Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
309results about How to "Minimize effort" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
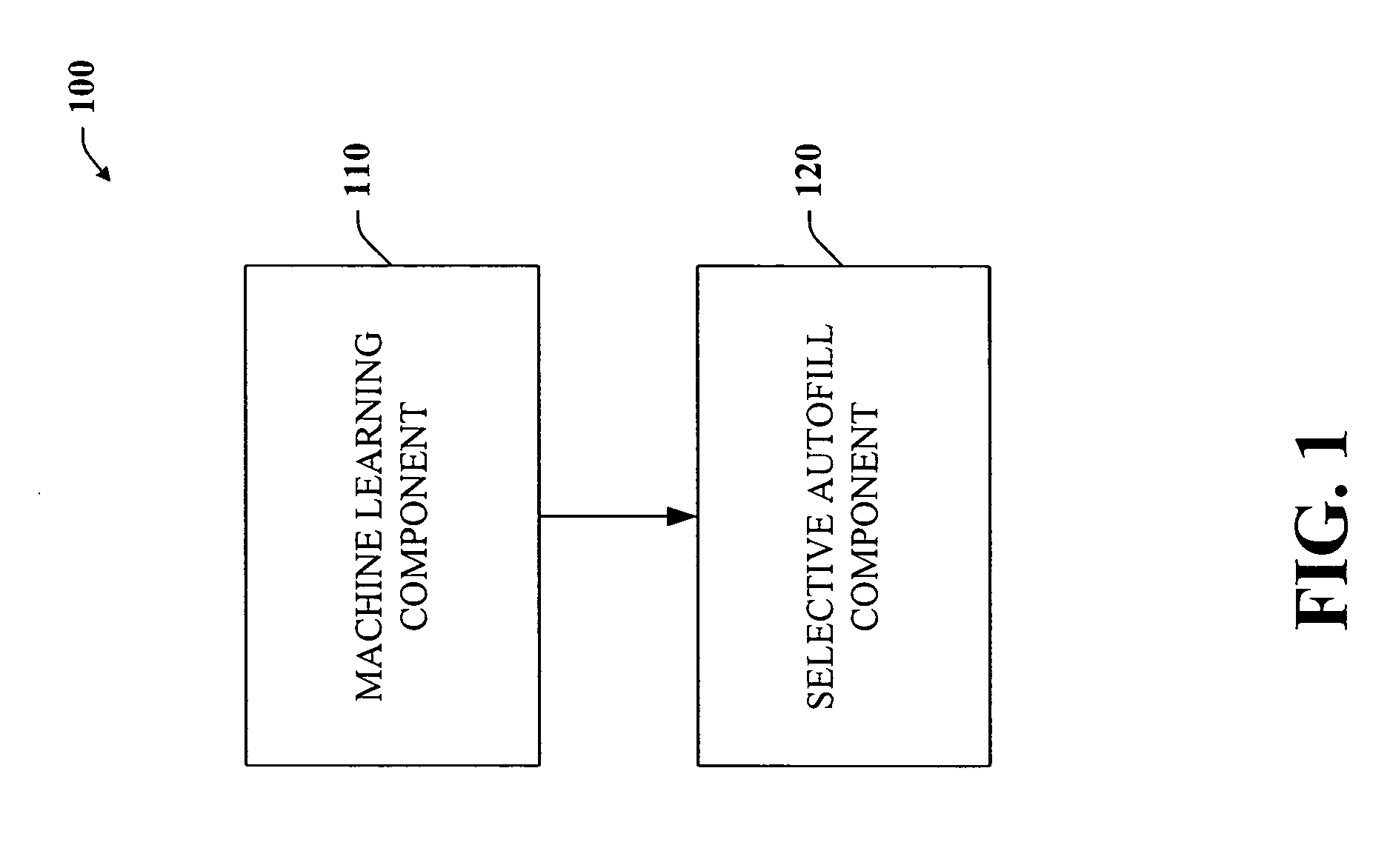
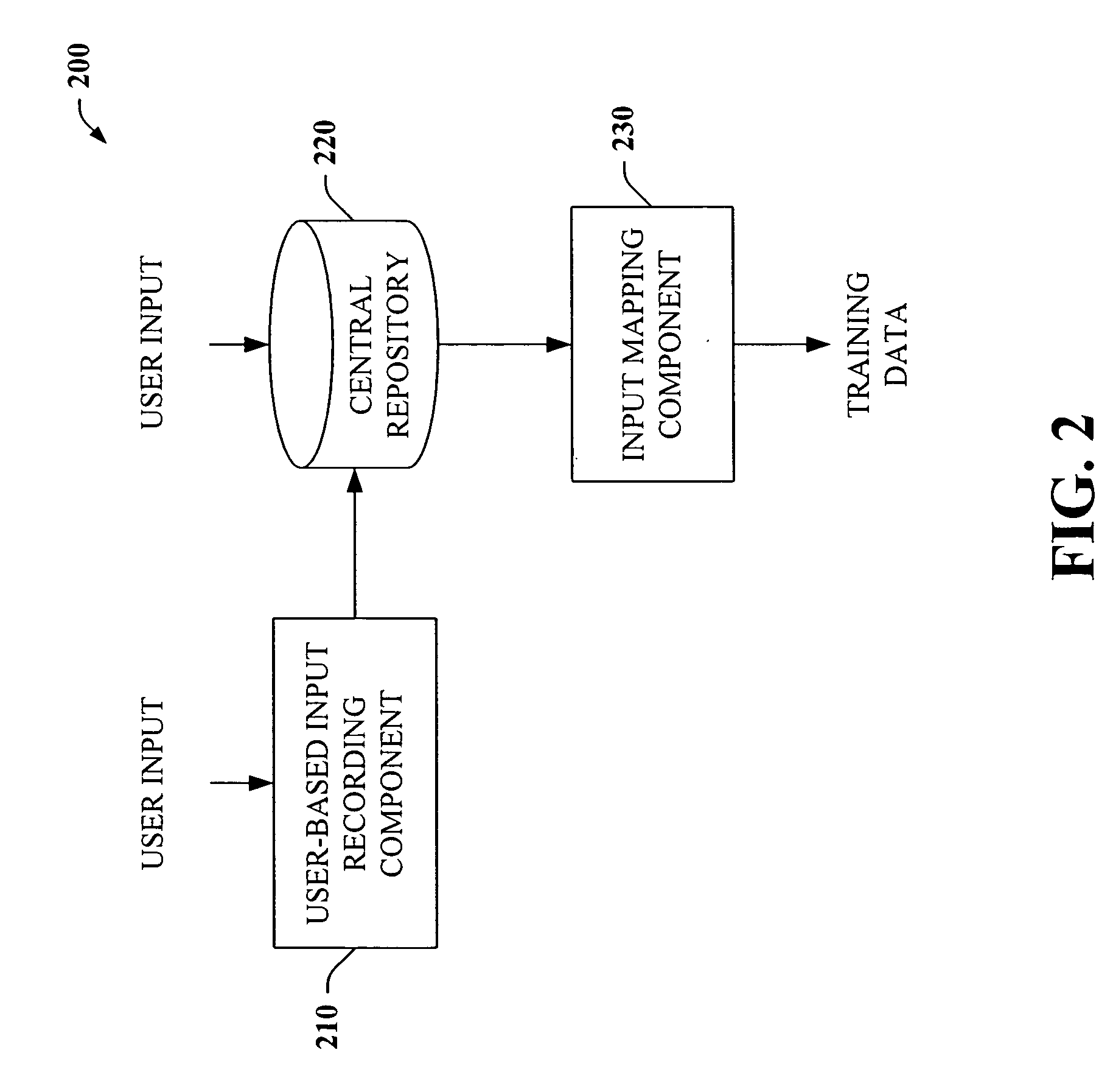
Intelligent autofill
InactiveUS7254569B2Minimize effortData augmentationData processing applicationsMetal-working feeding devicesData miningData entry
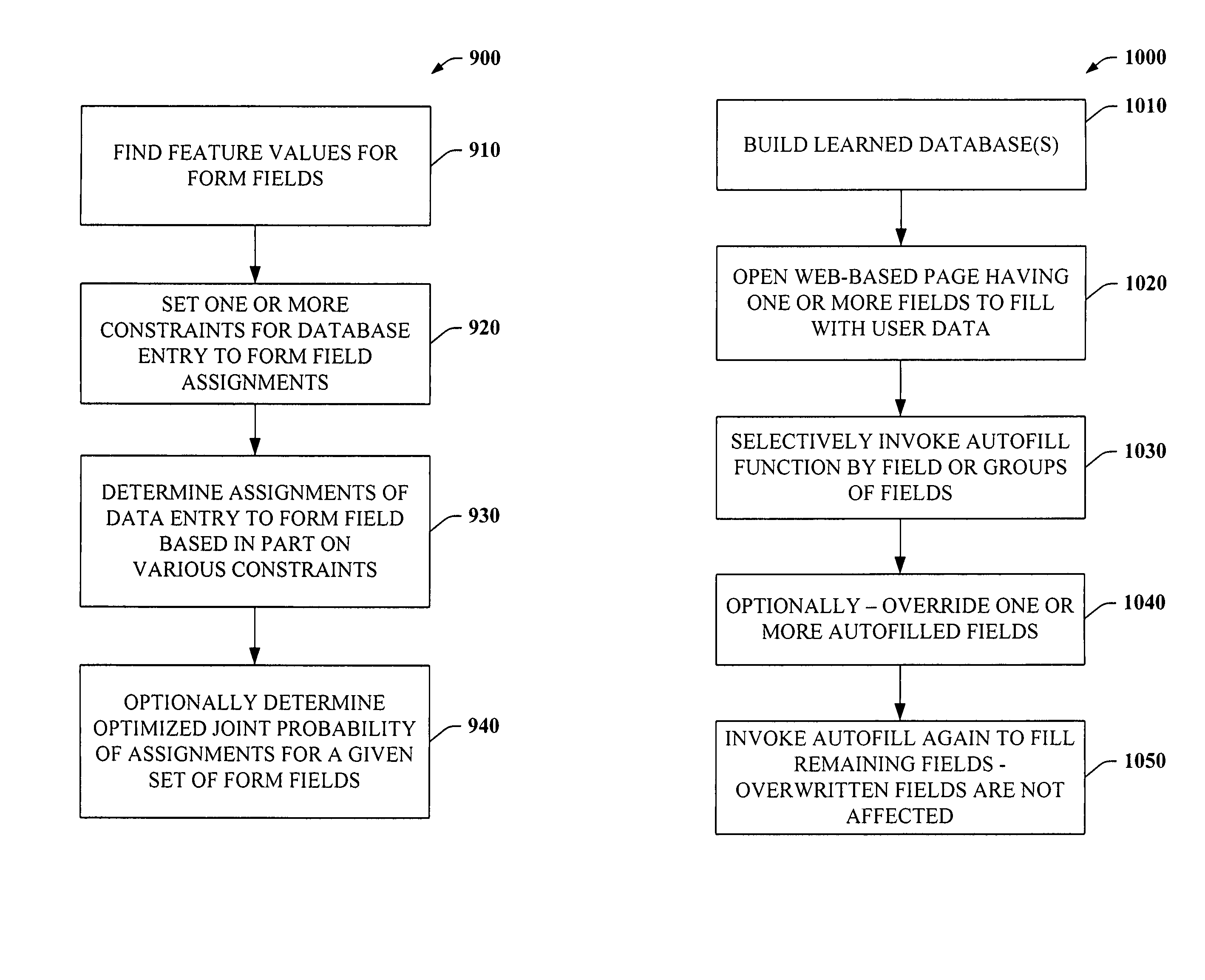
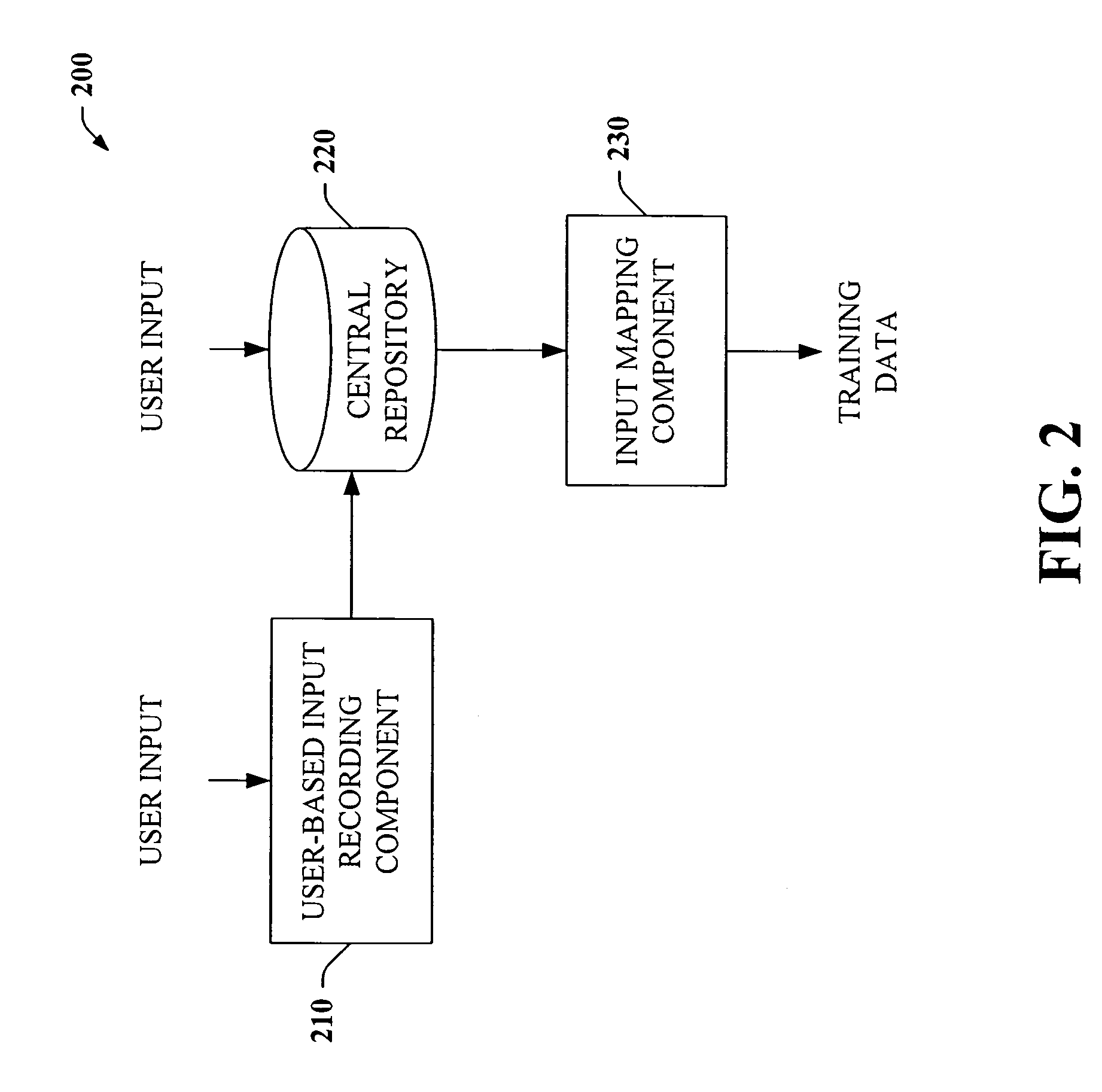
The present invention provides a unique system and method that can employ machine learning techniques to automatically fill one or more fields across a diverse array of web forms. In particular, one or more instrumented tools can collect input or entries of form fields. Machine learning can be used to learn what data corresponds to which fields or types of fields. The input can be sent to a central repository where other databases can be aggregated as well. This input can be provided to a machine learning system to learn how to predict the desired outputs. Alternatively or in addition, learning can be performed in part by observing entries and then adapting the autofill component accordingly. Furthermore, a number of features of database fields as well as constraints can be employed to facilitate assignments of database entries to form values—particularly when the web form has never been seen before by the autofill system.
Owner:MICROSOFT TECH LICENSING LLC
Intelligent autofill
InactiveUS20050257148A1Minimize effortData augmentationData processing applicationsMetal-working feeding devicesDatabaseCentral repository
The present invention provides a unique system and method that can employ machine learning techniques to automatically fill one or more fields across a diverse array of web forms. In particular, one or more instrumented tools can collect input or entries of form fields. Machine learning can be used to learn what data corresponds to which fields or types of fields. The input can be sent to a central repository where other databases can be aggregated as well. This input can be provided to a machine learning system to learn how to predict the desired outputs. Alternatively or in addition, learning can be performed in part by observing entries and then adapting the autofill component accordingly. Furthermore, a number of features of database fields as well as constraints can be employed to facilitate assignments of database entries to form values—particularly when the web form has never been seen before by the autofill system.
Owner:MICROSOFT TECH LICENSING LLC
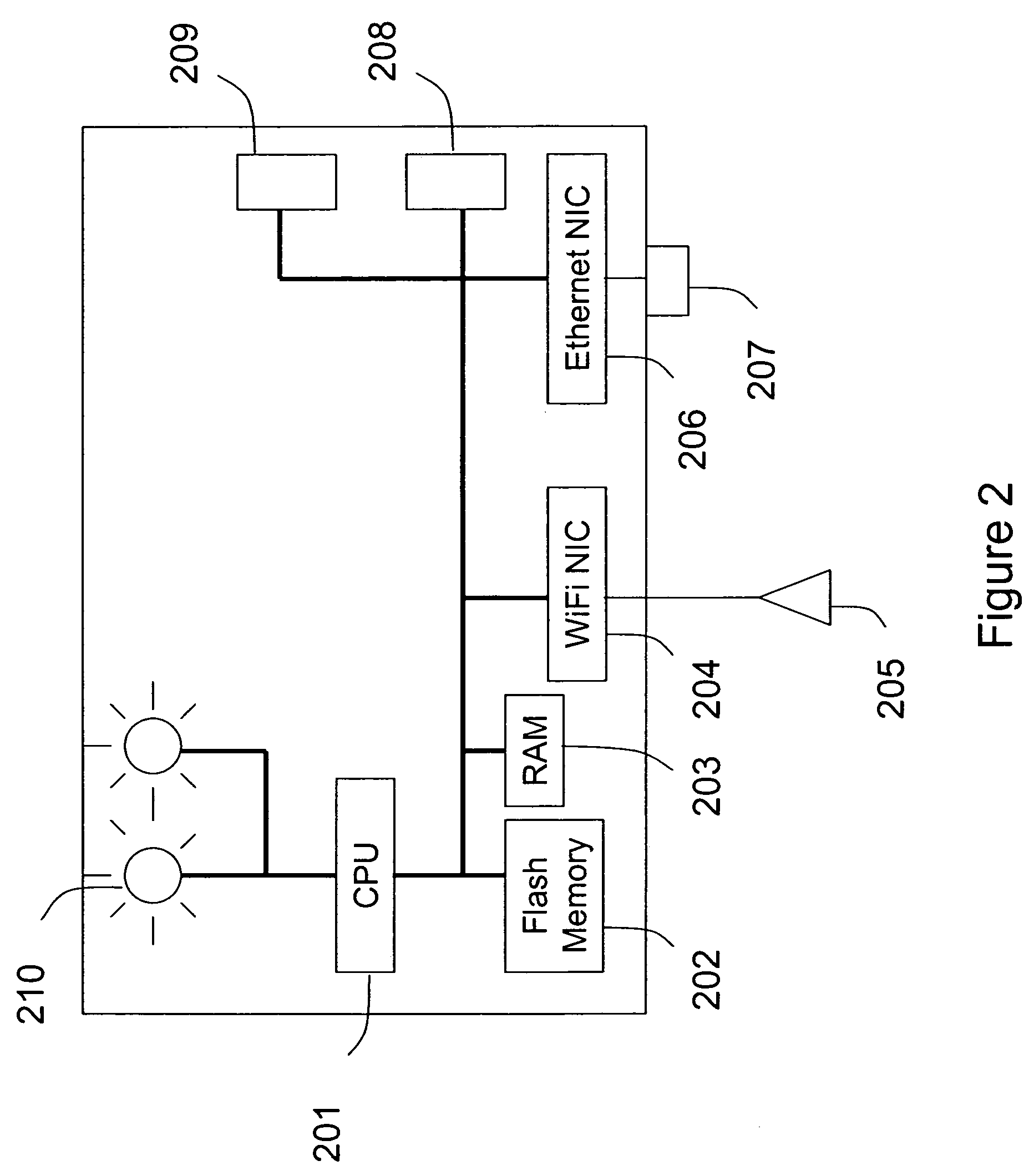
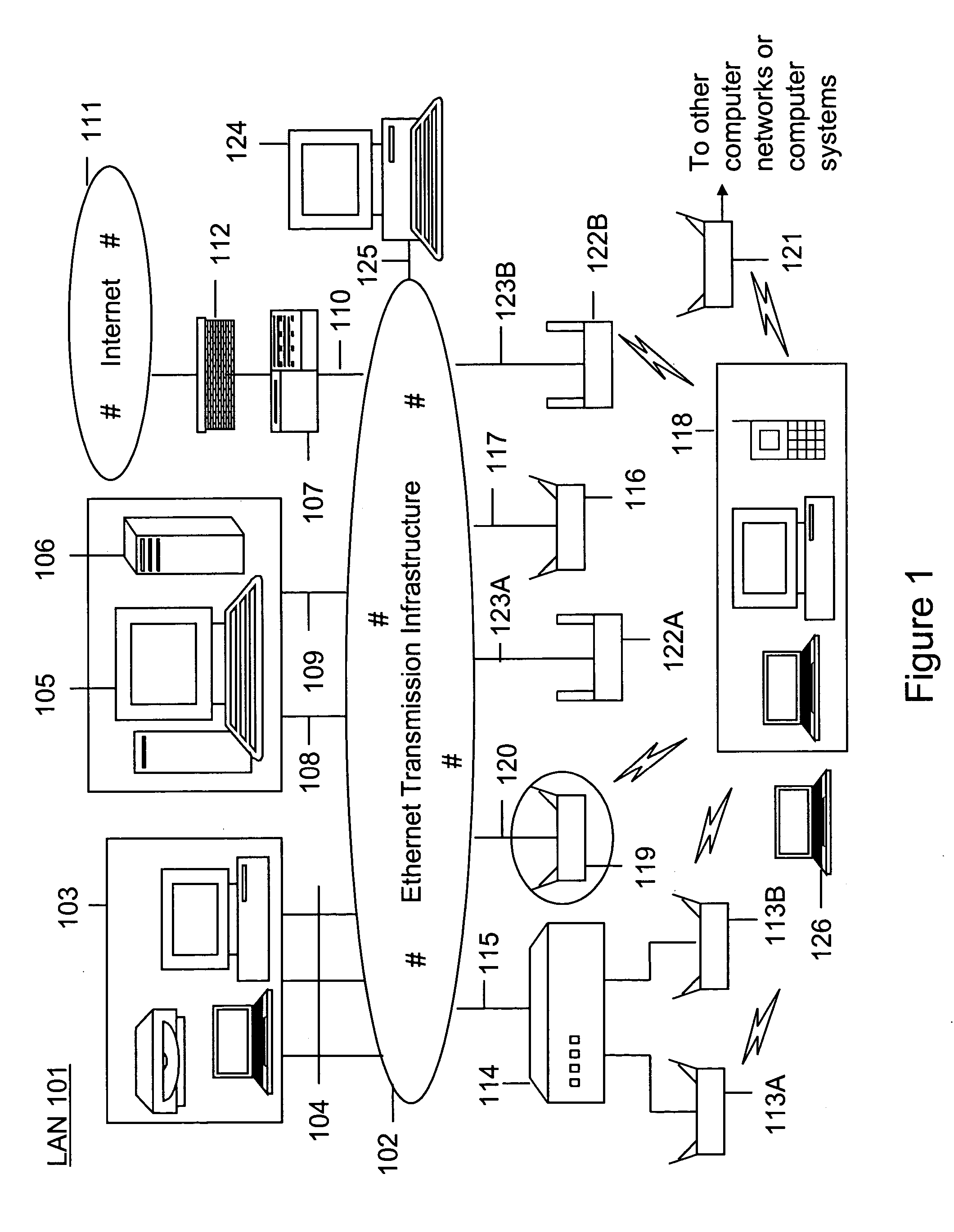
Method and system for detecting wireless access devices operably coupled to computer local area networks and related methods
InactiveUS7440434B2Easy to usePrevent unauthorized wireless accessMemory loss protectionError detection/correctionAir spaceReal-time computing
Owner:ARISTA NETWORKS
Method and apparatus for an improved security system mechanism in a business applications management system platform
InactiveUS6850893B2Minimizing user input effortMinimize effortSpecific access rightsDigital data processing detailsSafety management systemsImproved method
The present invention provides a solution to the needs described above through an improved method and apparatus for an improved security system mechanism in a business applications management system platform. The security management system partitions a number of business objects into a number of hierarchical domains. A security list is then created and configured to grant a member the right to perform a security operation on the business object located within the hierarchical domain. The security list is created by adding the security operation to the security list, applying the security operation to one of the multiple domains, and adding members to the security list.
