Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
201 results about "Disk operating system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A disk operating system (abbreviated DOS) is a computer operating system that can use a disk storage device, such as a floppy disk, hard disk drive, or optical disc. A disk operating system must provide a file system for organizing, reading, and writing files on the storage disk. Strictly speaking, this definition does not apply to current generations of operating systems, such as versions of Microsoft Windows in use, and is more appropriately used only for older generations of operating systems.
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS10129211B2Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsFiberNetwork operating system
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
Method and system for automatically updating operating systems
InactiveUS20040117414A1BootstrappingProgram loading/initiatingOperational systemPick operating system
Methods and systems for updating operating systems are disclosed. A computer includes a disk drive that stores an operating system to be updated. The computer creates a backup image of a first partition of the disk drive, then deletes the first partition to create free space on the disk drive. The computer also places an image of a maintenance operating system into the free space, wherein the maintenance operating system is operable to manage an operating system update. Thereafter, the computer updates the stored operating system under control of the maintenance operating system.
Owner:CAPITAL ONE FINANCIAL
iSCSI boot drive system and method for a scalable internet engine
InactiveUS20050138346A1Digital computer detailsProgram loading/initiatingOperational systemThe Internet
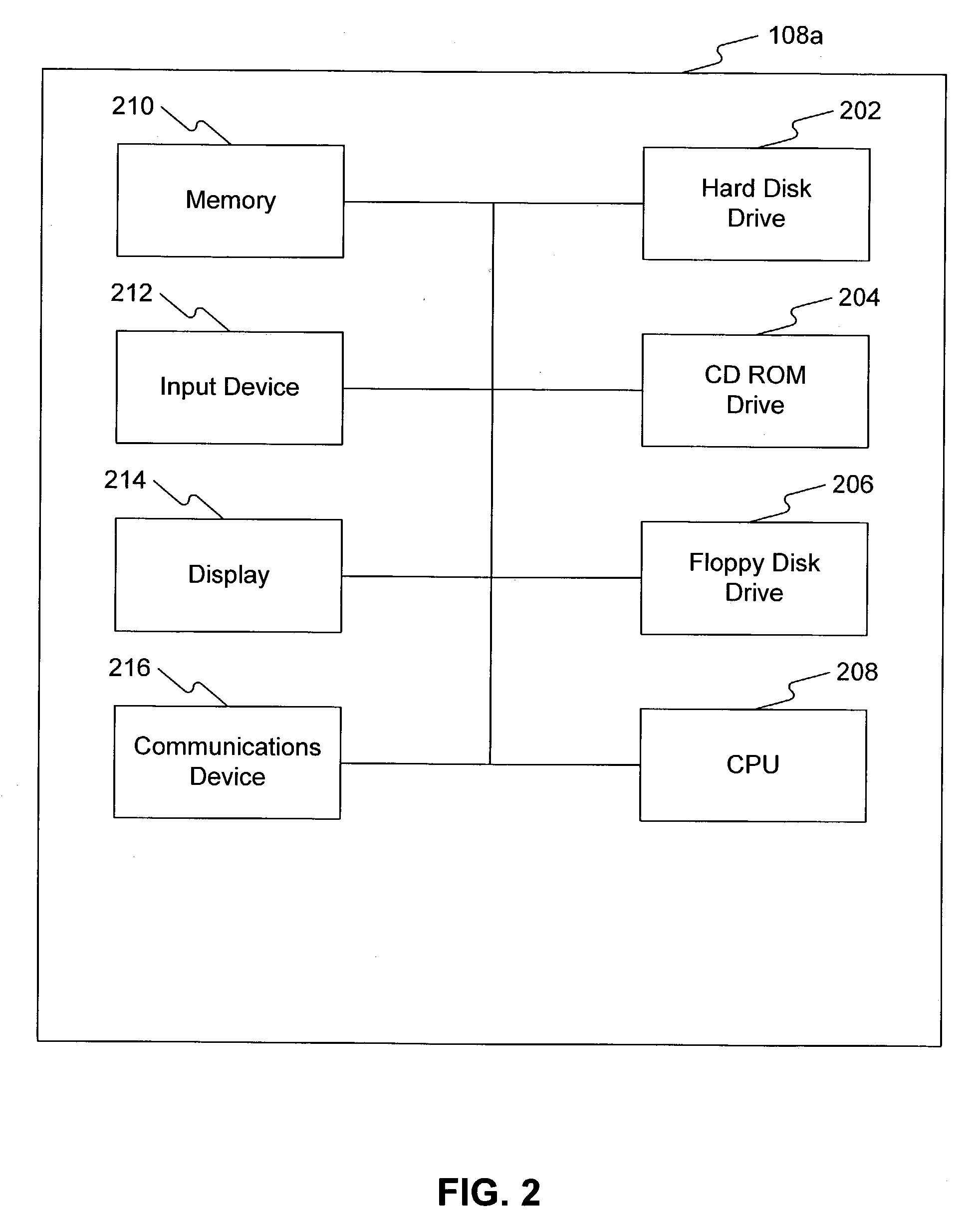
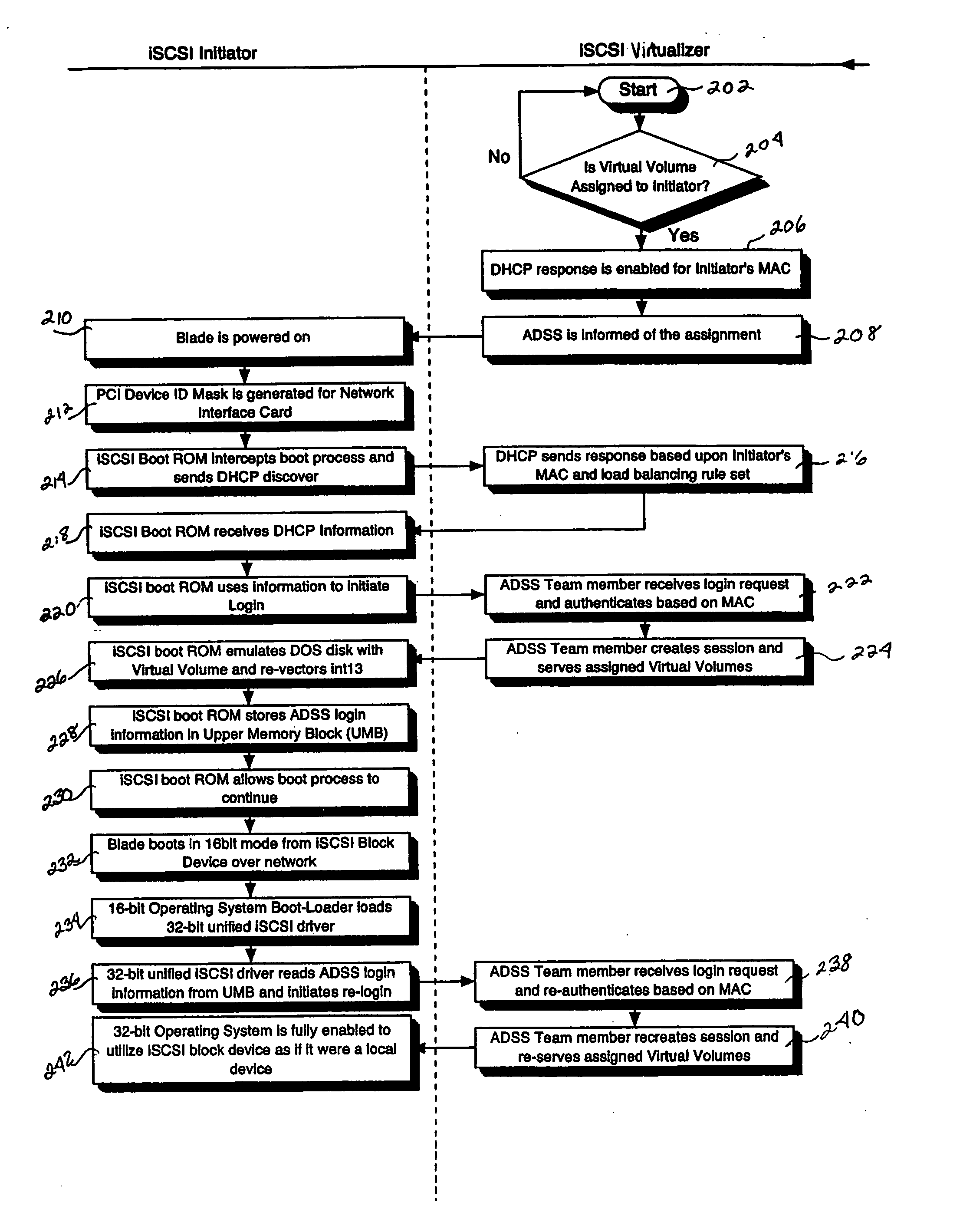
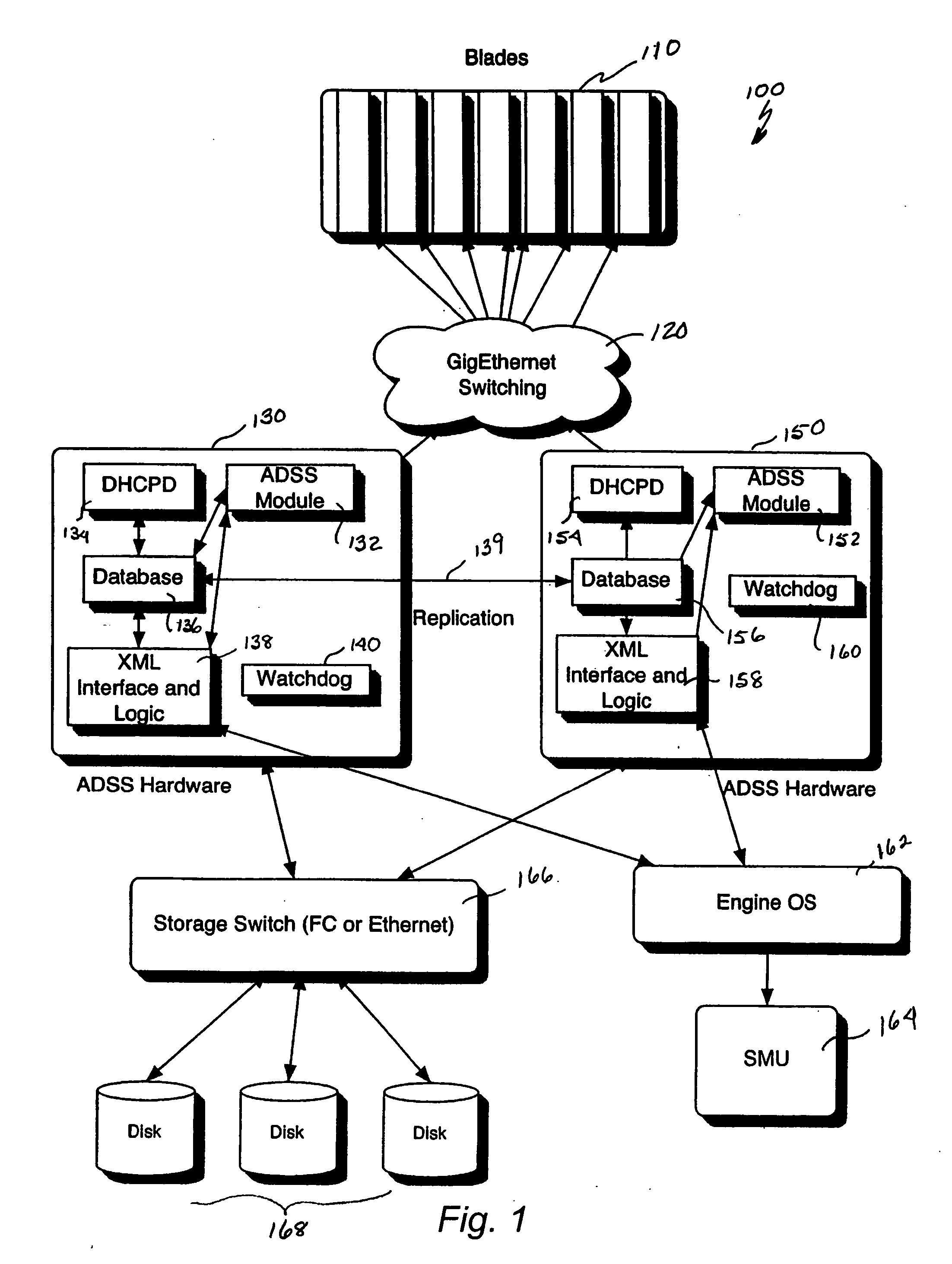
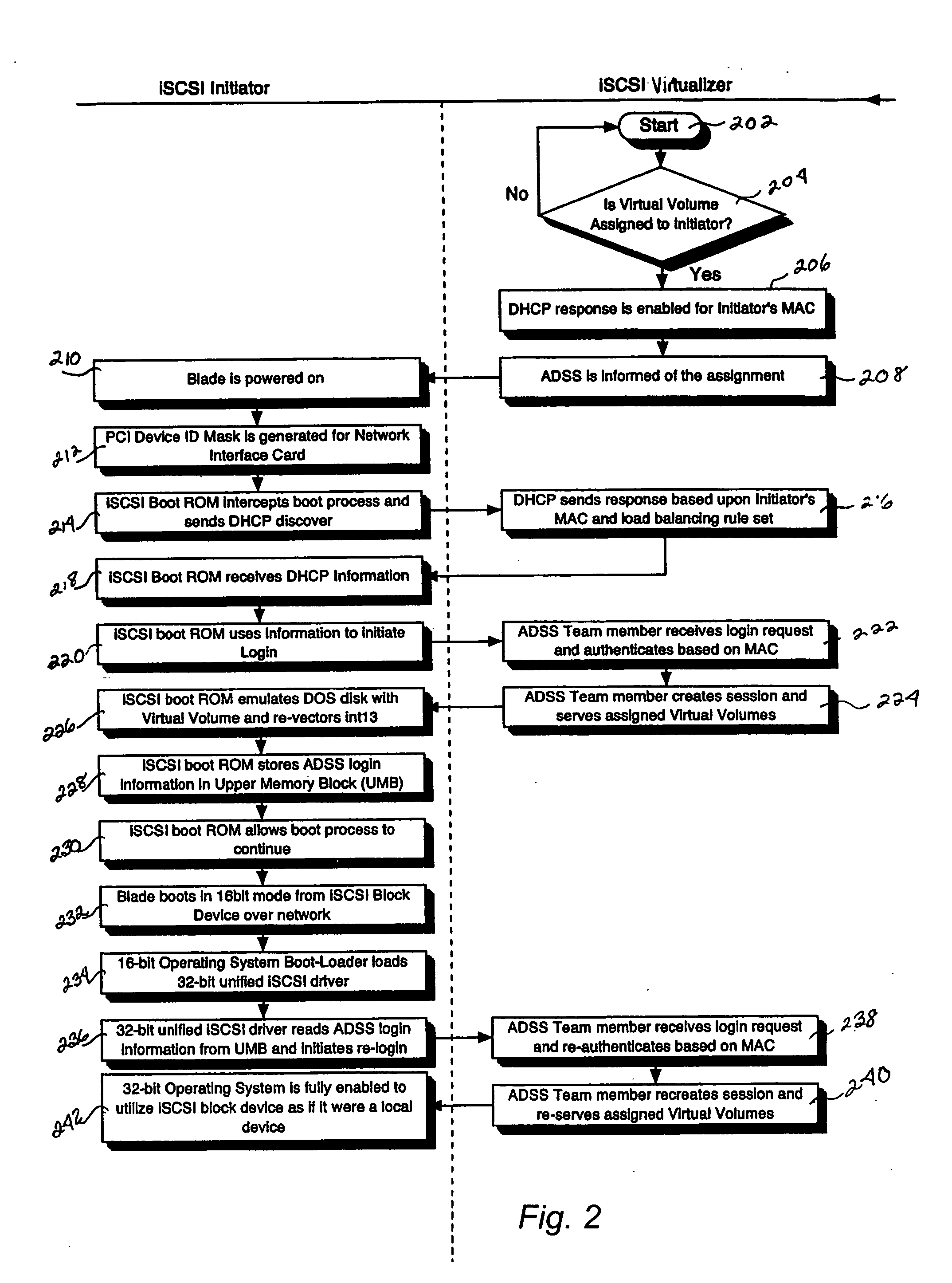
A system for remote booting of a server generally includes a client initiator, an iSCSI virtualizer, and an iSCSI initiator. The client initiator requests access to the server and the iSCSI virtualizer receives the access request. Then, the iSCSI initiator acts upon the request received by the iSCSI virtualizer to initiate login to the server through use of an iSCSI Boot ROM on the server and to emulate a disk operating system through use of the iSCSI Boot ROM, which enables the server to boot. The server boots in both an 8-bit and a subsequent 32-bit mode. The iSCSI Boot ROM appears as a local device upon the completion of the server boot. The iSCSI virtualizer authenticates the login at least twice. The iSCSI virtualizer includes a pair of replicated active directory service servers (ADSS).
Owner:RPX CORP
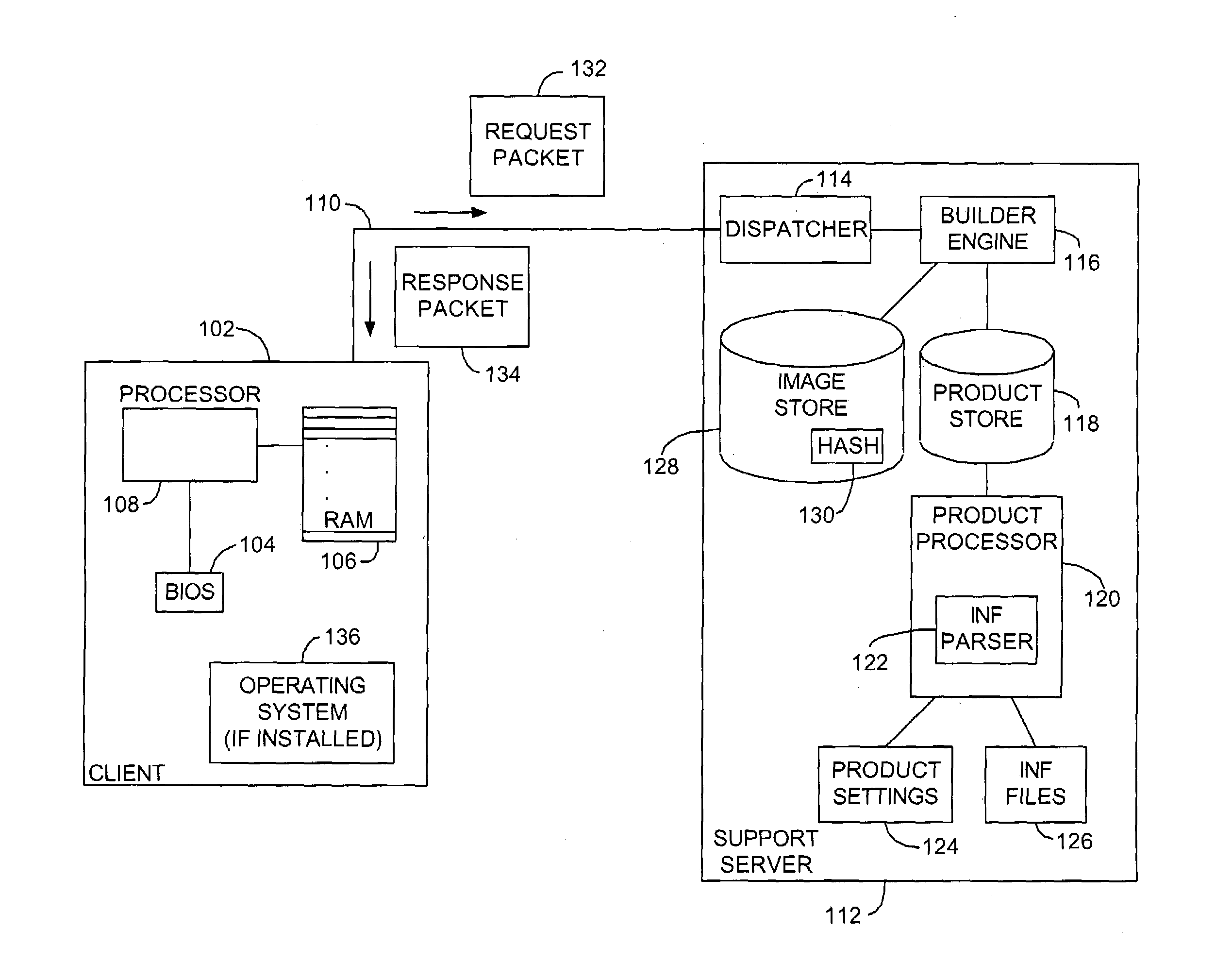
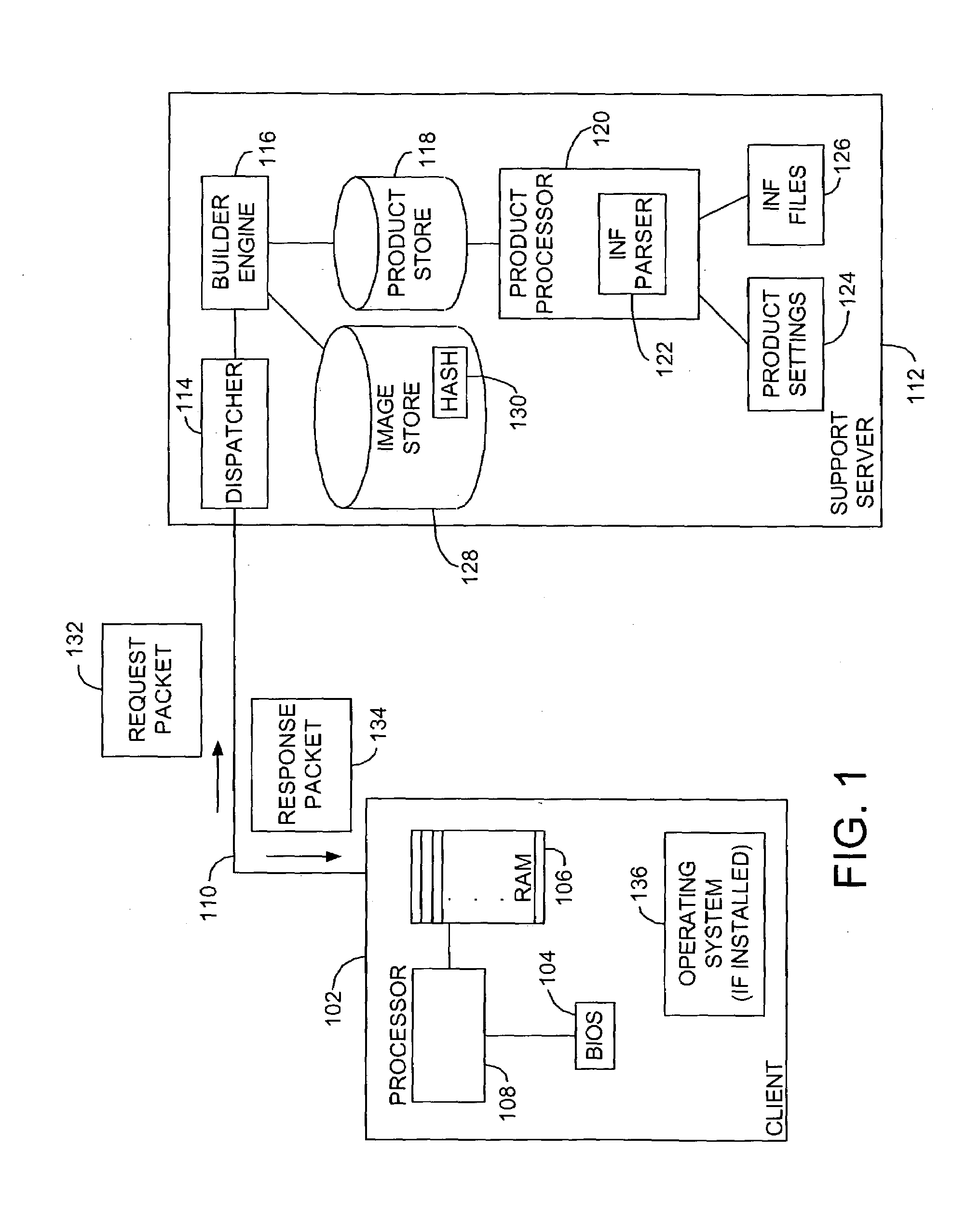
System and method for custom installation of an operating system on a remote client
A platform for remotely installing an operating system on a client machine includes a builder engine, for instance running on a support server. The builder engine may interrogate a remote client, for instance a diskless thin client or a machine having a disk but malfunctioning, and receive a machine state image from that machine. The builder engine may then assemble a customized image or kernel of an operating system such as Microsoft Windows™ for transmission to the client. A file system may be initialized in electronic memory, or otherwise and the machine may commence operation, without having executed an operating system setup process. In embodiments, the client machine may then link to a complete image of an operating system to reinstall a comprehensive version of that system, or perform other tasks.
