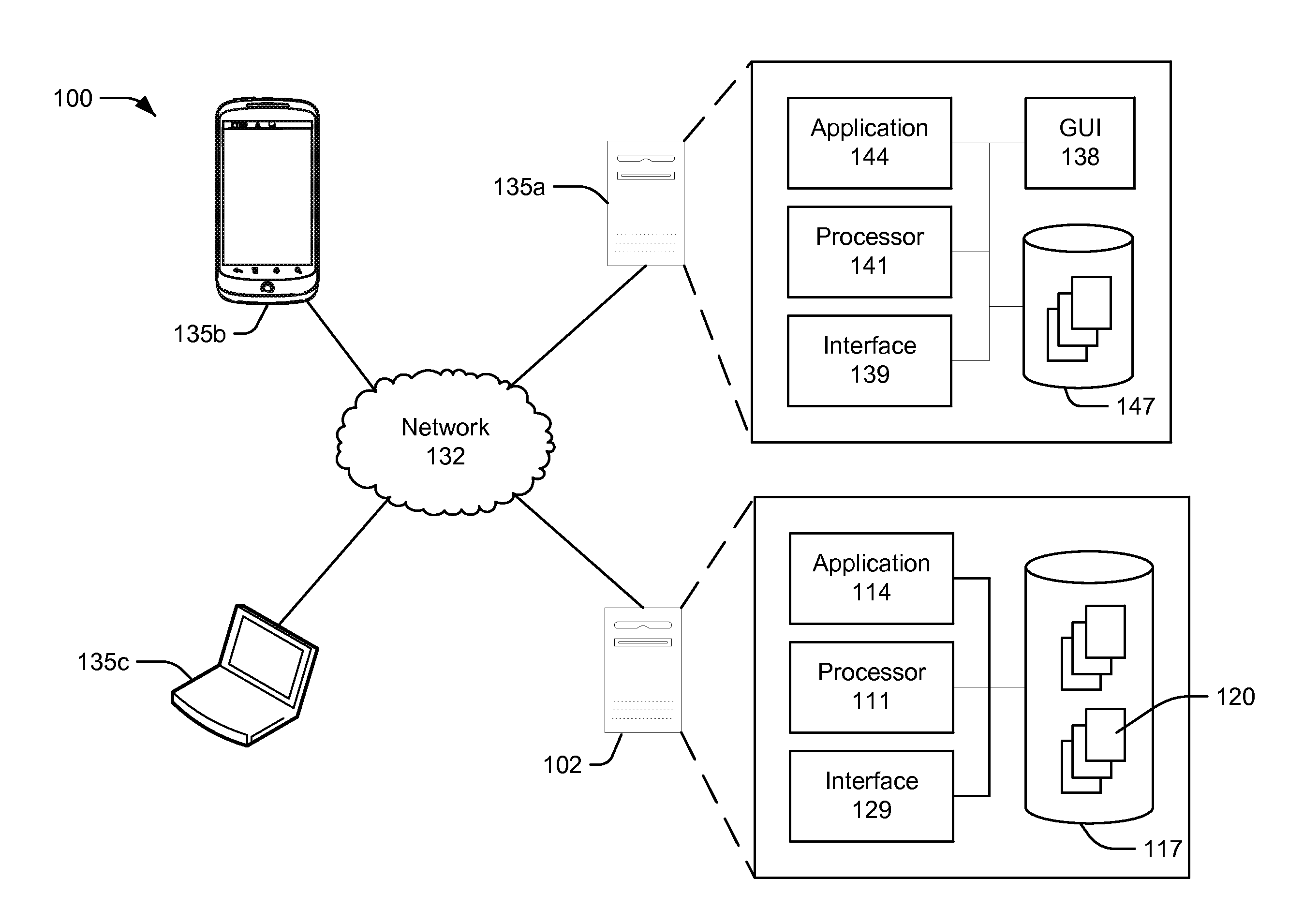
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
246 results about "Alias" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An alias is a feature of SQL that is supported by most, if not all, relational database management systems (RDBMSs). Aliases provide database administrators, as well as other database users, with the ability to reduce the amount of code required for a query, and to make queries simpler to understand. In addition, aliasing can be used as an obfuscation technique to protect the real names of database fields.
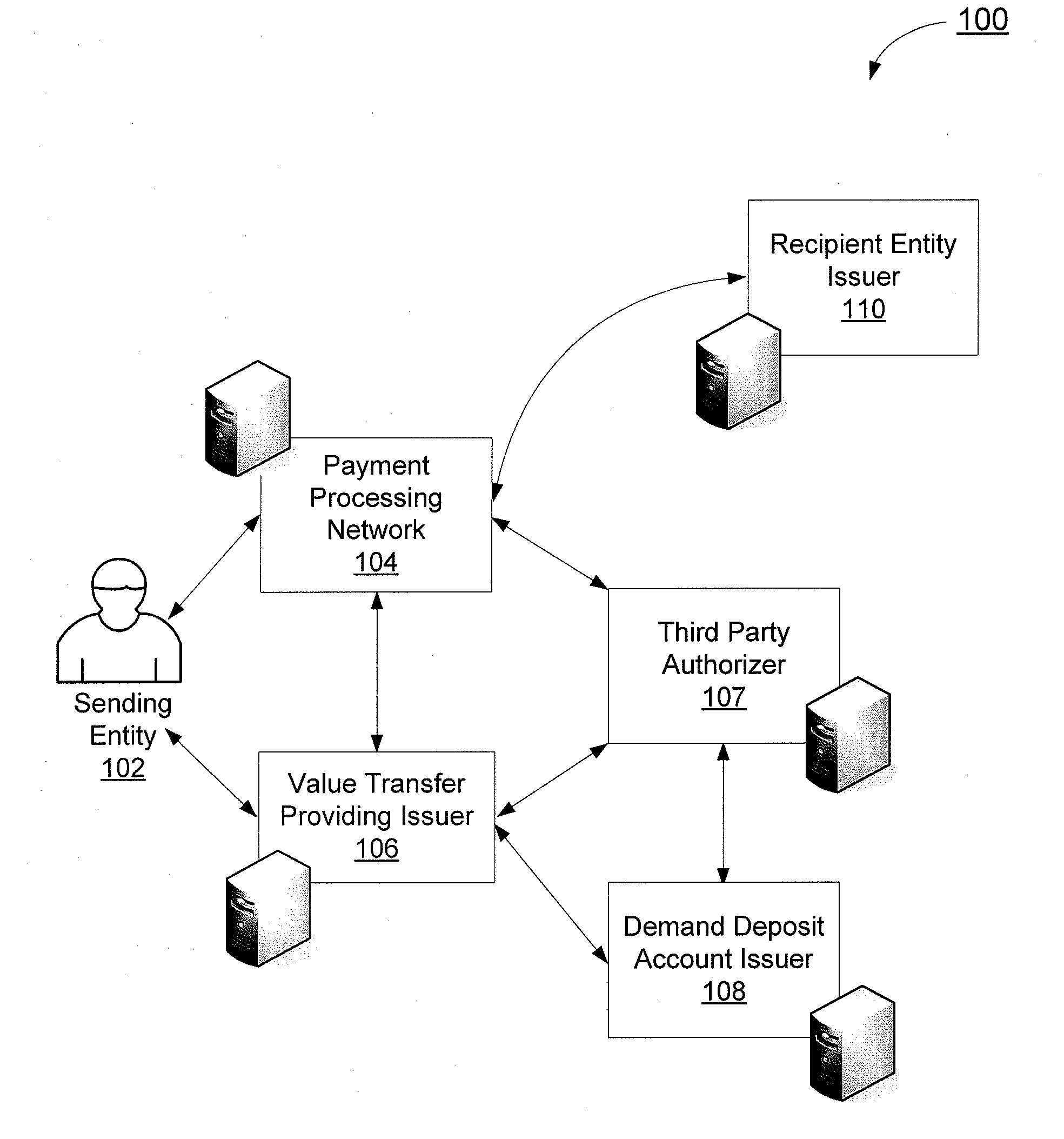
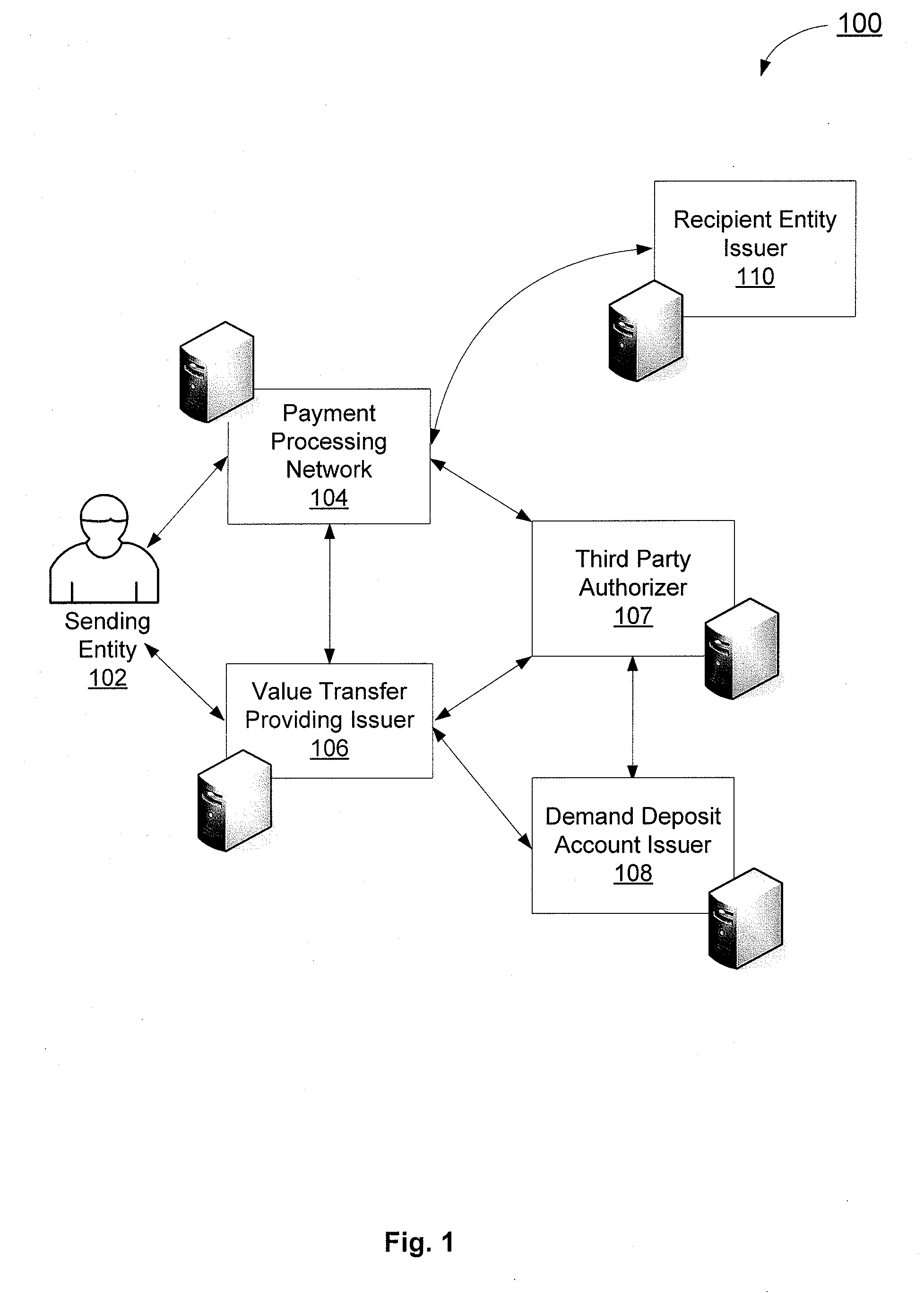
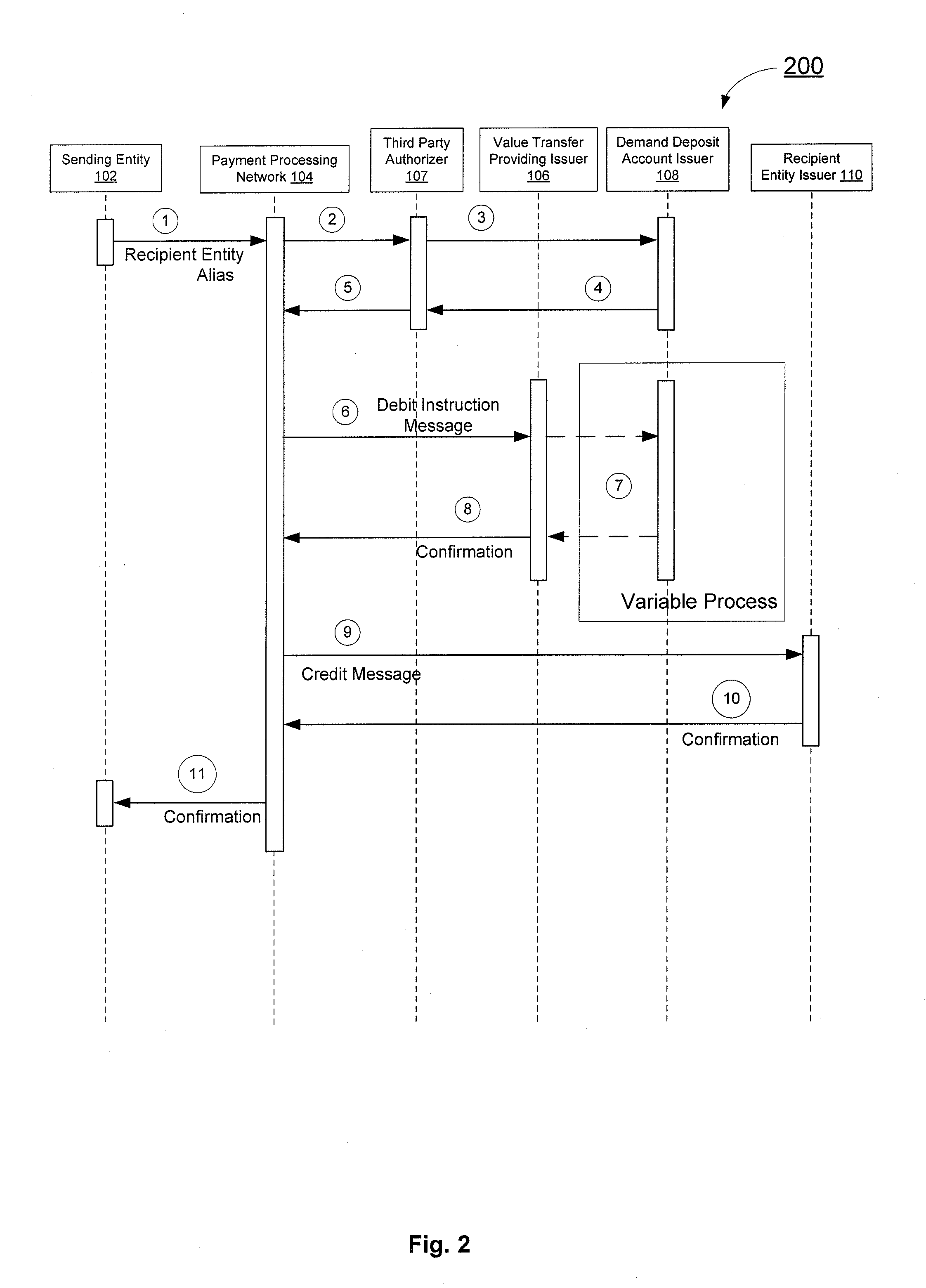
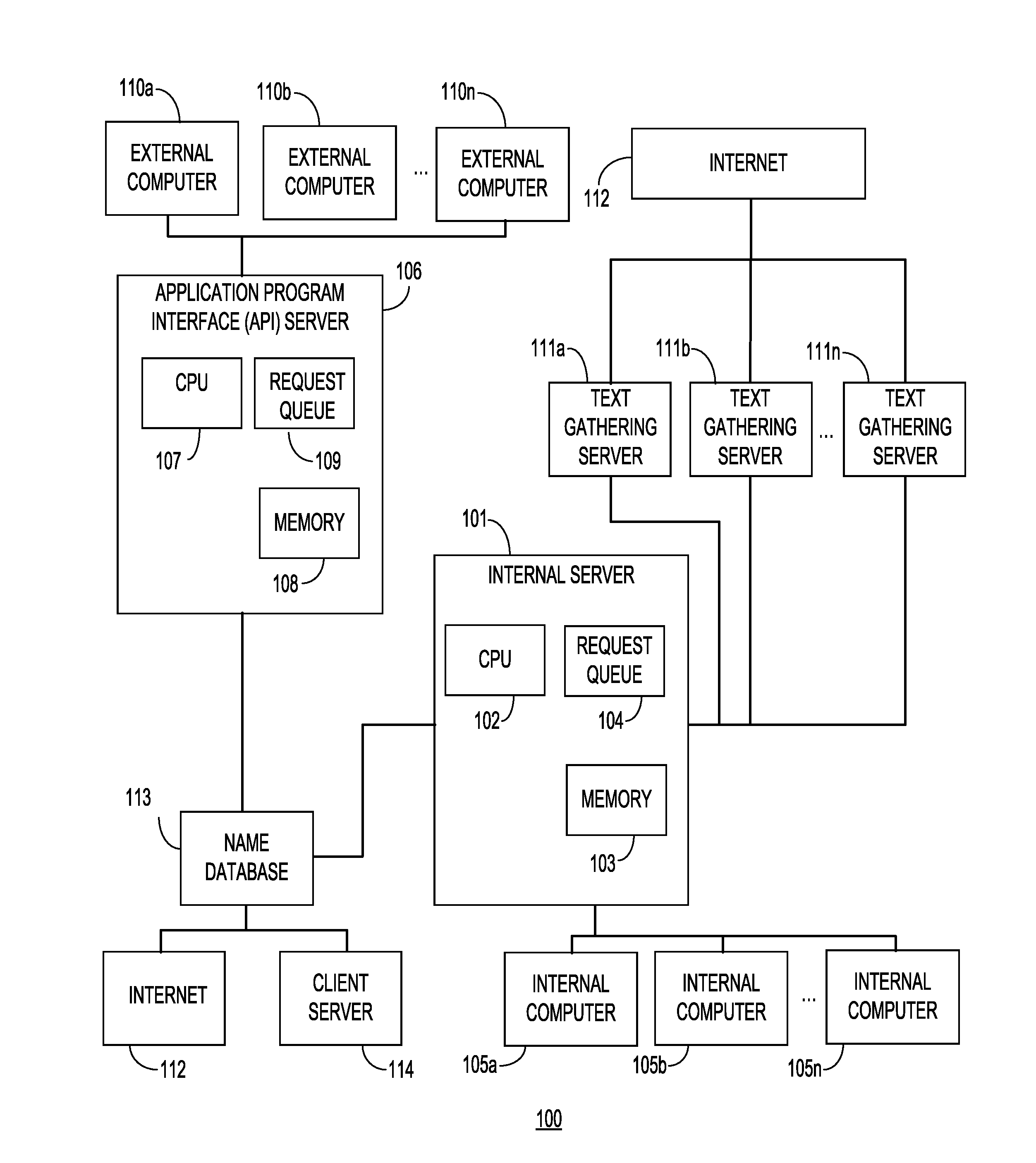
Alias management and off-us dda processing
An alias management and off-us demand deposit account processing system is disclosed. A sending entity initiates a value transfer with a payment processing network indicating a value transfer providing issuer which will conduct the value transfer and a demand deposit account issuer which hosts the demand deposit account that funds the value transfer. The sending entity is able to conduct a value transfer via a value transfer providing issuer using funds from an account with another issuer.
