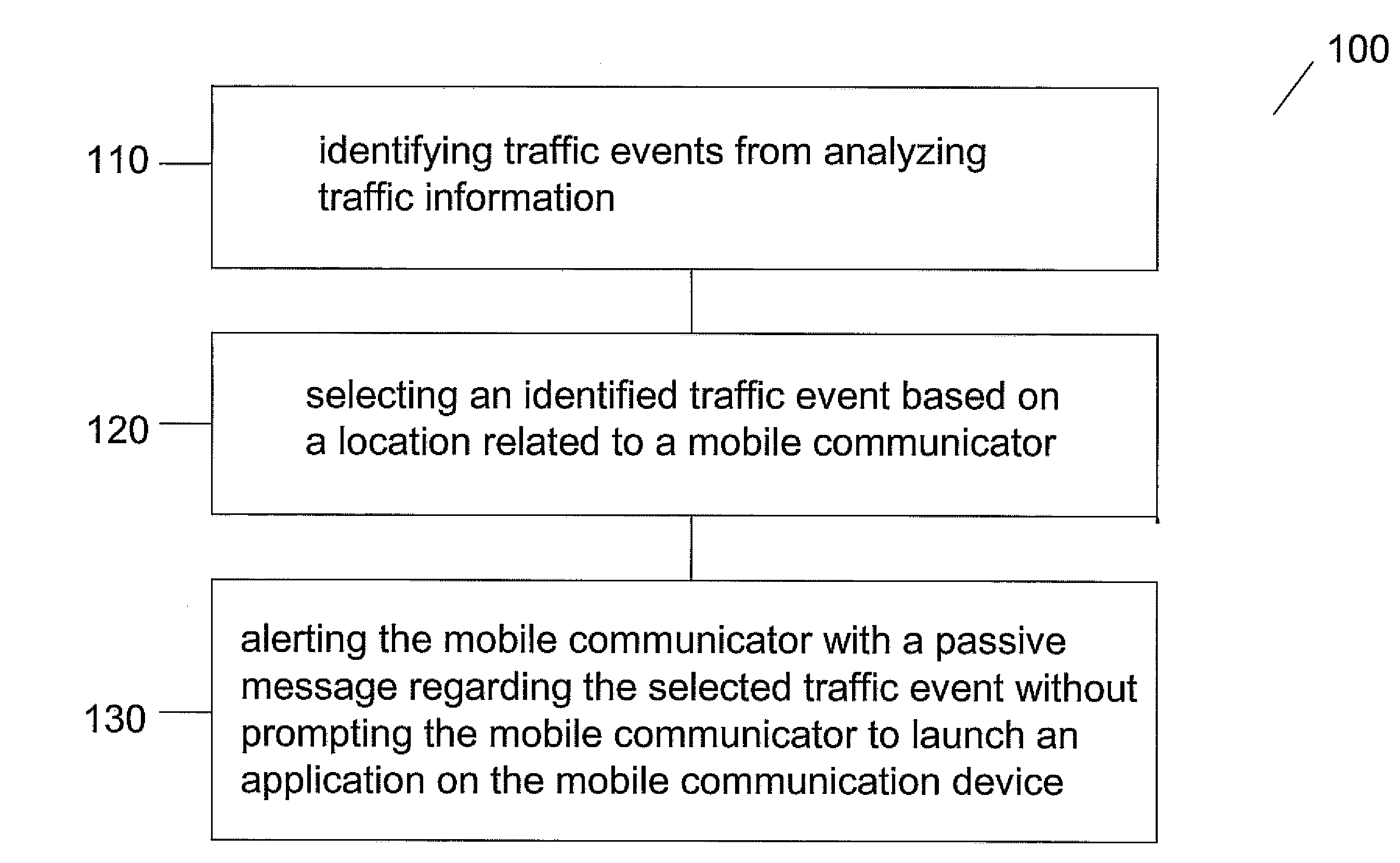
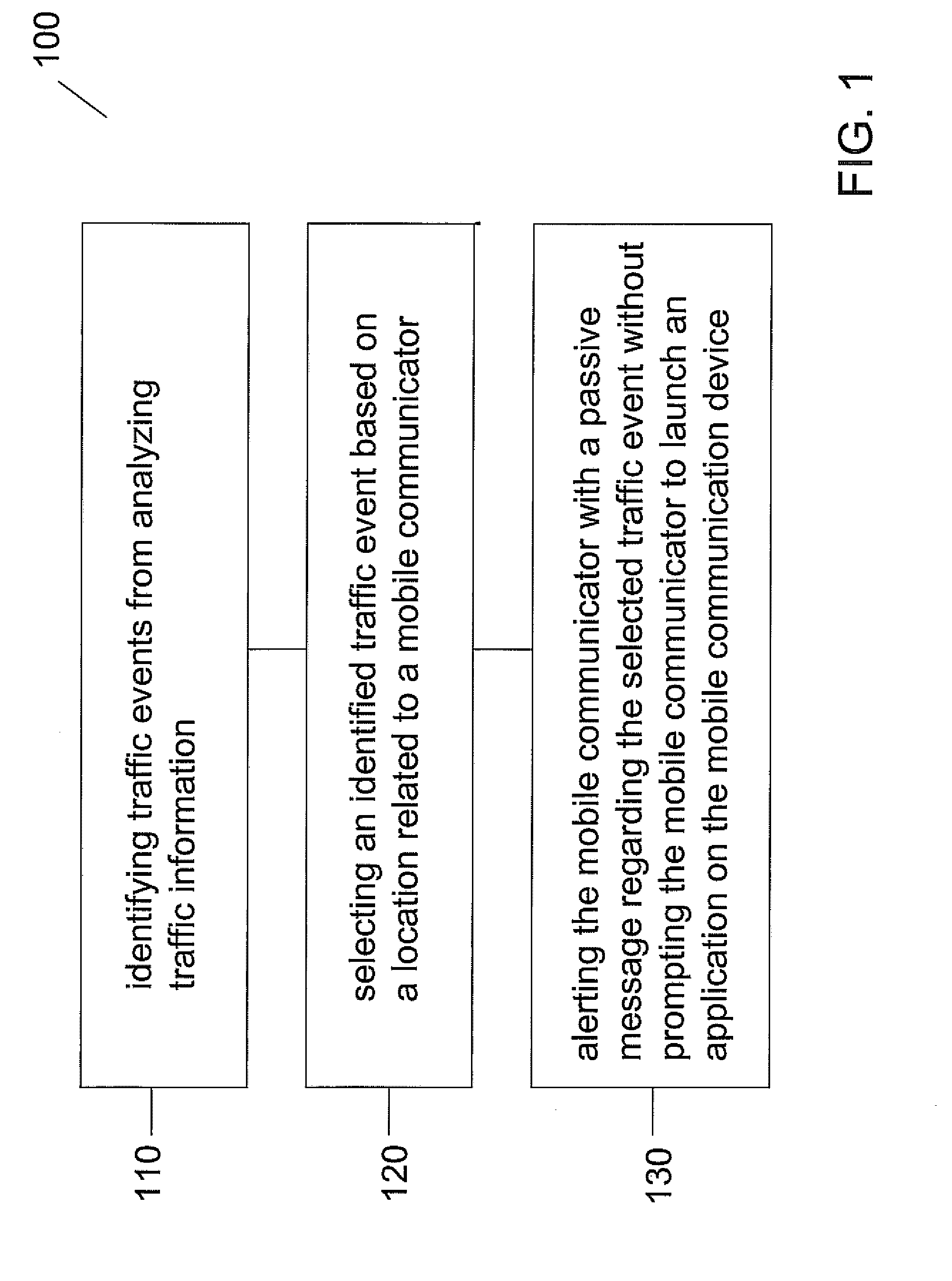
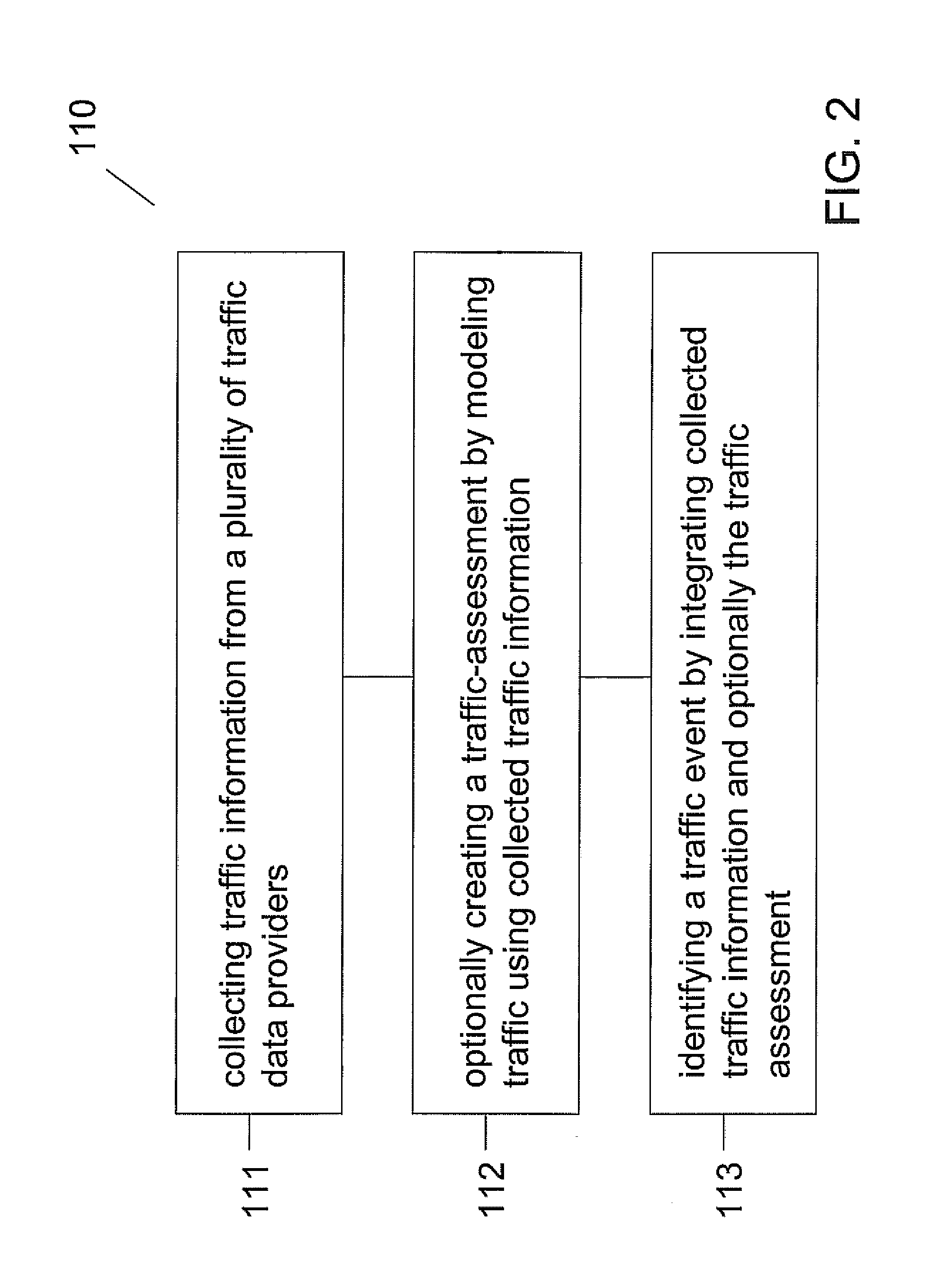
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
354 results about "Service policy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
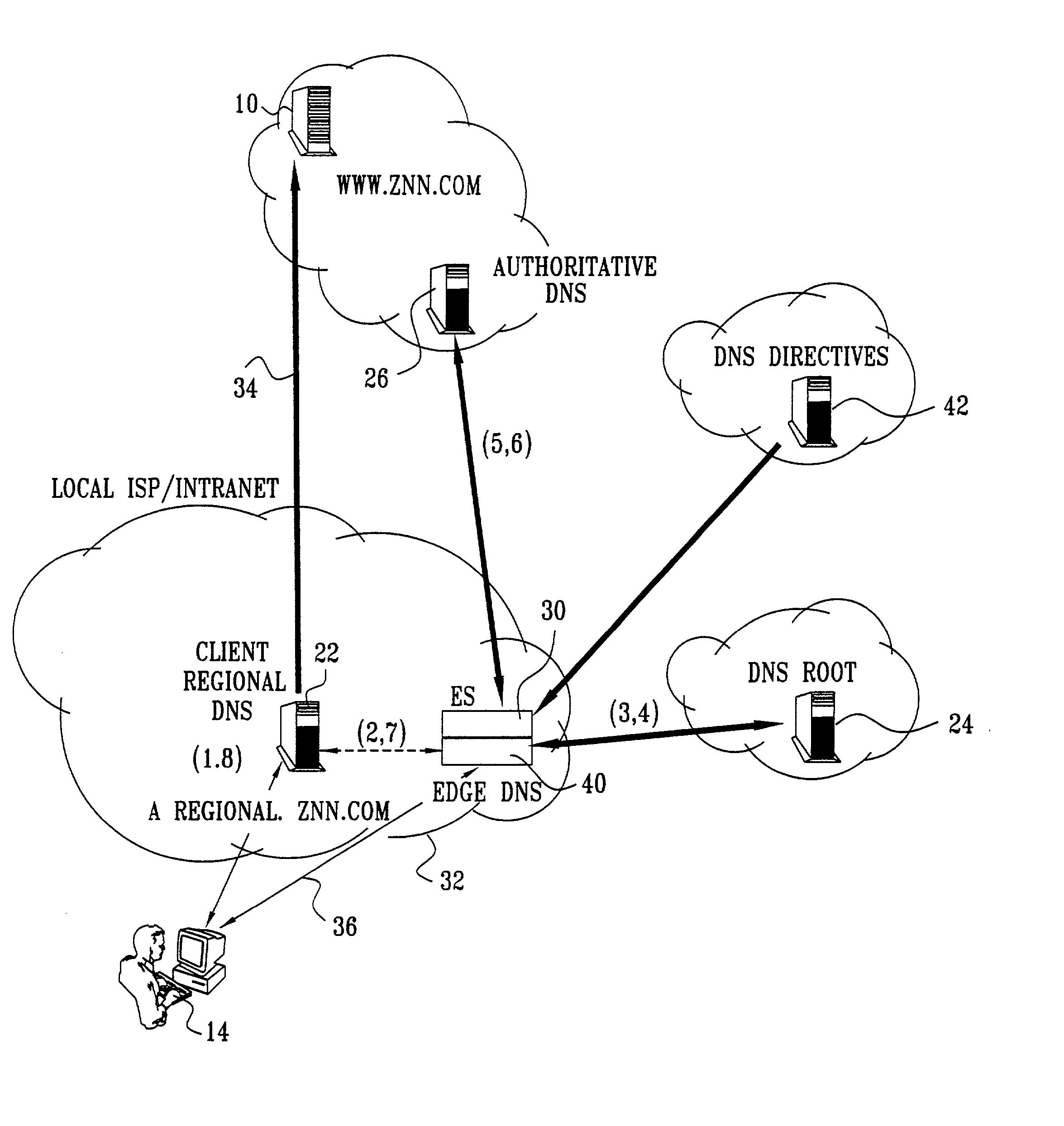
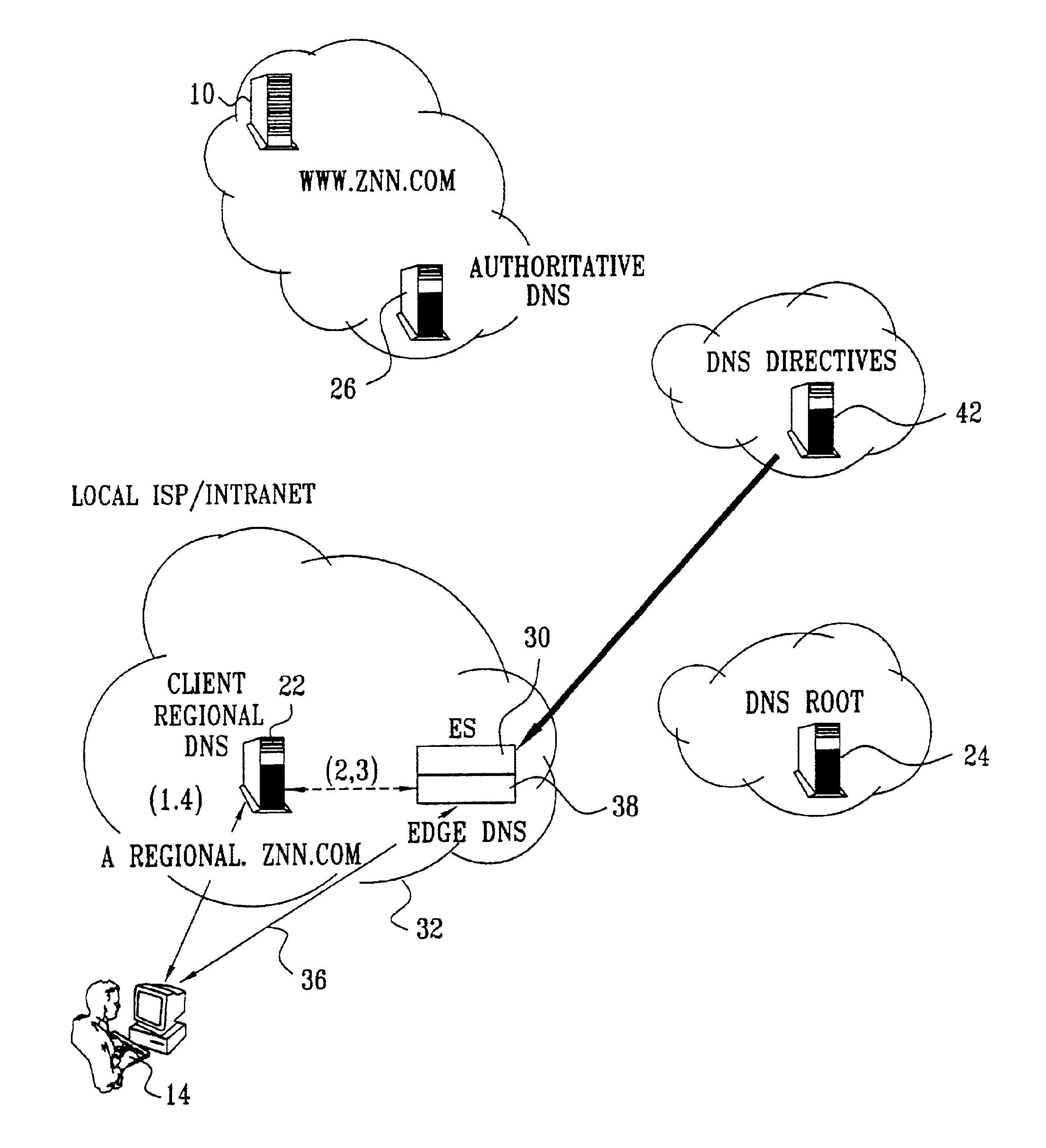
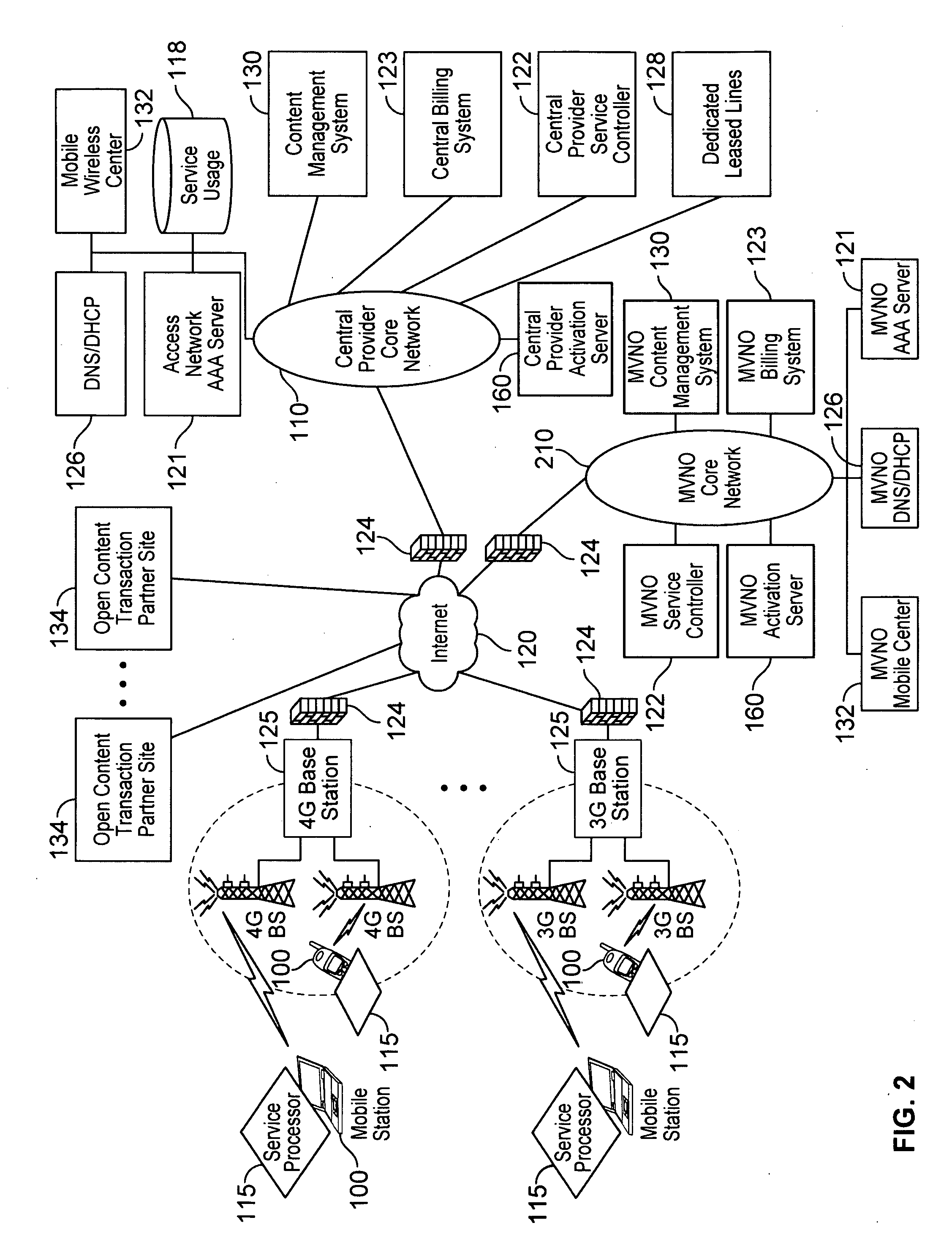
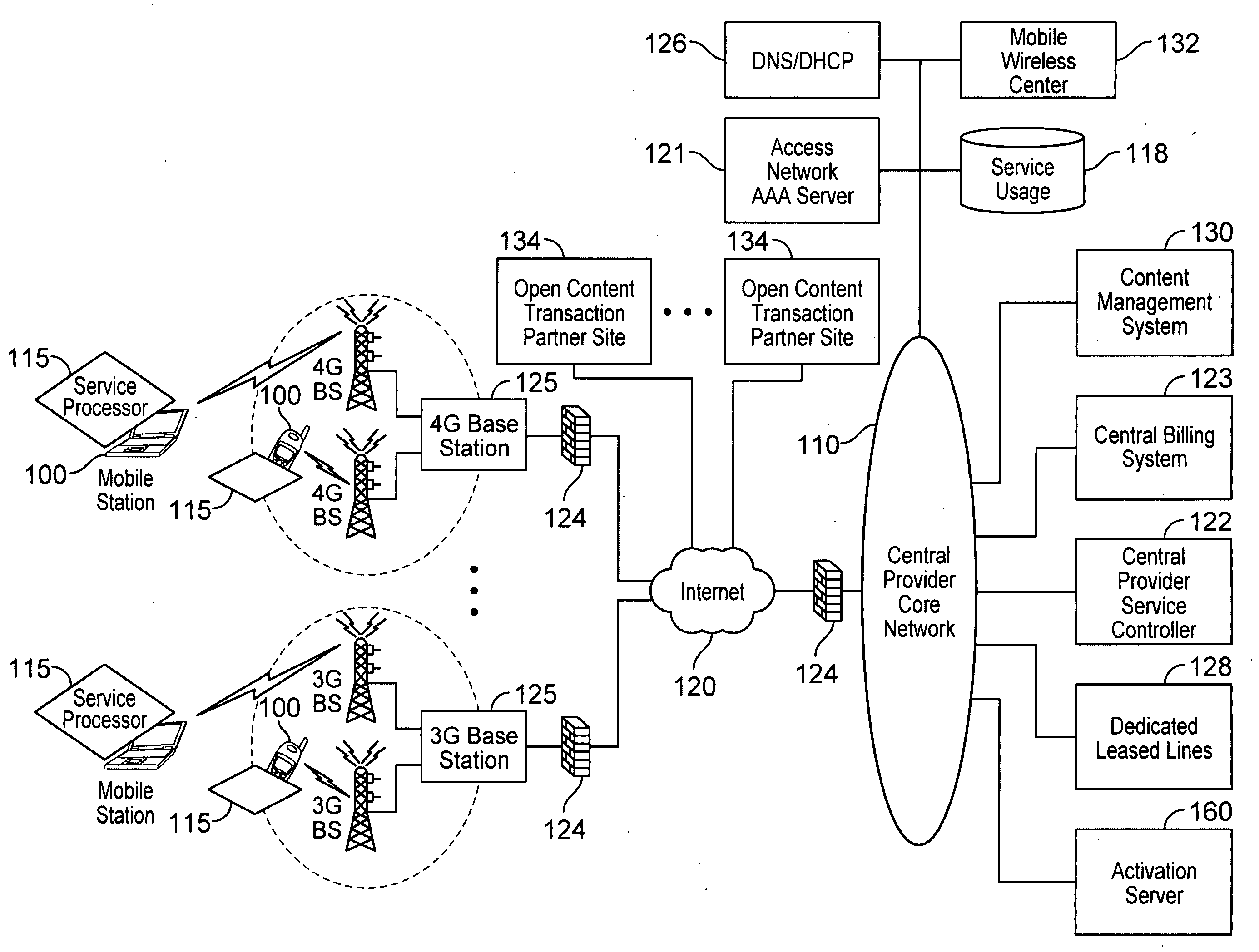
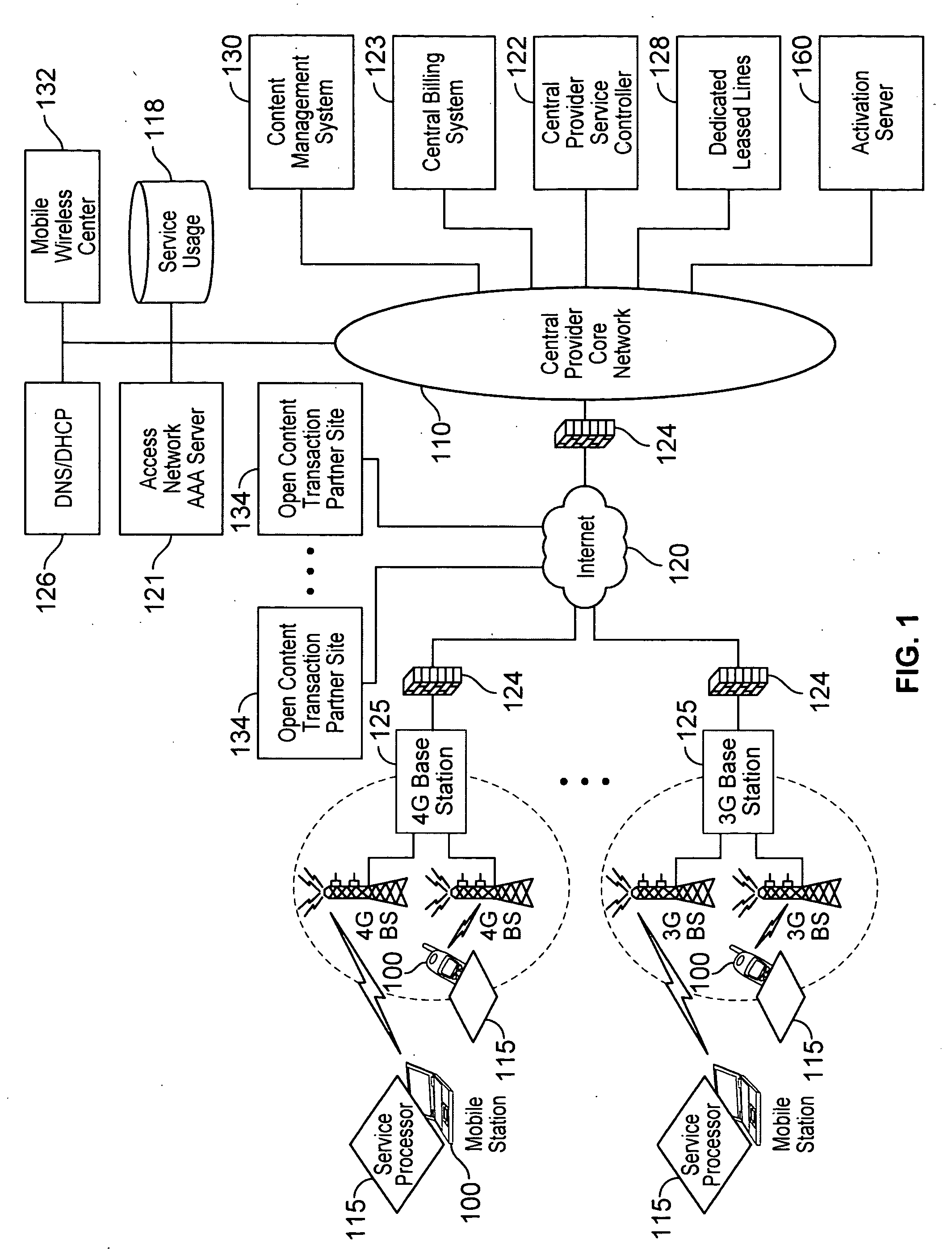
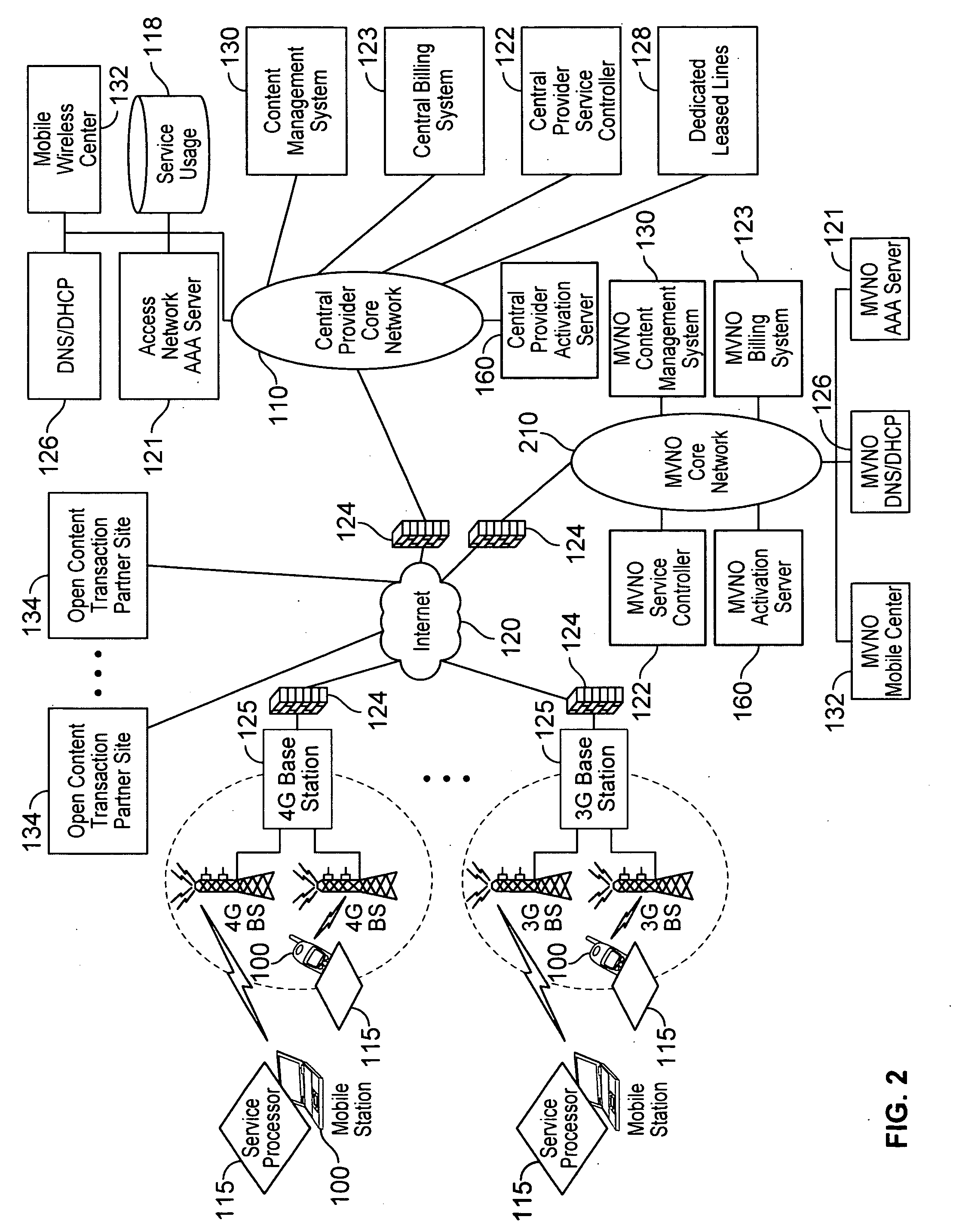
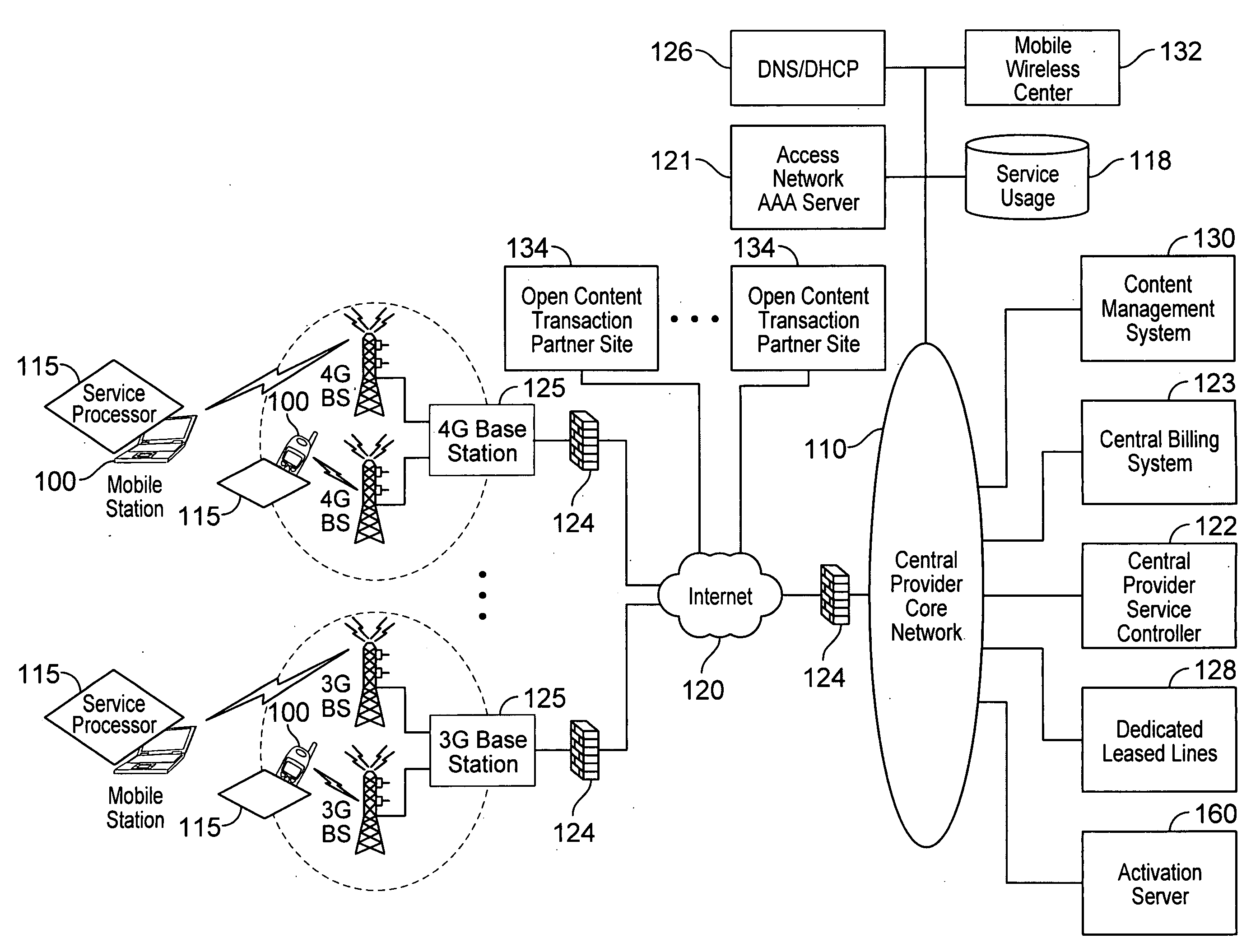
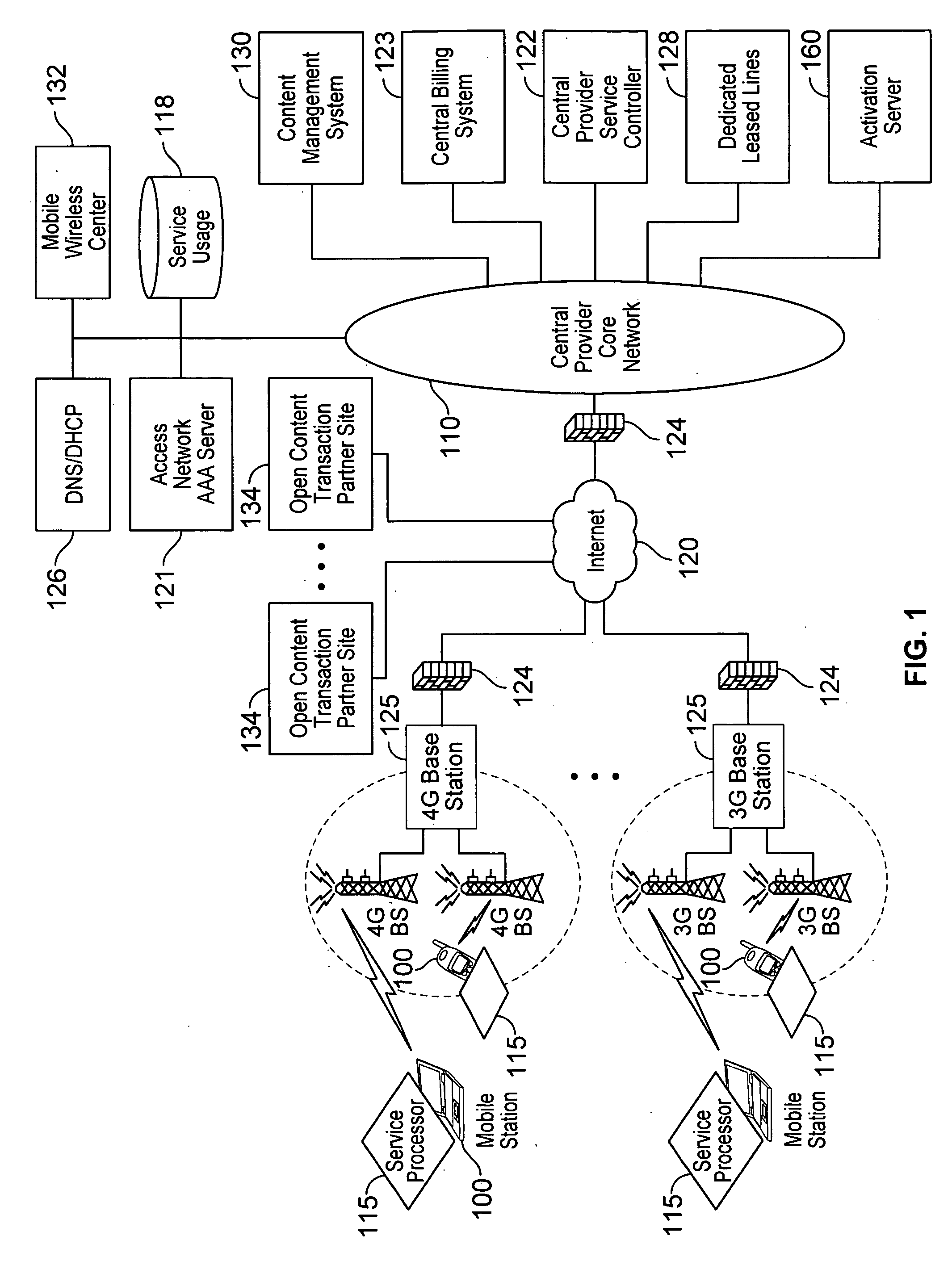
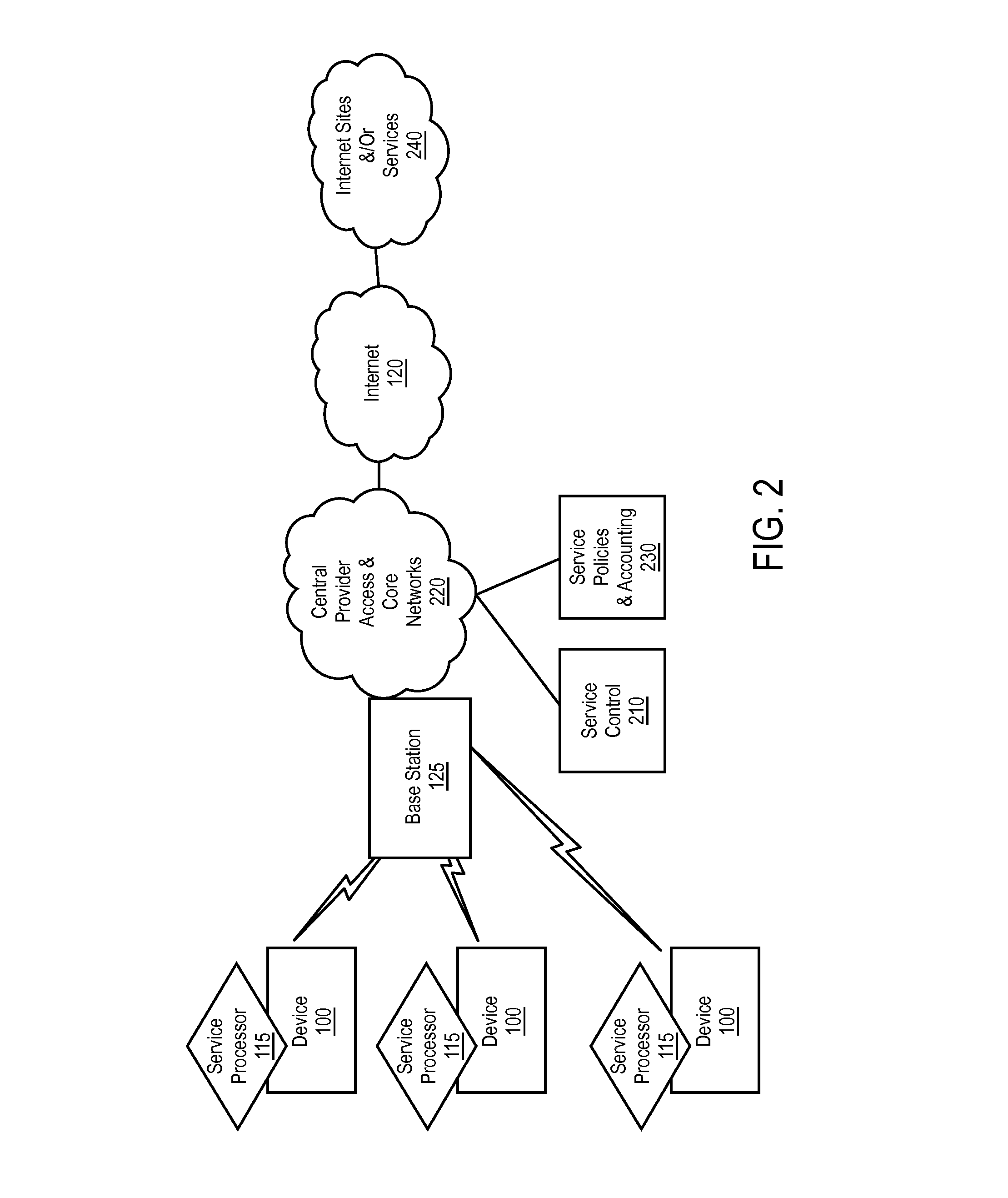
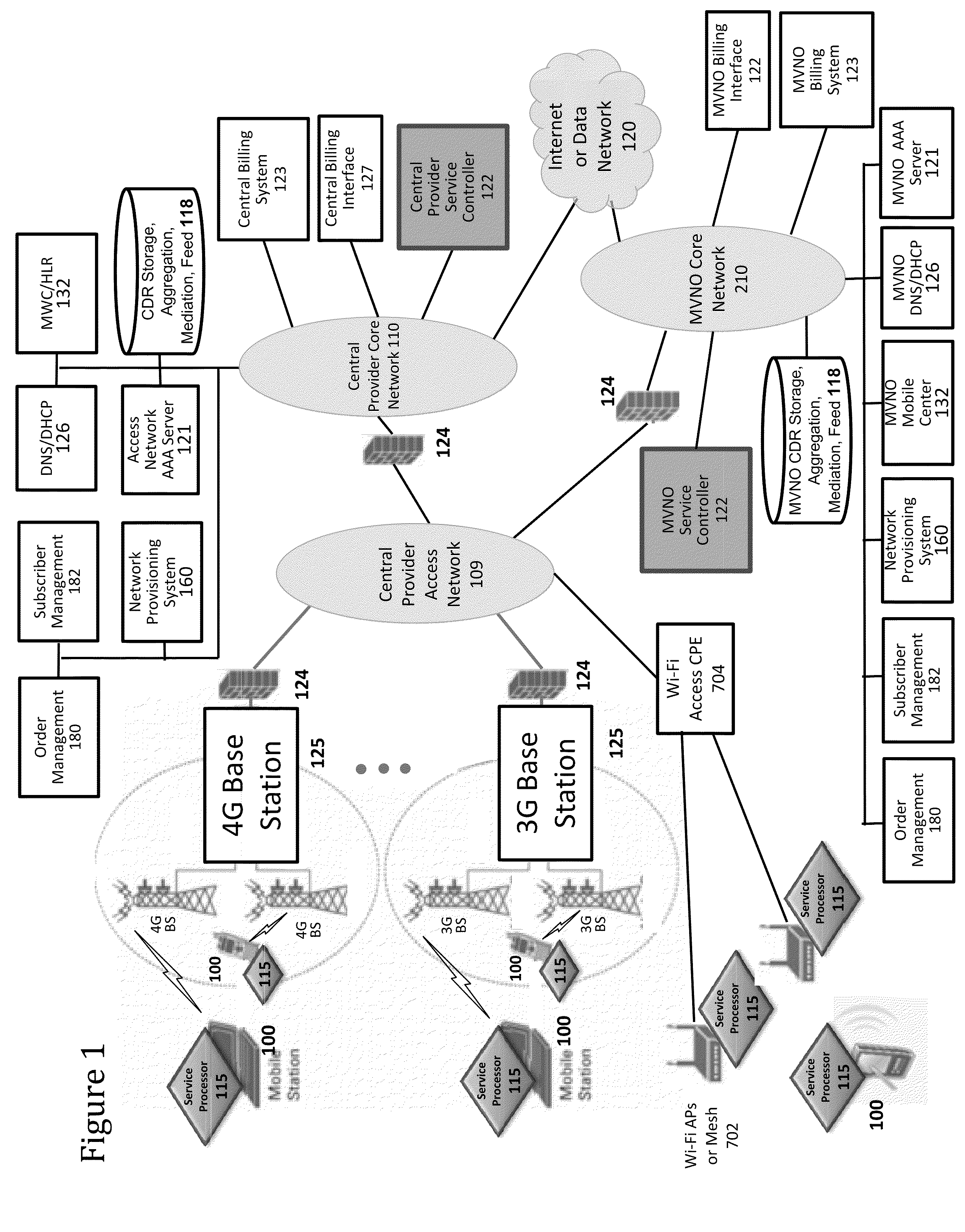
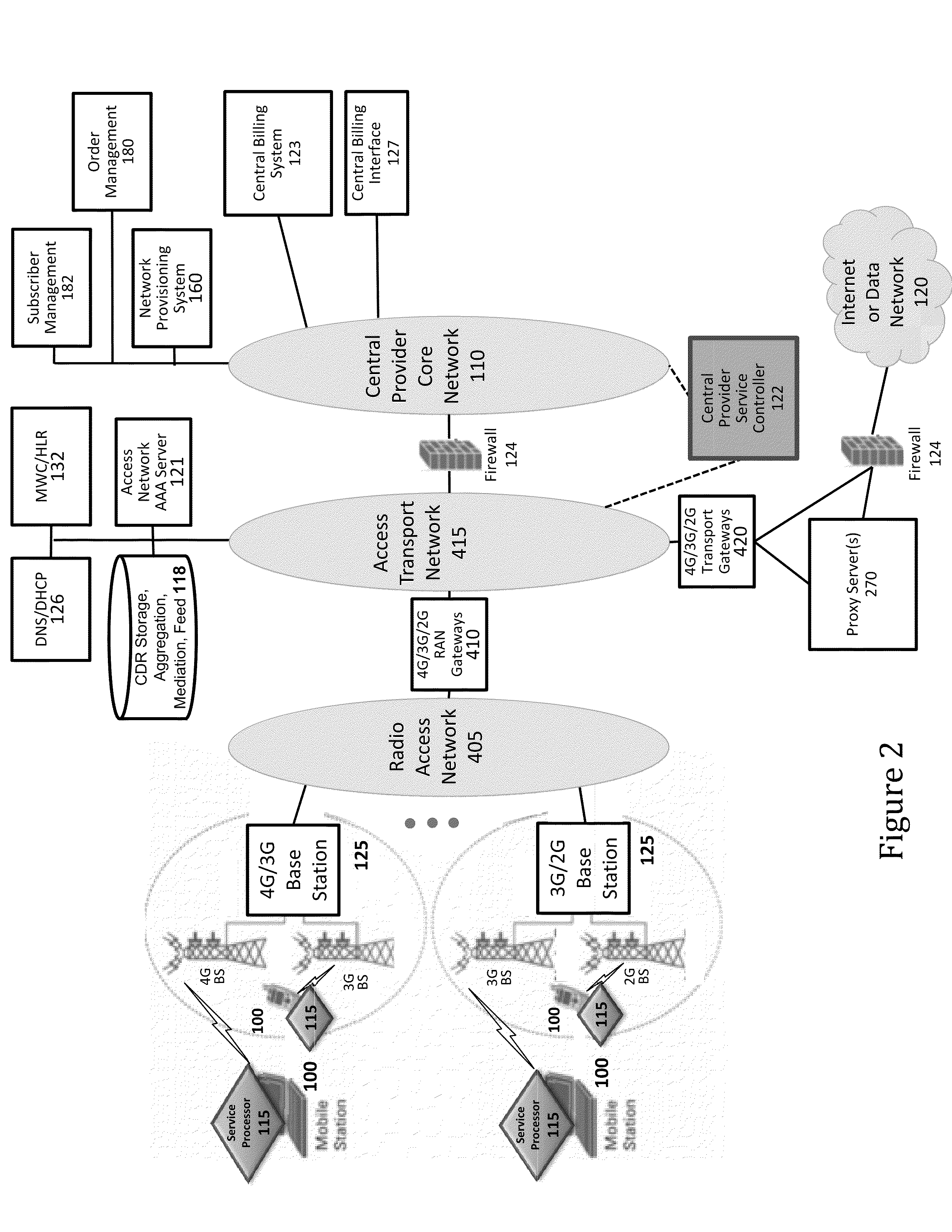
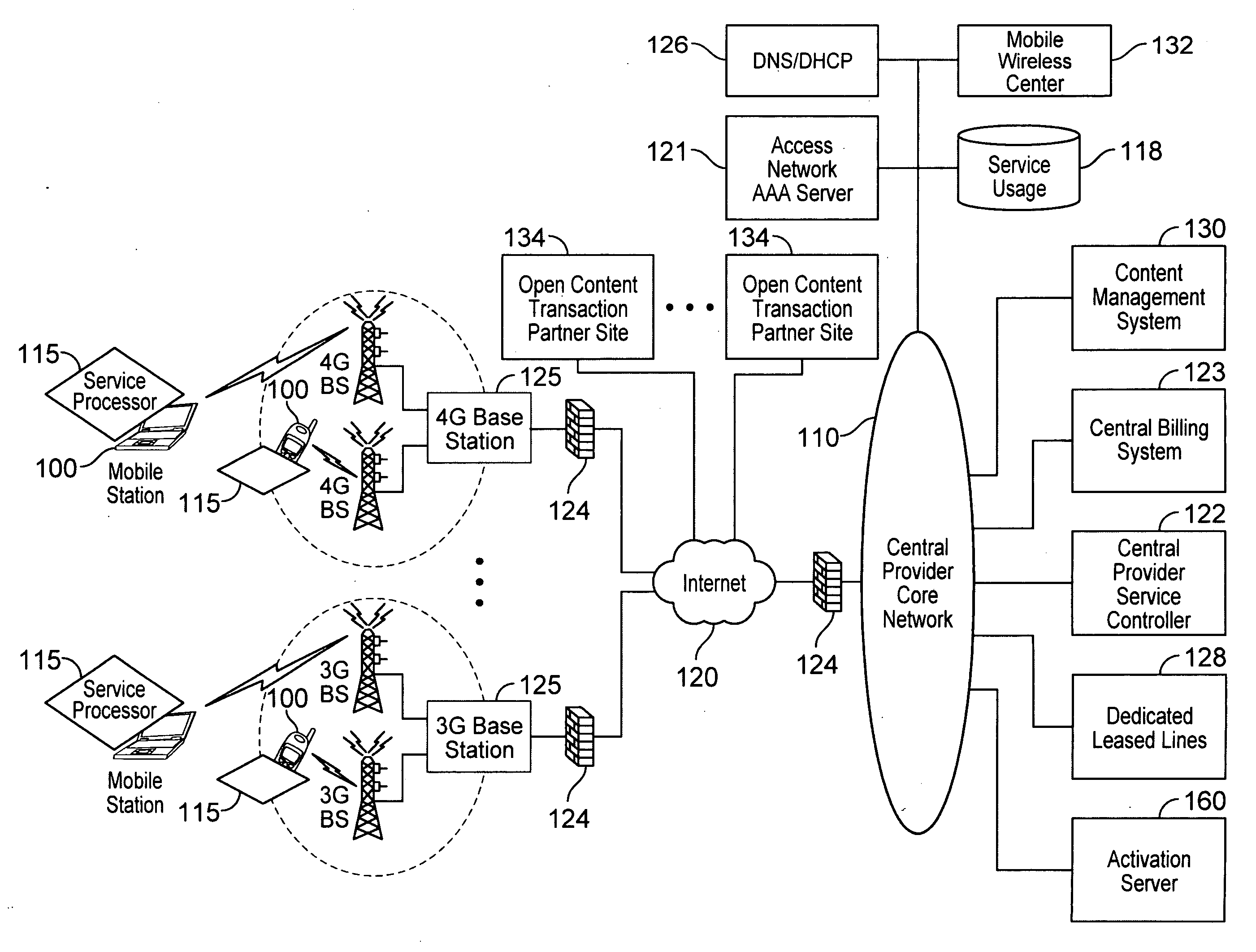
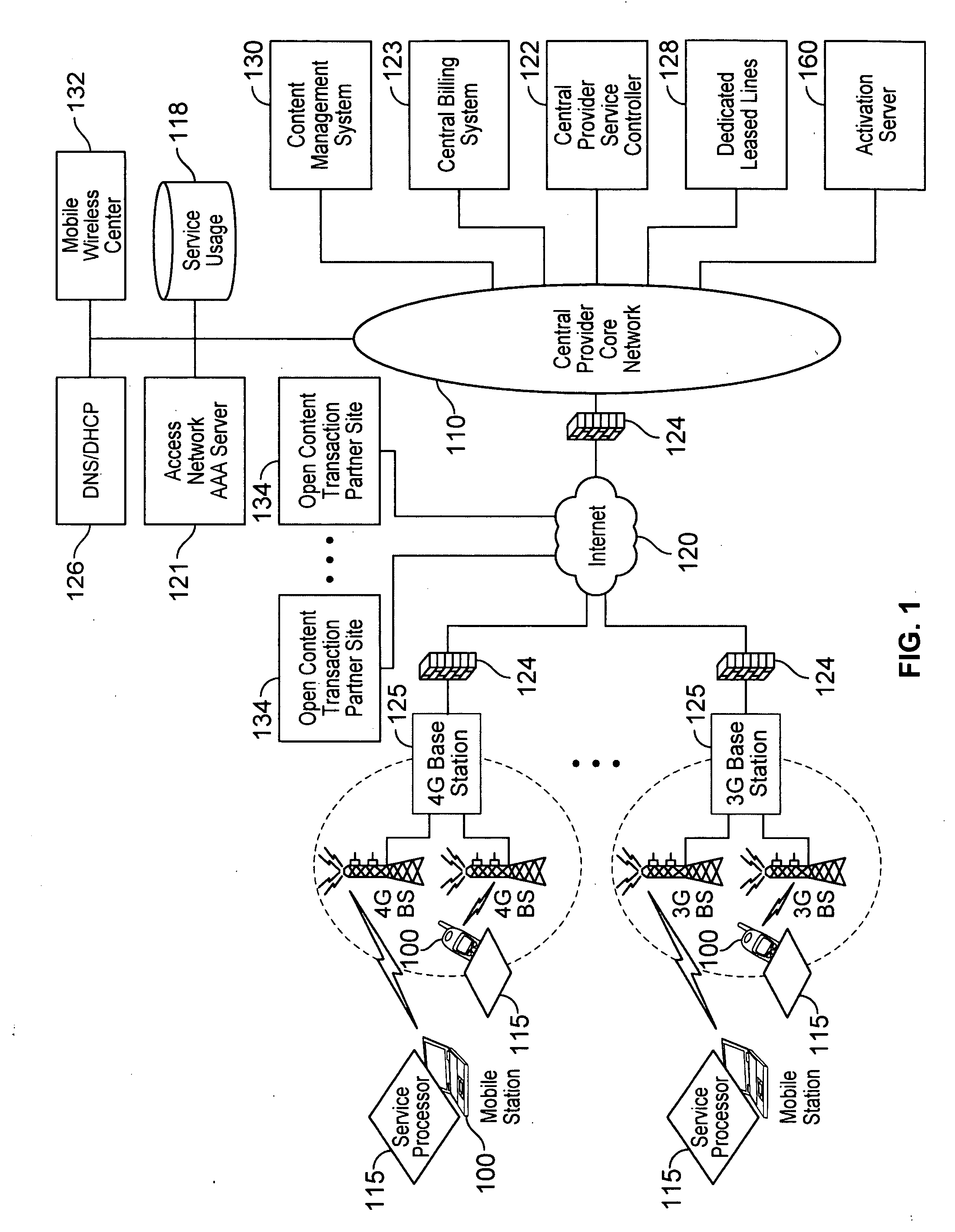
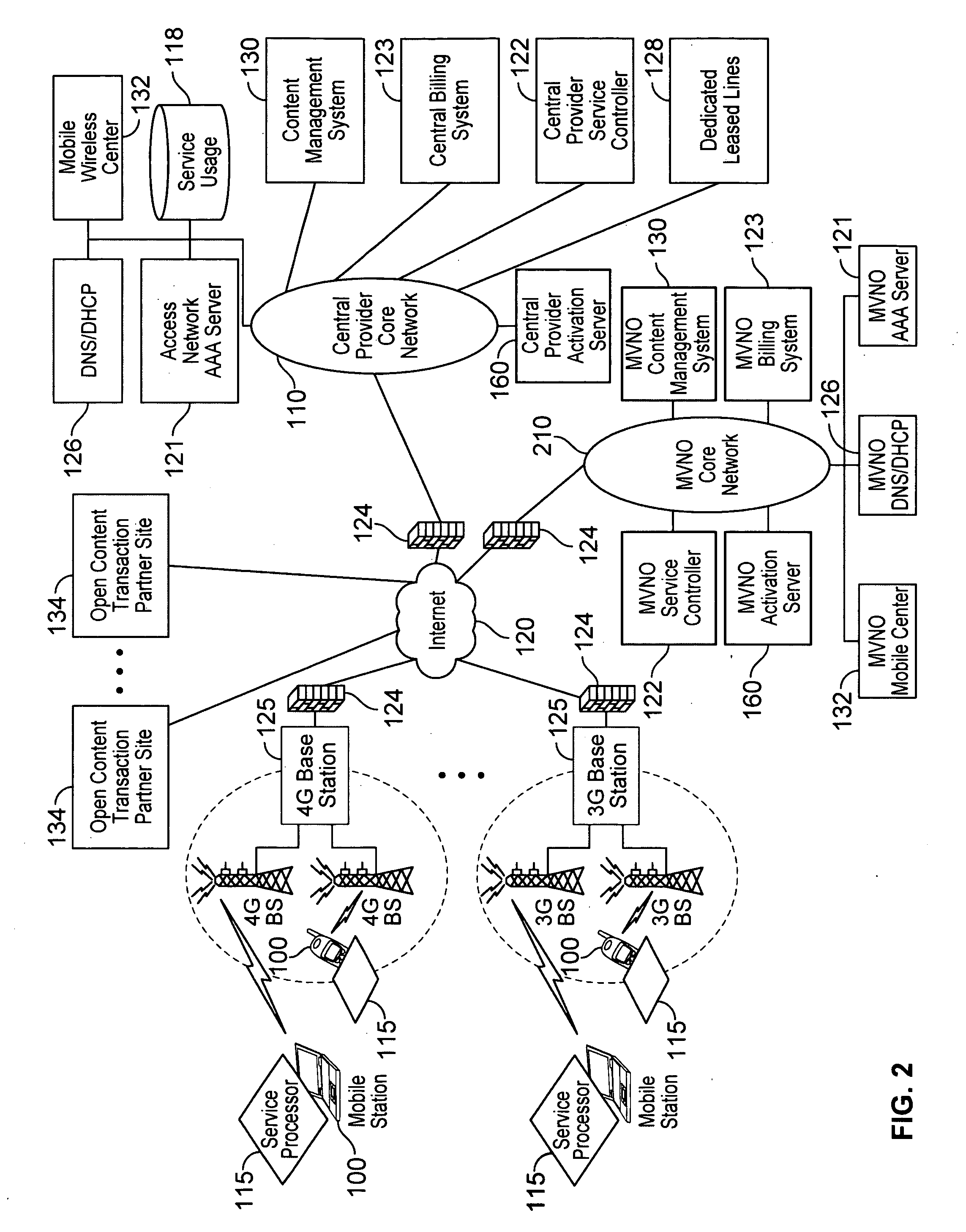
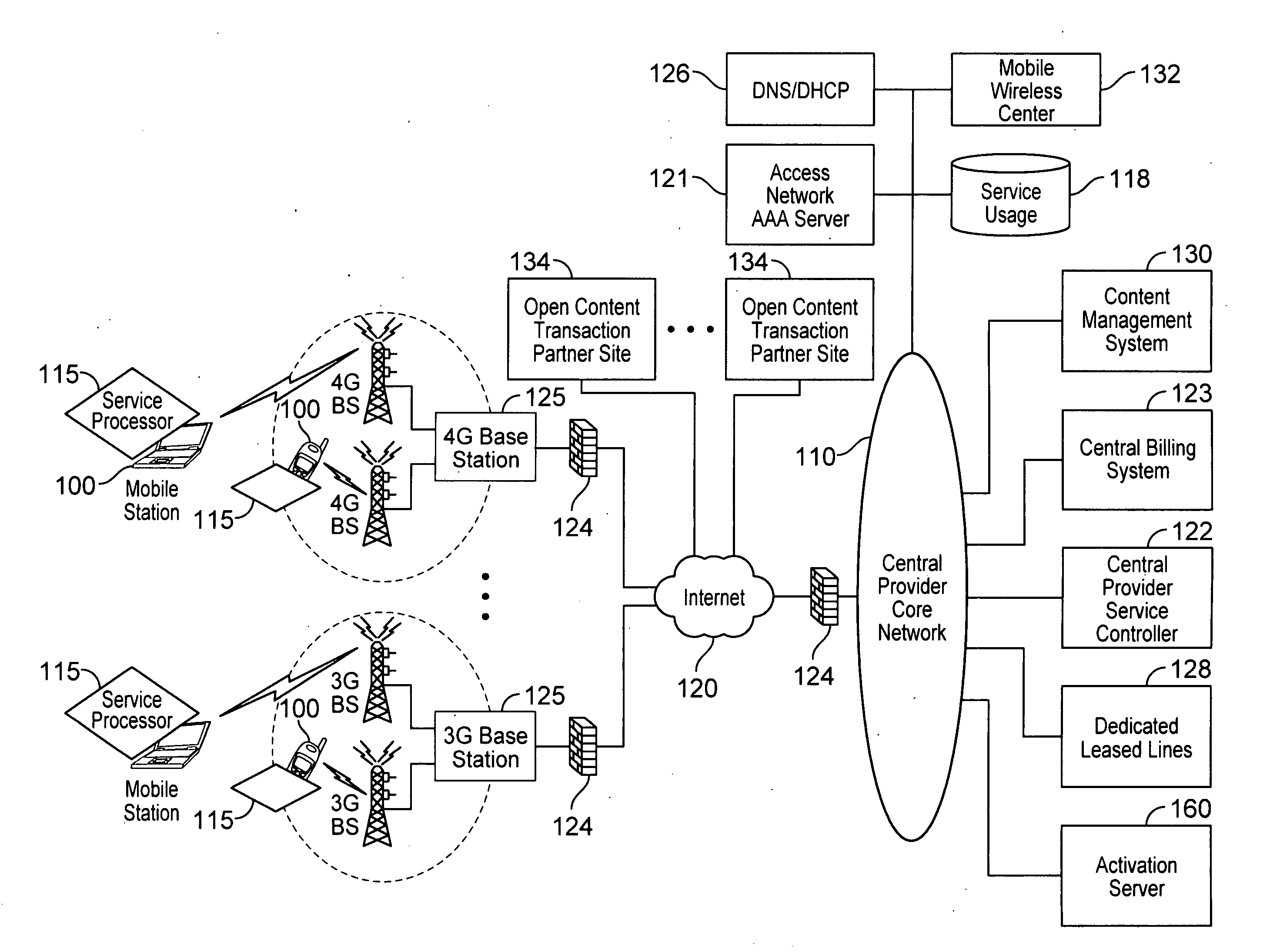
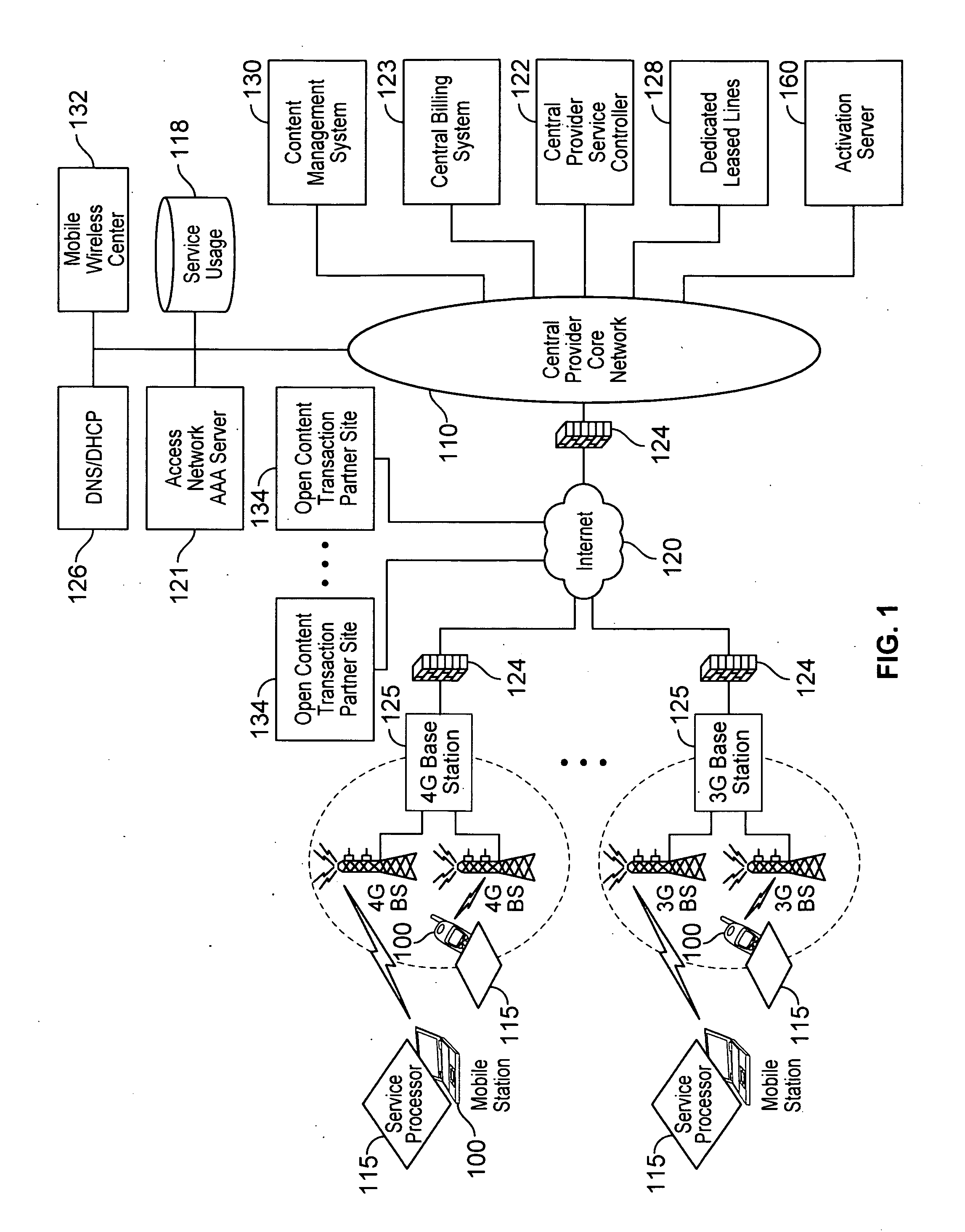