Owner:SABA SOFTWARE
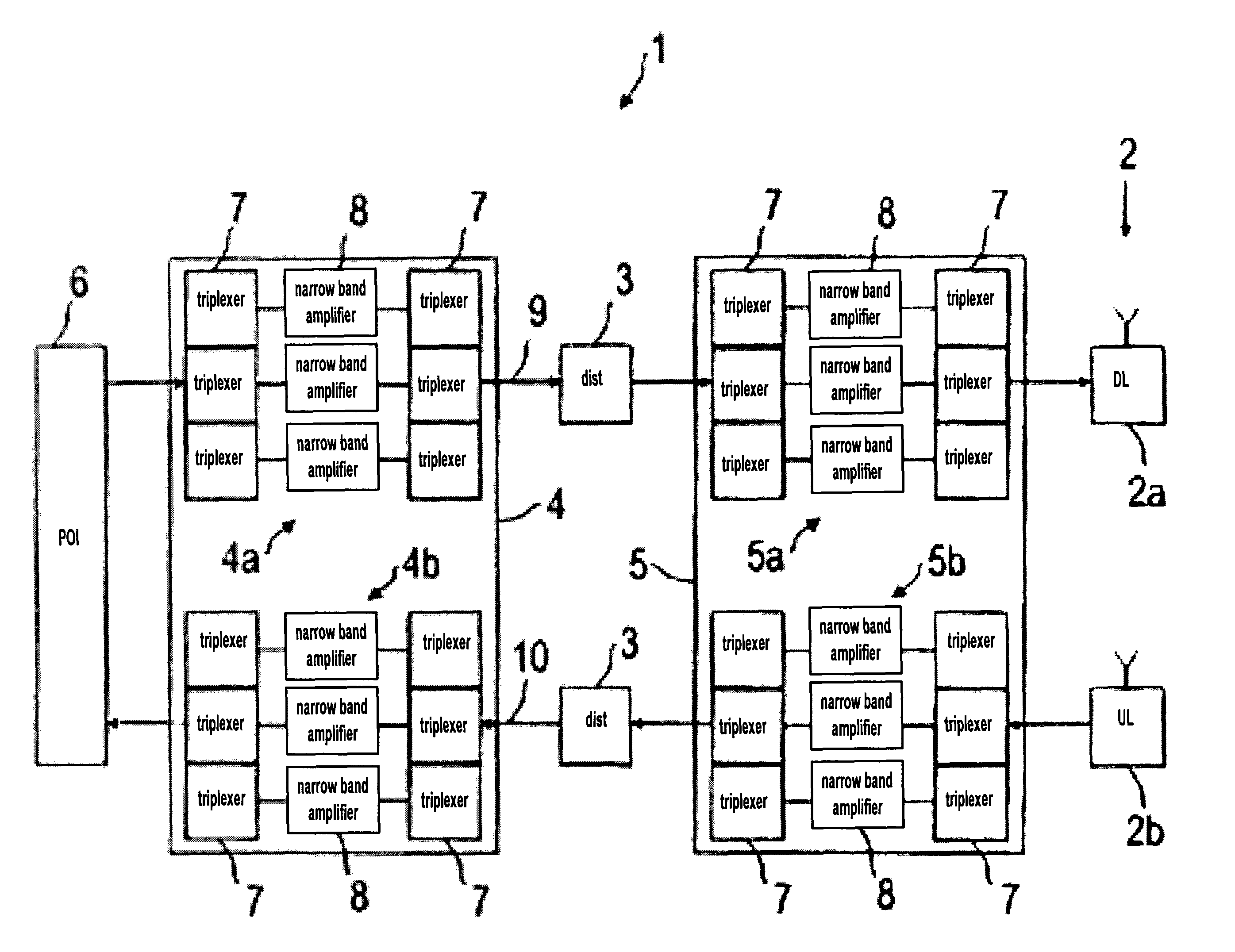
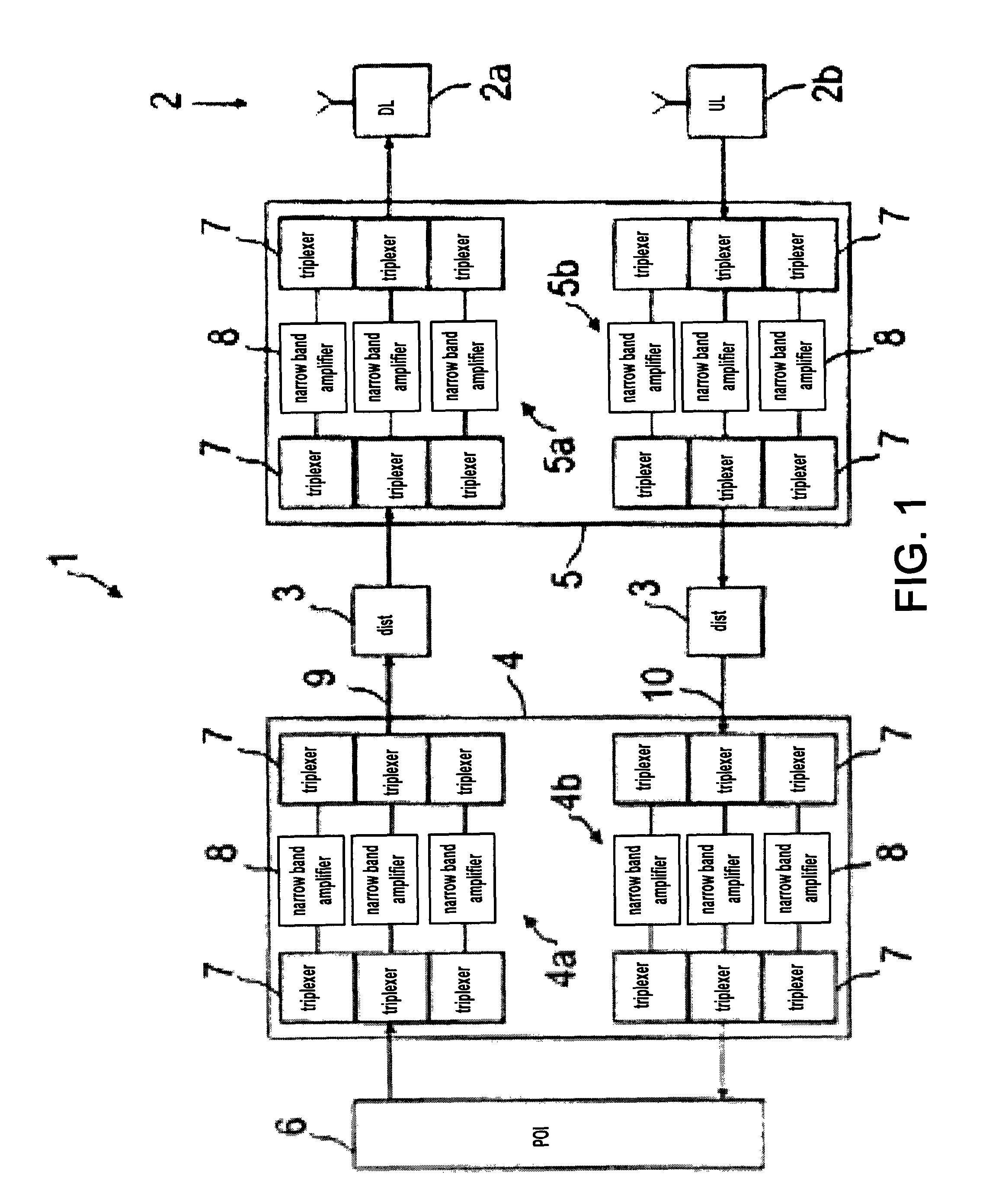
Radio frequency network
ActiveUS8428033B2Avoid intermodulationsReduce sizeFrequency-division multiplexWireless commuication servicesAudio power amplifierDistributed antenna system
Owner:RFS TECH INC
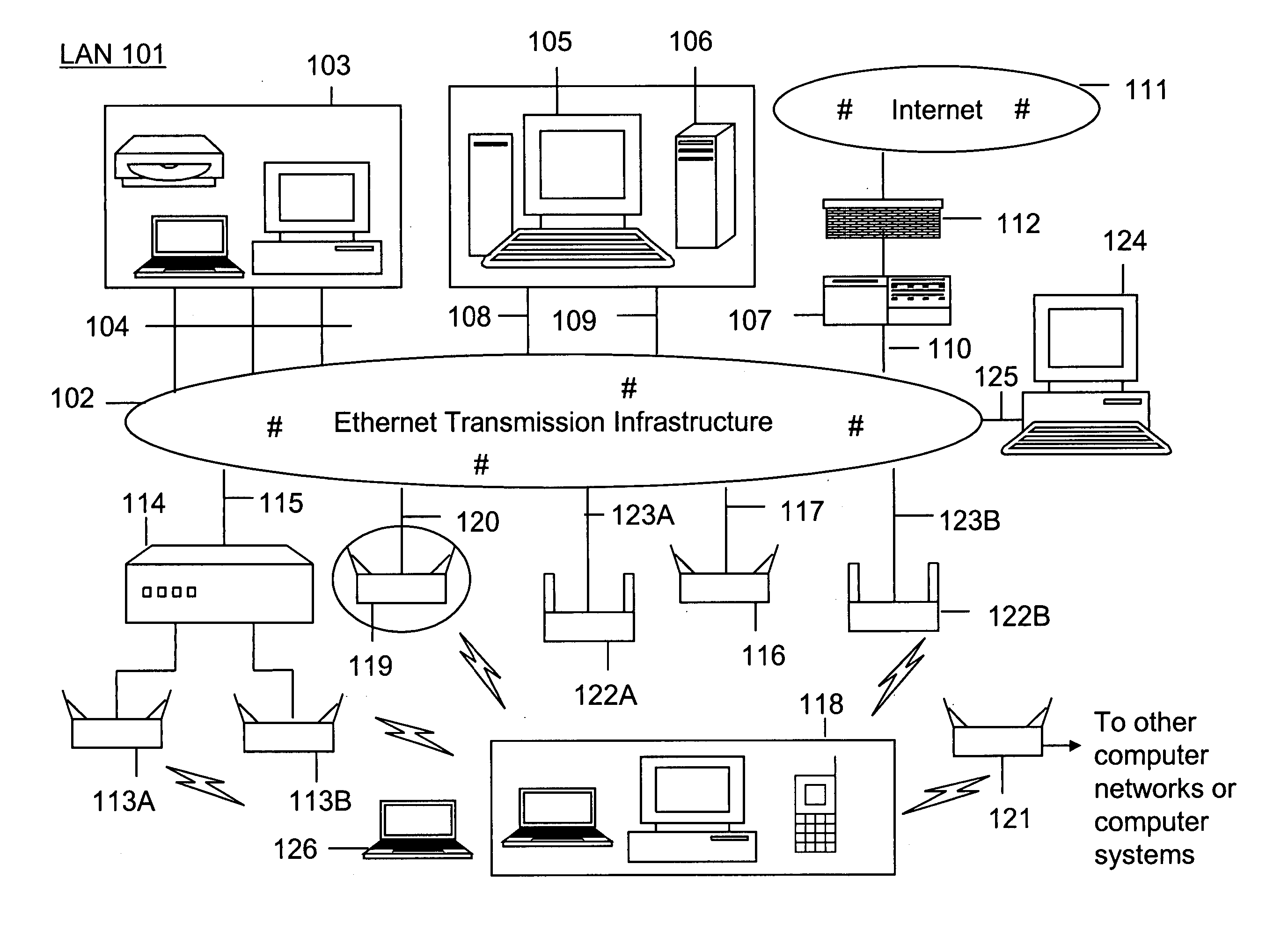
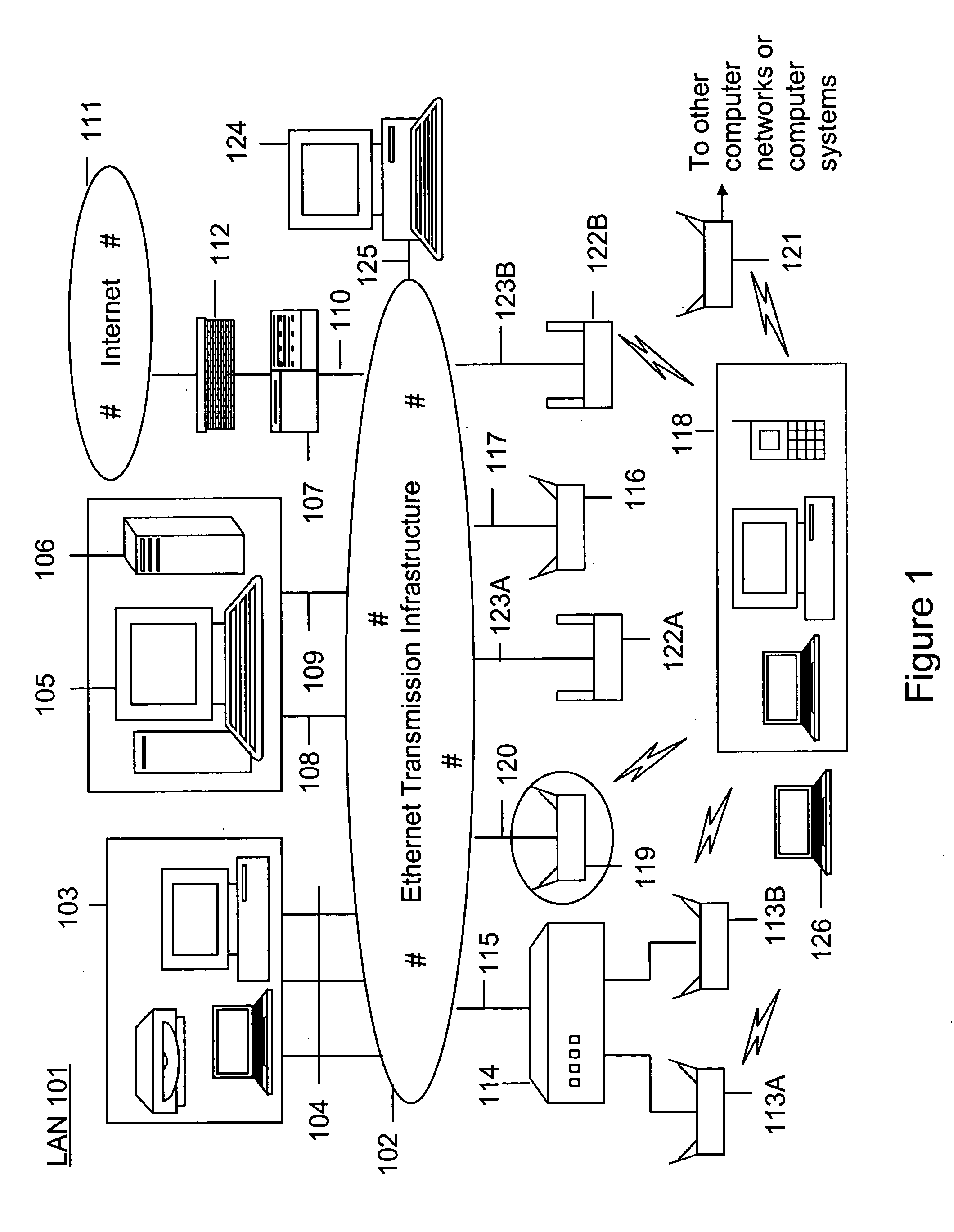
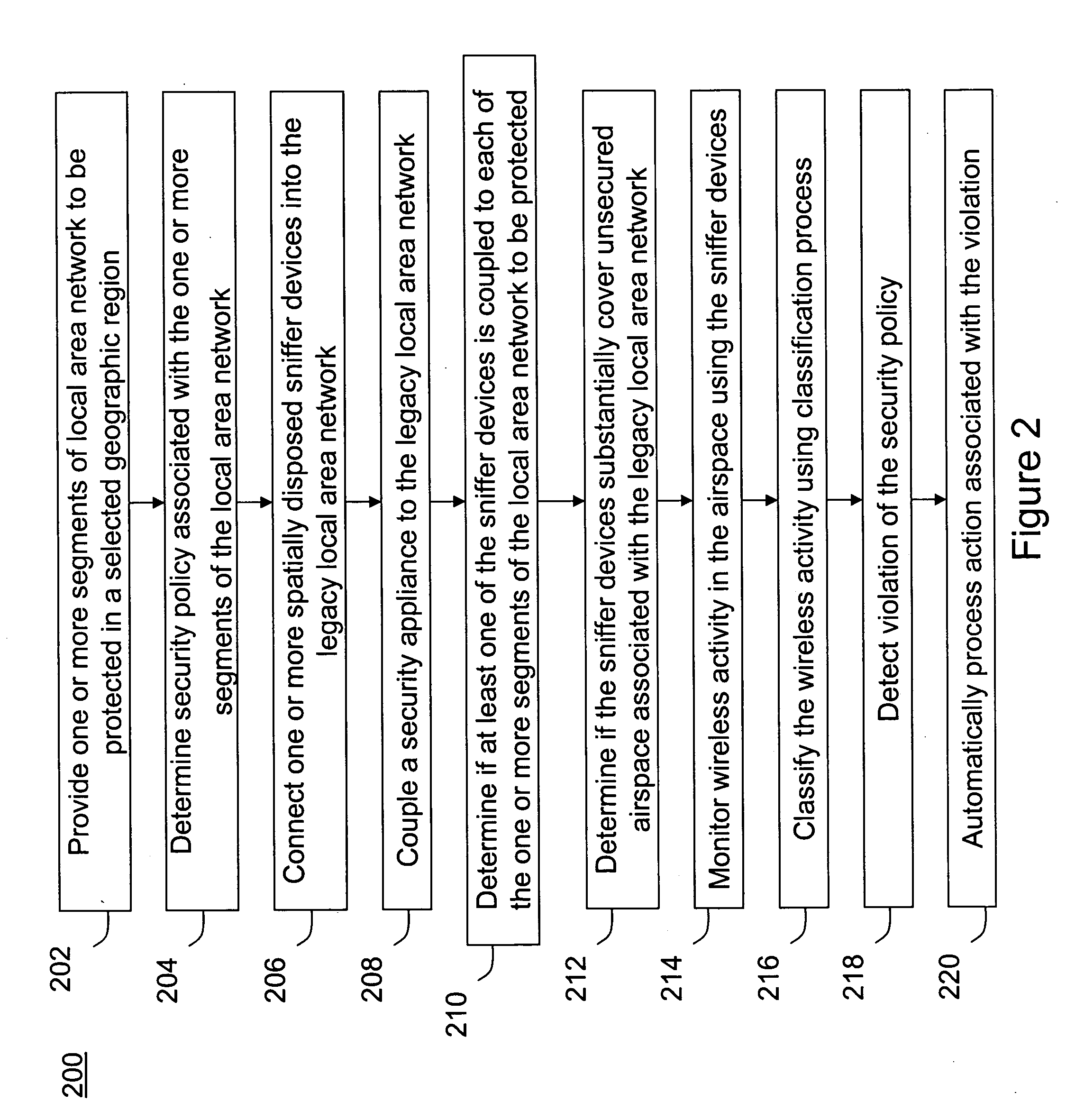
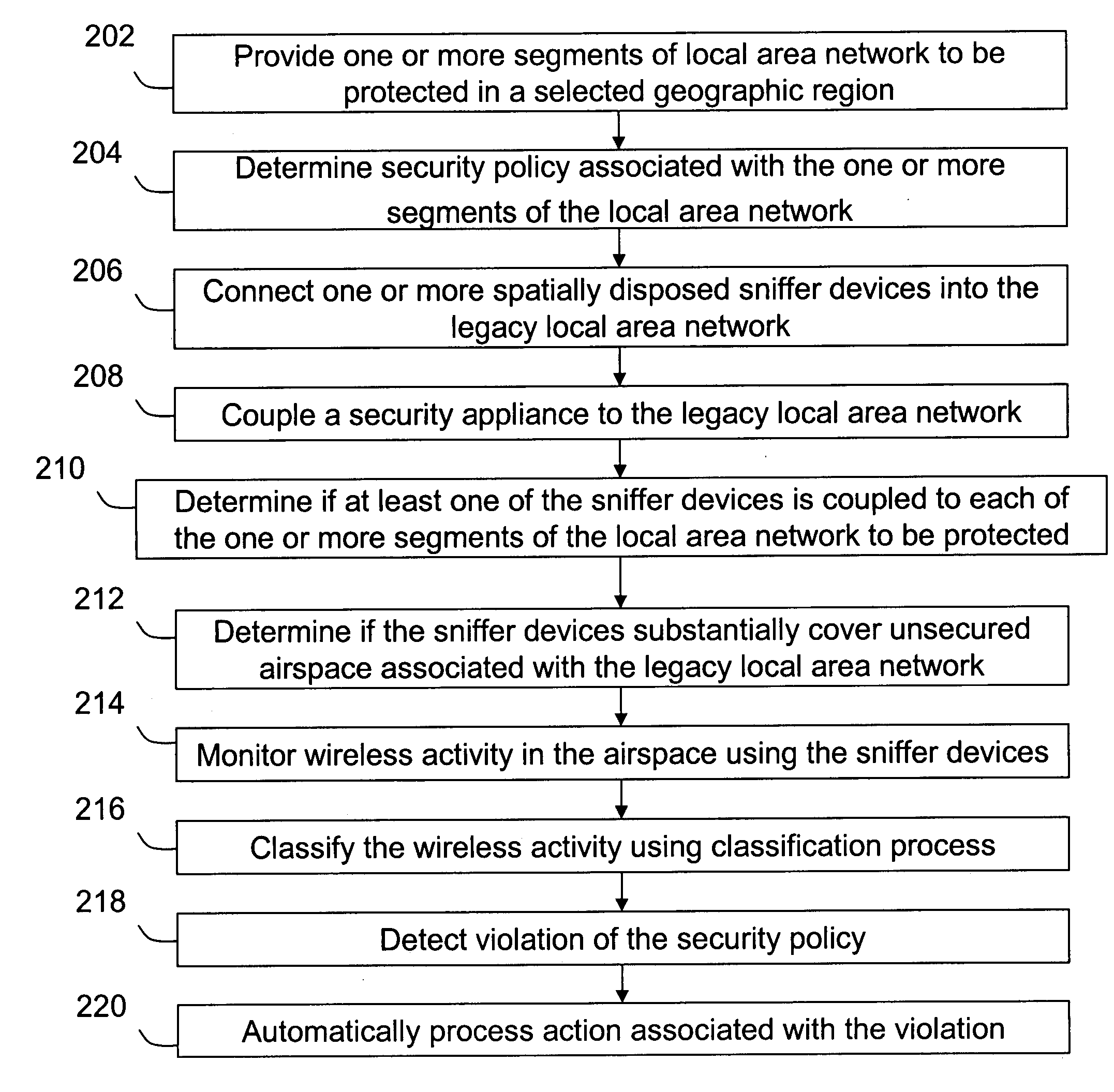
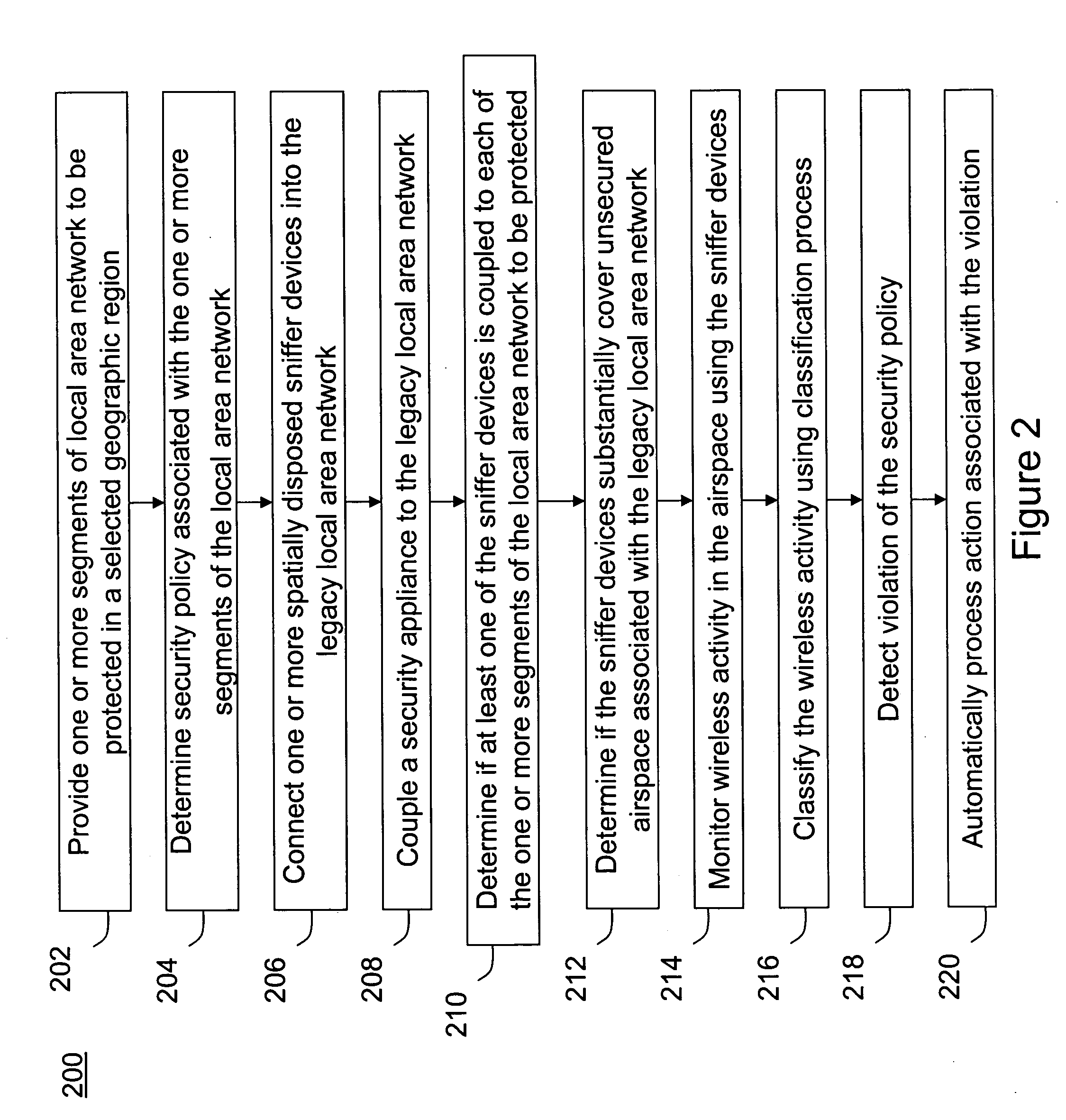
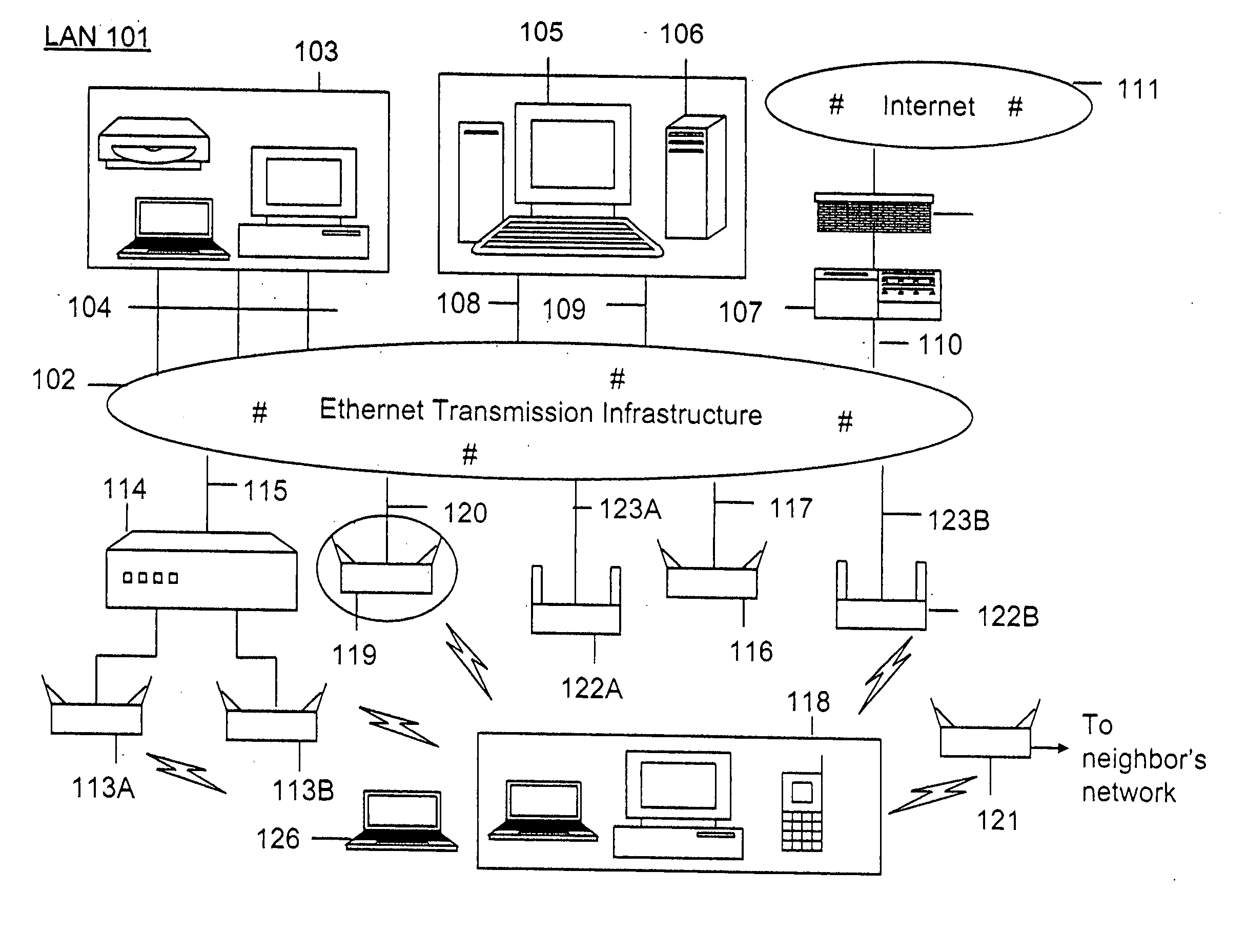
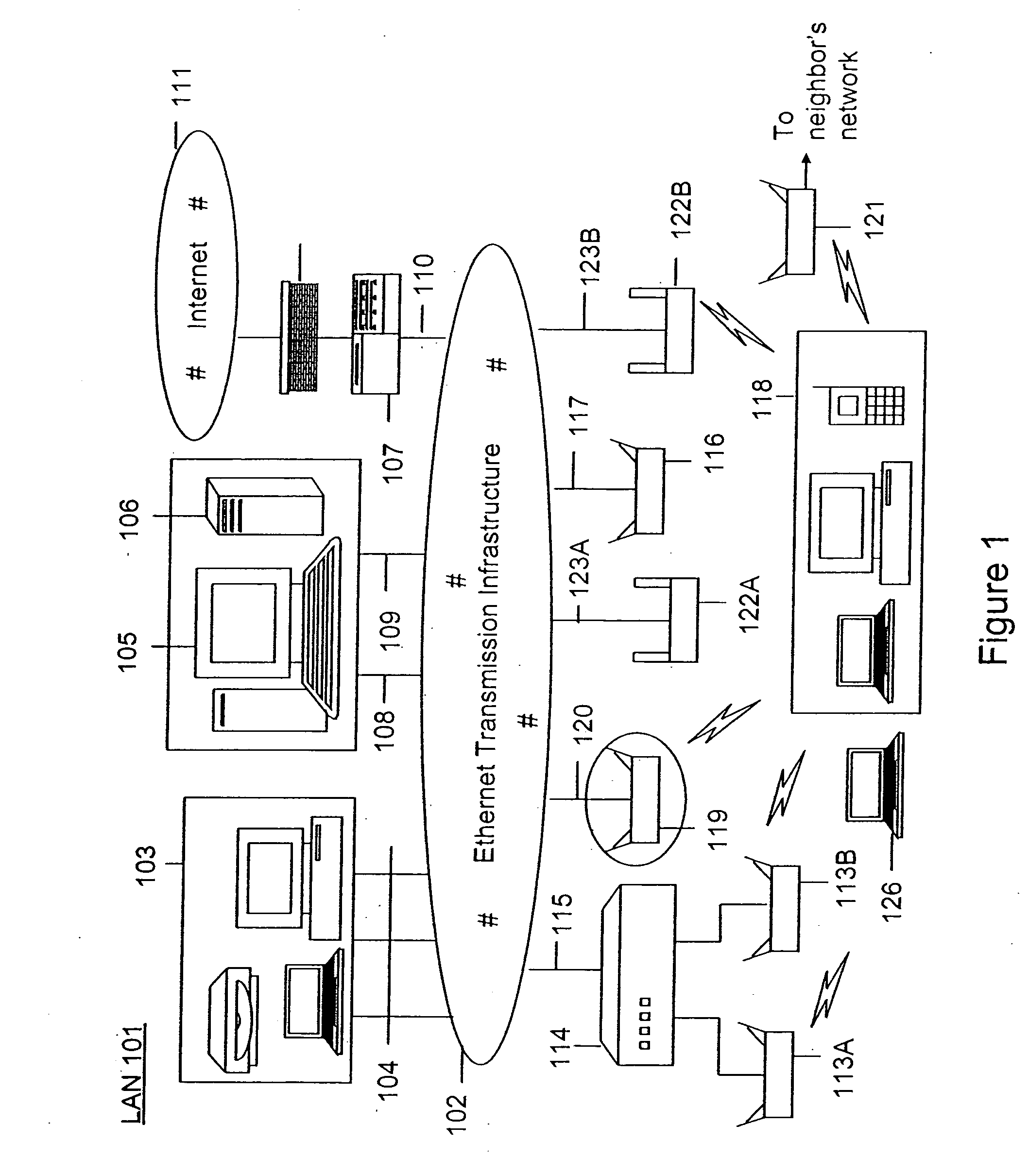
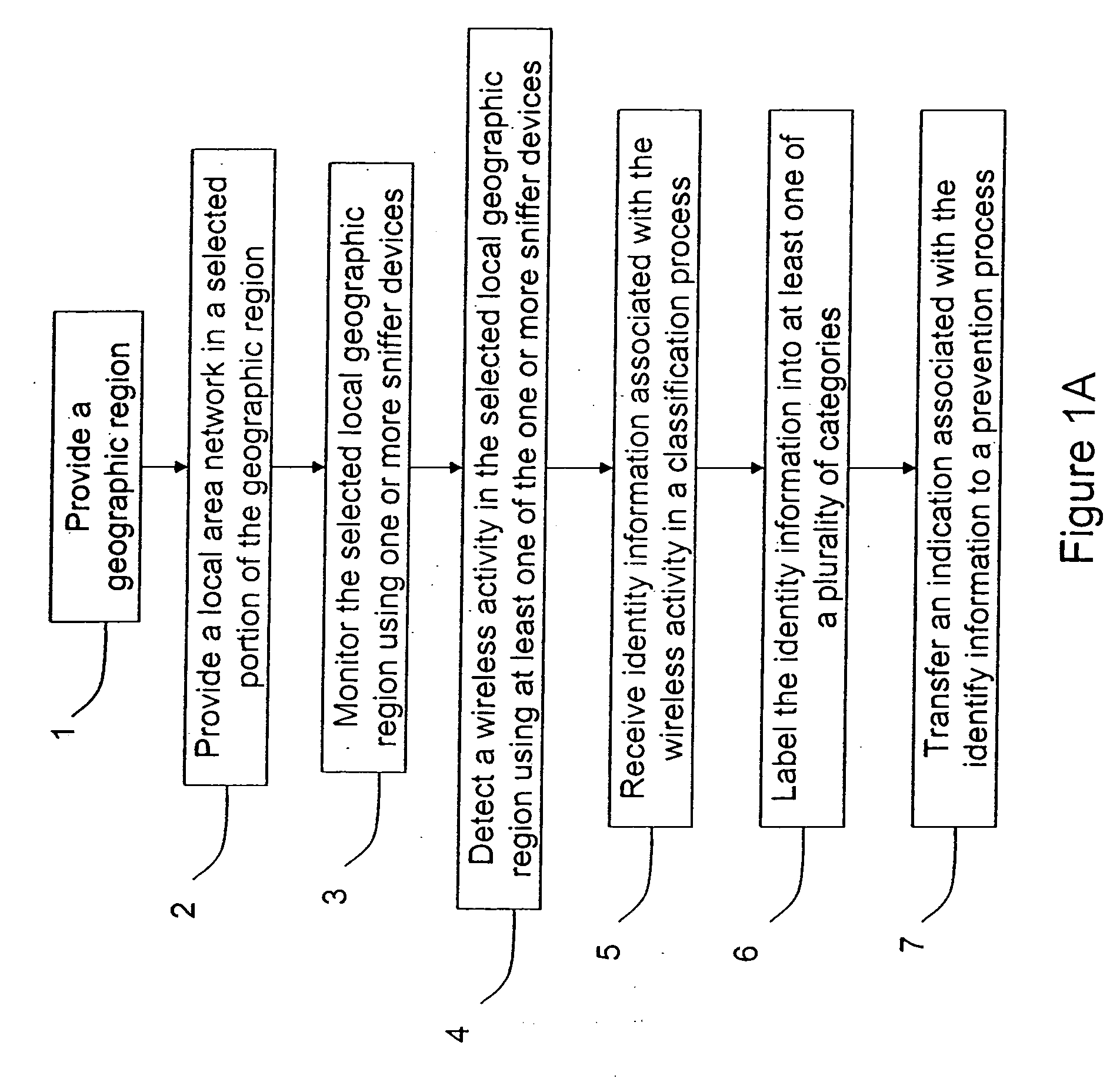
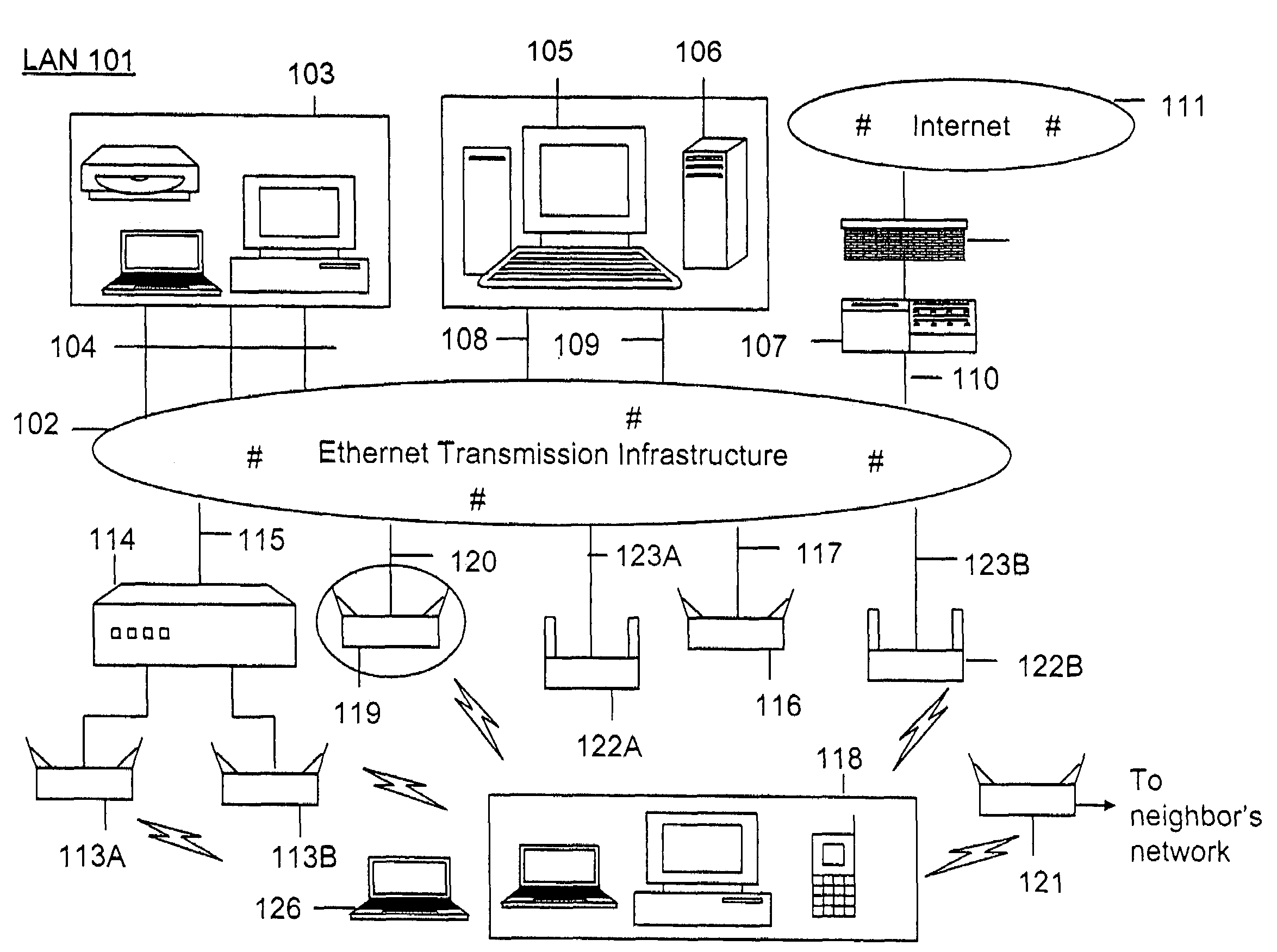
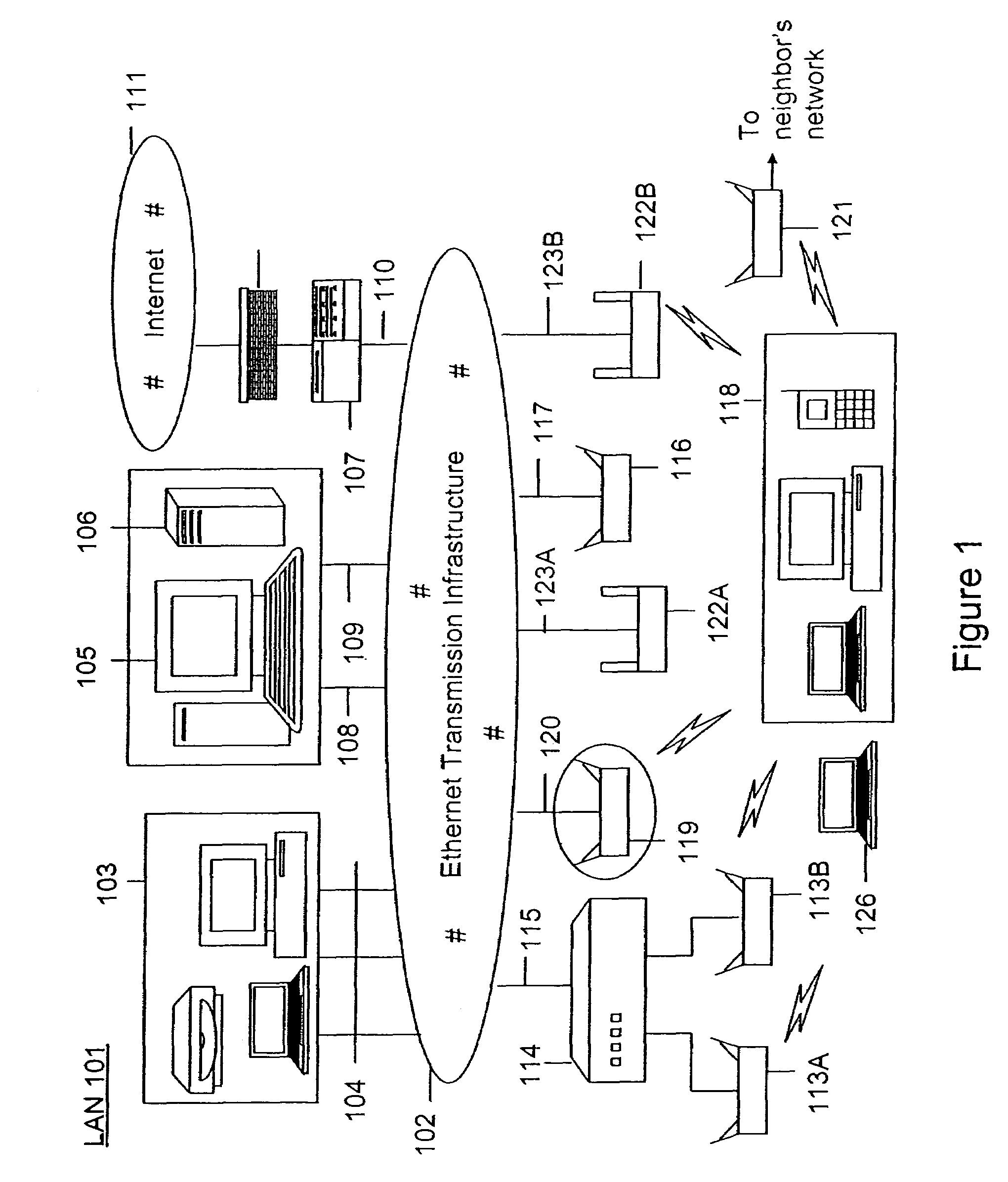
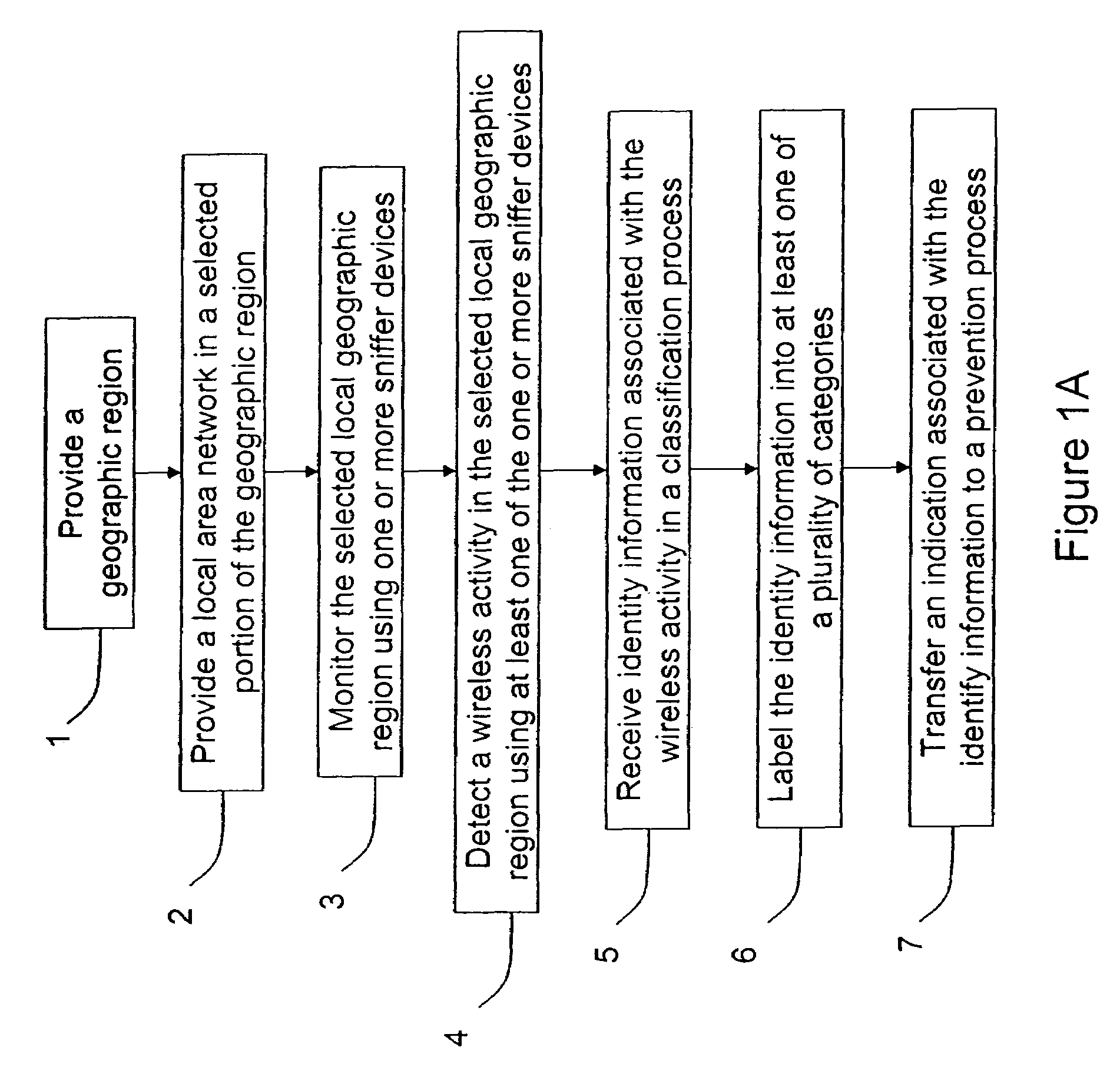
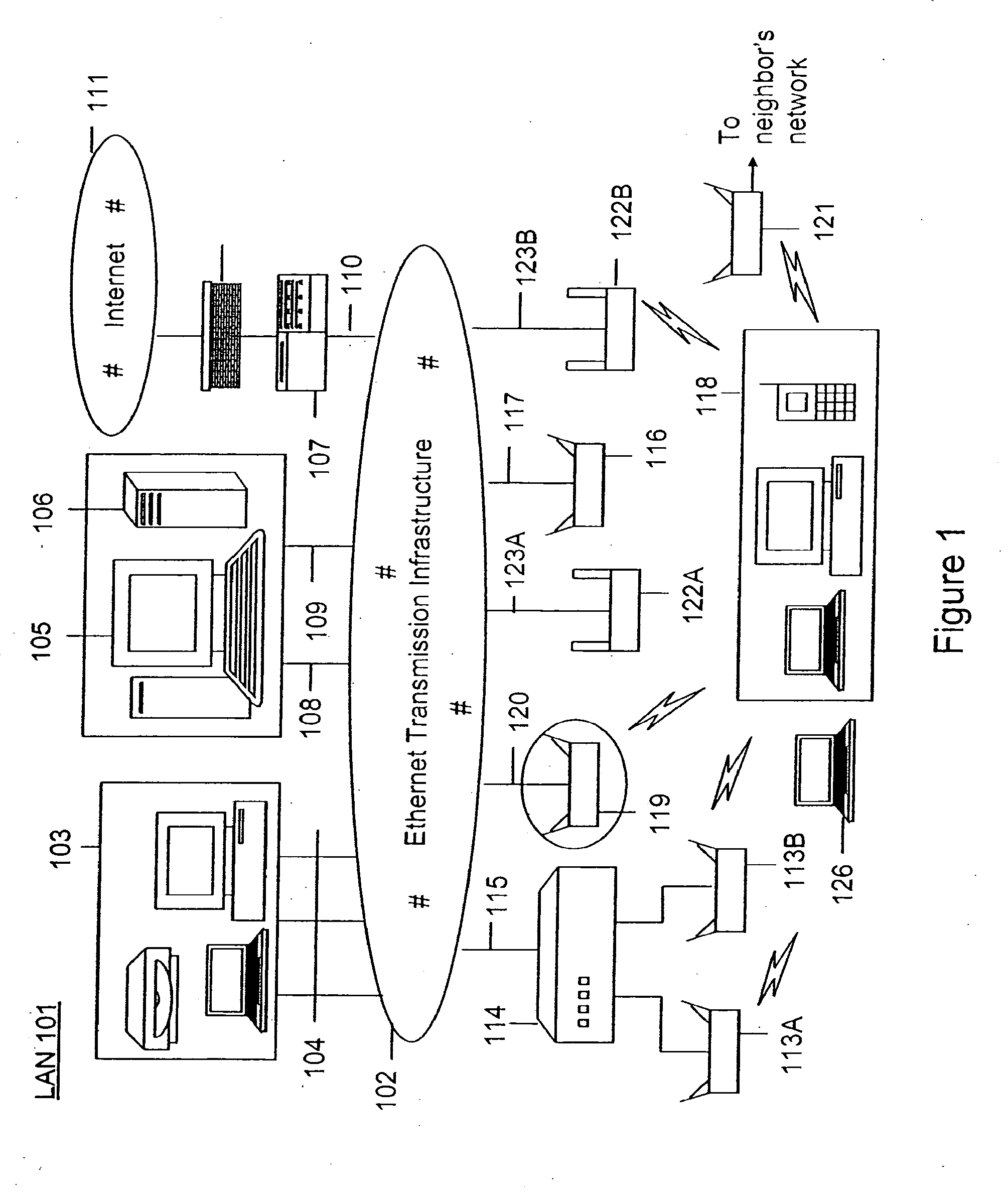
Method and system for monitoring a selected region of an airspace associated with local area networks of computing devices
ActiveUS20050128989A1Easy to usePrevent unauthorized wireless accessWave based measurement systemsData switching by path configurationBody area networkGeographic regions
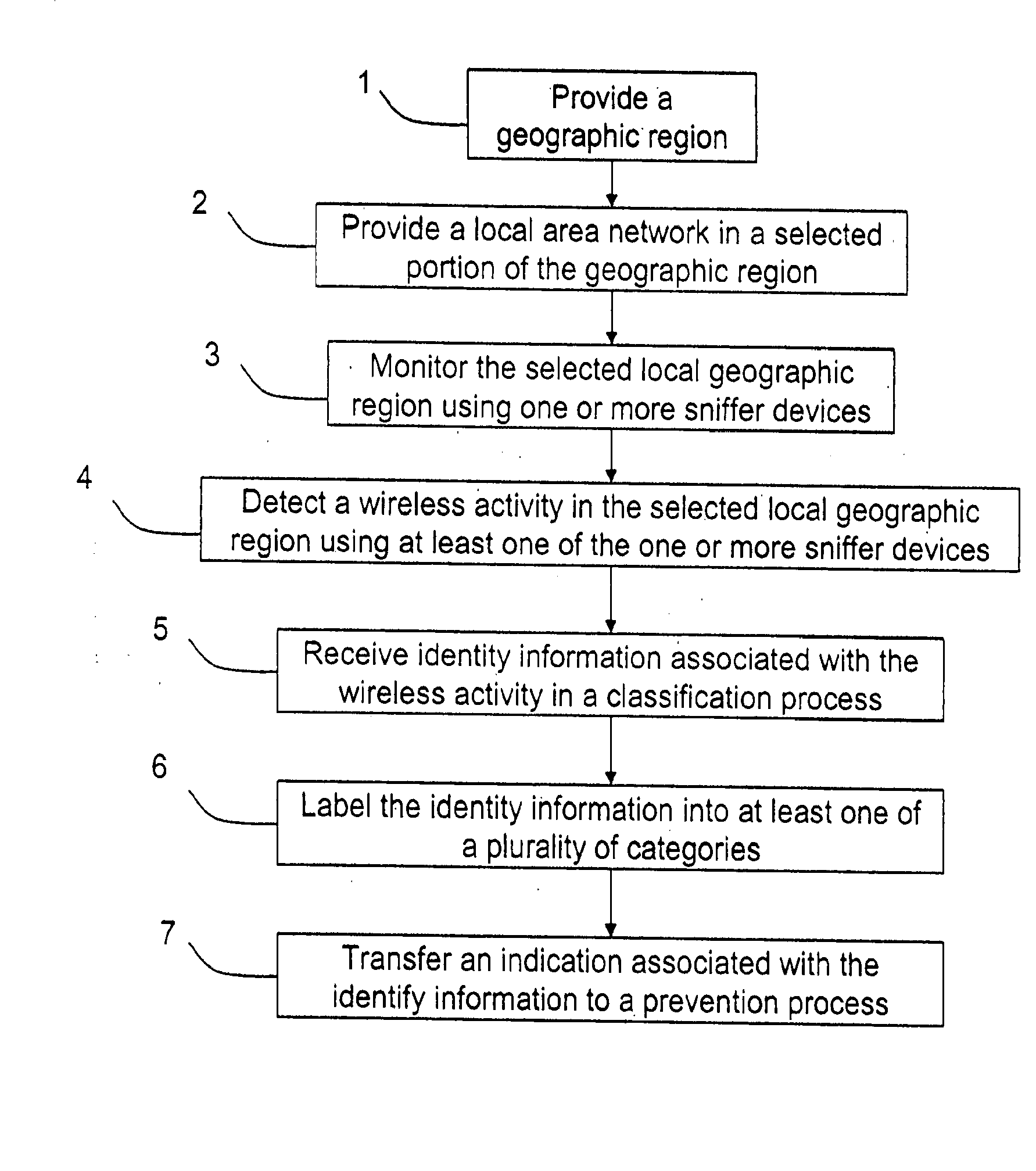
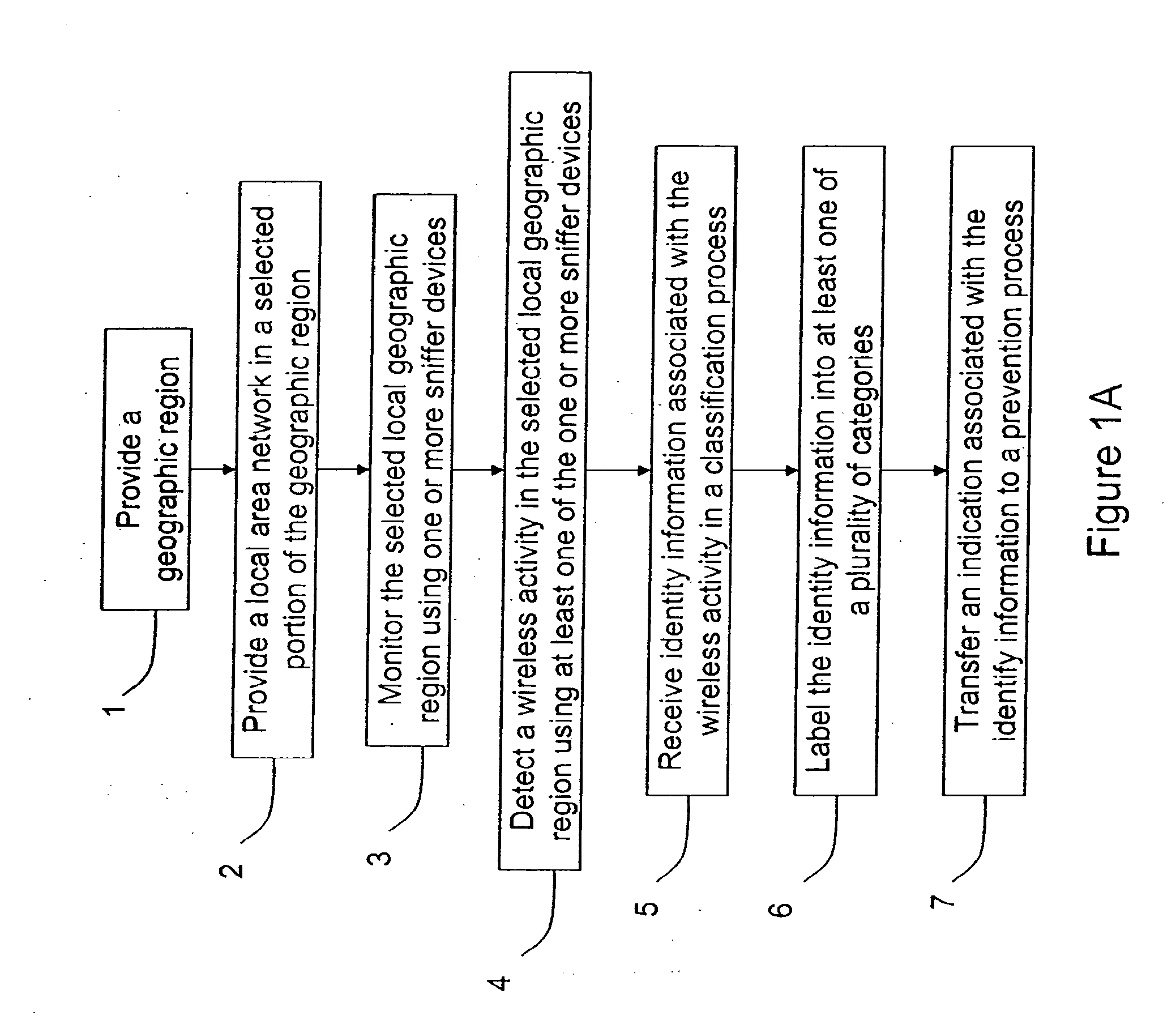
A method for monitoring a selected region of an airspace associated with local area networks of computing devices is provided. The method includes providing one or more segments of a legacy local area network to be protected in a selected geographic region. The legacy local area network is characterized by an unsecured airspace within the selected geographic region. The method includes determining a security policy associated with the one or more segments of the legacy local area network. The security policy at least characterizes a type of wireless activity in the unsecured airspace to be permitted, denied, or ignored. Additionally, the method includes connecting one or more sniffer devices into the legacy local area network. The one or more sniffer devices are spatially disposed within the selected geographic region to cause at least a portion of the unsecured airspace to be secured according to the security policy. Moreover, the method includes coupling a security appliance to the legacy local area network. The method also includes determining if at least one of the sniffer devices is