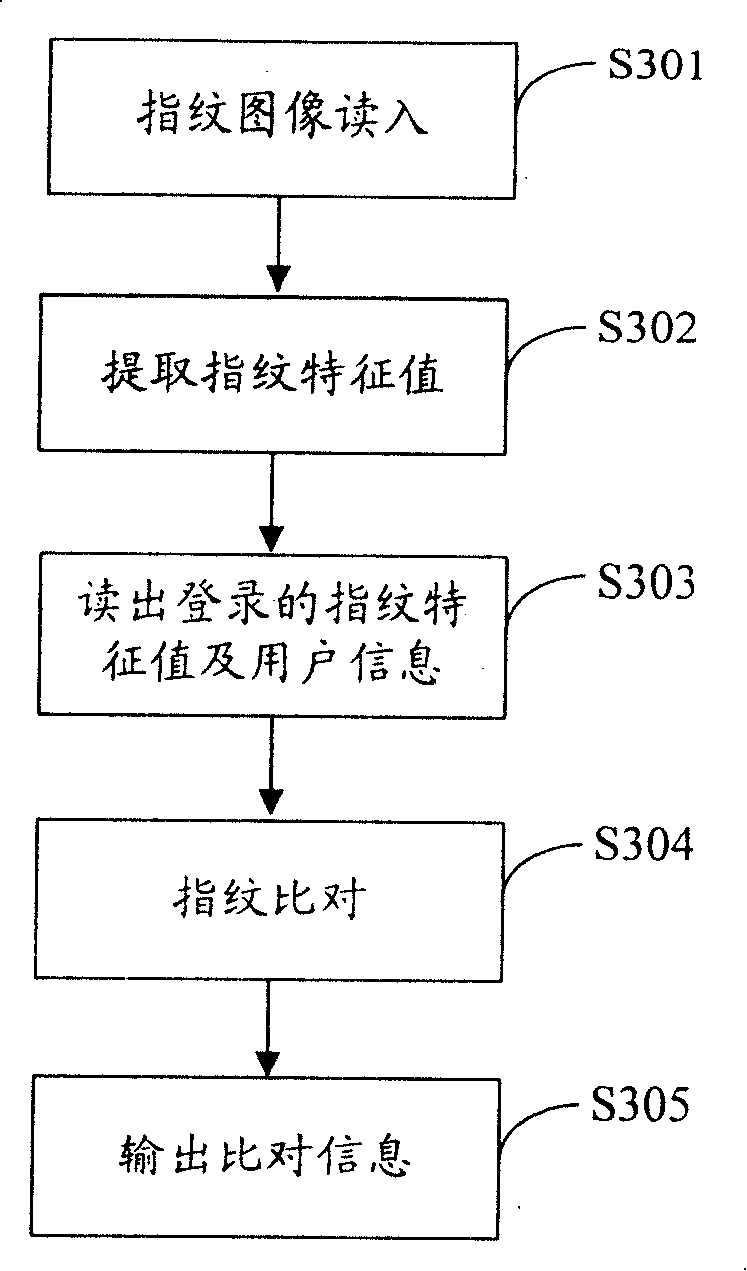
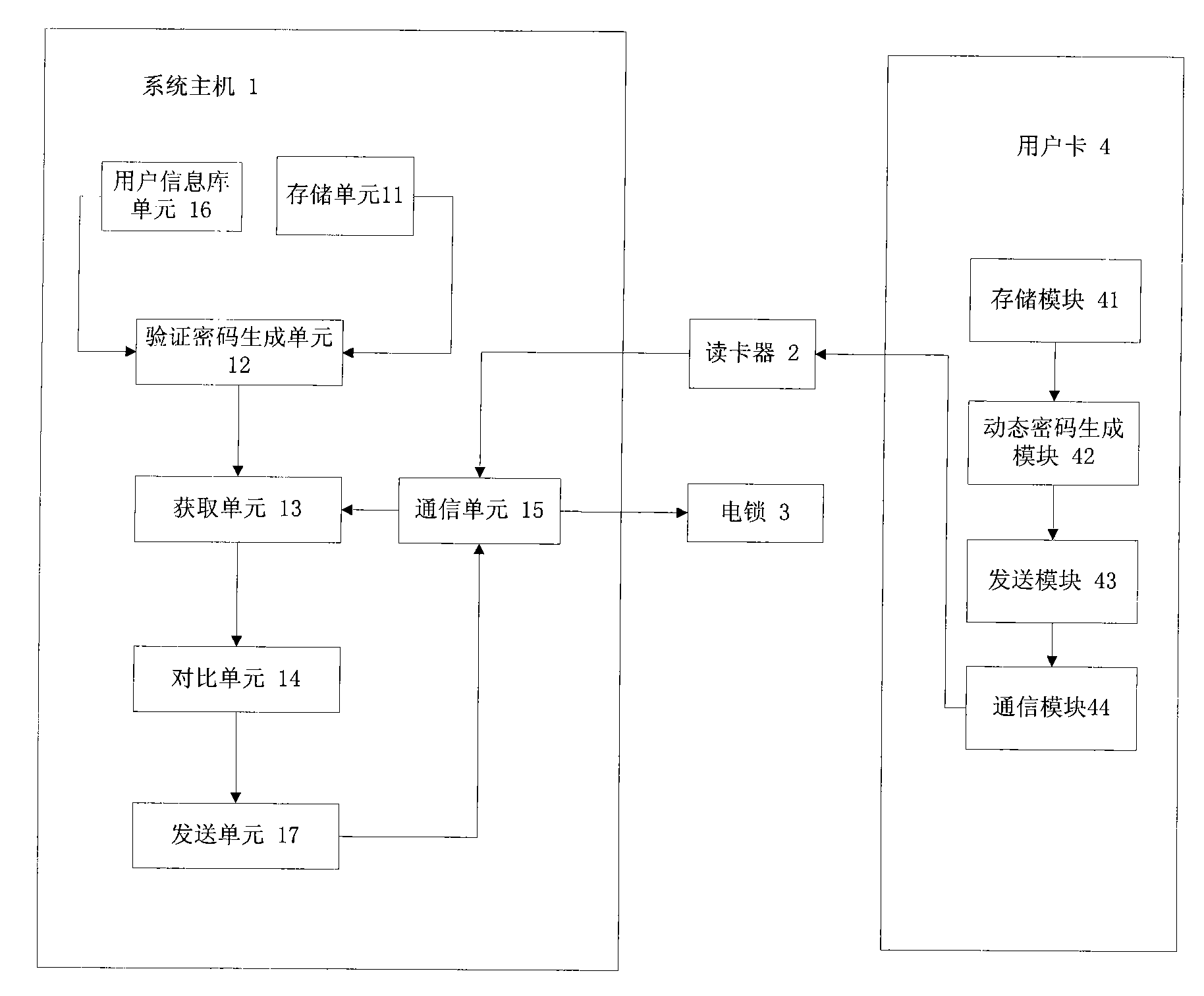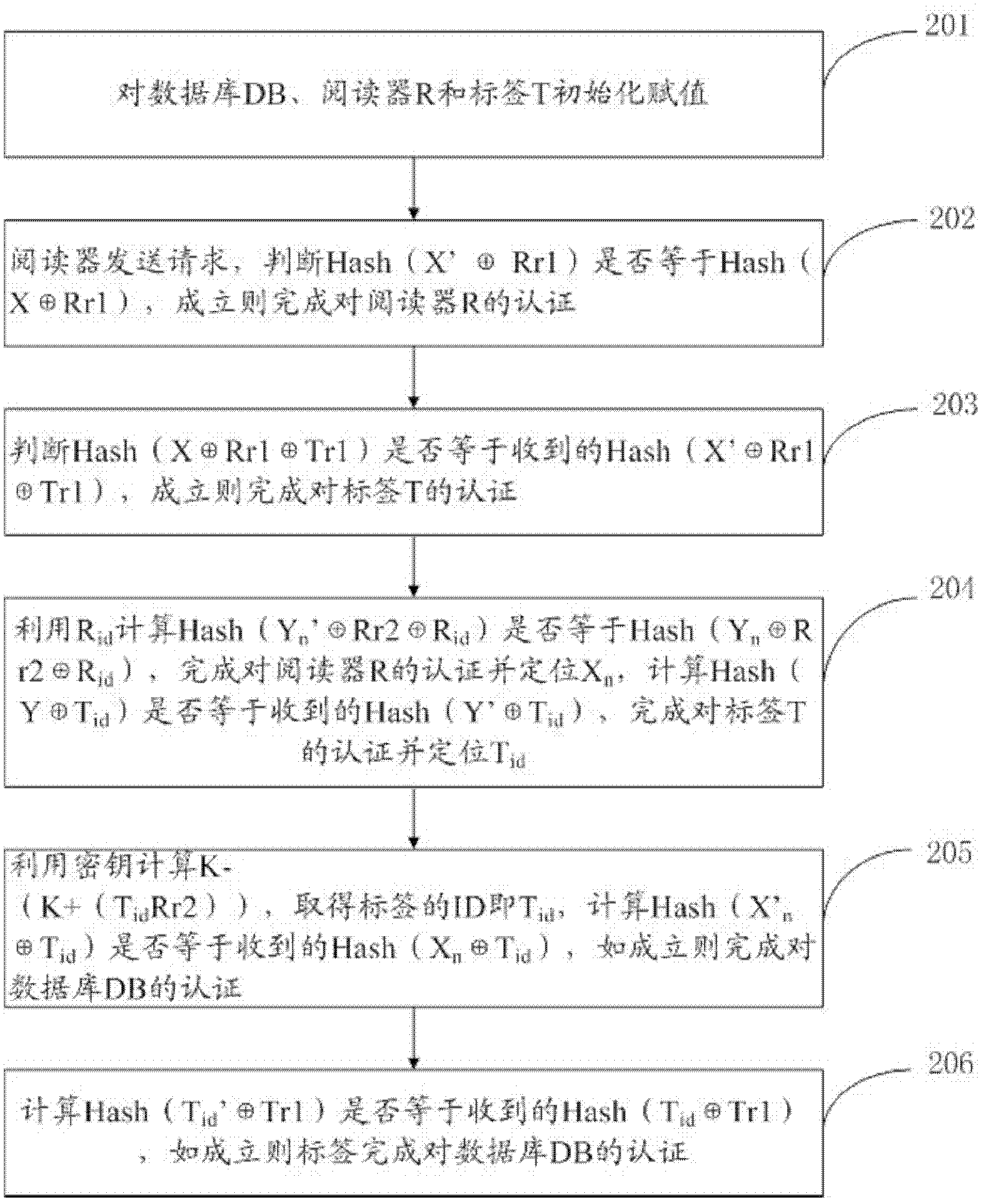Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2006 results about "Security authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
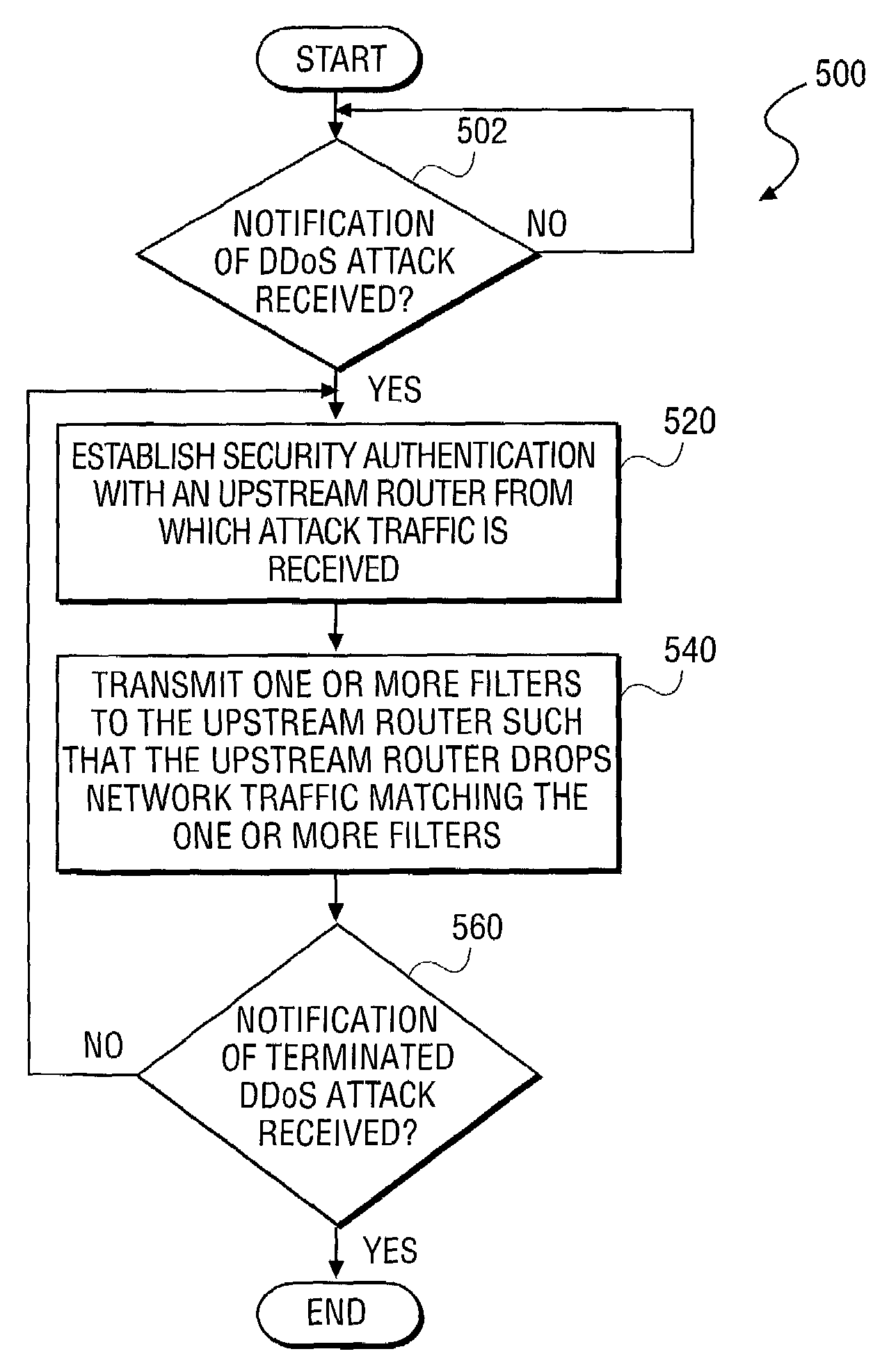
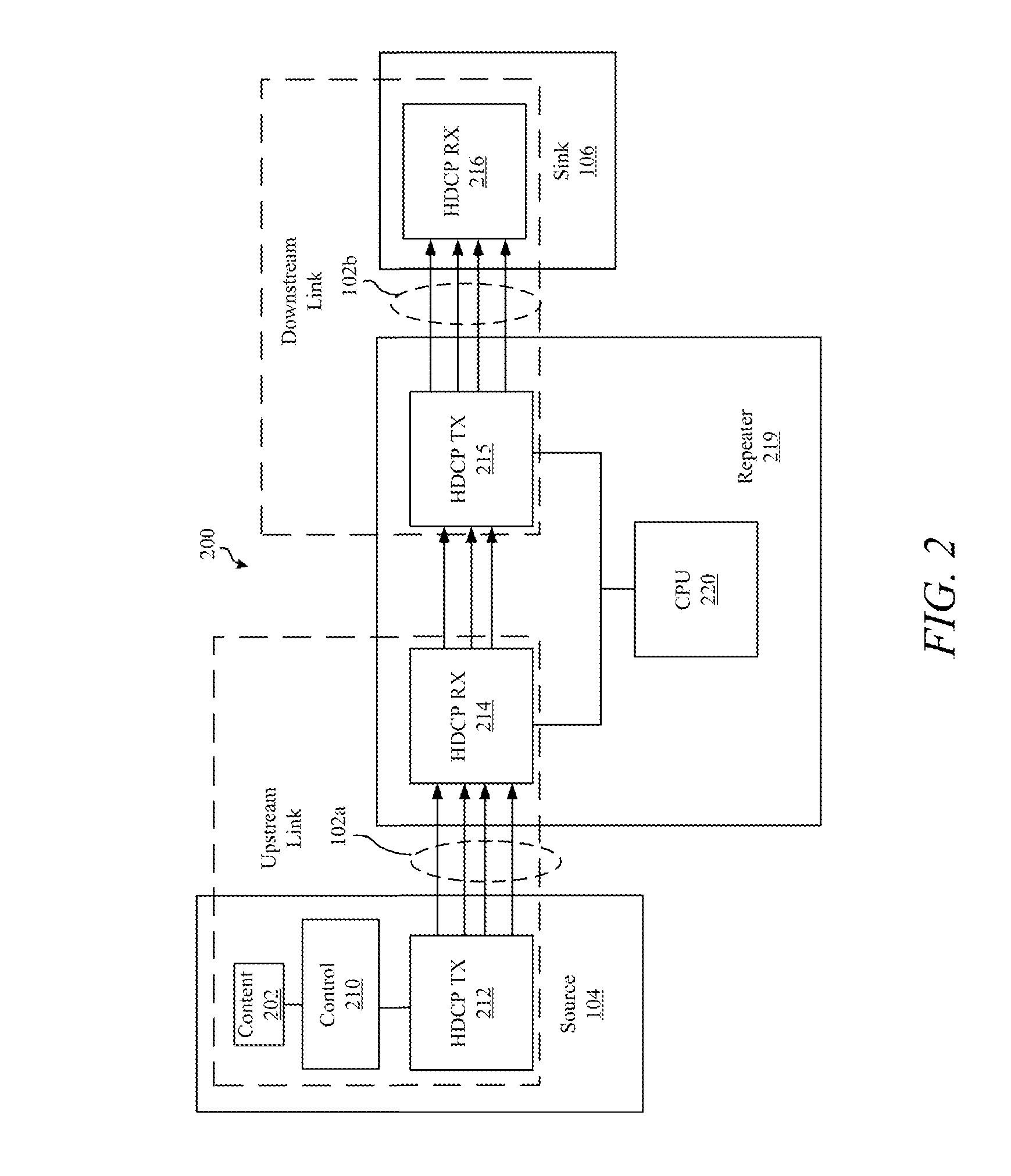
Apparatus and method for secure, automated response to distributed denial of service attacks
InactiveUS7028179B2Memory loss protectionError detection/correctionThe InternetSecurity authentication
An apparatus and method for secure, automated response to distributed denial of service (DDoS) attacks are described. The method includes notification of a DDoS attack received by an Internet host. Once received by an Internet host, the Internet host establishes security authentication from an upstream router from which the attack traffic, transmitted by one or more host computers, is received. The Internet host then transmits filter(s) to the upstream router generated based upon characteristics of the attack traffic. Once installed by the upstream router, the attack traffic is dropped to terminate a DDoS attack. In addition, the router may determine upstream router(s) coupled to ports from which attack traffic is received, and securely forward the filter(s) to the upstream routers as a routing protocol updated in order to drop the attack traffic at a point closer to a source of the DDoS attack.
Owner:INTEL CORP
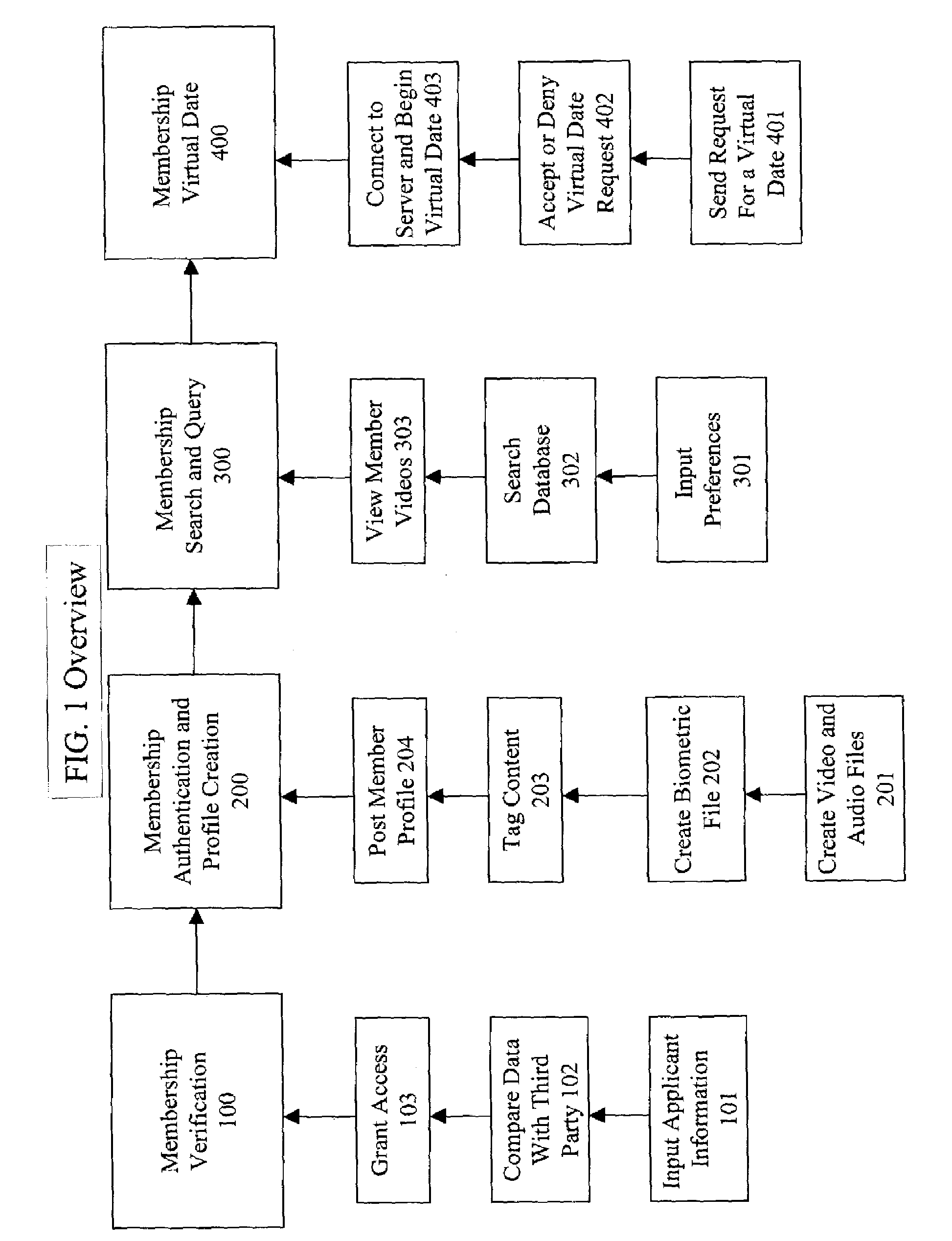
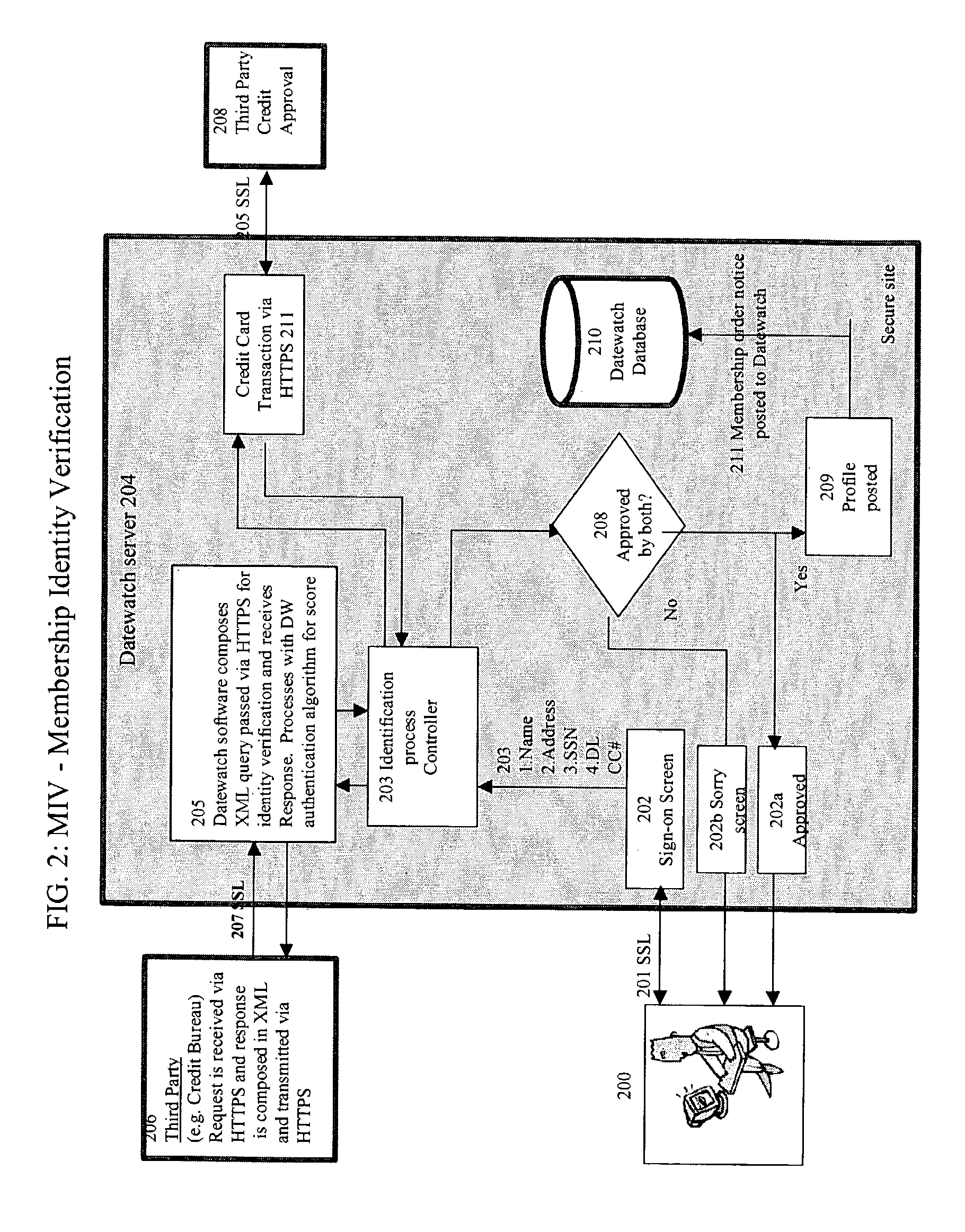
Method for user verification and authentication and multimedia processing for interactive database management and method for viewing the multimedia
InactiveUS7162475B2Improve audio qualityImprove video qualityDigital computer detailsDigital data authenticationUser verificationDigital video
A method for verifying specific profile, legal, and social preference data responses for generating a selectively approved membership database. Membership security is completed with a biometric security authentication of each member upon member logon. A media player is used for recording and delivering video on demand; live video broadcast communications, and video / audio relational database management as well as searching the database for Digital video and audio content defined by indexed unique hint track data. Live video conferencing is available utilizing bandwidth scheduling methods for quality video control and creating audit logs for member accountability and content control.
