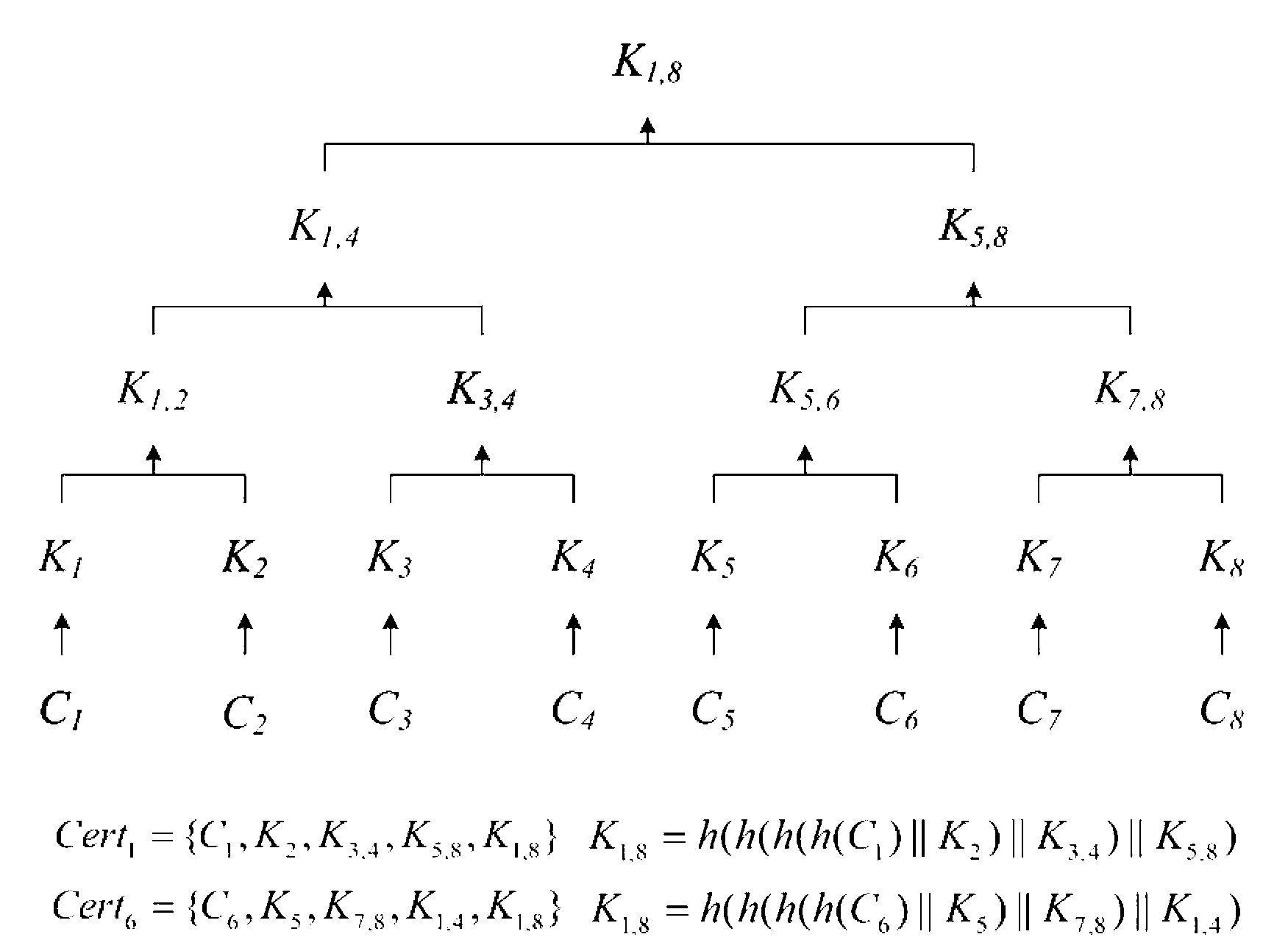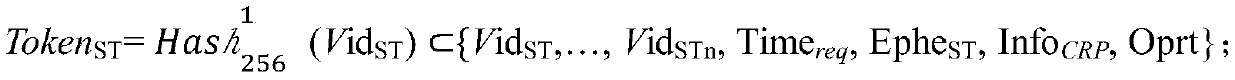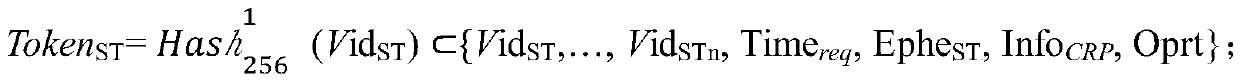Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
63results about How to "The certification process is reliable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
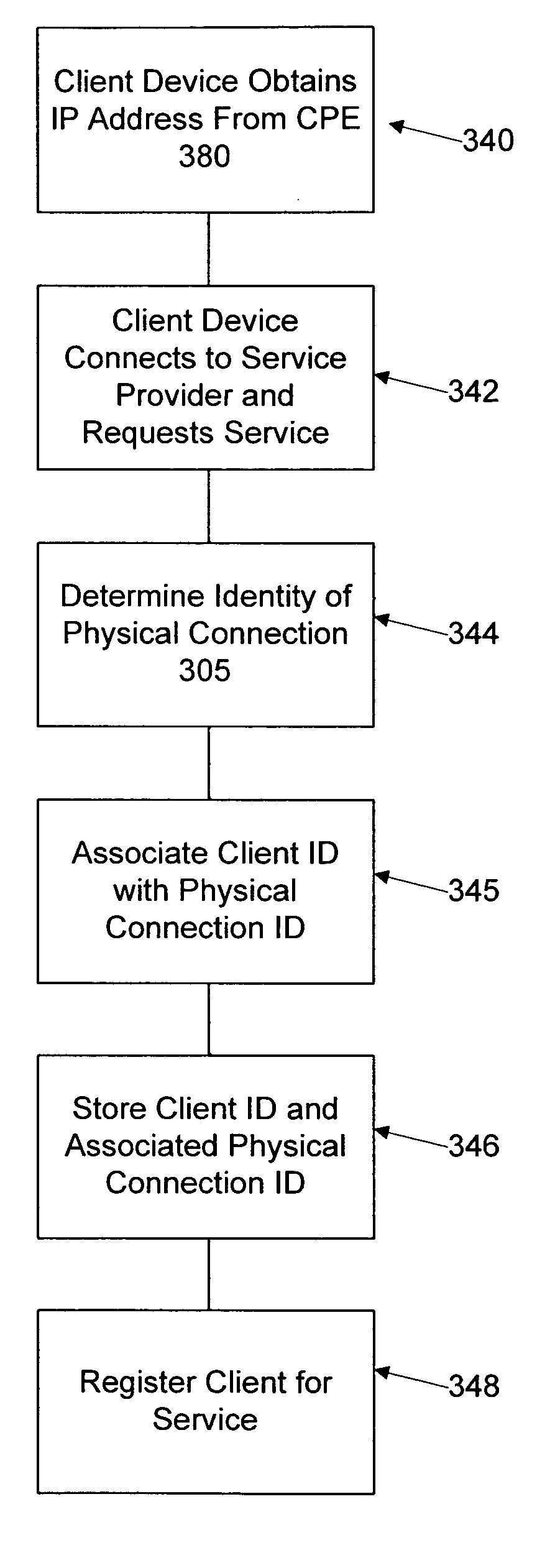
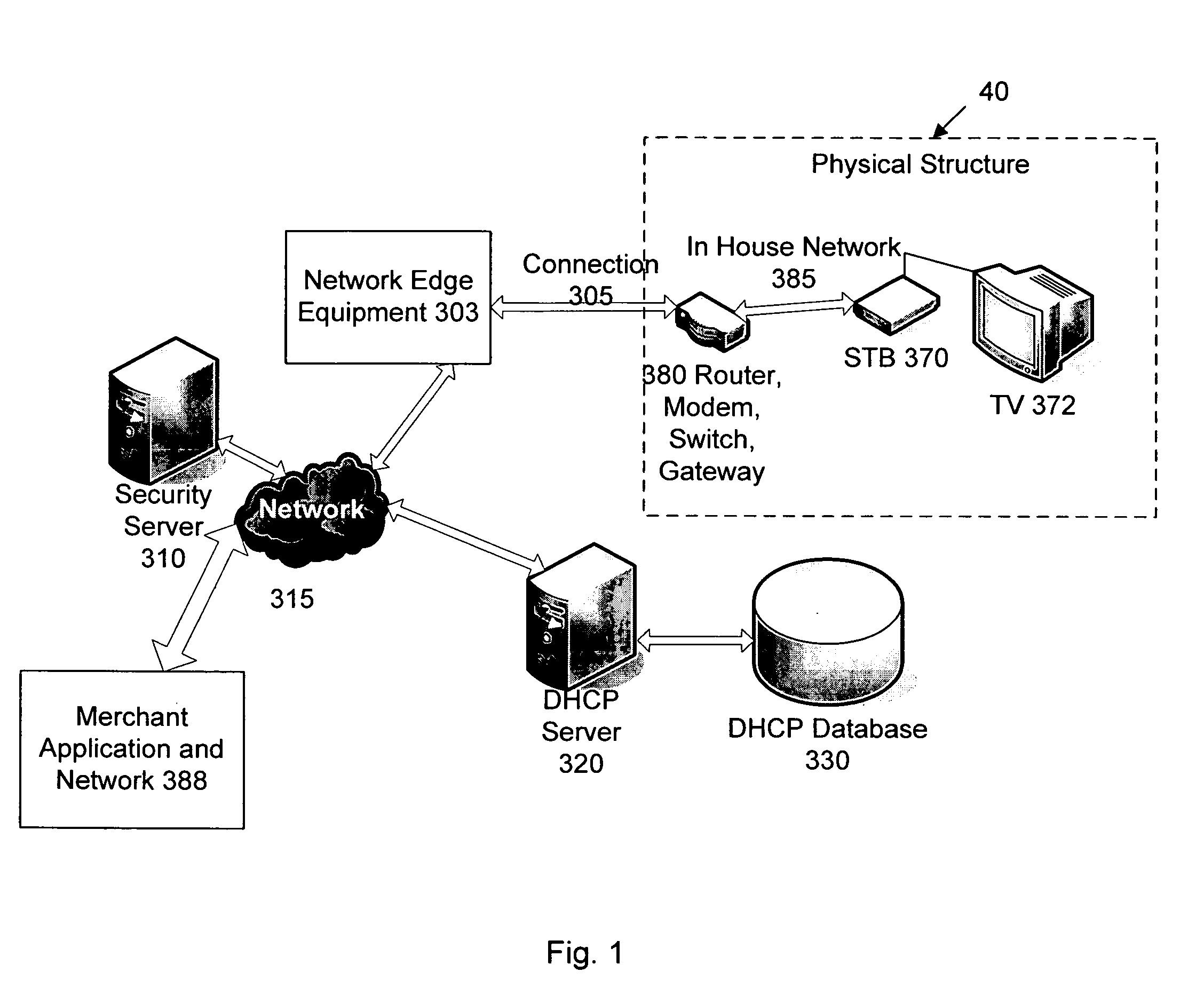
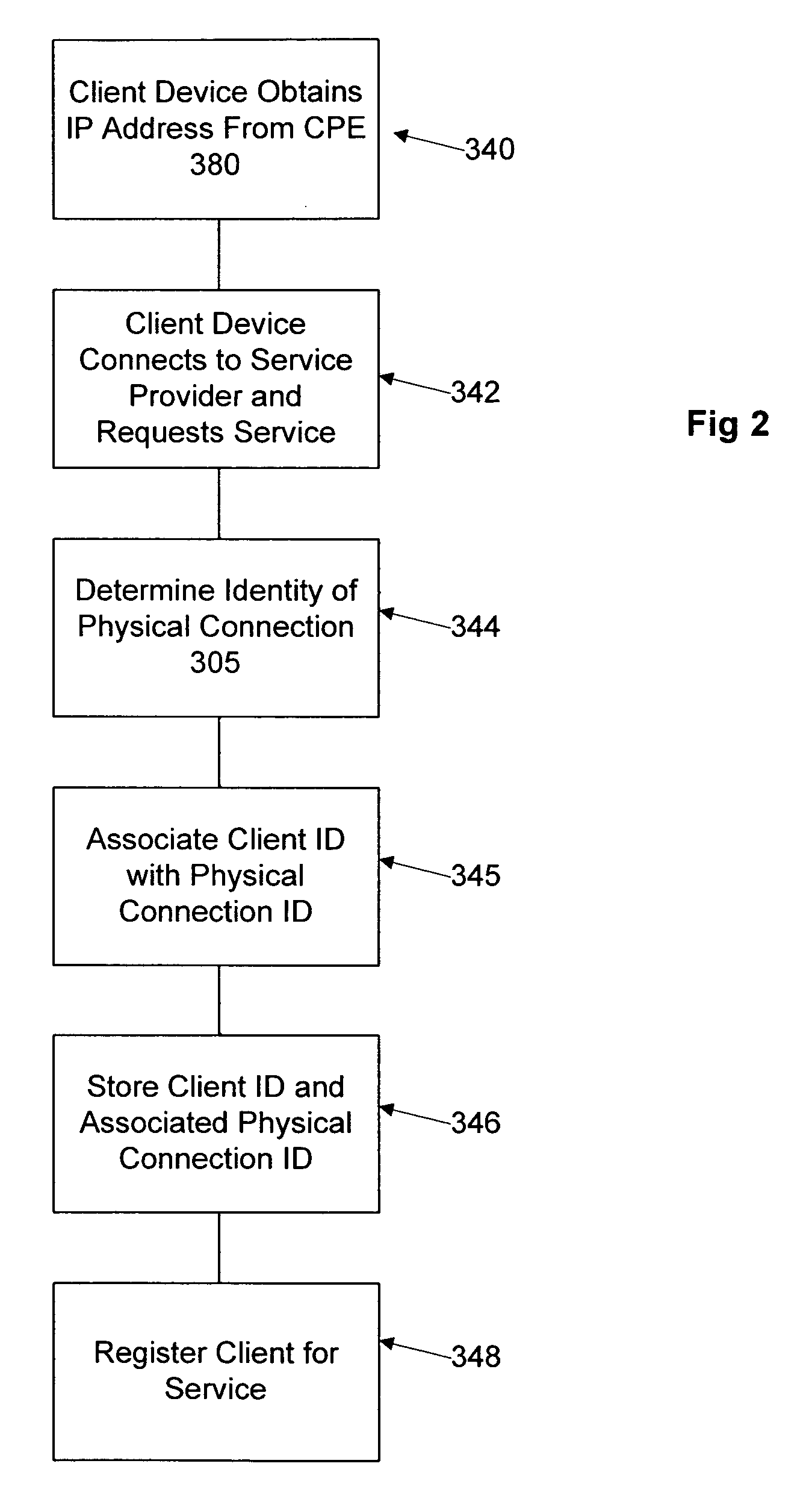
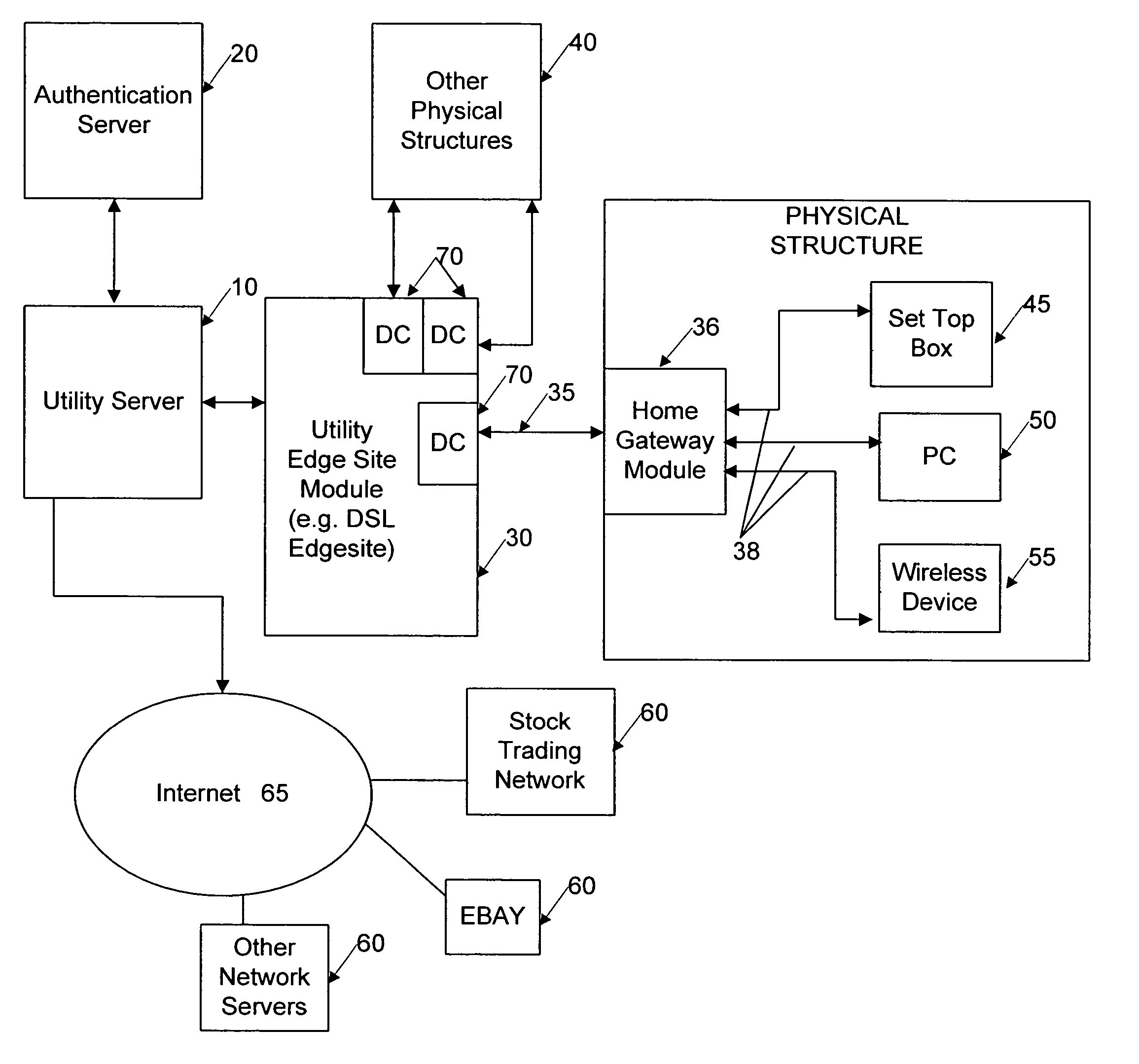
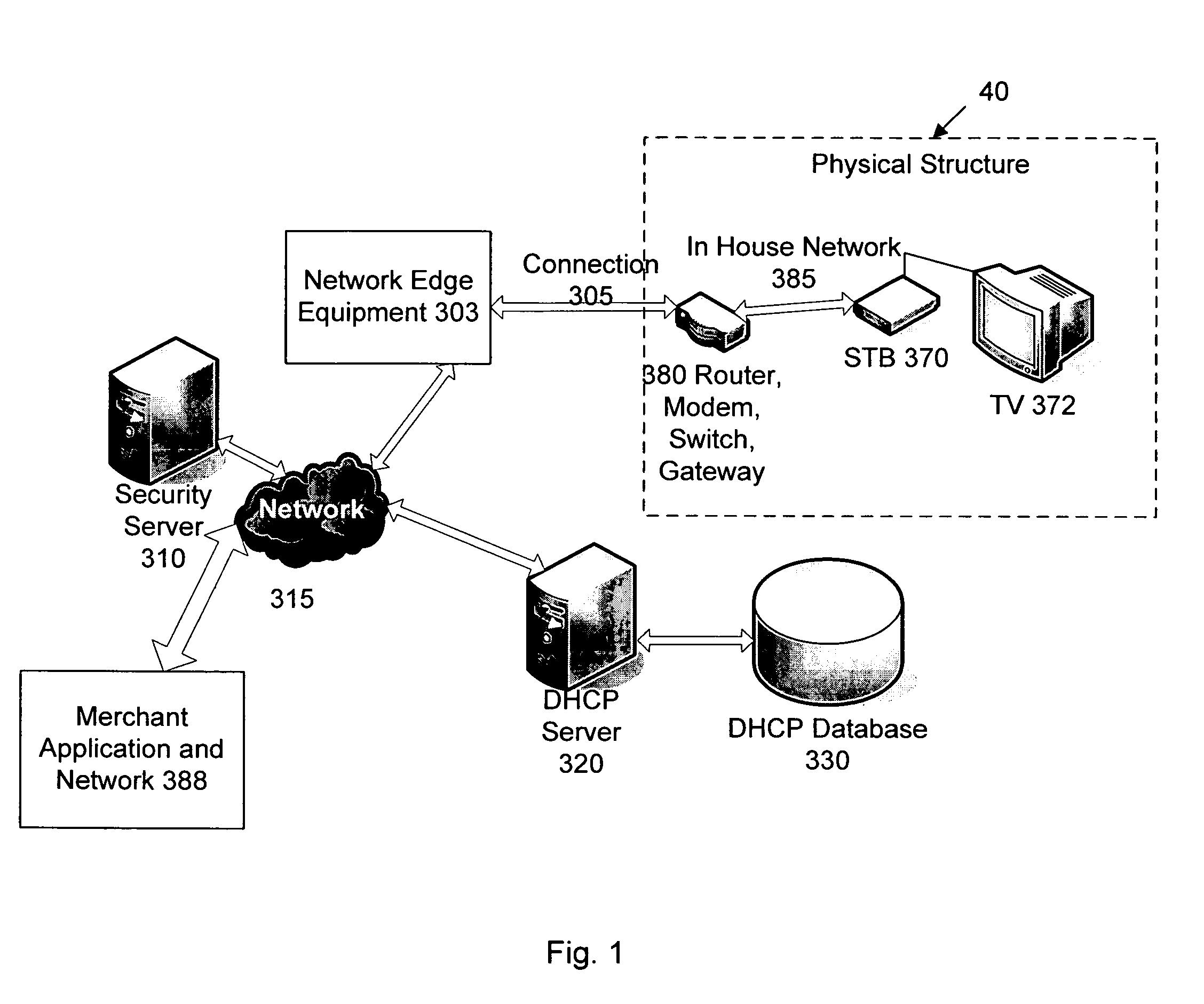
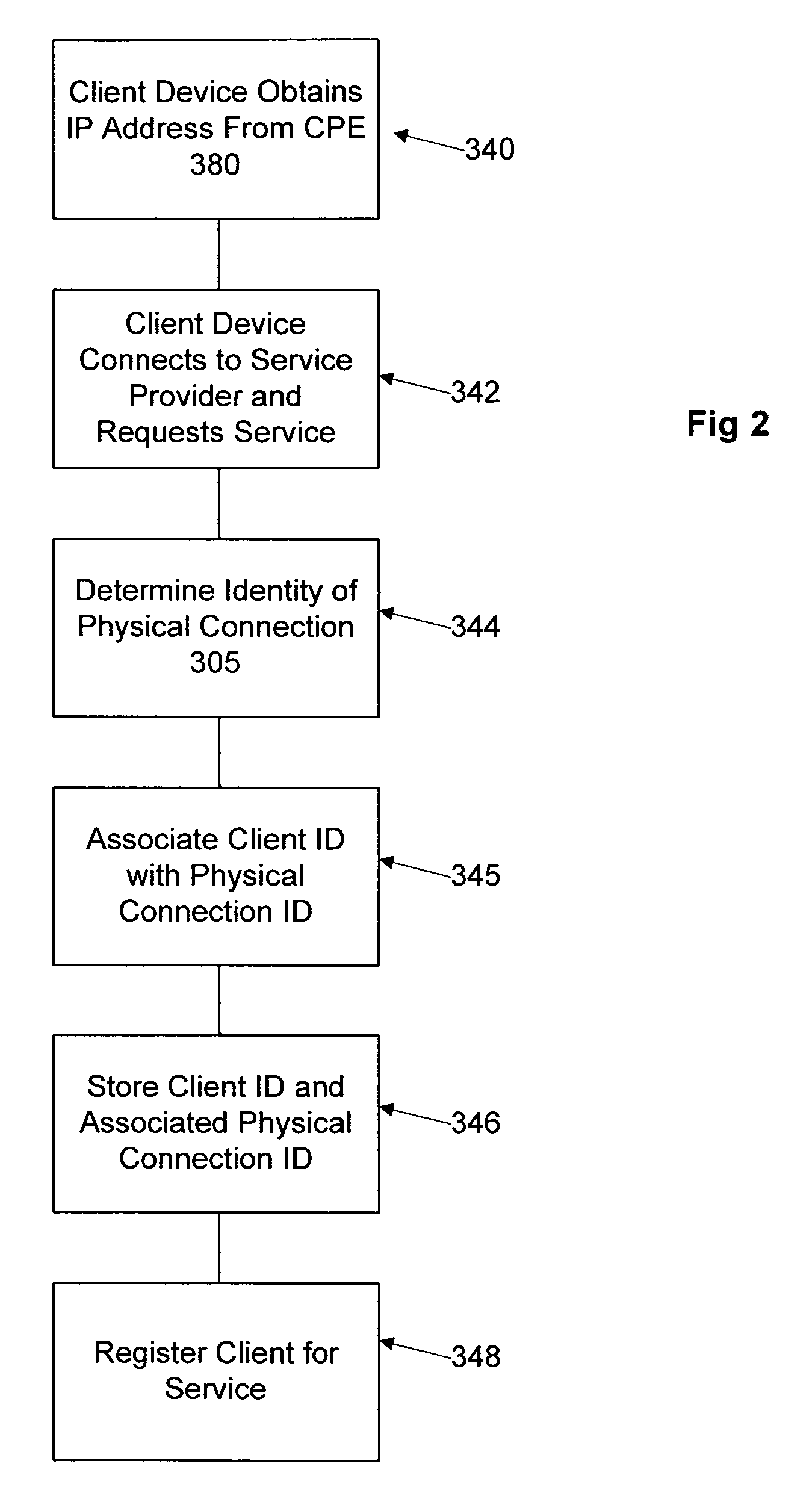
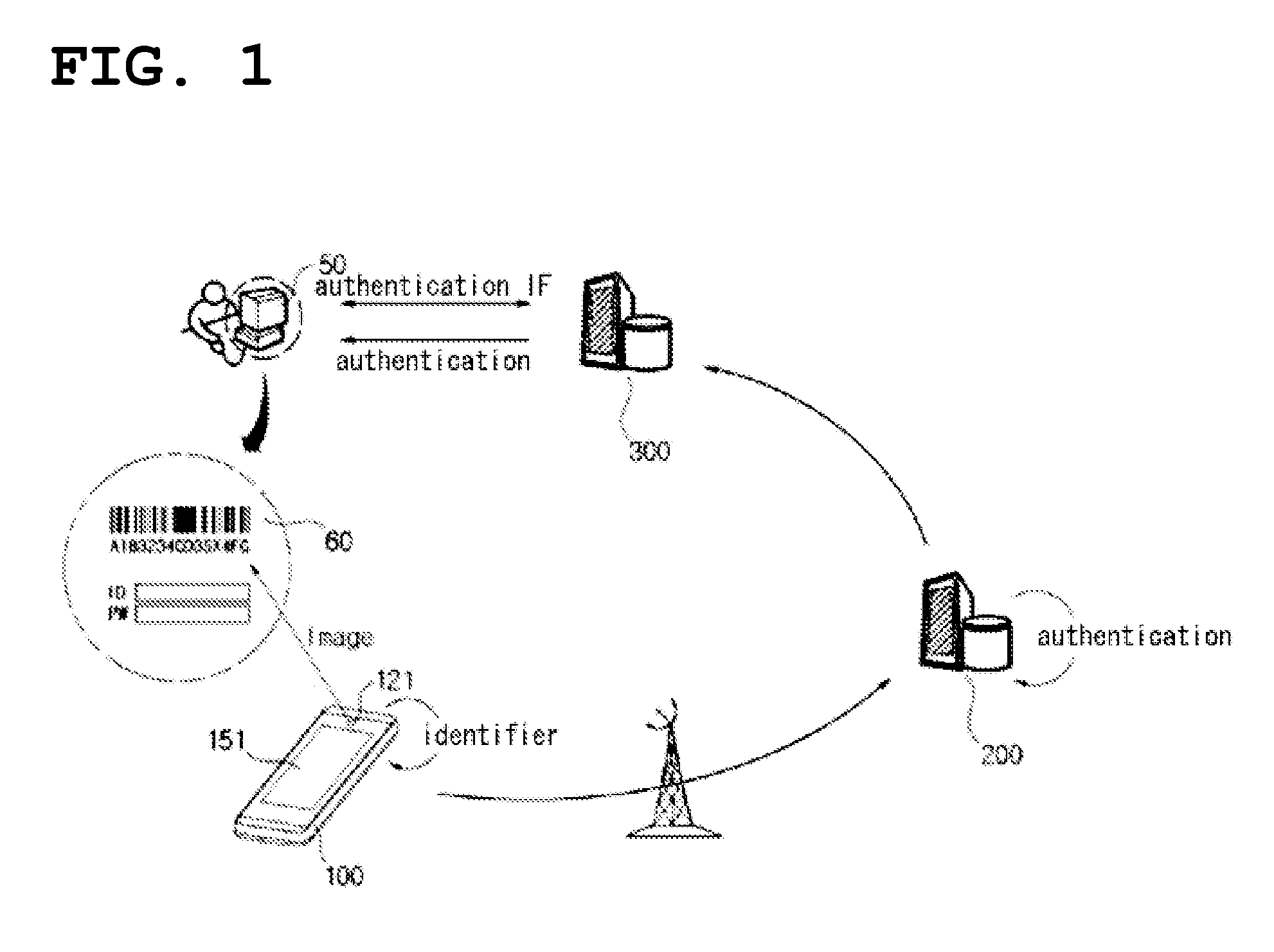
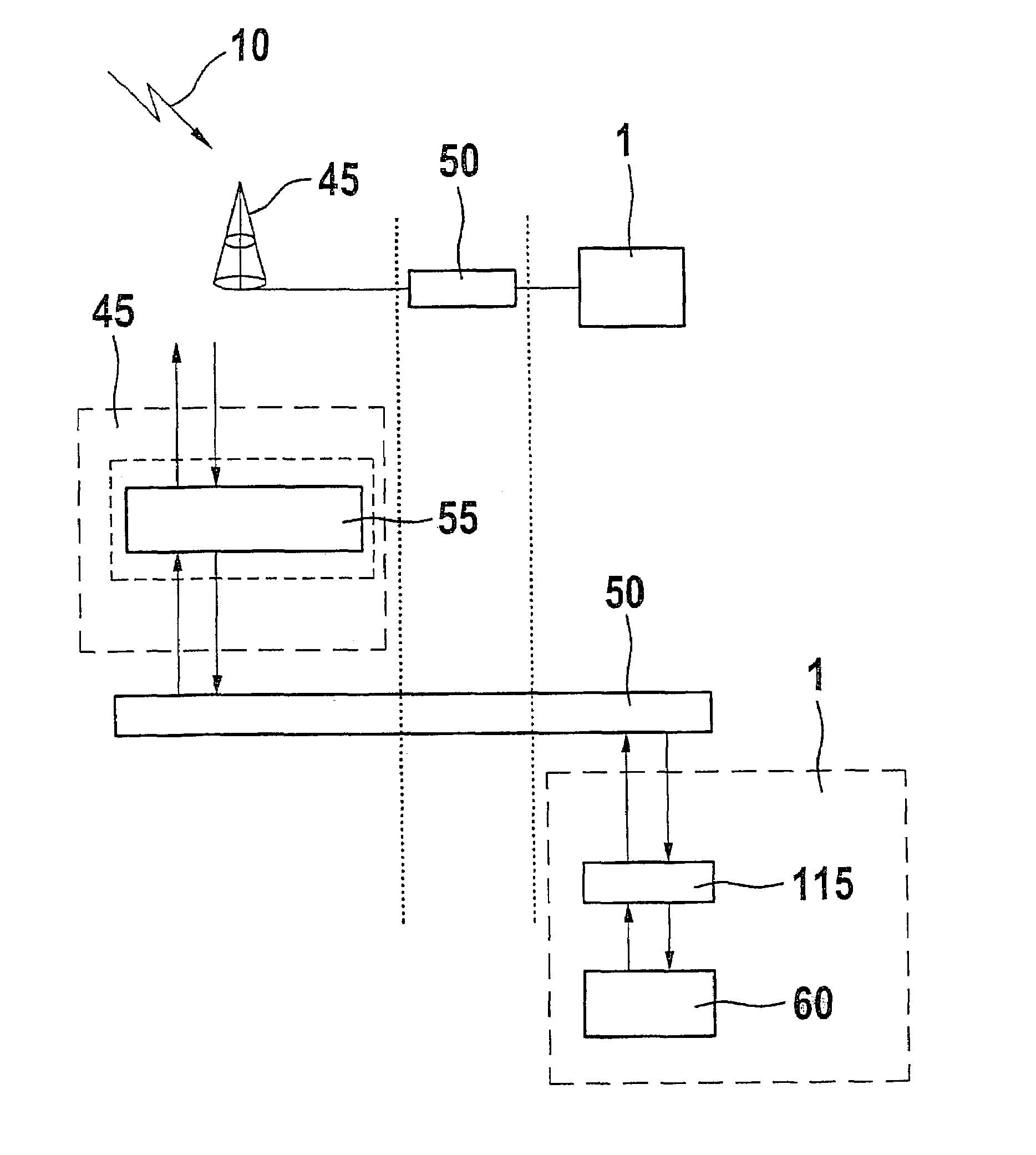
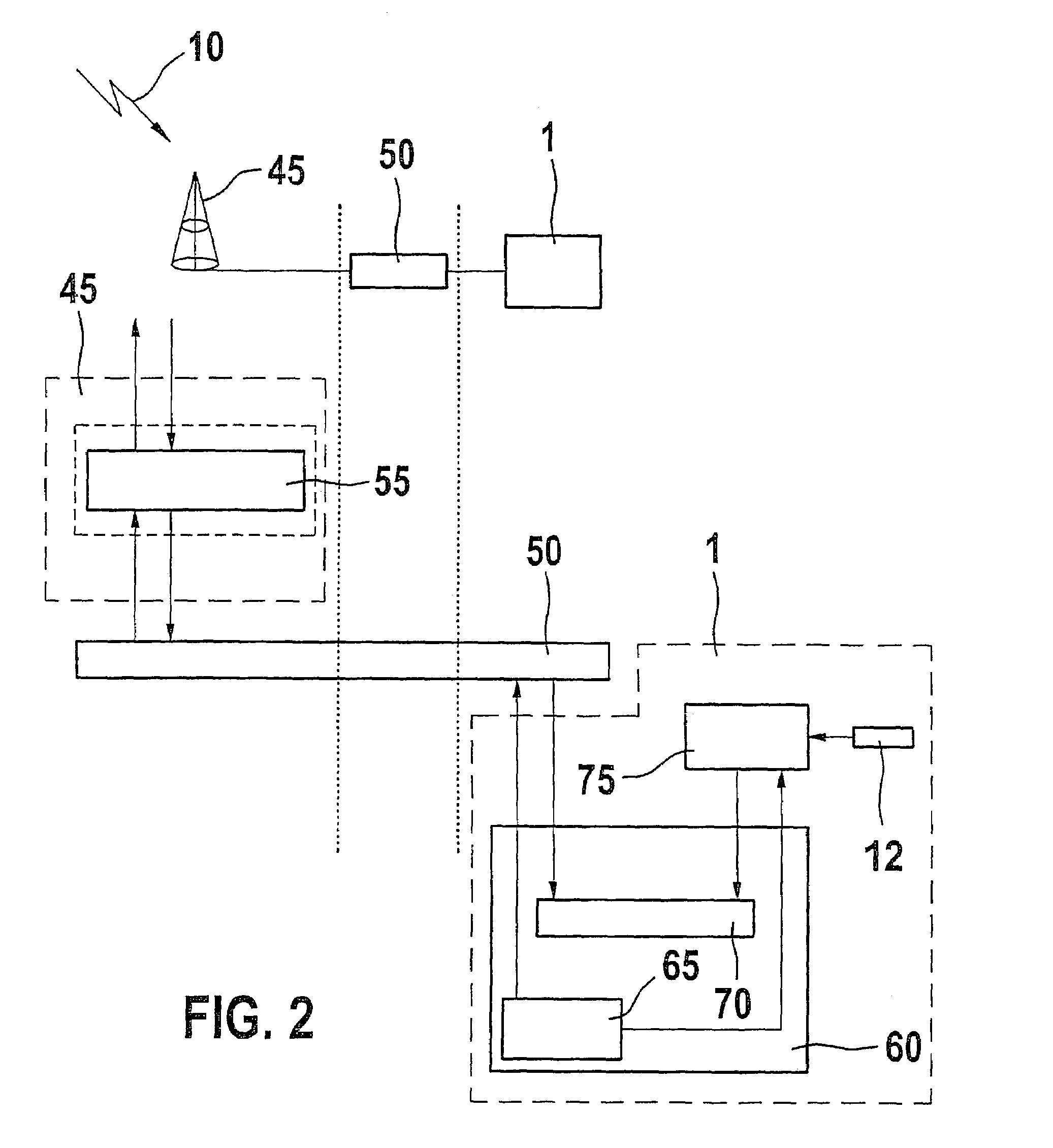
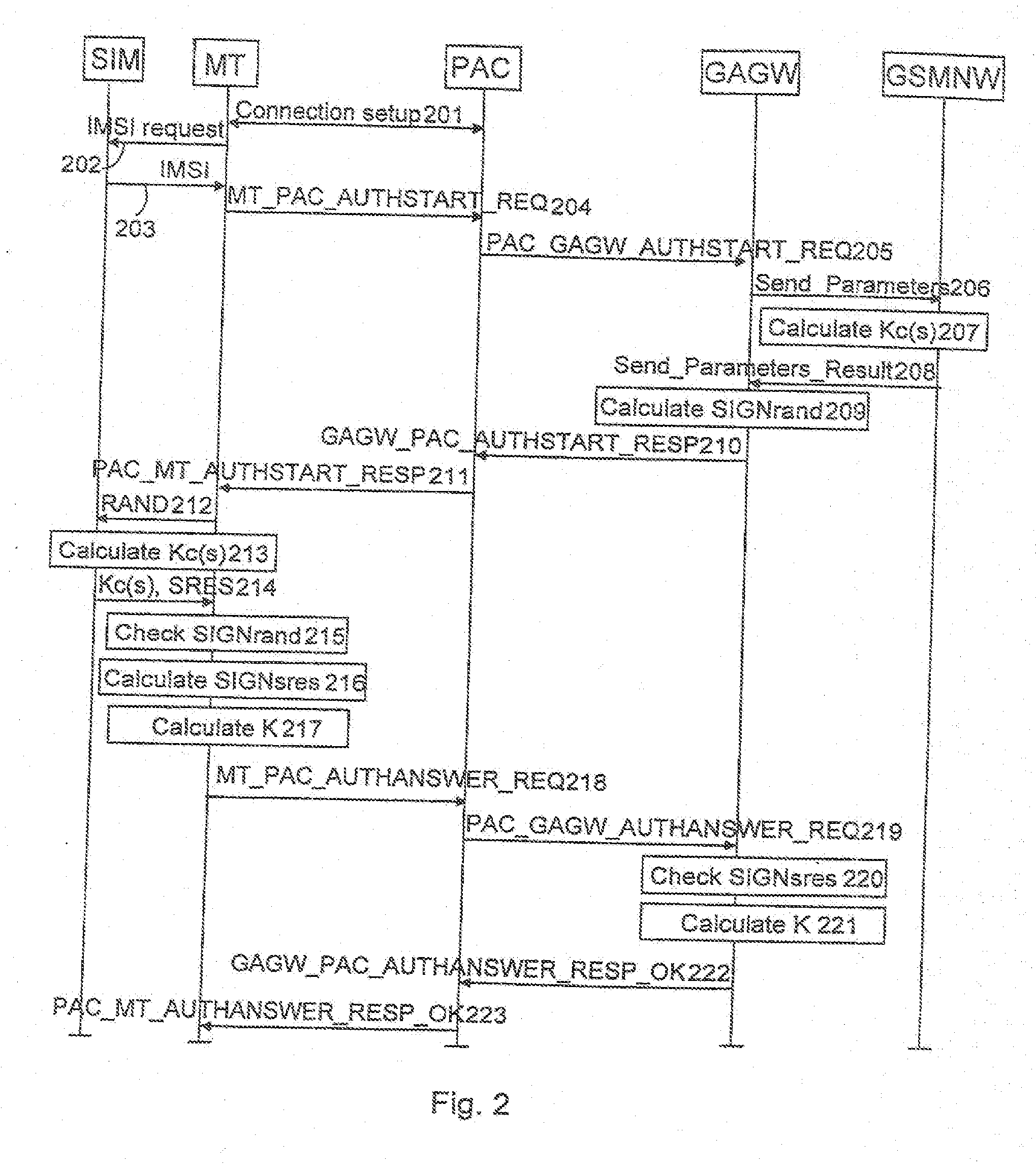
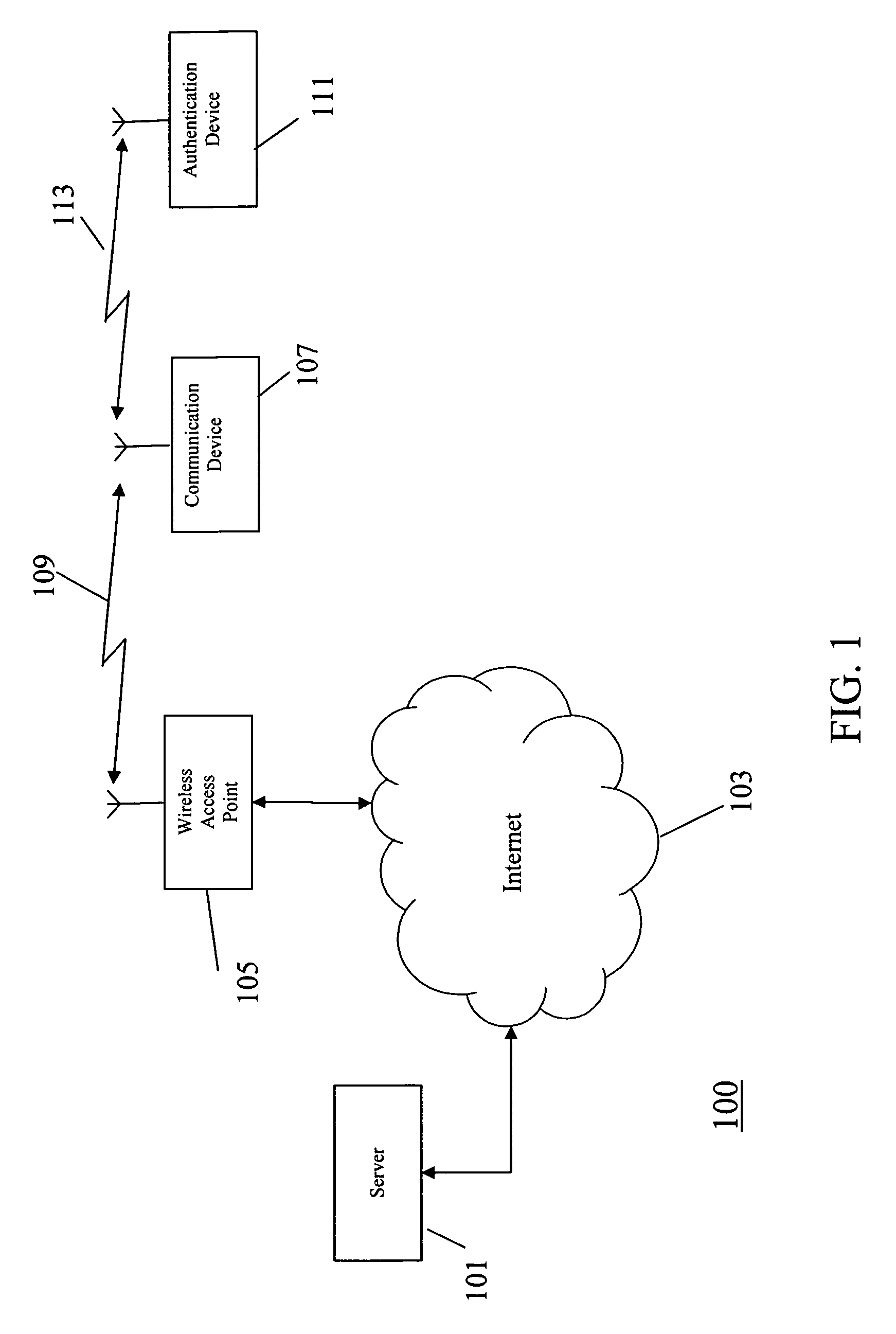
Network user authentication system and method
ActiveUS20070022469A1Removal difficult and impossibleThe certification process is reliableDigital data processing detailsUser identity/authority verificationUnique identifierAuthentication server
In a network user authentication system, a network user is identified for authentication purposes using the unique identifier for a dedicated physical communication line associated with the building in which the network user is located or a digital certificate which is associated with a secure component or communication line physically attached to a building. An authentication server initially verifies the identification of the dedicated communication line to be associated with a network service subscriber or issues a unique digital certificate to be associated with the dedicated communication line for authentication purposes. The digital certificate may be stored in a building gateway or in an edge site module which is connected to the secure components of a plurality of buildings and stores unique digital certificates for each building.
Owner:VERIMATRIX INC
Network user authentication system and method
ActiveUS8181262B2Removal difficult and impossibleThe certification process is reliableDigital data processing detailsUser identity/authority verificationComputer moduleUnique identifier
In a network user authentication system, a network user is identified for authentication purposes using the unique identifier for a dedicated physical communication line associated with the building in which the network user is located or a digital certificate which is associated with a secure component or communication line physically attached to a building. An authentication server initially verifies the identification of the dedicated communication line to be associated with a network service subscriber or issues a unique digital certificate to be associated with the dedicated communication line for authentication purposes. The digital certificate may be stored in a building gateway or in an edge site module which is connected to the secure components of a plurality of buildings and stores unique digital certificates for each building.
