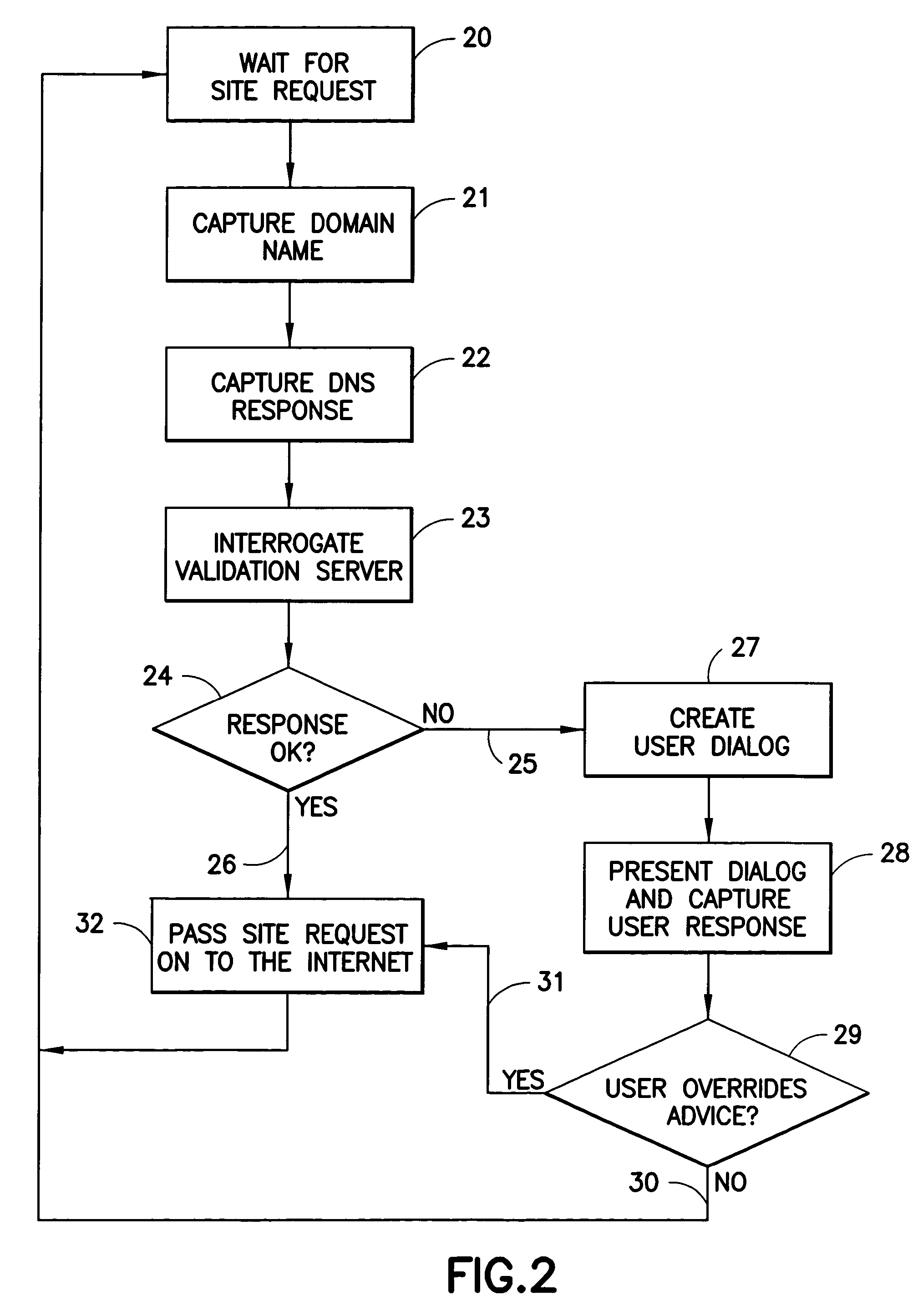
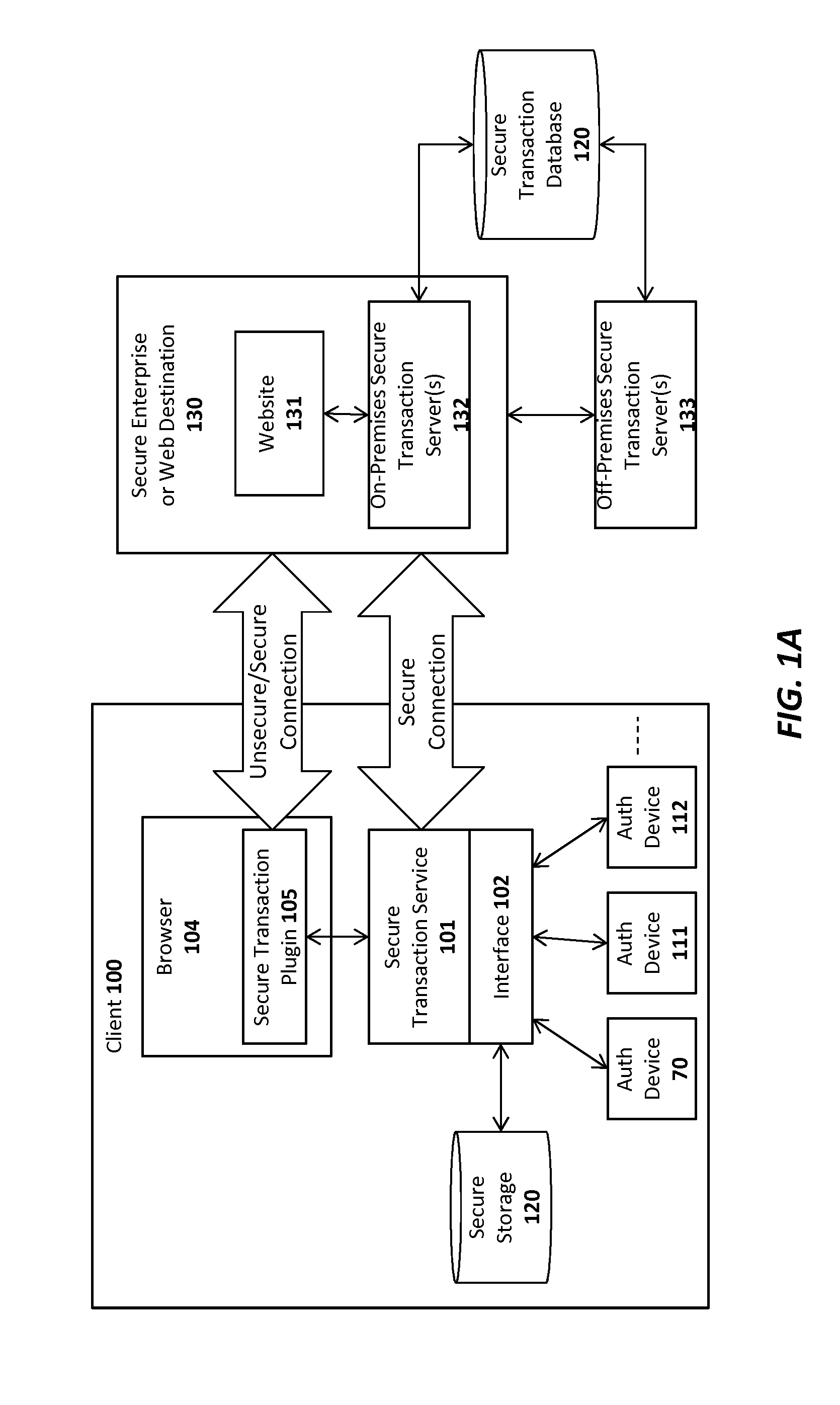
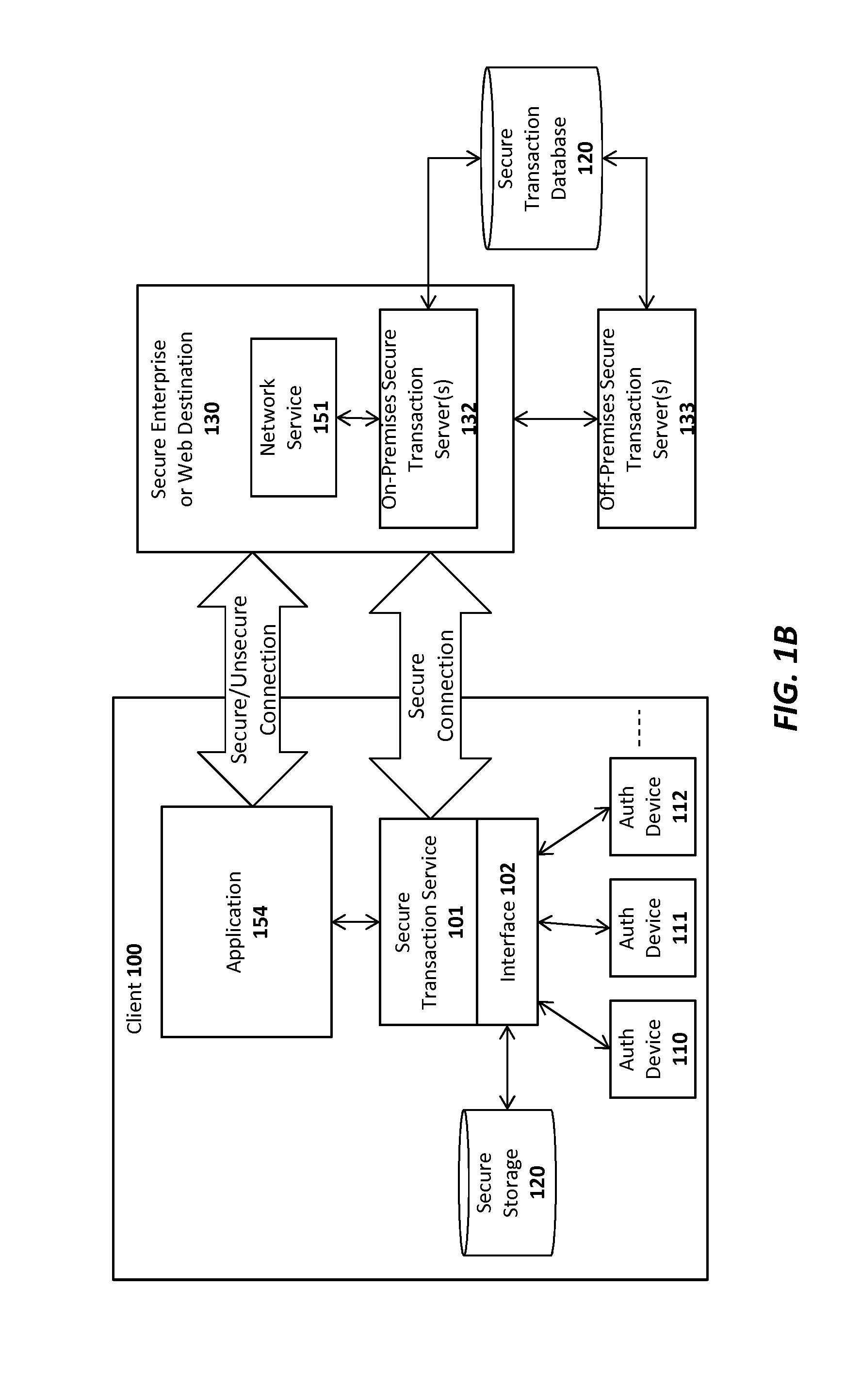
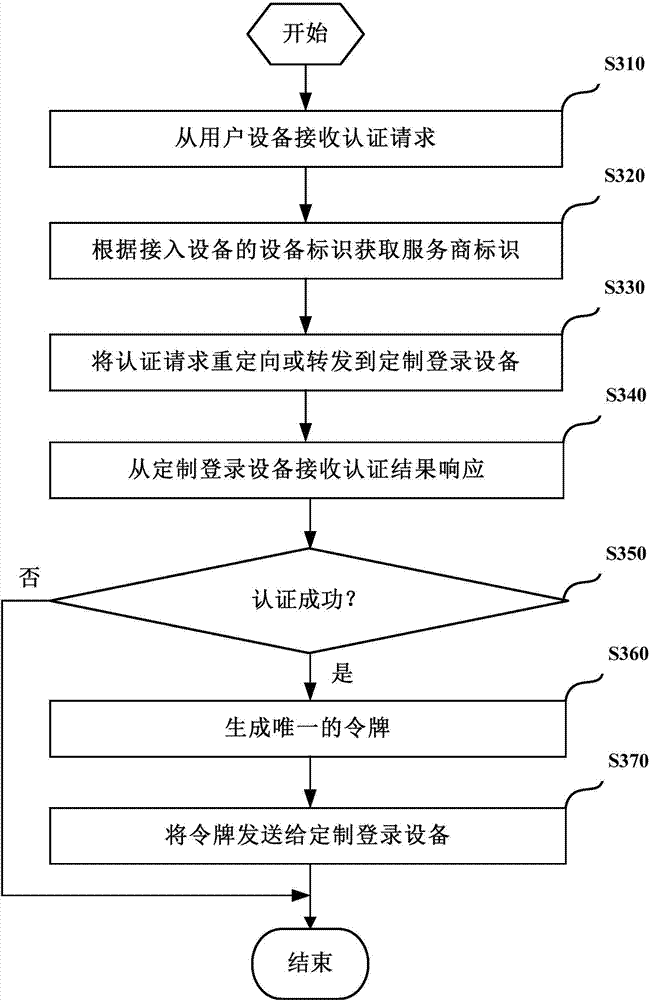
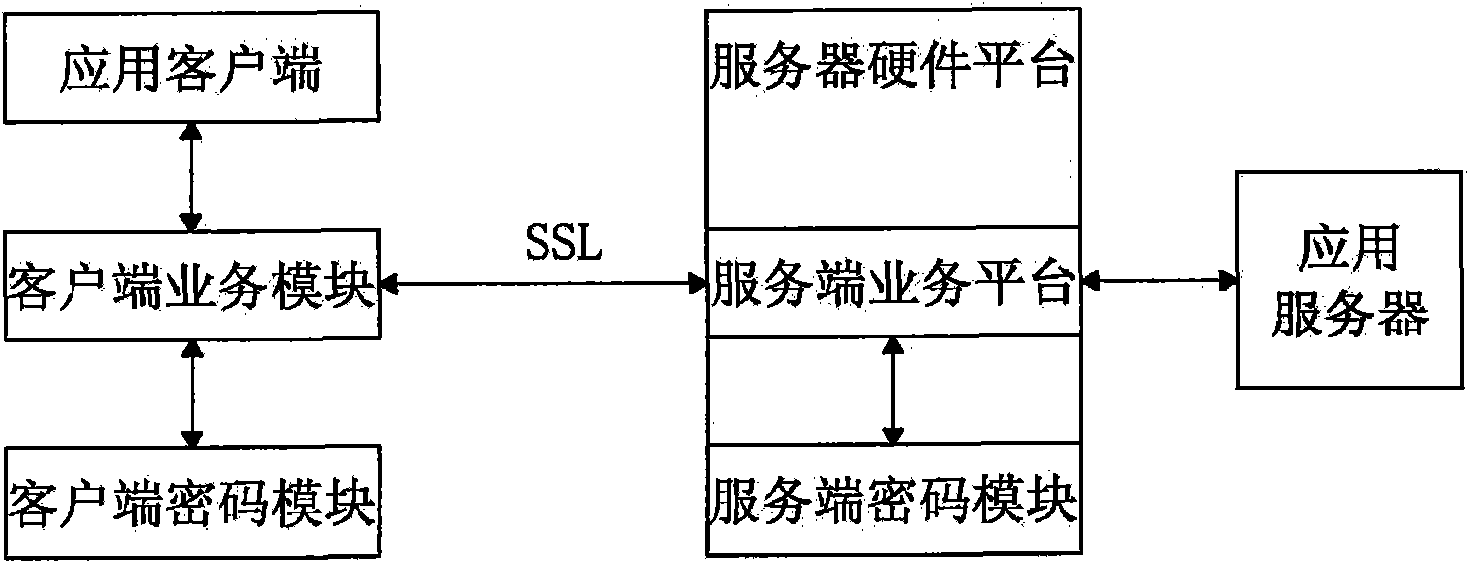
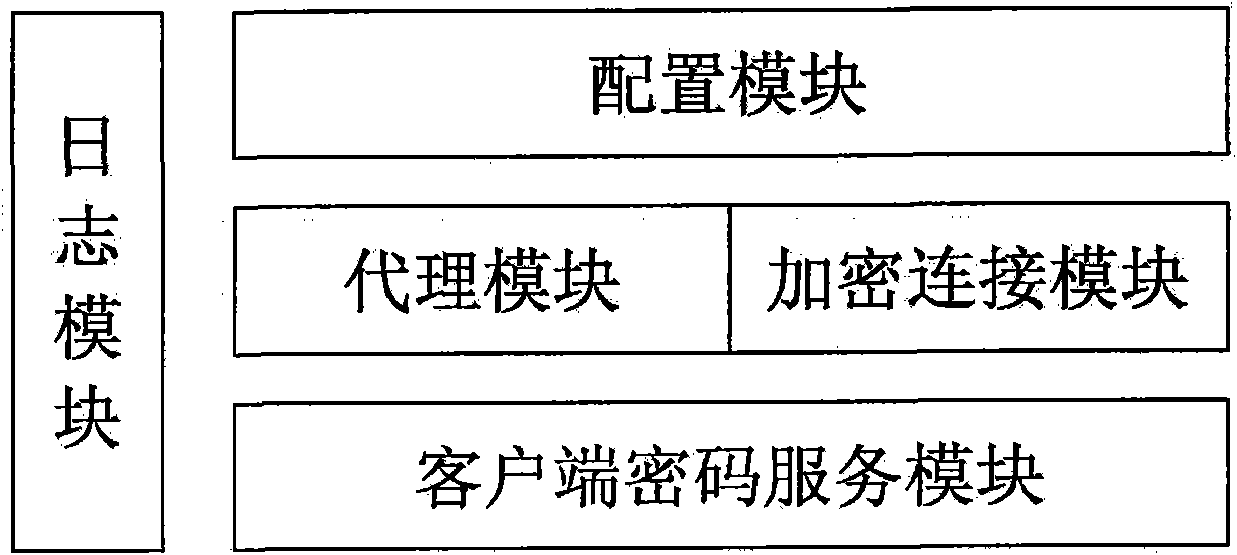
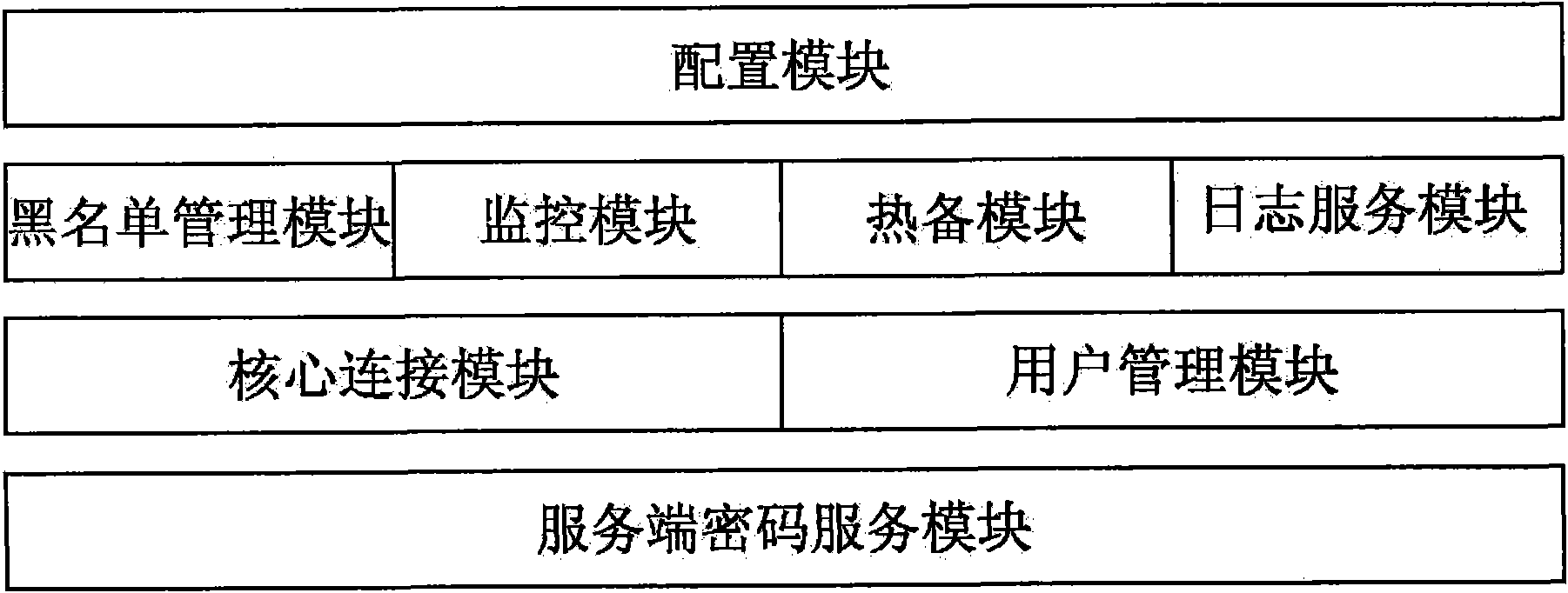
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
139 results about "Internet Authentication Service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
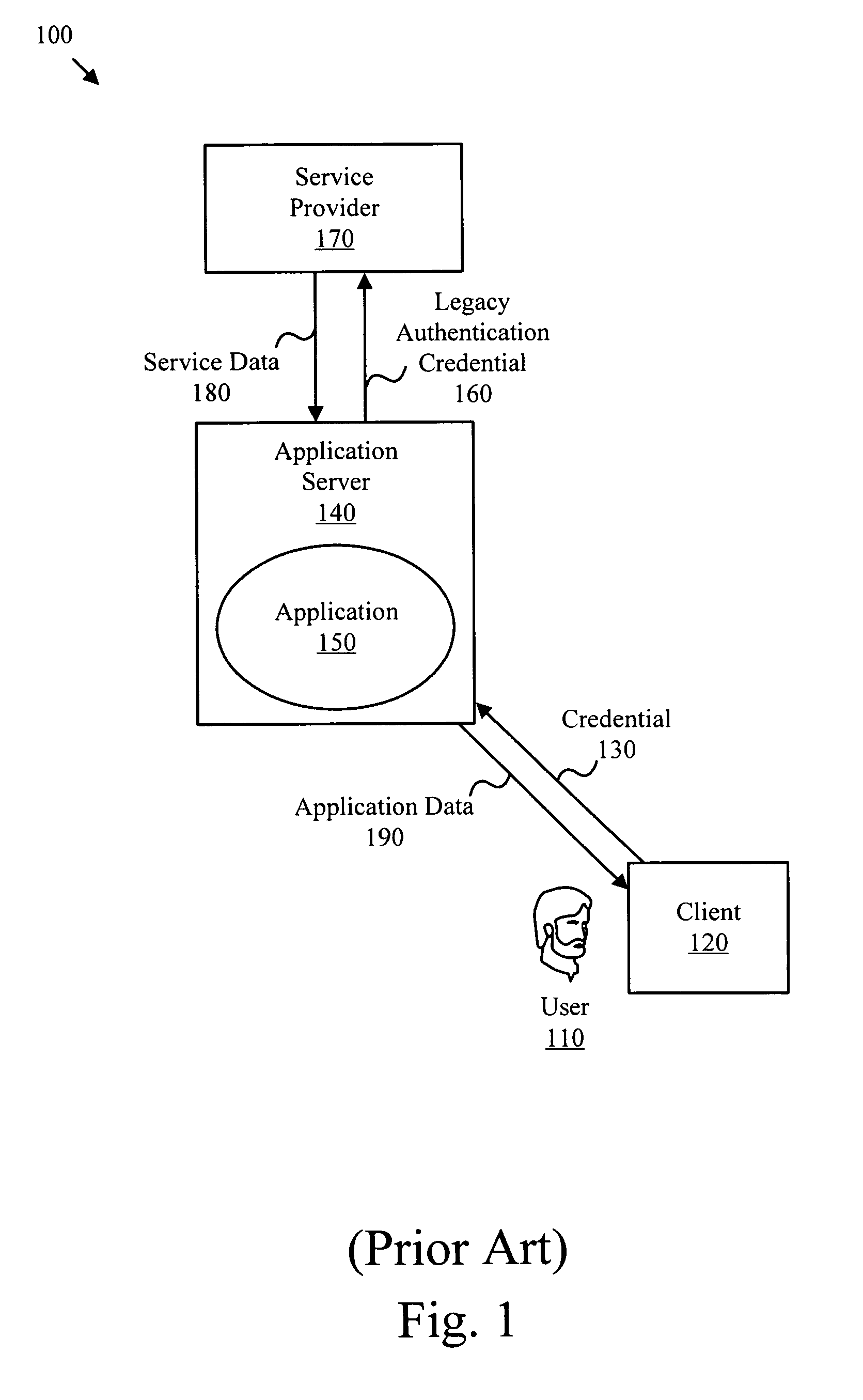
Internet Authentication Service (IAS) is a component of Windows Server operating systems that provides centralized user authentication, authorization and accounting.
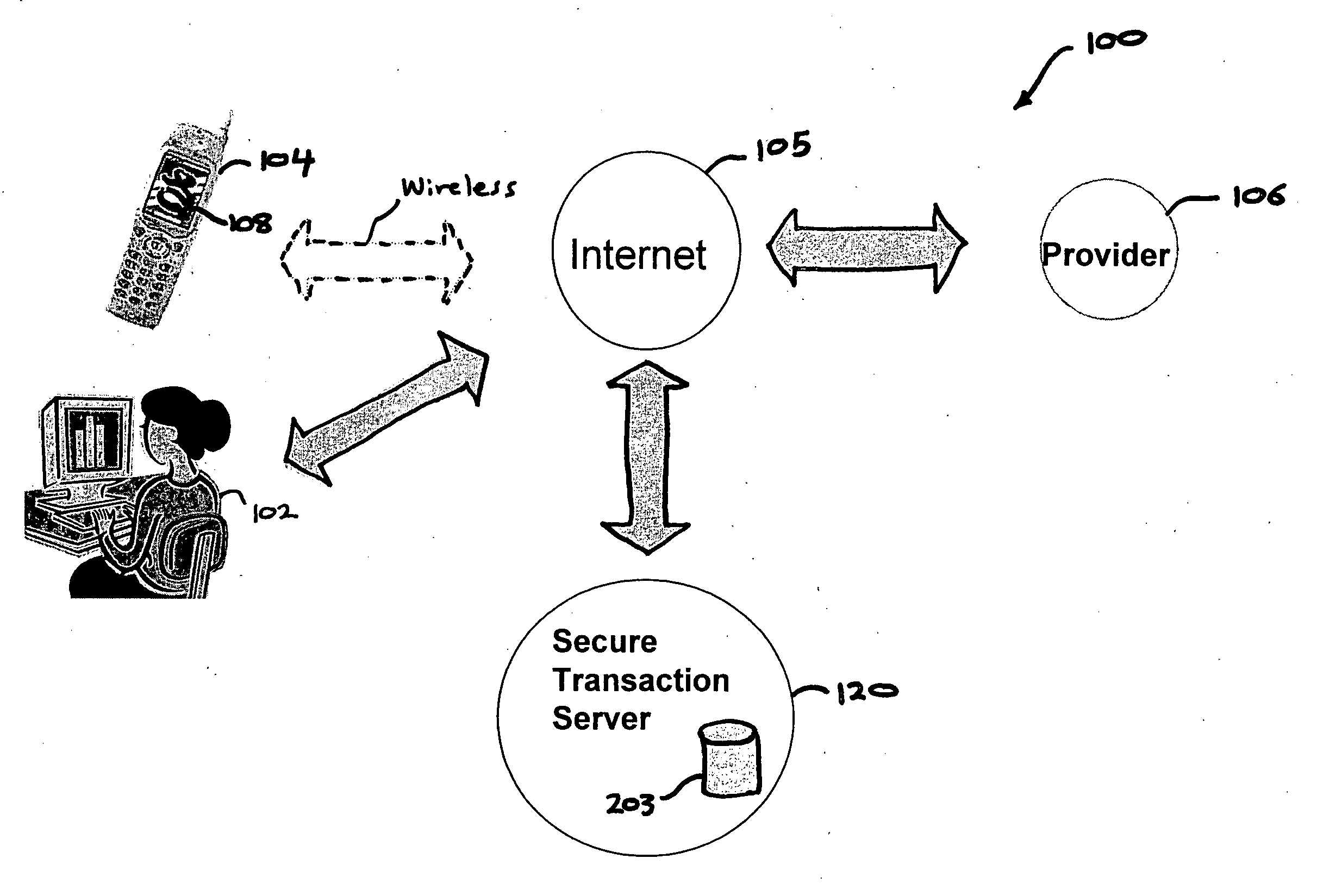
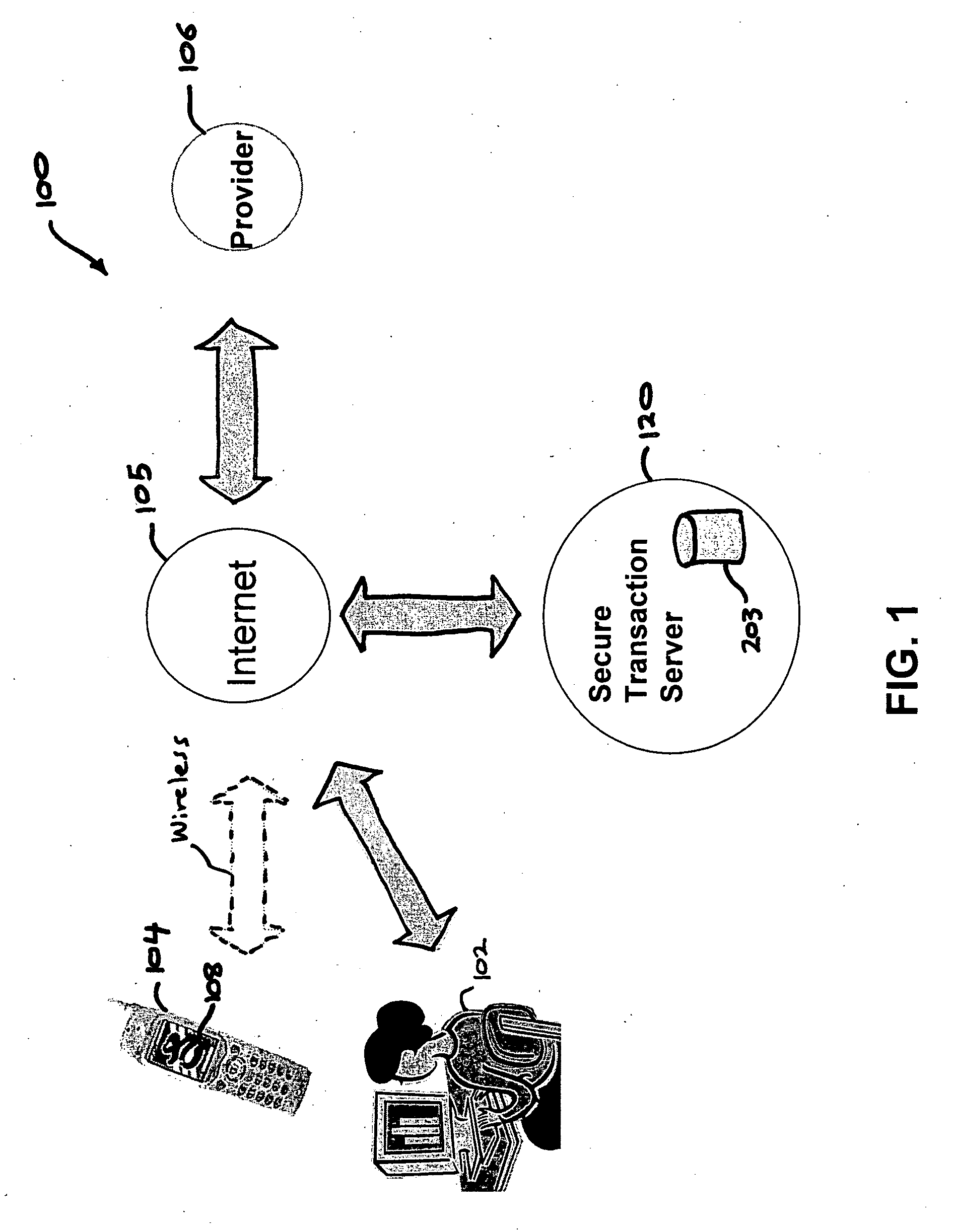
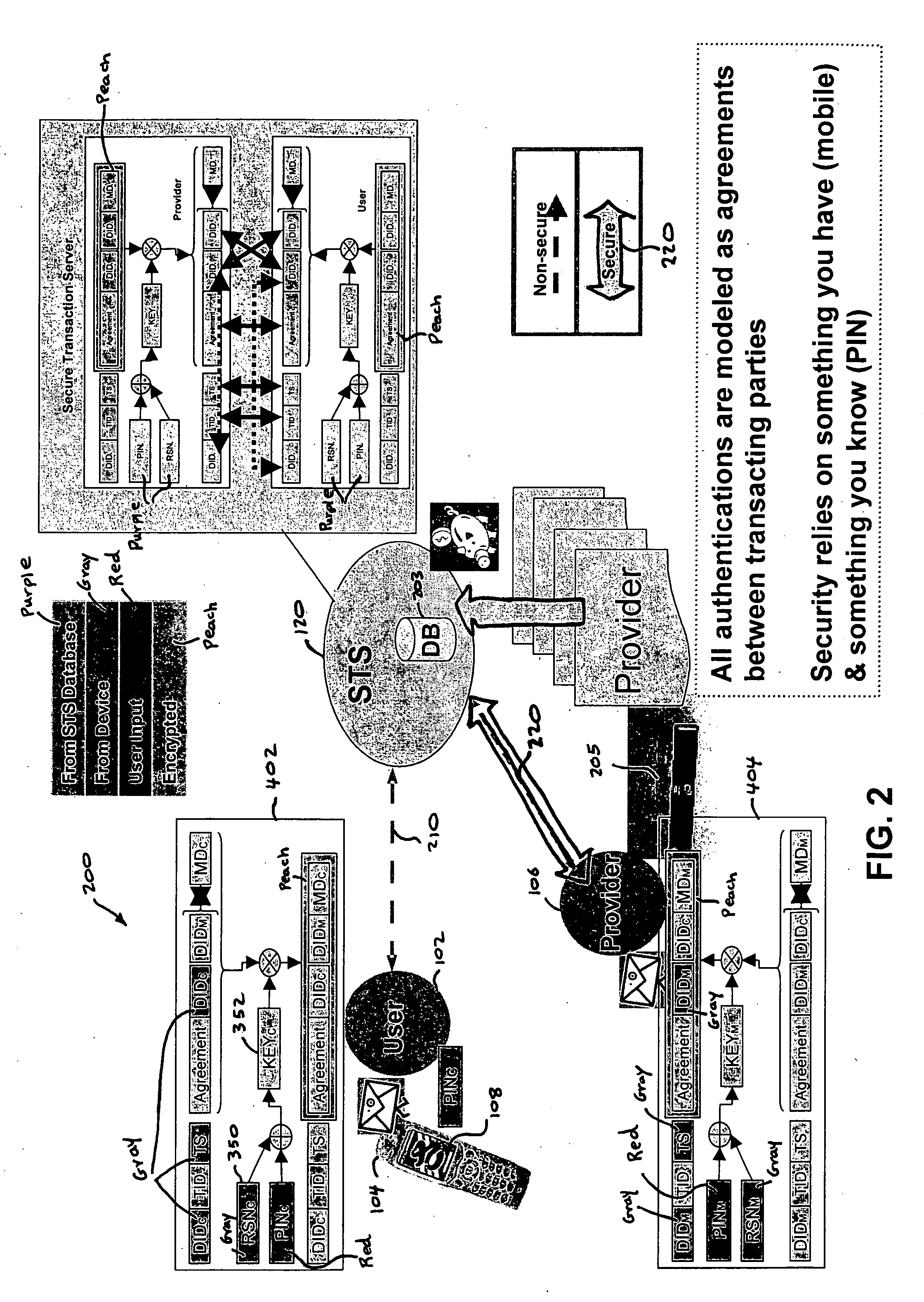
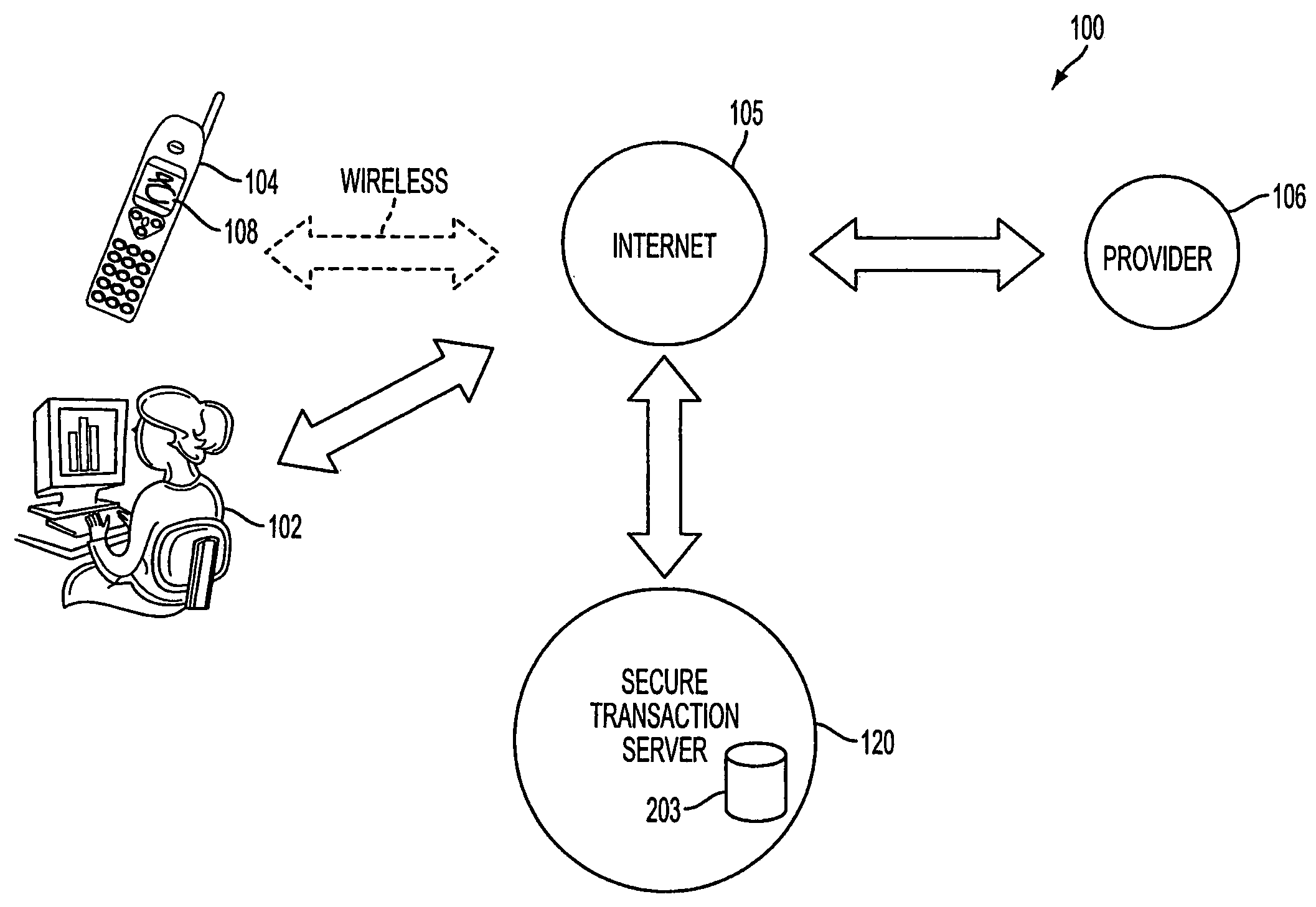
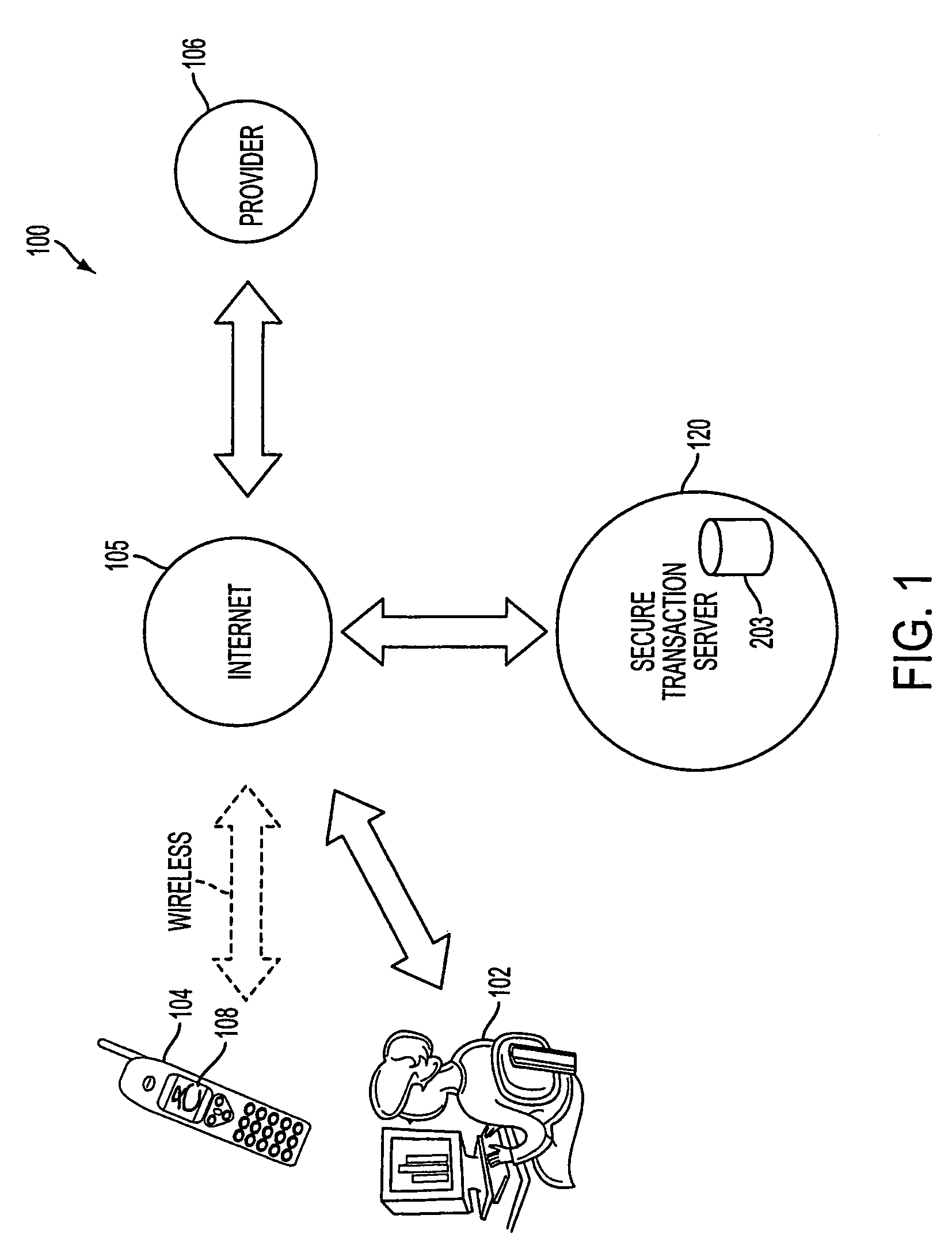
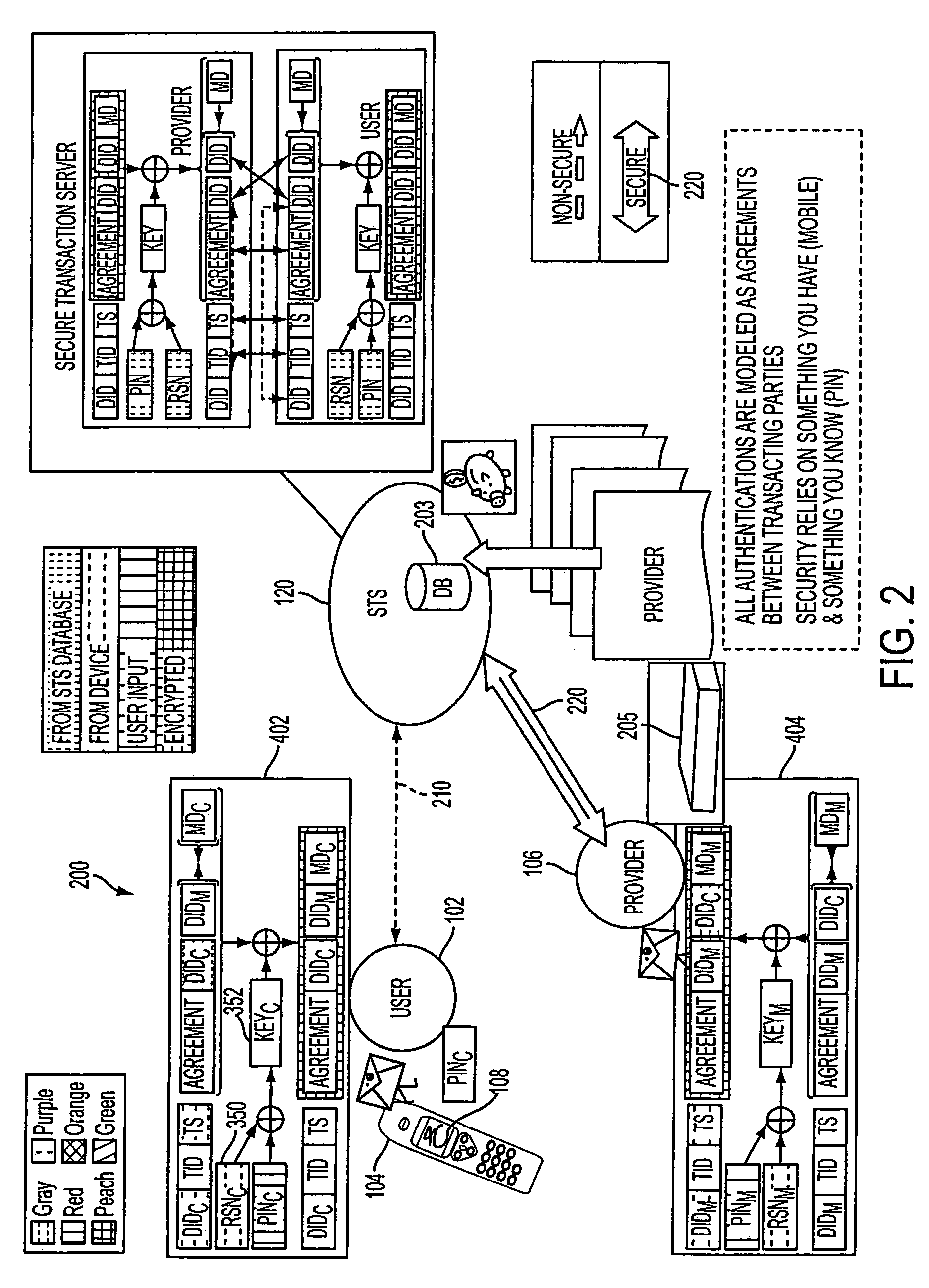
Authentication services using mobile device
InactiveUS20060206709A1Payment architectureATM softwaresInternet Authentication ServiceMobile device
A method, and an apparatus performing the method, is provided by authenticating a mobile device communicably connectable to a wireless network by an authentication parameter from a secure transaction server (STS), as a mobile device authenticator; providing an STS correlation between a personal identification entry (PIE) and the mobile device authenticator; and inputting, by a user, the PIE and a provider action, to the mobile device authenticator to transmit a transformed secure user authenticable authorization request to the STS over the wireless network to authorize an action with a provider.
Owner:PCMS HOLDINGS INC
Authentication services using mobile device
InactiveUS7606560B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet Authentication ServiceMobile device