coupled to each of the one or more segments of the legacy local area network to be protected and determining if the one or more sniffer devices substantially covers the portion of the unsecured airspace to be secured. The method additionally includes monitoring wireless activity in the airspace using the one or more sniffer devices, and automatically classifying, using a classification process, a portion of information associated with the monitoring of the wireless activity to at least determine if the wireless activity communicates to at least one of the one or more segments to be protected. Further, the method includes detecting a violation of the security policy based upon at least the classifying of the portion of the information from the monitoring of the wireless activity, and automatically processing an action associated with the violation in accordance to the security policy for the one or more segments in the legacy local area network to be protected.
Owner:ARISTA NETWORKS
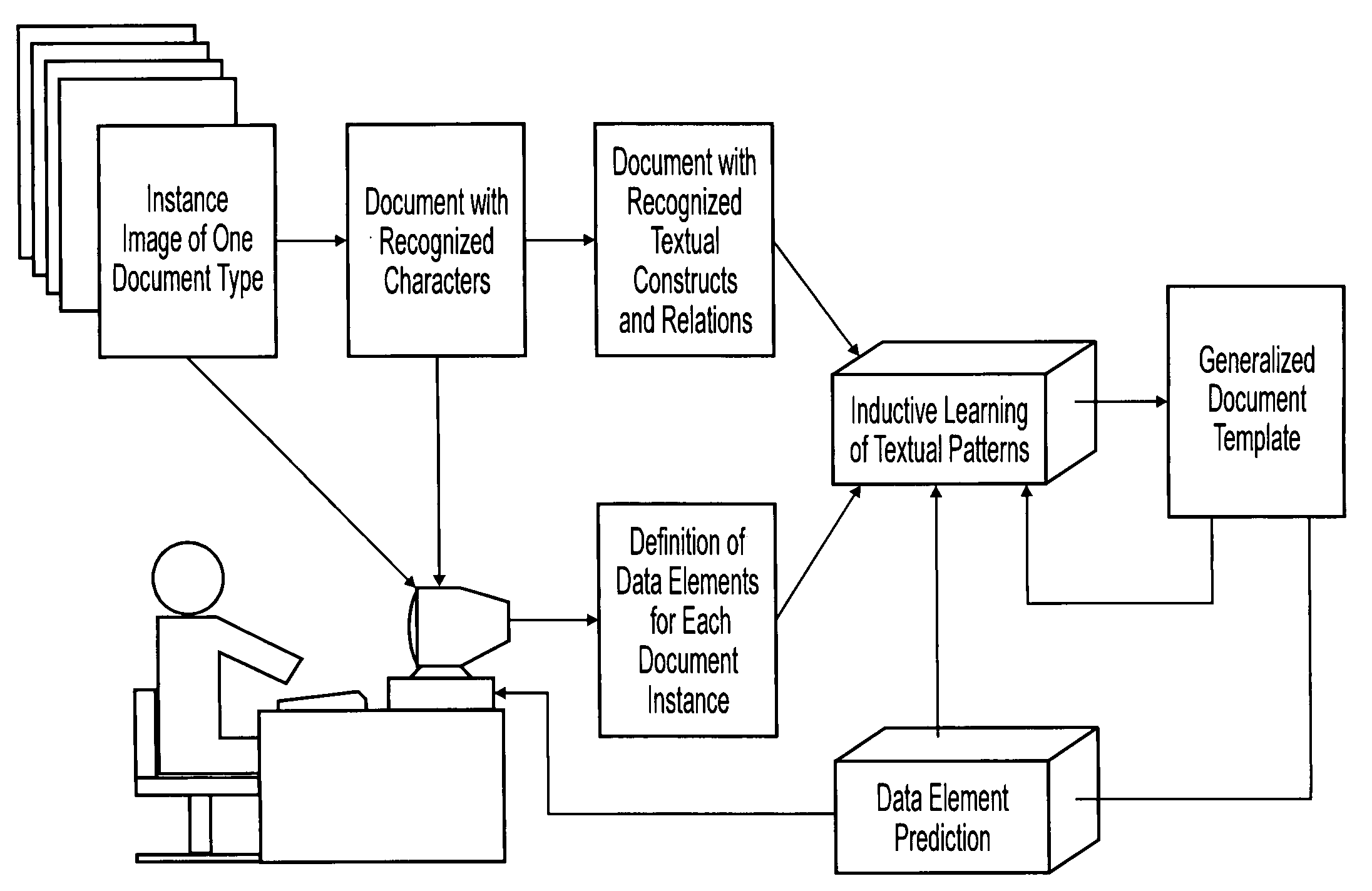
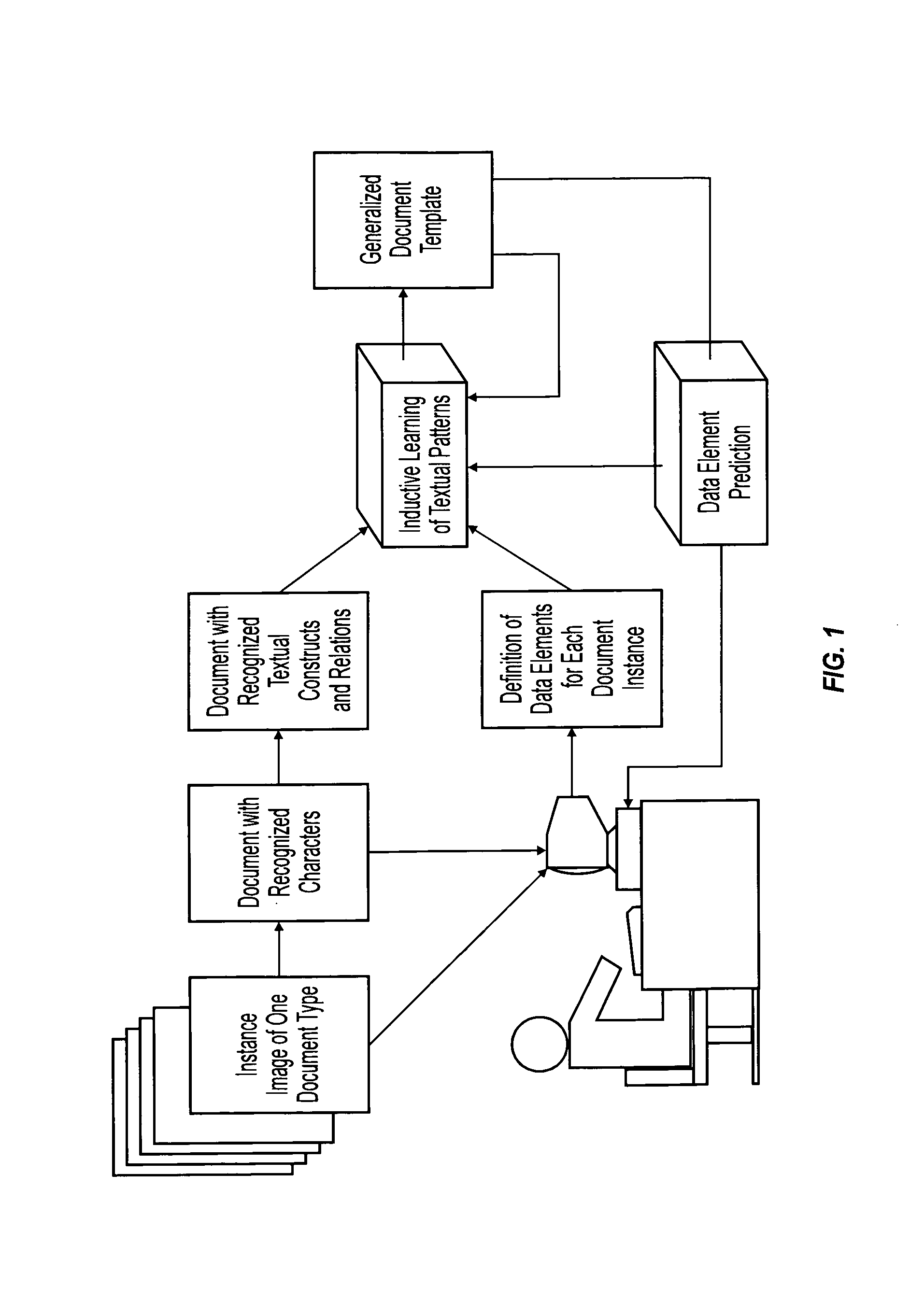
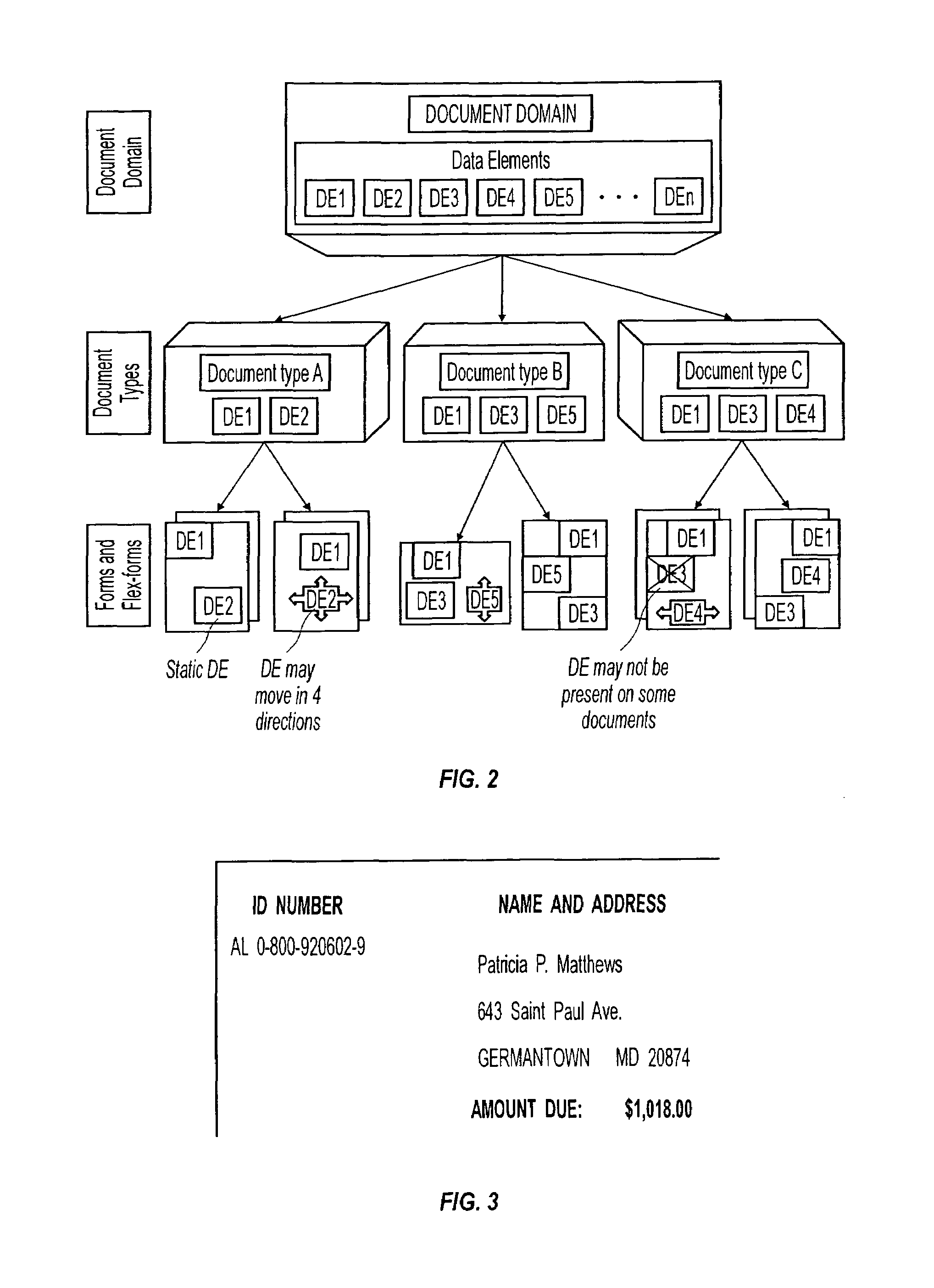
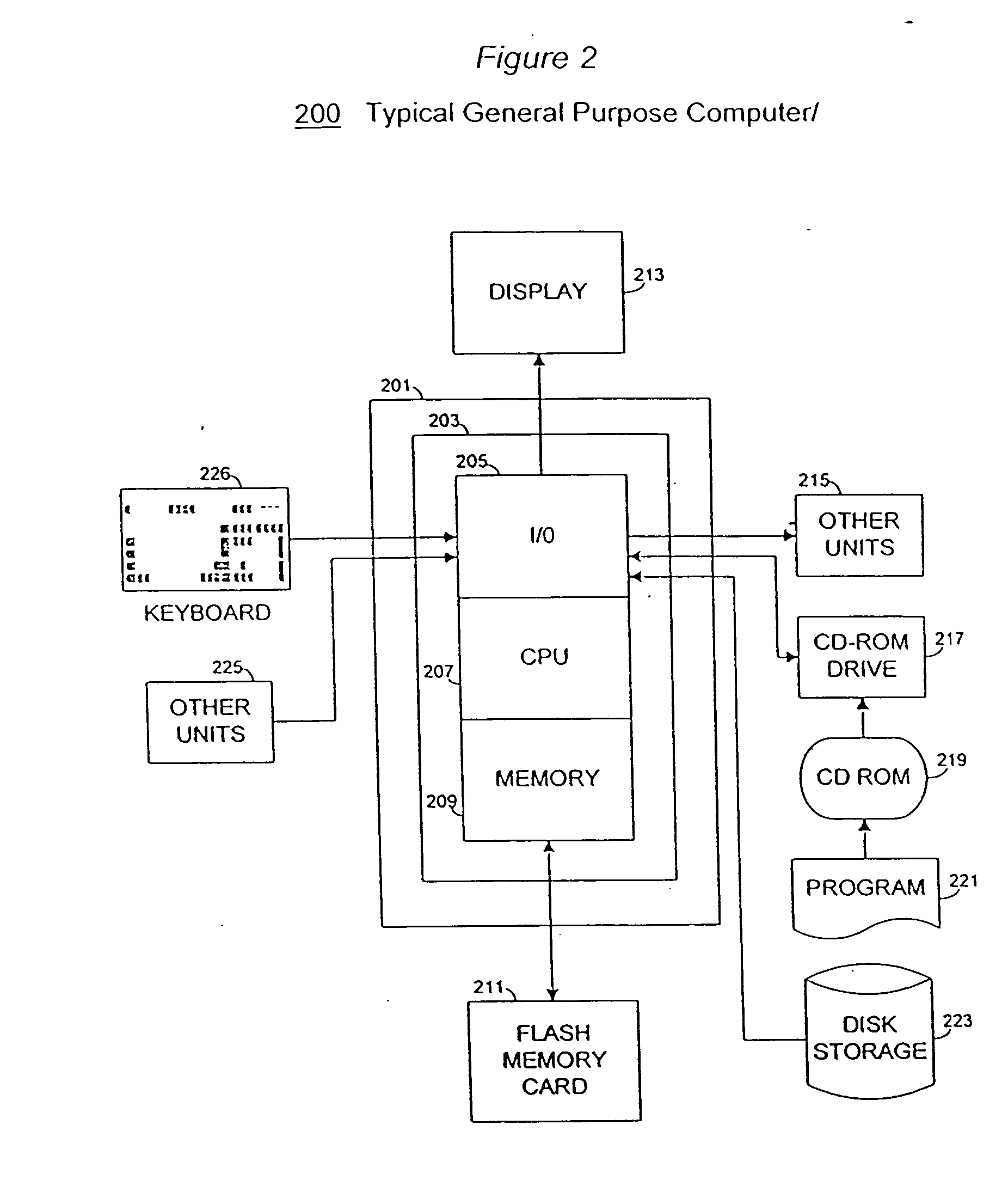
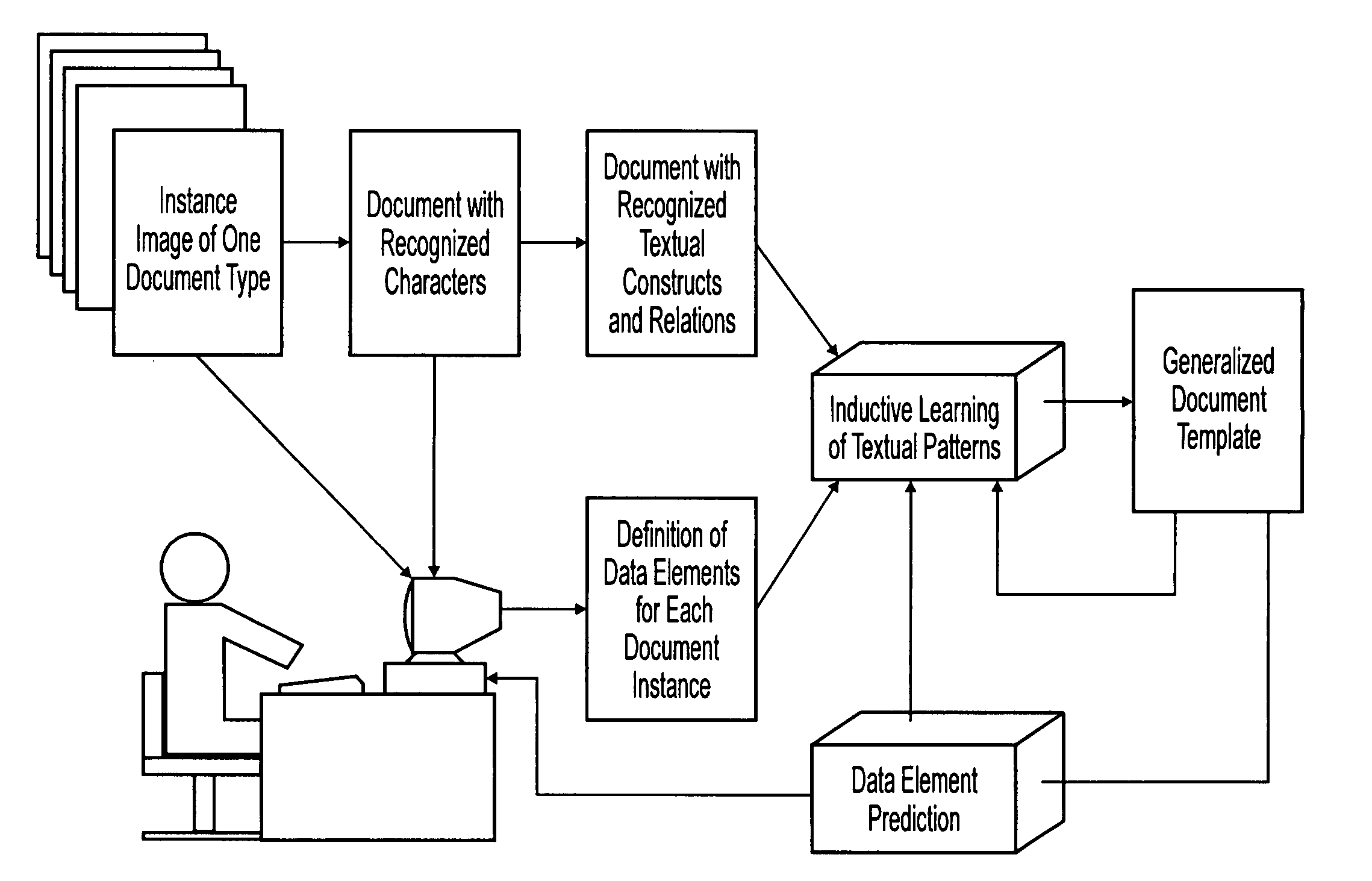
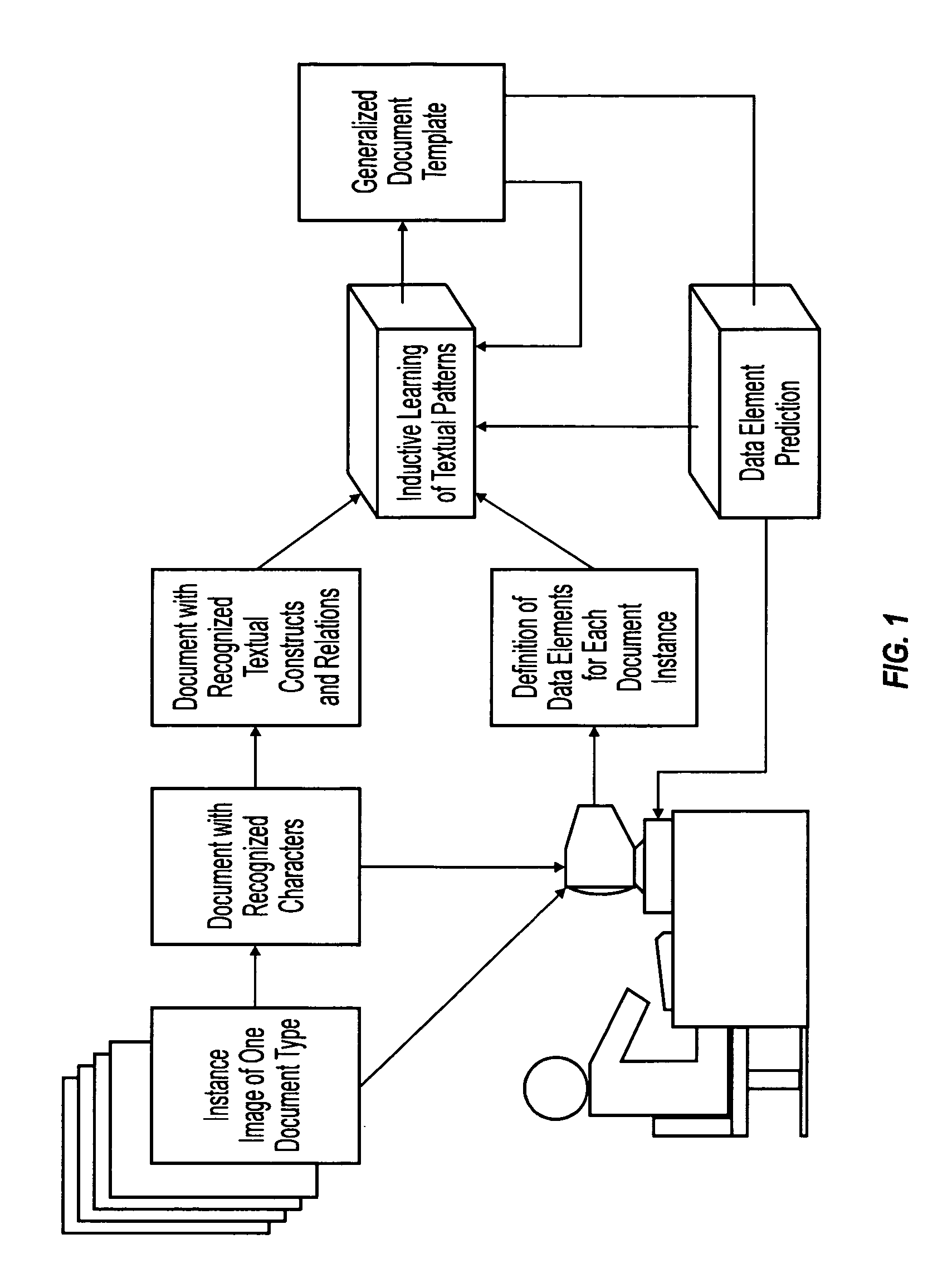
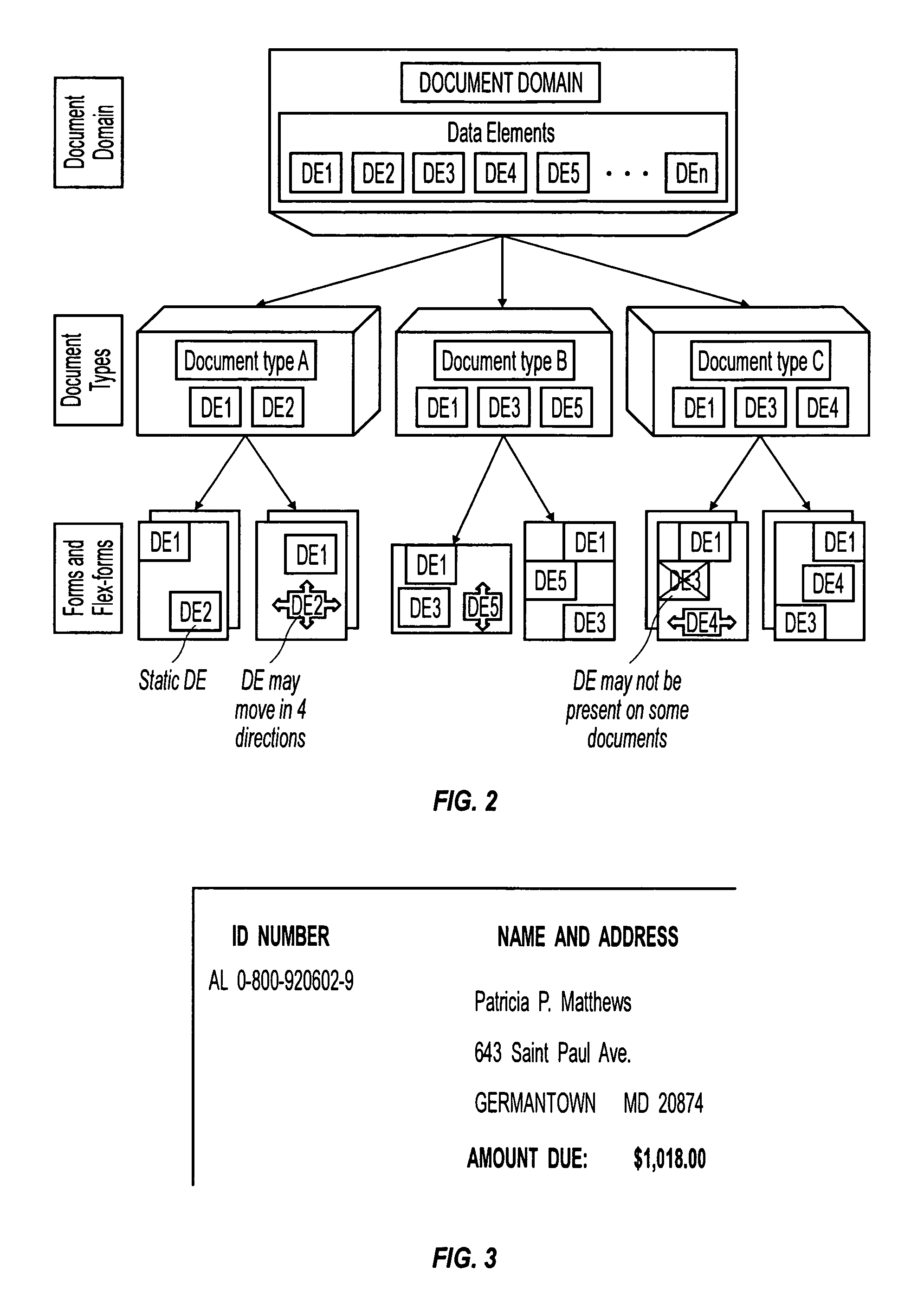
Machine learning of document templates for data extraction
InactiveUS7149347B1Quality assuranceMinimize effortCharacter recognitionData ingestionDocument preparation
The present system can perform machine learning of prototypical descriptions of data elements for extraction from machine-readable documents. Document templates are created from sets of training documents that can be used to extract data from form documents, such as: fill-in forms used for taxes; flex-form documents having many variants, such as bills of lading or insurance notifications; and some context-form documents having a description or graphic indicator in proximity to a data element. In response to training documents, the system performs an inductive reasoning process to generalize a document template so that the location of data elements can be predicted for the training examples. The automatically generated document template can then be used to extract data elements from a wide variety of form documents.
