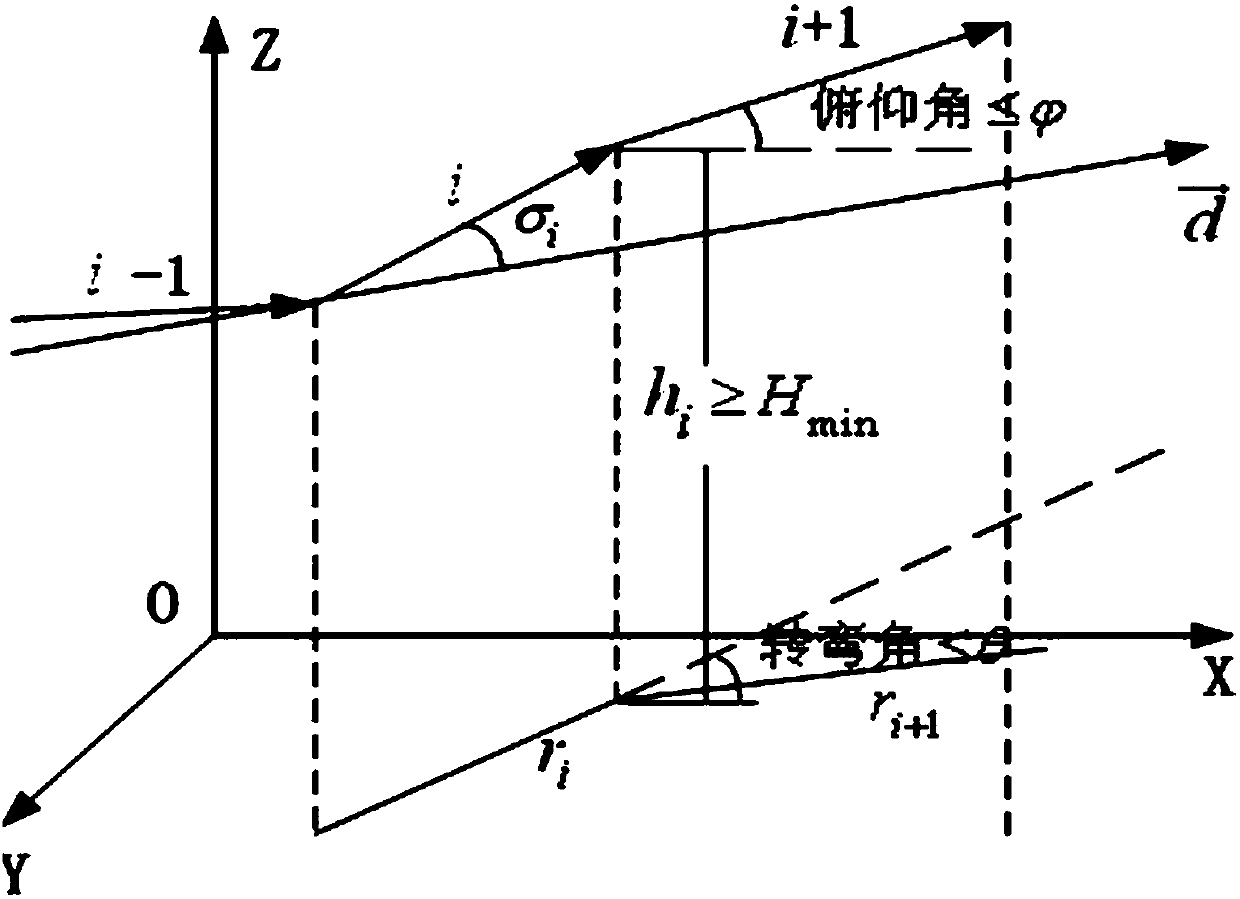
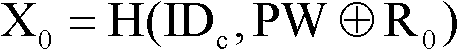Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
375results about How to "Guaranteed randomness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
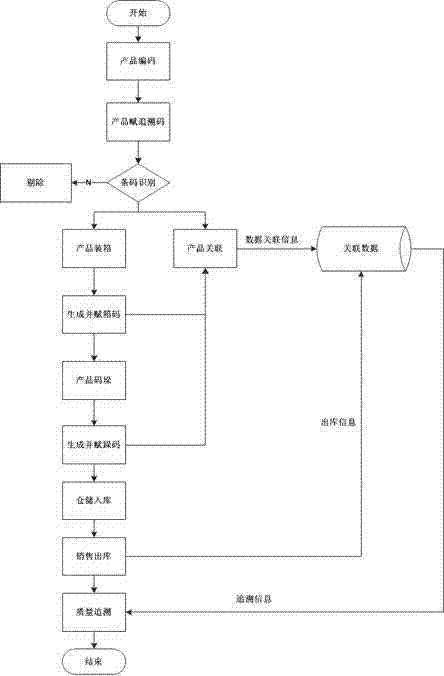
Quality safety tracing method for food processing enterprises
InactiveCN103761546ANo repeated codes appearMeet randomnessCo-operative working arrangementsDebit schemesProduction lineRelational database
The invention discloses a quality safety tracing method for food processing enterprises. The quality safety tracing method includes the steps that a laser coder generates random tracing codes according to a coding rule when a laser marking machine in a production line device is dynamically read in an on-line tagging mode; the laser marking machine carries out tracing mode marking on products on a production line, and two-dimension codes and plain codes are all marked on packages; a fixed reader is used for scanning and reading designated tagged code portions of the products; the two-dimension codes are successfully scanned and read, the tracing codes are recorded, and relevance between the tracing codes and commodity attribute information is completed; if the two-dimension codes fail to be scanned, the two-dimension codes will be removed through a removing device; the commodity tracing code information and the commodity attribute information are recorded into a relational database; after the products are packaged, package code data and product tracing code data are related; the products are stacked, stacking codes and tagged stacking codes are generated, and the stacking codes and the product package code data are related; the stacking codes are scanned, storage of the products is completed, delivery orders and the stacking codes are scanned to complete delivery, and the database records delivery information.
Owner:武汉华工赛百数据系统有限公司
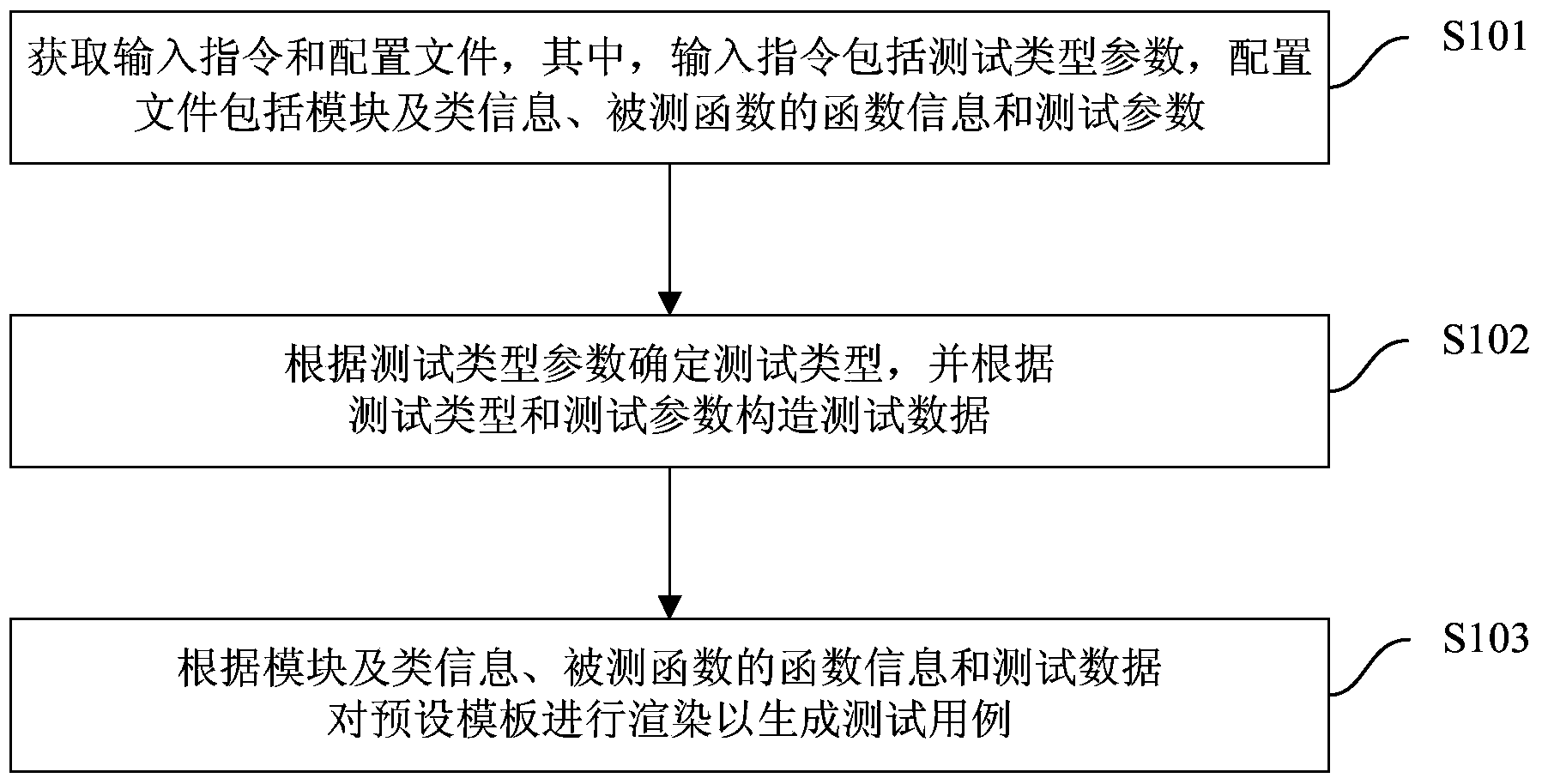
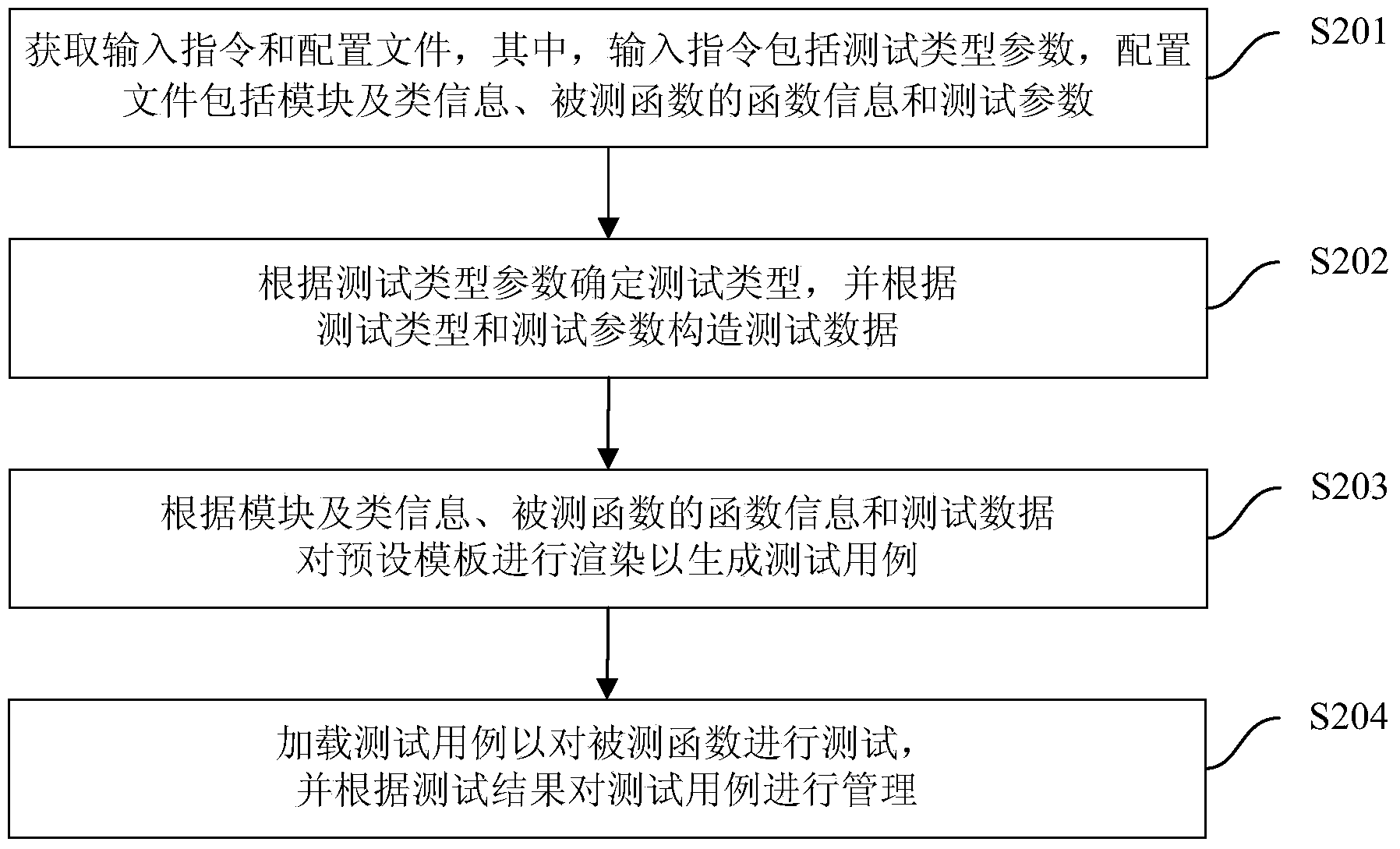
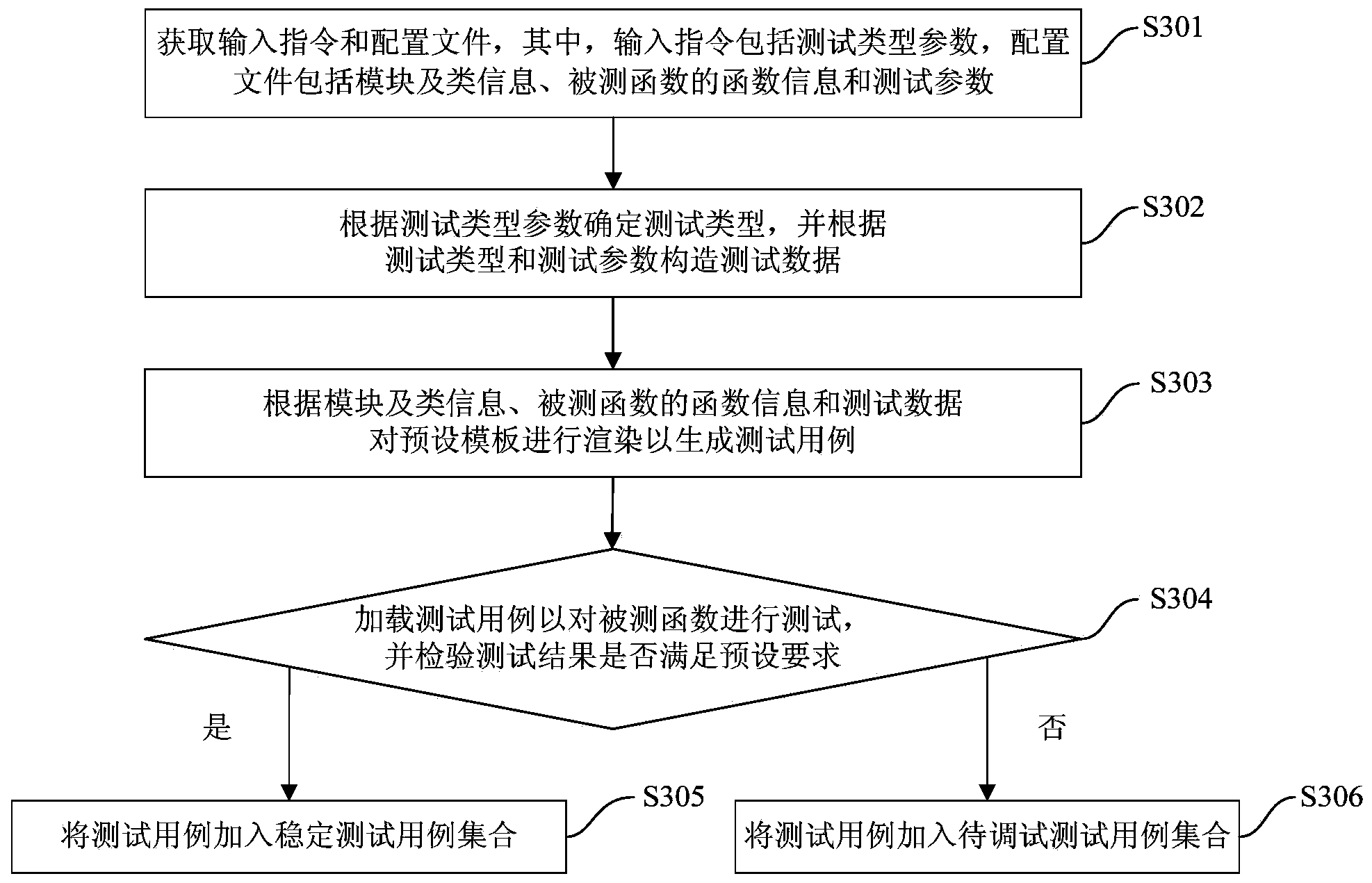
Method and device for generating test case
ActiveCN103631720AReduce maintenance costsGuaranteed randomnessSoftware testing/debuggingTest efficiencyComputer science
The invention proposes a method and a device for generating a test case. The method comprises the following steps: obtaining an input instrument and a configuration film, wherein the input instruction comprises a test type parameter; the configuration film comprises a module, class information, function information of the tested function and a test parameter; determining the test type according to the test type parameter, and structuring test data according to the test type and the test parameter; rendering the preset template according to the template, the class information, the function information of the tested function and the test data, so as to generate the test case. By adopting the method disclosed by the embodiment of the invention, on one hand, automatic generation of the function test case is achieved without artificially compiling the test case of the tested function, so as to improve the test accuracy, and on the other hand, the test type is determined according to the test type parameter, and support of a plurality of different test modes is achieved, so that the supported test modes are diversified.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Self-adaptation camouflage design method based on background
InactiveCN104318570AHigh synthesis efficiencyQuality assuranceImage analysisTexturing/coloringCluster algorithmSelf adaptive
The invention discloses a self-adaptation camouflage design method based on a background. According to the method, on the basis of a texture synthesis algorithm based on pixels, a whole camouflage image is synthesized pixel by pixel; in the synthesis process, a self coding algorithm is adopted to extract a texture primitive containing background sample complete texture features, and a neighborhood of the pixels to be synthesized is determined; by means of the neighboring correlation principle and a helix supplement search mechanism, a neighborhood matched with a target pixel neighborhood is searched for in a background sample; similarity matching is carried out through a pixel and texture similarity matching rule, pixels in the neighborhoods which are most similar in the sample are selected to serve as synthesis pixels, pixels of a target image are synthesized according to the sequence of scanning lines, and after synthesis, color quantization is carried out on the image by means of the clustering algorithm to generate a final camouflage image. By means of the method, similar camouflage images can be synthesized quickly according to the background, and the application aim of quickly camouflaging a target in a self-adaptation mode can be achieved.
