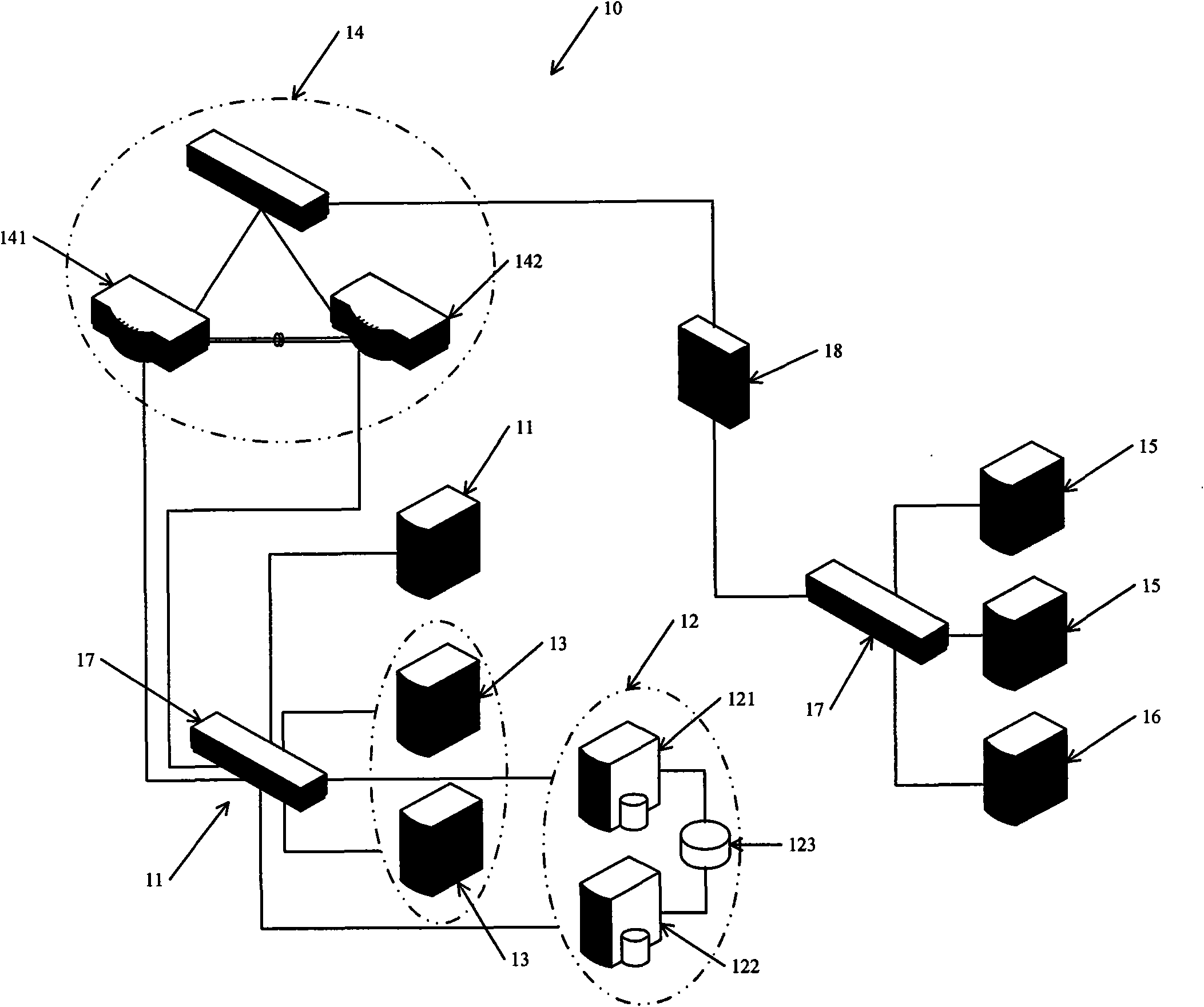
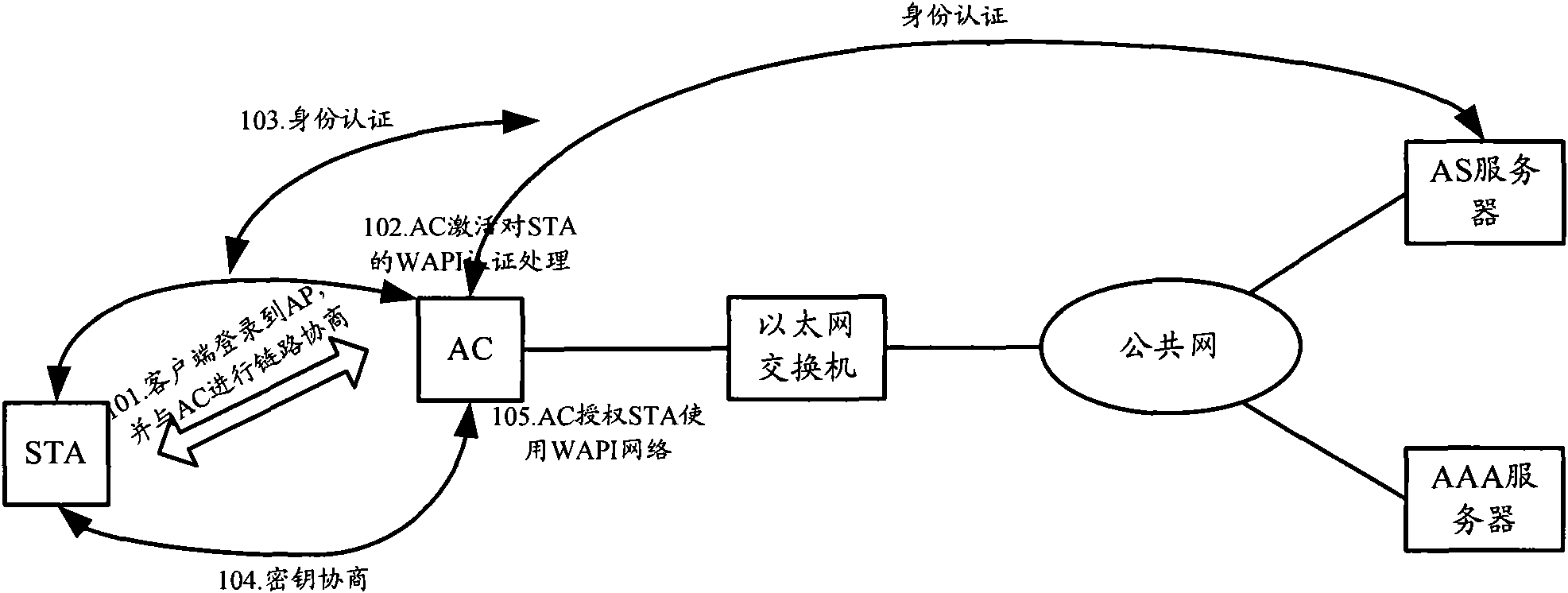
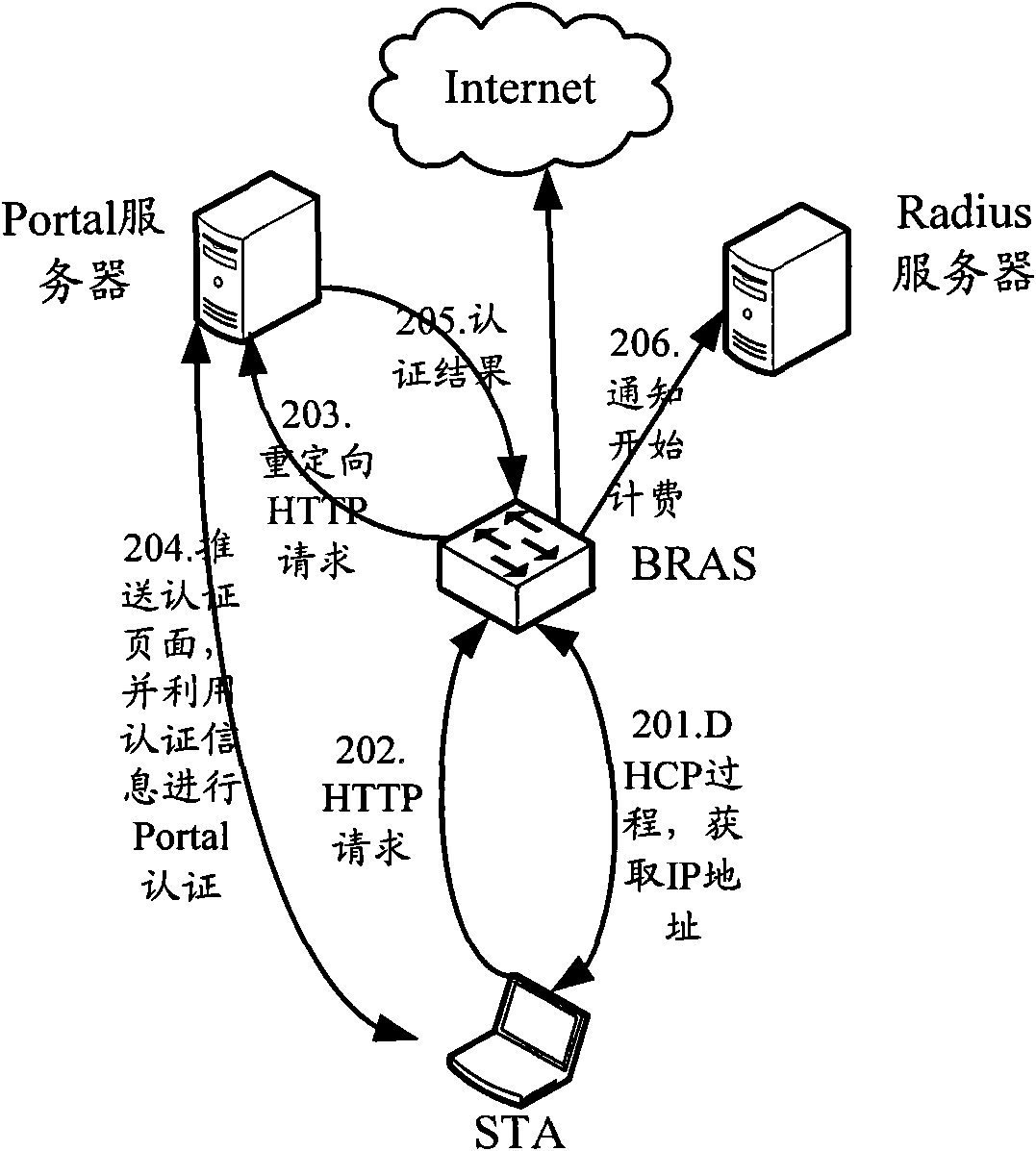
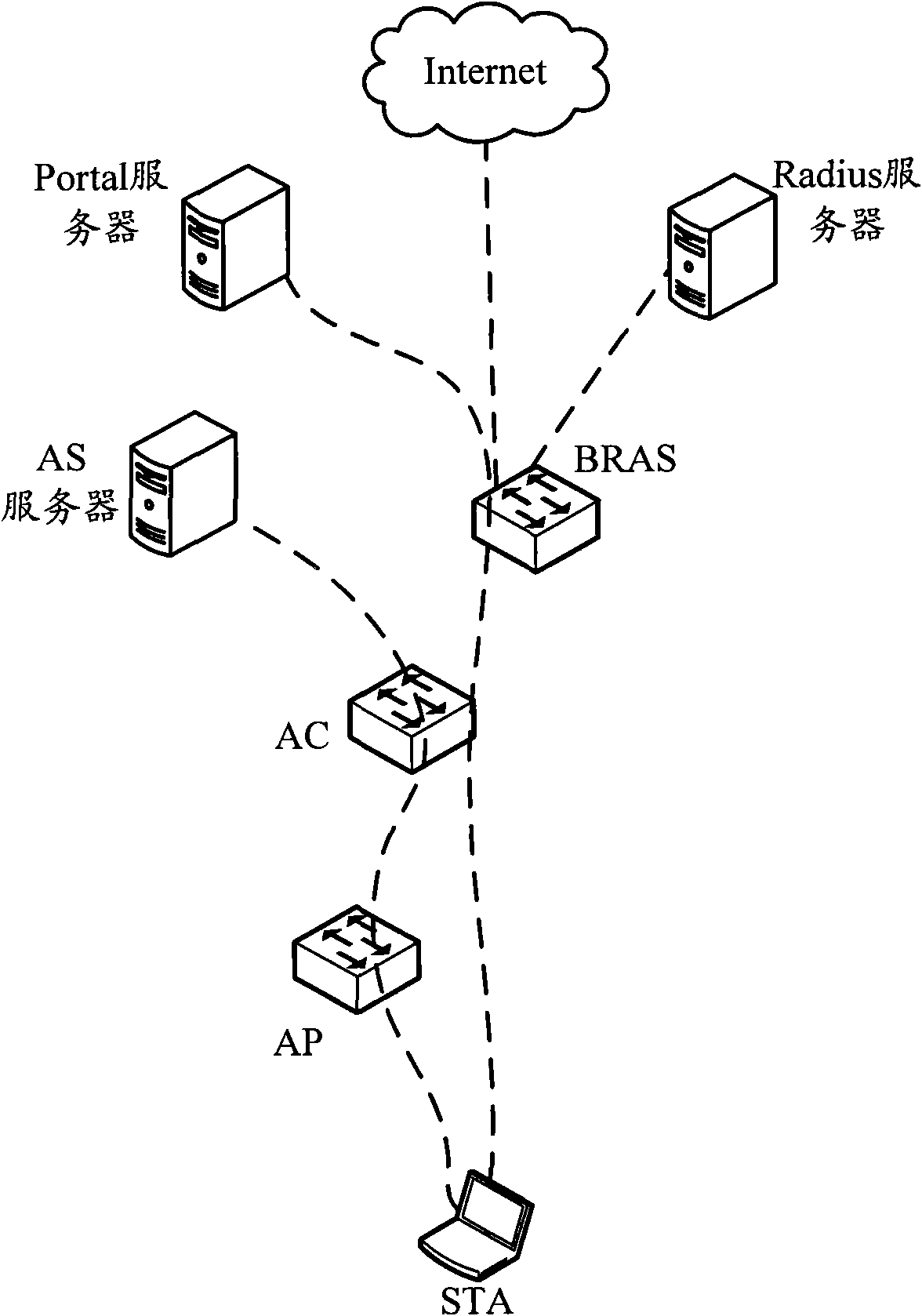
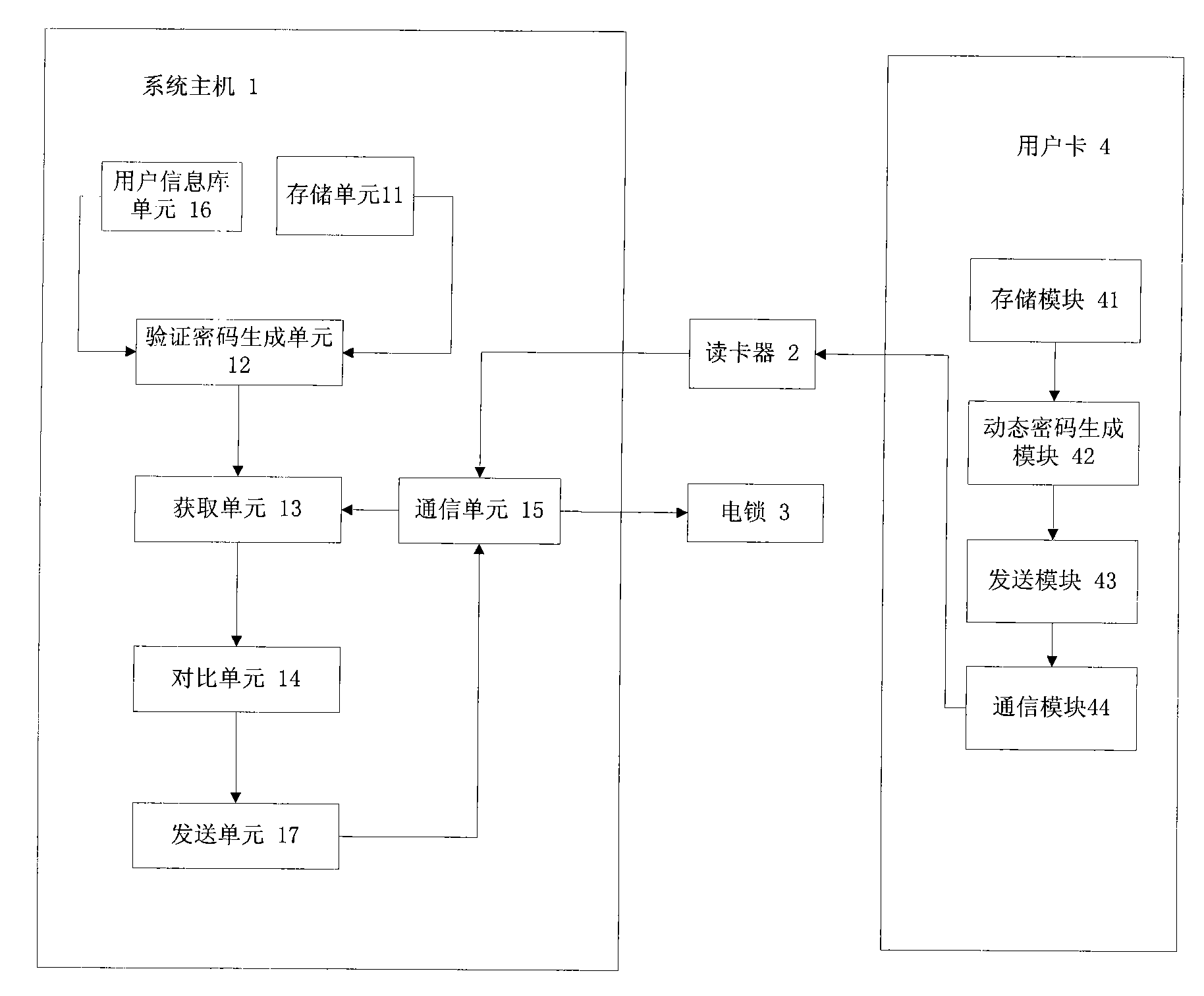Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
281 results about "Certificate server" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
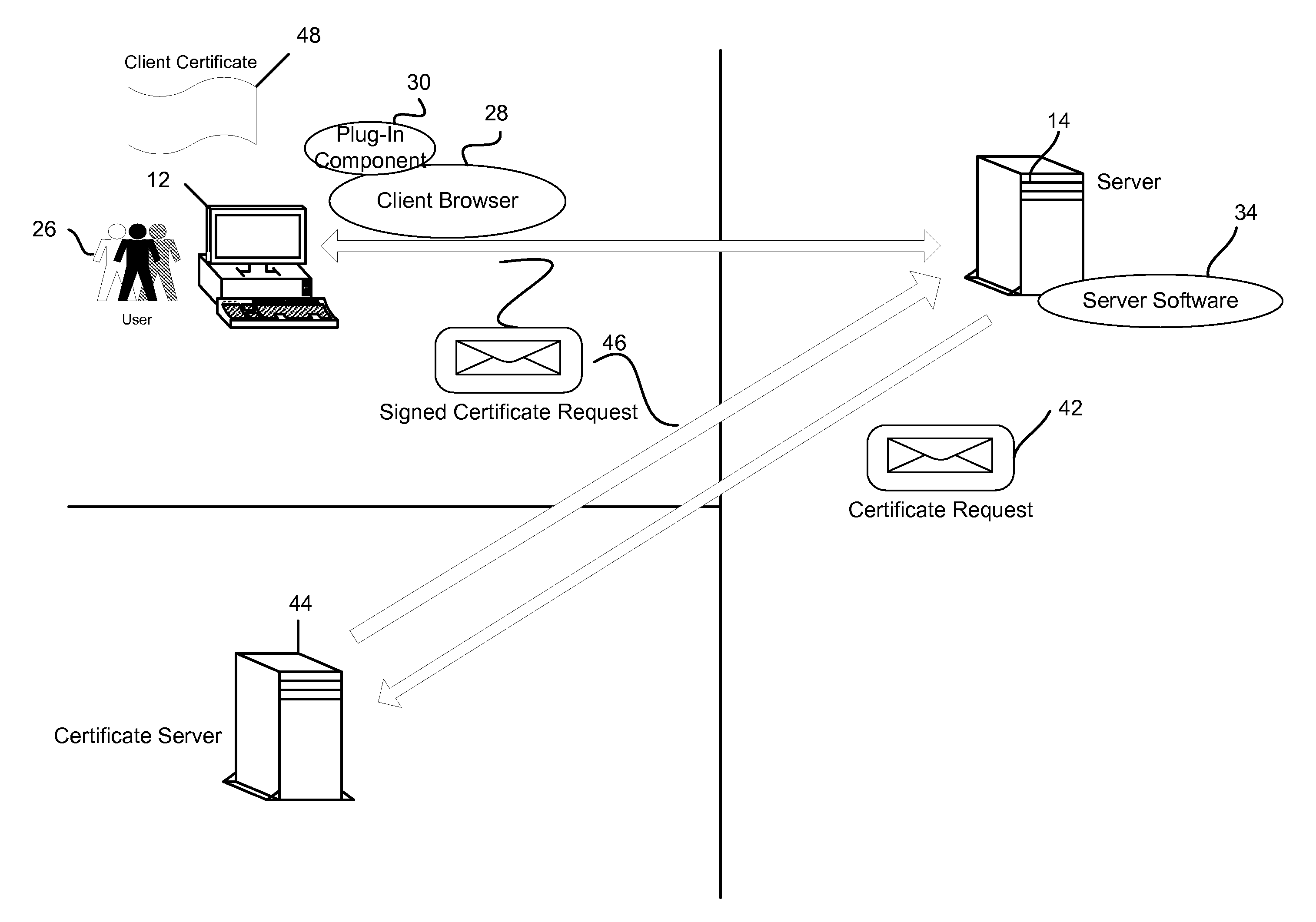
Certificate servers validate, or certify, keys as part of a Public key infrastructure. Keys are strings of text generated from a series of encryption algorithms that allow you to secure communication for a group of users. Many Web servers, such as Microsoft's Internet Information Services or Apache's mod_ssl create keys that after having been validated, can be applied to other servers such as News servers or Web servers. The purpose of this process is to create a way for people to communicate and be reasonably sure that others are not eavesdropping or assuming a false identity.
System and methods for providing network quarantine using IPsec
A system and method for ensuring that machines having invalid or corrupt states are restricted from accessing host resources are provided. A quarantine agent (QA) located on a client machine acquires statements of health from a plurality of quarantine policy clients. The QA packages the statements and provides the package to a quarantine enforcement client (QEC). The QEC sends the package to a quarantine Health Certificate Server (HCS) with a request for a health certificate. If the client provided valid statements of health, the HCS grants the client health certificate that may be used in IPsec session negotiation.
Owner:MICROSOFT TECH LICENSING LLC
Public Key Infrastructure based on the Public Certificates Ledger
InactiveUS20170346639A1Multiple keys/algorithms usagePublic key for secure communicationAs DirectedDigital signature
Systems and methods for managing public key certificates and supporting the users thereof. The certificates are cryptographically encapsulated objects that bind the identities of their owners to public keys and provide digital signature mechanisms for other users to verify the binding and correctness of other attributes of the certificate. Certificates include double links that reflect their validation and position in a public certificates ledger, thereby preventing insertion or removal of certificates in the ledger. Certificate protocols of the system include requesting issuance of certificates, issuing and returning certificates to their requesting users, storing certificates in the certificates ledger, requesting and distributing certificates to transaction partners, verification of certificates by transaction partners, and revoking certificates by their owners. These protocols are performed as direct peer-to-peer transactions between the members of the system.
