Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
57246results about "Digital data authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
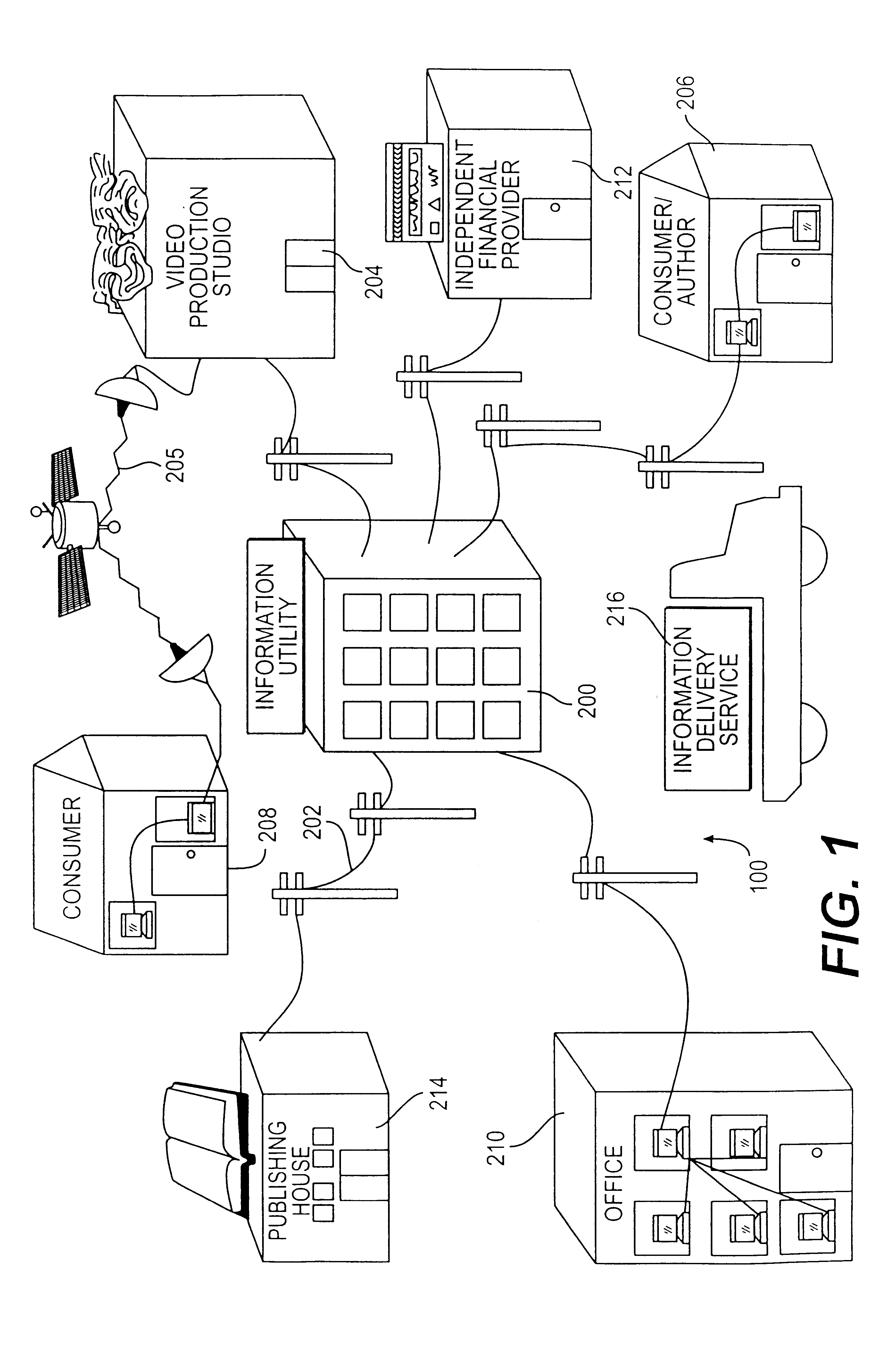
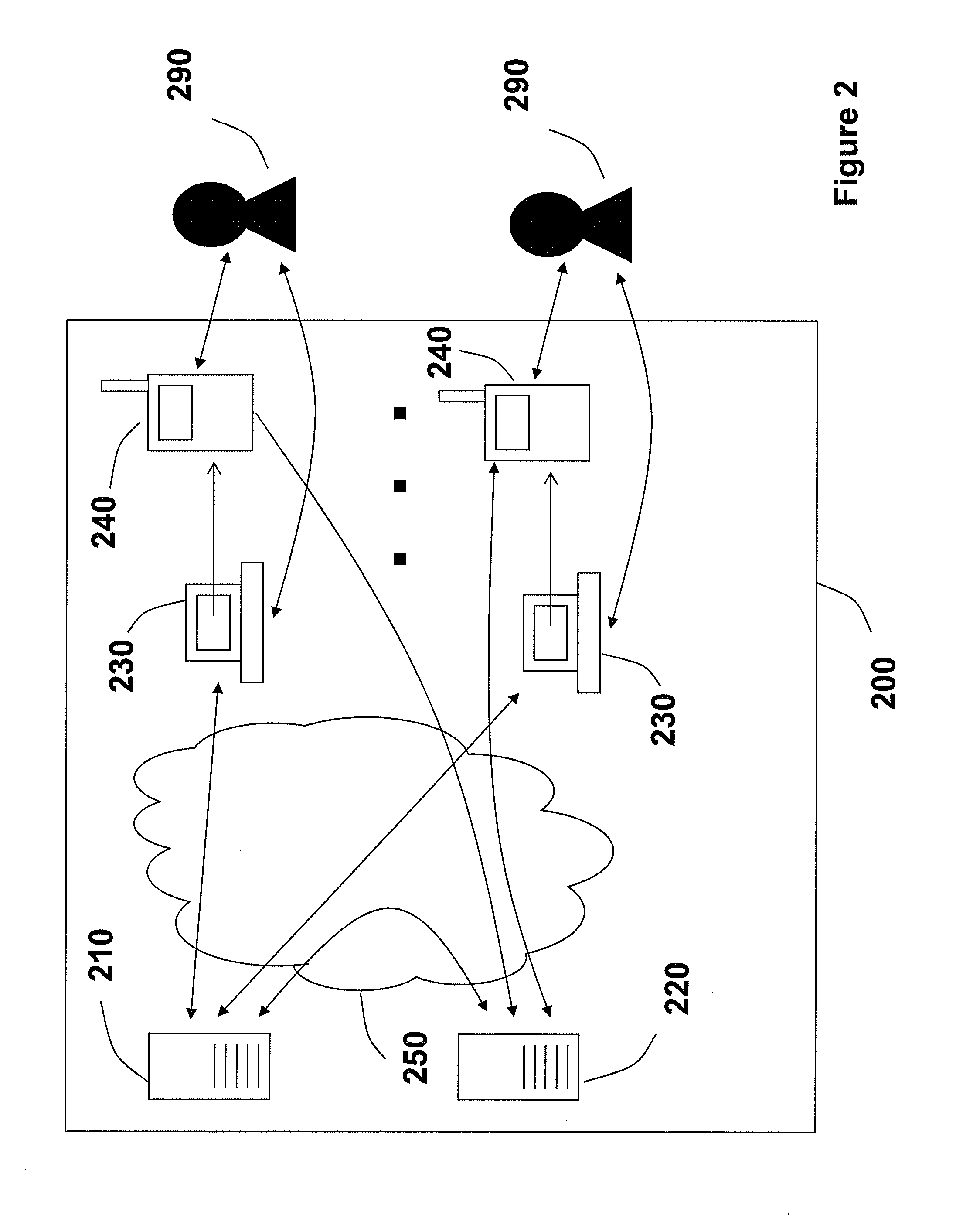
Systems and methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information
InactiveUS6112181AIncrease success rateCostly and inefficientUser identity/authority verificationSignalling system detailsRights managementUtility system
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
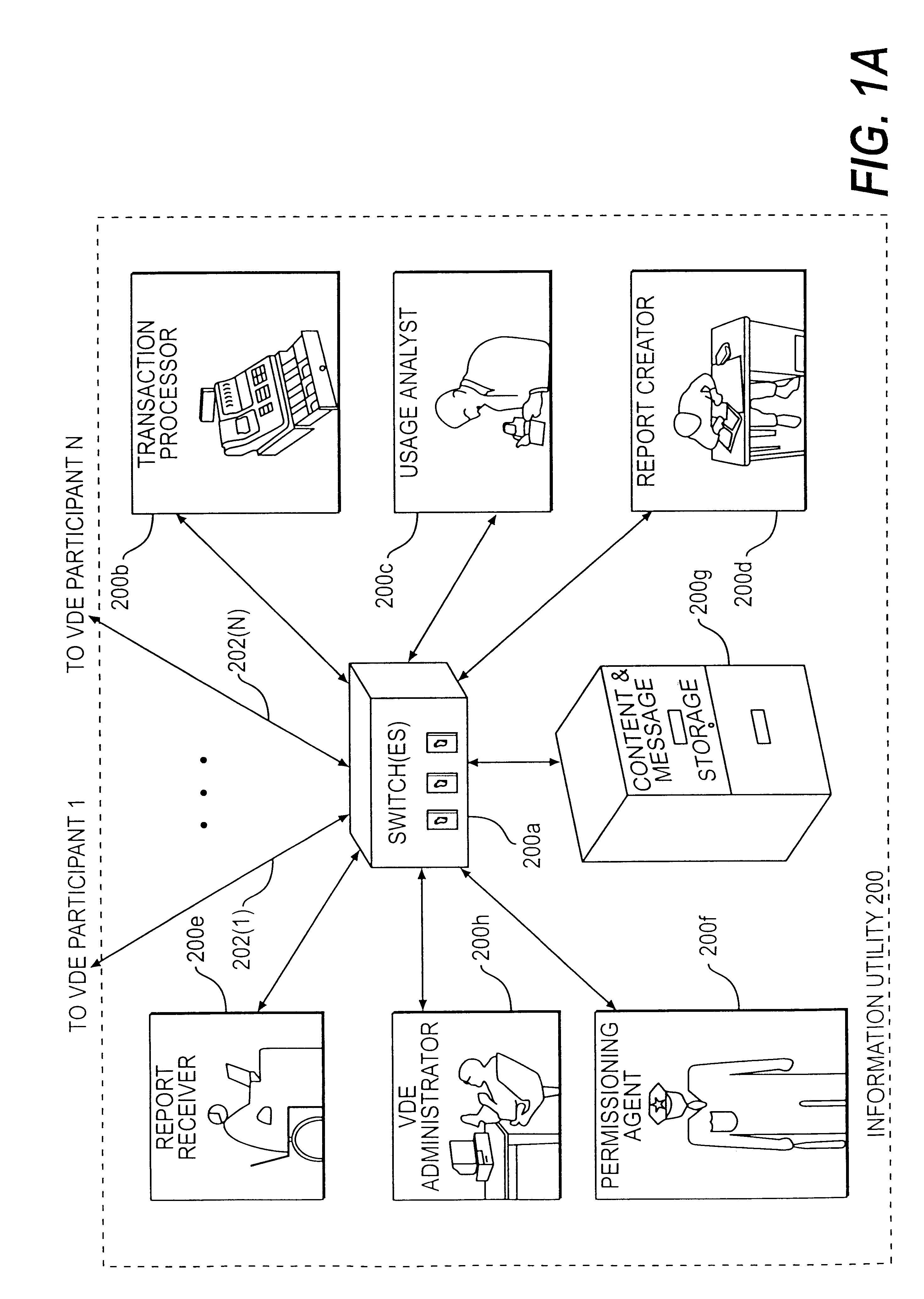
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
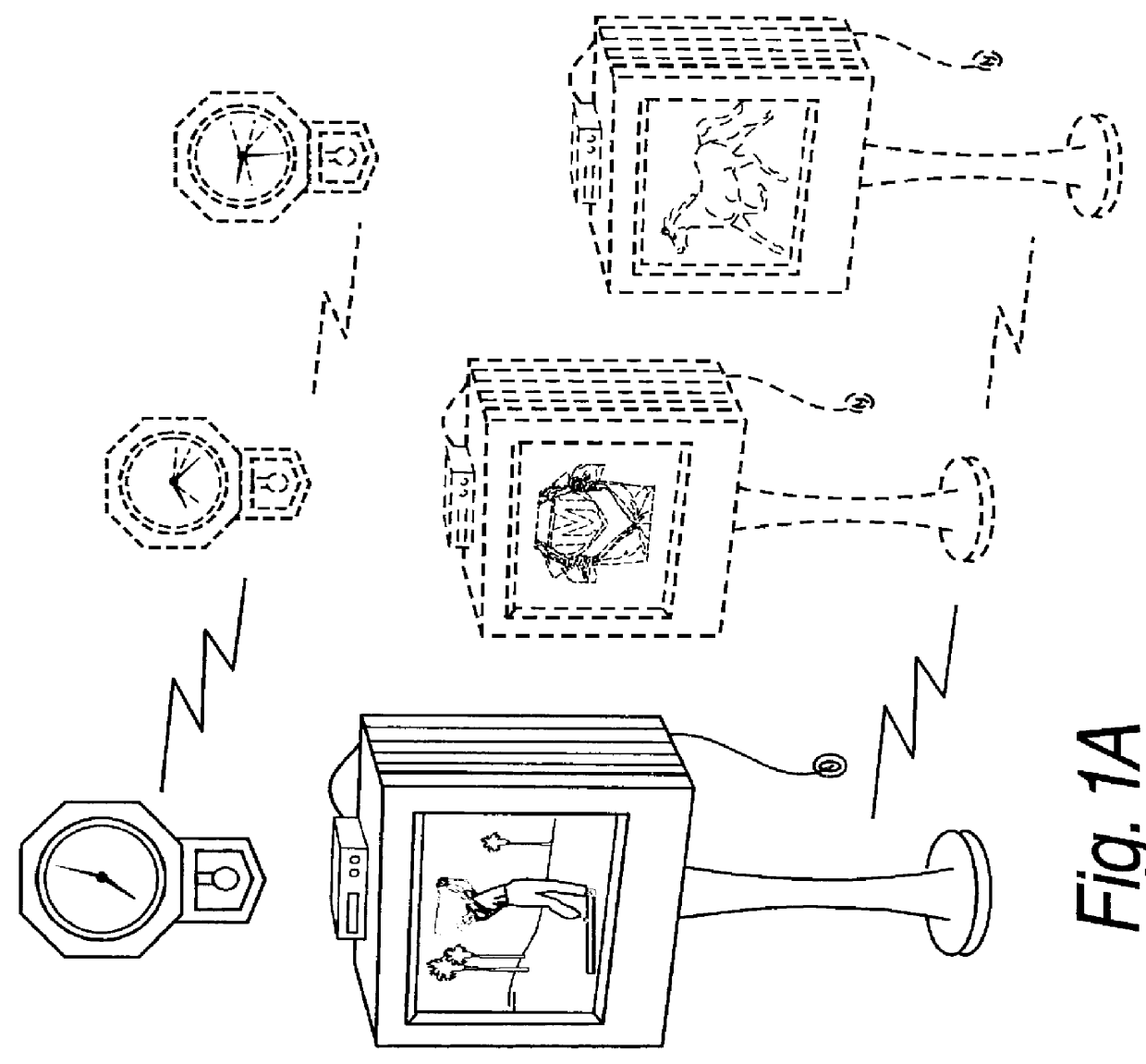
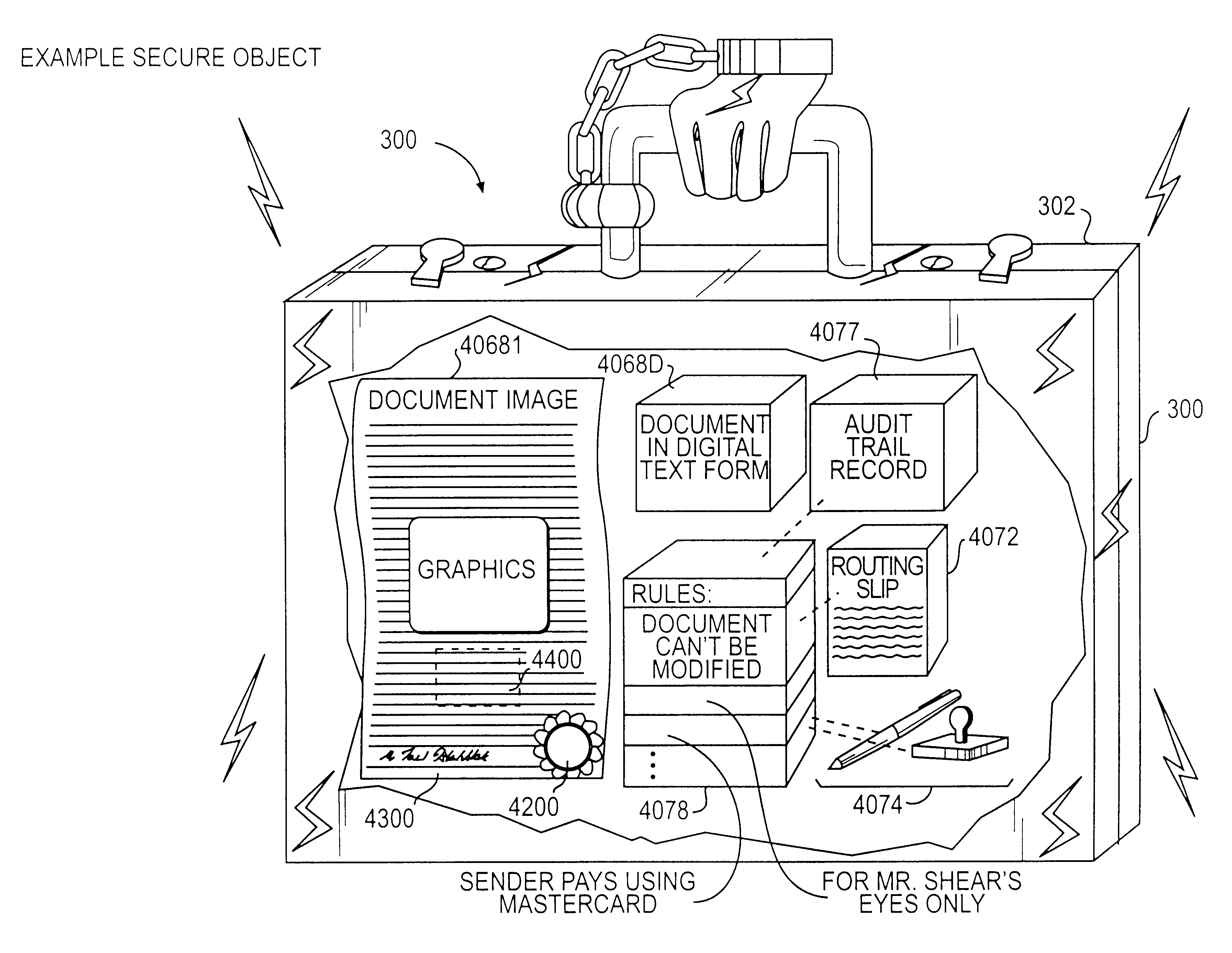
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
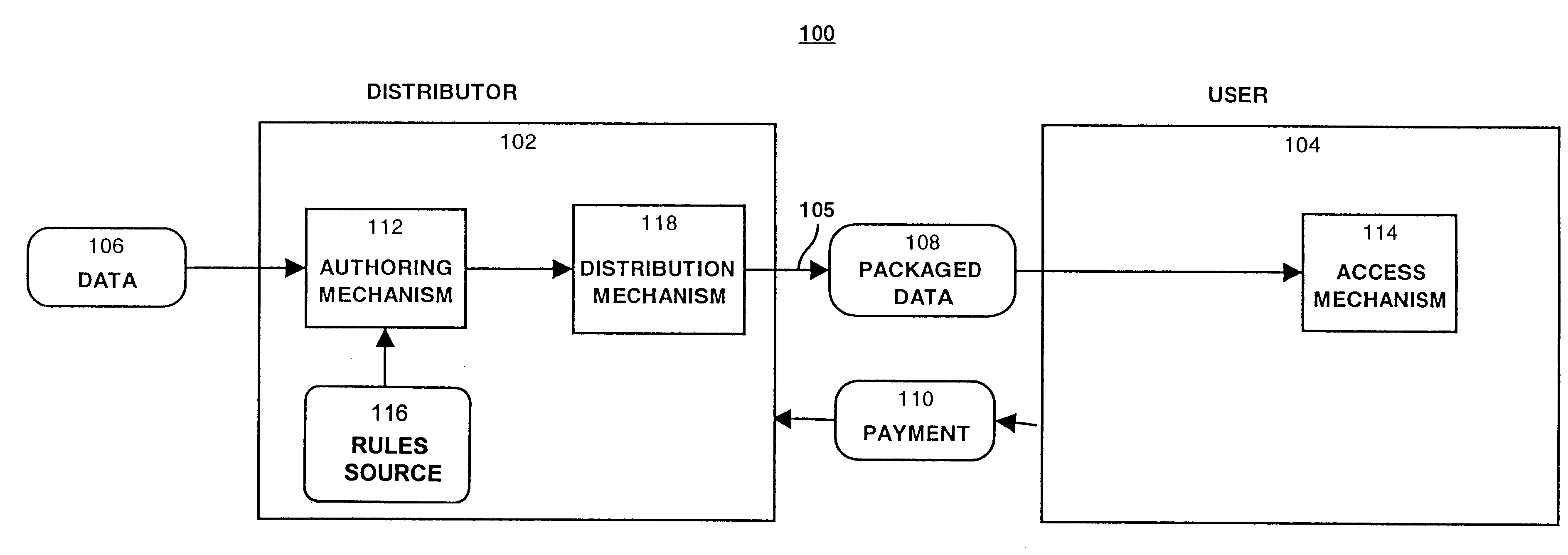
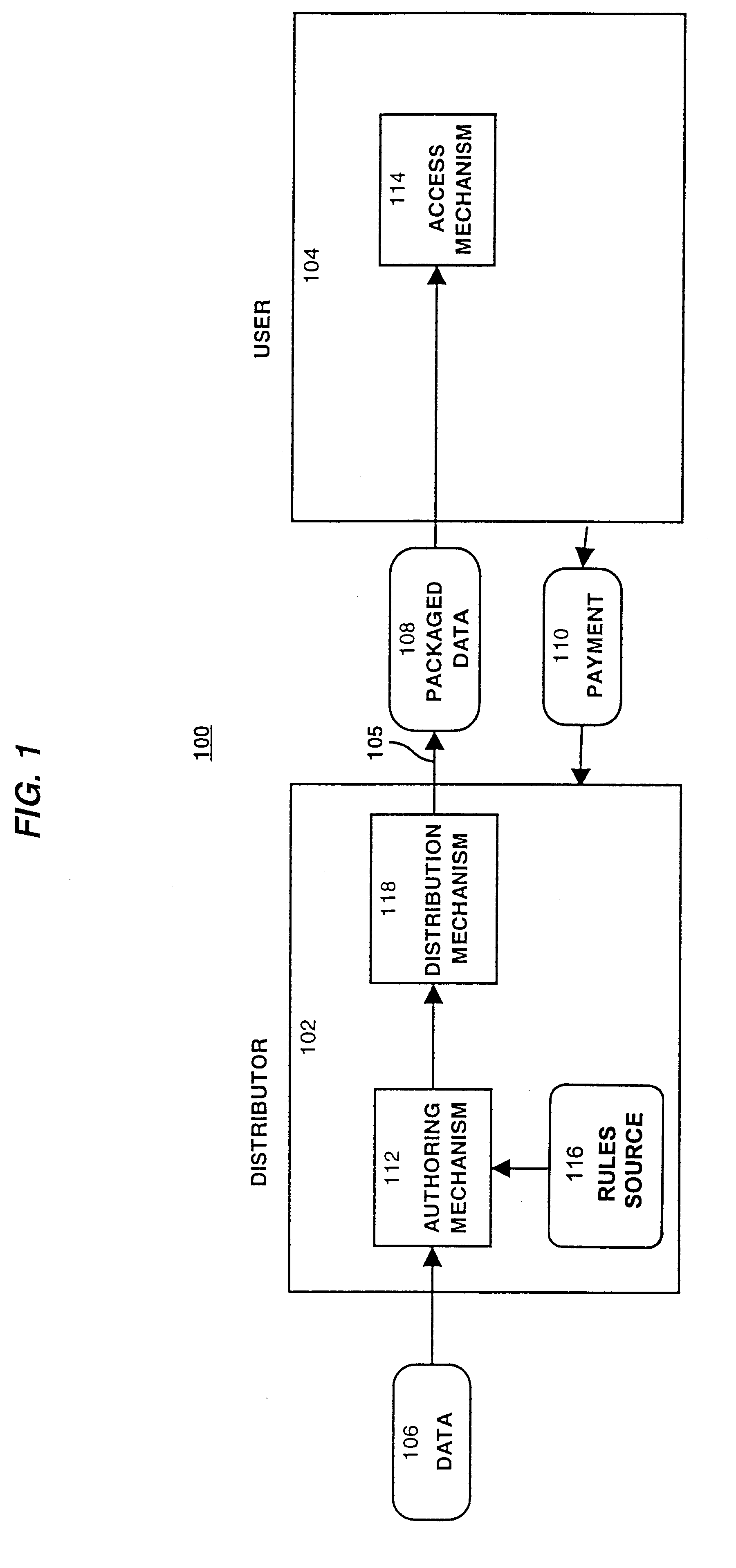
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
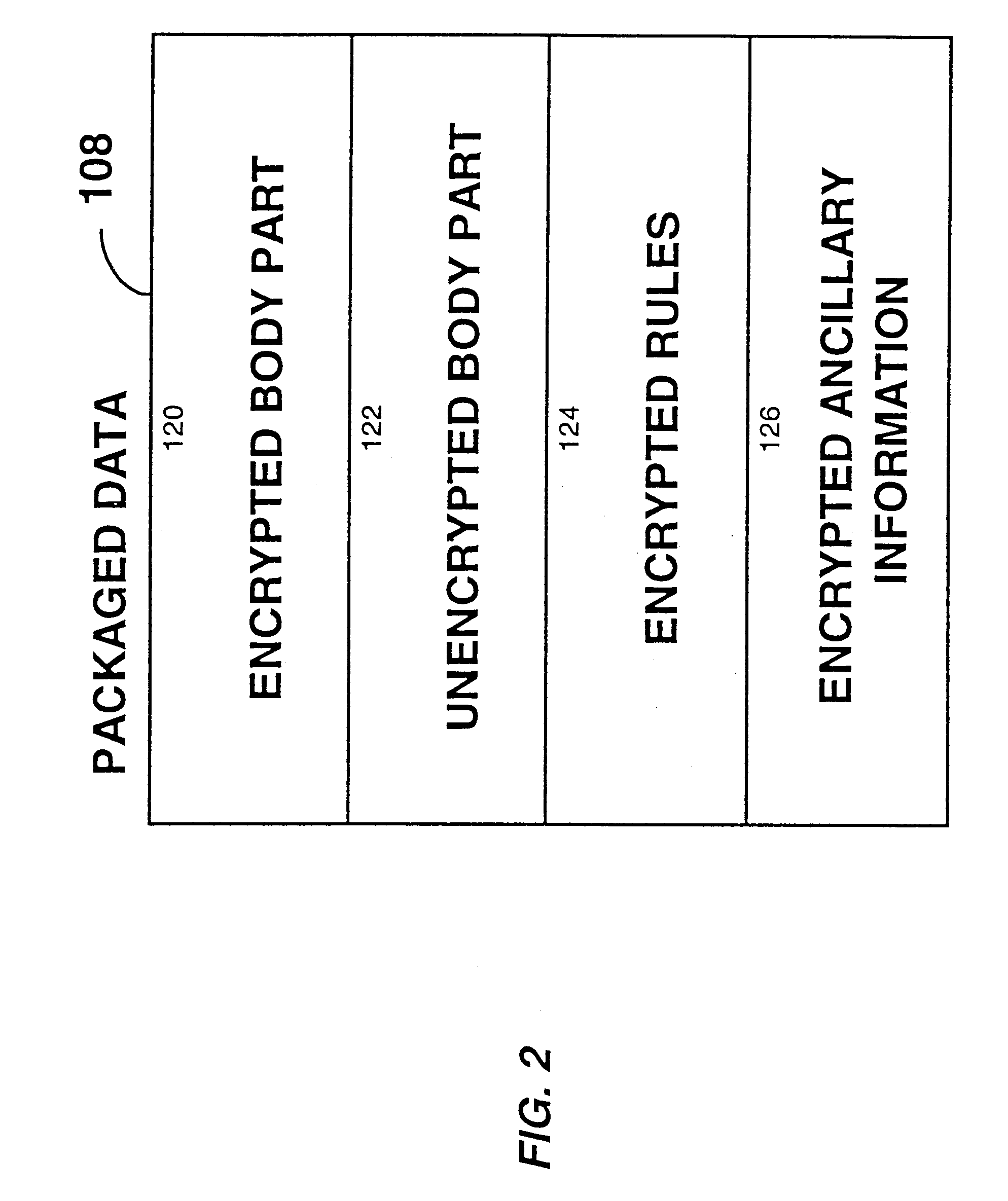
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
System and method for fraud monitoring, detection, and tiered user authentication
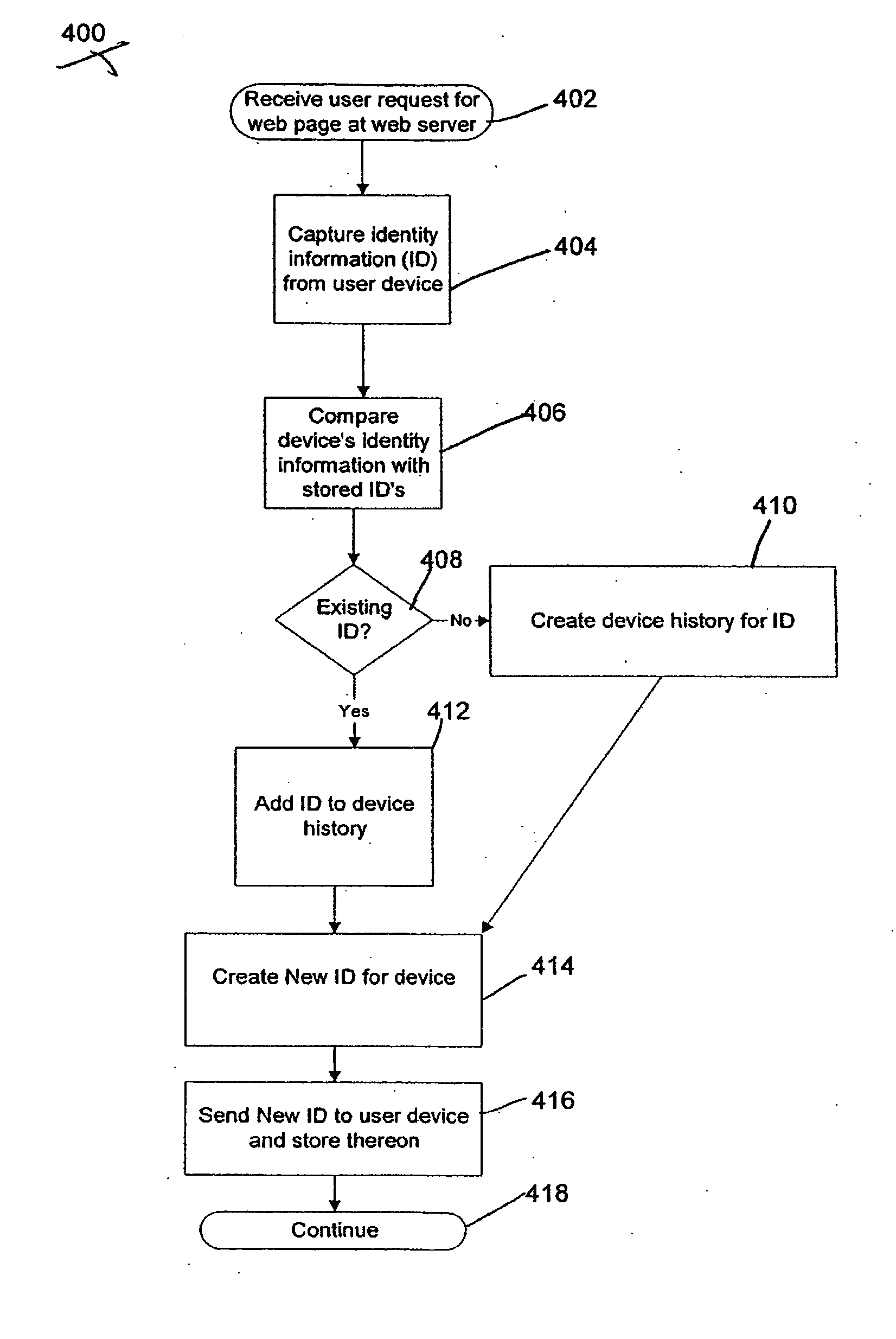