Owner:INTERNET BIOMETRIC SECURITY SYST
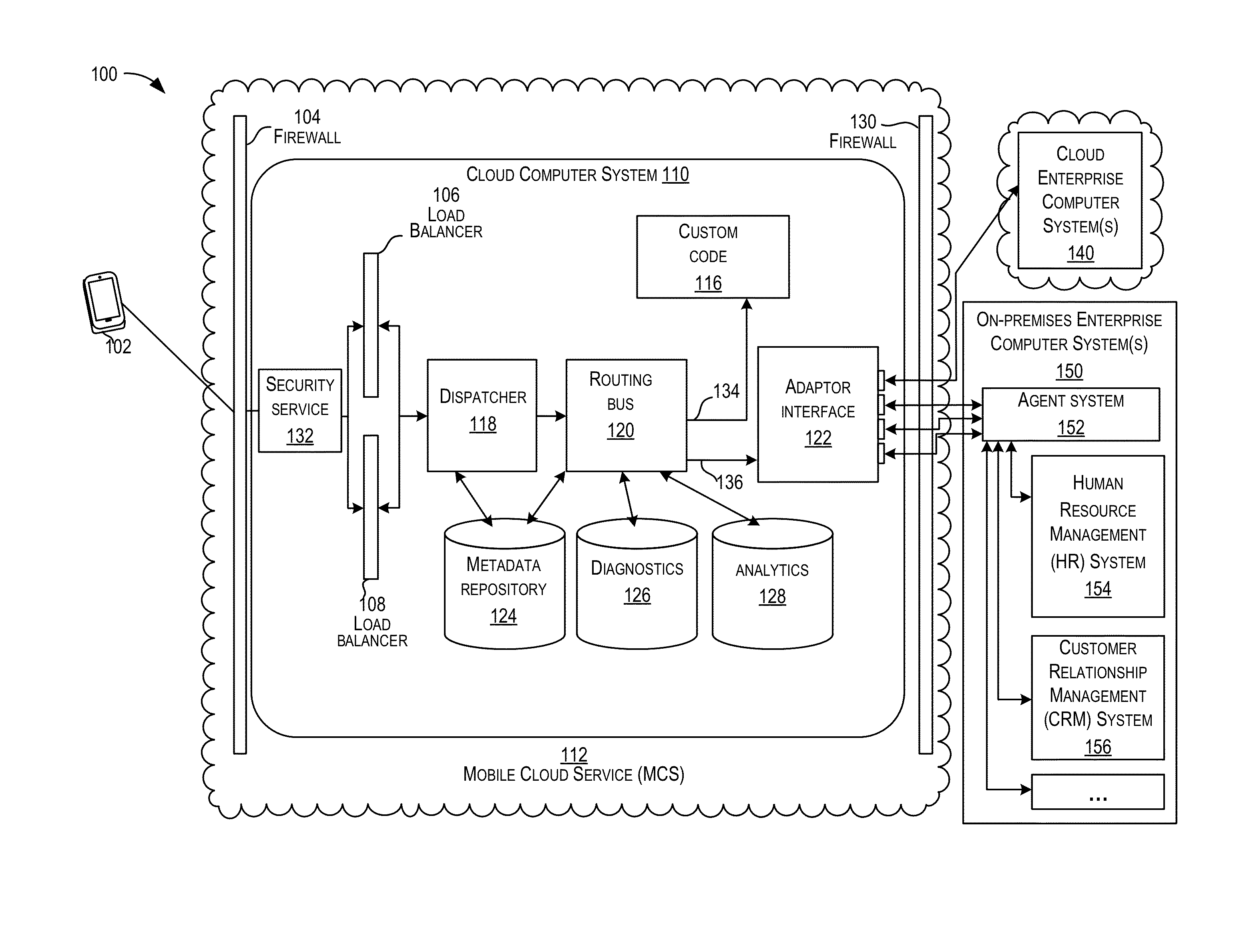
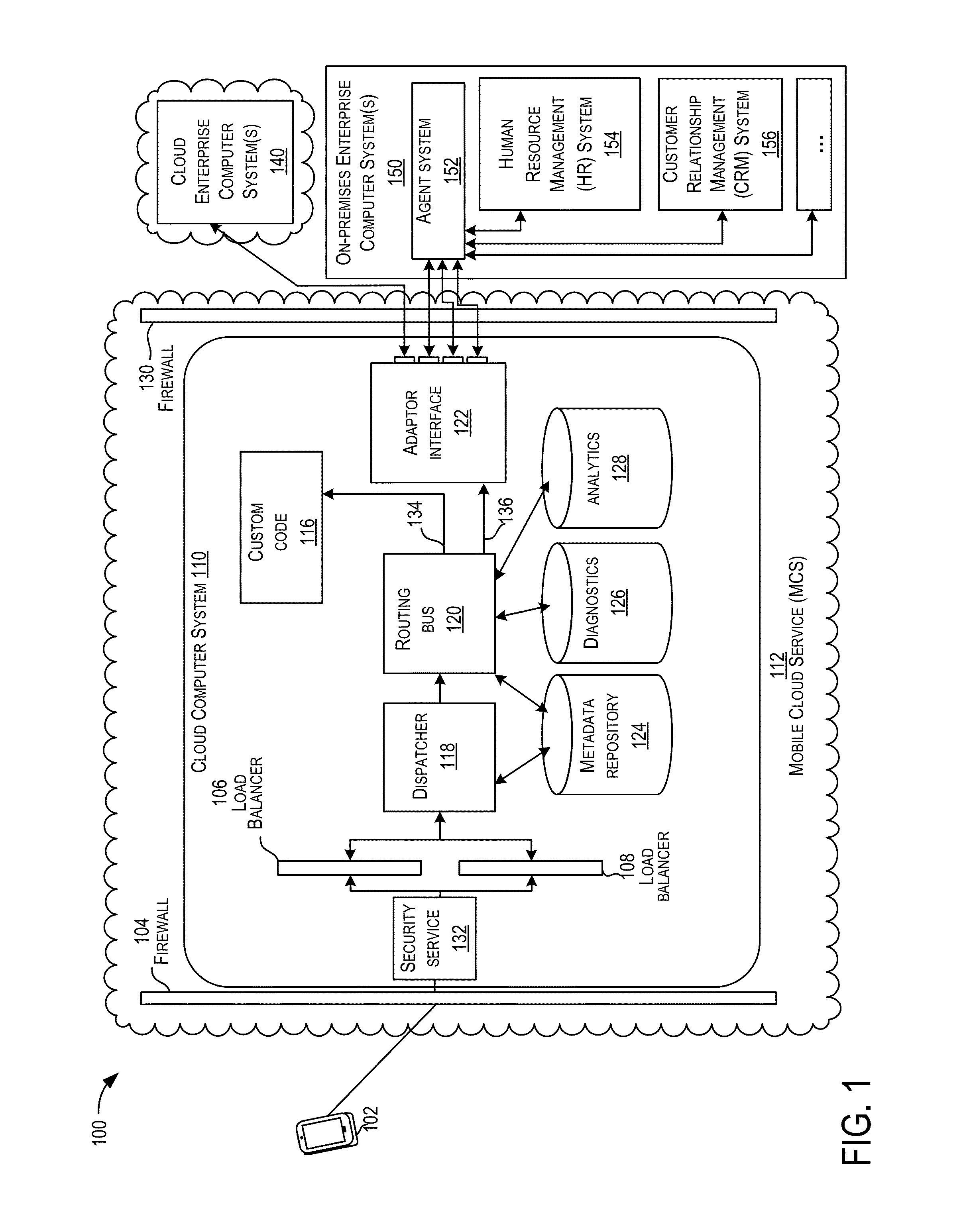
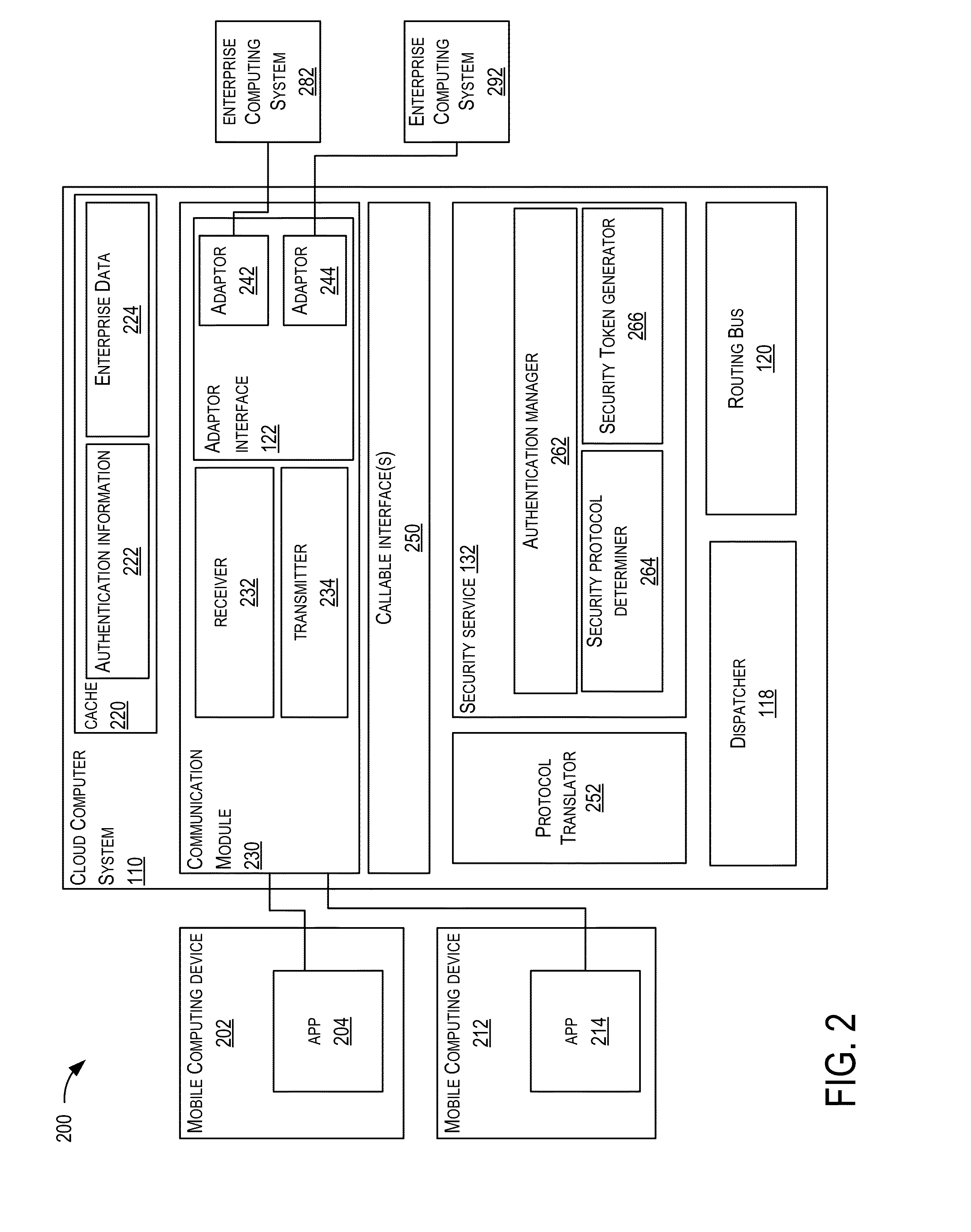
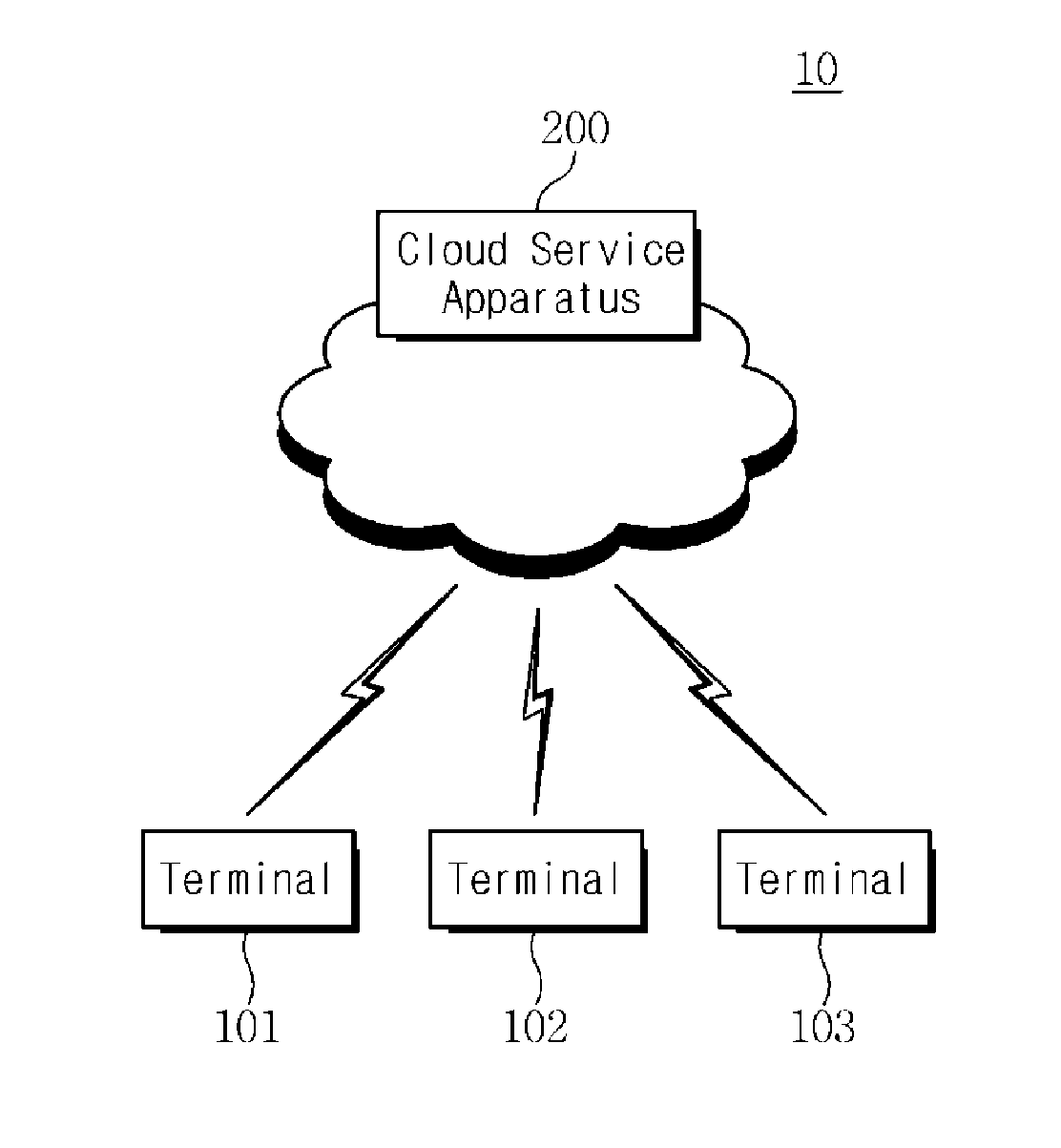
Mobile cloud service architecture
ActiveUS20150229638A1Facilitate communicationDigital data processing detailsInformation formatMobile cloudBusiness enterprise
Techniques are described for implementing a cloud computer system to facilitate communication between a computing device (e.g., a mobile computing device) and enterprise computer systems. In certain embodiments, the cloud computer system may receive, from a computing device, a request for a service provided by an enterprise computer system. The cloud computer system may determine security authentication of a user for the requested service. A security protocol may be determined for a requested enterprise computer system and a security token may be generated for the request according to the determined security protocol. The request may be sent to the requested enterprise computer system. In some embodiments, security authentication for a request to an enterprise computer system may be determined based on previous authentication. The cloud computer system may be configured to communicate with several different enterprise computer systems according to their supported protocols (e.g., communication protocol and / or security protocol).
Owner:ORACLE INT CORP
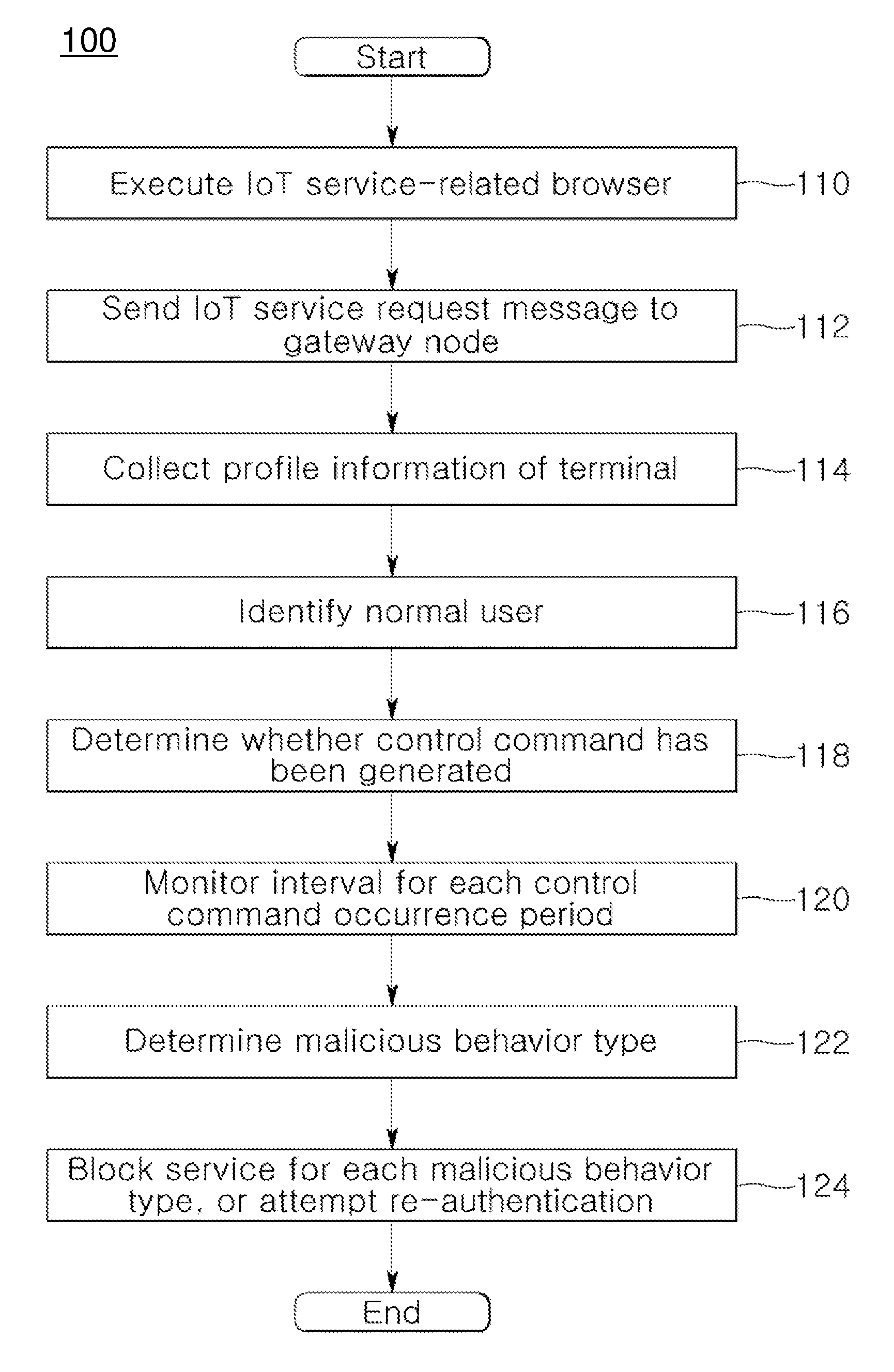
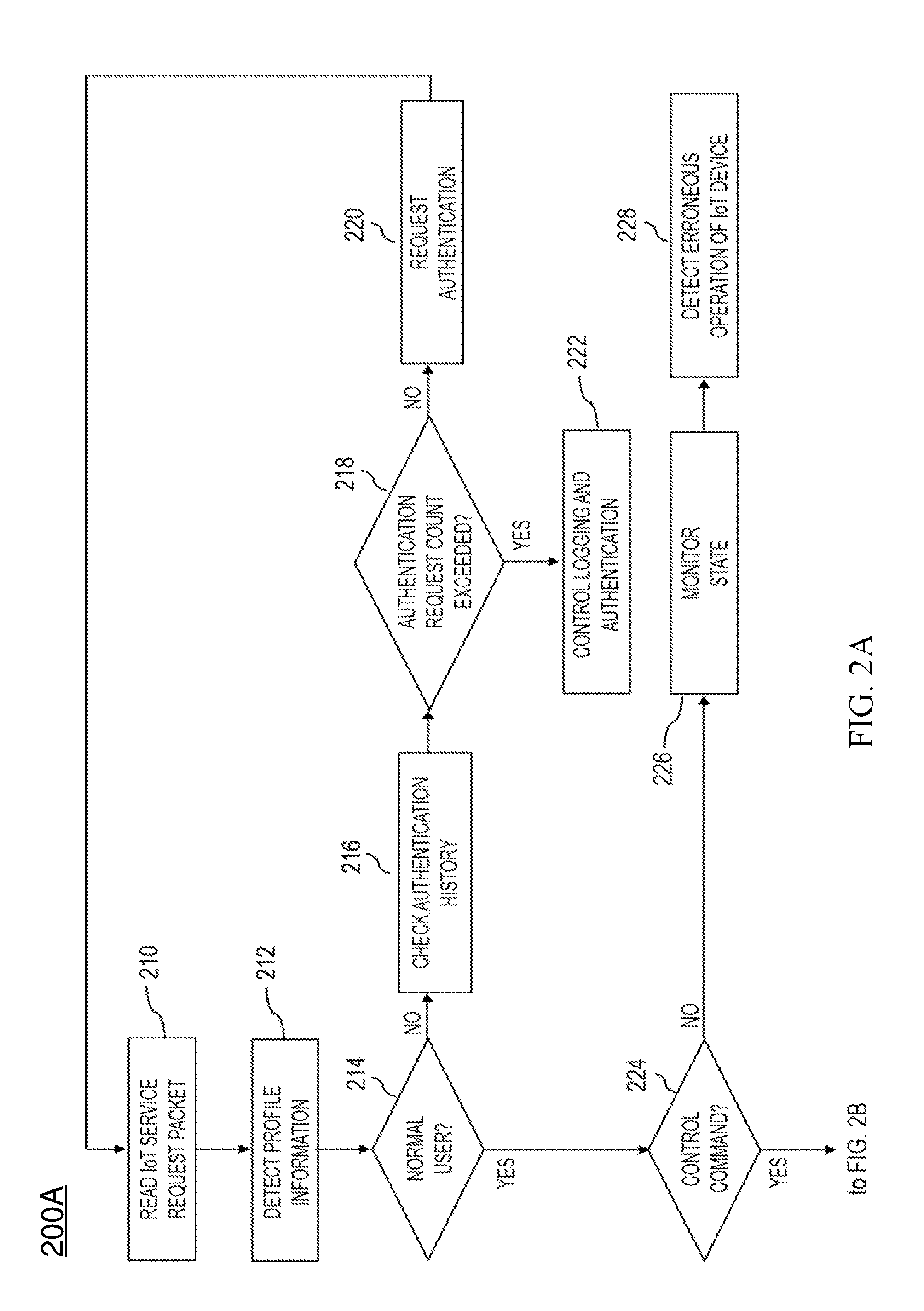
System and method for providing authentication service for internet of things security
ActiveUS20160173495A1Providing serviceUser identity/authority verificationMultiple digital computer combinationsInternet Authentication ServiceIot gateway
A system and method for providing authentication service for IoT security are disclosed herein. The system for providing authentication service for IoT security includes an Internet of Things (IoT) service server, and an IoT gateway node. The IoT service server supports an IoT communication service in accordance with an IoT communication service policy. The IoT gateway node receives an IoT service request from a terminal attempting to control an IoT device that supports the IoT communication service while operating in conjunction with the IoT service server, identifies whether the terminal attempting to control the IoT device is a normal user based on profile information, collected from the terminal via the IoT service request, via the IoT service server, and performs the security authentication of the IoT device.
Owner:WINS CO LTD
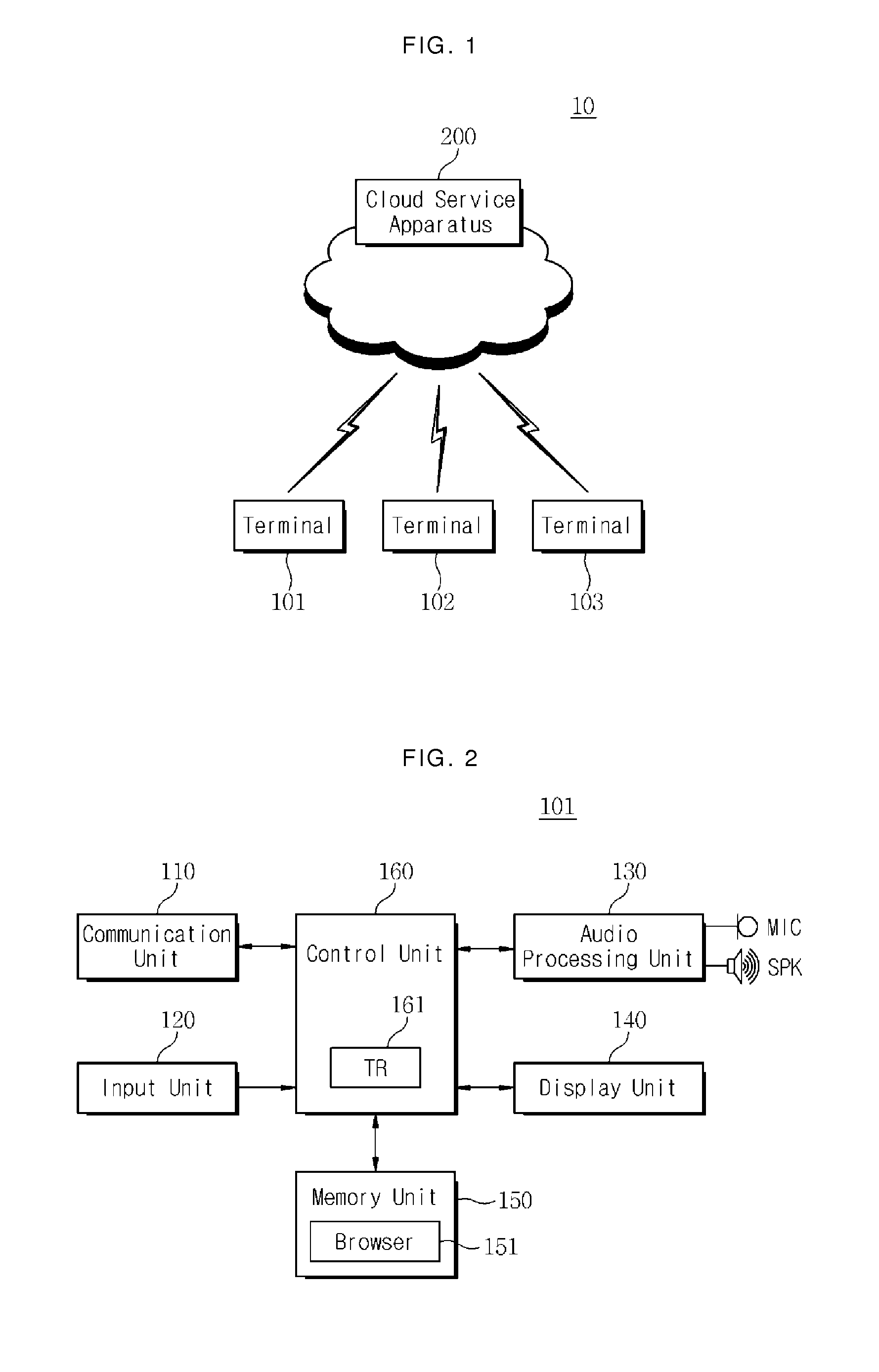
Cloud service system based on enhanced security function and method for supporting the same
ActiveUS20130333005A1Improve securityInhibition of informationDigital data processing detailsMultiple digital computer combinationsPasswordComputer terminal
The present invention relates to cloud service supporting technology. Particularly, a cloud service system based on an enhanced security function includes a terminal that includes a trusted platform therein and is configured to perform security authentication based on encrypted information provided by the trusted platform, to perform normal authentication based on preregistered ID and password information, and to use a cloud service according to the security authentication and the normal authentication, and a cloud service apparatus that is configured to provide the cloud service to the terminal after completing the security authentication and the normal authentication with the terminal that includes the trusted platform therein. The service apparatus, the terminal, and a method for supporting them are also disclosed.