Owner:VISA INT SERVICE ASSOC
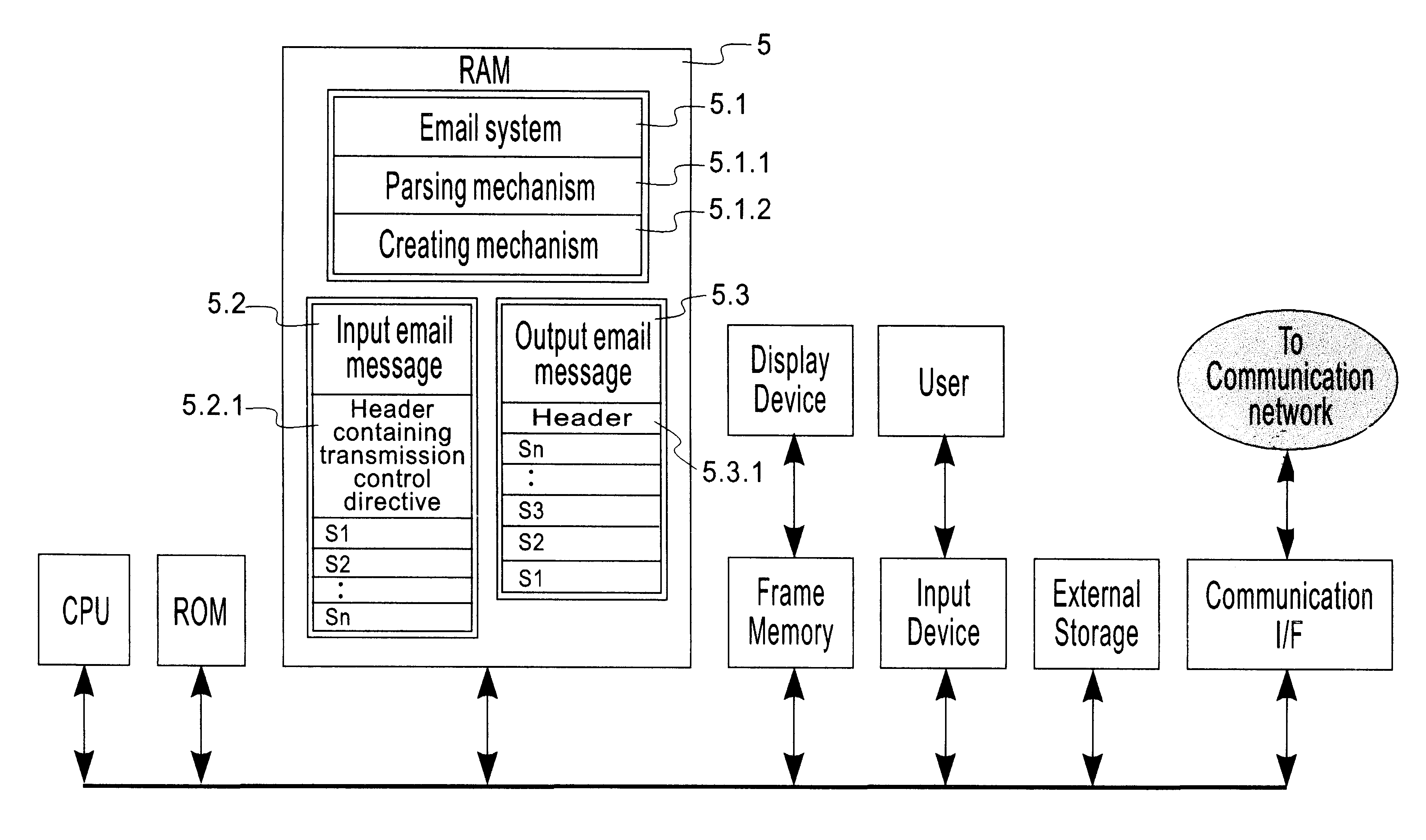
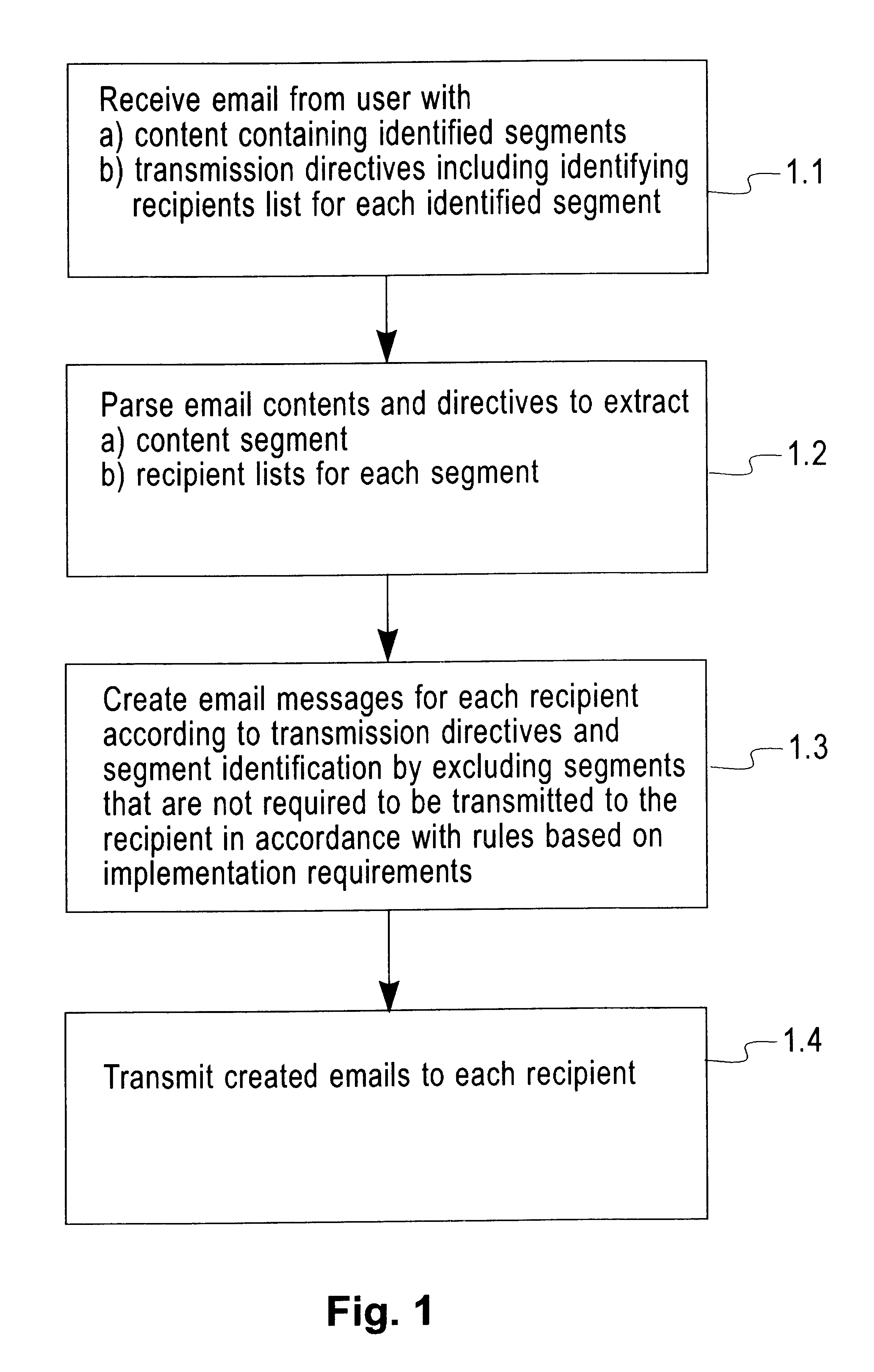
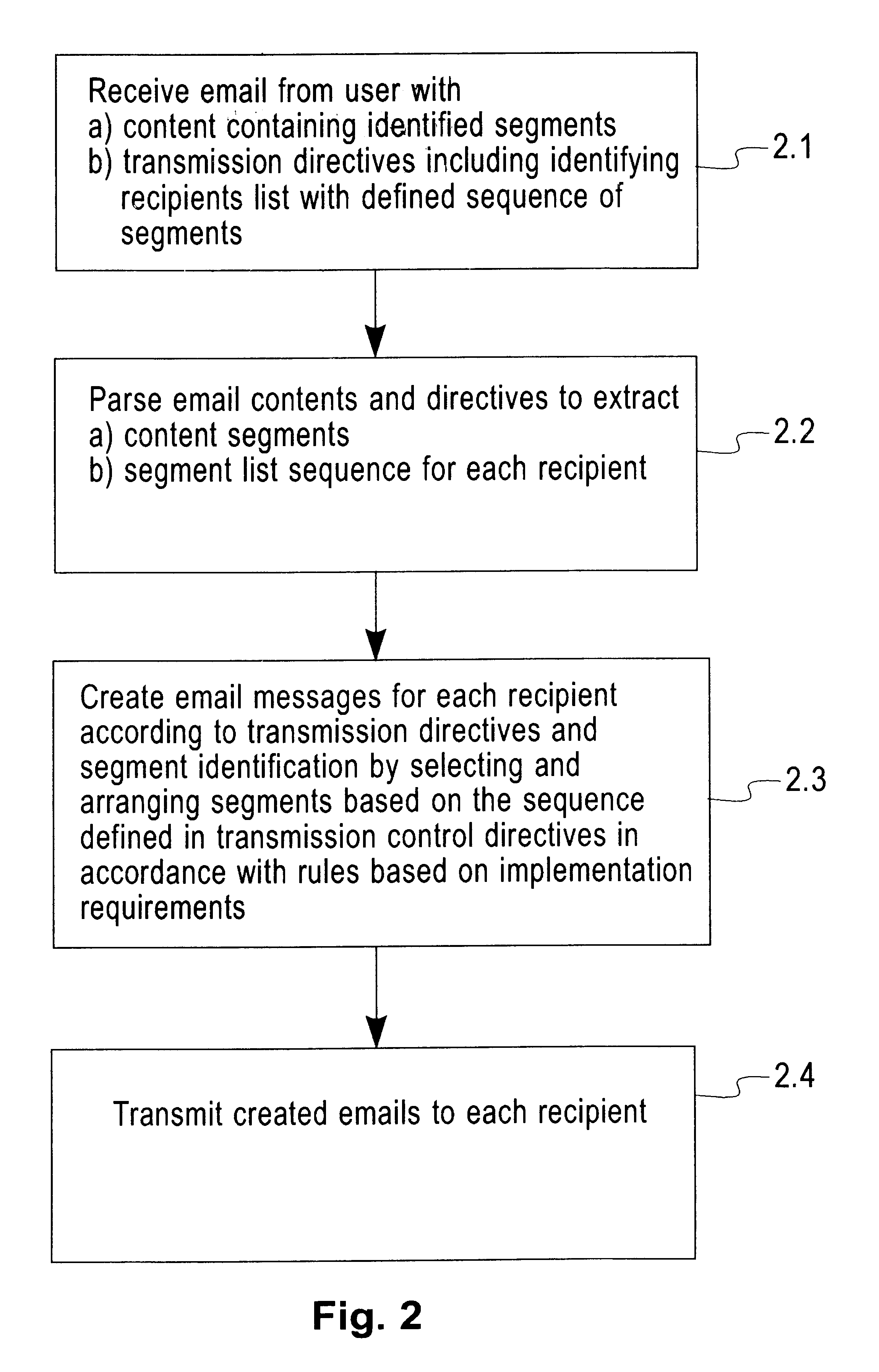
System for restructuring selected parts of email messages prior to transmission to plurality of recipients
InactiveUS6775689B1Multiple digital computer combinationsOffice automationWorld Wide WebElectronic mail
This invention relates to a method, apparatus and program product for restructuring email messages for transmission to a plurality of recipients by providing transmission control directives and email content segment identifiers supplied by the user, parsing the said directives and email contents, expanding aliases wherever necessary and applying the said directives to restructure the email contents by sending selected segments to selected recipients in identified lists. This invention further includes reordering the selected segments in a defined sequence prior to transmission. This invention also includes merging of selected identified corresponding segments from a plurality of email messages and transmitted to selected recipients in identified recipient lists. The selected merged segments may further be reordered in a defined sequence prior to transmission.
Owner:KYNDRYL INC
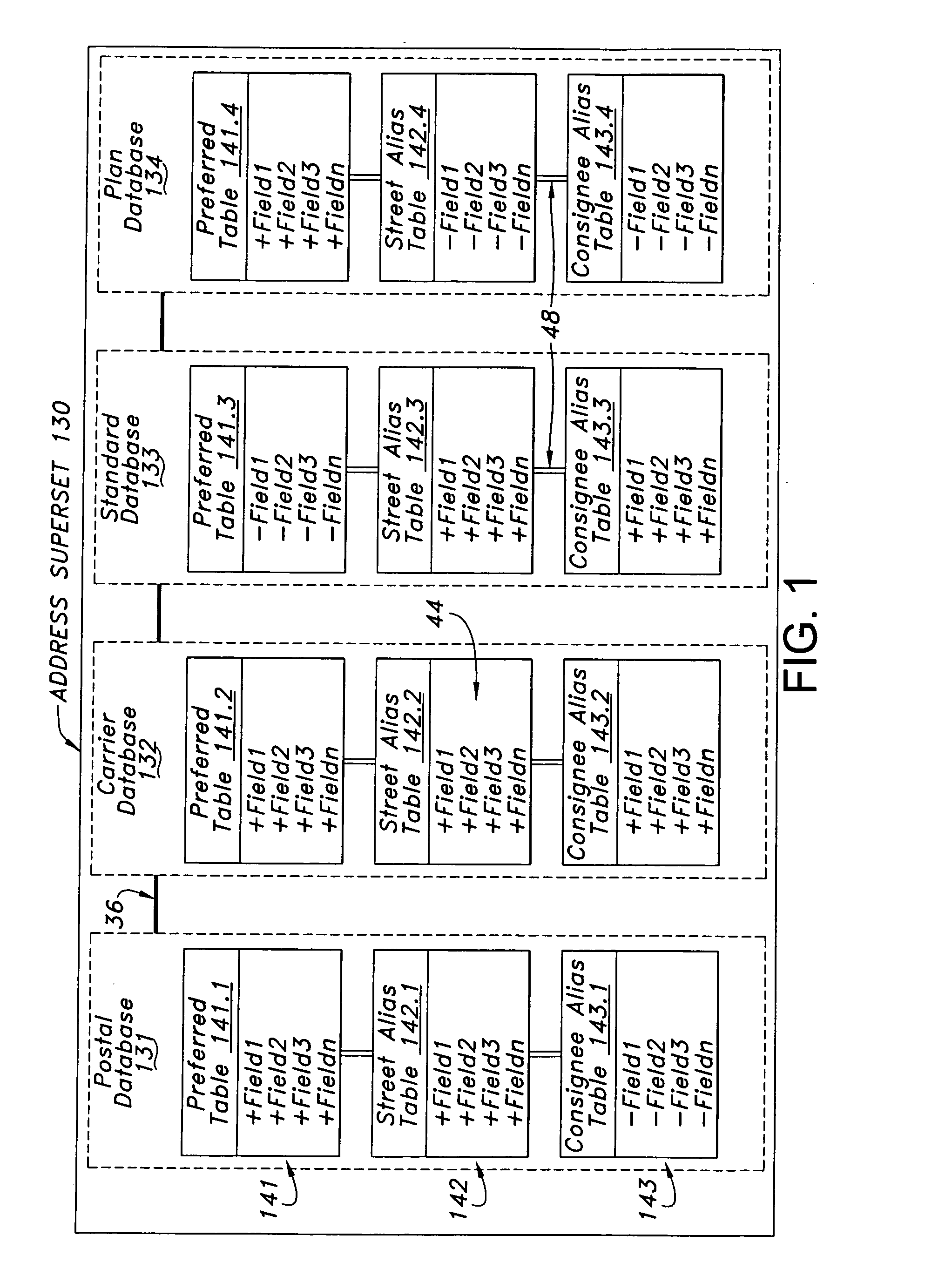
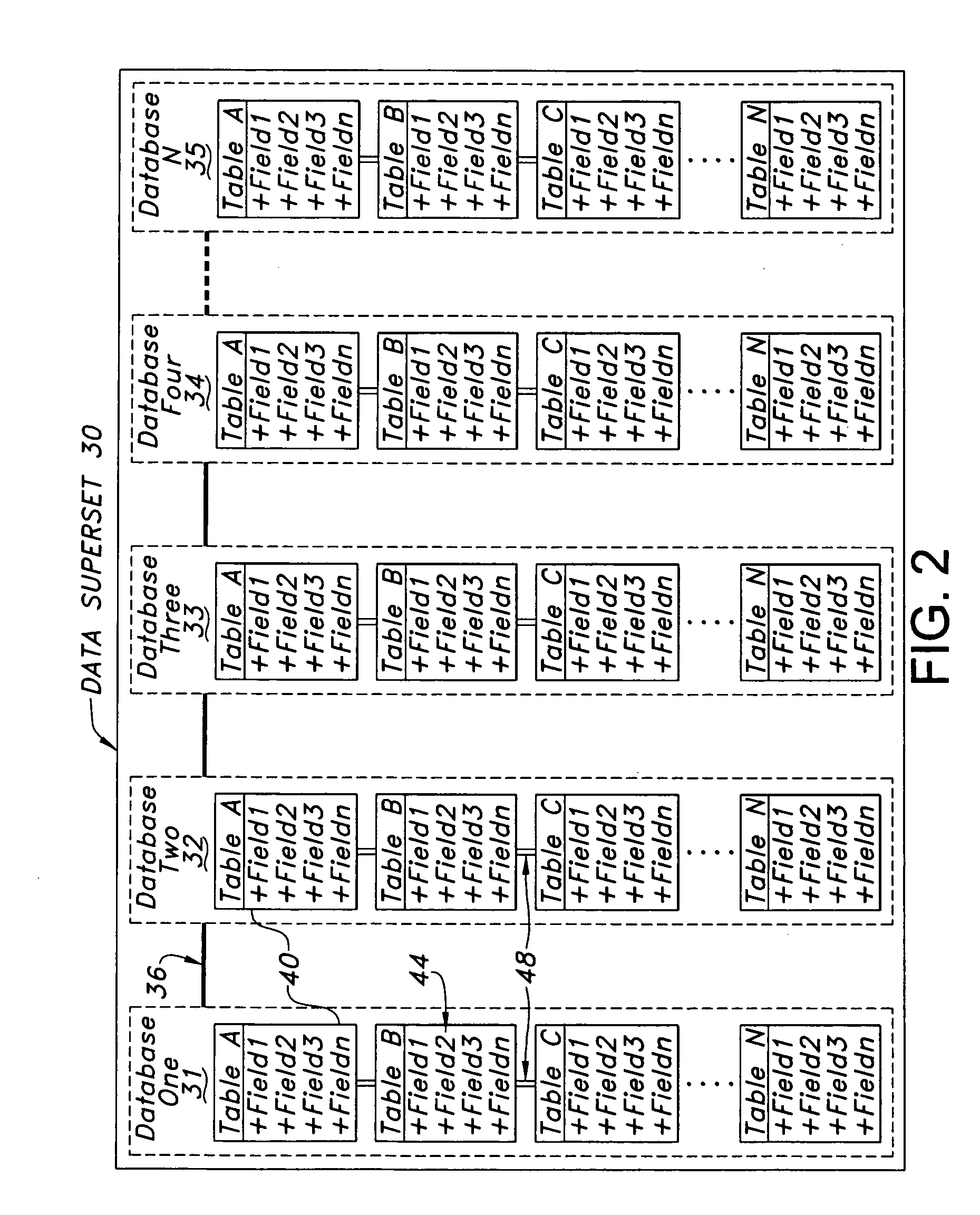
Data structure and management system for a superset of relational databases
ActiveUS20050086256A1Facilitate prompt and efficient validationEasy constructionData processing applicationsRelational databasesTable (database)Relational database
A data structure, database management system, and methods of validating data are disclosed. A data structure is described that includes a superset of interconnected relational databases containing multiple tables having a common data structure. The tables may be stored as a sparse matrix linked list. A method is disclosed for ordering records in hierarchical order, in a series of levels from general to specific. An example use with address databases is described, including a method for converting an input address having a subject representation into an output address having a preferred representation. Preferred artifacts may be marked with a token. Alias tables may be included. This Abstract is provided to comply with the rules, which require an abstract to quickly inform a searcher or other reader about the subject matter of the application. This Abstract is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
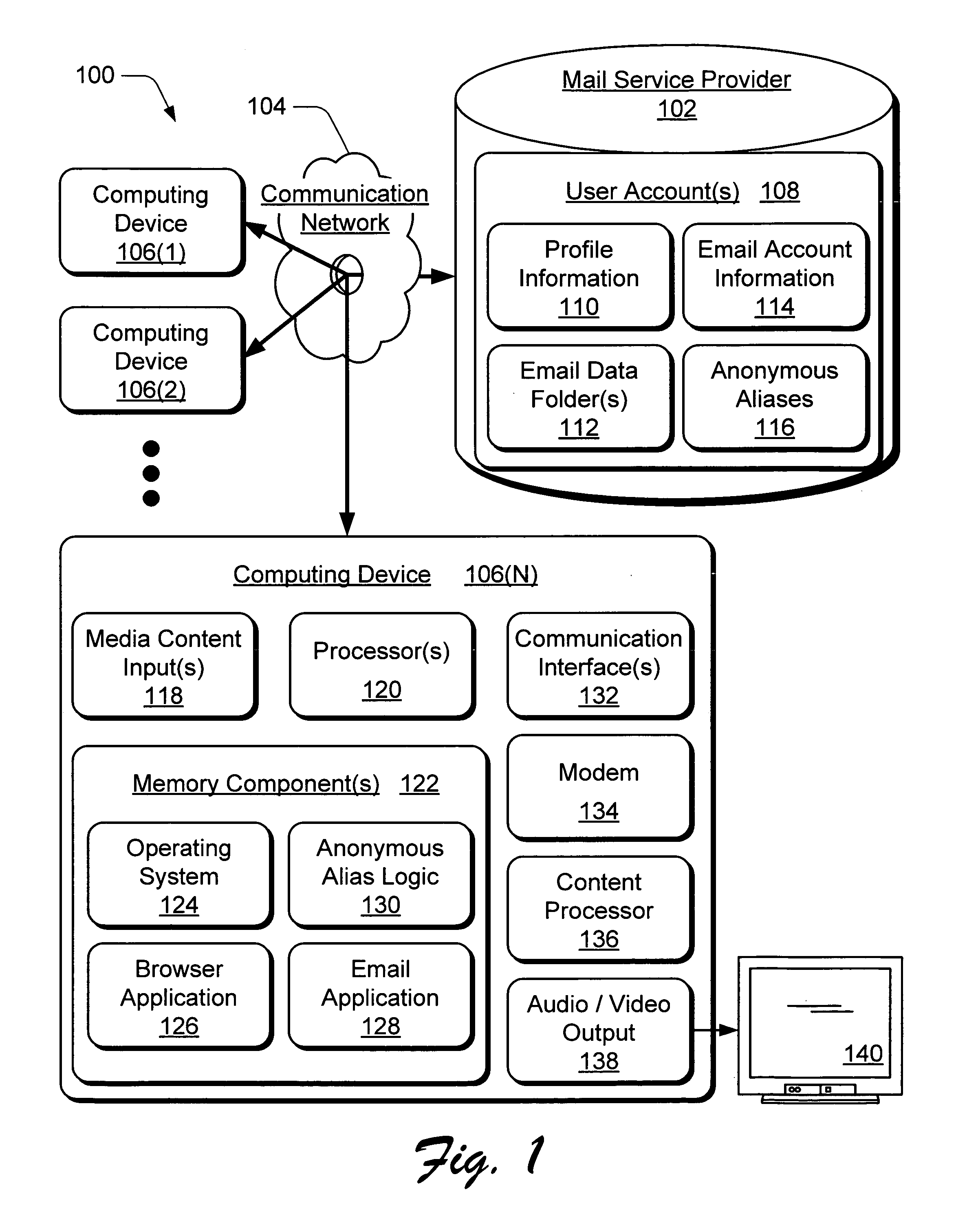
Anonymous aliases for on-line communications
InactiveUS20060026438A1Digital data processing detailsUser identity/authority verificationData miningDocumentation
Generation of anonymous aliases for on-line communications is described. In response to a user input to generate an anonymous alias, the anonymous alias is generated and associated with an established alias corresponding to the user, and an identification field in an on-line document is then determined and the anonymous alias is displayed in the identification field of the on-line document.
Owner:MICROSOFT TECH LICENSING LLC
Universal forms engine
InactiveUS7376891B2Simple methodSpeed up the processData processing applicationsNatural language data processingData validationThird party
A forms engine allows data sharing between customizable on-line forms, such as college admissions applications. Before applying, an applicant opens an account with a third party application servicer. After the applicant completes an application for one institution, the data is saved in a data base and automatically populates fields in subsequent application forms. The form for each institution is created from a form description file. Each form is branded for its institution and forms for different institutions differ in appearance and content so that the presence of the third party servicer is transparent to the applicant.The system is extensible without programming, allowing new applicant attributes to be readily incorporated into the system and allowing the content and appearance of the application to be readily changed by changing the description file. The use of aliases for applicant attributes permits data to be readily shared between forms even though labeled and arranged differently on different forms. Information stored about each attribute allows the specification of data validation rules and data sharing and grouping rules, as well as dependency rules that permit application page content to depend on applicant's responses on a previous page.