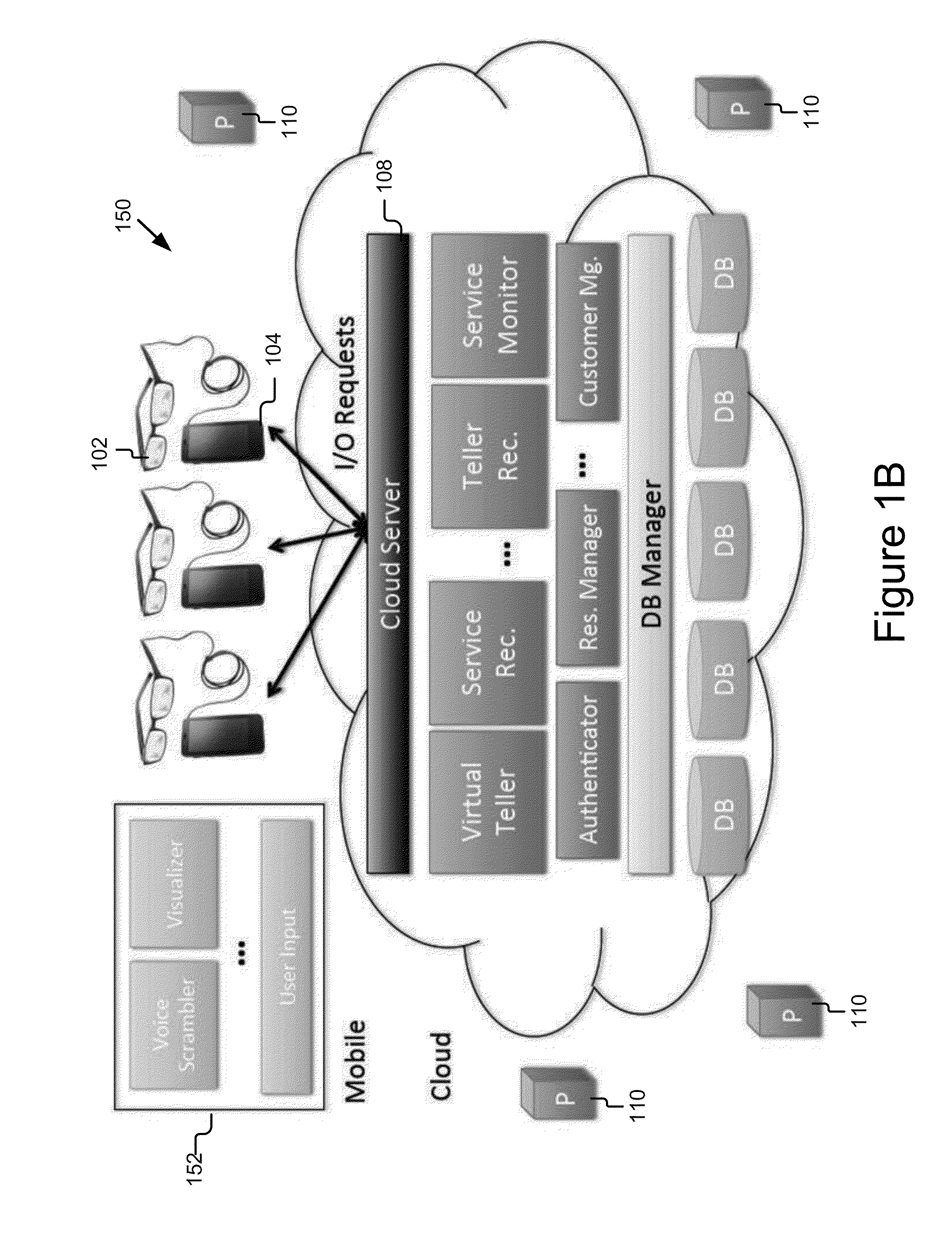
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
Authentication services using mobile device
InactiveUS20060206709A1Payment architectureATM softwaresInternet Authentication ServiceMobile device
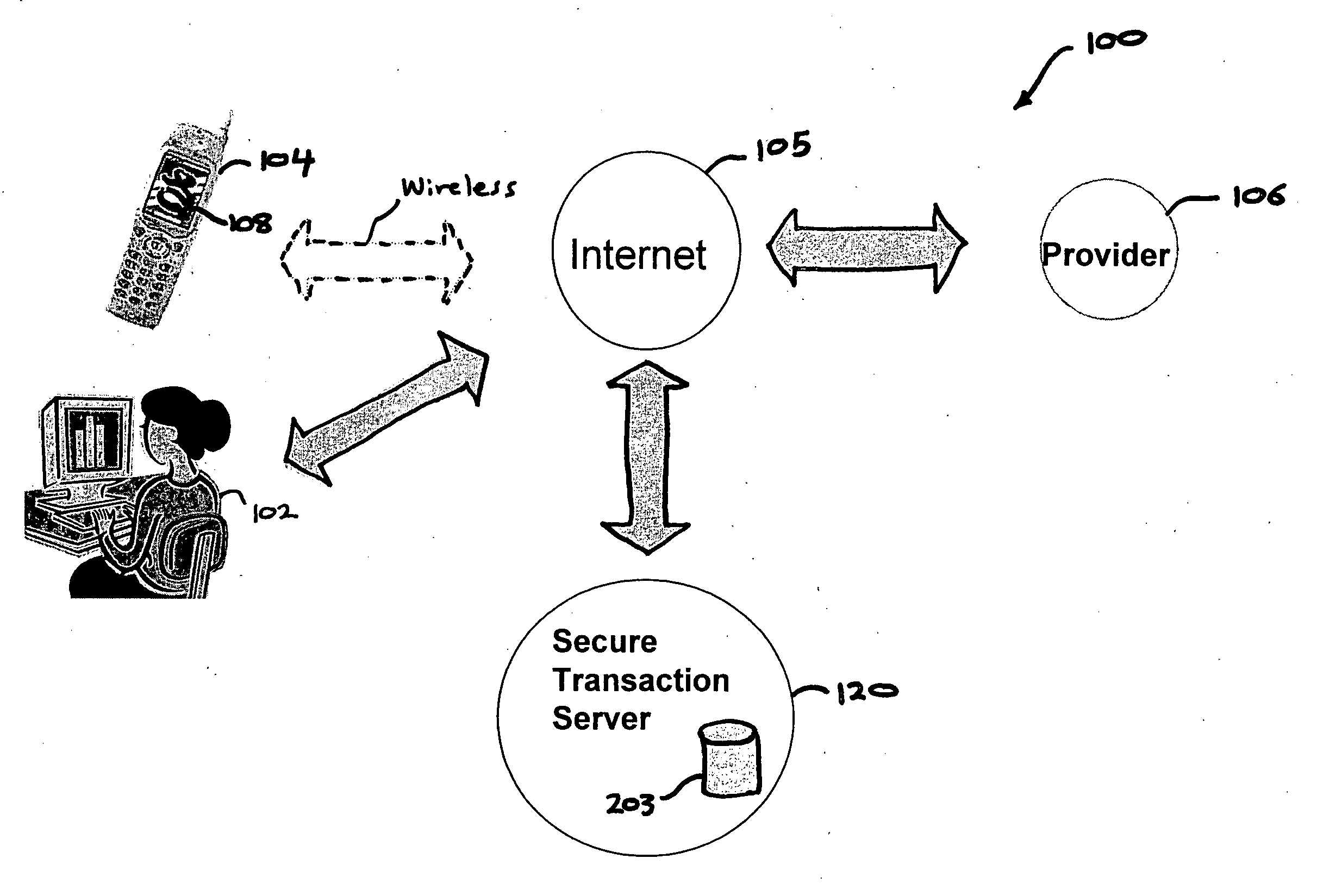
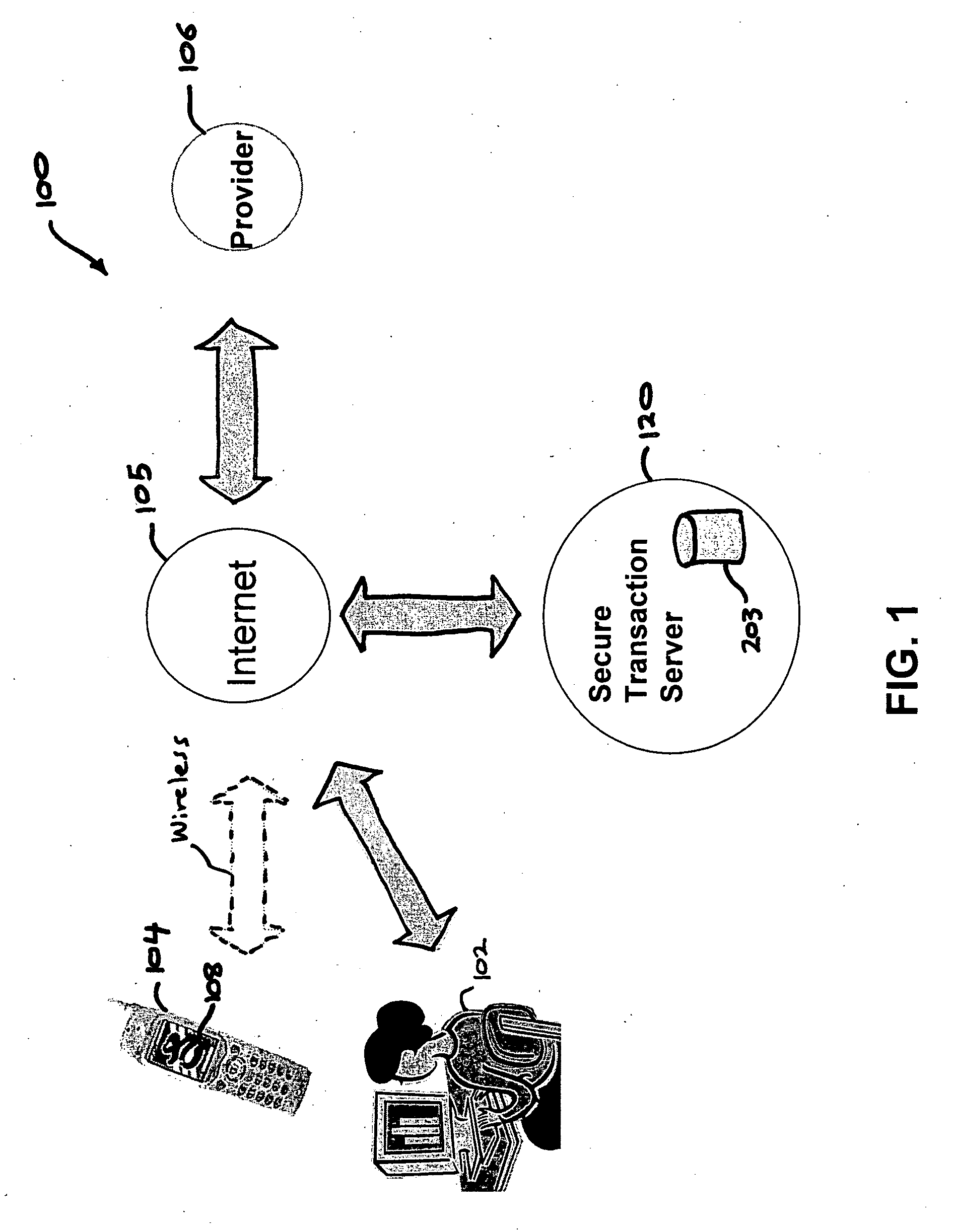
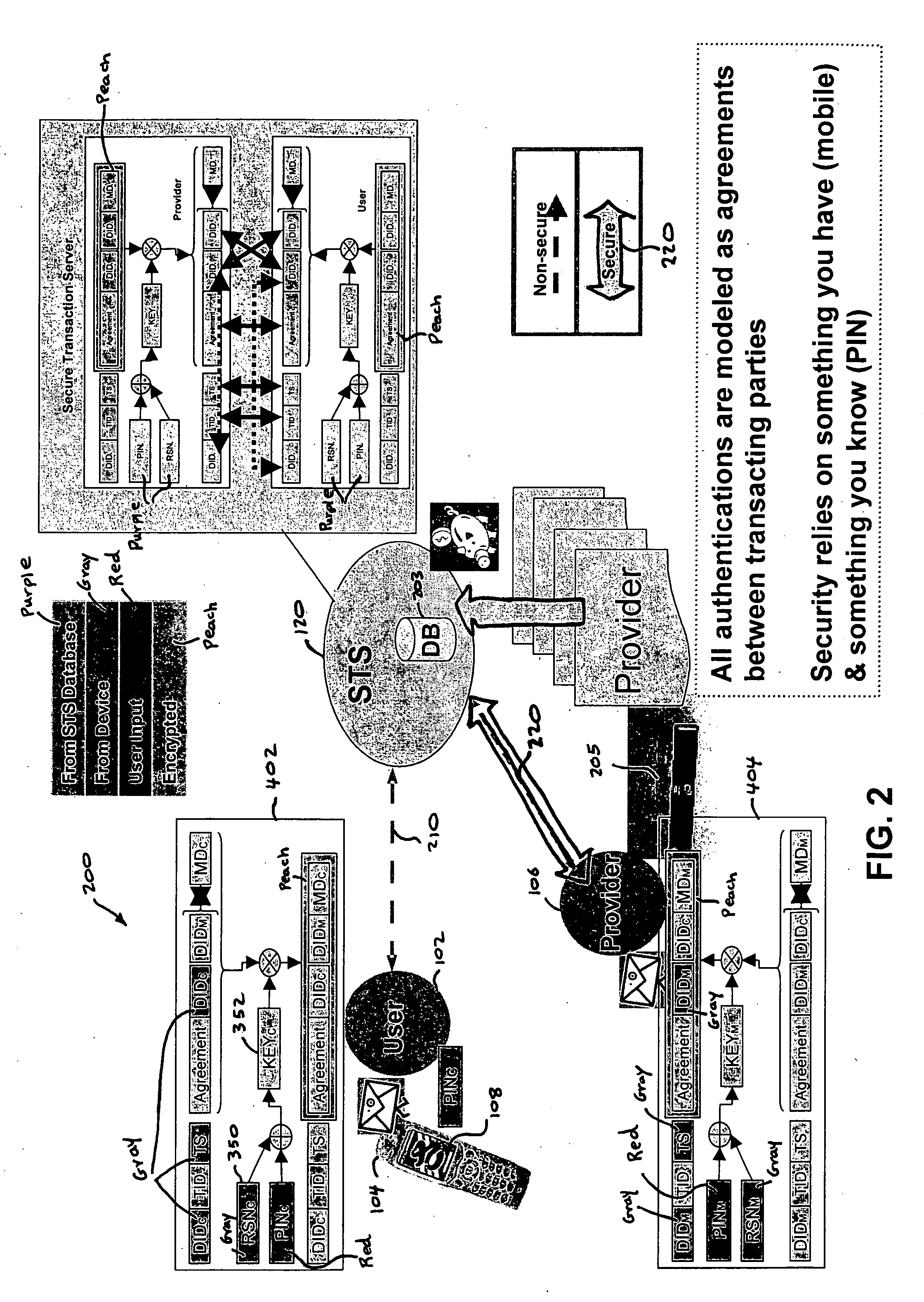
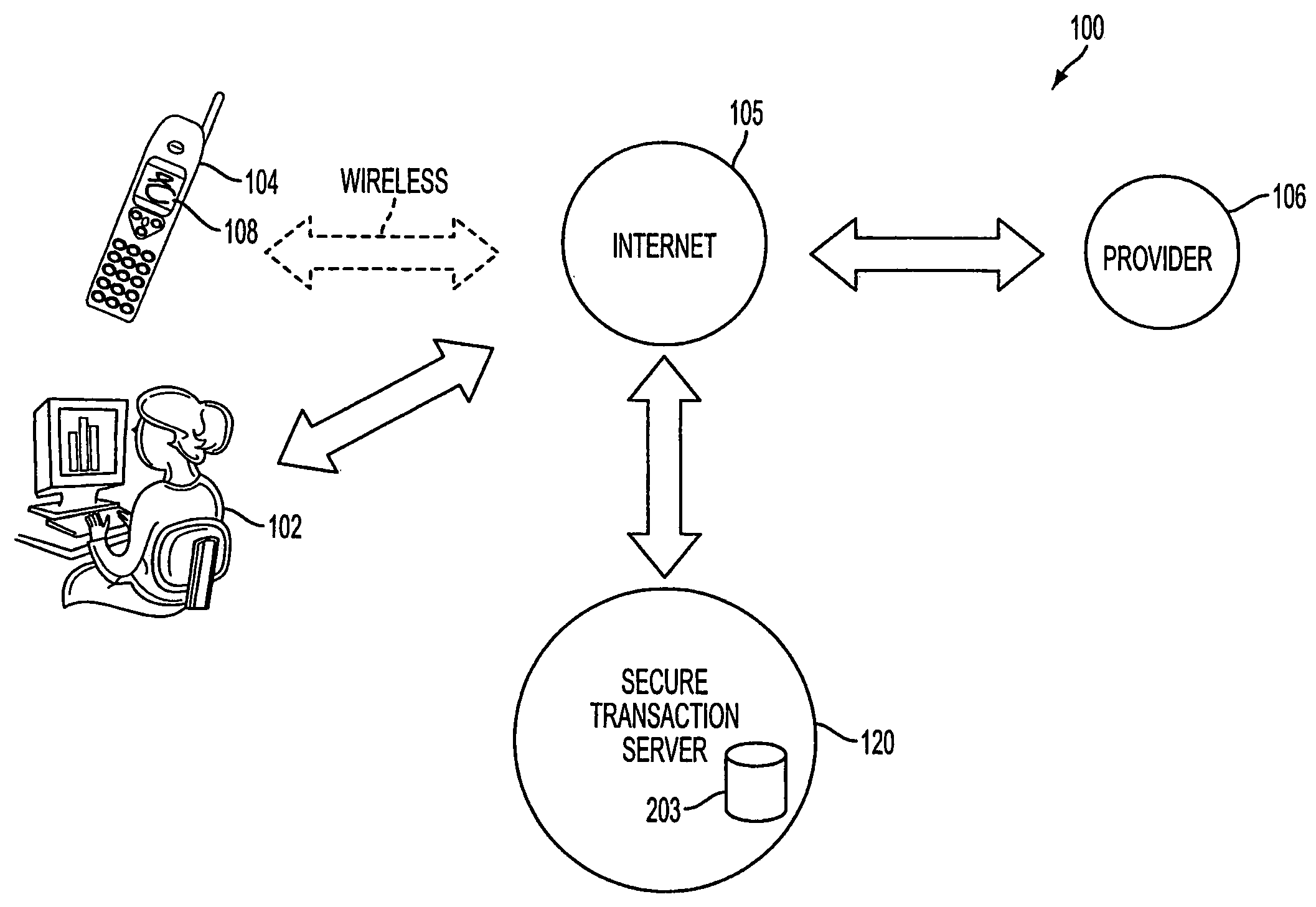
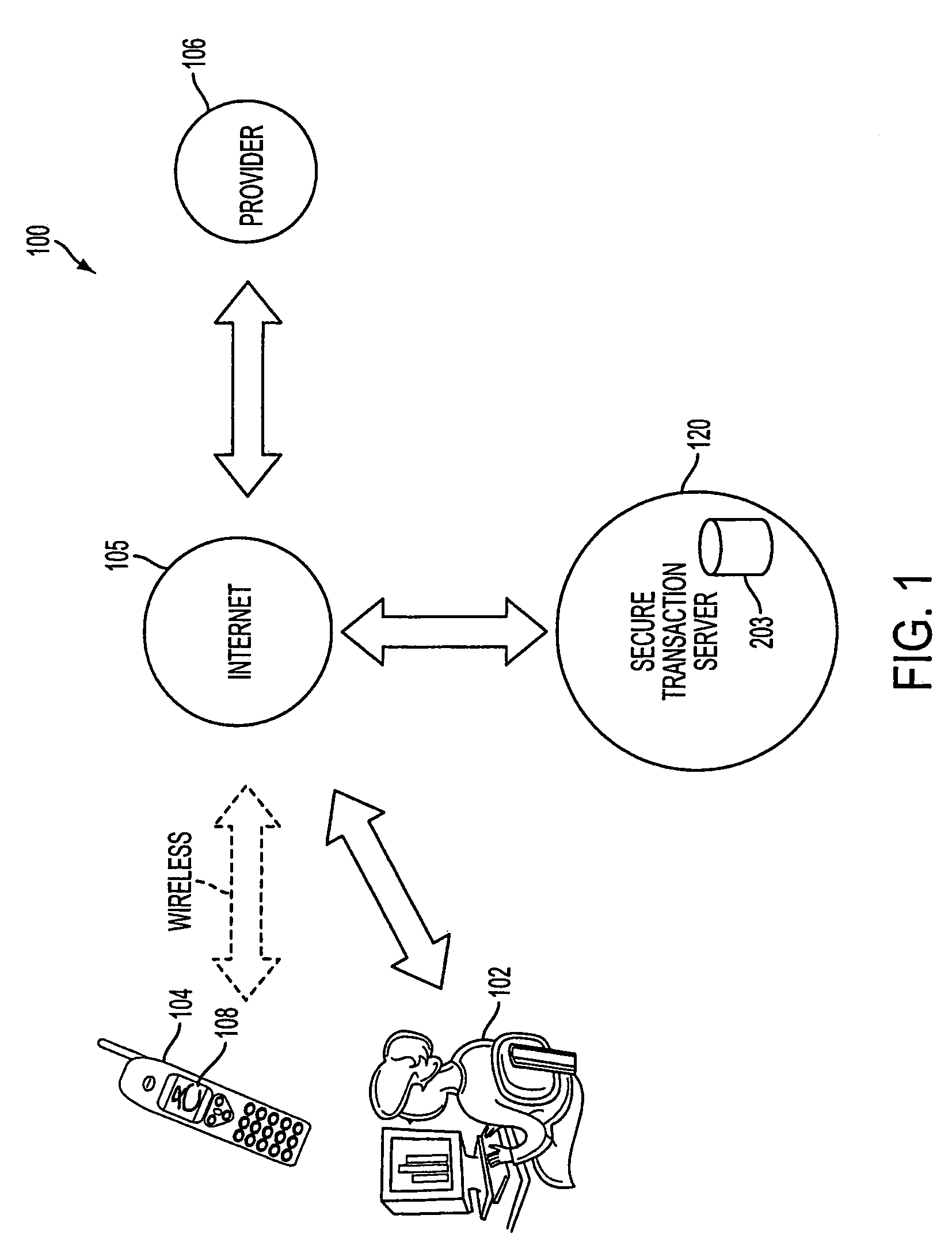
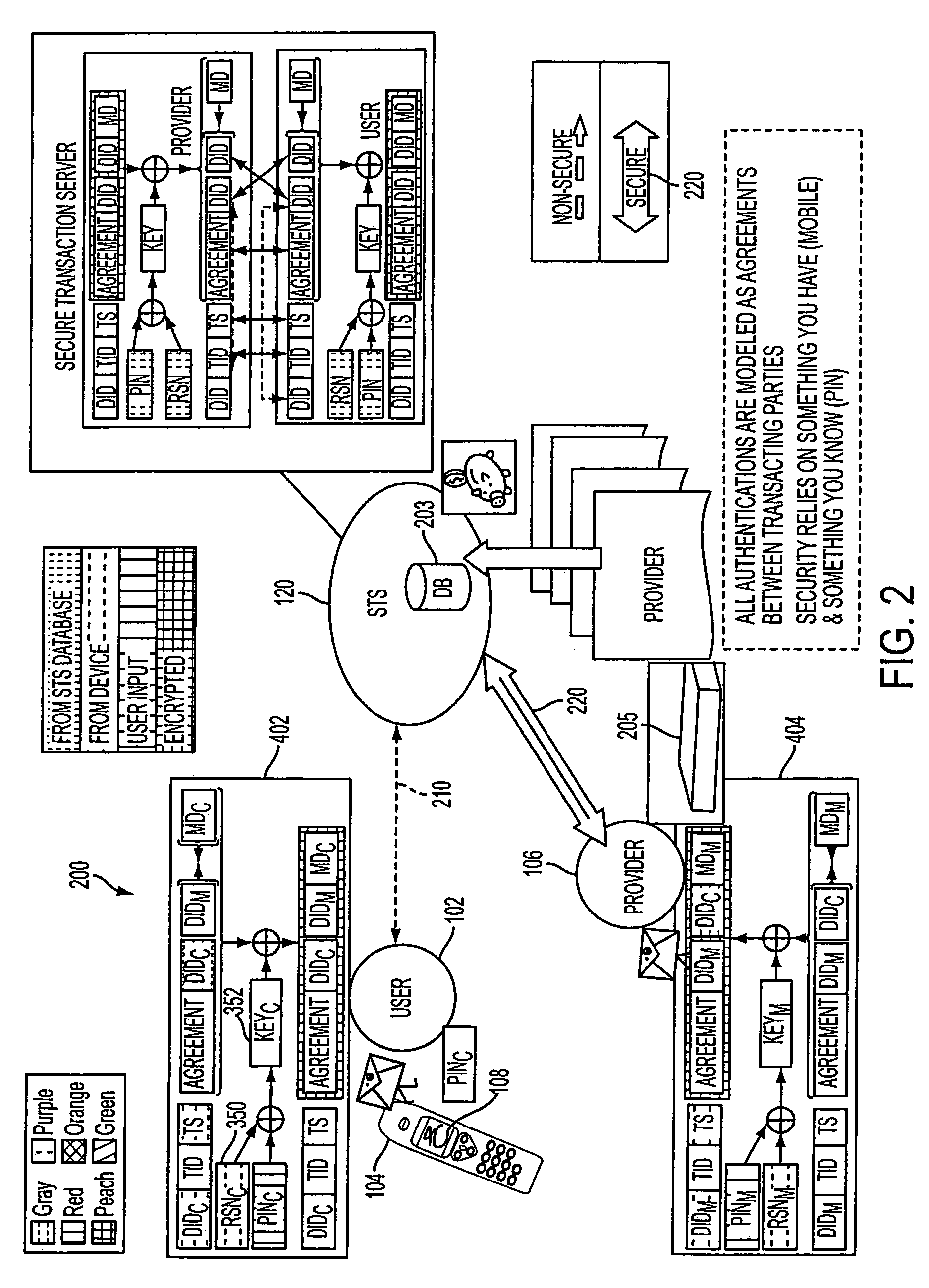
A method, and an apparatus performing the method, is provided by authenticating a mobile device communicably connectable to a wireless network by an authentication parameter from a secure transaction server (STS), as a mobile device authenticator; providing an STS correlation between a personal identification entry (PIE) and the mobile device authenticator; and inputting, by a user, the PIE and a provider action, to the mobile device authenticator to transmit a transformed secure user authenticable authorization request to the STS over the wireless network to authorize an action with a provider.