Owner:MUFTIC SEAD
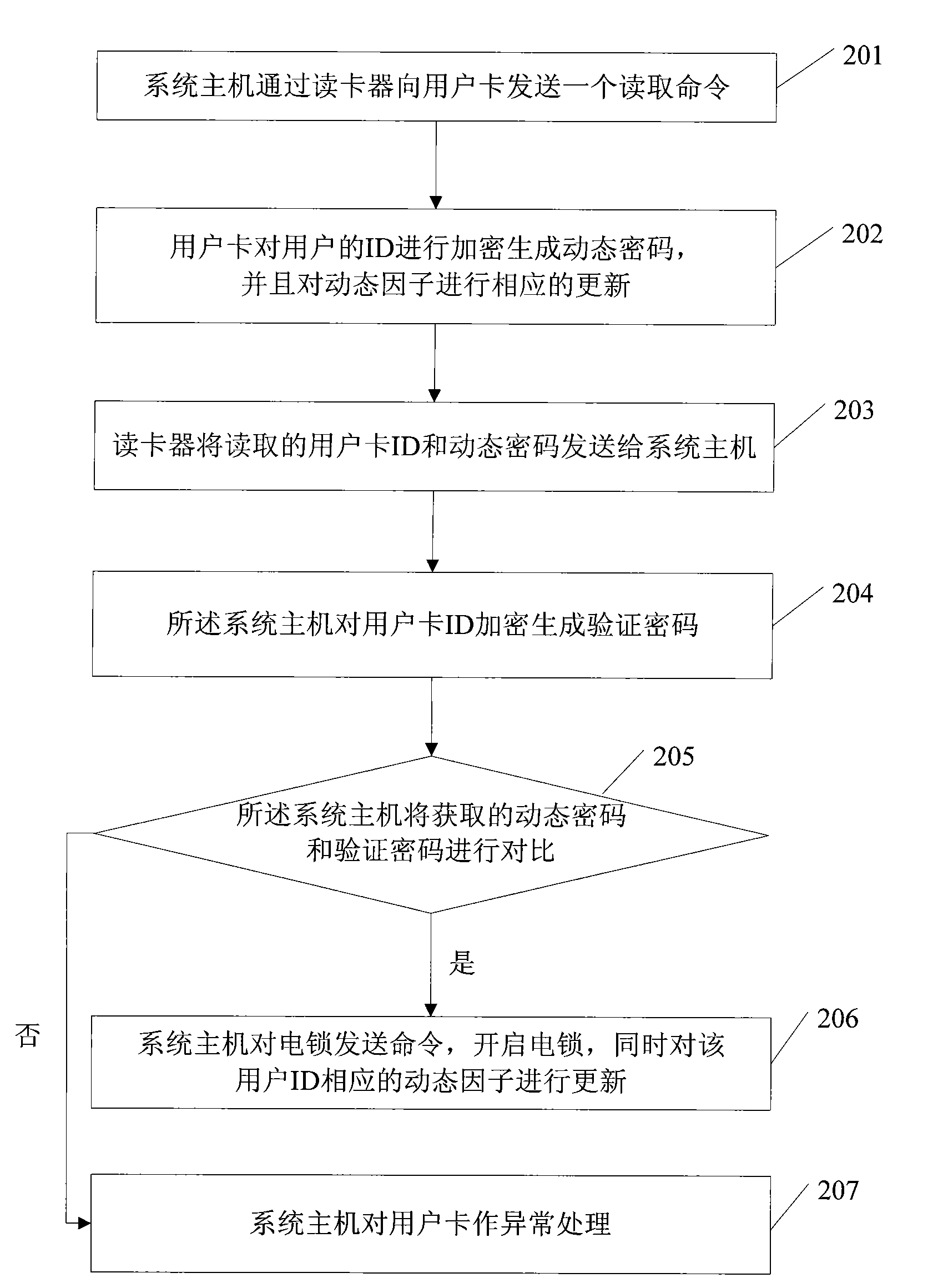
Access control system generated and verified on the basis of dynamic password and authentication method thereof
InactiveCN101593380ASynchronous generationUser identity/authority verificationIndividual entry/exit registersPasswordSecret code
The invention discloses an access control system generated and verified on the basis of dynamic password and an identity verification method, belonging to the field of security certificate. The system comprises a user terminal for generating dynamic password and a certificate terminal for verifying dynamic password, wherein, the user terminal comprises a storage module which is used for storing arithmetic, keys and dynamic factors, and the certificate terminal comprises a reading module, a locker module and a certificate server module. The method of the invention comprises the following steps: after receiving an order sent by the certificate terminal, the user terminal generates dynamic password, the certificate terminal generates verified password according to stored arithmetic and key which are identical to the user terminal and corresponding dynamic factors, and the dynamic password and the verified password are compared to verify the validity and availability of the dynamic password of the user terminal.
Owner:FEITIAN TECHNOLOGIES
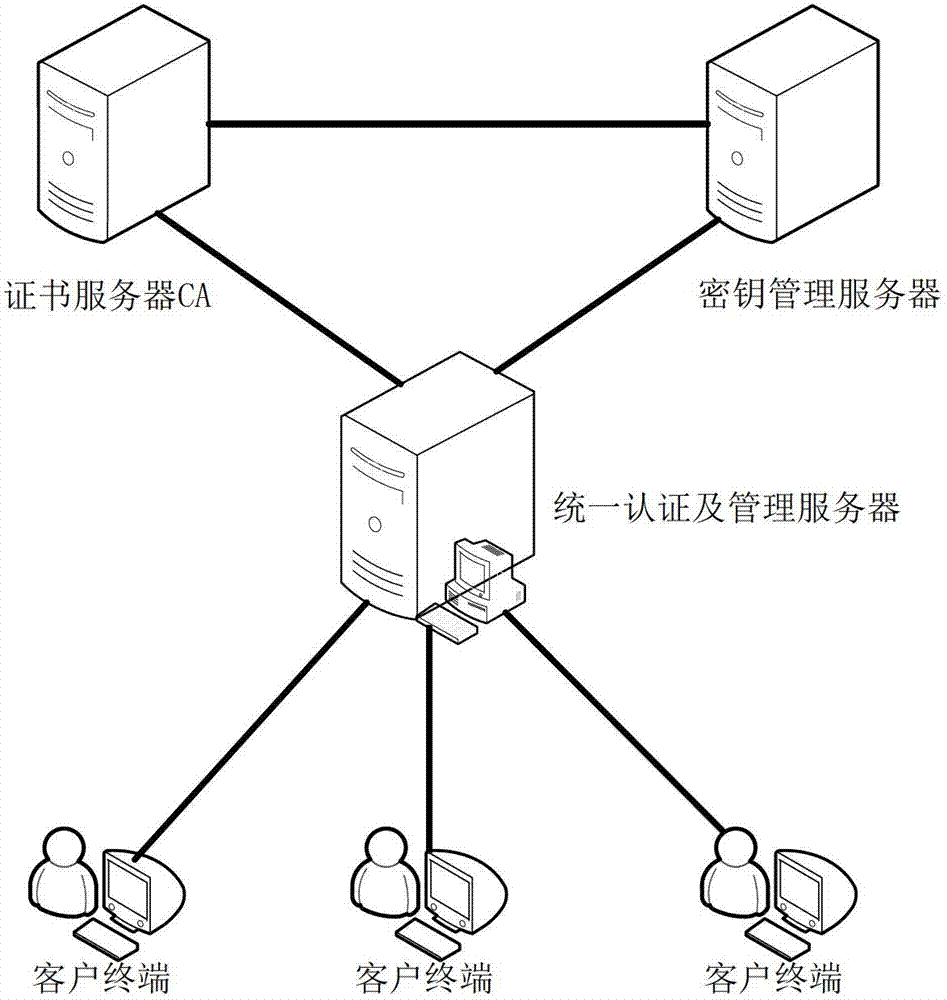
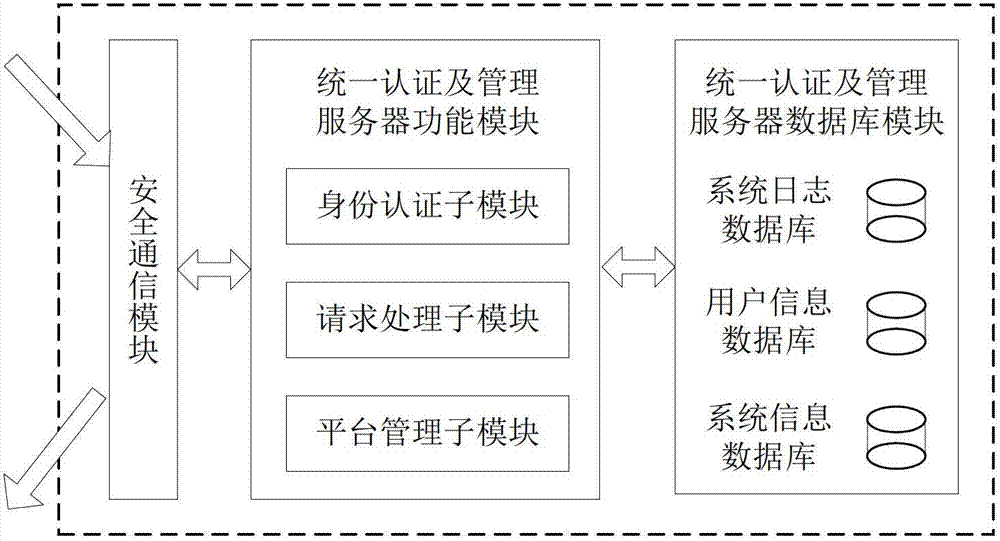
File safe protection system and method thereof
ActiveCN102970299ASimple structureEasy to buildKey distribution for secure communicationUser identity/authority verificationConfidentialityComputer terminal
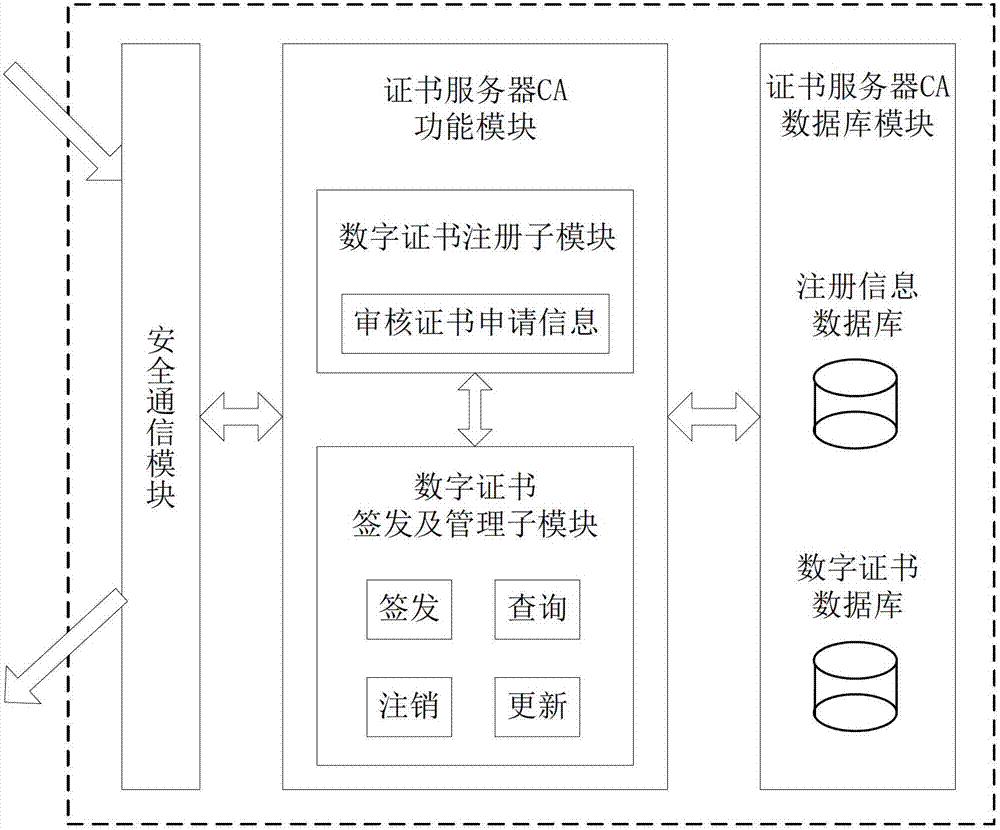
The invention discloses a file safe protection system and a method, which mainly solves the problems of network illegal invasion, information stealing and tamping, impersonation and weak deny resistance in the conventional information system. The file safe protection system consists of a unified authentication and management server, a certificate server CA, a secret key management server and a client terminal; the unified authentication and management server is used as a middle node and is used for processing or transmitting a service request sent by the client terminal; the certificate server CA processes a certificate service request of the client terminal and provides basic support for identification; and the secret key management server processes the secrete key service requests of the client terminal and the certificate server CA, and is used for encrypting and decrypting a file for the client terminal and providing parameter support for a digital certificate signed by the certificate server CA. With the adoption of the file safe protection system and method provided by the invention, identification, confidentiality, integration and non-repudiation services can be provided; and the file can be safely protected in transmission, storage, sharing and access processes.