Owner:VERIMATRIX INC
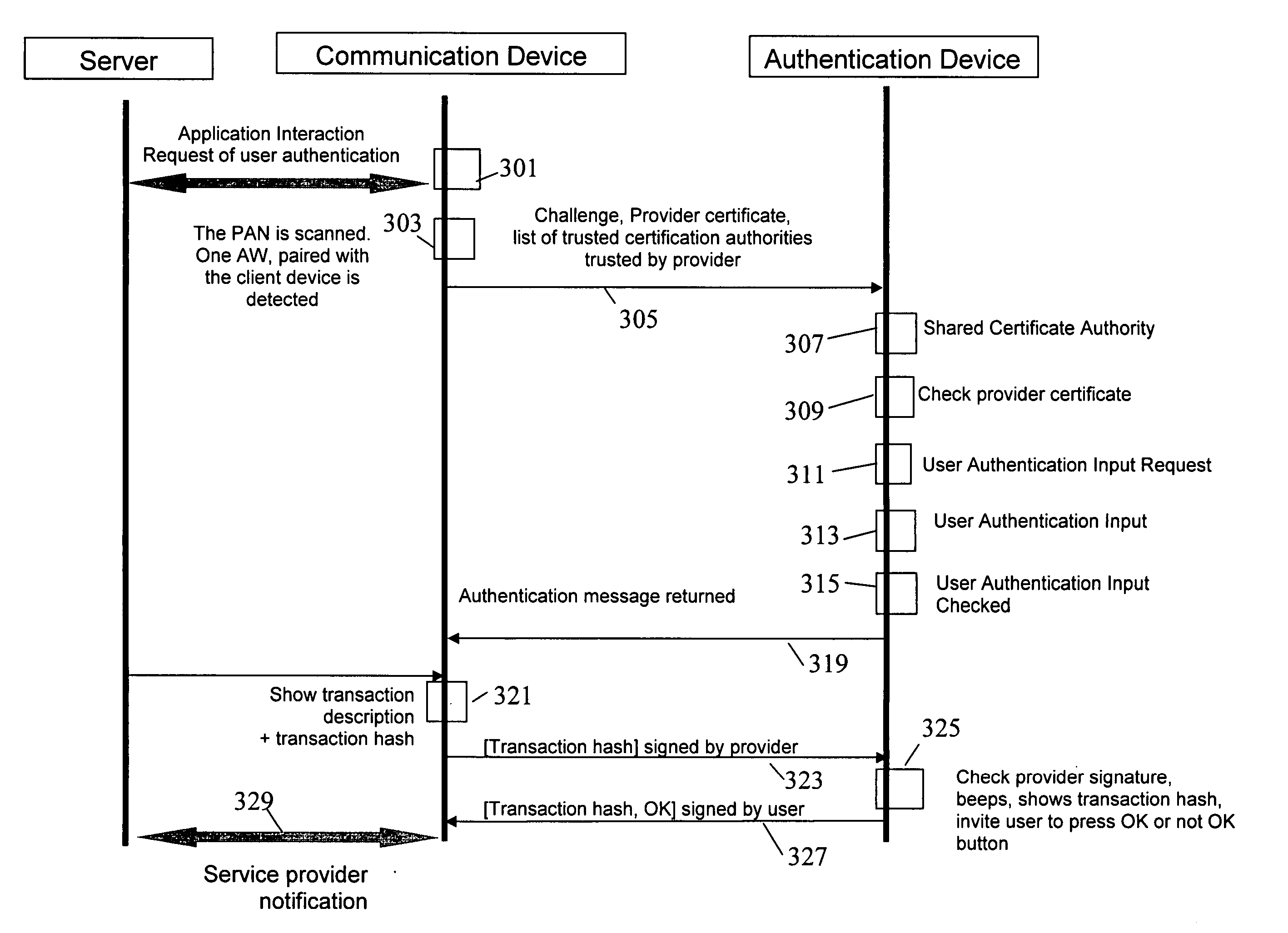
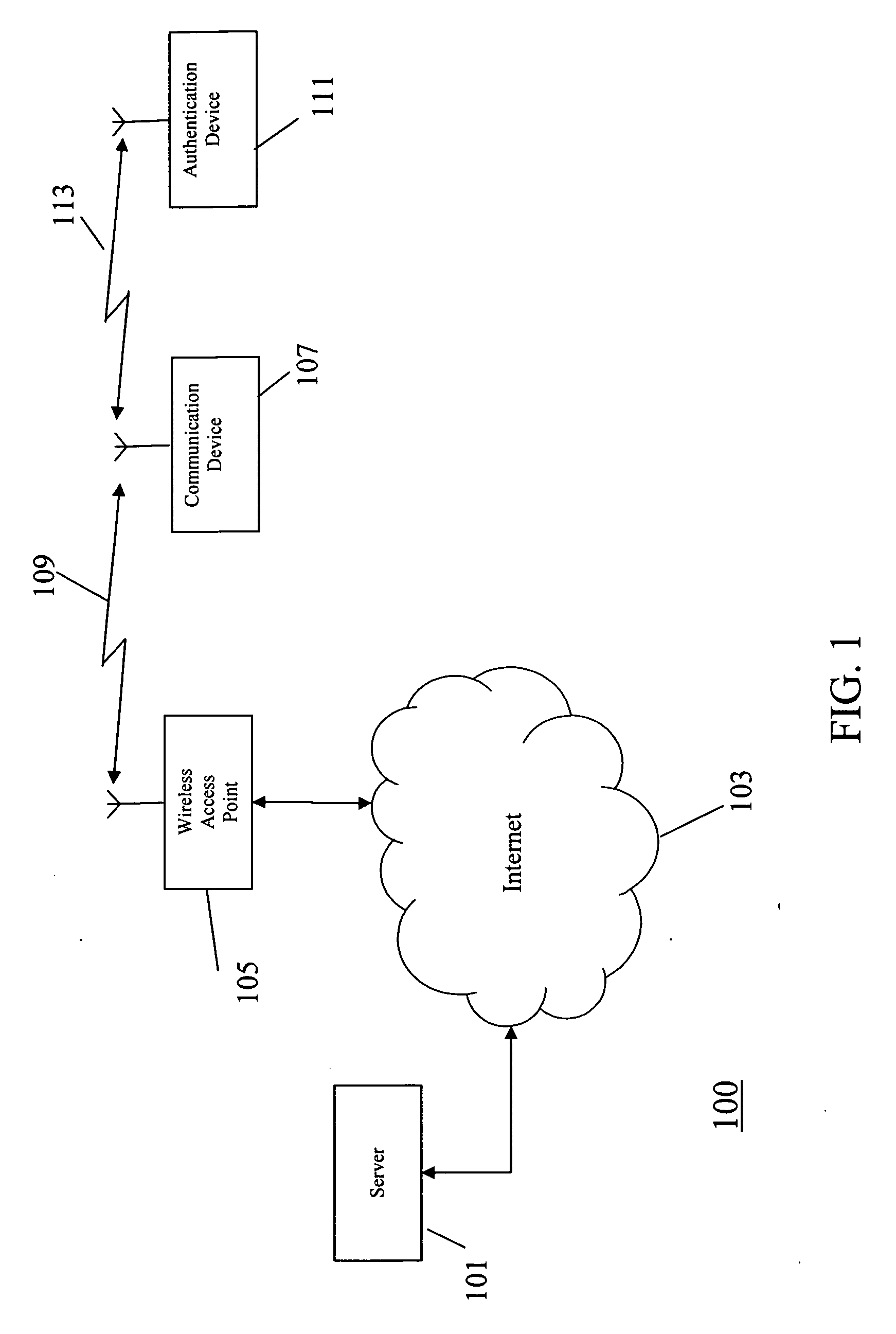
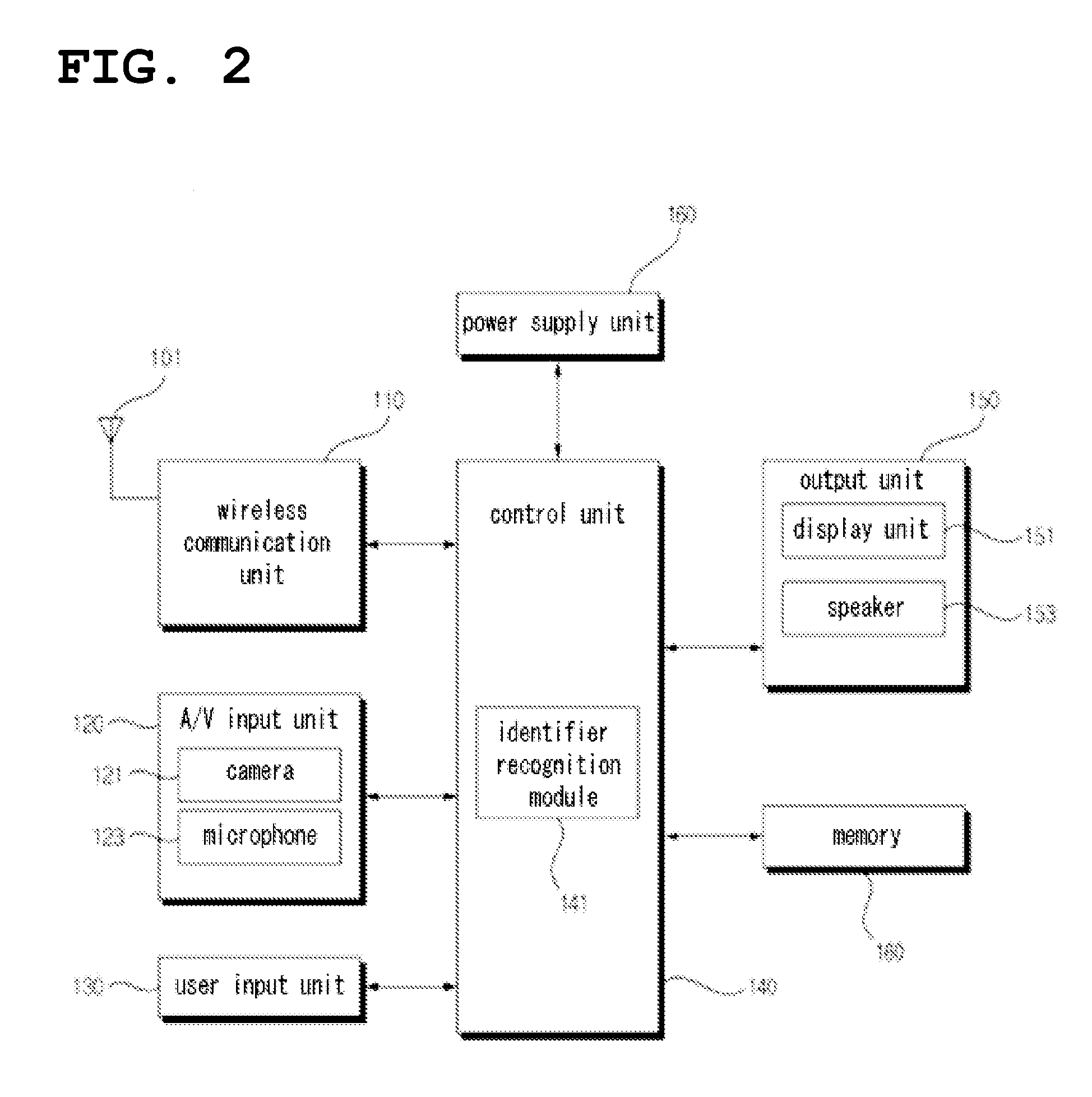
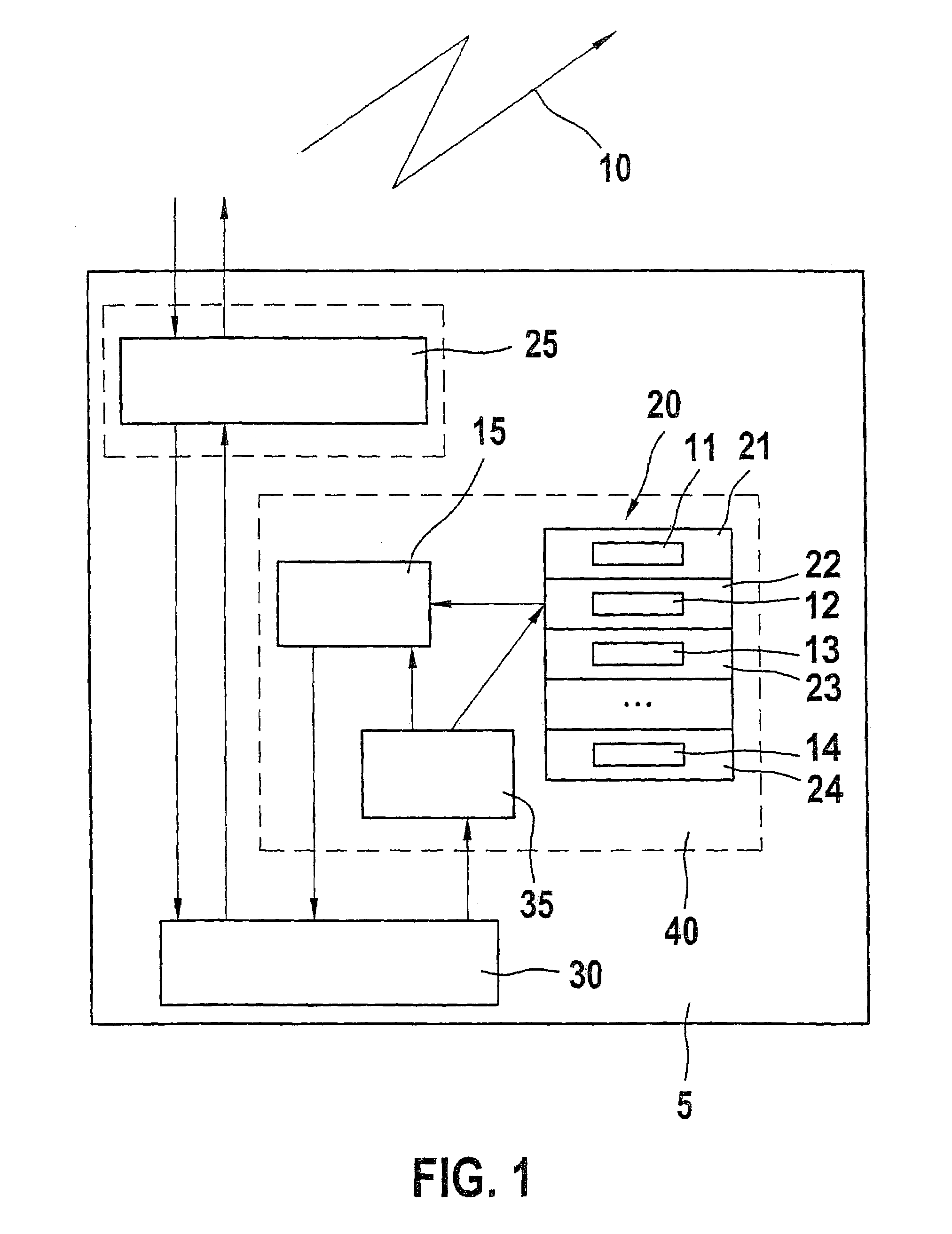
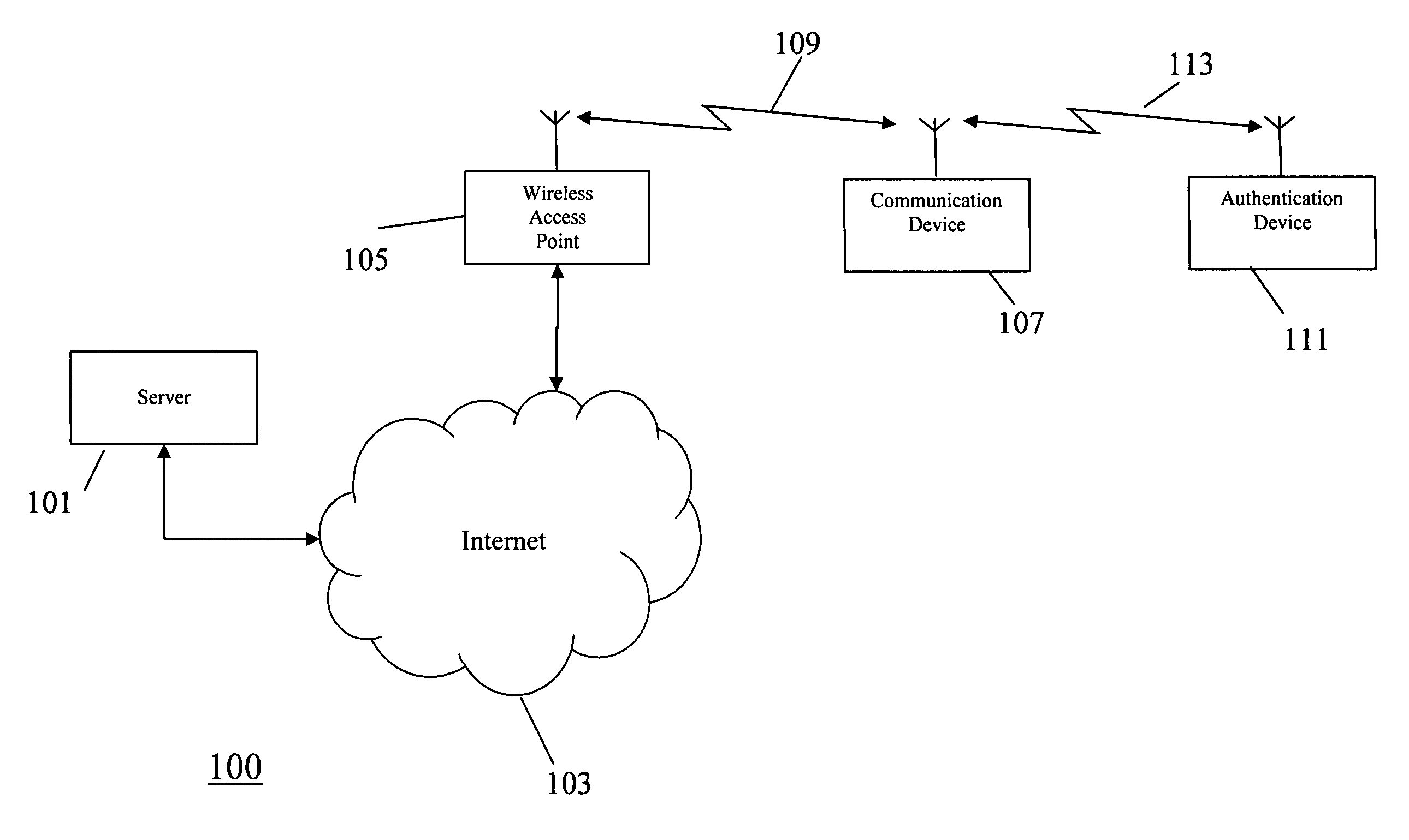
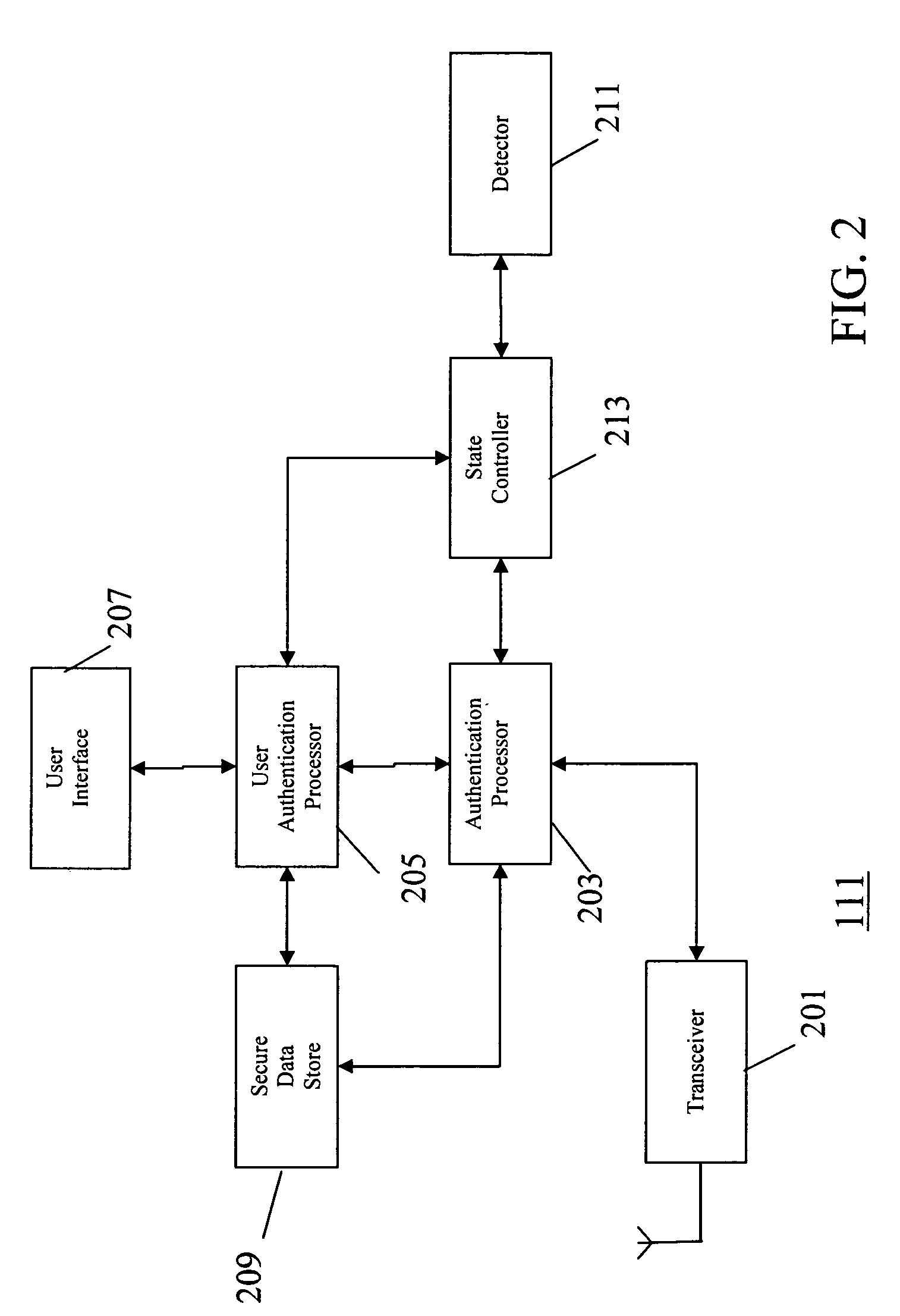
Method and apparatus for user authentication
ActiveUS20070050618A1The certification process is reliableEnhanced authenticationDigital data processing detailsUser identity/authority verificationUser inputData memory
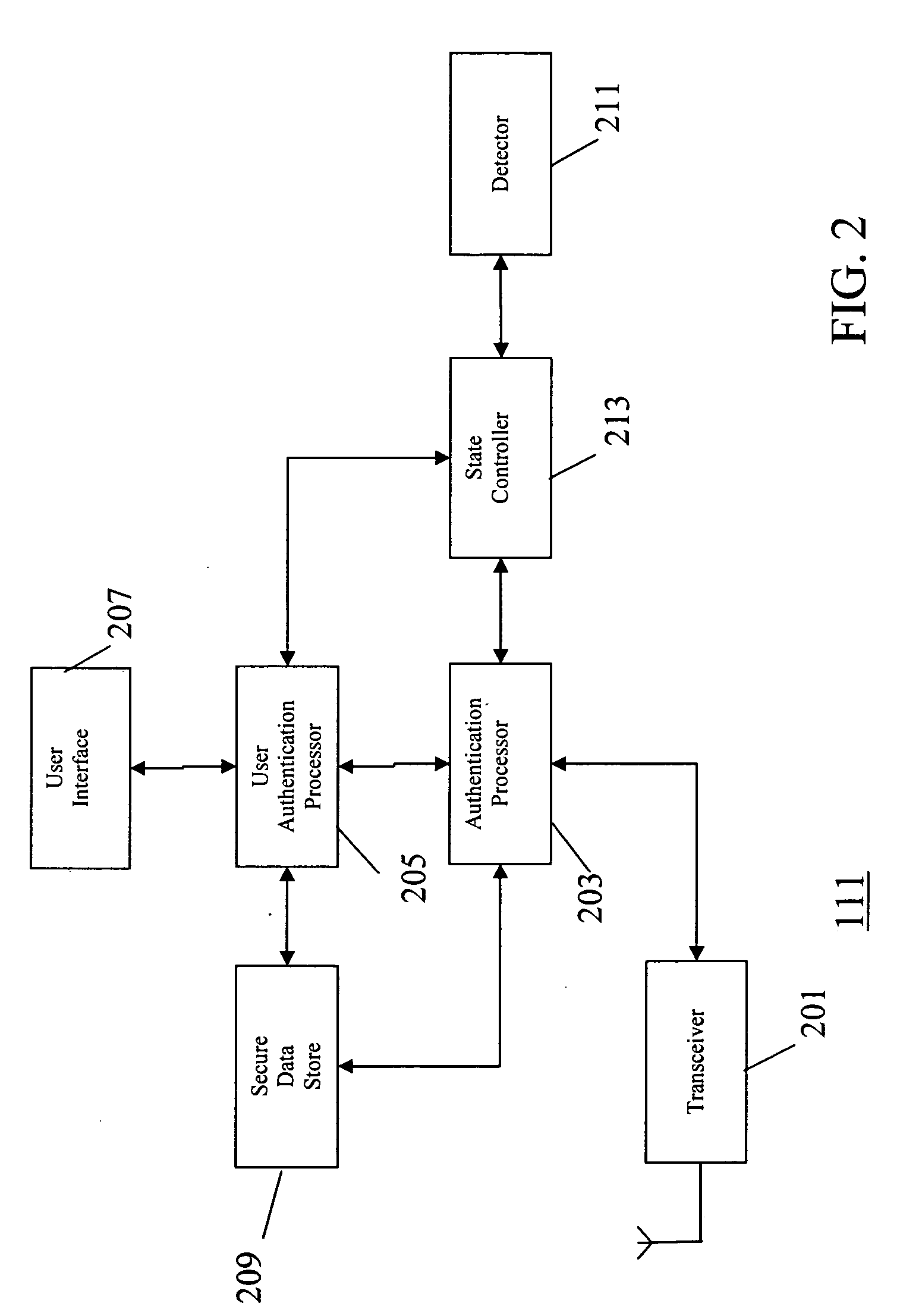
The invention provides for secure end-to-end user authentication by a remote server communicating with a communication device. The communication device further communicates with an authentication device, which provides a user authentication message to the communication device for forwarding to the remote server. The authentication device comprises a data store for storing user authentication credentials. A user authentication processor performs a local authentication of a user of the authentication device in response to a user input. An authentication processor generates the authentication message if the user authentication is valid. The authentication processor implements a cryptographic function based on the user authentication credentials. A transmitter then transmits the authentication message to the at least one communication device.
Owner:MOTOROLA SOLUTIONS INC
Method and a device to detect and manage non legitimate use or theft of a mobile computerized device
InactiveUS20170013464A1Improve reliabilityHigh precisionTransmissionSecurity arrangementComputer hardwareHand movements
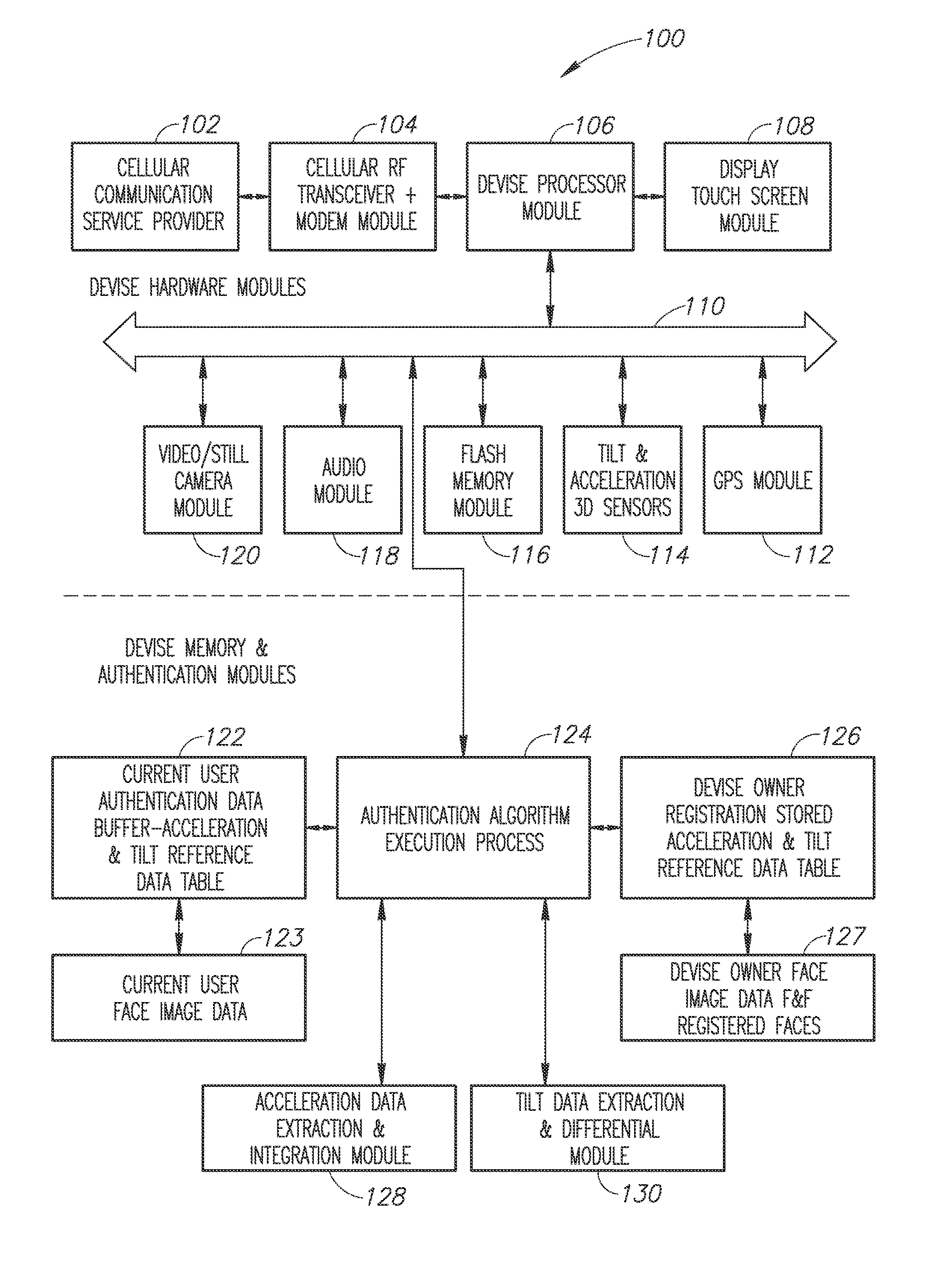
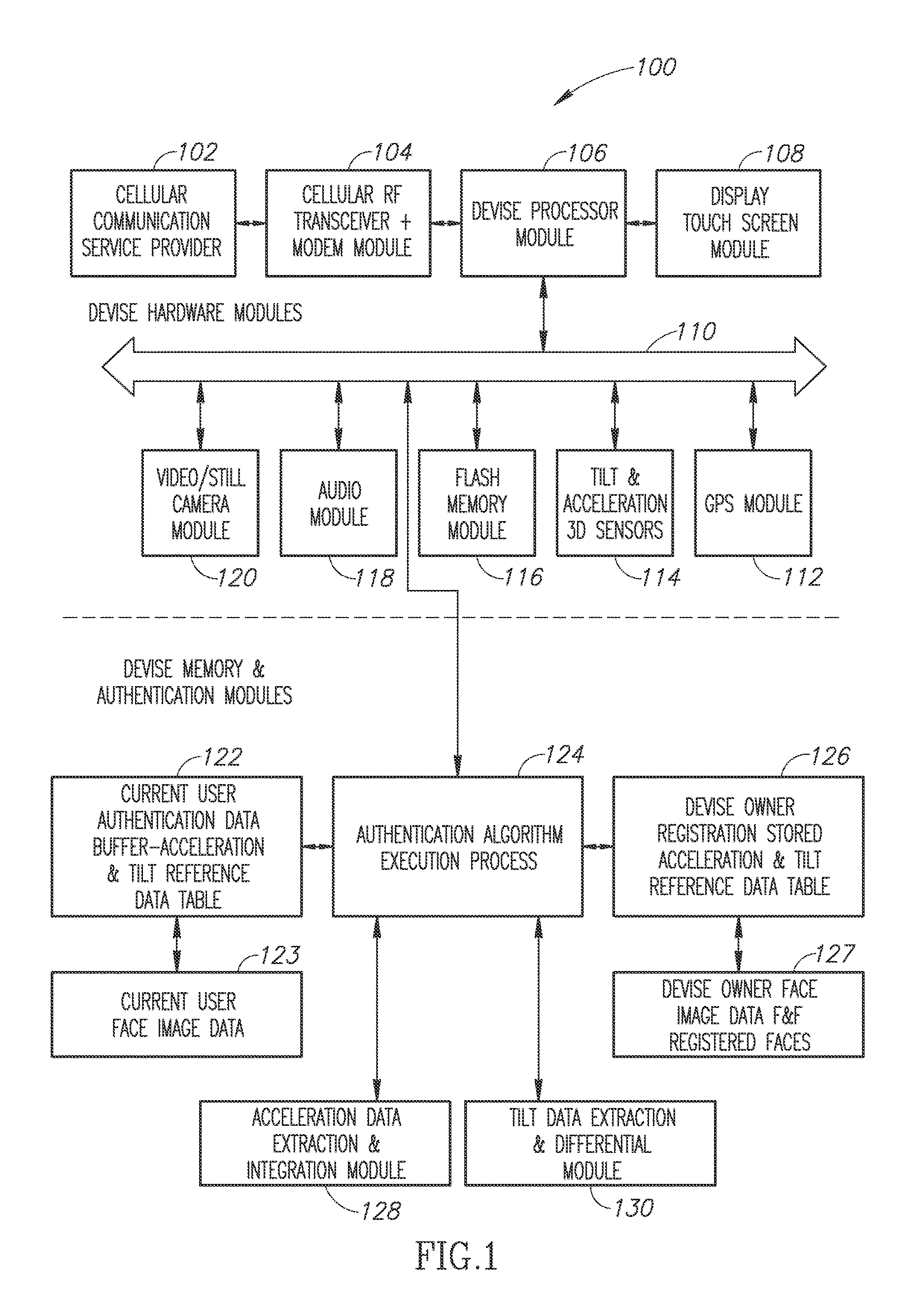
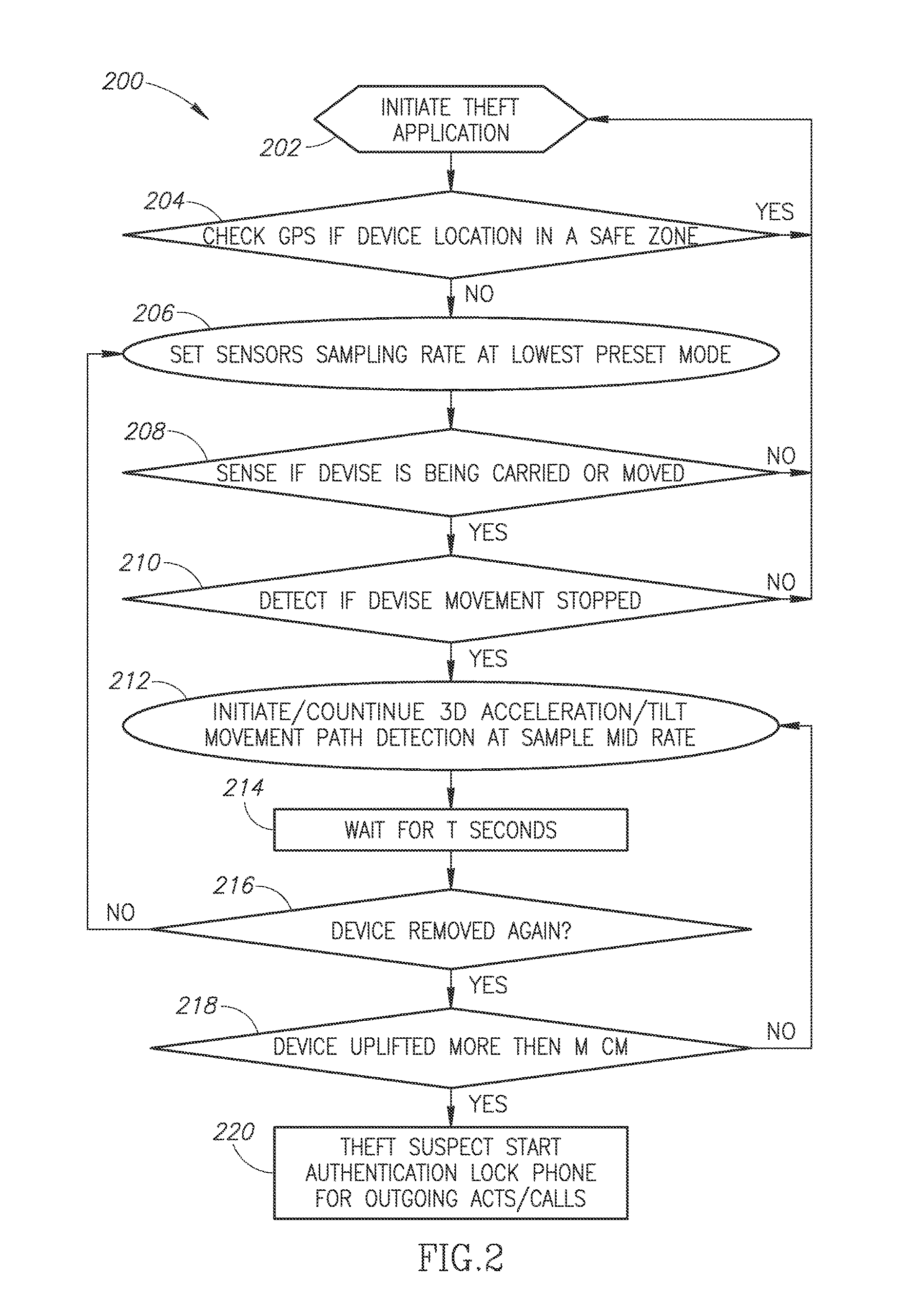
A method, a device and a system are provided for mobile devices theft protection and for avoiding none legitimate and misuse of the devices. It is based on a human 3D device holding hand movement, while creating a bio-authentication event of a user of the mobile device. In case of authentication failure it activates various types of alarms locally on the device, and / or deactivating or blocking one or more of the device operational functions, like communication or access to certain functions, stored data, or applications and it transmits alarms and illegitimate user images via text and image messages to remote locations. In other cases it generates and transmits also device's status and location to remote user's piers nearby, or to a monitoring center, all based on the user's device authentication failure and following activated action items.