Owner:COLLEGENET
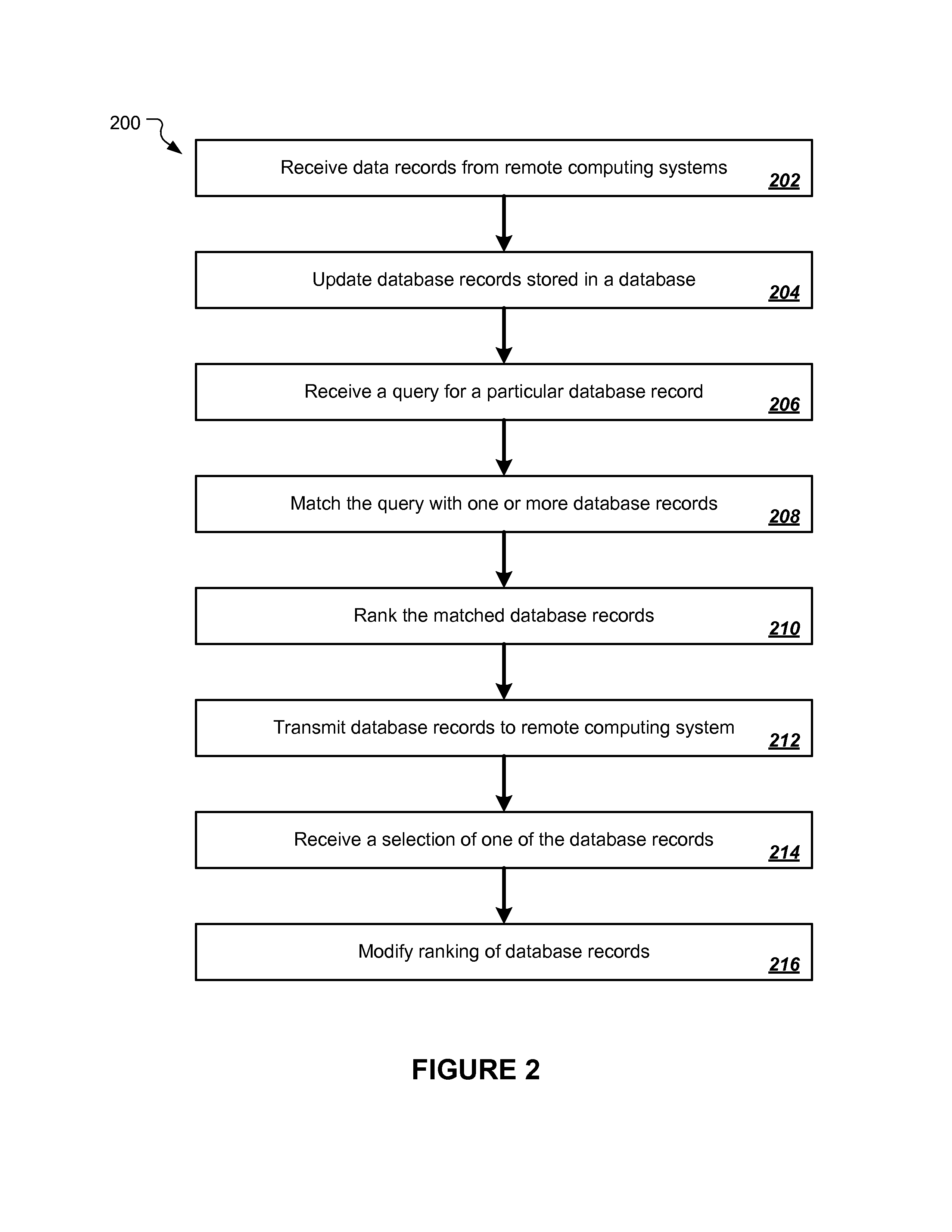
Entity Matching Using Machine Learning
ActiveUS20130185306A1Improve the level ofImprove precision and relevanceDigital data information retrievalDigital data processing detailsBusiness enterpriseData field
Techniques for information retrieval include receiving a plurality of data records, each data record including data fields associated with a business enterprise, the data fields including a name of the business enterprise; updating a plurality of database records associated with the received plurality of data records stored in a database, each database record including attributes including the name of the business enterprise and an alias associated with the name of the business enterprise; receiving a query for a particular database record, the query including at least one of the name of the business enterprise or the alias associated with the name of the business enterprise; and preparing for display, in response to the query, one or more of the database records based on at least one of the name of the business enterprise or the alias associated with the name of the business enterprise.
Owner:BUSINESS OBJECTS SOFTWARE
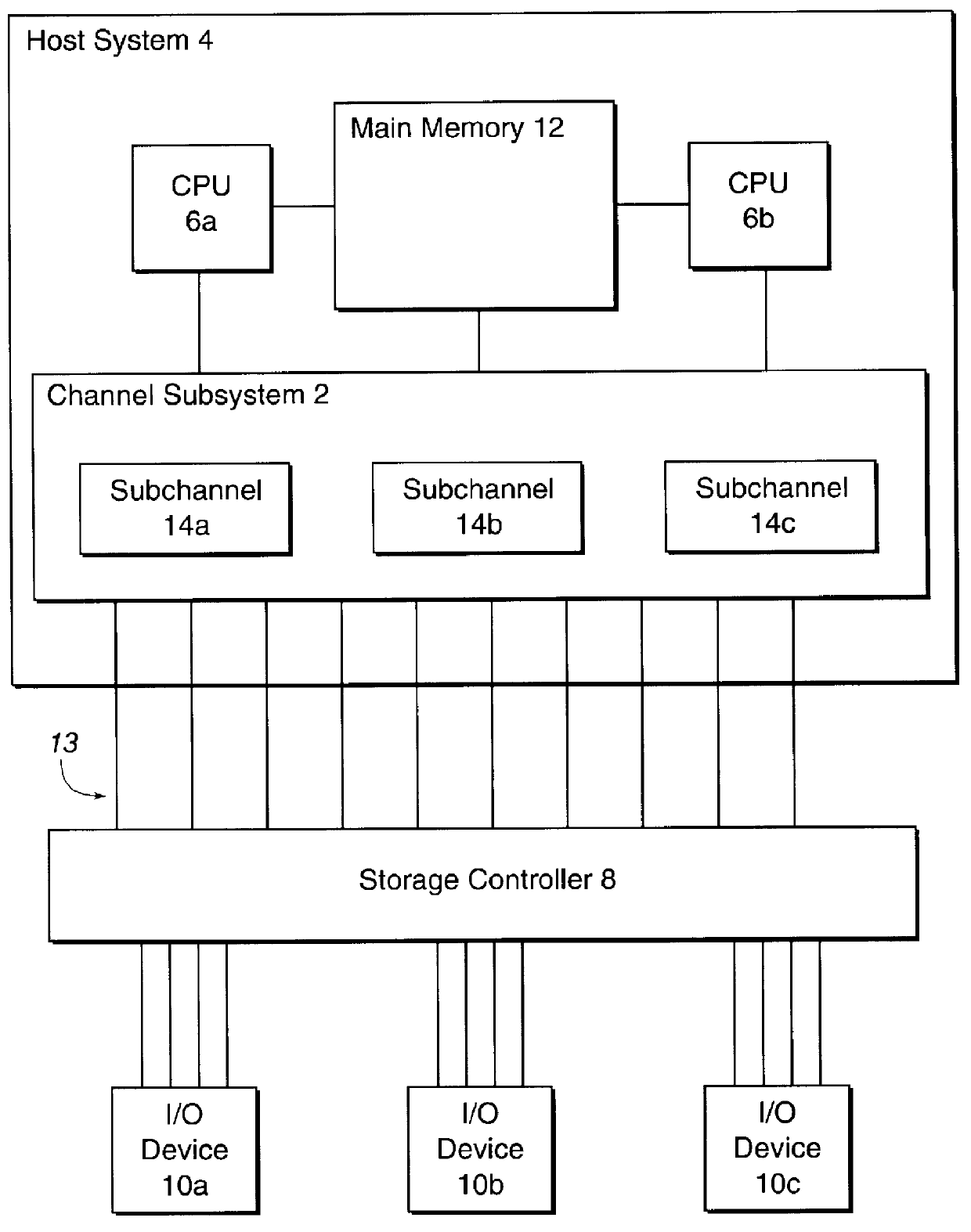
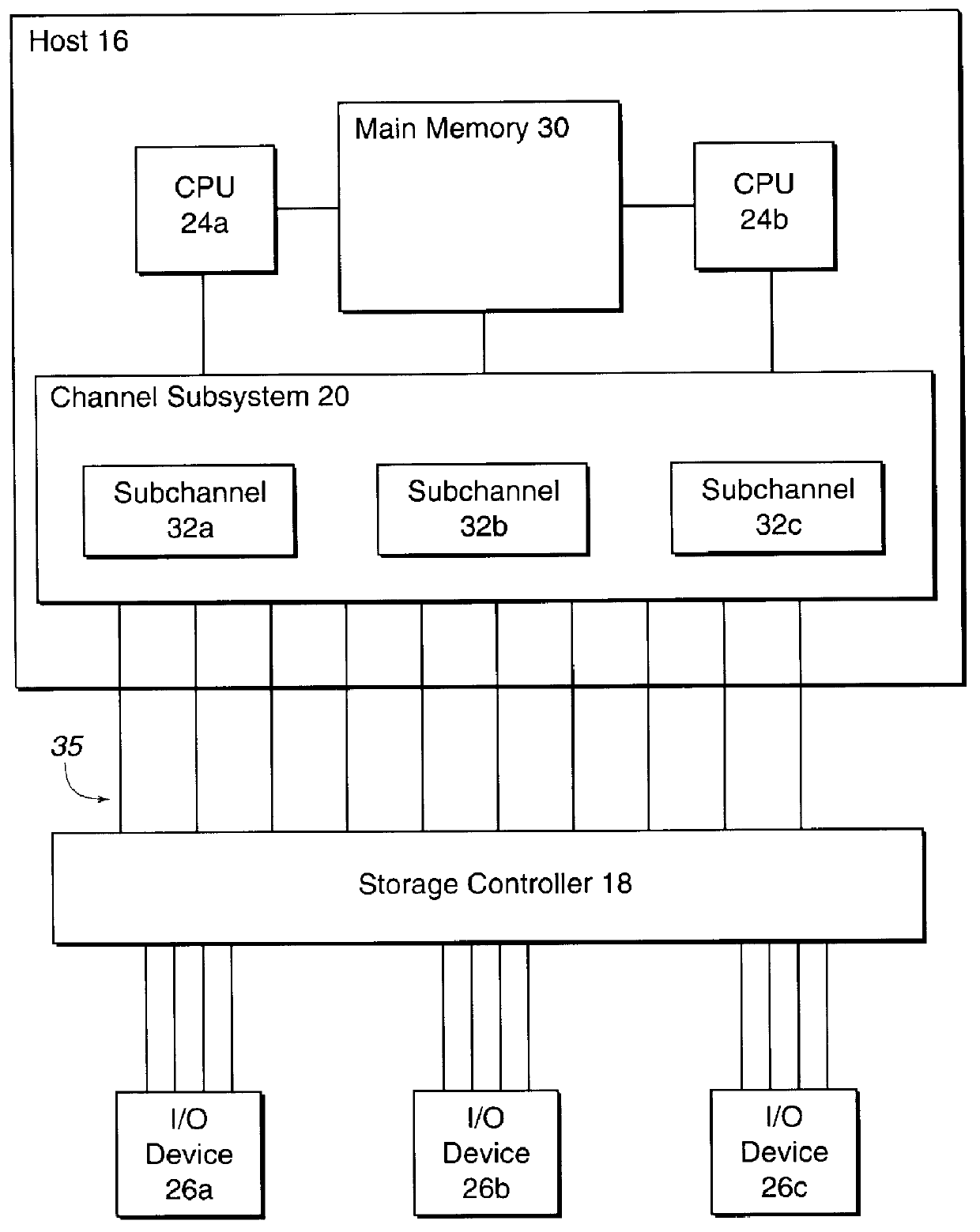
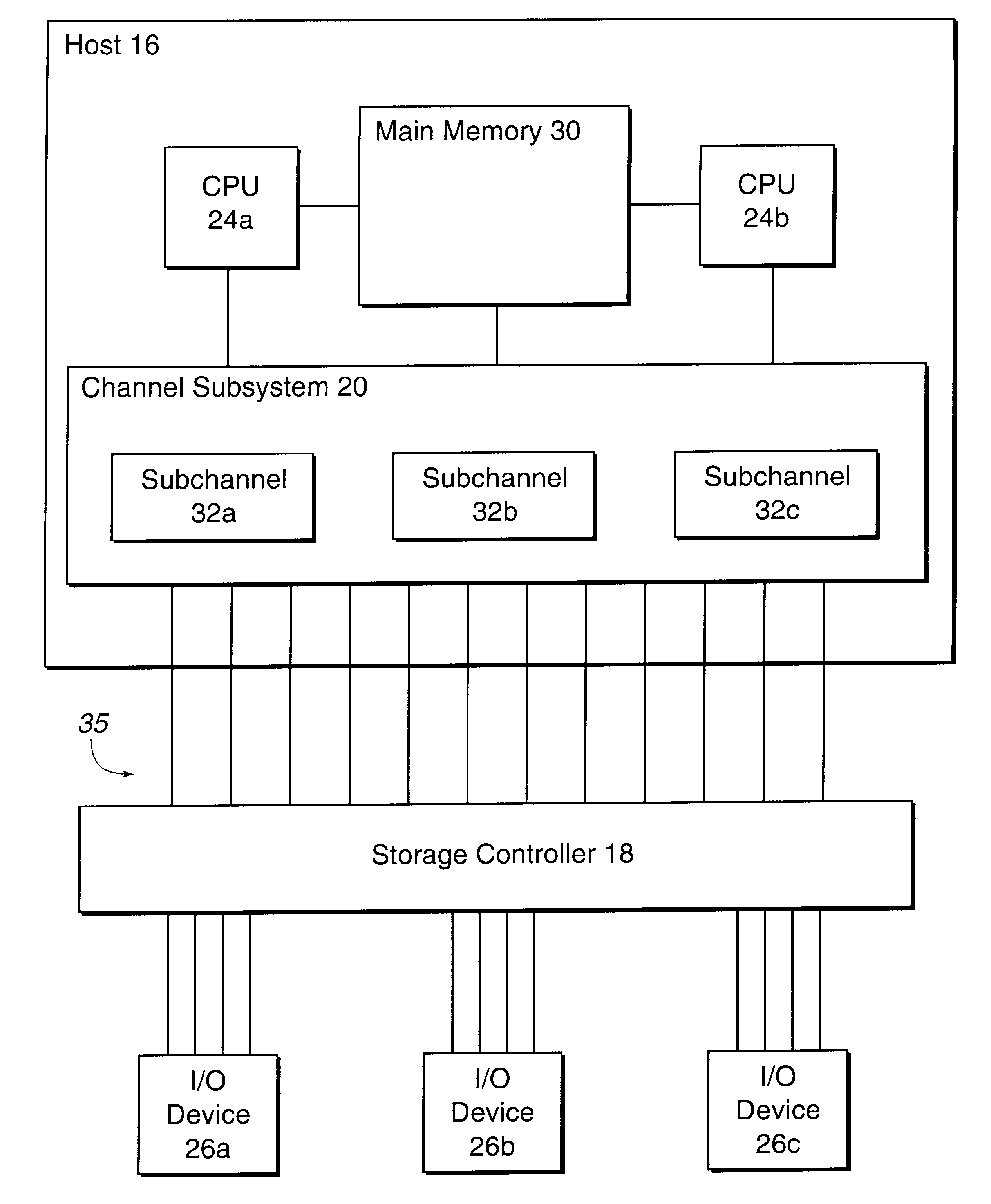
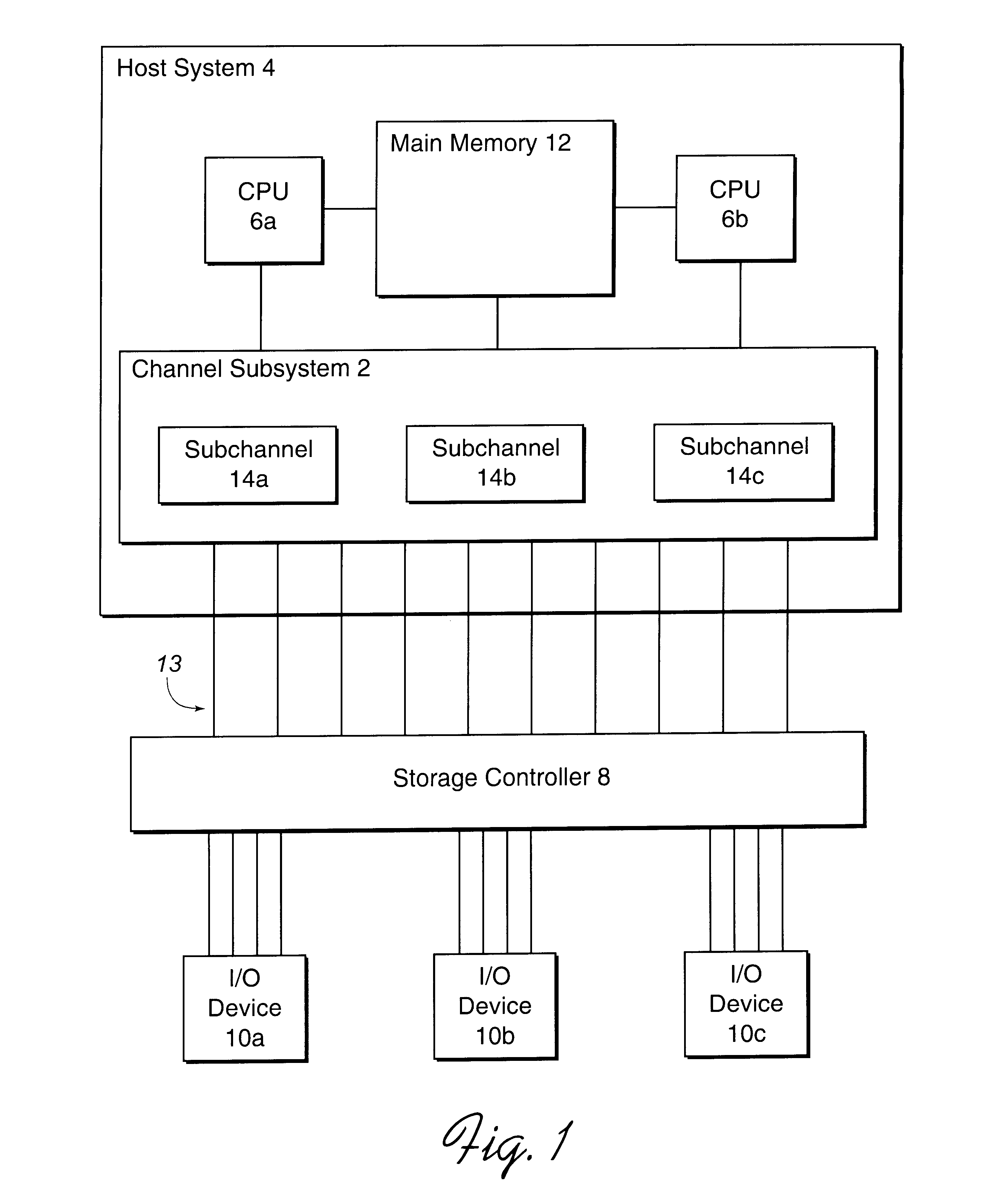
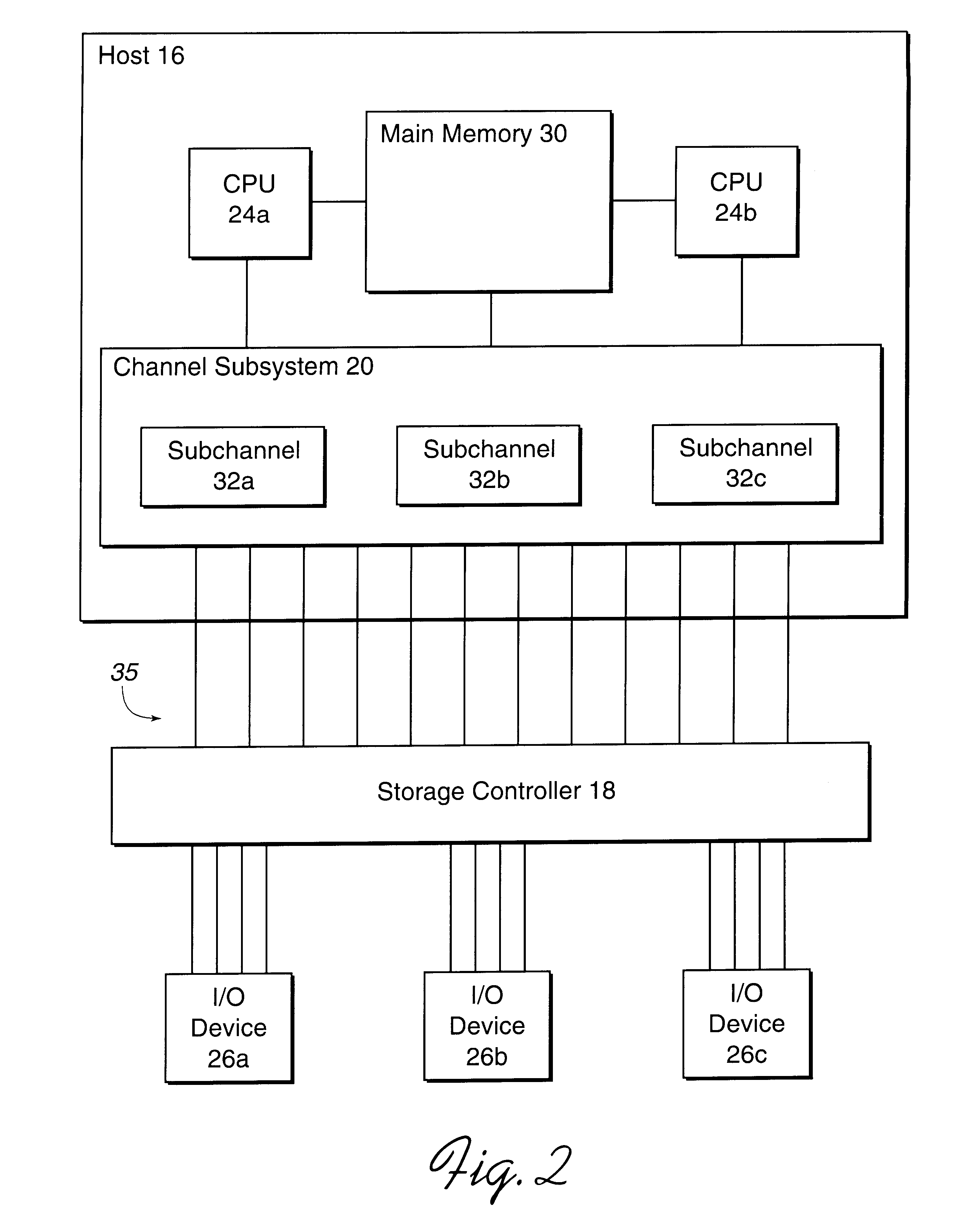
System for reassigning alias addresses to an input/output device
InactiveUS6167459AAvoid overheadReduce needMemory systemsInput/output processes for data processingInput/outputBase address
Disclosed is a system for reassigning addresses. A first processing unit, such as a storage controller, provides at least two base addresses for addressing devices, such as volumes of a direct access storage device (DASD) and a plurality of alias addresses. An alias address associated with a base address provides an address for addressing the device addressed by the base address. The first processing unit processes a command transmitted from a second processing unit, such as a host system that accesses the DASD through the storage controller, to reassign an alias address from a first base address to a second base address. The first base address addresses a first device and the second base address addresses a second device. The first processing unit then indicates that the alias address to reassign is not associated with the first base address and is associated with the second base address. The second device addressed by the second base addresses is capable of being addressed by the reassigned alias address. The first processing unit signals the second processing unit after the first processing unit indicates that the alias address was reassigned from the first base address to the second base address.
