Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
660 results about "Multiple domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
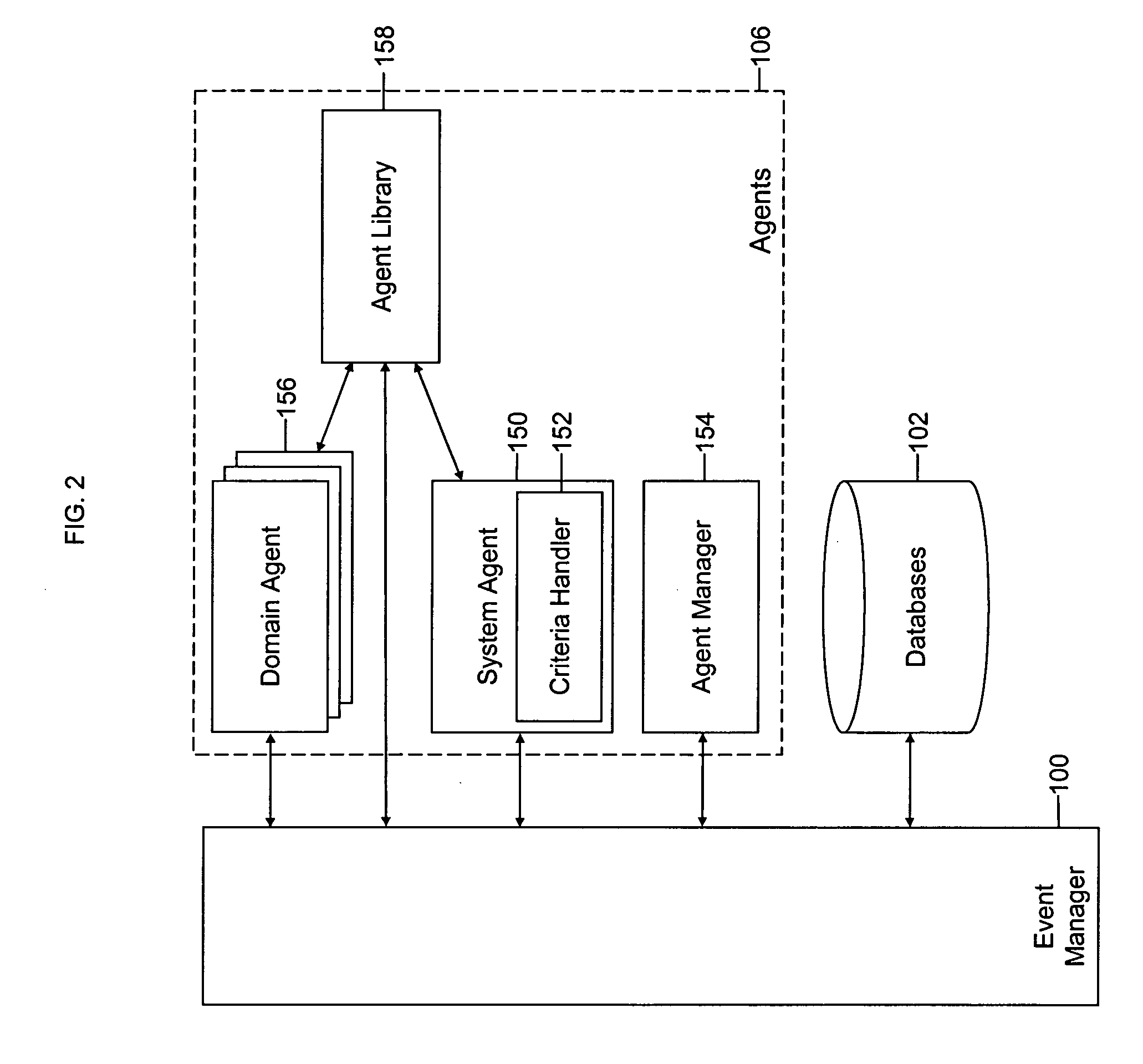
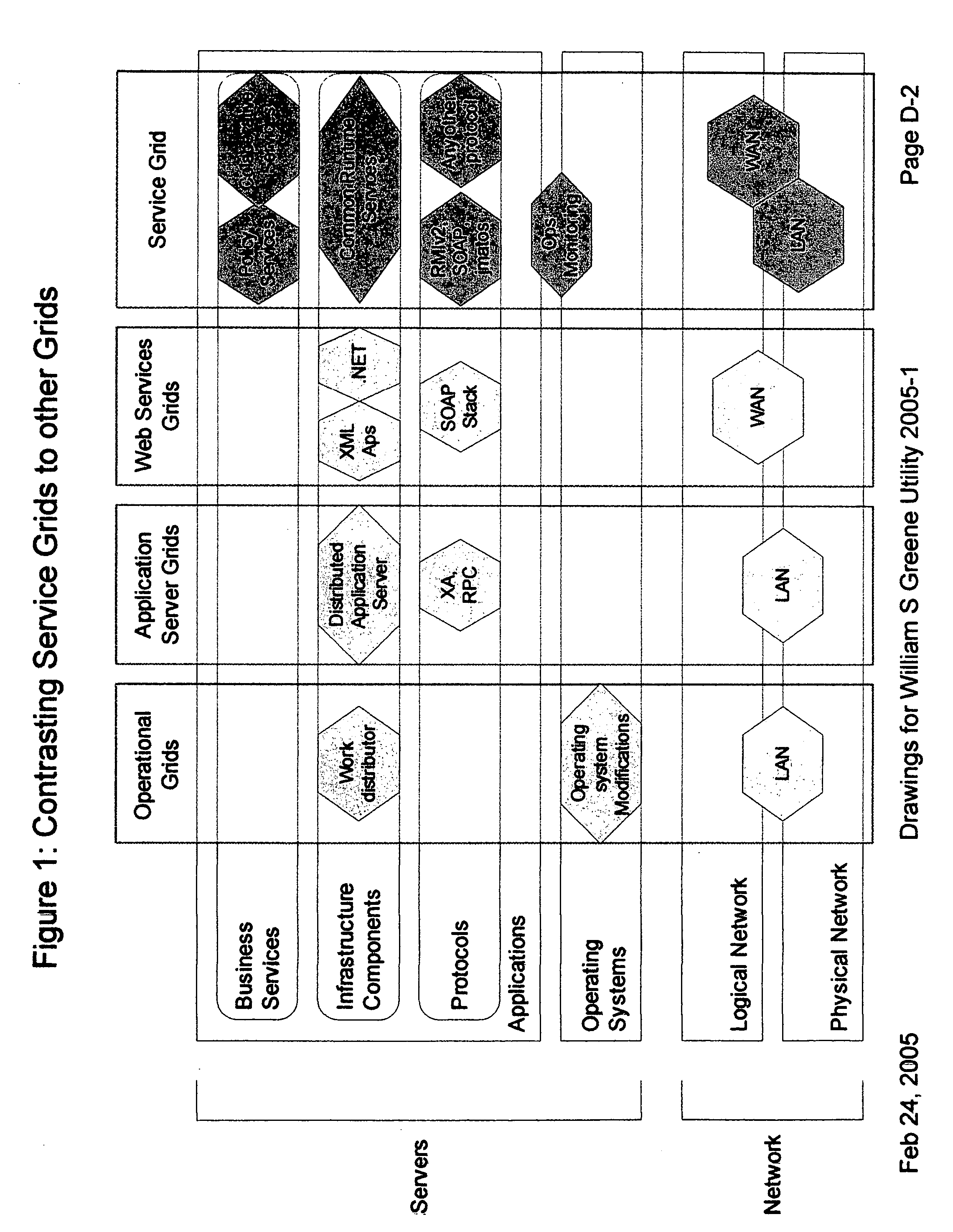
Multiple domains are add-on domains hosted on the sub-directory of a primary package. Each domain has its own web files, but share the disk space, database and traffic quotas of its parent account.
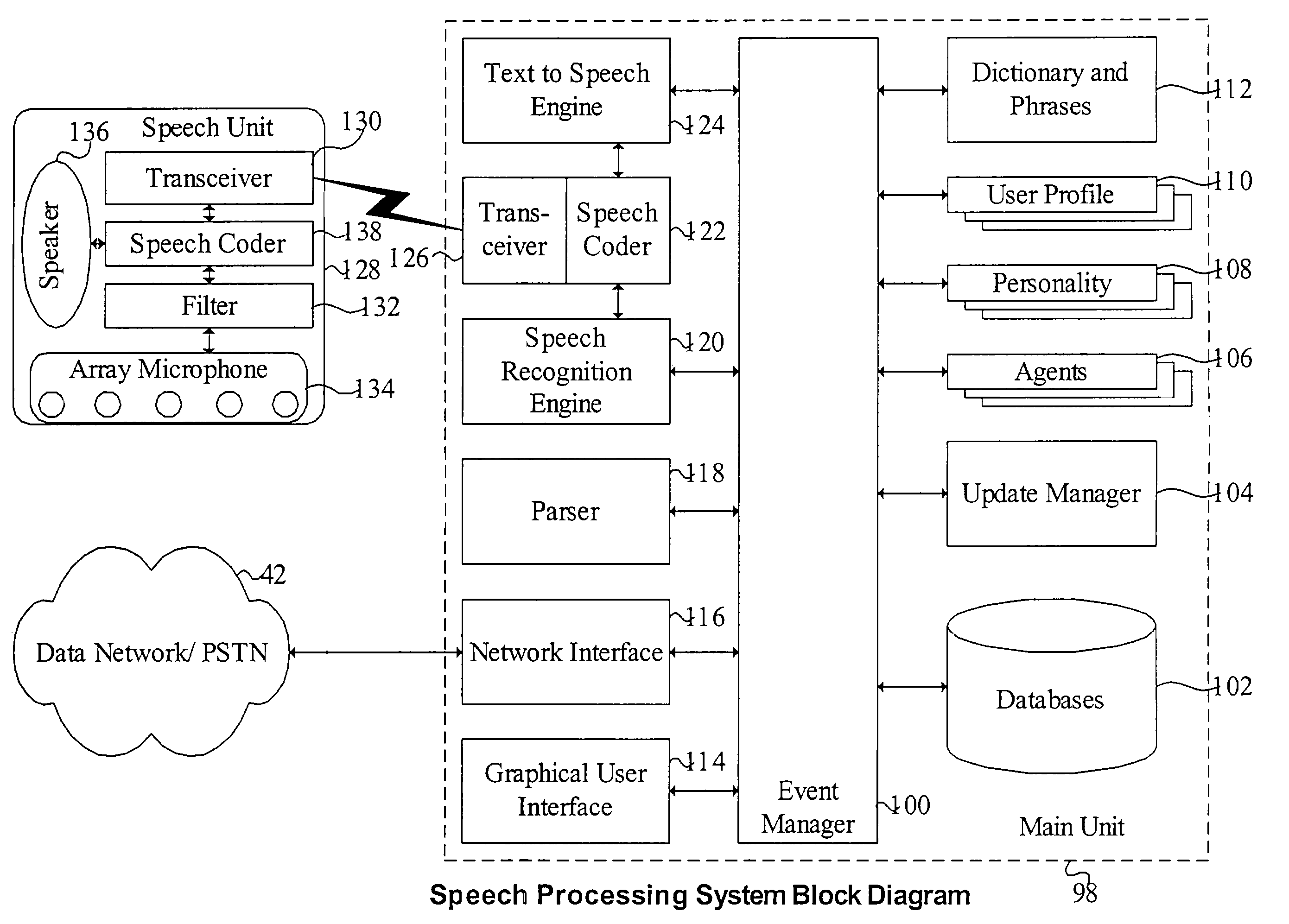
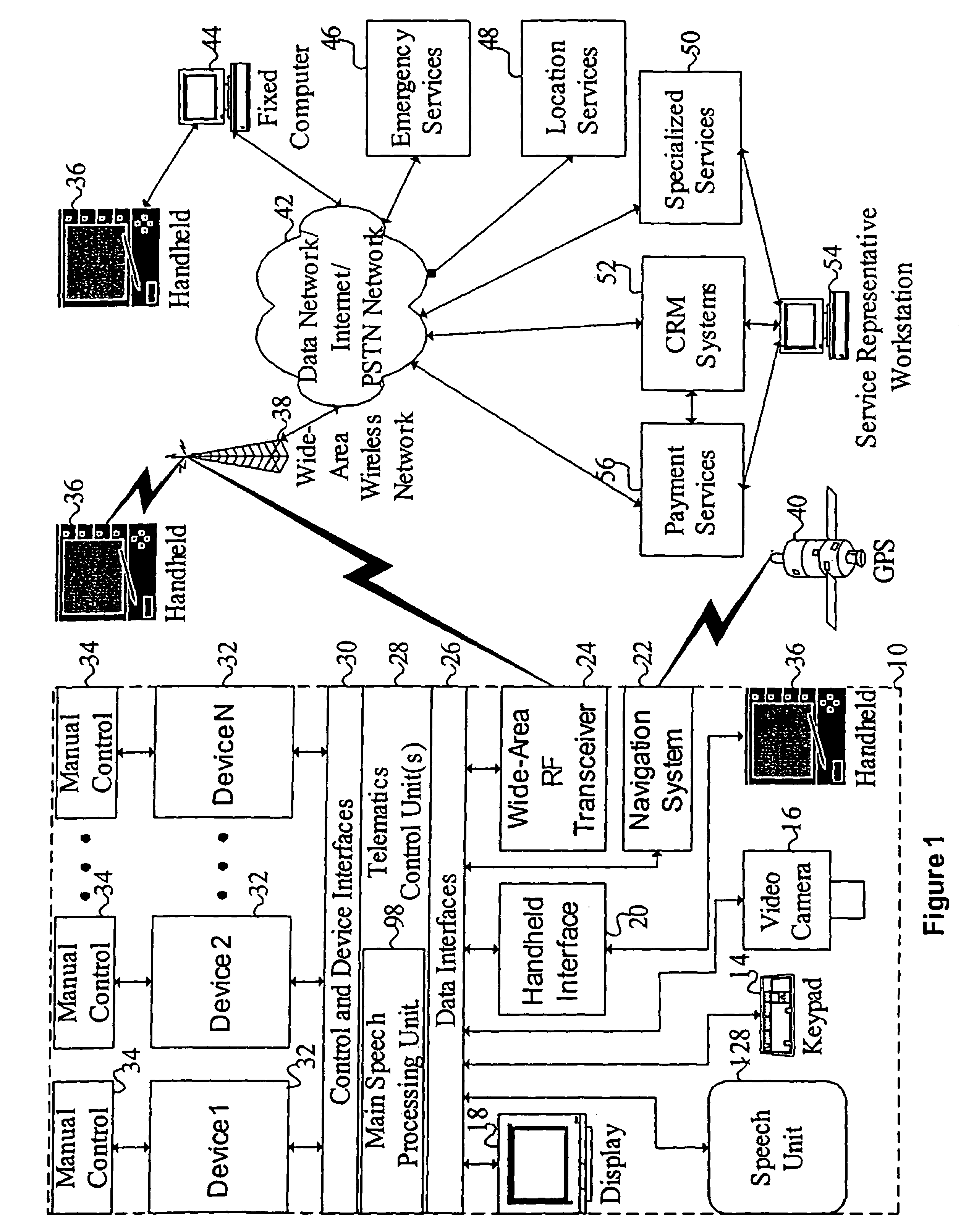
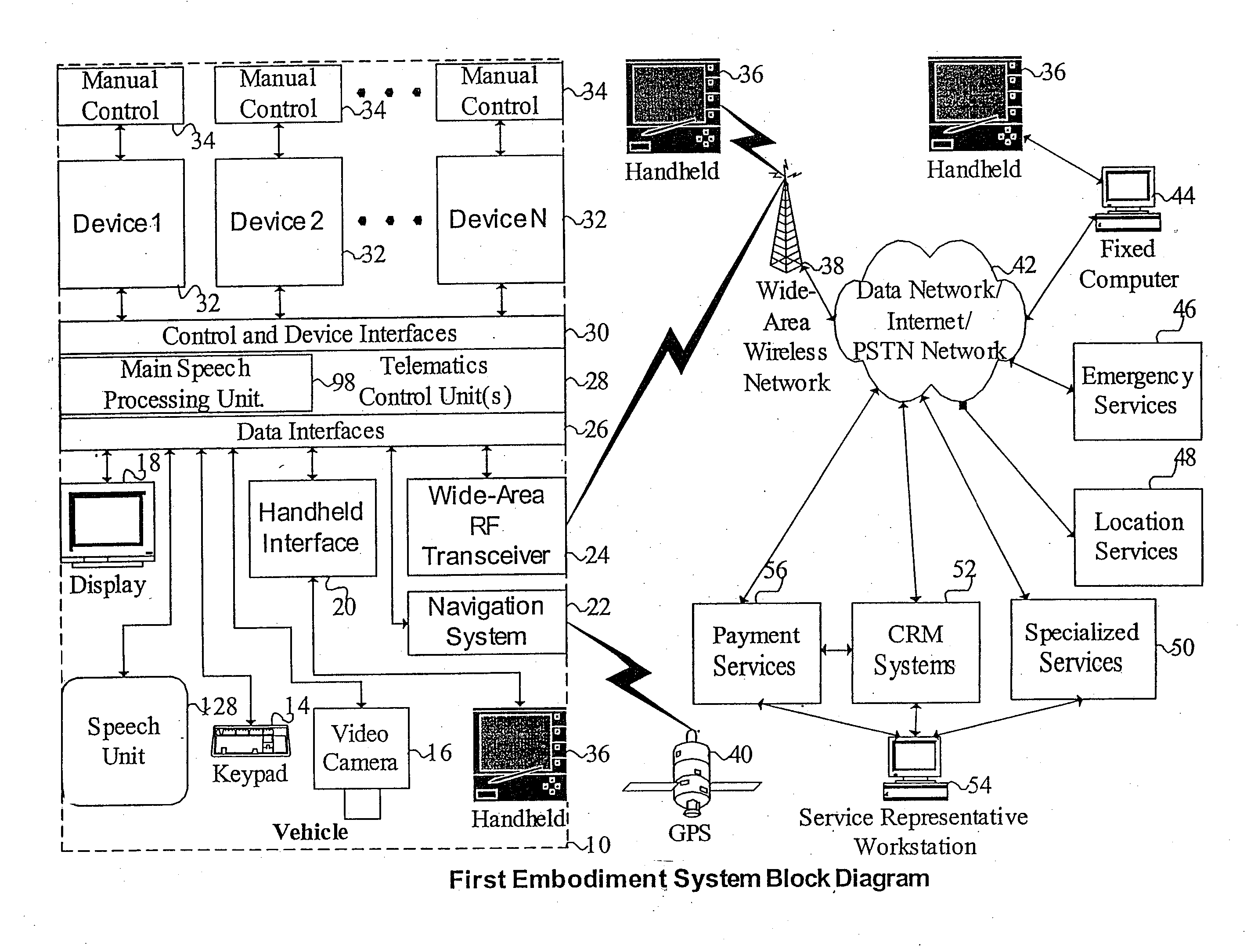
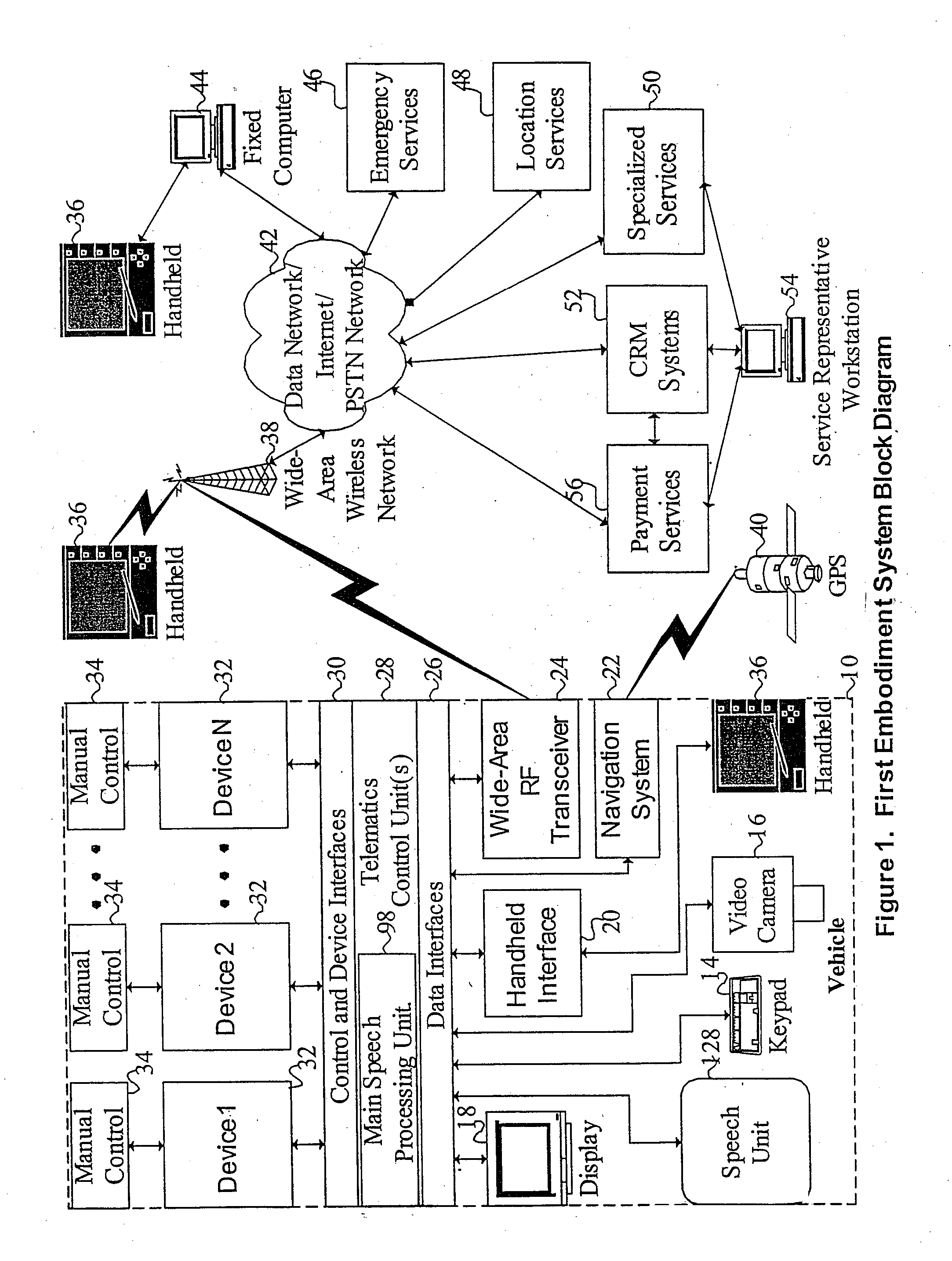
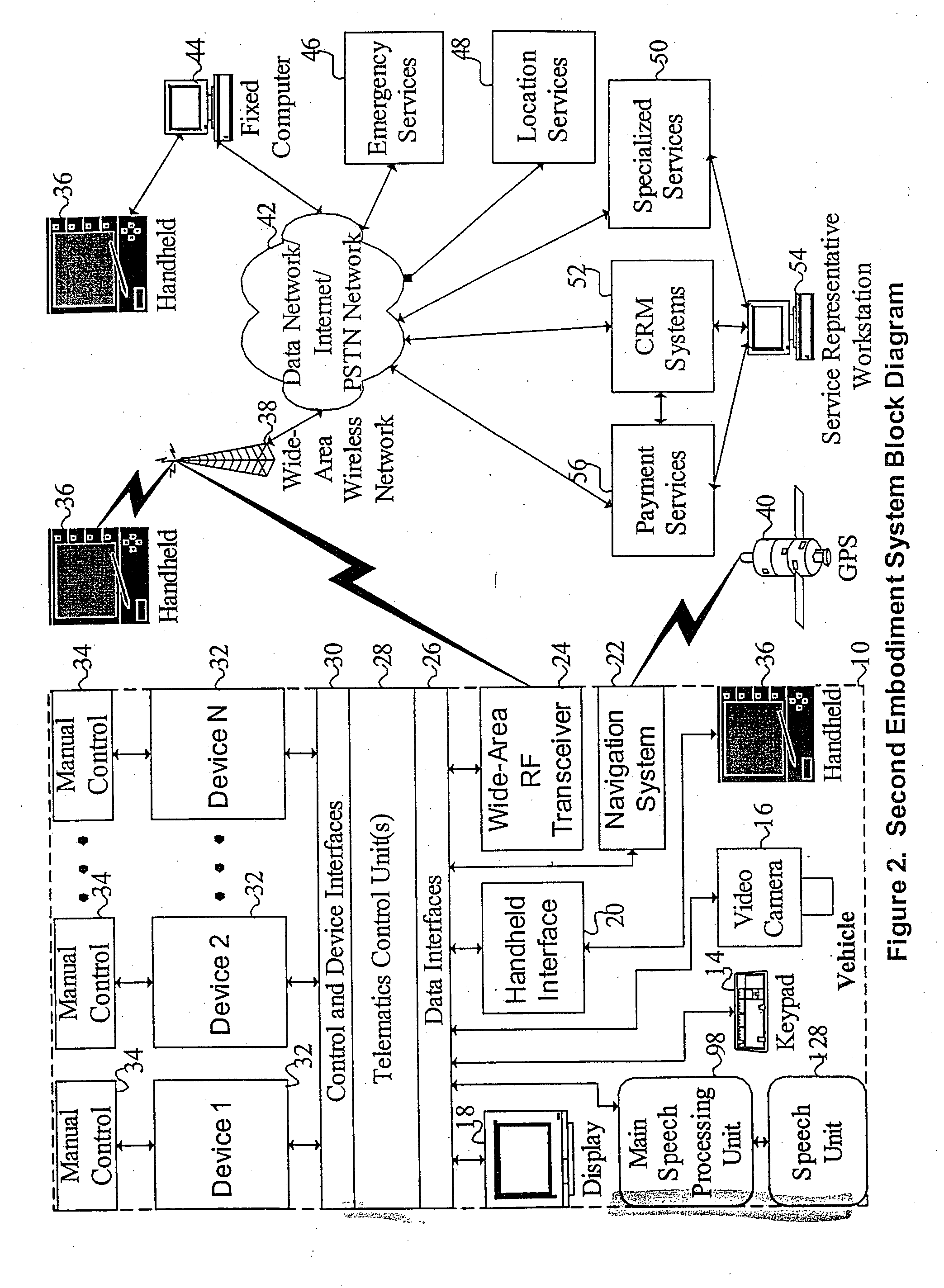
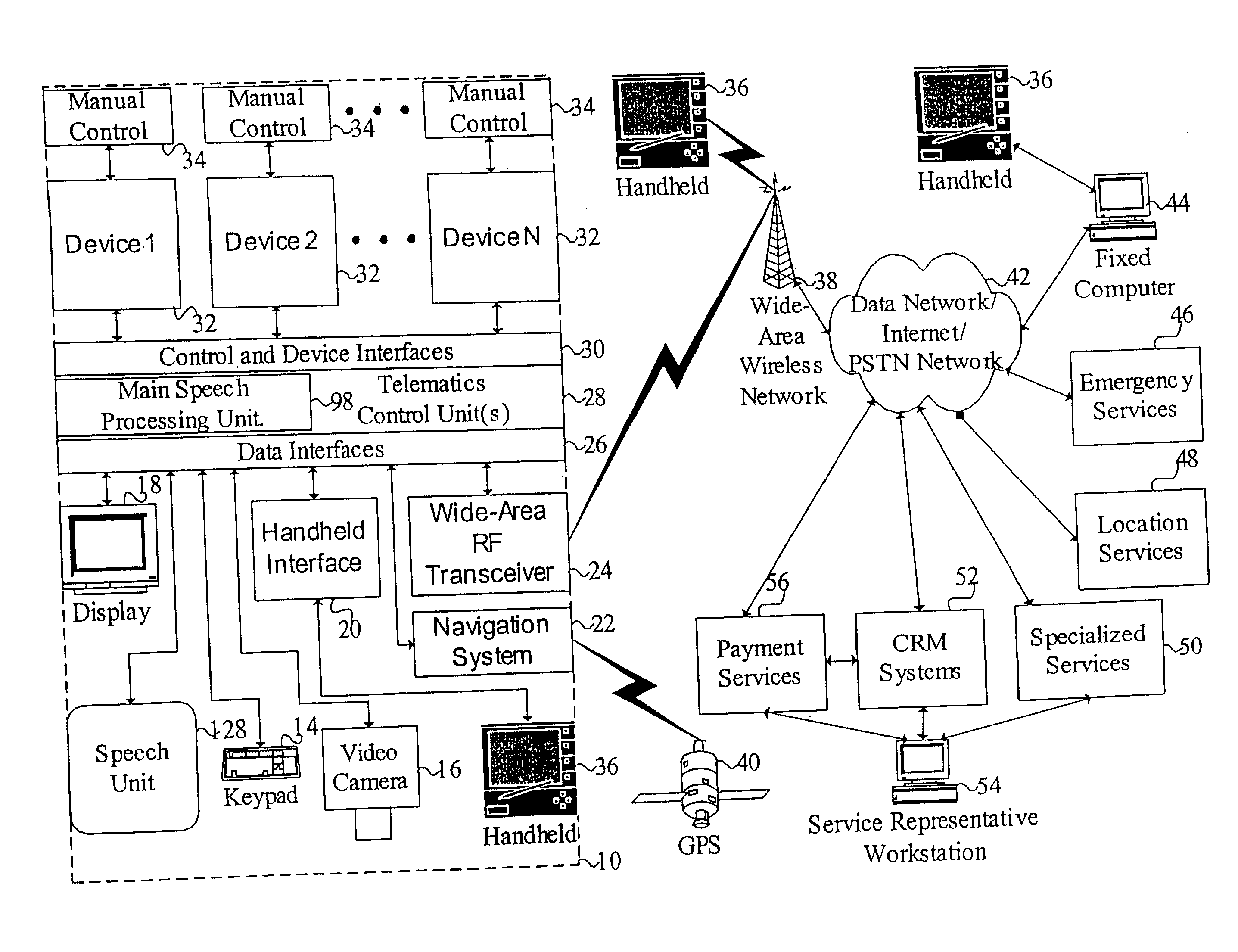
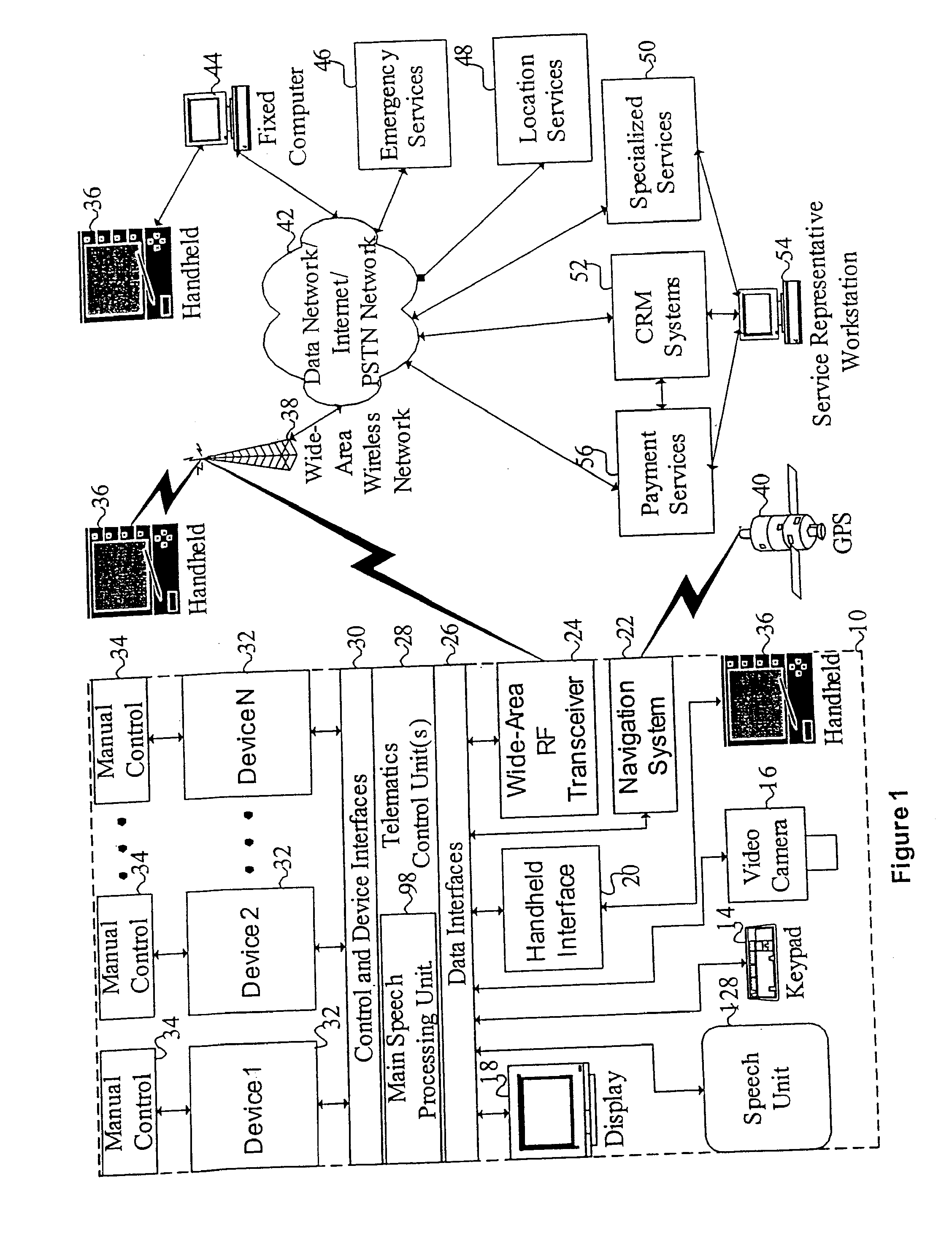
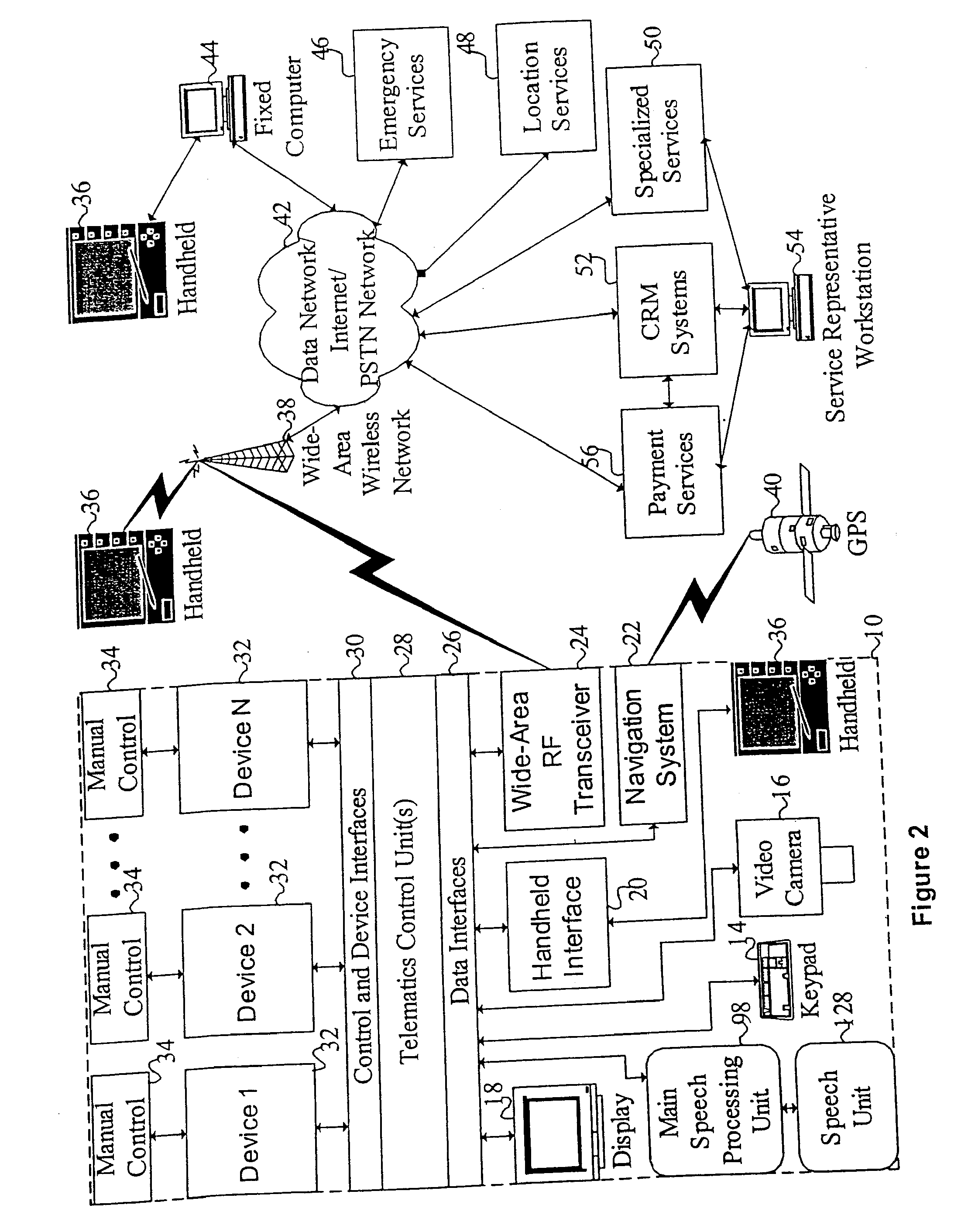
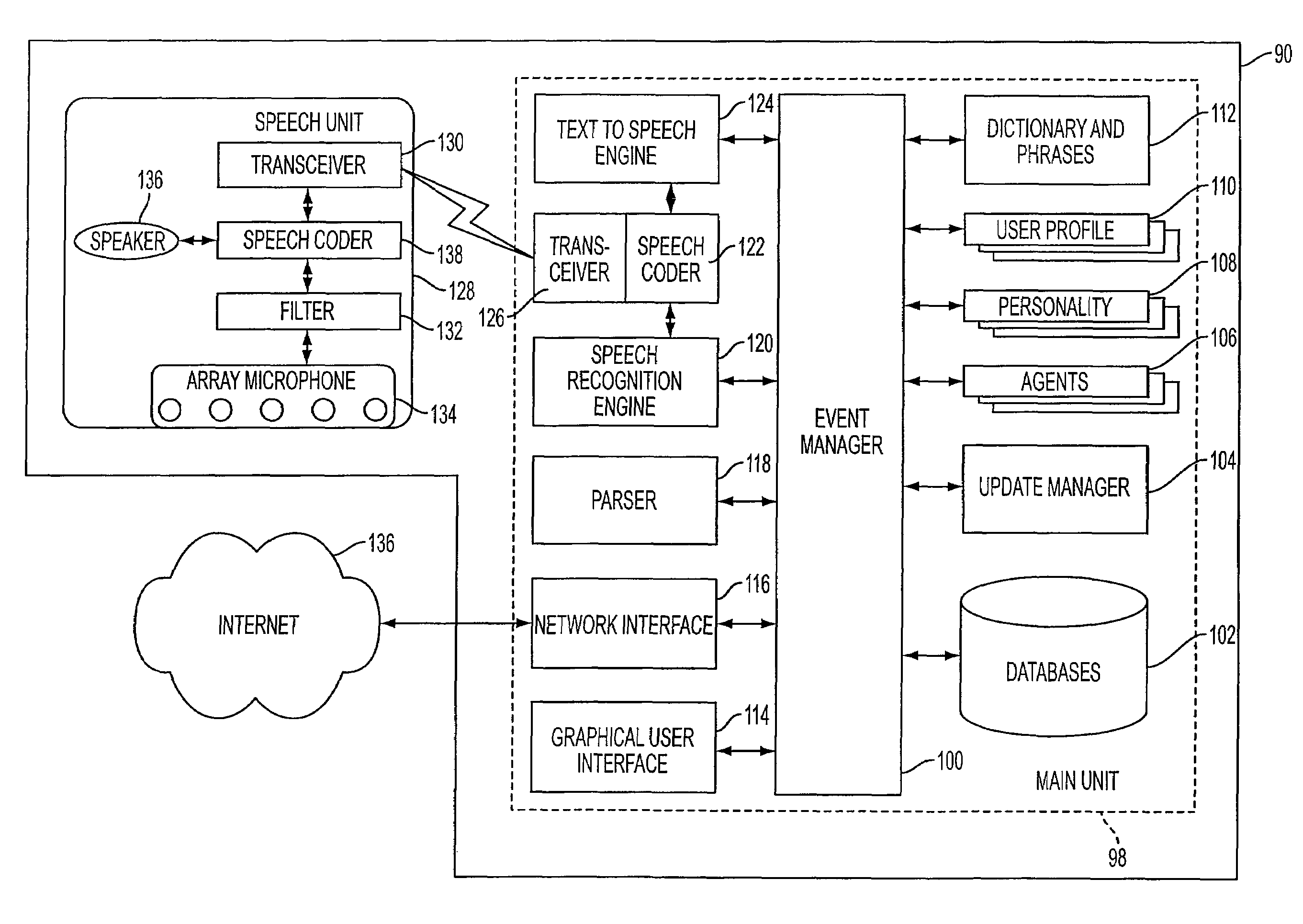
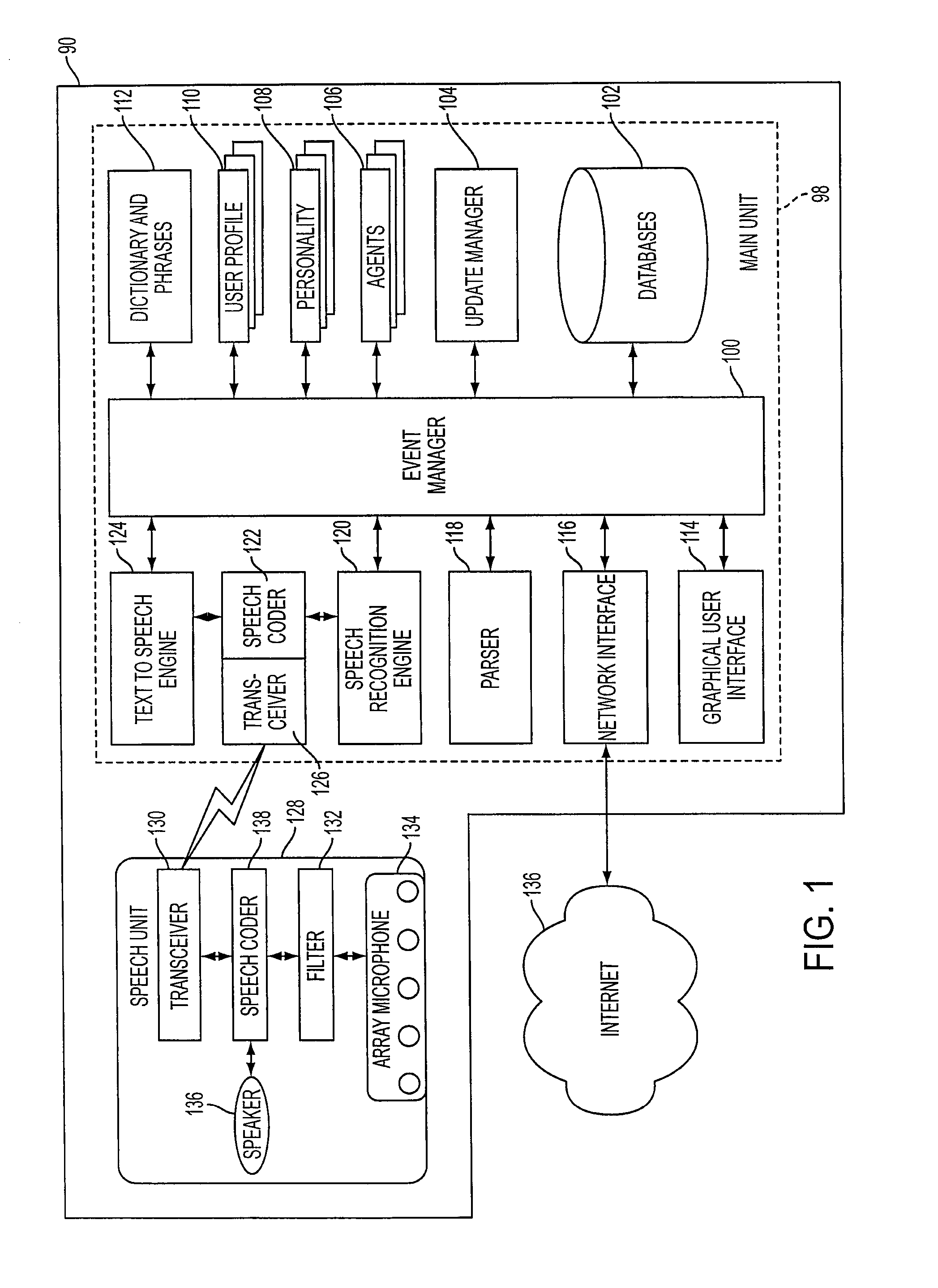
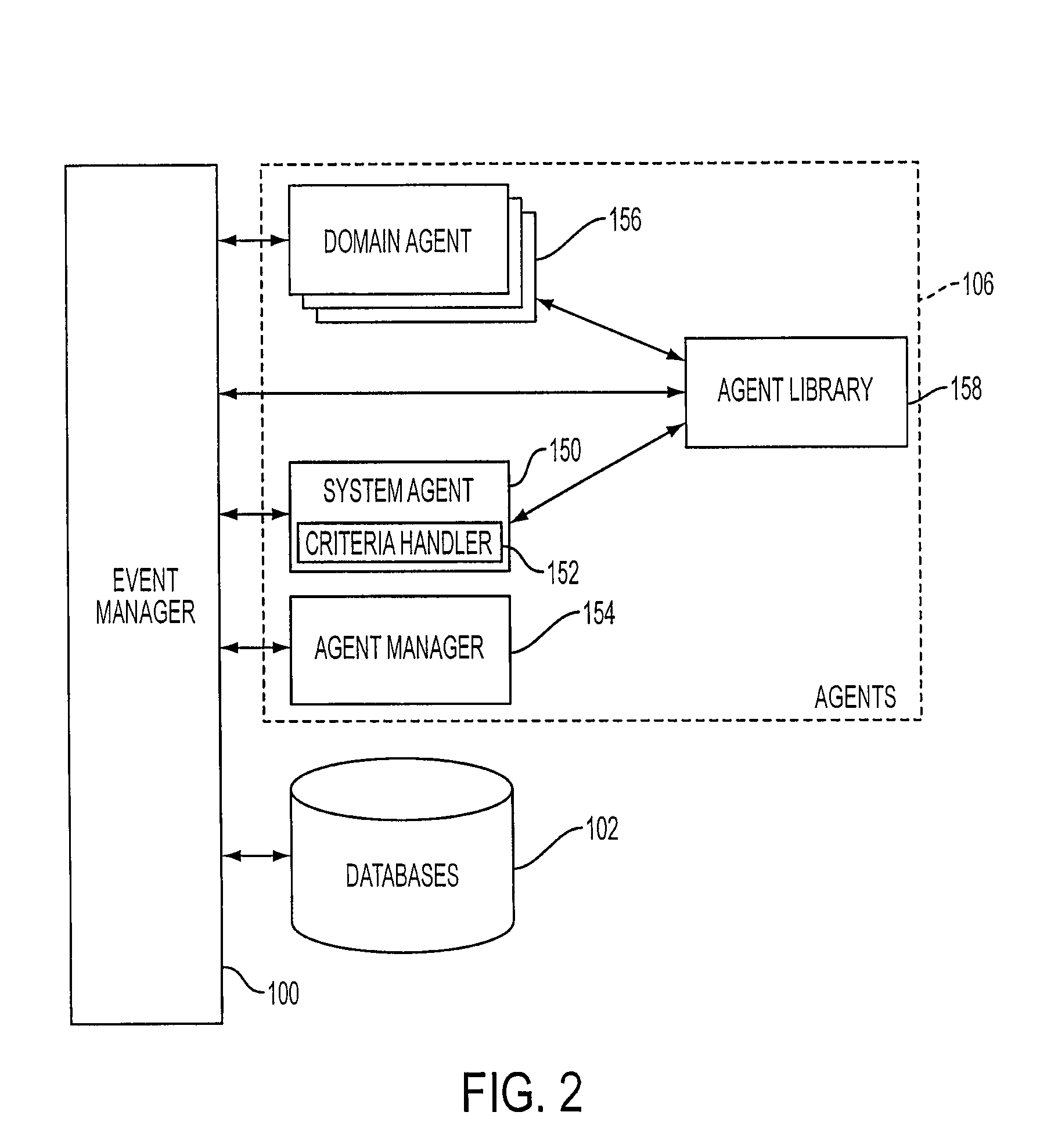
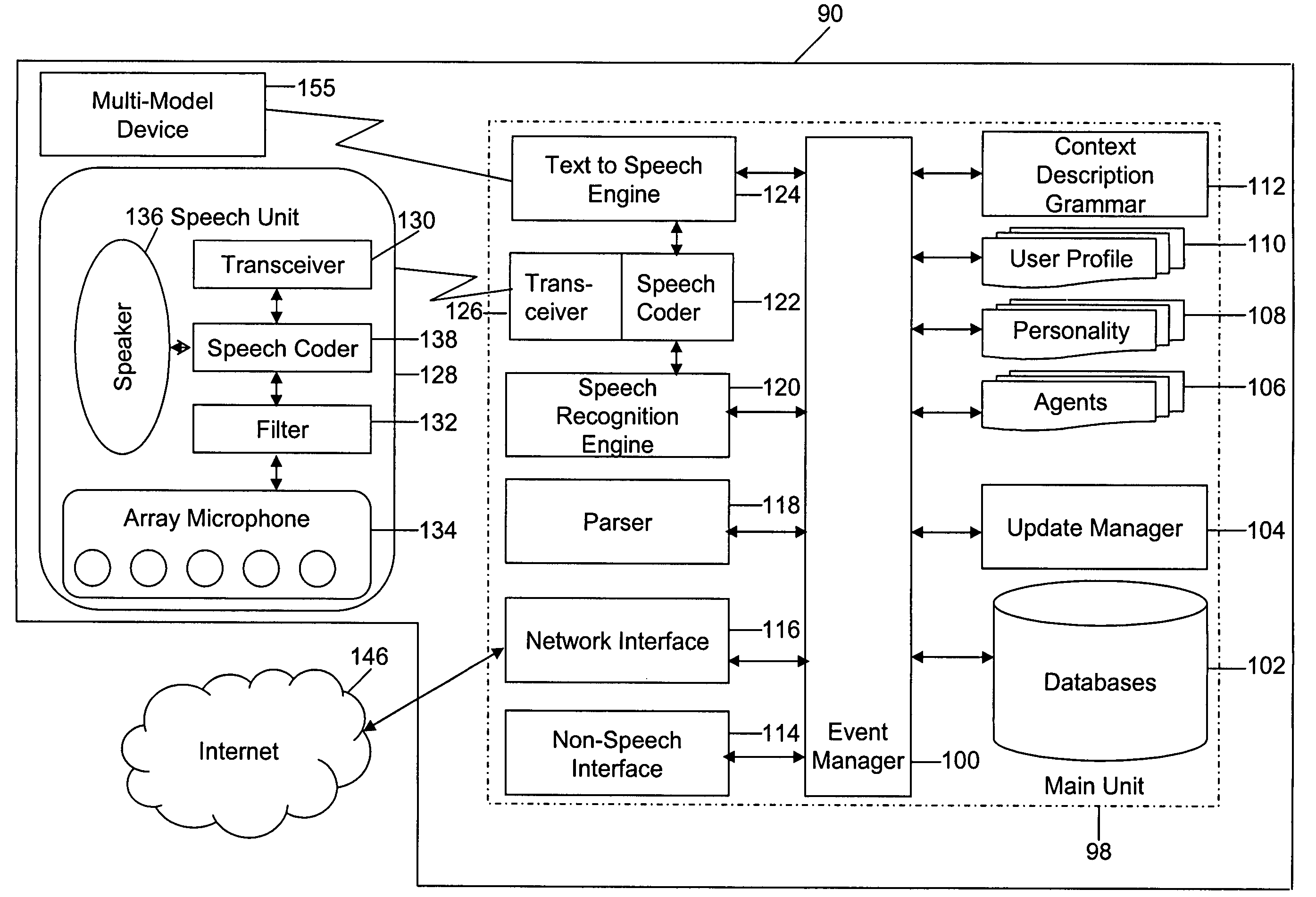
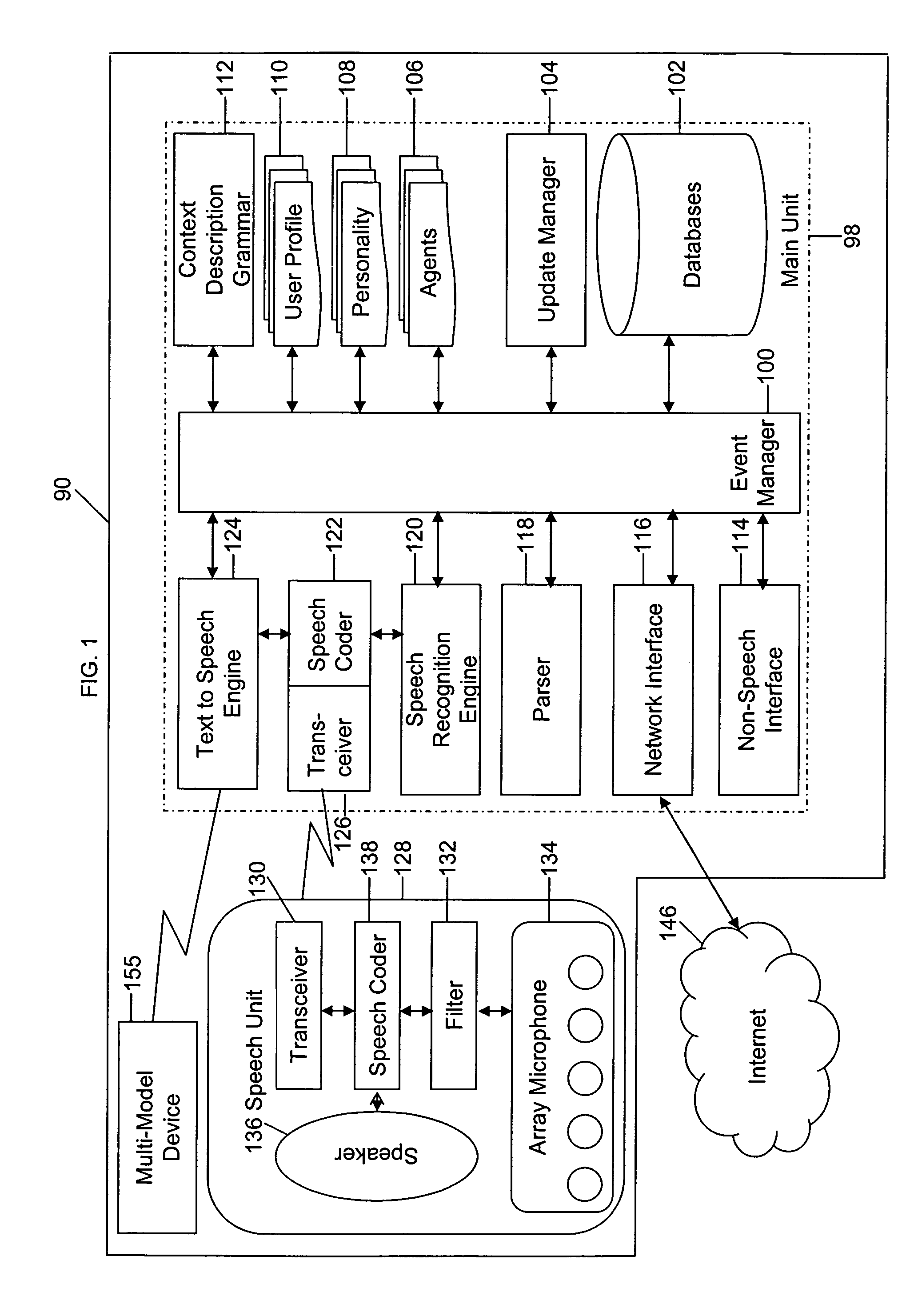
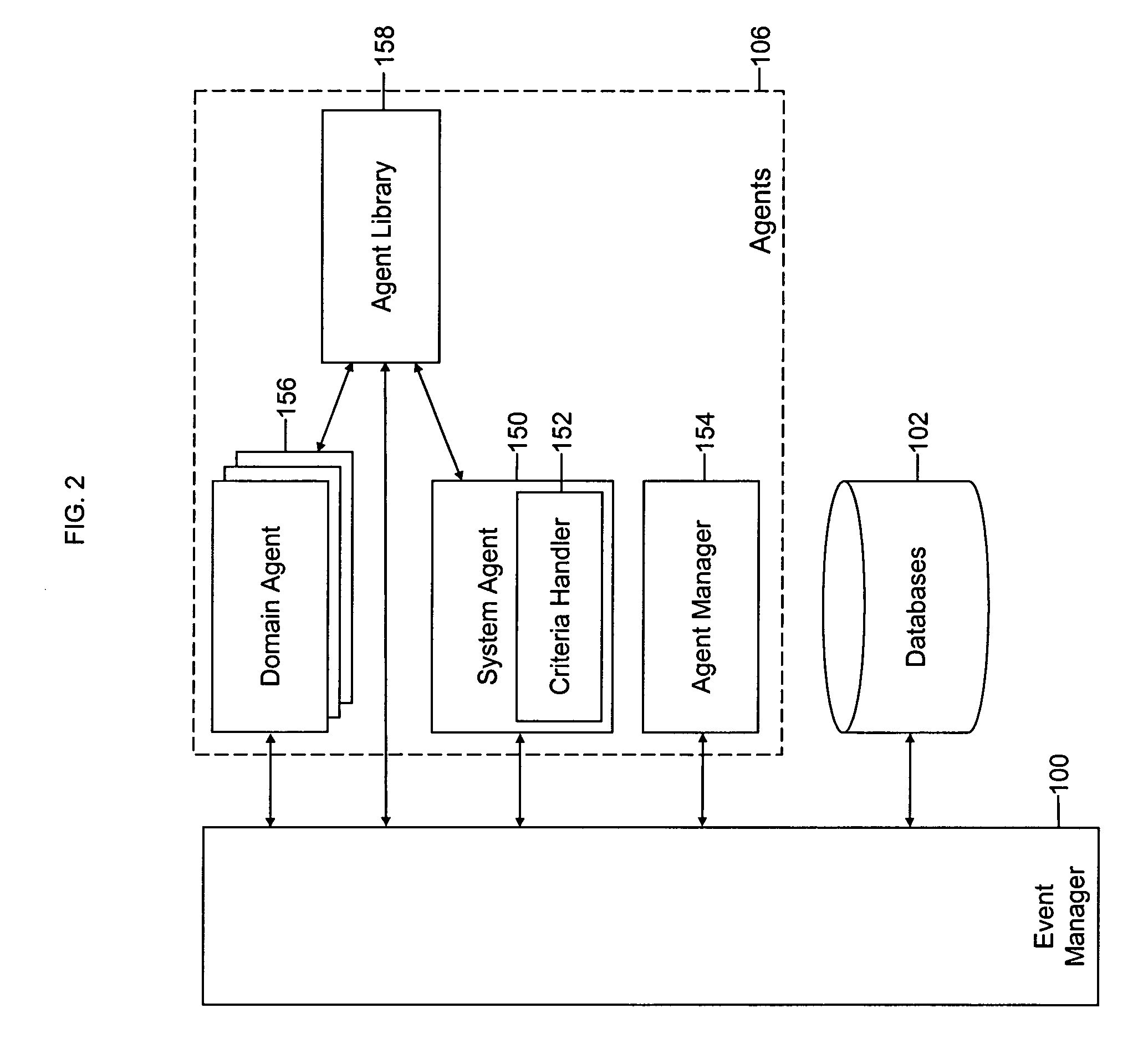
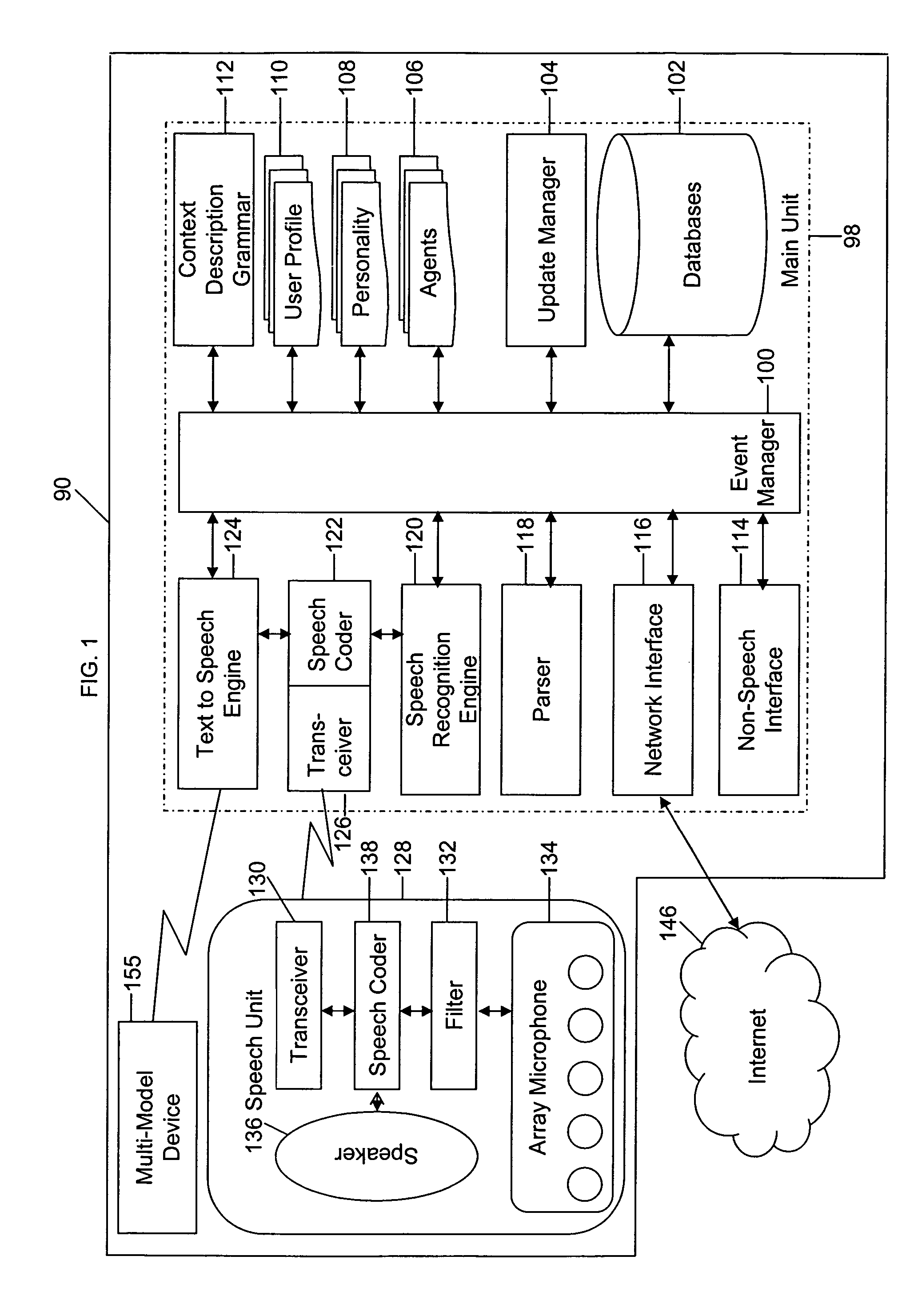
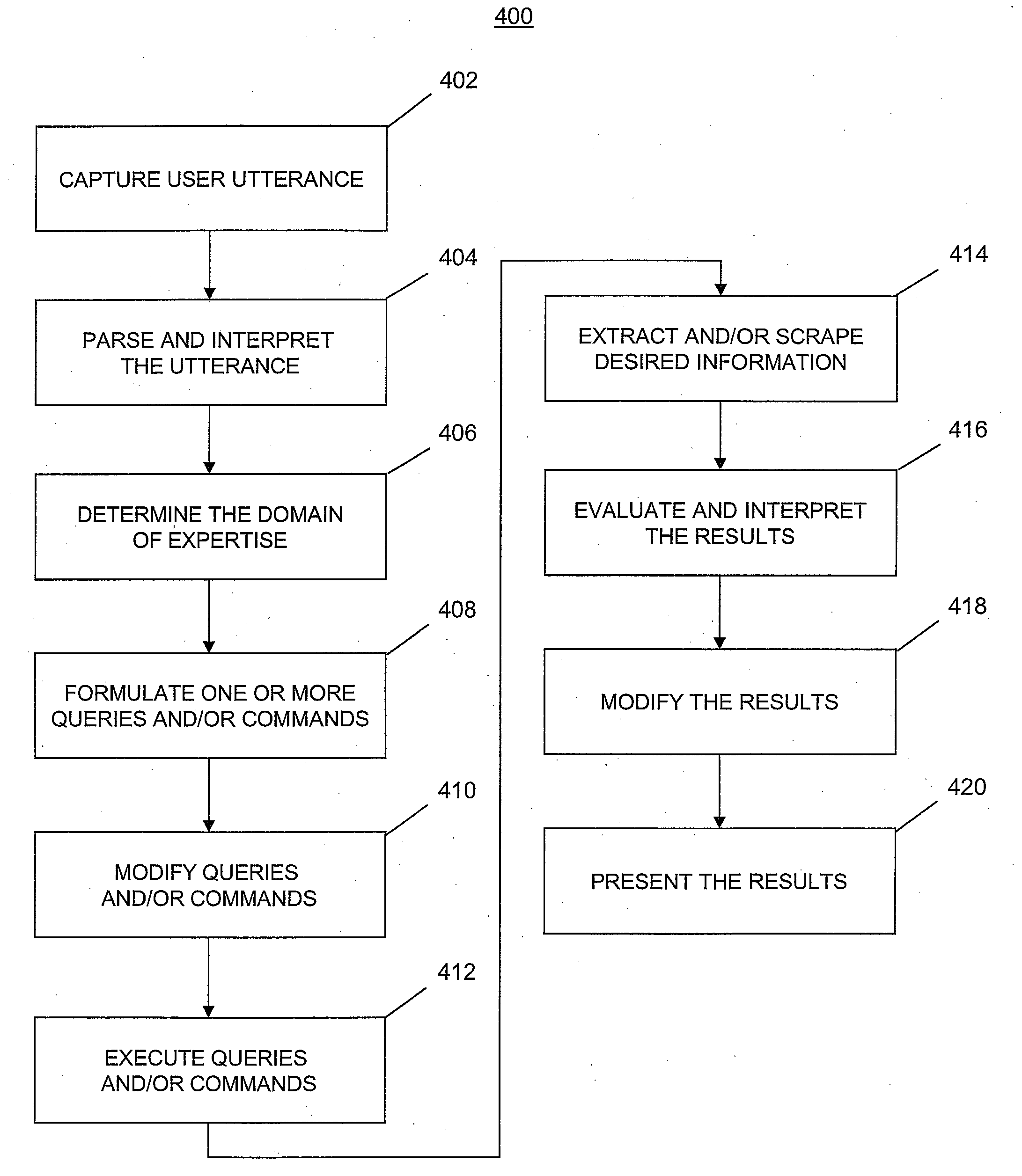
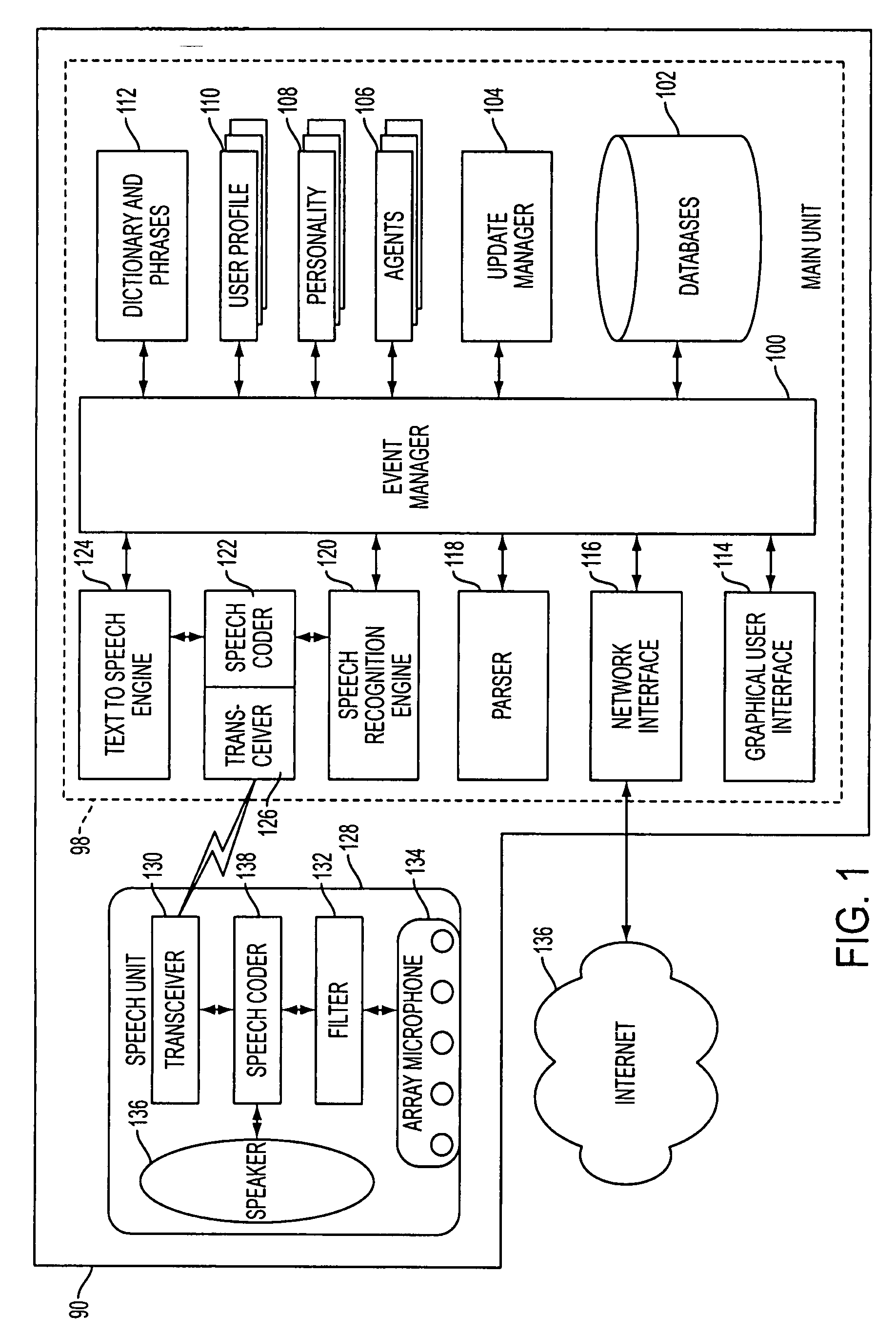
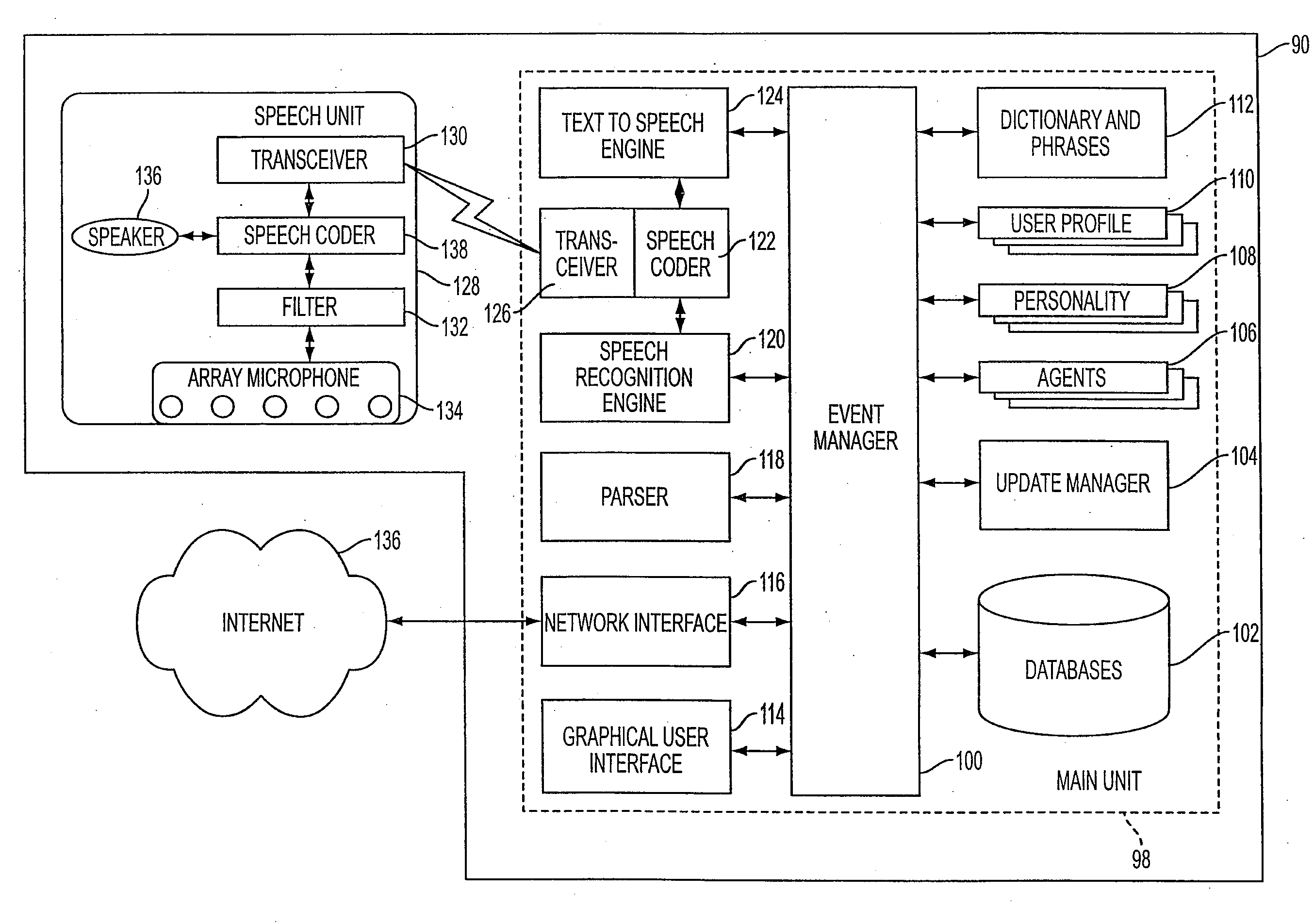
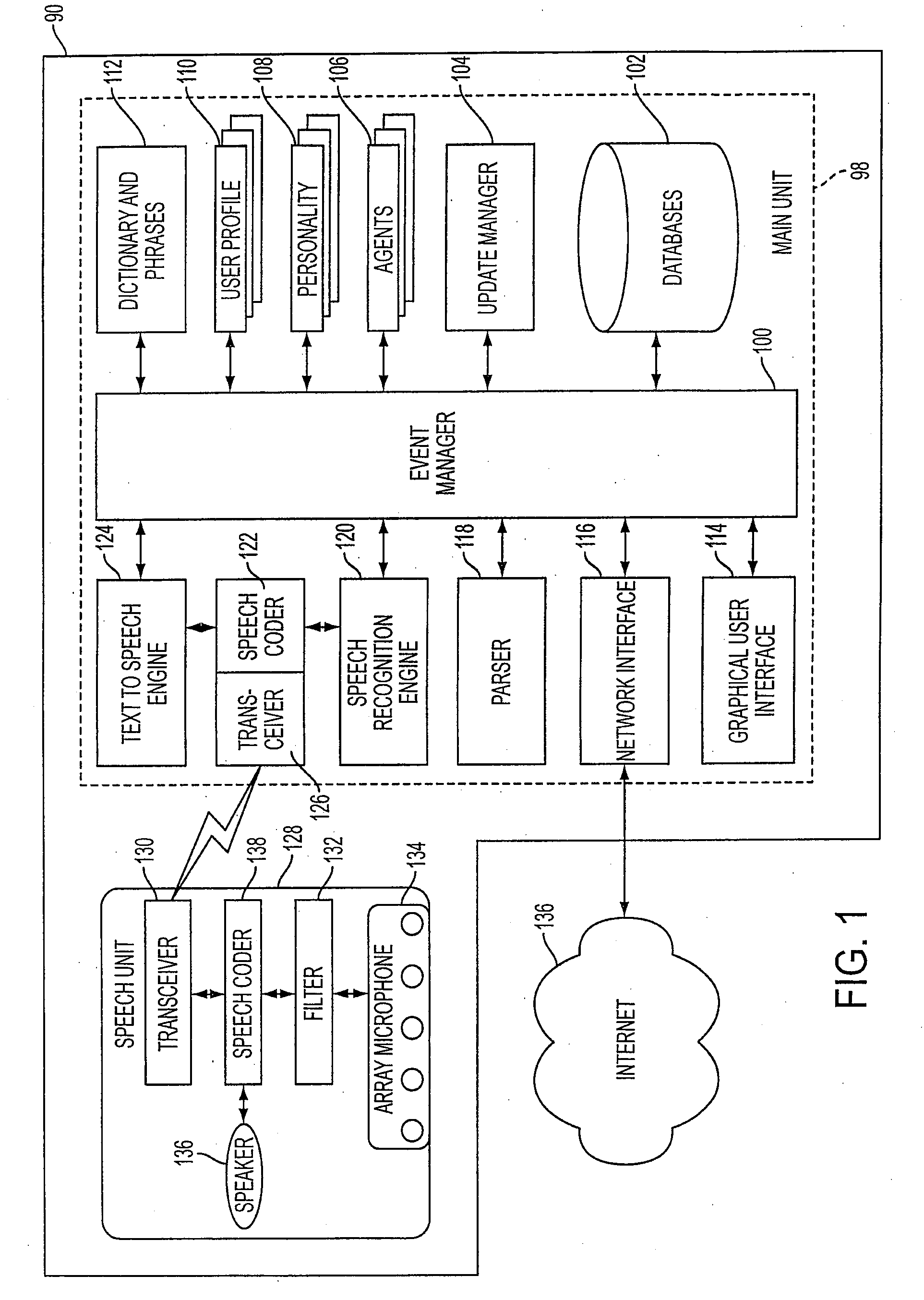
Mobile systems and methods for responding to natural language speech utterance
