Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1870 results about "End system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
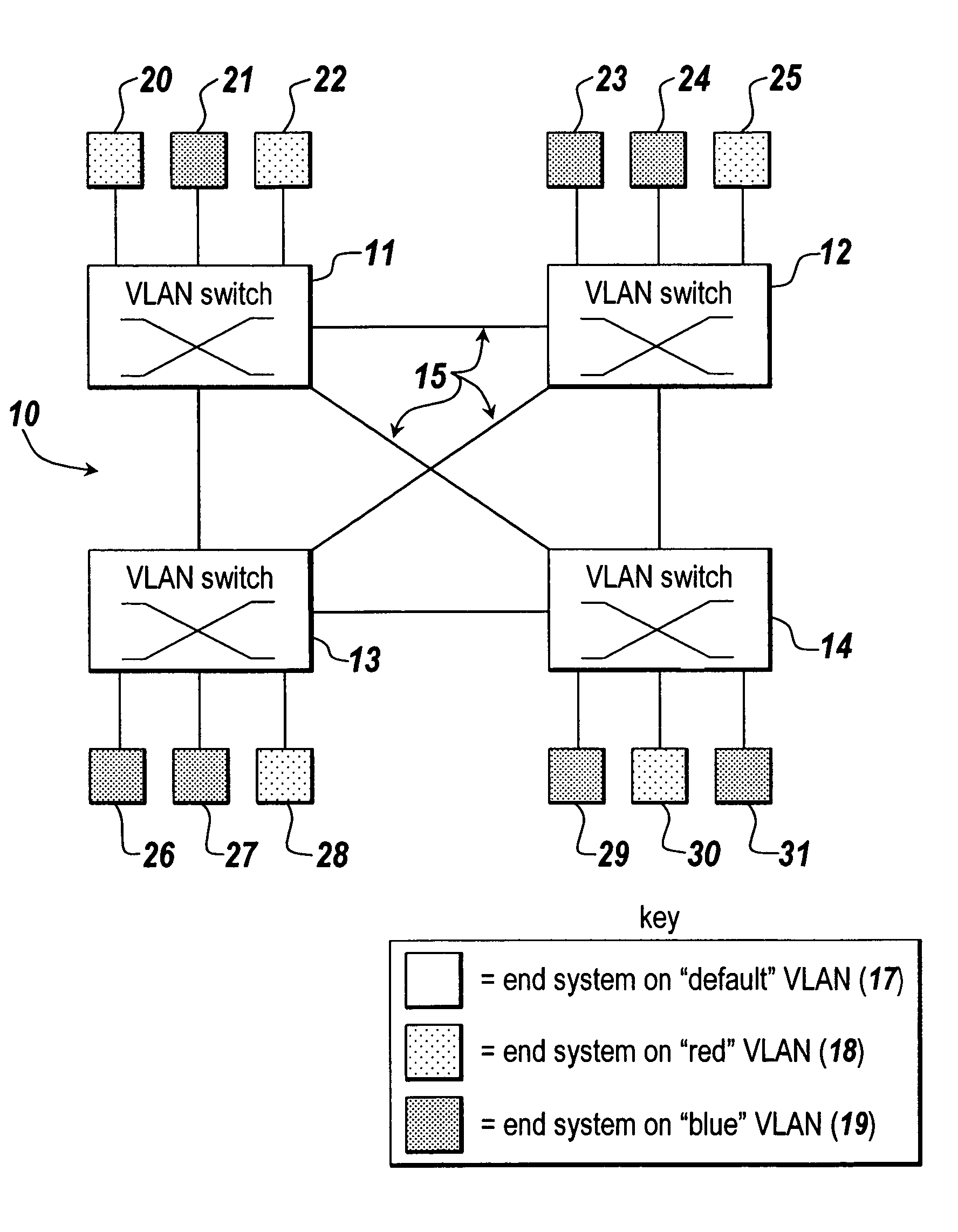
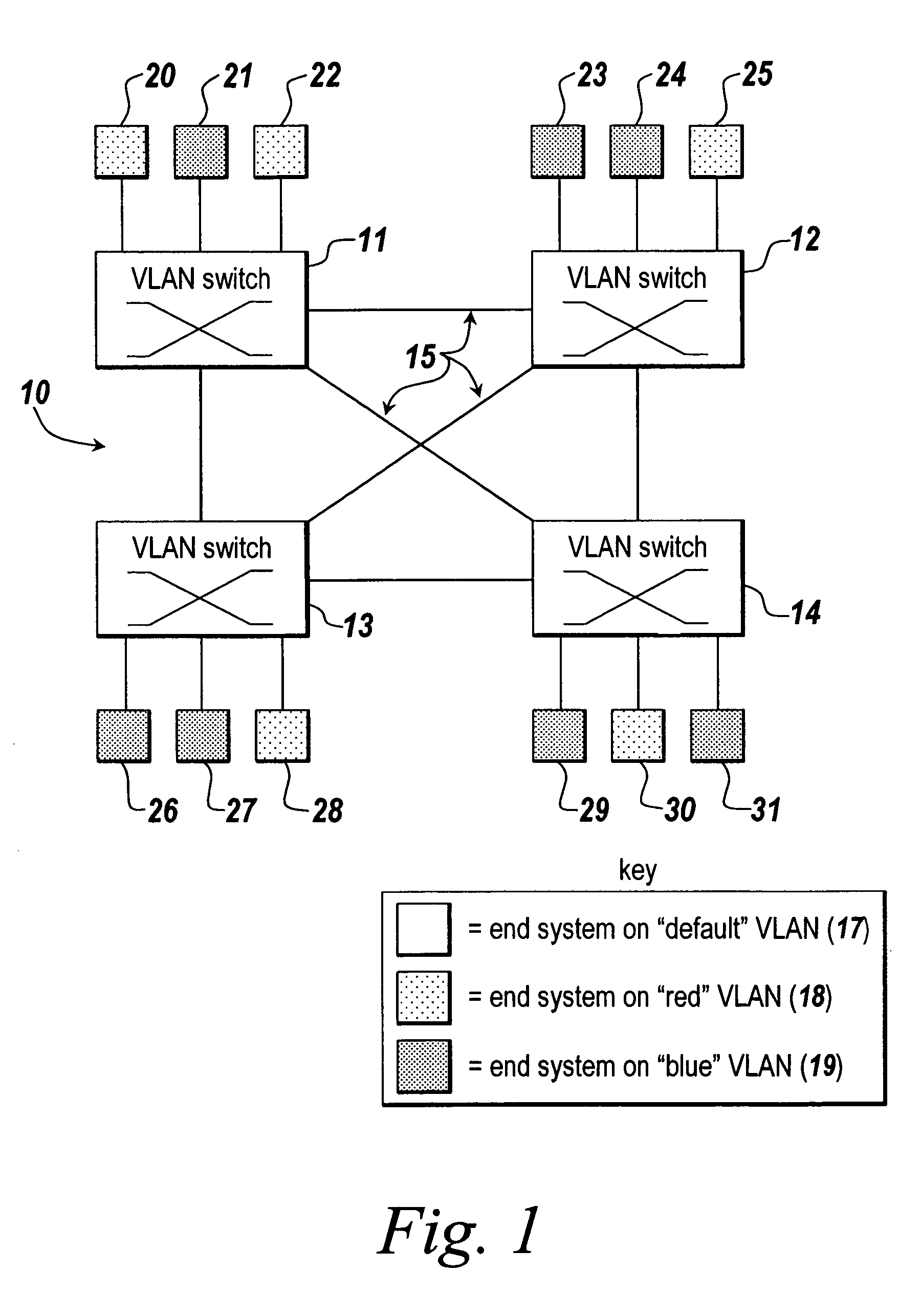
In networking jargon, the computers that are connected to a computer network are sometimes referred to as end systems or end stations. They are labeled end systems because they sit at the edge of the network. The end user always interacts with the end systems. End systems are the devices that provide information or services.
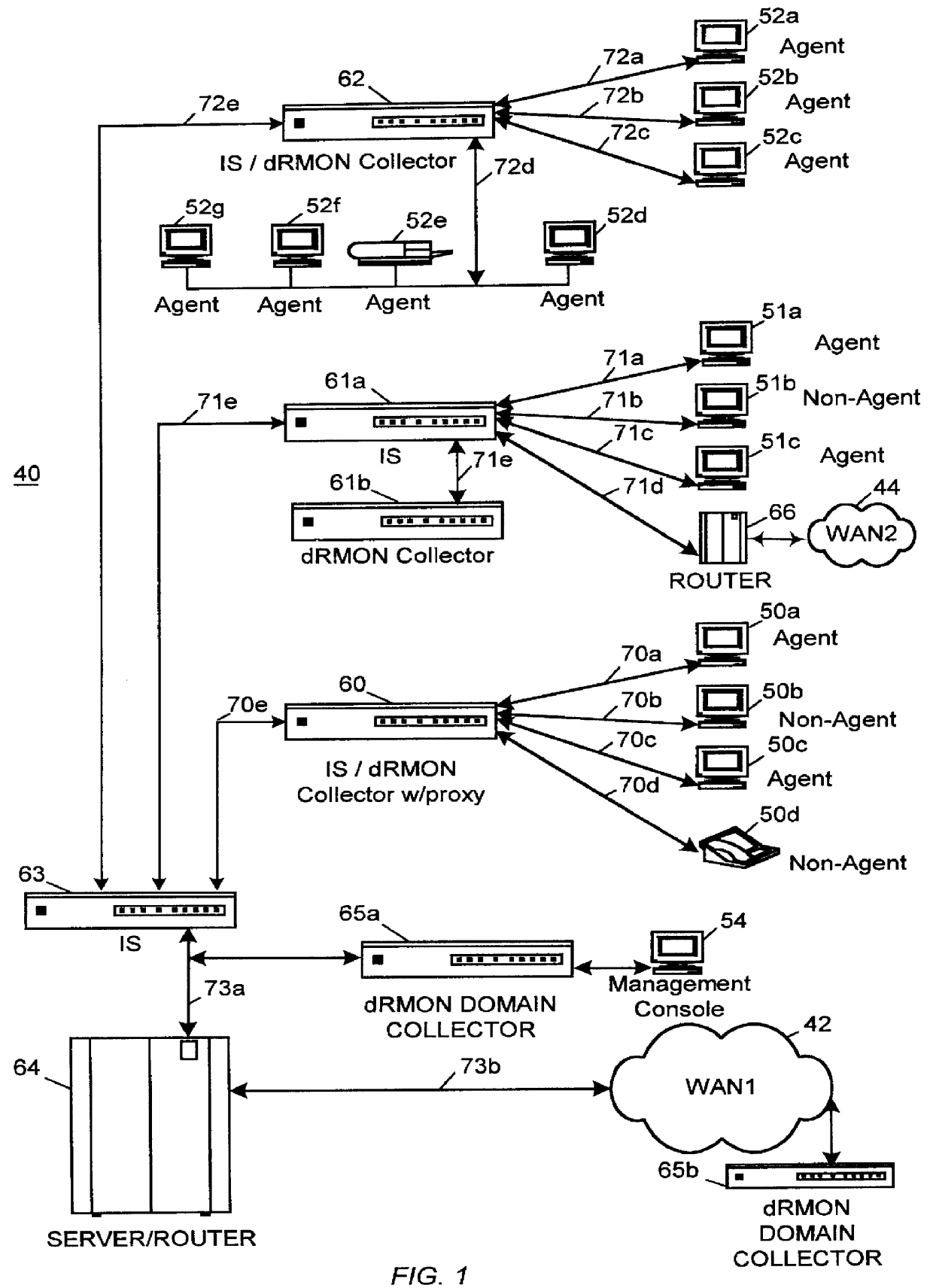
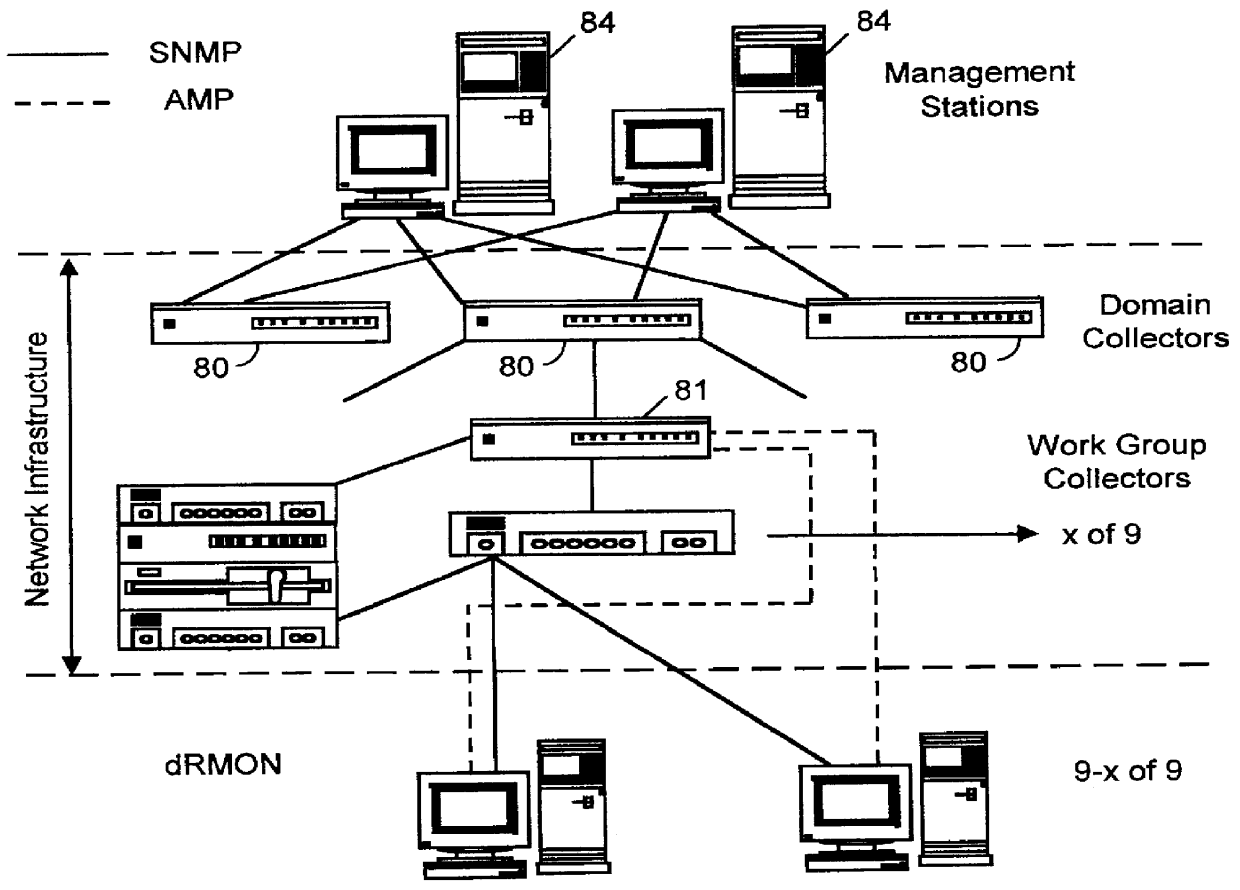
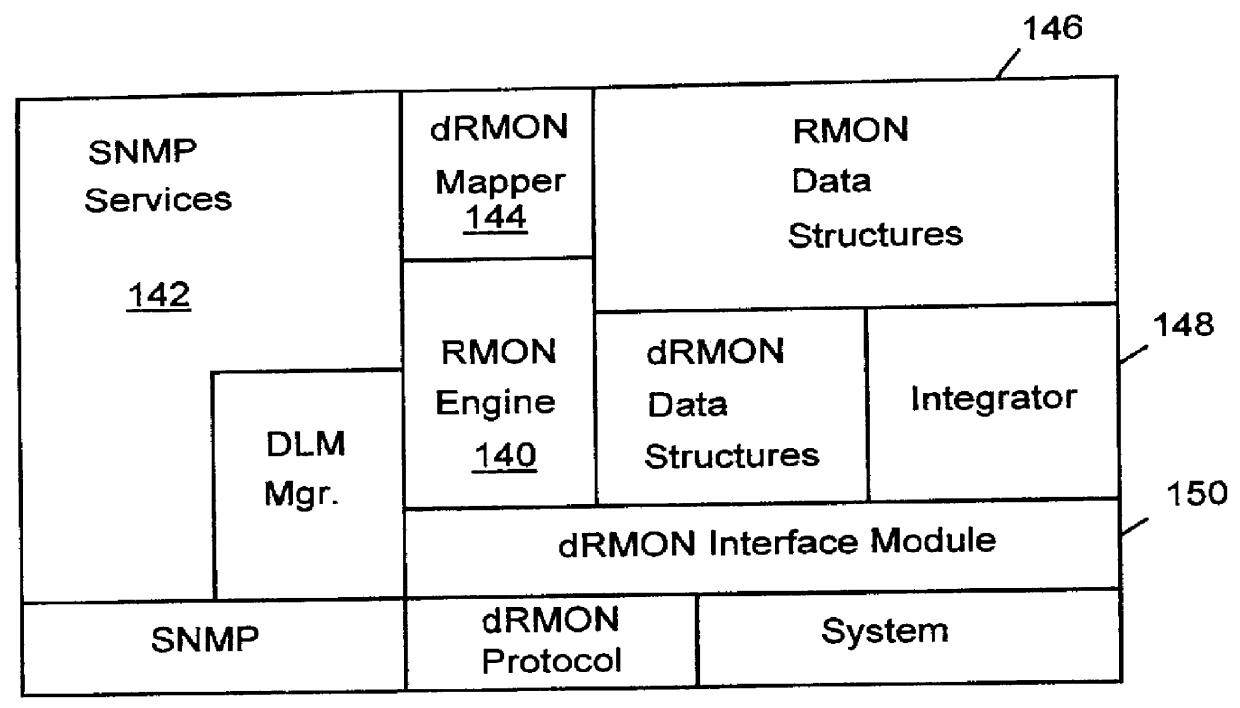
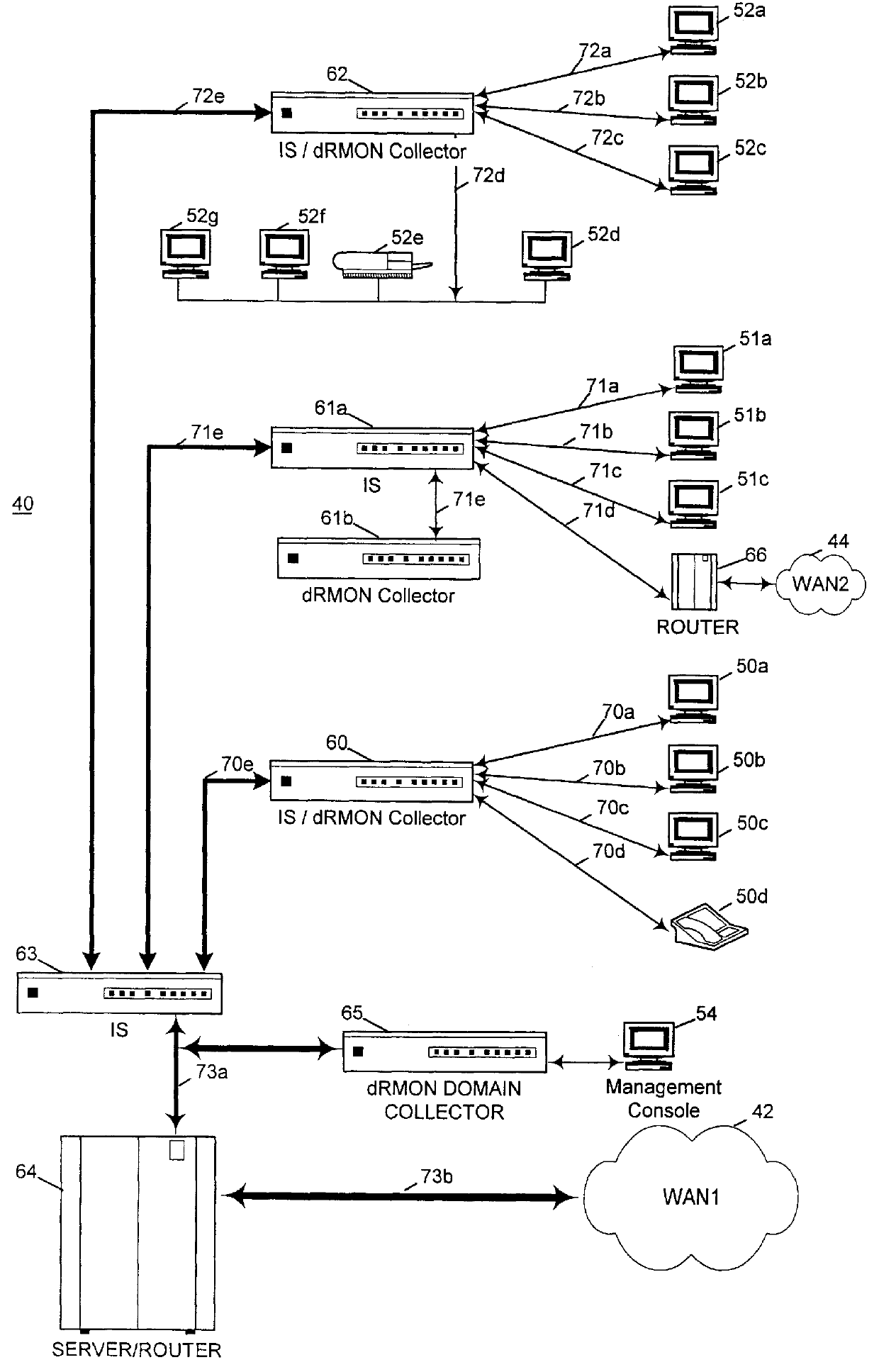
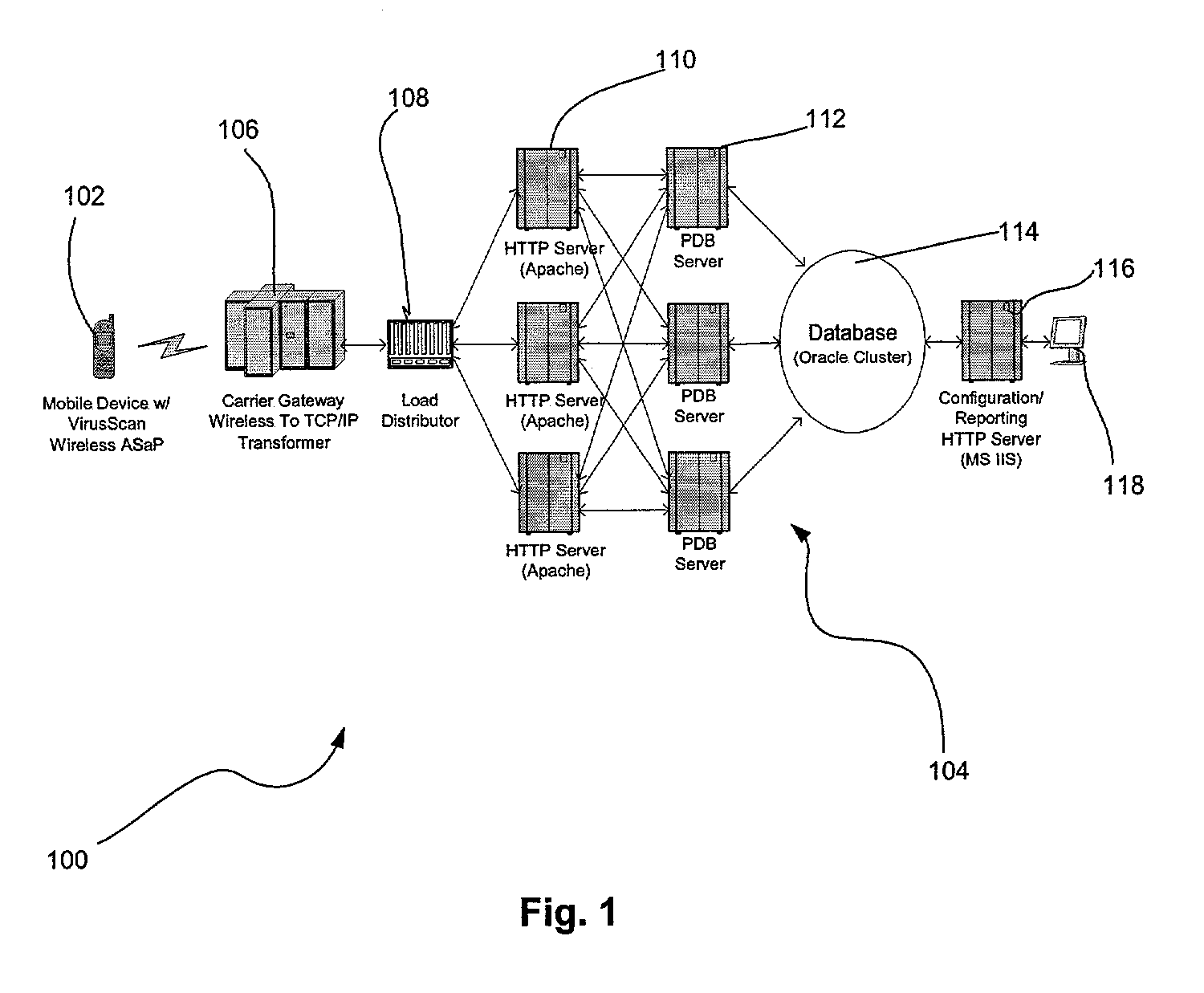
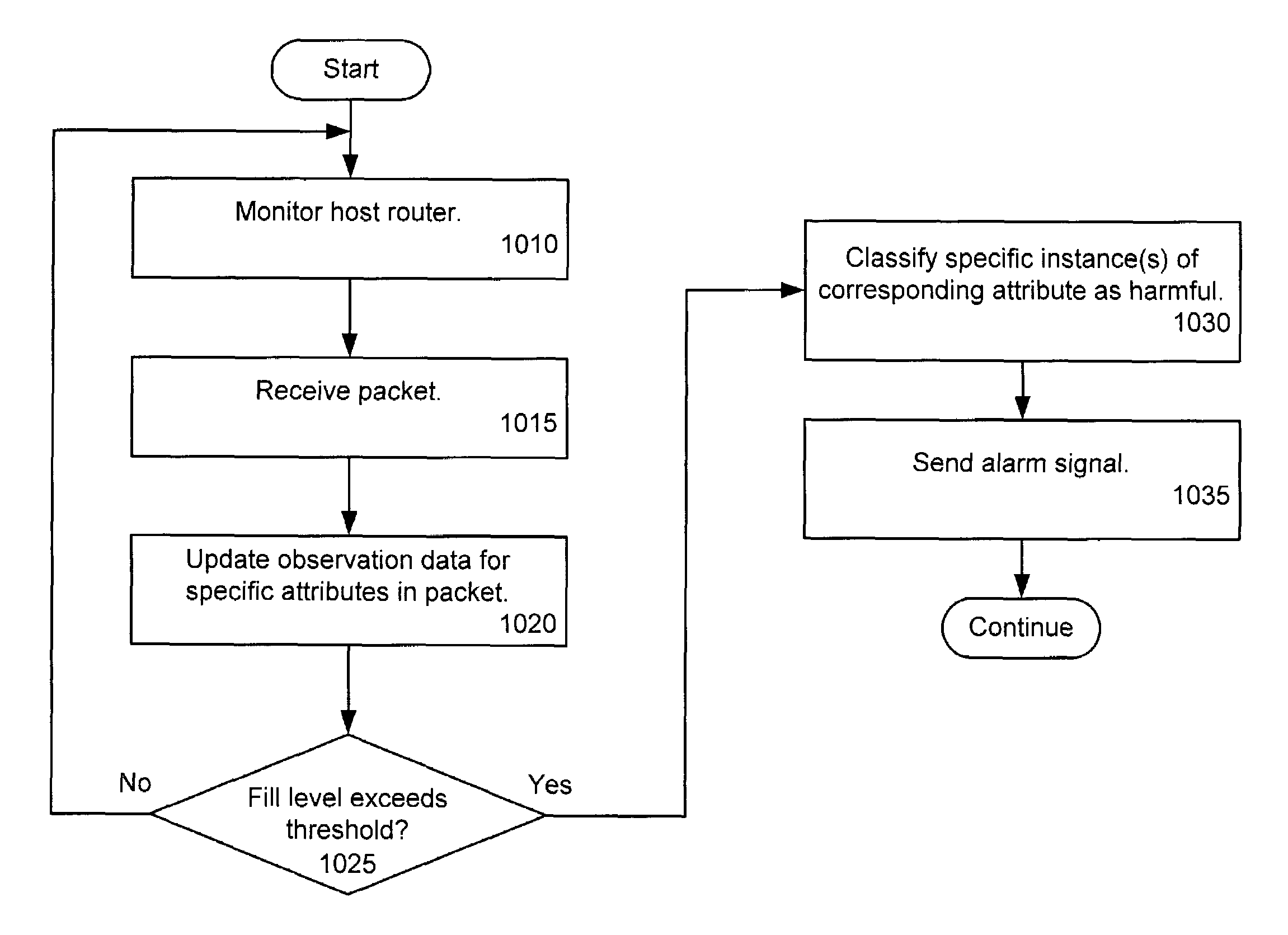
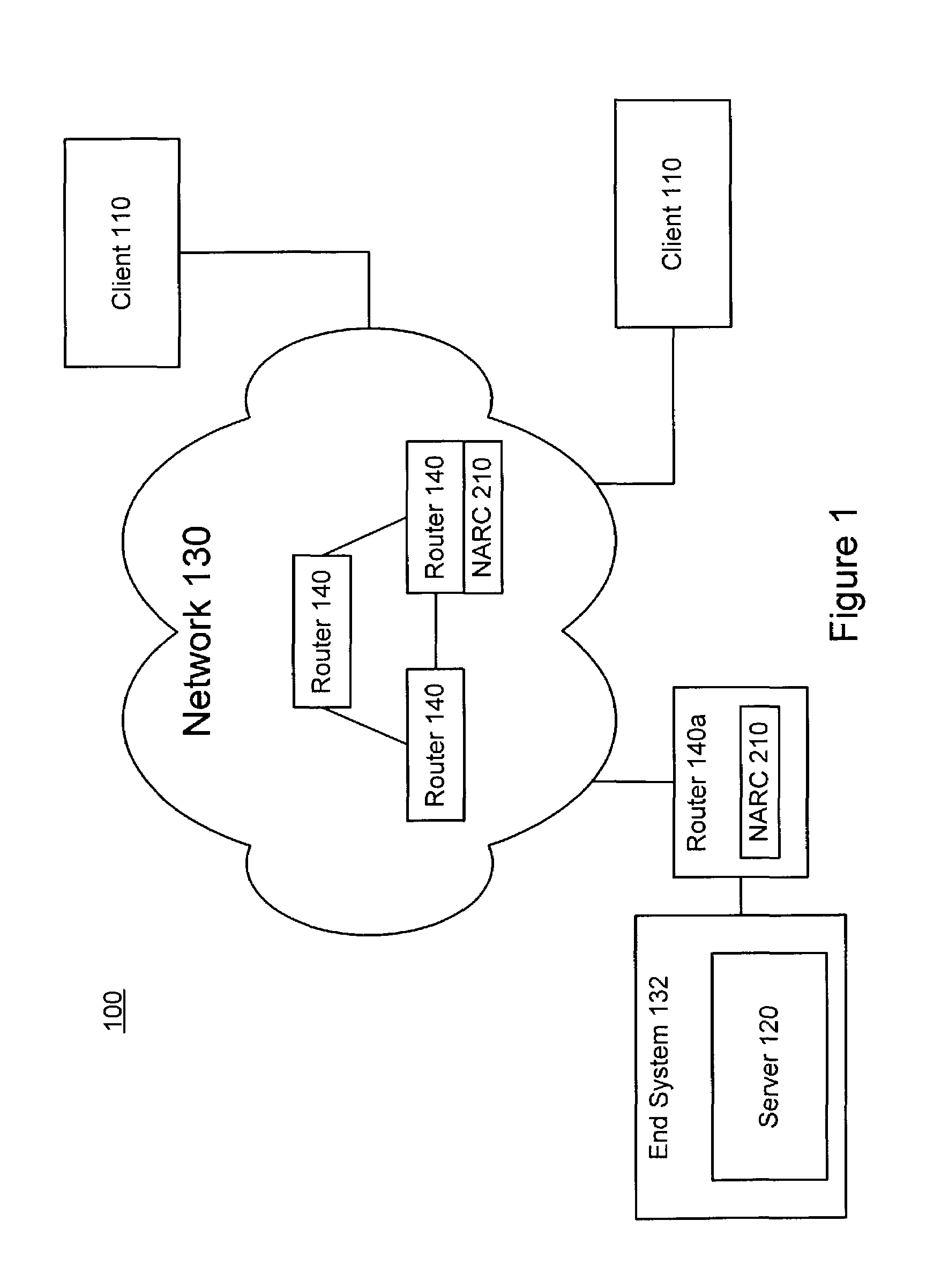
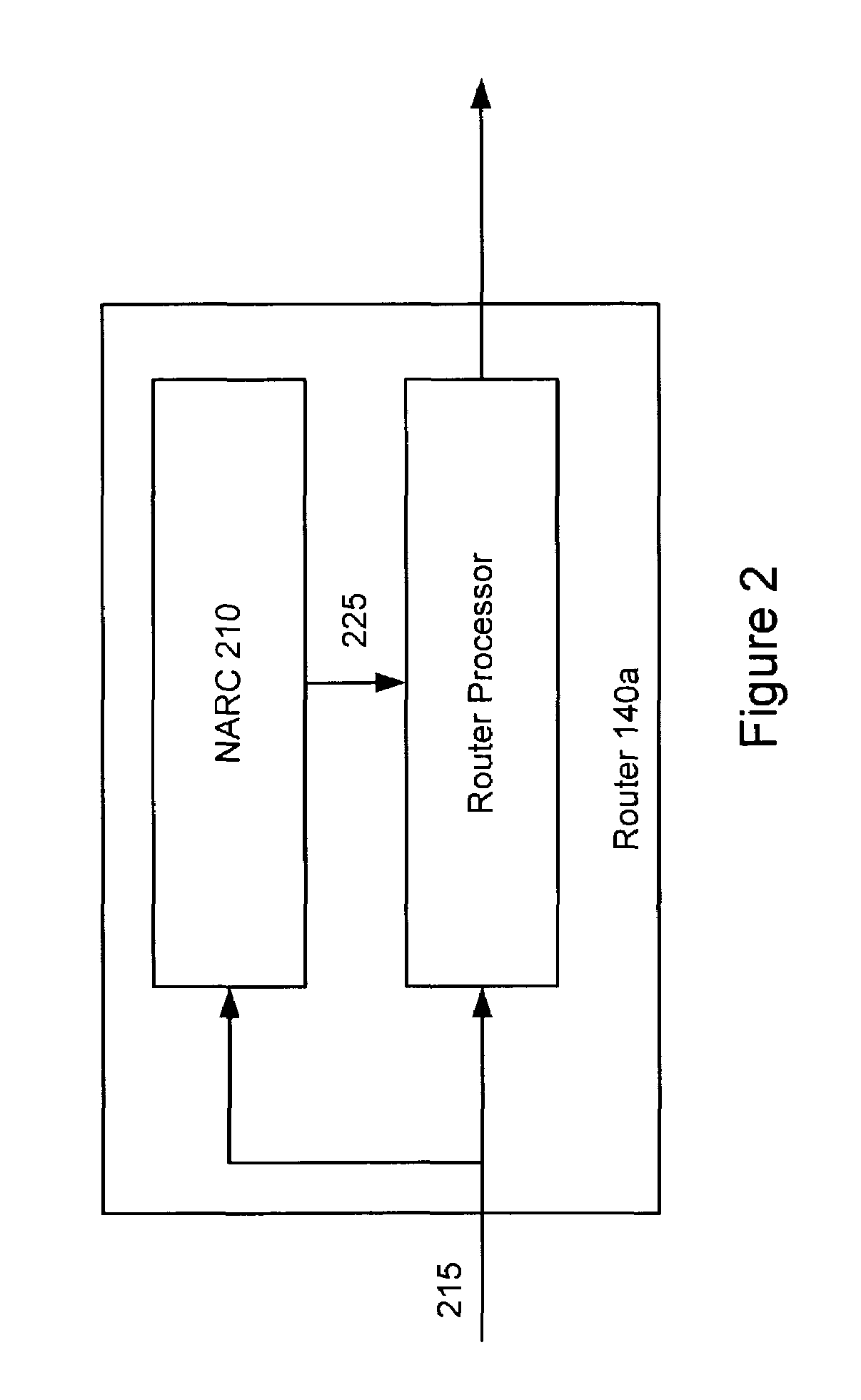
Distributed remote monitoring (dRMON) for networks
InactiveUS6108782AError preventionFrequency-division multiplex detailsNetwork operating systemOperational system
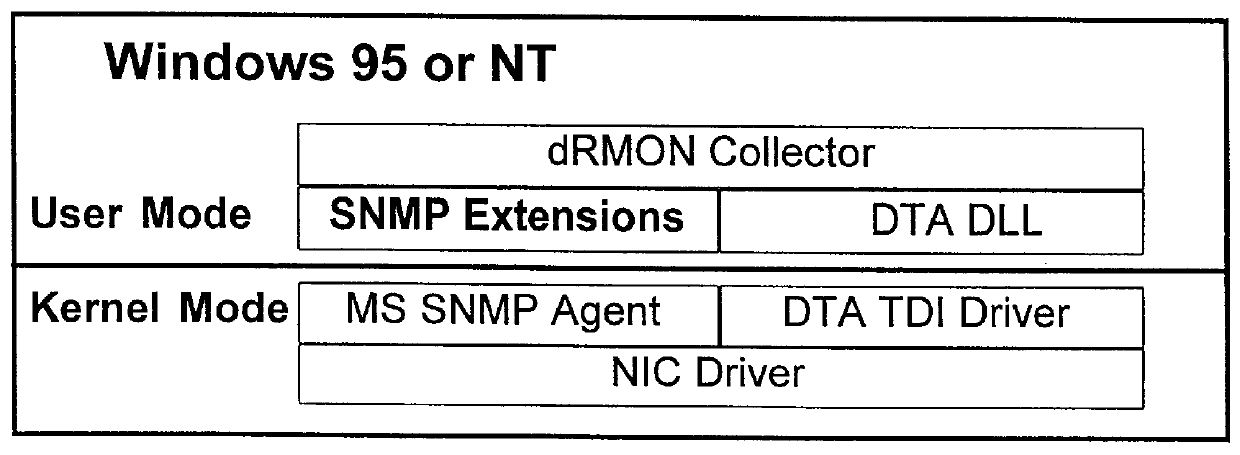
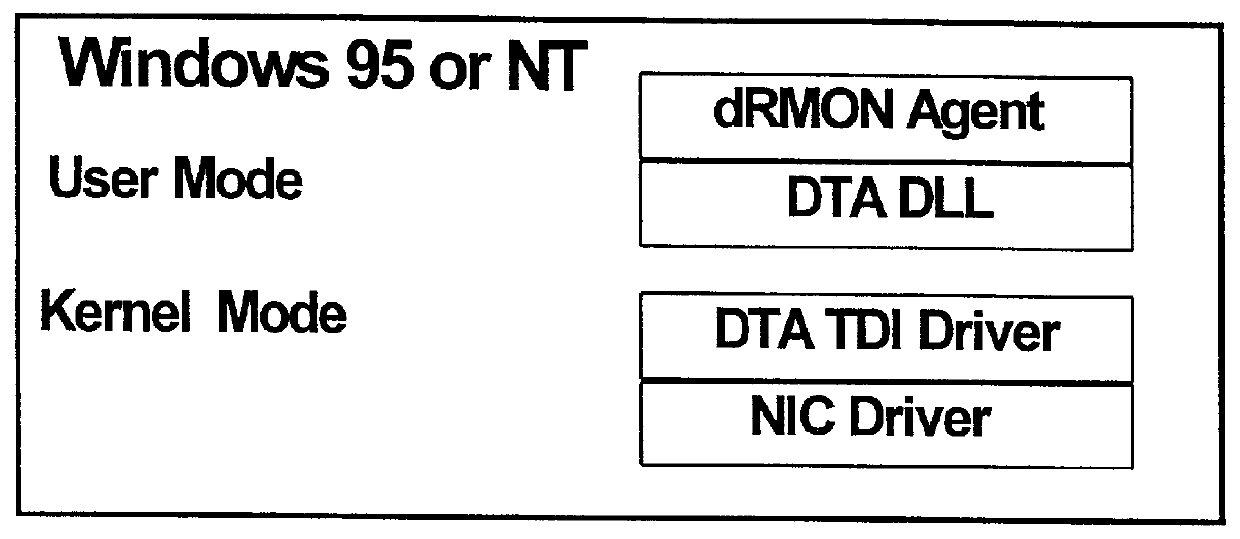
Distributed remote monitoring (dRMON) of network traffic and performance uses distributed nodes to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create combined views of network performance. A collector may mimic a prior art, non-distributed, network probe and may interact with network management software as though it were a stand alone network probe thereby simplifying a user's interaction with the distributed system. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments. The invention has applications in a variety of communication system environments including local area networks, cable television distribution systems, ATM systems, and advanced telephony systems. A specific embodiment of the invention solves is particularly optimized to work in LAN environments with end systems running under Windows-compatible network operating systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Distributed remote management (dRMON) for networks