Owner:FISH GILA +1
Communications Device Authentication
ActiveUS20140057599A1Authentication is efficient and rapidThe certification process is reliableUnauthorised/fraudulent call preventionEavesdropping prevention circuitsRadio access technologyCommunication device
There is described a method of accessing a resource requiring identity authentication, the method comprising: receiving at a communications device an encrypted token in response to an identity of the communications device being authenticated over a first radio access technology; decrypting the encrypted token using the identity of the communications device; and using the decrypted token over a second radio access technology to authenticate the identity of the communications device so as to allow access to the resource via the second radio access technology.
Owner:VODAFONE IP LICENSING
Authentication method and system using portable terminal
InactiveUS20130023241A1The certification process is reliableImprove convenienceUnauthorised/fraudulent call preventionDigital data processing detailsWeb siteAuthentication information
The present invention authenticates a user using identifiers and authentication information provided and displayed by the mobile terminal and the service server to and on the user terminal, in conjunction with each other. Accordingly, unless an external intruder collects information necessary for authentication from the mobile terminal, the service server, and the user terminal in the same time span, the external intruder cannot perform authentication in place of a user. The present invention can be used to process authentication in portal sites, websites of financial institutions such as banks, personal blogs, homepages, and a variety of other websites using the Internet.
Owner:IGROVE
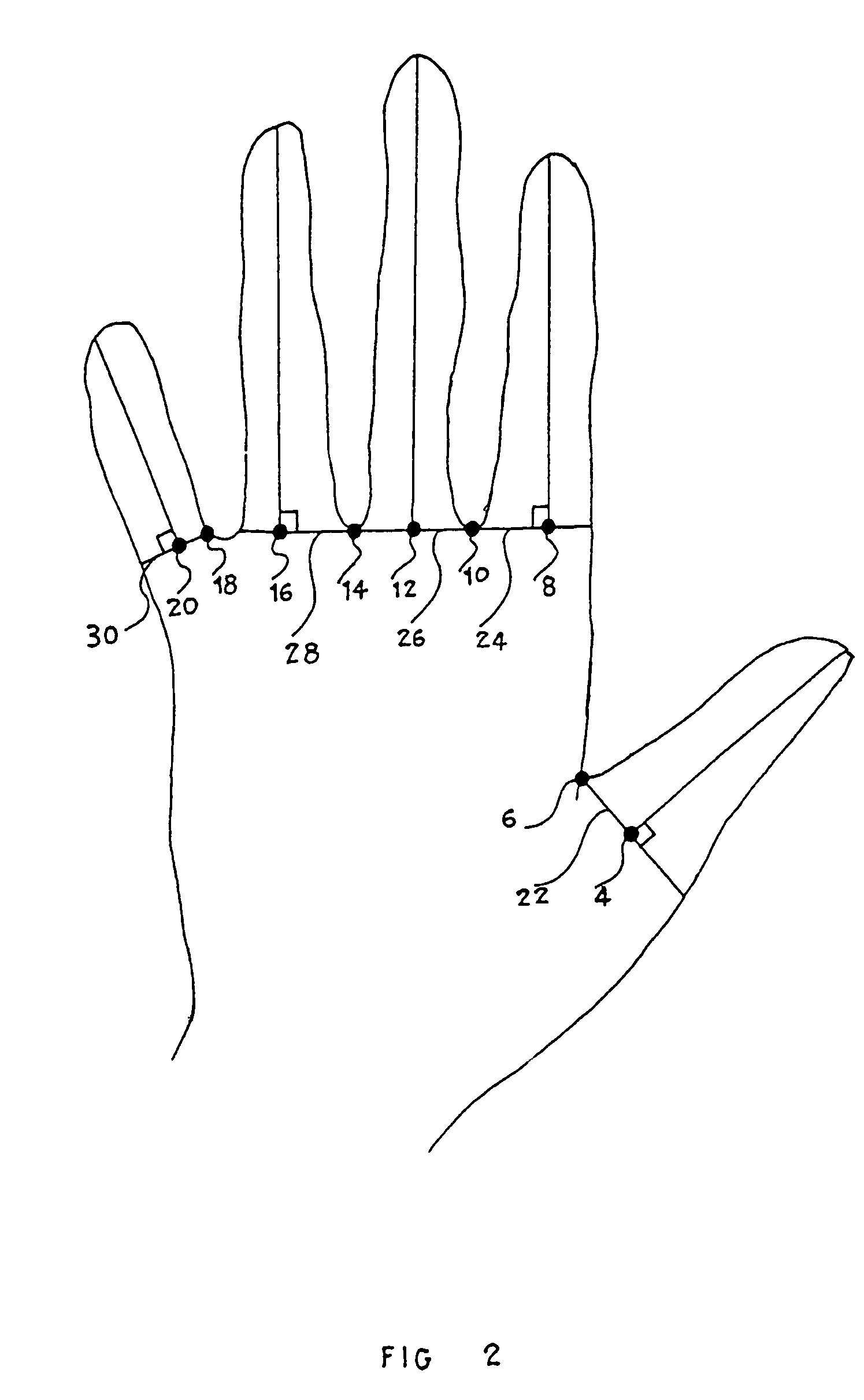
System and a method for person's identity authentication
InactiveUS7327858B2The certification process is reliableDigital data processing detailsDigital data authenticationComputer scienceAuthentication
The invention relates to a method for biometric authentication of an individual based on the unique characteristics of his hand, using a scanning unit of any size. The invention also relates to a system for use of said method.
Owner:WEISS GOLAN
Method and a server for processing a request from a terminal to access a computer resource
ActiveUS20140380048A1OptimizationEfficient use ofDigital data processing detailsUser identity/authority verificationComputer resourcesService provision
In one embodiment disclosed herein is a method of processing a request made by a terminal of a user to access a resource made available to a client entity by a platform of a cloud computer service supplier.