Owner:PCMS HOLDINGS INC
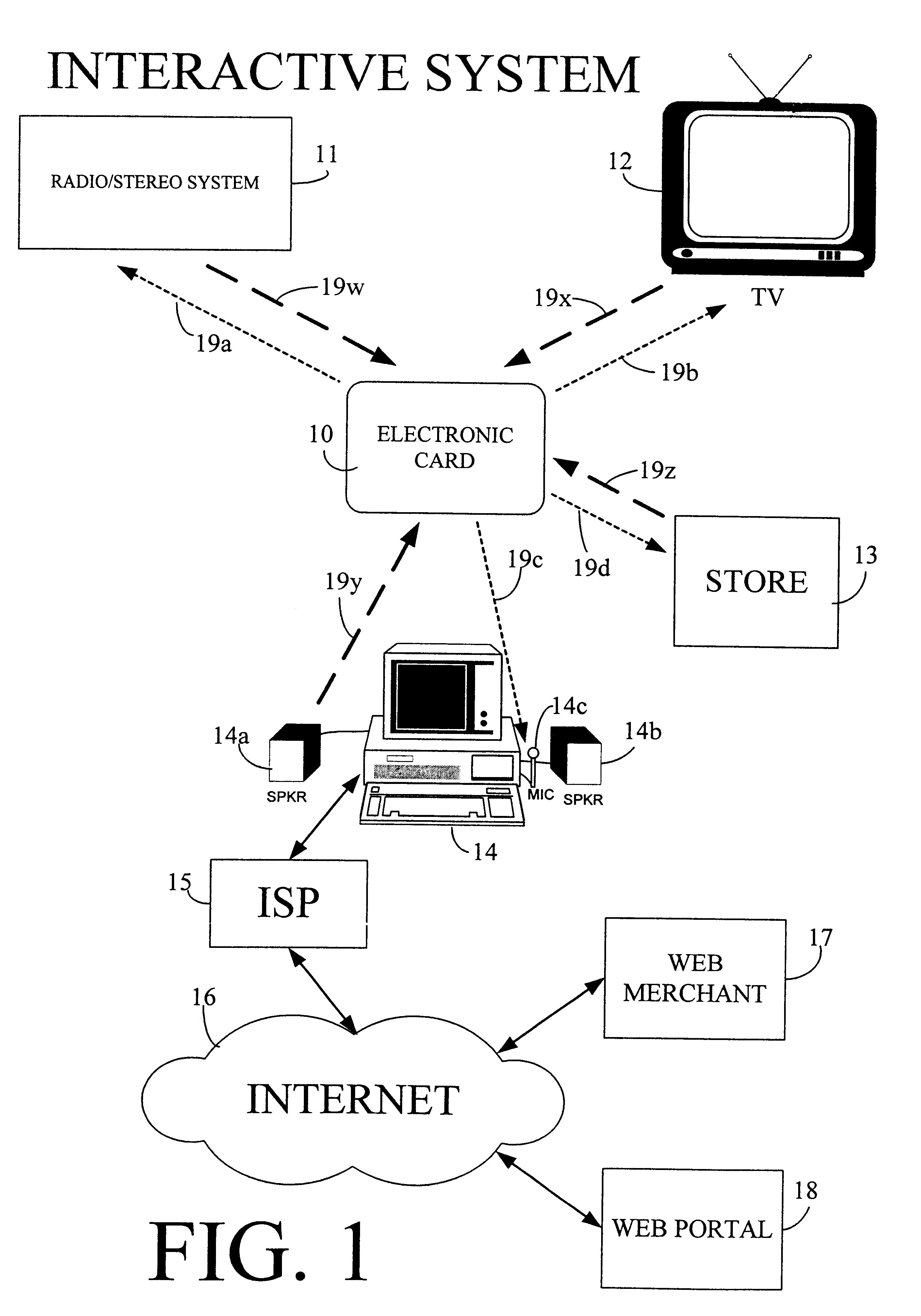
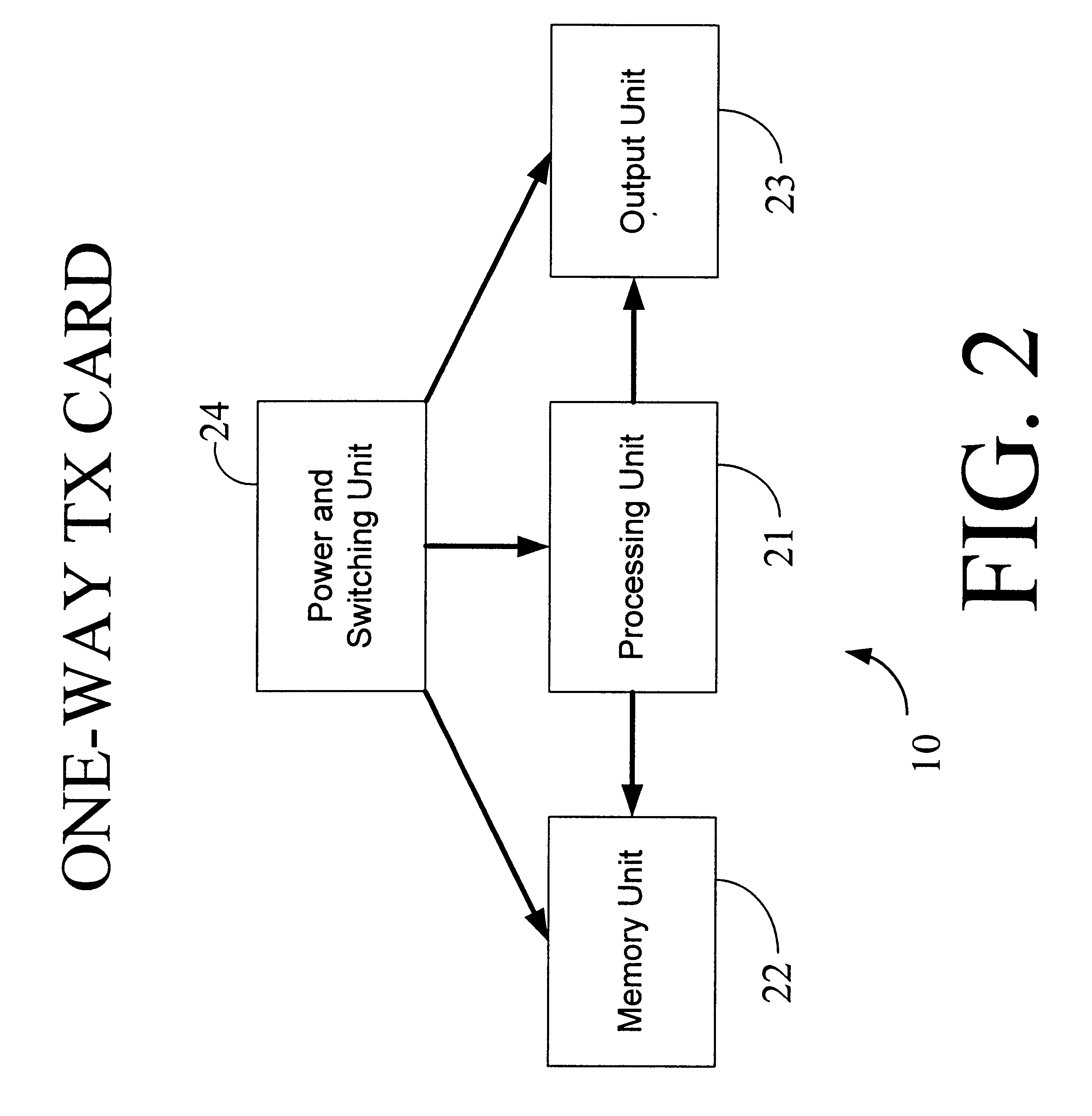
Physical presence digital authentication system
InactiveUS6607136B1Enhanced interactionMass scalableCredit registering devices actuationDiscounts/incentivesCrowdsAcoustic wave
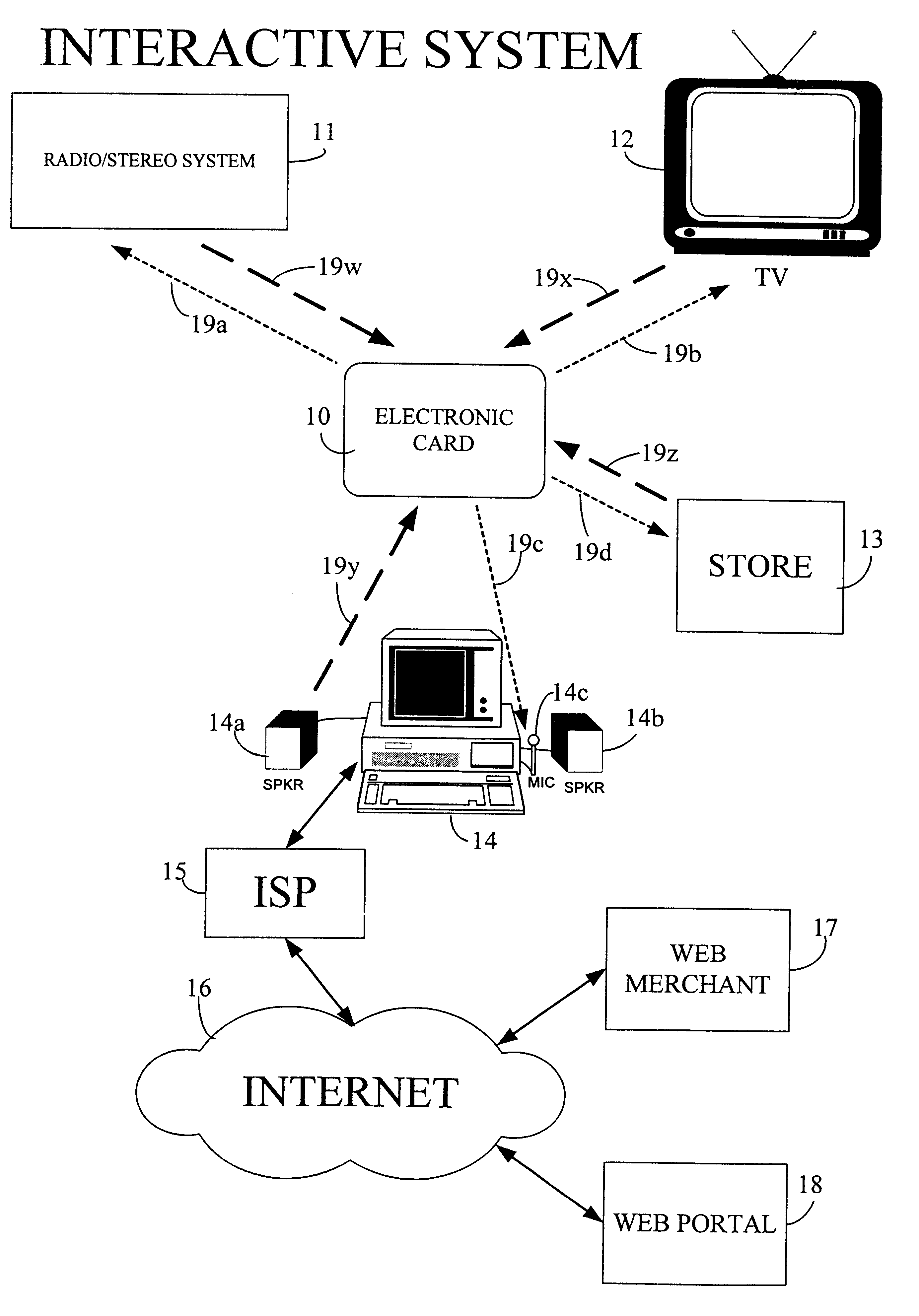
The interactive authentication system allows a consumer to interact with a base station, such as broadcast media (e.g., television and radio) or PC, to receive coupons, special sales offers, and other information with an electronic card. The electronic card can also be used to transmit a signal that can be received by the base station to perform a wide variety of tasks. These tasks can include launching an application, authenticating a user at a website, and completing a sales transaction at a website (e.g., by filling out a form automatically). The interaction between the base station and the electronic card is accomplished by using the conventional sound system in the base station so that a special reader hardware need not be installed to interact with the electronic card. The user is equipped with an electronic card that can receive and transmit data via sound waves. In the various embodiments, the sound waves can be audible or ultrasonic (which can be slightly audible to some groups of people).
Owner:SONIXIO INC
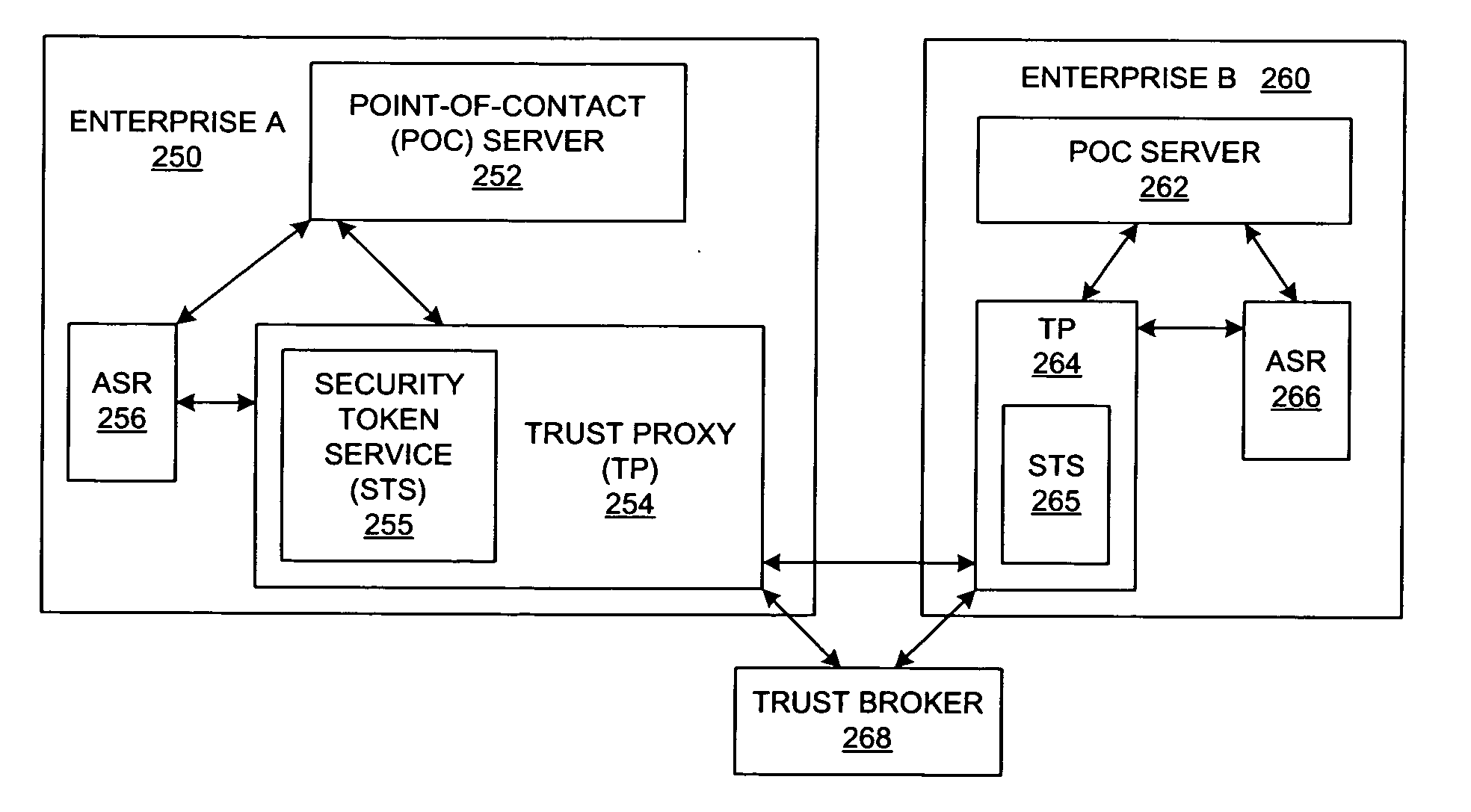
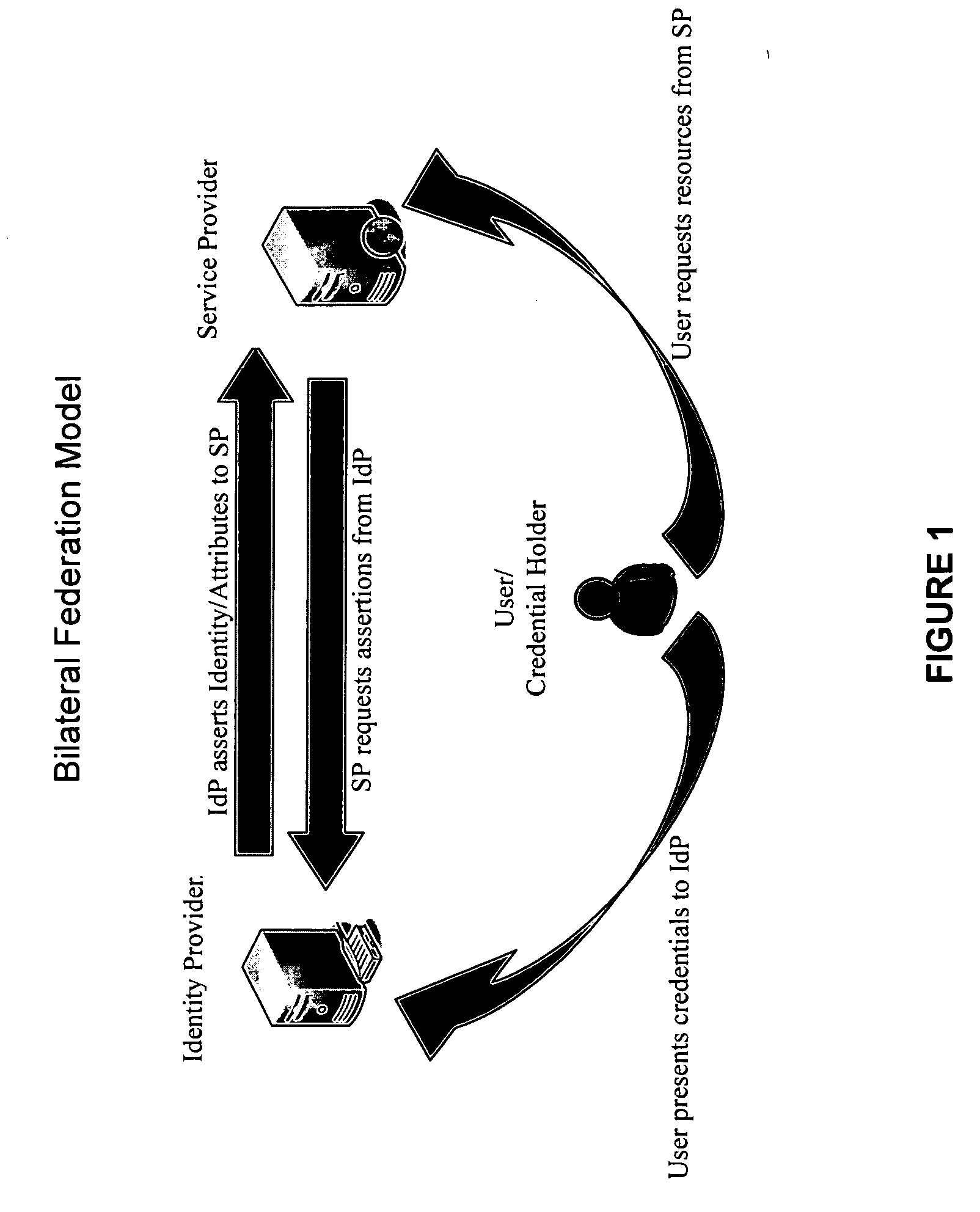
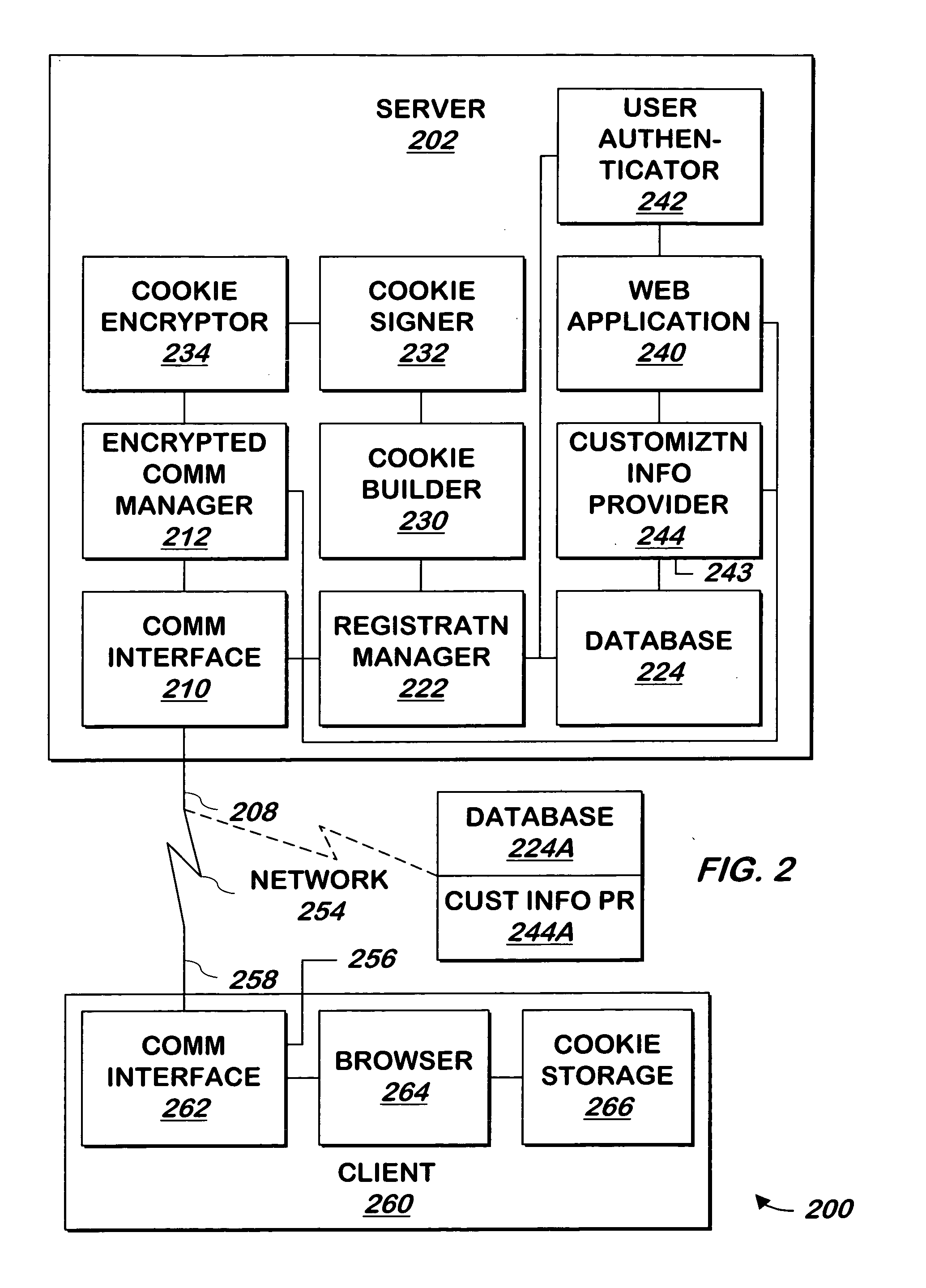
Method and system for federated provisioning
ActiveUS20060021019A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust relationship
A method and a system are presented in which federated domains interact within a federated environment. Domains within a federation can initiate federated single-sign-on operations for a user at other federated domains. A point-of-contact server within a domain relies upon a trust proxy within the domain to manage trust relationships between the domain and the federation. Trust proxies interpret assertions from other federated domains as necessary. Trust proxies may have a trust relationship with one or more trust brokers, and a trust proxy may rely upon a trust broker for assistance in interpreting assertions. When a user is provisioned at a particular federated domain, the federated domain can provision the user to other federated domains within the federated environment. A provision operation may include creating or deleting an account for a user, pushing updated user account information including attributes, and requesting updates on account information including attributes.
Owner:SERVICENOW INC
Advanced authentication techniques and applications
ActiveUS20140289833A1Digital data processing detailsMultiple digital computer combinationsEngineeringDatabase
A system, apparatus, method, and machine readable medium are described for performing advanced authentication techniques and associated applications. For example, one embodiment of a method comprises: receiving a policy identifying a set of acceptable authentication capabilities; determining a set of client authentication capabilities; and filtering the set of acceptable authentication capabilities based on the determined set of client authentication capabilities to arrive at a filtered set of one or more authentication capabilities for authenticating a user of the client.