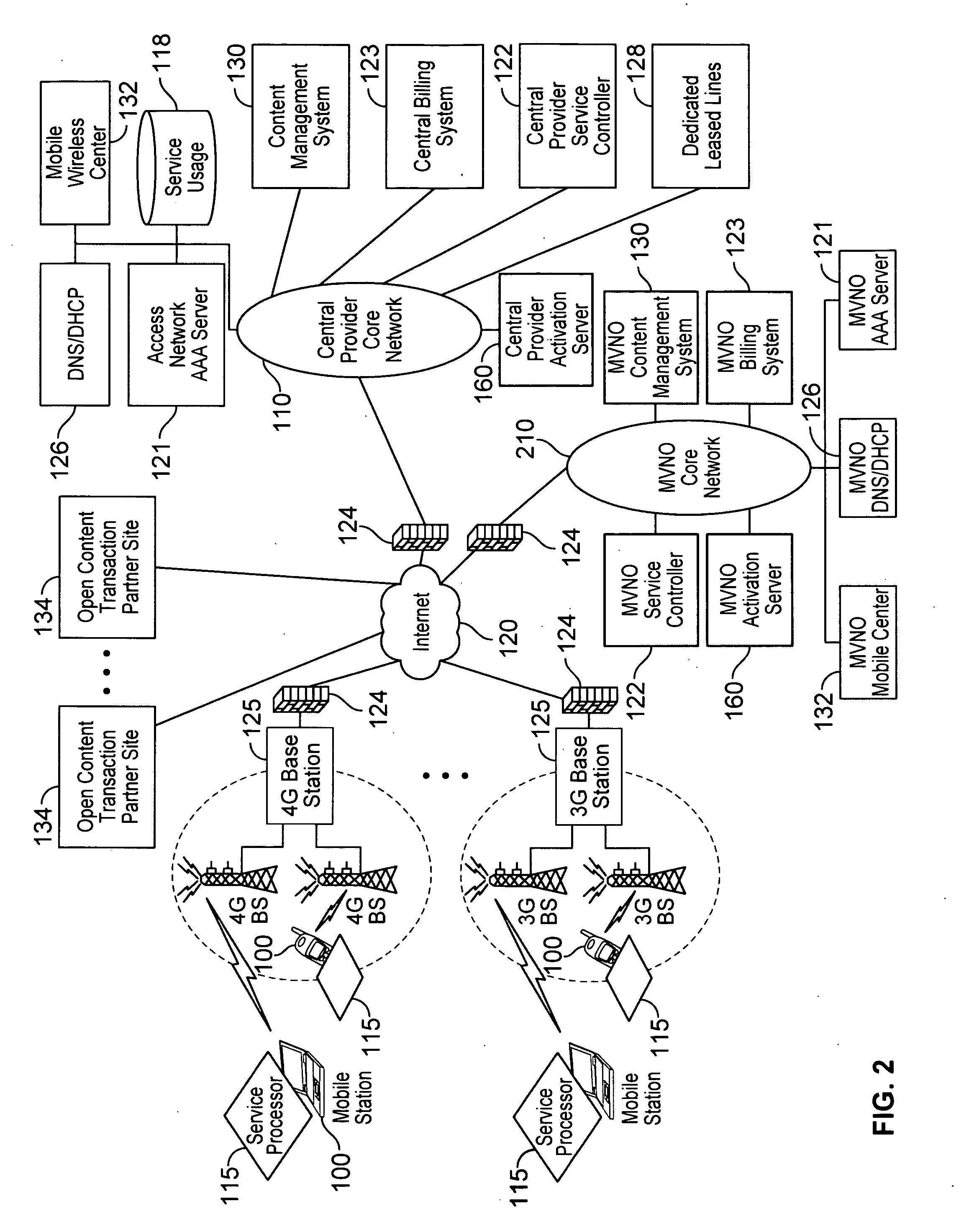
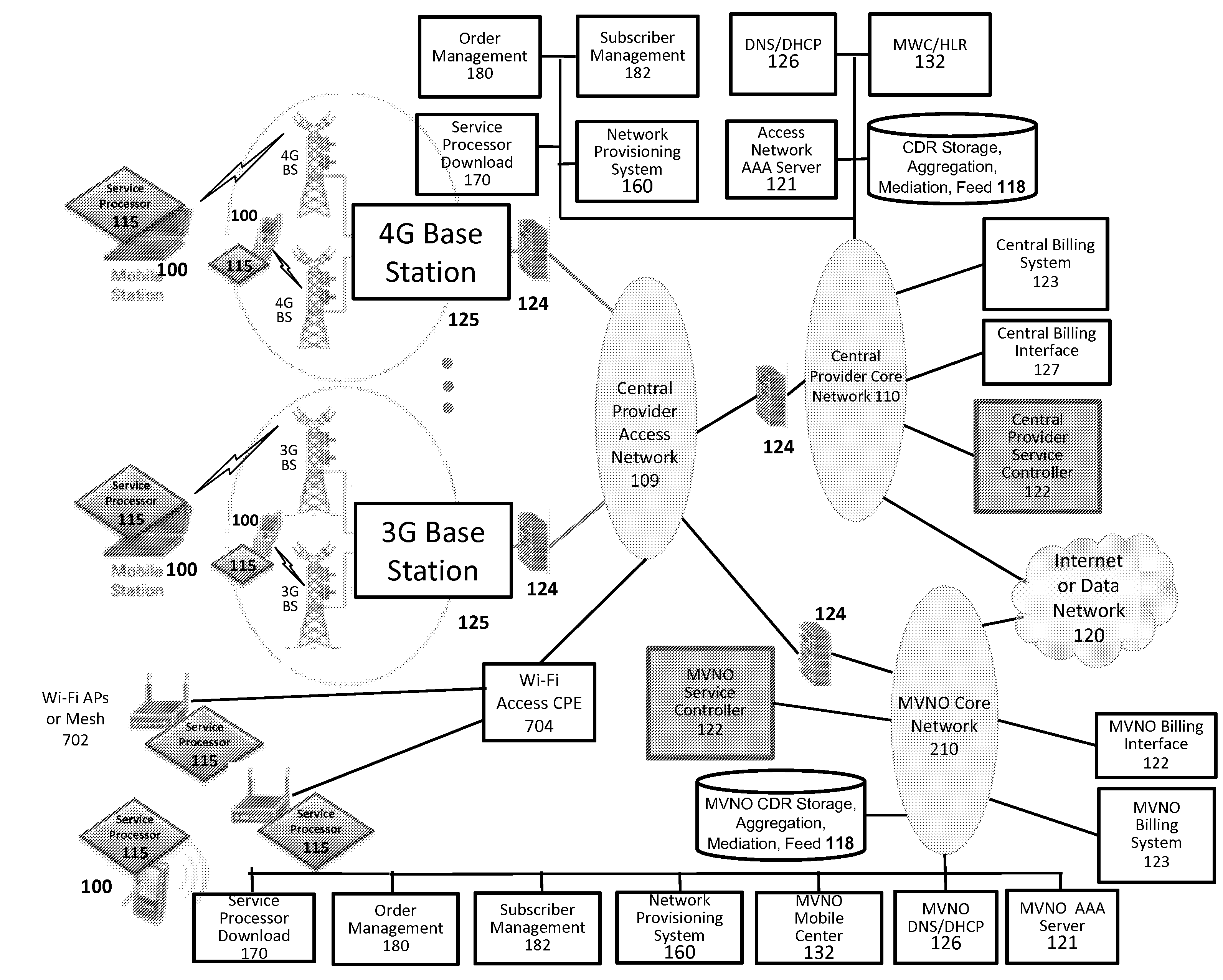
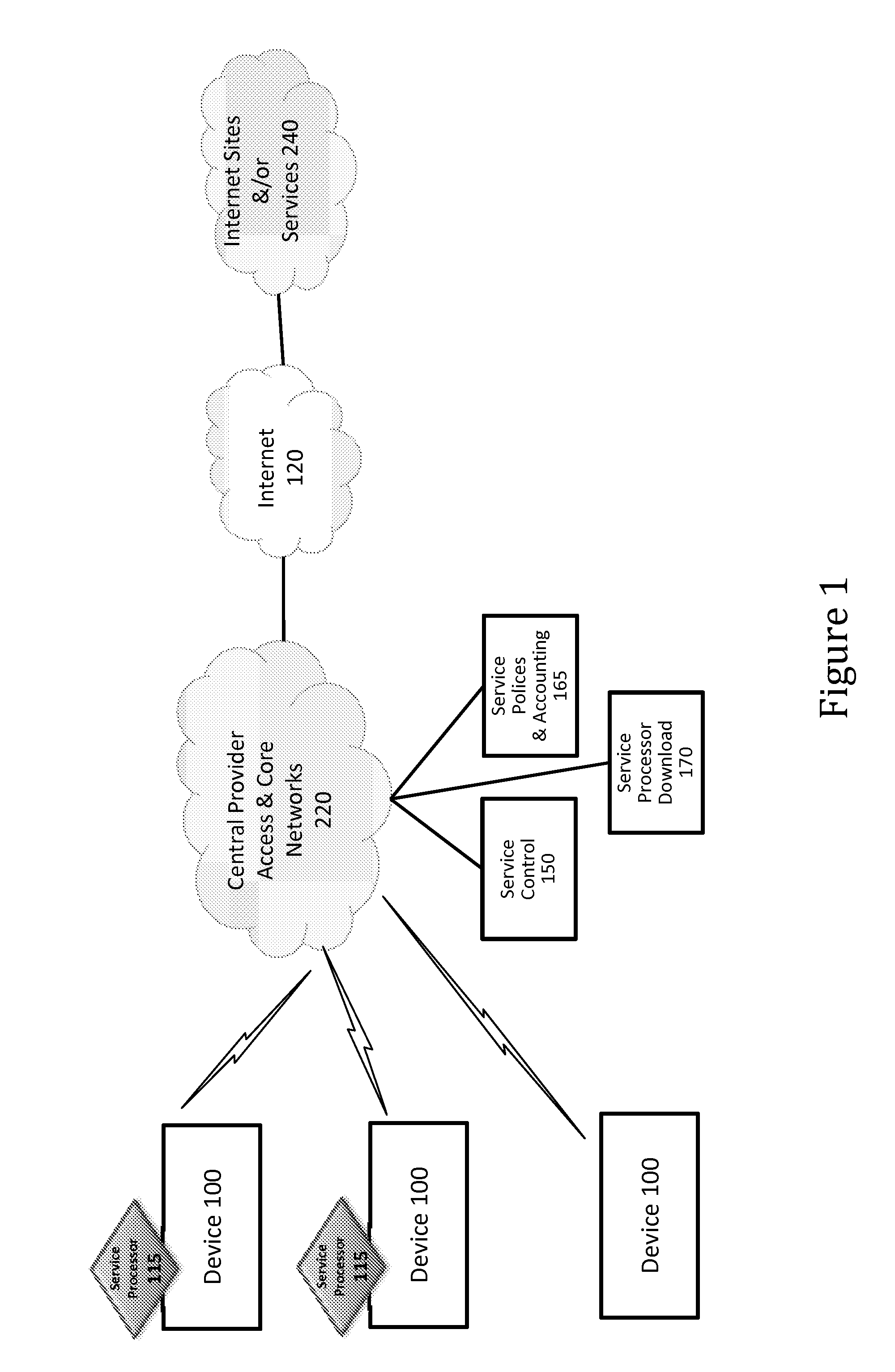
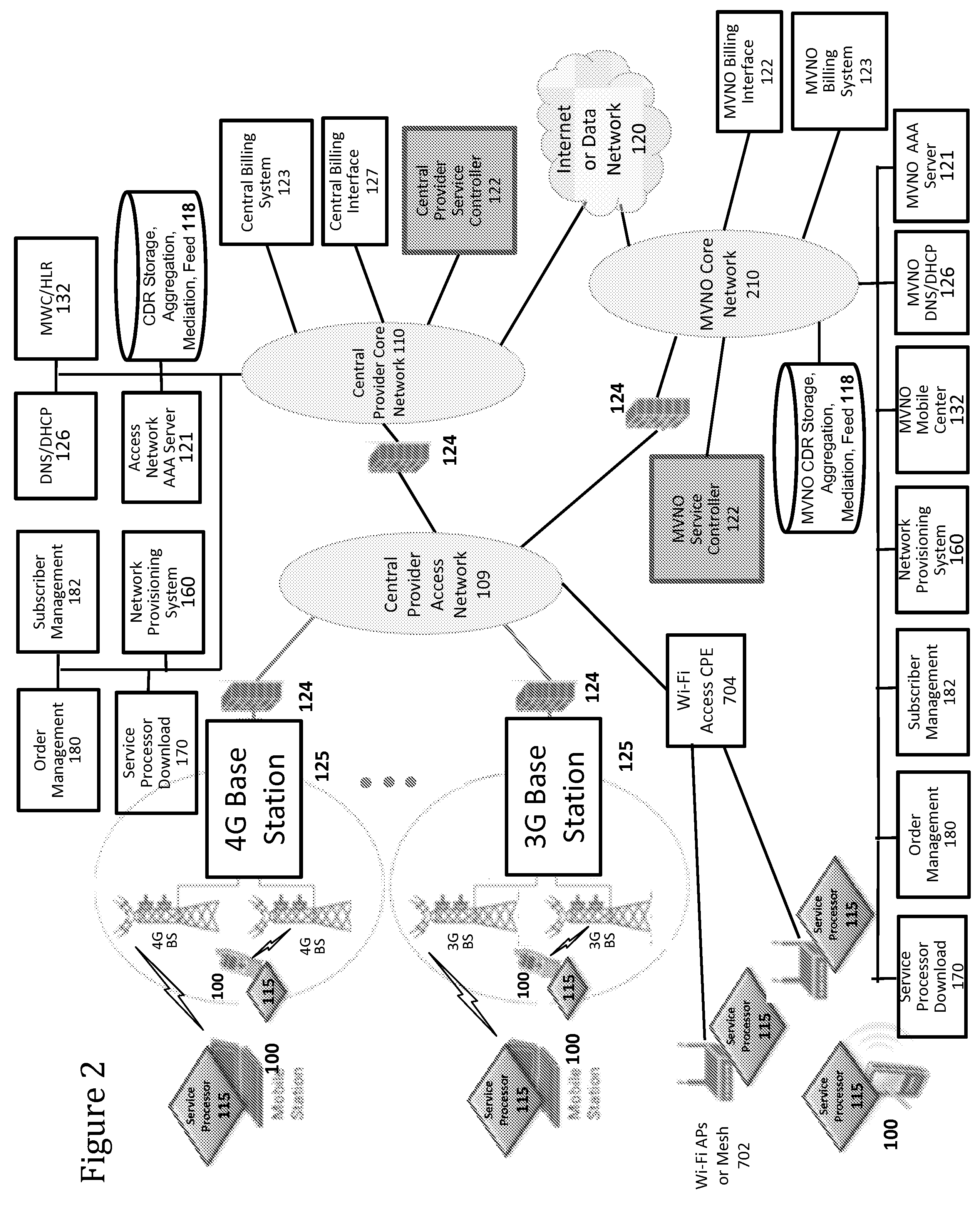
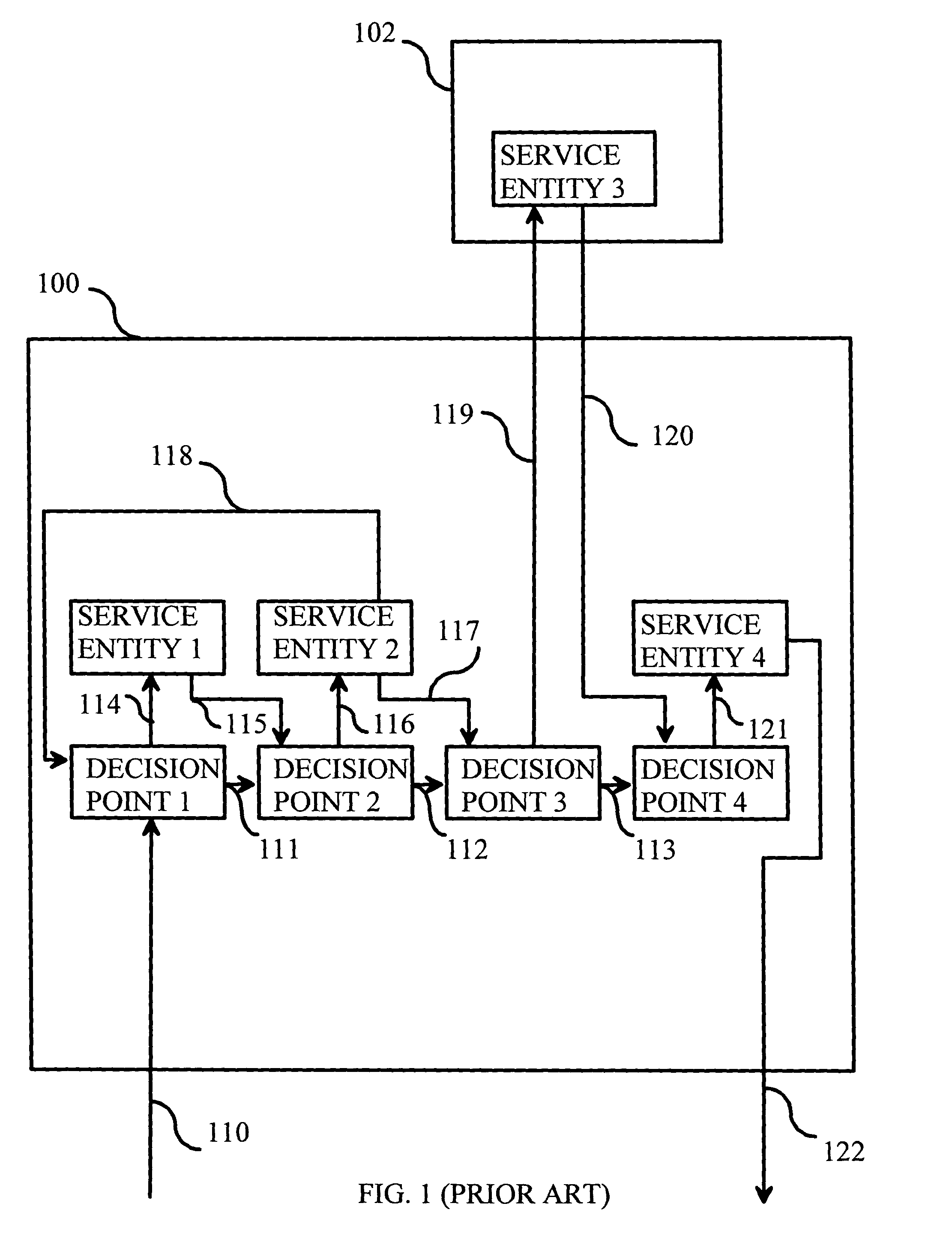
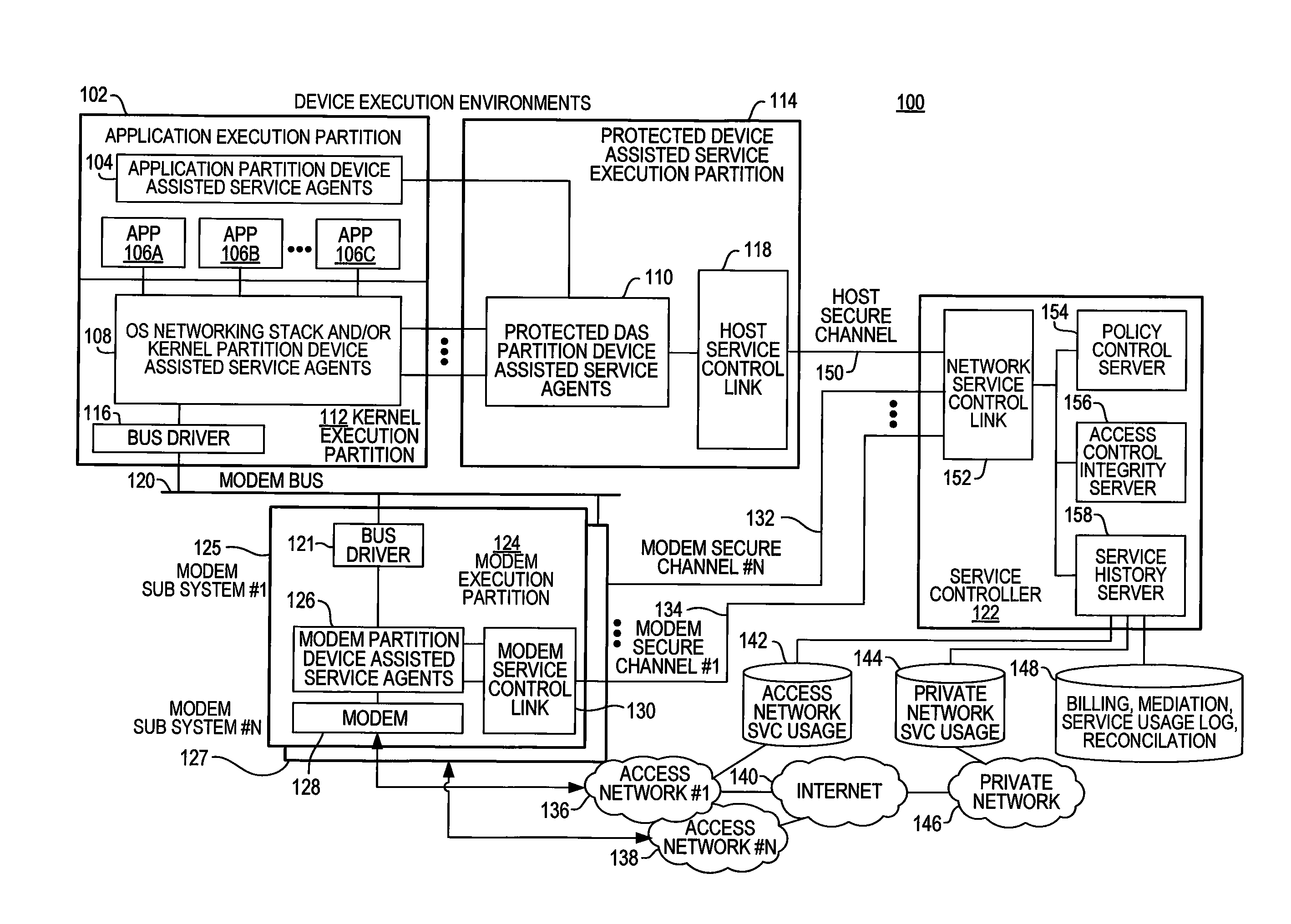
Defining service policies. A service policy is a named collection of service class and resource group specification overrides. When a policy is put into effect, the overrides are merged with the service class and resource group specifications in the service definition. A policy override is a way to change a goal or resource group capacity...
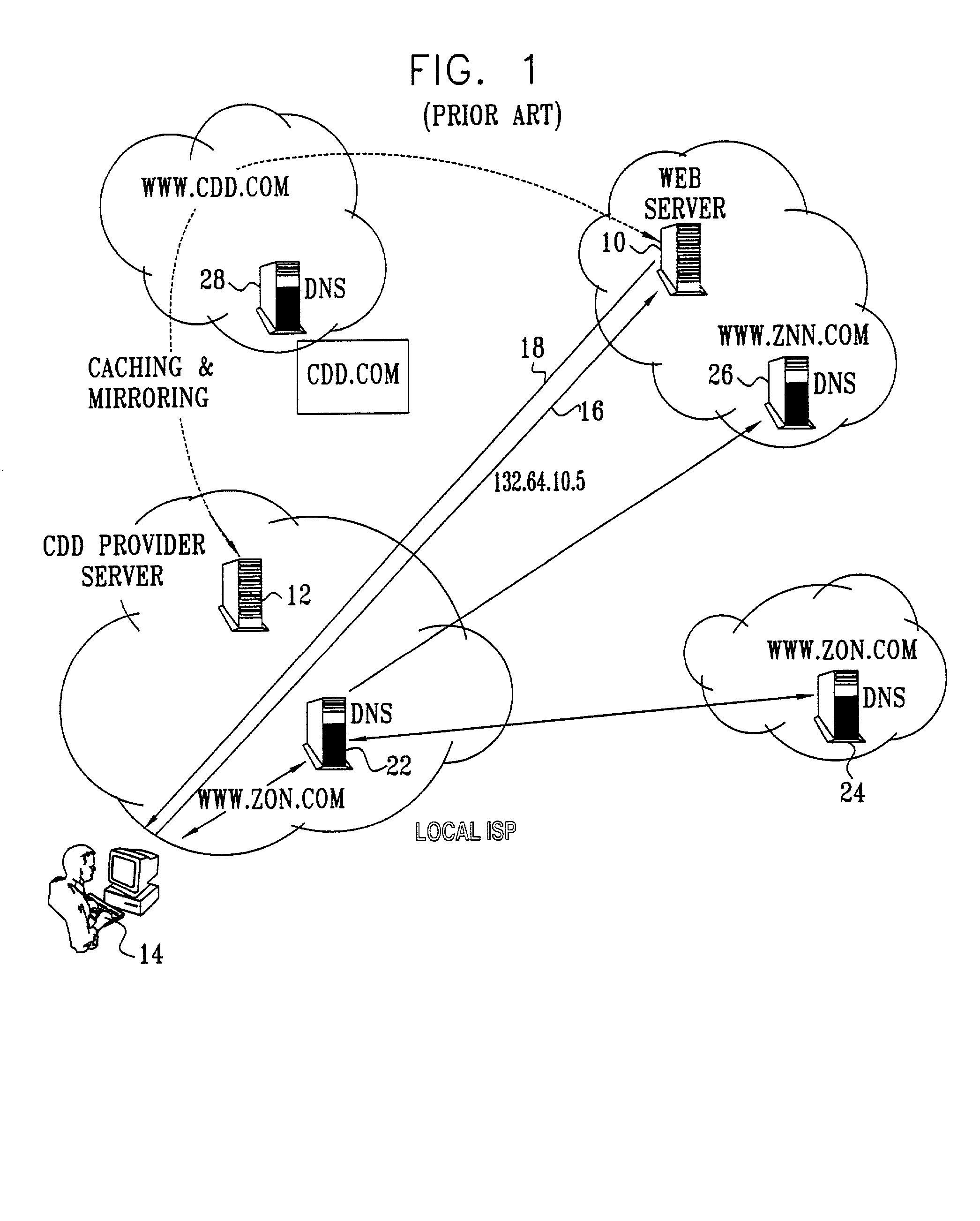
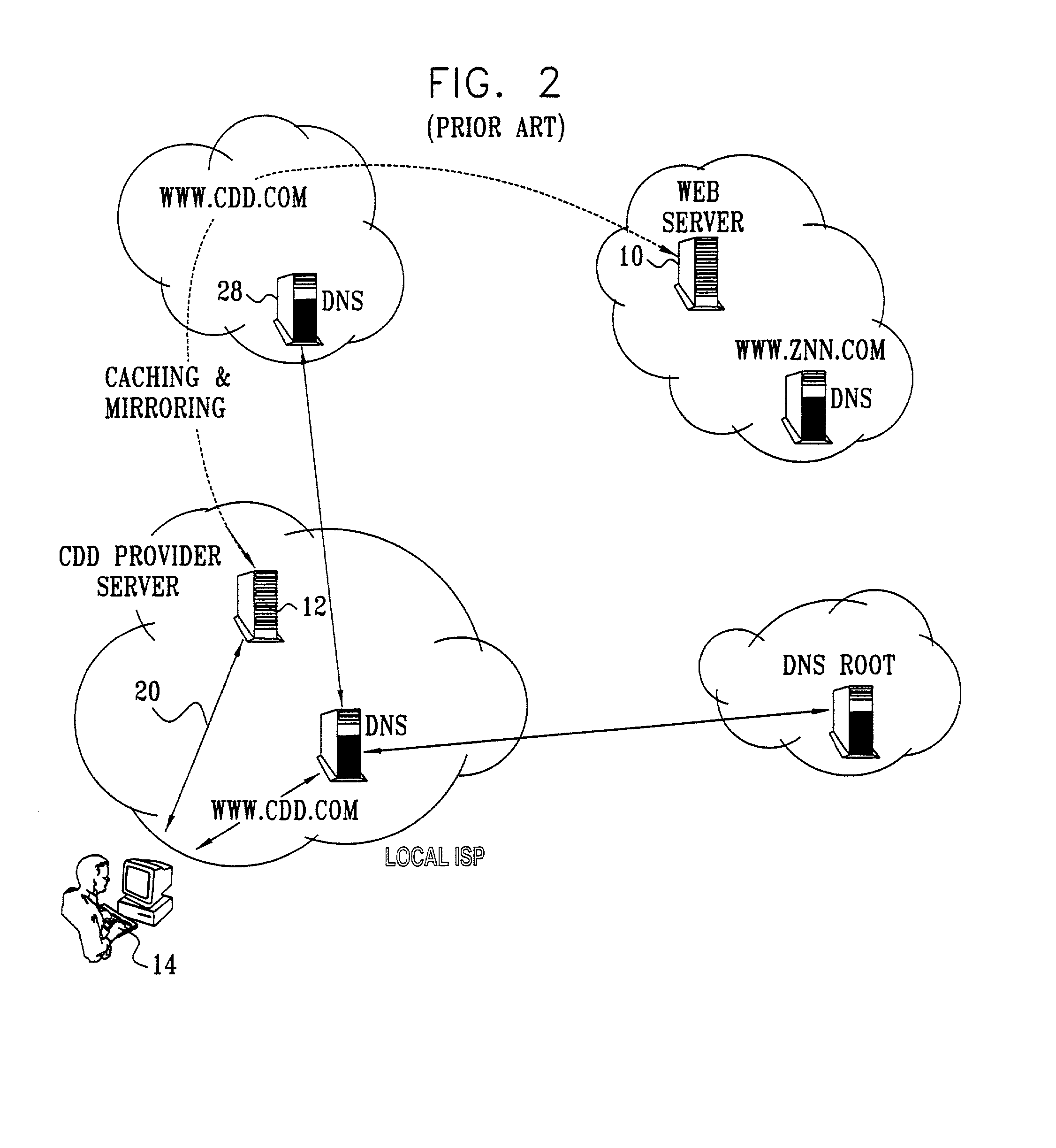
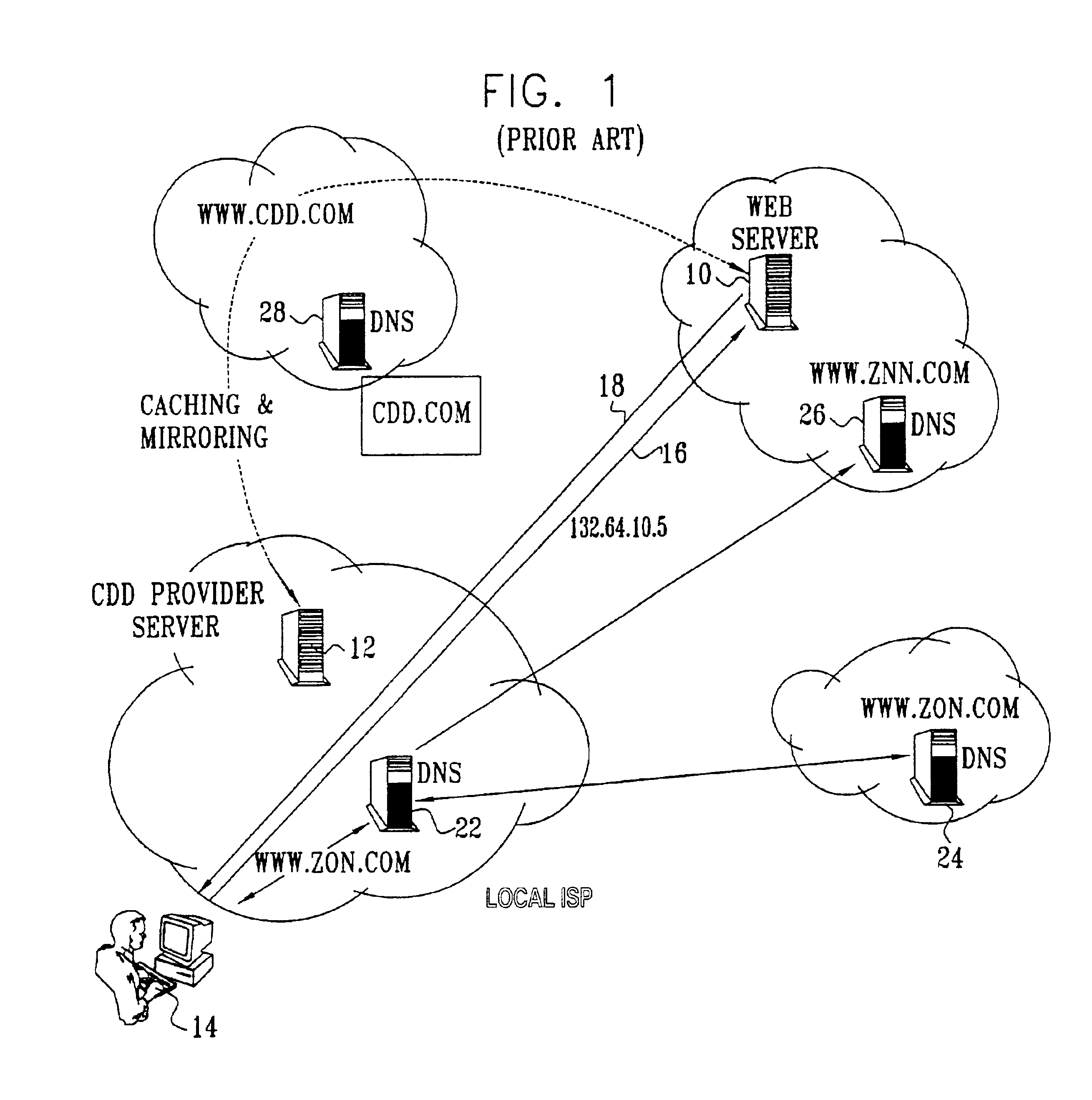
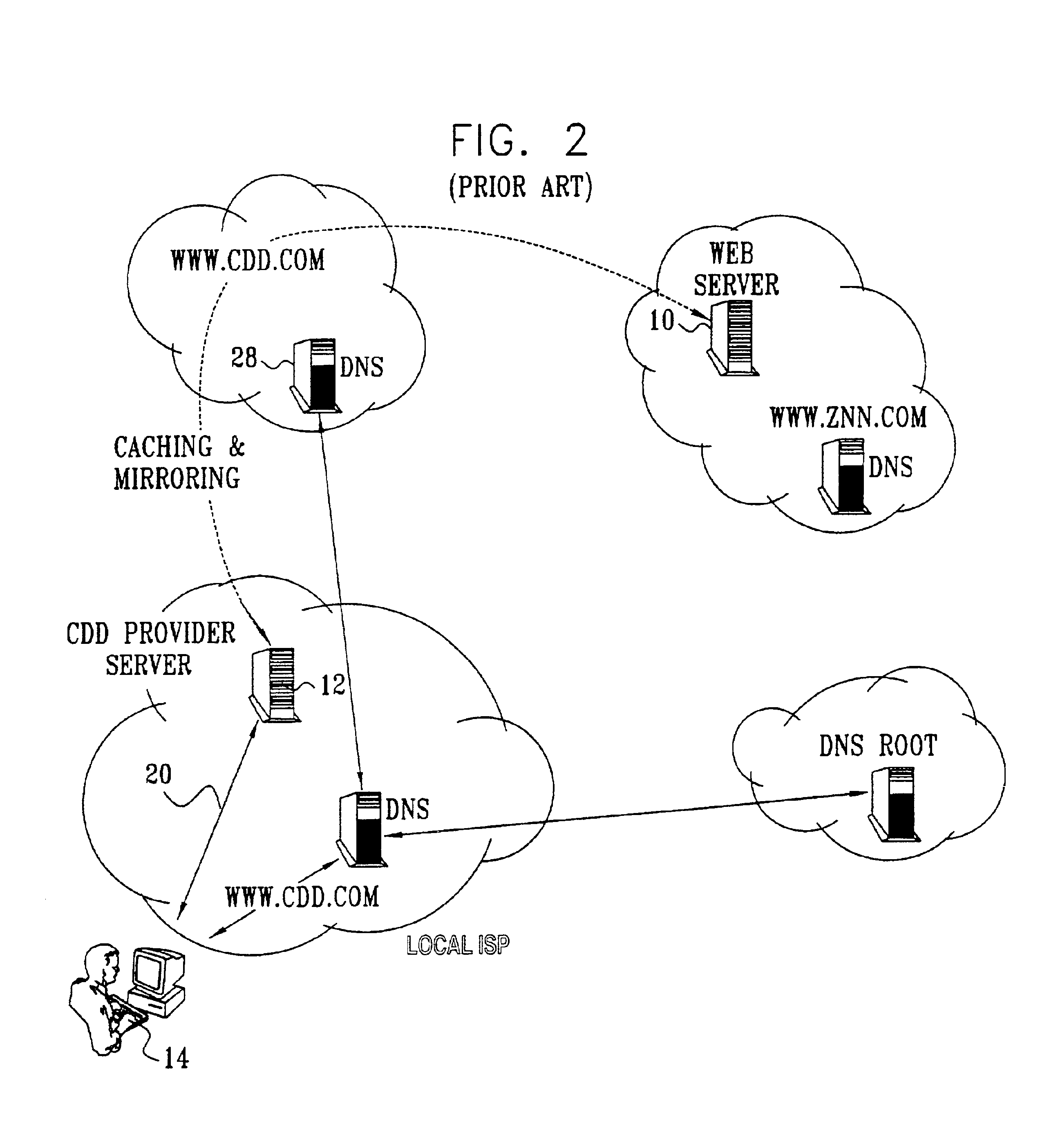
Differentiated content and application delivery via internet
InactiveUS20020010798A1Multiple digital computer combinationsWebsite content managementScalable systemEdge server
A technique for centralized and differentiated content and application delivery system allows content providers to directly control the delivery of content based on regional and temporal preferences, client identity and content priority. A scalable system is provided in an extensible framework for edge services, employing a combination of a flexible profile definition language and an open edge server architecture in order to add new and unforeseen services on demand. In one or more edge servers content providers are allocated dedicated resources, which are not affected by the demand or the delivery characteristics of other content providers. Each content provider can differentiate different local delivery resources within its global allocation. Since the per-site resources are guaranteed, intra-site differentiation can be guaranteed. Administrative resources are provided to dynamically adjust service policies of the edge servers.