Owner:ORANGE SA (FR)
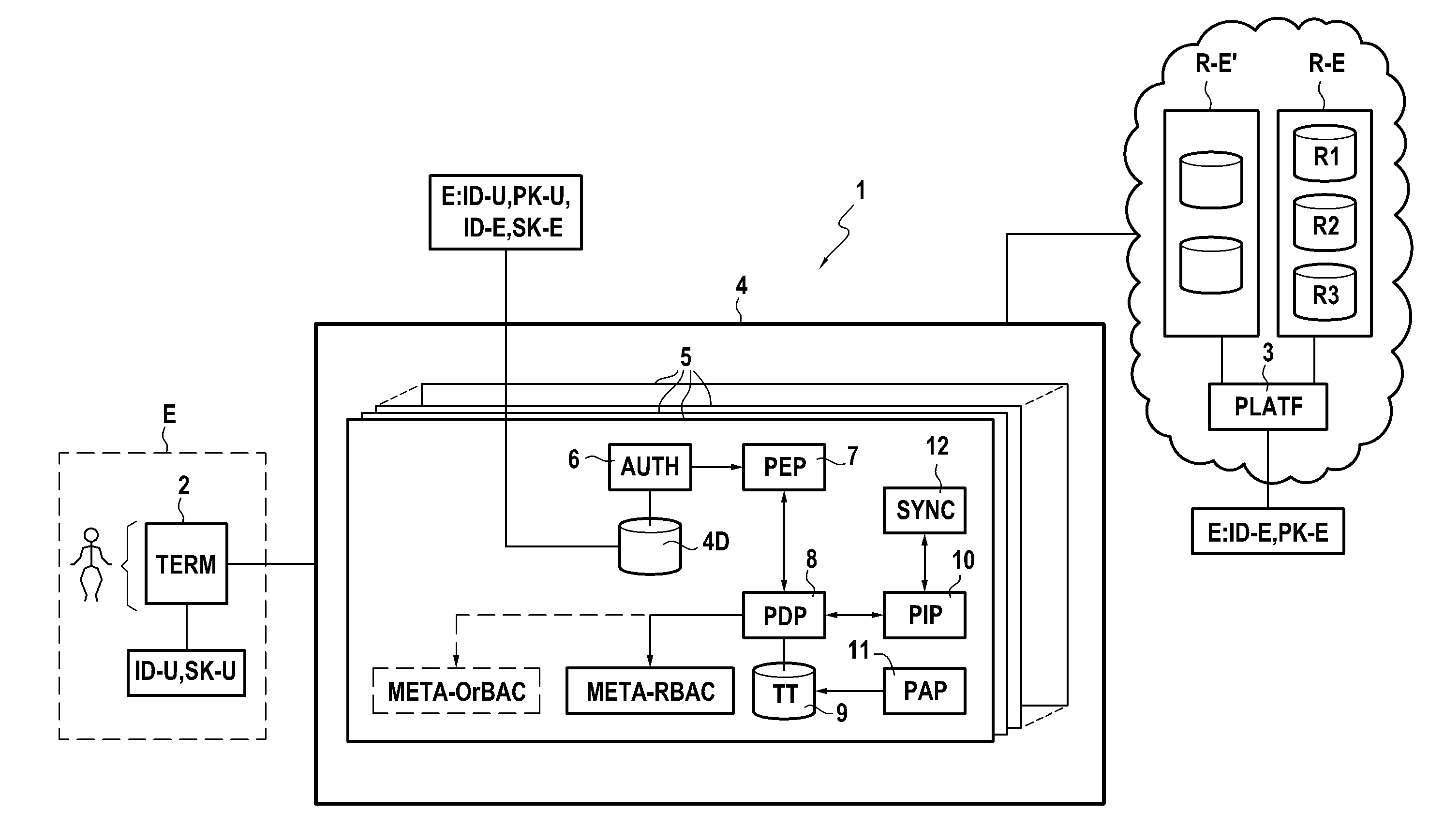
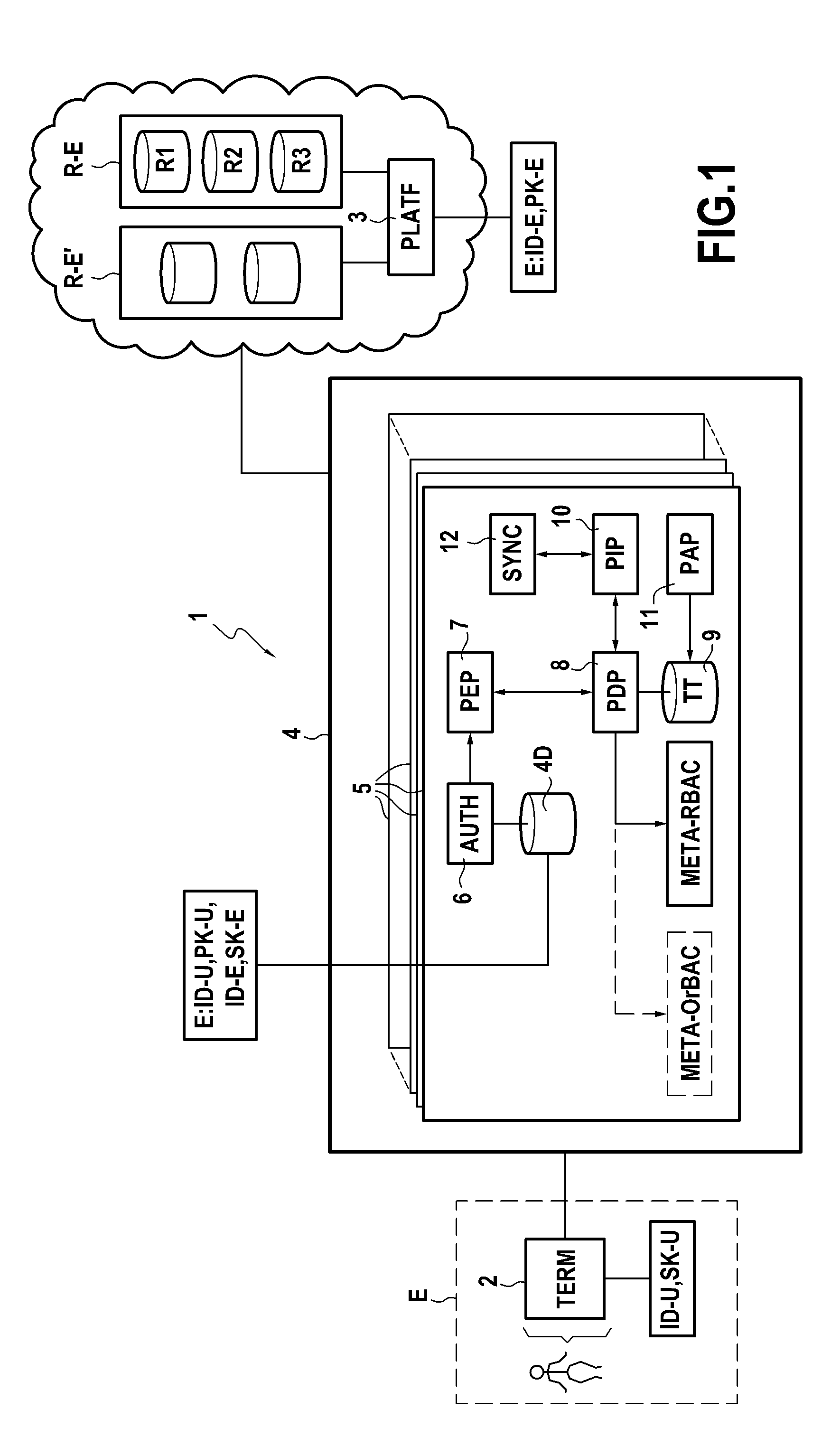
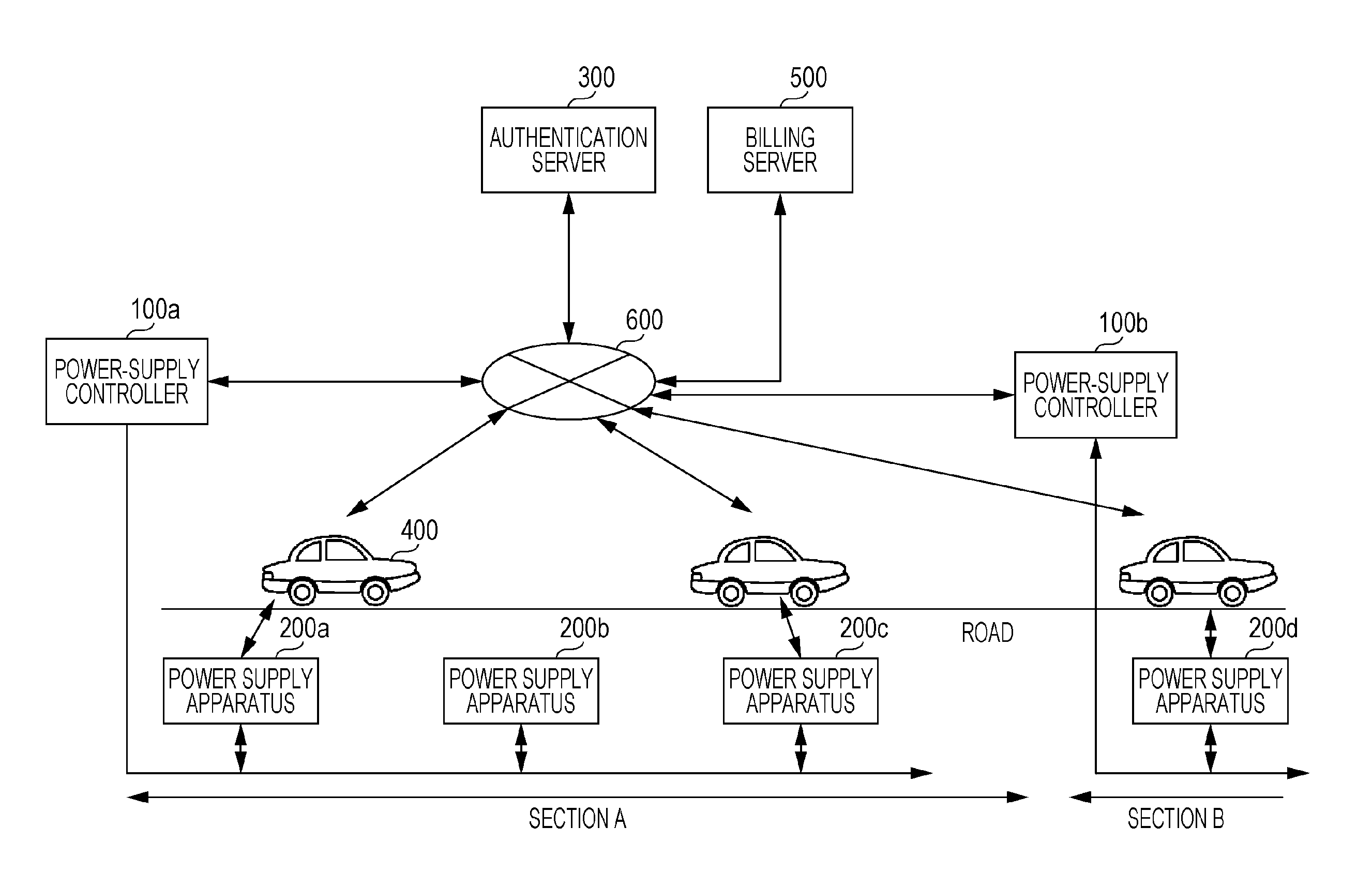
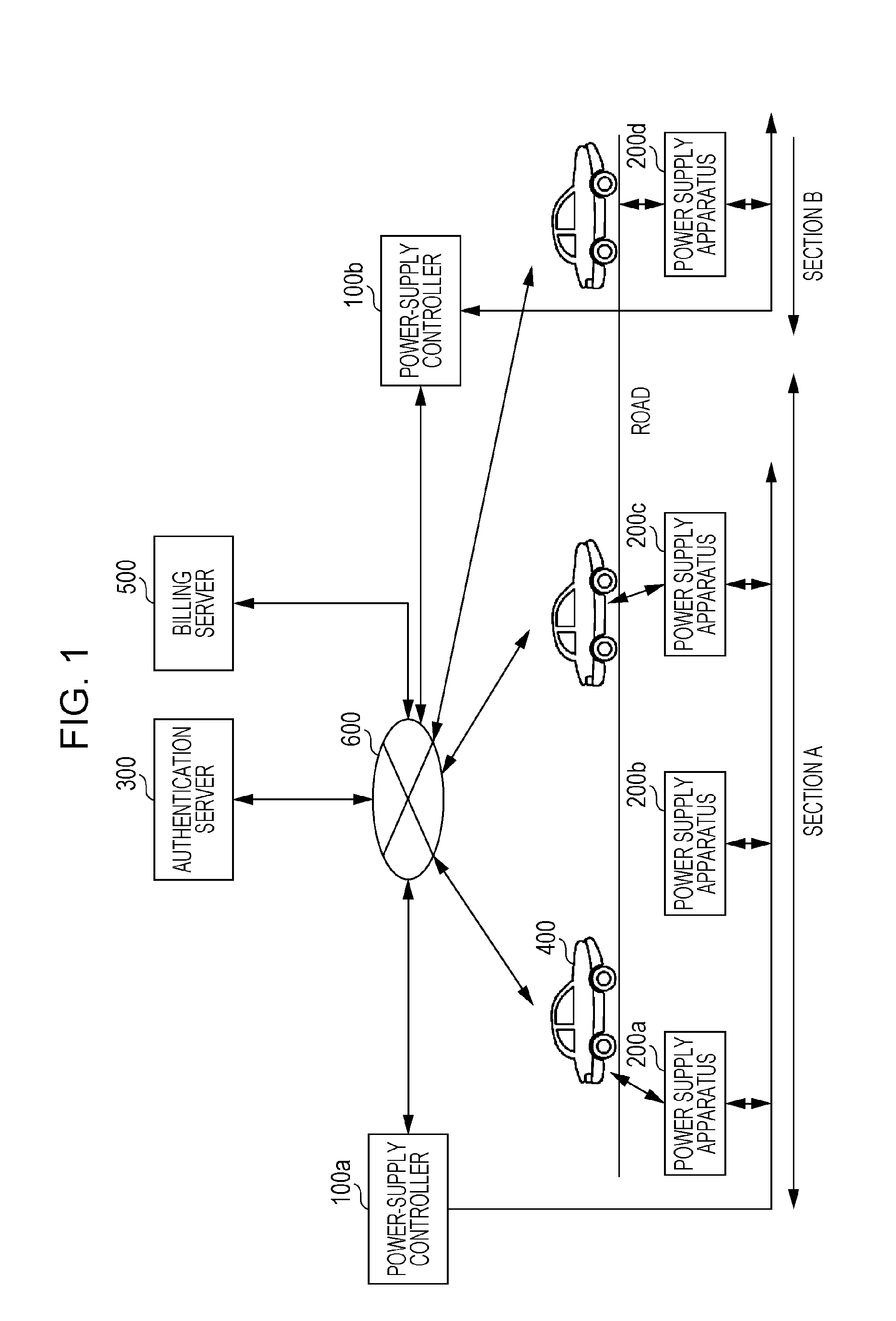
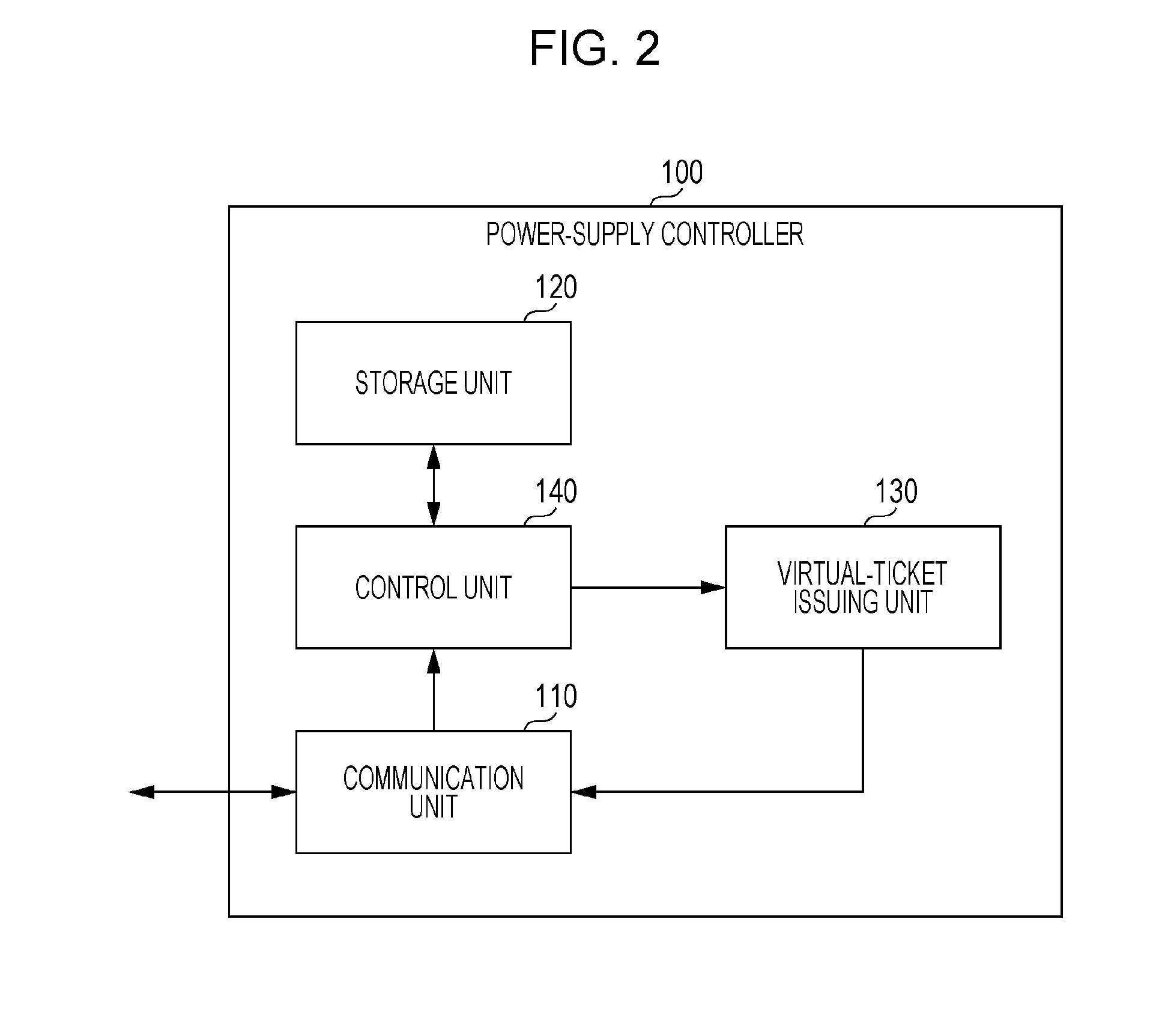
Power supply method, billing processing method, power supply system, power supply controller, power supply apparatus, power-supply control method, management server, electric vehicle, and billing serve
InactiveUS20150324798A1Highly reliable authenticationThe certification process is reliableCharging stationsFinancePower controllerAuthentication server
A power supply system includes an authentication server. Before receiving power supplied from a power supply coil of a power supply apparatus, an electric vehicle is authenticated by the authentication server. For receiving power supplied from the power supply coil, the electric vehicle gives a power-supply request to request a power-supply controller, which controls the power supply apparatus, to issue a temporary ticket for receiving power supply. The electric vehicle transmits the temporary ticket to the power supply apparatus, and upon determining that the temporary ticket is legitimate, the power supply apparatus executes power supply.
Owner:SOVEREIGN PEAK VENTURES LLC
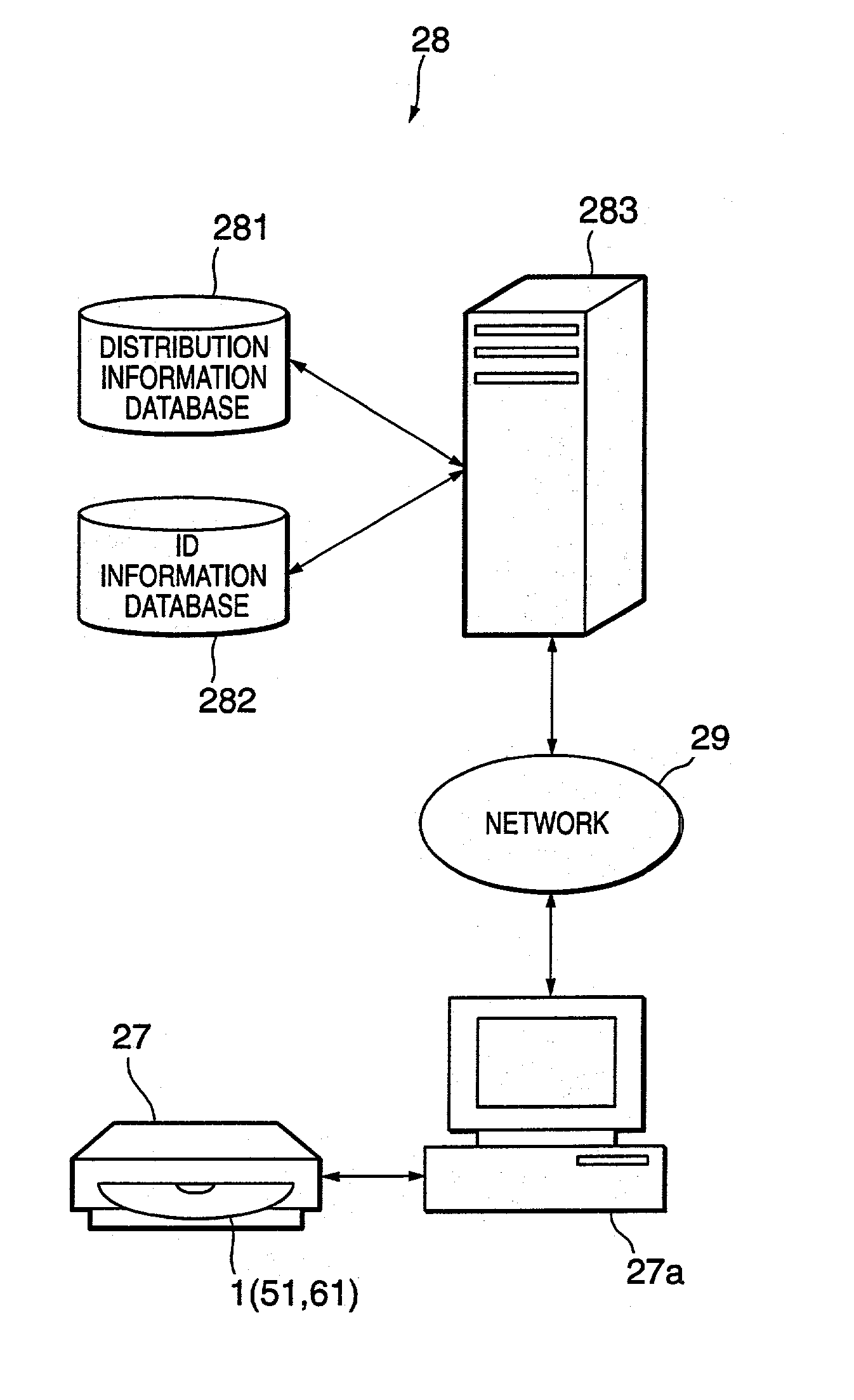
Information distribution method, information distribution system and information distribution apparatus
InactiveUS20020178145A1The certification process is reliableProtect information securityInformation arrangementDigital data processing detailsDistribution methodDistribution system
The present invention introduces an information distribution method capable of making an information distribution business for reliably authenticating a recording medium and distributing information in a prepaid manner. For this end, ID information recorded in a read-only area is read out from a disc-shaped recording medium having a read-only area and a recording and / or reading area. Judgment (or decision) is made whether or not information distribution to the recording medium is permitted based on the read-out ID information. The signal information distributed as a result of the judgment is recorded in the recording and / or reading area of the recording medium. The recording and / or reading area of the recording medium is rewritable. In case of reading the ID information out of the read-only area of the recording medium, erasing of recorded information for the recording and / or reading area is performed at the recording position for the ID information before reading the ID information.
Owner:SONY CORP
Authentication system and method for operating an authenitication system
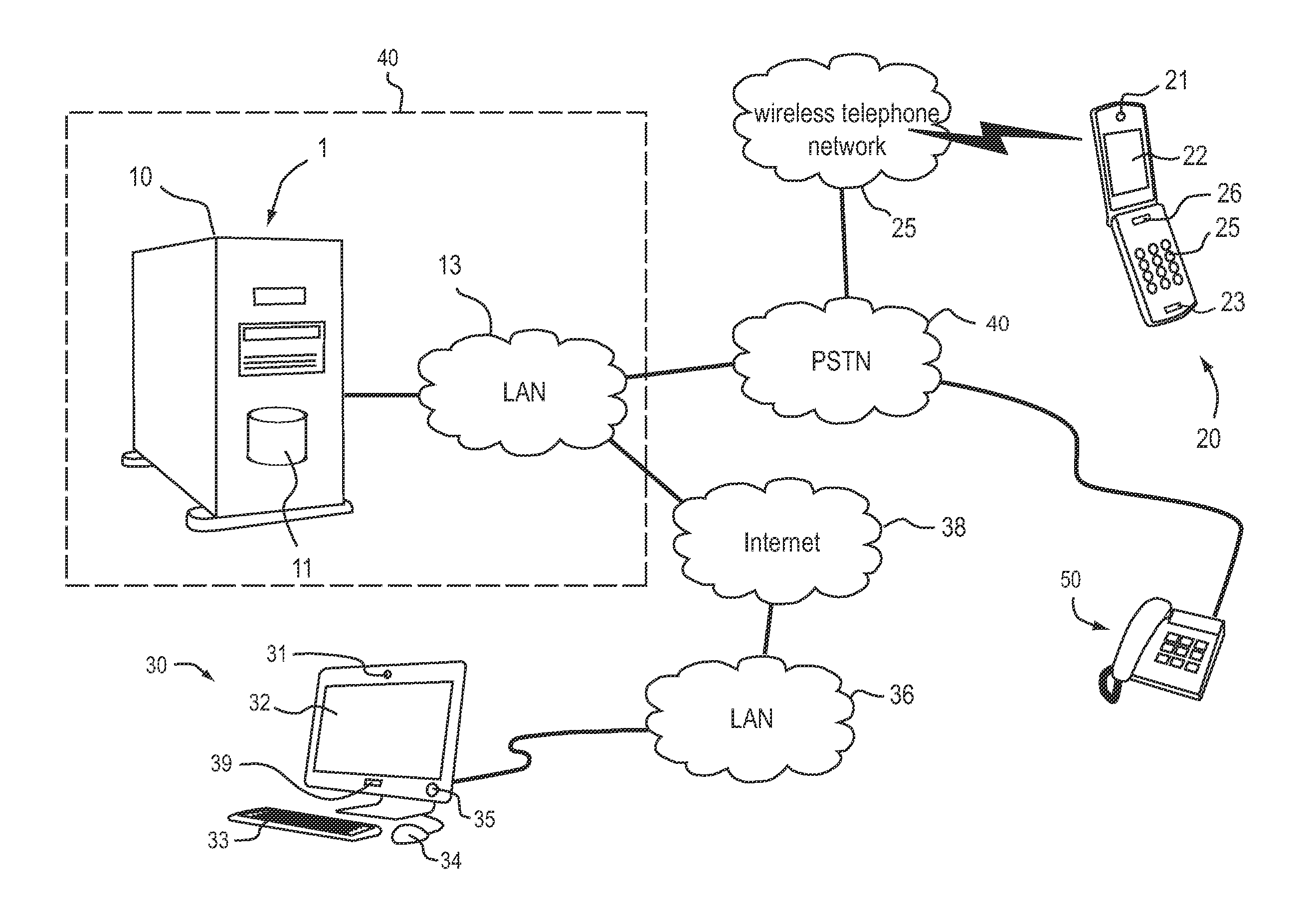
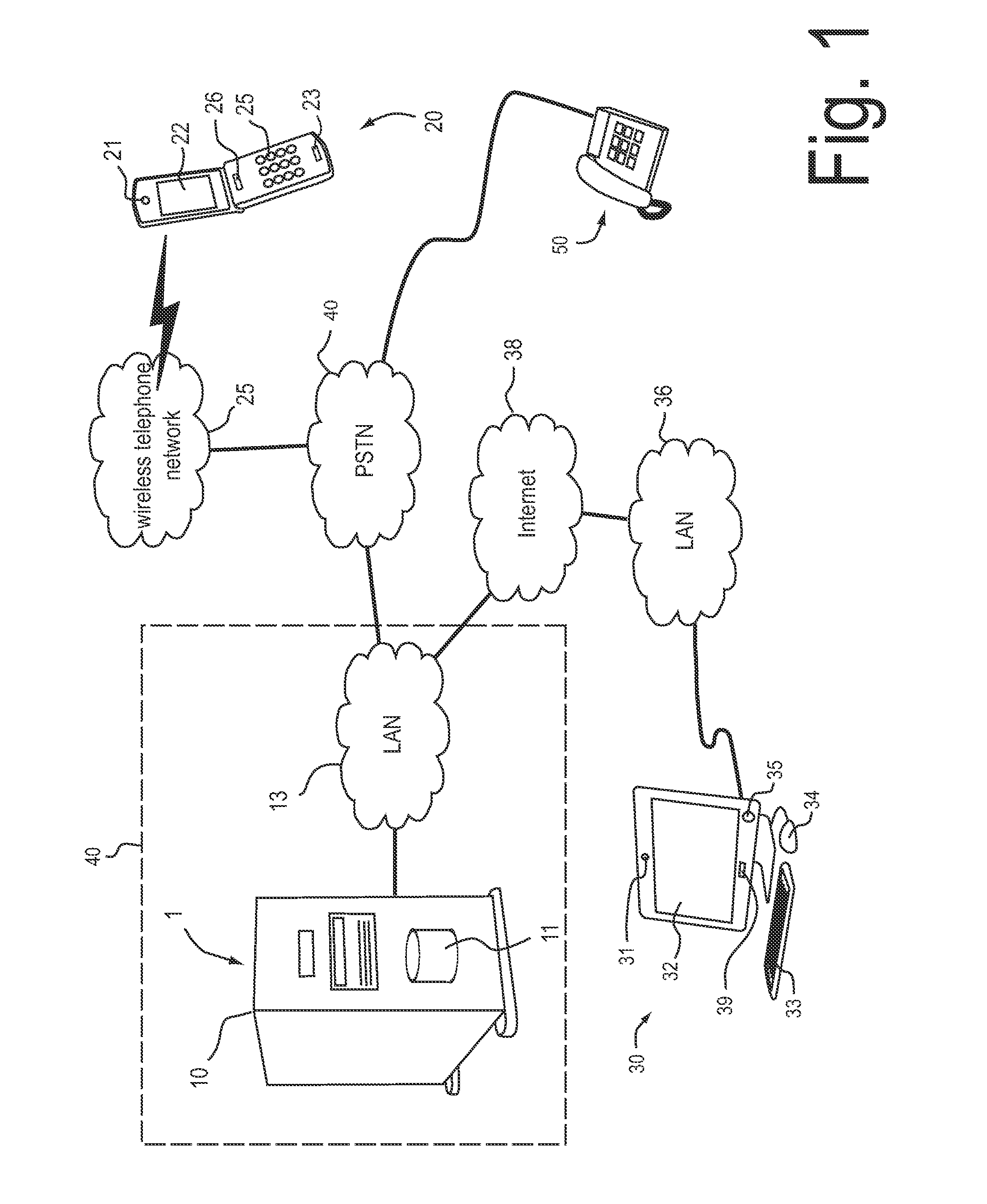
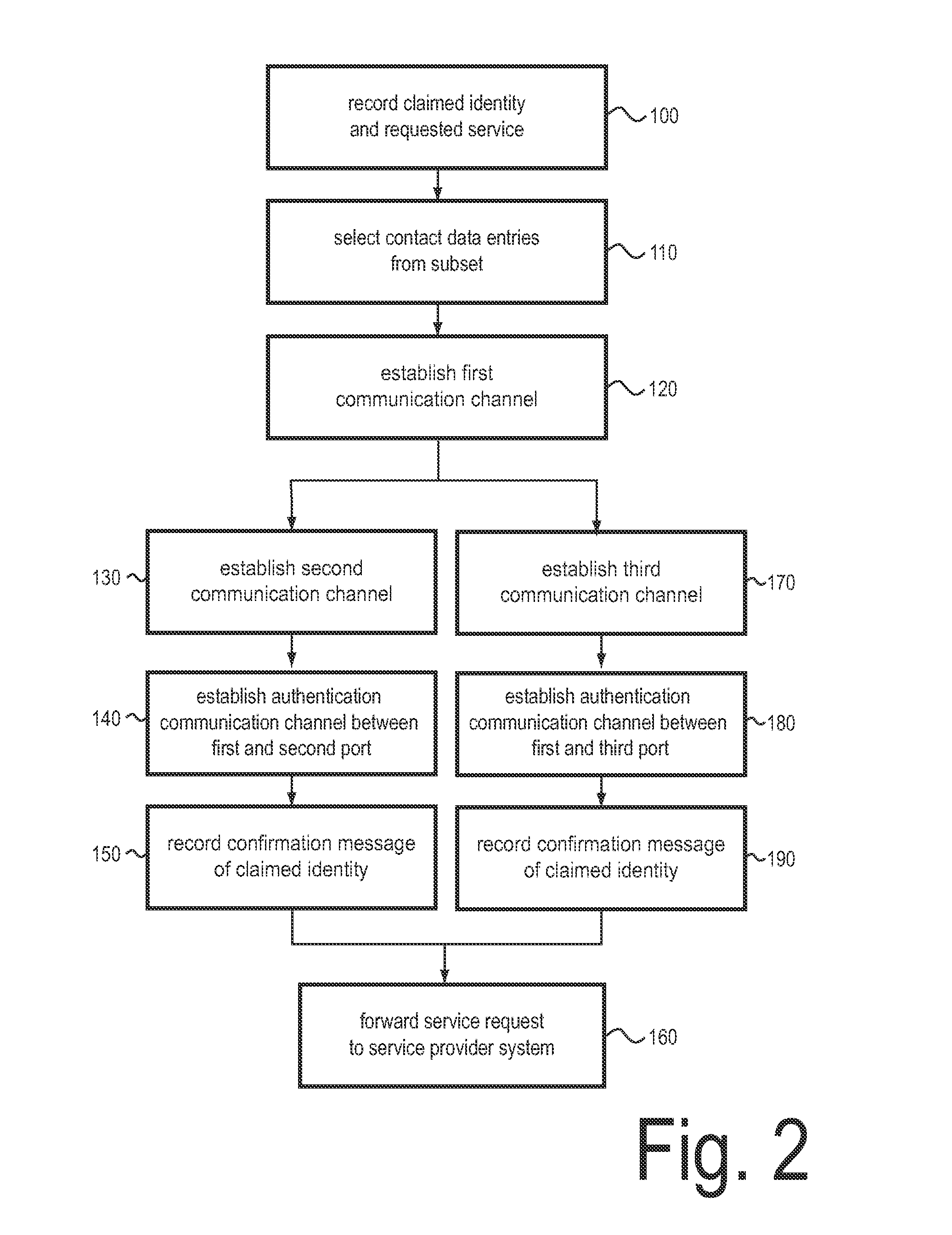
ActiveUS20130263231A1The certification process is reliableGood serviceDigital data processing detailsMultiple digital computer combinationsData streamComputer terminal
An authentication system for authenticating a human requester requesting a service, wherein the authentication system is configured to establish via a first and a second port of the authentication system an authentication communication channel comprising a first communication channel to the requester and a second communication channel to a human authenticator, such that at least one of an audio stream of a voice of the requester, a video stream of a face of the requester and a 3D-data stream of the face of the requester is transmittable between the end node device of the requester and the end node device of the authenticator; and to record a confirmation message of the authenticator, wherein the confirmation message confirms or rejects at least one of the claimed identity and the requested service.