Owner:NOK NOK LABS
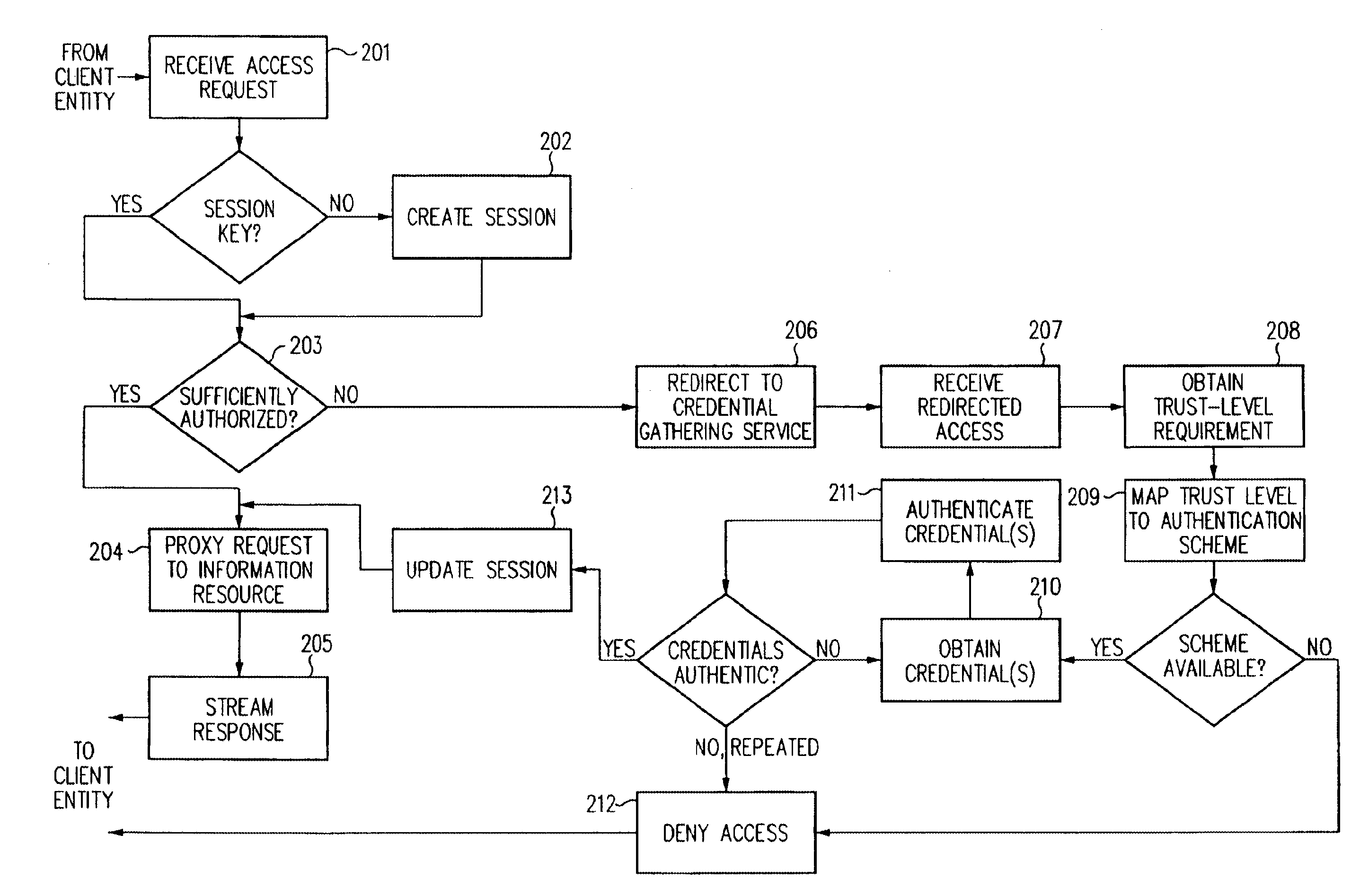
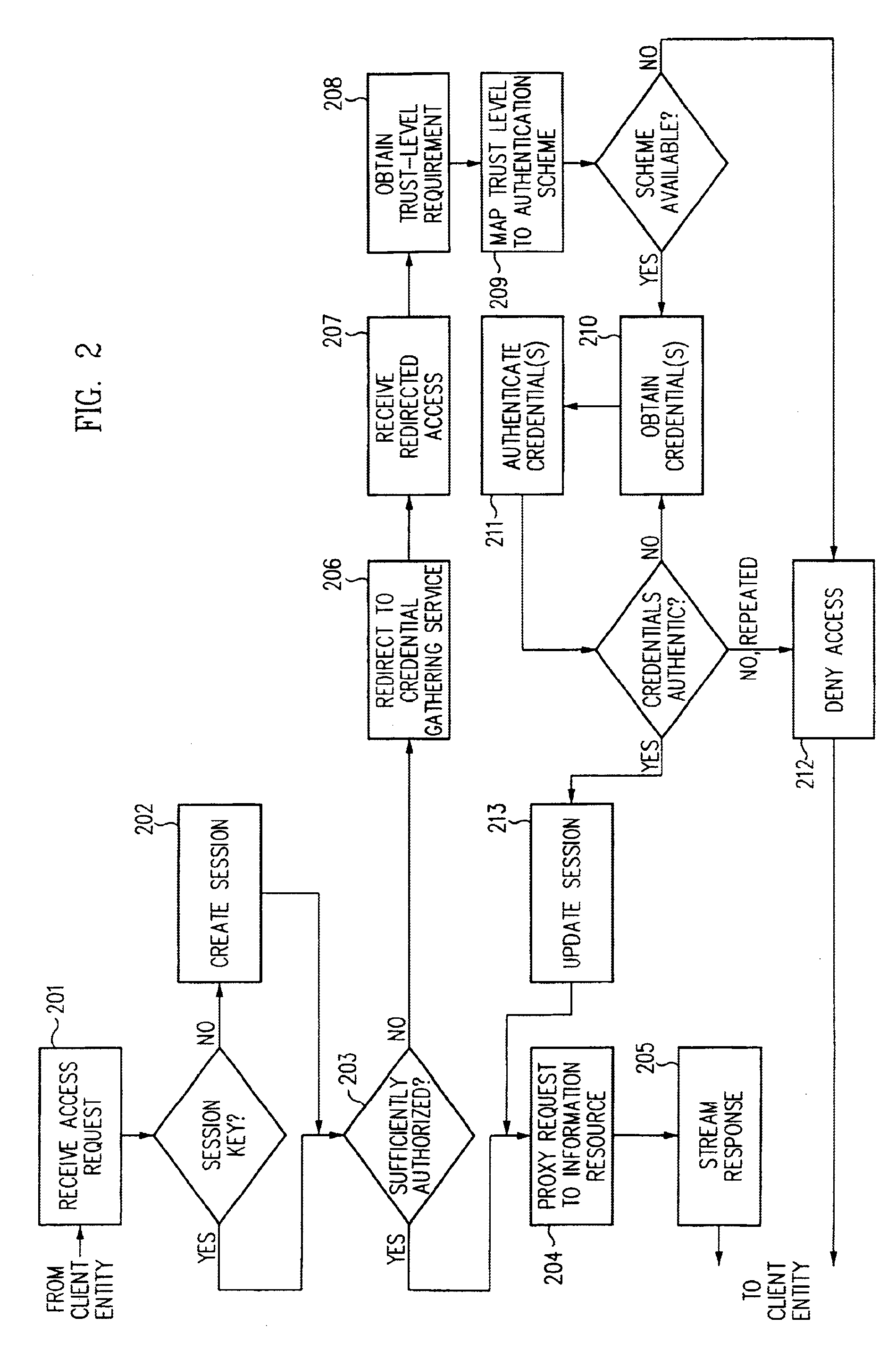
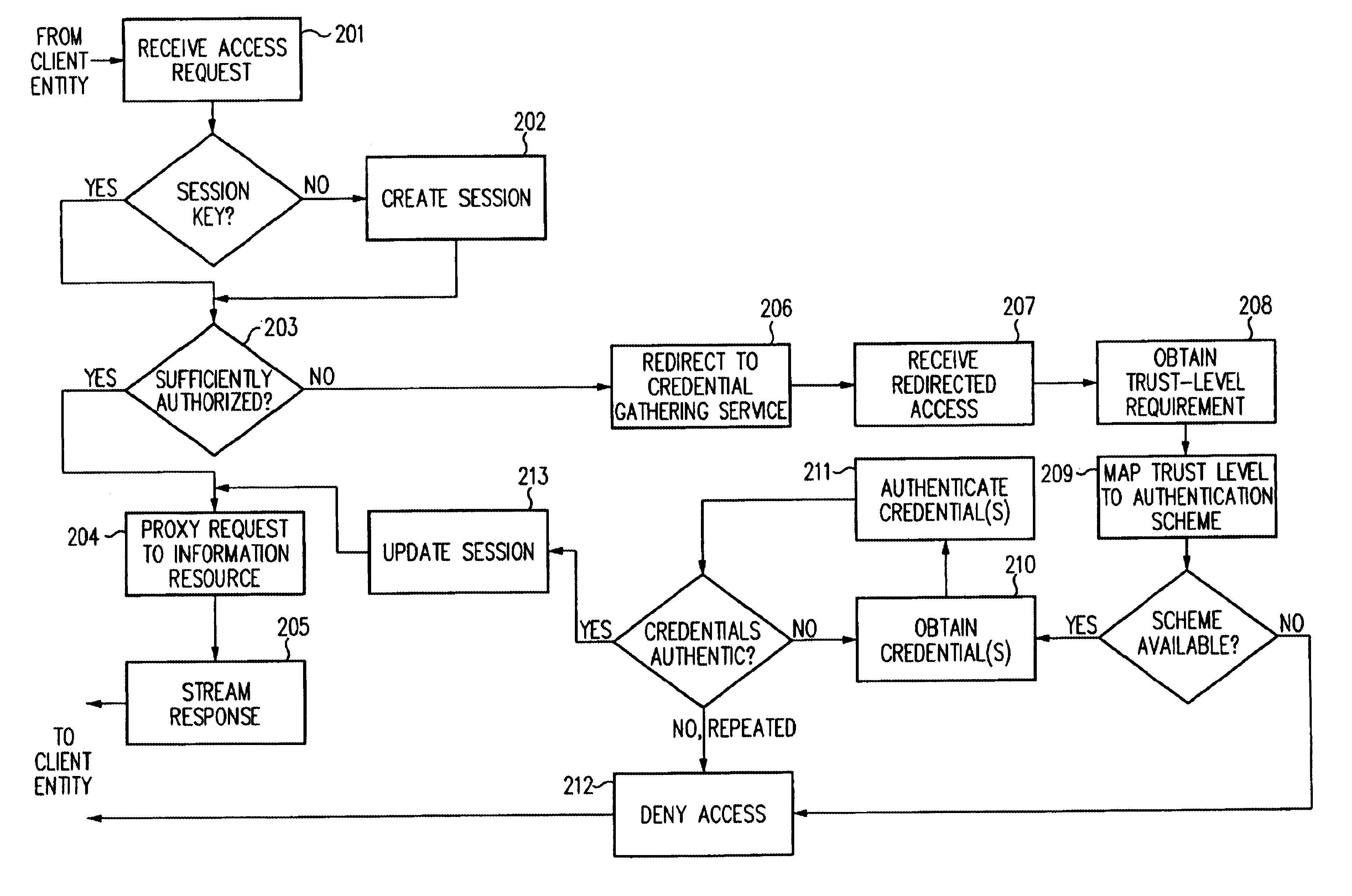
Log-on service providing credential level change without loss of session continuity
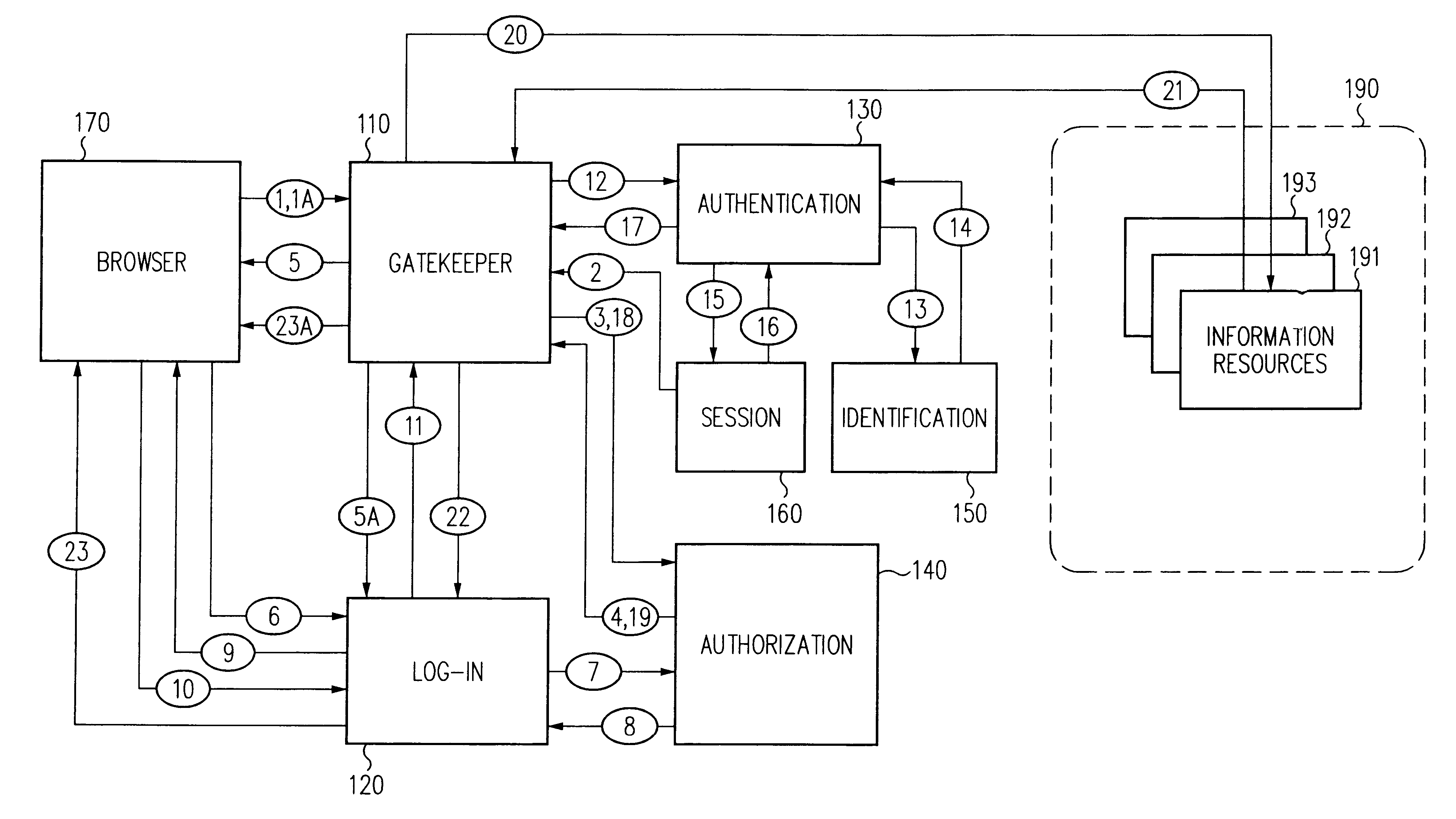
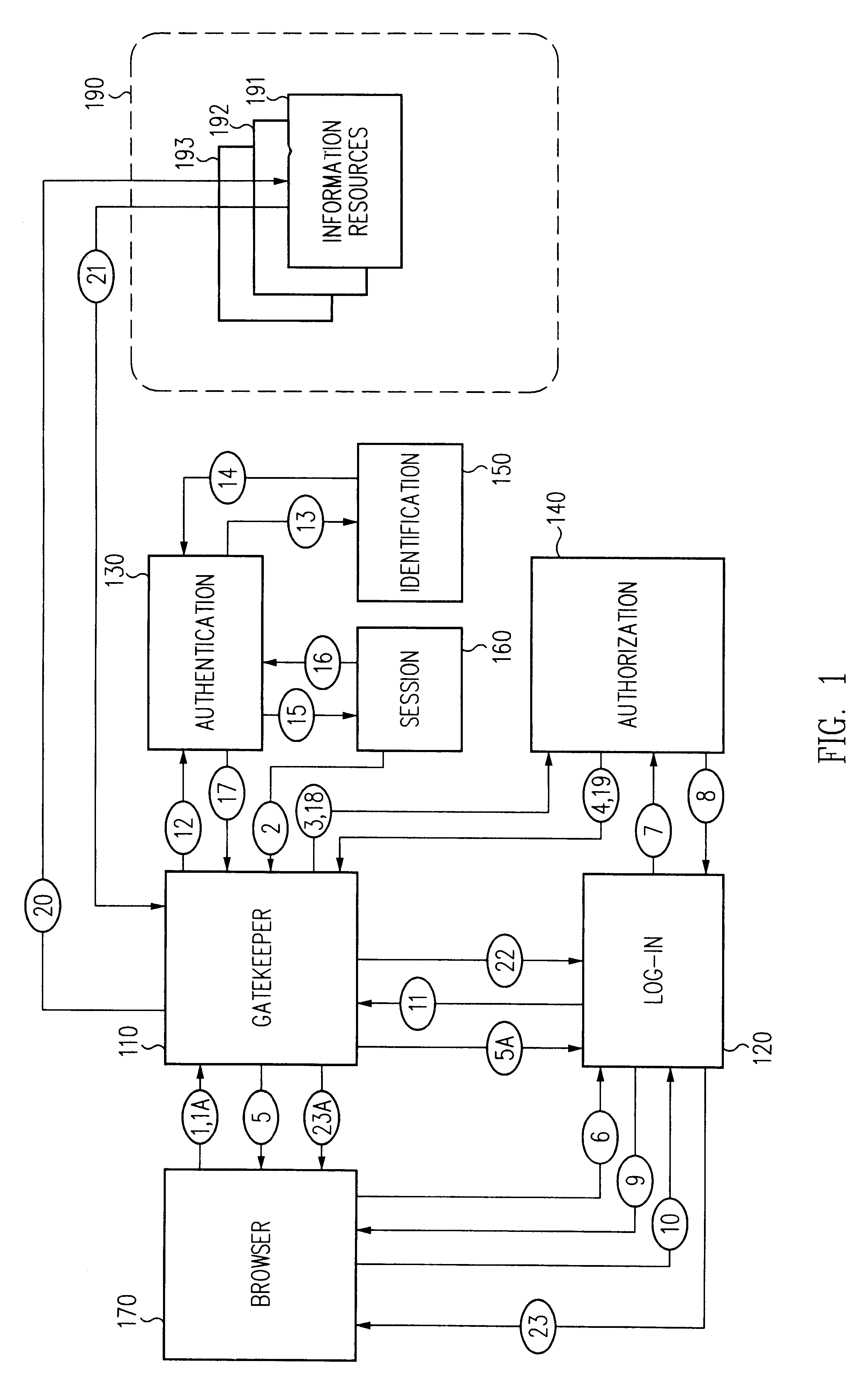
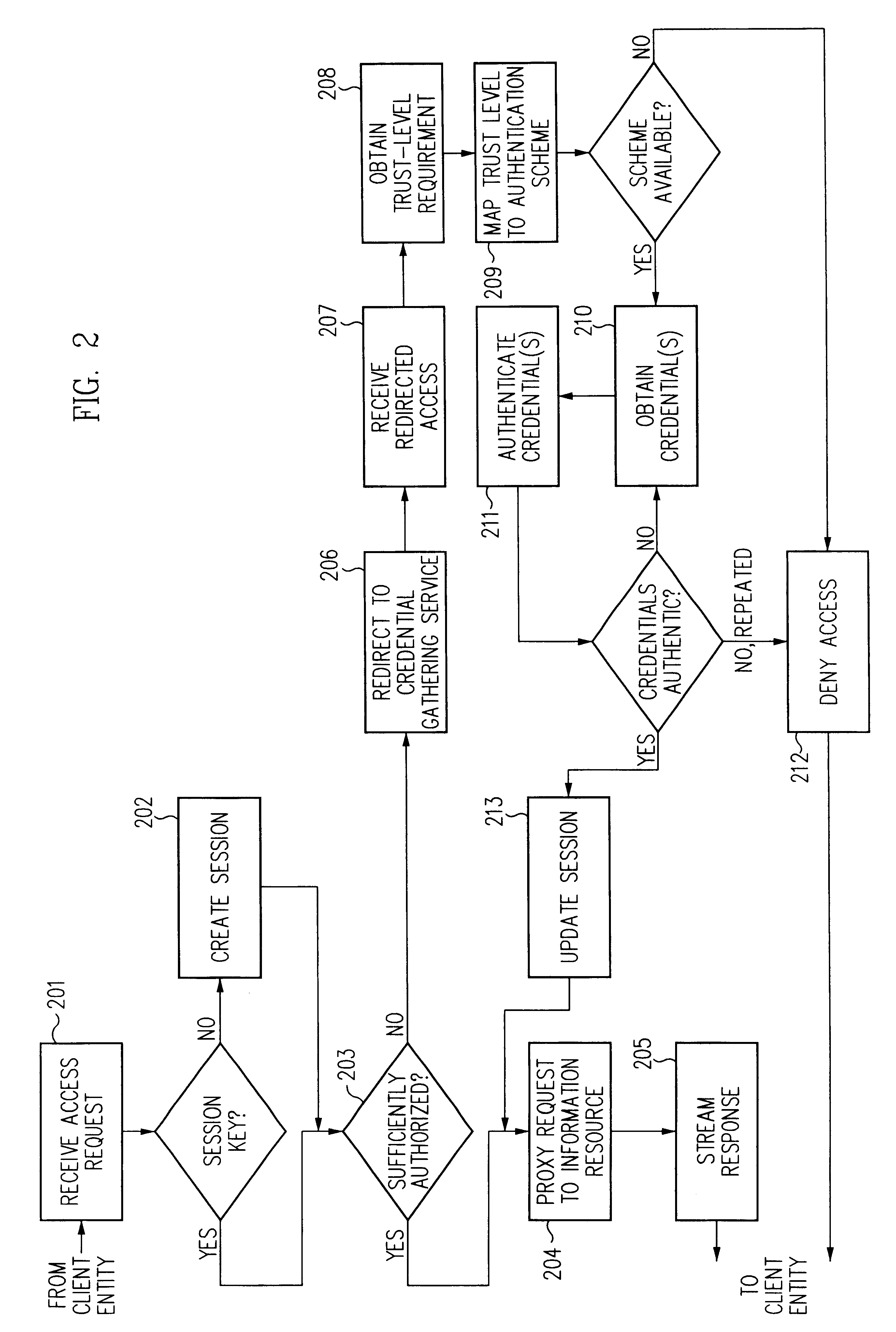
InactiveUS6609198B1Volume/mass flow measurementMultiple digital computer combinationsInformation resourceTrust level
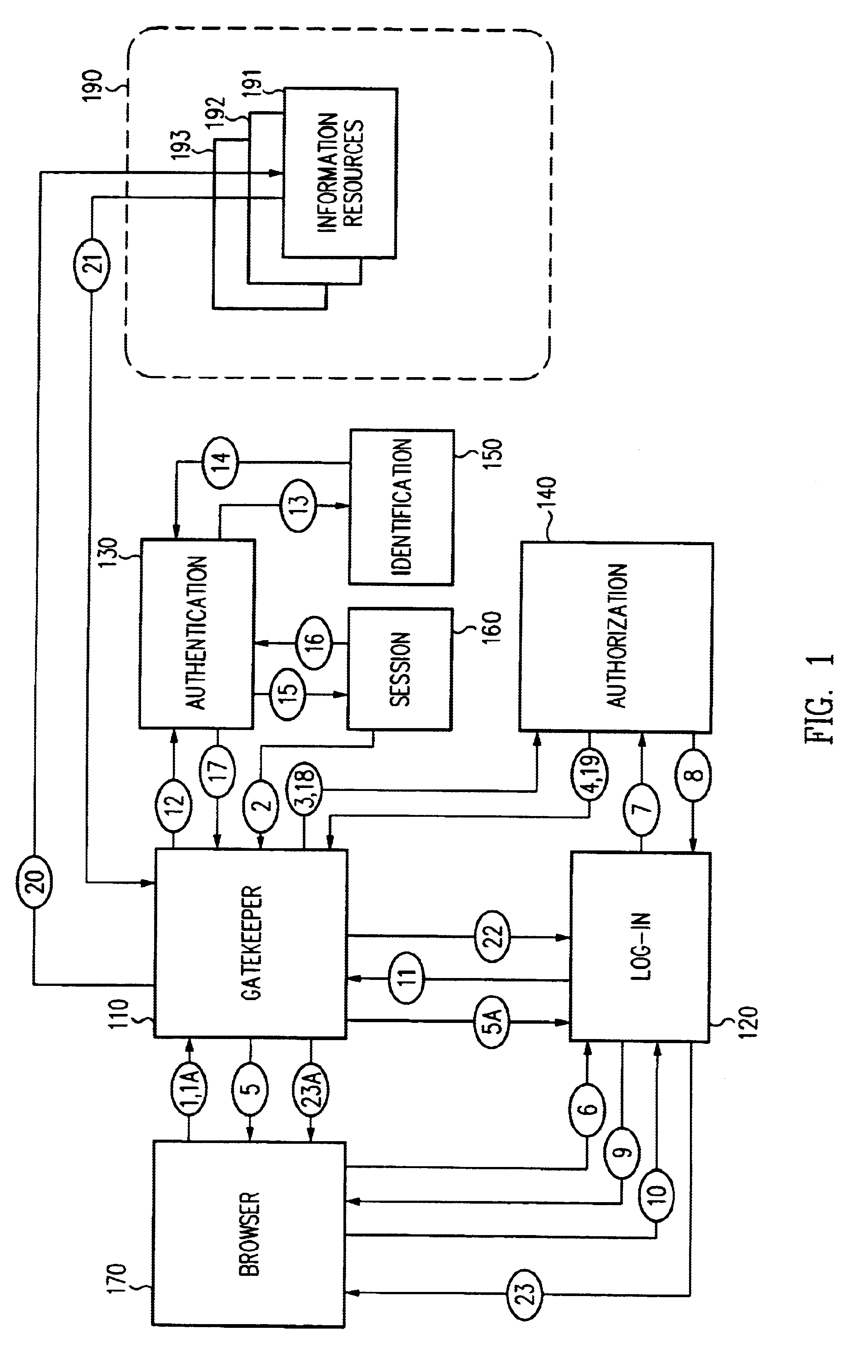
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient. The security architecture allows upgrade of credentials for a given session. This capability is particularly advantageous in the context of a single, enterprise-wide log-on. An entity (e.g., a user or an application) may initially log-on with a credential suitable for one or more resources in an initial resource set, but then require access to resource requiring authentication at higher trust level. In such case, the log-on service allows additional credentials to be provided to authenticate at the higher trust level. The log-on service allows upgrading and / or downgrading without loss of session continuity (i.e., without loss of identity mappings, authorizations, permissions, and environmental variables, etc.).
Owner:ORACLE INT CORP
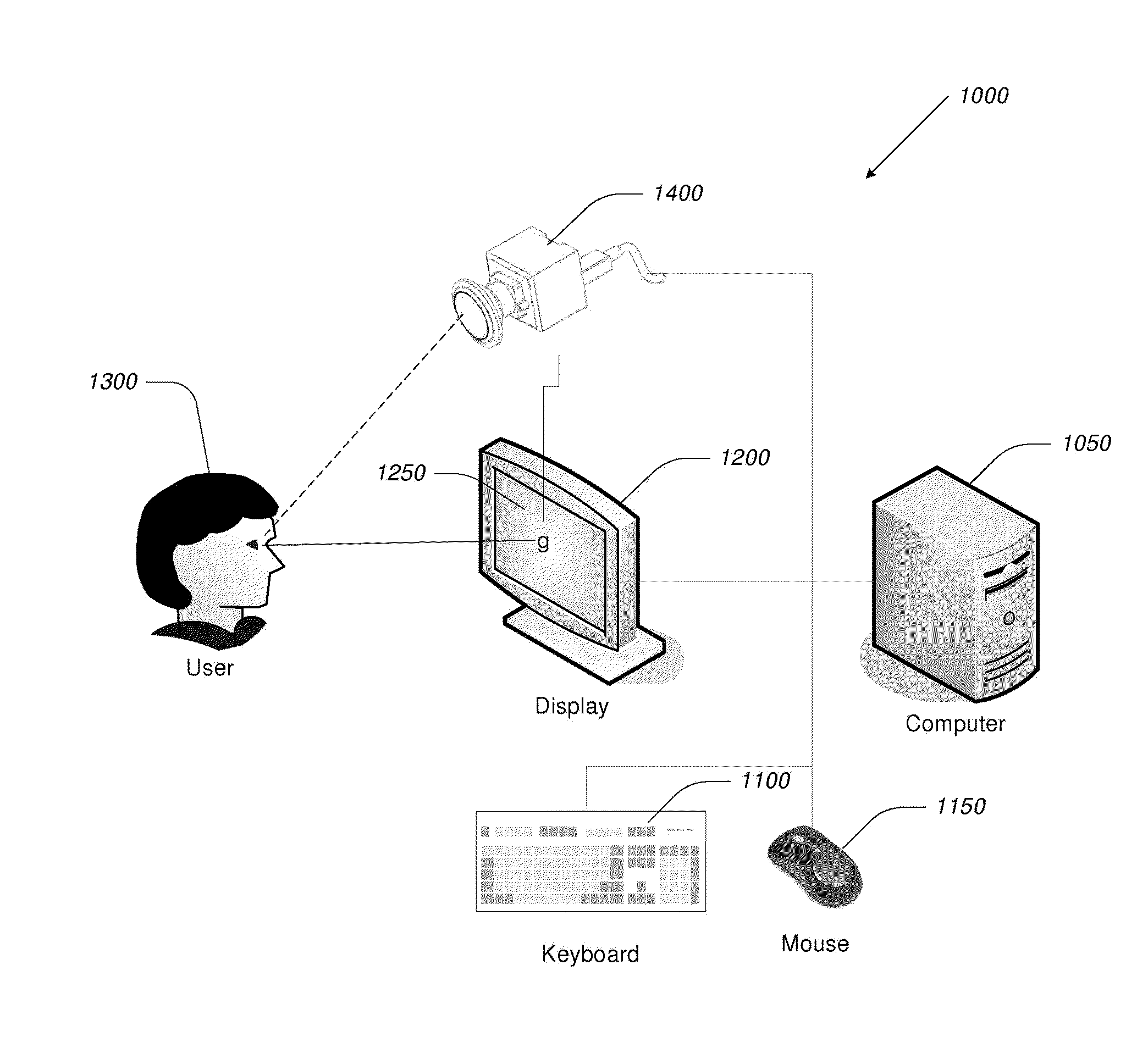
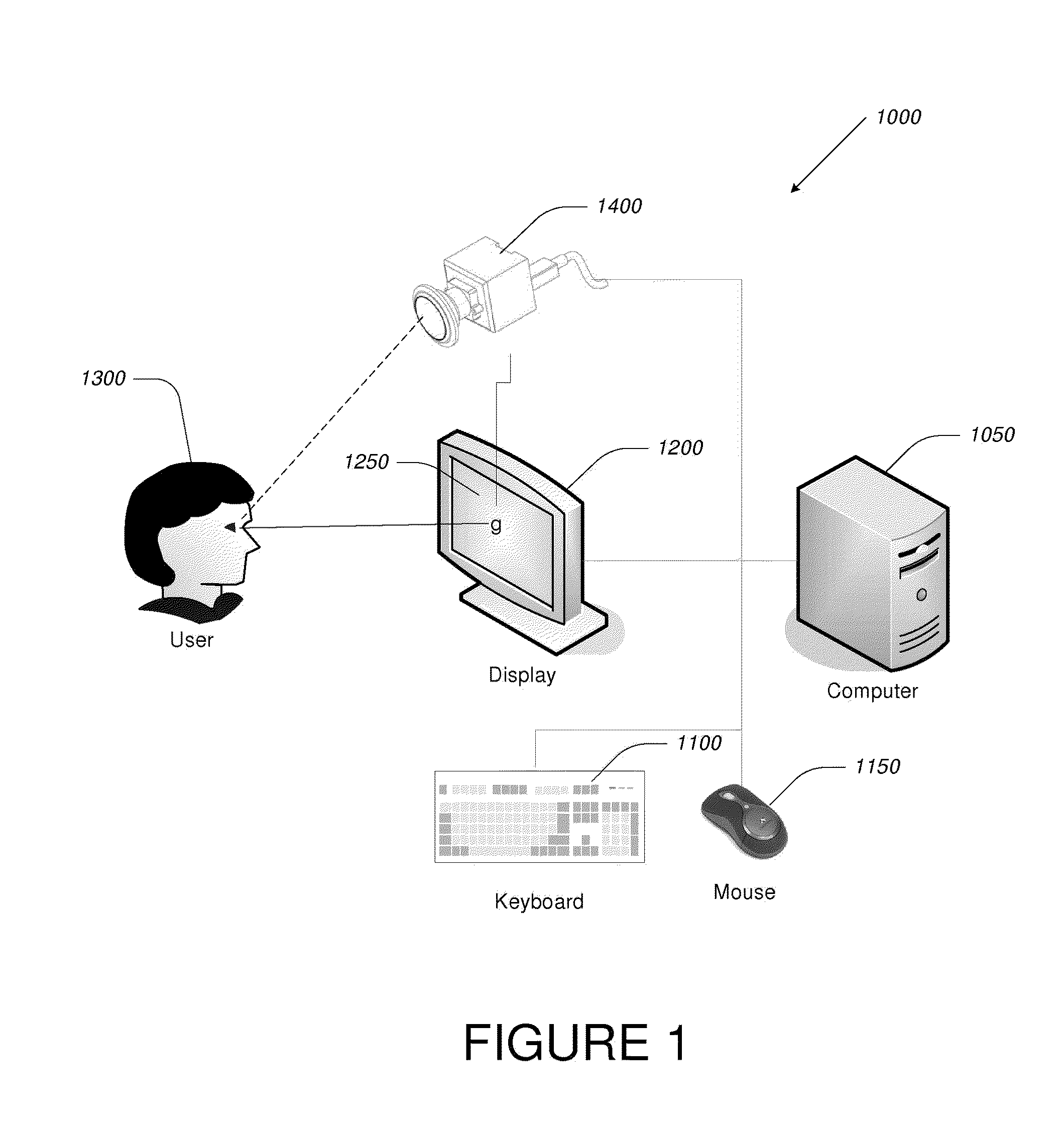
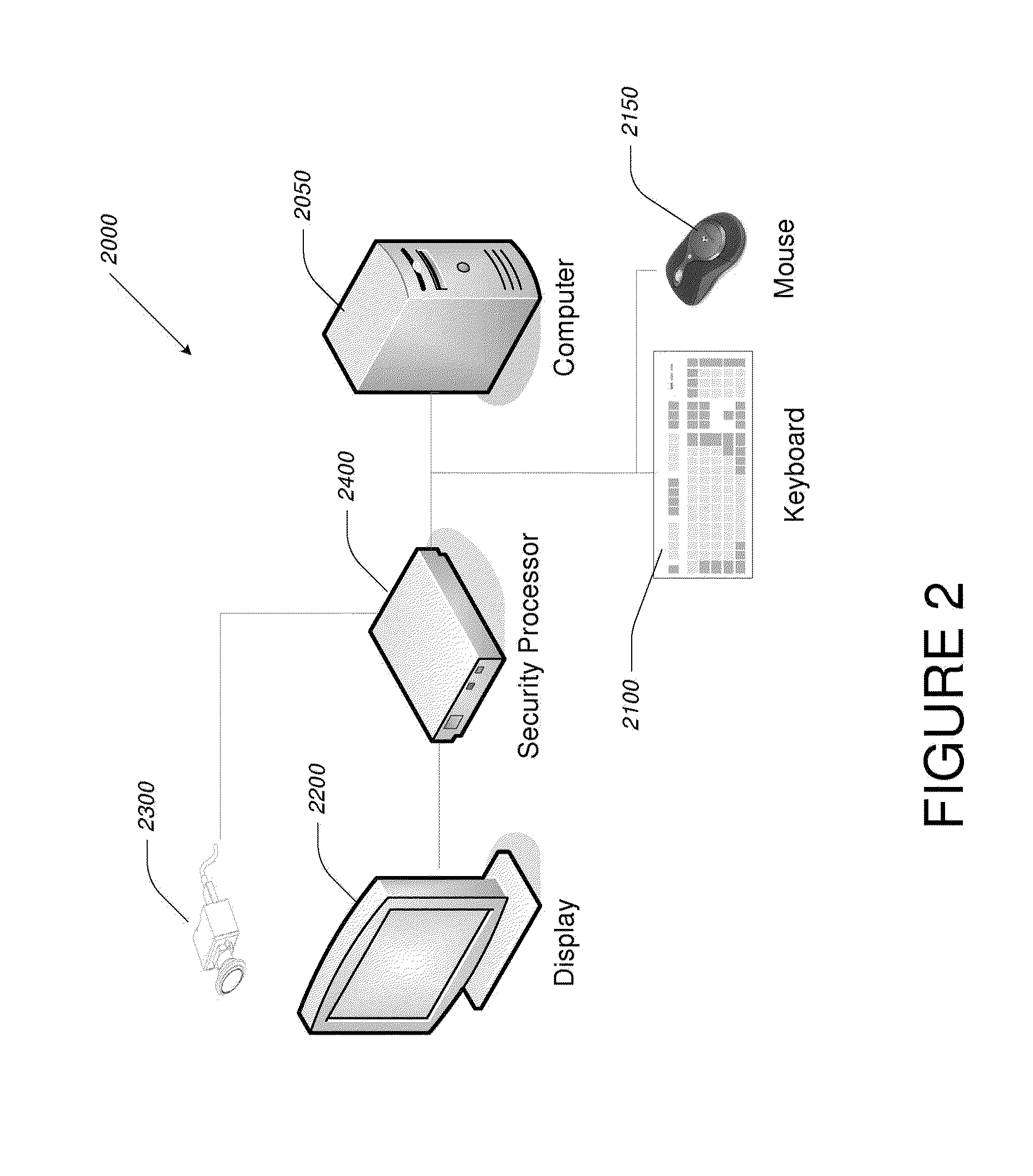
Video-Based Privacy Supporting System
ActiveUS20100205667A1Improve securityPrivacy protectionDigital data processing detailsUnauthorized memory use protectionDisplay deviceOutput device
Computer display privacy and security for computer systems. In one aspect, the invention provides a computer-controlled system for regulating the interaction between a computer and a user of the computer based on the environment of the computer and the user. For example, the computer-controlled system provided by the invention comprises an input-output device including an image sensor configured to collect facial recognition data proximate to the computer. The system also includes a user security parameter database encoding security parameters associated with the user; the database is also configured to communicate with the security processor. The security processor is configured to receive the facial recognition data and the security parameters associated with the user, and is further configured to at least partially control the operation of the data input device and the data output device in response to the facial recognition data and the security parameters associated with the user.