Owner:SHENYANG JIANZHU UNIVERSITY
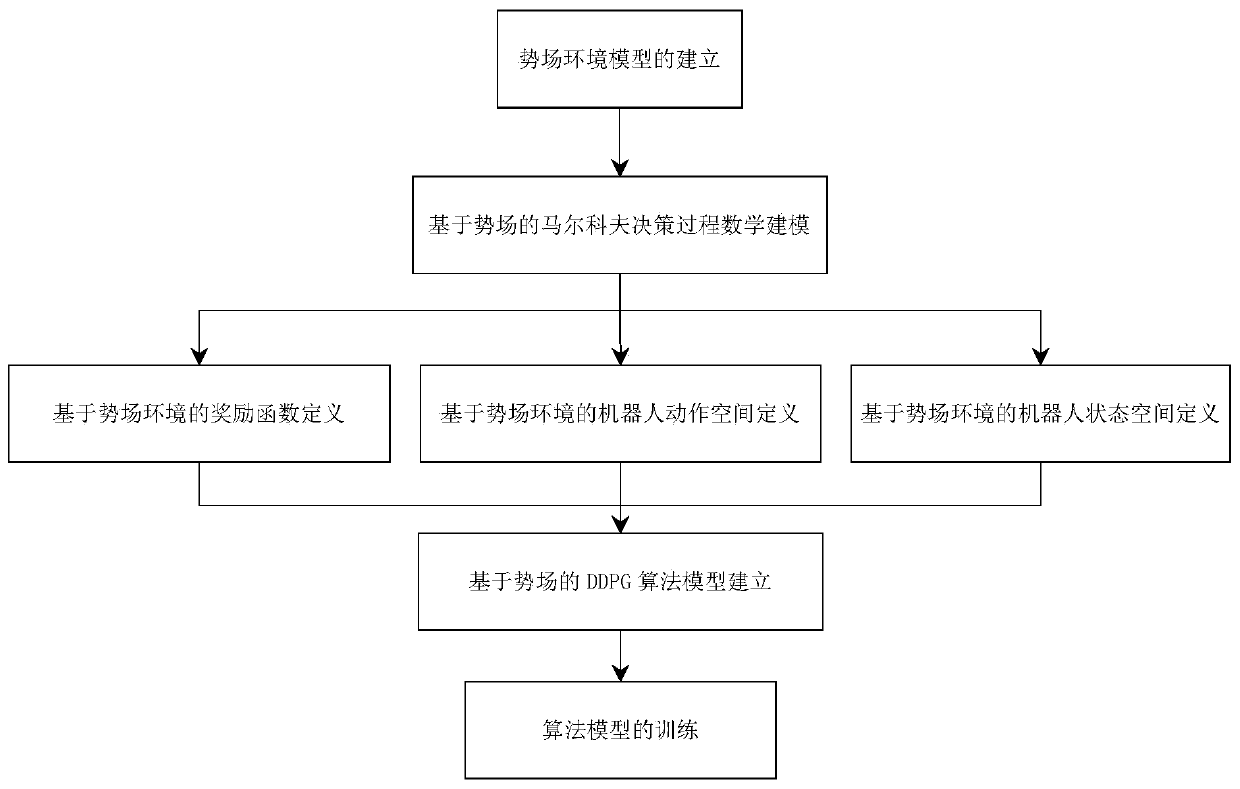
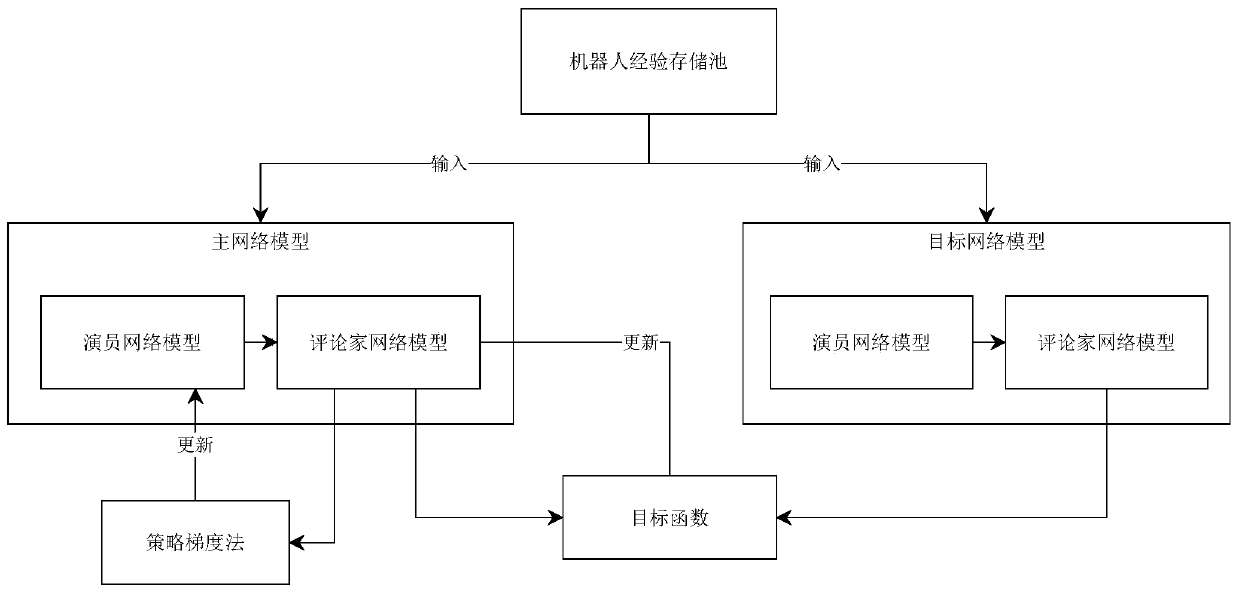
Reinforced learning path planning algorithm based on potential field
InactiveCN110794842ARealize path planningGuaranteed randomnessPosition/course control in two dimensionsReinforcement learning algorithmEngineering
The invention, which belongs to the field of intelligent algorithm optimization, provides a reinforced learning robot path planning algorithm based on a potential field in a complex environment, thereby realizing robot path planning in a complex dynamic environment under the environmental condition that a large number of movable obstacles exist in a scene. The method comprises the following steps:modeling environment space by utilizing the traditional artificial potential field method; defining a state function, a reward function and an action function in a Markov decision-making process according to a potential field model, and training the state function, the reward function and the action function in a simulation environment by utilizing a reinforcement learning algorithm of a depth deterministic strategy gradient; and thus enabling a robot to have the decision-making capability of performing collision-free path planning in a complex obstacle environment. Experimental results showthat the method has advantages of short decision-making time, low system resource occupation, and certain robustness; and robot path planning under complex environmental conditions can be realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Block chain consensus method and system
ActiveCN108737375AGuaranteed randomnessReduce security risksFinanceEncryption apparatus with shift registers/memoriesConsensus methodBlockchain
The invention discloses a block chain consensus method. The method comprises the following steps: establishing a Hash ring, and mapping a node and a Hash value of a virtual node thereof, and a Hash value of a block to the same Hash ring; determining the node capable of receiving a verification message and producing the next block right according to the address mapped to the Hash ring from the current block, wherein the node is the leader node, and the other nodes are follower nodes, the leader nodes adds the current block into the block chain after receiving the message that more than half follower nodes pass the current block verification, and broadcasts a confirm message and a packed next block content to the follower node; the follower node receives the broadcast message and adds the current block to the block chain when the message verification is passed, and then verifies the next block, and sends the verification message to the next leader node.
Owner:SUN YAT SEN UNIV
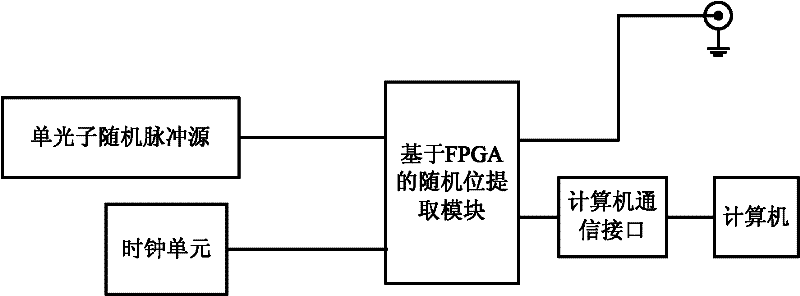
Truth random number producing method and device
InactiveCN102176199AGood randomnessProcessing speedRandom number generatorsCommunication interfaceFifo memory
The invention relates to a device and method for producing a truth random number; the device comprises a single photon random pulse source, a clock unit, a random bit extracting module based on an FPGA (field programmable gate array) and a computer; the random bit extracting module based on the FPGA comprises a controller, a counter, a multi-bit FIFO (first in first out) memory, a buffer unit, a comparator, 1-bit FIFO memory and a communication interface control module; the buffer unit comprises a first register and a second register. The technical problem that the current random number has great randomness, slow speed and bad stability is solved; and the random bit extracting method is circular, continuous, unlimited and high-speed.
