Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42905results about "Assess restriction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
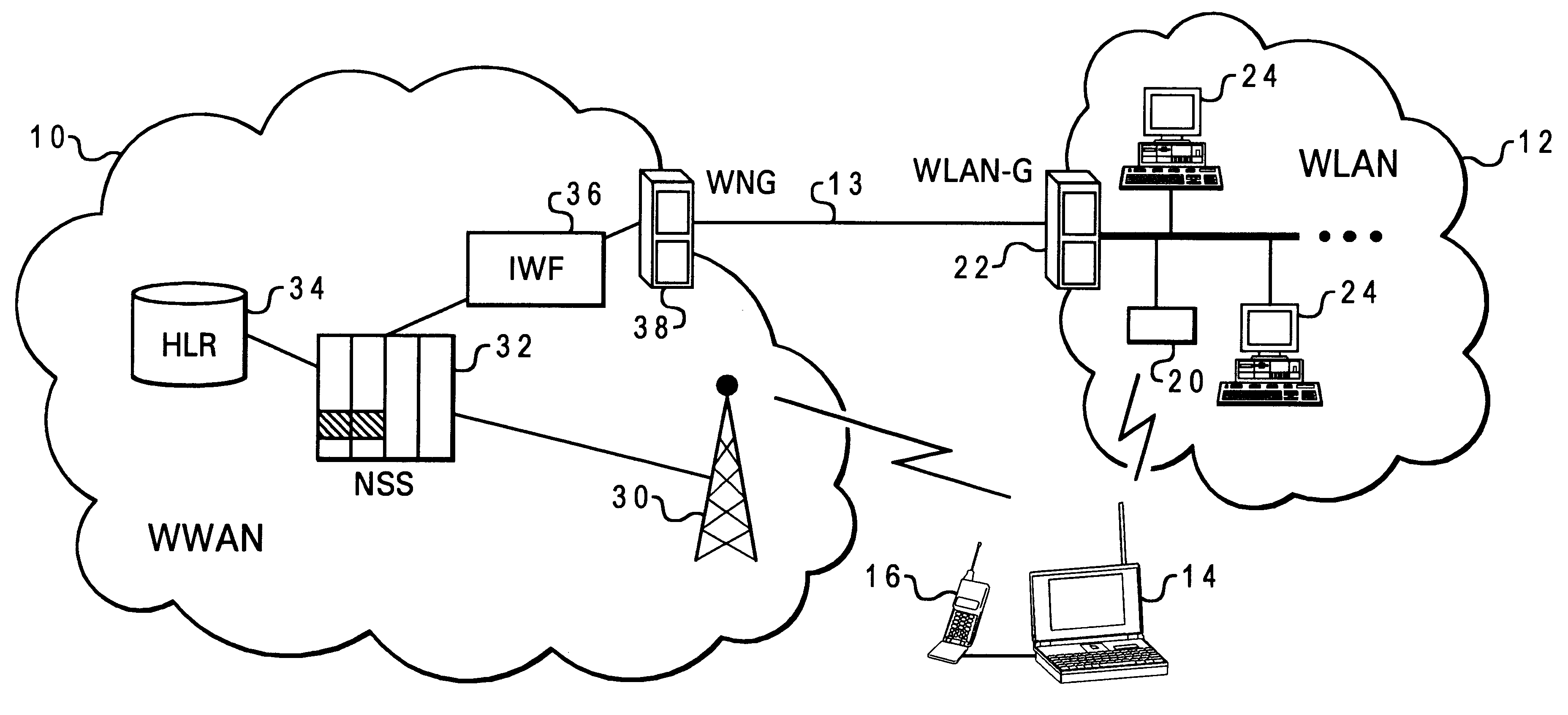
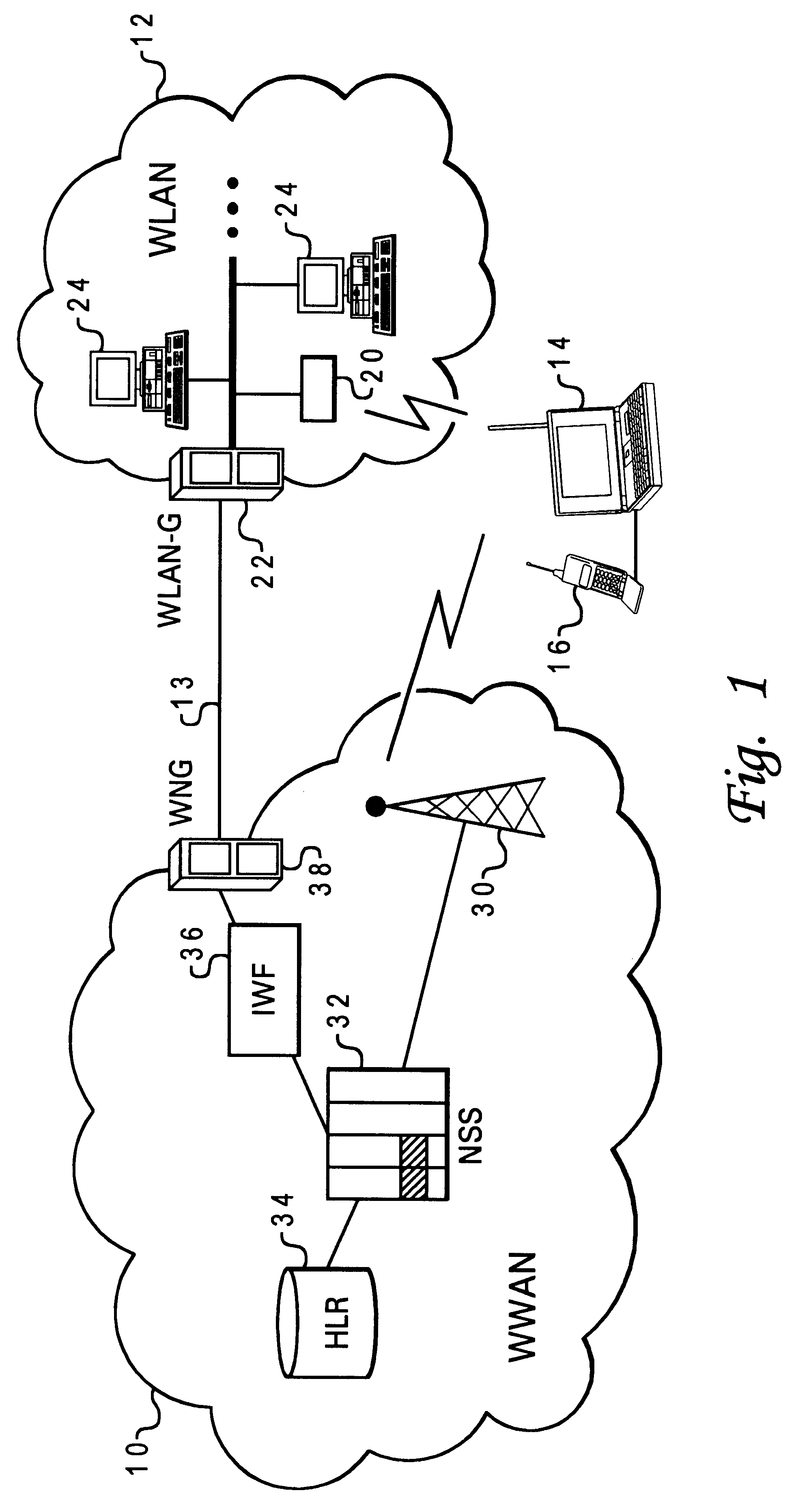
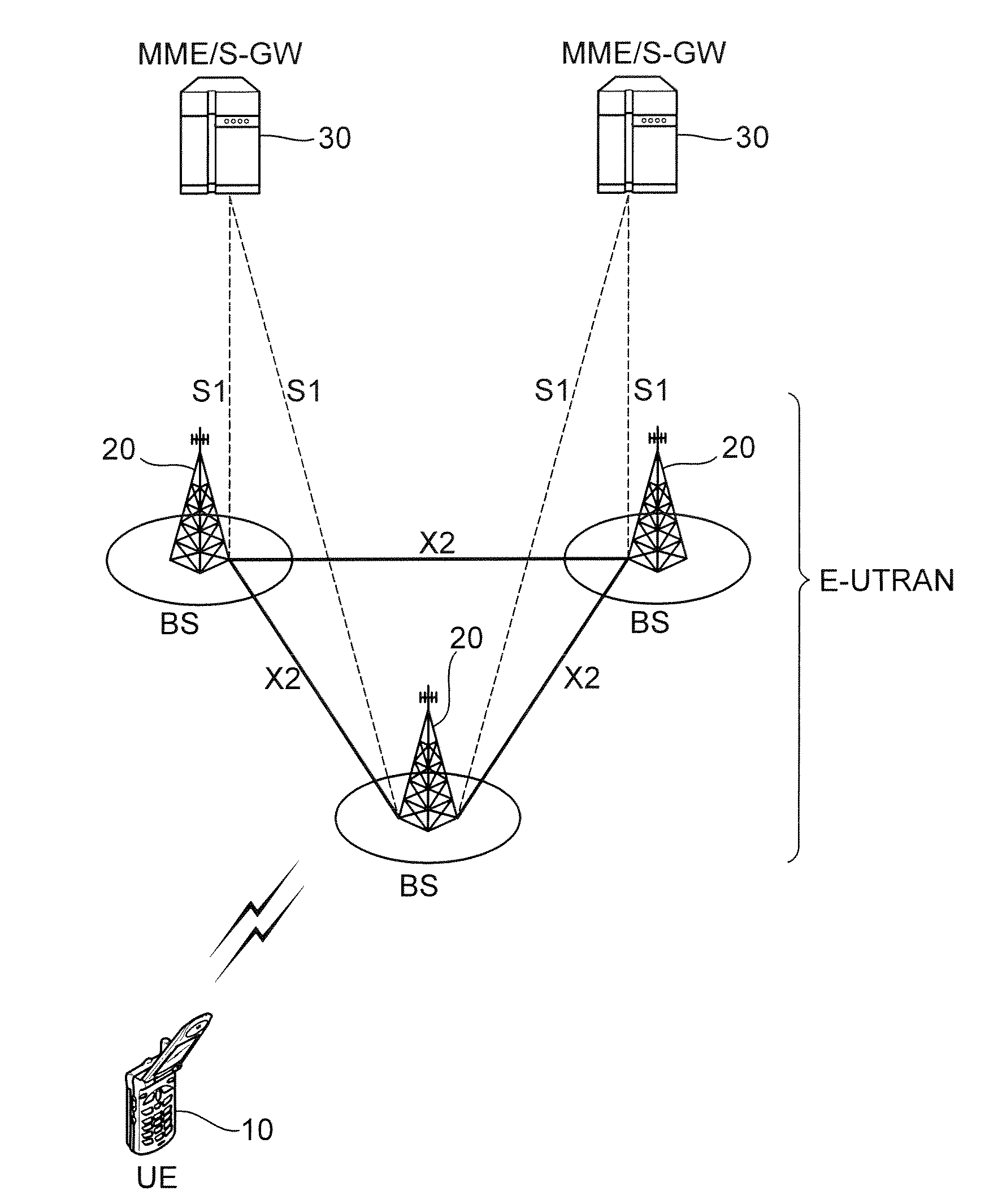
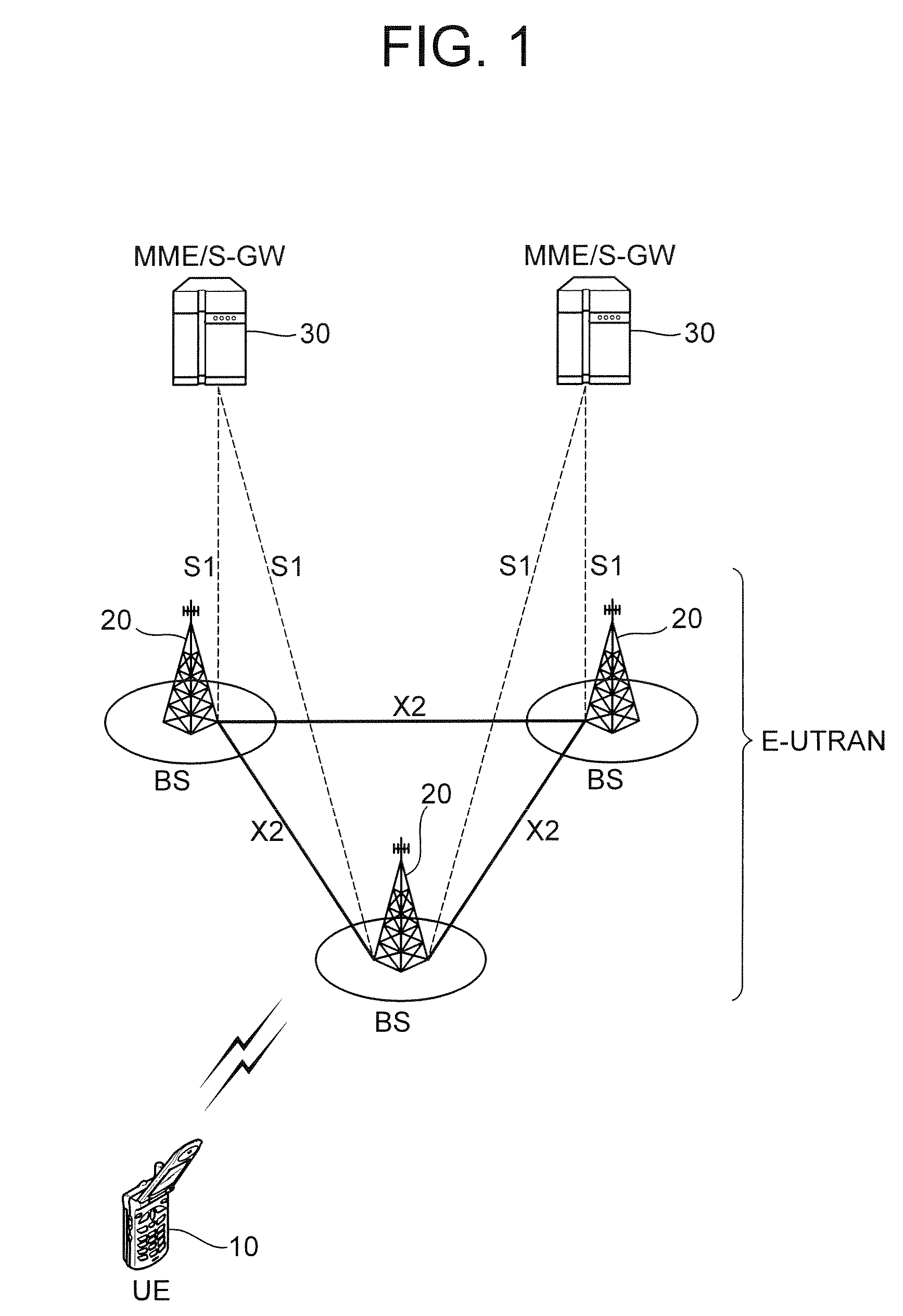
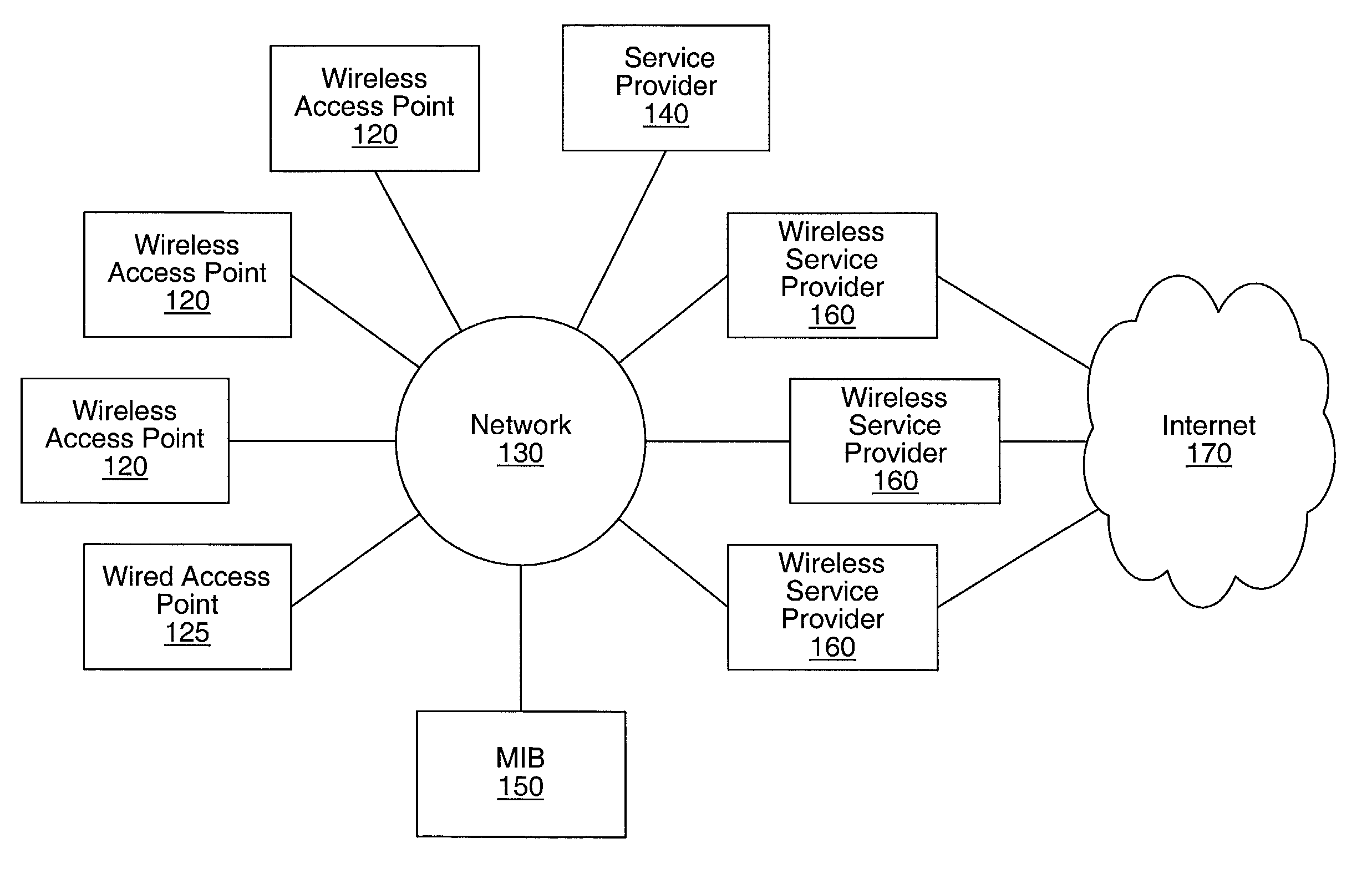
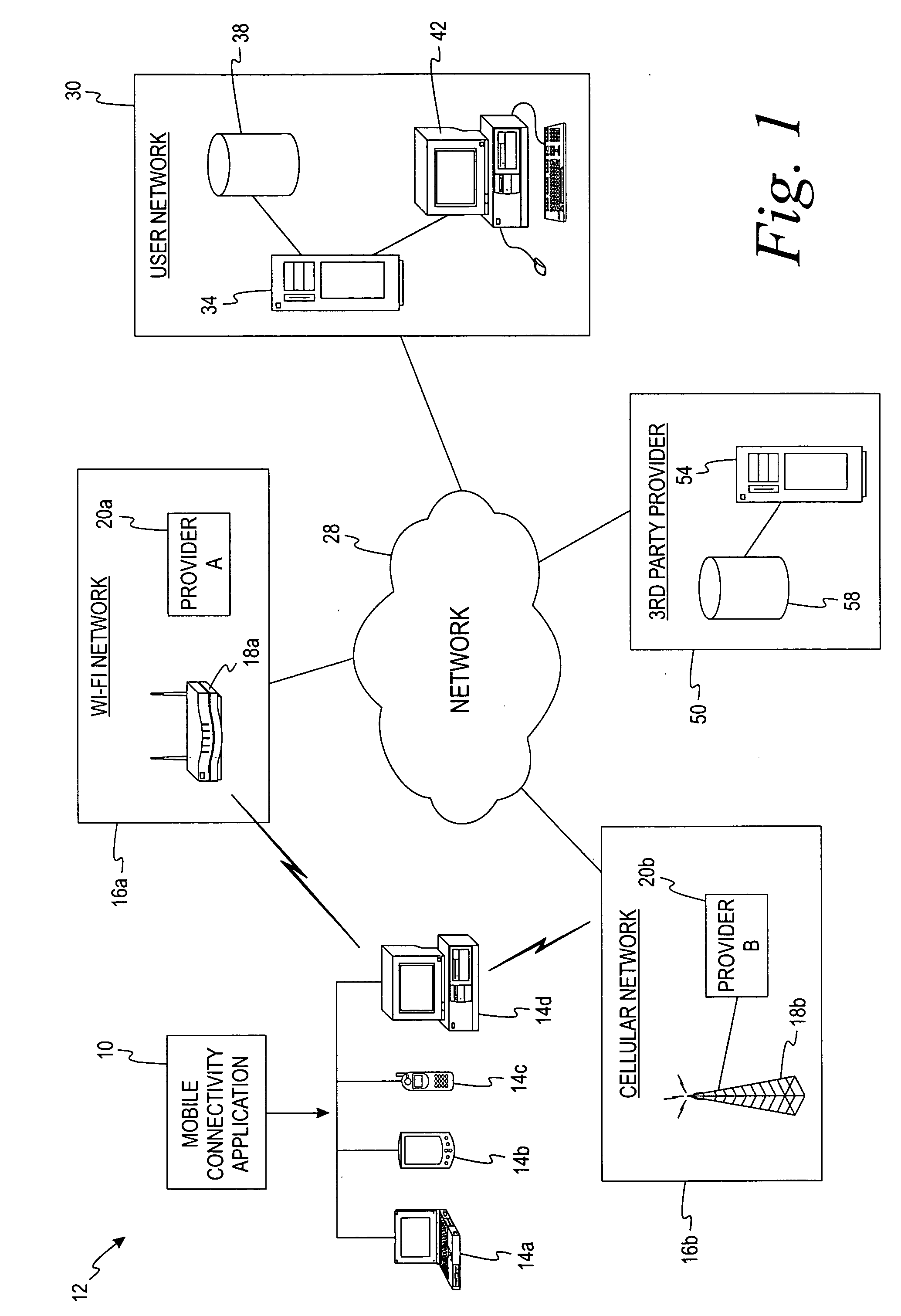
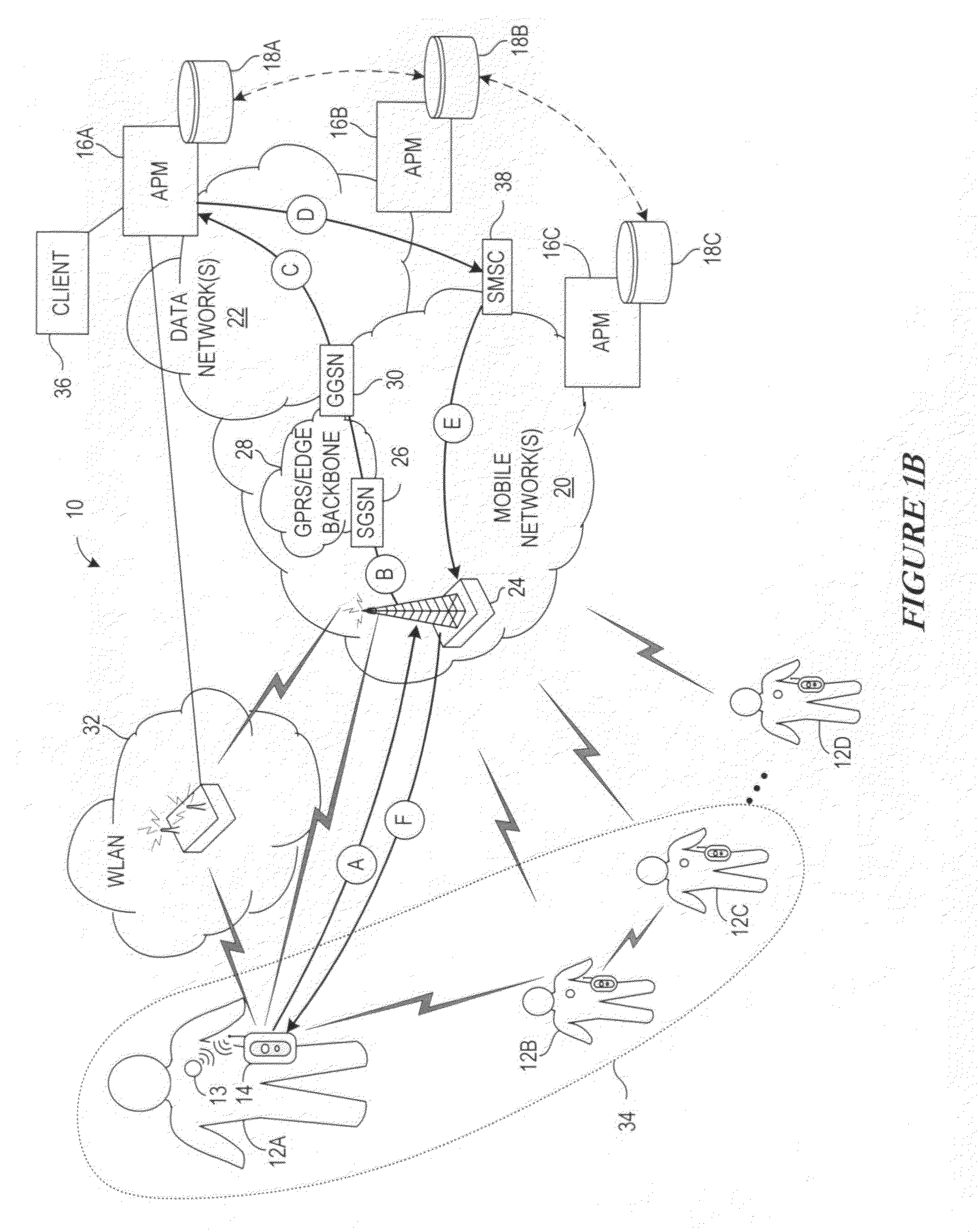
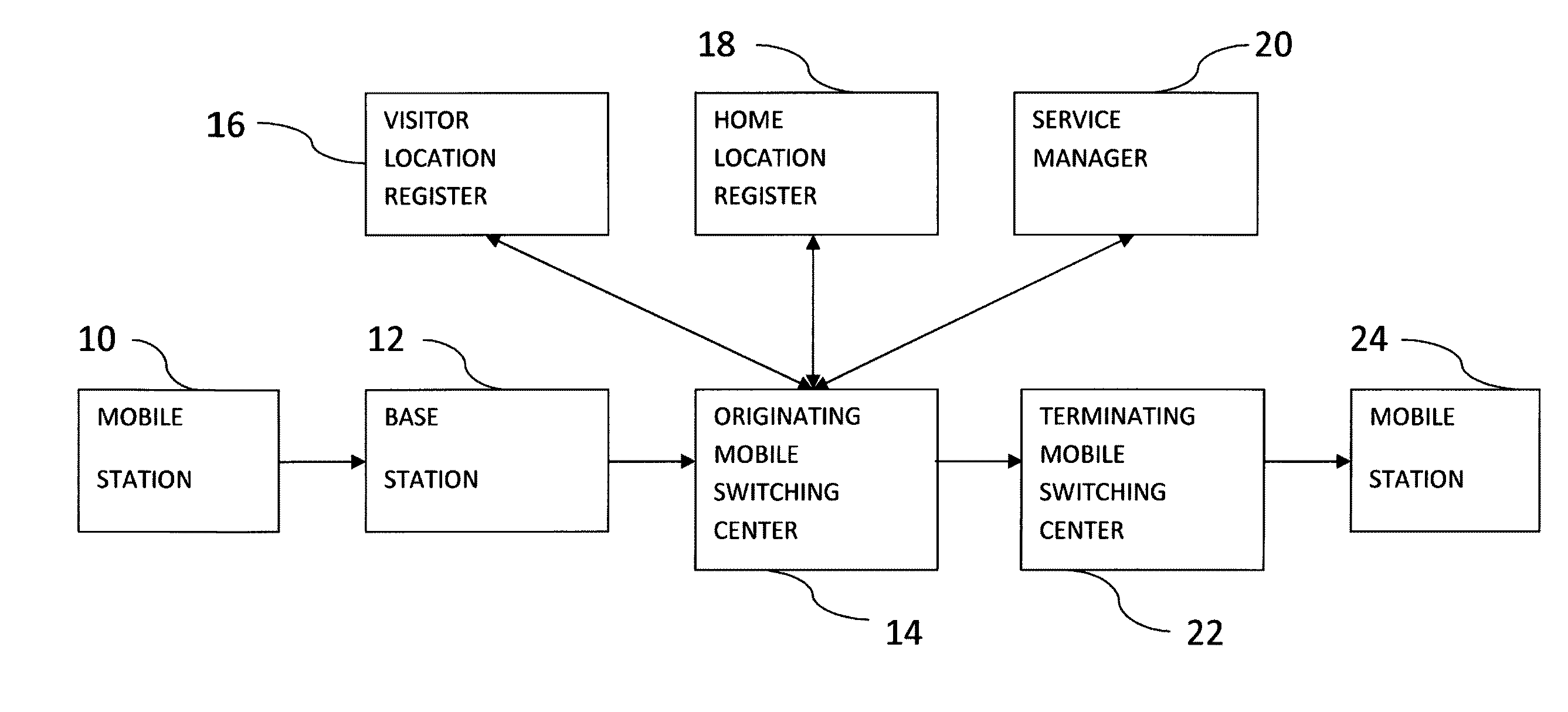
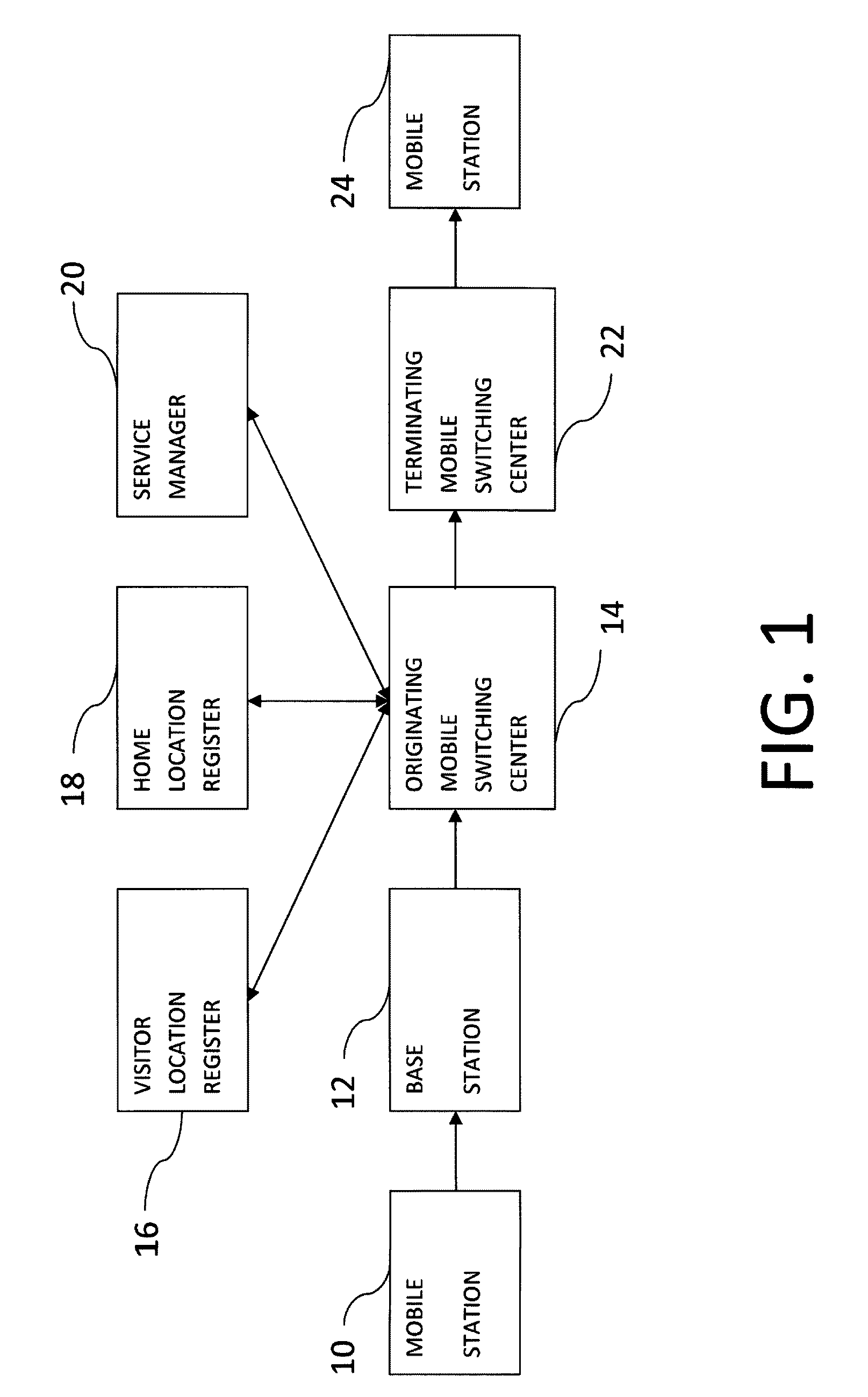
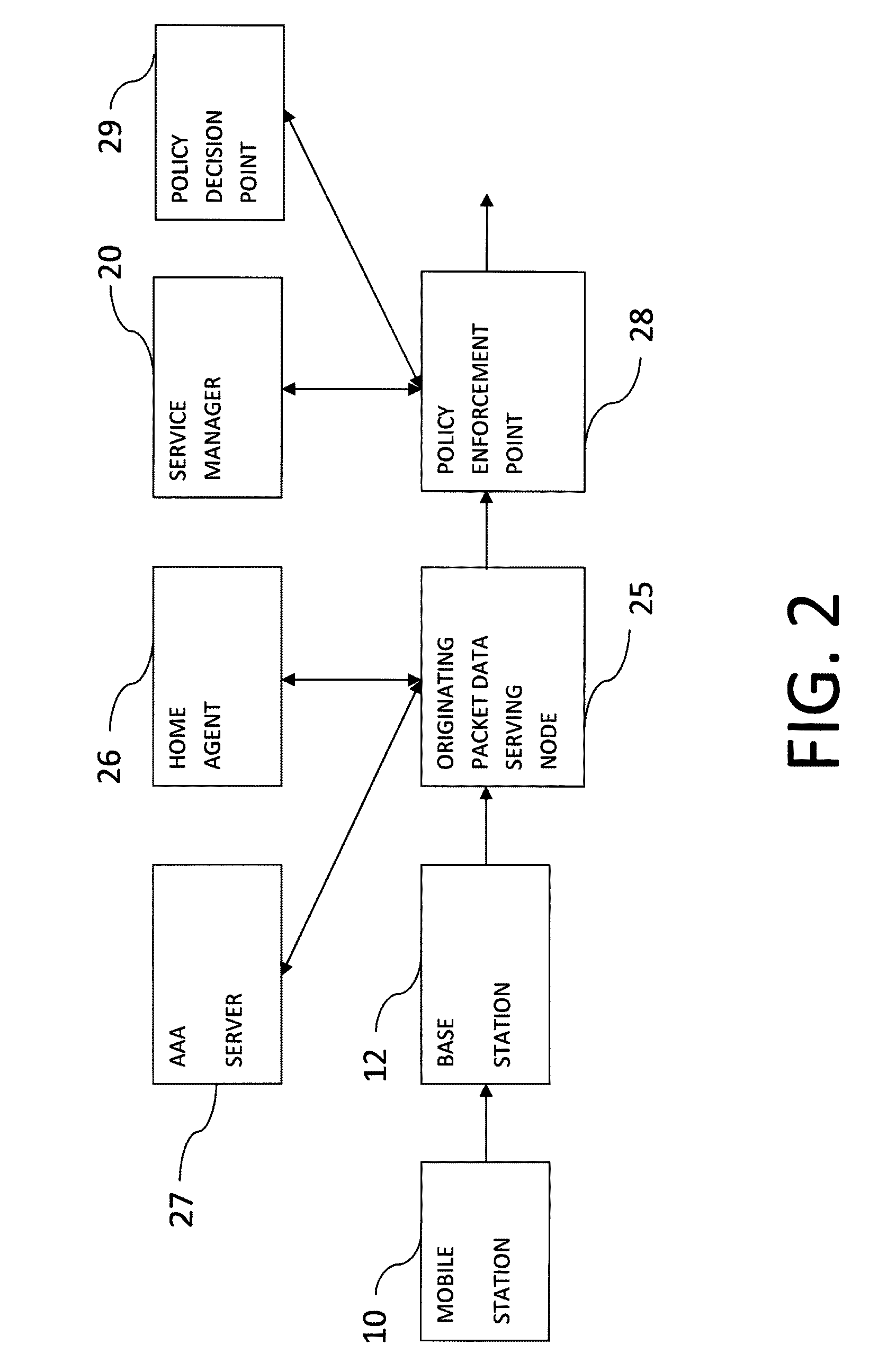
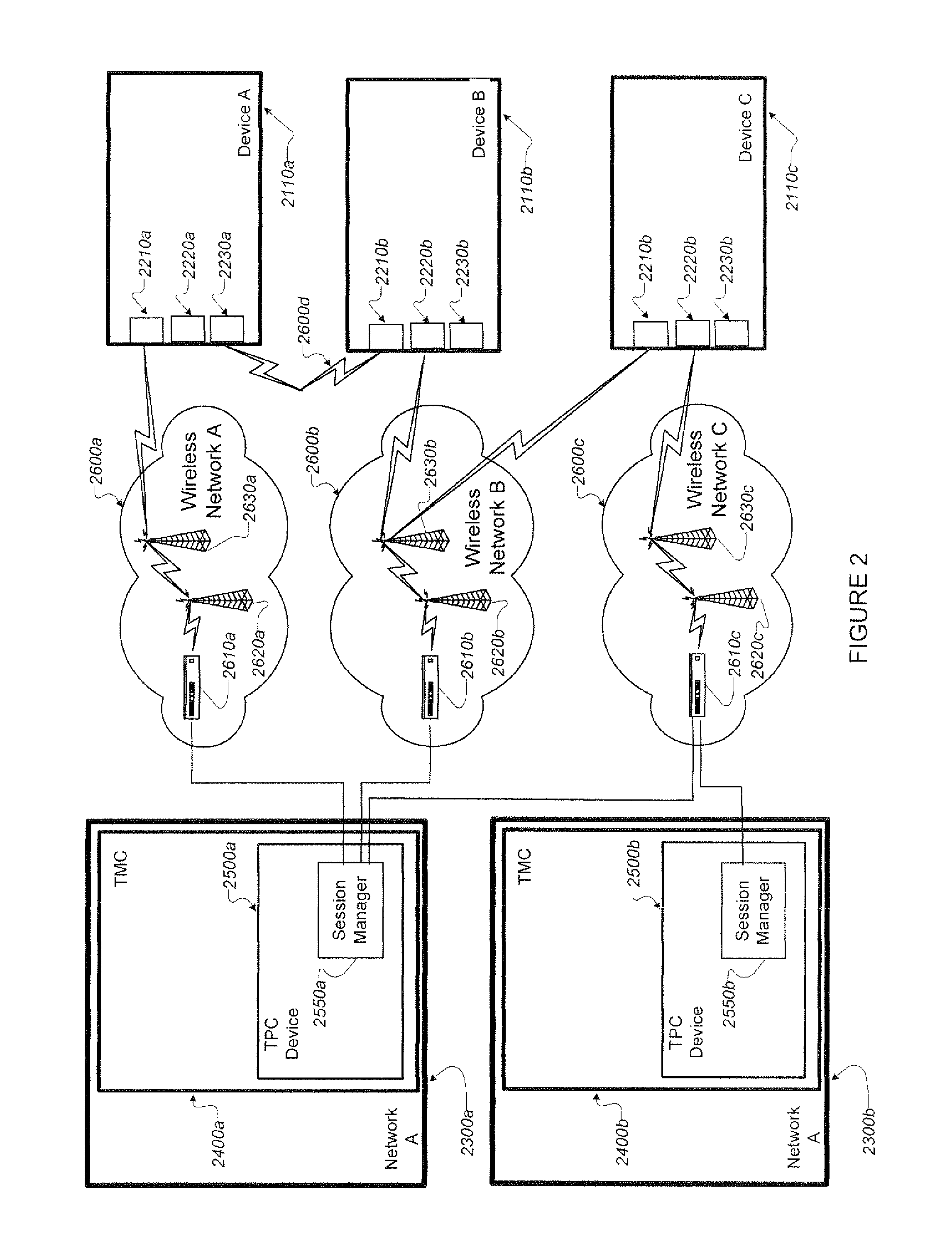
Method and system for seamless roaming between wireless communication networks with a mobile terminal
A mobile computer system capable of seamless roaming between wireless communication networks includes data processing resources for executing software, a plurality of wireless interfaces that supports simultaneous wireless connections with first and second wireless communication networks, and a network access arbitrator that routes data communicated between the software executed by the data processing resources and the first and second wireless communication networks. To permit seamless roaming, the network access arbitrator routes the data to the first wireless communication network via a first wireless interface and then seamlessly reroutes the data to a second wireless communication network via a second wireless interface. According to one embodiment, the network access arbitrator reroutes the data in response to the data bandwidths of the connections with the first and second wireless communication networks.