Owner:CISCO TECH INC
Differentiated content and application delivery via internet
InactiveUS6976090B2Decentralized and differentiatedAdvanced technologyMultiple digital computer combinationsWebsite content managementScalable systemEdge server
Owner:CISCO TECH INC
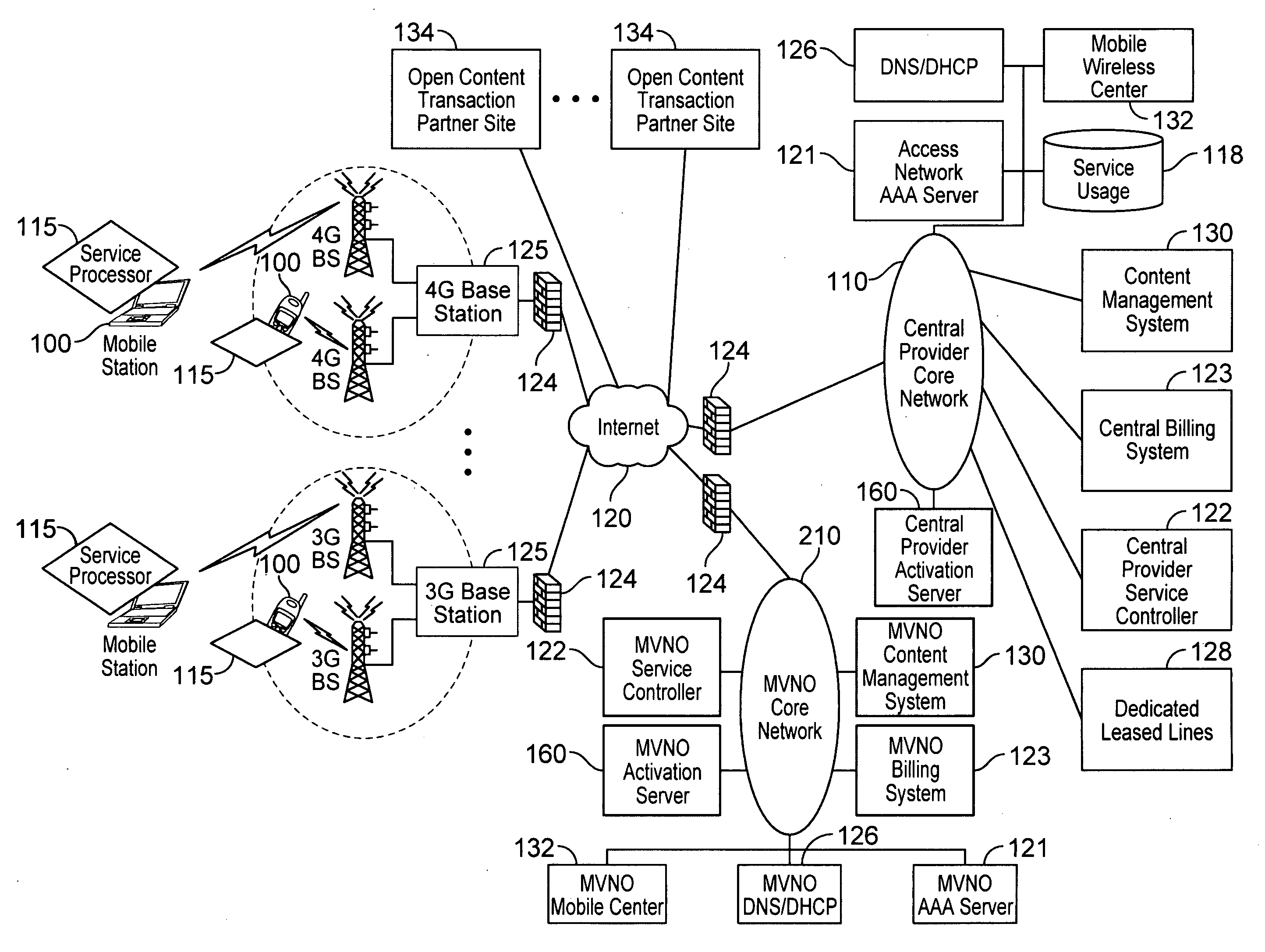
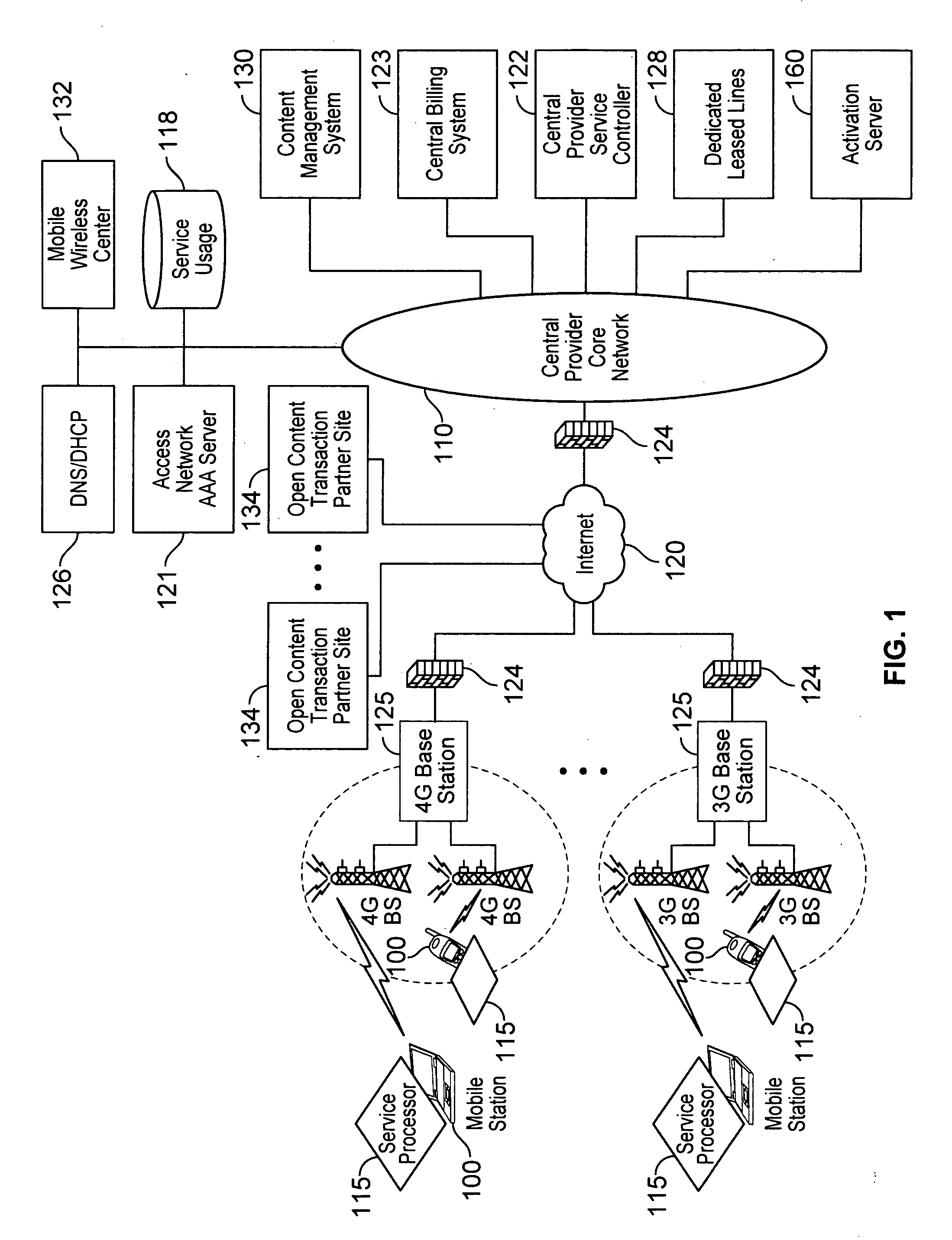
Automated device provisioning and activation
ActiveUS20100192212A1Digital data processing detailsTechnology managementCommunications systemBiological activation
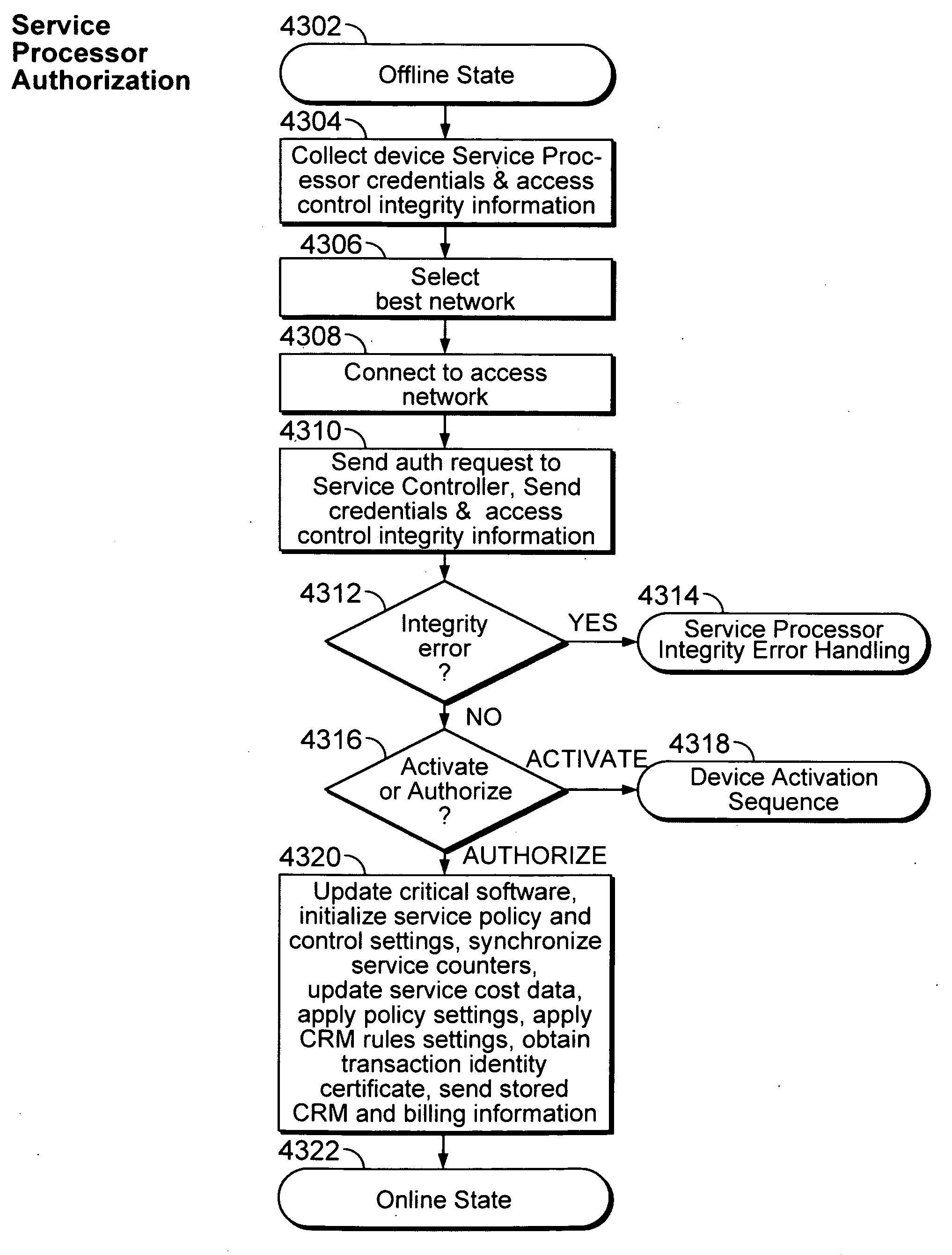
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device stores a set of device credentials for activating the communications device for a service on a network; and sends an access request to the network, the access request including the set of device credentials.
Owner:HEADWATER RES LLC
Verifiable device assisted service policy implementation
ActiveUS20100188975A1Error preventionFrequency-division multiplex detailsCommunications systemCommunication device
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting control of the communications device use of a service on a network; and monitors use of the service based on the service policy, in which the implementation of the service policy is verified.
Owner:HEADWATER RES LLC
Verifiable device assisted service usage monitoring with reporting, synchronization, and notification
ActiveUS20100191612A1Error preventionFrequency-division multiplex detailsControl communicationsService usage
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting control of the communications device use of a service on a network; and monitors use of the service based on the service policy, in which a local service usage is synchronized with a network based service usage.
Owner:HEADWATER RES LLC
Verifiable service billing for intermediate networking devices
ActiveUS8023425B2Error preventionFrequency-division multiplex detailsCommunications systemCommunication device
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, an intermediate networking device provides a service intermediary or intermediate connection between a network and one or more communications devices; implements a service policy set for assisting control of the intermediate networking device use of a service on the network, in which the service policy set includes one or more service policies, each policy being associated with either the intermediate networking device or a communications device; and monitors use of the service based on the service policy set; and in which the implementation of the service policy set is verified.
Owner:HEADWATER RES LLC
End user device that secures an association of application to service policy with an application certificate check
ActiveUS20120221955A1Input/output for user-computer interactionAccounting/billing servicesTraffic capacityApplication software
Network service provisioning is described. Network service provisioning to a device includes a mechanism for ensuring that network services are available based upon one or more of appropriate traffic control, billing, and notification policies. Ensuring that the policies are properly enforced on a device is a focus of this paper. The enforcement policies can be on the device or in the network.
Owner:HEADWATER RES LLC
Service profile management with user preference, adaptive policy, network neutrality and user privacy for intermediate networking devices
InactiveUS20100188992A1Error preventionFrequency-division multiplex detailsService profileCommunications system
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, an intermediate networking device provides a service intermediary or intermediate connection between a network and one or more communications devices; implements a service profile set for assisting control of the intermediate networking device use of a service set on the network, wherein the service profile set includes one or more service profiles, each profile being associated with either the intermediate networking device or a communications device, each profile further including a plurality of service policy settings; and monitors use of the service set based on the service profile set, in which the implementation of the first service profile set is verified.
Owner:ITSON
Verifiable device assisted service usage billing with integrated accounting, mediation accounting, and multi-account
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting billing for the communications device use of a service on a network; and monitors use of the service based on the service policy, in which a local service usage is synchronized with a network based service usage.
Owner:HEADWATER RES LLC
Adaptive ambient services
ActiveUS20100198698A1Error preventionFrequency-division multiplex detailsService profileWireless mesh network
Adaptive ambient services are provided. In some embodiments, an adaptive ambient service includes providing an ambient service profile. In some embodiments, an ambient service includes implementing an ambient service profile for assisting control of the communications device use of an ambient service on a wireless network, in which the ambient service profile includes a plurality of service policy settings, and in which the ambient service profile is associated with an ambient service plan that provides for initial access to the ambient service with limited service capabilities prior to activation of a new service plan; monitoring use of the ambient service based on the ambient service profile; and adapting the ambient service profile based on the monitored use of the ambient service.
Owner:HEADWATER RES LLC
Network based service profile management with user preference, adaptive policy, network neutrality, and user privacy
ActiveUS20100188990A1Error preventionFrequency-division multiplex detailsService profileControl communications
