Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
8237 results about "Anomaly detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In data mining, anomaly detection (also outlier detection) is the identification of rare items, events or observations which raise suspicions by differing significantly from the majority of the data. Typically the anomalous items will translate to some kind of problem such as bank fraud, a structural defect, medical problems or errors in a text. Anomalies are also referred to as outliers, novelties, noise, deviations and exceptions.
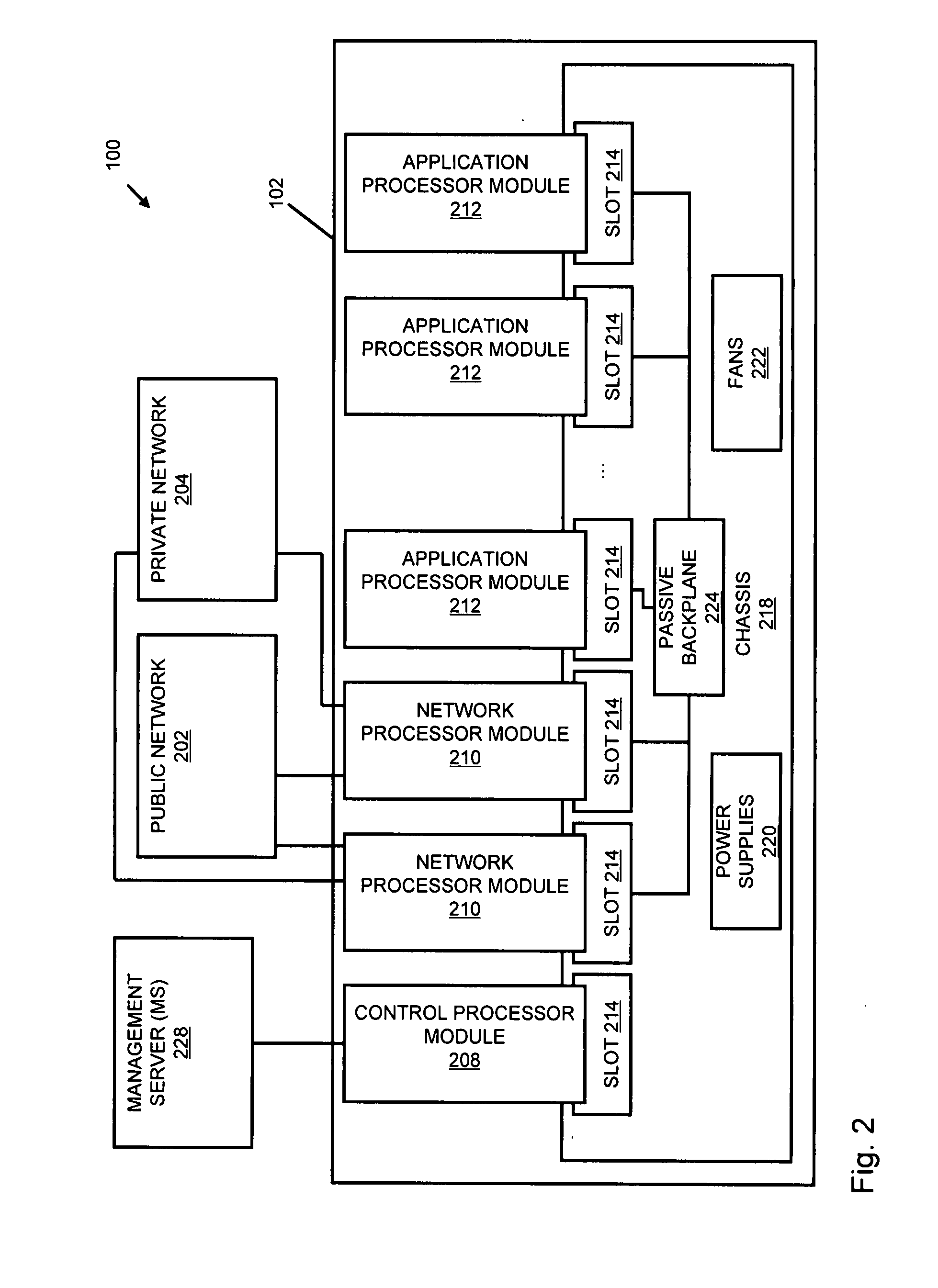
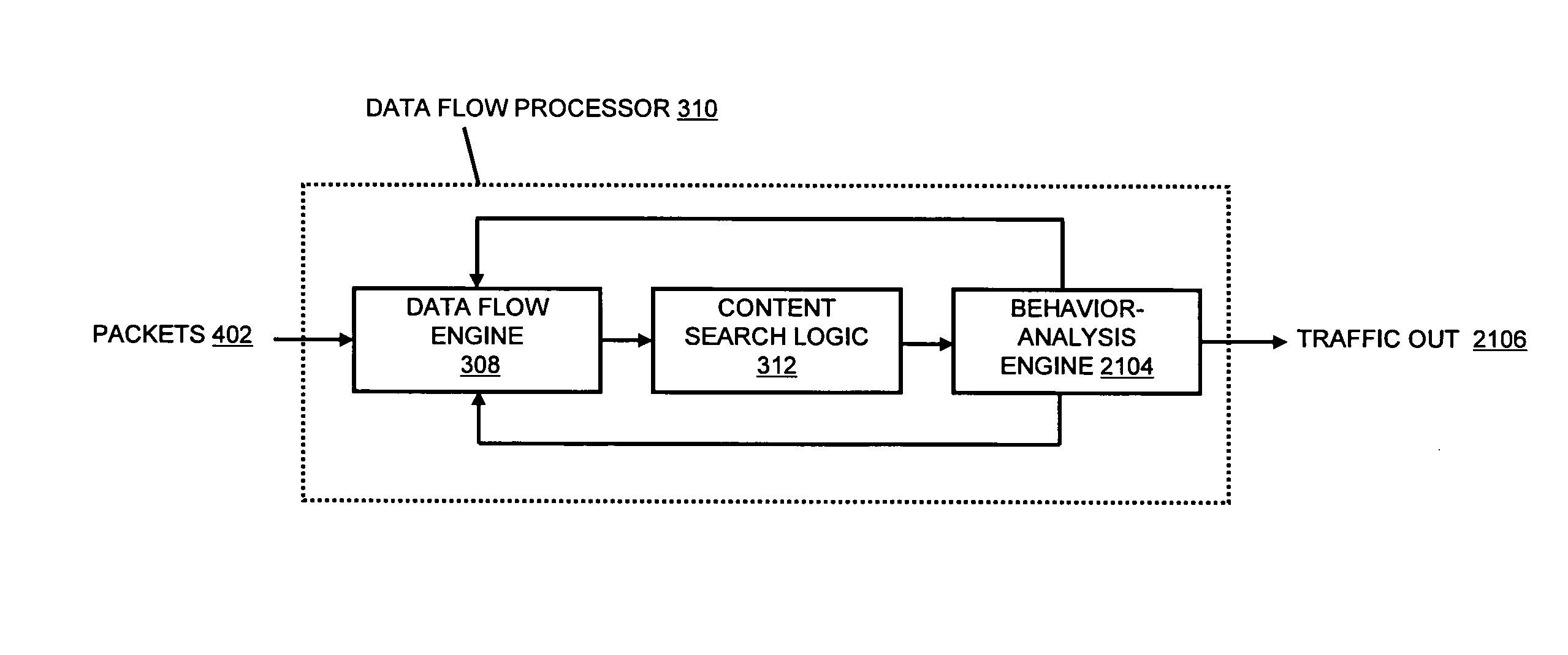
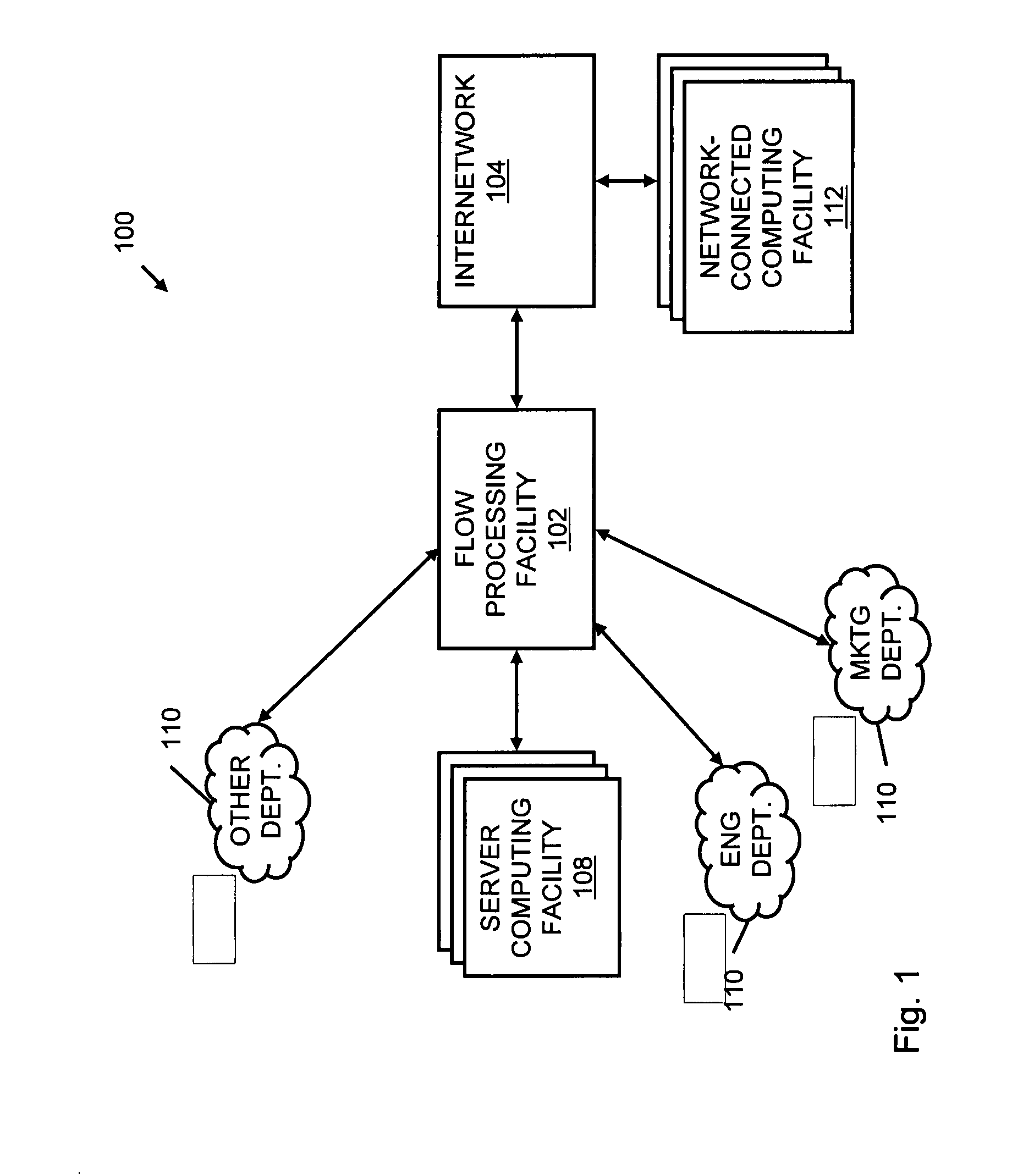
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
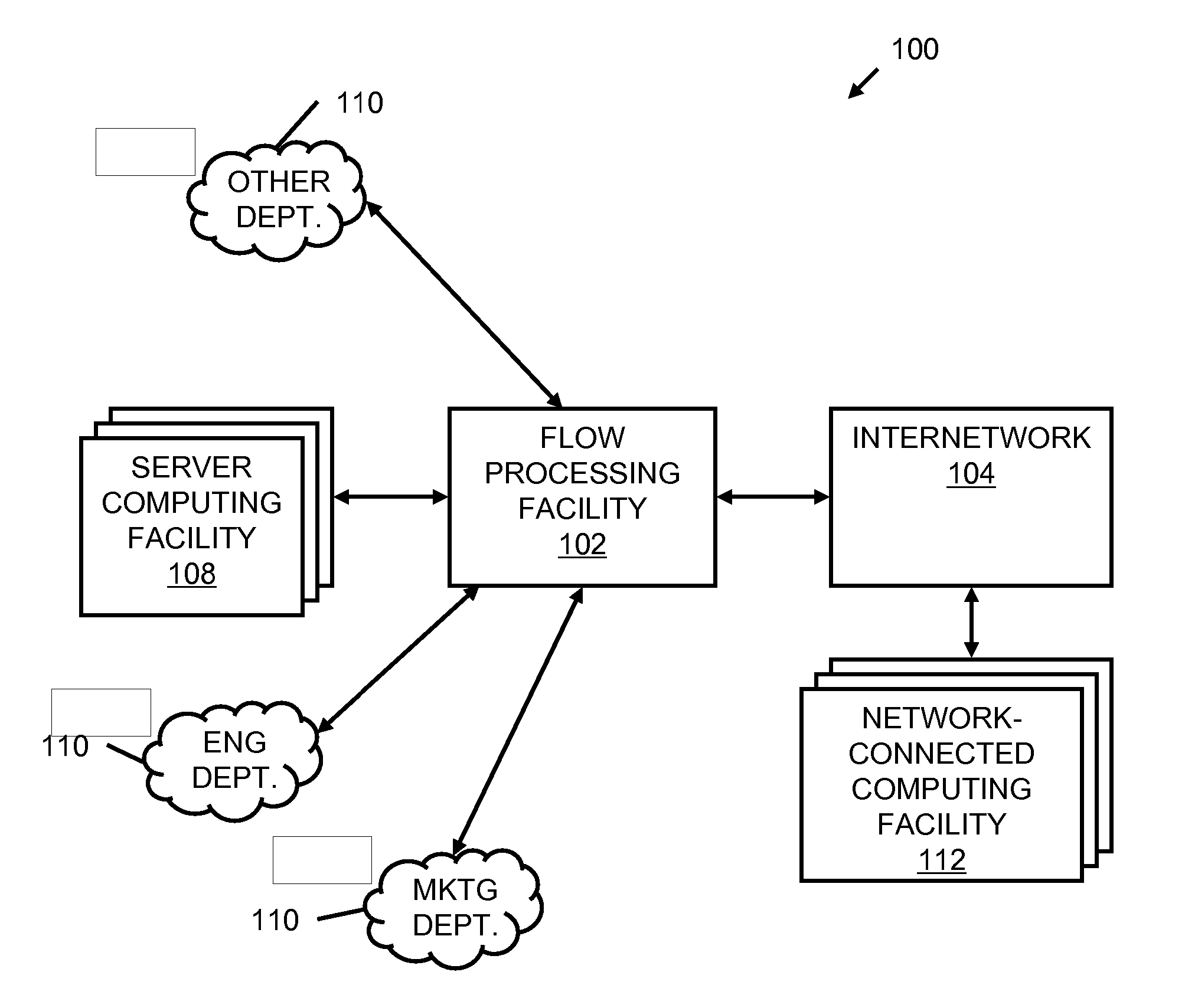
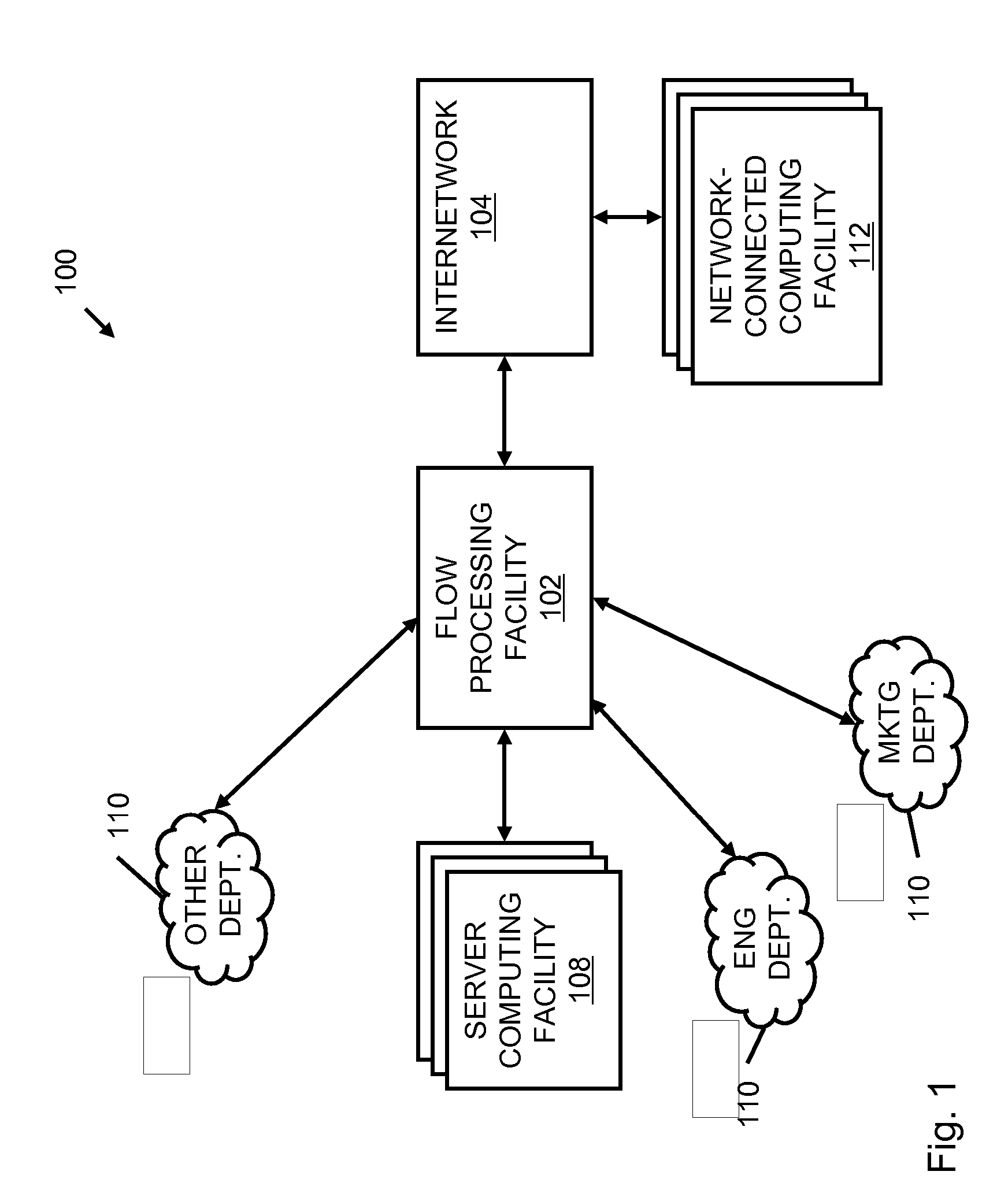
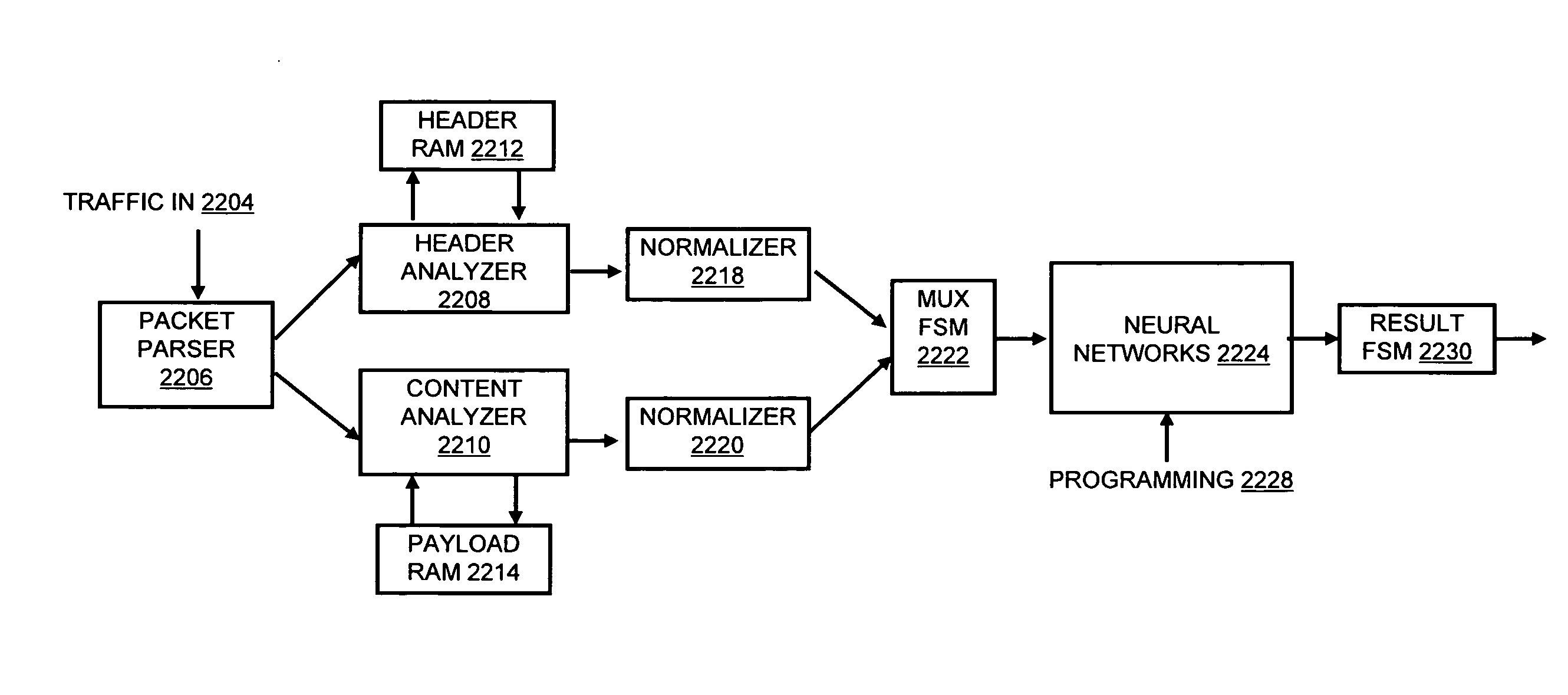
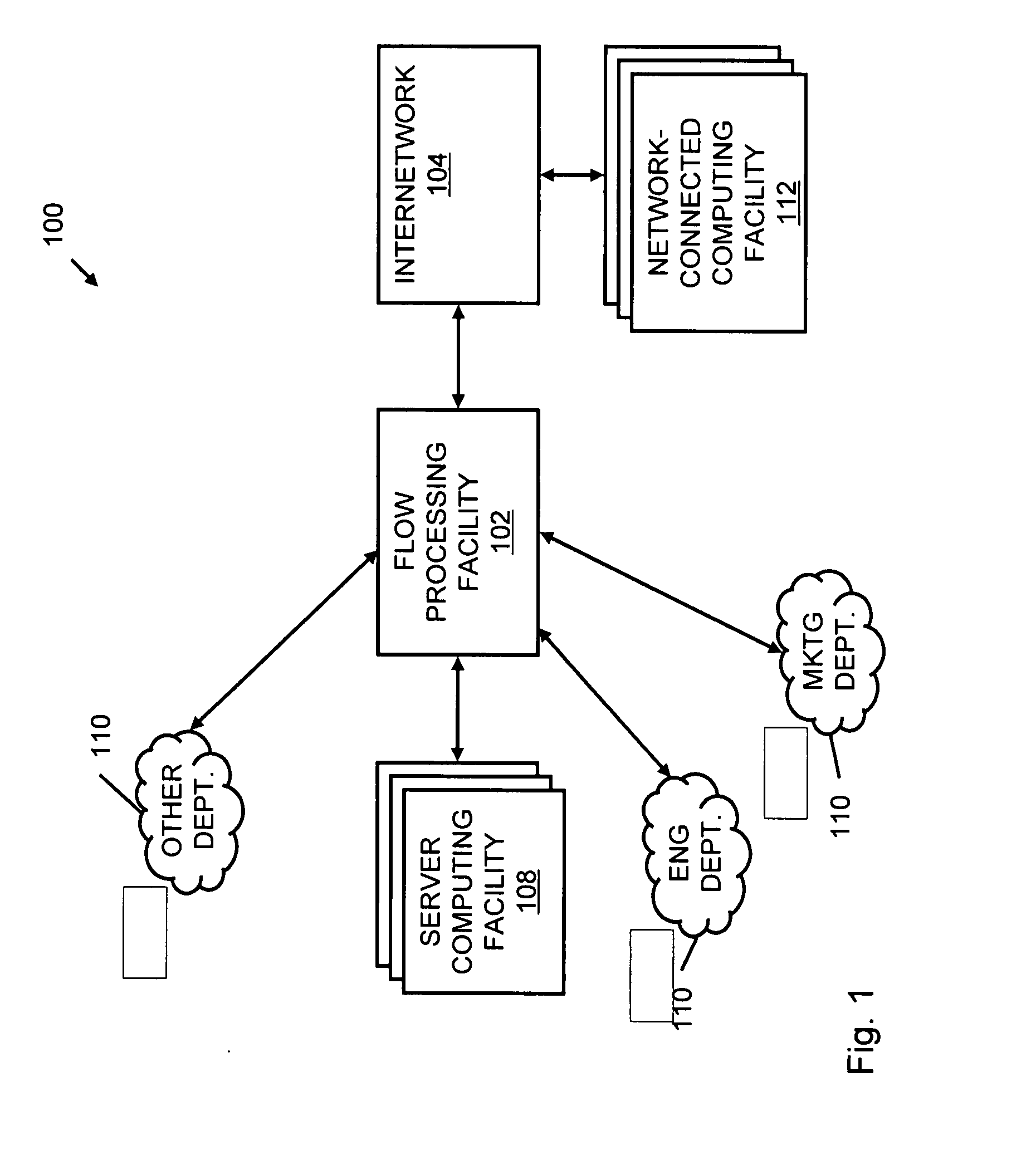
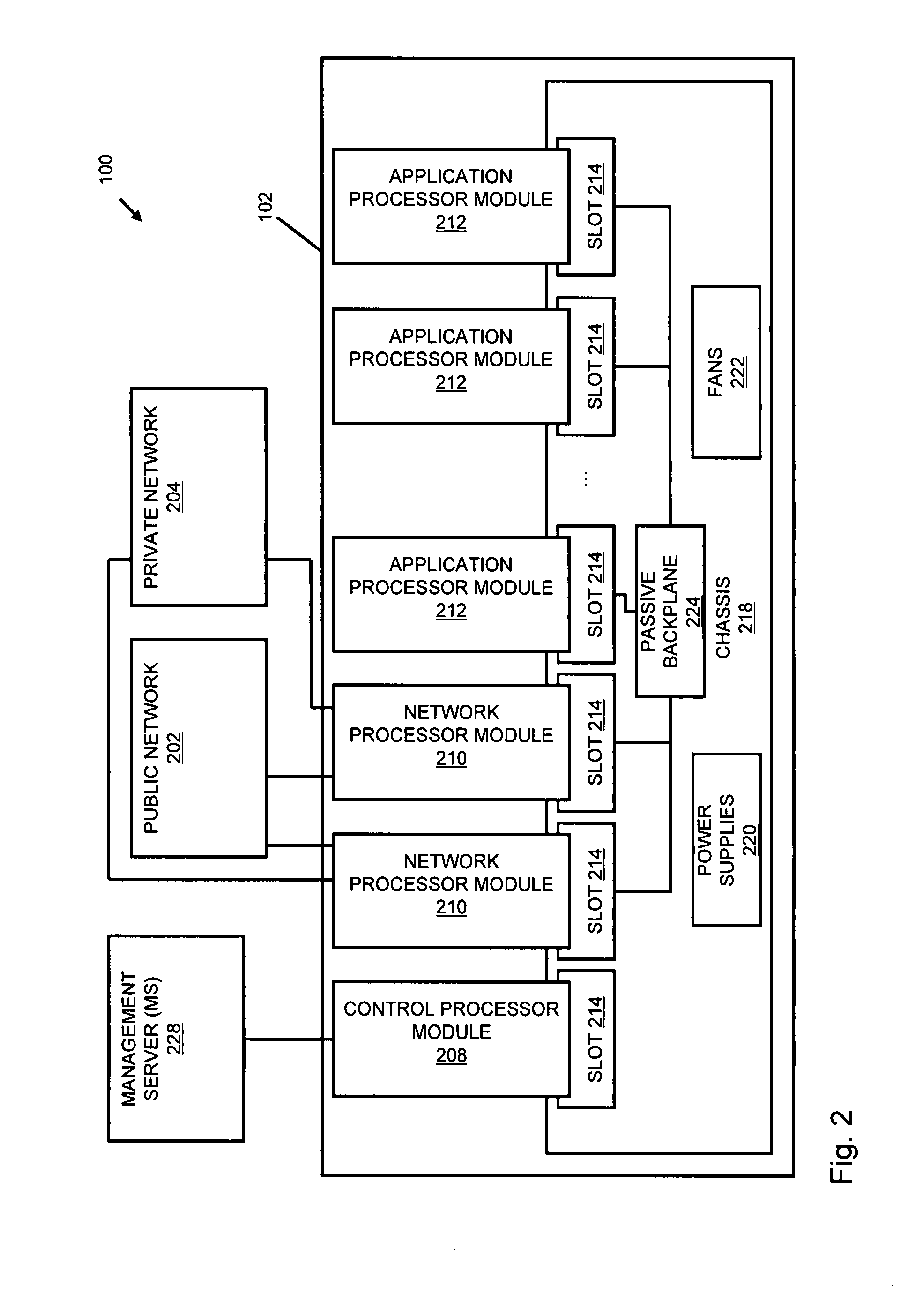
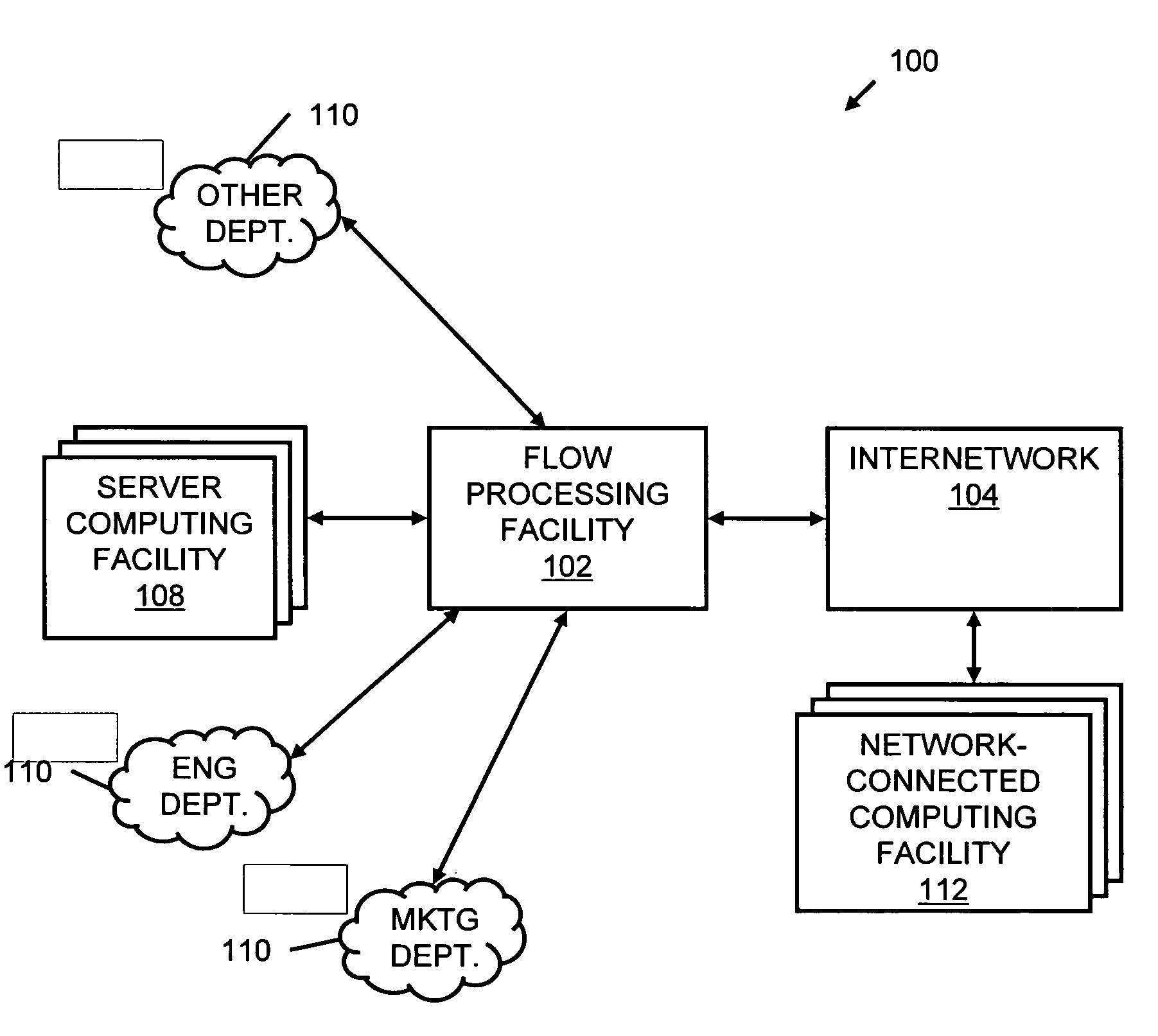
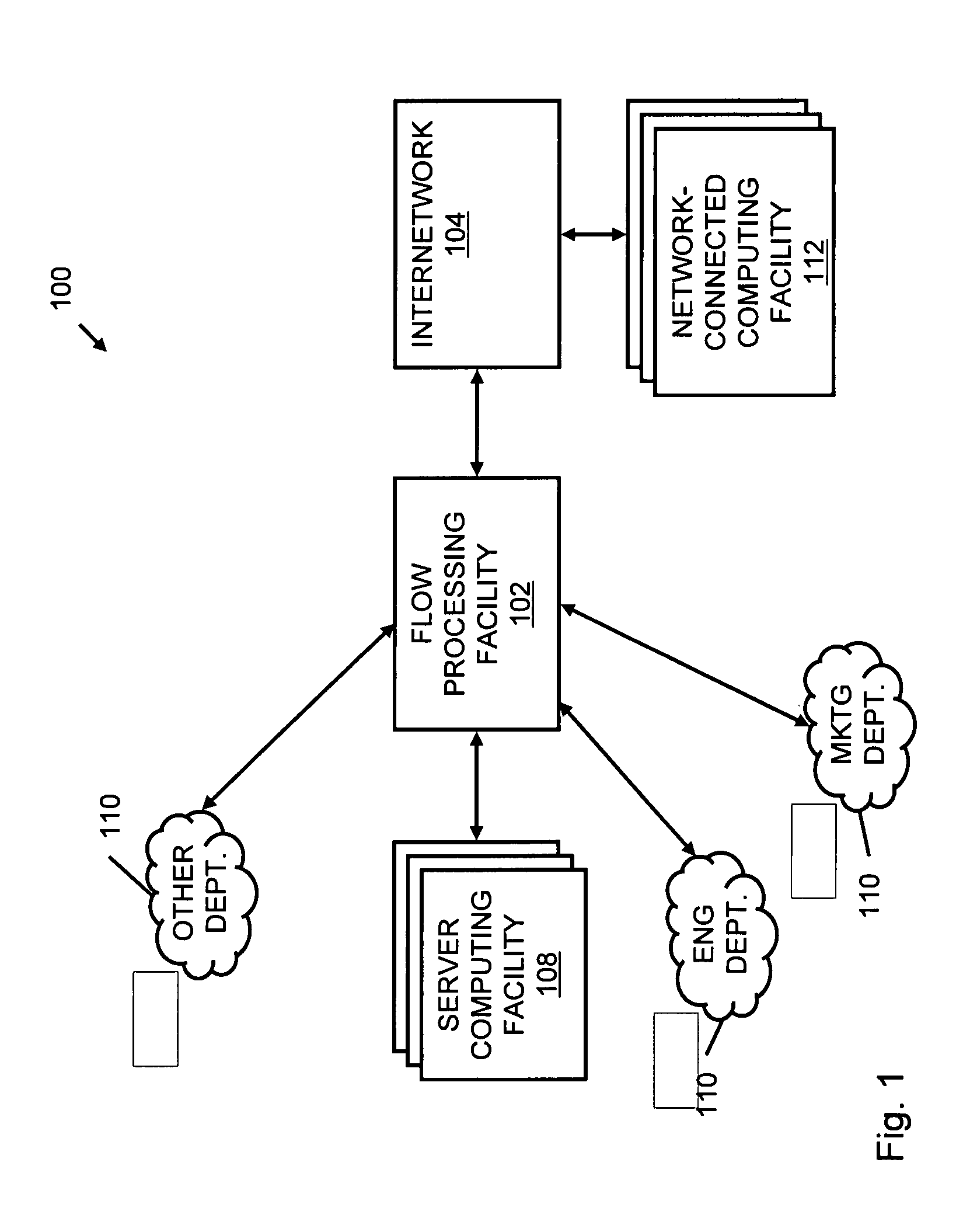
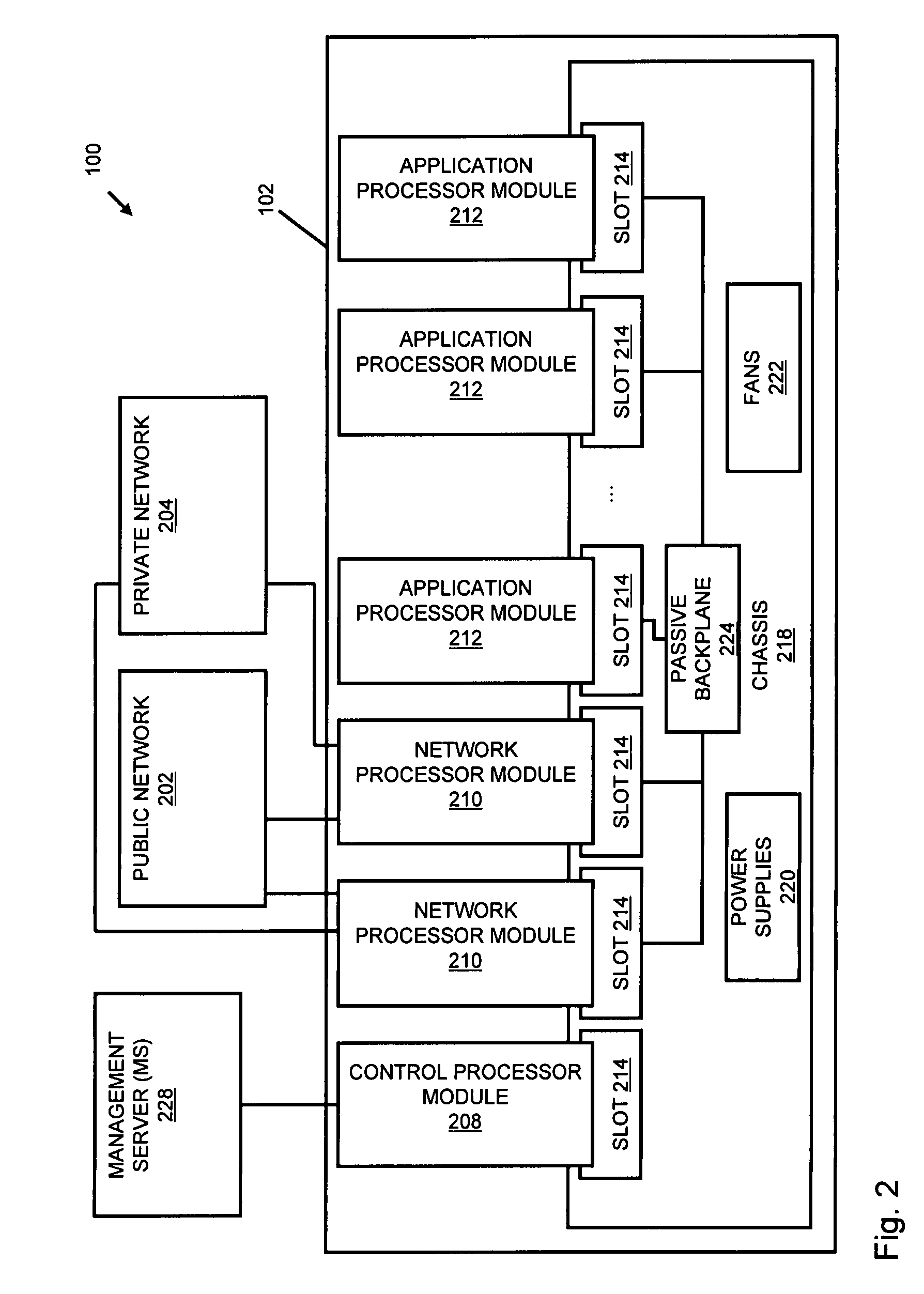
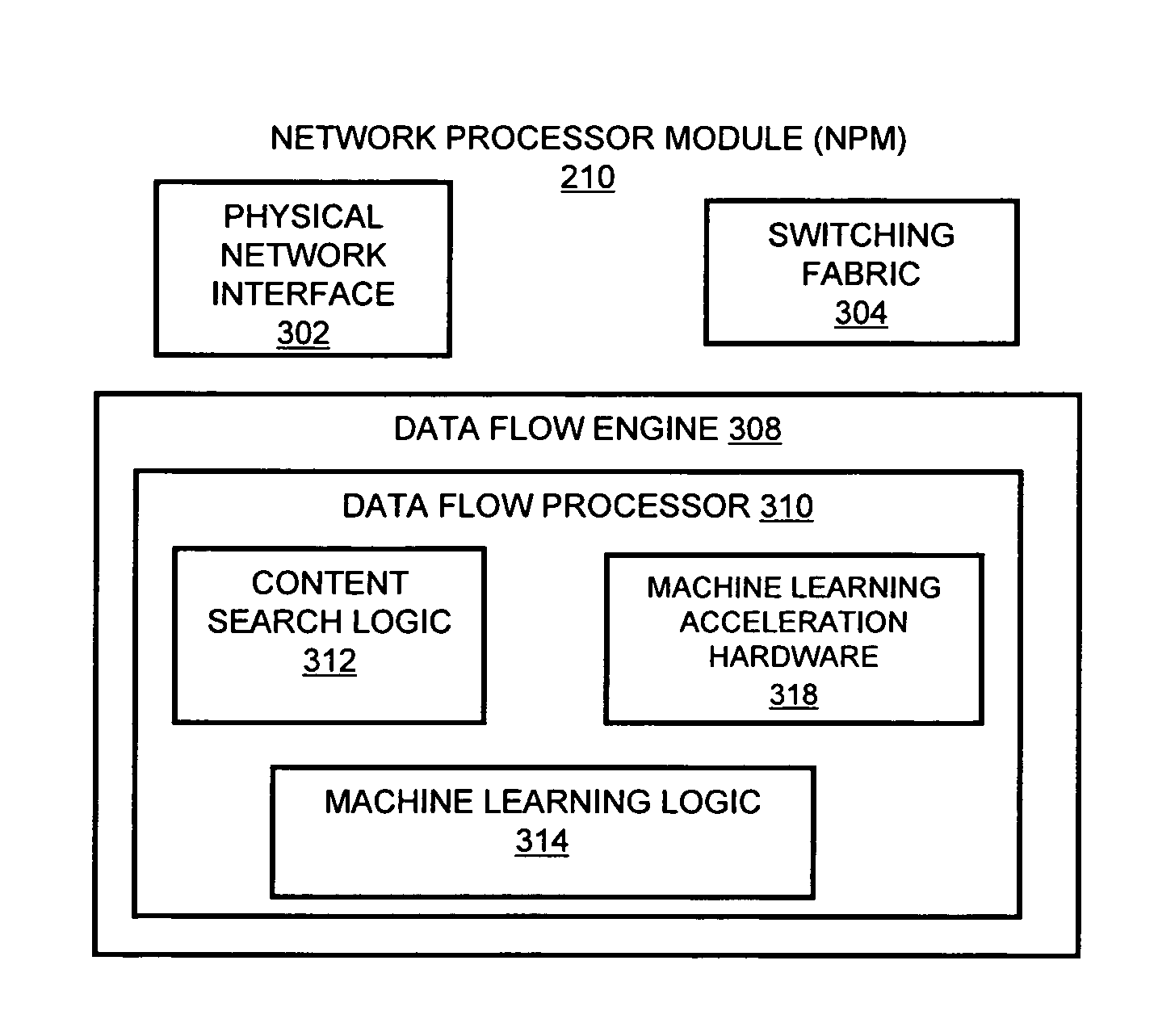
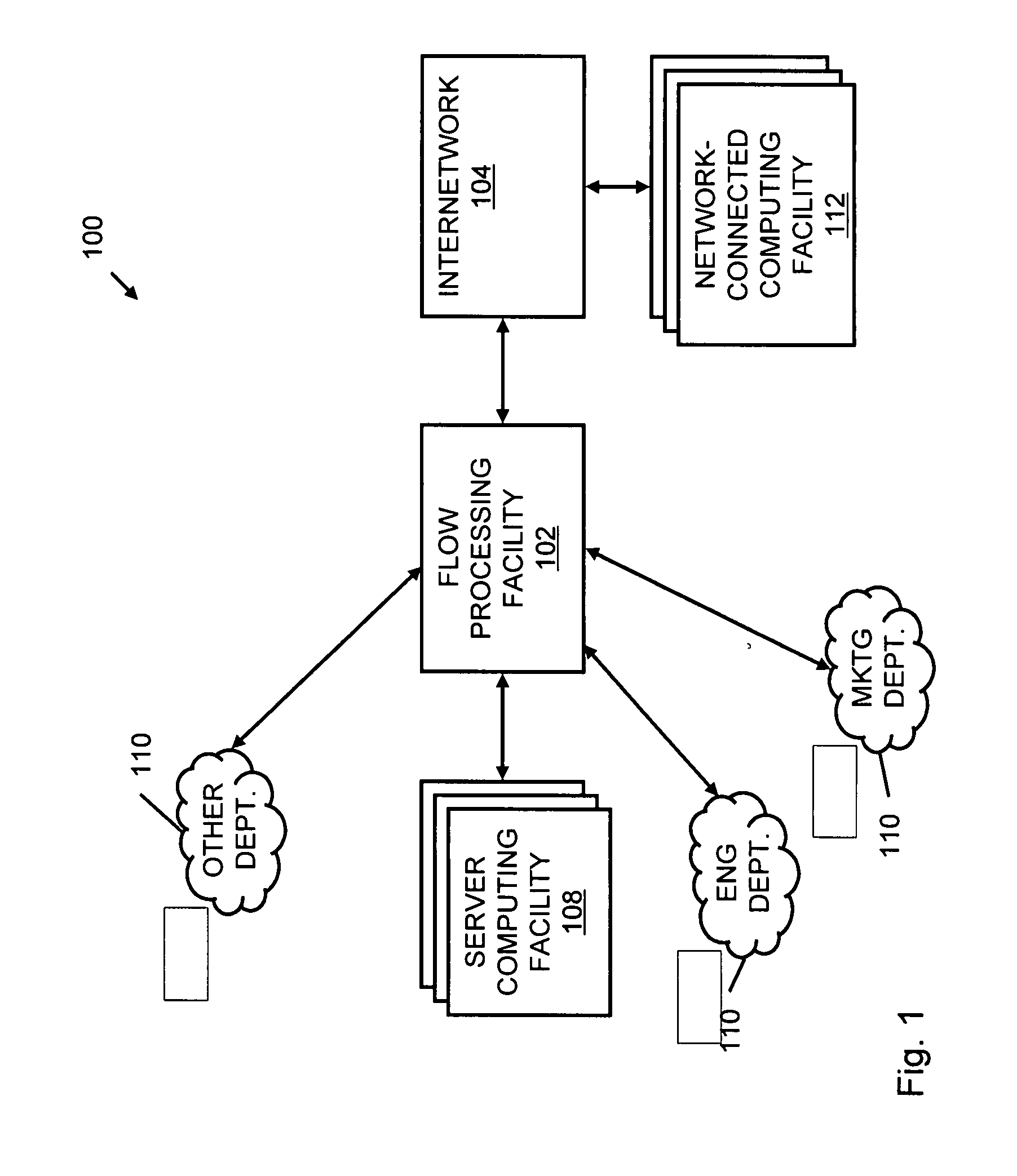
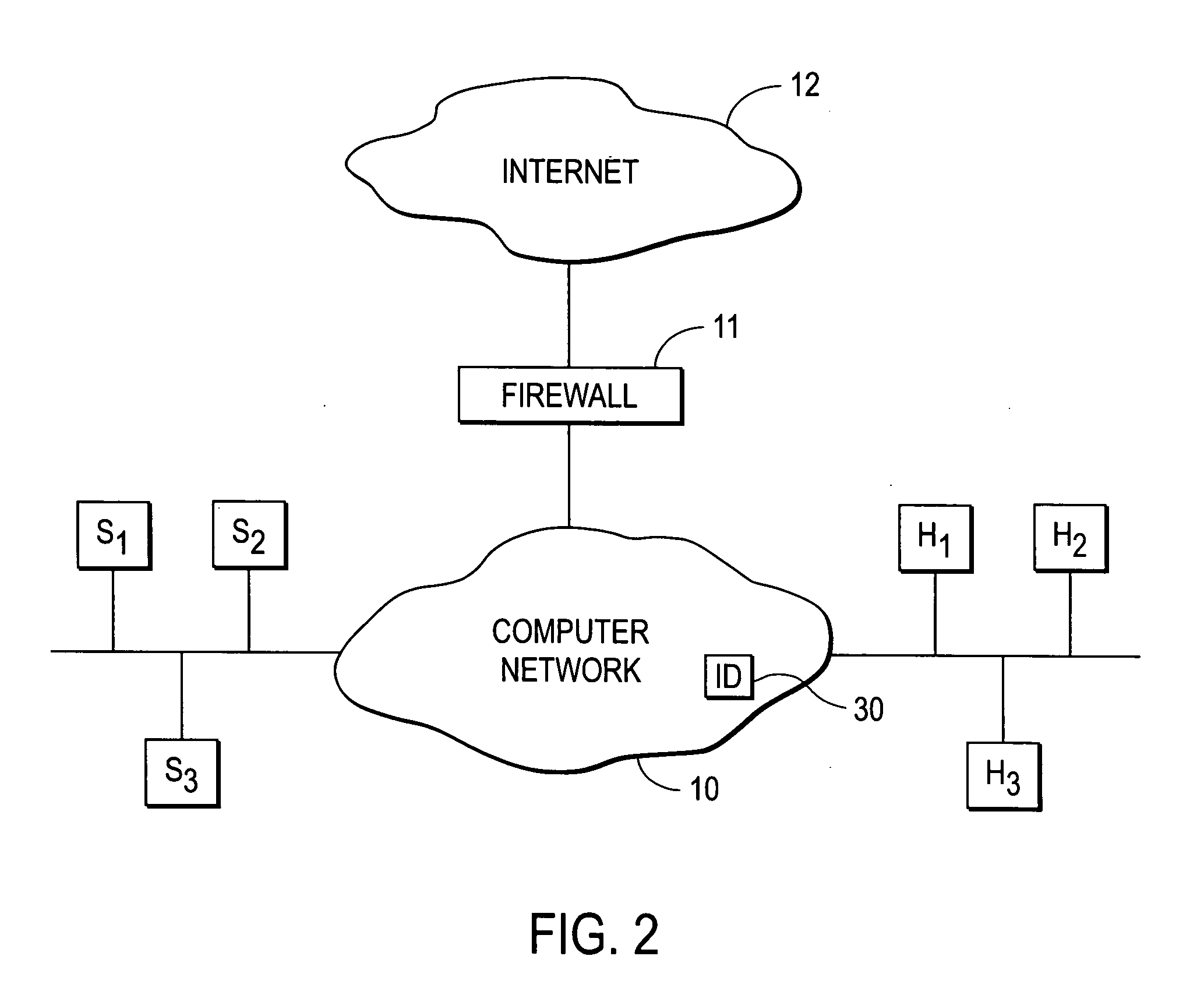
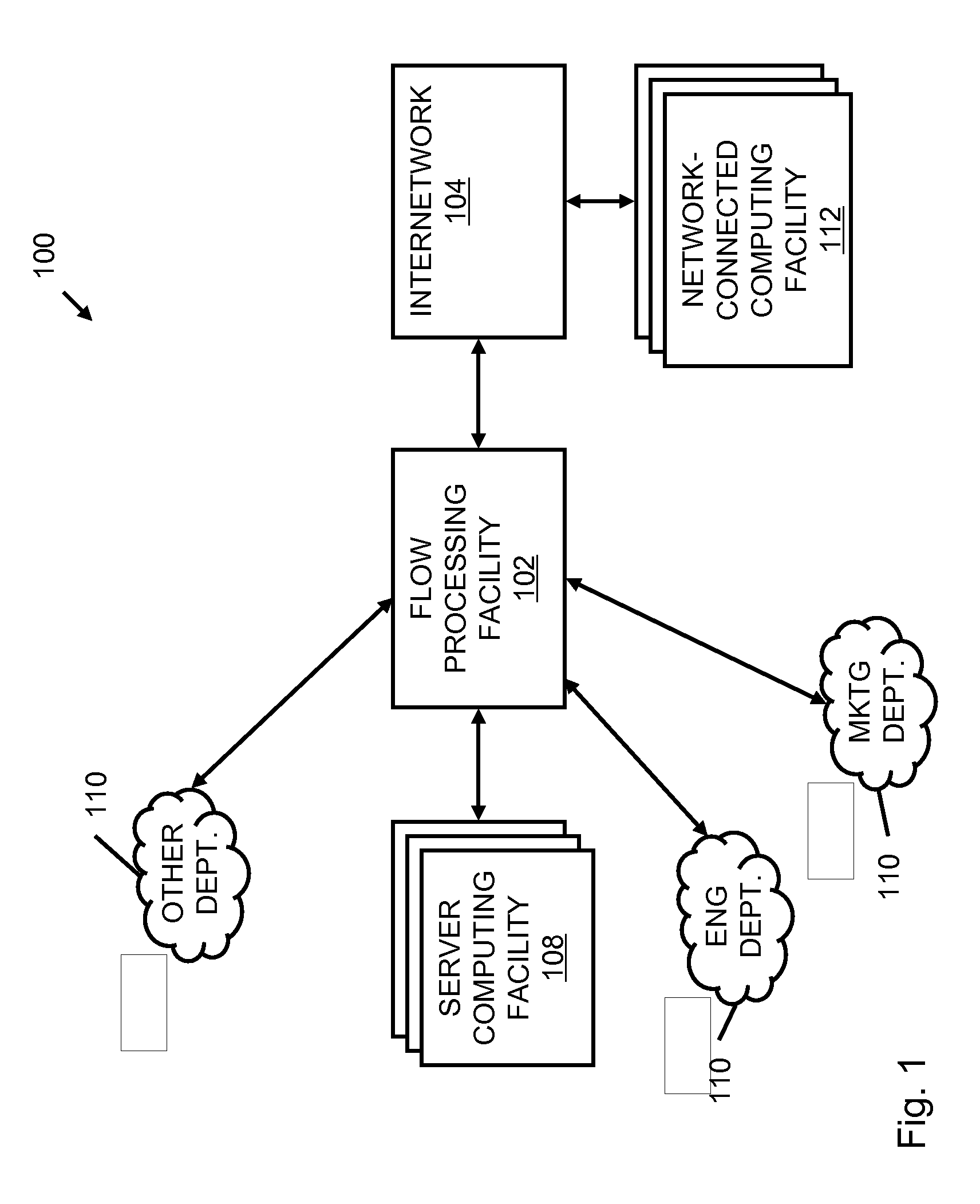
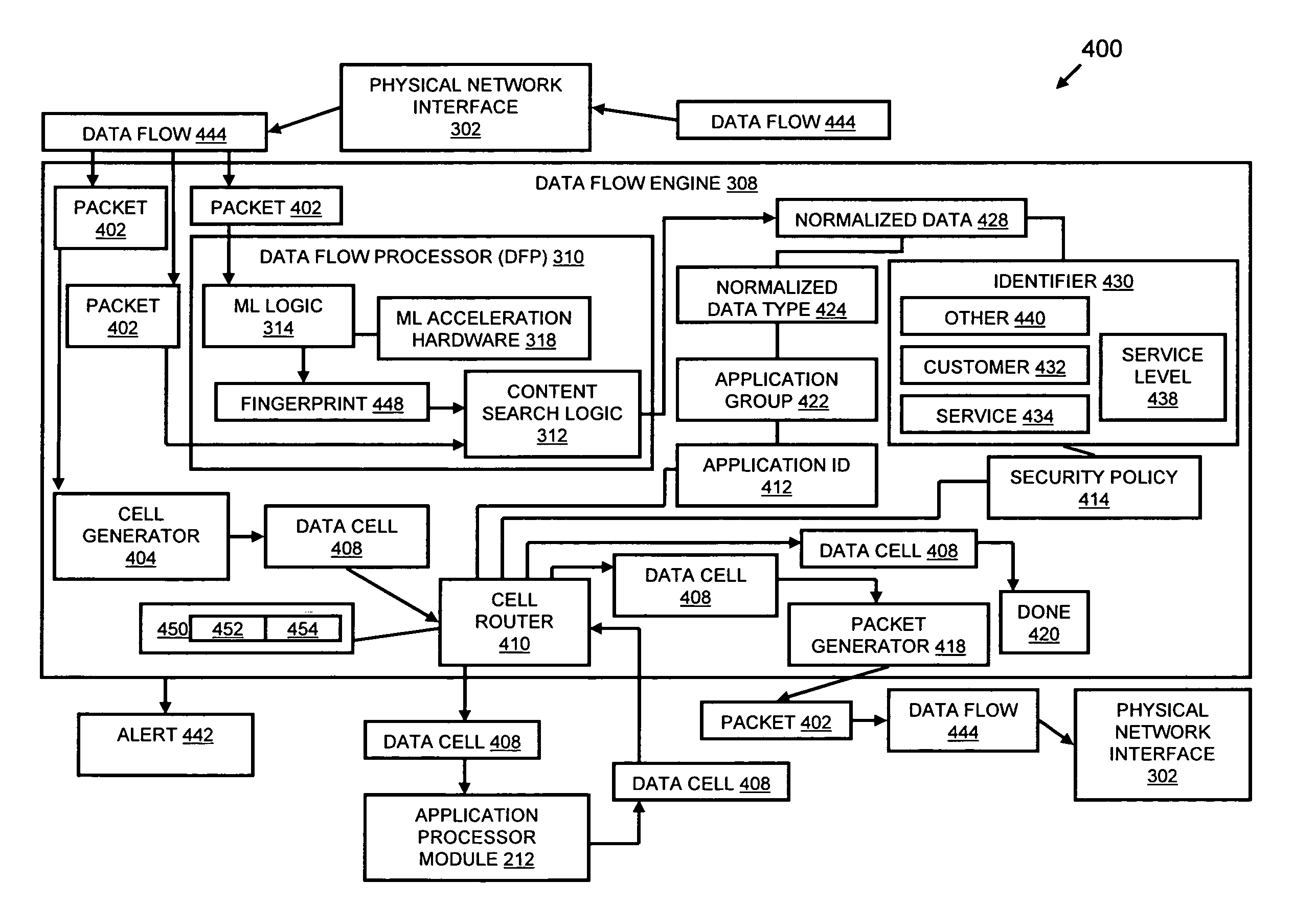
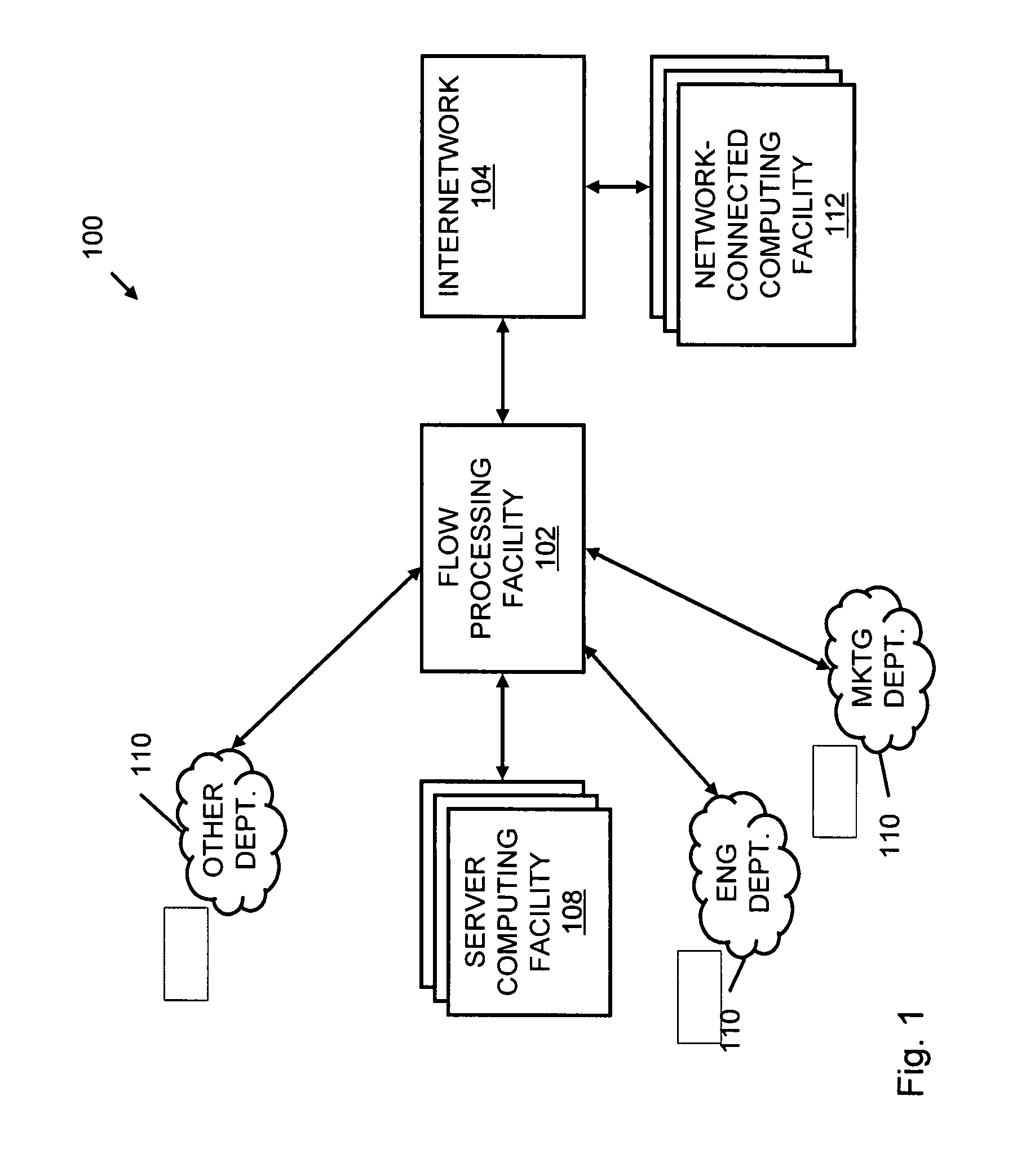
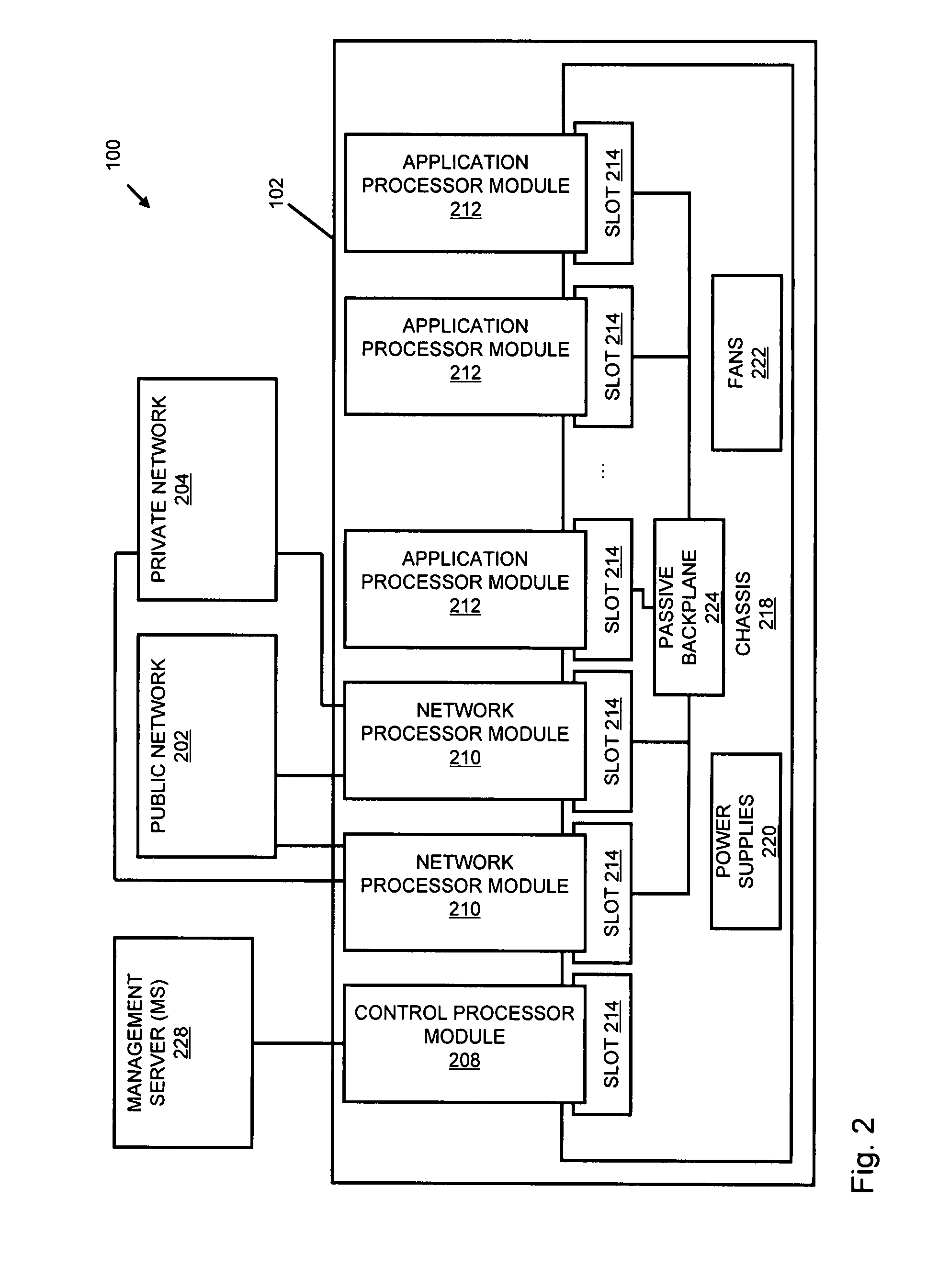
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS20070121596A1Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
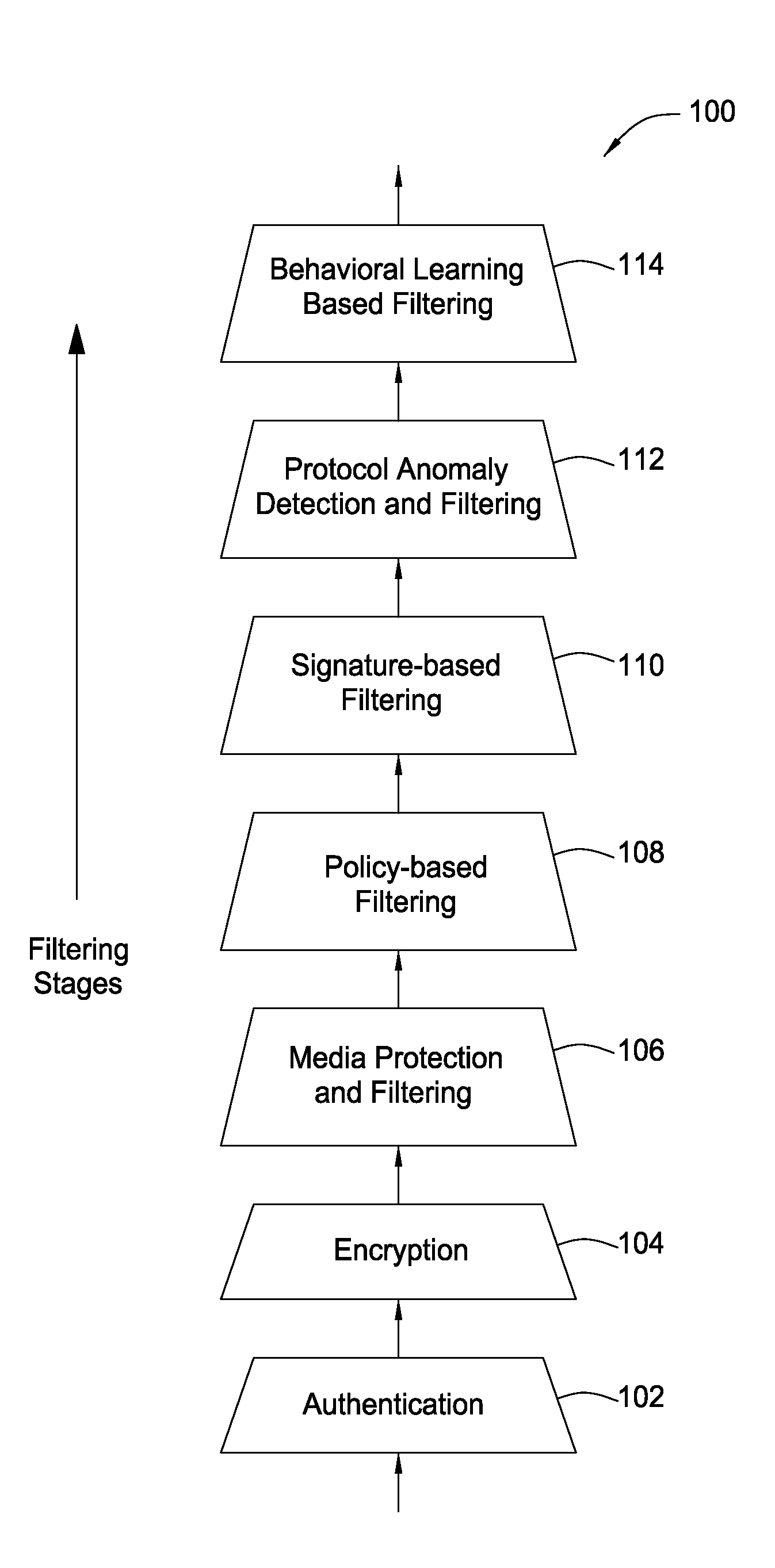