Owner:SK PLANET CO LTD
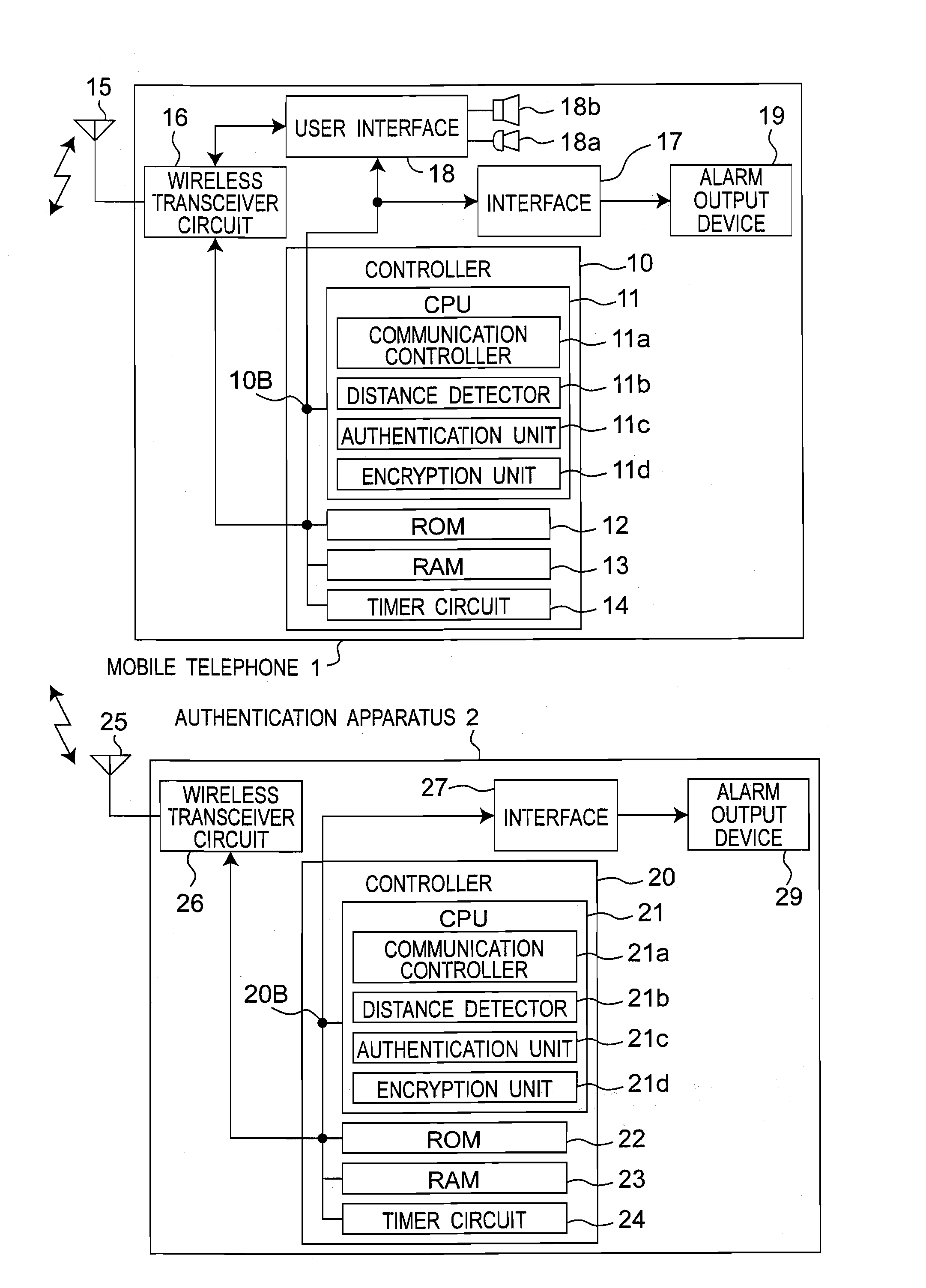
Wireless device monitoring system including unauthorized apparatus and authentication apparatus with security authentication function
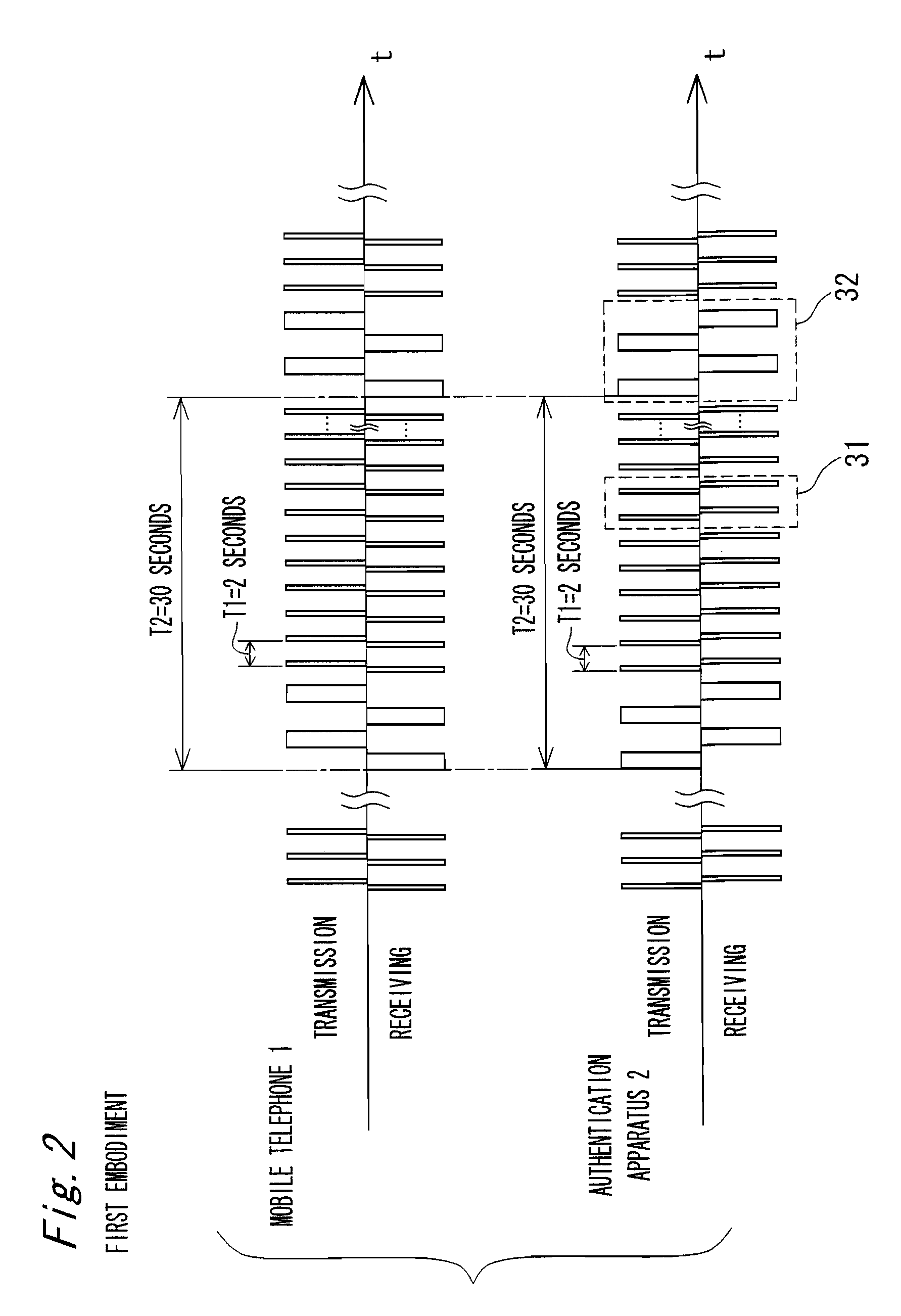
InactiveUS8145194B2Shorten communication timeKeep for a long timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMonitoring systemDistance detection
In a wireless device monitoring system including a mobile telephone and an authentication apparatus, a controller of the authentication apparatus repeatedly executes a distance detection processing based on a received level of a received wireless signal and an authentication processing based on authentication data included in the received wireless signal continuously at a first communication interval T1 and a second communication interval T2, respectively, and outputs an alarm signal or executes a predetermined control processing when a true counterpart electronic apparatus is not present or when the true counterpart electronic apparatus is apart from the electronic apparatus by a distance longer than the predetermined threshold distance. When a first communication time T11 for the distance detection processing is shorter than a second communication time T12 for the authentication processing, the T1 and the T2 are set to satisfy T1<T2.
Owner:PANASONIC CORP
Method and apparatus for providing adaptive VPN to enable different security levels in virtual private networks (VPNs)
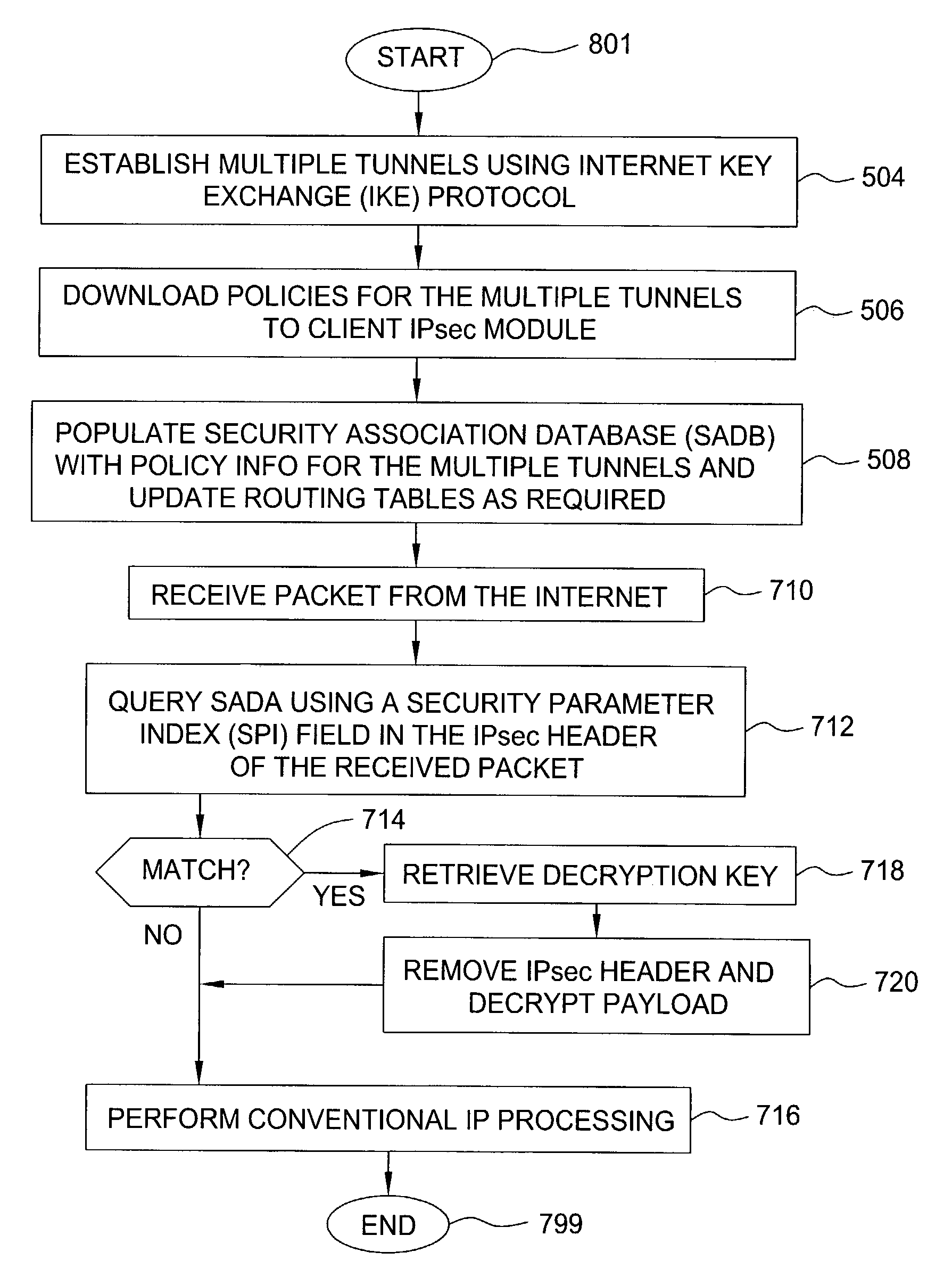
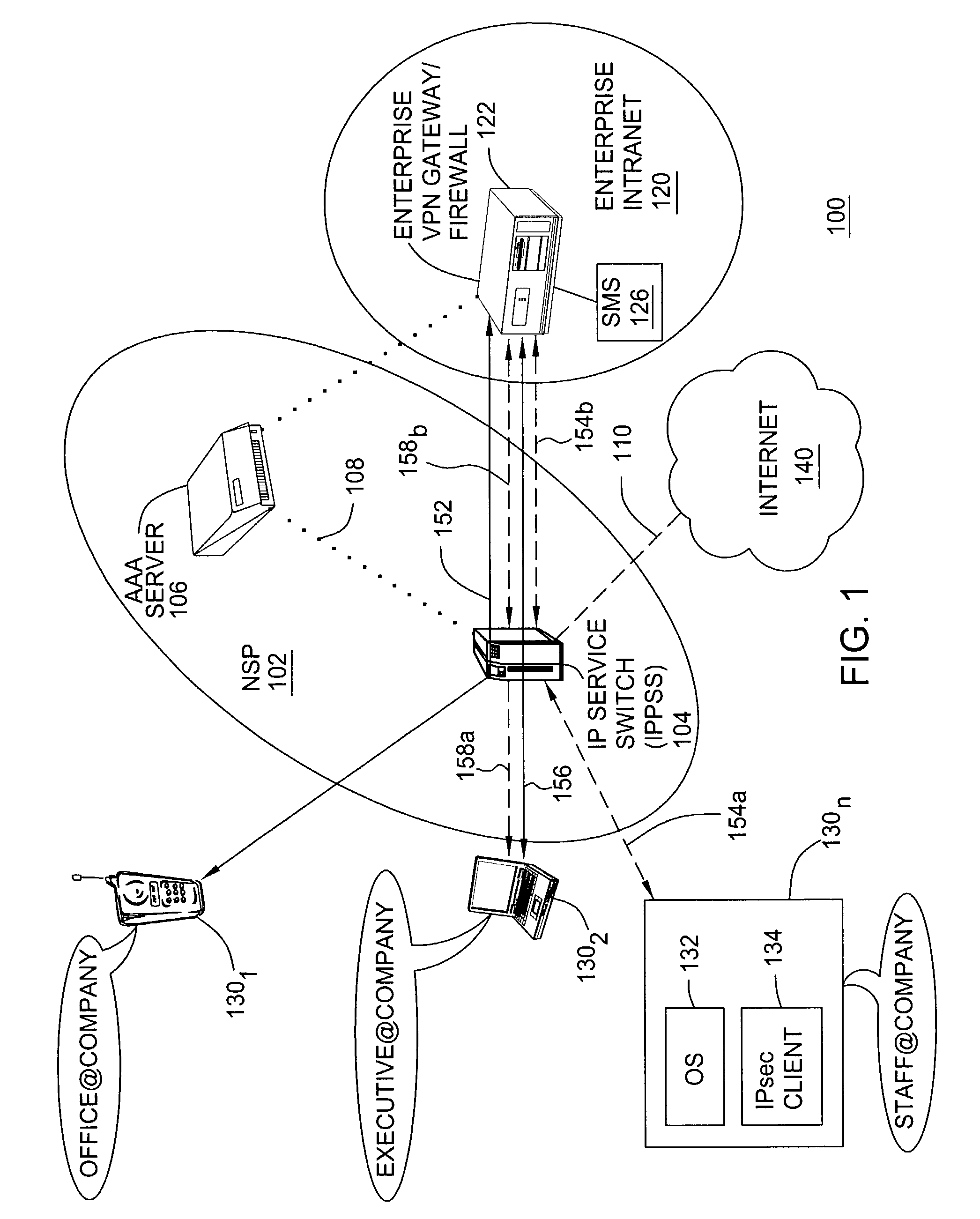
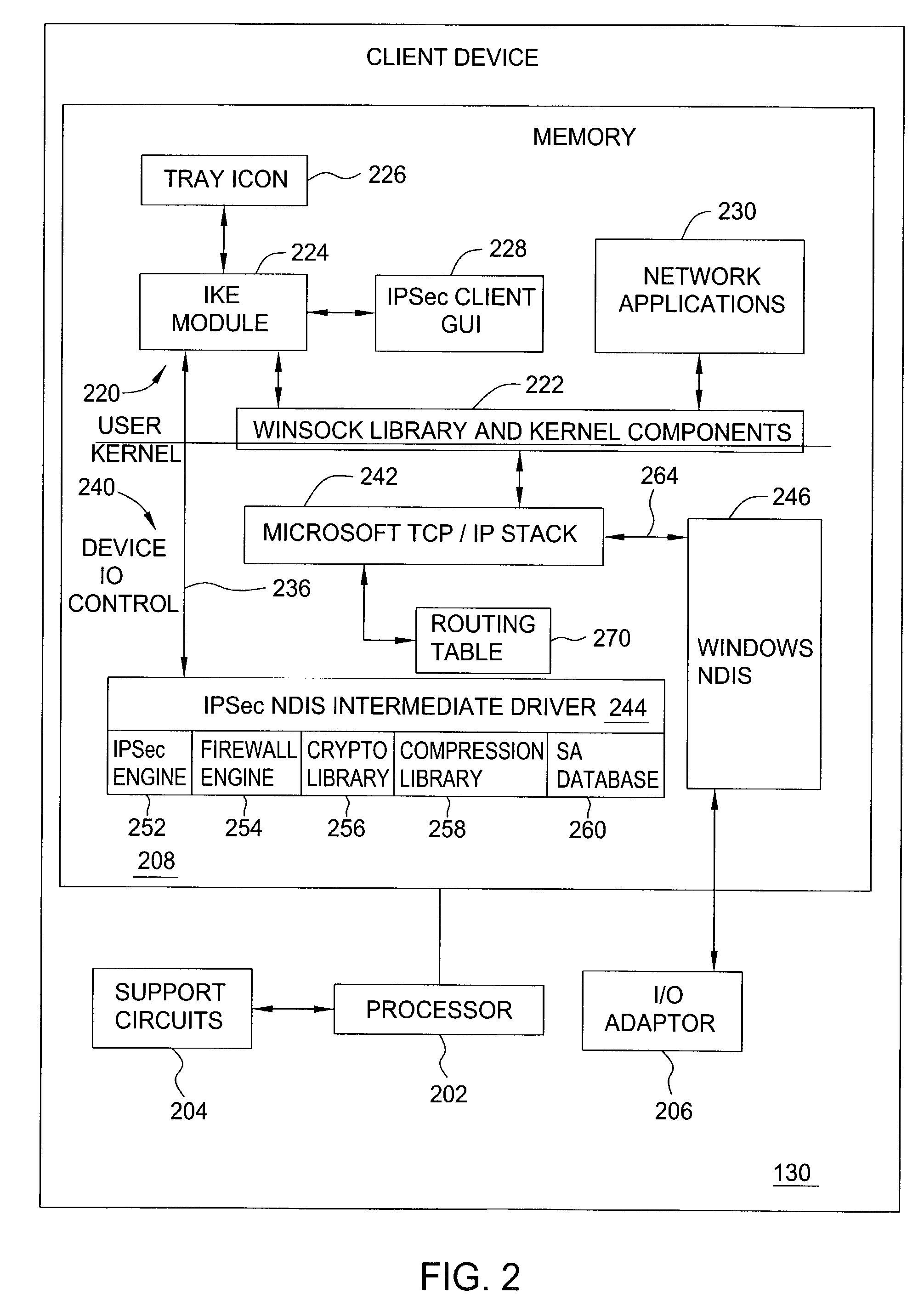
ActiveUS7478427B2Computer security arrangementsMultiple digital computer combinationsRouting tableIp address
A method and apparatus for providing at least two virtual private network VPN tunnels from a client device in a VPN network having an enterprise gateway and a network VPN gateway. The method and apparatus includes a client device having an Internet Key Exchange (IKE) module for establishing the at least two tunnels using an IKE protocol wherein a first tunnel is an end-to-end VPN tunnel to the enterprise gateway, and a second tunnel is a network-based tunnel to the network VPN gateway. An IPsec Network Driver Interface interfaces with the IKE module, which includes a security authentication database (SADB) that stores downloaded enterprise security policies respectively for each of the at least two tunnels. A routing table stores IP addresses of local presences and hosts respectively associated with the at least two tunnels, whereby packets are routed over the at least two tunnels based on the downloaded policies.
Owner:ALCATEL-LUCENT USA INC
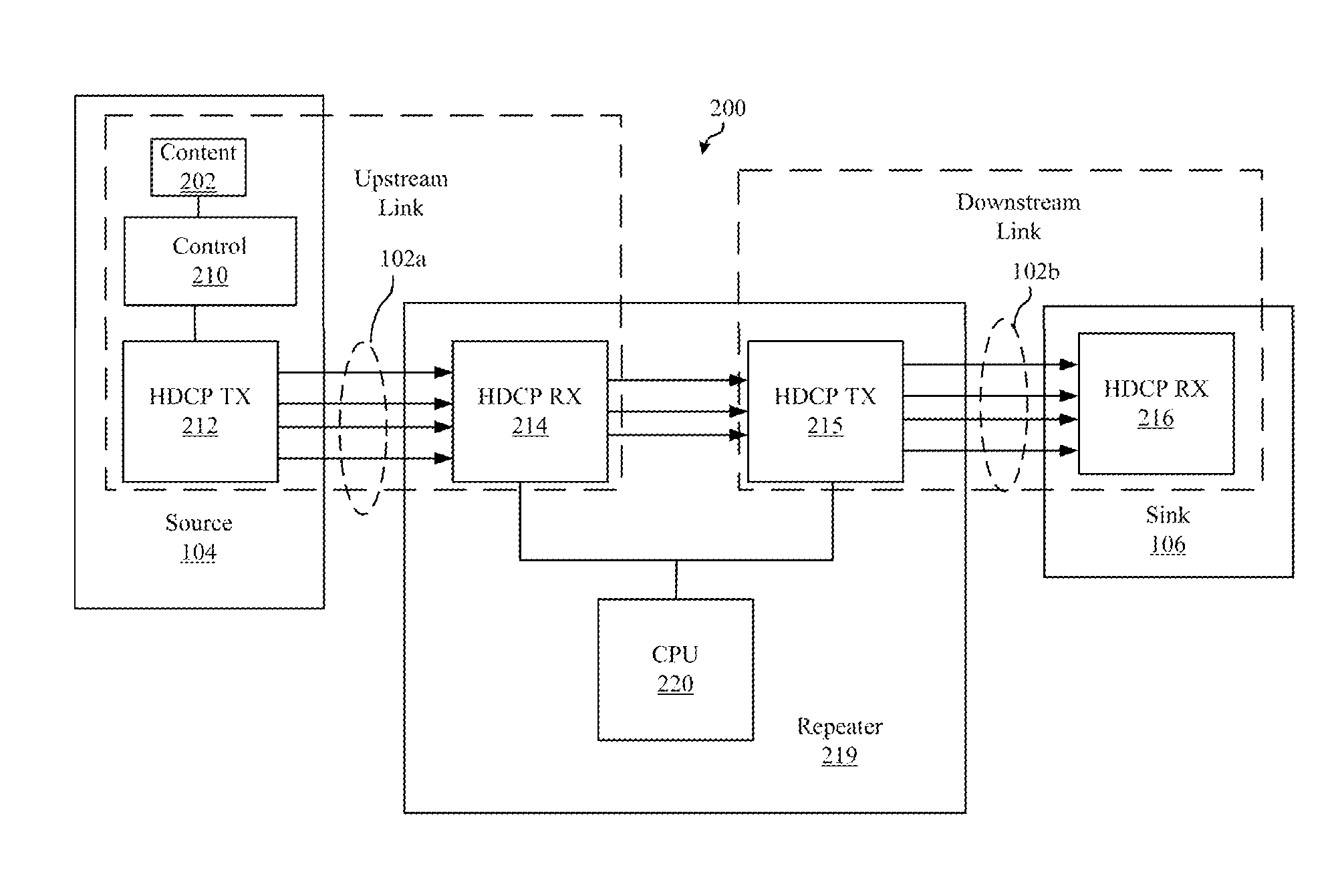
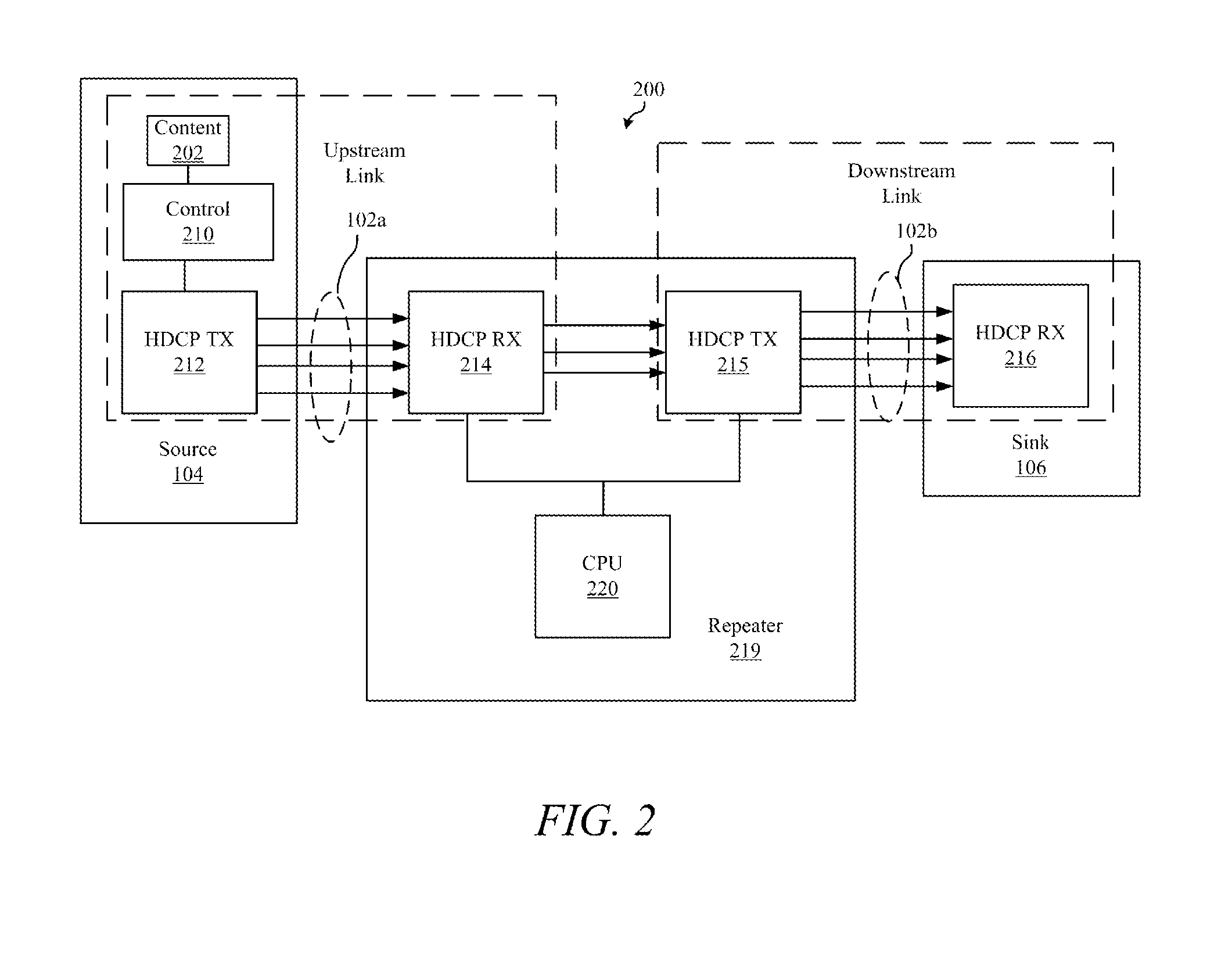
Systems, Devices and Methods for Reducing Switching Time in a Video Distribution Network
ActiveUS20150020088A1Reduce switching delayReducing actual and perceived switching timeAnalogue secracy/subscription systemsTwo-way working systemsSecurity authenticationSwitching time
When switching sources, resolutions or refresh rates in a video distribution network, switching times are reduced by maintaining video lock and security authentication between a video switcher and a video sink. The scaler maintains video lock and security authentication by continuing to generate video timing data during switching events. The scaler also facilitates an aesthetically pleasing transition by generating image content data prior to and after the switching event.