Owner:TOBII TECH AB
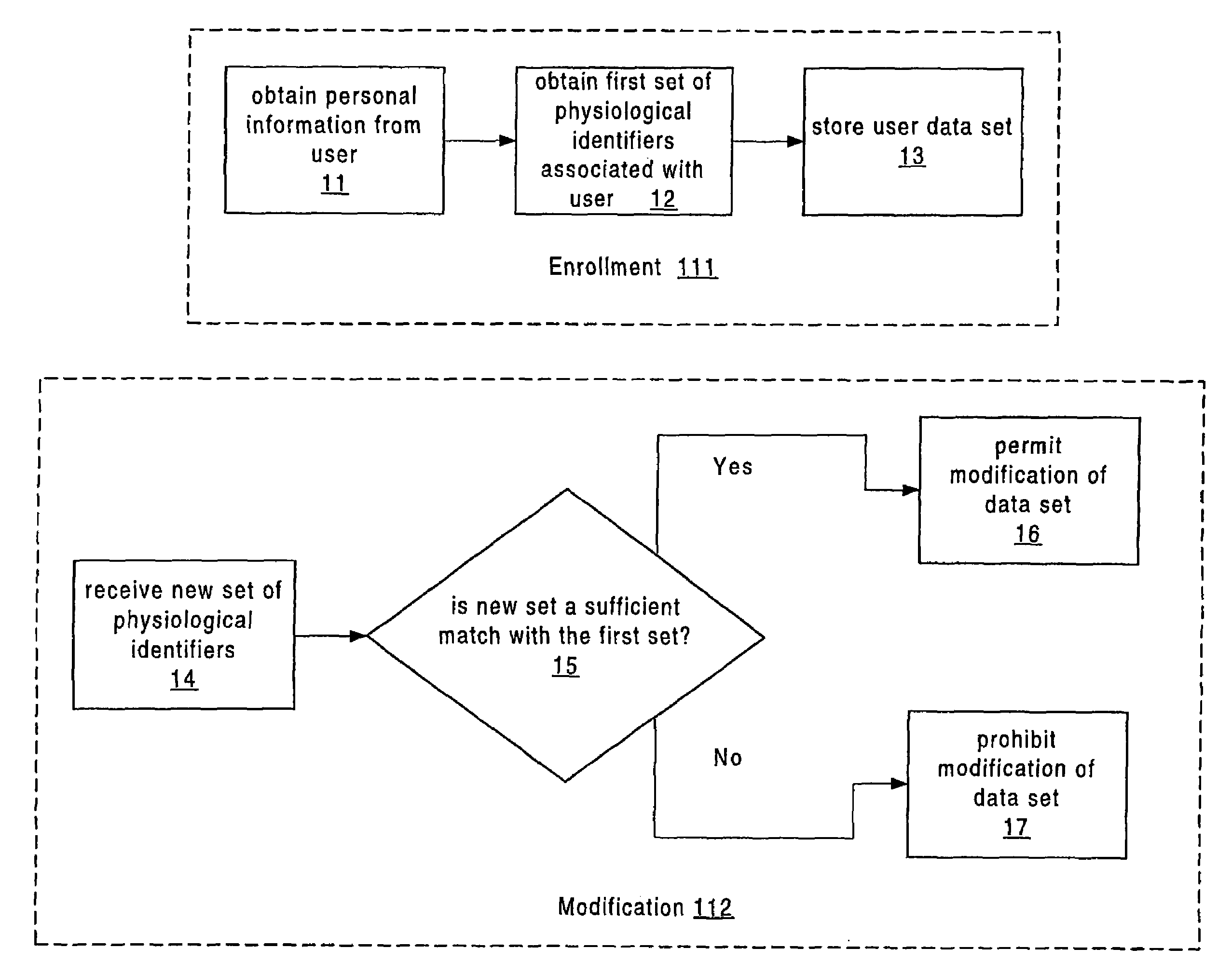
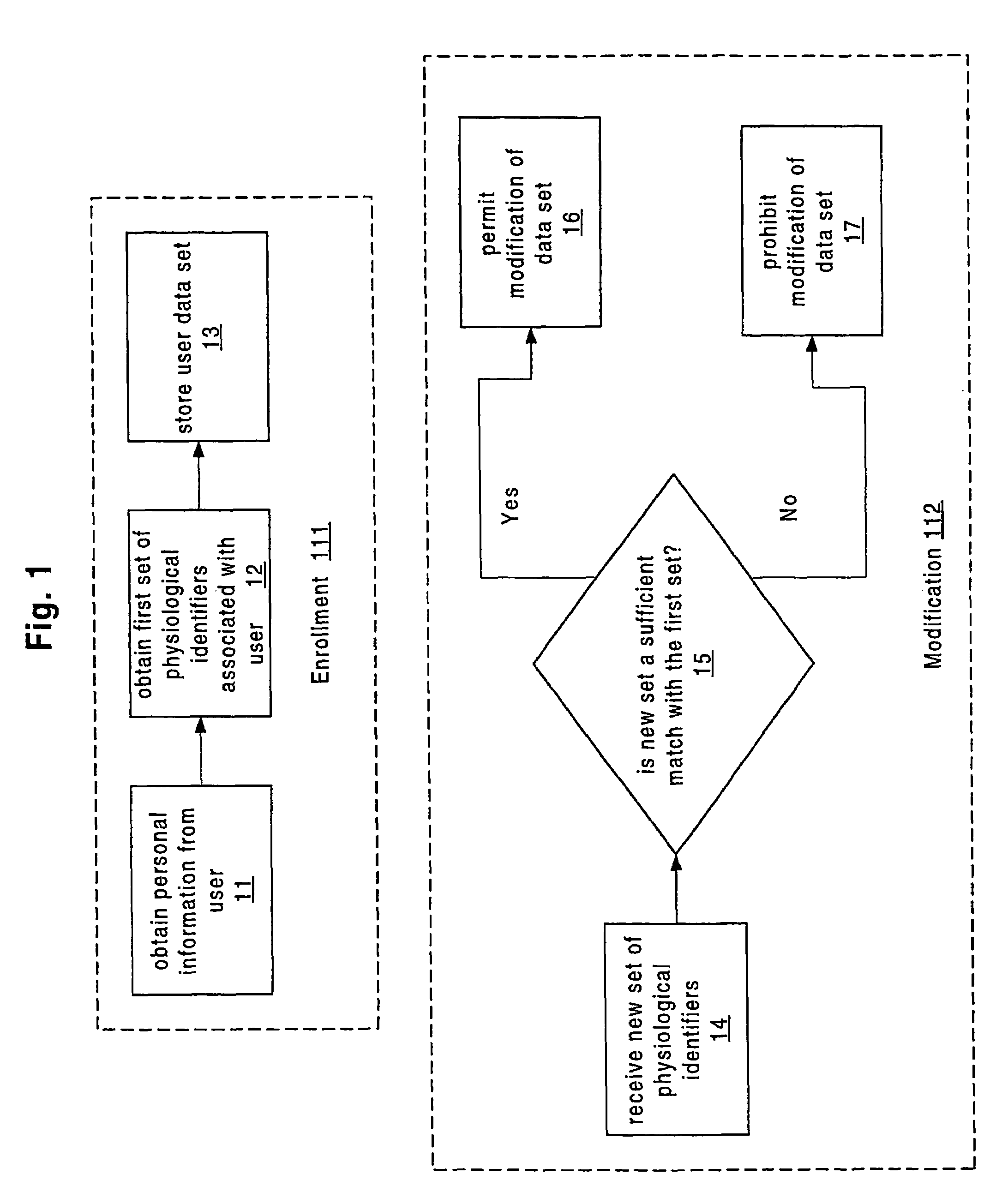
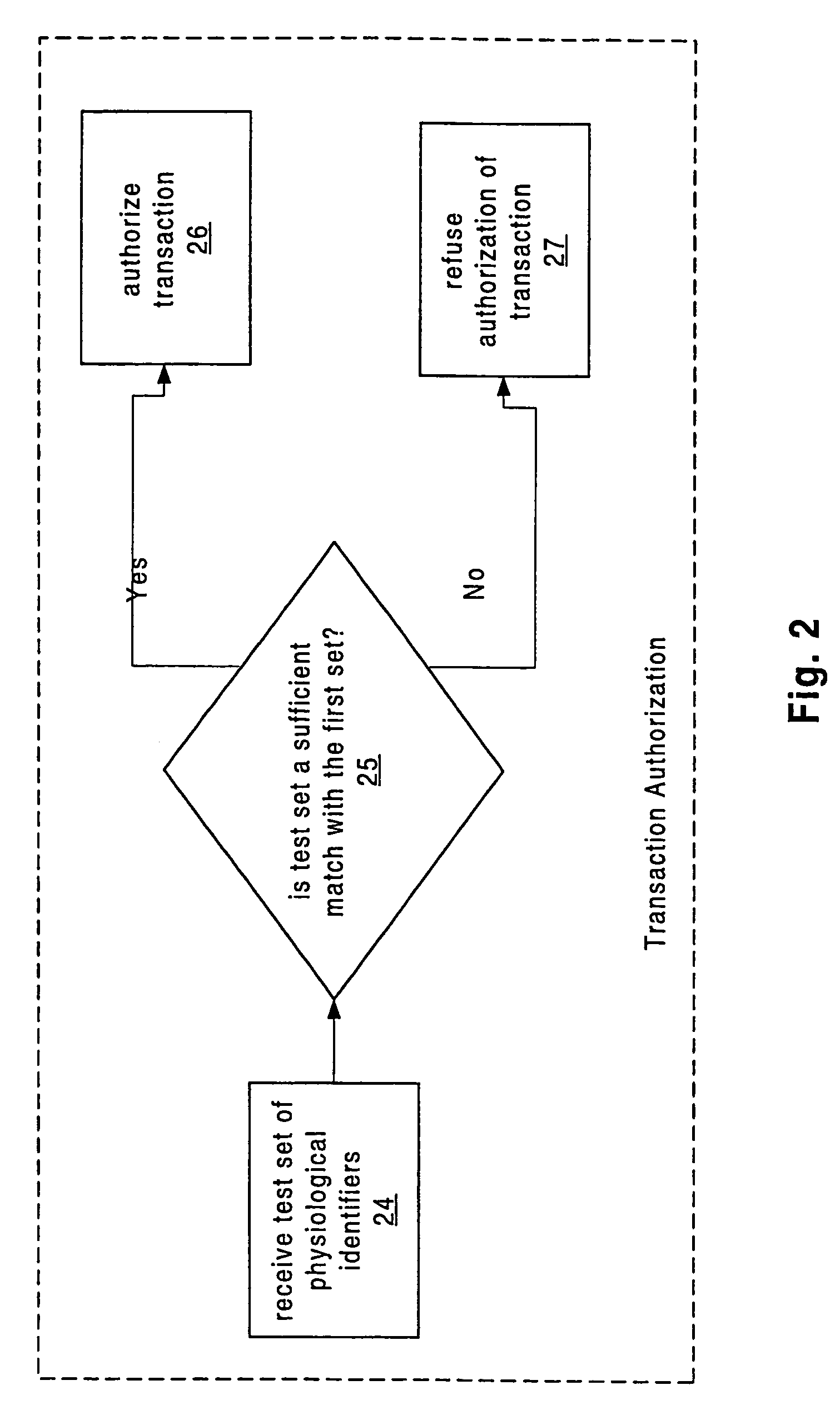
System and method for authenticating users using two or more factors
ActiveUS20050268107A1Easy to useLess increased securityPayment architectureDigital data authenticationComputer science
A system and method authenticates users via any two or three of 1) Something the user knows; 2) Something the user has; and 3) A physical characteristic of the user.
Owner:EMC IP HLDG CO LLC
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20090132813A1Save bandwidthSaving response timeDigital data processing detailsUser identity/authority verificationElectronic systemsFinancial transaction
Apparatus and methods perform transactions in a secure environment between an individual and another party, such as a merchant, in various embodiments. The individual possesses a mobile electronic device, such as a smartphone, that can encrypt data according to a public key infrastructure. The individual authenticates the individual's identity to the device, thereby unlocking credentials that may be used in a secure transaction. The individual causes the device to communicate the credentials, in a secure fashion, to an electronic system of a relying party, in order to obtain the relying party's authorization to enter the transaction. The relying party system determines whether to grant the authorization, and communicates the grant and the outcome of the transaction to the device using encryption according to the public key infrastructure.
Owner:SURIDX
Administration of protection of data accessible by a mobile device
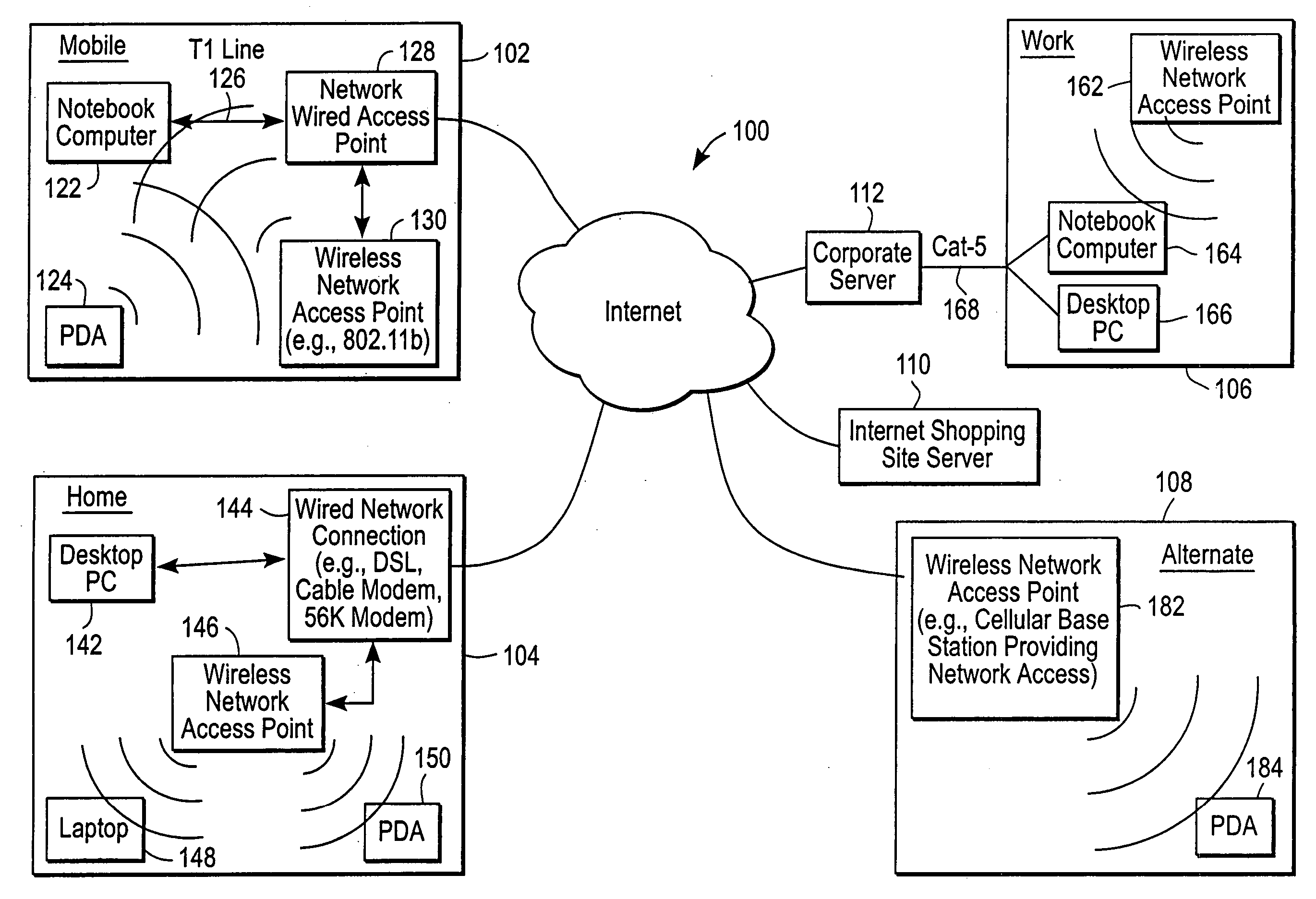
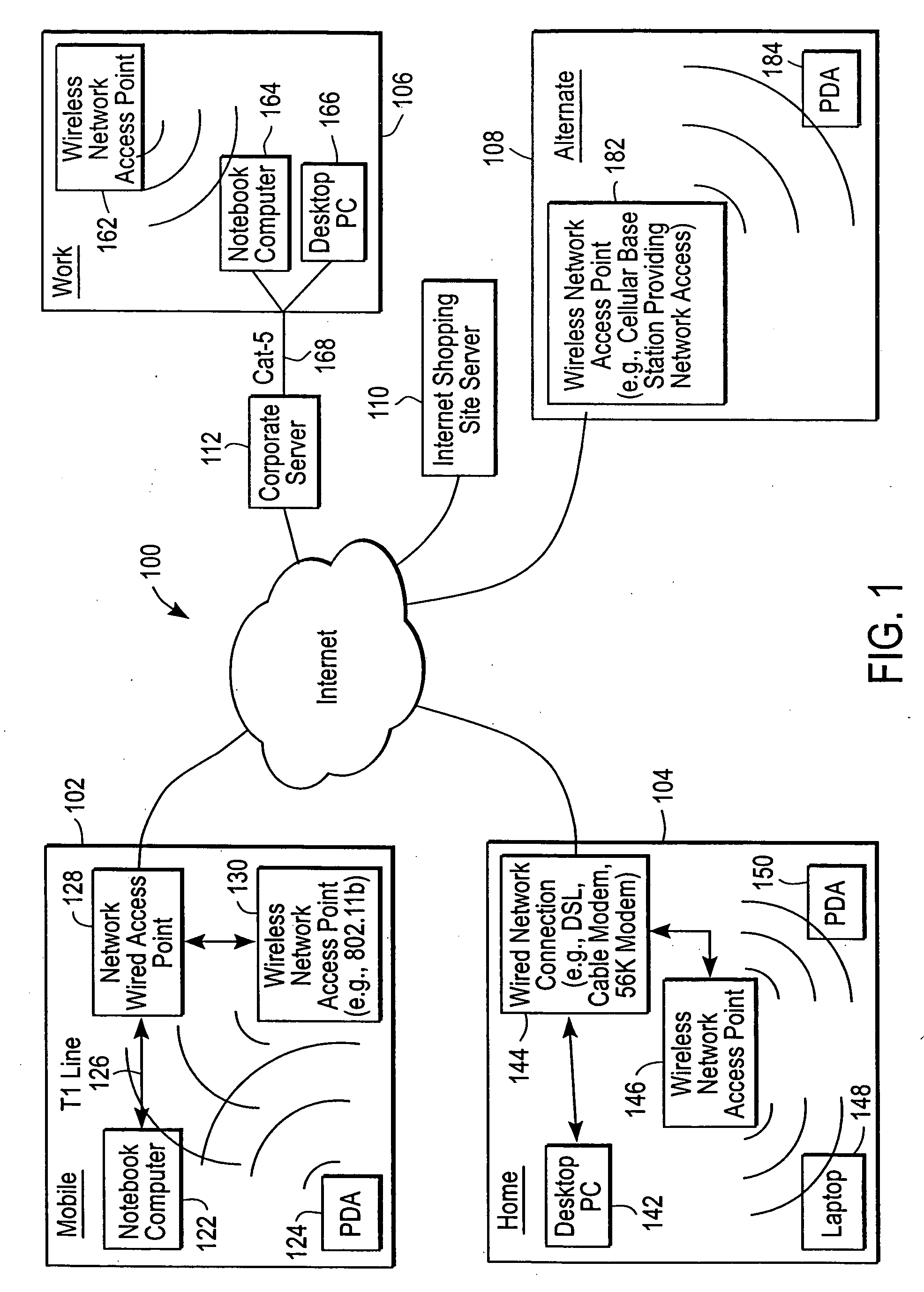
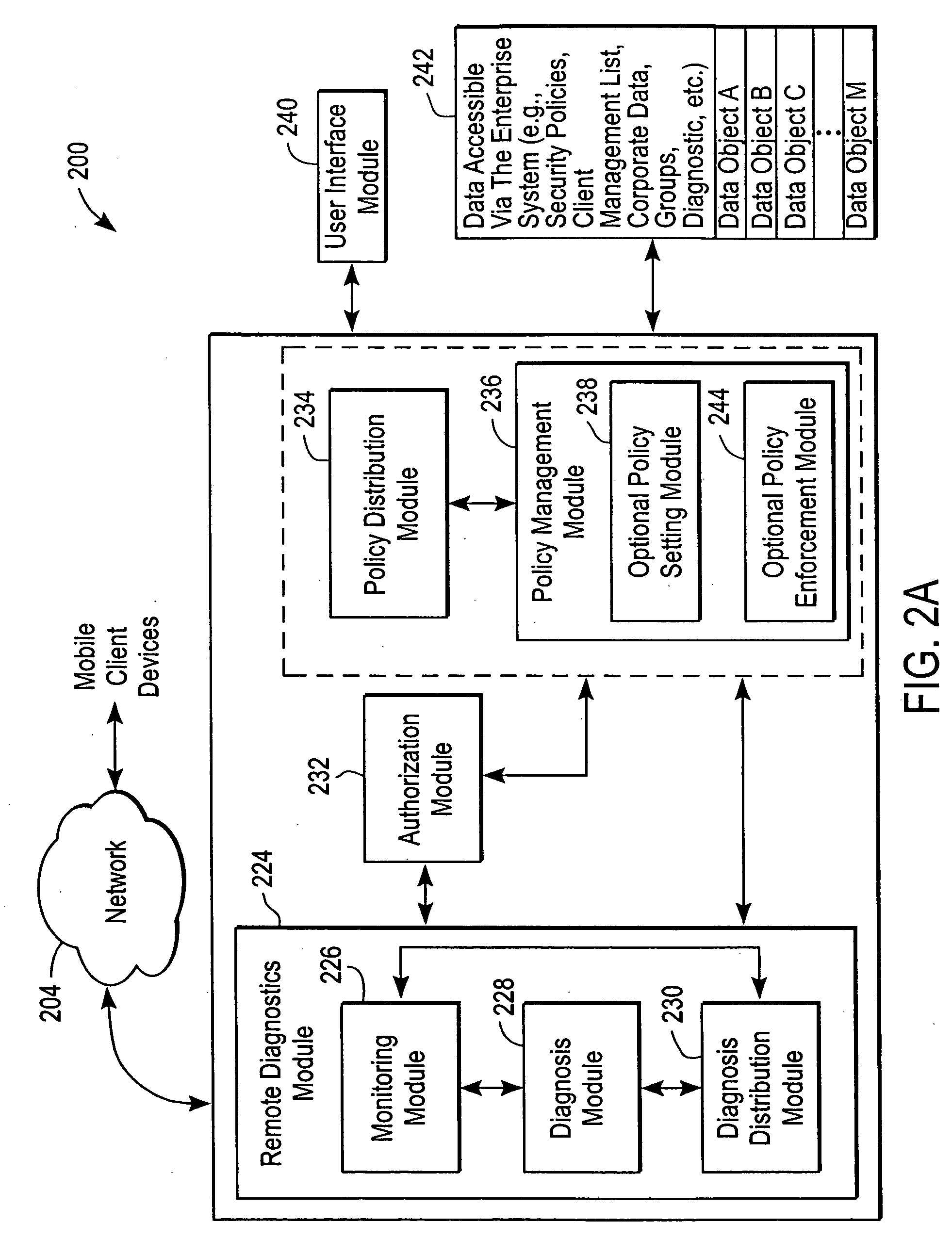
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
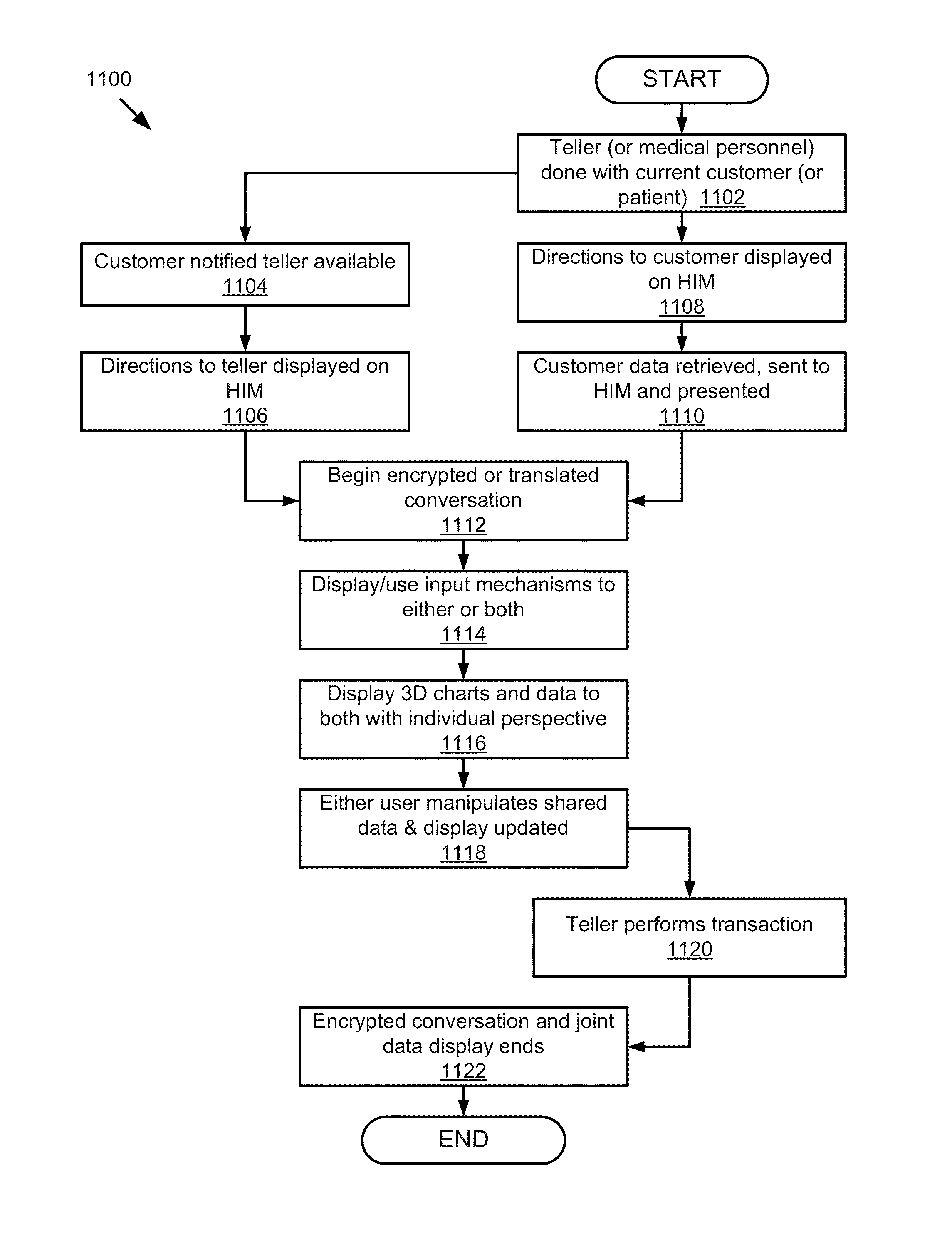
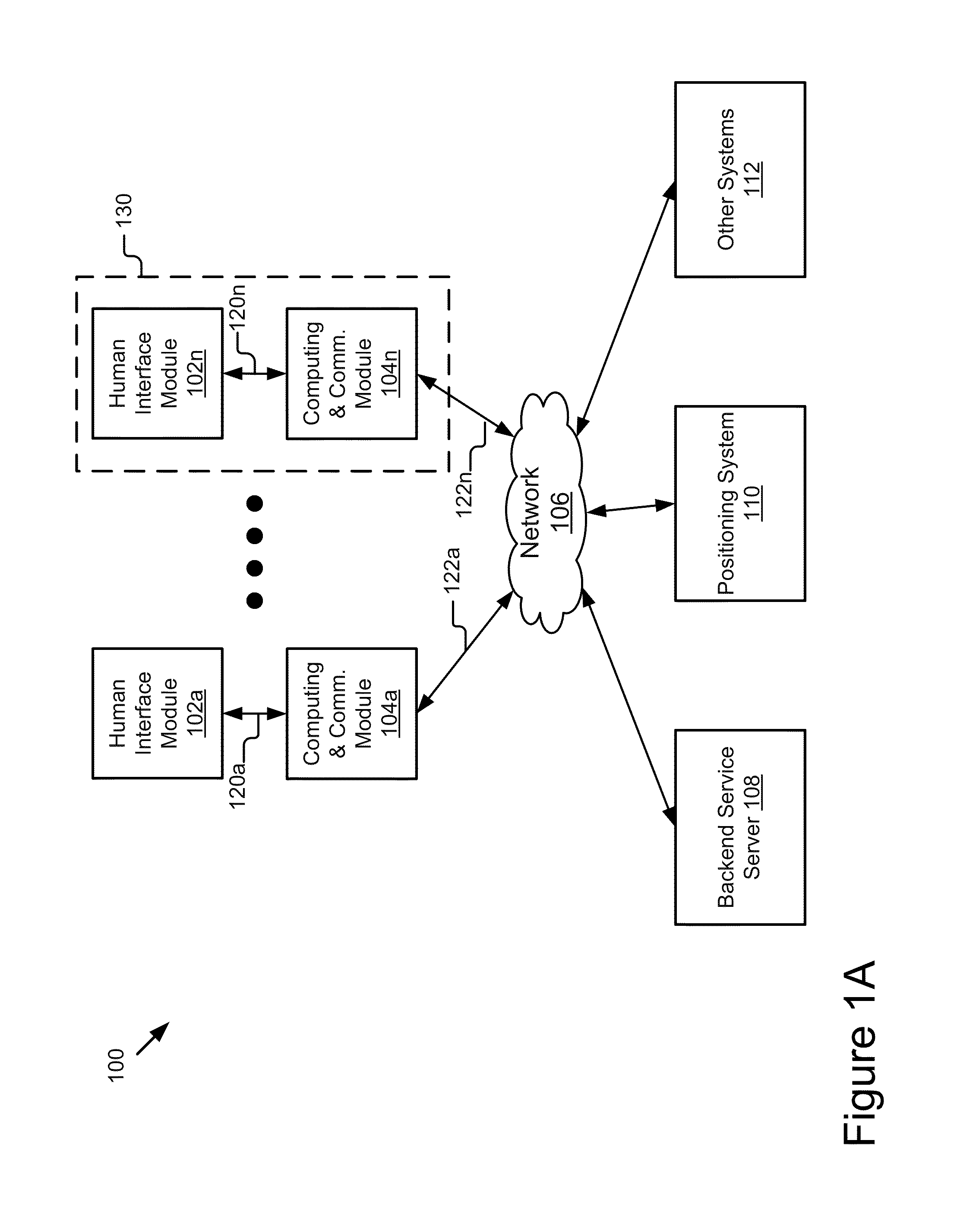
Mobile Information Gateway for Home Healthcare
A mobile information gateway comprises: a wearable human interface module having an image delivery and display mechanism for presenting information with a wide field of view and in three dimensions, a computing and communication module coupled for communication with the human interface module; and a backend service server coupled for communication with the computing and communication module, the backend service server for processing data for home healthcare. The present invention also includes a method for using the mobile information gateway for home healthcare comprises; capturing information with a wearable human interface module; processing the captured information to determine an identity of a user of the wearable human interface module; authenticating the identity of user; retrieving information using the captured information and the authenticated identity; and presenting the retrieved information using the wearable human interface module.
