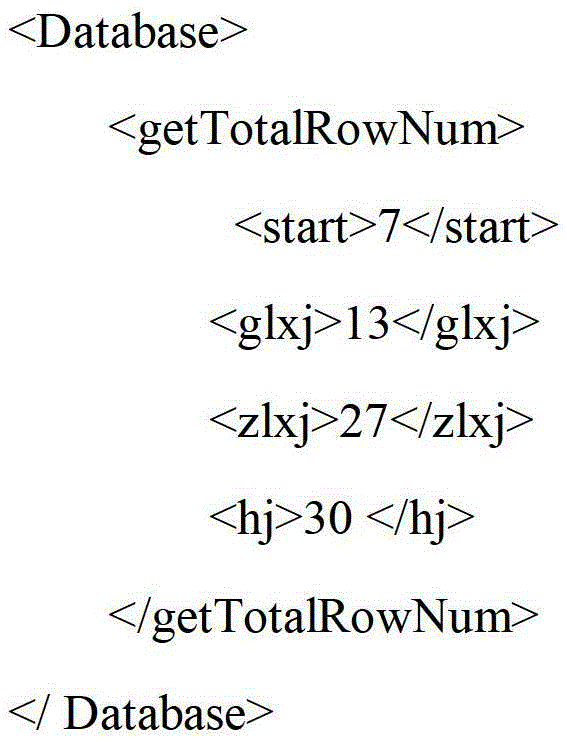Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
381 results about "Load file" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
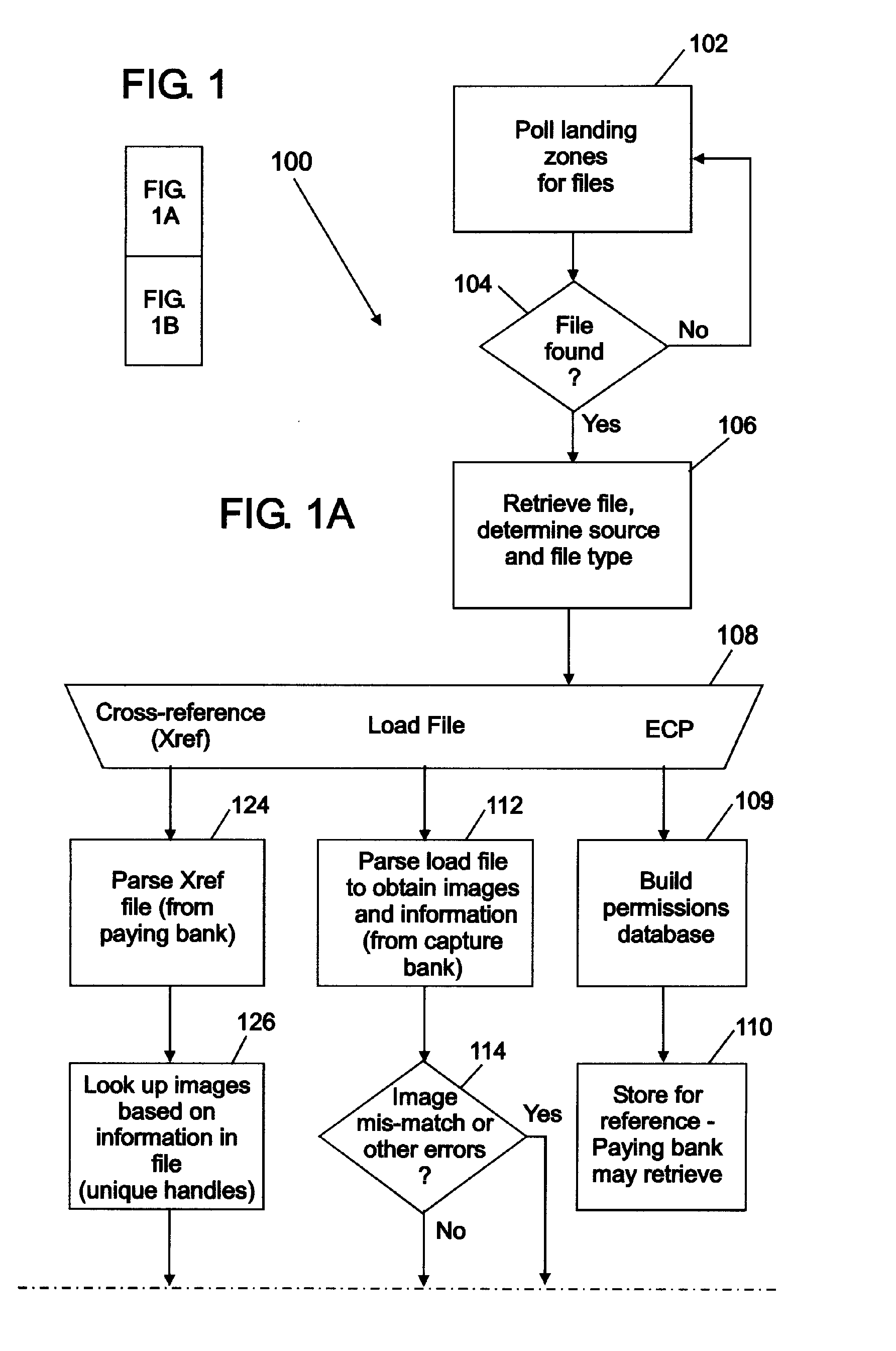
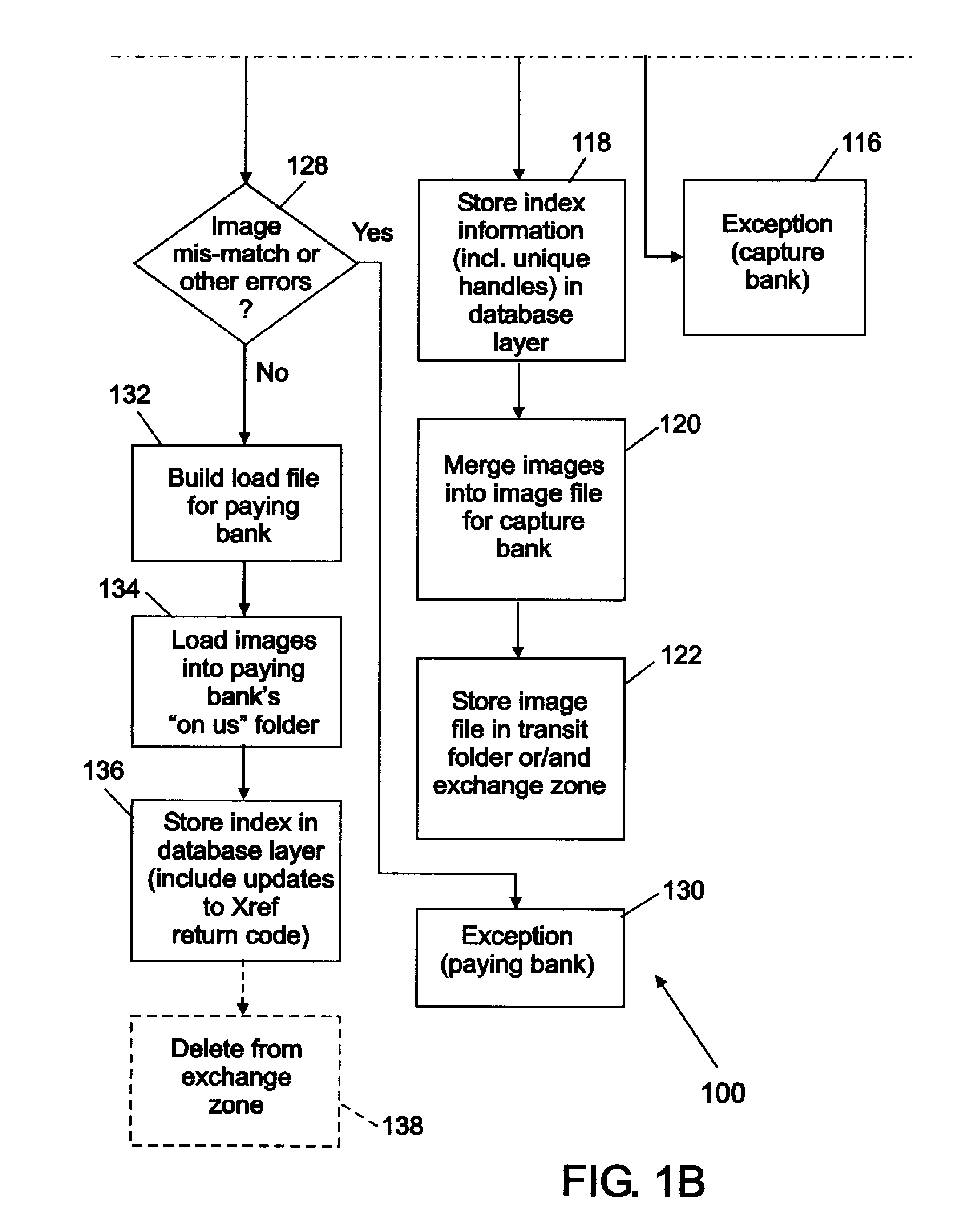
A load file in the litigation community is commonly referred to as the file used to import data (coded, captured or extracted data from ESI processing) into a database; or the file used to link images. These load files carry commands, commanding the software to carry out certain functions with the data found in them.
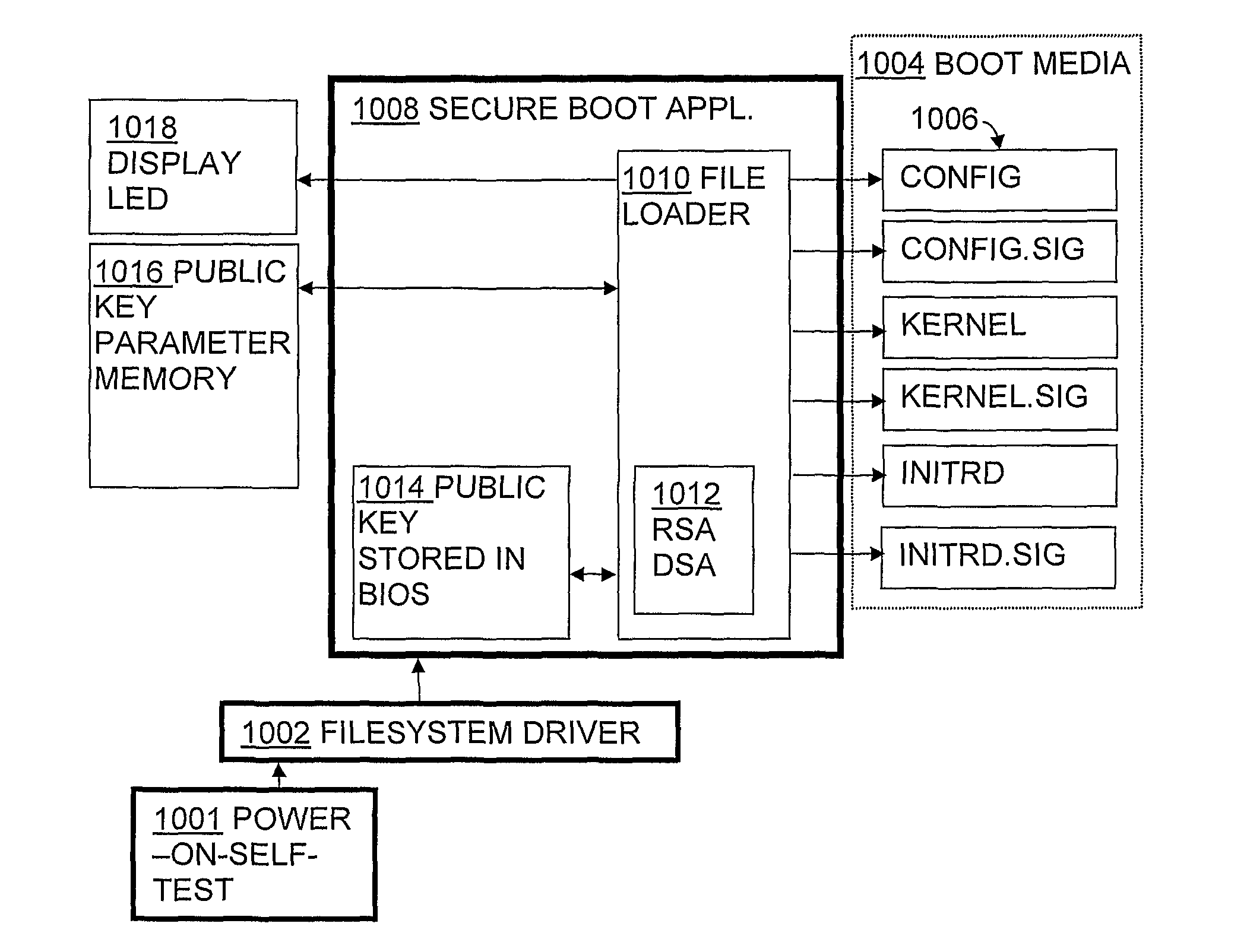
Method and system for secure software provisioning
A method and system for the provisioning of software that enable large scale installation and management of software in computer units in a highly secure manner. The BIOS of the target computer unit is adapted such that upon power up the system attempts to boot from an external media. The BIOS features functions within the code for the implementing a system watchdog for assuring the system remains in a known state, a function for digital signature verification, and loads drivers for a file system. The external media includes the operating system (OS) image and other bootstrap files, each having been digitally signed with an asymmetric private key that corresponds to the public key. A programmable read-only parameter memory on the motherboard is configured to store the public keys and the (failure) state of the system independently of the primary and secondary media enabling reboot from an alternative boot path.
Owner:ONITEO
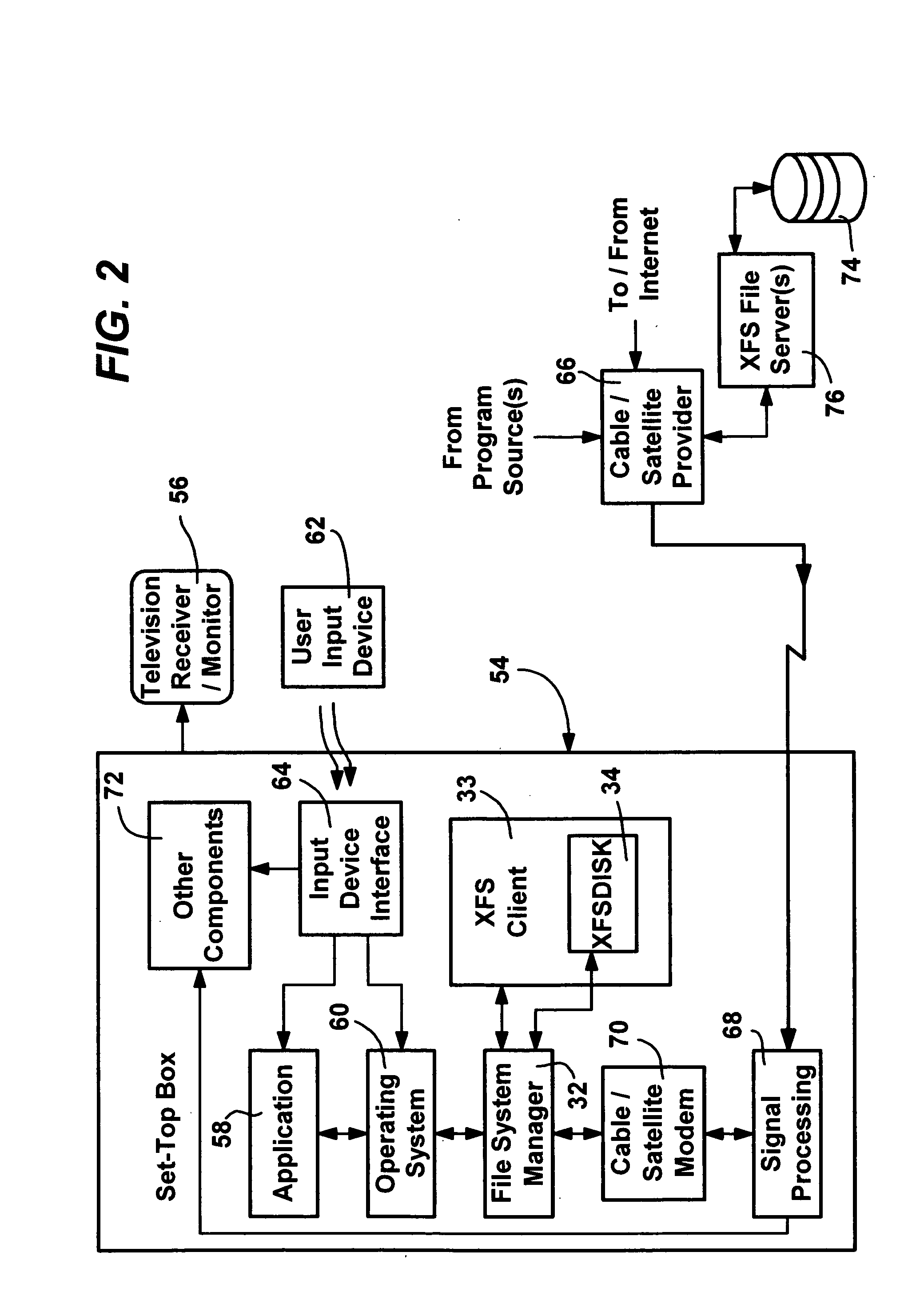
Extended file system
InactiveUS20050060316A1Fast communicationData processing applicationsNatural language data processingFile systemPersonal computer
A method and system for transparently combining remote and local storage to provide an extended file system such as a virtual local drive for a computer system client / user, e.g., a user of a pocket sized personal computer or a cable set-top box. A client device may load file system object data, storing the directories and files remotely, and retrieving the files only when required. Via its local storage, the extended file system handles unreliable connections and delays. When a connection to an extended file system server is present, the extended file system provides automatic downloading of information that is not locally cached, and automatically uploading of information that has been modified on the client. Extended file system attributes are employed to determine the actual location of file system data, and a lightweight protocol is defined to download or upload remote data by low-level components that make the remote source transparent from the perspective of the application. The system scales to large networks as it employs the lightweight protocol and establishes a connection only to retrieve and submit data.
Owner:MICROSOFT TECH LICENSING LLC
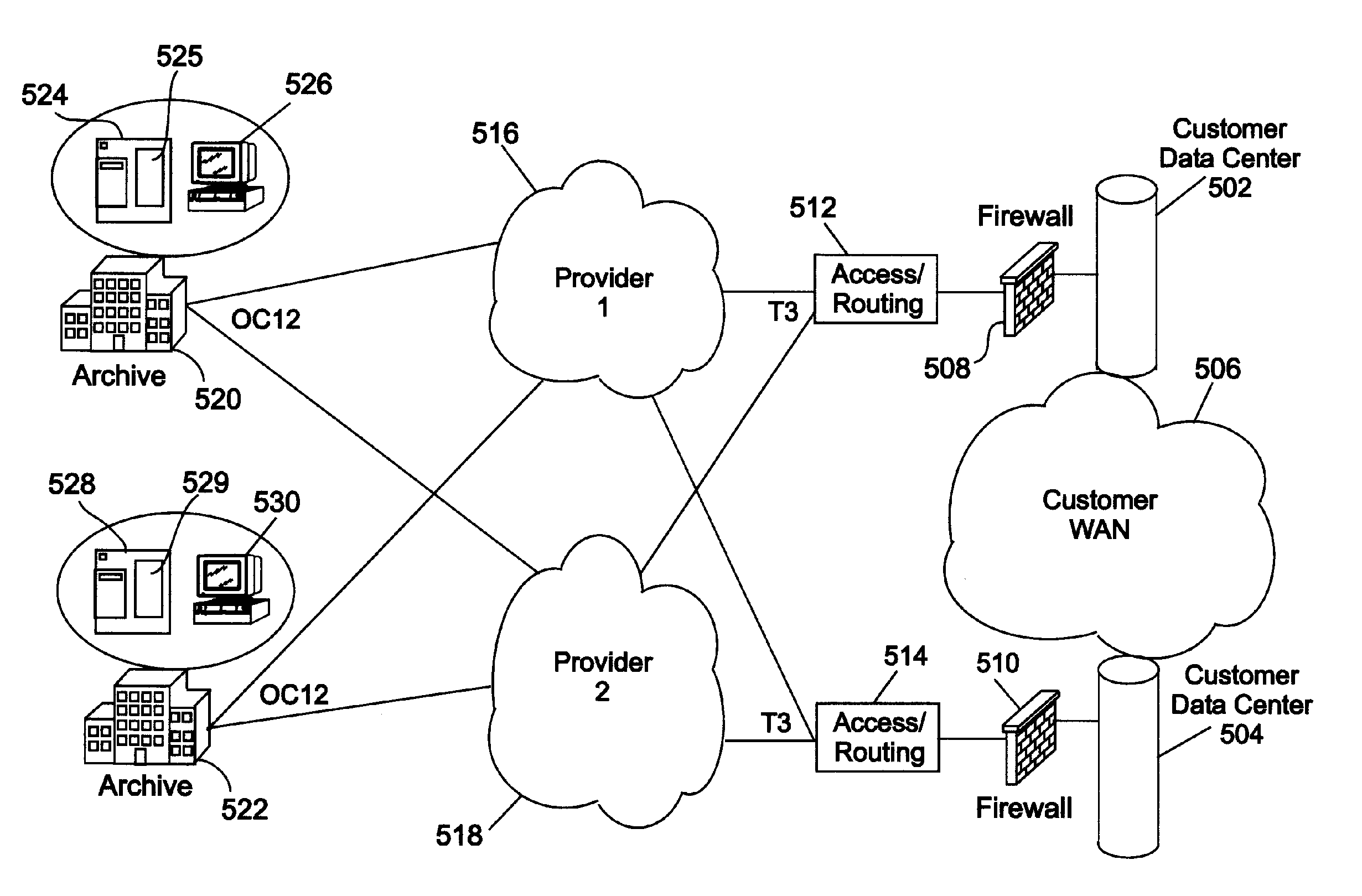
Centralized check image storage system
ActiveUS20050216409A1Reduce on-site image archive storage needSpeed reconciliationFinancePayment architectureInformation supportLanding zone
Centralized check image storage system. The present invention provides for sharing check images stored in a substantially centralized storage system between and / or among banks in support of the check collection process. In some embodiments, check images are received from the capture bank via a landing zone at the centralized storage facility. These images and information supporting the check collection process can be in the form of load file. A cross-reference file including information supporting the check clearing process such as unique handles identifying the check images is received from a paying bank, possibly also via a landing zone. Check images can be identified based on these unique handles, so that the check images can be made accessible to both the capture bank and the paying bank from the substantially centralized storage system.
Owner:VIEWPOINTE ARCHIVE SERVICES
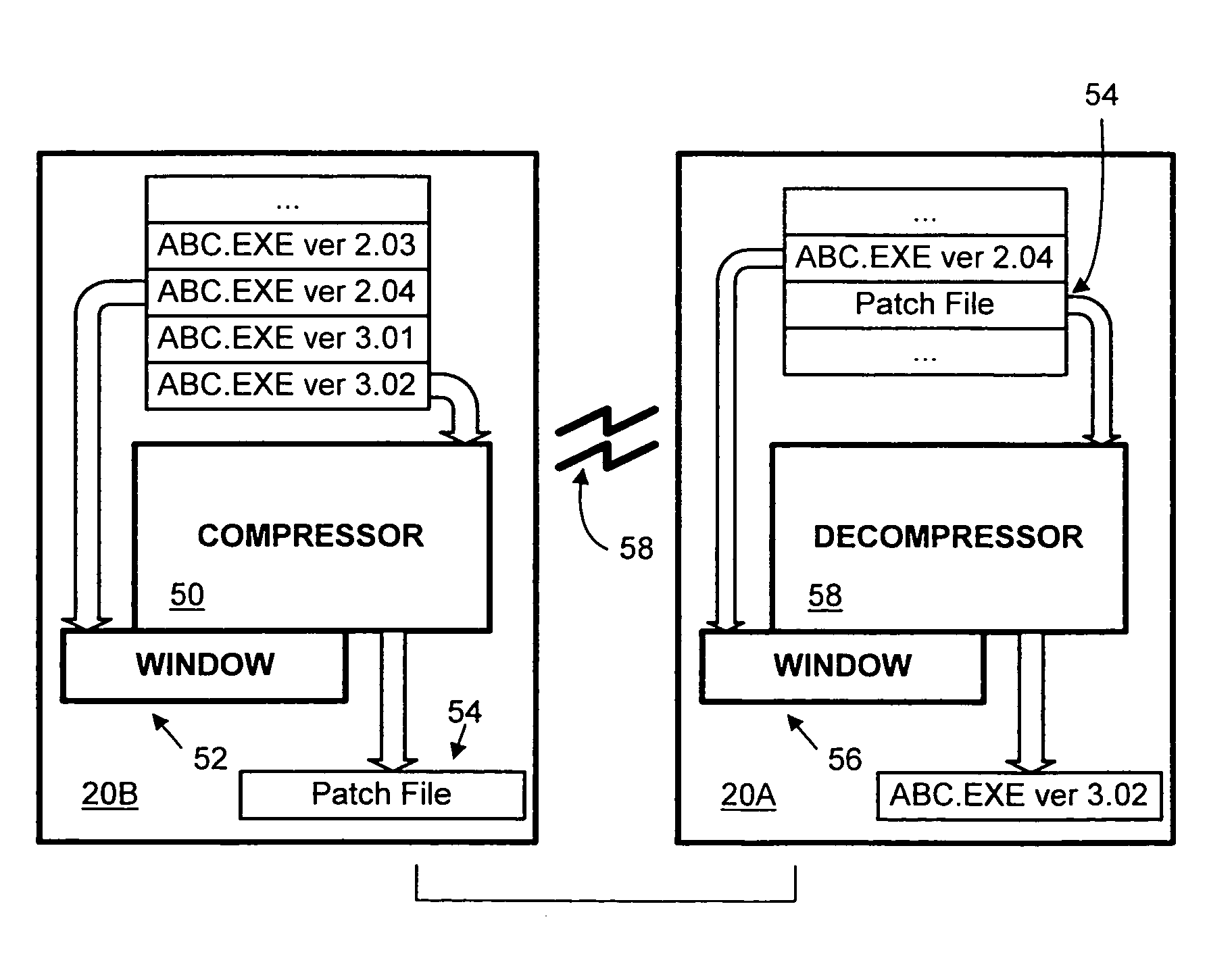
Method and system for updating software with smaller patch files
InactiveUS6938109B1More outputSmall sizeData processing applicationsProgram control using stored programsReduced sizeParallel processing
Rather than comparing an old file with a new file to generate a set of patching instructions, and then compressing the patching instructions to generate a compact patch file for transmission to a user, a patch file is generated in a single operation. A compressor is pre-initialized in accordance with the old version of the file (e.g. in an LZ77 compressor, the history window is pre-loaded with the file). The pre-initialized compressor then compresses the new file, producing a patch file from which the new file can be generated. At the user's computer, a parallel process is performed, with the user's copy of the old file being used to pre-initialize a decompressor to which the patch file is then input. The output of the decompressor is the new file. The patch files generated and used in these processes are of significantly reduced size when compared to the prior art. Variations between copies of the old file as installed on different computers are also addressed, so that a single patch file can be applied irrespective of such variations. By so doing, the need for a multi-version patch file to handle such installation differences is eliminated, further reducing the size of the patch file when compared with prior art techniques. Such variations are addressed by “normalizing” the old file prior to application of the patch file. A temporary copy of the old file is typically made, and locations within the file at which the data may be unpredictable due to idiosyncrasies of the file's installation are changed to known or predictable values.