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a network device implements a service profile for assisting control of a communications device use of a service on a network, in which the service profile includes service policy settings for the communications device; monitors use of the service by the communications device based on the service profile; and modifies a service policy setting to achieve a service usage goal.
Owner:HEADWATER RES LLC
Device assisted service profile management with user preference, adaptive policy, network neutrality, and user privacy
InactiveUS20100192170A1Analogue secracy/subscription systemsTechnology managementService profileControl communications
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service profile for assisting control of the communications device use of a service on a network, in which the service profile includes service policy settings; monitors use of the service based on the service profile; and modifies a service policy setting to achieve a service usage goal.
Owner:HEADWATER RES LLC
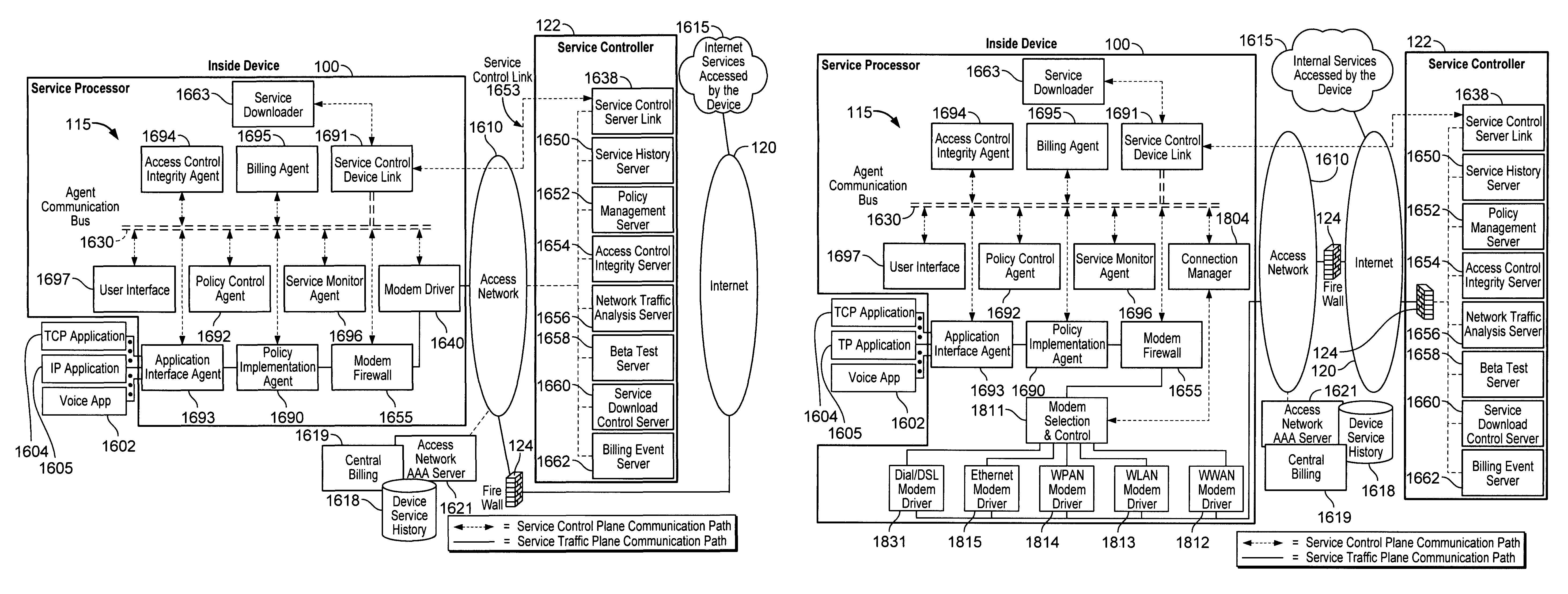
Device assisted services install
ActiveUS20100198939A1Accounting/billing servicesNetwork traffic/resource managementService profileControl communications
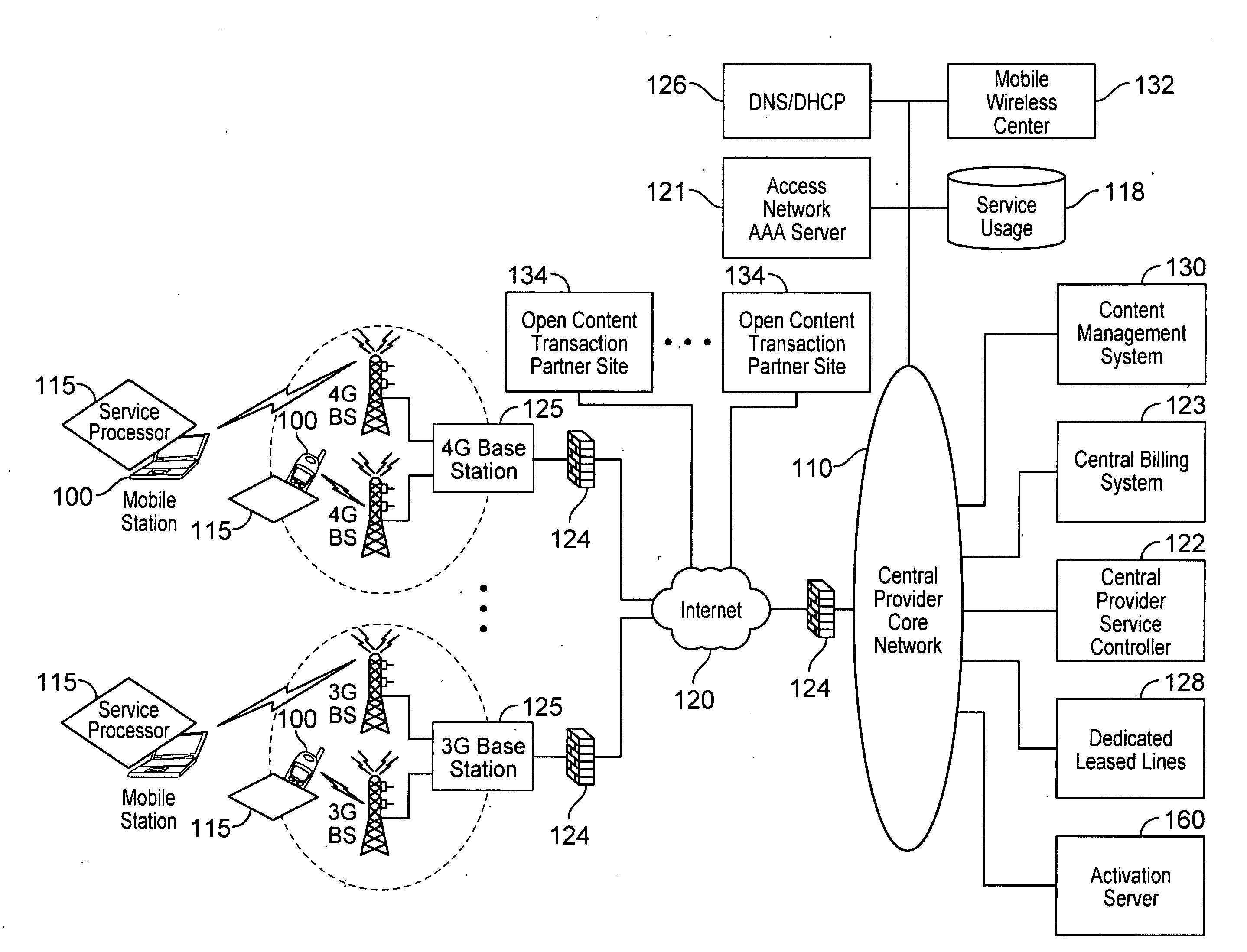
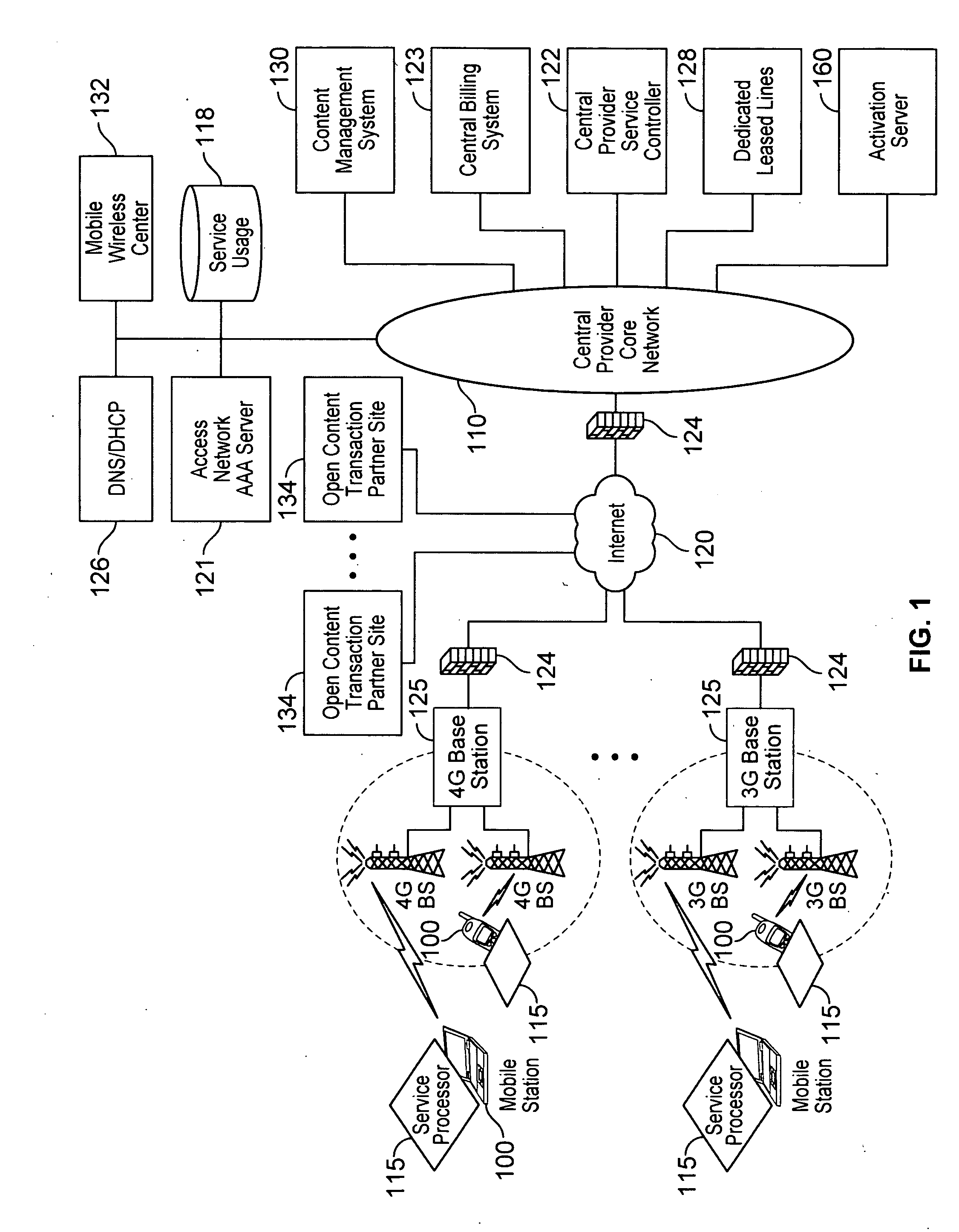
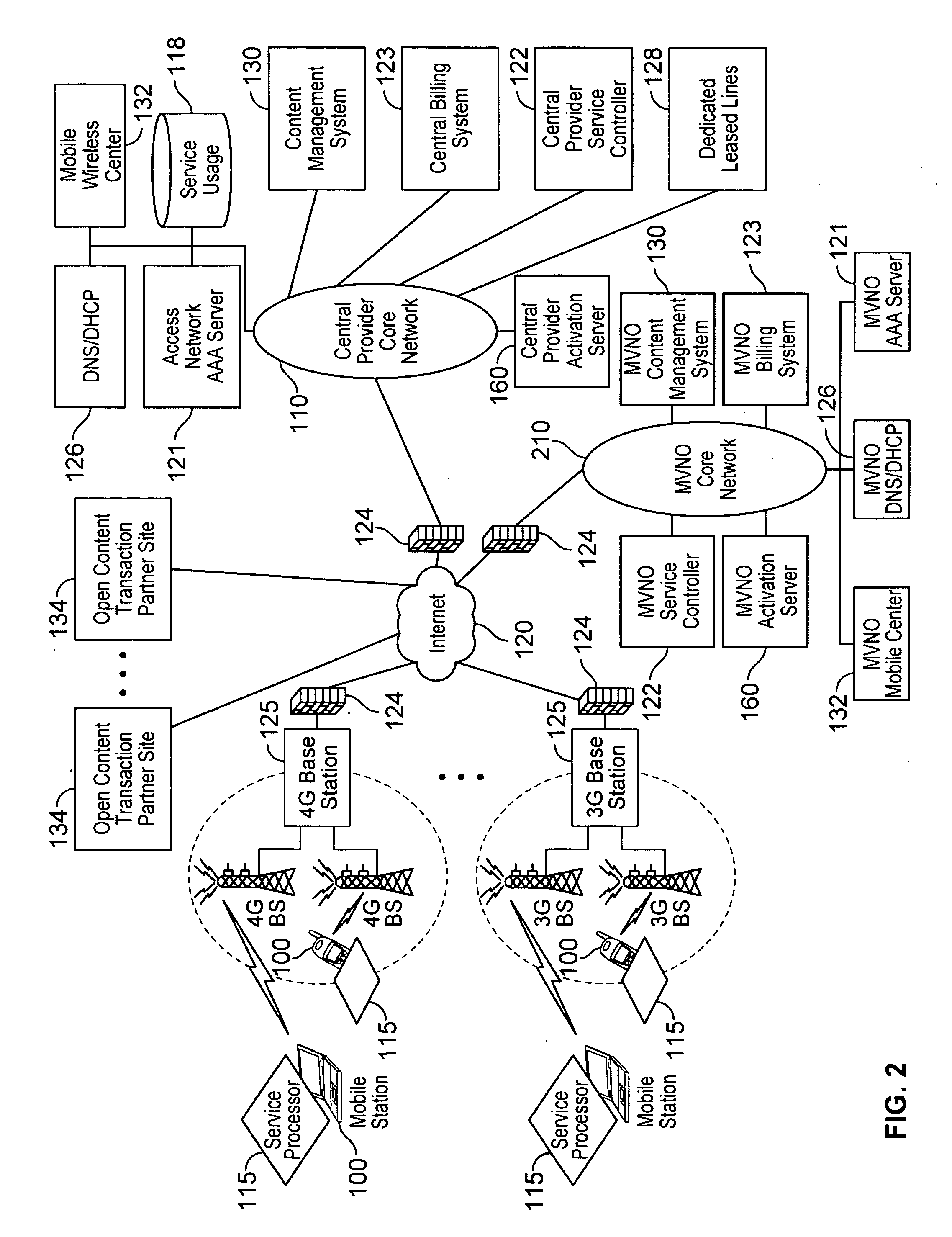
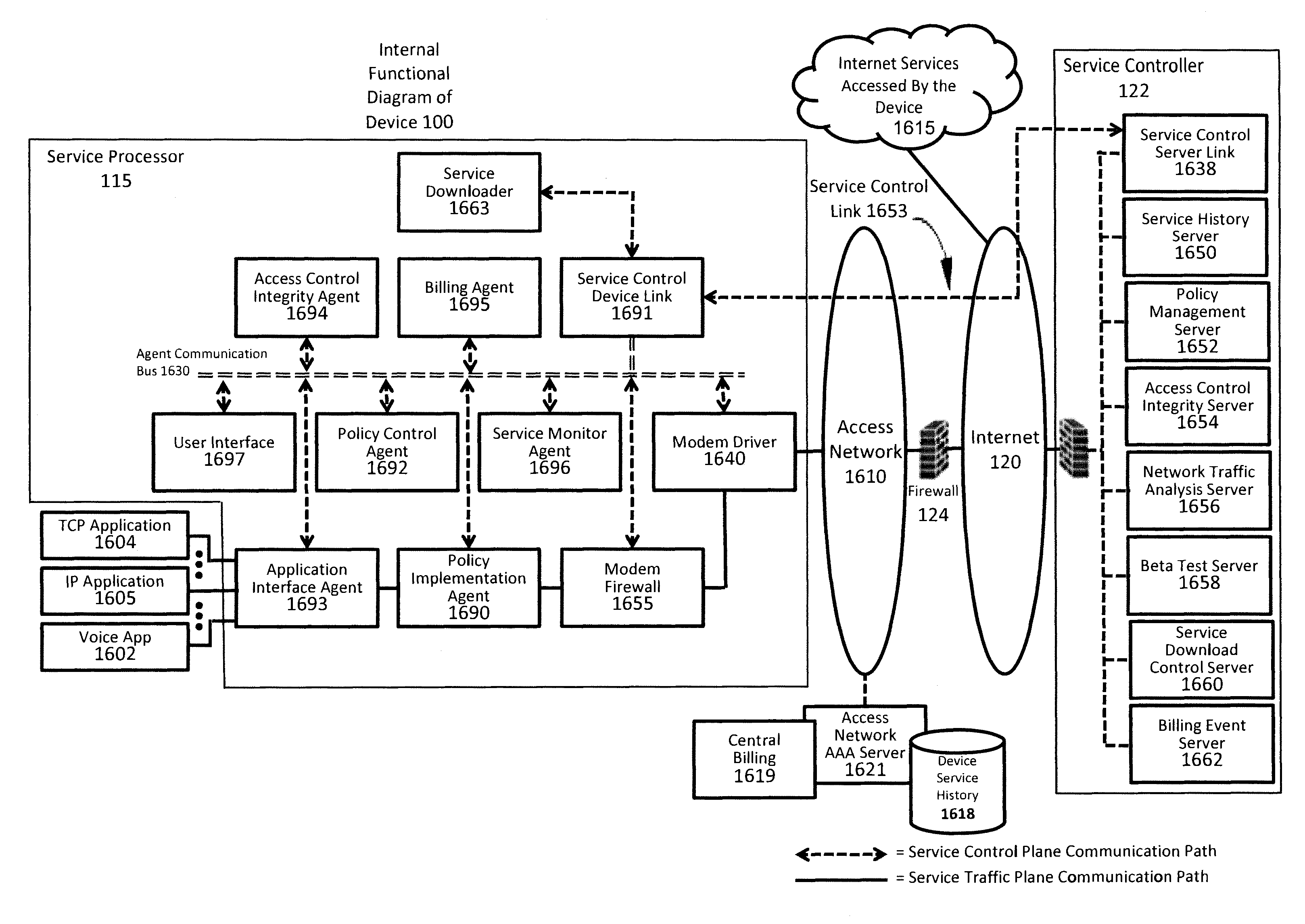
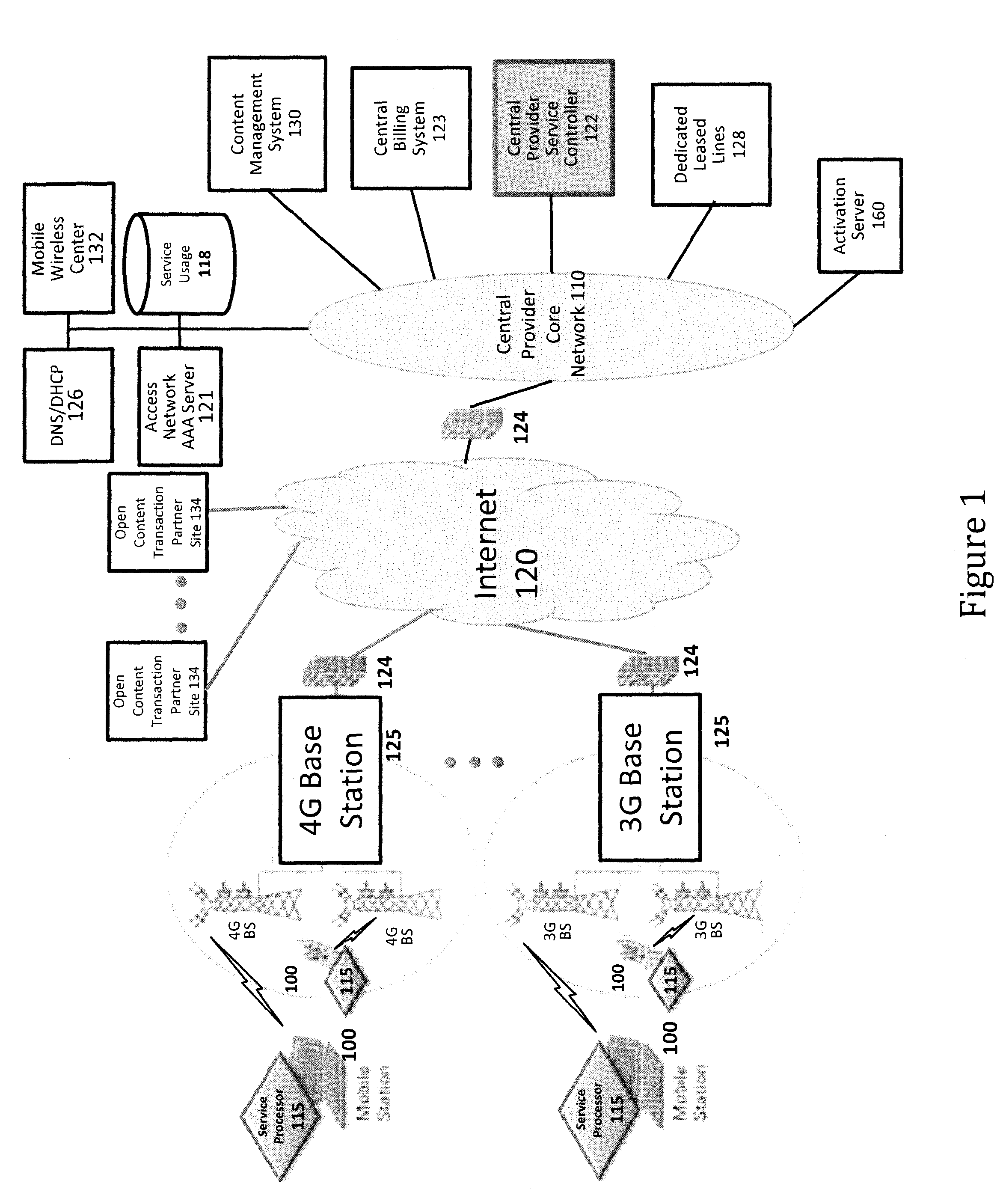
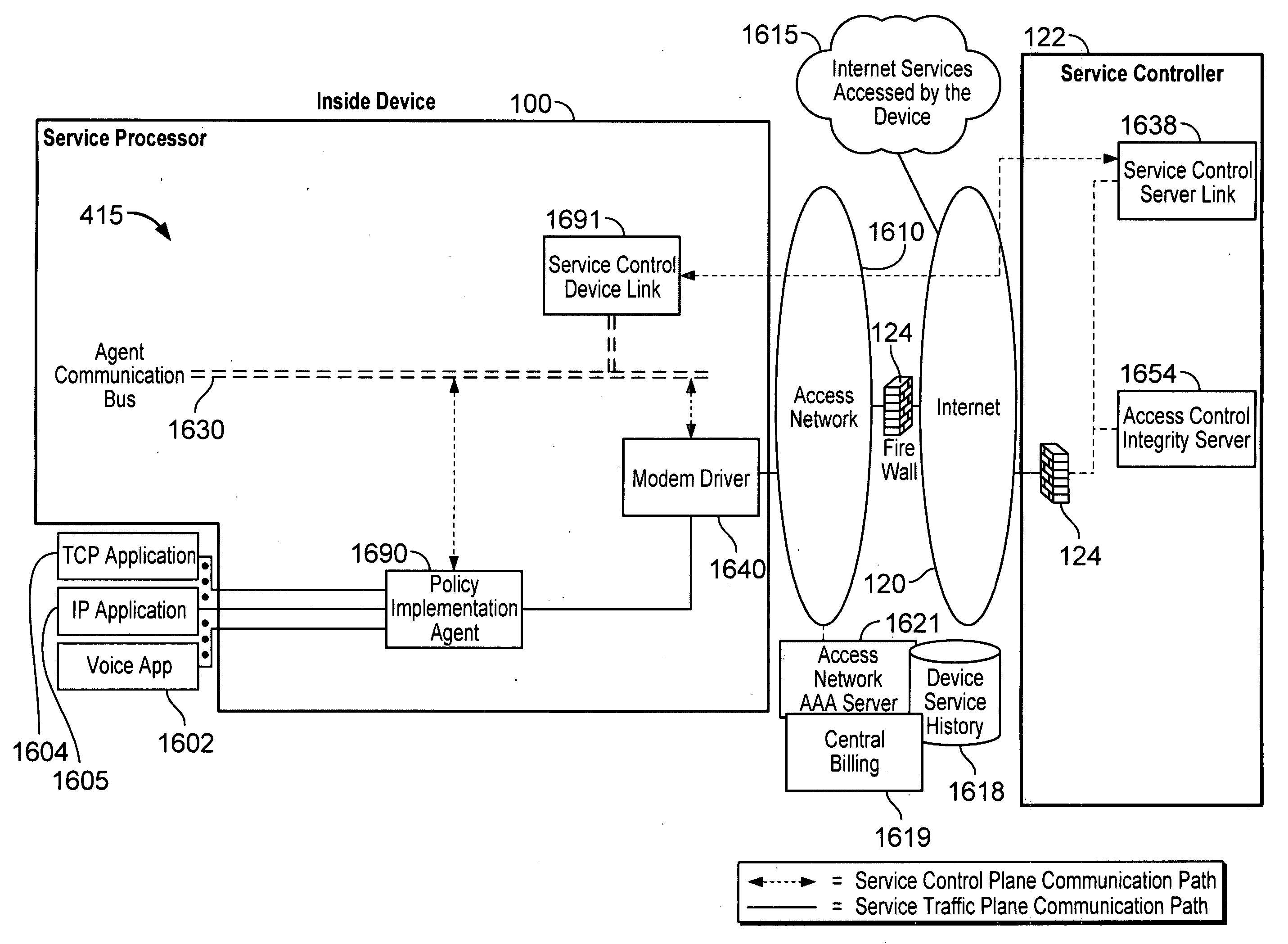
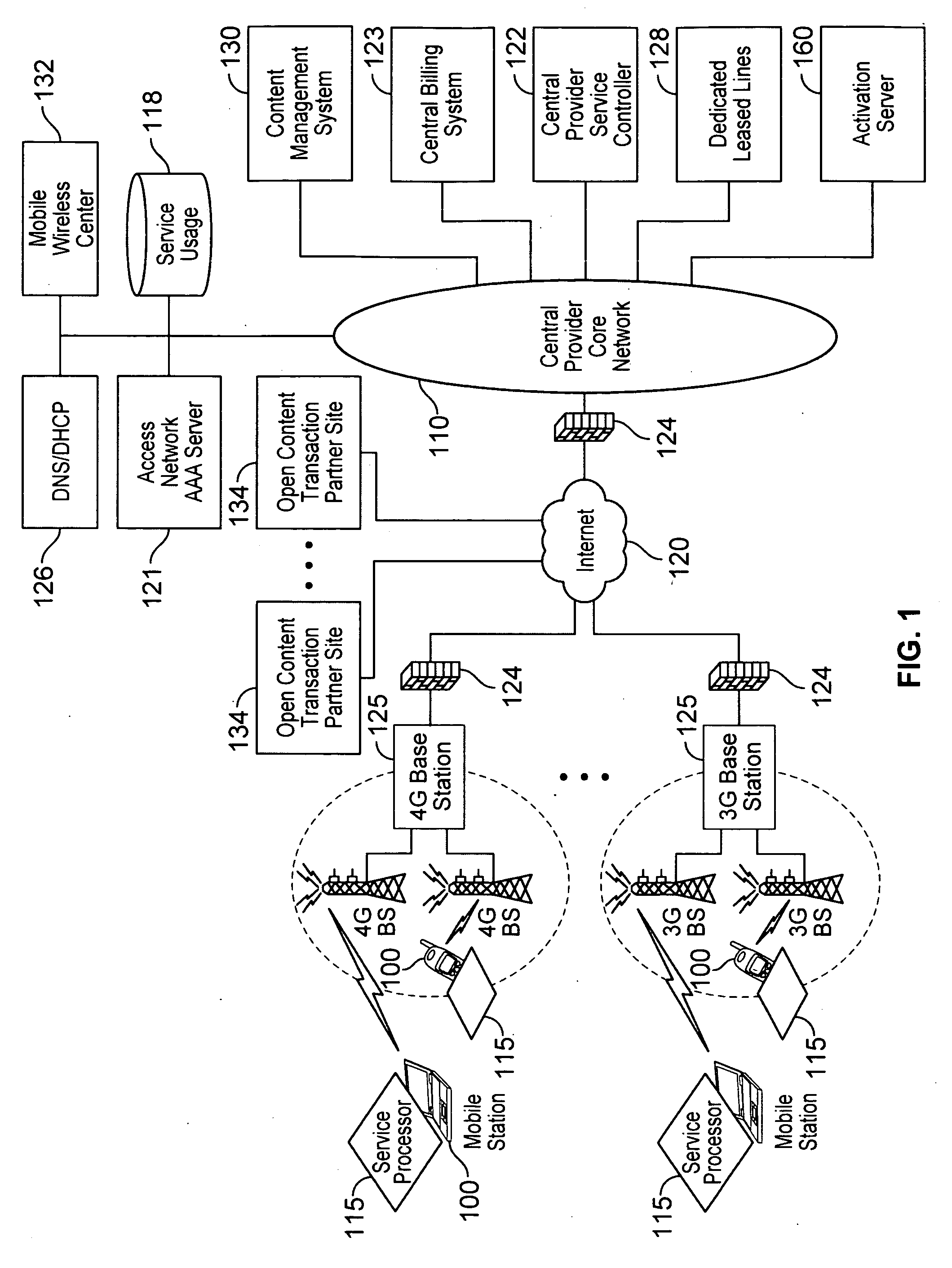
Device assisted services (DAS) install techniques are provided in accordance with some embodiments. In some embodiments, DAS install techniques for providing service processors for mobile devices are provided. In some embodiments, DAS install techniques for downloading / installing new and / or updated service processors for mobile devices are provided. In some embodiments, DAS install techniques for providing verified service processors for mobile devices are provided. In some embodiments, DAS install techniques for providing secured service processors for mobile devices are provided. In some embodiments, DAS install techniques include determining if a communications device in communication with a wireless network includes a service processor for assisting control of the communications device use of a service on the wireless network, in which the service processor includes a service profile that includes a plurality of service policy settings, and in which the service profile is associated with a service plan that provides for access to the service; and verifying the service processor. In some embodiments, DAS install techniques include providing a generic first version service processor for downloading and installing a second version service processor.
Owner:HEADWATER RES LLC
Controlling services in a packet data network
InactiveUS7948952B2Increase flexibilityEasy to configureConnection managementData switching by path configurationSession controlTerminal equipment
Owner:WSOU INVESTMENTS LLC
Verifiable device assisted service usage billing with integrated accounting, mediation accounting, and multi-account
ActiveUS8351898B2Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemService usage
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting billing for the communications device use of a service on a network; and monitors use of the service based on the service policy, in which a local service usage is synchronized with a network based service usage.
Owner:HEADWATER RES LLC
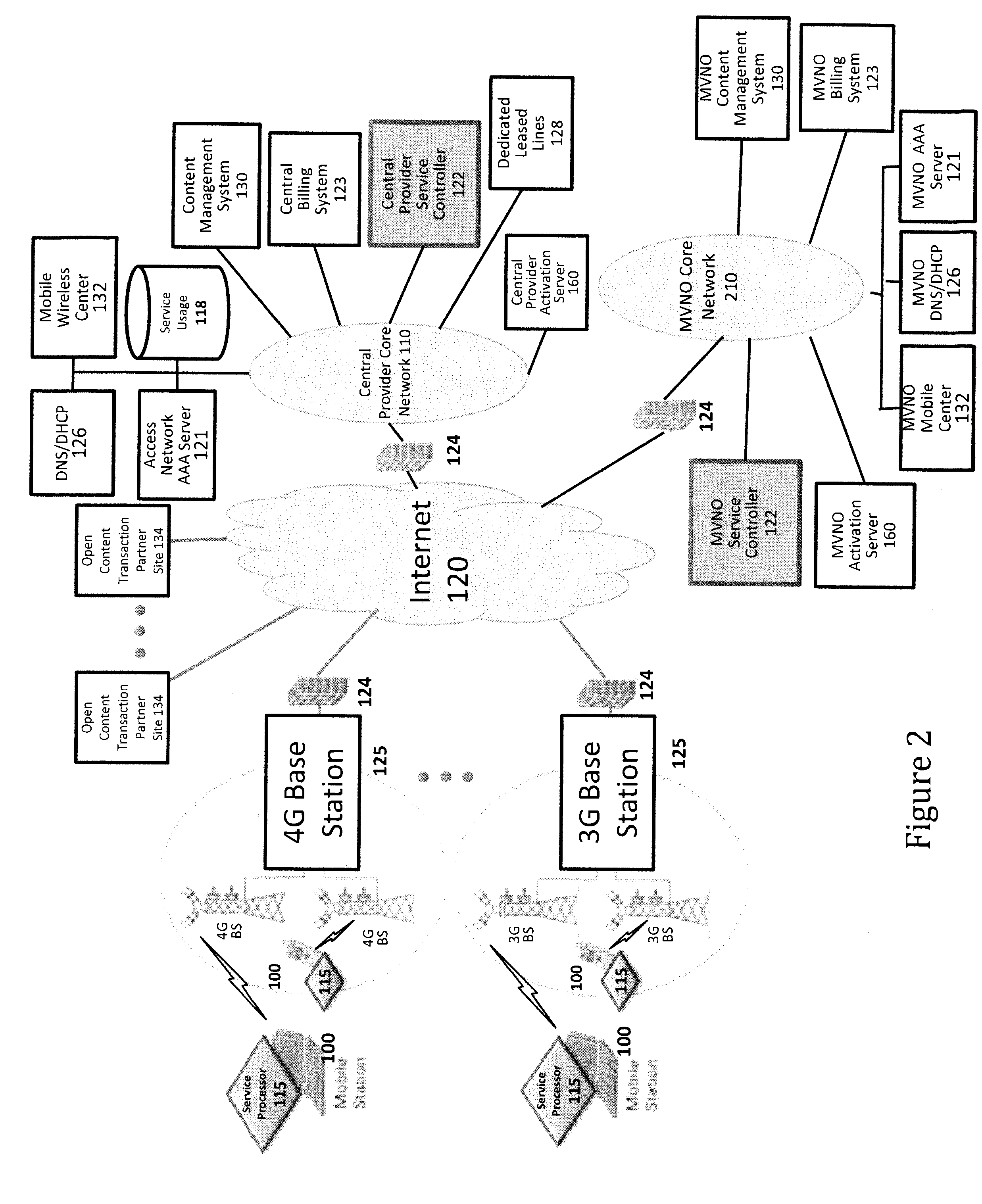
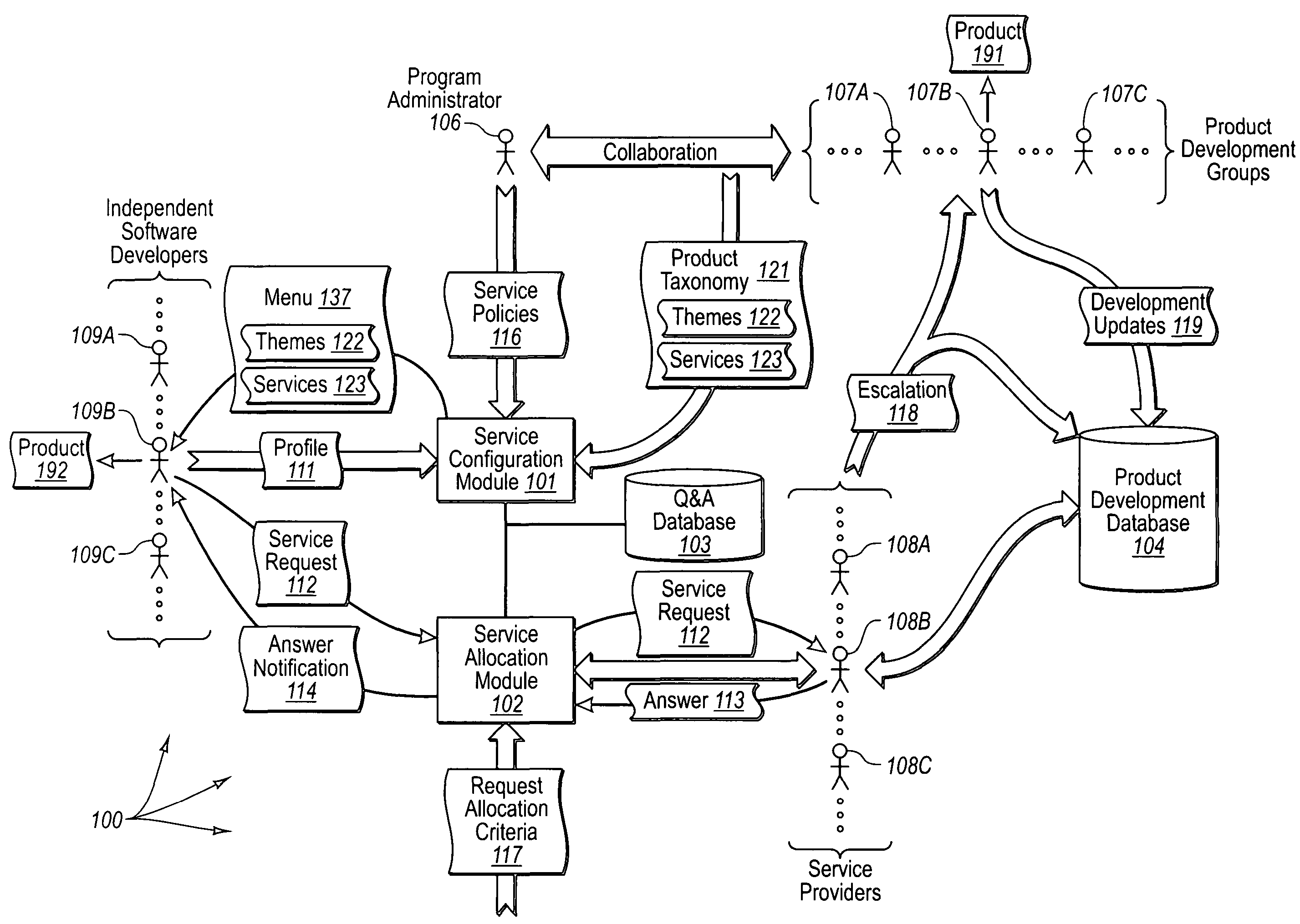
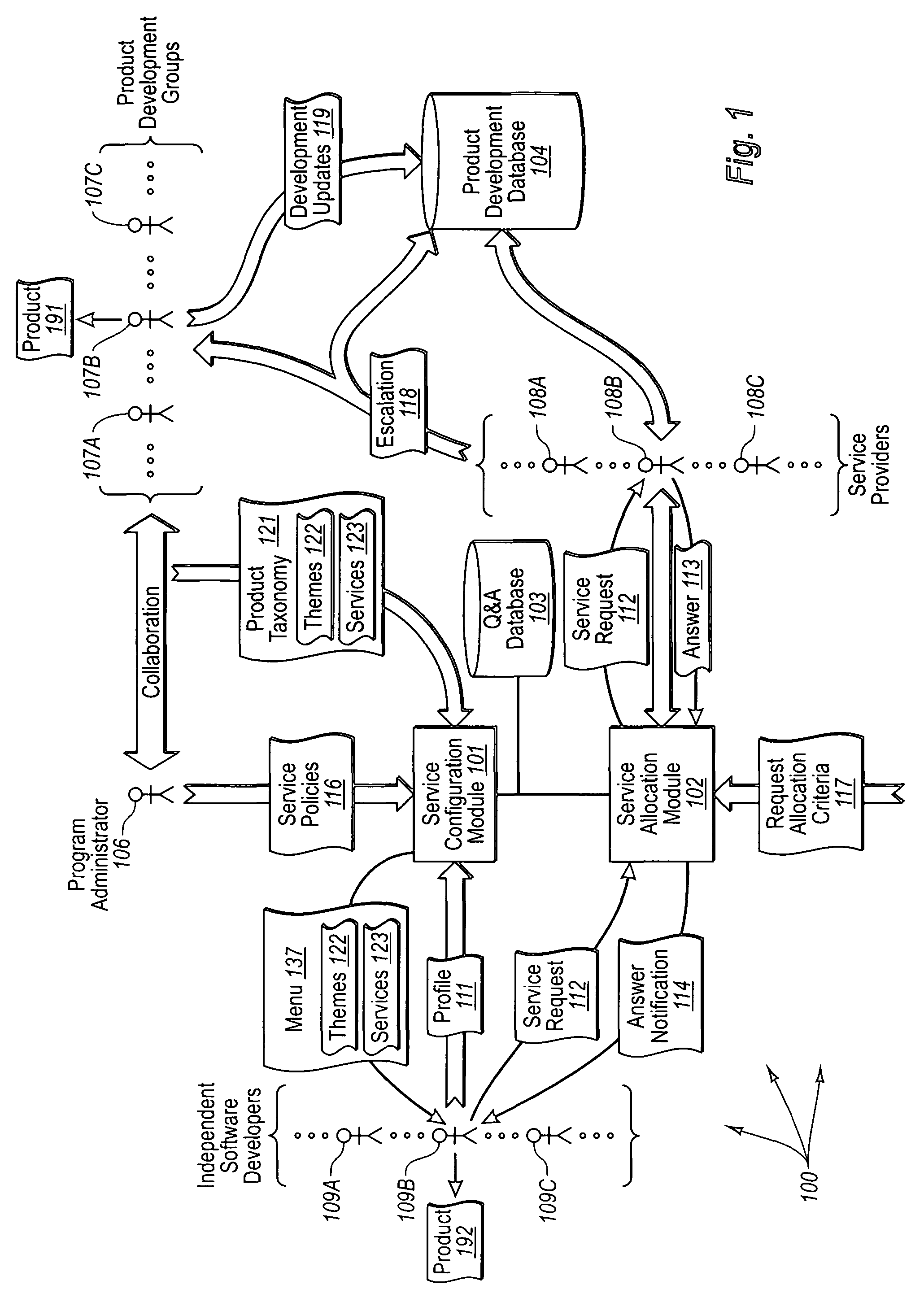
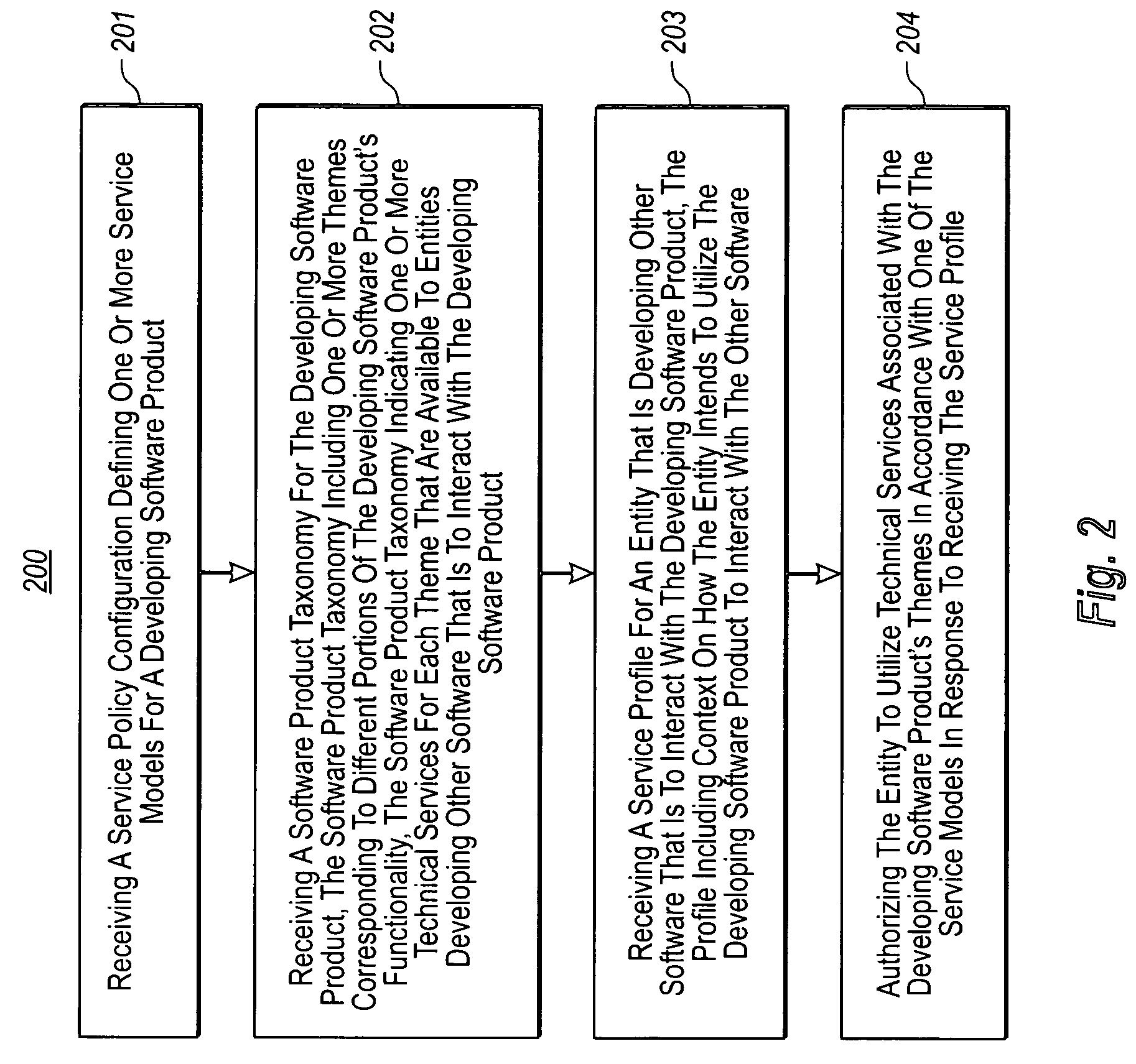
Configuring and allocating software product technical services
The present invention extends to methods, systems, and computer program products for configuring and allocating software product technical services. A service policy configuration defining one or more service models for the developing software product is received. A software product taxonomy, including one or more themes and corresponding technical services, for the developing software product is received. A service profile, including context on how the entity intends to utilize the developing software product, is received. The entity is authorized to utilize technical services associated with the developing software product in accordance with one of the service models in response to receiving the service profile. In other embodiments, a service request selection is made from a menu that lists themes and technical services associated with a software product. The service request is allocated to the identified service provider based on request allocation criteria. An entity is at least notified of a received answer.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for the use of dynamic XML message formats with web services
InactiveUS20050050228A1Natural language data processingMultiple digital computer combinationsService profileWeb site
A service proxy is used to automatically supply the message-format parameters required for incoming message communications to a web-service provider from client applications through a message-conversion system that the web-service provider previously sets up. For outgoing messages from the web service to client businesses, the service proxy automatically supplies the required message-format parameters according to service policies that client businesses set up previously through the web-service provider's web-site interface. The format of client application messages is predefined for a web service policy, and a configuration interface is established for context variables and message format variables. This service profile is recalled in order to apply the proper message format parameters for a web service request.