Owner:NORTEL NETWORKS LTD
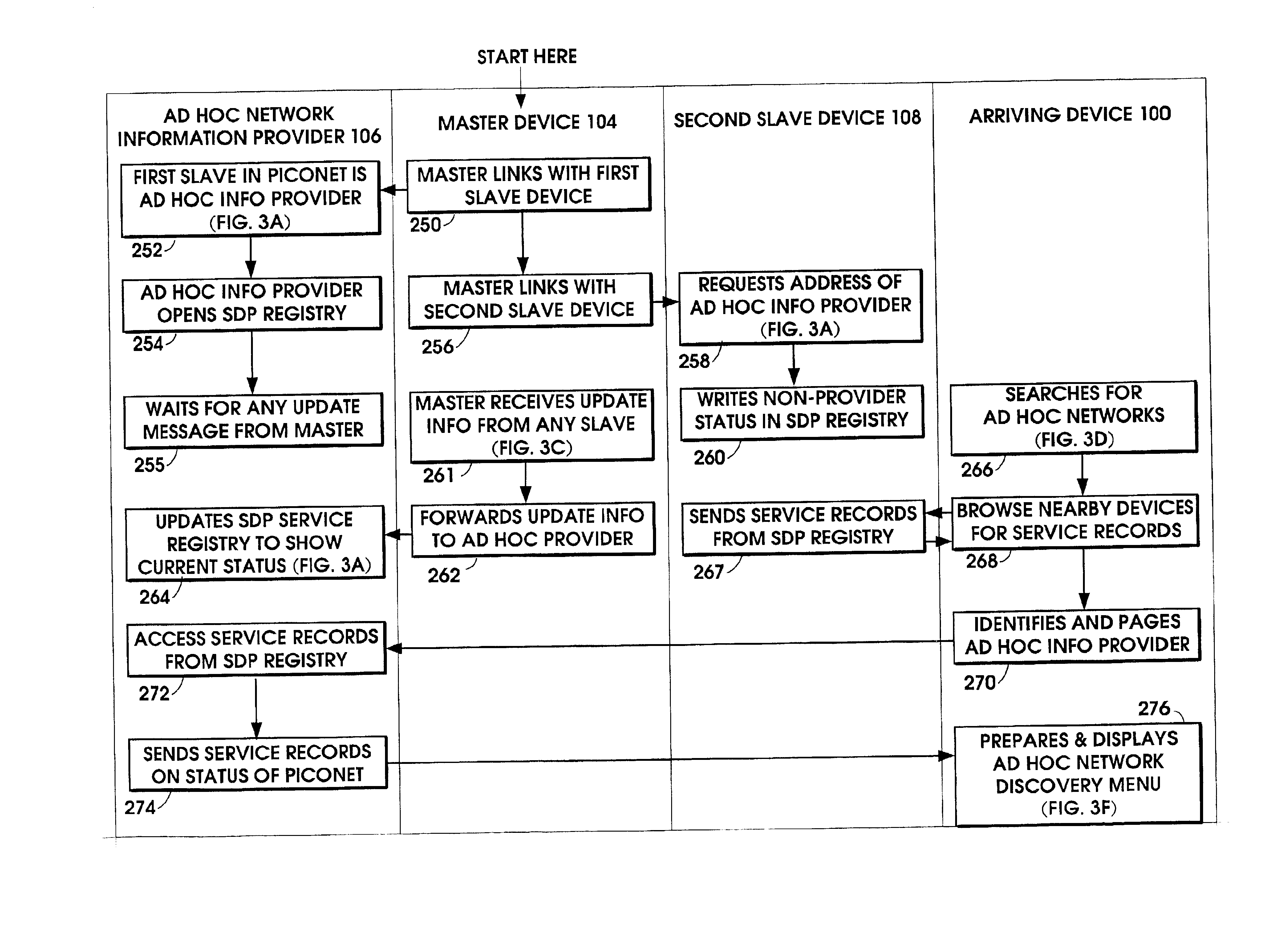
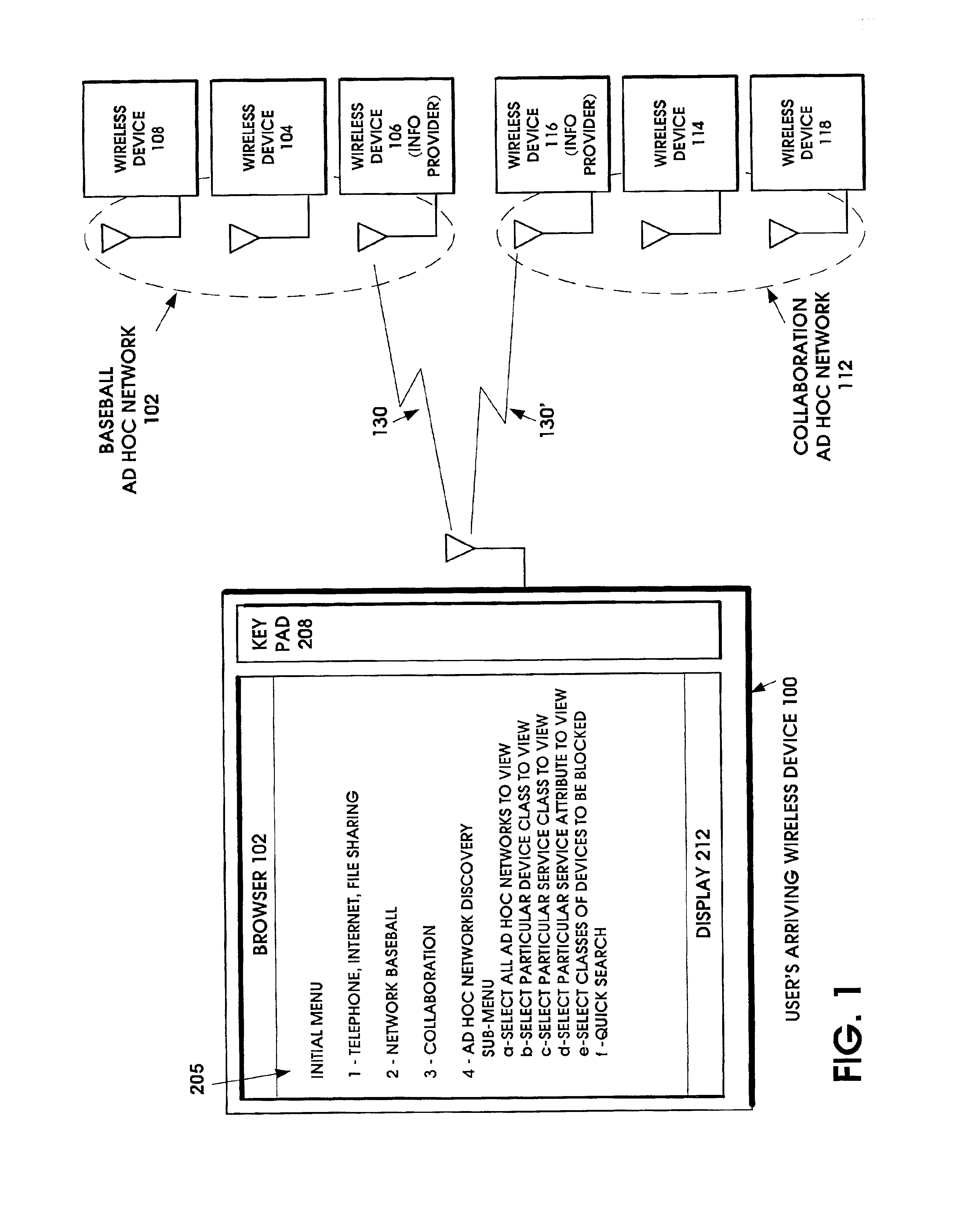
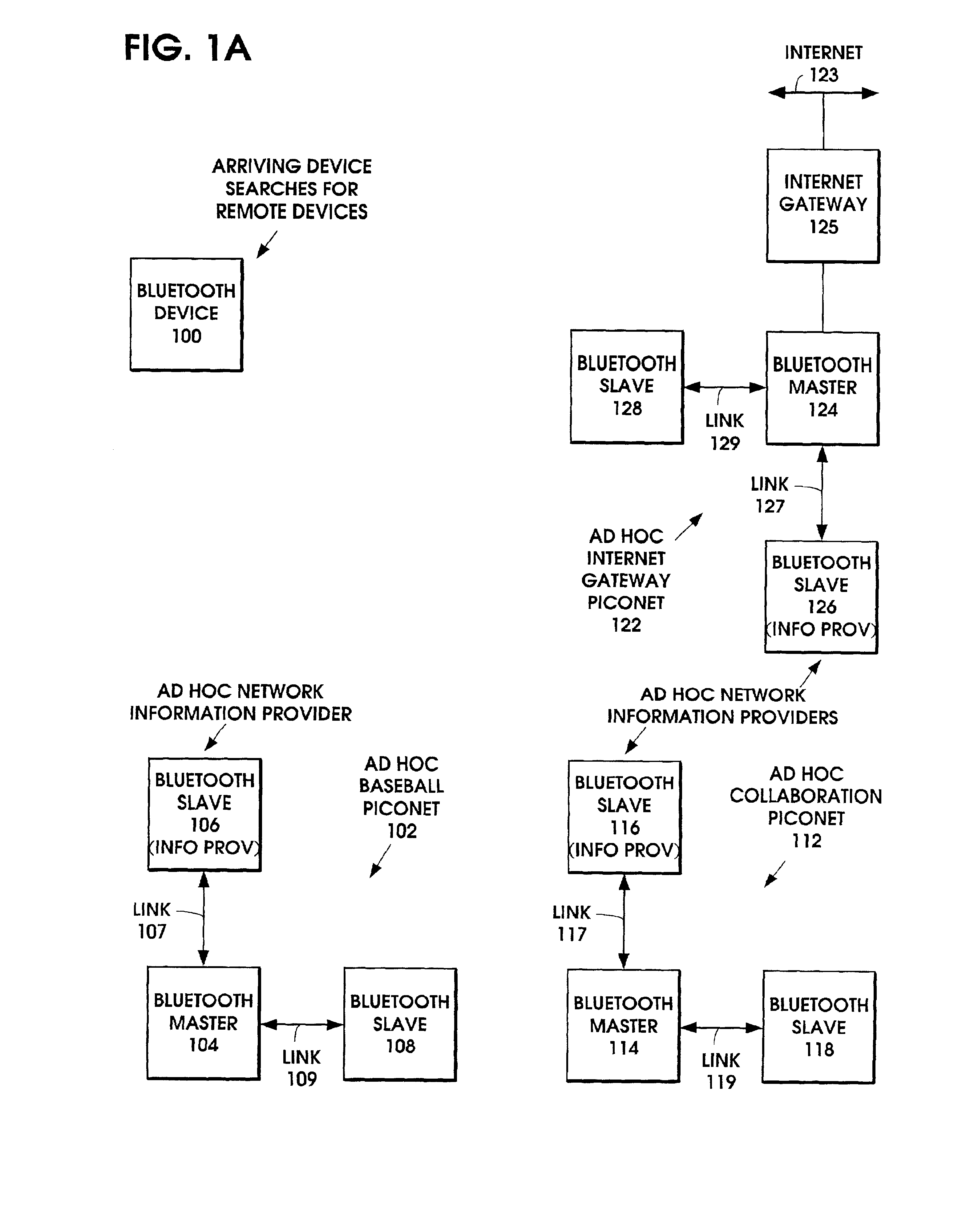
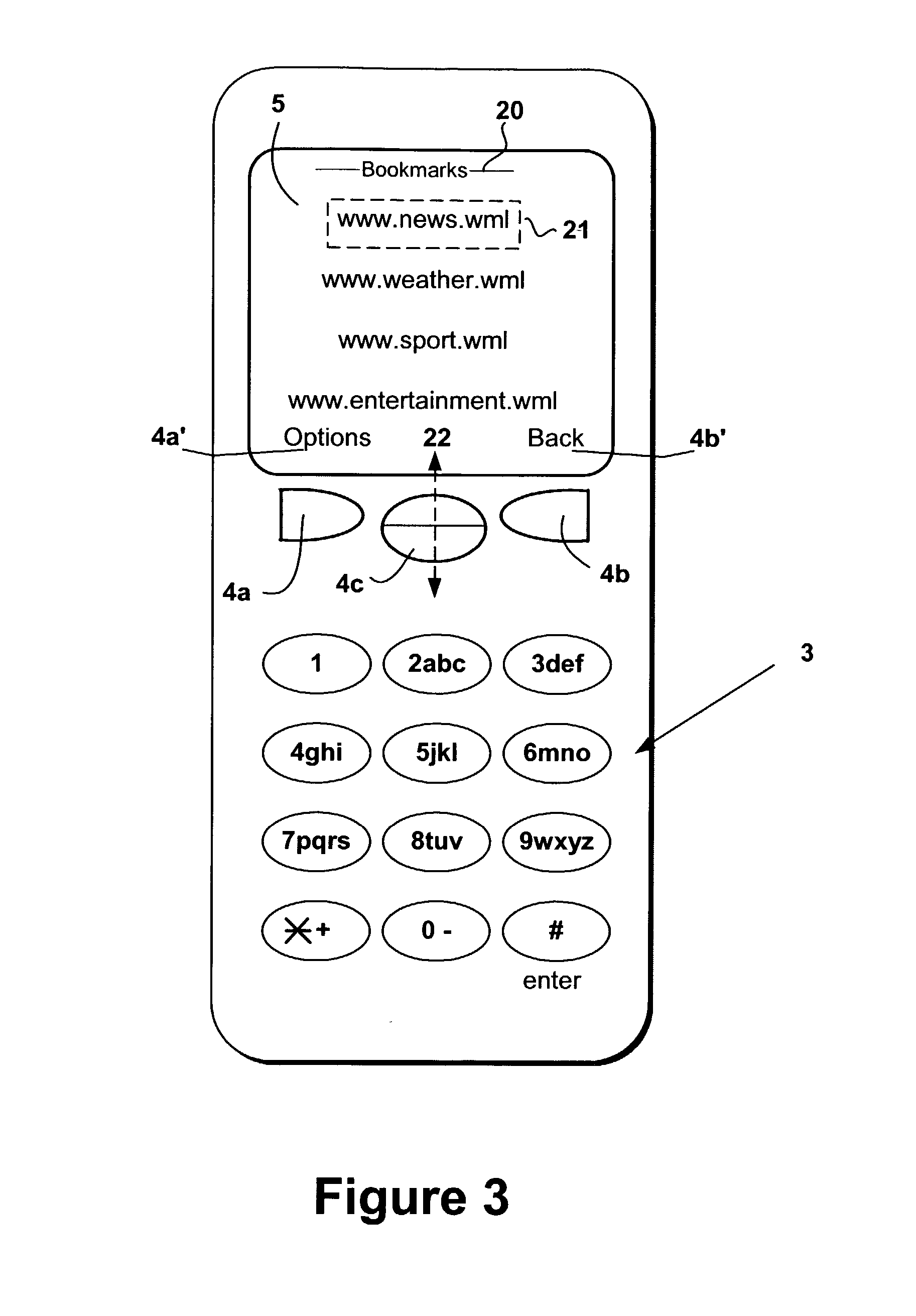
Ad hoc network discovery menu
When an ad hoc network is formed between short range wireless devices, at least one device assumes the role of an ad hoc network information provider for the new piconet. In this role, the device allocates a browsing hierarchy of service classes in its service registry. The service classes will provide a record to characterize the ad hoc network. When a new wireless device arrives within the communication range of any member of the ad hoc network, its inquiry signals are answered by the first member detecting the inquiry. If that first member is an ad hoc network information provider, it responds with information accessed from its service registry characterizing the ad hoc network. If, instead, an ordinary device in the ad hoc network is the first to respond to the inquiry signals of the arriving device, the device responds with the address of the ad hoc network information provider. The arriving device then pages the ad hoc network information provider to obtain information characterizing the ad hoc network.
Owner:NOKIA TECHNOLOGLES OY
System and method for providing context sensitive recommendations to digital services
ActiveUS20040043758A1Reducing or minimizing the processing load and memoryReduces privacy concernInterconnection arrangementsDigital data information retrievalComputer networkRelevant information
A system and method is disclosed to provide recommendations to a wireless device, based on stored bookmark / short-cut data. When a wireless device accesses services, data pertaining to the service access, along with any context related information is transmitted within the wireless device, or to a remote server. The data is processed in conjunction with bookmarks / short-cuts specified within the device, and are organized and presented to the wireless device in accordance with preference instructions specified within the wireless device.