Owner:XIDIAN UNIV
Performing client authentication using certificate store on mobile device
ActiveUS20140108810A1User identity/authority verificationSecurity arrangementInternet privacyBarcode
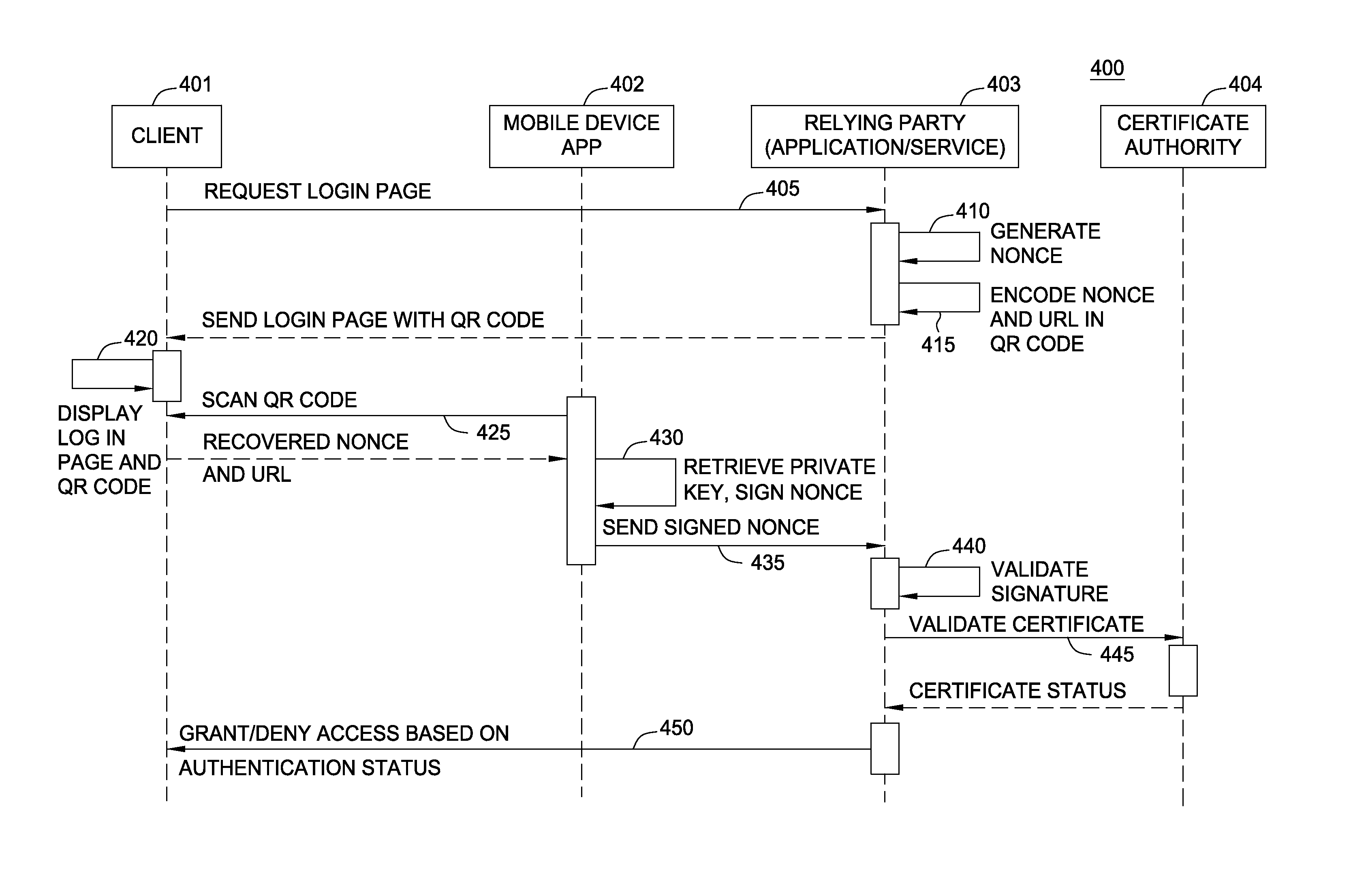
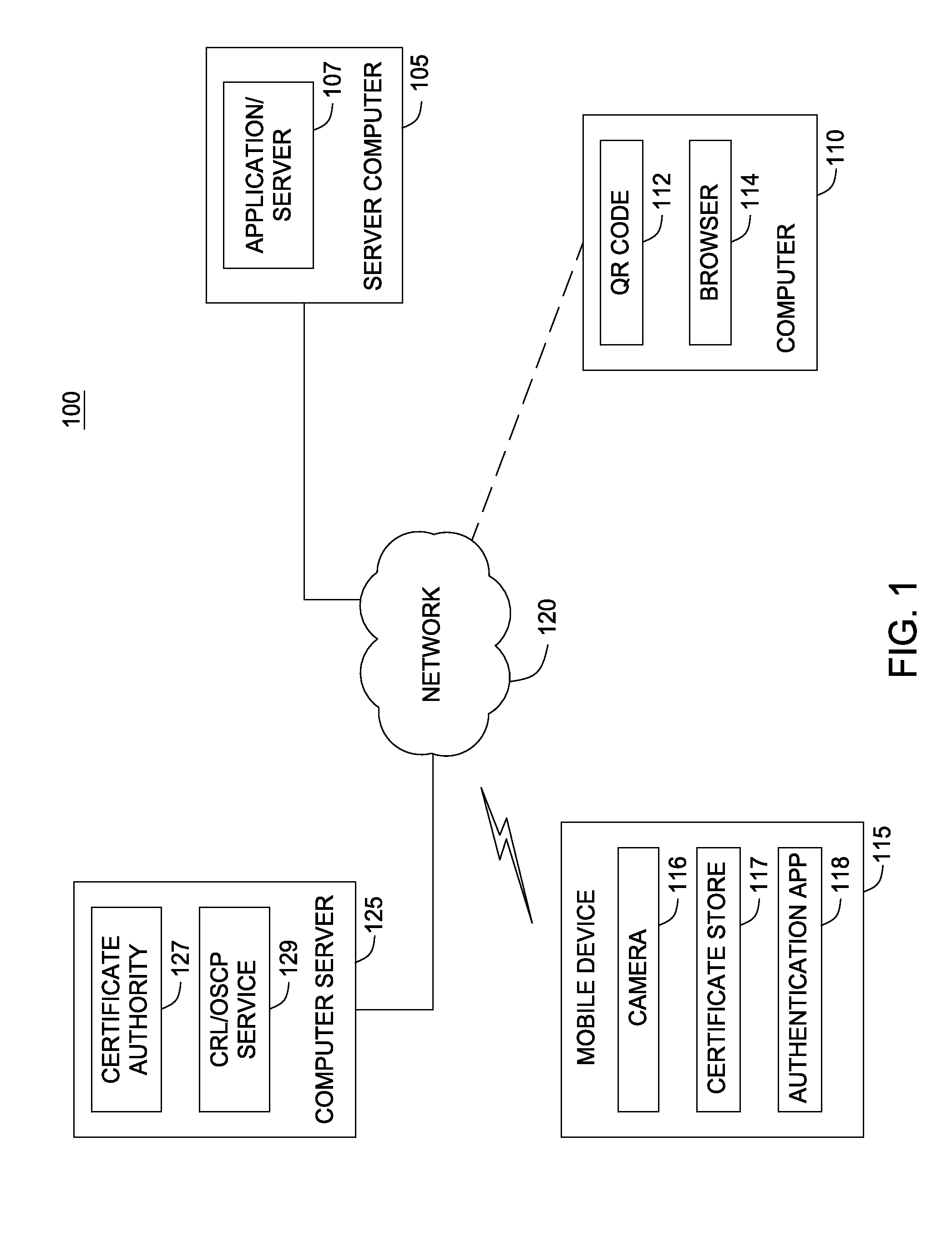
Techniques are disclosed for authenticating users to a computing application. A relying application transmits a login page to a user requesting access to the application. The login page may include a QR code (or other barcode) displayed to the user. The QR code may encode a nonce along with a URL address indicating where a response to the login challenge should be sent. In response, the user scans the barcode with an app on a mobile device (e.g., using a camera on a smart phone) to recover both the nonce and the URL address. The mobile device may also include a certificate store containing a private key named in a PKI certificate. The app signs the nonce using the private key and sends the signed nonce in to the URL in a response message.
Owner:CA TECH INC
System and method for secured network access utilizing a client .net software component
InactiveUS20090307486A1Accurate informationUser identity/authority verificationOperational systemWeb browser
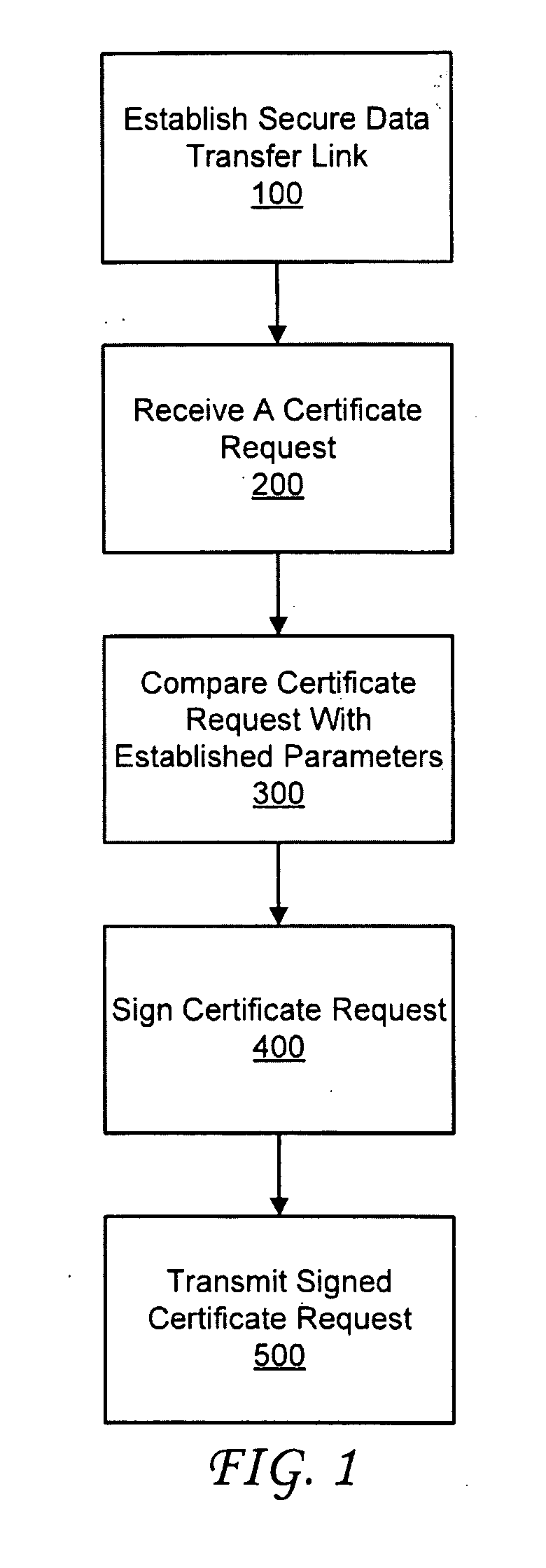
A method for self-service authentication of a client and a server. The method includes the server receiving an initialization command from the client. The initialization command may be transmitted to the server via a client web browser over an unsecured data transfer link. The method continues with requesting authentication information from the client. In response to receiving the authentication information from the client, the server transmits a client software component to the client. The client software component utilizes a client-side library installed on the operating system of the client to generate the various client credentials described above. Thereafter, the certificate signing request may be transmitted to a certificate server for signing the certificate signing request. The signed certificate signing request is then received by the client via the client web browser. The client utilizes the information associated with the signed certificate signing request with the client-side library installed on the client to generate a client certificate.