Owner:XI'AN INST OF OPTICS & FINE MECHANICS - CHINESE ACAD OF SCI
Social video information security method and system
InactiveCN102833246AIntegrity guaranteedGuaranteed randomnessKey distribution for secure communicationSelective content distributionData streamAttack
The invention discloses a social video information security method and a system. The method comprises the following four steps of identity authentication, key negotiation, encryption communication and rekeying and video integrity. The method comprises the following steps that a server carries out identity legitimacy authentication to connected users; two parties consult a post-communication key through asymmetric encryption and information digest algorithms; in the communication process, data streams are encrypted by using a chaotic pseudorandom sequence; and the server ensures that the video integrity is not damaged through two aspects of adding plaintext watermark and saving integrity information. The method and the system are applied, so that the user identity can be authenticated, imitation and attack are avoided, the randomness of every communication key is ensured, the personal information and the privacy of the users are prevented from being stolen, and the fact that the copyright of the videos shared by the users is not illegally infringed is effectively ensured. The technical scheme of the method and the system has a good development prospect.
Owner:NANJING UNIV
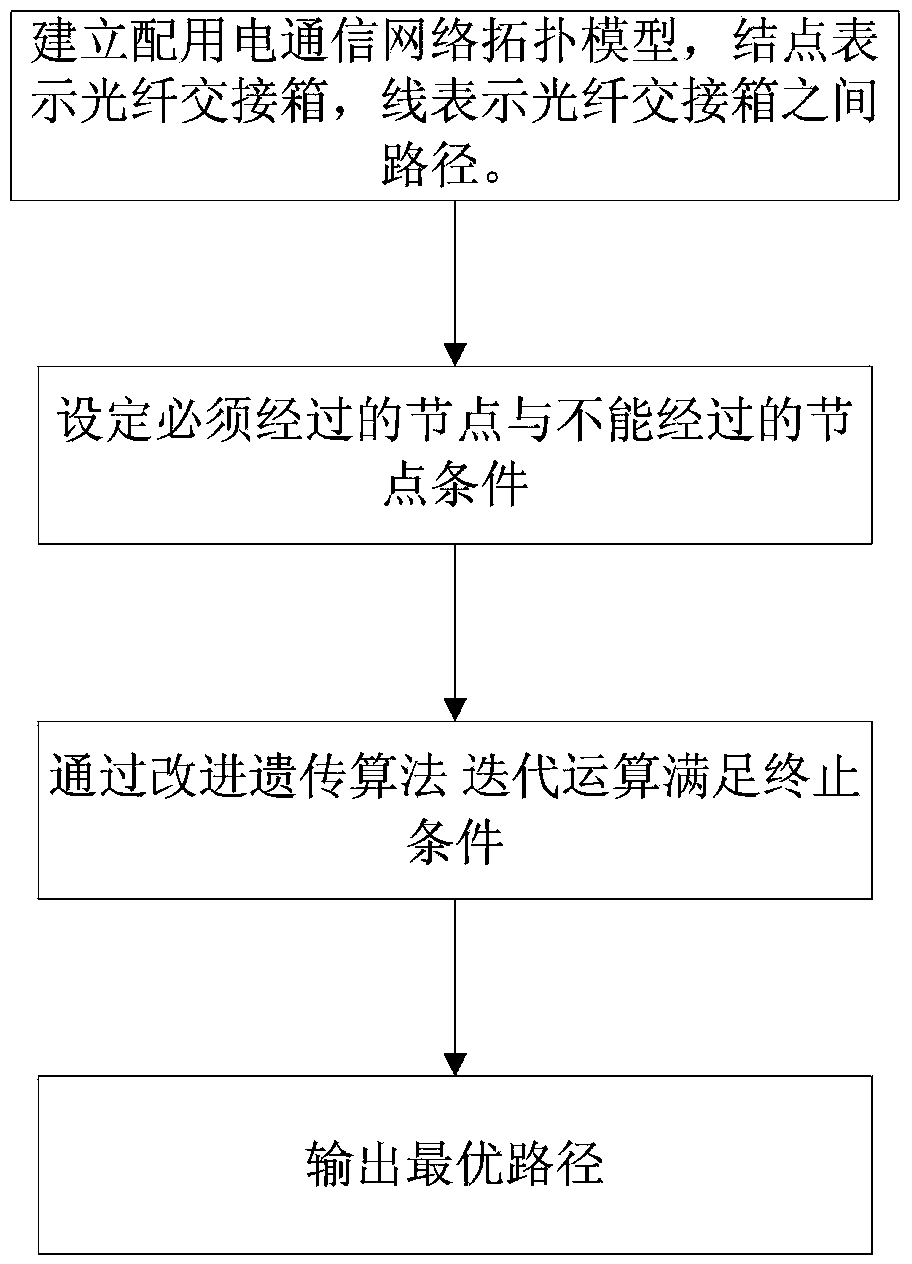
Method for selecting optimal path of power distribution and utilization communication network based on genetic algorithm
InactiveCN104299053AReduce the number of debuggingShorten the timeForecastingGenetic algorithmsGenetic algorithmComputer science
The invention discloses a method for selecting the optimal path of a power distribution and utilization communication network based on the genetic algorithm. The method is characterized by including the following steps that first, a unidirectional topology network is established; second, the population is initialized through binary coding; third, the number of iterations is set; fourth, selecting operation is performed; fifth, crossover operation is performed; sixth, mutation operation is performed; seventh, judgment is performed; eighth, the optimal path is output. On the basis of meeting the constraint conditions, the optimal path is efficiently found so that the search efficiency can be improved and the search complexity can be reduced.
Owner:STATE GRID CORP OF CHINA +1
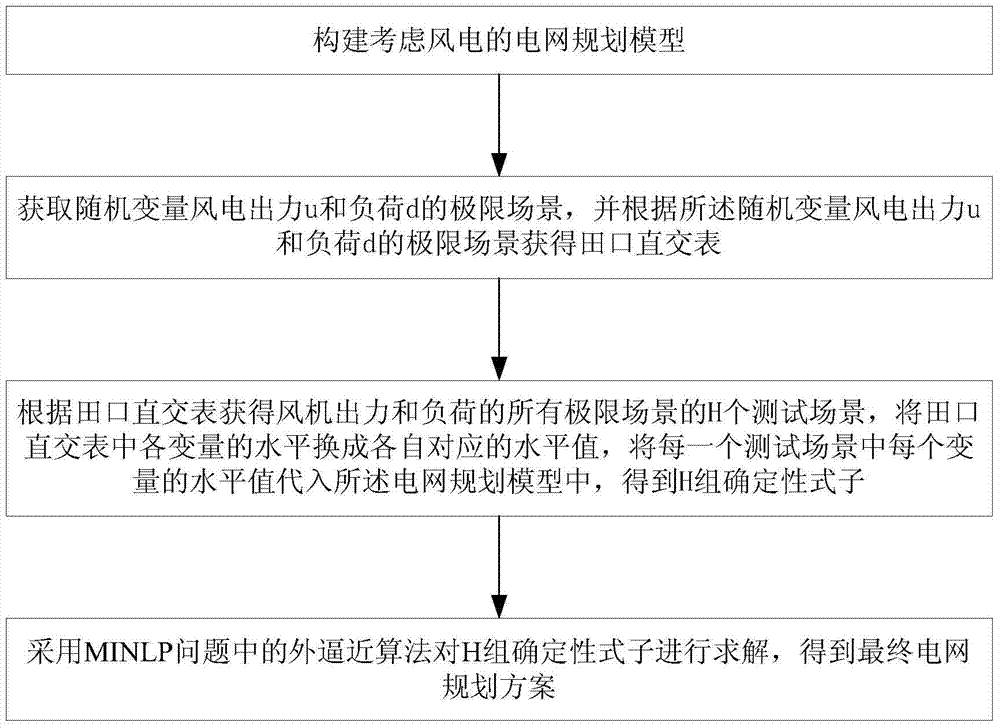
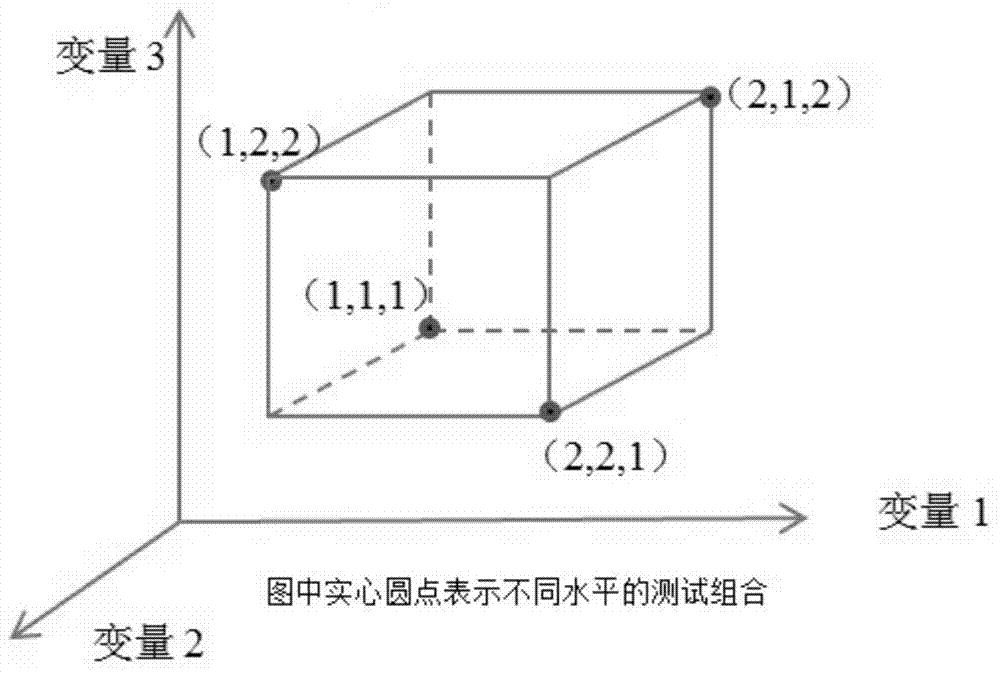
Electric power system power network planning method suitable for taking wind power random characteristic into account
ActiveCN103793612AGuaranteed randomnessData processing applicationsSpecial data processing applicationsElectricityElectric power system
The invention discloses an electric power system power network planning method suitable for taking the wind power random characteristic into account includes the steps that a power network planning model taking wind power into account is constructed, limit scenes of random variable wind power output and loads are acquired, H test scenes of all the limit scenes of the output and the loads of a fan are acquired according to a Taguchi orthogonal table, variables in the Taguchi orthogonal table are horizontally converted into respective corresponding horizontal values, the horizontal value of each variable in each test scene is substituted into the power network planning model, and thus H sets of deterministic formulae are obtained; the H set of deterministic formulae are solved with an outer approximation algorithm in the MINLP problem, and then the final power network planning scheme is obtained. On the basis of obtaining the wind power output probability characteristic, the wind power output limit value is selected, the constructed model is solved through the outer approximation algorithm based on the Taguchi orthogonal table, then the electric power system power network planning method suitable for taking the wind power random characteristic into account is obtained, and thus it can be guaranteed that an electric power system can adapt to the randomness of wind power.
Owner:GUANGXI UNIV
Dynamic password-based electronic lock system and authentication method thereof
InactiveCN102477820AEasy to manageEnsure safetyUser identity/authority verificationElectric permutation locksTime informationPassword
The invention discloses a dynamic password-based electronic lock system and authentication method thereof. The dynamic password-based electronic lock system comprises an electronic lock and a dynamic token, wherein the dynamic token comprises a clock module, a dynamic password generation module, a display module and a power module; the electronic lock comprises a clock module, a password generation module, a control module and a power module; the dynamic password generation module and the password generation module are in time synchronization; the dynamic password generation module is used for generating the dynamic password according to the current time information of the clock module of the dynamic token; and the password generation module is used for generating a group of dynamic passwords according to the time information within the current time vicinity of the clock module of the electronic lock. According to the invention, the safety, the irrepeatability and the randomness of the password of the electronic lock can be effectively ensured.
Owner:贾松仁
File security management system applied to network and management method thereof
InactiveCN101815063AEasy to useDecide how to useCharacter and pattern recognitionTransmissionNetwork connectionServer-side
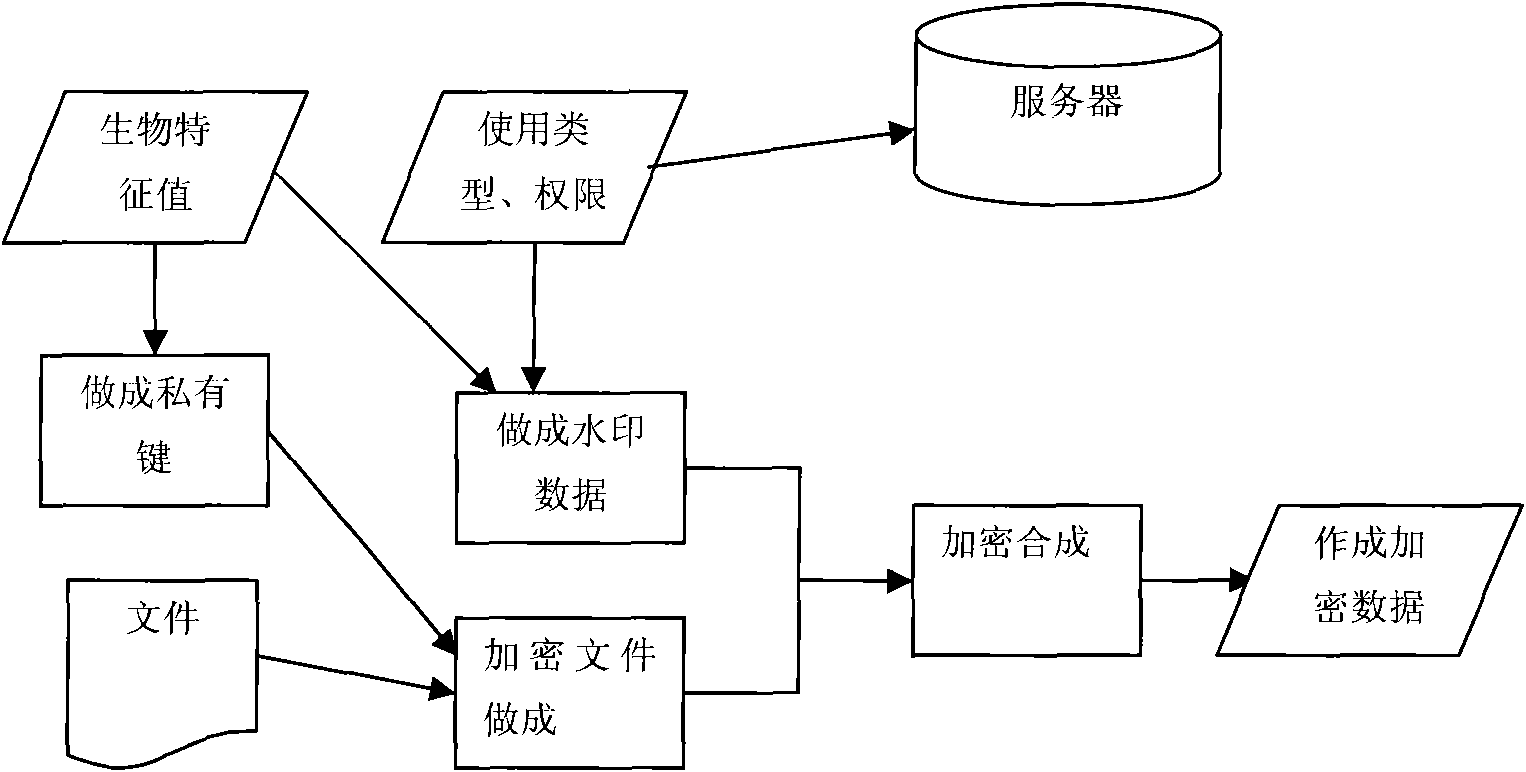
The invention provides a file security management system applied to a network, which comprises server and a user which are connected through the network, wherein the server is provided with file encryption equipment and user biological characteristic receiving equipment; the server stores and transmits files encrypted by using user biological characteristics as keys to the user; the user is provided with user biological characteristic acquisition equipment and file decryption equipment; and the user decrypts the files transmitted by the server by adopting the user biological characteristics. The file security management system effectively solves the security management problem of the files in the network.