Owner:NOKIA TECHNOLOGLES OY
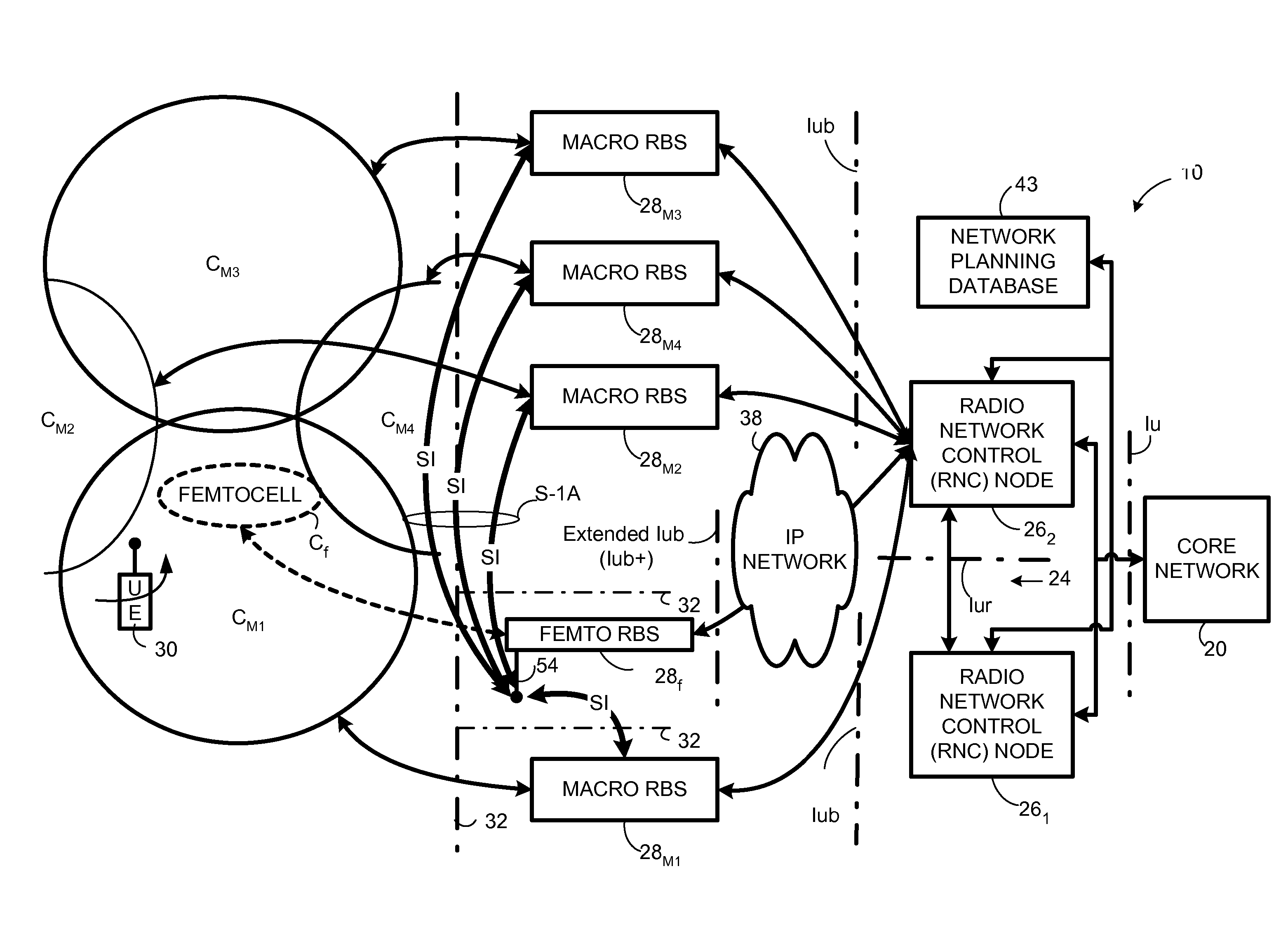
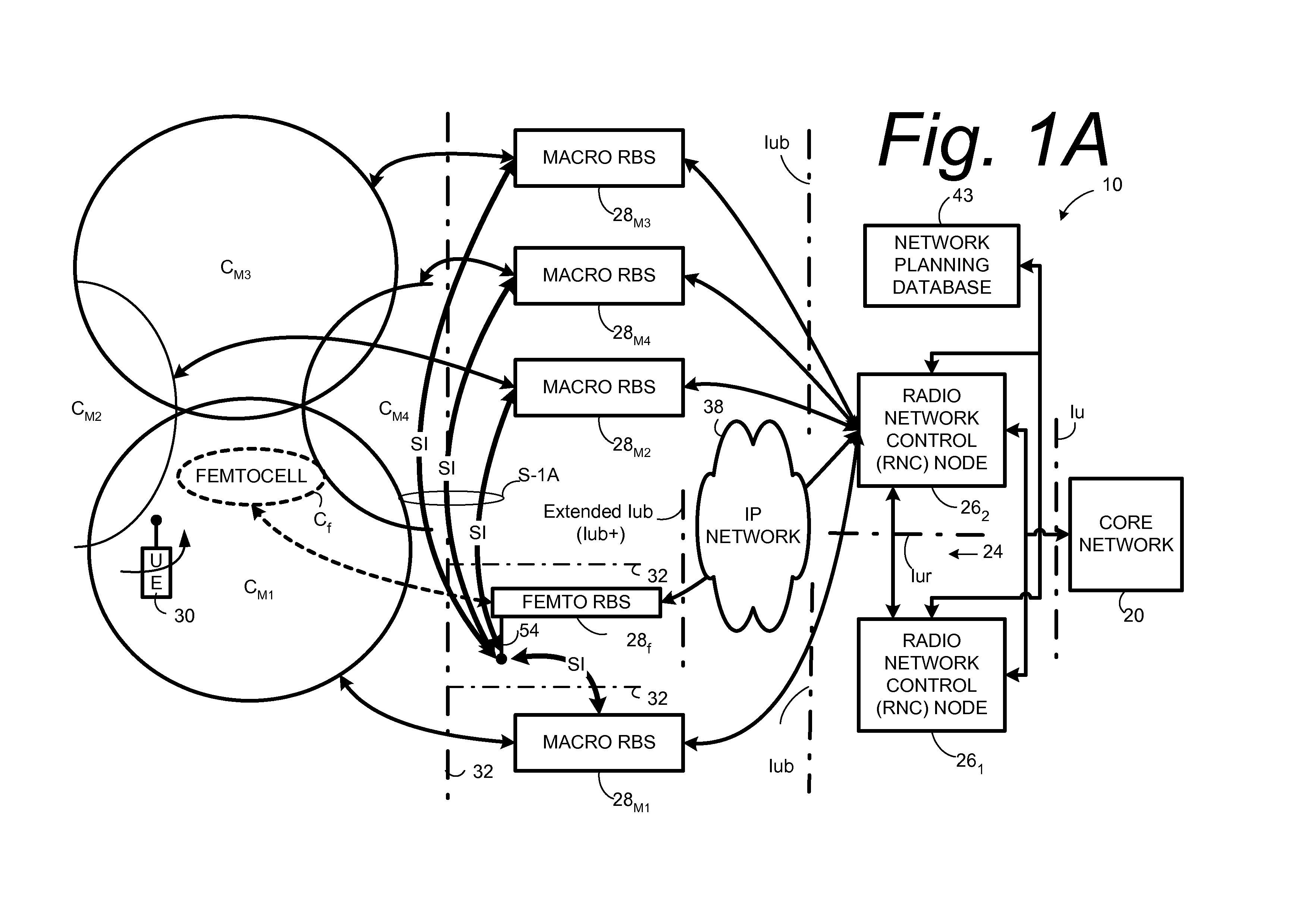
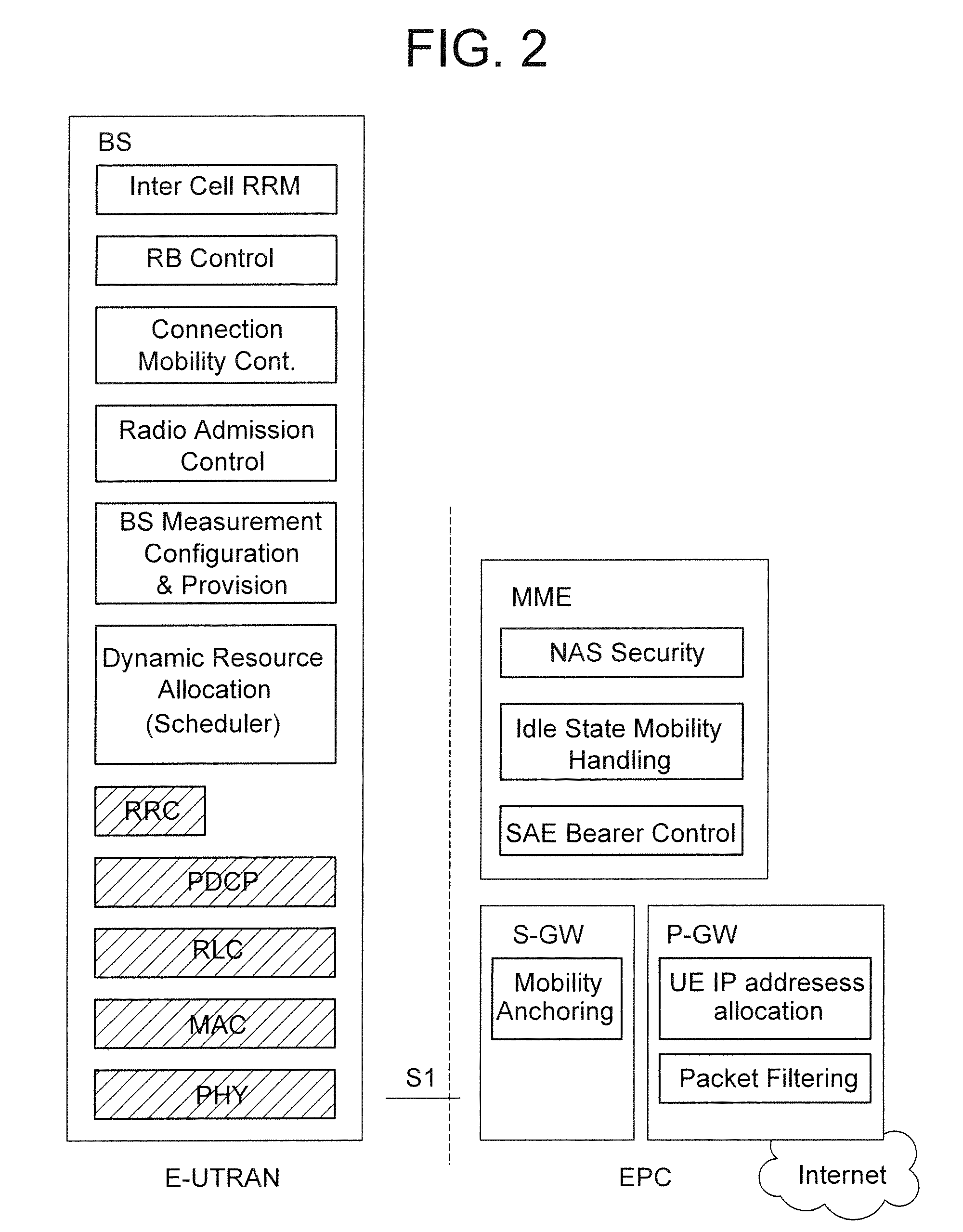
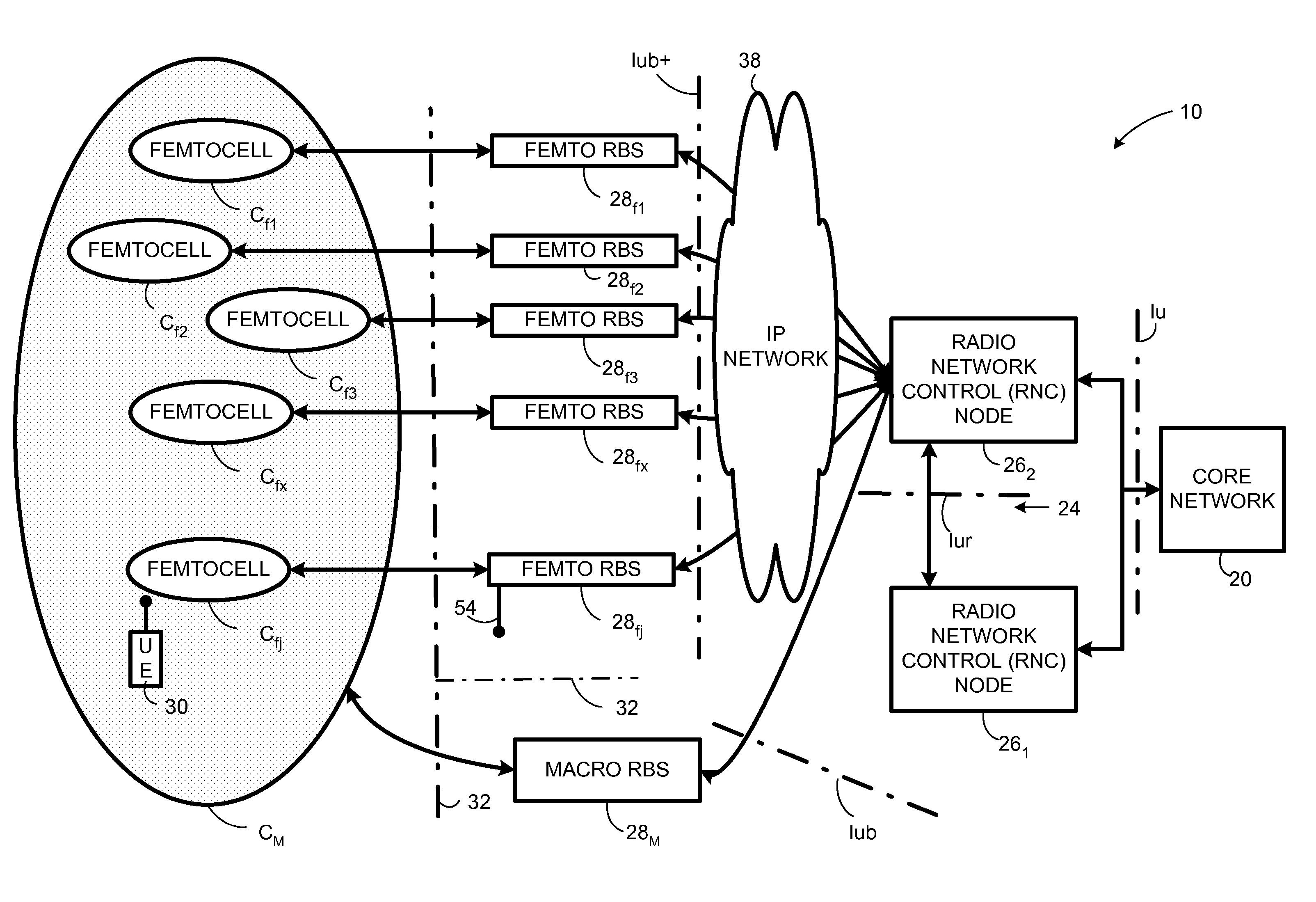
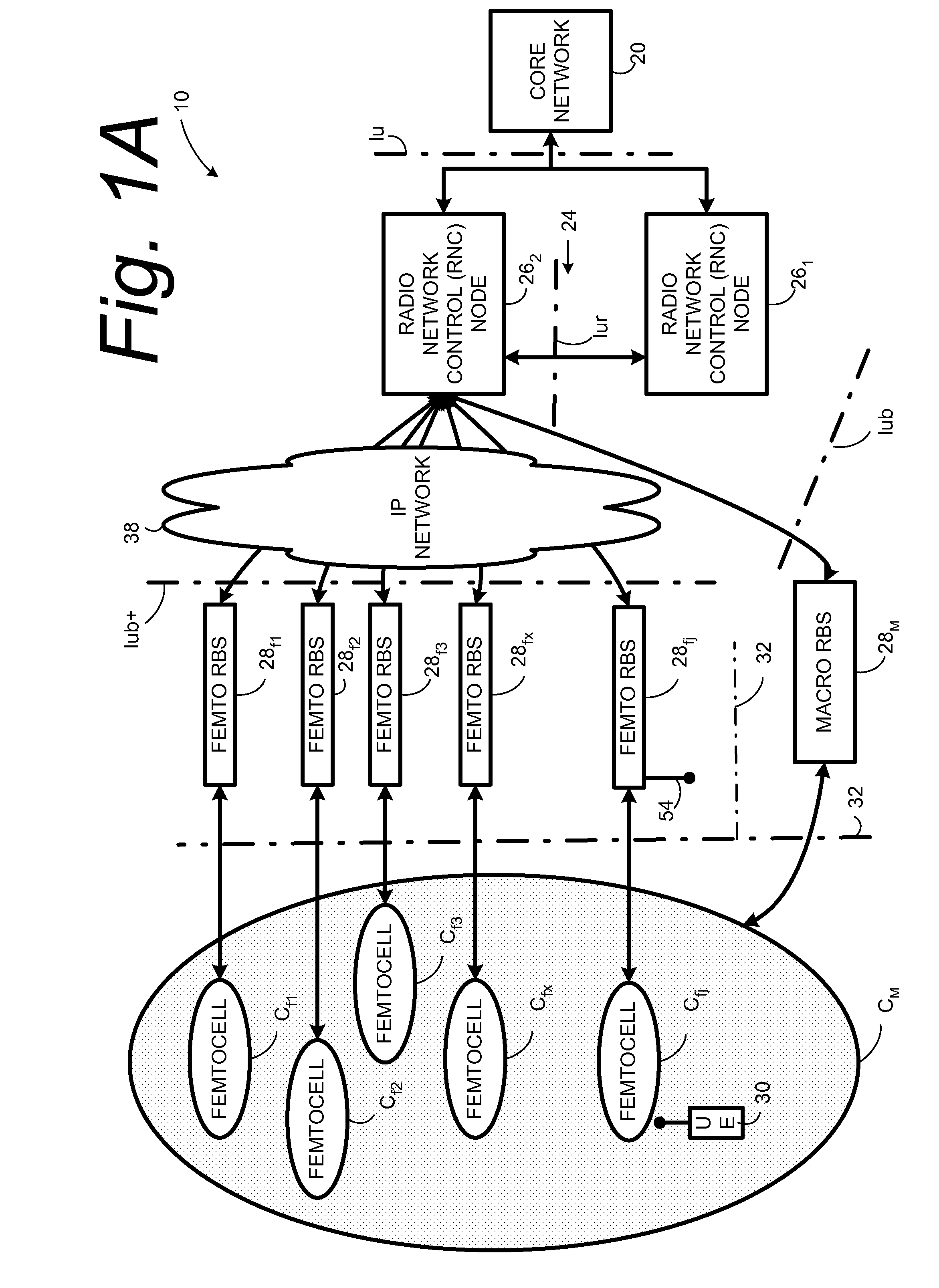
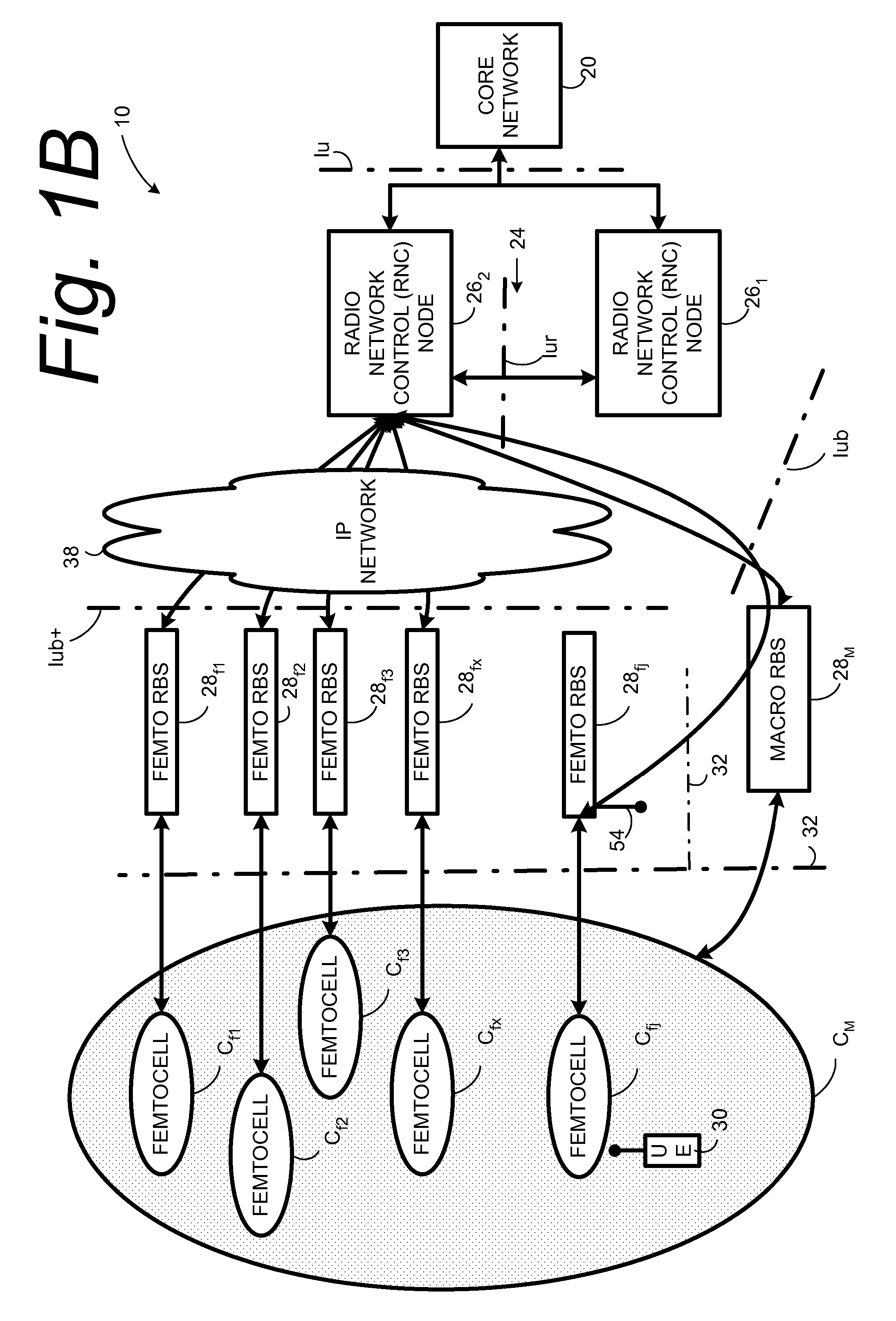
Automatic configuration of pico radio base station
Methods and apparatus configure a femto radio base station ( 28 f). A macro receiver of the femto radio base station ( 28 f) is used to acquire detected coverage information of a radio access network ( 24 ). The detected coverage information is used to determine an operation parameter for use by the macro transceiver ( 52 ) of the femto radio base station ( 28 f). In one embodiment, the detected coverage information is transmitted to a control node ( 26 ) of the radio access network. The control node ( 26 ) determines the operation parameter and communicates the operation parameter to the femto radio base station ( 28 f). The femto radio base station ( 28 f) is accordingly configured using the operation parameter for further operation towards UEs ( 30 ) accessing the femto radio base station ( 28 f).
Owner:TELEFON AB LM ERICSSON (PUBL)
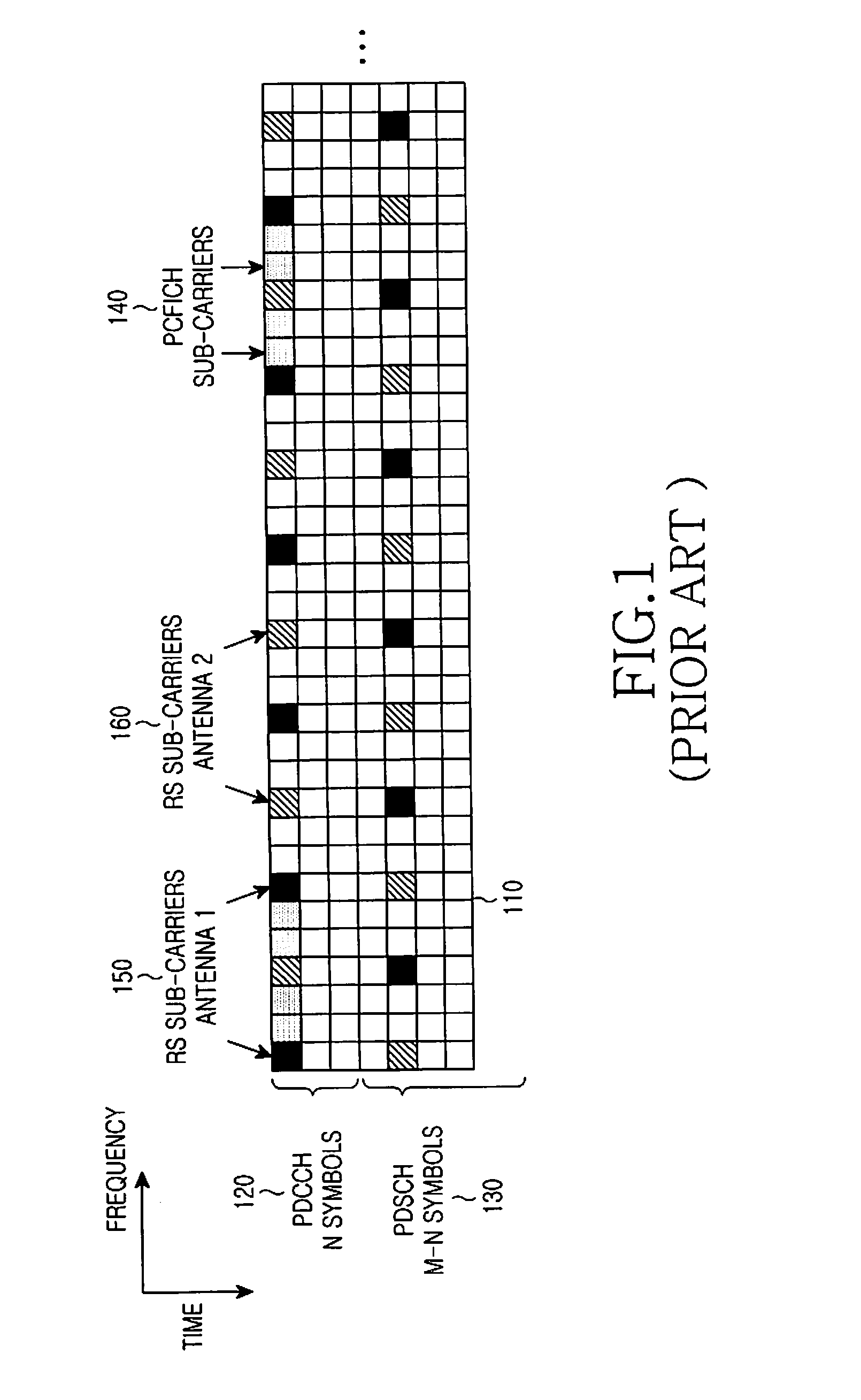
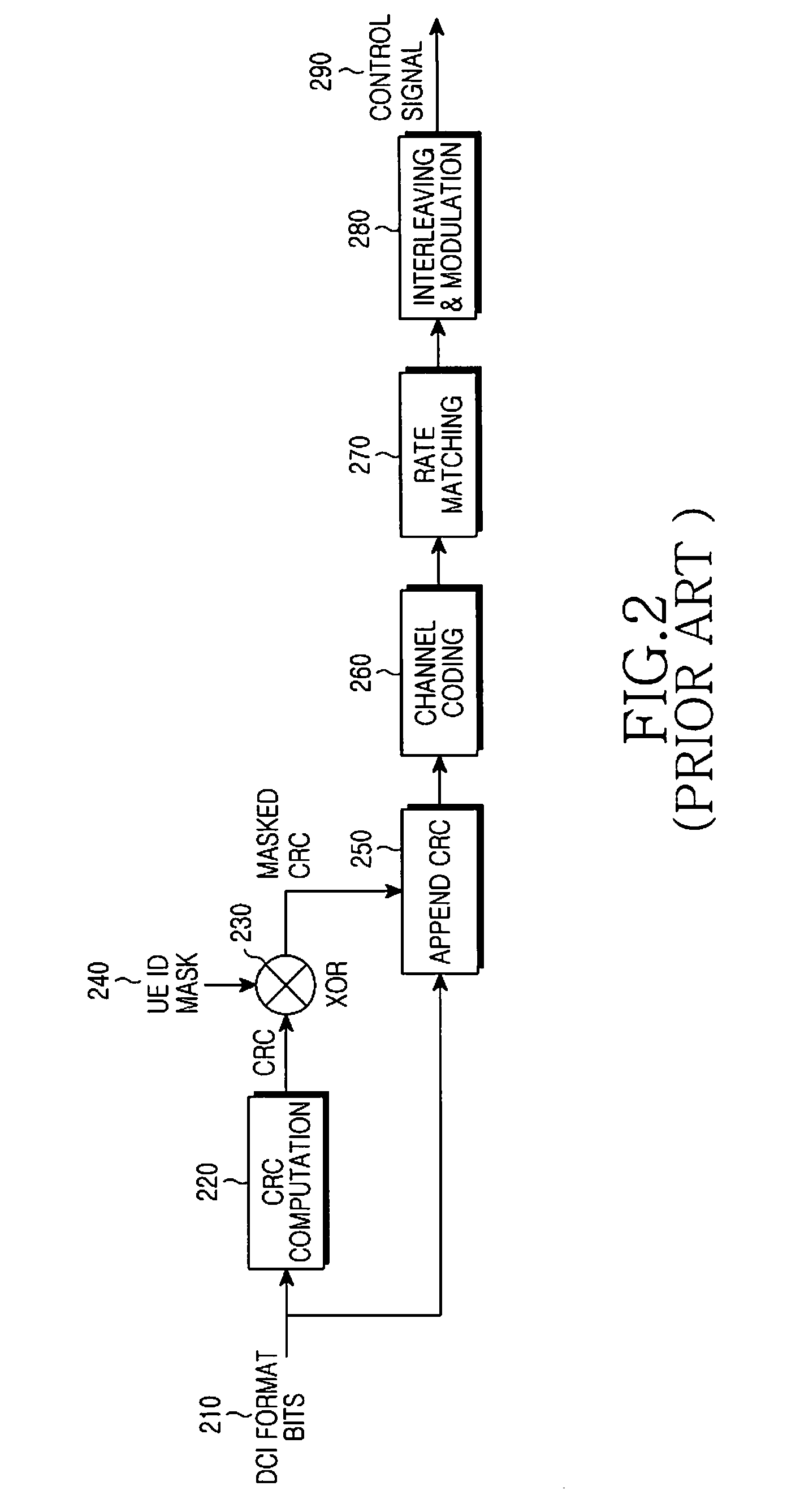
Wireless communication system for monitoring physical downlink control channel
ActiveUS20090088148A1Reduce in quantityTransmission path divisionAssess restrictionCommunications systemTelecommunications
A method of monitoring a physical downlink control channel (PDCCH) in a wireless communication system is provided. A user equipment monitors a set of PDCCH candidates for a search space in a subframe. The search space includes a common search space monitored by all user equipments in a cell and a UE-specific search space monitored by at least one UE in the cell.
Owner:LG ELECTRONICS INC
Wi-Fi Intelligent Selection Engine
Devices, systems, and methods are disclosed to offload the usage of a cellular network by intelligent selection of broadband network connections such as Wi-Fi access points. A Wi-Fi transceiver on a mobile device is activated when certain conditions are met, such as a time, location, recognition of a radiofrequency (RF) environment, etc. The conditions are correlated with a database of known locations in which a one or more Wi-Fi access points are determined to exist. The Wi-Fi transceiver on the mobile device is activated and commanded to connect to a particular Wi-Fi access point. Dynamic intelligence ensures that the appropriate connection method is used, and minimizes handovers to networks or access points that are unreliable or that are predicted to become inaccessible to the mobile device.
Owner:AT&T MOBILITY II LLC
Dynamic Network Connection System and Method
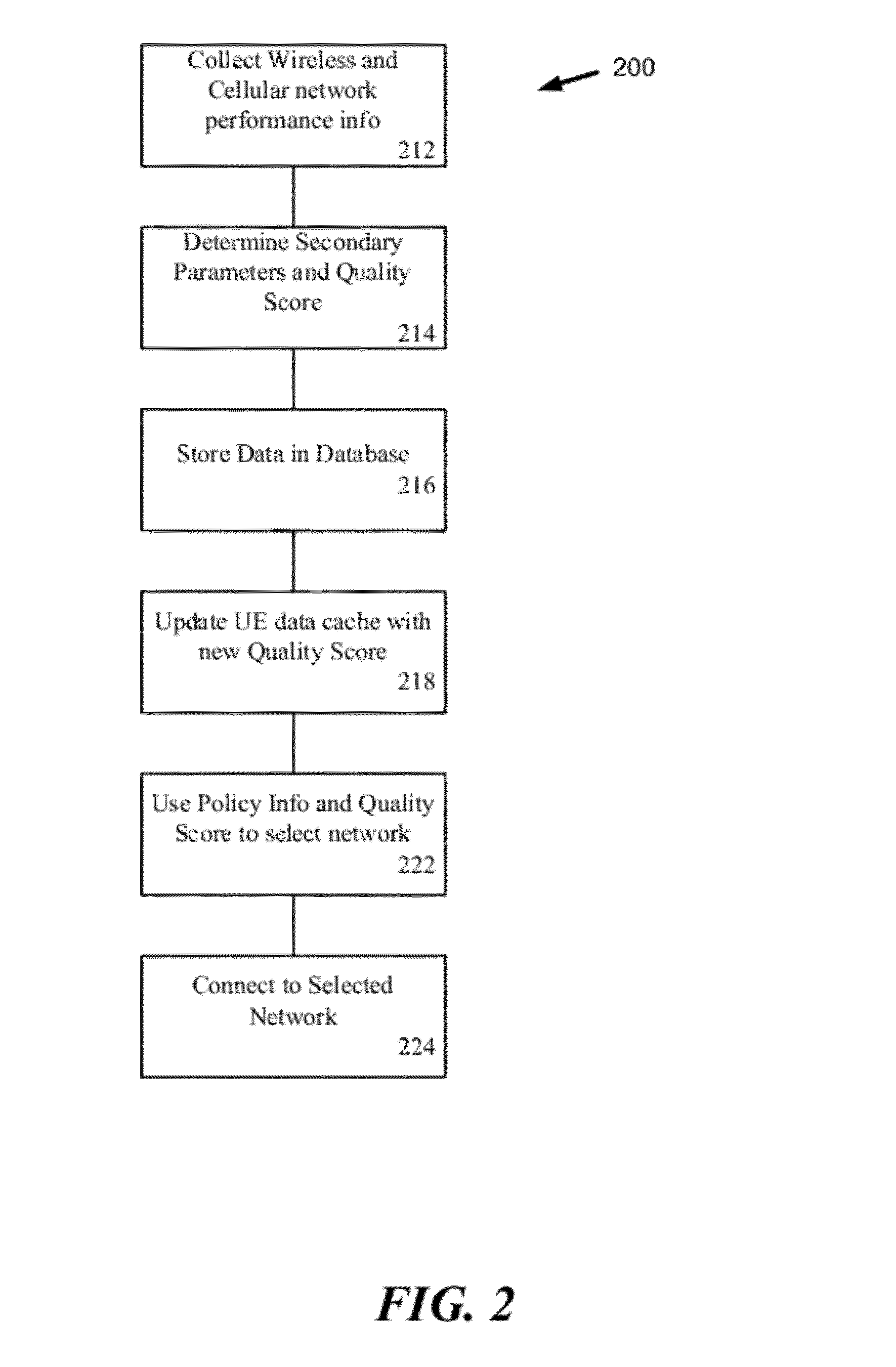
ActiveUS20120196644A1Reduce error rateReduce noiseAssess restrictionRadio transmissionNetwork connectionChoice making
A method and system for selecting a network to establish a connection to from a set of available network includes a network database providing historical information about each of the networks and sends the database information to end user terminals. The end user terminals monitor real-time performance information about each of the available networks and can send this information to the network database. The end user terminals also include network connection policy information which can be used to make the selection decision. The end user terminal determines a network quality score for each available network as a function of the historical information from the network database, the real-time performance information about each available network and the network connection policy information. The end user terminal can select the available network as a function of the network quality score, for example, selecting the available network with the highest network quality score.
Owner:WEFI
Method and system for selecting and providing a relevant subset of wi-fi location information to a mobile client device so the client device may estimate its position with efficient utilization of resources
Methods and systems for selecting and providing a relevant subset of Wi-Fi location information to a mobile client device so the client device may estimate its position with efficient utilization of resources.A method of providing a relevant subset of information to a client device is based in part on scanning for Wi-Fi access points within range of the client device, using a Wi-Fi database that covers a large target region to retrieve information about these access points, using this information to estimate the position of the mobile client device, selecting a limited region in the vicinity of the estimated location of the client device, and providing information about Wi-Fi access points within this limited region to the client. For efficient transfer and maintenance of data, the target region may be divided into a hierarchy of fixed geographical tiles.