ActiveUS7693720B2Promotes feeling of naturalOvercome deficienciesDigital data information retrievalSpeech recognitionRemote systemTelematics
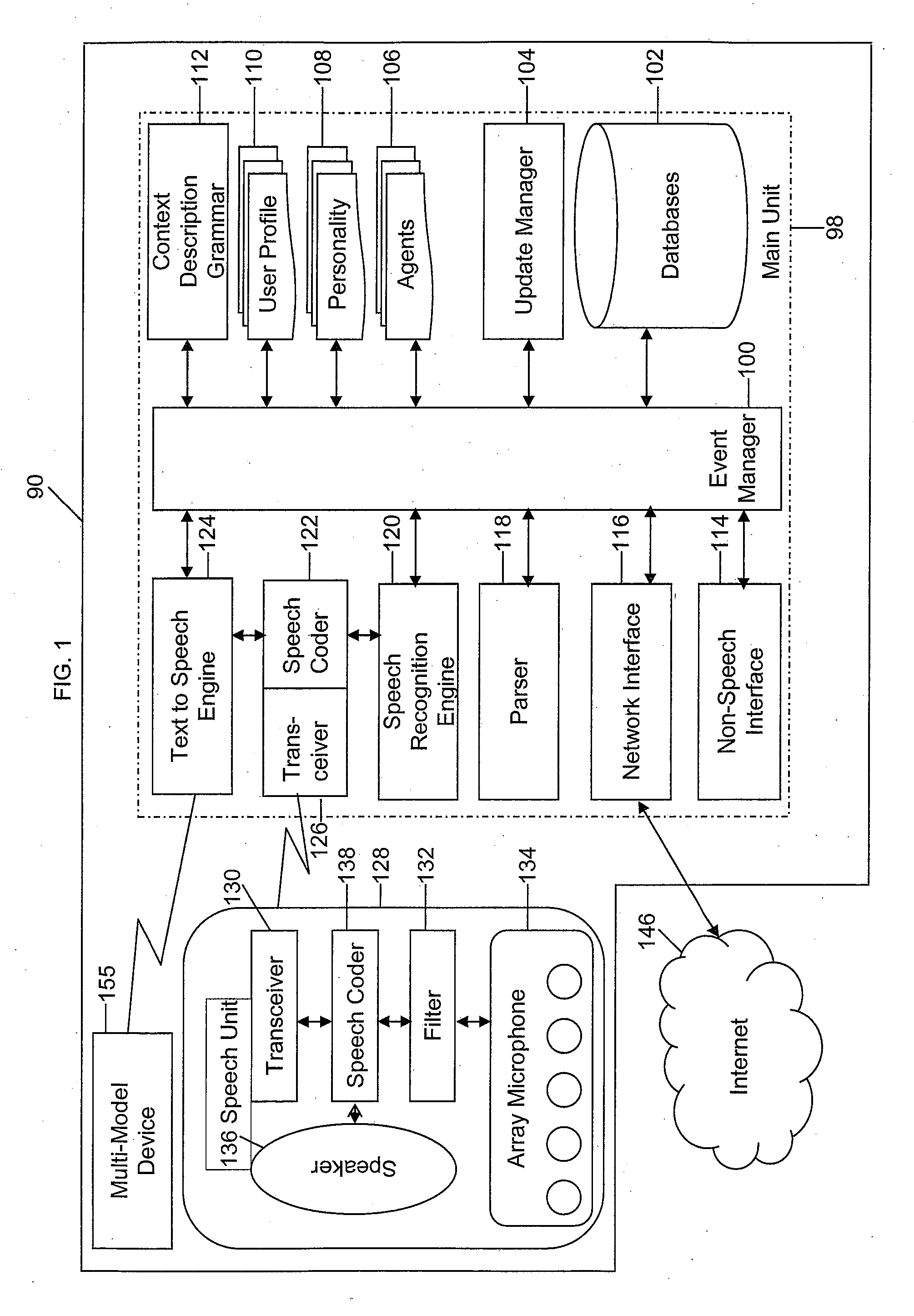
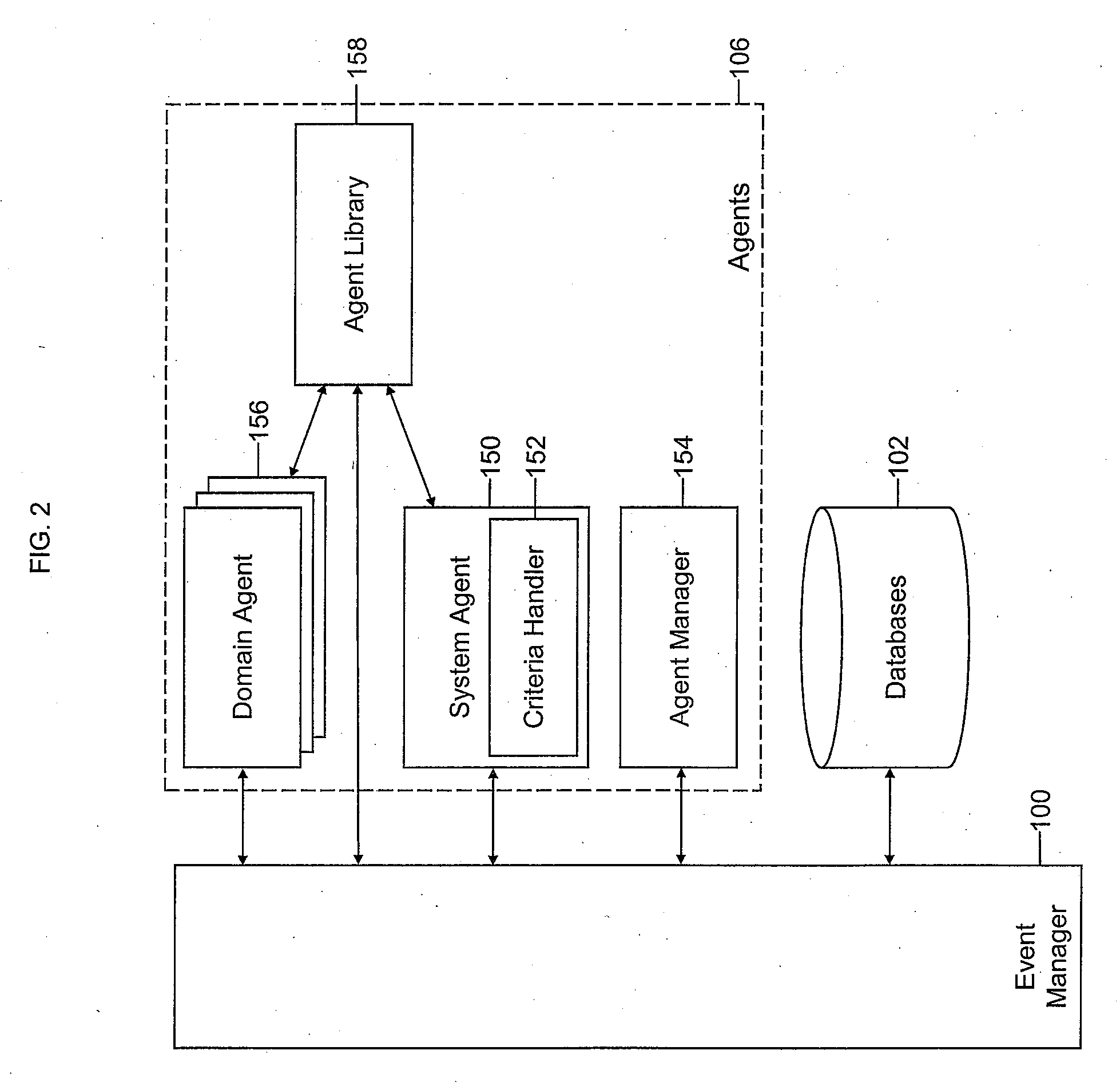
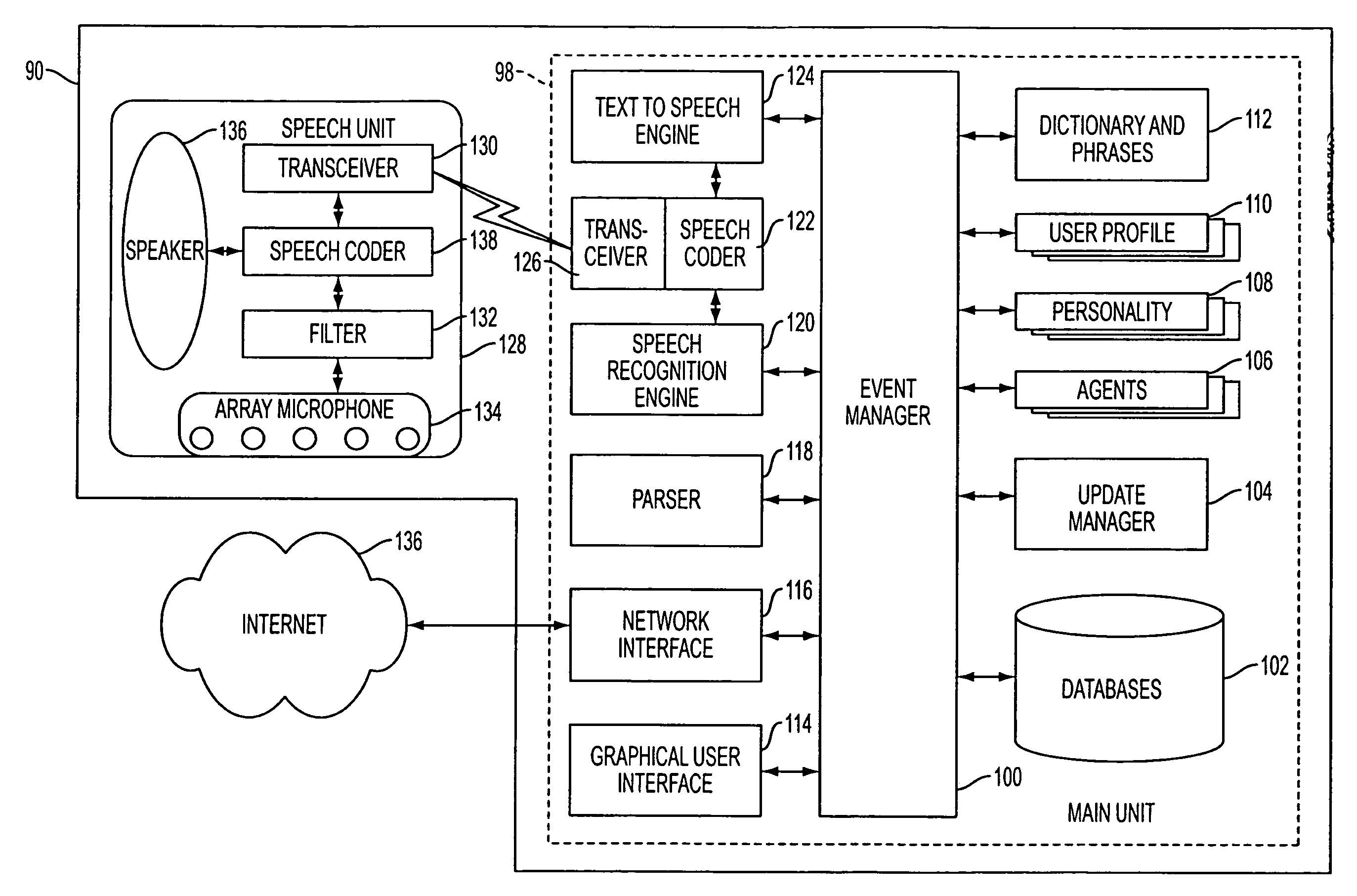
Mobile systems and methods that overcomes the deficiencies of prior art speech-based interfaces for telematics applications through the use of a complete speech-based information query, retrieval, presentation and local or remote command environment. This environment makes significant use of context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for one or more users making queries or commands in multiple domains. Through this integrated approach, a complete speech-based natural language query and response environment can be created. The invention creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context and presenting the expected results for a particular question or command. The invention may organize domain specific behavior and information into agents, that are distributable or updateable over a wide area network. The invention can be used in dynamic environments such as those of mobile vehicles to control and communicate with both vehicle systems and remote systems and devices.