Owner:LEIDOS
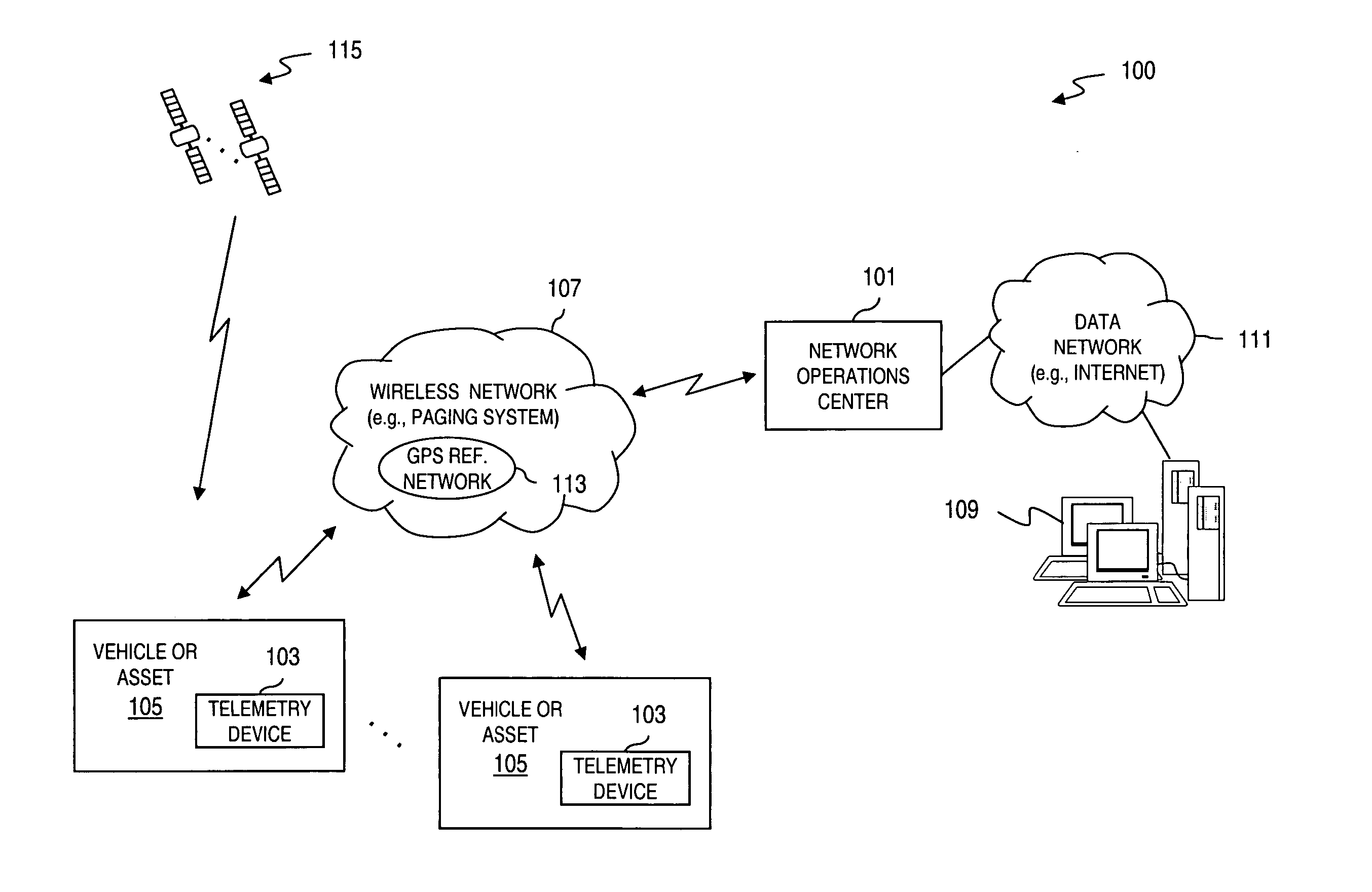
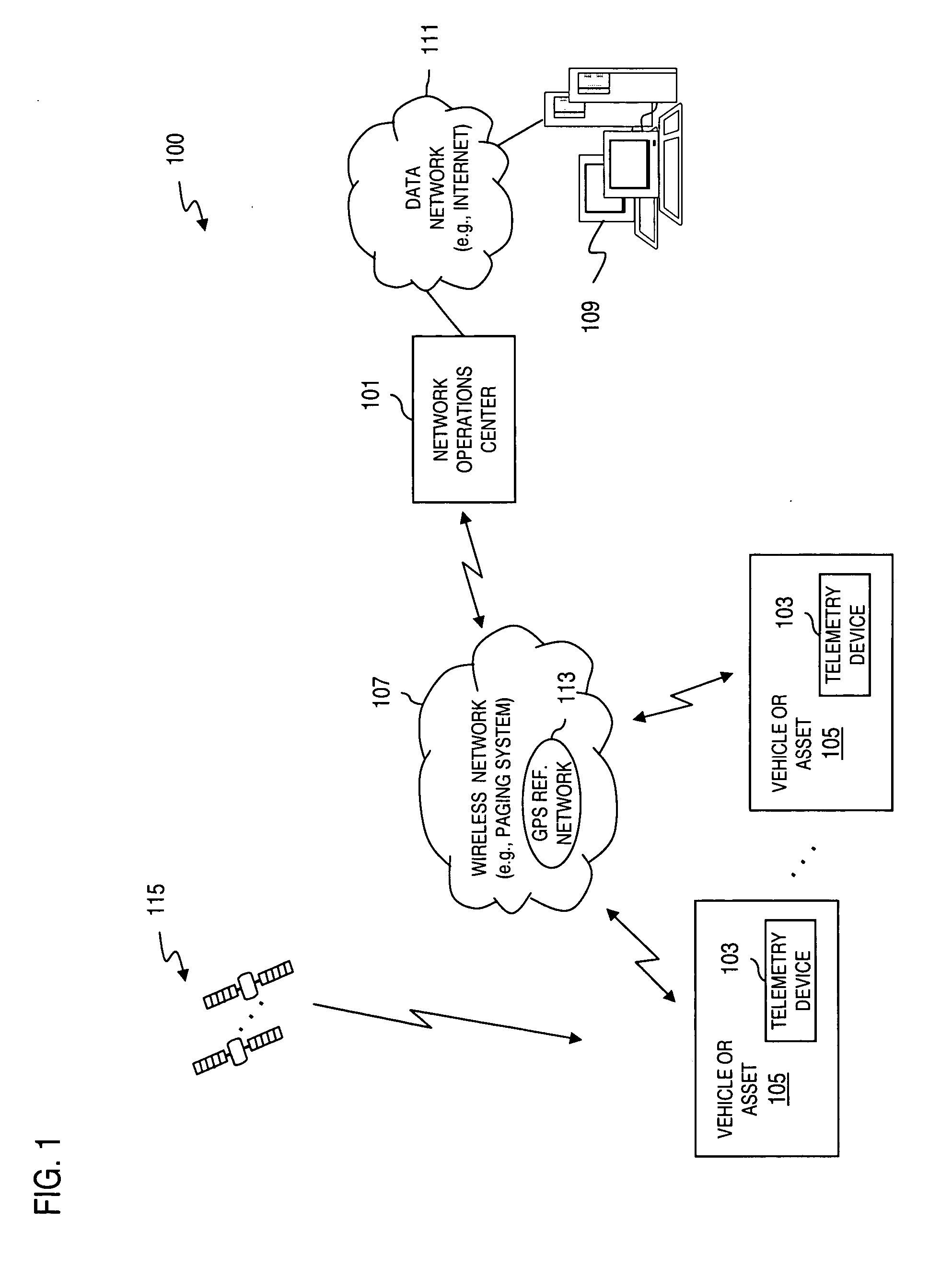
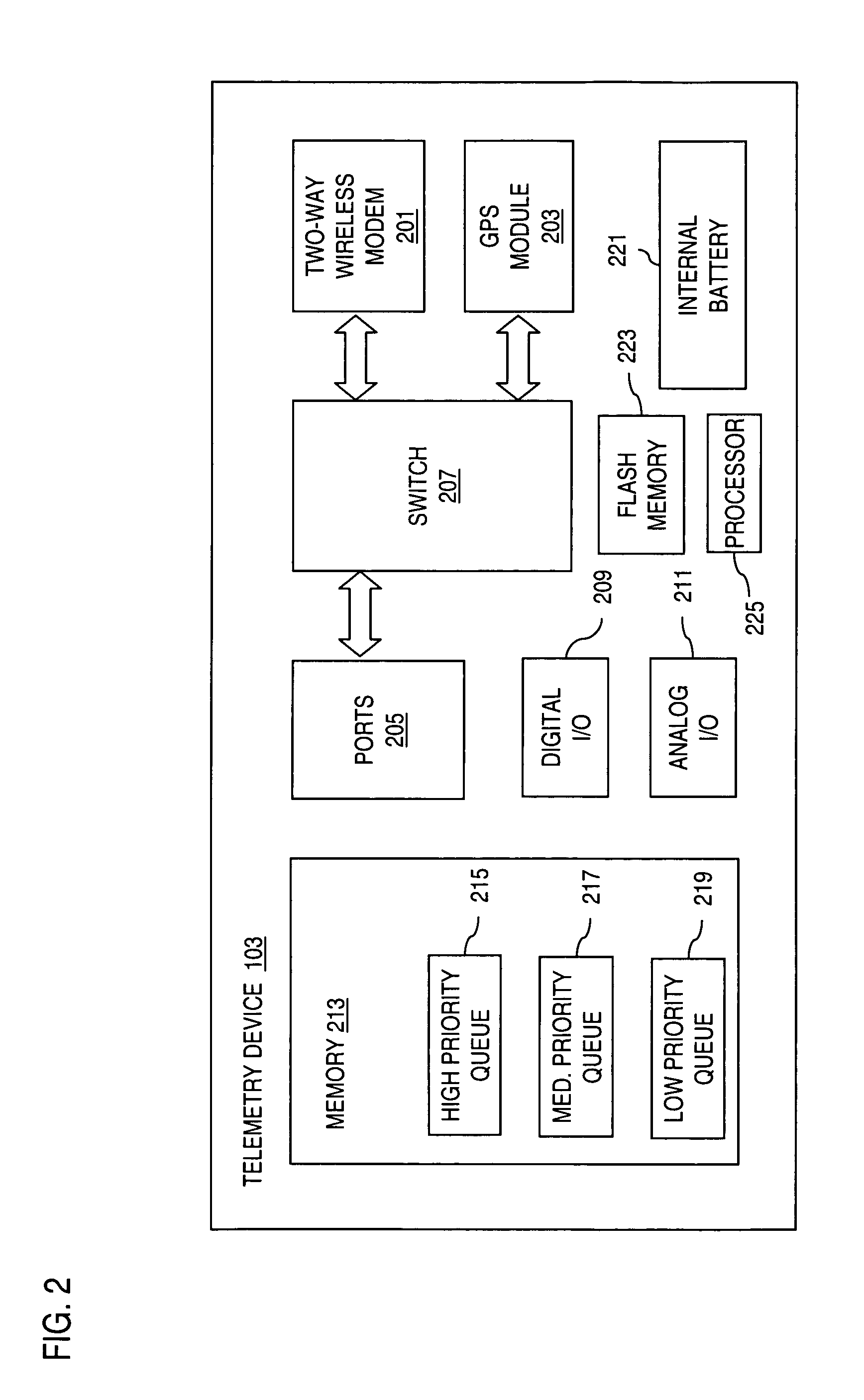
Method and system for interfacing with mobile telemetry devices
InactiveUS20050156715A1Minimize initial download timeMinimizing programmer/developer effortFrequency-division multiplex detailsComputer controlWeb browserTelemetry Equipment
An interface is provided for managing a plurality of tracked objects, each tracked object associated with a corresponding telemetry device. A request is received from a web browser for at least one action to be performed by the telemetry device. A message including information indicating the at least one action is transmitted, to the corresponding telemetry device. The web browser is configured to display at least one geographical map indication of at least one location of each tracked object.
Owner:SKYGUARD
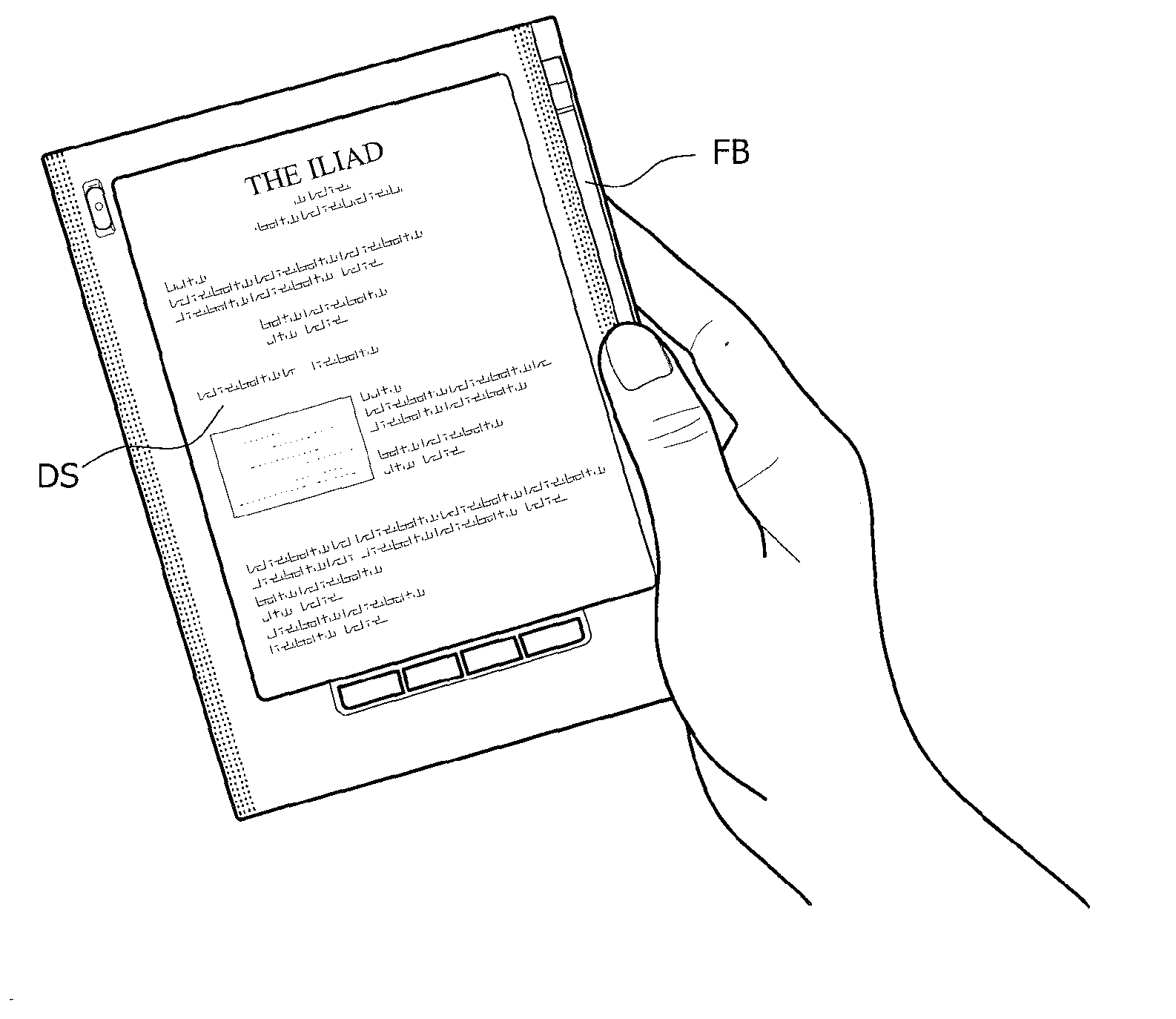
Electronic Reading Device Mimicking a Reading experience of a Paper Document
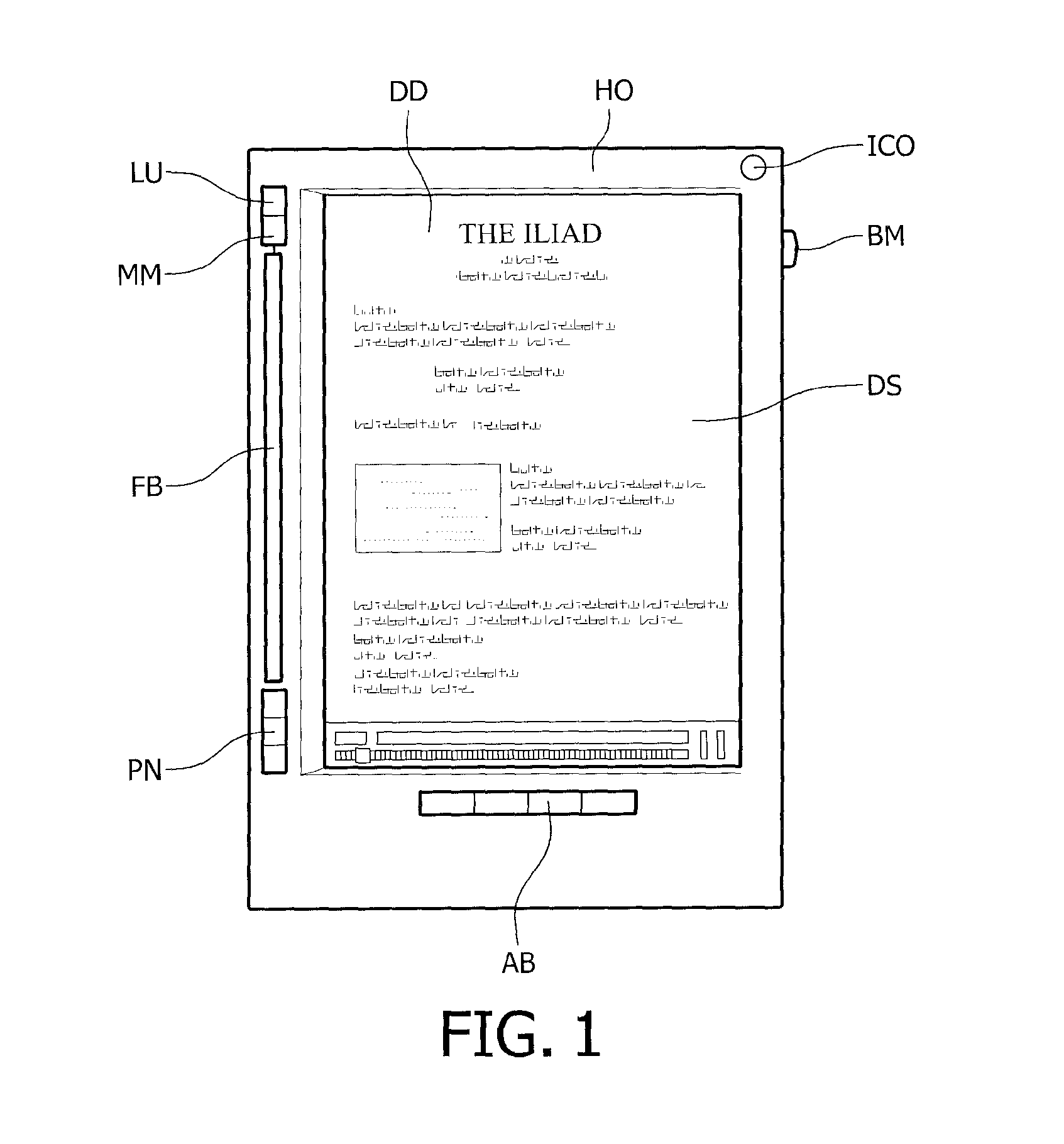
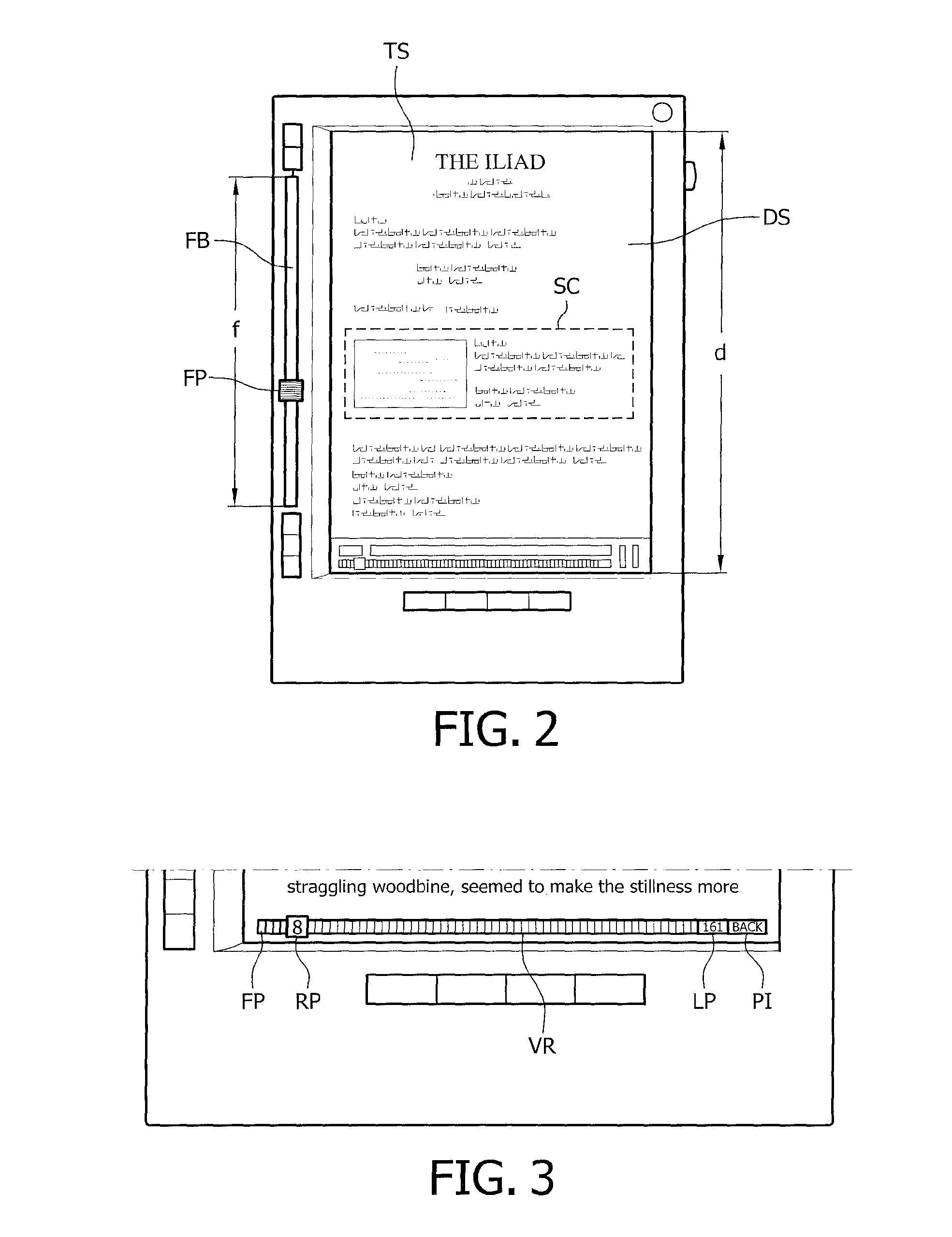
InactiveUS20080259057A1Minimize effortHelp positioningDigital computer detailsCathode-ray tube indicatorsBiological activationDocumentation
An apparatus comprises a display screen (DS) for visualizing digital information page by page, and a flip bar (FB) being movable upon user activation in at least two directions for flipping pages of the digital information back and forth, respectively. Such an apparatus may be an electronic reading device mimicking a reading experience of a paper document.
Owner:IRX IP
Intelligent autofill
ActiveUS20050257134A1Minimize effortData augmentationData processing applicationsMetal-working feeding devicesDatabaseCentral repository
The present invention provides a unique system and method that can employ machine learning techniques to automatically fill one or more fields across a diverse array of web forms. In particular, one or more instrumented tools can collect input or entries of form fields. Machine learning can be used to learn what data corresponds to which fields or types of fields. The input can be sent to a central repository where other databases can be aggregated as well. This input can be provided to a machine learning system to learn how to predict the desired outputs. Alternatively or in addition, learning can be performed in part by observing entries and then adapting the autofill component accordingly. Furthermore, a number of features of database fields as well as constraints can be employed to facilitate assignments of database entries to form values—particularly when the web form has never been seen before by the autofill system.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for monitoring a selected region of an airspace associated with local area networks of computing devices
ActiveUS7002943B2Easy to usePrevent unauthorized wireless accessWave based measurement systemsData switching by path configurationBody area networkGeographic regions
A method for monitoring a selected region of an airspace associated with local area networks of computing devices is provided. The method includes providing one or more segments of a legacy local area network to be protected in a selected geographic region. The legacy local area network is characterized by an unsecured airspace within the selected geographic region. The method includes determining a security policy associated with the one or more segments of the legacy local area network. The security policy at least characterizes a type of wireless activity in the unsecured airspace to be permitted, denied, or ignored. Additionally, the method includes connecting one or more sniffer devices into the legacy local area network. The one or more sniffer devices are spatially disposed within the selected geographic region to cause at least a portion of the unsecured airspace to be secured according to the security policy.