Owner:MICROSOFT TECH LICENSING LLC
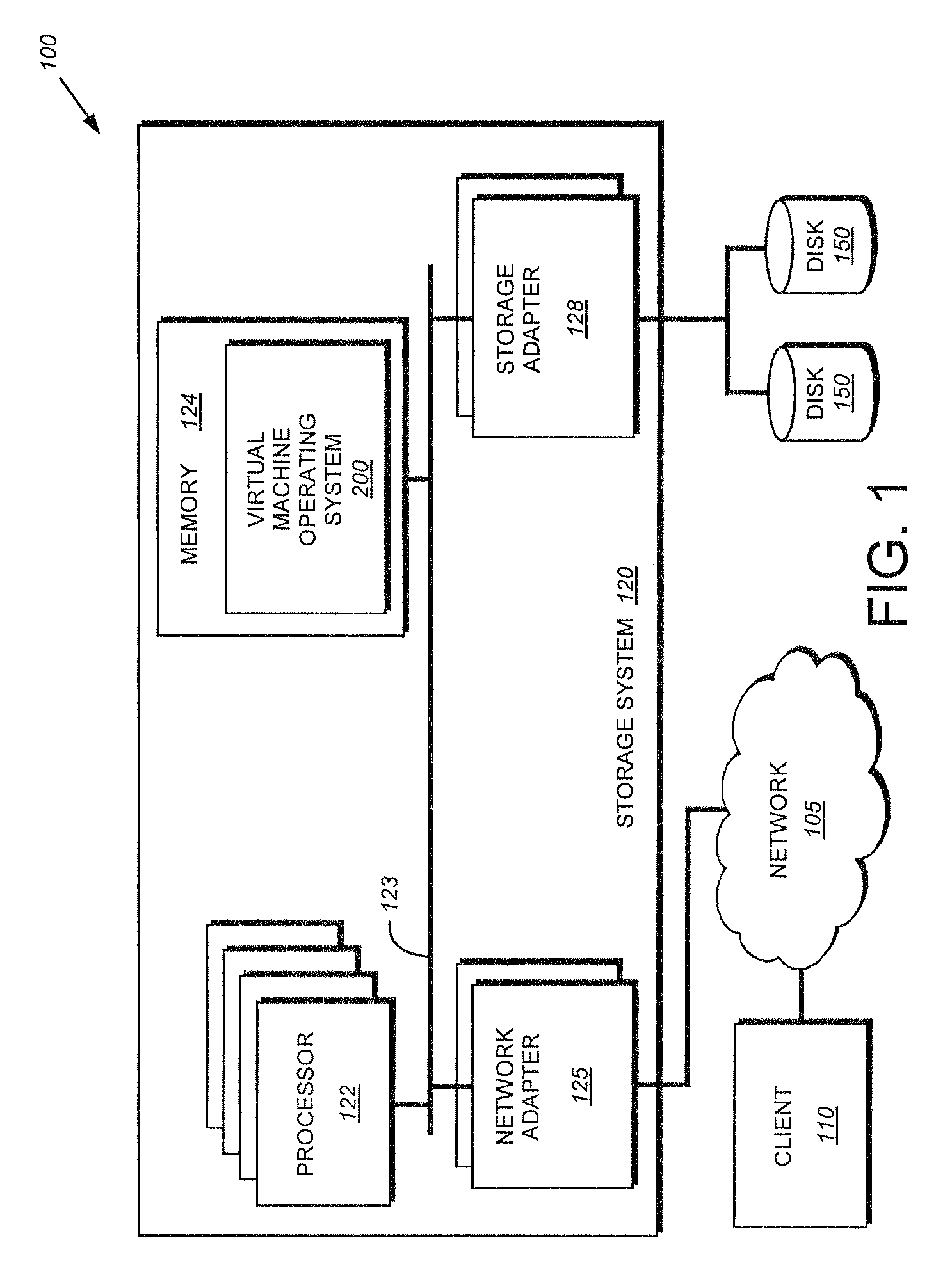
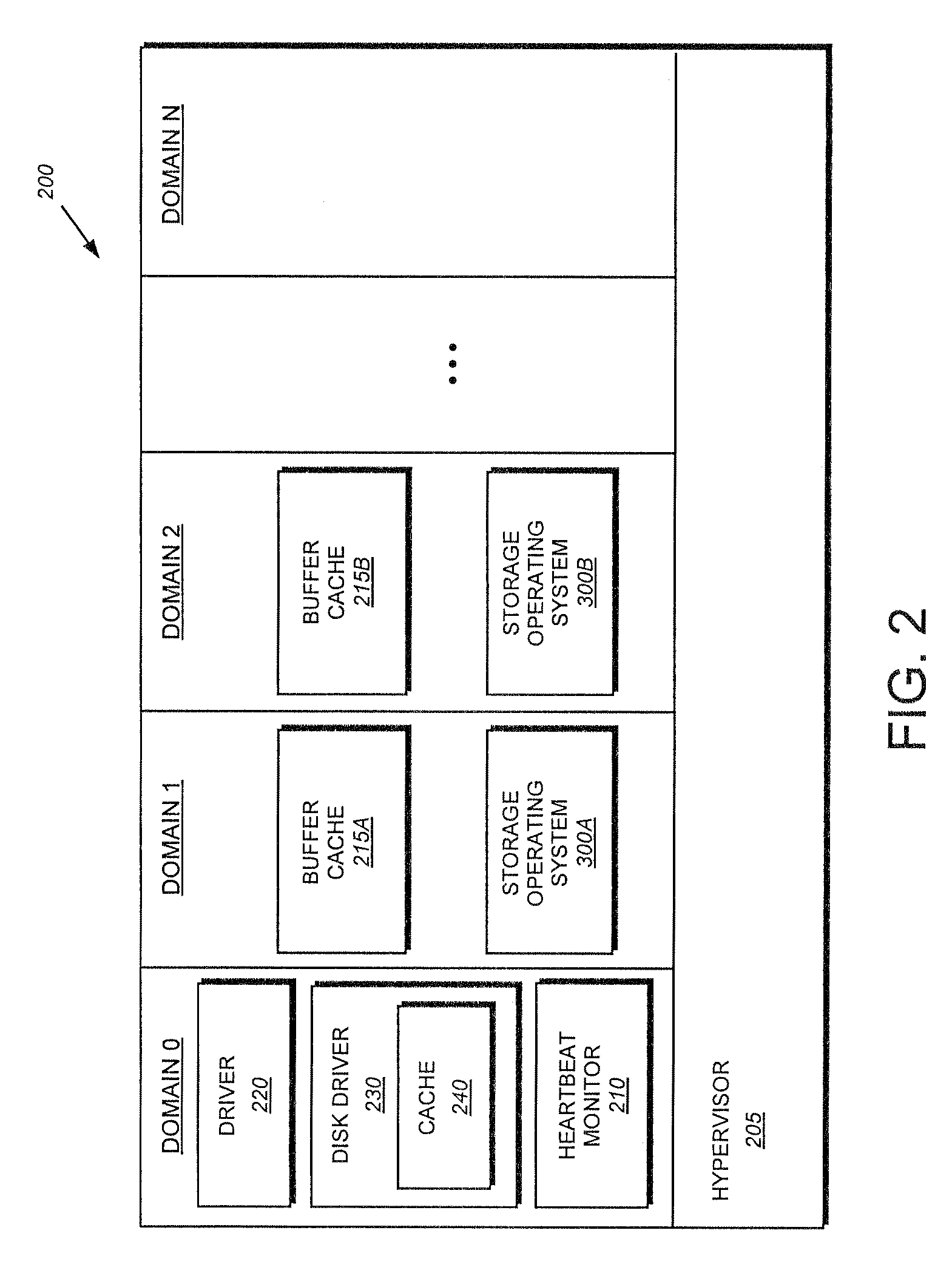
System and method for fast restart of a guest operating system in a virtual machine environment
ActiveUS8006079B2Short amount of timeShorten the timeDigital computer detailsData resettingVirtual machineDisk operating system
The present invention provides a system and method for fast restart of a guest operating system executing on a virtual machine operating system in a virtual machine environment. During initialization, the guest operating system saves a set of checkpoint information to persistent storage. Upon detection of an error condition during operation, the guest operating system begins a re-initialization procedure in accordance with an illustrative embodiment of the present invention. During the re-initialization procedure, the guest operating system retrieves the checkpoint information and configures itself using the retrieved information. By utilizing the retrieved information, the guest operating system avoids the need to perform lengthy configuration discovery routines, thereby shortening the re-initialization time substantially.
Owner:NETWORK APPLIANCE INC
Method and apparatus for display of windowing application programs on a terminal
InactiveUS7720672B1Cathode-ray tube indicatorsTransmissionOperational systemNetwork Communication Protocols
A video display terminal capable of operating with a graphical user interface such as Windows provides windowing functionality to permit use of popular applications programs resident on a server, without requiring more than application data to be transmitted from the server, and keyboard and mouse information to be transmitted from the terminal to the server. The terminal includes processing means, not fully compatible with personal computer BIOS or disk operating systems and incapable of executing windowing applications locally, adapted to receive windowing information supplied by programs executing on a remotely located application server. The terminal also includes a display for the windowing information supplied by programs executing on the remotely located application server. The invention provides FTP and SNMP capabilities along with a number of user interface enhancements, DHCP and SNMP enhancements. File information is transferred to and from the terminal using a communications protocol. One or more image upgrades are transferred to the terminal from the remotely located application server. Configuration data for the terminal can also be transferred to the terminal from the remotely located application server. The present invention further provides for simultaneously maintaining more than one connection between the terminal and server and establishing more than one virtual machine on the terminal with each virtual machine running an open session. Each virtual machine stops sending and receiving data to and from the server when an application resides in the background session. Each virtual machine commands the server to refresh the data for the application when the application is switched to the foreground.
Owner:DELL MARKETING CORP
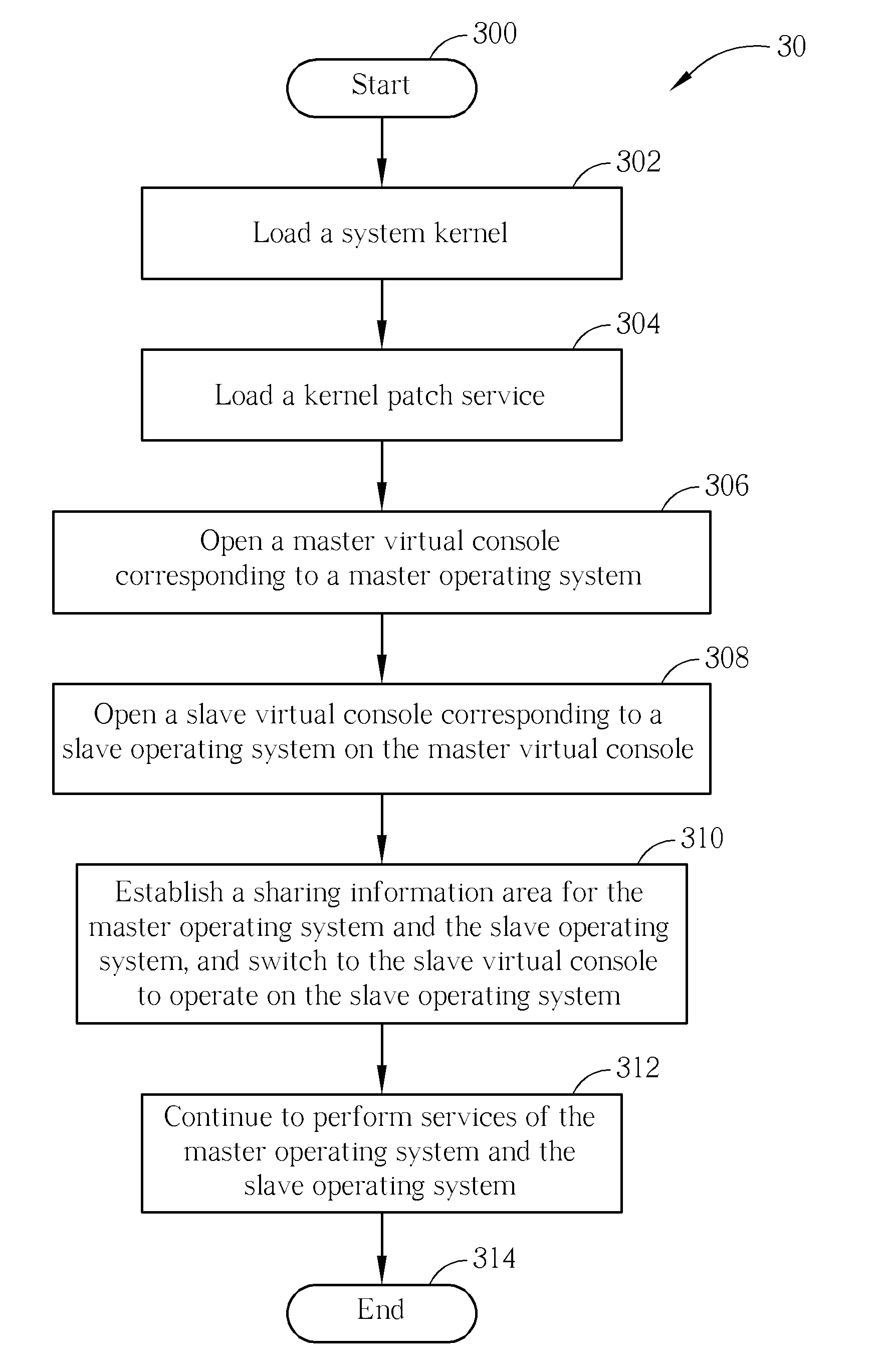
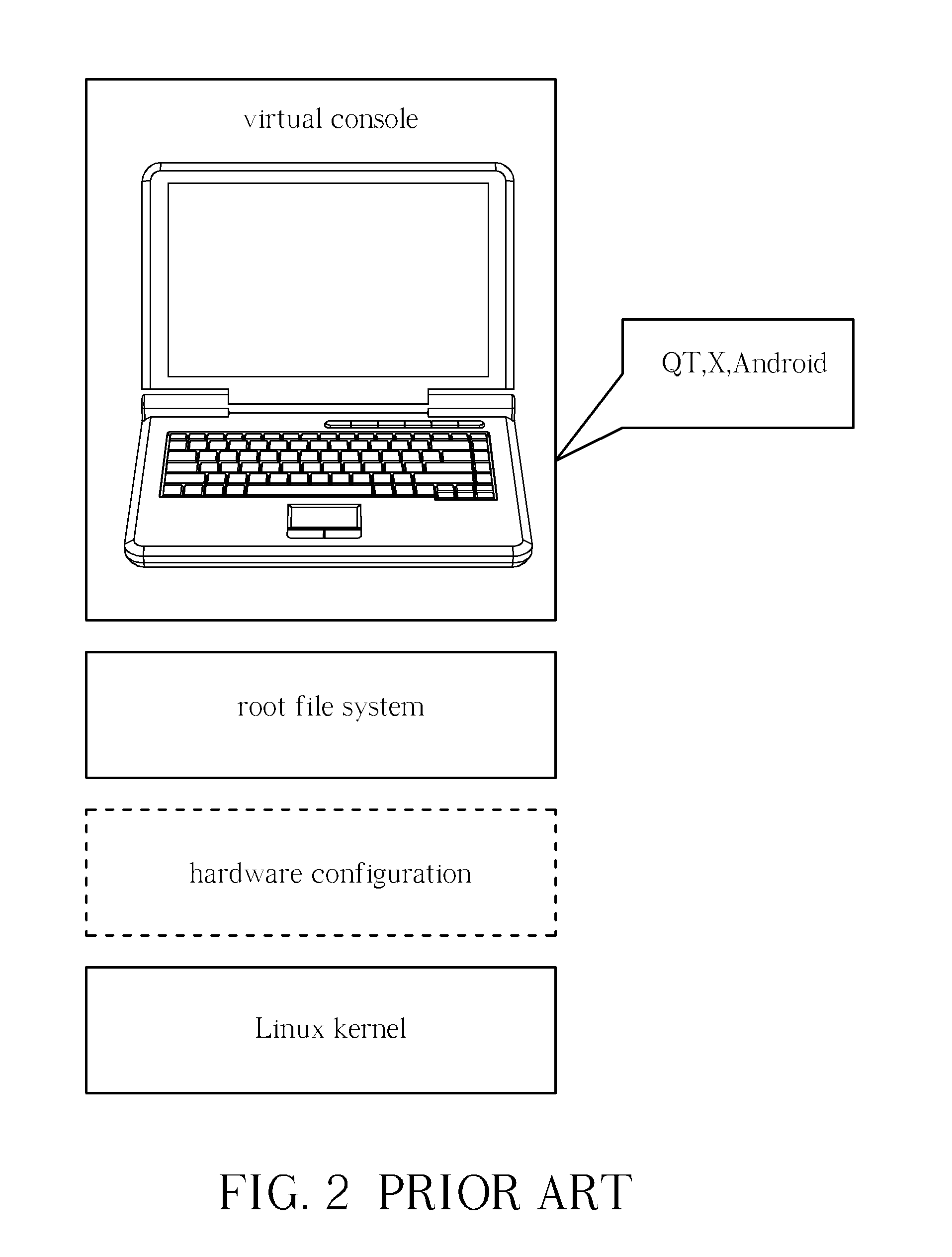
Application method for integrating heterogeneous operating systems based on the same system kernel
An application method for integrating heterogeneous operating systems based on the same system kernel is disclosed. The application method includes opening a master virtual console corresponding to a master operating system, opening a slave virtual console corresponding to a slave operating system in the master virtual console, and establishing a share information area for the master operating system and the slave operating system and switching to slave virtual console to operate on the slave operating system.
Owner:WISTRON CORP
Operation method and device of application program on the basis of application program programming interface
ActiveCN105607895AReduce development costsIncrease flexibilitySpecific program execution arrangementsOperational systemApplication programming interface
The embodiment of the invention provides an operation method and device of an application program on the basis of an application program programming interface. The method comprises the following steps: when an application program programming interface calling request sent from the application program is received, extracting a calling parameter from the calling request; according to the calling parameter, looking up the corresponding application program programming interface; calling the application program programming interface, and obtaining a processing result based on a system component; and returning the processing result to the application program. The design of the Hybrid API (Application Program Interface) of the embodiment of the invention faces various types of client sides, an API library which consistently calls a Native function is provided for a Web environment, the API library can operate on different operating systems including an Android system, an IOS (Iphone Operating System) system and the like, a use range is greatly improved, meanwhile, codes do not need to be complied according to different operating systems, and therefore, development cost is greatly reduced.