Owner:DIALECT LLC
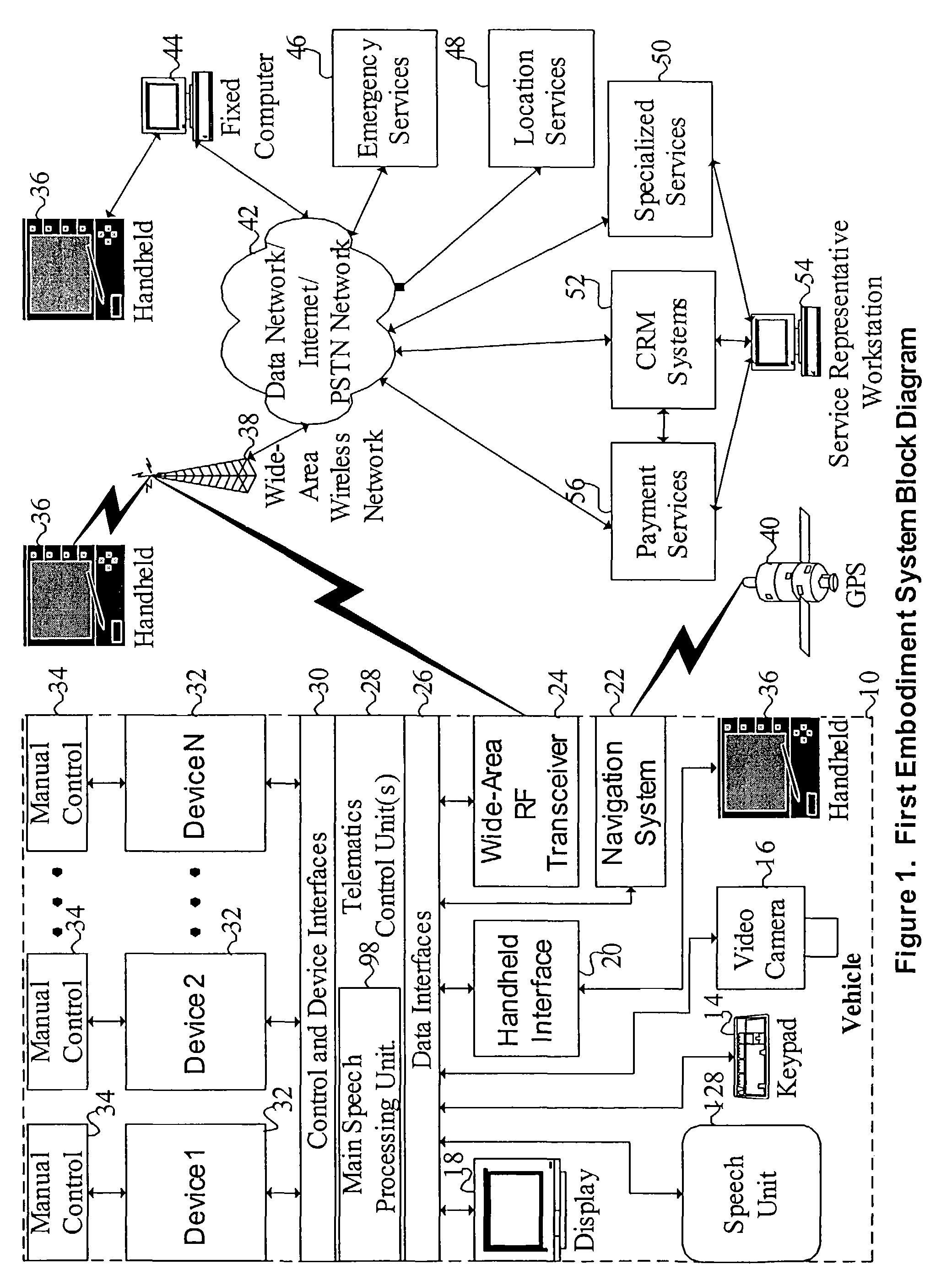
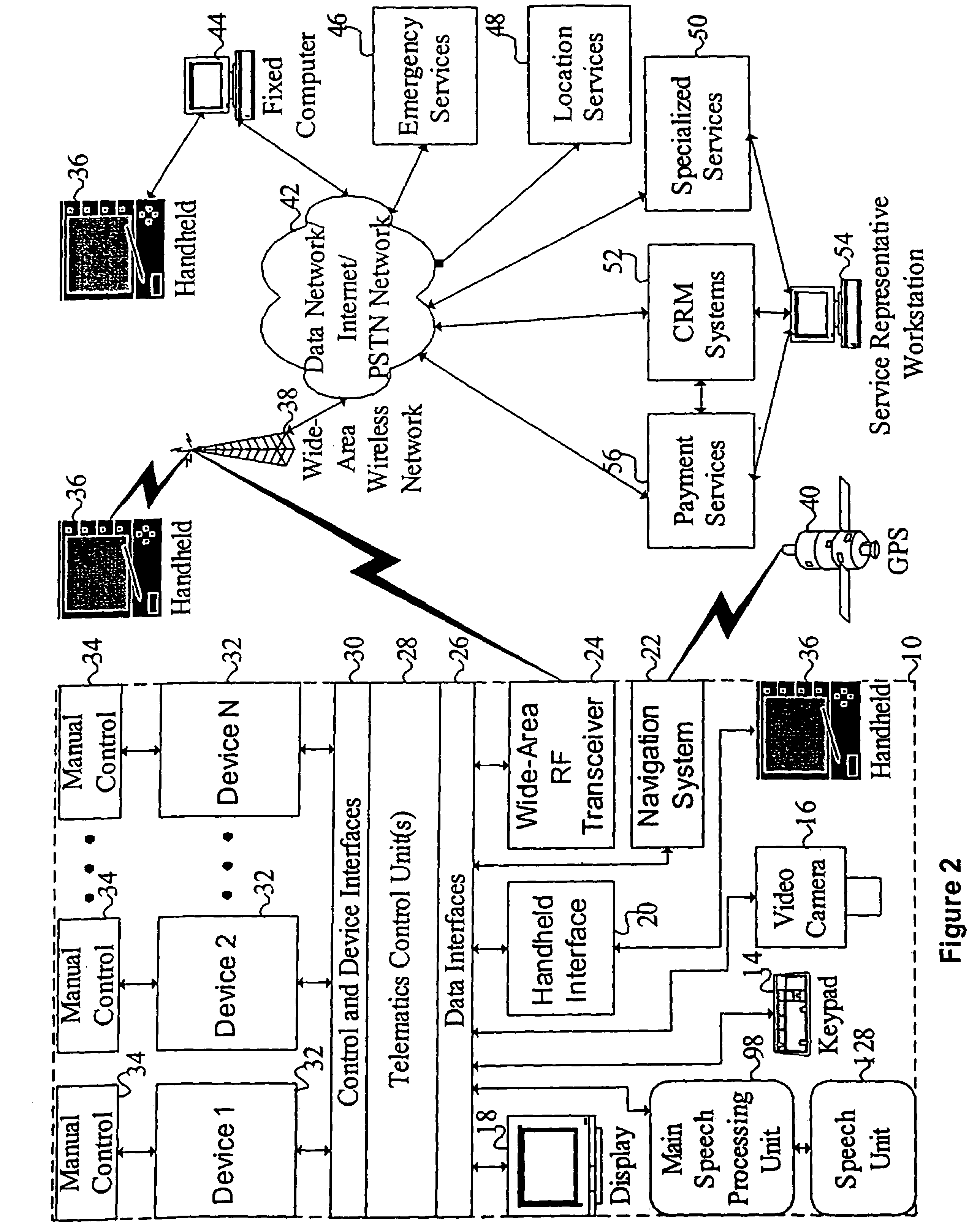
Mobile systems and methods of supporting natural language human-machine interactions
ActiveUS7949529B2Promotes feeling of naturalConvenient timeWeb data indexingDevices with voice recognitionTelematicsWide area network
A mobile system is provided that includes speech-based and non-speech-based interfaces for telematics applications. The mobile system identifies and uses context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for users that submit requests and / or commands in multiple domains. The invention creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context and presenting the expected results for a particular question or command. The invention may organize domain specific behavior and information into agents, that are distributable or updateable over a wide area network.
Owner:DIALECT LLC
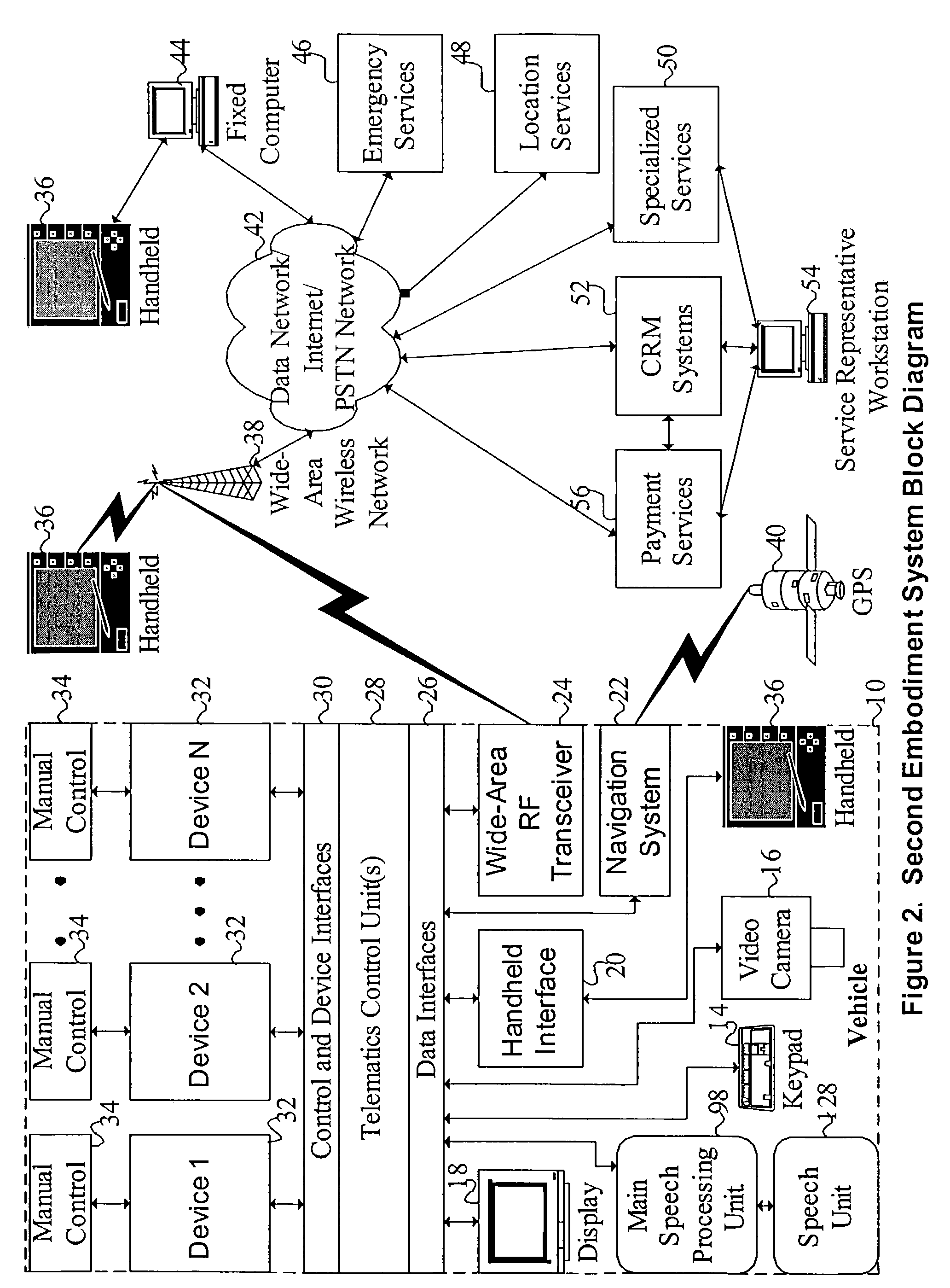
Mobile systems and methods for responding to natural language speech utterance
ActiveUS20100145700A1Promotes feeling of naturalOvercome deficienciesVehicle testingInstruments for road network navigationInformation processingRemote system
Owner:DIALECT LLC
Mobile systems and methods of supporting natural language human-machine interactions
ActiveUS20110231182A1Promotes feeling of naturalConvenient timeWeb data indexingDevices with voice recognitionEngineeringSpeech sound
A mobile system is provided that includes speech-based and non-speech-based interfaces for telematics applications. The mobile system identifies and uses context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for users that submit requests and / or commands in multiple domains. The invention creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context and presenting the expected results for a particular question or command. The invention may organize domain specific behavior and information into agents, that are distributable or updateable over a wide area network.
Owner:DIALECT LLC
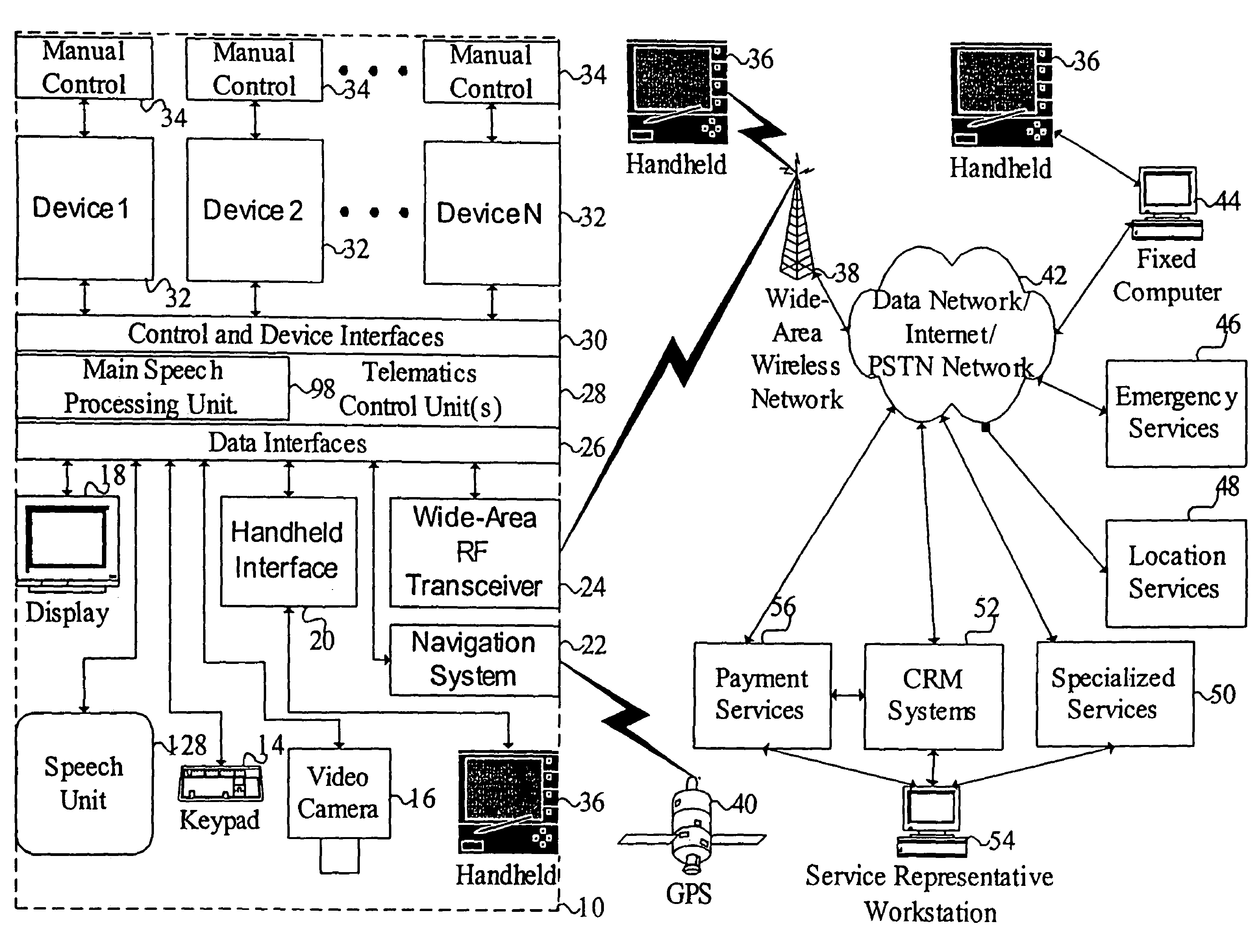
Systems and methods for responding to natural language speech utterance
ActiveUS7398209B2Promotes feeling of naturalOvercome deficienciesData processing applicationsNatural language data processingPrior informationDependability
Systems and methods for receiving natural language queries and / or commands and execute the queries and / or commands. The systems and methods overcomes the deficiencies of prior art speech query and response systems through the application of a complete speech-based information query, retrieval, presentation and command environment. This environment makes significant use of context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for one or more users making queries or commands in multiple domains. Through this integrated approach, a complete speech-based natural language query and response environment can be created. The systems and methods creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context and presenting the expected results for a particular question or command.
Owner:DIALECT LLC
Systems and methods for responding to natural language speech utterance
ActiveUS7640160B2Promotes feeling of naturalSignificant to useDigital data information retrievalSemantic analysisPrior informationSpeech sound
Systems and methods are provided for receiving speech and non-speech communications of natural language questions and / or commands, transcribing the speech and non-speech communications to textual messages, and executing the questions and / or commands. The invention applies context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for one or more users presenting questions or commands across multiple domains. The systems and methods creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context of the speech and non-speech communications and presenting the expected results for a particular question or command.
Owner:DIALECT LLC
Systems and methods for responding to natural language speech utterance
ActiveUS20070033005A1Improve maximizationHigh bandwidthDigital data information retrievalSemantic analysisPrior informationVoice communication
Owner:DIALECT LLC
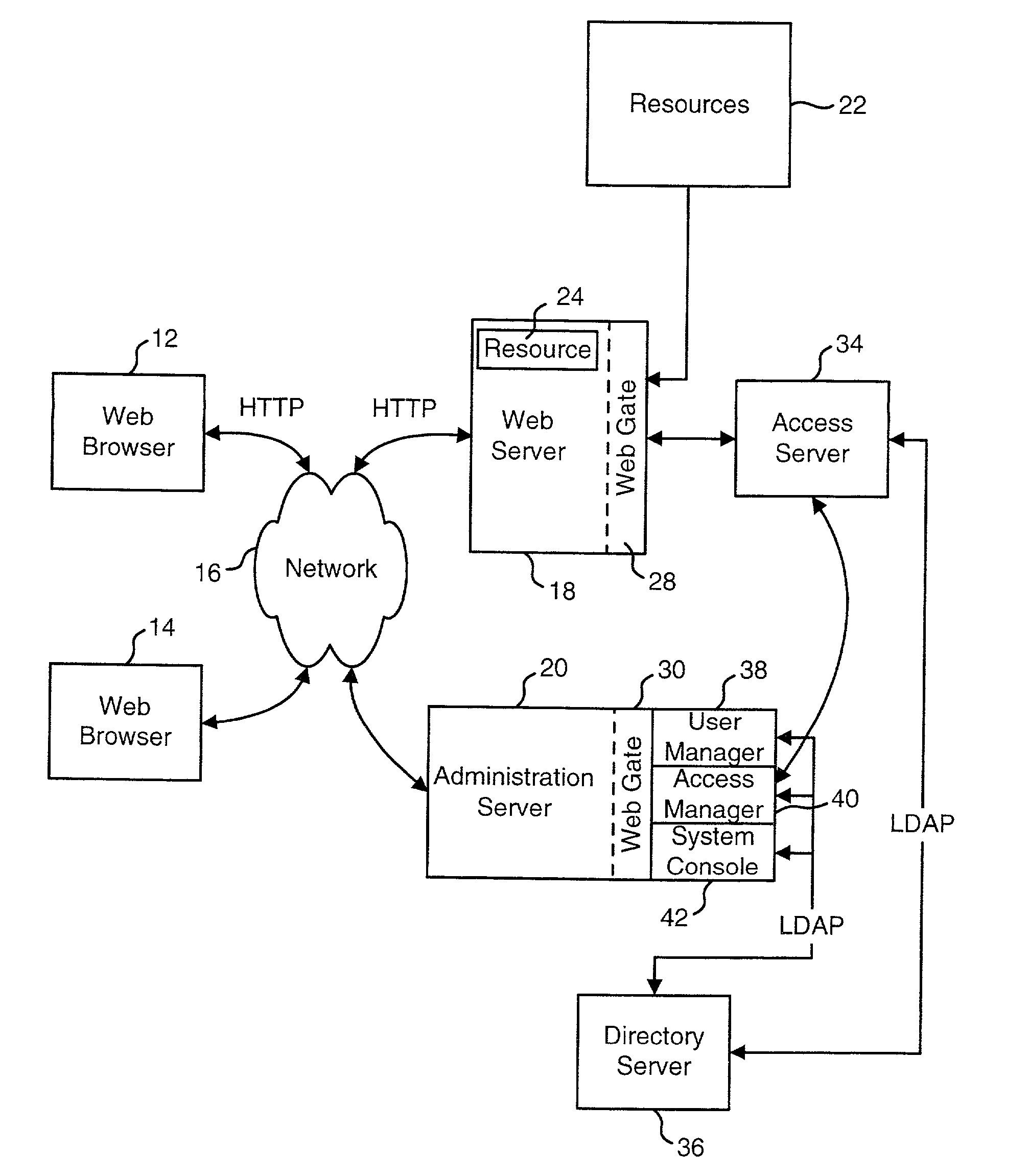
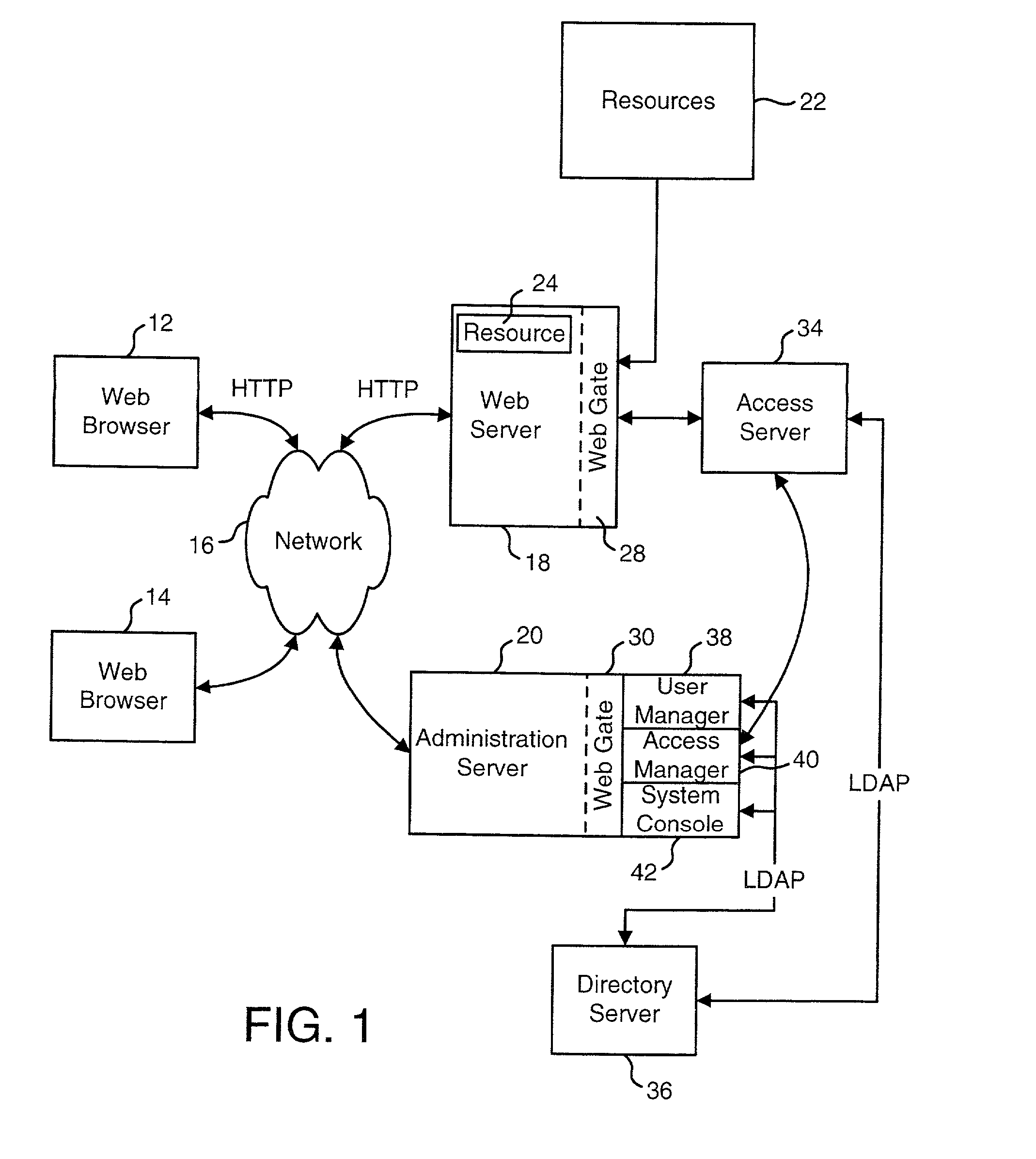
User Authentication
InactiveUS20020112155A1Easy mappingDigital data processing detailsUser identity/authority verificationInternet privacyUser authentication
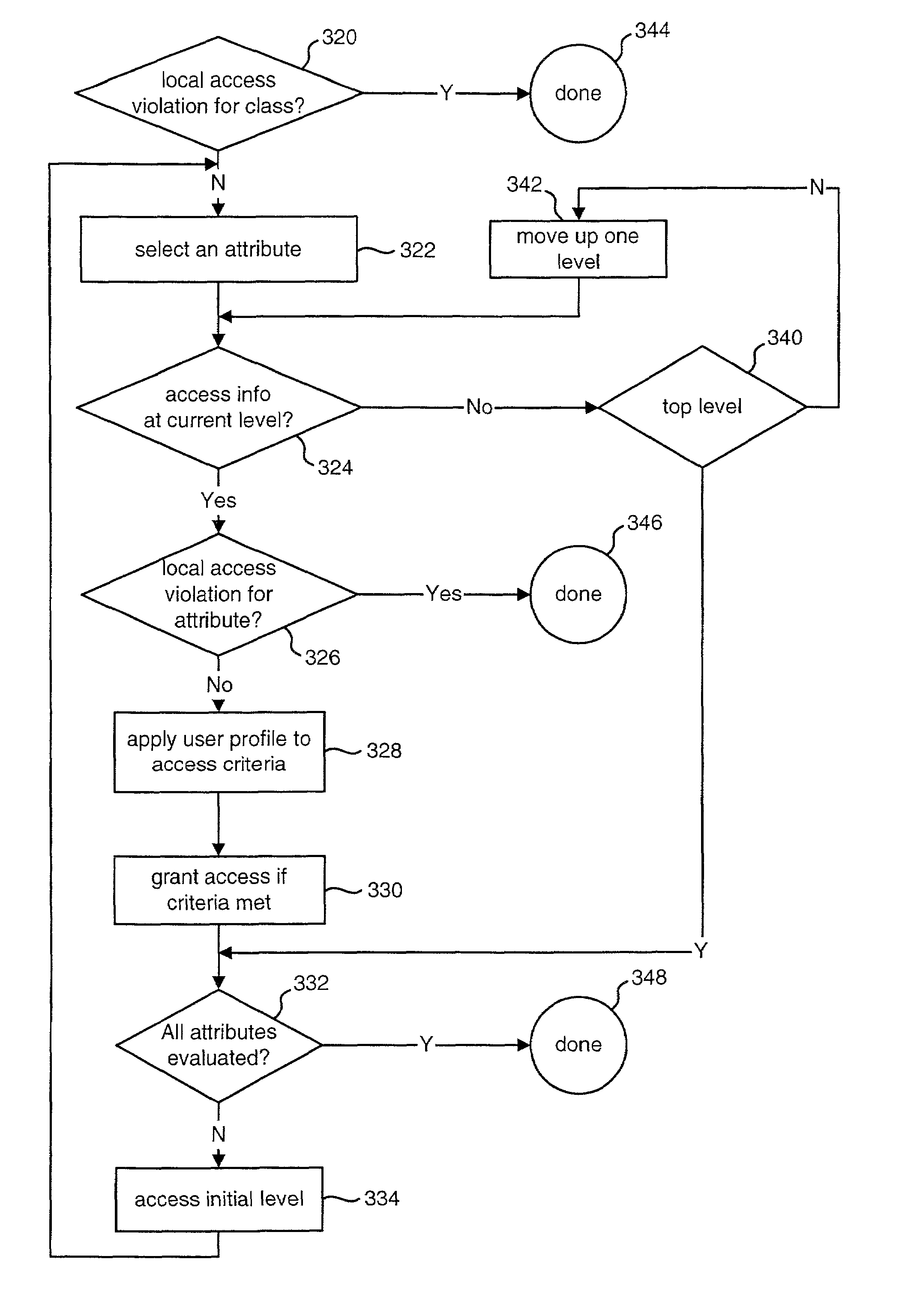
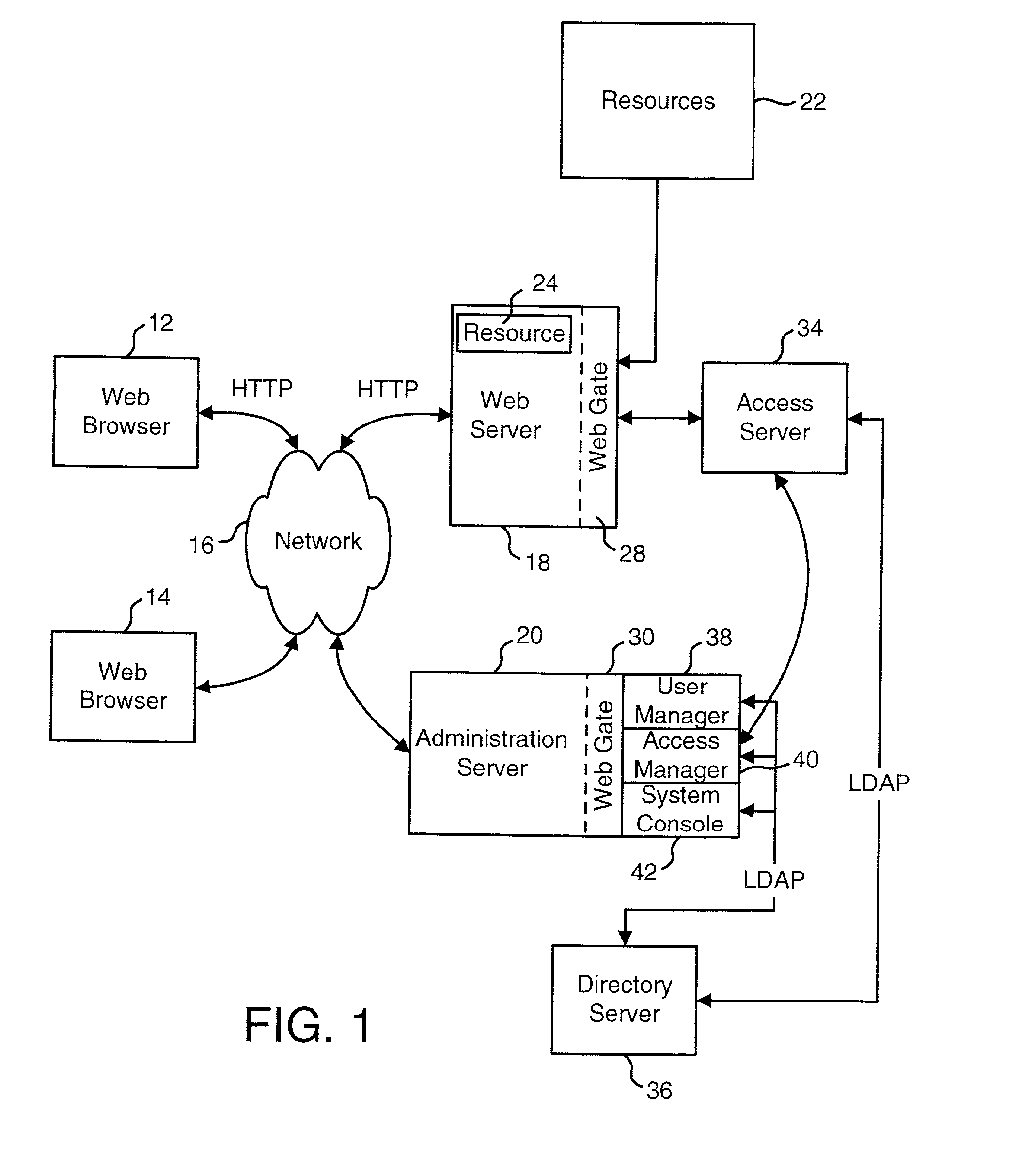
The present invention authenticates a user for multiple resources distributed across multiple domains through the performance of a single authentication. User access requests for a protected resource in a first domain are received and redirected to a second domain. User authentication is performed at the second domain. In one embodiment, the system transmits an authentication cookie for the second domain to the user after authentication at the second domain. In another embodiment, the system further redirects subsequent resource requests for resources in the first domain or a third domain to the second domain. The second domain confirms the user's authentication for applicable portions of the first, second, and third domains using the cookie.