Owner:强敏
Model training method and device for training data
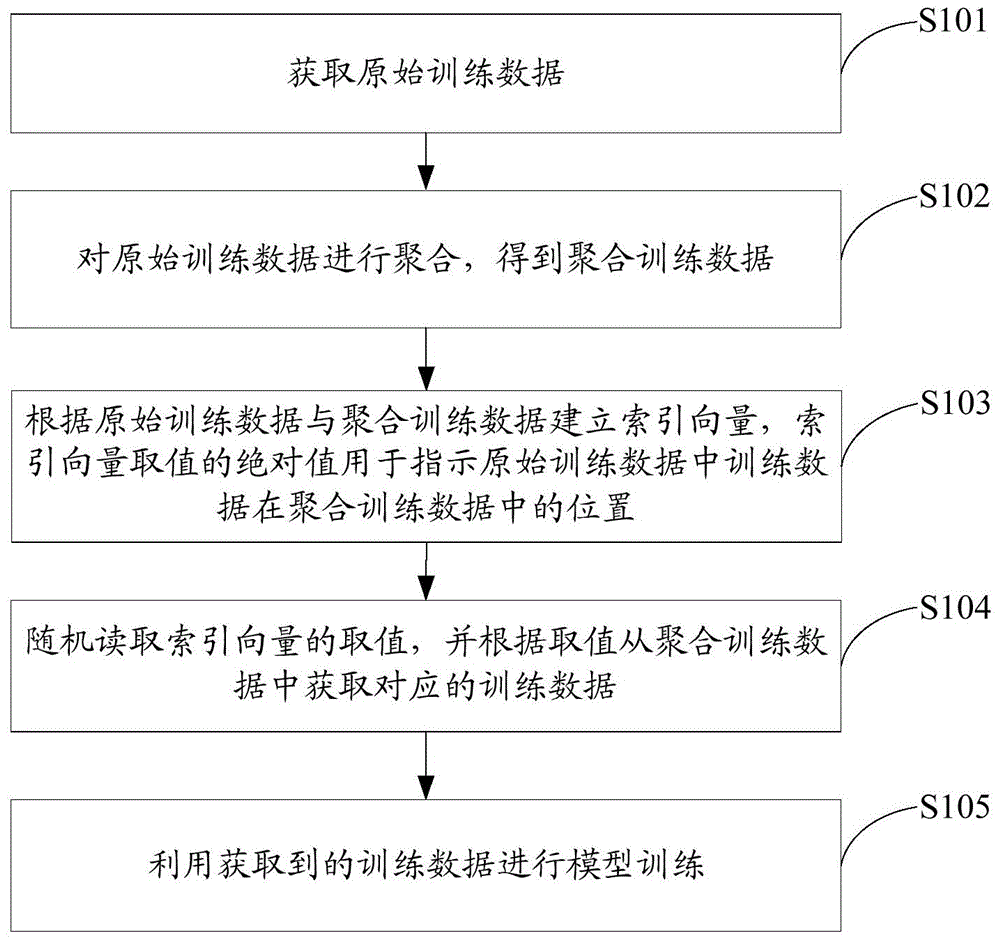
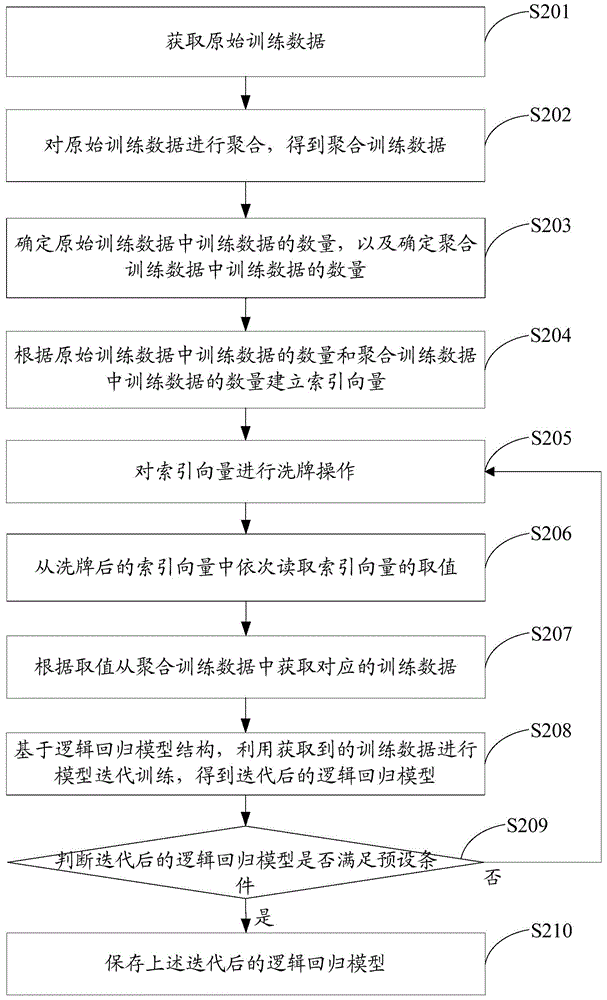
ActiveCN105045819AGuaranteed randomnessImprove training effectSpecial data processing applicationsData aggregatorMachine learning
The invention discloses a model training method and device for training data. The method comprises the following steps: obtaining original training data; carrying out aggregation on the original training data to obtain aggregated training data; according to the original training data and the aggregated training data, establishing an index vector, wherein the absolute value of an index vector value is used for indicating the position of the training data in the aggregated training data in the original training data; randomly reading the value of the index vector, and obtaining corresponding training data from the aggregated training data according to the value; and utilizing the obtained training data to carry out model training. On the premise of training data aggregation, the value of the index vector is randomly read, the corresponding training data can be obtained from the aggregated training data, and the randomness of the training data used for the model training is guaranteed so as to improve a model training effect on the basis of memory saving.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Method and equipment for testing compatibility after upgrading of system
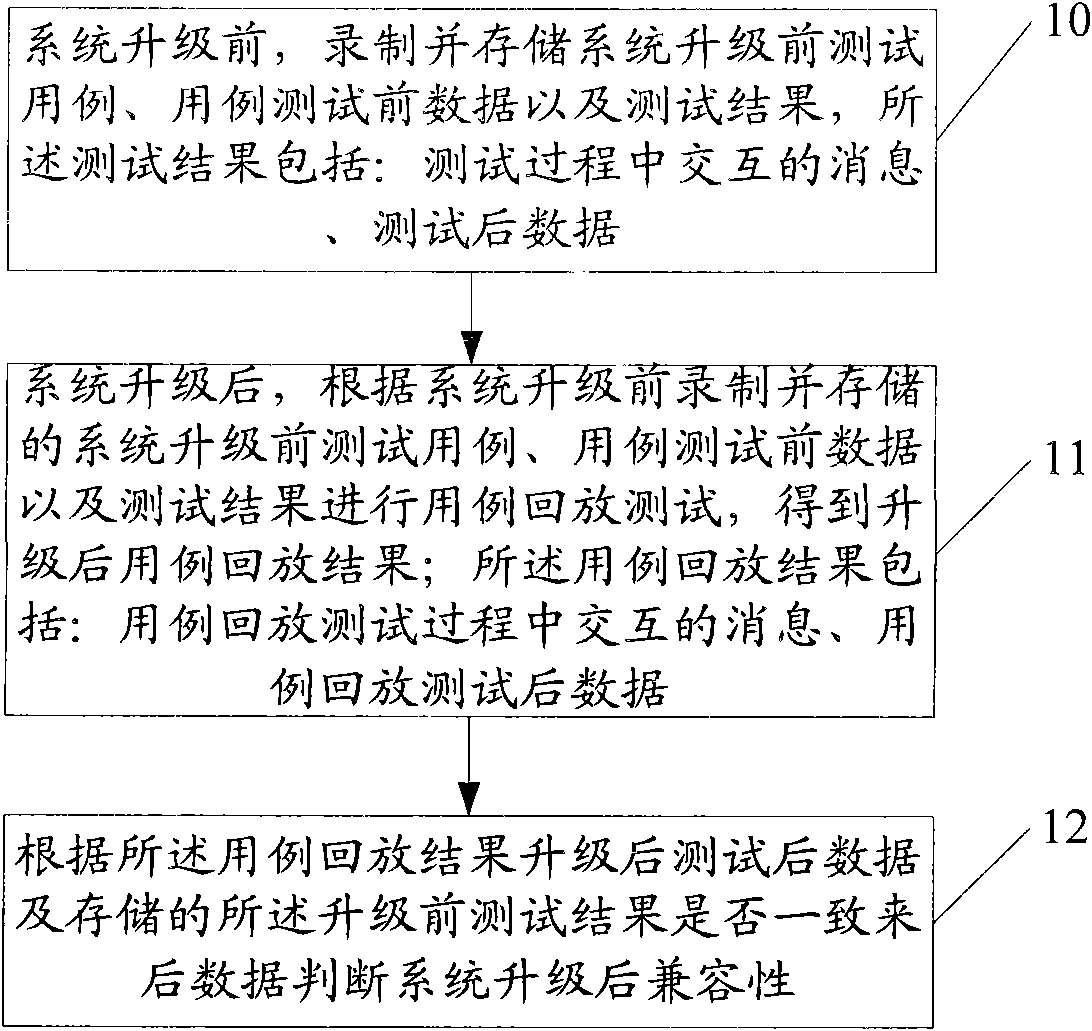
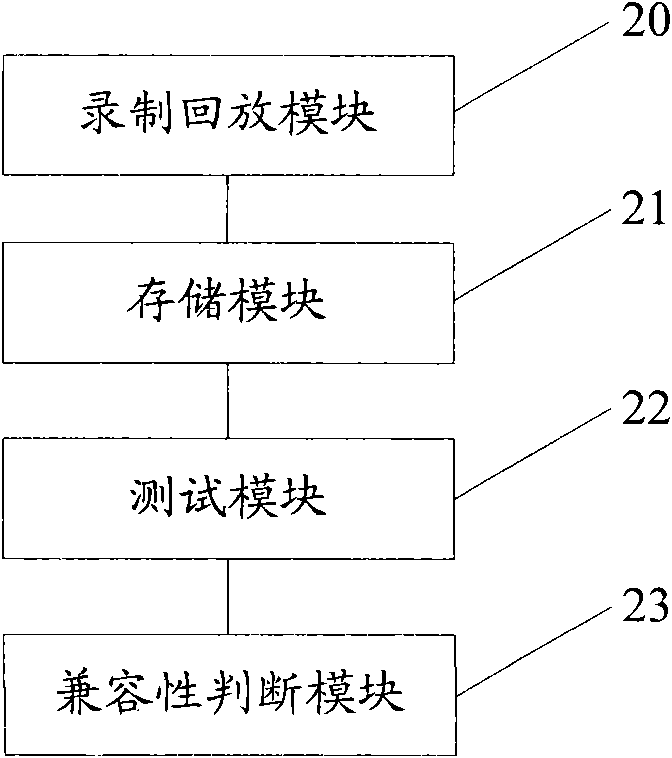
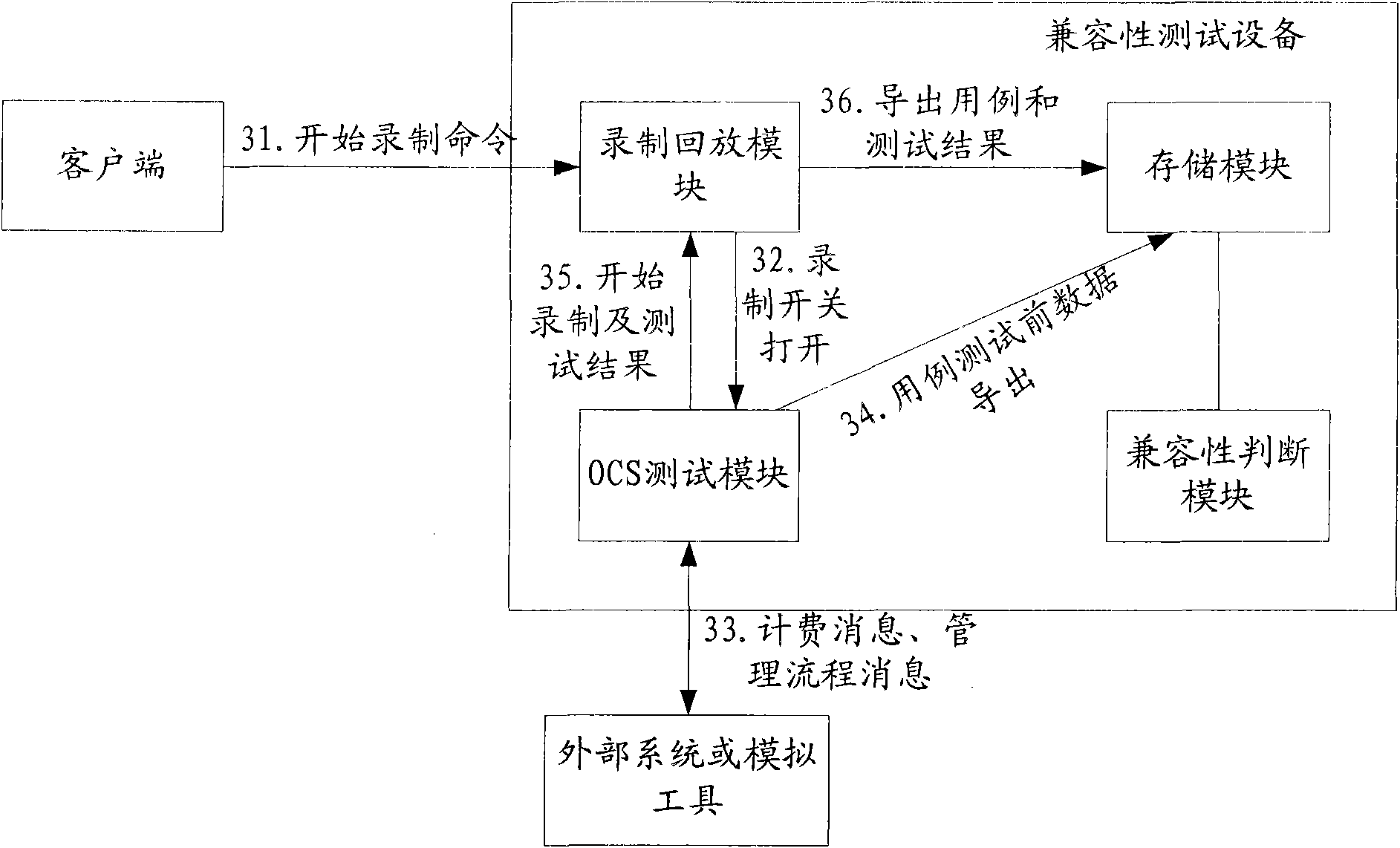
ActiveCN102045191AGuaranteed randomnessGuaranteed complexityData switching networksTest efficiencyComputer compatibility
The embodiment of the invention relates to a method and equipment for testing compatibility after upgrading of a system. The method comprises the following steps of: before the system is upgraded, recording and storing a test case before upgrading of the system, date before testing of a use case, and a test result; after the system is upgraded, performing use case playback testing according to the test case before upgrading of the system, the date before testing of the use case, and the test result which are recorded and stored before the system is upgraded to obtain a use case playback result after upgrading; and judging the compatibility after upgrading of the system according to the consistency between the use case playback result and the recorded and stored test result. In the invention, various test scenes before upgrading of the system are recoded and are played back after upgrading, data is not needed to be constructed in advance, randomness and complexity of the use case can be guaranteed, the automation degree of a test is improved, and the test efficiency is effectively improved.