Owner:MICROSOFT TECH LICENSING LLC
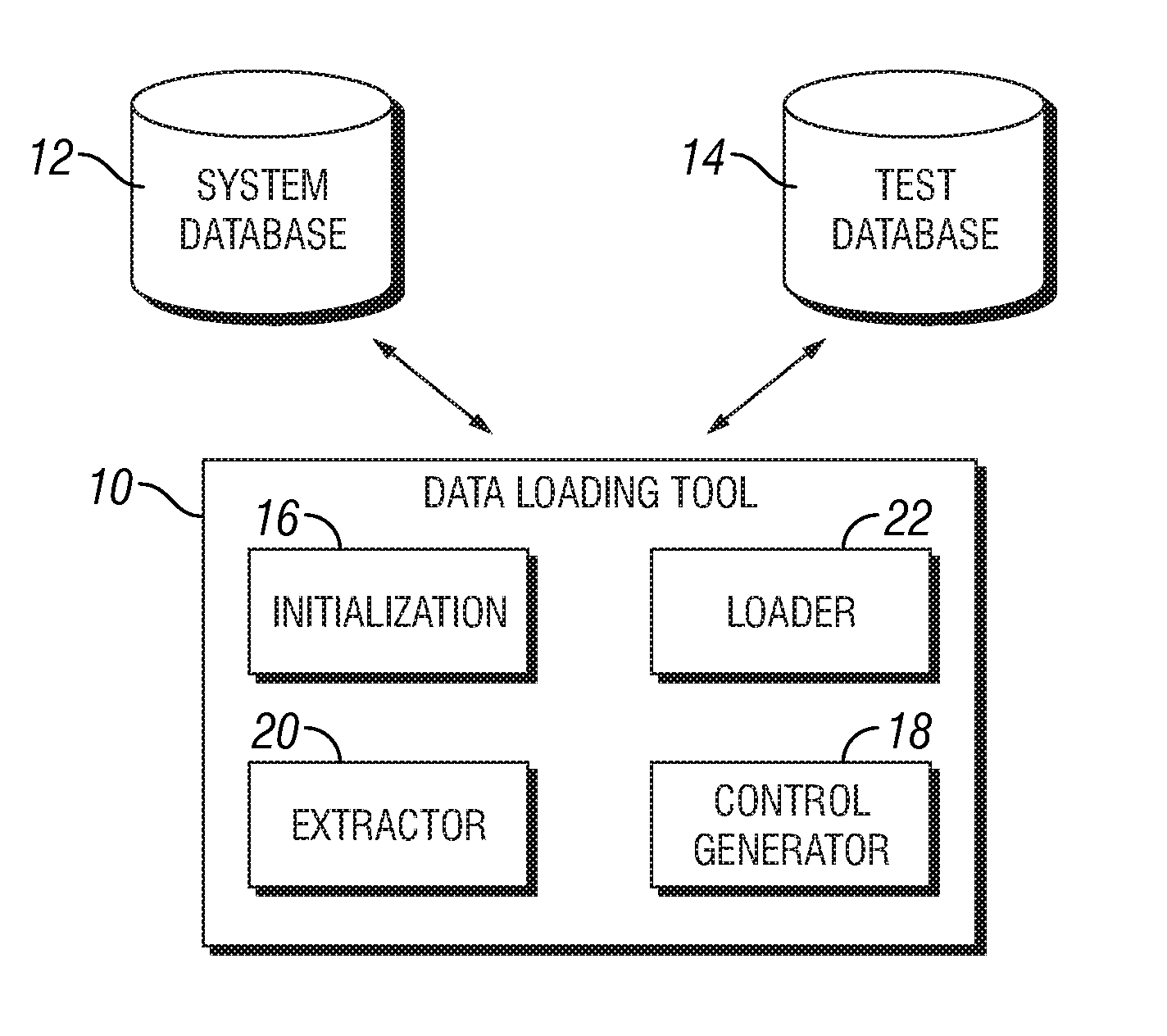
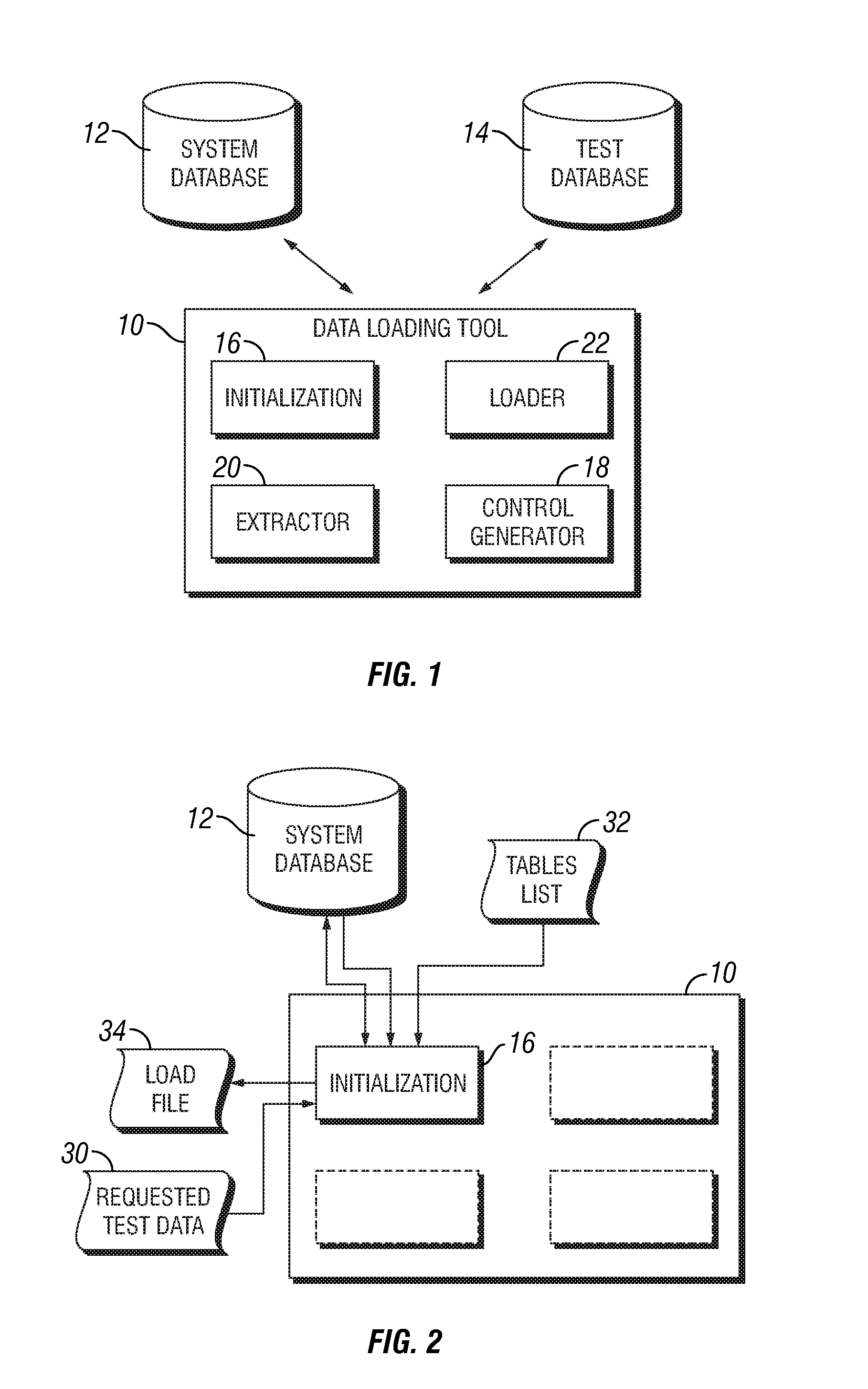
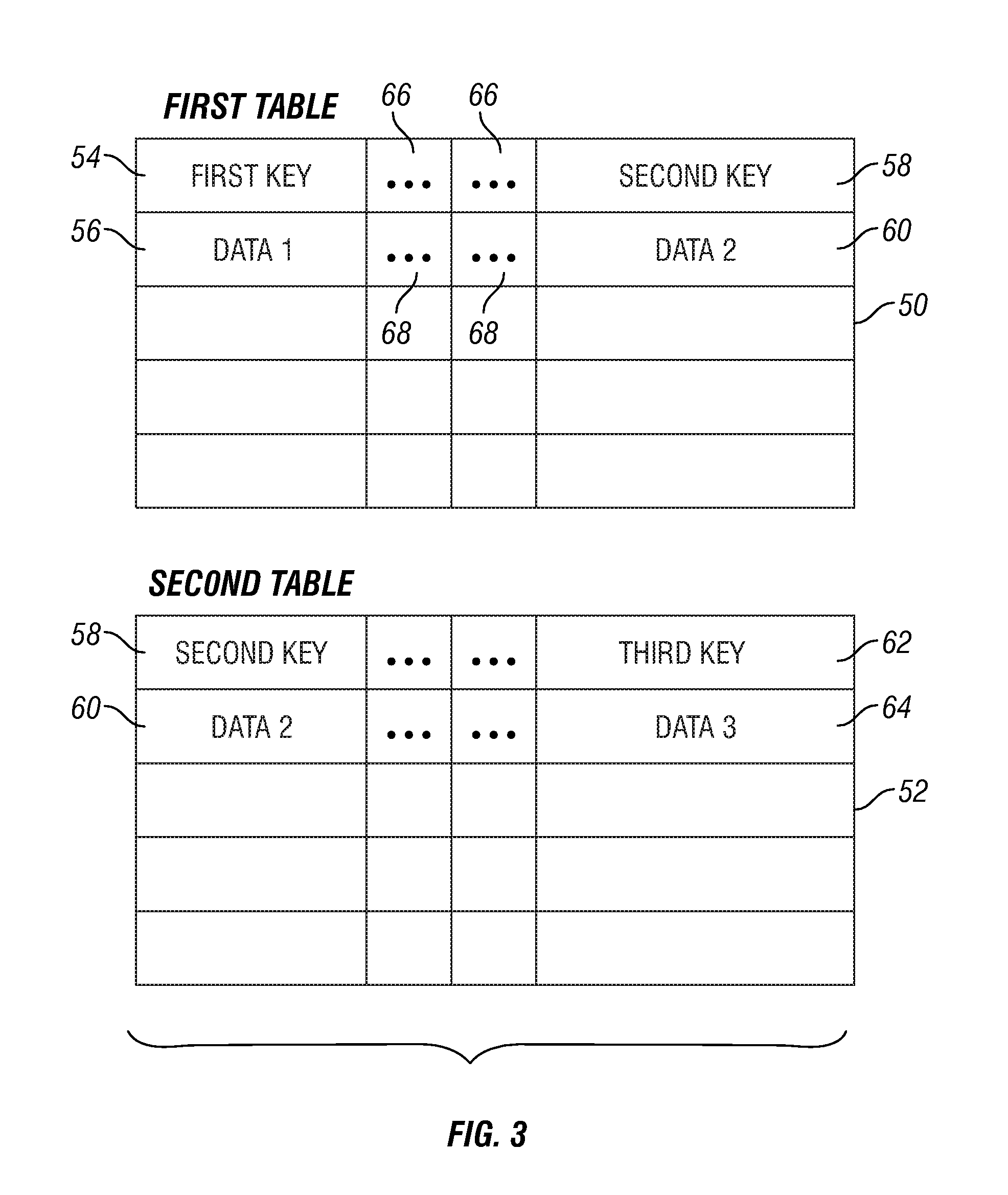
Data loading tool for loading a database
InactiveUS7337176B1Digital data information retrievalSpecial data processing applicationsTarget databaseLoad file
A data loading tool for loading a target database is provided. The data loading tool includes an initialization component operable to utilize data and a key of a first table of a database to generate a load file identifying related keys and associated data in the database. The data loading tool further comprises a control generator, an extractor component and a loader component. The control generator is operable to generate at least one control file related to the database. The extractor component is operable to extract data from the database based on the load file and the loader component is operable to load the data extracted by the extractor component into the target database utilizing the at least one control file. A method for loading a target database is provided.
Owner:SPRINT CORPORATION
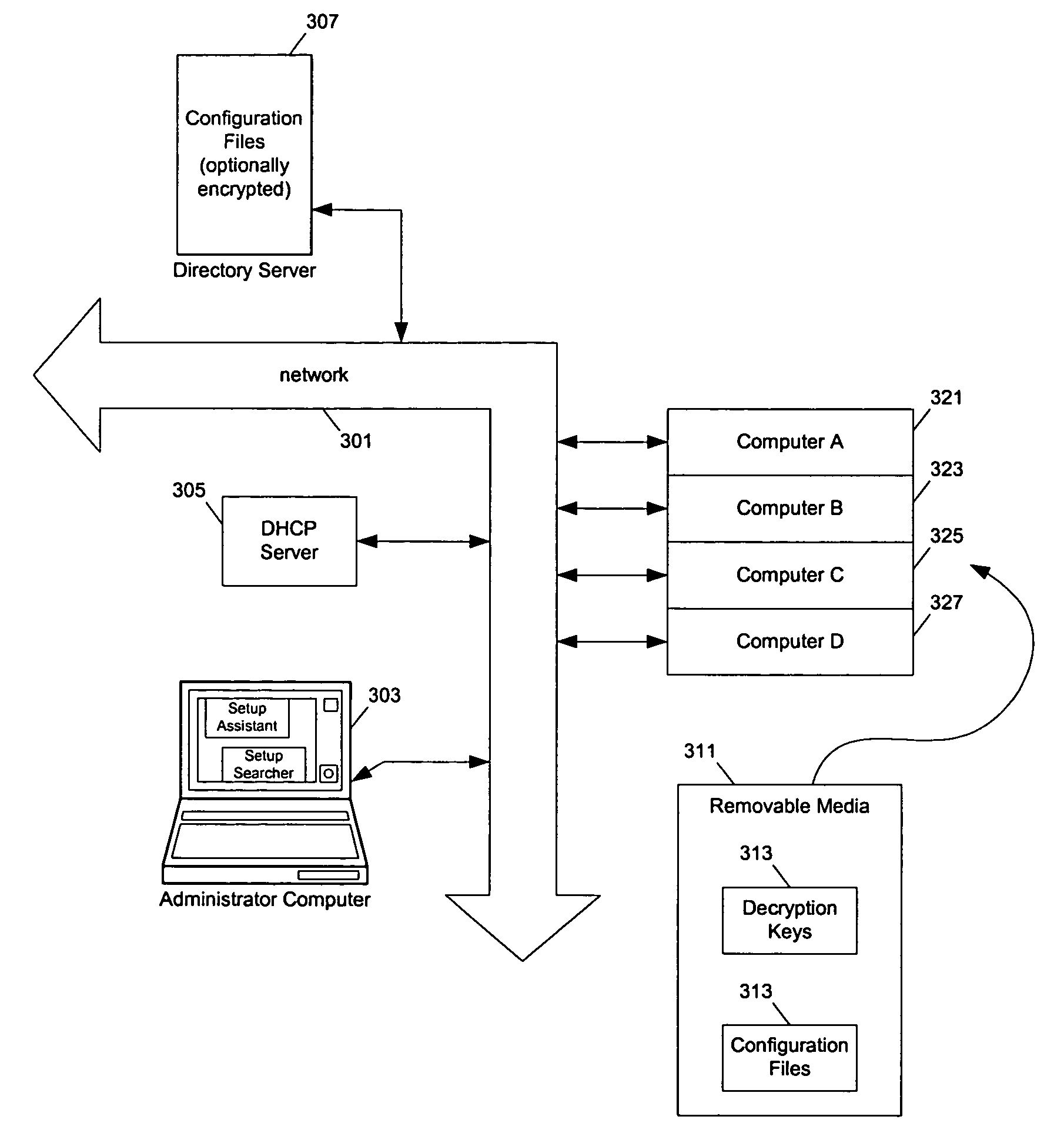
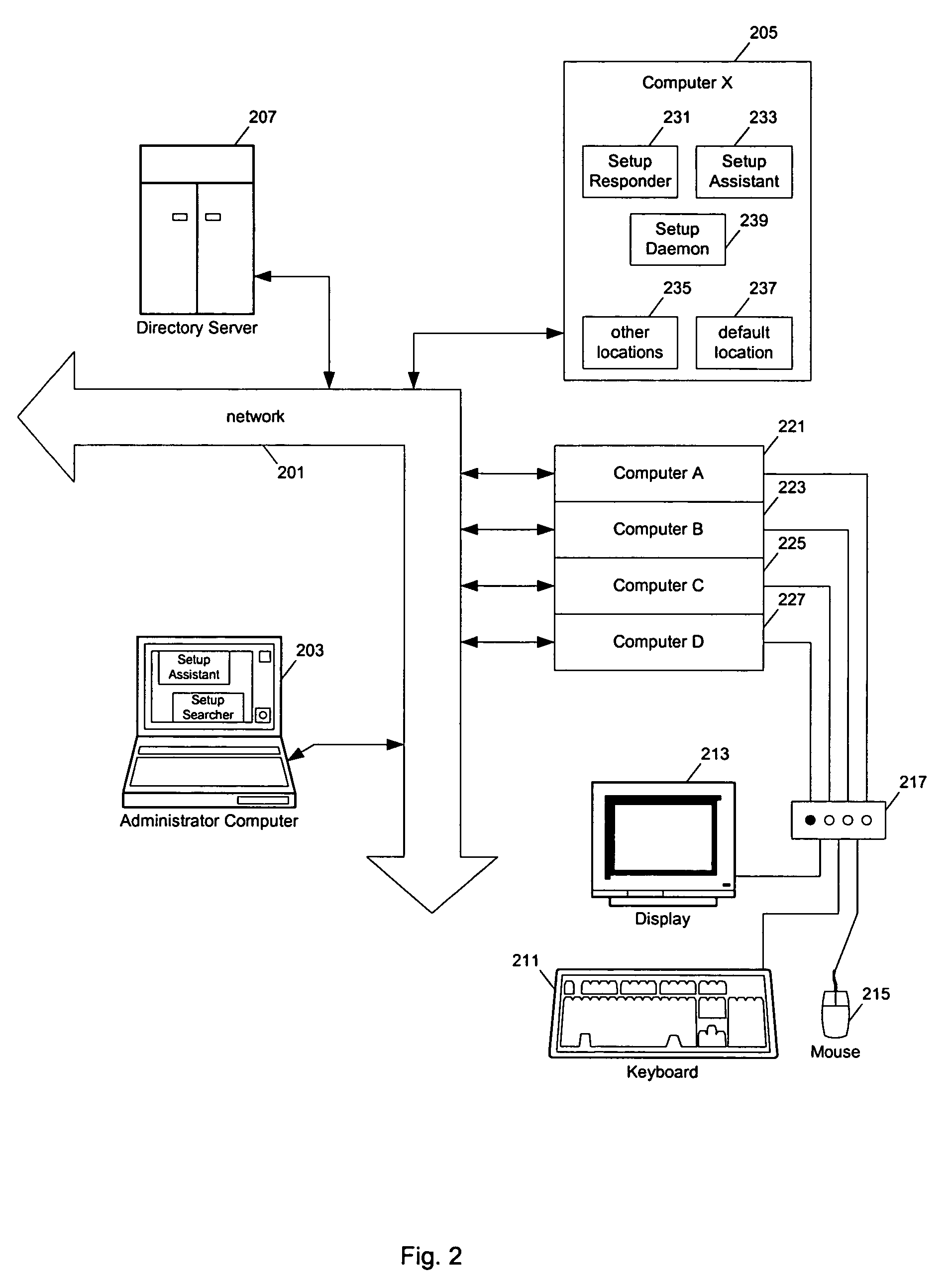
Software setup system
Methods and apparatuses for automatic system setup. At least one embodiment of the present invention stores the setup configuration information (e.g., in files and / or in directory servers). The setup configuration information is stored (e.g., using a configuration file naming scheme) so that the configuration information for a particular machine can be found. A setup daemon on the machine searches for suitable configuration information in a number of places, such as: in a location in a local file system, in locations in mounted file volumes, and directory servers. The configuration information may be encrypted, and the setup daemon searches for the decryption key in a similar fashion.
Owner:APPLE INC
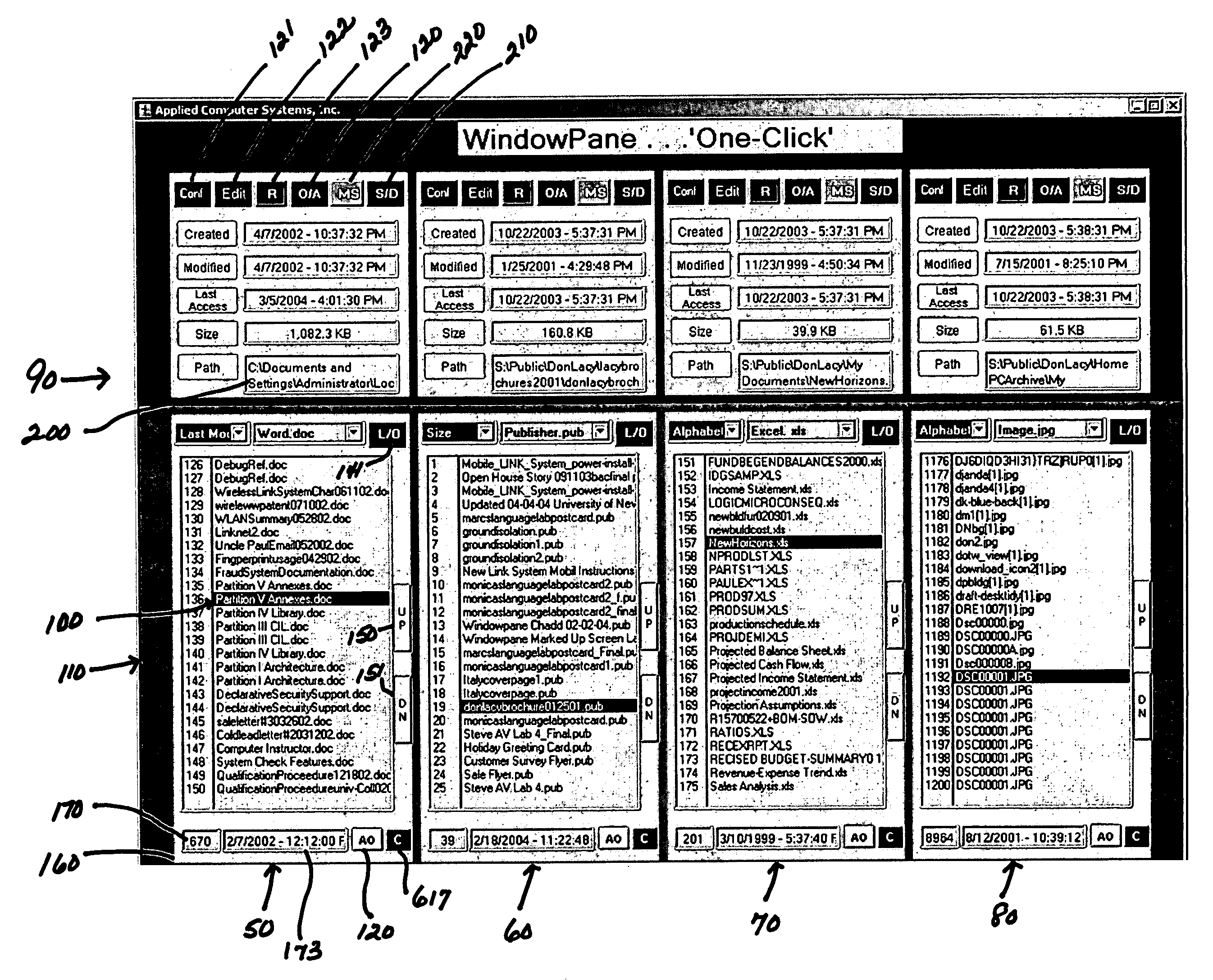
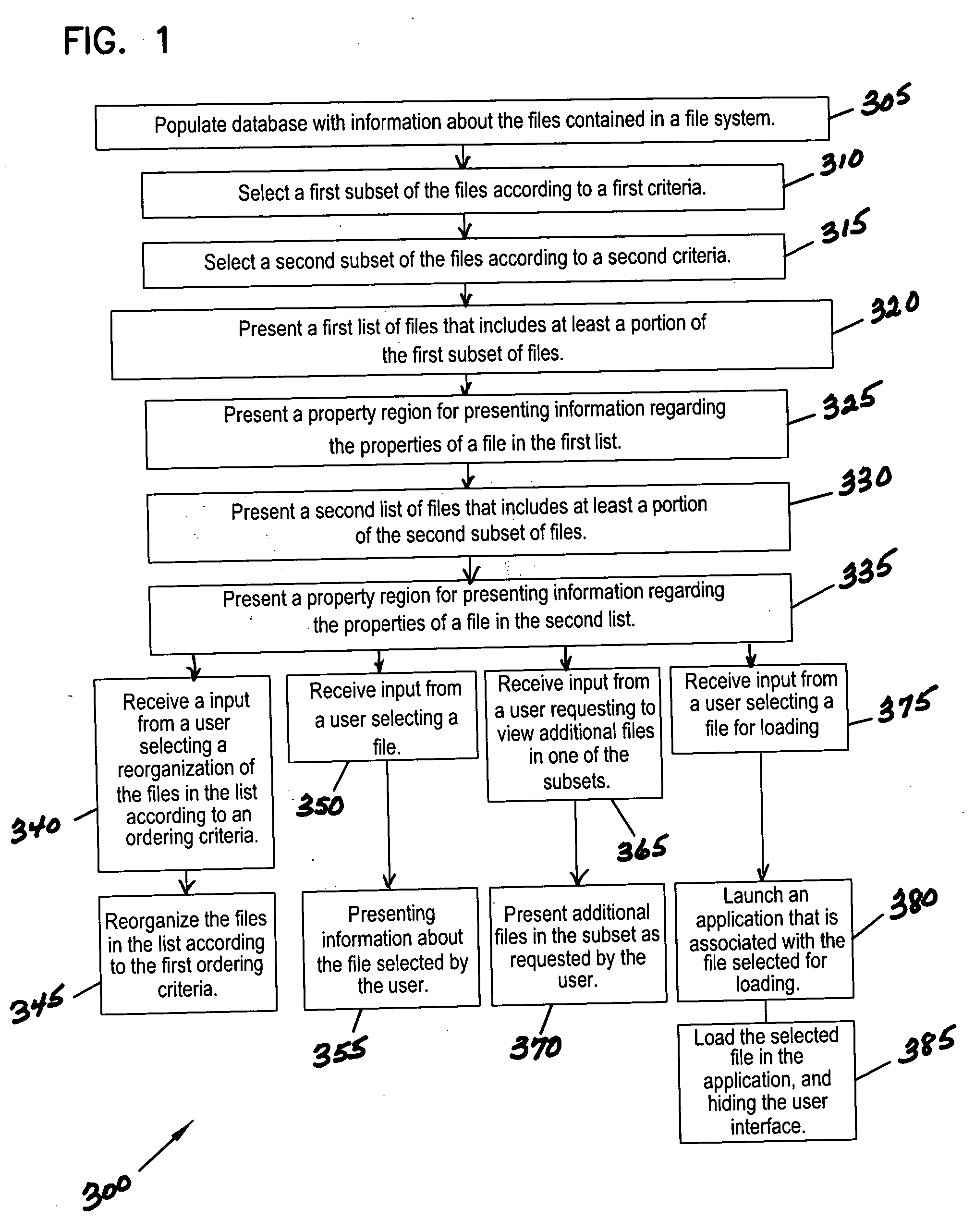
Method and system for displaying files to a user
InactiveUS20050246640A1Data processing applicationsSpecial data processing applicationsApplication softwareMetadata
A method and system for displaying files to a user by presenting several lists of files and allowing a user to view metadata about particular files. The lists may be organized according to projects, software applications, or other criteria. To help the user locate the appropriate file, metadata or file property information of one file each list is displayed in a window pane for that list. The order of the files in the list may be rearranged according to properties such as size, date of last modification, etc. To reduce the input required from a user to load files, multiple files can be selected and then loaded into related software applications.