Owner:RICOH KK
Techniques for fraud monitoring and detection using application fingerprinting
ActiveUS20090089869A1Acutation objectsDigital data processing detailsMultiple contextApplication software
Techniques for fraud monitoring and detection using application fingerprinting. As used herein, an “application fingerprint” is a signature that uniquely identifies data submitted to a software application. In an embodiment, a plurality of historical application fingerprints are stored for data previously submitted to a software application. Each historical application fingerprint is associated with one or more contexts in which its corresponding data was submitted. When new (i.e., additional) data is subsequently submitted to the application, a new application fingerprint is generated based on the new data, and the new application fingerprint is associated with one or more contexts in which the new data was submitted. The new application fingerprint is then compared with one or more historical application fingerprints that share the same, or substantially similar, context(s). Based on this comparison, a risk score is generated indicating a likelihood that the new data was submitted for a fraudulent / malicious purpose.
Owner:ORACLE INT CORP
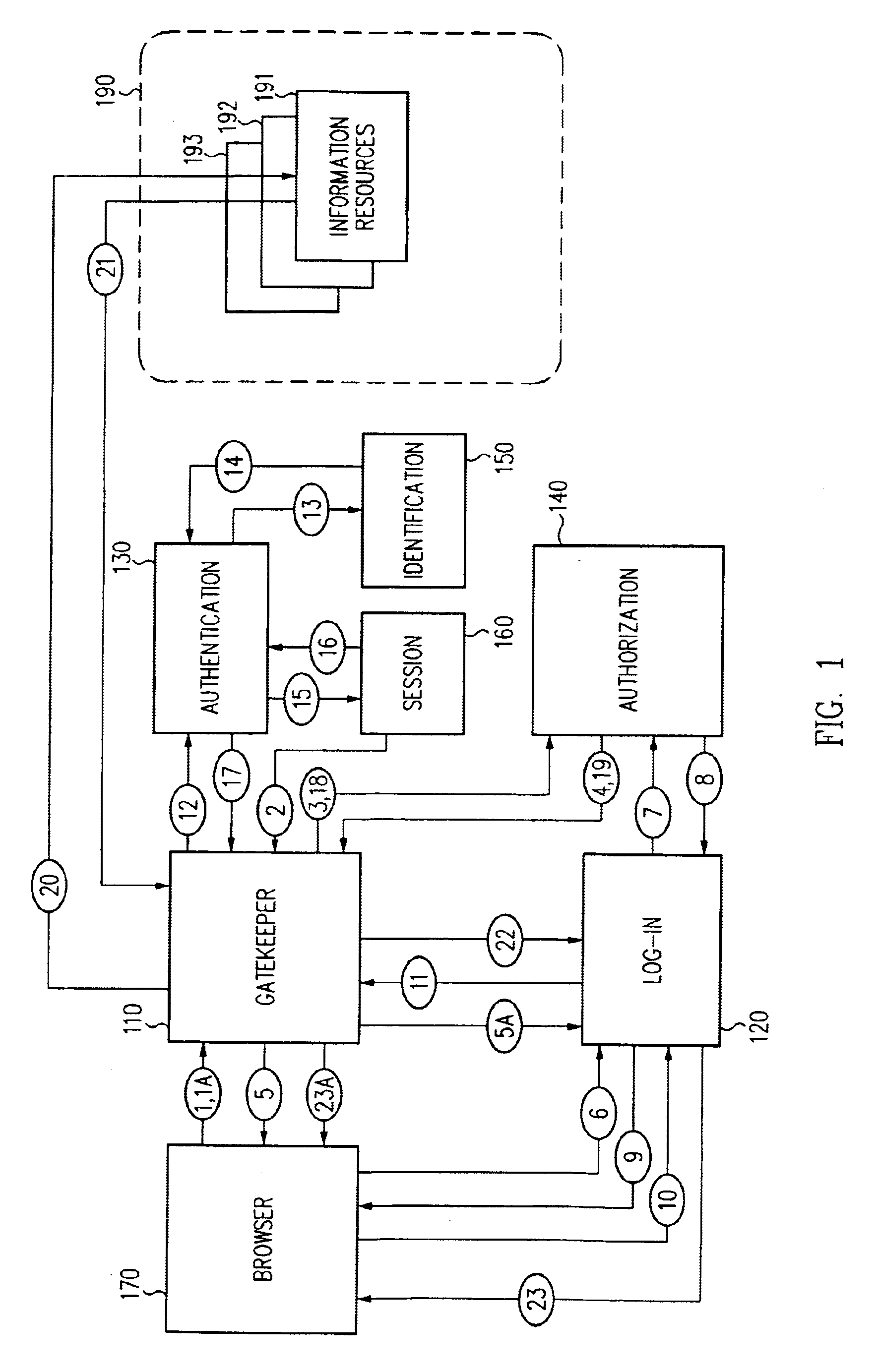
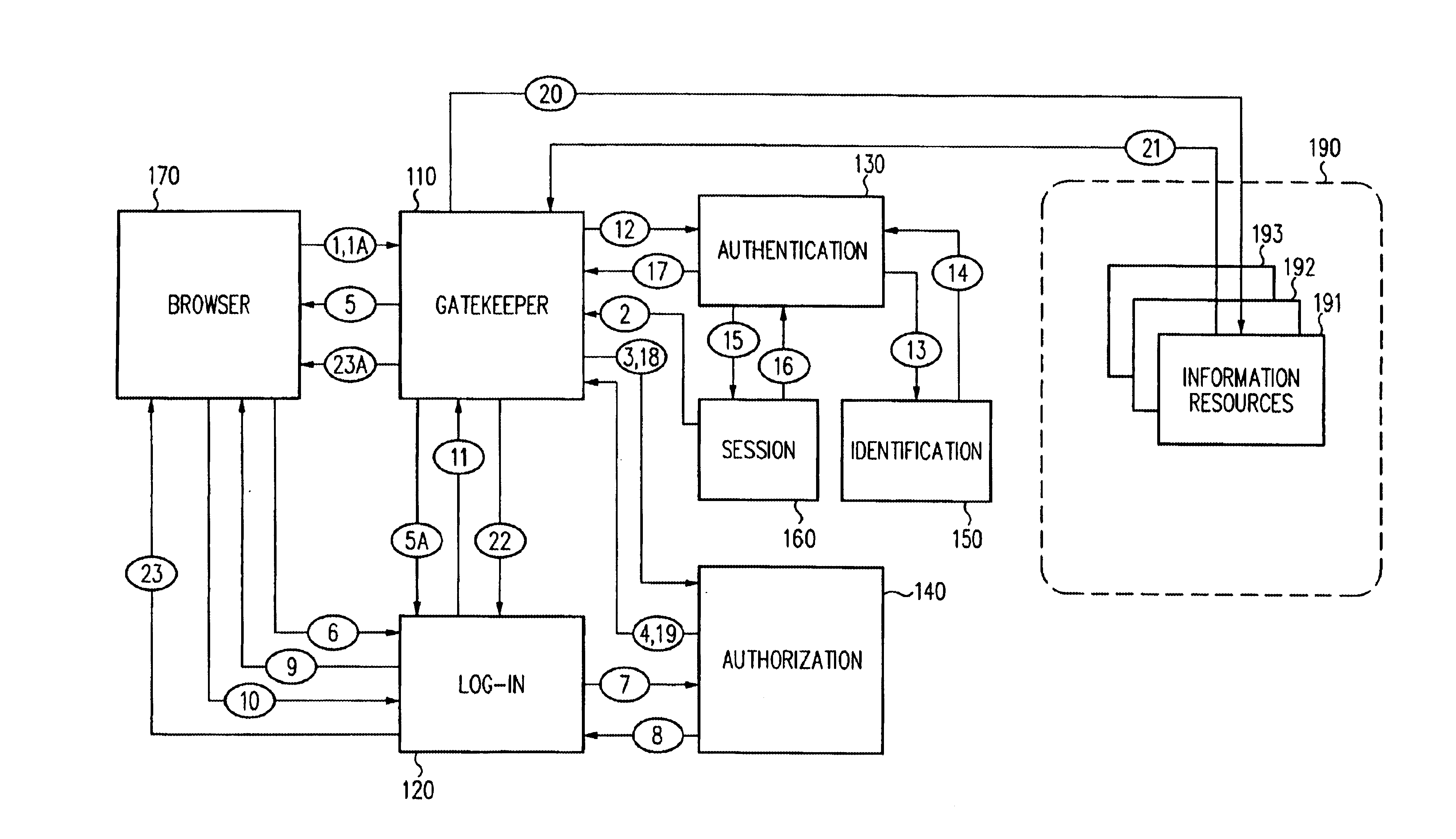
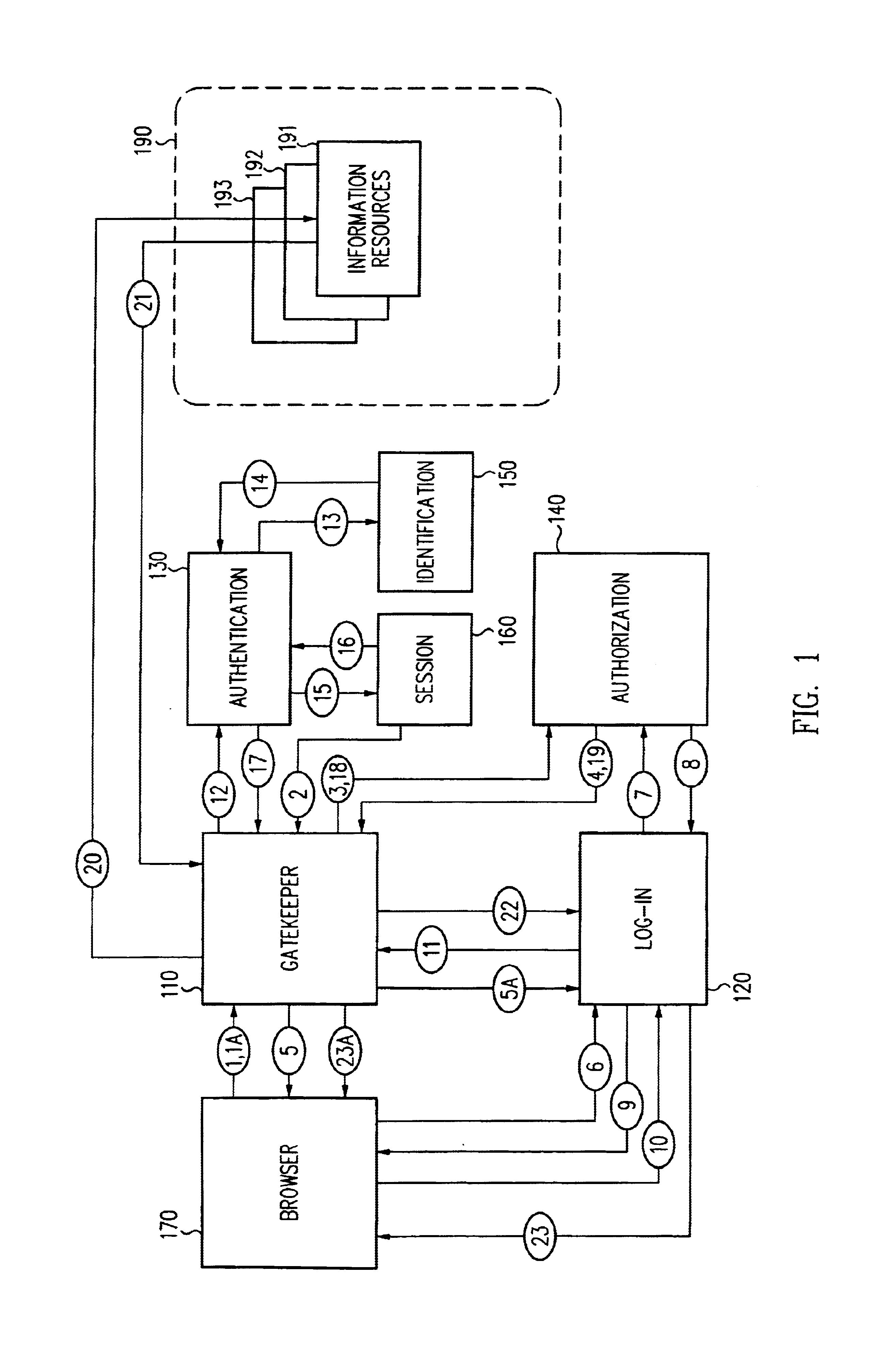
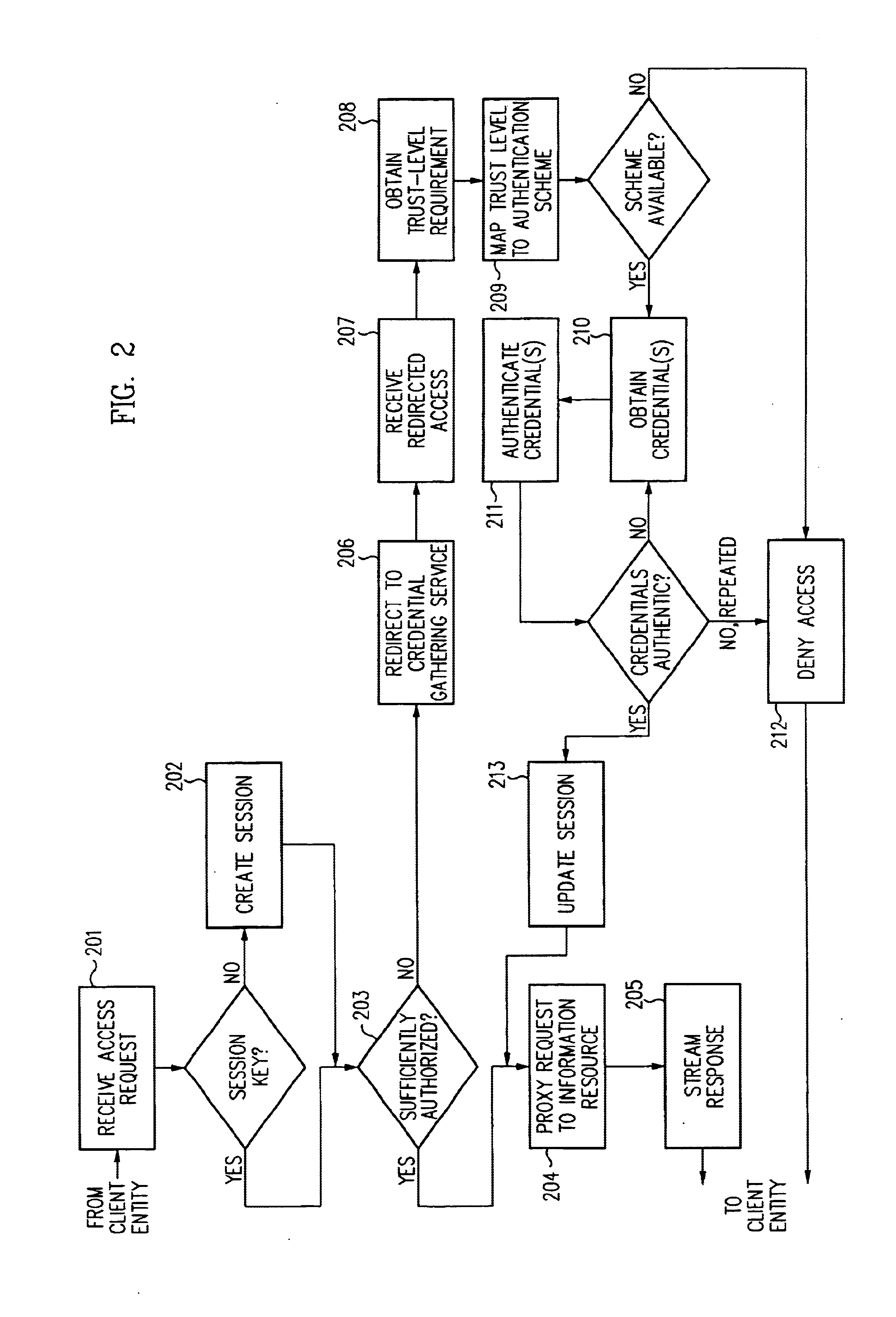
Single sign-on framework with trust-level mapping to authentication requirements
InactiveUS6892307B1Digital data processing detailsUser identity/authority verificationPasswordInformation resource
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels and a log-on service obtains credentials for an entity commensurate with the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:ORACLE INT CORP
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
Authentication services using mobile device
InactiveUS7606560B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet Authentication ServiceMobile device
A method, and an apparatus performing the method, is provided by authenticating a mobile device communicably connectable to a wireless network by an authentication parameter from a secure transaction server (STS), as a mobile device authenticator; providing an STS correlation between a personal identification entry (PIE) and the mobile device authenticator; and inputting, by a user, the PIE and a provider action, to the mobile device authenticator to transmit a transformed secure user authenticable authorization request to the STS over the wireless network to authorize an action with a provider.
Owner:PCMS HOLDINGS INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Screen icon manipulation by context and frequency of use
ActiveUS20110072492A1More user confidenceDigital data processing detailsMultiple digital computer combinationsTemporal informationOutbound communication
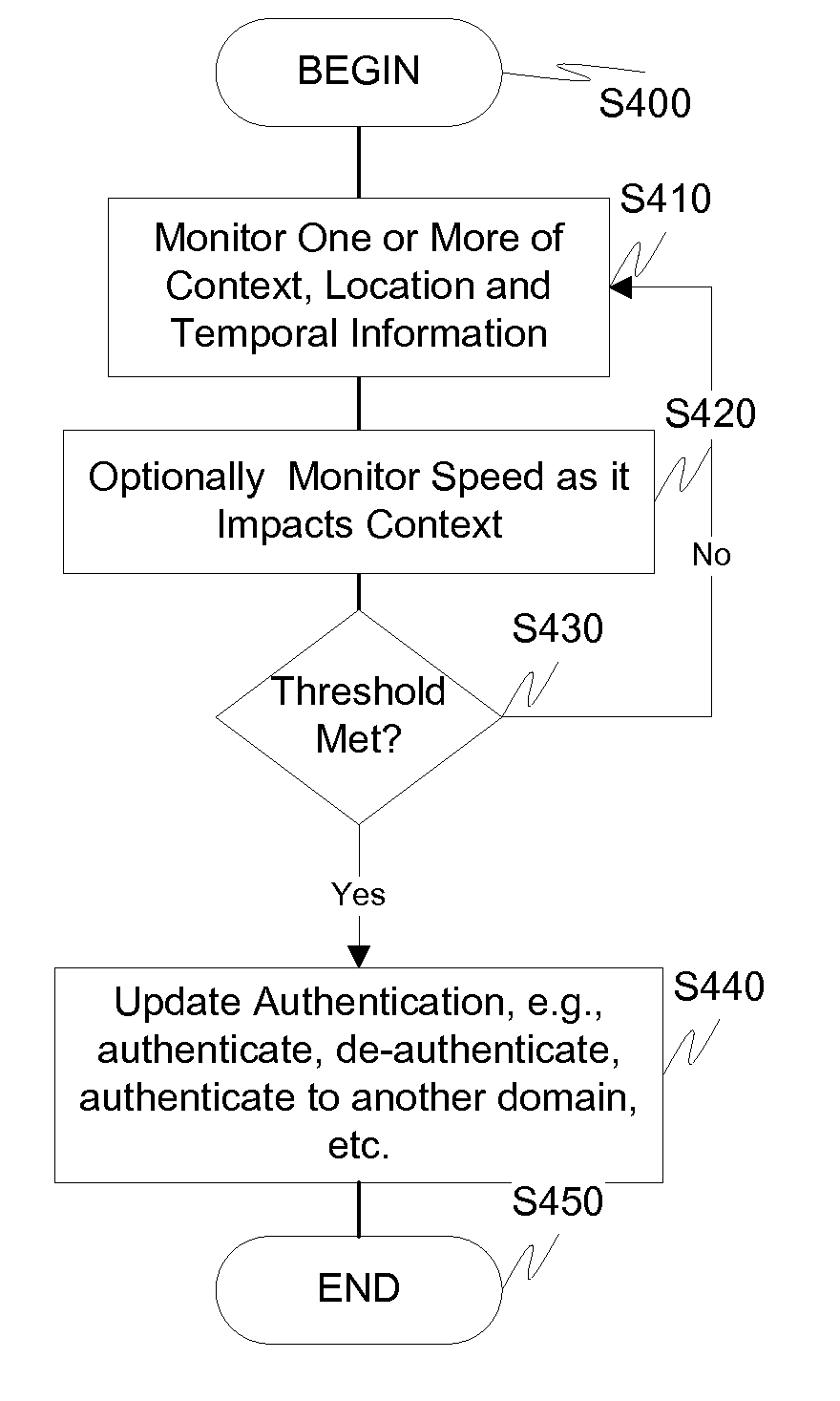
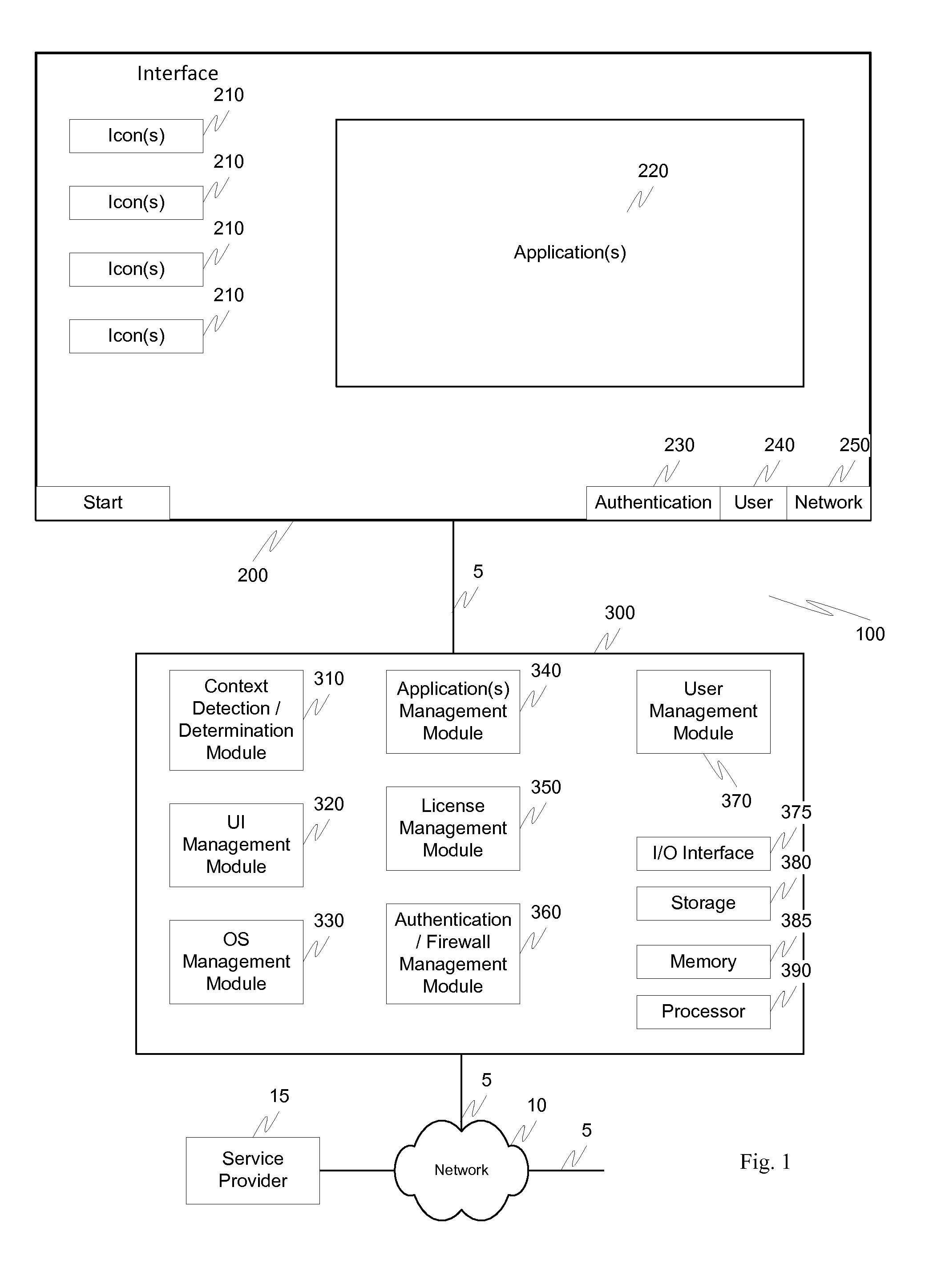