Owner:HUAWEI TEHCHNOLOGIES CO LTD
Attack-defense countermeasure considered intelligent planning method for unmanned aerial vehicle track
InactiveCN108318032AFully reflect tactical availabilityReflect tactical availabilityNavigational calculation instrumentsPosition/course control in three dimensionsPath planSurvival probability
The invention relates to an attack-defense countermeasure considered intelligent planning method for an unmanned aerial vehicle track. According to the method, on an occasion that an attack-defense countermeasure exists in a task execution process of an unmanned aerial vehicle, an optimal objective function of a survival probability is converted from a product maximization form into a minimizationform, and a topographic condition and a constraint condition for track planning are added into a search algorithm, so that a planned track better conforms to an actual situation, and furthermore, a search space is reduced, and the track planning efficiency is improved. Compared with the prior art, the attack-defense countermeasure considered intelligent planning method disclosed by the inventionhas the advantages of capability of realizing efficient and rapid path planning for the unmanned aerial vehicle under the conditions of an air defense threat and a performance limit.
Owner:SHANGHAI JIAO TONG UNIV
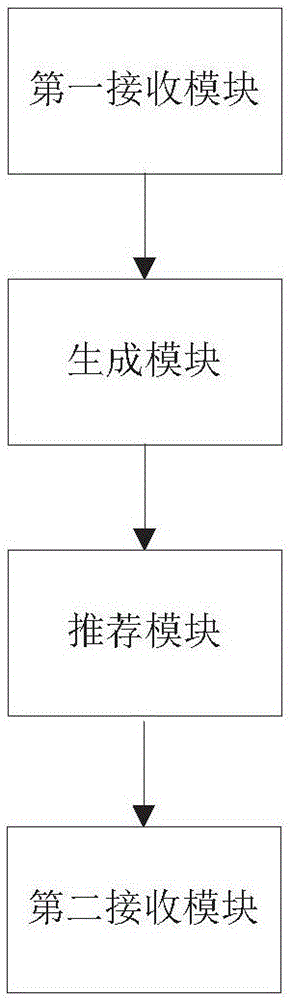
Learning resource recommendation system
ActiveCN106156354AReduce workloadQuality improvementElectrical appliancesSpecial data processing applicationsComputer scienceLearning resource
The invention provides a learning resource recommendation system. The system comprises a first receiving module, a generation module, a recommendation module and a second receiving module, wherein the first receiving module is used for receiving the curriculum, the push time of the curriculum and a question bank, and the question bank comprises the tile corresponding to each curriculum chapter; the generation module is used for generating test paper corresponding to each curriculum chapter according to the question bank, setting the recommendation time for the test paper, generating a classroom answer sheet by combining the test paper with the recommendation time and sending the classroom answer sheet to the recommendation module; the recommendation module is used for pushing the classroom answer sheet and the tiles of the curriculum chapters; the second receiving module is used for receiving search conditions, obtaining search results and receiving answers of the classroom answer sheet.
Owner:HUAIHAI INST OF TECH
Method and device for implementing dynamic load balancing
InactiveCN102541655AOvercome limitationsGuaranteed randomnessResource allocationDynamic load balancingDistributed computing
The invention provides a method for implementing dynamic load balancing in a distributed system. The distributed system comprises a plurality of servers. The method is used for determining a server for processing a request in a plurality of servers by the following steps of: respectively setting weights for a plurality of servers; calculating a range of each server according to the weights and calculating a total weight W; generating a random number R in the range of 1 to W; and judging the range M which the random number R falls into and reversely mapping the range M to determine the server for processing the request.
Owner:CHINA UNIONPAY
A block chain consensus method based on credibility evaluation
ActiveCN109949034AGuaranteed randomnessEnsure fairnessEncryption apparatus with shift registers/memoriesUser identity/authority verificationRankingDistributed computing
The invention relates to a block chain consensus method based on credibility assessment. According to the method, a weighted voting consensus based on trust values is adopted, and a consensus group isdynamically and randomly formed according to trust value ranking. Member of each consensus group has a voting weight in direct proportion to a trust value of the consensus group, and the trust valueis determined by long-time accumulated comprehensive performance. Therefore, only honest nodes show long-time normality and regularity, and can become one member of the consensus group. A miner in theconsensus group is randomly selected as a leader, the leader can generate a micro-block to pack the transaction, other nodes consensus the micro-block, and a round of work is finished. The method hasthree improvements: firstly, a novel leader and consensus group creation method is invented to ensure the randomness and fairness of selection; And secondly, a trust value calculation mode is createdbased on long-time accumulated comprehensive performance. And thirdly, a consensus algorithm based on the improved raft is created, and the throughput can be increased.
Owner:BEIJING UNIV OF TECH
Driving simulation method, device and equipment and storage medium
ActiveCN110069887AReduce manual operationsImprove construction efficiencyGeometric CADAutonomous decision making processReference distanceSimulation methods
The embodiment of the invention discloses a driving simulation method, device and equipment and a storage medium. The method comprises the following steps of obtaining basic parameters through a firstconfiguration interface, determining a vehicle reference distance, a vehicle reference speed and the number of background vehicles of a target lane according to the basic parameters; sequentially determining the initial position of each background vehicle on the target lane based on the position of the tested vehicle, the vehicle reference distance and the random distance deviation; based on thevehicle reference speed and the random speed deviation, sequentially determining the initial speed of each background vehicle located on the target lane, and conducting automatic driving simulation based on the initial position and the initial speed of each background vehicle. According to the method, the number of parameters required for setting the background vehicle in the simulated traffic environment can be reduced, the building efficiency of the simulated traffic environment is improved, and manual operation is simplified.
Owner:TENCENT TECH (SHENZHEN) CO LTD
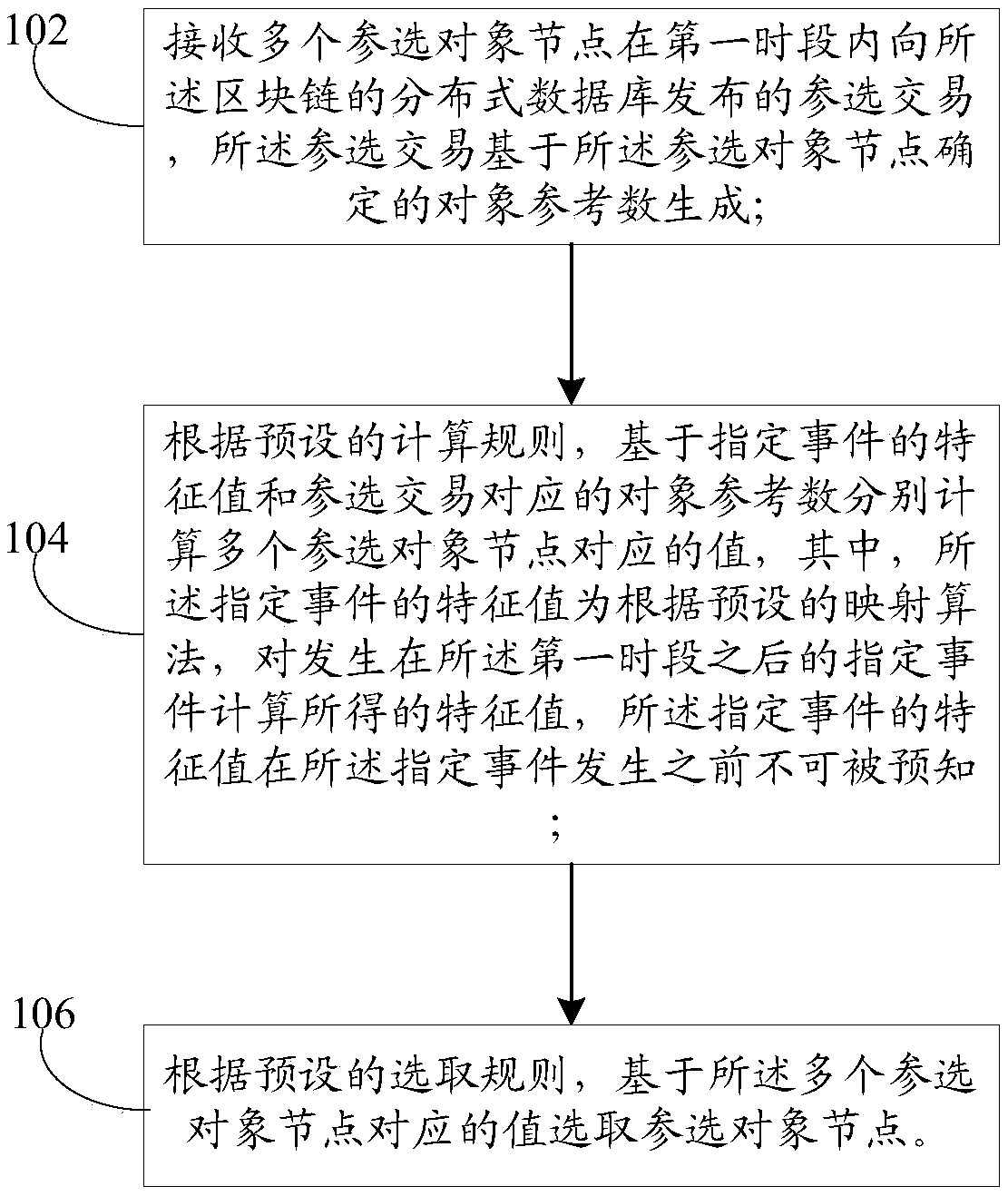
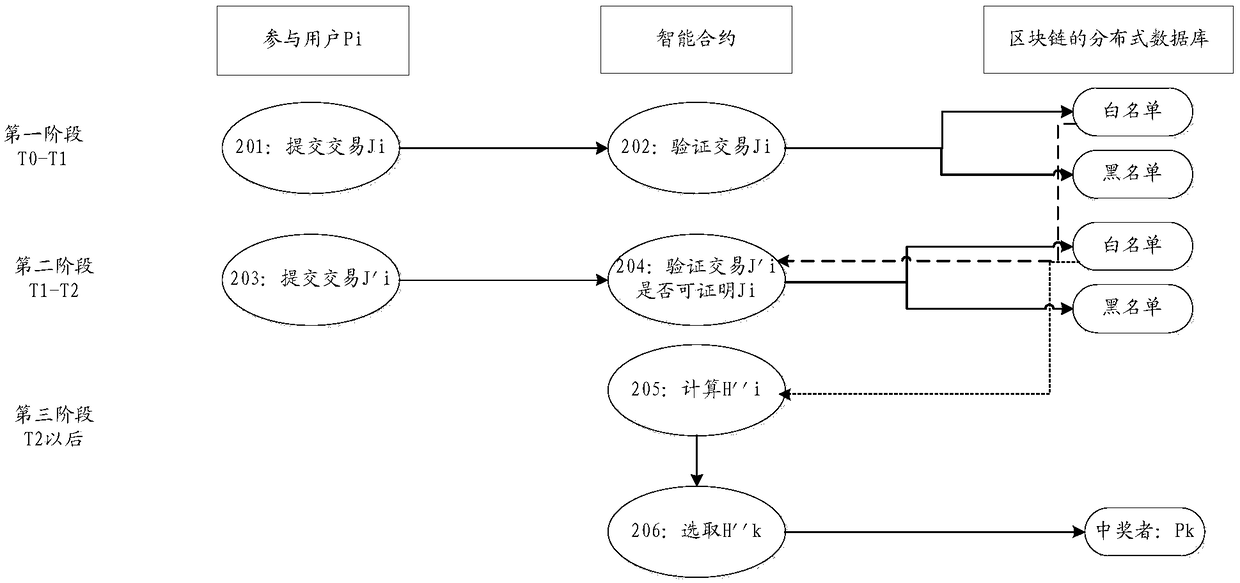
A method and apparatus for random object selection based on block chain
One or more embodiments of the present specification provide a block chain based random object selection method and apparatus, The method comprises: receiving a plurality of selected object nodes publishing a selected transaction to a distributed database of the block chain in a first period of time, the selected transaction being generated based on an object reference number determined by the selected object nodes; and receiving a selected transaction from a plurality of selected object nodes. According to the preset calculation rules, calculating values corresponding to a plurality of selected object nodes based on the eigenvalues of the specified events and the object reference numbers corresponding to the selected transactions, wherein an eigenvalue of the specified event is a eigenvalue calculated for a specified event occurring after the first period according to a preset mapping algorithm, the eigenvalue of the specified event being unpredictable before the specified event occurs; According to the preset selection rule, the selected object nodes are selected based on the values corresponding to the plurality of selected object nodes.
