Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2105results about How to "Uniqueness guaranteed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
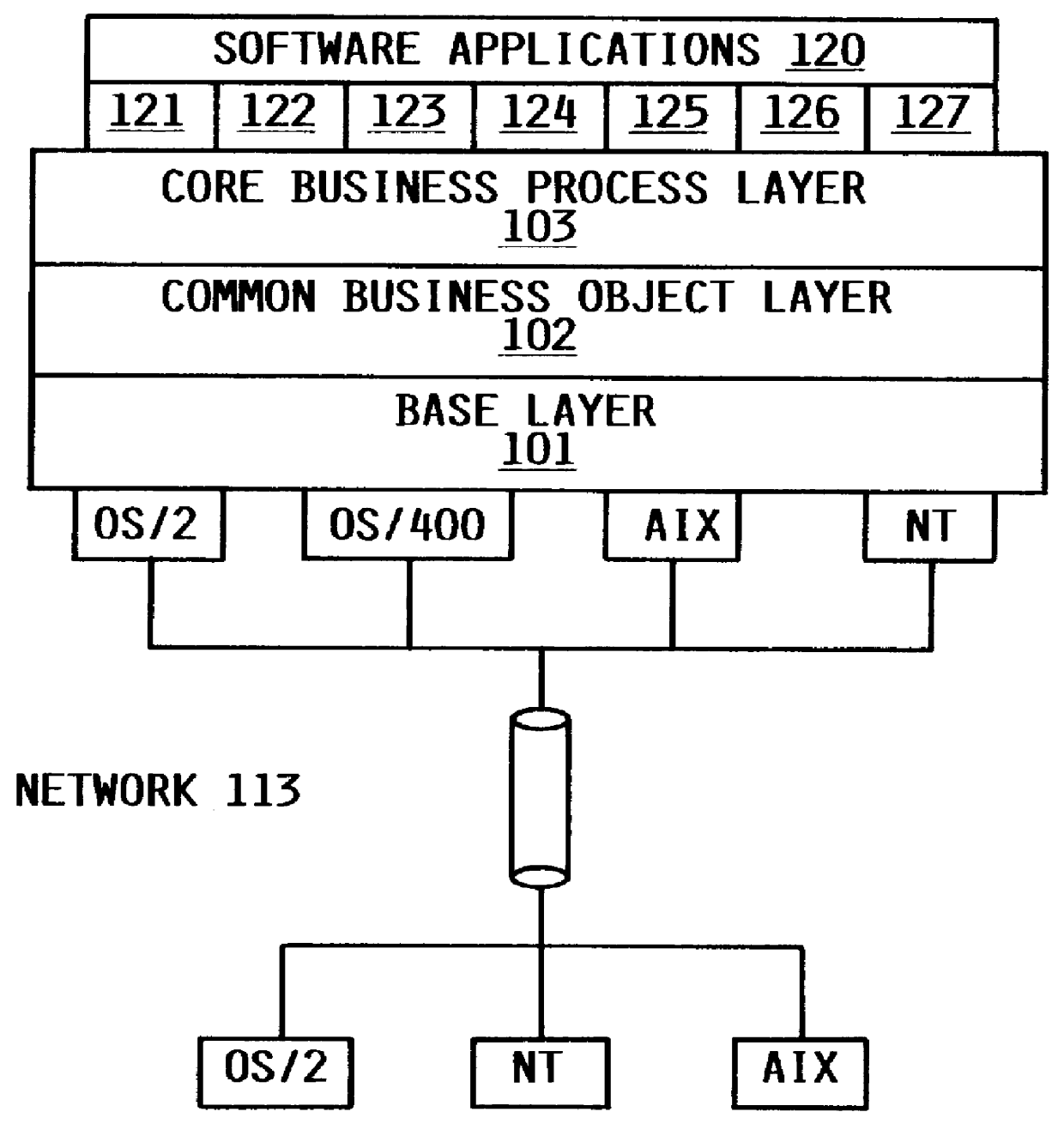
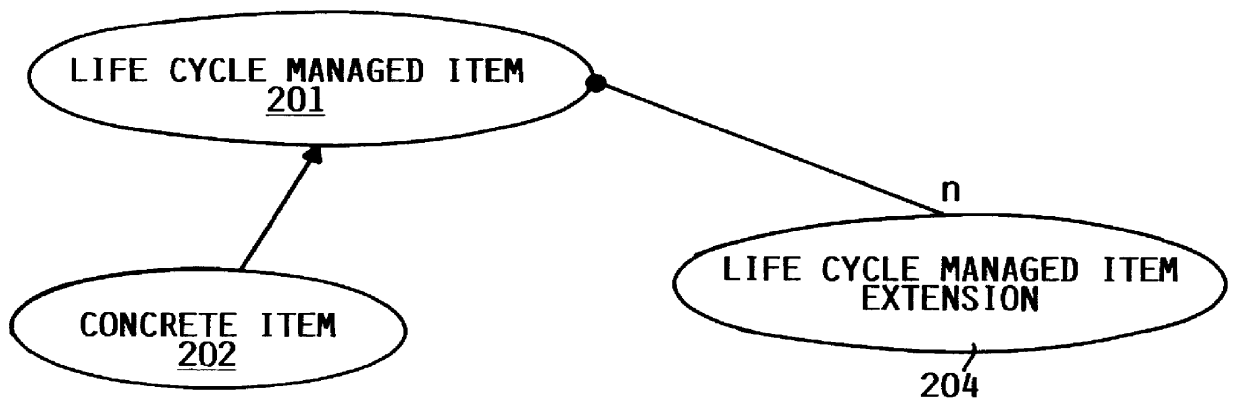
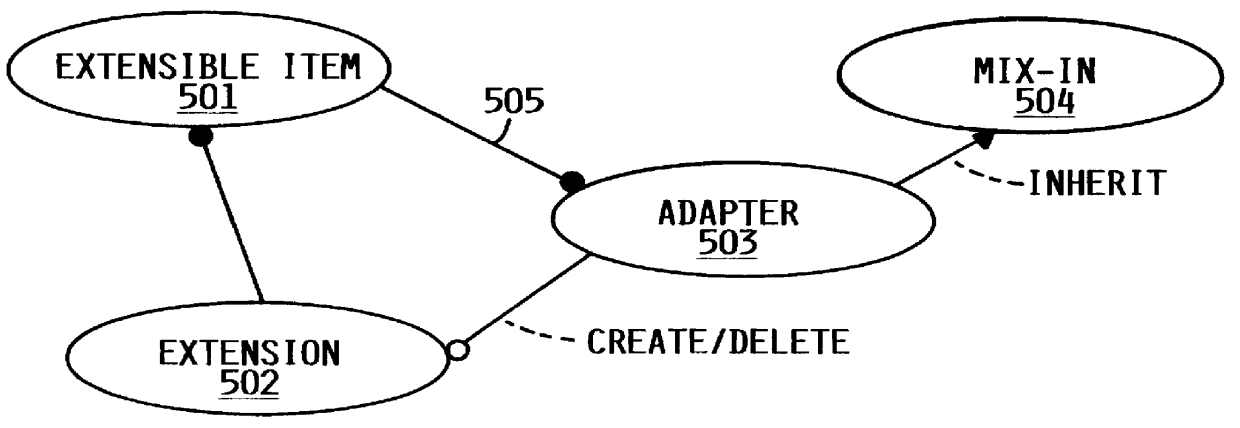
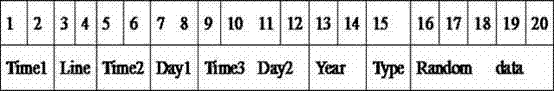
Method of developing a software system using object oriented technology
InactiveUS6106569AUniqueness guaranteedData processing applicationsSoftware designSoftware systemSoftware engineering
A method of developing a software system using Object Oriented Technology and frameworks. The problem of allowing an object to acquire and lose ability and function and to modify responsibilities on an object dynamically or, in other words, to allow an object to acquire and lose the ability to do things dynamically, is addressed. This problem is solved with a framework to be used for developing a software system, e.g. for a business application. The framework comprises a number of classes which are to be processed by a computer system. The framework further comprises a Life Cycle as a description of state transitions through which an object can proceed as it is processed by an application. This is applicable in the technical field of application development of software systems, e.g. for a business application as Financial or Logistic and Distribution, wherein it is the purpose of frameworks to provide significant portions of the application that are common across multiple implementations of the application in a general manner, easy to extend for specific implementation.
Owner:IBM CORP
Entrance guard access method and system based on two-dimension code and face identification
InactiveCN105741395AUniqueness guaranteedEnsure safetyIndividual entry/exit registersAccess methodComputer science
An entrance guard access method based on a two-dimension code and face identification comprises the steps that a resident applies to a background server for the visitor gate pass two-dimension code through an entrance guard APP intelligent terminal; a visitor acquires the visitor gate pass two-dimension code from the background sever through the entrance guard APP intelligent terminal, and uploads a face image to the server to be related with a visitor ID; an entrance guard controller reads the visitor gate pass two-dimension code displayed on the entrance guard APP intelligent terminal through an input device, and takes the picture of the face image of the visitor; the entrance guard controller judges the consistency of generated decoding information and stored authentication information.Two-dimension code appointment and face identification are combined, so that the uniqueness and safety of appointment verification are guaranteed; furthermore, the whole identification process is achieved through an entrance guard identifier, cost is saved, and more importantly, time is saved, efficiency is improved, and using is quite convenient.
Owner:WRT INTELLIGENT SCI & TECH
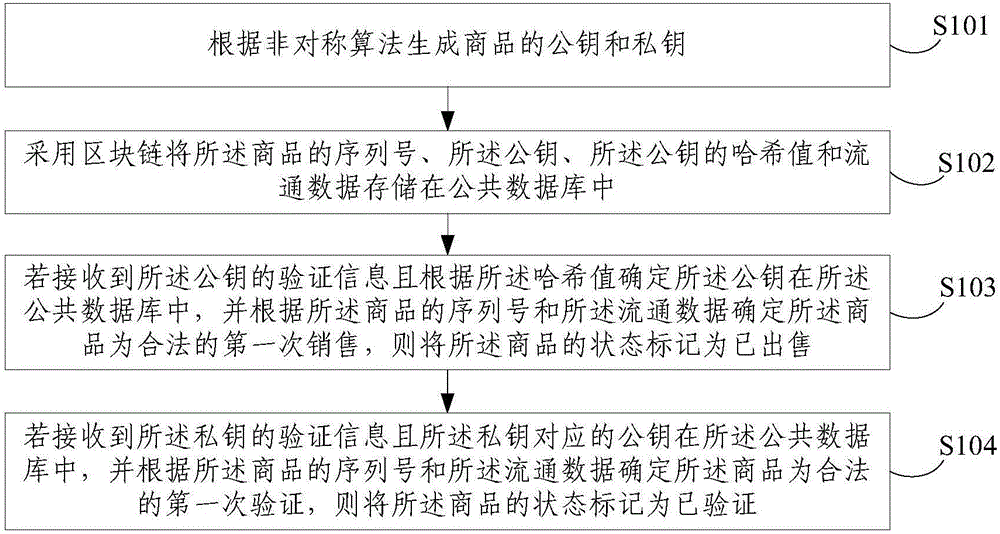
Commodity anti-counterfeiting method and device
InactiveCN106570710AGuaranteed readabilityGuaranteed verifiabilityCommerceRecord carriers used with machinesSerial codeReadability
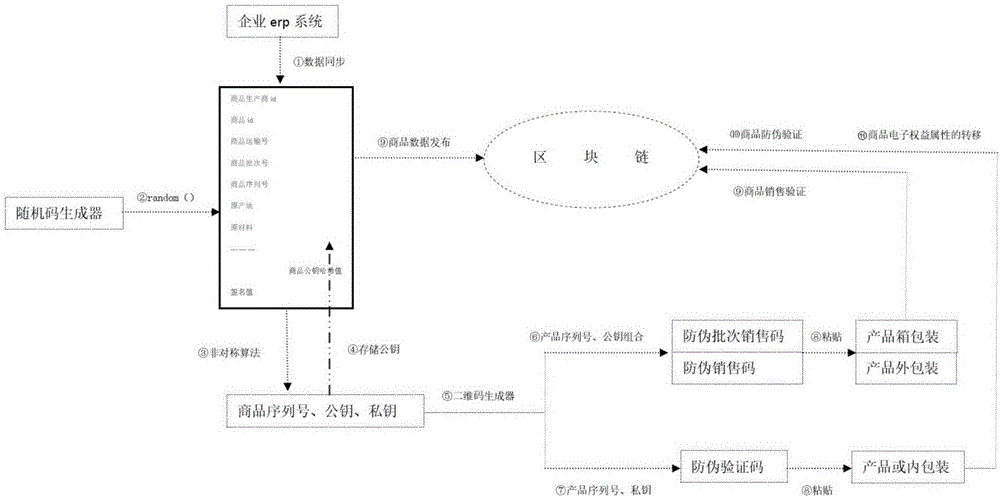
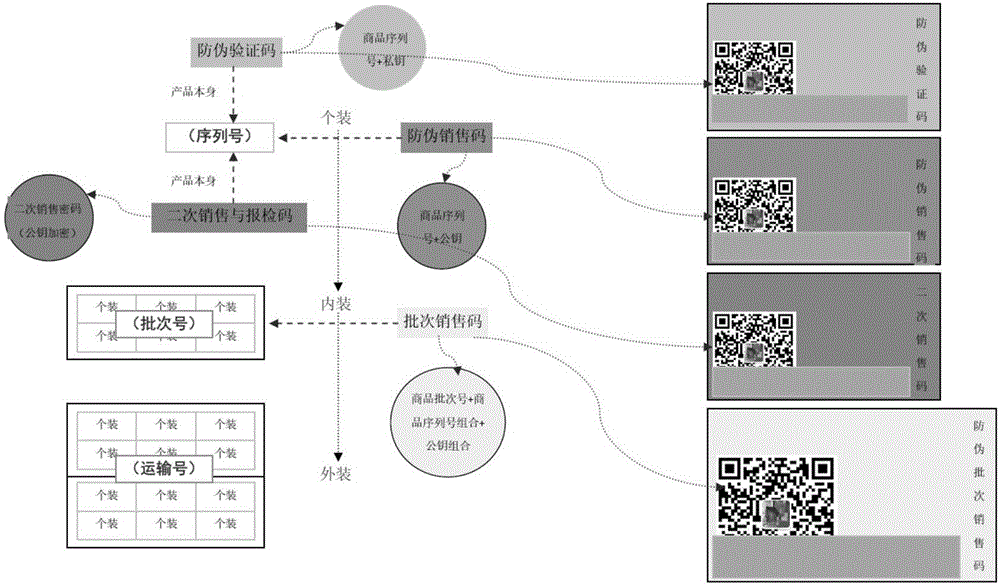
The embodiment of the invention discloses a commodity anti-counterfeiting method and a device. The method comprises the following steps of generating the public key and the private key of a commodity; storing the hash values of the serial number, the public key and the private key of the commodity and the circulation data of the commodity in a common database by using a block chain; upon receiving the verification information of the public key of the commodity and determining the stored state of the public key in the common database, determining the first legal sales state of the commodity according to the serial number and the circulation data of the commodity, and marking the state of the commodity to be sold out; upon receiving the verification information of the secret key of the commodity and determining the stored state of the public key corresponding to the secret key in the common database, determining the first legal verification state of the commodity according to the serial number and the circulation data of the commodity, and marking the state of the commodity to be verified. Through preparing the public key and the private key of the commodity into special two-dimension codes and pasting the special two-dimension codes onto the outer package and the surface of the commodity, the readability, the verifiability and the binding performance of anti-counterfeiting marks are ensured. Meanwhile, by means of the block chain, the commodity circulation traceability and the commodity source uniqueness are ensured. At the same time, the cost is reduced.
Owner:纸飞机(北京)科技有限公司
Quality safety tracing method for food processing enterprises
InactiveCN103761546ANo repeated codes appearMeet randomnessCo-operative working arrangementsDebit schemesProduction lineRelational database
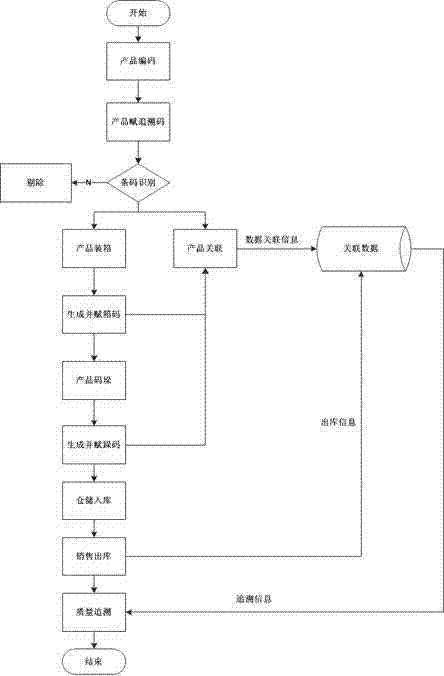
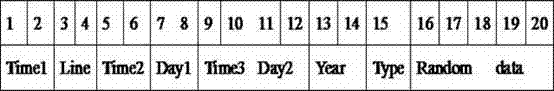
The invention discloses a quality safety tracing method for food processing enterprises. The quality safety tracing method includes the steps that a laser coder generates random tracing codes according to a coding rule when a laser marking machine in a production line device is dynamically read in an on-line tagging mode; the laser marking machine carries out tracing mode marking on products on a production line, and two-dimension codes and plain codes are all marked on packages; a fixed reader is used for scanning and reading designated tagged code portions of the products; the two-dimension codes are successfully scanned and read, the tracing codes are recorded, and relevance between the tracing codes and commodity attribute information is completed; if the two-dimension codes fail to be scanned, the two-dimension codes will be removed through a removing device; the commodity tracing code information and the commodity attribute information are recorded into a relational database; after the products are packaged, package code data and product tracing code data are related; the products are stacked, stacking codes and tagged stacking codes are generated, and the stacking codes and the product package code data are related; the stacking codes are scanned, storage of the products is completed, delivery orders and the stacking codes are scanned to complete delivery, and the database records delivery information.