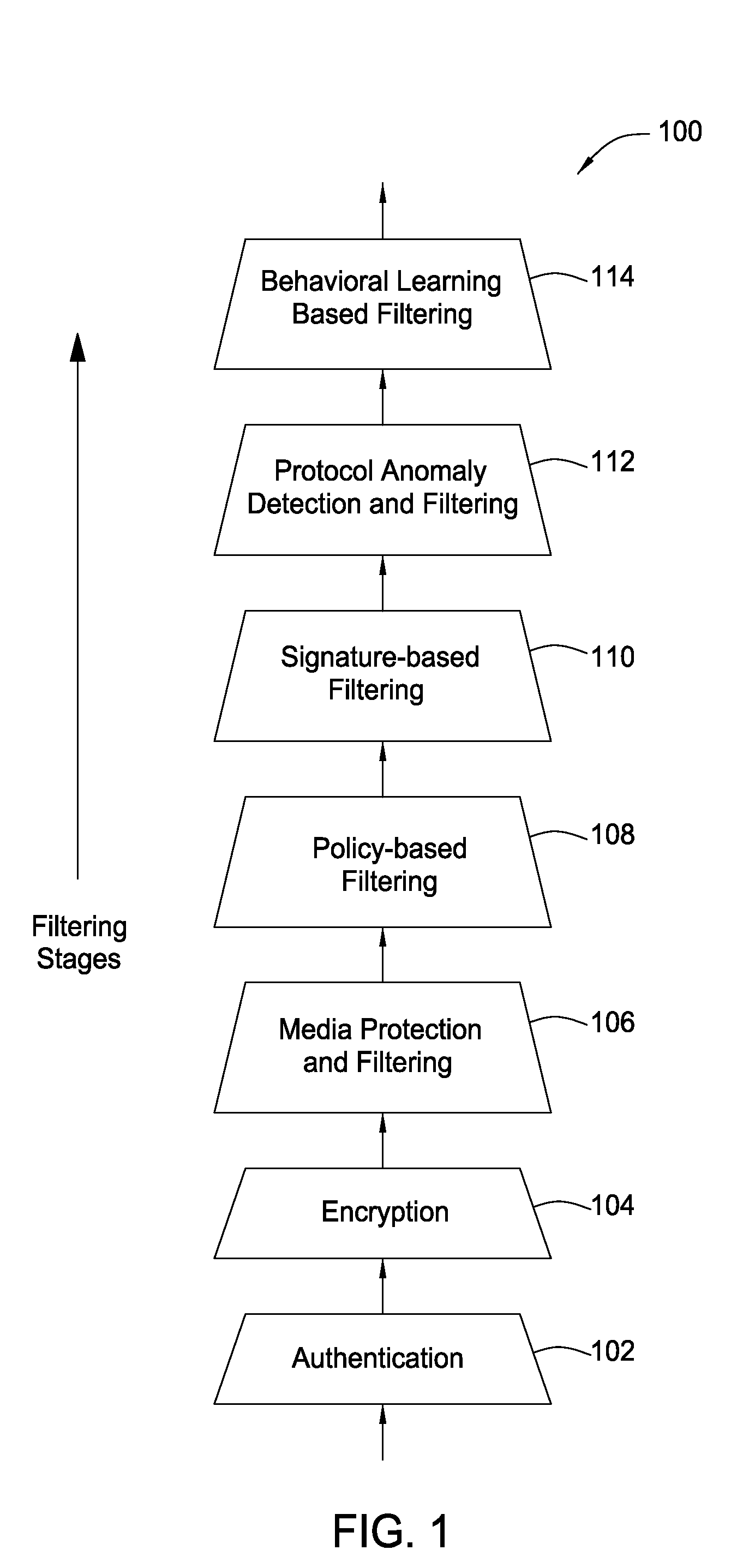
The present invention provides a system, method and apparatus for providing network level and nodal level vulnerability protection in VoIP networks by receiving a communication, filtering the received communication using three or more stages selected from the group comprising a media protection and filtering plane, a policy based filtering plane, a signature based filtering plane, a protocol anomaly detection and filtering plane and a behavioral learning based filtering plane, and either allowing or denying the received communication based the filtering step. The stages are applicable to one or more protocols including SIP, IMS, UMA, H.248, H.323, RTP, CSTA / XML or a combination thereof. In addition, the stages can be implemented within a single device or are distributed across a network (e.g., SIP network, a UMA network, an IMS network or a combination thereof).
Owner:AVAYA INC
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Robust anomaly detection and regularized domain adaptation of classifiers with application to internet packet-flows
InactiveUS20120284791A1Maximize aggregate statistical significanceMaximizesMathematical modelsMemory loss protectionCredit cardAlgorithm
Sound, robust methods identify the most suitable, parsimonious set of tests to use with respect to prioritized, sequential anomaly detection in a collected batch of sample data. While the focus is on detecting anomalies in network traffic flows and classifying network traffic flows