A method and apparatus for the distributed monitoring of network traffic deploys end system agents to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create higher level pictures of network performance. A collector may act as a proxy for a prior art standalone network probe and may interact with network management software as though it were a standalone network probe. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
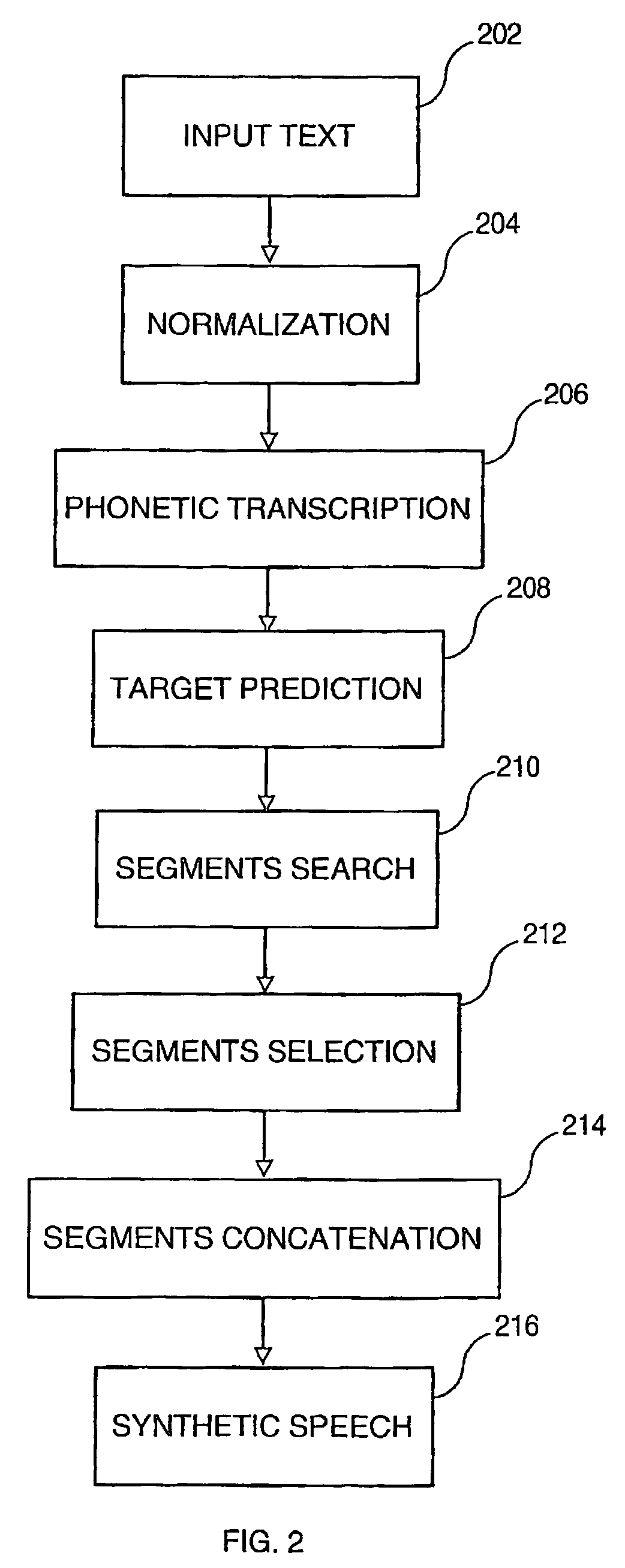
Systems and methods for selecting from multiple phonectic transcriptions for text-to-speech synthesis
ActiveUS7869999B2Quality improvementReduce in quantitySpeech synthesisEnd systemText to speech synthesis
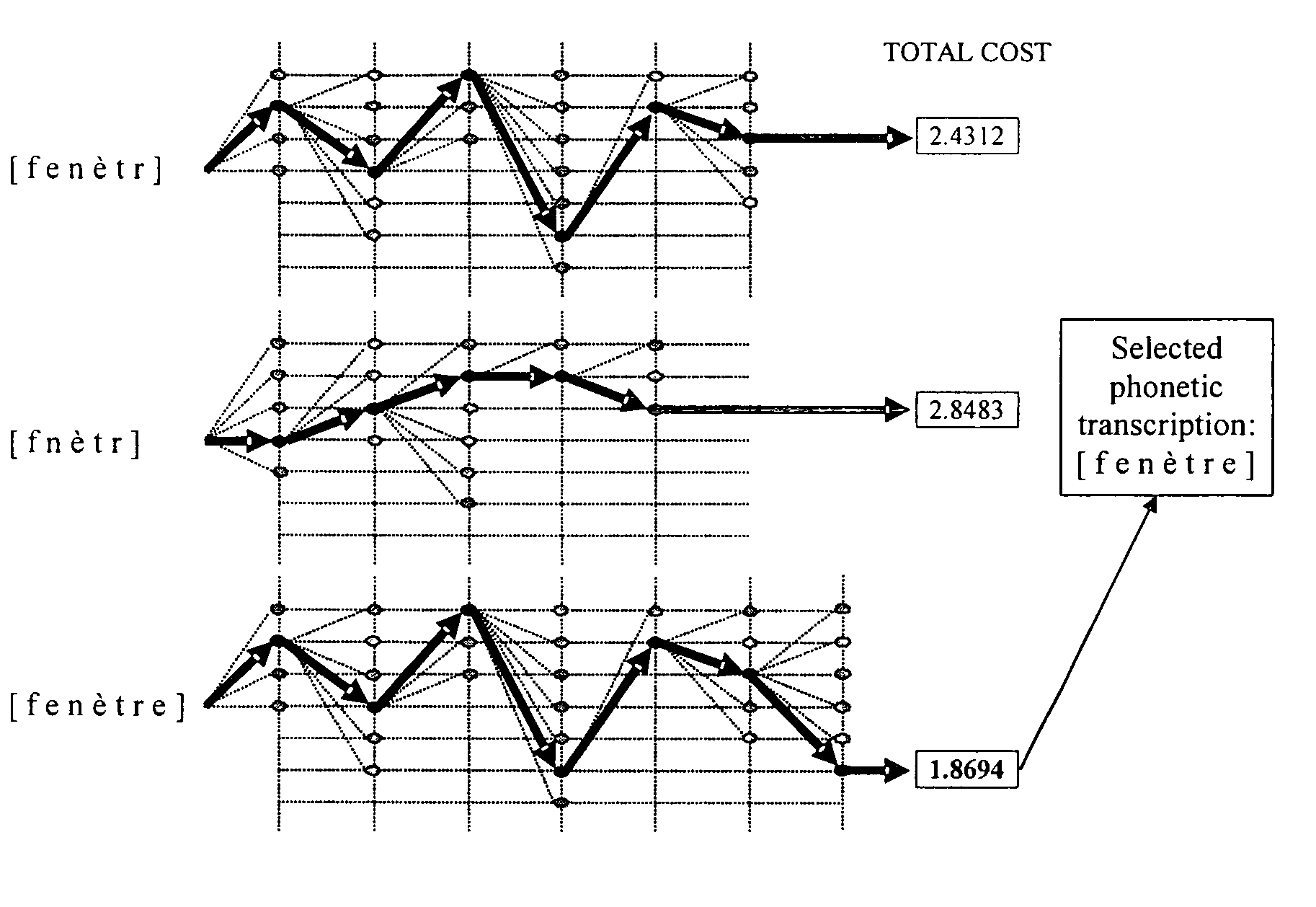
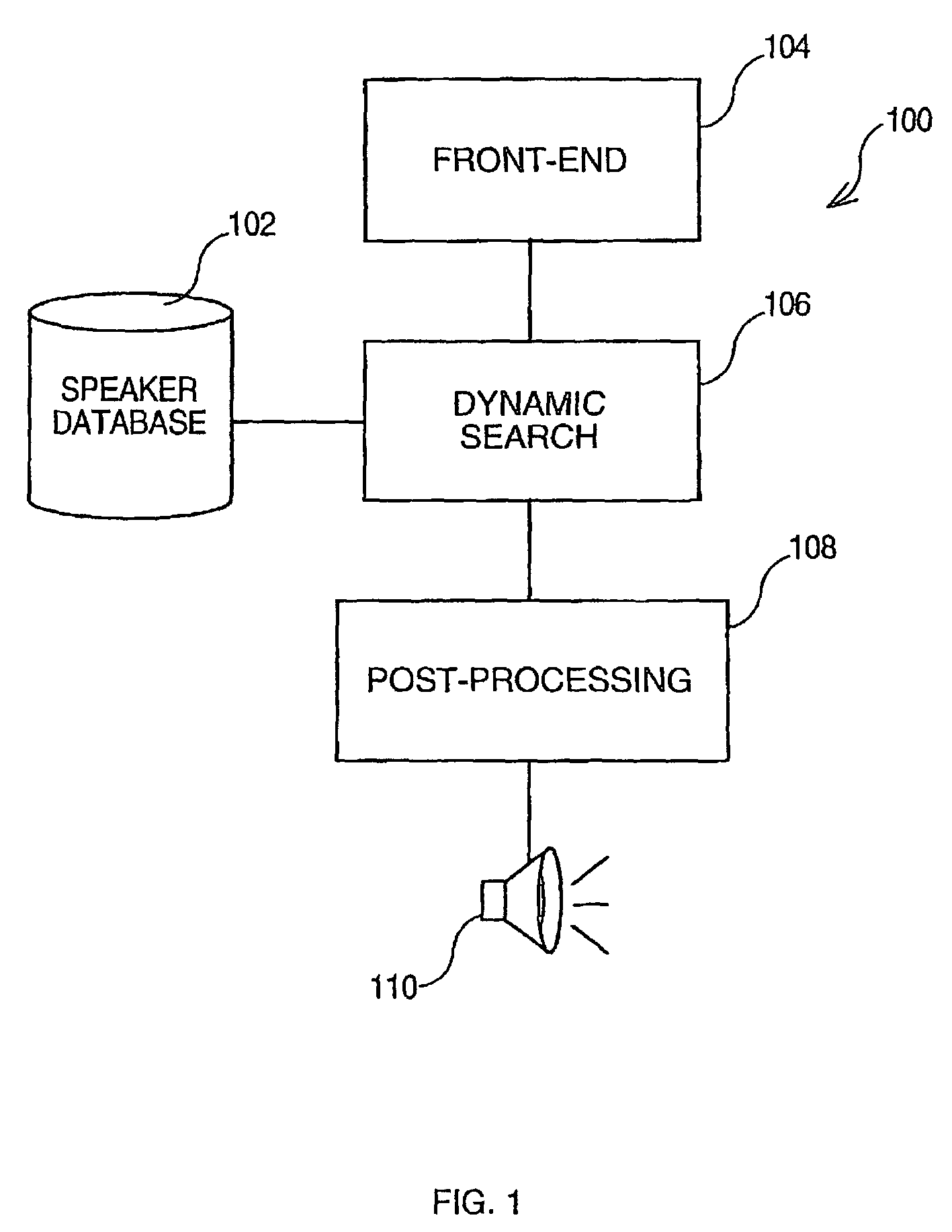
A system and method for generating synthetic speech, which operates in a computer implemented Text-To-Speech system. The system comprises at least a speaker database that has been previously created from user recordings, a Front-End system to receive an input text and a Text-To-Speech engine. The Front-End system generates multiple phonetic transcriptions for each word of the input text, and the TTS engine uses a cost function to select which phonetic transcription is the more appropriate for searching the speech segments within the speaker database to be concatenated and synthesized.
Owner:CERENCE OPERATING CO
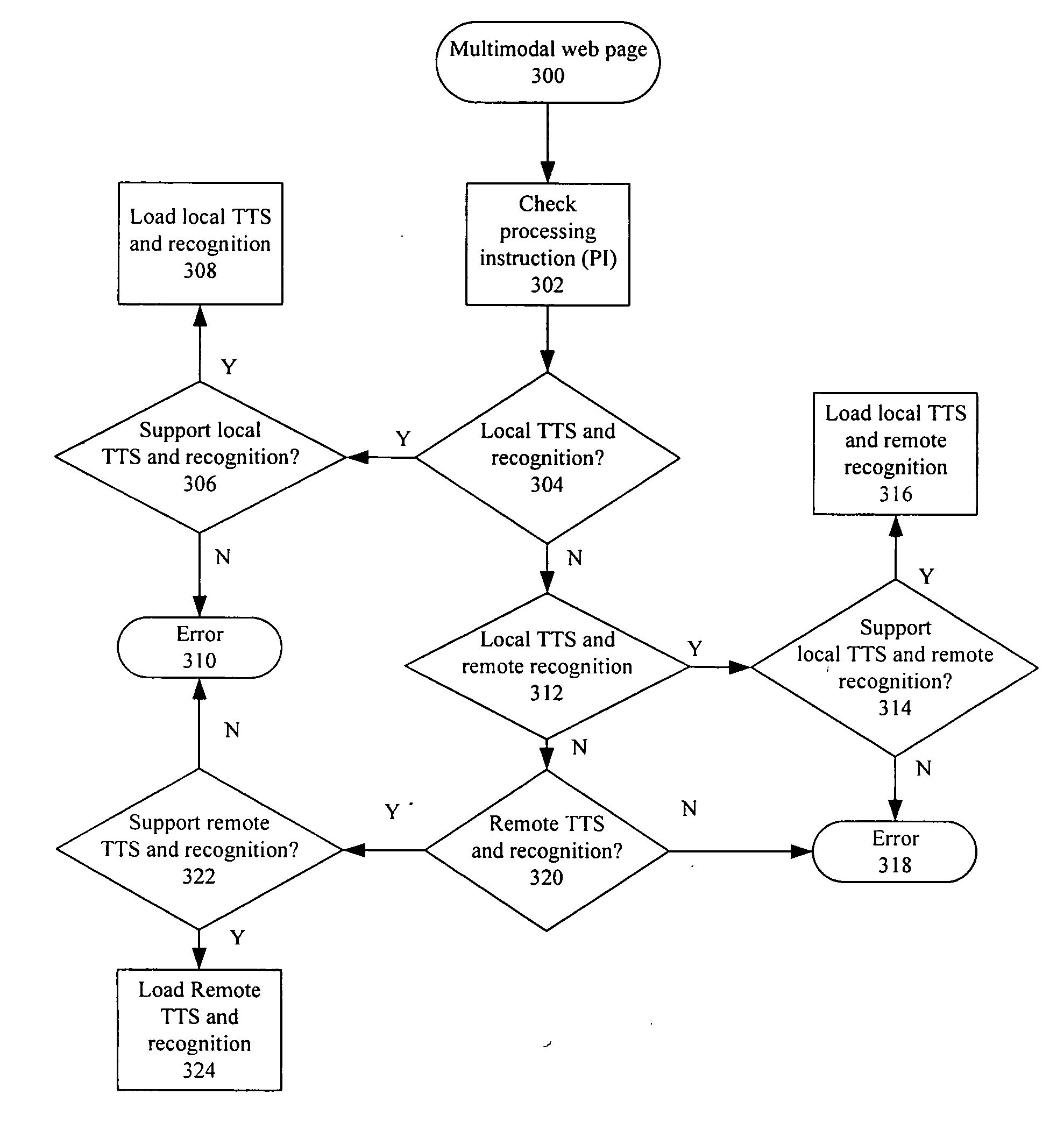
Dynamic switching between local and remote speech rendering
ActiveUS20060122836A1Devices with voice recognitionSubstation equipmentProcessing InstructionEnd system
A multimodal browser for rendering a multimodal document on an end system defining a host can include a visual browser component for rendering visual content, if any, of the multimodal document, and a voice browser component for rendering voice-based content, if any, of the multimodal document. The voice browser component can determine which of a plurality of speech processing configuration is used by the host in rendering the voice-based content. The determination can be based upon the resources of the host running the application. The determination also can be based upon a processing instruction contained in the application.