Owner:武汉华工赛百数据系统有限公司
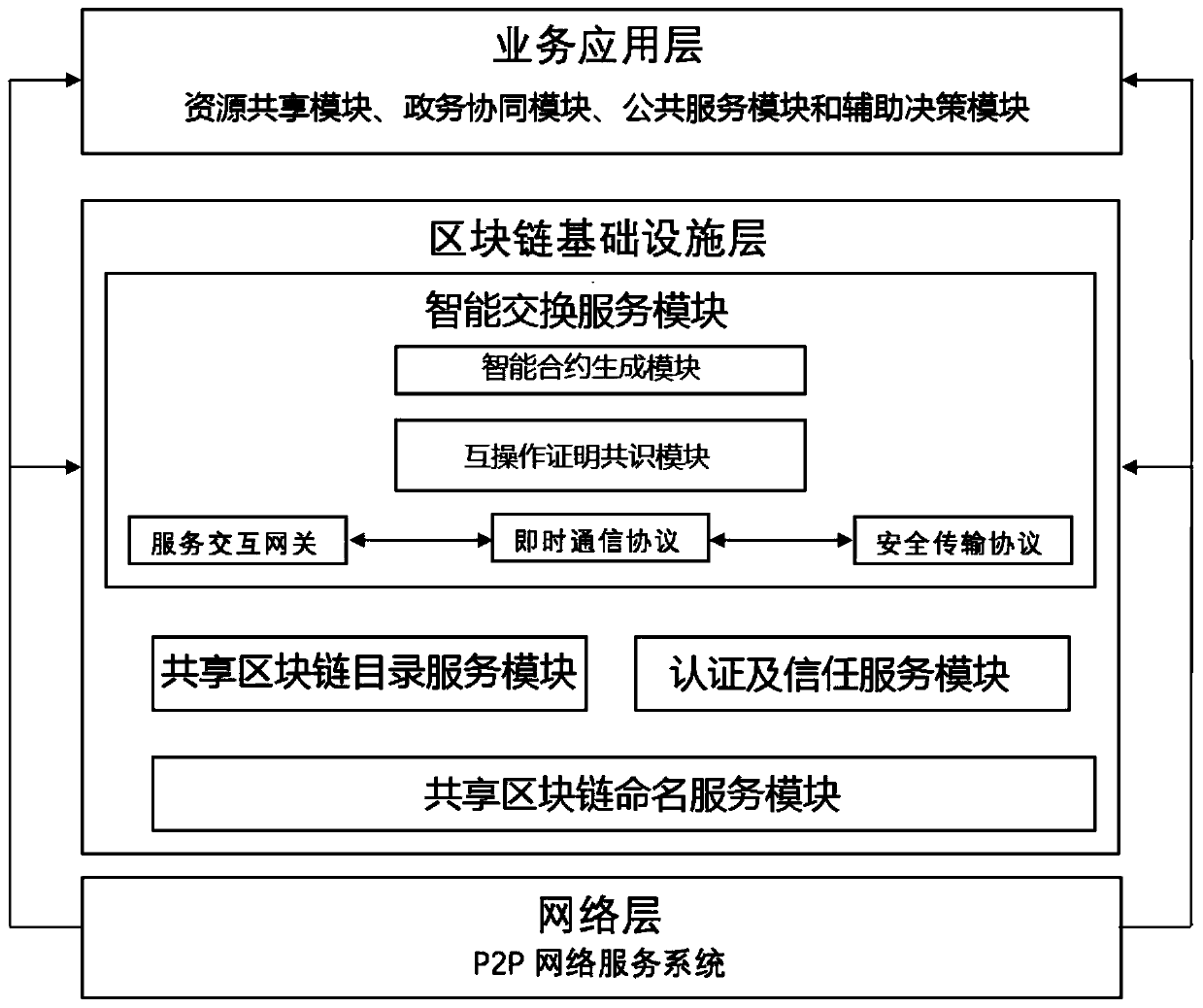
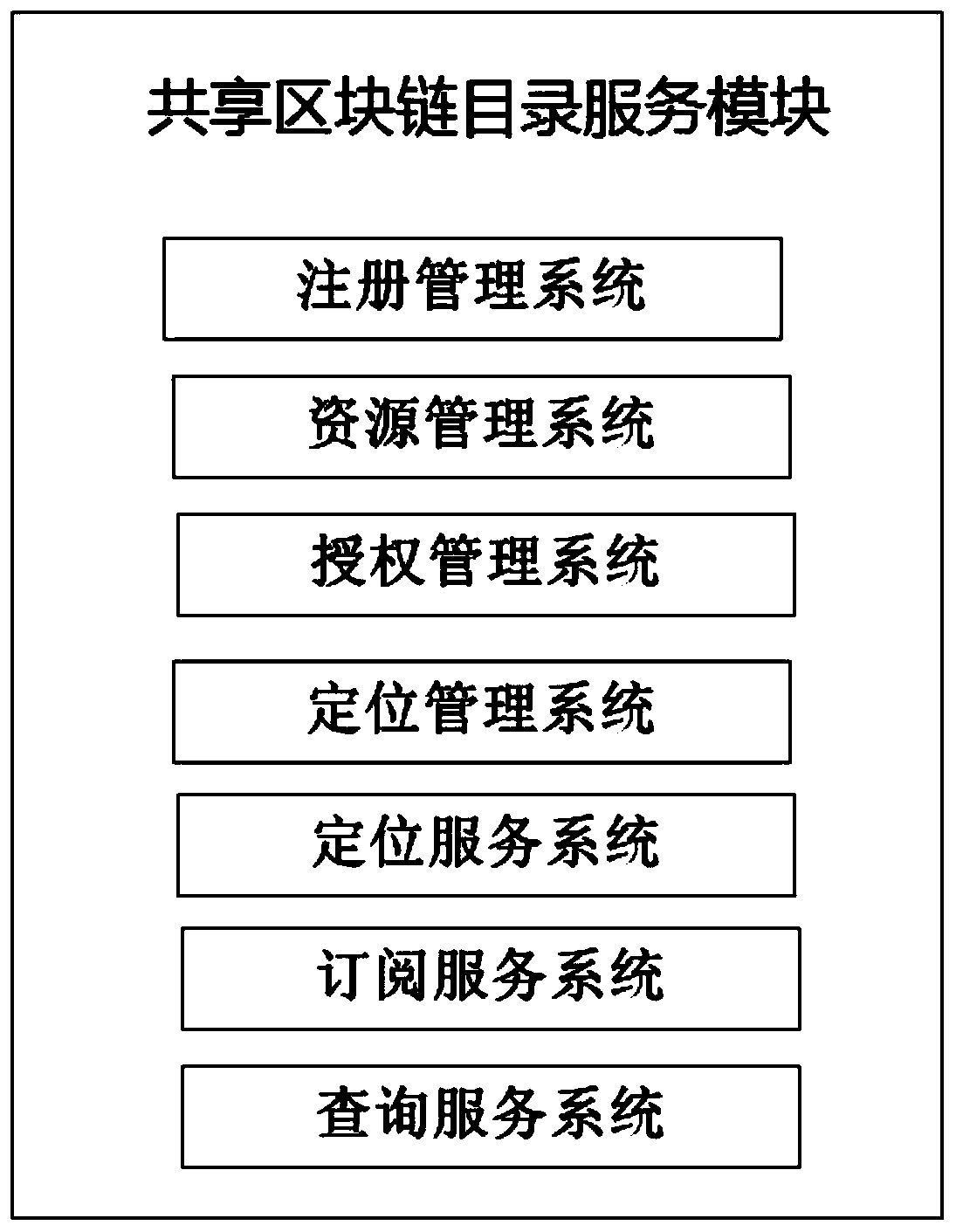
A government affair information resource sharing system based on a block chain
ActiveCN109787815AEnsure real-timeEnsure decentralizationData switching networksNon real timeExchange network
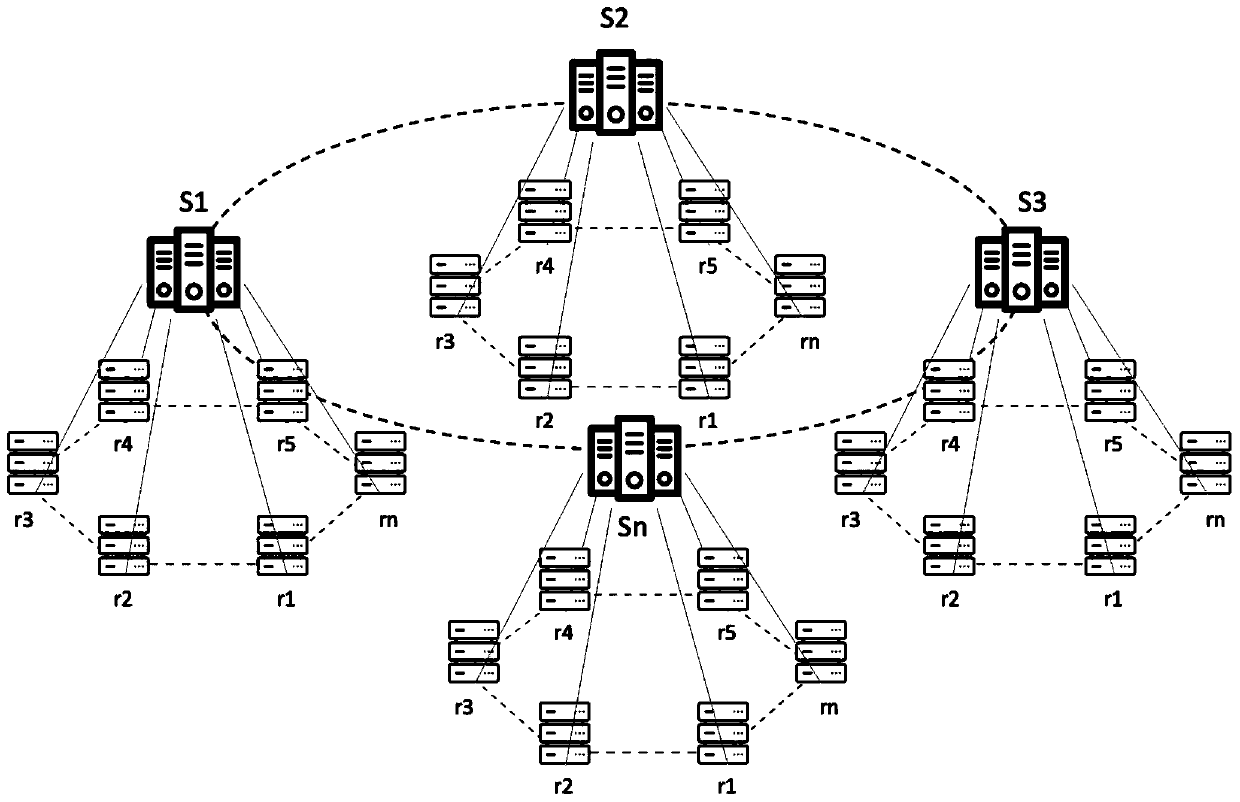
The invention discloses a government affair information resource sharing system based on a block chain, and belongs to the technical field of information sharing based on the block chain. By combiningP2P network, the cryptology and the artificial intelligence theory, the overall model architecture based on the block chain technology is provided, so that a government affair information resource sharing and exchange network system, a government affair information resource sharing and exchange block chain directory system, a certificate and trust system and an information resource sharing security intelligent exchange system are constructed. The government affair information sharing and exchanging system effectively solves the problems of trust islands, data ownership, peer-to-peer management, standard consistency, non-real-time exchange and the like in government affair information resource sharing application, and is high in safety, trustable, real-time exchange, data standard consistency, traceability and wide in sharing range.
Owner:YUNNAN UNIVERSITY OF FINANCE AND ECONOMICS
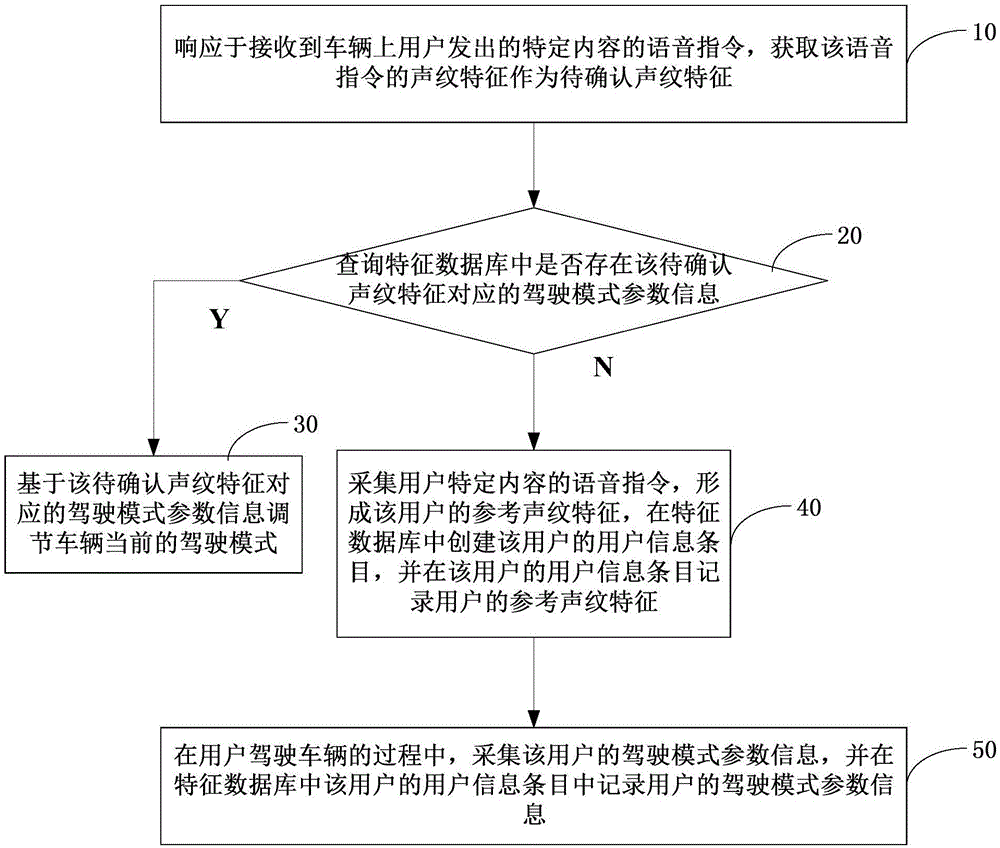
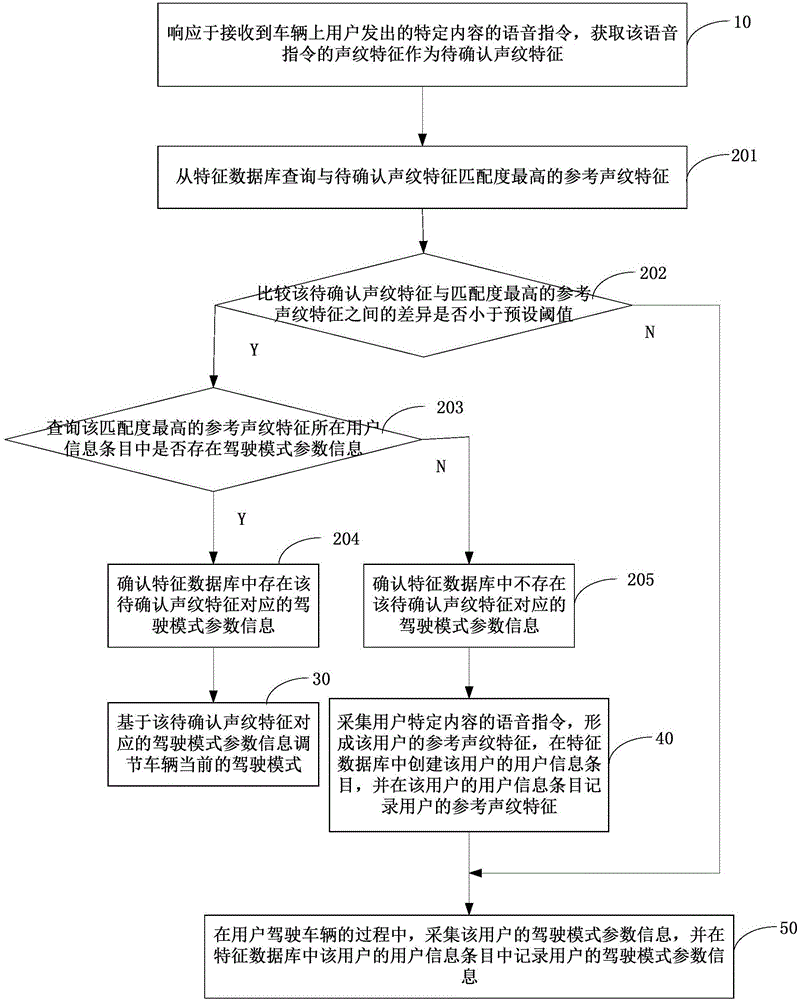
Method, device and system for adjusting driving modes and vehicle
ActiveCN106683673ARealize automatic adjustmentProtection securitySpeech recognitionPersonalizationVehicle driving
The invention discloses a method, a device and a system for adjusting driving modes and a vehicle. The method includes receiving a voice instruction; querying feature databases; determining parameter information of the driving modes on the basis of to-be-confirmed voiceprint features; acquiring the voice instruction and acquiring the parameter information of the driving modes in driving procedures. The method, the device, the system and the vehicle have the advantages that the vehicle can be adjusted to be in the most familiar and habitual driving modes by the aid of the single voice instruction, and accordingly users can be positioned in habitual driving environments without manually adjusting the parameter information of the driving modes; the parameter information of the driving modes of the users can be automatically acquired in the vehicle driving procedures of the users without being manually set by the users, the tedious properties of user operation can be prevented, specific physical buttons can be omitted, and influence on the aesthetics of internal environments of the vehicle can be prevented; the quantity of the parameter information of the driving modes of the users is unlimited for the same vehicle, and the personalized driving modes of the various users can be implemented.
Owner:ZHICHEAUTO TECH BEIJING
Metro ticket buying and checking method based on two-dimension code recognition
ActiveCN104134142AImprove comfortReduced comfortTicket-issuing apparatusUser identity/authority verificationKey issuesPublic key certificate
The invention discloses a metro ticket buying system and an entrance and exit ticket checking system based on the two-dimension code recognition technology. Smartphone terminals, smartphone application programs, a metro ticket selling and checking system background recharging server, automatic metro entrance and exit ticket checking systems and a CA center are included. The metro ticket selling and checking system background recharging server, each smartphone application program and each automatic metro entrance and exit ticket checking system respectively have a unified center public key issued by the CA center, a public key and a private key which are independent of each other and issued by the CA center and a public key certificate issued by the CA center. A user buys a ticket and has the ticket checked through the mobile phone program and two-dimension codes. The ticket buying efficiency is improved, the ticket buying time is saved, ticket card cost is reduced, paper is saved, timeliness and uniqueness of ticket cards are guaranteed, and metro tickets can be bought and checked fast, efficiently and safely.
Owner:SOUTHEAST UNIV
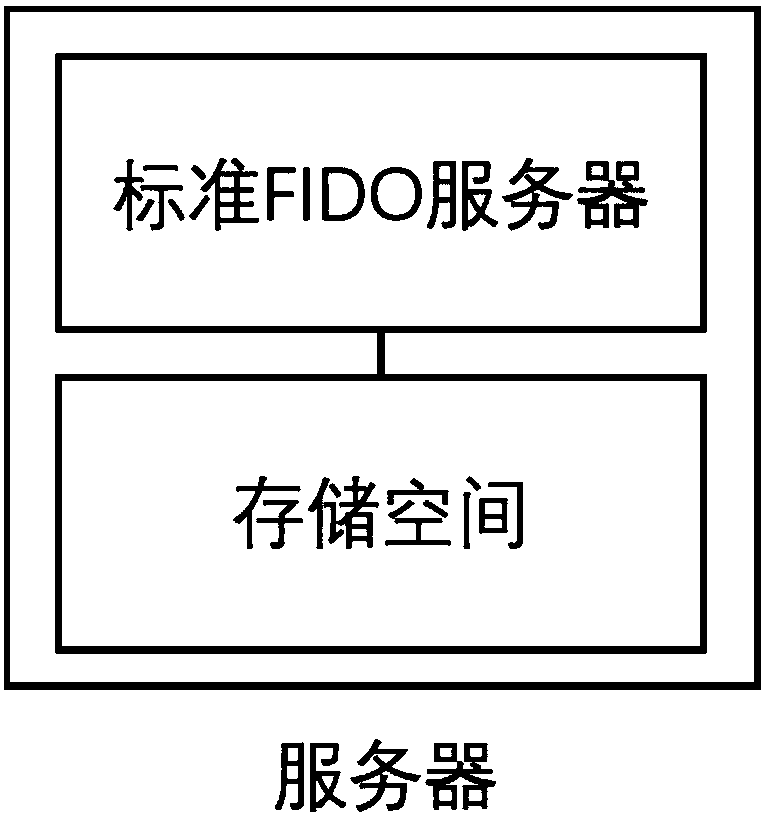
Identity authentication server and identity authentication token
ActiveCN108092776APrevent replay attacksAddressing leaked passwordsUser identity/authority verificationClient-sideNon-repudiation
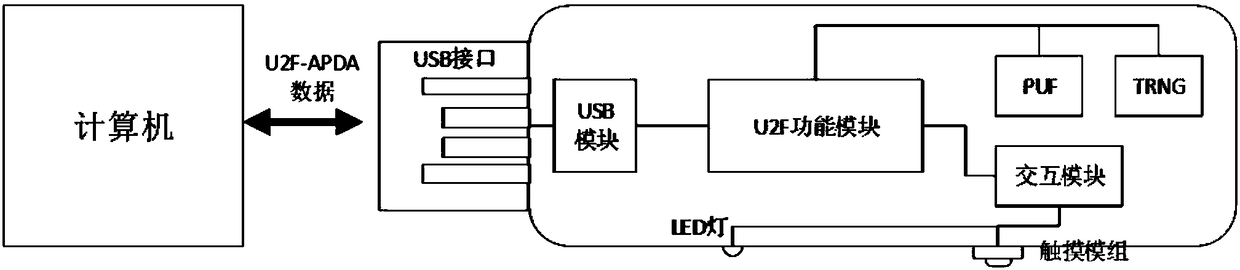
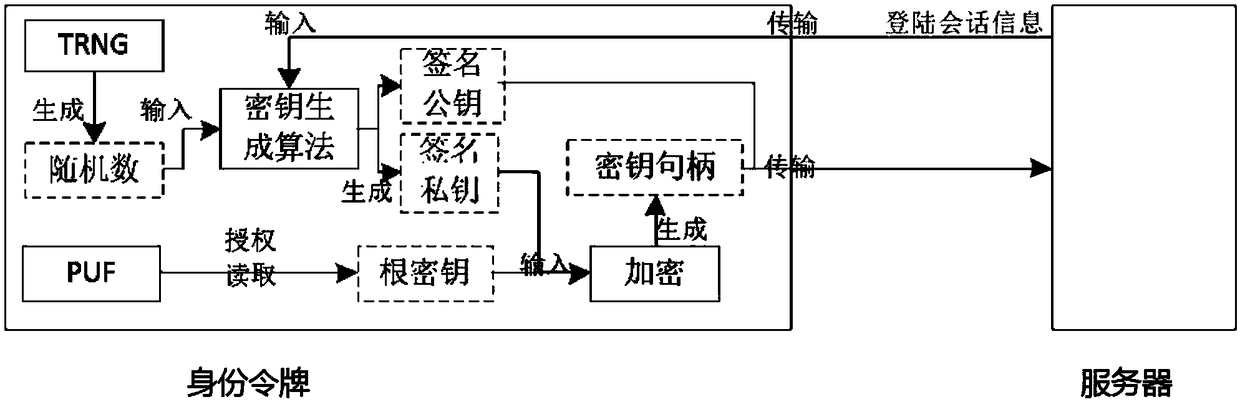
The invention discloses an identity authentication server and an identity authentication token, wherein the identity authentication server comprises a standard FIDO server and a storage space for storing keys, namely, a database, which are connected with each other; the identity authentication token is based on physical unclonable and the FIDO U2F protocol and comprises a U2F module, and a PUF module,a TRNG module, a USB module and an interaction module, which are connected with the U2F module, and a touch module connected with the interaction module; and an identity token interacts with a client browser, and the client browser in turn interacts with an FIDO server in the authentication server. According to the identity authentication server disclosed by the invention, the physical unclonable function is combined with the FIDO, the uniqueness and non-replicability of the token are ensured by the physical unclonable function, and the accuracy of the user identity and the non-defective modification and non-repudiation of the operation are ensured by the FIDO.