Owner:IBM CORP
Method and system for dynamically assigning addresses to an input/output device
InactiveUS6185638B1Memory systemsInput/output processes for data processingDirect-access storage deviceComputerized system
Disclosed is a system for dynamically assigning alias addresses to base addresses referencing an I / O device, such as a direct access storage device (DASD). In the system, at least one base control block indicates a base address and a plurality of alias control blocks indicate a plurality of alias addresses. Each control block is associated with an address for addressing an I / O device. A processing unit, such as a host computer system, processes at least one alias control block associated with the I / O device and determines a base control block associated with the I / O device with which the alias control blocks are associated. The processing unit then binds at least one alias control block to the determined base control block. The bound base and alias control blocks provide different addresses to address the same I / O device. Further, the bound base and alias addresses address the same I / O device for subsequent I / O operations until the processing unit detects a reassignment of the association of base and alias addresses.
Owner:IBM CORP
Method and systems for accessing information on a network using message aliasing functions having shadow callback functions
InactiveUS7058726B1Easy to rememberEasy inputMultiple digital computer combinationsTransmissionOperational systemHome page
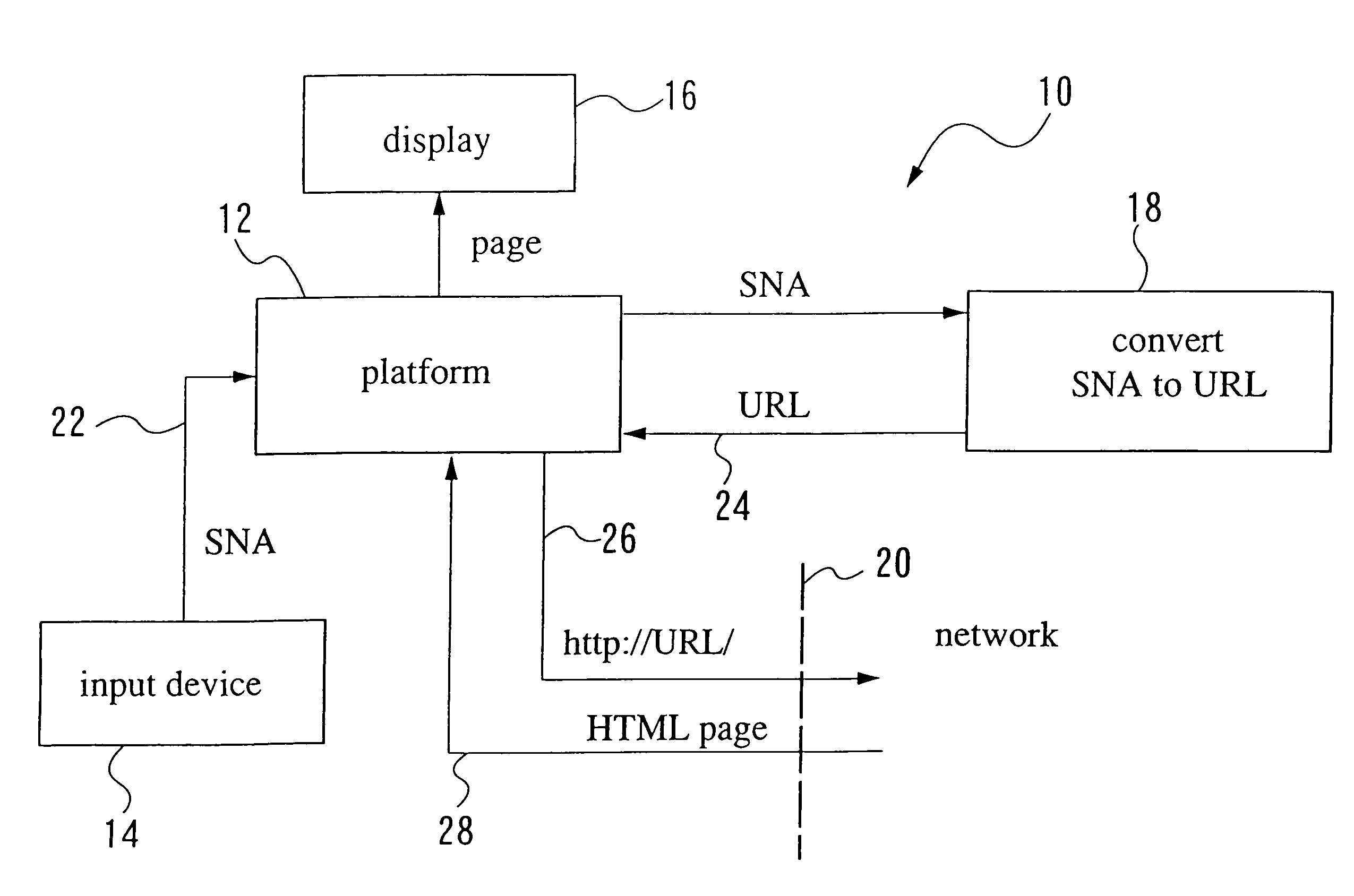
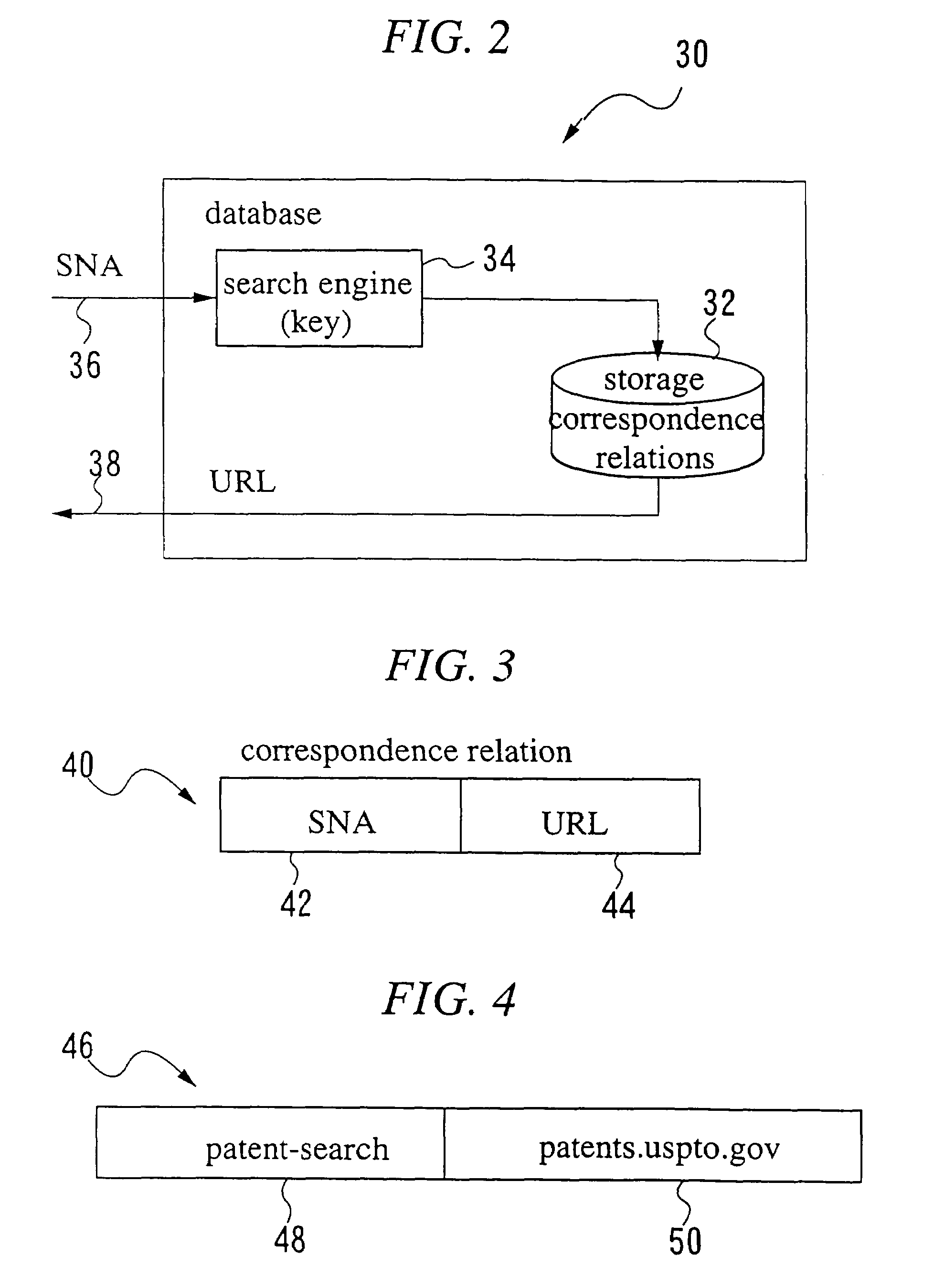
The present invention provides methods and systems for accessing a network URL through a pre-assigned simplified network address, correlating to the URL, and for displaying the home page having the URL as its address. These methods and systems provide easier URL and home page access because persons wanting to access the home page need only input the simplified network address, thereby avoiding the need to know and input the URL character string. The simplified network addresses of the present invention include numbers. Methods are provided for selecting numbers for assignment to URLs. The URL and home page access and display methods of the present invention include: assigning a simplified network address such as a number to a URL, storing the URL and number conversion in a network accessible storage system, inputting the assigned number in a network accessible computer, communicating the inputted number to the storage system, converting the number to the URL, retrieving the home page corresponding to the URL and displaying the home page on the computer. Additionally, the invention provides methods for use in message passing operating systems wherein system level messages to specific objects are intercepted, creating an alias message. The invention further defines networked systems and methods for operating the networked systems that rely on the interception and rule-based modification of messages passing between system applications.
Owner:INTERNET NUMBER
System and method for network security including detection of attacks through partner websites
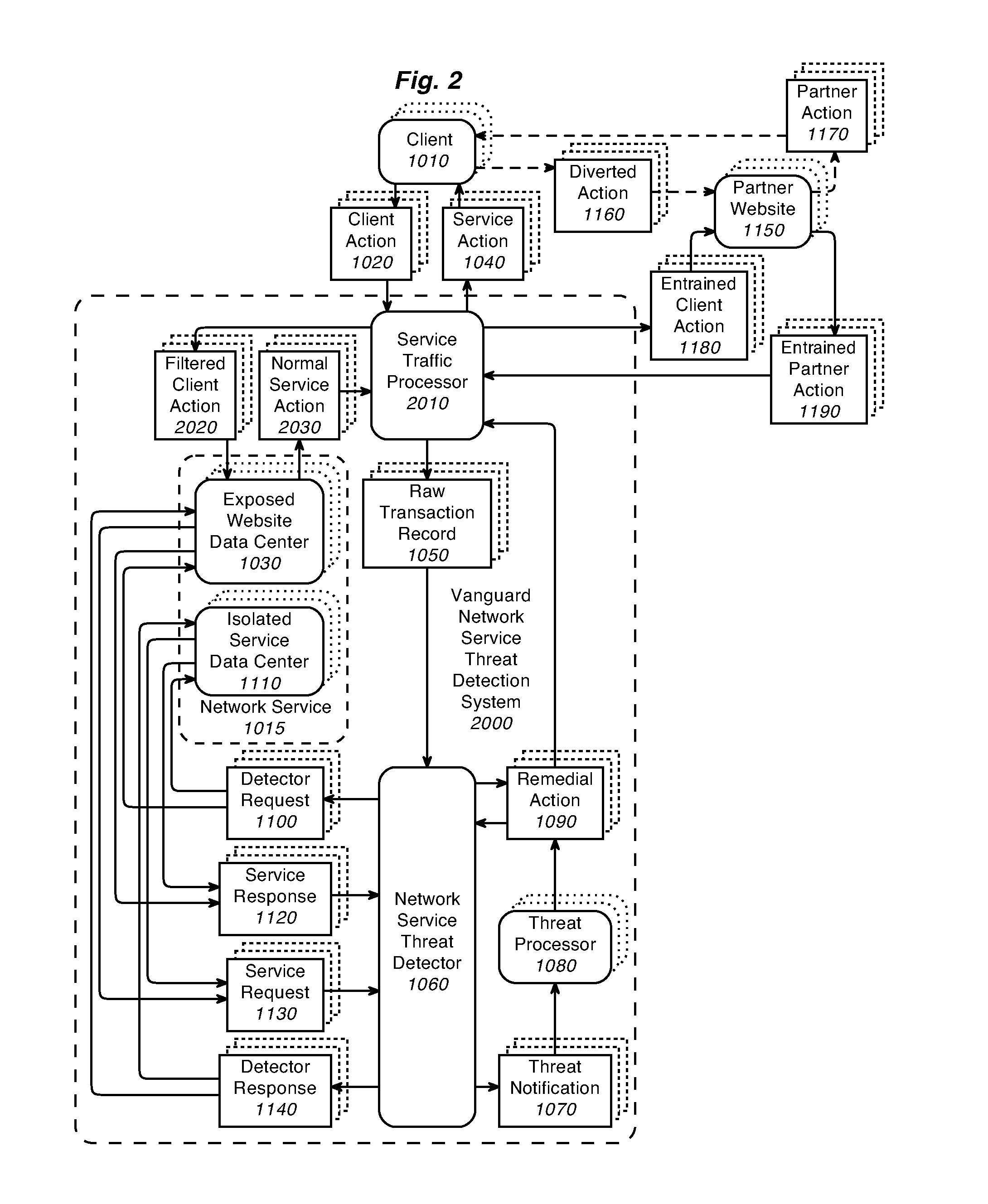
A computer readable storage medium with instructions executable on a host computer. The instructions record a relationship between a partner site and the host computer, substitute a reference to the partner site with a partner site alias referencing the host computer, deliver the partner site alias to a client, replace the partner site alias for the reference to the partner site in response to receiving the partner site alias from the client and augment the address of the client with an address alias. The address alias is sent to the partner site. A partner action and the address alias are received from the partner site. The address is exchanged for the address alias. The partner action is delivered to the client utilizing the address. These operations are monitored to identify client activity that constitutes a security threat at the host computer or the partner site.
Owner:EMC IP HLDG CO LLC
System and method for providing a roster list of temporary contacts having expiration periods designated by a user in an instant messaging environment
InactiveUS7096255B2Data processing applicationsMultiple digital computer combinationsCommunications mediaInstant messaging
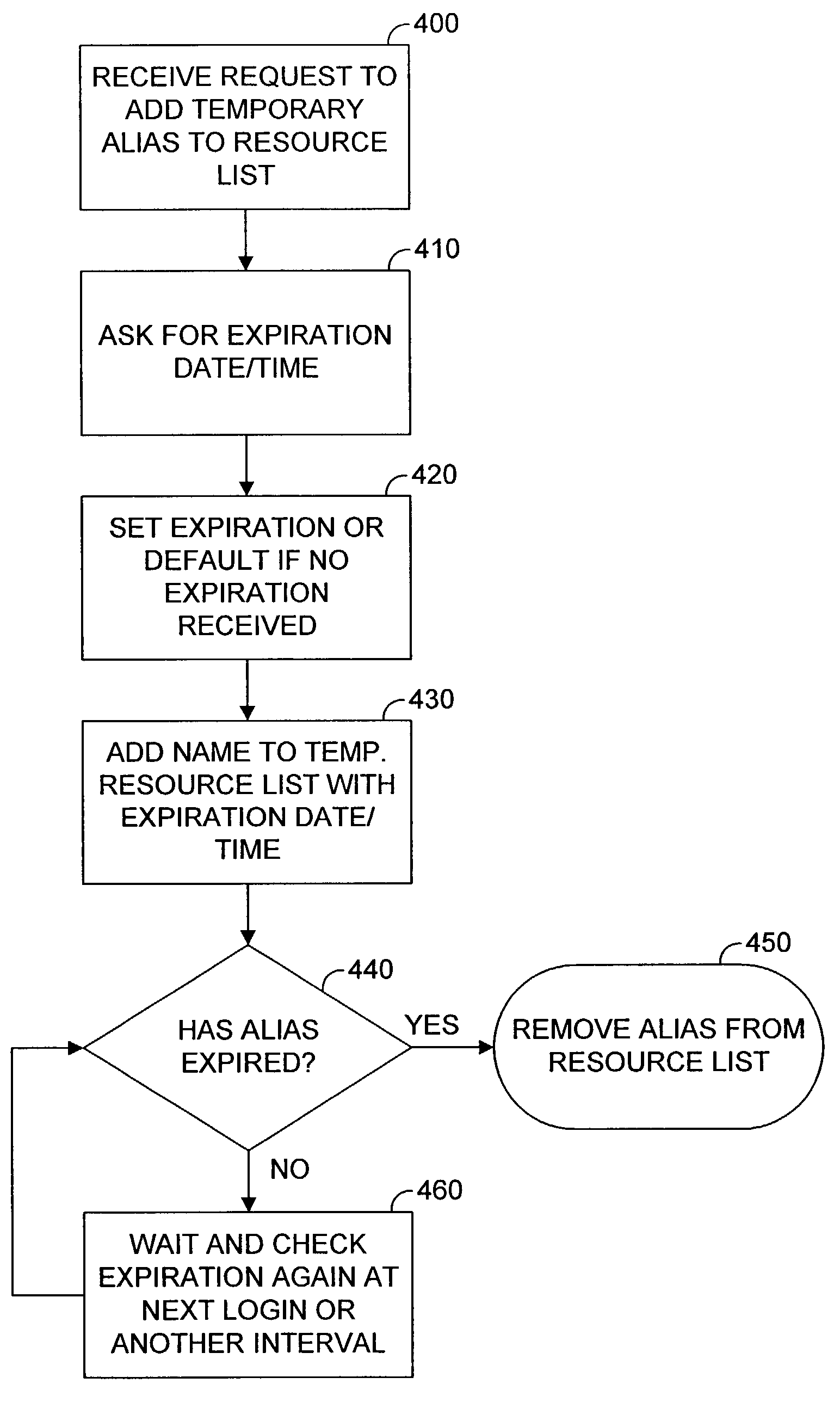
A system for providing temporary contact aliases is provided. A representative system includes a database system operable to store at least one resource list comprising a plurality of contacts associated with at least one user. The plurality of contacts comprising at least one temporary contact at the instruction of said at least one user, stored in said at least one resource list associated with said at least one user. The system further includes a network interface operable to communicate with a plurality of users, including said at least one user, over a network which is operable to provide a communication medium between the plurality of users. Methods and other systems for temporary contact alias are also provided.