Owner:MULTIFACTOR CORP
System and method for enabling bulk retrieval of certificates
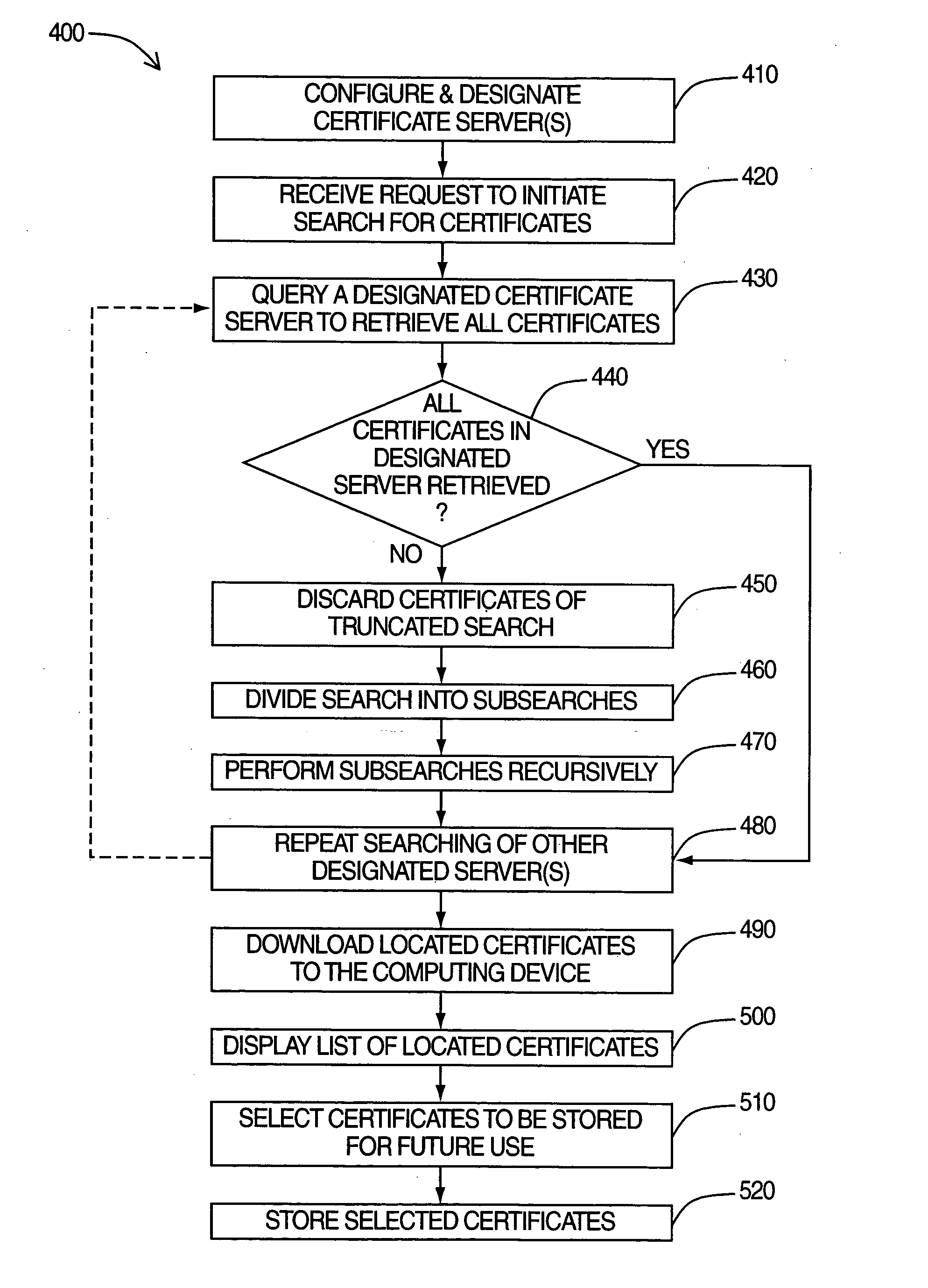
ActiveUS20060036848A1Efficient exchangeData processing applicationsUnauthorised/fraudulent call preventionApplication softwareCertificate server
A system and method for searching and retrieving certificates, which may be used in the processing of encoded messages. In one embodiment, a certificate synchronization application is programmed to perform certificate searches by querying one or more certificate servers for all of the certificates on those certificate servers. If all of the certificates on a certificate server cannot be successfully retrieved using a single search query, due to a search quota on the certificate server being exceeded for example, the search is re-performed through multiple queries, each corresponding to a narrower subsearch. The invention enables users to large amounts of certificates to be automatically searched for and retrieved from certificate servers, thereby minimizing the need for users to manually search for individual certificates.
Owner:MALIKIE INNOVATIONS LTD
System and method for implementing digital signature using one time private keys
InactiveUS20060020811A1Digital data processing detailsPublic key for secure communicationWeb browserDigital signature
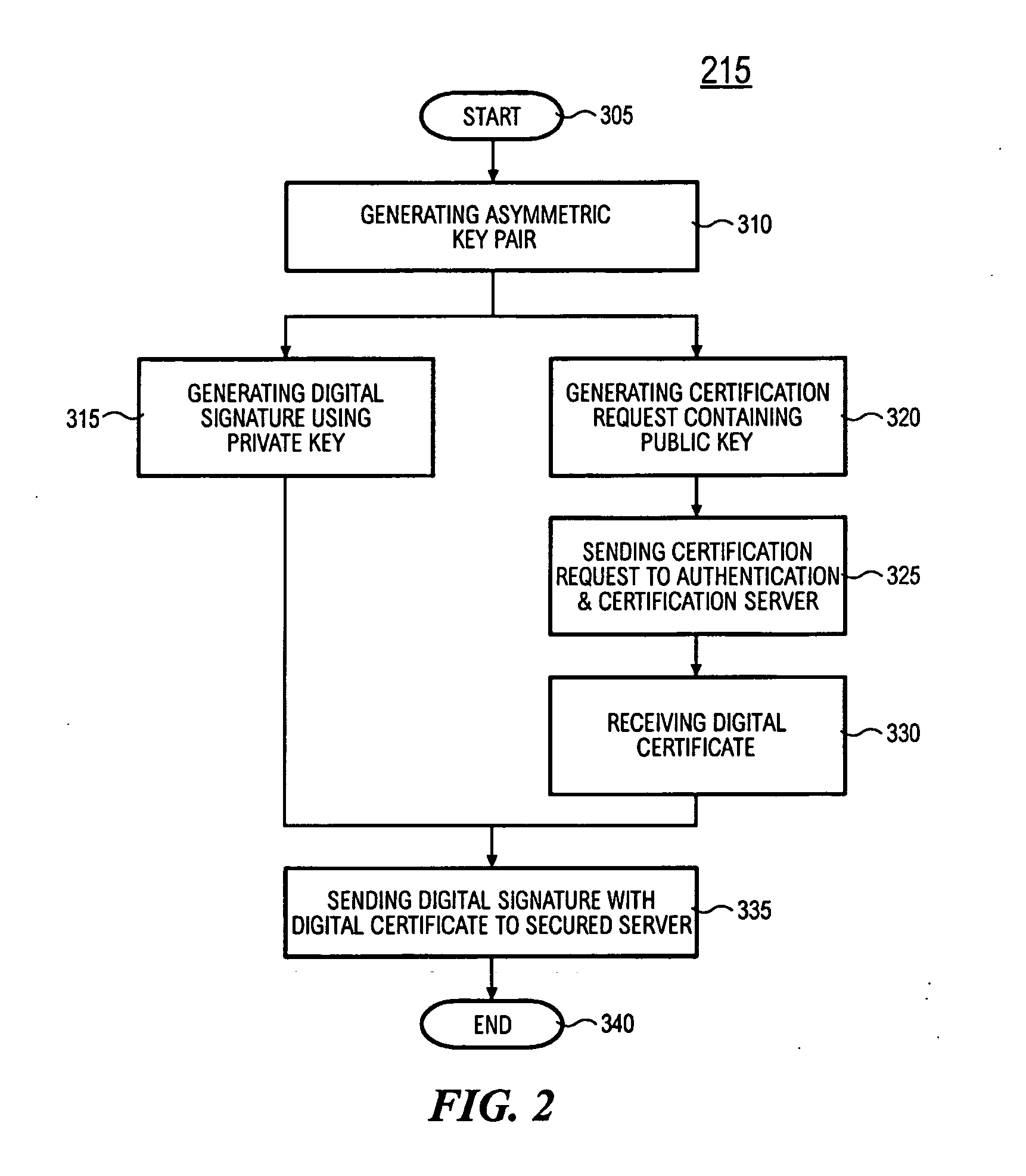
The OTPK module 40 is essential to the present embodiment. It may be considered to be a software module implemented on the signing entity 20. The OTPK module 40 may be dynamically downloaded for use or implemented as a pre-installed client plug-in. The OTPK module 40 may perform its role without significant intervention from a user when operating as the signing entity 20. The OTPK module 40 may be implemented as a PKCS#11 or CAPI DLL or a Java Applet or ActiveX plugin embedded within the Internet Web Browser. It may be automatically executed when performing secure transactions requiring digital signatures. The OTPK module 40 serves to independently and without additional instruction from a user carry out the steps of generating the asymmetric key pairs comprising the public key and the private key. The OTPK module 40 then contacts the authentication and certification server 50 for authenticating the identity of the signing entity 20. At this point, the user of the signing entity 20 may be prompted for a password or the password may have been entered earlier as part of a 2-factor authentication to the authentication and certification server 50. The private key is then automatically used to generate a digital signature for the signing entity 20. At this point onwards, the private key is then irretrievably deleted such that it cannot be re-used or copied for future use.
Owner:DATA SECURITY SYST SOLUTIONS PTE
System and method for storing client-side certificate credentials
InactiveUS20090240936A1Digital data authenticationSecuring communicationWeb browserDigital signature
A method and system is provided for storing a plurality of client certificate credentials via a client web browser into one or more keystore file(s). The client web browser is used to establish the secure data transfer link between the client and the server. The client web browser includes a plug-in software component. The plug-in software component is configured to generate the keystore file and a key pair. The method may continue with generating a certificate request on the client. The certificate request generated is then transmitted to a certificate server. The certificate server is configured to digitally sign the certificate request generated. The method continues with the client receiving a signed certificate request. The signed certificate request is received by the client via the client web browser. The method may conclude by storing the plurality of client certificate credentials associated with the signed certificate request in one or more keystore file(s).