Owner:STOPIC BOJAN
Method for encrypting data and a telecommunications terminal and access authorization card
InactiveUS7353211B2The certification process is reliableImprove efficiencyMultiple keys/algorithms usageDigital data processing detailsTelecommunications networkTelecommunications link
A method of encrypting data, a telecommunications terminal and an access authorization card are described, which permit utilization of services of one or more service providers independently of a network operator or manufacturer of the telecommunications terminal. Encrypted data is transmitted between a service provider and the telecommunications terminal over a telecommunications network. Data to be transmitted over the telecommunications network is encrypted as a function of the service provider selected.
Owner:IPCOM GMBH & CO KG
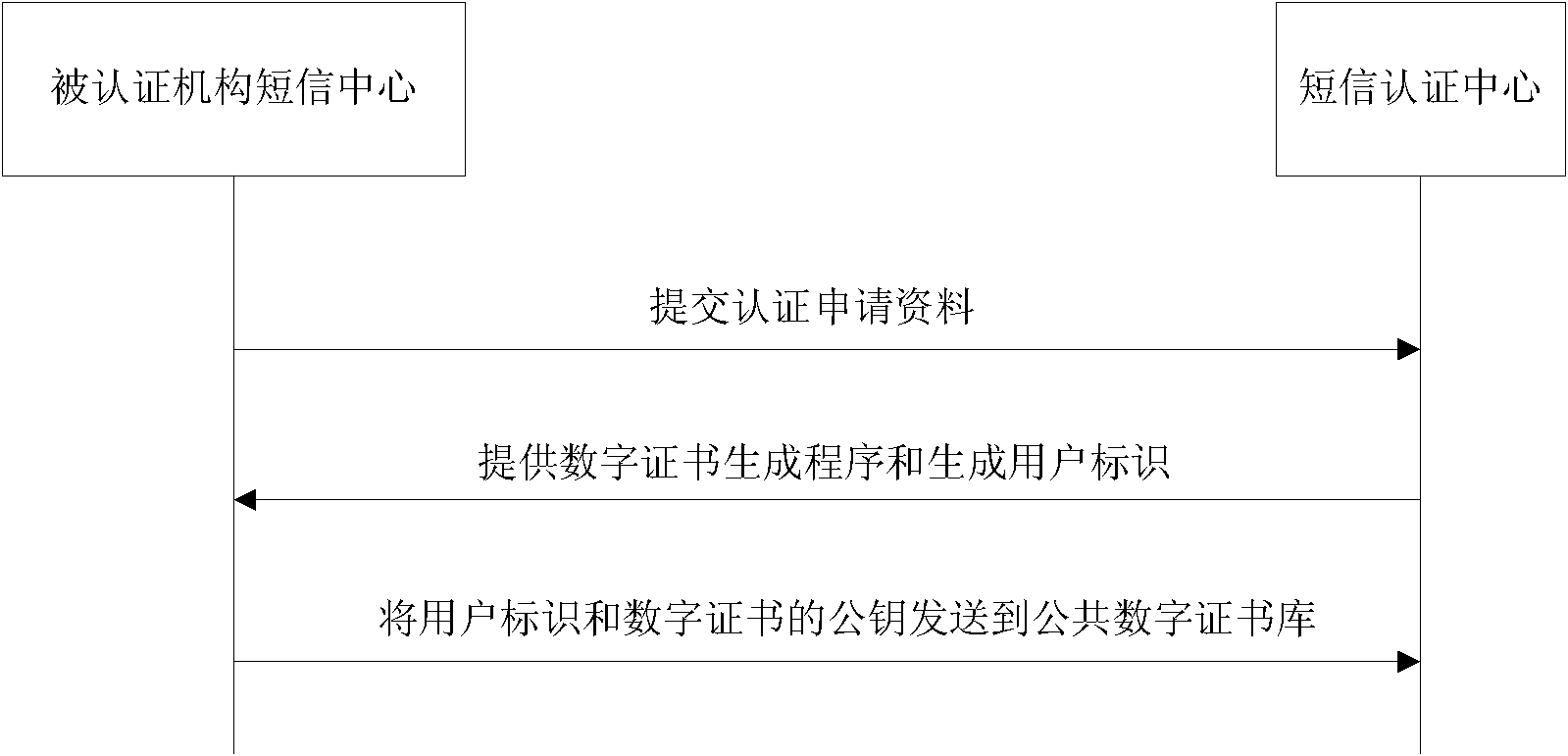
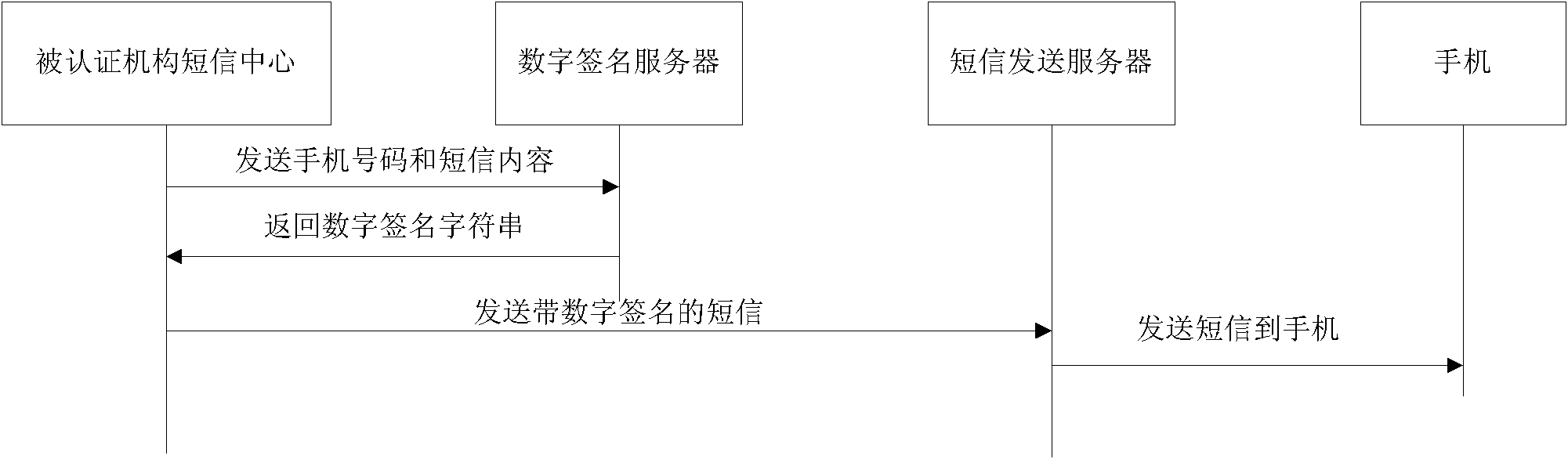
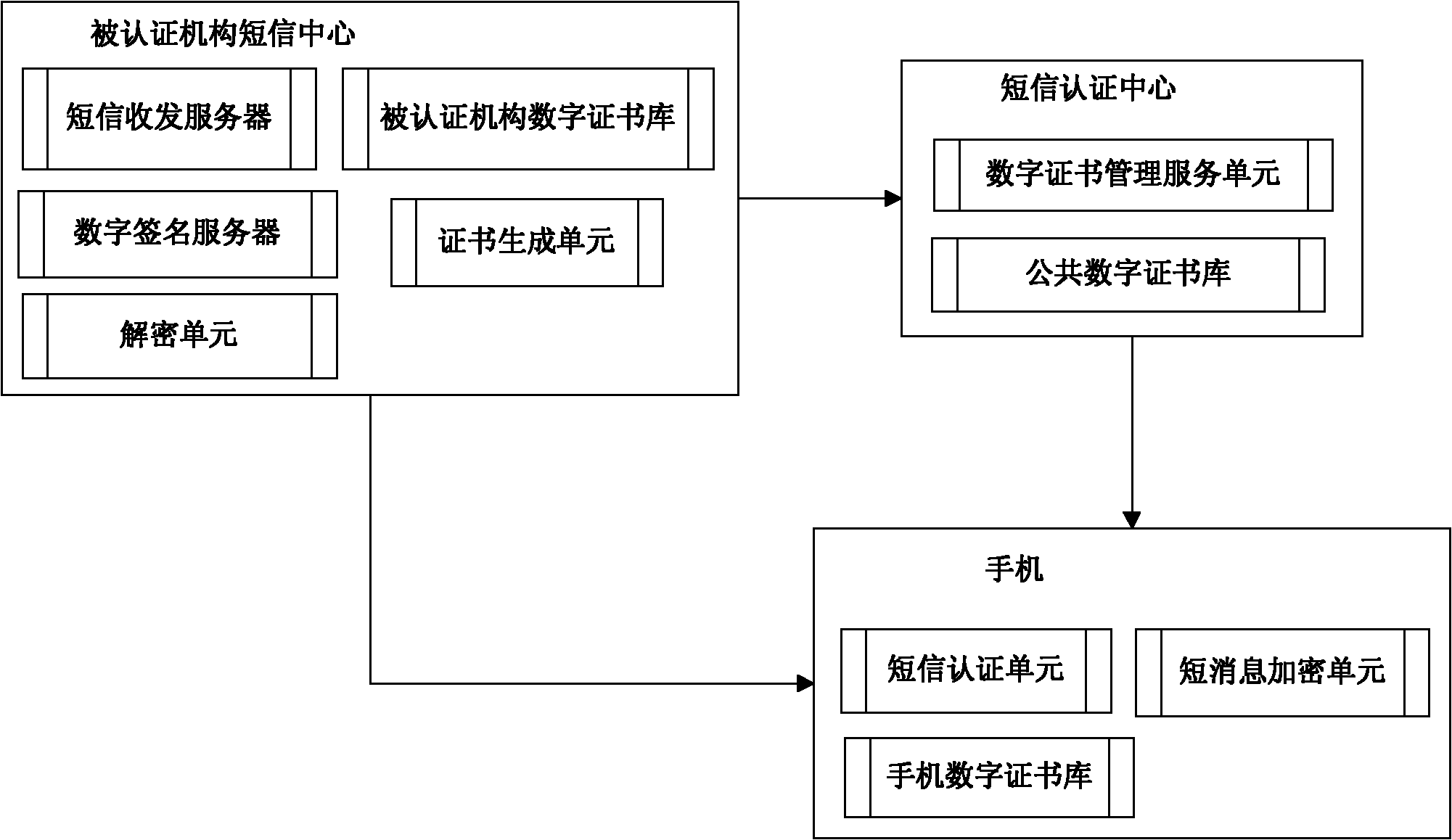
Short message service authenticated encryption system and method based on digital certificate
InactiveCN101895847AEnsure safetyPrevent leakageMessaging/mailboxes/announcementsSecurity arrangementConfidentialityFinancial transaction
The invention relates to a short message service (SMS) authenticated encryption system and method based on a digital certificate. The SMS authenticated encryption system comprises an SMS authentication center, an authenticated mechanism SMS center and a mobile phone. A digital certificate management service unit of the SMS authentication center provides procedures generated by the unique digital certificate of the authenticated mechanism according to the user identification, thus ensuring the safety of the digital certificate. The digital certificate is used for safety of two-way SMS communication. In the invention, the way that a plurality of different receivers respectively carry out encrypted transmission according to own keys based on the SMS numbers can be realized by only installing an SMS authentication and encryption procedure in the common mobile phone as the SMS authentication and encryption client. The invention can authenticate the received SMS contents, ensure the sent contents not to be falsified and ensure the authenticity of the senders, has good confidentiality, changes less existing SMS systems, occupies less resources, is easy to realize and can be applied to such fields as financial transactions, etc.
Owner:SHENZHEN ALL IN ONE NEW TECH LTD
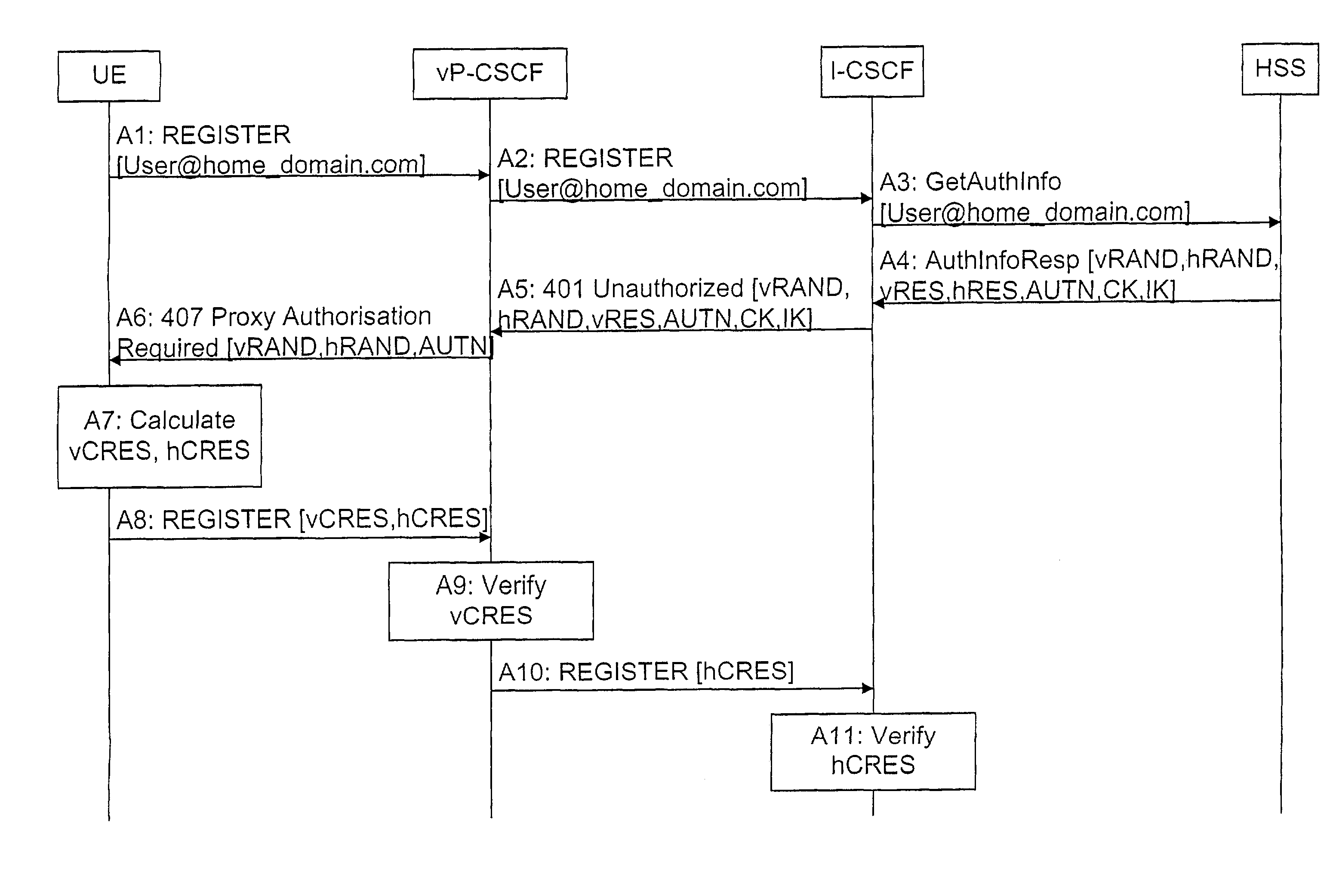
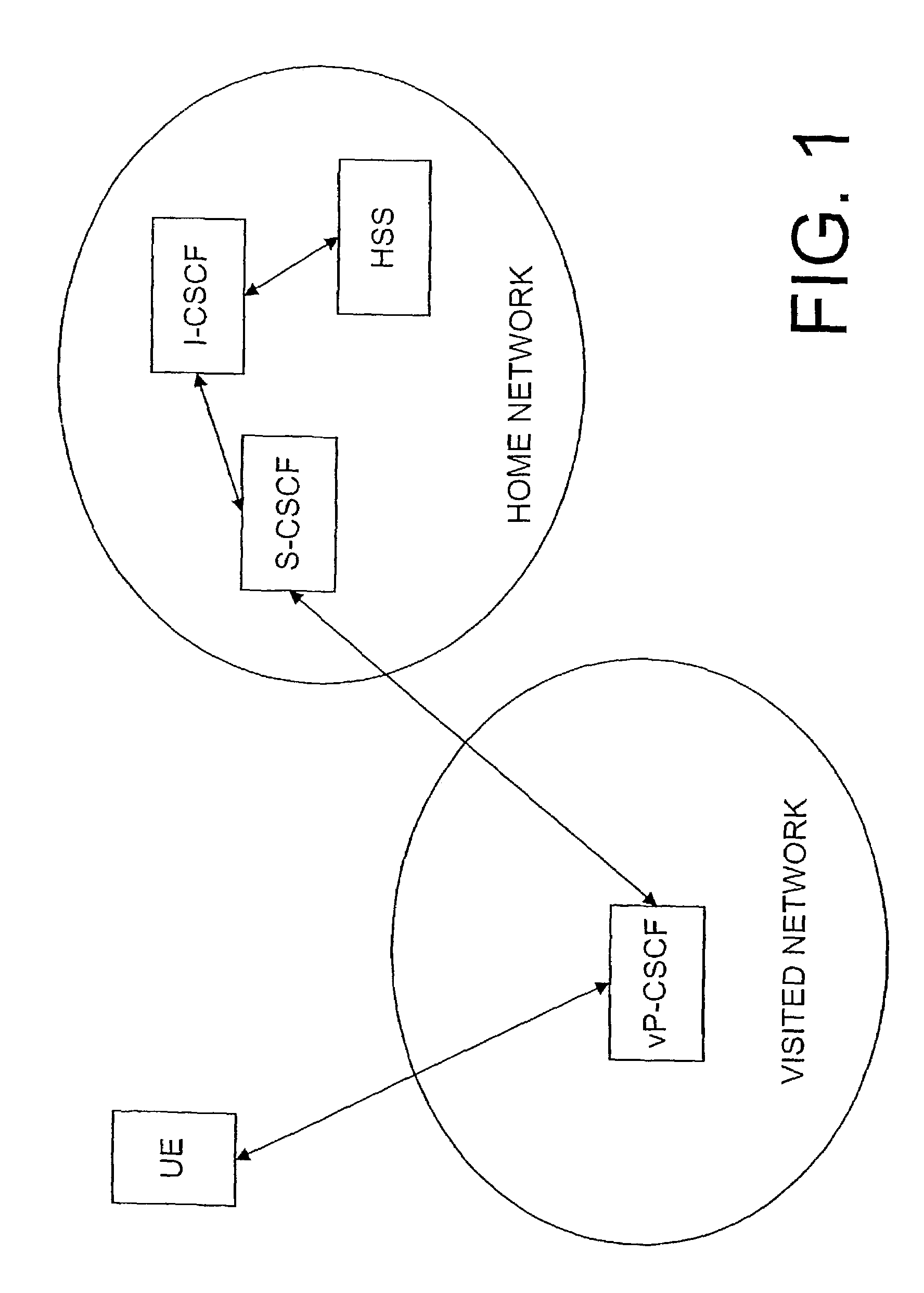
System and method for authentication of a roaming subscriber
InactiveUS7224800B1The certification process is reliableUser identity/authority verificationSecret communicationNetwork controlNetworked system
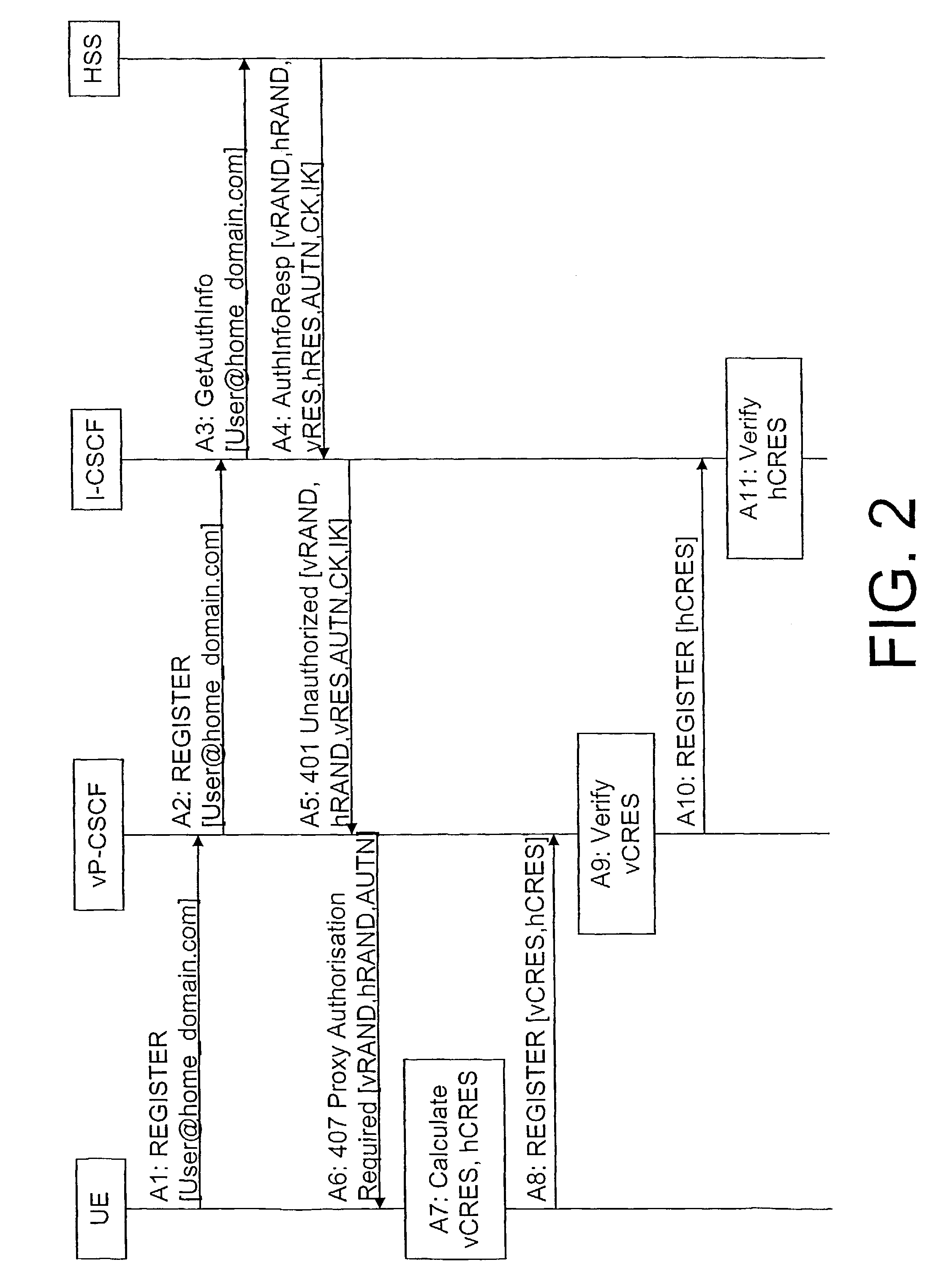
A network system is proposed comprising a first network control element in a visited network, a second network control element in a home network and a communication device (UE) associated to a subscriber, wherein the first network control element is adapted to perform a first authentication (A9) of a roaming subscriber requesting authentication, and the second network control element is adapted to perform a second authentication (A11) of the same subscriber. By this measure, both network control elements are able to verify that the authentication was performed correctly. Also a corresponding method is proposed.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Printed product with raised authentication feature
InactiveUS20120202021A1Accurate detectionThe certification process is reliableLayered productsMaterial analysis by optical meansEngineeringAuthentication
Printed products, printing methods and methods for verifying authenticity of a printed product are provided. In one aspect, the printed product has a receiver member and an image formed thereon by an electrophotographic process using toner particles, said image having at least one raised portion, wherein at least parts of said raised portion of said image comprise pearlescent toner particles. Methods for printing and authenticating the same are provided.