Owner:ORACLE INT CORP
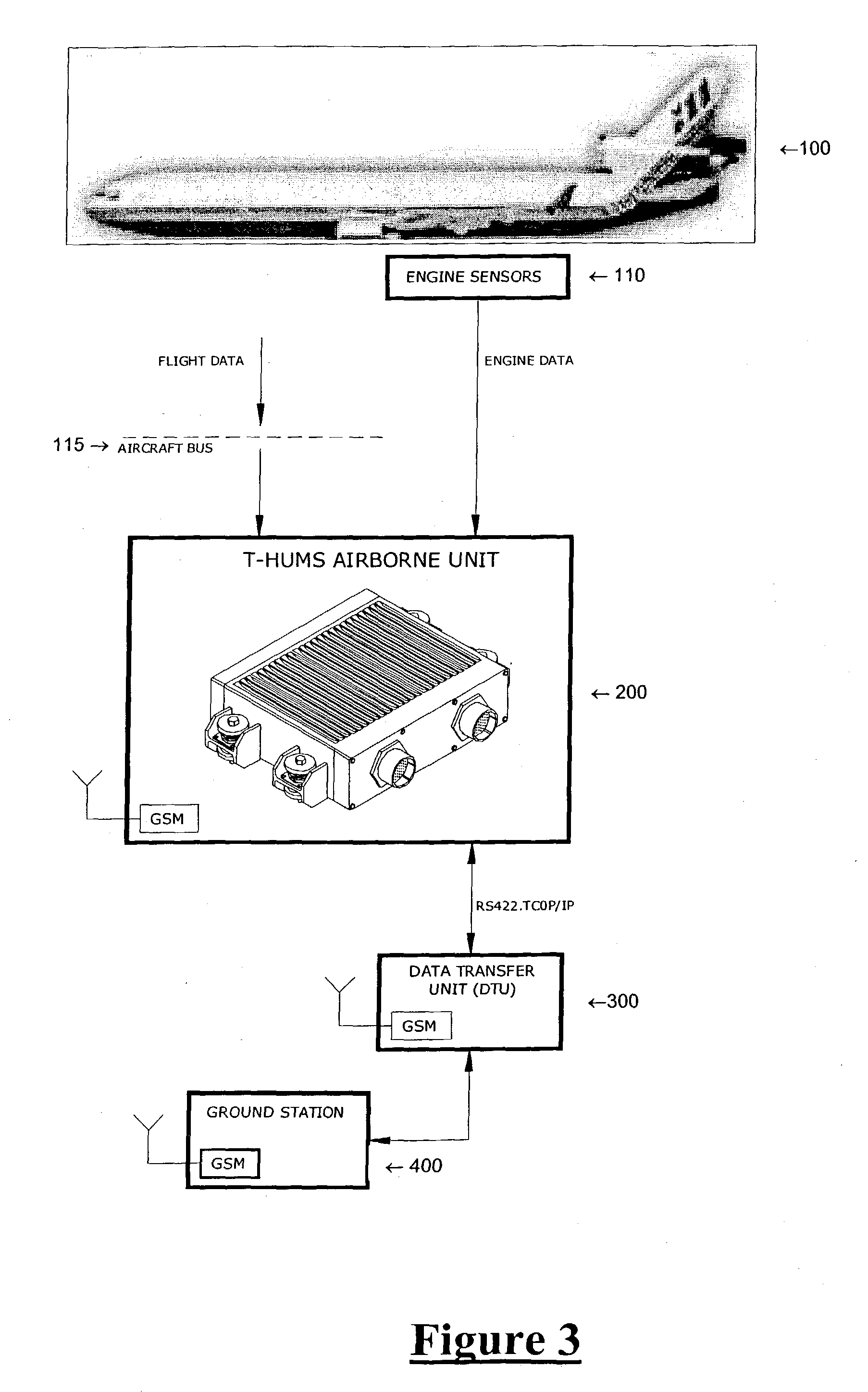
Device capability based discovery, packaging and provisioning of content for wireless mobile devices
ActiveUS7233790B2Digital data information retrievalNetwork traffic/resource managementWireless mobile devicesNetwork service
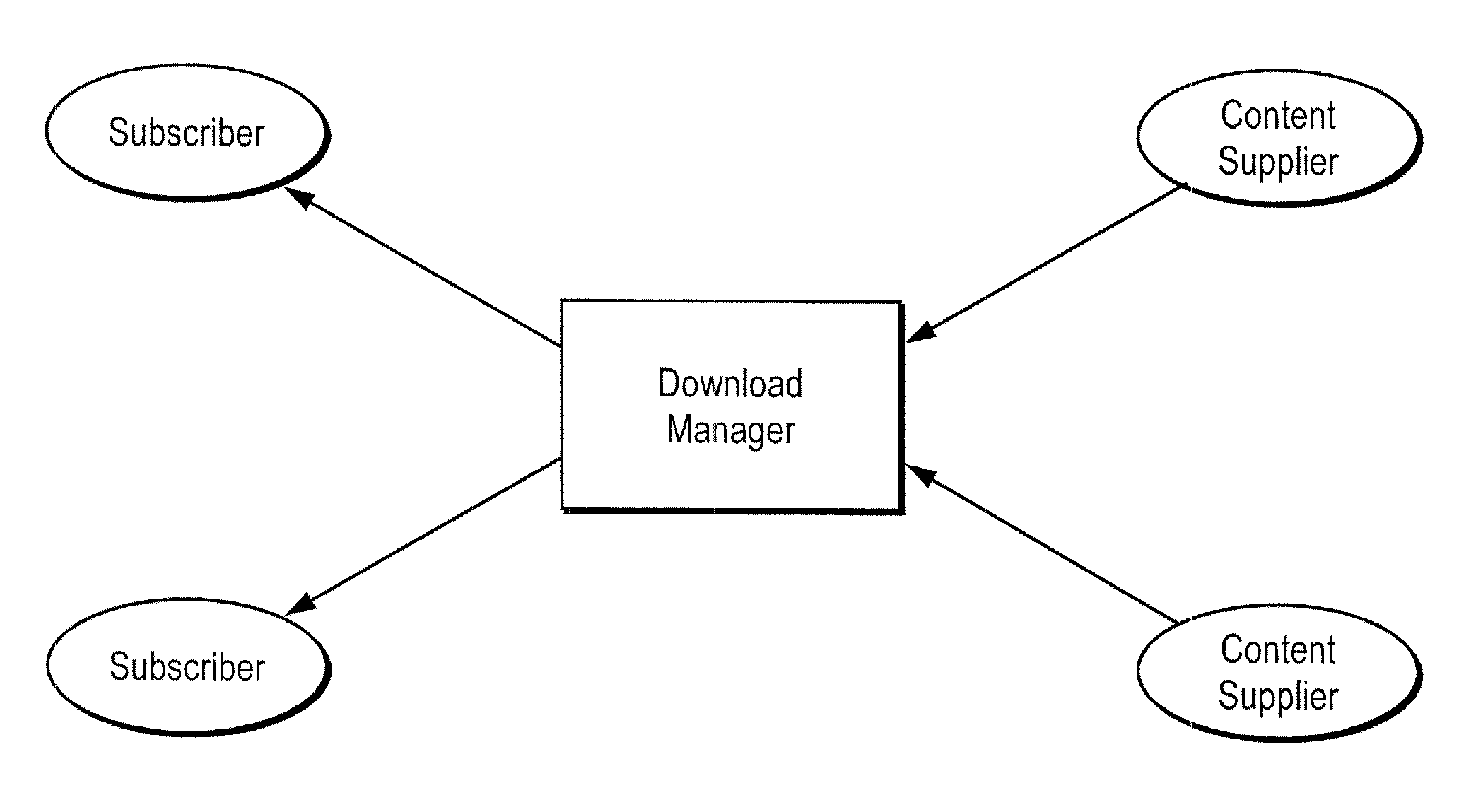
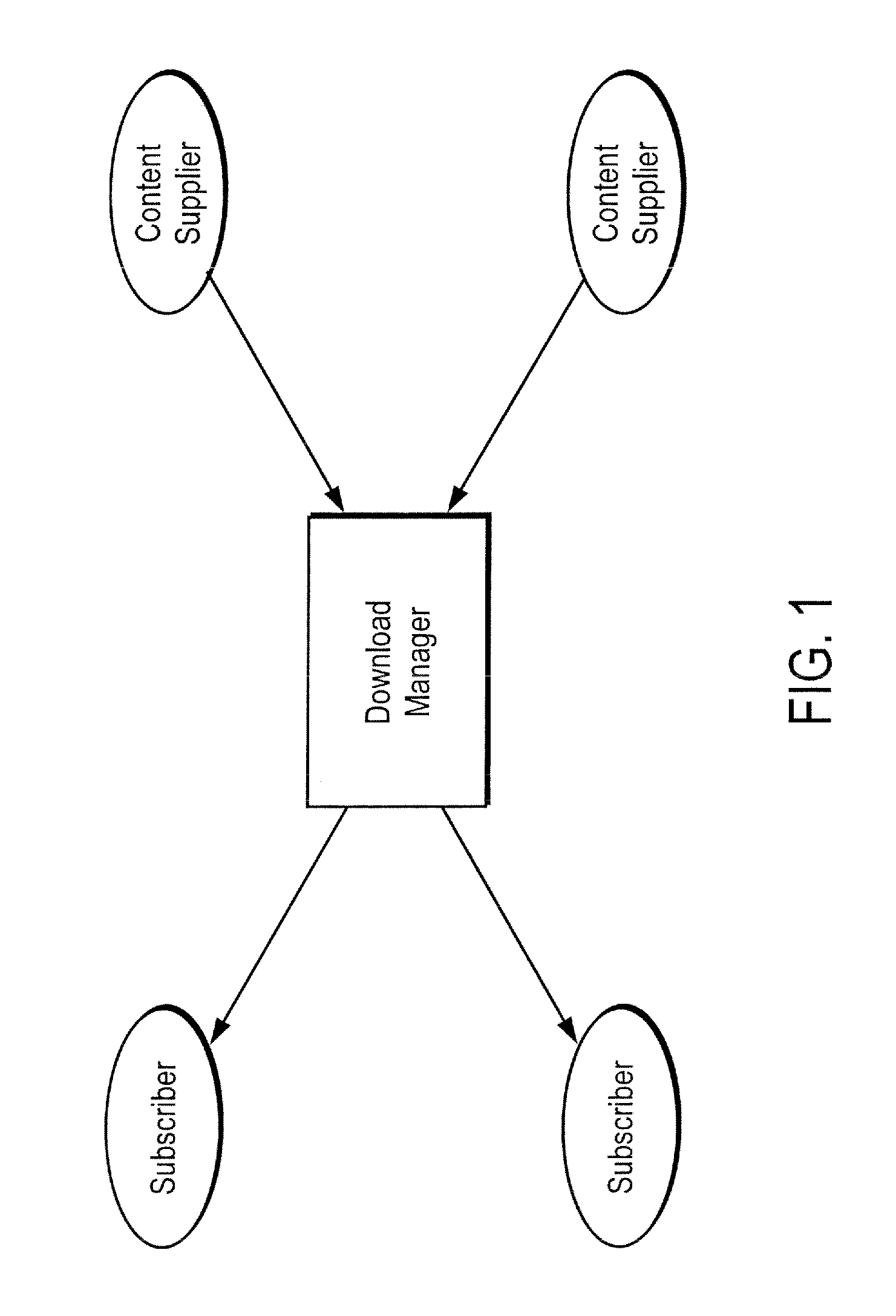
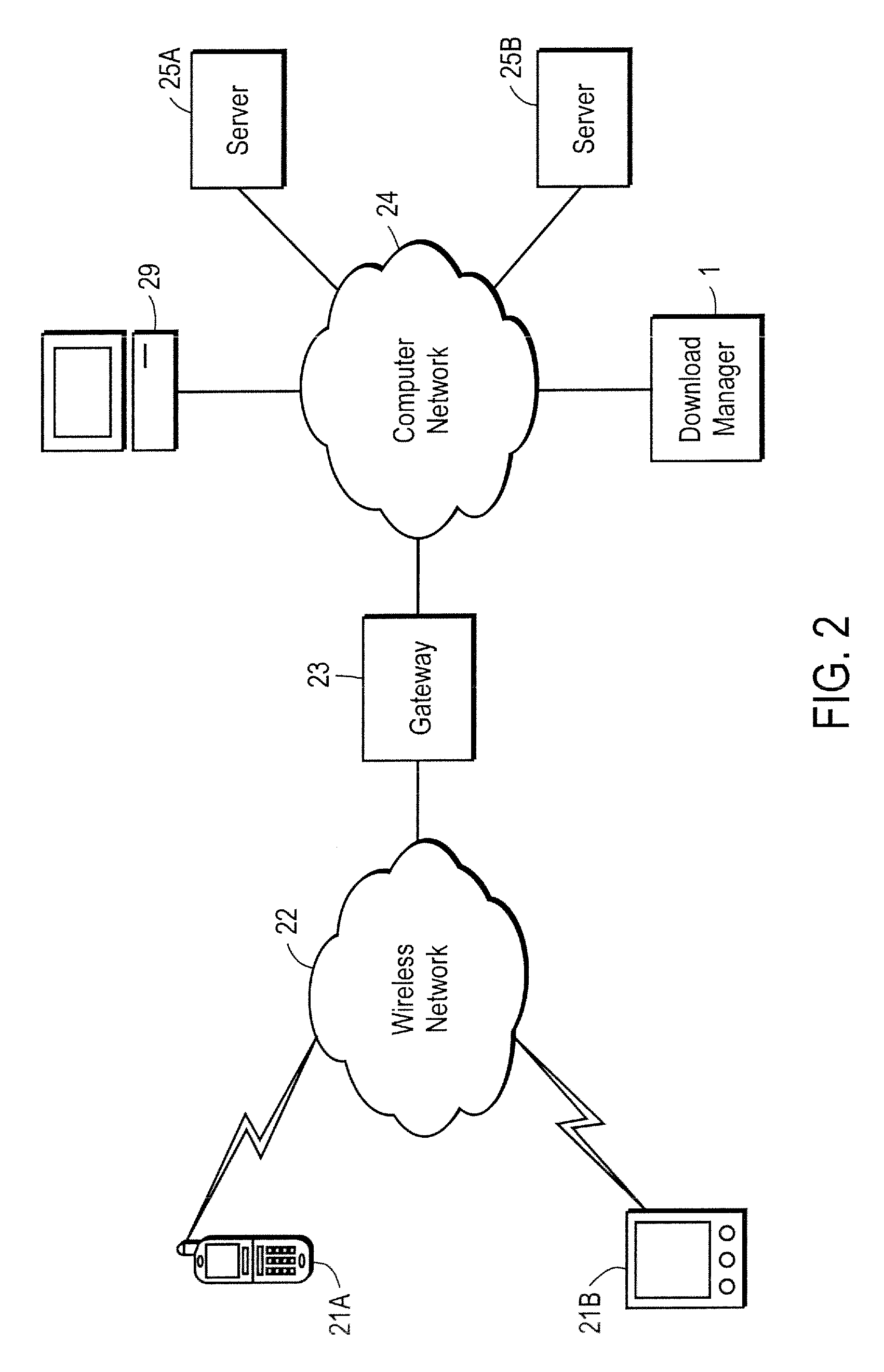
A network server system includes a download manager that manages the publication, purchase and delivery of digital products from multiple suppliers to wireless services subscribers in multiple domains. Product suppliers can publish and manage their products on the server system via a computer network and make their products available to the subscribers for purchase or licensing. The subscribers in each domain can access the server remotely to purchase rights to download and use the products on associated wireless communication devices. Multiple different implementations of any product can be maintained, where each implementation corresponds to a different set of device capabilities. Each product can also be associated with multiple different provisioning models, each corresponding to a different set of device capabilities.
Owner:VIDEOLABS
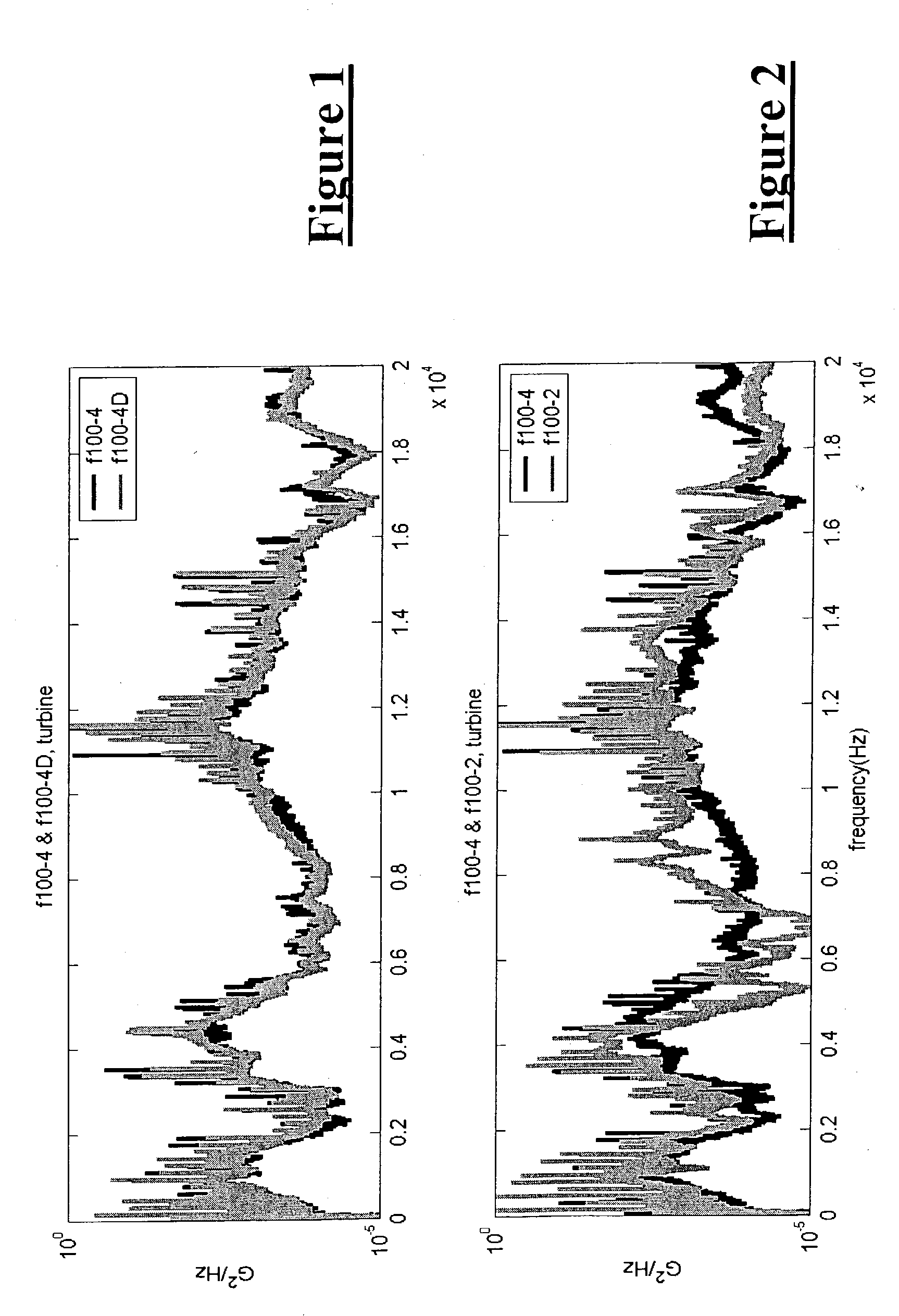
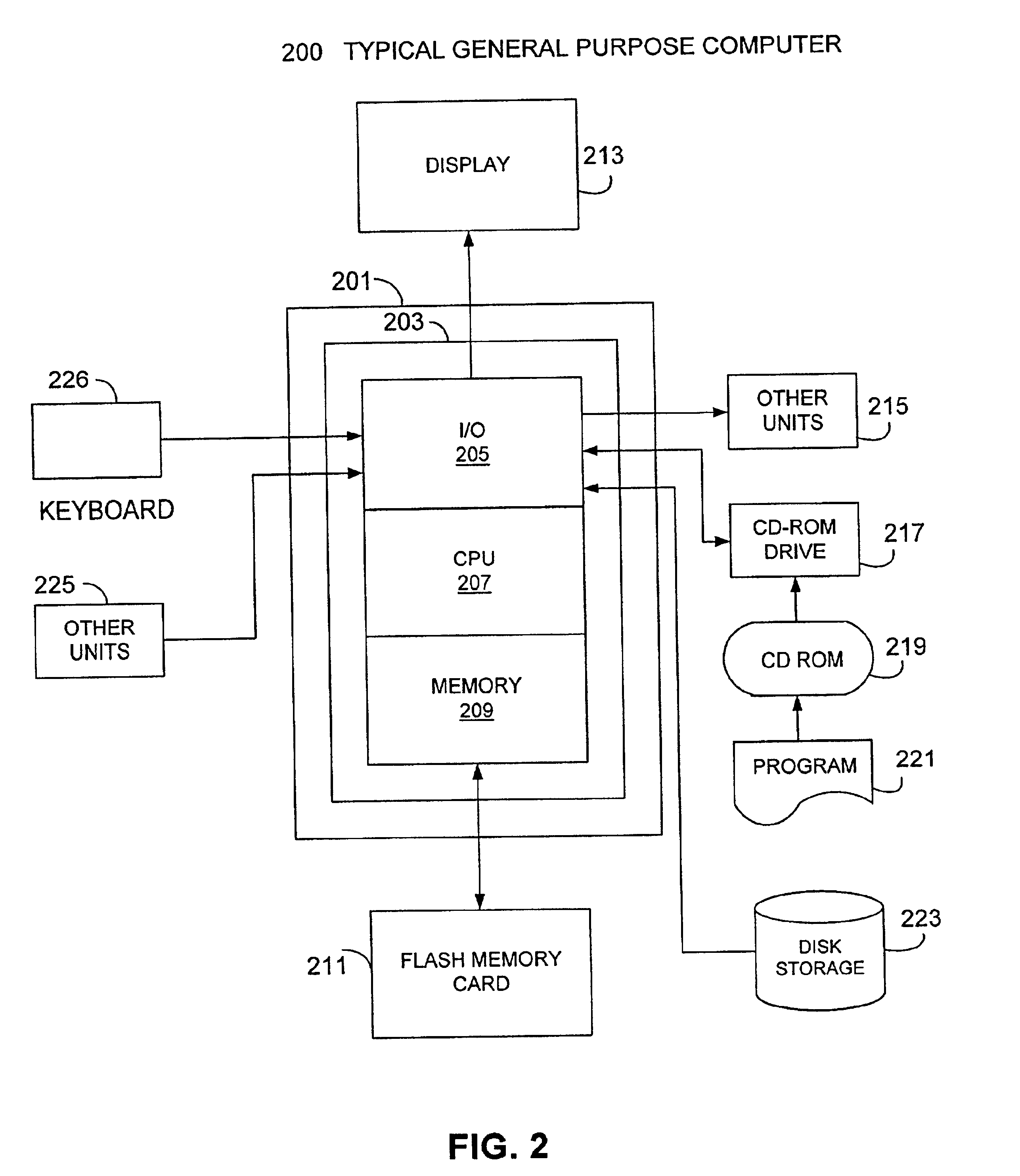
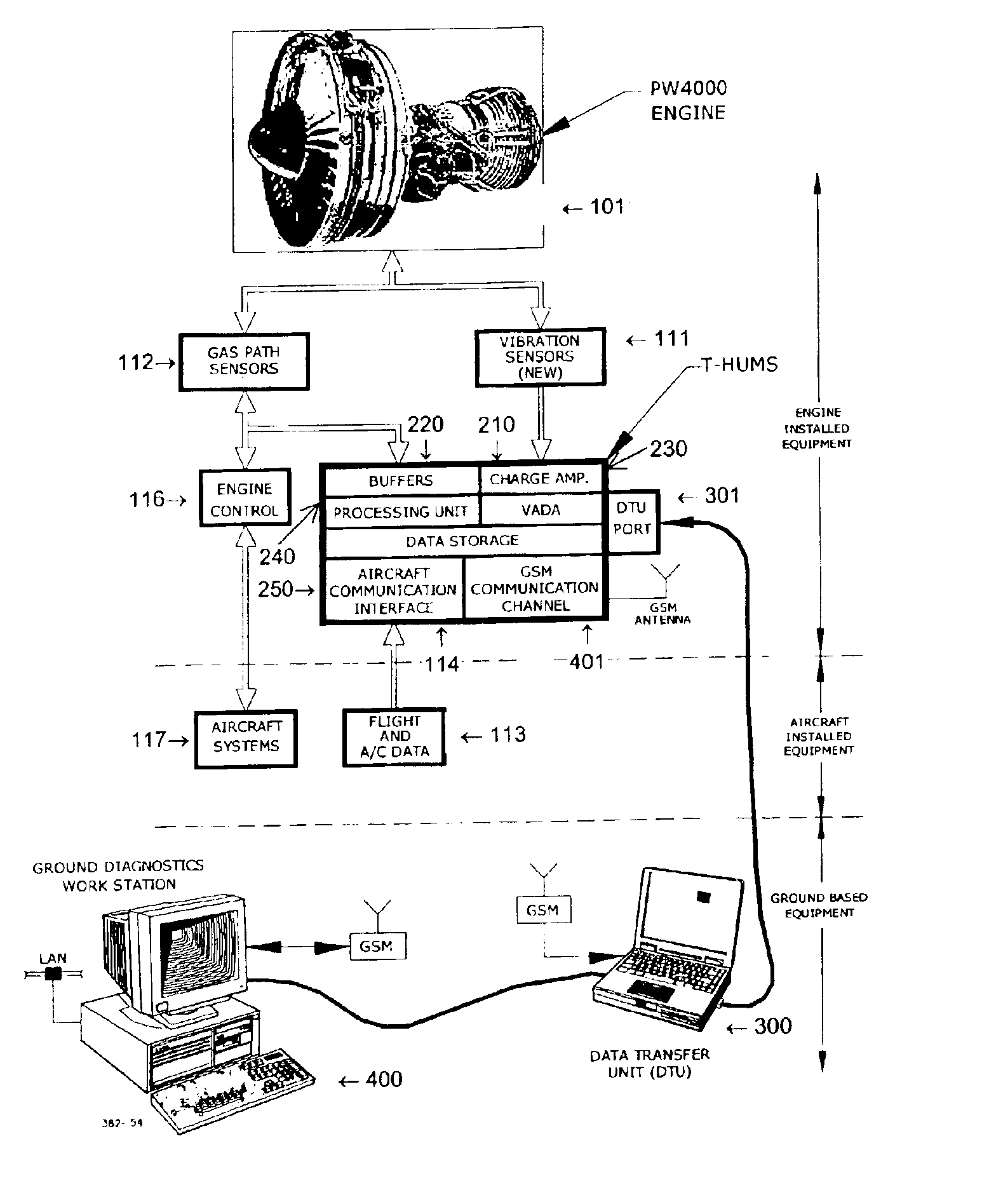
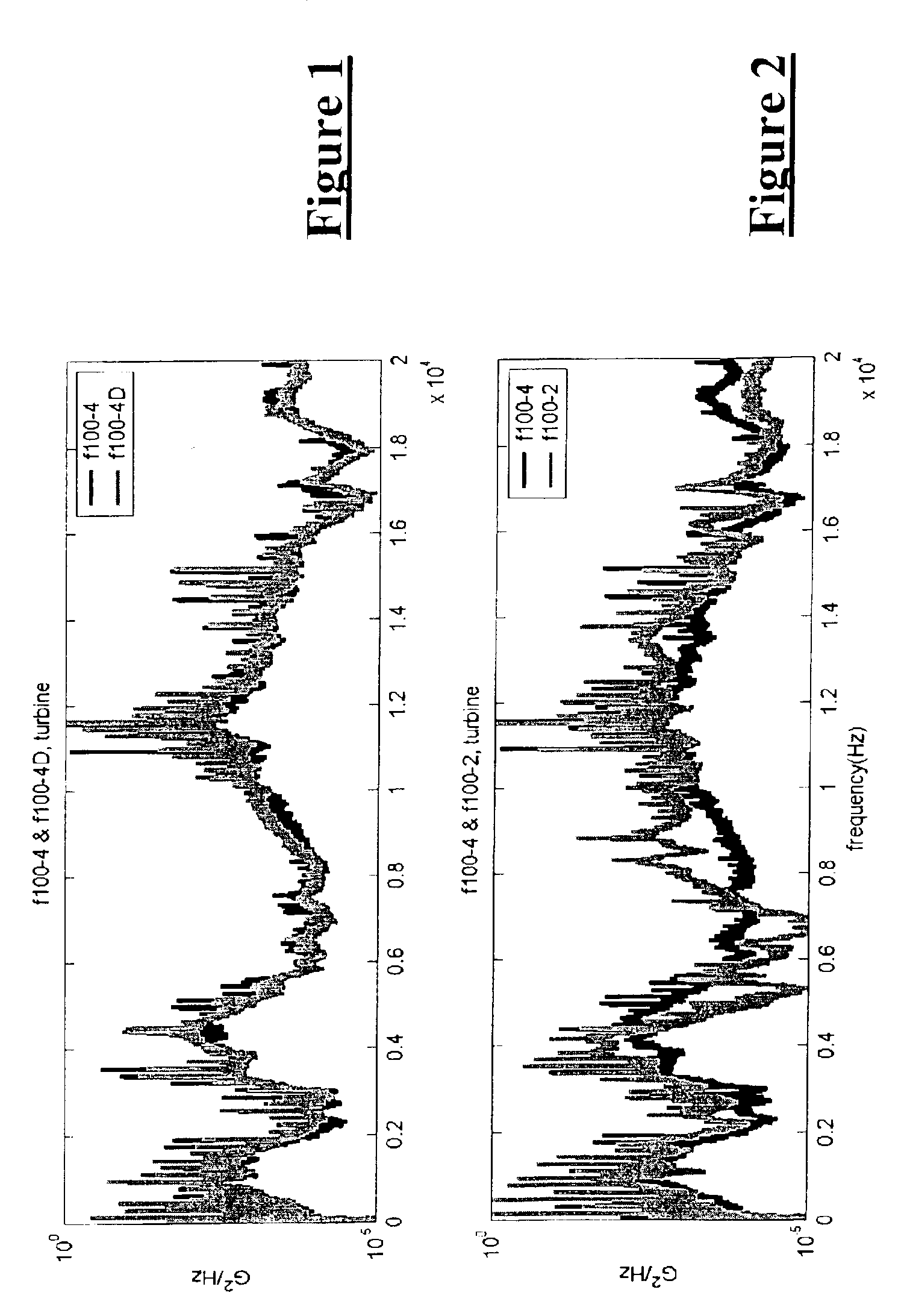
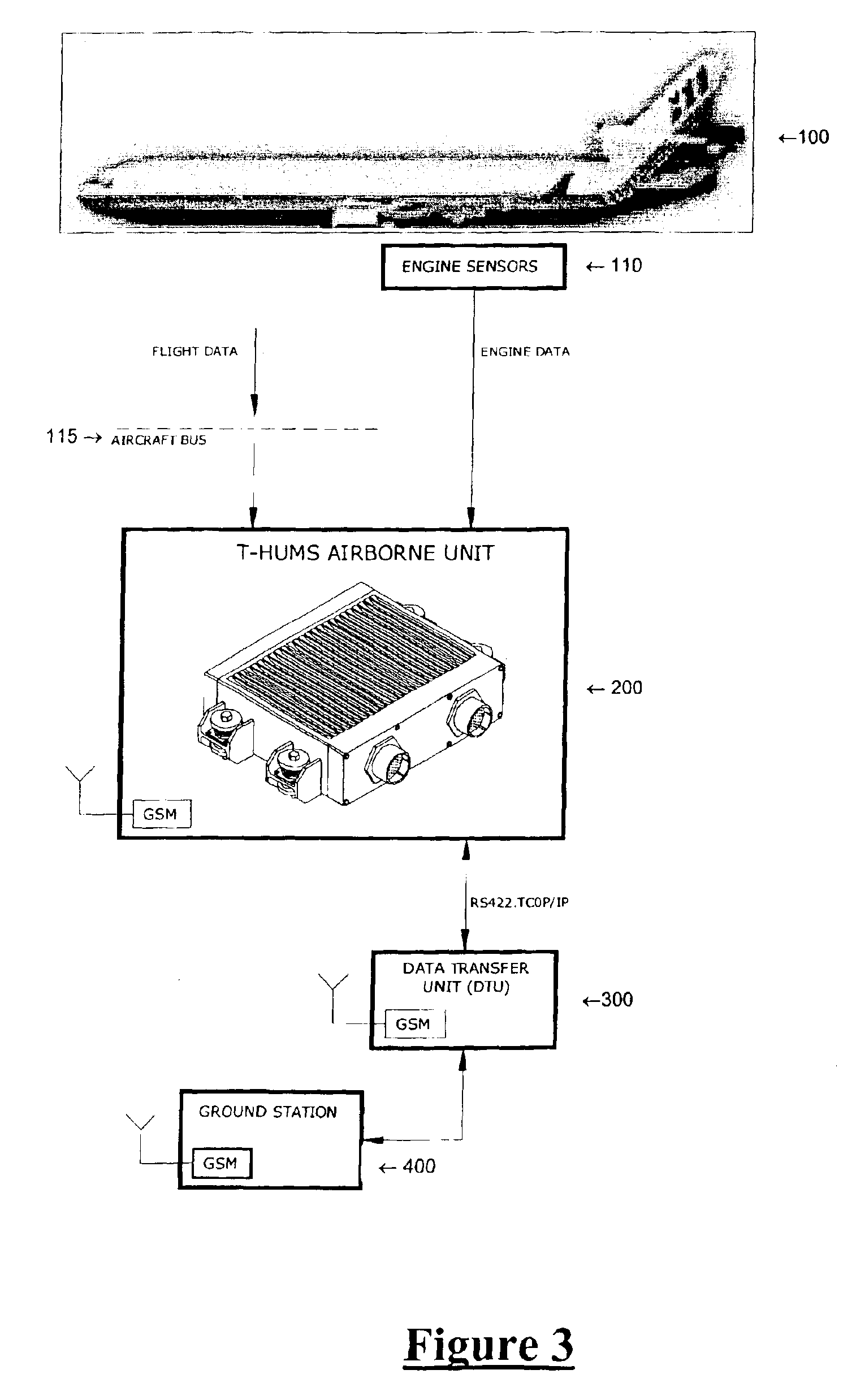
Method and system for diagnostics and prognostics of a mechanical system
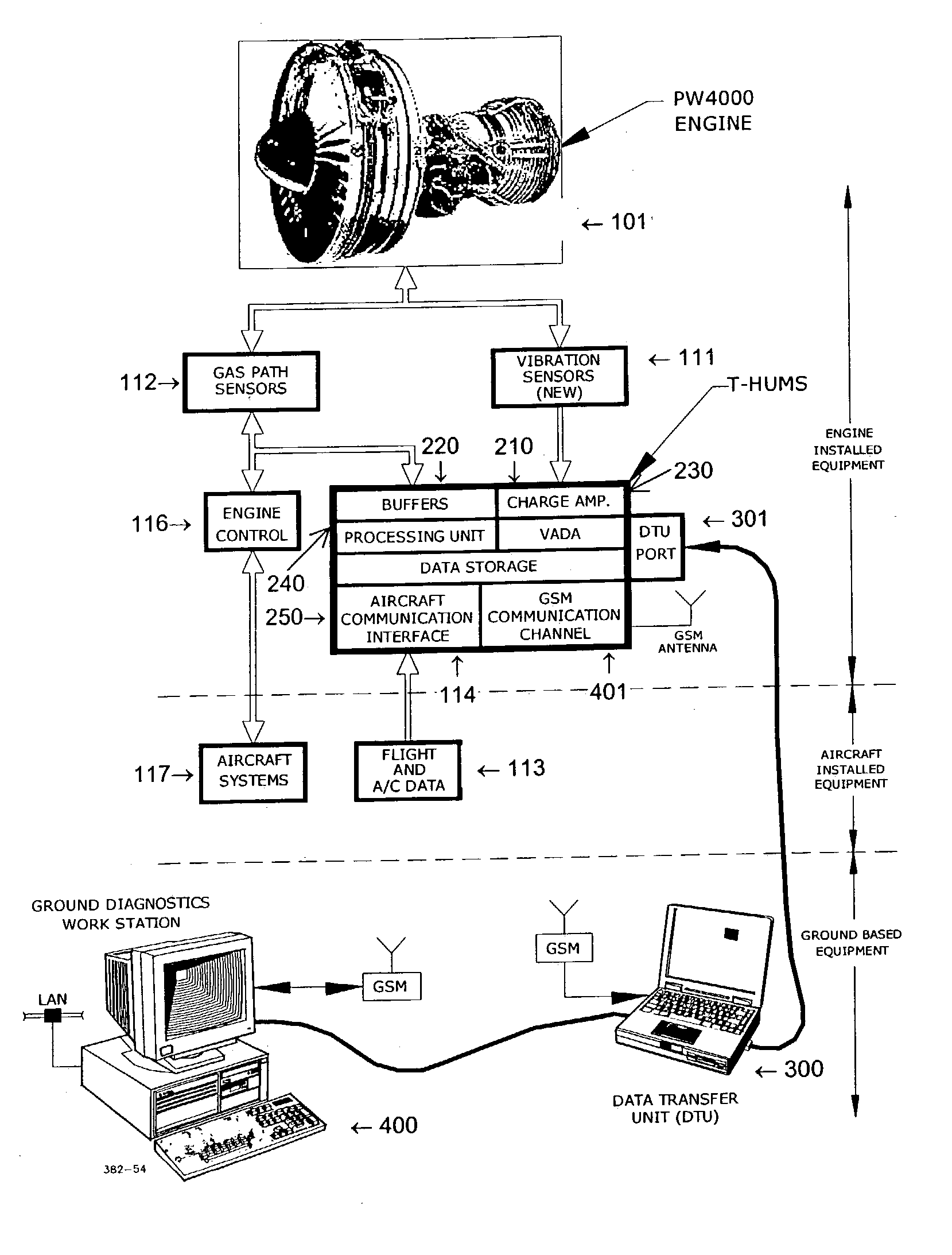
InactiveUS20050096873A1Robust and efficient diagnosing and trendingImprove reliabilityVibration measurement in solidsMachine gearing/transmission testingFeature dataComputer science
A vibrational analysis system diagnosis the health of a mechanical system by reference to vibration signature data from multiple domains. Features are extracted from signature data by reference to pointer locations. The features provide an indication of signature deviation from a baseline signature in the observed domain. Several features applicable to a desired fault are aggregated to provide an indication of the likelihood that the fault has manifested in the observed mechanical system. The system may also be used for trend analysis of the health of the mechanical system.