Owner:ATLASSIAN US INC
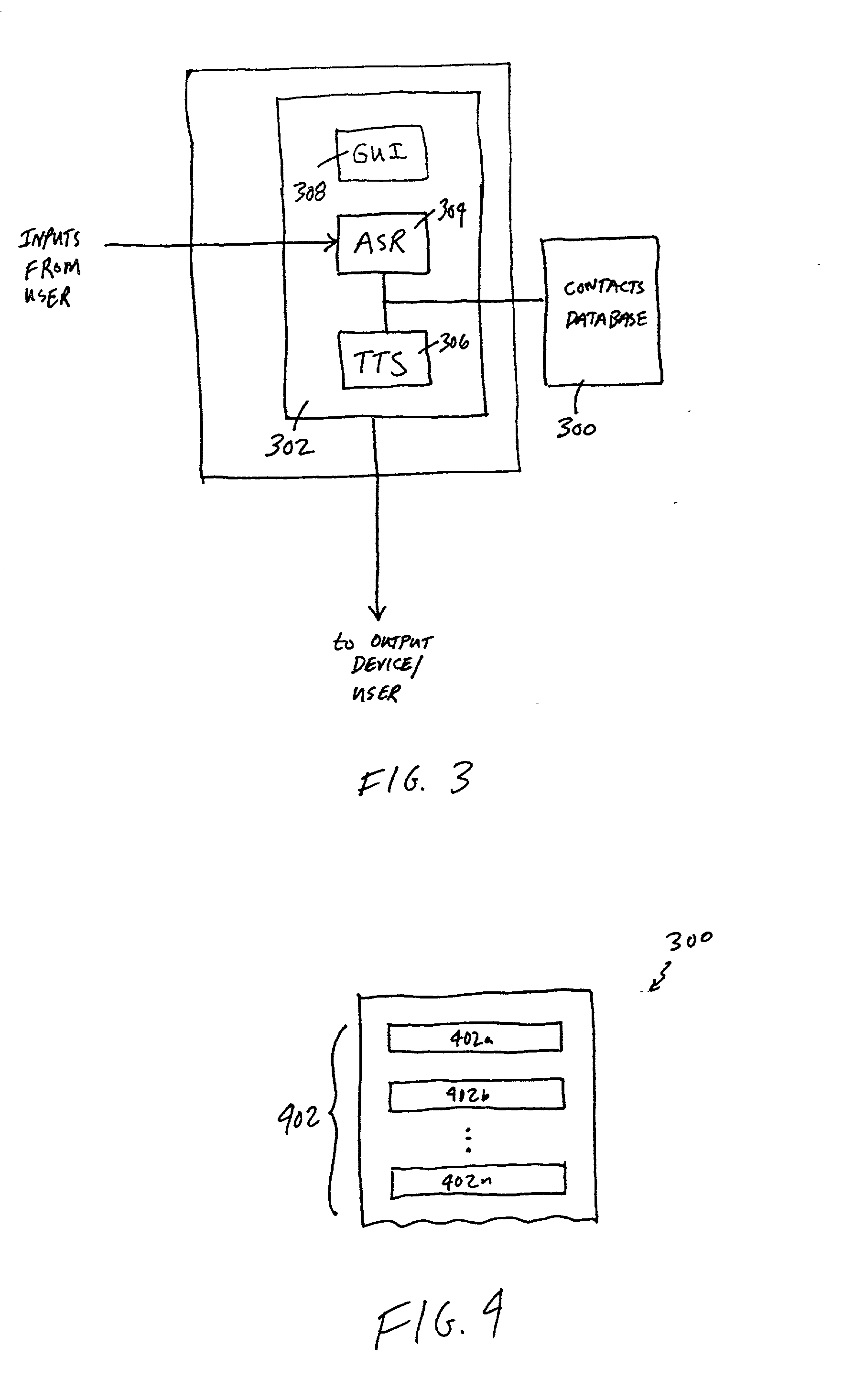
Embedded phonetic support and TTS play button in a contacts database
InactiveUS6462616B1Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingGraphical user interfaceEngineering
Improved methods and arrangements are provided for use in a computer telephony system that supports dial by name operations. A multiple purpose contacts database is modified through a graphical user interface (GUI) to include corresponding phonetically spelled information and / or other alias information for a contact. Voice recognition capabilities in the computer telephony system, which support the dial by name operations, can be directly invoked through the GUI to playback the phonetically spelled information and / or other alias information.
Owner:ERICSSON BUSINESS NETWORKS
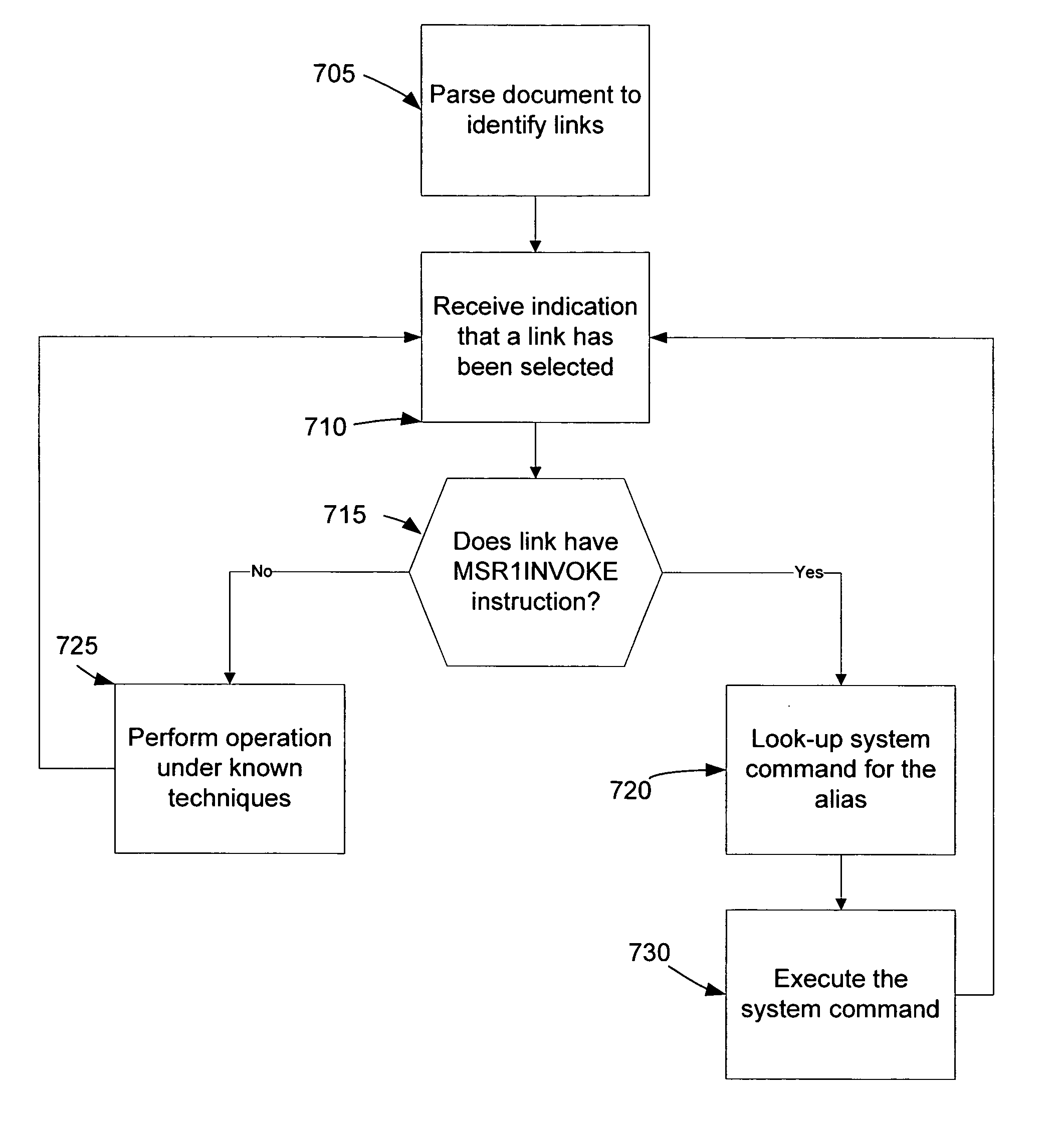
Techniques for invoking system commands from within a mark-up language document
InactiveUS7225400B2Text processingMultiple digital computer combinationsSoftware engineeringDocumentation
A method and apparatus for invoking system resources directly from within a mark-up language document. Links referencing a pre-defined system command to be invoked may be embedded within the document. The specific system command may be identified in the link by an alias, such as, for example, a numeric code. By clicking on the link, the system will analyze the contents of the link. If the link calls for invoking a system command, the system will extract the alias, determine the appropriate pre-defined system command referred to by the alias, and execute the system command.
Owner:MICROSOFT TECH LICENSING LLC
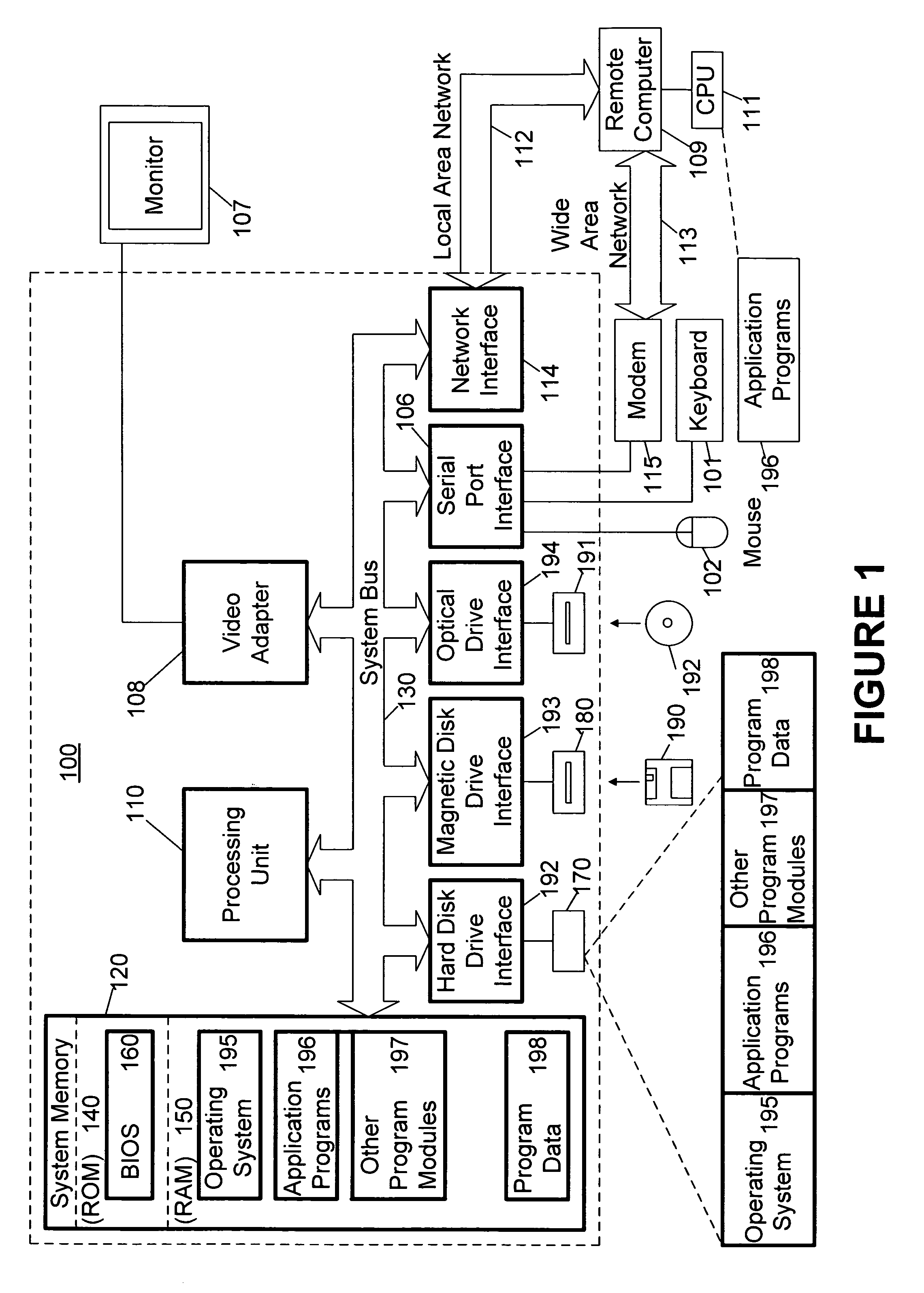
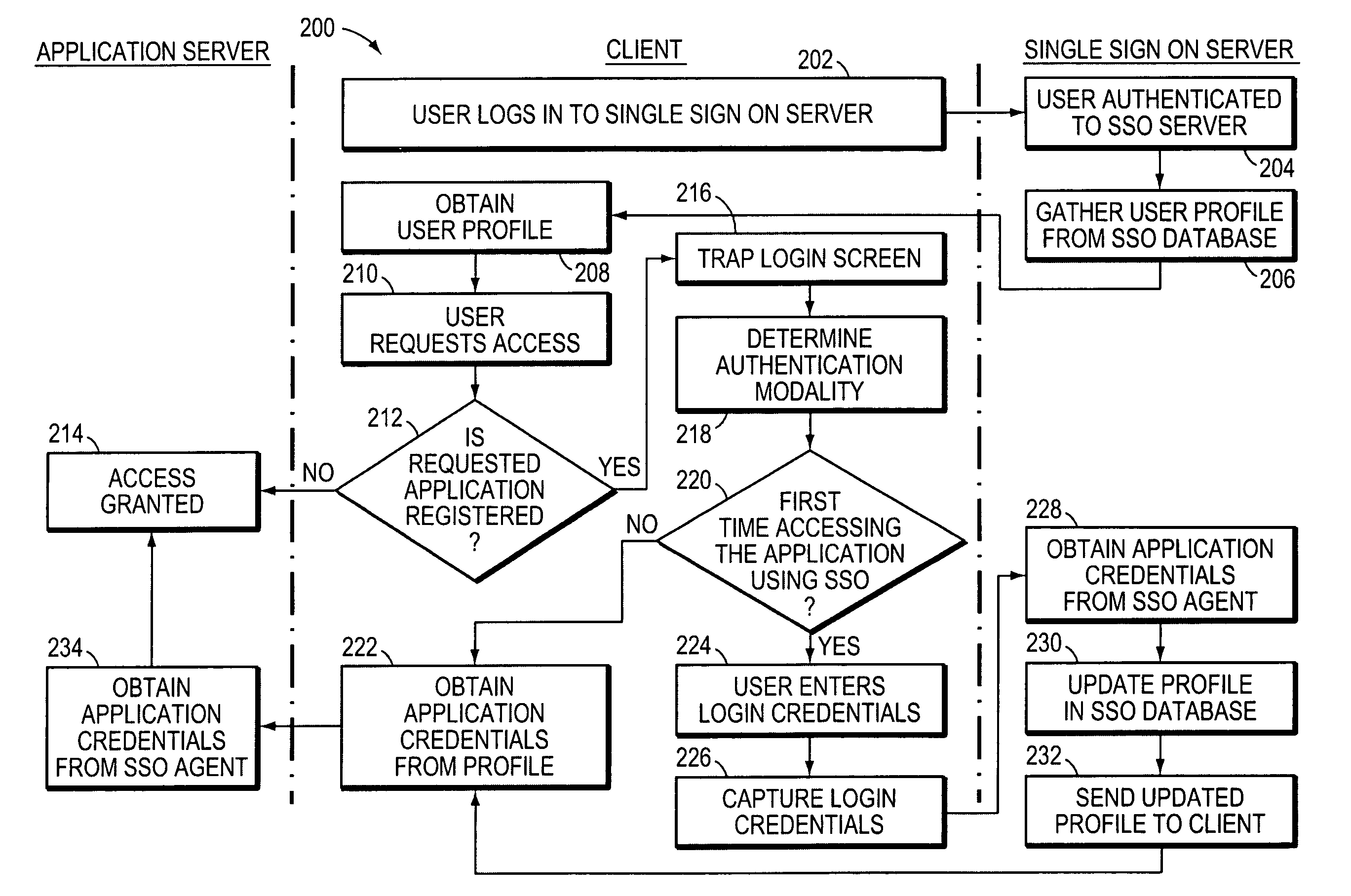
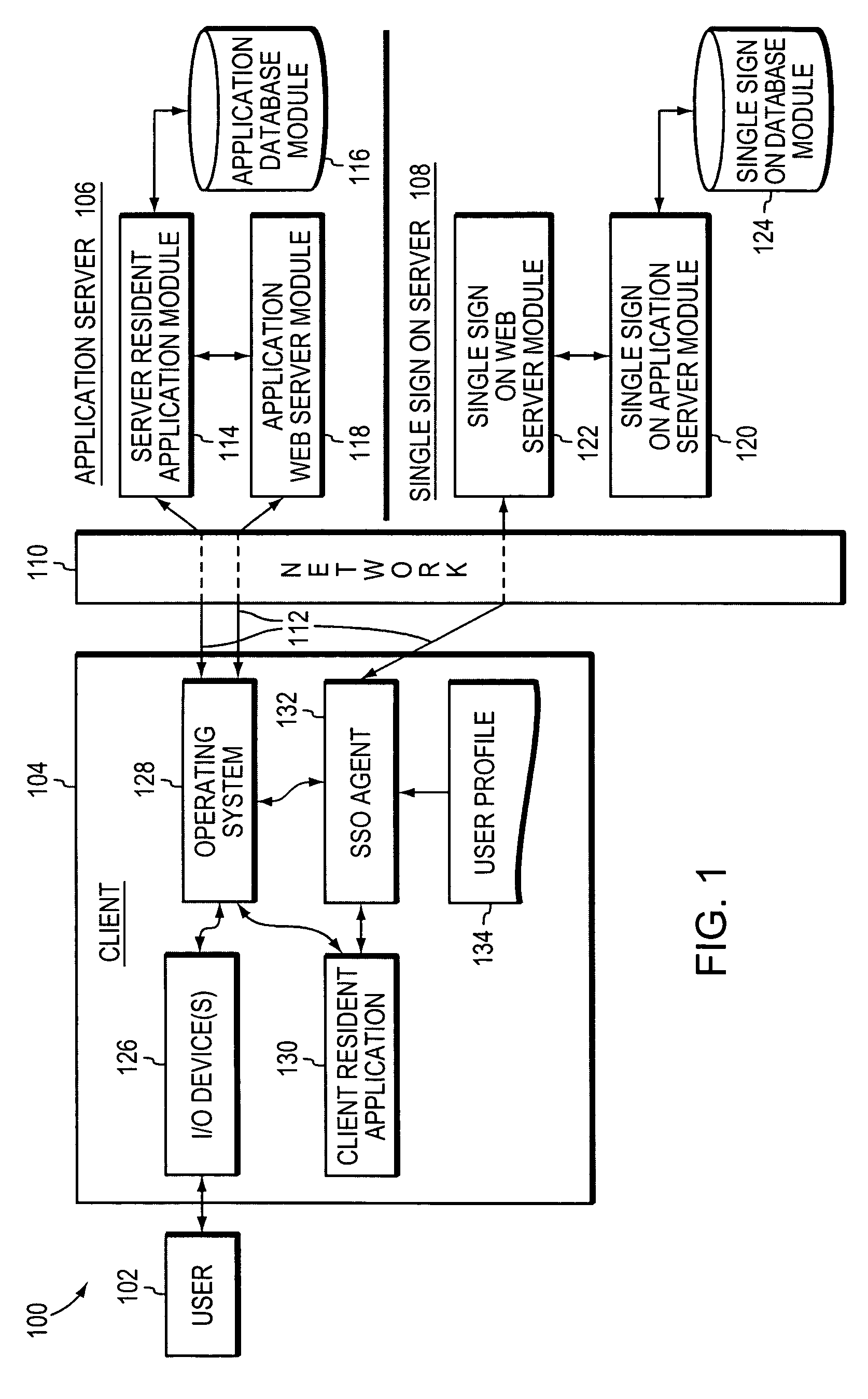
System and method for automated login
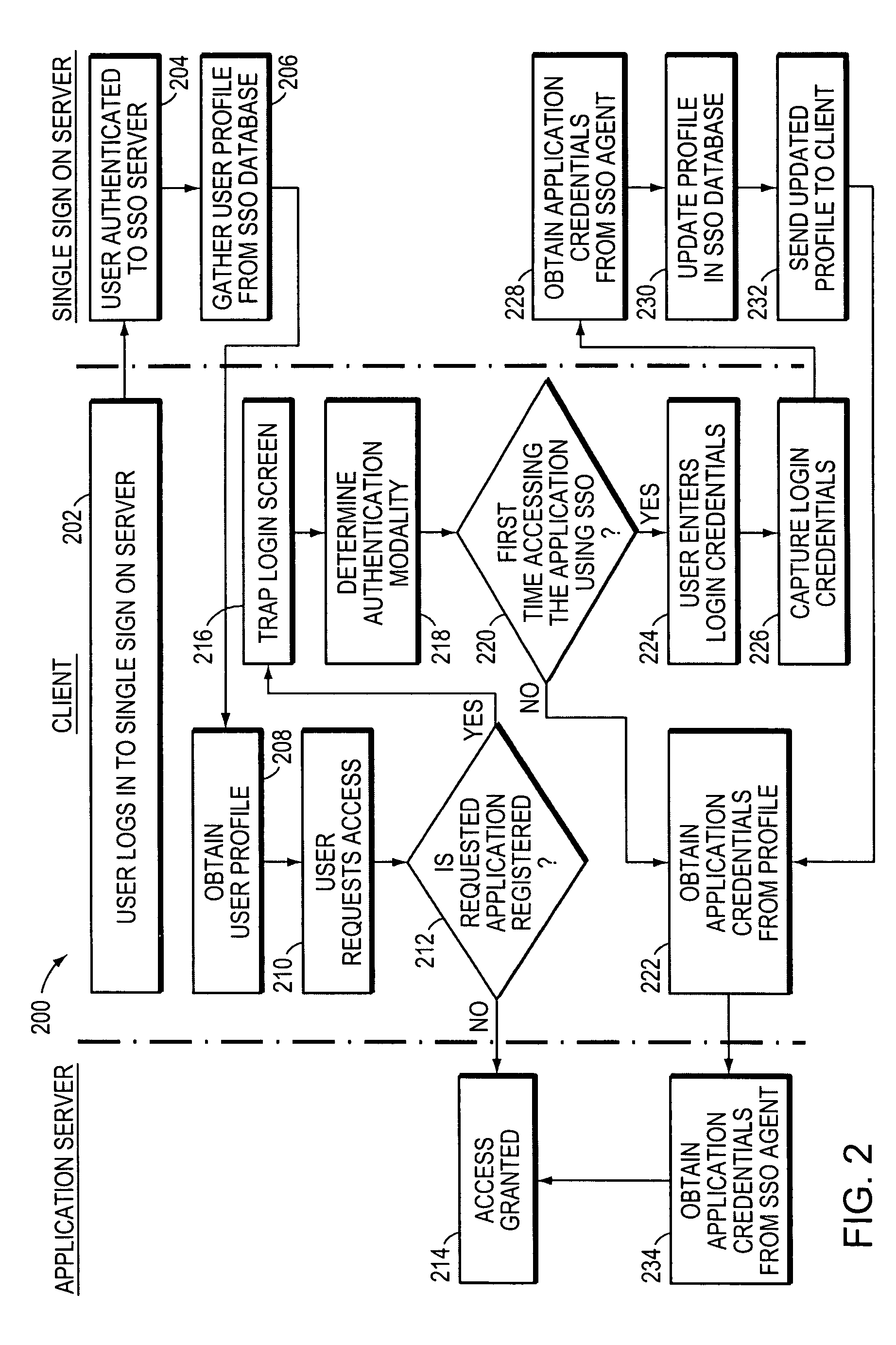
ActiveUS7660880B2Digital data processing detailsMultiple digital computer combinationsApplication softwareUser profile
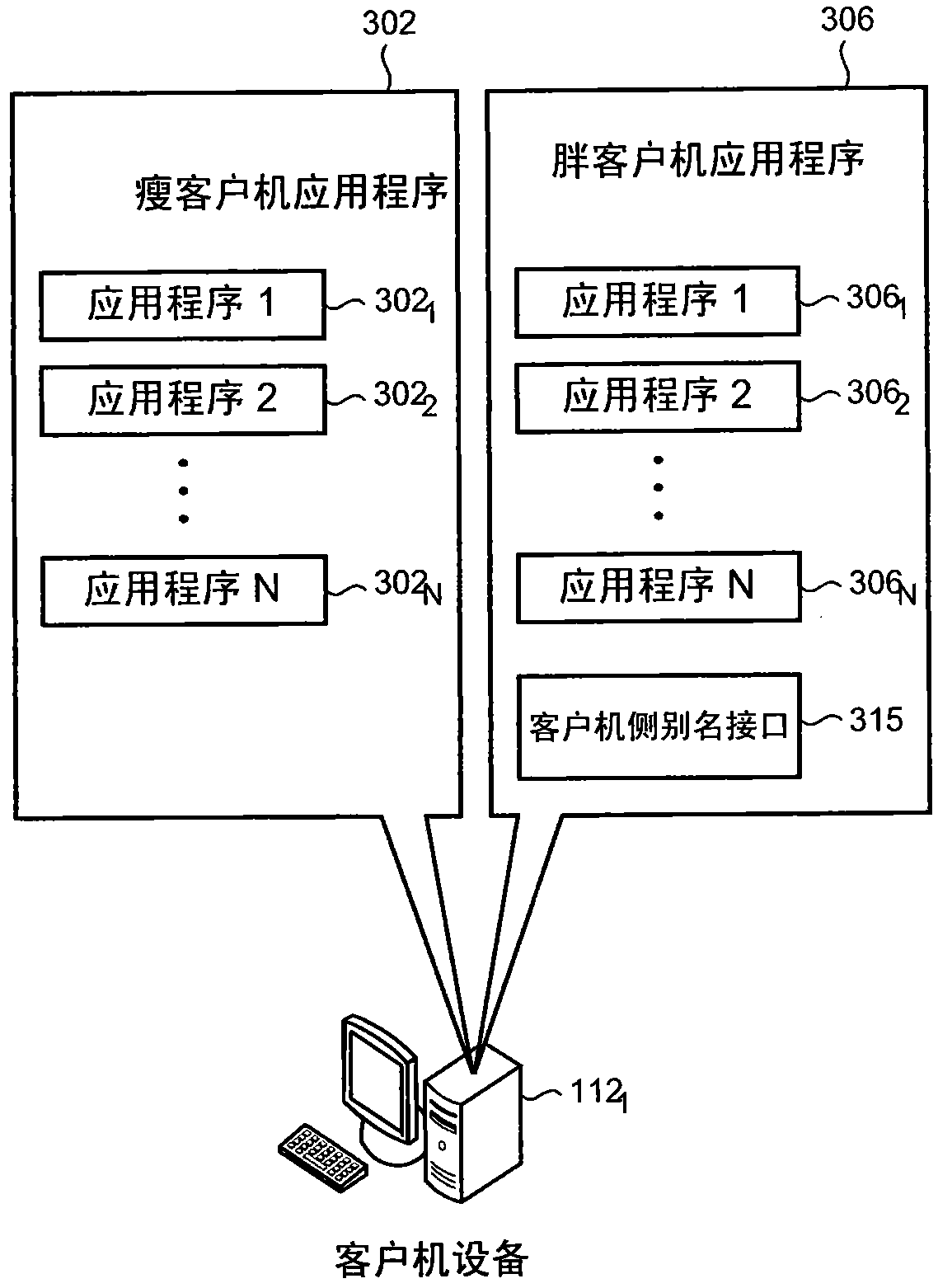
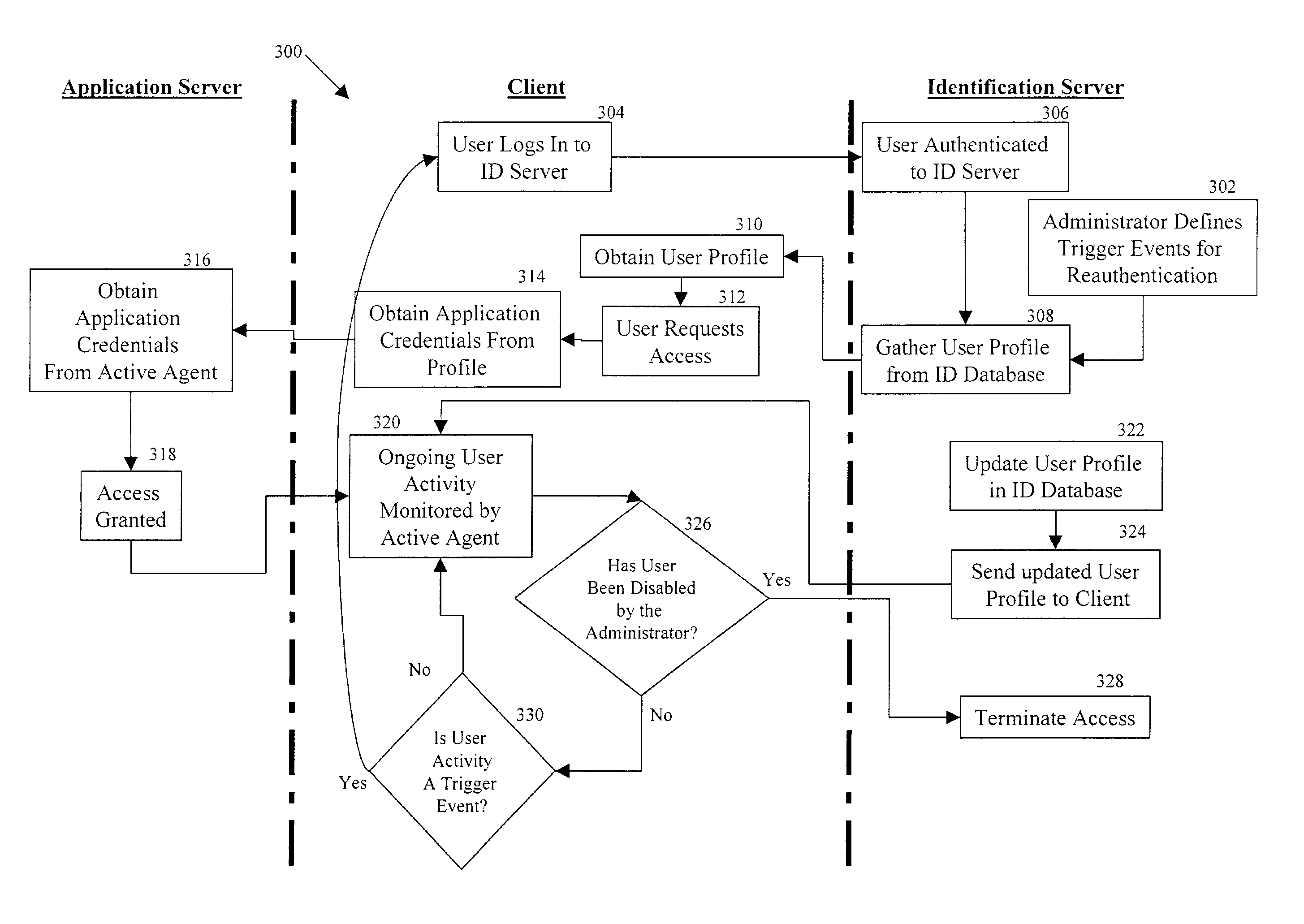
User access to applications is controlled by associating an alias for an individual with a user profile for the individual; the user profile typically contains data referring to one or more applications. Access to an application is obtained using the data in the user profile, e.g., through automatic completion of forms or screens within an application. In addition, the user profile may be employed to limit user access to parts of an application, or to terminate a user's access to an application.
Owner:IMPRIVATA
Method for patching virtually aliased pages by a virtual-machine monitor
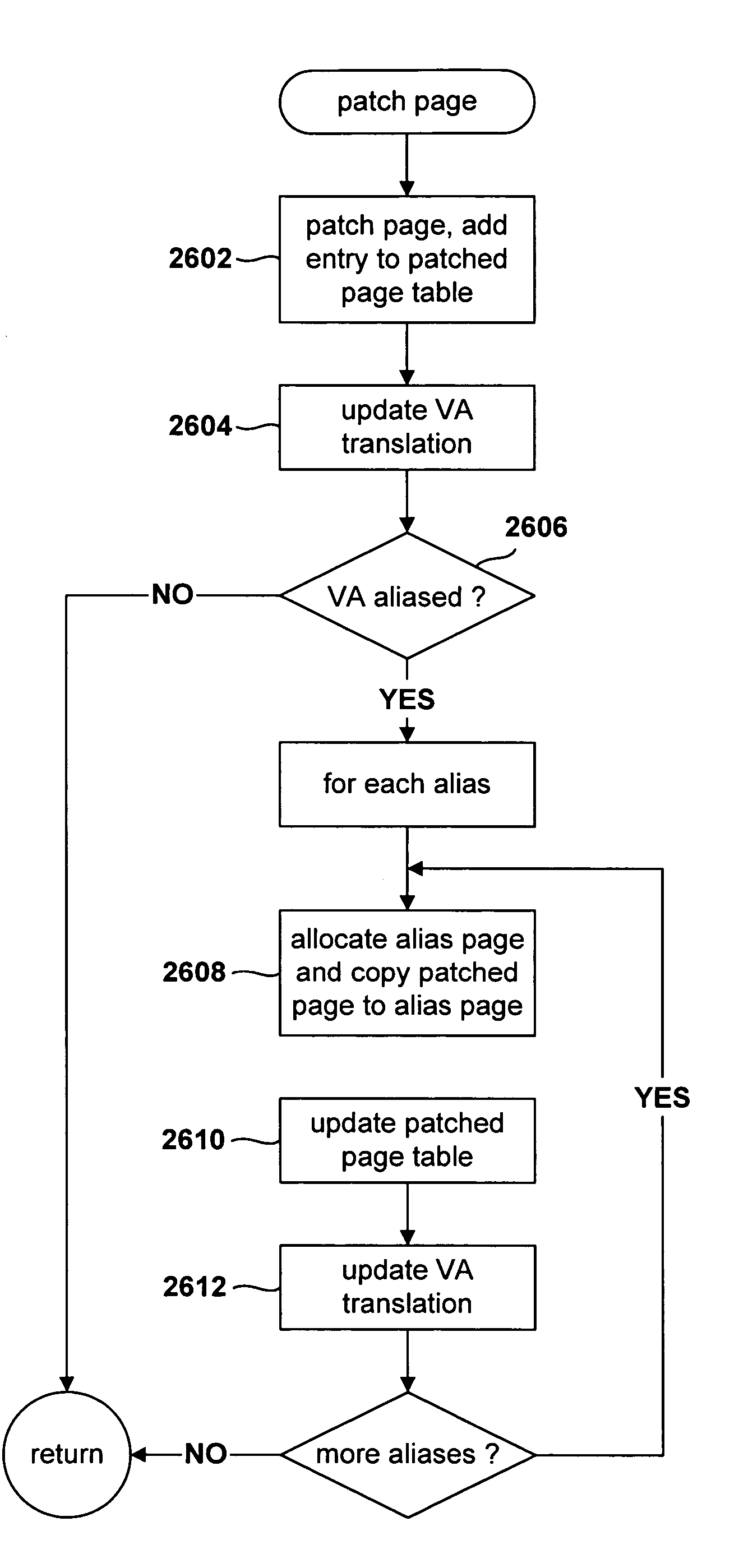
InactiveUS7213125B2Multiprogramming arrangementsSoftware simulation/interpretation/emulationContent replicationSoftware engineering
Various embodiments of the present invention are directed to methods by which a virtual-machine monitor can introduce branch instructions, in order to emulate privileged and other instructions on behalf of a guest operating system, into guest-operating-system code residing on virtually aliased virtual-memory pages. In a described embodiment of the present invention, the virtual-machine monitor physically aliases each virtual alias for a particular physical memory page by allocating a physical page for the virtual alias, copying the original contents of the physical memory page to the allocated physical page, or physical alias page, and subsequently patching each physical alias page appropriate to the physical address of the physical alias page.
Owner:HEWLETT PACKARD DEV CO LP
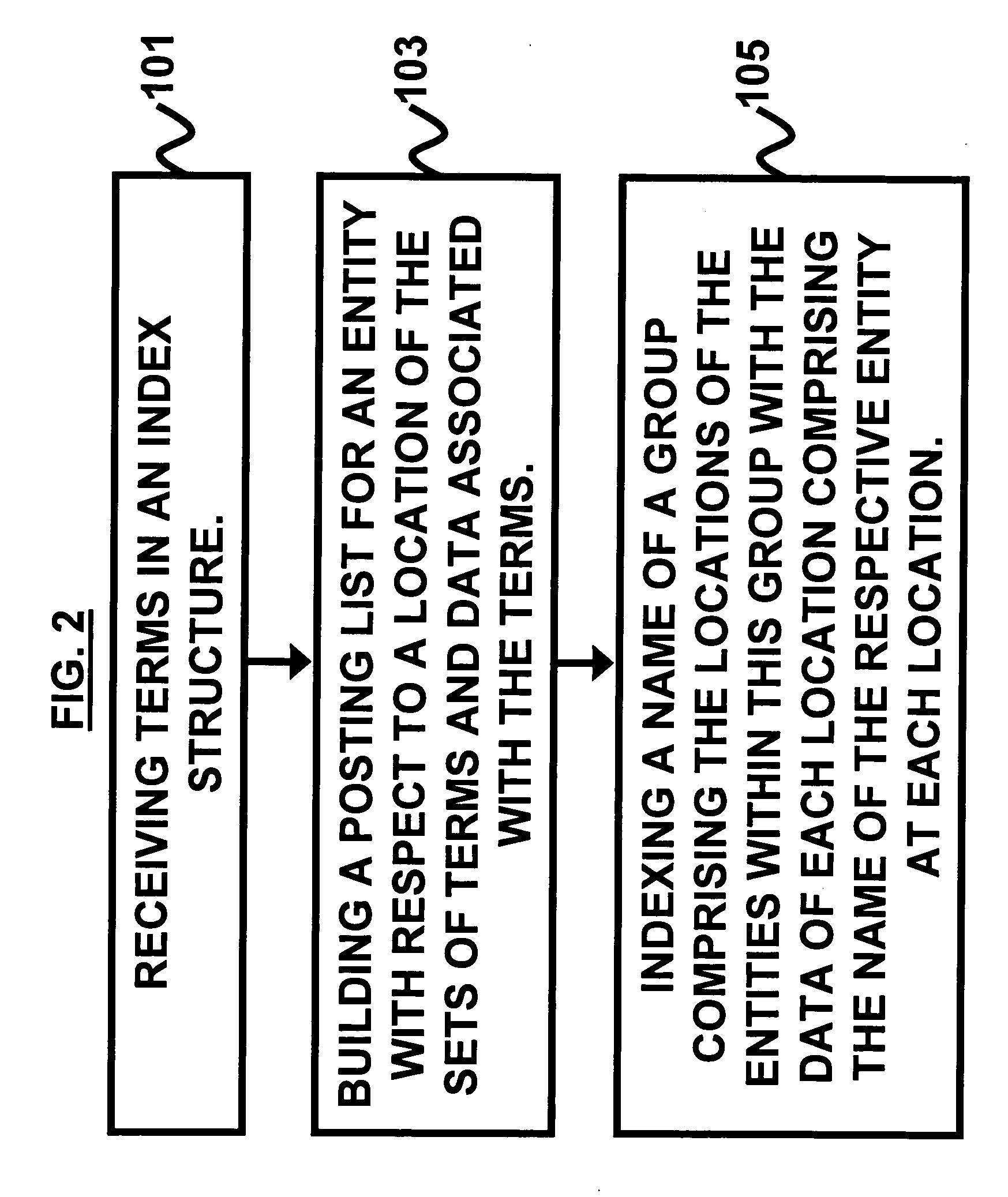