Owner:CRESTRON ELECTRONICS
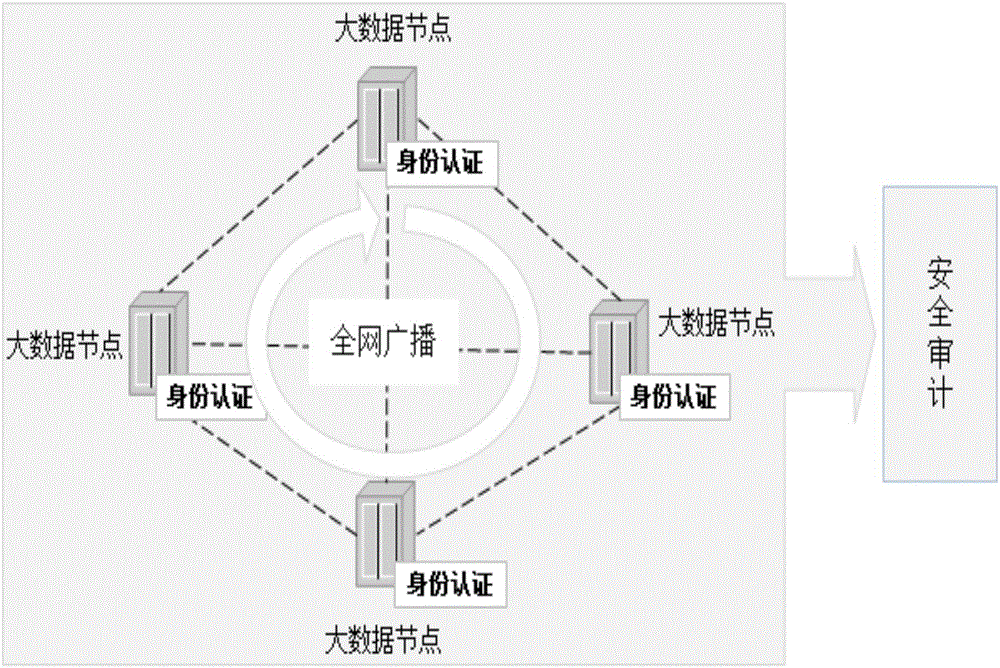
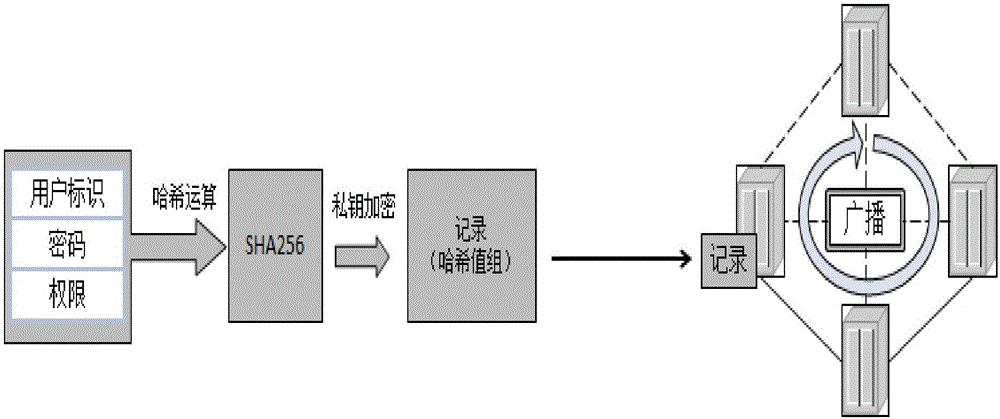
Block chain-based big data security authentication method and system
InactiveCN106375317AImprove robustnessFree to joinUser identity/authority verificationBlockchainSecurity authentication
The present invention discloses a block chain-based big data security authentication method and system. The method comprises the following steps that a big data node A broadcasts its identity authentication in the whole network; all other big data nodes in the whole network record the identity authentication; if the big data node A is accessed in authentication, the big data node A releases a transaction package including a timestamp in the whole network, the other big data nodes in the whole network check the transaction package, and determine whether the transaction package is consistent with transaction packages stored by the other big data nodes; if the determining results of other big data nodes are consistent, the transaction package is determined legal, and the big data node A is added to a big data block chain; and the security authentication of the big data node A succeeds. Through adoption of the method and system, the network robustness is improved, the management process is simplified, and the operation and maintenance cost is saved.
Owner:北京明朝万达科技股份有限公司
Devices, Systems and Methods for Reducing Switching Time in a Video Distribution Network
ActiveUS20130212613A1Reduce switching delayShorten the switching timeAnalogue secracy/subscription systemsSelective content distributionSecurity authenticationSwitching time
When switching sources, resolutions or refresh rates in a video distribution network, switching times are reduced by maintaining video lock and security authentication between a video switcher and a video sink. The scaler maintains video lock and security authentication by continuing to generate video timing data during switching events. The scaler also facilitates an aesthetically pleasing transition by generating image content data prior to and after the switching event.
Owner:CRESTRON ELECTRONICS
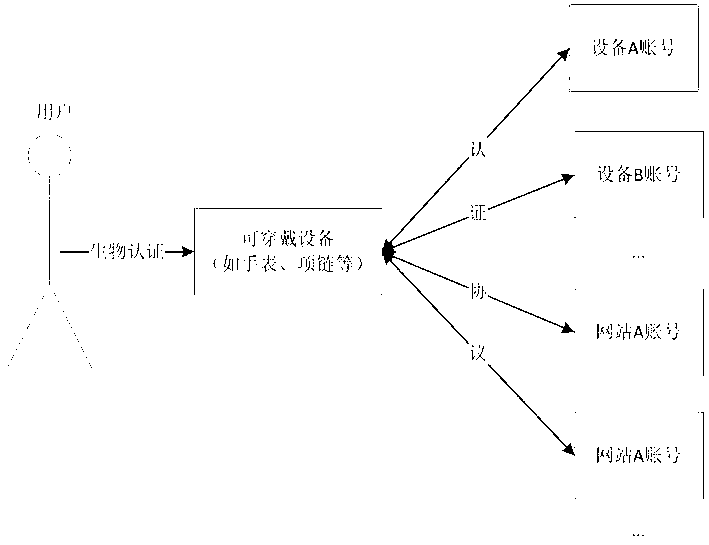
Man-machine fusion security authentication method based on wearable equipment
ActiveCN103310142AReduce dependenceEnsure safetyDigital data authenticationComputer hardwareDigital identity
The invention belongs to the field of personal identity authentication, and particularly relates to a man-machine fusion security authentication method based on wearable equipment. The wearable equipment in which user digital identity information is saved replaces a user to carry out identity authentication in a network space, and a command is not required to be inputted directly by the user. The method comprises the special steps as follows: a method user registers in the wearable equipment to become an authorized user; the method user stores the self digital identity into the wearable equipment; the method user passes the biometric-based identification authentication of the wearable equipment; and the wearable equipment automatically logs in other equipment or information systems in internet space through using the user digital identification stored in the wearable equipment. The method reduces the dependence of the user on a simple command, guarantees the information to be safer, and facilitates the monitoring and management better.
Owner:FUDAN UNIV
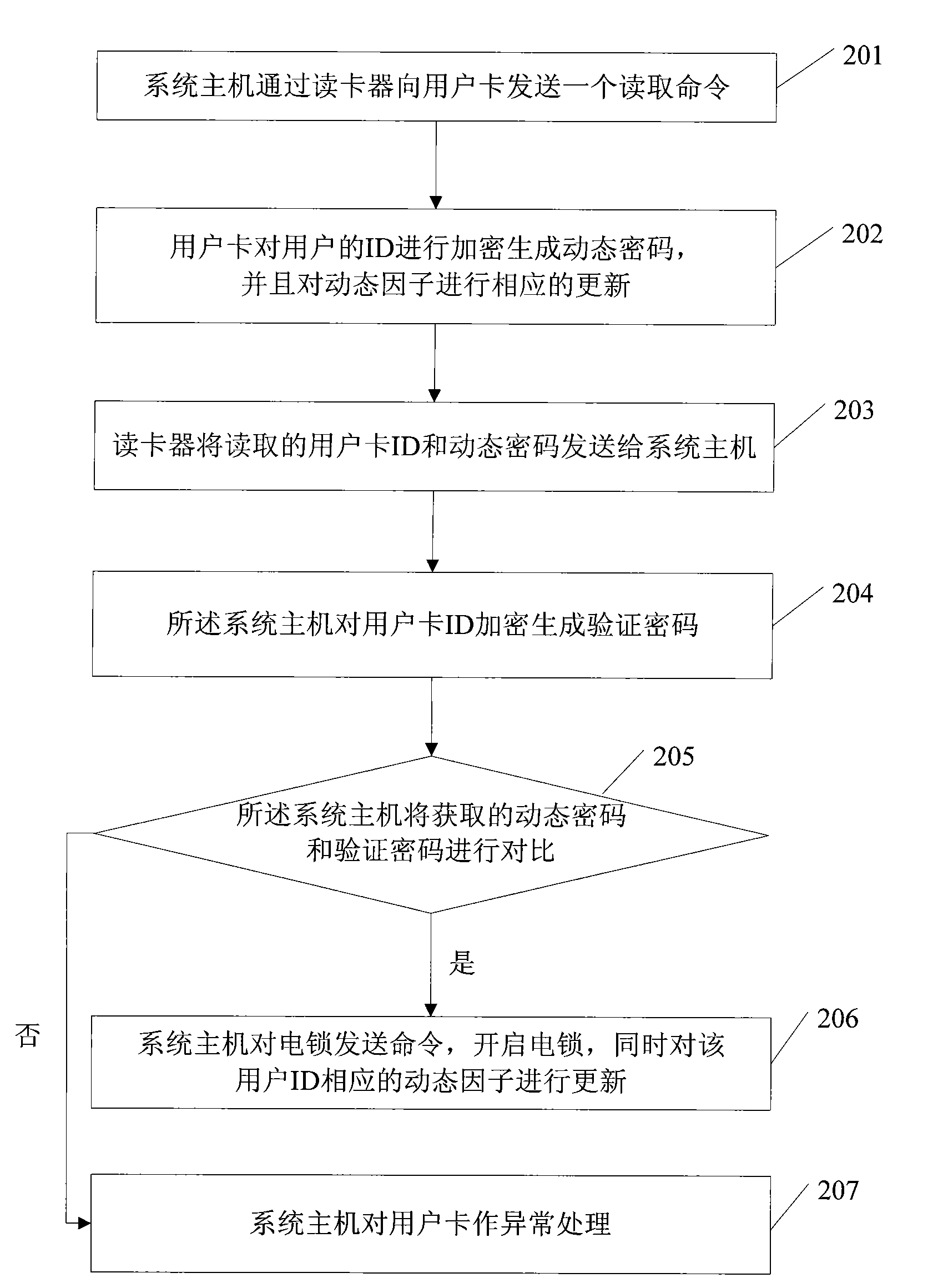
Access control system generated and verified on the basis of dynamic password and authentication method thereof
InactiveCN101593380ASynchronous generationUser identity/authority verificationIndividual entry/exit registersPasswordSecret code
The invention discloses an access control system generated and verified on the basis of dynamic password and an identity verification method, belonging to the field of security certificate. The system comprises a user terminal for generating dynamic password and a certificate terminal for verifying dynamic password, wherein, the user terminal comprises a storage module which is used for storing arithmetic, keys and dynamic factors, and the certificate terminal comprises a reading module, a locker module and a certificate server module. The method of the invention comprises the following steps: after receiving an order sent by the certificate terminal, the user terminal generates dynamic password, the certificate terminal generates verified password according to stored arithmetic and key which are identical to the user terminal and corresponding dynamic factors, and the dynamic password and the verified password are compared to verify the validity and availability of the dynamic password of the user terminal.
Owner:FEITIAN TECHNOLOGIES
Intelligent industrial security cloud gateway equipment system and method
InactiveCN107040459AUser identity/authority verificationNetwork connectionsData centerSecurity authentication
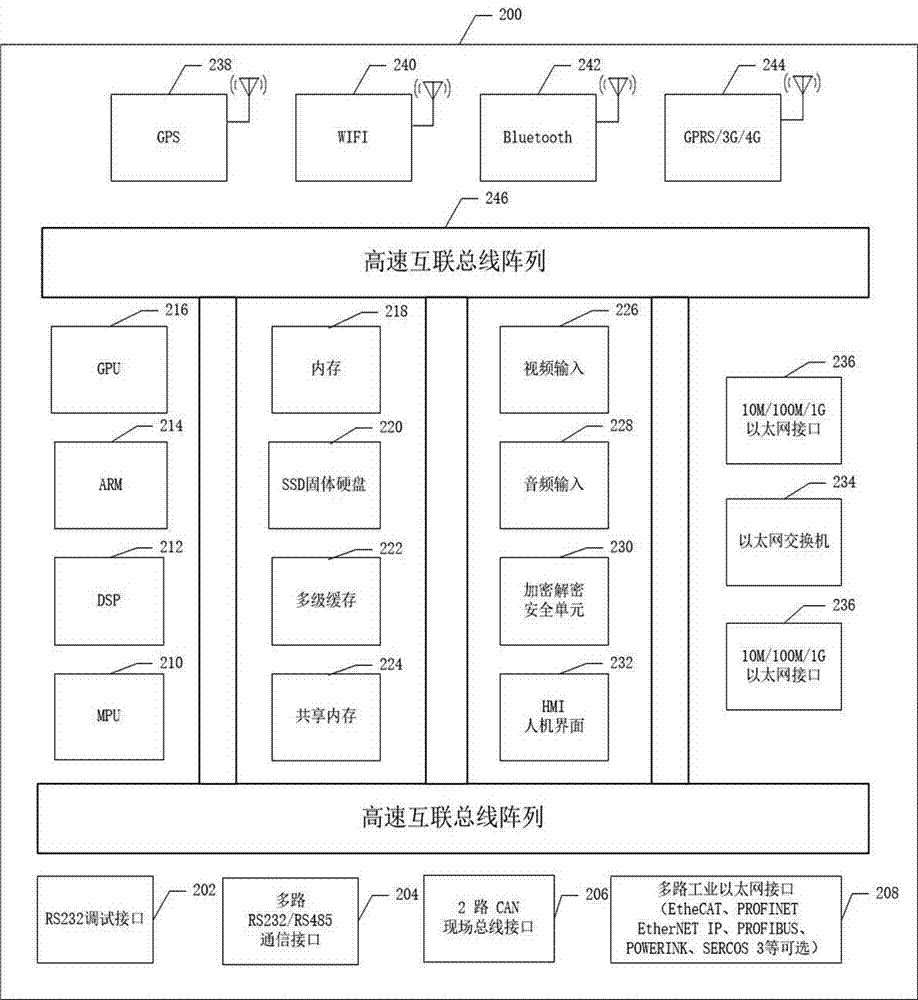
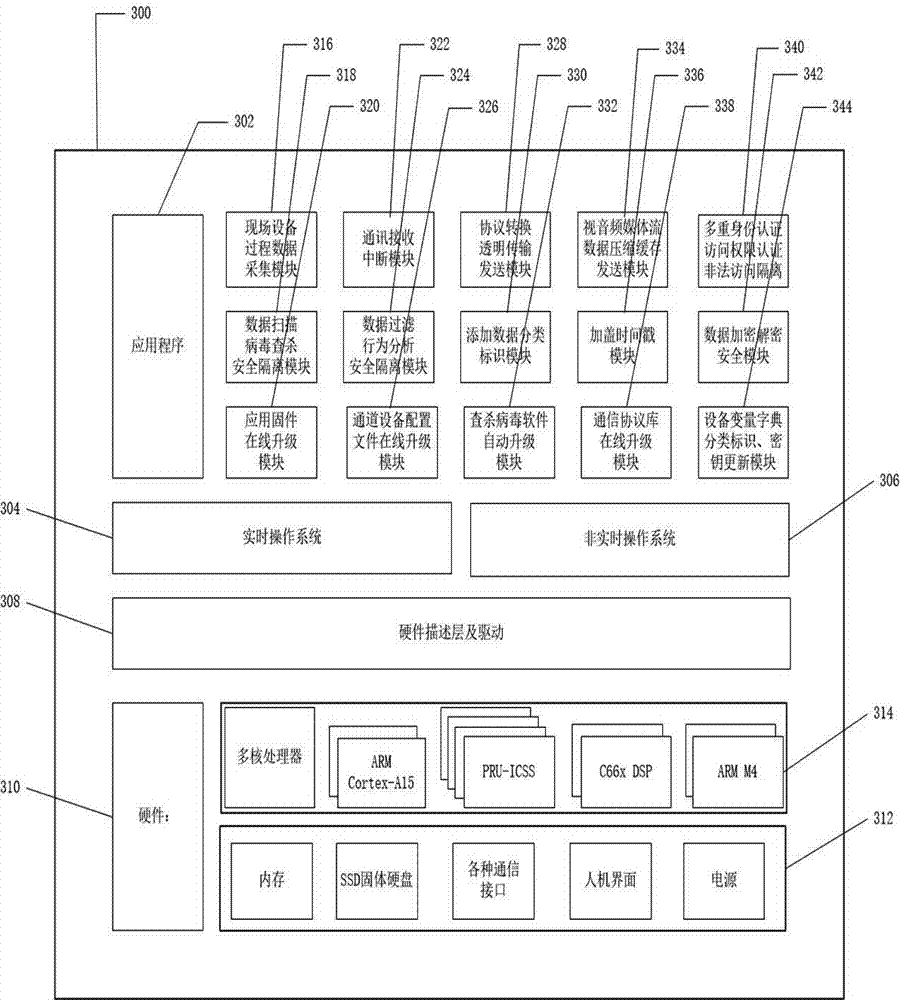
The invention discloses an intelligent industrial security cloud gateway equipment system and method. The industrial cloud security gateway equipment and method is characterized in that upper cloud data is encrypted and added with data classification identifiers and time stamps, and decryption, security scanning and multiple security authentication access control are carried out on data on downlink intelligent equipment, so that interconnection, protocol conversion, and multi-directional transparent and real-time transmission among cloud equipment, enterprise datacenter equipment and various intelligent equipment on an industrial field can be achieved. An intelligent industrial cloud security gateway is embedded intelligent equipment comprising various serial ports, communication interfaces for a field bus and field intelligent equipment such as the industrial Ethernet, communication interfaces for wireless mobile communication and wired Internet cloud equipment, wireless or wired local area network interfaces for Bluetooth, broadband and the like, an Ethernet switch, a GPS module, and embedded software. The intelligent industrial cloud security gateway can systematically prevent user data leakage and network virus attacks, is core equipment of a secure and reliable intelligent industrial cloud service system, and can serve intelligent industrial manufacturing.