into application types, the methods are also applicable to other anomaly detection and classification application settings, including detecting email spam, (e.g. credit card) fraud detection, detecting imposters, unusual event detection (for example, in images and video), host-based computer intrusion detection, detection of equipment or complex system failures, as well as of anomalous measurements in scientific experiments.
Owner:PENN STATE RES FOUND
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
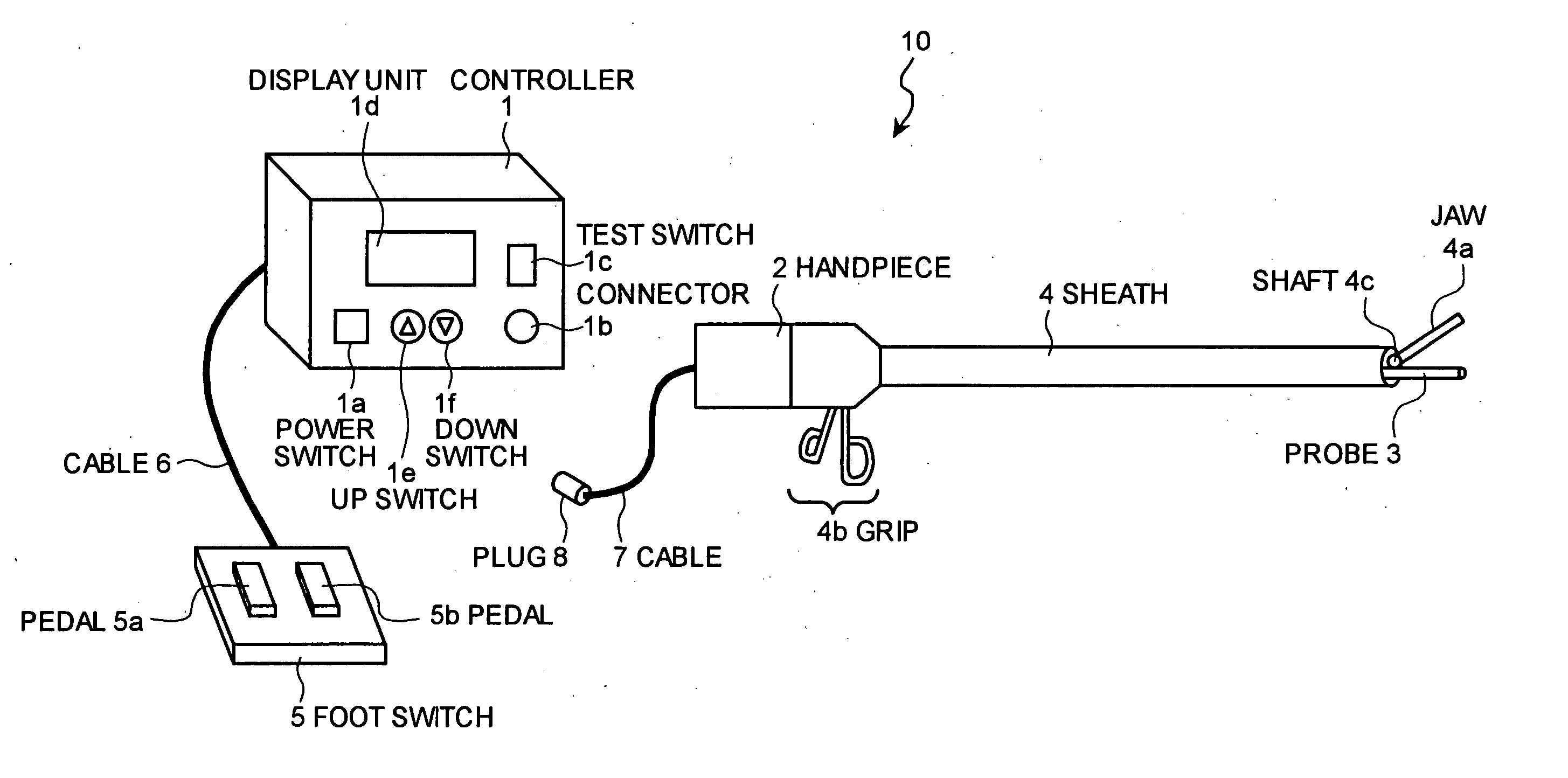
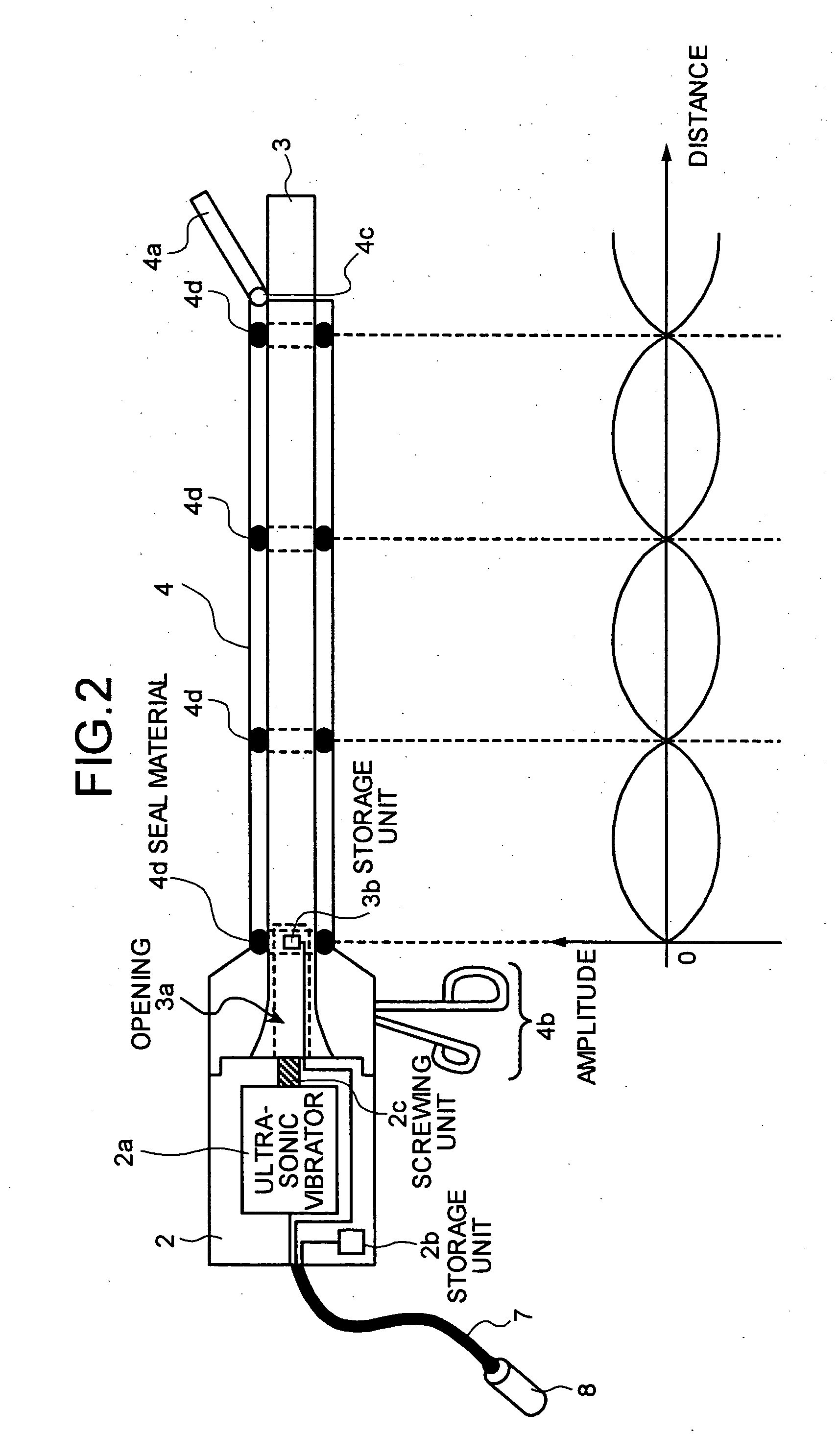
Ultrasonic surgical system, and abnormality detection method and abnormality detection program for ultrasonic surgical system
InactiveUS20050070800A1Solve problemsUltrasonic/sonic/infrasonic diagnosticsSurgical instrument detailsAnomaly detectionBiomedical engineering
An ultrasonic surgical system includes a handpiece having an ultrasonic vibrator; and a probe connected to the ultrasonic vibrator. The handpiece includes a first storage unit that stores first determination criterion information being a criterion of whether an abnormality occurs in the ultrasonic surgical system. The probe includes a second storage unit that stores second determination criterion information as a criterion of whether an abnormality occurs in the ultrasonic surgical system. The ultrasonic surgical system also includes a control unit that stops driving the ultrasonic vibrator based on the first and second determination criterion information.