Owner:IBM CORP
Method and system for content charging
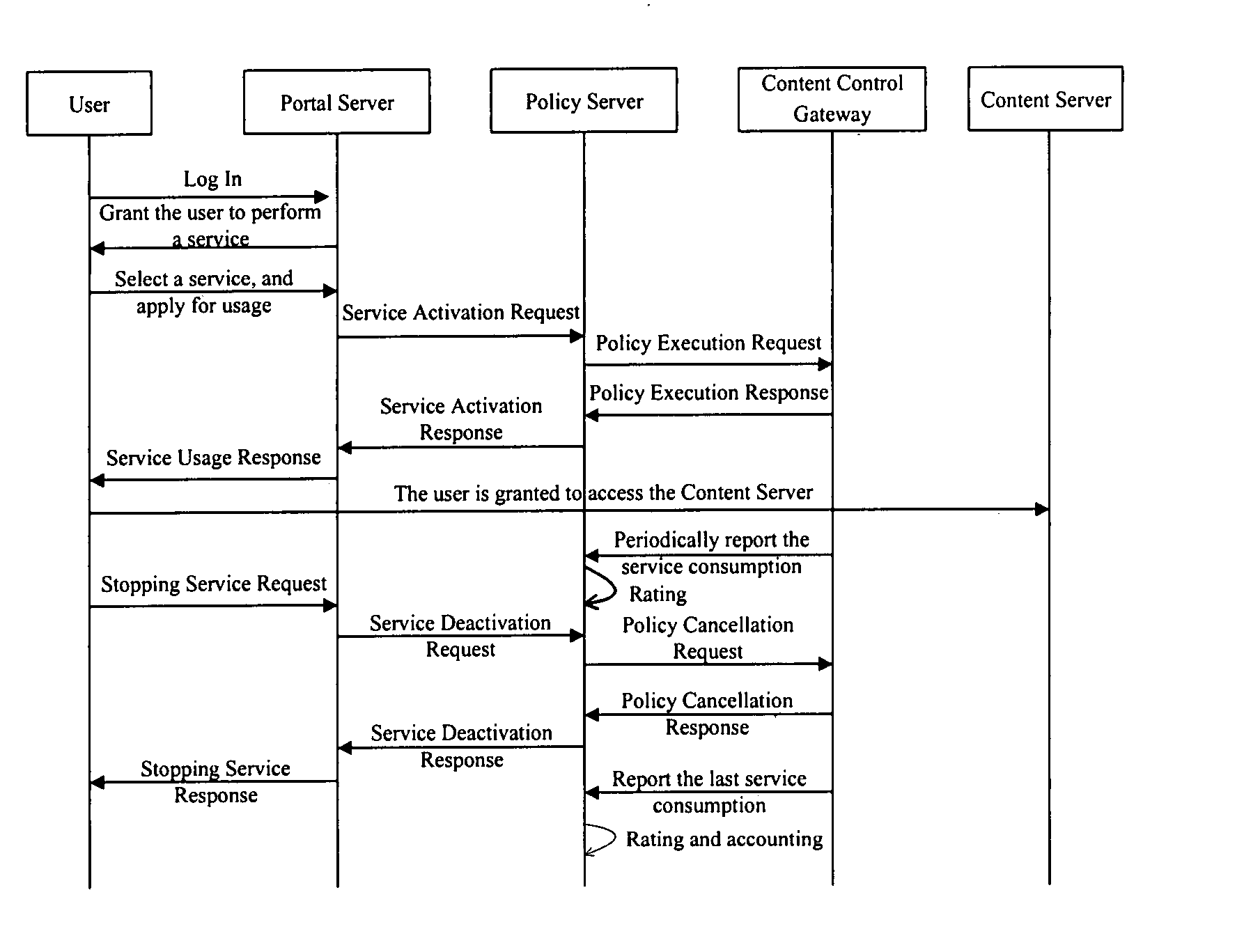
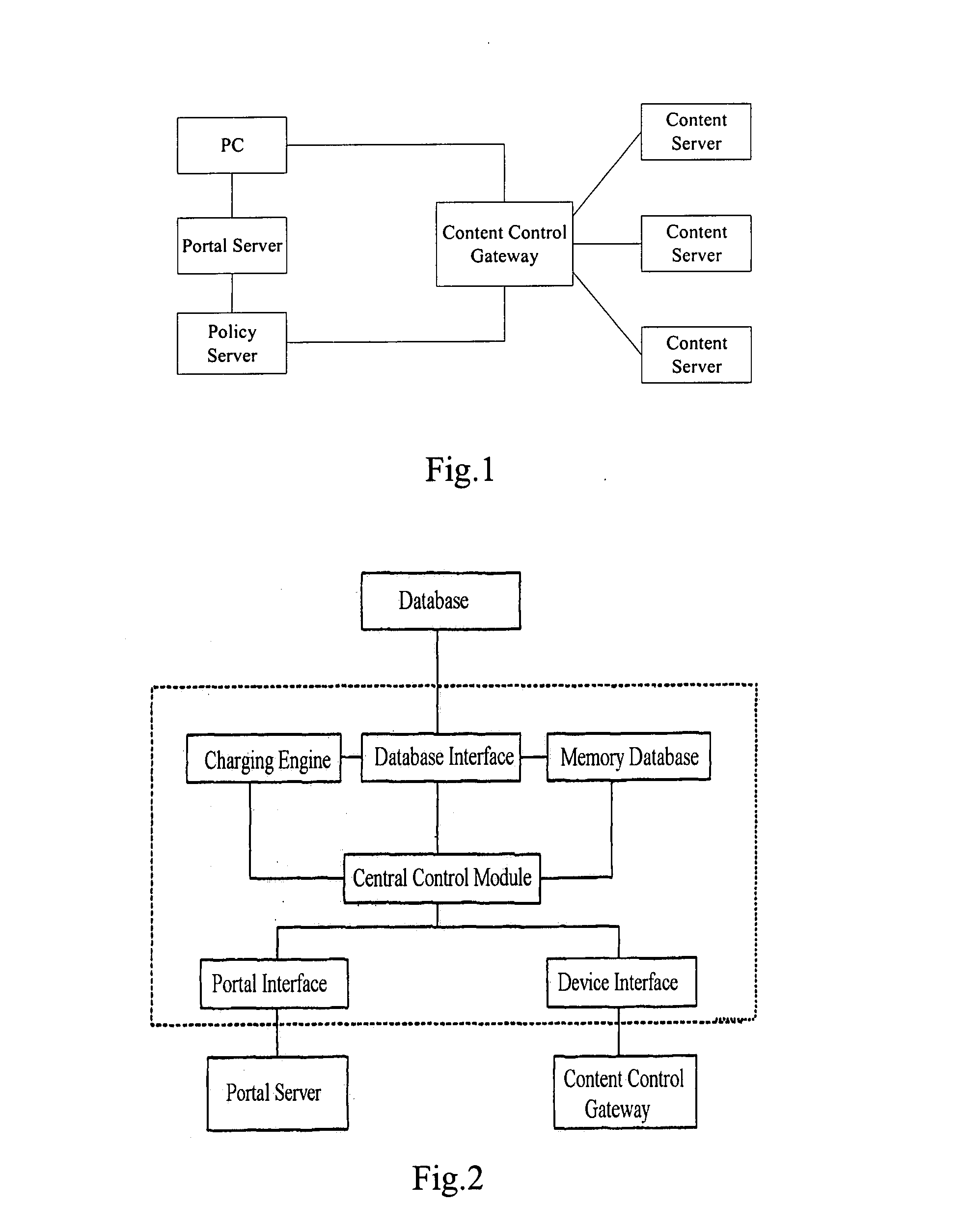
InactiveUS20080010379A1Interconnection difficulty and interconnection costEasy to handleMetering/charging/biilling arrangementsMultiple digital computer combinationsBiological activationService policy
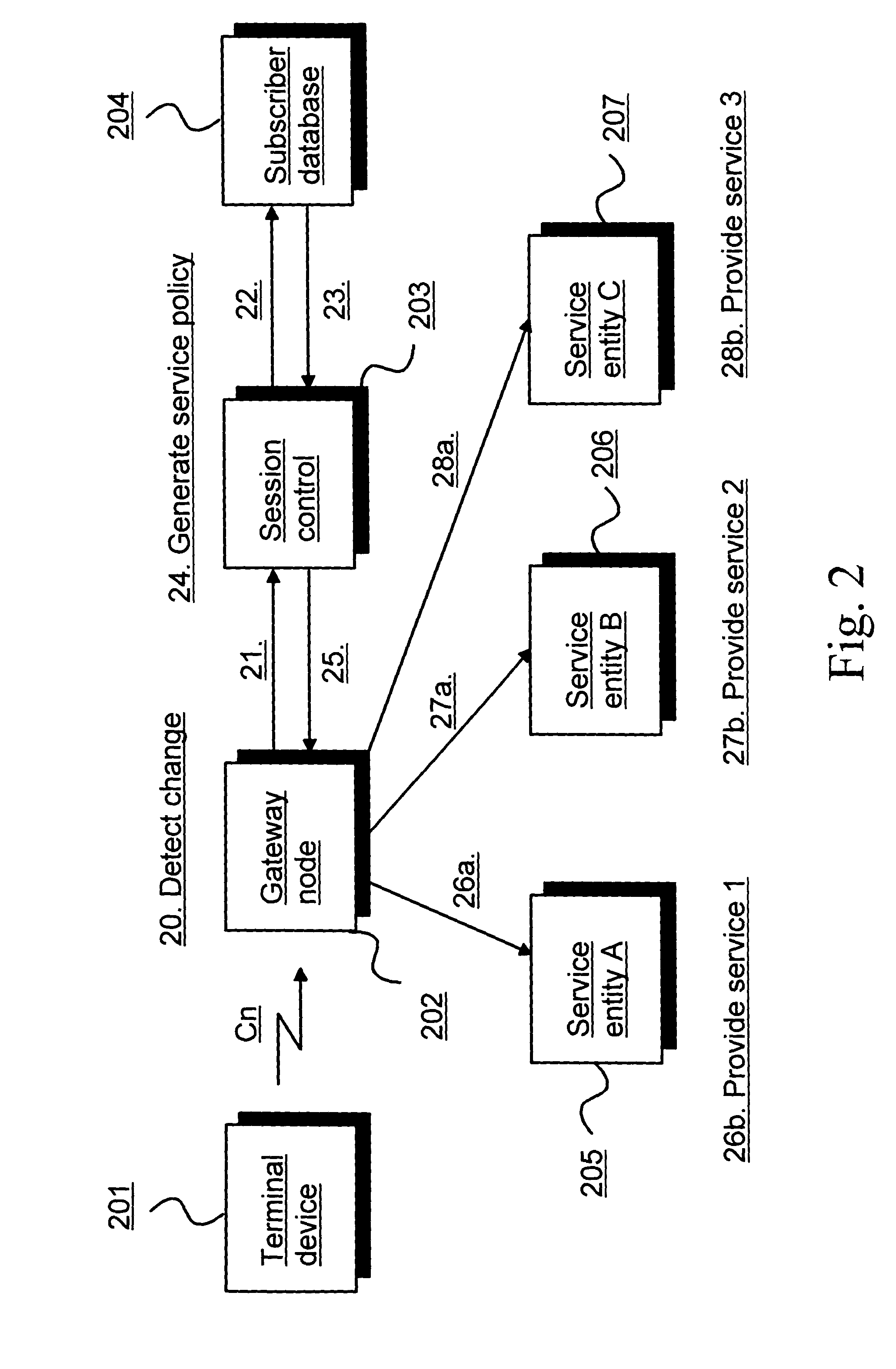
The present invention discloses a method for content charging, including: sending, by a Portal Server, a service activation request to a Policy Server based on a service request from a user; responding to the service activation request, determining the service policy corresponding to the service request, and delivering a service policy activation message to a content control gateway by the Policy Server; executing the service policy and reporting user service consumption information to the Policy Server by the content control gateway; performing charging, by the Policy Server, according to the user service consumption information. By using the technical solution of the invention, accurate and low-cost charging on content service may be realized, and the requirements of dynamic adjustment on content service QoS may be met.
Owner:HUAWEI TECH CO LTD
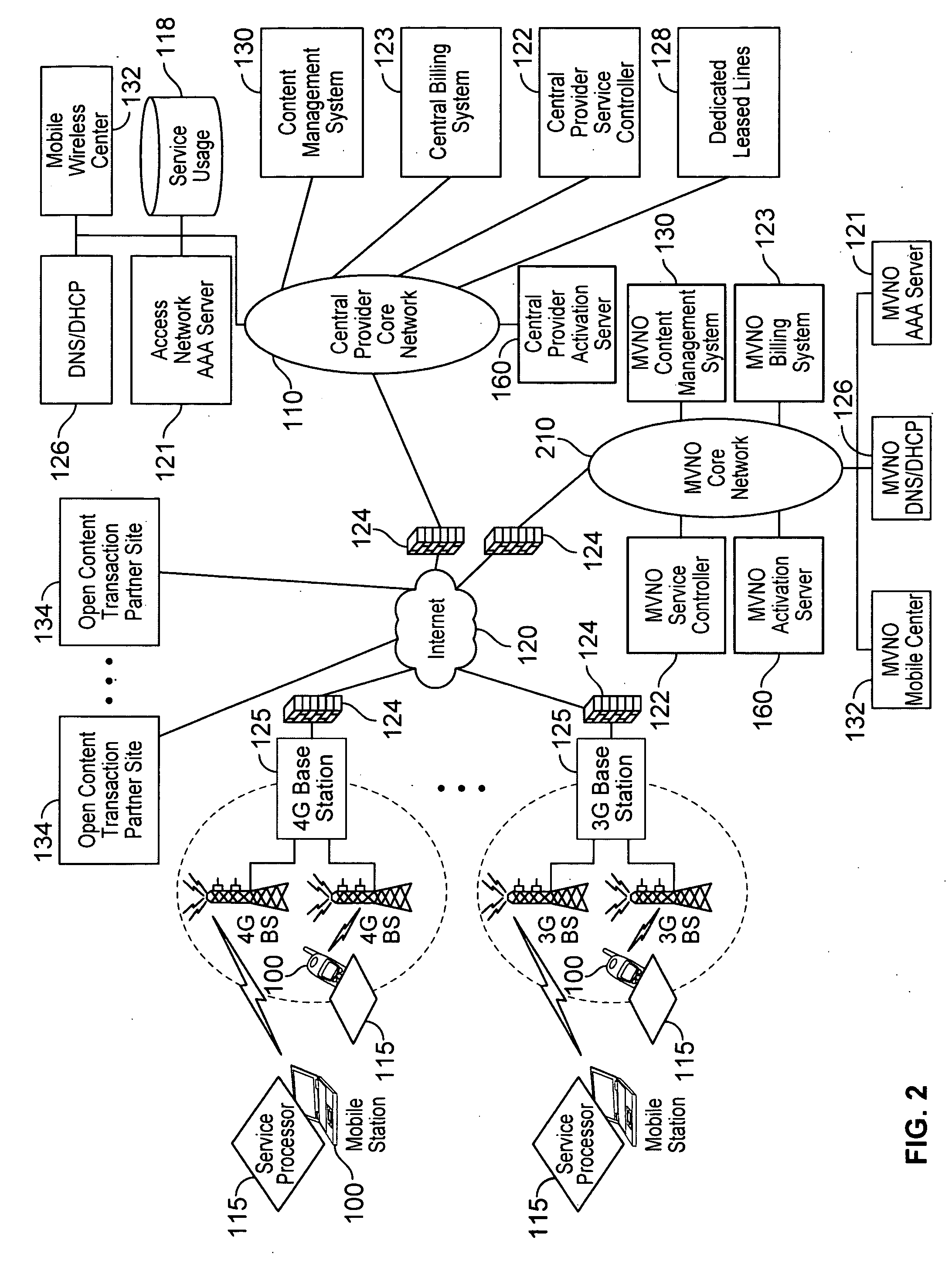
Virtual service provider systems
InactiveUS20100192207A1Digital data processing detailsTechnology managementCommunications systemService provision
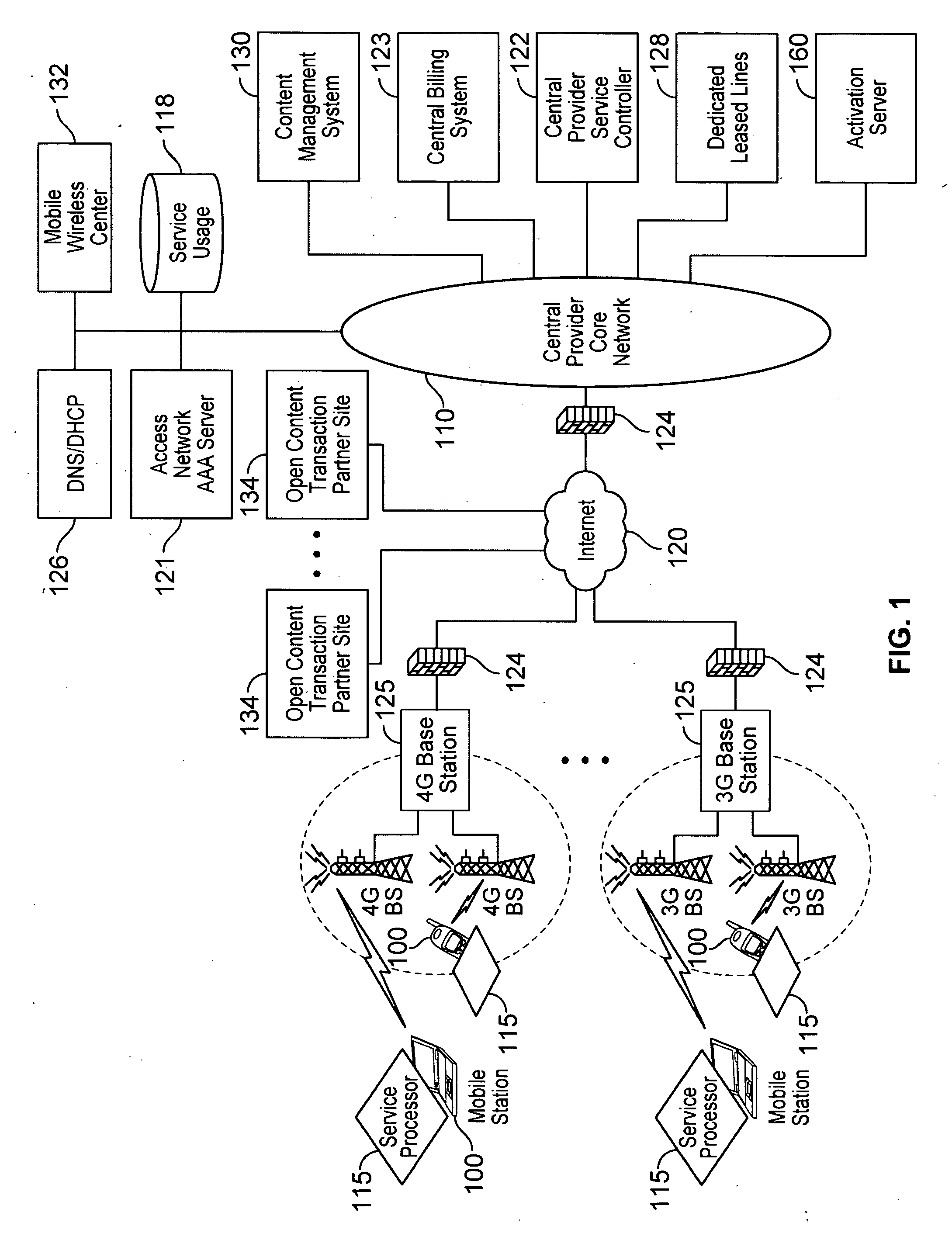
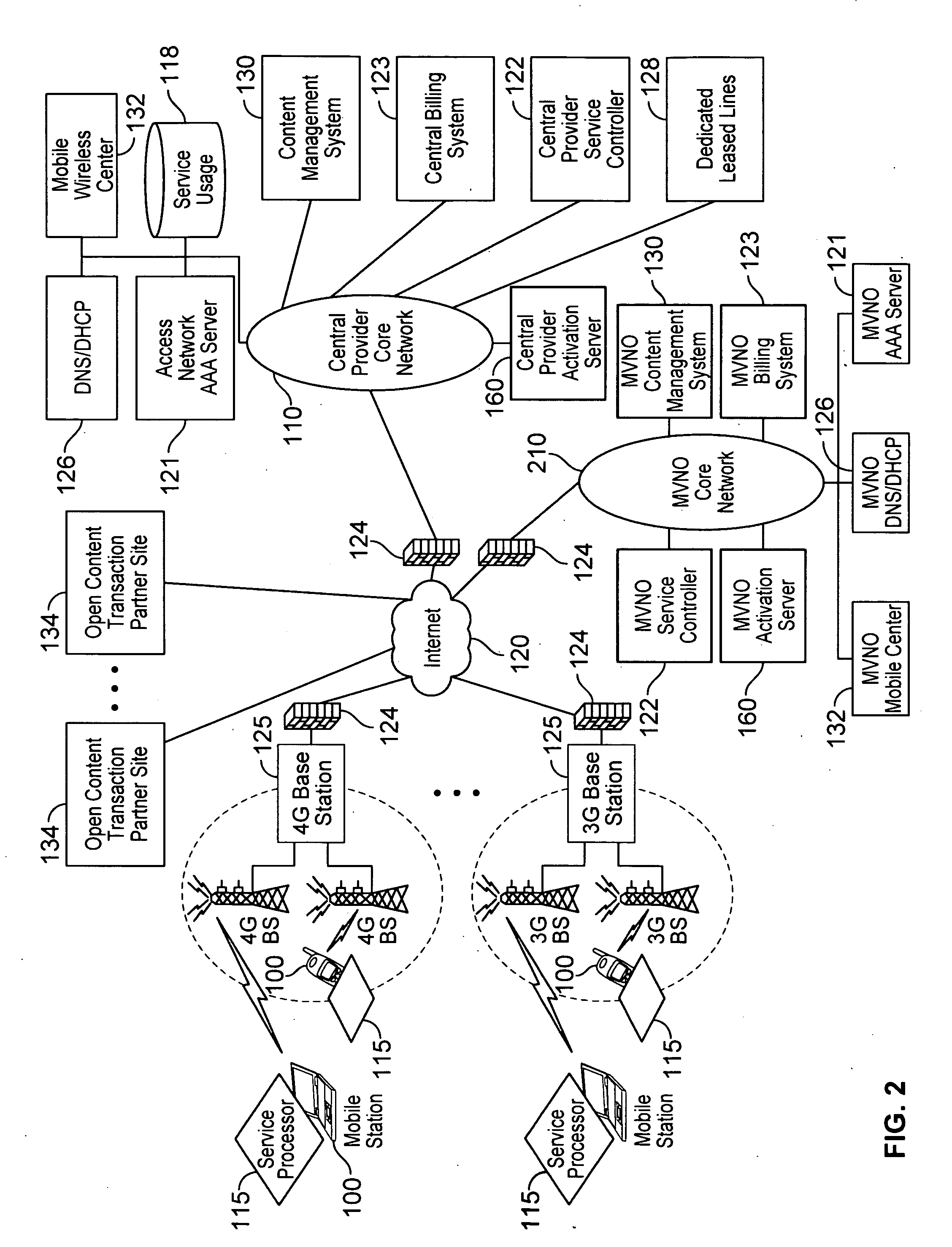
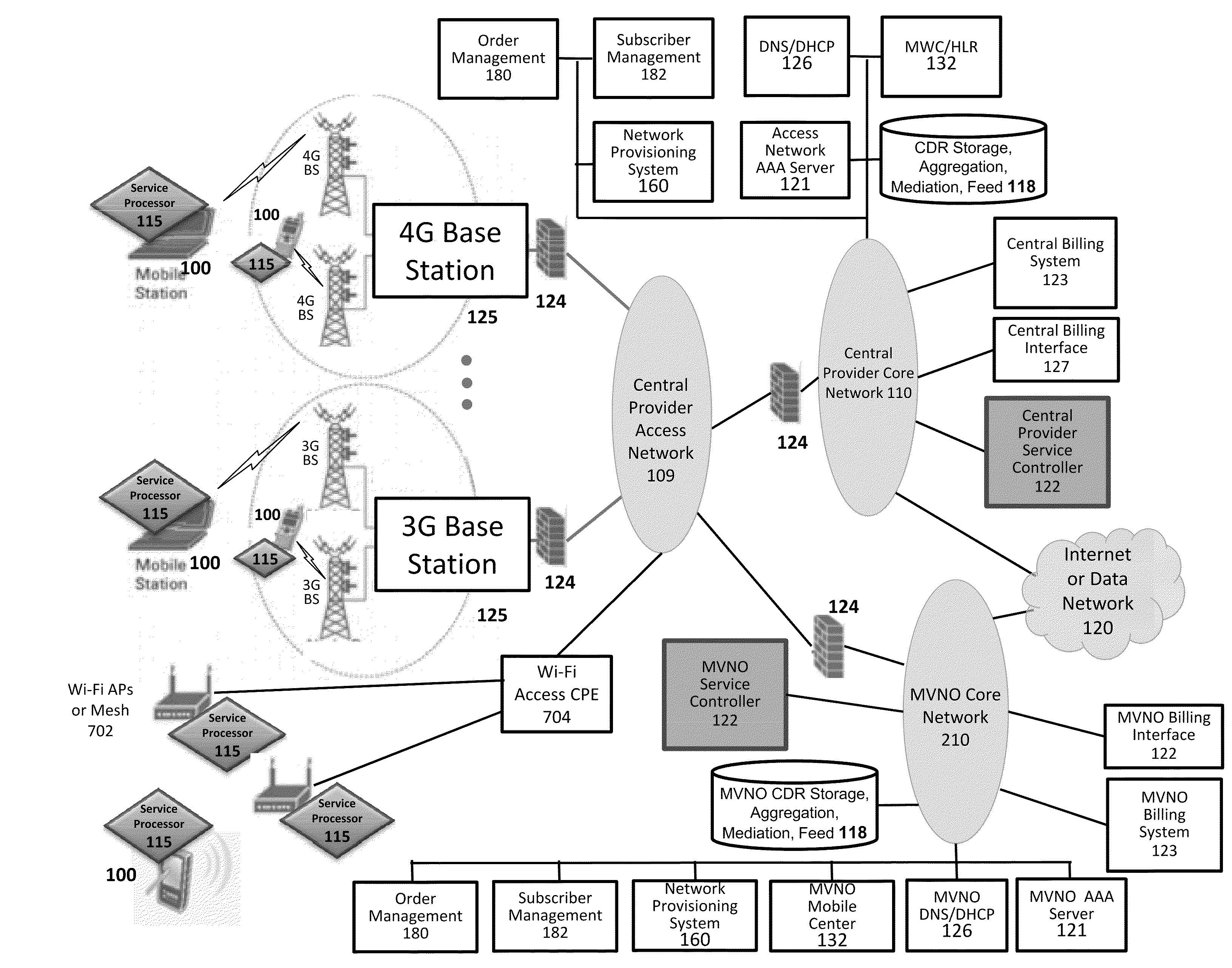
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a network device executes a service controller for a plurality of device groups, in which the service controller includes a capability to securely partition one or more device group database partitions, each device group partition includes service controller system settings, and each device group includes a plurality of communication devices controlled by a virtual service provider.
Owner:HEADWATER RES LLC
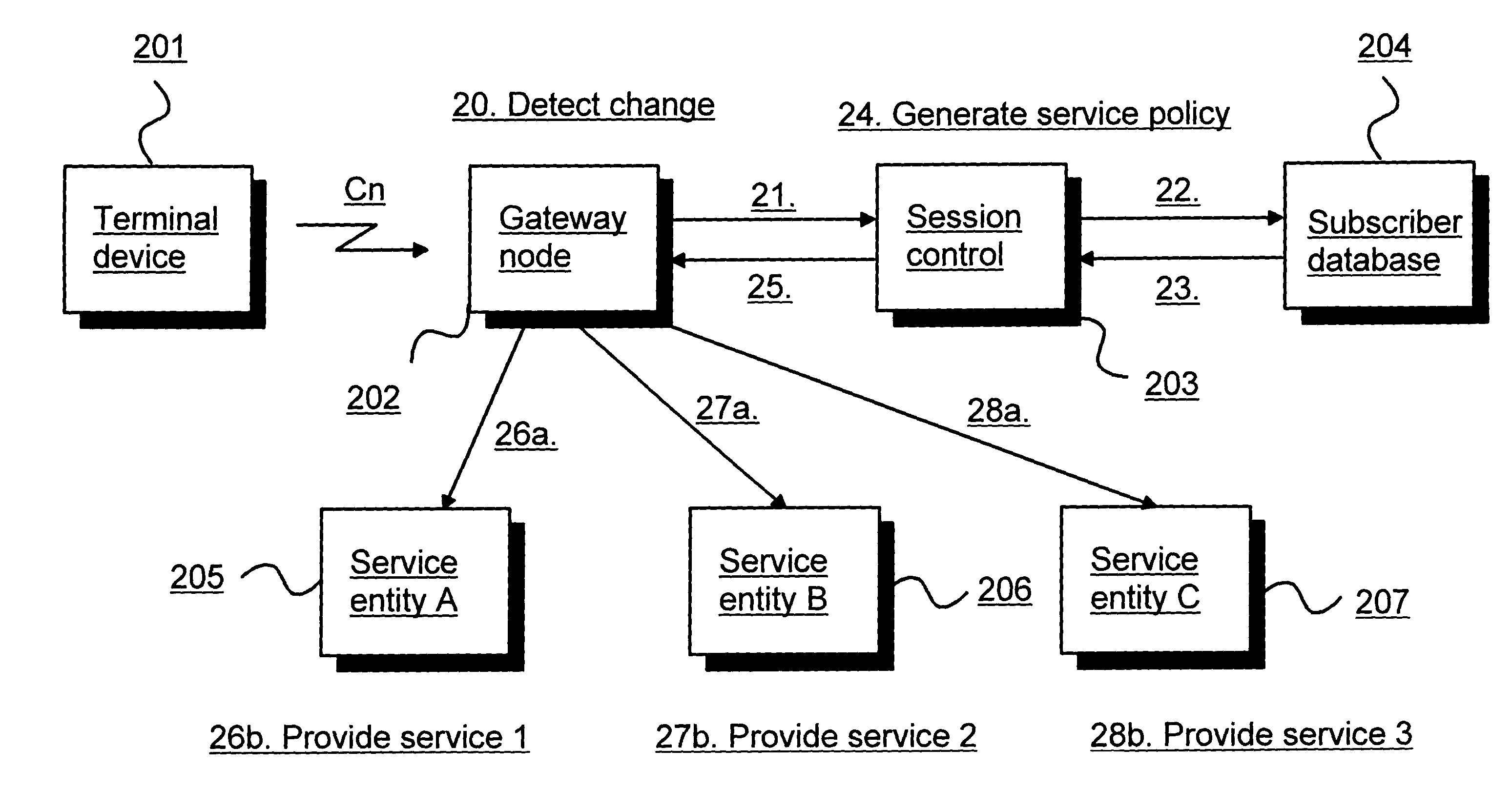
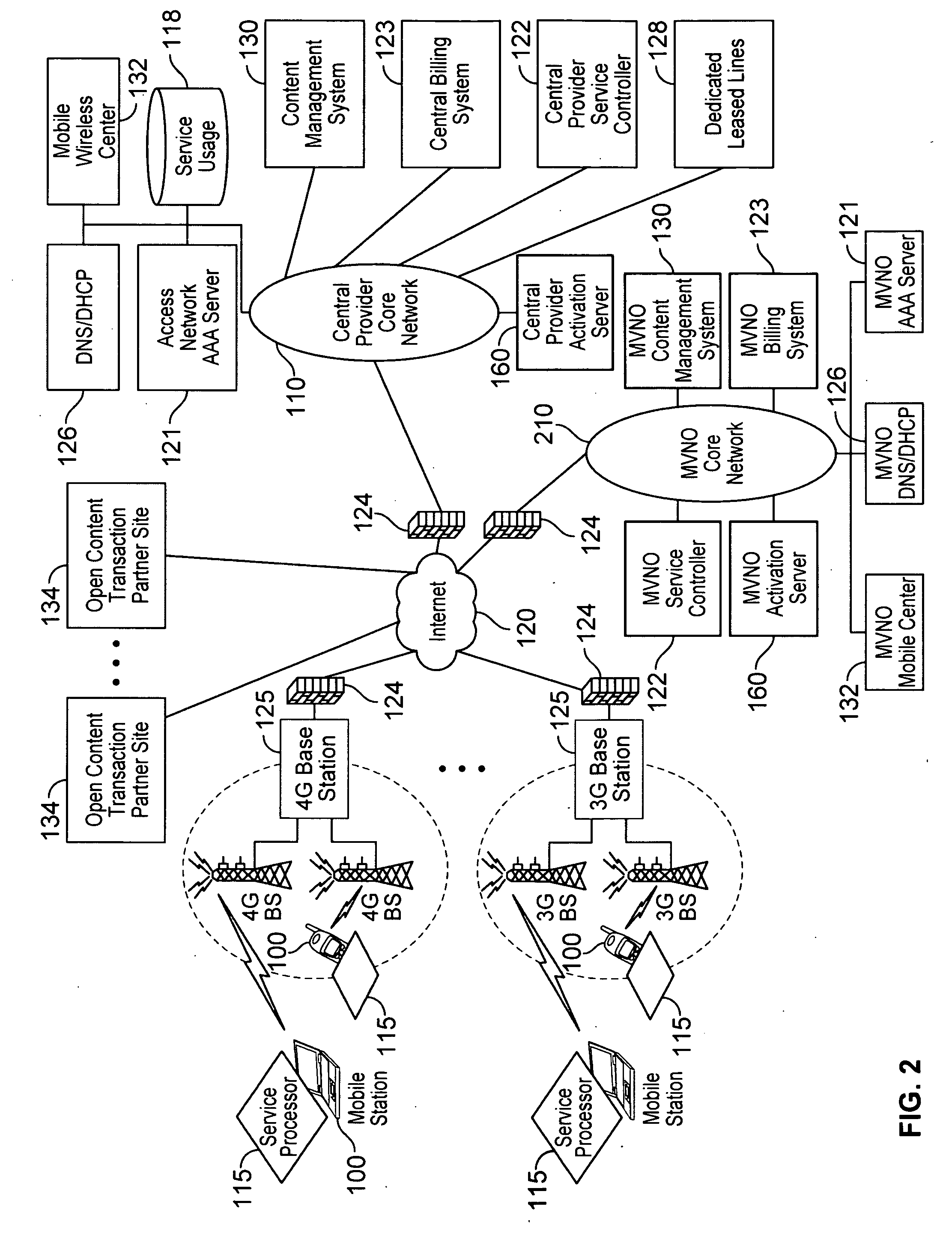
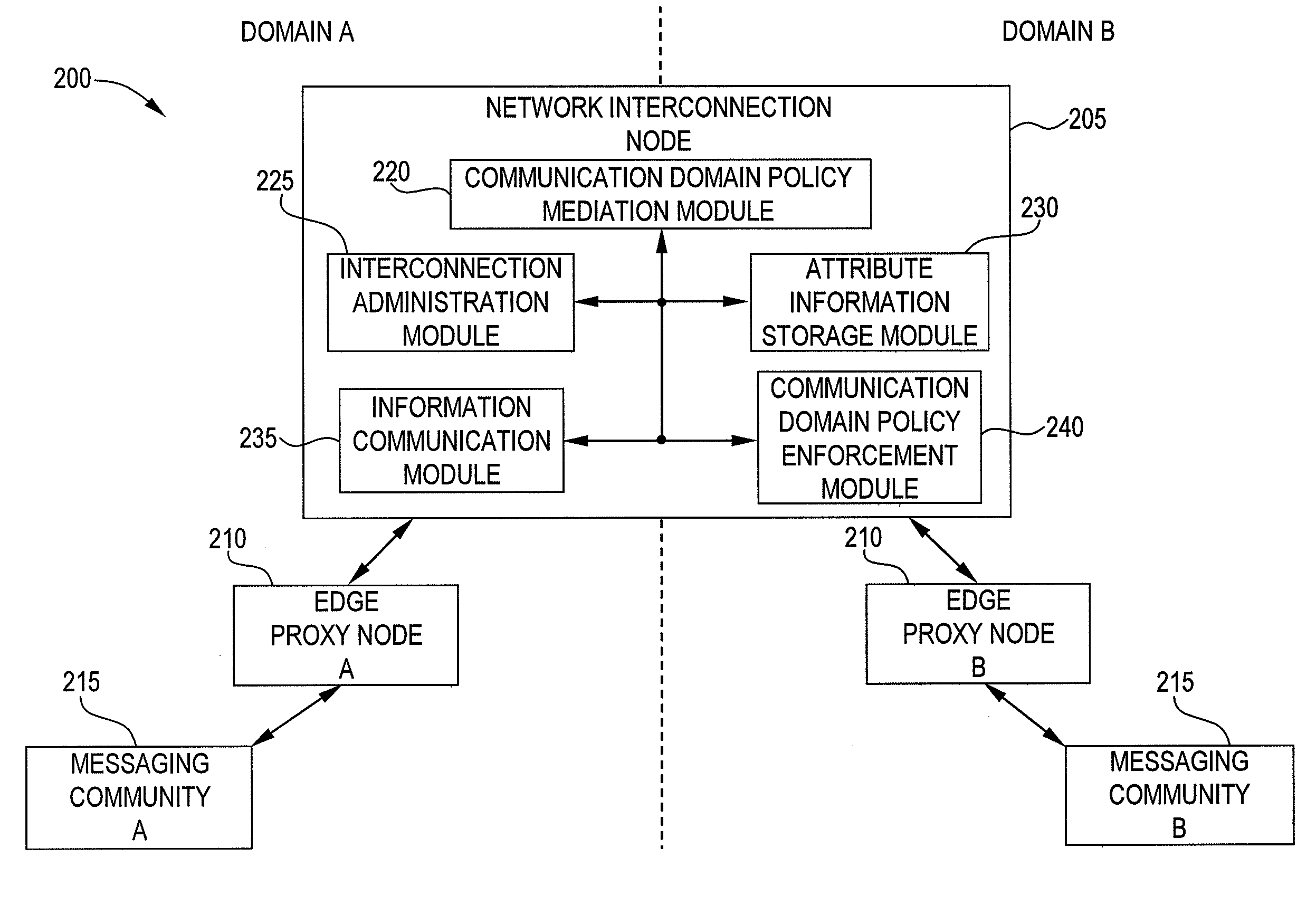
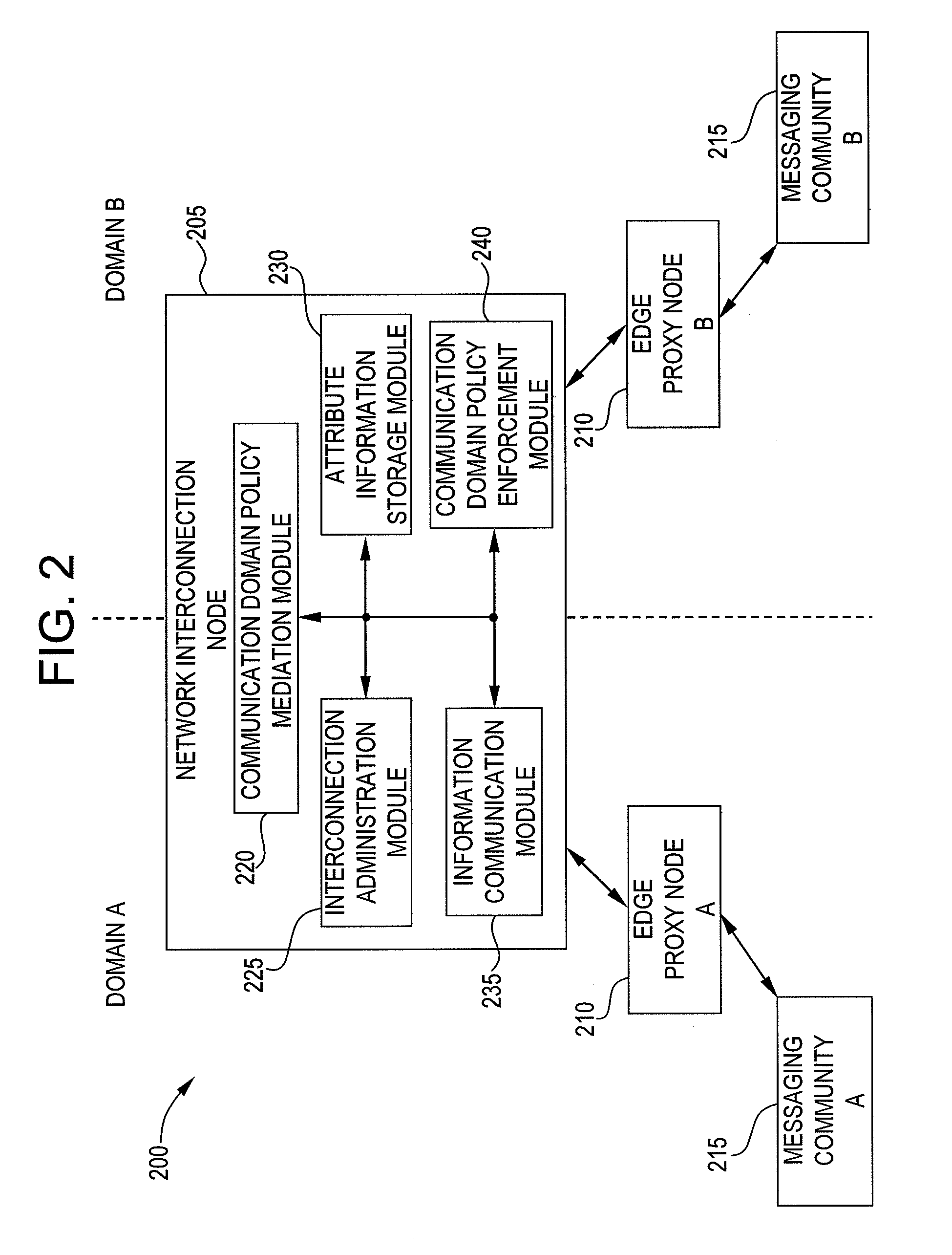
System and method for managing domain policy for interconnected communication networks
InactiveUS20080133729A1Digital computer detailsData switching networksInterconnectionLong-haul communications
The present invention is directed to a system and method for managing domain policy for interconnected communication networks. The present invention governs communication service policy for interconnection among remote communication services to allow users to communicate with other users in remote domains. Exemplary embodiments allow the local communication services to guarantee certain service aspects even when remote domains are involved. For example, the local service enablers can assert their local service policy across domains. A local service enabler can choose other service enablers in remote domains based on specific criteria that meets the local service enabler's settings and user preferences. The local service enabler can protect itself from connection to other service enablers that may contradict its local settings. Thus, the present invention can manage communication services across remote domains, while each domain can continue to be managed locally according to the needs and preferences of the local users.