Owner:NARI INFORMATION & COMM TECH
Shared names
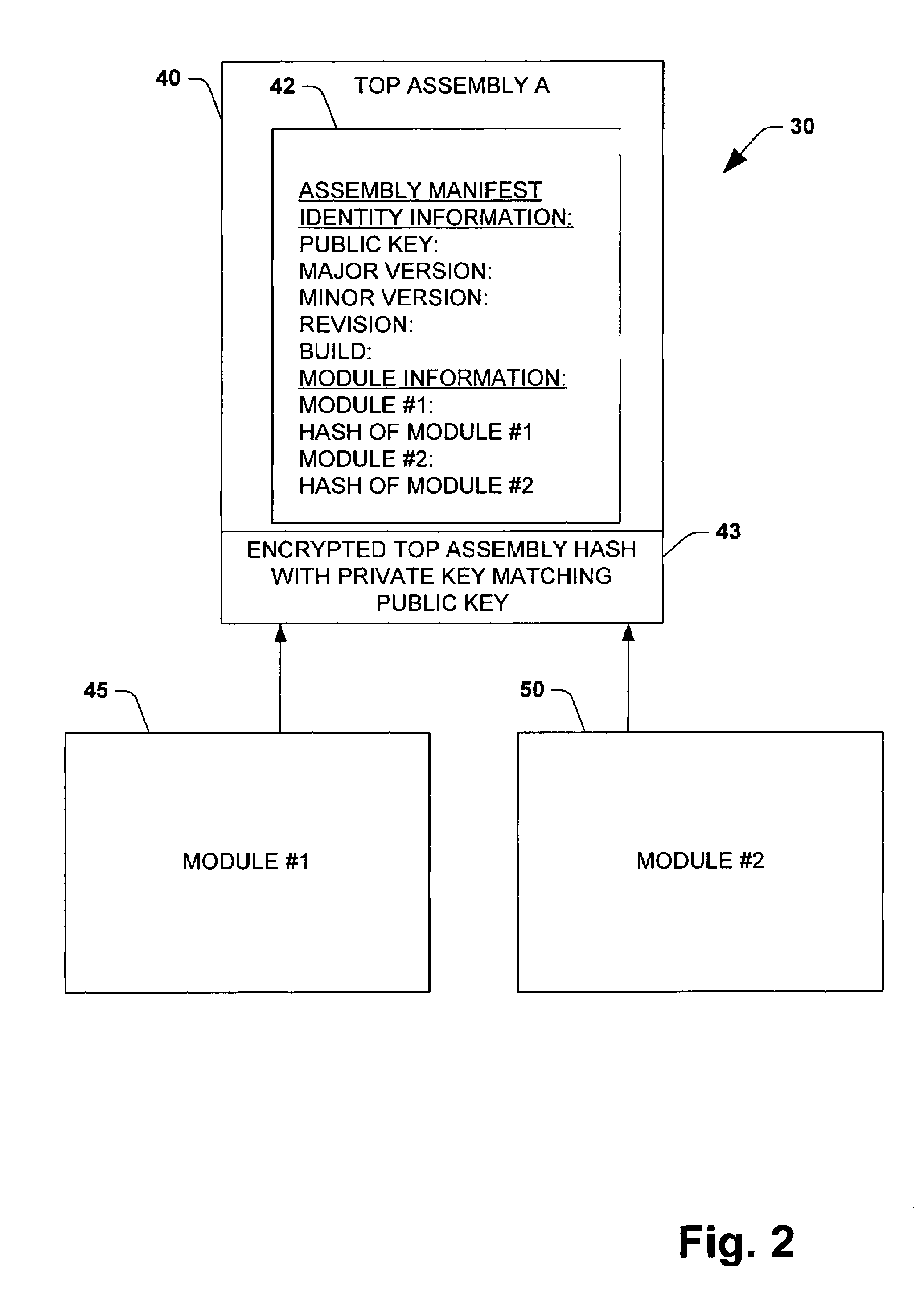
InactiveUS7117371B1Improve relationshipGuarantee name uniquenessKey distribution for secure communicationPublic key for secure communicationDigital signatureApplication software
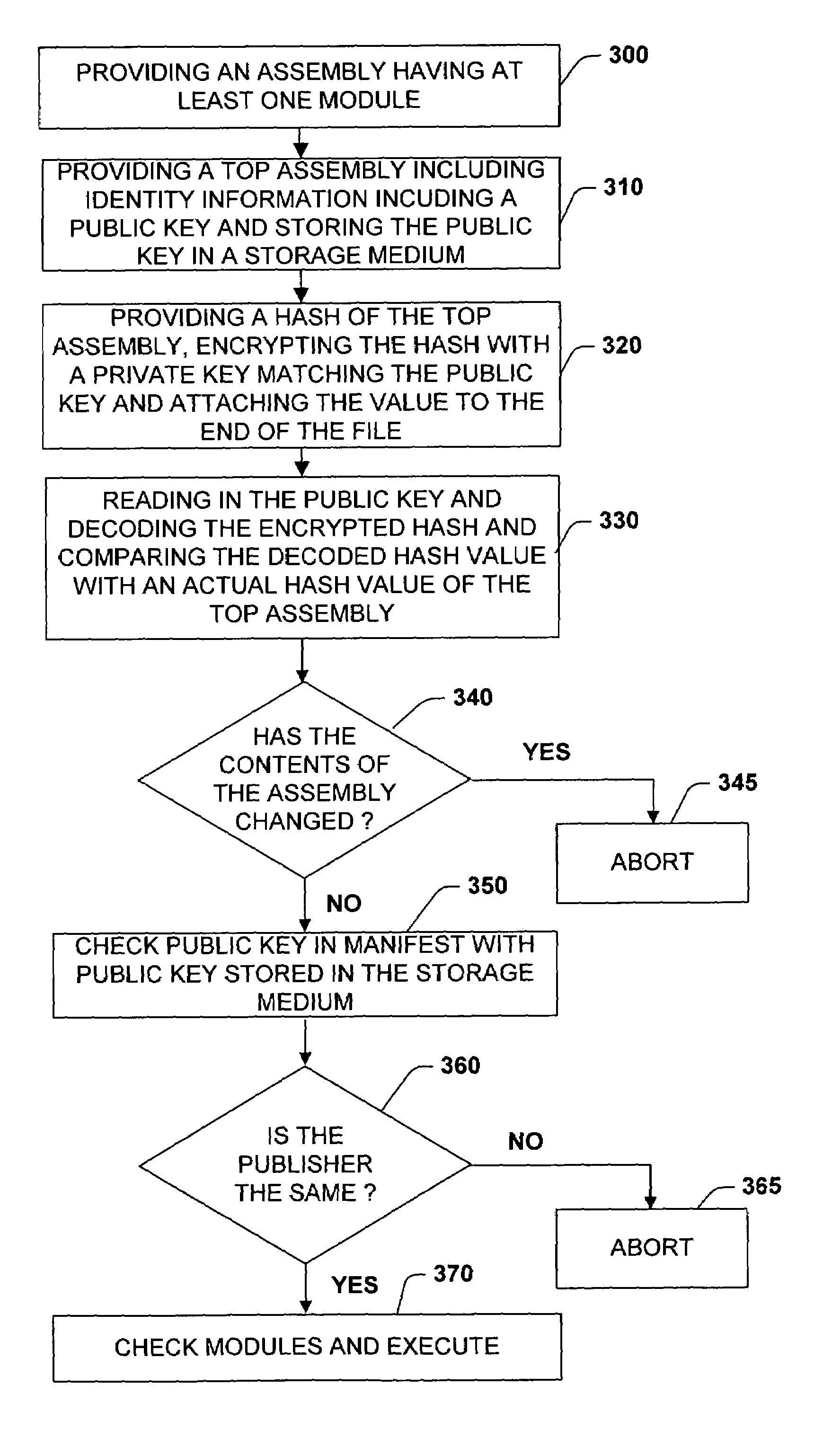
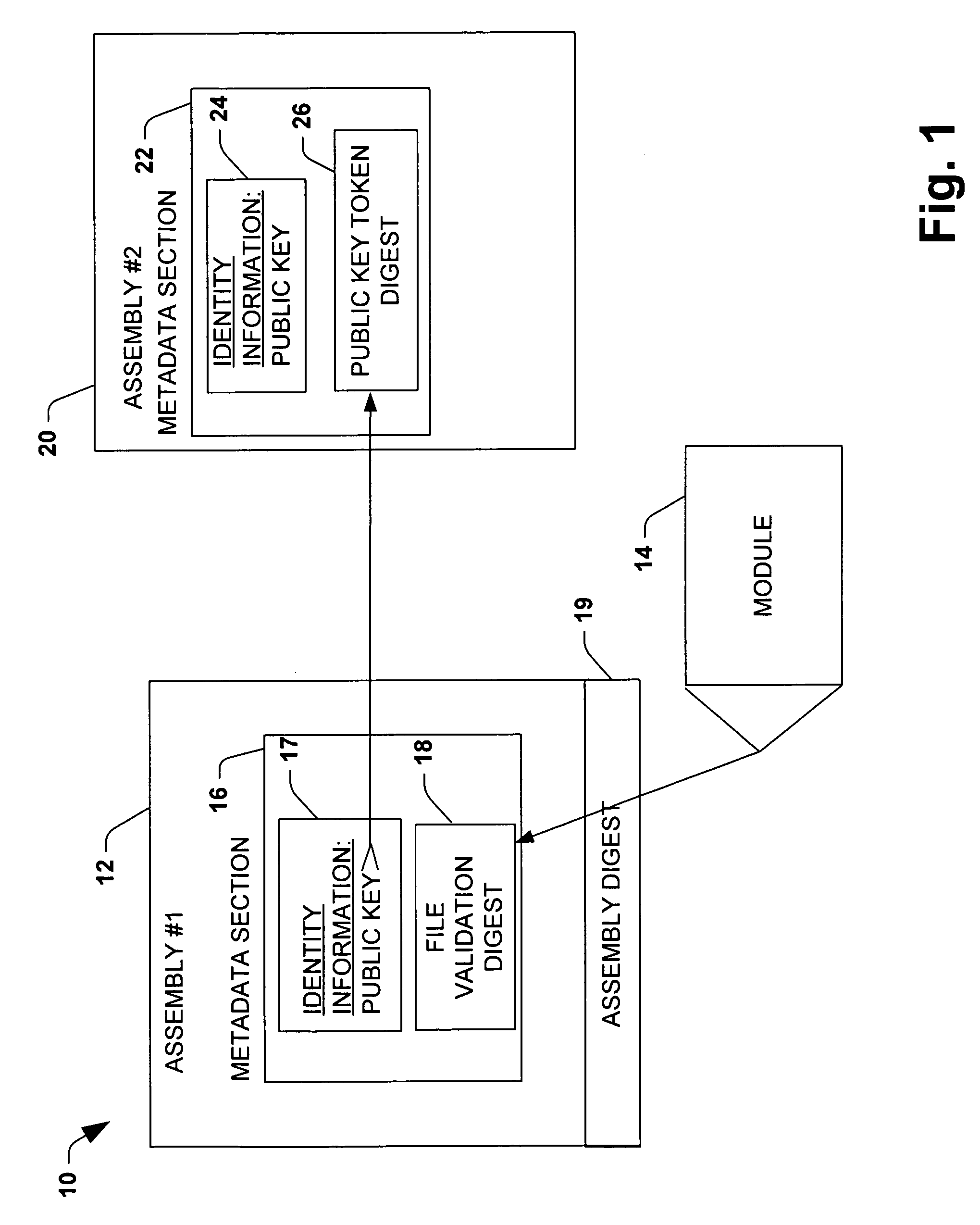
A system and method is provided for providing security to components or assemblies employed by application programs during runtime. The present invention employs digital signature keys to ensure that an assembly name that is published is unique because the assembly is published with a publisher's public key. This prevents others from publishing an updated version of an assembly that claims to be published from the same publisher. The present invention guarantees name uniqueness and prevents name spoofing because the original publisher is the only one with the private key matching the public key related to a published assembly. Due to the fact that the public keys are stored in each reference, the caller can be assured that the assembly that the caller is binding to at runtime comes from the same publisher that owns the private key.
Owner:MICROSOFT TECH LICENSING LLC
Universal remote controller
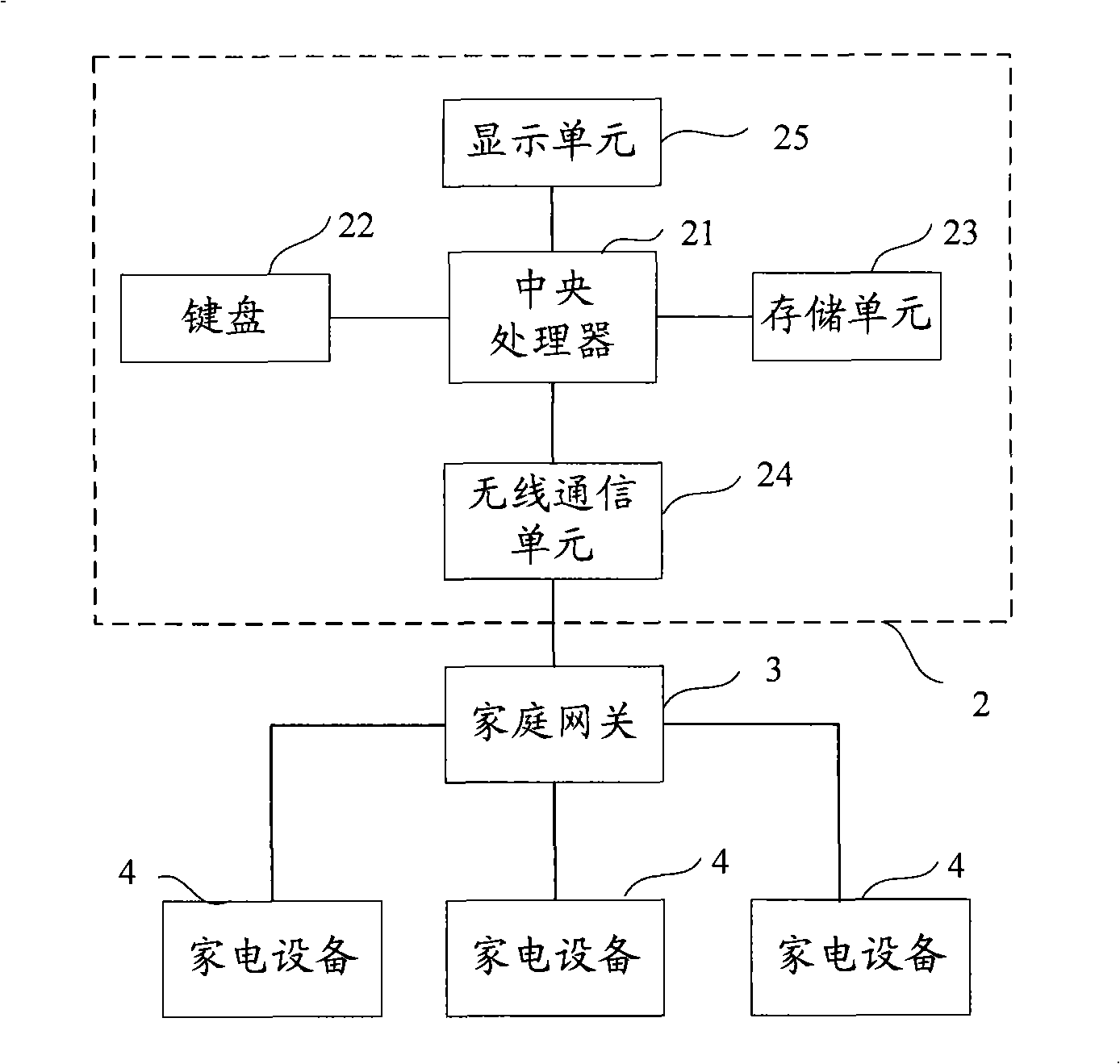
InactiveCN101315727AUniqueness guaranteedGuaranteed Unique SpecificityTelemetry/telecontrol selection arrangementsTransmission systemsCommunication unitHome area network
The invention discloses a general remote controller used for controlling household appliances which is connected with a home gateway, comprising a central processing unit, a keyboard connected with the central processing unit, a display unit, a wireless communication unit and a storage unit; the storage unit is used for storing description file of the household appliances; the wireless communication unit is used for communicating with the household appliances connected with the home gateway by the home gateway; the keyboard and the display unit are used for providing a man-machine interaction interface. The invention provides a general remote controller which can control the household appliances in home local area network and can ensure the uniqueness of a main control node.
Owner:HAIER GRP CORP +1
Multi-device interaction cooperative method, device, equipment and computer readable medium
InactiveCN107919119AGuaranteed experienceUniqueness guaranteedDigital data processing detailsSpeech recognitionTerminal equipmentSpeech identification
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Secure mobile terminal electronic authentication method and system
ActiveCN106506472AReduce manufacturing costUniqueness guaranteedUser identity/authority verificationPayment protocolsTrusted applicationApplication software
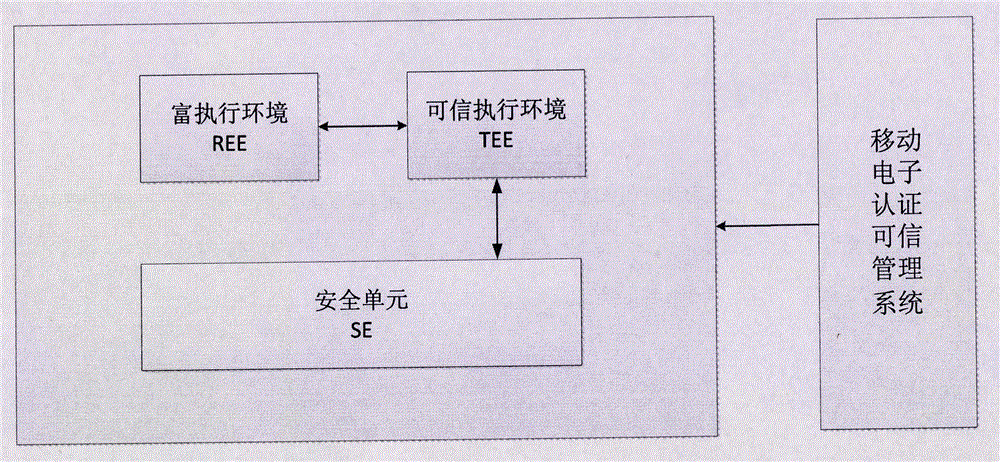
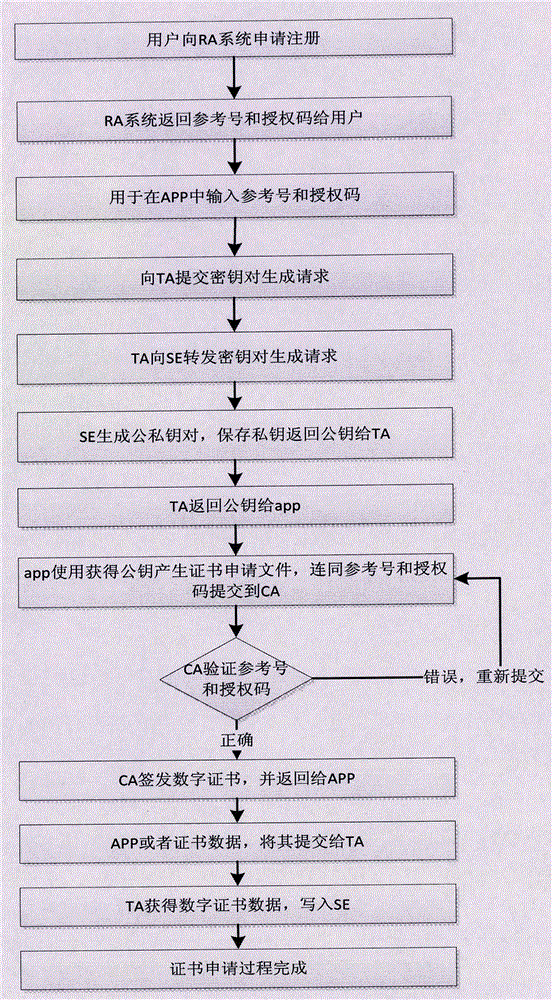
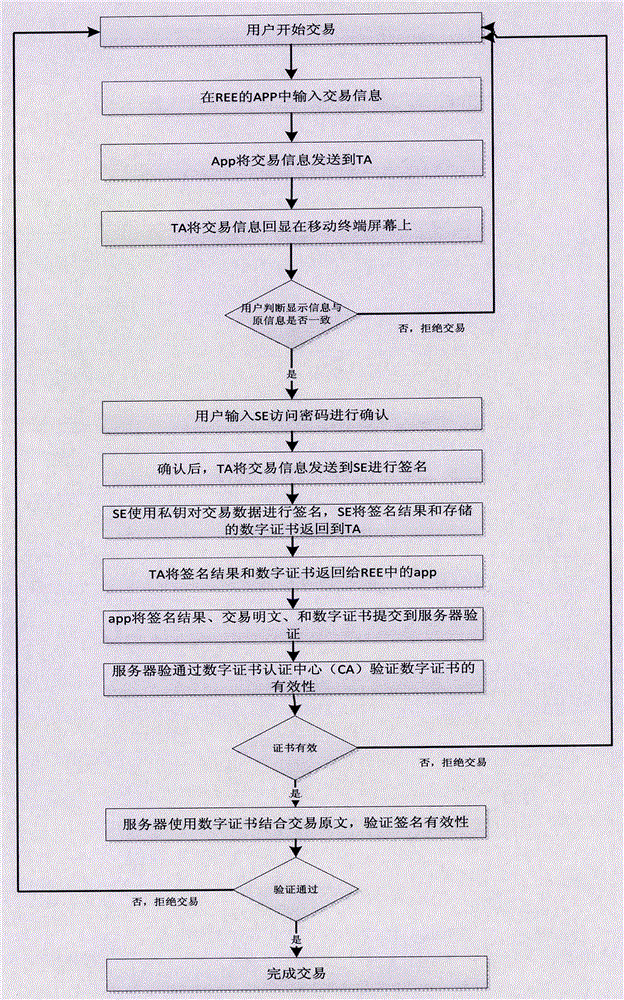
The invention provides a secure mobile terminal electronic authentication method and system. The secure mobile terminal electronic authentication system comprises a secure element (SE) which is arranged in a mobile terminal and can store a key, and a trusted execution environment (TEE) which is arranged in the mobile terminal; a secure application applet which can run in the secure element is arranged in the secure element (SE); the secure application can generate a public-private key pair for electronic signature; and a private key is stored in the secure element (SE) and cannot be exported or duplicated. A secure redisplay trusted application (TA) is arranged in the trusted execution environment (TEE), so that transaction correctness can be confirmed artificially by a user and the transaction cannot be attacked by trojan horse in a rich execution environment (REE). The secure mobile terminal electronic authentication method and system greatly reduce high cost caused by additionally required production of hardware devices, solve the problem of using and carrying inconvenience for the user, are conducive to energy conservation and emission reduction, and save the social resources.