Owner:ARISTA NETWORKS
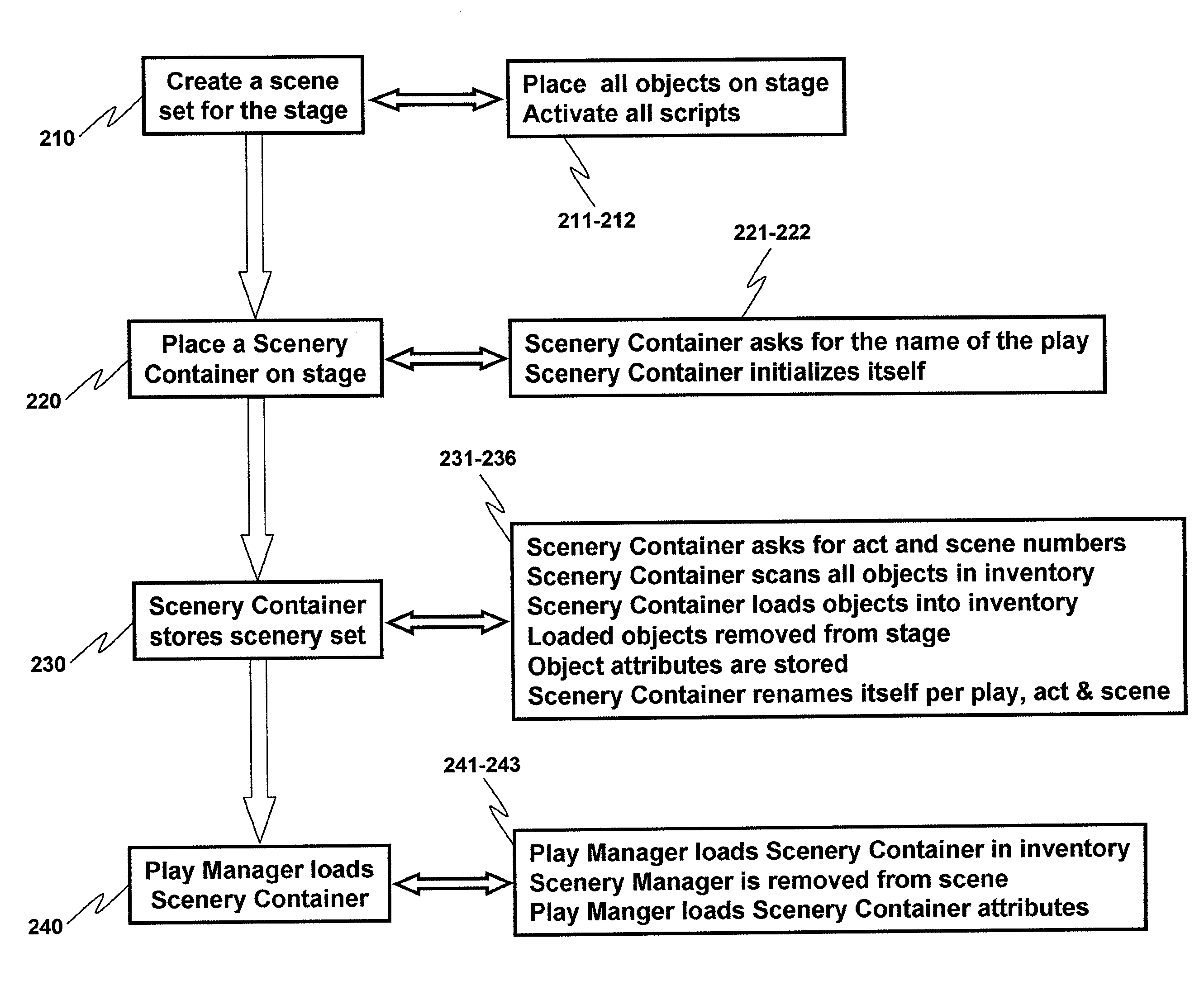
Method and system for rendering the scenes of a role playing game in a metaverse
ActiveUS8113959B2Speed maximizationMinimize effortTelevision system detailsColor television detailsRole playing gameVirtual world
In order to facilitate rendering of scenery elements in a role playing game, or in any other virtual universe (also known as a metaverse), there is provided a scenery container together with a play manager which cooperatively interact to achieve the loading, saving and storage of sets of scenery elements. Renderings are thus carried out more quickly and efficiently and with easier efforts on the part of the users.
Owner:ACTIVISION PUBLISHING
Method and apparatus for an improved security system mechanism in a business applications management system platform
InactiveUS20050154699A1Minimize effortSpecific access rightsDigital data processing detailsImproved methodSafe operation
Owner:SABA SOFTWARE
Machine learning of document templates for data extraction
InactiveUS7561734B1Speed up template developmentAssures template qualityNatural language data processingSpecial data processing applicationsData ingestionGraphics
The present system can perform machine learning of prototypical descriptions of data elements for extraction from machine-readable documents. Document templates are created from sets of training documents that can be used to extract data from form documents, such as: fill-in forms used for taxes; flex-form documents having many variants, such as bills of lading or insurance notifications; and some context-form documents having a description or graphic indicator in proximity to a data element. In response to training documents, the system performs an inductive reasoning process to generalize a document template so that the location of data elements can be predicted for the training examples. The automatically generated document template can then be used to extract data elements from a wide variety of form documents.
Owner:LEIDOS
Identification, storage and display of land data on a website
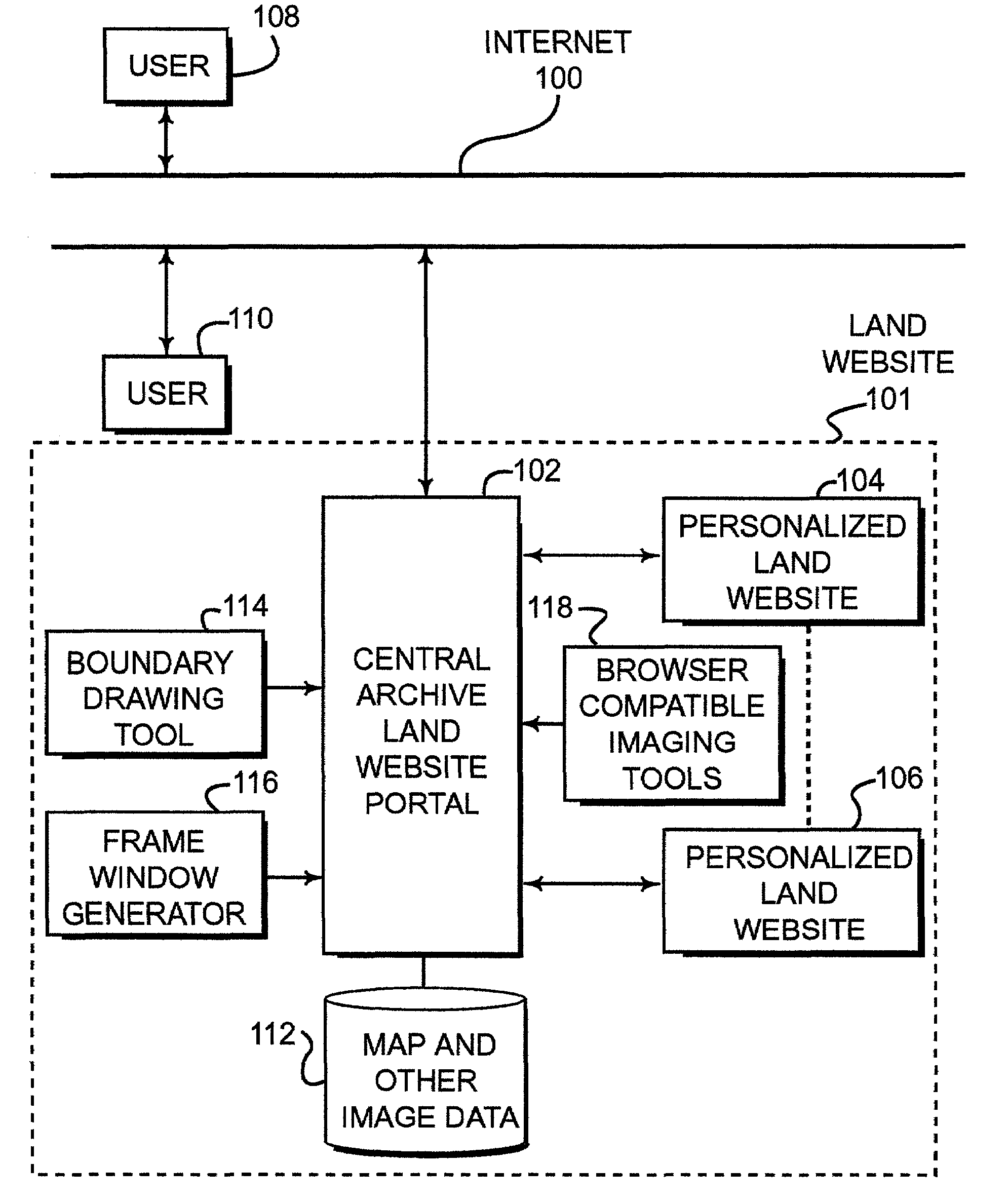
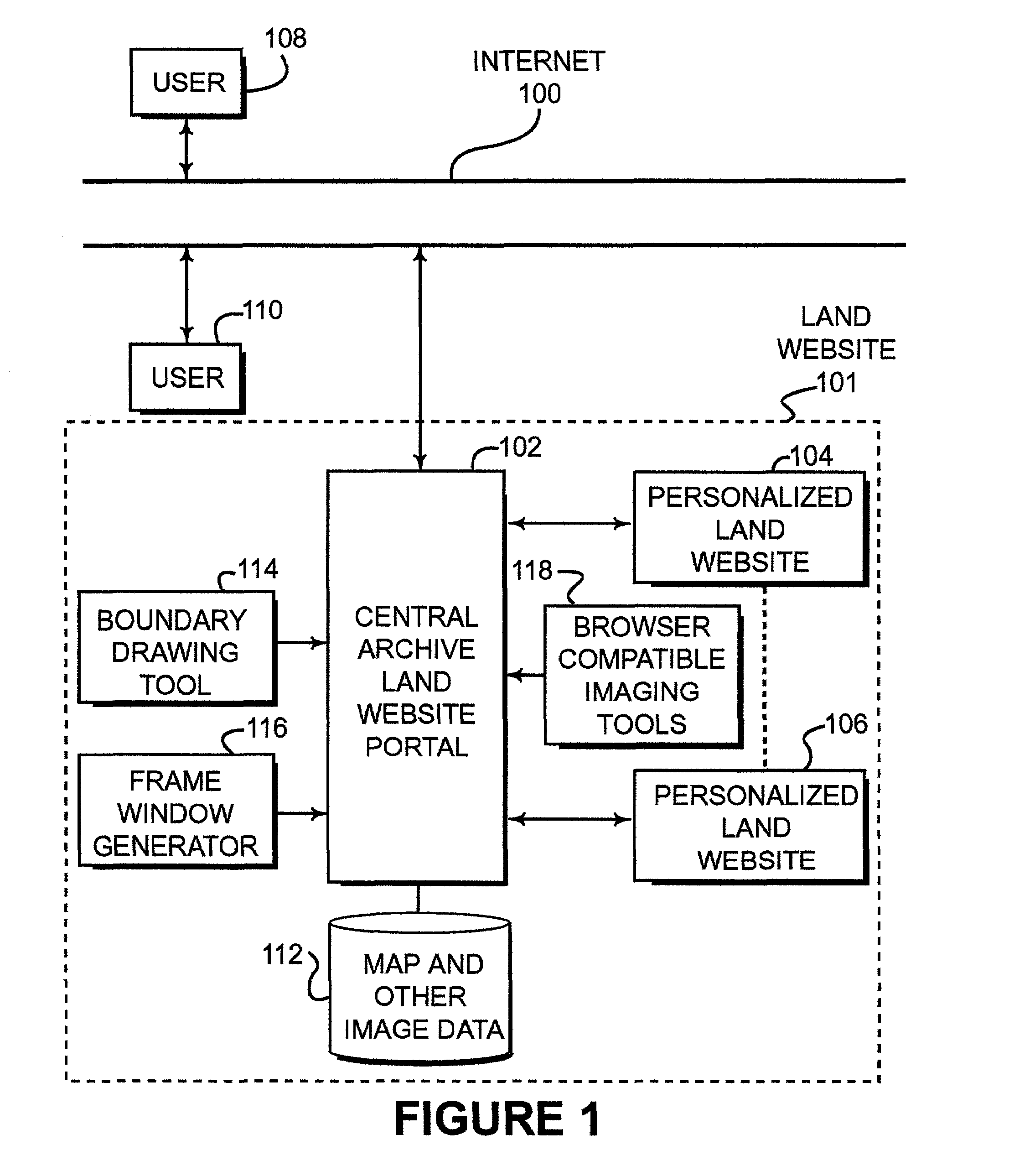
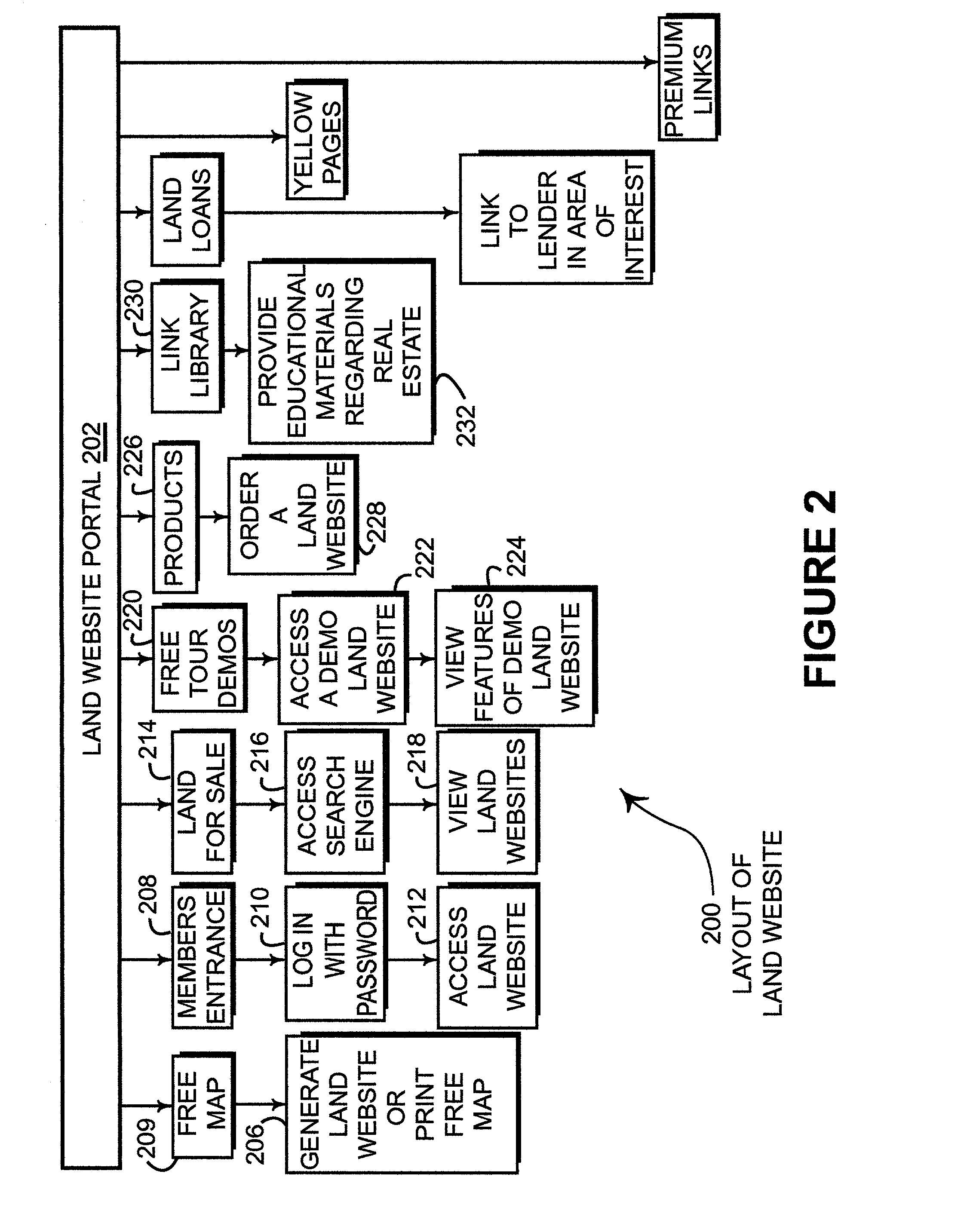
ActiveUS7171389B2Optimize locationLimited accessInstruments for road network navigationRoad vehicles traffic controlPersonalizationDocument preparation
Disclosed is a land website that provides a personalized database on which data can be stored, retrieved, customized and communicated (e.g., by e-mail) relating to a particular piece of property. The database can be accessible via a password and a security code over the Internet and may be encrypted for transmission. Land websites can be established that contain image data, map libraries, virtual tours, legal descriptions, title information, e-documents, actual pictures of property and various other information. Unique 3-D imaging of composite images can be provided on the land website as well as fly-around composite 3-D images. The land website provides a unique way of packaging information relating to a piece of land in a single, accessible location. A boundary applet tool is provided on the land website portal that allows a user to simply and easily draw boundaries around the property of interest and then submit an order for more detailed information about the property of interest. Various map data and image data are provided to assist the user in drawing the boundaries. Acreage amounts are automatically calculated based upon the size and area drawn by the user. Properties of interest can be easily accessed by a global coordinate system or by searching on map data that is provided on a wide range of scales.
Owner:LANDNET CORP
Automated sniffer apparatus and method for monitoring computer systems for unauthorized access
ActiveUS20050259611A1Easy to usePrevent unauthorized wireless accessMemory loss protectionError detection/correctionGeographic regionsNetwork interface device
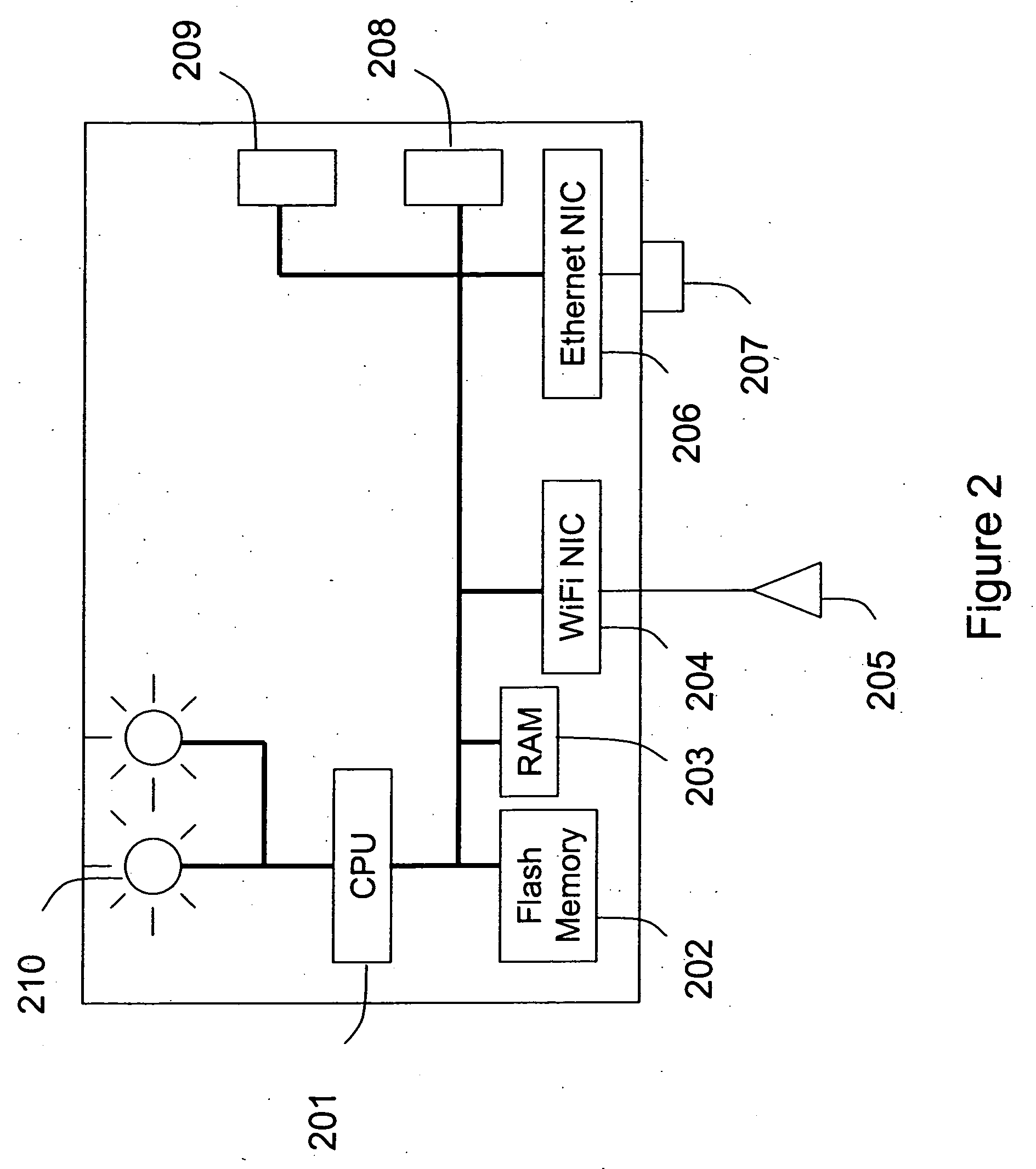
An apparatus for wireless communication including an automated intrusion detection process is provided. The apparatus has a portable housing, which may have a length no greater than 1 meter, a width no greater than 1 meter, and a height of no greater than 1 meter. A processing unit (e.g., CPU) is within the housing. One or more wireless network interface devices are within the housing and are coupled to the processing unit. The apparatus has an Ethernet (or like) network interface device within the housing and coupled to the processing unit. A network connector is coupled to the Ethernet network device. One or more memories are coupled to the processing unit. A code is directed to perform a process for detection of a wireless activity within a selected local geographic region. According to a specific embodiment, the wireless activity is derived from at least one authorized device or at least an other device. A code is directed to receiving at least identity information associated with the wireless activity from the detection process in a classification process. A code is directed to labeling the identity information into at least one of a plurality of categories in the classification process. Depending upon the embodiment, other codes may exist to carry out the functionality described herein.
Owner:ARISTA NETWORKS
Automated sniffer apparatus and method for monitoring computer systems for unauthorized access
ActiveUS7339914B2Easy to usePrevent unauthorized wireless accessMemory loss protectionError detection/correctionGeographic regionsNetwork connection
An apparatus for wireless communication including an automated intrusion detection process is provided. The apparatus has a portable housing, which may have a length no greater than 1 meter, a width no greater than 1 meter, and a height of no greater than 1 meter. A processing unit (e.g., CPU) is within the housing. One or more wireless network interface devices are within the housing and are coupled to the processing unit. The apparatus has an Ethernet (or like) network interface device within the housing and coupled to the processing unit. A network connector is coupled to the Ethernet network device. One or more memories are coupled to the processing unit. A code is directed to perform a process for detection of a wireless activity within a selected local geographic region. According to a specific embodiment, the wireless activity is derived from at least one authorized device or at least an other device. A code is directed to receiving at least identity information associated with the wireless activity from the detection process in a classification process. A code is directed to labeling the identity information into at least one of a plurality of categories in the classification process. Depending upon the embodiment, other codes may exist to carry out the functionality described herein.
Owner:ARISTA NETWORKS
Interactive spoken dialogue interface for collection of structured data
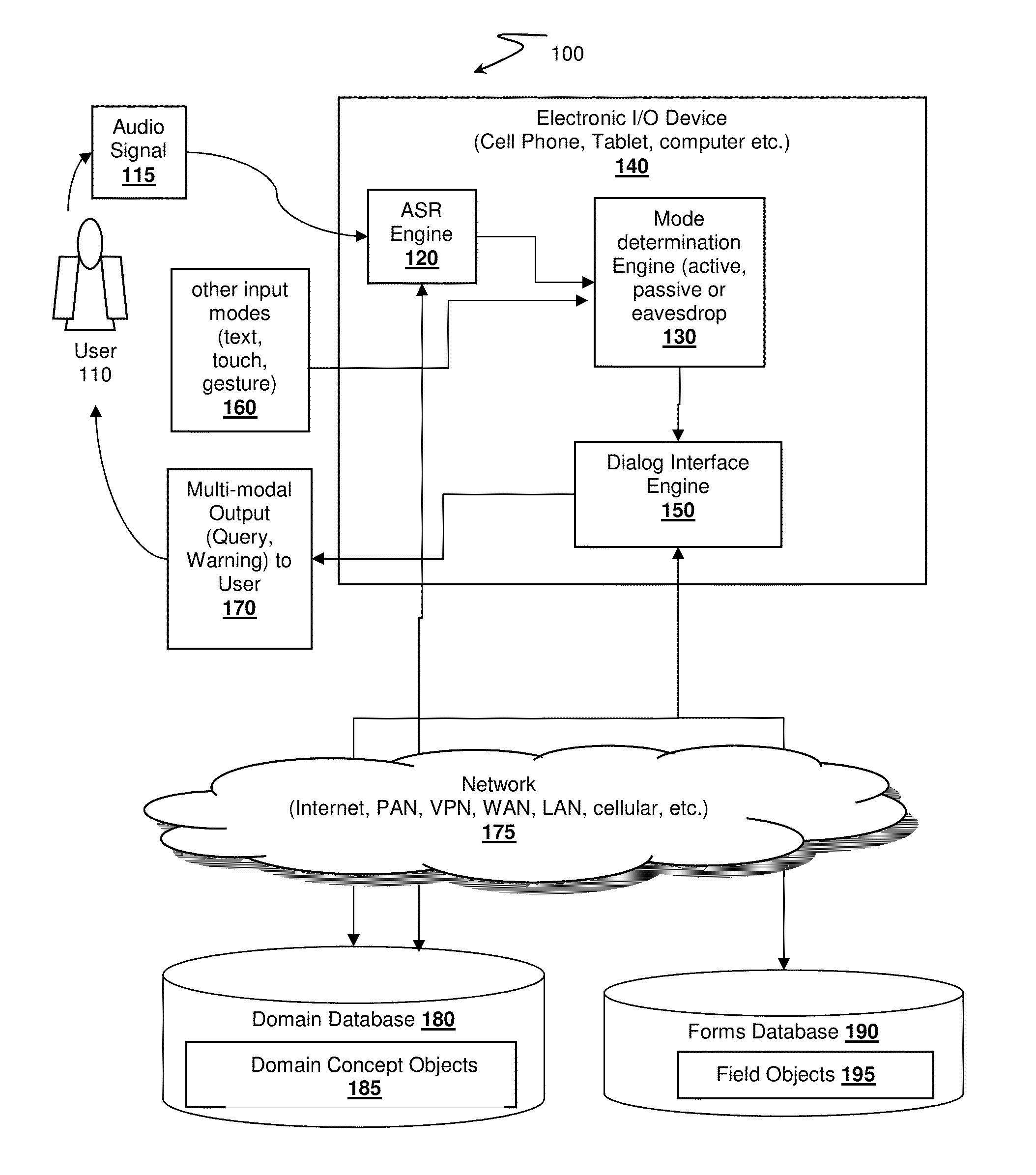
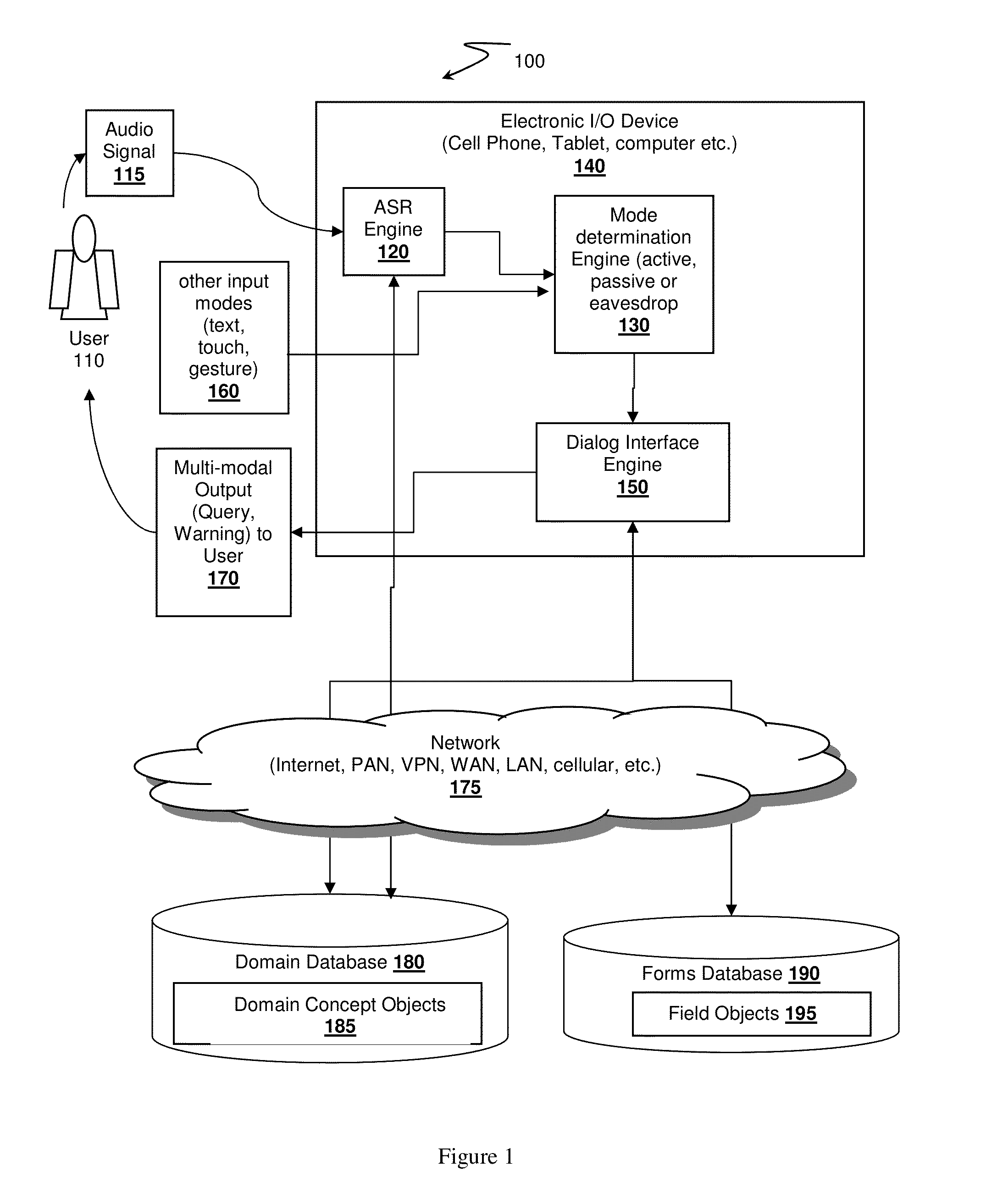
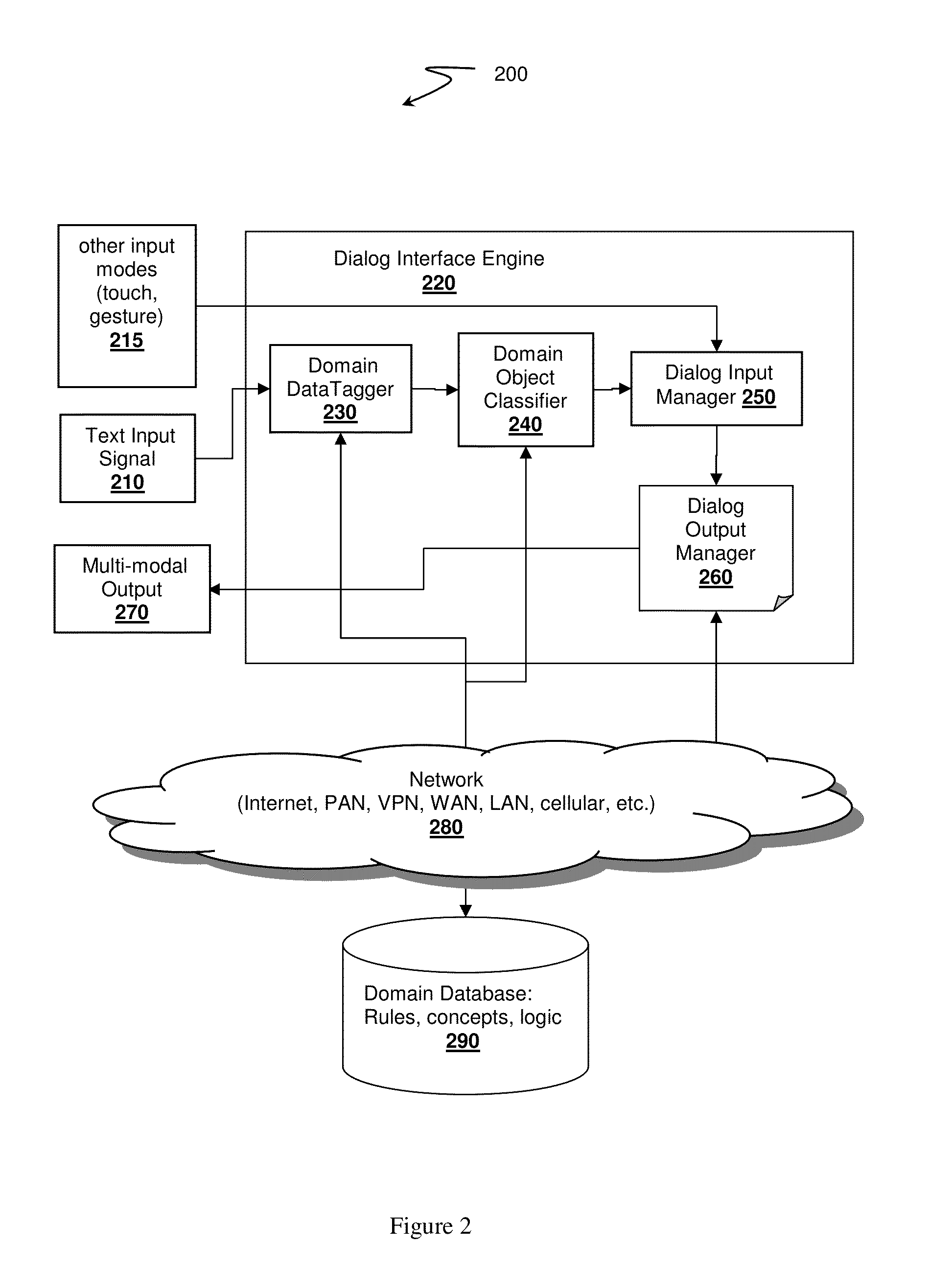
InactiveUS20130339030A1Enhanced interactionMinimize effortTherapiesMedical automated diagnosisMedical recordSpoken language
A multimodal dialog interface for data capture at point of origin is disclosed. The interface is designed to allow loading of forms needed for task record keeping, and is therefore customizable to wide range of record keeping requirements such as medical record keeping or recording clinical trial. The interface has a passive mode that is able to capture data while the user is performing other tasks, and an interactive dialog mode that ensures completion of all required information.