Owner:NUANCE COMM INC
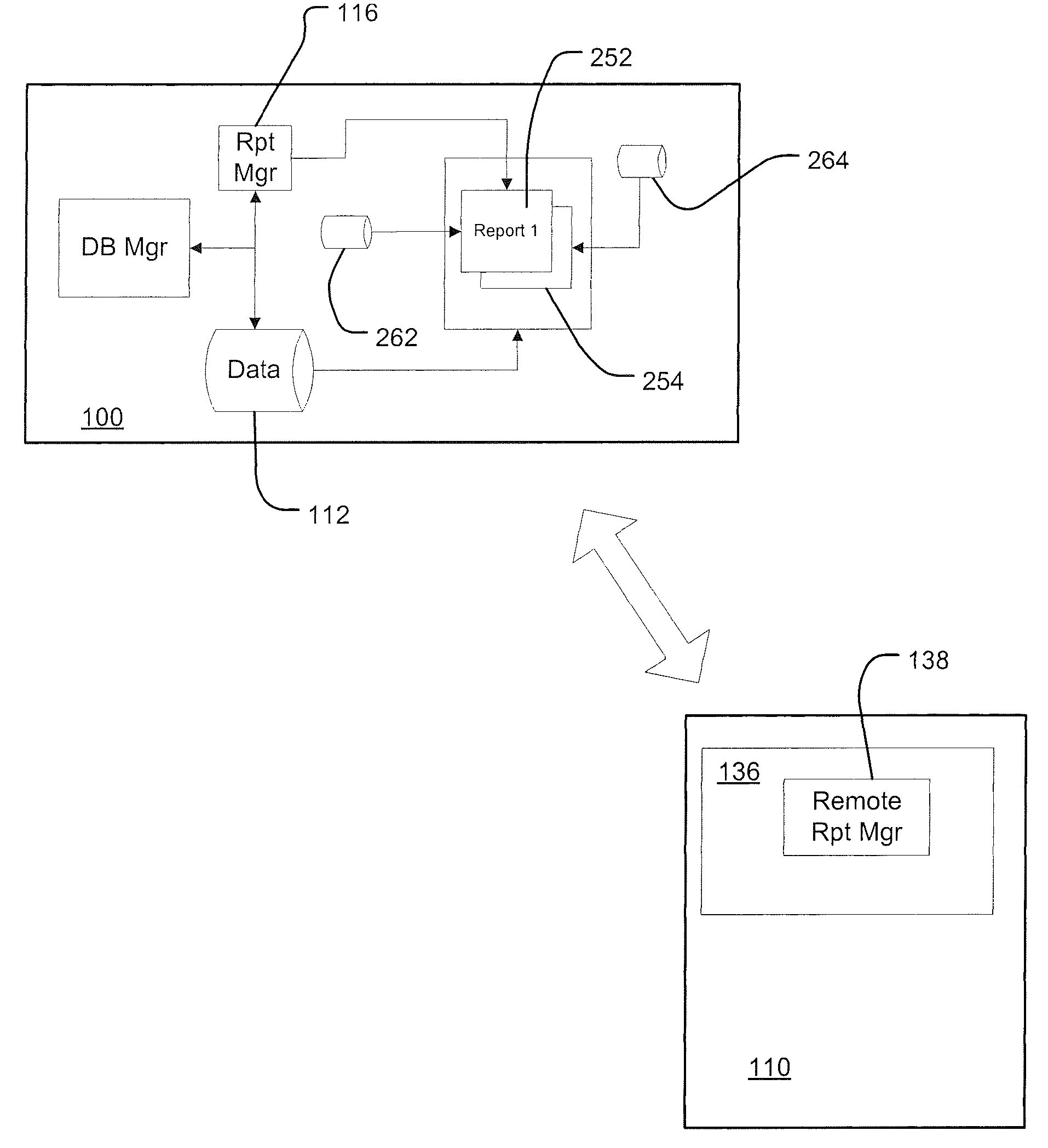
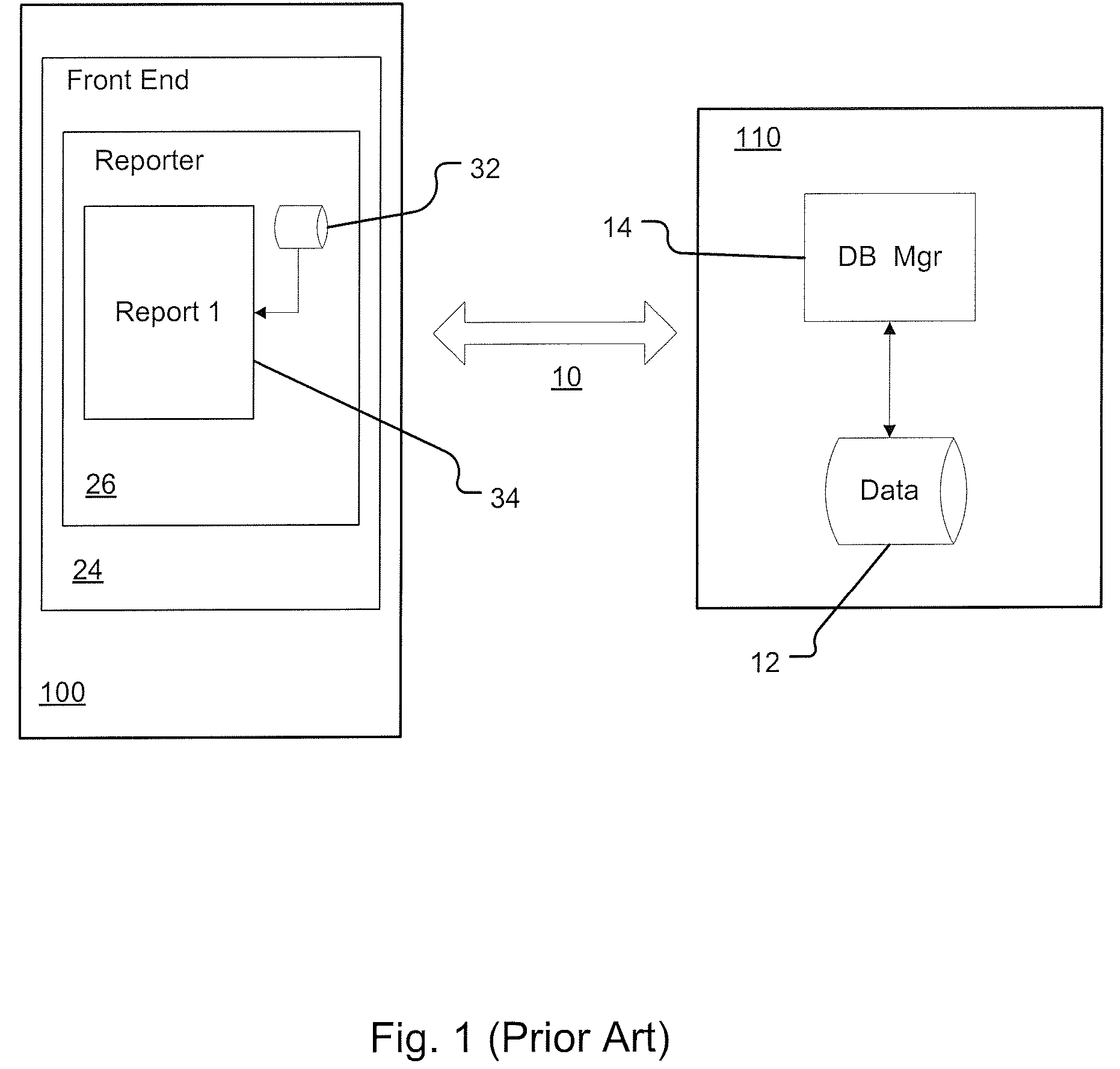
System for database reporting
A method of creating user-generated reports. The method begins with the step of receiving information related to consumer internet behavior. That information is then assembled into a database having facts and dimensions, in which the database resides on a server, the server being connected to a communications network. The method then provides a report generation system, including a report generation module resident on the server. The module generates a report, beginning with accepting user criteria for generating a report from a front end system resident on a client computer. It then generates from the database a dataset corresponding to the first report and forwards the same to the client computer, and it displays the report generated from the first dataset. The module then reiterates the report generation steps to generate a second report, the first report remaining resident on the client computer.
Owner:GULA CONSULTING LLC
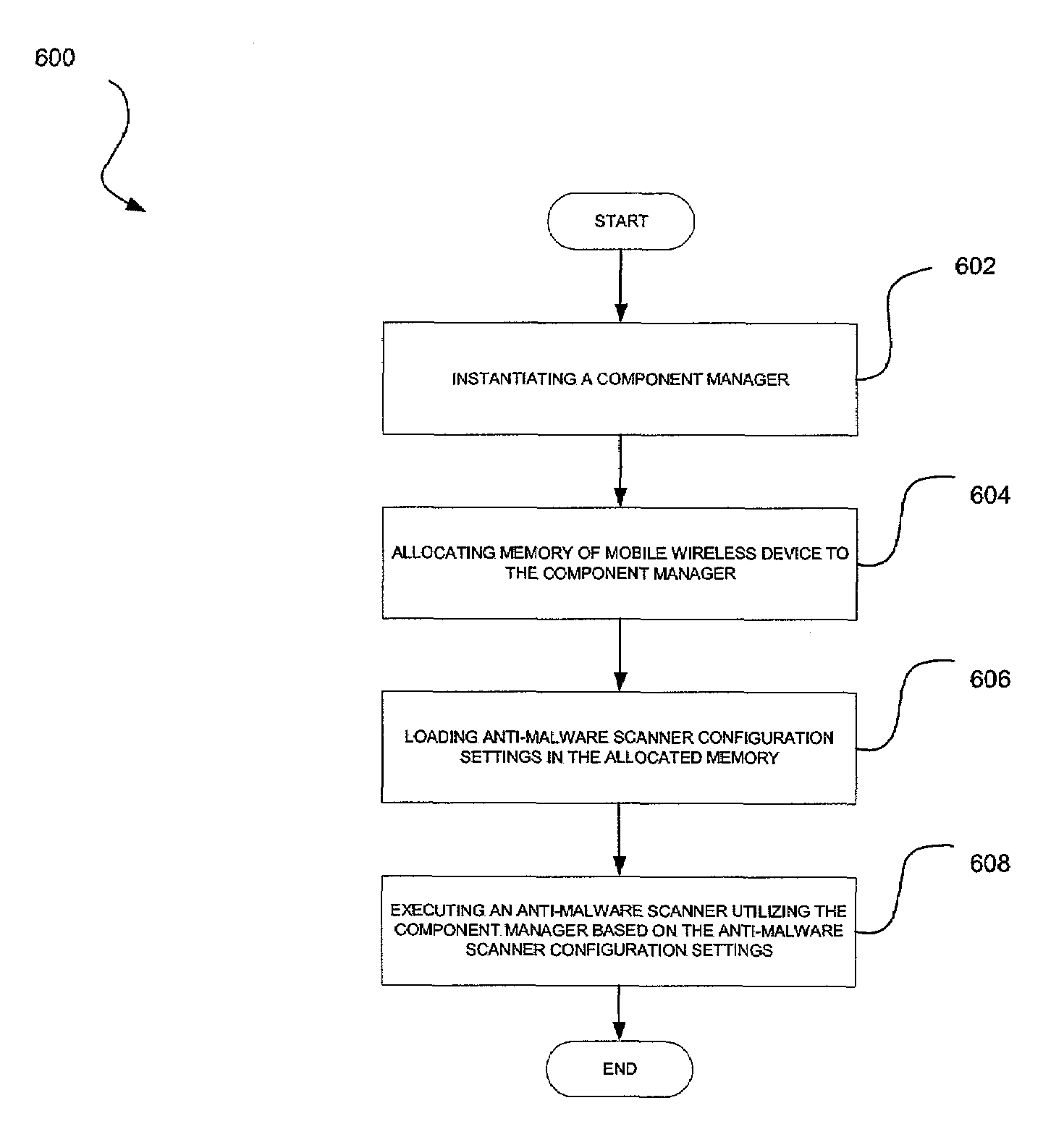
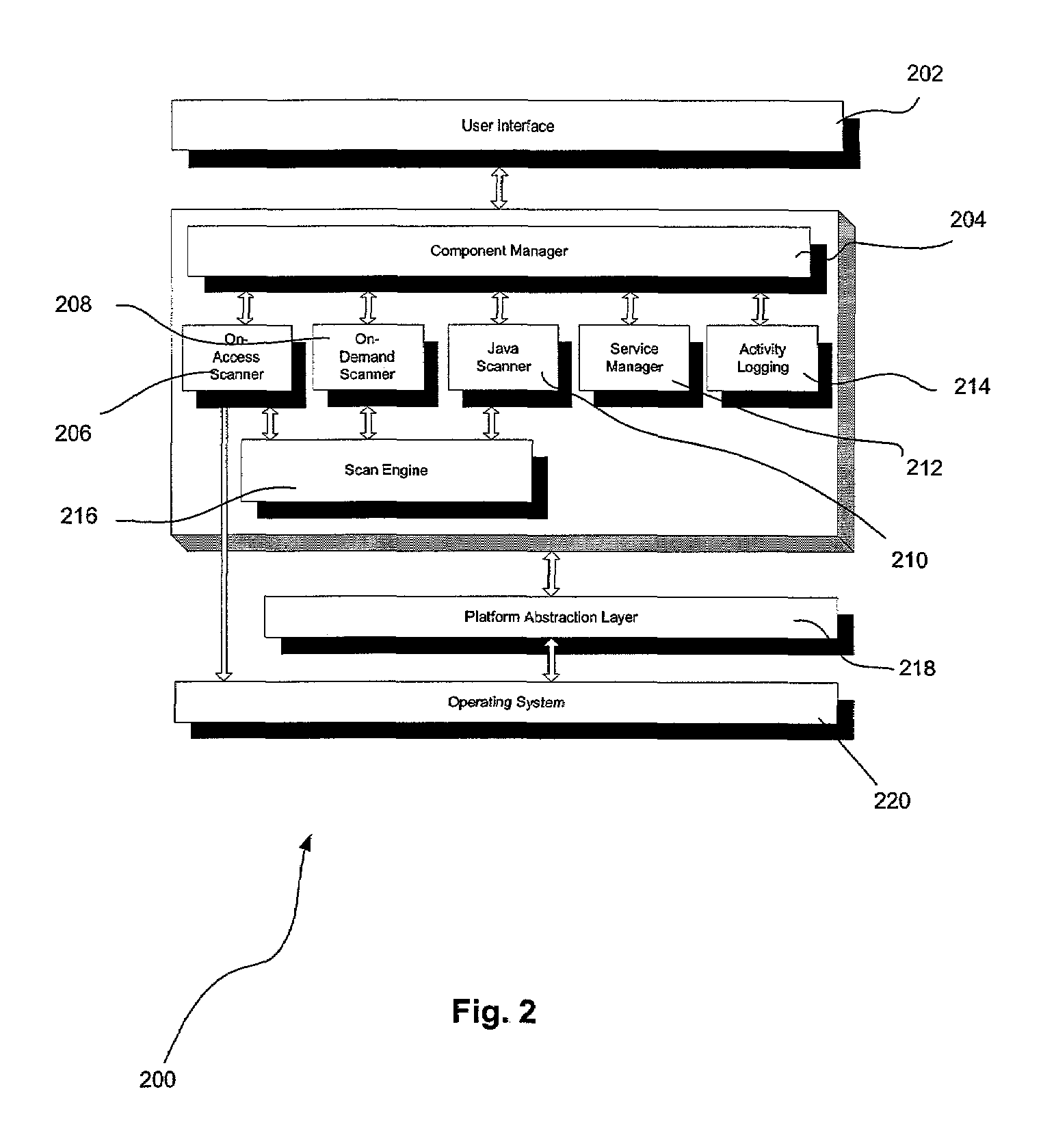
Wireless malware scanning back-end system and method
A system, method and computer program product are provided for scanning a plurality of mobile wireless devices for malware. A request is received to update an anti-malware scanner installed on a mobile wireless device over a wireless network. Further, an update tailored for the mobile wireless device is prepared using a back-end infrastructure. Such tailored update is then transmitted from the back-end infrastructure to the mobile wireless device over the wireless network.
Owner:MCAFEE LLC
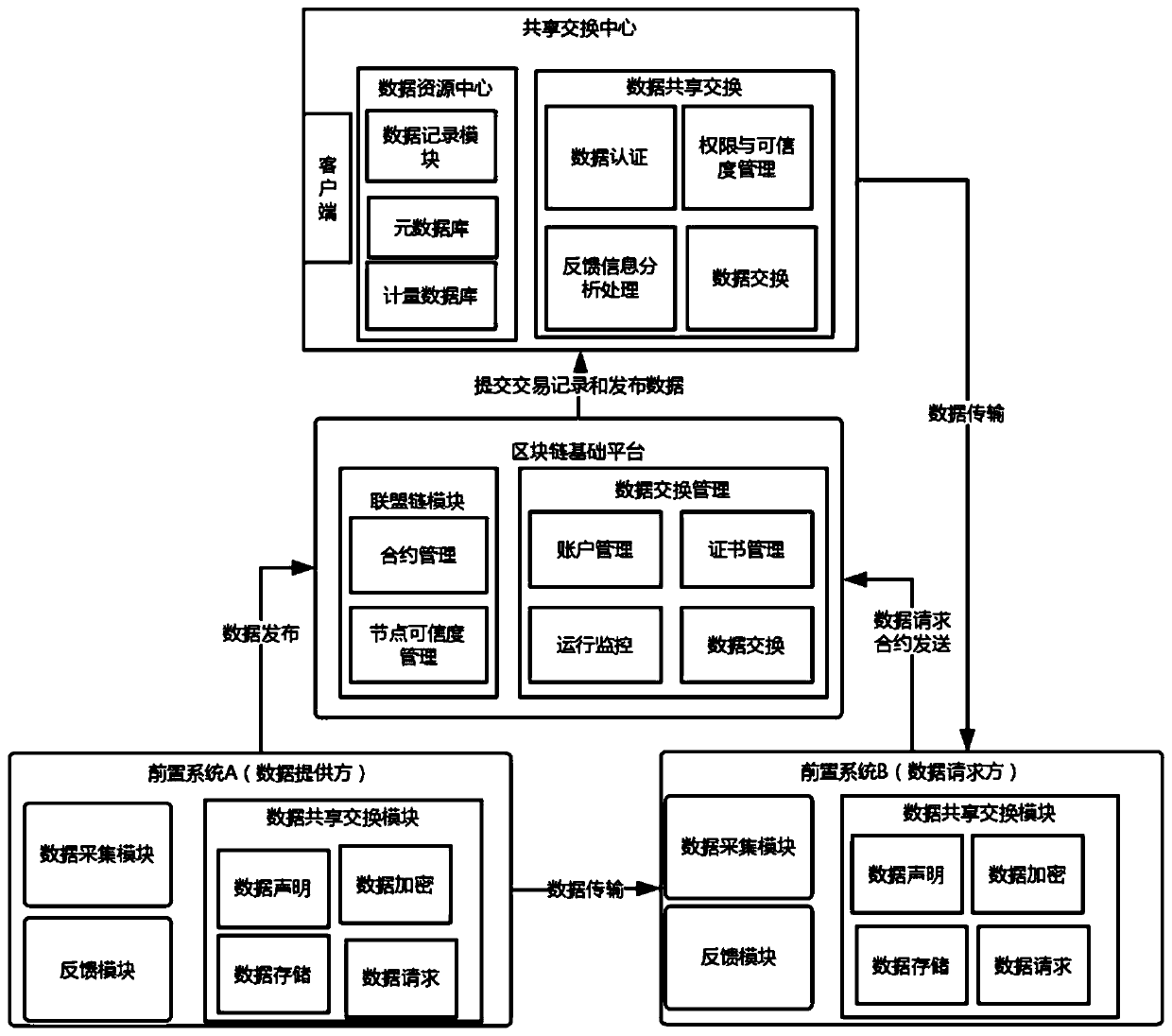
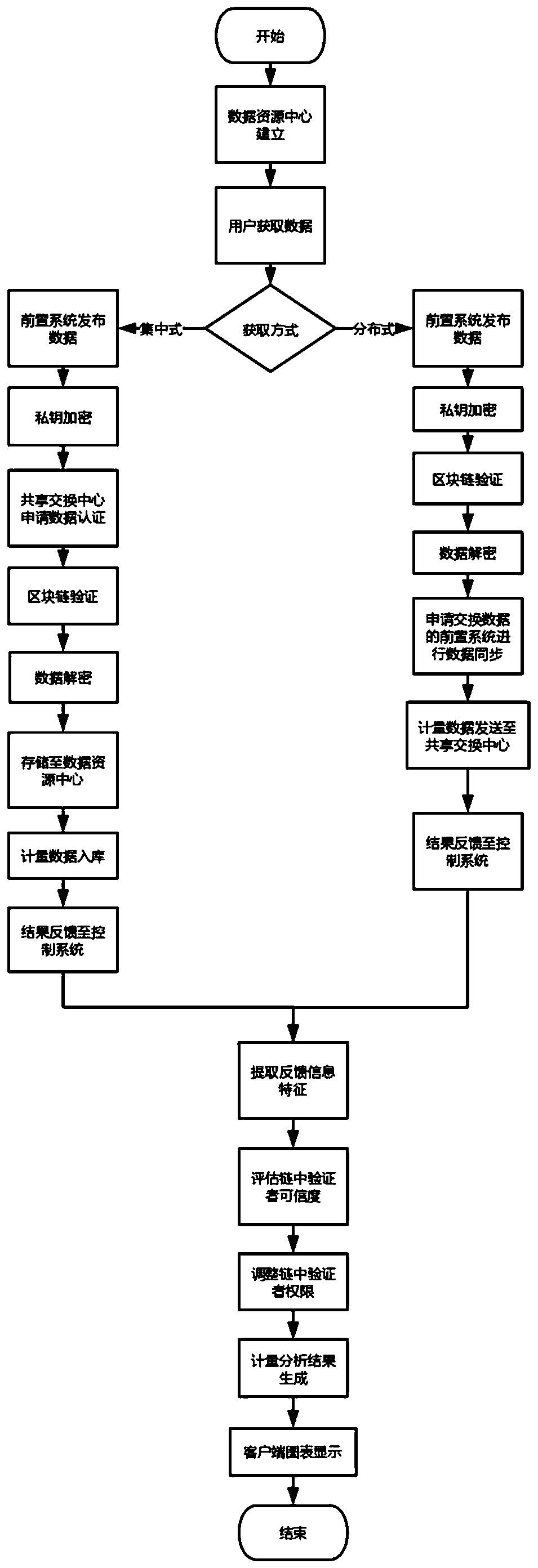
A data sharing exchange system and method based on a block chain
ActiveCN109729168AComply with shared exchange requirementsEasy to modifyUser identity/authority verificationDigital data protectionEnd systemControl system
The invention discloses a data sharing exchange system and method based on a block chain. The system comprises a data sharing exchange center, a front-end system and a block chain basic platform. Thedata sharing exchange center comprises a data sharing exchange control system, a data resource center and a client; The front-end system comprises a data acquisition system, a shared exchange module and a feedback module; The block chain basic platform comprises an alliance chain module and a data sharing exchange management module, the alliance chain module is responsible for intelligent contractand verifying credibility configuration of nodes, the intelligent contract generated in the data sharing exchange process is verified, and the data sharing exchange center communicates with the front-end systems in an alliance chain mode. According to the invention, the credit problem and the incentive problem of data sharing exchange in a multi-party participation environment are solved, the security and the reliability are ensured, the enthusiasm of a user for publishing and updating the sharing exchange data is promoted, and meanwhile, the guiding effect on user decision can be realized.
Owner:浙江成功软件开发有限公司
Examination of connection handshake to enhance classification of encrypted network traffic
ActiveUS7778194B1Easy to classifyError preventionFrequency-division multiplex detailsTraffic capacityEnd system
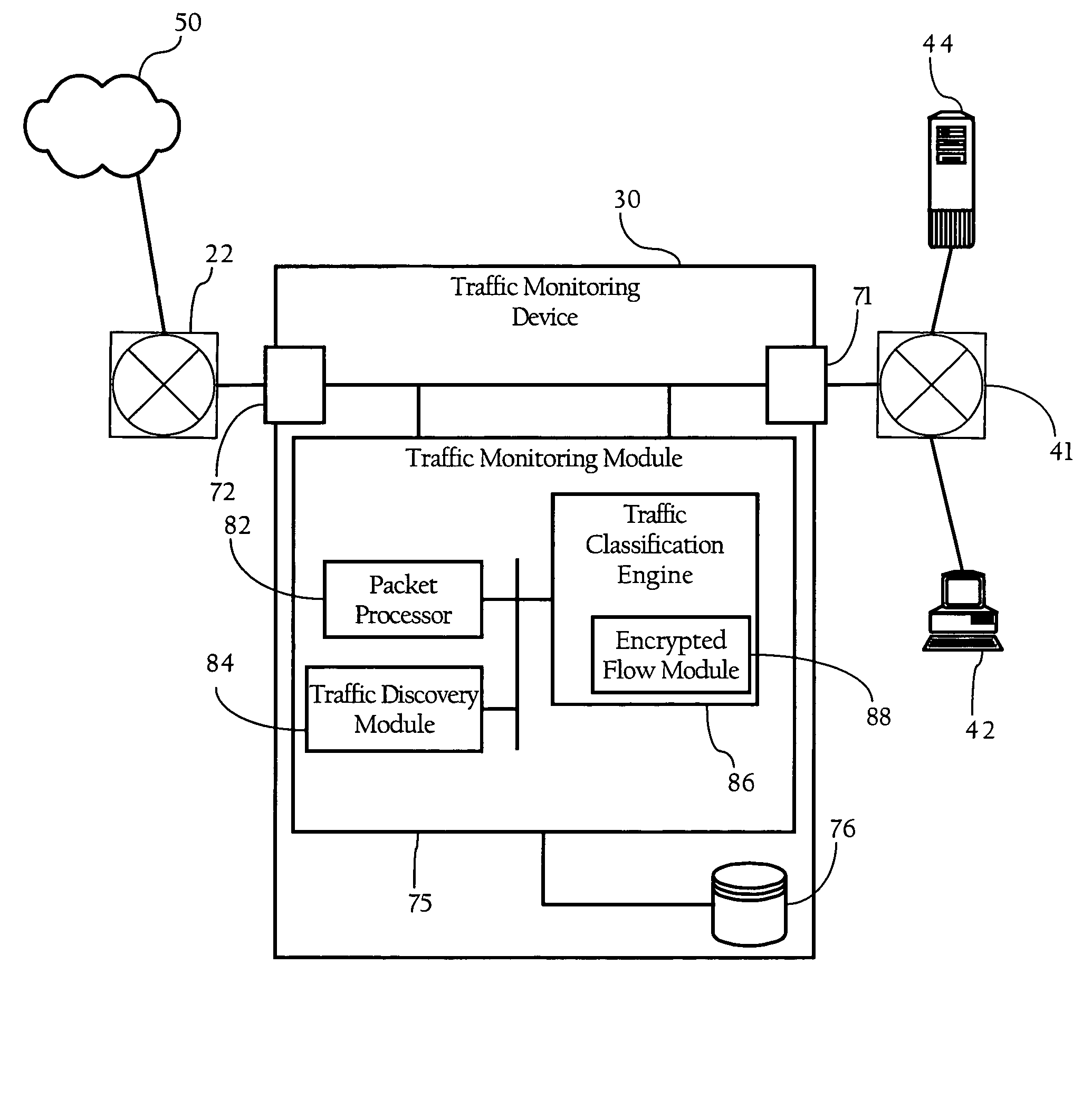
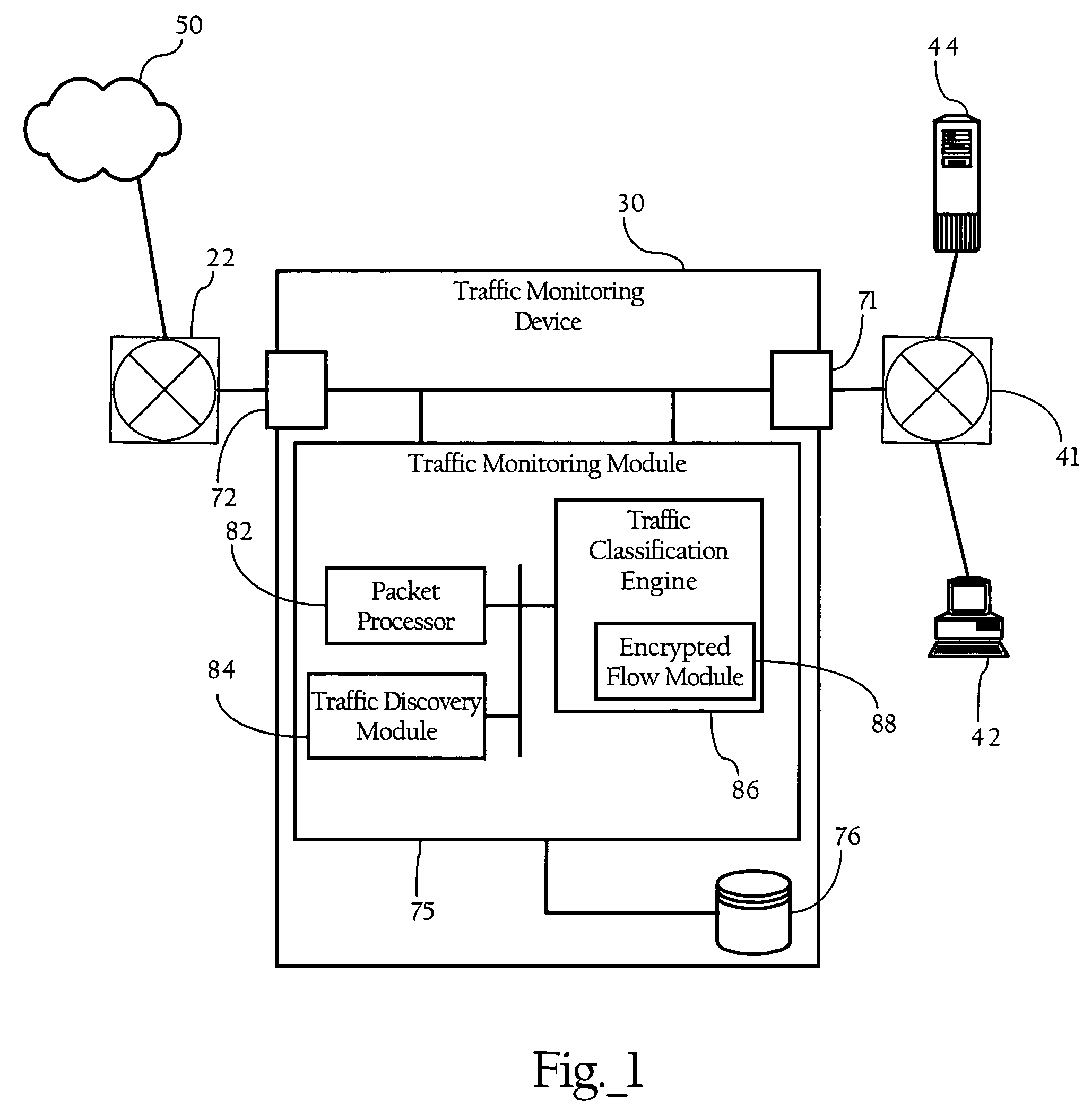
Methods, apparatuses and systems directed to the classification of encrypted network traffic. In one implementation, the present invention facilitates the classification of network traffic that has been encrypted according to a dynamically-created encryption mechanism involving a handshake between two end-systems, such as the SSL and TLS protocols. In one implementation, the present invention observes and analyzes attributes of the handshake between two nodes to enhance the classification of network traffic. In one embodiment, the enhanced classification mechanisms described herein operate seamlessly with other Layer 7 traffic classification mechanisms that operate on attributes of the packets themselves. Implementations of the present invention can be incorporated into a variety of network devices, such as traffic monitoring devices, packet capture devices, firewalls, and bandwidth management devices.