Method and framework to support indexing and searching taxonomies in large scale full text indexes
ActiveUS20070078880A1Digital data information retrievalDigital data processing detailsData storeIndex term
A system and method of indexing a plurality of entities located in a taxonomy, the entities comprising sets of terms, comprises receiving terms in an index structure; building a posting list for an entity with respect to the locations of the set of terms defining the entity and data associated with the respective terms; and indexing a name of a group comprising the entities within this group at the location of the entities with the data of the group comprising the name of the respective entity at each location. The building of the posting list comprises storing the location of the term and data associated with the term in an entry in the posting list for the term. The method comprises indexing aliases of the name of the group comprising the term, and using an inverted list index to associate data with each occurrence of an index term.
Owner:IBM CORP
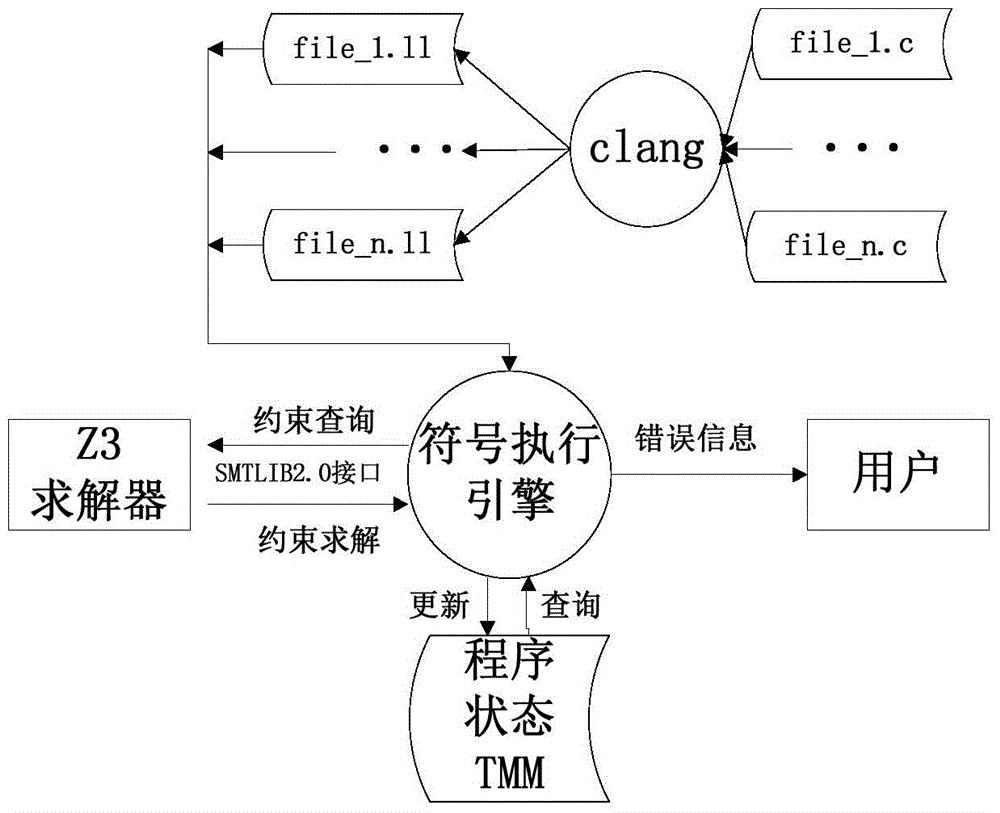
Code static detection method
ActiveCN104965788AEnable cross-language analysisRealize analysisSoftware testing/debuggingArray data structureSource code
The invention discloses a code static detection method, particularly relates to an LLVM IR (low level virtual machine intermediate representation) based symbol execution algorithm in the technical field of utilization of initial values of variable symbols of given programs, and solves the problems of single supported language and incapability of better processing pointers and aliases for a static detection method in the prior art and the problems in detecting potential program bugs and the like. The method comprises the steps of: (1) obtaining a source code, and preprocessing and converting the source code into an LLVM assembly program; (2) simulating interpretive execution of the LLVM assembly program obtained by conversion by applying the symbol execution algorithm, and recording the symbol value of each variable in different paths and the constraint conditions of each path; and (3) according to the recorded symbol value of each variable in different paths and constraint conditions of each path, calling an SMT (satisfiability modulo theories) solver Z3 to check whether the symbol value of the variable meets the path constraint and the bug constraint, and judging whether the program has potential bugs. The method is applied to array bound overflow, division by zero and null pointer dereference.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
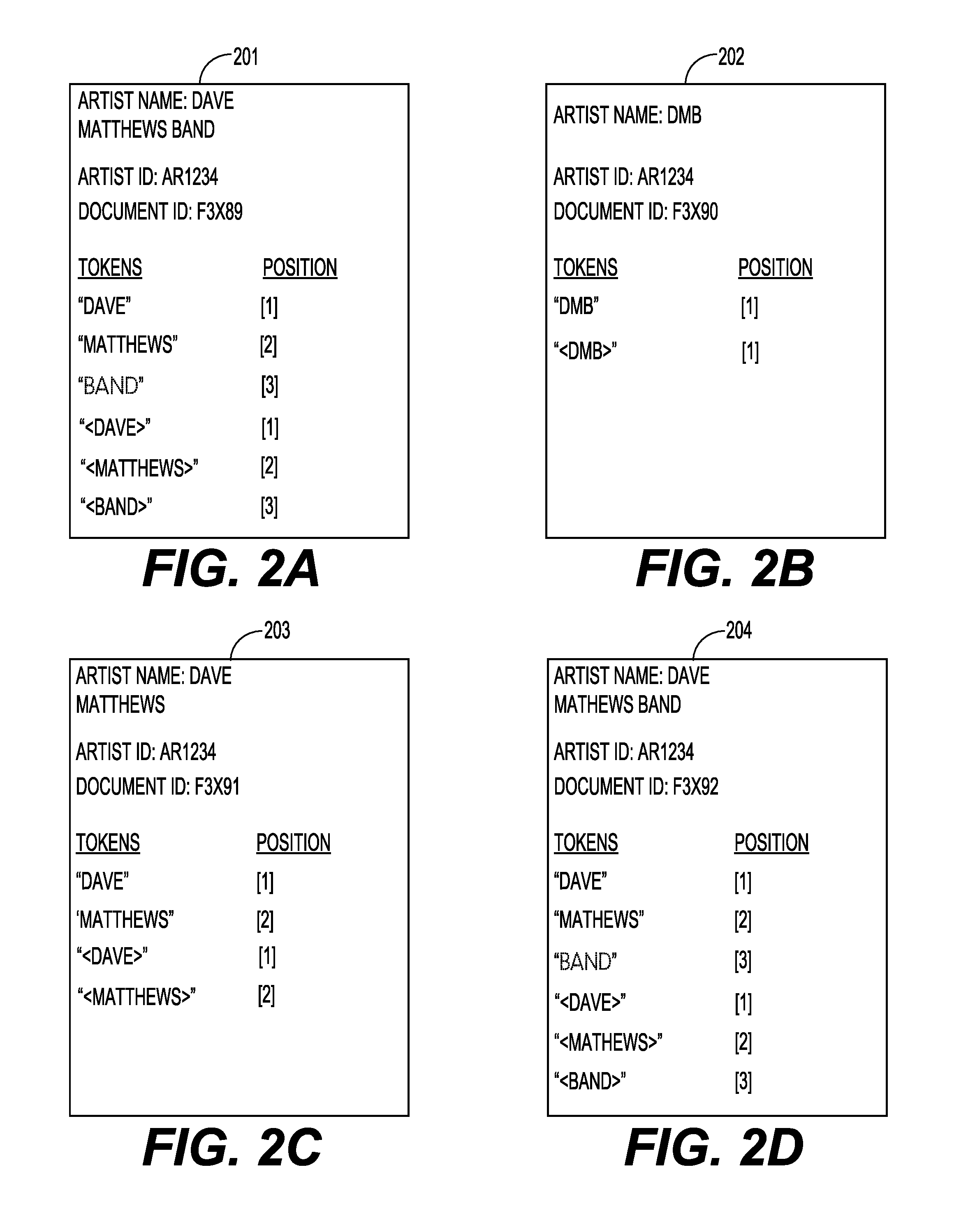
Named entity extraction from a block of text
A data processing method, program, and apparatus for identifying a document within a block of text. A block of text is tokenized into a plurality of text tokens according to at least one rule parser. Each of the plurality of text tokens is sequentially compared to a plurality of document tokens to determine if the text token matches one of the plurality of document tokens. The plurality of document tokens correspond to a plurality of documents which have been tokenized according to the one or more rule parsers. Each matched text token is filtered according to predetermined filtering criteria to generate one or more candidate text tokens. It is then determined whether sequence of candidate text tokens that occur in sequential order within the block of text match sequence of document tokens. If so, then it is determined that the document has been identified within the block of text. The document can correspond to an artist, a song names, and misspellings and aliases thereof.