Owner:APPLIED COMP SYST
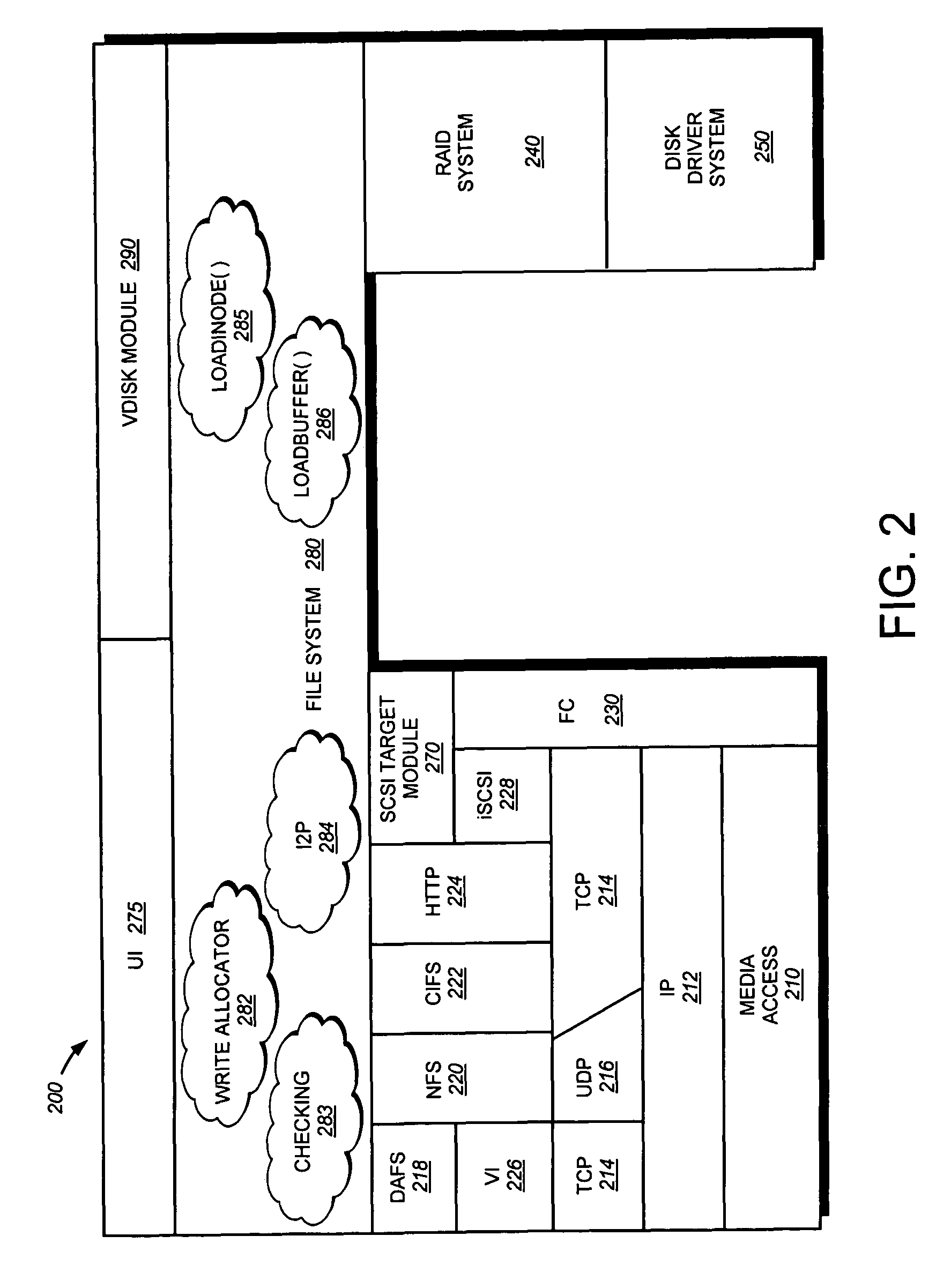
System and method for verifying and restoring the consistency of inode to pathname mappings in a filesystem
InactiveUS7707193B2Digital data processing detailsMultiple digital computer combinationsInodeOnline document
A system and method verifies and restores the consistency of inode to pathname mappings. In a first embodiment, an off-line verification procedure is modified to verify and correct the primary name inode to pathname mapping information within inodes of a file system. In a second embodiment, an on-line file system verification process is modified to verify inode to pathname mapping information upon the loading of each inode within the file system.
Owner:NETWORK APPLIANCE INC
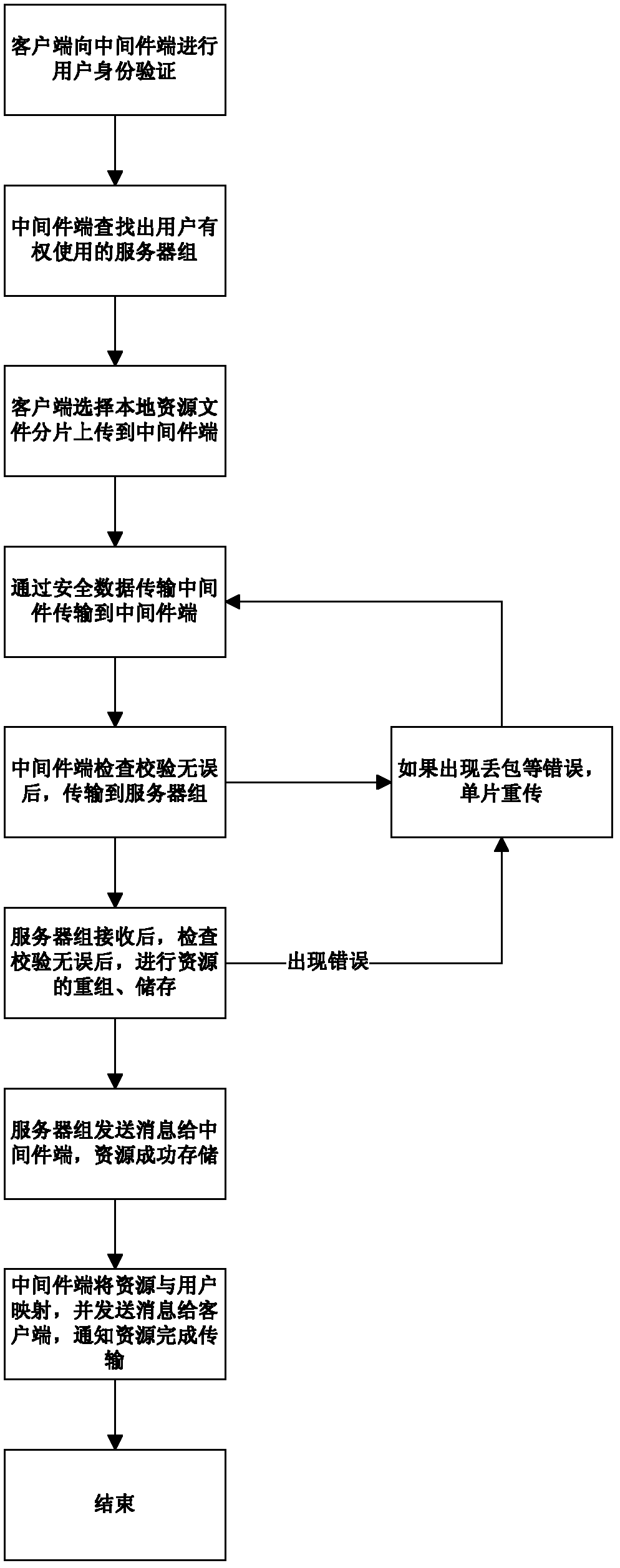
Cloud storage method for cloud computing server
InactiveCN102255974AFix security issuesGuaranteed correctnessTransmissionComputer network technologyClient-side
The invention discloses a cloud storage method for a cloud computing server, belonging to the technical field of computer networks. The method comprises the following steps: (1) a cloud computing server group server and a client registers on a middleware server respectively; (2) the middleware server searches a local database and looks up an operable file and a usable cloud computing server group for a current user; (3) the user selects an upload file, fragments the file and transmits the file fragments to the middleware server; (4) the middleware server verifies the upload file, requires the user to retransmit if the upload file is wrong, and transmits data to the cloud computing server group usable for the user if the upload file is correct; (5) the cloud computer server group rearranges and stores the received data and sends a success message to the middleware server; and (6) the middleware server establishes mapping between the name of the upload file and the user. According to the invention, the correctness and integrity of a data transmitting process and the privacy of data are ensured, and high reliability of normal work of the server group is ensured.
Owner:无锡中科方德软件有限公司
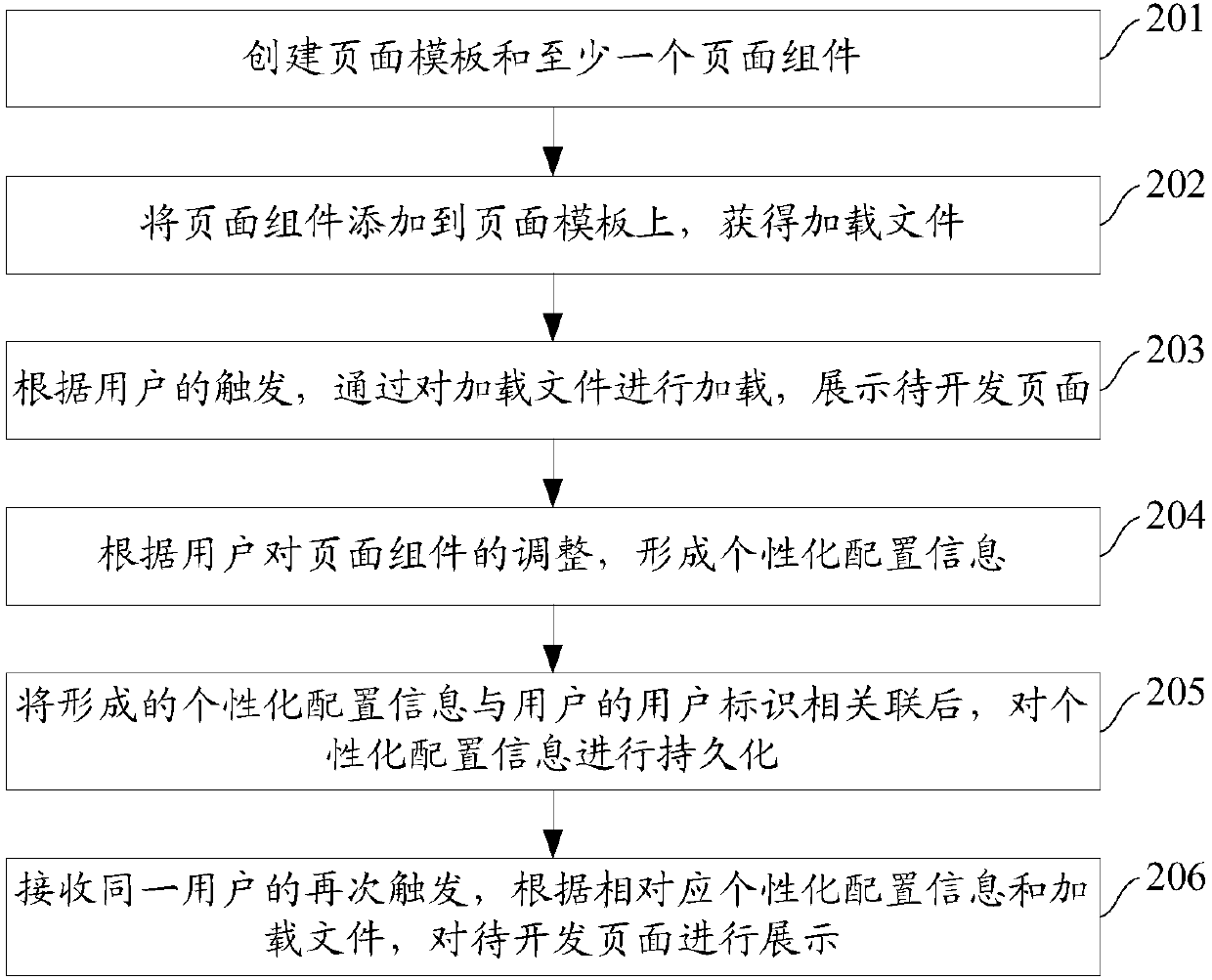
Page development method and device
The invention provides a page development method and device. The method comprises the following steps that: creating a page template and at least one page component, wherein each page component corresponds to at least one information displaying form; determining at least one piece of to-be-displayed information which needs to be displayed in a page to be developed; aiming at each piece of to-be-displayed information, obtaining the corresponding page component according to the information displaying form of the to-be-displayed information; obtaining the page template, and adding each obtained page component to the page template; independently configuring the position configuration information of each page component on the page template to determine the position of each page component on thepage template; independently configuring the data source configuration information of each page component to determine the data source of each page component; and carrying out persistence on the position configuration information and the data source configuration information corresponding to each page component to form the loading file of a to-be-developed page. By use of the scheme, page development efficiency can be improved.
Owner:INSPUR COMMON SOFTWARE
Virus scanning and killing method and device
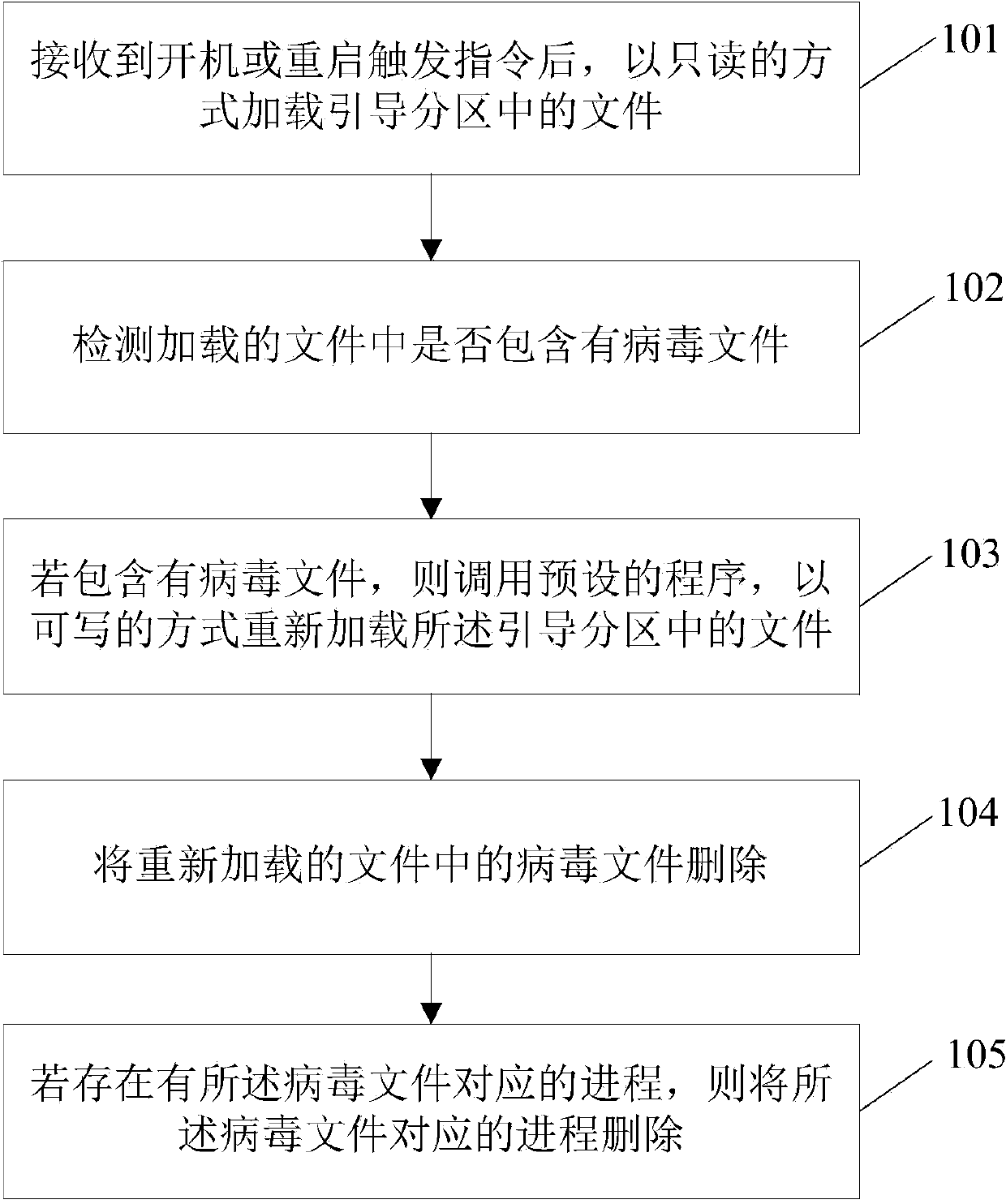
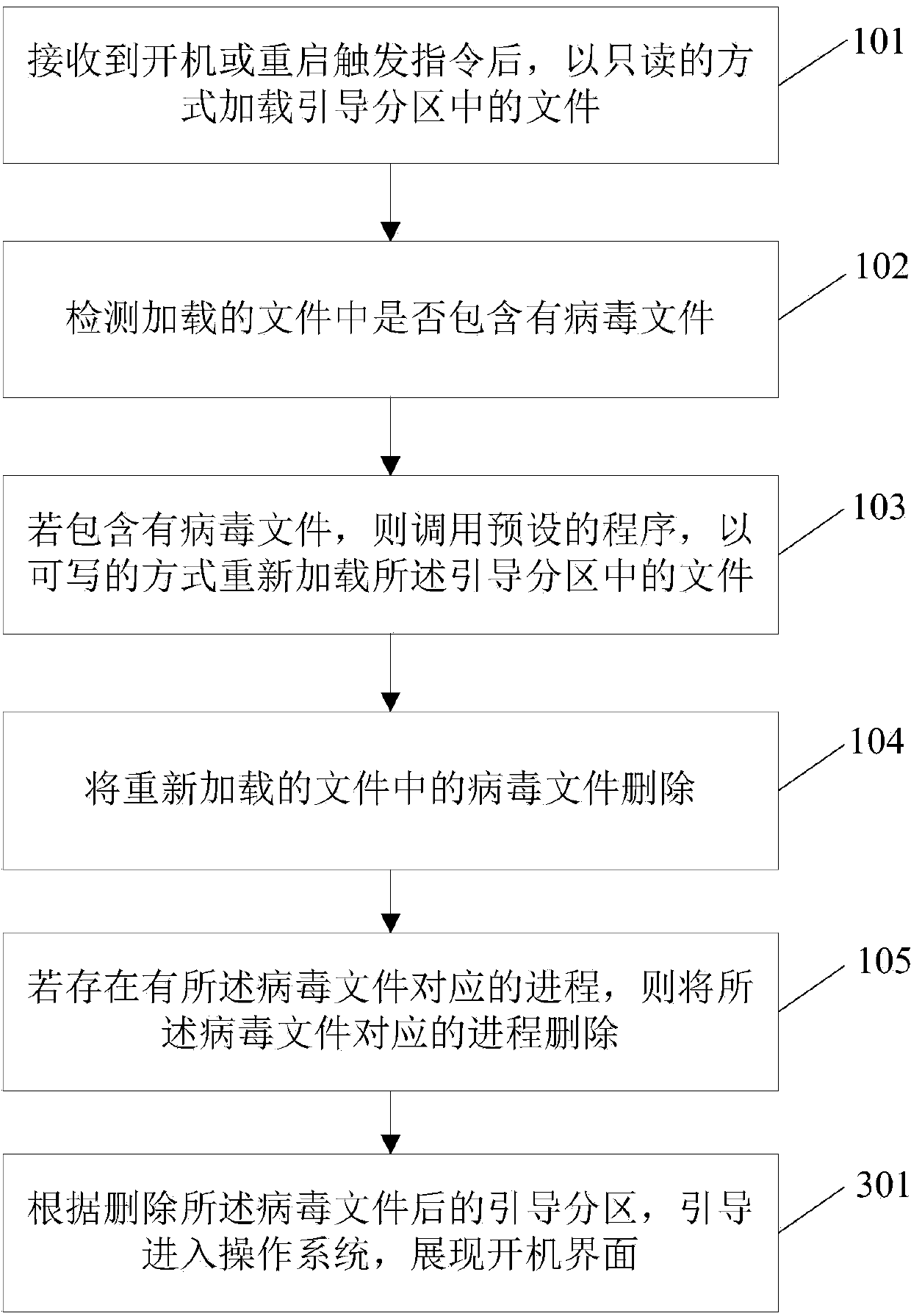
ActiveCN104008340AAvoid resurrectionImprove the safety of usePlatform integrity maintainanceVirusMobile phone
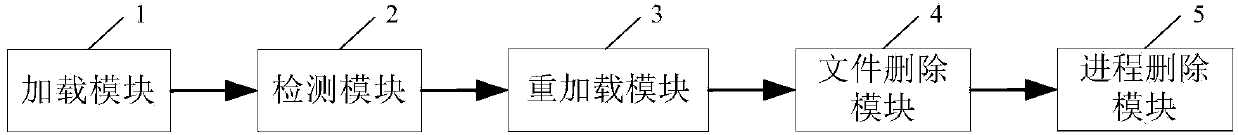
The invention relates to a virus scanning and killing method and a virus scanning and killing device, wherein the method comprises the following steps that after a boot or reboot triggering instruction is received, files in a boot partition are loaded in a read-only mode; whether the loaded files include virus files or not is detected; if the virus files are included, a preset program is called, and the files in the boot partition are reloaded in a writable mode; the virus files in the reloaded files are deleted; if processes corresponding to the virus files exist, the processes corresponding to the virus files are deleted. The technical scheme provided by the invention has the advantages that during boot or reboot of a mobile phone in each time, for the virus or rogue program written into the boot partition, both the loaded virus or rogue program files and the corresponding processes are deleted,, the reanimation of the virus or the rogue program after the boot or reboot is avoided, and the use safety of users is improved.