A method, and an apparatus performing the method, is provided by authenticating a mobile device communicably connectable to a wireless network by an authentication parameter from a secure transaction server (STS), as a mobile device authenticator; providing an STS correlation between a personal identification entry (PIE) and the mobile device authenticator; and inputting, by a user, the PIE and a provider action, to the mobile device authenticator to transmit a transformed secure user authenticable authorization request to the STS over the wireless network to authorize an action with a provider.
Owner:PCMS HOLDINGS INC
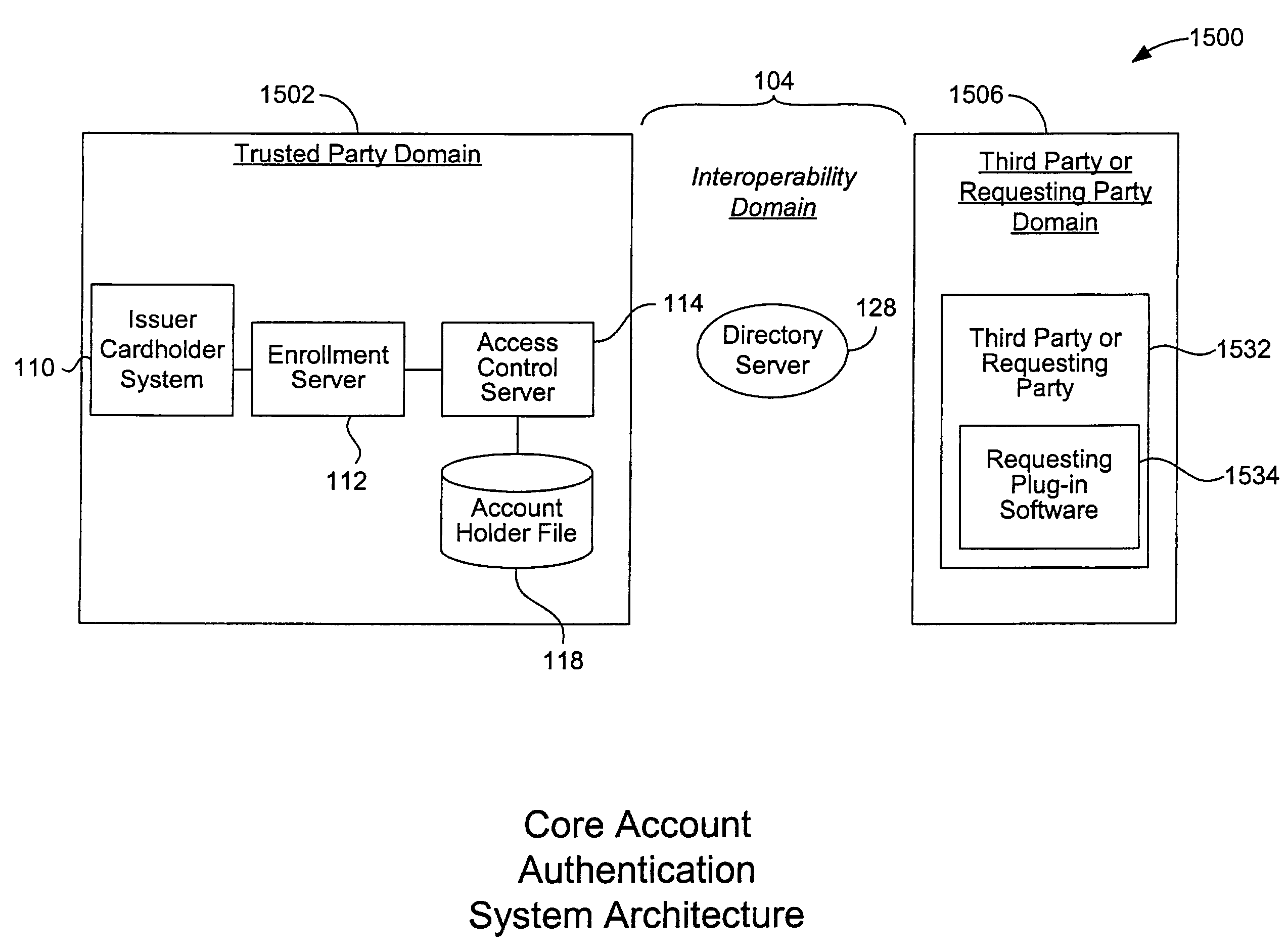
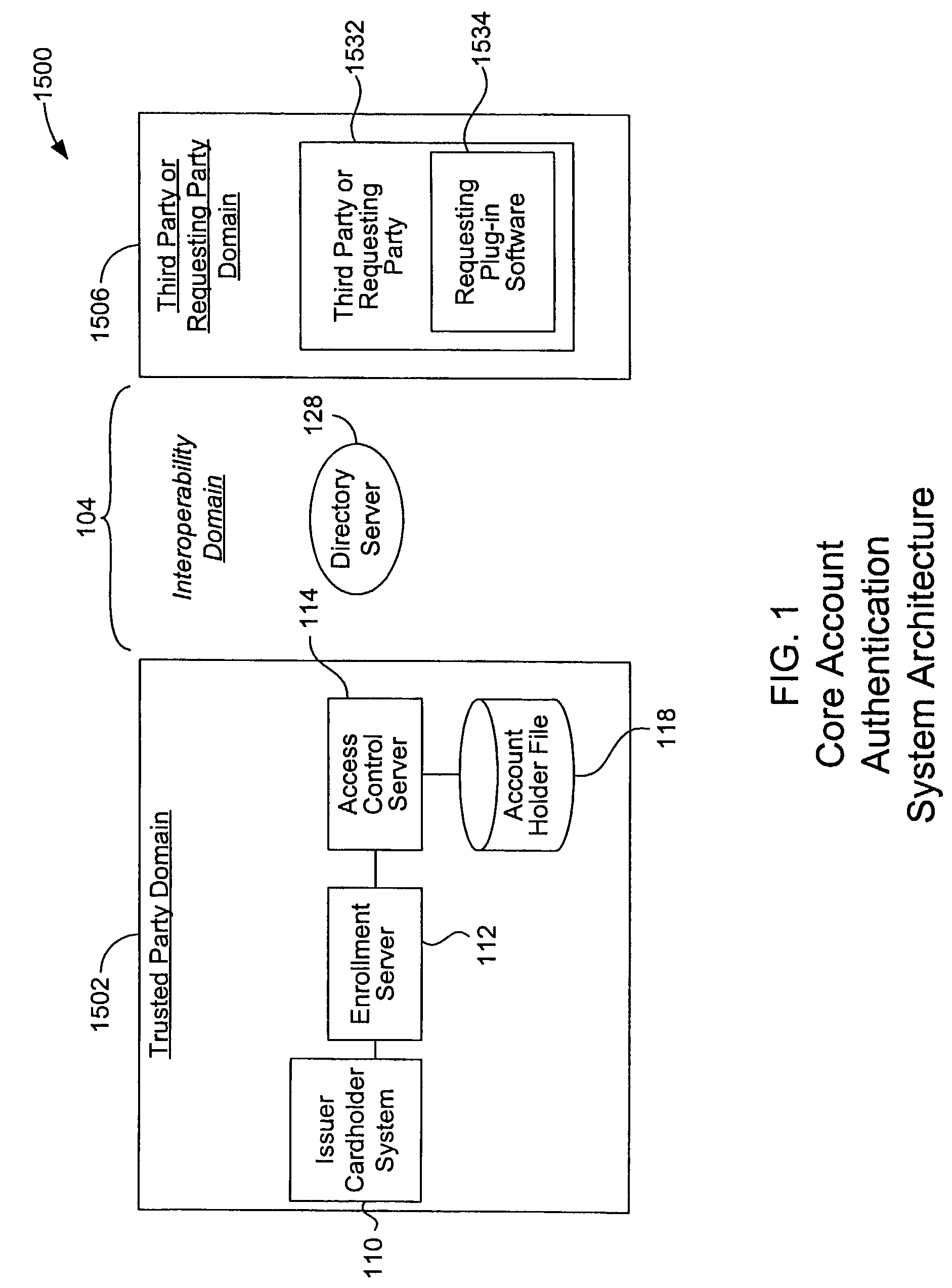
Mobile account authentication service
ActiveUS7707120B2Minimal investmentHigh level of interoperabilityComplete banking machinesFinanceInternet Authentication ServicePayment
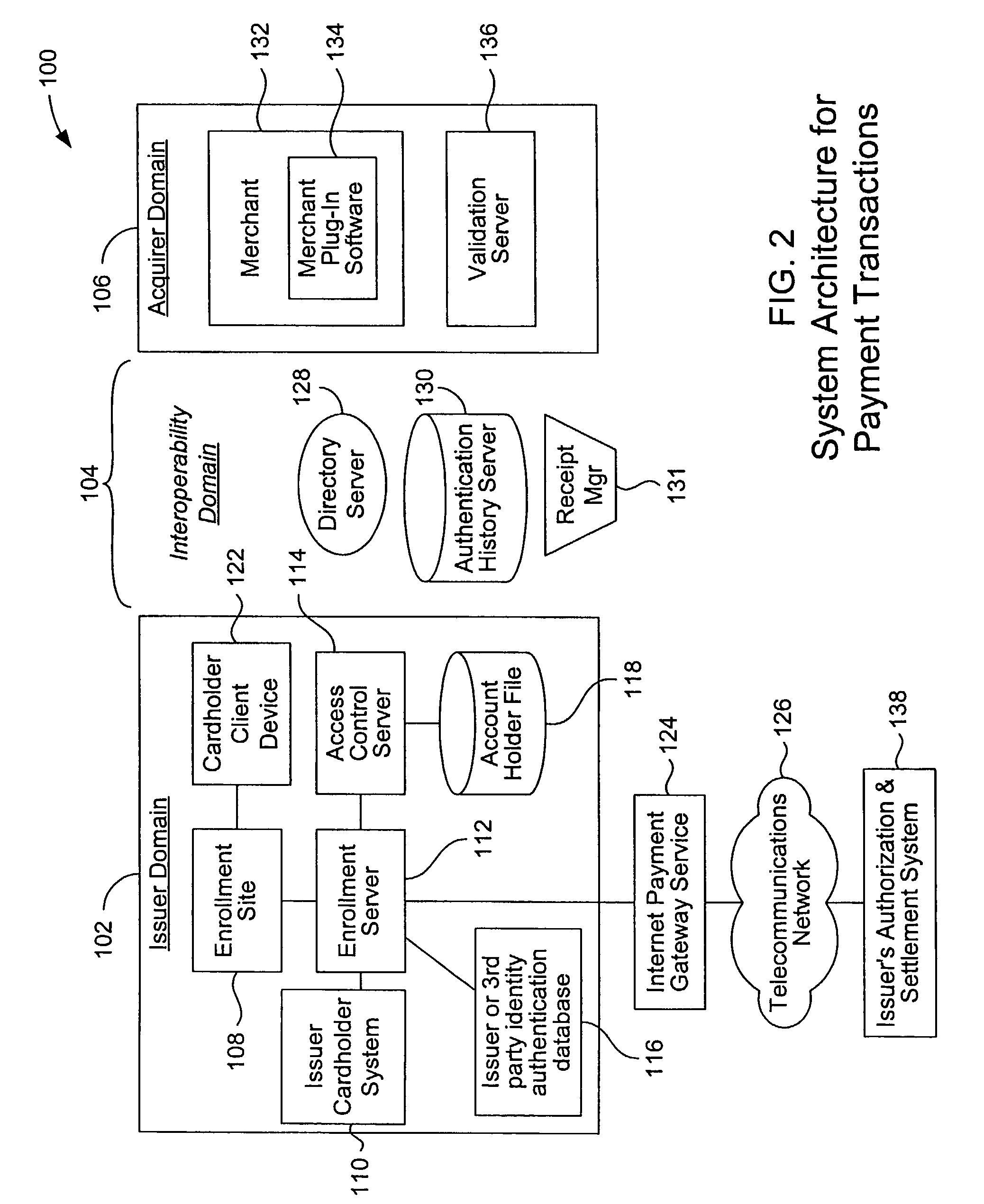
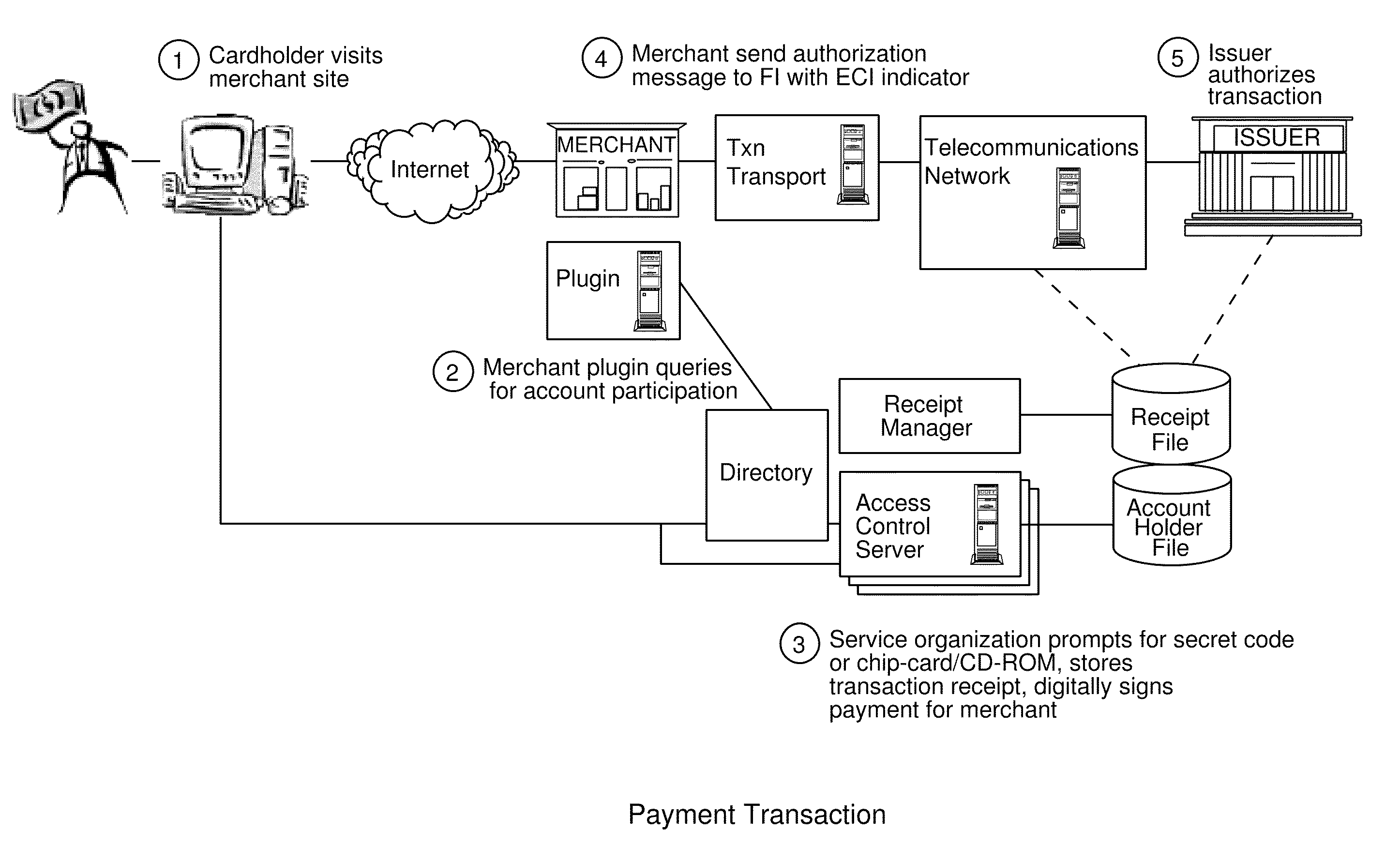
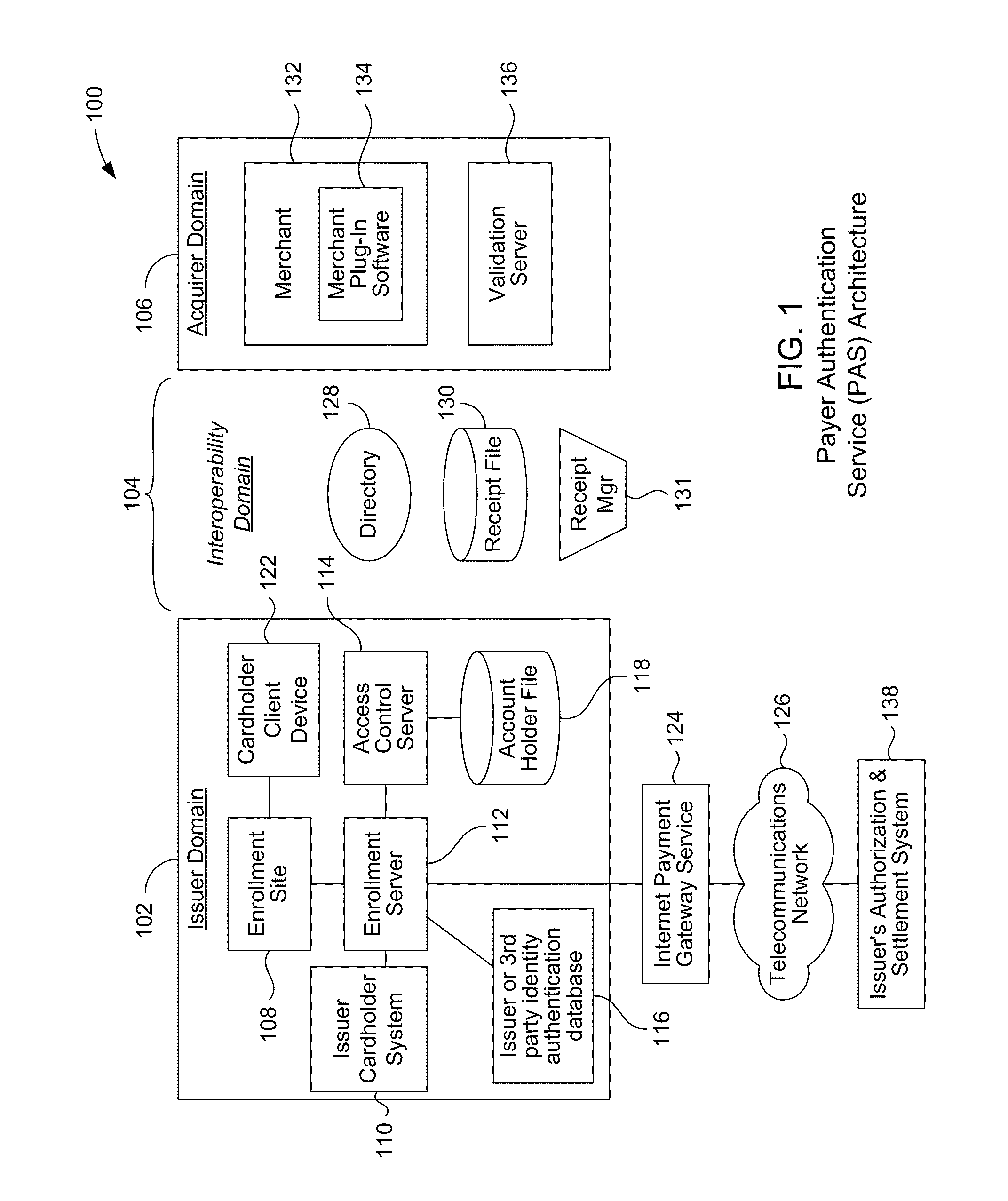
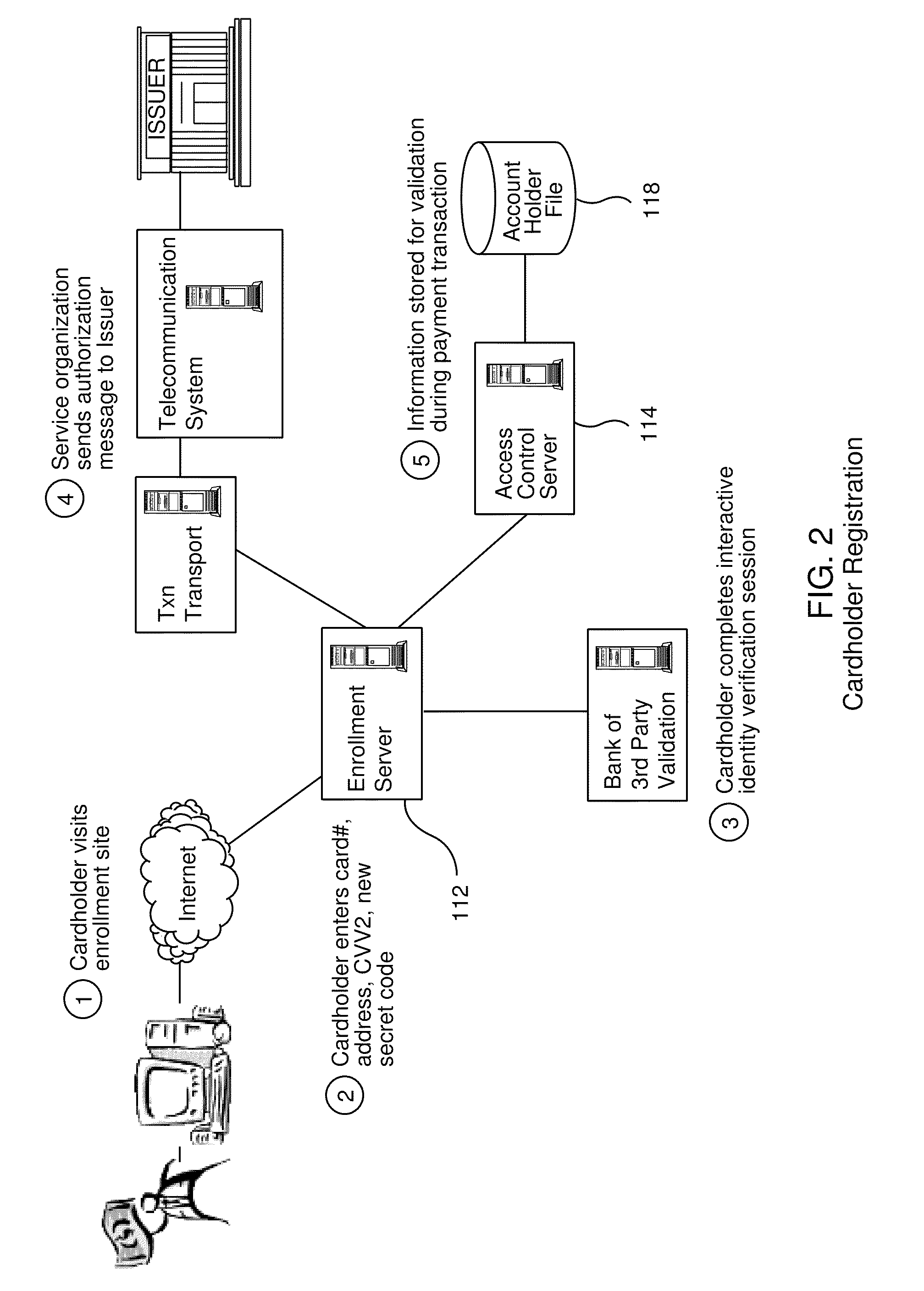
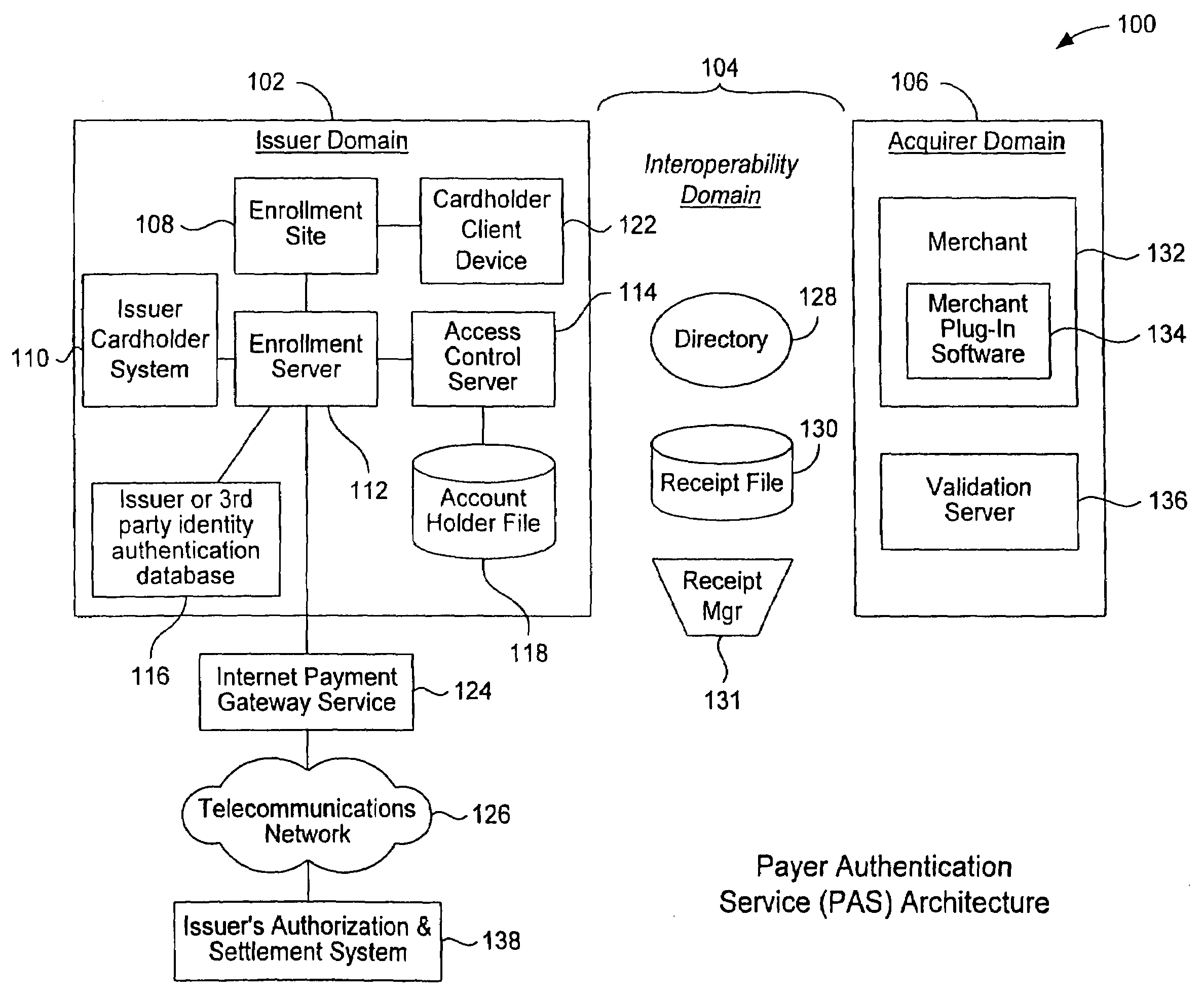
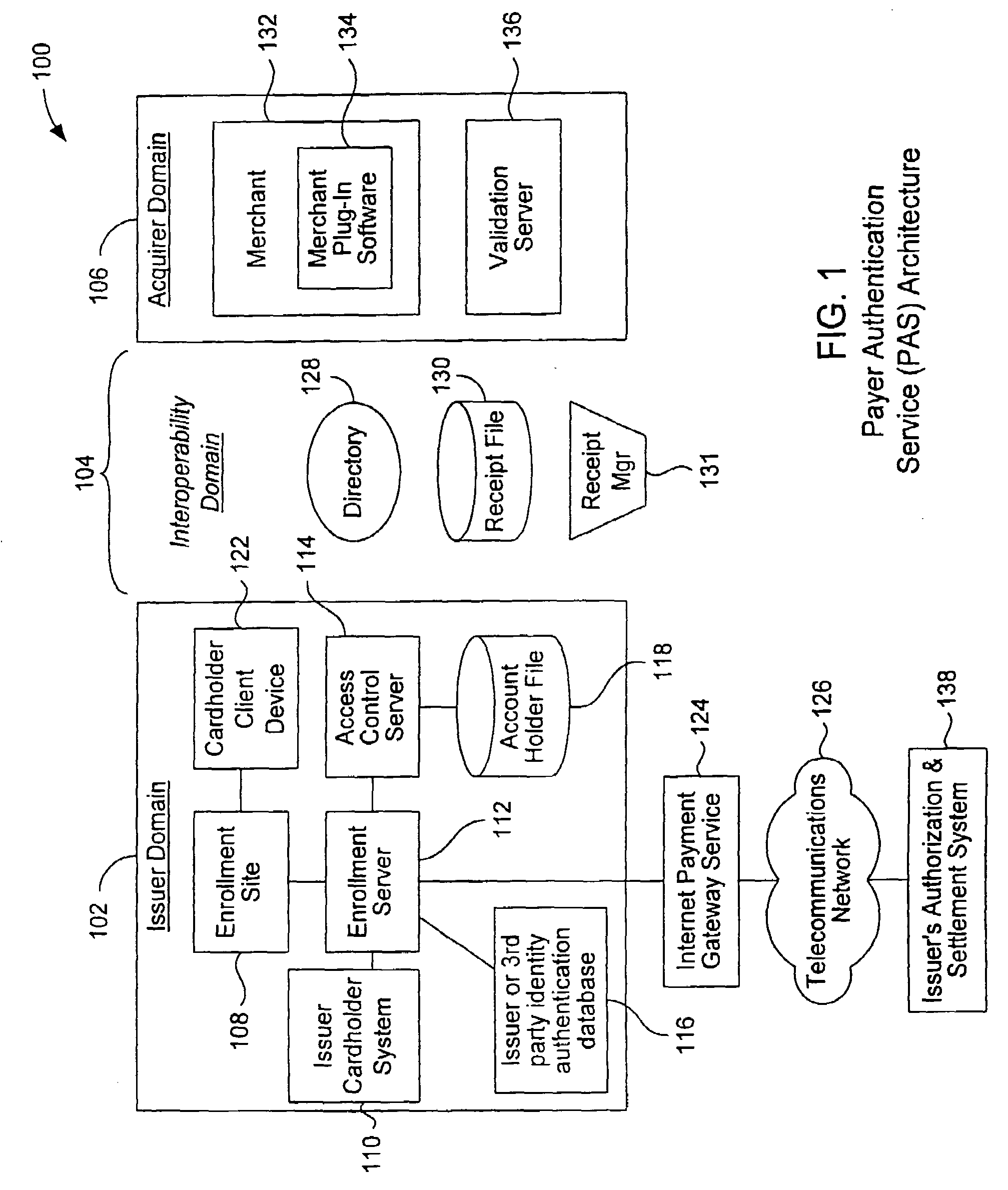
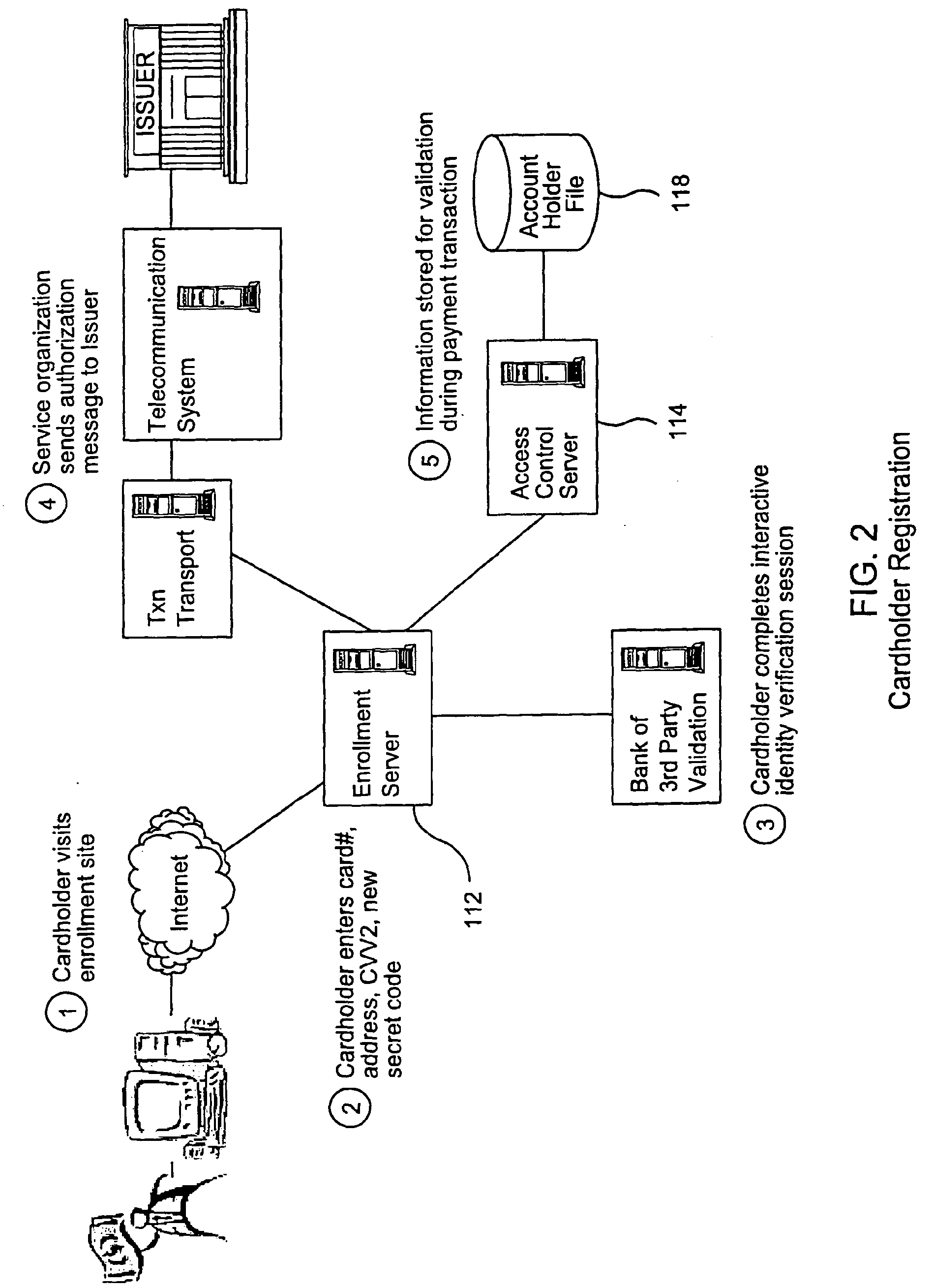
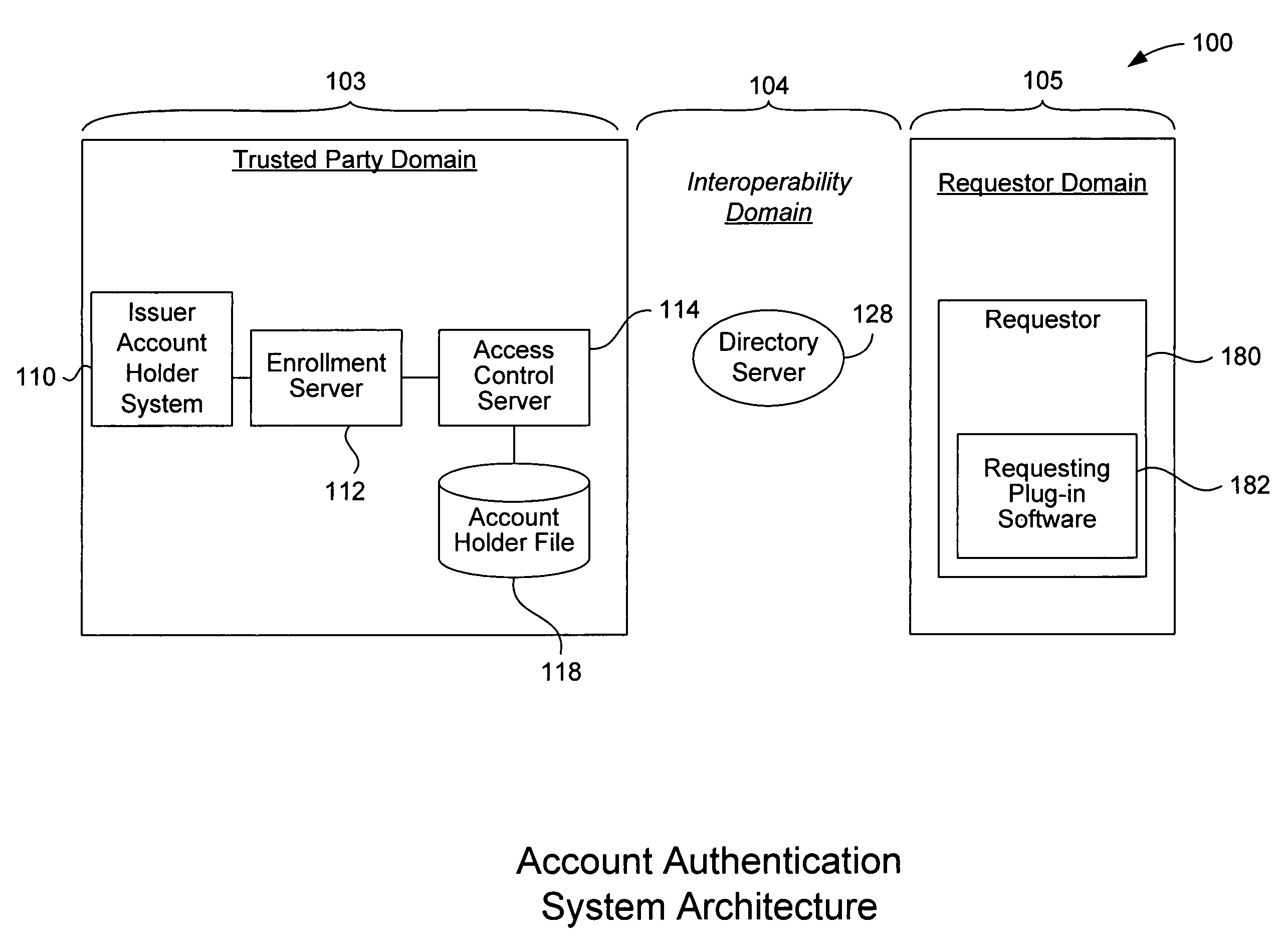
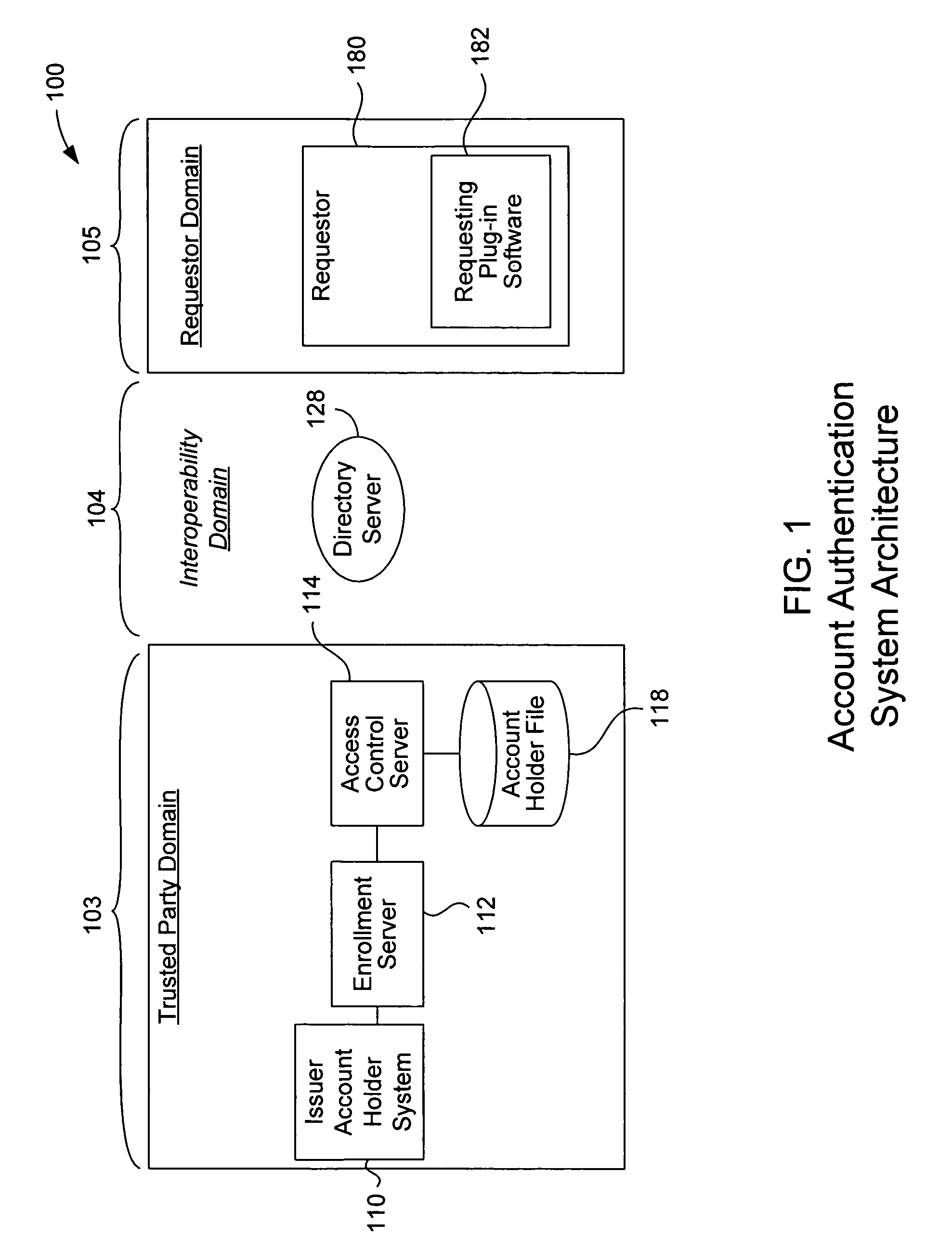
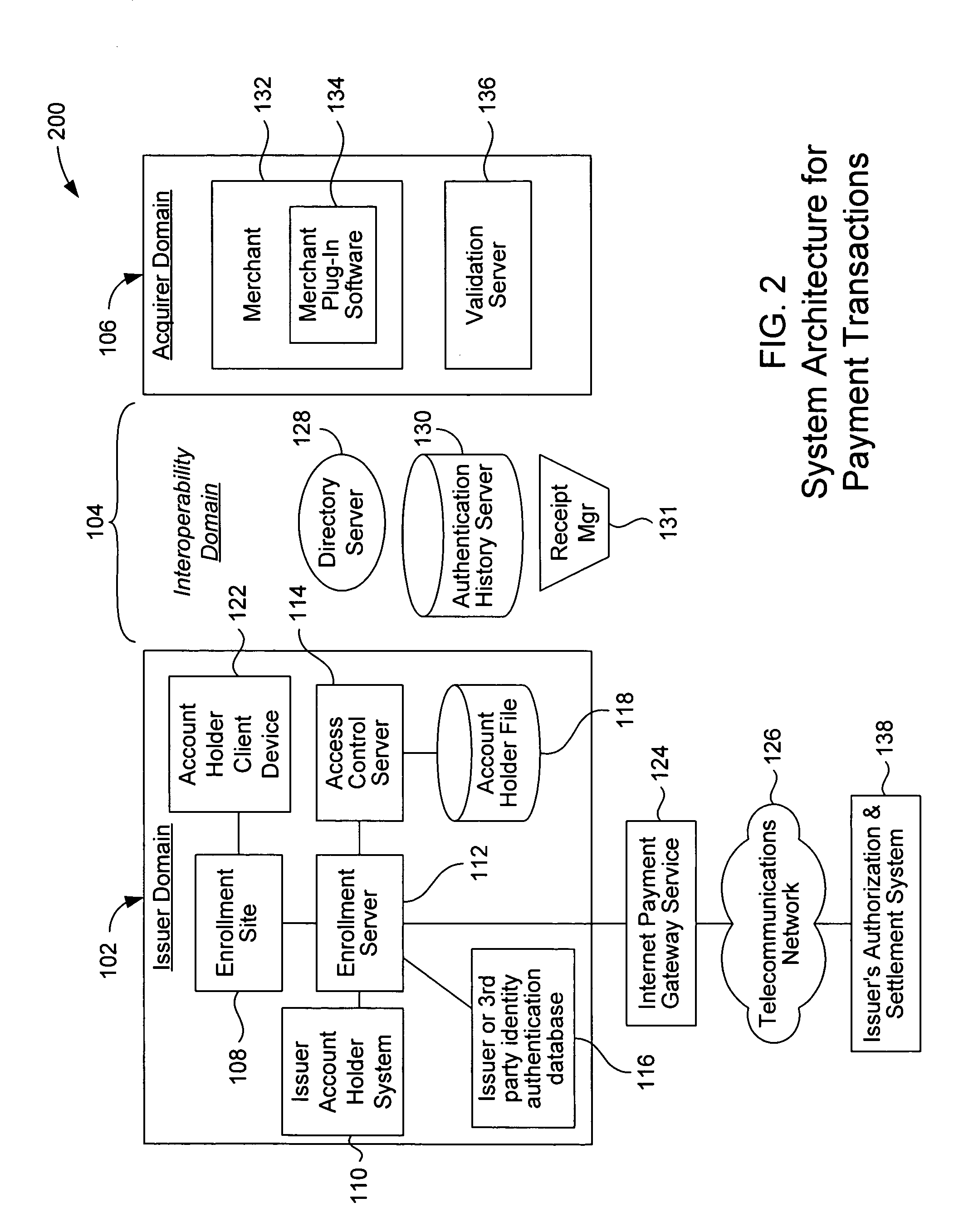
A payment authentication service authenticates the identity of a payer during online transactions. The authentication service allows a card issuer to verify a cardholder's identity using a variety of authentication methods, such as with the use of tokens. Authenticating the identity of a cardholder during an online transaction involves querying an access control server to determine if a cardholder is enrolled in the payment authentication service, requesting a password from the cardholder, verifying