Owner:OLYMPUS CORP
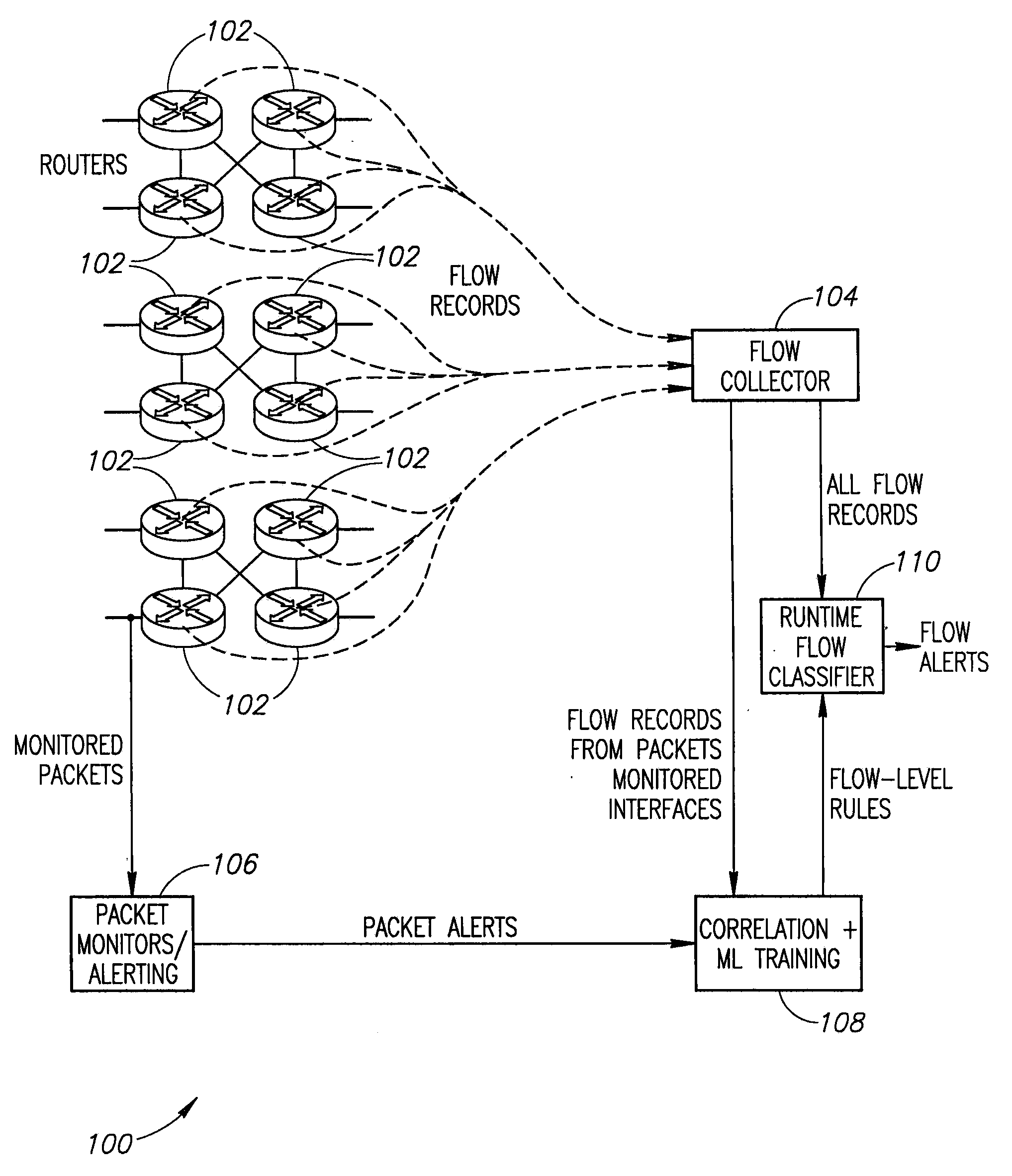
Systems and methods for rule-based anomaly detection on IP network flow
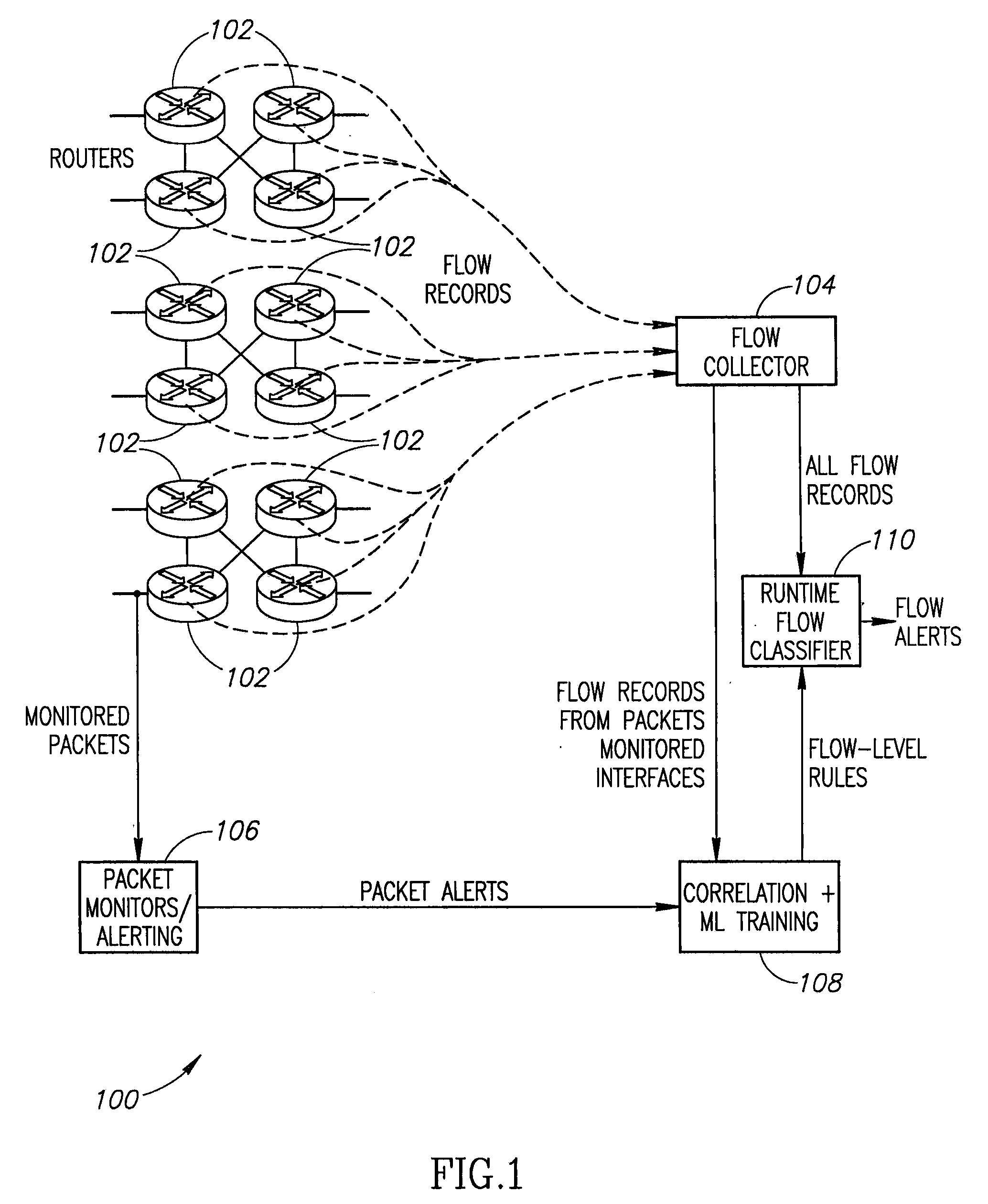
A system to detect anomalies in internet protocol (IP) flows uses a set of machine-learning (ML) rules that can be applied in real time at the IP flow level. A communication network has a large number of routers that can be equipped with flow monitoring capability. A flow collector collects flow data from the routers throughout the communication network and provides them to a flow classifier. At the same time, a limited number of locations in the network monitor data packets and generate alerts based on packet data properties. The packet alerts and the flow data are provided to a machine learning system that detects correlations between the packet-based alerts and the flow data to thereby generate a series of flow-level alerts. These rules are provided to the flow time classifier. Over time, the new packet alerts and flow data are used to provide updated rules generated by the machine learning system.
Owner:AT&T INTPROP I L P
Network activity anomaly detection
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
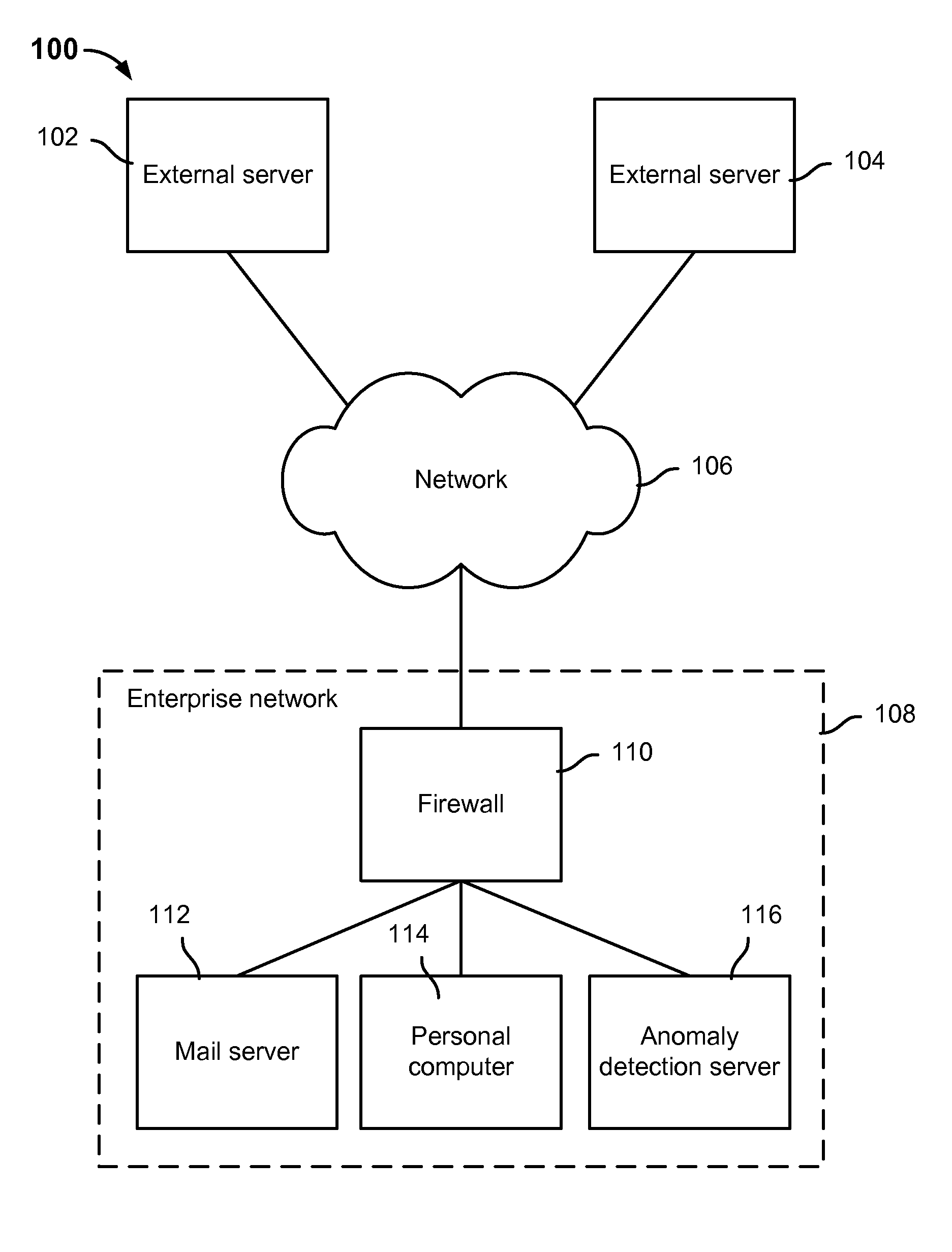
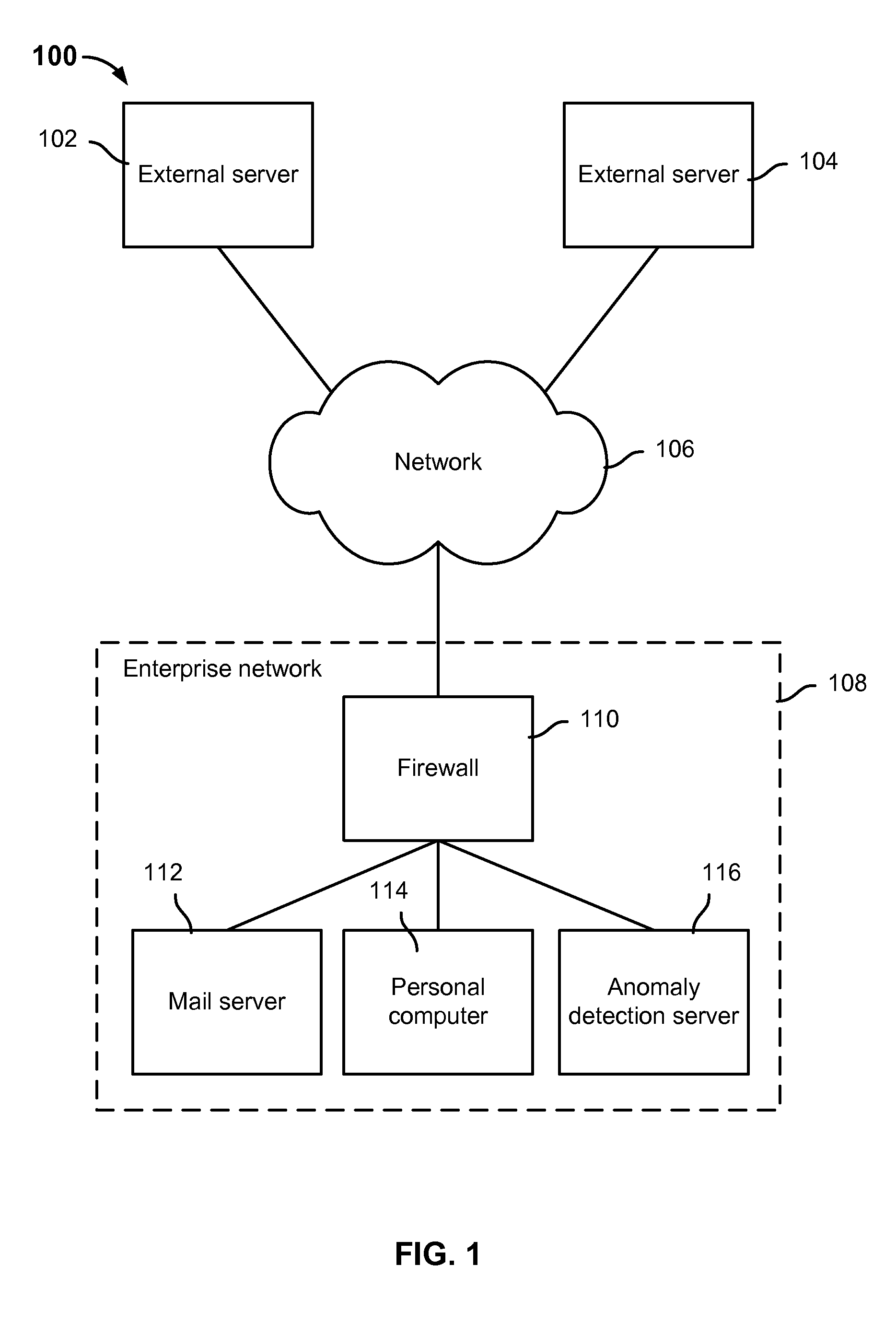
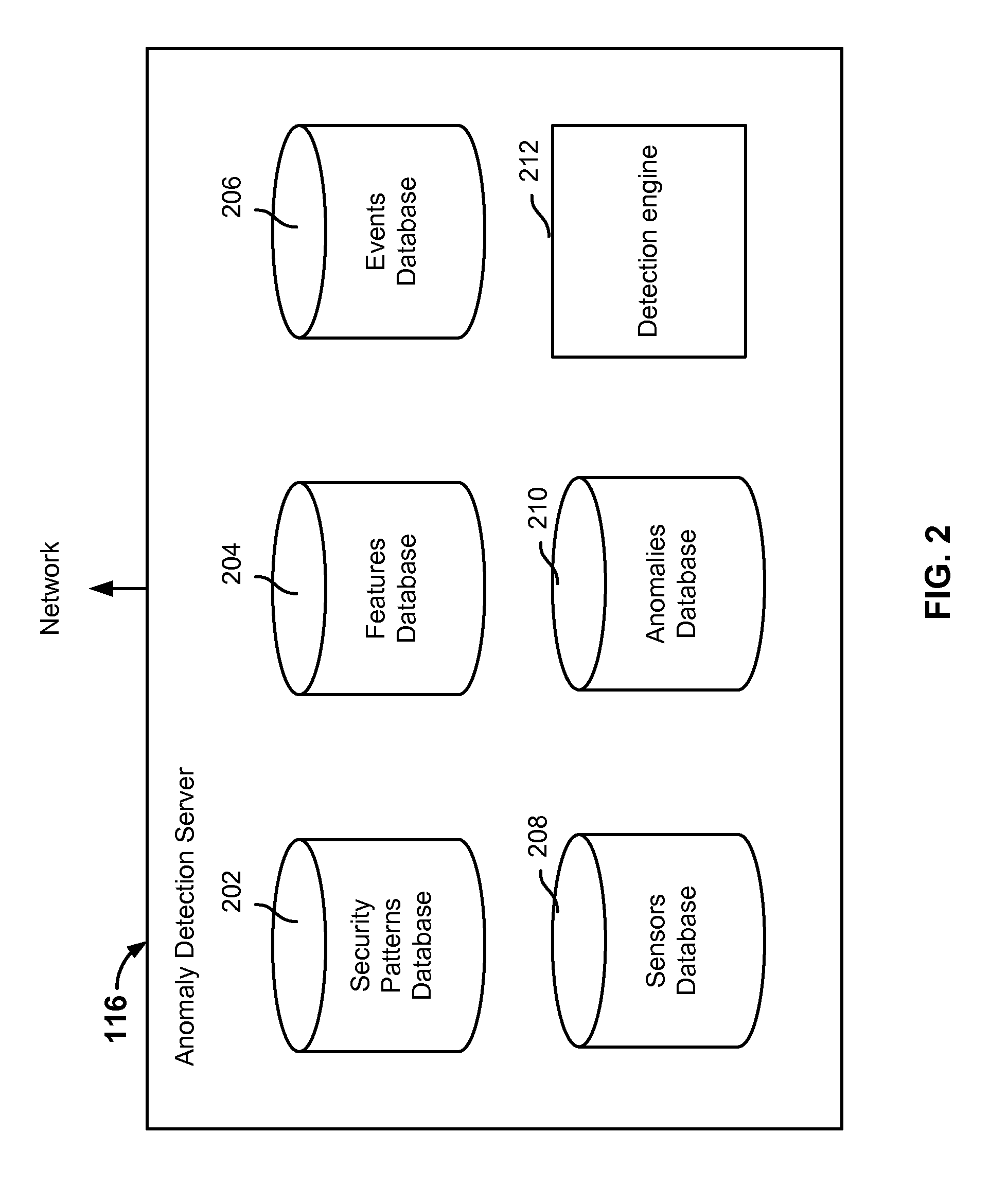
Anomaly detection system for enterprise network security
ActiveUS9112895B1Unauthorized memory use protectionComputer security arrangementsAnomaly detectionEnterprise networking
Anomaly detection is disclosed, including: determining a set of anomalous events associated with an enterprise network; and determining a path of interest based at least in part on at least a subset of the set of anomalous events.