Owner:ALIBABA GRP HLDG LTD
Concurrent patching of operating systems
InactiveUS8352933B2Software engineeringDigital computer detailsOperational systemComputerized system
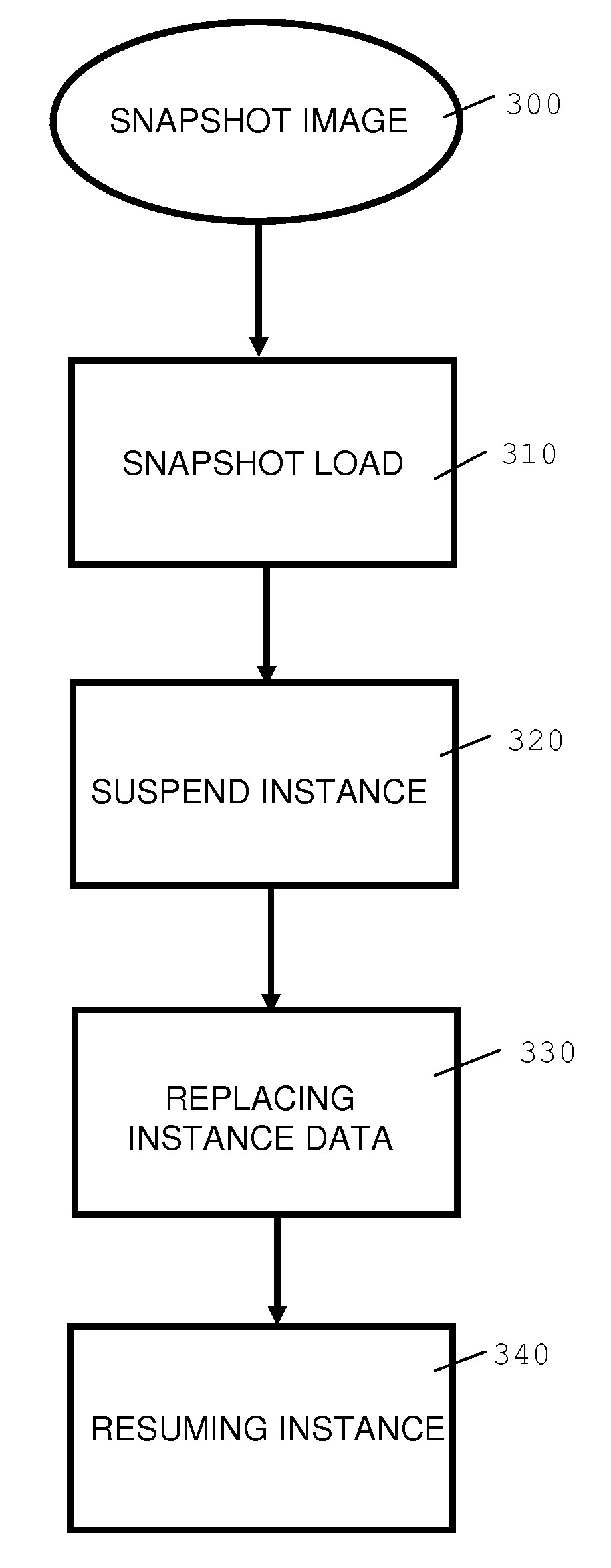
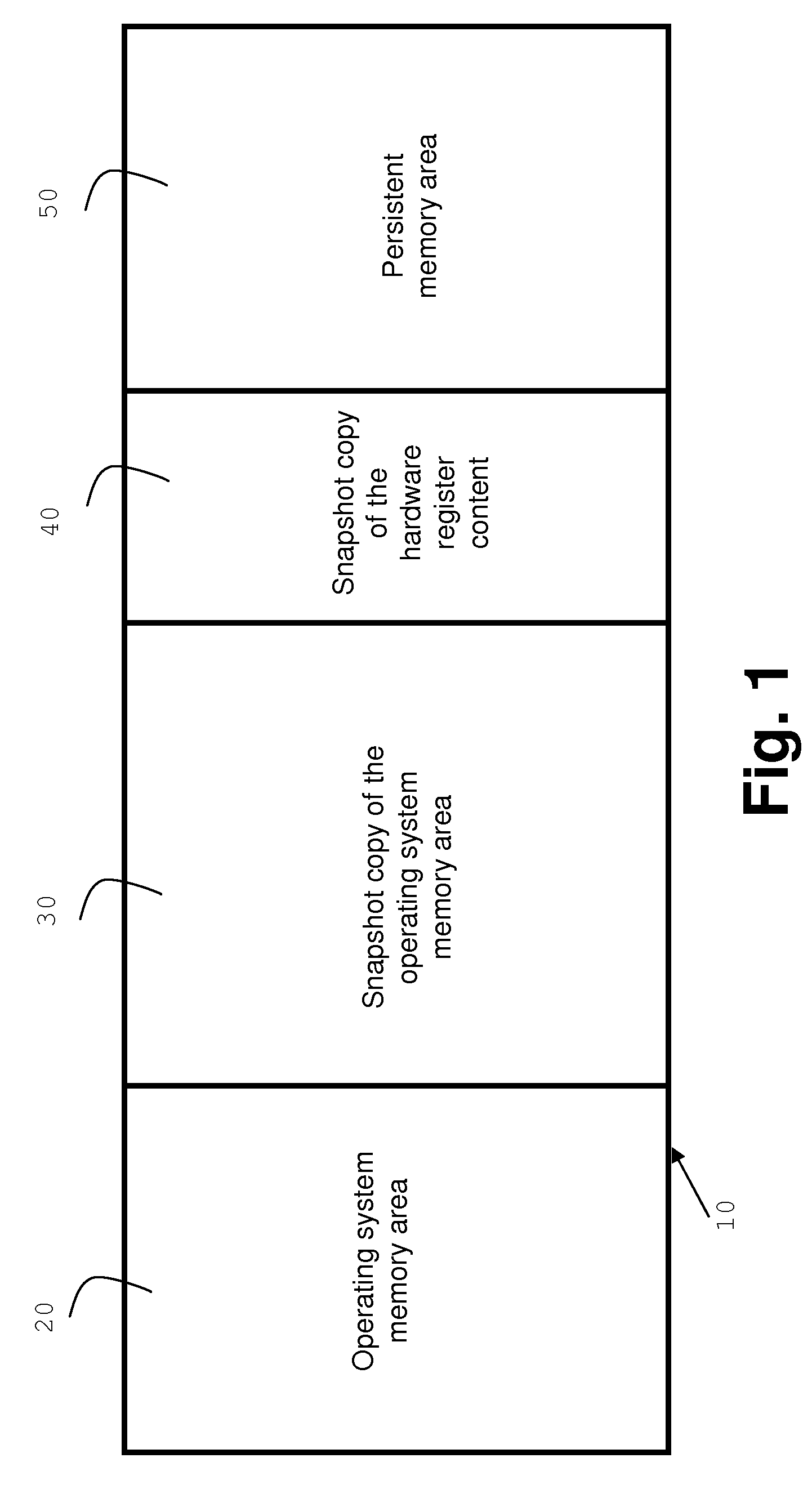
Replacing a computer program with a replacement version concurrently with its execution by a first instance of an operating system in a computer system, wherein a persistent memory area in the computer system is used to store selected data from the first instance. A snapshot image of a second instance of the operating system, wherein in the second instance the replacement version was executed instead of the computer program, is provided to the computer system. The execution of the first instance is suspended and the first instance is replaced with data from the snapshot image while preserving the persistent memory area. The execution of the first instance is resumed and data from the persistent memory area is restored in the first instance.
Owner:IBM CORP
Method for operating multiple operating systems and corresponding system and mobile equipment
ActiveCN104360900ASimple displaySimple input and outputMultiprogramming arrangementsDigital data authenticationVirtualizationOutput device
The invention relates to a method for operating multiple operating systems. The method comprises the following steps: operating a first operating system as a host operating system; starting a virtualization-supported virtual machine monitor program VMM on the host operating system; operating a second operating system on the VMM as a client operating system; selecting one of the first operating system and the second operating system as a foreground operating system and the other operating system as a background operating system to guarantee that the provided user experience is that the foreground operating system owns all input equipment and output equipment. The invention also relates to a corresponding system and mobile equipment.
Owner:SHANGHAI MICROVIRT SOFTWARE TECH
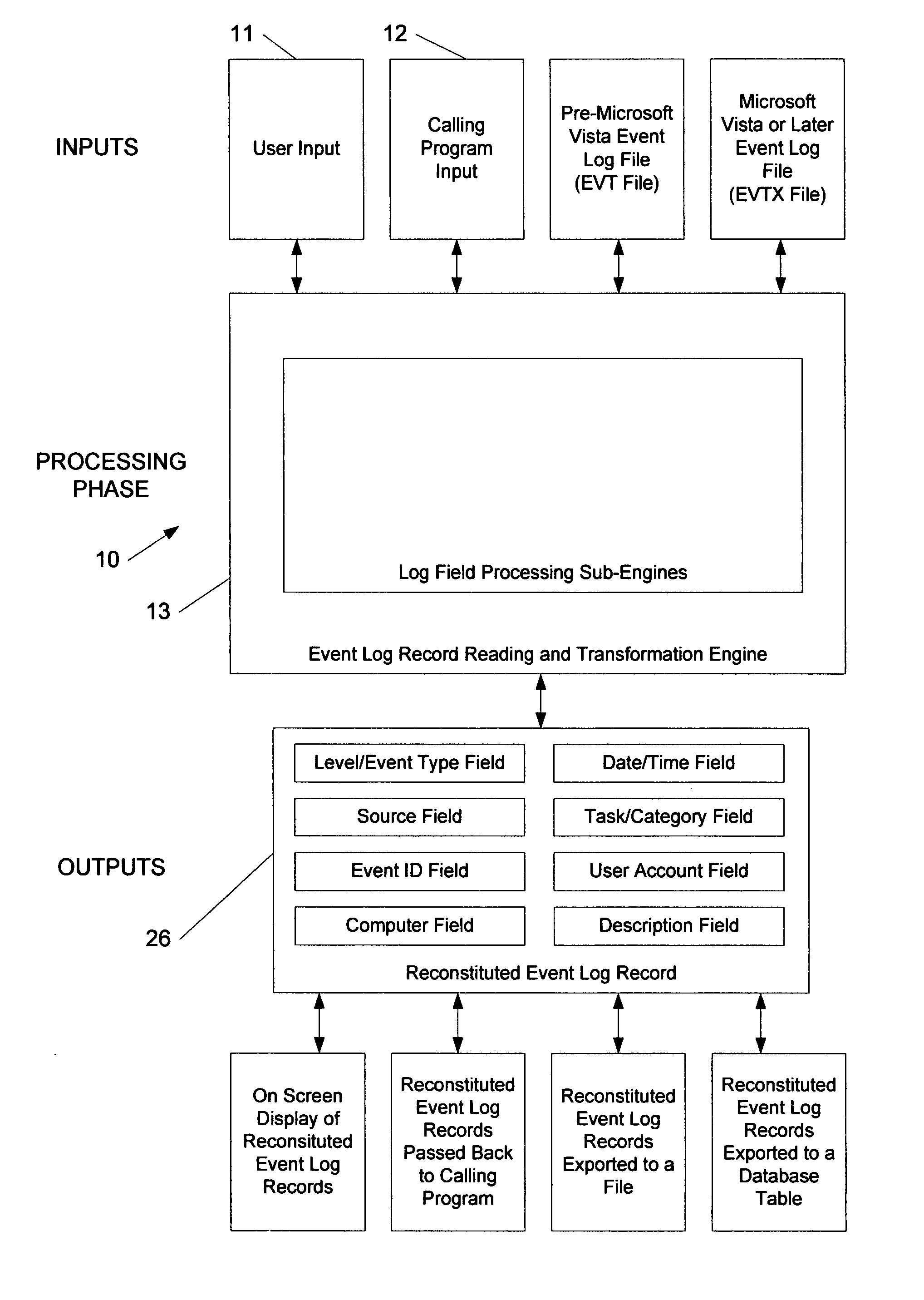
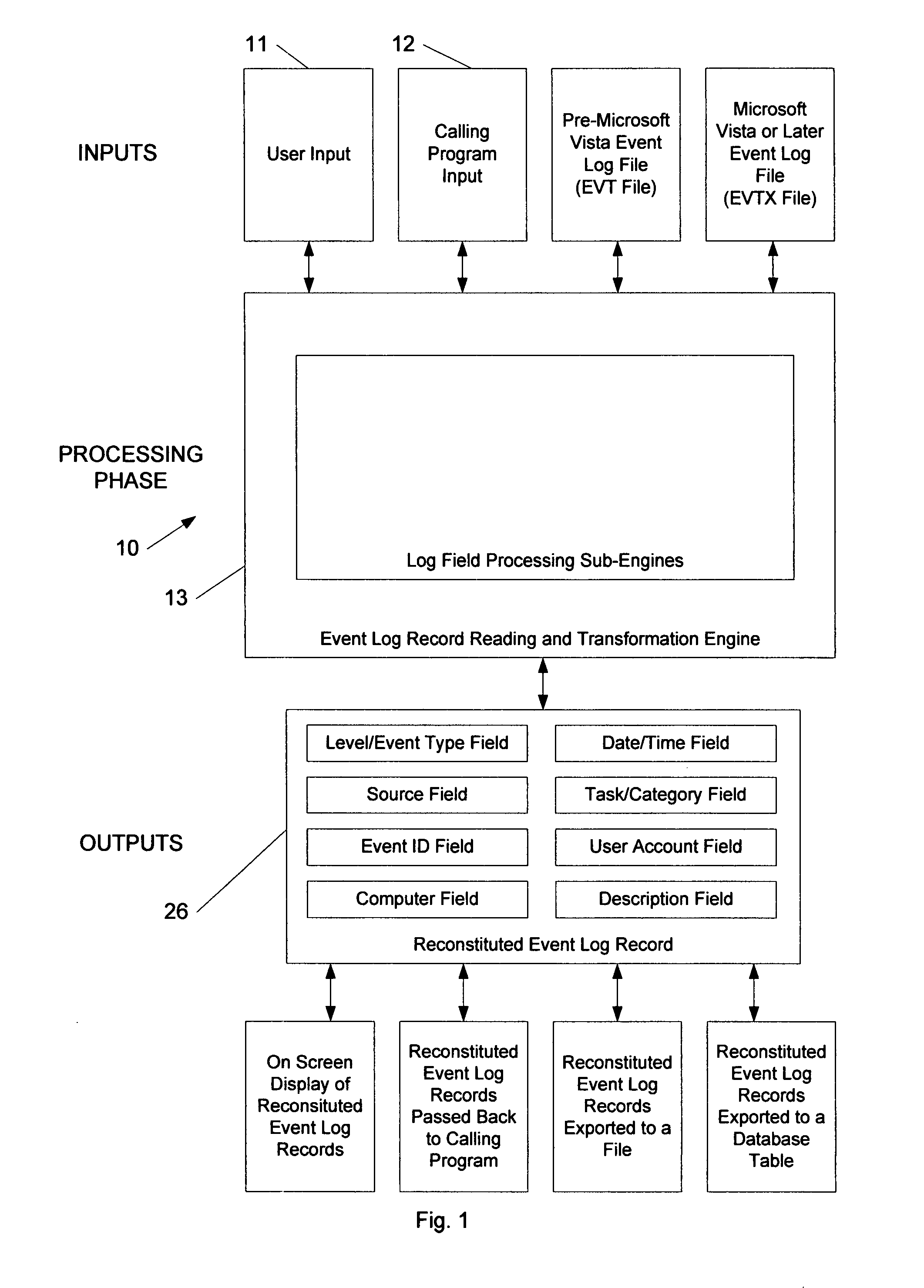
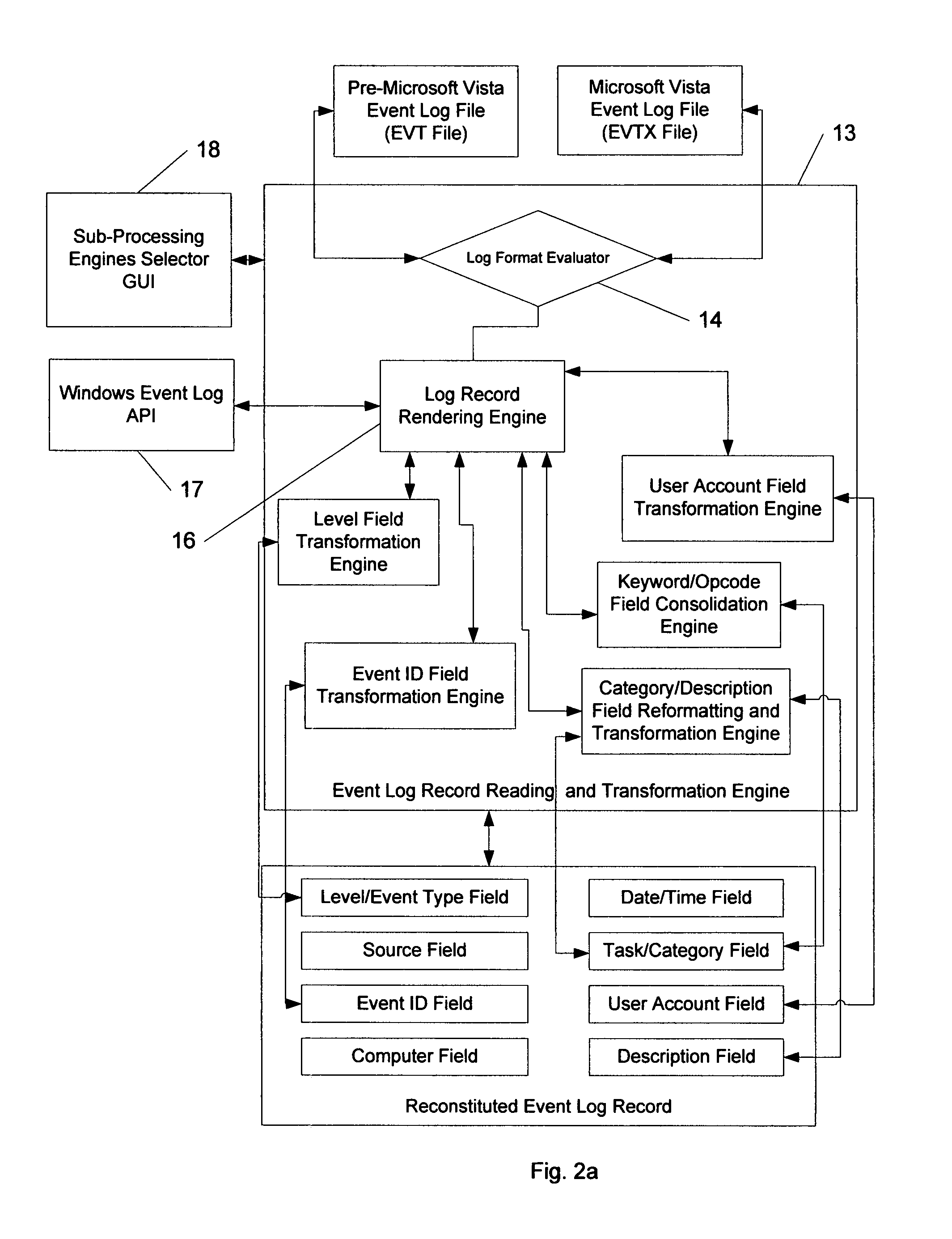
Method for transforming and consolidating fields in log records from logs generated on different operating systems
ActiveUS8086650B1Digital data information retrievalDigital data processing detailsOperational systemLog management
An event log translator for reading and translating, when necessary, the event log records from two distinct event log file formats (e.g. EVT and EVTX formats). Moreover, it is a system for consolidating the log records contained in either of the above formats into a common set of fields, which can be displayed to the user of a computer, exported into different formats (e.g. text files, database tables, etc) or consumed by an event log management system.