Owner:黄付营
Identification authentication apparatus based on finger biologic characteristics
InactiveCN101408938AImprove anti-counterfeiting performanceImprove securityCharacter and pattern recognitionVeinInterphalangeal Joint
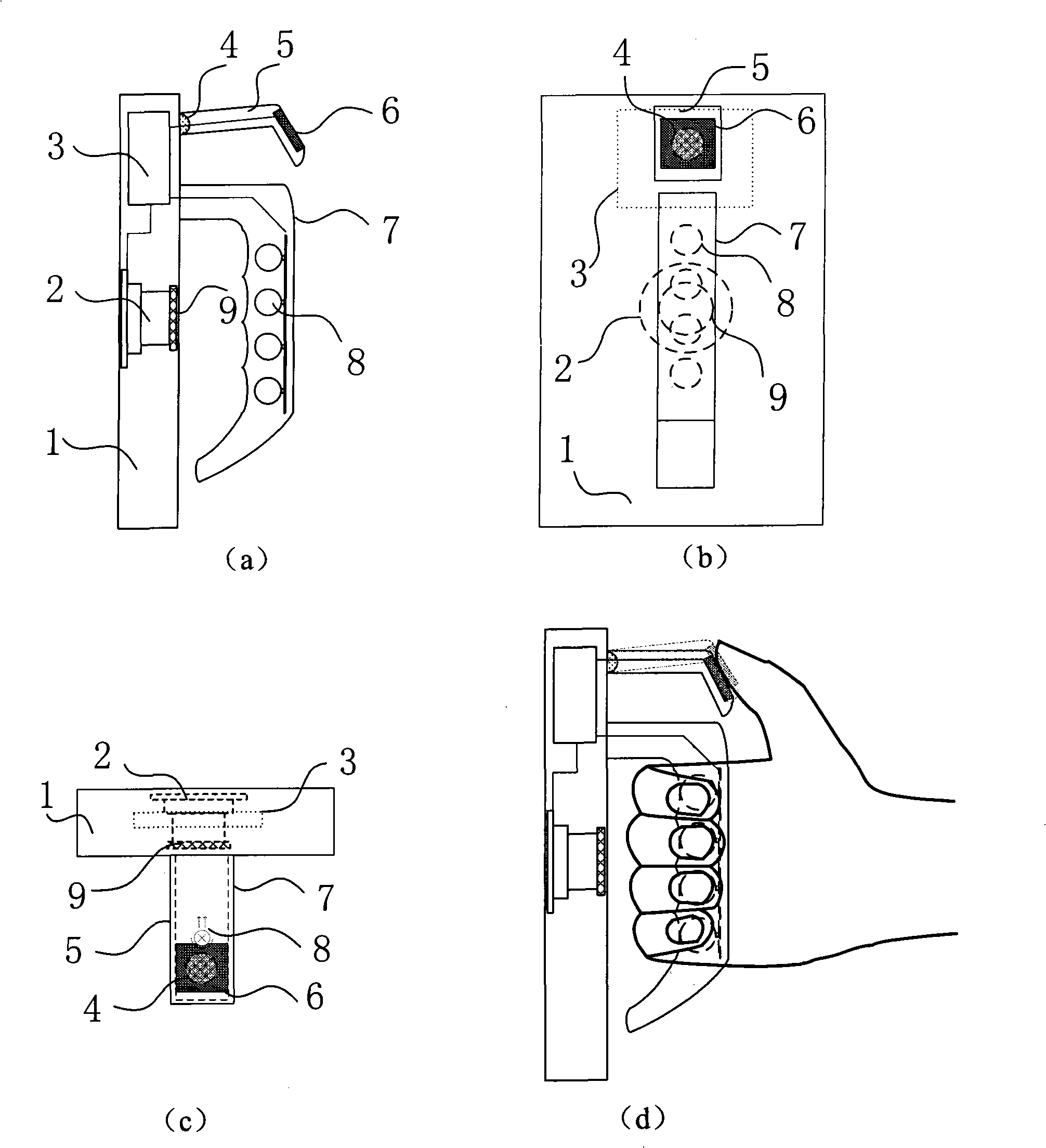
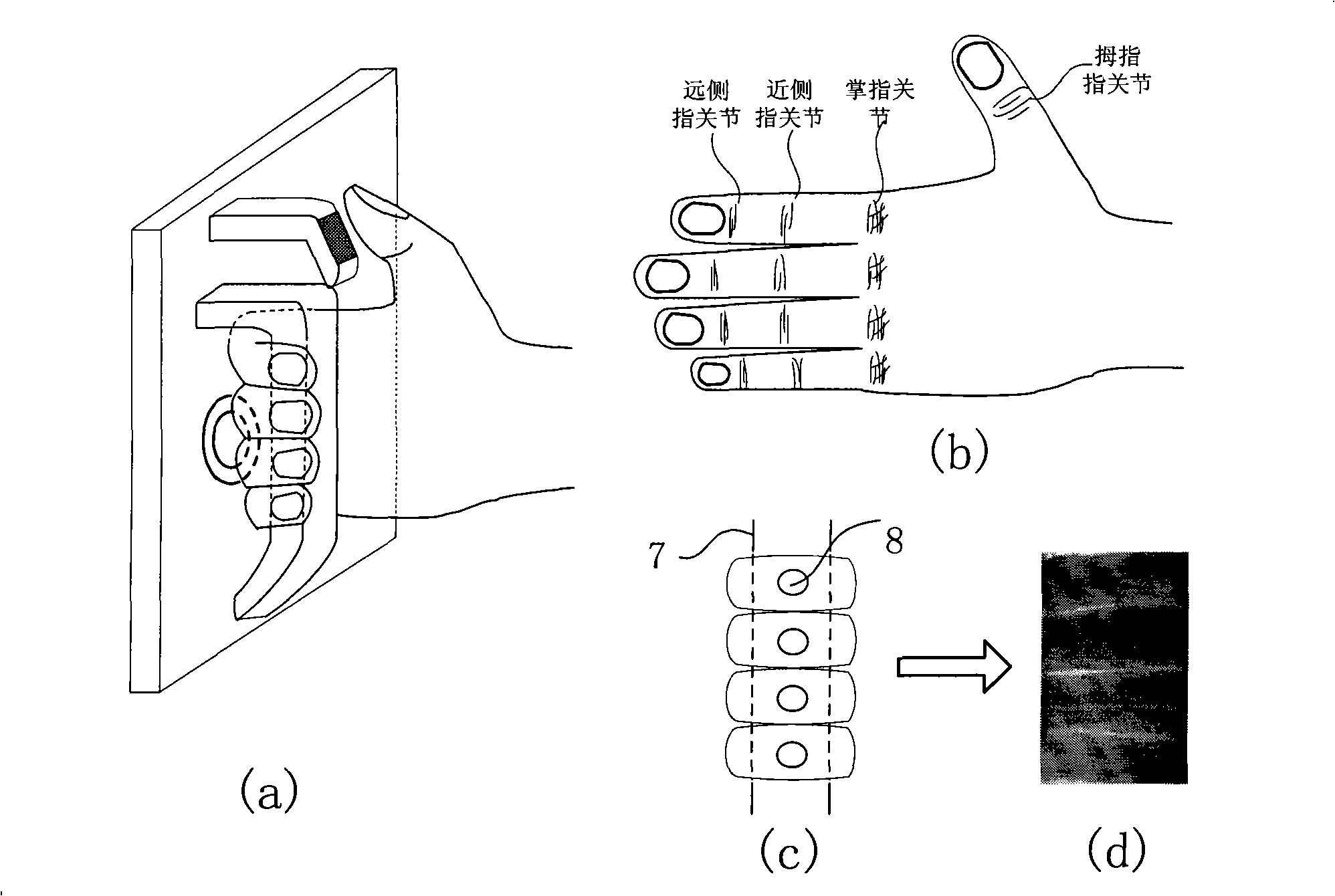
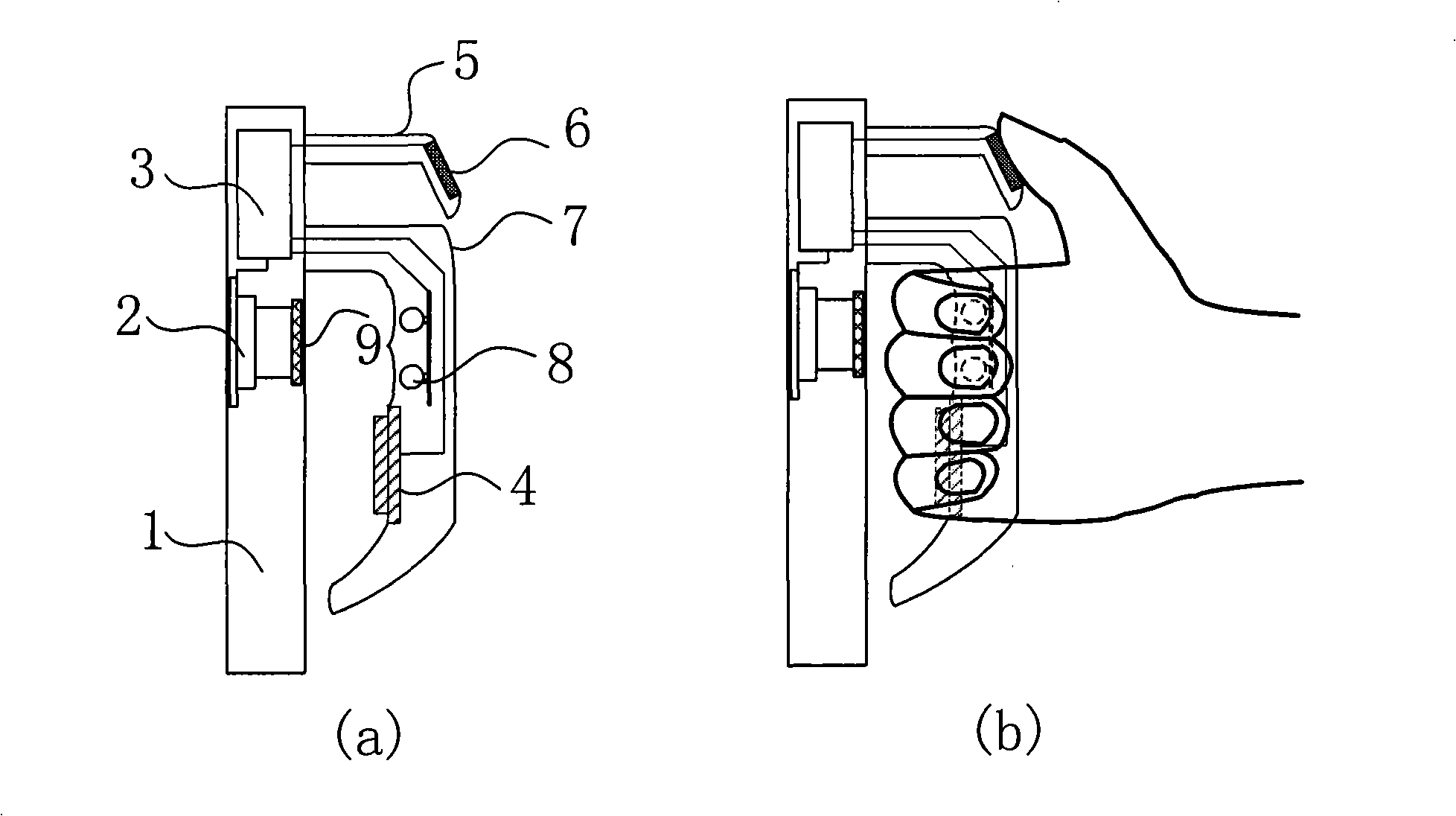
The invention discloses an identification and authentication device based on finger biometric. The device comprises a handle part, a fingerprint collection part, a light source, an image pickup part, a tact switch and a processing part. The processing part is respectively connected with the tact switch, the fingerprint collection part, the light source and the image pickup part. The device is usually in standby state, and a system starts to work when the tact switch is triggered: first, the light source is started to illuminate the position between the knuckle at a proximal interphalangeal joint of a finger and a distal interphalangeal joint of the finger, and the image pick-up part obtains a finger vein image; meanwhile, the fingerprint collection part collects a thumb fingerprint image, then the two images are subject to preprocessing and feature extraction respectively, and matched with the finger vein feature and the fingerprint feature stored in a database; finally, the judgment whether the authentication is successful is obtained by evaluating the similarity thereof. The invention fully utilizes two different biometrics at different cutaneous layers of the finger, can enhance the anti-counterfeiting property, the security and the accuracy of the system.
Owner:SOUTH CHINA UNIV OF TECH
Commodity double-layer anti-fake method based on technologies of internet of things
Provided is a commodity double-layer anti-fake method based on technologies of internet of things. The commodity double-layer anti-fake method based on the technologies of the internet of things comprises a plain code layer, a code layer, a mobile terminal, a server and a database. The plain code layer only contains inquiry codes which are used for inquiry of commodity information. A user obtains an inquiry code through the mobile terminal, and the inquiry code is automatically sent to the server. The server obtains a commodity information code through a decipherment algorithm, inquires corresponding commodity information from the database, and then sends the commodity information back to the mobile terminal. The code layer only contains verification codes which are used for verification of authenticity of a commodity, wherein a verification code and a corresponding inquiry code are a pair of rule codes which are bound in a one-to-one correspondence mode. The user obtains the verification code through the mobile terminal which is provided with identification software of two-dimension codes, bar codes or digital codes, and the verification code is automaticlly sent to the server. The server matches the verification code and the inquiry code, and sends a matching result back to the mobile terminal. The commodity double-layer anti-fake method based on the technologies of the internet of things has the advantages of being good in anti-fake performance, providing convenience, and being high in encryption performance, rapid, not prone to being forged, and beneficial for protecting rights and interests of consumers and enterprises.
Owner:HUNAN IOT ONLINE TECH
Anticounterfeit mark comprising a plurality of small signs and method for forming the same
InactiveCN1350274APrevent forgeryBig investmentStampsOther printing matterMarking outComputer science
An anti-fake mark composed of a plurality of minute markers or patterns and forming method thereof to identify an article whether a forgery and prevent forgery. The method for identifying the article includes forming at least one unique mark comprising a plurality of minute markers or patterns, which is randomly dispersed in the mark. The invention has a advantage of preventing forgery of an article by a forger as well as easily identifying and comparing.
Owner:蔡 嘉伦
Energy management and coordination control system and method for wind and solar energy distributed power generation independent micro grid
InactiveCN104092303AMeet the need for timeliness of controlAchieve energy balanceCircuit arrangementsSustainable buildingsMicro gridDC-BUS
The invention discloses an energy management and coordination control system and method for a wind and solar energy distributed power generation independent micro grid. The energy management and coordination control system is composed of a distributed power generation system, a wireless communication system and a monitoring system, and an AC and DC hybrid topology structure is adopted. Specifically, main power generation units are composed of the wind power generation unit, the photovoltaic power generation unit and other micro power supplies, an energy storage device is of a hybrid energy storage type including a lead-acid storage battery and a super capacitor, the micro wind power generation unit and the solar photovoltaic power generation unit are converged to a DC bus through a power electronic conversion device, the hybrid energy storage device is connected with the DC bus through a bidirectional power converter, the DC bus exchanges energy with an AC bus through a DC / AC converter, and a medium wind power generator is connected with the AC bus. According to the energy management and coordination control system and method, a multi-agent coordination control system can be applied to a micro grid monitoring system and is developed based on a JADE platform, and energy management and optimal scheduling of the micro grid can be achieved.