the password, and notifying a merchant whether the cardholder's authenticity has been verified. Systems for implementing the authentication service in which a cardholder uses a mobile device capable of transmitting messages via the Internet are described. Systems for implementing the authentication service in which a cardholder uses a mobile device capable of transmitting messages through voice and messaging channels is also described.
Owner:VISA INT SERVICE ASSOC
User authentication in a cloud environment
ActiveUS20140373126A1Well formedDigital data processing detailsComputer security arrangementsInternet Authentication ServiceData memory
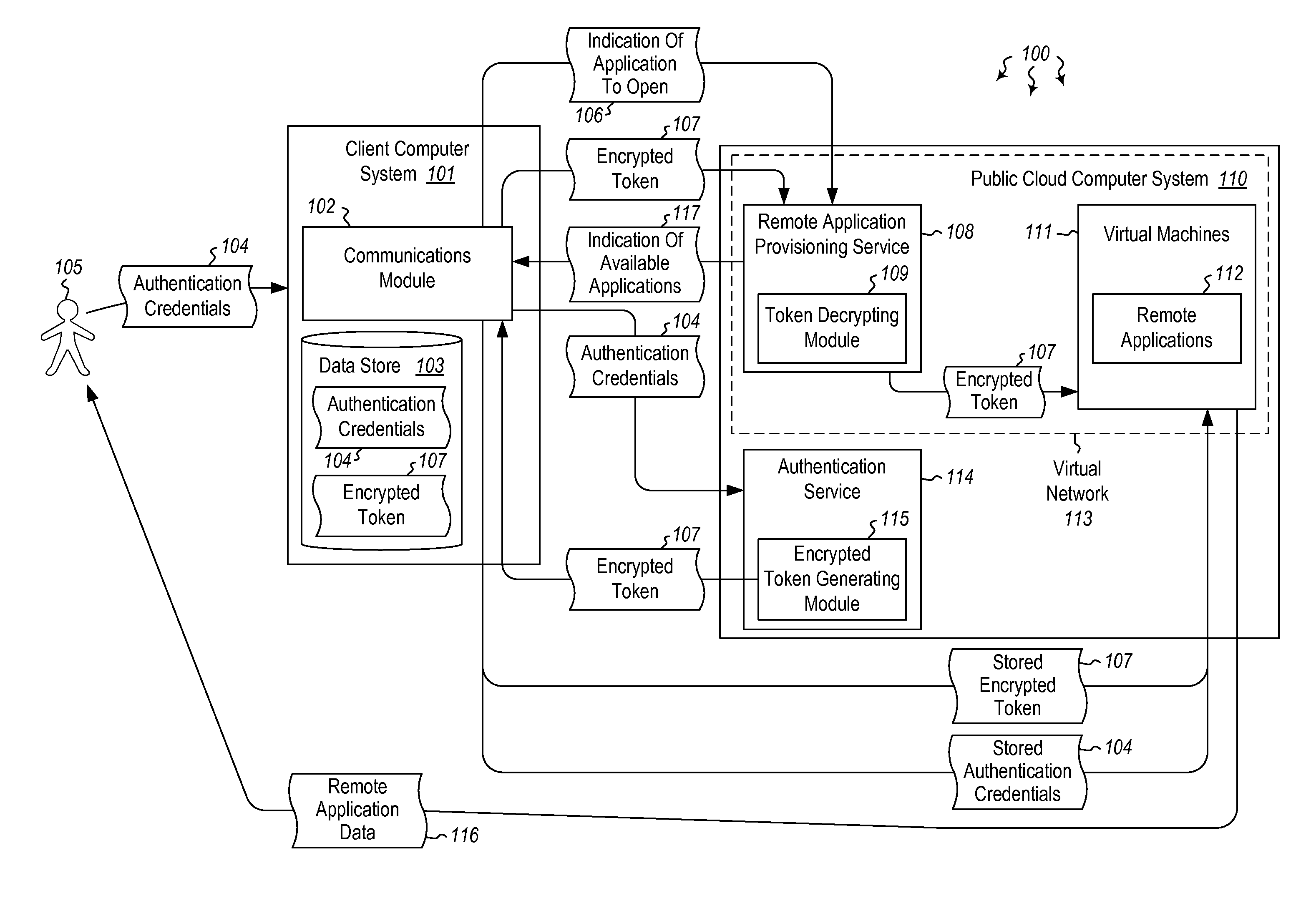
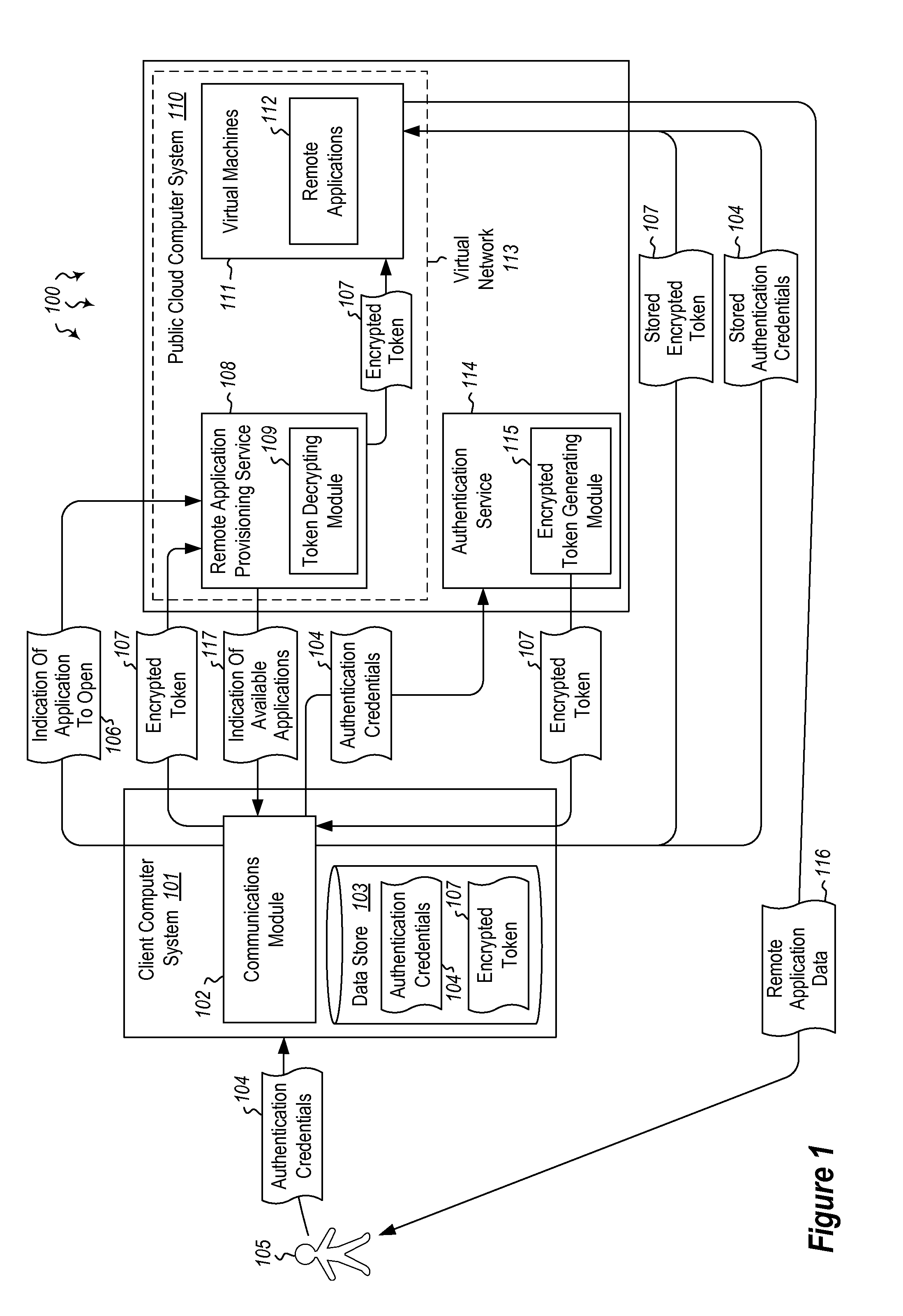
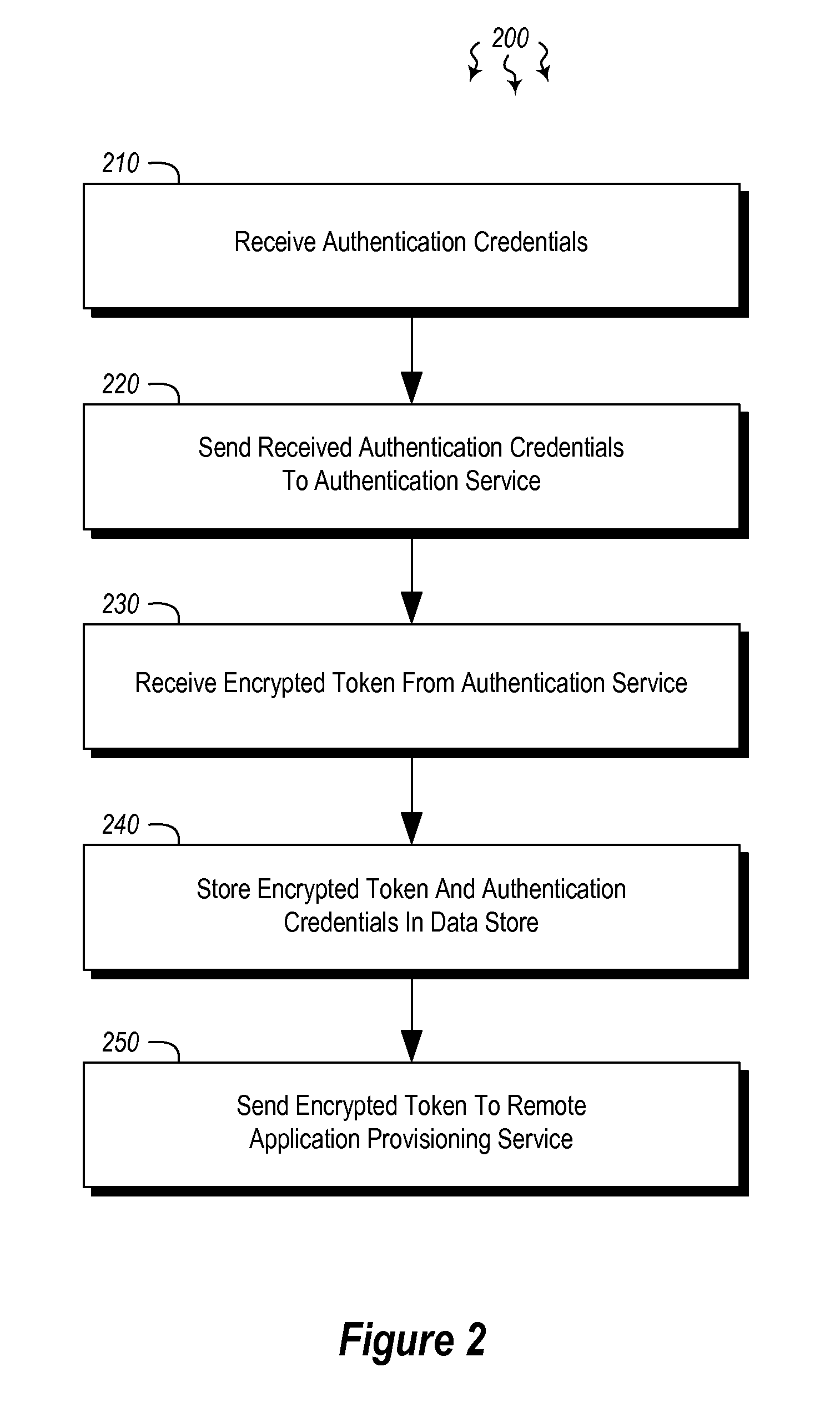
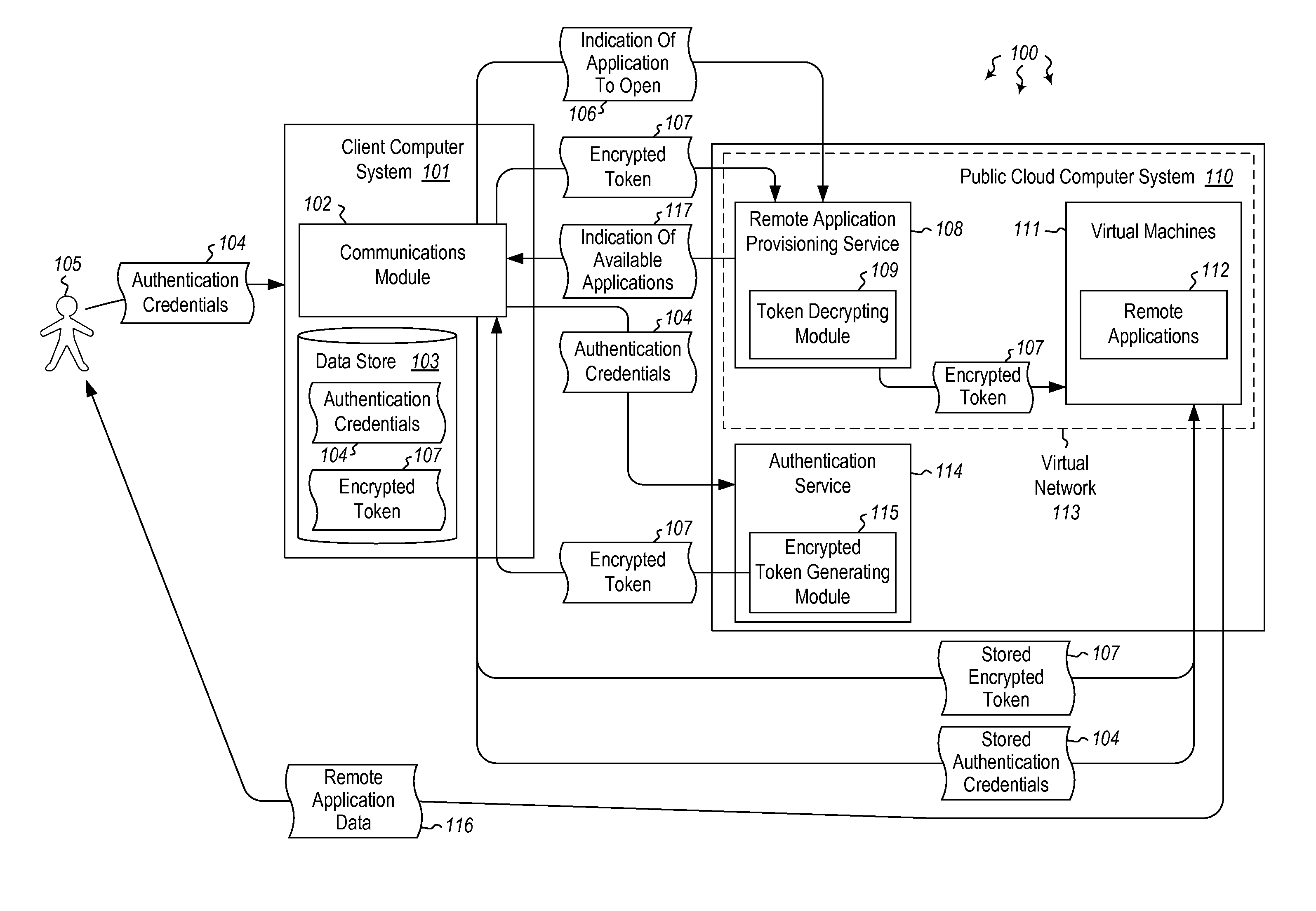
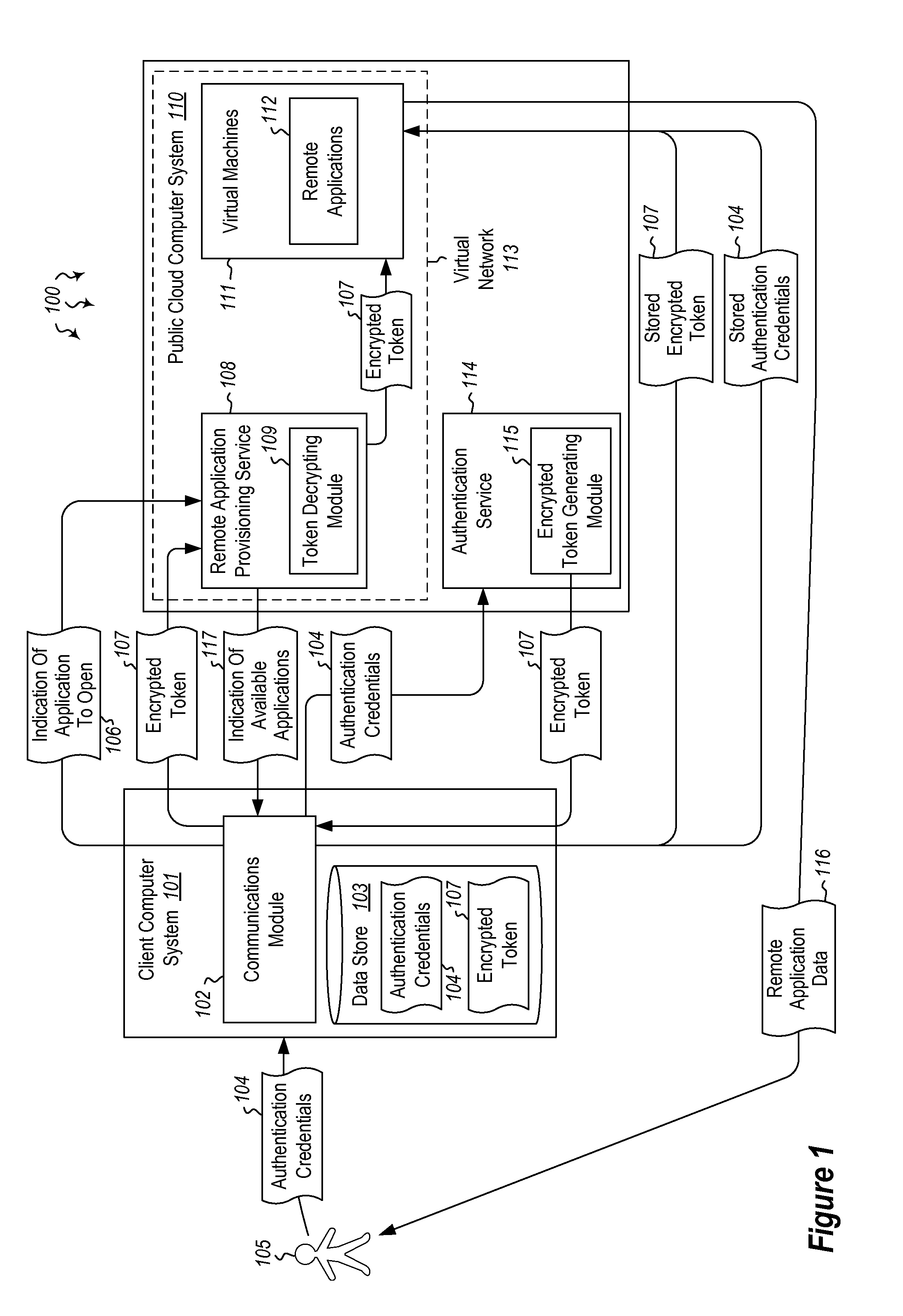
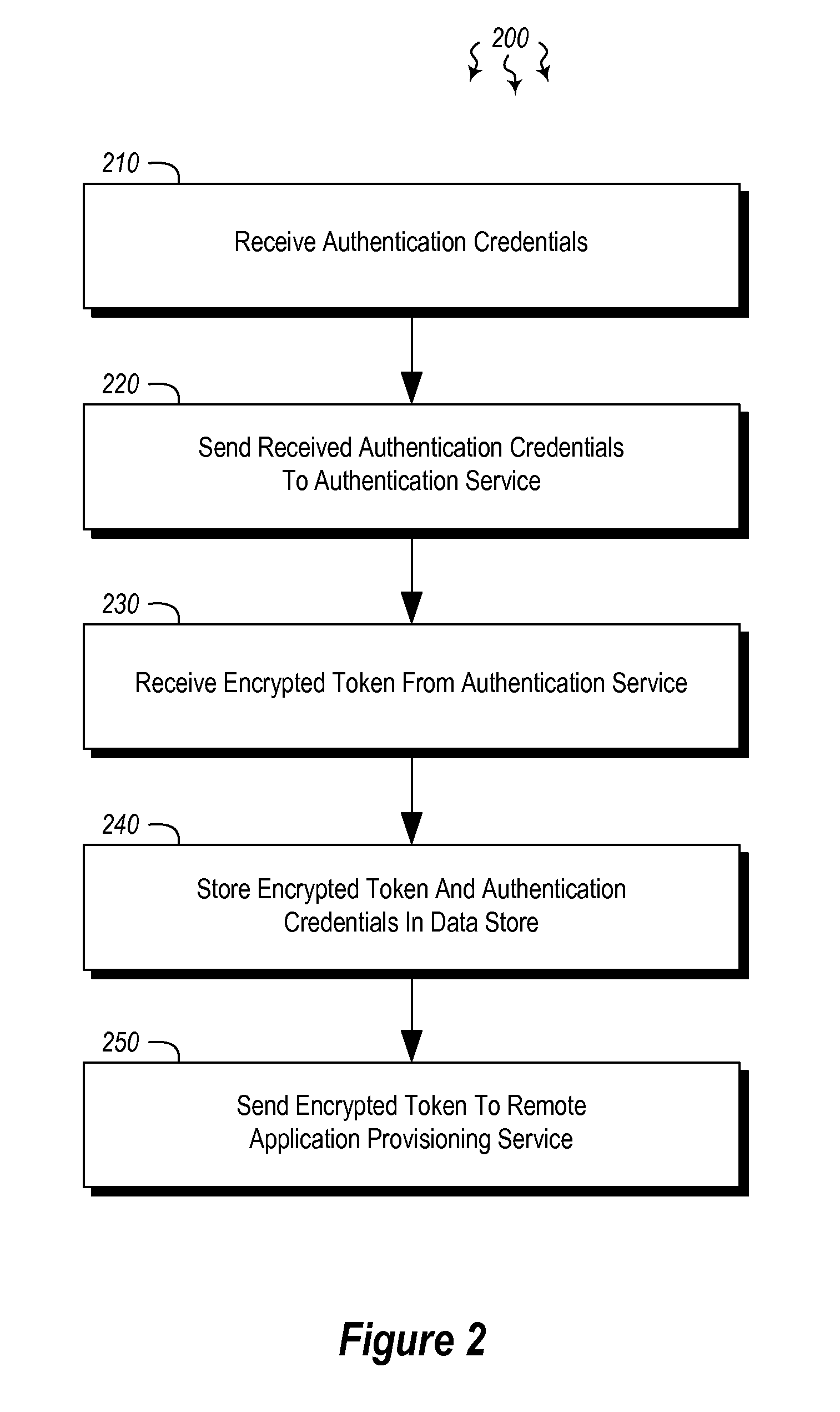
Embodiments are directed to authenticating a user to a remote application provisioning service. In one scenario, a client computer system receives authentication credentials from a user at to authenticate the user to a remote application provisioning service that provides virtual machine-hosted remote applications. The client computer system sends the received authentication credentials to an authentication service, which is configured to generate an encrypted token based on the received authentication credentials. The client computer system then receives the generated encrypted token from the authentication service, stores the received encrypted token and the received authentication credentials in a data store, and sends the encrypted token to the remote application provisioning service. The encrypted token indicates to the remote application provisioning service that the user is a valid user.