Owner:北京鸿享技术服务有限公司
Automatic analysis system and method for malicious code
InactiveCN1845120AImprove work efficiencyAccurate analysisProgram/content distribution protectionNetwork dataApplication software
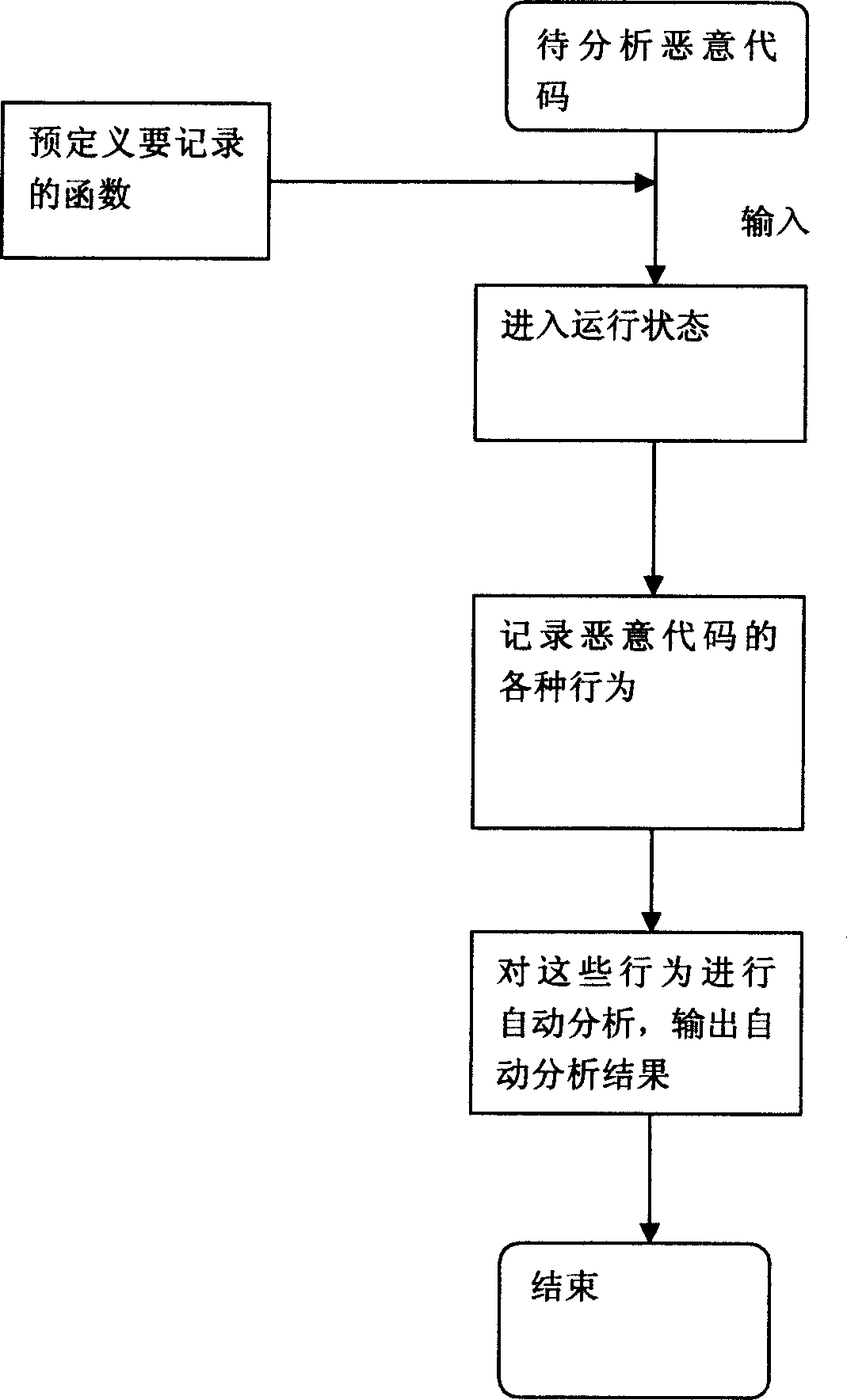
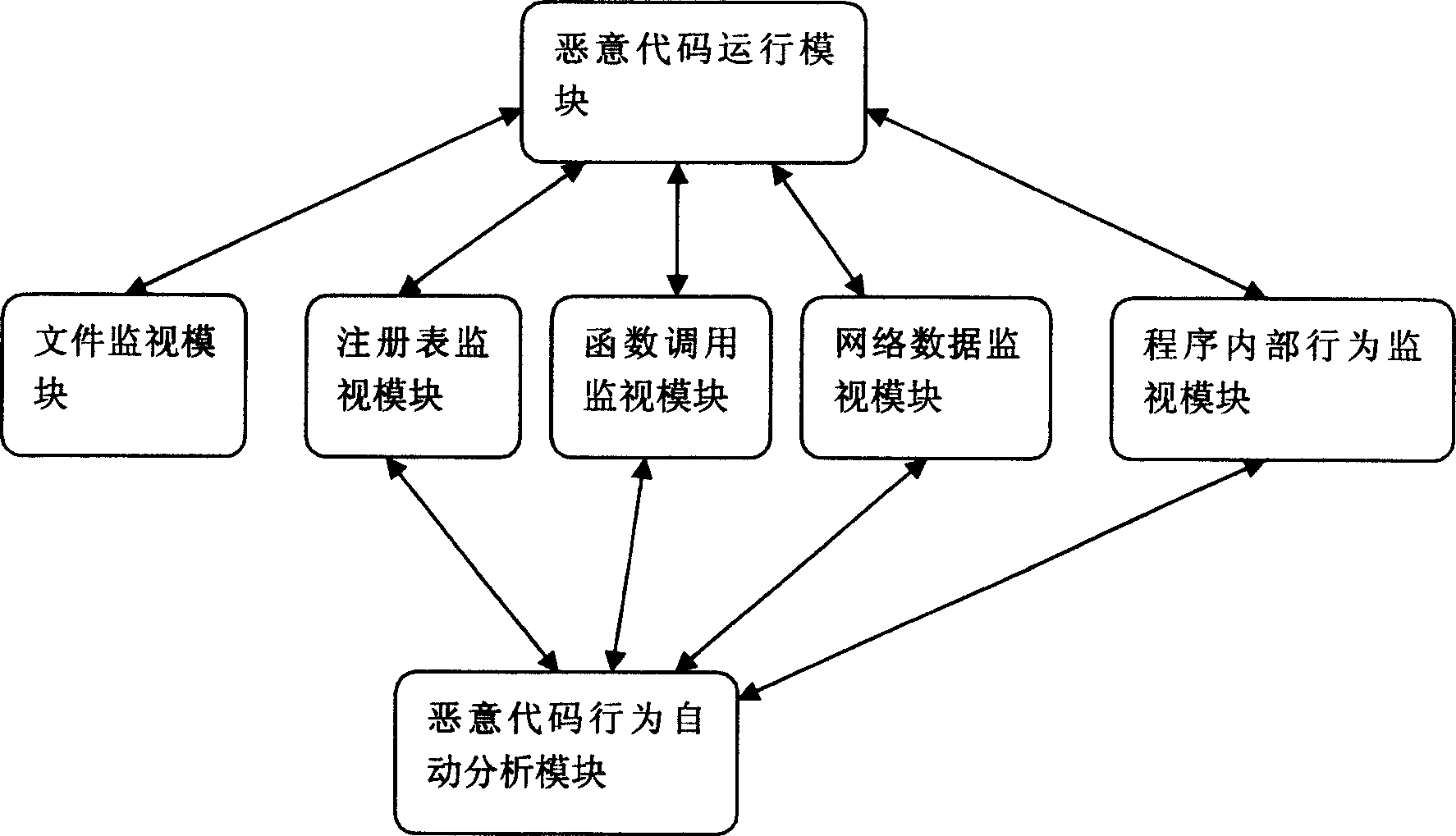
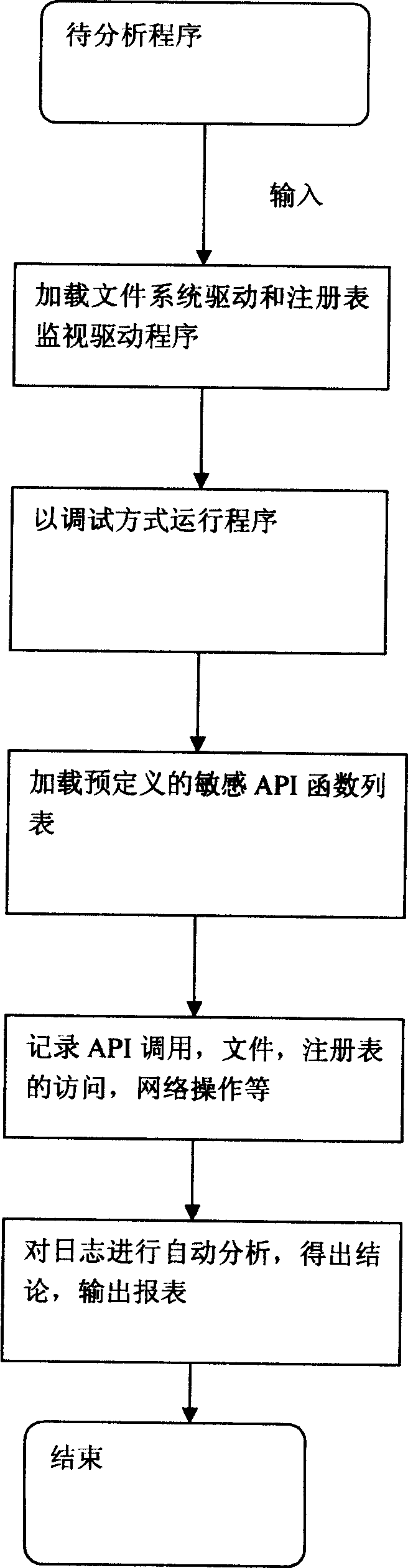
The invention discloses a malicious code automatic analyze system formed by several independent modules, as malicious code operating module, file detecting module, register detecting module, function transfer detecting module, network data detecting module, program inner operation detecting module, and malicious code operation automatic analyze module. Said method comprises: loading the driving programs of file detection and register detection; loading the sensitive function recorded in pre-definition; in the operation of malicious code, synchronously recording to the transfer of application program interfaced, the access of file and register, and network operation; when the malicious code is over and automatically leaves, the system automatically analyzes said operation, and outputs the result. The invention can completely record the operation of malicious code, without affected by the unknown frame or distortion frame of malicious code. The invention can improve the working efficiency and malicious code analyzer.
Owner:BEIJING VENUS INFORMATION TECH +1
Analog multiplier/divider applicable to prime field and polynomial field
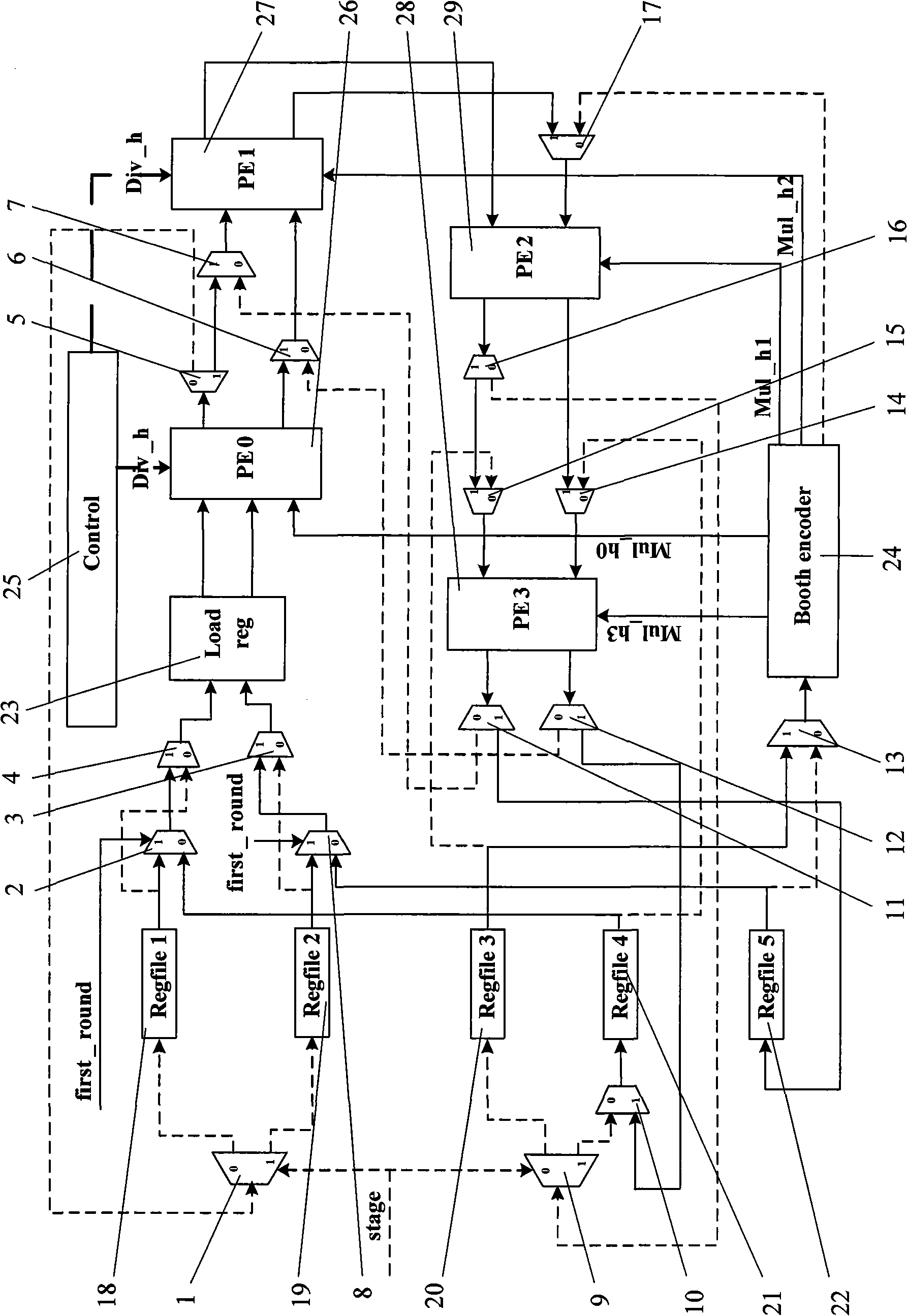
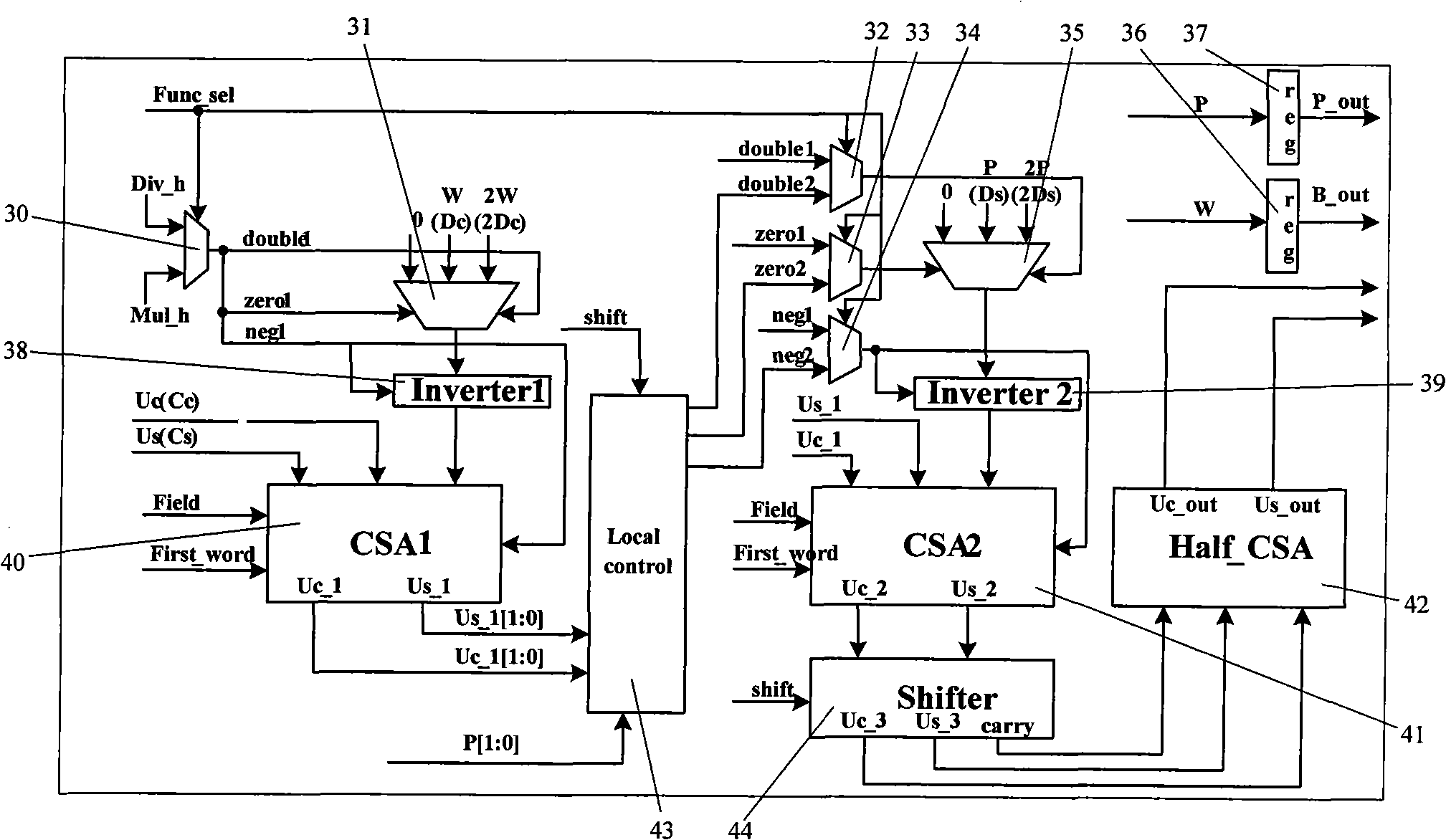
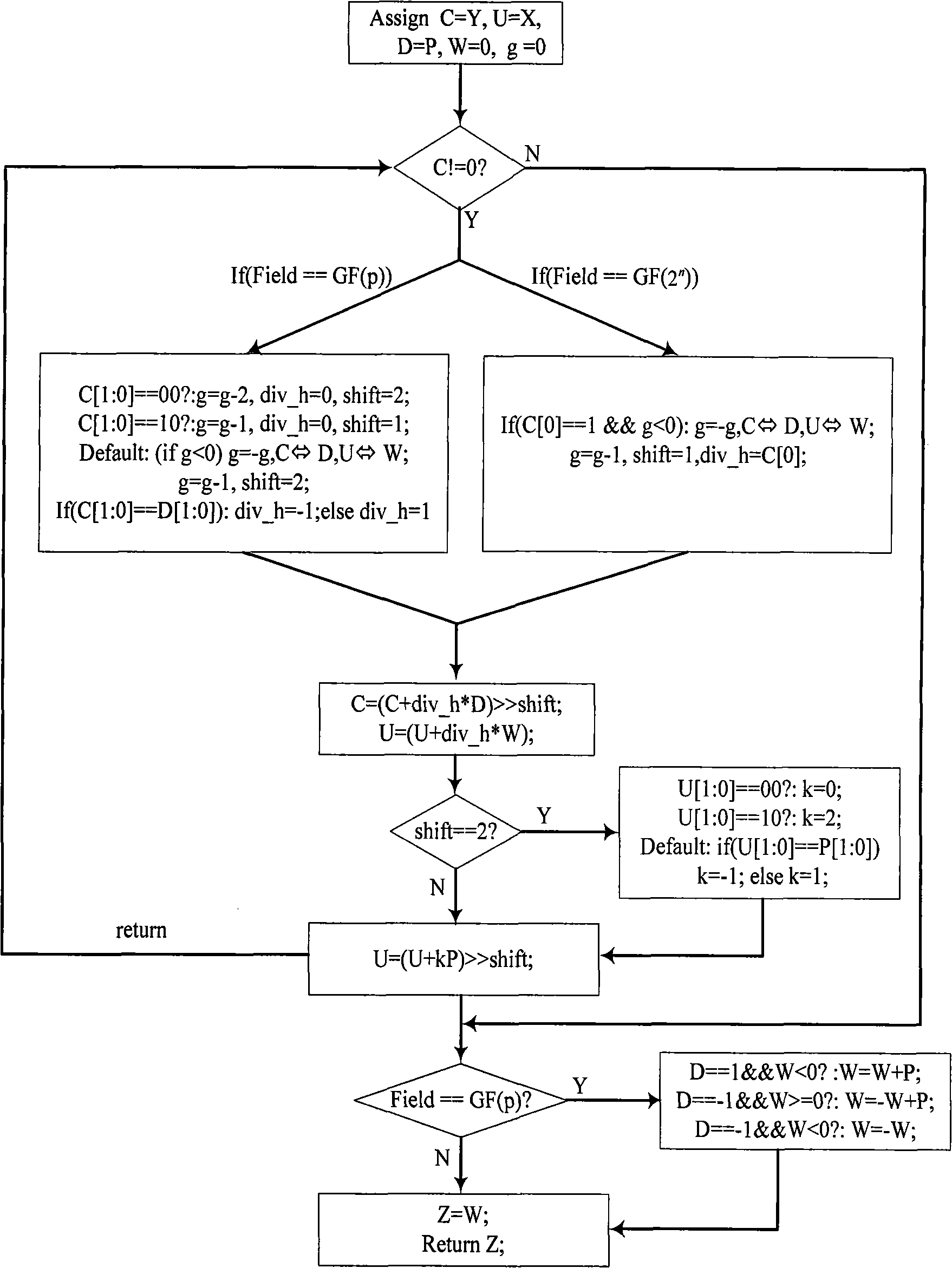
InactiveCN102122241AHigh speedReduce areaComputation using non-contact making devicesExtensibilityByte
The invention relates to a dual-field analog multiplier / divider which is suitable for an ECC (Elliptic Curve Cypher) algorithm required in high-speed network application and portable mobile equipment application. The analog multiplier / divider comprises four PE operating units, 5 register files (Regfile), a Booth encoding unit, an input register (Load file), a control module (control) and 17 multi-path selectors. The analog multiplier / divider changes the connection of the four PE operating units and the reading position of data through the 17 multi-path selectors so as to complete analog multiplying or analog dividing, has expandability, can support 480-bit analog multiplying / dividing operations maximally, and shares hardware units for multiplying / dividing operations so as to reduce the area of the hardware; and in the algorithm, addition and subtraction and shift operation of long operands are carried out by the unit of byte, therefore, the convergence rate of the algorithm is greatly accelerated, and further the operating speed is multiplied.
Owner:FUDAN UNIV
Communication protocol applicable to reliable multi-machine communication, encoding and decoding method and communication device
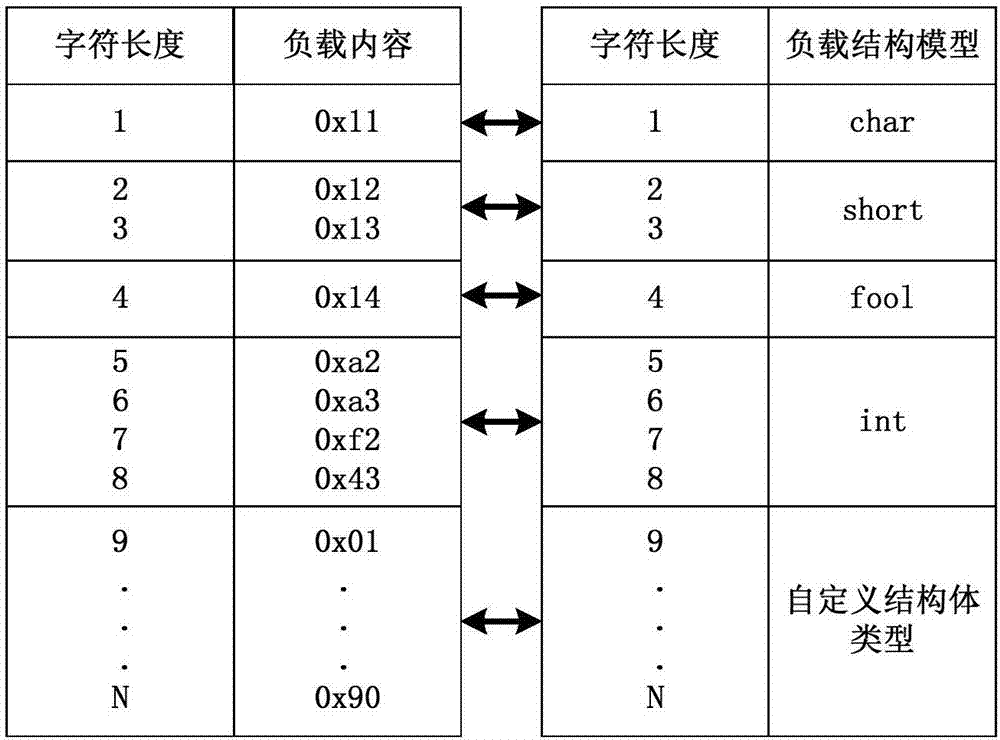
ActiveCN107147657AImprove frame and parsing efficiencyImprove readabilityBus networksTransmission format adaptationCode readabilityCommunication device
The invention discloses a communication protocol applicable to reliable multi-machine communication. The frame format of the communication protocol comprises a frame starting field, a frame header field, a load filed, a check field and an ending field, which are arranged in sequence from front to back, wherein the frame header field comprises a frame type field, a source address filed, a destination address filed, a load length filed and a functional codeword field, which are arranged in sequence from front to back; the load filed is expressed as a plurality of continuous data type fields according to the load contents to form a load structure model. According to the communication protocol, the frame header field comprises the source address filed and the destination address filed, thereby being applicable to multi-device communication. The load structure model is used for effectively improving the data framing and analysis efficiency. The frame header field comprises the frame type field, therefore classified analysis can be performed on the load data according to the frame type so as to effectively improve the readability and maintainability of the code.