Owner:INNER MONGOLIA UNIVERSITY
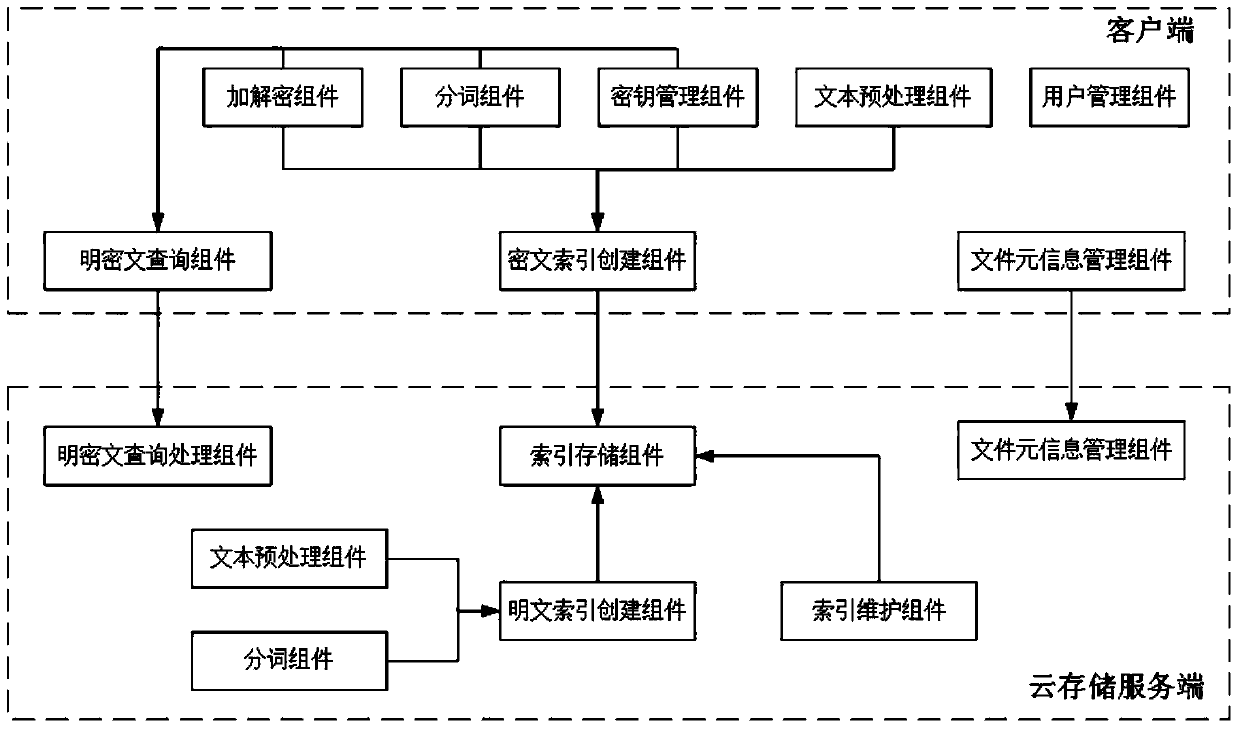
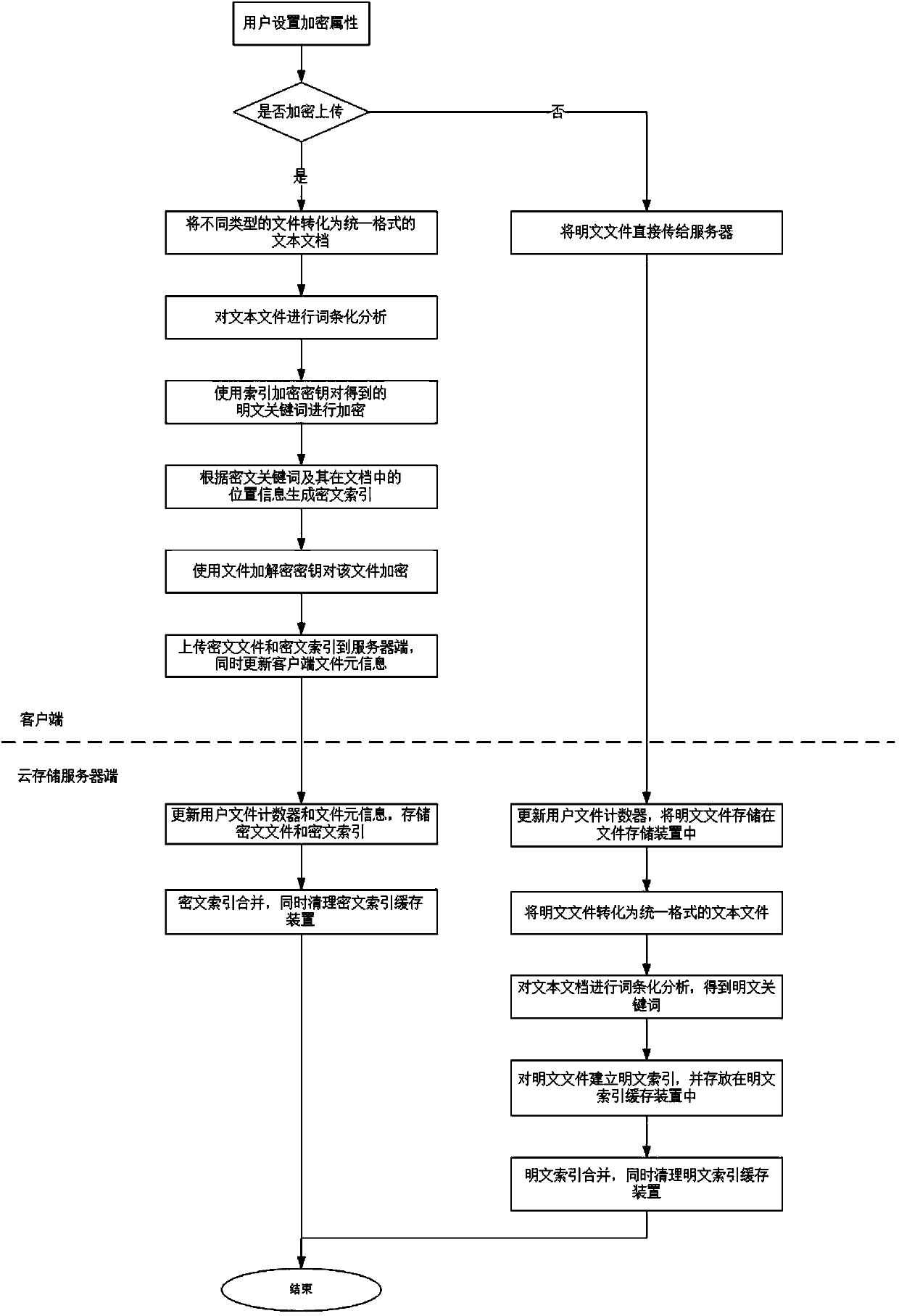
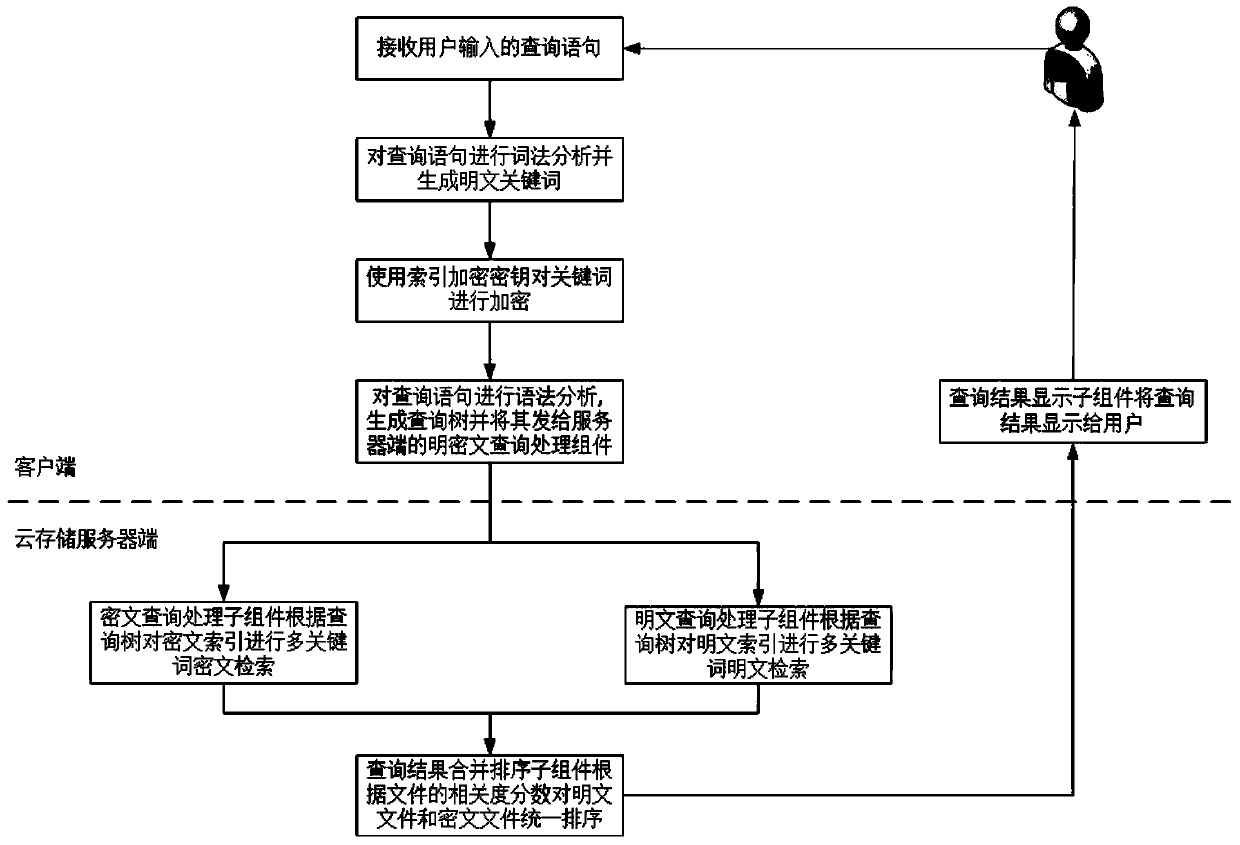
Multi-keyword plaintext and ciphertext retrieving method and device oriented to cloud storage
InactiveCN103593476AFix bugsAddress riskKey distribution for secure communicationComputer security arrangementsPlaintextComputer hardware
The invention relates to a multi-keyword plaintext and ciphertext retrieving method and device oriented to cloud storage and relates to the field of information safety. The method includes the following steps that firstly, a client terminal performs lexical analysis according to inquiry statements and generates plaintext keywords; secondly, a corresponding user index encryption key is obtained according to a main key bound with the identity of a user, and the plaintext keywords are encrypted with the encryption algorithm of the index encryption key, and ciphertext keywords are generated; thirdly, multi-keyword ciphertext retrieving is performed on a ciphertext index in a cloud storage server according to an inquire tree generated by the client terminal, and retrieved data element information and retrieved relevancy scores undergo inquiry result merging and sequencing; fifthly, inquiry result merging and sequencing are performed in the cloud storage server with the same method; sixthly, a unified sequence result is sent to the client terminal, and an inquiry result is displayed to the user. According to the multi-keyword plaintext and ciphertext retrieving method and device oriented to the cloud storage, a key management scheme which is higher in safety degree is provided, plaintext and ciphertext united retrieving can be supported and multi-keyword retrieving can be provided.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
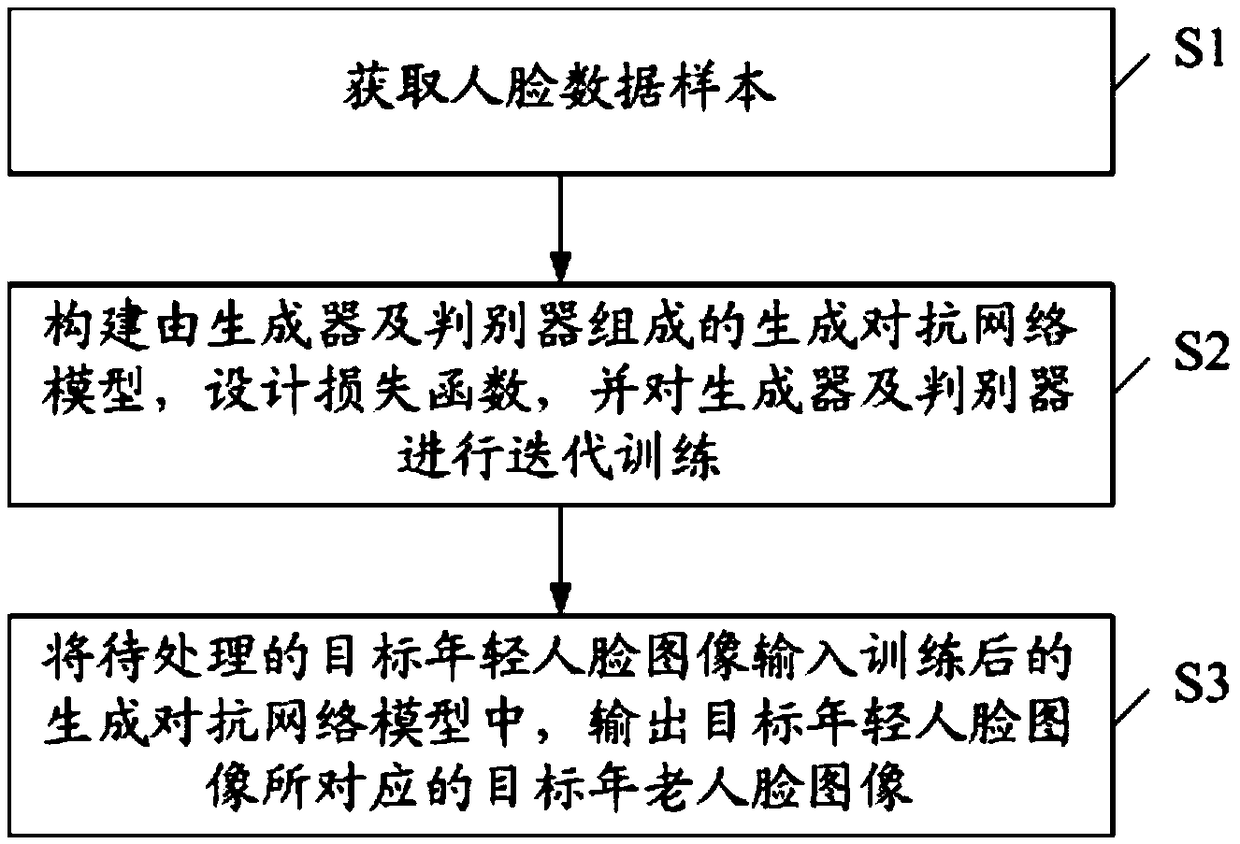
A method for predict face change based on generate antagonistic network
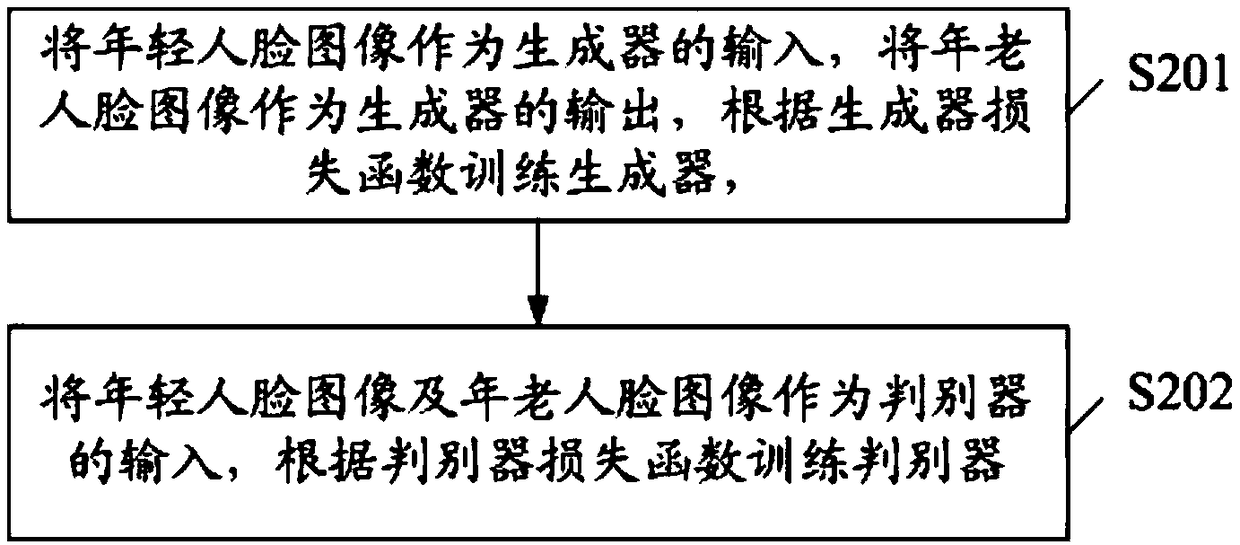
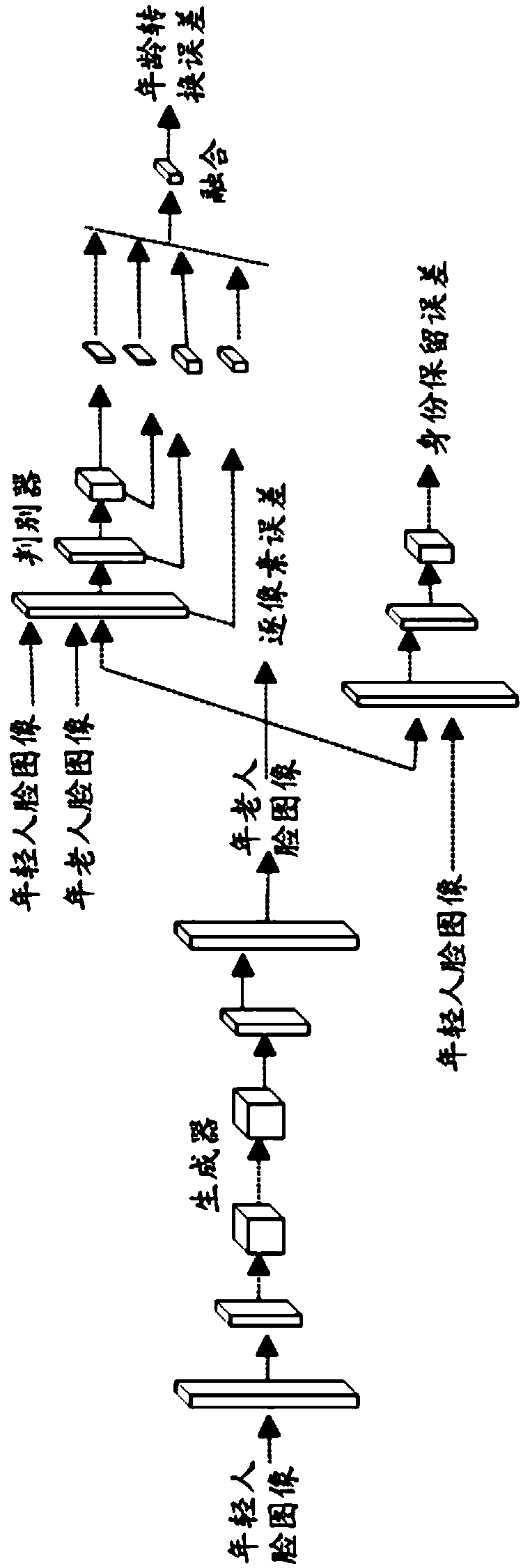
InactiveCN109308450AUniqueness guaranteedReduce complexityCharacter and pattern recognitionDiscriminatorOlder people
The invention discloses a face change prediction method based on a generation antagonism network, which comprises the following steps: S1, acquiring a face data sample; S2, constructing a generation antagonism network model composed of a generator and a discriminator, designing a loss function, and iteratively training the generator and the discriminator; S3, inputting the target young person faceimage to be processed into the generated antagonism network model after training, and outputting the target old person face image corresponding to the target young person face image. Adopting the invention, by constructing a unique generation antagonism network model and a loss function, the invention has good robustness to age change, and at the same time, the invention also considers the information changes of forehead and hair, and further improves the accuracy and uniqueness of prediction.
Owner:NEXWISE INTELLIGENCE CHINA LTD +1
Authentication authorization method and system
InactiveCN101303724AEasy to useImprove securityComplete banking machinesAcutation objectsUser needsPassword
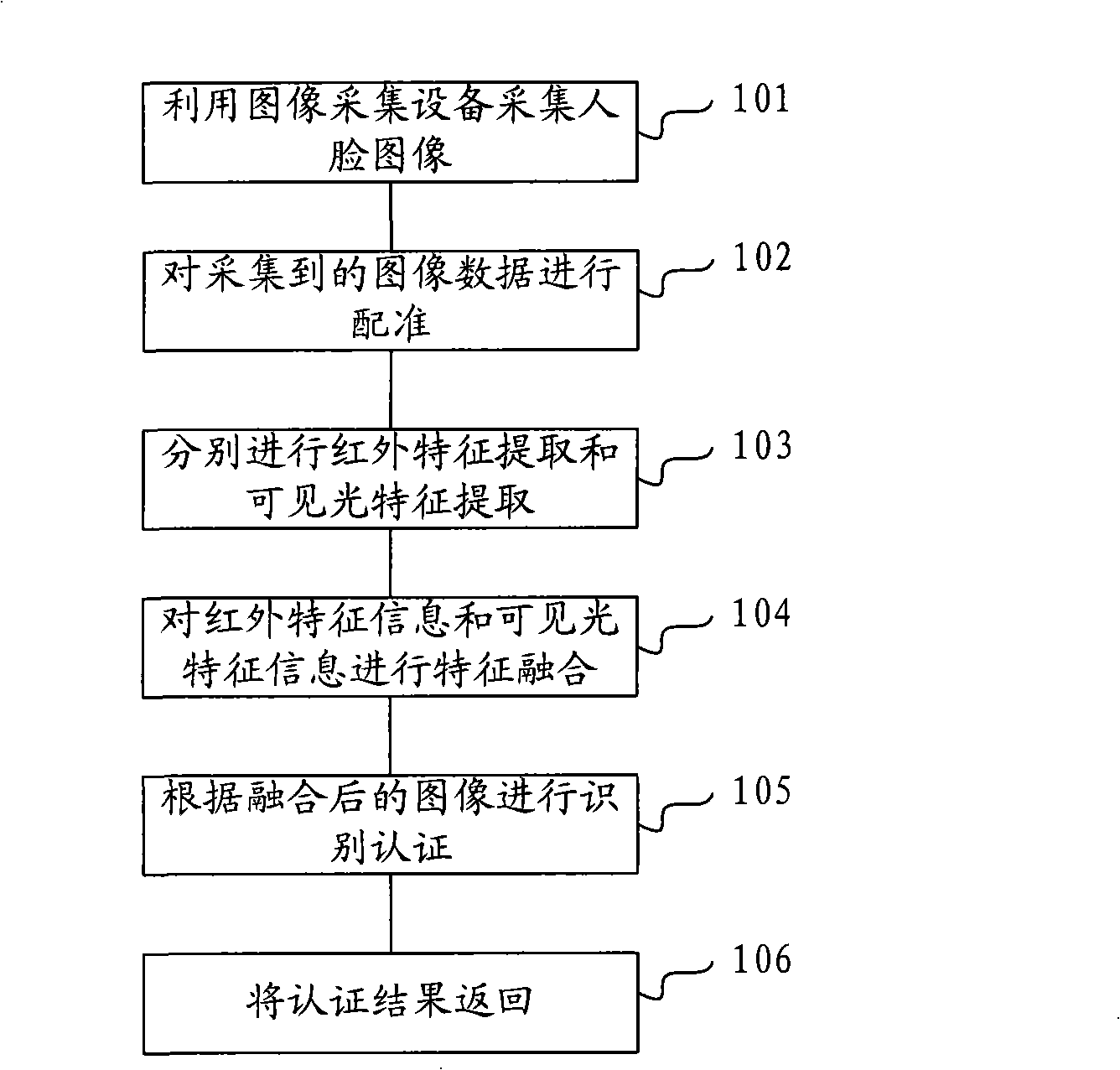
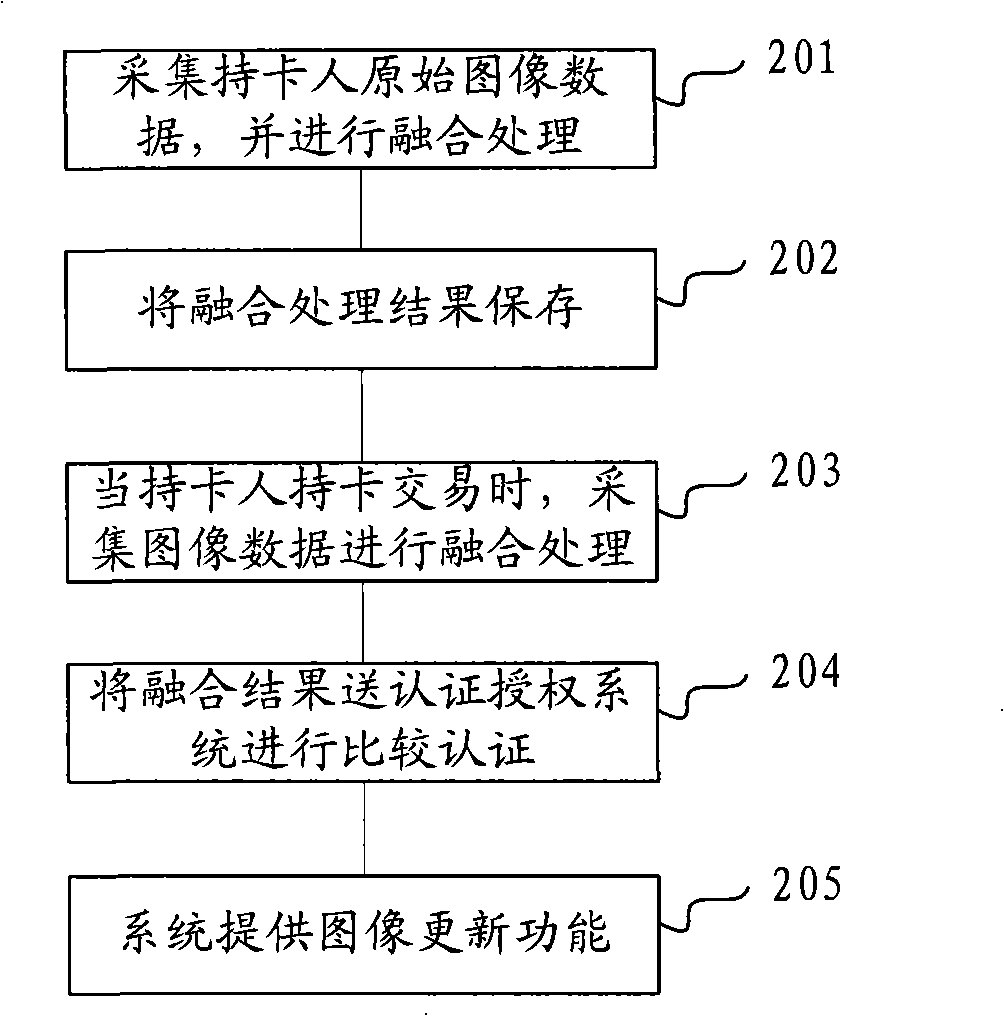
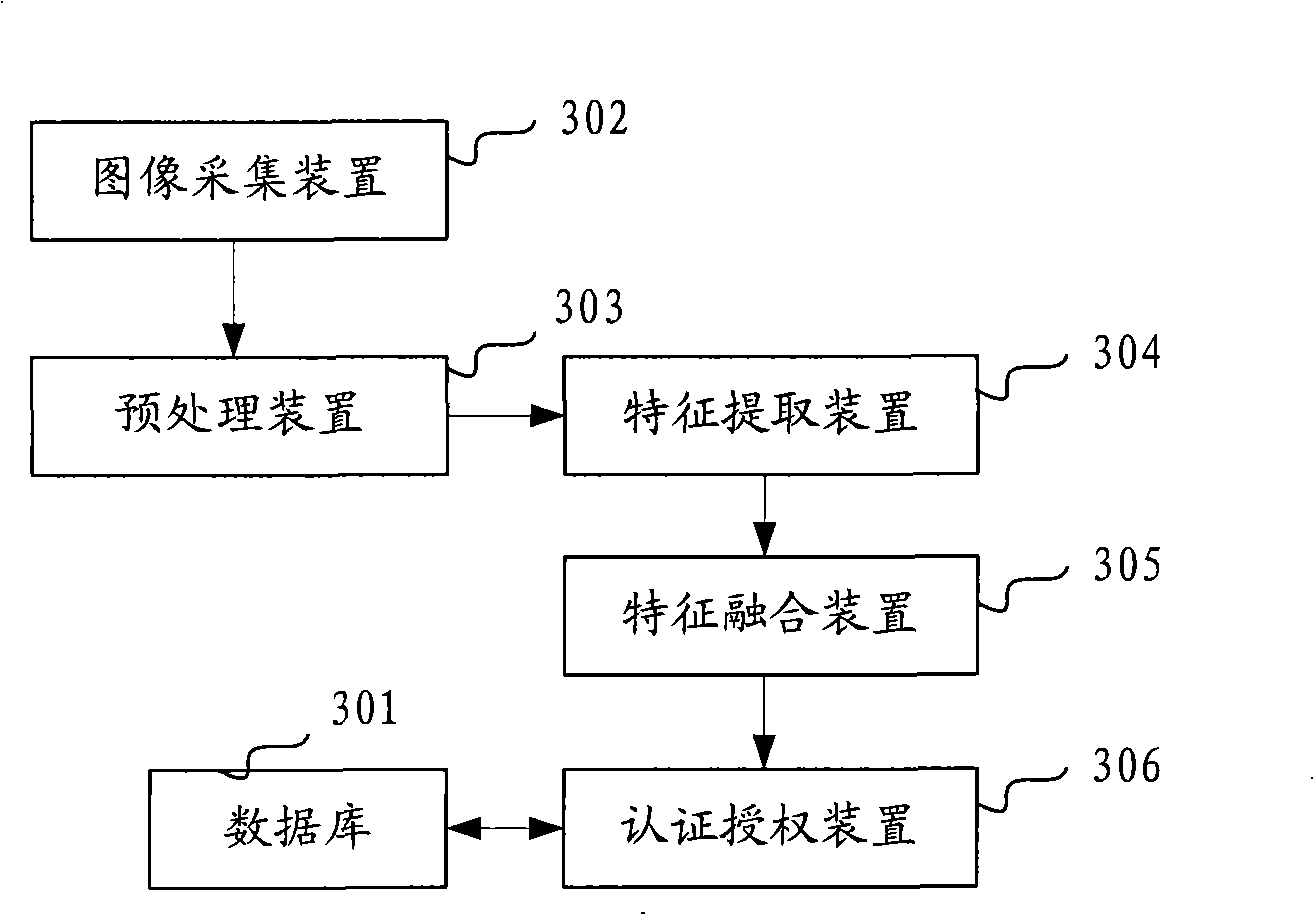
The invention discloses an authentication authorization method and an authentication authorization system and solves the problem that the traditional authentication authorization method is ineffective when the passwords are deciphered or stolen. The method includes: respectively collecting infrared image data and visible light image data on the same image; extracting the infrared characteristic information and the visible light characteristic information; carrying out characteristic integration treatment on the infrared characteristic information and the visible light characteristic information to generate the characteristic information of one image; comparing the image characteristics after being integrated with the pre-memorized image characteristics to carry out authentication authorization. Compared with the traditional password authentication authorization method, the authentication authorization method of the invention based on face identification has high safety and no dangers that the passwords are deciphered or stolen; besides, a user need not to memorize the passwords, thus being more convenient for using. The invention also discloses an authentication authorization system and a terminal system that is matched to be used. The invention can be used in the authentication process of face identification.