Owner:MICROSOFT TECH LICENSING LLC
User authentication in a cloud environment
ActiveUS9124569B2Digital data processing detailsDigital data authenticationInternet Authentication ServiceData memory
Embodiments are directed to authenticating a user to a remote application provisioning service. In one scenario, a client computer system receives authentication credentials from a user at to authenticate the user to a remote application provisioning service that provides virtual machine-hosted remote applications. The client computer system sends the received authentication credentials to an authentication service, which is configured to generate an encrypted token based on the received authentication credentials. The client computer system then receives the generated encrypted token from the authentication service, stores the received encrypted token and the received authentication credentials in a data store, and sends the encrypted token to the remote application provisioning service. The encrypted token indicates to the remote application provisioning service that the user is a valid user.
Owner:MICROSOFT TECH LICENSING LLC
Authorization services with external authentication
InactiveUS7231661B1Digital data processing detailsUser identity/authority verificationInternet Authentication ServiceIdentity management
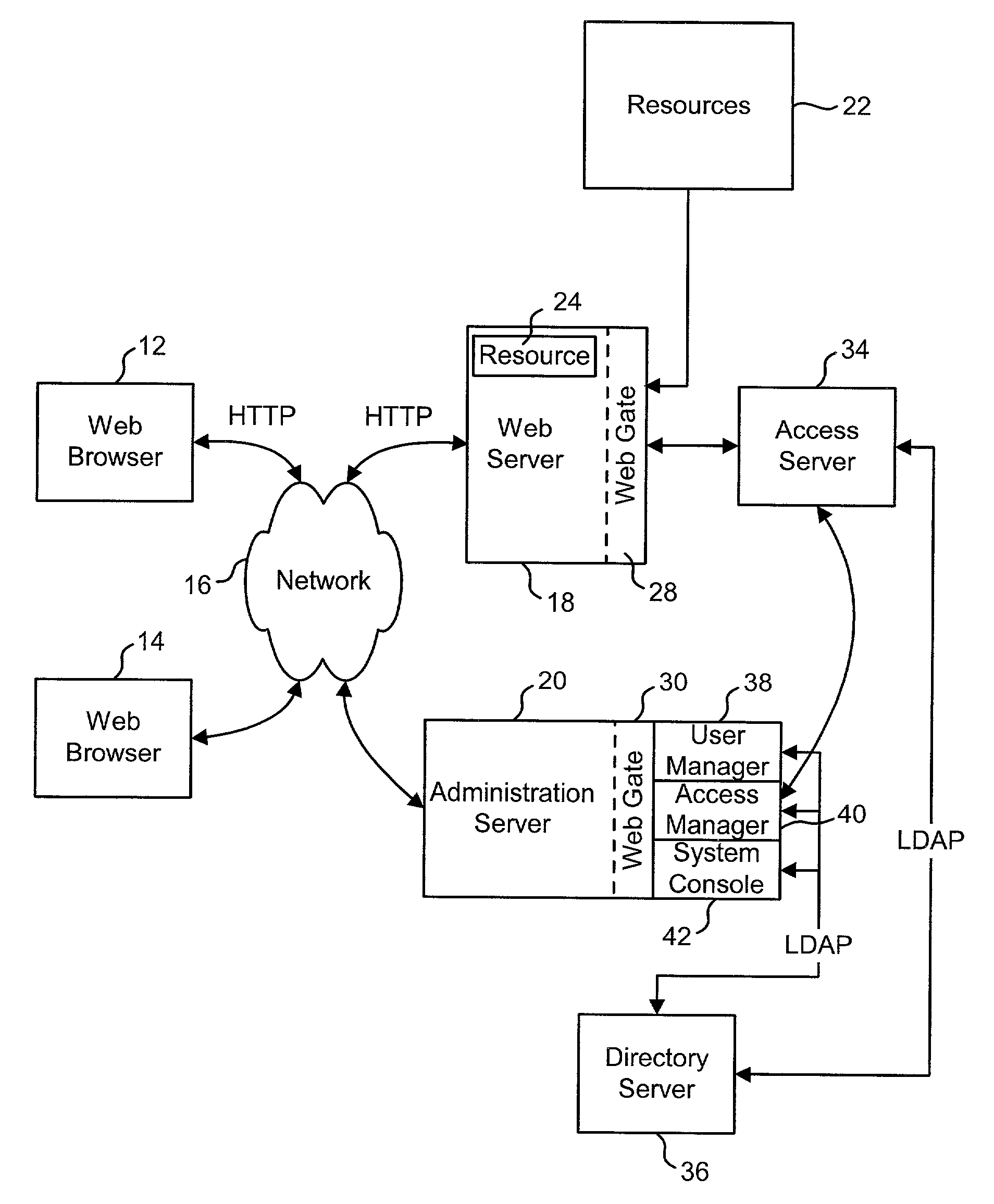
An Access System can provide identity management and / or access management services. Examples of access management services include authentication and authorization services. In some implementations, users of an Access System want to use the authorization services of the Access System but do not want to use the authentication services of the Access System. The present invention allows some or all of the resources protected by the Access System to use the authentication services of the Access System and some or all of the resources protected by the Access System to use external authentication services.
Owner:ORACLE INT CORP
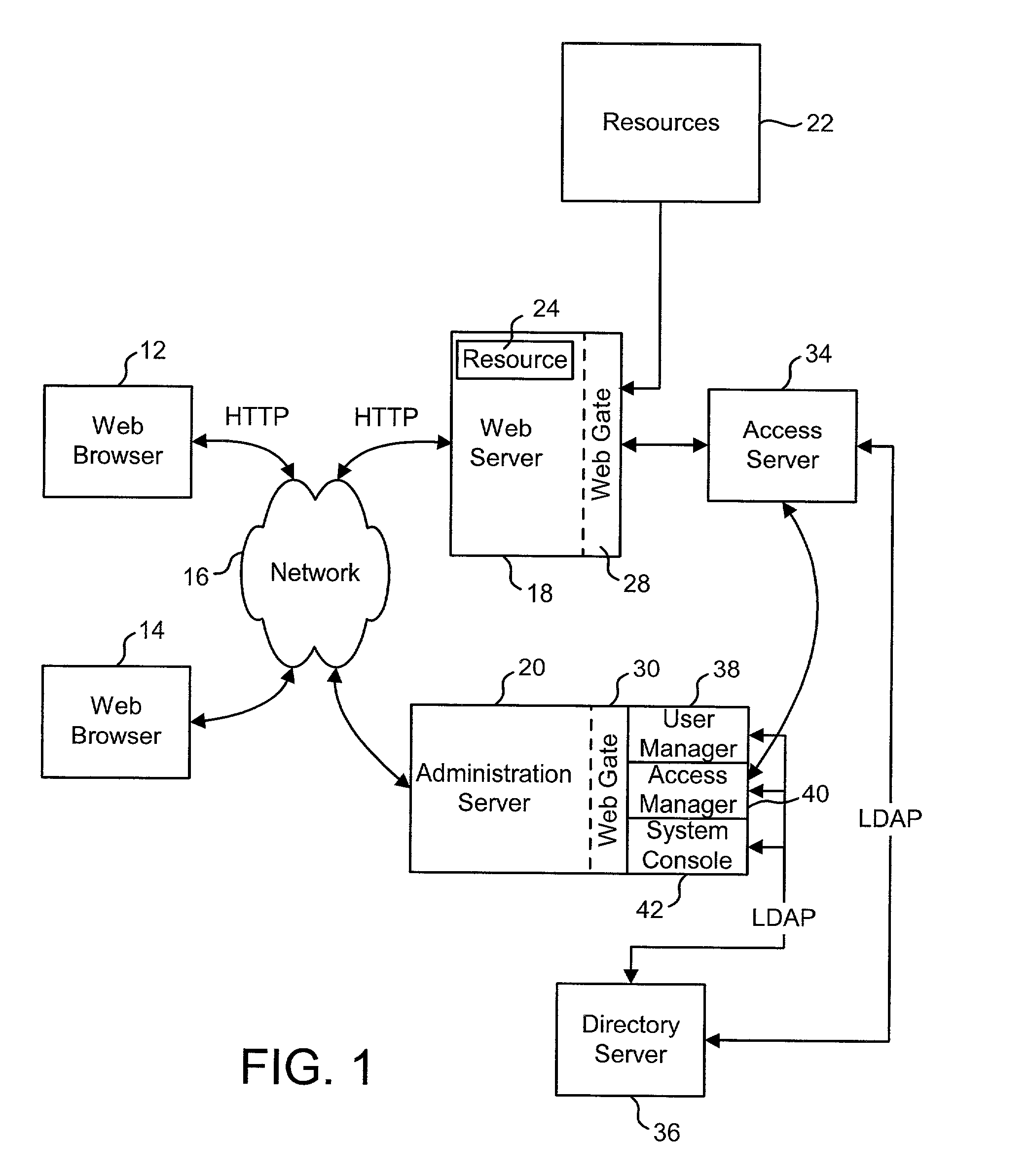
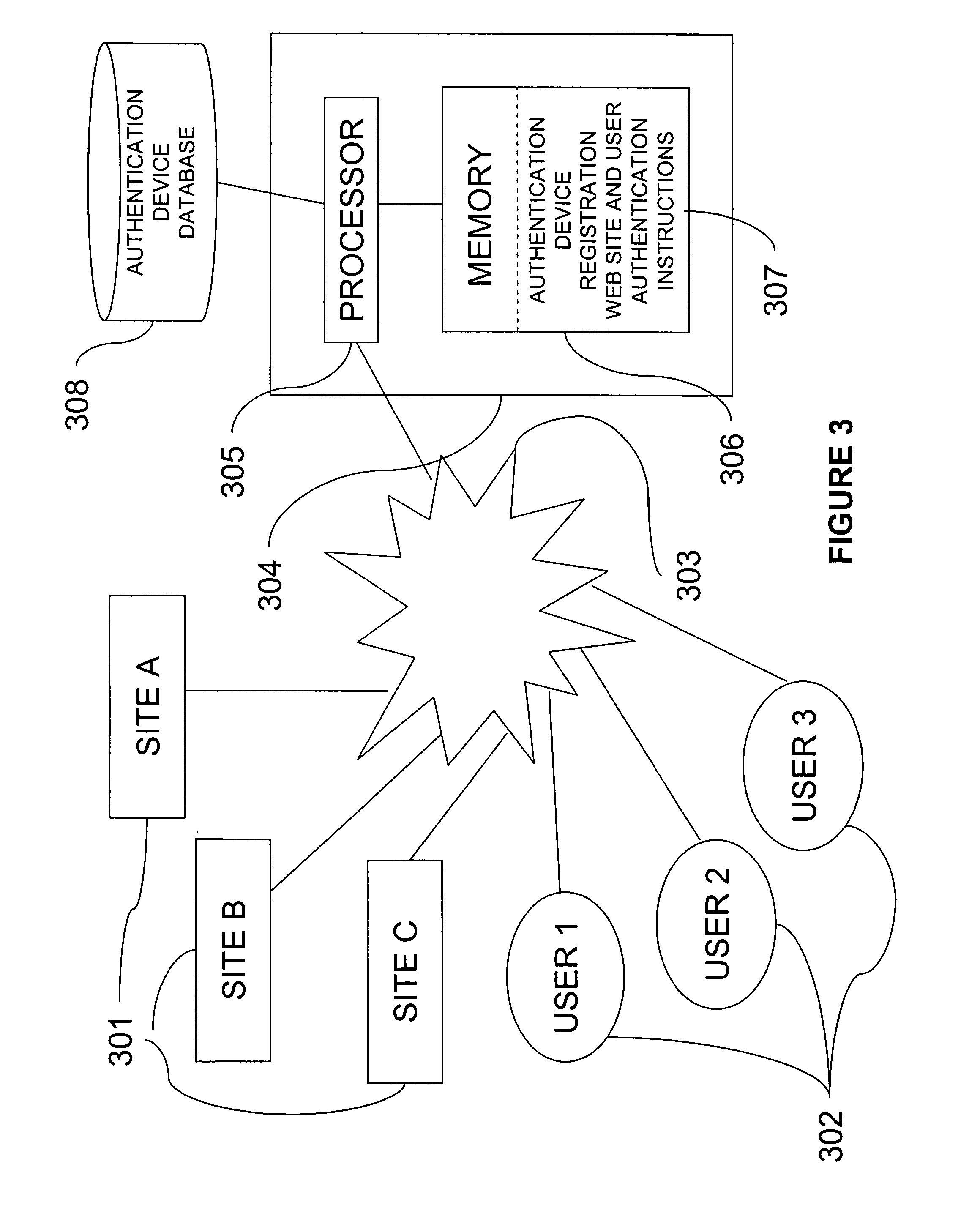
Web site authentication
ActiveUS20080109657A1Digital data processing detailsUser identity/authority verificationWeb siteInternet Authentication Service
A web site can be authenticated by a third party authentication service. A user designates an authentication device that is a shared secret between the user and the authentication service. A web site page includes a URL that points to the authentication service. The URL includes a digital signature by the web site. When the user receives the page, the user's browser issues a request to the authentication service, which attempts to authenticate the digital signature. If the authentication is successful, it sends the authentication device to the user computer.
Owner:SYMANTEC CORP
Account authentication service with chip card
ActiveUS20100057619A1Minimal investmentHigh level of interoperabilityUser identity/authority verificationSpecial service for subscribersPaymentInternet Authentication Service
A payment authentication service authenticates the identity of a payer during online transactions. The authentication service of the present invention allows a card issuer to verify a cardholder's identity using a variety of authentication methods, such as the use of passwords. Also, the only system participant requiring a certificate is the issuing financial institution. One embodiment of the invention for authenticating the identity of a cardholder during an online transaction involves querying an access control server to determine if a cardholder is enrolled in the payment authentication service, requests a password from the cardholder, verifies the password, and notifies a merchant whether the cardholder's authenticity has been verified. In another aspect of the invention, a chip card and the authentication service independently generate cryptograms that must match in order for the service to verify that the correct chip card is being used by the cardholder.
Owner:VISA INT SERVICE ASSOC
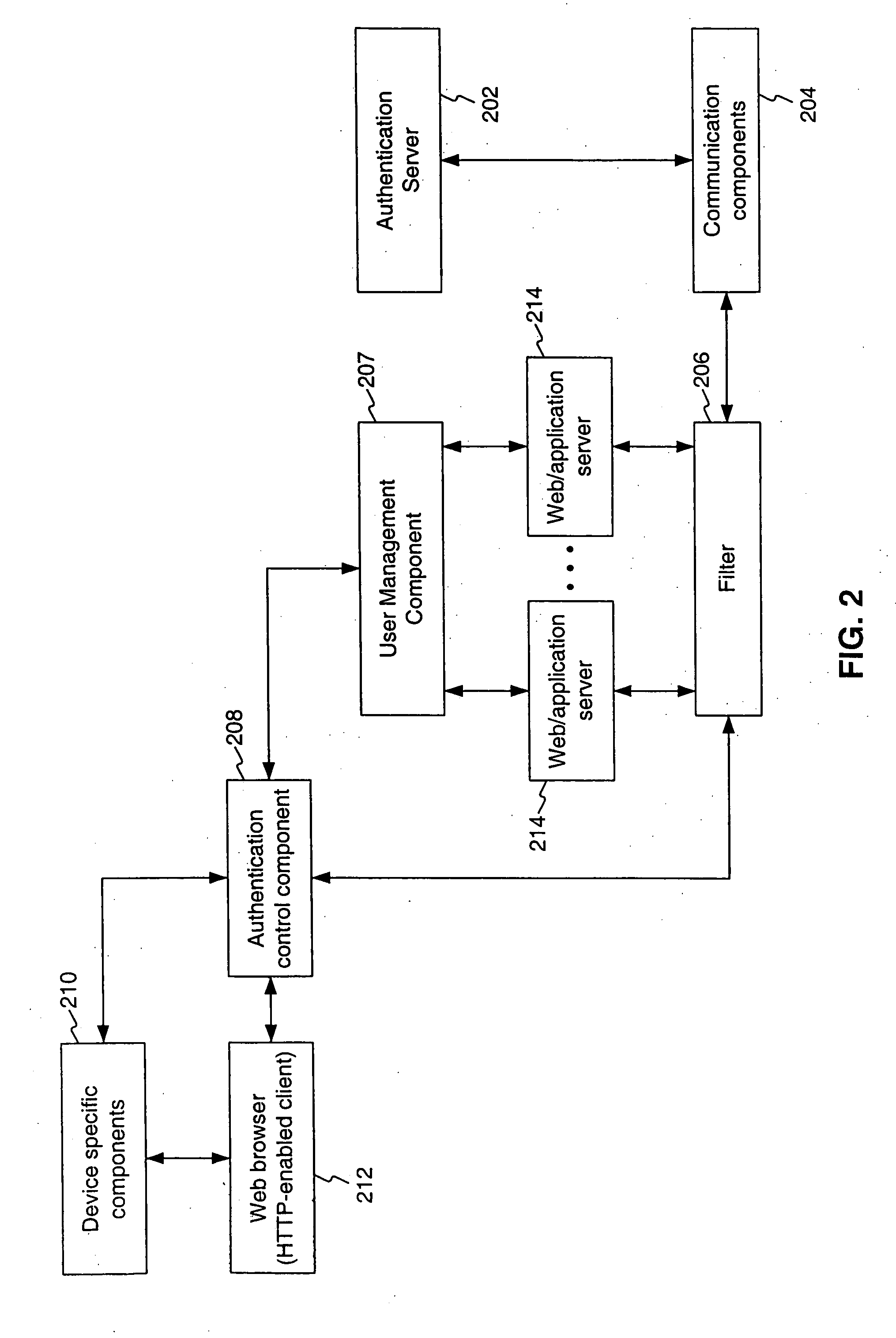
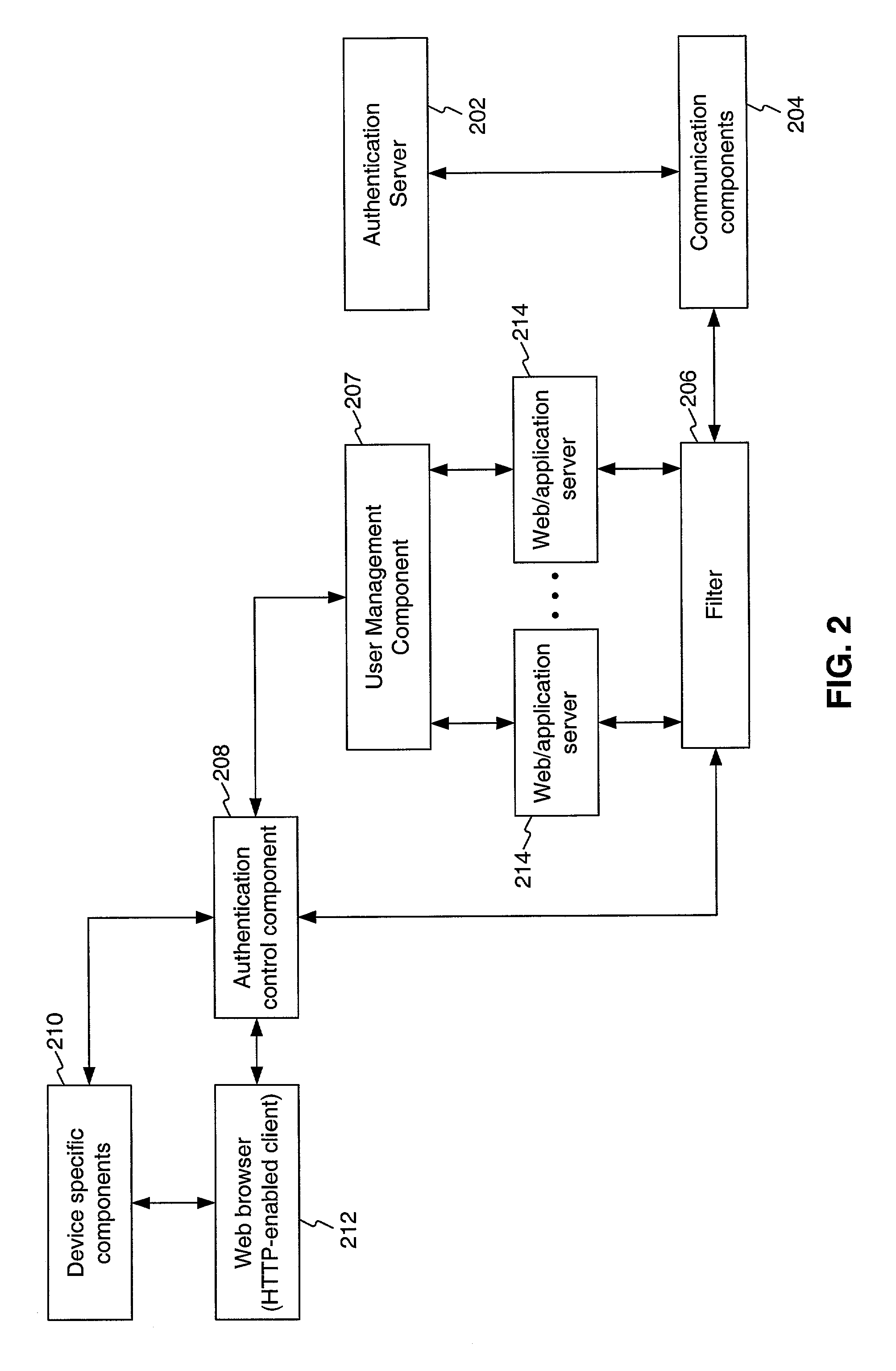
System, method and computer program product for providing unified authentication services for online applications
InactiveUS20090019534A1Digital data processing detailsUser identity/authority verificationInternet Authentication ServiceWeb application
A system and method remotely enrolls, authenticates and provides unified authentication services in an ASP setting to a user to access requested information via a communication medium. A filter is coupled to client side components via the communication medium and a user management component coupled to the client side components via the communication medium. The user management component allows end-users to register their credentials only once. In addition, the user management component allows end-users to define the level of protection of access to their web application accounts. This includes accounts that have been configured specifically for use with the present invention and particular user credentials and accounts that have been subsequently set up but configured to use the same user credentials. The present invention can then reuse those credentials to authenticate the user to one or more potentially unrelated web applications.
Owner:BIONETRIX SYST CORP
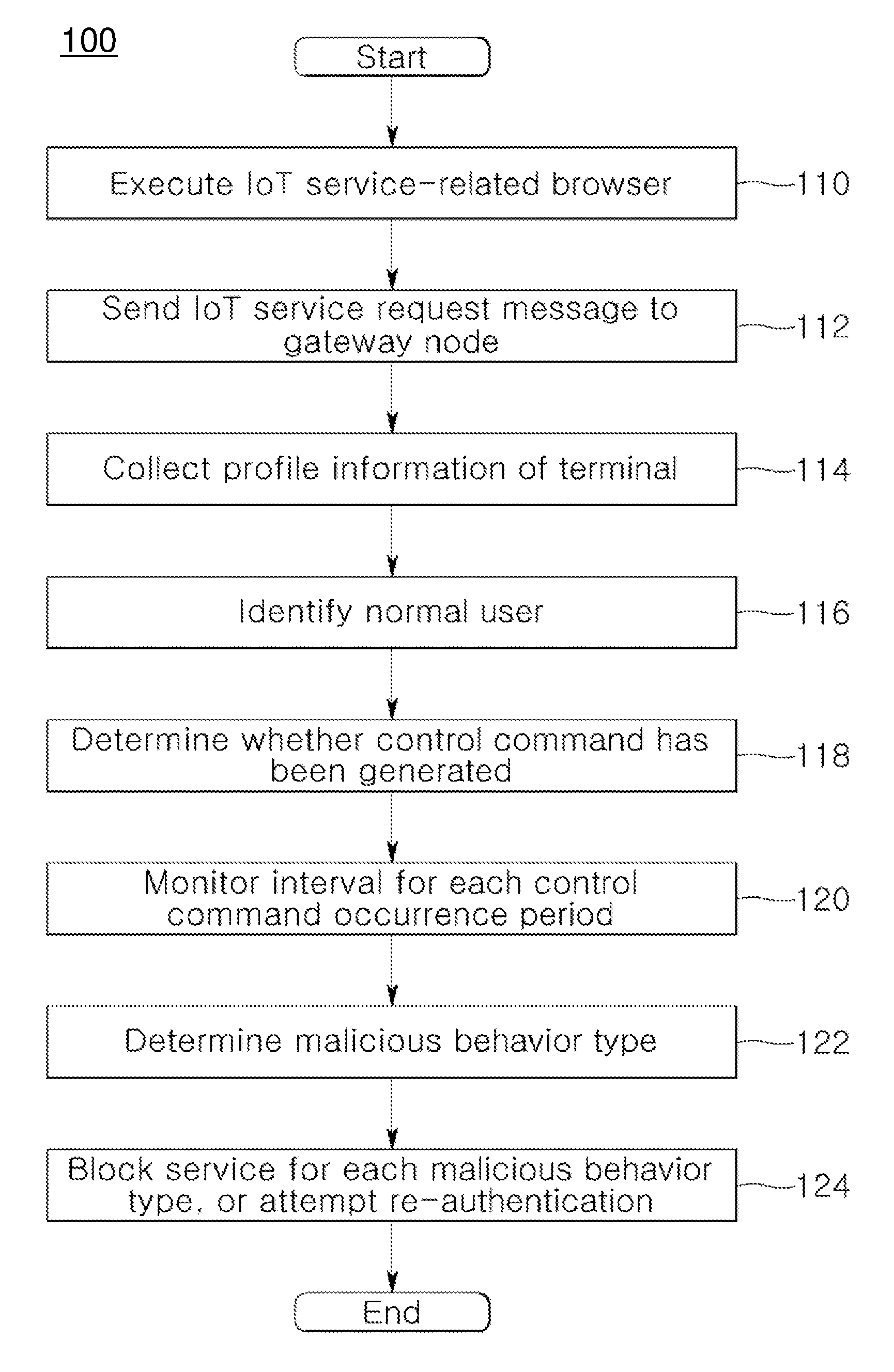
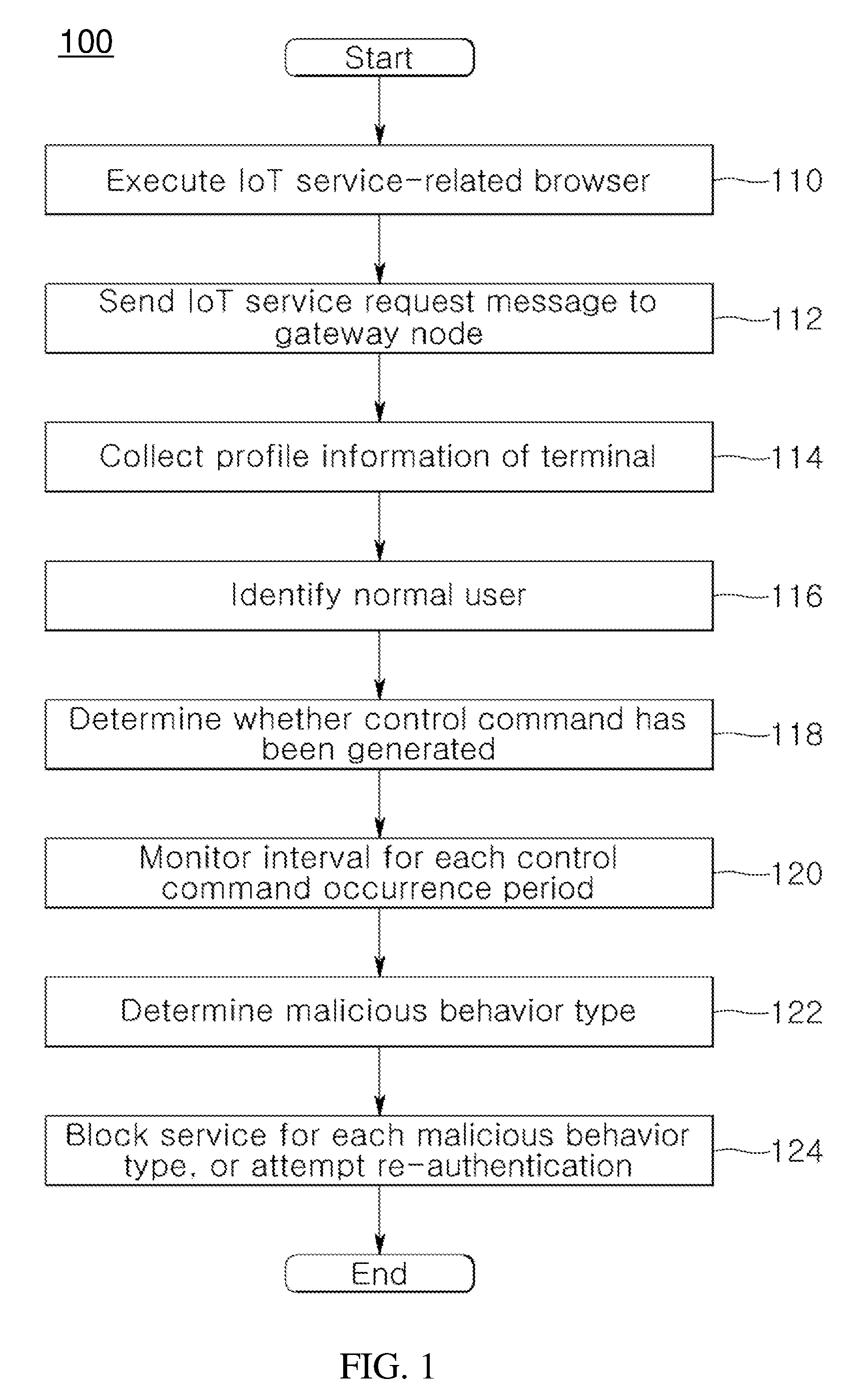
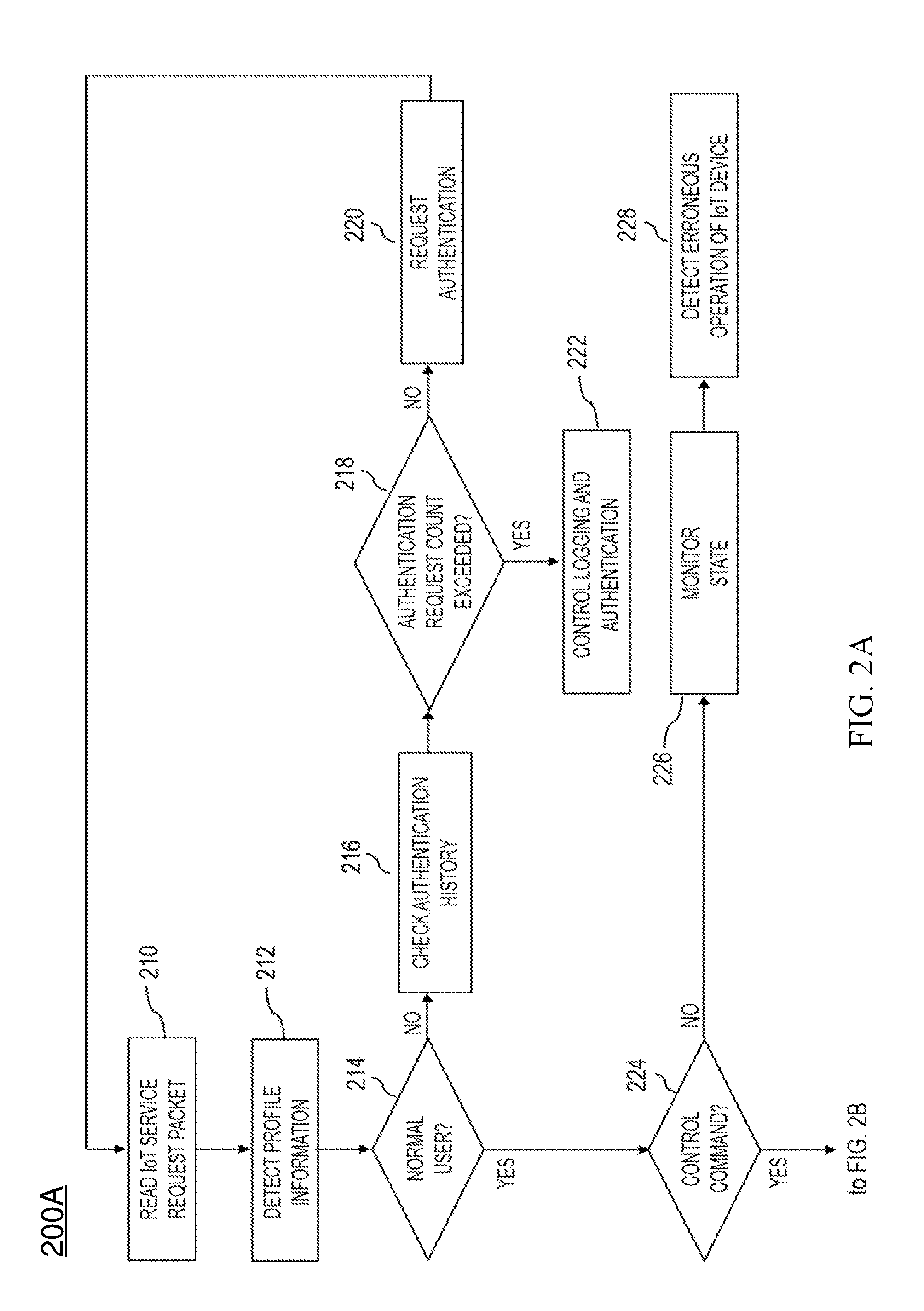
System and method for providing authentication service for internet of things security
ActiveUS20160173495A1Providing serviceUser identity/authority verificationMultiple digital computer combinationsInternet Authentication ServiceIot gateway
A system and method for providing authentication service for IoT security are disclosed herein. The system for providing authentication service for IoT security includes an Internet of Things (IoT) service server, and an IoT gateway node. The IoT service server supports an IoT communication service in accordance with an IoT communication service policy. The IoT gateway node receives an IoT service request from a terminal attempting to control an IoT device that supports the IoT communication service while operating in conjunction with the IoT service server, identifies whether the terminal attempting to control the IoT device is a normal user based on profile information, collected from the terminal via the IoT service request, via the IoT service server, and performs the security authentication of the IoT device.