Owner:ADVANCED NEW TECH CO LTD
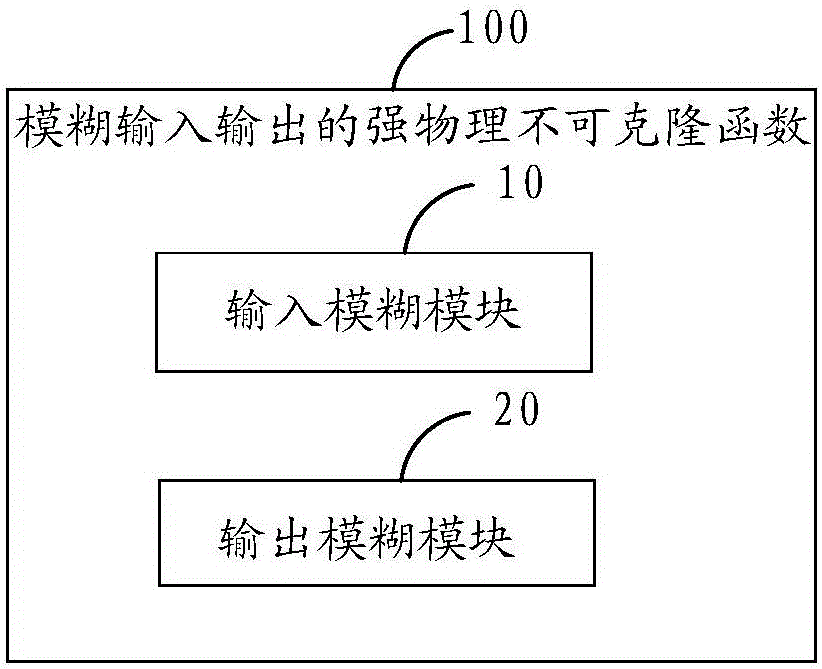
Strong physical unclonable function of fuzzy input and output
ActiveCN105809065AGuaranteed randomnessGuaranteed stabilityInternal/peripheral component protectionComputer hardwareComputer module
The invention is suitable for the technical field of information safety and integrated circuits, and provides a strong physical unclonable function of fuzzy input and output. The strong physical unclonable function comprises an input fuzzy module and an output fuzzy module, wherein the input fuzzy module is used for converting input excitation through a first random characteristic circuit and inputting the converted input excitation to the physical unclonable function; and the output fuzzy module is used for converting the output response of the physical unclonable function through a second random characteristic circuit and outputting the converted output response of the physical unclonable function to outside. The physical structure of the strong physical unclonable function of fuzzy input and output is that the strong physical unclonable functions and a weak physical unclonable function are integrated on a three-dimensional integrated circuit, wherein the weak physical unclonable function is positioned between two layers of strong physical unclonable functions. Therefore, the strong physical unclonable function can effectively resist modeling attack while the randomness and the stability of the strong physical unclonable function are guaranteed.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
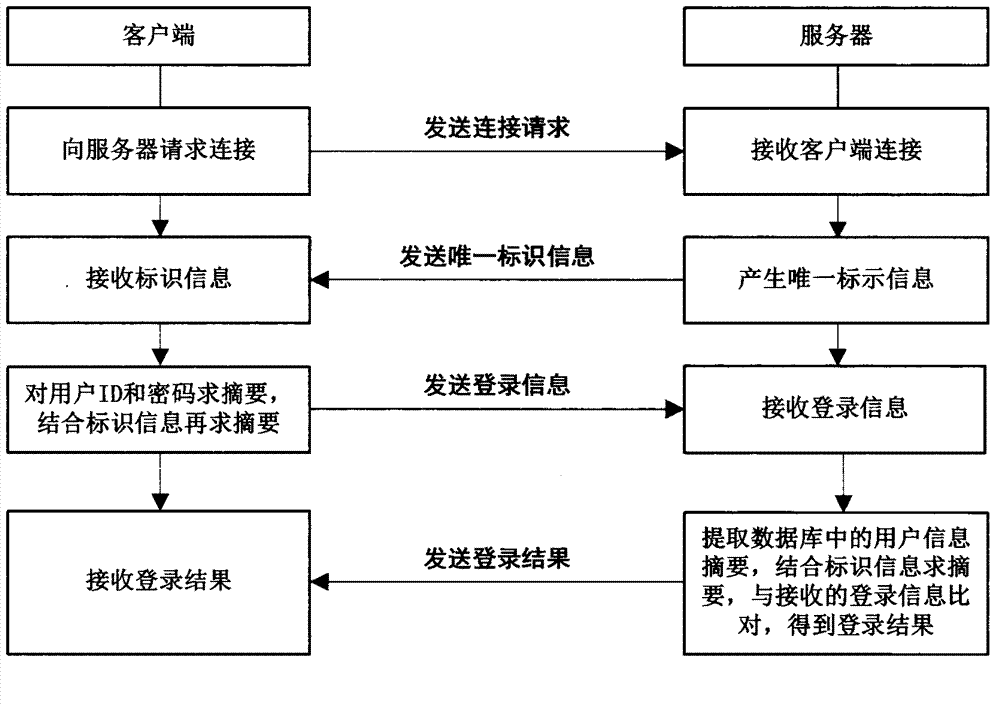
Bidirectional ID (Identity) authentication method based on dynamic password and digital certificate
ActiveCN101958913AImprove securityLower requirementUser identity/authority verificationPasswordAuthentication system
The invention relates to a computer network security technology, in particular to a bidirectional ID (Identity) authentication method based on a dynamic password and a digital certificate, solving the problem of system resource authorization risk in a traditional authentication system. The technical scheme comprises the following steps of: acquiring a user ID and a server ID in a certificate analysis mode; and authenticating a client and the server in a mode of combining the digital certificate with the dynamic password. The invention has the advantage of high security authentication between two communicating parties and is suitable for the secured communication of a network.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
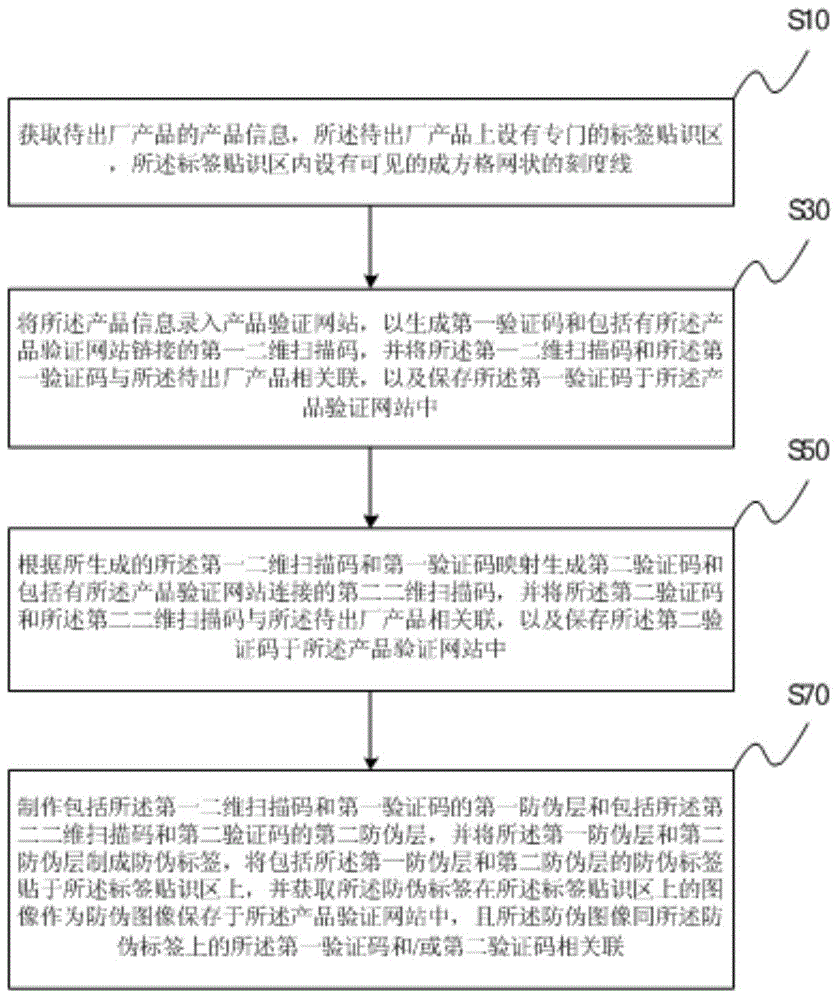
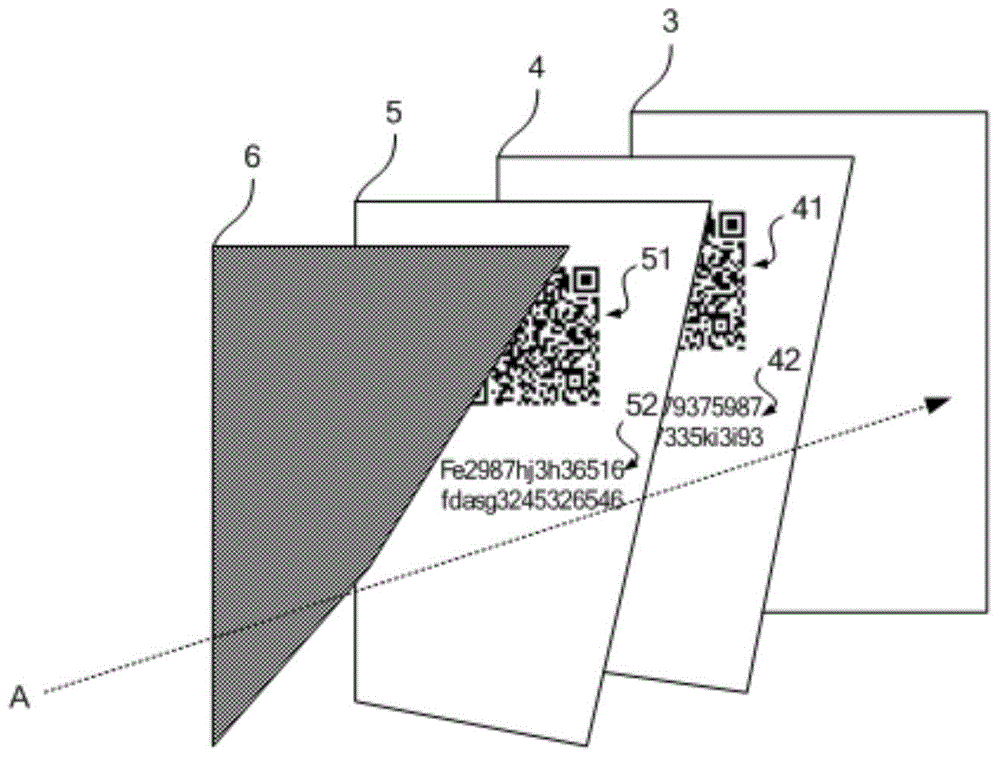
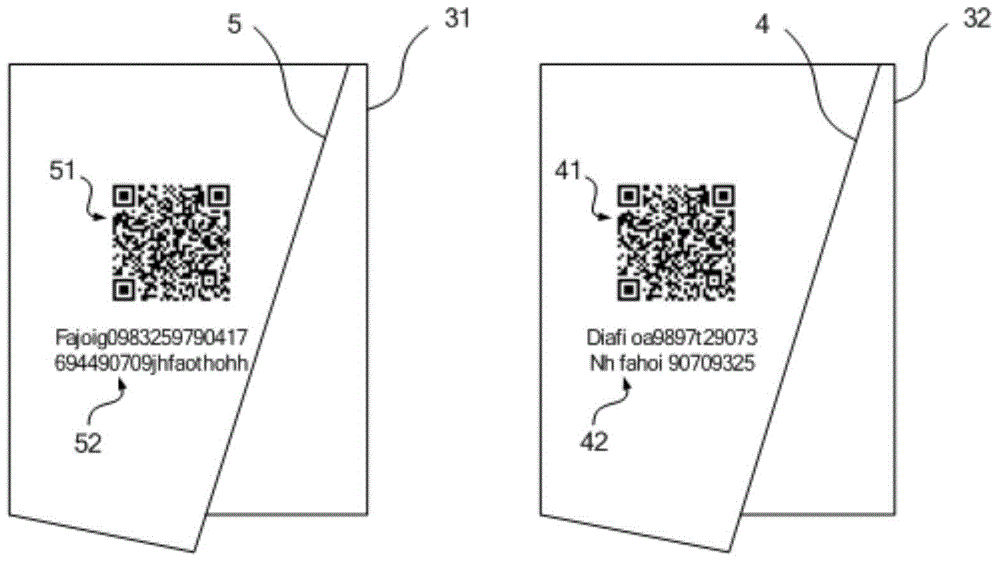
Product anti-counterfeiting method
InactiveCN104933569ARandomUniqueness guaranteedCommerceSensing by electromagnetic radiationComputer science
The invention provides a product anti-counterfeiting method used for the field of product anti-counterfeiting. According to the product anti-counterfeiting method, a two-dimensional code scanning technology and an internet technology are mainly utilized, a label pasting and identifying region is then arranged on a product which is going to leave a factory, and an image of an anti-counterfeiting label pasted in the label pasting and identifying region is obtained and used as an anti-counterfeiting image, so that the anti-counterfeiting safety of labels is enhanced, and the consistency between the anti-counterfeiting label on the product going to leave the factory and the label recorded before leaving the factory is ensured more effectively; in addition, an identifying code is arranged, and the identifying code is associated with production information of the product going to leave the factory and the anti-counterfeiting image, so that consistency and the unilateral control performance of the information associated with the product going to leave the factory are ensured. The invention further provides a product anti-counterfeiting system for realizing the method, so that an effective and safe anti-counterfeiting technology is provided to a product producer.