Owner:CA TECH INC
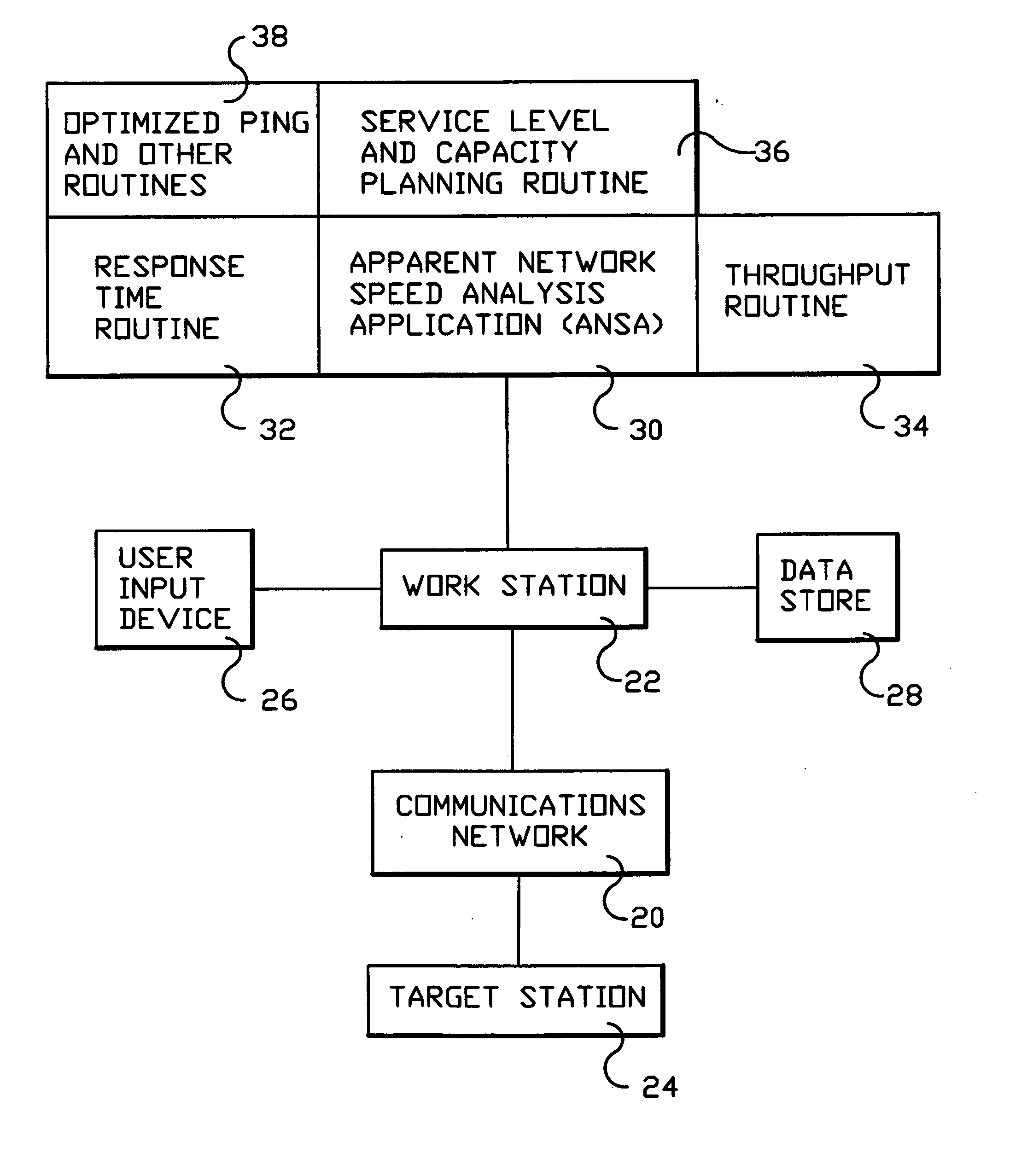
System and method for monitoring performance, analyzing capacity and utilization, and planning capacity for networks and intelligent, network connected processes
InactiveUS20050018611A1Error preventionFrequency-division multiplex detailsTotal responseTest sample
Analysis of networks and testing and analyzing intelligent, network connected devices. An instantaneous network utilization value is assigned for the worst surviving ping instance of between 90% and 99% (determined proportionately from the ratio of dropped test samples to surviving test samples), and then used to solve for average network message size and average utilization of the network. A plurality transactions of different types are transmitted across the network to intelligent end systems and the results mathematically evaluated to determine the portion of the total response time contributed by the network and by the end processors; the utilization of the end processor processing subsystems and of the end processor I / O subsystems; and the utilization of the end system as a whole; and of the network and end processors considered as a unitary entity. Steps include determining utilization of the network when test packets are dropped by the network; utilization of intelligent processor and other devices attached to the network when test transactions are dropped, and when not dropped; and response time for remote processes at both the network and processor level.
Owner:IBM CORP
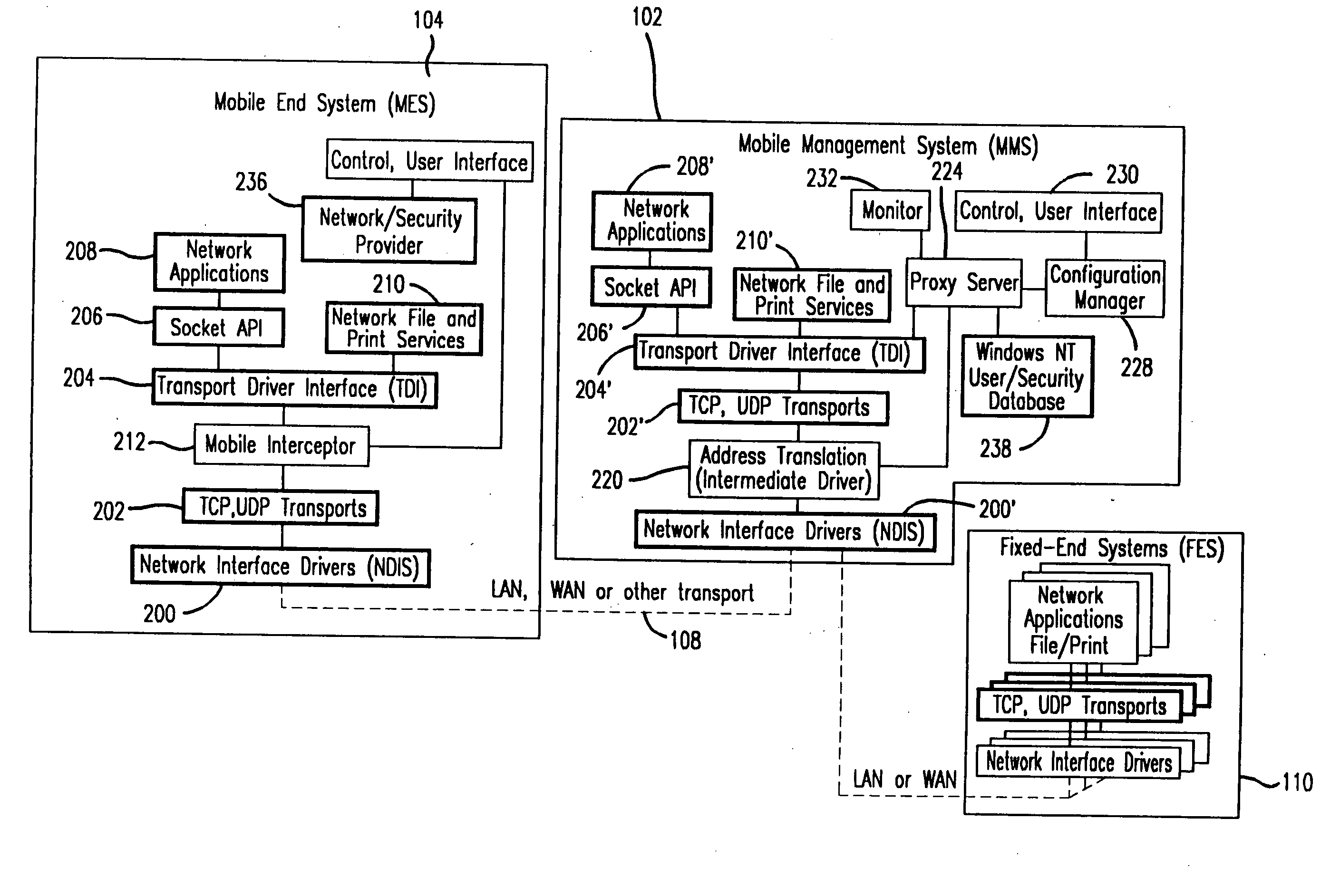
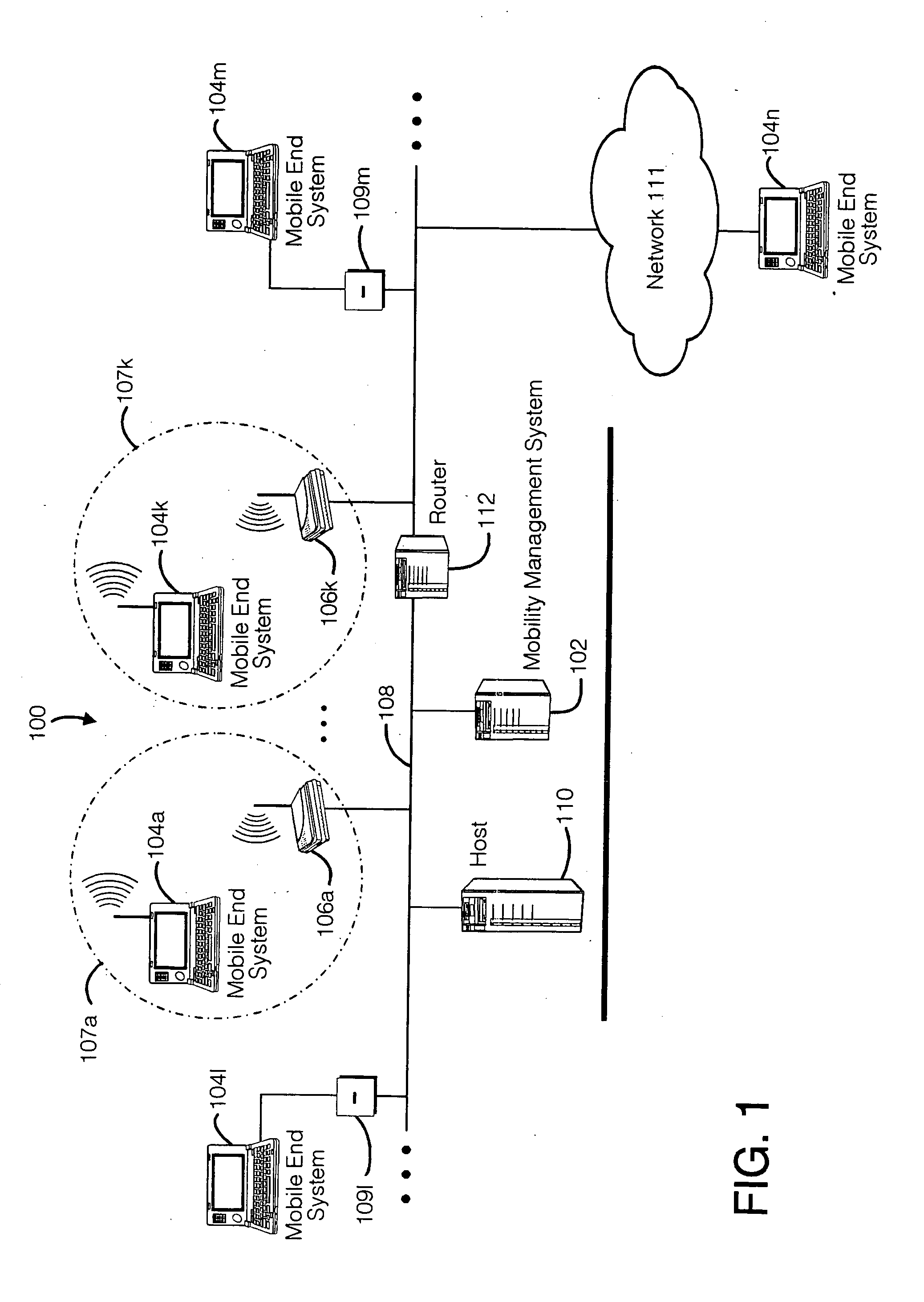
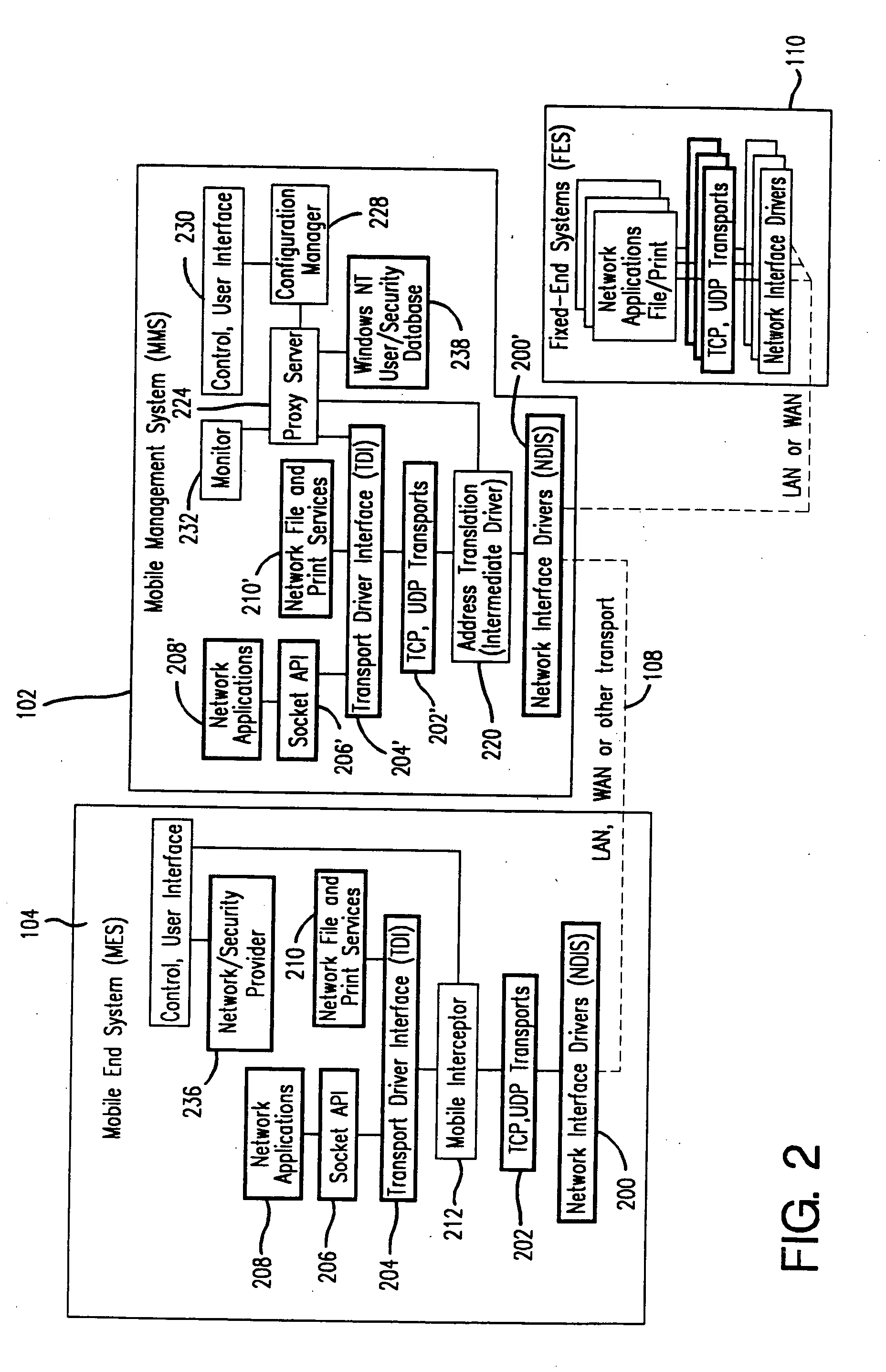
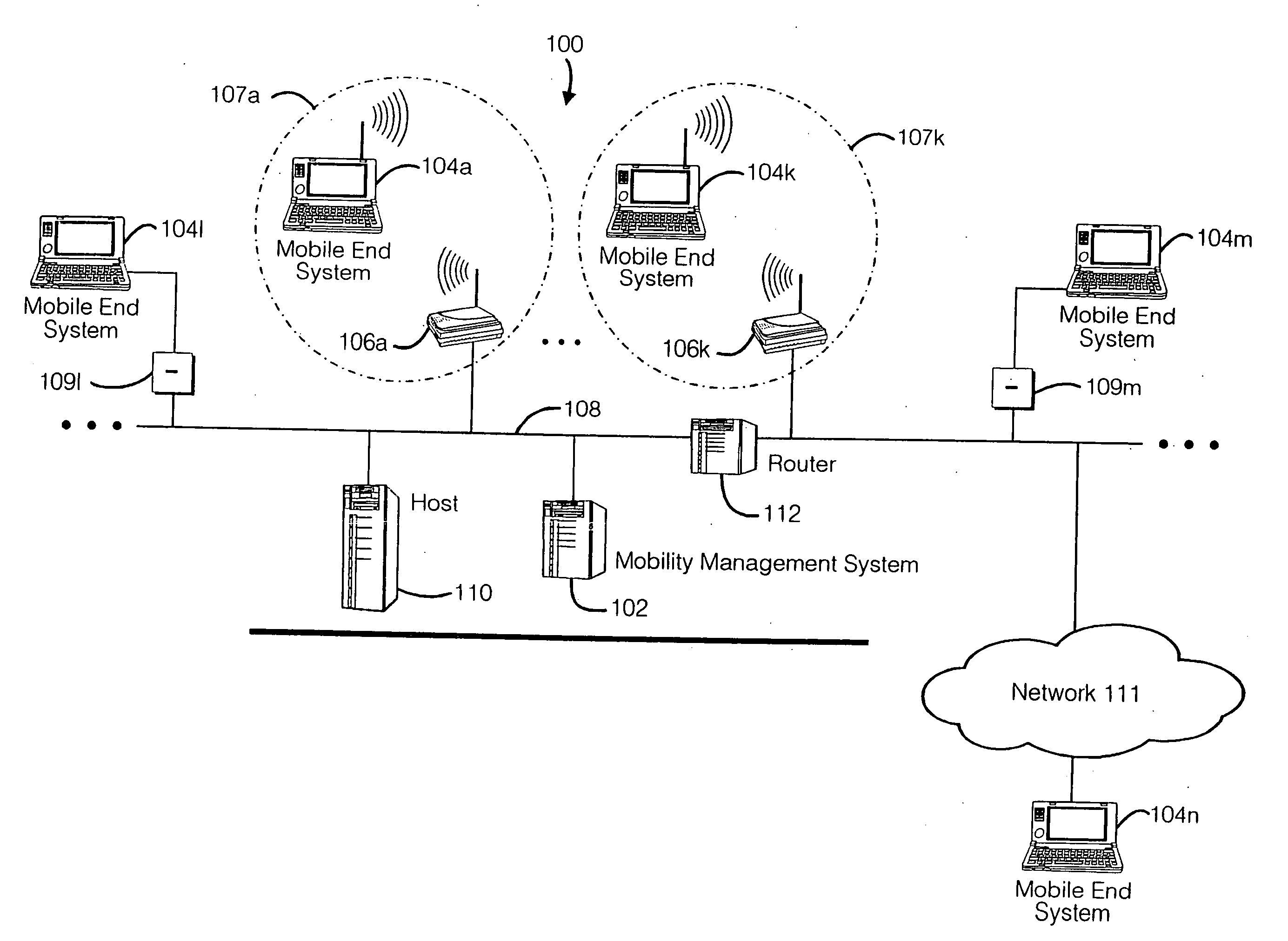
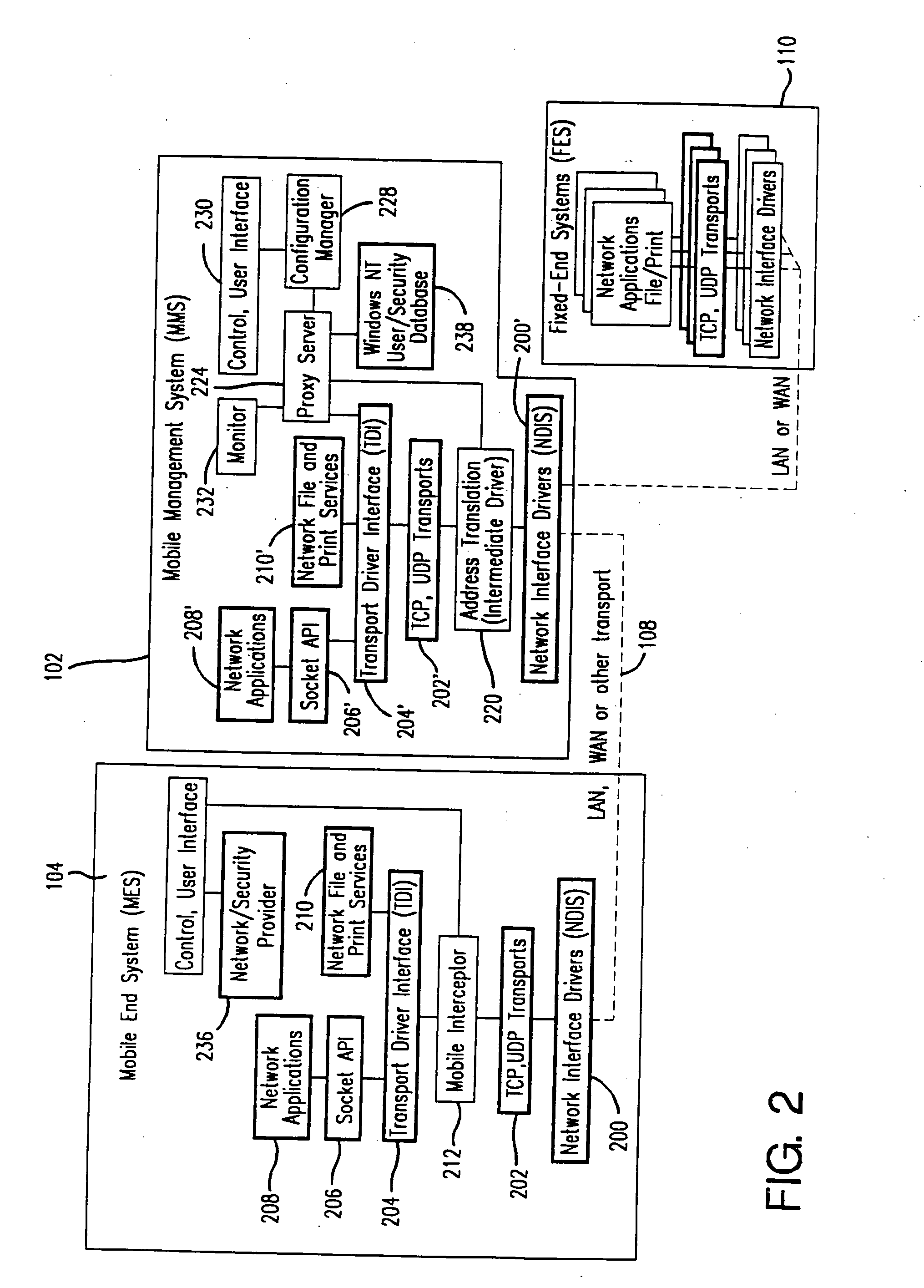
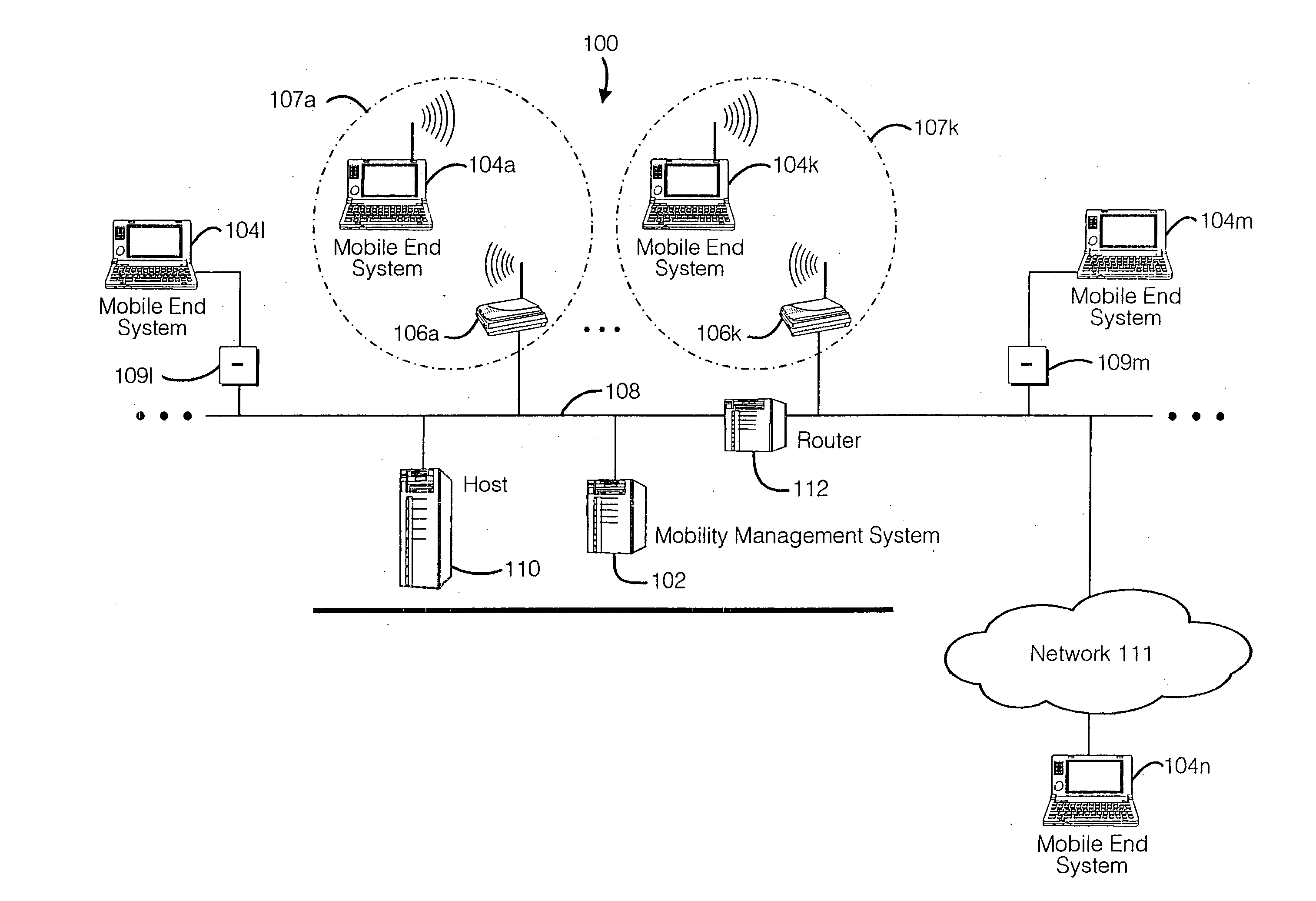
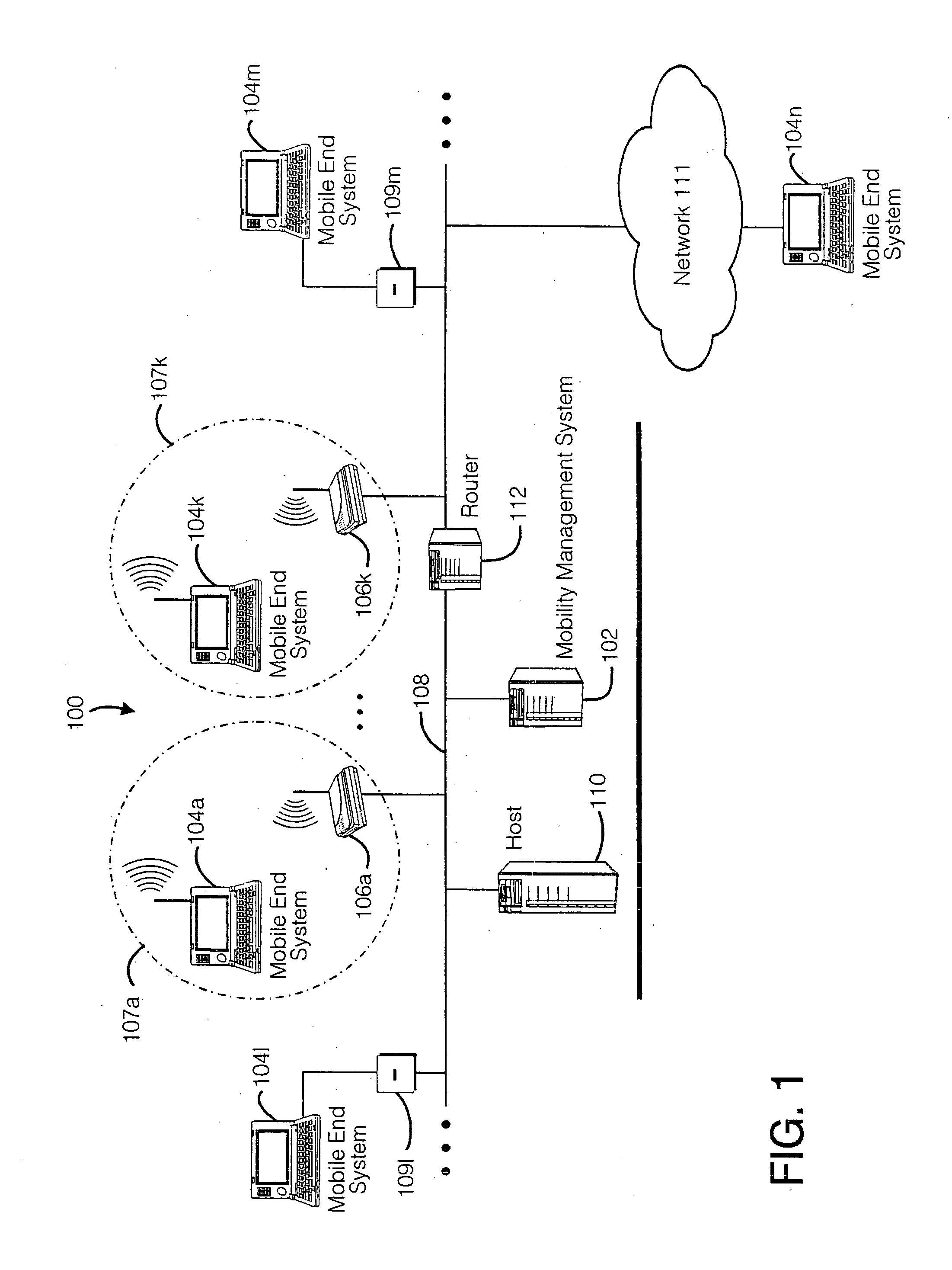
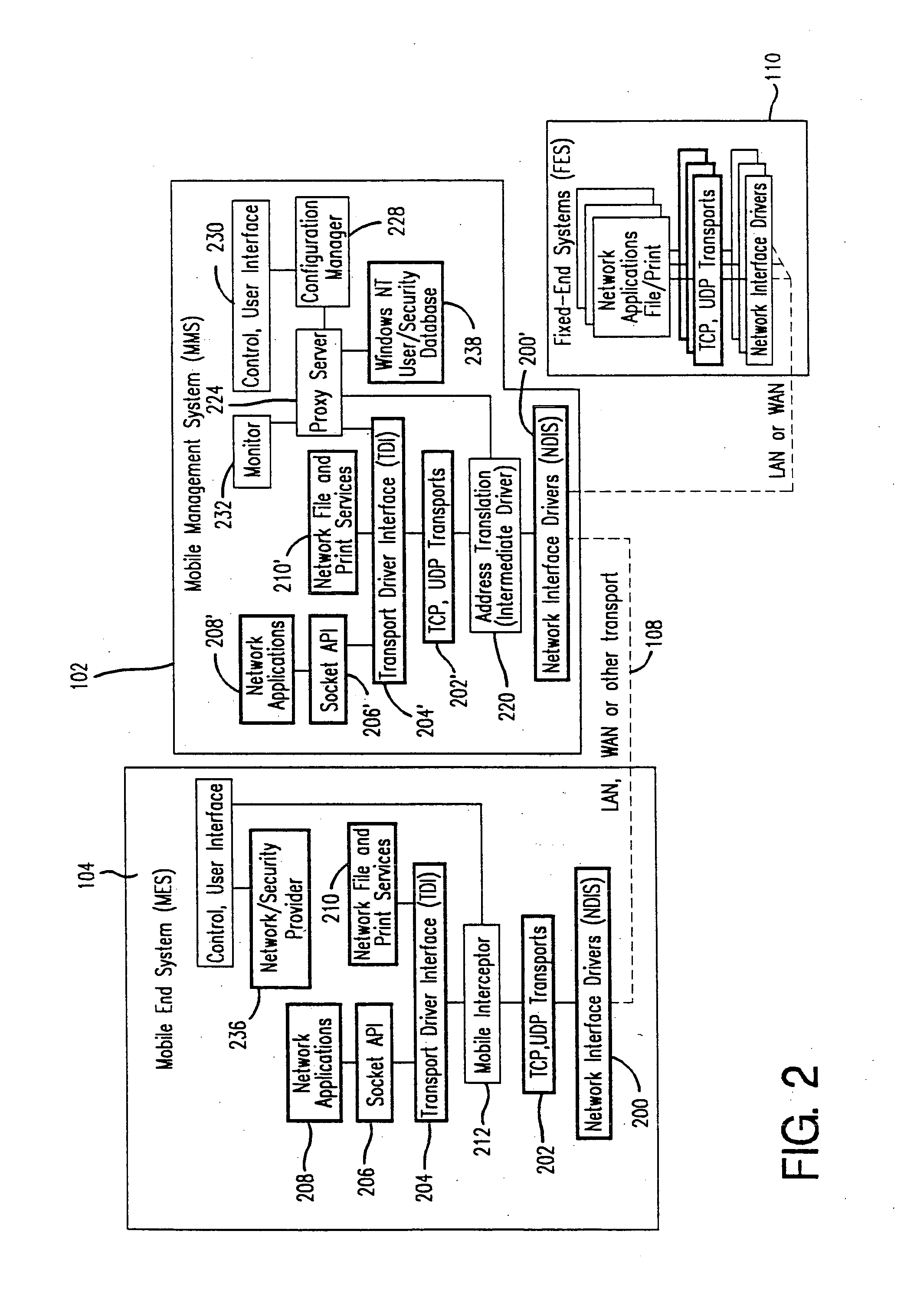
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS20060009213A1Take advantage ofEasy accessRepeater circuitsRadio/inductive link selection arrangementsMobile endNetwork address
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. An interface-based listener uses network point of attachment information supplied by a network interface to determine roaming conditions and to efficiently reestablish connection upon roaming. The Mobility Management Server can distribute lists to Mobile End Systems specifying how to contact it over disjoint networks.