Owner:EMC IP HLDG CO LLC
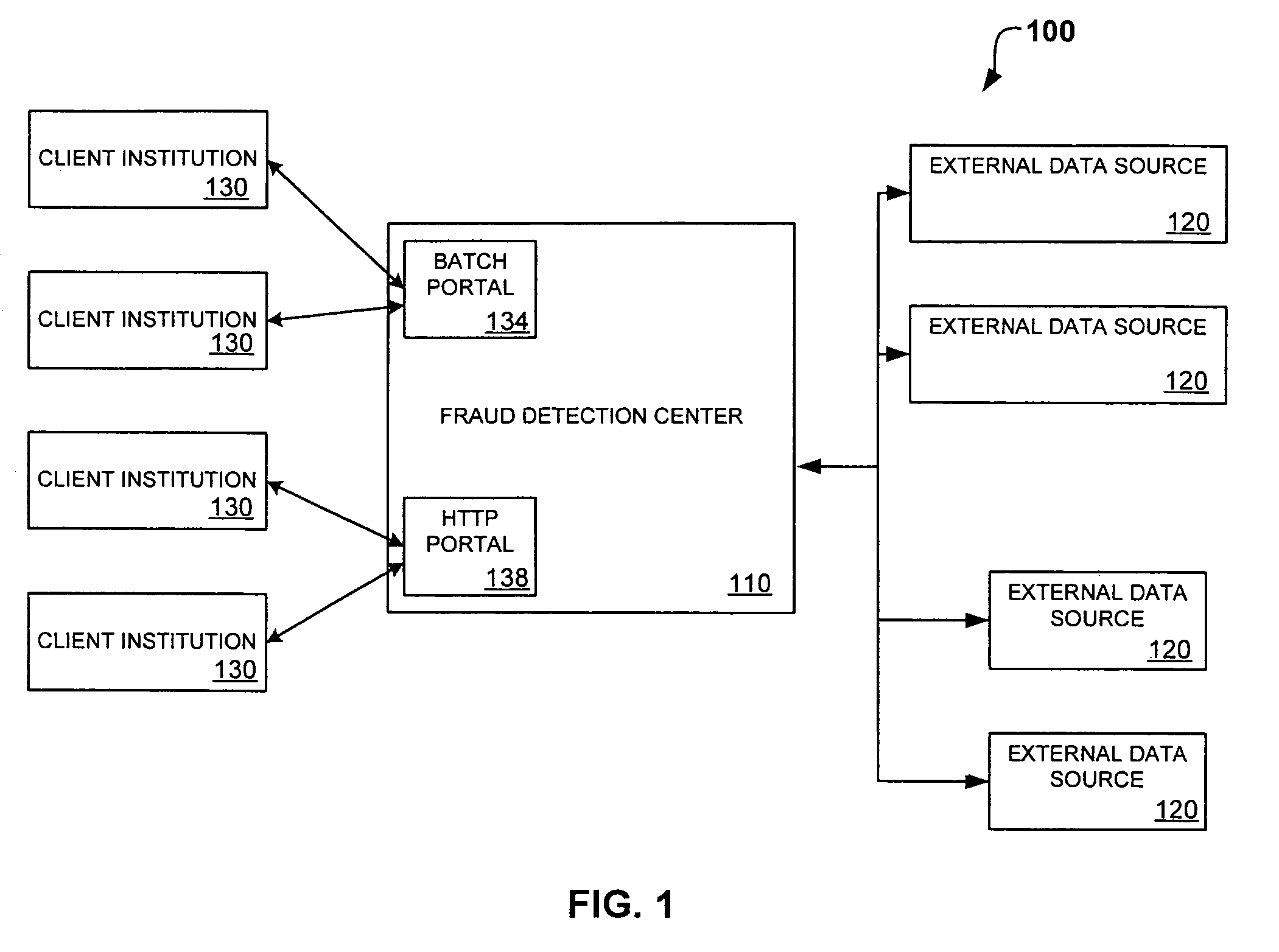
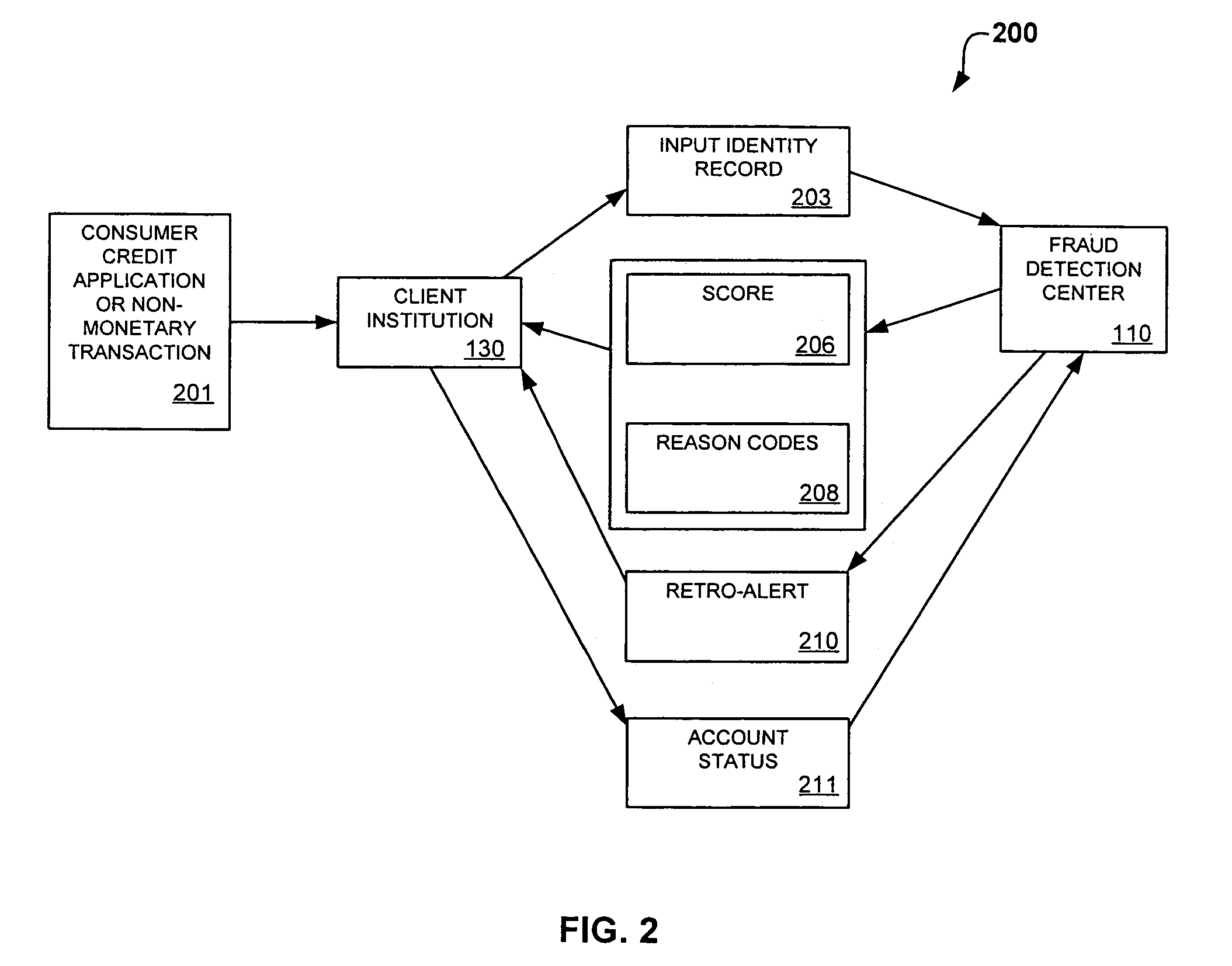
System and method for identity-based fraud detection through graph anomaly detection
A method for identifying a fraudulent account application includes receiving a new account application comprising a plurality of identity-related fields and linking the identity-related fields associated with the new account application with identity-related fields associated with a plurality of historical account applications. The links form a graphical pattern on which statistical analysis can be performed to determine the likelihood that the new account application is fraudulent. The statistical analysis can comprise comparing the graphical pattern to a known, or normal graphical pattern in order to detect differences, or anomalies occurring in the graphical pattern associated with the new account application.
Owner:LEXISNEXIS RISK SOLUTIONS FL
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
Method and system for user network behavioural based anomaly detection
InactiveUS20070245420A1Memory loss protectionError detection/correctionApplication softwareBehavioural analysis
A baseline can be defined using specific attributes of the network traffic. Using the established baseline, deviation can then be measured to detect anomaly on the network. The accuracy of the baseline is the most important criterion of any effective network anomaly detection technique. In a local area network (LAN) environment, the attributes change very frequently by many change agents; for example, new entities, such as users, application, and network-enabled devices, added to and removed from the LAN environment. The invention provides an improved method of establishing a baseline for network anomaly detection based on user's behaviour profiling. A user behaviour profiling is a distinct network usage pattern pertaining to a specific individual user operating on the LAN environment. No two users profiling would be the same. A group of users that have similar network usage attributes can be extrapolated using data mining technique to establish a group profiling baseline to detect network usage anomaly. By combining user and group profiling, a network anomaly detection system can measure subtle shift in network usage and as a result separate good user's network usage behaviour from the bad one. Using the said technique, a lower rate of false positives of network anomaly can be created that is suitable to operate in a highly dynamic LAN environment.
Owner:YONG YUH MING +1
System and method for site abnormality recording and notification
InactiveUS20130030875A1Improve system efficiencyAdvertisementsMultiprogramming arrangementsAnomaly detectionData memory
Method of notifying a user of site abnormalities via an application configured to access an event server having a first sensor abnormality detector connected to a first sensor, for detecting first abnormal behavior of first sub-events sensed by the first sensor, the first abnormal behavior corresponding to a first abnormal behavior value, a second sensor abnormality detector connected to a second sensor, for detecting second abnormal behavior of second sub-events sensed by the second sensor of a type different from the first sensor, the second abnormal behavior corresponding to a second abnormal behavior value, a correlator for correlating the first and second abnormal behavior values and logging correlated values as a composite event, a data store, the application having a viewer configured to show, on the device, data associated with a plurality of composite events, the viewer further configured to display the plurality of composite events in a temporal order.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Onboard vehicle data mining, social networking, and pattern-based advertisement
ActiveUS20110258044A1High throughput data streamLimited communication-bandwidthVehicle testingArrangements for variable traffic instructionsSystems designData stream mining
The present invention is an improvement of methods and systems using mobile and distributed data stream mining algorithms for mining continuously generated data from different components of a vehicle. The system is designed for both on-board and remote mining and management of the data in order to (1) detect the effect of various engine parameters on fuel consumption behavior, (2) predictive classification of driving patterns and associative indexing of driver performance matrix, (3) resource-constrained anomaly detection for onboard health monitoring, (4) vehicle-to-vehicle social networking and distributed data mining, (5) adaptive placement of advertisements based on vehicle performance profile and (6) onboard emissions analytics computation for wireless emissions monitoring and smog test.
Owner:AGNIK
Automatic anomaly detection and resolution system
ActiveUS20160350173A1Maximizing SLA compliant periodLow costNon-redundant fault processingData switching networksAnomaly detectionReal-time computing
An anomaly detection and resolution system (ADRS) is disclosed for automatically detecting and resolving anomalies in computing environments. The ADRS may be implemented using an anomaly classification system defining different types of anomalies (e.g., a defined anomaly and an undefined anomaly). A defined anomaly may be based on bounds (fixed or seasonal) on any metric to be monitored. An anomaly detection and resolution component (ADRC) may be implemented in each component defining a service in a computing system. An ADRC may be configured to detect and attempt to resolve an anomaly locally. If the anomaly event for an anomaly can be resolved in the component, the ADRC may communicate the anomaly event to an ADRC of a parent component, if one exists. Each ADRC in a component may be configured to locally handle specific types of anomalies to reduce communication time and resource usage for resolving anomalies.
Owner:ORACLE INT CORP
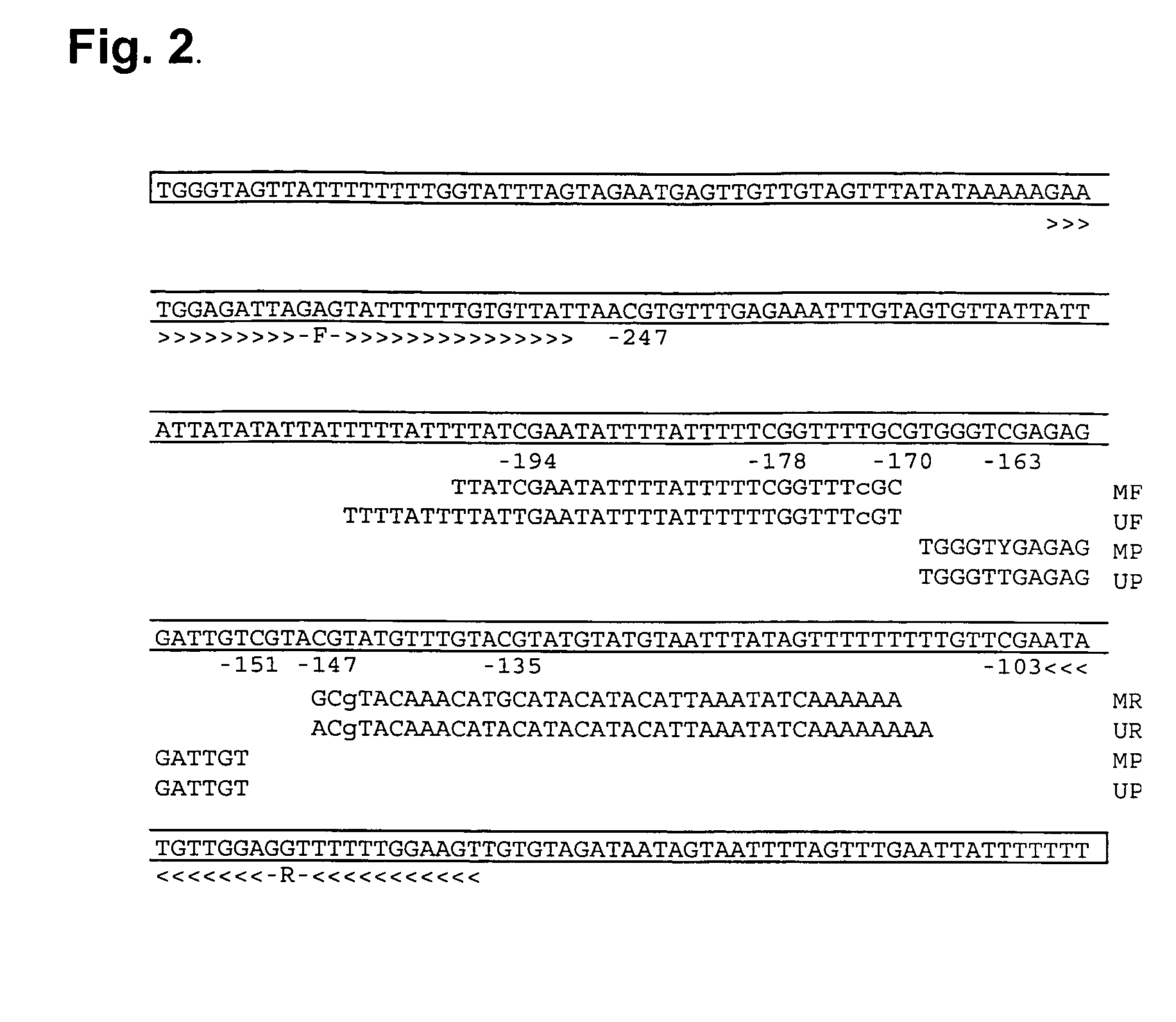
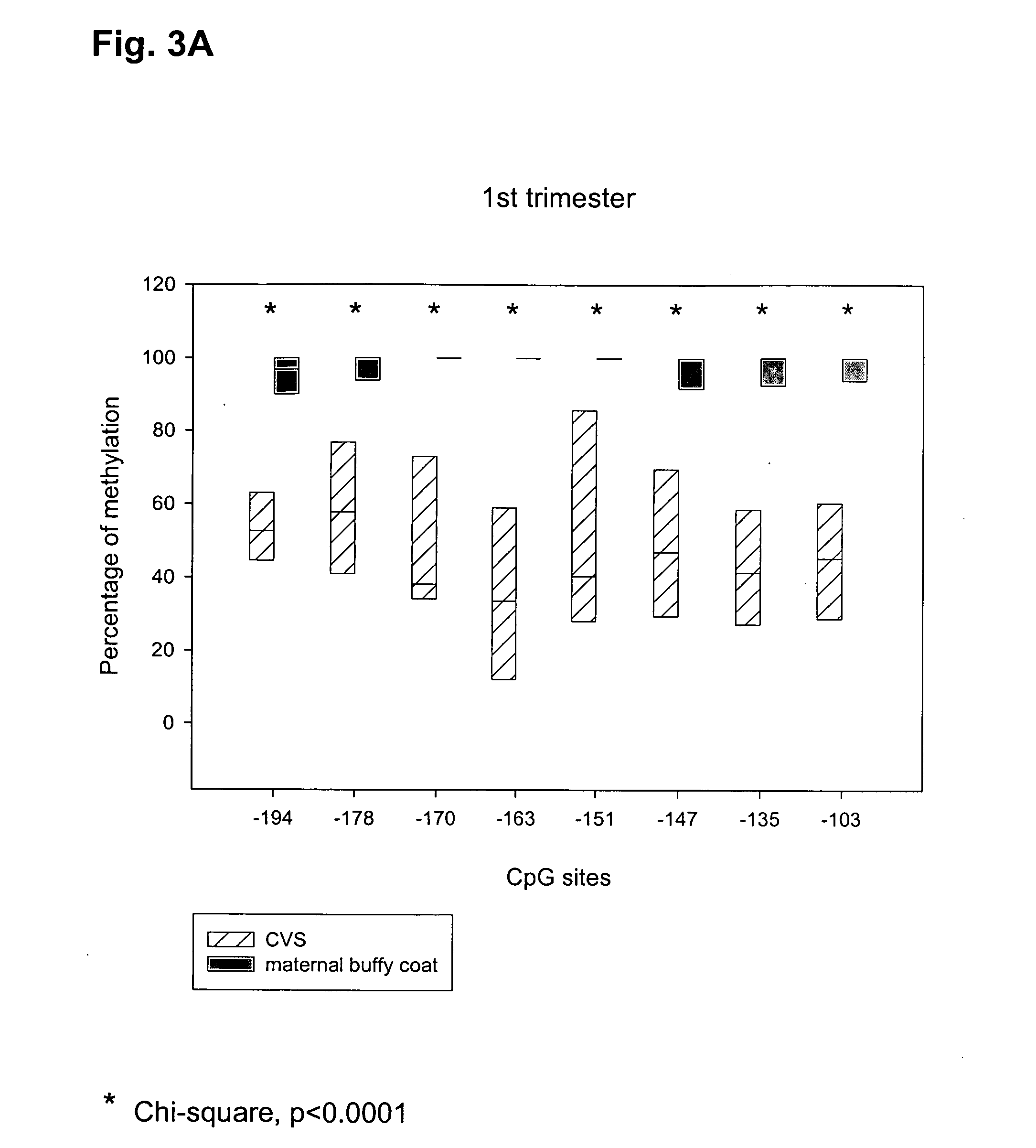
Marker for prenatal diagnosis and monitoring
The present invention relates to new methods for diagnosing a pregnancy-associated disorder by analyzing fetal DNA present in the mother's blood. More specifically, this invention relies on the discovery that the maspin gene is differentially methylated in fetal DNA and in maternal DNA and provides these new diagnostic methods, which distinguish fetal DNA from maternal DNA and detect prenatal disorders based on abnormalities in fetal DNA level and methylation status.
Owner:THE CHINESE UNIVERSITY OF HONG KONG
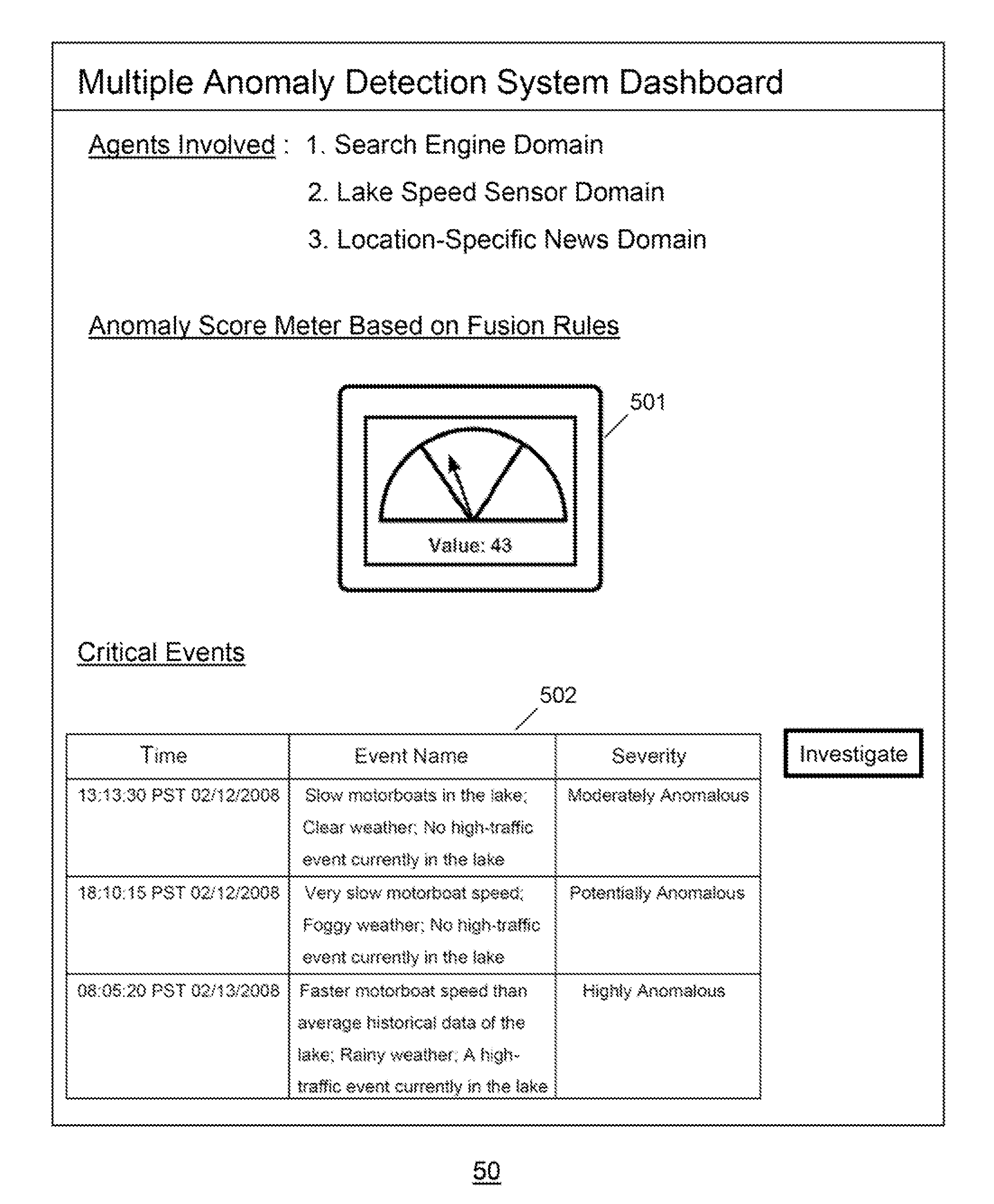
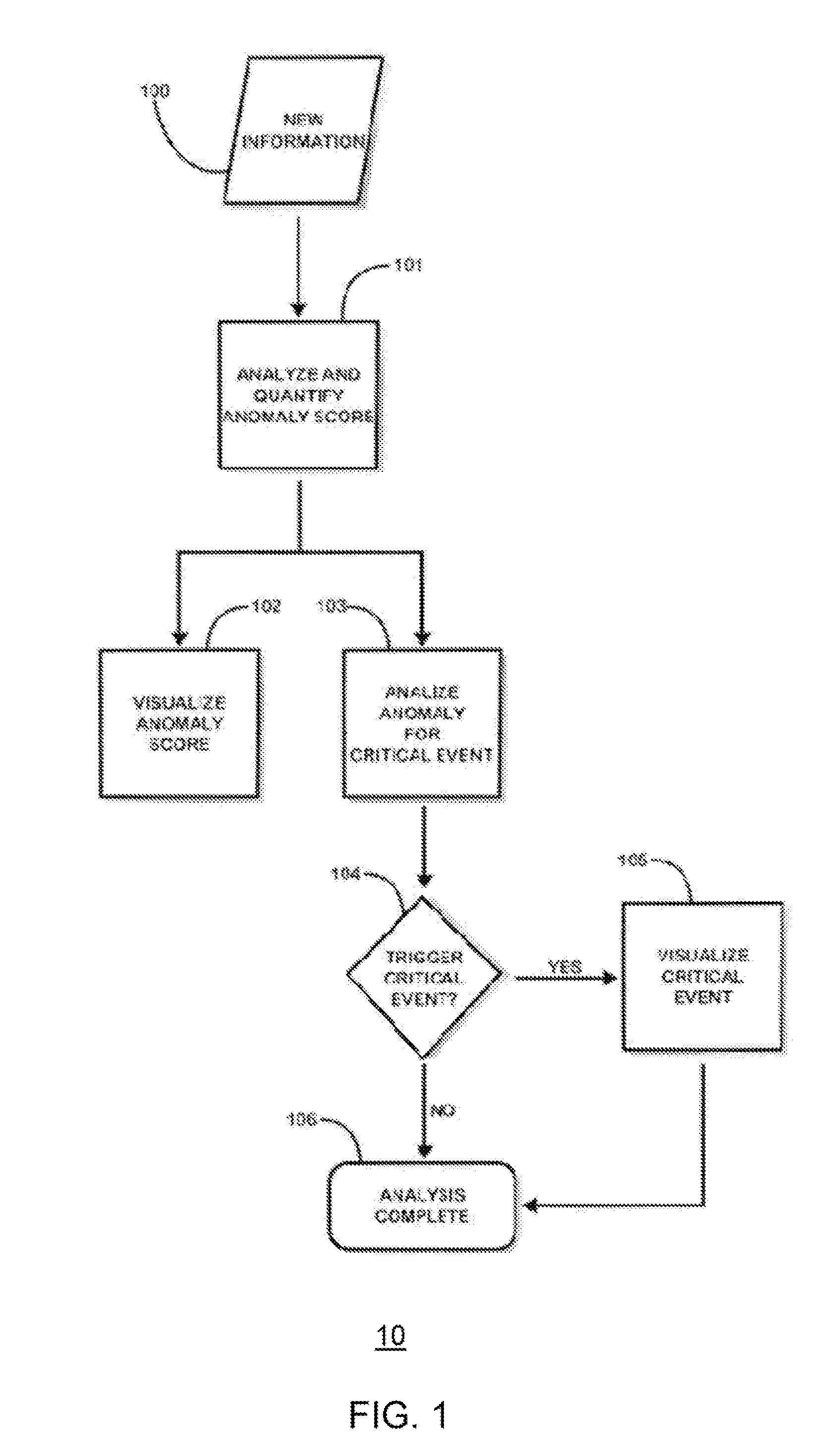
Multiple Domain Anomaly Detection System and Method Using Fusion Rule and Visualization
ActiveUS20110295783A1Digital data information retrievalDigital computer detailsAnomaly detectionDomain analysis
The present invention discloses various embodiments of multiple domain anomaly detection systems and methods. In one embodiment of the invention, a multiple domain anomaly detection system uses a generic learning procedure per domain to create a “normal data profile” for each domain based on observation of data per domain, wherein the normal data profile for each domain can be used to determine and compute domain-specific anomaly data per domain. Then, domain-specific anomaly data per domain can be analyzed together in a cross-domain fusion data analysis using one or more fusion rules. The fusion rules may involve comparison of domain-specific anomaly data from multiple domains to derive a multiple-domain anomaly score meter for a particular cross-domain analysis task. The multiple domain anomaly detection system and its related method may also utilize domain-specific anomaly indicators of each domain to derive a cross-domain anomaly indicator using the fusion rules.