Owner:NEUSTAR
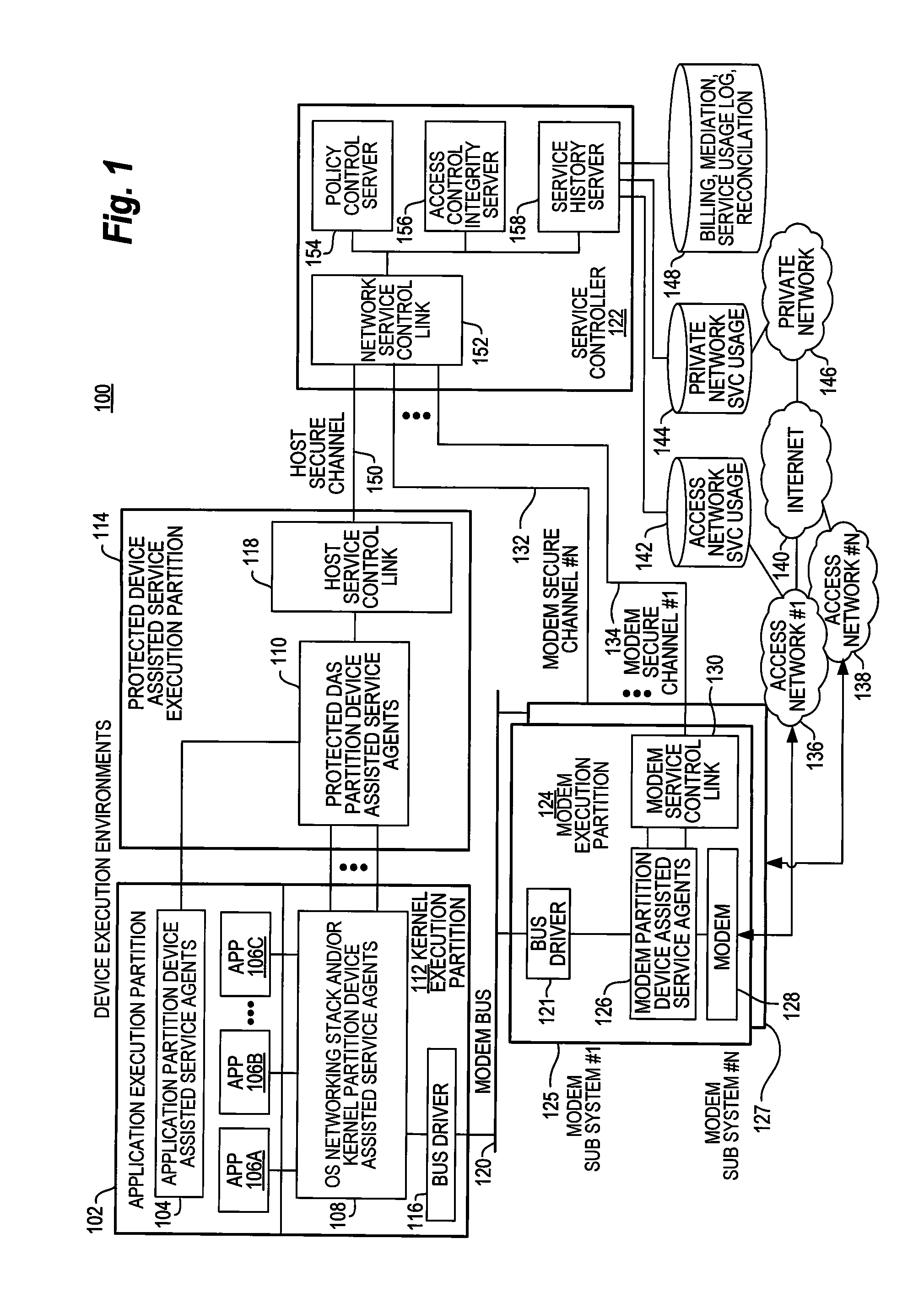
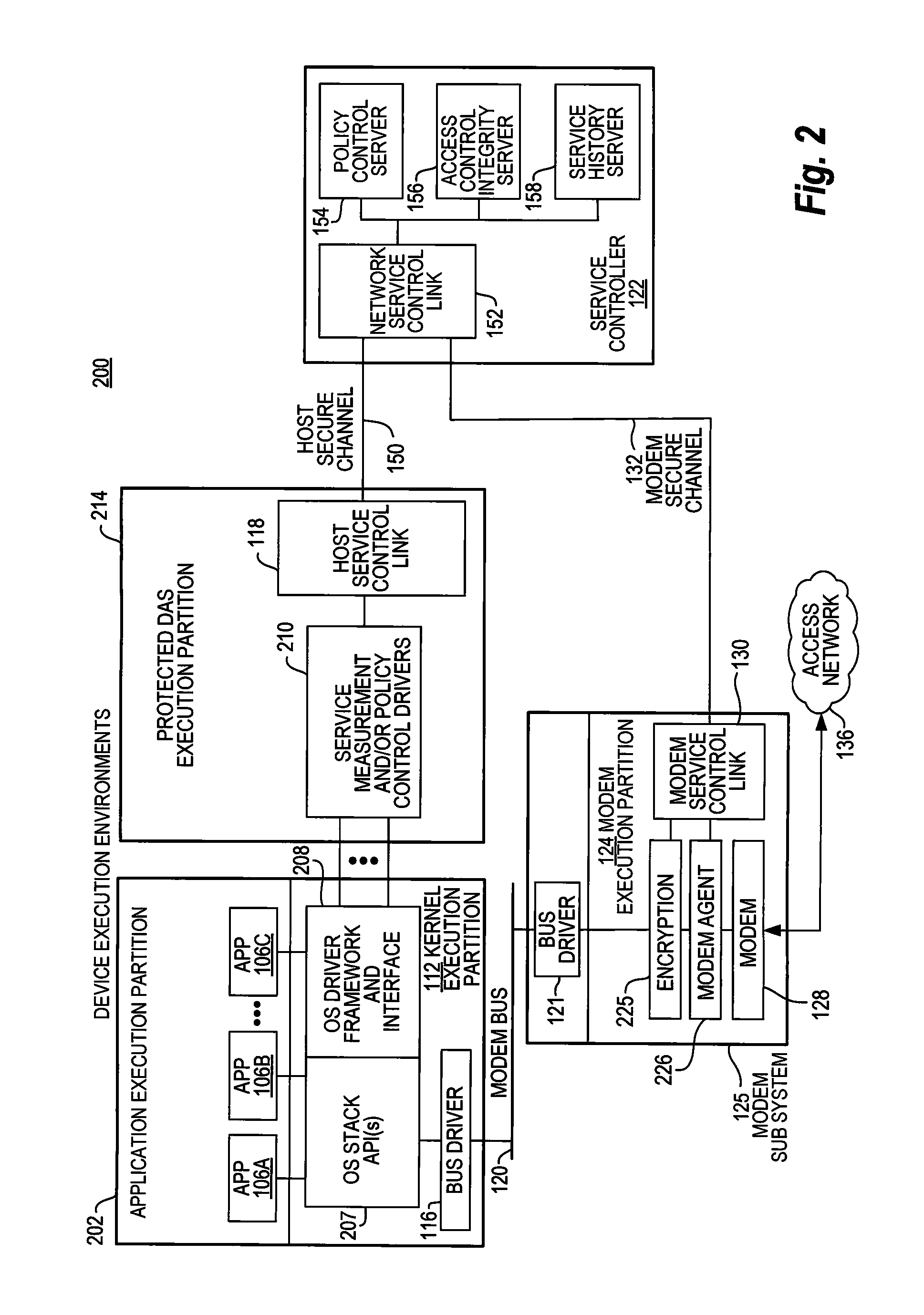
Security techniques for device assisted services
ActiveUS8391834B2Digital data processing detailsTechnology managementService profileService planning
Security techniques for device assisted services are provided. In some embodiments, secure service measurement and / or control execution partition is provided. In some embodiments, implementing a service profile executed at least in part in a secure execution environment of a processor of a communications device for assisting control of the communications device use of a service on a wireless network, in which the service profile includes a plurality of service policy settings, and wherein the service profile is associated with a service plan that provides for access to the service on the wireless network; monitoring use of the service based on the service profile; and verifying the use of the service based on the monitored use of the service.
Owner:HEADWATER RES LLC
Associating multiple display units in a grouped server environment
InactiveUS6915347B2Multiple digital computer combinationsTransmissionComputer moduleAncillary service
A method for grouping Human Interface Devices (HIDs) into a multi-head display is provided. The HIDs are identified as either “primary” or “secondaries”. A computational-service policy module is consulted when a new HID connects to the network. If the HID is identified as a secondary, the module consults all servers within a group to see if the primary presently has an active session connected to any of the servers. If the primary is being controlled by the same server to which the secondary is connected, the session connection information for the primary is augmented to indicate that the secondary is attached to the same session, and this information is disseminated to the interested software entities. The associated session may then provide multi-head outout to the secondary. If the primary is being controlled by another server in the group, the secondary re-attaches to the server that is hosting the primary.
Owner:ORACLE INT CORP
Verifiable device assisted service usage billing with integrated accounting, mediation accounting, and multi-account
ActiveUS20120089845A1Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemService usage
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting billing for the communications device use of a service on a network; and monitors use of the service based on the service policy, in which a local service usage is synchronized with a network based service usage.
Owner:HEADWATER RES LLC
Mobile alerting network
ActiveUS20090209233A1Sufficient operationUnauthorised/fraudulent call preventionRoad vehicles traffic controlApplication service providerVerification system
A system for providing a mobile application includes a Mobile Subscriber Detection Authorization and Verification System (MSDAVS), to request and receive confidential information from a confidential information owner relating to a user who opted-in to a mobile service application, and to communicate the received confidential information to a mobile application service provider. The MSDAVS can include an opt-in database, to store opt-in or registration data of the opted-in users of the mobile service application and a service policy database. The mobile application service can be a mobile traffic alerting service, the confidential information owner a telephone number database of one of a wireless carrier or a telephone number database operator, and the requested confidential information a list telephone numbers of opted-in users in an alert area, defined by the mobile traffic alerting service.
Owner:GLOBAL TRAFFIC NETWORK INC
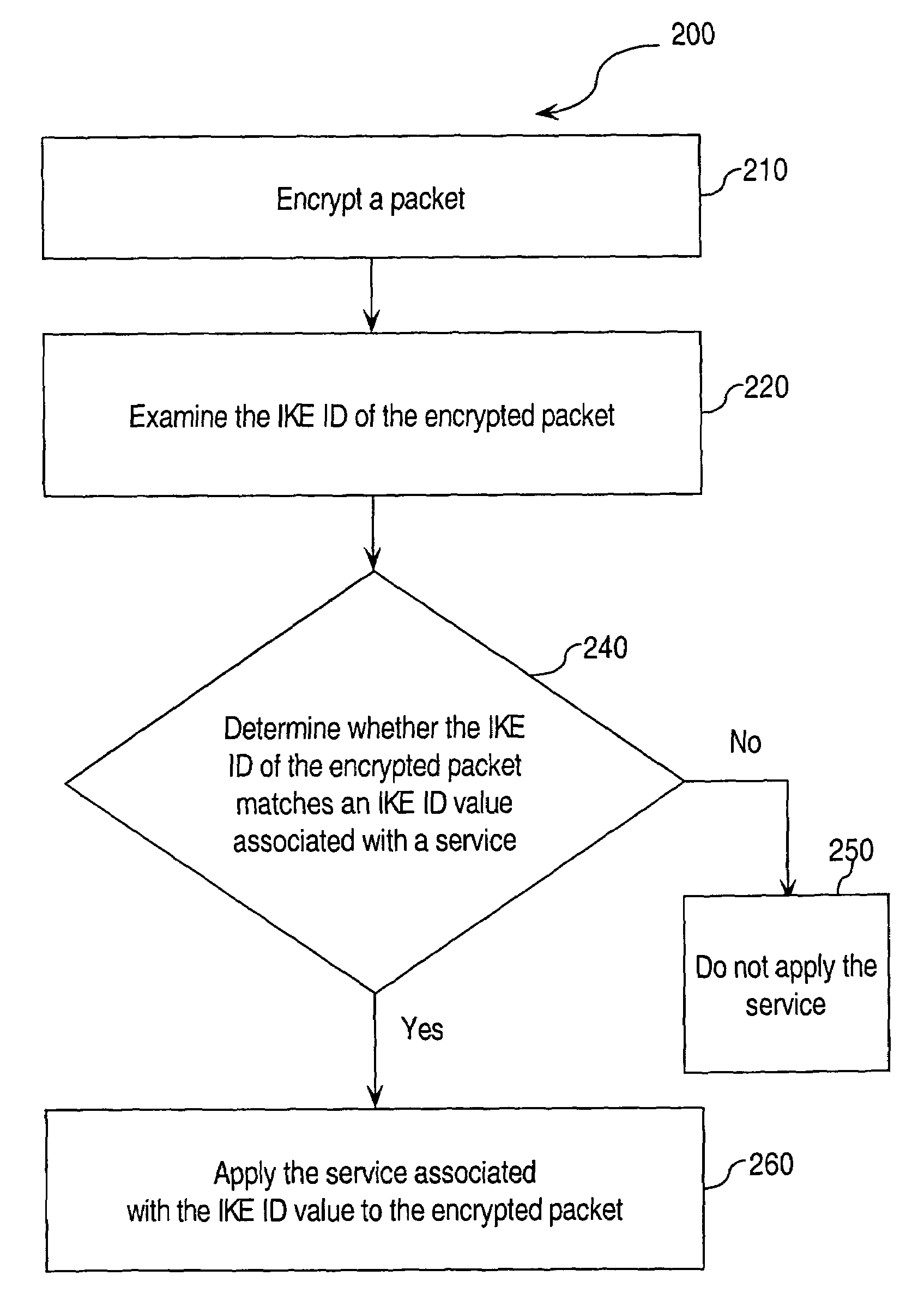
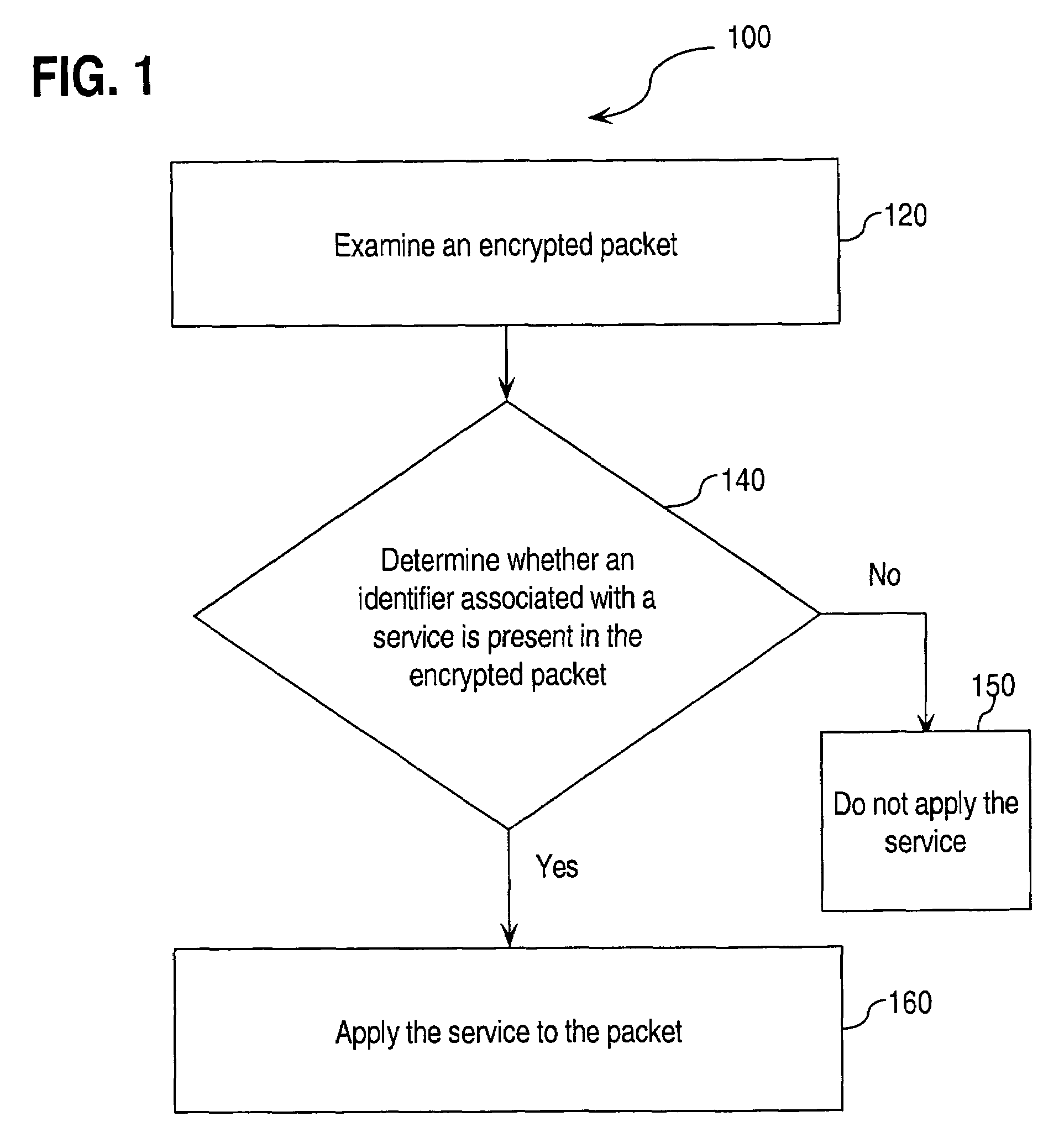
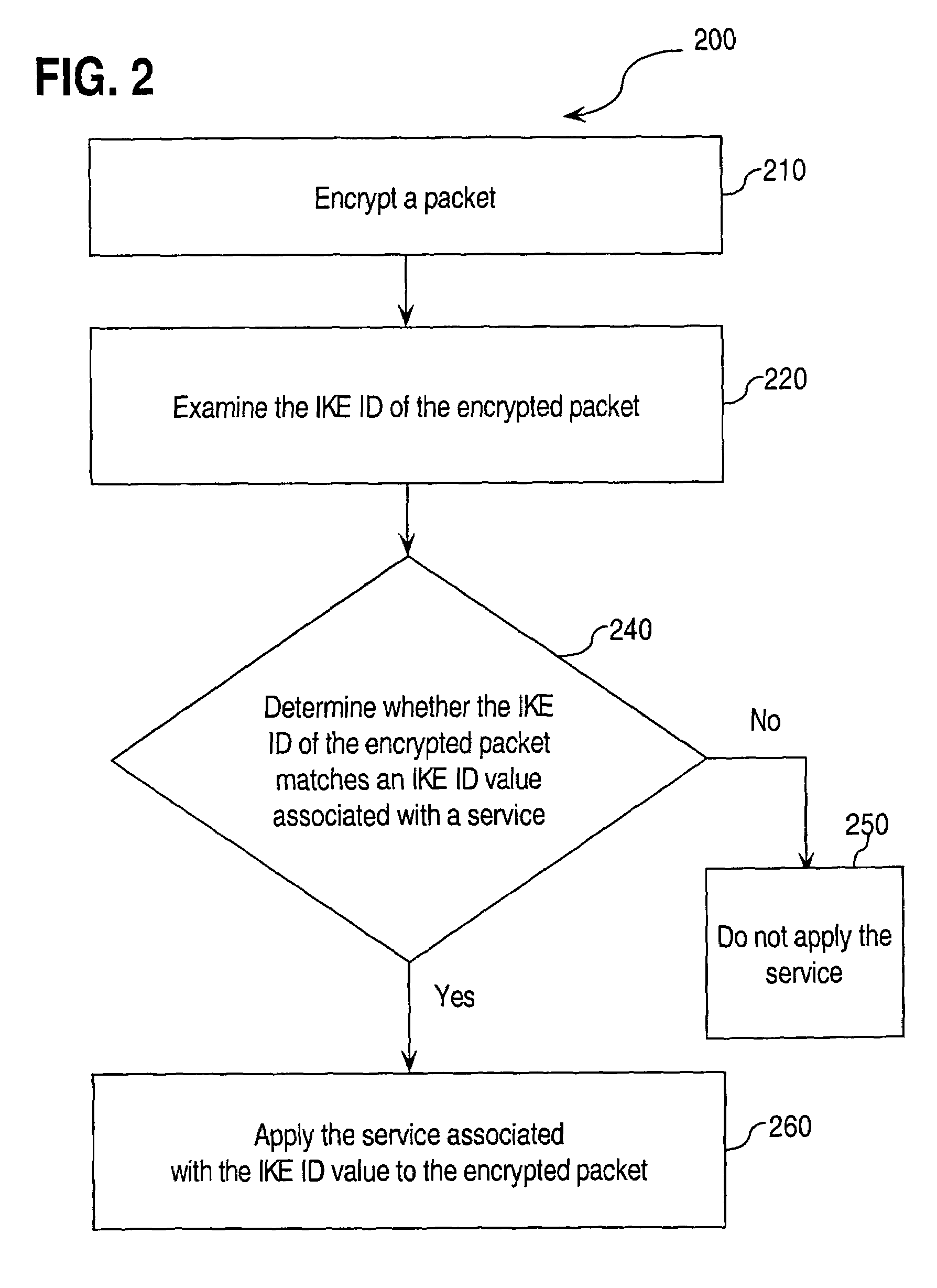
Approaches for applying service policies to encrypted packets
InactiveUS7562213B1Avoiding and reducing relianceSecuring communicationKey exchangeInternet Key Exchange
Approaches for applying service polices to encrypted packets are disclosed. One approach comprises examining an encrypted packet, determining whether an identifier associated with a service is present in an encrypted packet, and if it is determined that the identifier is present in the encrypted packet, applying the service to the encrypted packet. In an embodiment, the identifier is the Internet Key Exchange (IKE) ID of the encrypted packet.
Owner:CISCO TECH INC
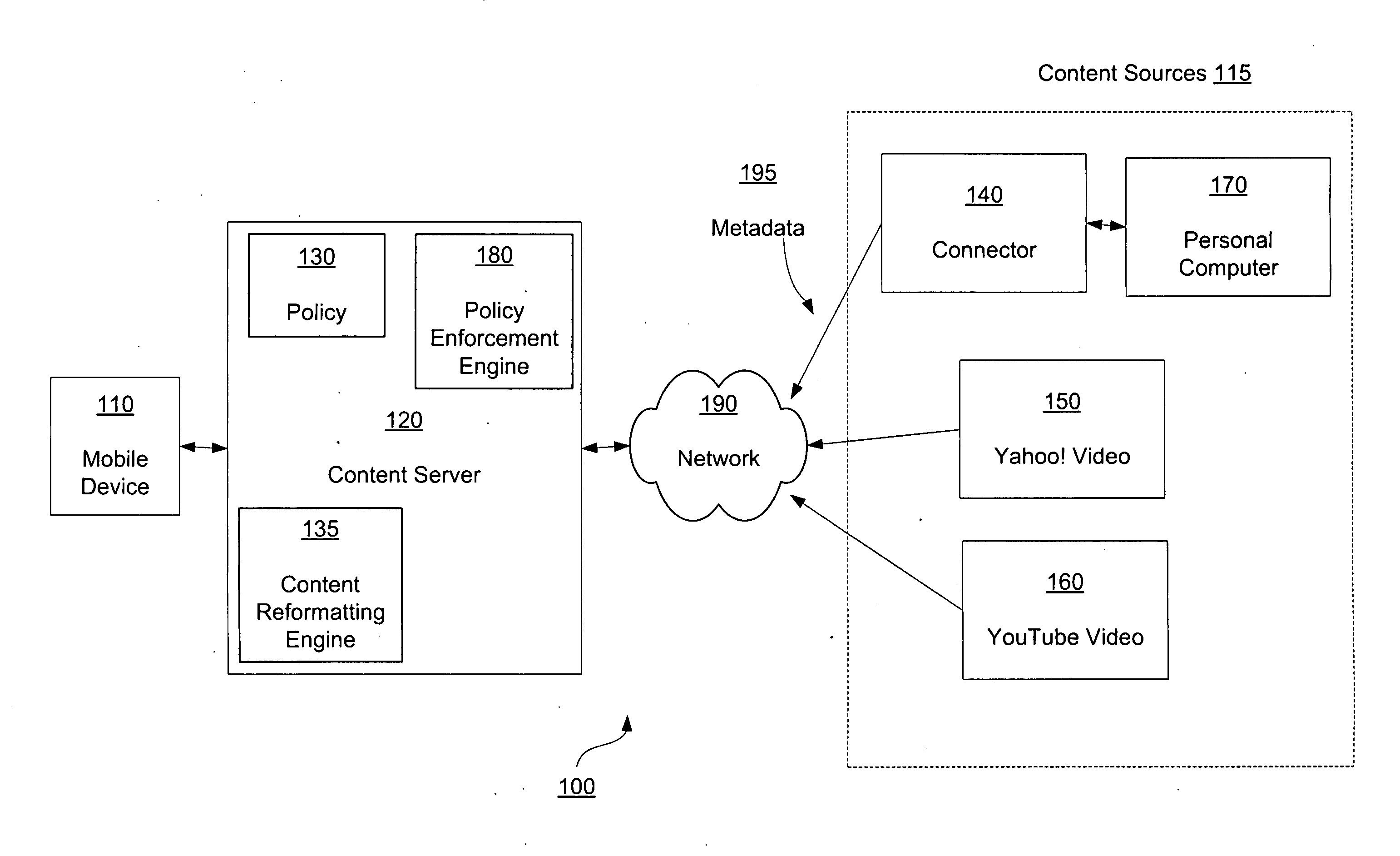
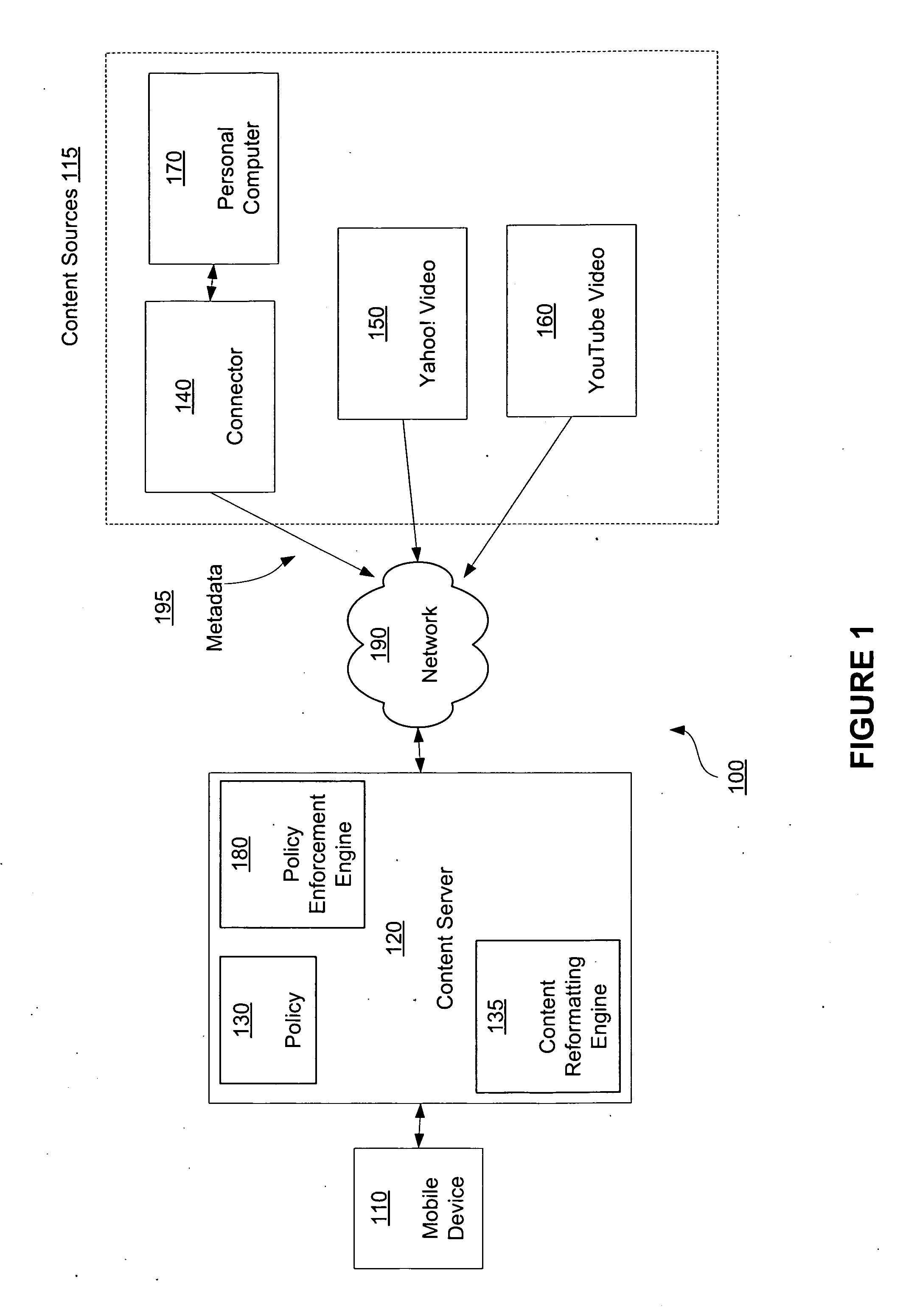
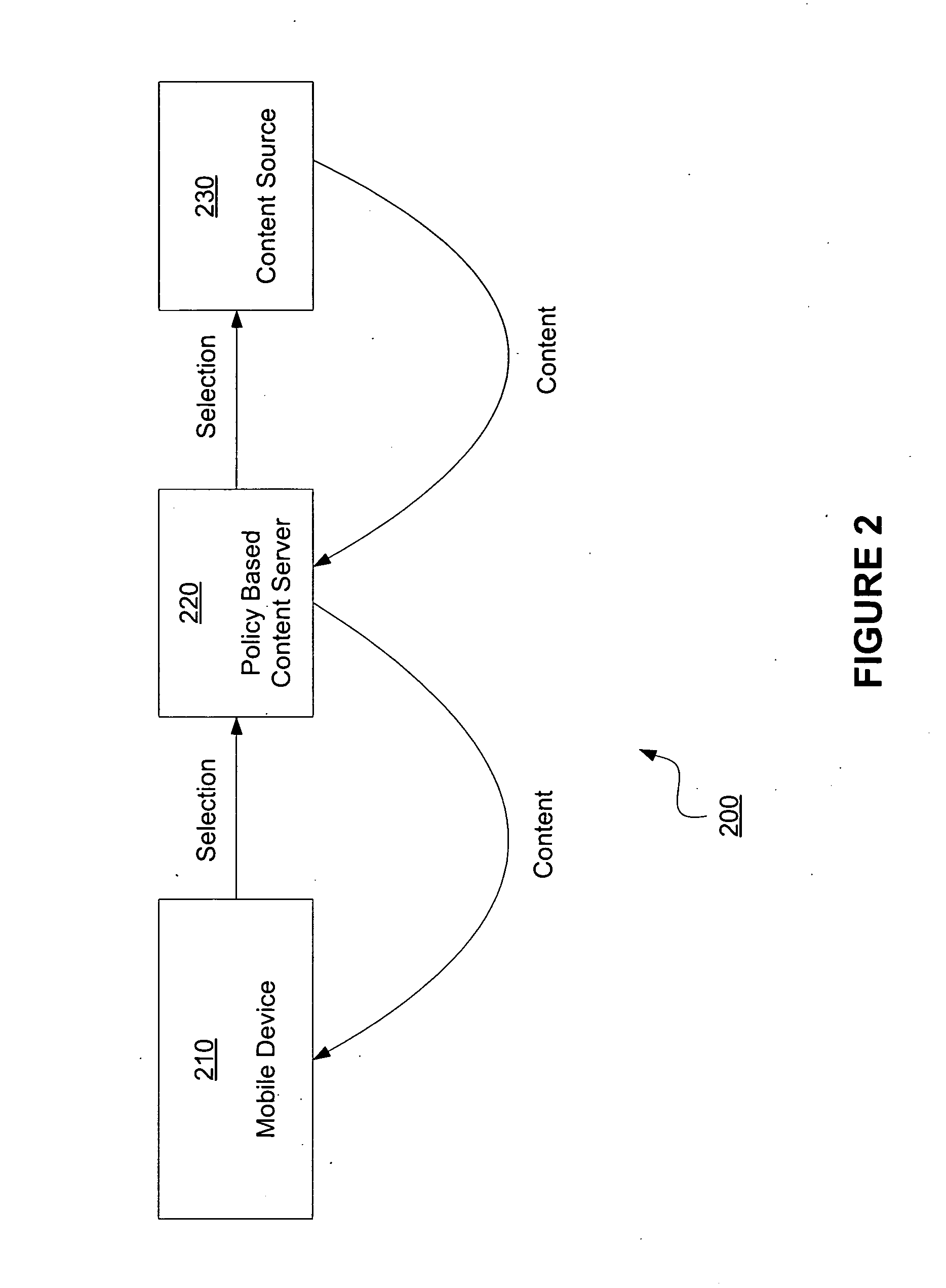
Policy based content service
InactiveUS20090164560A1Digital data information retrievalMultiple digital computer combinationsNetwork conditionsMobile device
Serving user selected content in accordance with a service policy is disclosed. The user may select content from a content source to be accessed at a mobile device. The desired content is modified as necessary such that transmission of the content complies with a policy. Alternatively, only content that complies with the policy may be made available for selection. The manner in which a policy is defined and the content provided may be determined by various factors including mobile device capabilities, user preferences, and network conditions.