Owner:高岩
Method and system for internet of things information transmission
ActiveCN103166919AImprove securityGuaranteed privacyUser identity/authority verificationInformation transmissionThe Internet
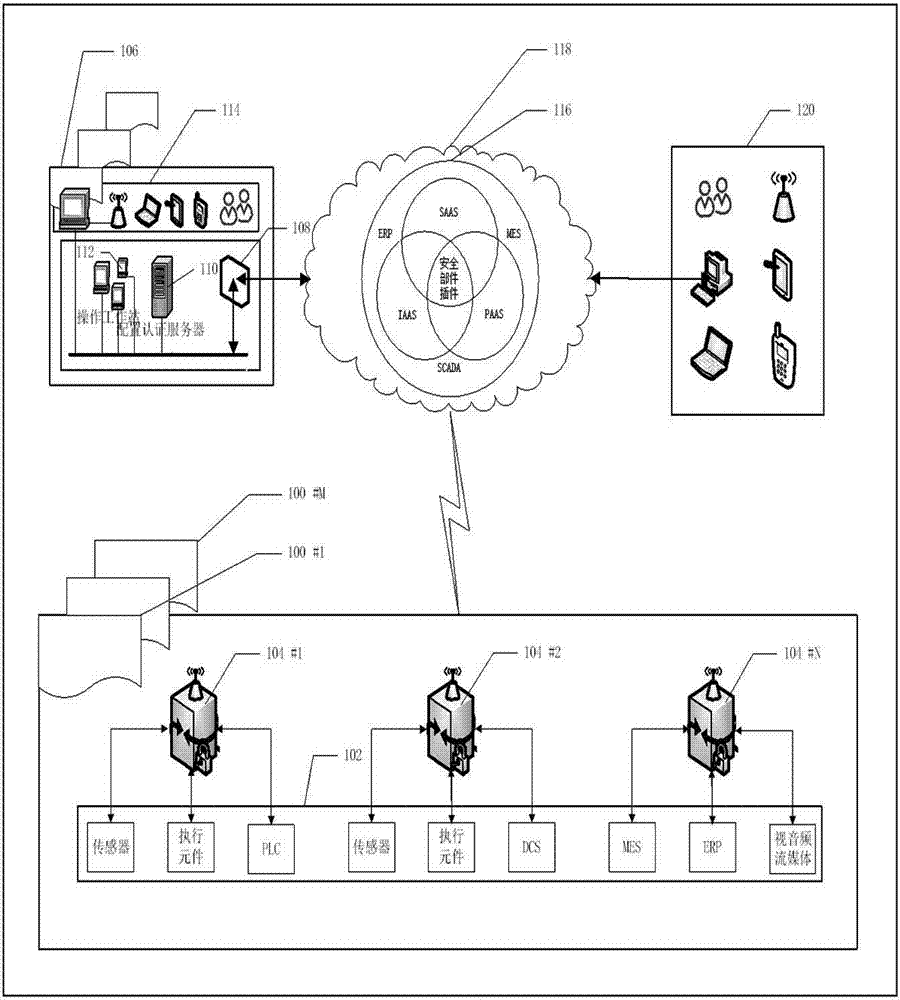
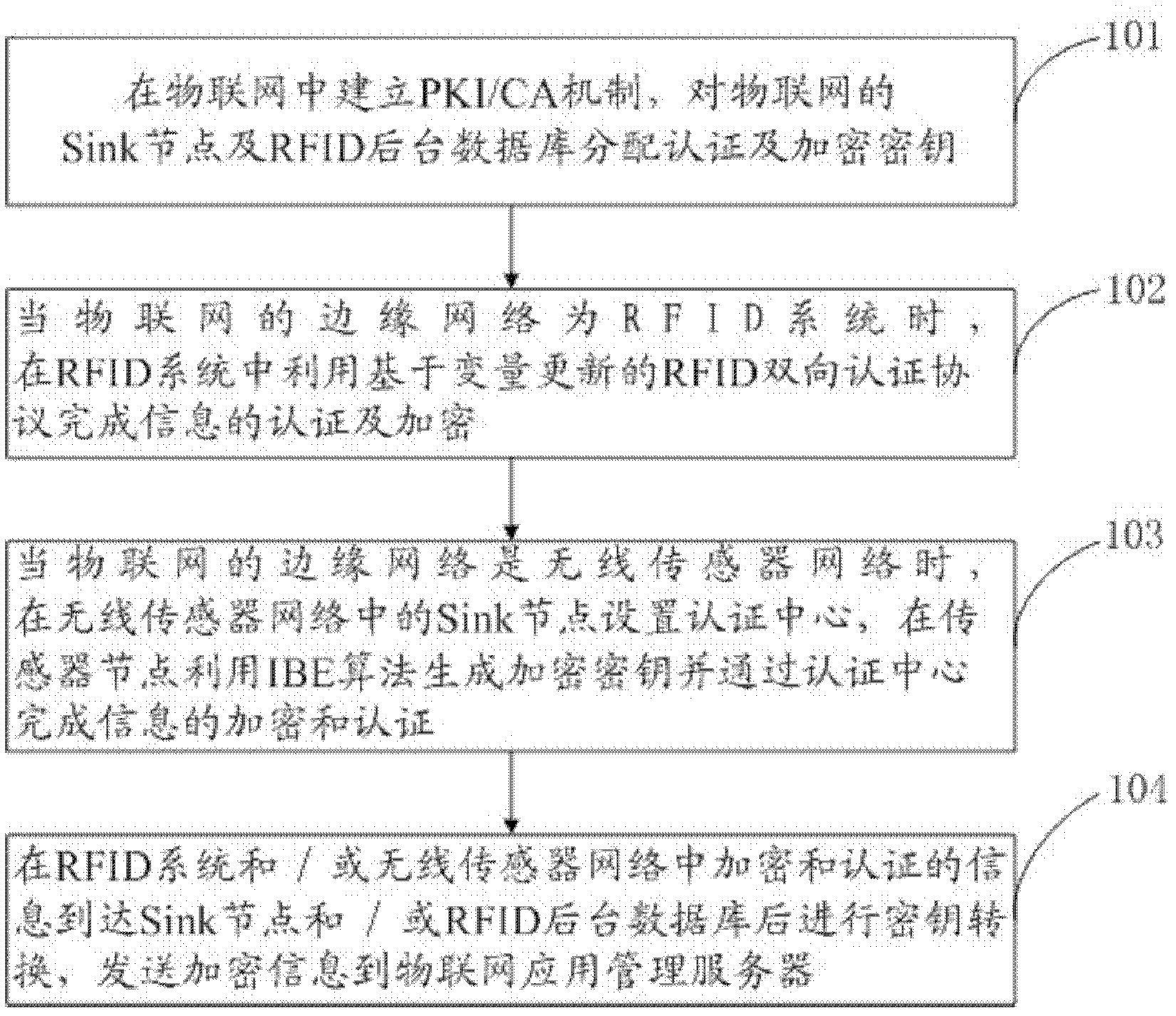
The invention discloses a method and a system for internet of things information transmission. Firstly, a public key infrastructure / certificate authority (PKI / CA) mechanism is established in the internet of things and an authentication key and an encryption key are distributed to an aggregation node of the internet of things; transmitted information is encrypted and authorized in an edge network of the internet of things; and key conversion is conducted after the encrypted and authorized information reaches the aggregation node of the internet of things and the information encrypted again is sent to an application management server of the internet of things. According to the method and the system for the internet of things information transmission, the internet of things can effectively resist interior attack, information safety transmission level is improved and complexity of encryption and safety authentication calculation in the edge network of the internet of things is reduced.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
Methods and systems for security authentication and key exchange
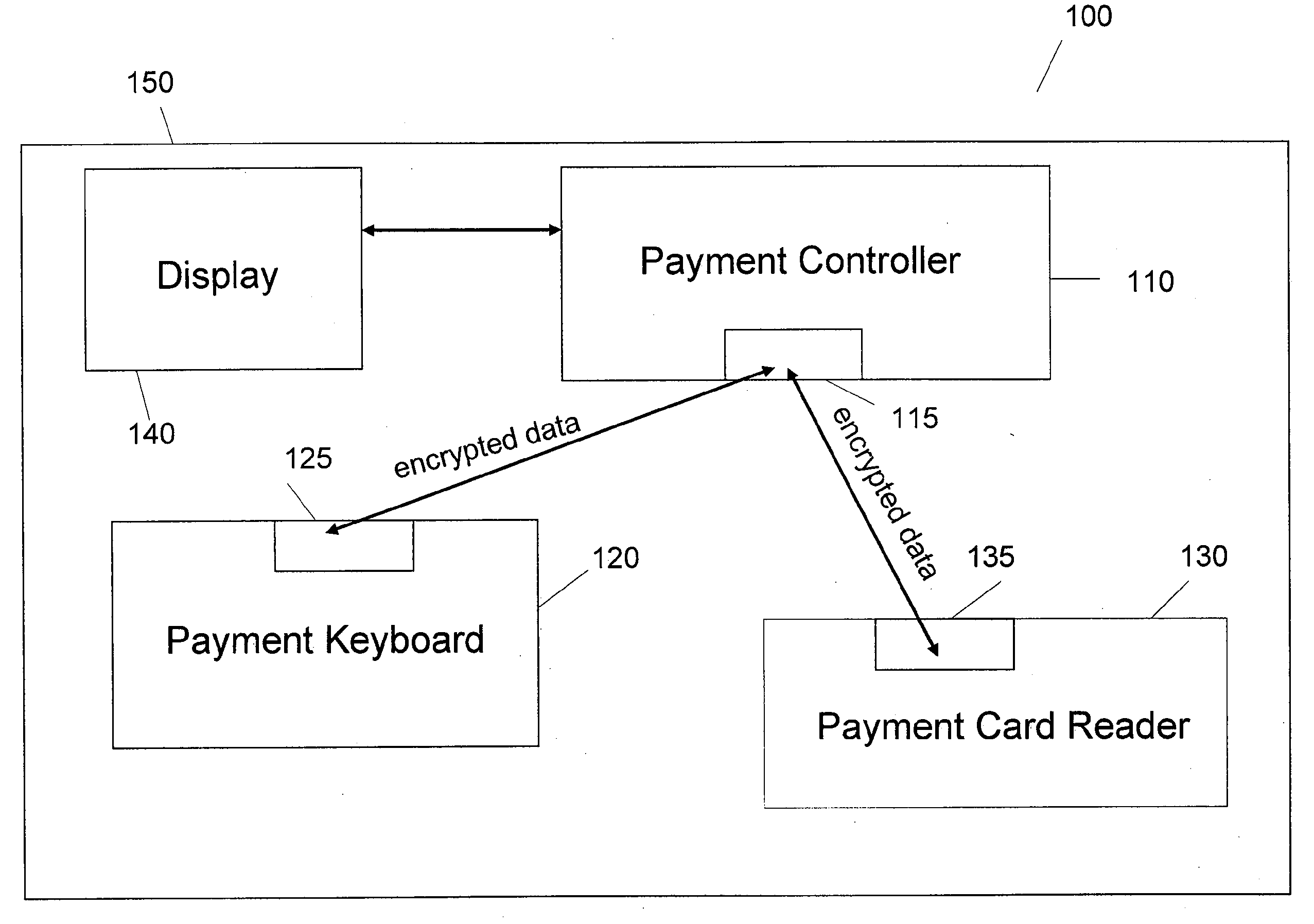
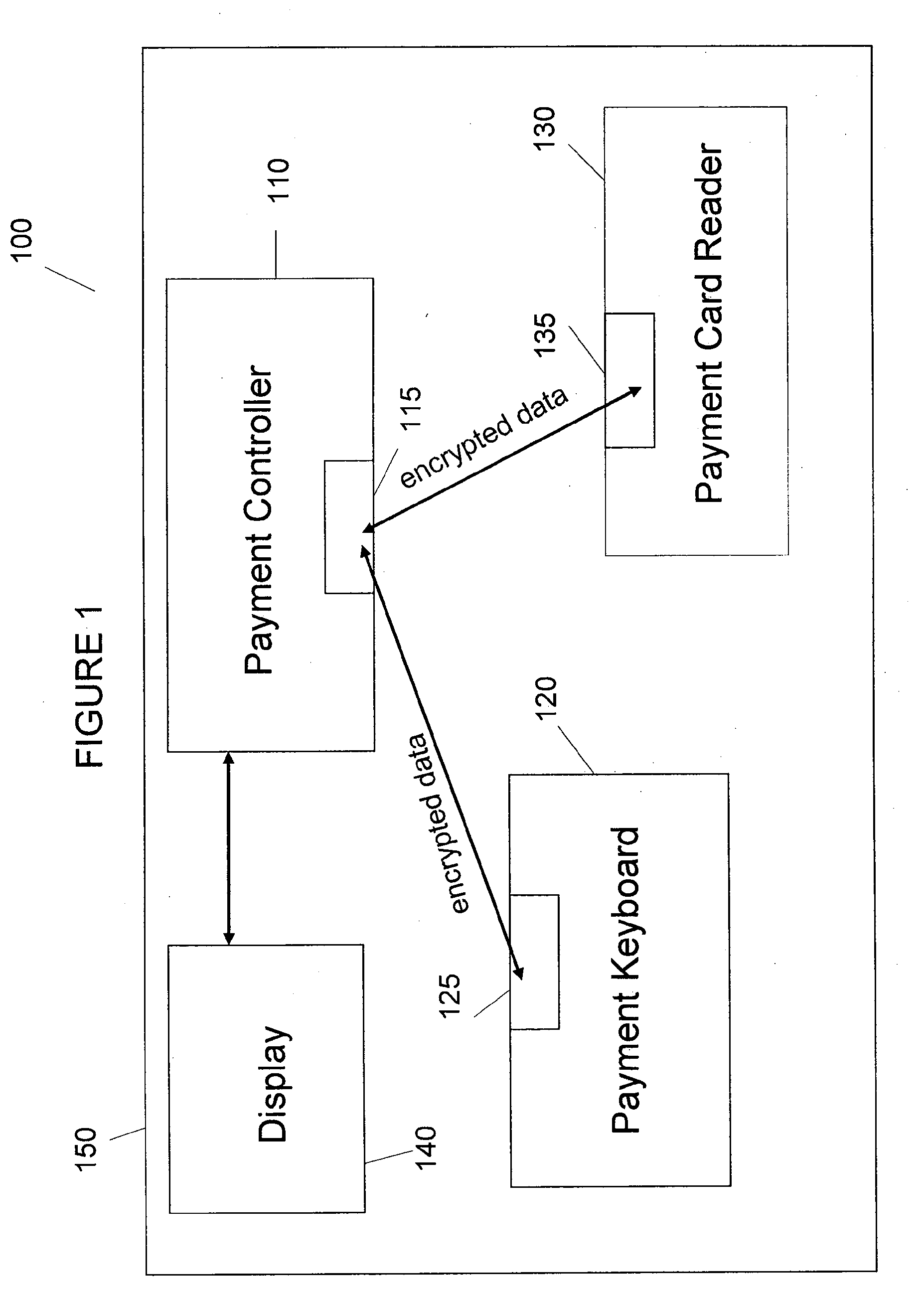
This is for a payment device that may be constructed from separate modules in a secure fashion such that the aggregation of the modules constitutes an overall secure device without the use of additional covers, cases, or tamper-resistant housings. The methods and system are provided whereby the devices within a modular payment system can exchange data between each-other in a secure fashion. While data encryption is being used elsewhere, the present invention extends the security zone from each secure payment module within a modular device out over the cable to the next device. This allows the user to purchase payment device components, place them as they see fit, and not have to obtain certification on their end product as a POS-A level payment device.
Owner:HYPERCOM CORP
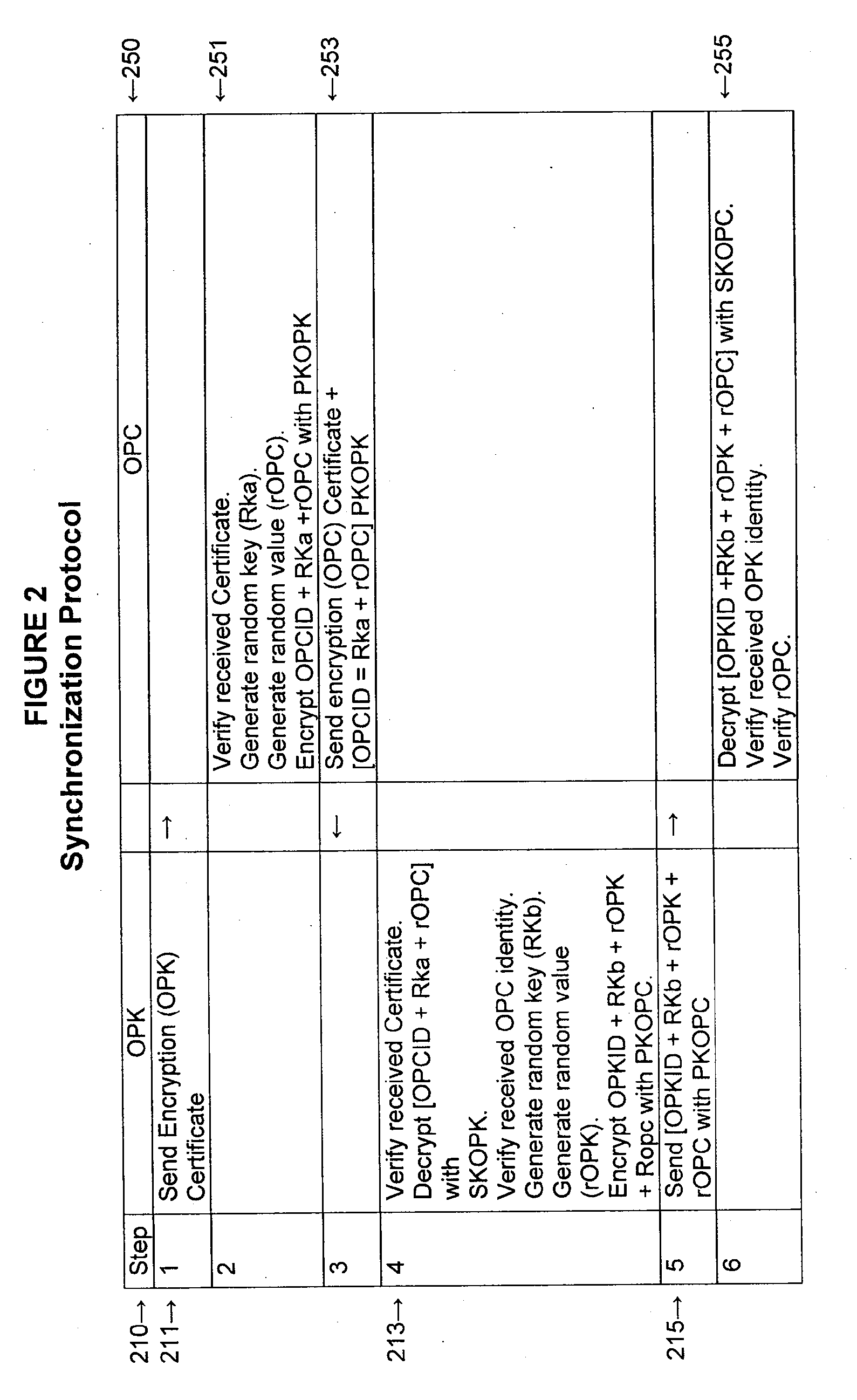
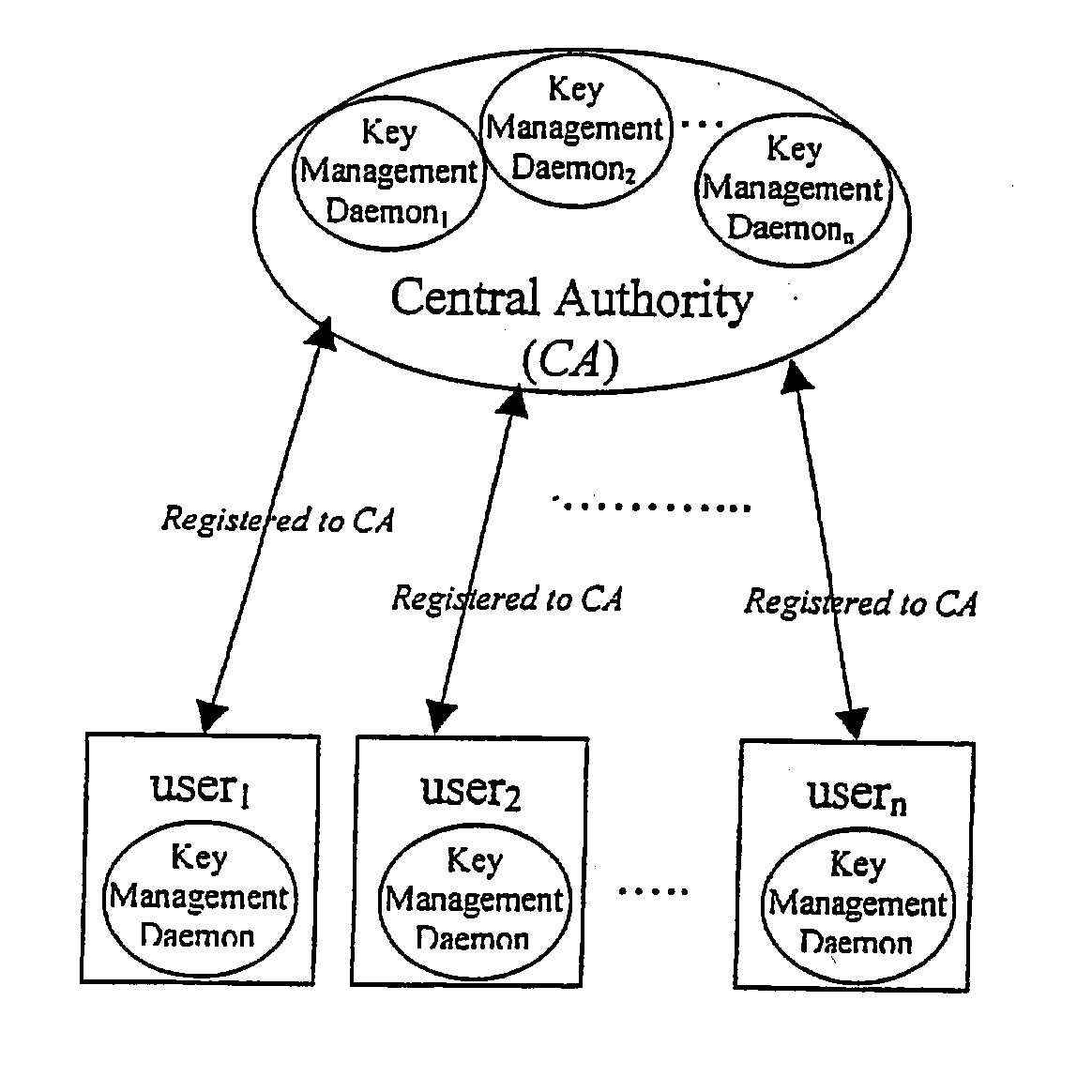
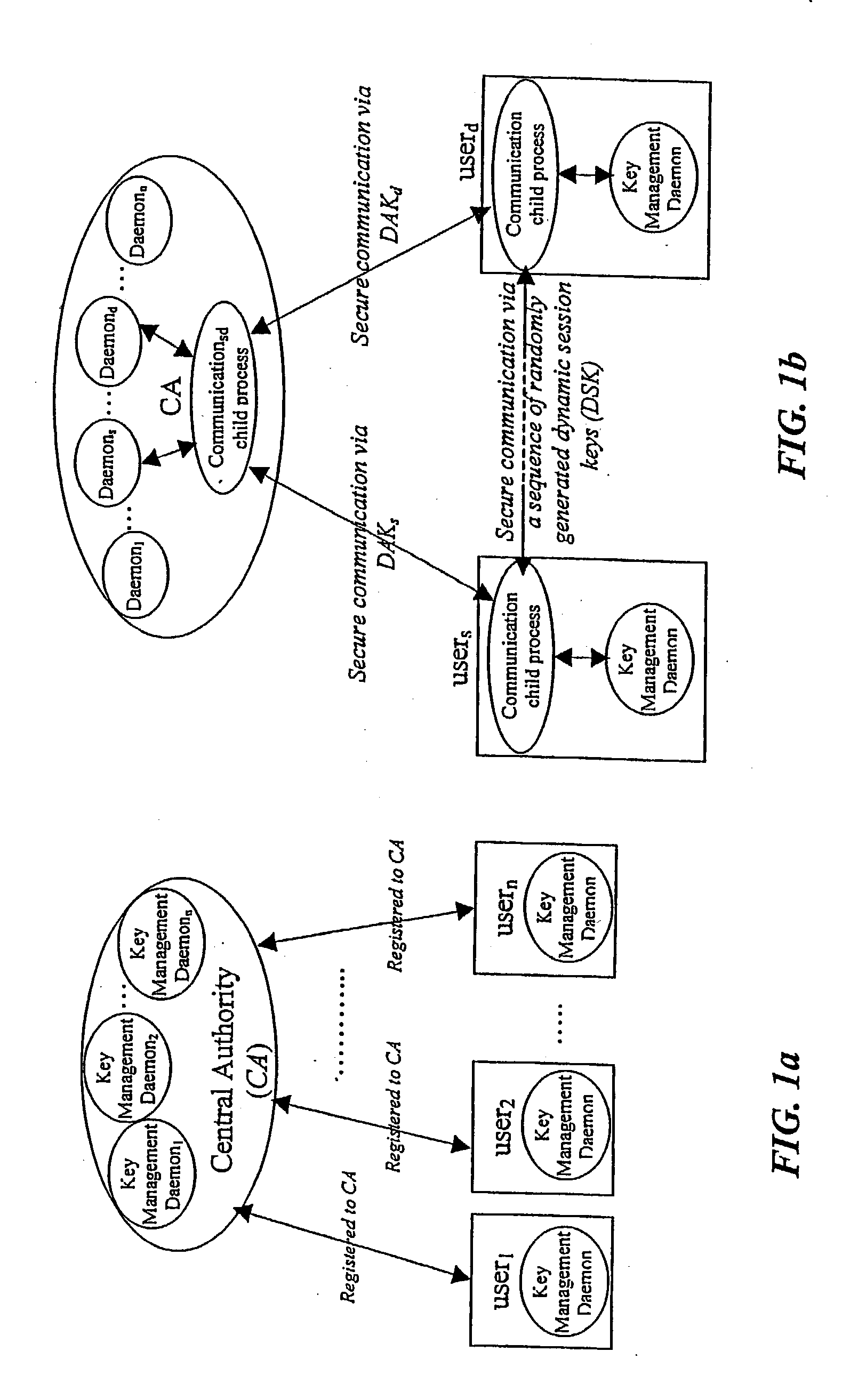
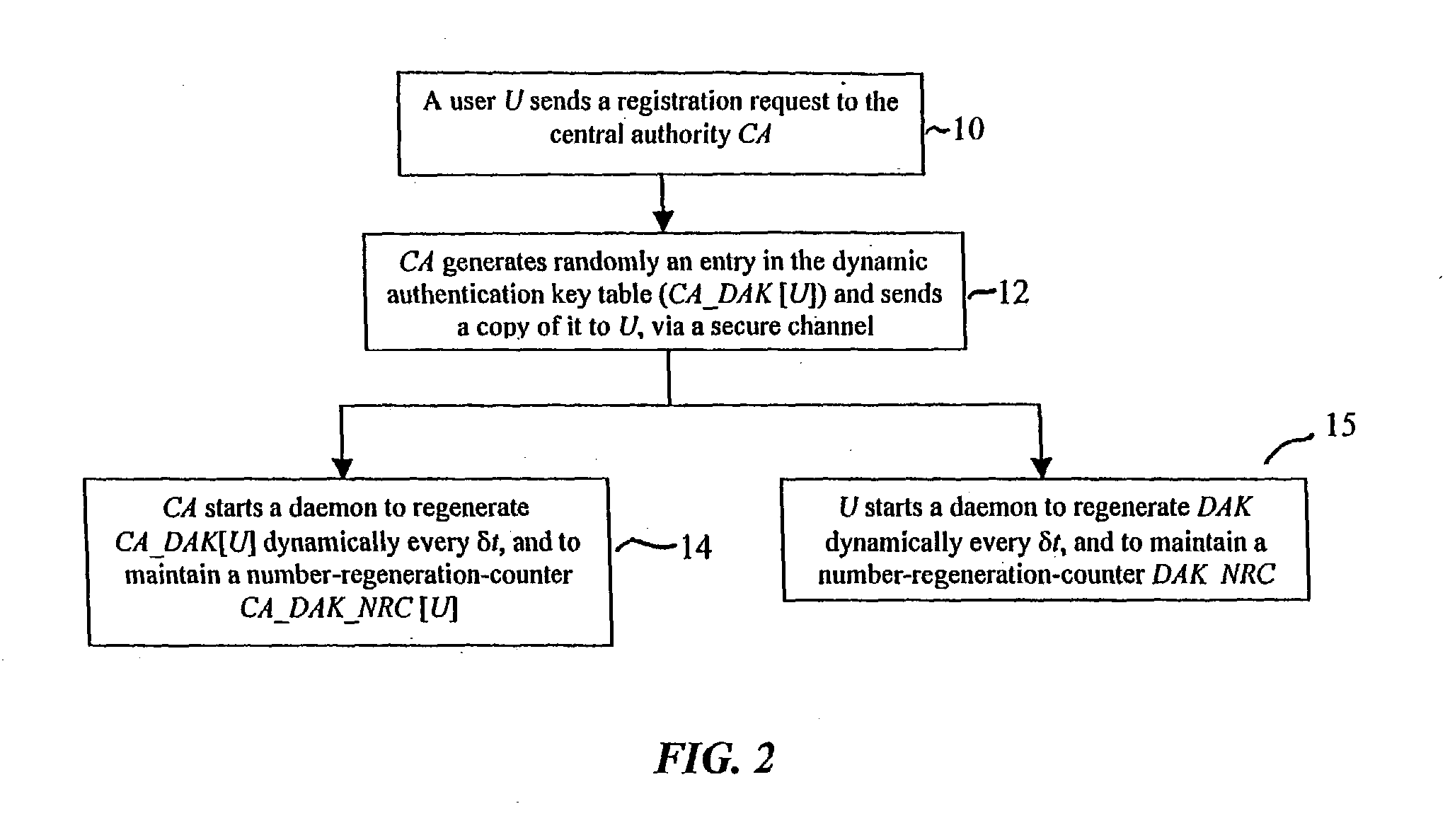
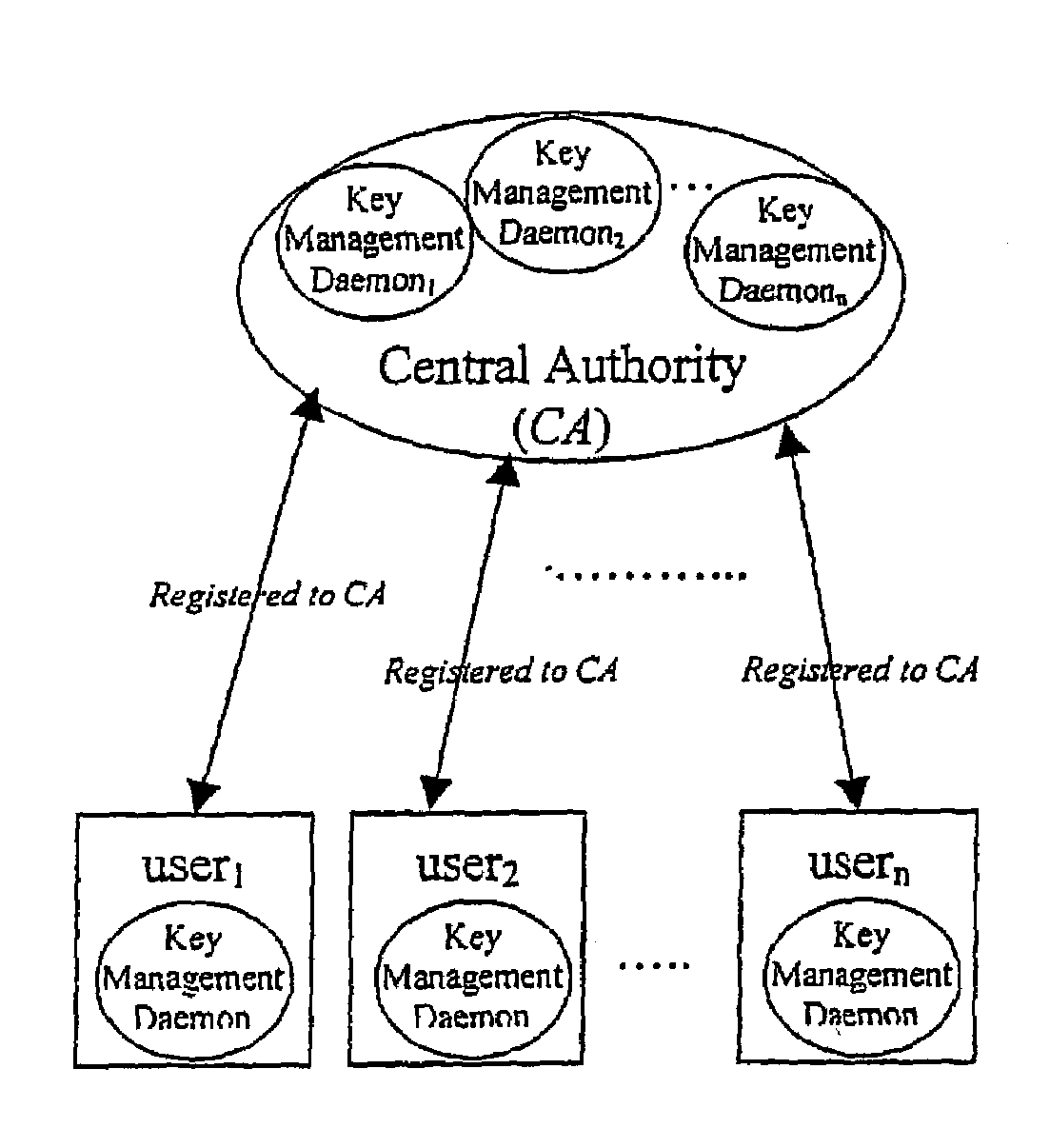
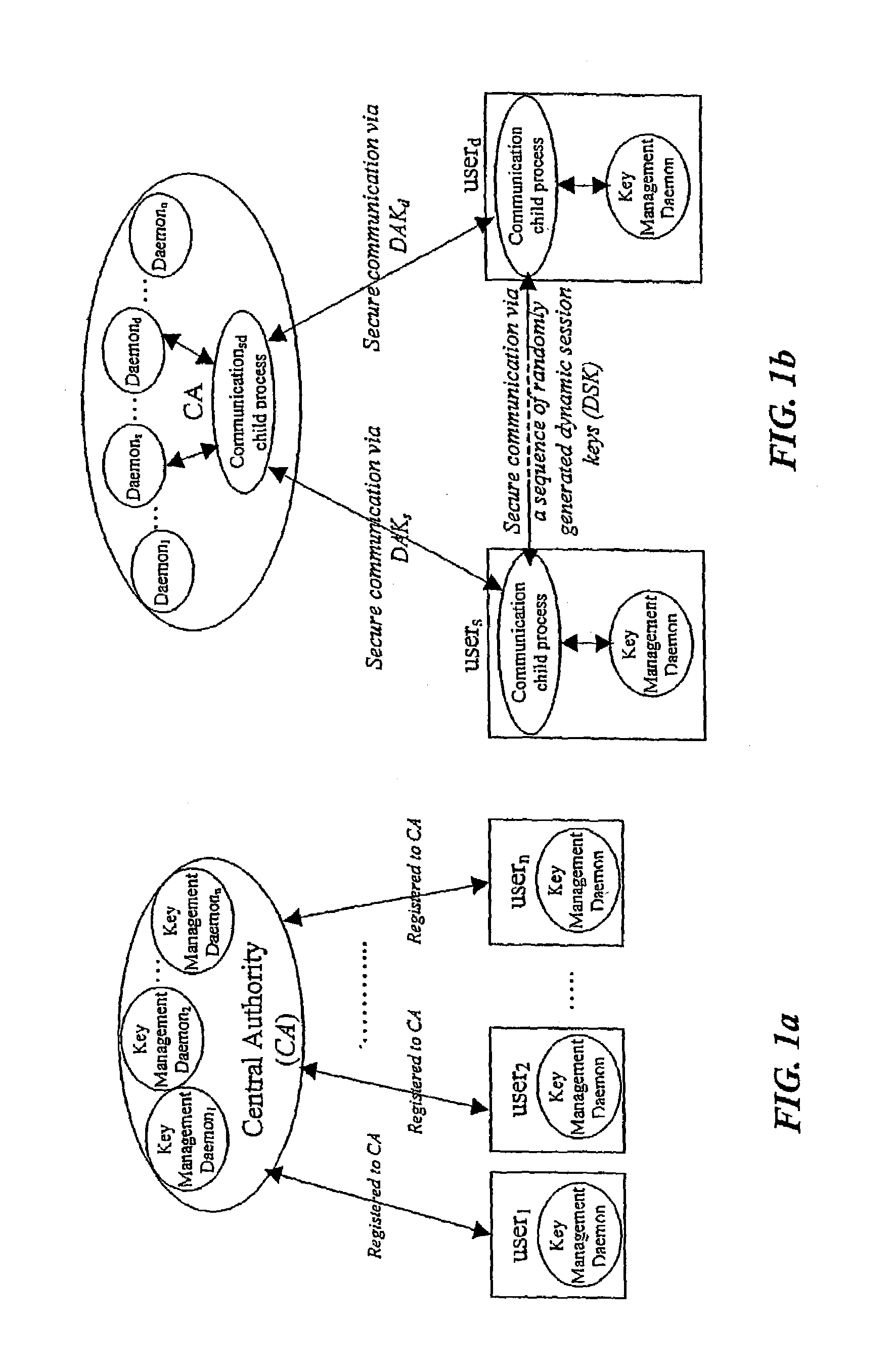
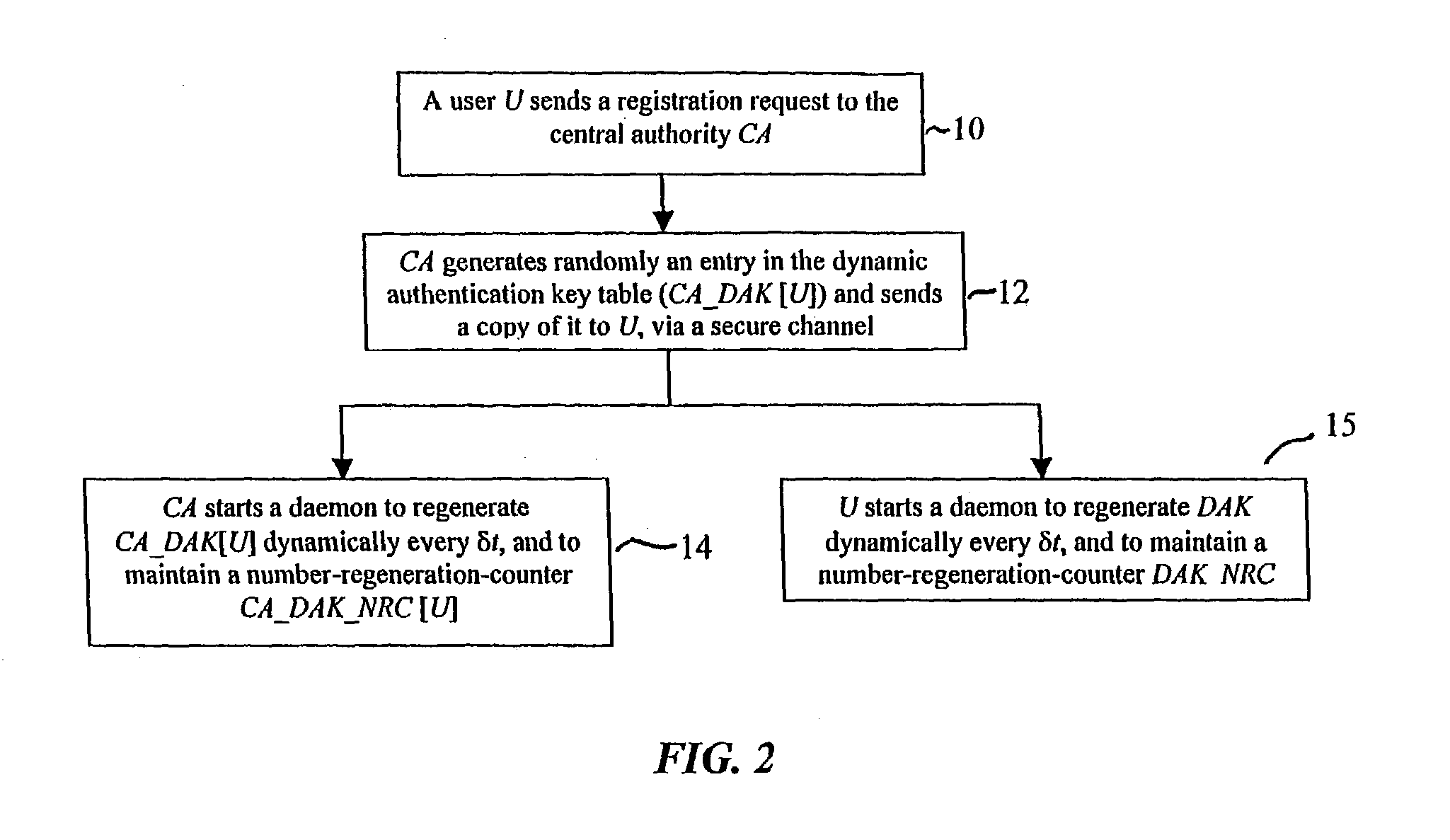
Dynamic security authentication for wireless communication networks
ActiveUS20040179690A1Minimize exchangeMinimization of wasted bandwidthKey distribution for secure communicationSynchronising transmission/receiving encryption devicesSystemic approachAuthentication server
In a first embodiment, a dynamic computer system security method and system using dynamic encryption and full synchronization between system nodes. A data record created by a source user is encrypted with an initial dynamic session key. A new dynamic session key is generated based upon a data record and a previous dynamic session key. A central authority is used to synchronize and authenticate both source and destination users with constantly regenerated dynamic authentication keys. In a second embodiment, a method of providing dynamic security authentication between wireless communication network nodes. An initial authentication key and an address are assigned to certain of the nodes. The address along with information encrypted by the initial authentication key is sent to an authentication server. The authentication server and node or nodes synchronously regenerate authentication keys based upon the initial authentication key. Secure handovers occur between nodes via an authentication key.