Owner:WINS CO LTD
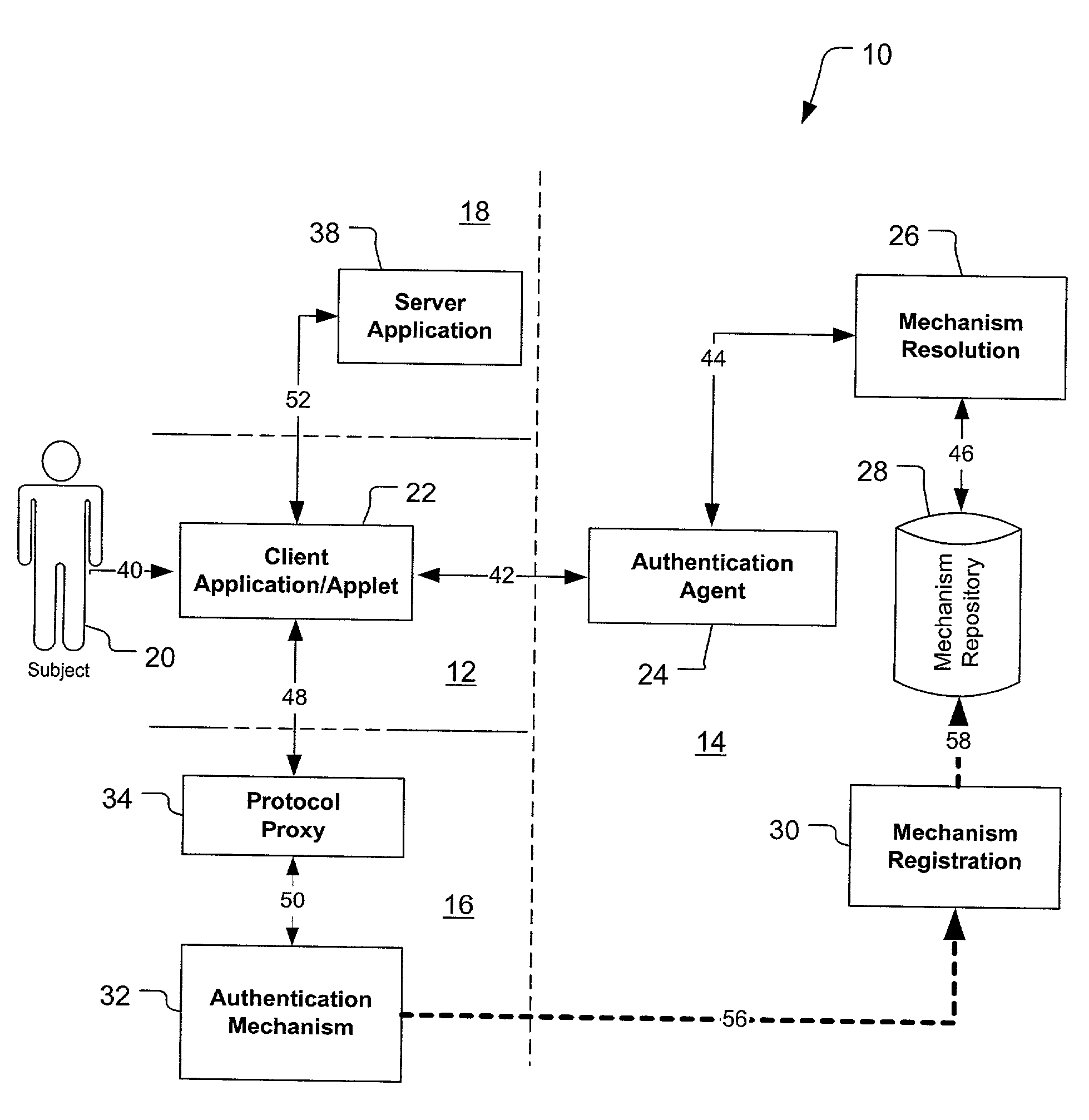
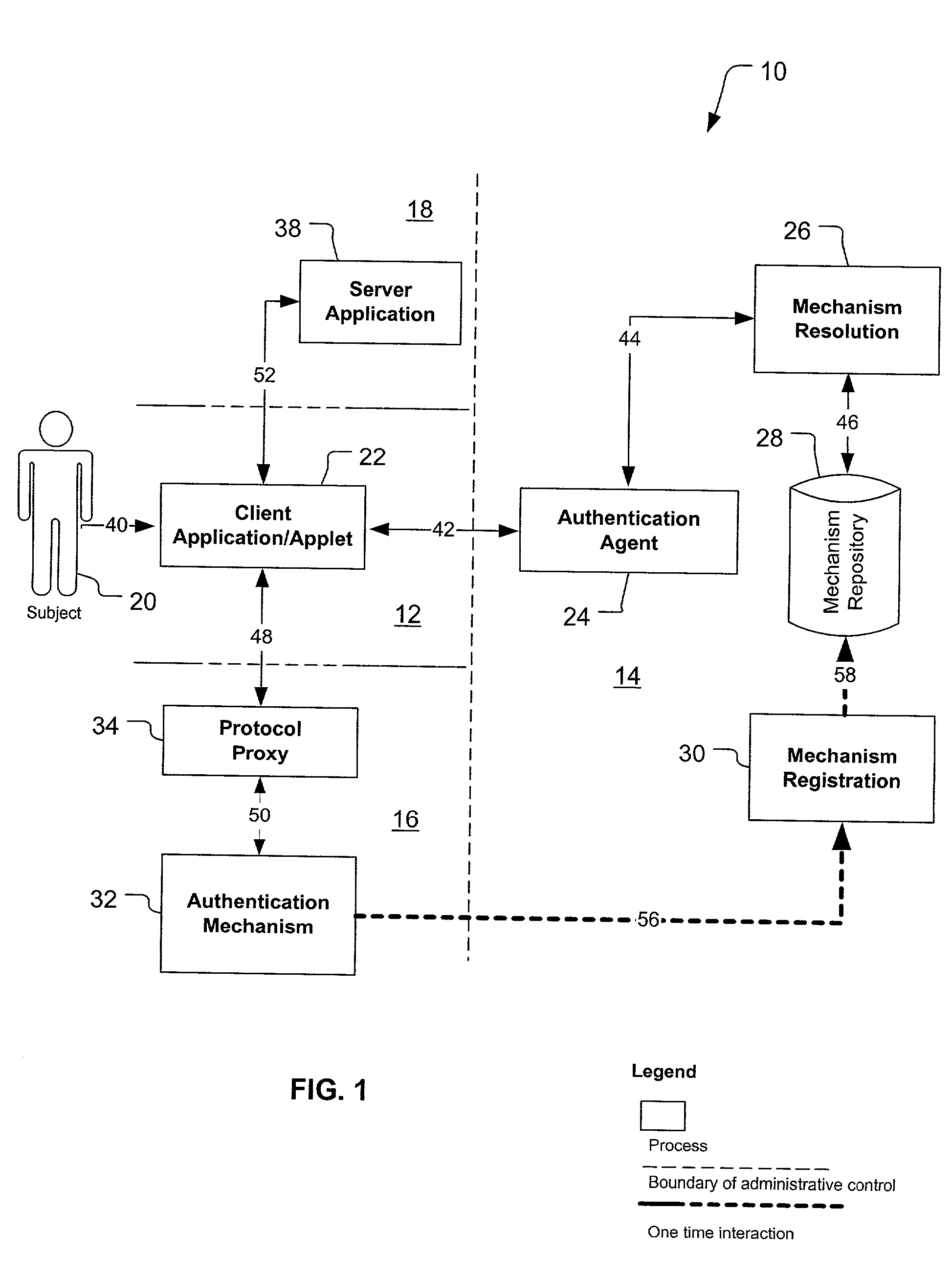
Federated authentication service
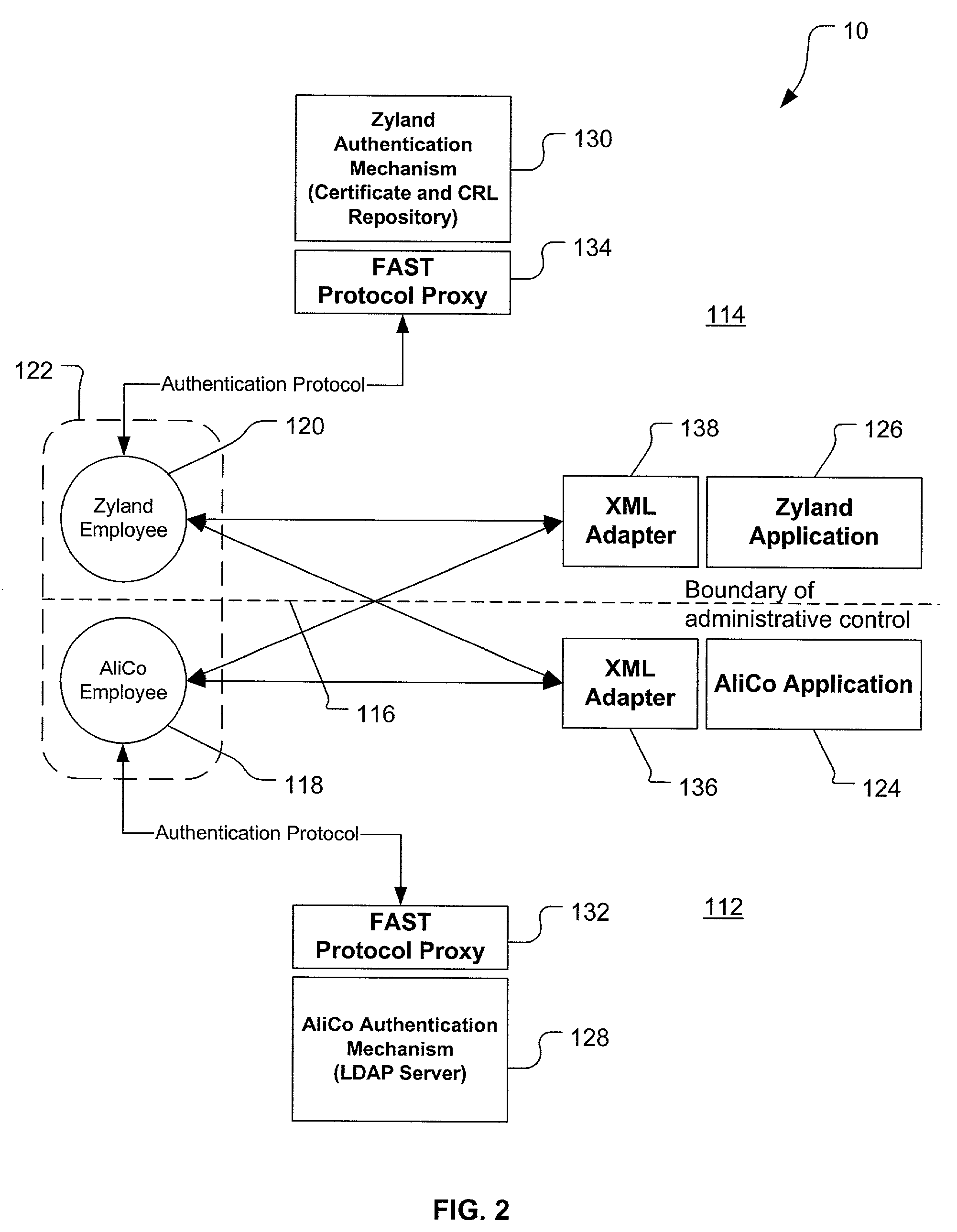
InactiveUS20030046391A1Effectively abstractingEasy to manageUser identity/authority verificationMultiple digital computer combinationsInternet Authentication ServiceFederated identity
A federated authentication service technology (10) for authenticating a subject (20) residing in a subject domain (12) on a network to a server application (38) residing in a server domain (18), wherein an authentication mechanism (32) residing in an authentication domain (16) affects the service provided by the server application (38). A client (22), which may be integrated non-human instances of the subject (20), authenticates the subject (20) and a protocol proxy (34) mediates with the authentication mechanism (32) to obtain a name assertion which the client can use to access the server application (38). When multiple authentication mechanisms (32) are available, an optional agent (24), mechanism resolution process (26) and mechanism repository (28), all residing in an agent domain (14), may be used to resolve to one suitable authentication mechanism (32).
Owner:PROOFPOINT INC
Deterministic user authentication service for communication network
InactiveUS6874090B2Digital data processing detailsUser identity/authority verificationPersonalizationInternet Authentication Service
A user authentication service for a communication network authenticates local users before granting them access to personalized sets of network resources. Authentication agents on intelligent edge devices present users of associated end systems with log-in challenges. Information supplied by the users is forwarded to an authentication server for verification. If successfully verified, the authentication server returns to the agents authorized connectivity information and time restrictions for the particular authenticated users. The agents use the information to establish rules for filtering and forwarding network traffic originating from or destined for particular authenticated users during authorized time periods. An enhanced authentication server may be engaged if additional security is desired. The authorized connectivity information preferably includes identifiers of one or more virtual local area networks active in the network. Log-in attempts are recorded so that the identity and whereabouts of network users may be monitored from a network management station.
Owner:ALCATEL LUCENT SAS
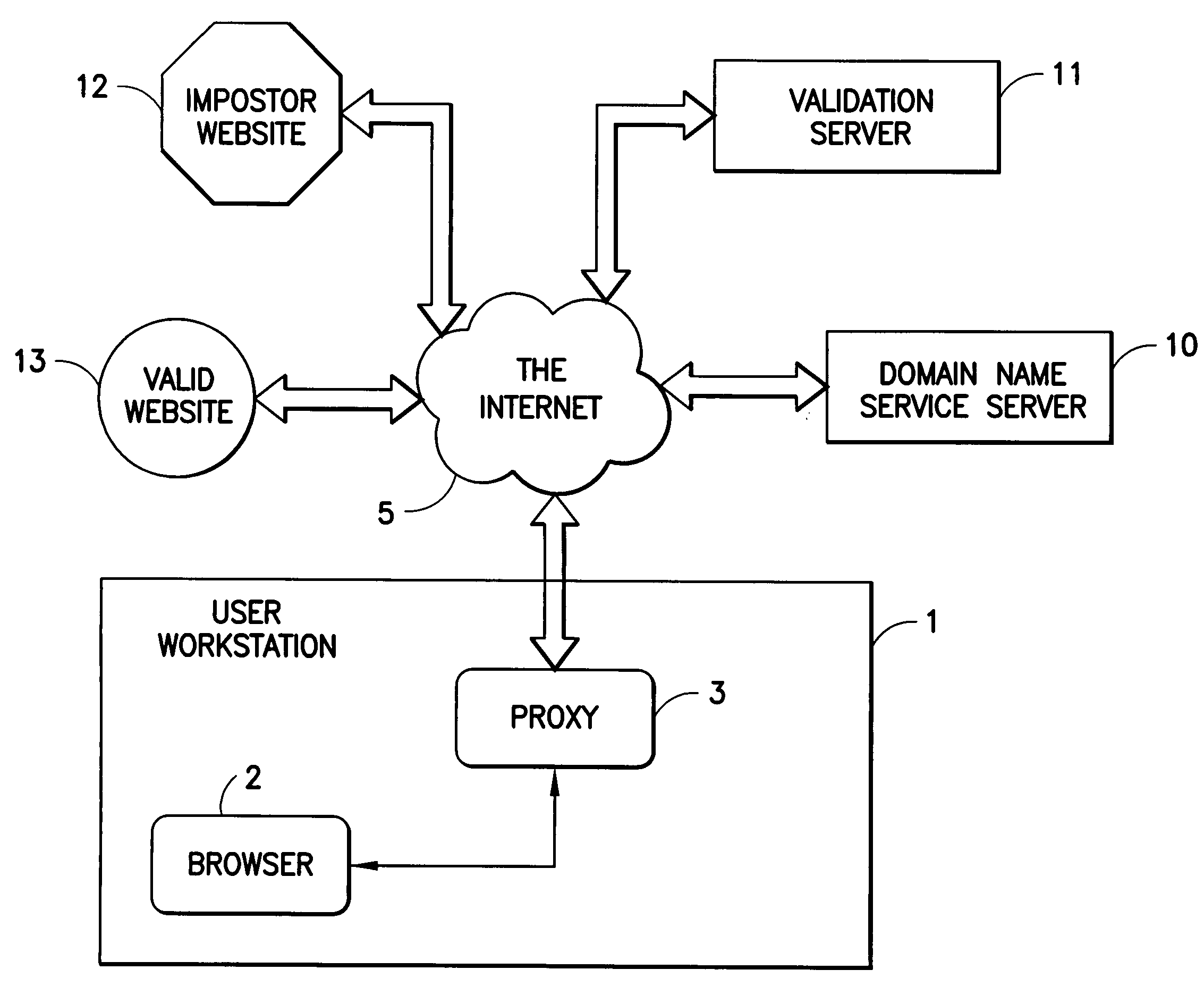
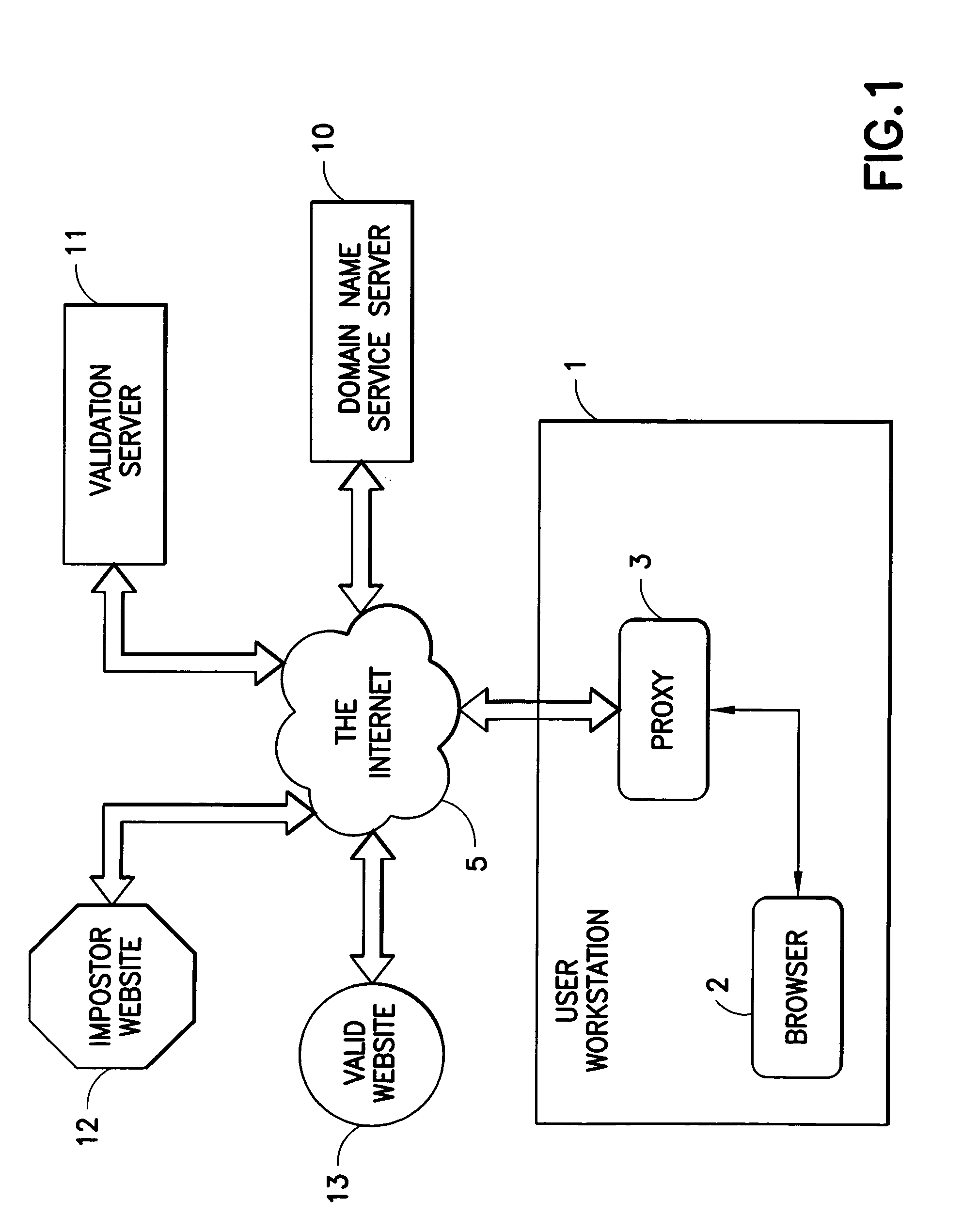
Internet site authentication service
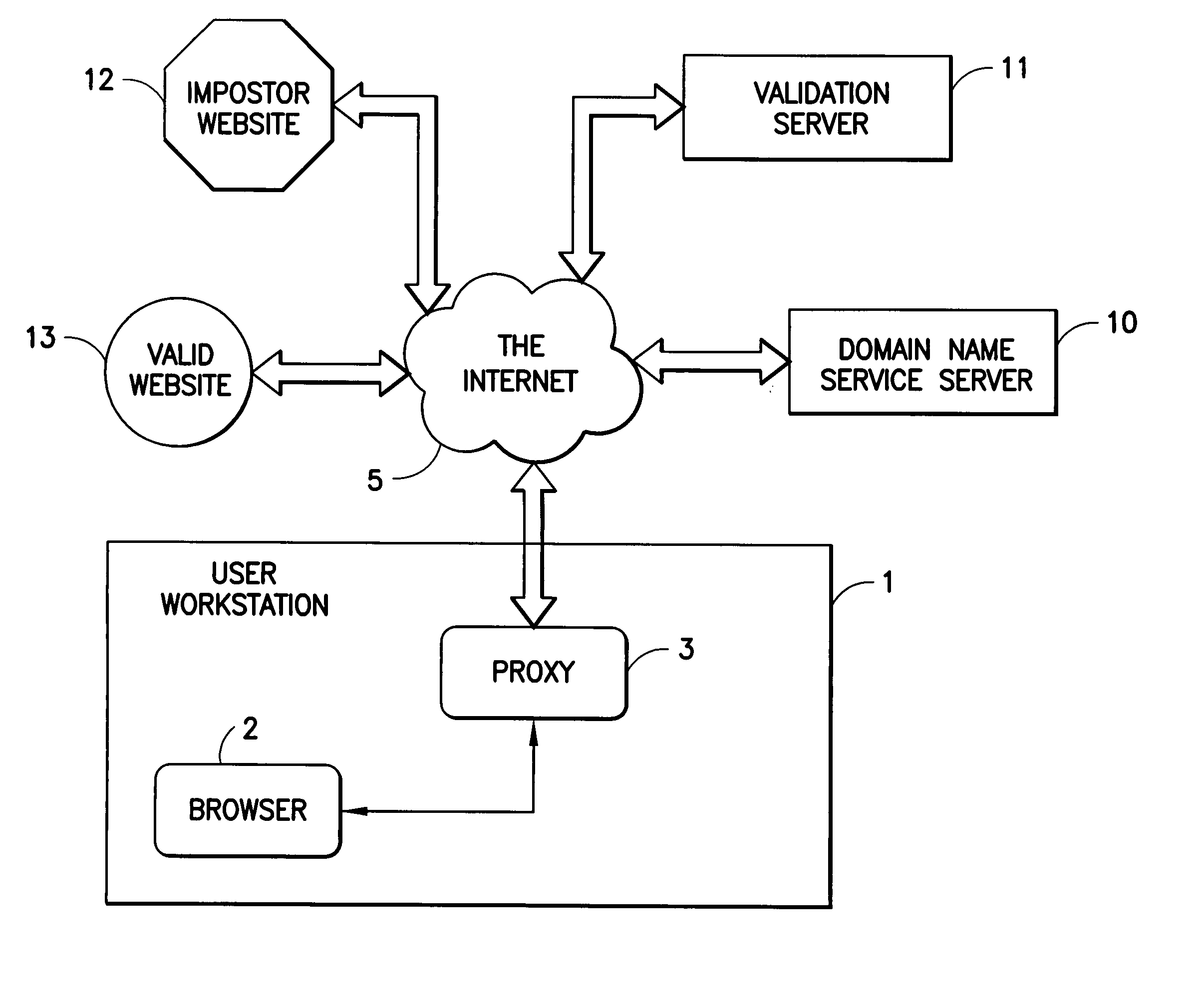
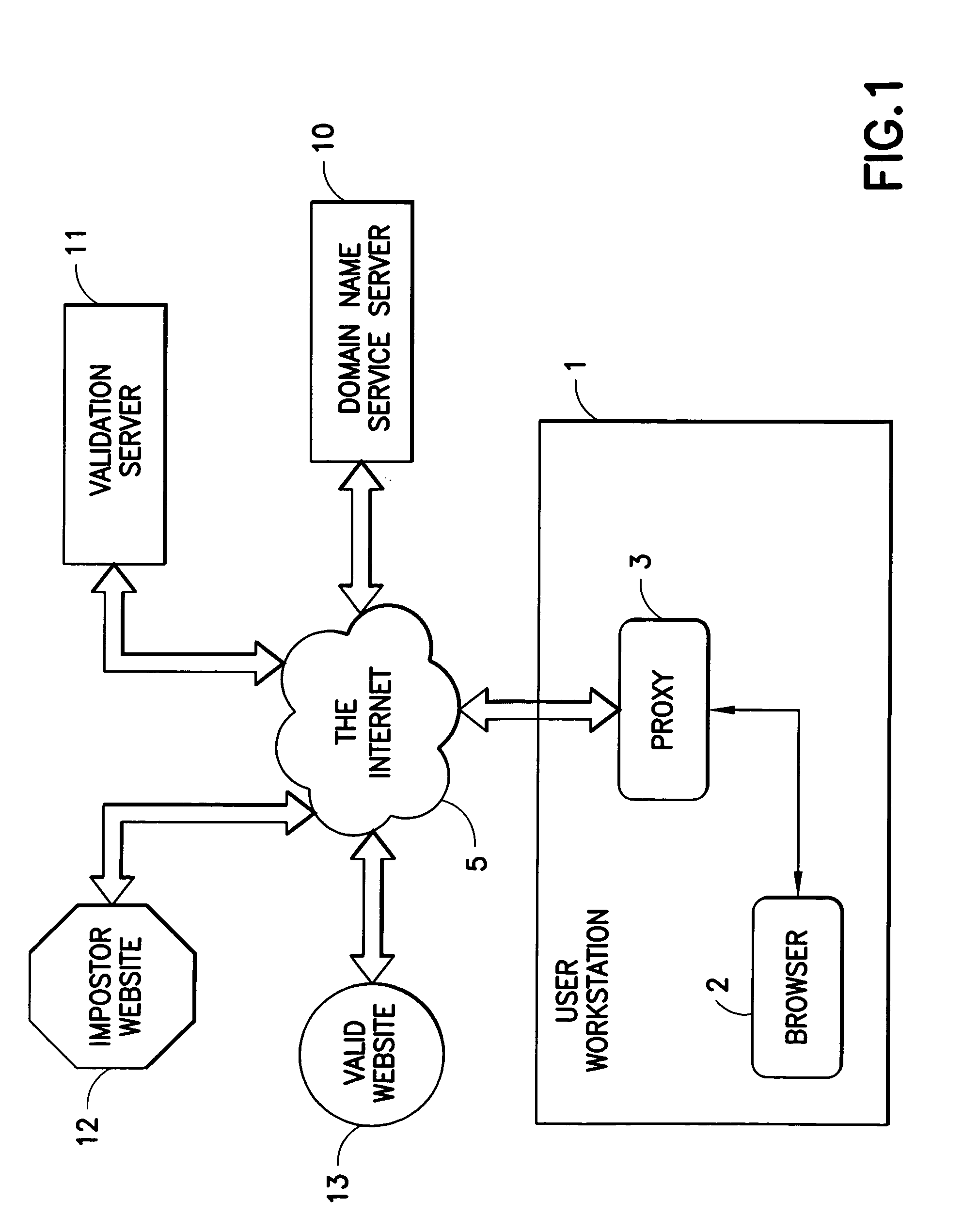
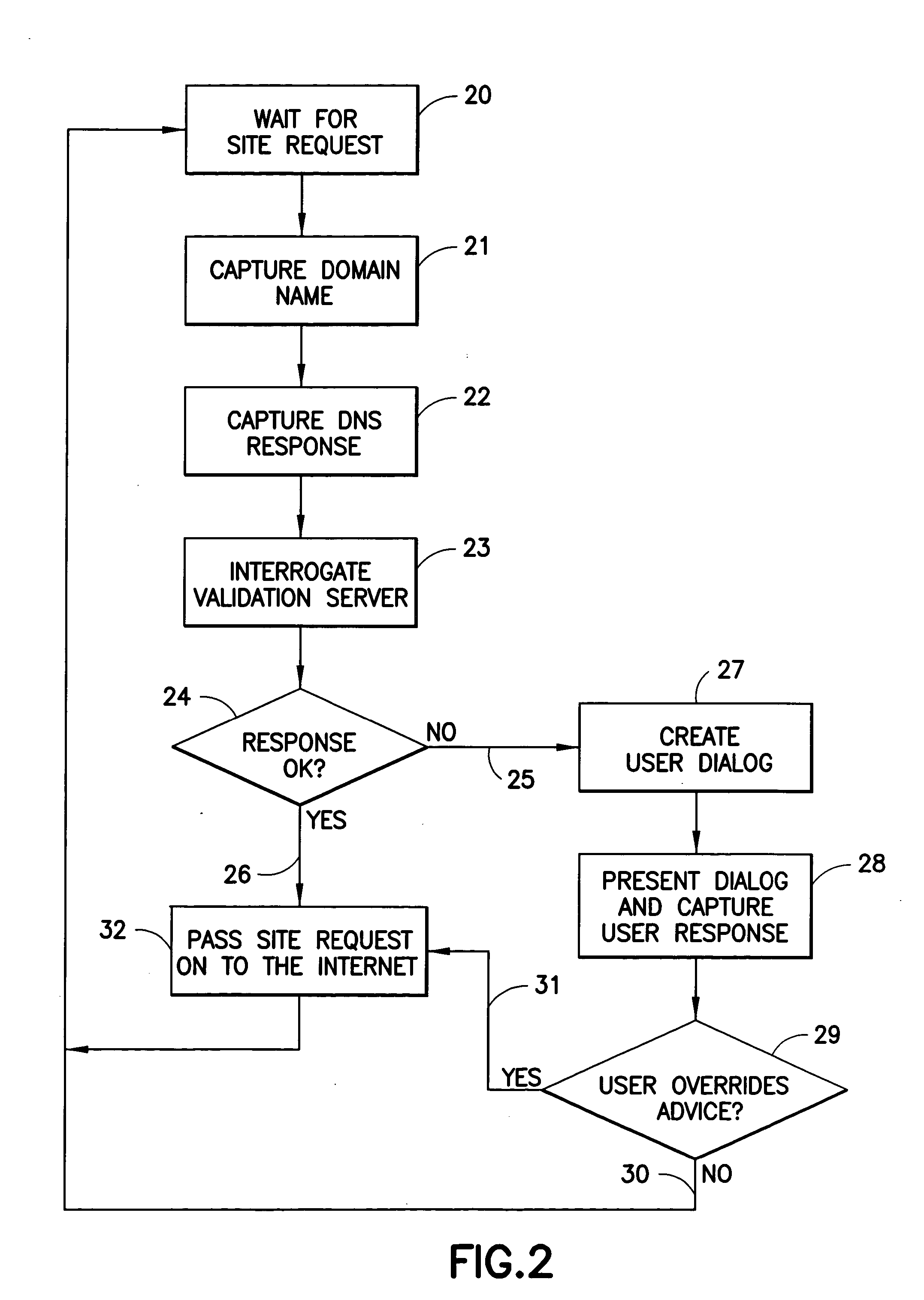
ActiveUS20050108569A1Memory loss protectionDigital data processing detailsInternet Authentication ServiceIp address
The authenticity of a website is tested with software that runs on a personal computing device and a service that is provided via the Internet. The software on the personal computing device is in the form of a proxy, or transparent component in the Internet Protocol implementation. The proxy receives all outbound messages, analyzes them and forwards or modifies them without the user's intervention. The service tests the IP address and / or the behavior of the target website.