Owner:RSL ELECTRONICS
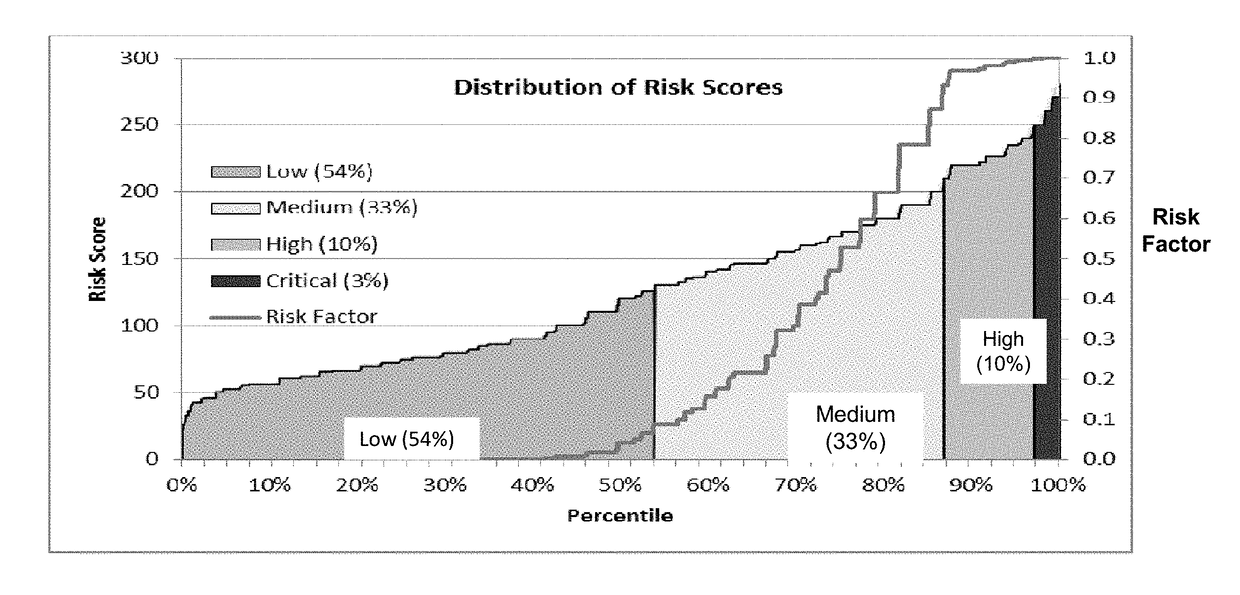
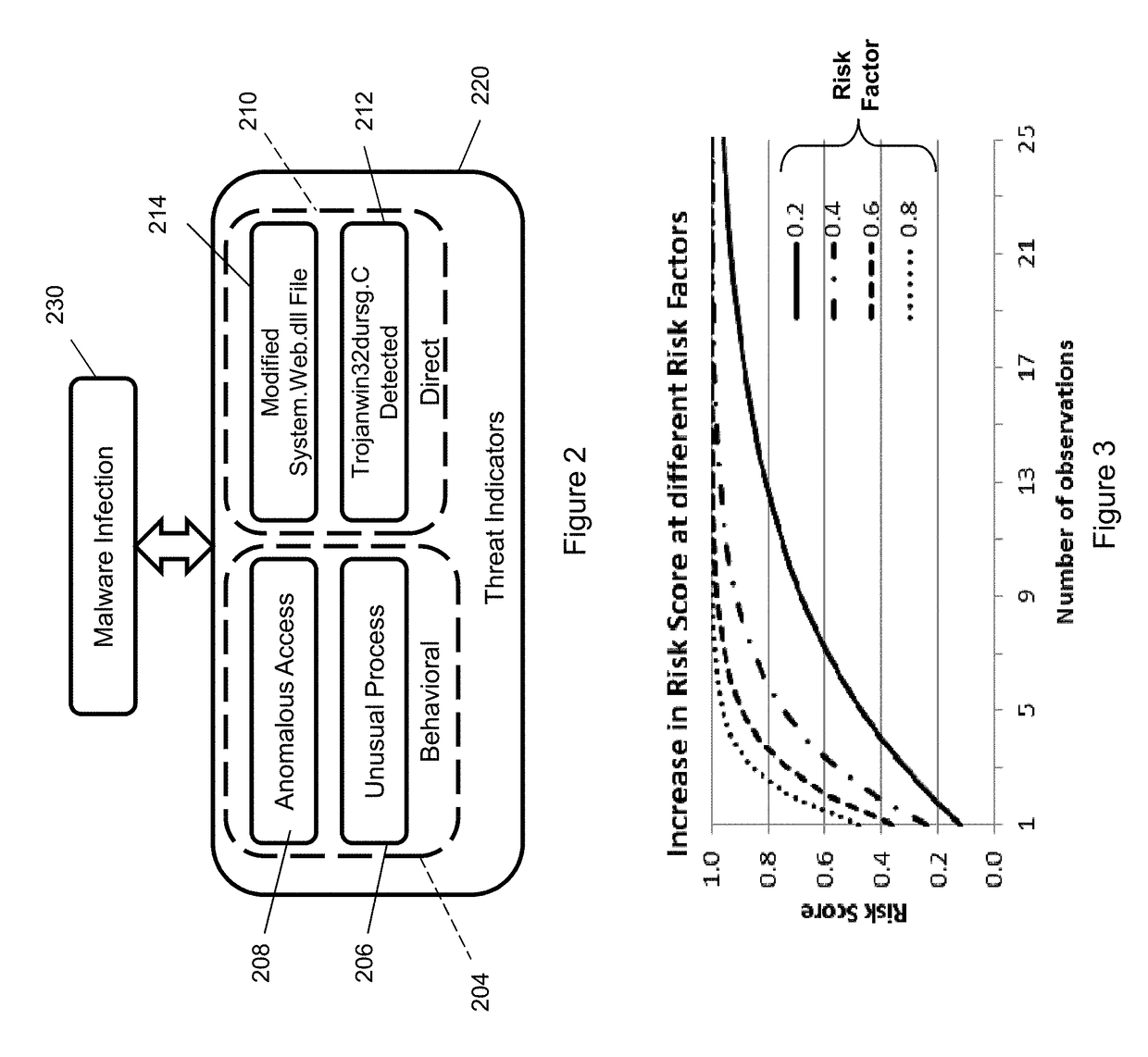
Risk scoring for threat assessment
Threat risks to an enterprise are detected and assessed by assembling singular threats identified using both direct and behavioral threat indicators into composite threats to create complex use cases across multiple domains, and to amplify risks along kill chains of known attacks for early detection. Composite threat risk scores are computed from risk scores of singular threats to exponentially increase with the number of events observed along the kill chain. Composite threats are combined with normalized values of static risk and inherent risk for an entity of the enterprise to produce an entity risk score representative of the overall risk to the entity.
Owner:SECURONIX INC
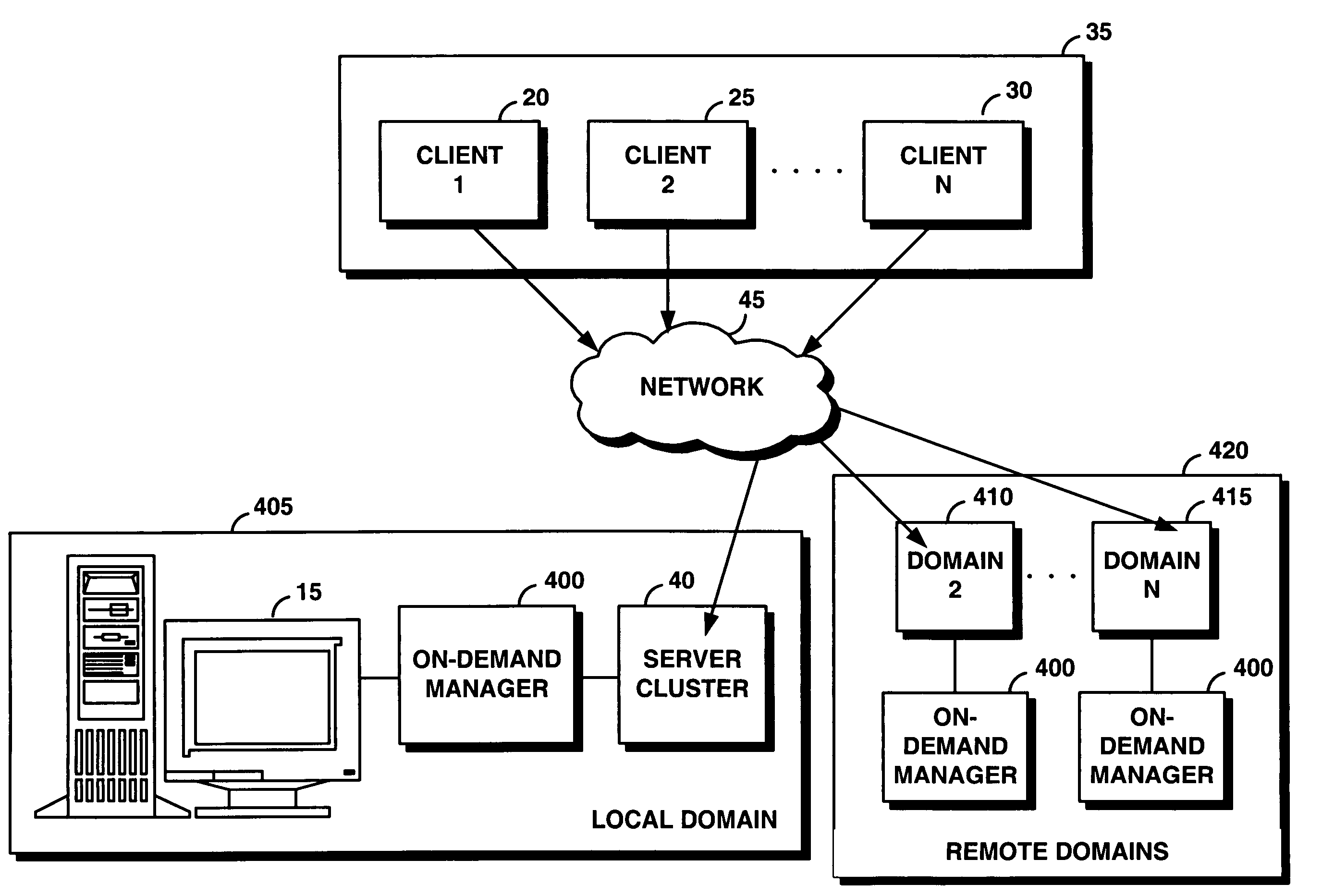
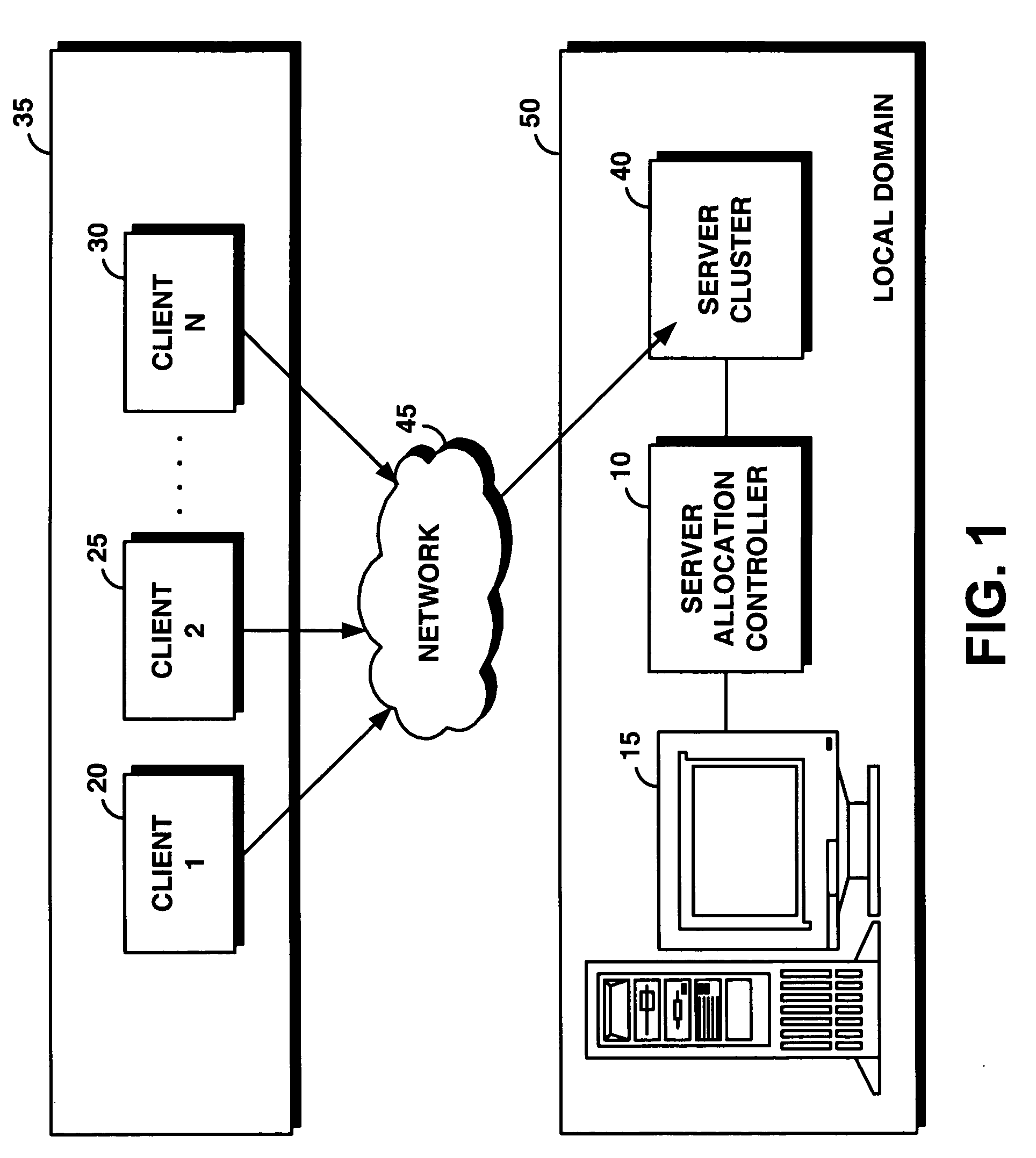
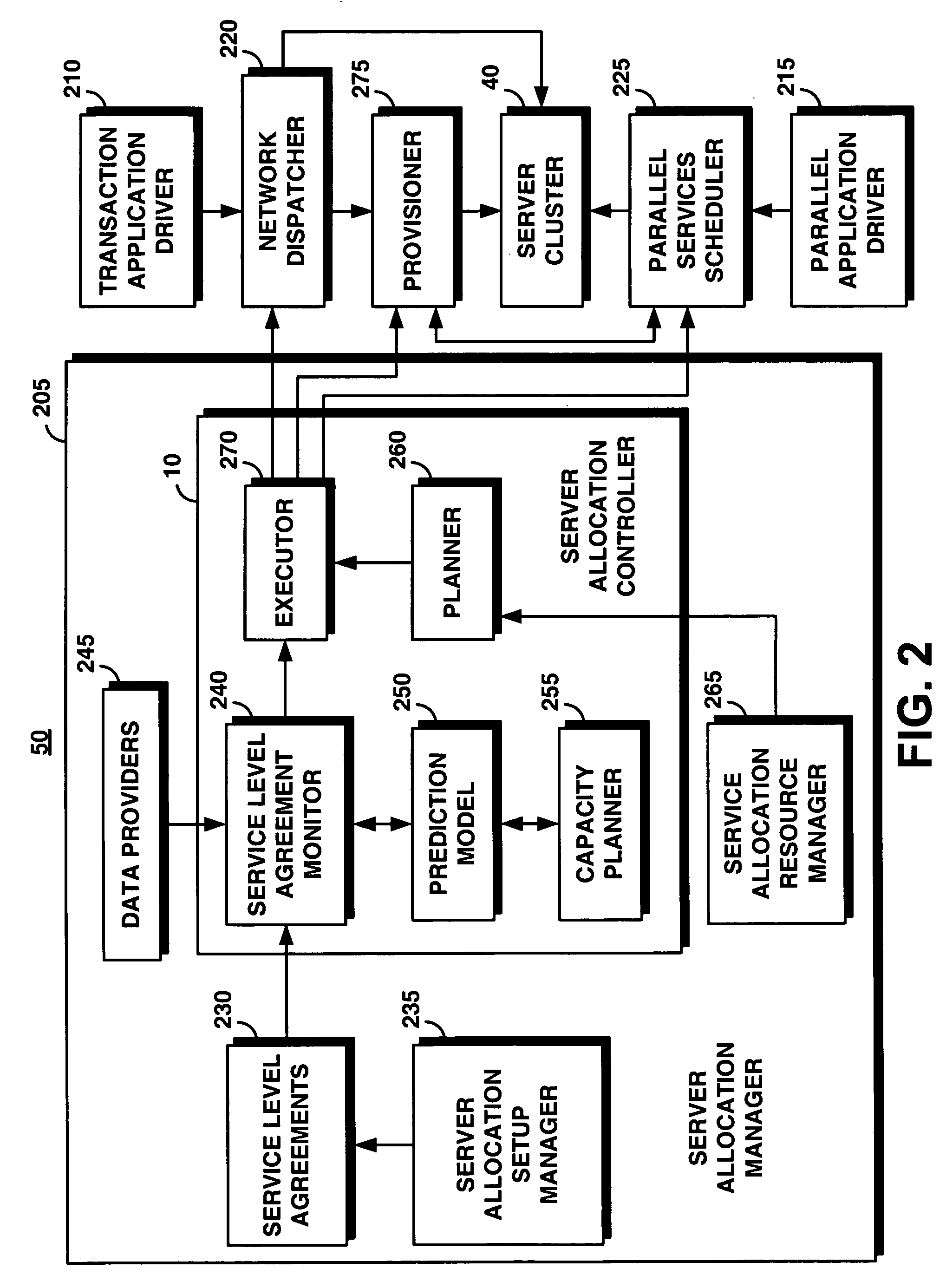
System and method for supporting transaction and parallel services across multiple domains based on service level agreenments
InactiveUS20050165925A1Facilitates dynamic allocationResource allocationDigital computer detailsService-level agreementData processing system
An on-demand manager provides an improved distributed data processing system for facilitating dynamic allocation of computing resources among multiple domains based on a current workload and service level agreements. Based on a service level agreement, the on-demand manager monitors and predicts the load on the system. If the current or predicted load cannot be handled with the current system configuration, the on-demand manager determines additional resources needed to handle the workload. If the service level agreement violations cannot be handled by reconfiguring resources at a domain, the on-demand manager sends a resource request to other domains. These other domains analyze their own commitments and may accept the resource request, reject the request, or counter-propose with an offer of resources and a corresponding service level agreement. Once the requesting domain has acquired resources, workload load balancers are reconfigured to allocate some of the workload from the requesting site to the acquired remote resources.
Owner:IBM CORP
Domain-based management of distribution of digital content from multiple suppliers to multiple wireless services subscribers
ActiveUS7299033B2Digital data information retrievalSpecial service for subscribersDigital contentBusiness enterprise
A network server system includes a download manager that manages the publication, purchase and delivery of digital content from multiple content suppliers to wireless services subscribers in multiple domains. Each domain is defined as a different grouping of subscribers, such as a wireless carrier or subsidiary thereof, a business enterprise, or other defined group of subscribers. The download manager maintains data defining the multiple domains and associations between the domains and wireless services subscribers. Digital content suppliers can publish and manage their products on the server system via a computer network and make their products available to the subscribers for purchase or licensing. The subscribers in each of the domains can access the server remotely to purchase rights to download and use the digital content on associated wireless communication devices.
Owner:UNWIRED PLANET
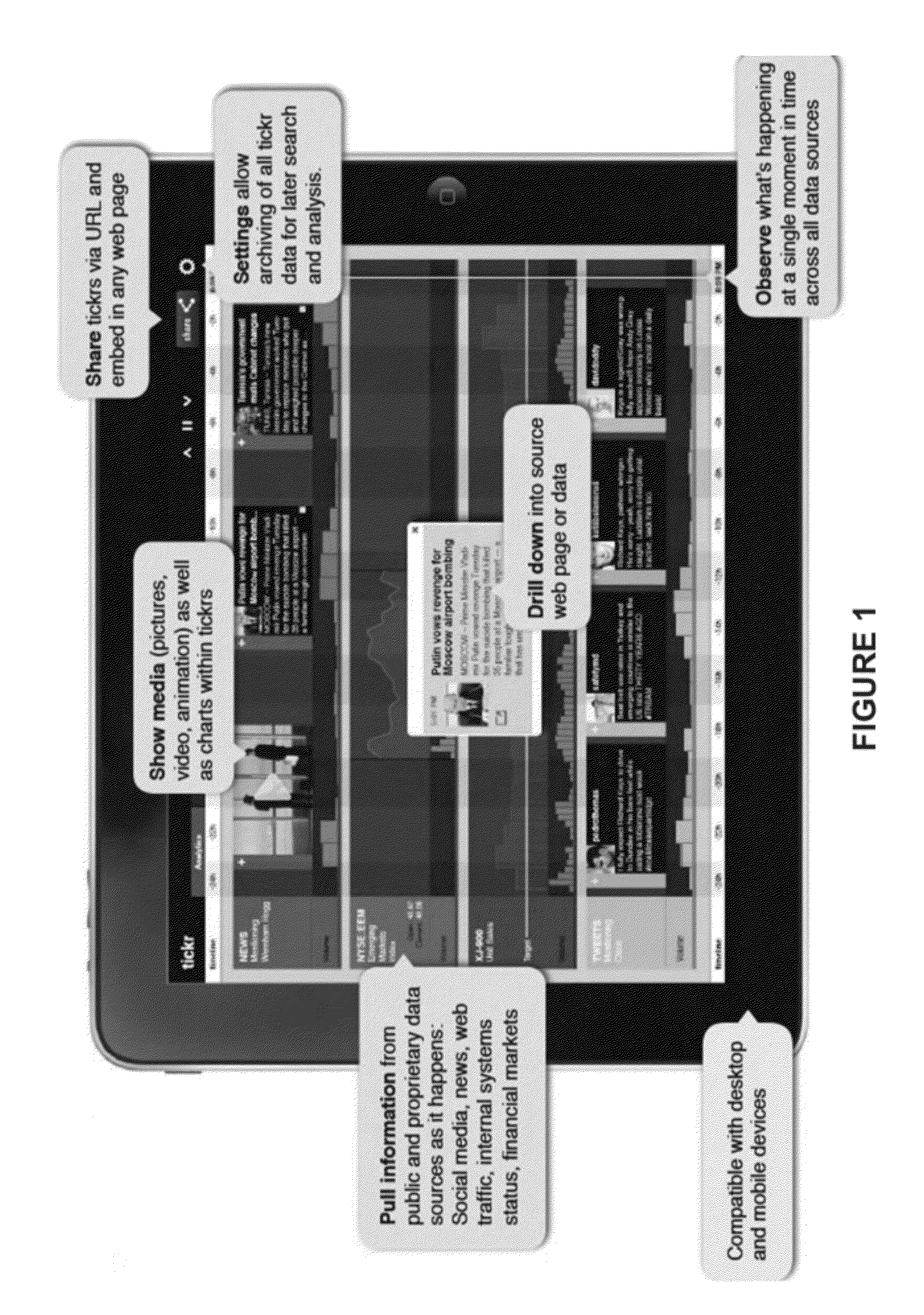
Multi-dimensional visualization of temporal information
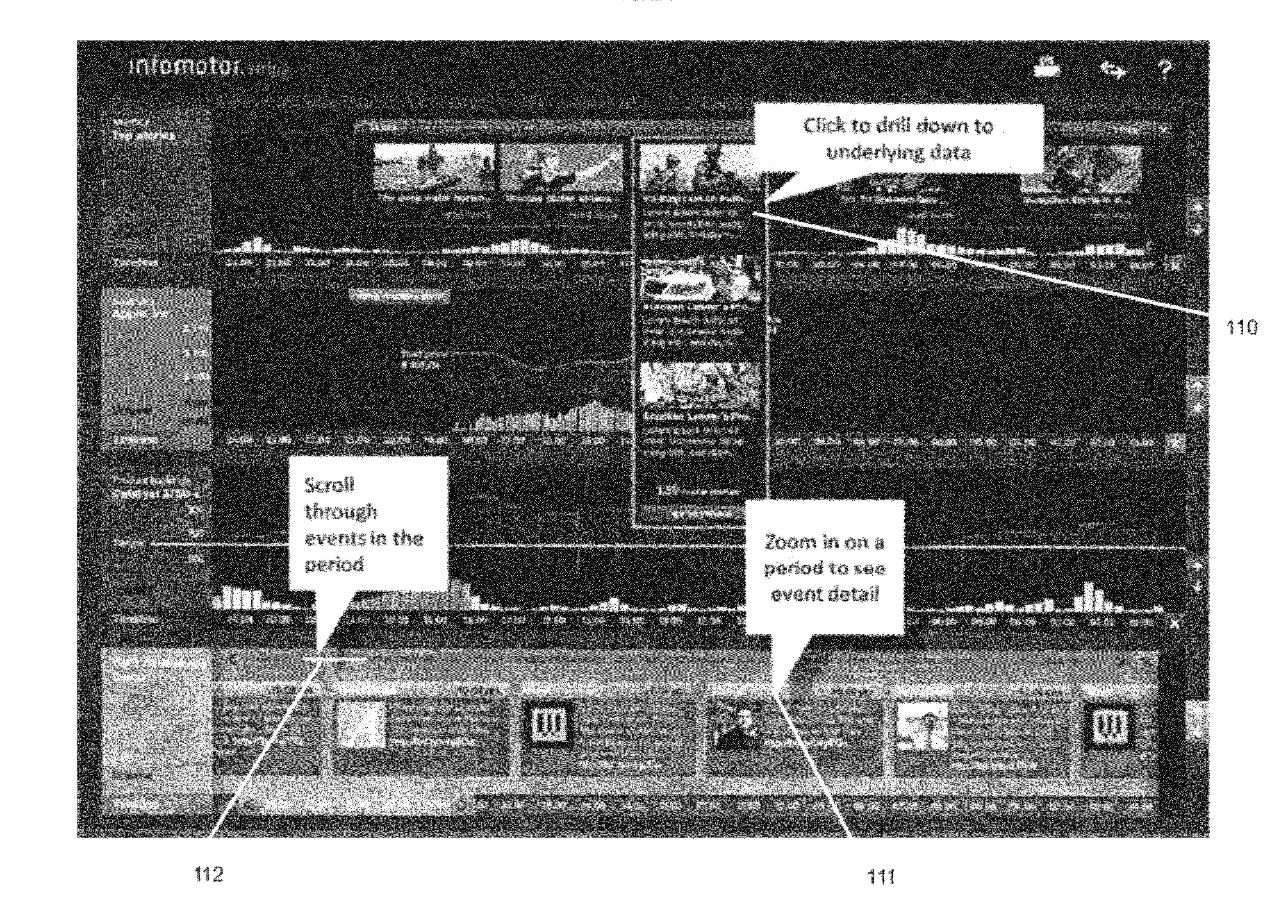
ActiveUS20120173985A1Not simpleDigital data information retrievalSpecial data processing applicationsTemporal informationRelevant information
Various kinds of business and other information are tracked in real time. A coherent information visualization, for example as a time line, automatically, simultaneously presents relevant information to a user across multiple dimensions. Tools are provided that allow the user to establish and manipulate multi-dimensional linkages to develop insights into information gathered from multiple domains.
Owner:TICKR
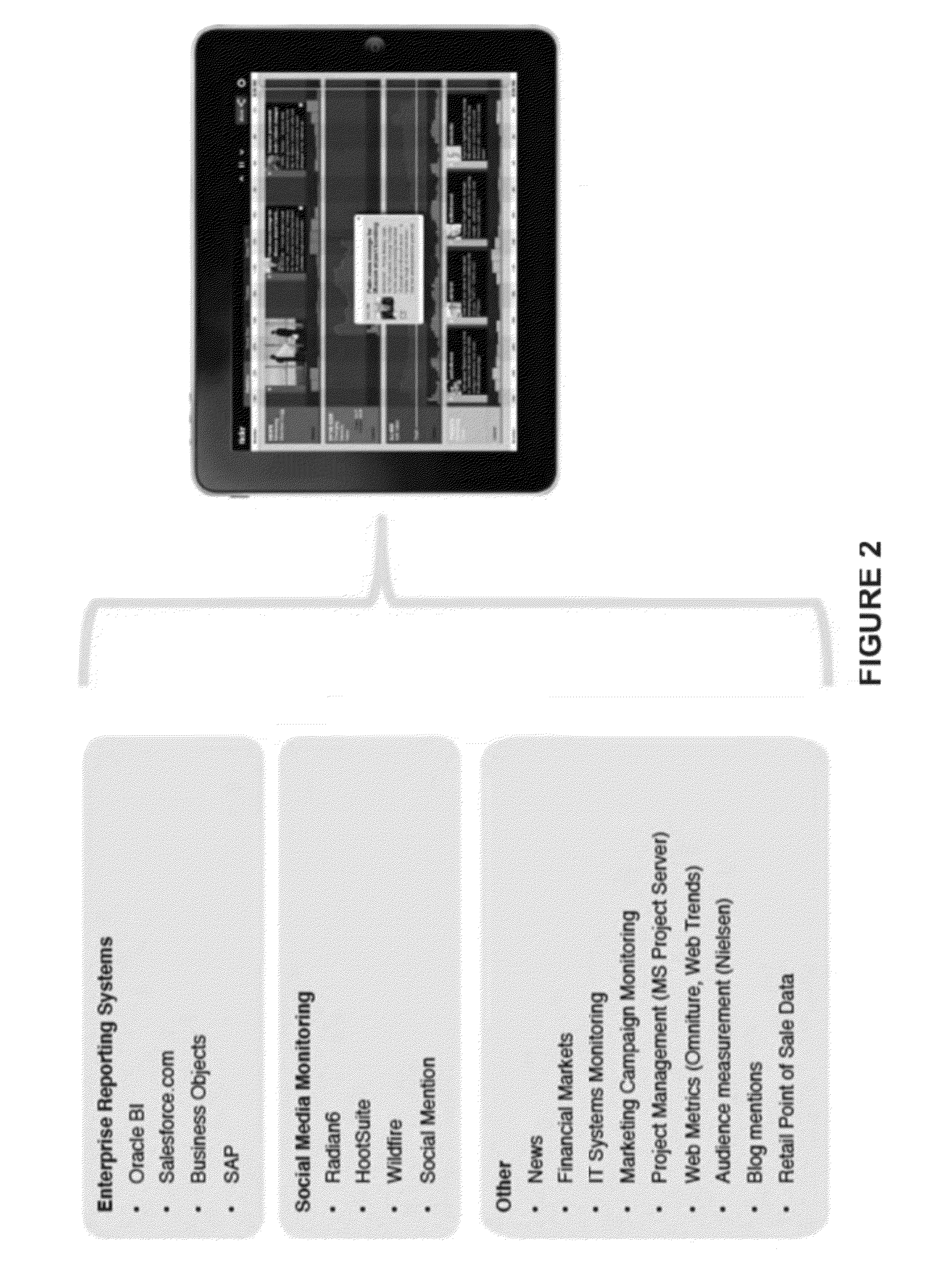
Shared view of customers across business support systems (BSS) and a service delivery platform (SDP)
ActiveUS8073810B2Overcome deficienciesDigital data processing detailsDatabase distribution/replicationData aggregatorCustomer information
Owner:ORACLE INT CORP
Systems and methods for responding to natural language speech utterance
ActiveUS20100057443A1Promotes feeling of naturalSignificant to useDigital data information retrievalSemantic analysisPrior informationSpeech sound
Systems and methods are provided for receiving speech and non-speech communications of natural language questions and / or commands, transcribing the speech and non-speech communications to textual messages, and executing the questions and / or commands. The invention applies context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for one or more users presenting questions or commands across multiple domains. The systems and methods creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context of the speech and non-speech communications and presenting the expected results for a particular question or command.