Owner:MOXCHANGE LLC
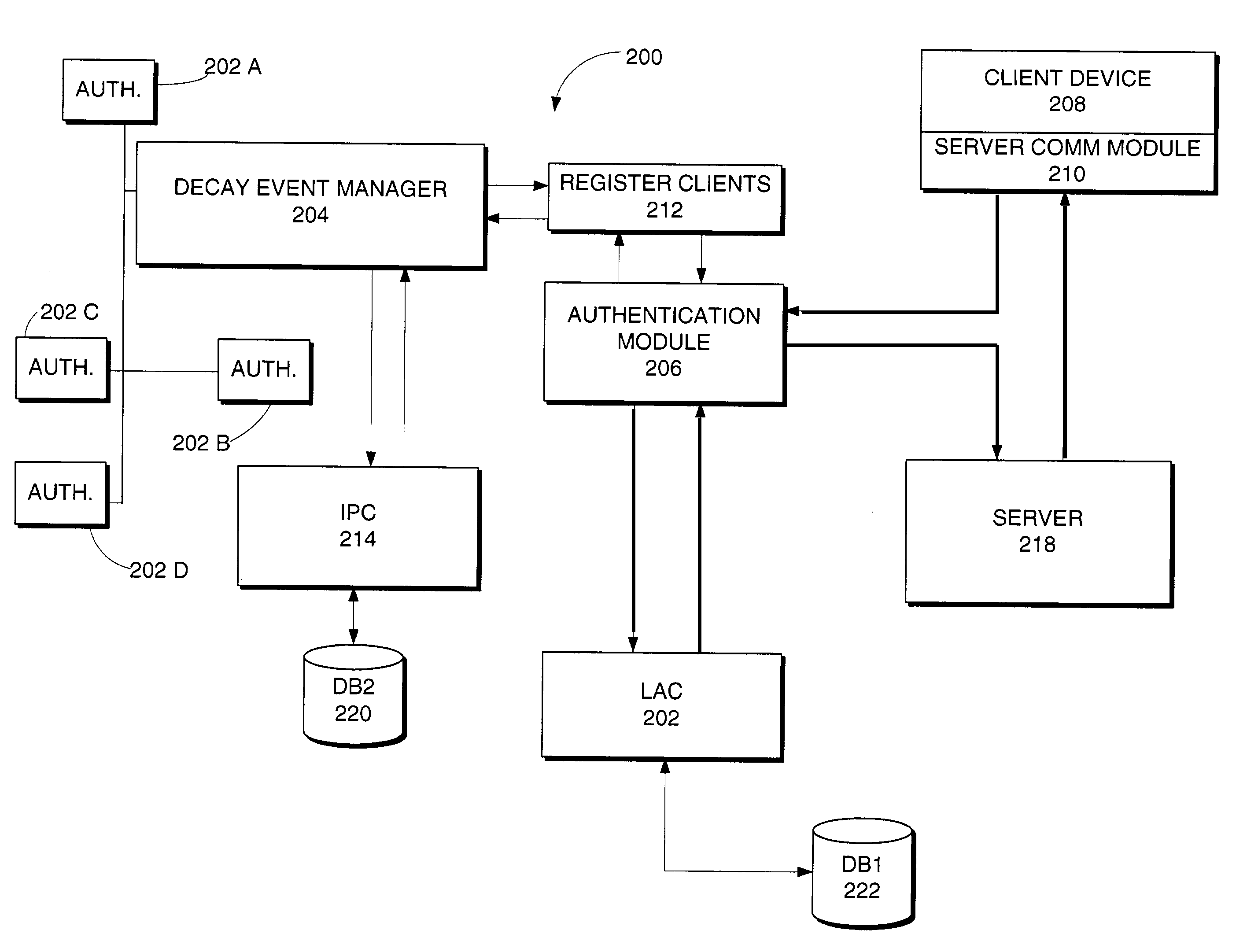
Authentication surety and decay system and method
InactiveUS7636853B2Digital data processing detailsUser identity/authority verificationIdentity theftUser authentication
The present invention is directed to a method and system for use in security authentication in a network environment. The present invention enables shared security information by networked devices. It also allows access to networked devices on the basis of authentication surety. The system assigns surety levels on the basis of the modes and methods of user authentication to the network. Further, the present invention allows the gradual decay, of user authentication and thus access to networked devices over time. Further still, the present invention distinguishes between individual identities and personas within the network environment. Surety levels associated with an authentication provide a predetermined level of access to networked devices or device features. The present invention provides improved security and diminishes the risk of fraudulent access to a network via identity theft.
Owner:MICROSOFT TECH LICENSING LLC
Safety identification method based on safe computer
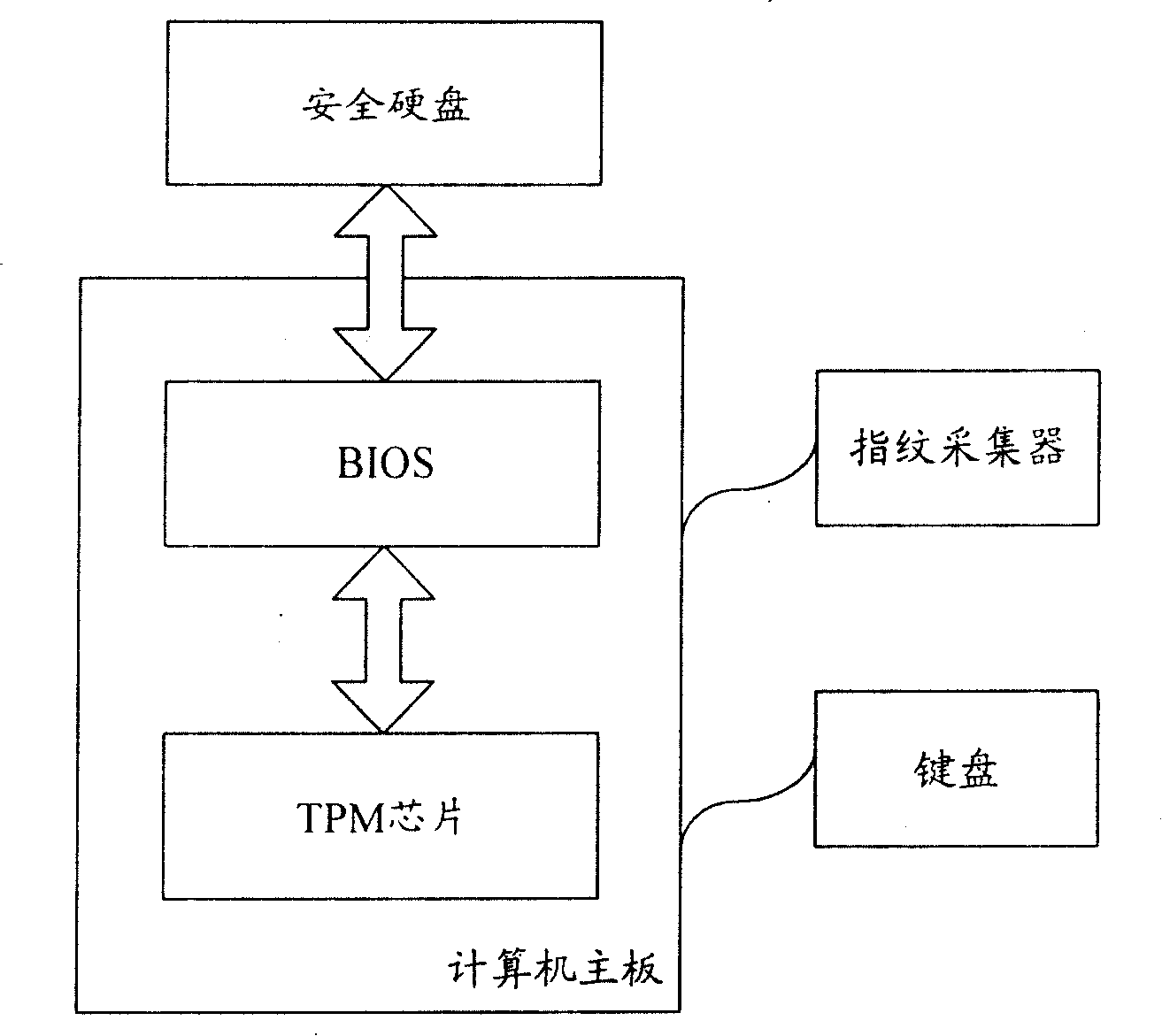
ActiveCN101165696AReduce operational complexityImprove usabilityInternal/peripheral component protectionDigital data authenticationLog managementTrusted Platform Module
Said security computer comprises a computer mother board, a security hard drive, a basic input / output system (BIOS) located on said mother board and a trusted platform module (TPM) chip. Both Said TPM chip and the security hard drive are respectively connected to the BIOS. The method comprises: after said BIOS completes the system self-testing and initialization and before the mutual authentication is made between the BIOS and security hard drive, the BIOS make a forced ID authentication for user powering the computer; after passing through the ID authentication, the BIOS and the security hard drive make mutual authentication each other; if the authentication is passed, then the security authentication is successful.
Owner:CHINA GREATWALL TECH GRP CO LTD
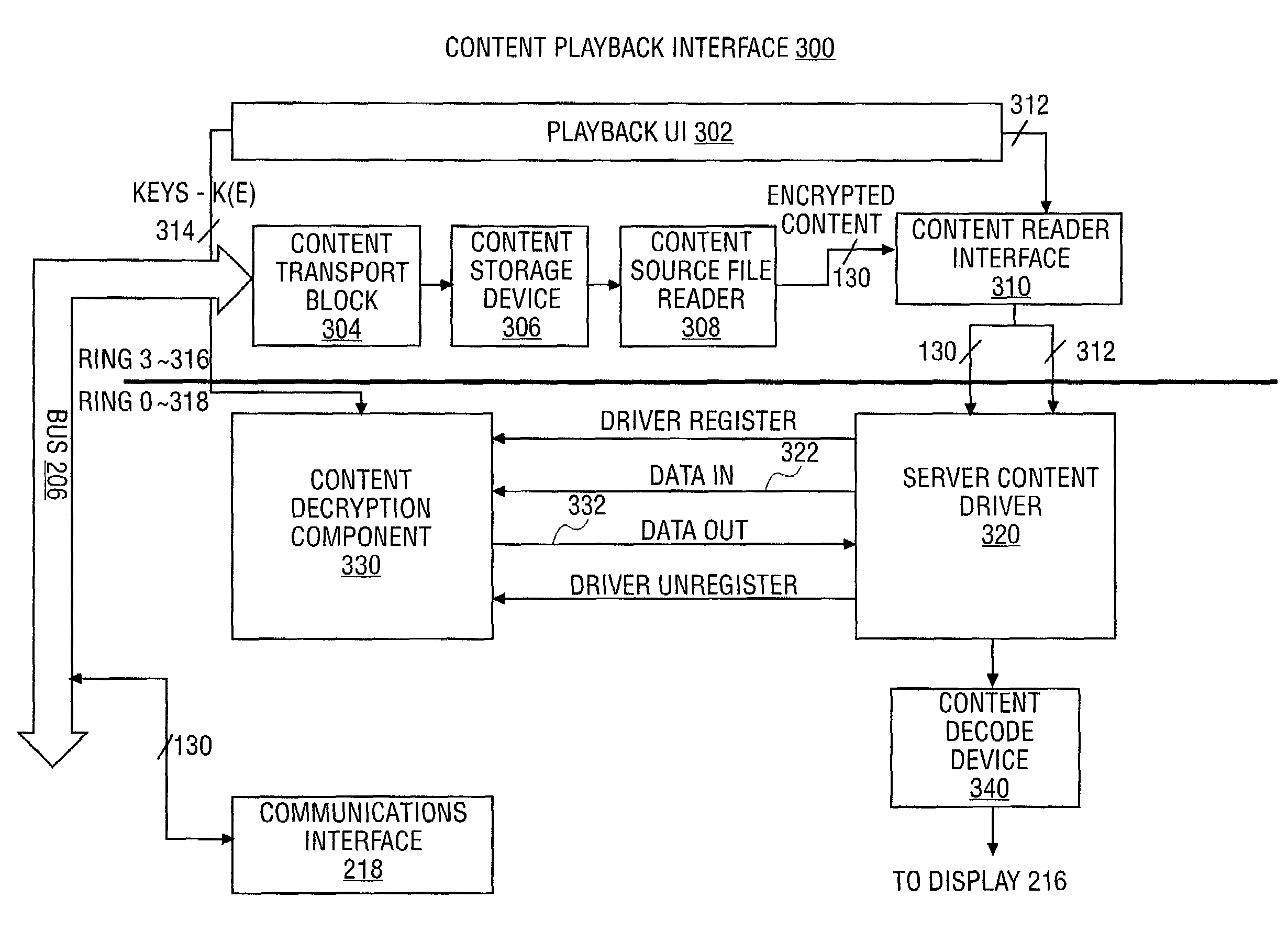
Apparatus and method for enabling secure content decryption within a set-top box
ActiveUS7328455B2Digital data processing detailsUser identity/authority verificationSecurity authenticationRunning time
An apparatus and method for enabling secure content decryption within a set-top box are described. The method includes performance of security authentication of a content driver by a content decryption component. Security authentication is performed in order to verify an identity of the content driver as a secure content driver. Next, the content decryption component receives an encrypted content stream from the secure content driver. Once received, the content decryption component performs integrity authentication of a run-time image of the secure content driver. Finally, while integrity authentication of the secure content driver is verified, the content decryption component streams decrypted content to the secure content driver to enable playback of the decrypted content to a user.