Owner:IBM CORP
System, method and computer program product for providing unified authentication services for online applications
InactiveUS7441263B1Digital data processing detailsComputer security arrangementsInternet Authentication ServiceInternet privacy
A system, method and computer program product for providing unified authentication services in an Application Service Provider (ASP) setting to a registered end-user of one or more online (or web) applications. The system includes client side components, a user management component coupled to the client side components and server side components coupled to the user management component. The client side components include an authentication control component that manages the process of capturing a user-determined policy for a first account and user credentials. This allows the user to define the level of protection to access the first account. This includes, but is not limited to, accounts / applications that have been configured specifically for used with the system and particular user credentials and accounts that have been subsequently set up but configured to use the same user credentials. The client side components then communicate the result of capturing the user-determined policy and user credentials to the user management component. The user management component stores the user-determined policy and user credentials in a centralized location. In addition, the user management component organizes the user-determined policy and user credentials such that the user credentials can be reused for user authentication to a second account. Finally, the server side components include an authentication server. The user management component indicates to the authentication server to use the user-determined policy for user authentication to the first account.
Owner:CITIBANK +1
Online payer authentication service
InactiveUS20080301056A1Reduce chargebacksReduce fraudUser identity/authority verificationCo-operative working arrangementsPaymentInternet Authentication Service
A payment authentication service authenticates the identity of a payer during online transactions. The authentication service of the present invention allows a card issuer to verify a cardholder's identity using a variety of authentication methods, such as the use of passwords. Also, the only system participant requiring a certificate is the issuing financial institution. One embodiment of the invention for authenticating the identity of a cardholder during an online transaction involves querying an access control server to determine if a cardholder is enrolled in the payment authentication service, requests a password from the cardholder, verifies the password, and notifies a merchant whether the cardholder's authenticity has been verified. In another aspect of the invention, a chip card and the authentication service independently generate cryptograms that must match in order for the service to verify that the correct chip card is being used by the cardholder.
Owner:WELLER KEVIN D +6
System and method for distributed authentication service
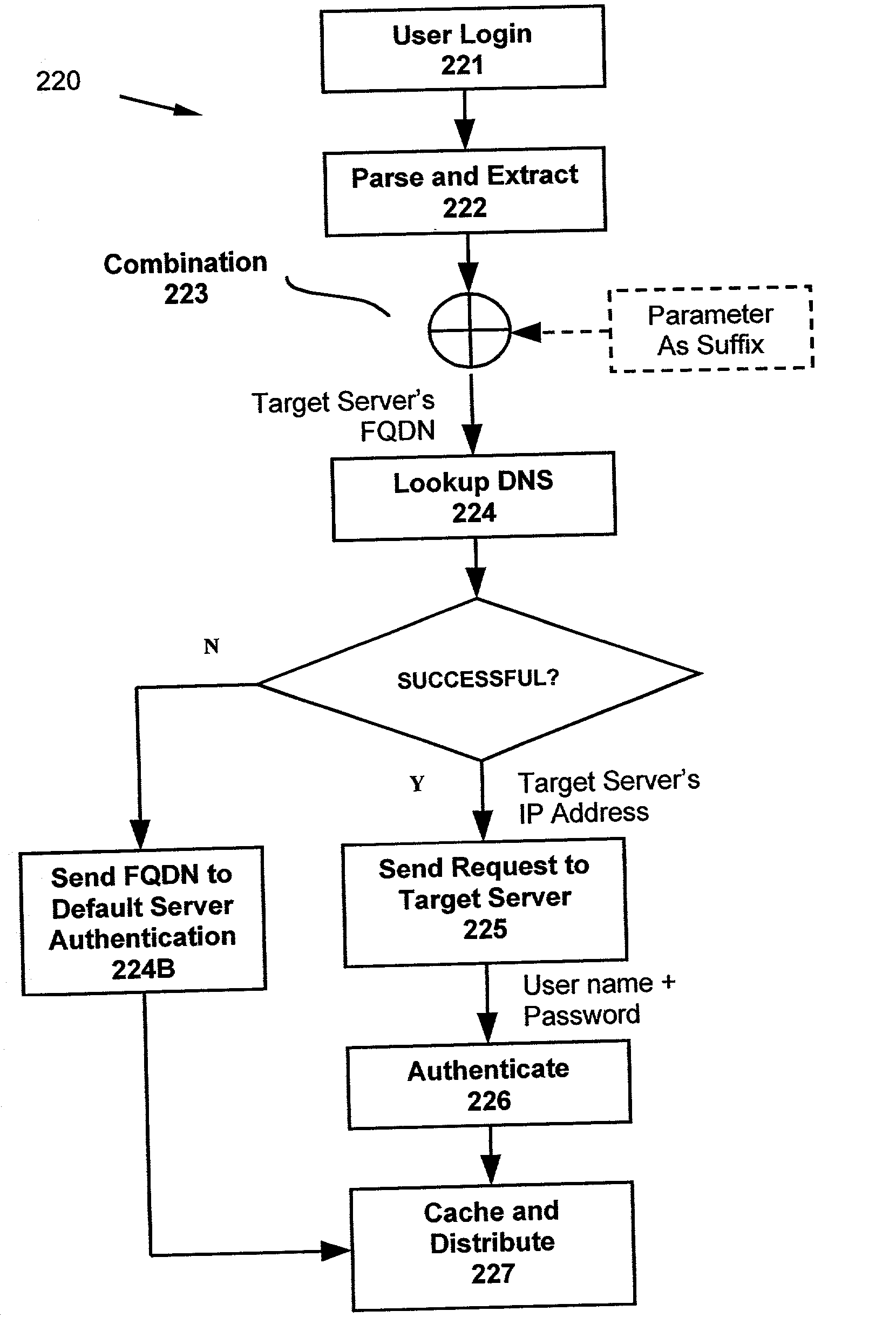
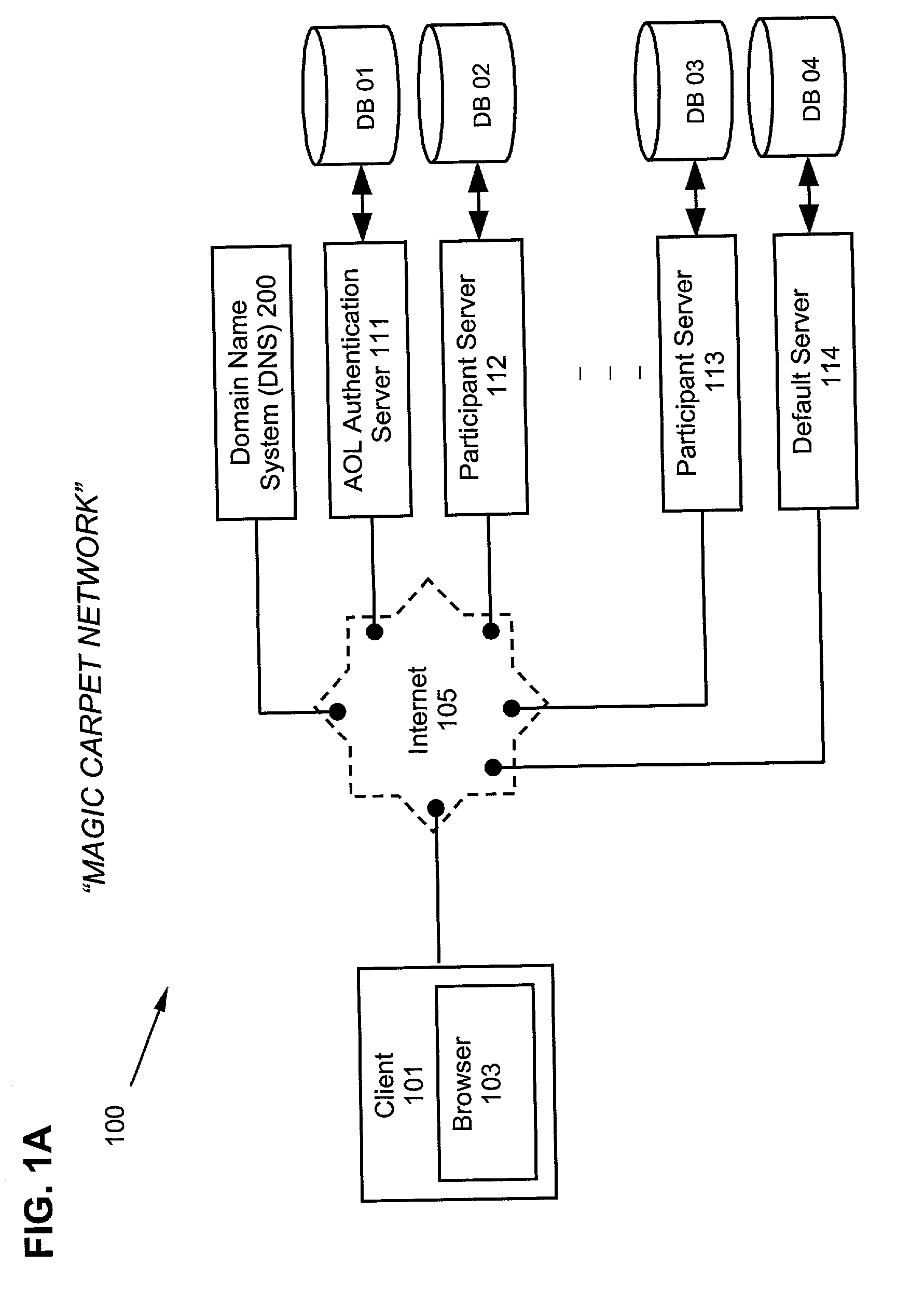
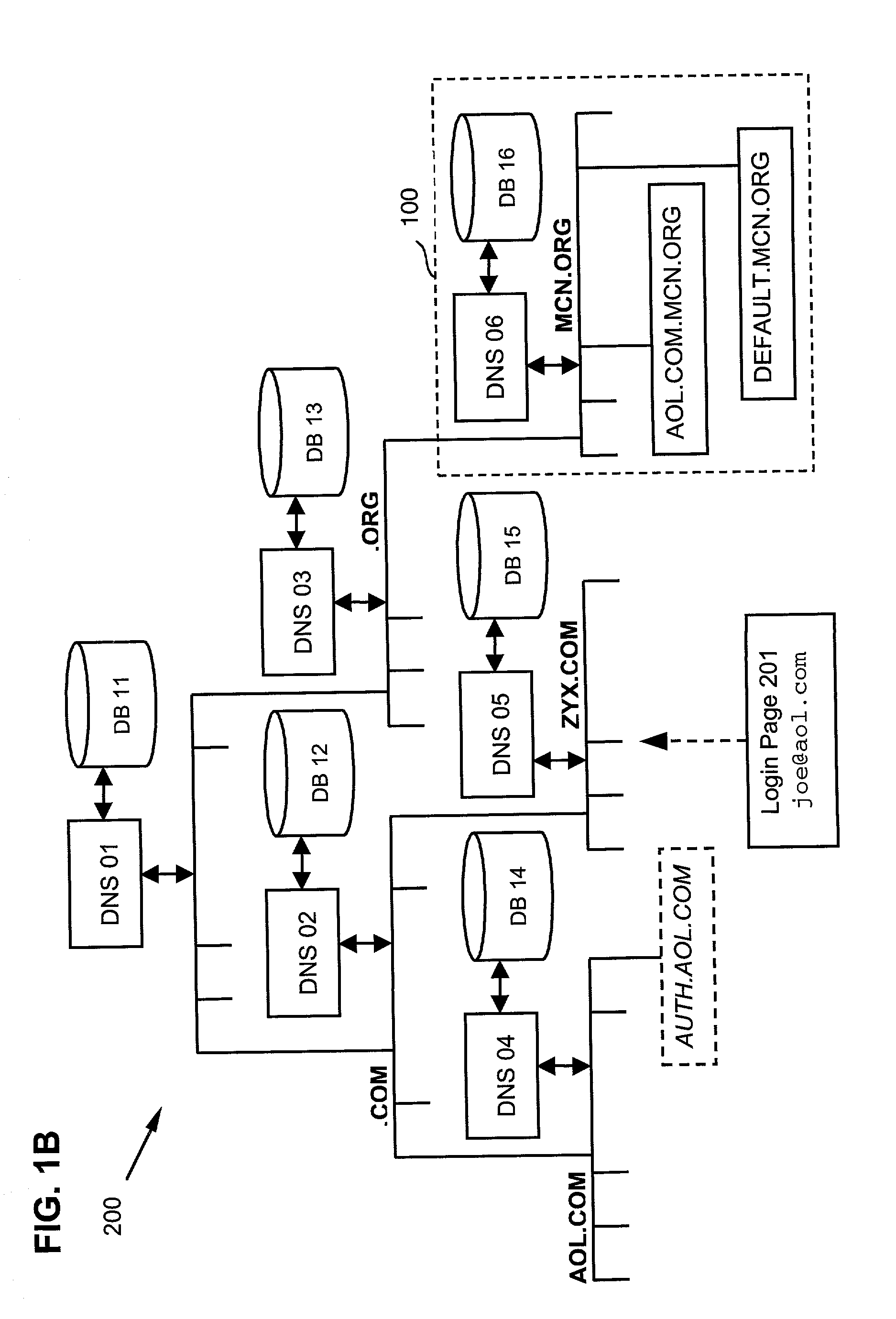
ActiveUS20030163730A1Digital data processing detailsUser identity/authority verificationInternet Authentication ServiceDomain name
A system and method for distributed authentication service is disclosed, which prevents any single participant from monitoring the logon rates of other participants is disclosed. In particular, there is no single central list that is consulted to identify where the authentication should be performed. Rather, the systems keys on the domain portion of the global user ID. The client portion parses the entered ID and re-directs the submission to the appropriate authentication service. Rather than consulting a global look-up table, the domain name is pre-pended to a central host domain and DNS is consulted to find the location of the underlying authentication servers. The DNS look-up is distributed and cached and, as a result, the look-up cannot be centrally monitored.
Owner:META PLATFORMS INC
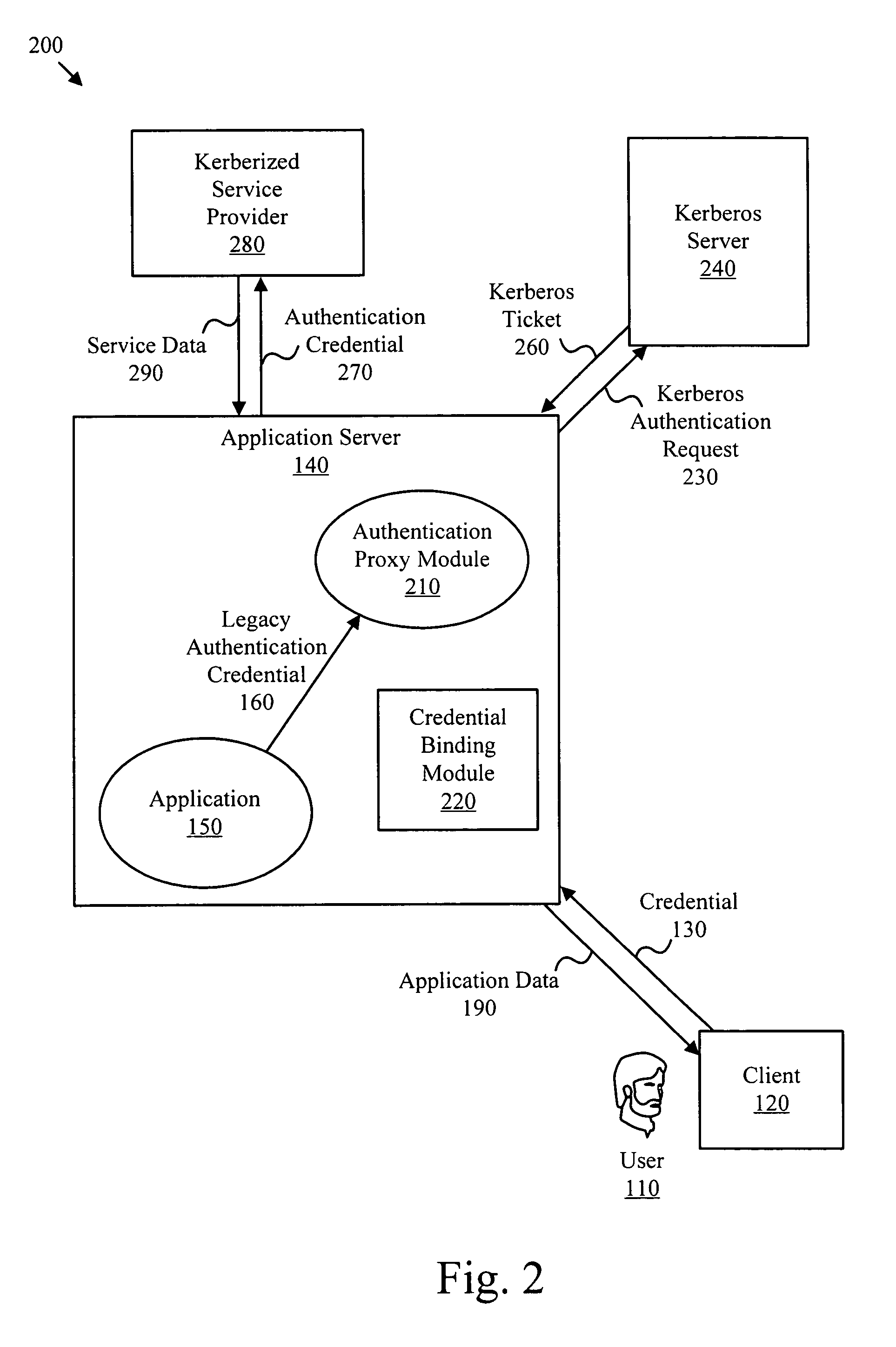
Apparatus, systems and methods to provide authentication services to a legacy application
ActiveUS7904949B2Digital data processing detailsUser identity/authority verificationInternet Authentication ServicePassword
Owner:QUEST SOFTWARE INC
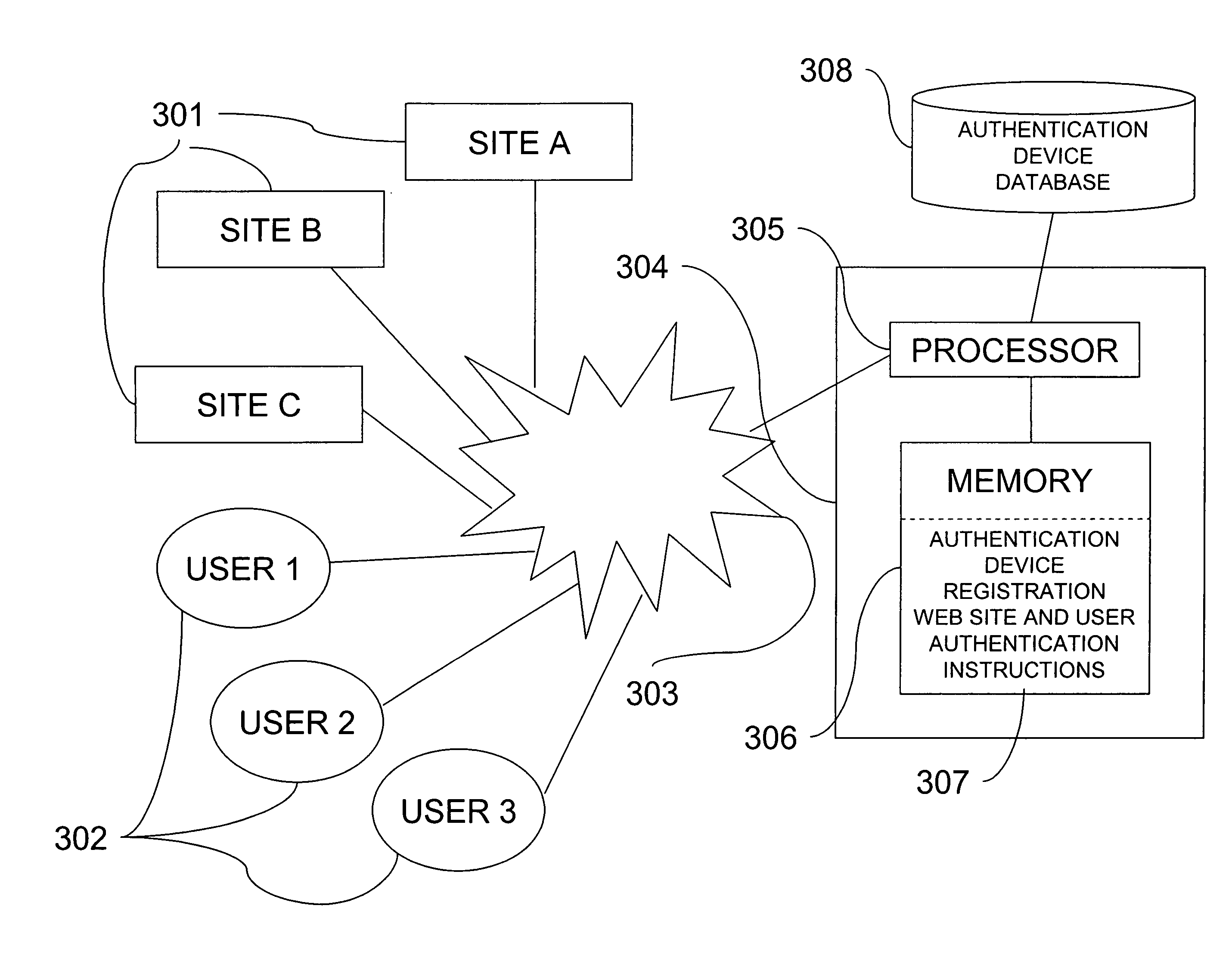
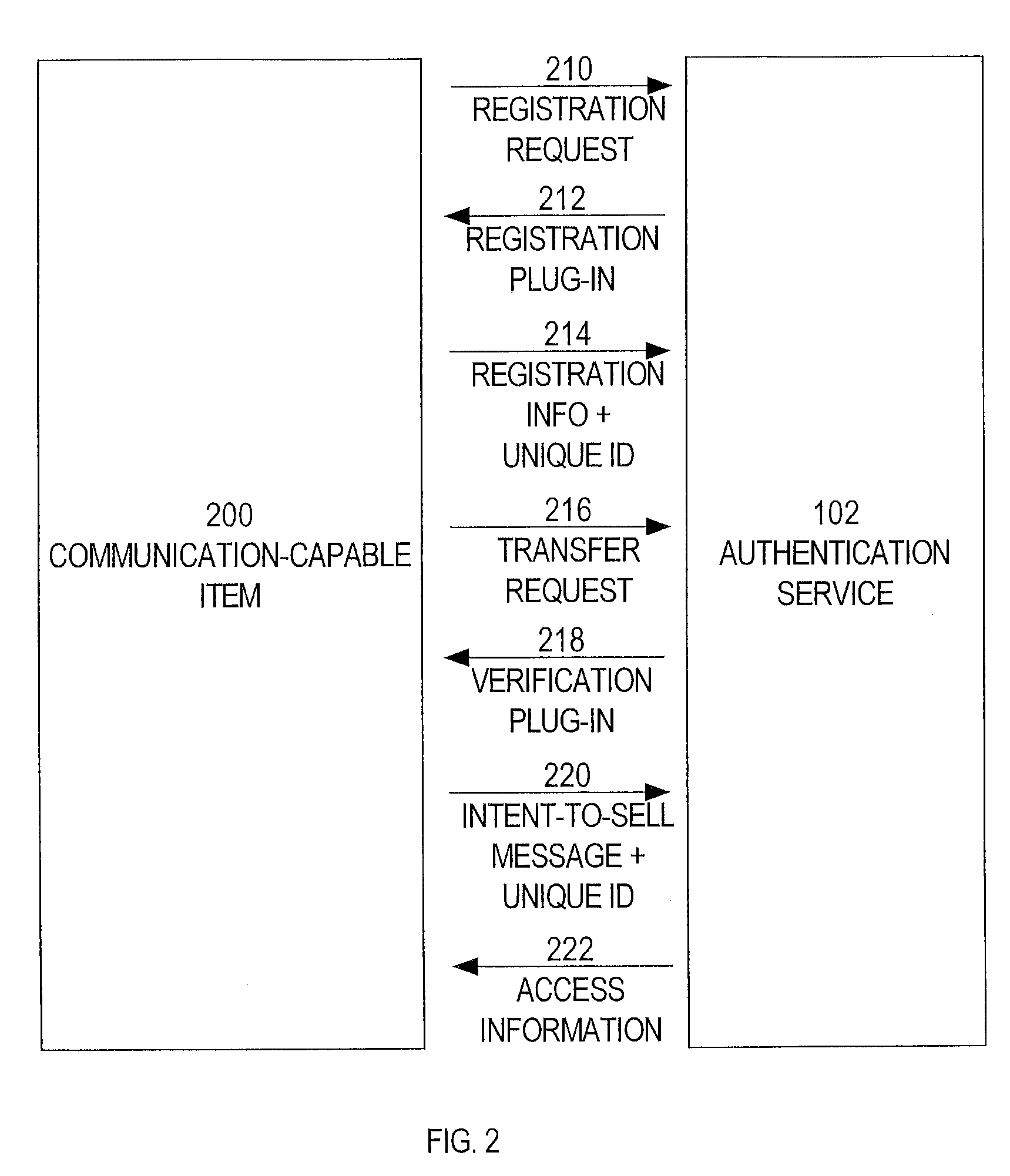
Authentication service for sales of goods and services
InactiveUS20110302096A1Buying/selling/leasing transactionsInternet Authentication ServiceAuthentication information
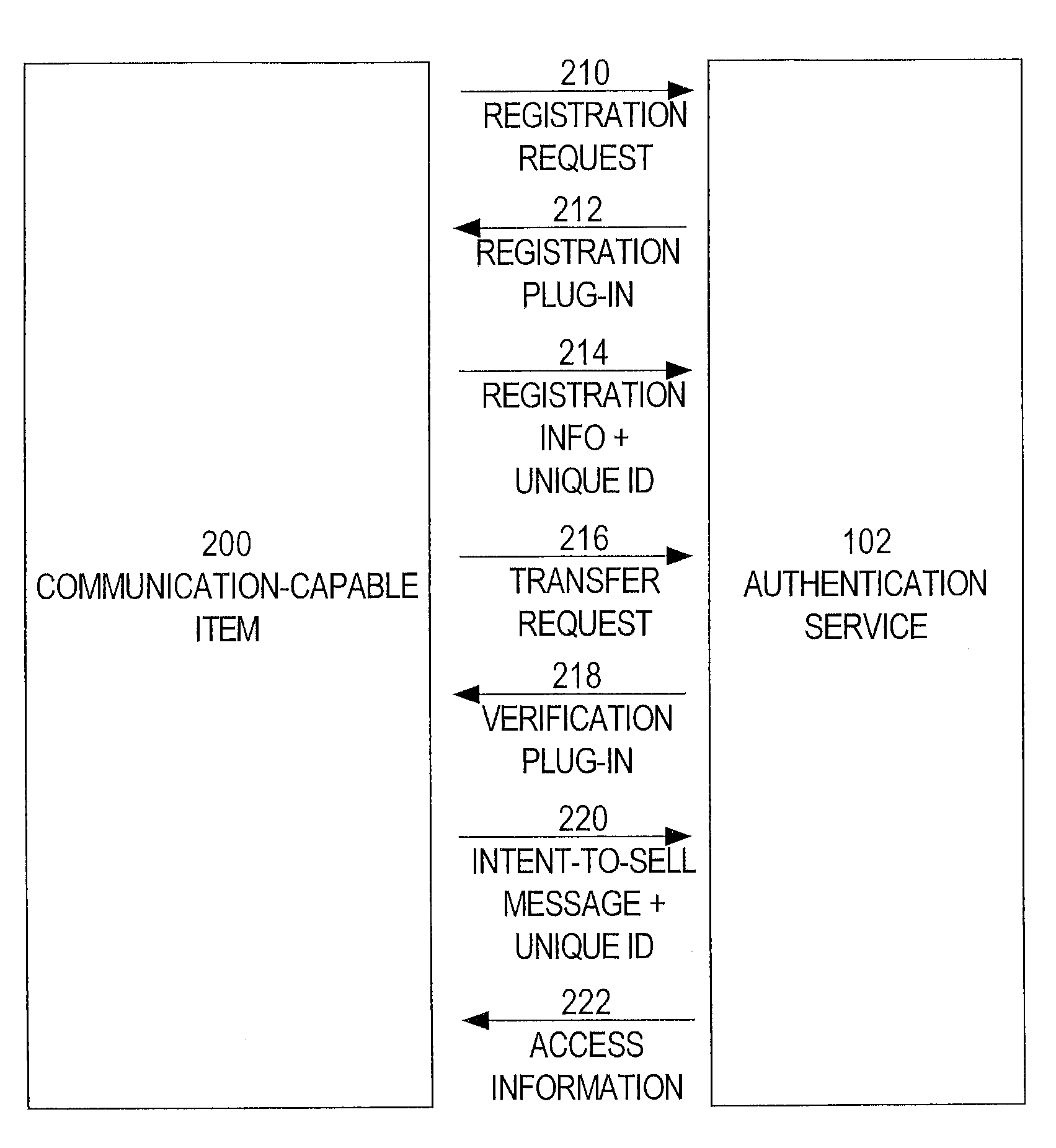
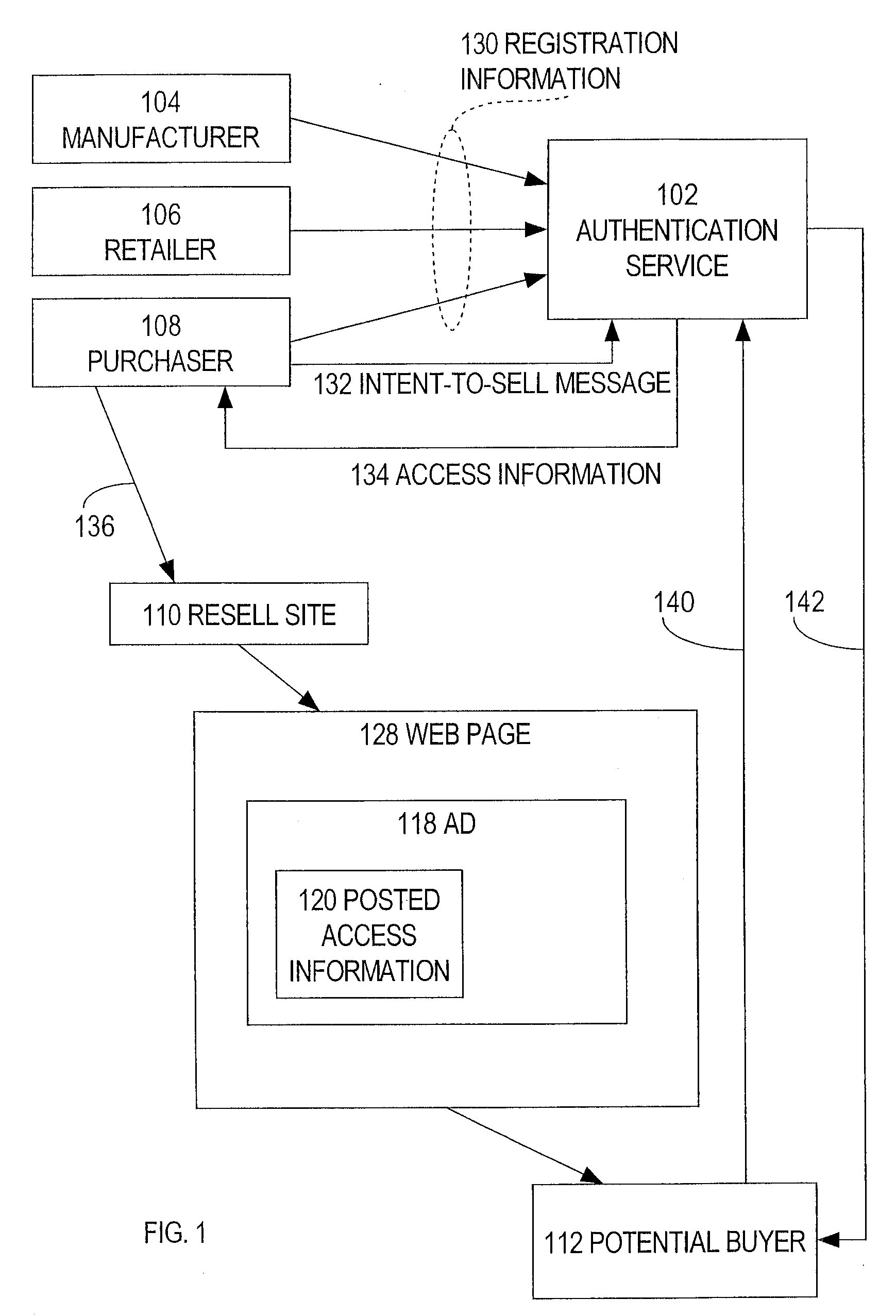
An authentication service provides authentication information to help potential buyers determine the legitimacy of an offer to sell a good or service. For example, an authentication service stores registration information that indicates (a) that a particular item was purchased by a particular party, and (b) contact information that indicates a particular address for communicating with the party. When the registered owner of an item wants to sell the item, the owner sends an intent-to-sell message to the authentication service. In response to receiving the intent-to-sell message, the authentication service sends access information to the particular address. The access information specifies a manner of receiving authentication information about the item from the authentication service. The registered owner includes the access information in his or her advertisements for the item. When a potential buyer sees the access information in an advertisement, the potential buyer can obtain the authentication information, directly from the authentication service, using the manner specified in the access information.