Owner:EASTMAN KODAK CO
Cuvette and method for authenticating a cuvette
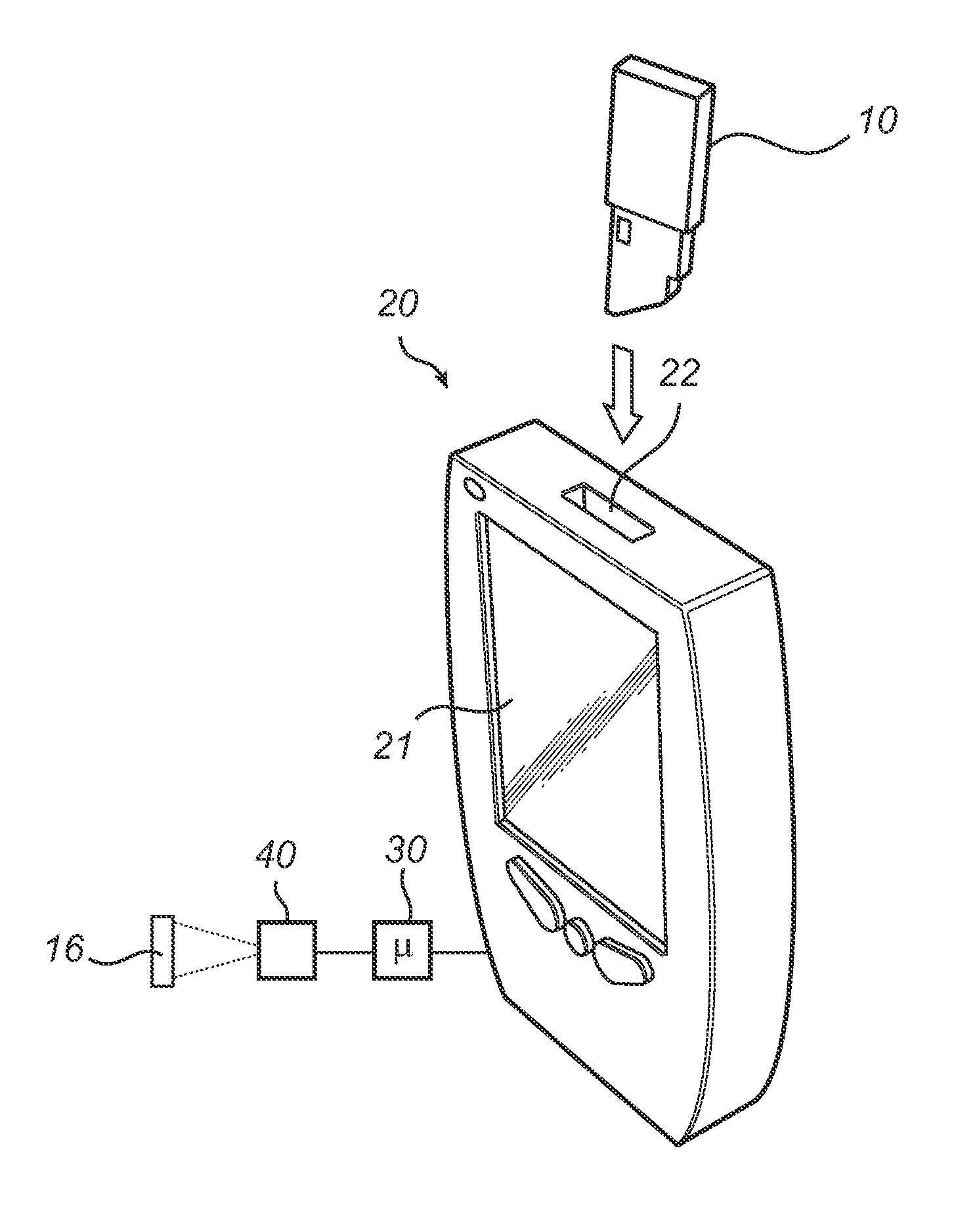
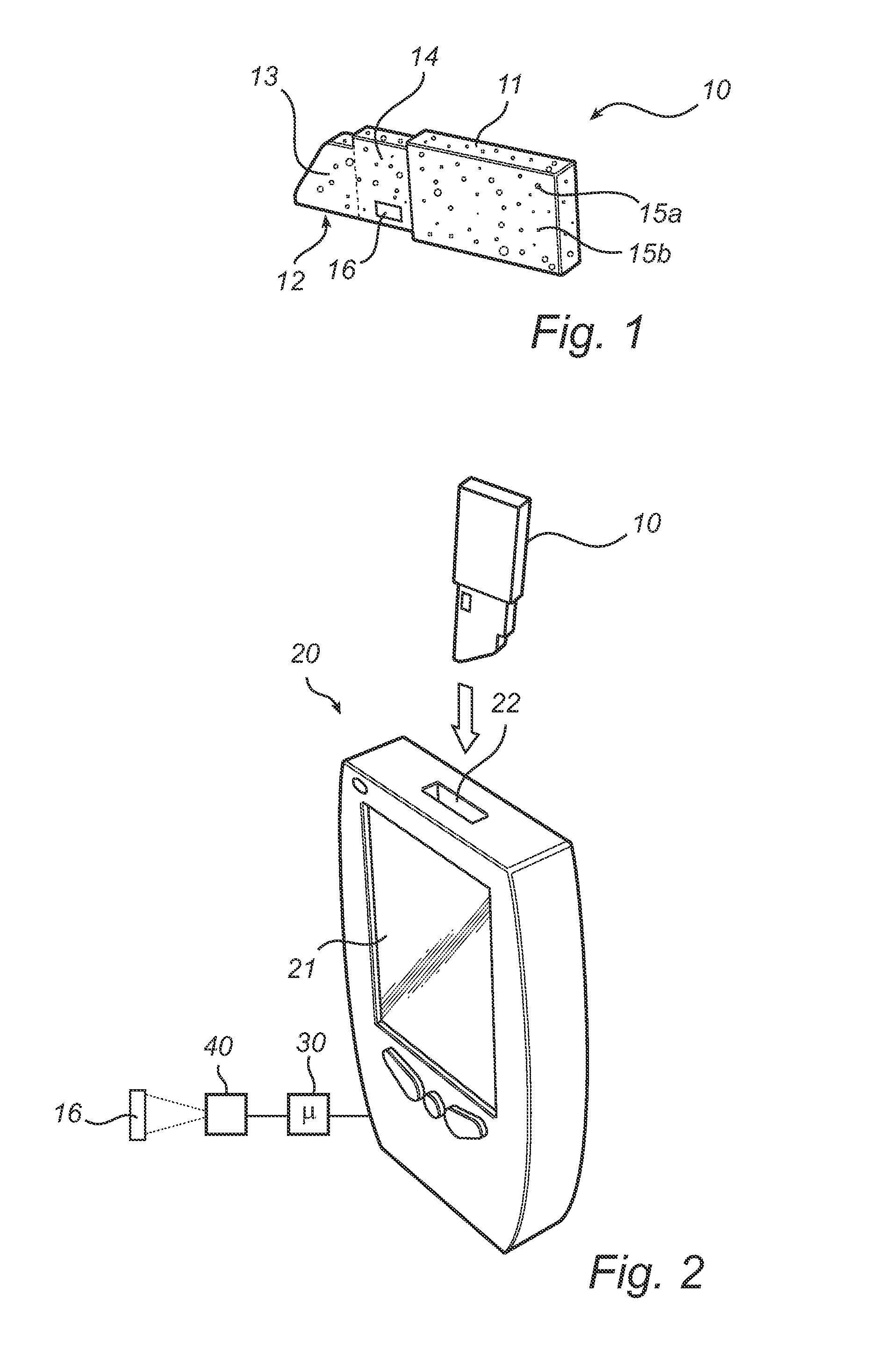
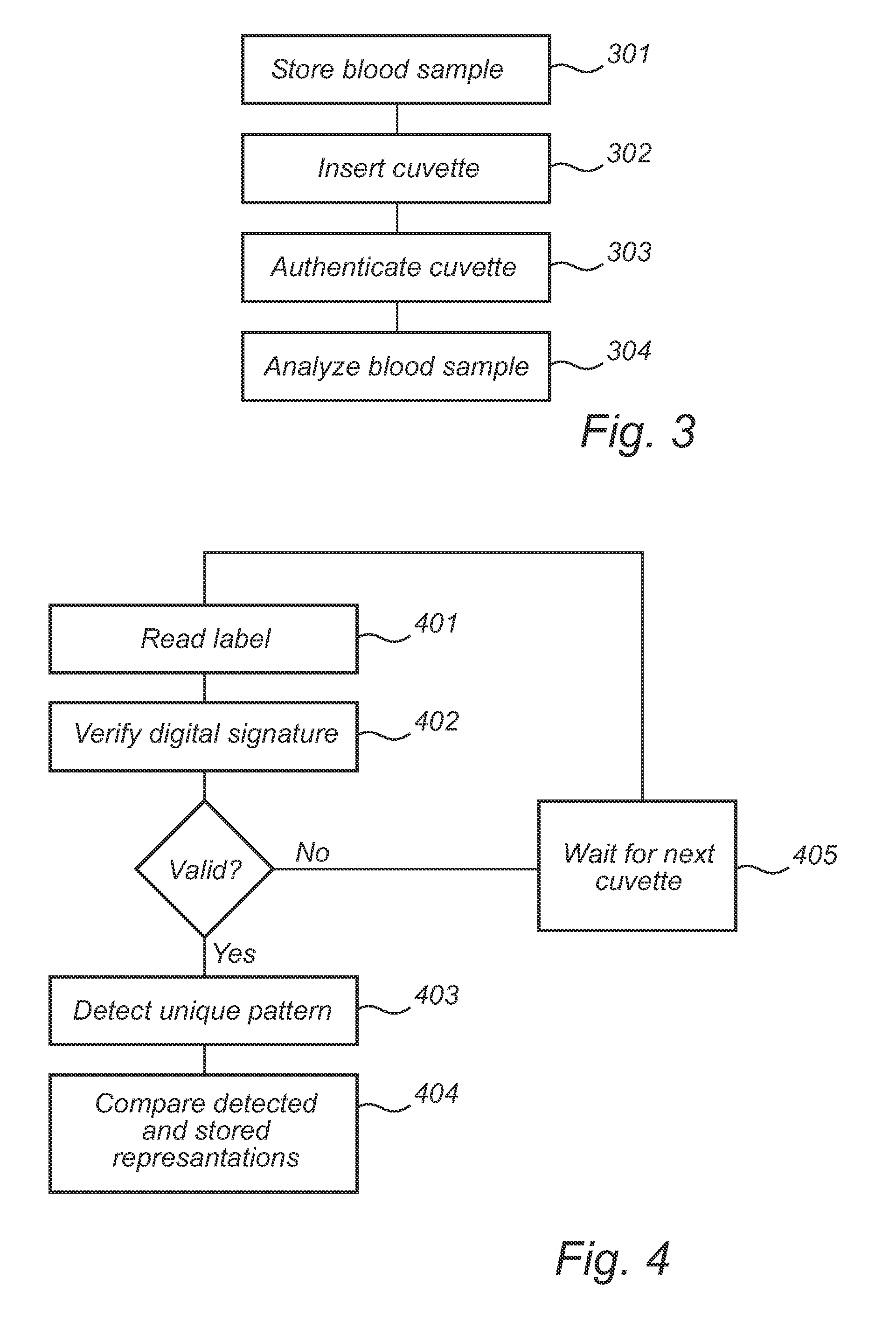
ActiveUS20110259091A1Reduce usageEffective and practicalSamplingMaterial analysis by optical meansCuvettePhysical property
A cuvette (10) for storing a biological sample to be analyzed by means of a predefined detection technique is disclosed. The cuvette (10) is formed from a moldable material that contains particles (15a, 15b) at a concentration within a predefined range. The particles (15a, 15b) are randomly distributed, in order to form a unique pattern. Moreover, the particles (15a, 15b) have measurable physical properties, so that the unique pattern is detectable using the detection technique that is used to analyze the biological sample. The unique properties obtained by the randomly distributed particles (15a, 15b) render copying nearly impossible, since it is more complicated to distribute the particles in a predetermined pattern than to let them distribute randomly.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
GF (27) finite field and dual authentication-based meaningful (K, N) image sharing and reconstructing method
ActiveCN105590297AThe certification process is reliableImprove visual qualityGeometric image transformationComputer hardwareBunker
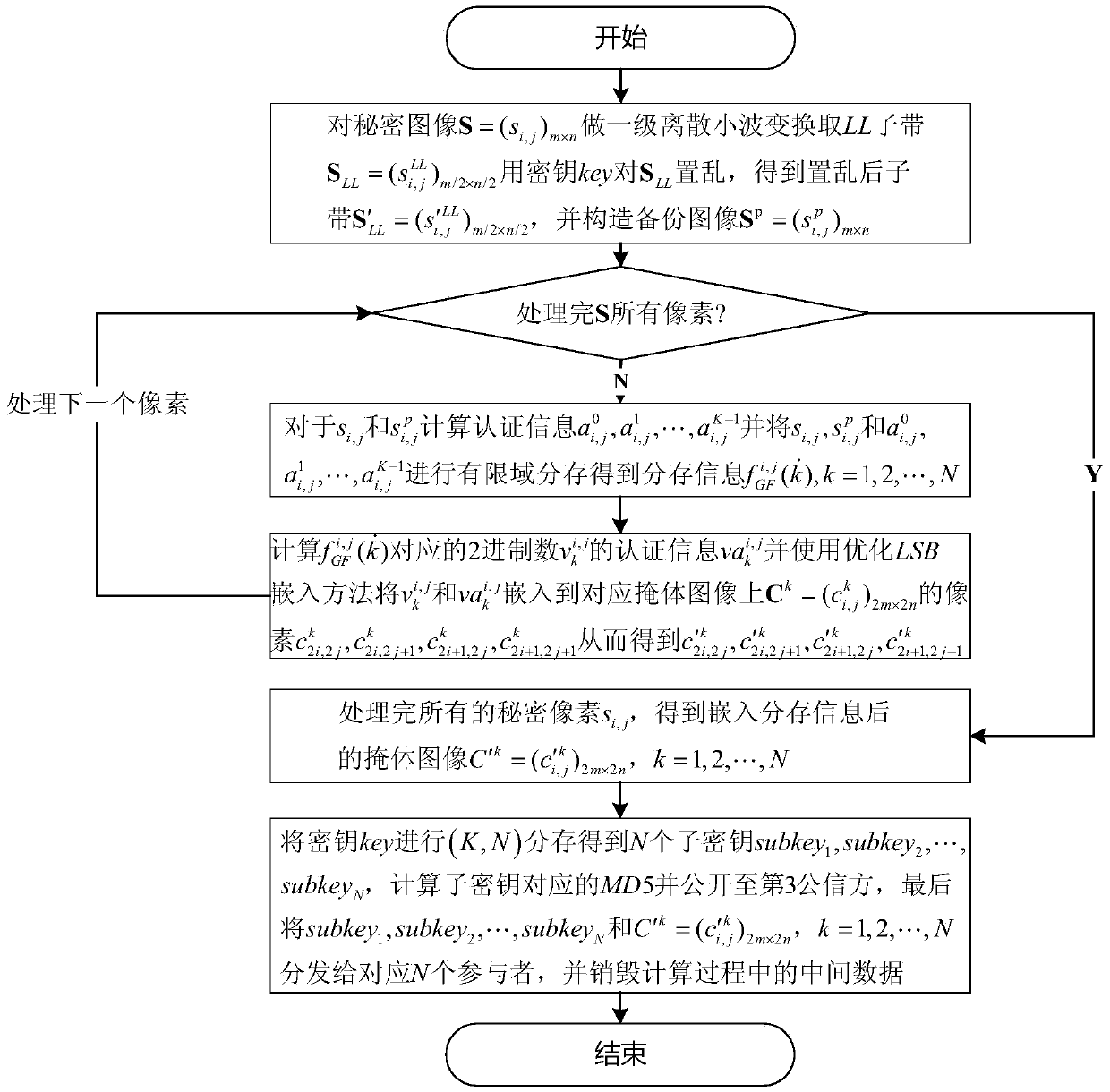
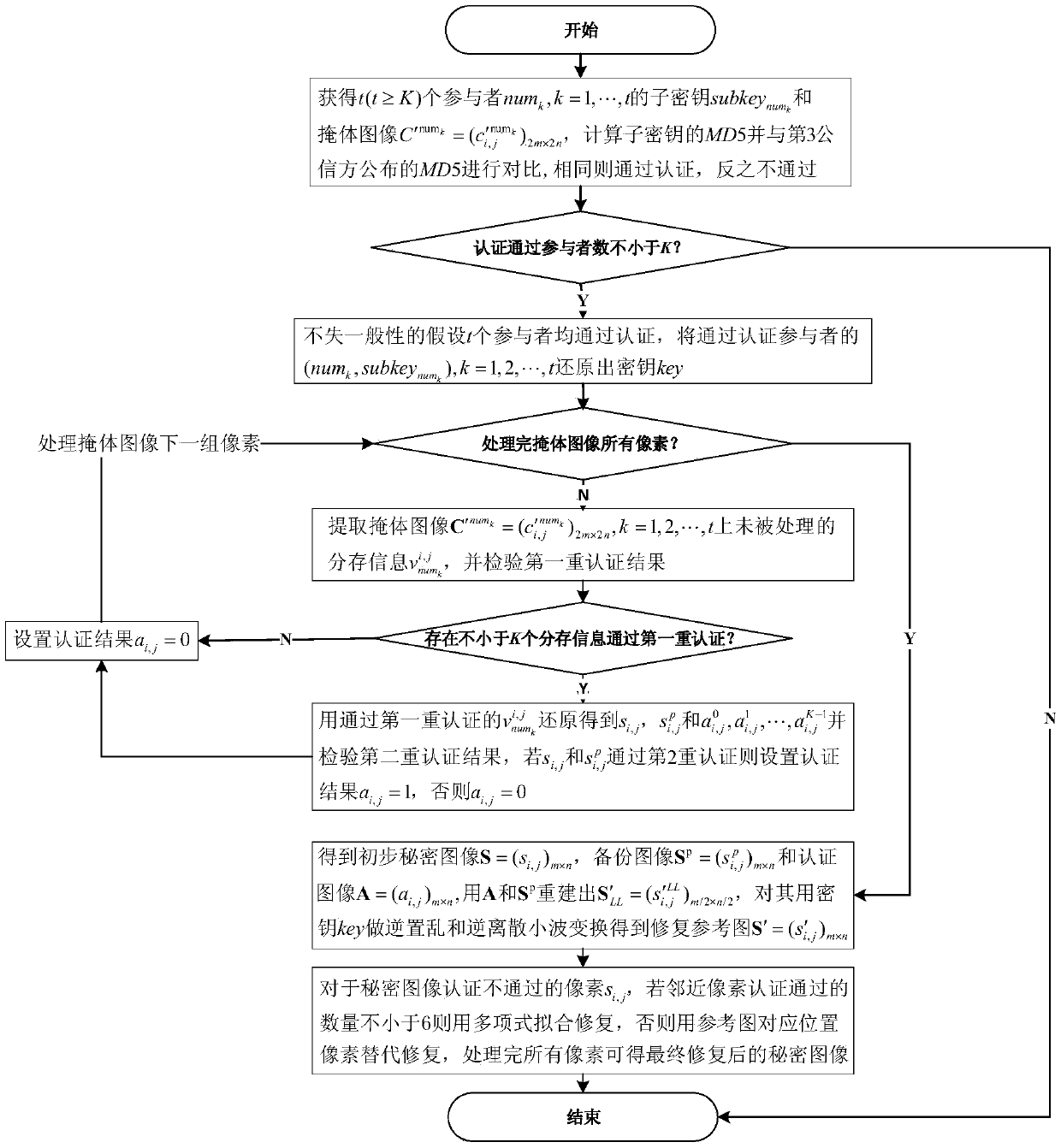
The invention provides a GF (27) finite field and dual authentication-based meaningful (K, N) image sharing and reconstructing method. Ring the sharing period, the sub-band of a secret image LL is scrambled, and the coefficients of bits are backed up by different numbers according to the degrees of importance thereof. Finally, a backup image of the same size with the secret image is formed. After that, secret pixels, backup pixels and the corresponding dual-authentication information are shared in the form of (K, N) in the GF (27) finite field. Based on the optimized LSB method, the shared information and primary authentication bits are embedded into the lower-order bits of a bunker block to maximally ensure the visual quality of distributed bunker images. During the reconstruction process, the shared information for recovery is screened through the primary authentication step. After that, the reliability of recovered secret pixels and the reliability of recovered backup pixels are verified through the secondary authentication step, so that an authentication image, a backup image and a preliminary secret image are formed. In combination with the secret image, a recovered reference image and the authentication image, the non-pass pixels of the secret image during the authentication process are subjected to polynomial fitting repair and alternative repair, so that the repair quality after the attack is better.
Owner:SHAANXI NORMAL UNIV
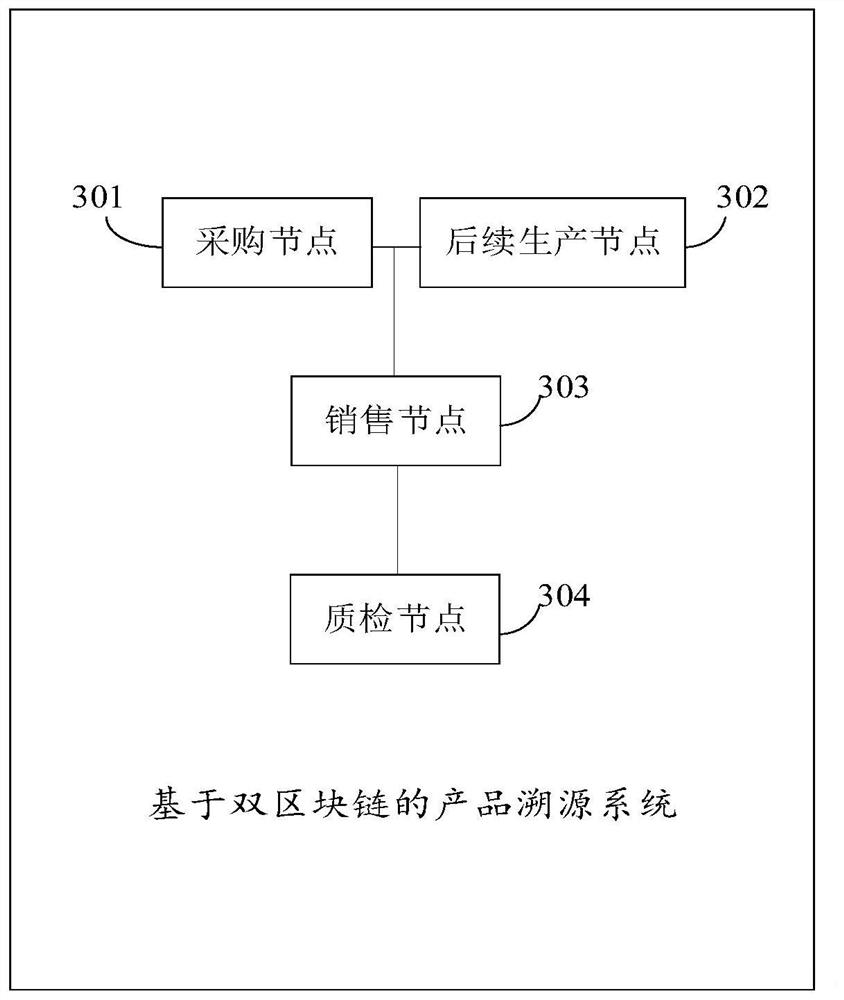
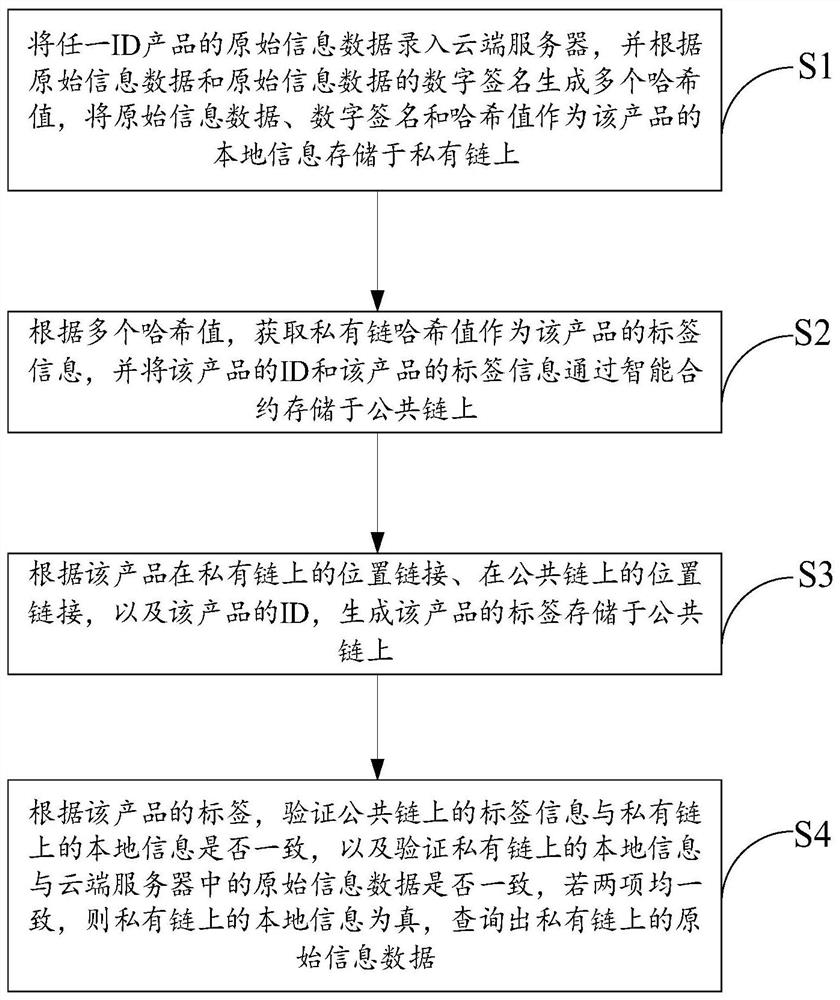
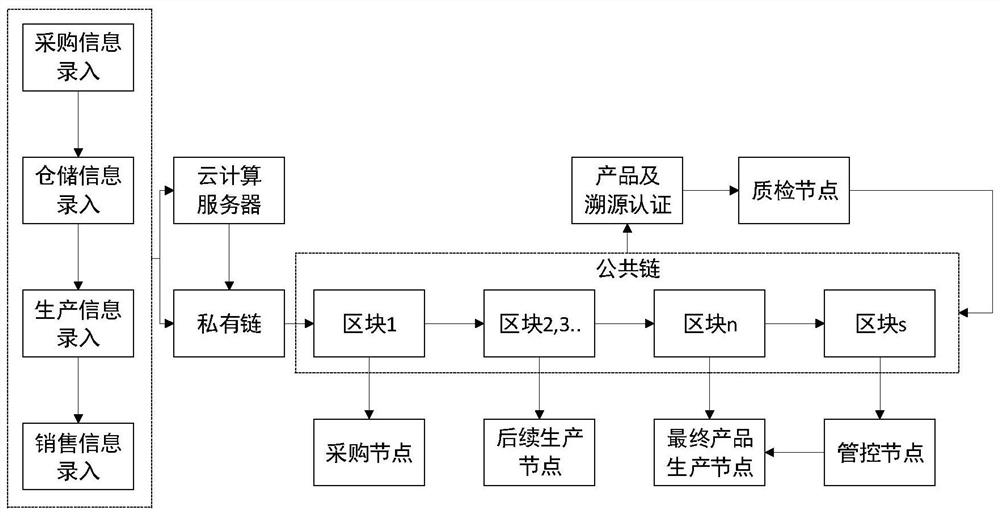
Product traceability method and system based on double block chains
PendingCN111667279AGuaranteed not to be tampered withGuaranteed follow-up verificationDatabase distribution/replicationDigital data protectionBusiness enterpriseProduct traceability
The embodiment of the invention provides a product traceability method and system based on double block chains, being characterized by processing existing cloud computing data and server resources ofan enterprise, constructing a double-blockchain fusion model based on a private chain and a public chain by combining a high-efficiency private chain mode and a cross-chain technology, effectively fusing the cloud computing data and the block chain, and extracting cloud computing data and recording hash values of the cloud computing data into a private chain, and the private chain traceability necessary data is uploaded to the public chain, so as to ensure data tampering prevention and subsequent verification, thus realizing high-efficiency interaction between cloud computing data and on-chaindata, reducing the difficulty of deploying a blockchain system by an enterprise, finally realizing intelligent generation of product traceability information, and meanwhile, eliminating human factorsof information circulation among main bodies of a supply chain, so that traceability information authentication which is more accurate, and more complete and more reliable than traditional product traceability is generated.