Owner:SPOTIFY
Embedded phonetic support and tts play button in a contacts database
InactiveUS20020041659A1Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingGraphicsGraphical user interface
Improved methods and arrangements are provided for use in a computer telephony system that supports dial by name operations. A multiple purpose contacts database is modified through a graphical user interface (GUI) to include corresponding phonetically spelled information and / or other alias information for a contact. Voice recognition capabilities in the computer telephony system, which support the dial by name operations, can be directly invoked through the GUI to playback the phonetically spelled information and / or other alias information.
Owner:ERICSSON BUSINESS NETWORKS
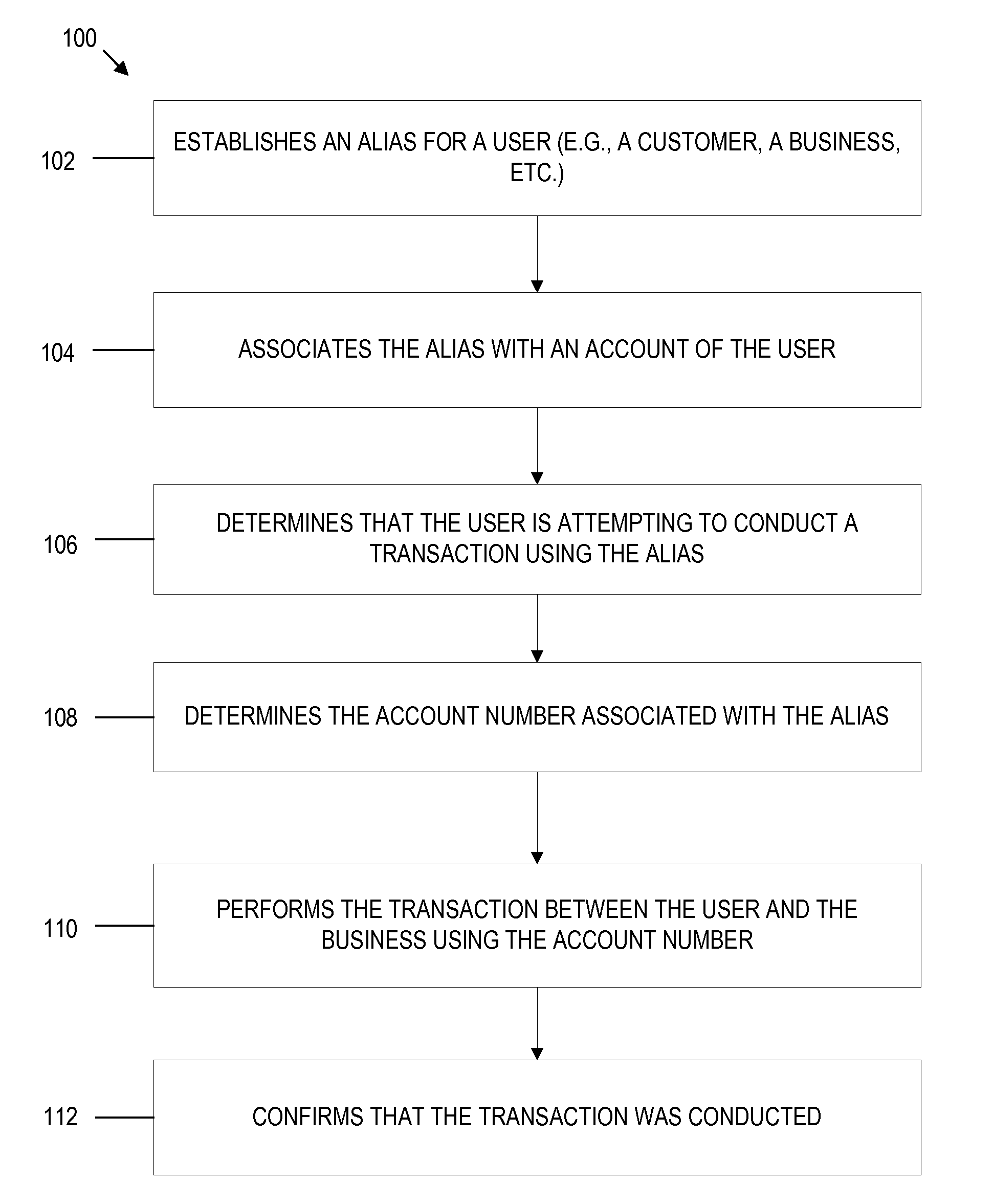
Alias-based merchant transaction system
InactiveUS20130018779A1User-friendly interfaceEasily register existing account and openFinanceFinancial transactionFinancial trading
A system and method for using an alias to conduct financial transactions at a merchant is provided. The system and method allows a user to provide an alias identifying the user or a business in order to conduct transactions without needing to know or provide actual account numbers. Aliases are associated with users and businesses and can be linked to financial accounts of the user and business. When the method determines that the user is attempting to conduct a transaction using the alias, the method determines the account number associated with the alias and completes the transaction using the alias. The method may also evaluate the transaction to determine whether pre-determined rules are complied with and provide confirmation to the user that the transaction has completed.
Owner:BANK OF AMERICA CORP
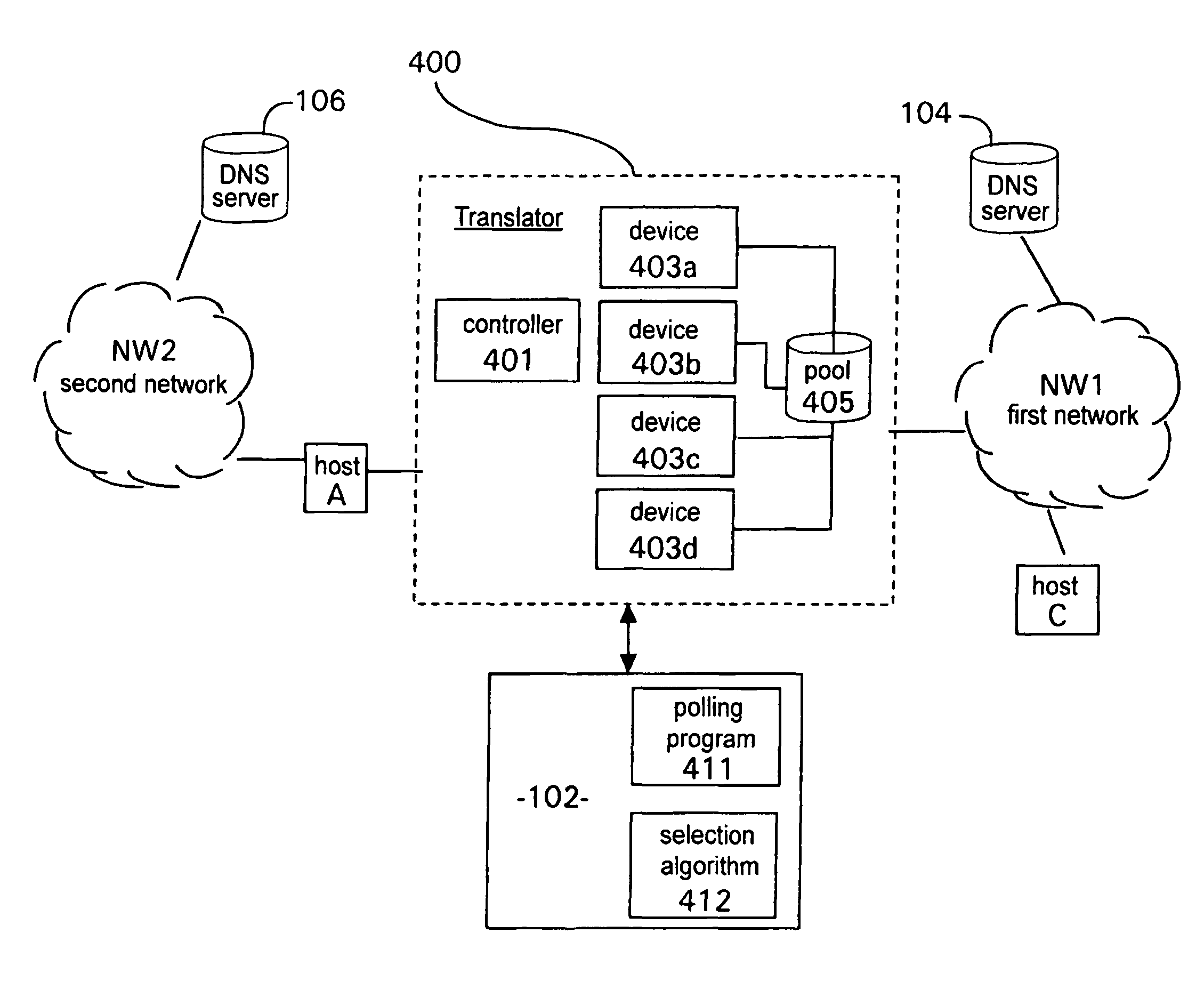
Inter-network address translator that is separately addressable from address alias assignment process
ActiveUS8046452B2Multiple digital computer combinationsNetwork connectionsNetwork Communication ProtocolsNetwork addressing
Communication between a network device in a first network and a network device in a second network is provided, where the first network operates in accordance with a first communication protocol and the second network operates in accordance with a second communication protocol. An alias is assigned to a target network device in the first network, the alias being compatible with the communication protocol of the second network The assigned alias is translated to an address for a target network device, the translated address being compatible with the communication protocol of the first network. Apparatus, for assigning the alias and for translating it are separately addressable in one or both of the networks, and the assigned alias corresponds to an address of the translating apparatus, such that, when a network device in the second network sends one or more communication(s) using an address including the assigned alias, each communication is routed to the translator, whereupon the translator translates the alias into the address of the target network device in the first network and sends the communication(s) into the first network.
Owner:BRITISH TELECOMM PLC
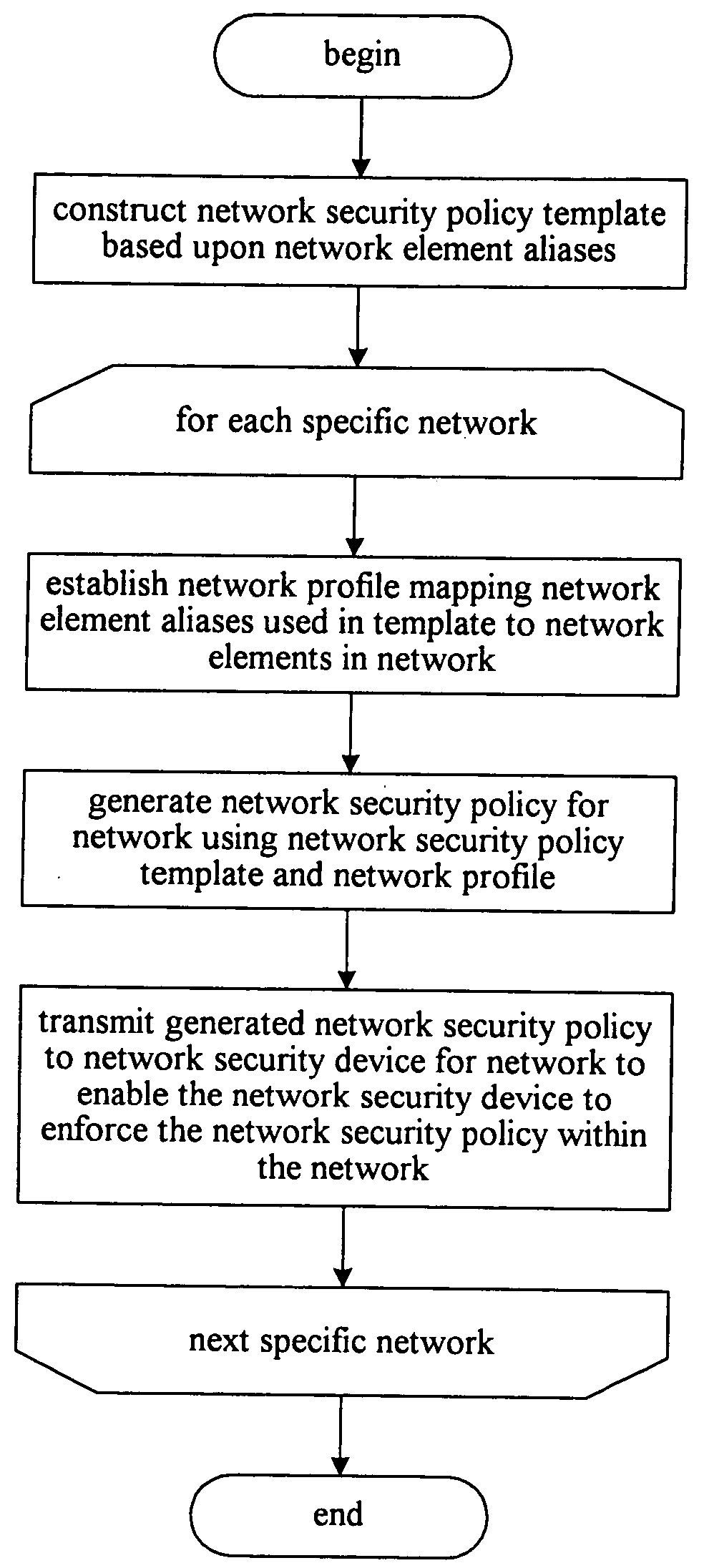
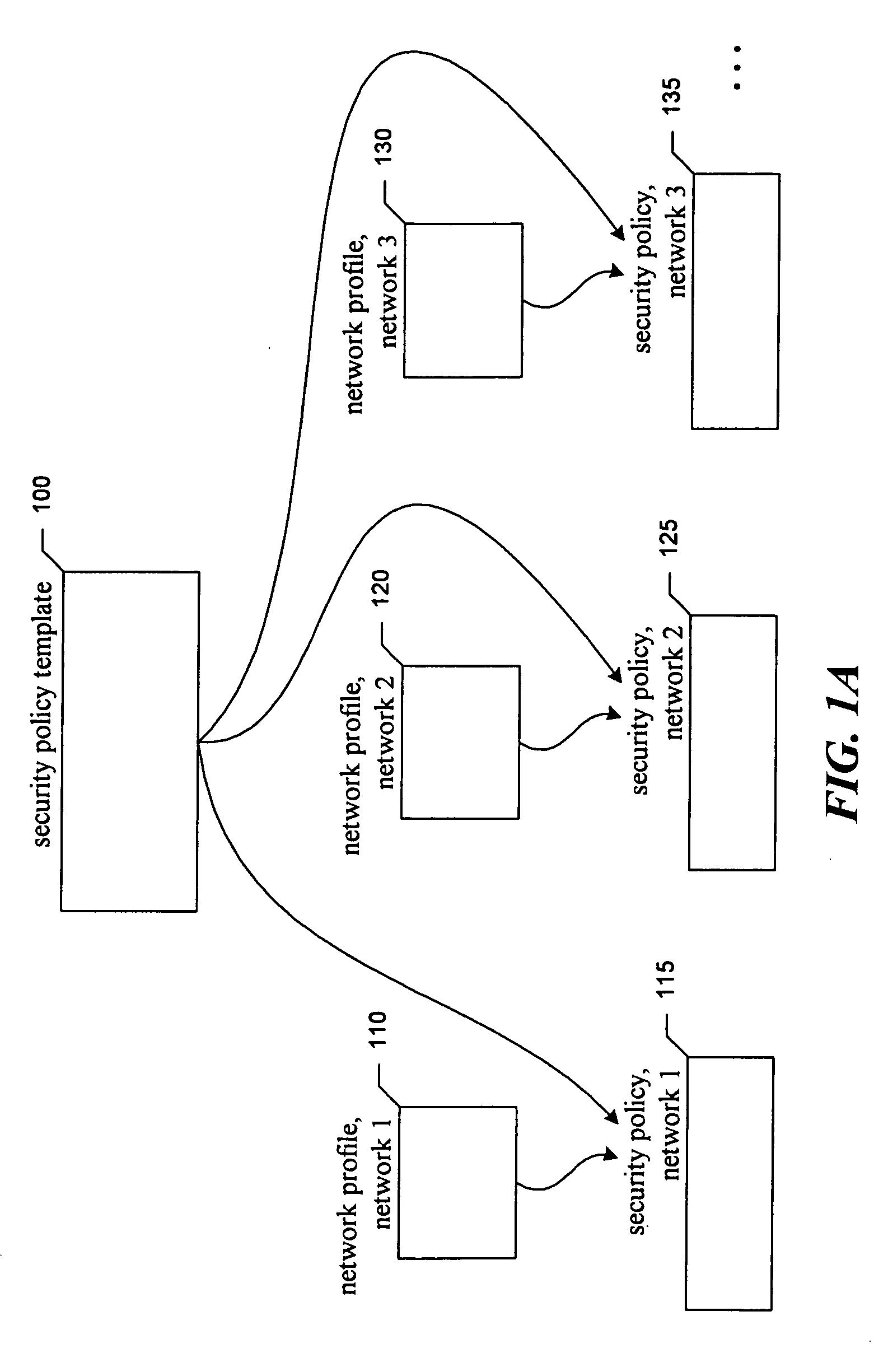
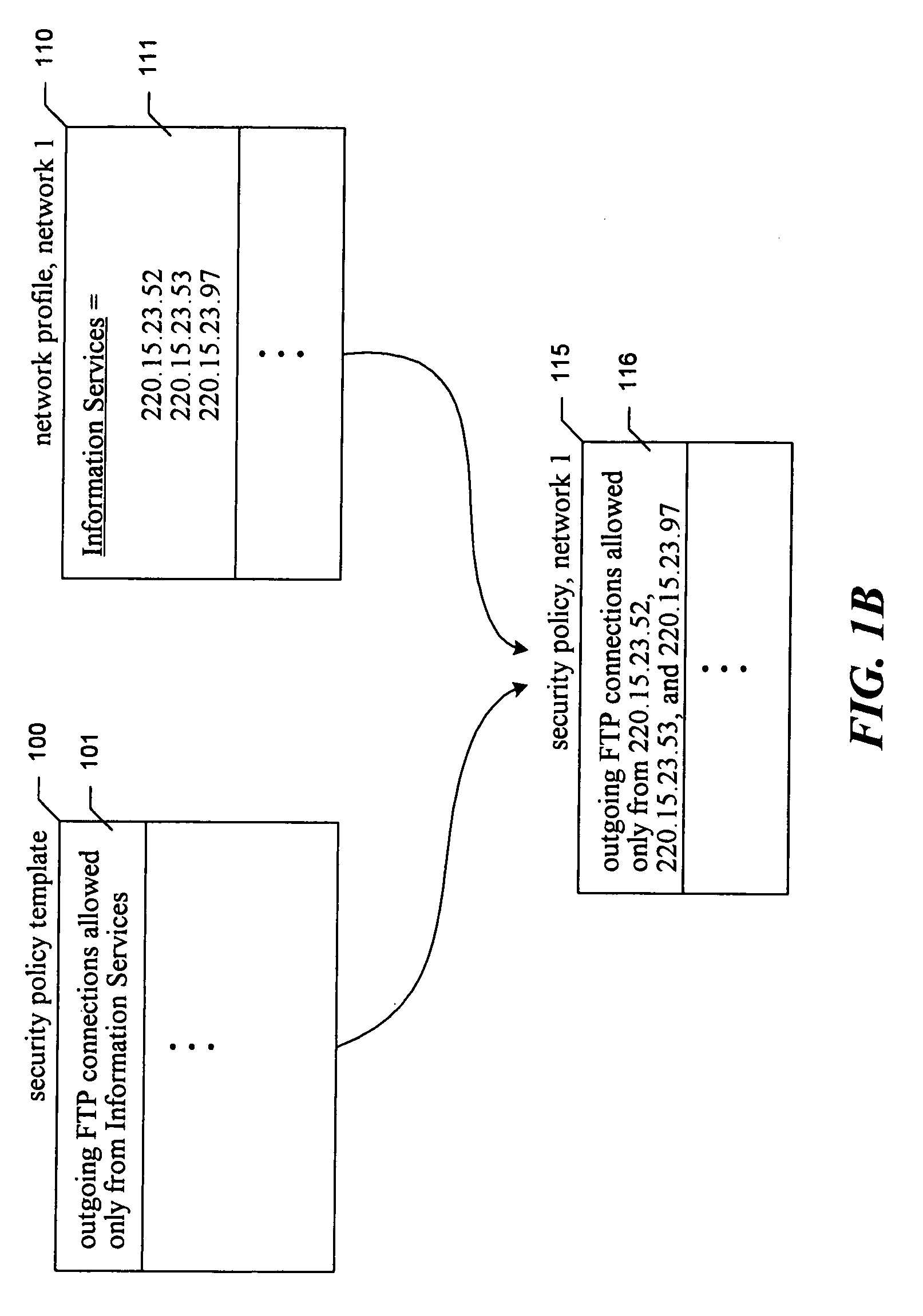
Generalized network security policy templates for implementing similar network security policies across multiple networks
InactiveUS20050022027A1Low costEfficient updateData processing applicationsDigital data processing detailsNetwork security policySecurity policy
The present invention is directed to a facility for adapting a network security policy model for use in a particular network. The facility retrieves the network security policy model, which comprises network security rules each specified with respect to one or more aliases. Each alias represents a role in a network for one or more network elements. The facility receives, for each alias included in the network security policy model, a list of one or more network elements in the network serving the role represented by the alias. The facility replaces each alias in the network security policy model with the received list of network security devices specified for the alias to produce a network security policy adapted for use in a network.