Owner:APPLE INC
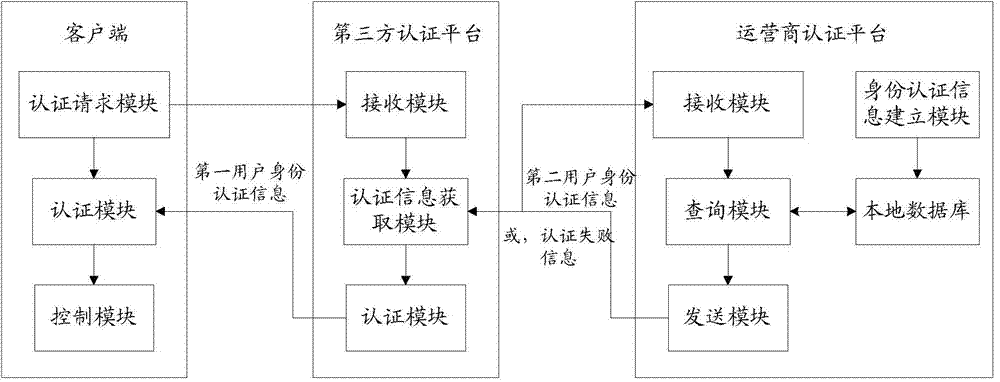
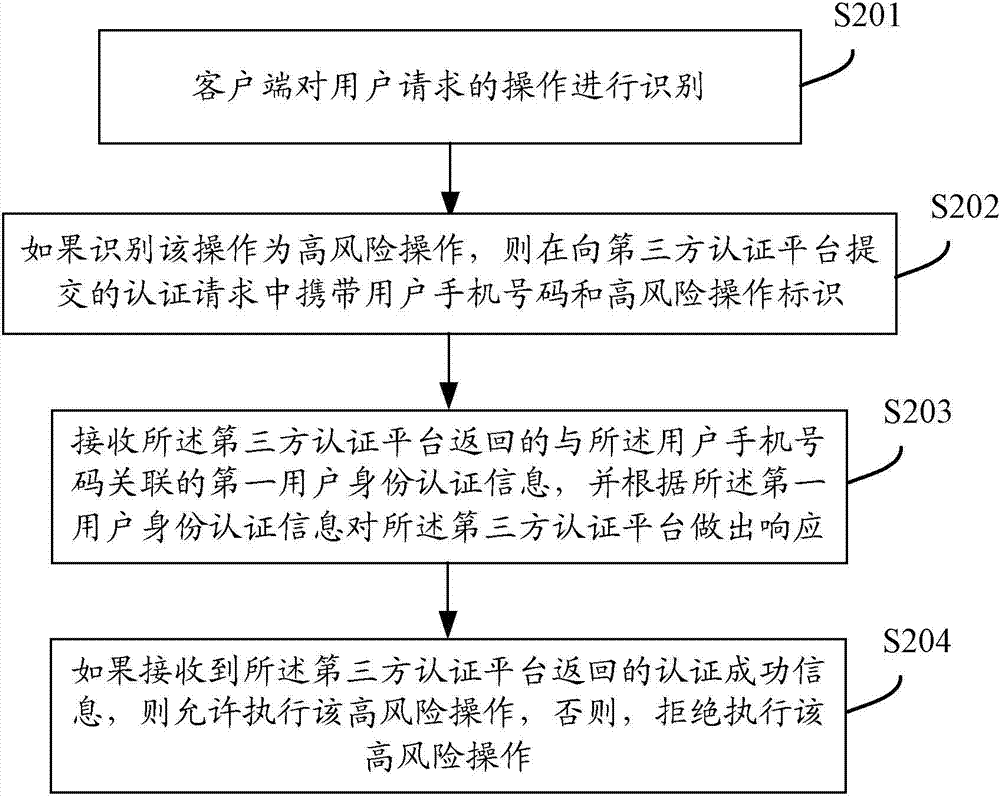
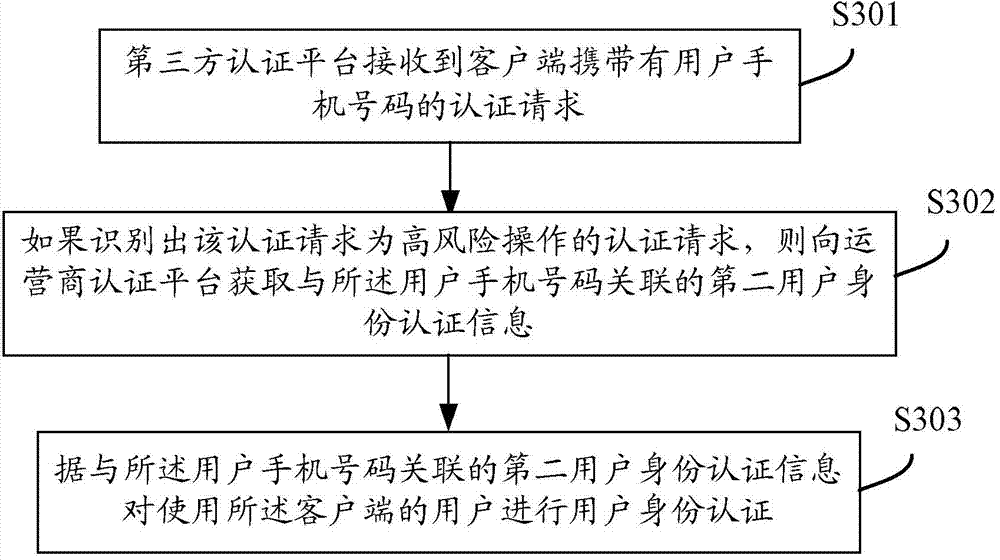
User identity authentication method, third-party authentication platform and operator authentication platform
ActiveCN103944737AEnsure safetyEnhanced Authentication ServicesUser identity/authority verificationInternet Authentication ServiceMobile Telephone Number
The invention discloses a user identity authentication method, a third-party authentication platform and an operator authentication platform all oriented to mobile applications. The system comprises a client, the third-party authentication platform and the operator authentication platform; the third-party authentication platform receives a high-risk operation authentication request carrying a user mobile phone number from the client, and then obtains user identity authentication information associated with the user mobile phone number from the operator authentication platform; the operator authentication platform sends the user identity authentication information which is associated with the user mobile phone number and found in a local database to the third-party authentication platform; the third-party authentication platform authenticates the identity of a user using the client according to the user identity authentication information associated with the user mobile phone number. The user information of the operator is fused with the authentication technology of the third-party applications, so that the authentication services with the mobile user identity as the core can be further enhanced, the authentication level can be increased and the security of the user and the third-party can be guaranteed.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Multiple party benefit from an online authentication service
An account authentication service where a trusted party verifies an account holder's identity for the benefit of a requestor during an online transaction. The account authentication involves requesting a password from the account holder, verifying the password, and notifying the requestor whether the account holder's authenticity has been verified. An alternative embodiment of the account authentication service includes a value-adding component where information about a customer is shared with a value-adding party. The customer information is rich in detail about the customer since it is collected by each of the parties in the account authentication process. The value-adding party can then use this information in various manners. All of the parties involved can benefit from sharing the customer information. The value-adding party can be, for example, a merchant, a shipper, a security organization, or a governmental organization. A transaction identifier identifies a specific transaction between a customer, a merchant, and the customer information.
Owner:VISA INT SERVICE ASSOC
One-point entry and access system based on authentication service acting information facing to service architecture
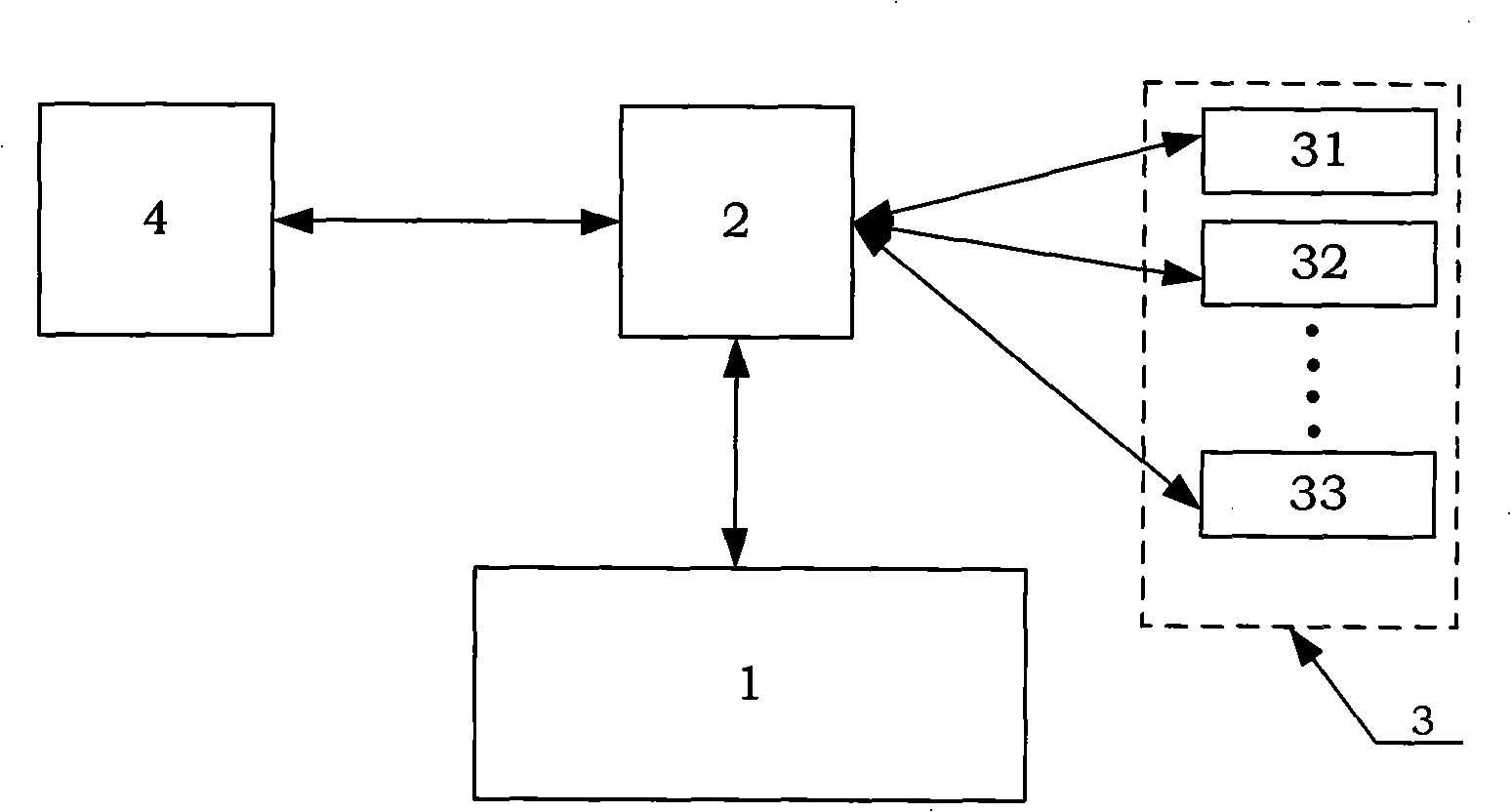
InactiveCN101277193AHigh degree of opennessSimple programming interfaceUser identity/authority verificationInternet Authentication ServiceService-oriented architecture
The invention discloses an information portal single sign-on and accessing system based on facing to service architecture authentication service agent. The system includes: an authentication service terminal (1) based on facing to service architecture, an authentication service agent (2), an application system (3) and a user browser (4). The authentication service terminal (1) is composed of an authentication service terminal date structure set (11), an authentication service terminal atomic service set (12) and an authentication service terminal assistant service set (13). The authentication service terminal date structure set (11) is used for bearing exchanged date in single sign-on execution process; the authentication service terminal atomic service set can complete single sign-on and accessing to the application system (3) through response calling request of the authentication service agent (2); the authentication service terminal assistant service set (13) is used for maintaining local user role mapping LURM, global user identity information GUII in single sign-on, and can assistant complete single sign-on and accessing to the application system (3).
Owner:BEIHANG UNIV
Internet site authentication service
ActiveUS7313691B2Memory loss protectionDigital data processing detailsWeb siteInternet Authentication Service
Owner:INT BUSINESS MASCH CORP
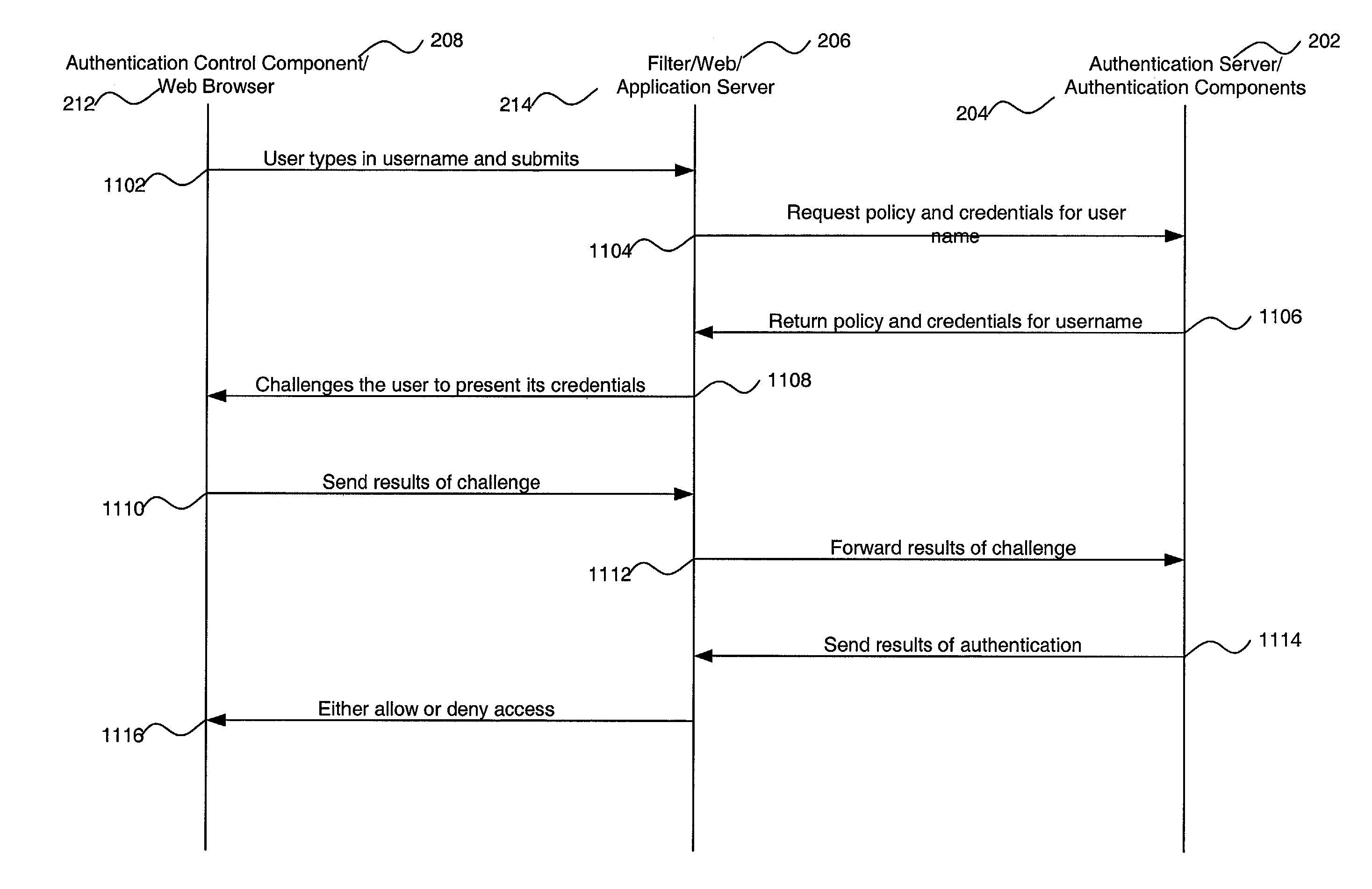
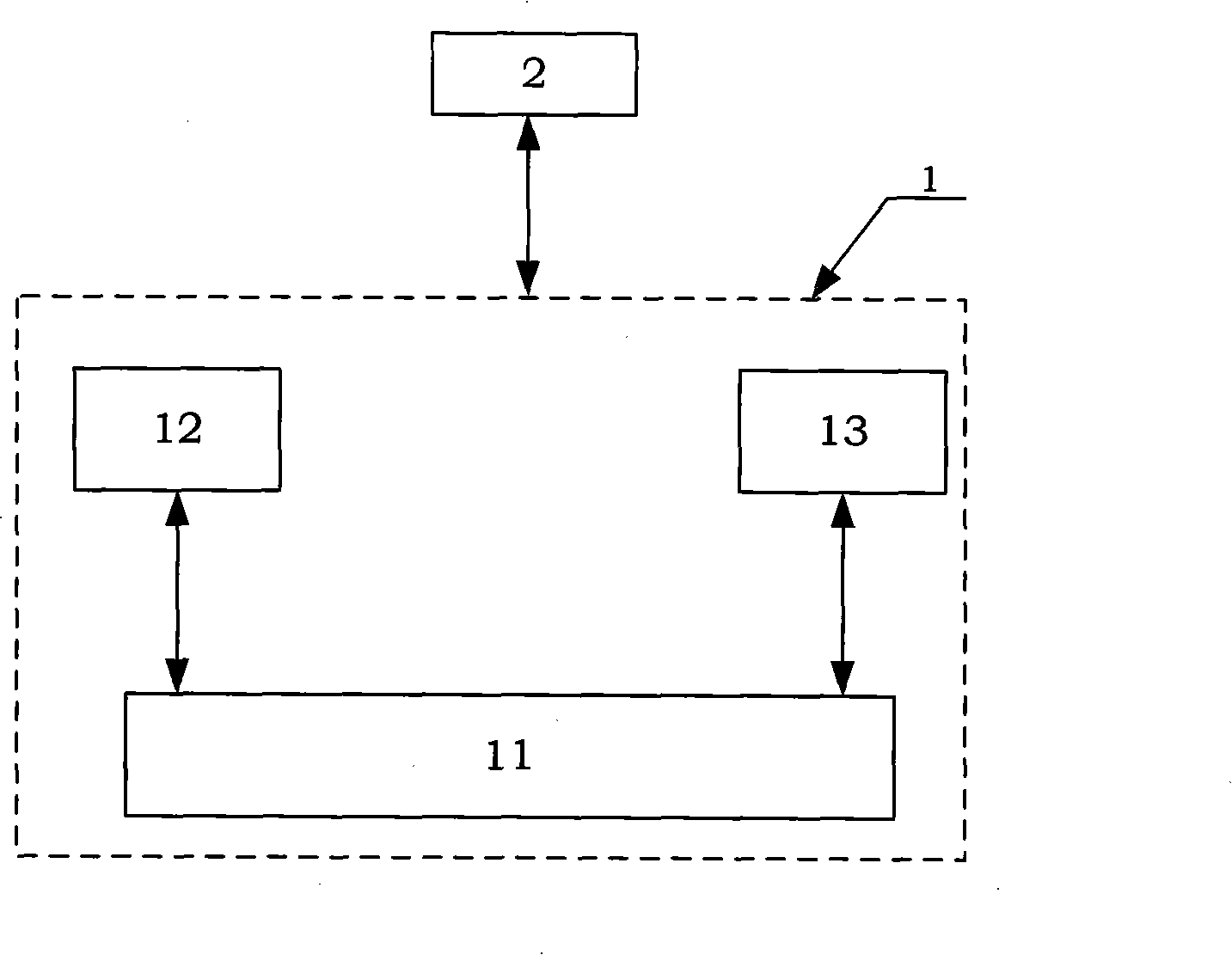
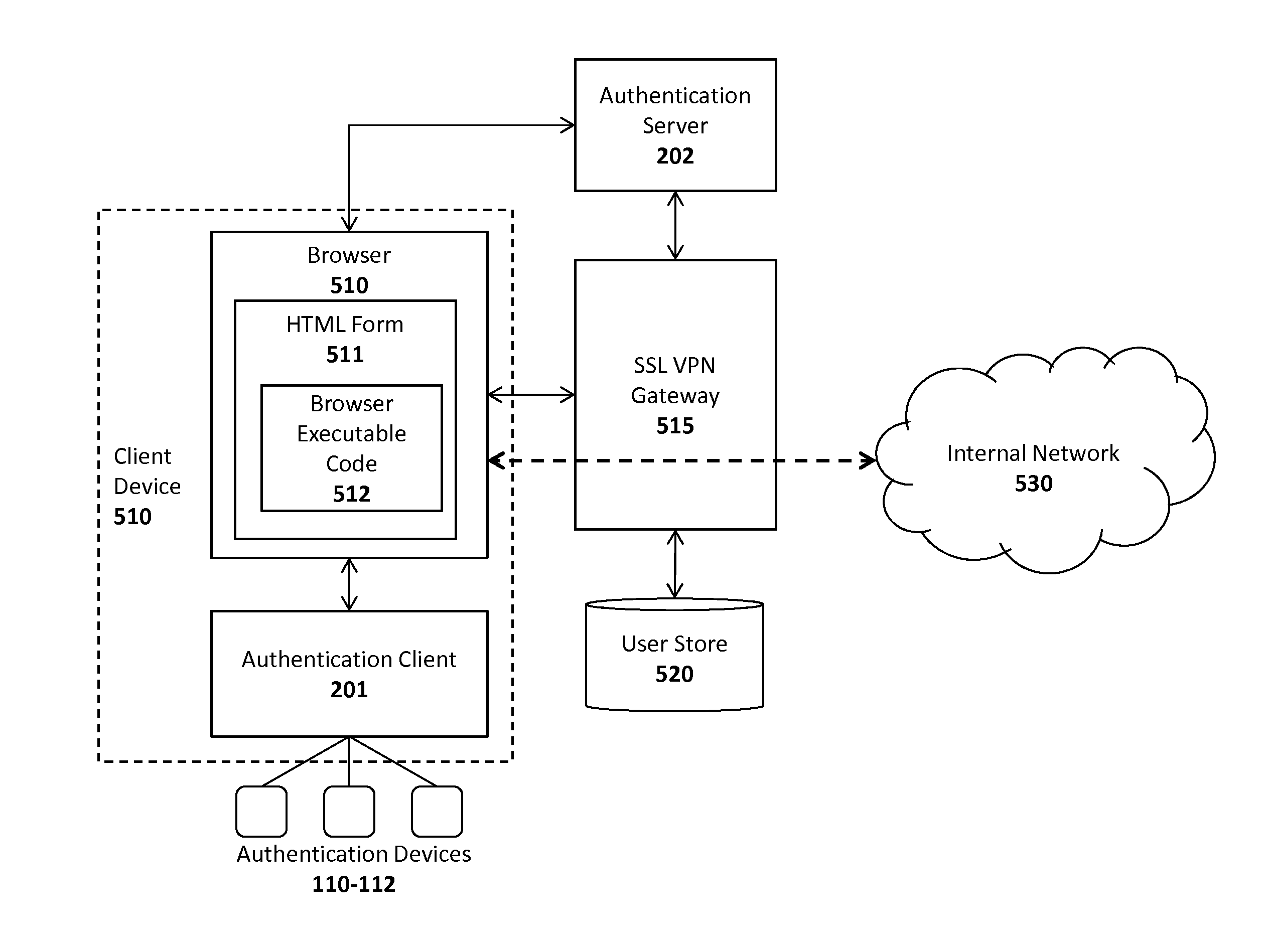
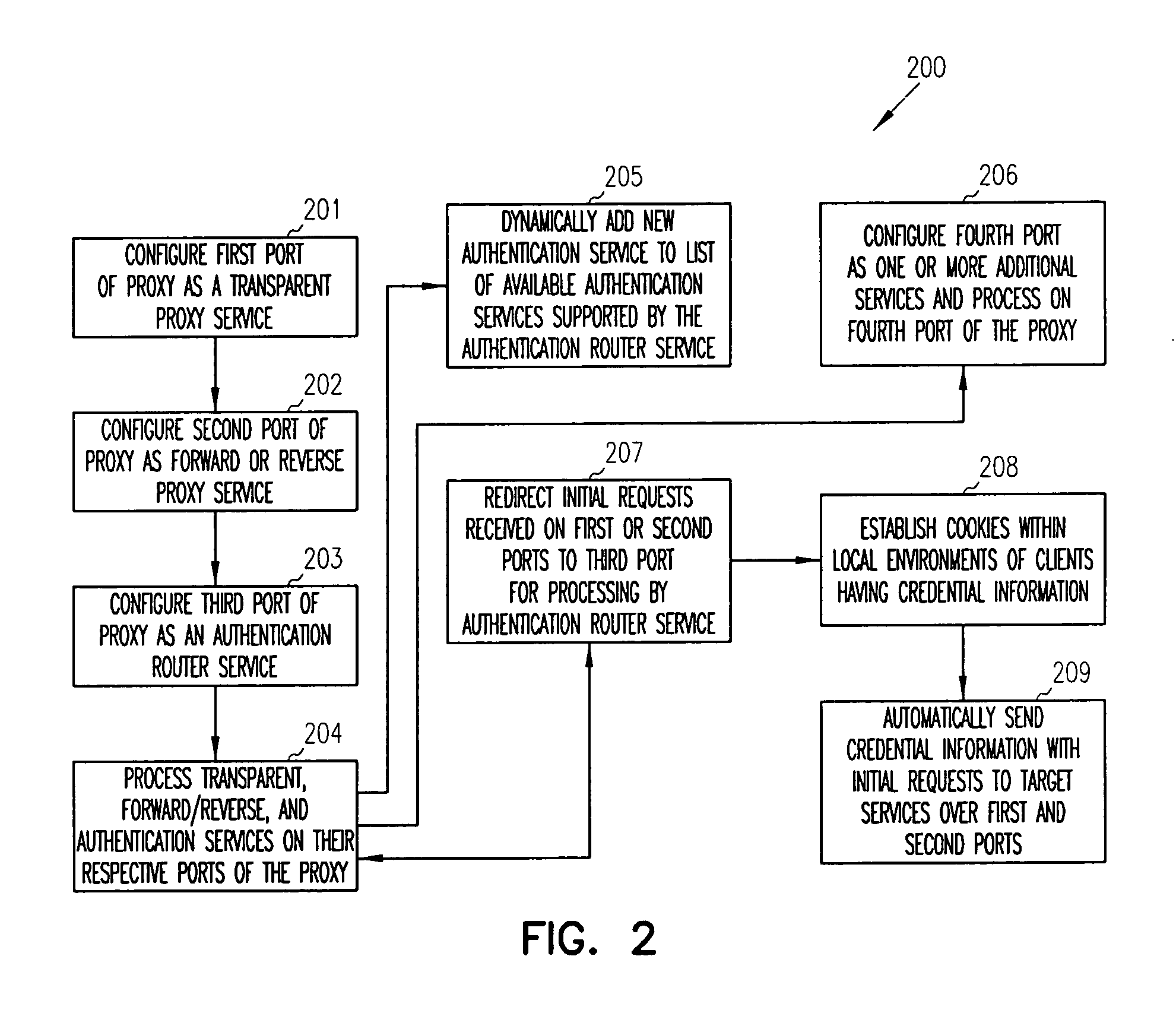
System and method for integrating an authentication service within a network architecture
A system and method are described for integrating an authentication service within an existing network infrastructure. One embodiment of a method comprises: configuring a gateway to restrict access to an internal network; configuring an authentication client of a client device to establish a communication channel with the authentication server and to register one or more authentication devices with the authentication server; authenticating the user with the authentication server using one or more of the registered authentication devices in response to an attempt to gain access to the internal network via the gateway; providing the client device with a cryptographic data structure in response to a successful authentication; providing the cryptographic data structure to the gateway as proof of the successful authentication; validating the cryptographic data structure with the authentication server; providing access to the gateway upon receiving an indication from the authentication server that the cryptographic data structure is valid.
Owner:NOK NOK LABS
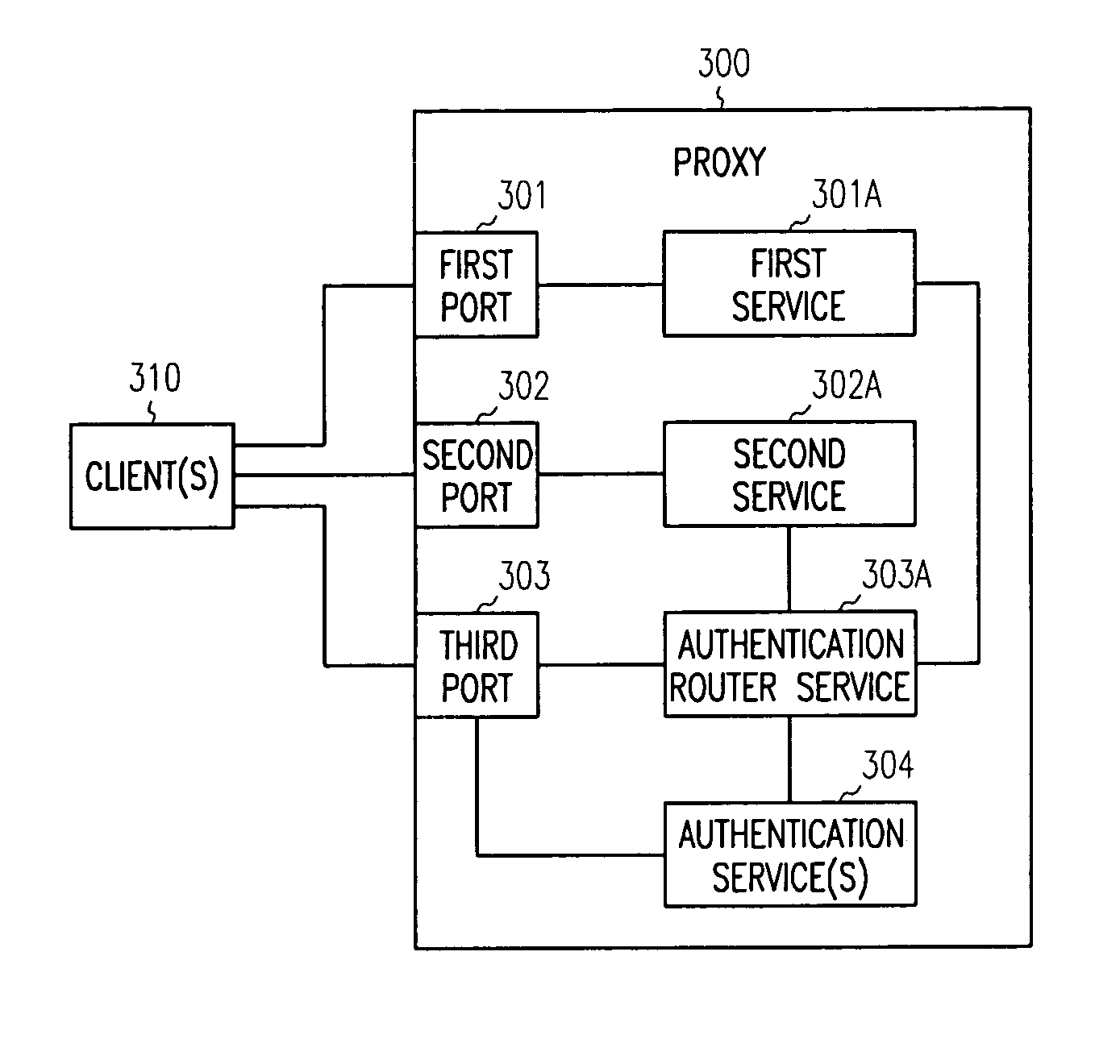
Proxy authentication
ActiveUS7681229B1Digital data processing detailsMultiple digital computer combinationsInternet Authentication Service
Techniques are provided for proxy authentication. A proxy includes a first port, a second port, and a secure port; each port processing a different service. Requests received on the first and second ports which require authentication are redirected to the secure port. The secure port processes an authentication router service. The authentication router service forwards requests for authentication to selective authentication services. The authentication services authenticate the requests over the secure port.
Owner:ORACLE INT CORP
One pass security
InactiveUS7281128B2Digital data processing detailsPublic key for secure communicationOne passInternet Authentication Service
A system and method for secure network communication. In various embodiments of the present invention, data needed for authentication an encryption is included in each communication pass between network devices, so that when a network connection is broken, a secure connection can be reestablished with the next pass. A client authentication service on the client receives a server request and searches for a current client-side session key. If one is not present, the client authentication service generates and encrypts an initial session key, acquires credentials, adds the credentials to the server request, and encrypts the server request with the initial session key. The encrypted server request and the encrypted session key are sent to the server, where a server authentication service decrypts the initial session key, decrypts the server request with the initial session key, and authenticates the credentials before allowing the server request to be acted upon. Where a current client-side session key is detected, the client authentication service acquires the current client-side session key, generates a next step session key, adds the next step session key to the server request, and encrypts the server request with the current client-side session key. The encrypted server request is sent to the server where the server authentication service decrypts the server request with a current server-side session key allowing the server request to be acted upon.