Owner:SKYHOOK WIRELESS
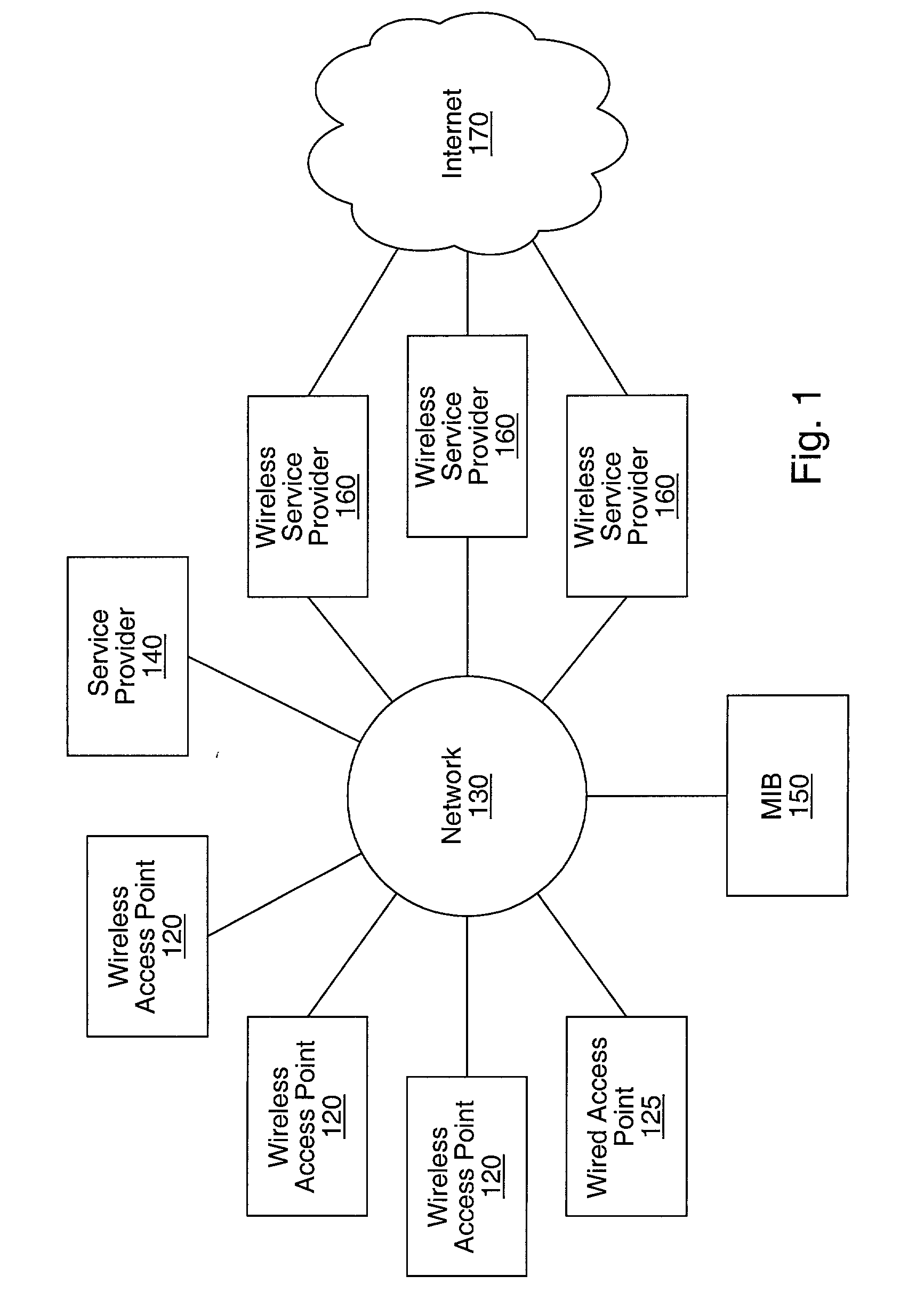
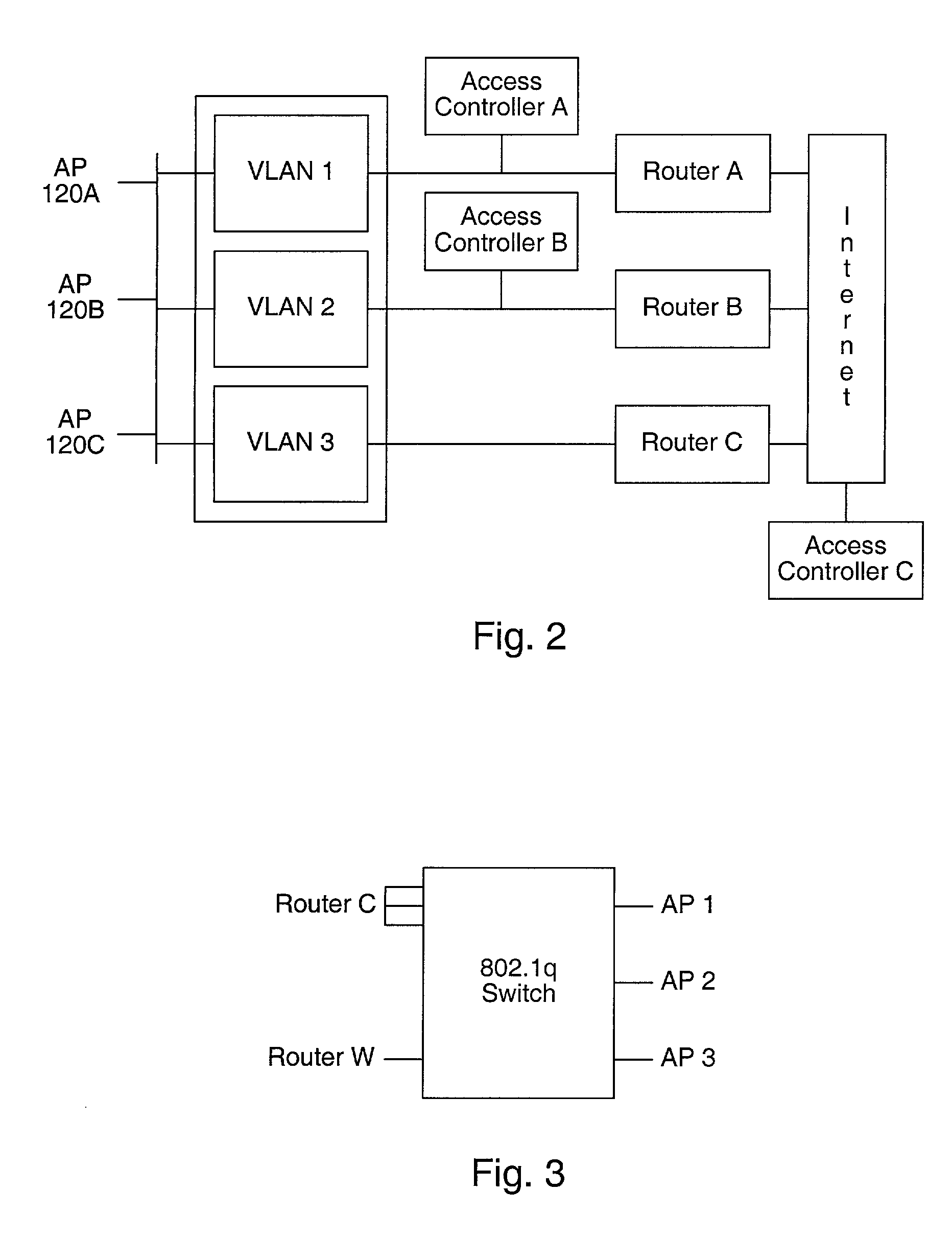
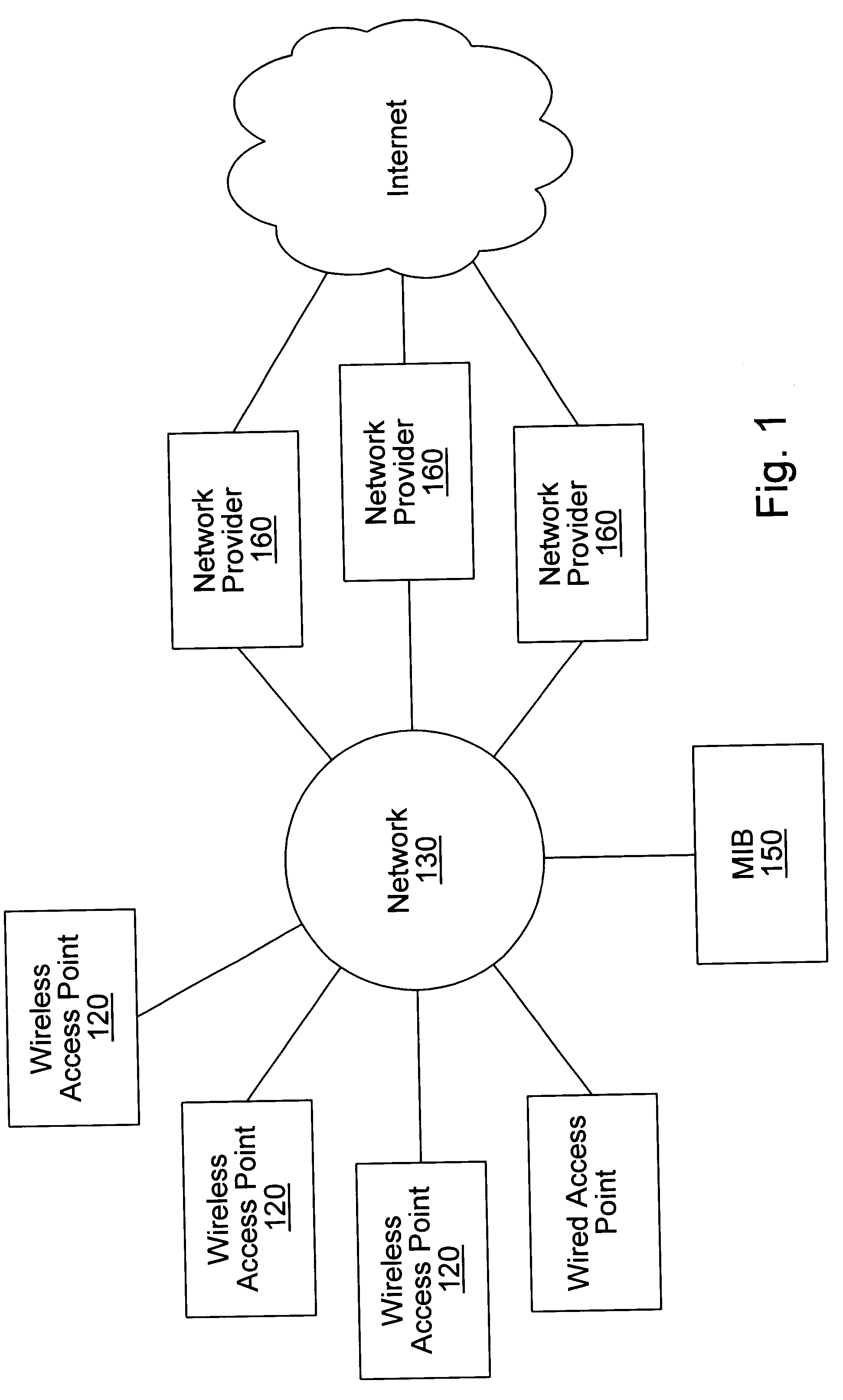
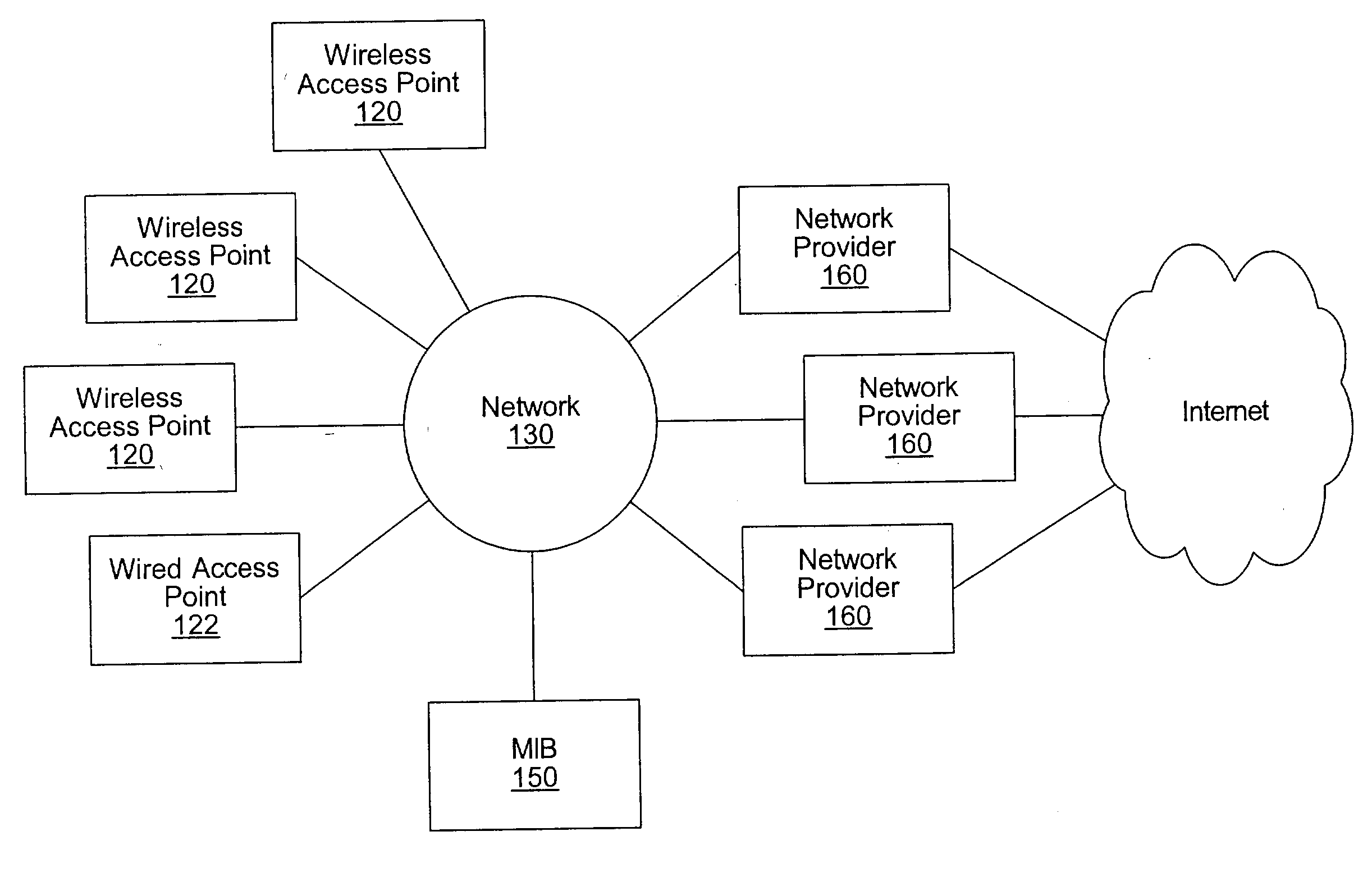
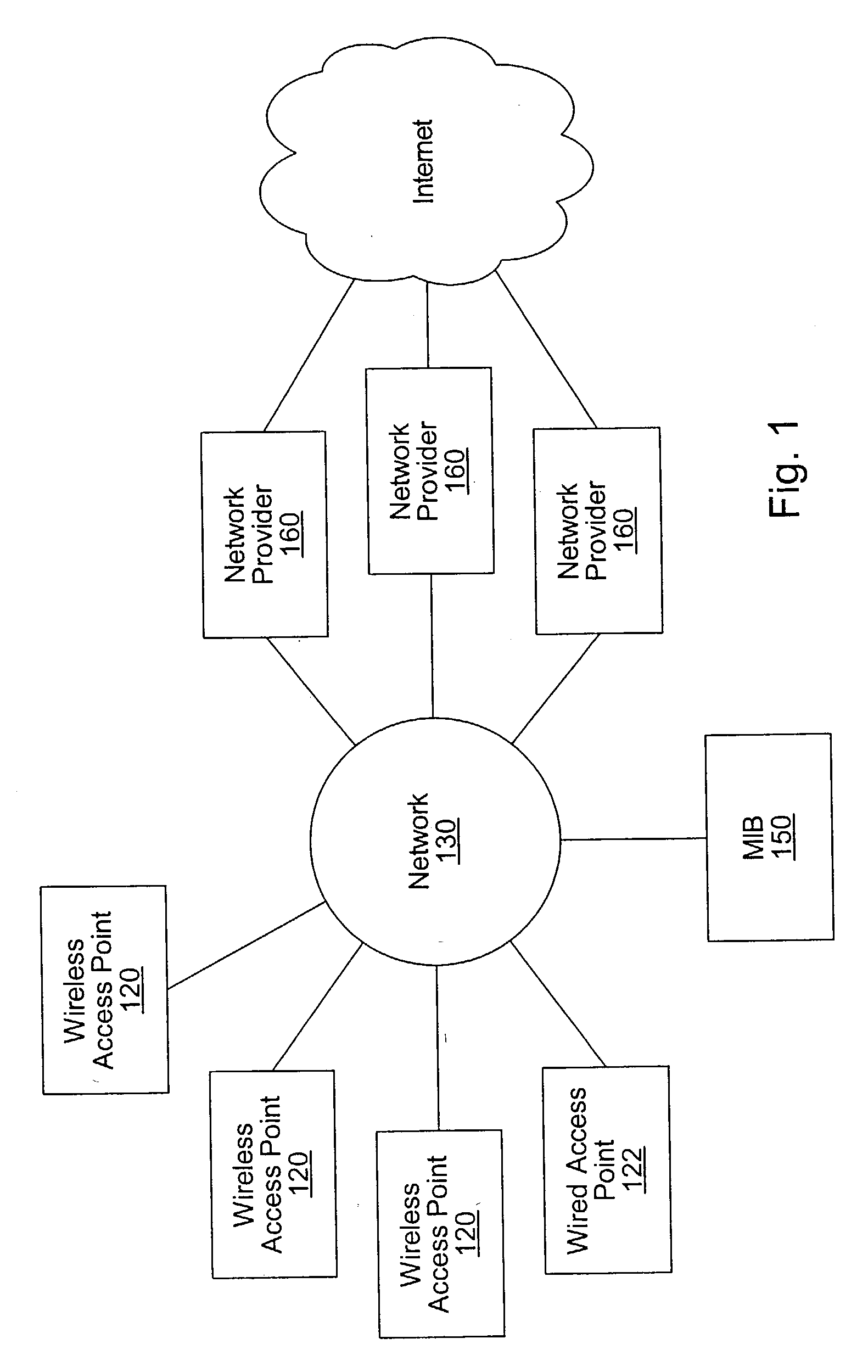
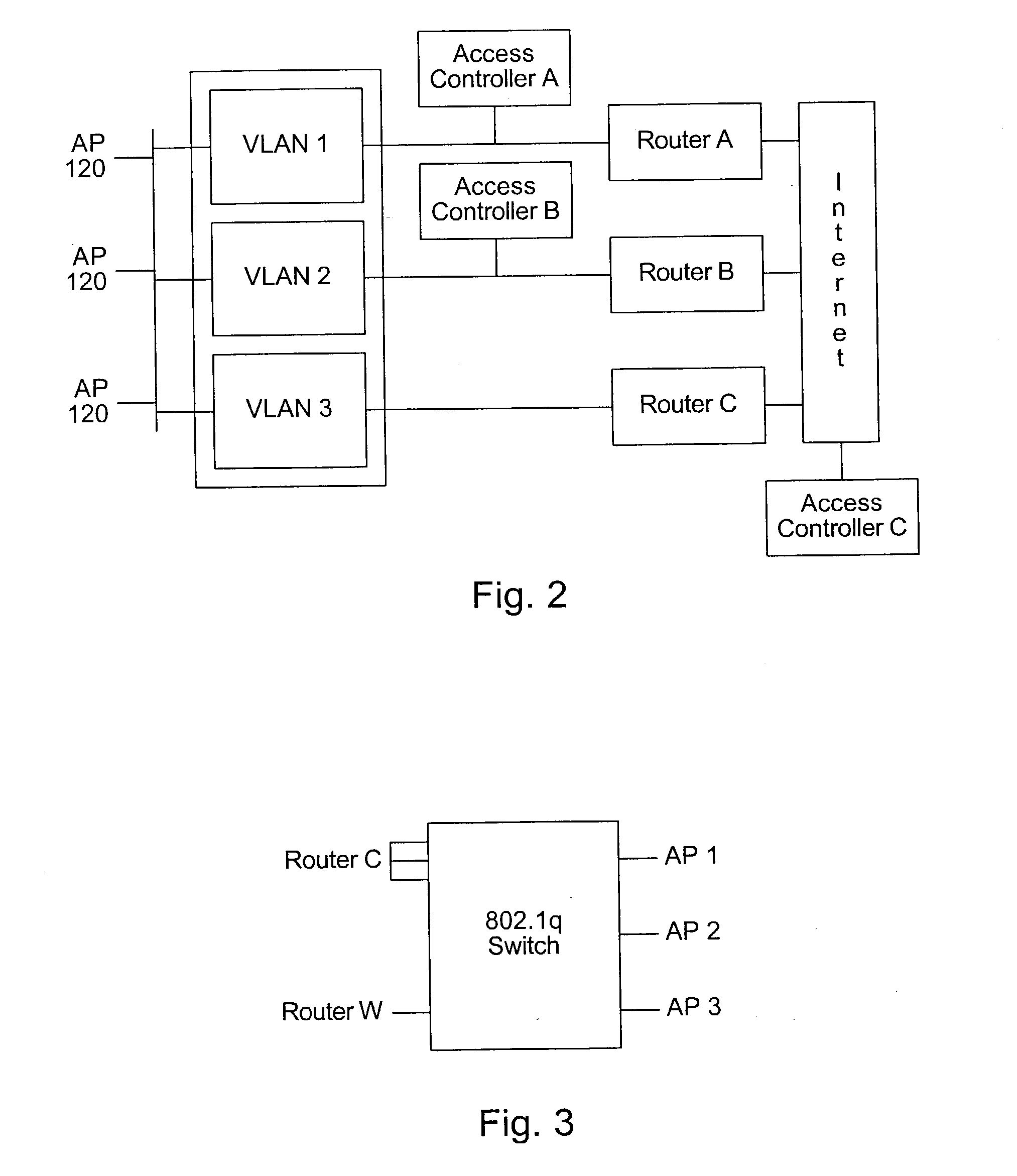
Distributed network communication system which allows multiple wireless service providers to share a common network infrastructure
System and method for providing access to multiple wireless service providers (WSPs) on a shared network infrastructure. The system includes a plurality of access points (APs) coupled to a network which may be distributed in airports, mass-transit stations, businesses, etc. The network may couple to a wide area network, such as the Internet. Each AP may include a plurality of virtual APs (VAPs), each corresponding to a WSP. A portable computing device (PCD) of a user stores identification information indicating a WSP of a plurality of possible WSPs, and which may include an access level of the user. Each AP "listens for" or detects identification information associated with numerous WSPs. When the AP receives the identification information from the PCD, it determines the VAP / WSP for the PCD using the identification information. Network access is then provided to the PCD through the determined WSP at the determined access level.
Owner:CISCO TECH INC
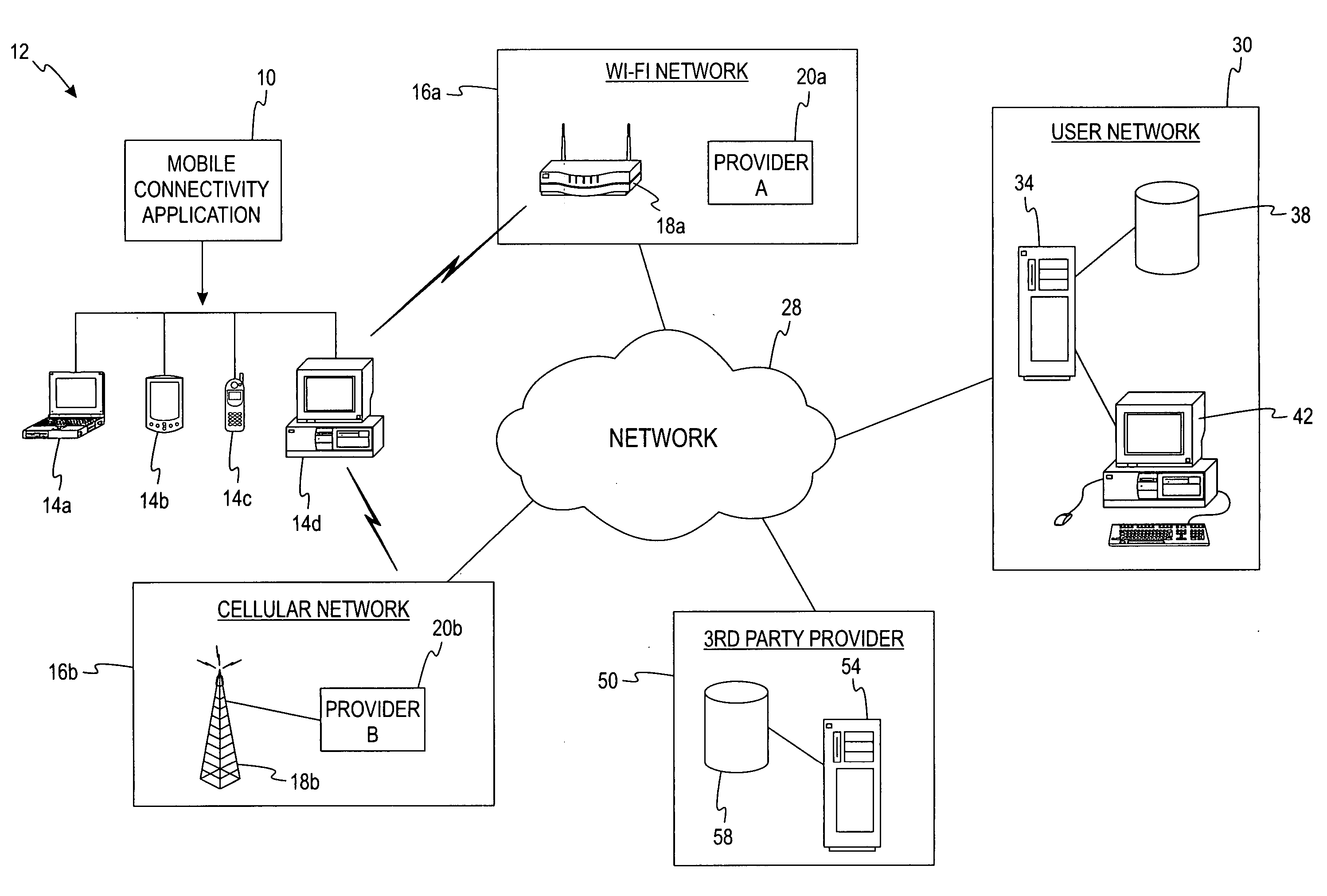
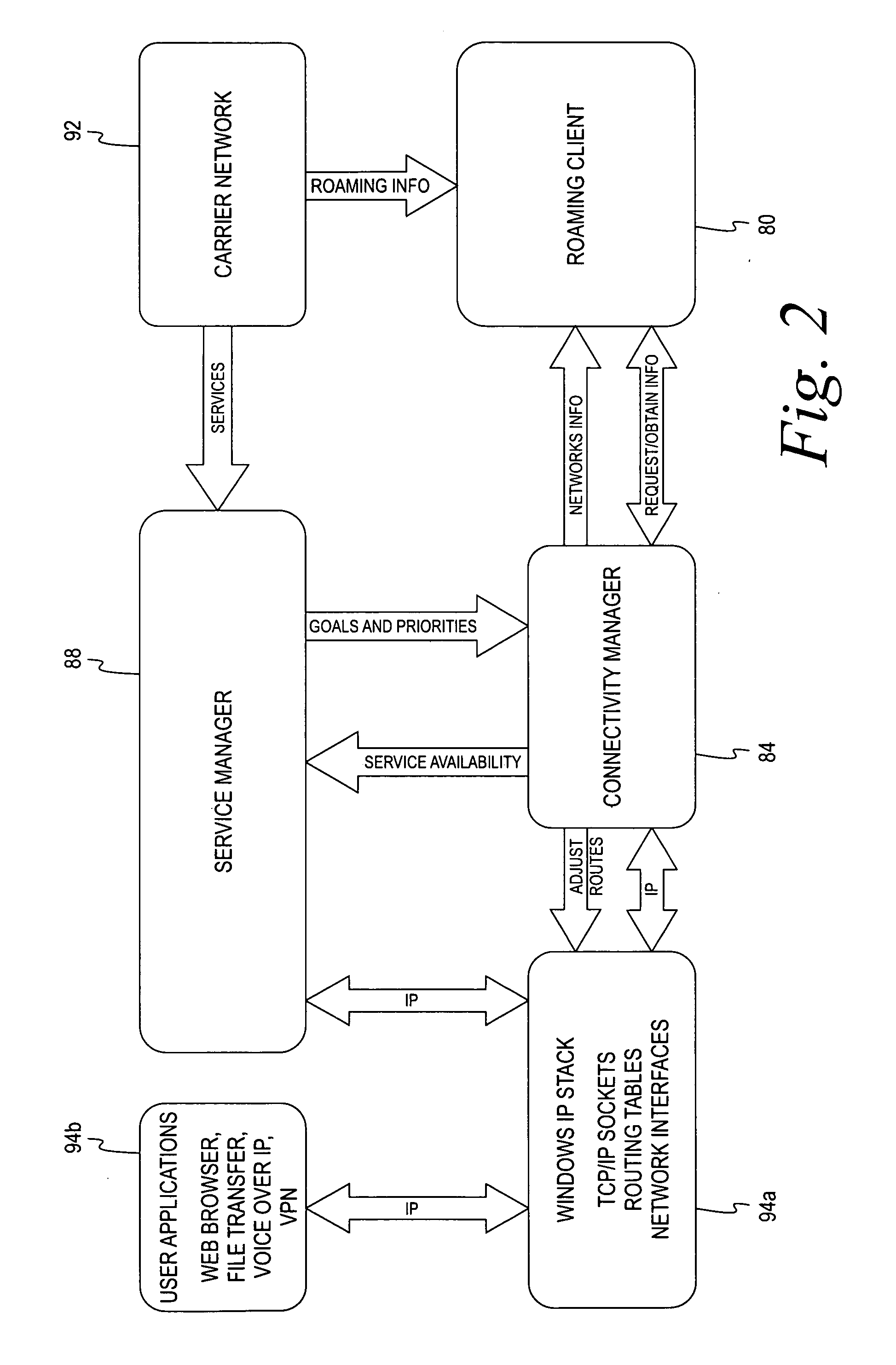
Mobile connectivity solution
A method and application for selecting a network from one or more candidate networks is disclosed. Information is gathered from one or more database relating to each of the one or more candidate networks and is harmonized in relation to an associated network type. The harmonized information is evaluated to allocate a weight to each of the candidate networks. The weight represents the desirability of each of the candidate networks. The required resources to connect to each of the candidate networks are determined from information contained within the service-provider database, from information obtained by the end-user, and by self-adaptive learning algorithms. At least one of the candidate networks is selected based on the allocated weight of the candidate network and the application attempts to connect to the candidate network. The method and application incorporates the ability to control and integrate a plurality of services on a user device via the candidate network.
Owner:DELL MARKETING CORP
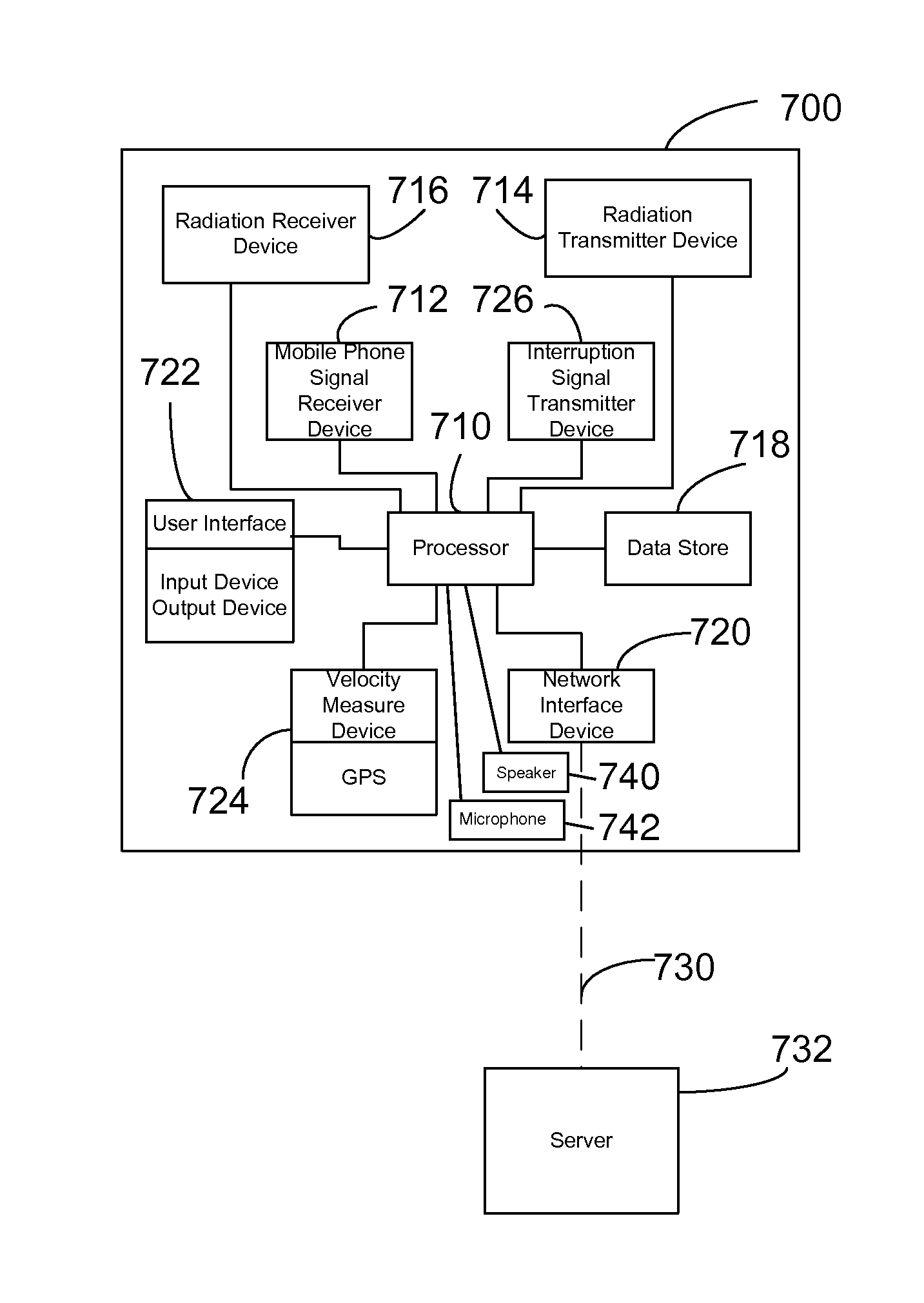
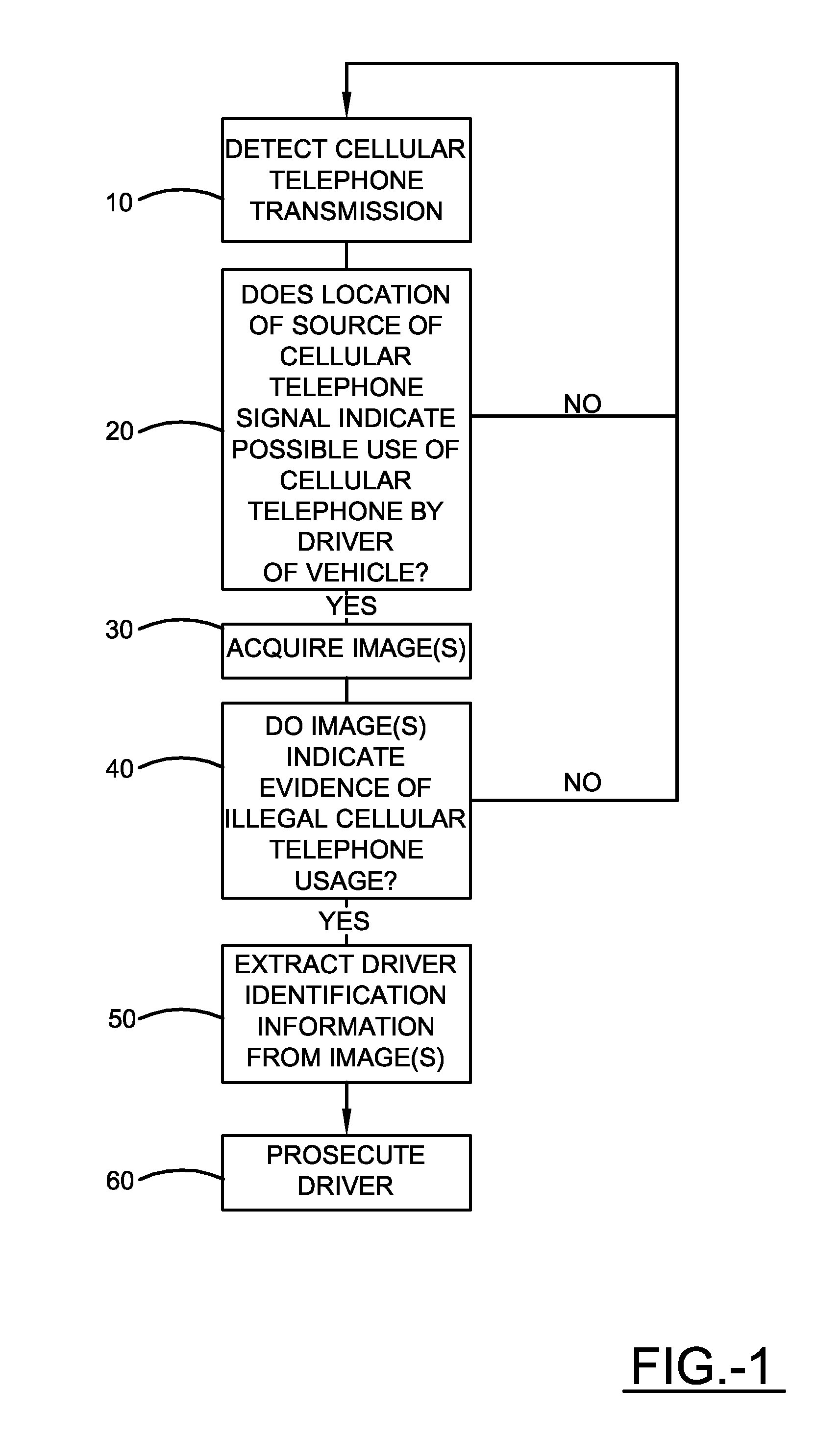
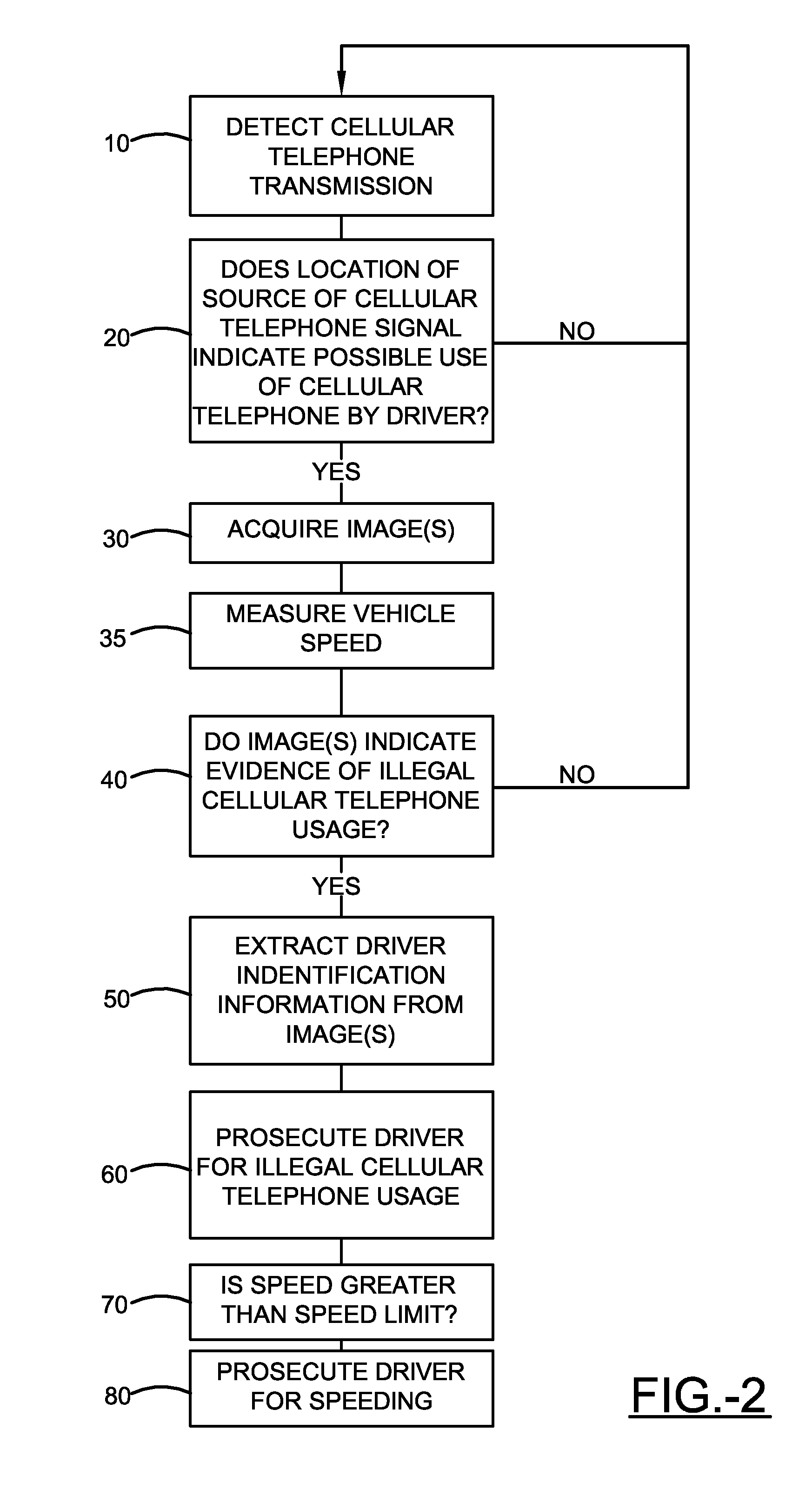
Method and apparatus for reducing mobile phone usage while driving
InactiveUS20130150004A1Reduce violationsAssess restrictionSpecial service for subscribersComputer scienceMobile telephony
An apparatus that includes a mobile phone detection system is provided. The detection system includes a processor and a plurality of sensors that are operative to be used by the processor to determine which individuals in a group of individuals are and are not transmitting a predetermined type of RF signals. The sensors include a frequency antenna operative to receive RF signals from locations associated with positions of each respective individual. The sensors include a further sensor that is operative to detect data that is used by the processor to corroborate which individuals in the group are and are not transmitting the predetermined type of RF signal. The detection system is operative to communicate to a remote server, data corresponding to at least a portion of the determination made regarding which of the individuals in the group are and are not transmitting the predetermined type of RF signal.