Owner:CHINA UNIONPAY
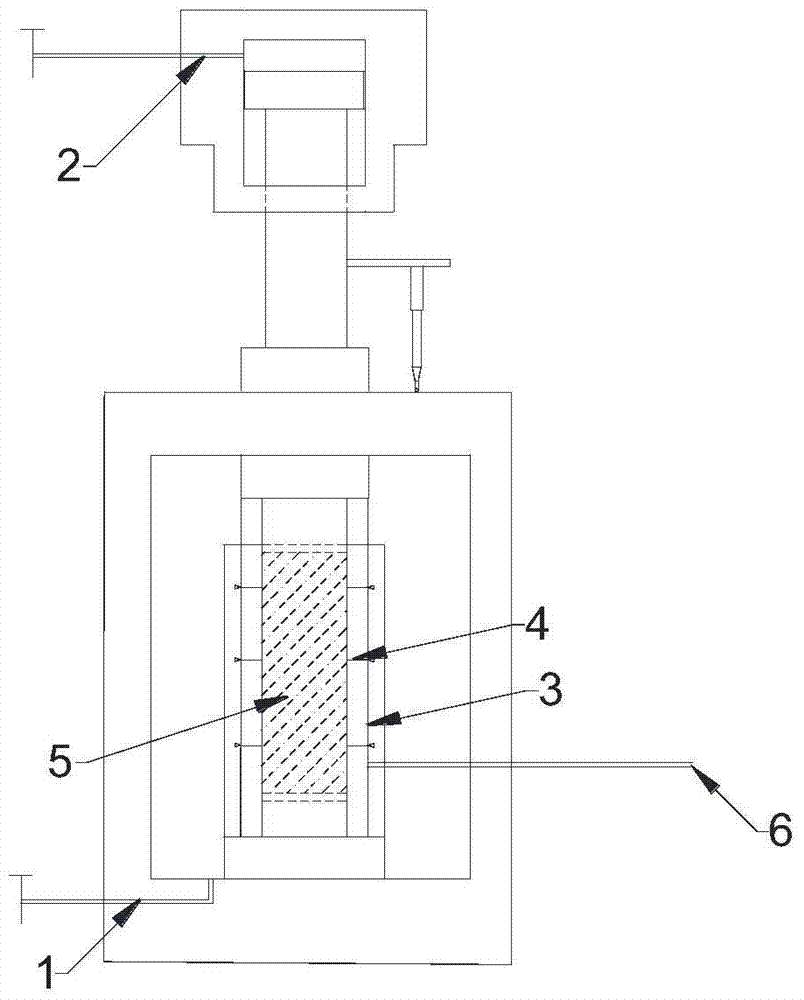
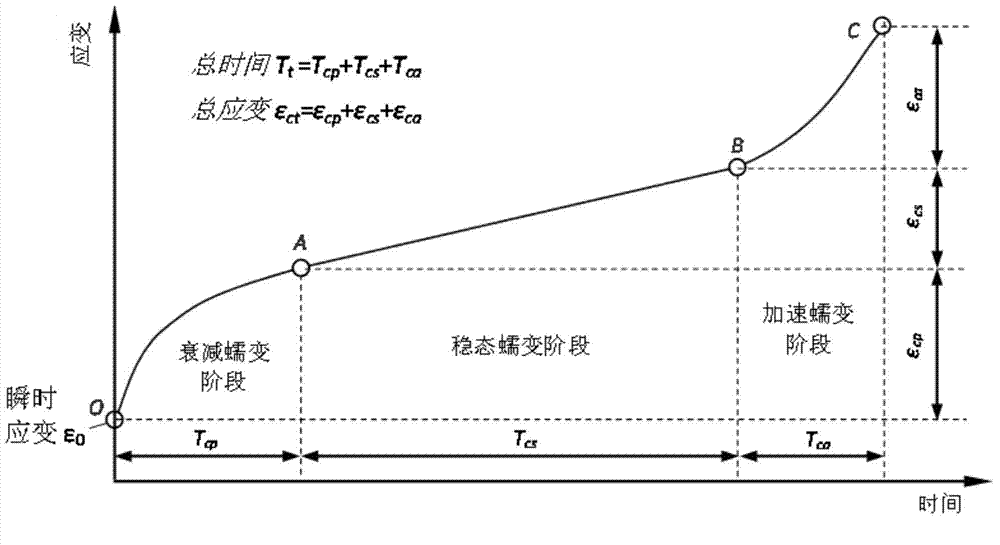
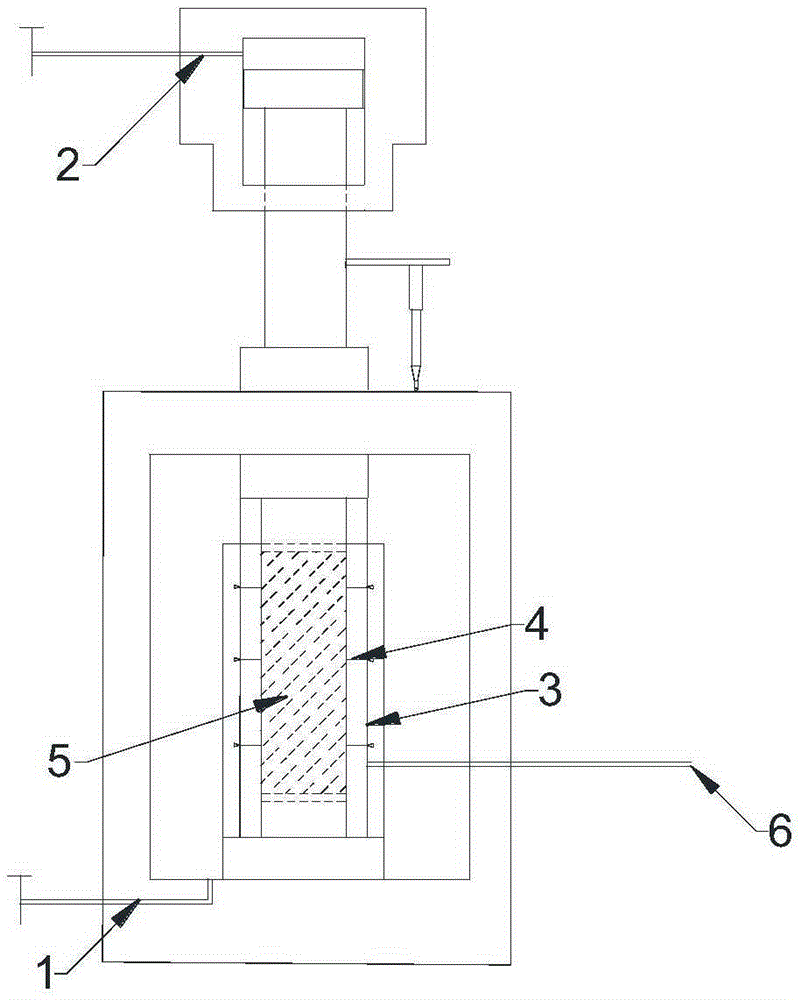
Method for determining long-period strength of rock through multistage stress staged loading creep mechanic test
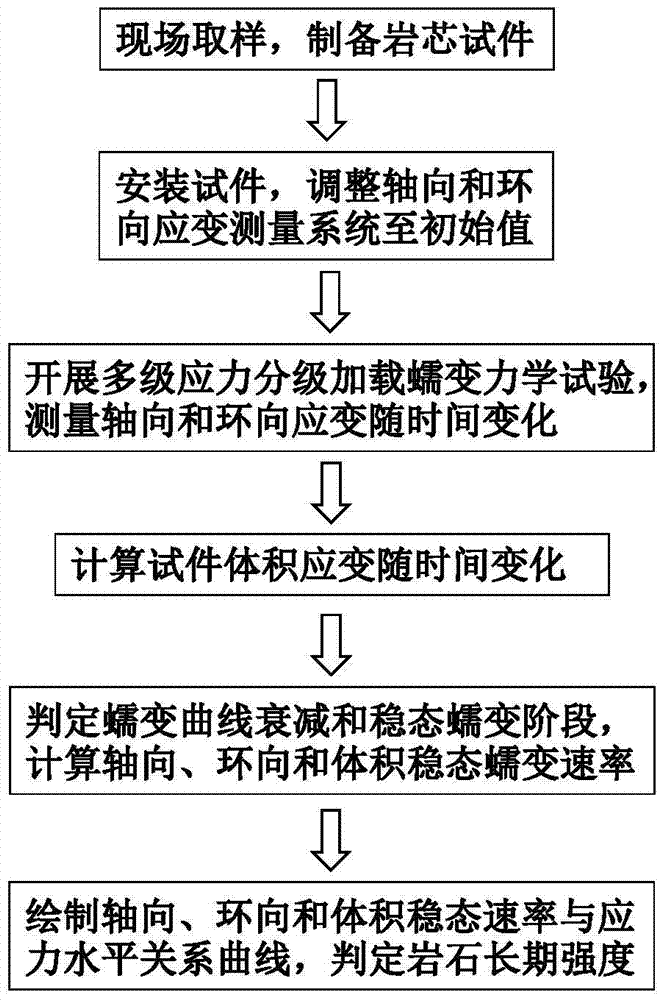
InactiveCN104849134ARemove subjective judgmentThe method is simple and reliableStrength propertiesRock coreTemporal change
The invention discloses a method for determining the long-period strength of rock through a multistage stress staged loading creep mechanic test. The method comprises the following steps that the in-site sampling is carried out, and a rock core test piece is manufactured; the test piece is arranged into a rock three-axis rheological mechanic test instrument, and an axial stress and annular stress system is regulated to an initial value; the test piece is subjected to multistage stress staged loading creep mechanic test in a stress load control mode until a specimen is damaged, and in the process, the change of the axial compression stress and the annular volume expanding stress along with the time in the whole test process under the effects of different stress is measured; the change of the size of the test piece along with the time is calculated; a rock creep curve is drawn, and the weakening creeping stage and the steady-state creep stage of the creep curve under the effect of each stage stress load are judged; the steady-state creep speed under the effect of each stage of stress load is calculated, the relationship curve of the change of the axial, annular and size steady-state creep speed along with the stress level is drawn, a crossing point is determined, and the stress corresponding to the crossing point is the long-period intensity of the rock.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
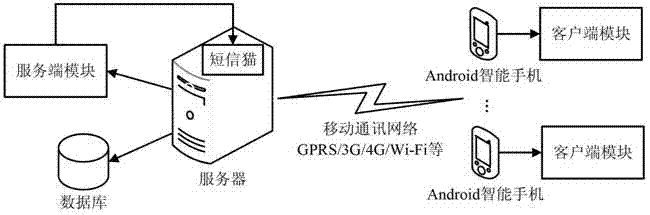
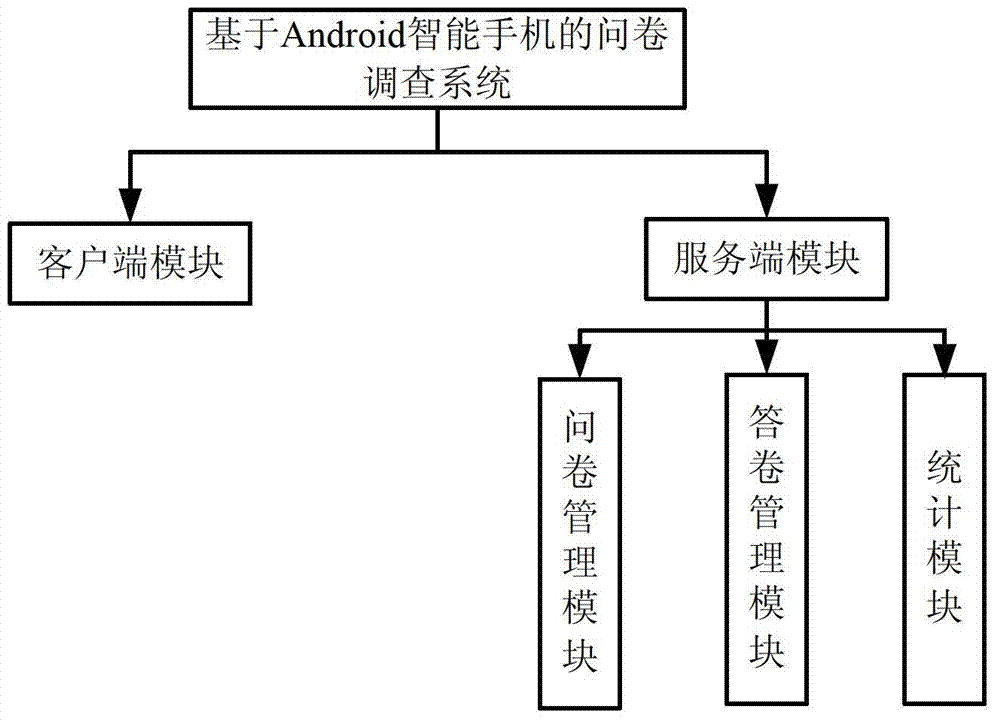
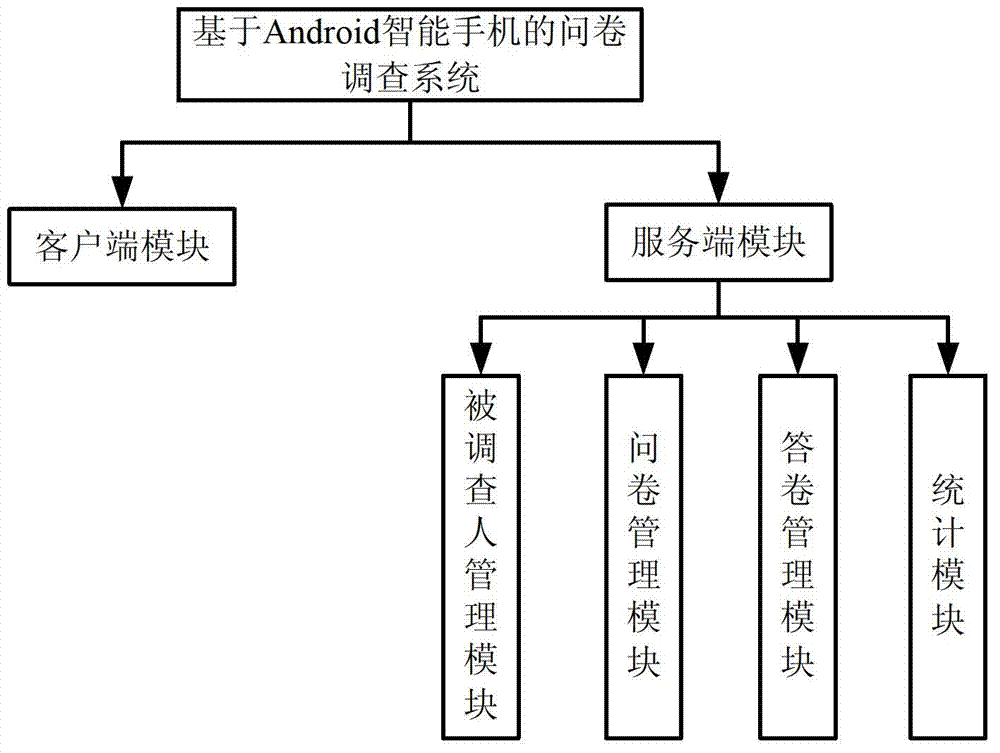
Questionnaire survey system on basis of intelligent mobile communication equipment and method thereof
InactiveCN102789606AComplete and true reflectionImprove investigation efficiencyOffice automationTransmissionSurvey resultComputer module
The invention relates to a questionnaire survey system on basis of intelligent mobile communication equipment, which comprises more than one intelligent mobile communication equipment and more than one server, wherein a client module is mounted in the intelligent mobile communication equipment and is used for realizing the recording of a questionnaire, participating in questionnaire survey and requesting for inquiring a statistical result of a survey answer sheet; a server module is mounted in the server; the server module comprises a questionnaire management module, an answer sheet management module and a statistic module; the server module is used for realizing the storage, starting and ending of the questionnaire survey, the checking and storage of the answer sheet and the statistics of the answer sheet; the questionnaire contains more than one question; each question is corresponding to more than one optional answer; the optional answer corresponding to each question can be autonomously added by an inquired person; and the client module is in data communication with the server module through a mobile communication network. The invention also provides a questionnaire survey method on the basis of the intelligent mobile communication equipment. According to the questionnaire survey method provided by the invention, a survey result is truly reflected and the survey is quick and convenient.
Owner:ZHUHAI ZAIZHOU SOFTWARE TECH
Two-dimensional code production method for wine bottle
ActiveCN105303220AEasy to participateUniqueness guaranteedCo-operative working arrangementsRecord carriers used with machinesThree levelLogistics management
The invention discloses a two-dimensional code production method for a wine bottle, and belongs to the field of bar code production, for solving the problems of logistics node management, fake and inferior products, out-zone sale and the like in the industry of liquor. Two-dimensional codes are generated by an encryption algorithm and are obtained through secondary encryption, verification and checking through a system, two-dimensional code pictures are generated, each product is endowed with a code, according to a three-level association sequence of bottles, boxes and pallets, the unique two-dimensional code of each wine bottle is acquired on a liquor filling streamline through a gatherer for association, and then the two-dimensional codes are enabled to be associated with such information as product specifications, production time, production batch numbers, groups, dealers, sale orders, delivery orders and the like through production scheduling and delivery, such that tracing of the quality of products in the whole life period, counterfeiting prevention, out-zone sale prevention, logistics monitoring, sale data monitoring, product stock monitoring and establishment of a basis of consumer group terminal client data can be realized, and vast users can rapidly and conveniently participate in quality tracing supervision.
Owner:泸州益和纸品包装有限公司
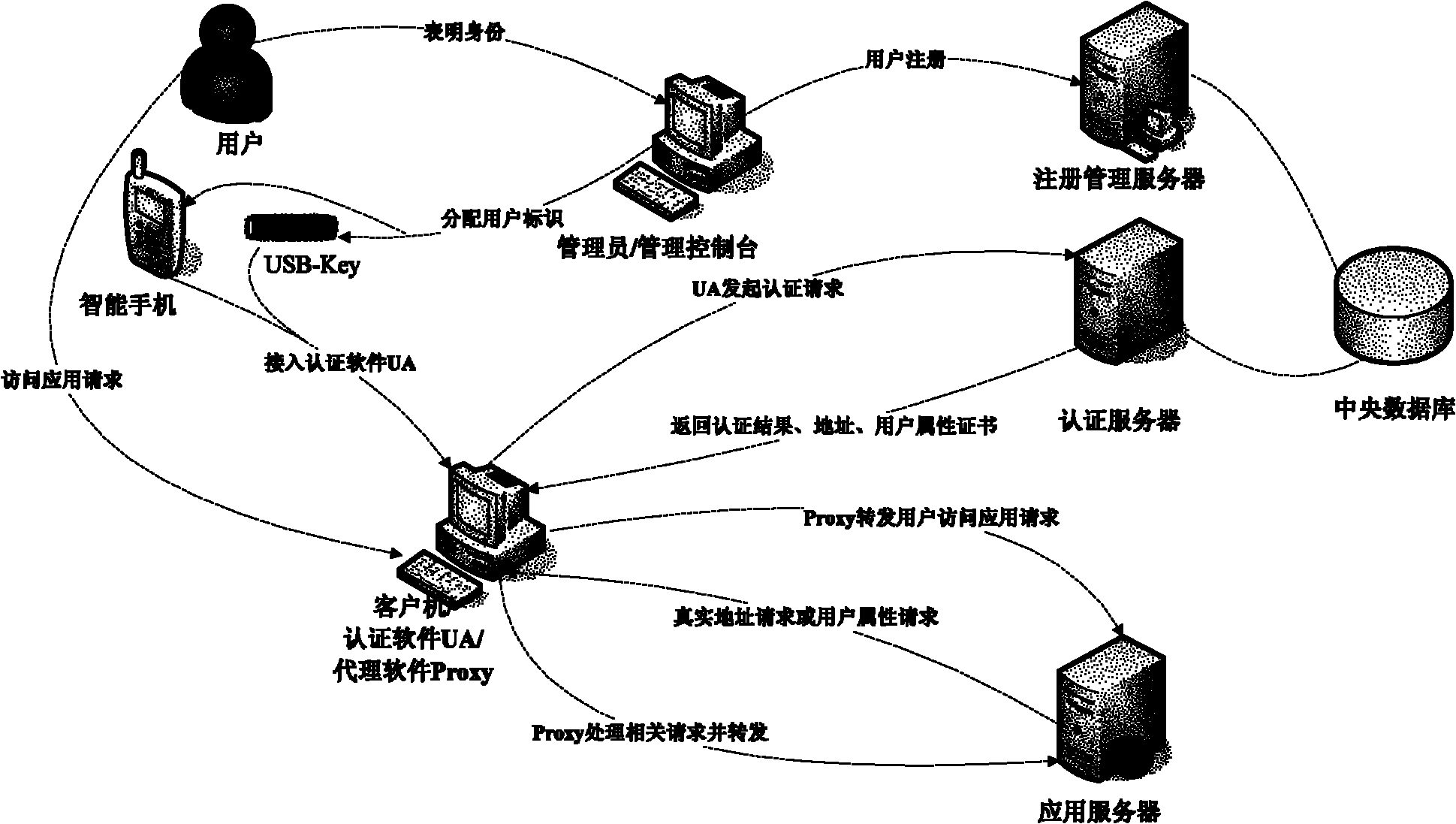
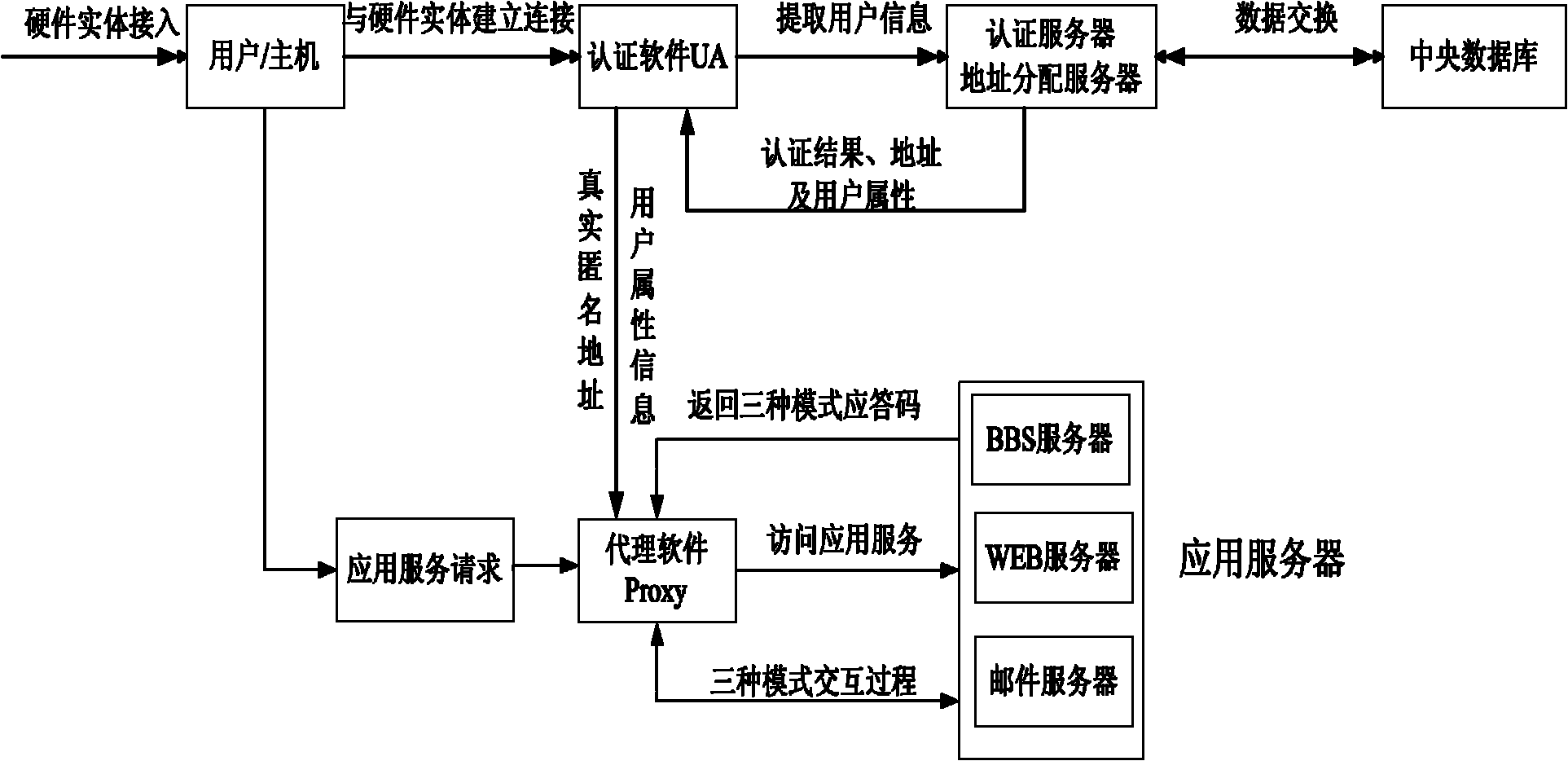
Trustworthy internet-oriented entity ID (Identity)-based ID authentication method and system
InactiveCN102006299AEnsure safetyUniqueness guaranteedTransmissionInternet Authentication ServiceStructure of Management Information
The invention discloses trustworthy internet-oriented entity ID (Identity)-based ID authentication method and system. Through distributing a user basic ID and a user ID certificate in one-to-one correspondence to a user and using a safer entity authentication mode to access the internet, the security and the uniqueness of user information are ensured, various entities attempting to enter the network through false or error ID marks are recognized and ID authentication services are provided for various network applications. The IPv6 (Internet Protocol Version 6) address structure is resigned corresponding to the user basic ID and the user ID certificate, two address types, i.e. a real address and an anonymous address to be distributed in authentication are provided, and the user ID is expanded to richer user attribute certificates so that the user is provided with three network access, i.e. access based on an anonymous address, access based on a real address and access based on the realaddress and the user ID certificate.