Owner:DIALECT LLC
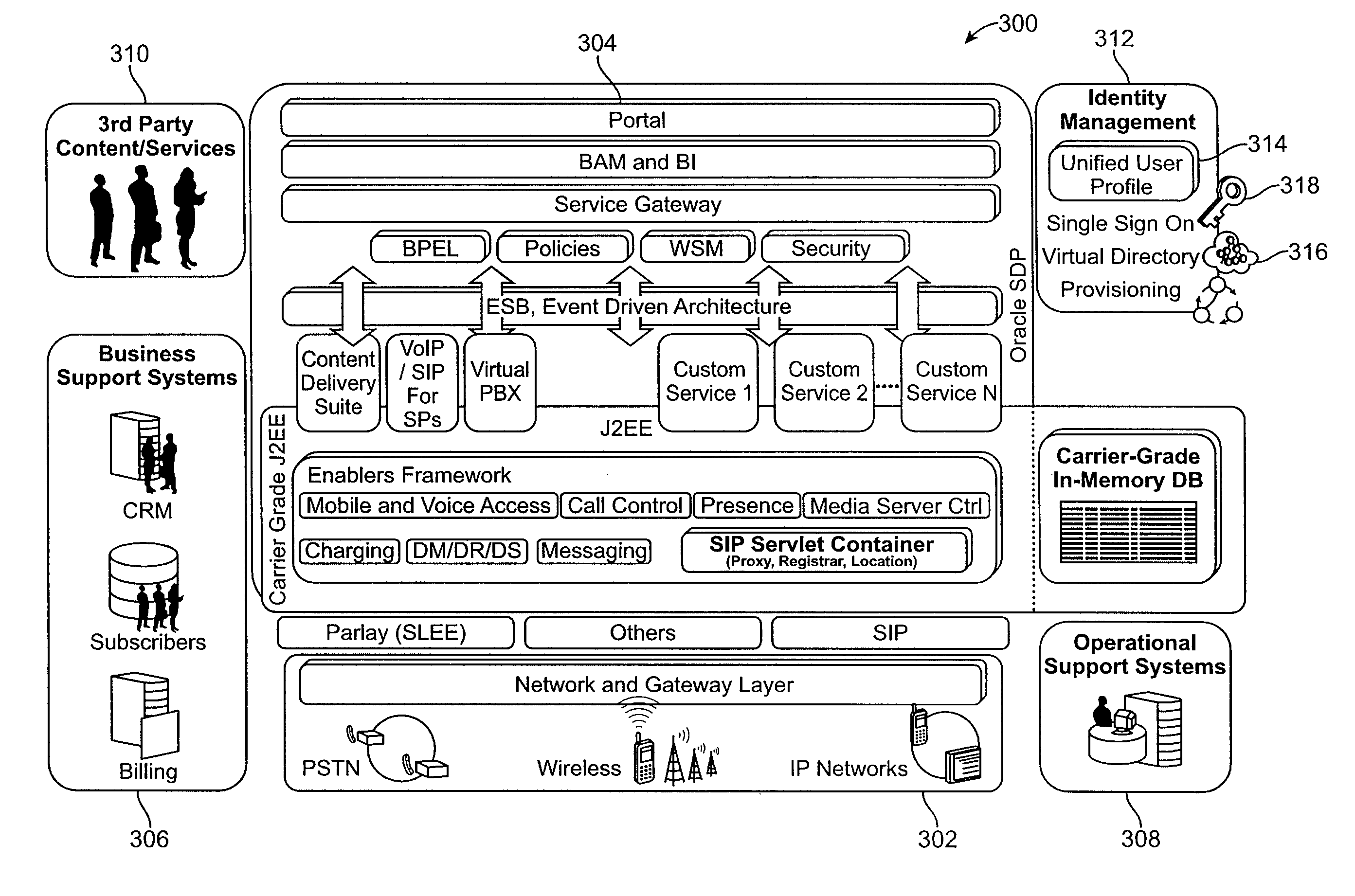
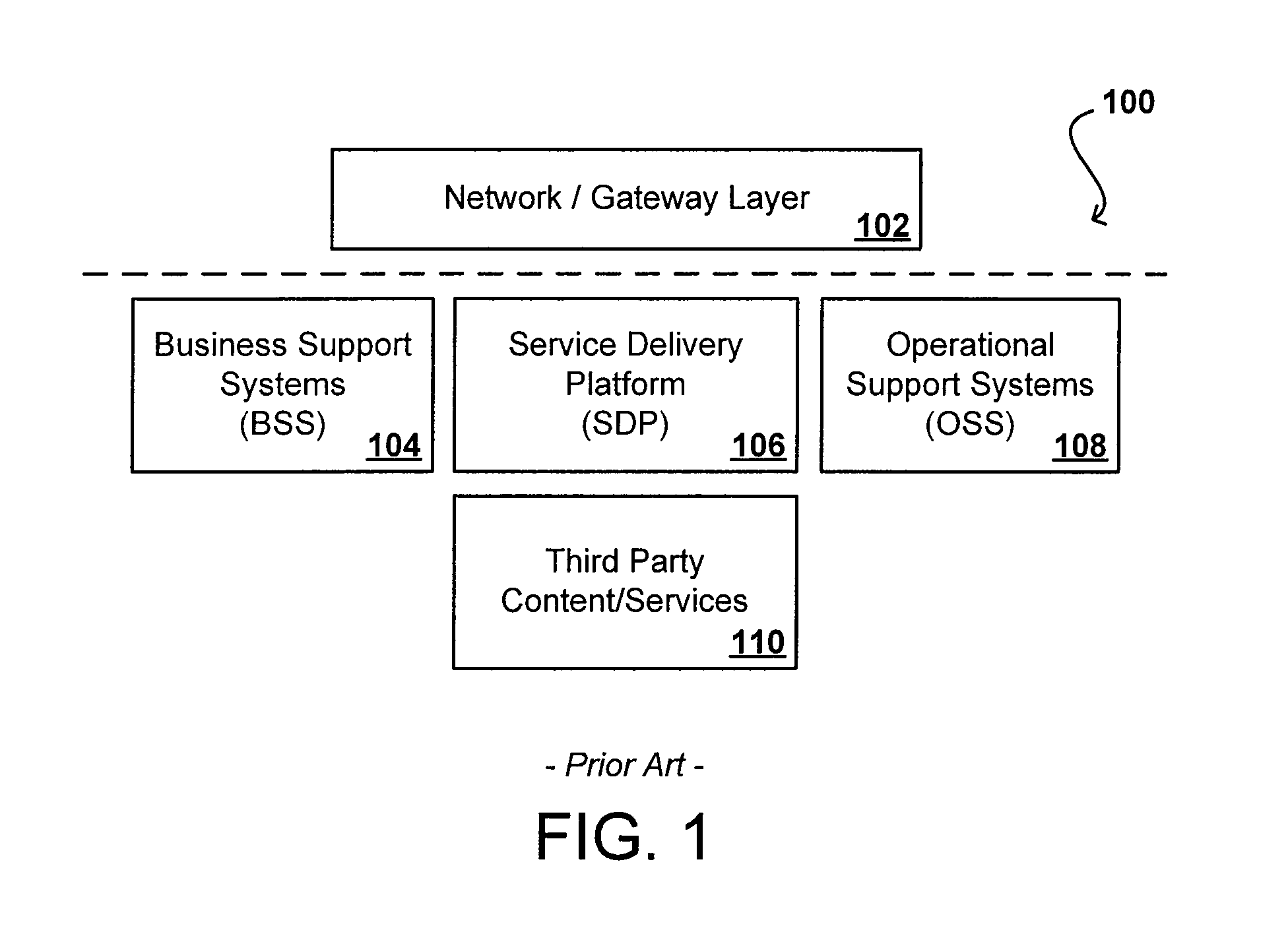
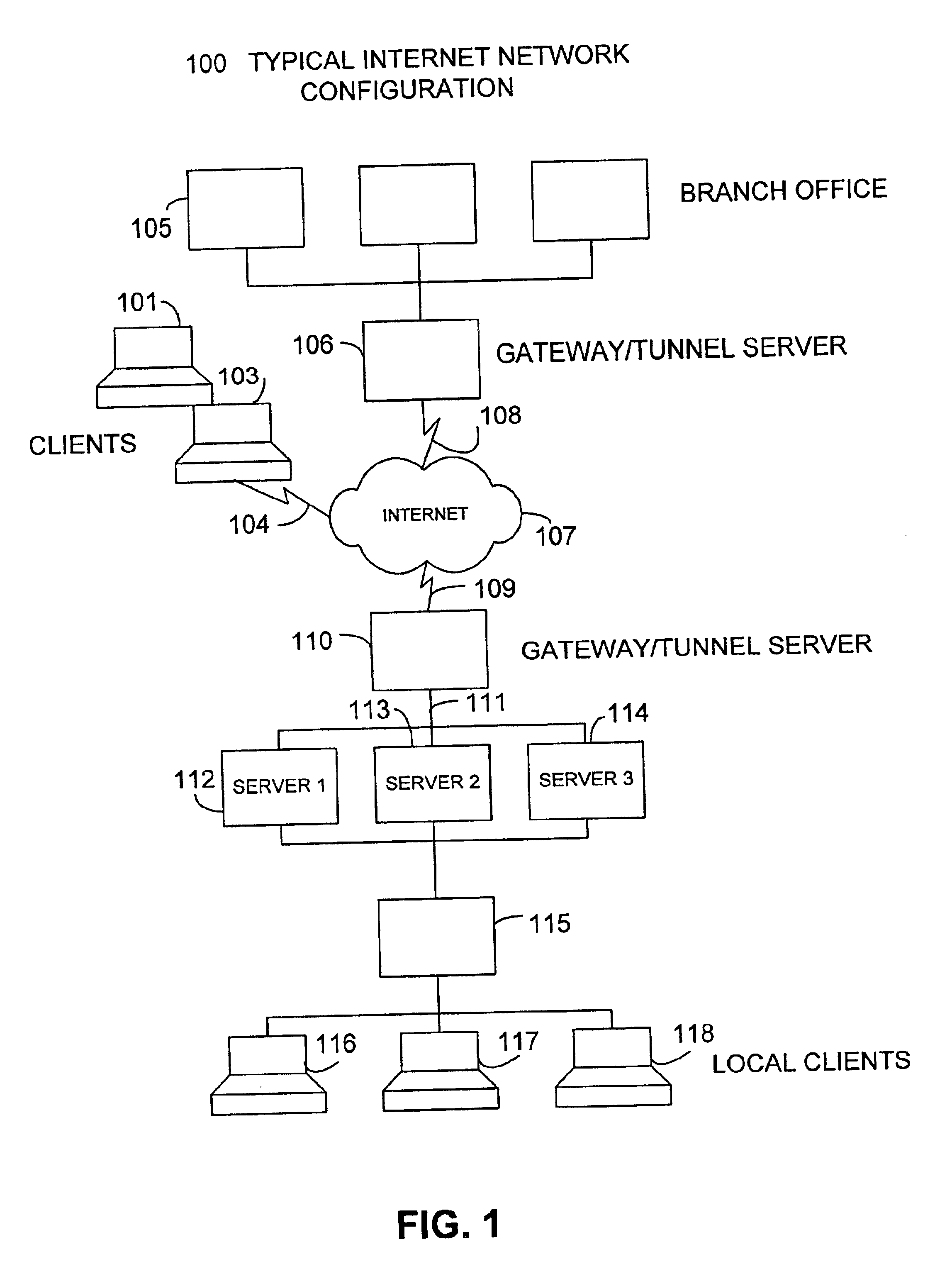
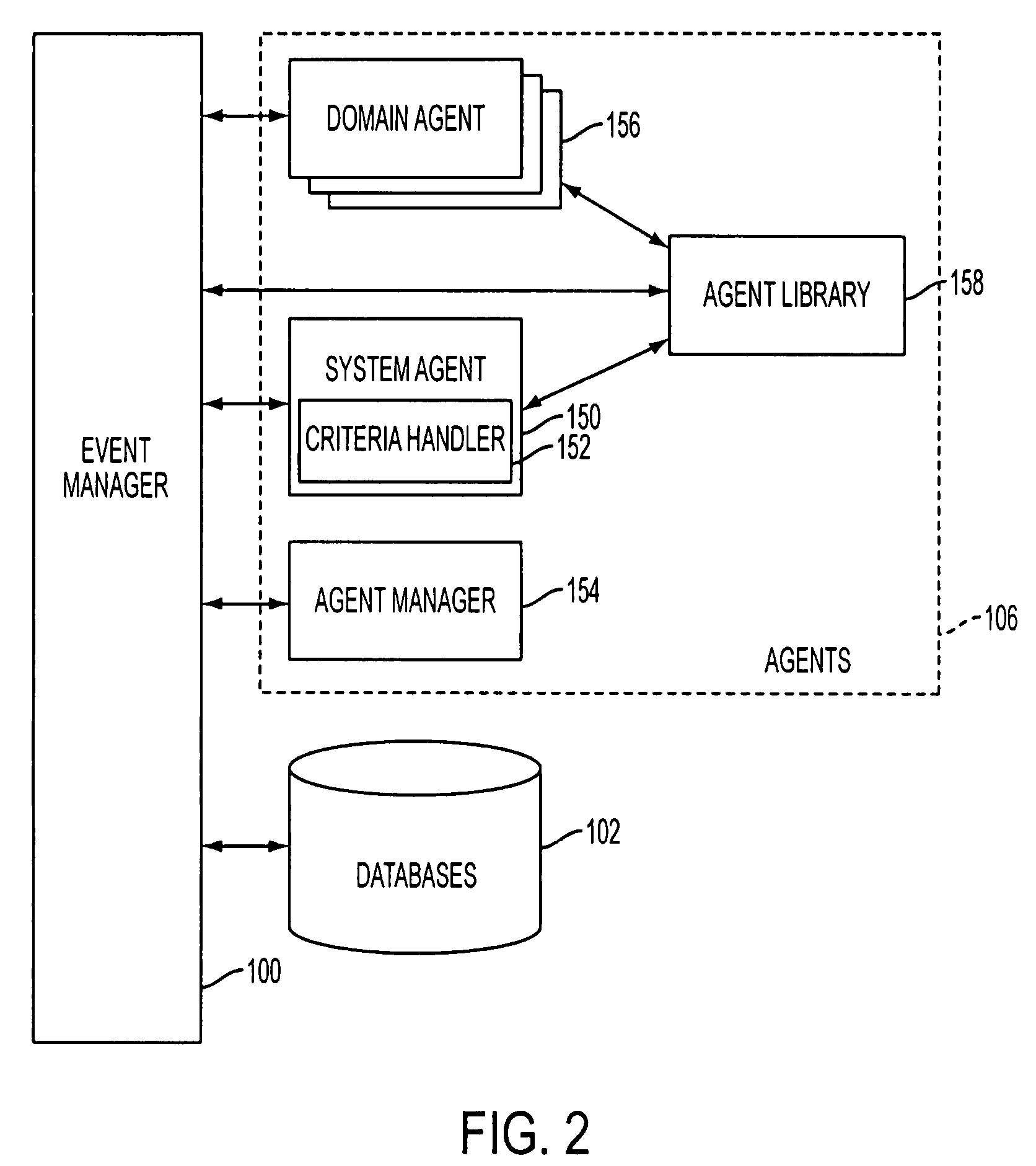
Reconfigurable service provision via a communication network
InactiveUS6330586B1Customer base for information services is particularly wideLarge capacityMultiplex system selection arrangementsData processing applicationsReconfigurabilityReusable software
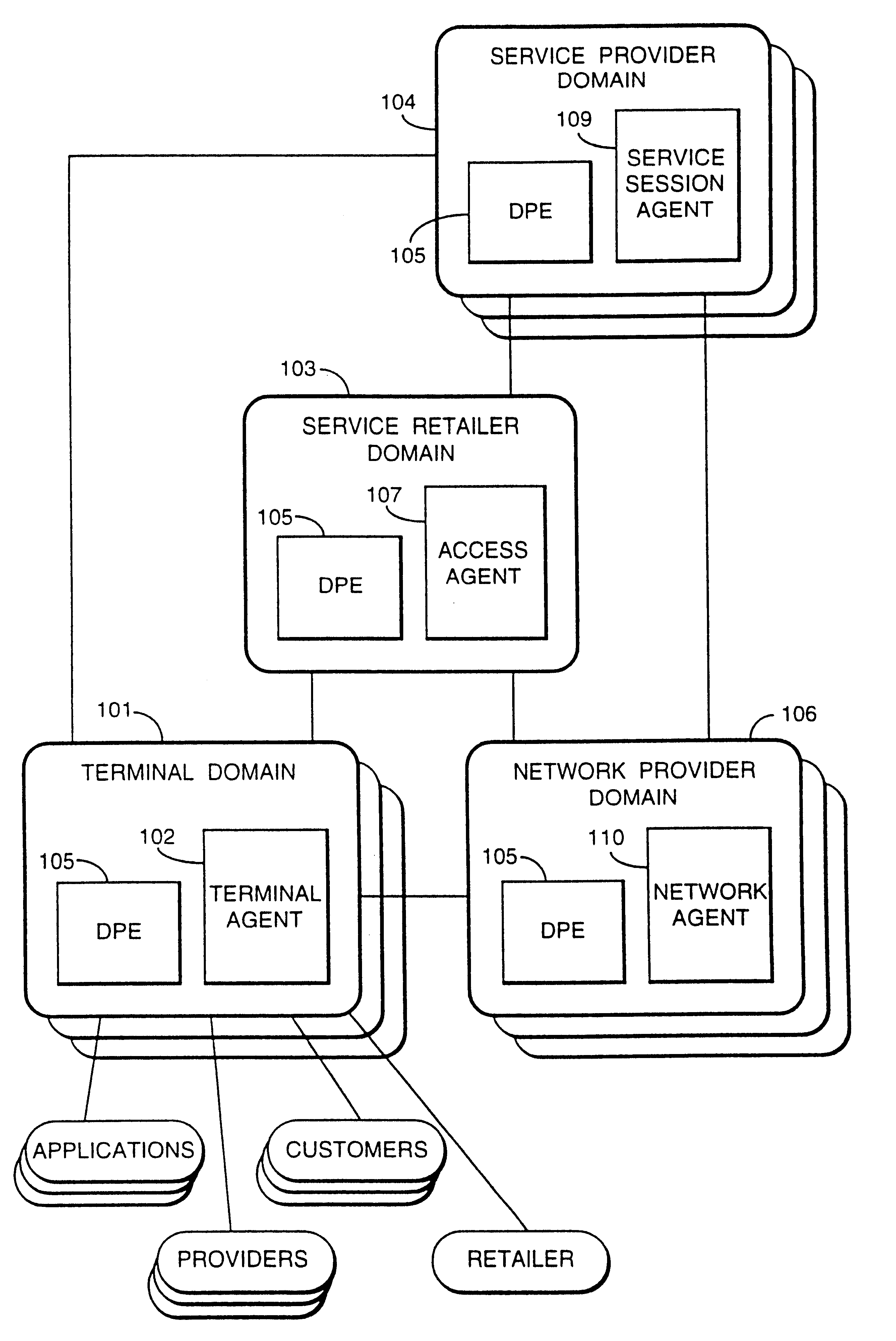
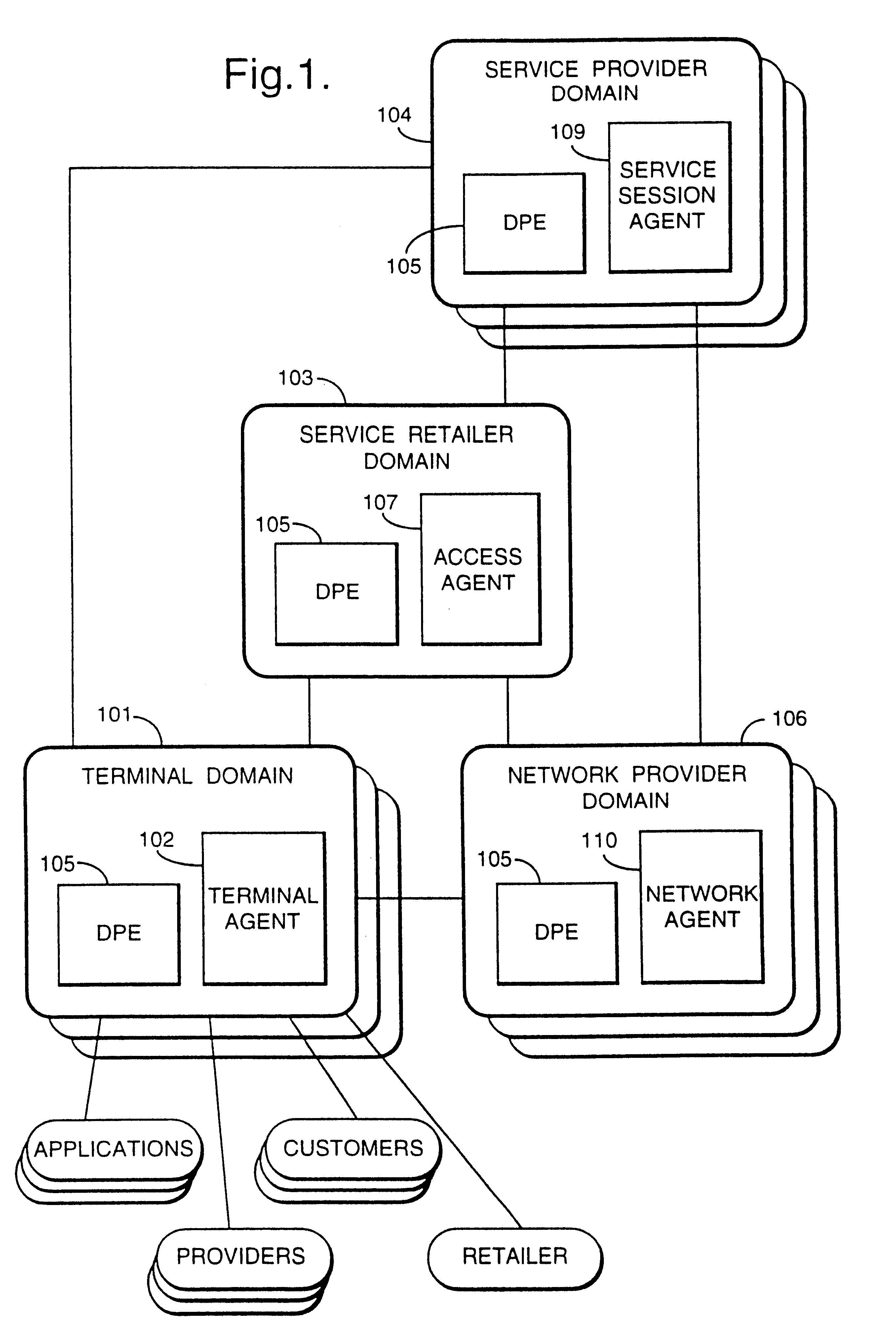
A services provision system provides information services over one or more communications networks and has a software infrastructure divided into domains. Each domain has an intelligent software agent and this community of agents sits in a computing environment represented in each domain by a DPE kernel. The community of agents co-operates to provide service and service management functionality to a user. At least one of the agents is reconfigurable to change the functionality the system makes available. Reconfigurability is based on the use of a plurality of reusable software modules, the agent reconfiguring by selecting a new combination of modules. The software modules themselves incorporate rules, or policies, which determine process steps offered by the modules at run-time. These policies are external to the modules and may be loaded at run-time, allowing dynamic modification to functionality of the system. The system as a whole offers functionality associated with using services, providing them and managing them and the reconfigurability allows it to offer the different types of functionality in an efficient way. It also allows access control to functionality at different levels with particularly good security against fraudulent use.
Owner:BRITISH TELECOMM PLC
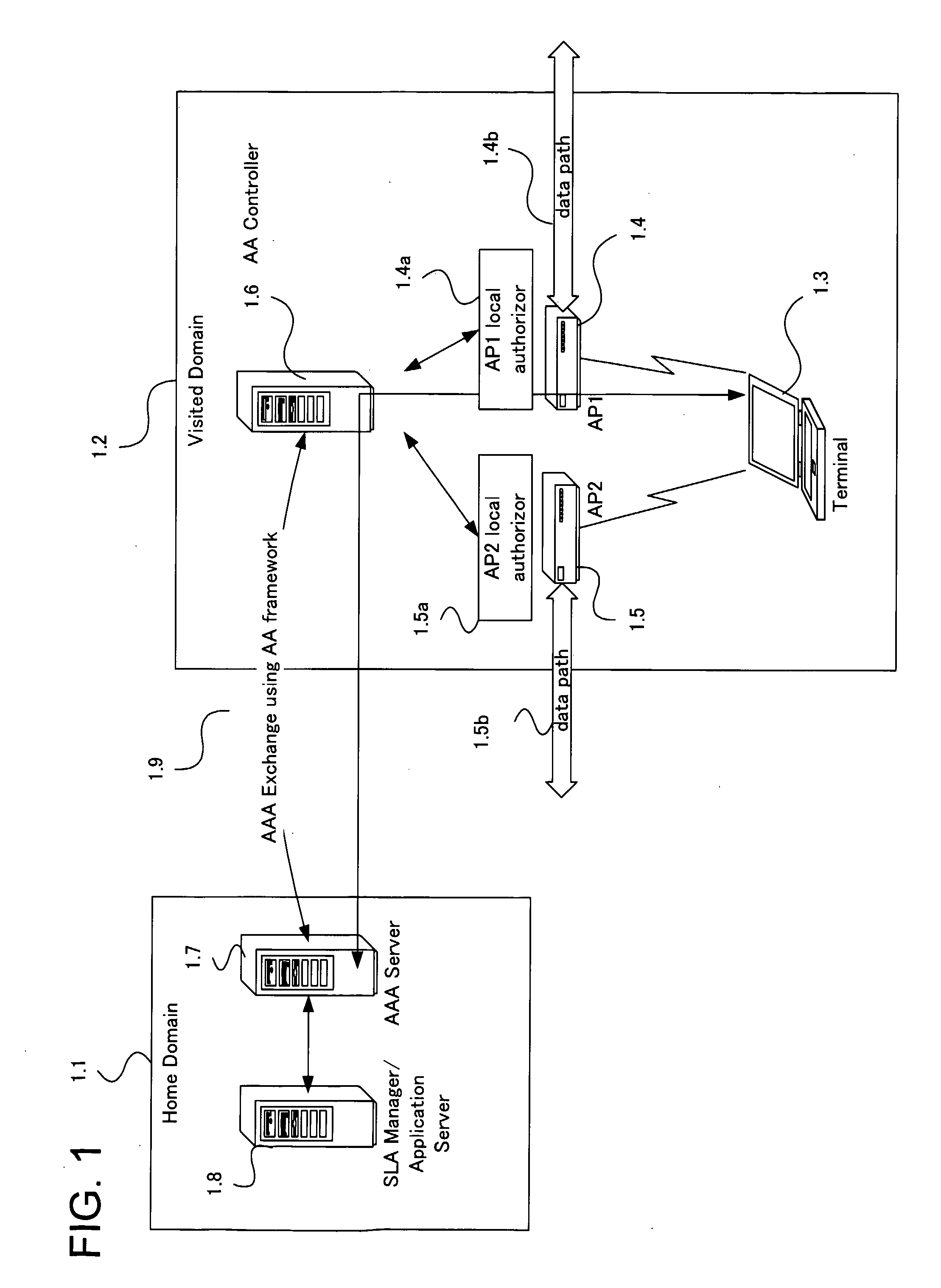
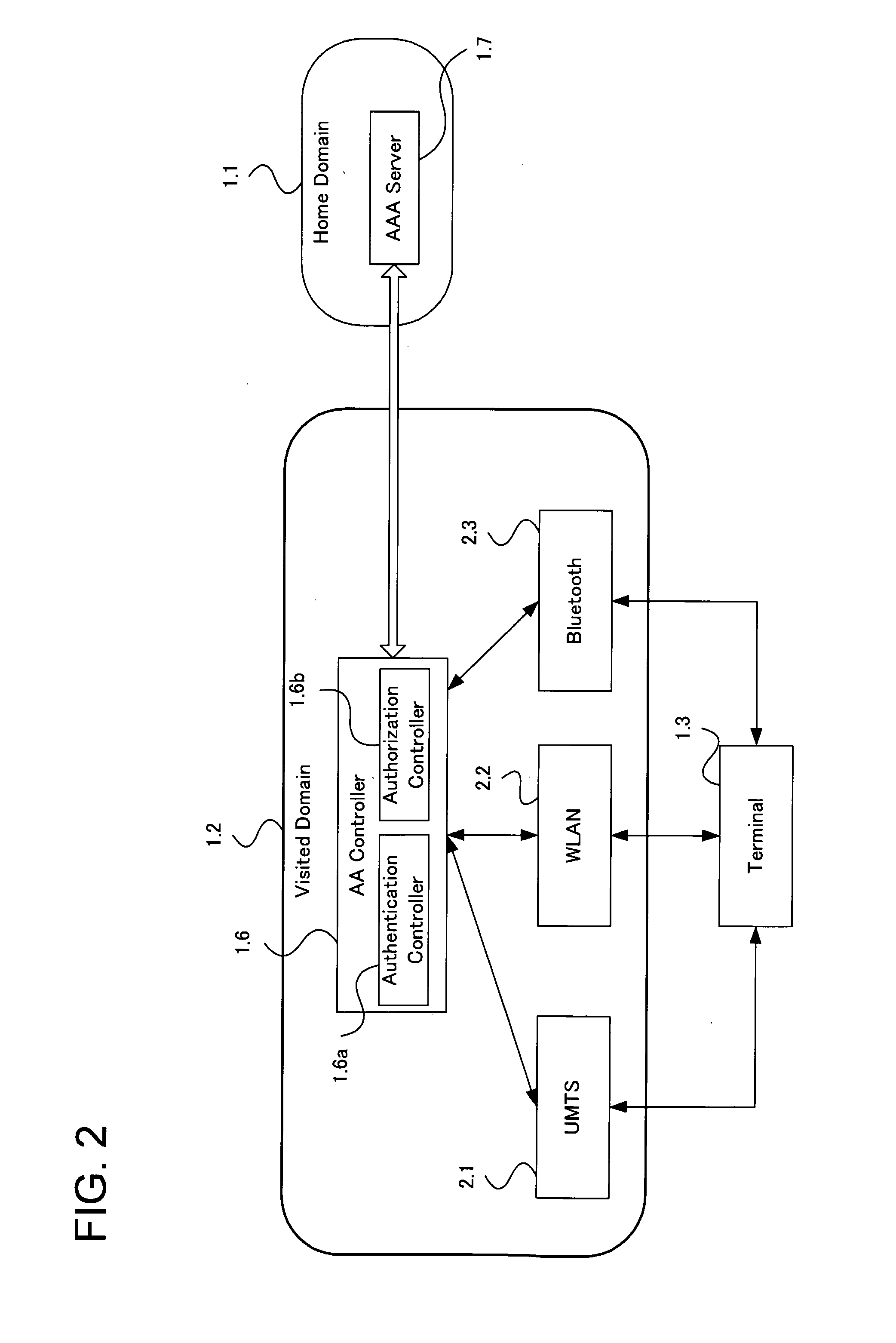
System And Method For Managing User Authentication And Service Authorization To Achieve Single-Sign-On To Access Multiple Network Interfaces
InactiveUS20080072301A1Timely controlShorten the timeDigital data processing detailsUser identity/authority verificationUser authenticationNetwork management
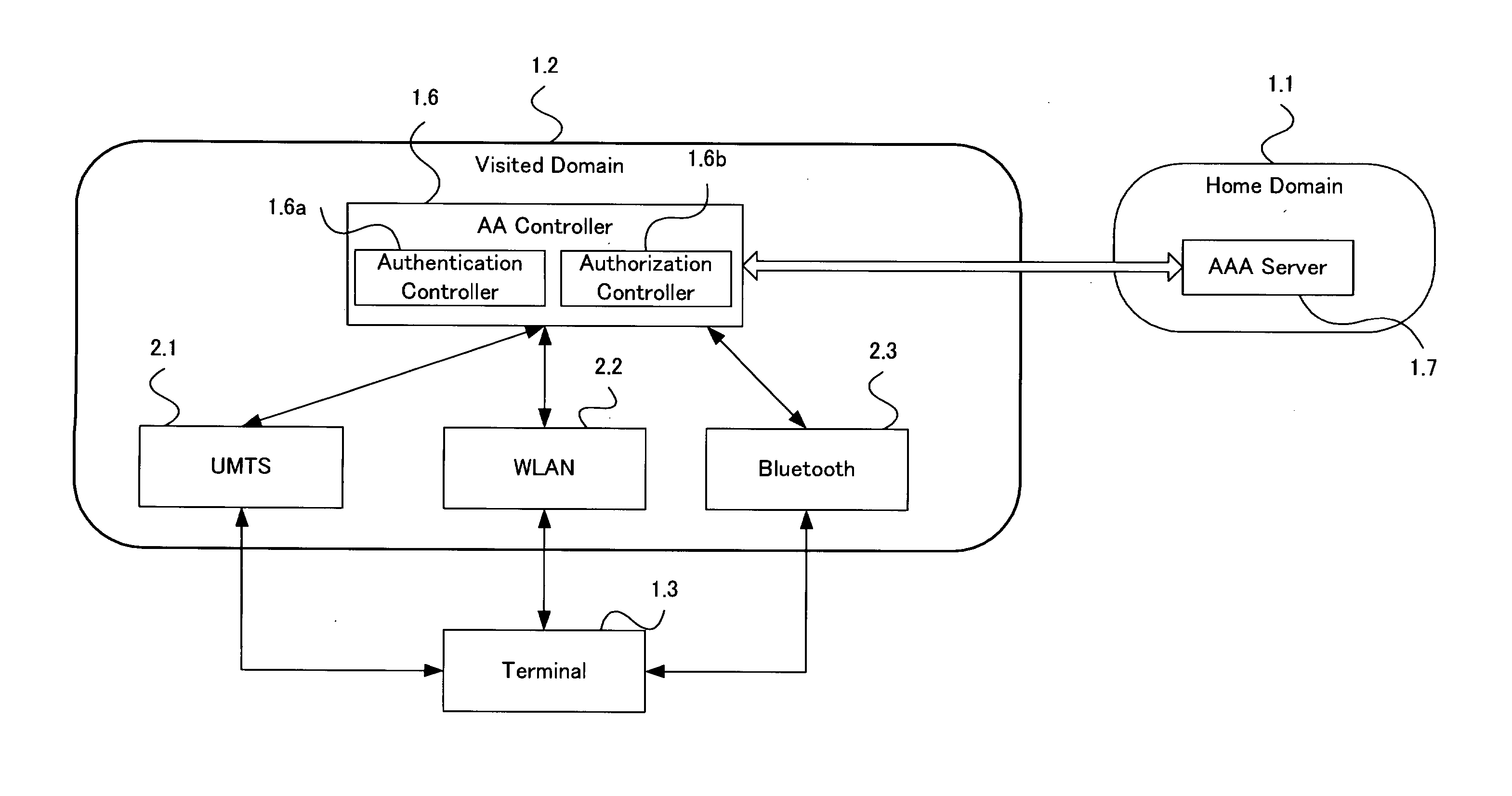
A single-sign-on to access multiple networks residing at multiple domains is disclosed. In particular the single-sign-on features refers to the authentication and the authorization process carried out among the different network administration domains so that the terminal using the end service need not explicitly initiate the authentication process each time it accesses a new service. This invention's single-sign-on feature can be extended for usage in a federated domain environment and non-federated domain environment. The non-federated domains are able to form an indirect federation chain through other domains in order to utilize this invention. Therefore discovery of intermediate domains to form a federation chain is also covered. The management of user credentials to allow a Visited Domain to perform authentication is also covered in this invention.
Owner:PANASONIC CORP
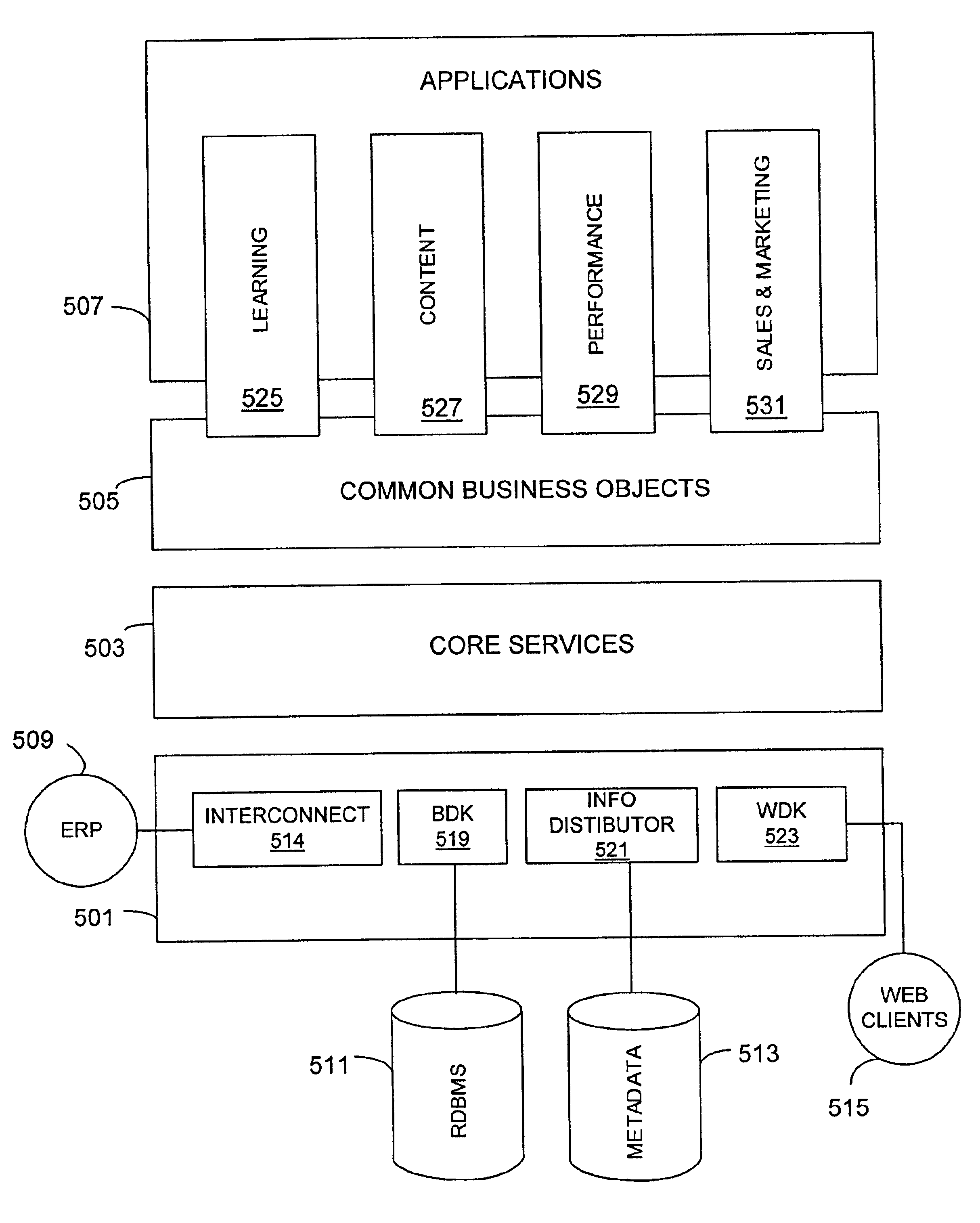
Method and apparatus for an improved security system mechanism in a business applications management system platform
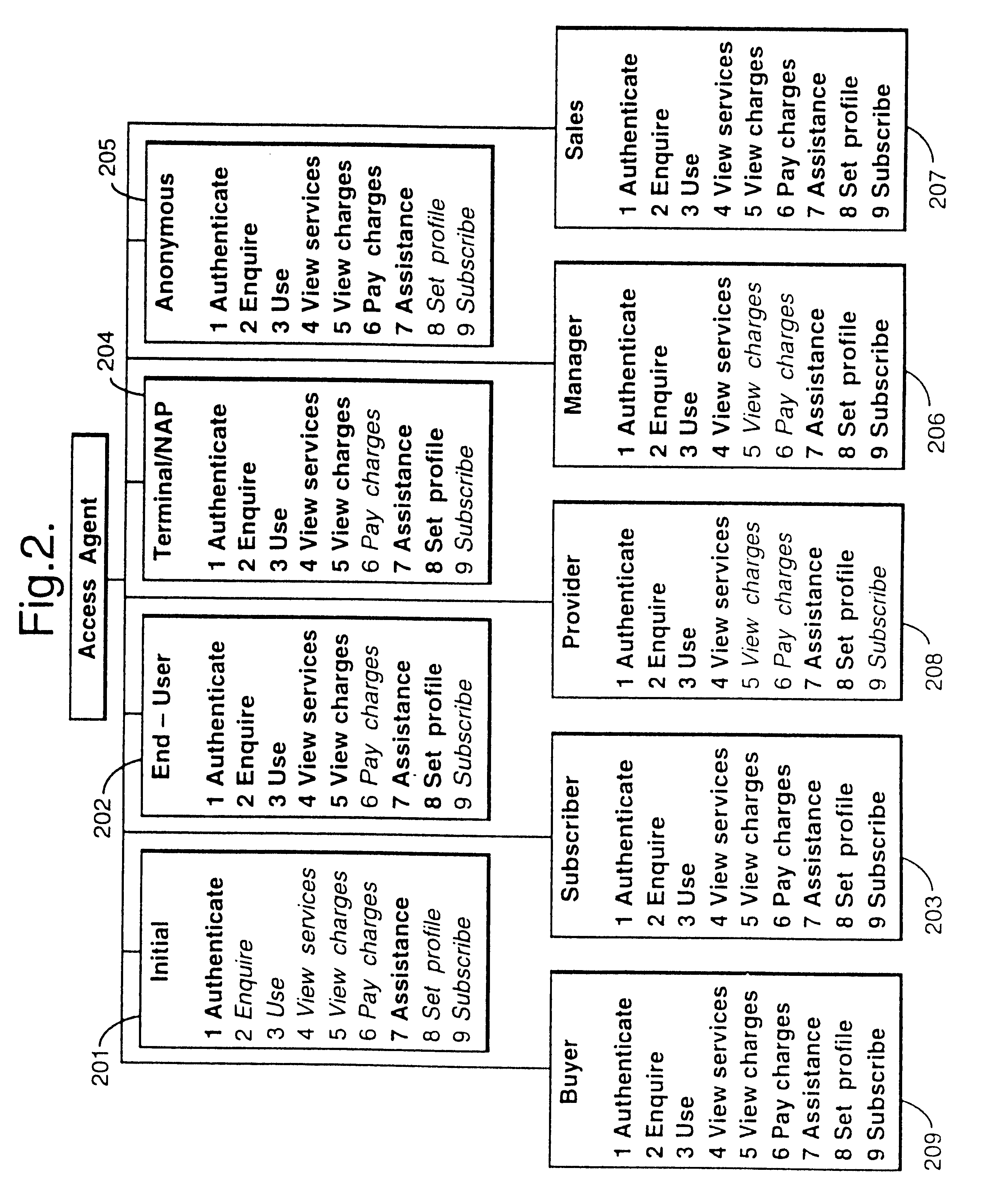
InactiveUS6850893B2Minimizing user input effortMinimize effortSpecific access rightsDigital data processing detailsSafety management systemsImproved method
The present invention provides a solution to the needs described above through an improved method and apparatus for an improved security system mechanism in a business applications management system platform. The security management system partitions a number of business objects into a number of hierarchical domains. A security list is then created and configured to grant a member the right to perform a security operation on the business object located within the hierarchical domain. The security list is created by adding the security operation to the security list, applying the security operation to one of the multiple domains, and adding members to the security list.
Owner:SABA SOFTWARE
Method and system for diagnostics and prognostics of a mechanical system
InactiveUS7027953B2Robust and efficient diagnosing and trendingImprove reliabilityVibration measurement in solidsMachine gearing/transmission testingSystem diagnosisComputer science
A vibrational analysis system diagnosis the health of a mechanical system by reference to vibration signature data from multiple domains. Features are extracted from signature data by reference to pointer locations. The features provide an indication of signature deviation from a baseline signature in the observed domain. Several features applicable to a desired fault are aggregated to provide an indication of the likelihood that the fault has manifested in the observed mechanical system. The system may also be used for trend analysis of the health of the mechanical system.