Owner:一飞智控(天津)科技有限公司
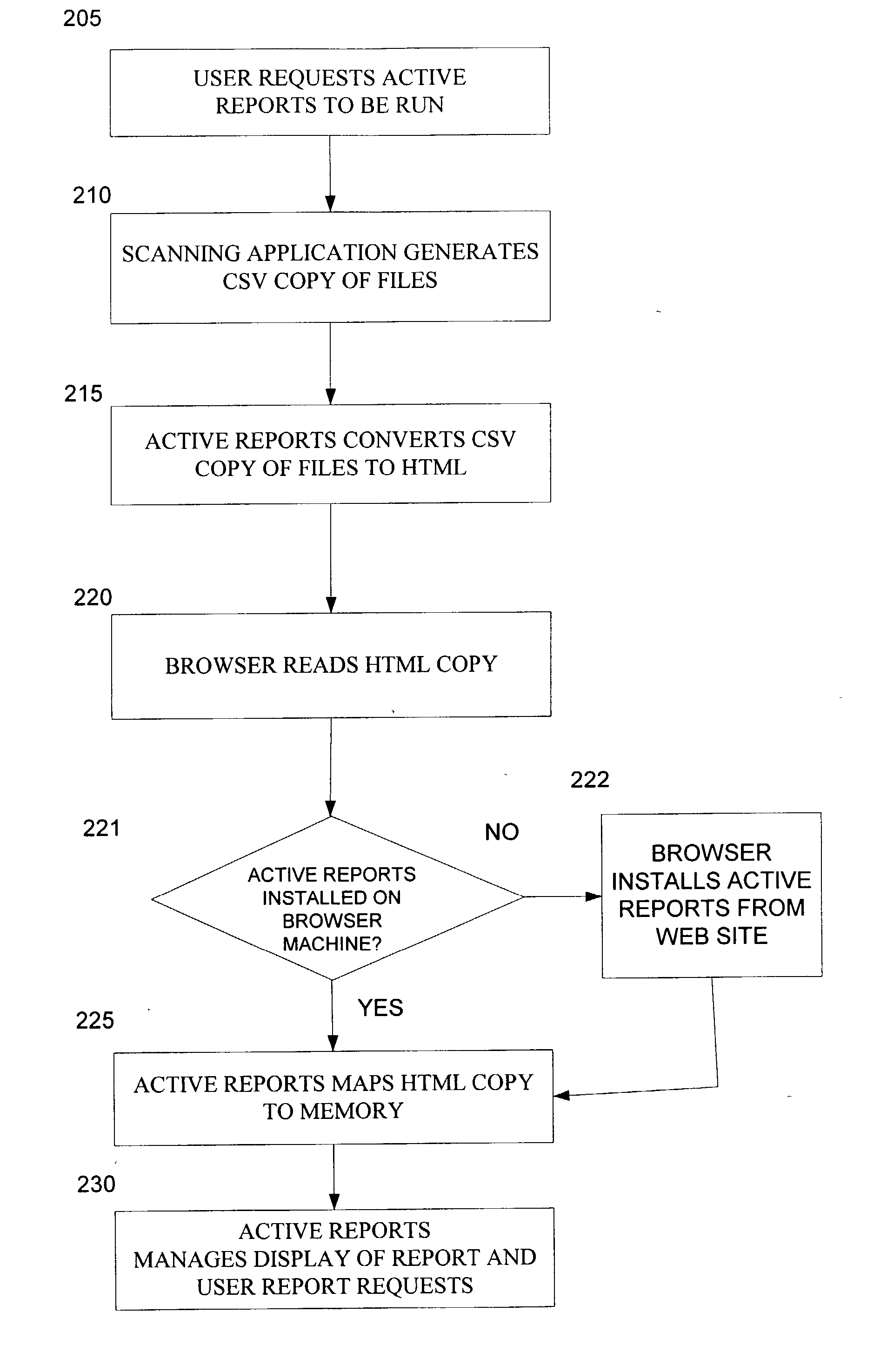
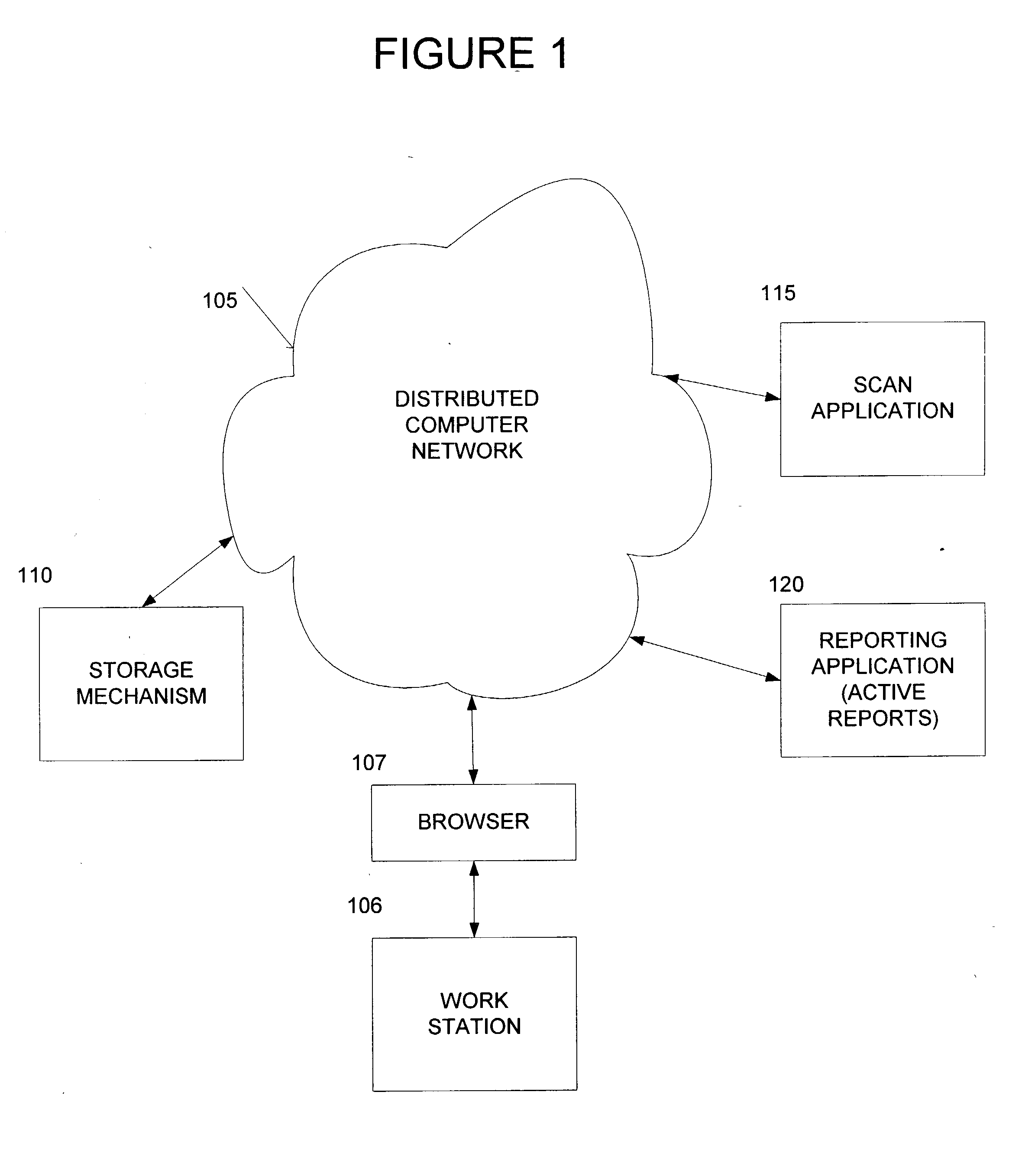
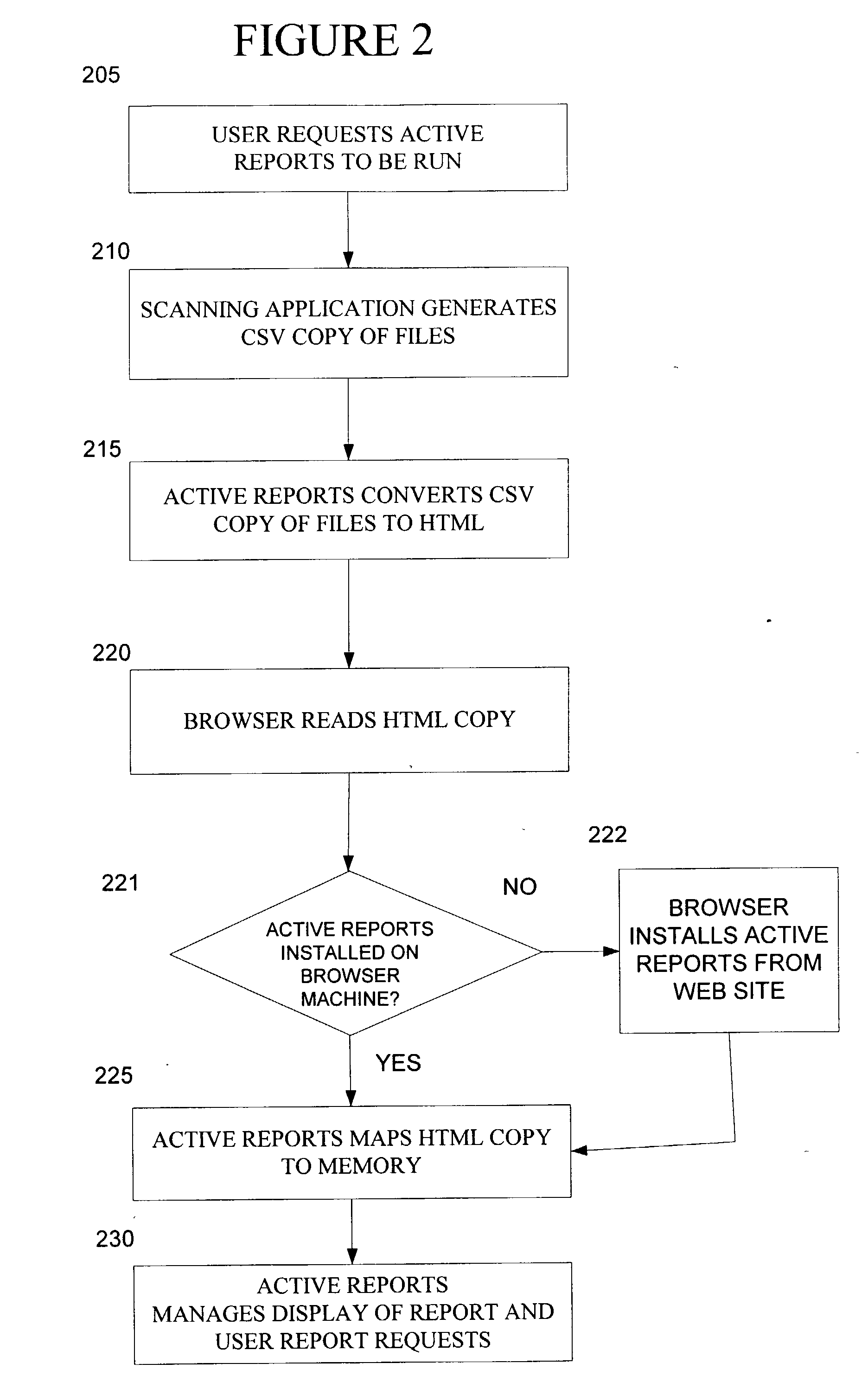
System for active reports with drill down capability using memory mapping of HTML files with embedded data
InactiveUS20020174140A1Data processing applicationsDigital data information retrievalDrill downElectronic form
A system and method for obtaining information on a large number of files, and to view and take action on those files. The present invention compiles a report on a file system in HTML format that is displayed by a browser. The report allows users to manage their files, or portions of their files, directly from the report, relieving system administrators of this burden. The method comprises: requesting Active Reports to be run; generating a CSV formatted copy of the files in the storage mechanism; converting the CSV formatted copy of the files to an HTML formatted copy of the files; reading the HTML formatted copy of the files so that the user can view the files; loading the file data by mapping the HTML formatted copy of the files to memory into a spreadsheet-like grid; and managing the display of the report and user report requests.
Owner:VERITAS TECH
Soft ware autonomous air upgrading method of wireless communication module, device and system thereof
ActiveCN101539885AAchieve upgradeSave spaceMemory adressing/allocation/relocationNetwork data managementGeneral Packet Radio ServiceExternal storage
The invention provides a data organizing method of a wireless communication module: in the wireless communication module, each submodule is linked and programmed to a fixed address in a memorizer with a modifying decentralizing and loading file; in each submodule, an indicating needle which points to a function which is needed to be called by the other submodule in the submodule or to a used global variable is put in an absolute segment; and the segment is linked to a first address of the submodule with the modifying decentralizing and loading file. The wireless communication module which organizes the data with the method starts a general packet radio service function periodically after networking, is connected with a server by the wireless network and is interacted with the server in a signally way so as to realize the automatic upgrade of current each submodule in the wireless communication module without special people on duty and external memory devices and can upgrade any protocol stack submodule or even whole protocol stack soft wares.
Owner:DATANG MICROELECTRONICS TECH CO LTD
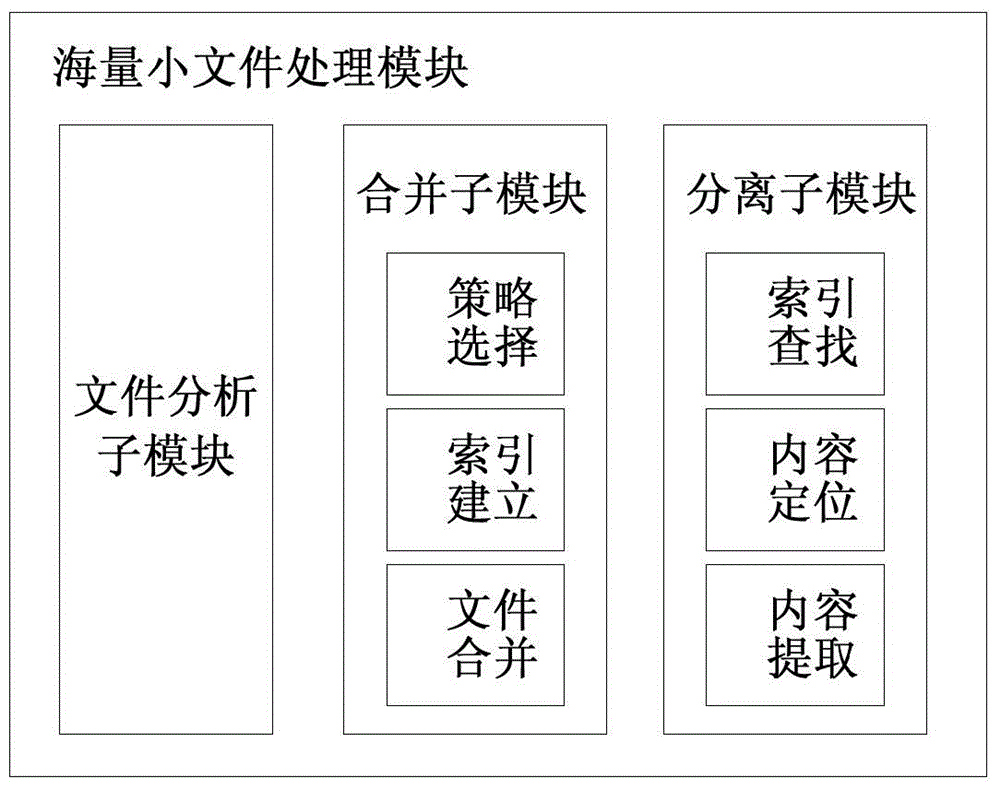
Backup method of mass small files and cloud store gateway
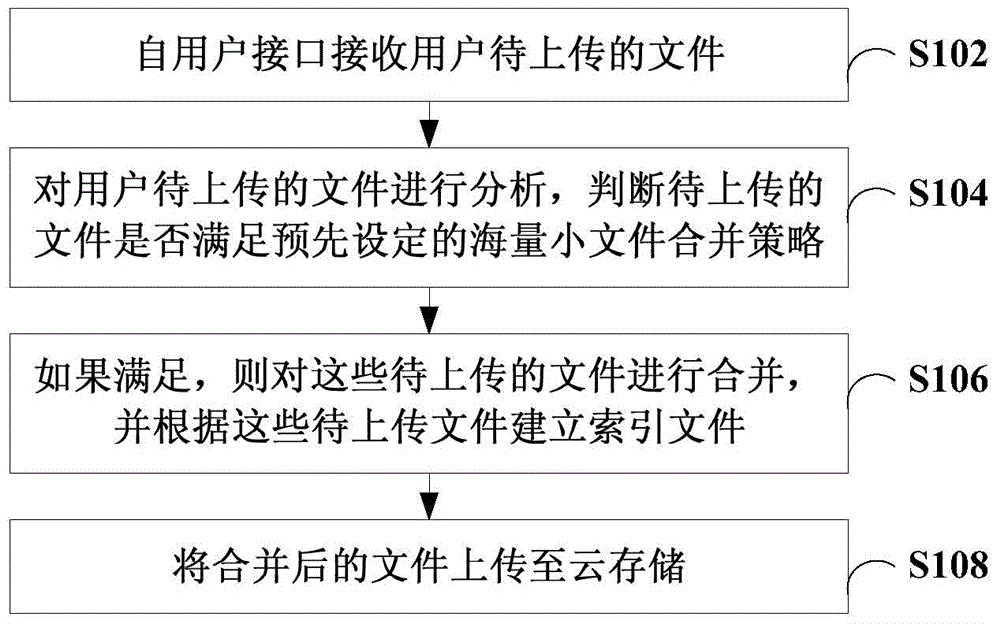
InactiveCN104978351AReduce frequent operationsReduce consumptionSpecial data processing applicationsCloud storageUser interface
The invention relates to a backup method of mass small files and a cloud store gateway. The method comprises the following steps: receiving the to-be-uploaded files of a user from a user interface; analyzing the to-be-uploaded files of the user, and judging whether the to-be-uploaded files meet a preset mass small file consolidation strategy or not; if the to-be-uploaded files meet the preset mass small file consolidation strategy, consolidating the to-be-uploaded files, and establishing an index file according to the to-be-uploaded files; and uploading the consolidated files to cloud storage. The backup method improves the backup efficiency of the mass small files.
Owner:CHINA TELECOM CORP LTD
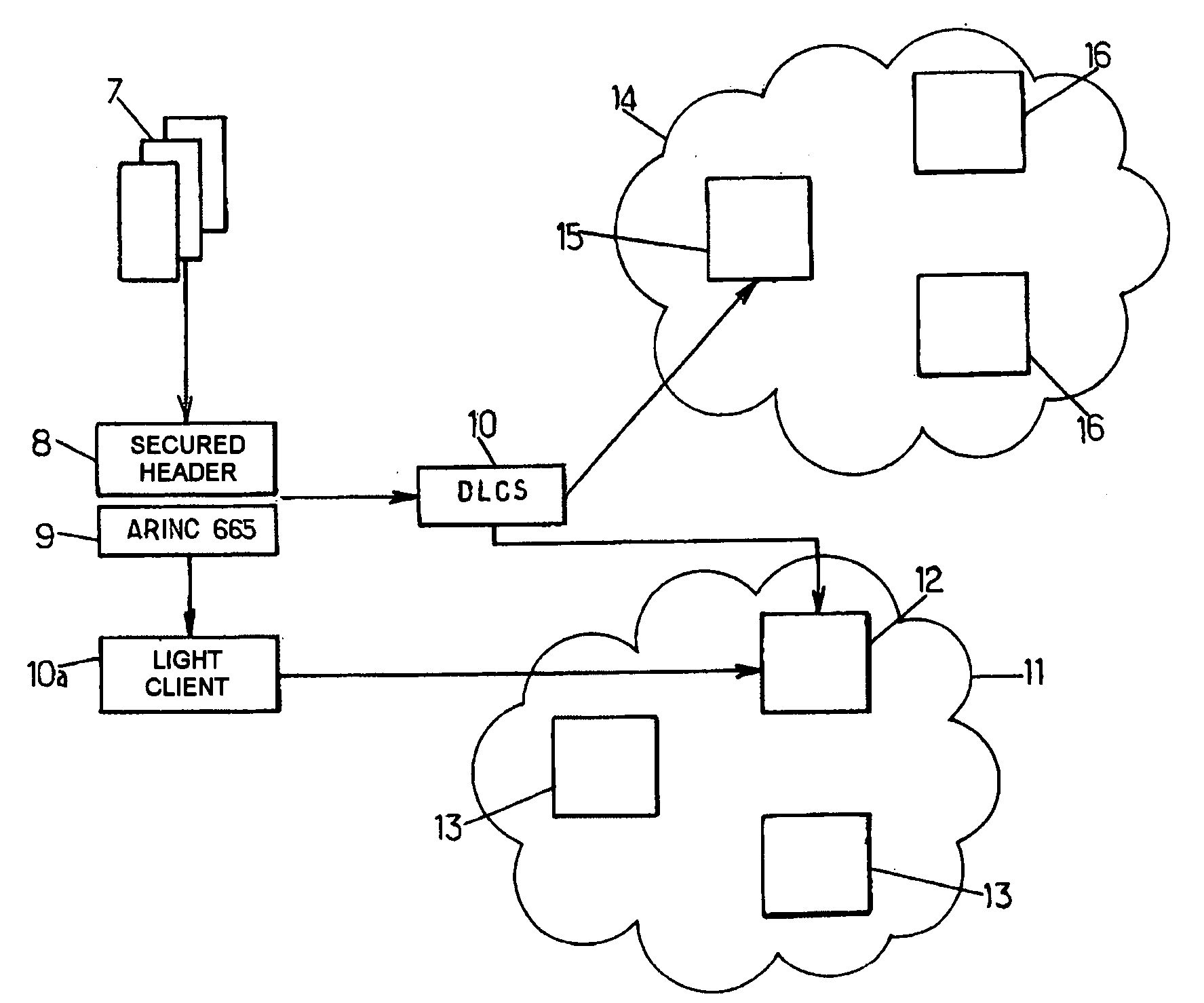
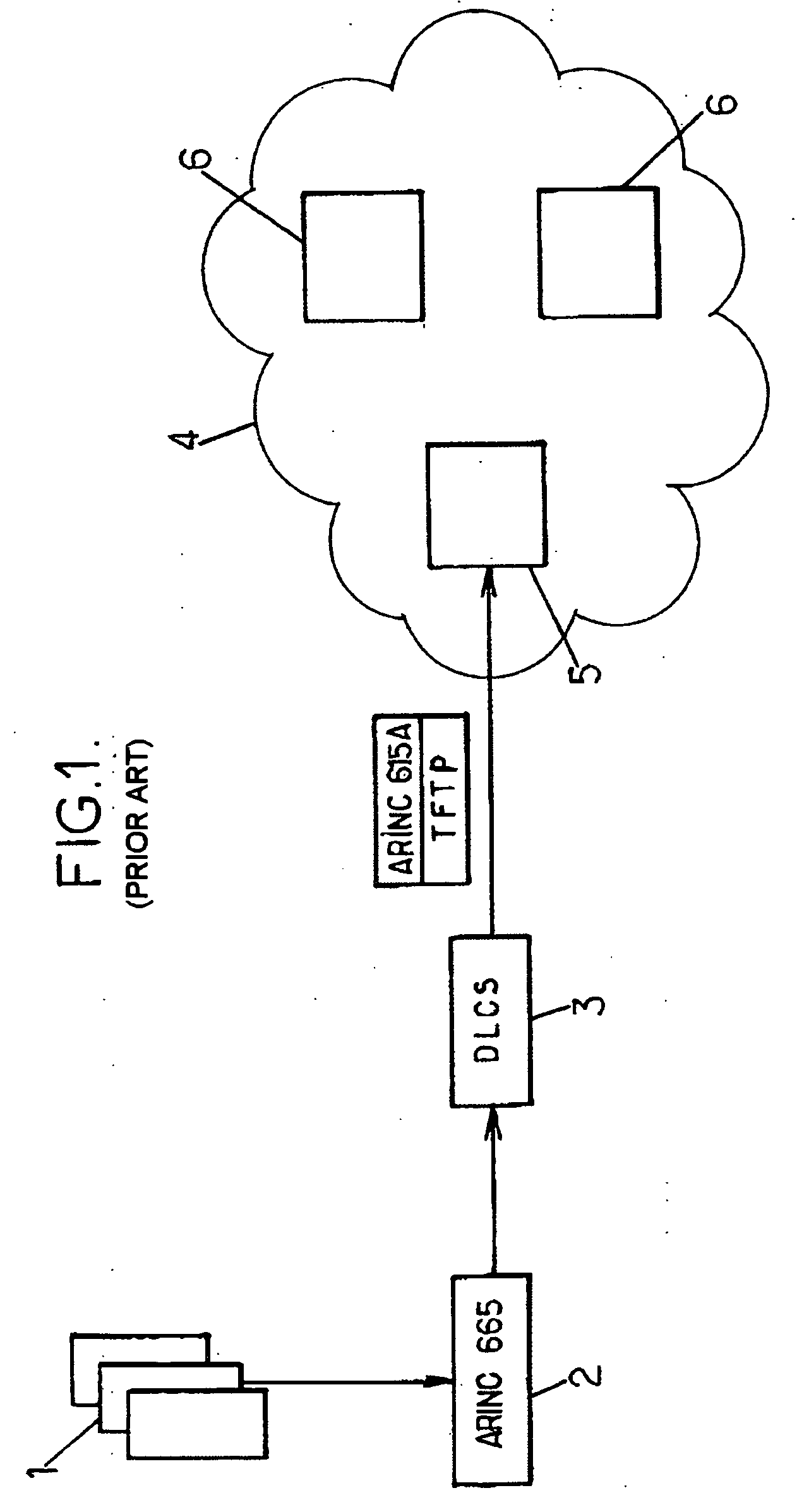
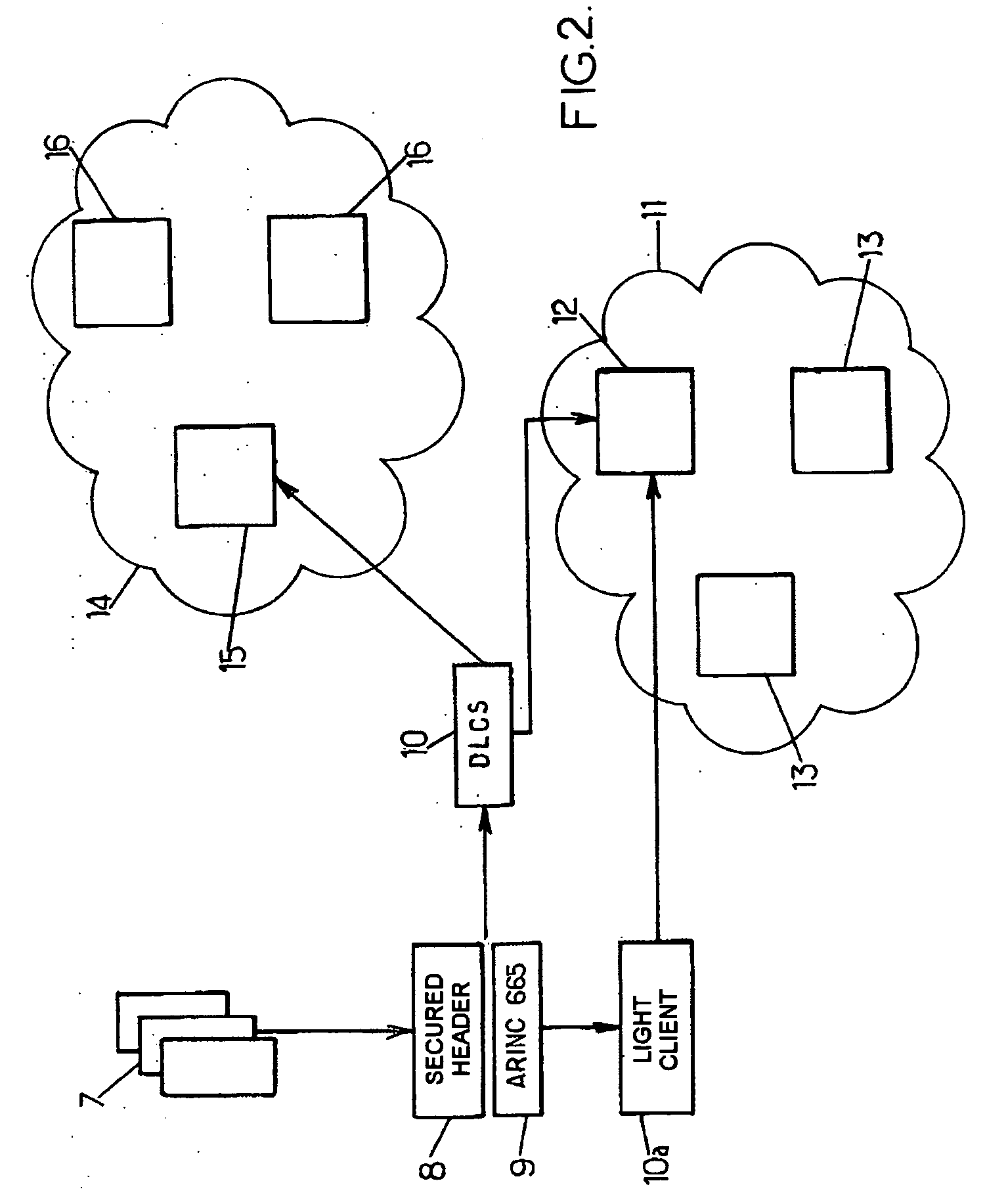
Method of loading files from a client to a target server and device for implementing the method
ActiveUS20050267860A1Ensures a certain degree of compatibility of the loading toolsDigital data processing detailsMultiple digital computer combinationsClient-sideComputer science
The invention proposes a method of loading files from a client to at least one target server, the method comprising the following steps: transmitting, from the client to the target server, a set of data obtained from said files to be loaded, at least some of the data of said set being encoded; requesting, from the client, an authenticity check, by the target server, on the data of said set from at least some of said encoded data; and when the authenticity of the data of said set has been checked successfully by the target server, loading said files according to a predetermined format from the client to the target server.