Owner:XI AN JIAOTONG UNIV
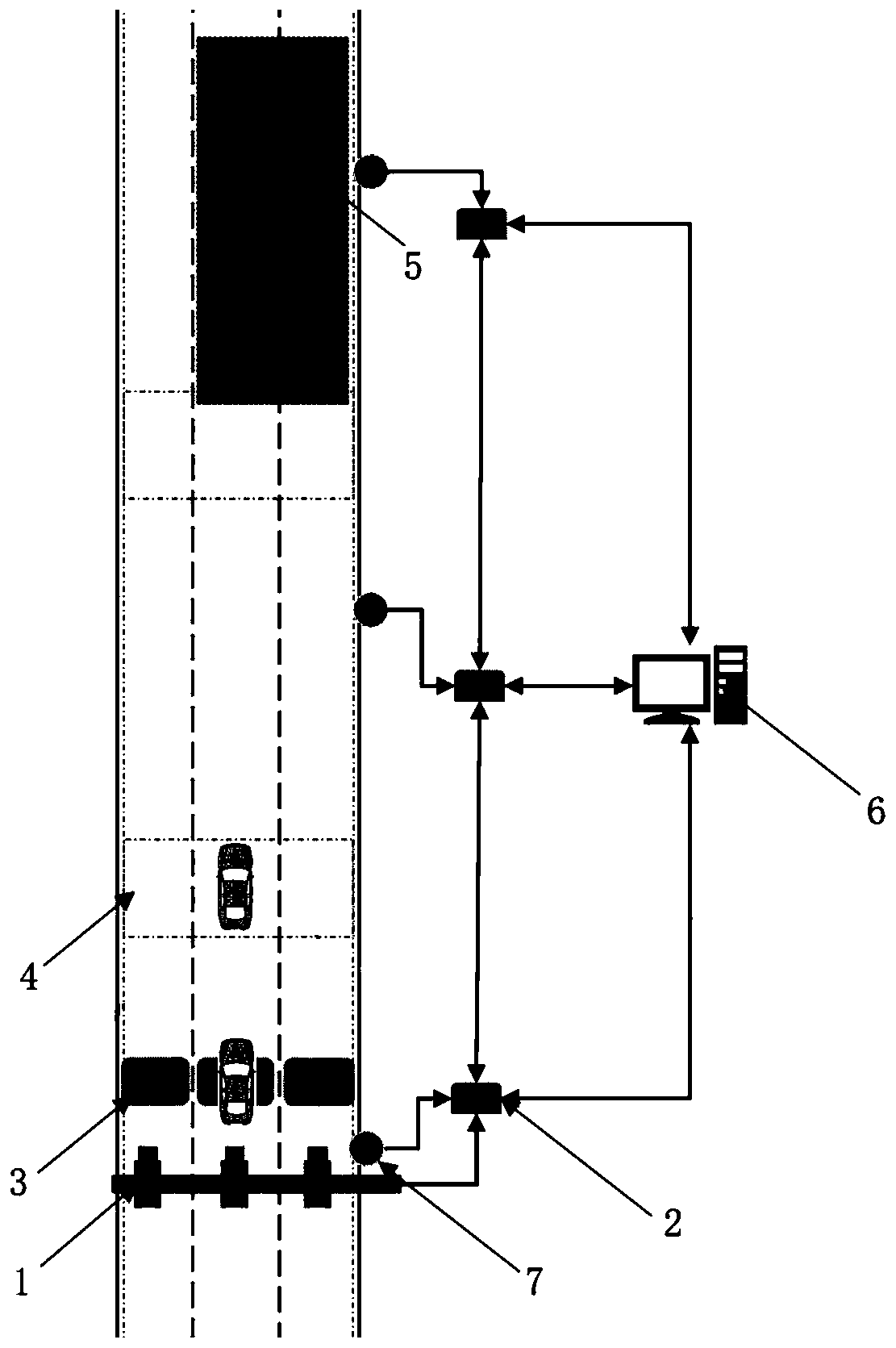
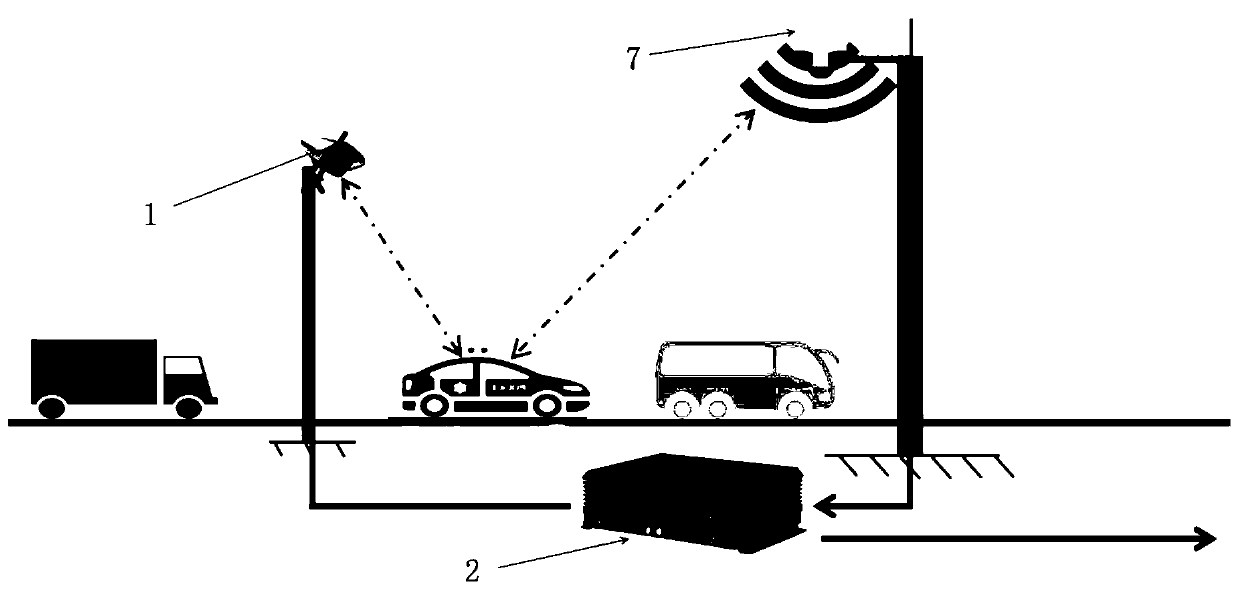
Active vehicle continuous tracking device, system and method
ActiveCN110930692AUniqueness guaranteedPrecise positioningDetection of traffic movementEmbedded systemReal-time computing
The embodiment of the invention discloses an active vehicle continuous tracking and positioning device, system and method. The vehicle continuous tracking device comprises: a vehicle continuous tracking unit; a radar sensor, a snapshot camera and a data processor, the radar sensor scans and acquires original data in a detection range; dynamic data and a unique ID number of each vehicle are formedafter the data is processed by the data processor; when the radar tracks the vehicle to enter a preset area; the data processor acquires information and synchronously triggers the snapshot camera to capture a vehicle image and send the vehicle image to the data processor to acquire vehicle feature information; the data processor associates and fuses the dynamic data and the characteristic data ofthe same vehicle according to a rule, and starts a data cross-radar handover mechanism when the vehicle enters an adjacent radar overwrapping area, thereby realizing a function of tracking and positioning the same vehicle in the whole process within a plurality of radar coverage ranges. According to the invention, the problems that highway vehicles cannot realize whole-course active tracking and positioning, the positioning is inaccurate, the information is incomplete, and the tracked vehicles are easy to lose are solved.
Owner:河北德冠隆电子科技有限公司
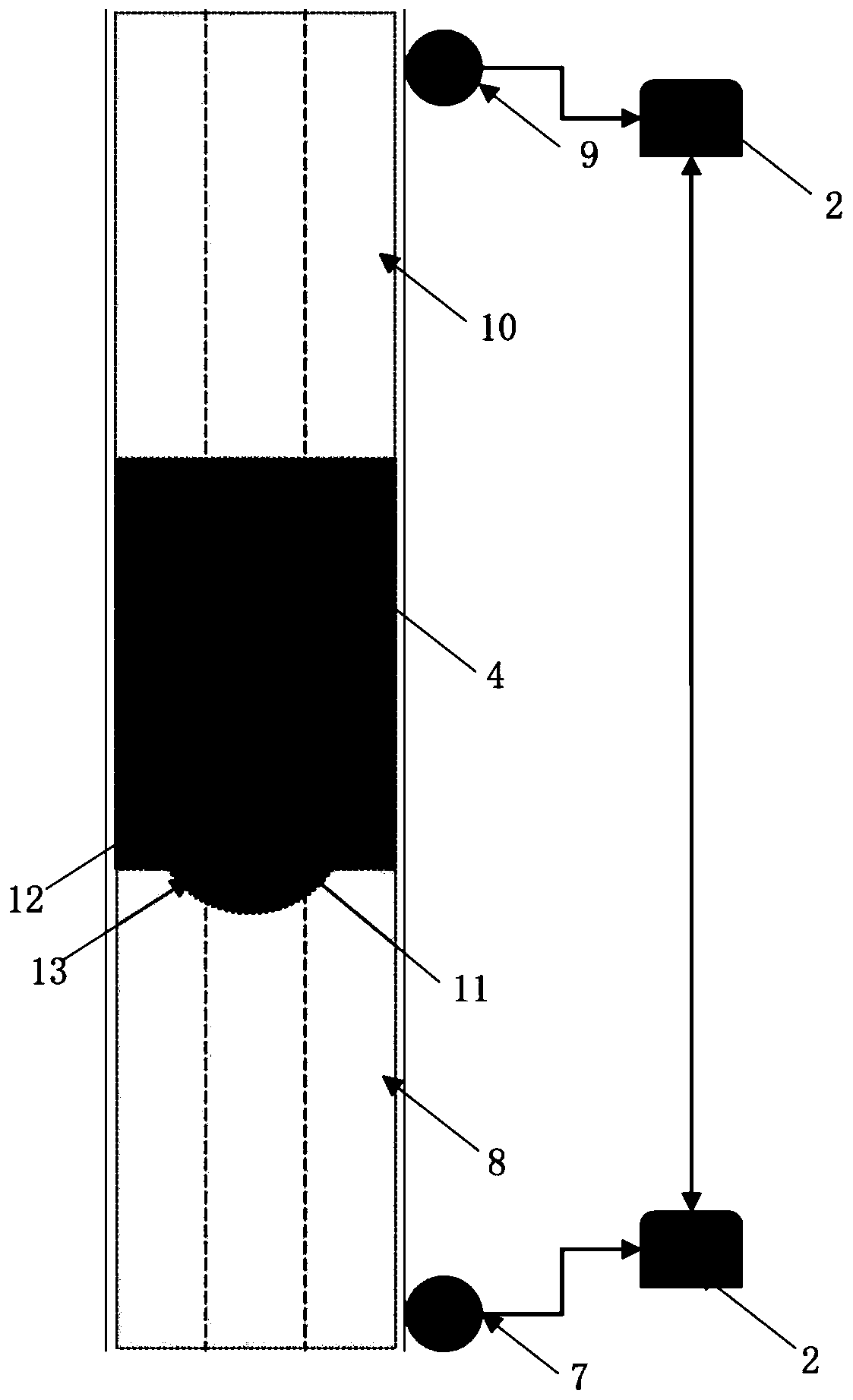
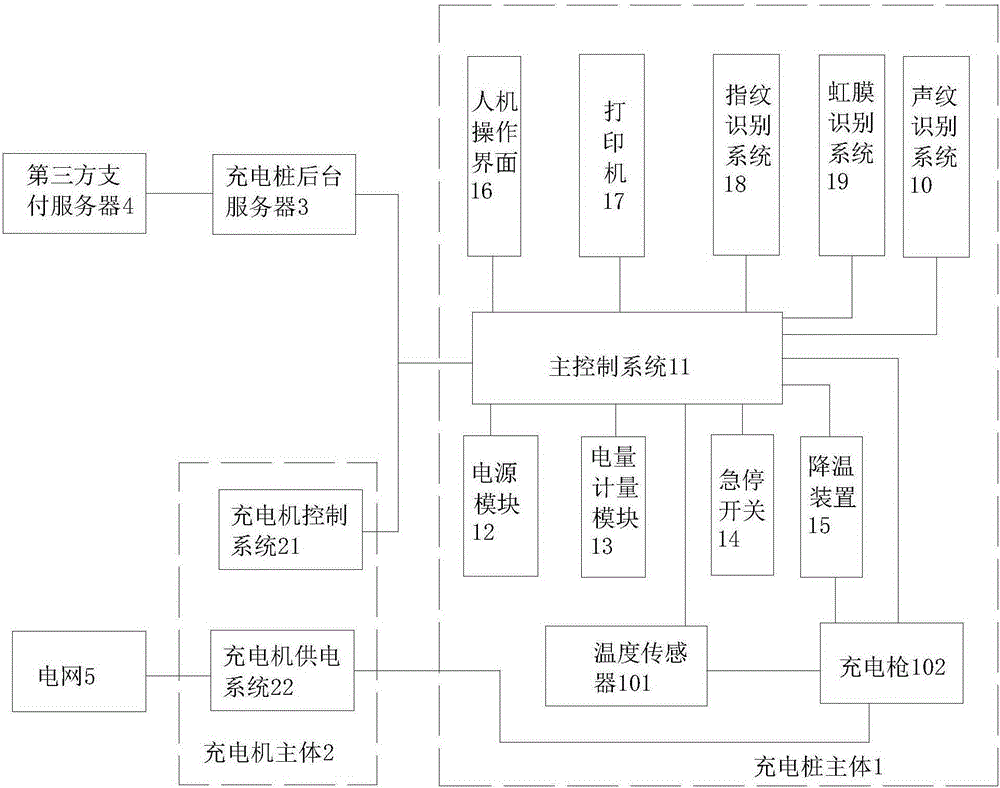
Human body fingerprint payment system and method for electric car charging pile
ActiveCN105186604AImprove securityUniqueness guaranteedBatteries circuit arrangementsCharacter and pattern recognitionElectricityElectrical battery
The invention discloses a human body fingerprint payment system for an electric car charging pile, and the system comprises a charging pile main body, a charging machine main body, a charging pile background server, and a third-side payment server, wherein the charging pile main body is electrically connected with the charging pile background server and the charging machine main body. The charging pile background server is connected to the third-side payment server. The charging machine main body is connected to a power grid. The charging machine main body is used for converting the electric energy of the power grid into the electric energy for charging an electric car battery. The charging pile background server is used for storing the account information of a user, and carries out settling of electric charge and the monitoring of a charging pile scene through the third-side payment server. The third-side payment server is used for a third-side payment platform. The charging pile main body is used for controlling the charging machine main body to charge an electric car according to the payment information of a user.
Owner:上海联会能源科技有限公司
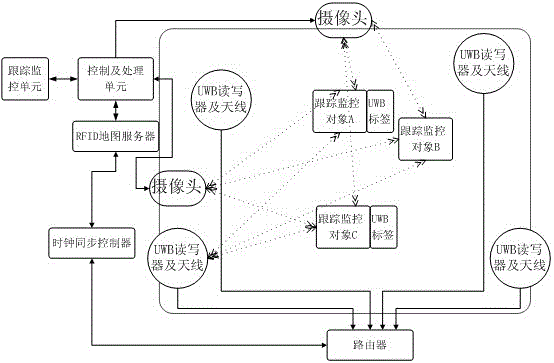
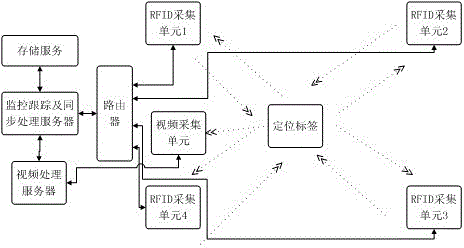
Personnel identification method and system combining video identification and UWB positioning technologies
InactiveCN105072381AEnhanced Smart Tracking ServiceUniqueness guaranteedClosed circuit television systemsTransmissionUltra-widebandReal time analysis
The invention provides a personnel identification method and system combining video identification and UWB (ultra-wideband) positioning technologies. The method comprise the steps of: A, in the simulation filed of a same supervision area, obtaining geographical positions of mobile positioning objects and the first quantity of the geographical positions according to video identification positioning, and obtaining positioning coordinates of positioning terminals and the second quantity of the positioning coordinates according to wireless positioning; B, comparing the first quantity and the second quantity at a same time, prompting abnormity and entering C if the first quantity is not equal to the second quantity, and prompting normality if the first quantity is equal to the second quantity; and C, obtaining abnormal geographical positions according to the matching between the positioning coordinates and the geographical positions. The method and system can efficiently monitor specific objects and specific occasions such as a campus, analyze and determine in real time position monitoring and video image monitoring information, and timely provide alarm response service, thereby enhancing campus safety service.