Owner:PROGRESS SOFTWARE
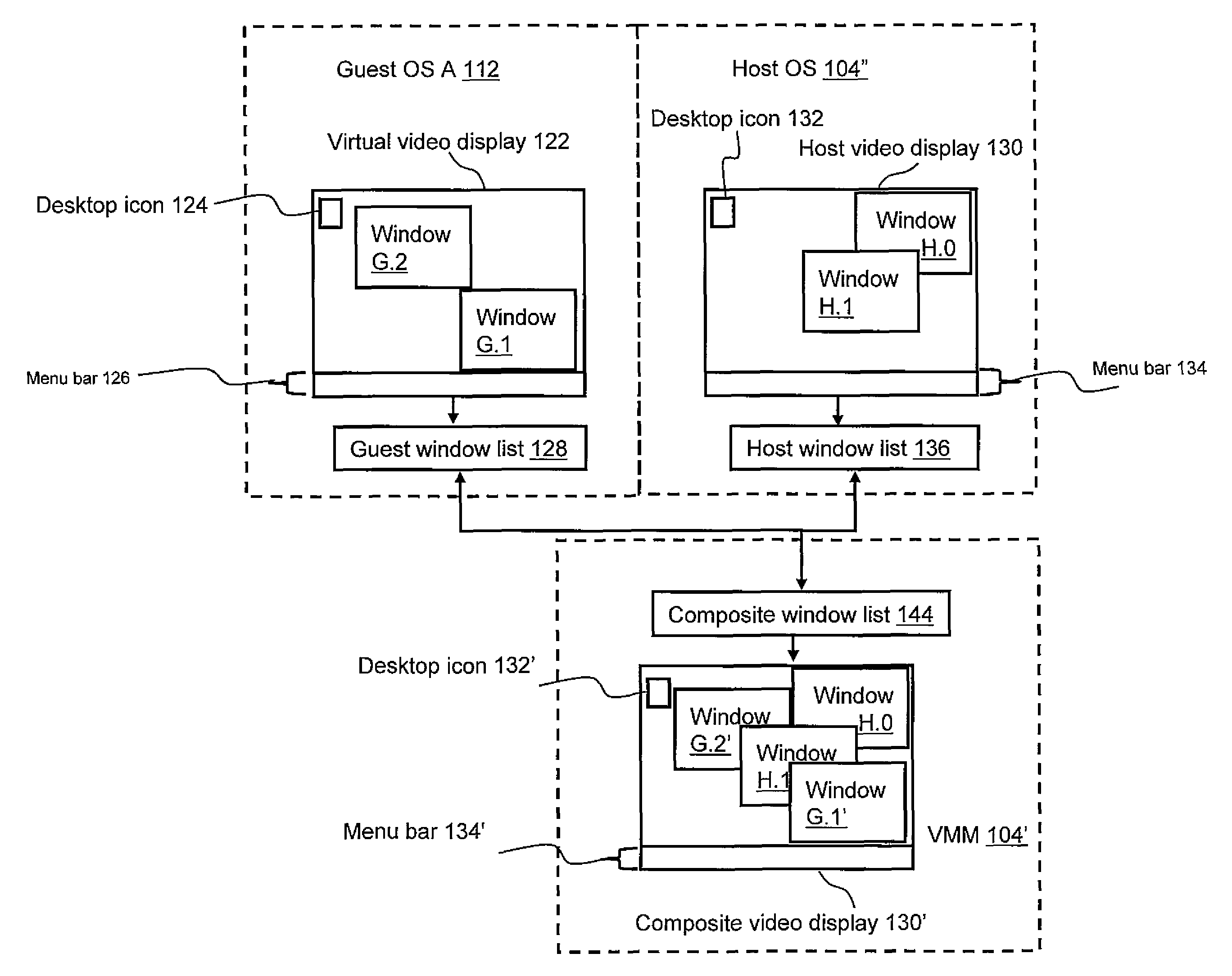
Systems and methods for integrating application windows in a virtual machine environment
ActiveUS7996785B2Reduce difficultyGood user interfaceExecution for user interfacesSoftware simulation/interpretation/emulationZ-orderComputer experience
The present invention includes systems for and methods of visually integrating application windows in a virtual machine environment. Embodiments of the present invention are directed to a system for and method of visually integrating application windows of host and guest operating system in a virtual machine environment in order to reduce difficulties that the users of computers experience in navigating between applications in a virtual machine environment. The present invention accomplishes this by using a composite window list in the virtual machine monitor (VMM) to manage the configuration, the focus, the geometry, the Z-order of the windows across guest and host operating systems, and the arrangement of doppelgangers (virtual application windows, in this case) in a way that allows host and guest application windows to appear integrated in a single display window.
Owner:MICROSOFT TECH LICENSING LLC
Upgrading method for operating systems and upgrading device for operating systems
ActiveCN104168557AImprove securityAvoid security issuesProgram loading/initiatingNetwork data managementOperational systemNetwork packet
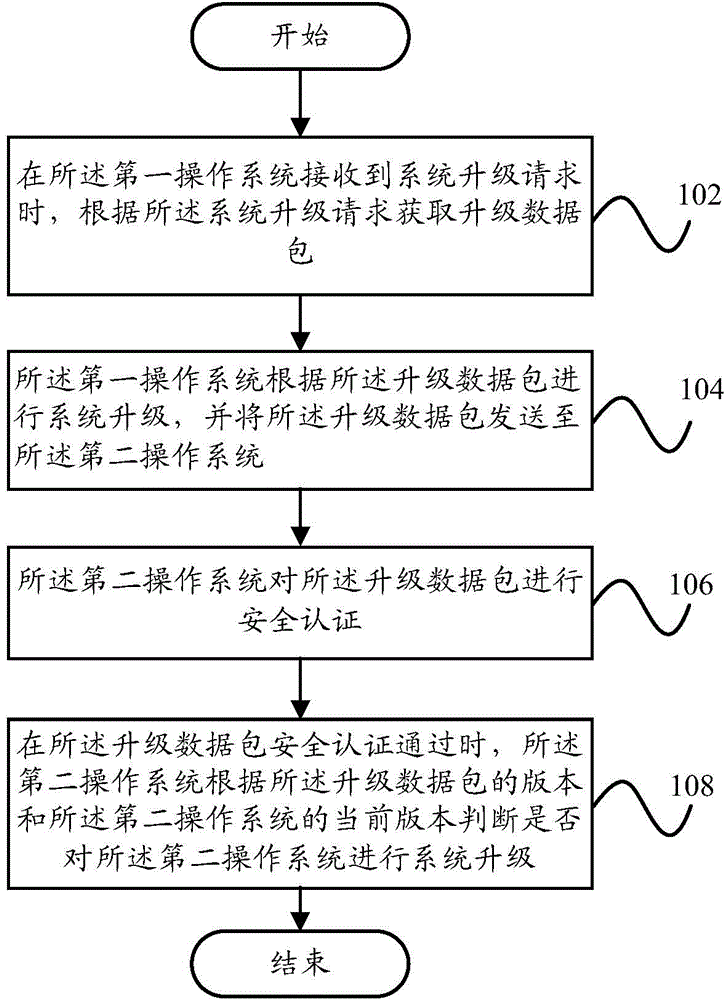
The invention provides an upgrading method for operating systems. The upgrading method is applied to a terminal. The terminal comprises the first operating system and the second operating system. The first operating system is allowed to have access to the Internet. The second operating system is forbidden to have access to the Internet. The upgrading method for the operating systems includes the steps that when the first operating system receives a system upgrading request, an upgrading data packet is obtained according to the system upgrading request; the first operating system is upgraded according to the upgrading data packet, and the upgrading data packet is sent to the second operating system; the second operating system conducts safety certification on the upgrading data packet; the second operating system judges whether to be upgraded or not according to the version of the upgrading data packet and the current version of the second operating system when the upgrading data packet passes safety certification. Accordingly, the invention further provides an upgrading device for the operating systems. According to the technical scheme, safety is ensured during upgrading while a safety system is upgraded.
Owner:COOLPAD SOFTWARE TECH (SHENZHEN) CO LTD
Storage network switch
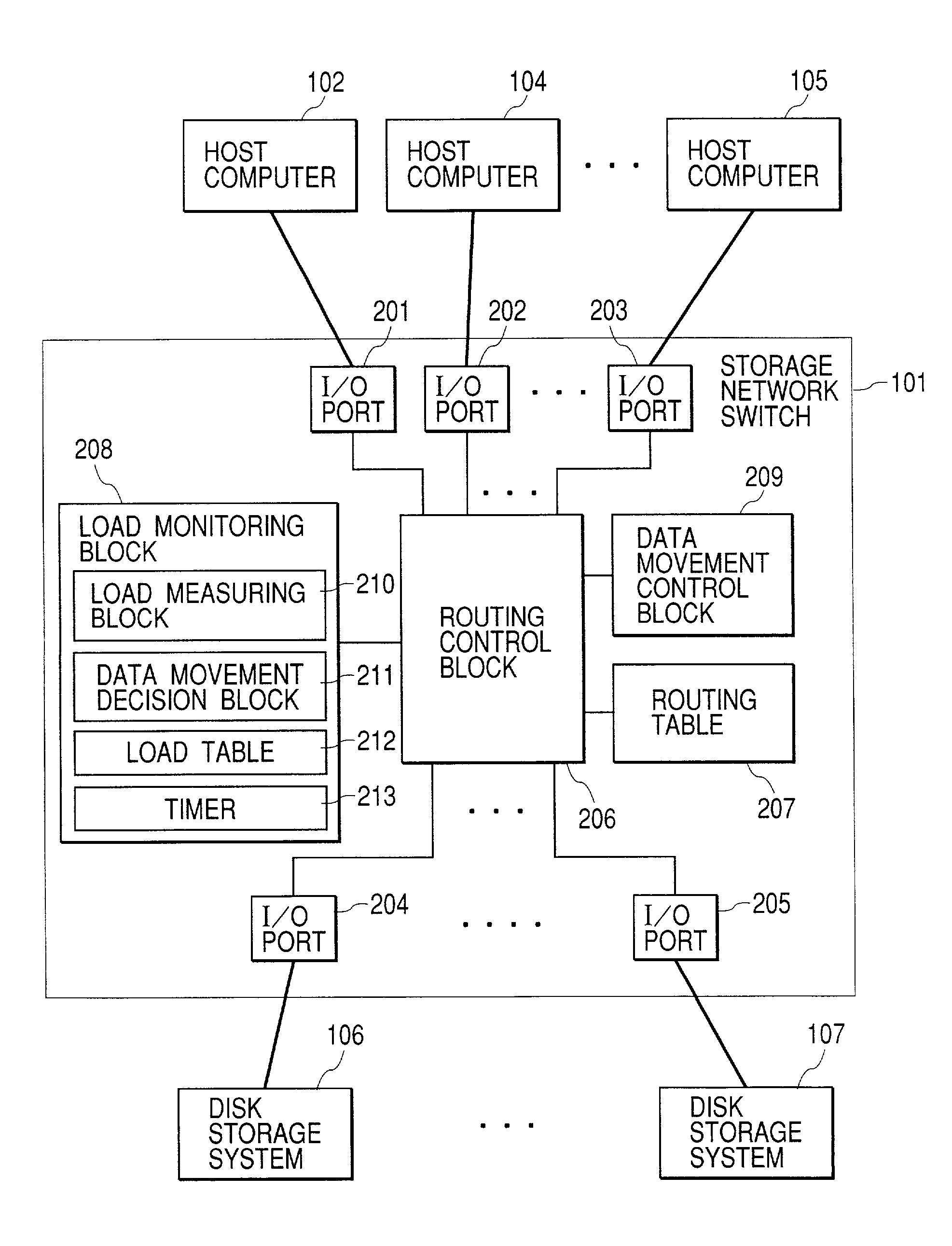
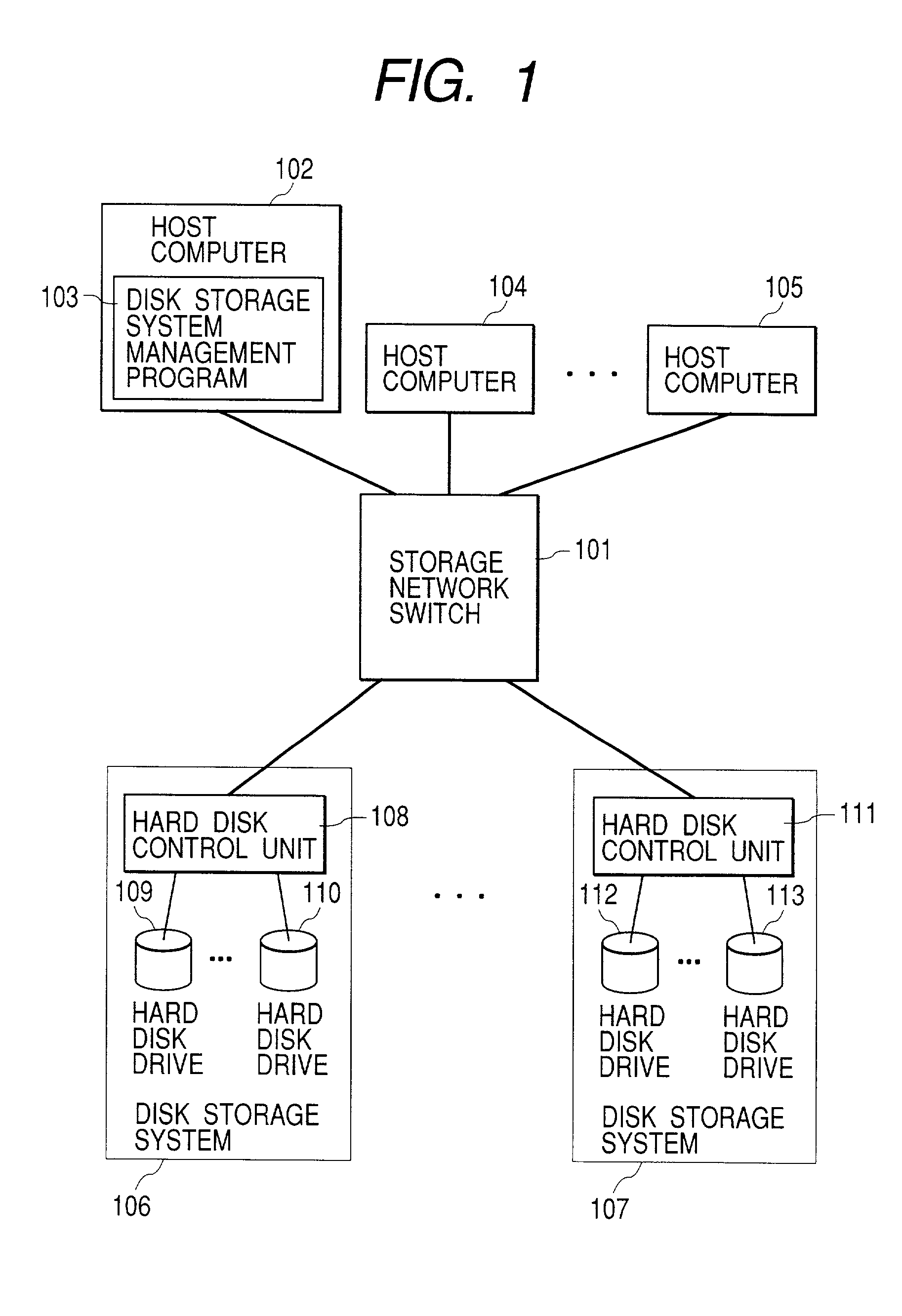
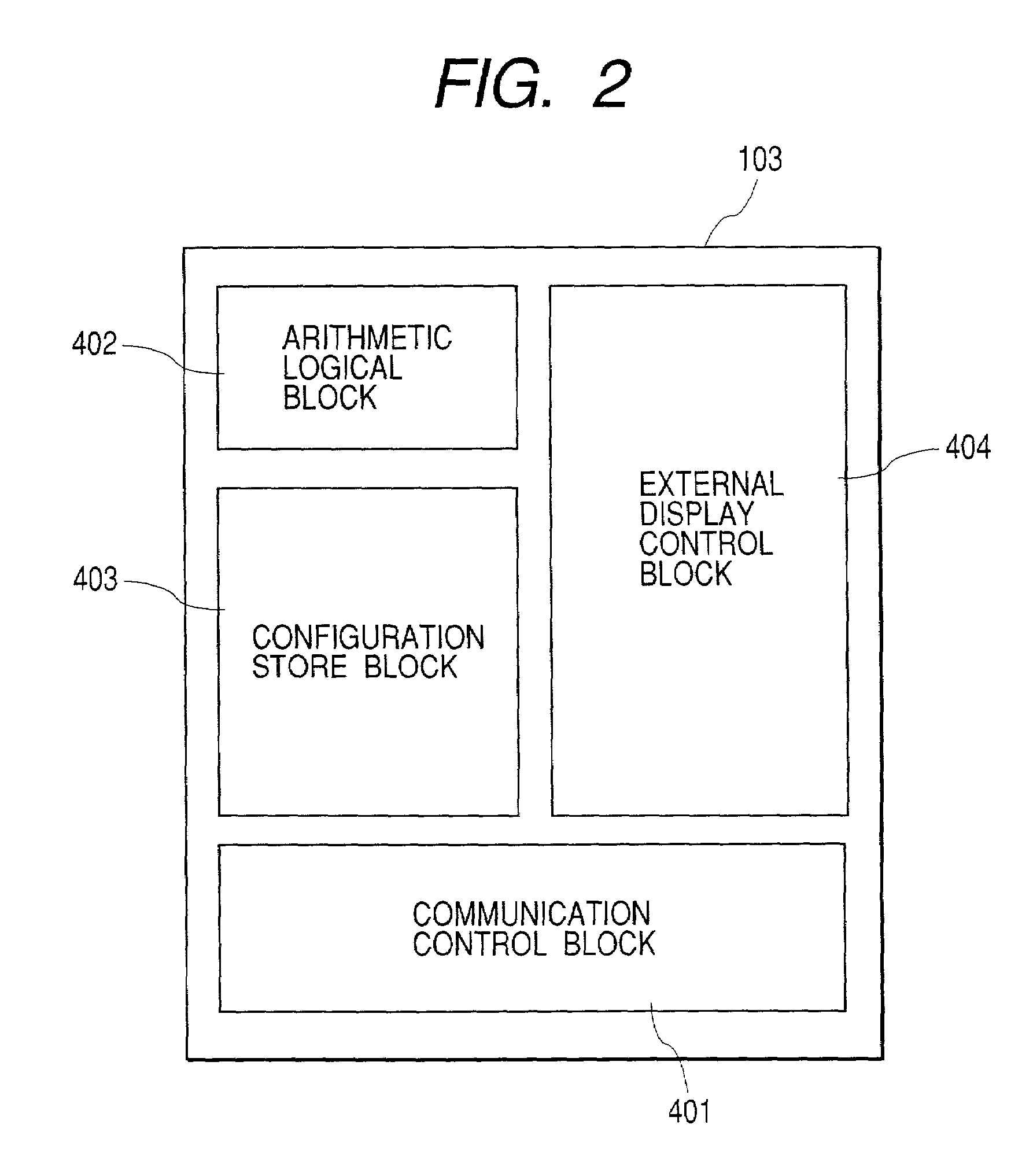
InactiveUS7356581B2Efficient load balancingReduce the burden onInput/output to record carriersResource allocationNetwork switchHybrid storage system
The present invention provides a storage network switch suitable for effective load balancing of a plurality of disk storage systems along with the mitigated burden of the host computer. The storage network switch for connecting a plurality of host computers to a plurality of disk storage systems has a load measuring means, and a data movement facility if required.
Owner:HITACHI LTD
Virtualization method based on operating system layer
InactiveCN102339229AReduce overheadImprove performanceSoftware simulation/interpretation/emulationVirtualizationNetwork operating system
The invention provides a bottom virtualization process (namely, virtualization for an operating system layer). According to a method, virtualization is realized by adding a virtual server function in an operating system layer. The bottom virtualization process comprises the following steps of: forming a virtualized layer on a hardware layer, thereby finishing virtualized integration of physical equipment; installing a plurality of client operating systems on the virtualized layer; and running an application program in the client operating systems. The client operating systems are communicated with the hardware through a VMM (Virtual Machine Monitor) in the virtualized layer, wherein the VMM is used for determining the access of all virtual machines to physical resources. In a virtualization solution, the VMM plays a role of a traditional operating system in a software set and the traditional operating system as the client operating system runs on the virtualized layer at a position of the application program. Compared with other virtualization processes, the bottom virtualization process has the advantages that a manager need not install and maintain a single operating system embodiment for each application, thereby lowering the management cost.