Owner:NANT HLDG IP LLC
Method and apparatus for monitoring multiple network segments in local area networks for compliance with wireless security policy
InactiveUS20060193300A1Prevent unauthorized wireless accessMinimizes human effortNetwork topologiesRadio/inductive link selection arrangementsGeographic regionsComputer science
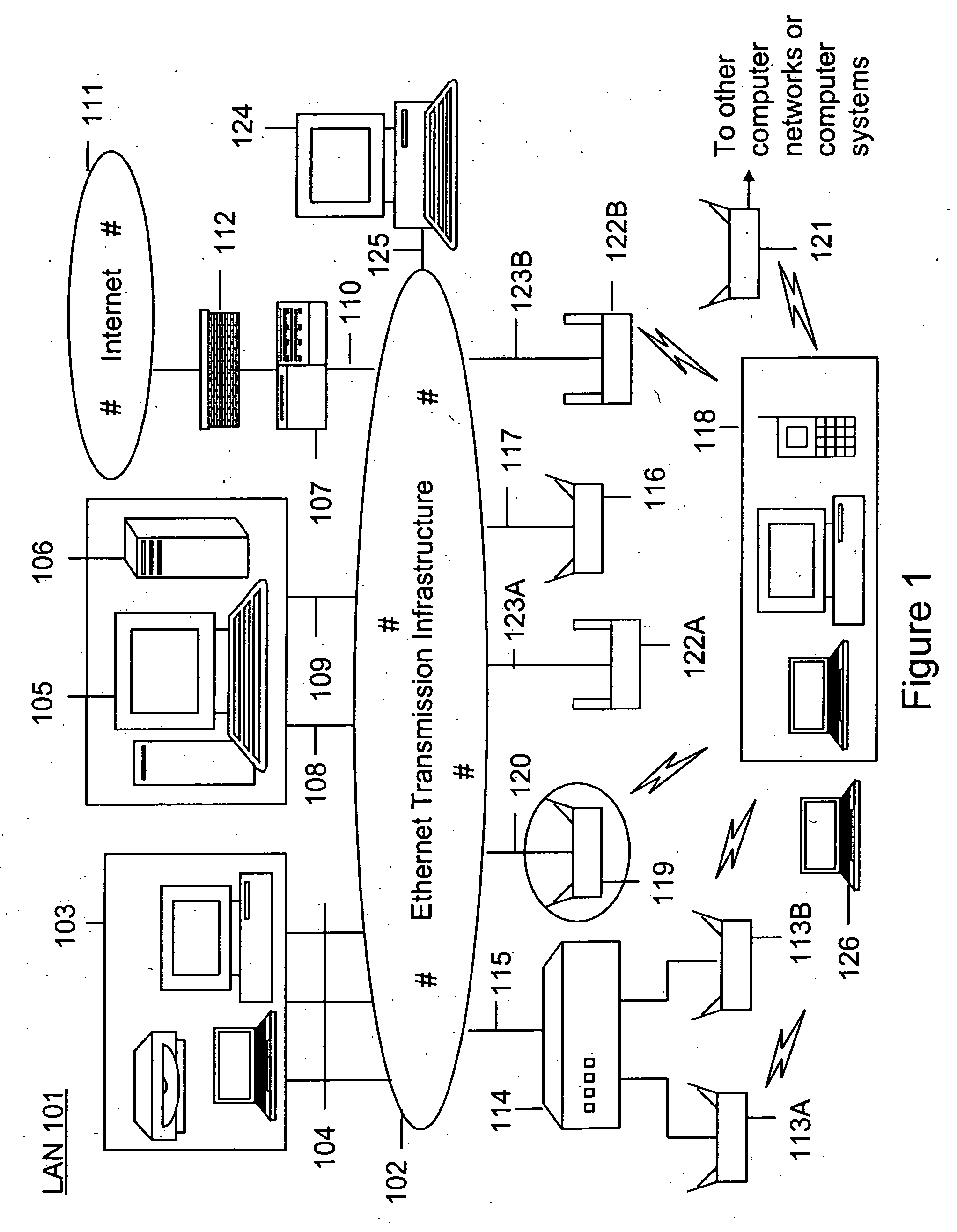
Method and system for monitoring a plurality of network segments in a local area network within a selected geographic region is provided. The monitoring is performed to check compliance with one or more wireless security policies. The method comprises providing a network monitoring device and coupling the network monitoring device to a connection port of the local are network. Moreover, the method includes providing one or more sniffers that are adapted to interact with a wireless medium. The sniffers are spatially disposed within and / or in a vicinity of the selected geographic region. The method includes determining a connectivity status of at least one wireless access device to the local area network.
Owner:AIRTIGHT NETWORKS
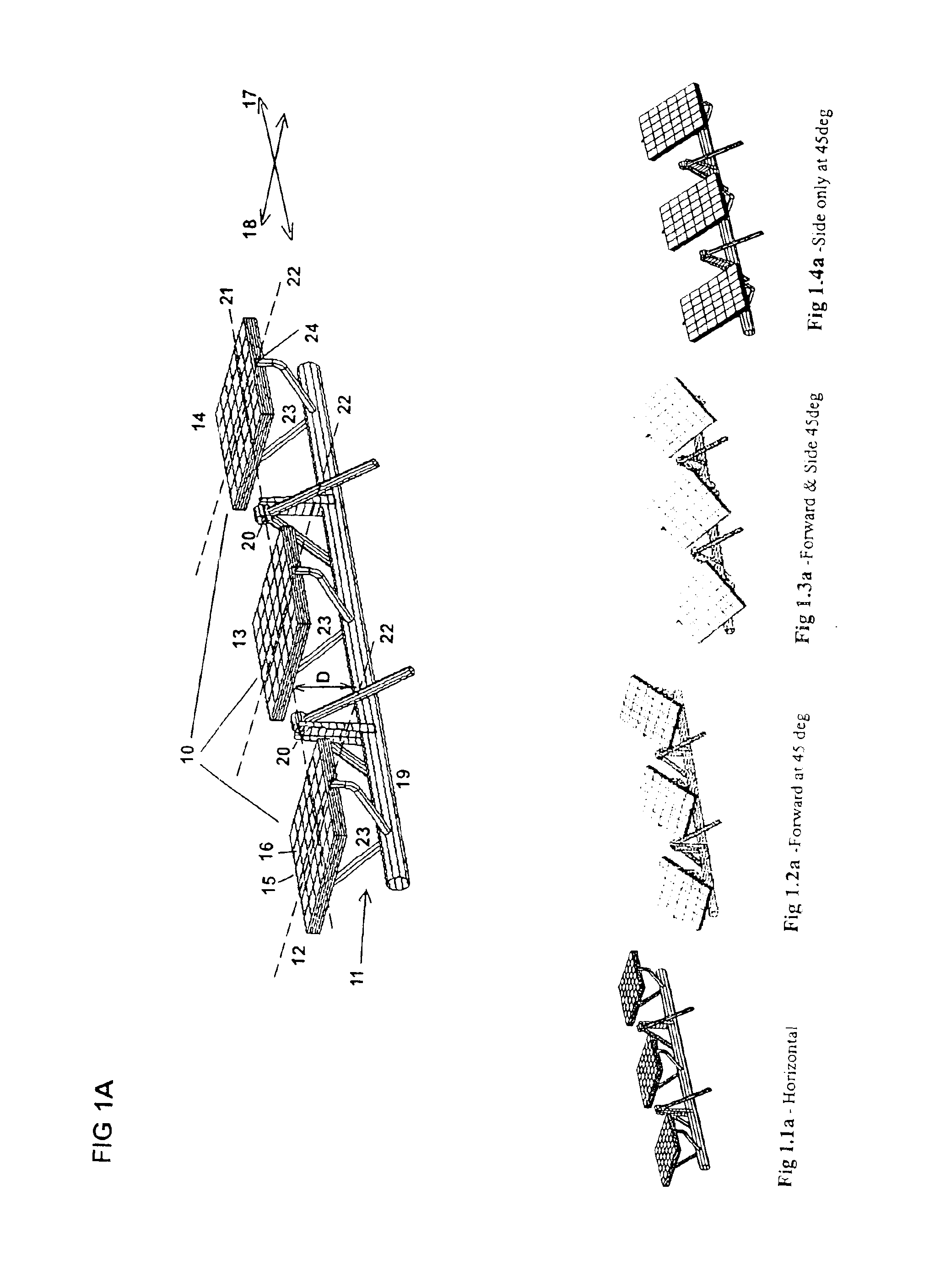
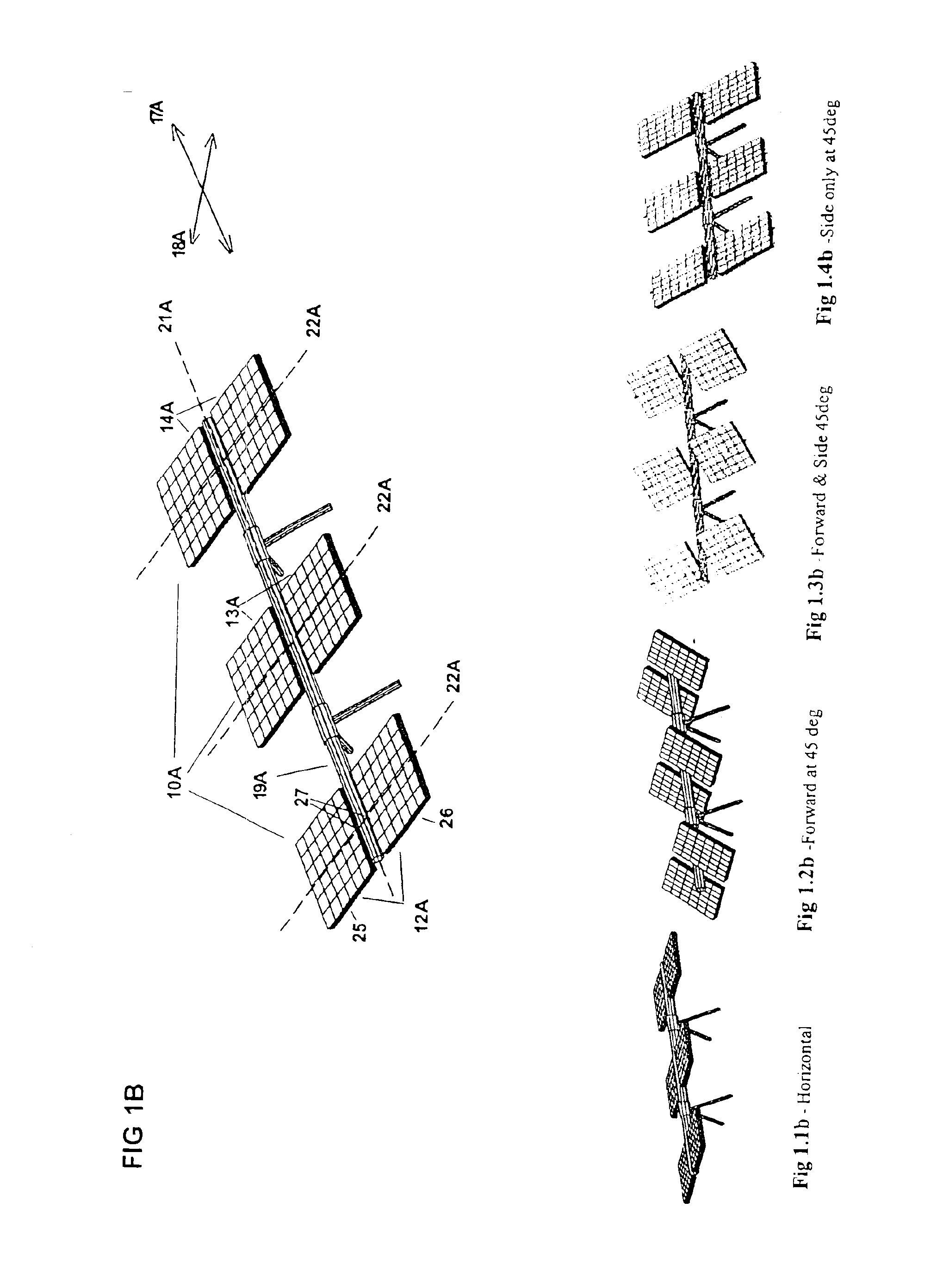
Solar panel tilt mechanism
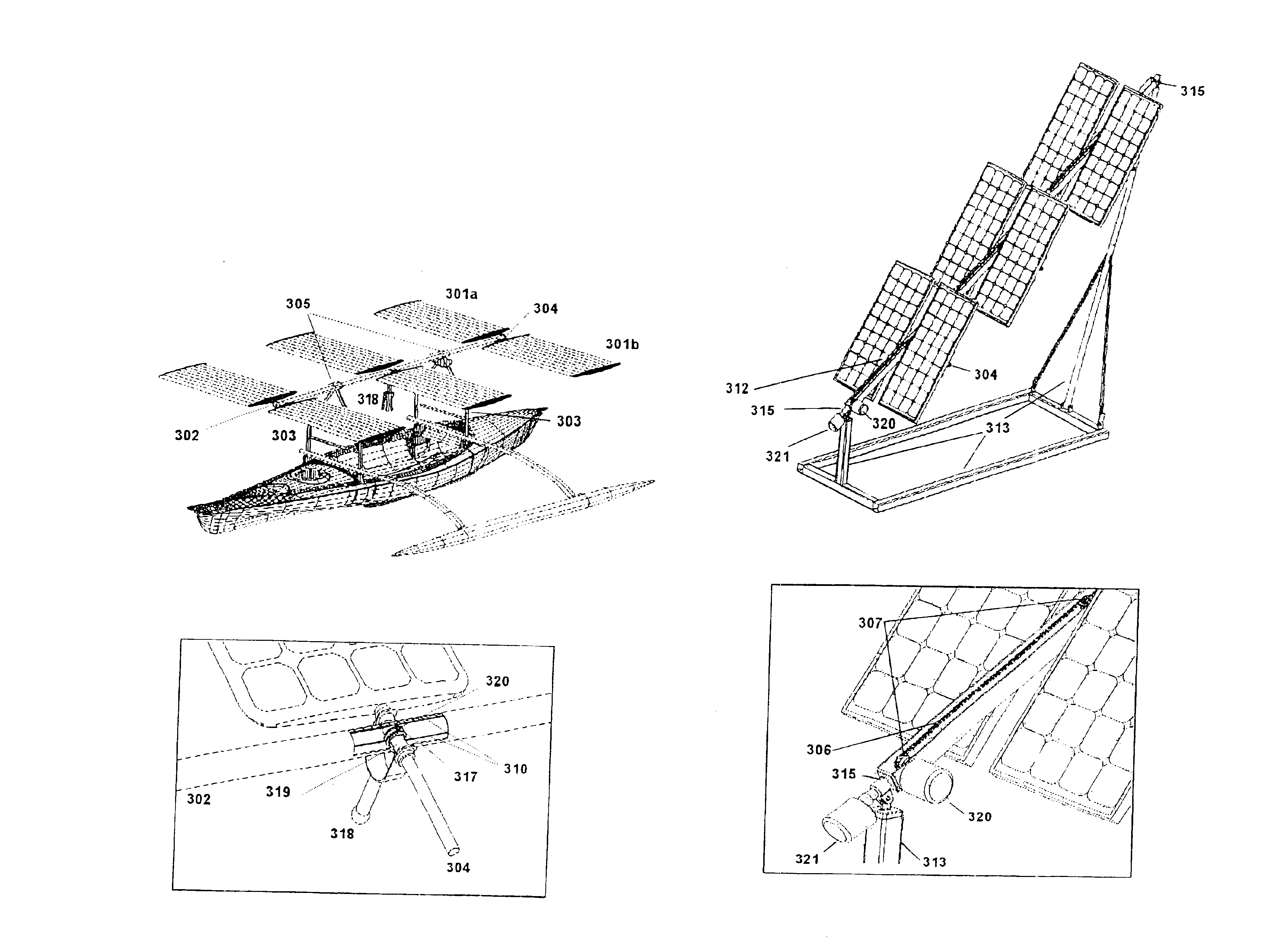
InactiveUS6848442B2Minimize effortPhotovoltaic supportsSolar heating energyAerospace engineeringEngineering
A tilt mechanism associated with a solar panel assembly whereby effort required to tilt panel assemblies comprising the solar panel assembly is reduced or minimized by appropriate placement of first and second tilt axes with respect to the center of mass and / or center of pressure of the panel assemblies due to wind. These arrays are suitable for use on mobile or static installations. The tilt mechanism is suited for harnessing wind energy if the panels are suitably shaped.
Owner:HABER MICHAEL B
Cuttable illuminated panel
InactiveUS20050251698A1Minimizing assembly effortReduce the amount requiredVolume/mass flow measurementLighting elementsLight equipmentDielectric surface
An illumination apparatus is provided having a panel including a plurality of circuit units on a dielectric surface. The circuit units include electrically conductive traces and at least one light emitting diode (LED). At least some of the circuit units have contacts for supplying power to the LED. The circuit units are preferably electrically interconnected so that power provided to one circuit unit also supplied power to at least a group of the circuit units. The apparatus with the circuit units may be cut or shaped to a predetermined or desired shape. Also provided are methods of manufacturing, assembling, and using the illumination apparatus.
Owner:DIAMOND CREEK CAPITAL LLC
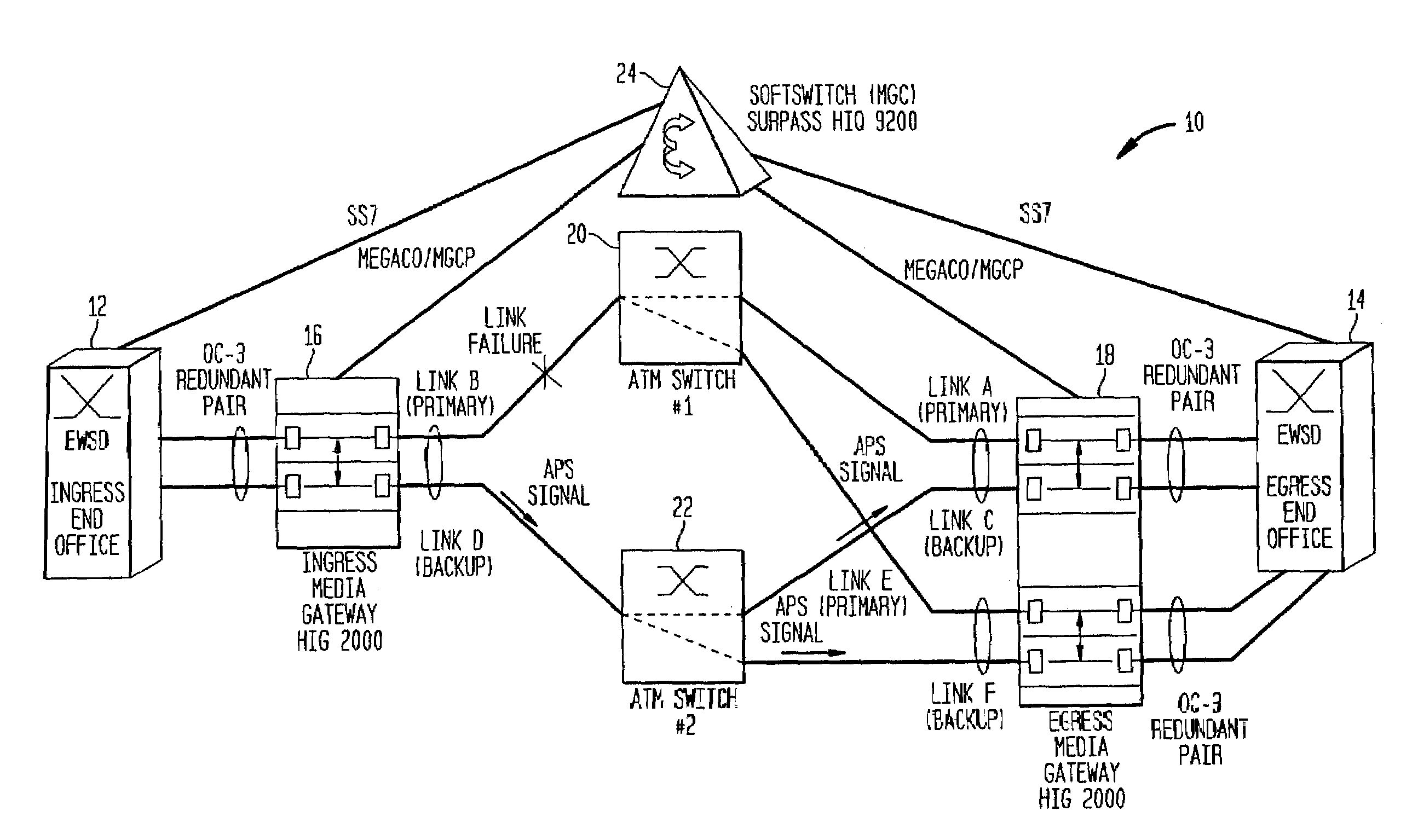
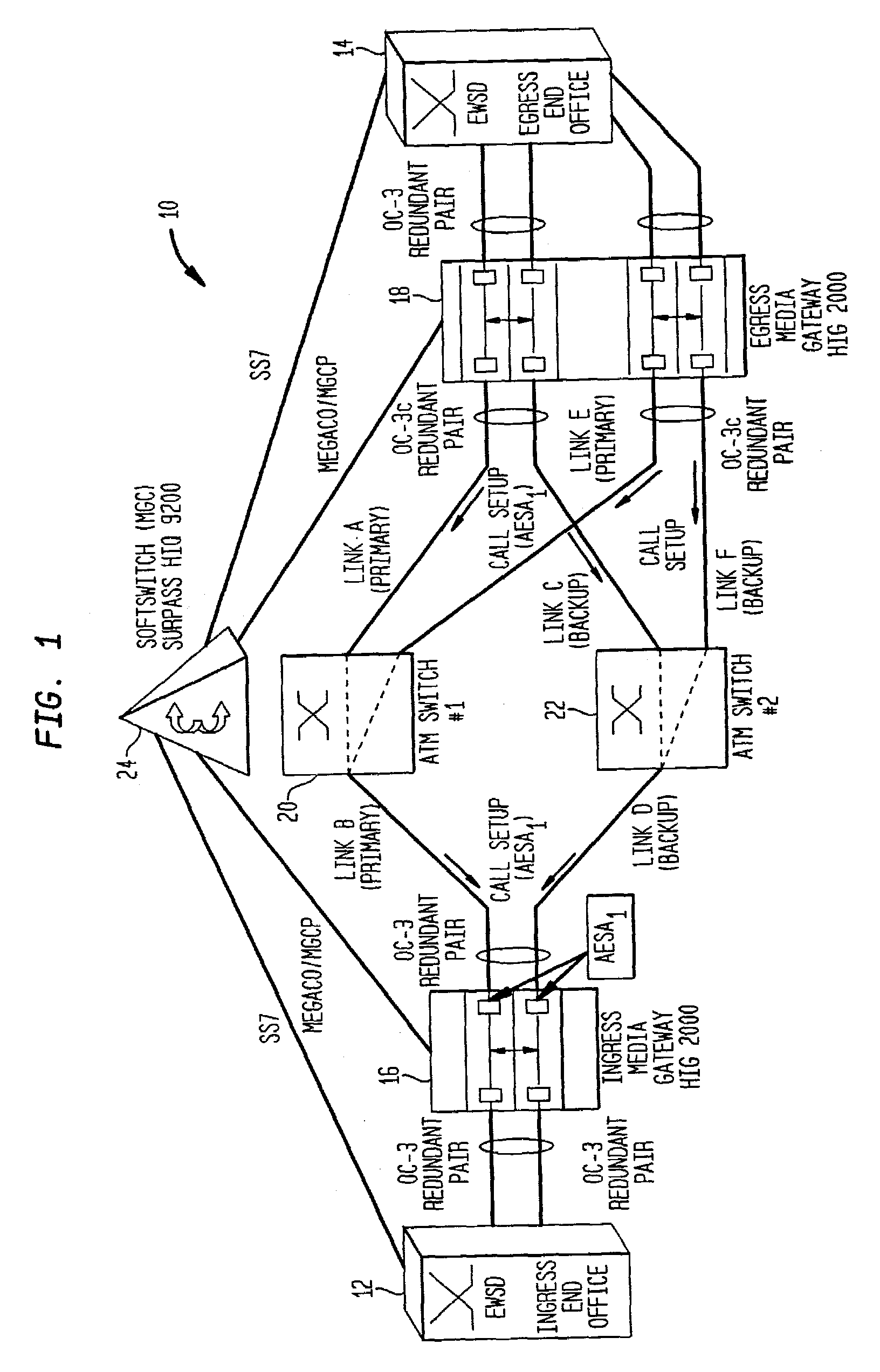
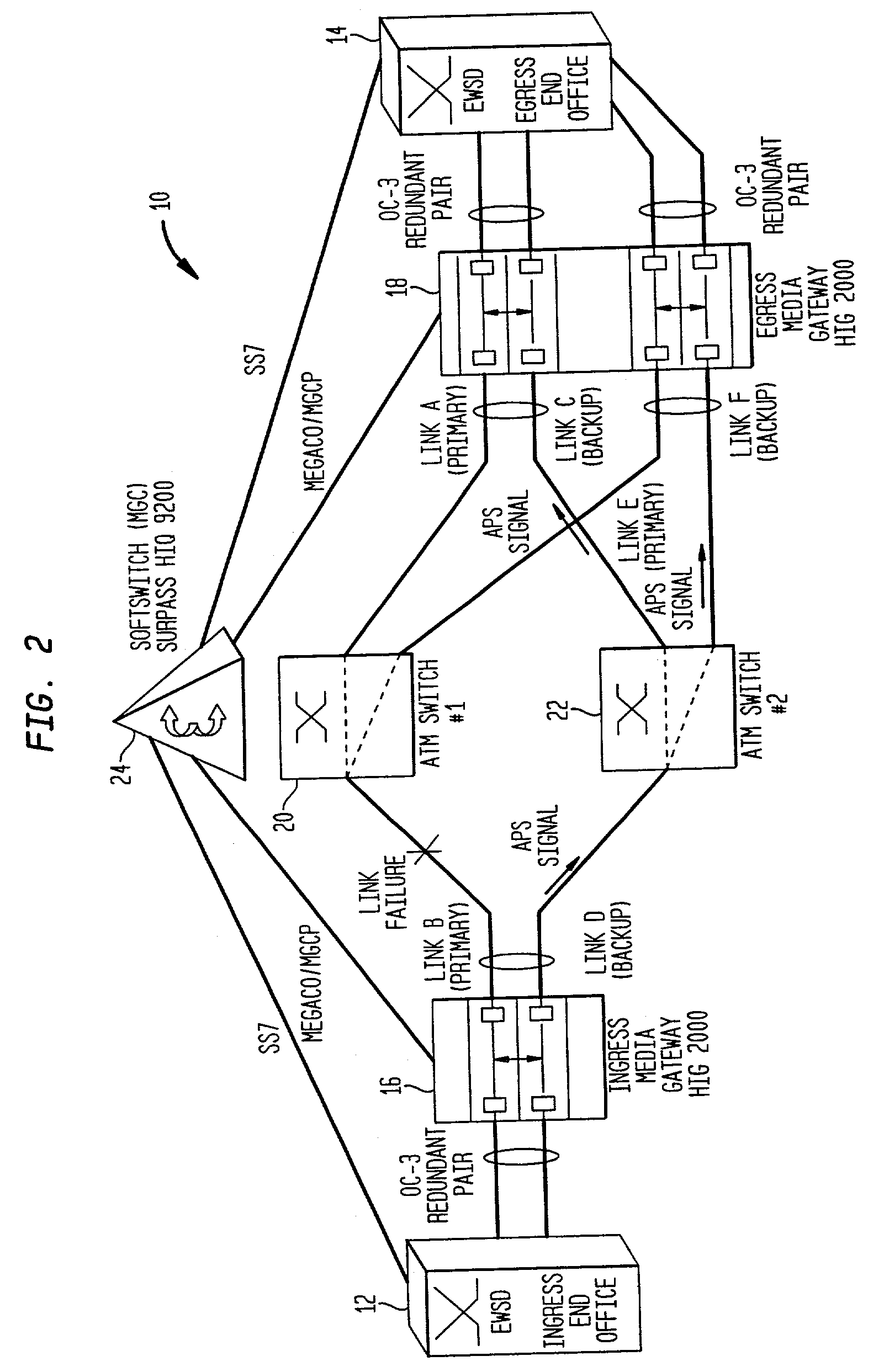
Method for resilient call setup through ATM networks for Softswitch applications
InactiveUS7065041B2Minimize effortEliminate needError preventionFrequency-division multiplex detailsEnd systemSoftswitch
A method establishes two redundant Switched Virtual Channel (SVC) connections through ATM Networks using the same ATM End System Address (AESA) from a source ATM End Point to a destination ATM End Point. The method provides end-to-end path protection without relying on any underlying resiliency features of an ATM Network so that the set-up model is transparent to the underlying ATM Network.