Owner:ROSEN MICHAEL
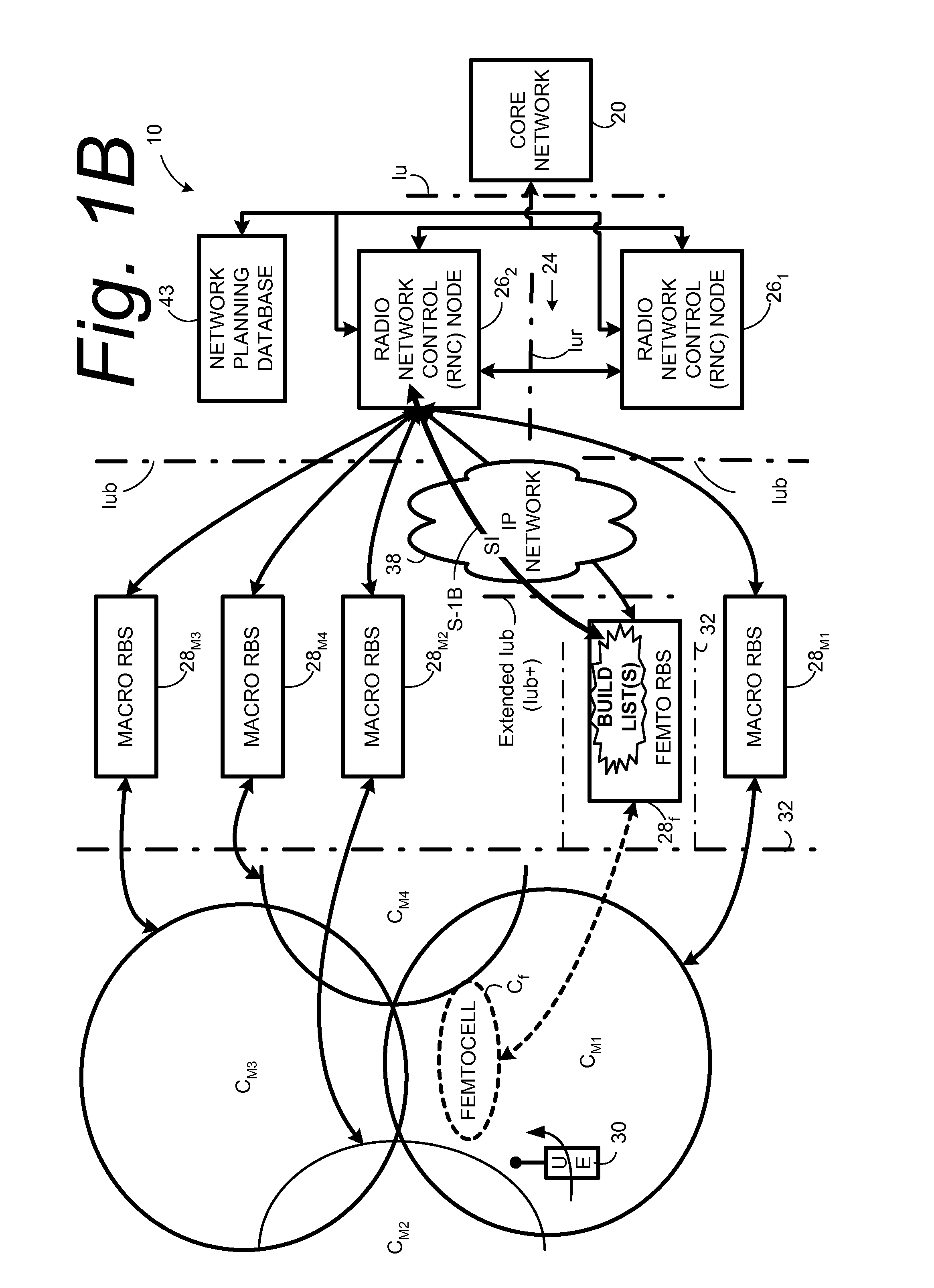
Automatic building of neighbor lists in mobile system
In a radio access network (24) a femto radio base station (28f) comprises a resident receiver (54) which acquires system information broadcast in a radio access network (24). At least part of the system information is used for building, at the femto radio base station (28f), a neighbor data structure (59) comprising information for neighboring cells. The neighbor data structure (59) is then used for building a neighbor list. The neighbor list is subsequently transmitted from the femto radio base station (28f) to a user equipment unit (30) served by the femto radio base station (28f). In some example embodiments and modes, the femto radio base station (28f) reports the neighbor data structure to a network node (26, 100) other than the femto radio base station. The other node (26, 100) uses the neighbor data structure for building the neighbor list at the other node. In some example embodiments and modes, acquisition of the system information comprises scanning a surrounding macro coverage area of the femto radio base station for obtaining cell identity information for detected cells. In other example embodiments and modes, the acquisition of the system information can additionally comprise camping on a macro cell and using / consulting at least one system information block in the camped-on macro cell is consulted / used for obtaining information about at least one neighboring cell.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and system for controlling a mobile communication device in a moving vehicle
ActiveUS20110021234A1Assess restrictionParticular environment based servicesMobile vehicleControl system
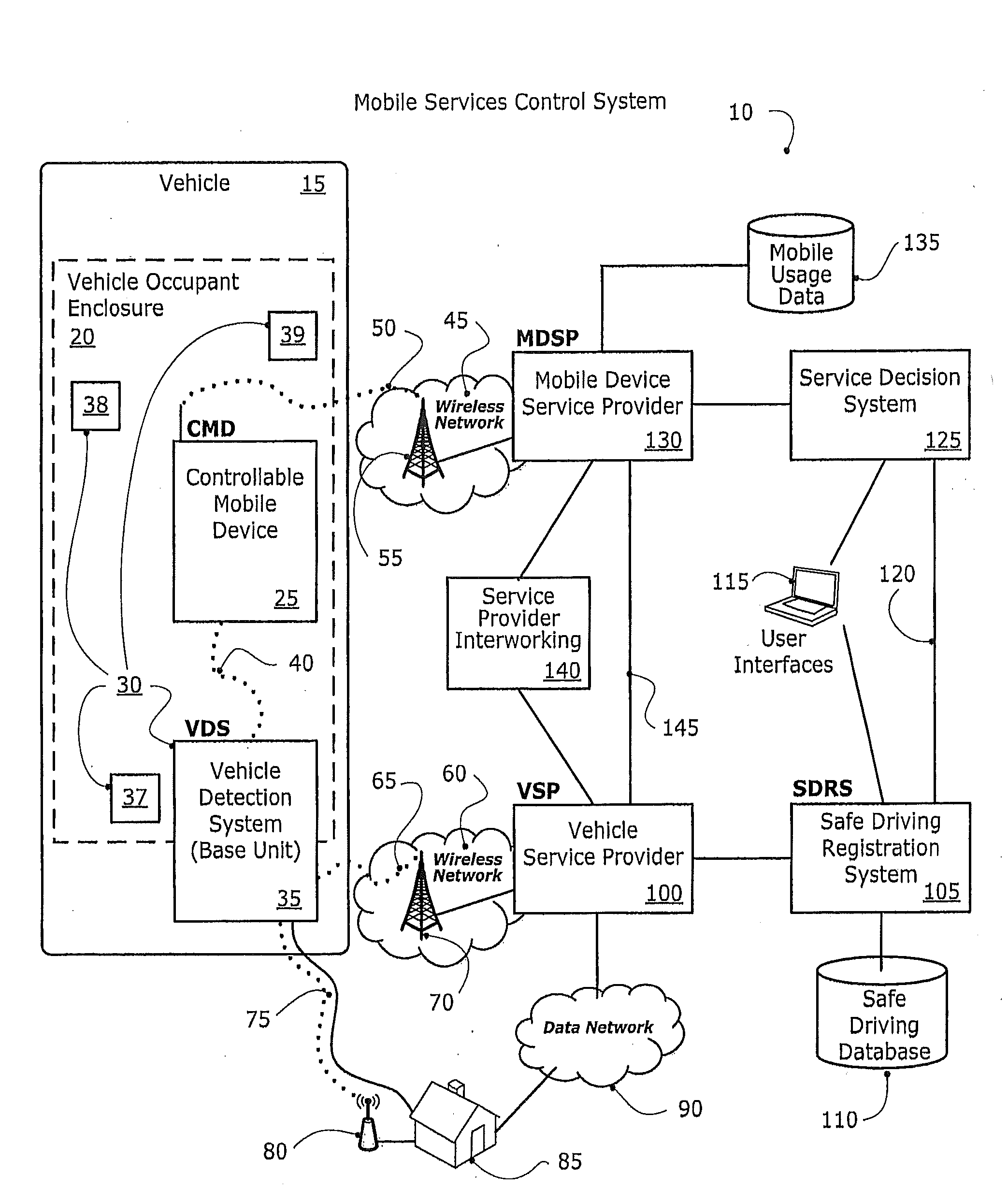
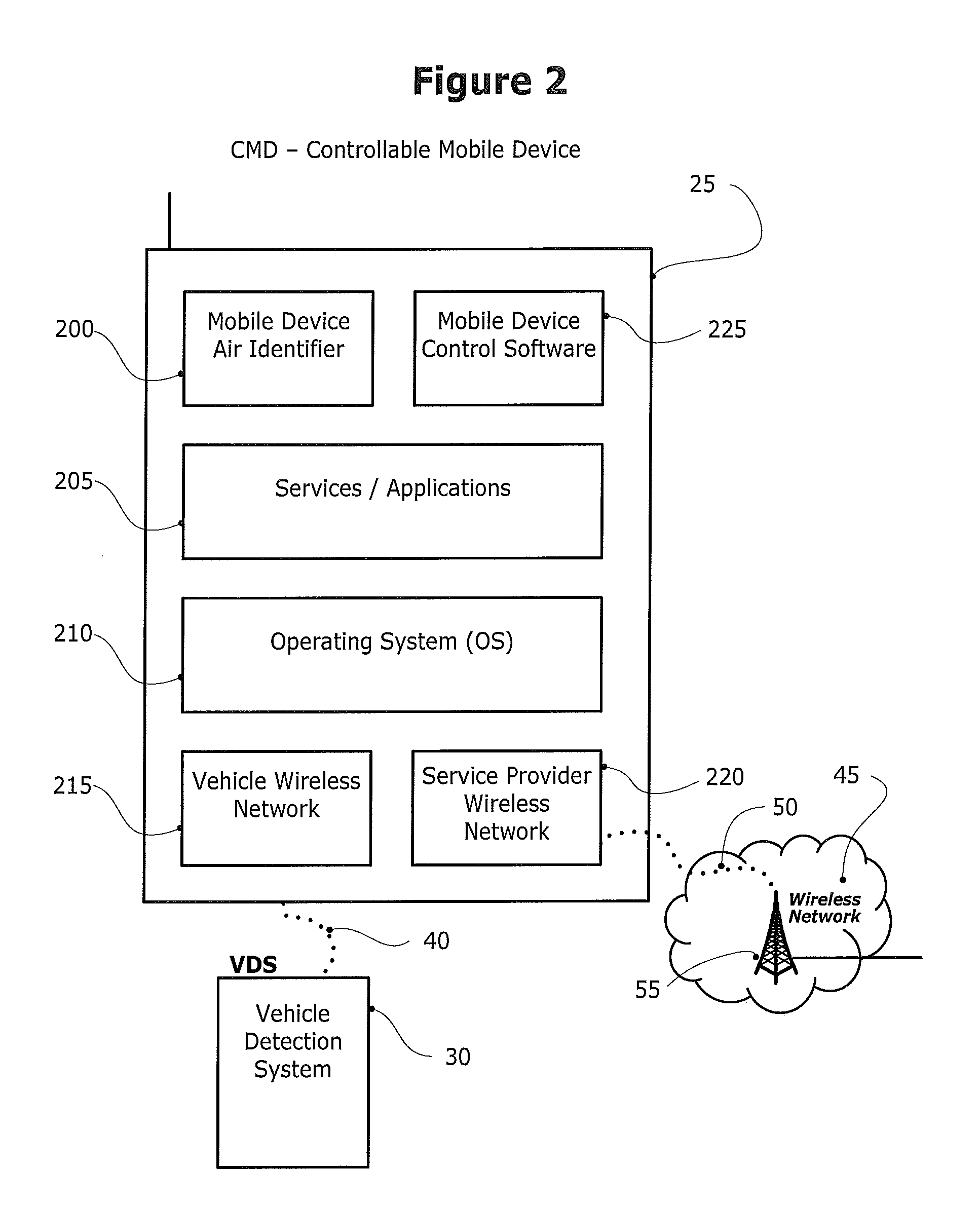
Disclosed herein is a method and system for detecting, monitoring and / or controlling one or more of mobile services for a mobile communication device (also referred to herein as a Controllable Mobile Device or CMD), and in particular, when the device is being used and the vehicle, operated by the user of the device, is moving. The present method and system determines whether the vehicle is being operated by a user that may also have access to a mobile communication device which, if used concurrently while the vehicle is in operation, may lead to unsafe operation of the vehicle. If the mobile services control system determines that a vehicle operator has potentially unsafe access to a mobile communication device, the mobile services control system may restrict operator access to one or more services that would otherwise be available to the operator via the mobile communication device.
Owner:KATASI
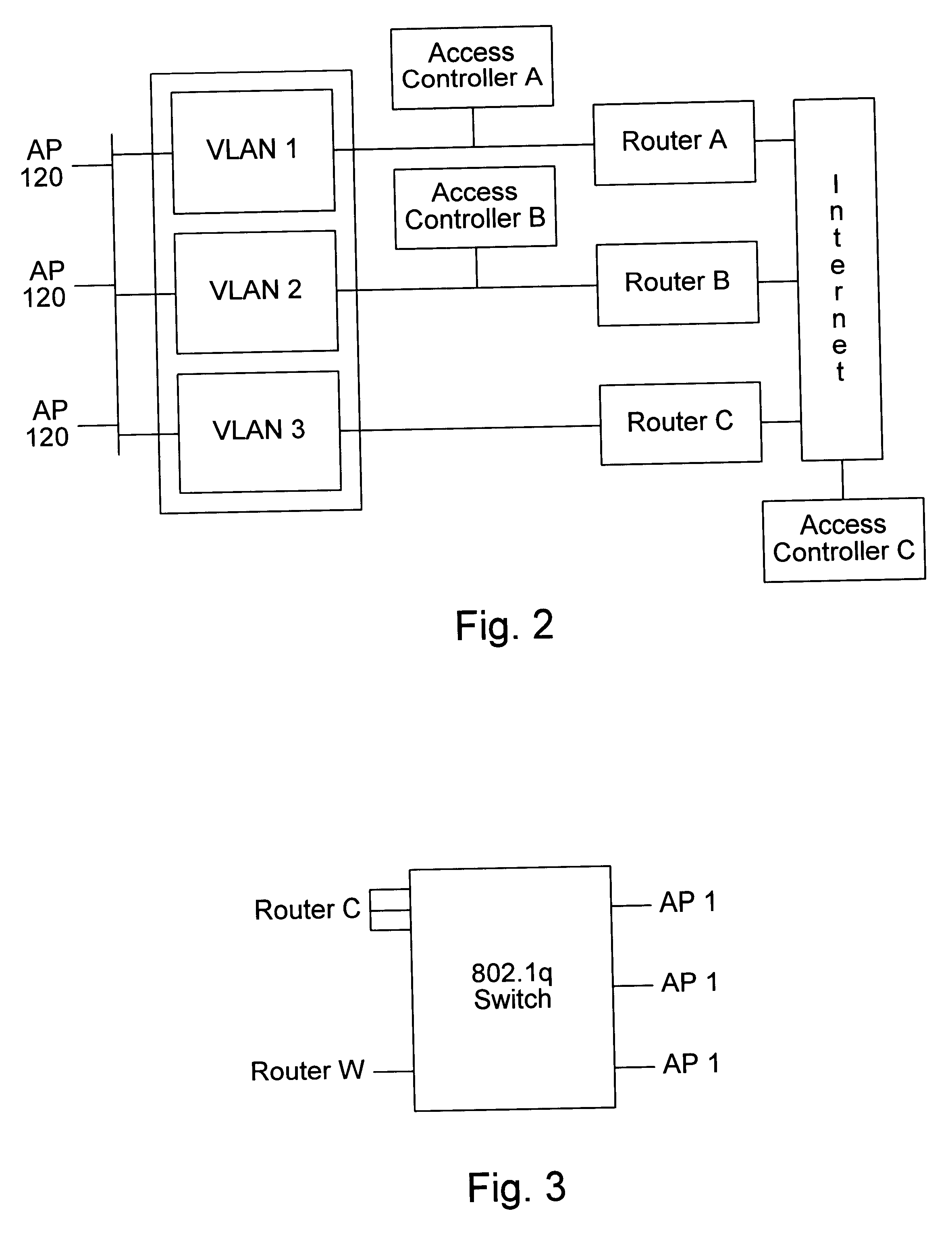
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
InactiveUS6732176B1Metering/charging/biilling arrangementsMultiple digital computer combinationsCommunications systemNetworked system
A system and method for providing access and / or roaming features on a network system. The network system includes a plurality of wireless and / or wired access points coupled to a network. A portable computing device (PCD) of a user may store identification information which uniquely indicates a network provider of a plurality of possible network providers. The identification information may also or instead indicate an access or privilege level of the user. When the access point receives the identification information from a PCD of a user, the access point may determine the appropriate network provider for the portable computing device using the identification information. Network access may then be provided to the portable computing device through the determined network provider.
Owner:CISCO TECH INC
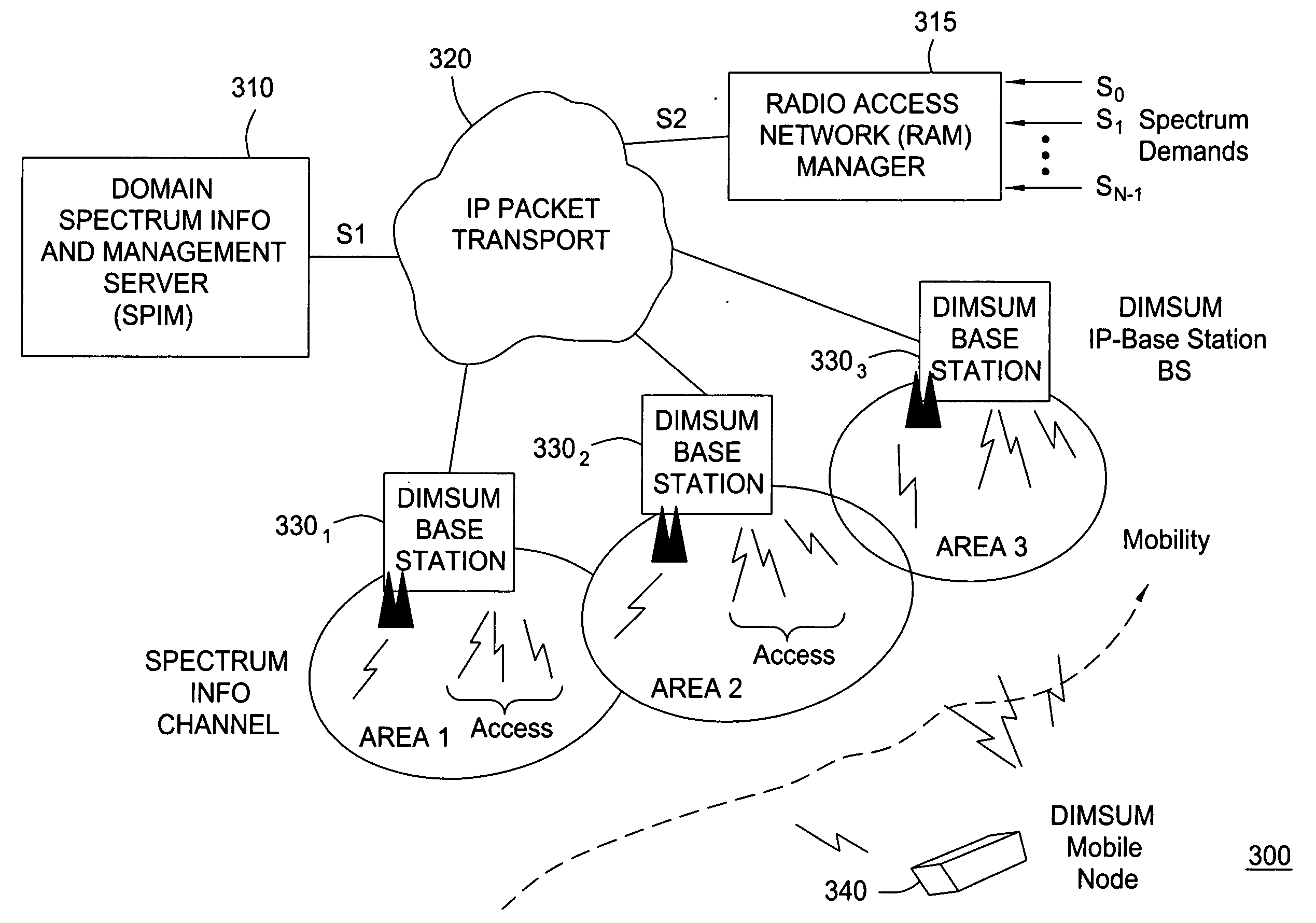
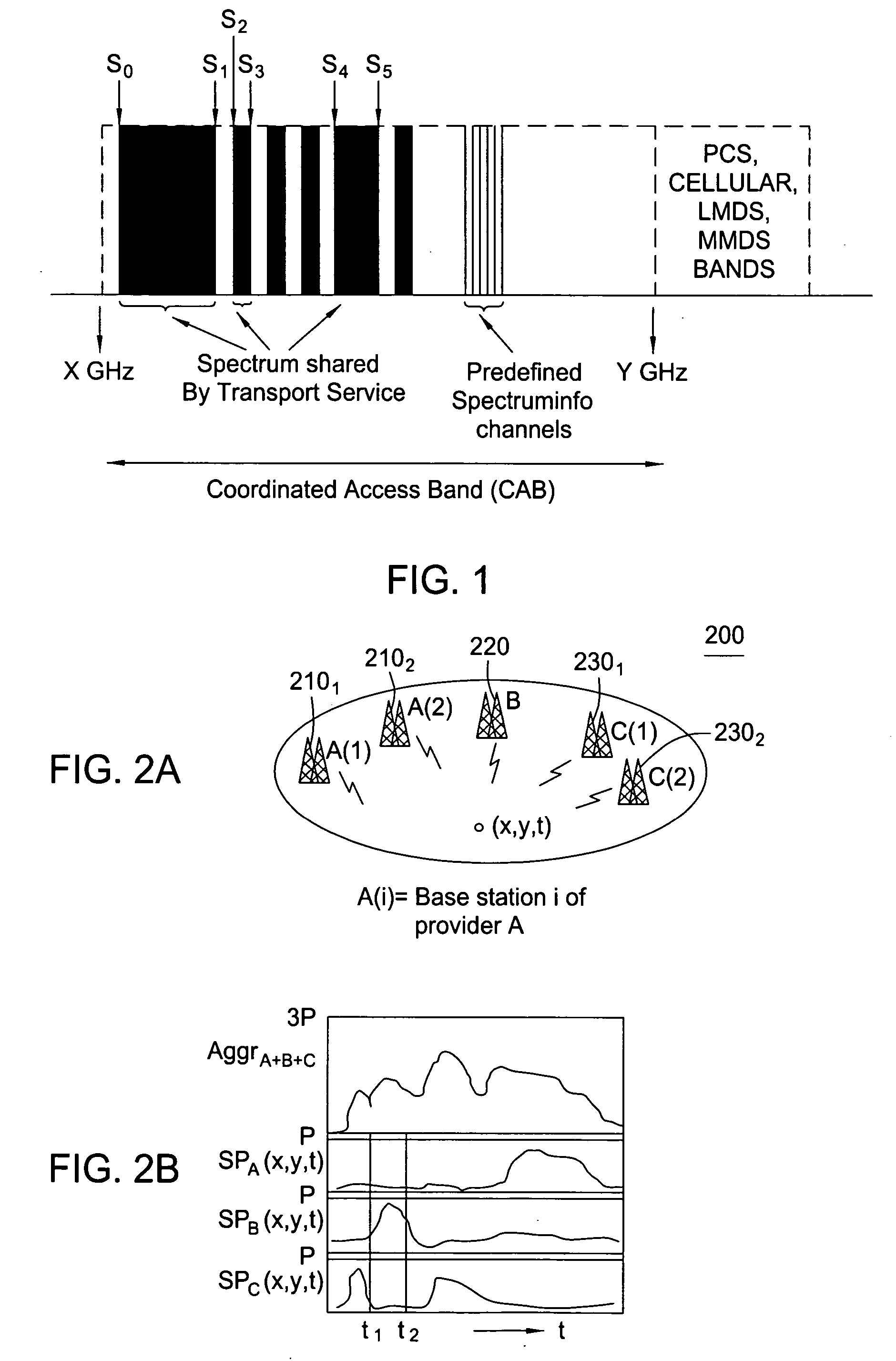
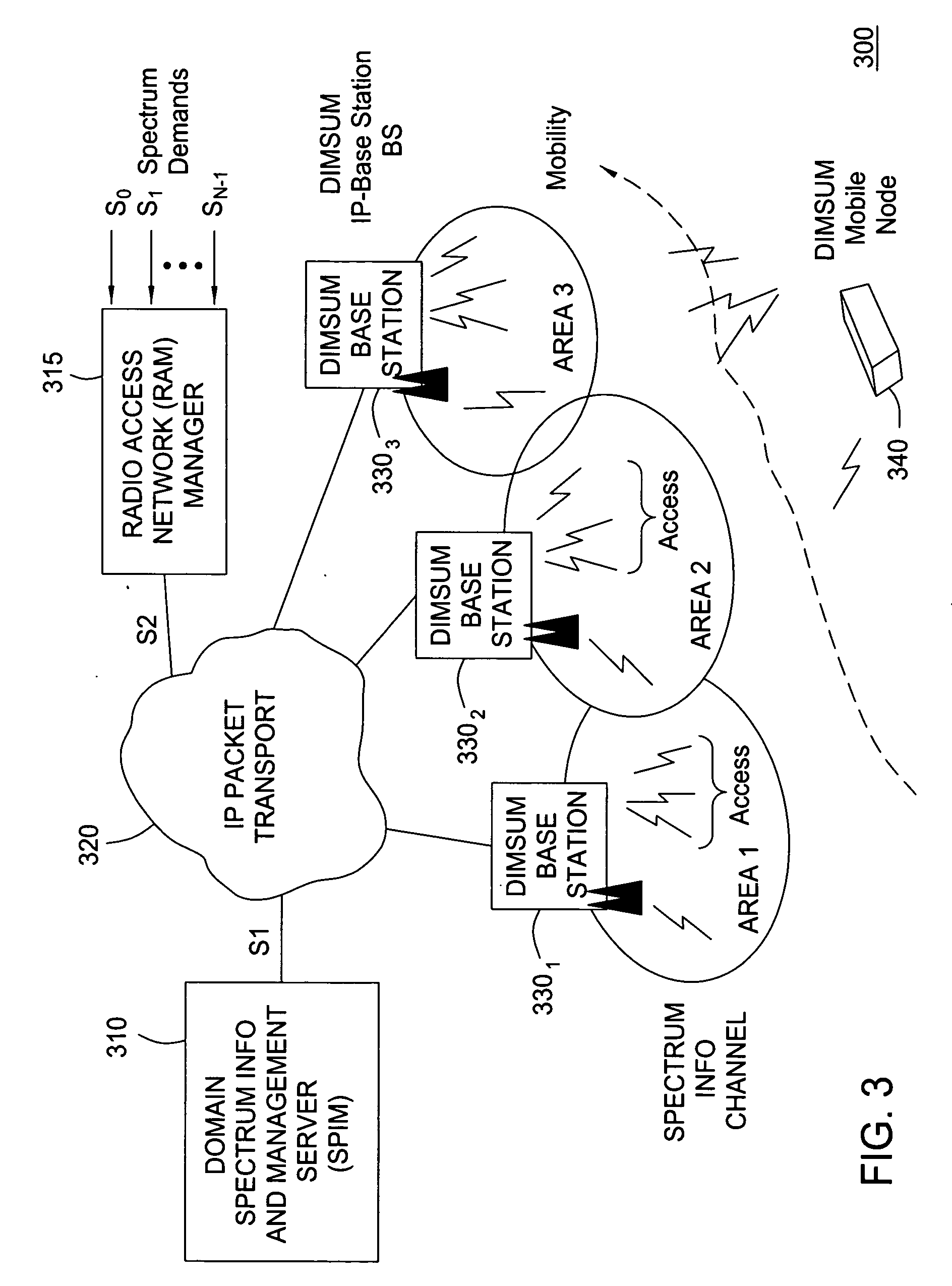
Method and system for wireless networking using coordinated dynamic spectrum access
ActiveUS20060083205A1Network traffic/resource managementAssess restrictionFrequency spectrumSpectrum broker
A method and system for coordinated dynamic access to radio spectrum for wireless networking includes defining a coordinated access band (CAB) from which radio access network (RAN) managers may request spectrum allocations in the form of time bound spectrum leases for their respective requesting base stations. In one embodiment of the present invention, a DIMSUMnet architecture is implemented to make some fundamental choices and to centralize the collection of information, such as spectral occupancy, thermal and adjacent frequency interference. Such collected information is subsequently used by a spectrum broker in making spectrum allocation decisions. The DIMSUMnet architecture of the present invention also introduces a RAN manager element to centralize the task of acquiring time bound spectrum leases and for configuring the base stations.