Owner:SAFRAN ELECTRONICS & DEFENSE
Table format customizable Excel table analysis method
InactiveCN103150380ARealize business needsMaintain accuracySpecial data processing applicationsTransaction managementWeb service
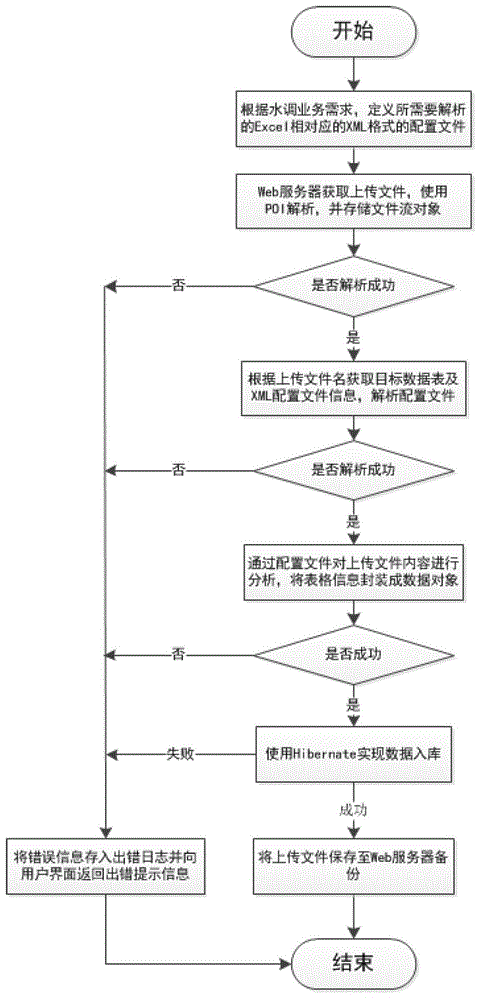
The invention discloses a table format customizable Excel table analysis method which comprises the steps of defining an XML (Extensive Makeup Language) format configuration file corresponding to an Excel table to be resolved according to water diversion business requirements, uploading an Excel file to a Web server through a browser, resolving the file, obtaining a target data sheet of the file and information of the corresponding XML configuration file according to a filename of the uploaded file, resolving the configuration file, analyzing contents of the uploaded file through the information of the configuration file, packaging the information to be warehoused into a data object, warehousing data with Hibernate, and uploading a file backup to the server. According to the method, general resolution of complicated Excel is realized through the configurable file, the method is particularly applicable to processing river basin water diversion business tables, and a precise error information prompt mechanism and a transaction management mechanism ensures accuracy and consistency of the data of a database.
Owner:HOHAI UNIV
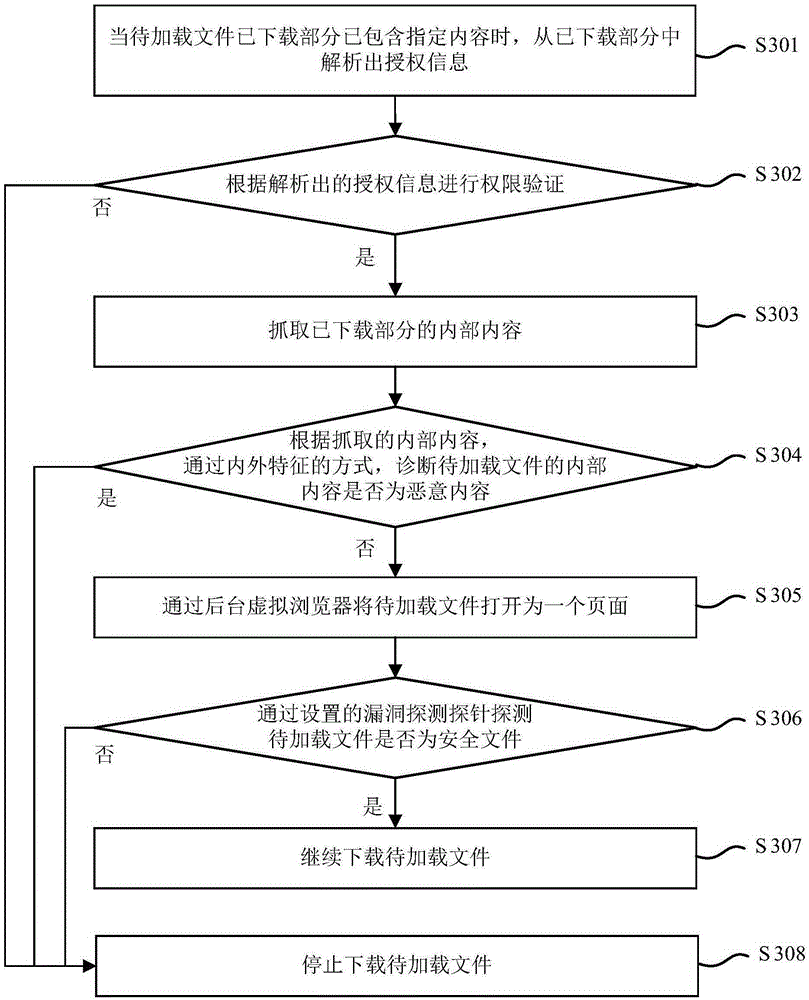
File secure loading implementation method and apparatus
ActiveCN105320883AReduce exclusionReduce cleanup timePlatform integrity maintainanceTraffic capacityAuthorization
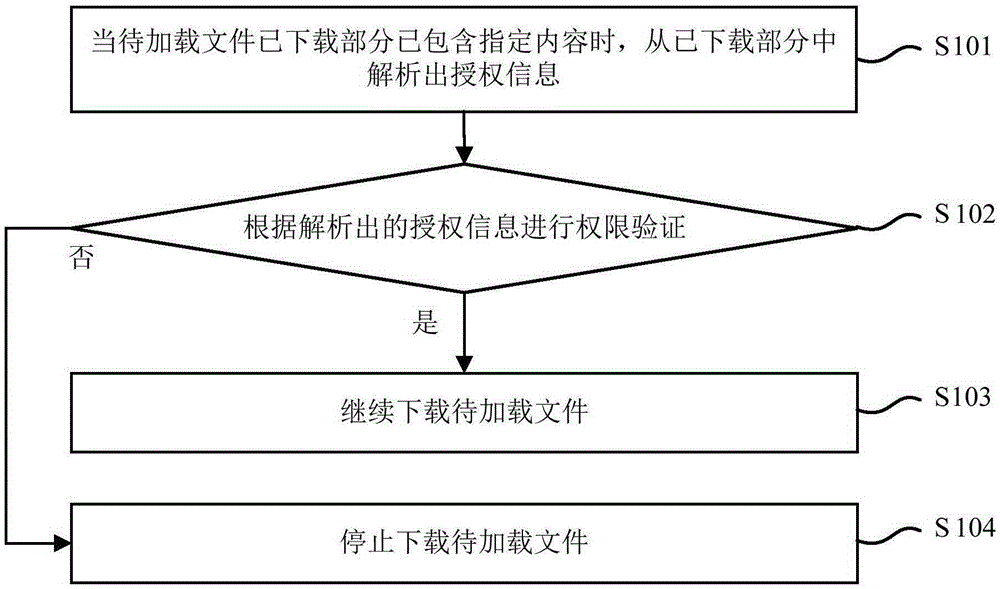
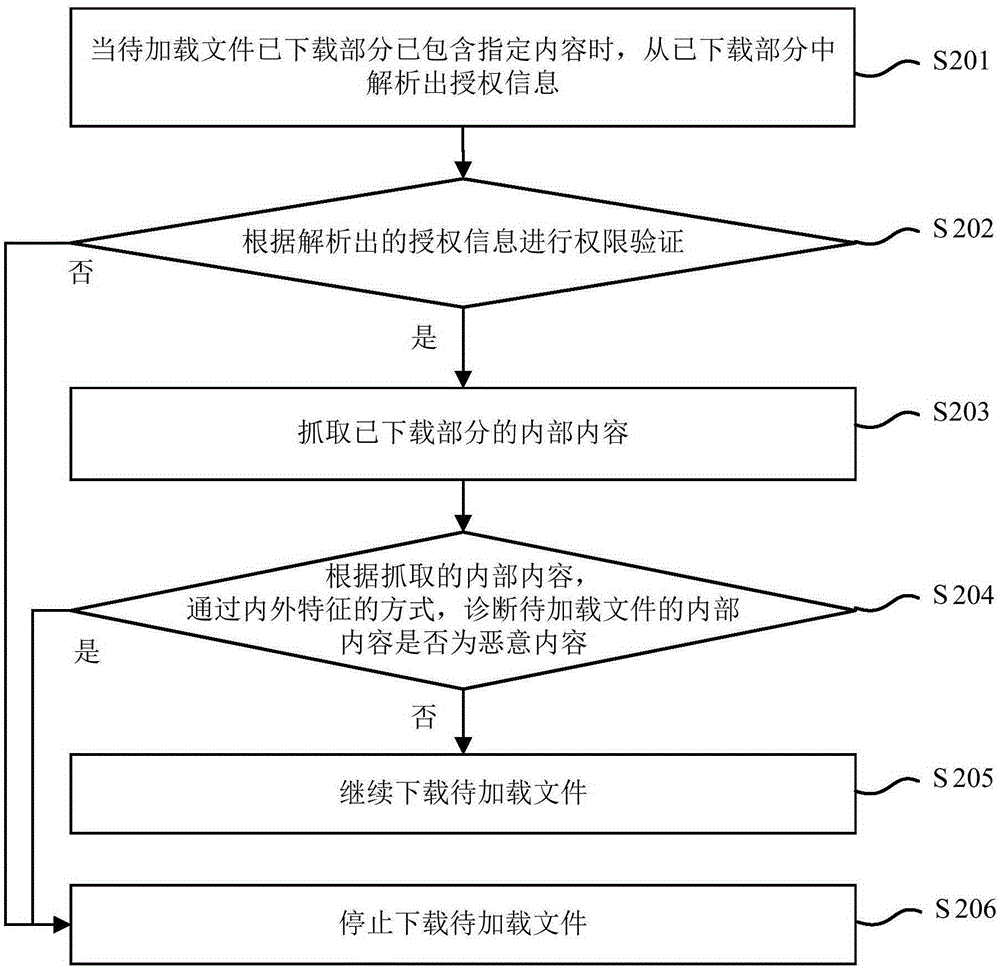
The present invention provides a file secure loading implementation method and apparatus. The method comprises: when a downloaded portion of a to-be-loaded file comprises a specified content, parsing authorization information from the downloaded portion; according to the authorization information, performing authority verification; when the verification is not passed, stopping downloading the to-be-loaded file; and when the verification is passed, continuing downloading the to-be-loaded file. According to file secure loading implementation method and apparatus provided by the present invention, unsafe to-be-loaded files can be found in time during a download process rather than after downloading is completed, so that the speed and efficiency of excluding the unsafe files are improved, a download volume is reduced, download traffic is saved, and waste of system resources is avoided.
Owner:BEIJING QIHOO TECH CO LTD
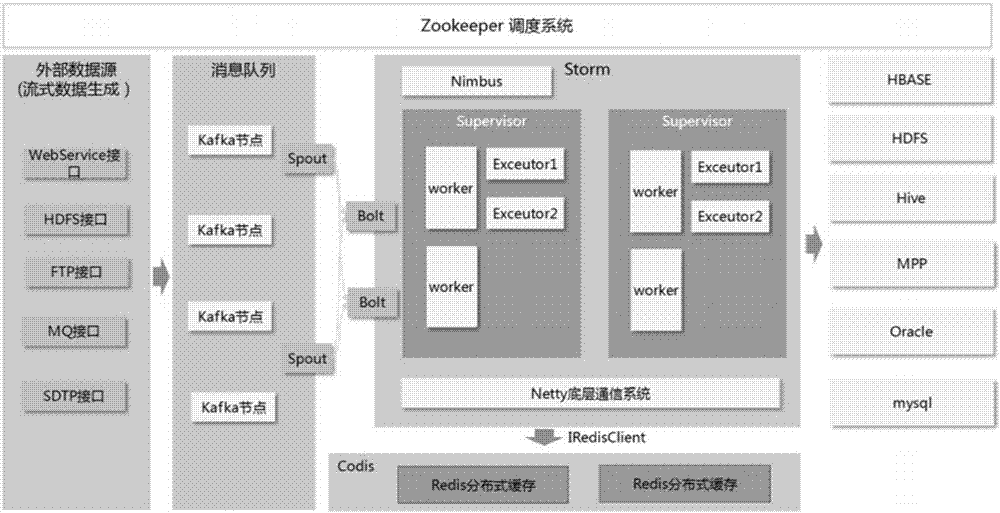
Communication network optimization system and streaming data processing device in communication network optimization system
InactiveCN107070890ATaking into account real-timeTaking into account the needsNetwork topologiesData switching networksThird partyStreaming data
The invention provides a communication network optimization system and a streaming data processing device in the communication network optimization system. The streaming data processing device comprises a streaming data generating module for loading file data obtained by different data sources as the streaming data and pushing the streaming data to a Kafka processing module; the Kafka processing module used for uniformly loading the streaming data to a Kafka cluster so as to be called by a Storm processing module; the Storm processing module which comprises a Spout node and a Bolt node, wherein the Spout node is used for reading data from the Kafka cluster and pushing the read data to the Bolt node, the Bolt node is used for performing a corresponding computation on the data pushed by the Spout node according to a preconfigured application scene and summarizing the computing result in real time, and storing the summarization result in a Redis cluster at fixed period; a Redis storage module for caching the summarized data in the memory; a data output module for providing the streaming processing result to a third-party data provider in a standard interface. By use of the streaming data processing device provided by the invention, the network optimization system can provide the real-time sensing analysis function in the user level.
Owner:BEIJING MATARNET TECH
Method for automatically converting data between dynamics analysis software and finite element analysis software
InactiveCN101727527AExcellent mechanical propertiesImprove performanceSpecial data processing applicationsKinematicsFinite element analysis software
The invention discloses a method for automatically converting data between dynamics analysis software and finite element analysis software, comprising the following steps of: starting the finite element analysis software to perform model flexiblization and outputting a modal neutral file (MNF); starting the dynamics analysis software, loading a virtual prototype model, reading the MNF, performing kinematics and dynamics analysis and outputting a load file; applying a load in the load file to a flexible body, performing stress and strain analysis on the flexible body and outputting stress and strain data; and circularly performing the steps and outputting an optimal operating condition and the stress and strain data. The method for automatically converting data can really integrate the powerful finite element function of the finite element analysis software and the powerful dynamics analysis function of the dynamics analysis software for combined application and provide an automatic, simple, convenient, high-efficiency and reliable realization means for achieving the mechanical property analysis and the operating condition analysis of a mechanical system.
Owner:CHINA AGRI UNIV
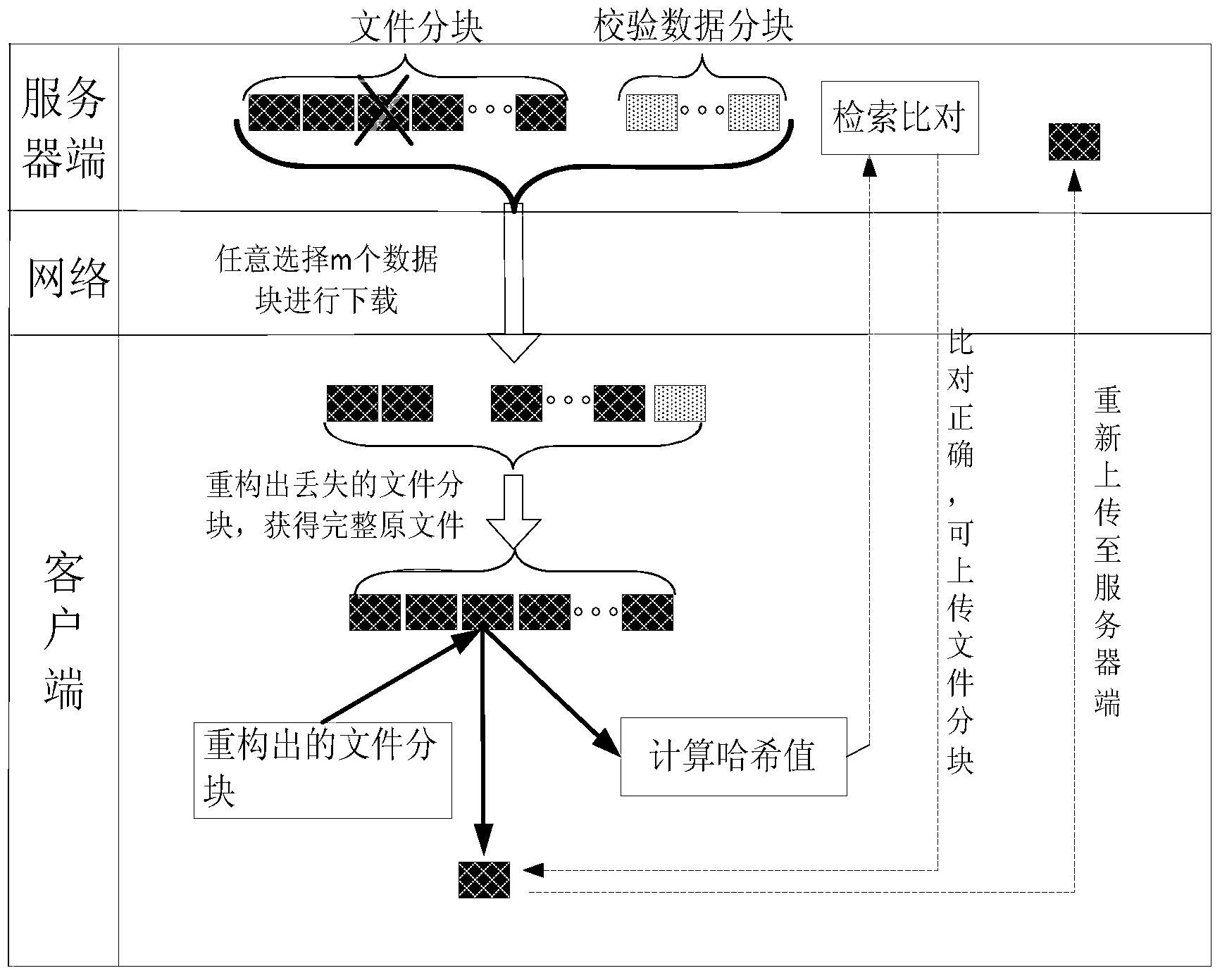
Self-adaptation data storage and reconstruction method for coding redundancy storage system
InactiveCN103916483AReduce the impactTroubleshoot maintenance bandwidth issuesTransmissionCode redundancyData center
The invention provides a self-adaptation data storage and reconstruction method for a coding redundancy storage system. The self-adaptation data storage and reconstruction method includes the following steps: (1) a client terminal calculates a Hash value of a file to be stored and uploads the Hash value to a server terminal; (2) the Hash value of the file to be stored is compared with Hash values of files already stored in the server terminal; (3) if the Hash value equal to the Hash value of the file exists, the server terminal does not accept uploading of the file to be stored, if the Hash value equal to the Hash value of the file does not exist, the server terminal accepts uploading of the file to be stored, the uploaded file is partitioned, Hash values of the file partitions are calculated and stored, and the file partitions are encoded to generate verification data partitions. Compared with the prior art, the self-adaptation data storage and reconstruction method has the advantages that the Hash value of the file to be stored and the Hash values of the file partitions are recorded, the corresponding file storage and reconstruction method is selected according to conditions of the system and the client terminal, and therefore network bandwidth pressure and calculation pressure, caused by data reconstruction, on a data center are reduced.