Owner:上海快捷科技发展有限公司
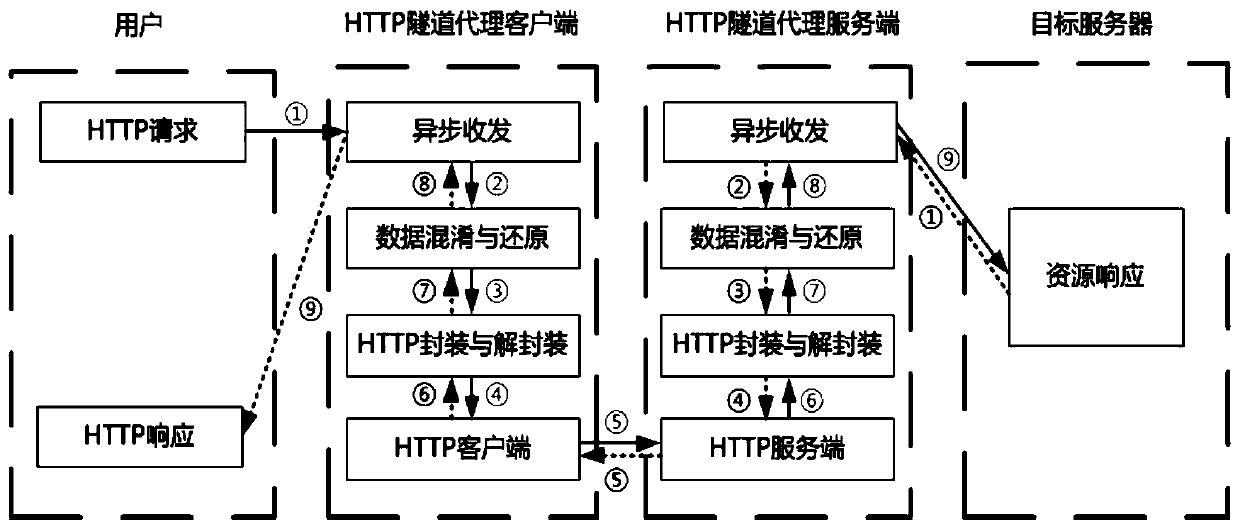
high-hiding network agent method and system based on an HTTP protocol
ActiveCN109756501AGuaranteed randomnessReduce the amount of calculationTransmissionTraffic capacityTraffic flow analysis
The invention provides an HTTP-based high-hiding network agent method and system, which are used for designing and realizing a set of agent communication scheme for improving agent efficiency and hiding property, and solving the problems that the concurrency capability is weak, the flow is easy to identify and the like in the existing agent application. And data hiding transmission based on an application layer protocol is realized through a tunnel technology, so that the concealment of proxy traffic is improved. Meanwhile, the load data is split, the characteristics of the original data are hidden, and the purpose of anti-flow analysis is achieved. The communication quality of the agent system under high concurrent access is ensured through an asynchronous transmission framework, and theuse experience of a user is improved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Method for achieving three-dimensional verification code
InactiveCN103514393AGuaranteed randomnessThree-dimensional prevention method is goodDigital data authenticationArray data structureRandom noise
The invention discloses a method for achieving a three-dimensional verification code. The method comprises the steps that a three-dimensional sphere capable of rotating is drawn and each point on the spherical surface of the three-dimensional sphere is expressed through a vector; a set of noise points are randomly added to the spherical surface of the three-dimensional sphere according to a preset rule; generated characters in the verification code are projected onto the three-dimensional sphere; two points are randomly chosen from the spherical surface of the three-dimensional sphere and are connected to form a line, so that a random noise line is generated; the random noise line is displayed on a verification interface to be identified by a user. A method for drawing the three-dimensional sphere capable of rotating comprises the steps that an icosahedron is drawn and coordinates of the icosahedron are stored in an array; in terms of each triangular face, midpoints of the three sides are obtained, and the length of the vector of each midpoint is adjusted to be identical to the radius of the sphere; each triangle is divided into four parts, the icosahedron is subdivided into an eighty-face body and a three-hundred-twenty-face body according to the recursive algorithm, and by parity of reasoning, the icosahedron is divided until a body similar to the sphere is obtained.
Owner:SHANGHAI HIGH SCHOOL
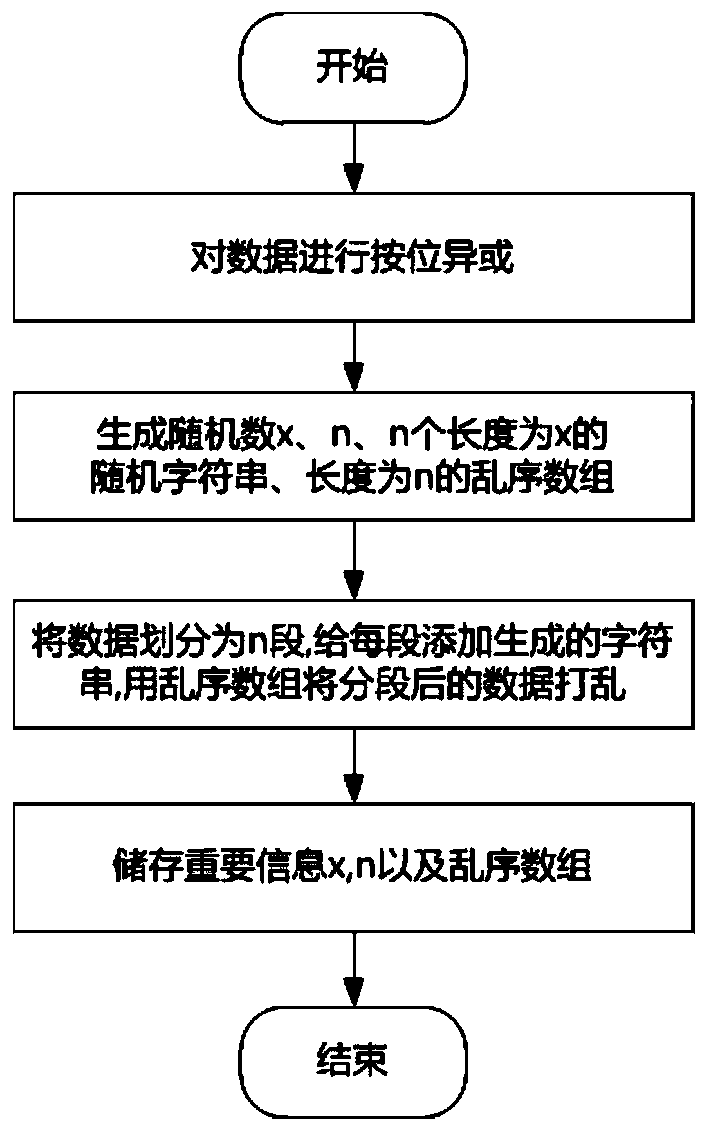
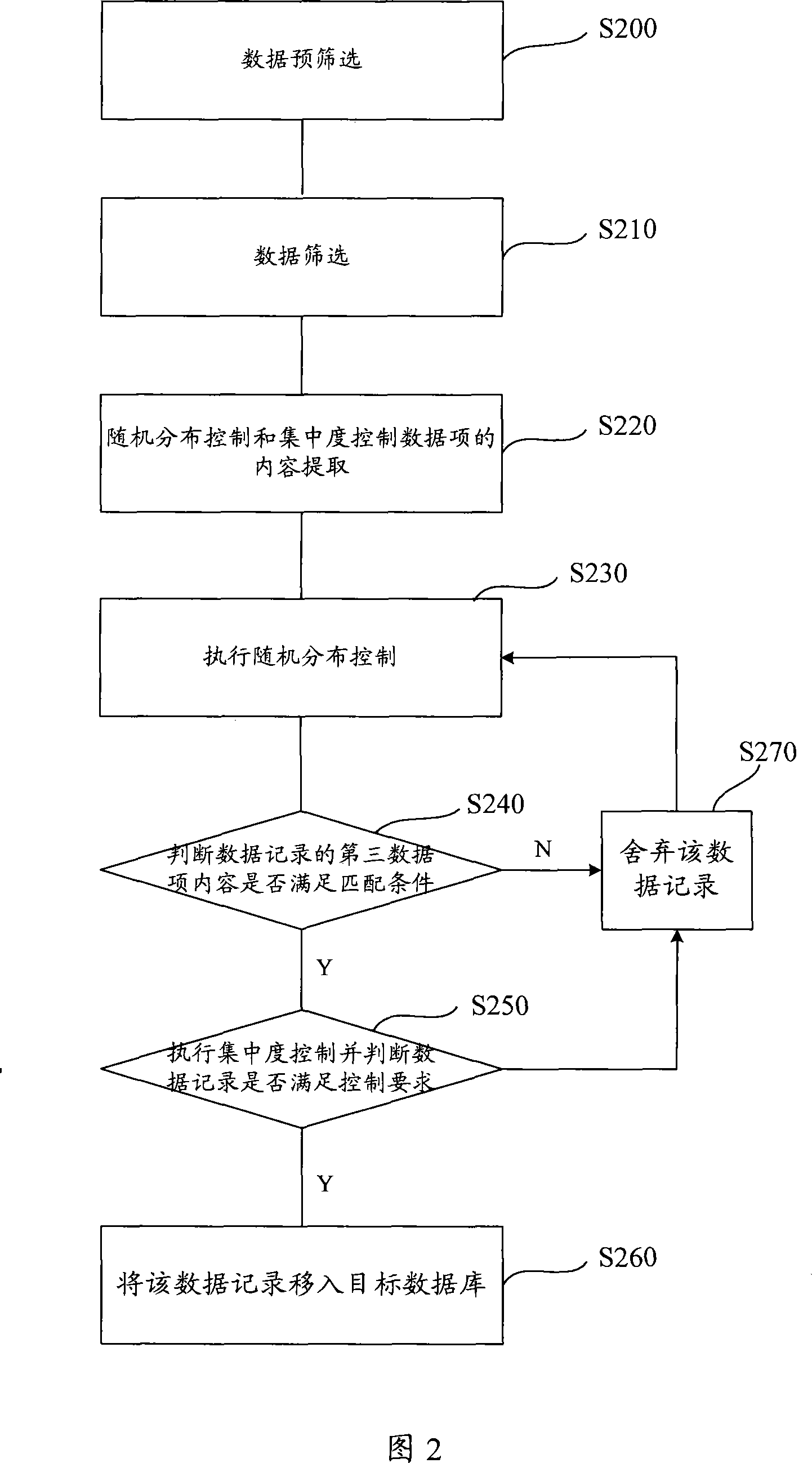
Data screening method and device, and securitization loan screening method and device
ActiveCN101221578AReduce process overheadShorten screening timeFinanceSpecial data processing applicationsDistribution controlData records
The invention discloses a method for data sieving and is applied in the sieving of the data records in a database at least comprising a first data item, a second data item and a third data item. The invention comprises that: the pre-sieving is executed, the data records which can not meet the sieving requirement are get rid of to form a preselection base; the data records which meet the sieving conditions are sieved from the preselection base to form a candidate base; the content of the first data item used for random distribution control and the content of the second data item used for concentration degree control are extracted; the random distribution control is executed according to the content of the first data item, a data record is randomly sieved, then the concentration degree control is made to the data record according to the content of the second data item; if the record meets the requirement of the concentration degree, whether the content of the third data item of the data record meets the matching conditions is judged, if the content of the third data item of the data record meets the matching conditions, the data record is moved into a target database. The invention also provides a data sieving device as well as a sieving method and a sieving device for securitization loan. The invention has less time consumption and higher efficiency during the data sieving.
Owner:CHINA CONSTRUCTION BANK
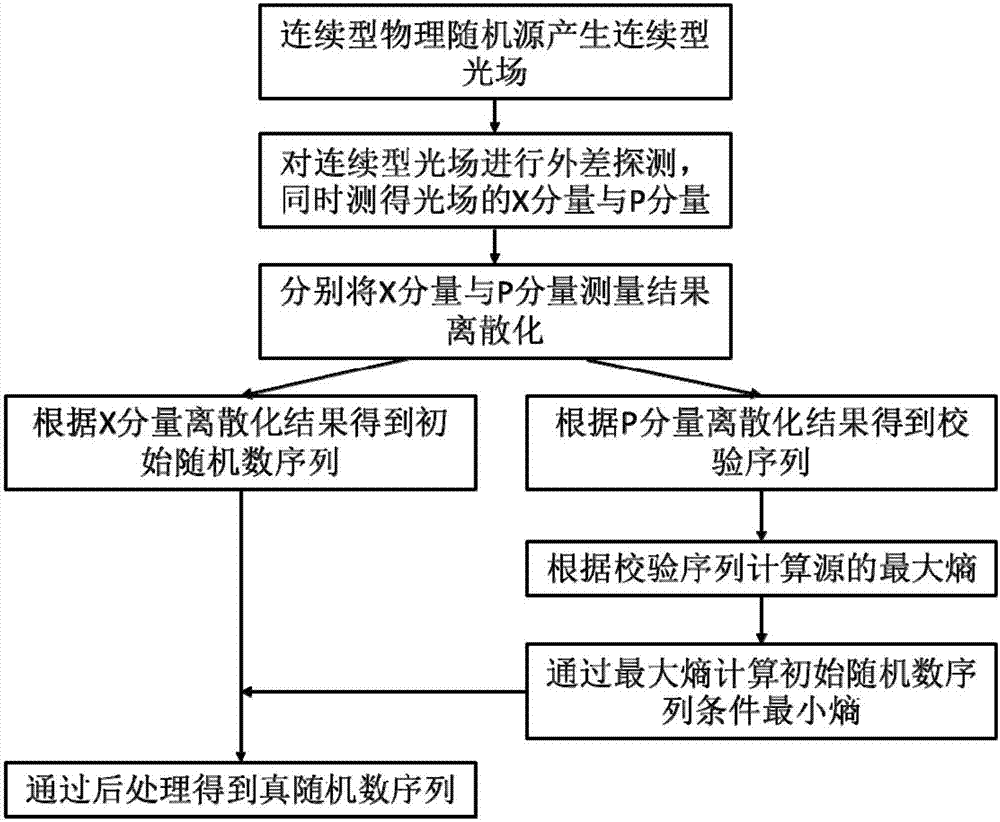
Generation method and device for source independent continuous quantum random number
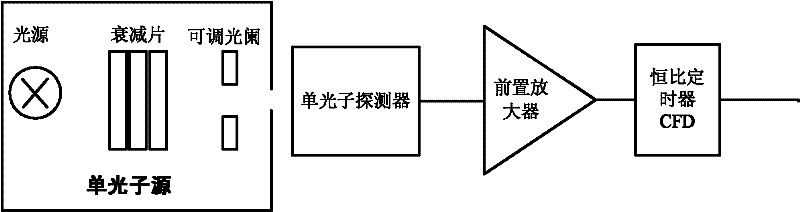
InactiveCN107368282ARealize measurementGuaranteed randomnessRandom number generatorsContinuous lightContinuous measurement
The invention puts forward a generation method and device for a source independent continuous quantum random number. The method comprises the following steps that: a continuous physical random source generates a continuous light field; the continuous light field is subjected to heterodyne detection, and meanwhile, two non-commutative mechanical quantities of the light field are measured, wherein the two non-commutative mechanical quantities are a component X (regular coordinate) and a component P (regular momentum); the continuous measurement results of the two mechanical quantities are discretized to independently obtain an initial random sequence under one component and a checking sequence under the other component; according to the checking sequence, the maximum entropy of a continuous random source is calculated; and through an entropy uncertainty principle and a maximum entropy calculation result, the conditional minimum entropy of the initial random sequence is obtained, and a completely random binary system true random sequence is obtained through postprocessing. By use of the method, additional random number does not need to be provided, the method does not depend on a hypothesis for sources, a "trusted" part in the physical random source can be effectively extracted, and the quantum random number is generated.