Owner:MOBILE SONIC INC
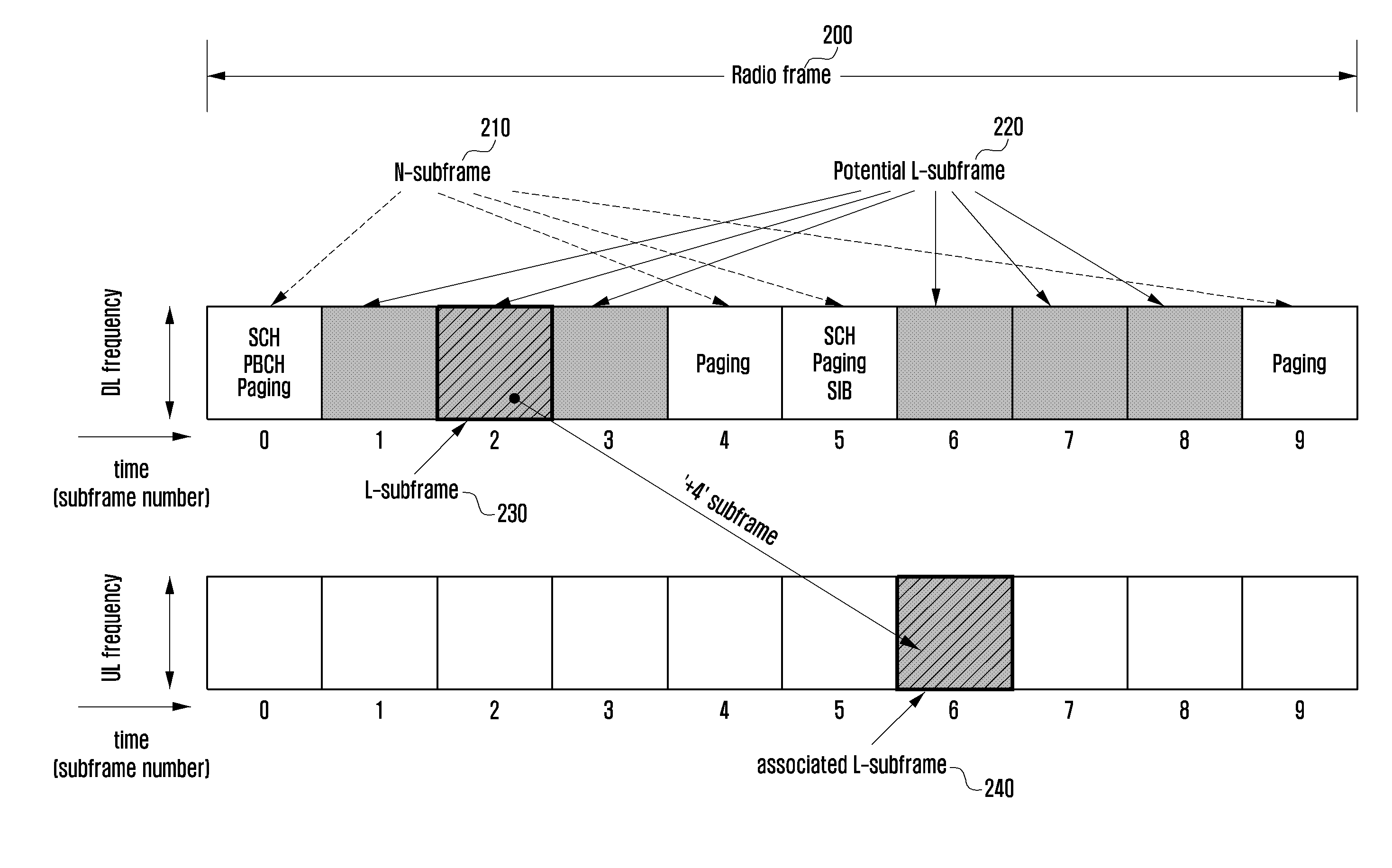
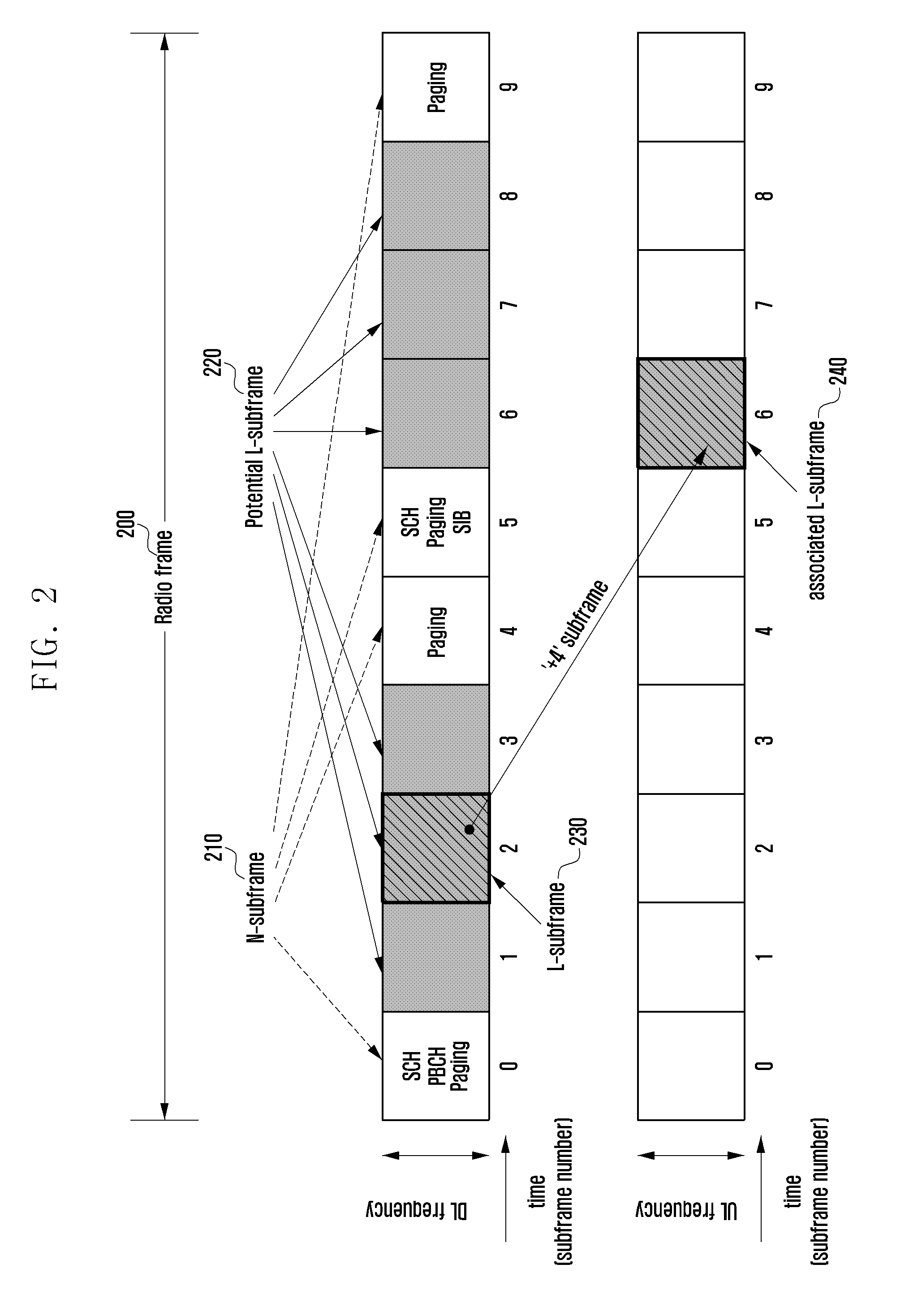
System access method and apparatus of a narrowband terminal in a wireless communication system supporting wideband and narrowband terminals
ActiveUS20130077582A1Synchronisation arrangementWireless commuication servicesCellular radioAccess method
A system access method of a narrowband terminal is provided for supporting both wideband and narrowband terminals in a cellular radio communication system. The method includes broadcasting a Shared CHannel (SCH) for a terminal to acquire system synchronization; transmitting a Low-end Master Information Block (L-MIB) including control information on an L-subframe configuration for supporting a second type terminal and a sub-band configuration of the L-subframe; transmitting a Low-end System Information Block (L-SIB) including information on downlink reception and uplink transmission of the second type terminal; and performing a random access procedure, when an attach request is received from one of the first type terminals and the second type terminals.
Owner:SAMSUNG ELECTRONICS CO LTD
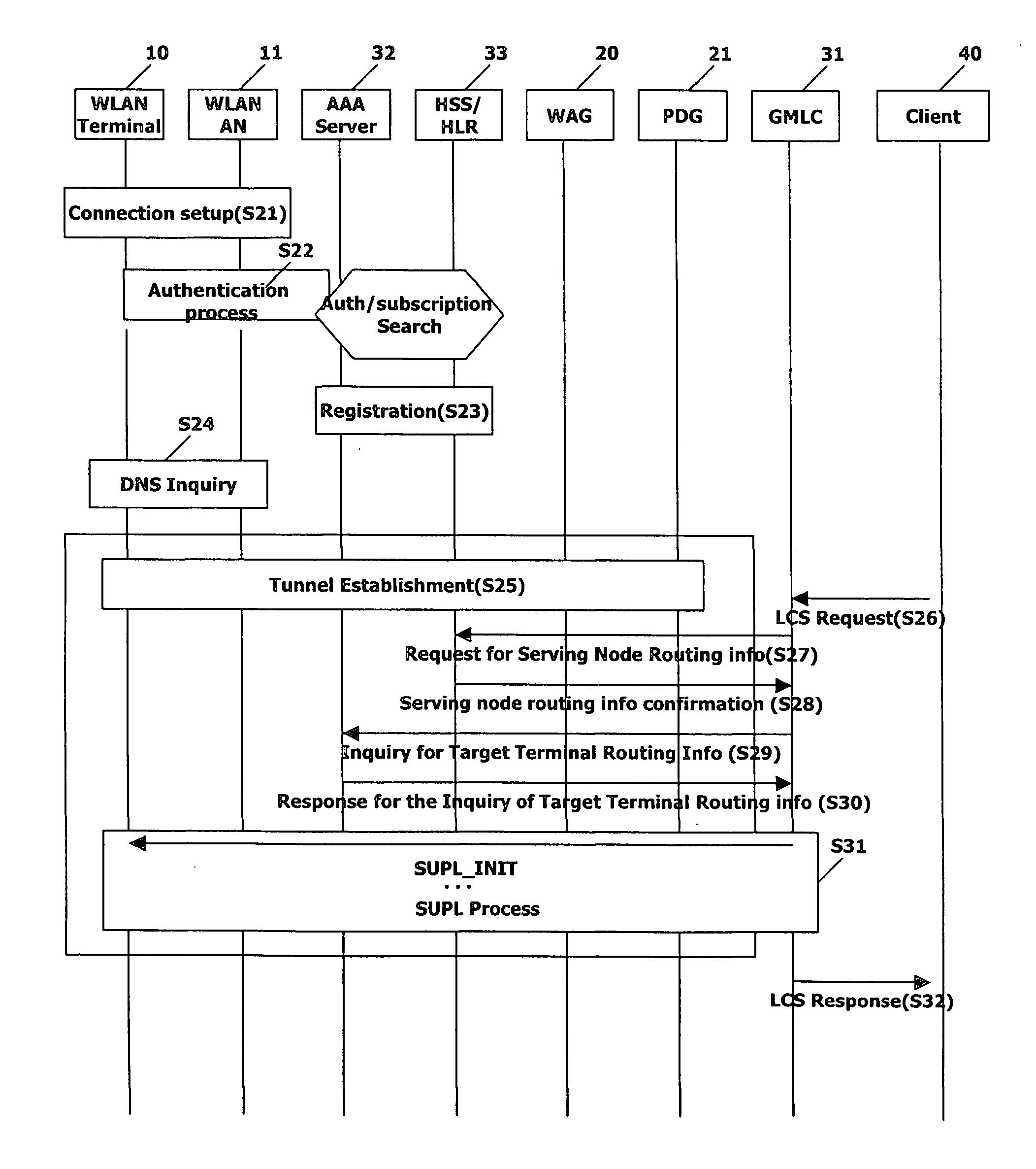
Terminal, system and method for providing location information service by interworking between WLAN and mobile communication network
InactiveUS20060245406A1Network topologiesData switching by path configurationTerminal systemMobile communication network
A WLAN terminal, system and method for providing a SUPL service, are discussed. According to an embodiment, the WLAN terminal includes a controller to establish an IP connection with a mobile communication network through interworking between the mobile communication network and a WLAN, and selectively perform a SUPL procedure with a location server of the mobile communication network through the IP connection in response to a request for location information of the WLAN terminal from the location server.
Owner:LG ELECTRONICS INC
Mobile networking system and method
ActiveUS20060123079A1Take advantage ofEasy accessMultiple digital computer combinationsWireless network protocolsMobile endNetwork address
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. An interface-based listener uses network point of attachment information supplied by a network interface to determine roaming conditions and to efficiently reestablish connection upon roaming. The Mobility Management Server can distribute lists to Mobile End Systems specifying how to contact it over disjoint networks. Architectures are provided for bridging between IPv4 and IPv6 Internet Protocols.
Owner:MOBILE SONIC INC
Plant-level comprehensive supervision platform
InactiveCN105187771ARealize centralized managementQuality improvementClosed circuit television systemsTransmissionVideo monitoringIntelligent lighting
The invention relates to a monitoring system and specifically relates to a plant-level comprehensive supervision platform. The plant-level comprehensive supervision platform comprises a front-end system, a transmission network and a master station system, wherein the front-end system is integrated with subsystems of video monitoring, environmental monitoring, security guard, fire alarm, one-card-through, entrance and exit control, maloperation prevention, gps positioning, intelligent lighting, intelligent control and the like in a thermal power plant; the transmission network functions as a bridge for connecting the front end and the platform; the master station system comprises a local monitoring center, a cloud computing system, an application platform and a whole network operation and maintenance platform. The comprehensive supervision platform is a large online monitoring system integrated with hardware, software and network; the platform software is taken as the core to realize centralized management on all zones; besides, centralized monitoring and uniformed management on the front-end system can be realized at a regulation and control center; in short, the plant-level comprehensive supervision platform escorts the smart grid.
Owner:SHANDONG CHUANGDE SOFTWARE TECH
Systems and methods for coordinating wireless traffic for heterogeneous wireless devices
InactiveUS20060215556A1Good effectError preventionFrequency-division multiplex detailsTraffic capacityPHY
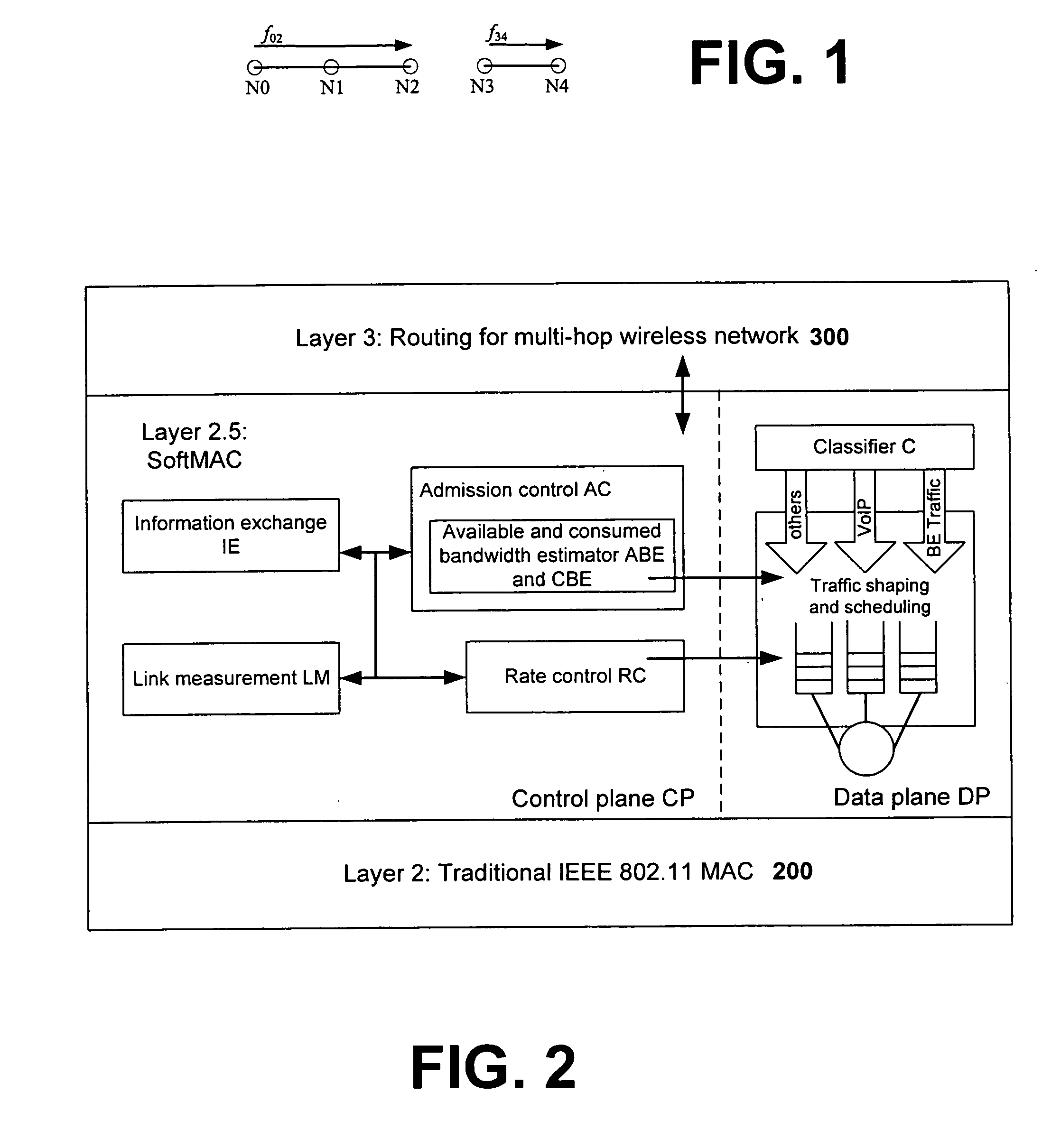
In view of the foregoing, the present invention provides a unified software framework or architecture for distributed coordination of wireless devices and radios, referred to as Layer 2.5 Software MAC (or ‘SoftMAC’), which resides between the standard 802.11 MAC layer (Layer 2) and IP layer (Layer 3) to regulate and control the amount of traffic (both real-time and “best effort”) delivered to 802.11 MAC DCF interfaces. The software based design can be ported to different OS platforms and systems and is capable of handling new hardware interfaces and MAC mechanisms (e.g., 802.11e) with only a software upgrade. The invention thus provides a natural way to make end systems support coordination of different radios of device(s), achieving better performance. Advantages of the 2.5 layer software MAC in accordance with the invention include: (a) there are no hardware constraints; (b) heterogeneous wireless / radio support is provided at the 2.5 layer; and (c) an evolutionary and extensible solution with the ability to support future wireless MAC / PHY chip combinations.
Owner:MICROSOFT TECH LICENSING LLC
Enterprise workflow screen based navigational process tool system and method
InactiveUS6990636B2Improve developmentLess expenseCathode-ray tube indicatorsOffice automationClient server systemsApplication software
Computer processes for carrying out almost any process may be defined as a series of steps using a plurality of standardized user-interface screens. These standardized interface screens may be linked together in predetermined orders to implement on a client computer activities for which the standardized screens are appropriate to accomplish a pre-defined process. Any number of computer processes may be developed and deployed using the standard interfaces. The computer process automatically takes a user from screen to screen, prompting the user to review or provide information or take appropriate action. Processes may be represented using metadata. Metadata may provide data to a screen rendering process running on a user's workstation with details on how to render one of a plurality of standard screens in a manner which is specific to a particular process. Metadata may be provided to define the steps of the process for enabling navigational capabilities. Metadata may stored in a database and communicated by a process server to a client computer, which acts as a user's workstation. This client-server system architecture allows maintenance of the computer processes in a central location and remote management of their use within a network. Furthermore, any number of application-specific computer processes may be made available and distributed to users without detailed programs for those processes having to be stored at each user workstation. Furthermore, basic interface functions with legacy databases and back-end systems may be provided to each user workstation in a network through the server system.
Owner:IBM CORP
Communication method for packet switching systems
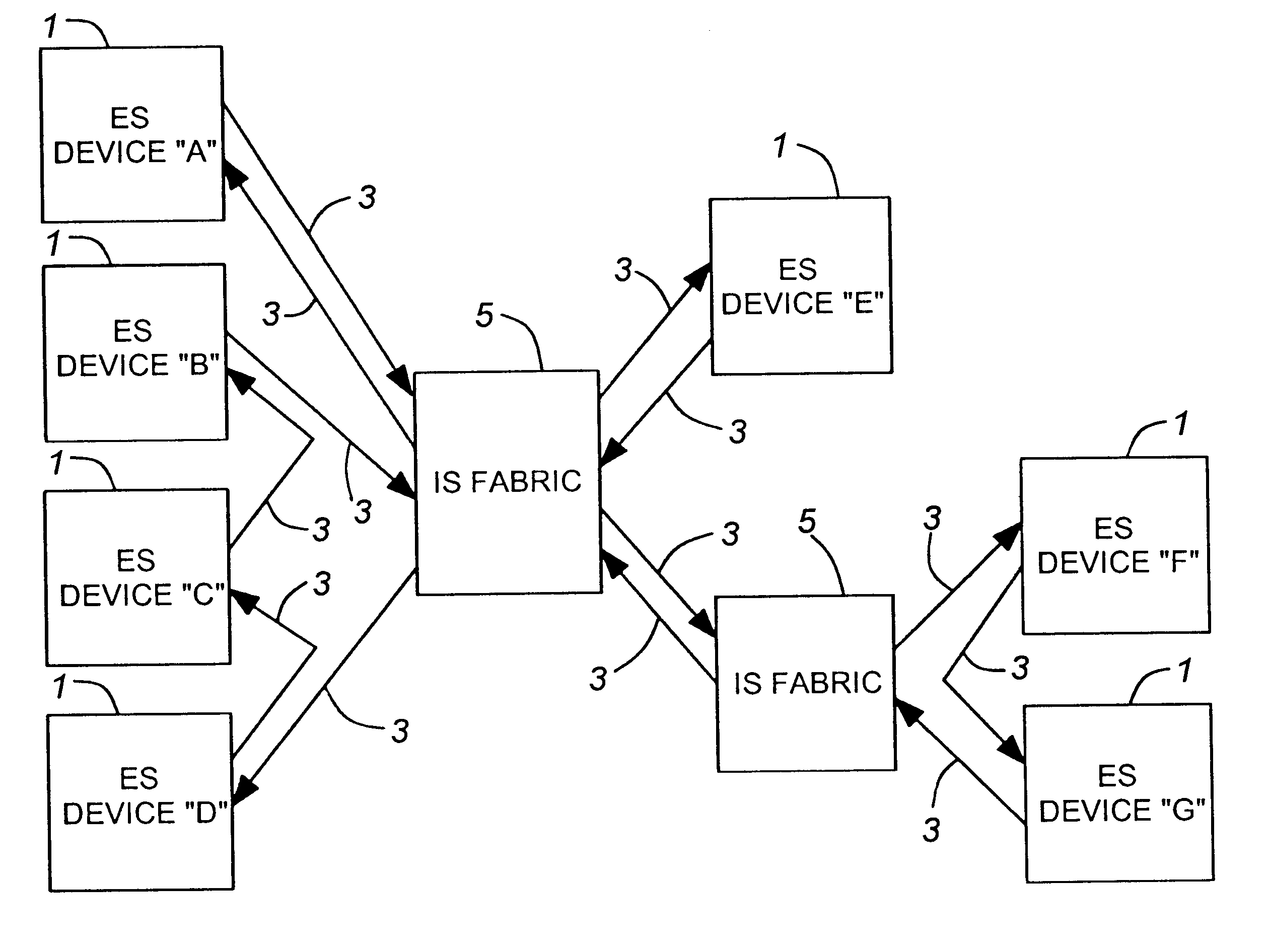
A method of communicating data frames between nodes in a network comprised of one or more end system nodes where each end system node has a unidirectional ingress port and a unidirectional egress port. The method comprises transmitting a data frame from an egress port of one end system node to the ingress port of another end system node, the receiving end system node then determining whether it is the final destination for the data frame. If the receiving end system node is the final destination of the data frame, the receiving end system node absorbs the message. If not, the receiving end system node buffers and then retransmits the data frame through its own egress port. The method provides scalability, low cost, distributed pipeline scheduling, maximum complexity of the network fabric, and maximum speed.