Owner:BONN DAVID WAYNE +1
SFC (Service Function Chaining) OAM (Operation, Administration and Maintenance) method and node device
The invention discloses an SFC OAM method and a node device, and relates to the field of Internet equipment. The SFC OAM method comprises that when a source-end service node carries out OAM operation on alias information, the source-end service node determines an SFC or a service function path bound to the alias information; and the source-end service node carries out OAM operation on the determined SFC or service function path to generate a corresponding OAM message and send the OAM message to a target-end service node of the OAM operation. According to the technical scheme of the invention, an operator can obtain link information of the service chain simply and rapidly, and diagnose and locate the link information of the service chain, and thus, different SFC OAM can be realized rapidly and simply.
Owner:ZTE CORP
Identity and authentication system using aliases
InactiveCN102171712APrivacy protectionPayment architectureDigital data authenticationEmail addressThe Internet
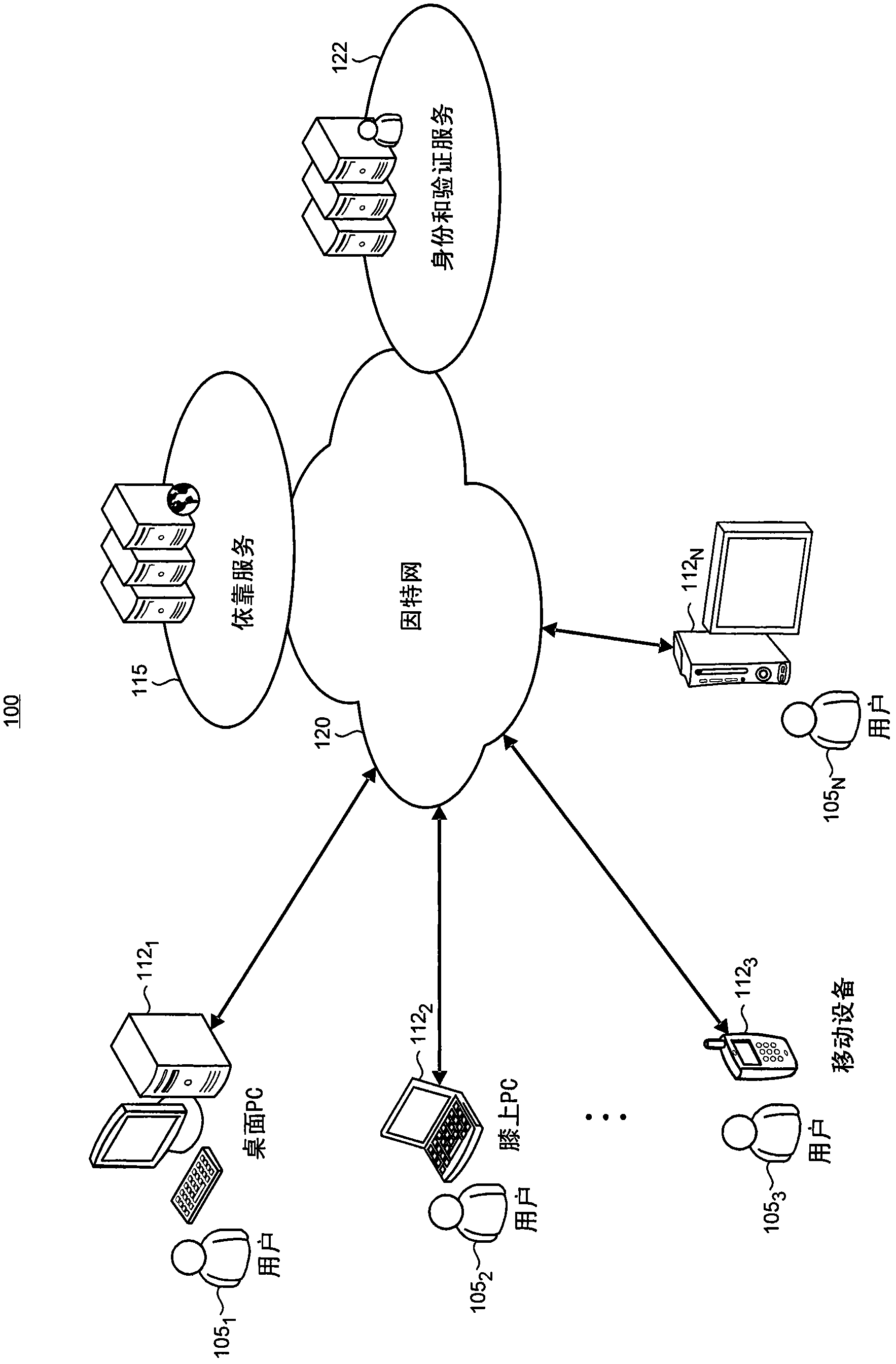
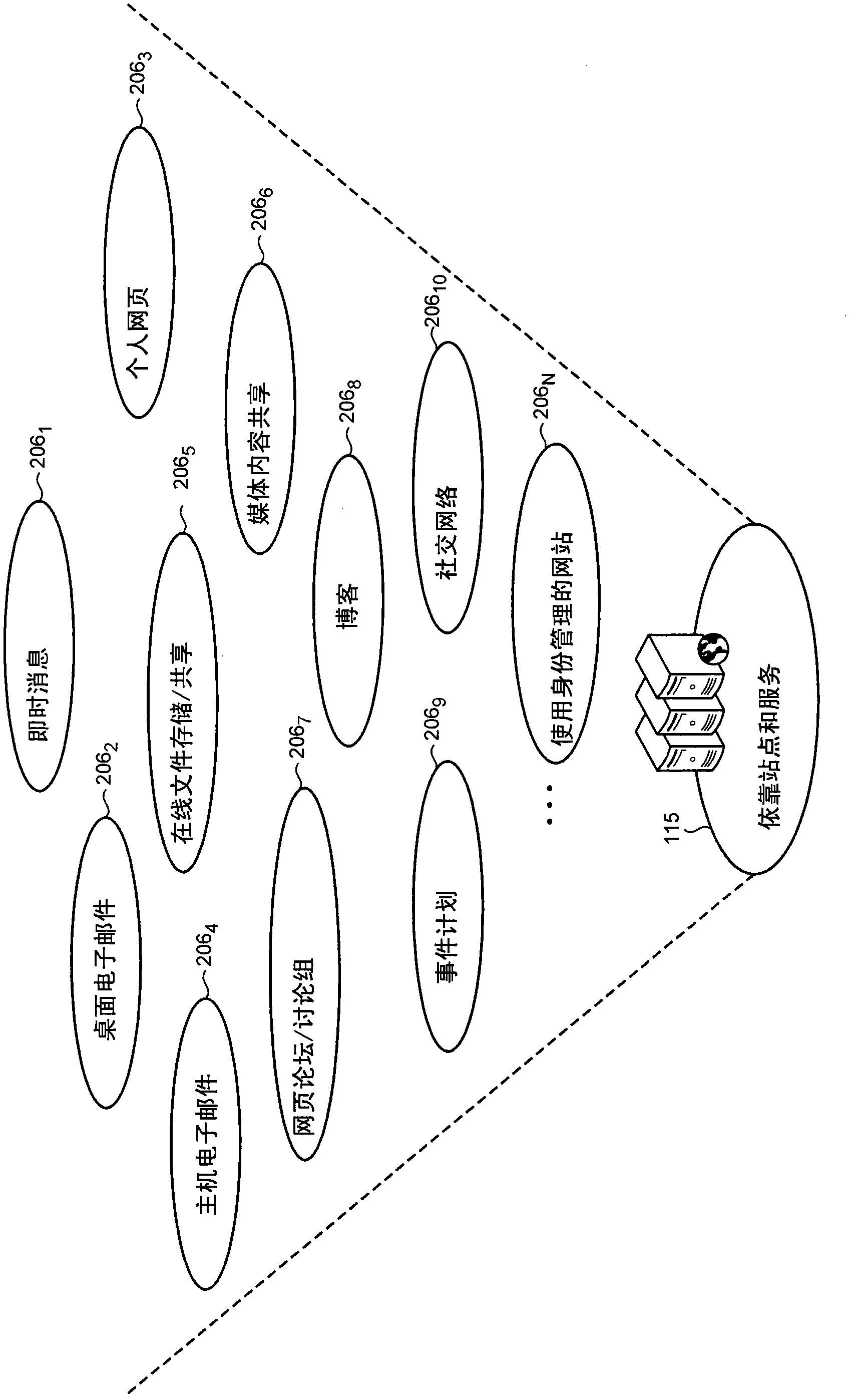
An identity and authentication platform (122) utilizes a data model (400) that enables multiple identities such as e-mail addresses, mobile phone numbers, nicknames, gaming IDs, and other user IDs to be utilized as aliases (505) which are unique sub-identities of a main account name (512). A user (105) may utilize the aliases (505) supported by the platform (122) to project multiple different on-line identities while using the authentication credentials of the main account (512). The platform (122) is configured to expose the aliases (505) to various client applications and Internet-accessible sites and services (206) such as e-mail, instant messaging, media sharing, gaming and social networks, and the like, to enable the implementation of a variety of usage scenarios that employ aliases (505).
Owner:MICROSOFT CORP
System and method for audit tracking
ActiveUS7941849B2Allow accessMemory loss protectionError detection/correctionApplication softwareUser profile
User activities in various applications are audited using a client-resident agent. An alias for an individual is associated with a user profile for the individual user. The user profile may contain data pertaining to the user's activities within one or more applications. Data in the user profile may be used to determine which actions are audited, and how the audit data is used.
Owner:IMPRIVATA
Static detection method on basis of embedded software and system thereof
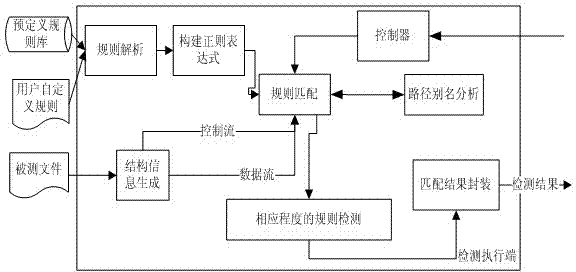
InactiveCN102968367AReduce false positive informationSoftware testing/debuggingStreaming dataPathPing
The invention provides a static detection method on the basis of embedded software. The method overcomes the defects in an existing static detection technology and is used for carrying out static detection by combining control flow information, data stream information and path alias information. The method adopts a detection executing end module and a client module. A client provides support for editing a graphical rule file, a tester can execute static detection on a source file after completing the work of editing a source file, and the client sends a command to notify a detection execution end to start static detection; the detection execution end receives the detection starting command sent by the client, analyzes the structure of the source file, calls a rule analysis module to analyze the rule file, generates a matching result after processing, carries out packaging by a matching result packaging module and sends a detection result generated by packaging to the client for analysis and display; and the client carries out analysis and mapping on the detection result and the client is updated according to the detection result, so that a developer can visually view the static detection result and visually view the rule breaking condition.
Owner:SOUTH CHINA UNIV OF TECH
Method and system for managing file aliases
InactiveUS20070124271A1Digital data information retrievalSpecial data processing applicationsMulti fieldDisplay list
A method, system, or computer program manages file names as multi-field character strings by defining each file name in a list of file names as a multi-field character string, displaying the list of file names, receiving a command selecting a field within the displayed list of file names, and sorting the file names according to the selected field in the current displayed list.
Owner:IBM CORP
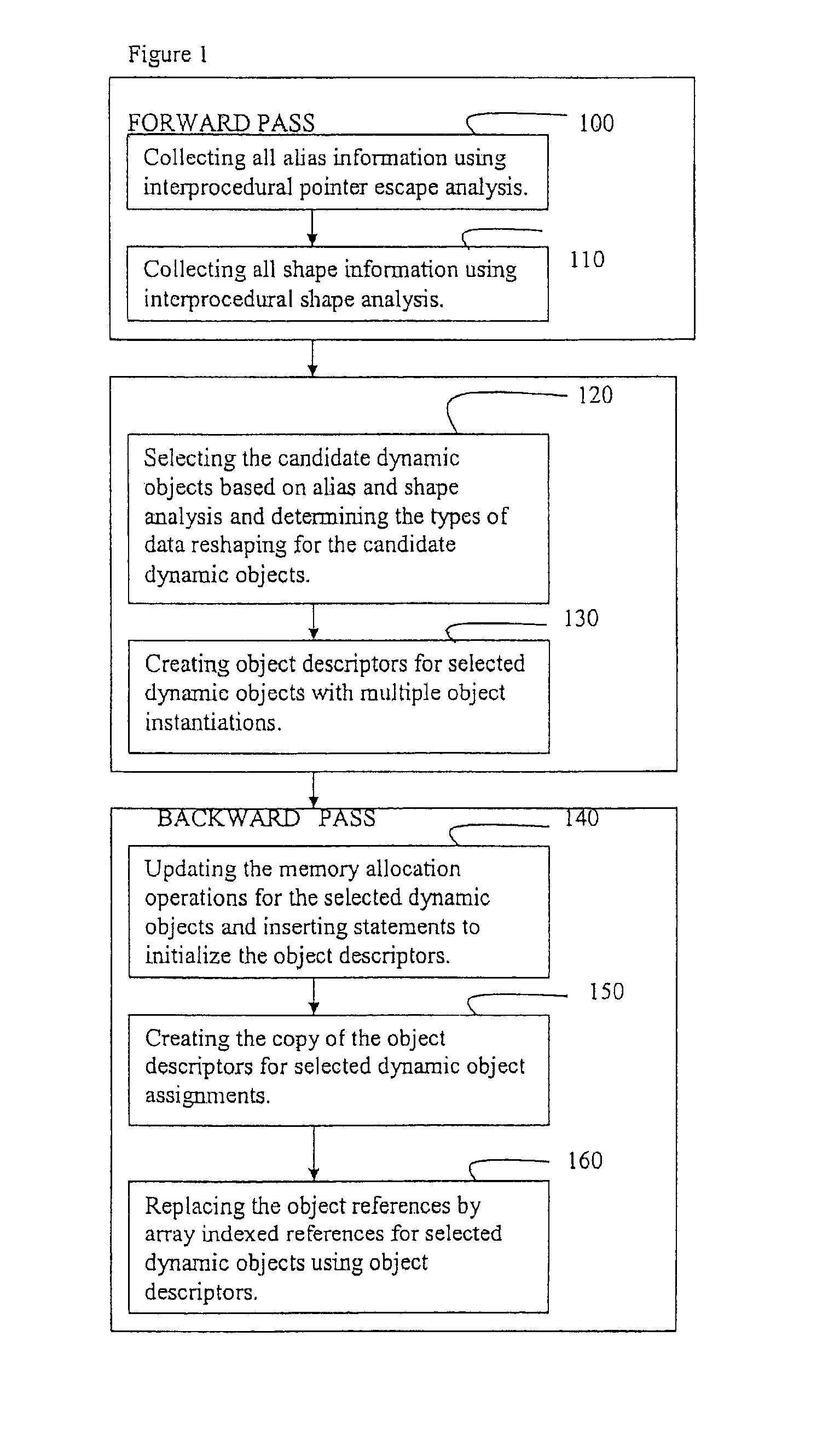
Efficient method of data reshaping for multidimensional dynamic array objects in the presence of multiple object instantiations
A method of data reshaping for multidimensional dynamic array objects in the presence of multiple object instantiations. The method includes collecting all alias information using interprocedural point escape analysis, and collecting all shape information using interprocedural shape analysis. The method progresses with selecting the candidate dynamic objects based on alias and shape analysis, and determining the types of data reshaping for the candidate dynamic objects. The method further includes creating objects for selected dynamic objects with multiple object instantiations. The method proceeds by updating the memory allocation operations for the selected dynamic objects and inserting statements to initialize object descriptors. The method further includes creating the copy of the object descriptors for selected dynamic object assignments. The method concludes by replacing the object references by array-indexed references for selected dynamic objects using object descriptors.
Owner:IBM CORP
Recognition information processing method and device
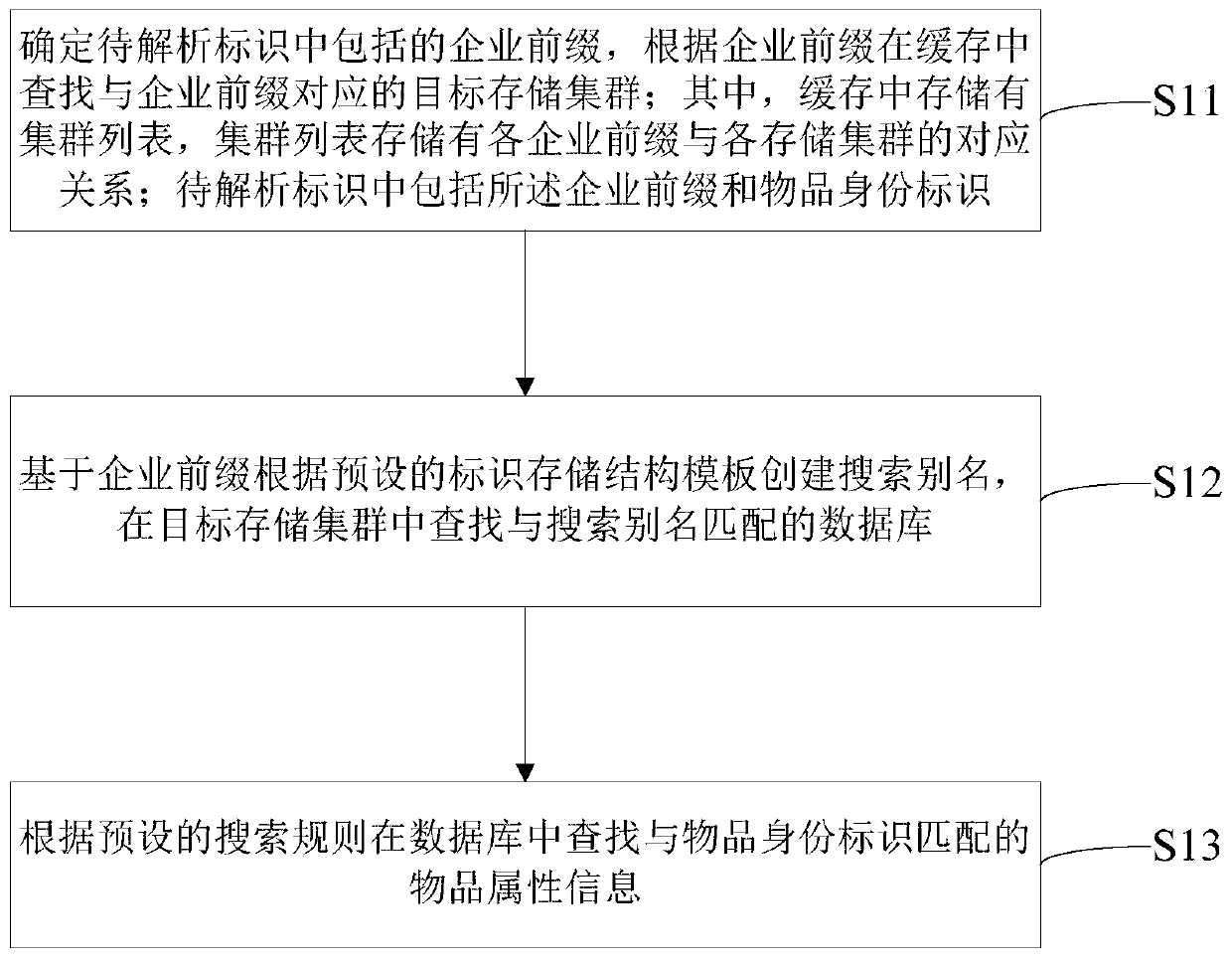
PendingCN111459985AReduce the amount of query dataImprove search efficiencyDigital data information retrievalSpecial data processing applicationsInformation processingInformation analysis
The invention relates to the technical field of Internet, and provides an recognition information processing method and device. The method comprises the steps: determining an enterprise prefix included in a to-be-analyzed recognition, and searching a target storage cluster corresponding to the enterprise prefix in a cache according to the enterprise prefix; wherein a cluster list is stored in thecache, and a corresponding relationship between each enterprise prefix and each storage cluster is stored in the cluster list; wherein the to-be-analyzed identifier comprises the enterprise prefix andan article identity identifier; creating a search alias according to a preset identifier storage structure template based on the enterprise prefix, and searching a database matched with the search alias in the target storage cluster; and searching article attribute information matched with the article identity identifier in a database according to a preset search rule. According to the recognition information processing method for the industrial Internet provided by the embodiment of the invention, the query of the sub-clusters and the sub-libraries is carried out through automatic recognition in the recognition information analysis process, so that the query data volume is reduced, and higher retrieval efficiency is provided.
Owner:MIDEA GRP CO LTD
Method of IP address de-aliasing
A method of internet protocol (IP) address de-aliasing that involves obtaining IP addresses from devices in a network, pinging pairs of the IP addresses by sending packets to pairs of the IP addresses, obtaining ping response orders for the packets, and determining whether the pairs of IP addresses are aliases of the same network device based on the obtained ping response orders.
Owner:AVAYA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com