Owner:戴元顺
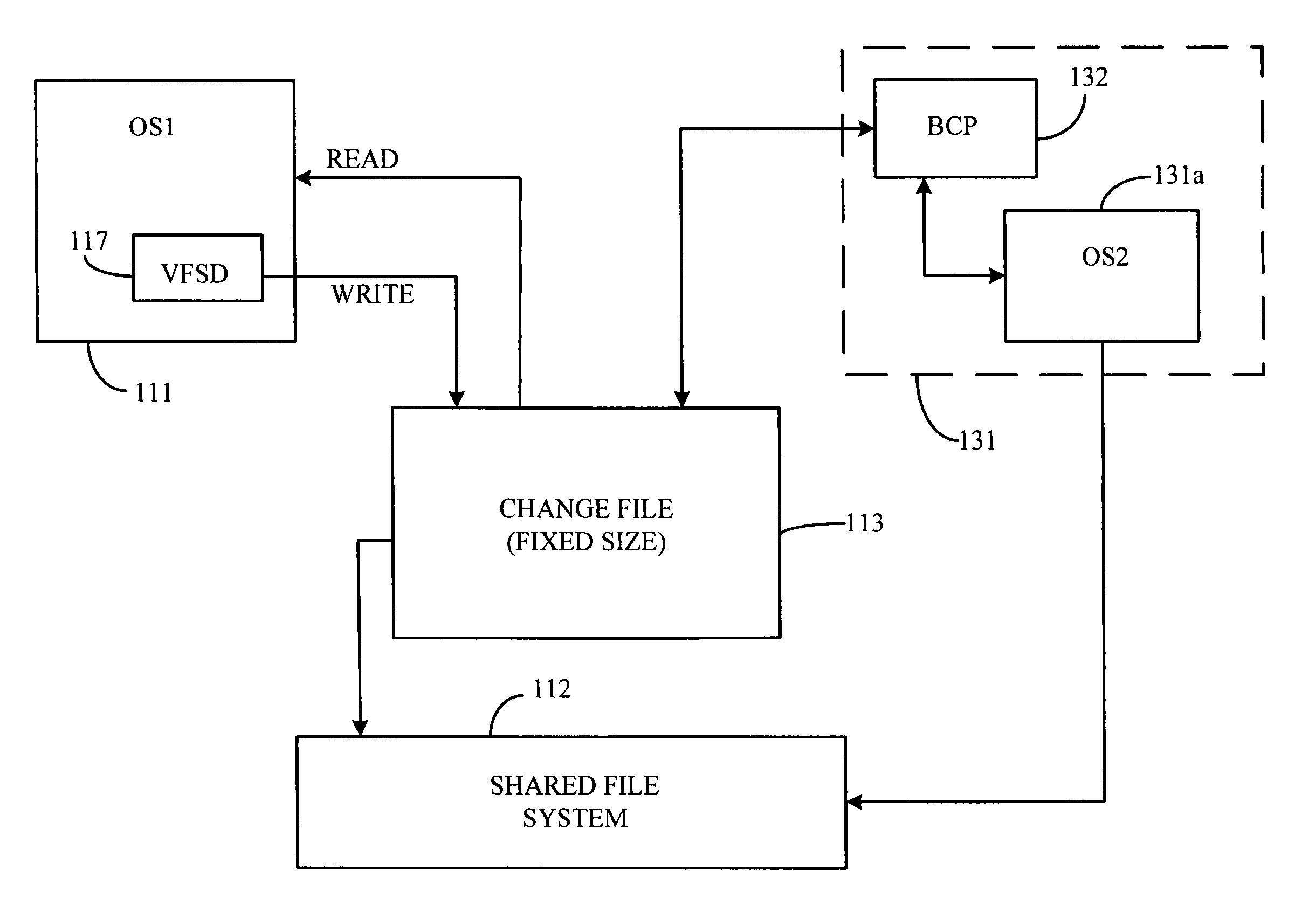
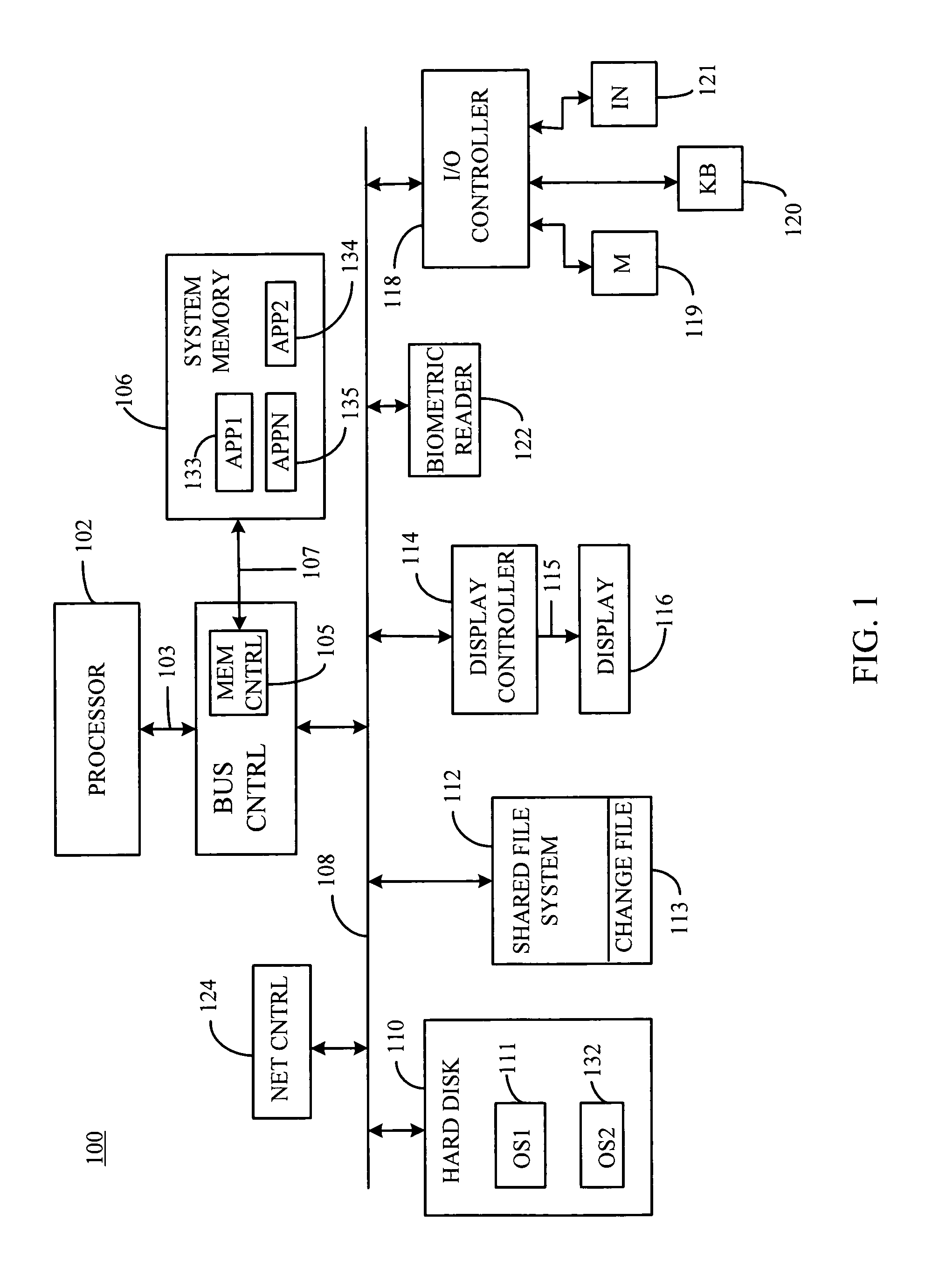
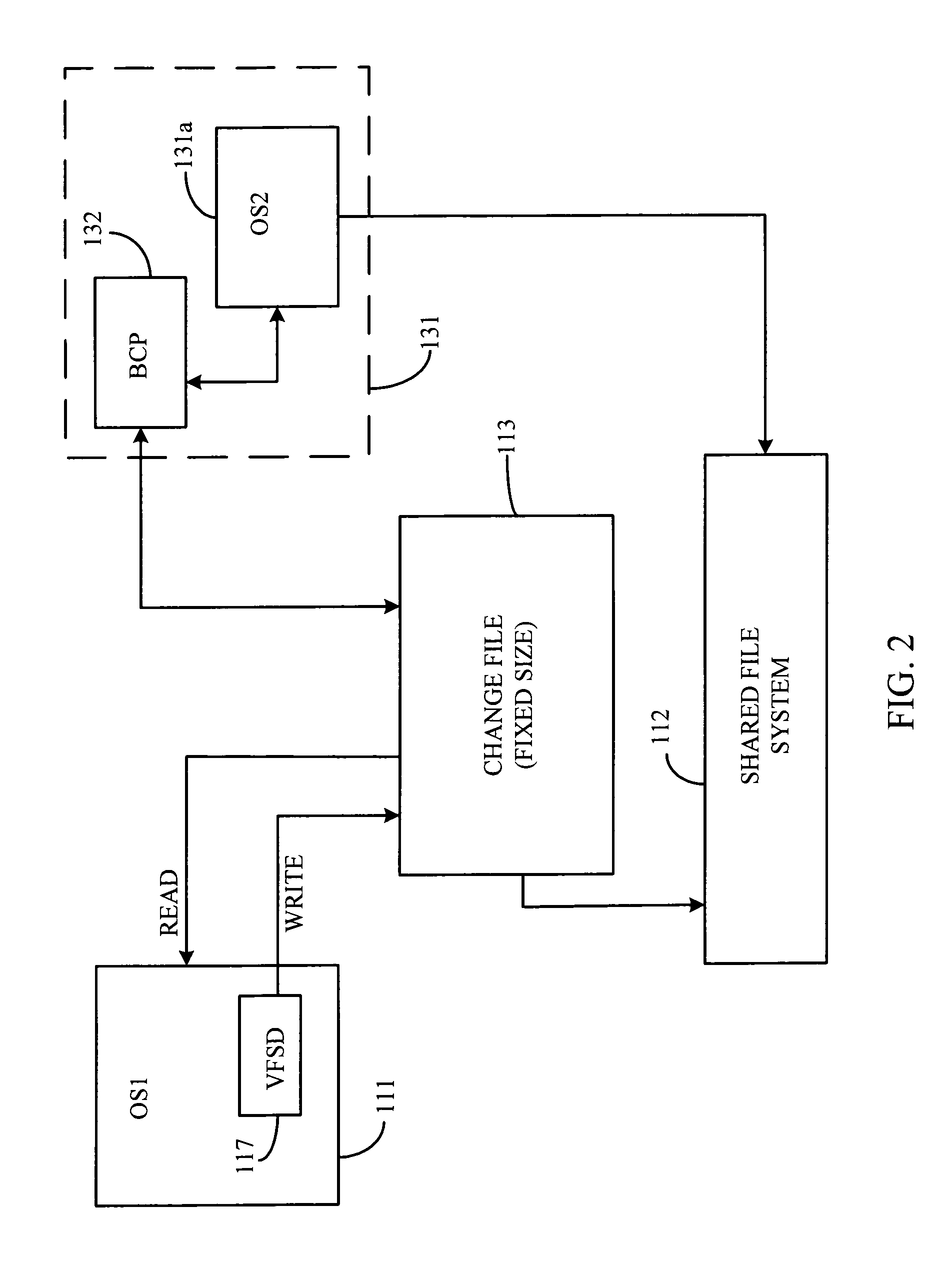
Shared file system management between independent operating systems
ActiveUS8195624B2Preventing conflicts during file system updatingDigital data information retrievalDigital data processing detailsFlash file systemOperational system
A shared file system may be updated by a non-native operating system writing information to a change file, while a native operating system is in a suspend or hibernation mode; after writing, the non-native operating system is placed in a suspend or hibernation mode and the native system activates and then retrieves the updated information from the change file and writes the updated information to a shared file system. The native operating system returns to a suspend or hibernate state before the non-native operating resumes operation. The updated information may be written as provided by the non-native operating system, or further updated by the native operating system before being written to the shared file system. The change file is created by the native operating system, and may be a reserved portion of the shared file system or may be a separate portion of non-volatile memory. The native and non-native operating systems operate both concurrently and independent of one another; thereby, preventing conflicts during file system updating.
Owner:INSYDE SOFTWARE CORP
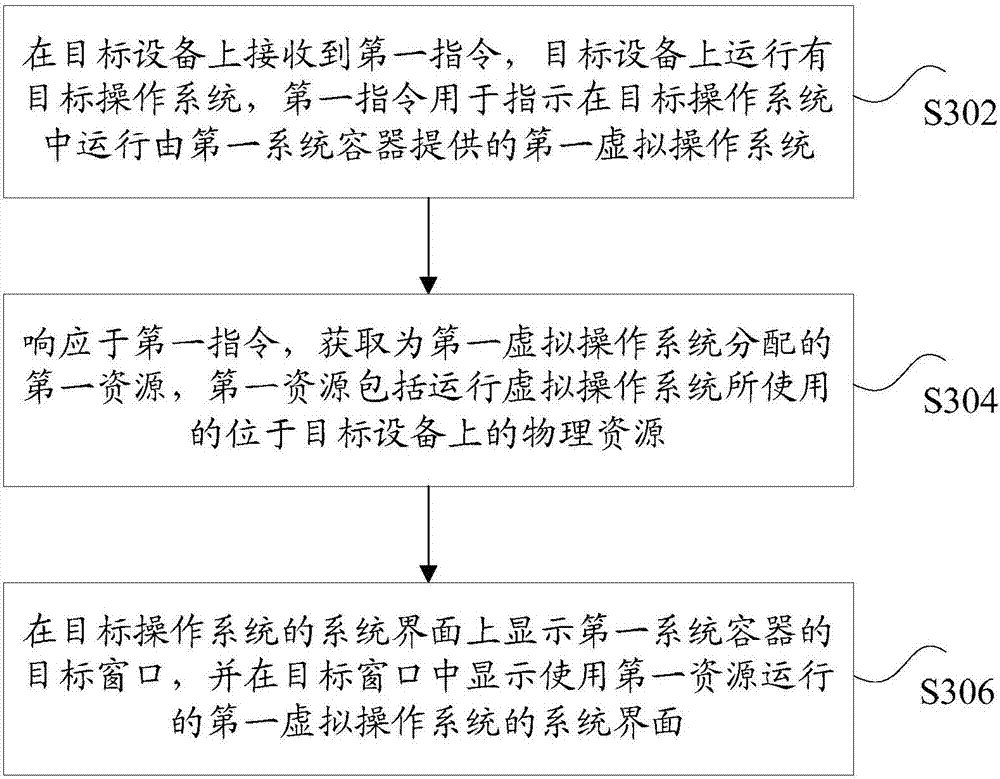
Running method and device of virtual operating systems
ActiveCN107463402ASolve technical issues with slow startupFast startupProgram loading/initiatingSoftware simulation/interpretation/emulationVirtual machineDisk operating system
The invention discloses a running method and device of virtual operating systems. The method includes: receiving a first instruction on a target device, wherein a target operating system is run on the target device, and the first instruction is used to indicate running of a first virtual operating system, which is provided by a first system container, in the target operating system; in response to the first instruction, acquiring first resources allocated for the first virtual operating system, wherein the first resources include physical resources which are used by running the virtual operating system and located on the target device; and displaying a target window of the first system container on a system interface of the target operating system, and displaying a system interface of the first virtual operating system, which is run by using the first resources, in the target window, wherein a system kernel of the first virtual operating system is a system kernel of the target operating system, and system drivers of the first virtual operating system are system drivers of the target operating system. The method solves the technical problem that starting of virtual machines is slower in the related art.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Swapping “fixed system” hard disk
InactiveUS7949814B2Attach and detachDigital data processing detailsDigital computer detailsMotherboardPower management
Method for ‘Cool-Swap’, ‘Warm-Swap’ and ‘Hot-Swap’ of ‘Fixed’‘System’ hard disk(s) in and out of the computer and for re-cycling the computer between ‘diskly’ state to ‘diskless’ state by combining the following features in one way or the other: separating the power supply of the ‘Fixed’‘System’ hard disk(s) from the internal power supply that is supplying power to other components of the computer, in particular the motherboard; taking the operating system, capable of being taken to run as ramdisk-based operating system, in control of the computer to run as ramdisk-based operating system; putting the computer into different power management states; and issuing commands or instructions for logical disconnection and / or re-connection of hard disk(s).
Owner:CHAN KAM FU
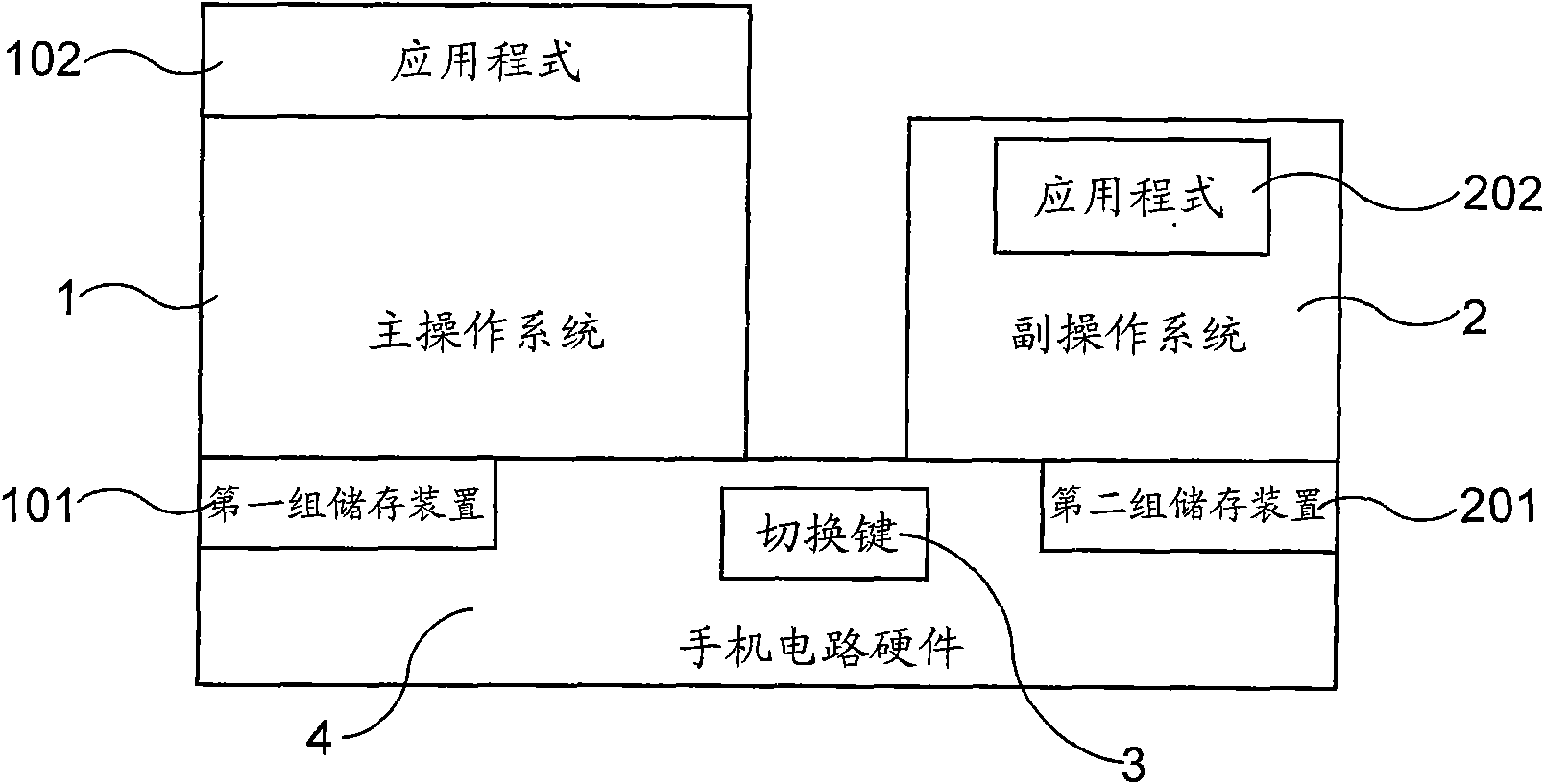
High-safety two-operating system mobile phone capable of resisting hackers and being used for Internet banking
The invention relates to a high-safety two-operating system mobile phone capable of resisting hackers and being used for Internet banking, which comprises two mutually independent operating systems, namely a main operating system (1) and an auxiliary operating system (2), and a switching key (3), wherein the main operating system (1) is equivalent to a general operating system of a mobile phone and provides various convenient and easy functions; the auxiliary operating system (2) is a limited operating system which can only execute the internal programs of the auxiliary operating system (2) but can not execute other external programs, can avoid invasion of virus or Trojan programs, and can be used for applications with high safety requirements, such as Internet banking service, processing of confidential documents, sending and receiving of e-mails and the like; and the switching key (3) is used for selecting the running operating system, and when the mobile phone responds to the action of the switching key (3), the switching key (3) can immediately suspend the operation of the current operating system, and then switches to the other operating system, and a user can select the main operating system (1) or the auxiliary operating system (2) at any time by the switching key (3).