Owner:RSL ELECTRONICS
User authentication
InactiveUS7194764B2Digital data processing detailsUser identity/authority verificationInternet privacyUser authentication
The present invention authenticates a user for multiple resources distributed across multiple domains through the performance of a single authentication. User access requests for a protected resource in a first domain are received and redirected to a second domain. User authentication is performed at the second domain. In one embodiment, the system transmits an authentication cookie for the second domain to the user after authentication at the second domain. In another embodiment, the system further redirects subsequent resource requests for resources in the first domain or a third domain to the second domain. The second domain confirms the user's authentication for applicable portions of the first, second, and third domains using the cookie.
Owner:ORACLE INT CORP
Systems and methods for responding to natural language speech utterance
InactiveUS20070265850A1Disseminate their knowledgeImprove system performanceData processing applicationsNatural language data processingPrior informationConfigfs
Systems and methods for receiving natural language queries and / or commands and execute the queries and / or commands. The systems and methods overcomes the deficiencies of prior art speech query and response systems through the application of a complete speech-based information query, retrieval, presentation and command environment. This environment makes significant use of context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for one or more users making queries or commands in multiple domains. Through this integrated approach, a complete speech-based natural language query and response environment can be created. The systems and methods creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context and presenting the expected results for a particular question or command.
Owner:DIALECT LLC
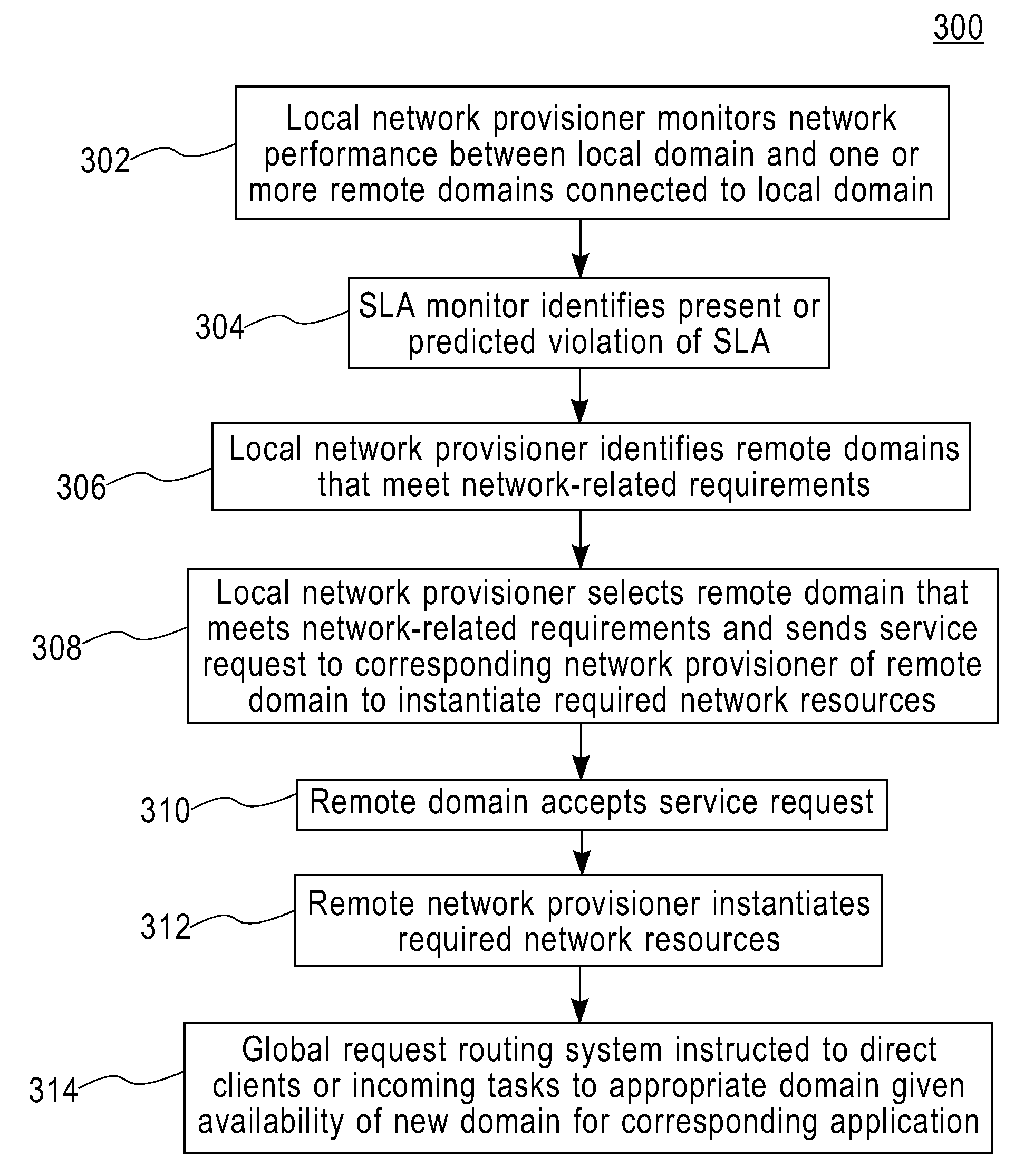
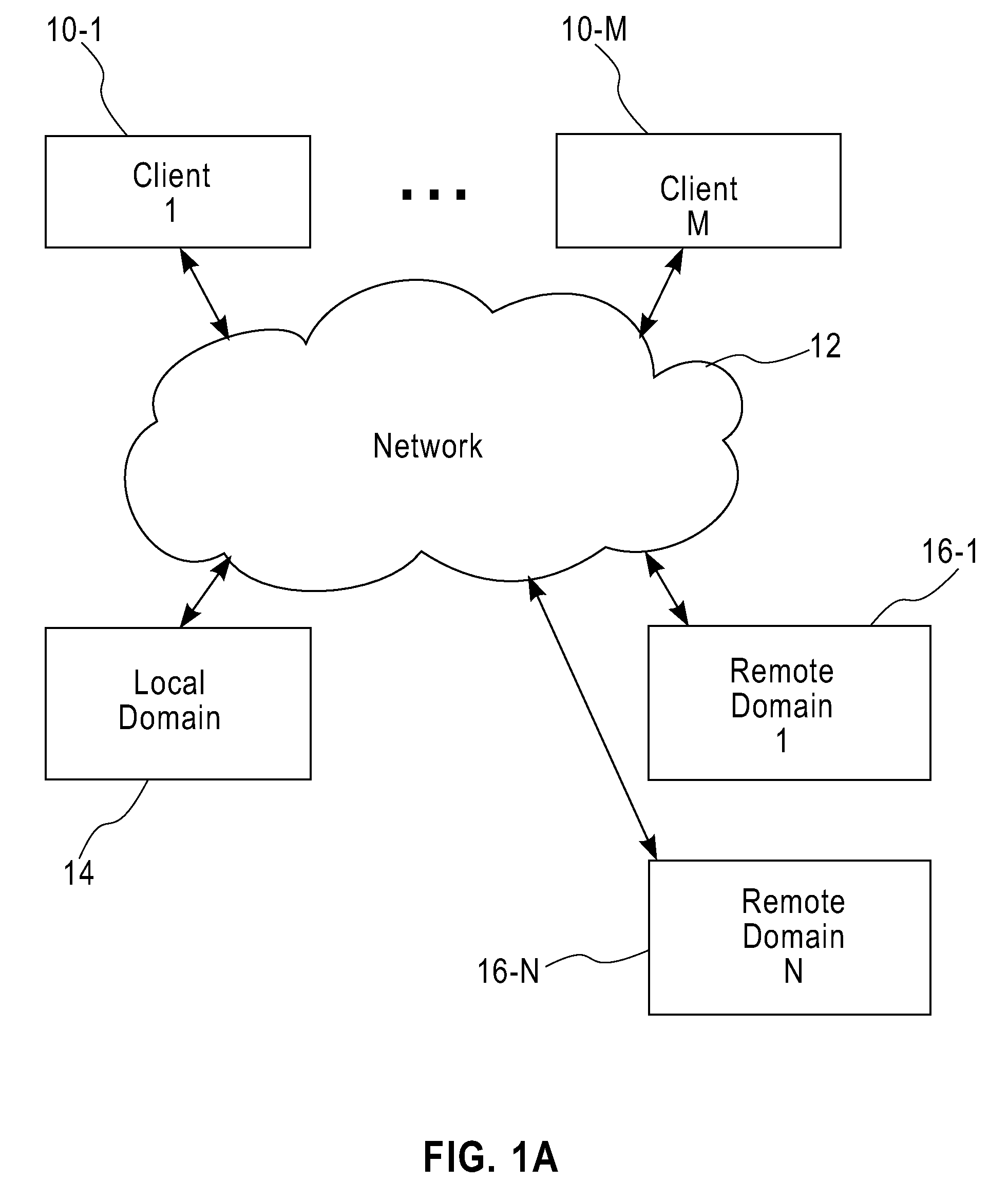
Method and apparatus for network distribution and provisioning of applications across multiple domains
ActiveUS20080240150A1Error preventionTransmission systemsService-level agreementAdministrative domain
Techniques are disclosed for network distribution and provisioning of applications, such as transactional applications and parallel applications, across multiple administrative domains that ensure compliance with service level agreements. For example, a method of provisioning one or more resources in a distributed computing network to ensure compliance with a service level agreement associated with a computer application includes the following steps. Network performance is monitored between a local domain and one or more cooperating domains connected to the local domain by network paths. A present or predicted violation of the service level agreement is identified based on at least a portion of results of the monitoring step. One or more cooperating domains are selected that can effect compliance with the service level agreement by instantiating one or more network resources within at least one of the selected cooperating domains in response to a request from the local domain. Reconfiguration of the local domain is effectuated to allow the computer application to make use of the one or more newly instantiated network resources within the selected cooperating domain.
Owner:DAEDALUS BLUE LLC
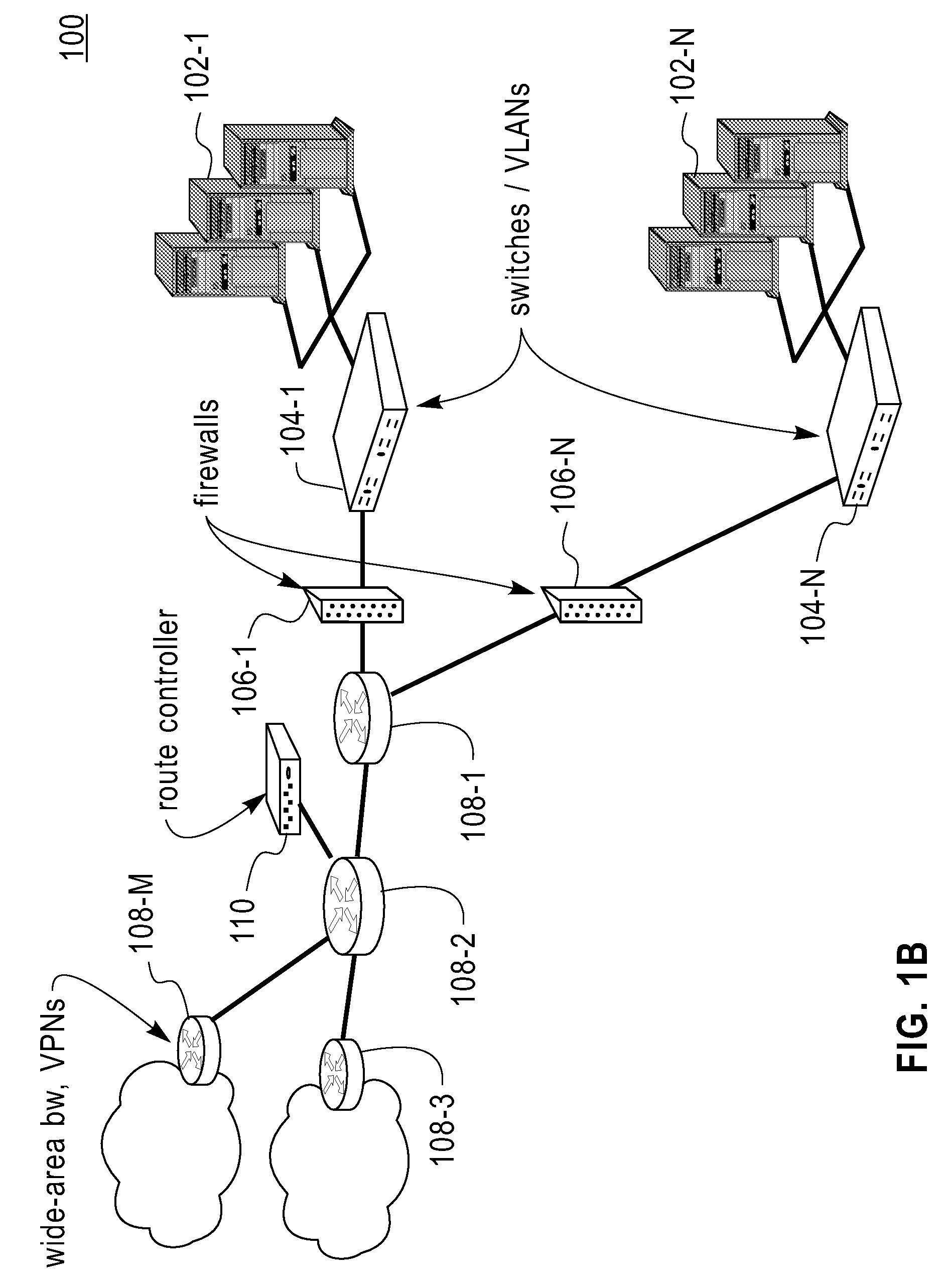
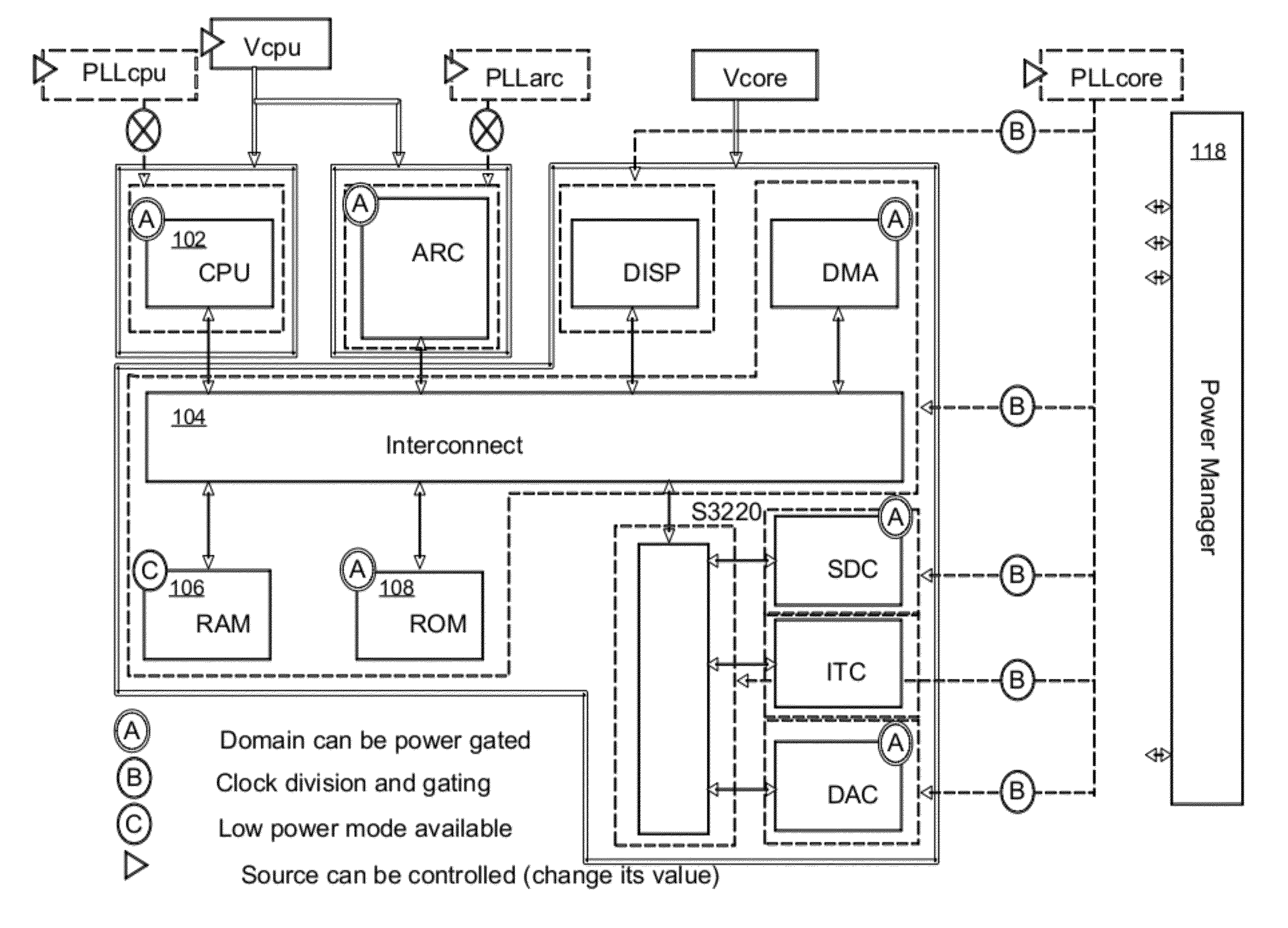
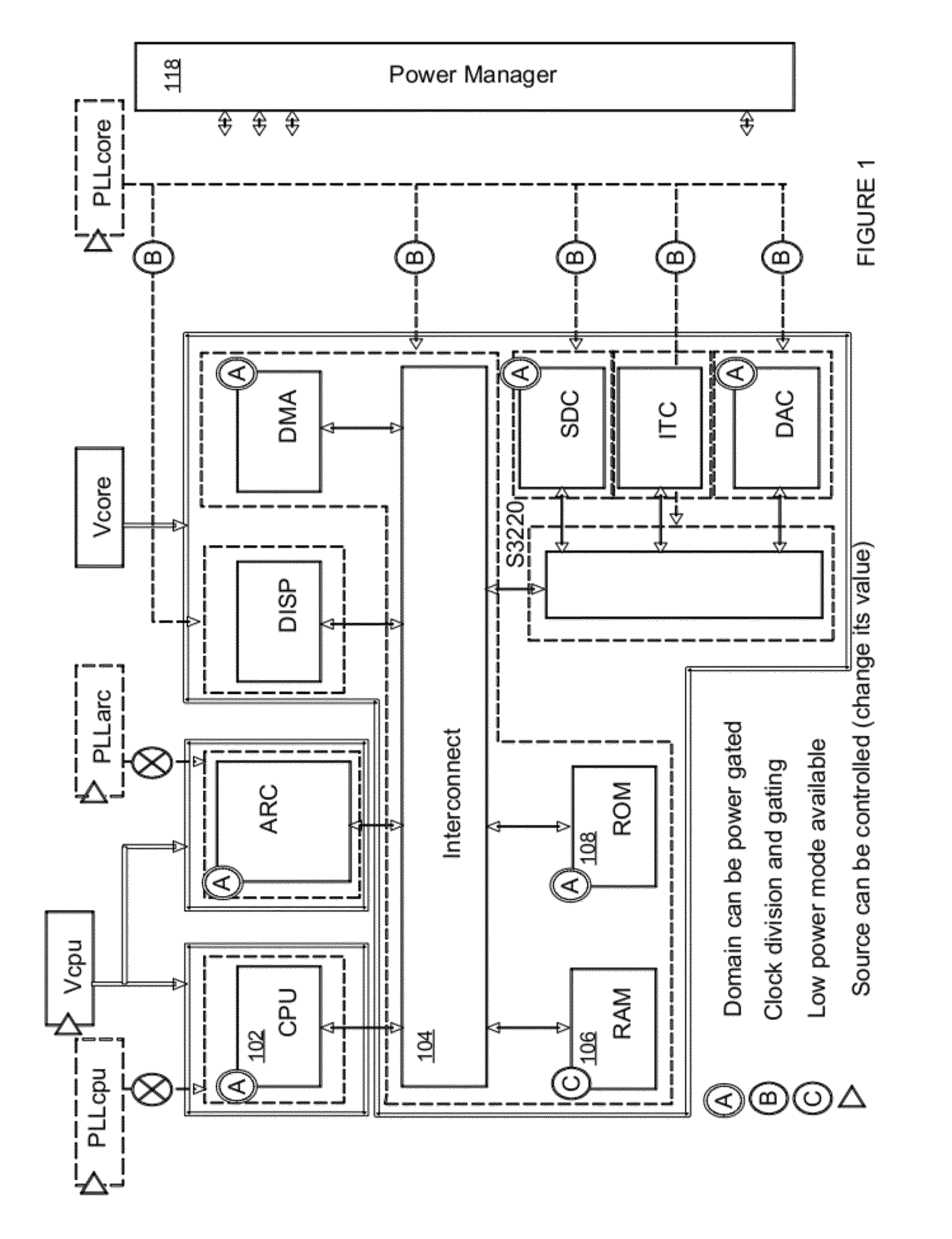
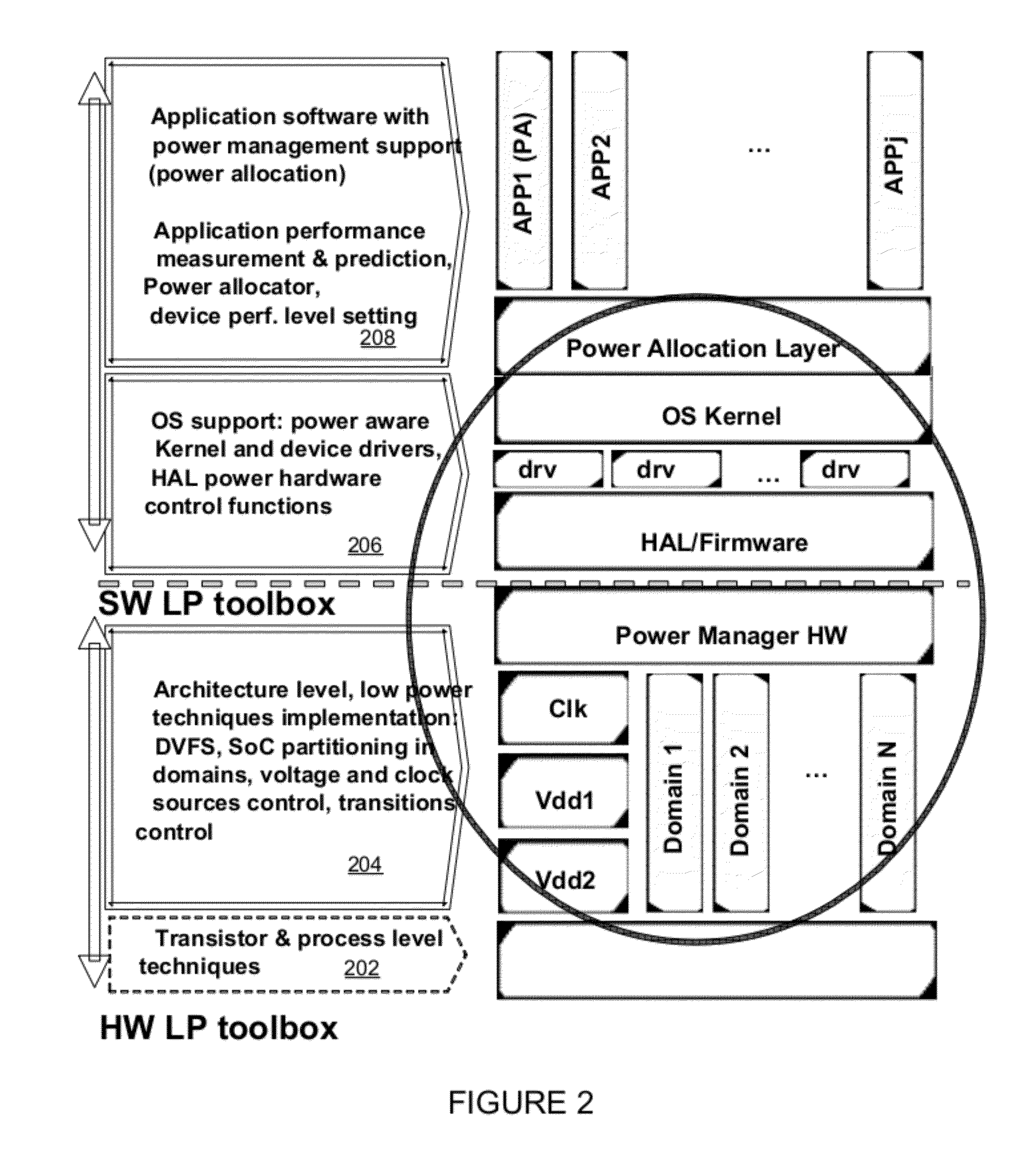
Intelligent power controller
ActiveUS20120054511A1Volume/mass flow measurementDigital storagePower controllerIntellectual property
A method, apparatus, and system in which an interconnect for an integrated circuit communicates transactions between one or more initiator Intellectual Property (IP) cores and one or more target IP cores coupled to the interconnect, including a power manager having a hierarchy of two or more layers including a hardware logic portion to control a power consumption of two or more domains in the integrated circuit, where each layer of the power manager performs its own function; wherein the power manager has its own dedicated CPU or dedicated state machine to execute power management instructions; and wherein the power manager controls the power consumption of two or more domains without using a CPU IP core utilized by other IP cores on the integrated circuit to execute power management instructions.
Owner:META PLATFORMS TECH LLC
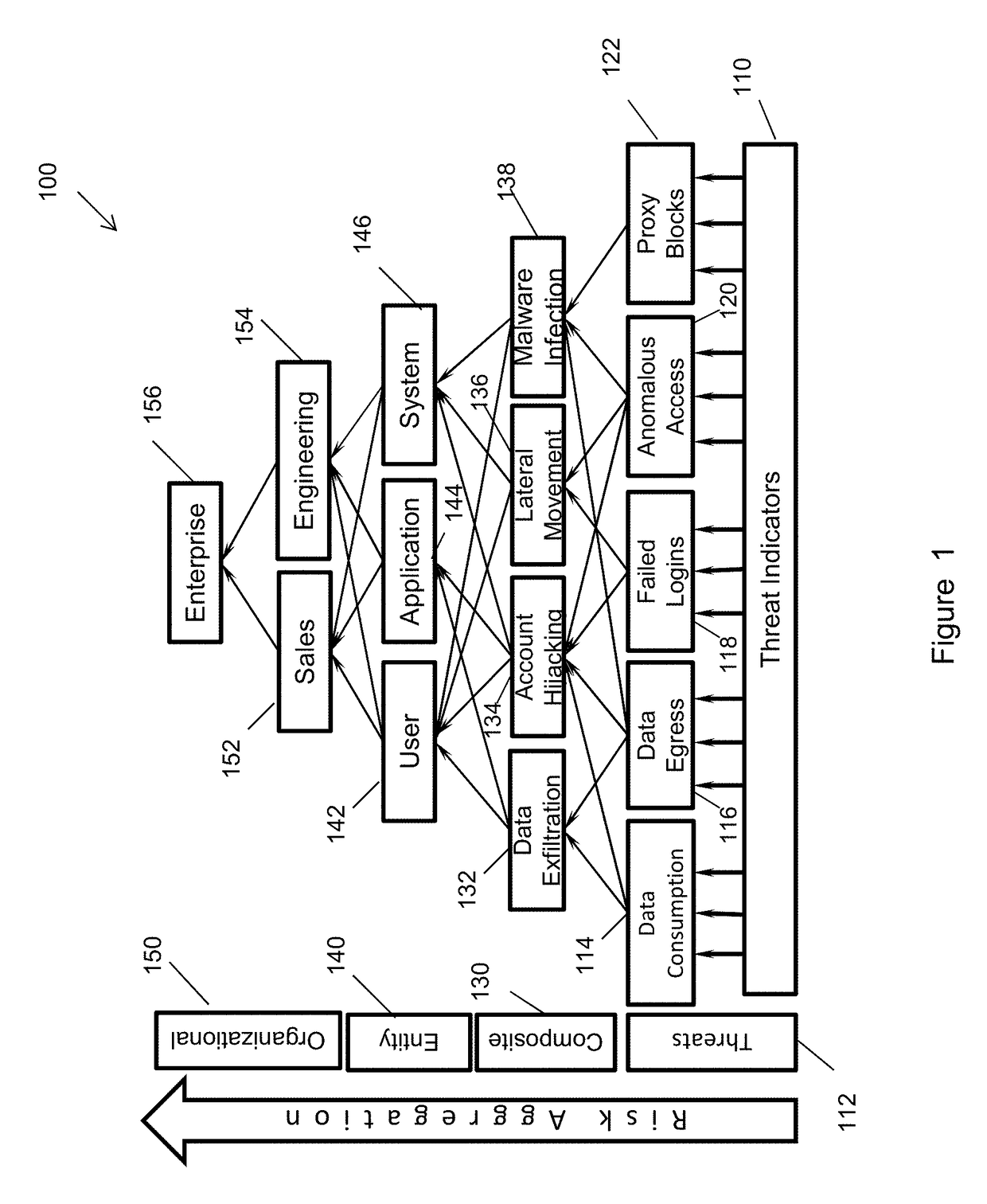
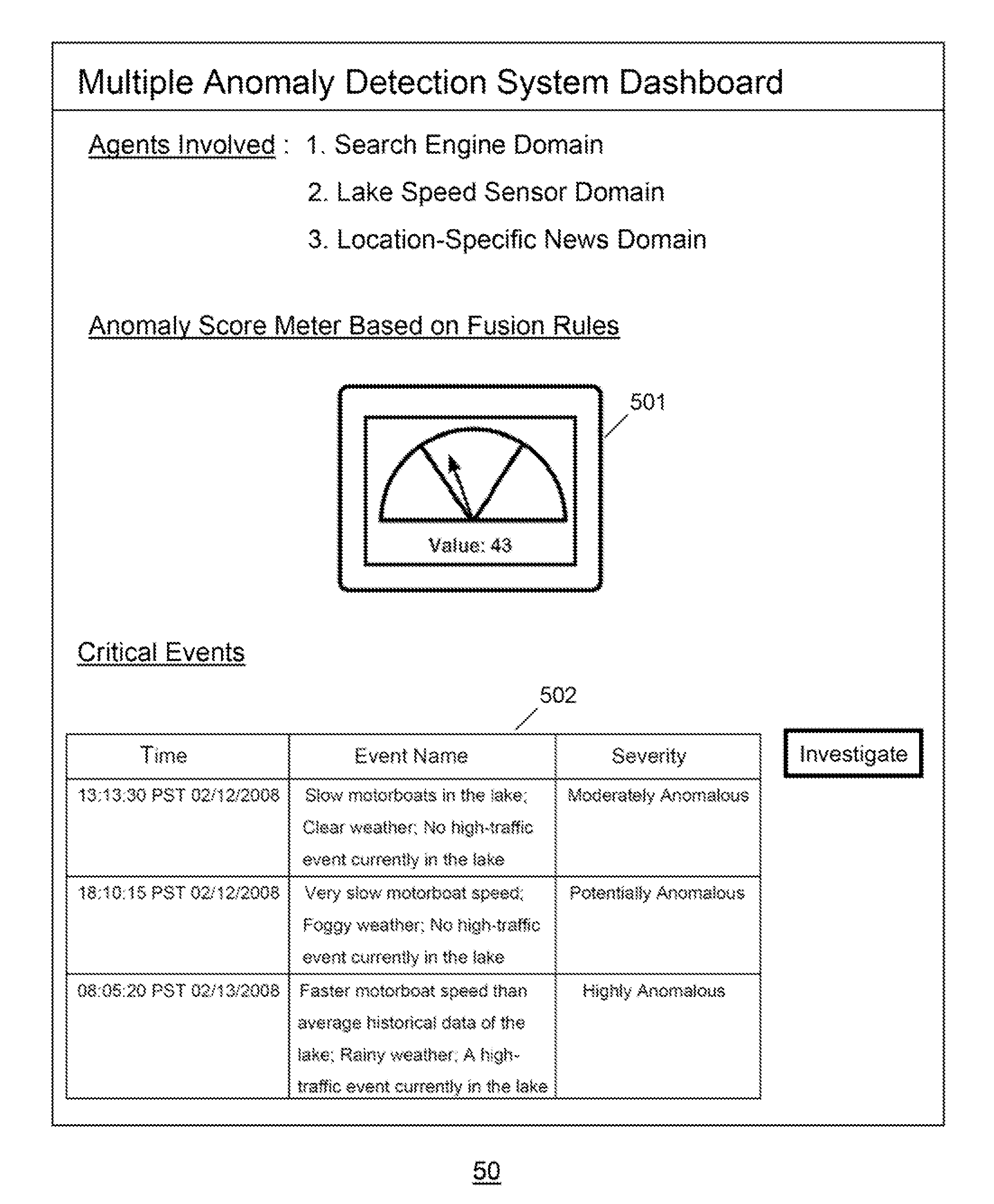
Multiple Domain Anomaly Detection System and Method Using Fusion Rule and Visualization
ActiveUS20110295783A1Digital data information retrievalDigital computer detailsAnomaly detectionDomain analysis
The present invention discloses various embodiments of multiple domain anomaly detection systems and methods. In one embodiment of the invention, a multiple domain anomaly detection system uses a generic learning procedure per domain to create a “normal data profile” for each domain based on observation of data per domain, wherein the normal data profile for each domain can be used to determine and compute domain-specific anomaly data per domain. Then, domain-specific anomaly data per domain can be analyzed together in a cross-domain fusion data analysis using one or more fusion rules. The fusion rules may involve comparison of domain-specific anomaly data from multiple domains to derive a multiple-domain anomaly score meter for a particular cross-domain analysis task. The multiple domain anomaly detection system and its related method may also utilize domain-specific anomaly indicators of each domain to derive a cross-domain anomaly indicator using the fusion rules.
Owner:ZHAO YING +2
Systems and methods for responding to natural language speech utterance
ActiveUS20080235023A1Promotes feeling of naturalOvercome deficienciesData processing applicationsDigital data processing detailsWorld Wide WebHuman language
Systems and methods for receiving natural language queries and / or commands and execute the queries and / or commands. The systems and methods overcomes the deficiencies of prior art speech query and response systems through the application of a complete speech-based information query, retrieval, presentation and command environment. This environment makes significant use of context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for one or more users making queries or commands in multiple domains. Through this integrated approach, a complete speech-based natural language query and response environment can be created. The systems and methods creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context and presenting the expected results for a particular question or command.