Owner:WUHAN UNIV OF TECH
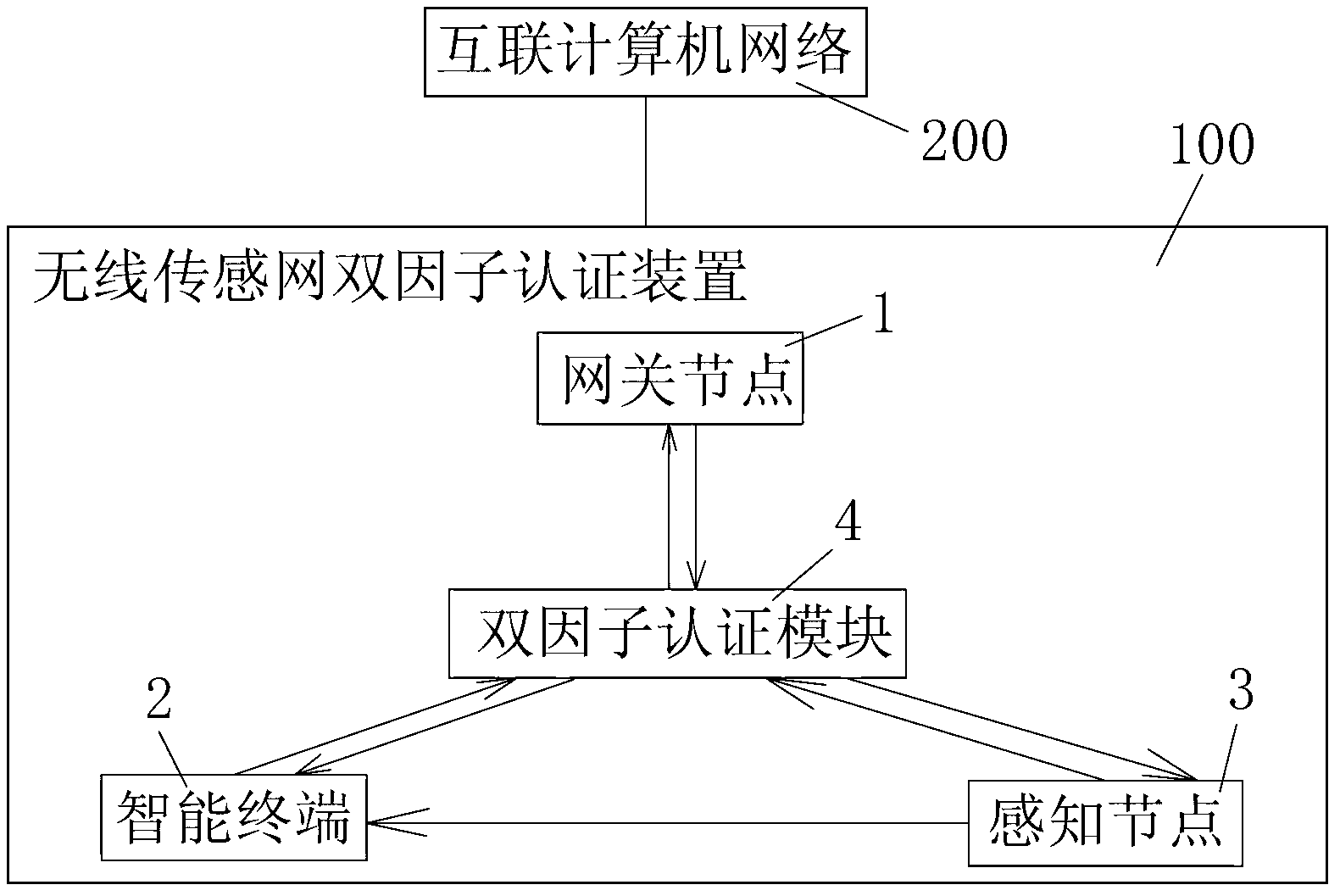
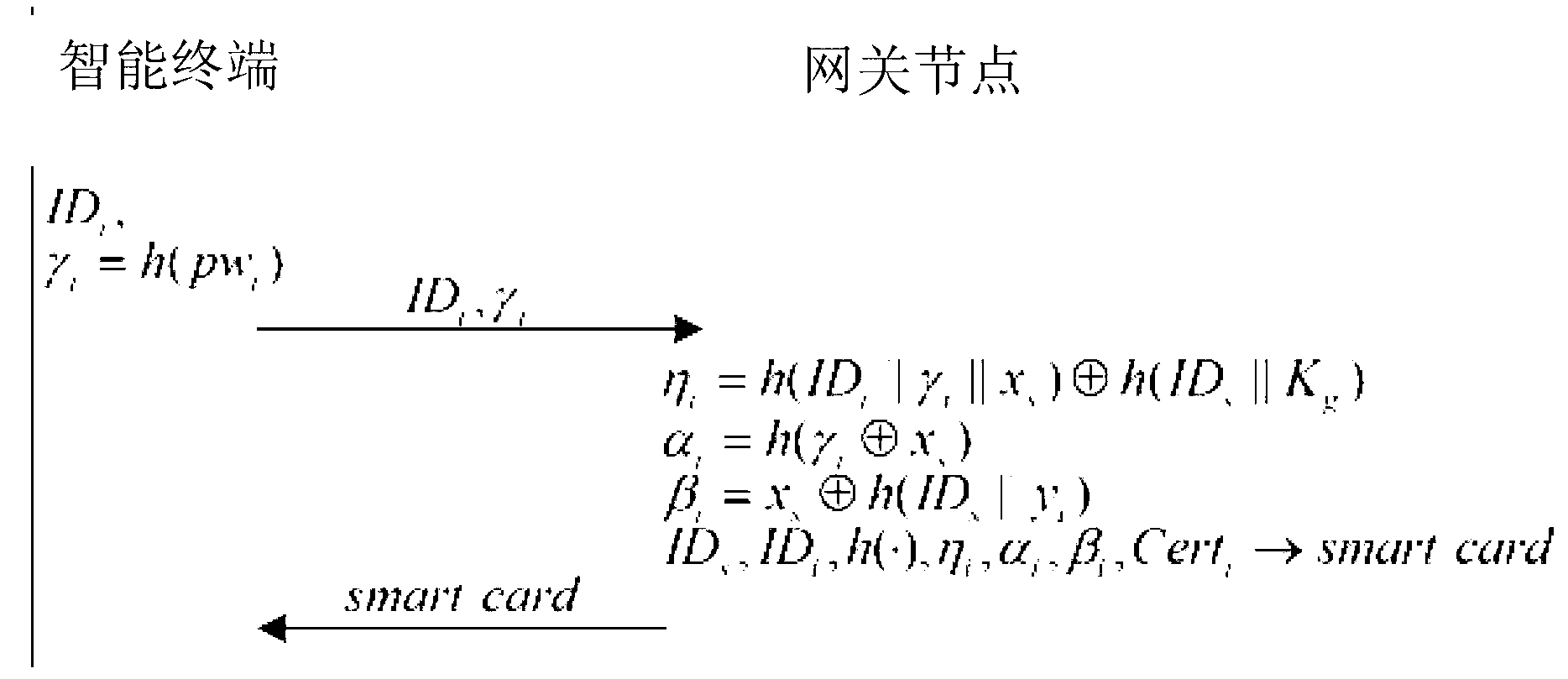
Two-factor authentication method and two-factor authentication device for wireless sensor network and network comprising two-factor authentication device
ActiveCN103313246AAuthentication securityThe certification process is reliableTransmissionSecurity arrangementPersonalizationInterconnection
The invention discloses a two-factor authentication method and a two-factor authentication device for a wireless sensor network and a network comprising the two-factor authentication device. The two-factor authentication device comprises a gateway node, an intelligent terminal, a sensor node and a two-factor authentication module, and the gateway node, the intelligent terminal and the sensor node are communicated with each other. The Merkle hash tree based two-factor authentication method for the wireless sensor network is applied to the two-factor authentication module. The two-factor authentication method includes the steps of gateway pre-authentication: performing DoS (disk operating system)-attack resisting gateway pre-authentication on the basis of the Merkle hashtree; bidirectional authentication among gateway and sensor nodes: authenticating the sensor node by the gateway node after the sensor node finishes in authenticating an access request from the gateway node, wherein during bidirectional authentication, one-way hash is performed after connection with sensor node ID (identification) is established, so that personalized safety parameters for the sensor node are formed to resist attacks from gateway counterfeit and data counterfeit caused by leakage of the safety parameters. The invention further provides an interconnection computer network comprising the two-factor authentication device for the wireless sensor network.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI +1
Method and system for realizing mixed authentication
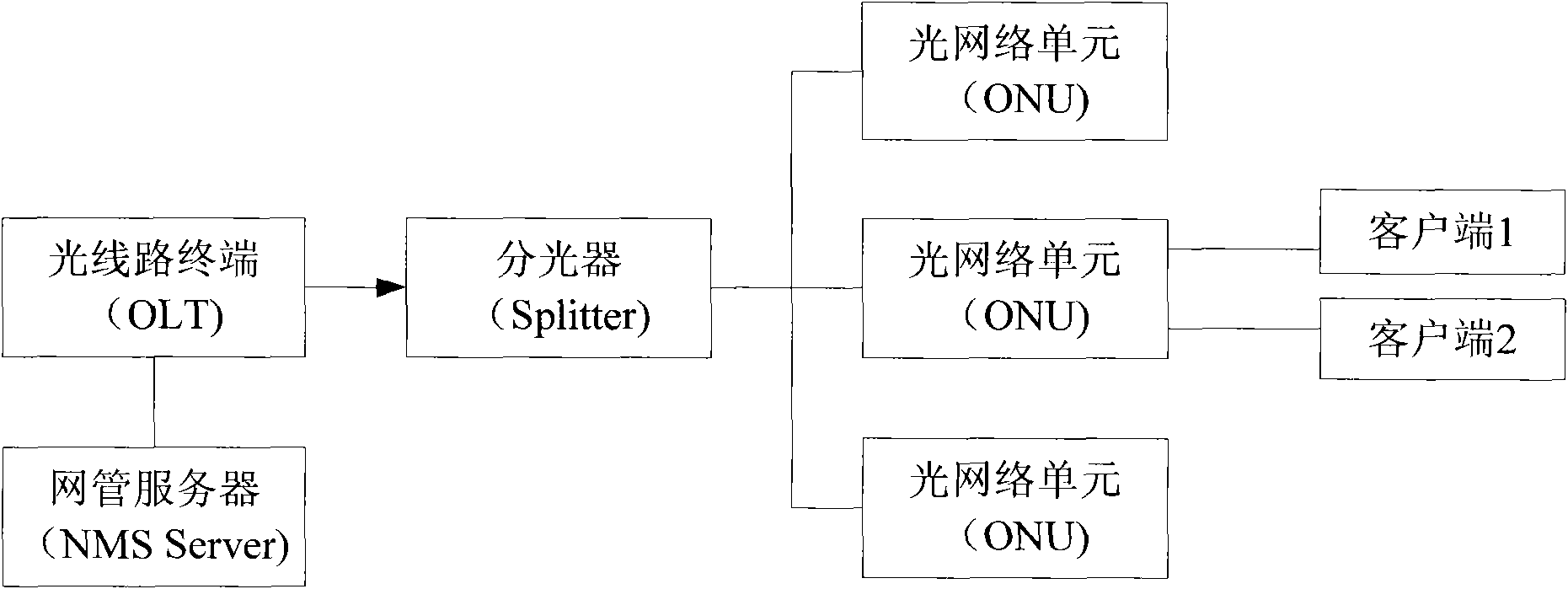
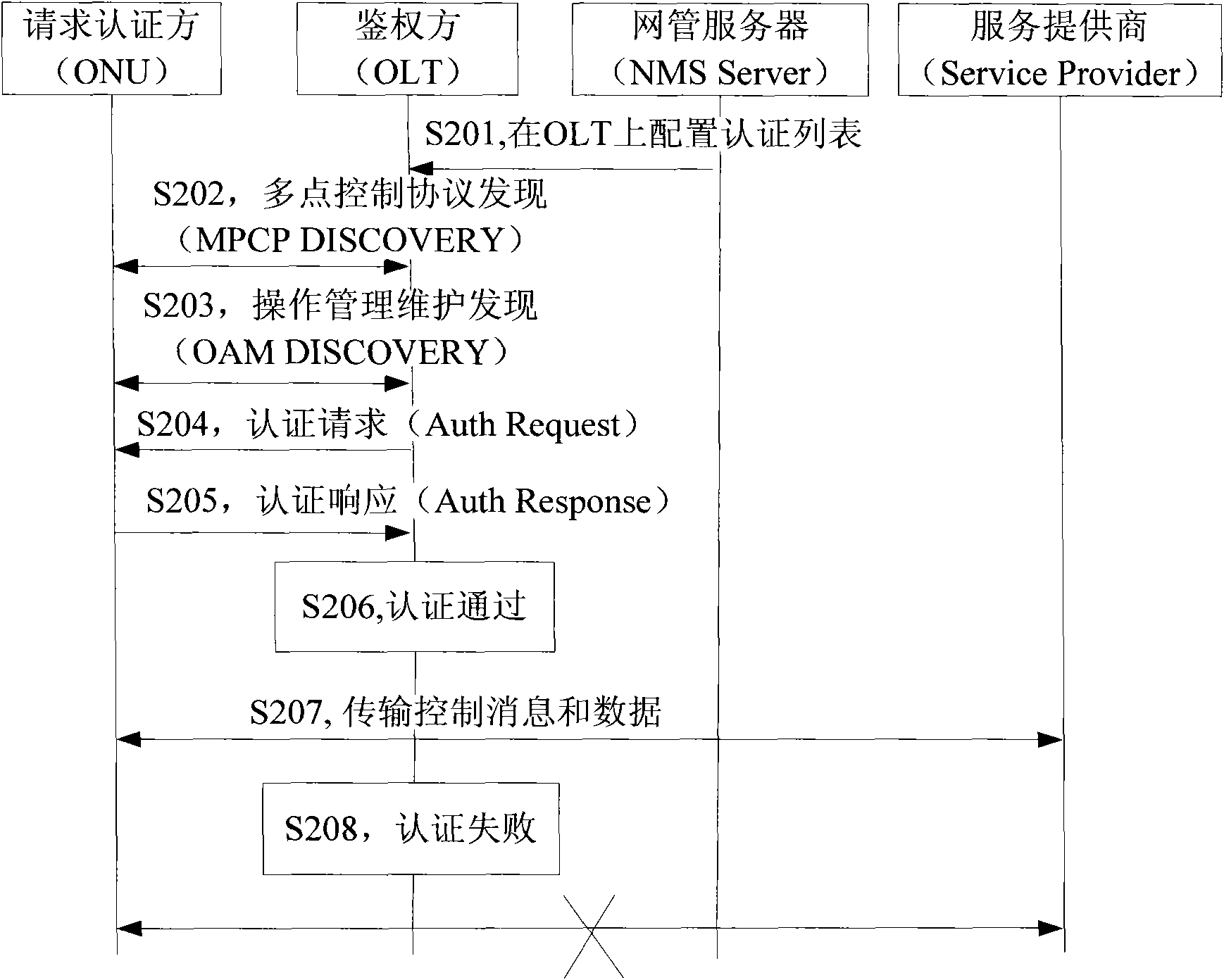
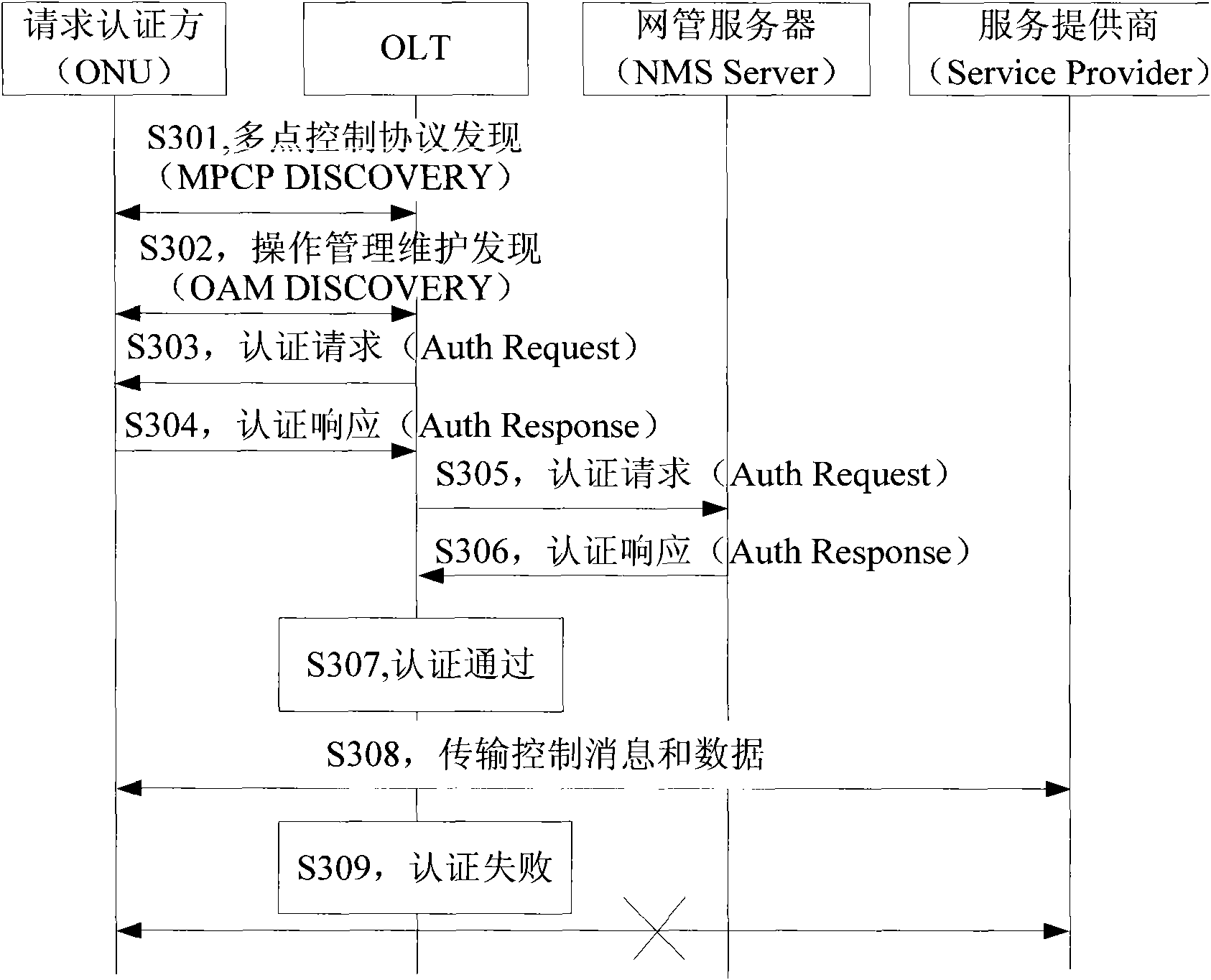
InactiveCN102170421AThe certification process is reliableAuthentication securityMultiplex system selection arrangementsData switching networksOptical network unitComputer science
The invention provides a method for realizing mixed authentication. The method comprises the steps of obtaining a logic identifier and a physical identifier of an optical network unit; authenticating according to the logic identifier and the physical identifier; enabling the optical network unit to pass the authentication while the logic identifier and the physical identifier are legal; and otherwise, obtaining that the optical network unit fails to pass the authentication. The invention also provides a system for realizing the mixed authentication. By using the method and the system disclosed by the invention, the reliability and security of the ONU (Optical Network Unit) authentication process are improved.
Owner:ZTE CORP
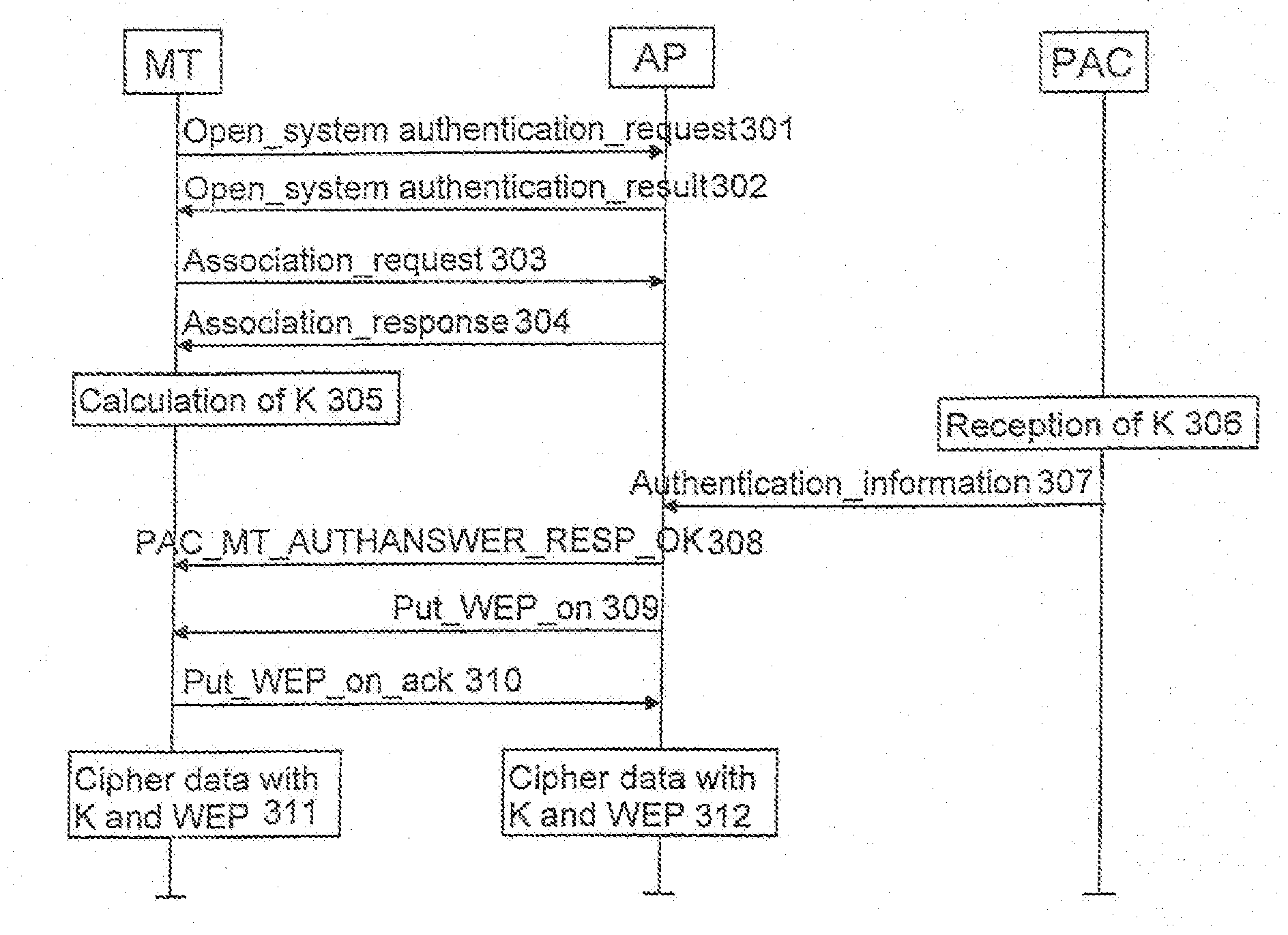
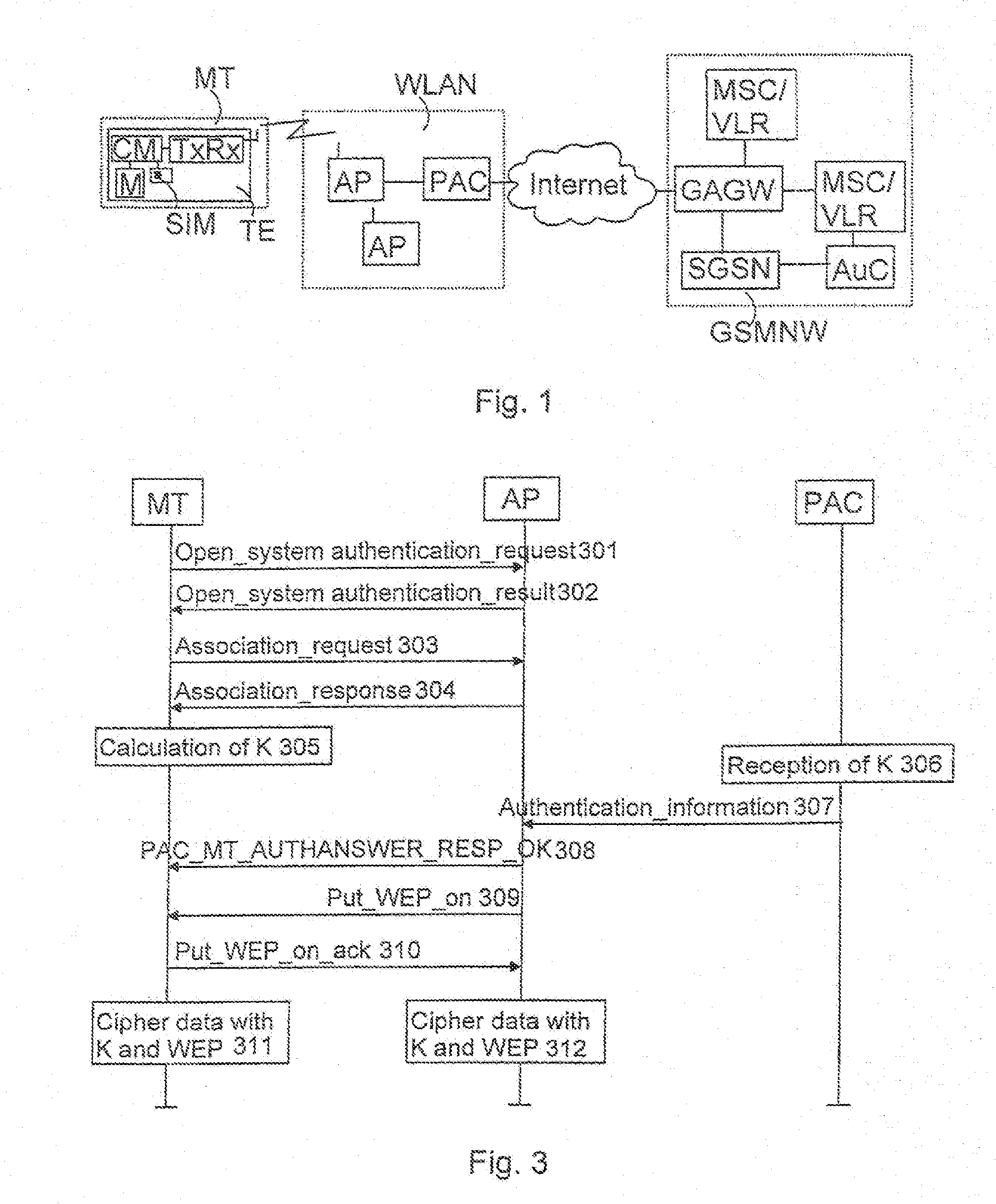
Arranging data ciphering in a wireless telecommunication system
InactiveUS20110058670A1The certification process is reliableEnsure reliabilityKey distribution for secure communicationUnauthorised/fraudulent call preventionPublic land mobile networkComputer terminal
Arranging data ciphering in a telecommunication system comprising at least one wireless terminal, a wireless local area network and a public land mobile network. At least one first ciphering key according to the mobile network is calculated in the mobile network and in the terminal for a terminal identifier using a specific secret key for the identifier. Data transmission between the mobile network and the terminal is carried out through the wireless local area network. A second ciphering key is calculated in the terminal and in the mobile network using said at least one first ciphering key. The second ciphering key is sent from the mobile network to the wireless local area network. The data between the terminal and the network is ciphered using said second ciphering key.
Owner:INTELLECTUAL VENTURES I LLC
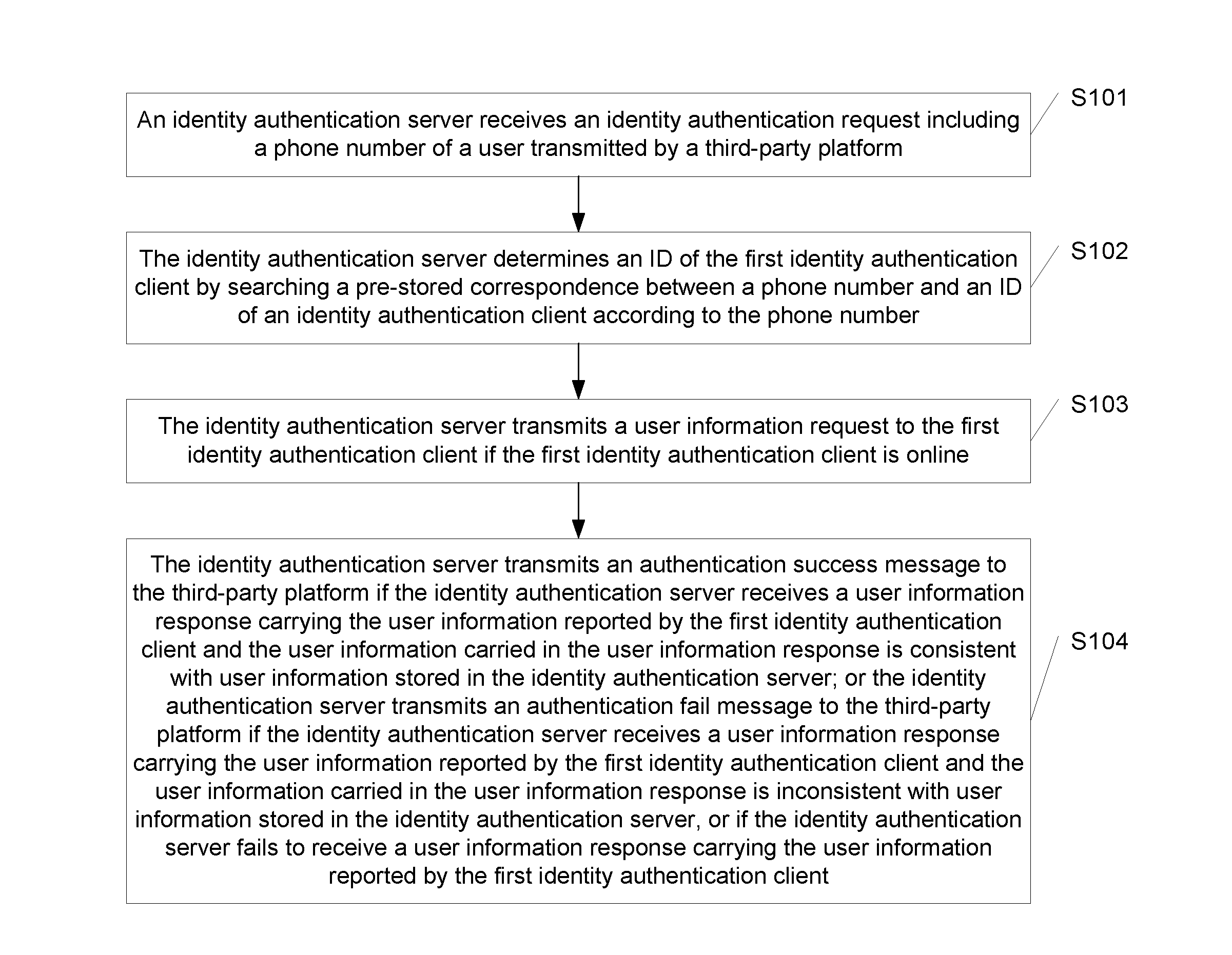
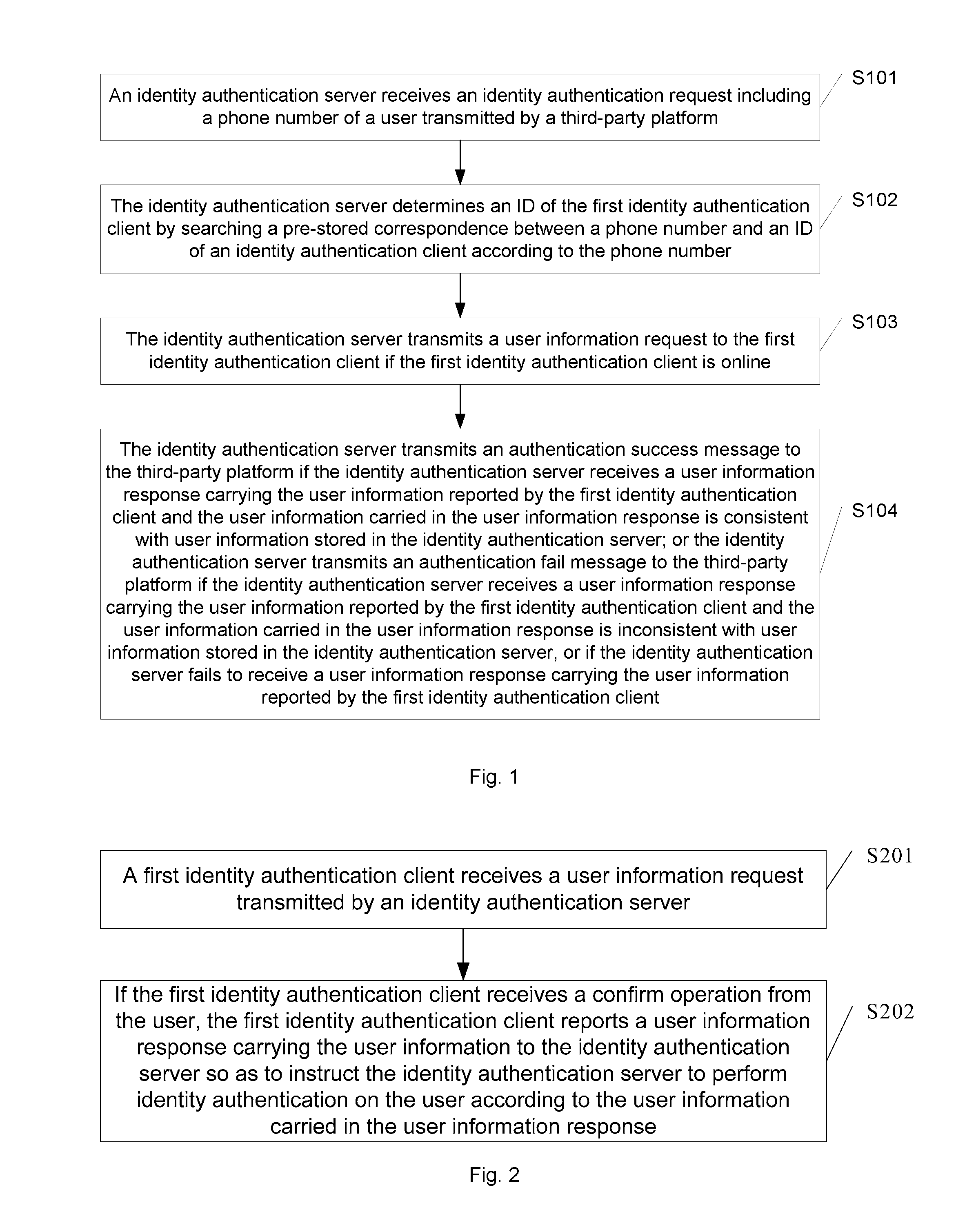
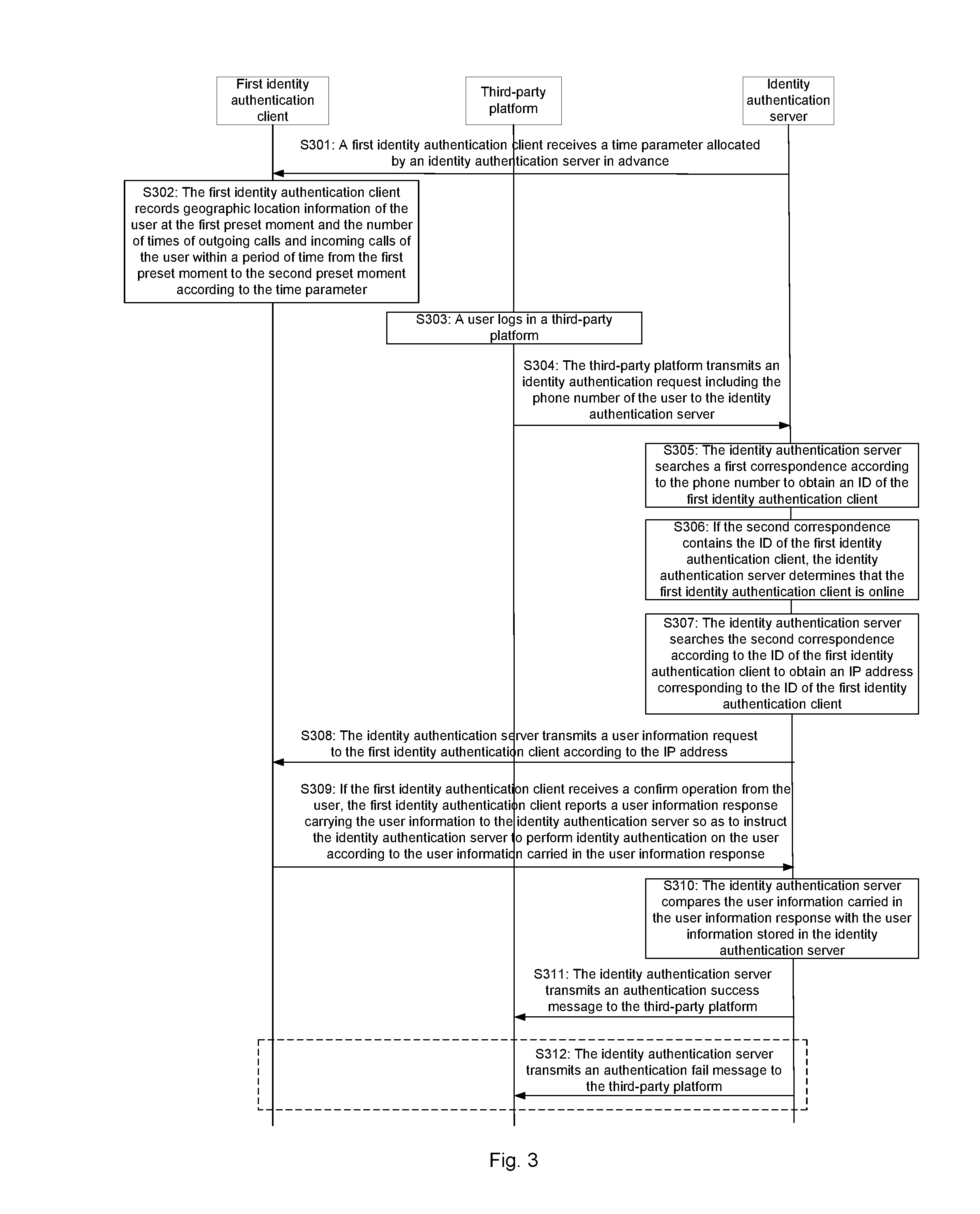
Identity authentication method and device
InactiveUS20170041307A1Complex the user name and the passwordImprove securityTransmissionSecurity arrangementThird partyInternet privacy
Embodiments of the present disclosure disclose an identity authentication method and device. The method comprises: receiving, by an identity authentication server, an identity authentication request transmitted by a third-party platform; determining, according to the phone number, an ID of a first identity authentication client by searching a pre-stored correspondence; if the first identity authentication client is online, transmitting a user information request; transmitting an authentication success message to the third-party platform if a user information response carrying the user information is received and the user information is consistent with user information stored in the identity authentication server; or transmitting an authentication fail message to the third-party platform if the user information is inconsistent with user information stored in the identity authentication server, or if a user information response carrying the user information is not received.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Method and system for safely receiving and sending mails
ActiveCN103428077AEnsure safetyImplement encryptionUser identity/authority verificationData switching networksSecure transmissionClient-side
The invention discloses a method and a system for safely receiving and sending mails. Mail receiving and sending safety authentication and safety transmission of the mails are realized. The method includes the steps: connecting a mail client with a login platform to perform identity authentication; returning a token message to the mail client after authentication success; accessing a first address in the token message by the mail client; receiving a first message including a second address by the mail client; calling an interface of a safety management platform and transmitting the first message to the safety management platform by the mail client; generating a second message and transmitting the second message to the mail client and a mail gateway by the safety management platform; acquiring a user policy message from the safety management platform through the second message by the mail client; carrying the second message by the mail client and authenticating the second message at the mail gateway; connecting the mail gateway with a mail server and starting receiving and sending the mails after passing authentication.