Owner:INTEL CORP
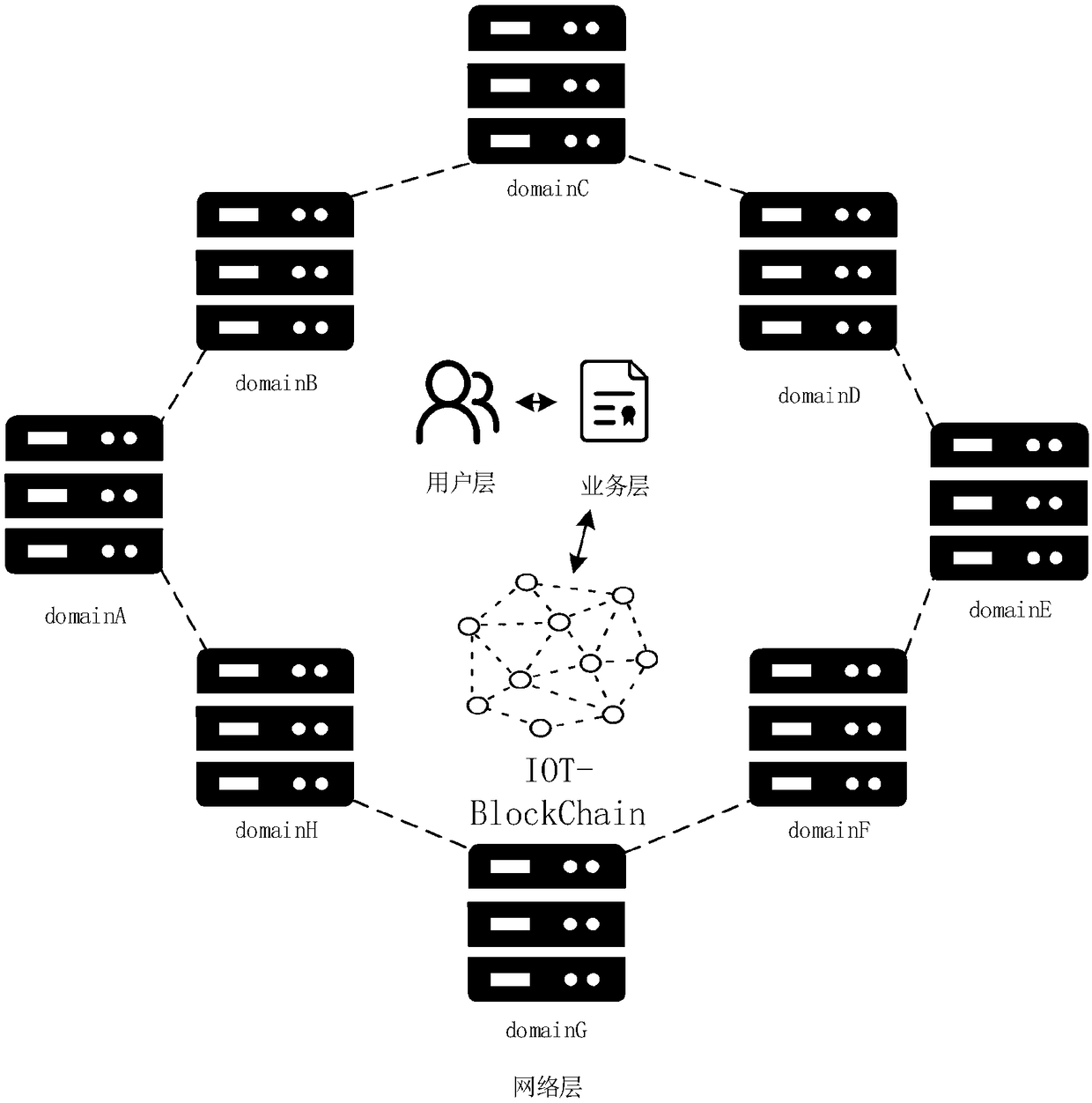
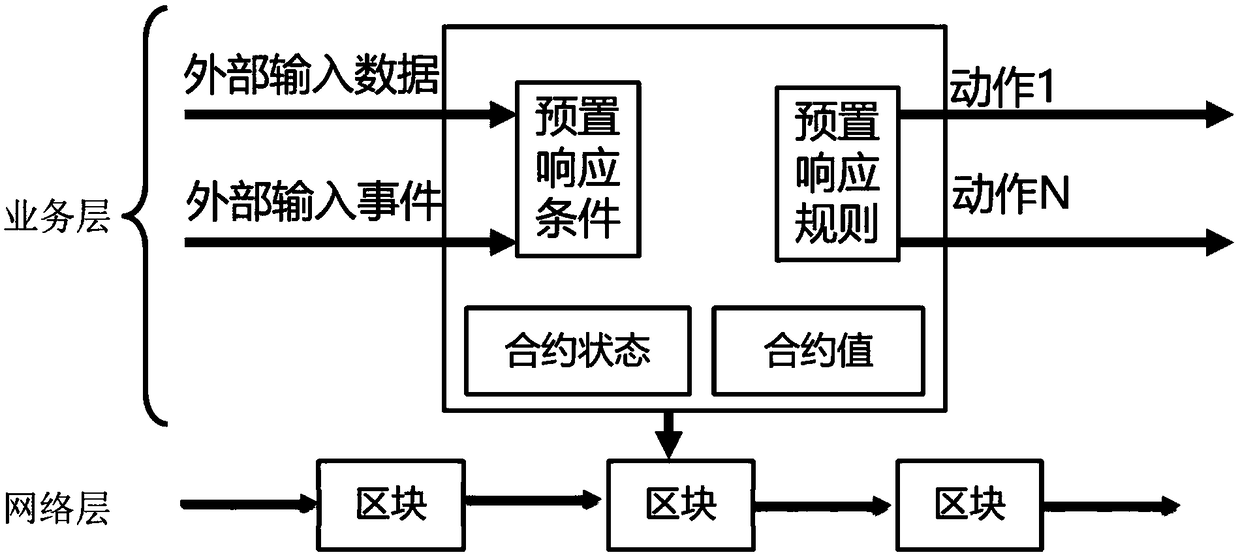
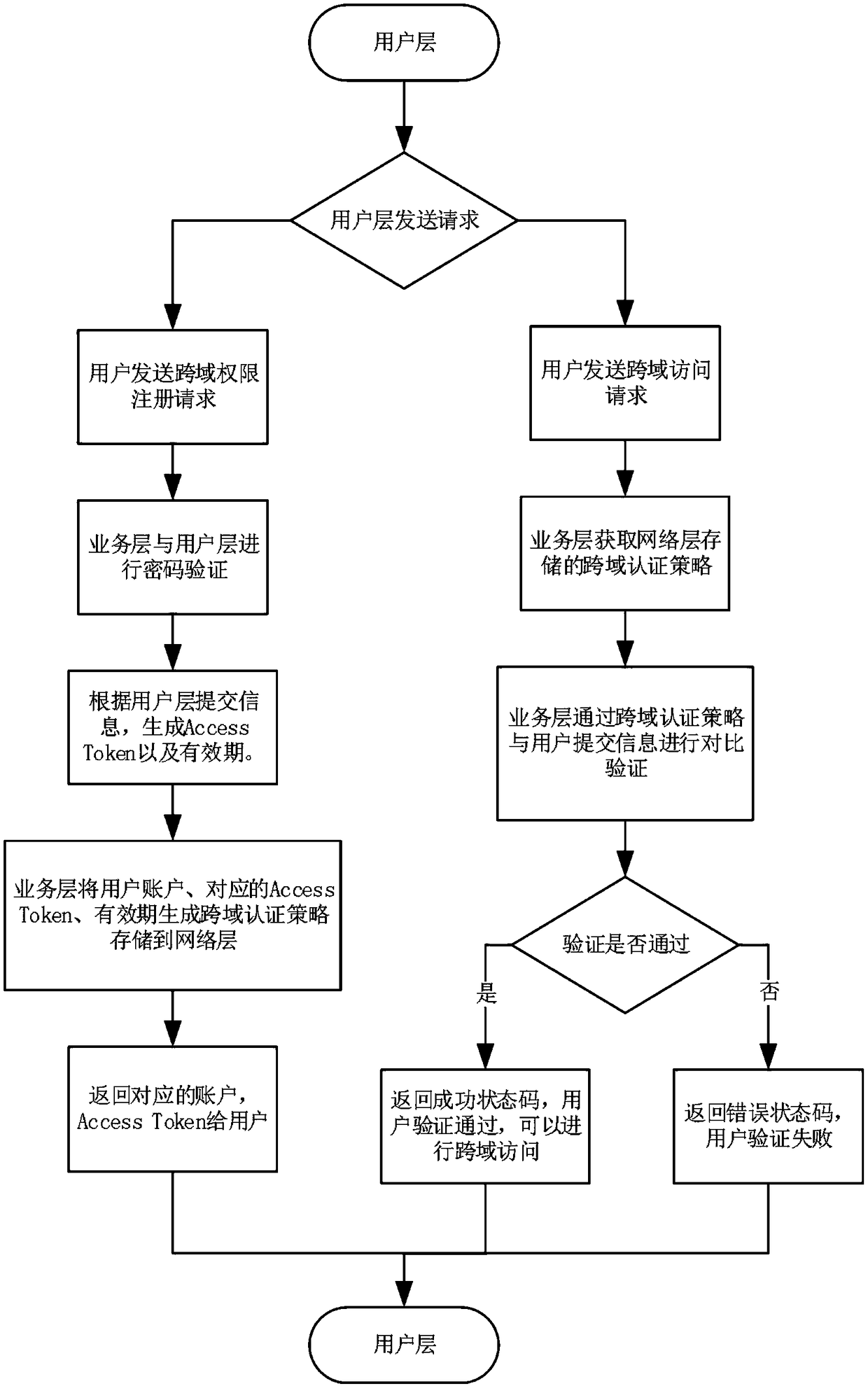
Internet of Things (IoT) cross-domain authentication system and method based on block chain
ActiveCN108737370AAchieve sharingImplement a trustless mechanismTransmissionThe InternetInteraction interface
The invention belongs to the technical field of the Internet of Things (IoT) security authentication, and discloses an IoT cross-domain authentication system and an IoT cross-domain authentication method based on a block chain. The system comprises a network layer, a service layer and a user layer. The network layer is a block chain network, and is an allied block chain formed by each domain separately serving as a network node; the service layer is a distributed application intelligent contract developed based on a block chain network, and can execute a complex machine language; and the userlayer is based on a user interaction interface developed based on the node of each domain, for implementing binding of the authenticated domain and distribution of an authentication key. According tothe system and method provided by the invention, the cross-domain authentication system based on security of the block chain can be implemented, the distributed storage of authentication schemes is implemented, and the authentication schemes are recorded on the block chain in the form of an account book, so as to be unable to tamper.
Owner:XIDIAN UNIV
Supply chain management method based on sovereign blockchain
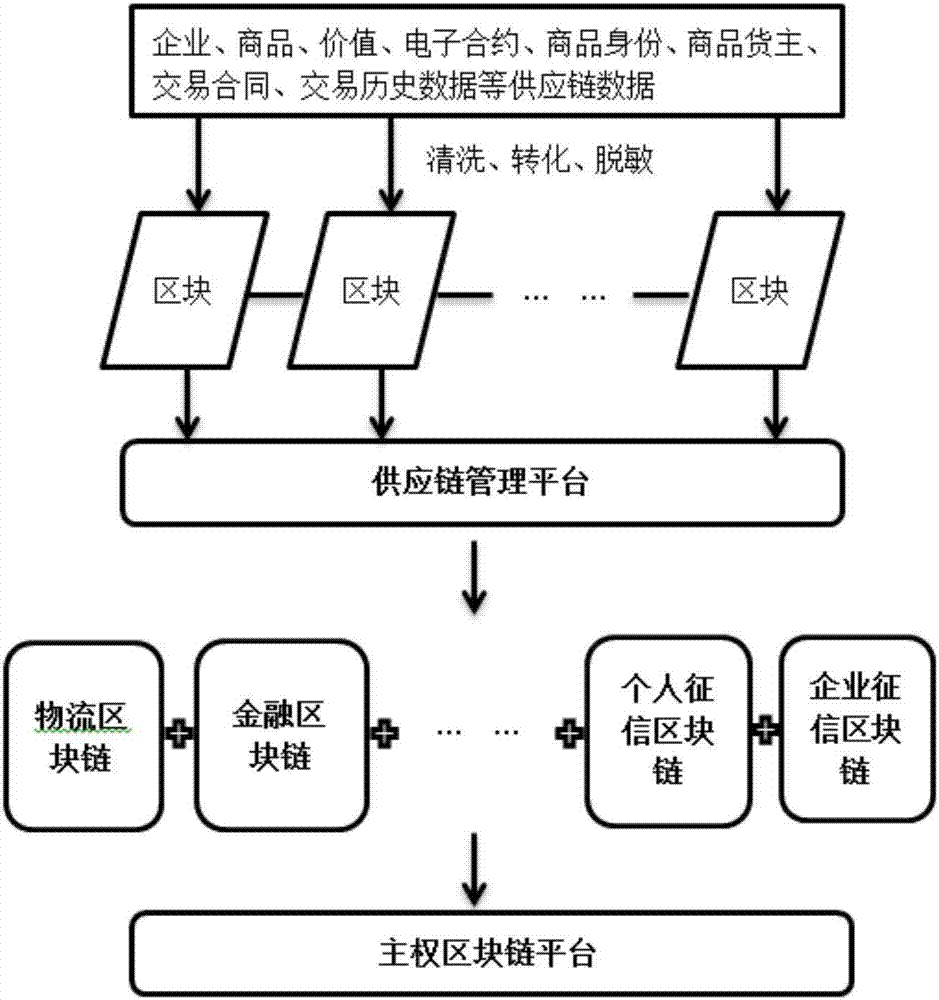
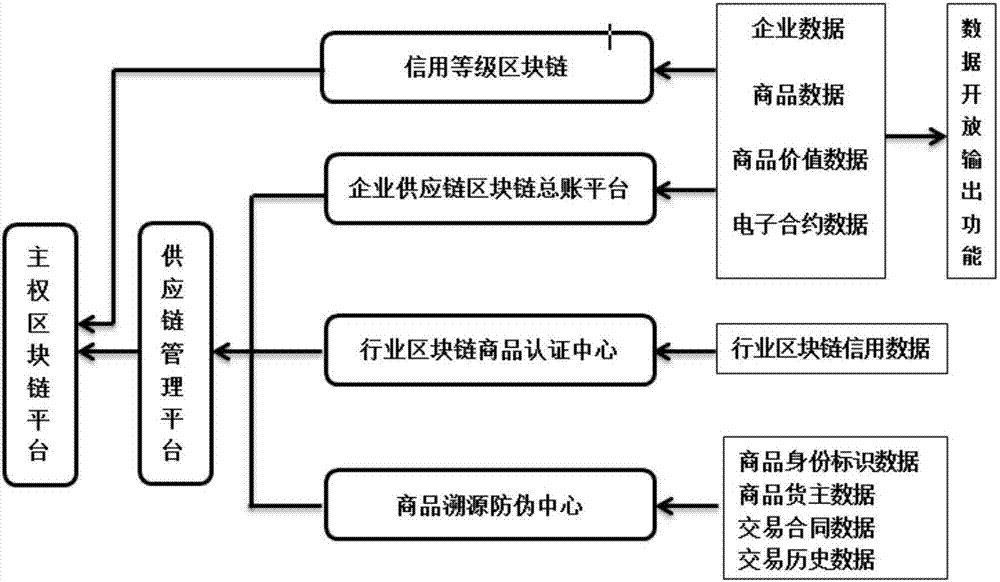
InactiveCN107103480AImprove management transparencyIncrease the scope of applicationCo-operative working arrangementsBuying/selling/leasing transactionsEngineeringSecurity authentication
The invention discloses a supply chain management method based on a sovereign blockchain. The method comprises establishing the sovereign blockchain based on national sovereignty and blockchain technology, establishing a supply chain management platform on the sovereign blockchain, establishing an enterprise supply chain blockchain general ledger service platform, an industry blockchain product certification center and a commodity traceability security authentication center on the supply chain management platform, acquiring supply chain-related information, and establishing a blockchain to be stored in the sovereign blockchain platform so as to connect various dispersive links in the supply chain and to achieve data storage, sharing and authentication in the supply chain through the blockchain.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
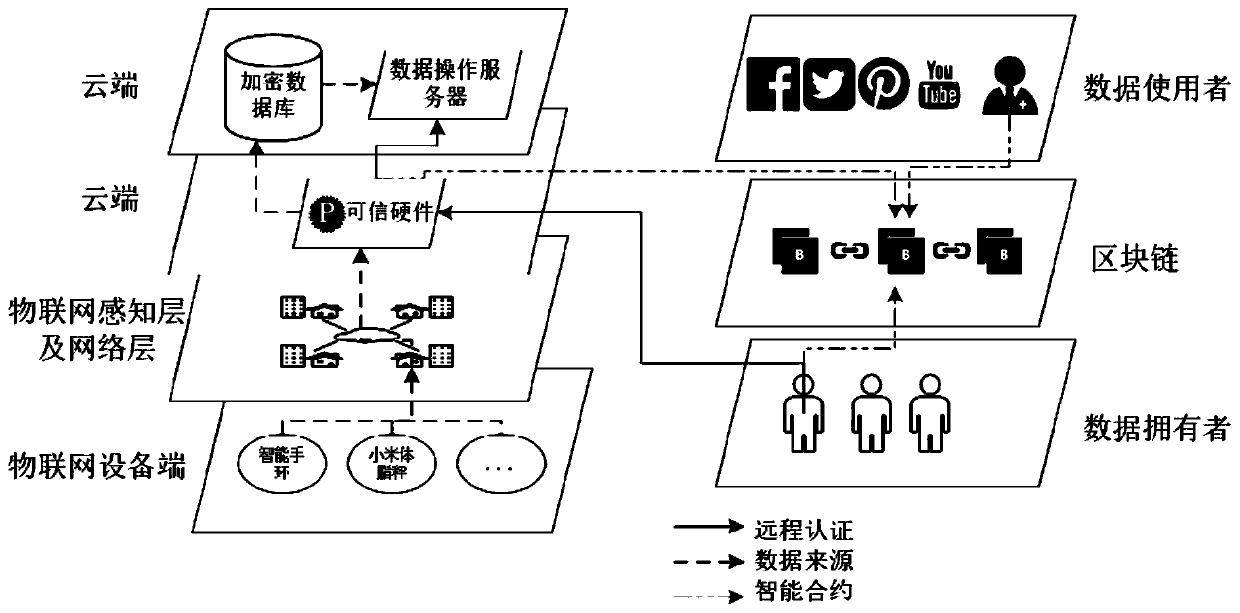
Internet of Things data privacy protection method based on block chain and trusted hardware
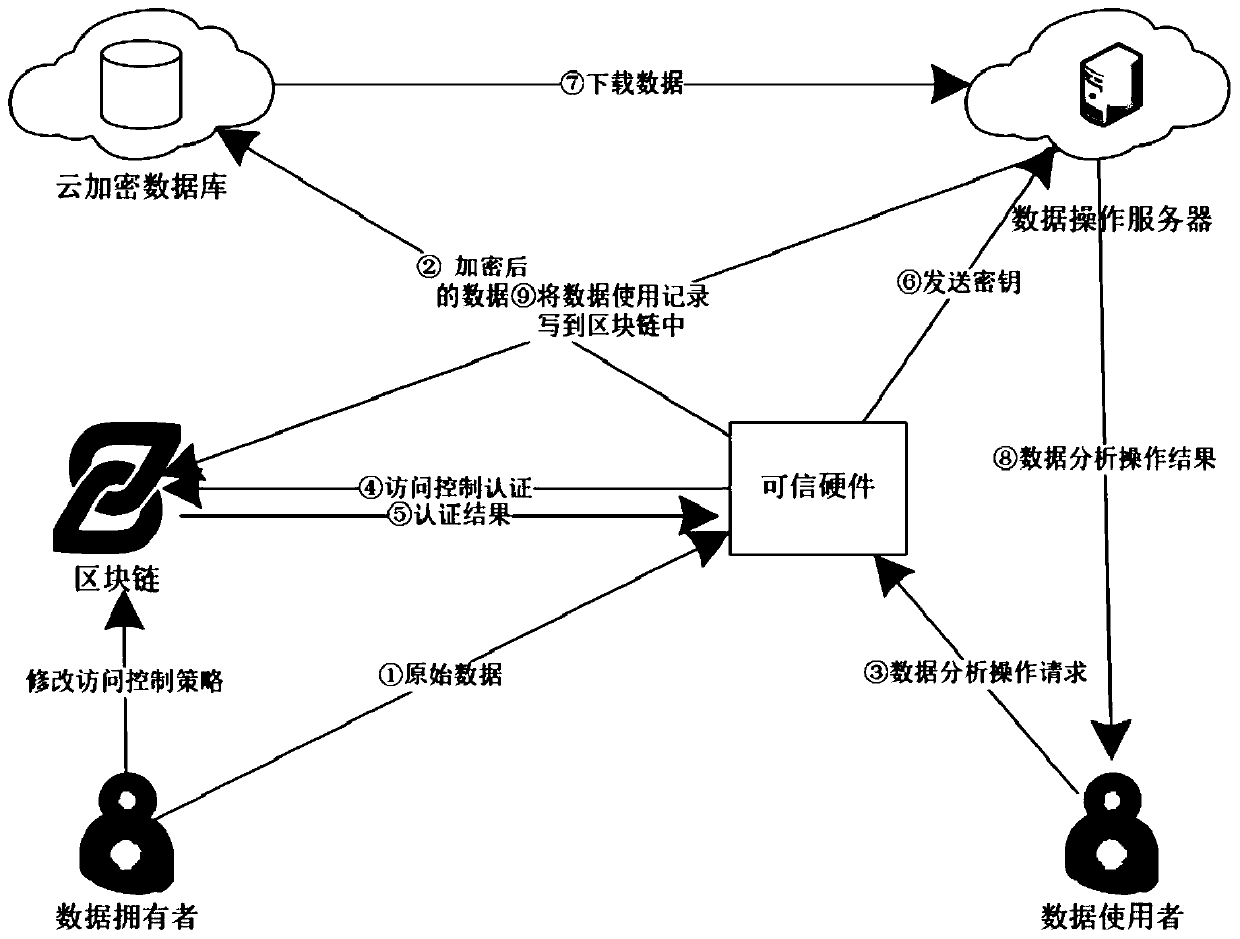
ActiveCN110086804AEnsure safetyGuaranteed reliabilityUser identity/authority verificationDigital data protectionData privacy protectionTrusted hardware
The invention relates to an Internet of Things data privacy protection method based on a block chain and the trusted hardware. The method comprises three stages of secret key management and data generation, data access control strategy definition and intelligent contract deployment and data access and intelligent contract execution, and Internet of Things data is encrypted by a hardware trusted entity IDA and uploaded to a cloud for storage; when there is an operation request, the trusted entity calls an access control authentication interface of the smart contract to carry out authority authentication; after the authority authentication passes, the trusted entity carries out security authentication on the operation execution server and sends the secret key to the data operation executionserver through a security channel; and the server downloads the data from the cloud, then decrypts the data and executes the operation, and writes the data use record into the block chain after the data analysis operation is completed. According to the scheme, the block chain is combined with the trusted entity, the data is effectively operated under the condition that the original data privacy isnot leaked, and the integrity and the safety of the data use records are guaranteed.
Owner:GUANGZHOU UNIVERSITY
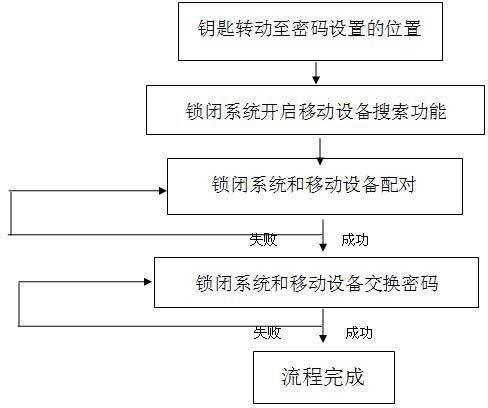
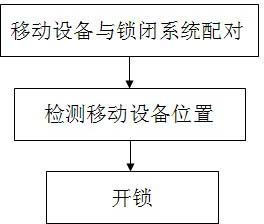
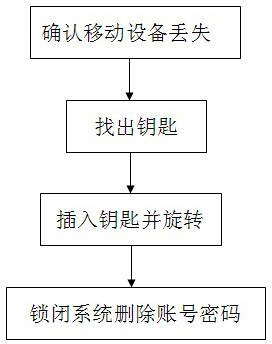
Method for controlling locking system by mobile equipment
The invention discloses a method for controlling a locking system by mobile equipment. The method is used for solving the problem that complex operation such as key using and the like are required in the conventional locking system and reducing human activities which are required in an unlocking process to the maximum extent. An implementation method comprises the following steps of: using external linking functions of the current mobile equipment, such as wireless fidelity (wifi), Bluetooth, infrared and the like; sending unlocking and locking commands to the locking system by using the mobile equipment; and performing multiple security authentication such as inputting of a display name, a password and a dynamical password between the locking system and the mobile equipment, and resetting to ensure that the locking system executes unlocking and locking operation, and the processes of unlocking and locking are implemented.