Owner:黄金富
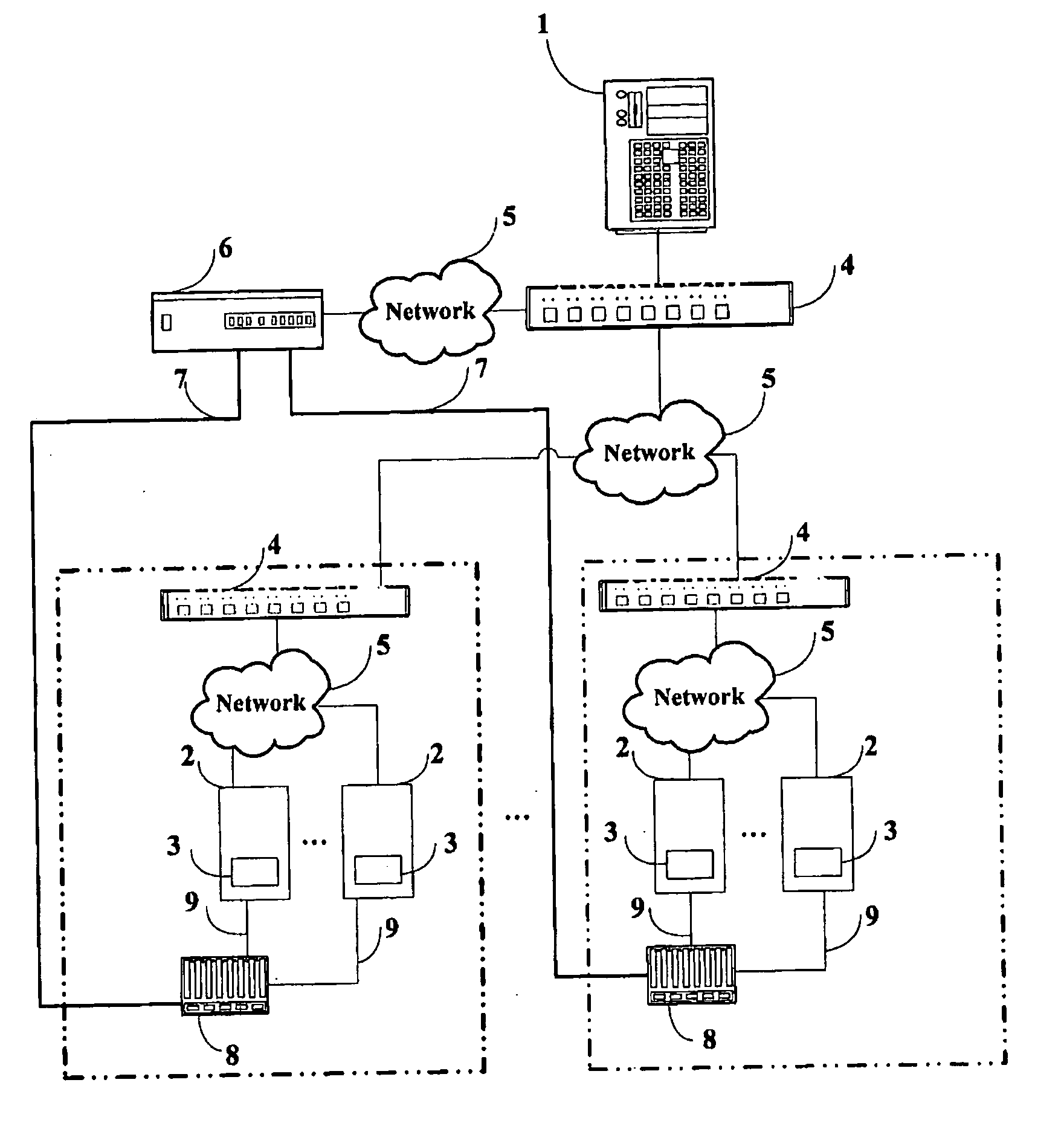
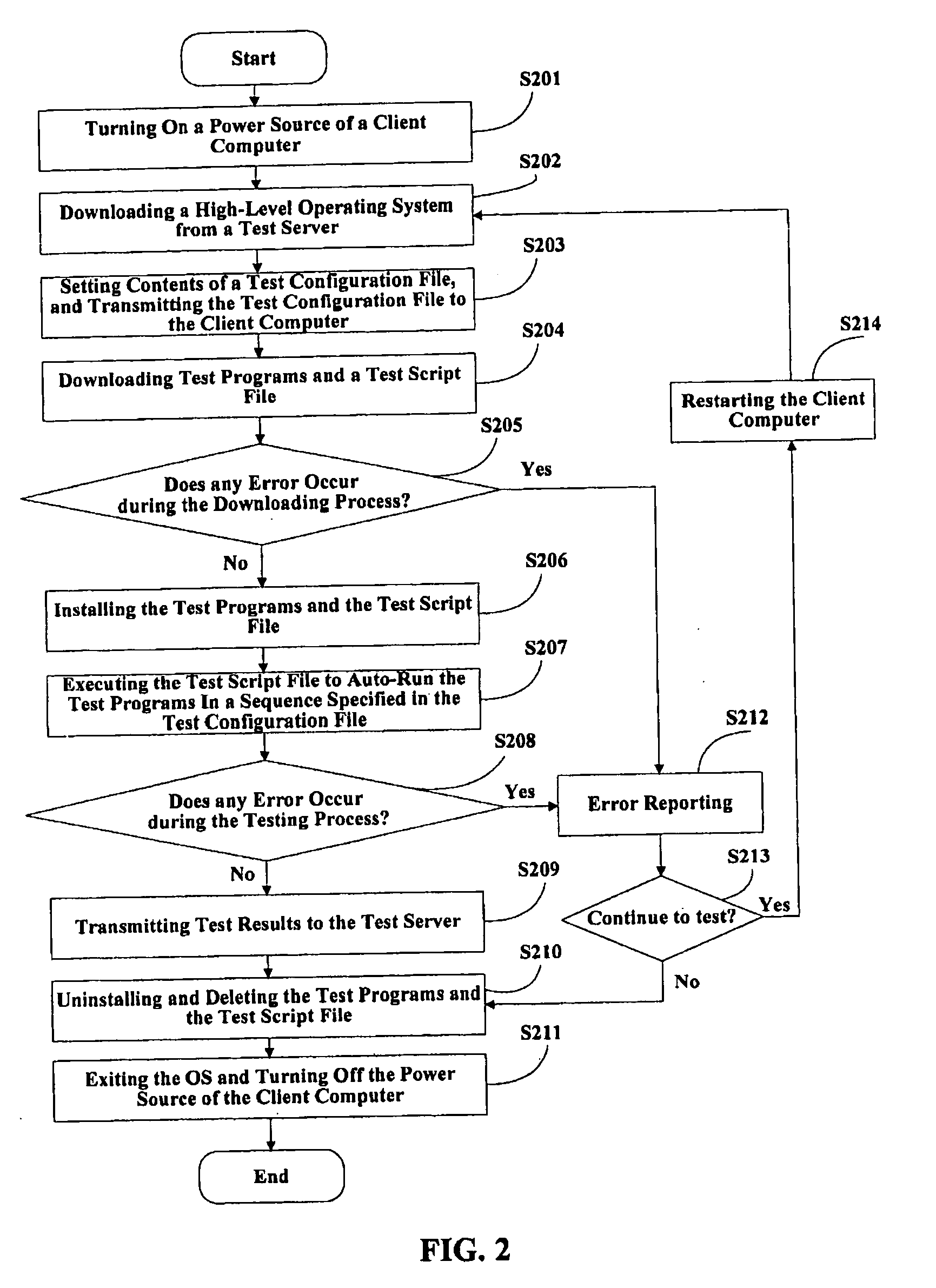
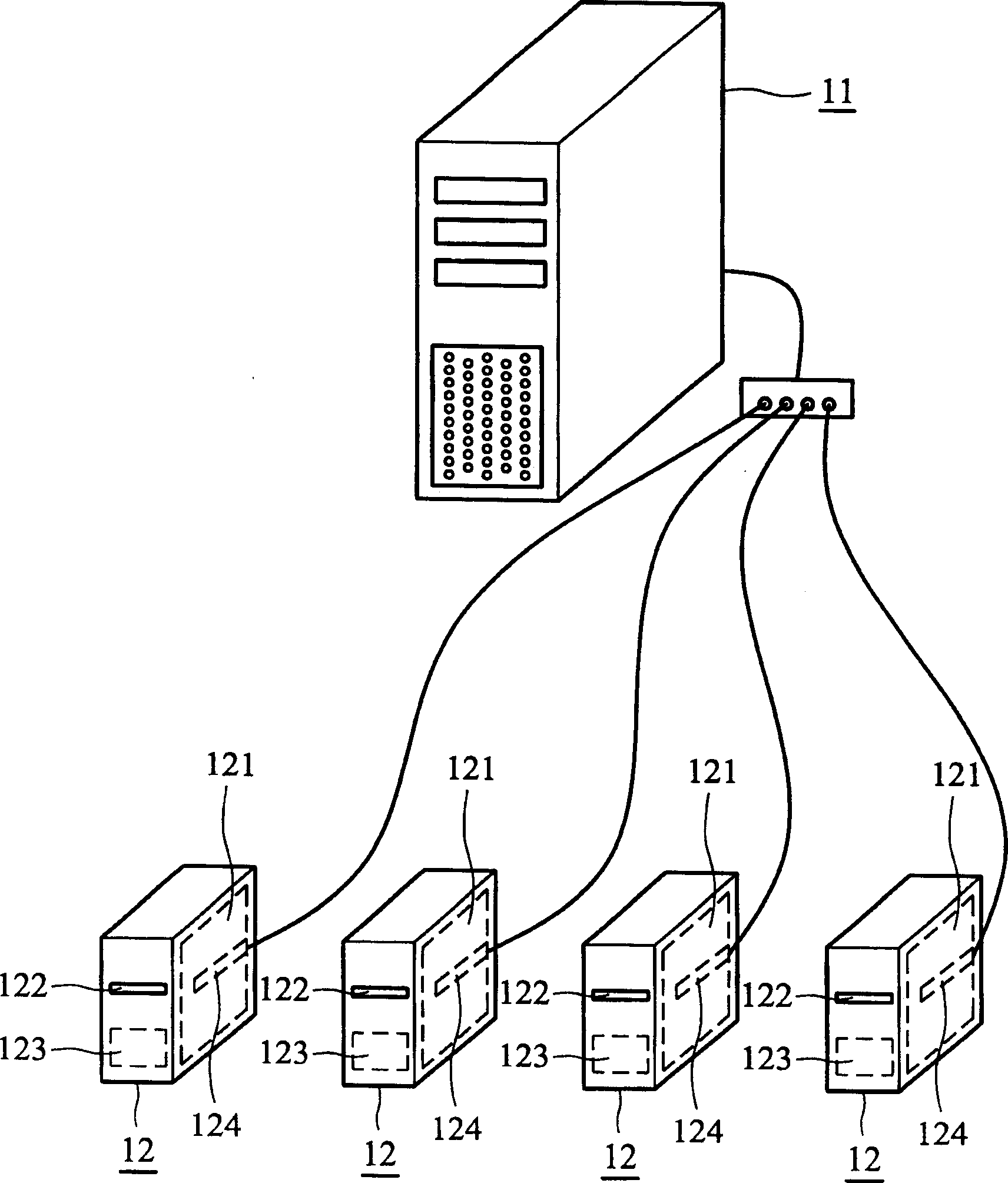
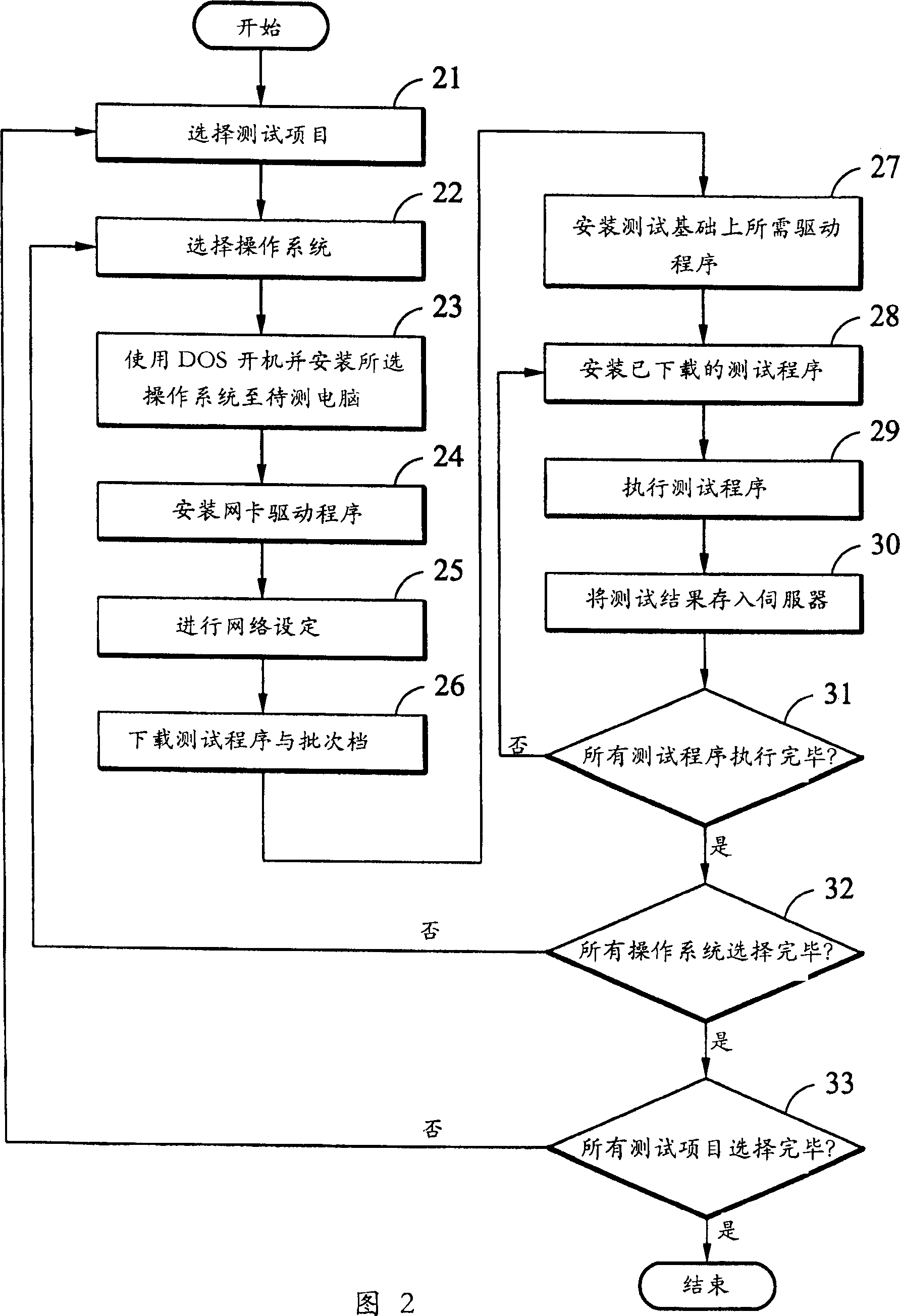
System and method for automatically testing motherboards
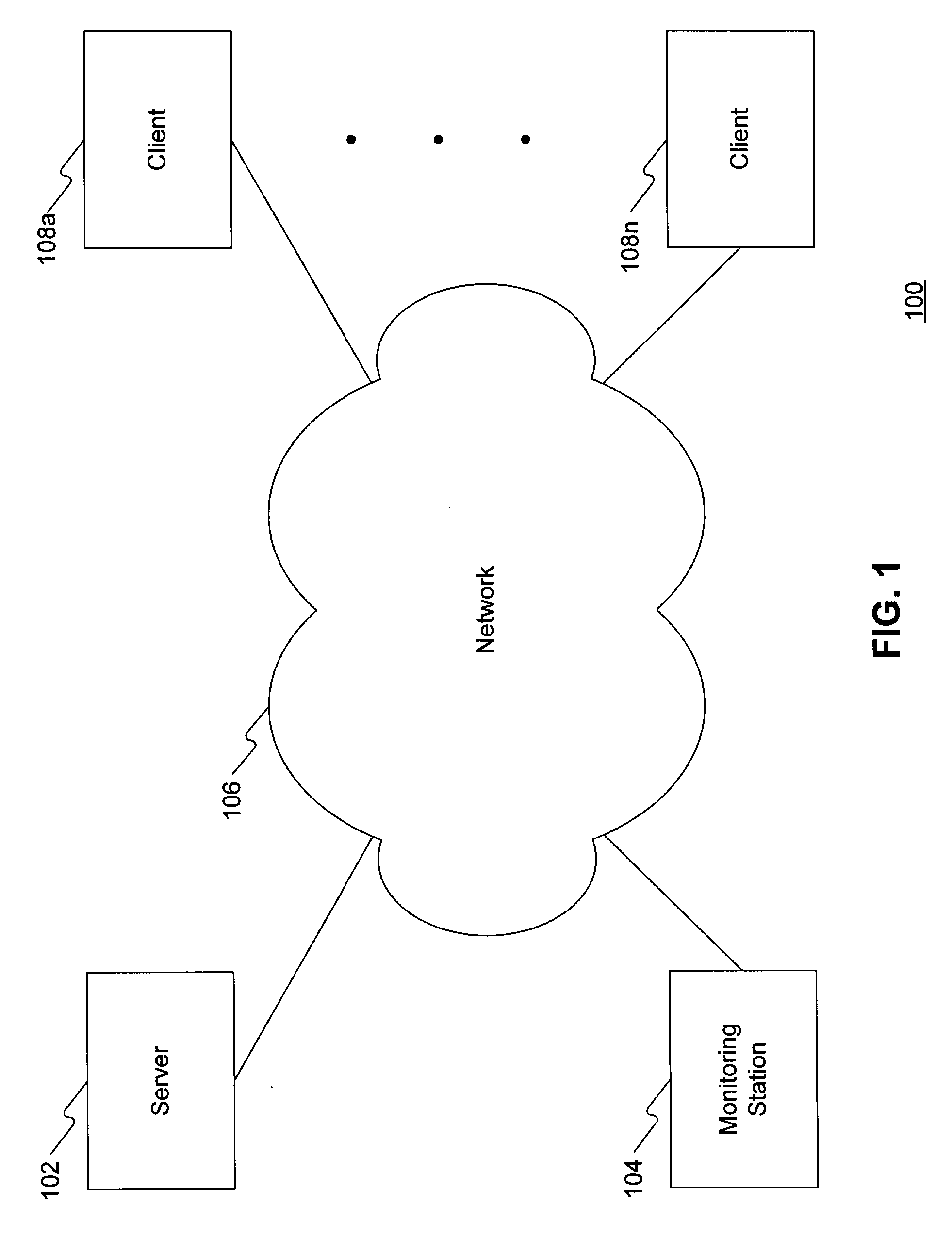
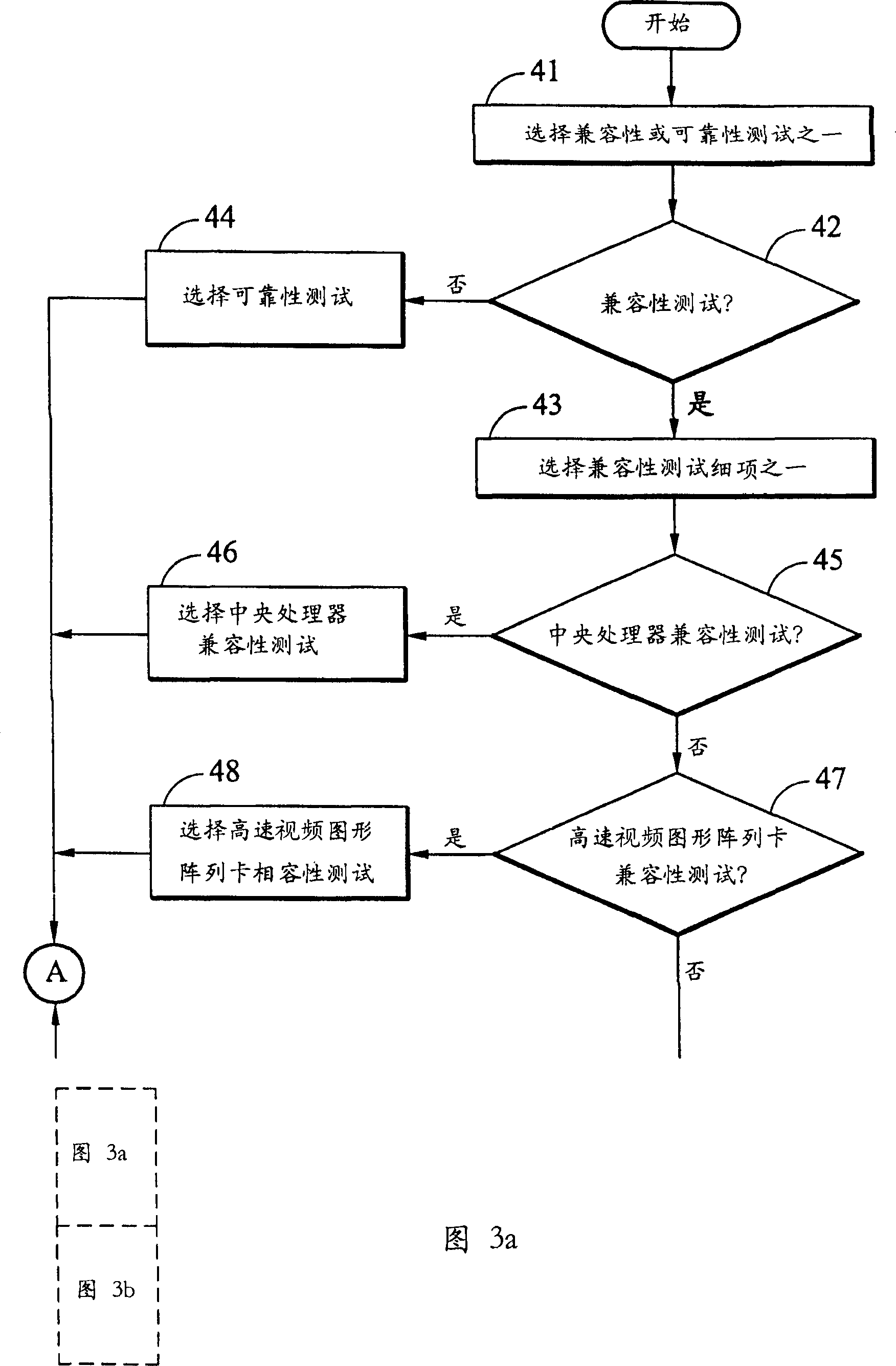
InactiveUS20050246589A1Resistance/reactance/impedenceDetecting faulty hardware by remote testTest scriptOperational system
A system for automatically testing motherboards includes a test server (1), client computers (2), and a network (5) connecting the test server with the client computers. The test server is for storing a plurality of high-level OSs (Operating Systems), test programs and test script files, for setting contents of test configuration files, and for storing test results. Each client computer has a motherboard installed therein, and is operated under a DOS (Disk Operating System). The client computer downloads and installs a high-level OS from the test server, downloads and installs one or more test programs and a test script file according to a test configuration file set by the test server, executes the test script file to auto-run test programs in a sequence specified in the test configuration file, and then transmits test results to the test server.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
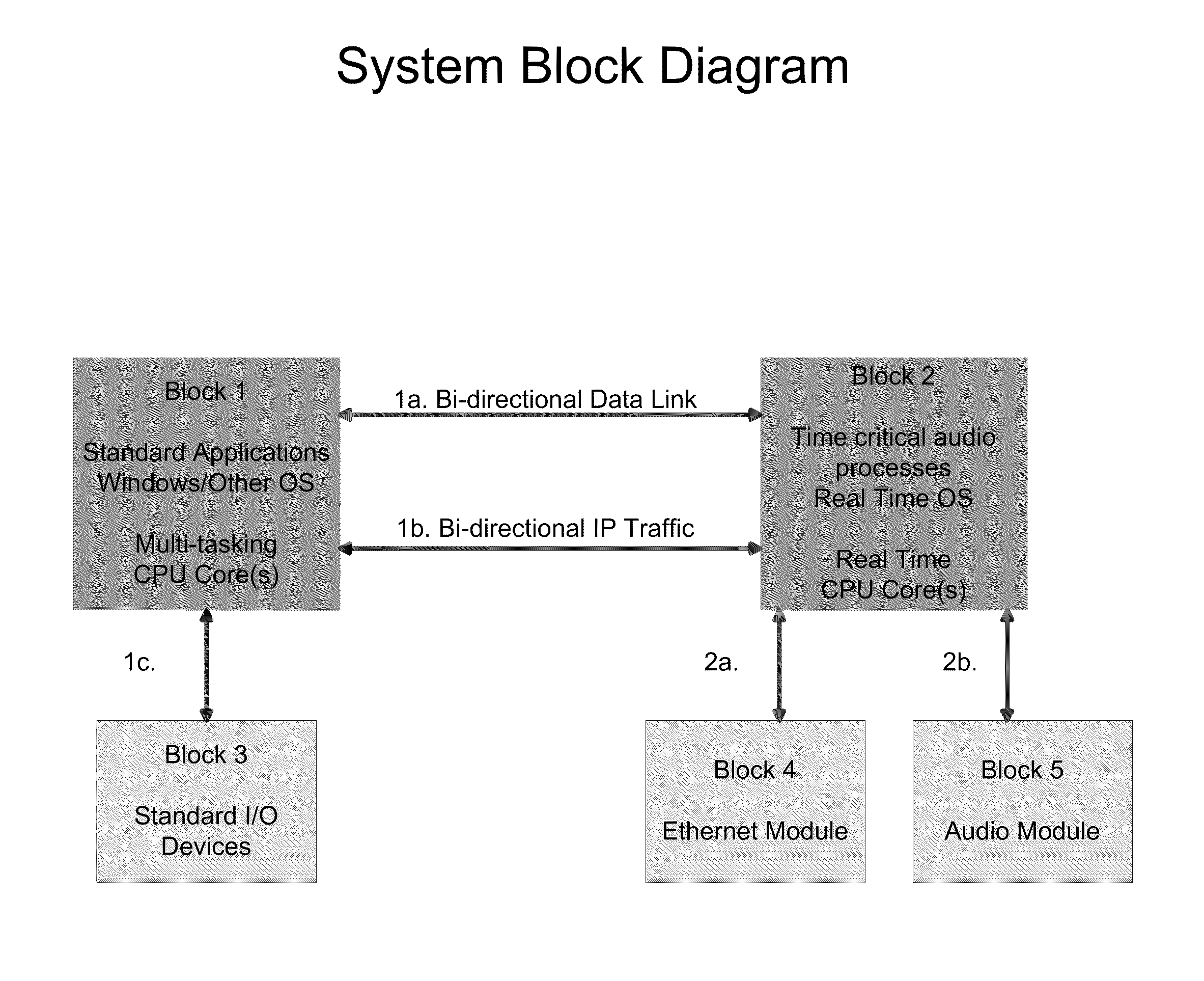
Audio Processing Utilizing a Dedicated CPU Core and a Real Time OS
InactiveUS20110106282A1Lower latencyMultiprogramming arrangementsSpecial data processing applicationsOperational systemGNU/Linux
This invention claims a novel software application that facilitates streaming and mixing audio and / or video with nearly zero latency, using a computer having Windows or Linux operating systems.Typical computer operating systems are not structured sufficiently to transmit or receive audio and / or video data in a real time. Alternatively, Application Specific Integrated Circuits (ASICs) and Field Programmable Arrays (FPGAs} are used to transmit and receive audio and / or video data via the network. This requires extra hardware, space and cost.The attributes of this invention are significant contributions to successful products in modern markets.