Owner:北京明朝万达科技股份有限公司
Method and apparatus for user authentication
ActiveUS7725717B2The certification process is reliableEnhanced authenticationDigital data processing detailsUser identity/authority verificationUser inputEncrypted function
The invention provides for secure end-to-end user authentication by a remote server communicating with a communication device. The communication device further communicates with an authentication device, which provides a user authentication message to the communication device for forwarding to the remote server. The authentication device comprises a data store for storing user authentication credentials. A user authentication processor performs a local authentication of a user of the authentication device in response to a user input. An authentication processor generates the authentication message if the user authentication is valid. The authentication processor implements a cryptographic function based on the user authentication credentials. A transmitter then transmits the authentication message to the at least one communication device.
Owner:MOTOROLA SOLUTIONS INC
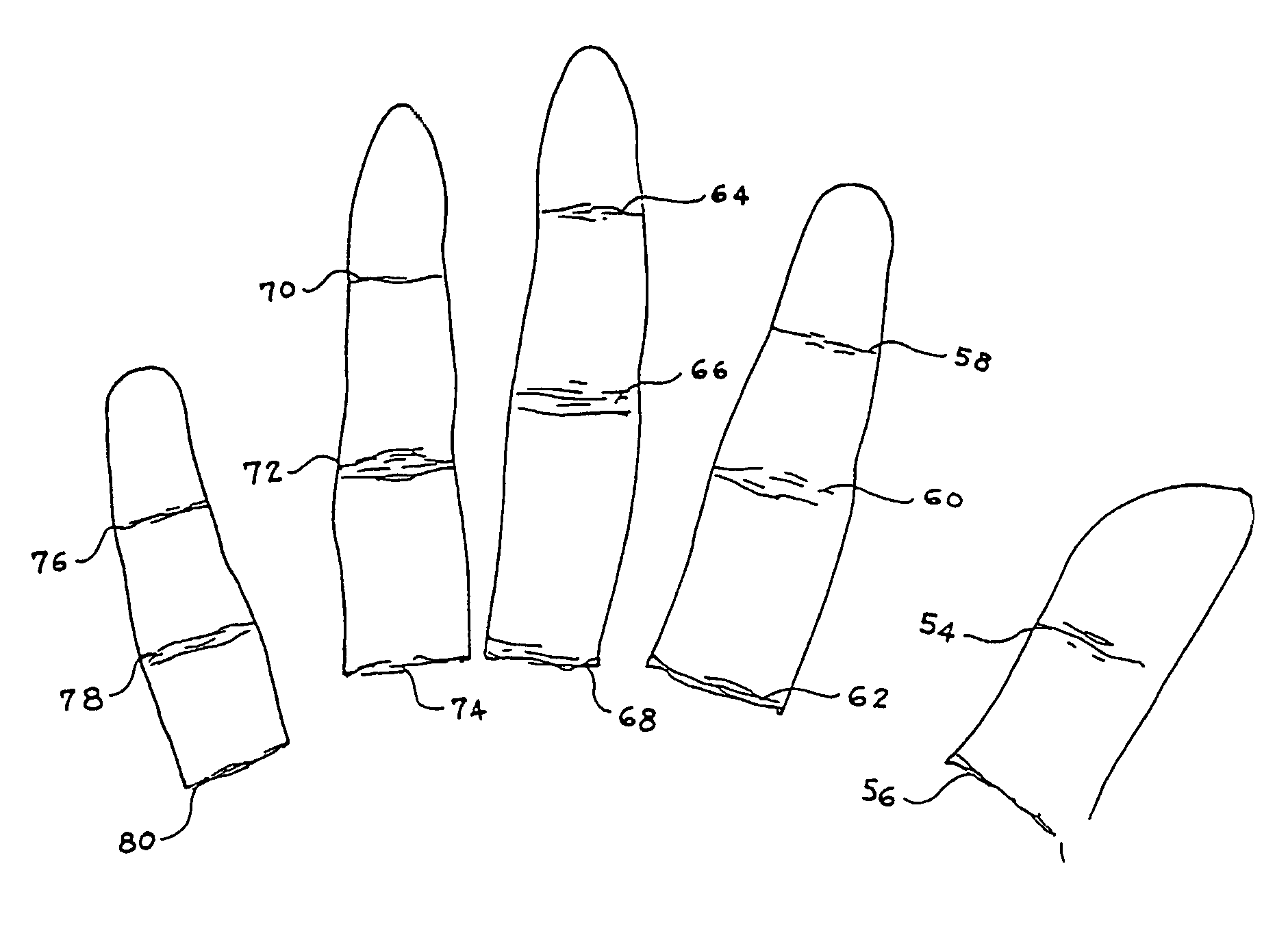
Method, device and computer program for authenticating a user
ActiveUS20170339137A1Authentication of user can be reliableReliable matchImage enhancementTelevision system detailsLivenessInternet privacy
The present invention concerns a method for authenticating a user, comprising:an initial biometric authentication of the user, based on biometric features extracted from one or a plurality of image frames corresponding to a first portion of the user's hand and / or wrist, captured with a camera (12) of a wearable device (10);a subsequent step of confirming said biometric authentication of the user and / or verifying his liveness, based on at least a measure of a second portion of the user's hand or wrist made when said wearable device is worn against the user's hand or wrist;the surface of said second portion being smaller than the surface of said first portion.
Owner:BIOWATCH SA
identification mark
ActiveCN102265311ACompact structureImprove carryIndividual entry/exit registersCommunications systemIdentification device
An identification device for identifying persons on an authenticated basis includes a support layer, an authentication device with a non-volatile, re-writeable semiconductor memory, a person-related feature, a communication system with a communication connector, and a first electronic key which is linked to the person-related feature and is stored in the memory. In a further aspect, an identification device for identifying persons on an authenticated basis includes an electronic data set in which an electronic image of a person-related feature and a first electronic key are stored, and the first electronic key is linked to the person-related feature. Also provided is a method of identifying and authenticating a person by an identification device.
Owner:ASMAG HLDG
Method for realizing security key authentication of pure electric vehicle
ActiveCN110310397APrevent theftImprove authentication securityKey distribution for secure communicationAnti-theft devicesCiphertextKey authentication
The invention discloses a method for realizing the security key authentication of a pure electric vehicle. The method comprises the steps: waking up a smart key, feeding back a high-frequency key coordinate signal and a unique key ID of the smart key to a vehicle body controller; generating a first random number by the vehicle body controller and encrypting the Key ID, the first random number anda low-frequency wake-up signal by the vehicle body controller and the smart key based on an HITAG2 algorithm; completing authentication of the vehicle body controller and the smart key under the condition of consistence of the vehicle body controller and a ciphertext obtained by smart key encryption; generating a second random number Key and a third random number Key1 by the vehicle body controller and sending the second random number Key and the third random number Key1 to an overall vehicle controller; generating a fourth random number Key2 and a fifth random number Key3 by the overall vehicle controller and replying the fourth random number Key2 and the fifth random number Key3 to the vehicle body controller; and carrying out two-way authentication by the vehicle body controller and theoverall vehicle controller by using the second random number Key, the third random number Key1, the fourth random number Key2, the fifth random number Key3, and a conventional number A to realize starting of a pure electric vehicle.
Owner:浙江新吉奥汽车有限公司
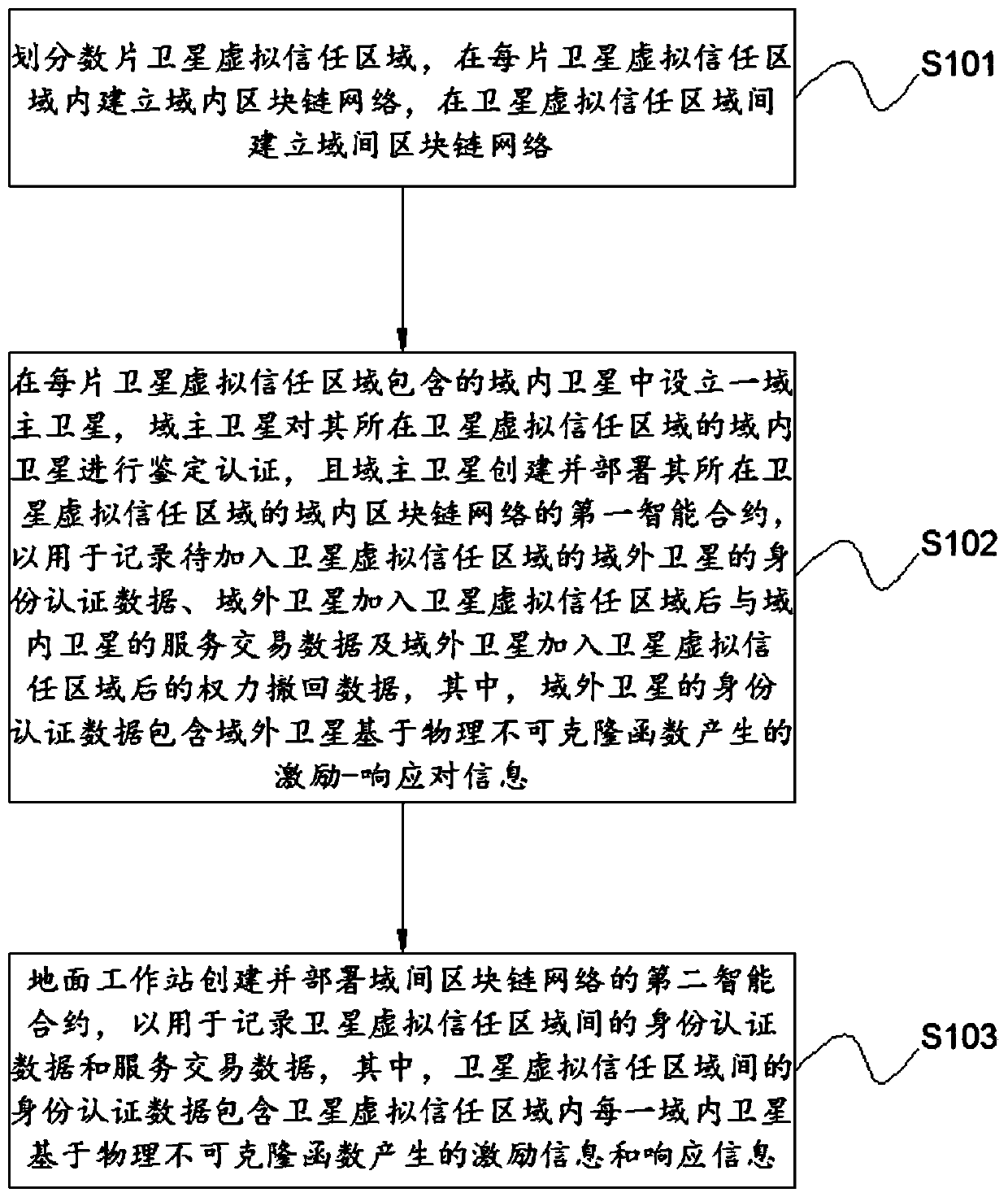
Satellite management method based on blockchain and physical unclonable function
ActiveCN111200500AAvoiding Zero Trust ProblemsThe certification process is reliableFinanceUser identity/authority verificationData domainEngineering
The invention discloses a satellite management method based on a blockchain and a physical unclonable function. The method comprises the steps of dividing a plurality of satellite virtual trust regions, building an intra-domain blockchain network in each satellite virtual trust region, and building an inter-domain blockchain network between the satellite virtual trust regions; setting a domain main satellite in intra-domain satellites contained in each satellite virtual trust area; enabling the domain main satellite to create and deploy a first intelligent contract of the intra-domain block chain network so as to record identity authentication data of an out-domain satellite to be added into the satellite virtual trust area, service transaction data of the out-domain satellite and the intra-domain satellite and power withdrawal data of the out-domain satellite; and enabling a ground workstation to create and deploy a second smart contract of the inter-domain blockchain network so as torecord identity authentication data and service transaction data between the satellite virtual trust areas. According to the method, the performance defects of a traditional satellite network can beovercome, and better safety performance can be obtained.
Owner:GUANGXI UNIV +1
User authentication system and method thereof
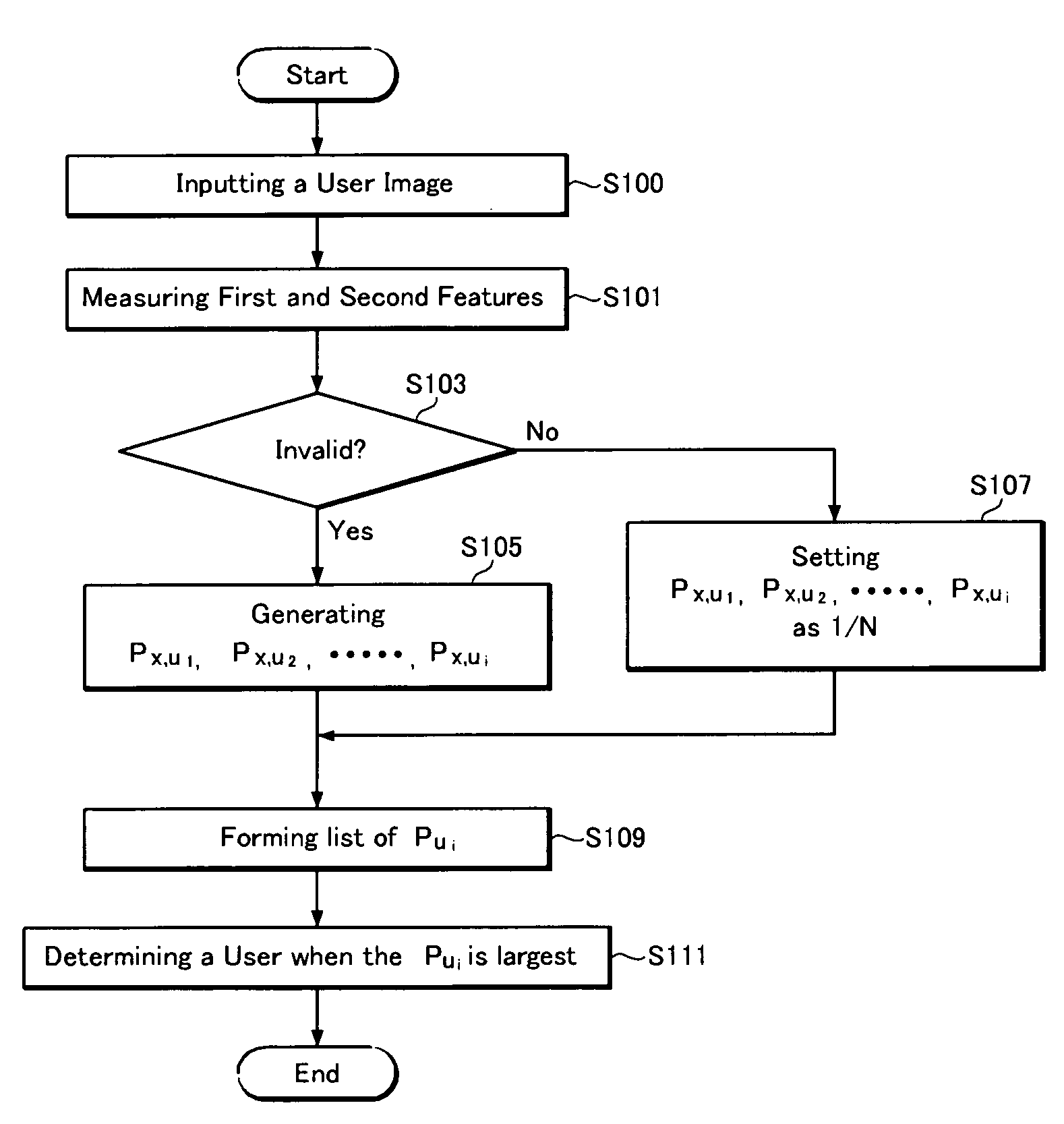
InactiveUS7634113B2The certification process is reliableProgramme controlElectric signal transmission systemsInternet privacyUser authentication
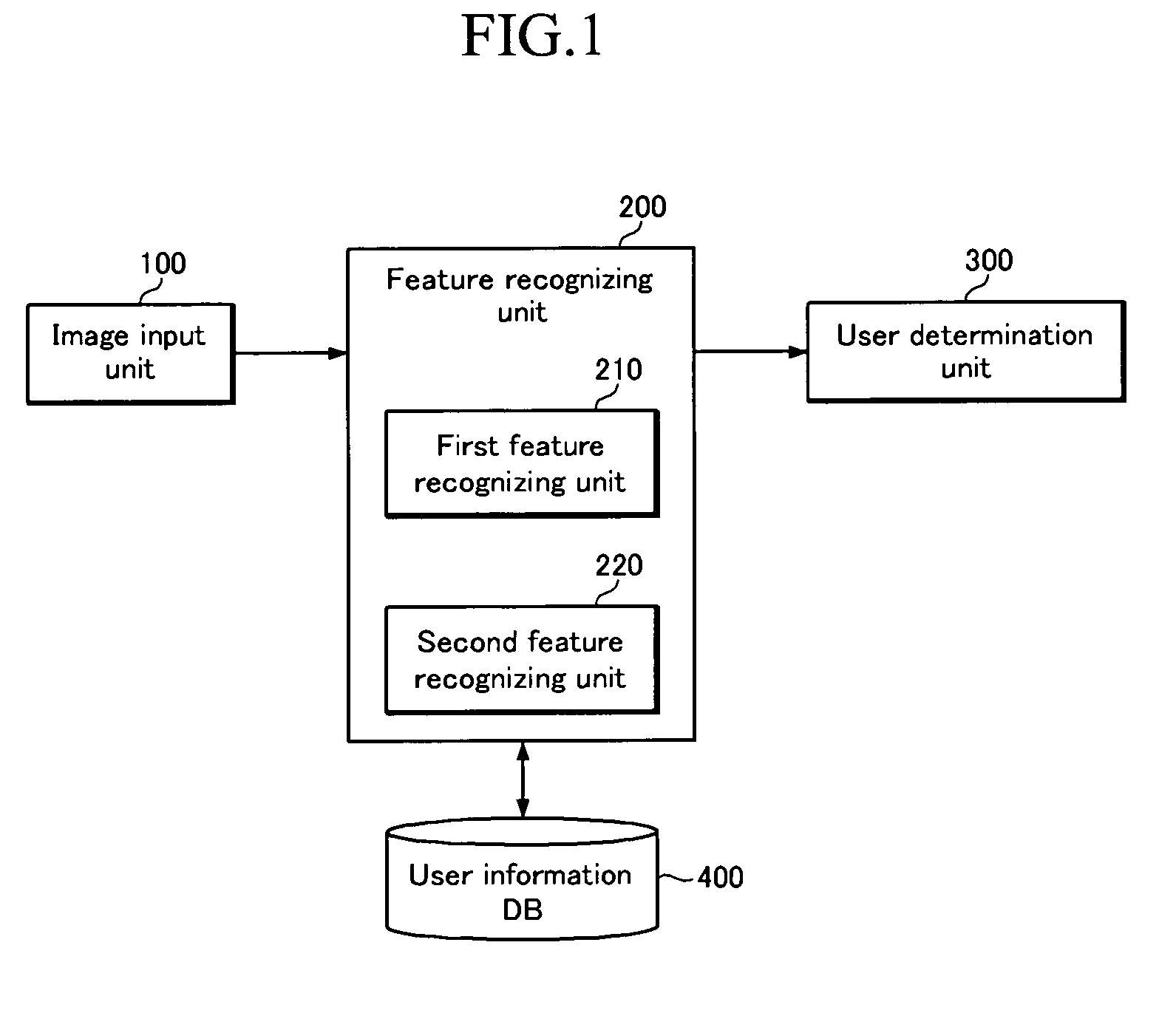
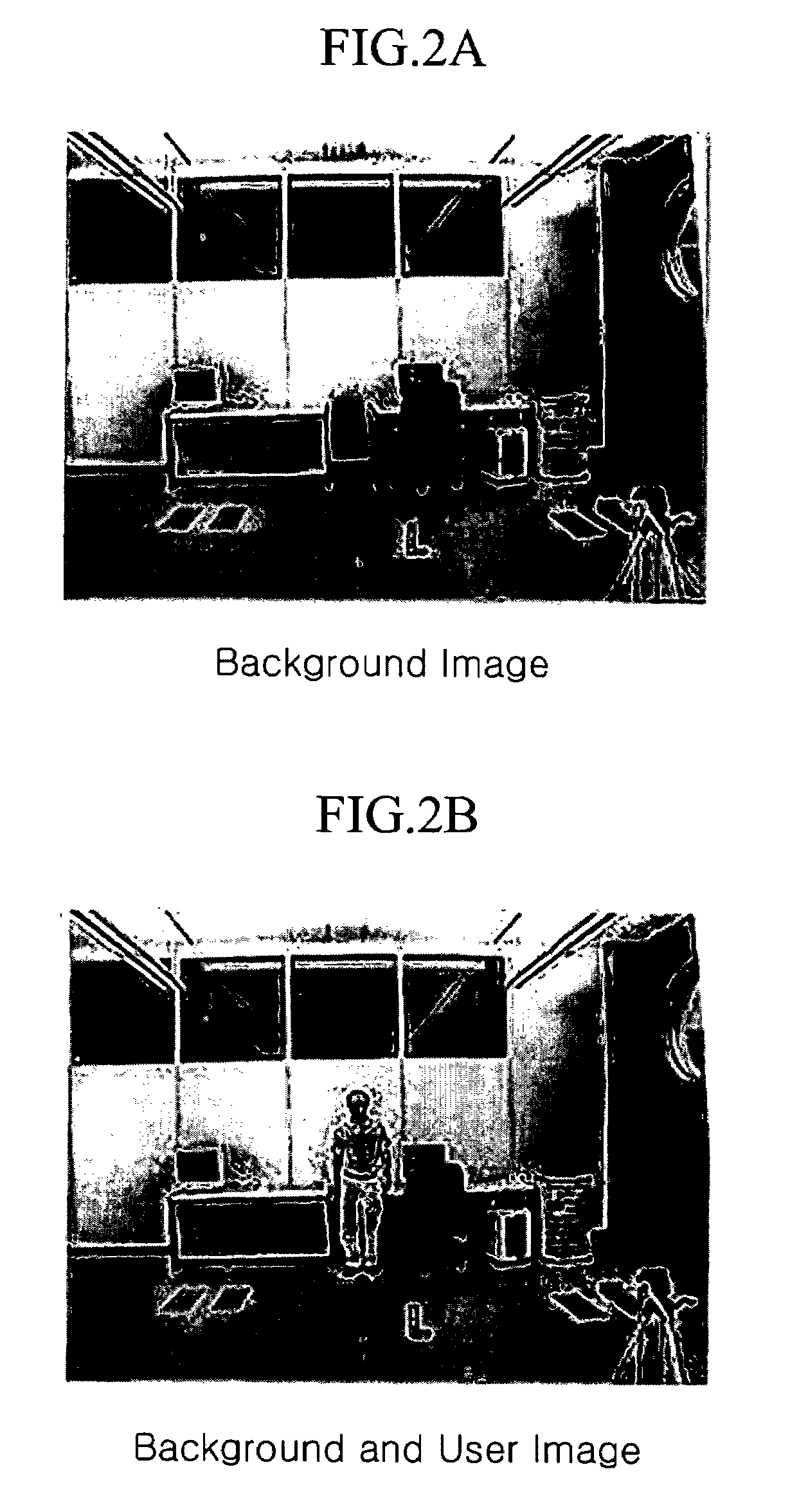
A user recognizing system and method is provided. According to the user recognizing system and method, user ID and predetermined user feature information are stored, first and second user feature information are extracted from the user image data transmitted from the image input unit, and first and second probabilities that the extracted first and second user feature information determine the predetermined user are respectively generated based on the information stored at the user information database, the first user feature information being absolutely unique biometric information and the second user feature information being unique semibiometric information under a predetermined condition, and ID of the input image is finally determined by combining the first probability and the second probability. According to the user recognizing system and method, a user identity can be authenticated even when the user freely moves.
Owner:ELECTRONICS & TELECOMM RES INST
Distributed identity authentication method and system
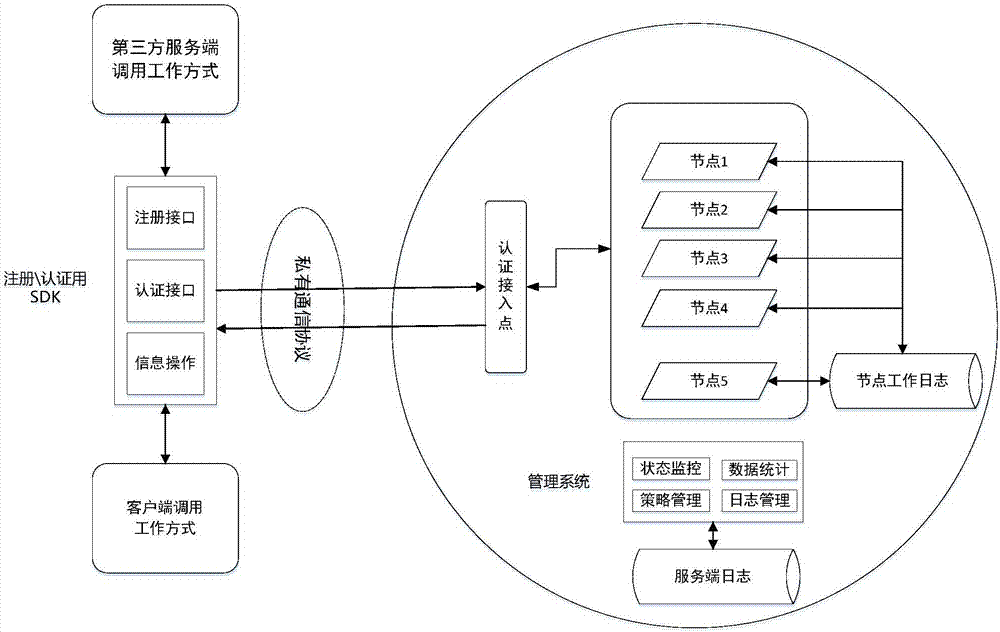
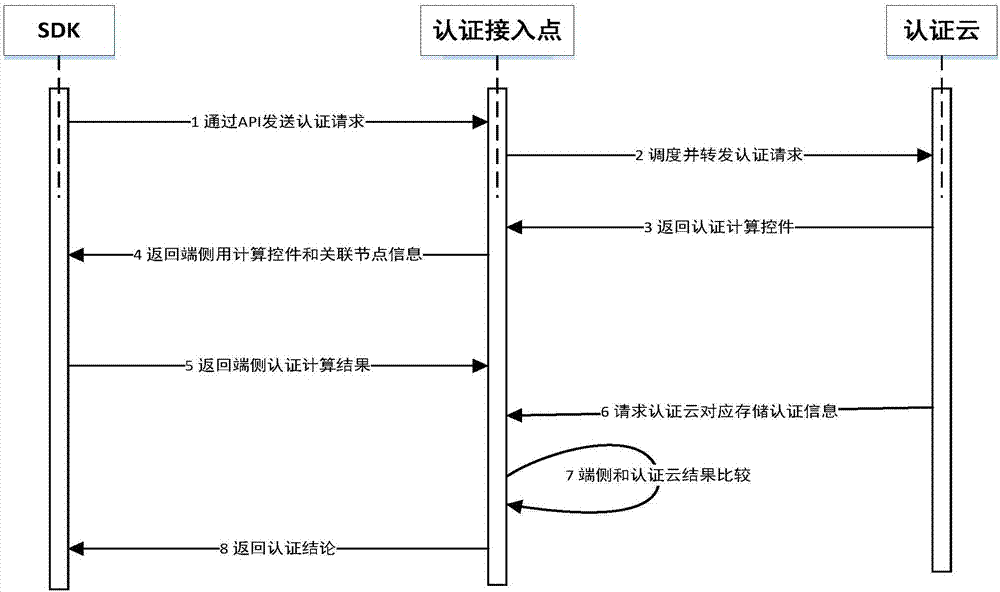
InactiveCN107196957AReliable authenticationThe certification process is reliableDigital data authenticationTransmissionAuthentication serverClient-side
The invention discloses a distributed identity authentication method and system. The method comprises the following steps that a client sends an authentication request to an authentication server; the client receives returned authentication calculation control and association node information; the client carries out calculation according to the authentication calculation control, thereby obtaining authentication information result CRL; and an authentication access node receives the authentication information result CRL, compares the authentication information result CRL with authentication information SAL and returns an authentication result to the client. Through application of the scheme, the identity authentication efficiency and stability are improved, and local processing resources are saved.
Owner:北京明朝万达科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com