Owner:CHENGDU INST OF BIOLOGY CHINESE ACAD OF S
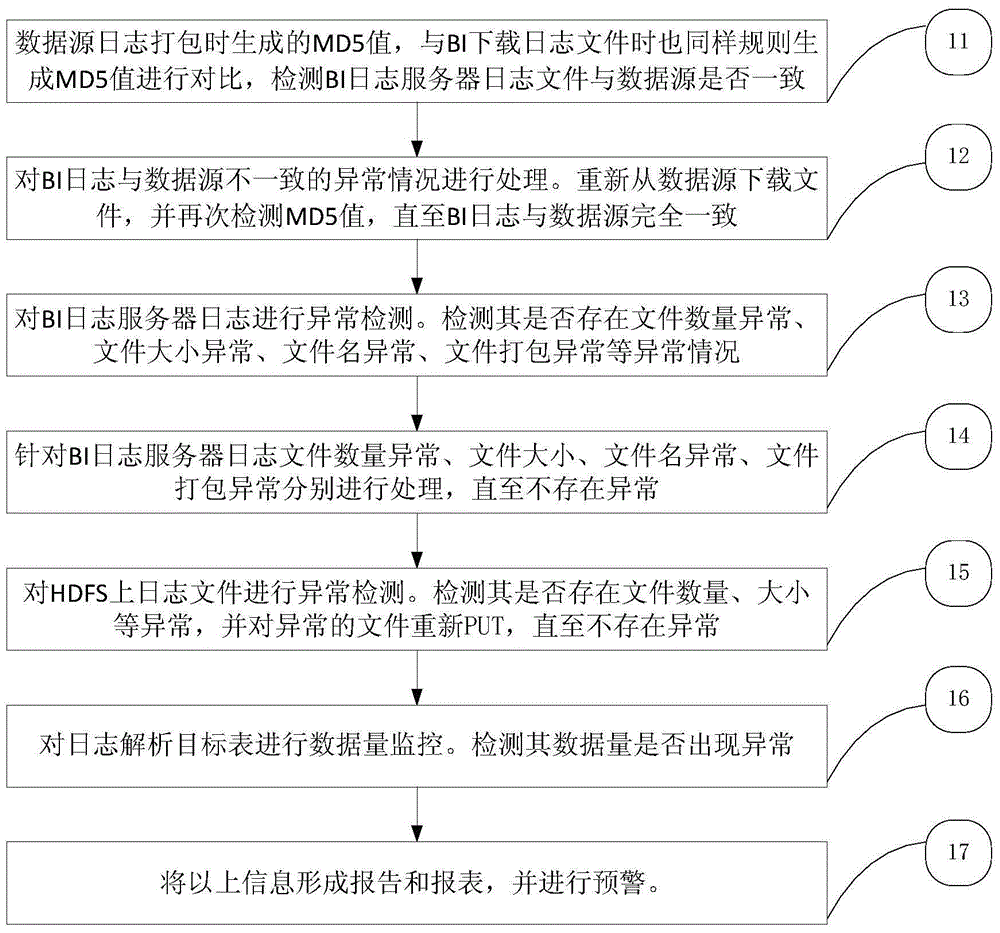
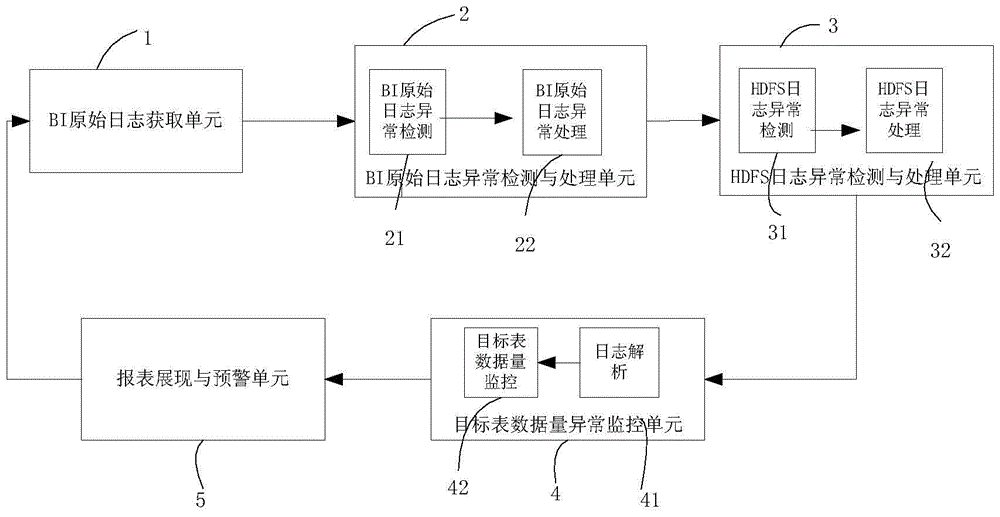
Method and device for abnormity detection and processing of log files
ActiveCN105700989AImprove analytical performanceComplete and accurate analysisHardware monitoringServer logAnomaly detection
The invention discloses a method for abnormity detection and processing of log files. The method comprises the following steps: 1) abnormity monitoring and processing of a BI log server log and a data source MD5: (1) comparing the BI log server log with the data source MD5 and detecting whether the BI log server log and the data source MD5 are abnormal, and (2) processing the abnormal condition that a BI log server log file is inconsistent with a data source MD5 file; 2) abnormity monitoring and processing of the BI log server log file and the data source MD5 file: (1) detecting whether the BI log server log file is abnormal, (2) identifying content in the file, and when records not under the date of a folder exist in the file under the folder or records under the date and records not under the date coexist in the file, considering that the log file has packaging error, and (3) abnormity processing of the BI log server log file: carrying out abnormity detection on the BI log server log file and carrying out processing after abnormity is found; and 3) abnormity detection and processing of an HDFS file.
Owner:FOCUS TECH
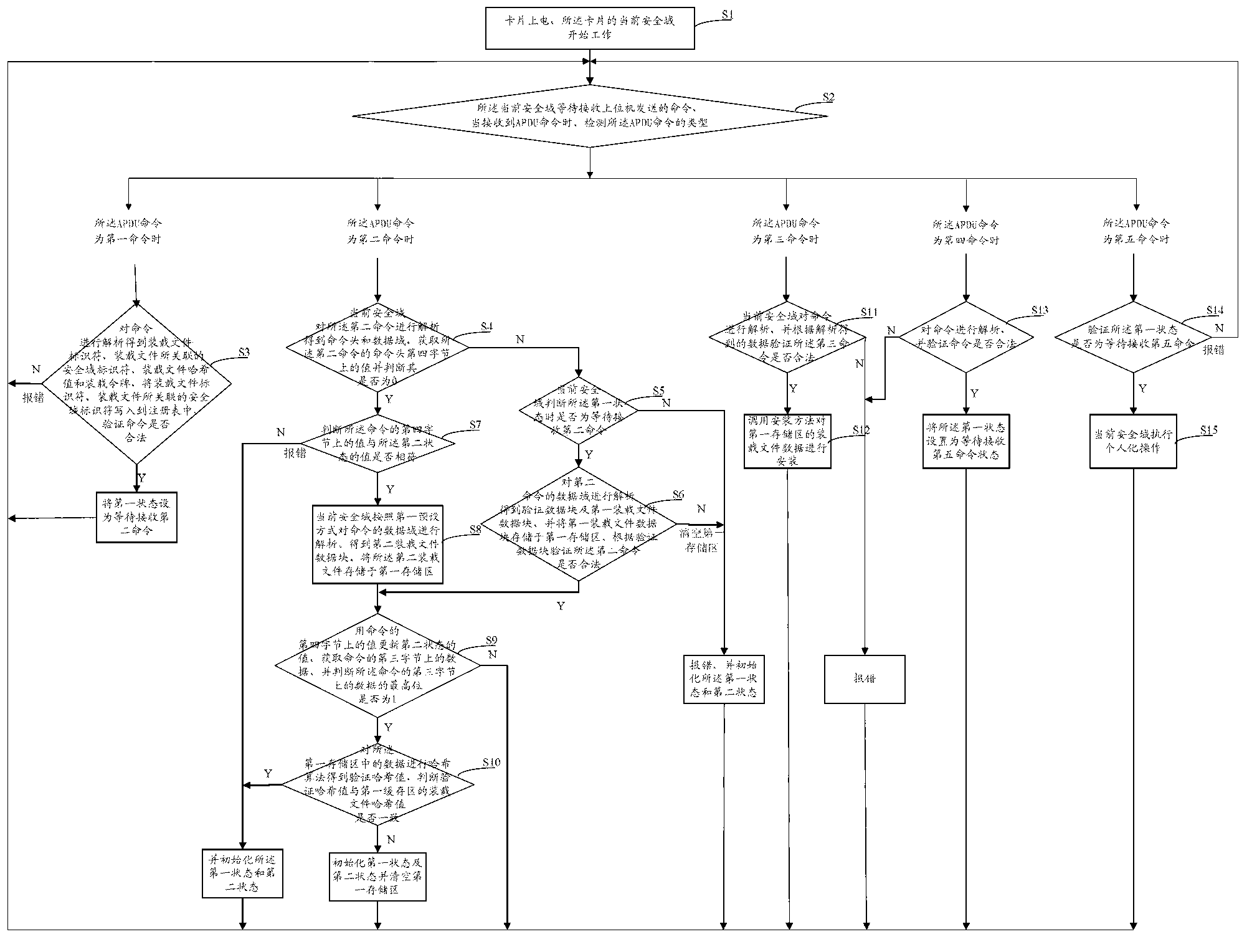
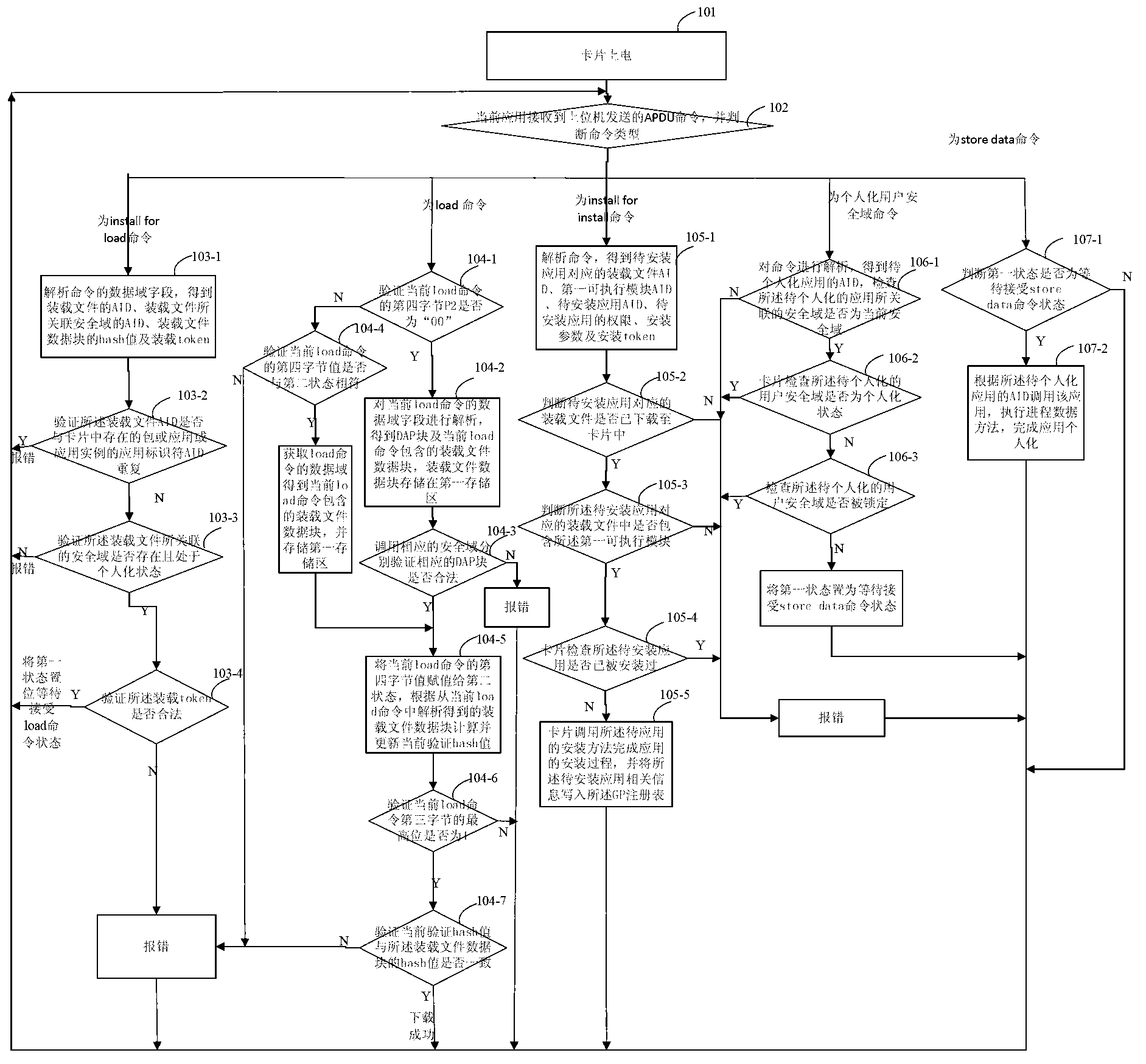
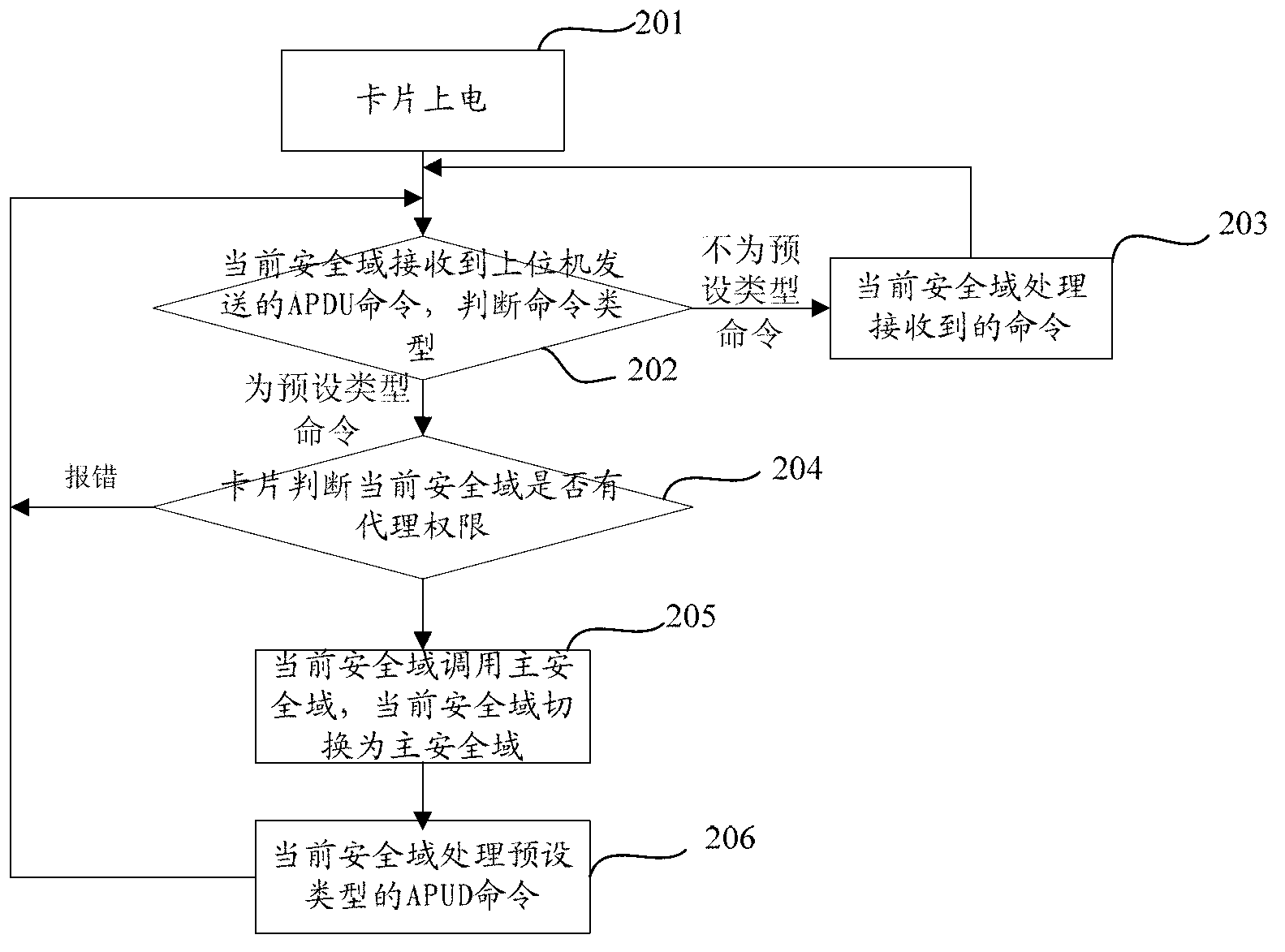
Realization method for security domain on java card
ActiveCN102801705AFlexible Management InterfaceImprove securityUser identity/authority verificationPersonalizationData validation
The invention discloses a realization method for a security domain on a java card, and relates to the field of smart cards. The method comprises the following steps of: receiving and resolving a first command by using a current security domain to obtain application related information, and setting a first state into waiting for the reception of a second command; receiving and resolving the second command to obtain a loaded file data block, storing the loaded file data block into a first memory area, verifying whether the second command is legal or not, continuing the method if the second command is legal, otherwise reporting an error; receiving and resolving a third command, verifying whether the third command is legal or not according to resolved data, and if the third command is legal, calling an installation method, and installing application according to the data of the first memory area; receiving and resolving a fourth command, judging whether the fourth command is legal or not, and if the fourth command is legal, setting the first state into waiting for the reception of a fifth command; and receiving the fifth command, and executing application personalization operation. By using the scheme, the security of application downloading, installation and personalization processes of the card is ensured.
Owner:FEITIAN TECHNOLOGIES
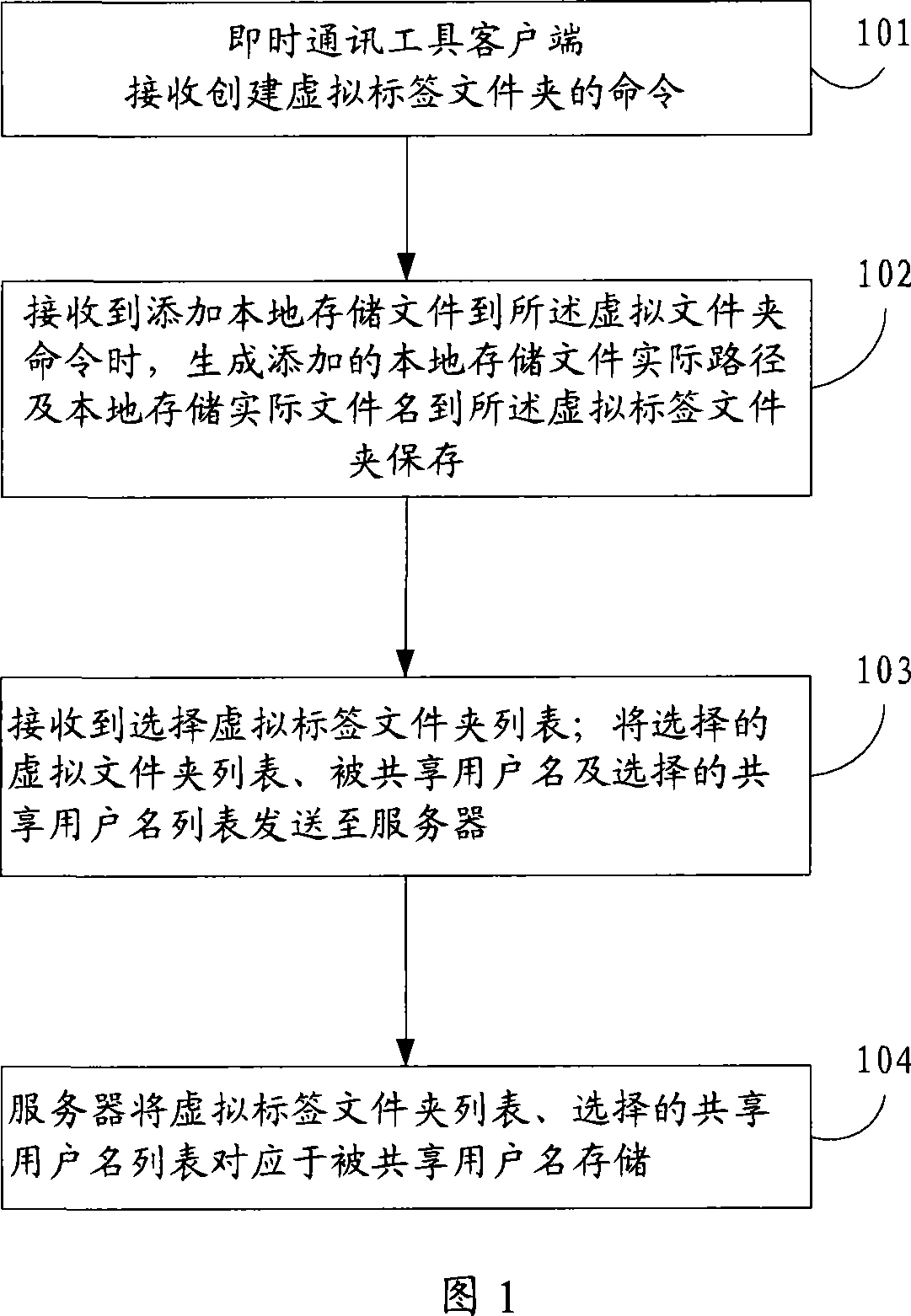
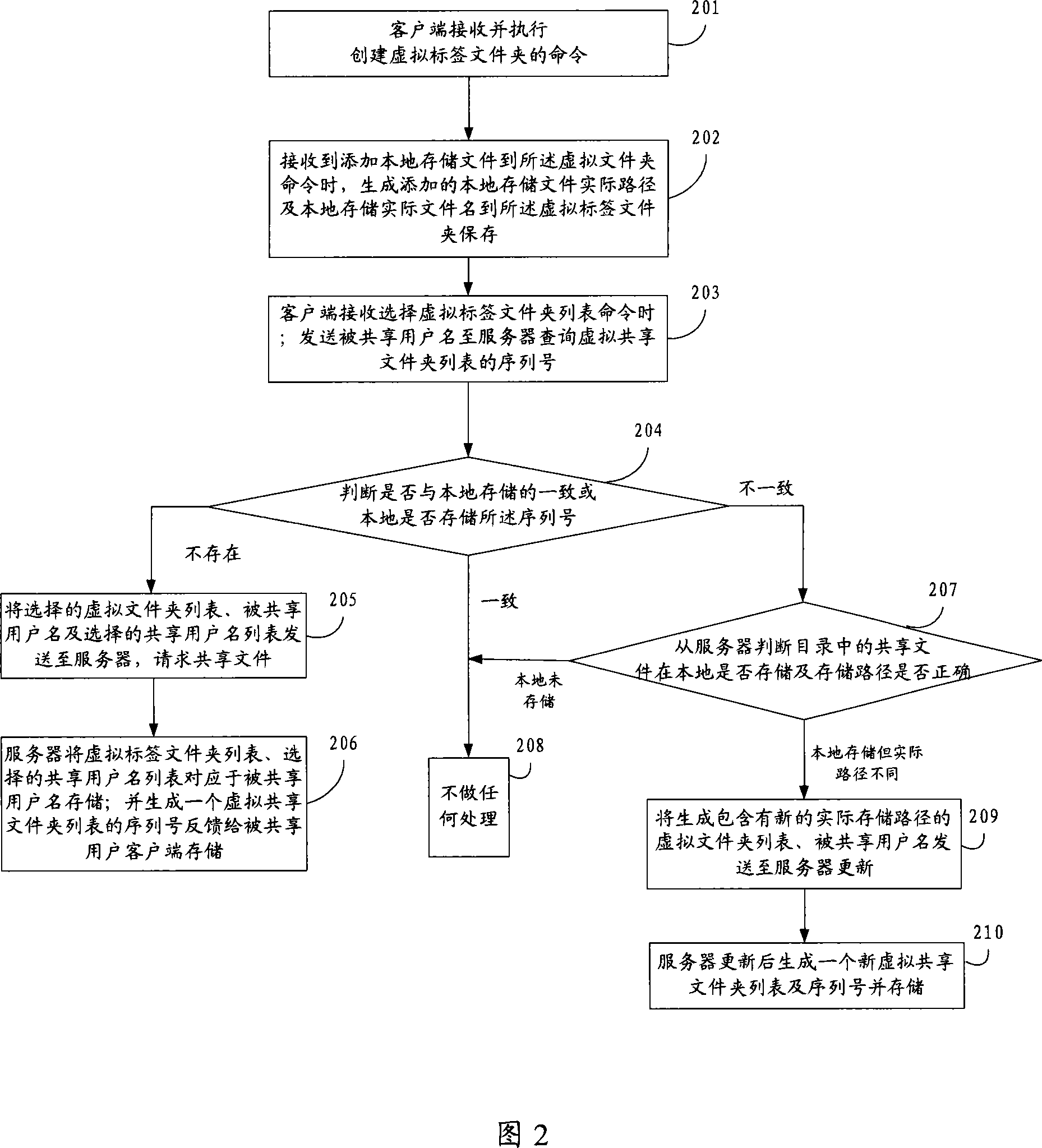
Method for creating virtual label file, sharing and download file
This invention provides a method for setting up visual label files including: when receiving an order of setting up a virtual label file, a prompt communication customer end generates a virtual label file with the virtual label name and stores it, and generates an additive actual path for storing local files and actual file name in the virtual file and stores them when receiving an order of adding local stored file in the label file, a method for sharing files, a server and a customer end, so long as a sharing user shares a necessary shared label to other user, it can share all corresponding shared files to the user at one run.