Owner:PMC-SIERRA
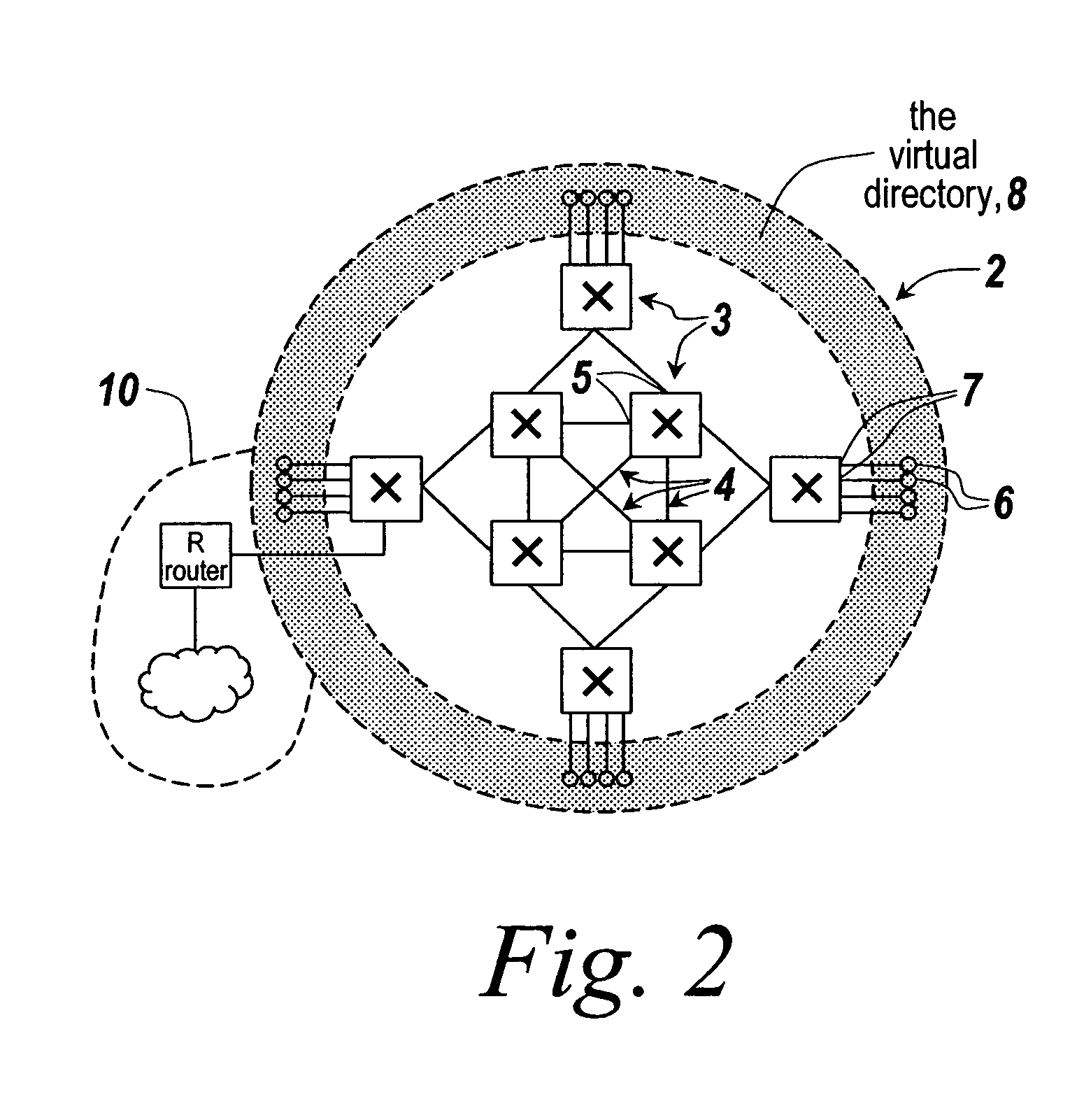
Distributed connection-oriented services for switched communication networks
InactiveUS7720076B2Special service provision for substationDigital computer detailsMAC addressTraffic capacity
Owner:EXTREME NETWORKS INC
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
ActiveUS20050223115A1Reduce network trafficMaximum performanceError preventionConnection managementMobile endNetwork address
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. The solution extends the enterprise network, letting network managers provide mobile users with easy access to the same applications as stationary users without sacrificing reliability or centralized management. The solution combines advantages of existing wire-line network standards with emerging mobile standards to create a solution that works with existing network applications. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. In one example, Mobility Management Server communicates with Mobile End Systems using Remote Procedure Call and Internet Mobility Protocols.
Owner:MOBILE SONIC INC
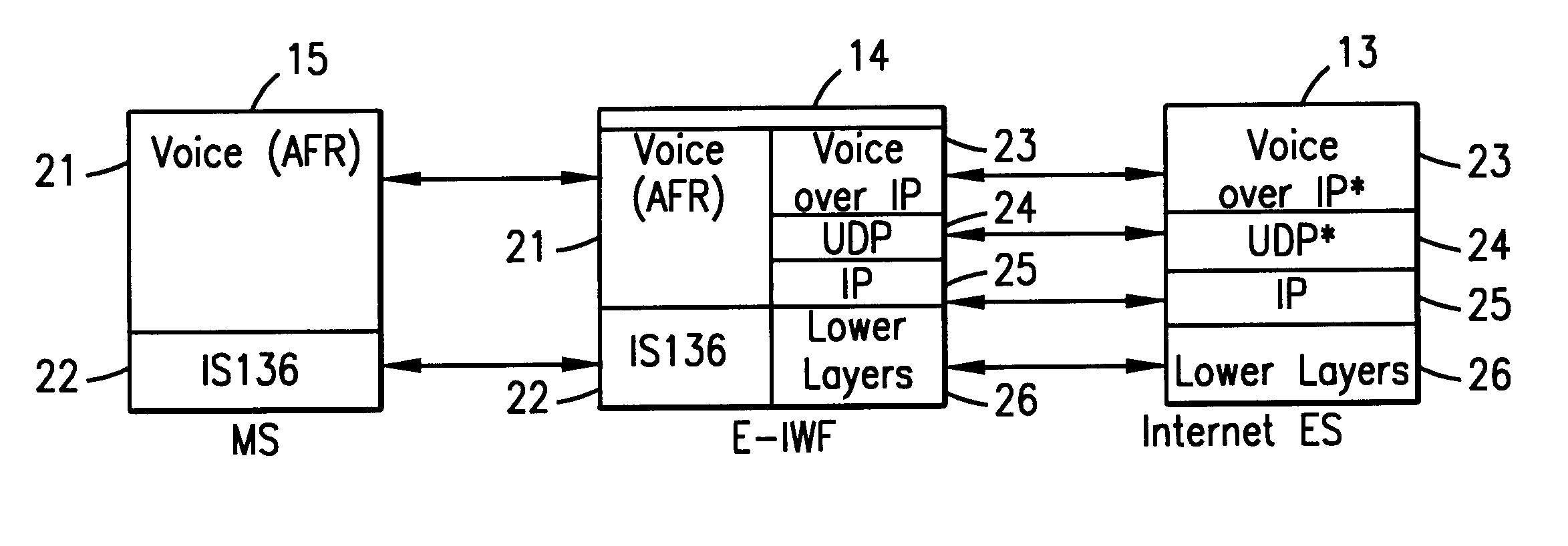
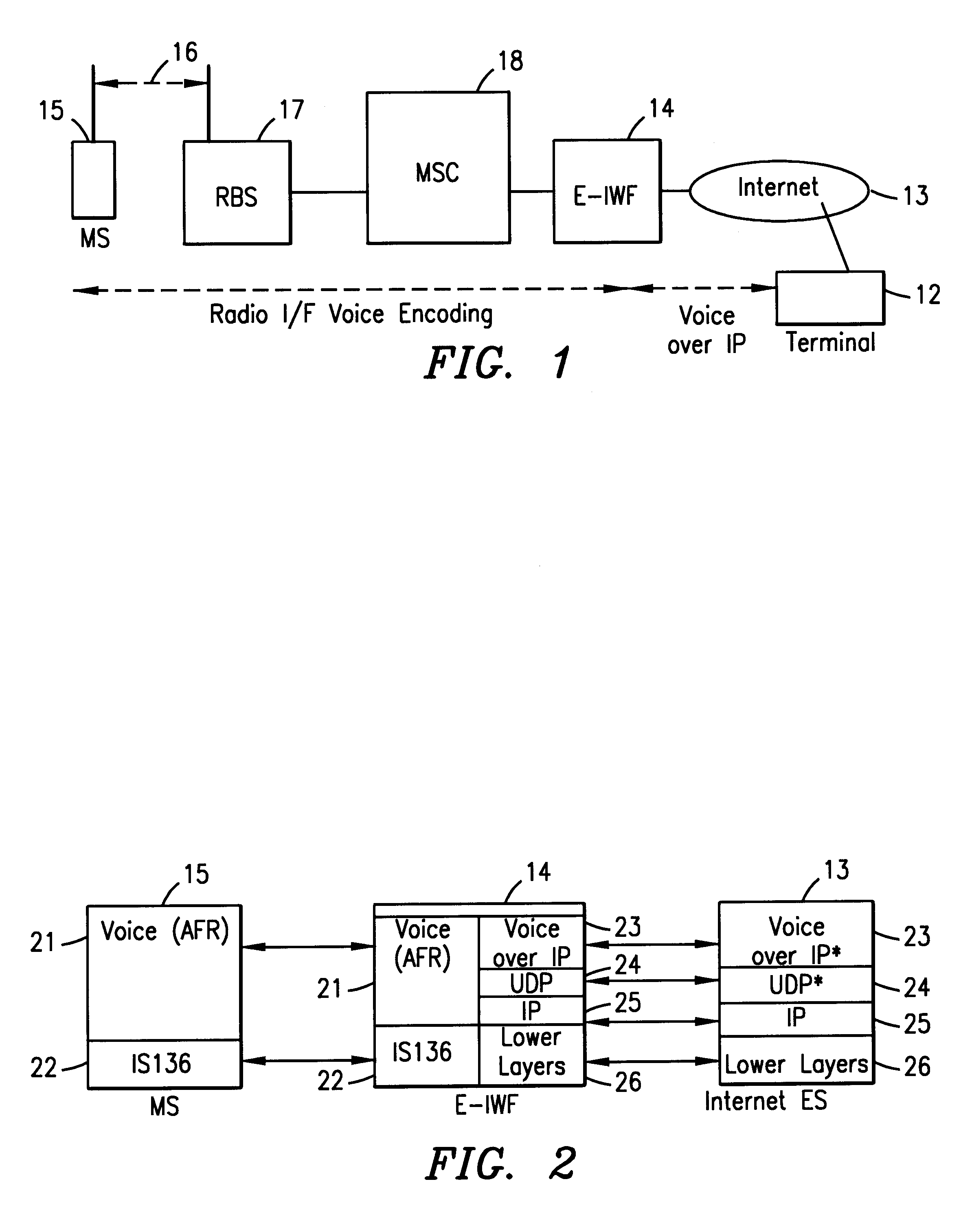
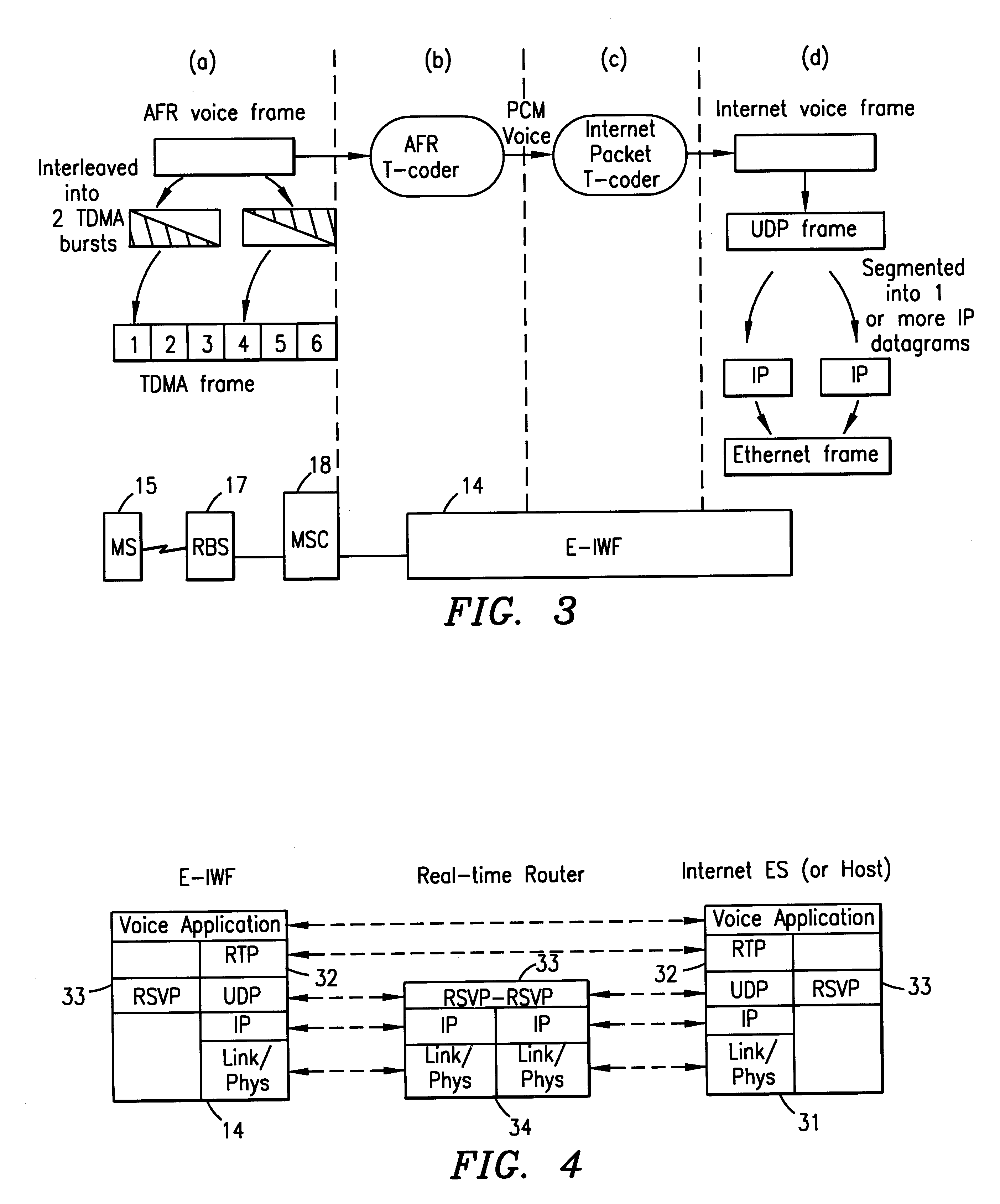
Enhanced interworking function for interfacing digital cellular voice and fax protocols and internet protocols
Owner:TELEFON AB LM ERICSSON (PUBL)
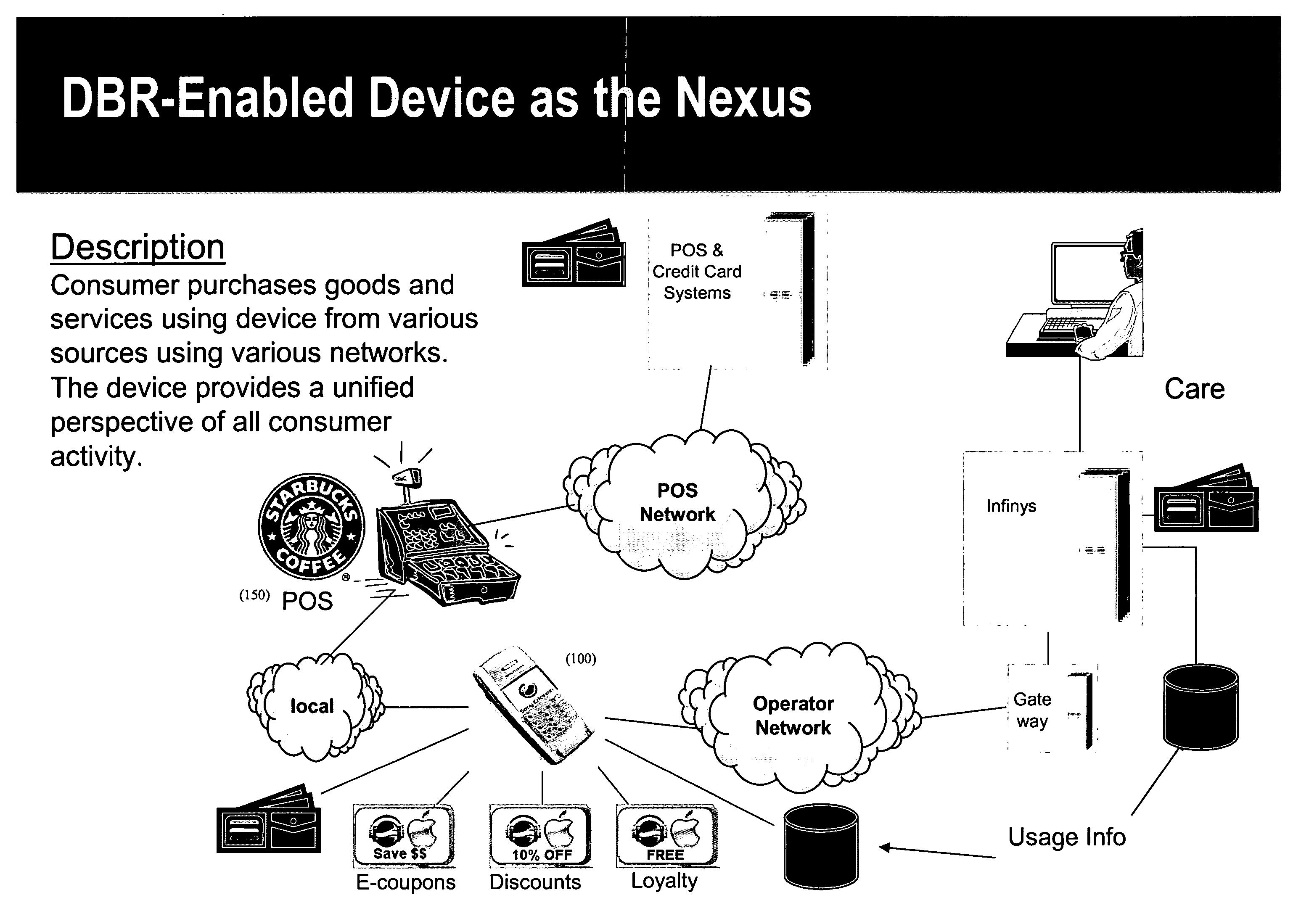
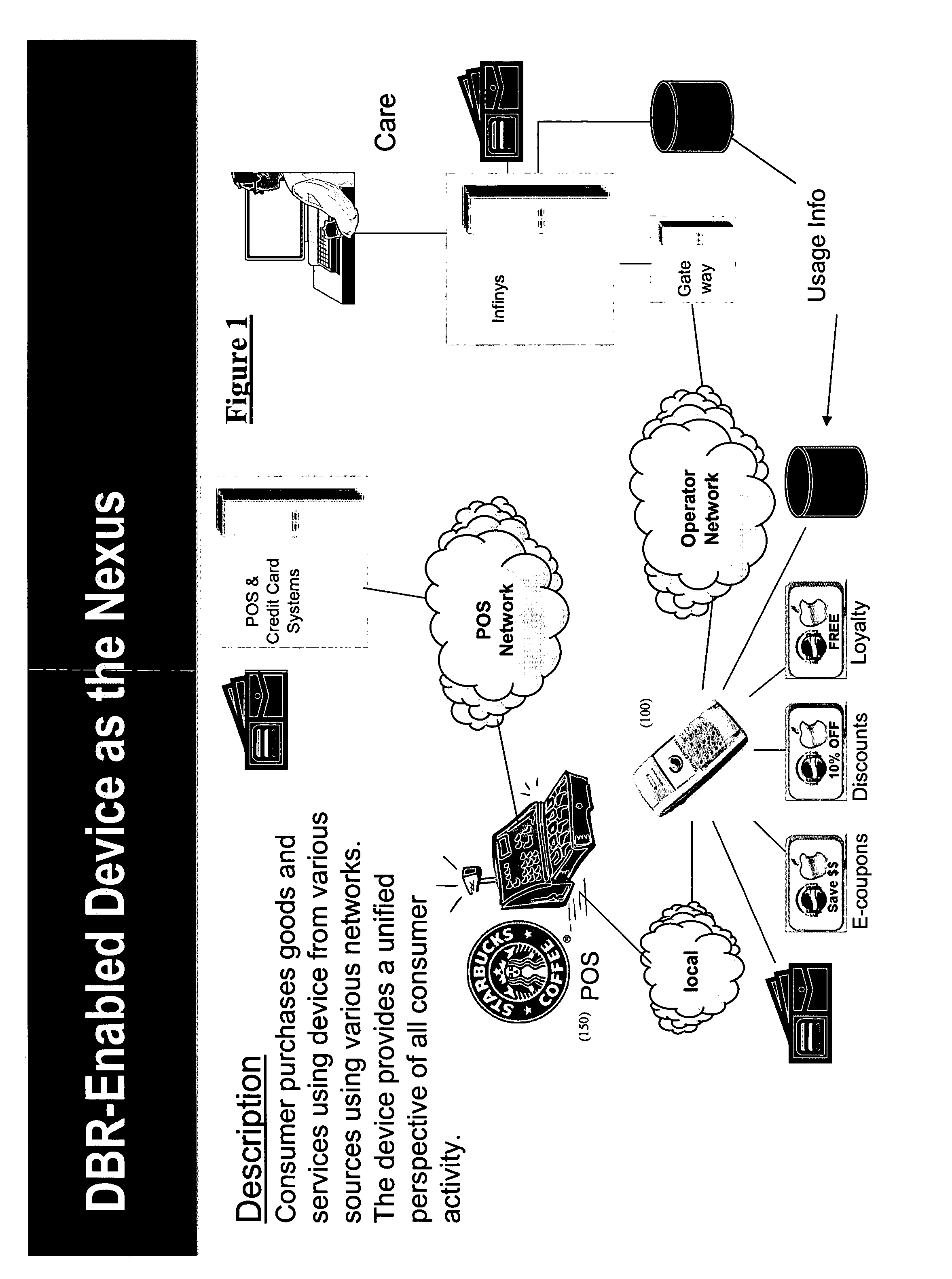
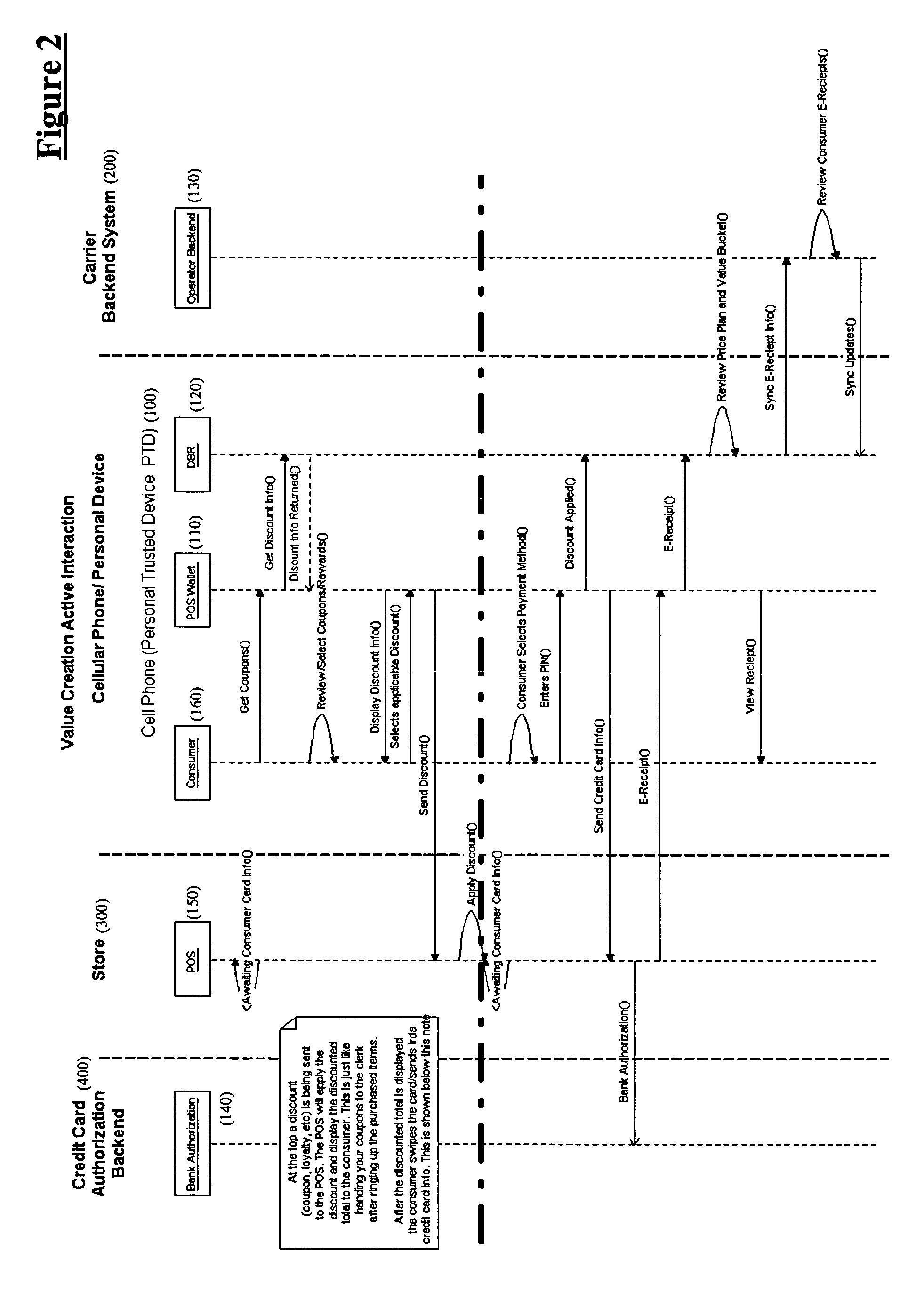
System and method for value creation
There is disclosed a system and method for creating value by facilitating third party participation in mobile commerce transactions, providing consumers with a unified perspective of commercial activity, and selectively implementing discounts. The system may include a computerized engine and a point of sale wallet, which may be embedded in a personal trusted device. The computerized engine may be programmed to selectively implement a discount associated with a particular transaction. The personal trusted device may comprise a wireless communications technology, which enables the device to communicate with a back-end system and / or other point of sale devices. The personal trusted device may serve as the nexus of consumer transactions by facilitating payment as well as receipt and storage of electronic receipts. The personal trusted device may also be configured to transmit electronic receipts via the communications technology.
Owner:NETCRACKER TECH SOLUTIONS
Dynamic DoS flooding protection
Detecting and protecting against denial of service flooding attacks that are initiated against an end system on a computer network. In accordance with one aspect of the invention, a filter is established at a network location. The filter prevents data packets received at a first network location and deemed responsible for the denial of service flooding condition from being forwarded to a subsequent network location. Data packets received at the first network location are then monitored to determine whether the flow of any data packets from a network source exhibit a legitimate behavior, such as where the flow of data packets exhibits a backoff behavior. The filter is then modified to permit data packets that exhibit legitimate behavior to pass through the filter.