Owner:COREVALUS SYST
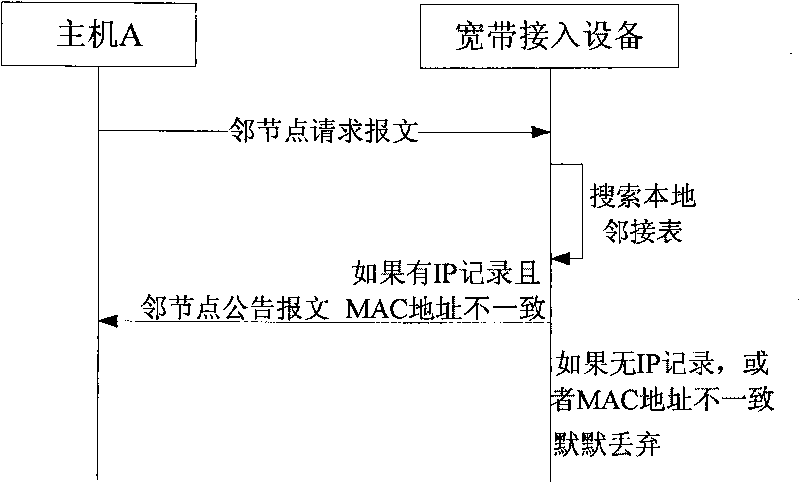
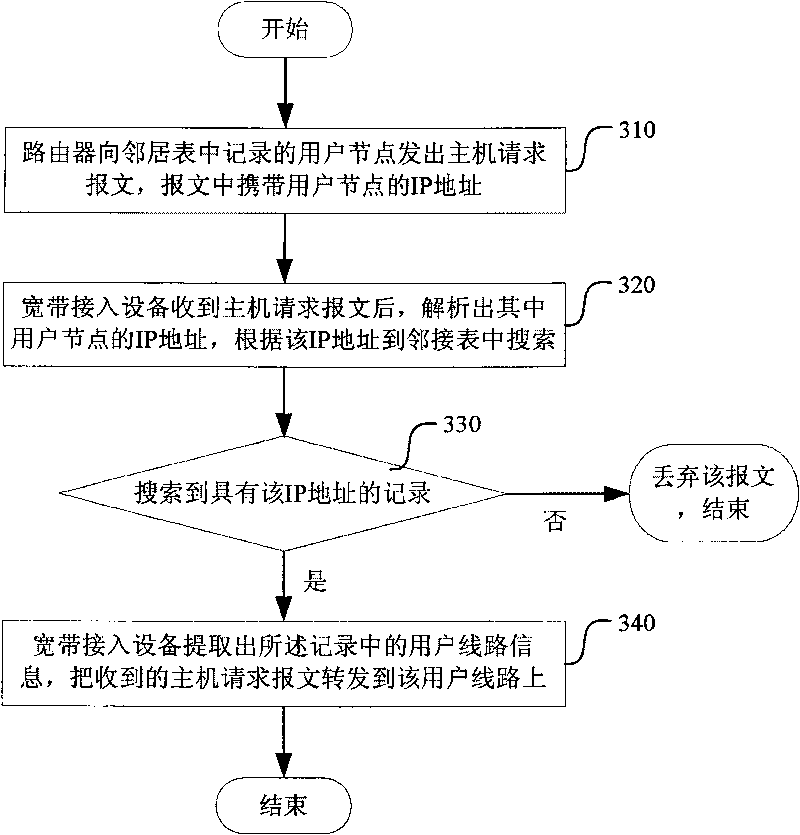
Method for improving neighbor discovery safety in IPv6 (Internet Protocol Version 6) environment and broadband access equipment
ActiveCN101764734AAvoid paralysisBlock communicationWireless network protocolsData switching networksIp addressBroadband
The invention relates to a method for improving neighbor discovery safety in IPv6 (internet protocol version 6) environment and broadband access equipment. When carrying out duplicate address detection on a temporary IP (internet protocol) address, a user node transmits an adjacent node request message to the broadband access equipment to which the user node belongs and the adjacent node request message carries the temporary IP address and an MAC (media access control) address of the user node; and when receiving the adjacent node request message, the broadband access equipment returns an adjacent node notice message to the user node when judging that a record containing the temporary IP address exists in the adjacent list but the MAC address in the record is different from the MAC address in the adjacent node request message. The method can effectively prevent duplicate address detection on DoS (Disk Operating System) attacks, blocks the communication among nodes attacked by a DoS and avoids the communicating paralysis of the whole link.
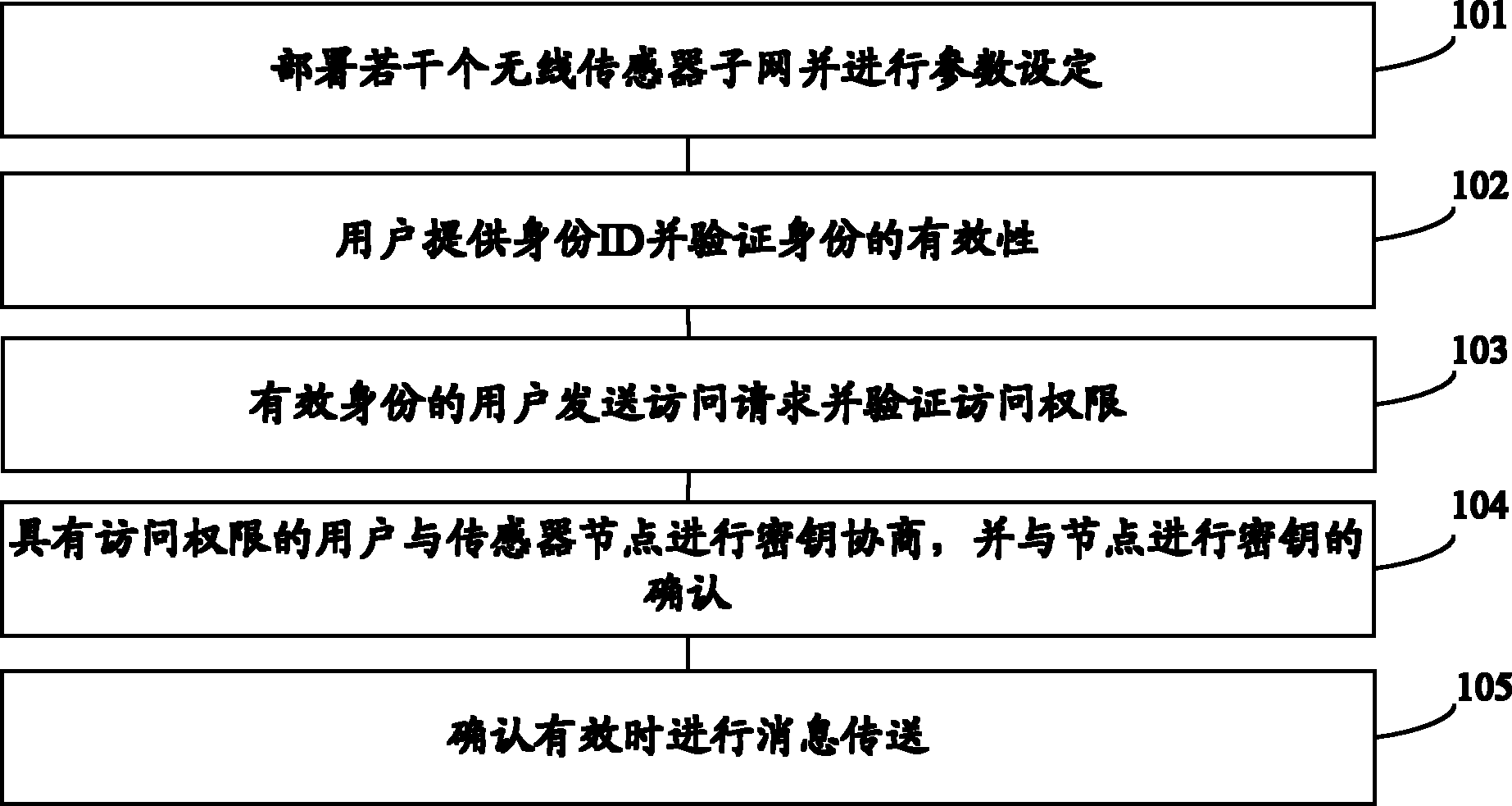
Owner:ZTE CORP
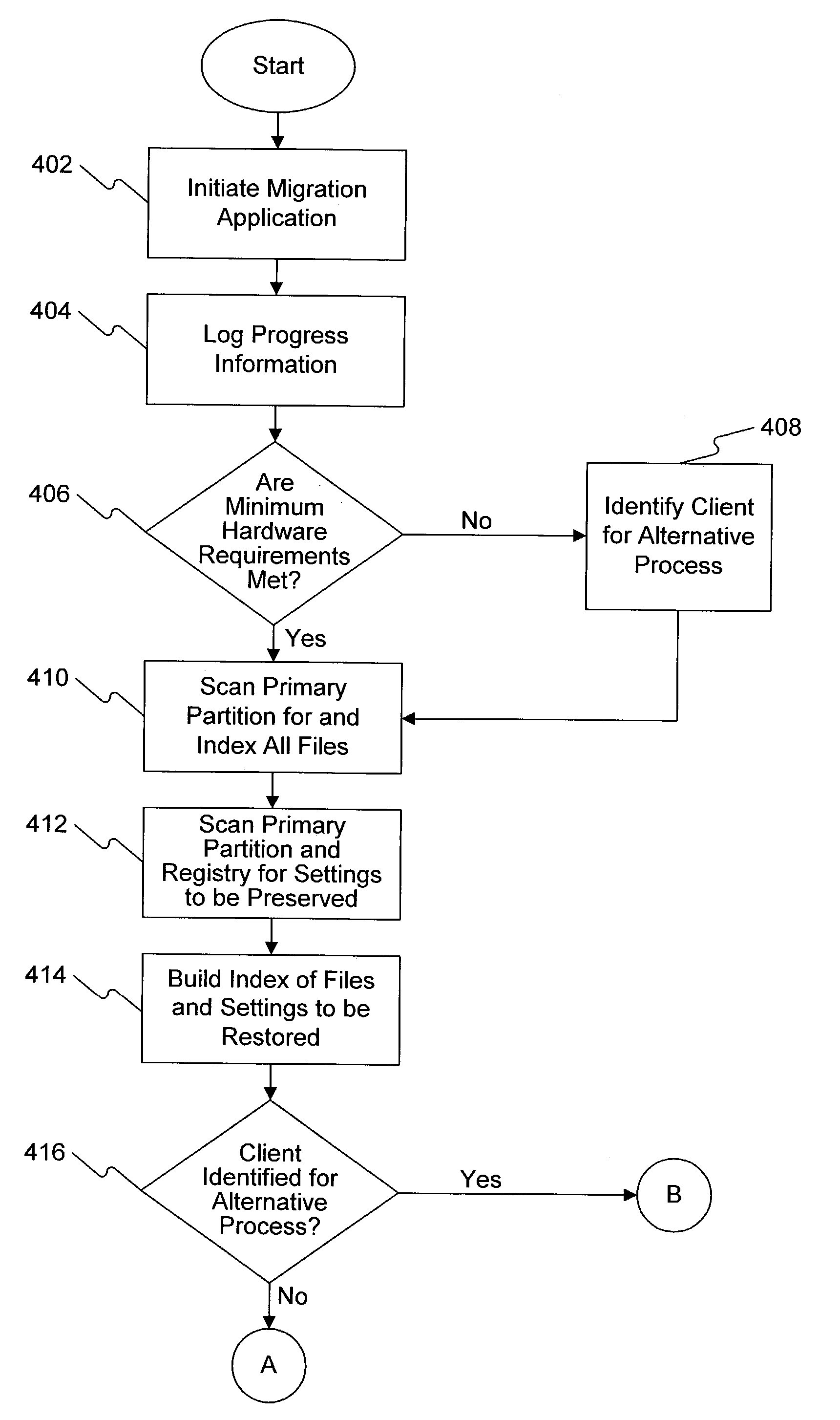
Automatic main board test system and methods
InactiveCN1431595ATest integrity and resilienceSave human effortDetecting faulty computer hardwareProgram loading/initiatingOperational systemChoice test
The method is utilized to test the main board to be tested installed in computers. The method includes following steps. (1) The test items for the main board to be tested are selected. (2) The high-level operation system is selected. The computer to be tested is connected to the server through network under a disk operation system control and the high-level operation system is also installed on the computer to be tested from the server. The testing programs needed for the selected test items are down loaded and installed on the computer to be tested from the server. (3) Under the control of the selected high-level operation system, the computer to be tested is on-line with the server to carry out the test programs, and the tested results are sent back to storage of the server.
Owner:VIA TECH INC
Wireless sensor network DOS (disk operating system) attack lightweight detection method based on random forest
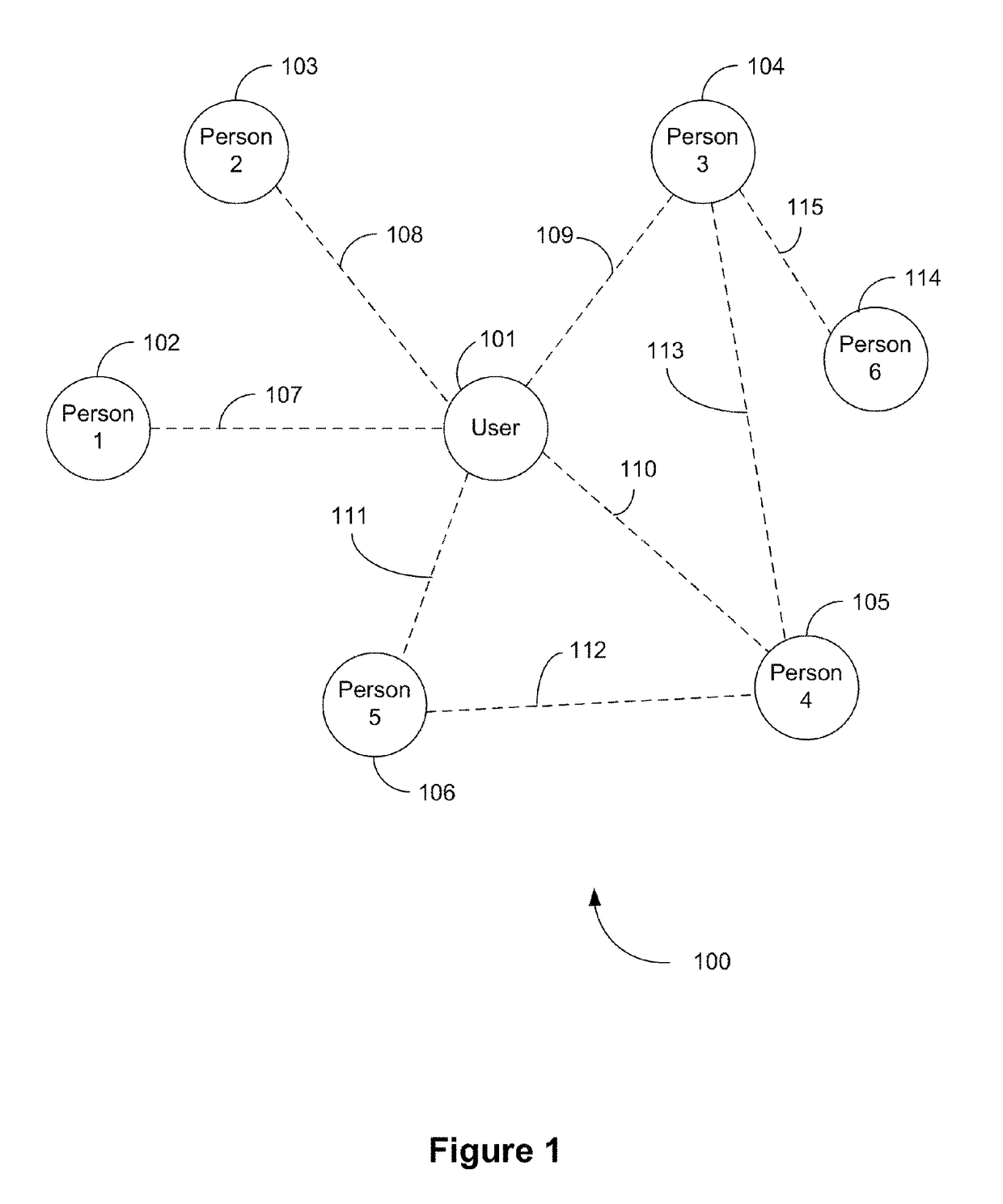
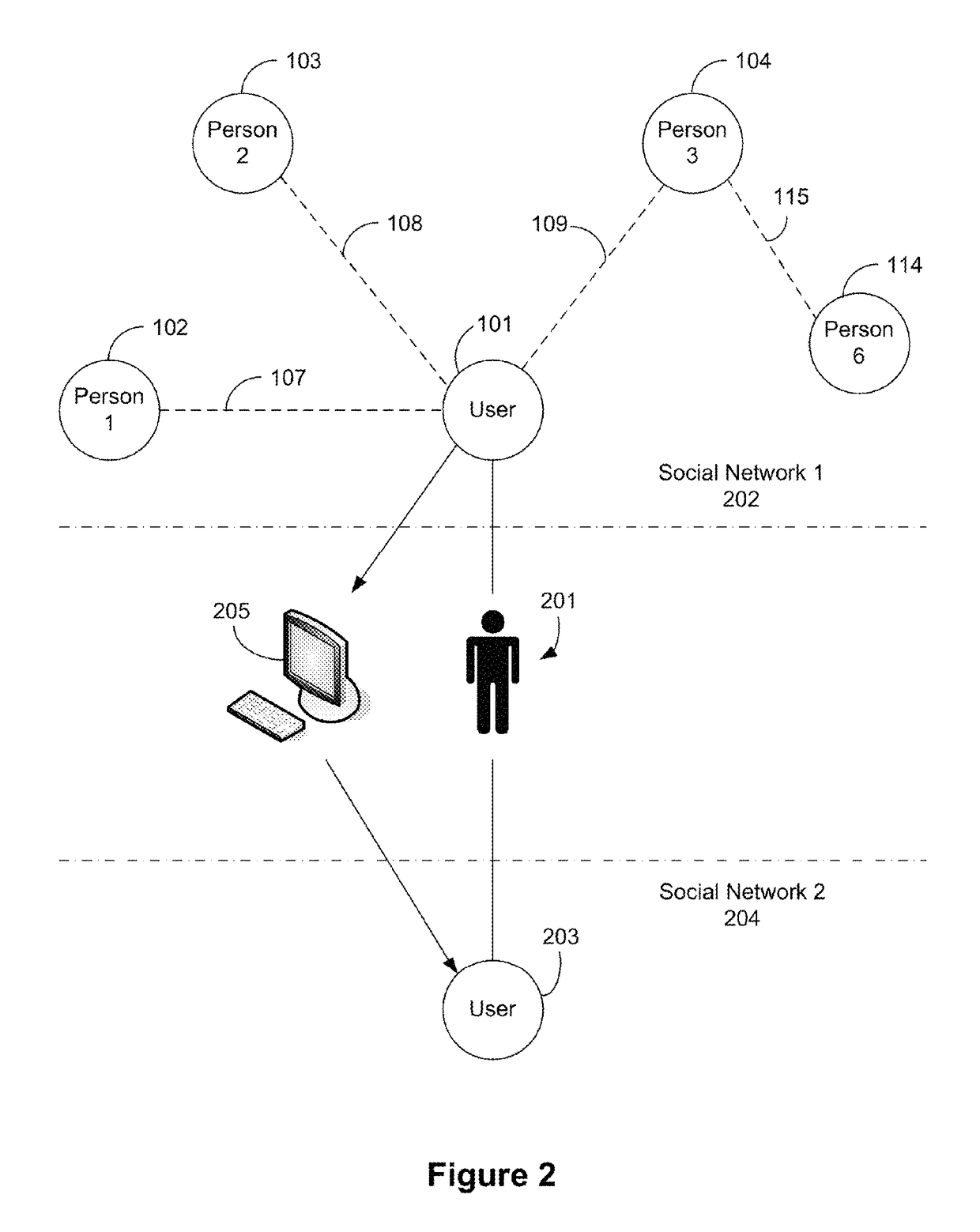
ActiveCN107872460AImprove generalization abilityWork lessNetwork topologiesTransmissionLine sensorInformation security
The invention provides a wireless sensor network DOS (disk operating system) attack lightweight detection method based on a random forest, and relates to the field of wireless sensor network information security. The method includes the steps: collecting one group of monitoring data by wireless sensor network monitoring nodes every other a fixed time, and transmitting the monitoring data to a basestation; generating detection characteristics (A) and (B) according to perception data attack characteristics of DOS attack on the base station, and standardizing the detection characteristics (A) and (B) into (A*) and (B*); combining a training set with the detection characteristics (A*) by a k-means++ algorithm to obtain normal data and noise data, and adding a certain attack data into the normal data obtained at the stage to train the random forest; firstly judging each sample to be detected is noise or not according to the detection characteristics (A*), and detecting whether DOS attack happens or not by the aid of a random forest and the detection characteristics (B*) if not. The method is implemented on the base station, DOS attack is detected without additional contribution of themonitoring nodes, and node calculation, storage and energy are saved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Virtual jukebox
InactiveUS6937541B2Easy accessEasy to createRecord information storageBuying/selling/leasing transactionsHard disc driveMass storage
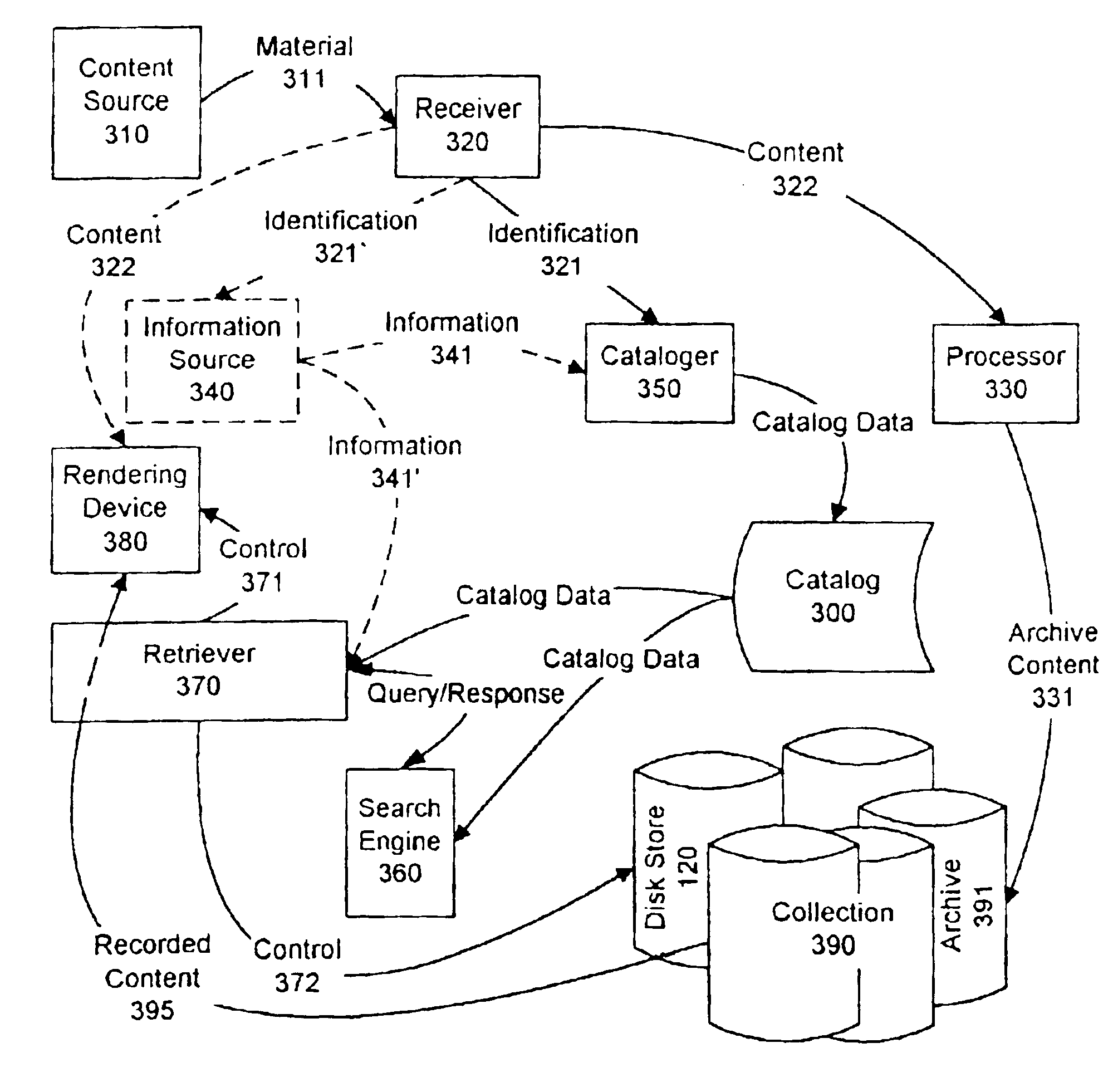
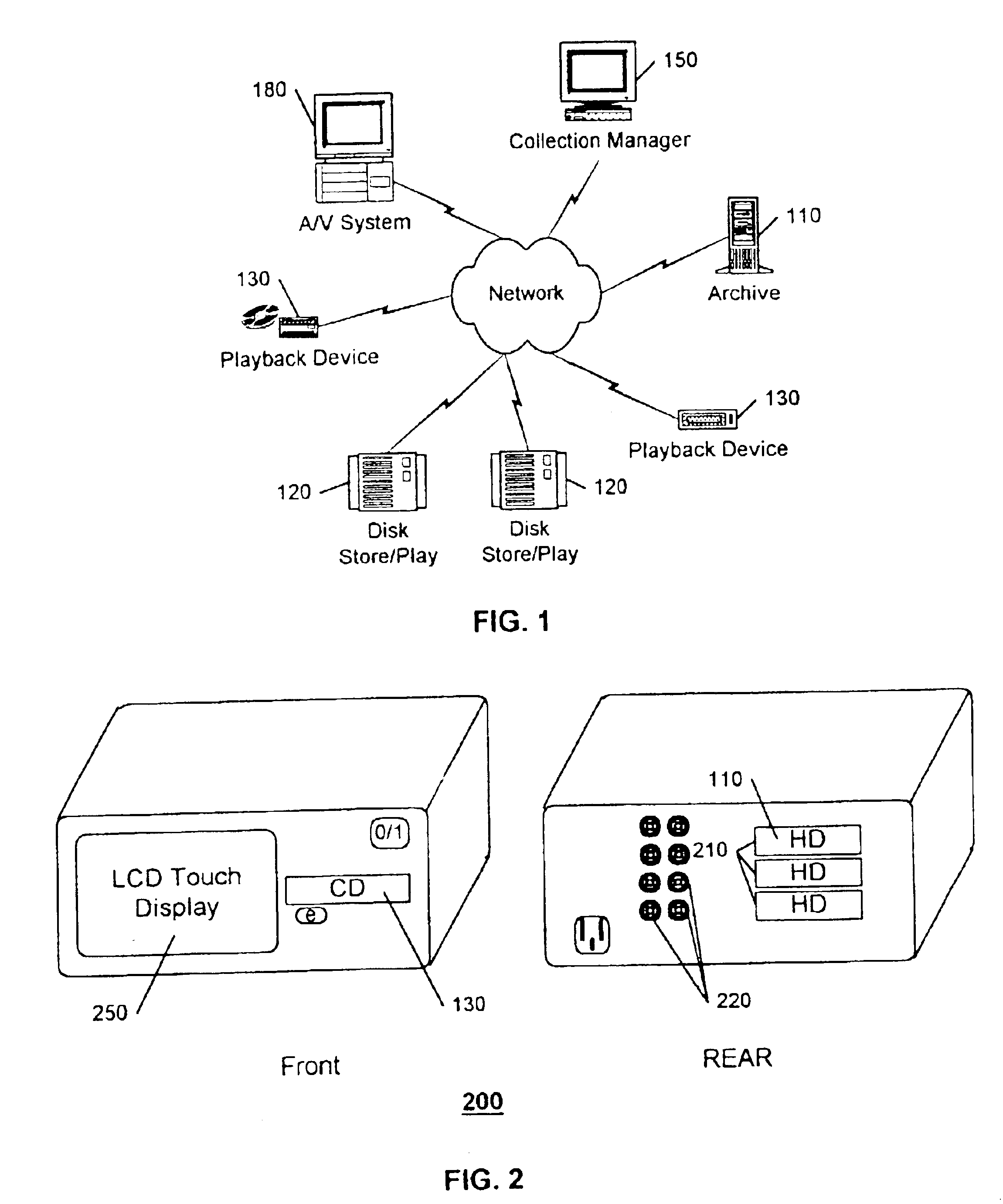
A collection management system, or virtual jukebox, is provided for a collection of recordings that is independent of the physical media upon which the material is recorded. The system forms a part of a network that includes storage media and playback devices, and provides an easy to use system for collection cataloging, archiving, and retrieval. In a preferred embodiment, a collection management system resides on a consumer electronic (CE) device, or a personal or home computer (PC), and the collection includes recordings that are stored on one or more hard drives associated with the CE device or the PC. The collection management system includes a user interface that facilitates the retrieval of recordings for playback from one or more storage devices, based on an individual selection of genre, author, and so on. By storing the recordings on a hard disc drive or other mass storage device with an associated disk operating system, immediate access is available to each recording on the drive, and additional drives can be added to the system as new material is added to the collection.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method for implementing startup of double operating systems on embedded board
ActiveCN105260205AFunction increaseImprove good performanceProgram loading/initiatingGNU/LinuxEmbedded system
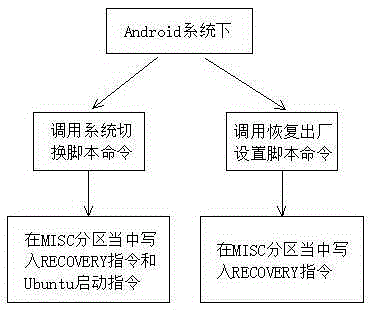