Owner:SEVEN NETWORKS INC
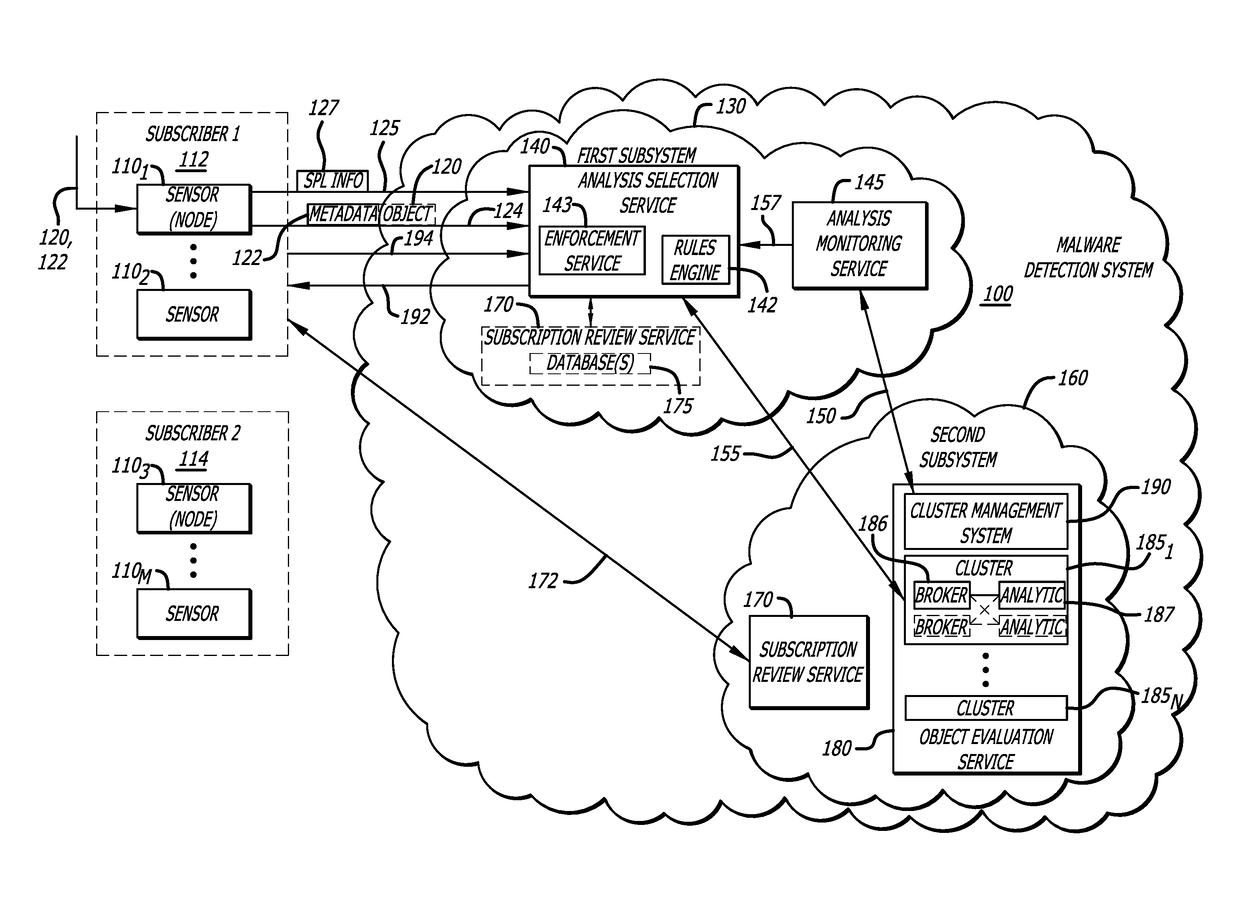
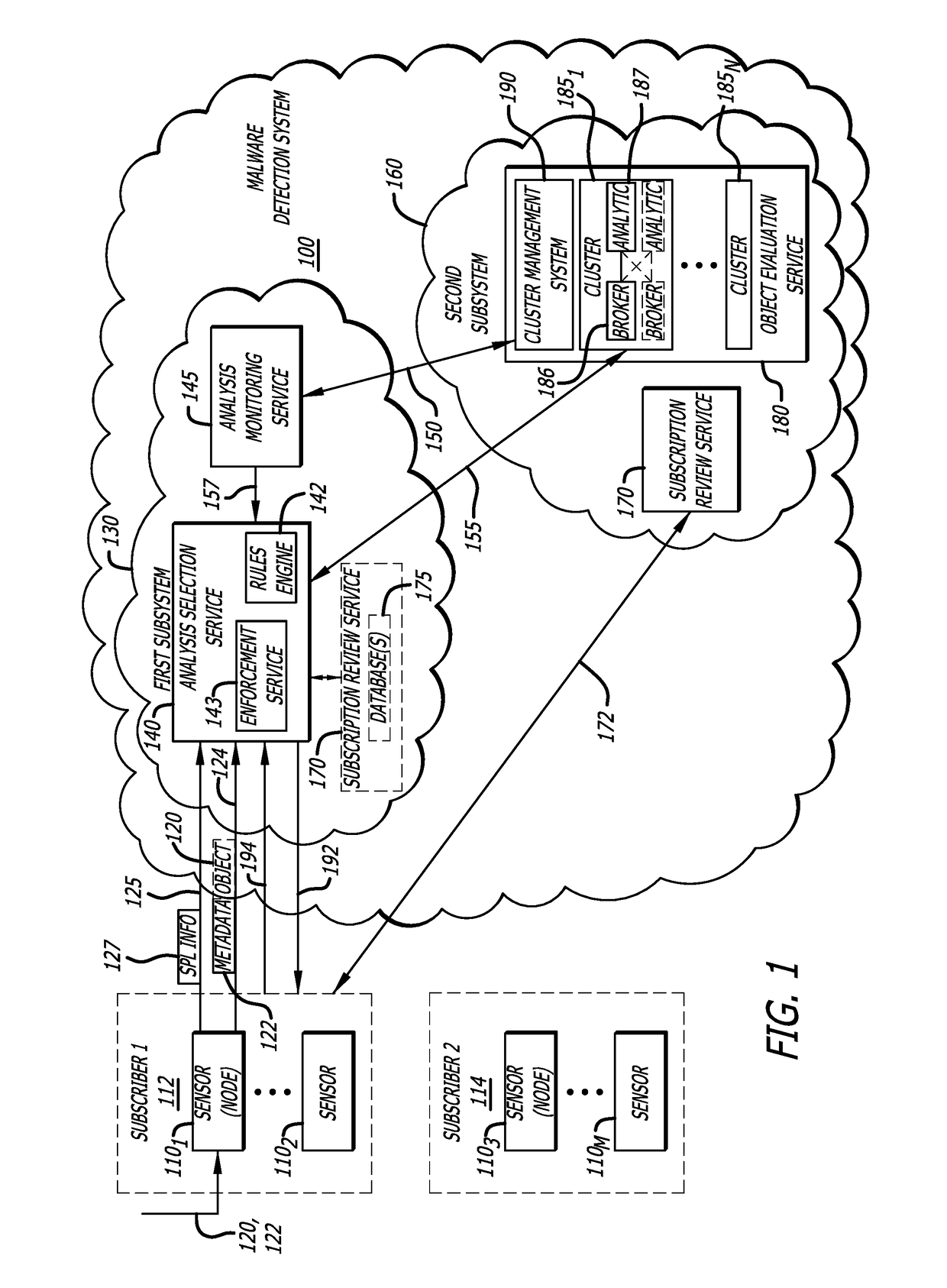
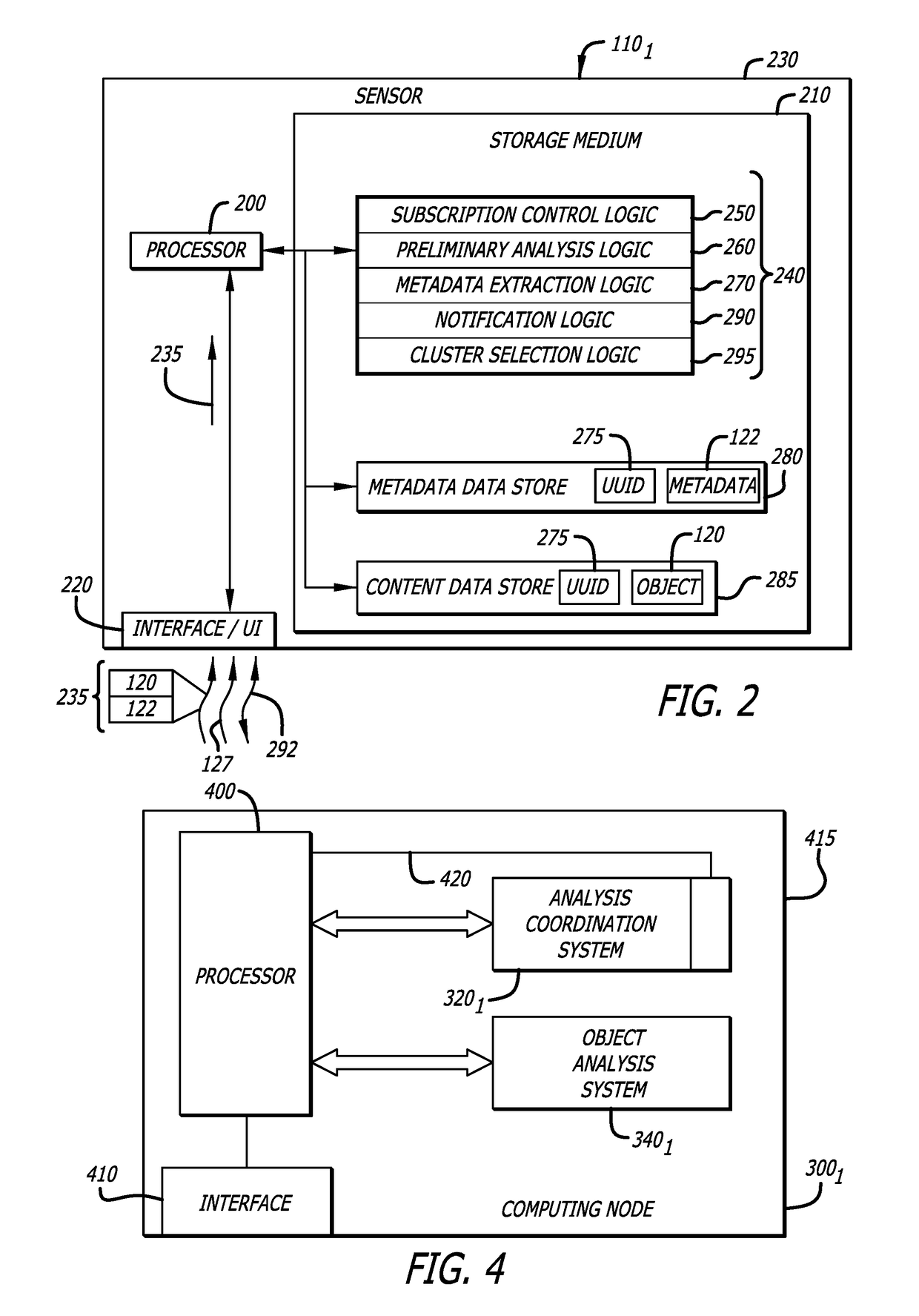
Attribute-controlled malware detection
A computerized method for authenticating access to a subscription-based service to detect an attempted cyber-attack. The method features operations by the cloud broker that include receiving service policy level information and information based on operational metadata. The service policy level information includes at least subscription attributes to identify one or more performance criterion in analyses conducted on one or more objects submitted by a sensor for malware representing an attempted cyber-attack. The operational metadata includes metadata that pertains to an operating state of one or more clusters of a plurality of clusters of the subscription-based service. The cloud broker, using both the service policy level information and the information based on the operational metadata, selecting a cluster of the plurality of clusters to analyze the one or more objects submitted by the sensor and establishes a communication session between the sensor and the cluster via the cloud broker.
Owner:FIREEYE SECURITY HLDG US LLC
System and method for providing authentication service for internet of things security
ActiveUS20160173495A1Providing serviceUser identity/authority verificationMultiple digital computer combinationsInternet Authentication ServiceIot gateway
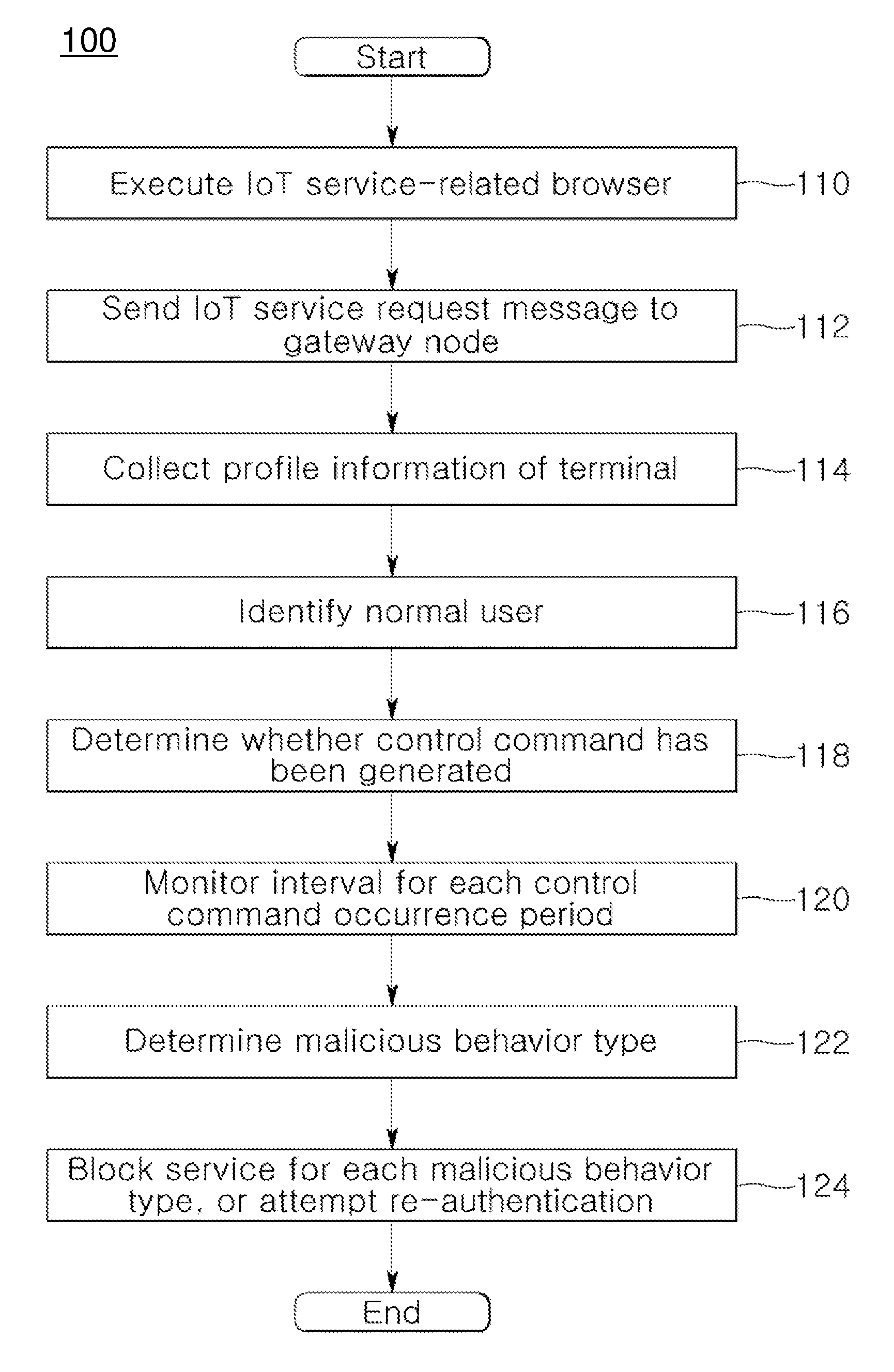
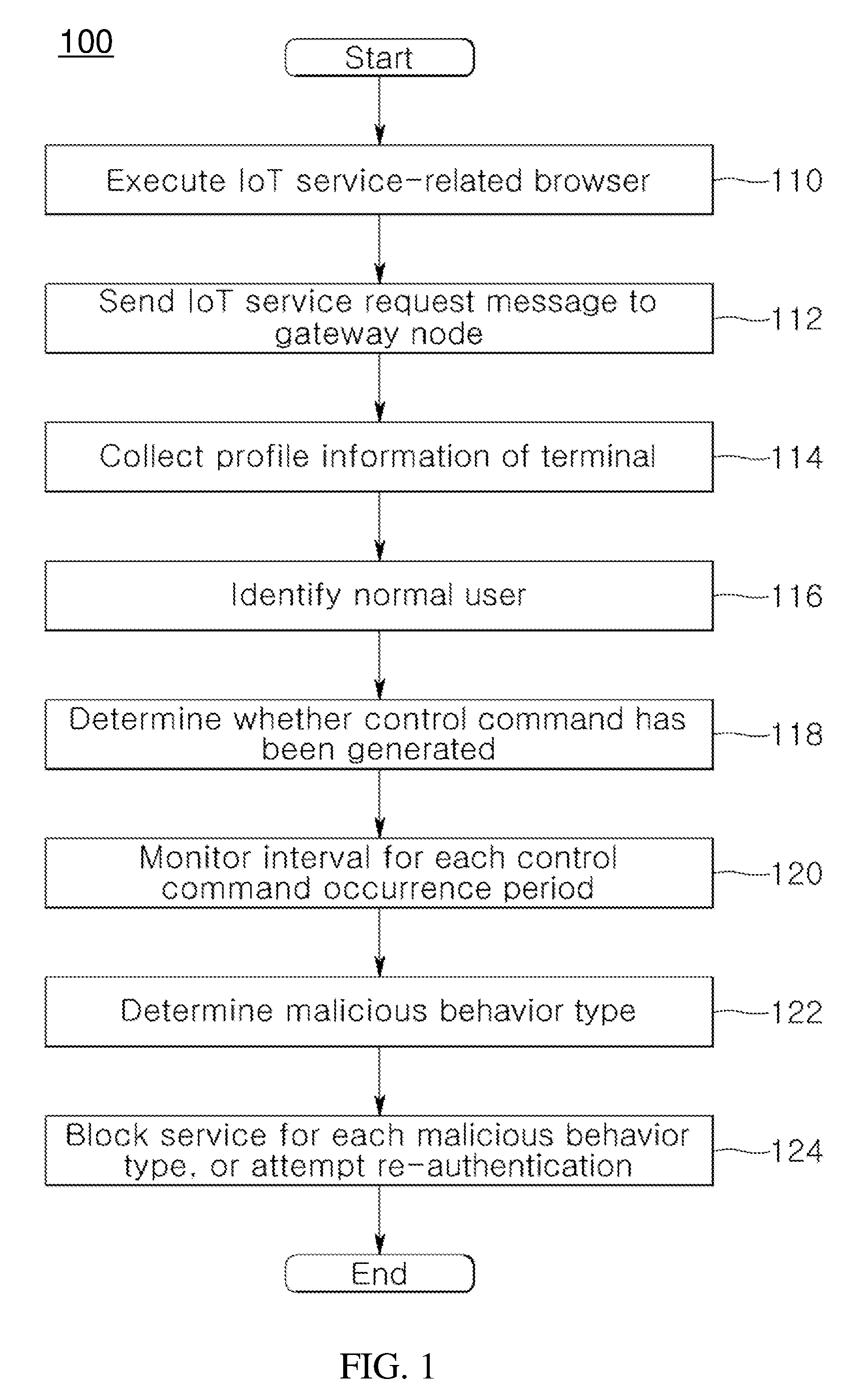
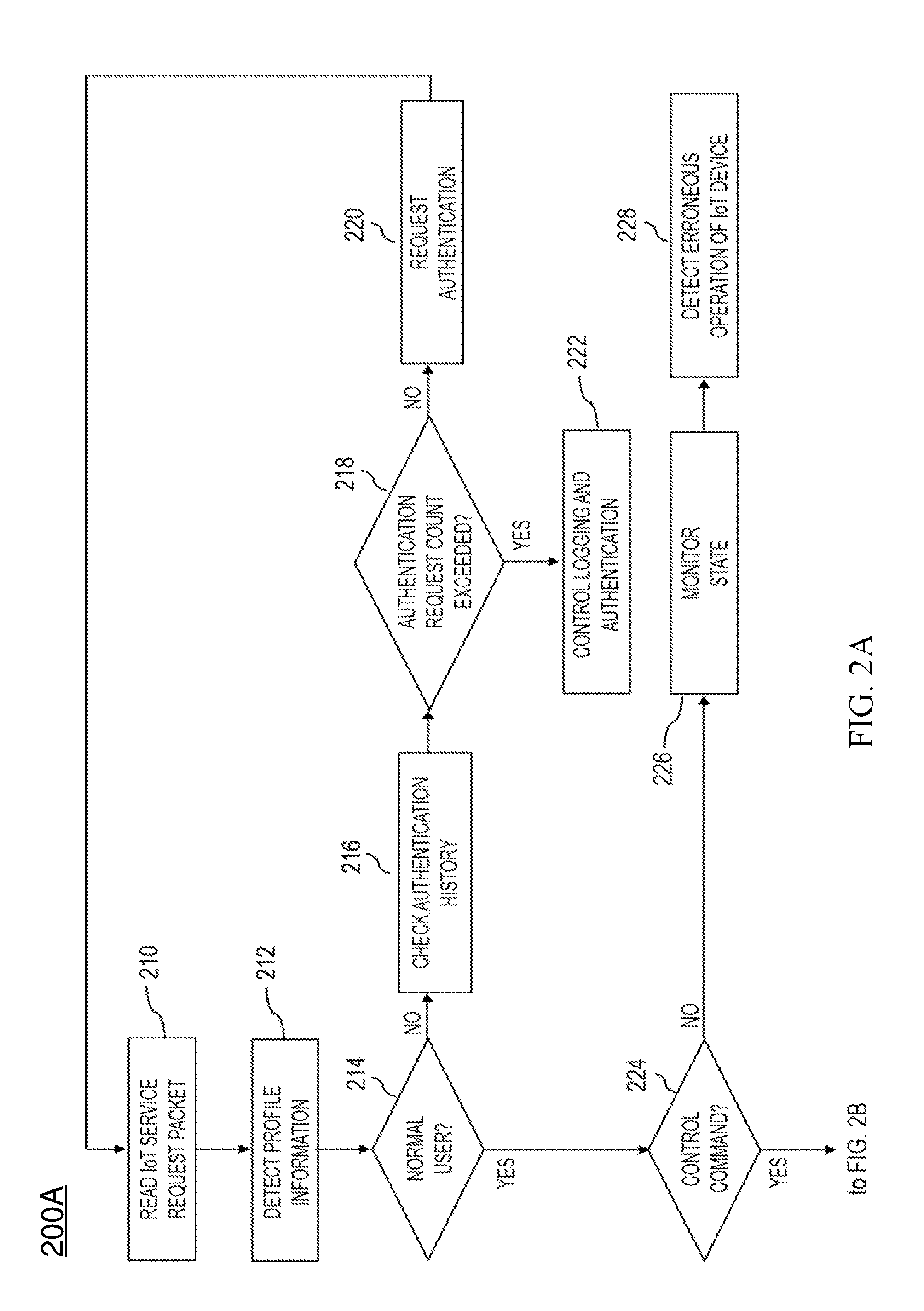
A system and method for providing authentication service for IoT security are disclosed herein. The system for providing authentication service for IoT security includes an Internet of Things (IoT) service server, and an IoT gateway node. The IoT service server supports an IoT communication service in accordance with an IoT communication service policy. The IoT gateway node receives an IoT service request from a terminal attempting to control an IoT device that supports the IoT communication service while operating in conjunction with the IoT service server, identifies whether the terminal attempting to control the IoT device is a normal user based on profile information, collected from the terminal via the IoT service request, via the IoT service server, and performs the security authentication of the IoT device.
Owner:WINS CO LTD
Providing desired service policies to subscribers accessing internet
InactiveUS6952728B1Minimize the numberFast forwardMultiple digital computer combinationsElectric digital data processingAccess networkContent-addressable storage
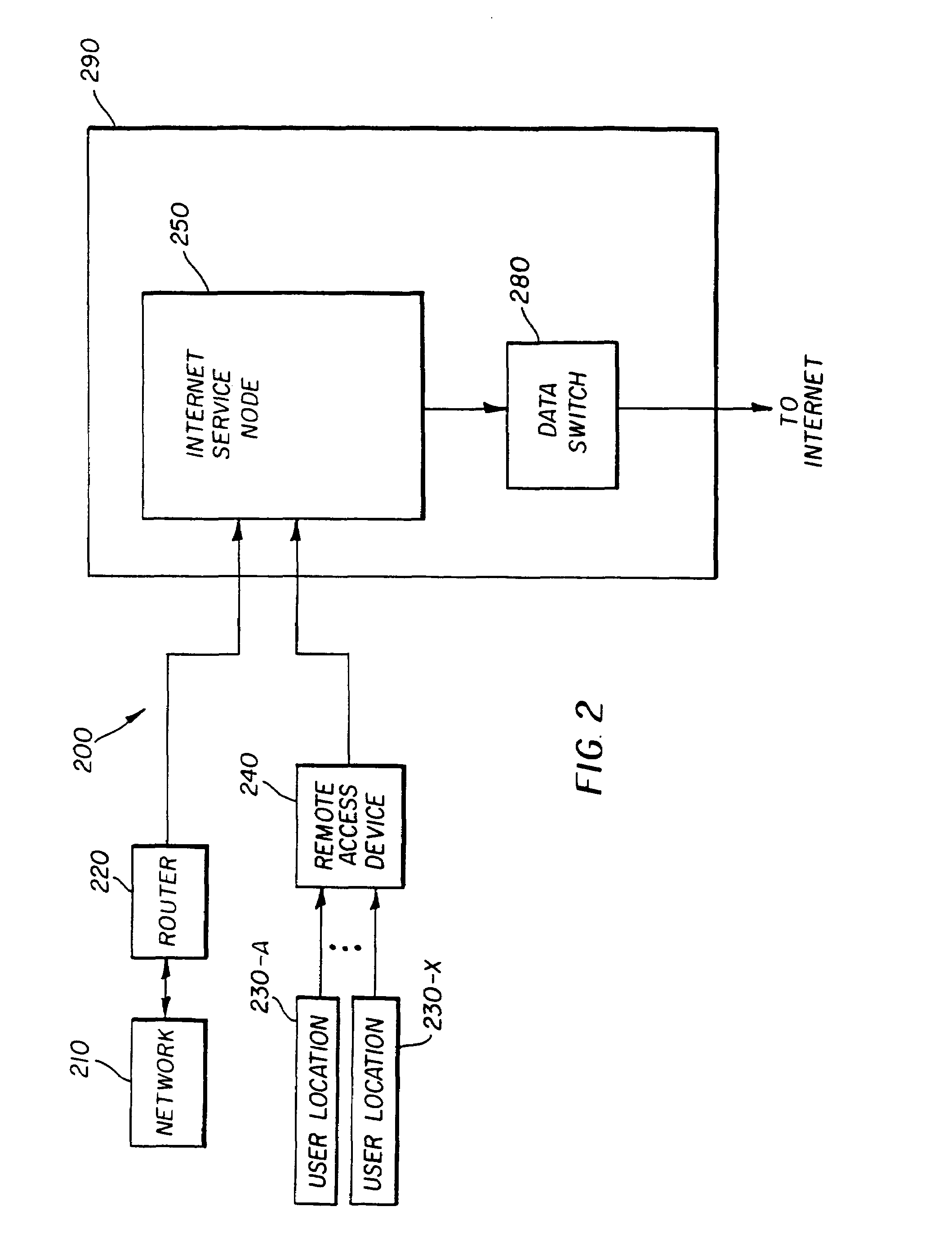
An internet service node (ISN) enabling the provision of desired service policies to each subscriber. The ISN may contain multiple processor groups, with each subscriber being assigned to a processor group. The assigned processor group may be configured with the processing rules, which provide the service policies desired, by a subscriber. A port may determine the specific processor group to which received data is to be forwarded. A content addressable memory with masks for individual locations may be implemented to quickly determines the processor group to which received data is to be assigned to. Due to the features of the present invention, an ISN may be able to serve a large number of subscribers efficiently. The ISN may be used at the edge of an access network.
Owner:RPX CLEARINGHOUSE
Sticky Service Sessions in a Datacenter
ActiveUS20160094661A1Connection managementMultiple digital computer combinationsCloud baseData center
Some embodiments provide novel inline switches that distribute data messages from source compute nodes (SCNs) to different groups of destination service compute nodes (DSCNs). In some embodiments, the inline switches are deployed in the source compute nodes datapaths (e.g., egress datapath). The inline switches in some embodiments are service switches that (1) receive data messages from the SCNs, (2) identify service nodes in a service-node cluster for processing the data messages based on service policies that the switches implement, and (3) use tunnels to send the received data messages to their identified service nodes. Alternatively, or conjunctively, the inline service switches of some embodiments (1) identify service-nodes cluster for processing the data messages based on service policies that the switches implement, and (2) use tunnels to send the received data messages to the identified service-node clusters. The service-node clusters can perform the same service or can perform different services in some embodiments. This tunnel-based approach for distributing data messages to service nodes / clusters is advantageous for seamlessly implementing in a datacenter a cloud-based XaaS model (where XaaS stands for X as a service, and X stands for anything), in which any number of services are provided by service providers in the cloud.
Owner:NICIRA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com