Owner:上海真灼科技股份有限公司
Identification analysis system implementation method based on blockchain technology and identification coding technology
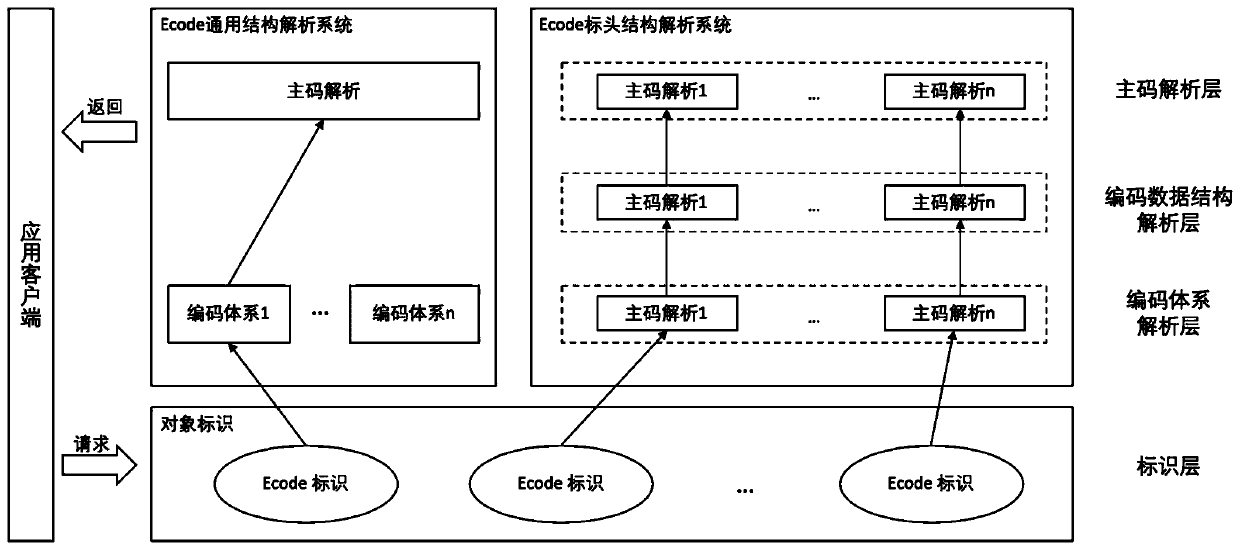
ActiveCN110941611AEnsure safetyGuaranteed reliabilityDatabase distribution/replicationSpecial data processing applicationsThe InternetEngineering
The invention discloses an identification analysis system implementation method based on a blockchain technology and an identification coding technology. The method comprises the following steps: A, establishing a consensus node mechanism; B, carrying out on-chain deployment by utilizing an intelligent contract technology so as to guarantee an identification rule; cC generating a data tree management mode for producing a full link based on a distributed account book technology; D, establishing a component model; E, querying the component model; if a result is inquired, directly entering the step G, otherwise, entering the step F; F, performing intercommunication analysis of the identification system; and G, outputting identification information. According to the method, the management efficiency of the identification data can be effectively enhanced, identification codes are unified, the method is unified with the construction of a national identification analysis system, the identification information management of all elements and all links of an industrial internet identification analysis ecosphere is realized, and an interconnected and intercommunicated data ecological chain isformed between the method and other identification systems.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
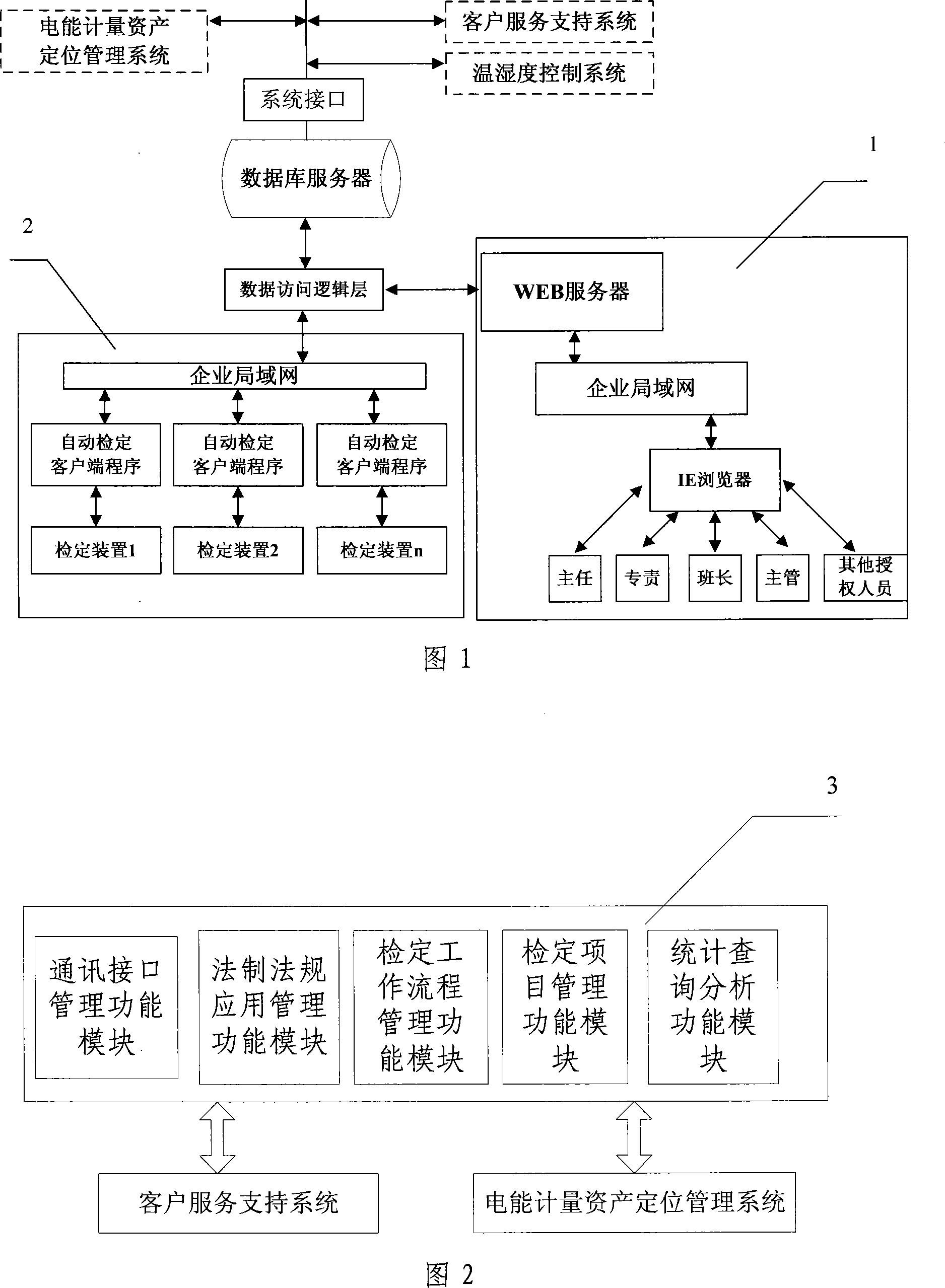
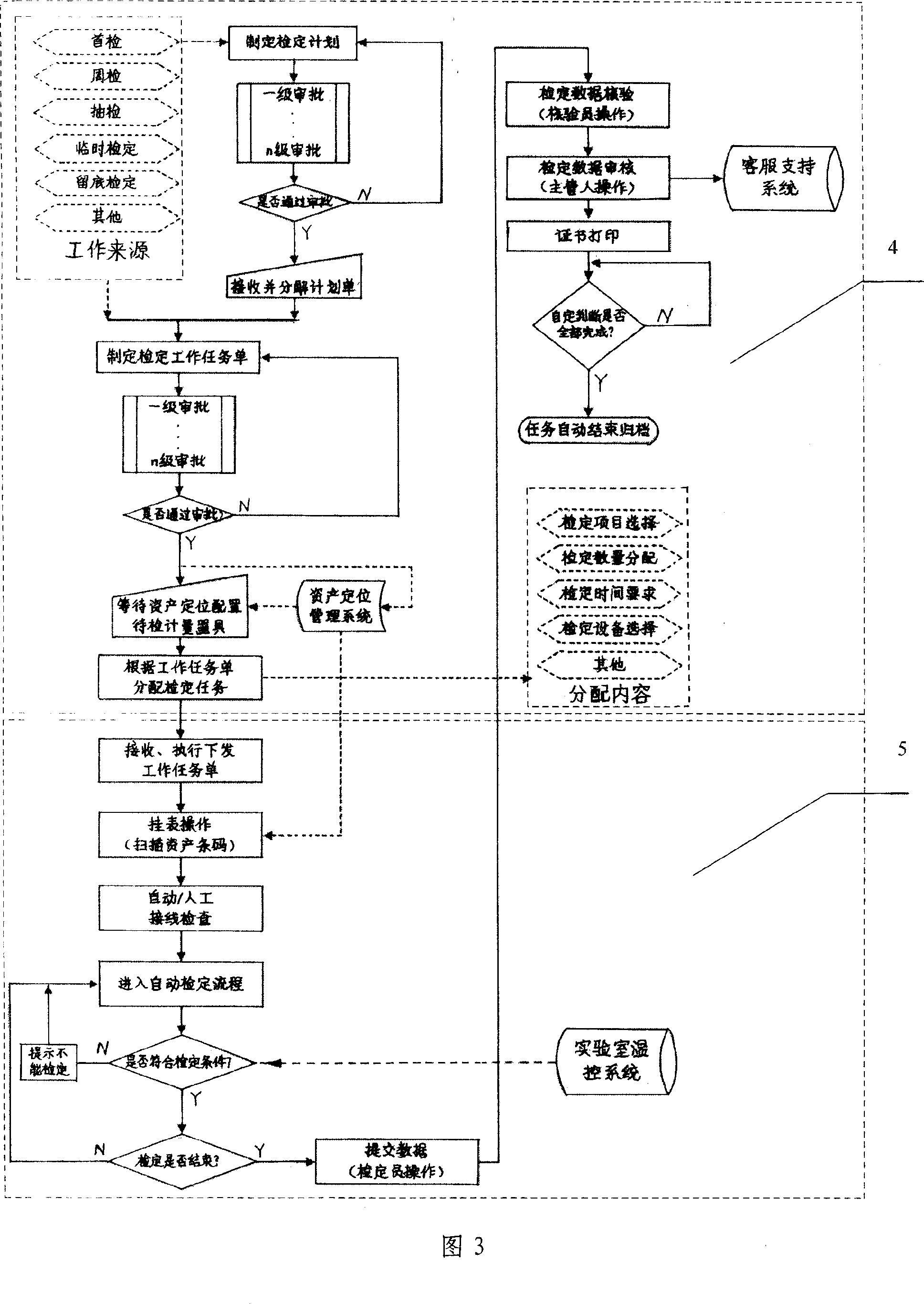
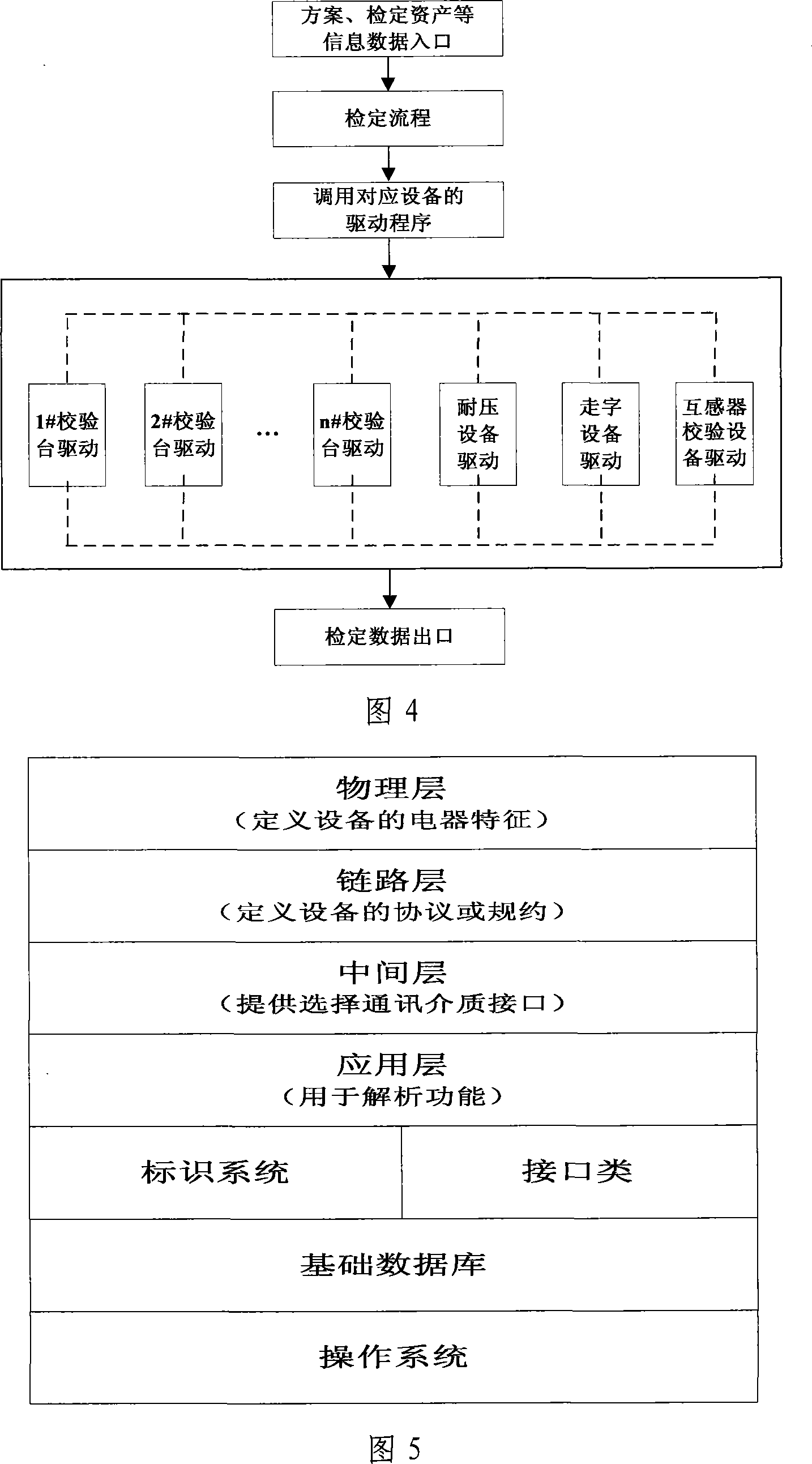
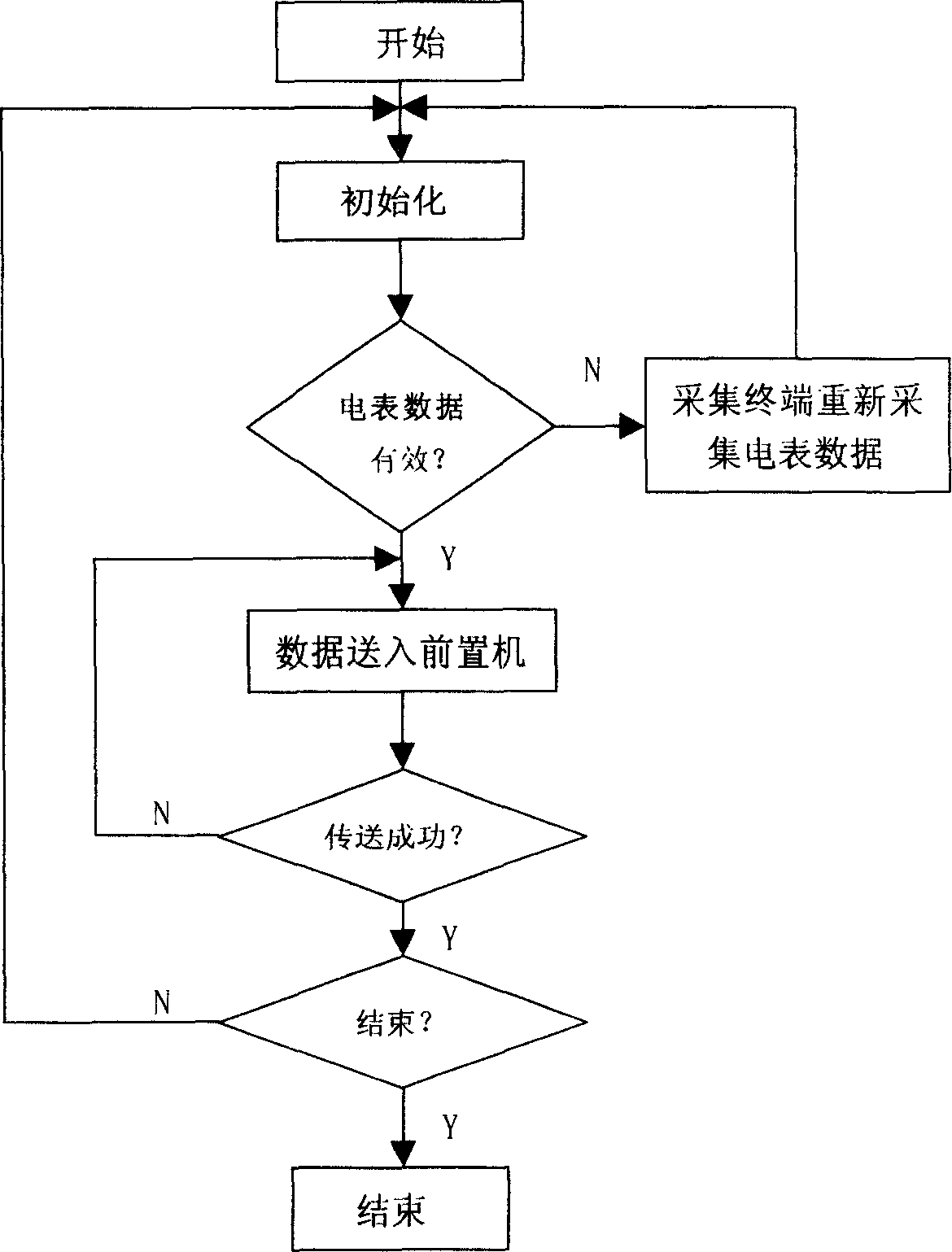
Electrical energy metering automatic verification integrative management platform system
The present invention provides a comprehensive managing platform system for automatically rating the electric energy measurement, and consists of a database server, a data accessing logic layer, an automatic rating user end, a WEB server, and a system interface part. The system adopts a C / S and B / S configuration coexisting net combining method, adopts a device communication unified interface design, and connects the technologies which are irrelevant to the device with different measuring devices. The present invention can realize the standardization, the unification, and the standardization of the electric energy measuring task by five function modules of the communication interface managing function, the legal system and law application managing function, the rating work flow managing function, the rating item managing function, and the statistic searching and analyzing function, thereby ensuring the multi-machine work by one person justly and rightly according to the law.
Owner:SHANXI YINXING POWER ELECTRONICS TECH
Metering and charging system of electric energy amount
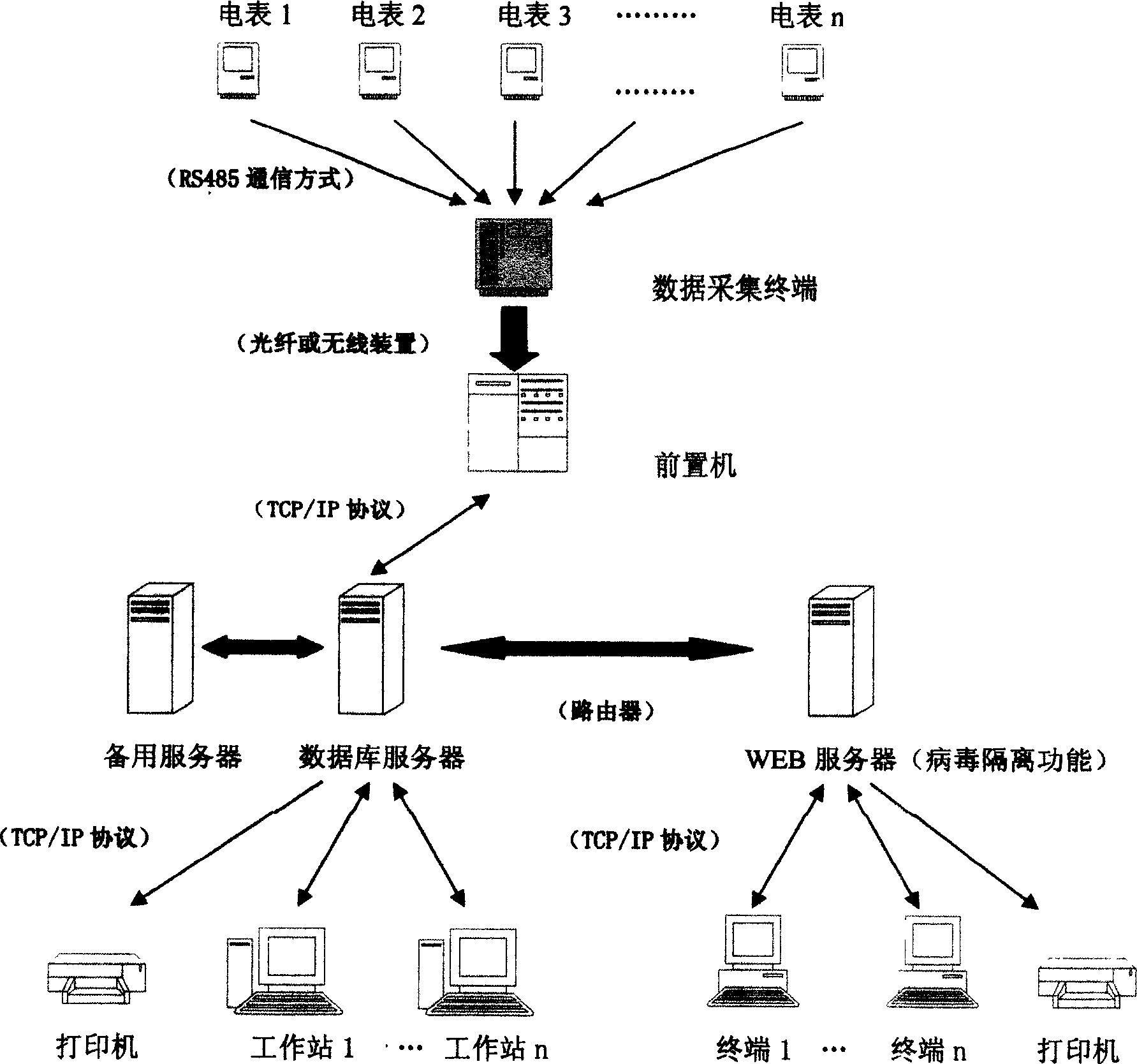
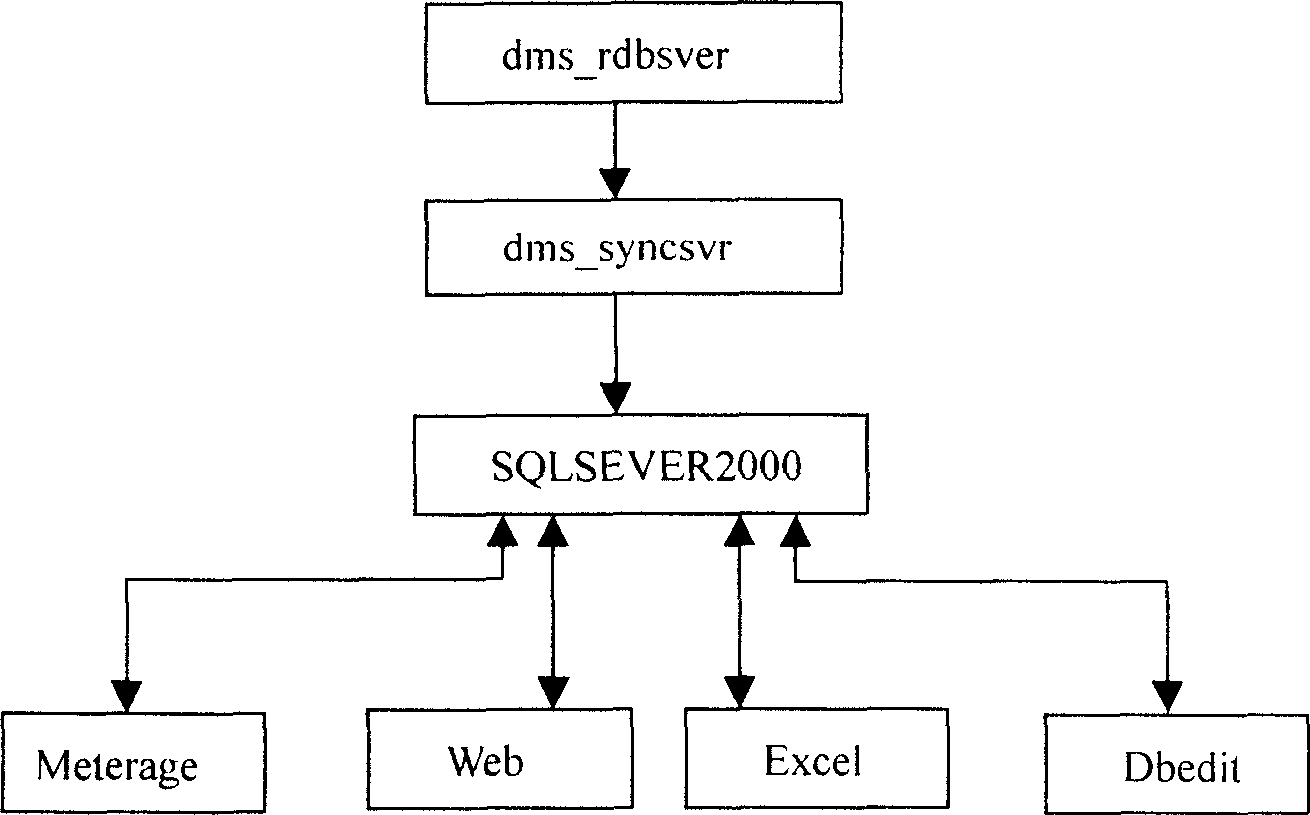
InactiveCN1680817AUniqueness guaranteedIntegrity guaranteedElectric signal transmission systemsTariff metering apparatusData platformData acquisition
A metering and charging system of electric energy consists of four parts of data collection, data management, network browse and electronic report. It is featured as using data collection unit and data management unit to form databank for application, using network browse unit to browse data in databank and using electronic report unit to print out required data. The system has unified data platform being able to obtain remote electric energy data and it can ensure uniqueness, completeness and correctness of the data.
Owner:南京迪玛斯电气有限公司
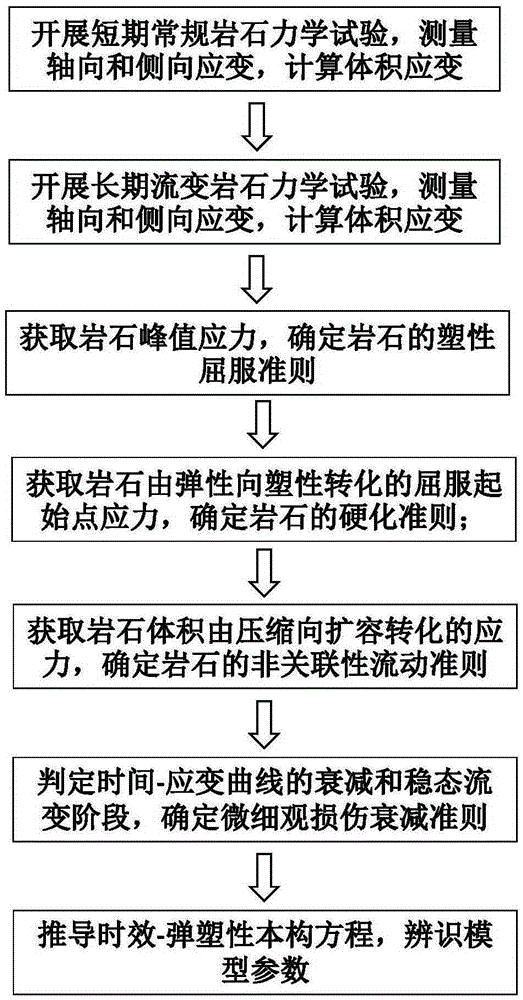
Method for establishing rock material ageing and elastic-plastic mechanics constitutive model
InactiveCN105259035AImprove accuracyWide applicabilityMaterial strength using tensile/compressive forcesUltrasound attenuationDynamic balance
The invention discloses a method for establishing a rock material ageing and elastic-plastic mechanics constitutive model. The method includes the steps that the triaxial short-long term test result of rock is used as the basis first, and the volumetric strains of a rock test piece under different test conditions are calculated; by drawing a stress-axial and lateral strain relation curve and a stress-volumetric strain relation curve, the yield criterion, the non-associated flow rule and the hardening criterion of the rock are determined, and an elastic-plastic mechanics model is established; then by combining material micro and fine damage attenuation ageing evolution dynamic equilibrium, the micro and fine ageing damage rule of the rock is determined, the model is popularized, a relation matrix of strain increment and stress increment at the ageing-elasticoplastic deformation stage is established, and accordingly the rock material ageing and elastic-plastic mechanics constitutive model is obtained. According to the model, the mechanics significance is definite, the expression is unique, the number of parameters is small and can be obtained based on the test results, hence, solving uniqueness and accuracy are guaranteed, and wide applicability and expansibility are achieved.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com