Owner:ZHAO YING +2
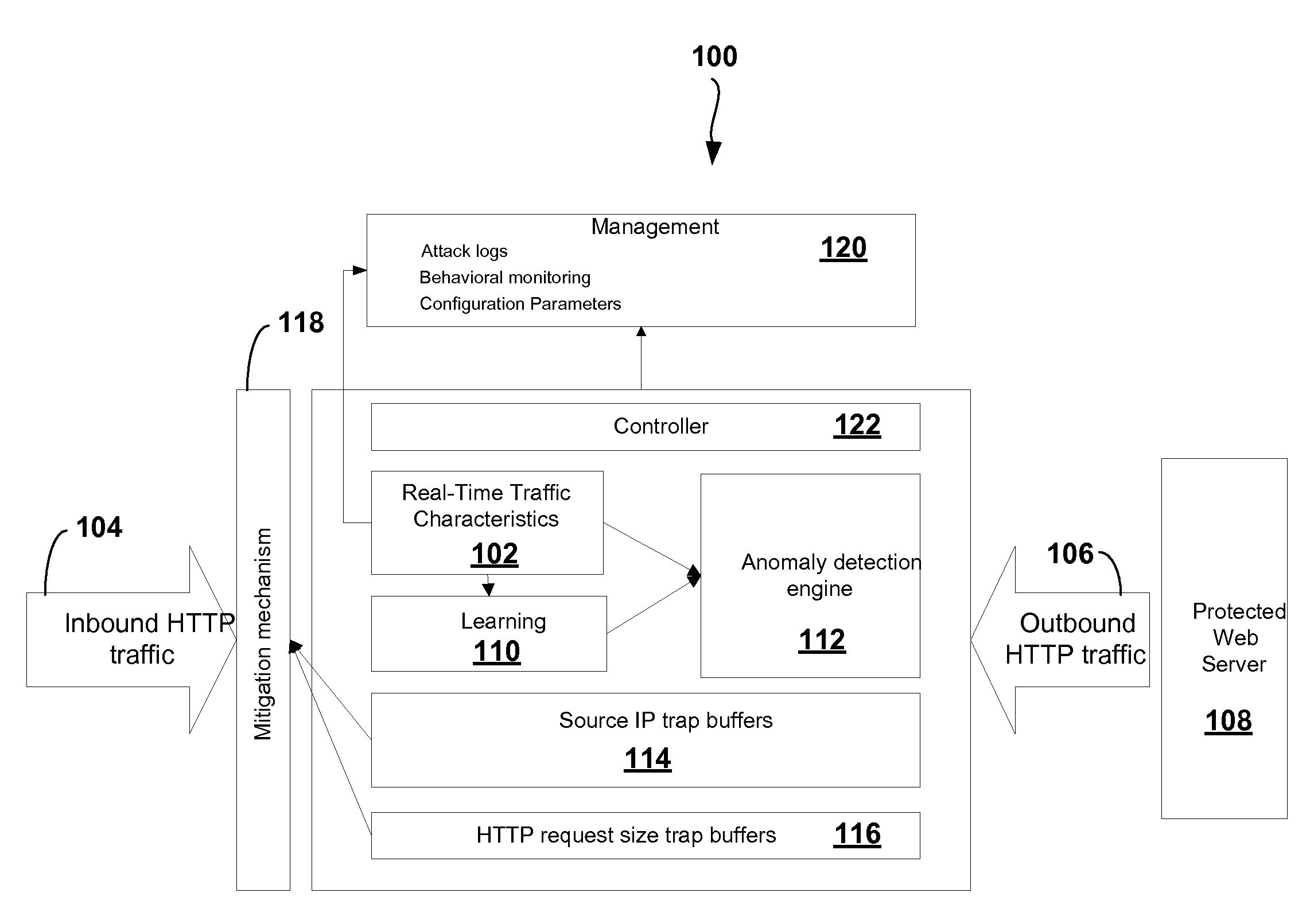
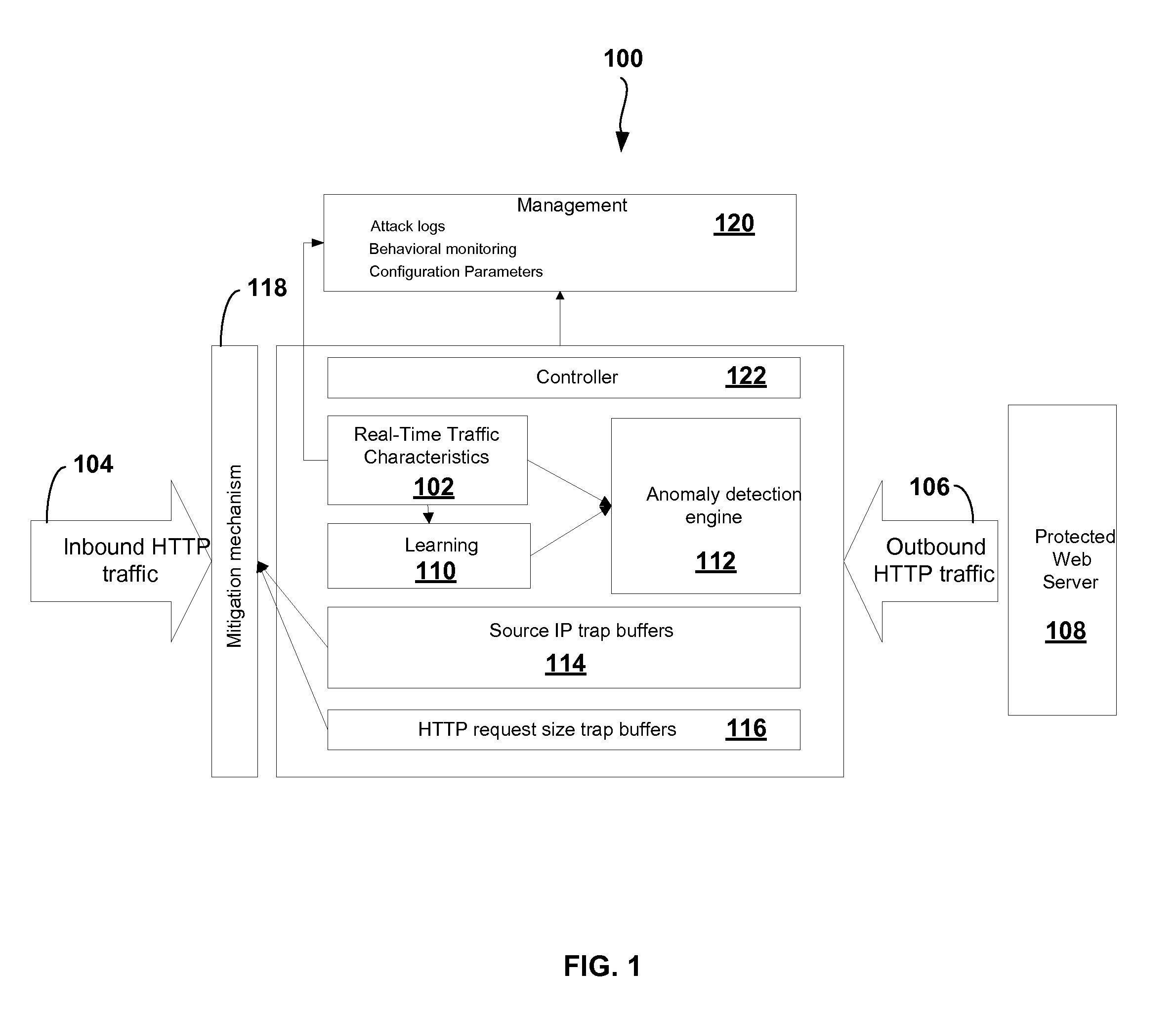
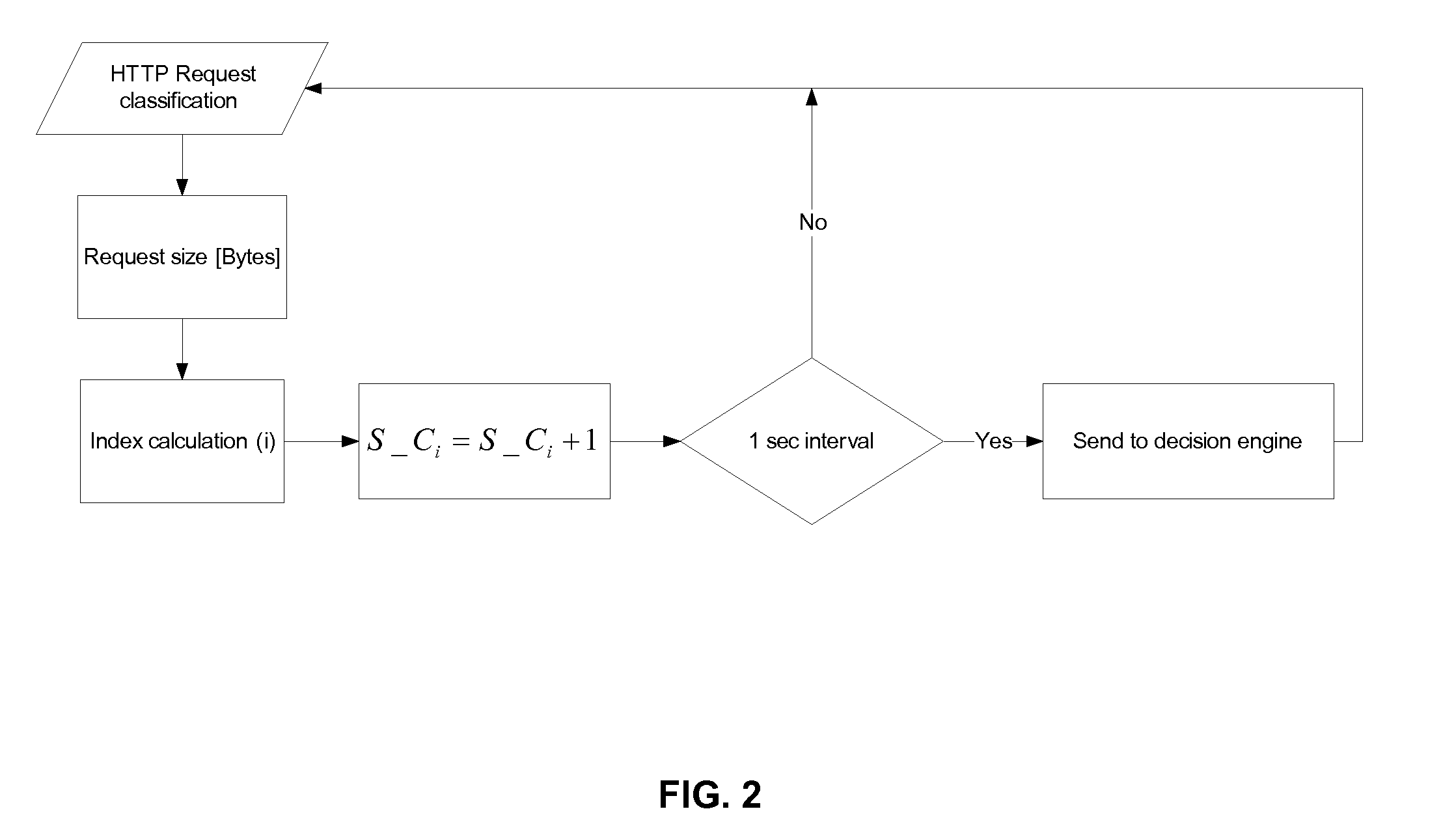
Adaptive Behavioral HTTP Flood Protection
A system and method to detect and mitigate denial of service and distributed denial of service HTTP “page” flood attacks. Detection of attack / anomaly is made according to multiple traffic parameters including rate-based and rate-invariant parameters in both traffic directions. Prevention is done according to HTTP traffic parameters that are analyzed once a traffic anomaly is detected. This protection includes a differential adaptive mechanism that tunes the sensitivity of the anomaly detection engine. The decision engine is based on a combination between fuzzy logic inference systems and statistical thresholds. A “trap buffer” characterizes the attack to allow an accurate mitigation according to the source IP(s) and the HTTP request URL's that are used as part of the attack. Mitigation is controlled through a feedback mechanism that tunes the level of rate limit factors that are needed in order to mitigate the attack effectively while letting legitimate traffic to pass.
Owner:RADWARE
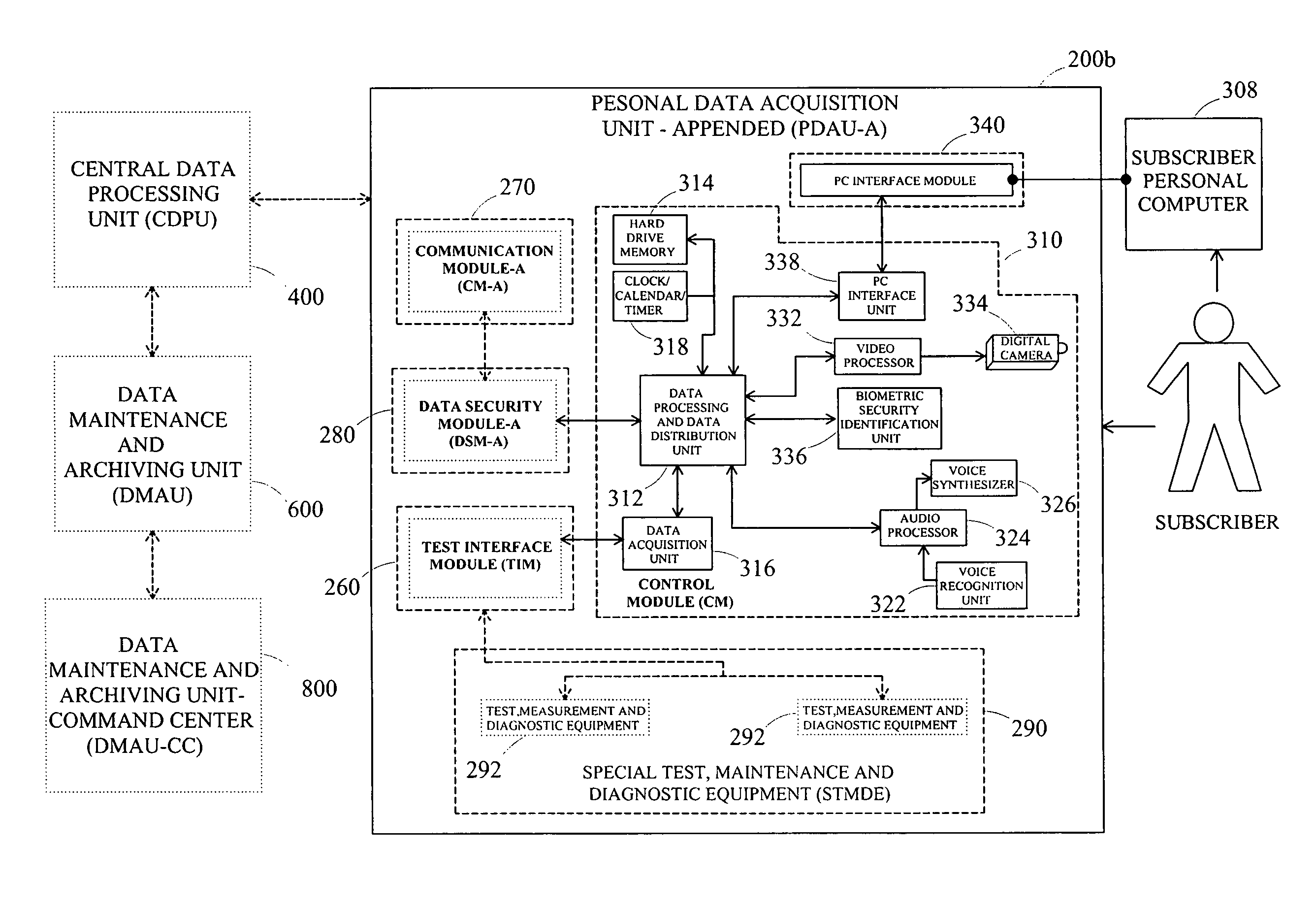
Health maintenance system
ActiveUS7953613B2Easy retrievalData processing applicationsDrug and medicationsAnalysis dataAnomaly detection
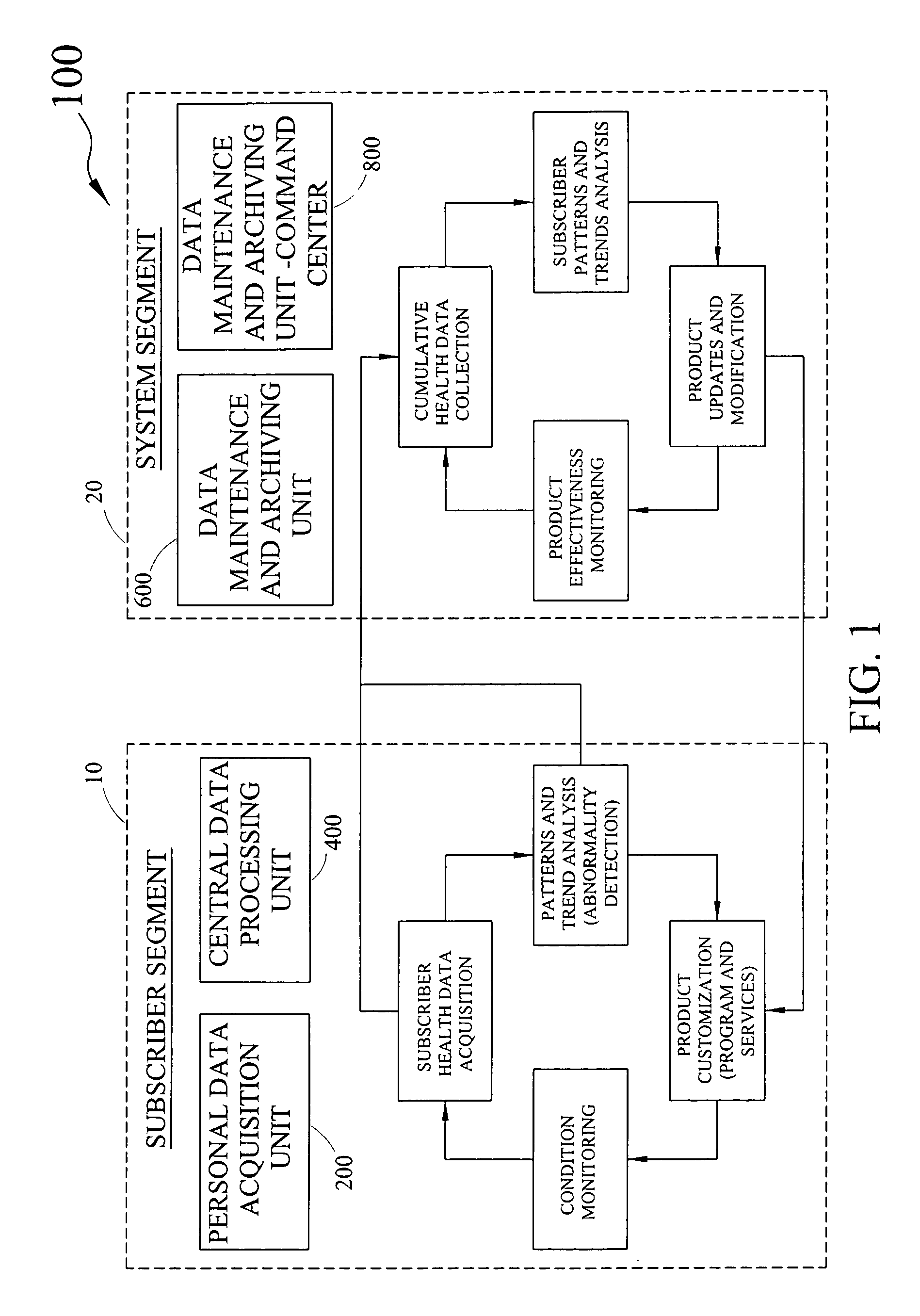
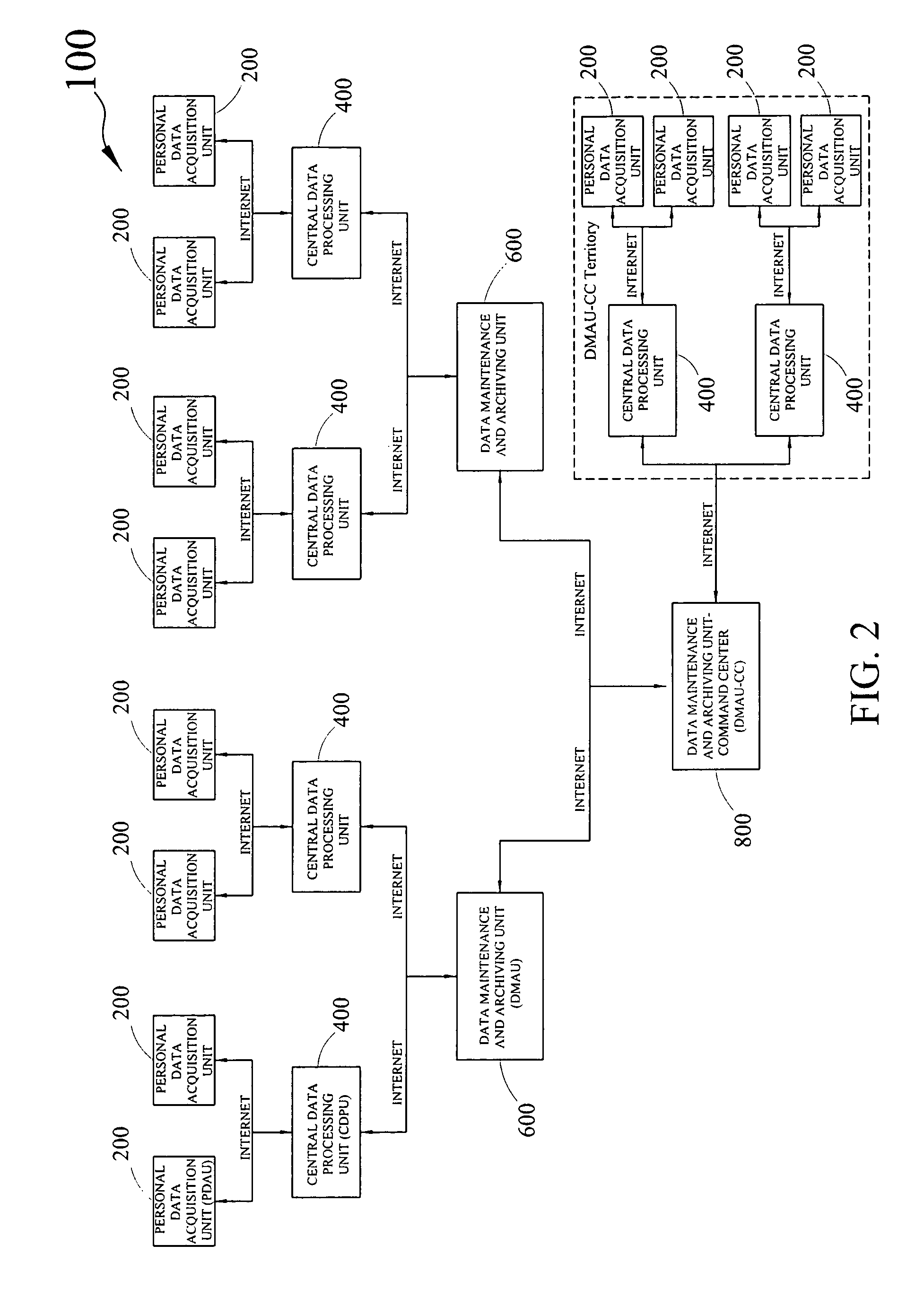
Disclosed is a health maintenance system for comprehensive health assessment, abnormality detection, health monitoring, health pattern and trend detection, health strategy development, and health history archiving. The health maintenance system comprises a subscriber segment and a system segment, communicatively coupled. The subscriber segment acquires subscriber personal and health data from at least one subscriber, analyzing the data; identifies specific health abnormalities; prescribes at least one customized subscriber health product, instructs the subscriber on the implementation of the prescribed health product, compiles and preserves the subscriber's health history data—including abnormalities and prescribed health products, and performs monitoring of subscriber health conditions. The subscriber segment acquires subscriber data from the subscriber segment, stores and maintains the data, facilitates retrieval of data by the subscriber and emergency medical personnel analyzes subscriber patterns and trends, develops new health products and modifies existing health products, and monitors the effectiveness of health products.