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG
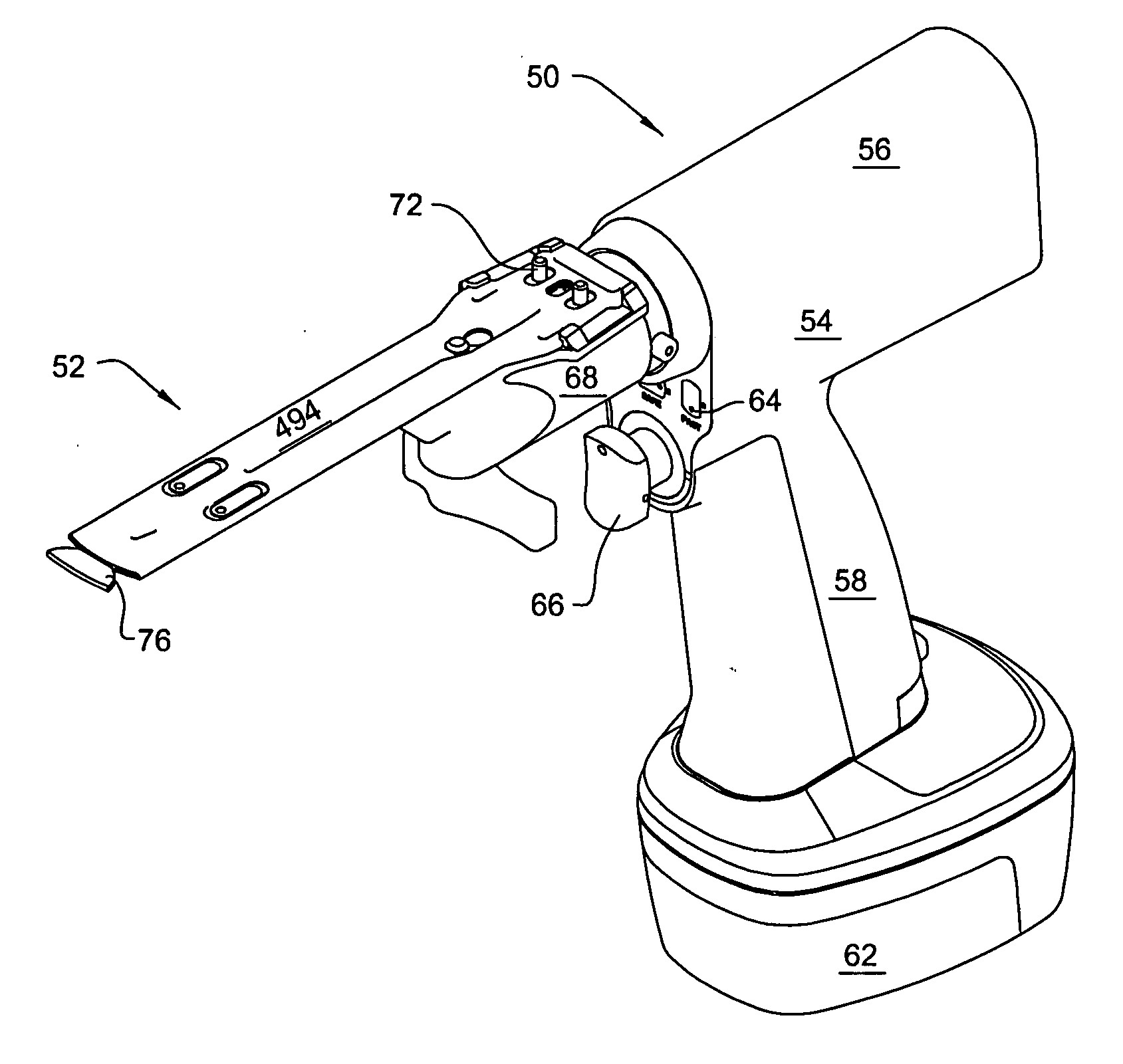
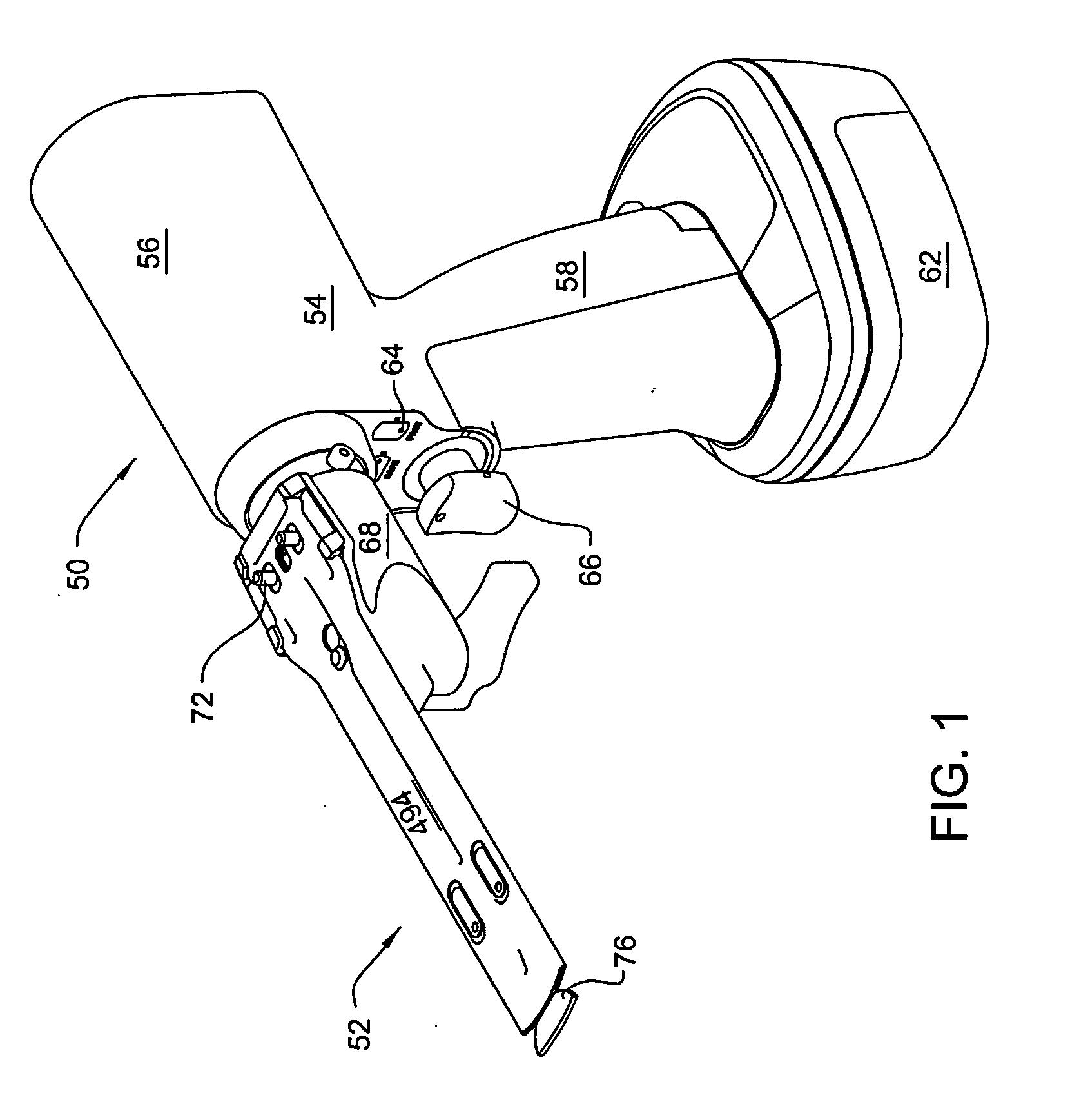
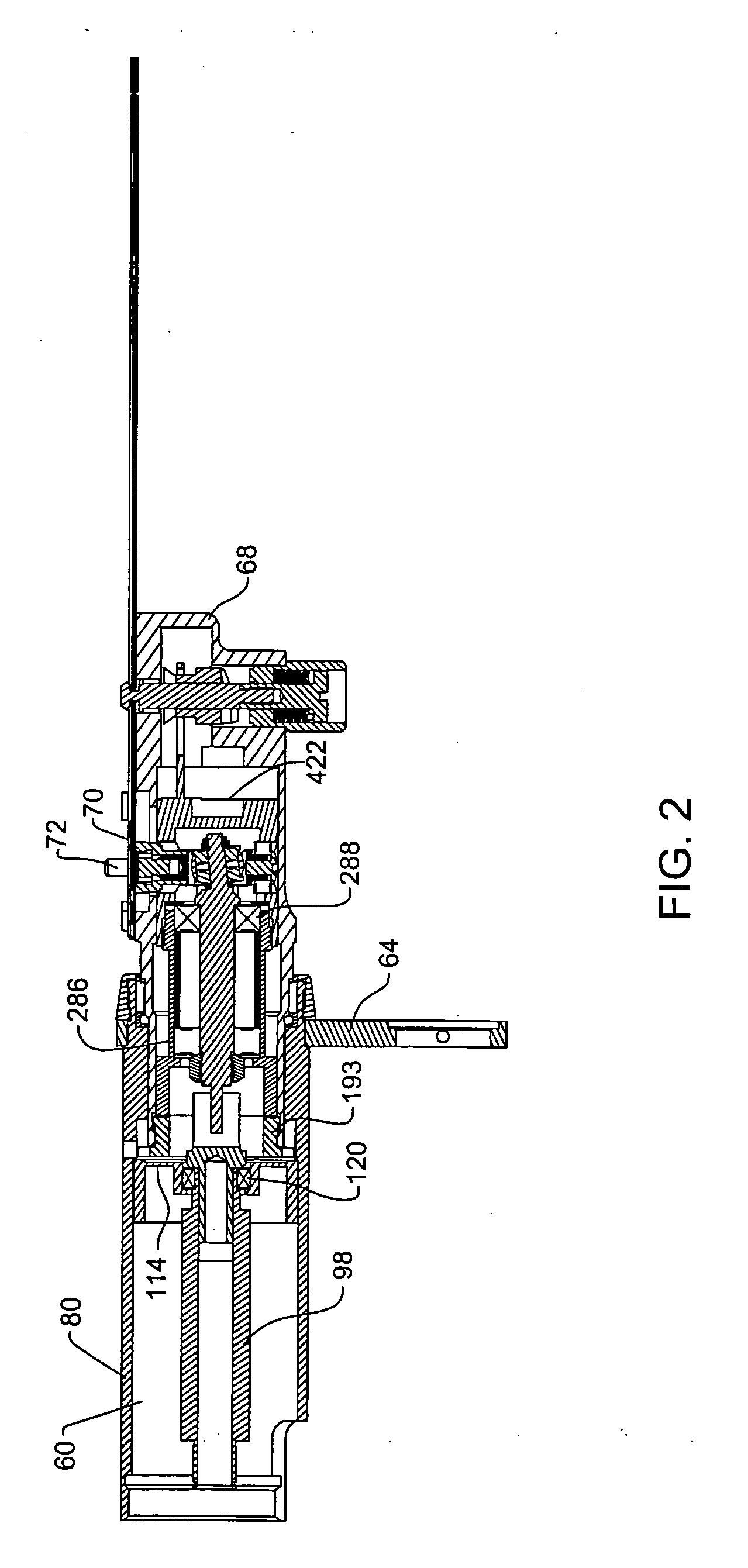
Surgical sagittal saw with indexing head and toolless blade coupling assembly for actuating an oscillating tip saw blade and oscillating tip saw blade with self cleaning head
ActiveUS20070119055A1Facilitated releaseMinimize effortDiagnosticsSurgical navigation systemsCouplingKnife blades
A surgical sagittal saw with an indexing head. The saw actuates a blade assembly that includes a bar from which a blade head extends. An oscillating head extends upwardly from the saw head. The oscillating head, in addition is mounted to the saw head to be able to rotate around its longitudinal axis and so that it can move along the saw head. A biasing spring normally holds the oscillating head in a fixed position. When the oscillating head is in the fixed position, the oscillating head holds the blade assembly against a restraining bracket integral with the saw head. Manual force is used to overcome the biasing spring to allow replacement and removal of the blade assembly.
Owner:STRYKER EURO OPERATIONS HLDG LLC
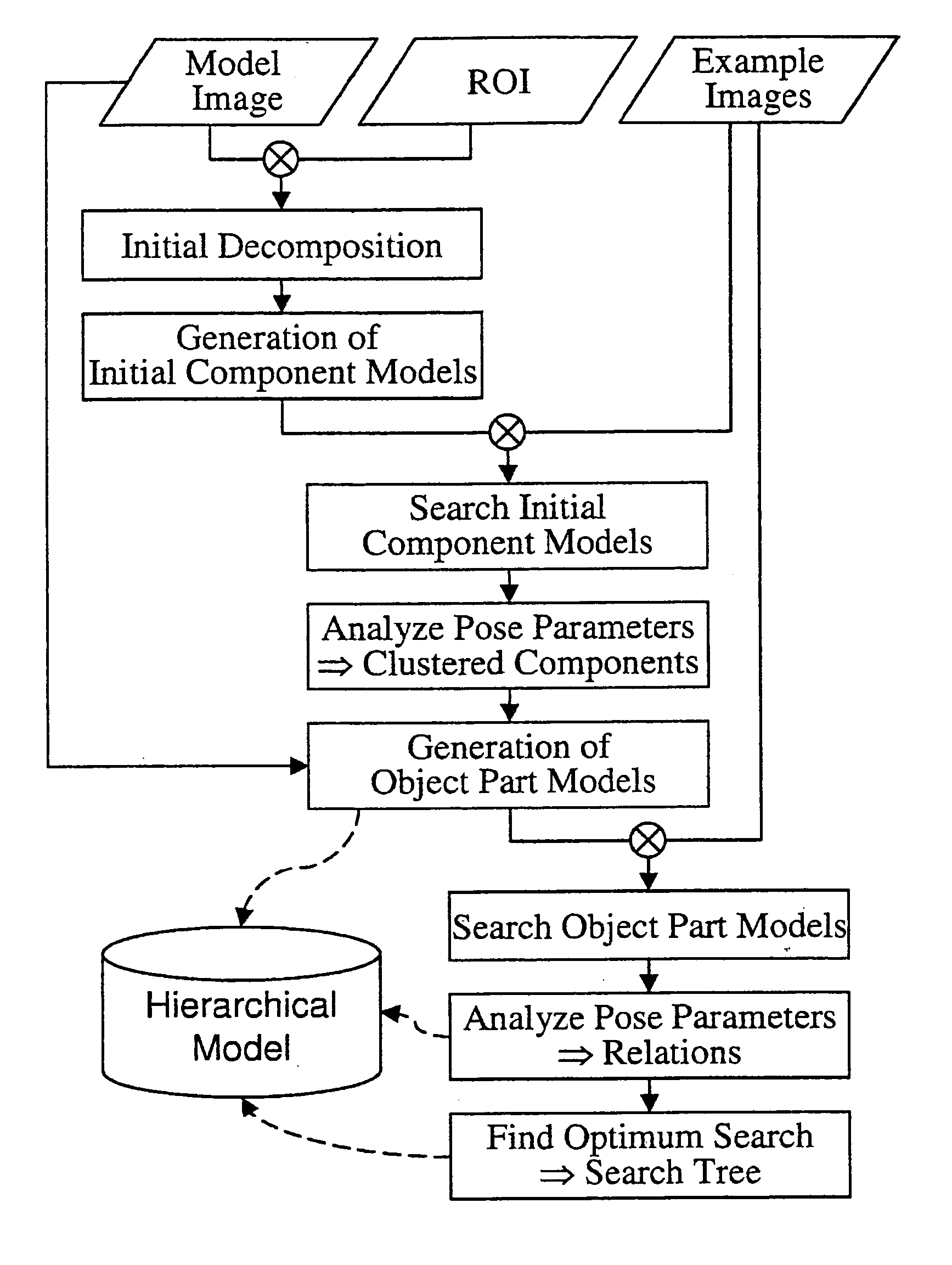
Hierarchical component based object recognition
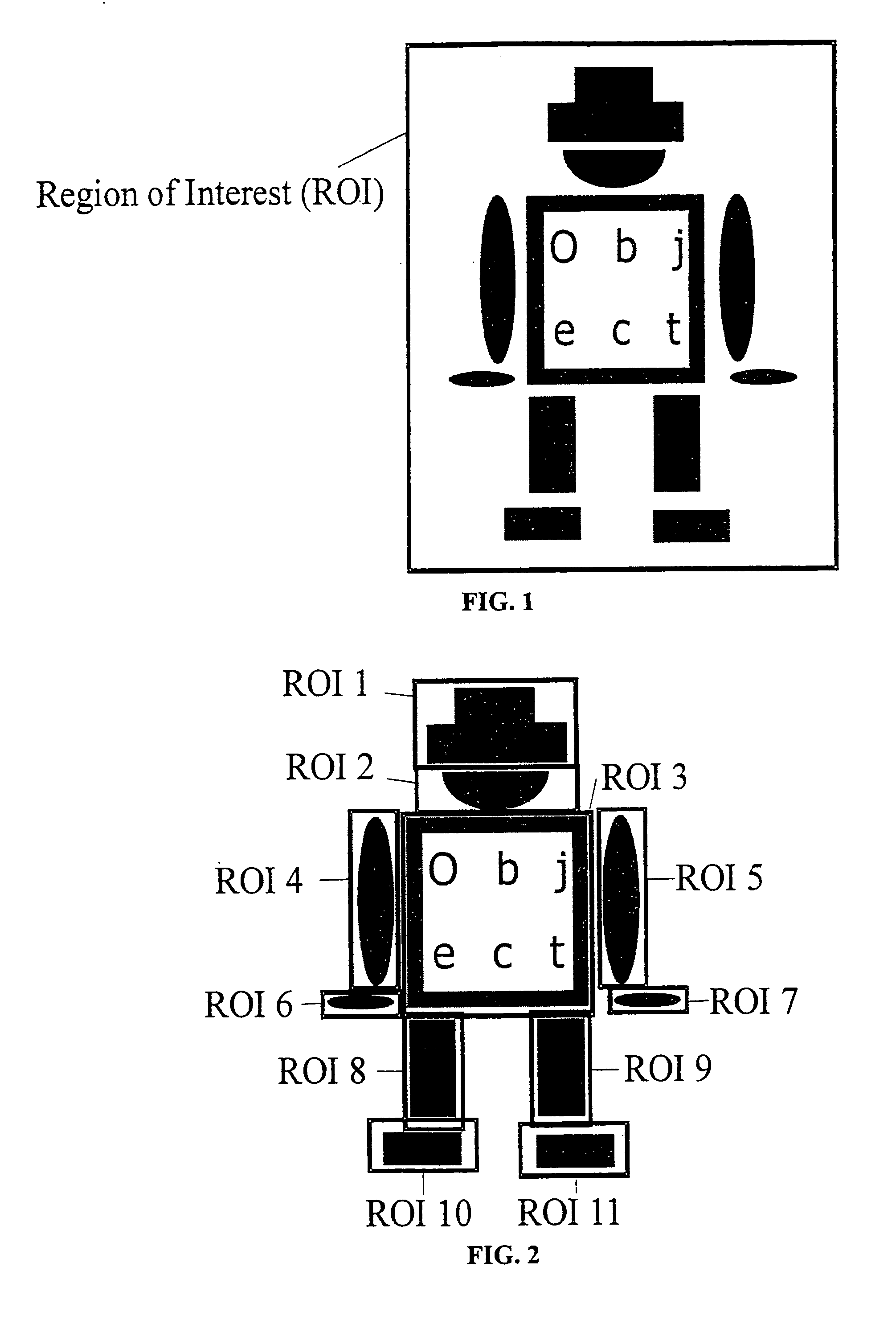
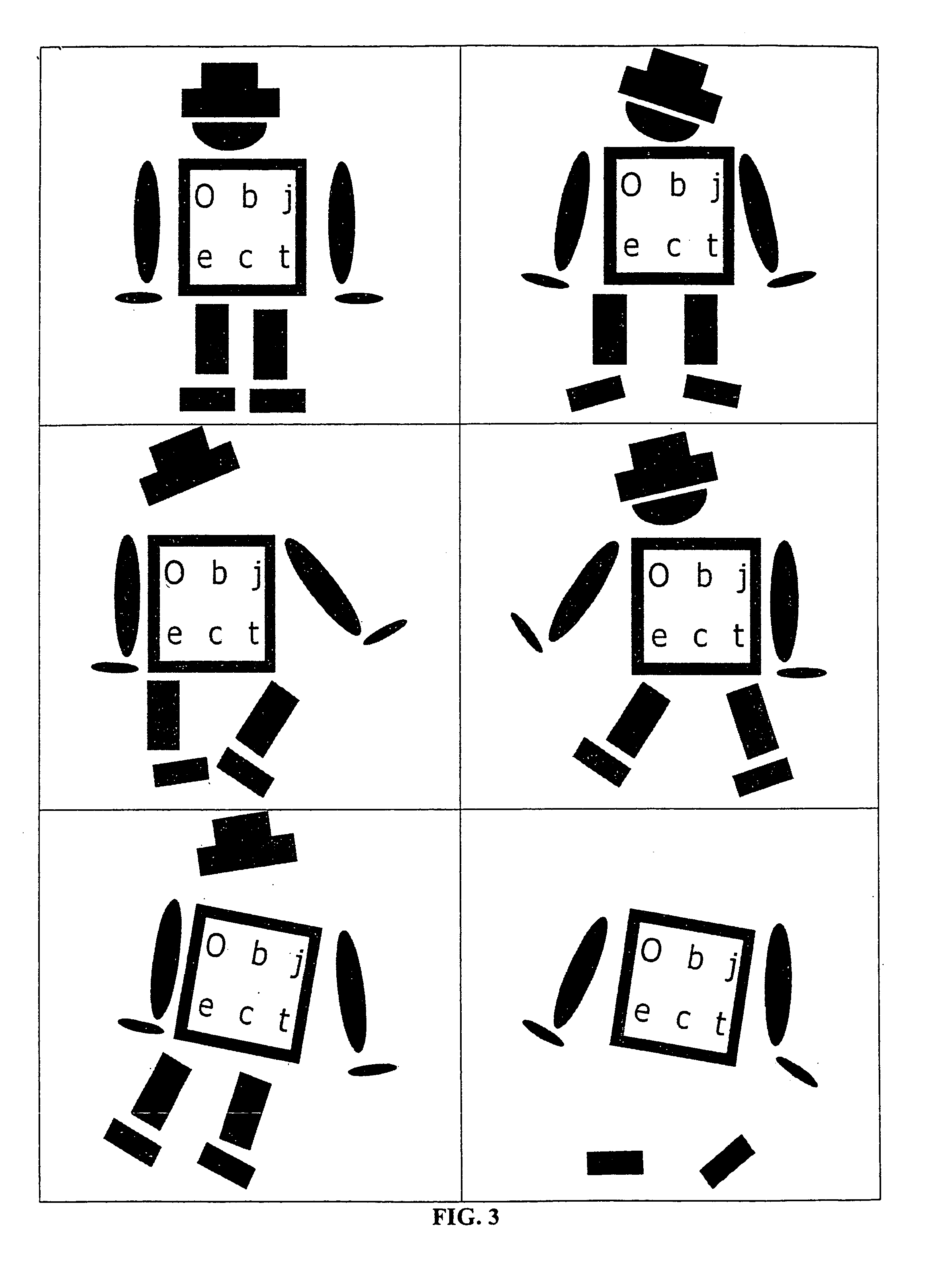
ActiveUS7239929B2Scale upMinimize effortImage analysisCharacter and pattern recognitionHough transformRelative motion
The present invention provides a method for the recognition of objects in an image, where the objects may consist of an arbitrary number of parts that are allowed to move with respect to each other. In the offline phase the invention automatically learns the relative movements of the single object parts from a sequence of example images and builds a hierarchical model that incorporates a description of the single object parts, the relations between the parts, and an efficient search strategy. This is done by analyzing the pose variations (e.g., variations in position, orientation, and scale) of the single object parts in the example images. The poses can be obtained by an arbitrary similarity measure for object recognition, e.g., normalized cross correlation, Hausdorff distance, generalized Hough transform, the modification of the generalized Hough transform, or the similarity measure. In the online phase the invention uses the hierarchical model to efficiently find the entire object in the search image. During the online phase only valid instances of the object are found, i.e., the object parts are not searched for in the entire image but only in a restricted portion of parameter space that is defined by the relations between the object parts within the hierarchical model, what facilitates an efficient search and makes a subsequent validation step unnecessary.
Owner:MVTEC SOFTWARE
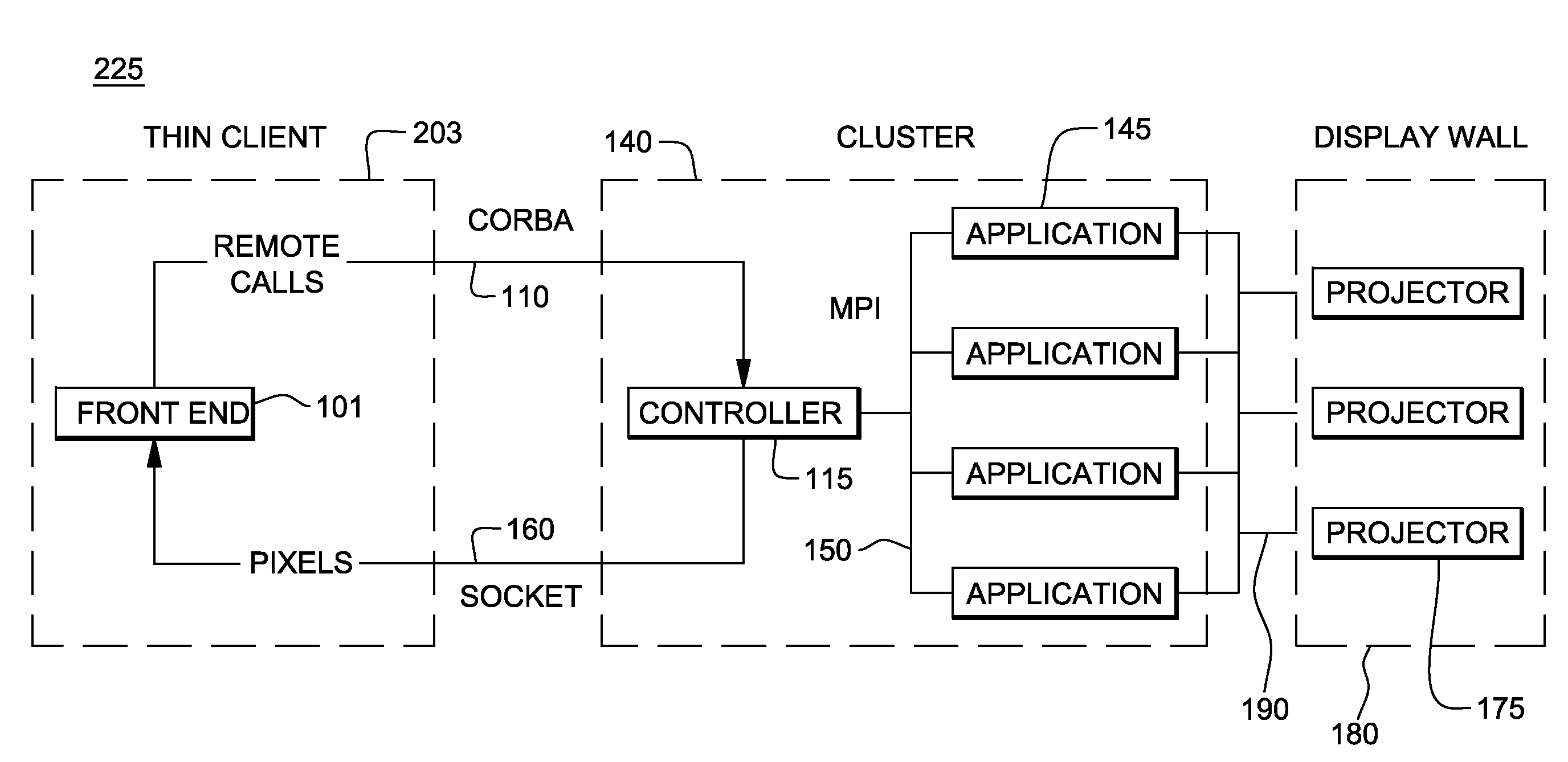
System, mechanism, and apparatus for a customizable and extensible distributed rendering api
InactiveUS20100289804A1Improve utilizationImprove effectivenessProgram controlGraphicsApplication programming interface
A system and method for providing an Application Programming Interface (API) that allows users to write complex graphics and visualization applications with little knowledge of how to parallelize or distribute the application across a graphics cluster. The interface enables users to develop an application program using a common programming paradigm (e.g., scene graph) in a manner that accommodates handling parallel rendering tasks and rendering environments. The visualization applications written by developers take better advantage of the aggregate resources of a cluster. The programming model provided by APT function calls handles scene-graph(s) data in a manner such that the scene and data management are decoupled from the rendering, compositing, and display. As a result, the system and method is not beholden to one particular graphics rendering API (e.g. OpenGL, Direct X, etc.) and provides the ability to switch between these APIs even during runtime.
Owner:IBM CORP
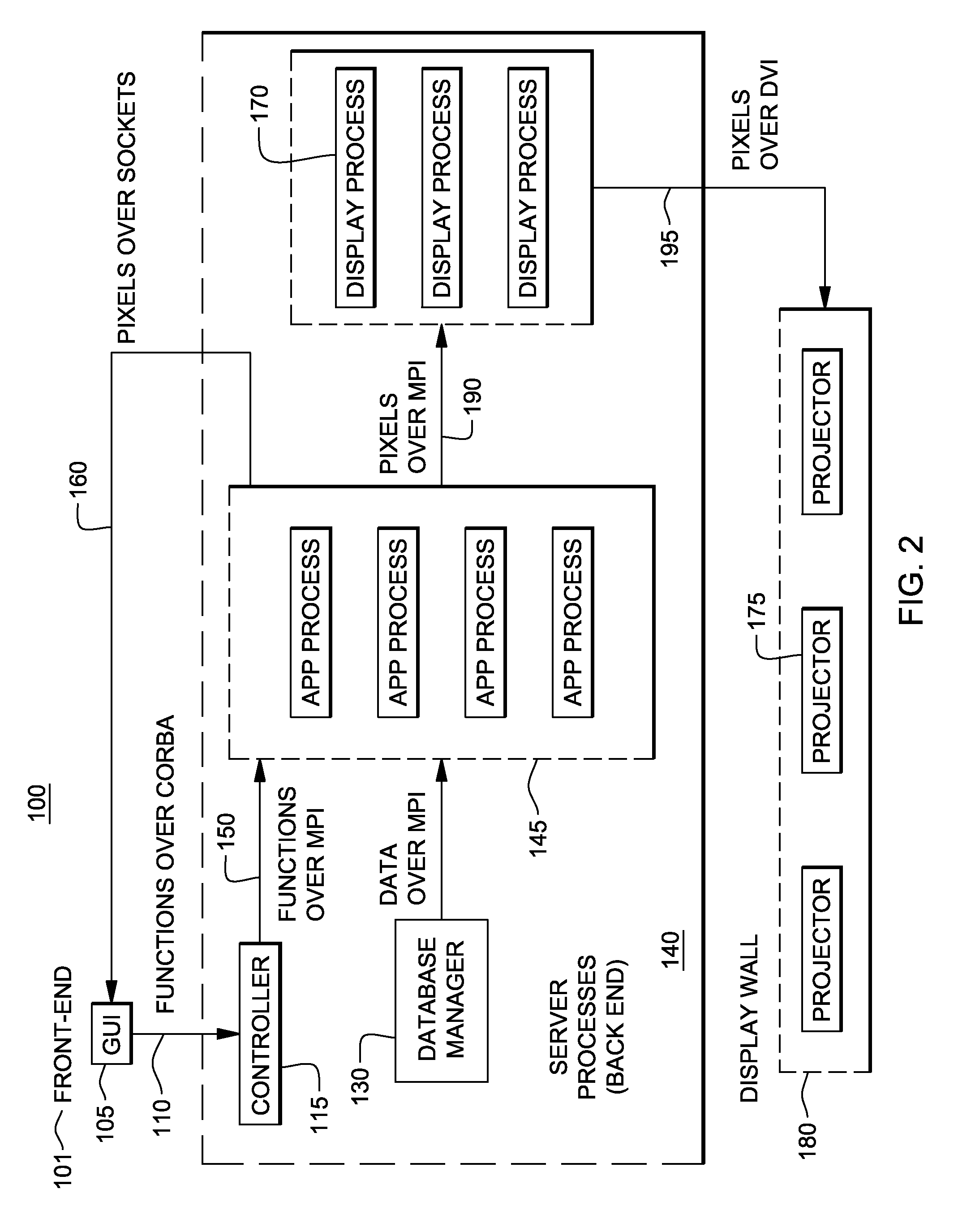
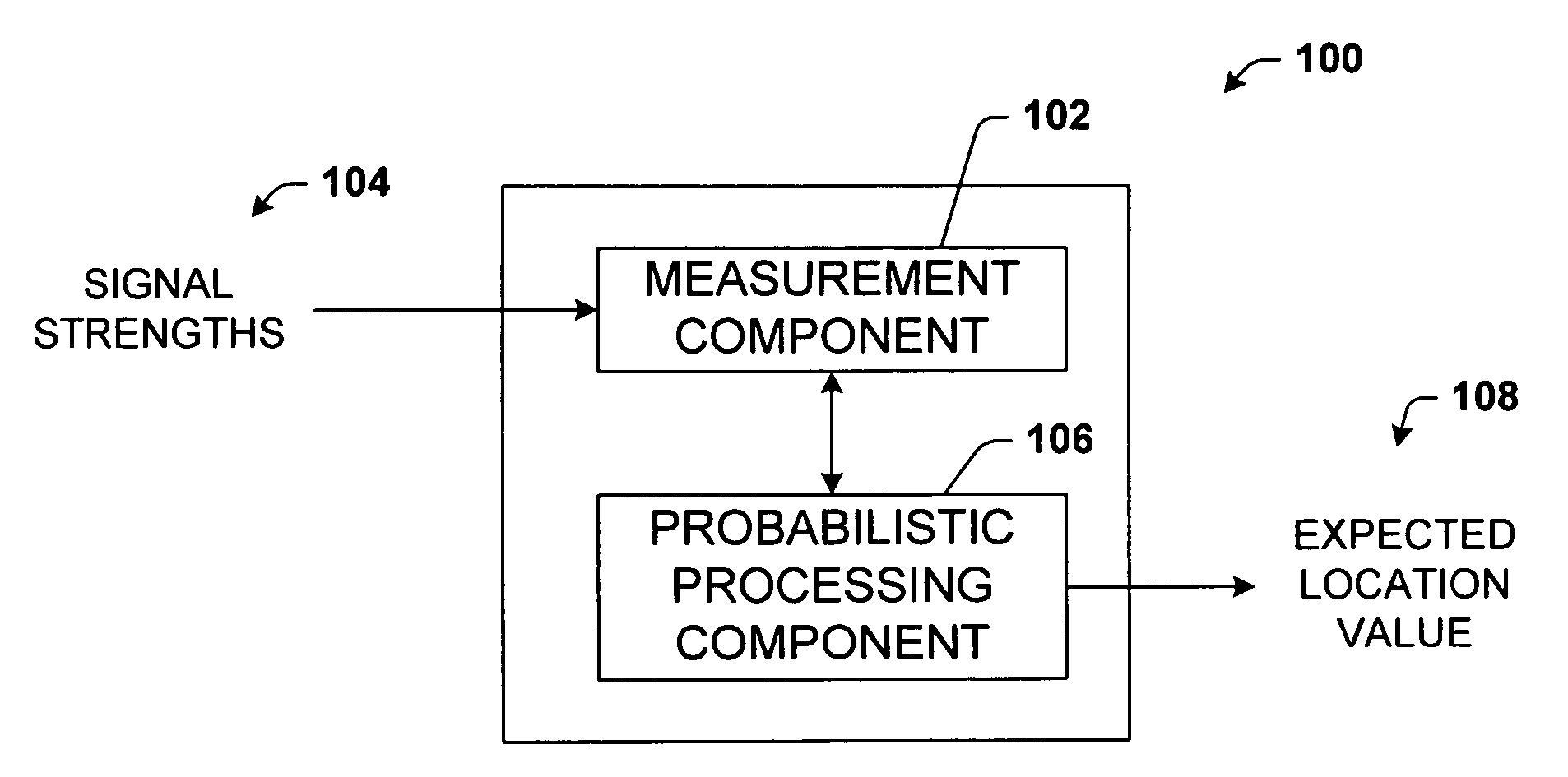
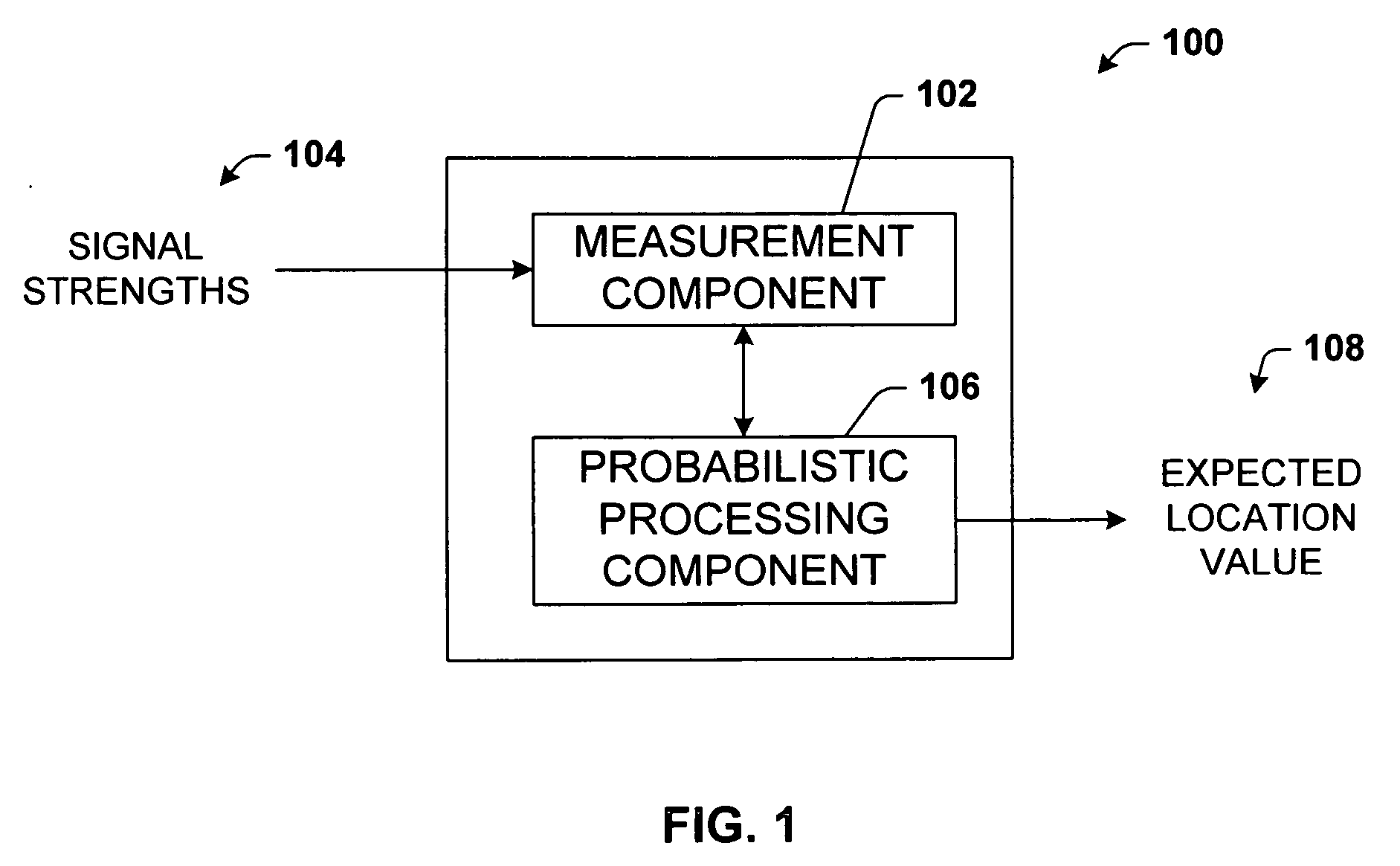
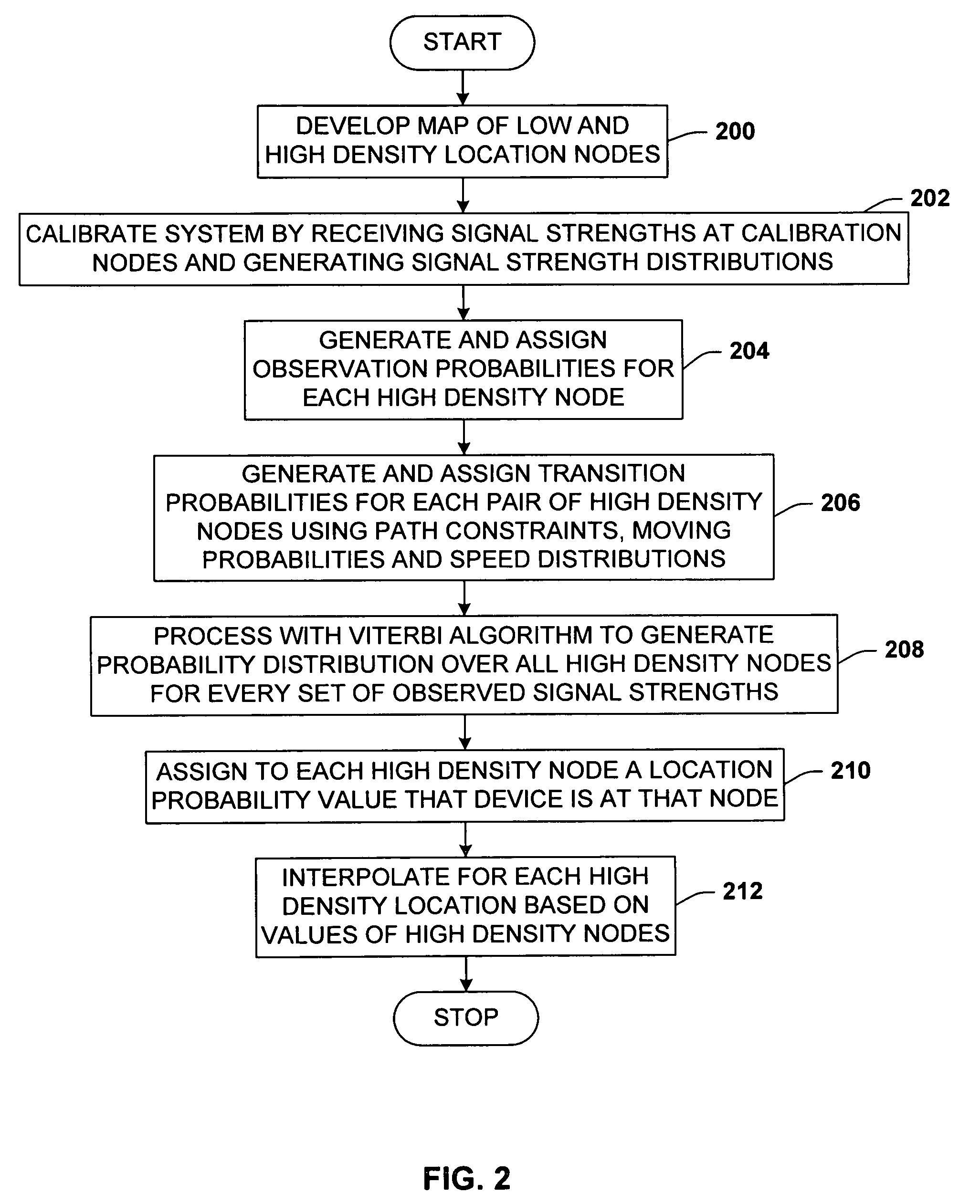
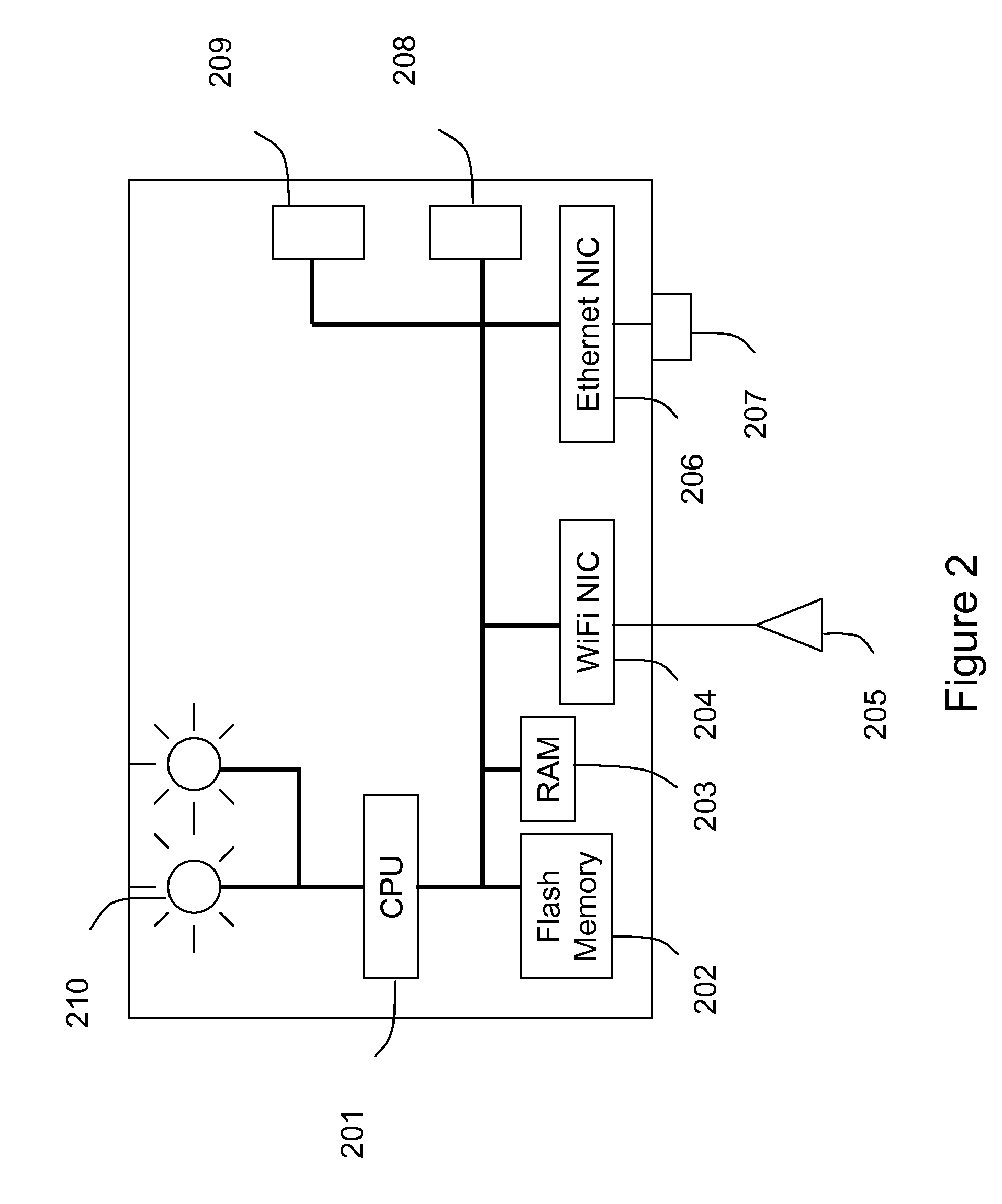
System and methods for determining the location dynamics of a portable computing device
InactiveUS20050270236A1Easy to trackFacilitate communicationData processing applicationsDirection finders using radio wavesProgram planningFloor plan
Owner:MICROSOFT TECH LICENSING LLC
Automated sniffer apparatus and method for monitoring computer systems for unauthorized access
InactiveUS20080109879A1Easy to usePrevent unauthorized wireless accessDigital data processing detailsError detection/correctionGeographic regionsNetwork interface device
An apparatus for wireless communication including an automated intrusion detection process is provided. The apparatus has a portable housing, which may have a length no greater than 1 meter, a width no greater than 1 meter, and a height of no greater than 1 meter. A processing unit (e.g., CPU) is within the housing. One or more wireless network interface devices are within the housing and are coupled to the processing unit. The apparatus has an Ethernet (or like) network interface device within the housing and coupled to the processing unit. A network connector is coupled to the Ethernet network device. One or more memories are coupled to the processing unit. A code is directed to perform a process for detection of a wireless activity within a selected local geographic region. According to a specific embodiment, the wireless activity is derived from at least one authorized device or at least an other device. A code is directed to receiving at least identity information associated with the wireless activity from the detection process in a classification process. A code is directed to labeling the identity information into at least one of a plurality of categories in the classification process. Depending upon the embodiment, other codes may exist to carry out the functionality described herein.