Owner:SECUREAUTH CORP
Security identification system of wireless application service and login and entry method thereof
ActiveCN101183932AReduce the risk of obtainingImprove the safety of useKey distribution for secure communicationWireless Application ProtocolSecure authentication
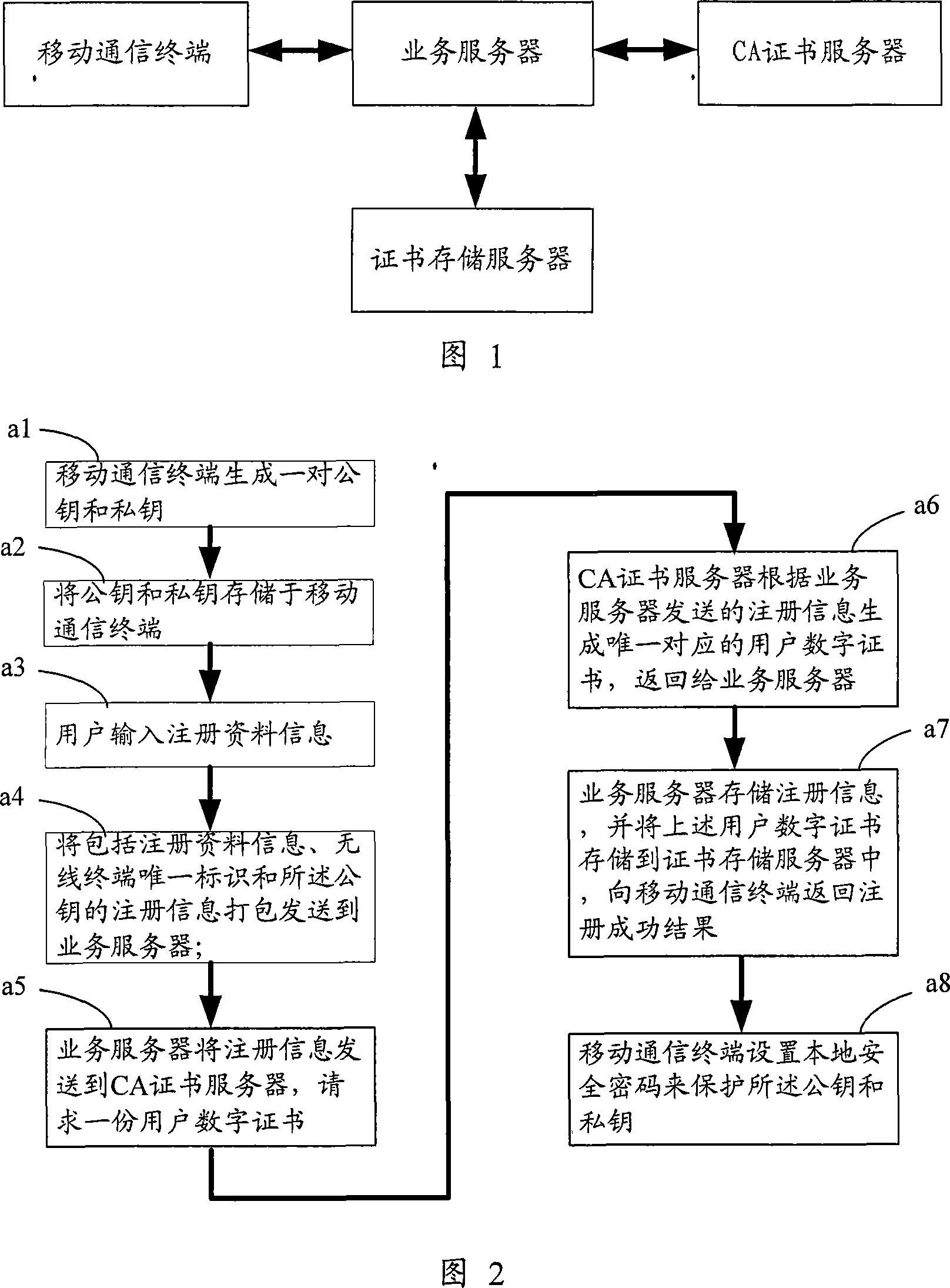
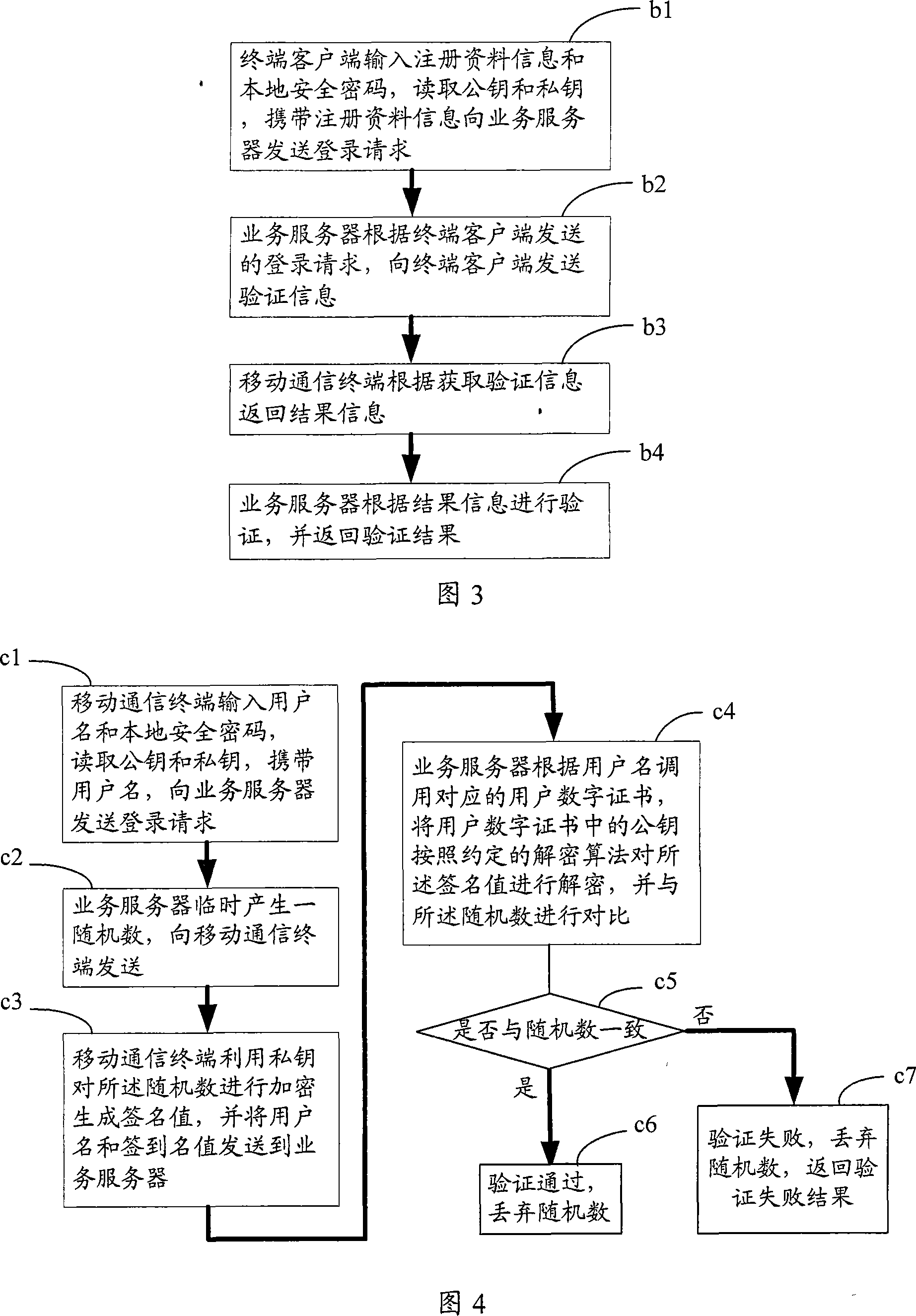
The invention discloses a safety certification system for wireless application service and the registration and login method. The system comprises a plurality of mobile communication terminals, a business server, a CA certificate server, and a certificate storage server, wherein the mobile communication terminals, the business server and the CA certificate server are orderly connected with each other though the wireless network or wired network, and the certificate server is connected with the business server; the registration method is as follow: a couple of public key and private key are generated by the mobile communication terminal; the registration request is sent to the business server; the registration result is sent back to the business server; the user digital certificate is generated by the OA certificate server, and stored in the certificate storage server; the login method is as follow: the login request is sent to the business server by the mobile communication terminal, and checked by the business server; the checked result is sent back. The invention is characterized in that the public key and the private key are generated by the mobile communication terminal, and protected by the local safety code which is never transmitted in the network. The invention has the advantages of great risk reduction of the public key and the private key acquired, and improved use security of application service in wireless network.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and system for management and notification of electronic certificate changes
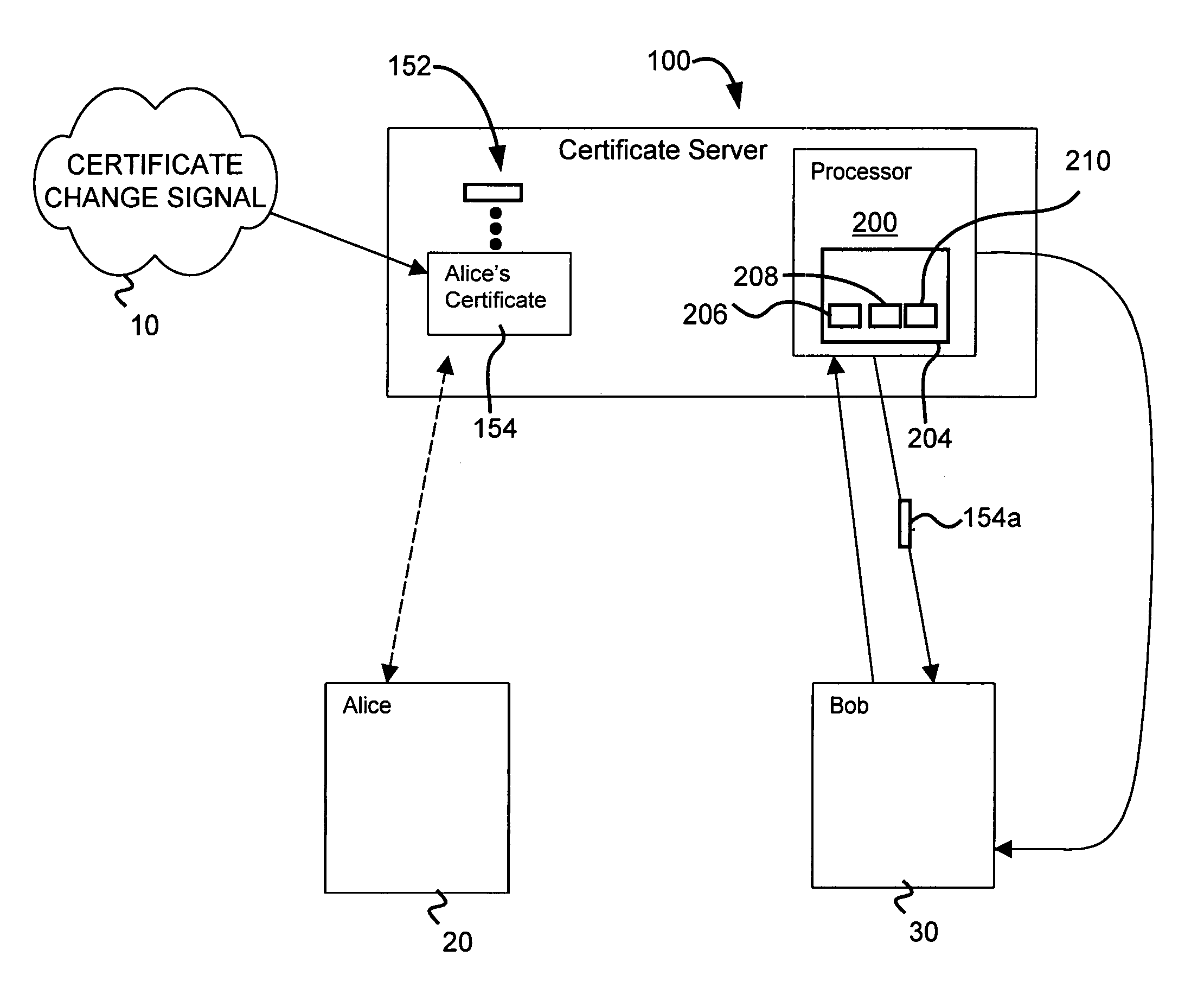
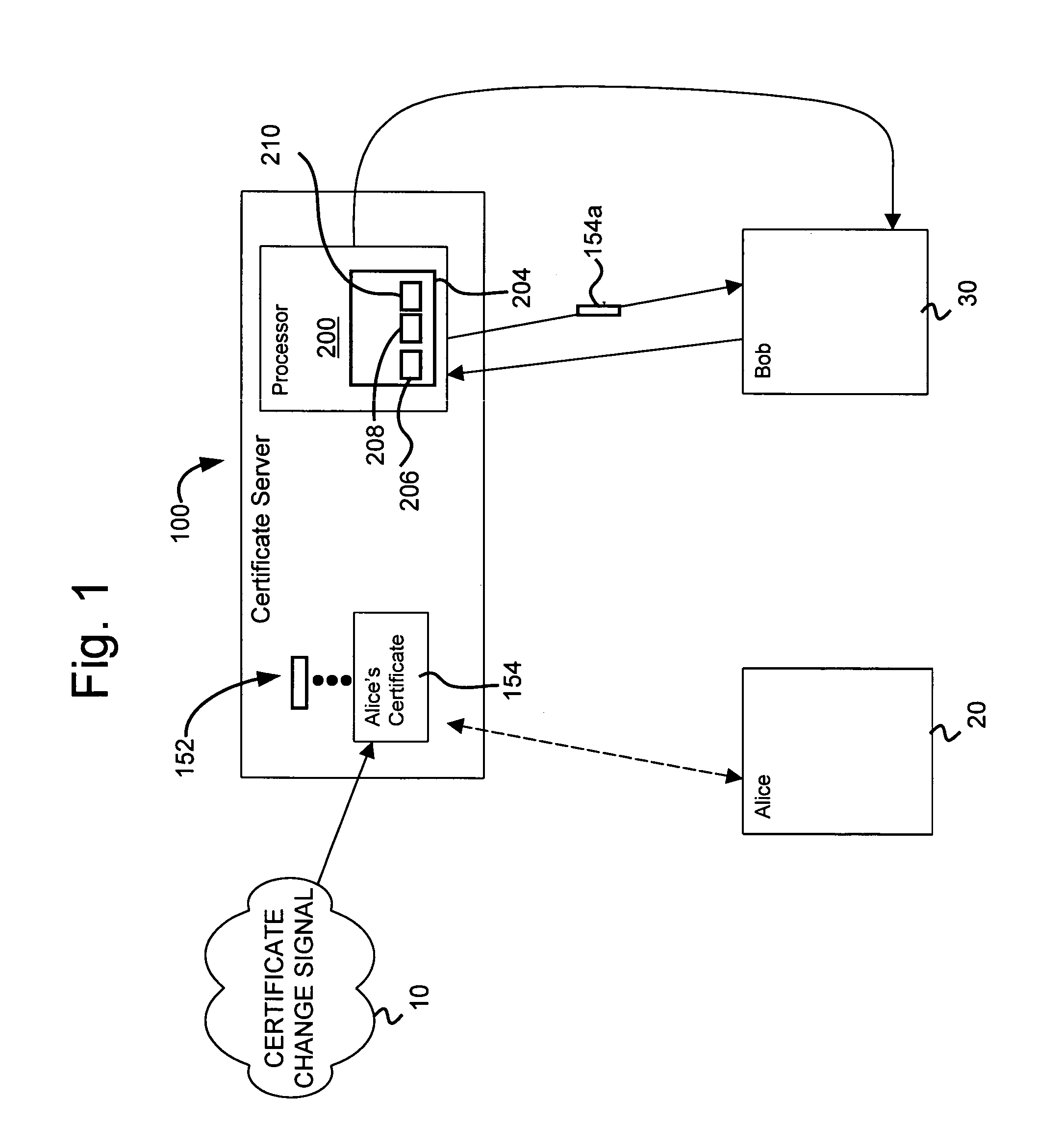
InactiveUS6950933B1Digital data processing detailsUser identity/authority verificationCertificate serverComputer program
A system for notification of a change in condition of an electronic certificate is disclosed. The system includes a certificate server comprising a processor having a computer program comprising a plurality of executable modules that are executable on the processor. A first executable module is for detecting a change in condition of an electronic certificate. A second executable module in the computer program is for notifying a user of the electronic certificate of the change in condition. The computer program may comprise a third module for negotiating a contract, called a certificate action point (CAP), with the certificate user regarding the type of change in condition the second module notifies the certificate user of, the way the second module notifies the certificate user, the diligence with which the second module notifies the certificate user of the change in condition, and a price for notifying the certificate user. The change in condition may comprise revocation of, roll-over of, change in field of, disablement of, expiration of the electronic certificate, or other type of change in condition of an electronic recognized by those skilled in the art. An updated electronic certificate may be forwarded to the certificate user, thereby updating the electronic certificate with respect to the certificate user to the new version of the electronic certificate. Alternatively, the certificate user may selectively download an updated version of the electronic certificate from the certificate server.