Owner:GIZEWSKI THEODORE M
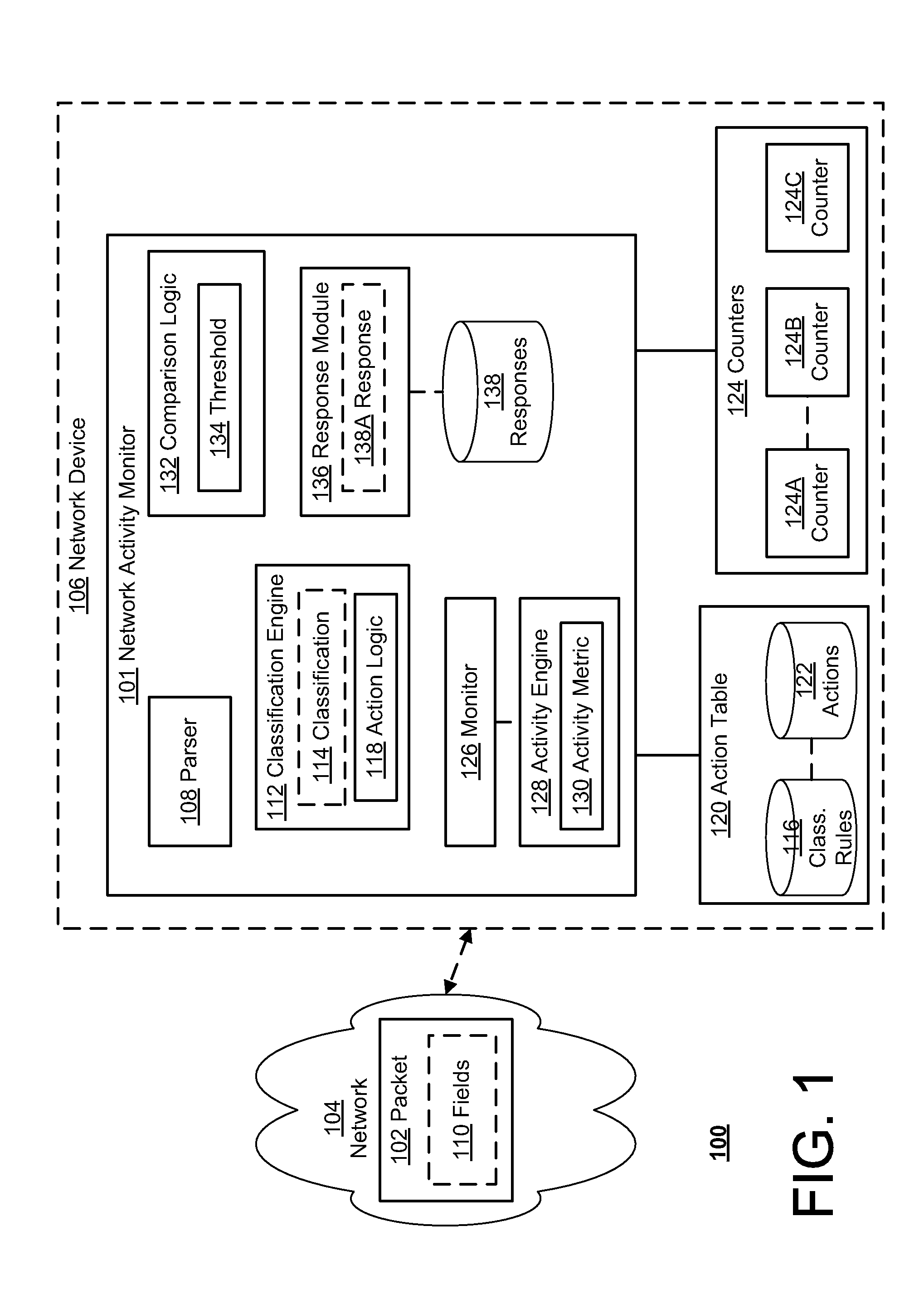
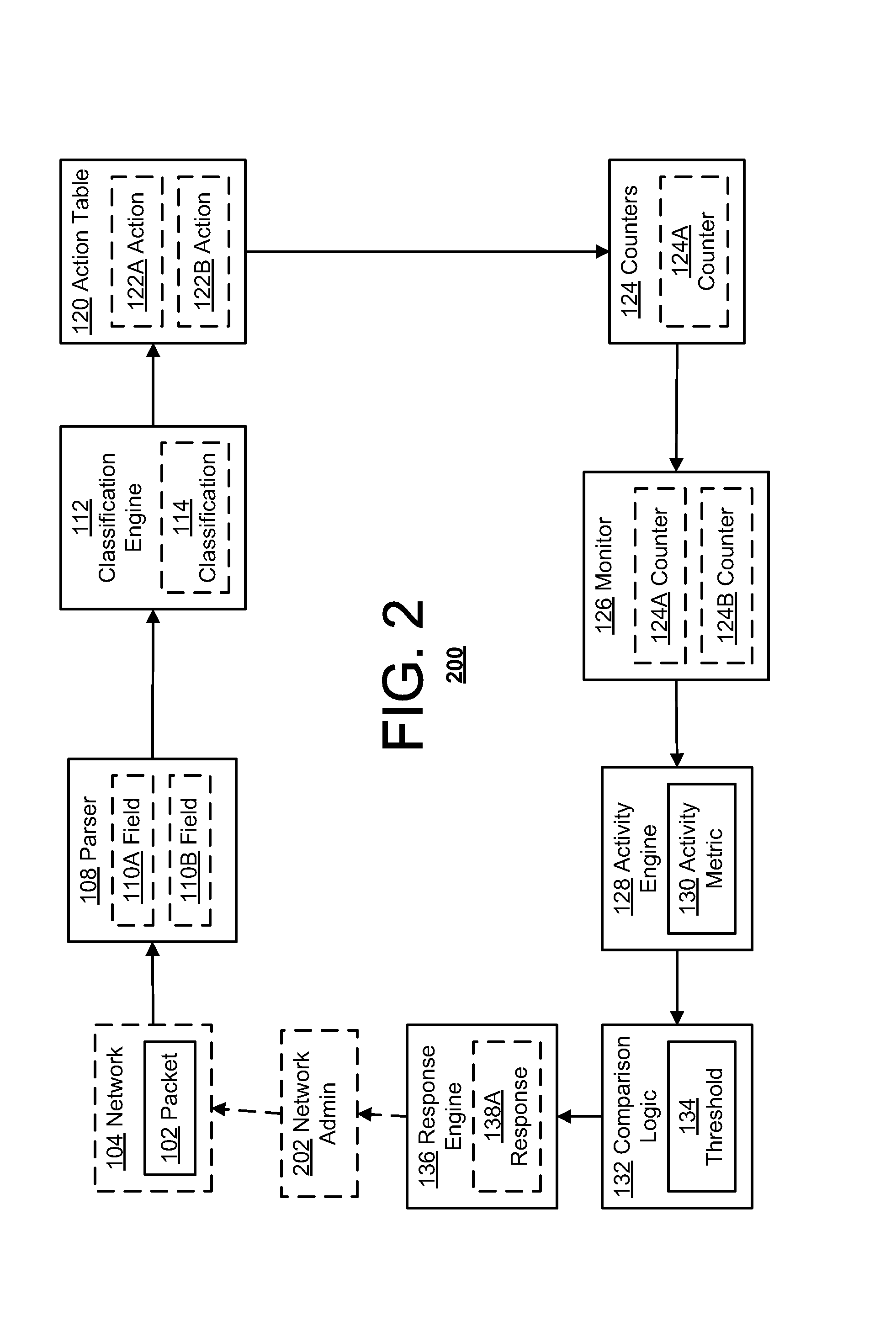
Network intrusion detection system having application inspection and anomaly detection characteristics
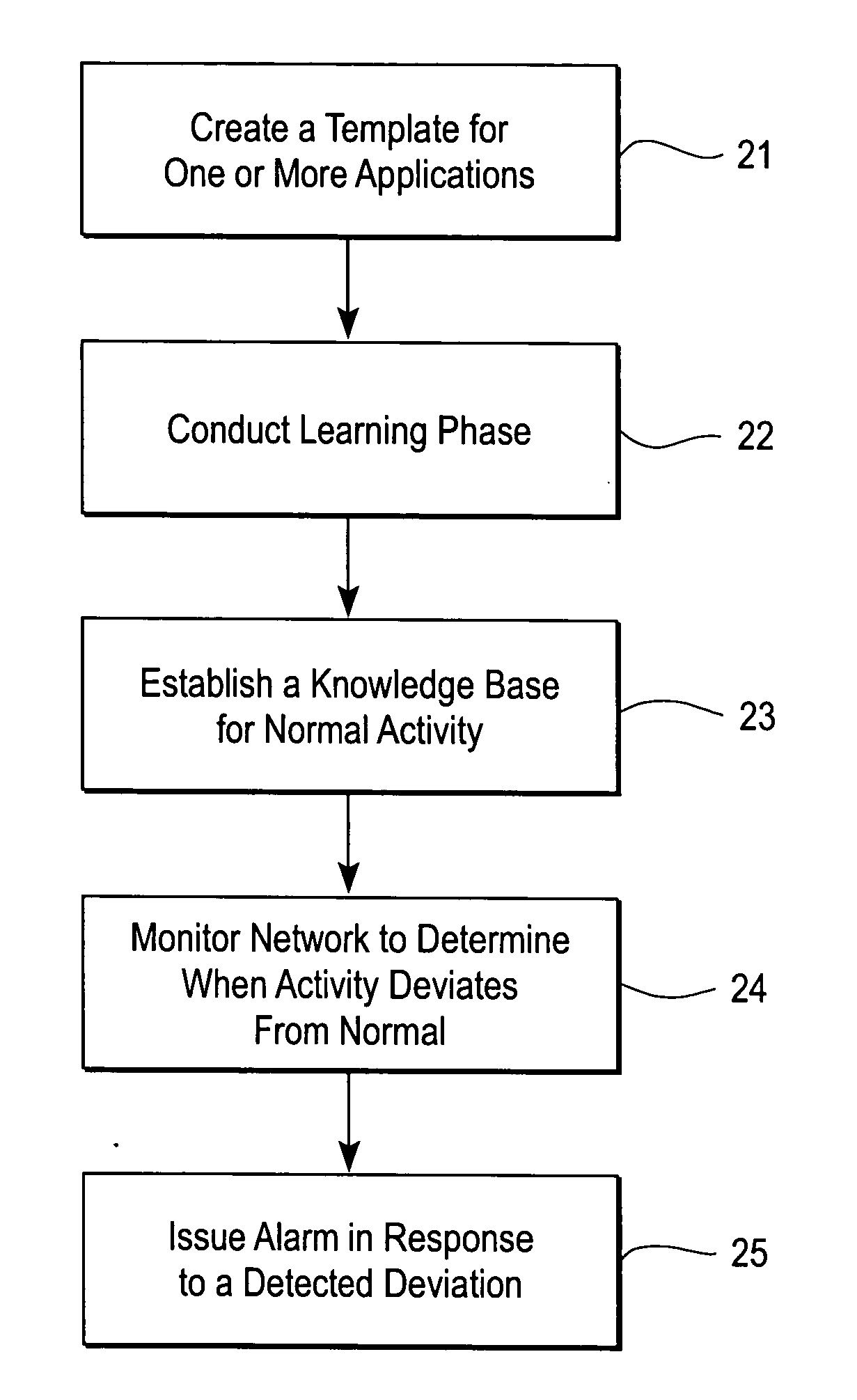
An intrusion detection system and method for a computer network includes a processor and one or more programs that run on the processor for application inspection of data packets traversing the computer network. The one or more programs also obtaining attribute information from the packets specific to a particular application and comparing the attribute information against a knowledge database that provides a baseline of normal network behavior. The processor raises an alarm whenever the attribute information exceeds a predetermined range of deviation from the baseline of normal network behavior. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
Systems and methods for processing data flows
InactiveUS20080133517A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
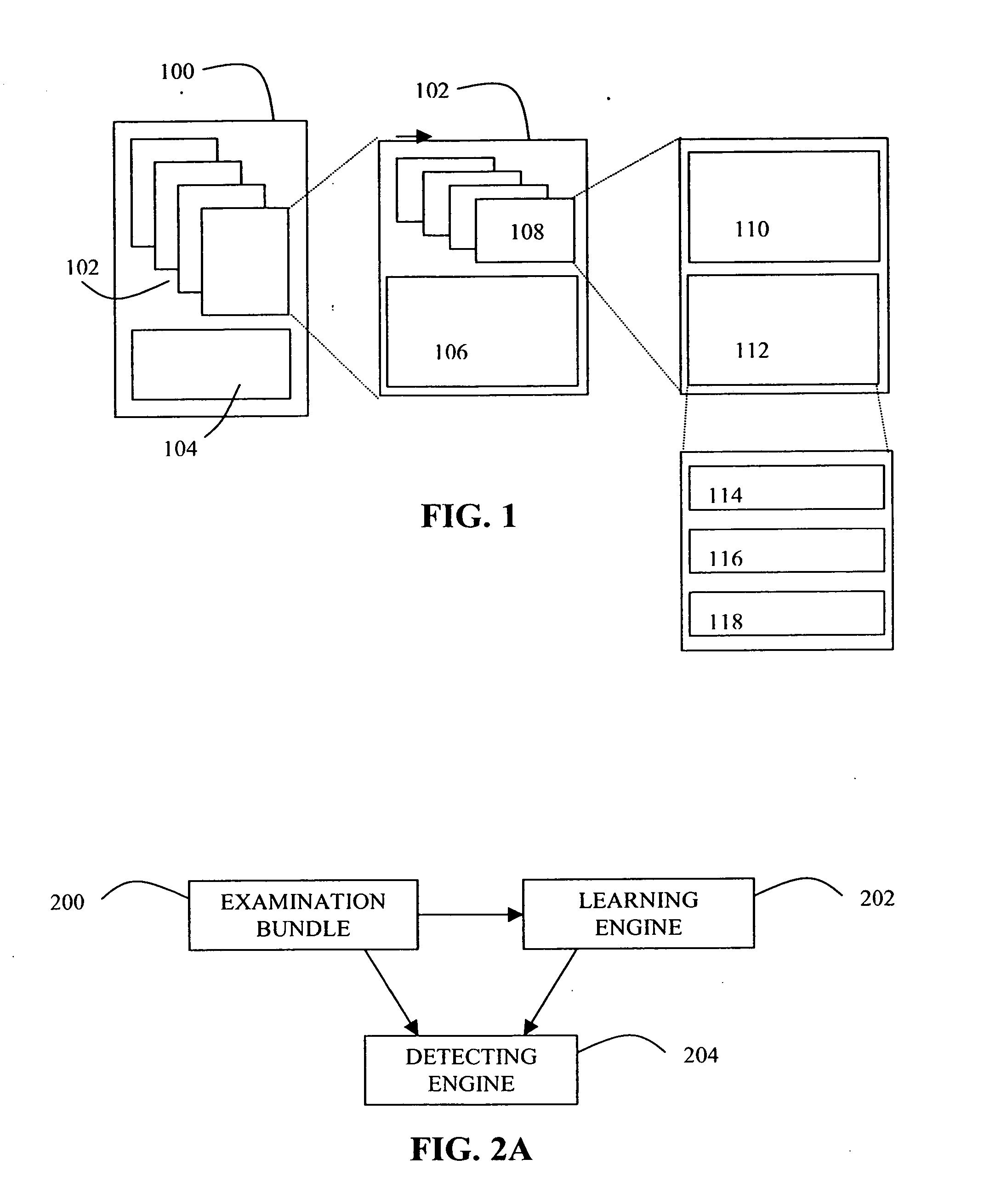
Abnormality detection in medical images
A system for the detection of abnormalities in a medical image of a subject. The system includes an examination bundle, a learning engine, and a detecting engine. The examination bundle includes at least one medical image of the subject from a first modality and at least one medical image of the subject from a second modality. The learning engine is employed for determining the characteristics of abnormalities within the at least one medical image from the first modality and the at least one medical image from the second modality. The detecting engine is employed for detecting abnormalities within at least one of the medical images comprising the examination bundle.
Owner:CARESTREAM HEALTH INC
Systems and methods for processing data flows
InactiveUS8010469B2Increased complexityAvoid problemsMemory loss protectionError detection/correctionData streamSelf-organizing map
Methods and systems for flow processing and switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security are described. Such flow processing facilities may be used for inspecting network traffic packet payloads to detect security threats and intrusions across accessible layers of the network IP stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources.
Owner:CA TECH INC
Sna-based anomaly detection
ActiveUS20080109730A1Enhance intrusion detectionEasy to detectMemory loss protectionError detection/correctionAnomaly detectionEngineering
A method, system, and computer program product for enabling dynamic detection of anomalies occurring within an input graph representing a social network. More specifically, the invention provides an automated computer simulation technique that implements the combination of Social Network Analysis (SNA) and statistical pattern classification for detecting abnormal social patterns or events through the expanded use of SNA Metrics. The simulation technique further updates the result sets generated, based on observed occurrences, to dynamically determine what constitutes abnormal behavior, within the overall context of observed patterns of behavior.
Owner:NORTHROP GRUMMAN SYST CORP
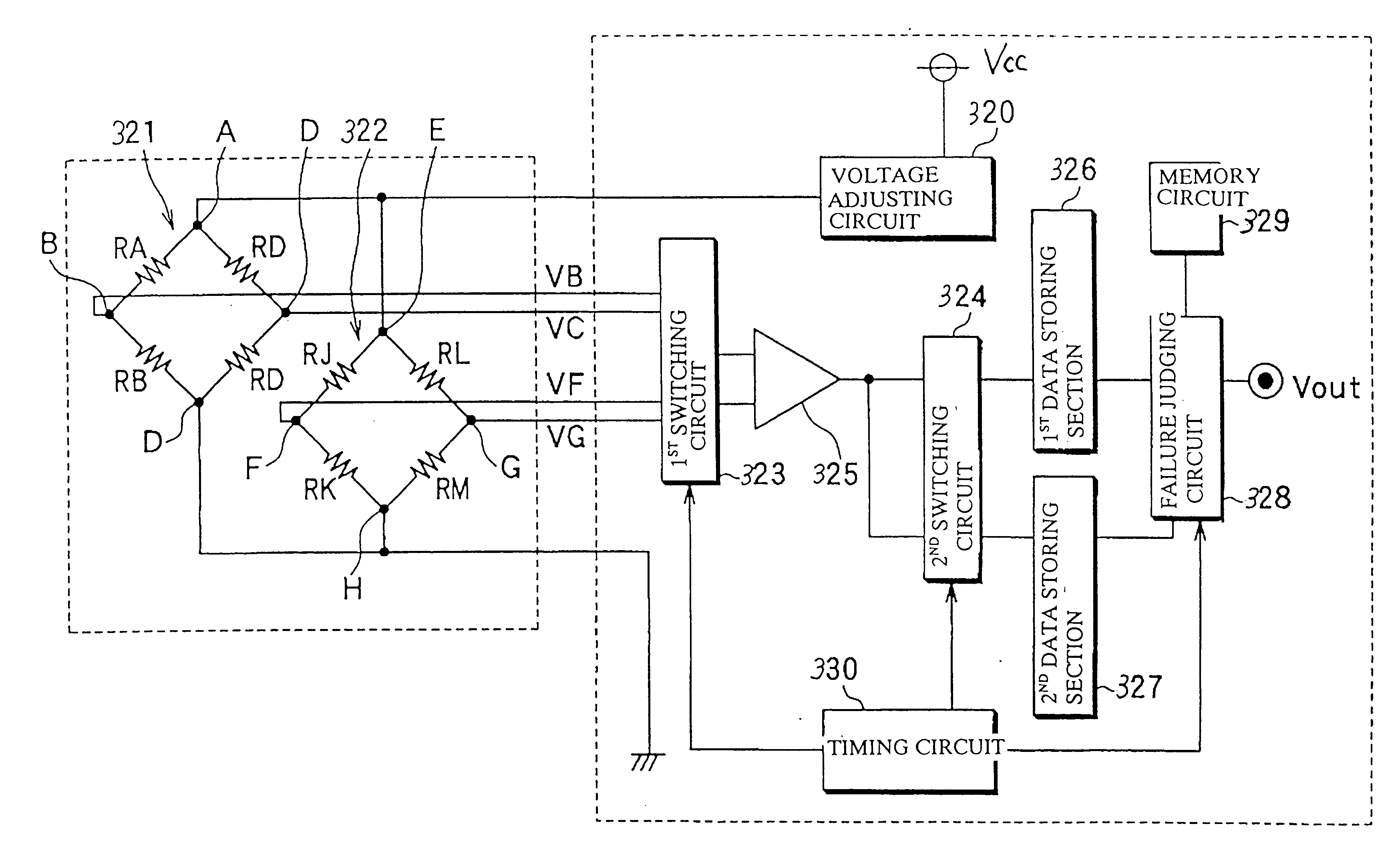
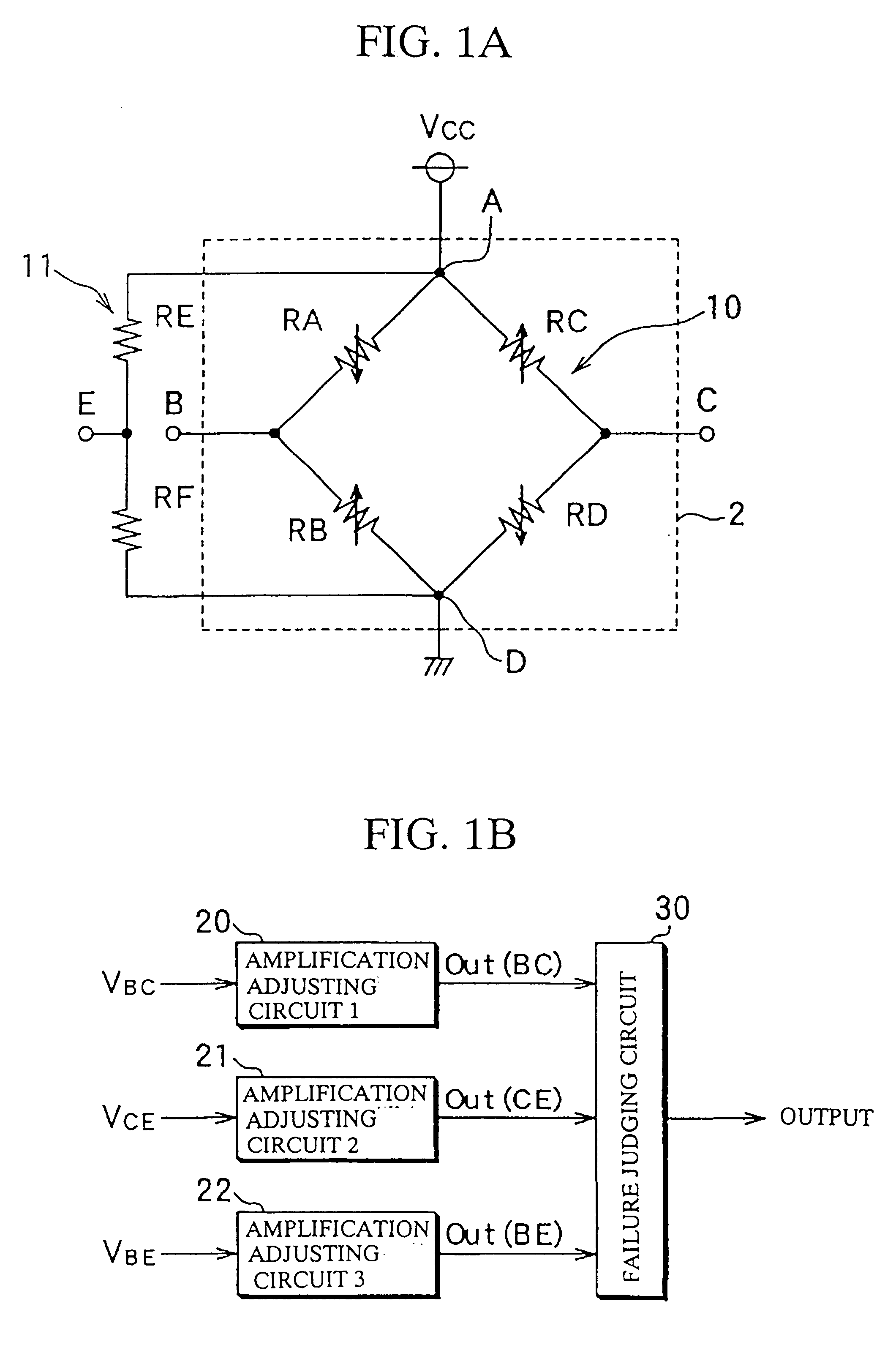
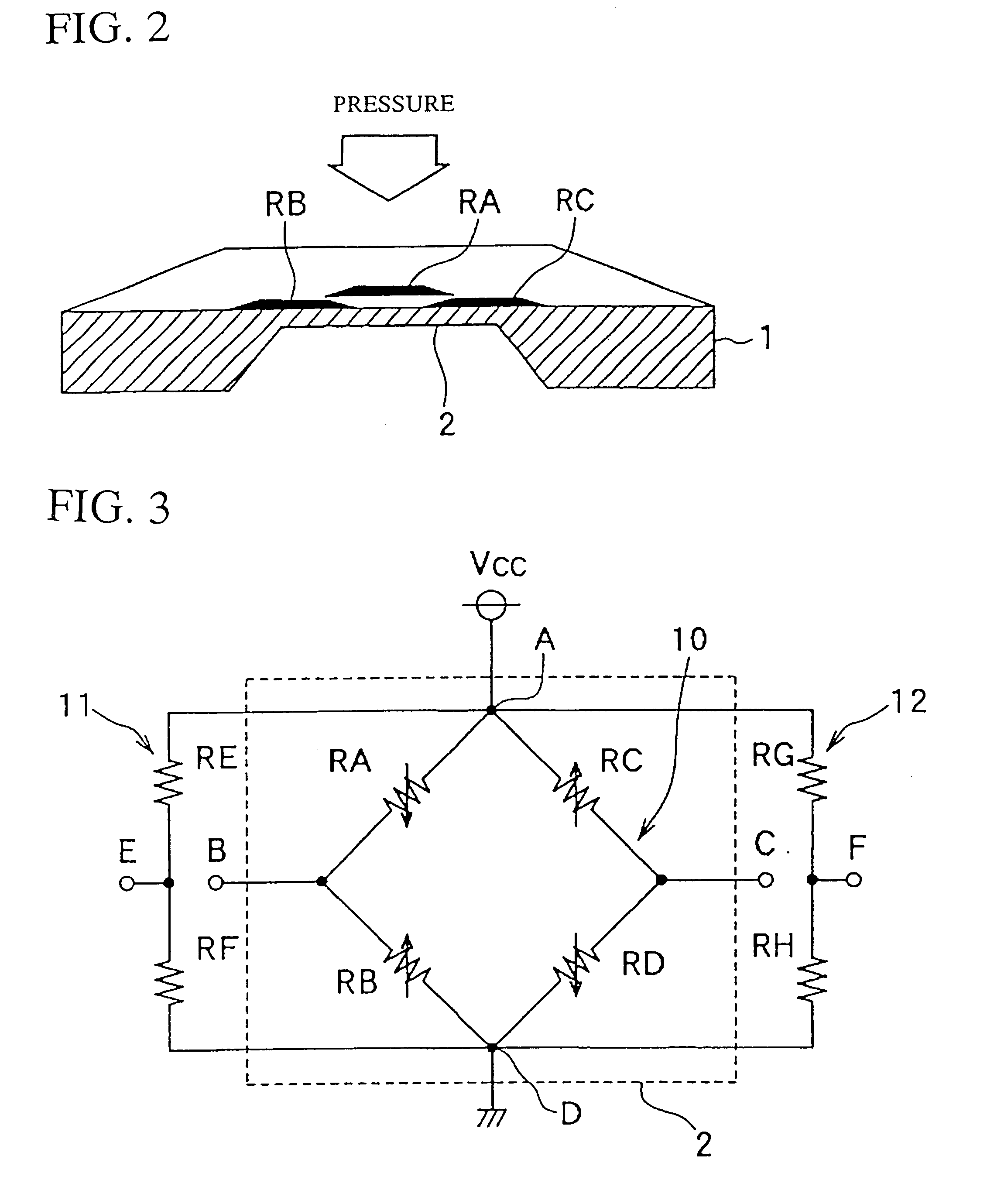
Sensor failure or abnormality detecting system incorporated in a physical or dynamic quantity detecting apparatus
InactiveUS6422088B1Detect failureFluid pressure measurement using ohmic-resistance variationForce measurementElectrical resistance and conductanceAnomaly detection
A reference voltage generating circuit is constituted by resistors RE and RF each having a resistance not influenced by an application of pressure. The reference voltage generating circuit is connected between one and the other ends of a bridge circuit. A failure judgement of the bridge circuit is performed based on a comparison of a voltage difference VBC between two midpoints B and C of the bridge circuit and voltage differences VCE and VBE between a reference voltage level of the reference voltage generating circuit and the voltage levels of two midpoints B and C.