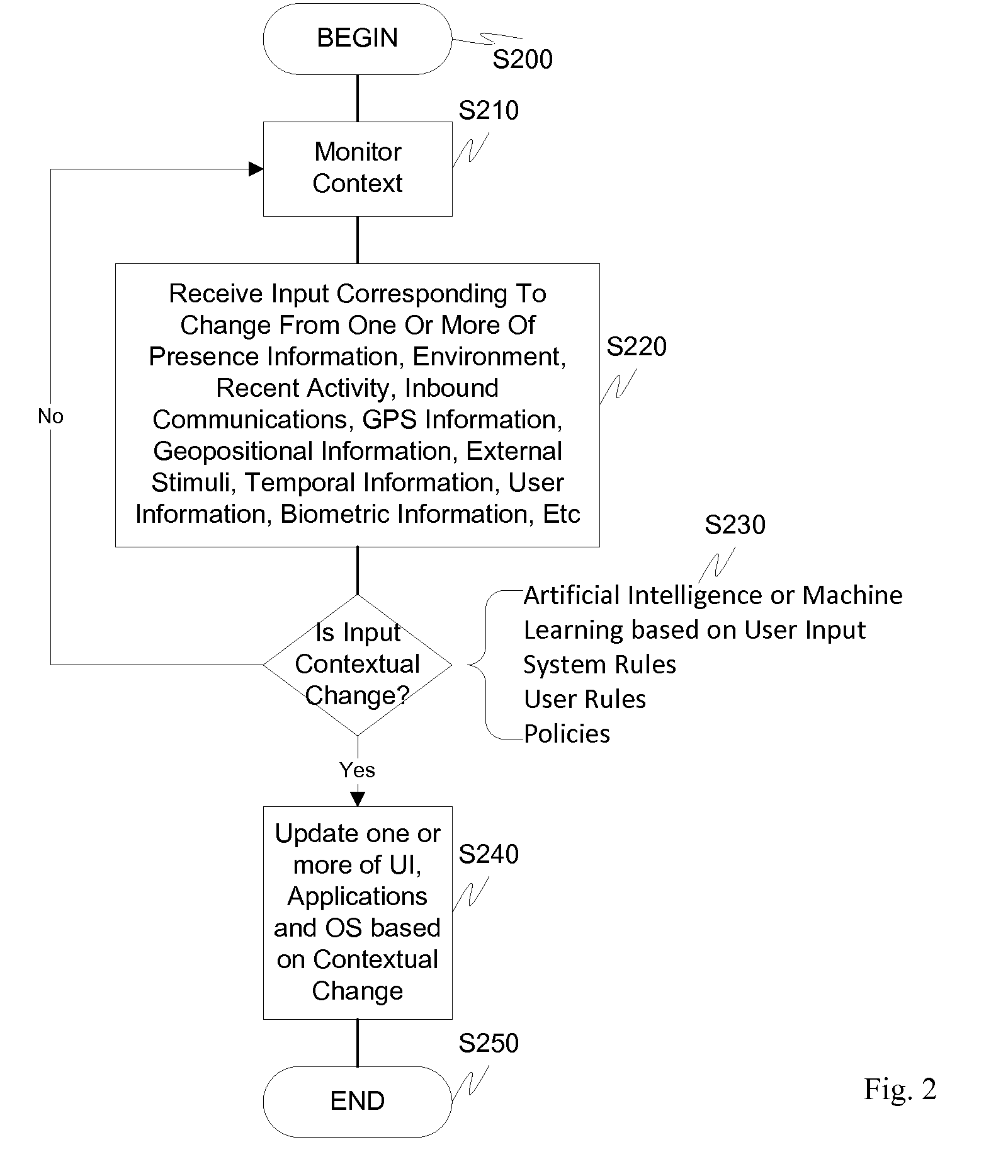
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
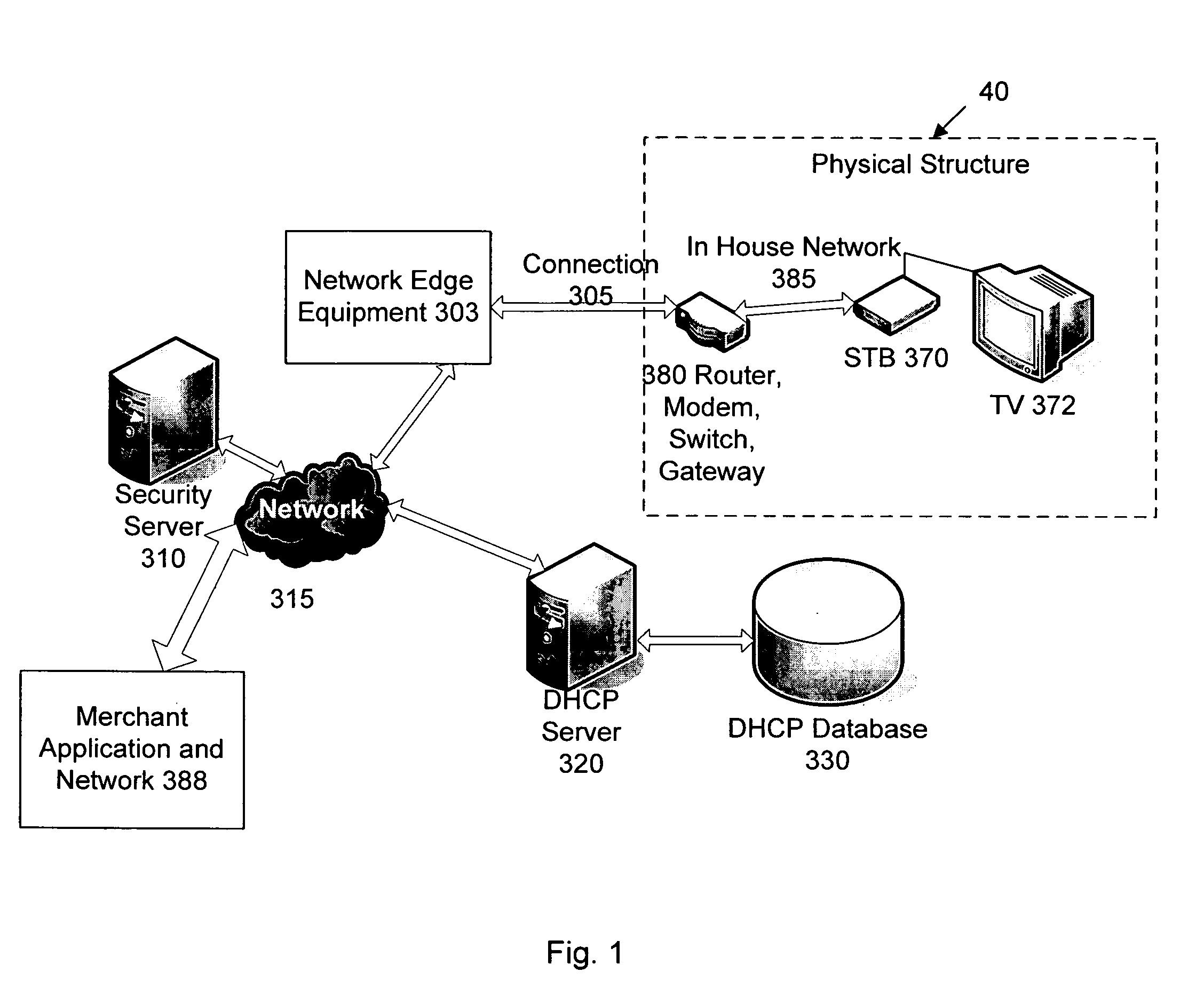
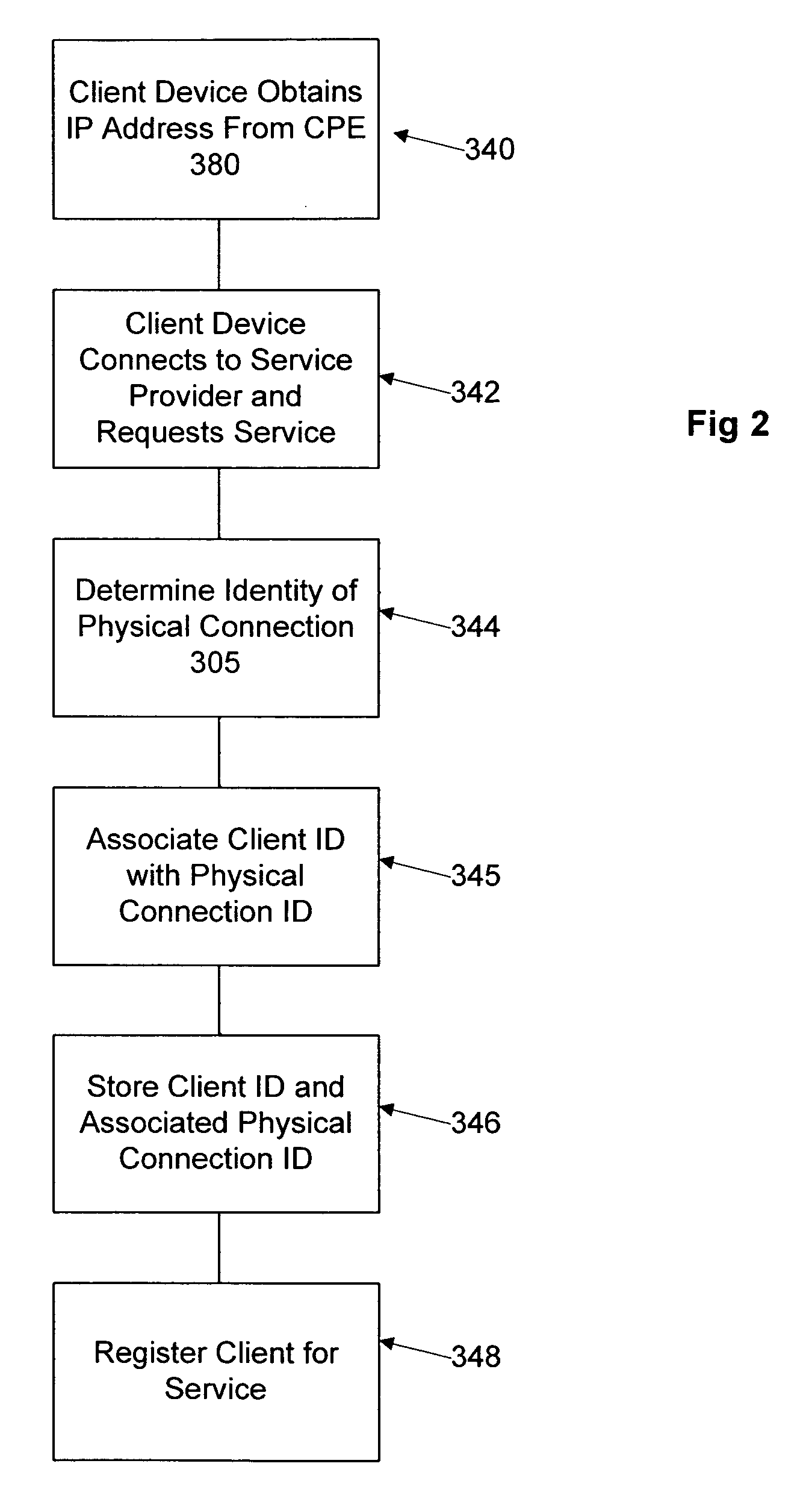
Network user authentication system and method
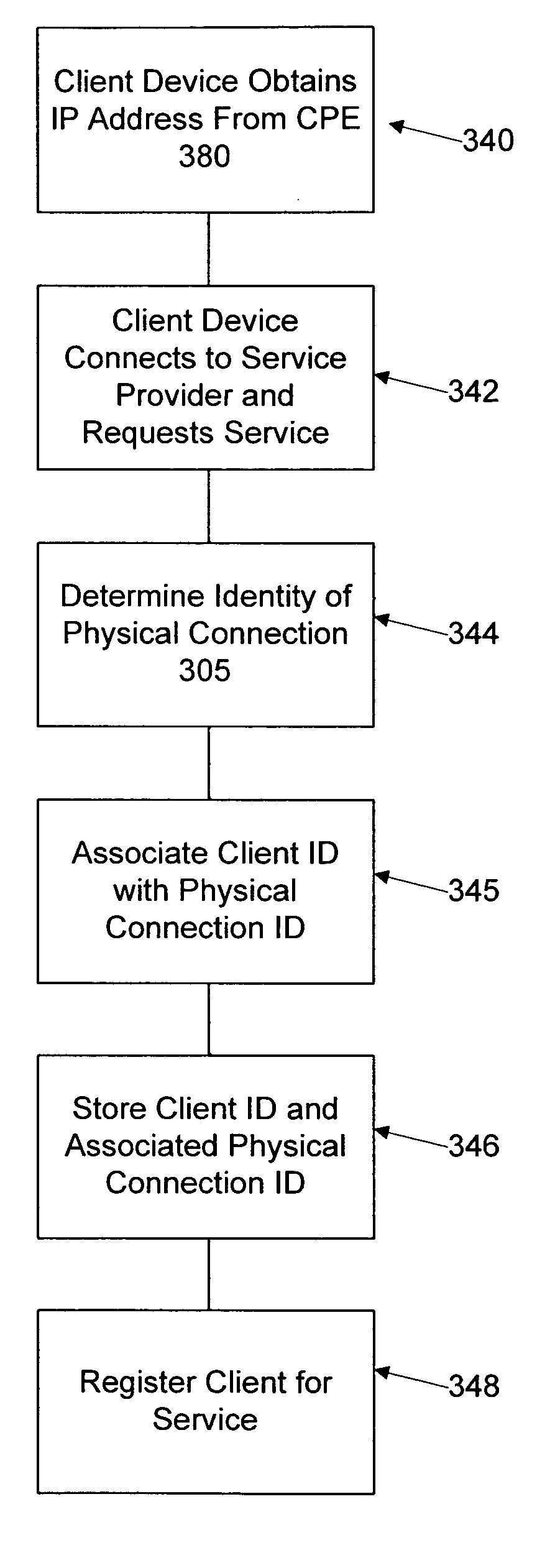
ActiveUS20070022469A1Removal difficult and impossibleThe certification process is reliableDigital data processing detailsUser identity/authority verificationUnique identifierAuthentication server
In a network user authentication system, a network user is identified for authentication purposes using the unique identifier for a dedicated physical communication line associated with the building in which the network user is located or a digital certificate which is associated with a secure component or communication line physically attached to a building. An authentication server initially verifies the identification of the dedicated communication line to be associated with a network service subscriber or issues a unique digital certificate to be associated with the dedicated communication line for authentication purposes. The digital certificate may be stored in a building gateway or in an edge site module which is connected to the secure components of a plurality of buildings and stores unique digital certificates for each building.
Owner:VERIMATRIX INC
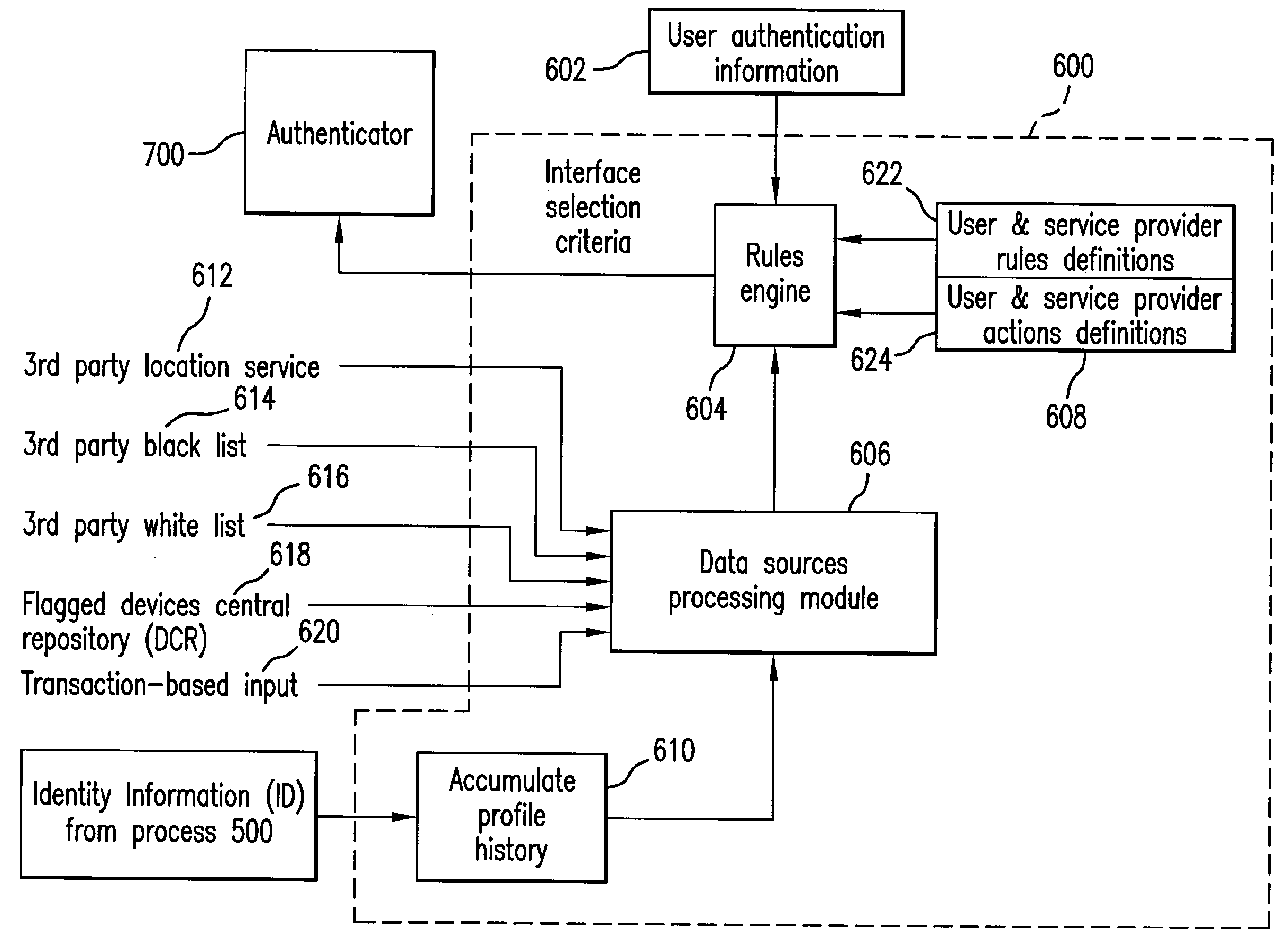
Security architecture with environment sensitive credential sufficiency evaluation
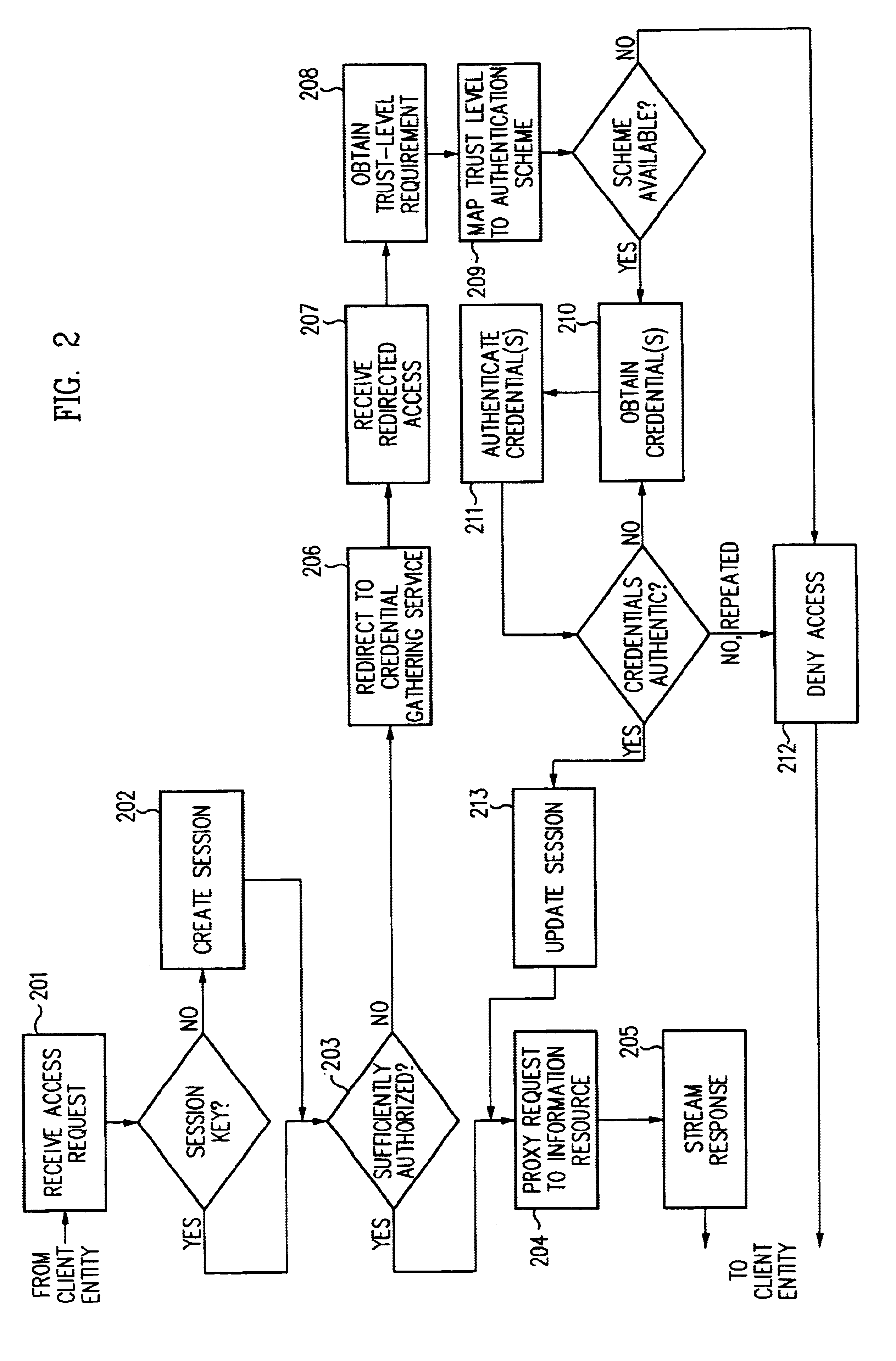
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
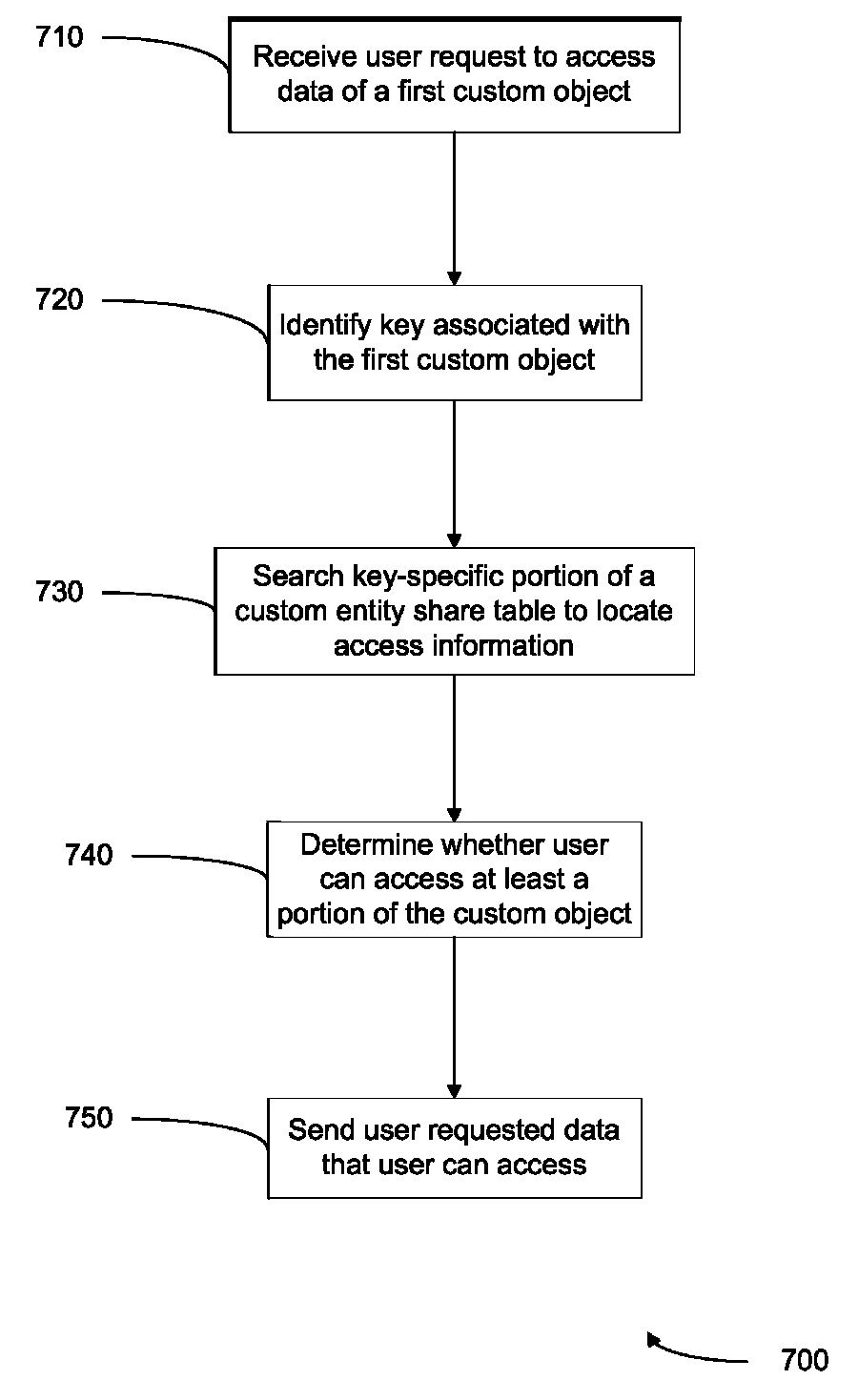
Methods and systems for controlling access to custom objects in a database
ActiveUS8095531B2Data processing applicationsDigital data processing detailsWorld Wide WebData library
Owner:SALESFORCE COM INC
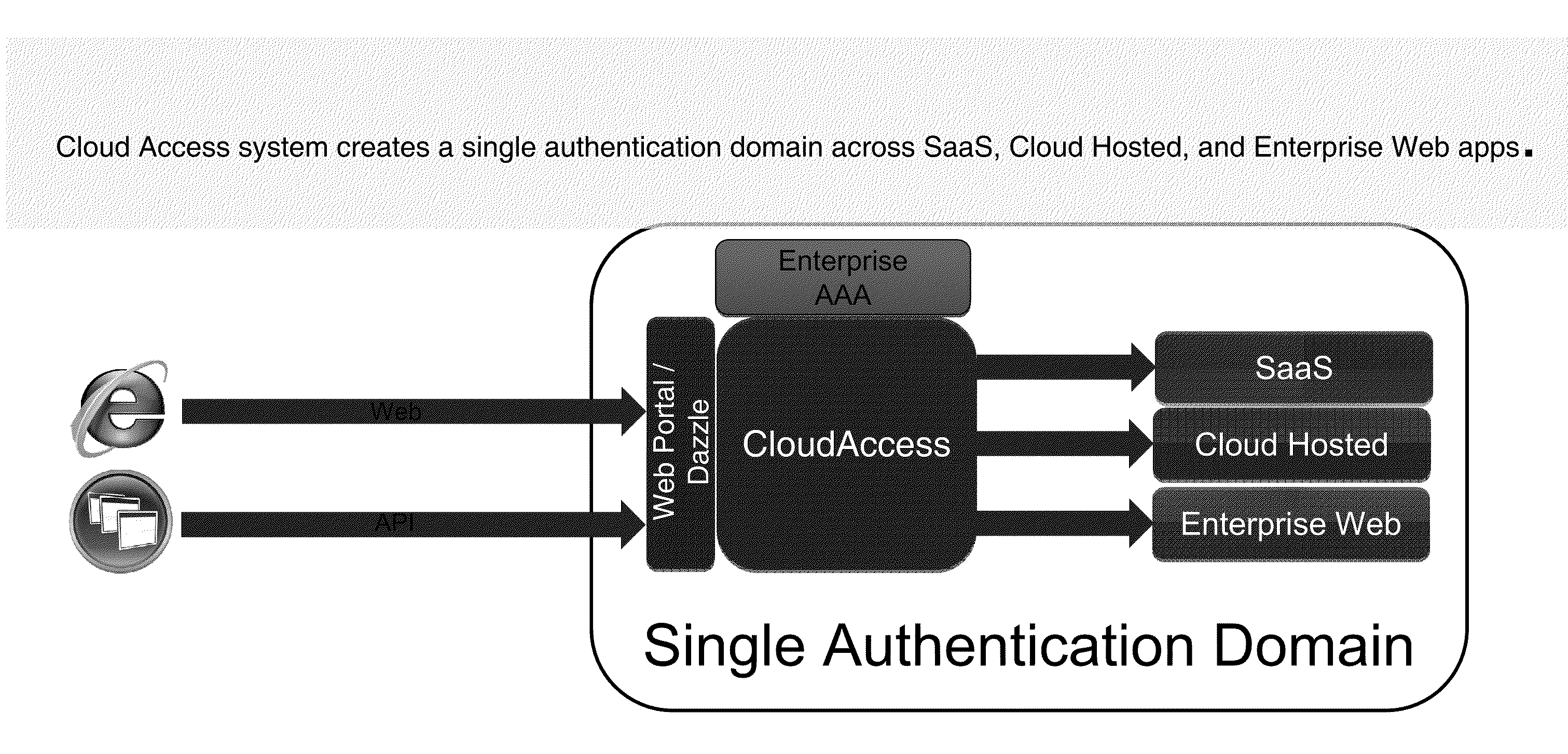
Systems and Methods for Providing a Single Click Access to Enterprise, SAAS and Cloud Hosted Application
ActiveUS20110277027A1Input/output for user-computer interactionDigital data processing detailsThird partyGraphics
The present disclosure is directed to methods and systems of providing a user-selectable list of disparately hosted applications. A device intermediary to a client and one or more servers may receive a user request to access a list of applications published to the user. The device may communicate to the client the list of published applications available to the user, the list comprising graphical icons corresponding to disparately hosted applications, at least one graphical icon corresponding to a third-party hosted application of the disparately hosted applications, the third party hosted application served by a remote third-party server. The device may receive a selection from the user of the at least one graphical icon. The device may communicate, from the remote third party server to the client of the user, execution of the third party hosted application responsive to the selection by the user.