Owner:ALCATEL LUCENT SAS
System and method for user access to a distributed network communication system using persistent identification of subscribers
InactiveUS20030233332A1Market predictionsMetering/charging/biilling arrangementsDevice registerCommunications system
A system and method for providing network access are disclosed. After connecting to a network at an access point, a user of a computing device registers for network access with a network provider. In response to the registration, the network provider sends a completion page to the computing device. The completion page includes a link to an embedded file such as a small, transparent GIF image. When the computing device retrieves the embedded file, the embedded file is associated with a header than includes an instruction to generate a network system identifier (e.g., a cookie). The network system identifier may be stored by the computing device and later used to identify the computing device as a registrant for network access with the network provider. The embedded file may also be sent at other times, such as after authentication of the user for network access.
Owner:WAYPORT
Systems and methods for monitoring data and bandwidth usage
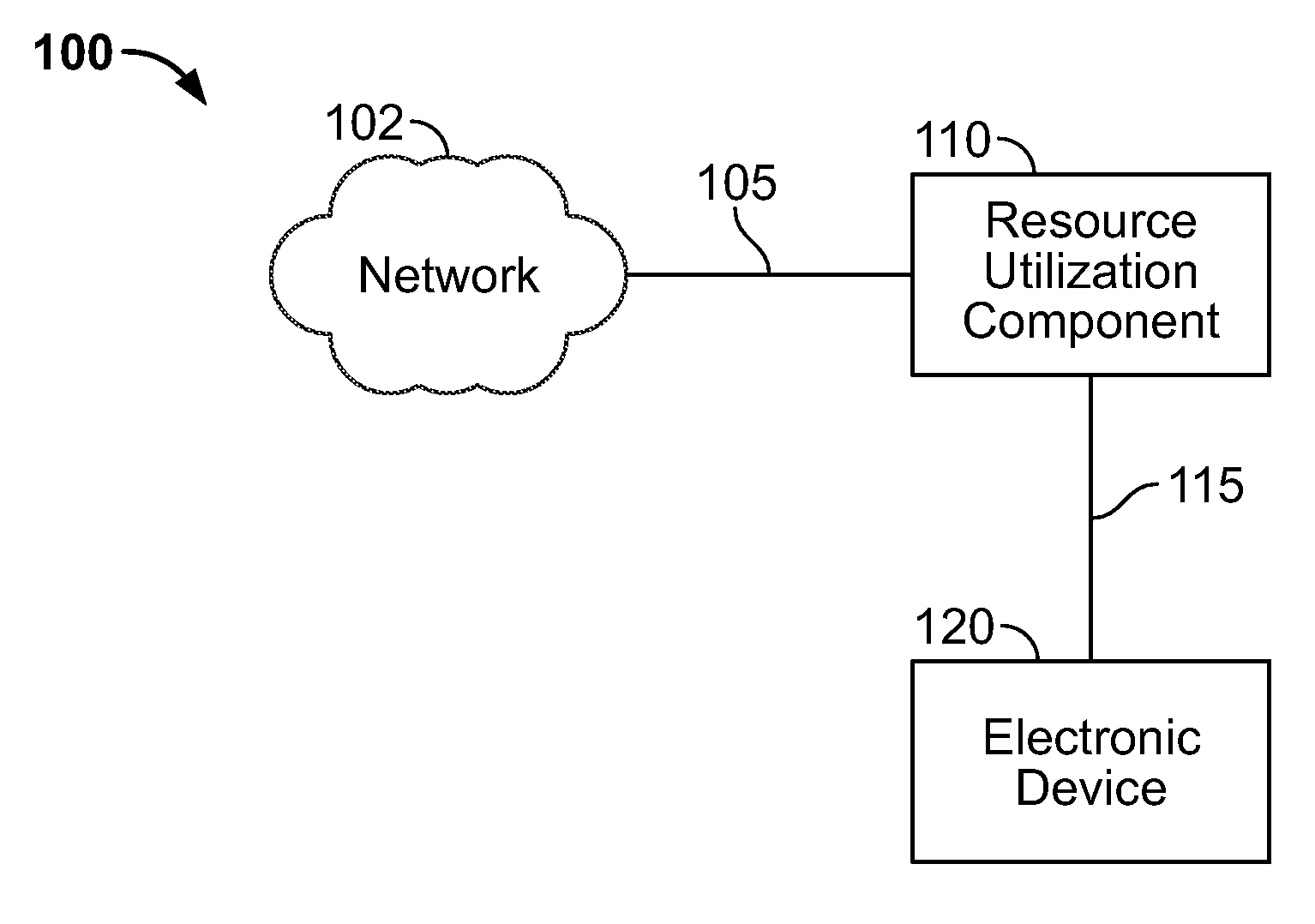
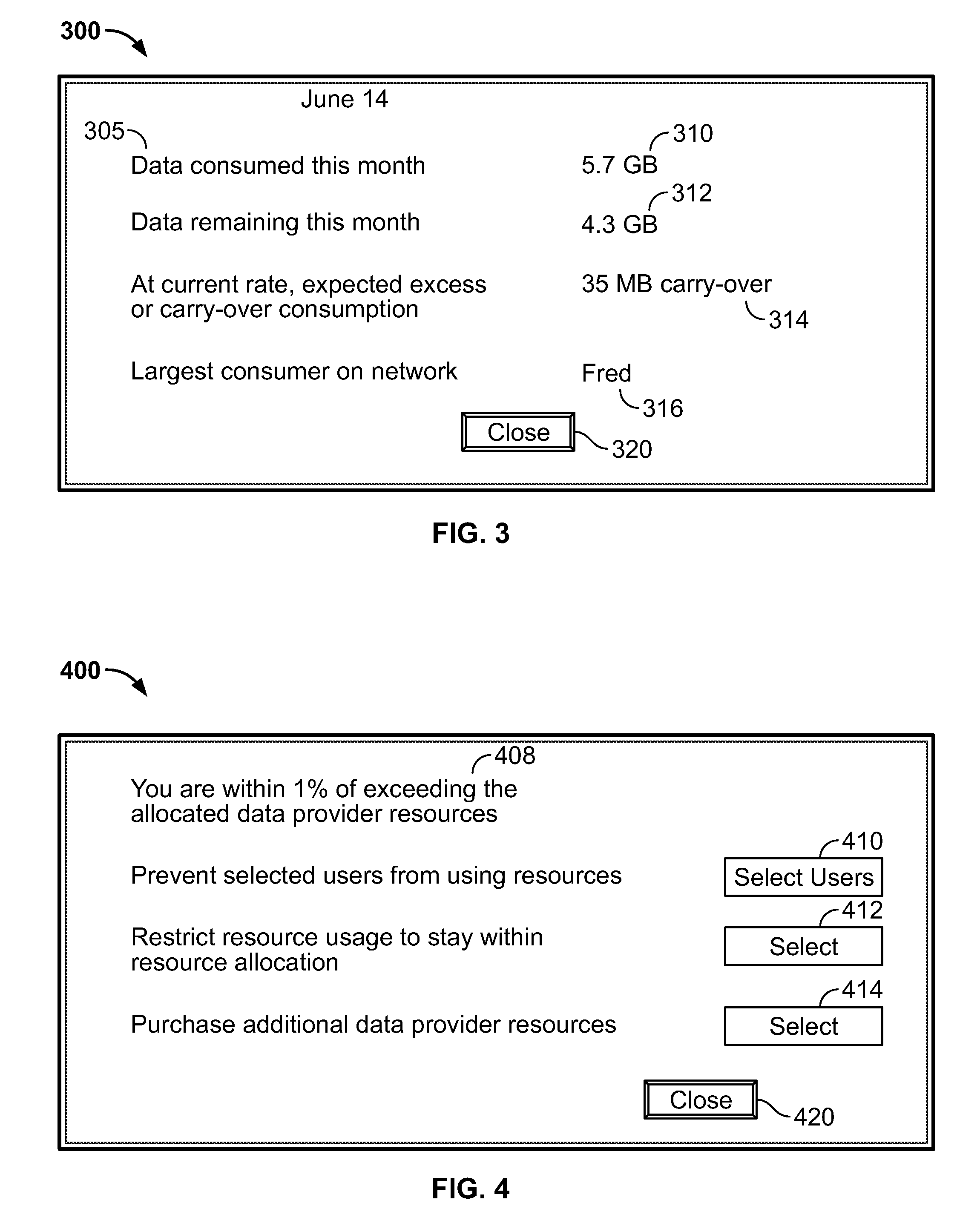
ActiveUS20100017506A1Assess restrictionMultiple digital computer combinationsResource consumptionResource utilization
Access to a communications network may be provided via a data provider that may charge for access. In some cases, the access fee may be related to the amount of network resources consumed (e.g., amount of data downloaded or bandwidth used). In some cases, a user may have access to a particular amount of data provider resources and be required to pay an additional fee for using resources in excess of the particular amount. To assist the user in managing his data resource consumption, a resource utilization component may provide different alerts and notices informing the user of current consumption, expected future consumption, and recommendations for reducing data provider resources consumed (e.g., stopping particular processes or data provider requests, such as downloading media). If several electronic devices in a network are connected to the same data provider resources, a network component may manage the data provider resource use among the several electronic devices (e.g., allow only particular users or devices access).
Owner:APPLE INC
Controlling Mobile Device Functions
ActiveUS20110195699A1Limited abilityAutomatically disabling the texting ability of mobile deviceAssess restrictionSpecial service for subscribersDistractionDriver/operator
This provides for controlling mobile device functions and features, along with systems incorporating these devices and methods. For example, it limits or disables the use of some of mobile device features which could cause distraction to the user, when the user is engaged in another activity. In an example, it enables other mobile device features based on occurrence of events related to the user or environment. Another example addresses controlling the mobile device features, such as SMS, while the user is in a vehicle or driving. Another example restricts the ability of the driver of a vehicle to text, while the vehicle is in motion, by automatically disabling the texting ability of mobile device within and around the perimeter of the driver's seat. Other variations, examples, improvements, detection mechanisms, models, techniques, calculations, verification mechanisms, and features are also described in details.
Owner:HYUNDAI MOTOR CO LTD
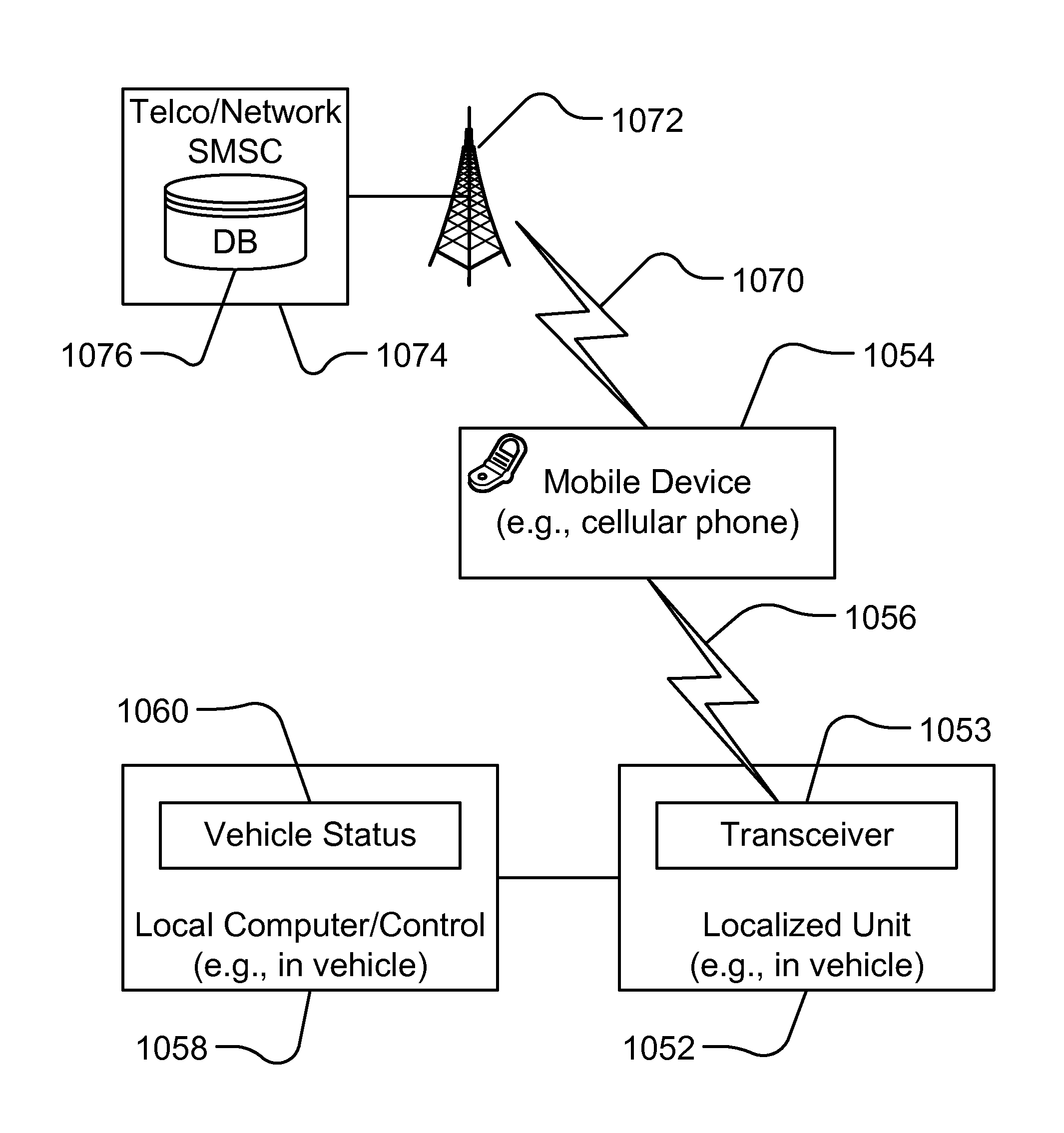
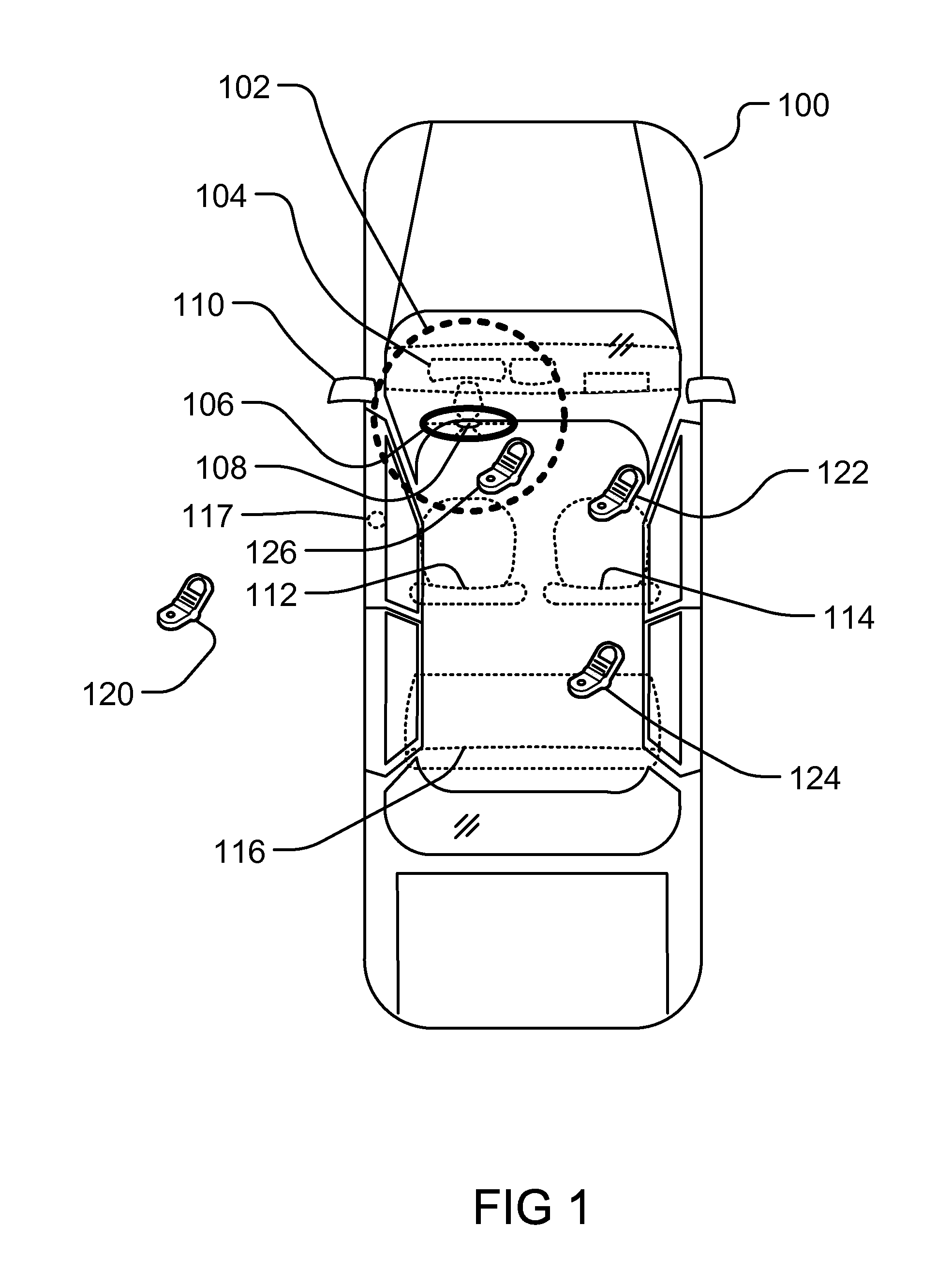
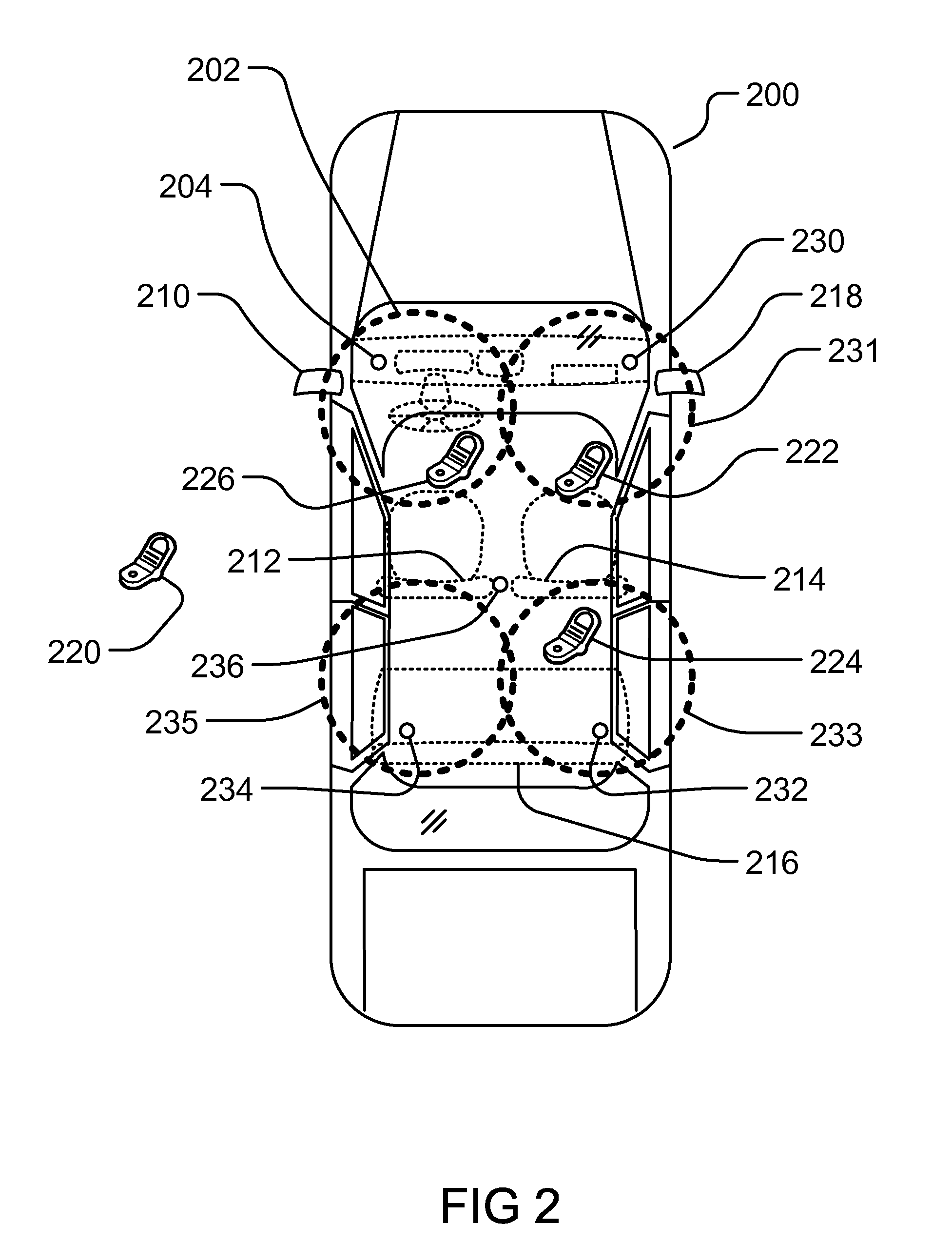
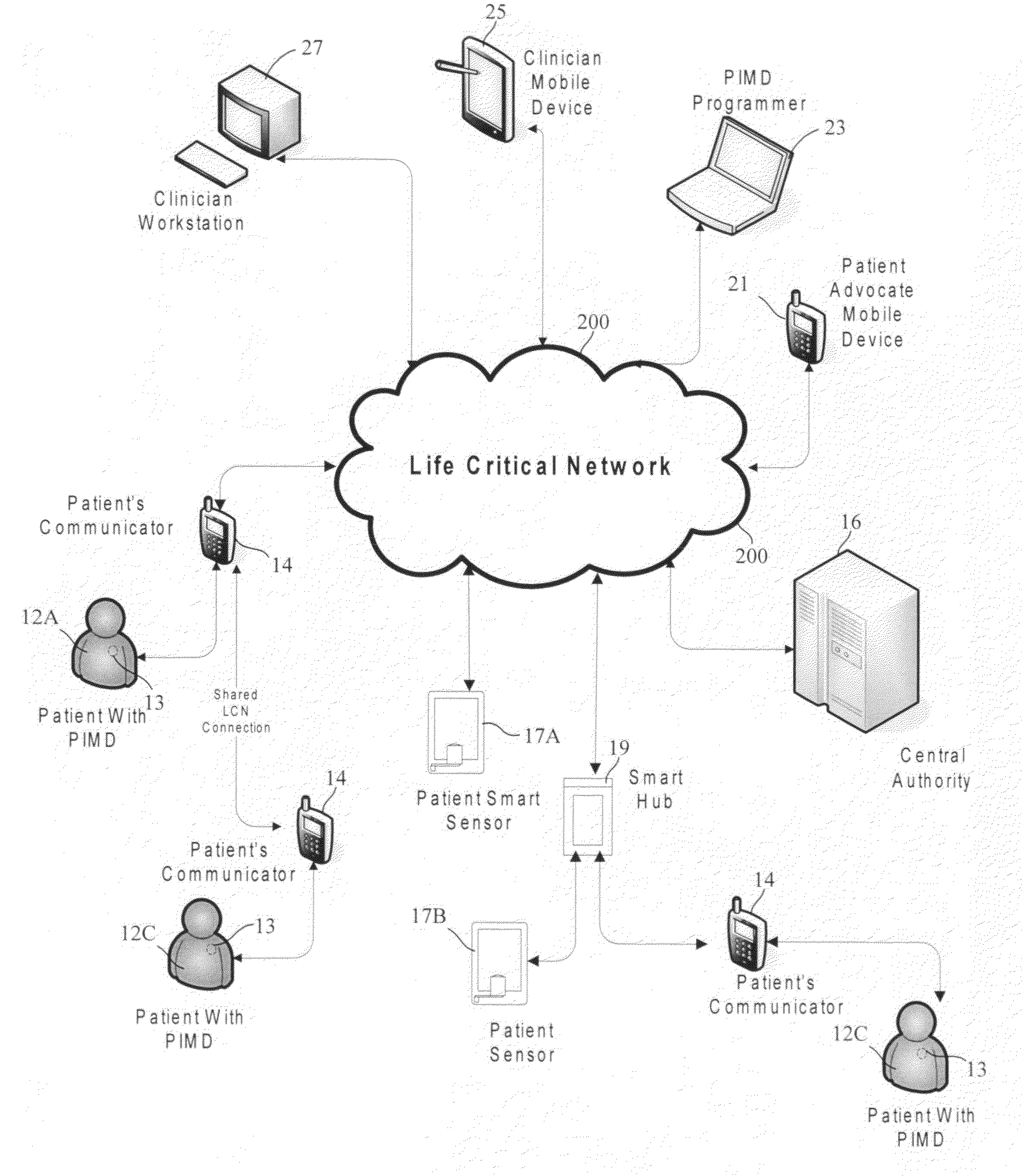
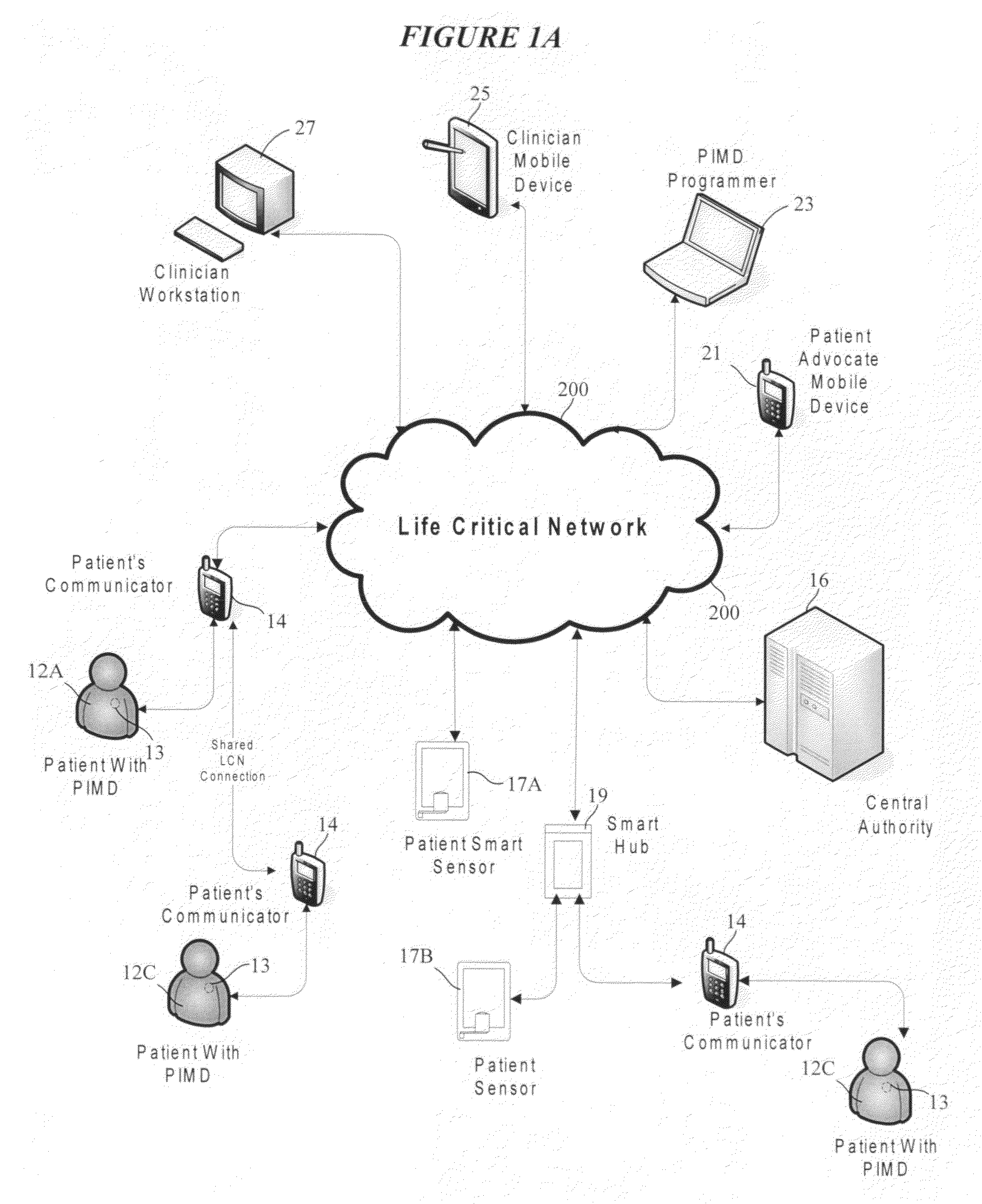
Medical data transport over wireless life critical network employing dynamic communication link mapping
ActiveUS20090063187A1ElectrotherapyMeasuring/recording heart/pulse rateTelecommunications linkNetwork connection
A portable source medical device determines communication links of a network presently available to effect communications with a target component when the source medical device is at each of a multiplicity of geographical locations. A profile is generated comprising information about each available communication link and attributes associated with each available communication link for each geographical location. When the source medical device is at a particular geographical location, a profile associated with the particular geographical location is accessed and a network connection is established between the source medical device and the target component using a communication link associated with the particular profile. Medical information is transferred between the source medical device and the target component via the communication link associated with the particular profile.