Owner:DENSO CORP
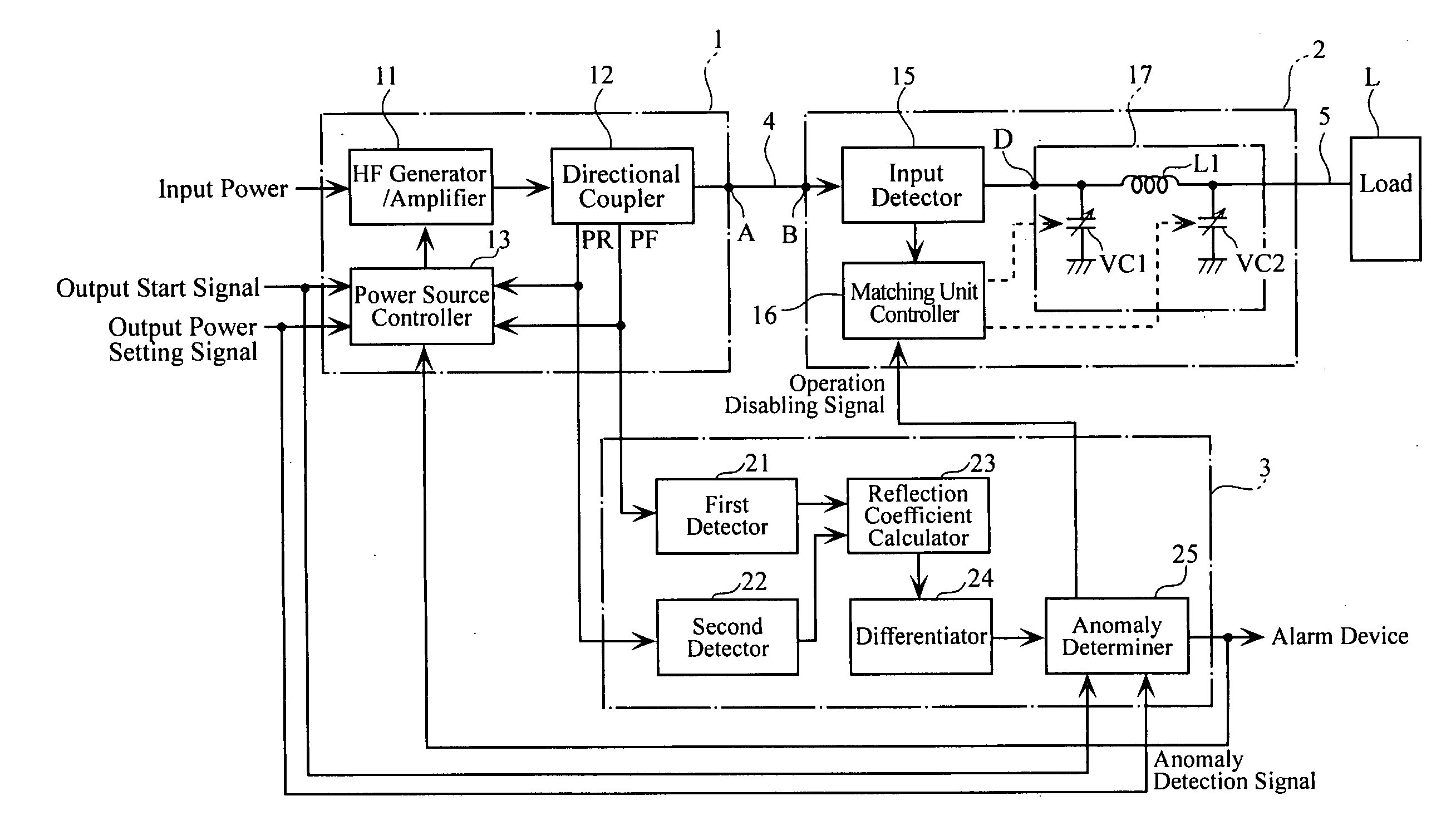
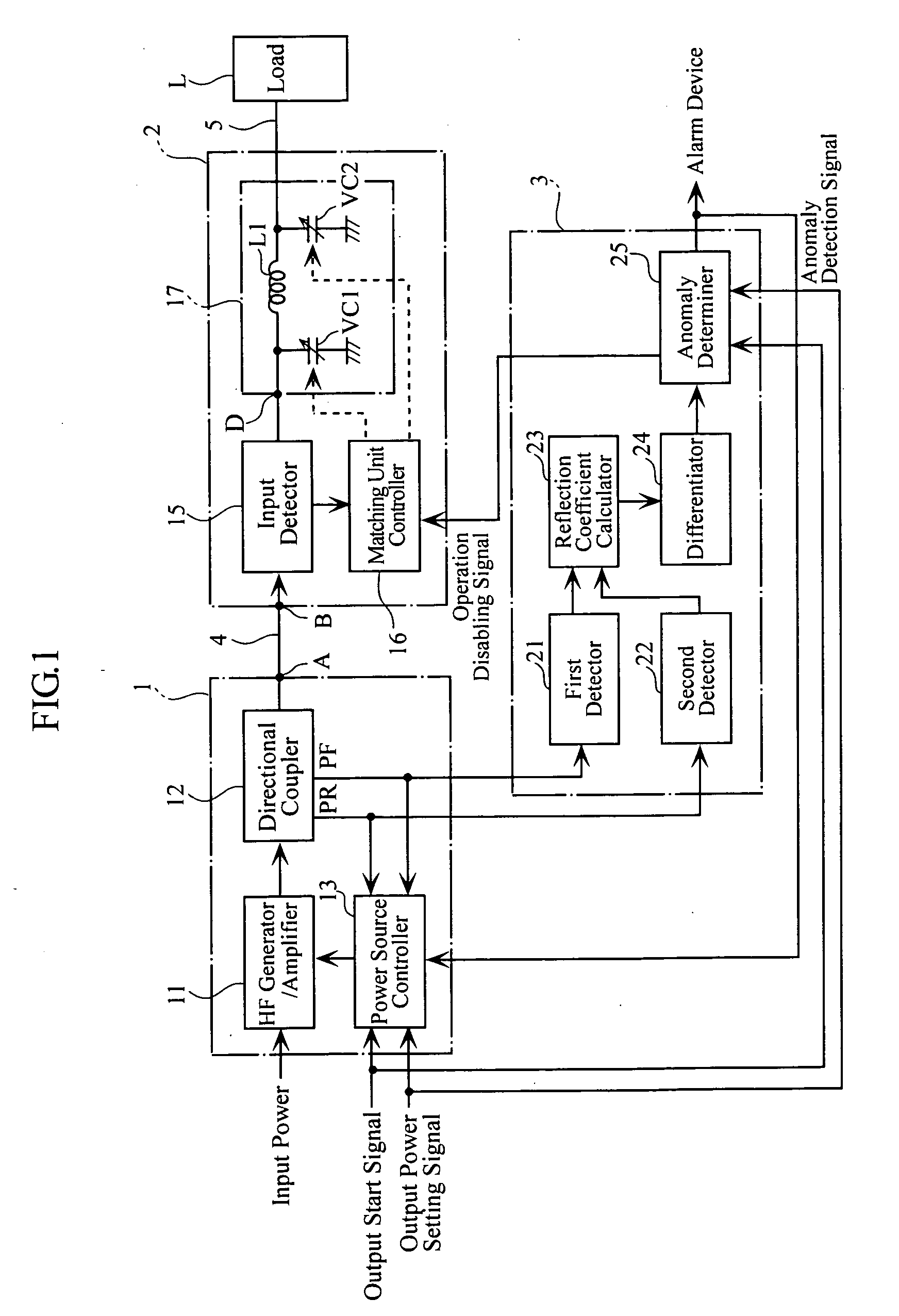
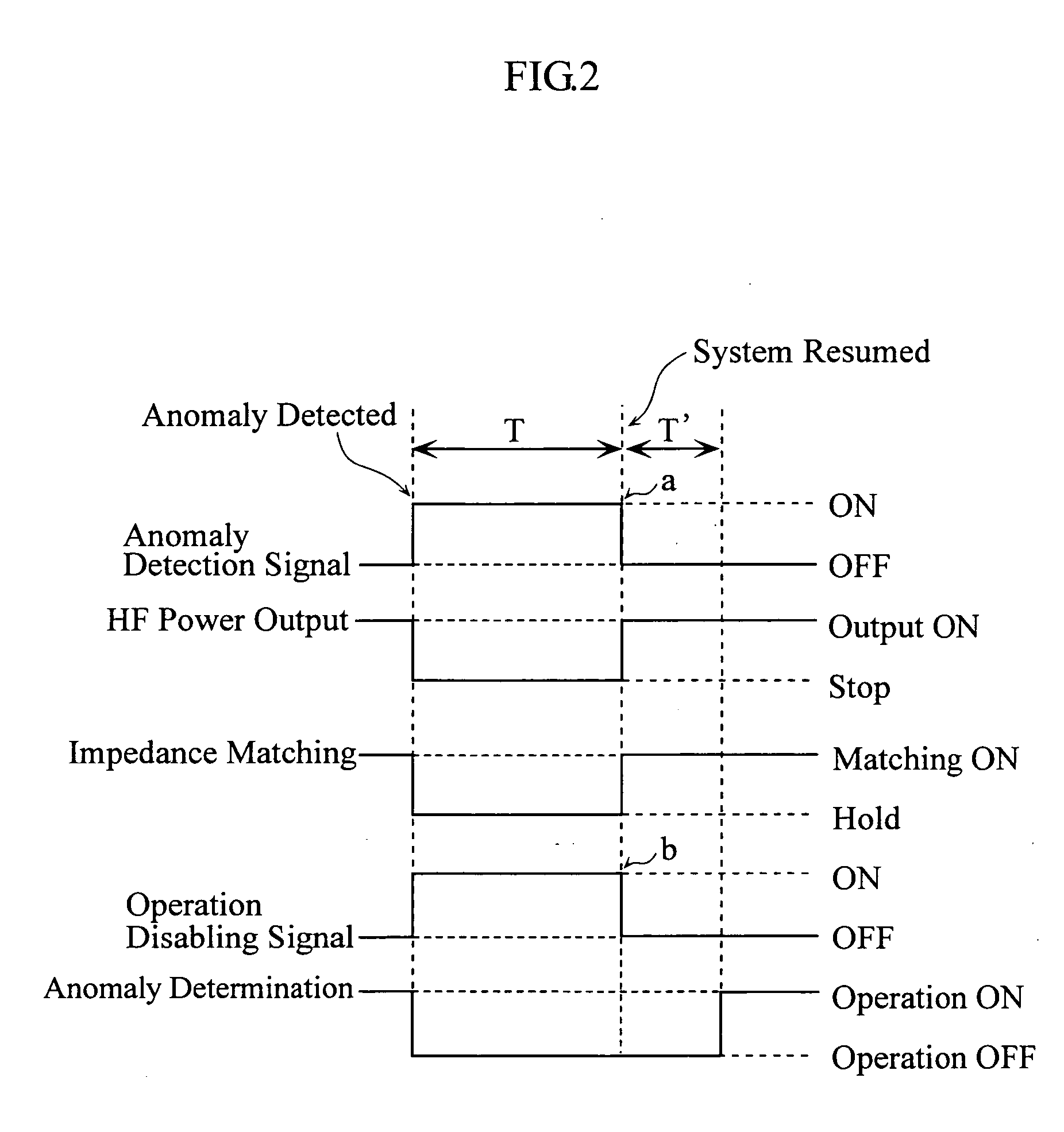
High-frequency power supply system
InactiveUS20070121267A1Multiple-port networksElectric discharge tubesDifferentiatorHigh frequency power
A high-frequency power supply system includes an anomaly detector 3 which detects an anomaly occurring in a circuit on the side of a load L as from an outputting end A of a high-frequency power source 1. The anomaly detector 3 includes a first detector 21 which detects a voltage value Vf of a high-frequency forward wave, a second detector 22 which detects a voltage value Vr of a high-frequency reflected wave, a reflection coefficient calculator 23 and a differentiator 24 which calculate a reflection coefficient differential value dΓ / dt from the forward wave voltage value Vf and the reflected wave voltage value Vr, and an anomaly determiner 25 which determines of an occurrence of an anomaly based on the reflection coefficient differential value dΓ / dt. When the anomaly detector 3 outputs an anomaly detection signal to the high-frequency power source 1, high-frequency power source 1 stops its power output operation.
Owner:DAIHEN CORP
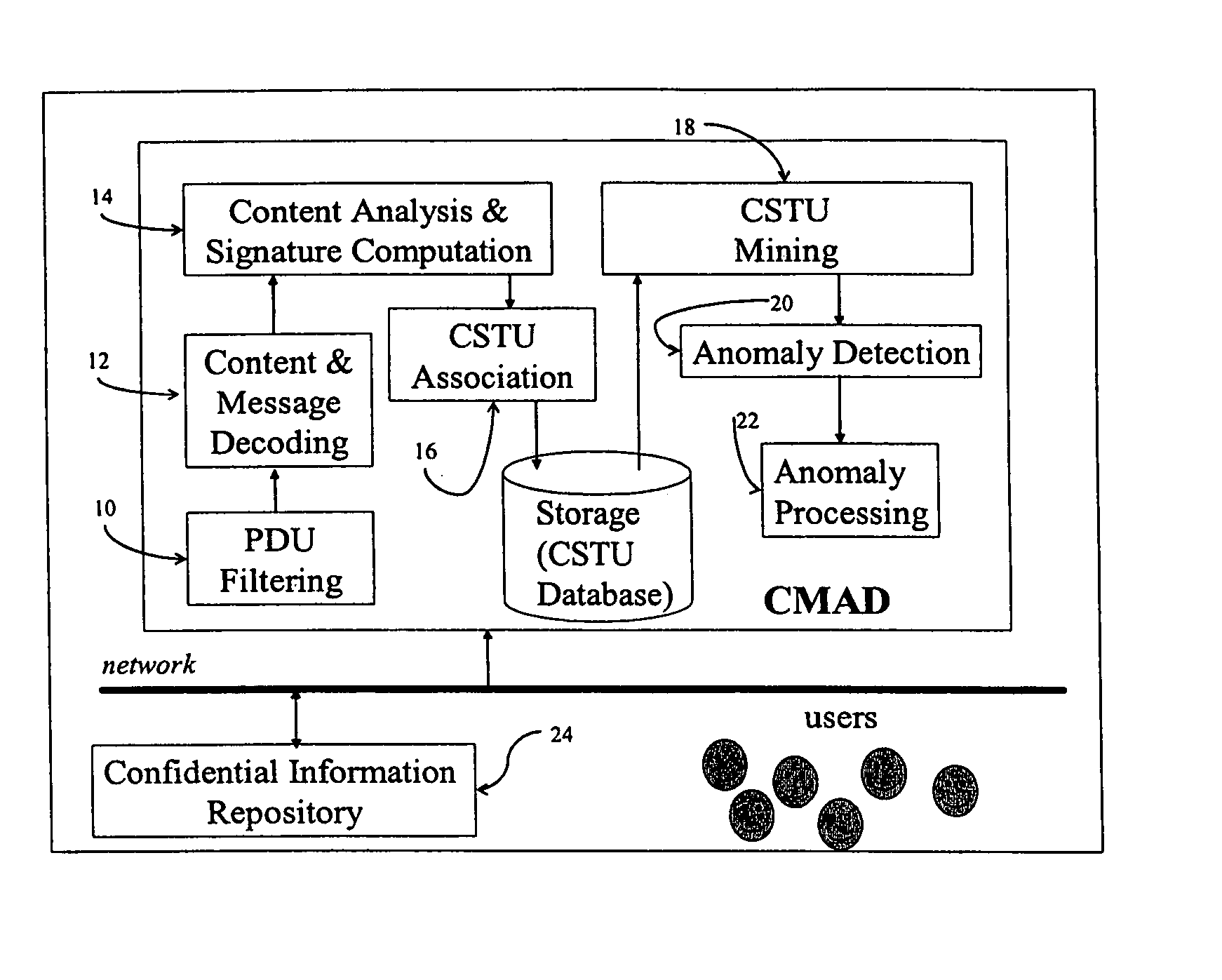
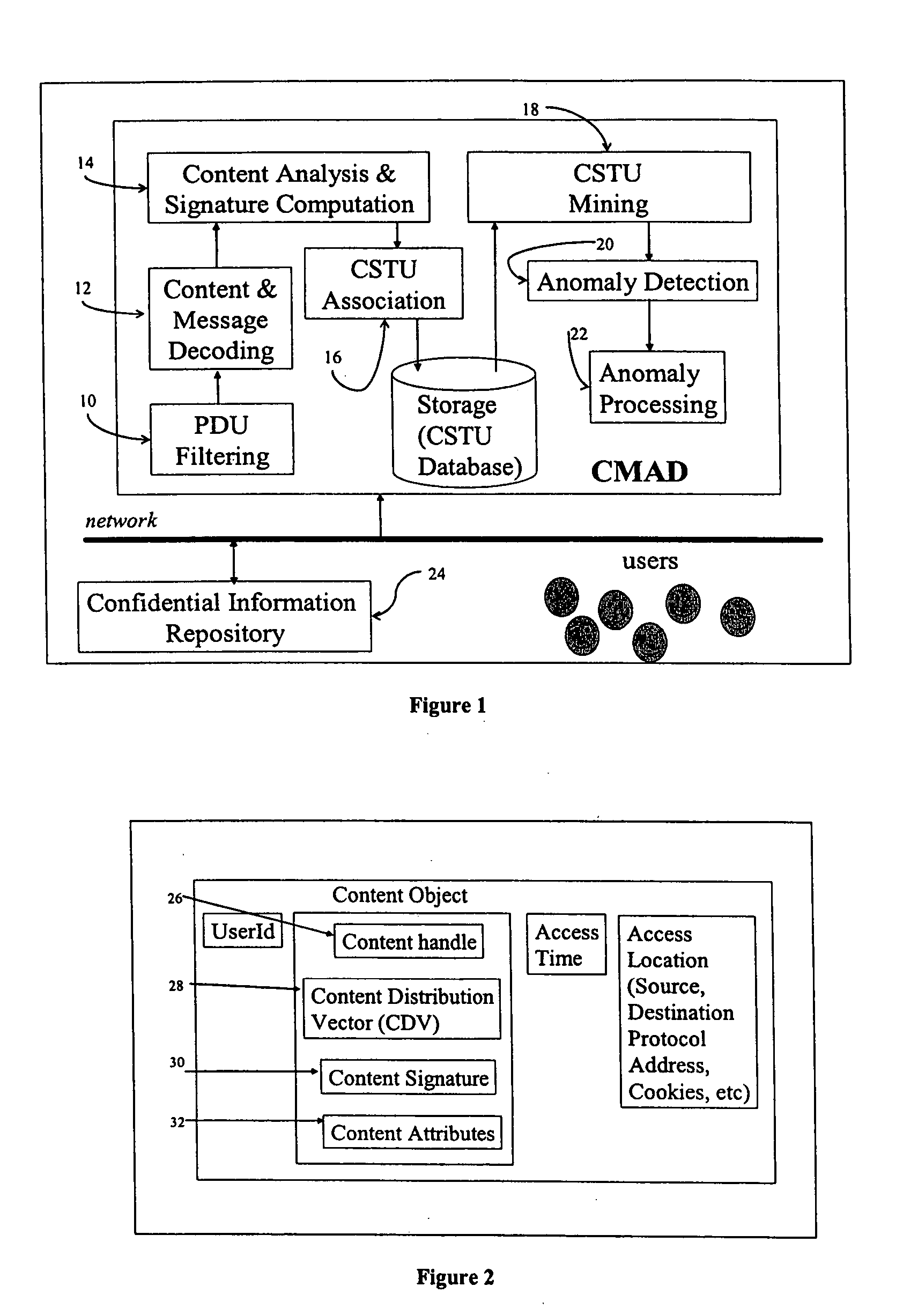
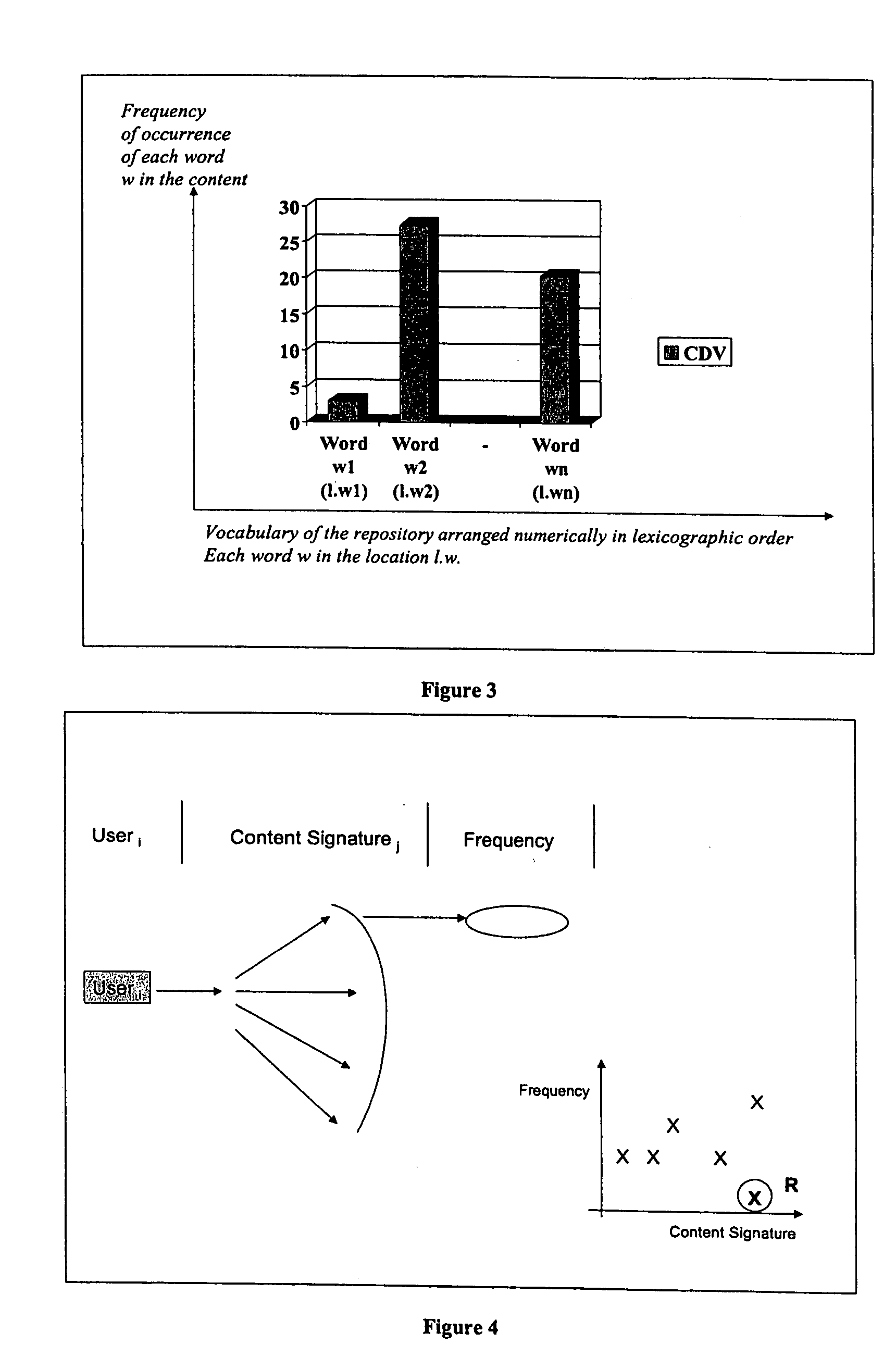
Method and apparatus to detect unauthorized information disclosure via content anomaly detection
ActiveUS20050091532A1Memory loss protectionError detection/correctionInternet privacyAnomaly detection
Method and apparatus to monitor and detect anomalies of information content flows, the method comprising the steps of capturing information access packets, filtering packets to extract information, decoding packets to determine information content, deriving content signatures, trending prototypical behavior, and detecting anomalies of information access, and said apparatus comprising a computing device comprising a network based device that captures the information and produces anomaly information.
Owner:IBM CORP
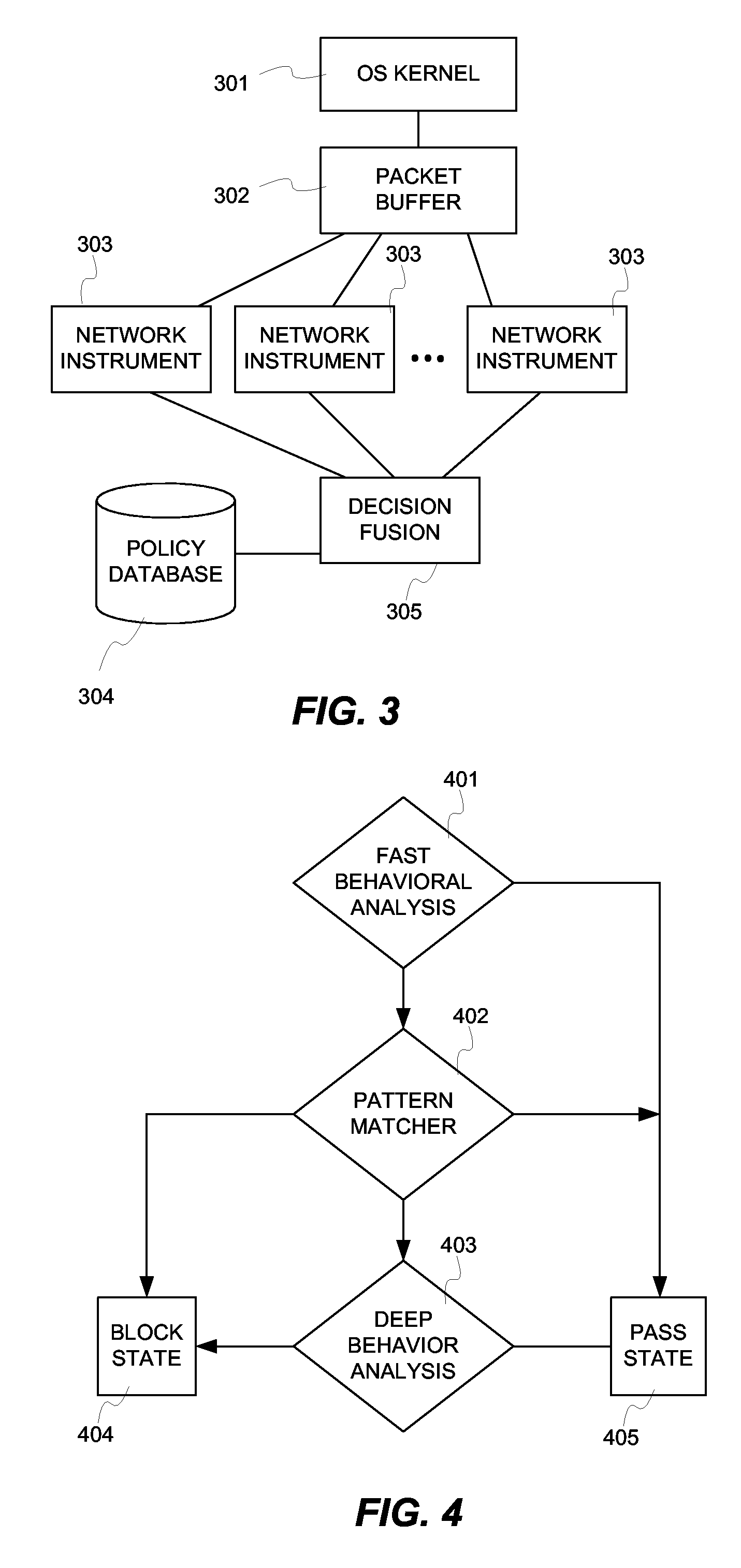
Fusion instrusion protection system
InactiveUS20070056038A1Solve the high false positive rateEfficient Anomaly DetectionMemory loss protectionError detection/correctionAnomaly detectionSensor fusion
An intrusion protection system that fuses a network instrumentation classification with a packet payload signature matching system. Each of these kinds of systems is independently capable of being effectively deployed as an anomaly detection system. By employing sensor fusion techniques to combine the instrumentation classification approach with the signature matching approach, the present invention provides an intrusion protection system that is uniquely capable of detecting both well known and newly developed threats while having an extremely low false positive rate.
Owner:LOK TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com