Owner:MCAFEE LLC
System and method for searching and retrieving certificates
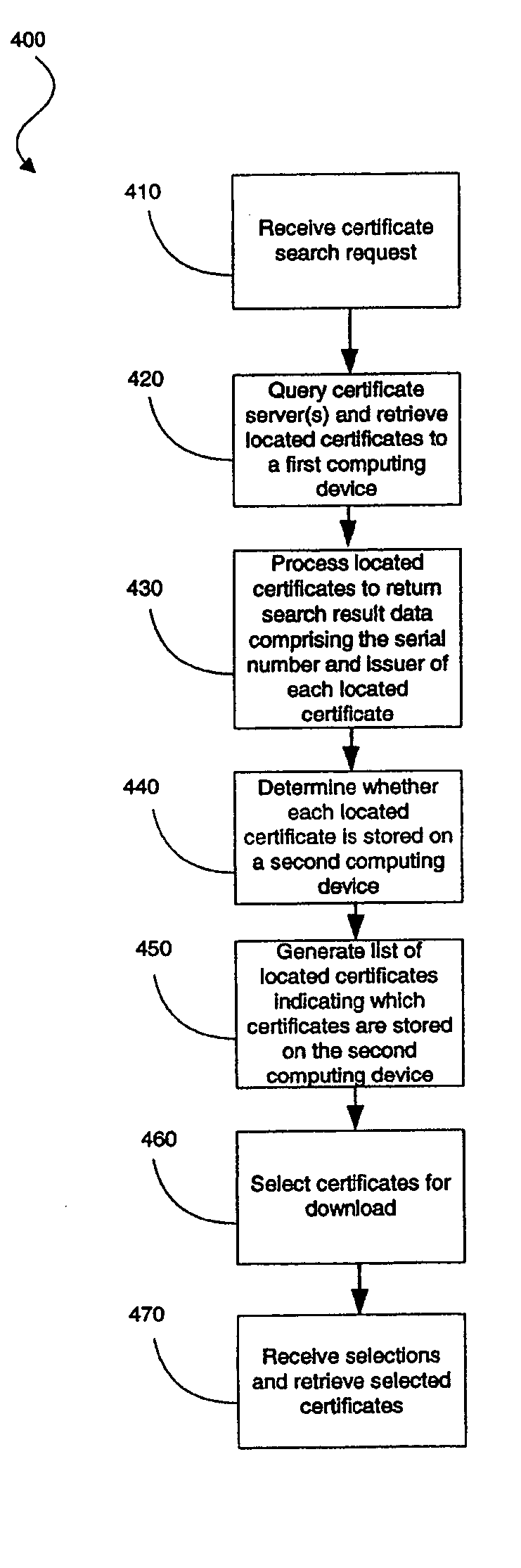
ActiveUS20060059332A1Efficient searchUser identity/authority verificationMobile deviceCertificate server
A system and method for searching and retrieving certificates, which may be used in the processing of encoded messages. In one broad aspect, a method is provided in which a certificate search request is received, a search of one or more certificate servers for certificates satisfying the request is performed, located certificates are retrieved and processed at a first computing device to determine data that uniquely identifies each located certificate, and search result data comprising the determined data is communicated to a second device (e.g. a mobile device) for use in determining whether each located certificate is already stored on the second device.
Owner:MALIKIE INNOVATIONS LTD
Fingerprint payment certificate server, fingerprint payment method and system thereof
InactiveCN101901517ABreak through limitationsAvoid the problem of lack of impartiality of proofComplete banking machinesAcutation objectsThird partyInternet privacy
The invention discloses a fingerprint payment certificate server, a fingerprint payment method and a system thereof. The server comprises a prepositioned server, which receives packaged data transmitted by a payment terminal which transacts based on fingerprint information, and comprises a preprocessing unit, a memory and a transaction server, wherein the preprocessing unit unpacks and deciphers the packaged data to obtain fingerprint information data and transaction data; the memory prestores user identity information including pre-acquired user fingerprint characteristic data; the transaction server is in signal connection with the prepositioned server and the memory, and certifies the user identity by comparing the fingerprint information data acquired by the prepositioned server with the fingerprint characteristic data of a corresponding user in the memory; and when the user identity is certified successfully, the transaction data is transmitted to a bank server. The fingerprint payment certificate server plays a role of a third party authenticator between the user and the bank, avoids the problem that impartiality deficiency of proof existing in unilateral certificate, and improves the convenience for user payment at the same time.
Owner:开店宝支付服务有限公司
Method, system and device of security certificate
ActiveCN101651682AImprove experienceData switching networksSecurity arrangementBroadbandAuthentication server
The invention provides a method, a system and a device of security certificate. The method comprises the followings steps: encapsulating an empty certificate request in a protocol message of a remoteuser dial certification system (Radius) after an access controller (AC) activates the empty certificate of mobile termination (STA), sending the empty certificate request to an empty certificate server by a broad band access server (BRAS), and receiving the Radius protocol message in which a certificate result is encapsulated, returned by the empty certificate server through the BRAS; when the certificate result succeeds, authorizing the STA to be accessed to a wireless network, and permitting the STA to be accessed to a metropolitan area network after the BRAS determines the certificate result to be successful. The BRAS is fused in the empty certificate process, and the empty security certificate and the security certificate of accessing to the metropolitan area network are realized whileadopting the one-time empty certificate process. The invention has simple realization and brings user better user experience.
Owner:NEW H3C TECH CO LTD
Computer safety protective method based on software identity identifying technology
InactiveCN1900941AMeet safety requirementsStop runningPlatform integrity maintainanceProtection mechanismAuthentication server
The present invention relates to computer security technology, and is a client end computer security protecting mechanism established around the certificating server based on software identity certification. The present invention includes: 1. establishing security certificating database with the unique flag code as ID; 2. establishing certificating server for providing software security certificating function with the security certificating database as kernel; 3. establishing security policy for limiting the software running in the client end; 4. monitoring the client end computer and extracting the unique ID and submitting it to the certificating server before starting the executable file; 5. inquiring the security certificating database with the certificating server and feeding back the corresponding security information to the client end computer; and 6. the client end computer judging whether to execute the software. Compared with traditional antivirus method, the present invention has more wide protection.
Owner:傅玉生
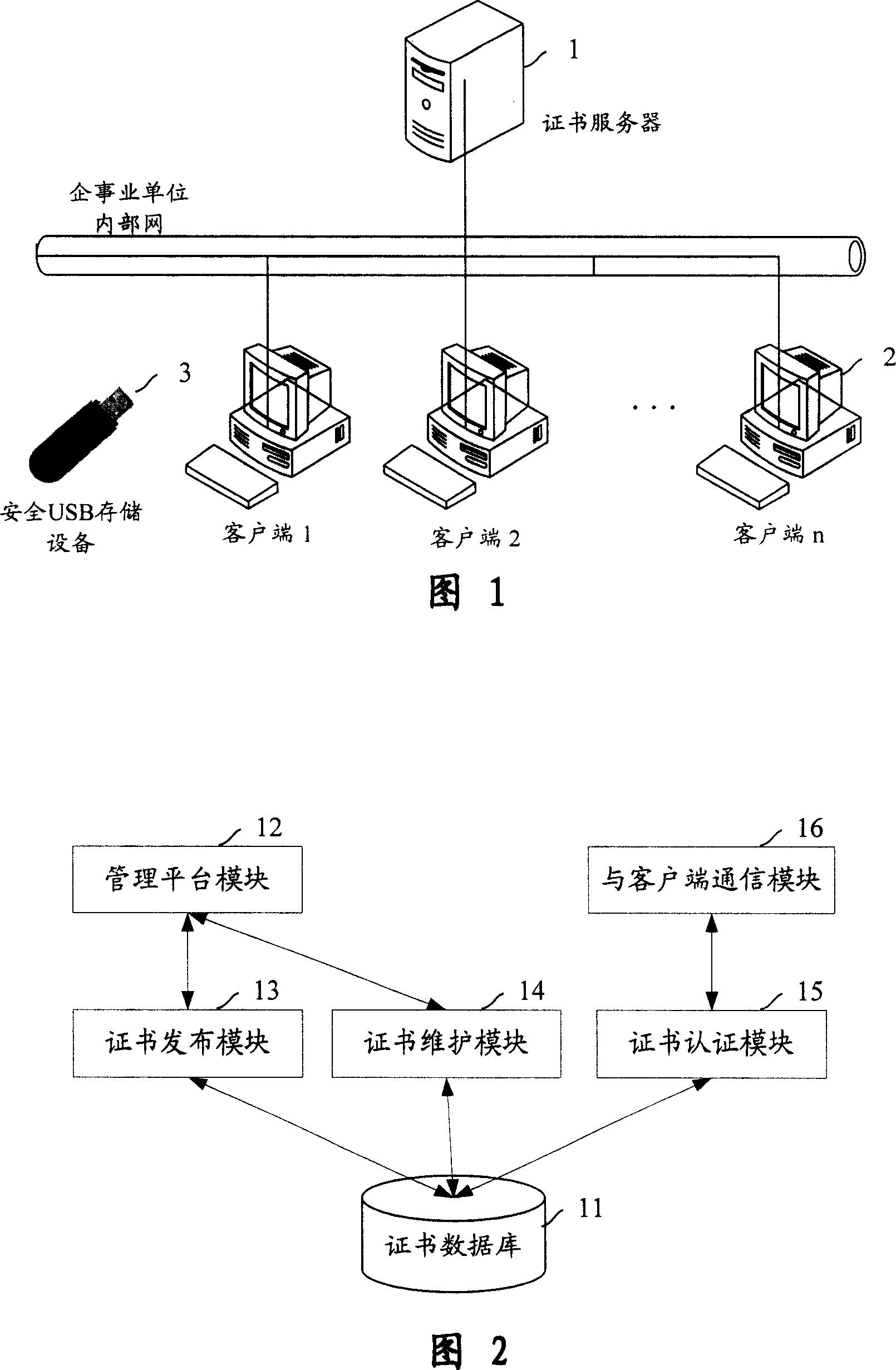
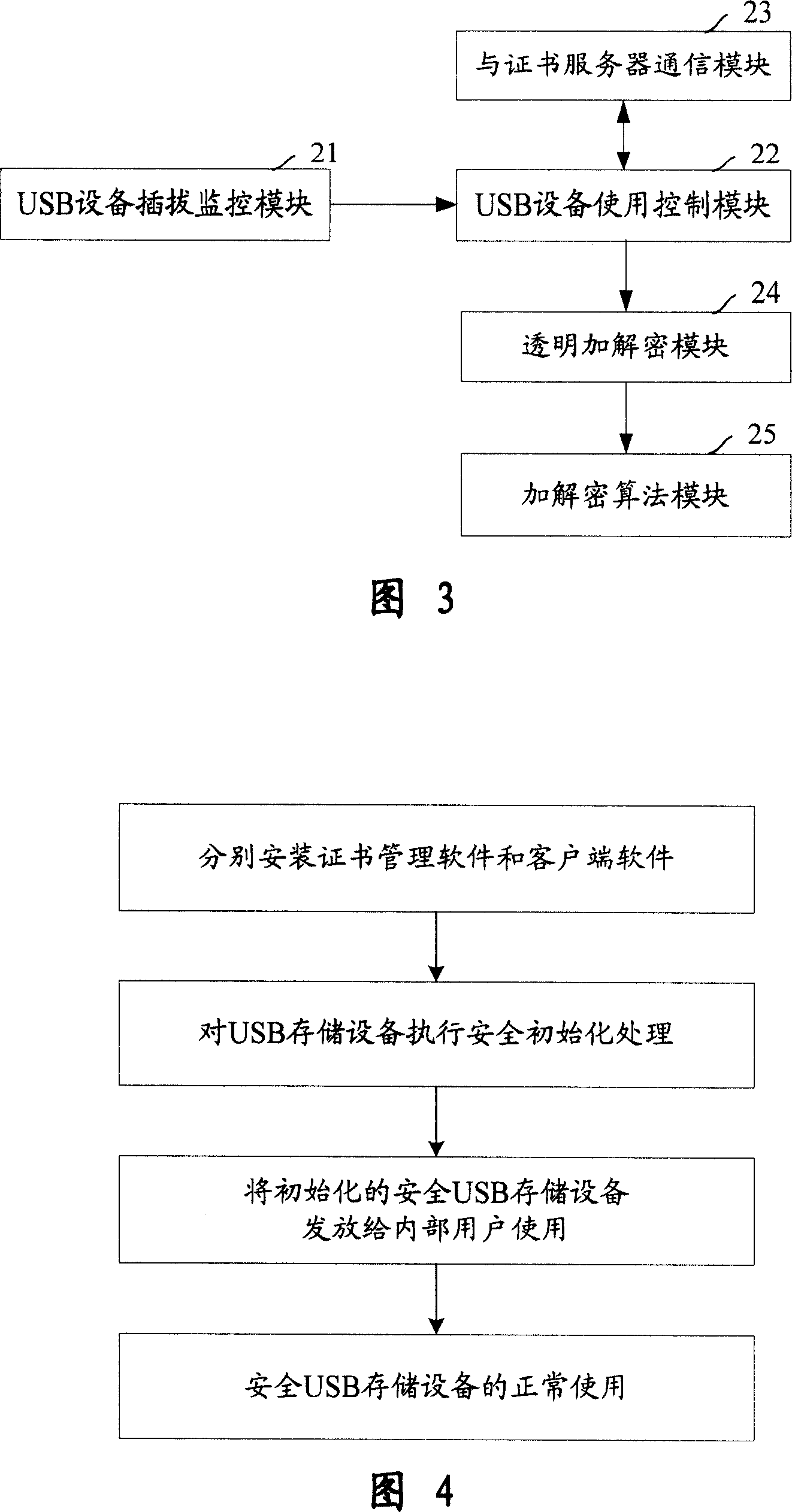
Divulging secrets prevention system of USB storage device date based on certificate and transparent encryption technology
InactiveCN101017525APrevent leak riskReduce the Risk of ConfidentialityUser identity/authority verificationUnauthorized memory use protectionClient-sideUSB
This invention relates to one USB memory data anti-leakage system based on certificate and transparent coding technique, which comprises the following parts: one certificate management software; certificate servo with physical isolation and network protection actions, inner network host to customer end with customer end software; safety USB memory device by multiple common USB devices through the servo. The method comprises the following steps: a, separately fixing certificate management software and customer end software in network servo and each host; b, executing safety initial process in certificate servo on USB memory device; c, sending the memory device to inside user; d, safety USB memory device is for normal use.