Owner:CARDIAC PACEMAKERS INC
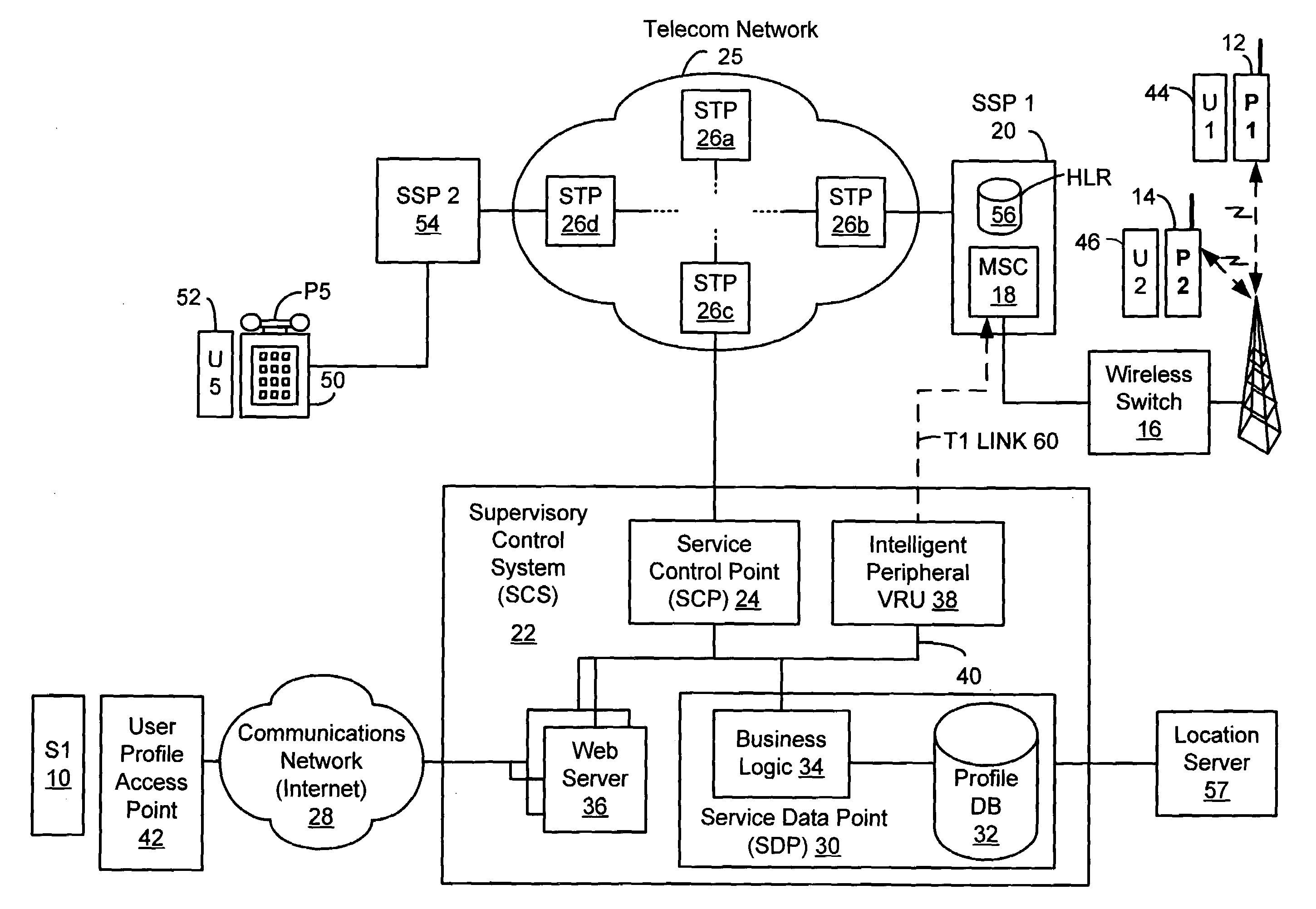
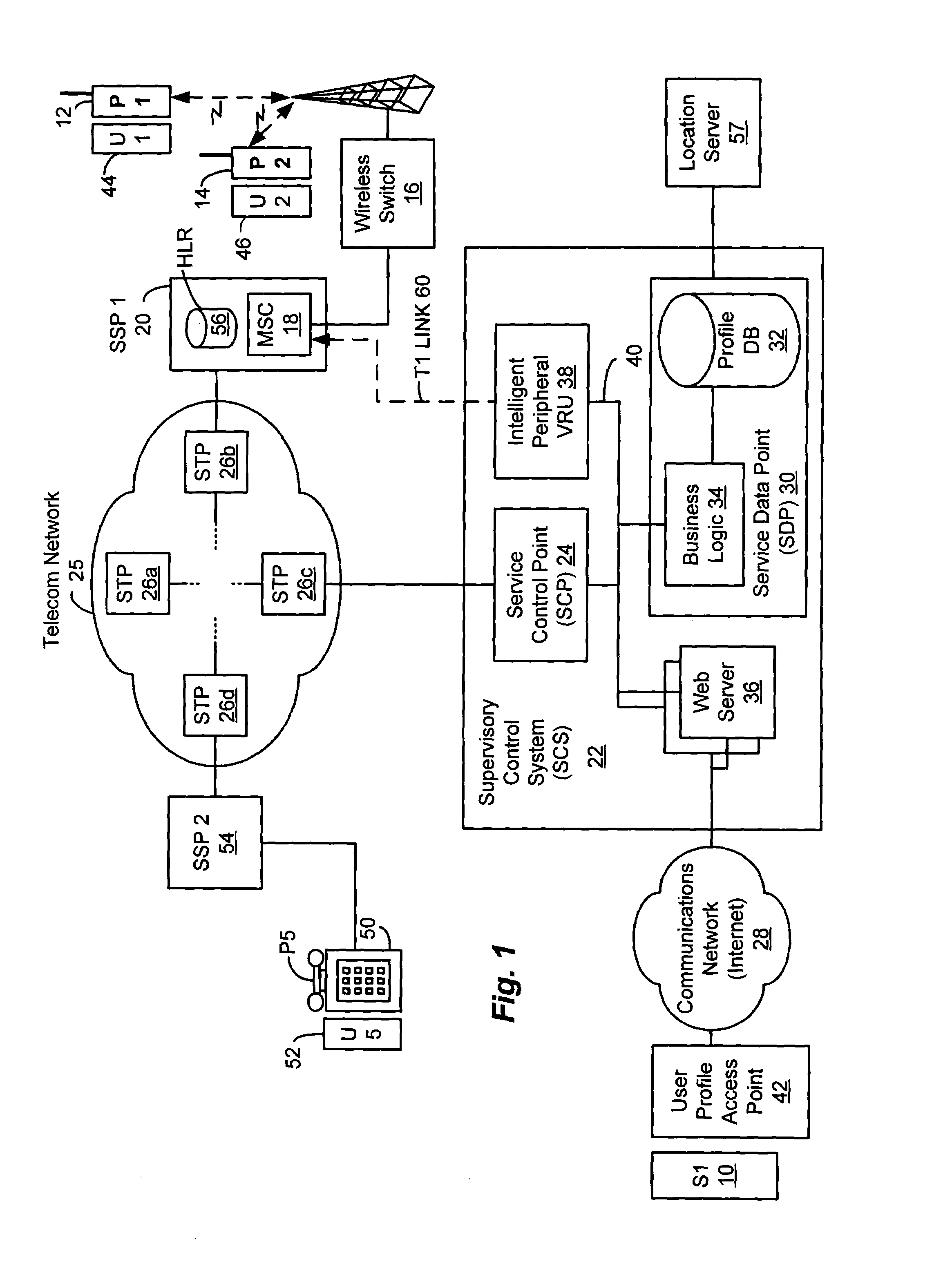
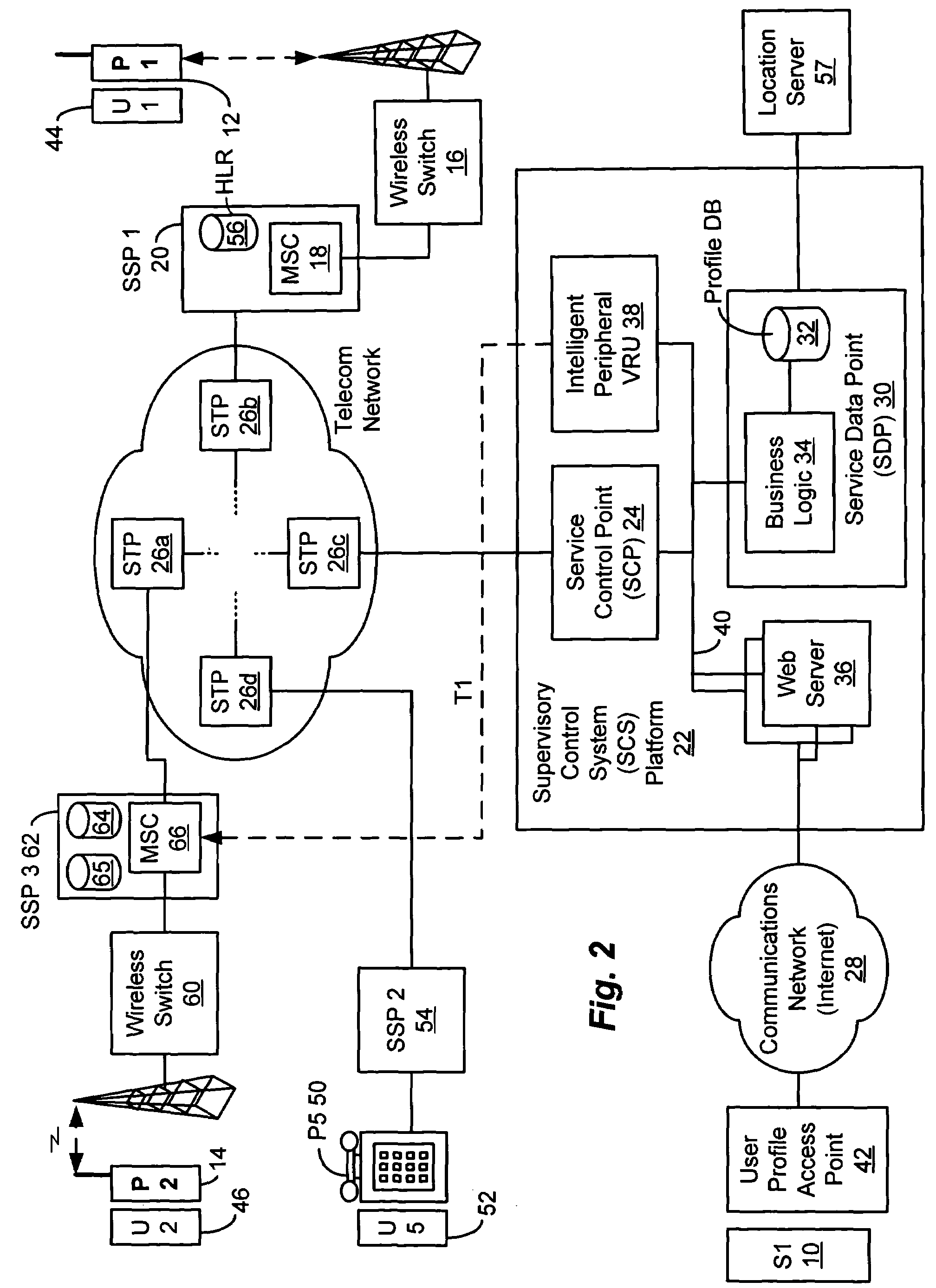
Method and system for providing supervisory control over wireless phone usage
InactiveUS7197321B2Reduce usageAccounting/billing servicesUnauthorised/fraudulent call preventionUser profileControl period
A system for controlling wireless phone usage enables a supervisor to establish user profiles for supervised users of wireless phones across a range of parameters which are stored in a user profile database. Such parameters may include one or more locations at which use of the wireless phone is restricted or permitted. In addition, restrictions on phone use may be provided based upon total phone usage within a specified control period, time periods, dates or days of the week during which phone use is restricted or permitted. One or more lists including numbers that are always-accessible may be provided and one or more lists including numbers that are never-accessible may also be provided. In the event a call does not satisfy predefined criteria, the call is blocked. Predetermined messages may be played to the called or calling party as applicable when a call is blocked. Boolean combinations of restrictions and permissive use criteria for the wireless phone may be specified to provide for flexibility when establishing use criteria for the wireless phone.
Owner:BOSTON COMM GROUP
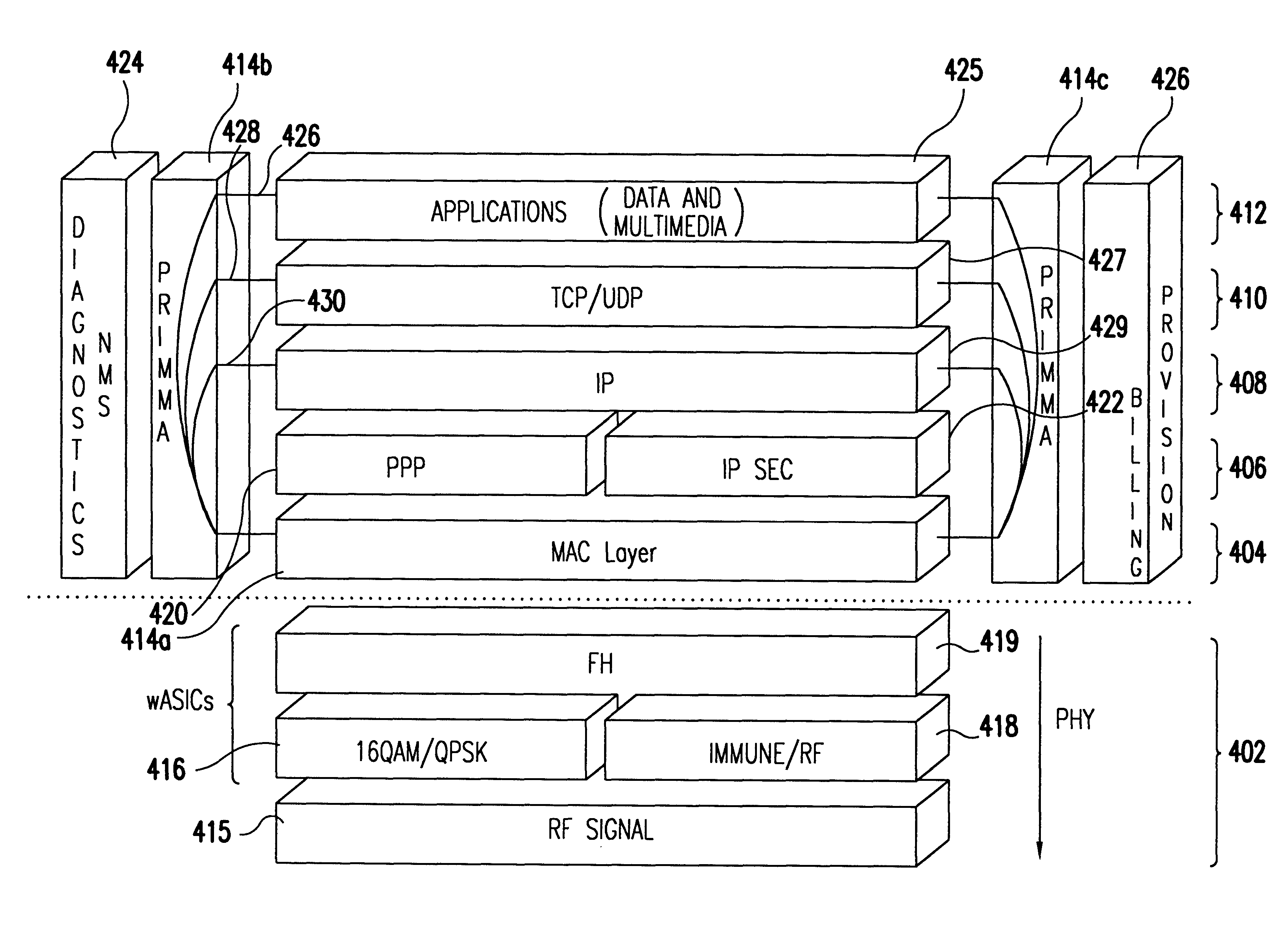
Transmission control protocol/internet protocol (TCP/IP) packet-centric wireless point to multi-point (PTMP) transmission system architecture
InactiveUS6862622B2Special service provision for substationError detection/prevention using signal quality detectorTransport systemWorkstation
A packet-centric wireless point to multi-point telecommunications system includes: a wireless base station communicating via a packet-centric protocol to a first data network; one or more host workstations communicating via the packet-centric protocol to the first data network; one or more subscriber customer premise equipment (CPE) stations coupled with the wireless base station over a shared bandwidth via the packet-centric protocol over a wireless medium; and one or more subscriber workstations coupled via the packet-centric protocol to each of the subscriber CPE stations over a second network. The packet-centric protocol can be transmission control protocol / internet protocol (TCP / IP). The packet-centric protocol can be a user datagram protocol / internet protocol (UDP / IP). The system can include a resource allocation means for allocating shared bandwidth among the subscriber CPE stations. The resource allocation is performed to optimize end-user quality of service (QoS). The wireless communication medium can include at least one of: a radio frequency (RF) communications medium; a cable communications medium; and a satellite communications medium. The wireless communication medium can further include a telecommunications access method including at least one of: a time division multiple access (TDMA) access method; a time division multiple access / time division duplex (TDMA / TDD) access method; a code division multiple access (CDMA) access method; and a frequency division multiple access (FDMA) access method.The first data network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN). The second network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN).
Owner:INTELLECTUAL VENTURES I LLC
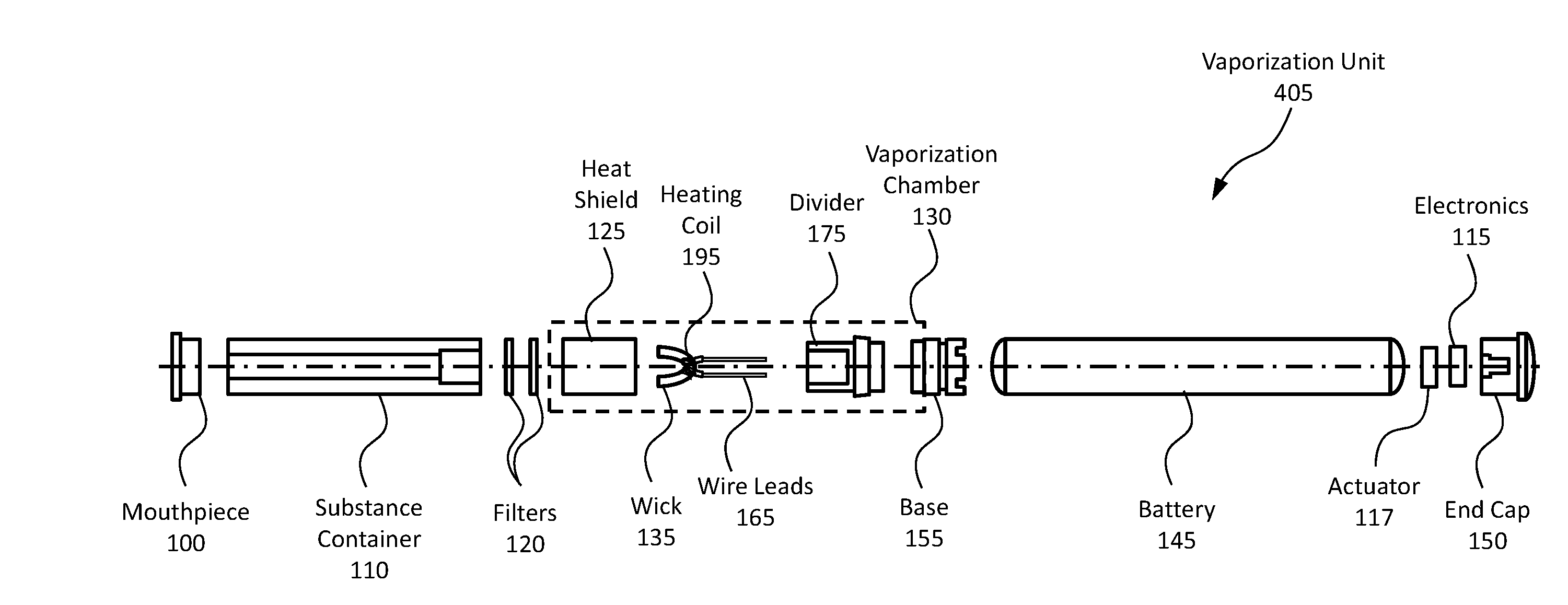
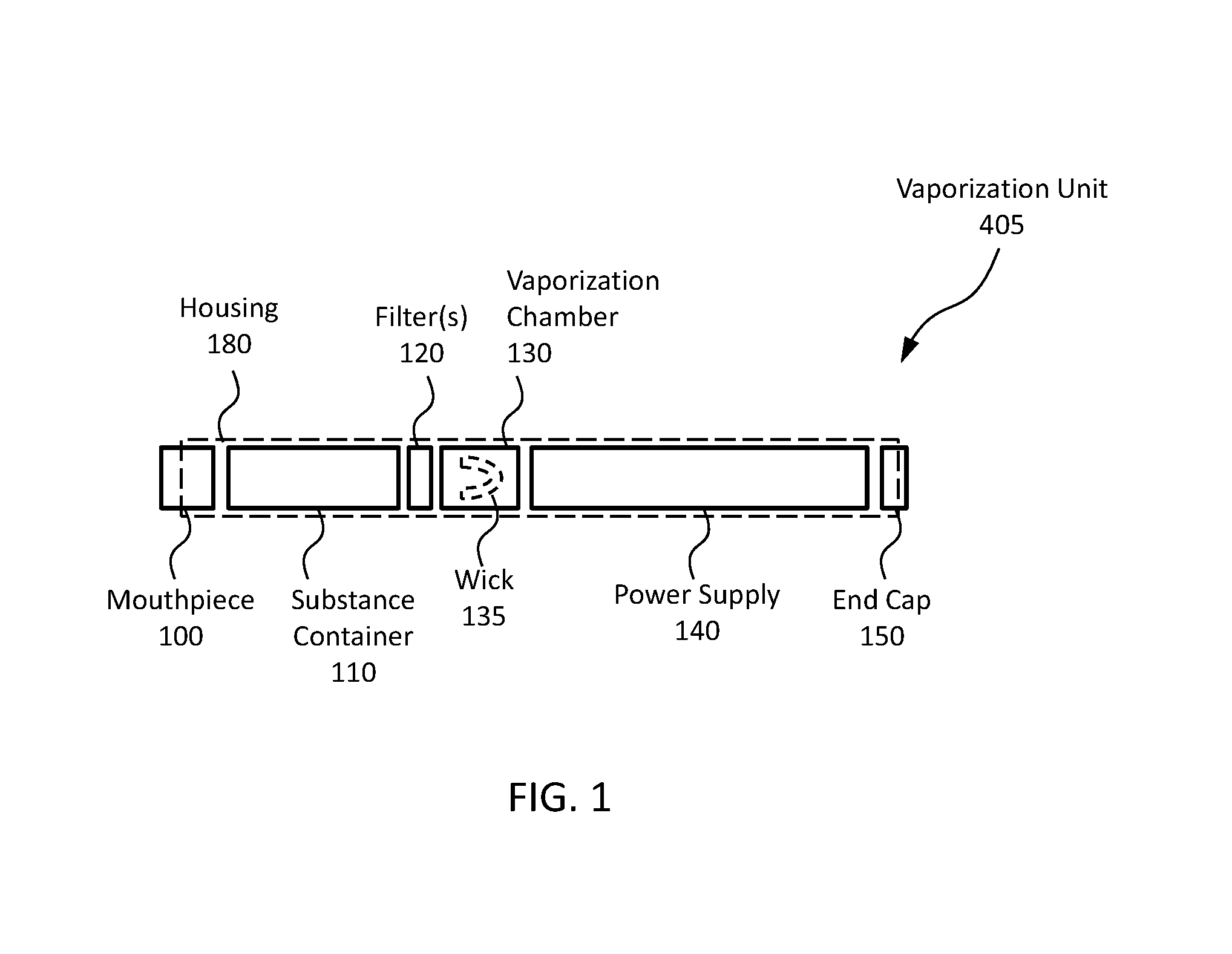
Systems and methods for a vaporization device and product usage control and documentation
Owner:CANOPY GROWTH CORP
Feature management of a communication device
A system and method for the real-time management of a device, and more particularly to the establishment and enforcement of policies or rules associated with the feature or functions that may be performed with the device. Modern communication devices are capable of many things, including making and receiving calls, exchanging data, playing games and music, sending and receiving email, accessing web sites, and paying for goods and services. Depending on who is using the communication device, such as a child or an employee, there may be a need or desire to regulate how that communication device can be used and to determine who will pay for what goods or services. In addition to providing all of the features associated with a device, service providers need to be able to establish and enforce rules (policies) regulating how and when that device can be used and who will pay for a good or service requested by the user of the device.
Owner:KAJEET
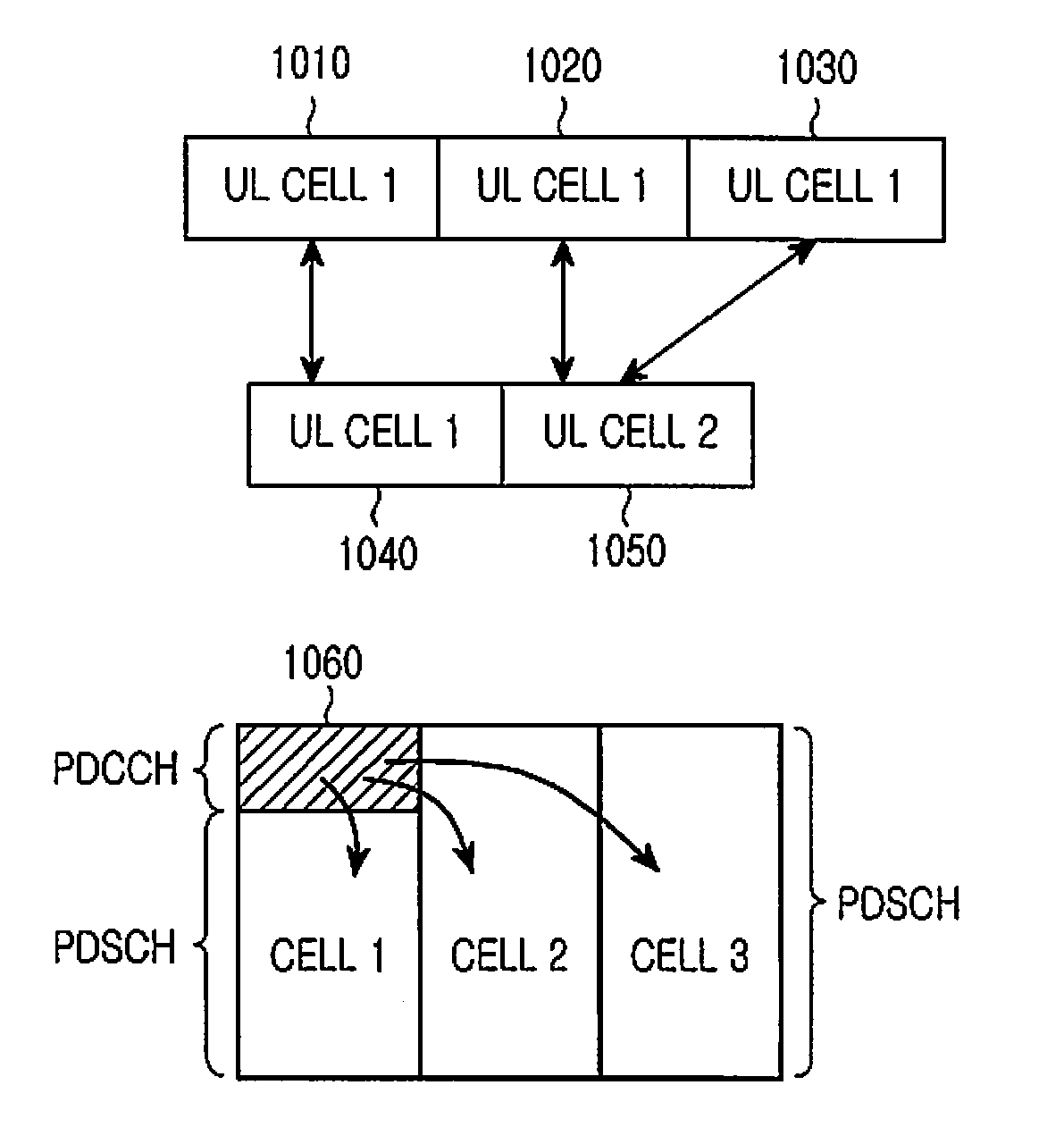
Extending physical downlink control channels
ActiveUS20110075624A1Limit regionSynchronisation arrangementTransmission path divisionTelecommunicationsControl channel
Methods and apparatus for transmitting and receiving Downlink Control Information (DCI) in a single cell in order to support communication over multiple cells. The DCI is conveyed by DCI formats transmitted through Physical Downlink Control CHannels (PDCCHs) in a UE-Common Search Space (UE-CSS) and in a UE-Dedicated Search Space (UE-DSS). A distinct UE-DSS is defined in the single cell for each of the multiple cells. Each distinct UE-DSS has the same structure as a conventional UE-DSS and a location that is determined by the same parameters as the location of the conventional UE-DSS and by the respective cell identity (Cell_ID).