Owner:DIALECT LLC
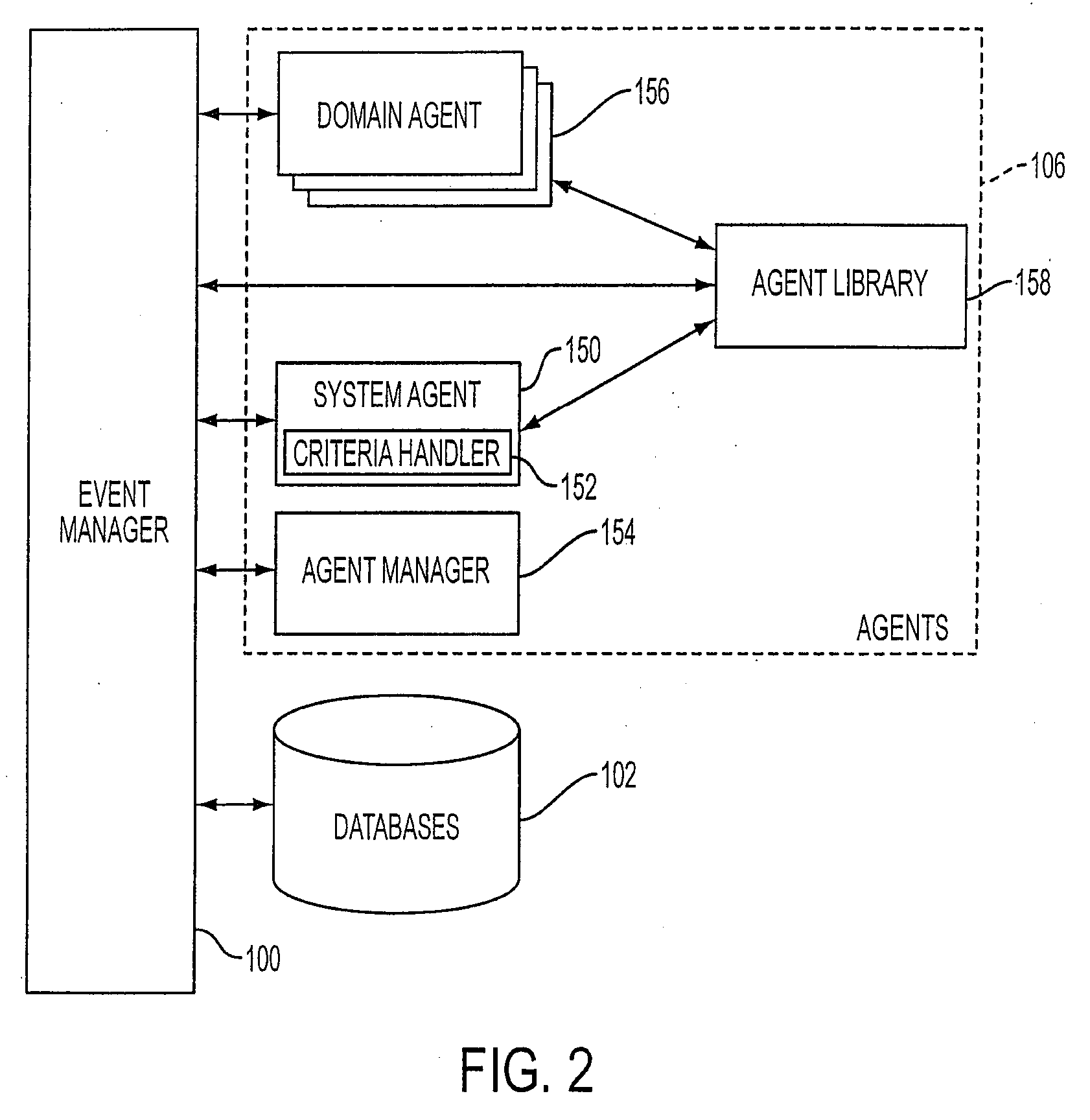
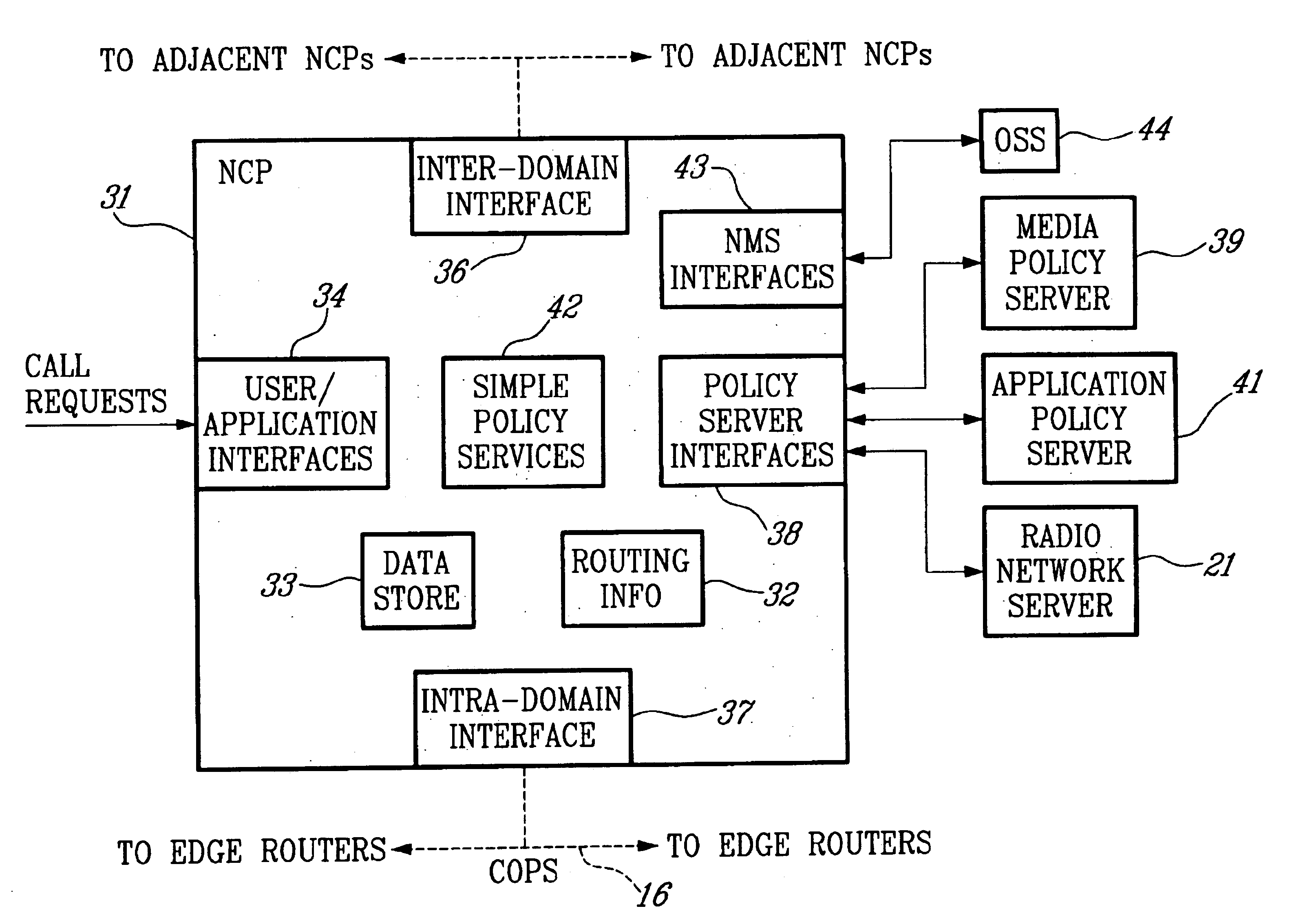
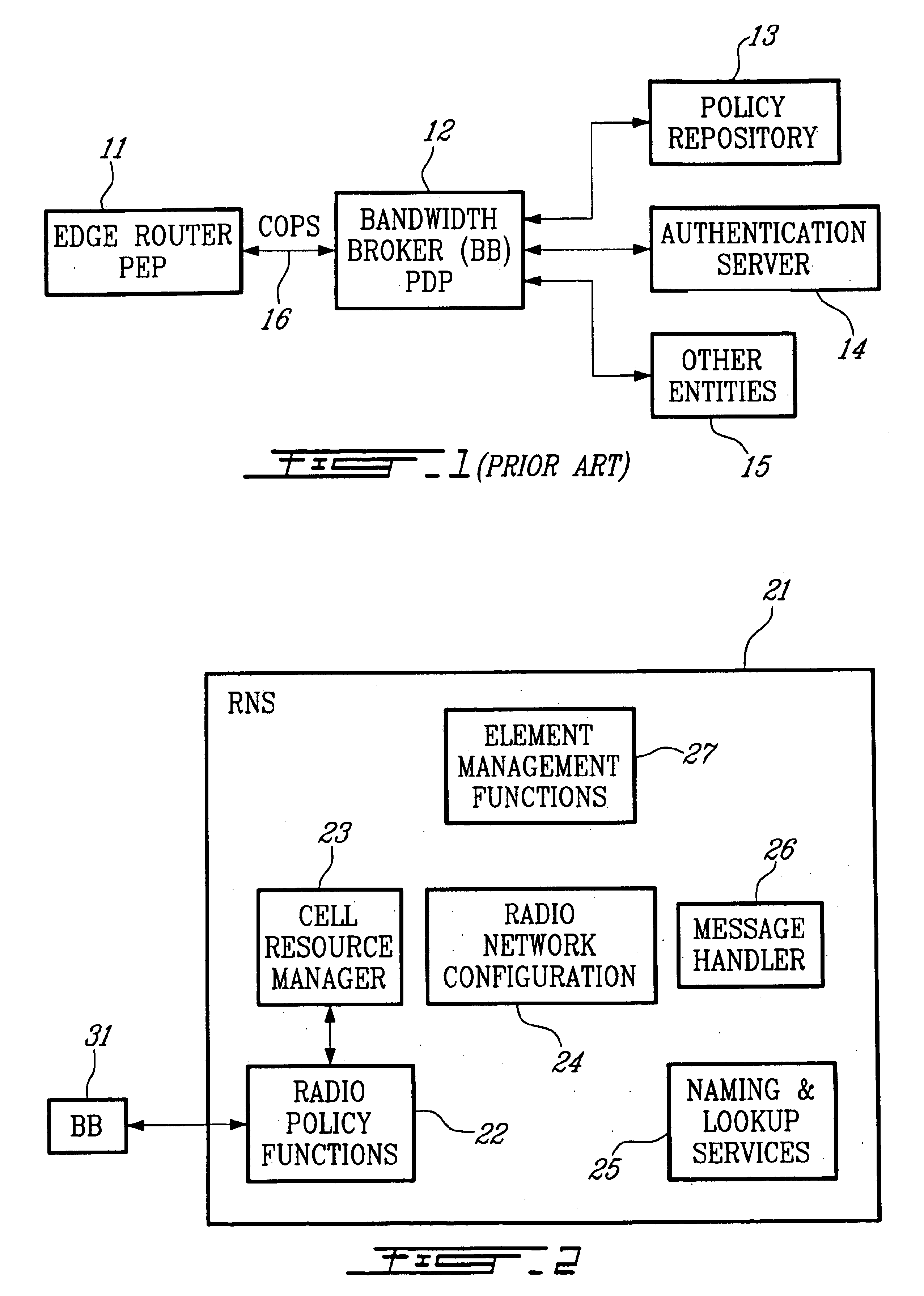
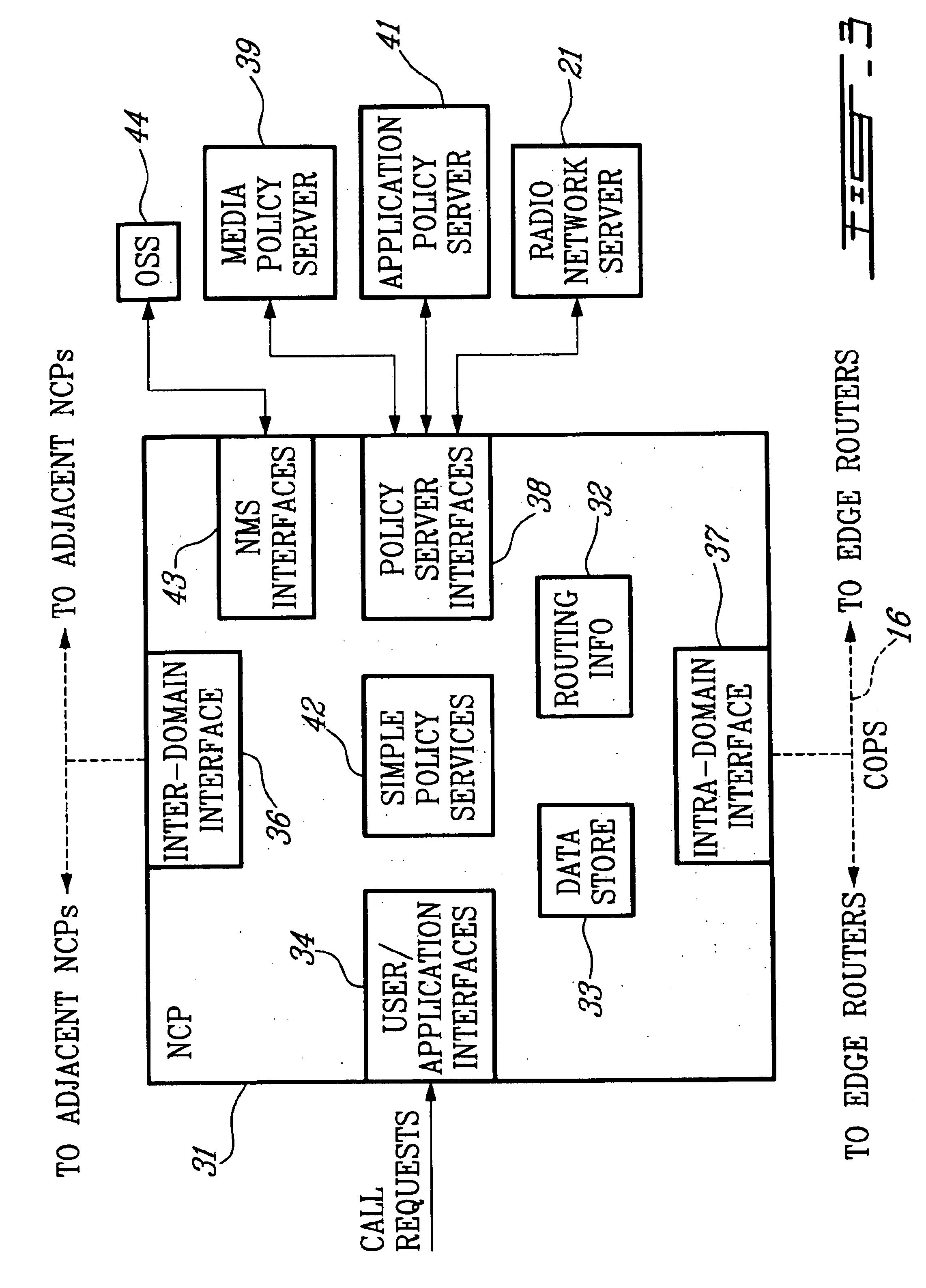
Policy server and architecture providing radio network resource allocation rules
A Radio Network Server (RNS) is modified to function as a policy server providing radio network resource allocation rules in an integrated third generation wireless IP network. The RNS determines a level of availability of radio network resources, and determines whether the level is sufficient to satisfy requests for resources in accordance with policy rules. The RNS informs a Bandwidth Broker (BB) whether the radio network resources are available. The BB functions as a Policy Decision Point (PDP) for its domain, and either allows or denies requests from users for network resources based on the input from the RNS. A plurality of edge routers in each domain interface with the BB utilizing the Common Open Policy Service (COPS) protocol interface. The edge routers function as Policy Enforcement Points (PEPs) for their domain to enforce policy decisions made by the BB. The BB may interface with BBs in other domains for calls that span multiple domains.
Owner:TELEFON AB LM ERICSSON (PUBL)
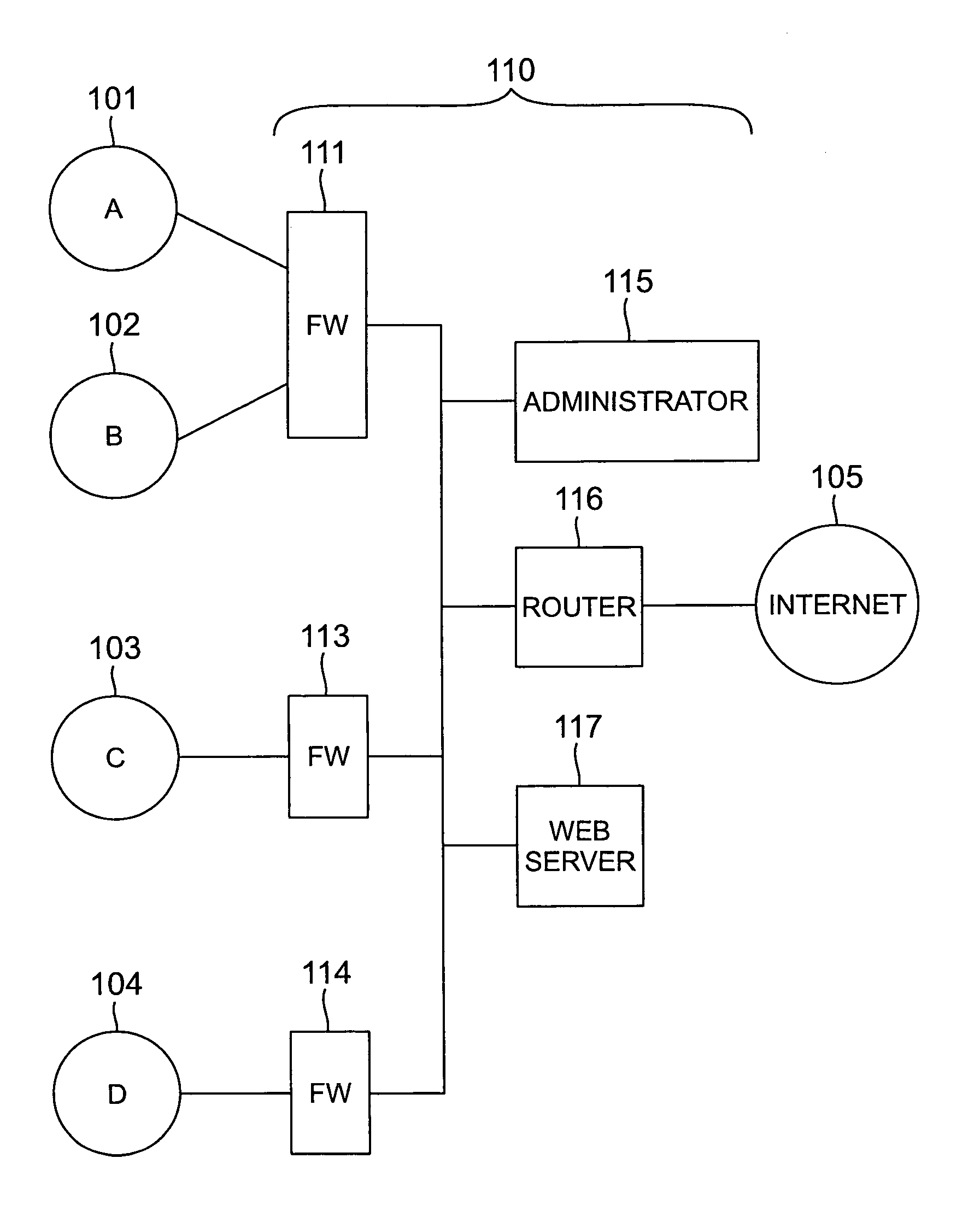
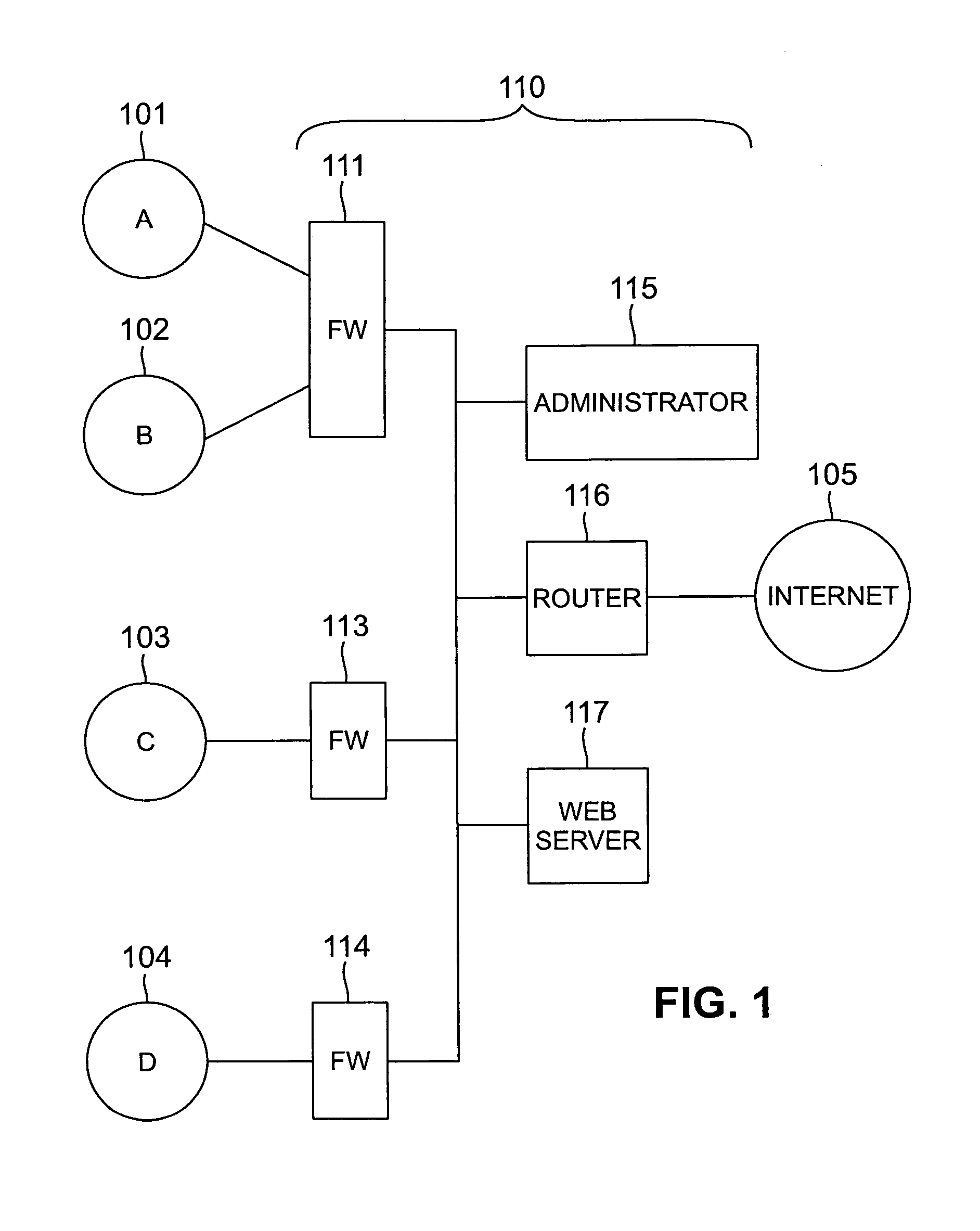
Methods and apparatus for a computer network firewall with multiple domain support
InactiveUS7143438B1Improve processing efficiencyIncrease access rule flexibilityUser identity/authority verificationHardware monitoringData packEngineering
The invention provides improved computer network firewalls which include one or more features for increased processing efficiency. A firewall in accordance with the invention can support multiple security policies, multiple users or both, by applying any one of several distinct sets of access rules. The firewall can also be configured to utilize “stateful” packet filtering which involves caching rule processing results for one or more packets, and then utilizing the cached results to bypass rule processing for subsequent similar packets. To facilitate passage to a user, by a firewall, of a separate later transmission which is properly in response to an original transmission, a dependency mask can be set based on session data items such as source host address, destination host address, and type of service. The mask can be used to query a cache of active sessions being processed by the firewall, such that a rule can be selected based on the number of sessions that satisfy the query. Dynamic rules may be used in addition to pre-loaded access rules in order to simplify rule processing. To unburden the firewall of application proxies, the firewall can be enabled to redirect a network session to a separate server for processing.
Owner:LUCENT TECH INC
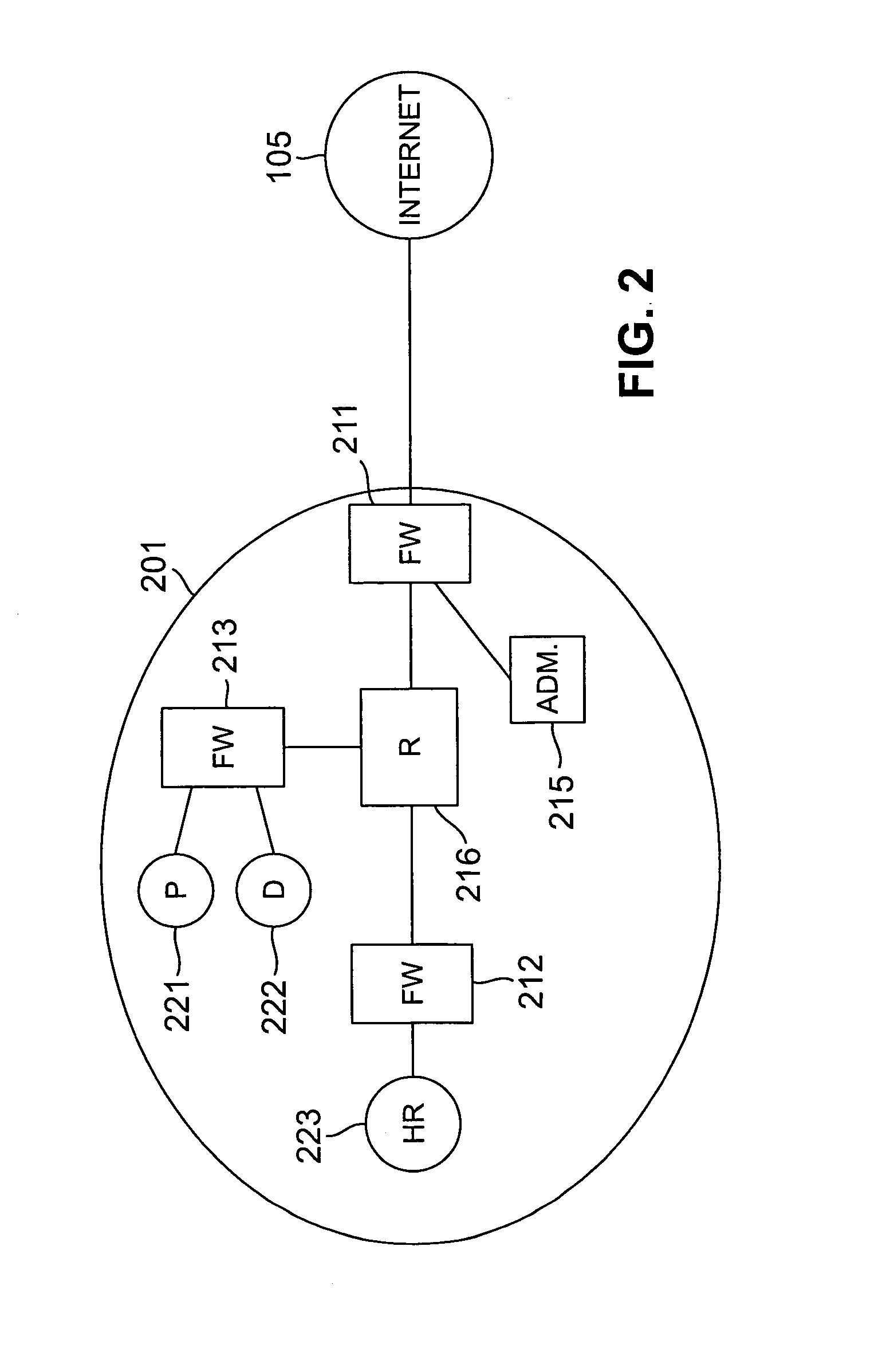
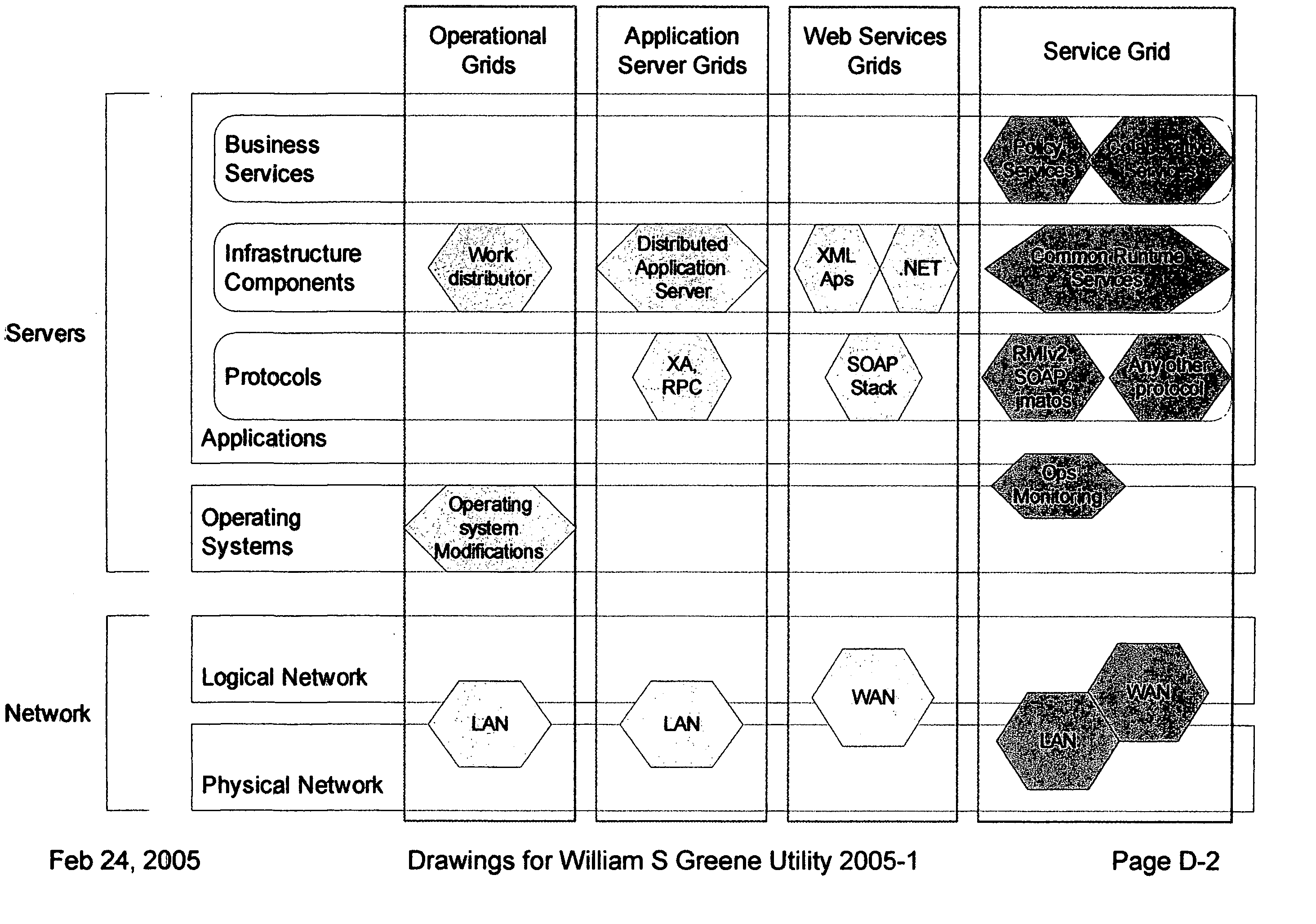
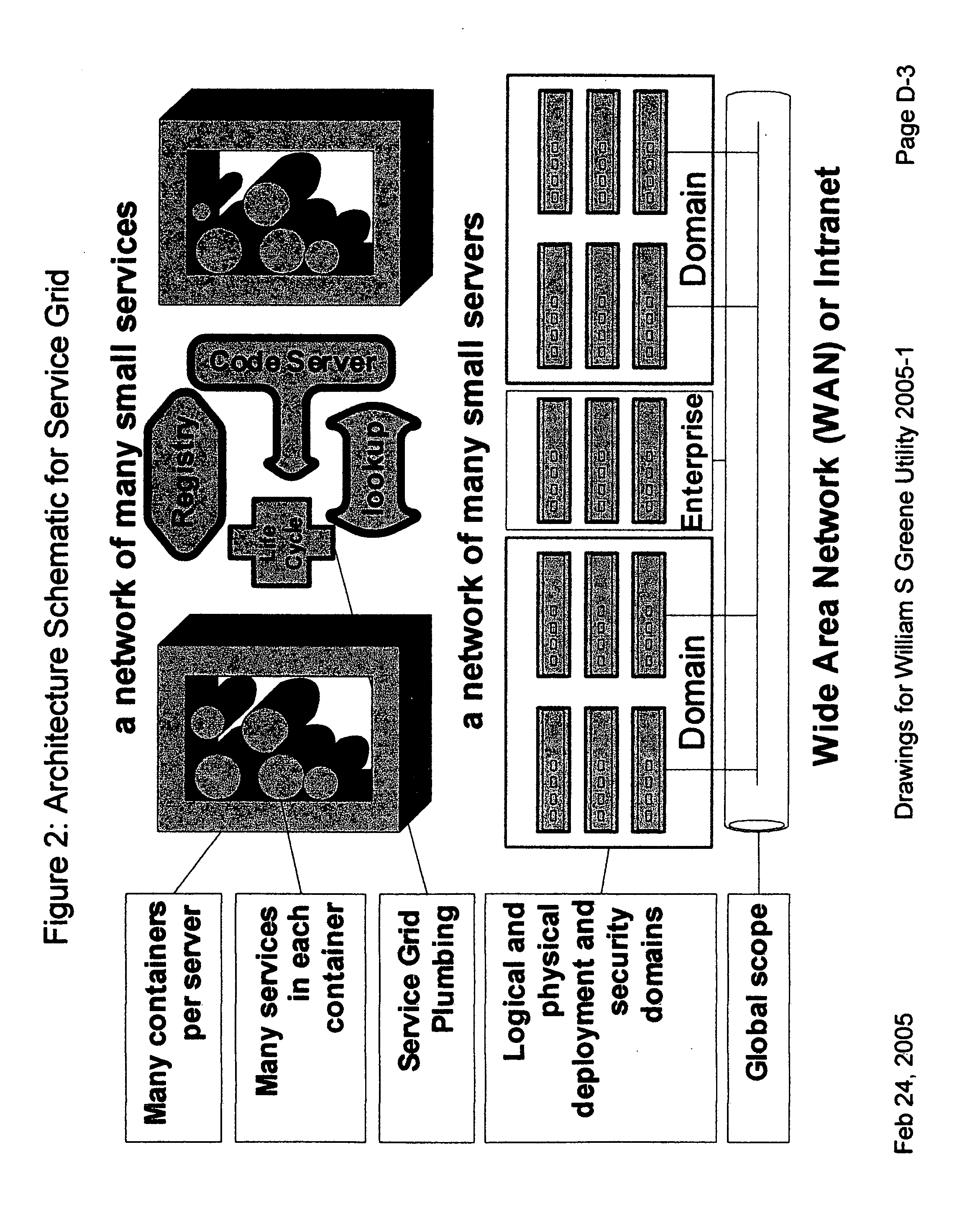
Providing secure data and policy exchange between domains in a multi-domain grid by use of a service ecosystem facilitating uses such as supply-chain integration with RIFD tagged items and barcodes
InactiveUS20050193222A1Simple methodImprove securityDigital data processing detailsMultiple digital computer combinationsSecurity domainRadio frequency
A system, method, and software implemented system of services provides enhanced security and management to multiple domain grids and allows intercommunications between the different grid domains providing for secure data exchange, policy exchange, and agent exchange between grids or grid domains. Via the exemplary example, utilizing the unique characteristics of the Service Grid and mobile agents, this is extended to provide enhanced security and management to supply chains: providing data exchange, policy exchange, and agent exchange between supply chain nodes and supply chain partners—facilitating enhanced methods of supply chain automation when using barcodes and Radio Frequency Identity (RFID) tags to identify and track goods through supply chains and consumer uses. Agents transport data and policy between supply-chain partners over an extranet, migrating across corporate boundaries and security domains, locating near where items are identified to provide local control, environmentally responsive policy, and ongoing permanent data capture & history.
Owner:GREENE WILLIAM SPROTT
Apparatus and method for managing access to a memory
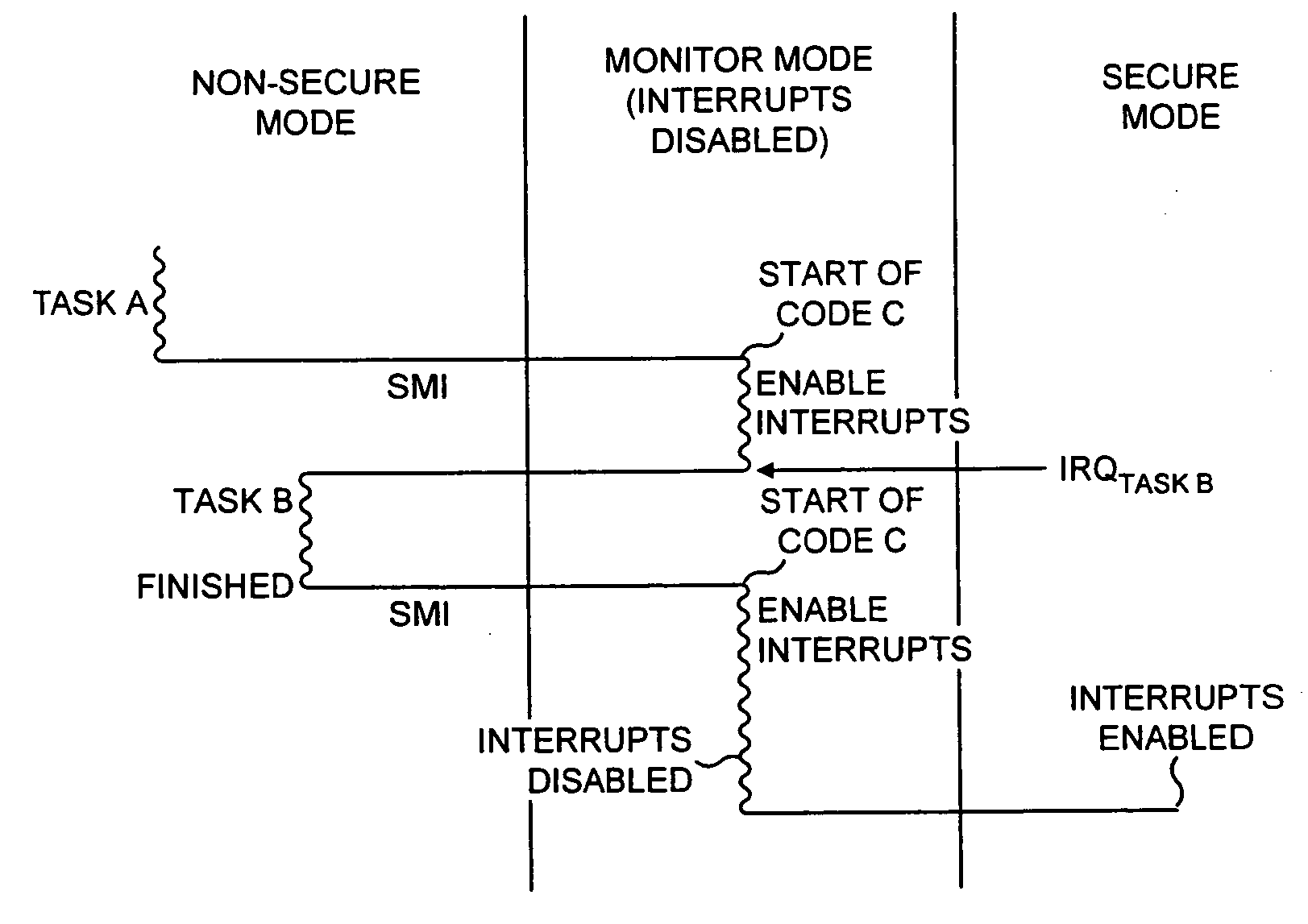
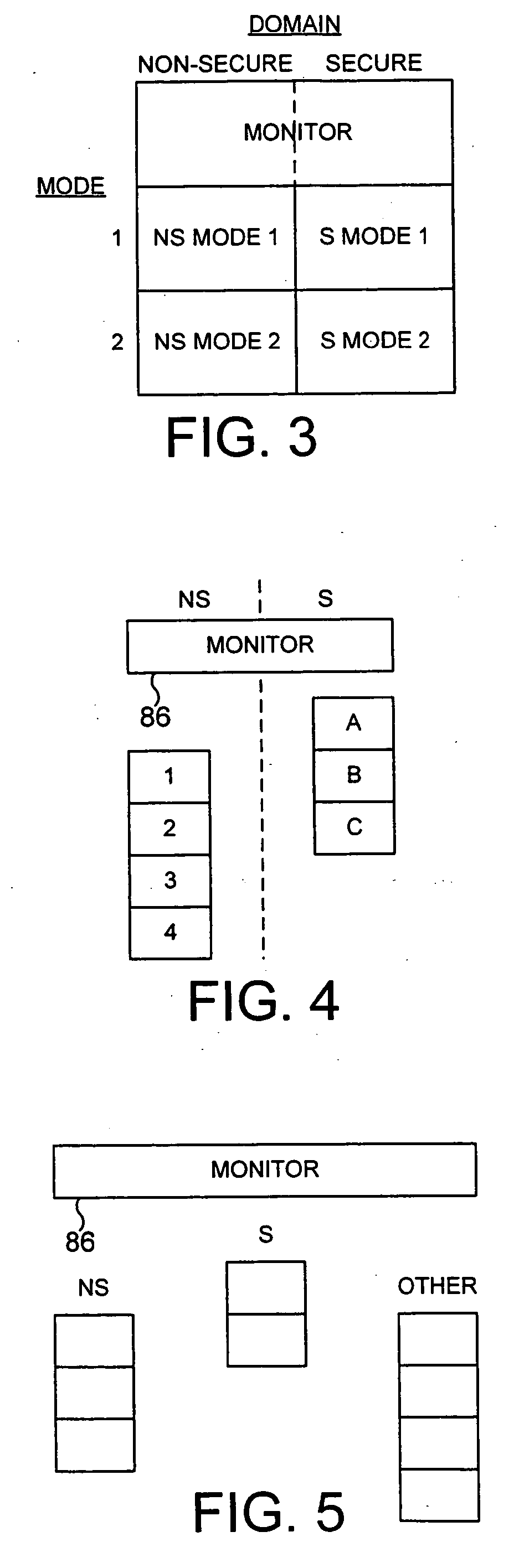
ActiveUS20040177269A1Performance is not affectedEasy to operateMemory architecture accessing/allocationDigital data processing detailsManagement unitMultiple modes
The present invention provides a data processing apparatus and method for managing access to a memory within the data processing apparatus. The data processing apparatus comprises a processor operable in a plurality of modes and a plurality of domains, said plurality of domains comprising a secure domain and a non-secure domain, said plurality of modes including at least one non-secure mode being a mode in the non-secure domain and at least one secure mode being a mode in the secure domain, said processor being operable such that when executing a program in a secure mode said program has access to secure data which is not accessible when said processor is operating in a non-secure mode. Further, a memory is provided for storing data required by the processor, and consists of secure memory for storing secure data and non-secure memory for storing non-secure data. The memory further contains a non-secure table and a secure table, the non-secure table being within the non-secure memory and arranged to contain for each of a number of first memory regions an associated descriptor, and the secure table being within the secure memory and arranged to contain for each of a number of second memory regions an associated descriptor. When access to an item of data in the memory is required by the processor, the processor issues a memory access request, and a memory management unit is provided to perform one or more predetermined access control functions to control issuance of the memory access request to the memory. The memory management unit comprises an internal storage unit operable to store descriptors retrieved by the memory management unit from either the non-secure table or the secure table, and in accordance with the present invention the internal storage unit comprises a flag associated with each descriptor stored within the internal storage unit to identify whether that descriptor is from the non-secure table or the secure table. By this approach, when the processor is operating in a non-secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the non-secure table. In contrast, when the processor is operating in a secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the secure table. This approach enables different descriptors to be used for the control of accesses to memory in either the secure domain or the non-secure domain, whilst enabling such different descriptors to co-exist within the memory management unit's internal storage unit, thereby avoiding the requirement to flush the contents of such an internal storage unit when the operation of the processor changes from the secure domain to the non-secure domain, or vice versa.
Owner:ARM LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com