Owner:TENCENT TECH (SHENZHEN) CO LTD
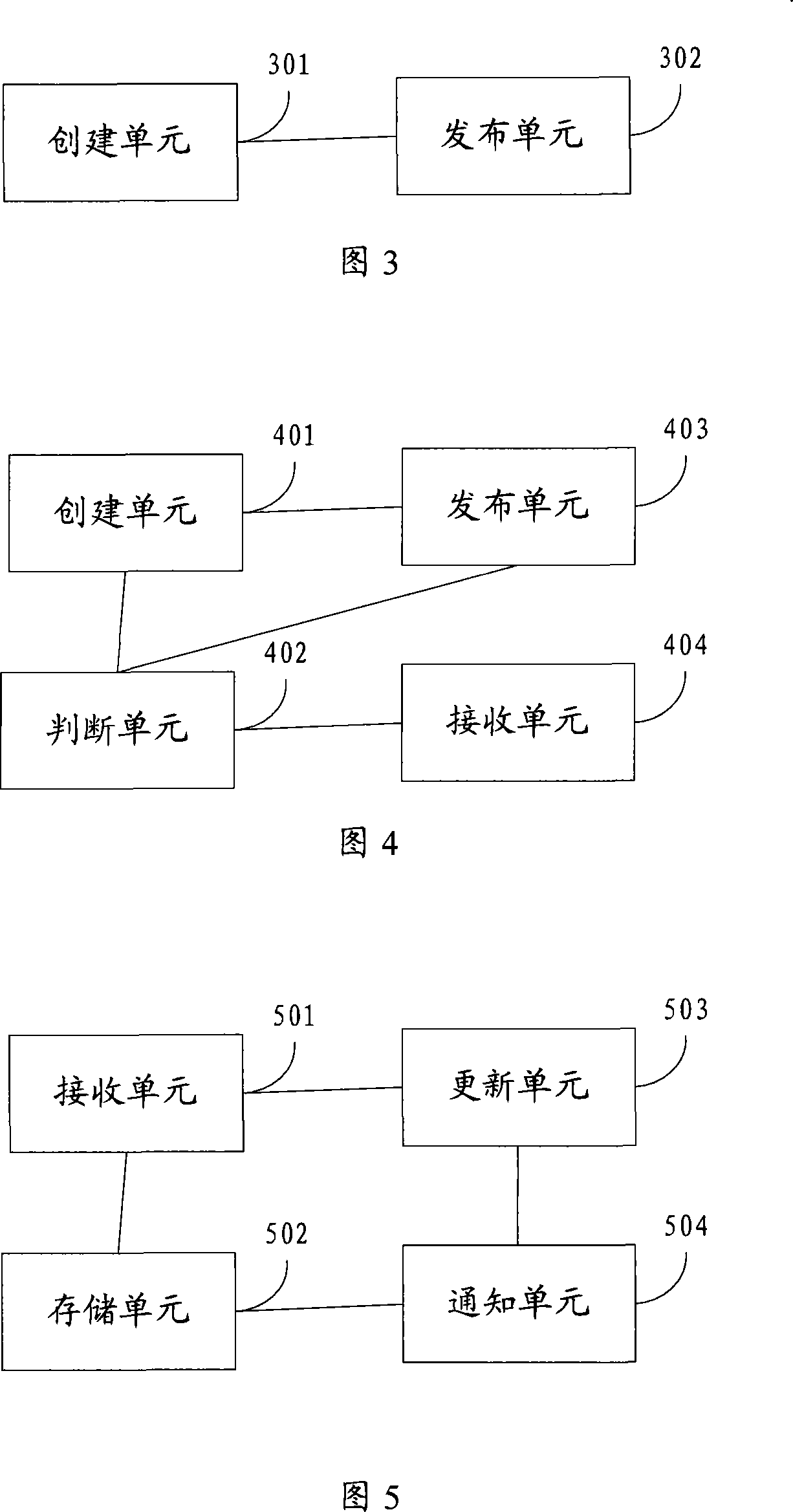
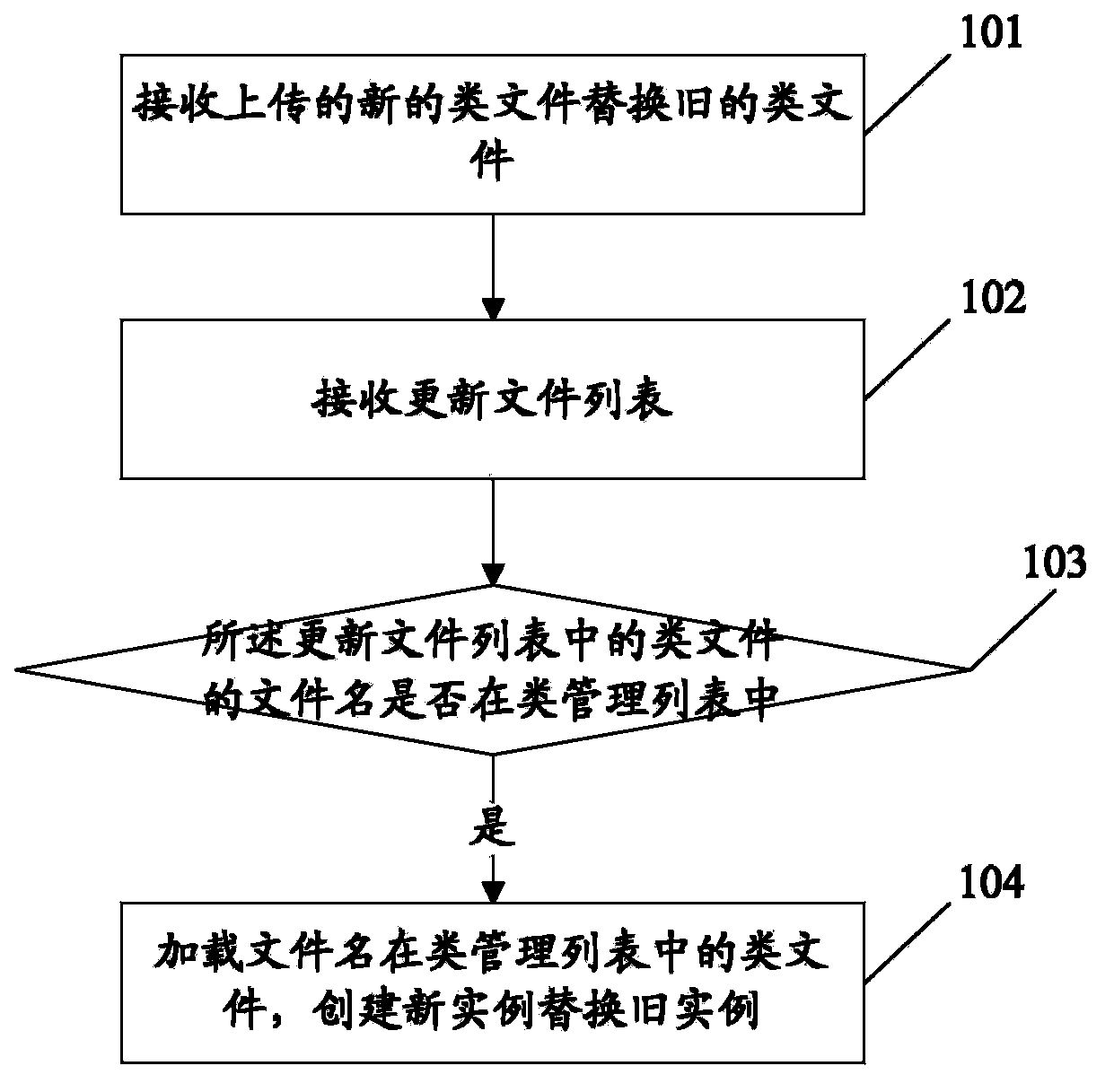
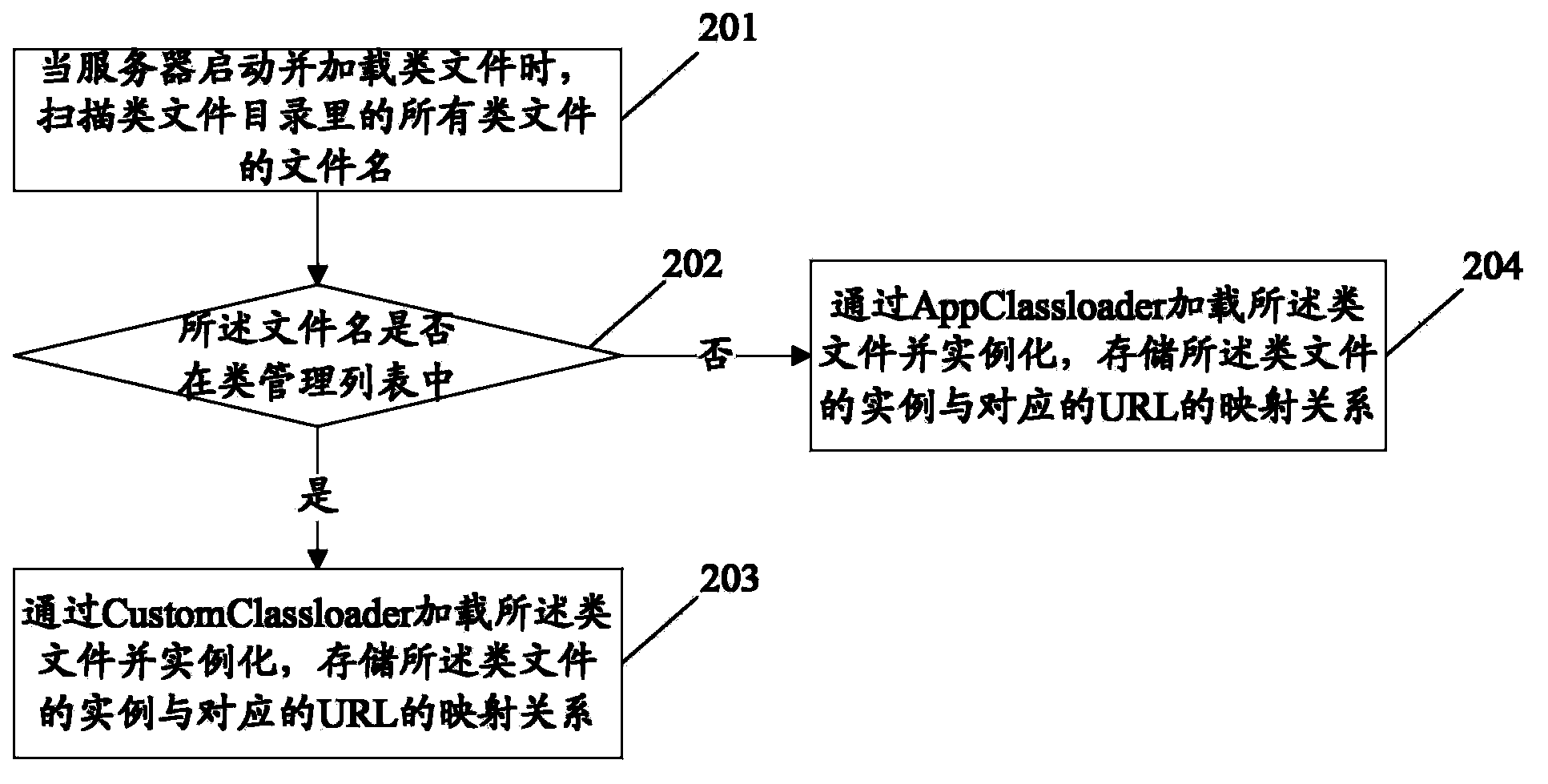
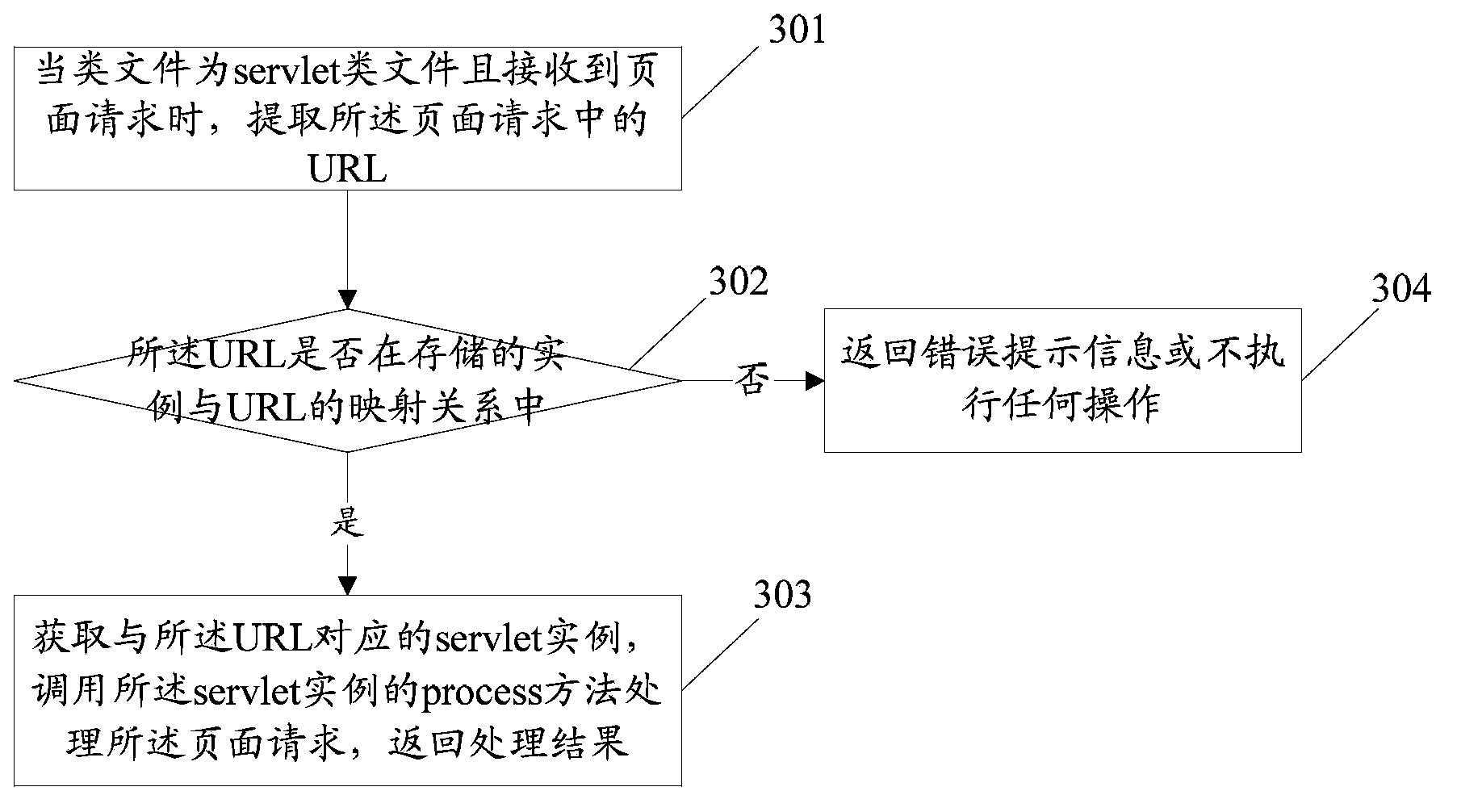
Processing method and device for realizing hot deployment and server
The invention discloses a processing method for realizing hot deployment. The method comprises the following steps: receiving a new uploaded class file for replacing an old class file, and receiving an update file list; determining that the file name of the class file in the update file list is in a class management list, loading the class file of which the file name is in the class management list, and creating a new example for replacing an old example, wherein the file name of the class file which allows hot deployment is recorded in the class management list. The invention further discloses a processing device for realizing hot deployment and a server. Through the scheme of the invention, a hot deployment function can be realized by the server without always scanning an application deployment catalog, so that the occupation on resources during update of a system is reduced, the update efficiency is increased, and user experience is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for simultaneously loading multiple FPGA using CPU
InactiveCN101165652AImprove loading speedImprove reliabilityProgram loading/initiatingProcessor registerAddress bus
The method is used in a system comprising one or more FPGAs and CPUs, and comprises: 1) generating a FPGA loading file by means of combining multi FPGA loading bit-stream files; 2) making logical expand for the address bus of the CPU to get the registers and latch units required by loading said multi FPGAs; 3) said CPUs reads said FPGA loading files and sends the files to the expending memory of said CPU; said CPU controls said register and latch units to generate the loading time sequence in order to make loading for one of multi FPGAs.
Owner:ZTE CORP
Animation processing method, apparatus and device
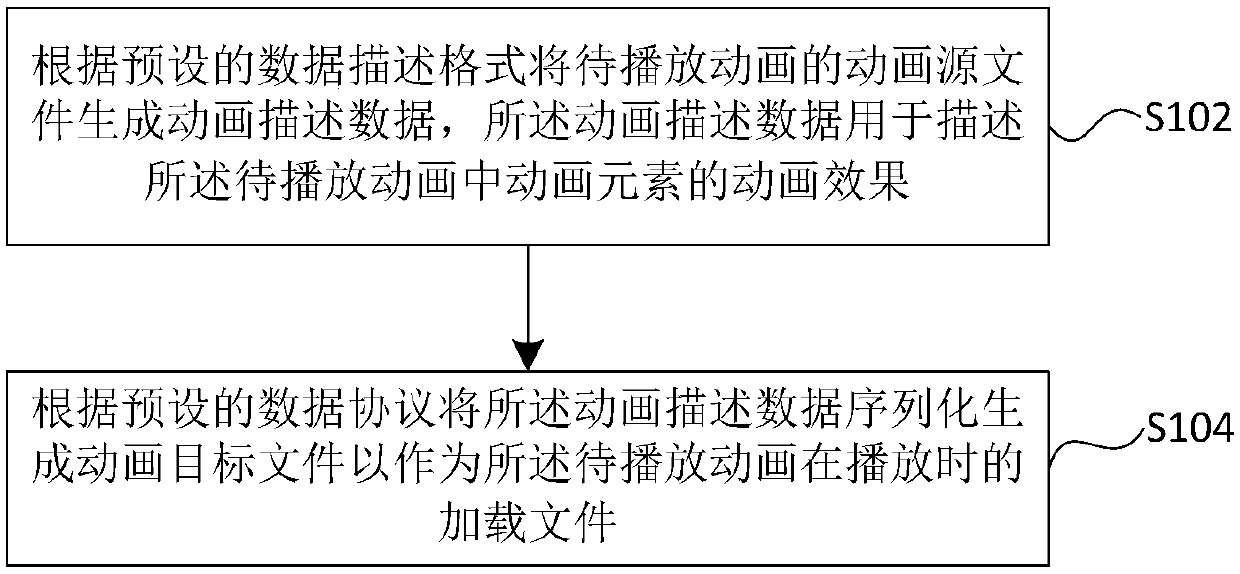
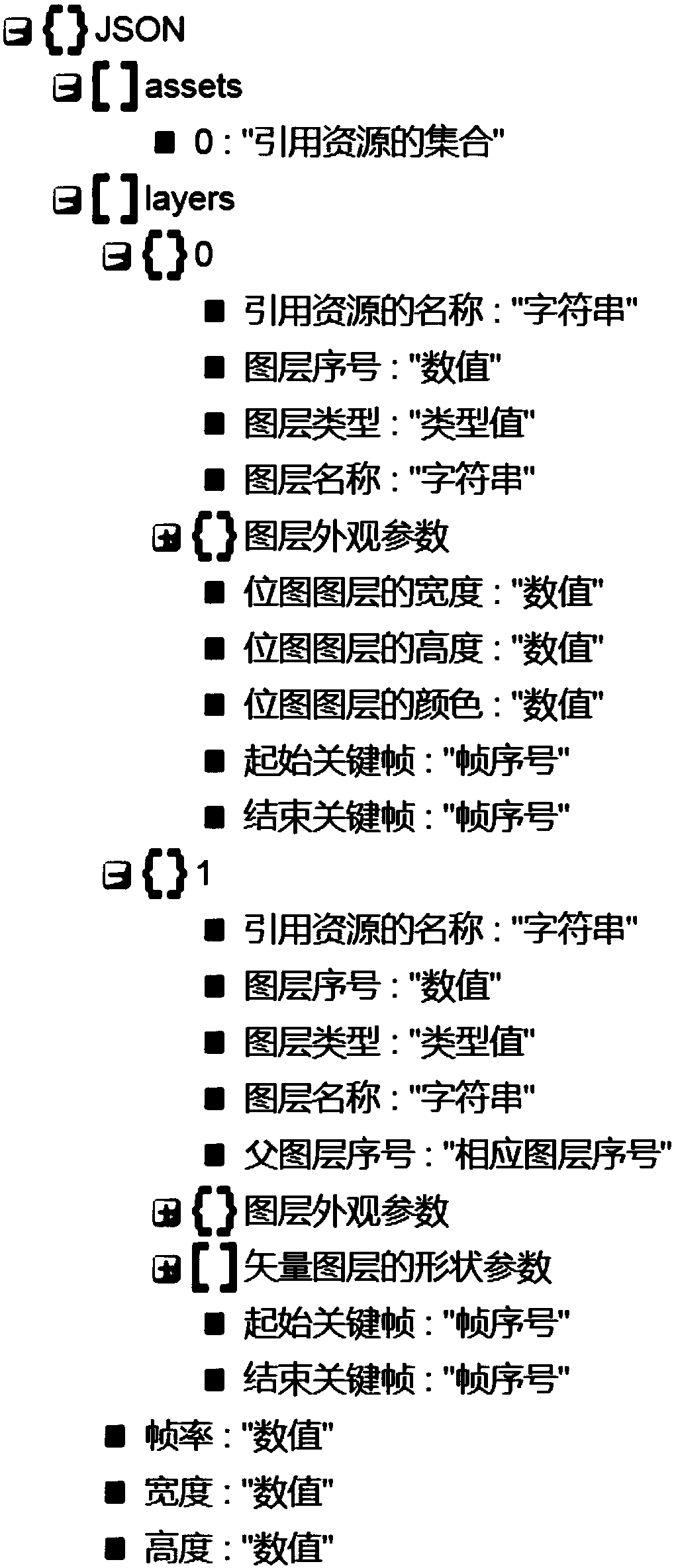
Embodiments of the present specification disclose an animation processing method, apparatus, and device. The scheme includes: describing the animation effect of the animation elements in the animationto be played by using the animation description data, and serializing the animation description data to generate the animation object file as the loading file of the animation to be played in order to facilitate the application processing of the subsequent animation playing.
Owner:ADVANCED NEW TECH CO LTD
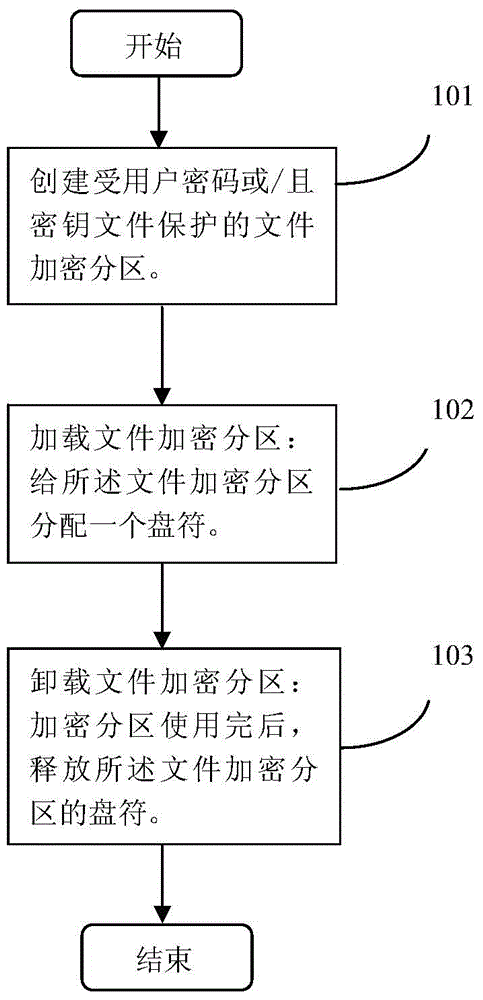
File encryption and decryption method and device on the basis of partitions
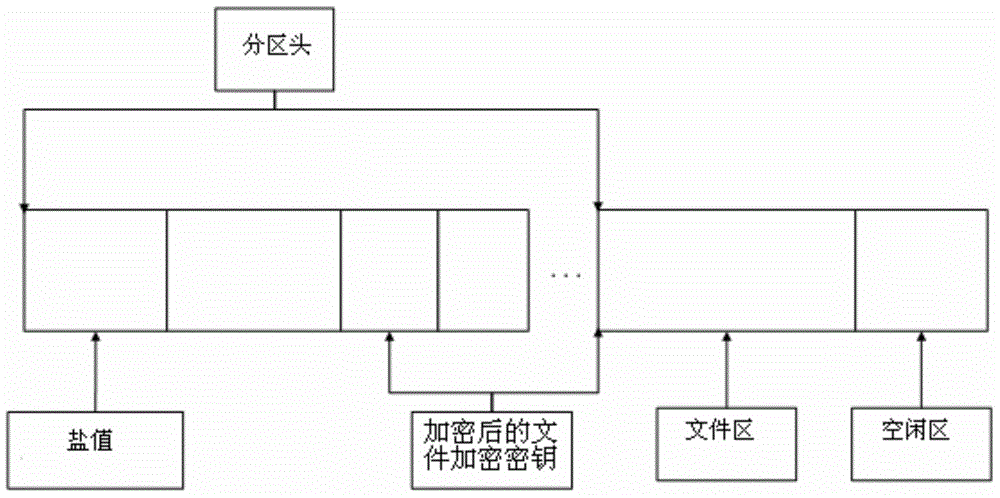
InactiveCN103914666AIncreased complexityEnsure safetyInternal/peripheral component protectionComputer hardwarePassword
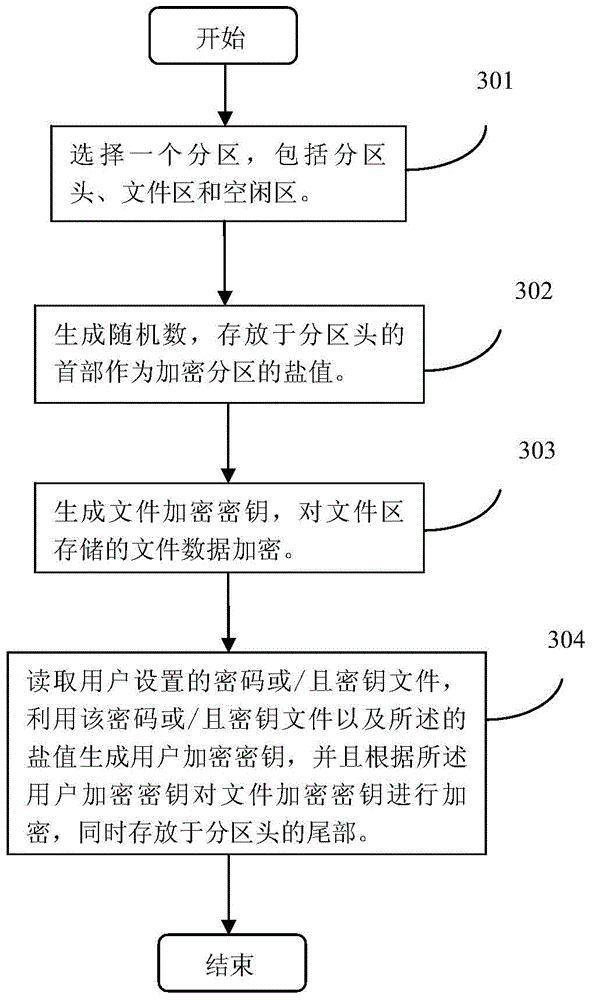
The invention discloses a file encryption method and device on the basis of partitions. The method includes that file encryption partitions which are protected by user password and / or key file are established; firstly, one of partitions is selected, which comprises a partition head, a file area and an idle area; then a random number is generated and stored as a salt figure in a first part of the partition head, and a file encryption key is generated to encrypt file data of the file area; the password and / or the key file set by a user are / is read, a user encryption key is generated by the password and / or the key file and the salt figure, and the file encryption key is encrypted according to the generated user encryption key to be stored on a tail portion of the partition head; a file encryption partition is loaded, which includes that a drive is distributed to the file encryption partition; after the use of the encryption partition is finished, the file encryption partition is unloaded, which includes that the drive of the file encryption partition is released. Thereby, by means of the method and the device, strength and encryption strength of the file password can be improved.
Owner:ASIA EURO BOLOD INFORMATION SECURITY TECHHUNAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com