Owner:EXTENDED SYST
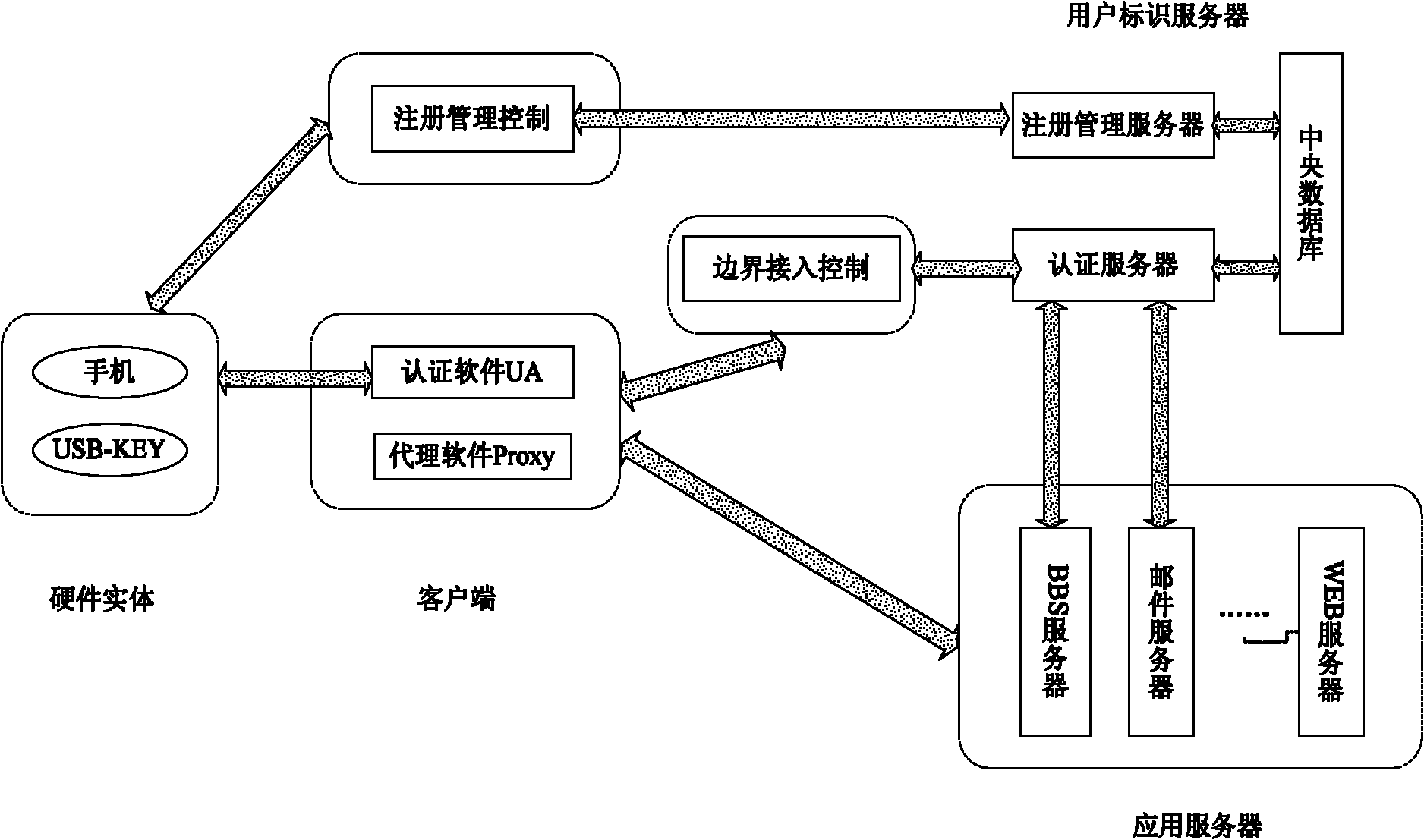
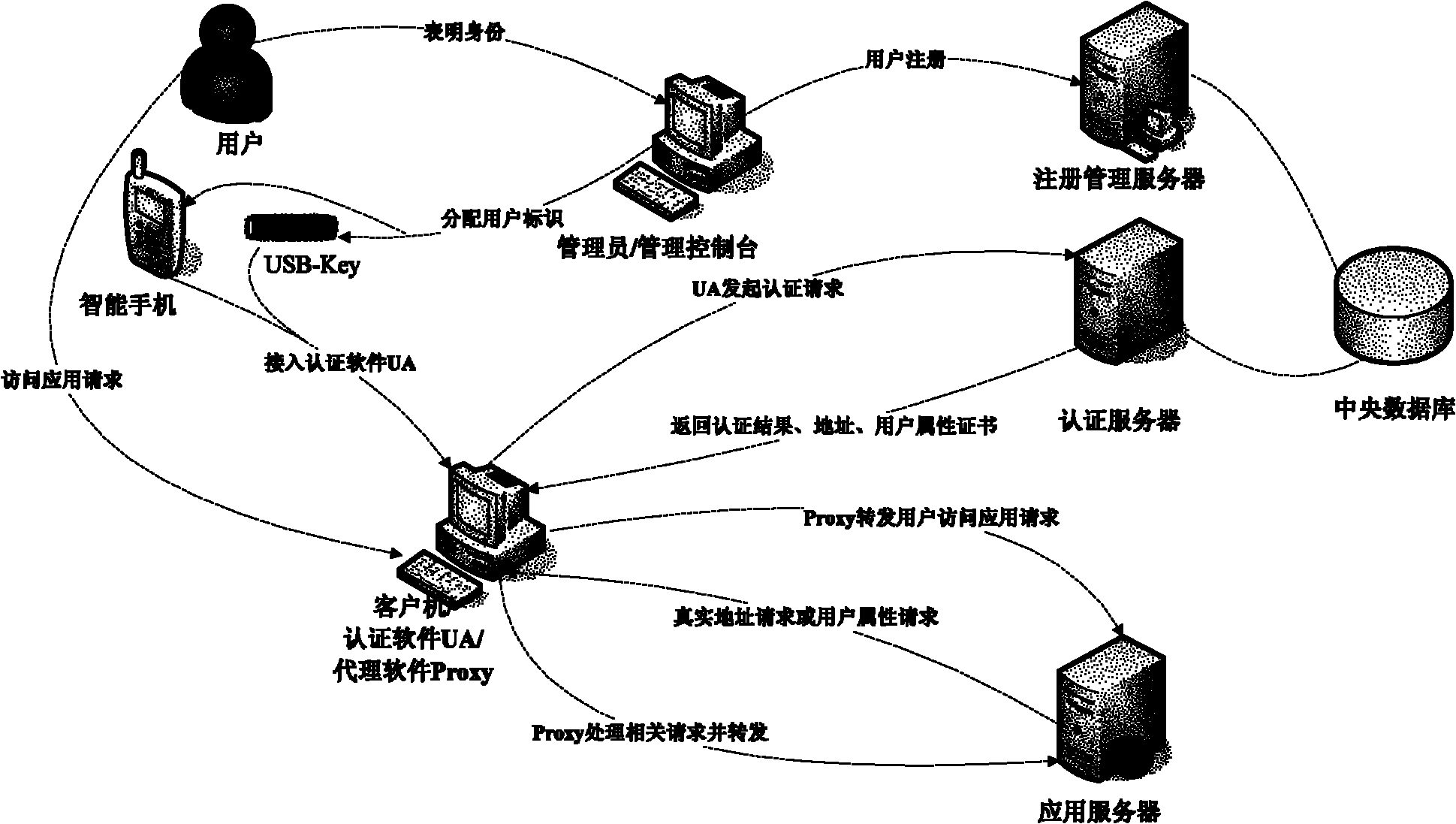
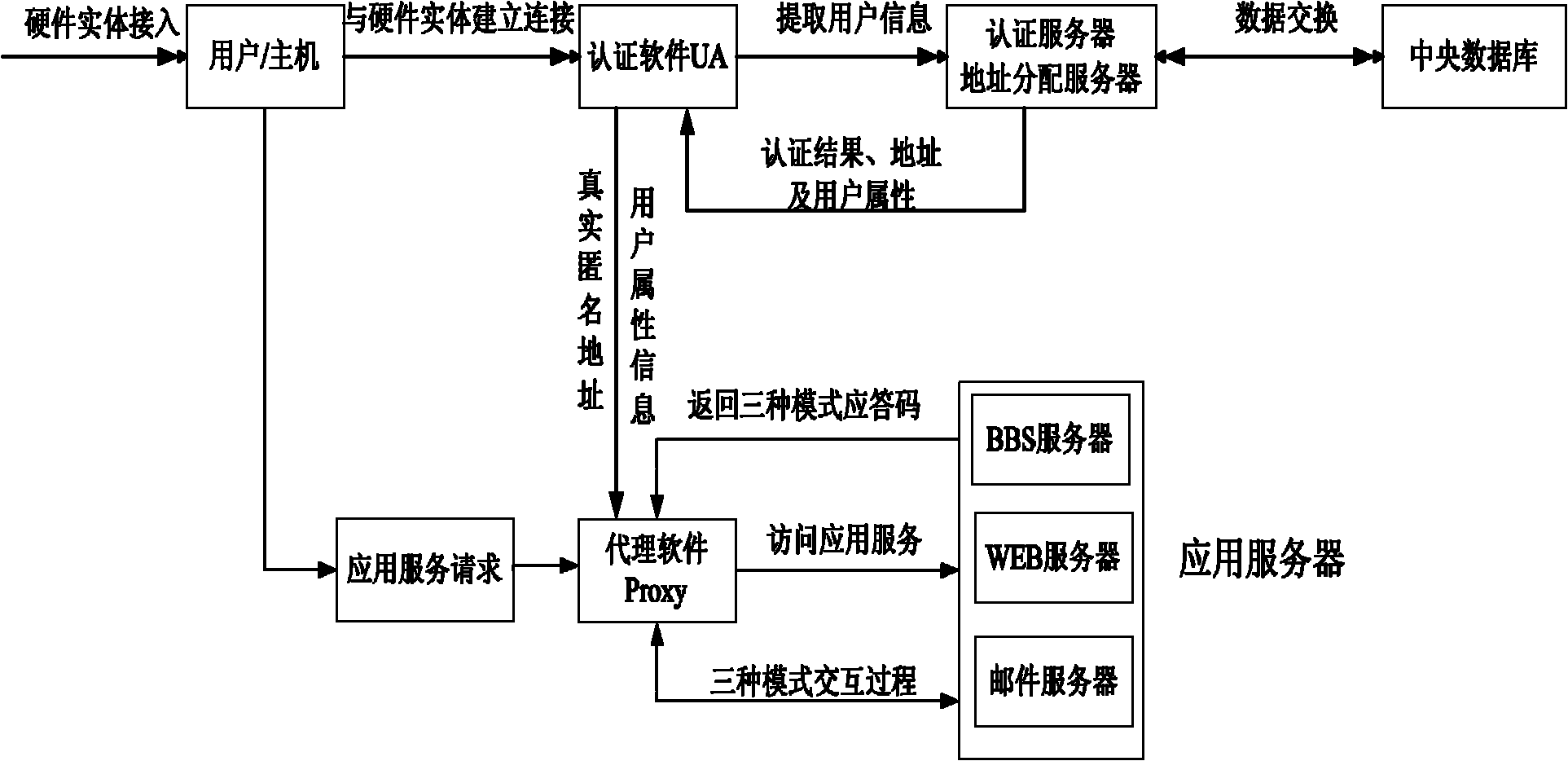
Trustworthy internet-oriented entity ID (Identity)-based ID authentication method and system
InactiveCN102006299AEnsure safetyUniqueness guaranteedTransmissionInternet Authentication ServiceStructure of Management Information
The invention discloses trustworthy internet-oriented entity ID (Identity)-based ID authentication method and system. Through distributing a user basic ID and a user ID certificate in one-to-one correspondence to a user and using a safer entity authentication mode to access the internet, the security and the uniqueness of user information are ensured, various entities attempting to enter the network through false or error ID marks are recognized and ID authentication services are provided for various network applications. The IPv6 (Internet Protocol Version 6) address structure is resigned corresponding to the user basic ID and the user ID certificate, two address types, i.e. a real address and an anonymous address to be distributed in authentication are provided, and the user ID is expanded to richer user attribute certificates so that the user is provided with three network access, i.e. access based on an anonymous address, access based on a real address and access based on the realaddress and the user ID certificate.
Owner:XI AN JIAOTONG UNIV
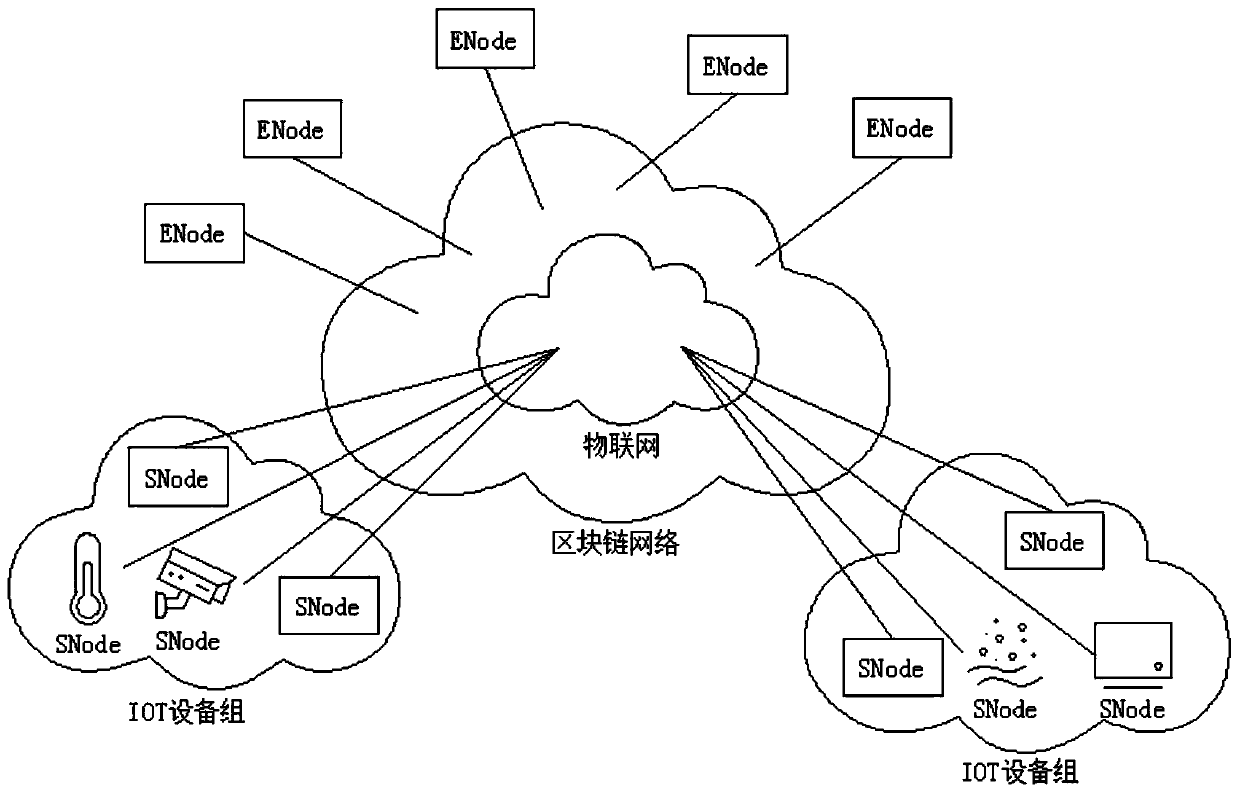
Decentralized Internet of Things security authentication system, equipment registration and identity authentication method
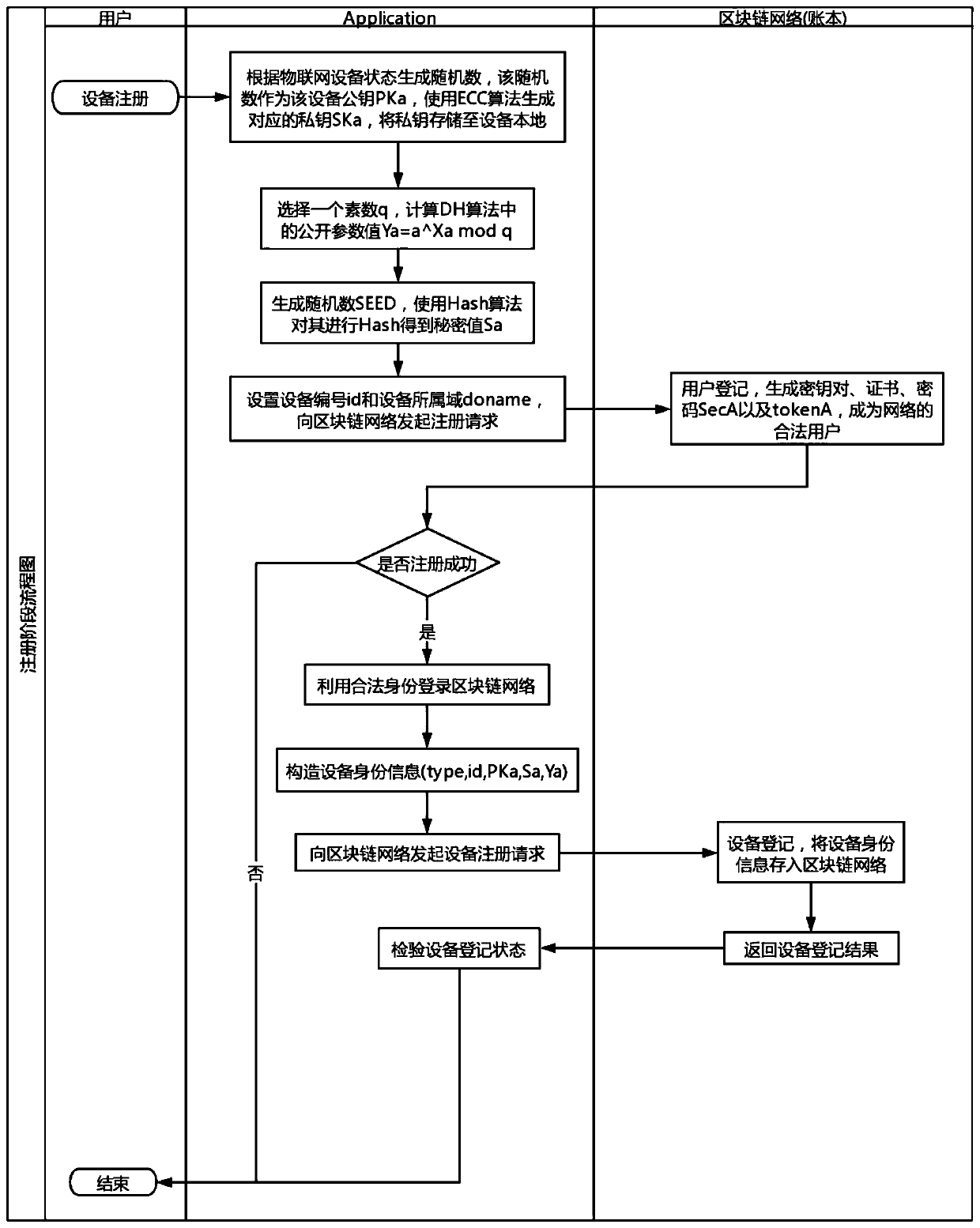
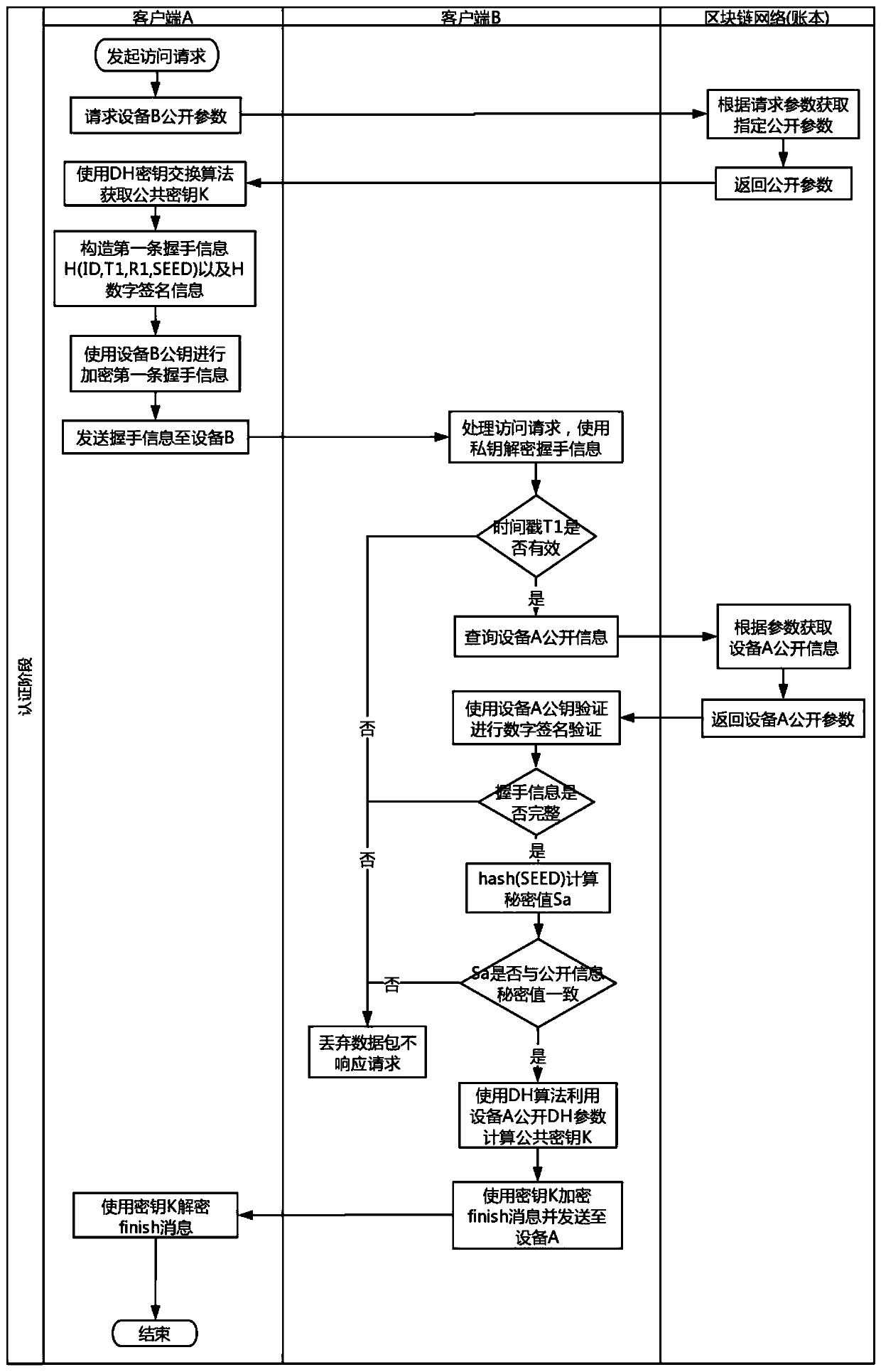
ActiveCN109768988AConnect securelyRealize dynamic changesUser identity/authority verificationInternet Authentication ServiceCommunications security
The invention discloses a decentralized Internet of Things security authentication system, an equipment registration method and an identity authentication method, and belongs to the technical field ofInternet and network, the system comprises a bookkeeping node and a light node, and Internet of Things equipment in the system is the light node; and the system core module comprises an equipment certificate generation module, a key management module, a block chain basic service module, a security authentication service module and a visual management module. According to the invention, the blockchain basic service is operated in a system kernel mode; the method comprises the following steps: providing a security authentication service, a network basic service, a key management service, an equipment certificate generation service and a security authentication service, realizing complete protection of equipment and communication security assurance between the equipment based on the services, and providing services such as DDOS attack detection and defense schemes, point-to-point key distribution and blockchain application generation and deployment.
Owner:安捷光通科技成都有限公司
Method and device for equipment authentication and authentication service system
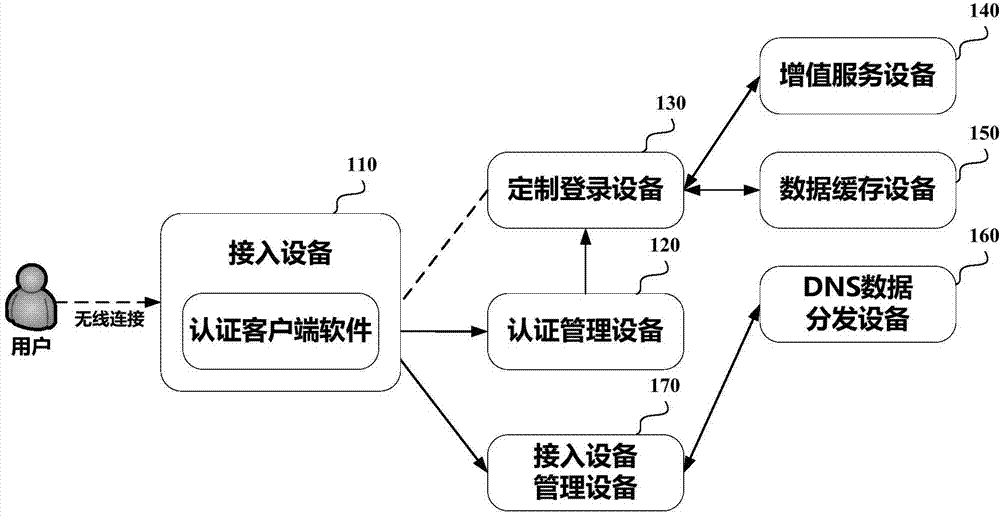
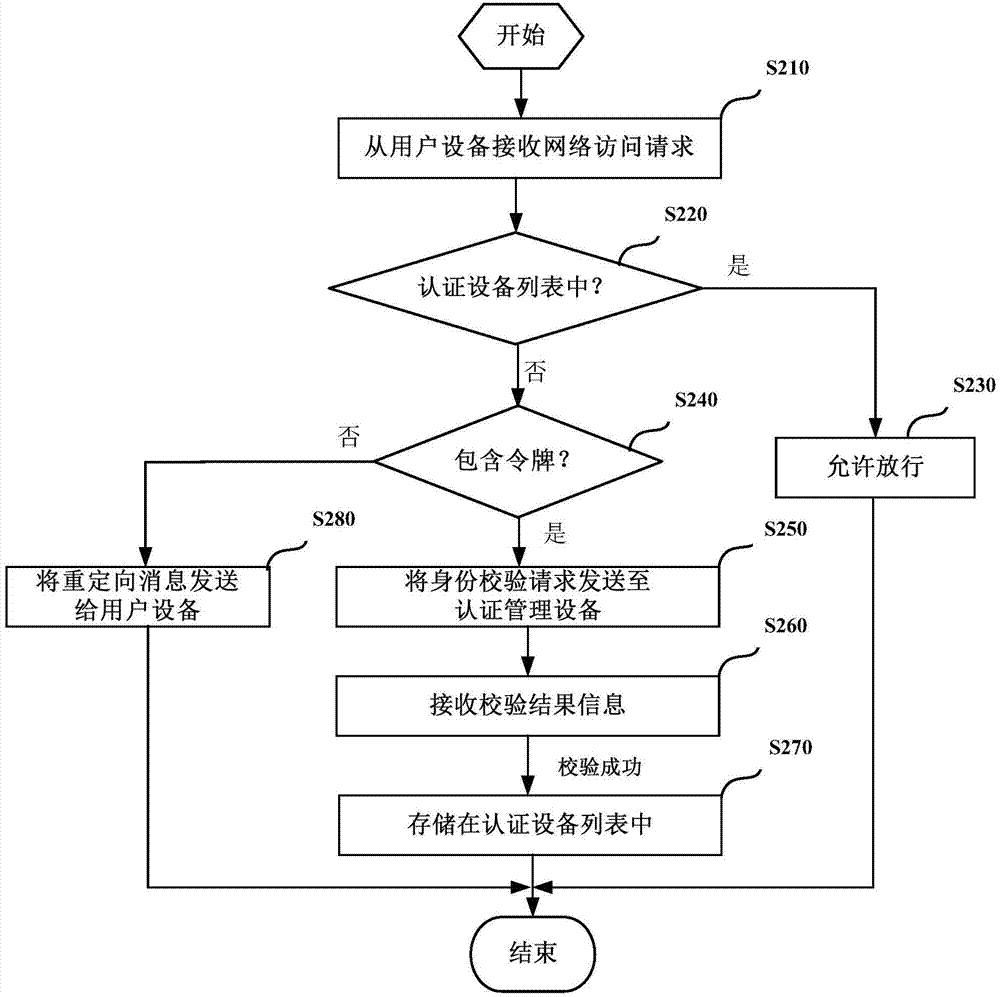
ActiveCN104506510AQuick buildNetwork topologiesTransmissionInternet Authentication ServiceUser equipment
The invention provides a method and a device for equipment authentication and an authentication service system. The method for the equipment authentication comprises the following steps: receiving a network access request from user equipment; if an equipment identifier of the user equipment is contained in an equipment list, approving the network access request; if the equipment identifier of the user equipment is not contained in the equipment list and a token is not contained in the network access request, sending redirecting information, which is used for indicating the user equipment to authenticate authentication managing equipment, to the user equipment. A customized authentication service is supplied to a merchant, the merchant is assisted in building a WiFi (Wireless Fidelity) internet service system and a complex WiFi authentication process is shielded for the merchant.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Security certificate gateway
InactiveCN102111349ARealize data transmission securityAchieving Valid AuthenticationNetwork connectionsInternet Authentication ServiceRemote desktop
The invention discloses a security certificate gateway, comprising a client crypto module, a client business module, a service business module and a service crypto module, wherein the client business module is used as an agent of an application client and used for calling the client crypto module and the service business module interactively to build an encrypted connection; and the service business module is used for calling the service crypto module and the service business module to build a secure encrypted channel. Based on the high-strength identity authentication service, the high-strength data link encryption service and the digital signature and authentication service of a digital certificate, the gateway provided by the invention effectively protects secure access of network resources, and supports B / S applications of a hypertext transport protocol (HTTP) and hypertext transfer protocol secure (HTTPS) as well as common C / S applications of a file transfer protocol (FTP), a remote desktop and the like.
Owner:KOAL SOFTWARE CO LTD
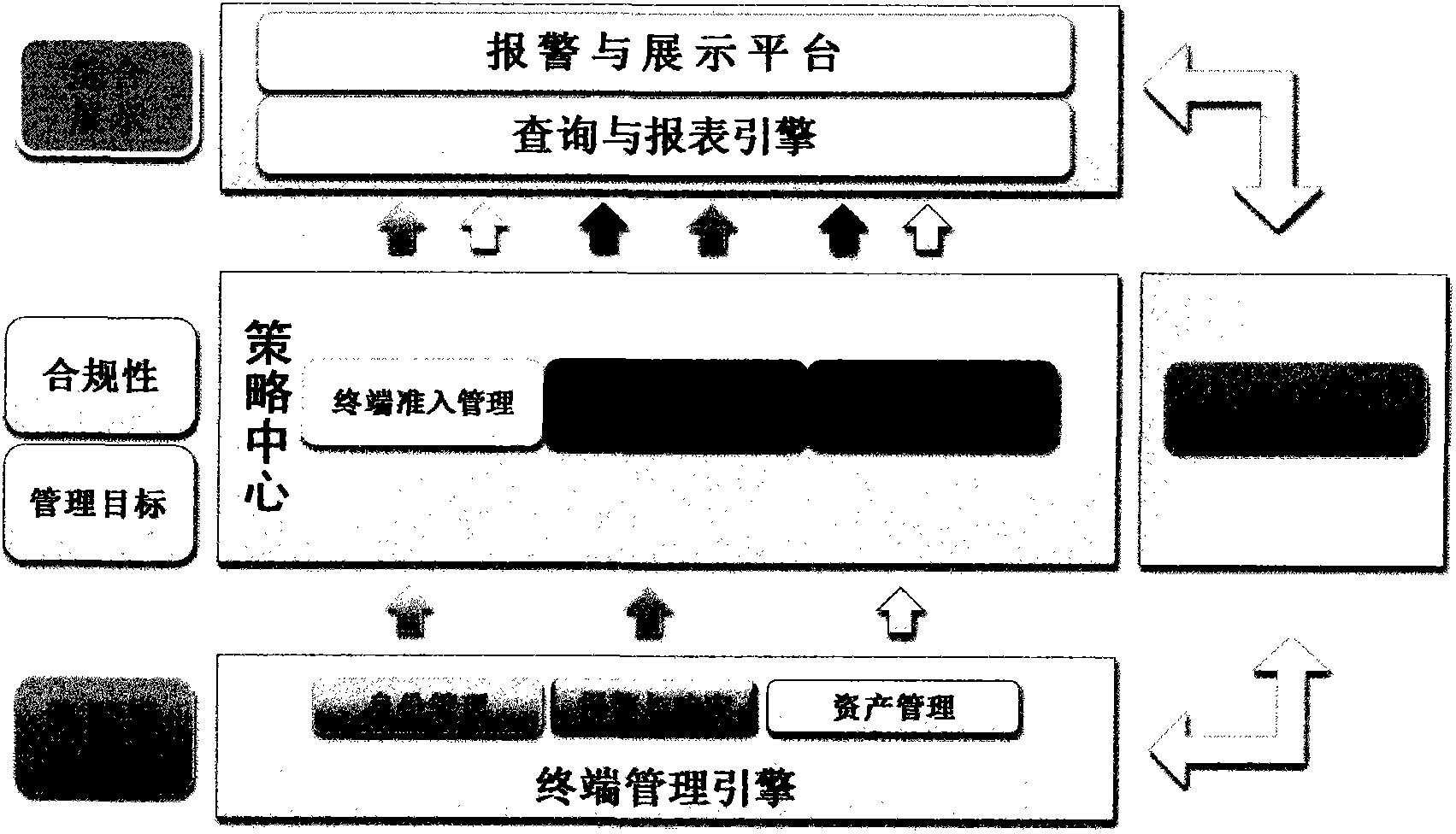
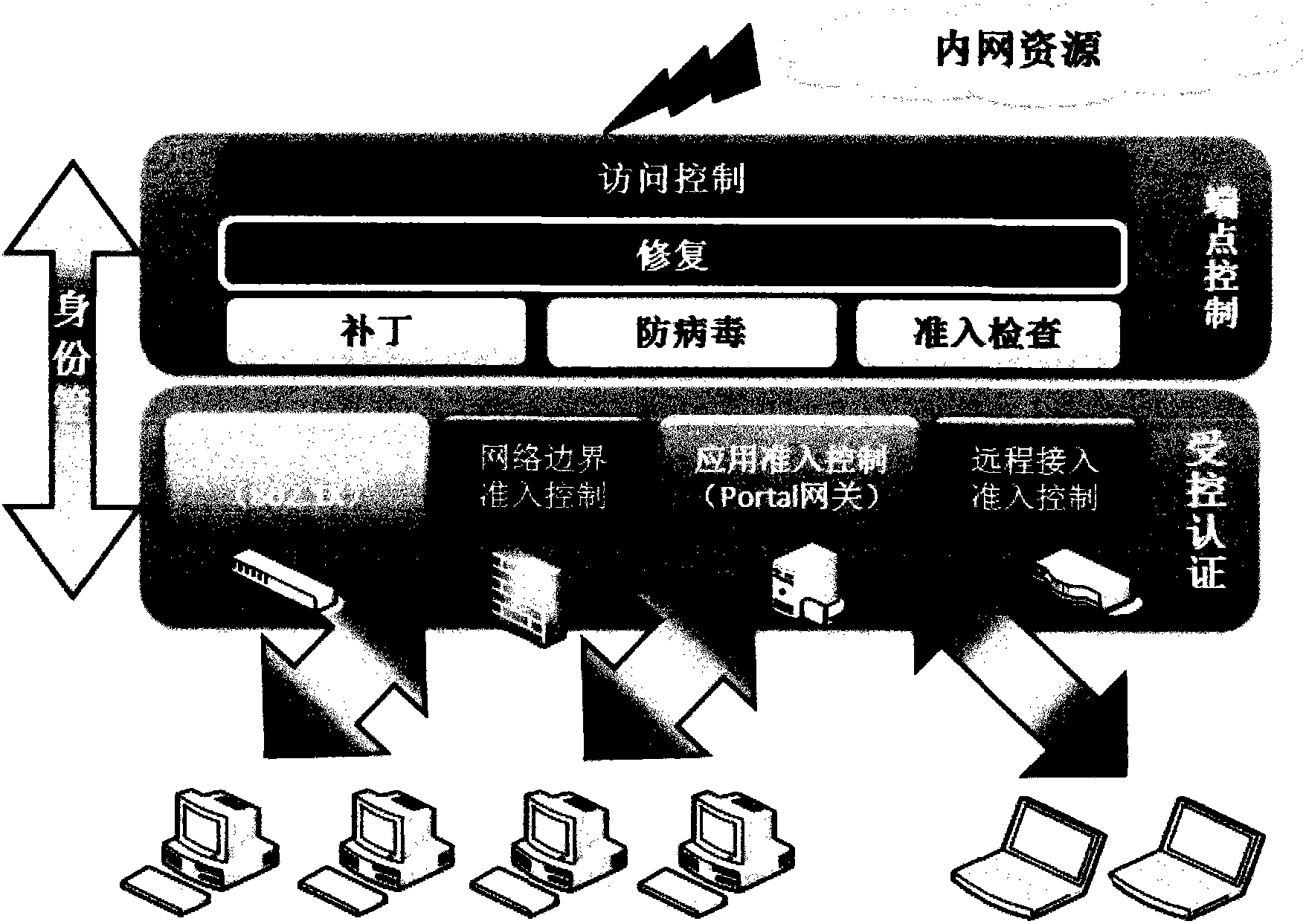
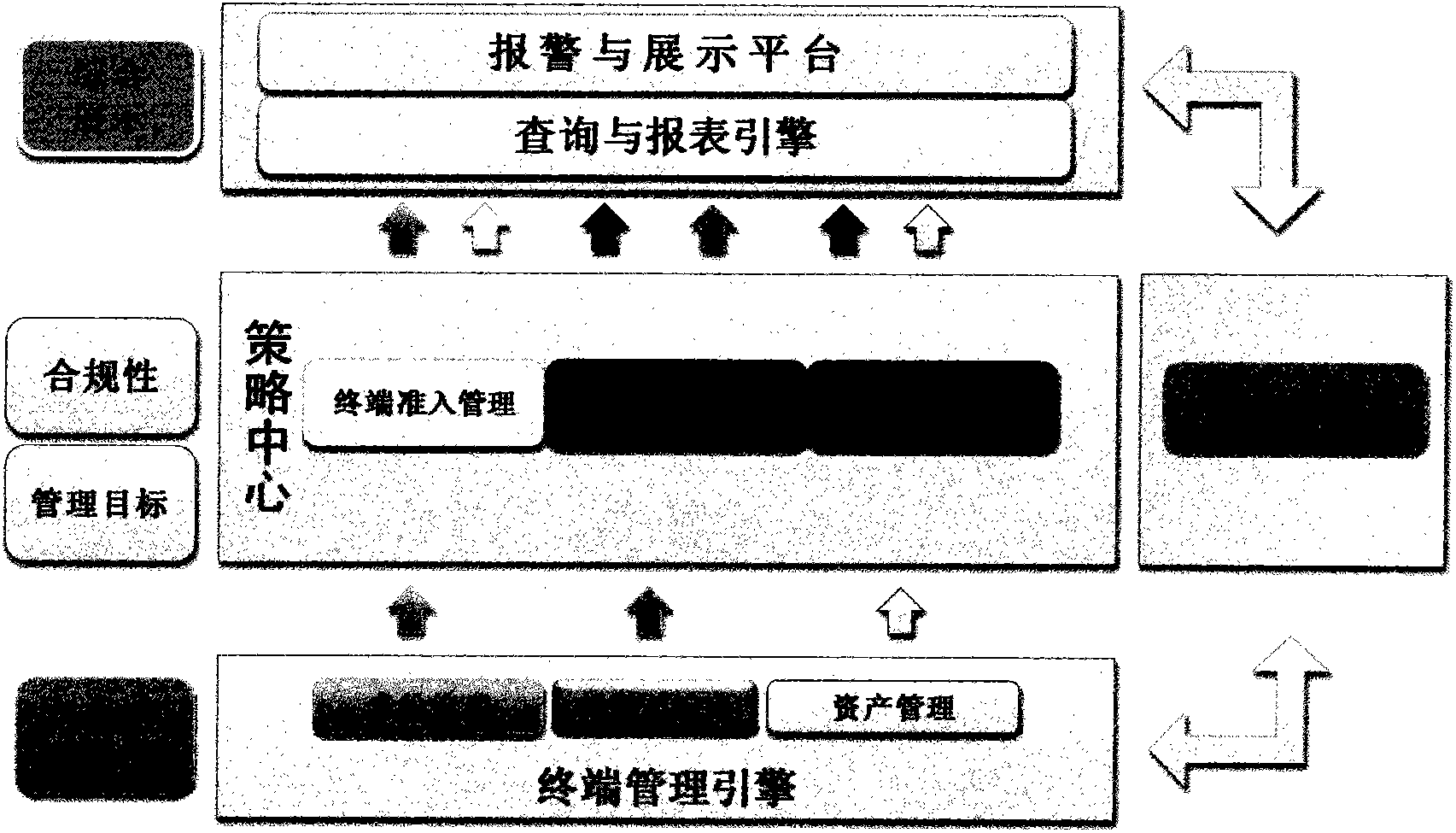
Terminal security management and authentication method and system
The invention discloses a security management and authentication method and system. The system comprises a terminal manager. The terminal manager comprises an identity authentication service chip / module, a strategic management service chip / module and an alarm platform, wherein the identity authentication service chip / module is used for authenticating the identity of a terminal, and returning an authentication response message to the terminal after the terminal passes the identity authentication; the strategic management service chip / module comprises a memory / module used for storing management strategies corresponding to different users and terminals, and a management strategy configuration chip / module used for receiving the command of a system manager so as to manage and maintain the management strategies in a management strategy database module; and the alarm platform is used for sending an alarm to maintenance personnel. The security management method can be implemented by adding user information, a password corresponding to the user information, inherent characteristic information of the terminal and use authority information required by the user into the transmitted authentication message request.
Owner:LIAONING GOETHINK TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com