Owner:SAMSUNG ELECTRONICS CO LTD
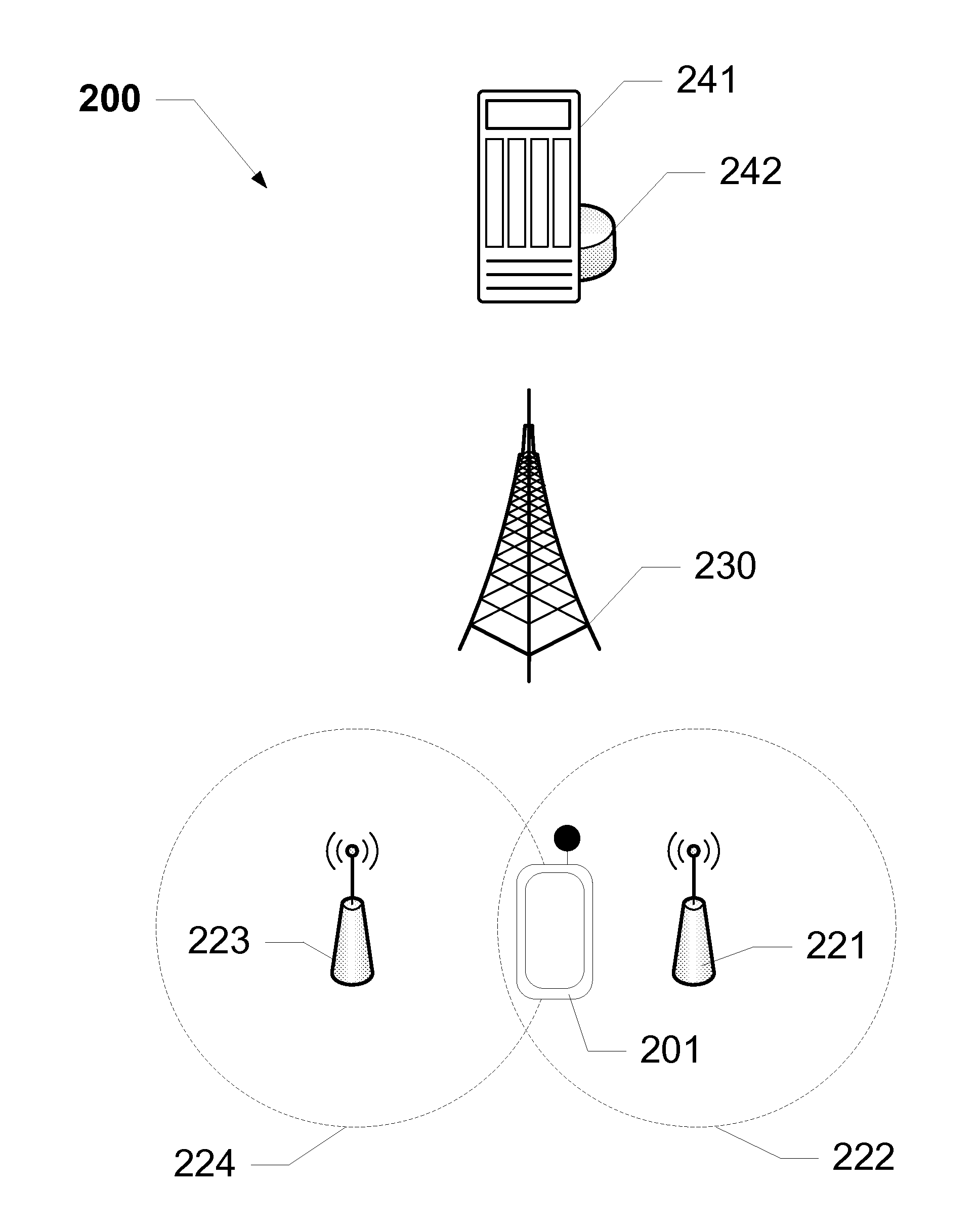
Method for selecting an air interface using an access list on a multi-mode wireless device
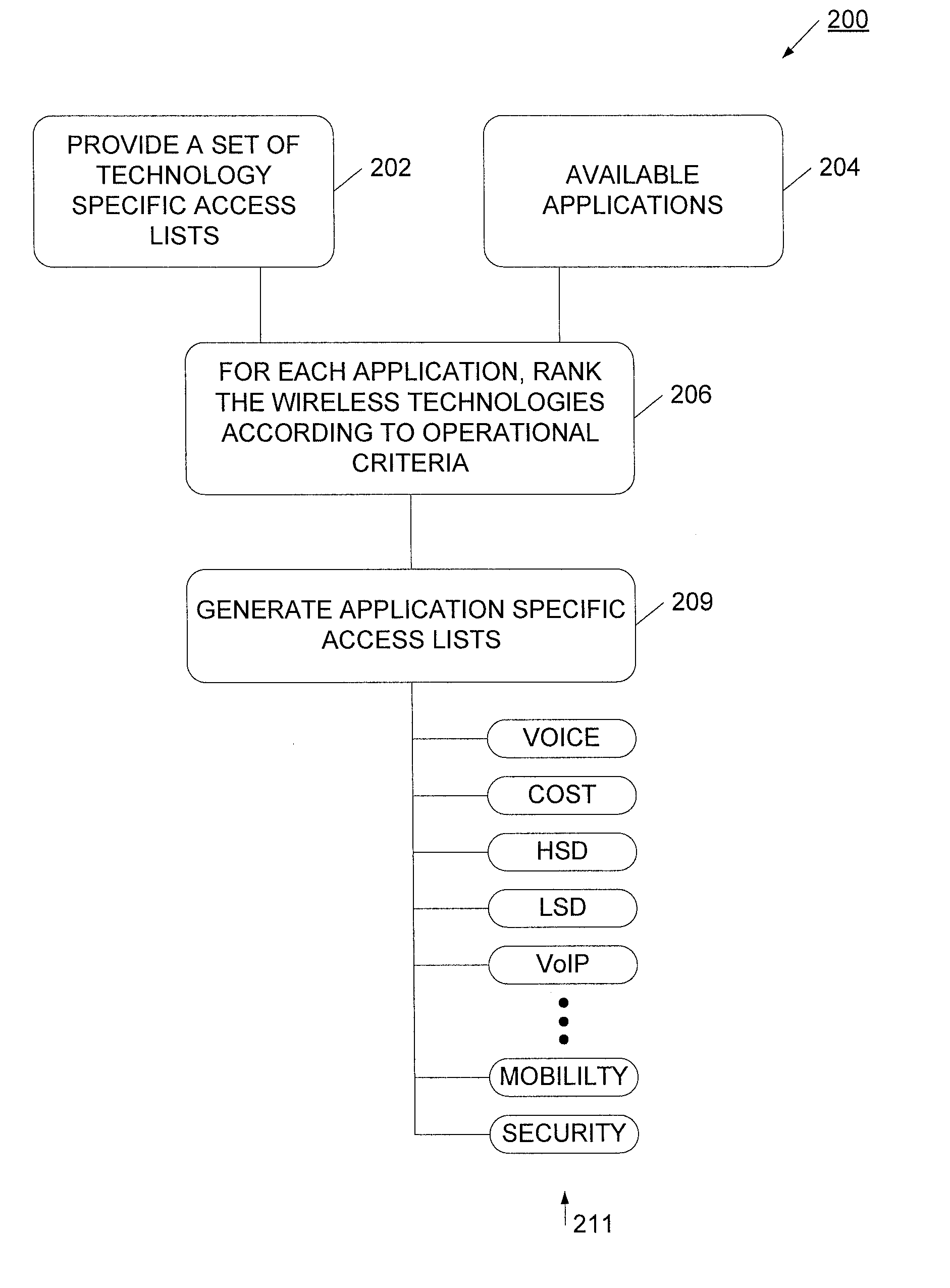
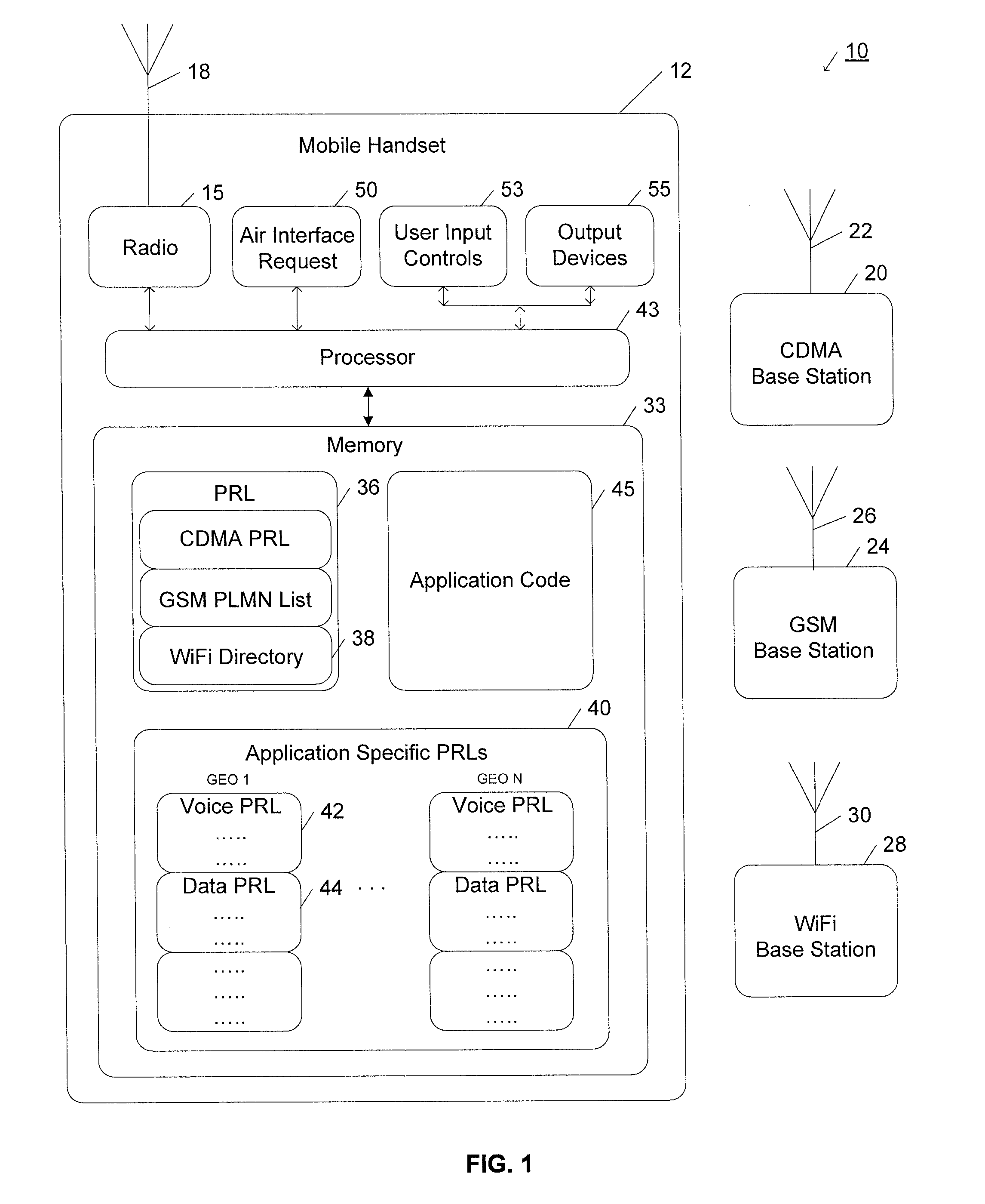
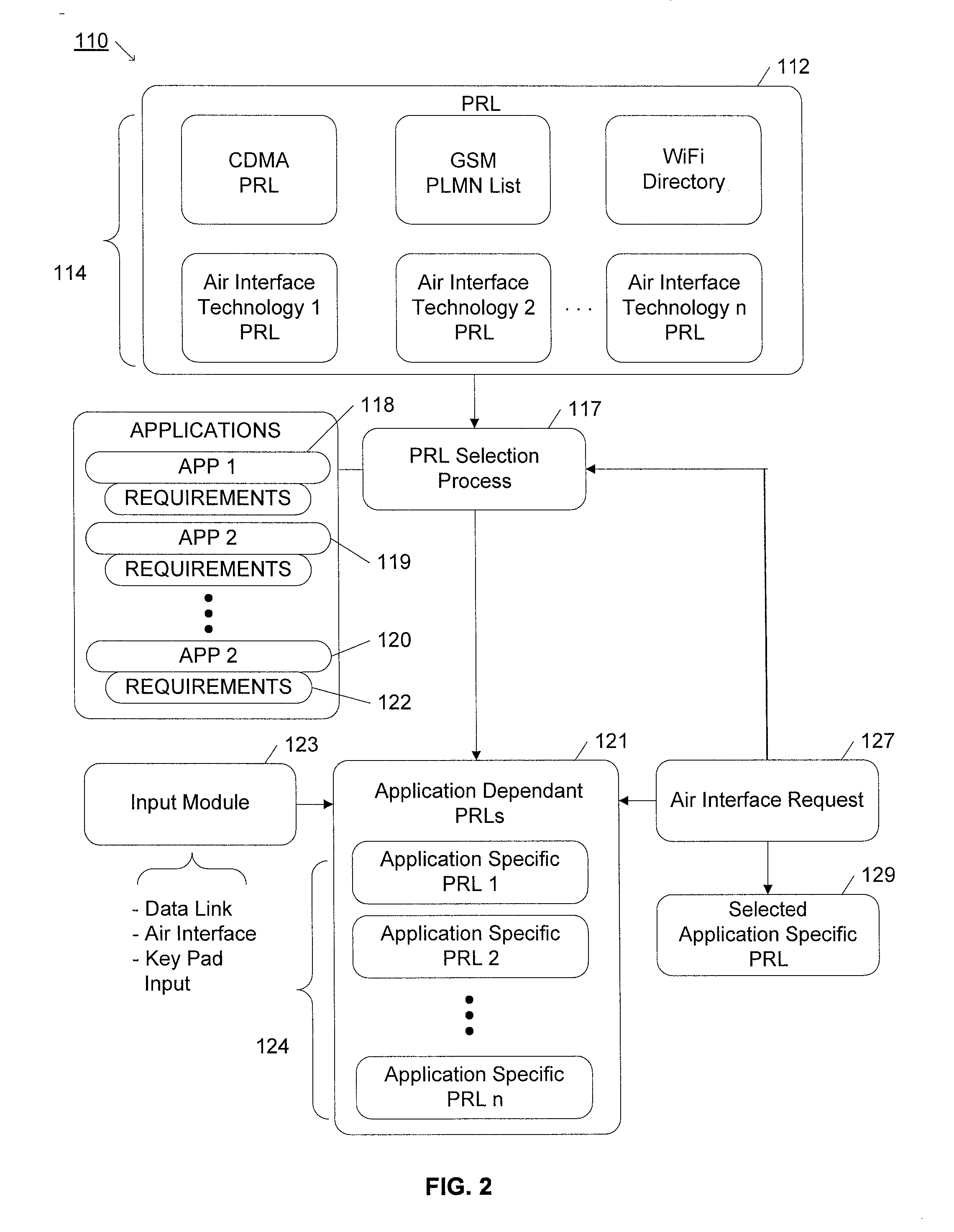
InactiveUS20070255797A1Shorten the timeEfficient identificationAssess restrictionMultiple digital computer combinationsAir interfaceApplication specific
Application-specific access lists are provided for a multimode mobile wireless device. The multimode mobile device has an access list for each wireless technology. Typically, these technology specific access lists are standard for each technology, and are provided by a service provider or the manufacturer of the multimode mobile device. For each application the multimode wireless device is a likely to operate, an application-specific access list is generated. The application-specific access list ranks the wireless technologies according to its relative desirability for the application. In this way, when the multimode mobile device request an application, the application-specific access list may be used to efficiently acquire a network preferred for that particular application. The application-specific access lists may be updated from time to time as applications are added or changed, as technology specific access lists are updated, or as geographic location changes.
Owner:KYOCERA CORP
Adaptive ambient services
ActiveUS20100198698A1Error preventionFrequency-division multiplex detailsService profileWireless mesh network
Adaptive ambient services are provided. In some embodiments, an adaptive ambient service includes providing an ambient service profile. In some embodiments, an ambient service includes implementing an ambient service profile for assisting control of the communications device use of an ambient service on a wireless network, in which the ambient service profile includes a plurality of service policy settings, and in which the ambient service profile is associated with an ambient service plan that provides for initial access to the ambient service with limited service capabilities prior to activation of a new service plan; monitoring use of the ambient service based on the ambient service profile; and adapting the ambient service profile based on the monitored use of the ambient service.
Owner:HEADWATER RES LLC
System and method for dynamic automatic communication path selection, distributed device synchronization and task delegation
InactiveUS20100124196A1Limited bandwidthConducive to diversificationError preventionAssess restrictionTelecommunications linkCommunication link
Systems, software, and apparatuses that provide wired and wireless telecommunications under conditions where signal strength is poor or intermittent, the coordination and synchronization of data and workflows across various communication links under such conditions, especially intermittent or unreliable communications links, and the management of wireless mobile applications in such environments. The present invention technology herein relates to the fields of computer science, telecommunications, and data management.
Owner:JUMPSTART WIRELESS CORP
Method for radio resource control
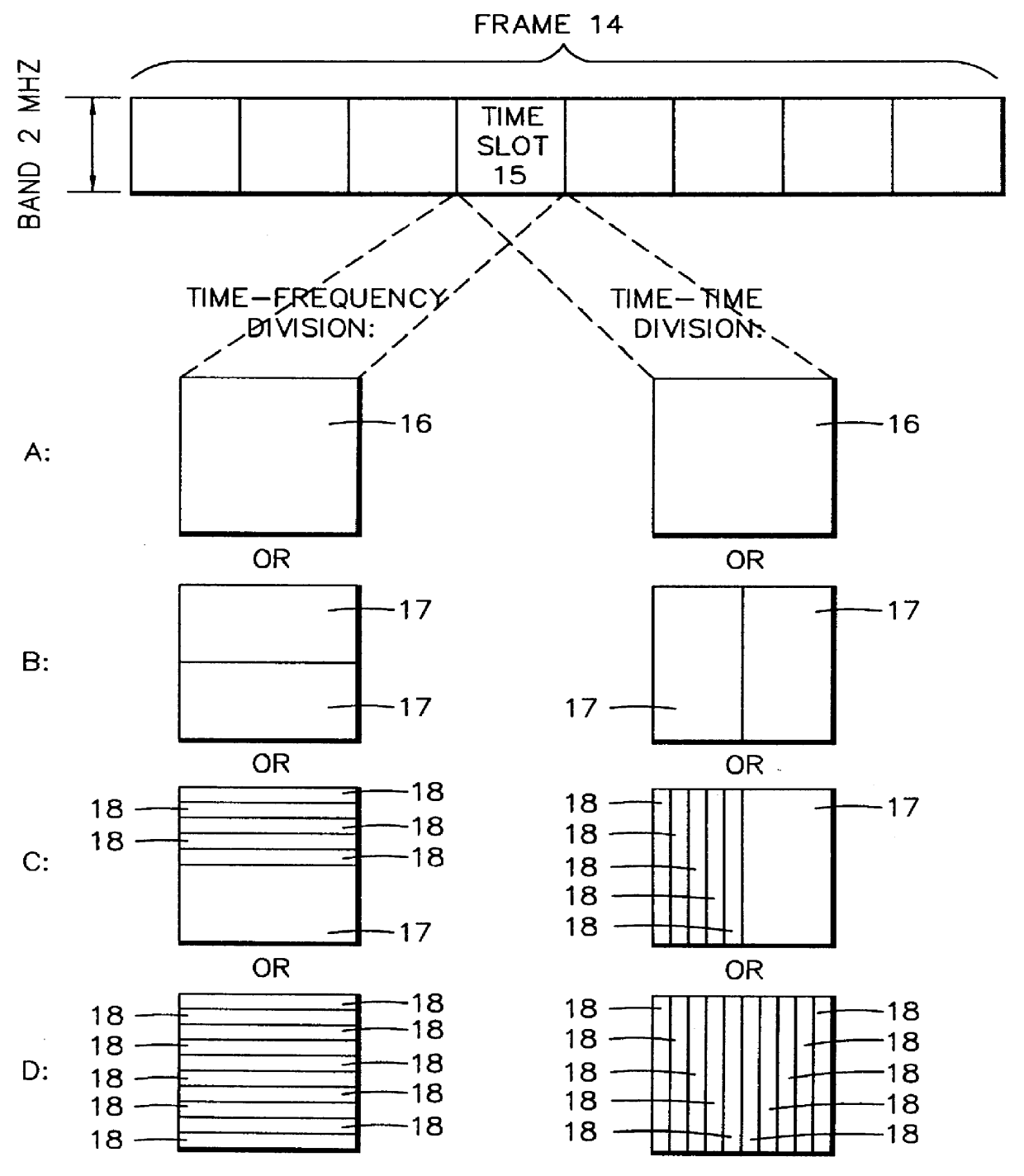
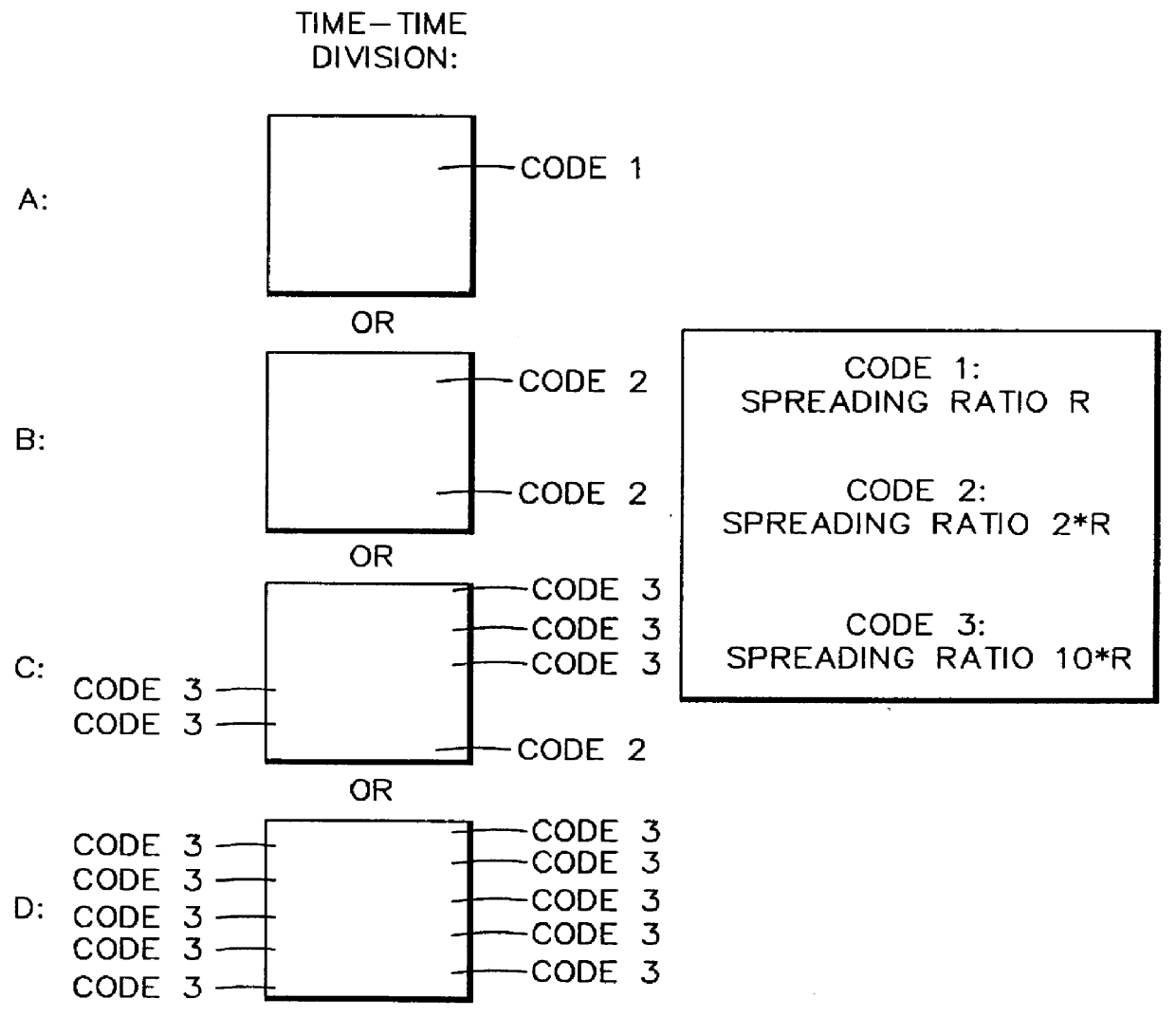
In order to control the use of physical radio resources, the physical radio resources are divided into chronologically consecutive frames (14), so that a frame contains slots (16, 17, 18) of various sizes, which slots represent a given share of the physical radio resources contained in the frame and can be individually allocated to different radio connections. The first dimension of a frame is time and the second dimension can be time, frequency or code. In the direction of the second dimension the slots represent various sizes, and a given first integral number of slots of the first size can be modularly replaced by another integral number of slots of another size. A certain number of consecutive frames form a superframe (19), in which case frames with corresponding locations in consecutive superframes are equal in slot division and allocations, if the data transmission demands do not change. Changes in the state of occupancy of the slots are possible at each superframe. In order to form an uplink connection, the mobile station sends a capacity request, where it indicates the type of requested connection and the demand of resources. In order to form a downlink connection, the base station subsystem sends a paging call, where it indicates the location in the superframe of the slots allocated to the connection. In order to indicate the state of occupancy, the base station subsystem maintains a superframe-size parametrized reservation table.
Owner:NOKIA TECHNOLOGLES OY
Wireless power receiver and control method thereof
Methods and apparatus are provided for controlling a wireless power receiver for wirelessly receiving power. A drive power for driving the wireless power receiver is received from a wireless power transmitter. A communication network is established with the wireless power transmitter. A wireless power network that is controlled by the wireless power transmitter is joined. A charge power is received from the wireless power transmitter.
Owner:SAMSUNG ELECTRONICS CO LTD
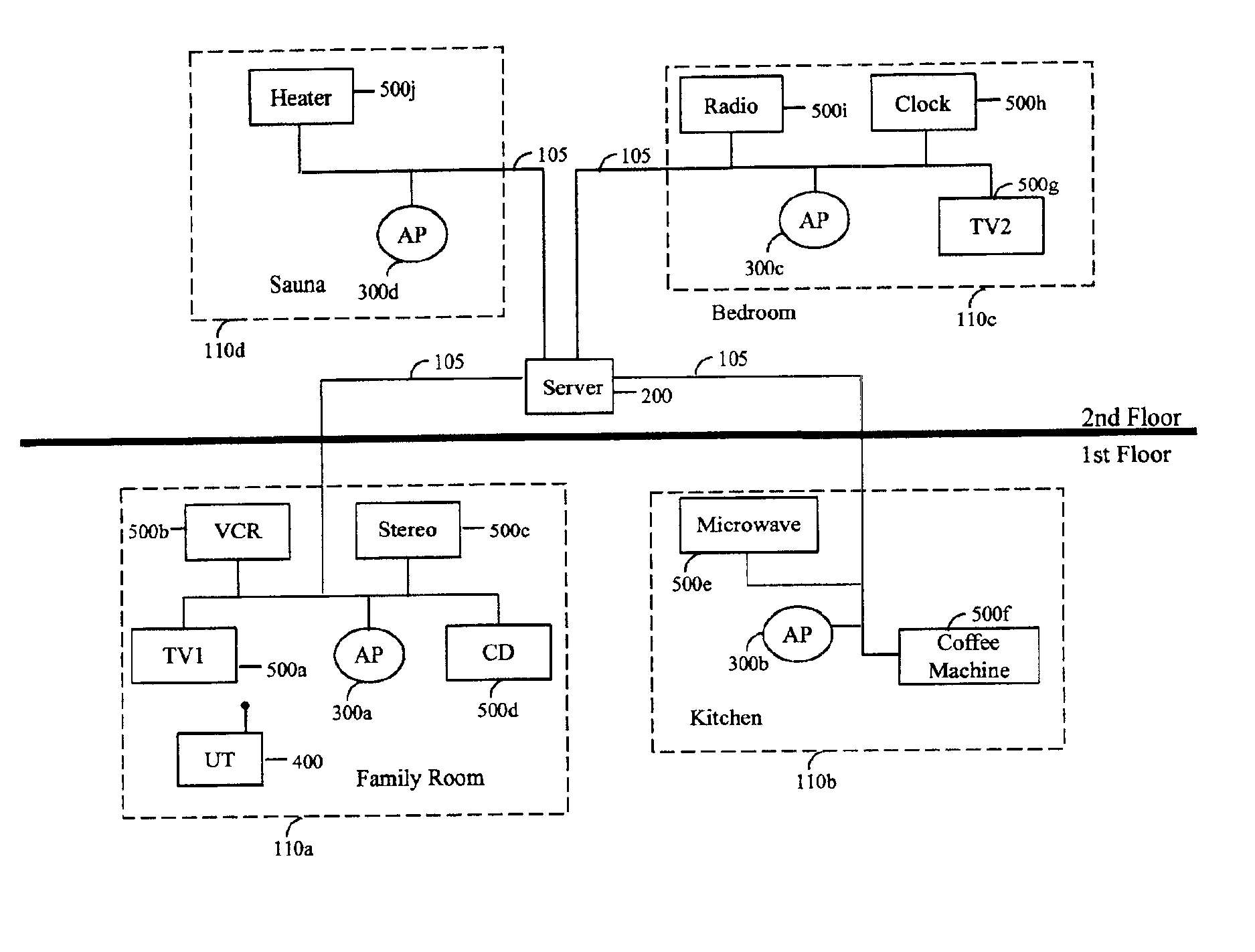
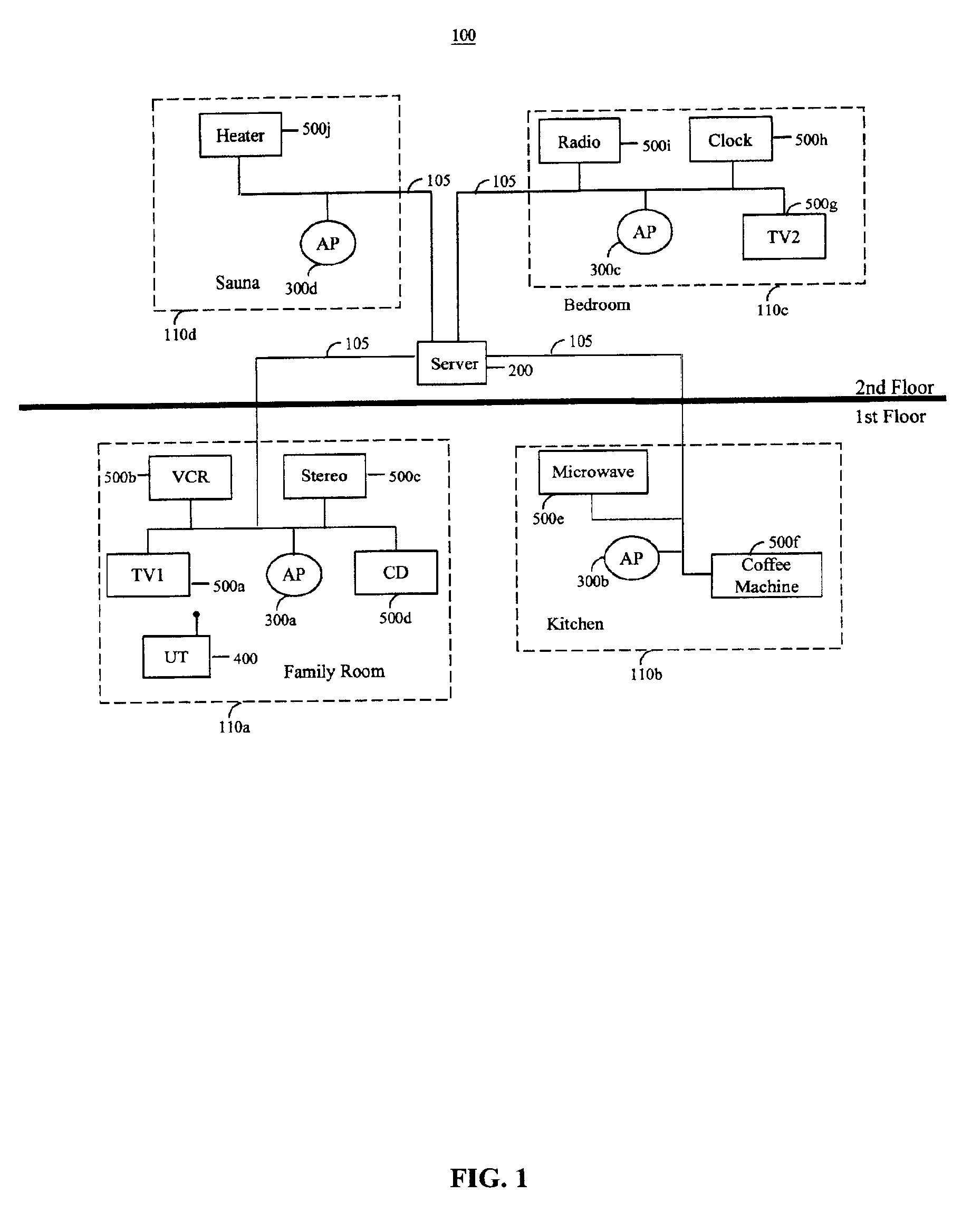
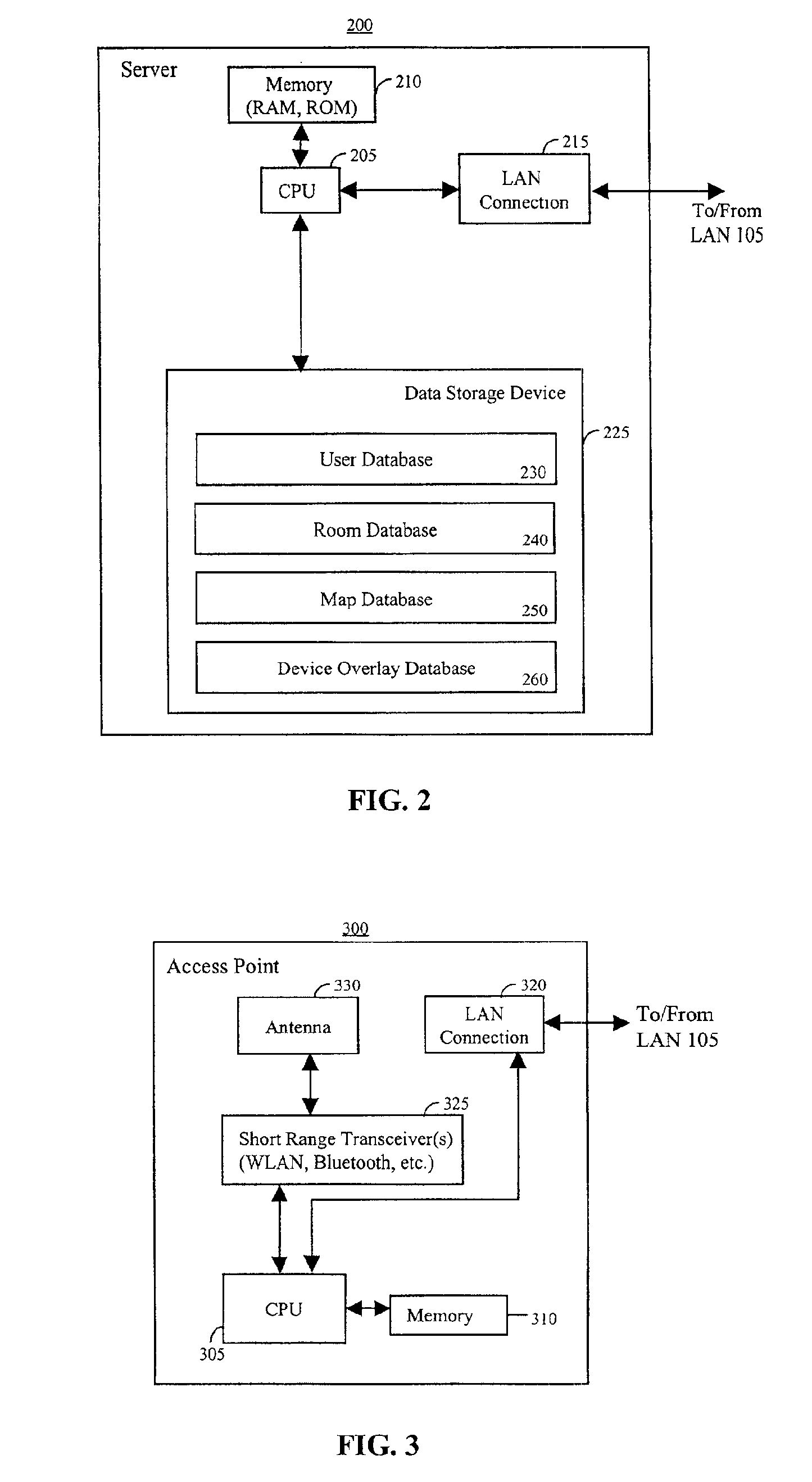
System and method for accessing ubiquitous resources in an intelligent environment
InactiveUS6885362B2Electric signal transmission systemsFrequency-division multiplex detailsIntelligent environmentRemote control
A system and method for enabling a wireless terminal to access and operate ubiquitous devices (“UDs”), such as televisions, DVD players, etc. The system comprises a server coupled to access points and UDs via a LAN or a WLAN. Each access point is associated with both a map of an associated area and an overlay indicating the location of the UDs within that area. In response to wireless terminal requests relayed by an access point, the server retrieves the map and overlay associated with the access point, and transmits that data to the terminal for display. Alternatively, a list of UDs may be transmitted. Selection of a UD from the display causes an image of the UD's control panel to be displayed, from which the device may be remotely controlled by the user. A mechanism is also provided to permit users to display maps of areas other than the one in which the user is currently located to permit remote control of UDs in such areas.
Owner:NOKIA TECHNOLOGLES OY
Popular searches
Data switching by path configuration Wireless network protocols Substation equipment Radio/inductive link selection arrangements Wireless commuication services Network data management Automatic call-answering/message-recording/conversation-recording Supervisory/monitoring/testing arrangements Broadcast information generation Special data processing applications
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com