Owner:杭州赛脑智能科技股份有限公司
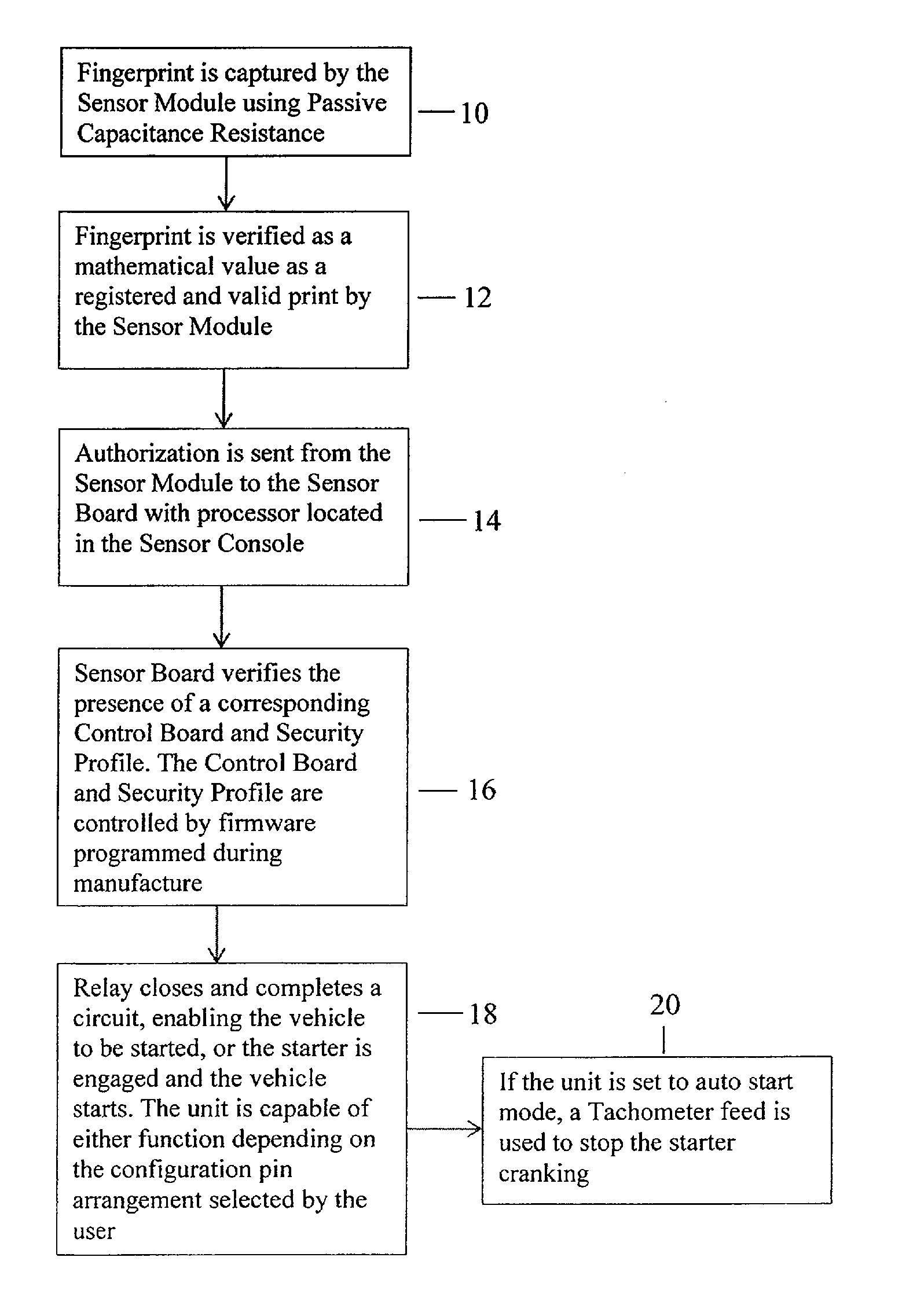
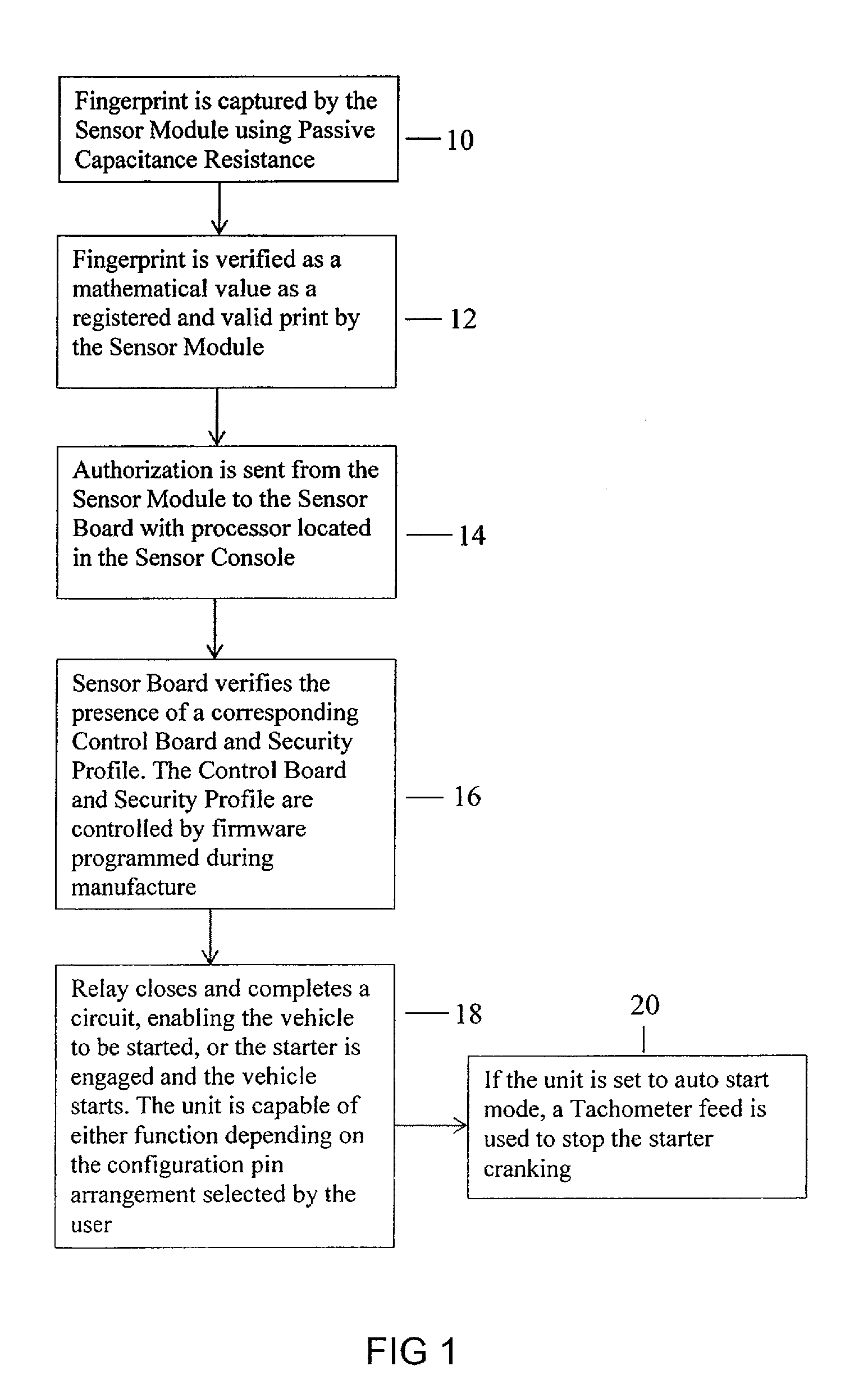
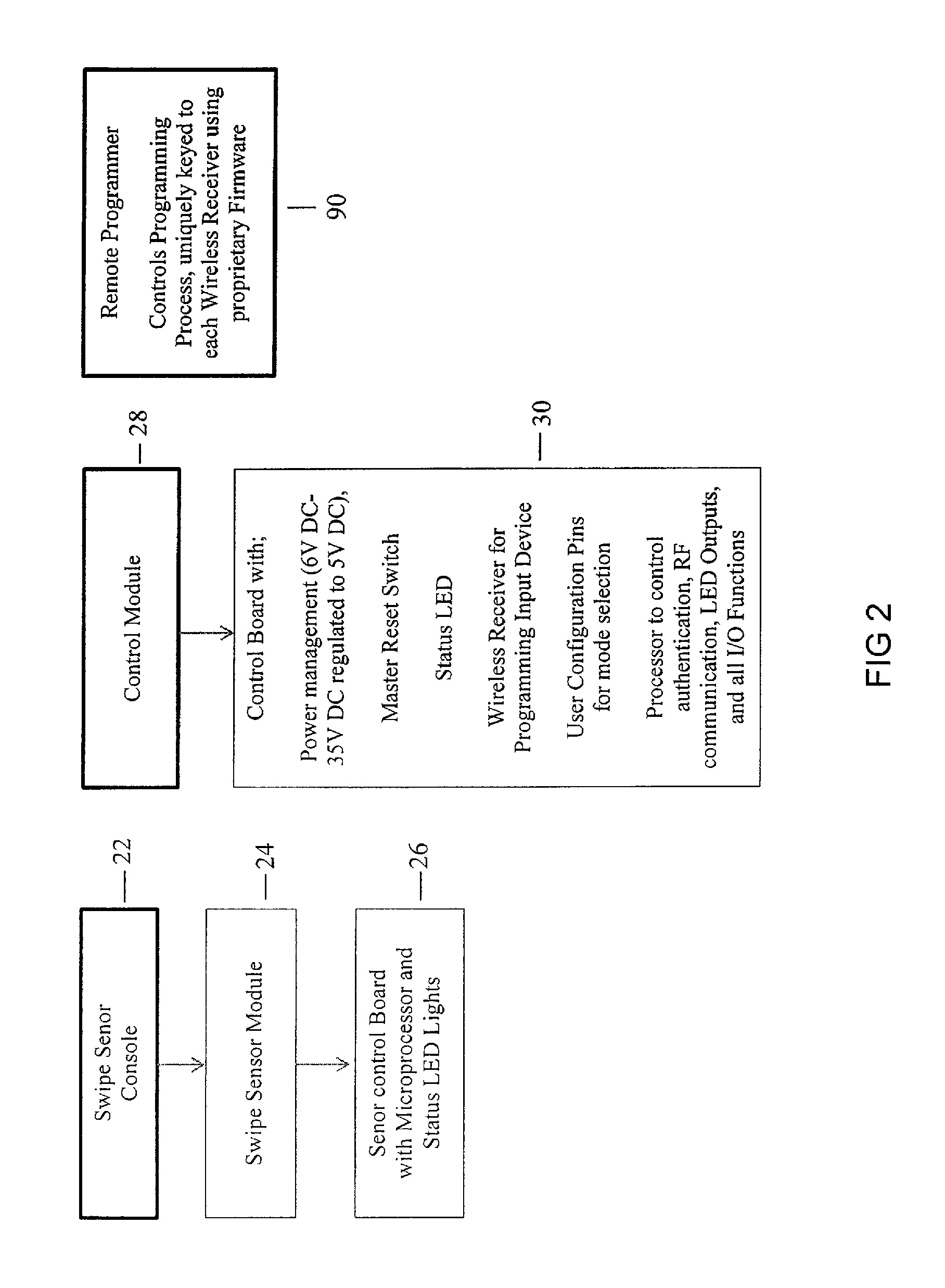
Apparatus and Method for Vehicle Operation Using Biometric Fingerprint identification
InactiveUS20140002237A1Improve the level ofEasy to installElectric signal transmission systemsImage analysisElectricitySecurity authentication
Disclosed is a fingerprint authentication system having a particular benefit for use in protecting vehicles. The system includes a wireless handheld programmer for easy setup and configuration of a multifactor security authentication console having multicolor LED indicator lights that provide programming and user interface feedback by universal symbols. The system is electrically coupled to a vehicle by use of a relay allowing most any vehicle on / off function to be controlled. Once the operator's identity has been authenticated, the device allows operation of the vehicle. A valet mode is provided wherein the unit can be deactivated or programmed to allow a single user. A sensor module operates as the swipe device allowing for the inconspicuous placement on most any vehicle.
Owner:FIST ENTERPRISES
Dynamic security authentication for wireless communication networks
ActiveUS7233664B2Minimize exchangeMinimize wasteKey distribution for secure communicationSynchronising transmission/receiving encryption devicesSystemic approachAuthentication server
In a first embodiment, a dynamic computer system security method and system using dynamic encryption and full synchronization between system nodes. A data record created by a source user is encrypted with an initial dynamic session key. A new dynamic session key is generated based upon a data record and a previous dynamic session key. A central authority is used to synchronize and authenticate both source and destination users with constantly regenerated dynamic authentication keys. In a second embodiment, a method of providing dynamic security authentication between wireless communication network nodes. An initial authentication key and an address are assigned to certain of the nodes. The address along with information encrypted by the initial authentication key is sent to an authentication server. The authentication server and node or nodes synchronously regenerate authentication keys based upon the initial authentication key. Secure handovers occur between nodes via an authentication key.
Owner:MOXCHANGE LLC
Internet bank security authentication method and system
ActiveCN102737311ASafe and convenient transaction methodPayment protocolsSmart cardComputer terminal
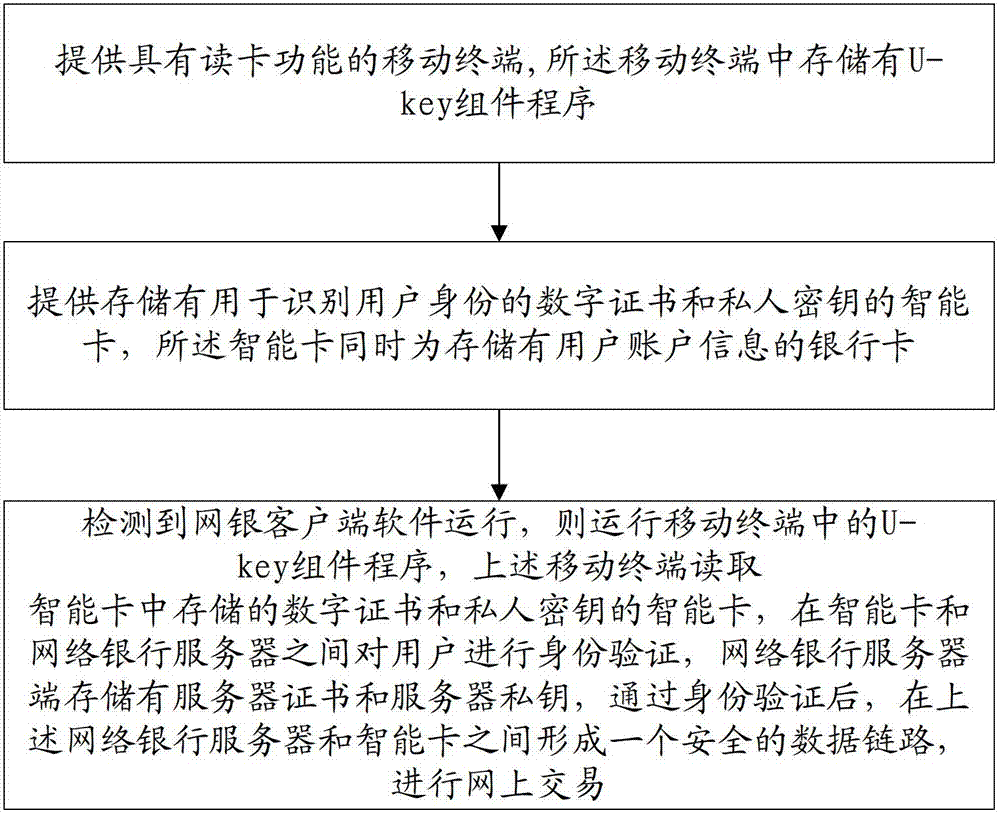
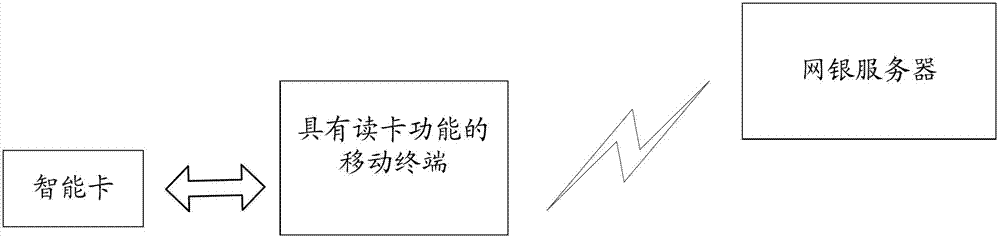
The invention discloses an internet bank security authentication method which comprises the steps of: providing a mobile terminal with a card reading function, wherein U-key assembly program is stored in the mobile terminal; providing an intelligent card stored with a digital certificate and a private key, wherein the digital certificate and the private key are used for identifying user identity, and the intelligent card is also used as a bank card for storing information of a user account; reading the intelligent card for storing the digital certificate and the private key by the mobile terminal, conducting identity authentication on a user between the intelligent card and an internet bank server side, wherein internet bank server side is used for storing a server certificate and a server private key; and after the identity authentication is passed, forming a safety data link between the internet bank server side and the intelligent card so as to conduct networked transaction. According to the invention, the safety information is stored in the intelligent card, safety and convenient transaction can be realized by the mobile terminal and user identity authentication between the intelligent card and the internet bank server side. The invention further discloses an internet bank security authentication system.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Security certificate method based on fingerprint, cryptographic technology and fragile digital watermark
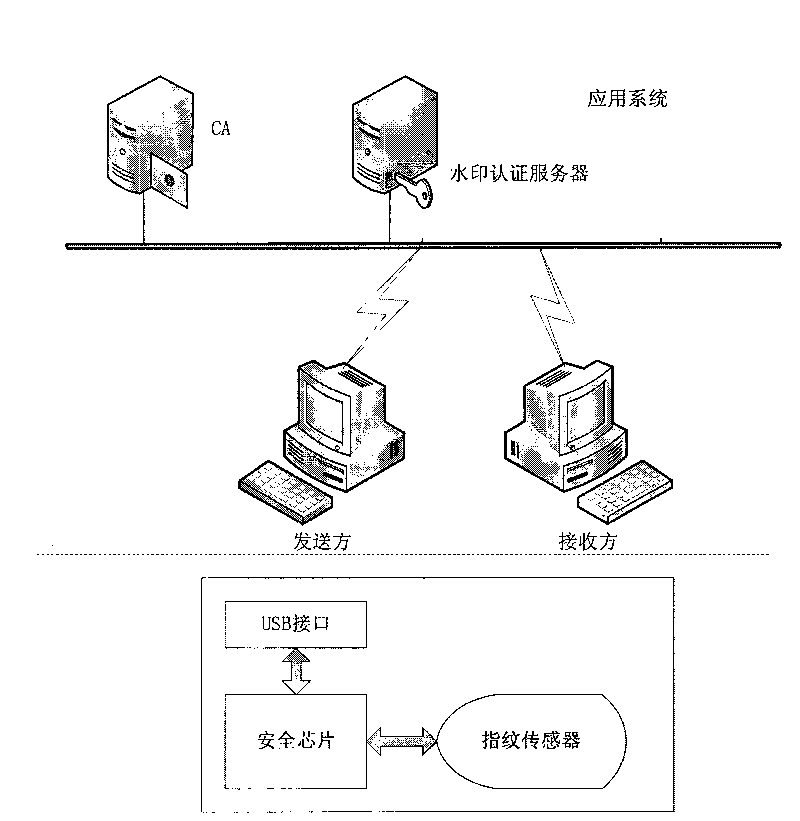
ActiveCN101729256AAuthenticityAvoid the risk of being stolenUser identity/authority verificationImage data processing detailsDigital signatureSecure authentication
The invention discloses a security certificate method based on fingerprint, cryptographic technology and fragile digital watermark, comprising the following steps: a sender collects a fingerprint image, calculates summary information of the fingerprint image and inserts the summary information, a secret key and digital information which is digitally signed and encrypted into the fingerprint image as a watermark; the fingerprint of the sender is collected, the fingerprint image inserted with the watermark is sent to a receiver after the fingerprint of the sender is qualified; after receiving information, the receiver firstly detects and verifies whether the fingerprint image is inserted with the digital watermark and whether the digital watermark is right or not so as to indentify identity authenticity; digital watermark information is extracted from the received image; the summary information of the fingerprint image from which the watermark is extracted is calculated; and the summary information is compared with the summary information of the fingerprint image recorded in the watermark information to approve information authenticity. The invention can effectively overcome the defects that the existing digital signature security certificate can not approve the legal KEY holder and the fingerprint in the fingerprint certificate is easy to clone and embezzle.
Owner:SHENZHEN POKA ELECTRONICS EQUIP +1
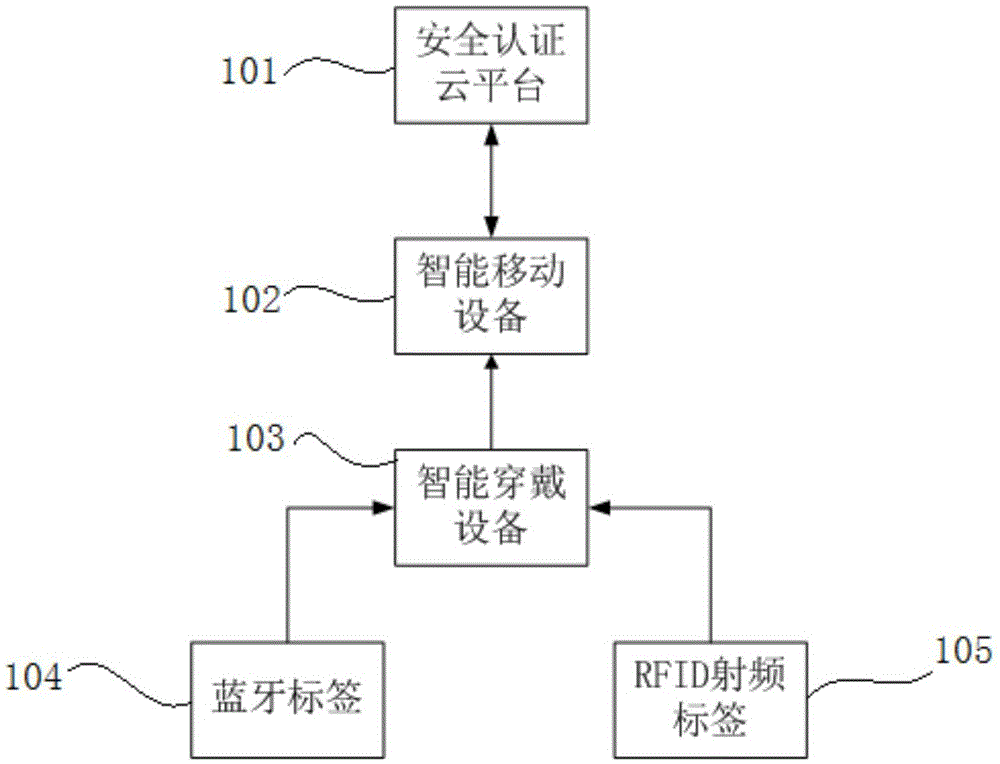
Intelligent wearable terminal based child behavior monitoring and developing method and system
InactiveCN105608654AAchieve recordIncrease the database of dynamic behavior habitsCo-operative working arrangementsOffice automationWi-FiData information
The present invention discloses an intelligent wearable terminal based child behavior monitoring and developing system and method. The system comprises an intelligent wearable device, a Bluetooth tag, an RFID radio-frequency tag, an intelligent mobile device, a security authentication cloud platform and a data cloud platform. The method comprises: based on a position relationship, establishing a Bluetooth tag based on a Bluetooth Ad Hoc network, and a radio-frequency tag, and according to the Bluetooth tag and the radio-frequency tag, monitoring a behavior of a child wearing an intelligent wearable terminal; uploading a monitoring result to a cloud-end server; establishing a classifiable dynamic behavior habit database according to child basic data information and child daily behavior data; and comparing child behavior data in the dynamic behavior habit database with behavior data in a preset standard behavior database, and outputting early-warning and prompting information. According to the method and system disclosed by the present invention, by integrating technologies such as Bluetooth, RFID and Wi-fi, child behavior monitoring and development are implemented.
Owner:刘国正
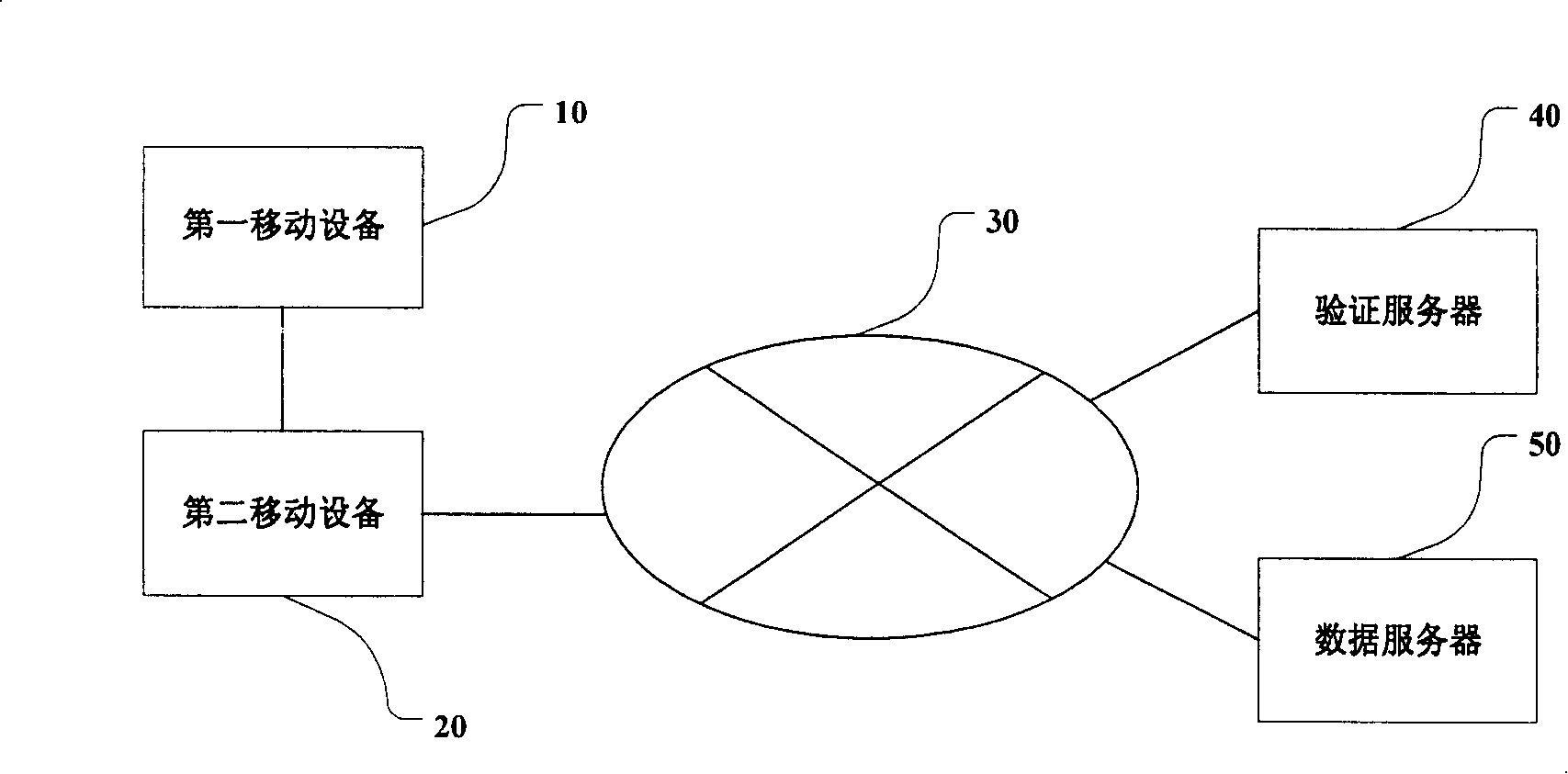
Method and system for security verification of data among non-contact equipments
InactiveCN101202621AImprove securityKey distribution for secure communicationThird partyShortest distance
The invention discloses a method and a system for carrying through security authentication on data among non-contact devices. The invention includes the steps of transmitting a data voucher form a first movable device to a second movable device by a short distance communicating mode; launching an authentication request of the data voucher to a third party from the second movable device through a safe data transmission channel; the third party carries through authentication on the data voucher by utilizing the key information shared by the first movable device based on the authentication request; transmitting a data access description to the second movable device through the safe data transmission channel under the situation that the authentication result of the data voucher carried out by the third party is positive; and the second movable device acquires safe data corresponding to the data voucher through the data access description. By utilizing the invention, the security for carrying through data transmission among the non-contact devices can be improved.
Owner:LENOVO (BEIJING) CO LTD
Method, system and device of security certificate
ActiveCN101651682AImprove experienceData switching networksSecurity arrangementBroadbandAuthentication server
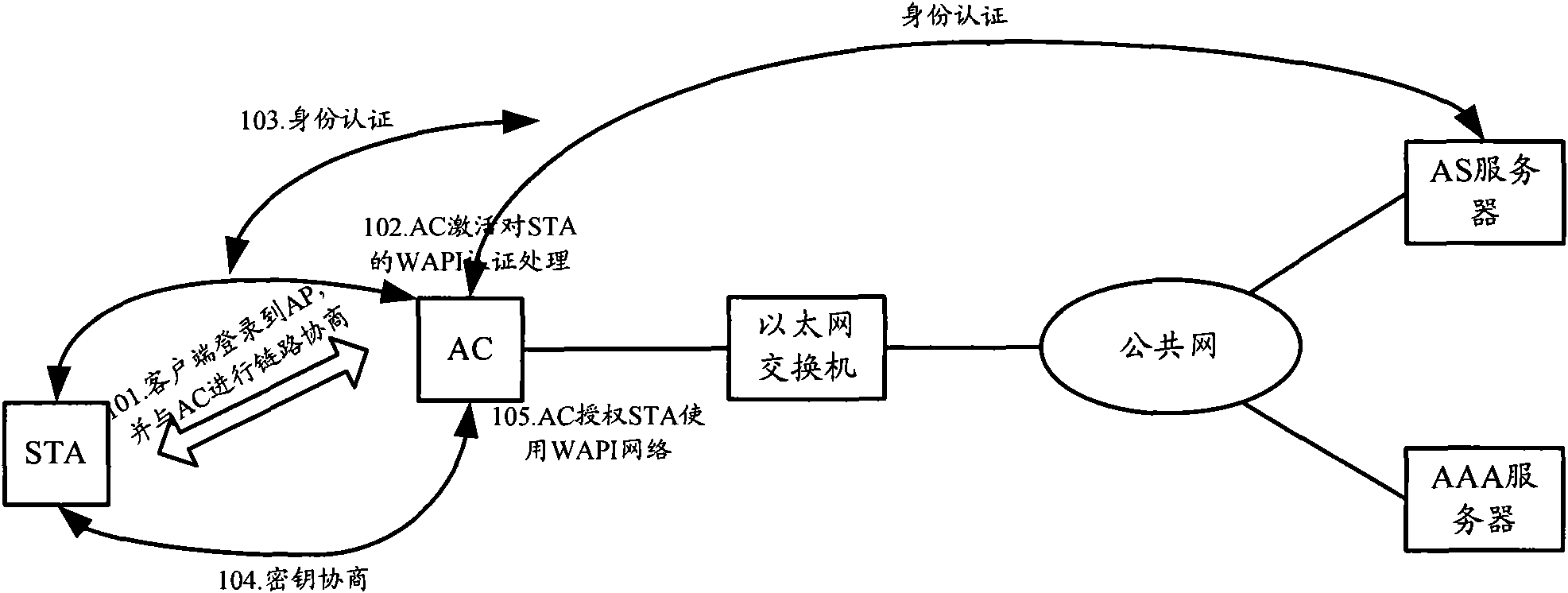
The invention provides a method, a system and a device of security certificate. The method comprises the followings steps: encapsulating an empty certificate request in a protocol message of a remoteuser dial certification system (Radius) after an access controller (AC) activates the empty certificate of mobile termination (STA), sending the empty certificate request to an empty certificate server by a broad band access server (BRAS), and receiving the Radius protocol message in which a certificate result is encapsulated, returned by the empty certificate server through the BRAS; when the certificate result succeeds, authorizing the STA to be accessed to a wireless network, and permitting the STA to be accessed to a metropolitan area network after the BRAS determines the certificate result to be successful. The BRAS is fused in the empty certificate process, and the empty security certificate and the security certificate of accessing to the metropolitan area network are realized whileadopting the one-time empty certificate process. The invention has simple realization and brings user better user experience.
Owner:NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com