Owner:AIRTIGHT NETWORKS
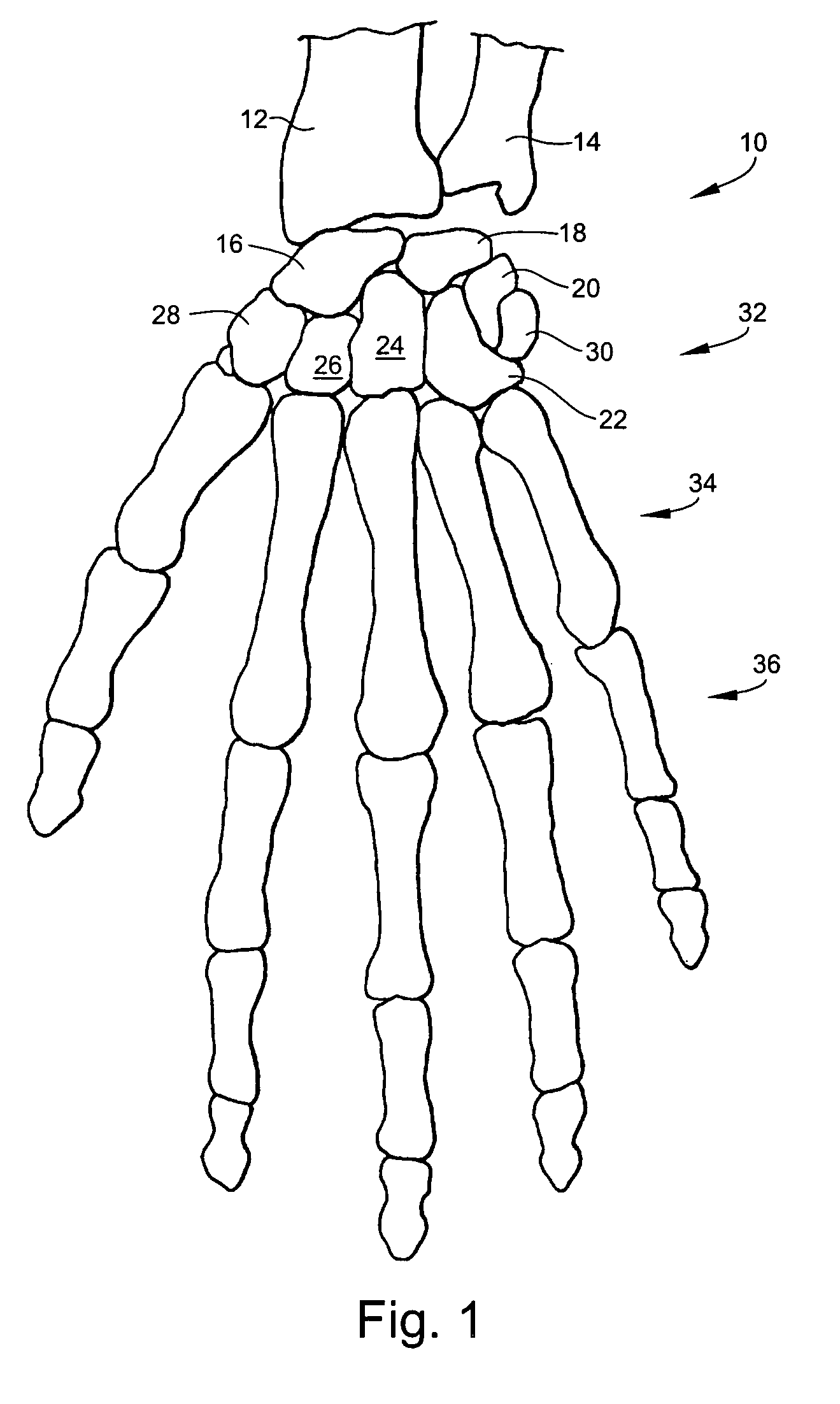
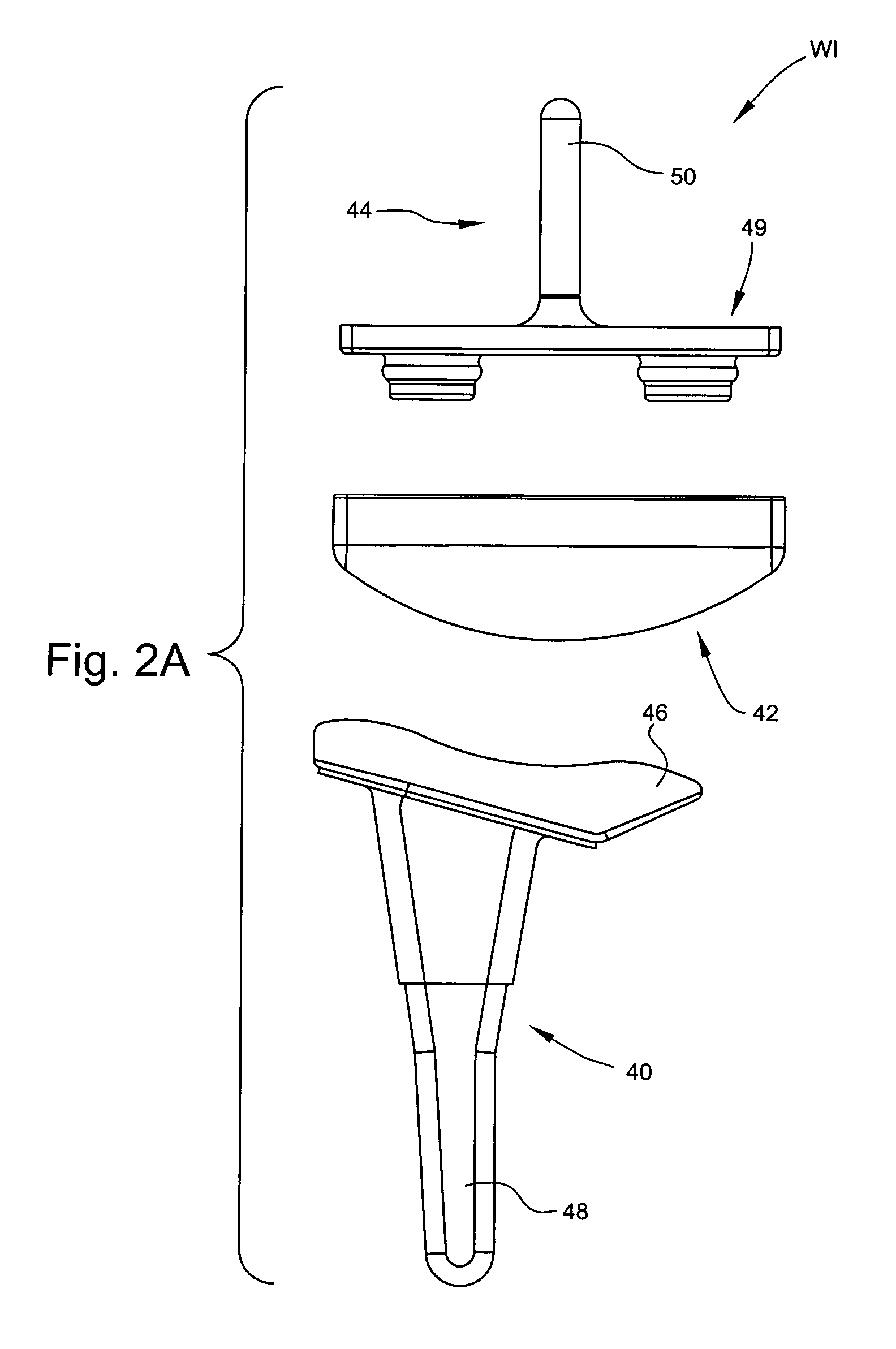
Wrist implant apparatus and method
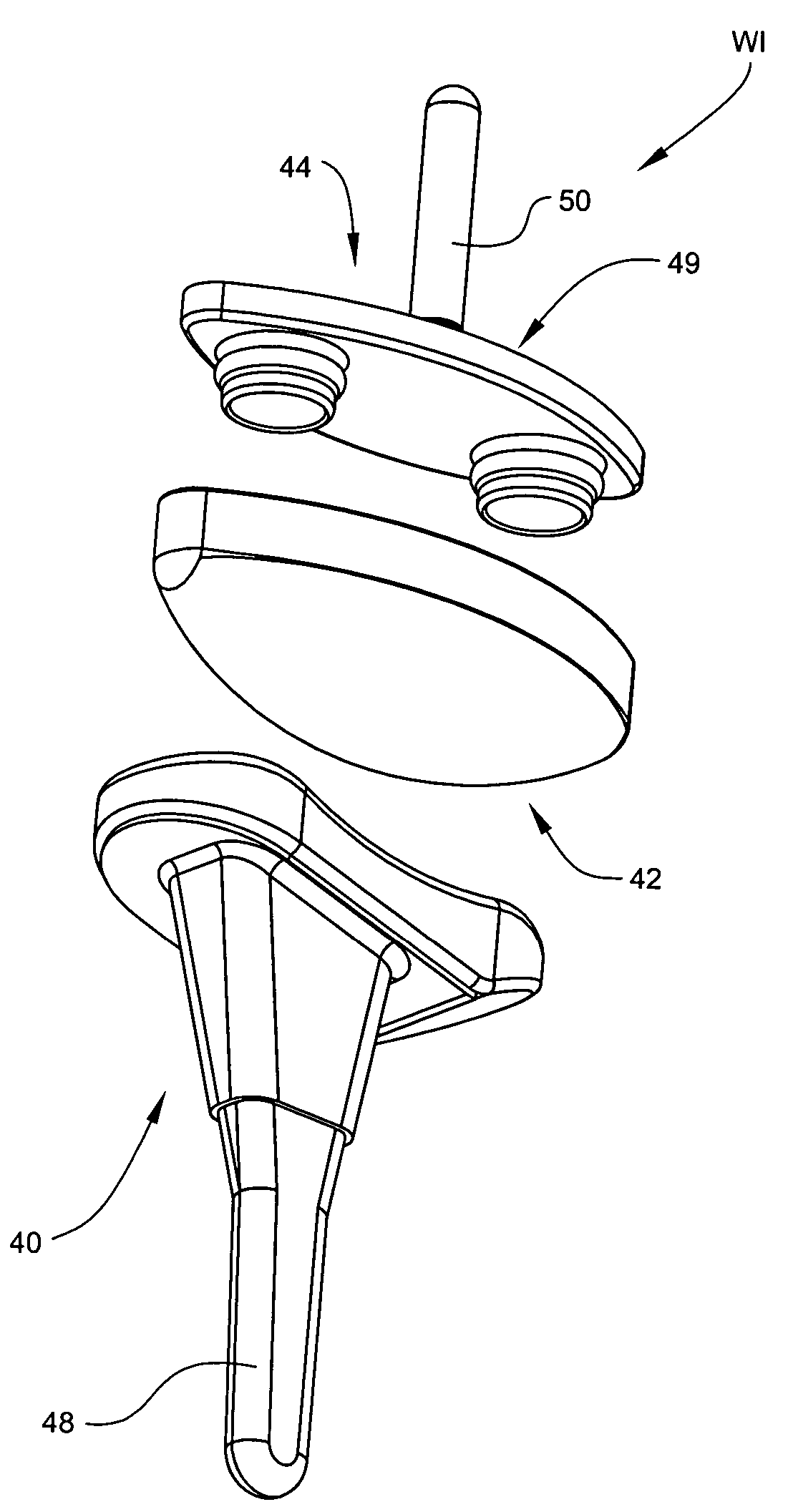
ActiveUS7531003B2Large range of motionAcceptable flexionWrist jointsAnkle jointsProsthesisCarpal bones
Prosthetic wrist implants and methods are provided. The prosthetic wrist implant includes a radial component including a base member having an upper bearing surface and a lower surface having an elongated radial stem for fixation to a radius bone. The elongated radial stem can be in an off-center position in relation to a center of the lower surface. A carpal component is also provided including a substantially planar base member having an upper surface and a lower surface with at least one socket protrusion extending therefrom, and may further included an elongated carpal post member for fixation to one or more carpal bones. An articulating bearing component for placement between the radial and carpal components is provided and includes an upper surface defining at least one socket recess and a lower bearing surface for cooperative engagement with the upper bearing surface of the radial component. The socket protrusion of the carpal component is adapted to linearly engage the socket recess of the bearing component to desirably limit rotational and translational movement of the carpal component relative to the bearing component.
Owner:SMITH & NEPHEW INC
Method and system for monitoring of wireless devices in local area computer networks
ActiveUS7970894B1Easy to usePrevent unauthorized wireless accessUser identity/authority verificationNetwork topologiesPointing deviceAuthentication
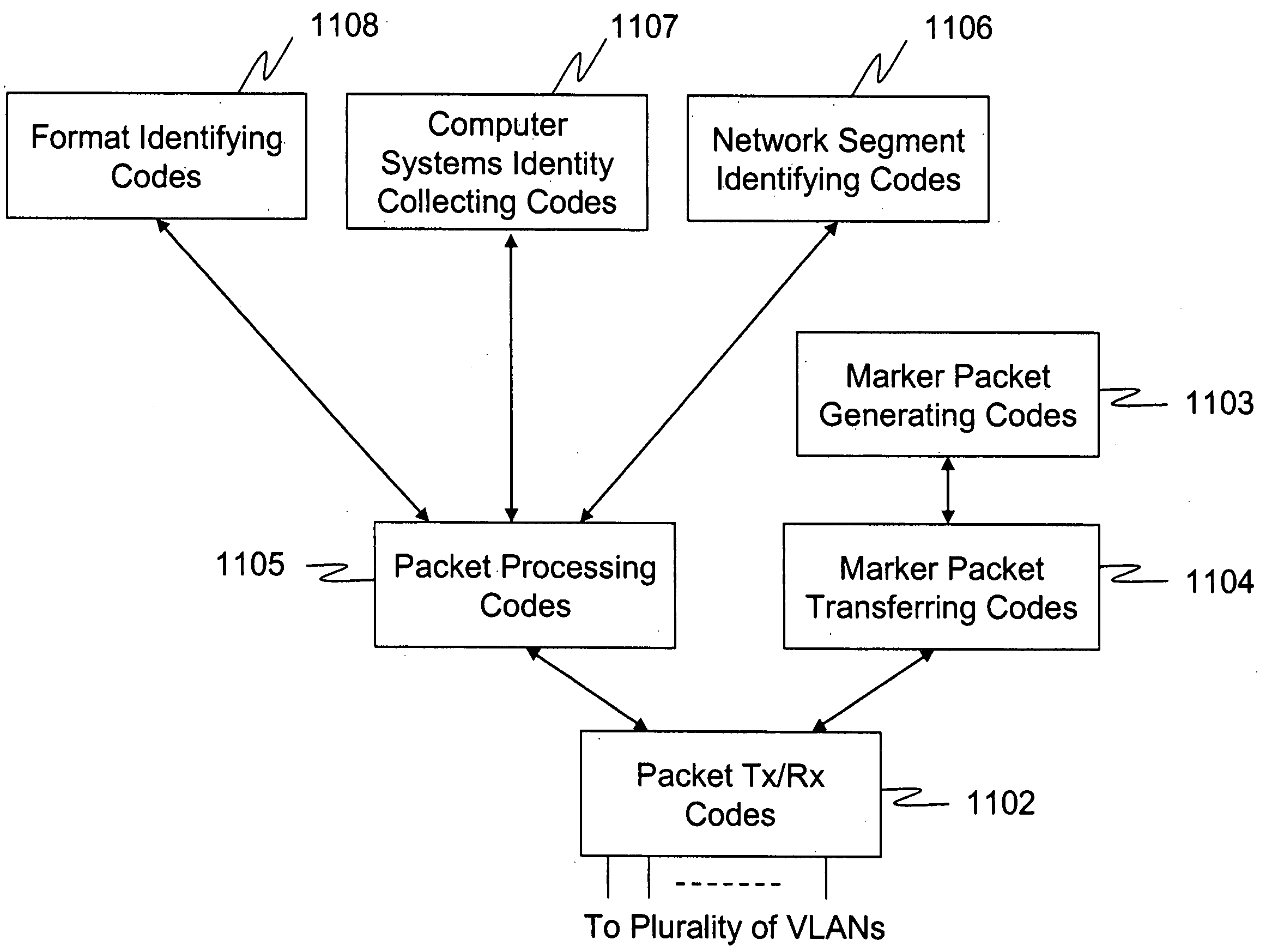
A method and a system for detecting access point devices that provide unauthorized wireless access to local area computer networks is provided. The method includes transferring one or more marker packets to the wired portion of the local area network. The one or more marker packets include an authentication data that is computed based at least upon identify of the wirelessly active access point device and a secret key. The method includes processing one or more wireless frames transmitted from the wirelessly active access point device to extract and to verify at least a portion of the authentication data.
Owner:ARISTA NETWORKS
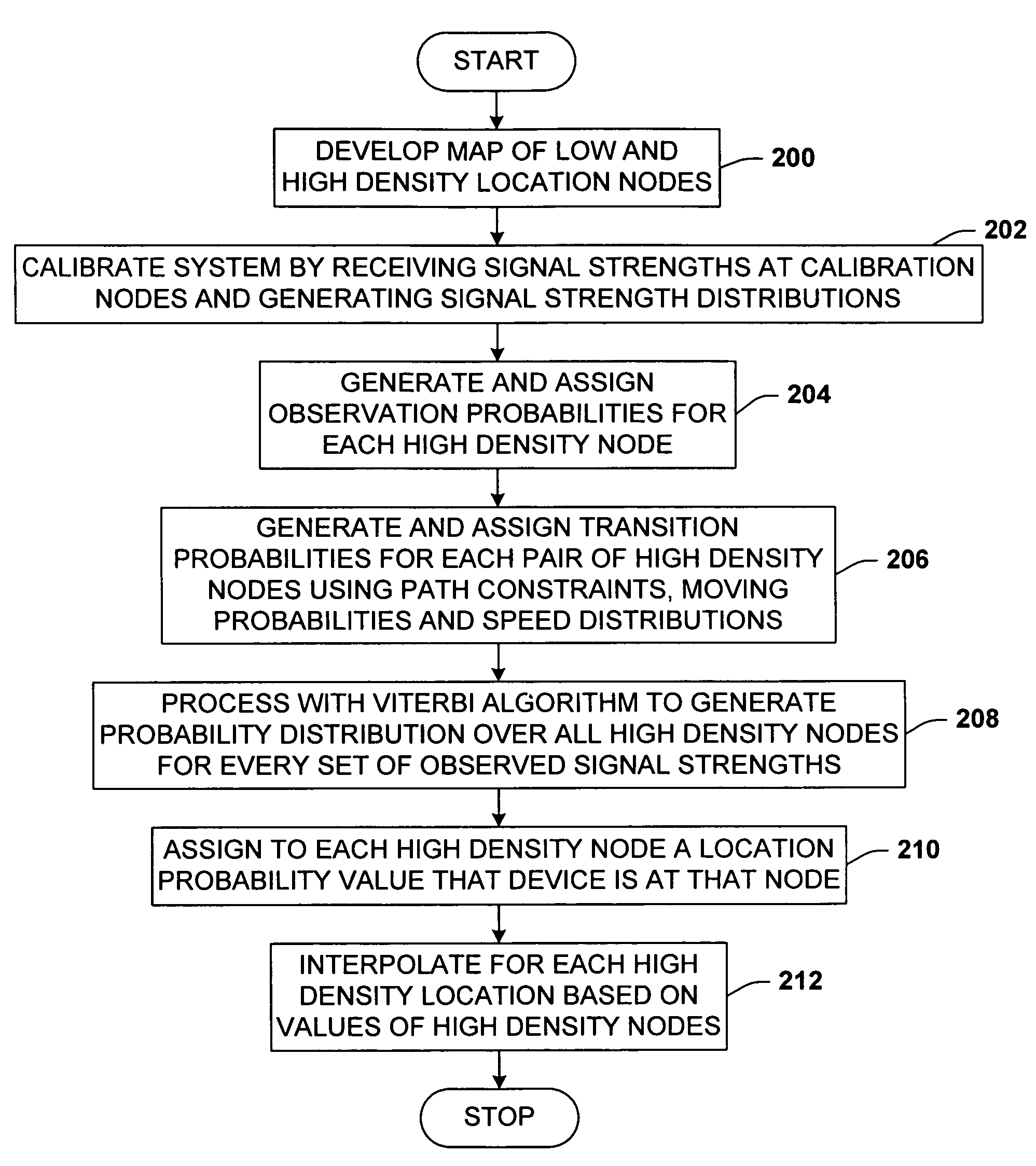
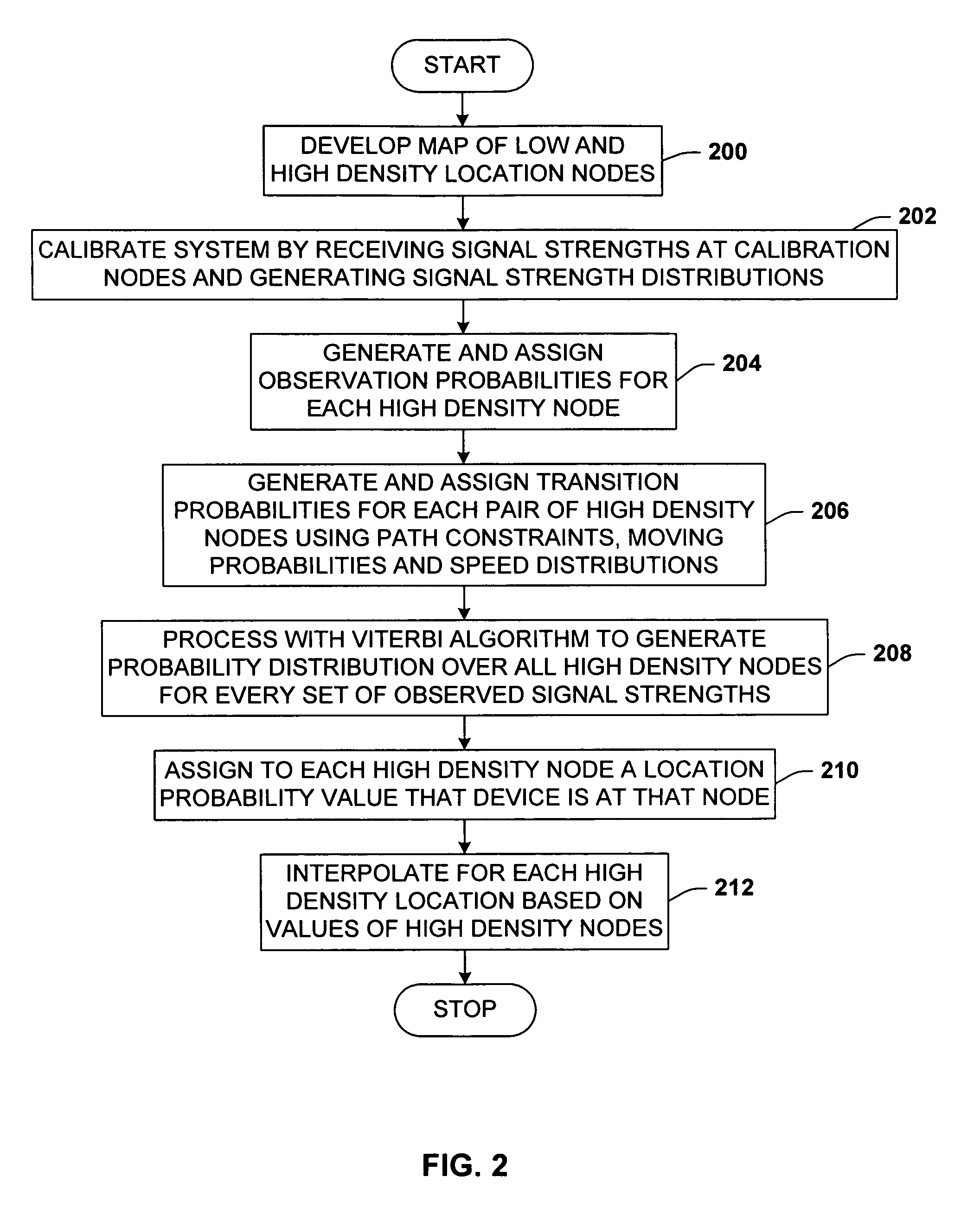
System and methods for determining the location dynamics of a portable computing device
InactiveUS7053830B2Easy to trackFacilitate communicationData processing applicationsDirection finders using radio wavesSimulationPositioning system
A location system for locating and determining the motion and velocity of a wireless device. The methods include direct inferences about whether a device is in motion versus static based on a statistical analysis of the variation of radio signal strengths over time. The system is trained according to a sparse set of identified locations from which signal strengths are measured. The system uses the signal properties of the identified locations to interpolate for a new location of the wireless device. The system uses a probabilistic graph where the identified locations of the floor plan, expected walking speeds of pedestrians, and independent inference of whether or not the device is in motion are used to determine the new location of the device.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com