In order to implement startup and switching of both an Android system and a Linux system on an embedded board card, the present invention discloses a method for starting double operating systems. The method comprises the operation steps of an initial setting step, a system switching step and a reduction start-up step. Particularly, the method comprises: transferring a rescue system in a Recovery partition of the Android system to another idle partition, such as a backup partition; writing into a kernel and a booting system of the Linux system; and by modifying a script command of an MISC partition, guiding to switch and load the Android system and the Linux system. According to the method disclosed by the present invention, minimum modification on the systems is ensured, the problems of trouble transplanting process, high cost and the like of a dual-system startup mode are solved, the embedded board card supports the dual systems and retains an emergency mode of the Android system, and the Android system can carry out operations of restoring factory settings, OTA upgrading and the like.
Owner:T CHIP ELECTRONICS TECH CO LTD
Swapping "Fixed System" Hard Disk
InactiveUS20080215871A1Eliminate needDigital computer detailsPower supply for data processingHot swappingMotherboard
Method for ‘Cool-Swap’, ‘Warm-Swap’ and ‘Hot-Swap’ of ‘Fixed’‘System’ hard disk(s) in and out of the computer and for re-cycling the computer between ‘diskly’ state to ‘diskless’ state by combining the following features in one way or the other: separating the power supply of the ‘Fixed’‘System’ hard disk(s) from the internal power supply that is supplying power to other components of the computer, in particular the motherboard; taking the operating system, capable of being taken to run as ramdisk-based operating system, in control of the computer to run as ramdisk-based operating system; putting the computer into different power management states; and issuing commands or instructions for logical disconnection and / or re-connection of hard disk(s).
Owner:CHAN KAM FU
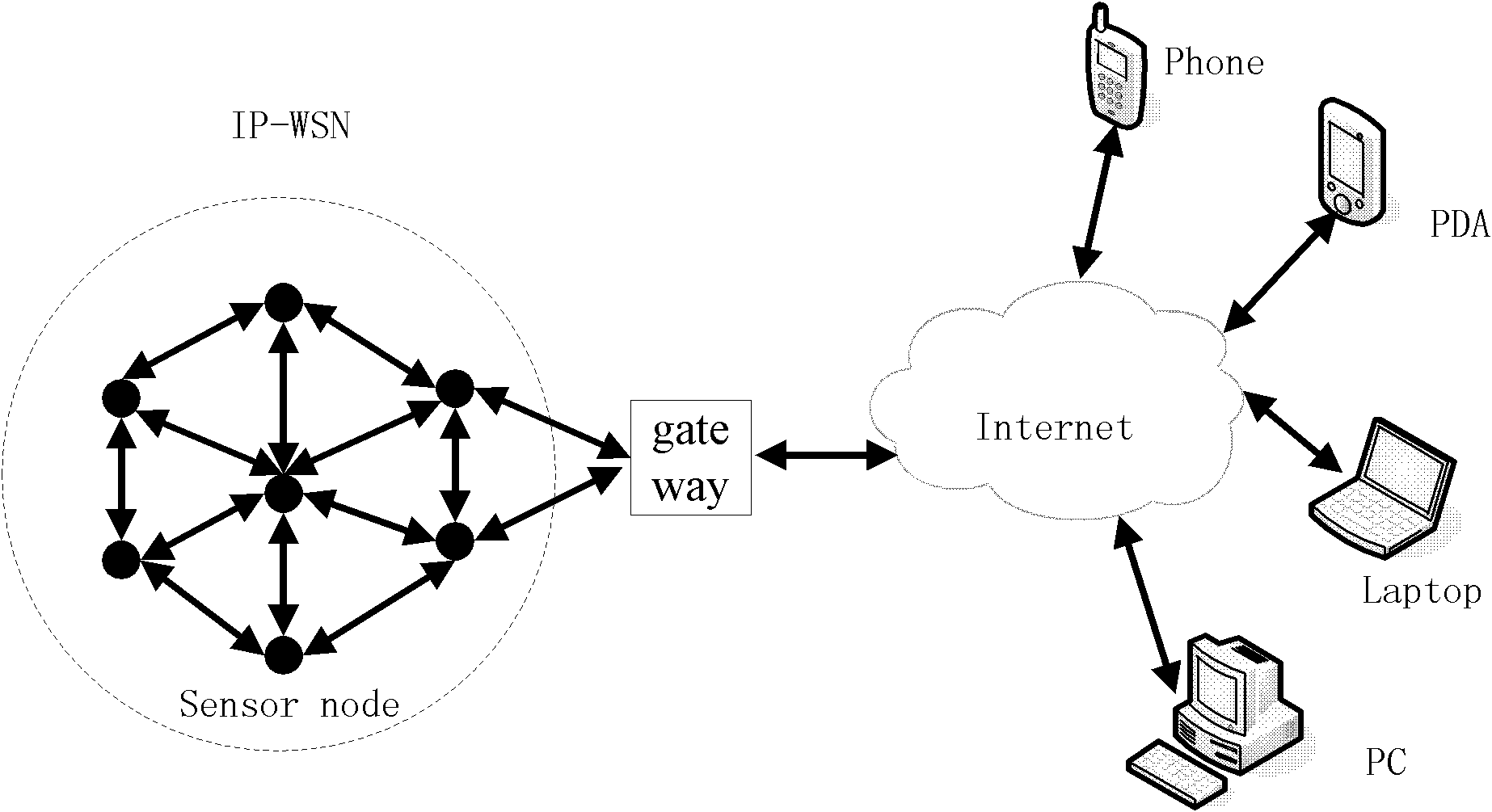
End-to-end safety control method for wireless sensor network and internet intercommunication
InactiveCN102546650AReduce energy consumptionEnhanced Access ControlKey distribution for secure communicationUser identity/authority verificationEnd to end securityWireless mesh network
The invention provides an end-to-end safety control method for wireless sensor network and internet intercommunication. Part of the certification and access control work is transferred to the gateway of the wireless sensor network, an asymmetric key negotiation mode based on elliptic-curve signcryption technology is adopted to place unsigncryption operation with large computing amount in an Internent remote terminal, and the symmetric key decryption operation is placed in the sensor nodes. Compared with the improved ECC (Elliptic Curve Cryptography)-based SSL (Security Socket Layer) protocol and the improved TLS (Transport Layer Security) protocol based on elliptic-curve identity, the energy consumption of the sensor nodes is effectively reduced, access control and privacy protection are enhanced and Dos (Disk Operating System) attack can be resisted.
Owner:BEIJING UNIV OF TECH
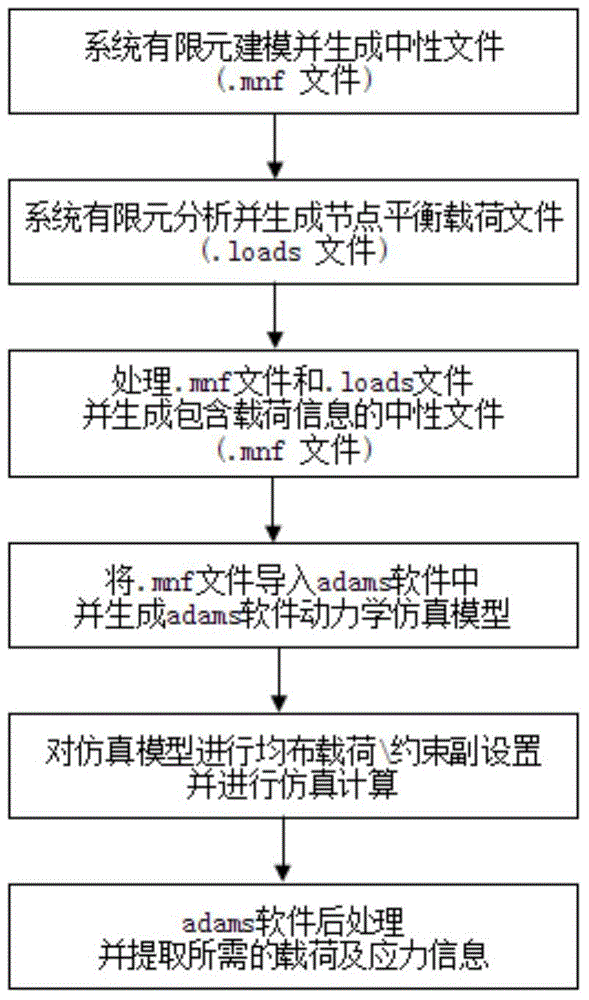
Dynamics simulation analysis method of uniformly distributed load bearing system
InactiveCN105005671AAvoid not being able to realistically simulate system loading at the same timeAvoid the disadvantages of mutual constraint relationship between partsSpecial data processing applicationsElement modelSystem design process
The invention relates to a dynamics simulation analysis method of a uniformly distributed load bearing system. The method comprises the following steps of: (1) performing finite element modeling on the system in Patran software environment; (2) applying uniformly distributed load to a built system model, adding constraints, and generating a node balance load file of a finite element model; (3) processing a neutral format file and the load file through a DOS (Disk Operating System) to generate the neutral format file, wherein the neutral format file can be input by Adams software and includes load information; (4) inputting the neutral format file including the load information into the Adams software to generate an Adams dynamics simulation model of the analyzed system; (5) performing pre-processing setting on the simulation model, and performing simulation calculation; and (6) performing post-processing on the calculation result of the Adams software, and completing the subsequent system intensity analysis work. The method has the advantages that the analysis model consistent with the real loaded and constraint condition of the system is built; the calculation precision and the reliability in the system design process are effectively improved; the development period is shortened; and the development cost is reduced.
Owner:AVIC SAC COMML AIRCRAFT
IPv4 and IPv6-based detection method and system for denial of service attacks
ActiveCN103248607AHigh detection rate and accuracyShield interferenceTransmissionService flowDetection rate
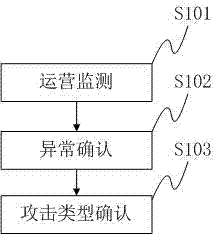
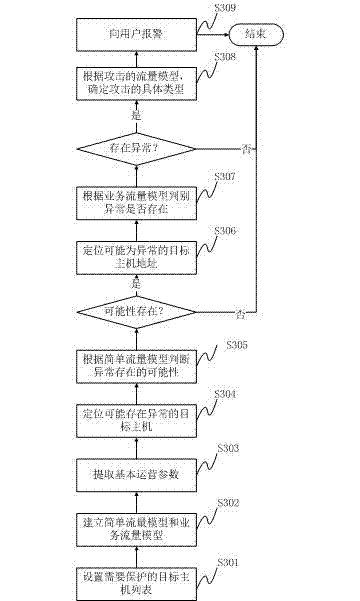
The invention discloses an IPv4 and IPv6-based detection method for denial of service attacks. The method comprises the following steps: during usual operation detection, a system only picks up basic operation parameters in flow, and a simple flow model is used for judging possible abnormalities; under the condition that abnormalities exist, a service flow model is used for judging abnormalities; and under the condition that abnormalities are confirmed, an attack flow model is used for judging attack types. The invention further discloses an IPv4 and IPv6-based detection system for denial of service attacks, wherein the system comprises a flow model module, an operation monitoring module, an abnormality conforming module, and an attack type conforming module and handling module. The method and the system provided by the invention basically shield interference of large flow data of the whole network to analysis, and are high in relevance ratio accuracy of DOS (disk operating system) / DDOS (diagnostic disk operating system) attacks.
Owner:HARBIN ANTIY TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com