Owner:VIRTUAL INSTR CORP
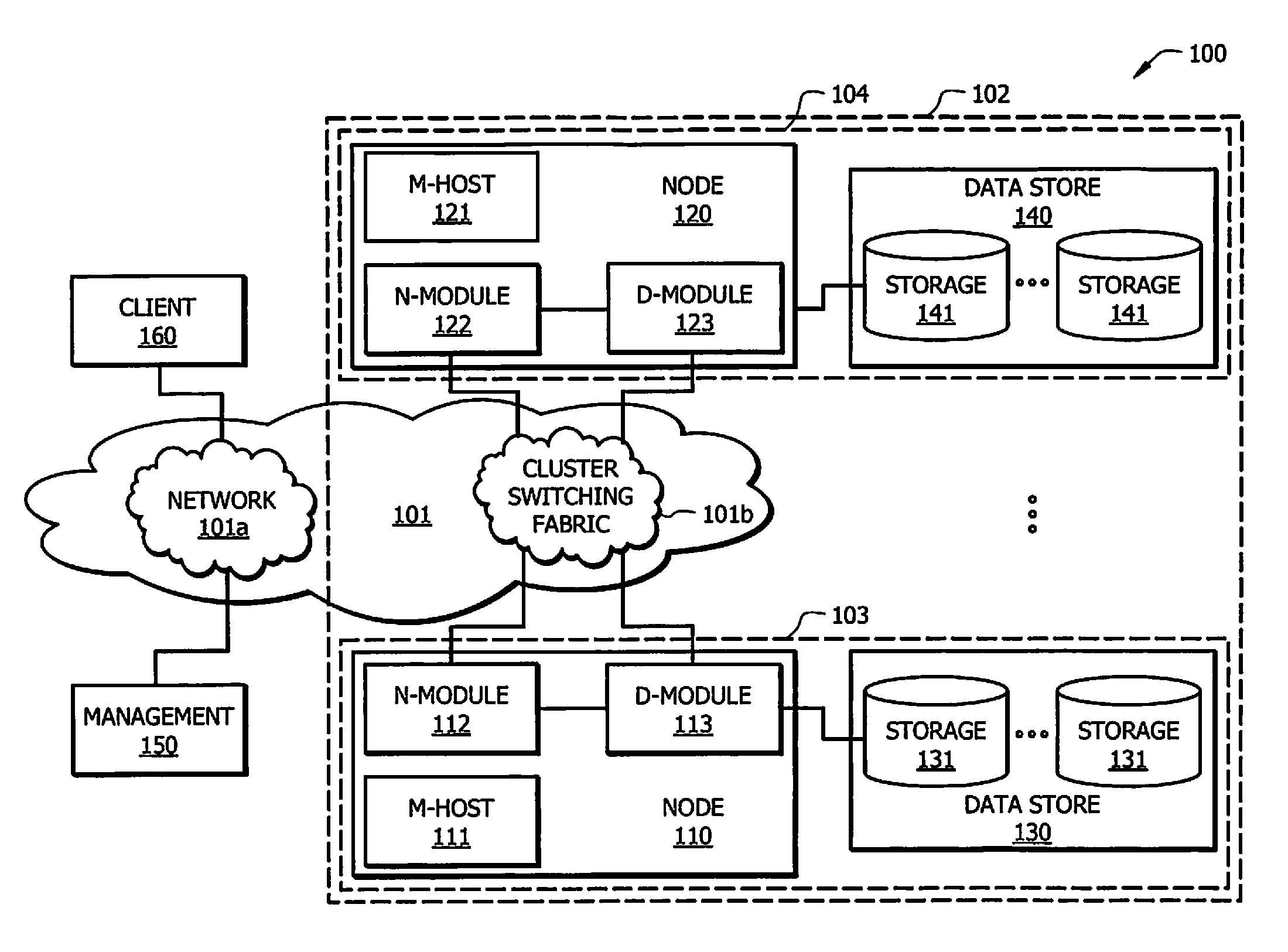
Systems and methods for providing intelligent automated support capable of self rejuvenation with respect to storage systems
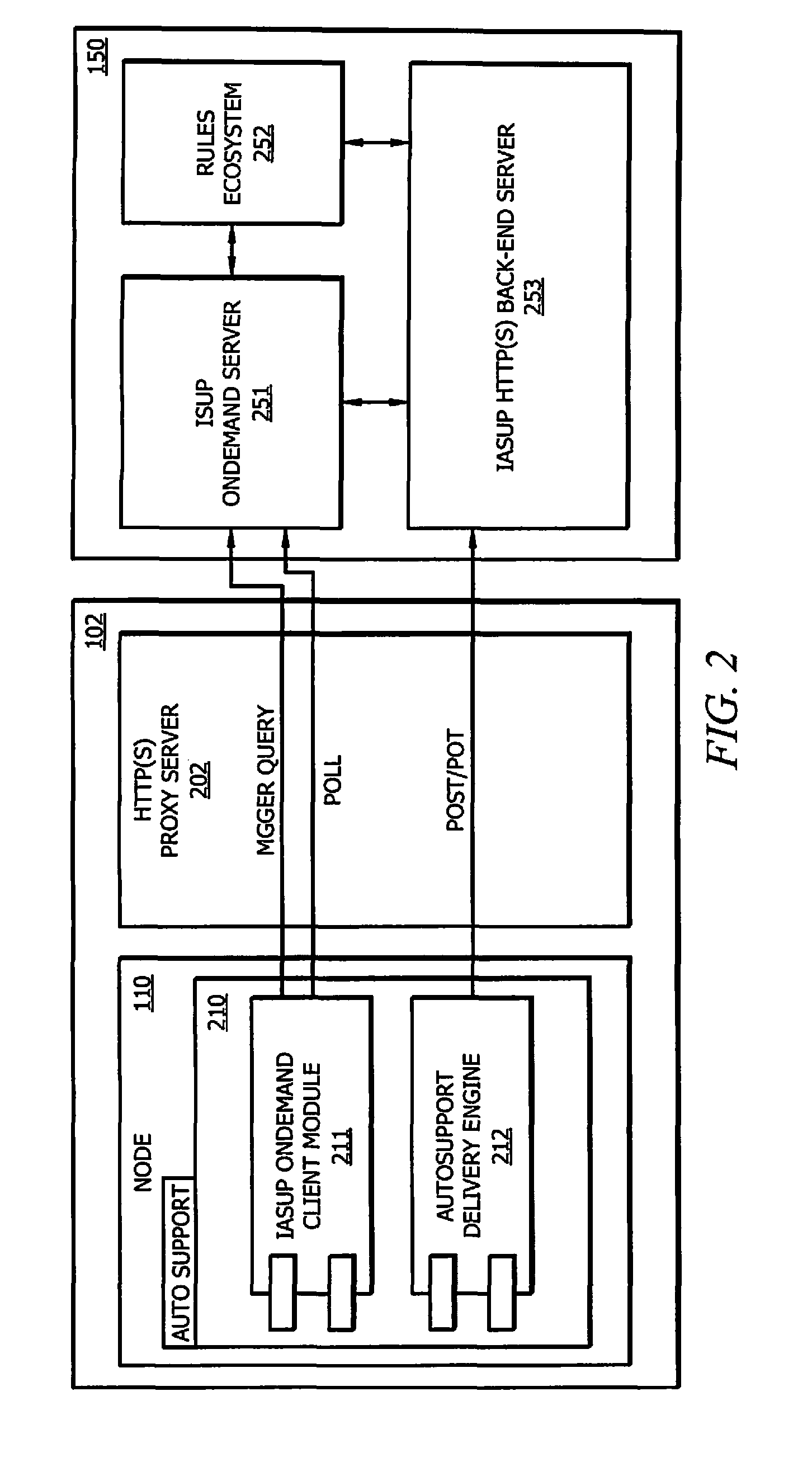
ActiveUS8825752B1Facilitate IASUPEasy to collectMemory loss protectionError detection/correctionEnd systemHybrid storage system
Systems and methods which provide an intelligent automated support (IASUP) architecture in which logic is implemented to control support messaging in an automatic, timely, and meaningful fashion to imbibe intelligent automated support functionality are disclosed. Embodiments of an IASUP architecture implement bidirectional communication links between storage systems and IASUP back-end systems providing data collection. The bidirectional communication links supported by IASUP architectures of embodiments facilitate automated storage system rejuvenation functionality whereby an IASUP back-end system provides processing and analysis with respect to storage system data to initiate manipulation or control of one or more components of a storage system.
Owner:NETWORK APPLIANCE INC
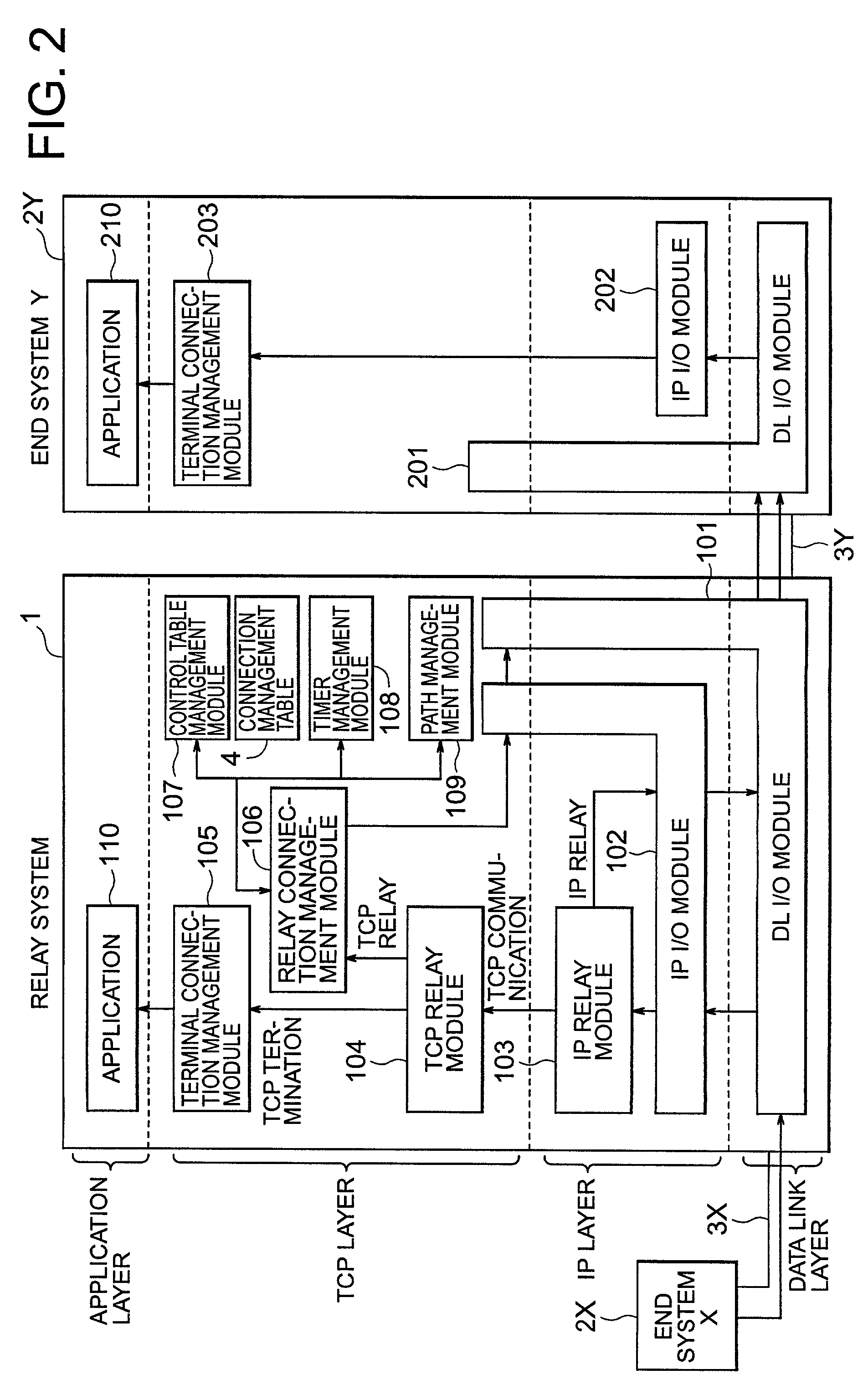
Relay connection management program, relay connection management method, relay connection management apparatus and recording medium which stores relay connection management program
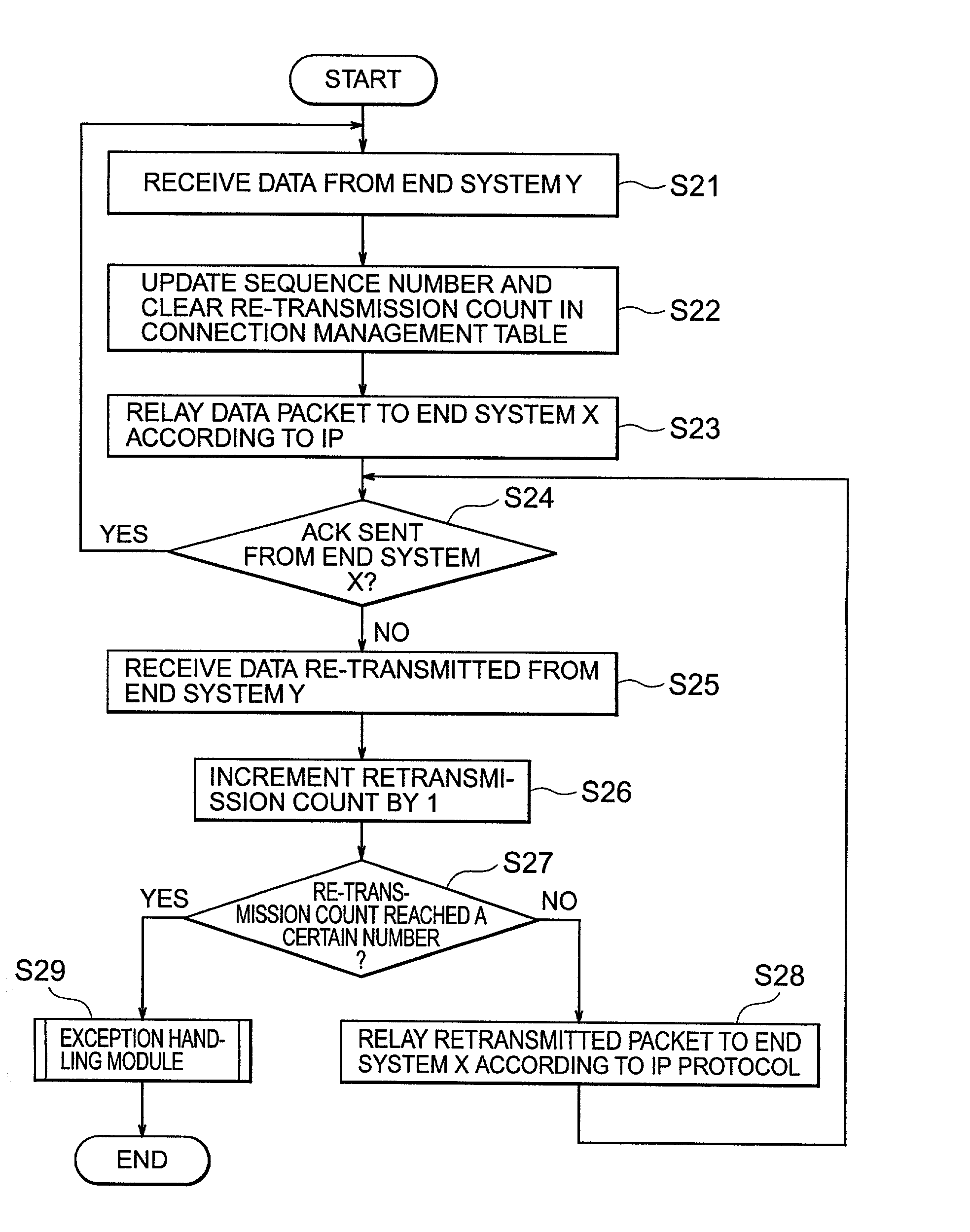
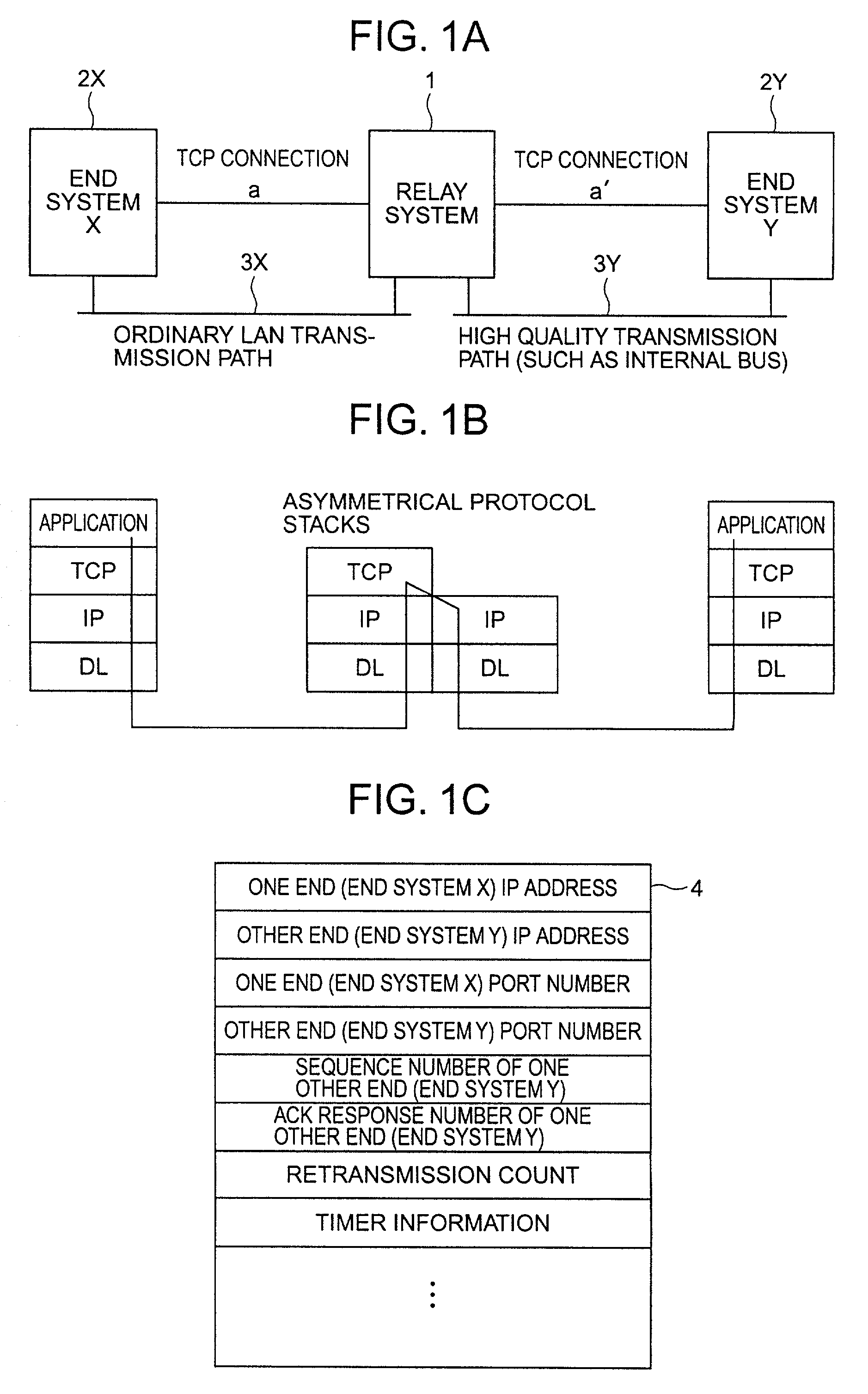
InactiveUS7227868B2Simplify the management processReduce processing burden and memory usageError prevention/detection by using return channelTransmission systemsEnd systemNetwork packet
A relay system stores destination information of both end systems for which communications are relayed, the sequence number of the one of the end systems is connected with a high quality transmission path, an ACK response number, a re-transmission count, etc. in a connection management table. Upon receiving a re-transmitted packet from the one of end systems, the relay system searches for the connection management table containing a matching sequence number, and increments the re-transmission count in the table by 1. If the re-transmission count has not reached a certain number, the relay system relays the re-transmitted packet as it is to the other end system.
Owner:FUJITSU LTD
Distributed connection-oriented services for switched communication networks
InactiveUS20050083949A1Special service provision for substationDigital computer detailsBroadcastingMAC address
Method and apparatus providing connection-oriented services for packet switched data communications networks. Directory services include distributed discovery of MAC addresses and protocol alias addresses. Topology services include a link state topology exchange among switches, which provides each switch with a complete topology graph of the network. This enables an access switch receiving a data packet to determine a complete path from a source end system to a destination end system. Another service includes resolution of broadcast frames to unicast frames, in order to reduce the amount of broadcast traffic. Policy restrictions may be applied prior to connection setup. Path determination services enable multiple paths from a source to a destination. Connection management includes source routed mapping of connections on the desired path. A distributed call rerouting service is provided wherein if a link on an active path fails, each switch receives a topology change notification and unmaps any connection involving the failed link. A broadcast / unknown service provides restricted flooding of nonresolvable packets. Furthermore, connection-oriented switching is provided based on the source and destination MAC addresses as a connection identifier. Still further, resolution of networks outside the switch domain is enabled by access switches listening for network and server route advertisements and maintaining best routes to said networks and servers. The best route metrics may be combined with best path metrics to determine a path from a first access switch to an egress switch connected to the external network.
Owner:EXTREME NETWORKS INC
Multi-network transaction analysis
Techniques described herein relate to analyzing location-based transaction systems, based on data from multiple client devices detected and received via multiple communication networks, and providing customized data to client devices associated with particular locations and / or users of the transaction system. The characteristics of a transaction system and / or specific client locations of the transaction system may be determined, based on data received from multiple client devices. A back-end system may receive data from one or more digital kiosk systems associated with particular locations in a transaction system network, various mobile computing devices of users, and client computers within the transaction system. One or more back-end servers may analyze the data to determine various characteristics of the transaction system and / or characteristics of one or more particular locations in the transaction system network.
Owner:THE WESTERN UNION CO
Deterministic user authentication service for communication network
InactiveUS6874090B2Digital data processing detailsUser identity/authority verificationPersonalizationInternet Authentication Service
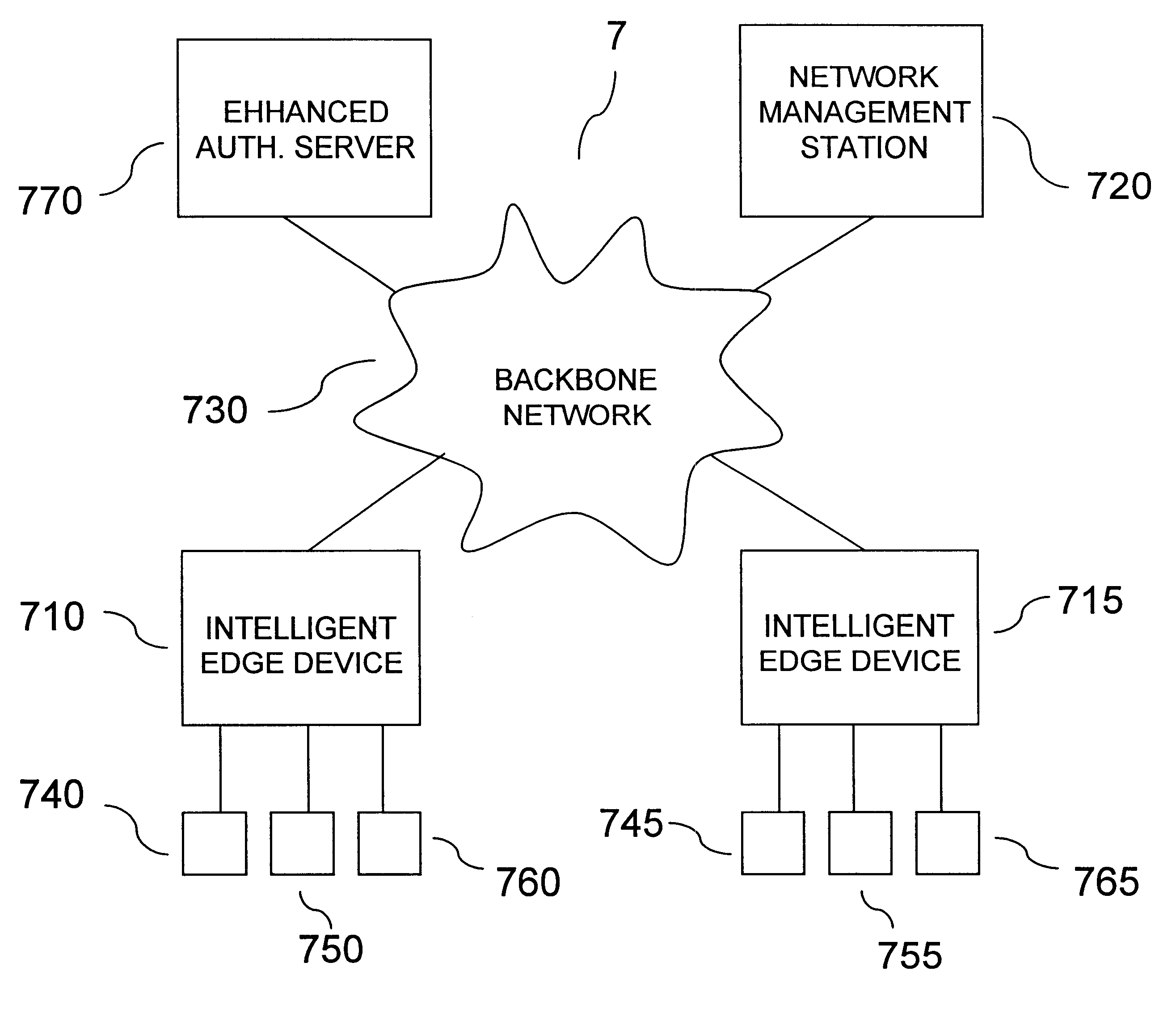
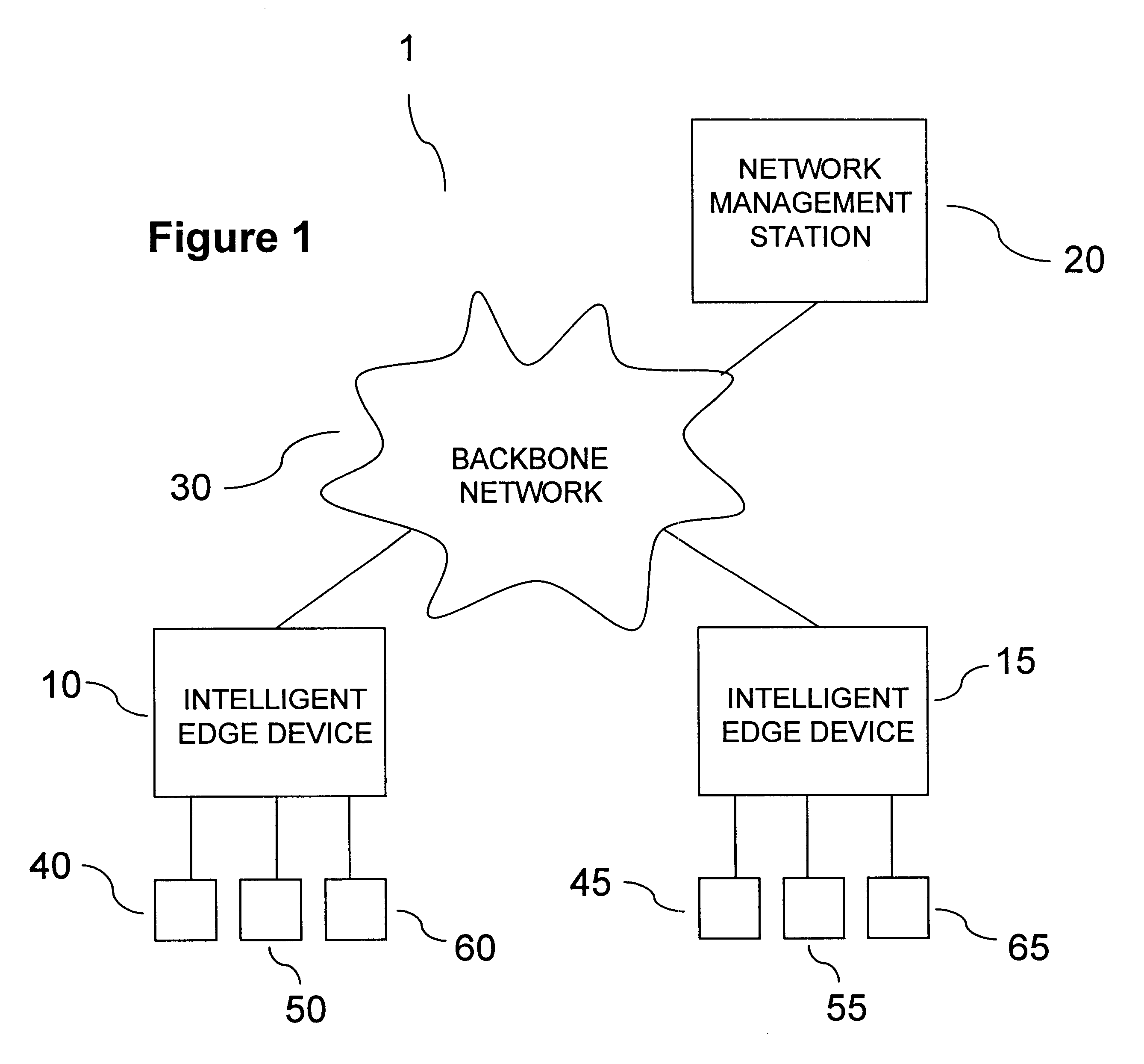
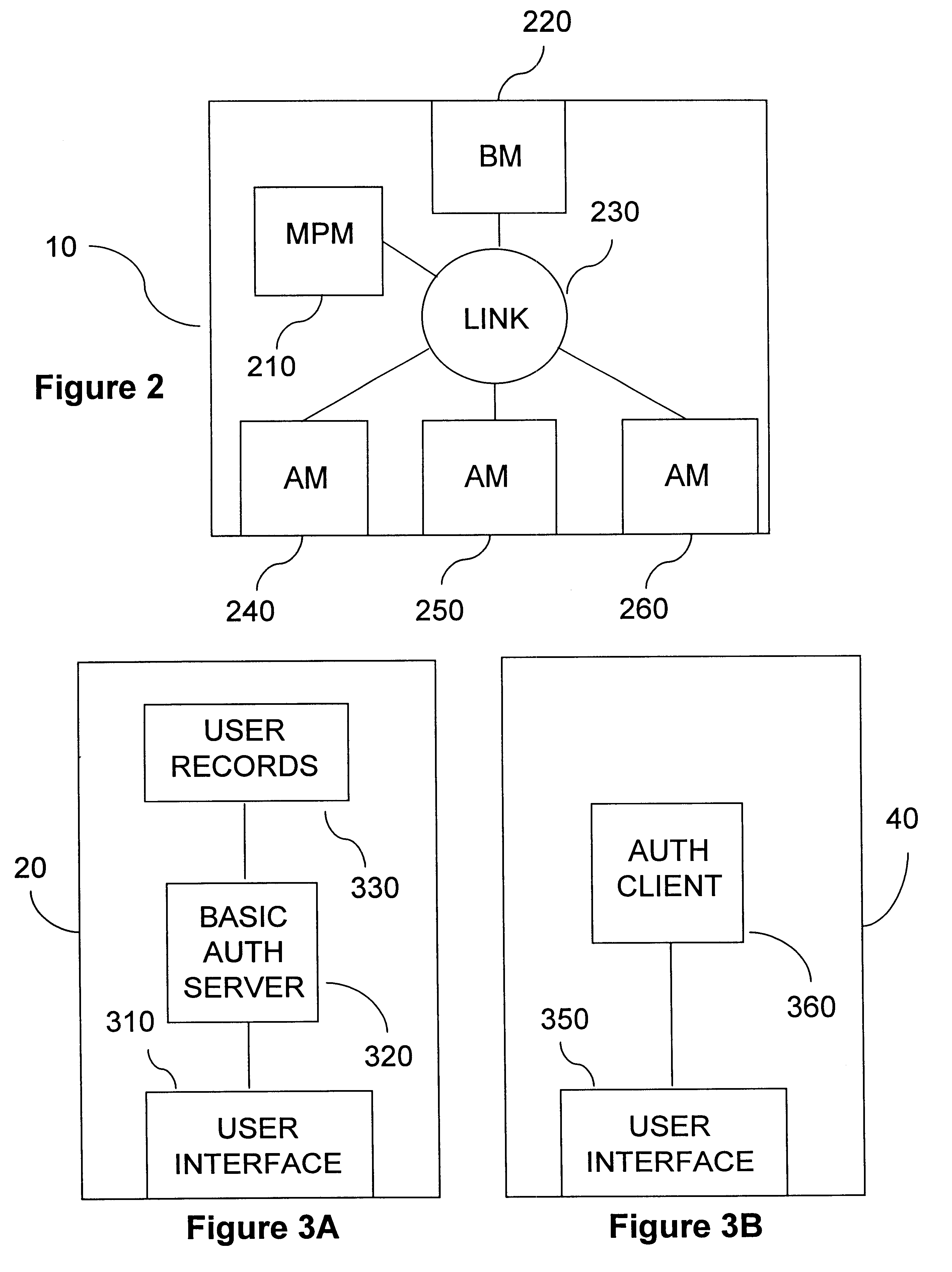
A user authentication service for a communication network authenticates local users before granting them access to personalized sets of network resources. Authentication agents on intelligent edge devices present users of associated end systems with log-in challenges. Information supplied by the users is forwarded to an authentication server for verification. If successfully verified, the authentication server returns to the agents authorized connectivity information and time restrictions for the particular authenticated users. The agents use the information to establish rules for filtering and forwarding network traffic originating from or destined for particular authenticated users during authorized time periods. An enhanced authentication server may be engaged if additional security is desired. The authorized connectivity information preferably includes identifiers of one or more virtual local area networks active in the network. Log-in attempts are recorded so that the identity and whereabouts of network users may be monitored from a network management station.