Owner:CITRIX SYST INC
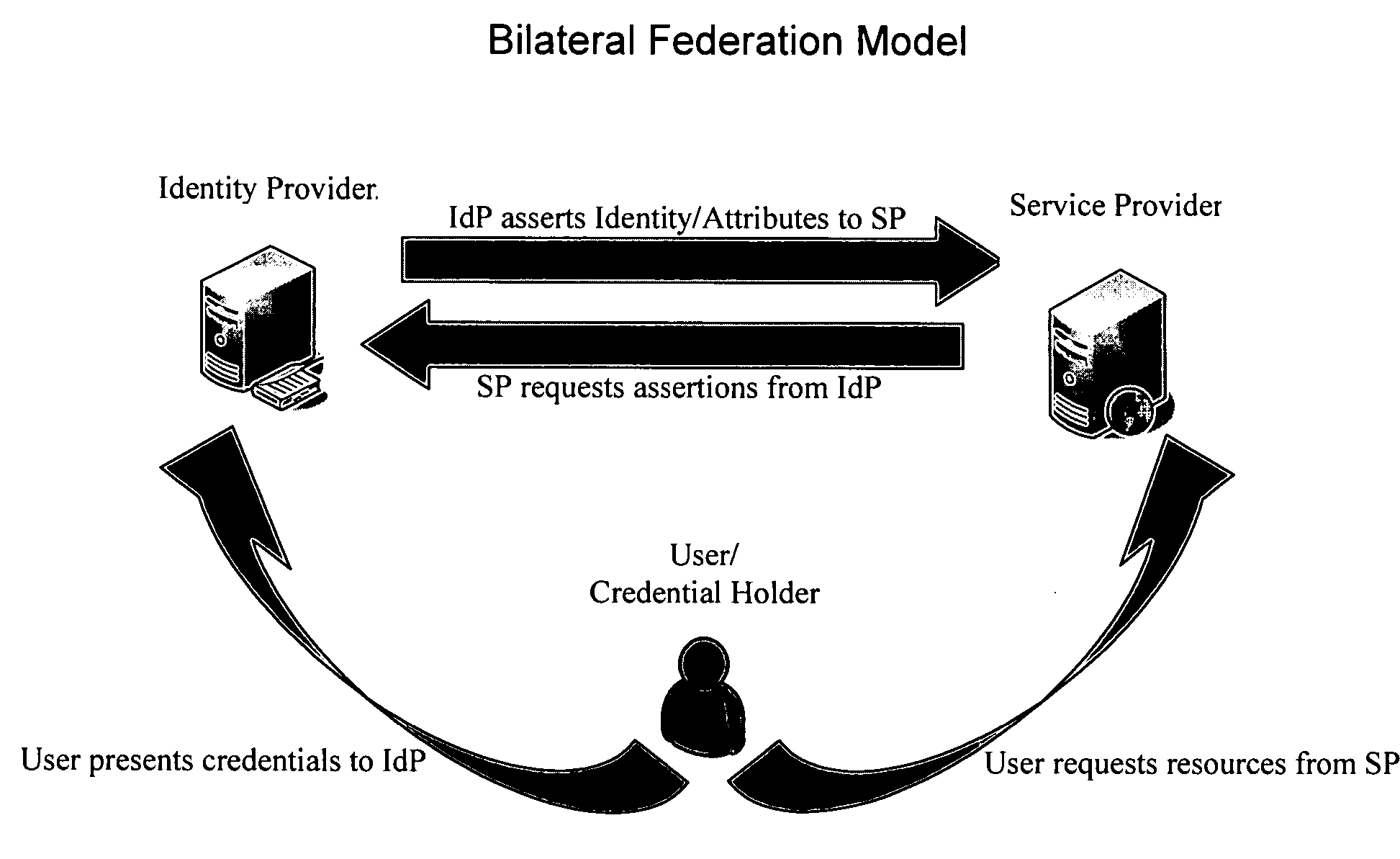
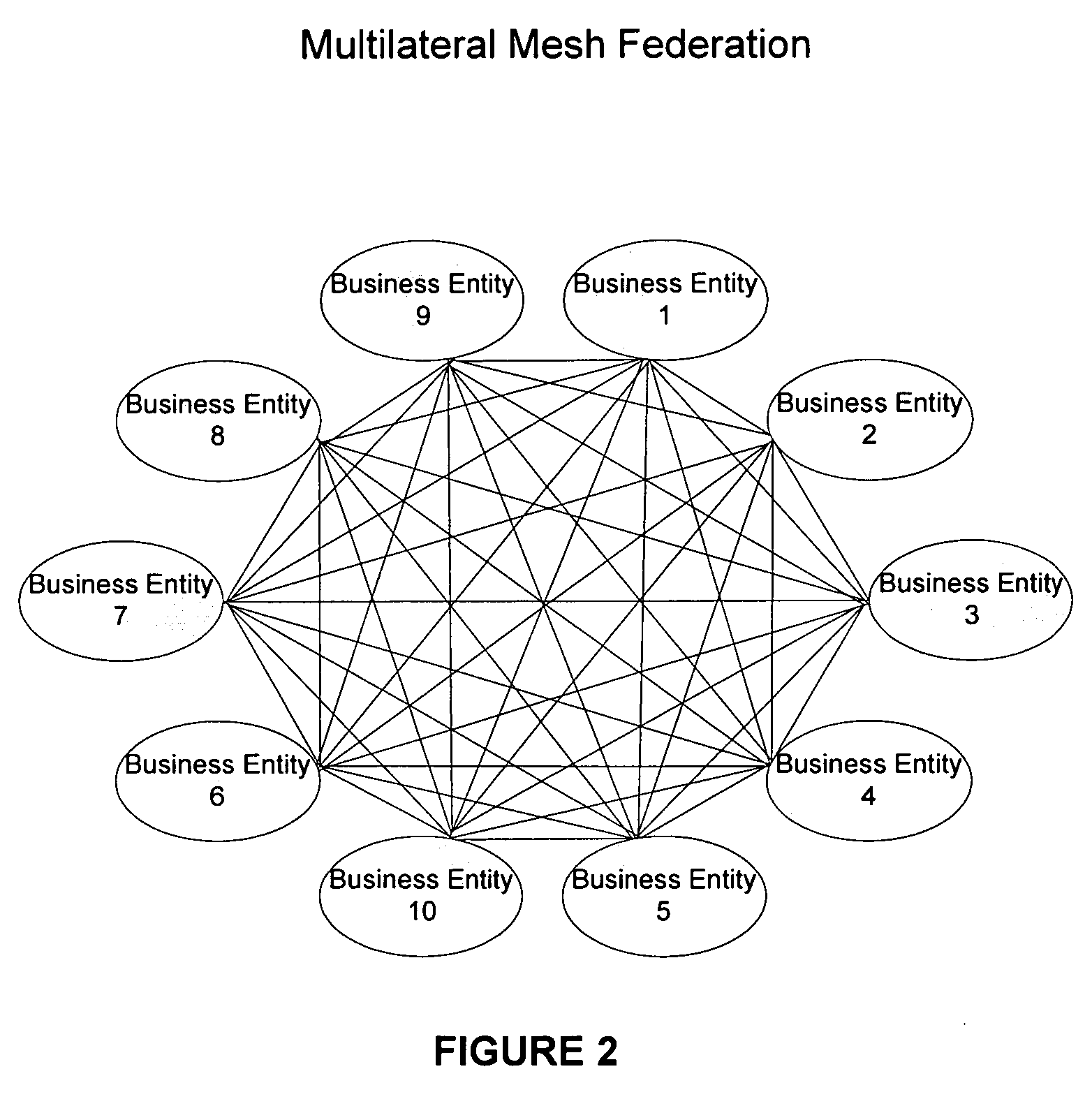
Systems and methods for enabling trust in a federated collaboration
ActiveUS20060129817A1Ensure complianceDigital data processing detailsUser identity/authority verificationThird partySuccessful completion
Systems and methods consistent with the present invention enable explicit and multilateral trust across a community of federated servers via a network. A trusted third party establishes a framework of policies and procedures governing a federation. Organizations joining the federation submit to an audit process of internal policies and procedures to ensure compliance with the policies and procedures of the federation. Upon successful completion of an audit, an organization may receive a digital certificate containing the digital public key of the organization and indicating approval of the trusted third party. The organization may then use the associated digital private key for signing security assertions associated with a request for resources from another federation service provider. The service provider may trust the assertion from the organization based on trust placed in trusted third party by the service provider and the trust placed in the organization by the trusted third party.
Owner:EXOSTAR CORP
User-convenient authentication method and apparatus using a mobile authentication application
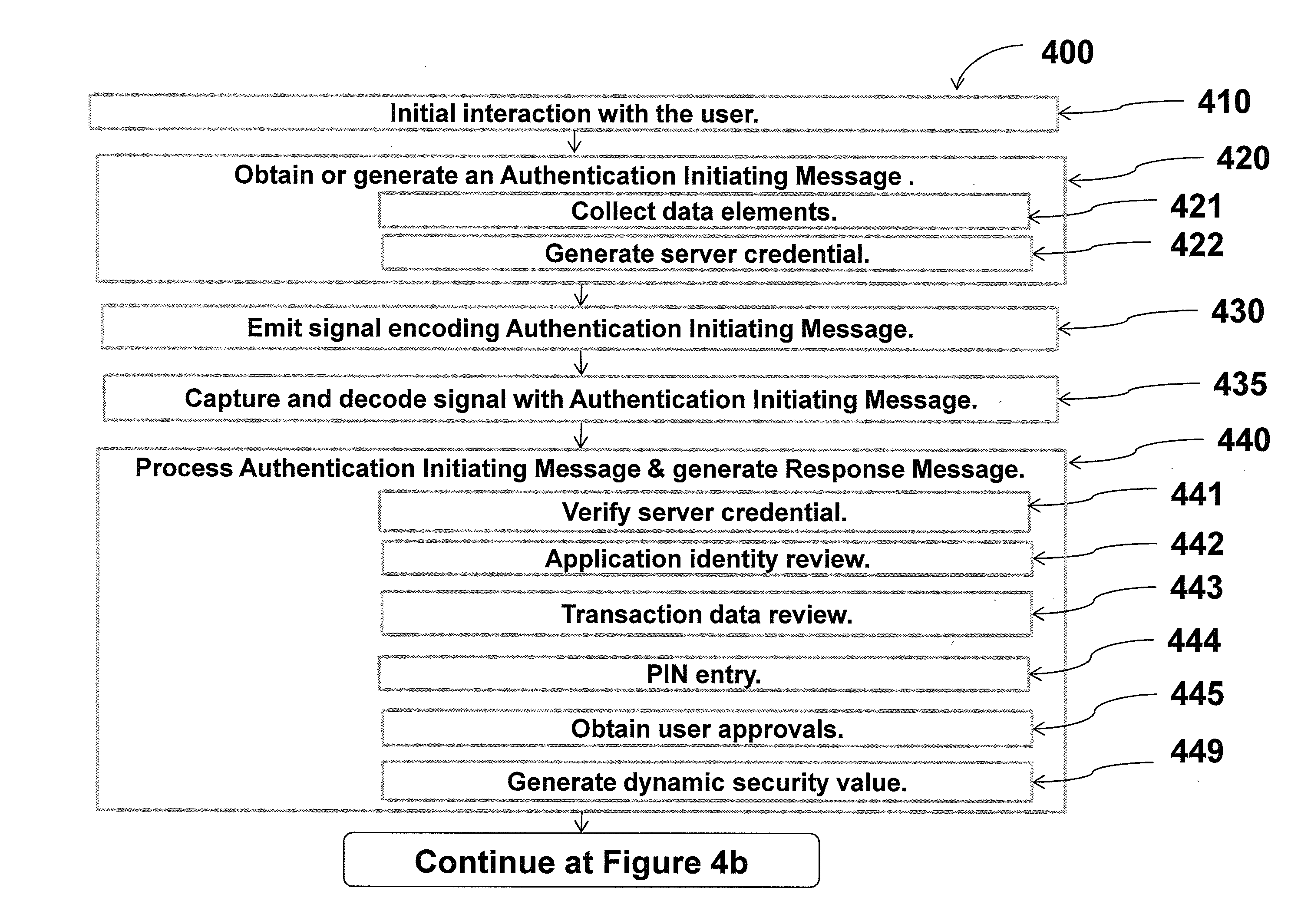
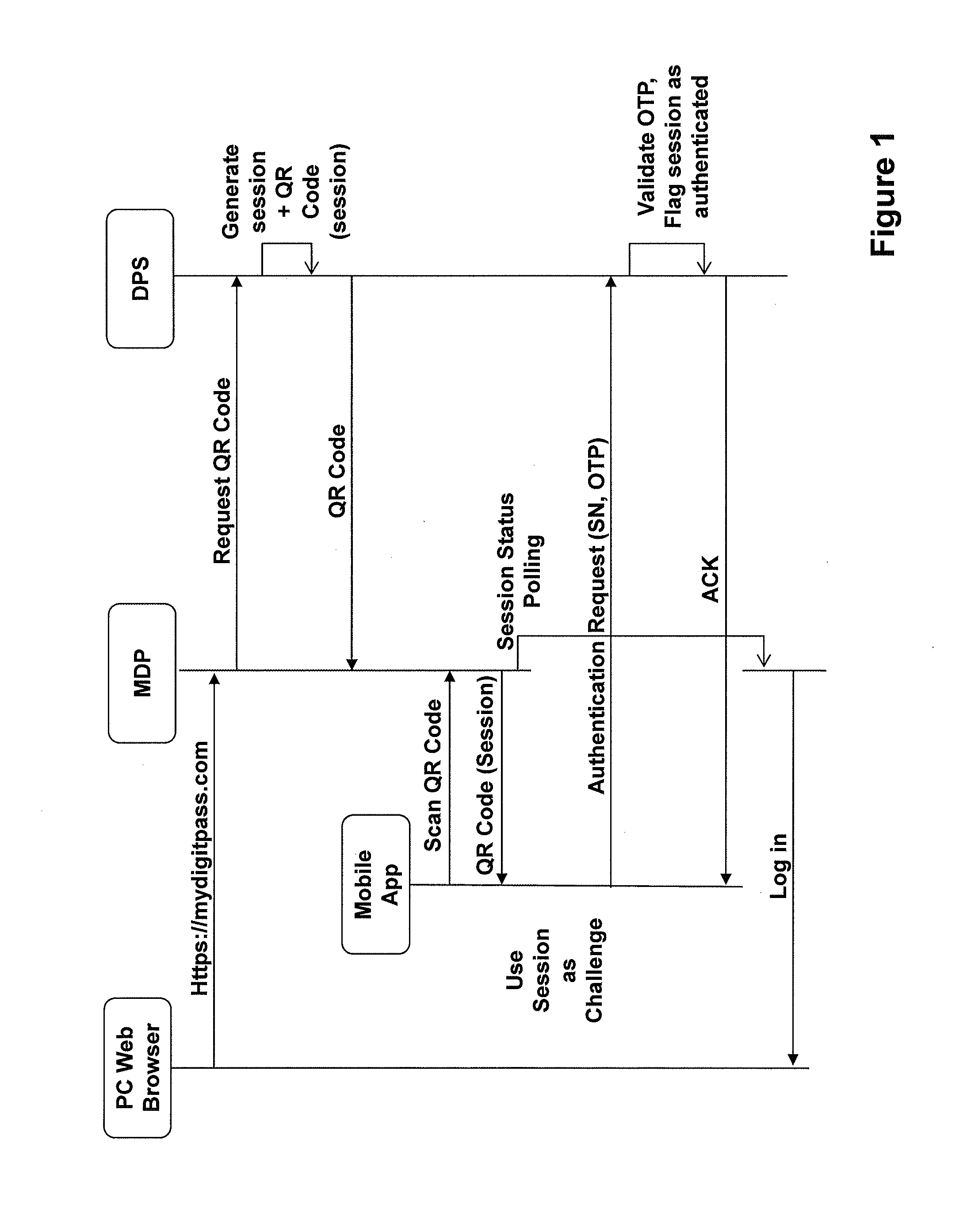
ActiveUS20140040628A1Authentication process can be made convenientCost-effectiveDigital data authenticationCoding/ciphering apparatusUser authenticationApplication software
Methods, apparatus, and systems for securing application interactions are disclosed. Application interactions may be secured by, at a user authentication device, capturing a signal emitted by an access device encoded with an authentication initiating message including an application identifier, decoding the signal and obtaining the authentication initiating message, retrieving the application identifier, presenting a human interpretable representation of the application identity to the user, obtaining user approval to generate a response message available to a verification server, generating a dynamic security value using a cryptographic algorithm that is cryptographically linked to the application identity, and generating a response message including the generated dynamic security value; making the response message available to a verification server; and, at the verification server, receiving the response message, verifying the response message including verifying the validity of the dynamic security value, and communicating the result of the verification of the response message to the application.
Owner:ONESPAN NORTH AMERICA INC
Apparatus and method for authenticated multi-user personal information database
InactiveUS6985887B1Improve reliabilityLower level of reliabilityStampsError preventionInternet privacyMulti-user
Owner:GOLD STANDARD TECH
Method and apparatus for authentication of users and web sites
InactiveUS7100049B2Digital data processing detailsUser identity/authority verificationWeb siteS system
Owner:EMC IP HLDG CO LLC
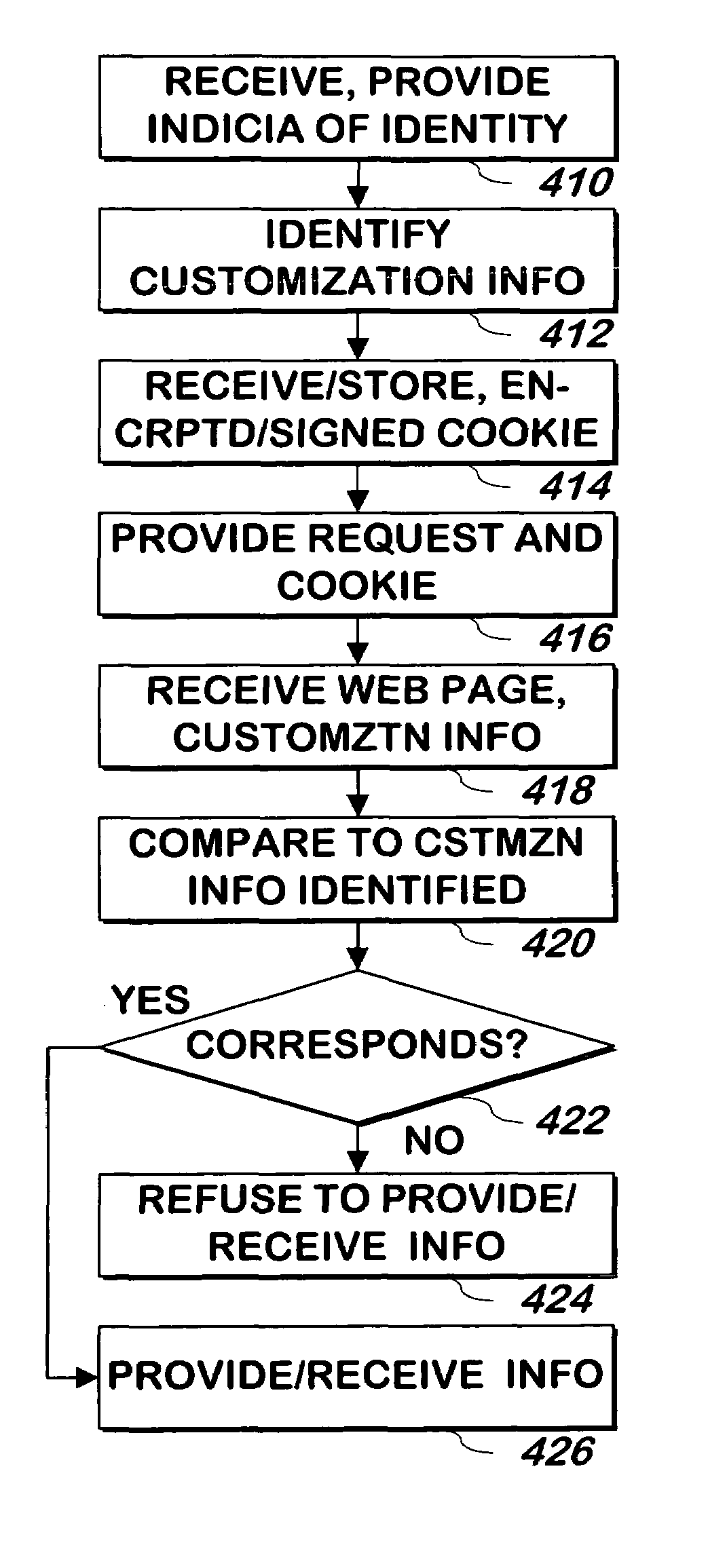
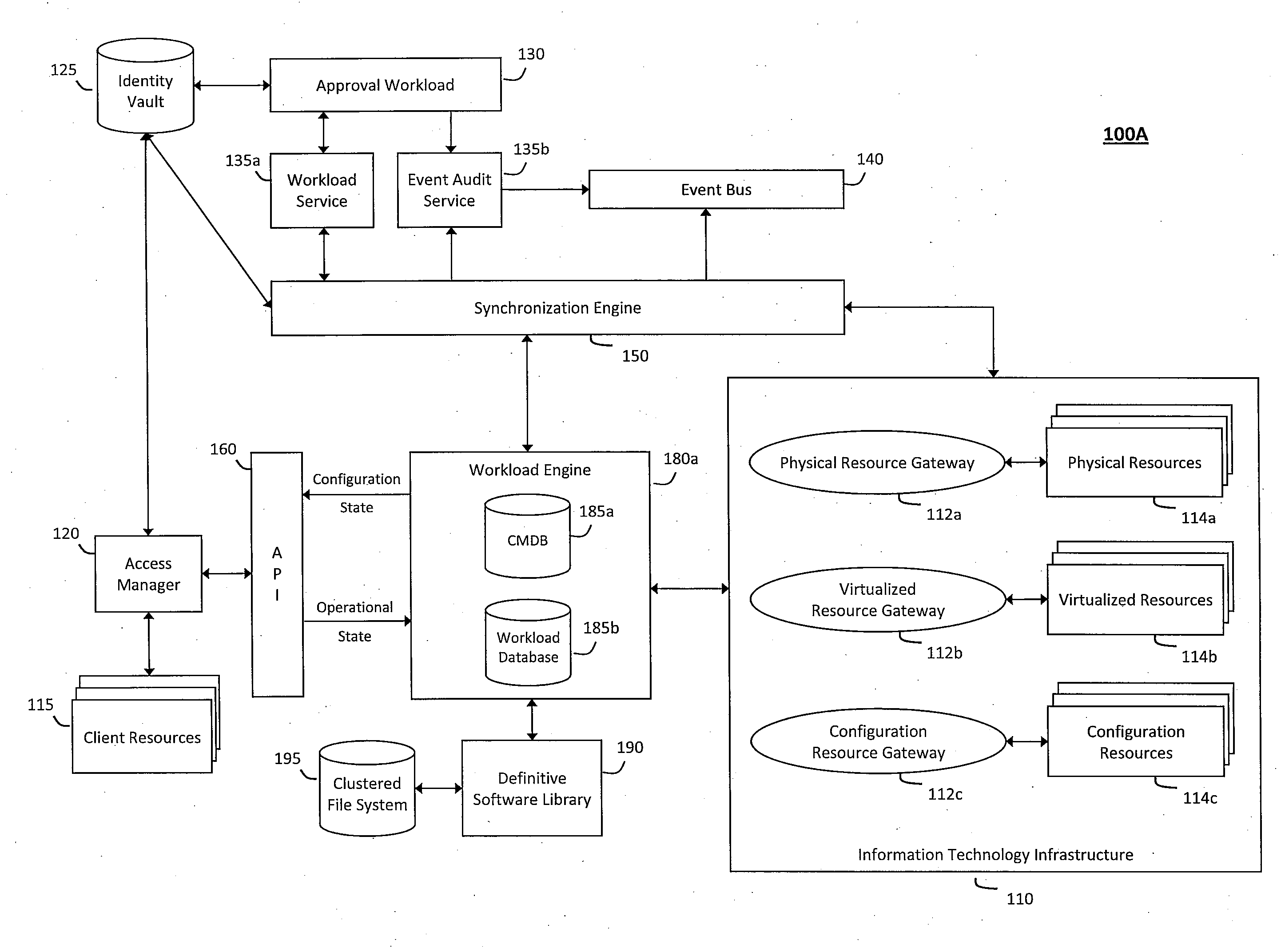
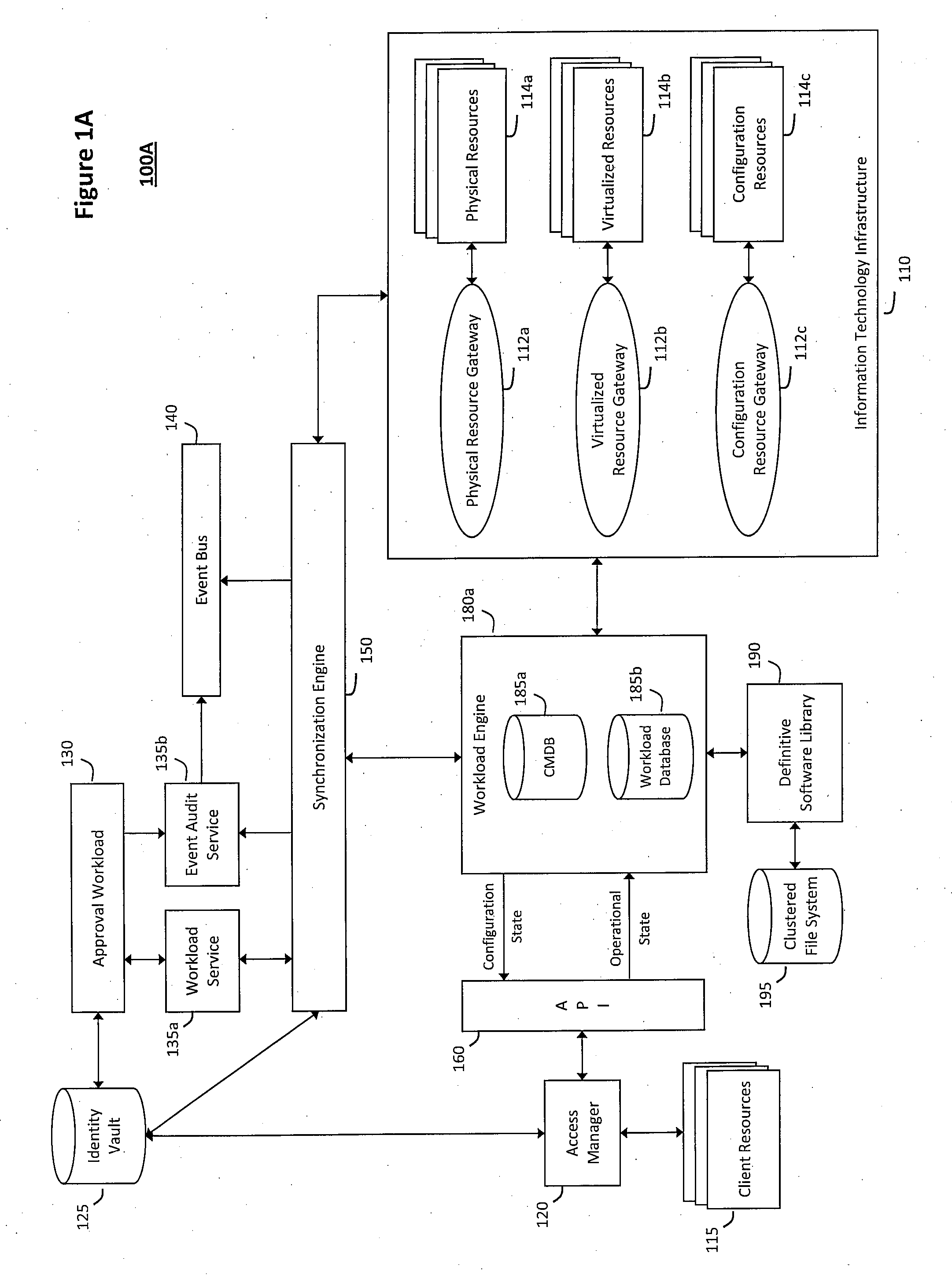
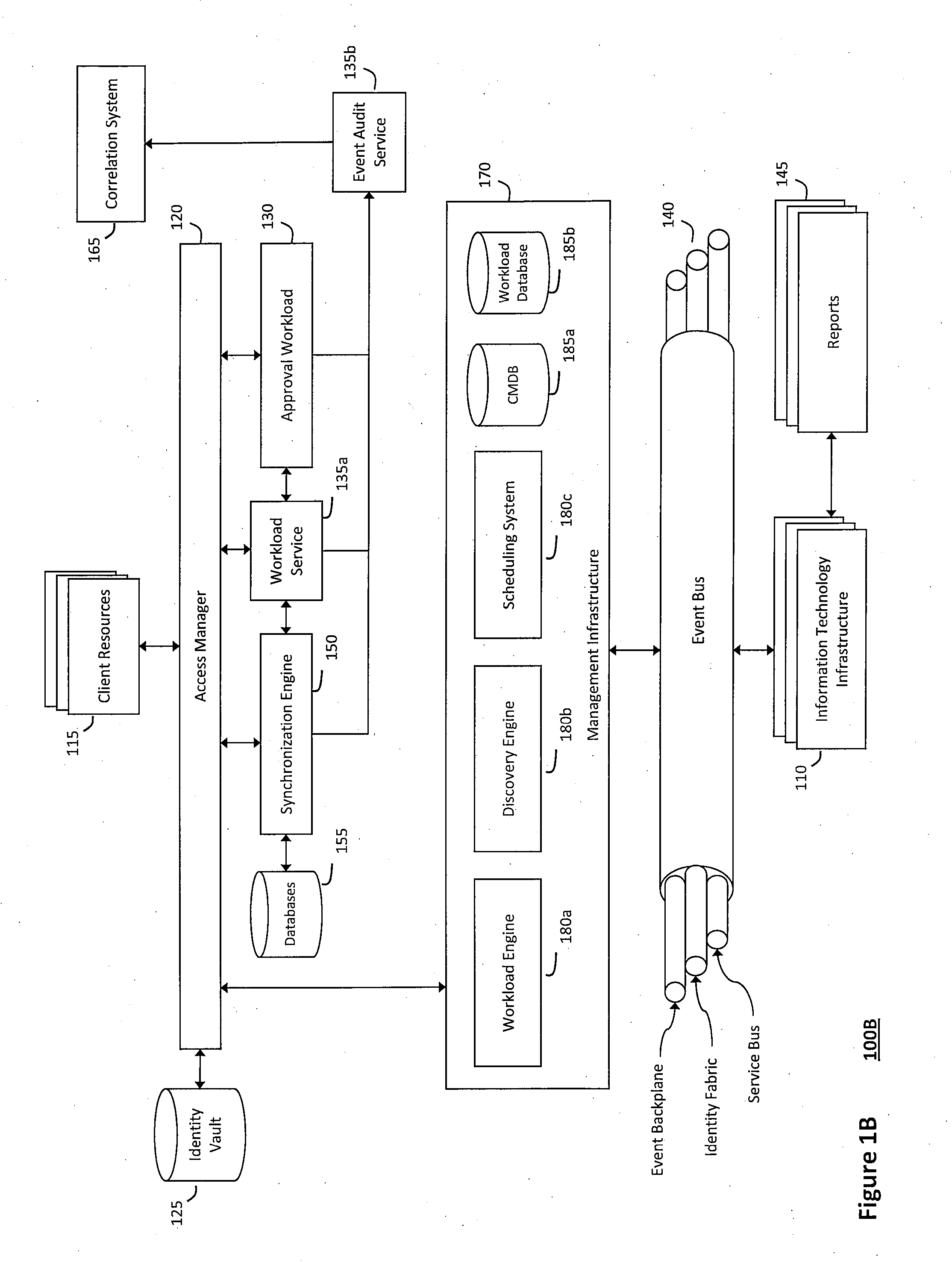
System and method for controlling cloud and virtualized data centers in an intelligent workload management system
InactiveUS20110126197A1Free computational resourceAgile and flexible managementDigital computer detailsDigital data authenticationData centerService-oriented architecture
The system and method for controlling cloud and virtualized data centers described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, and further to creating cloud images having embedded management agents and identity services for validating the cloud images prior to deployment into the cloud and virtualized data centers and controlling, monitoring, and auditing activity associated with the cloud images following deployment into the cloud and virtualized data centers.
Owner:MICRO FOCUS SOFTWARE INC
Popular searches
Electric/electromagnetic visible signalling Buying/selling/leasing transactions Program/content distribution protection Special data processing applications Market data gathering Advertisements Analogue secracy/subscription systems Color television details Internal/peripheral component protection Two-way working systems
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com