Owner:PEKING UNIV
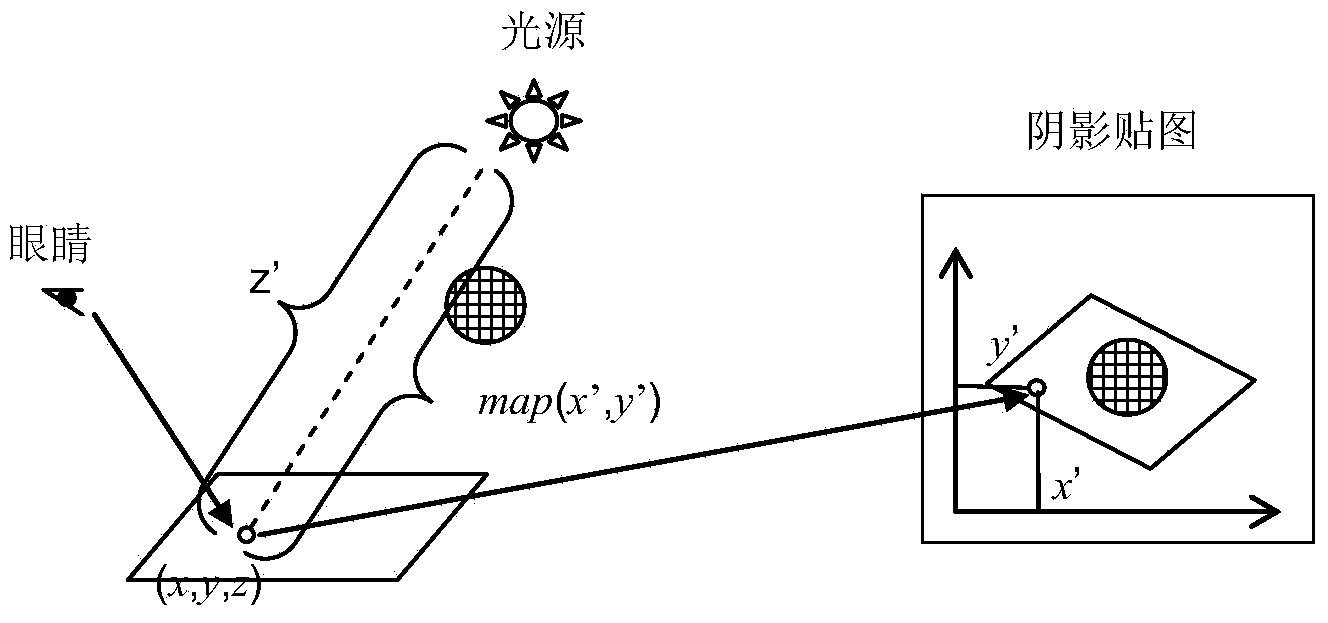
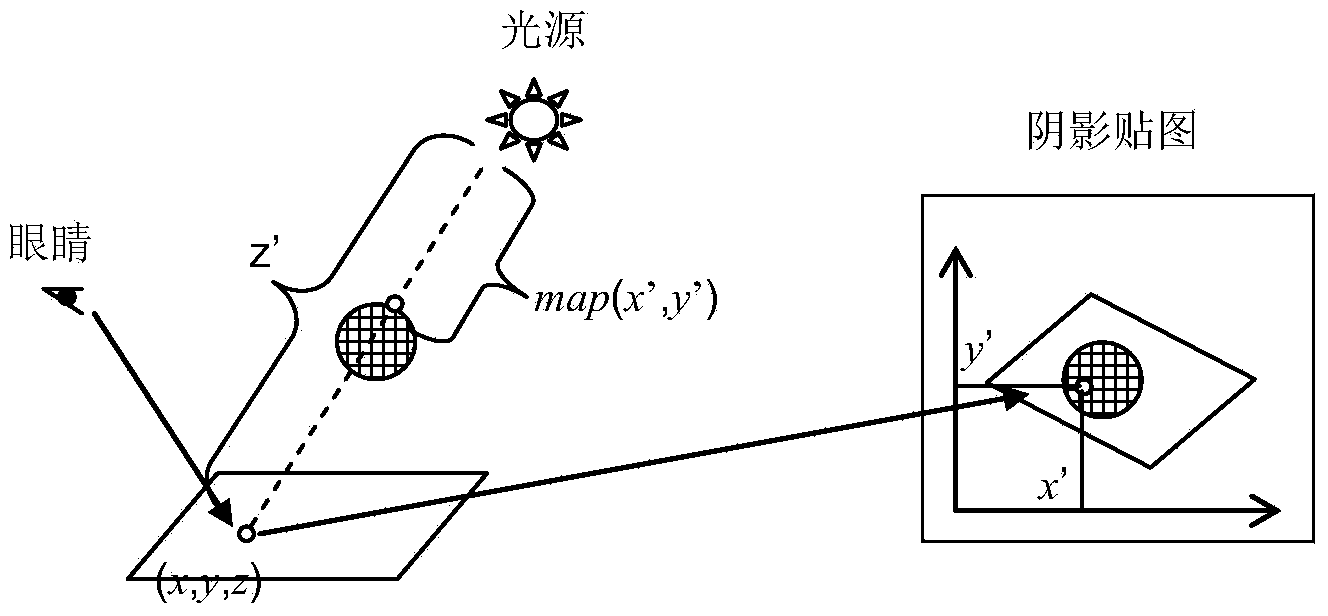
Method for shadow rendering in virtual home decoration indoor scene design
InactiveCN103903296AIncreased complexityImprove execution efficiency3D-image renderingDiffusionShadow mapping
The invention discloses a method for shadow rendering in virtual home decoration indoor scene design. The method comprises the steps of shadow mapping graph generation, half shadow estimation, percentage approximation filtering based on Poisson disc sampling and finally generation of a virtual home decoration indoor scene shadow effect graph with the reality sense through adding of diffusion reflection environment light. The method can effectively solve the problem of sawtooth deformation of a shadow mapping graph.
Owner:SOUTHEAST UNIV
Software system performance optimization method based on generative countermeasure network
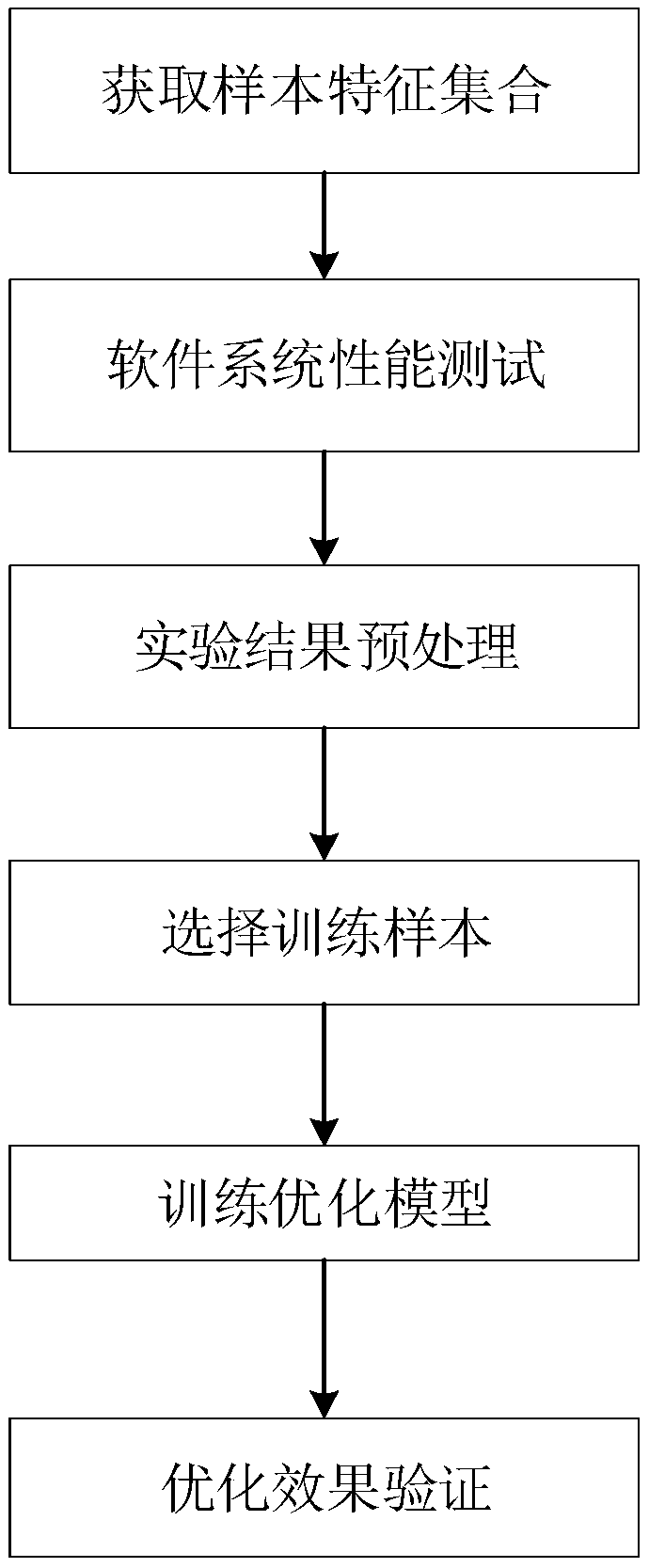
ActiveCN109388565AThe result is obviousEasy to trainSoftware testing/debuggingCountermeasureSoftware system
The invention discloses a software system performance modeling and optimization method based on a generating countermeasure network, which mainly solves the problems of high time cost, too much difficulty in training, easy collapse of training network and limited optimization space in the prior art. The implementation scheme is as follows: 1) acquiring the feature sample set of the software system; 2) fixing that hardware environment, configuring the software system, carry out performance testing according to the characteristic sample set, obtaining throughput or time delay, carry out pretreatment on the throughput or time delay, and sequentially carrying out single thermal coding and normalization to obtain structured data; 3) at that start of each iteration, randomly selecting half of the structured data from the step 1 as a training sample, iteratively train the generated antagonism network to obtain an optimized sample; 4) comparing the performance of the training sample and the optimization sample to verify the optimization effect. The invention reduces the time cost, improves the robustness and stability of the network, has obvious optimization effect, and can be used for theprocessing of the Internet and the big data.
Owner:XIDIAN UNIV
Two-dimensional code generation method and application thereof
ActiveCN104331728AUniqueness guaranteedGuaranteed randomnessCo-operative working arrangementsCommerceComputer hardwareSource tracing
The invention discloses a two-dimensional code generation method and an application thereof. The method is characterized by including the steps: 1 generating source tracing codes; 2 generating prefix codes; 3 generating Y-bit verification codes; 4 storing the source tracing codes, the prefix codes and the Y-bit verification codes into an anti-fake database, and generating an initial two-dimensional code by the aid of a bar code generator after the source tracing codes and the prefix codes are combined; embedding the Y-bit verification codes into the middle of the initial two-dimensional code to form a two-dimensional code. A lot of two-dimensional codes with high anti-fake performance and difficult simulation can be rapidly and stably generated, so that uniqueness of the two-dimensional code is effectively ensured, and the two-dimensional code is prevented from being copied or repeatedly used.
Owner:ANHUI GUOKE TESTING TECH CO LTD
Quadratic congruence equation-based method for resisting denial-of-service attacks of wireless network
InactiveCN102196432AReduce the number of negotiationsIncrease the number of negotiationsAssess restrictionSecurity arrangementWireless mesh networkBeacon frame
The invention discloses a quadratic congruence equation-based method for resisting denial-of-service attacks of a wireless network, which belongs to the technical field of network safety, and mainly solves the problem that the DoS (Denial-of-Service) attacks exist in a wireless access authentication process of an IEEE (Institute of Electrical and Electronic Engineers) 802.11i protocol. The method is implemented by the following steps: an AP (Access Point) adds parameters used for constructing a puzzle into a beacon frame and broadcasts the beacon frame periodically by using the beacon frame in the IEEE 802.11i protocol; a client STA (Special Temporary Authority) acquires the beacon frame, extracts puzzle parameters from the beacon frame, constructs and solves the puzzle in combination with the current global parameters of the wireless network, adds the puzzle parameters and the solution into an authentication request message, and sends an authentication request message to the AP; and the AP receives an open system authentication message of the STA, and the AP sends the authentication request message to the STA to complete the association process when the solution of the puzzle is correct, or the request of the STA is terminated. When the method is adopted, the negotiation times increased to construct the puzzle in a traditional client puzzle scheme are reduced, and the negotiation efficiency and the DoS attach resistance of the wireless access authentication protocol are improved.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com