Owner:ALCATEL LUCENT SAS
Method and system for process brokering and content integration for collaborative business process management
InactiveUS20030187743A1FinanceMultiple digital computer combinationsApplication softwareBusiness process management
Process Brokering Services (PBS) are implemented though the concept of Adaptive Documents to facilitate electronic commerce (e-commerce). PBS provides a single point of process control over the various fragmented execution flows and brings together the elements for process integration (views, content, flows) in a unified, scalable architecture on an industry standard platform. The two principal functions of the PBS are brokering of multiple business processes encapsulated in various back-end systems including workflow engines and business applications, and aggregating content from multiple enterprise information systems in the business context and managing the shared access to this based on the roles of the participants. The dynamic services provided by PBS are accessible to clients through the PBS Interface.
Owner:IBM CORP
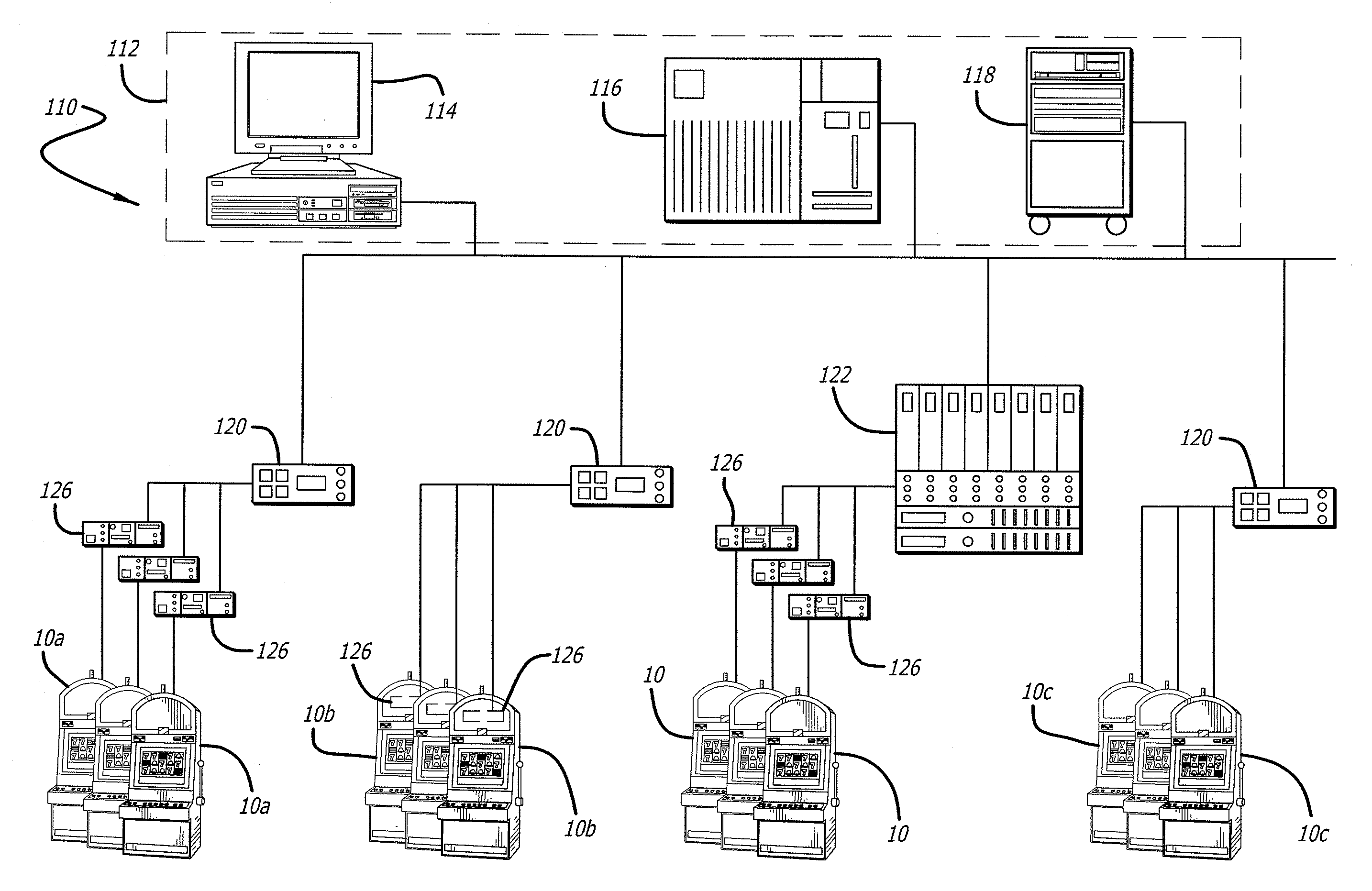
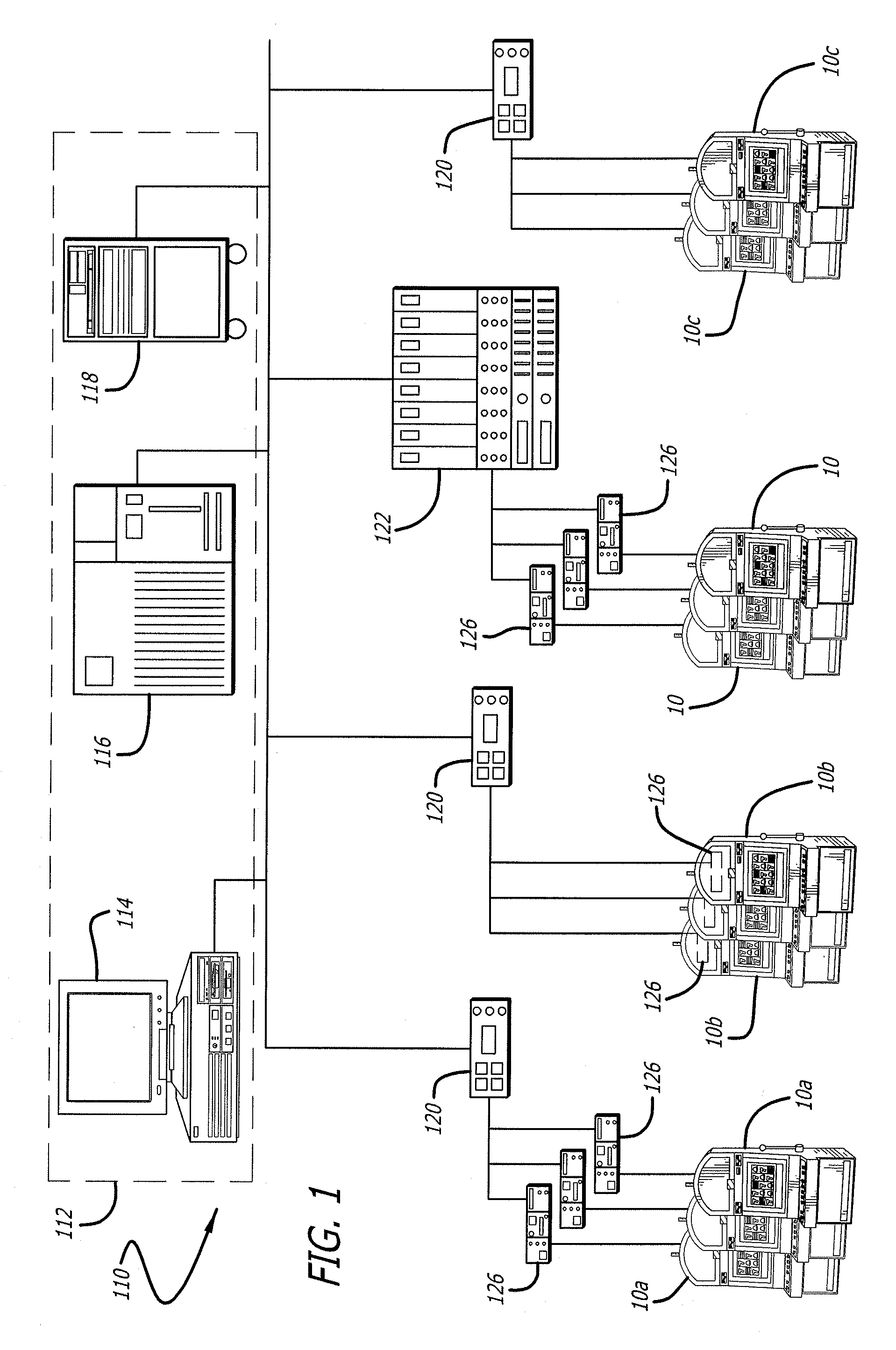
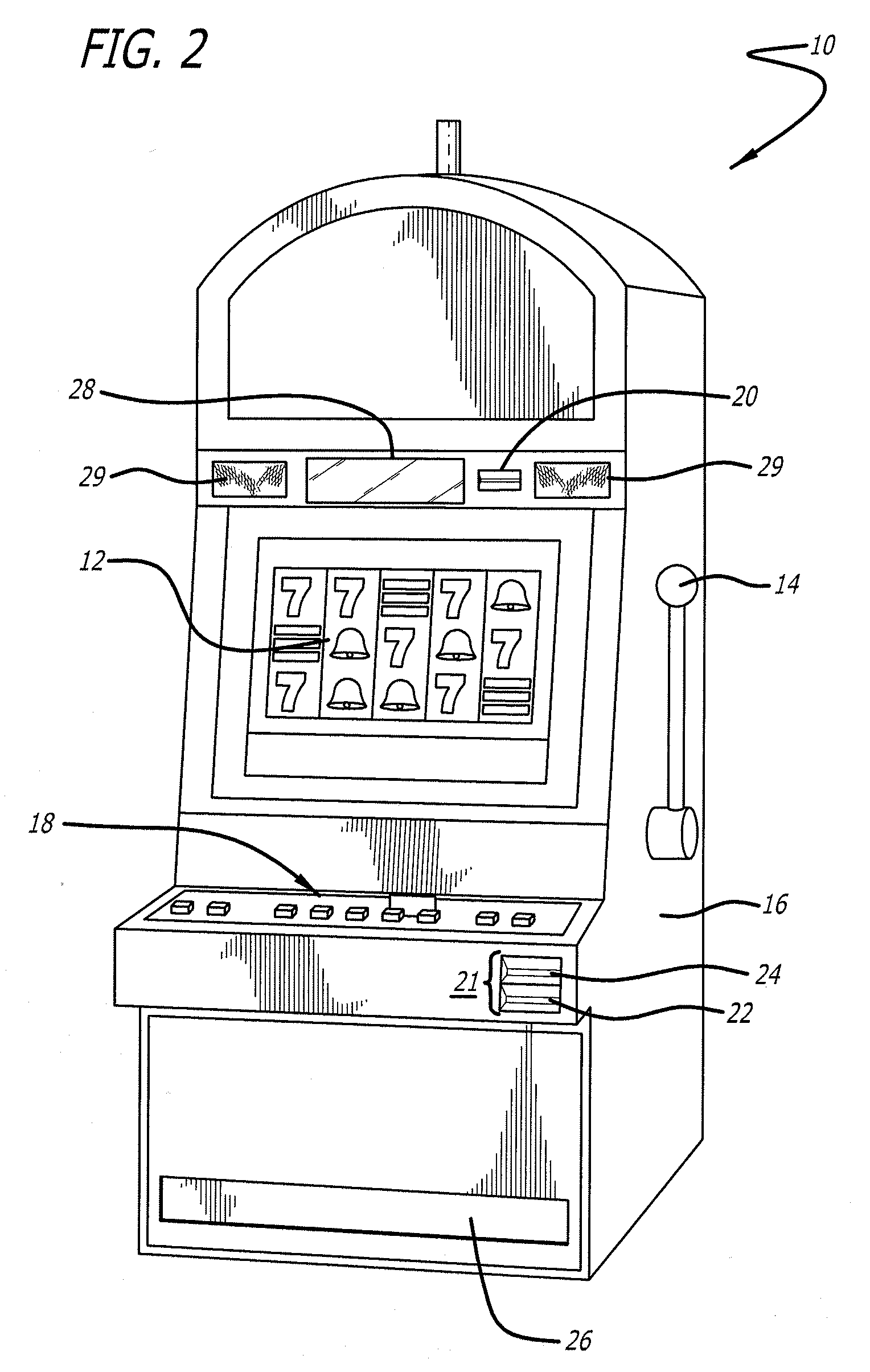
System for managing gaming devices
An embedded web server is disclosed. In one embodiment, a casino gaming system comprises a back end system having one or more servers. One or more gaming machines are operatively connected to the back end system via a network connection and one or more gaming devices operatively connected to at least one gaming machine. The gaming device includes an embedded web server and a web browser in communication with the web server, delivers a management user interface to the web browser for accessing the gaming device.
Owner:LNW GAMING INC
Tracking a user to support tasks performed on complex-system components
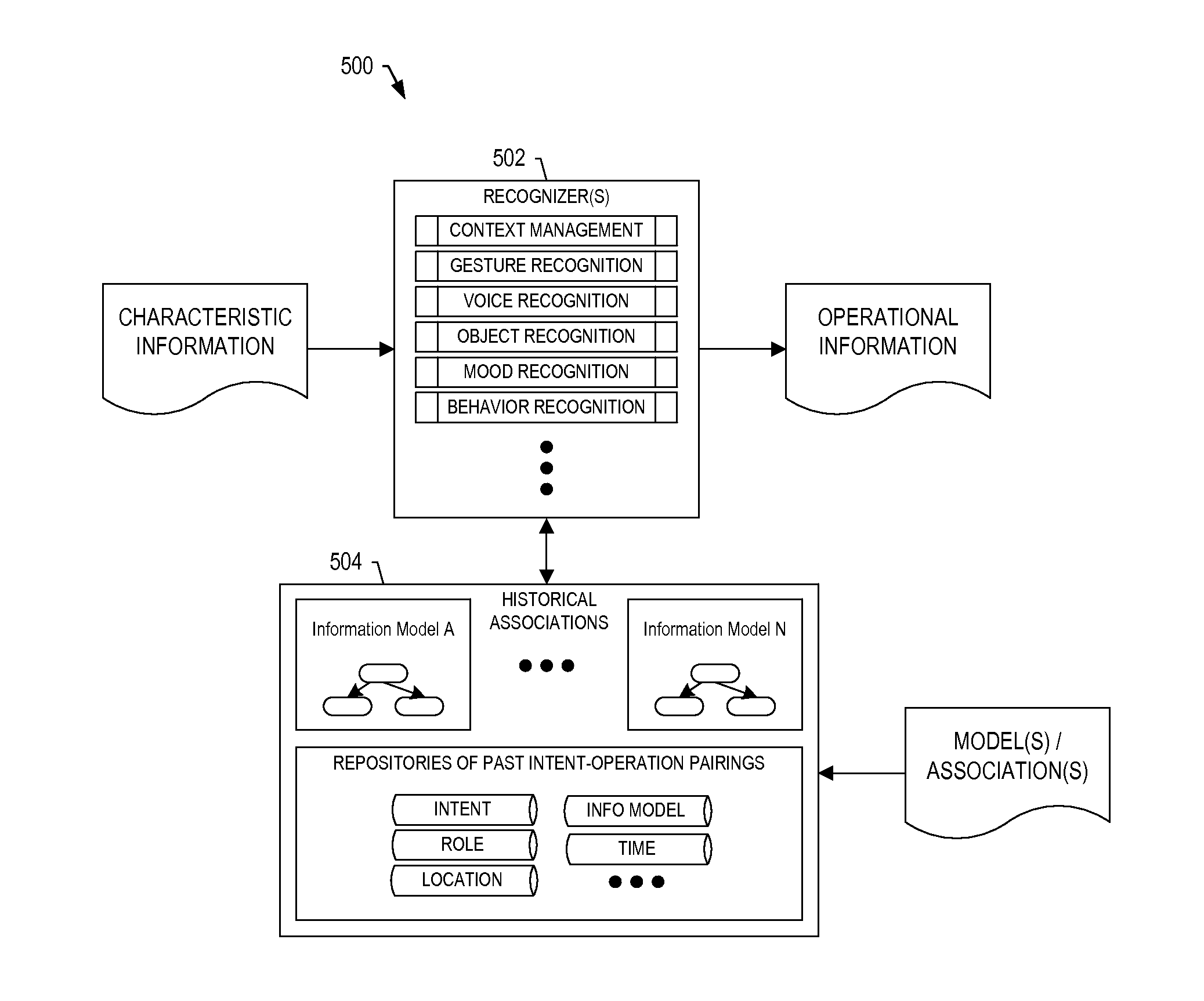
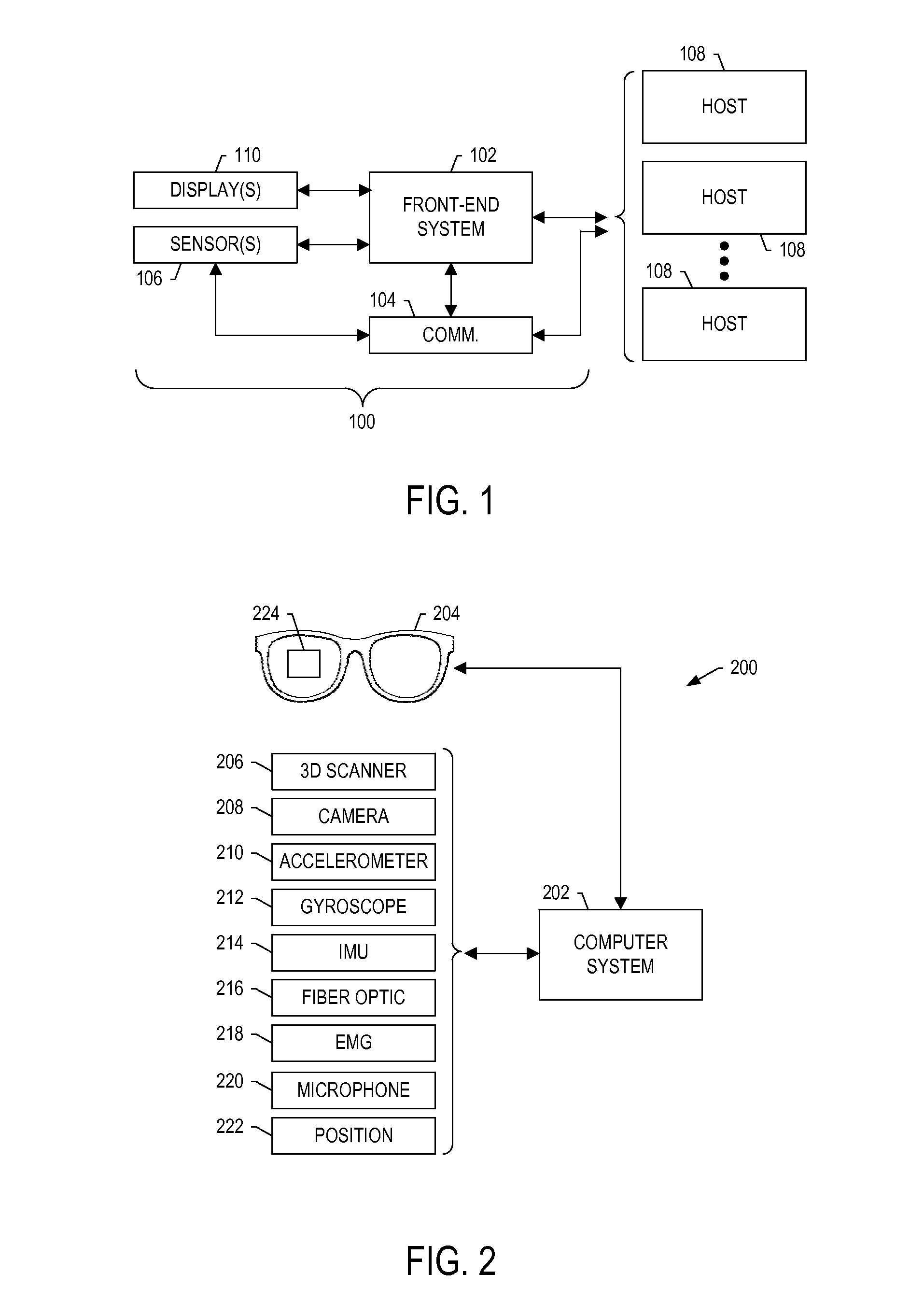
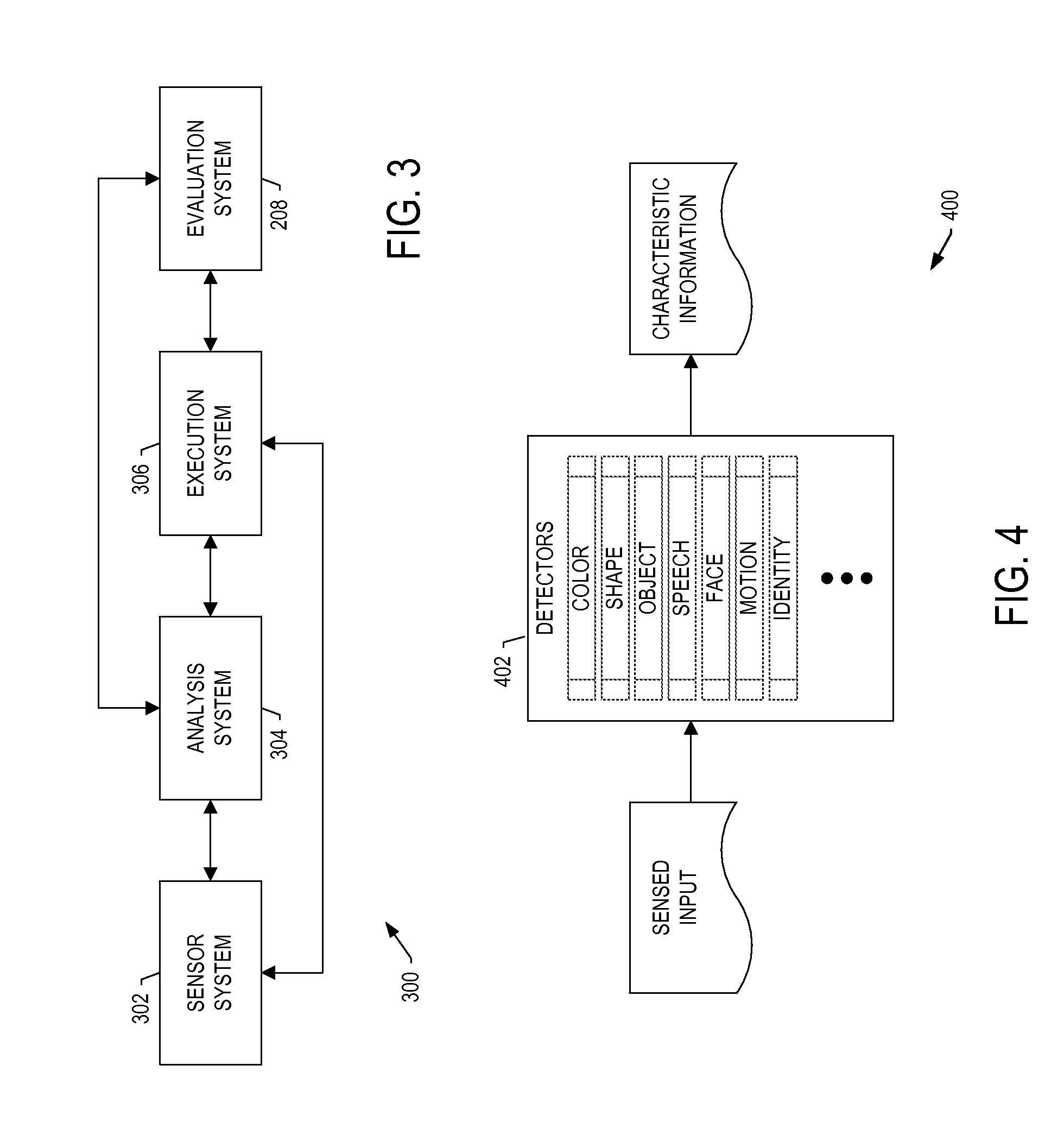
ActiveUS20140354529A1Input/output for user-computer interactionCathode-ray tube indicatorsEnd systemDisplay device
A system is provided that includes sensors(s) configured to provide sensed input including measurements of motion and / or orientation of a user during performance of a task to work a complex-system component. The system includes a front-end system configured to process the sensed input including the measurements to identify a known pattern that indicates a significance of the sensed input from which to identify operations of an electronic resource. The front-end system is configured to form and communicate an input to cause the electronic resource to perform the operations and produce an output. The operations include determination of an action of the user during performance of the task, or calculation of a process variable related to performance of the task, from the measurements. And the front-end system is configured to receive the output from the electronic resource, and communicate the output to a display device, audio output device or haptic sensor.
Owner:THE BOEING CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com