Owner:BEIJING UNIV OF POSTS & TELECOMM
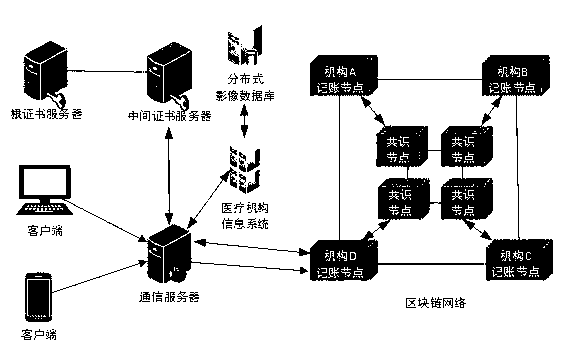
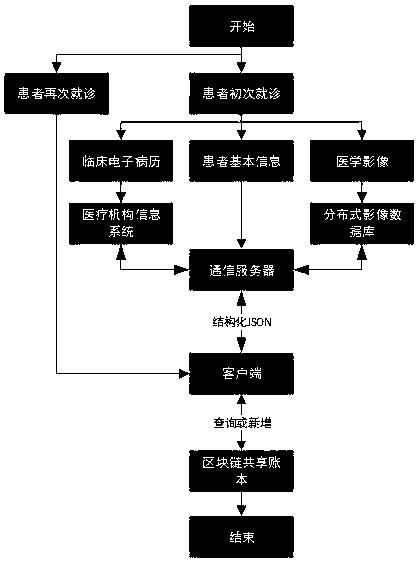
Medical data platform based on block chain technology
InactiveCN109243548AIsolation damageReduce risk of leakageDigital data information retrievalPublic key for secure communicationData synchronizationData platform
The invention discloses a medical data platform based on the block chain technology. The medical data platform comprises a terminal, a server module, a data storage module and a block chain network. The terminal exchanges data with the data storage module and the block chain network through the server module. The server module comprises a communication server, an intermediate certificate server and a root certificate server and is used for processing data interaction between the modules and allocating certificates to the block chain network nodes. The data storage module comprises a medical information system and a distributed image database and is used for data storage. The block chain network comprises multiple institutional accounting nodes and multiple consensus nodes. The accounting nodes perform mutual data synchronization. The medical data platform based on the block chain technology has the advantages that the existing medical information is stored in the block chain shared account book so that all the medical institutions can share the medical information related to the patients, and the privacy protection function of the medical data can be realized by using the encryption algorithm and thus sharing of the medical data can be facilitated and the security of the sensitive information can also be protected.
Owner:GUANGDONG UNIV OF TECH
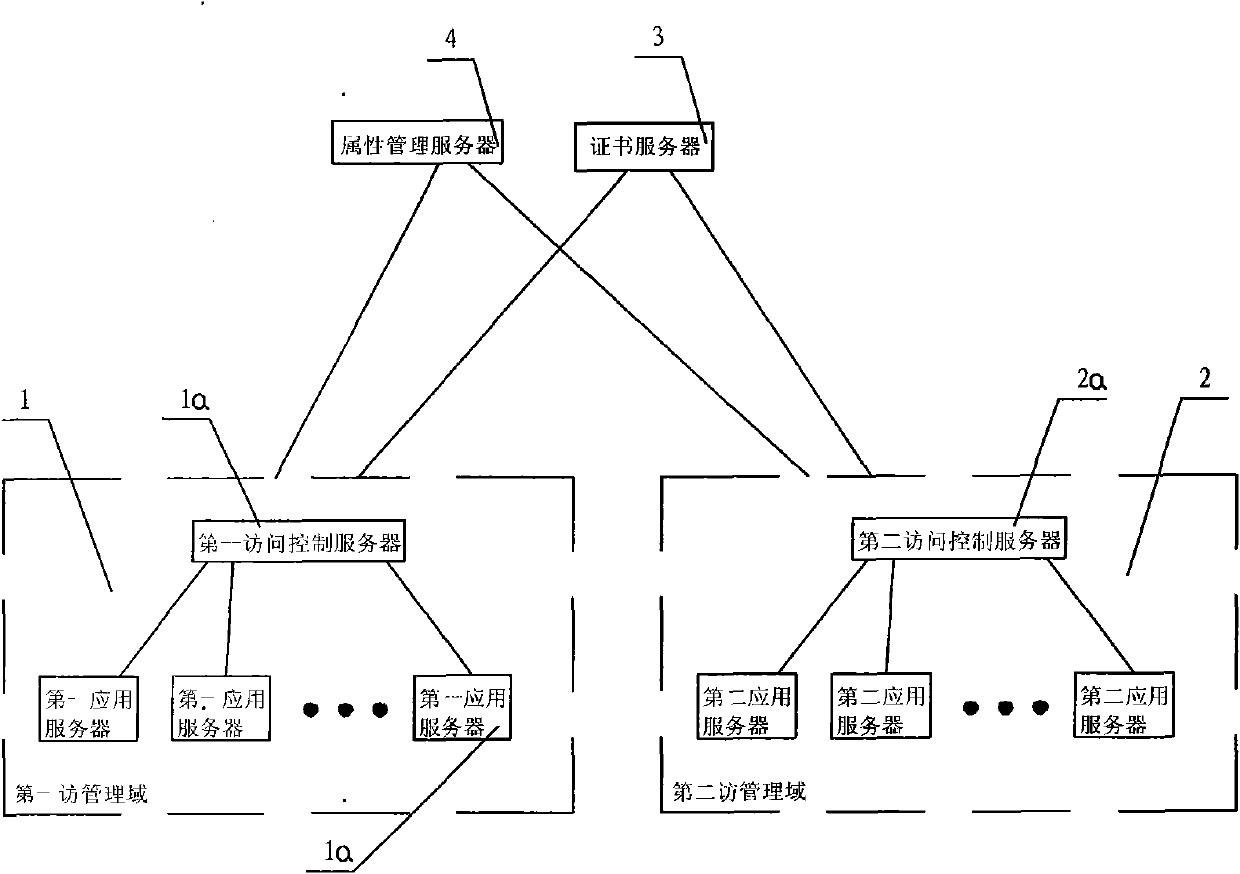
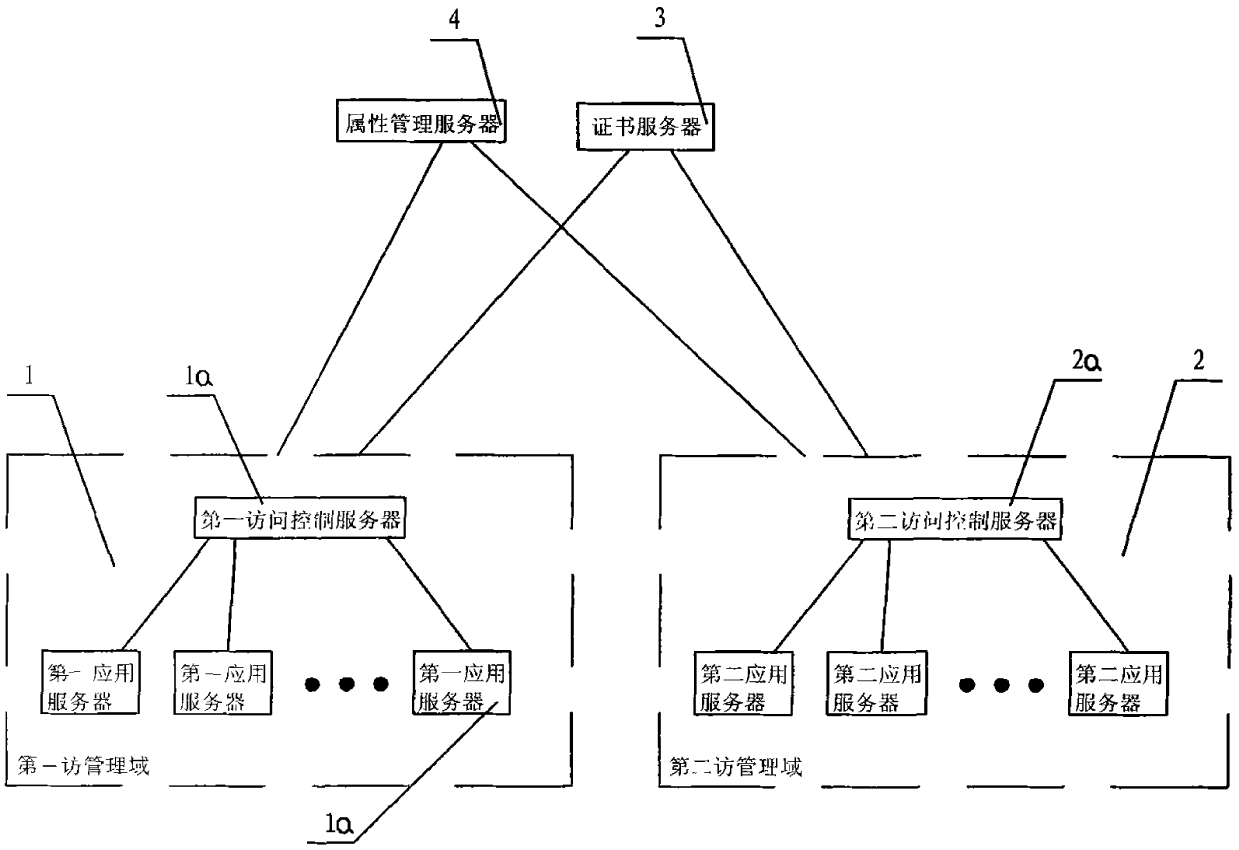
Attribute-based access control model and cross domain access method thereof
InactiveCN101997876ASolve the efficiency problem of user-role-permission assignmentImprove convenienceTransmissionAccess methodAdministrative domain
The invention discloses an attribute-based access control model and a cross domain access method thereof. The attribute-based access control model comprises a first management domain and a second management domain, and is characterized by comprising certificate servers and attribute management servers. The cross domain access method of the system comprises the following steps: the certificate servers are respectively used for awarding a server certificate for the first management domain and the second management domain; a user downloads an attribute certificate to a local disk for storage by logging on the first management domain; the user submits the attribute certificate to the second management domain; a second access control server verifies the attribute certificate; and the second access control server extracts an attribute value to judge the operation validity of the user. The attribute-based access control model and the cross domain access method thereof of the invention have the obvious advantages that the role of the user and the management domains can be considered as a single attribute of the user, the efficiency problem of user-role-authority valuation under the condition of complex role in a role-based access control (RBAC) model can be effectively solved, and the corresponding access control method is provided for an anonymous user in an open network environment.
Owner:CHONGQING UNIV
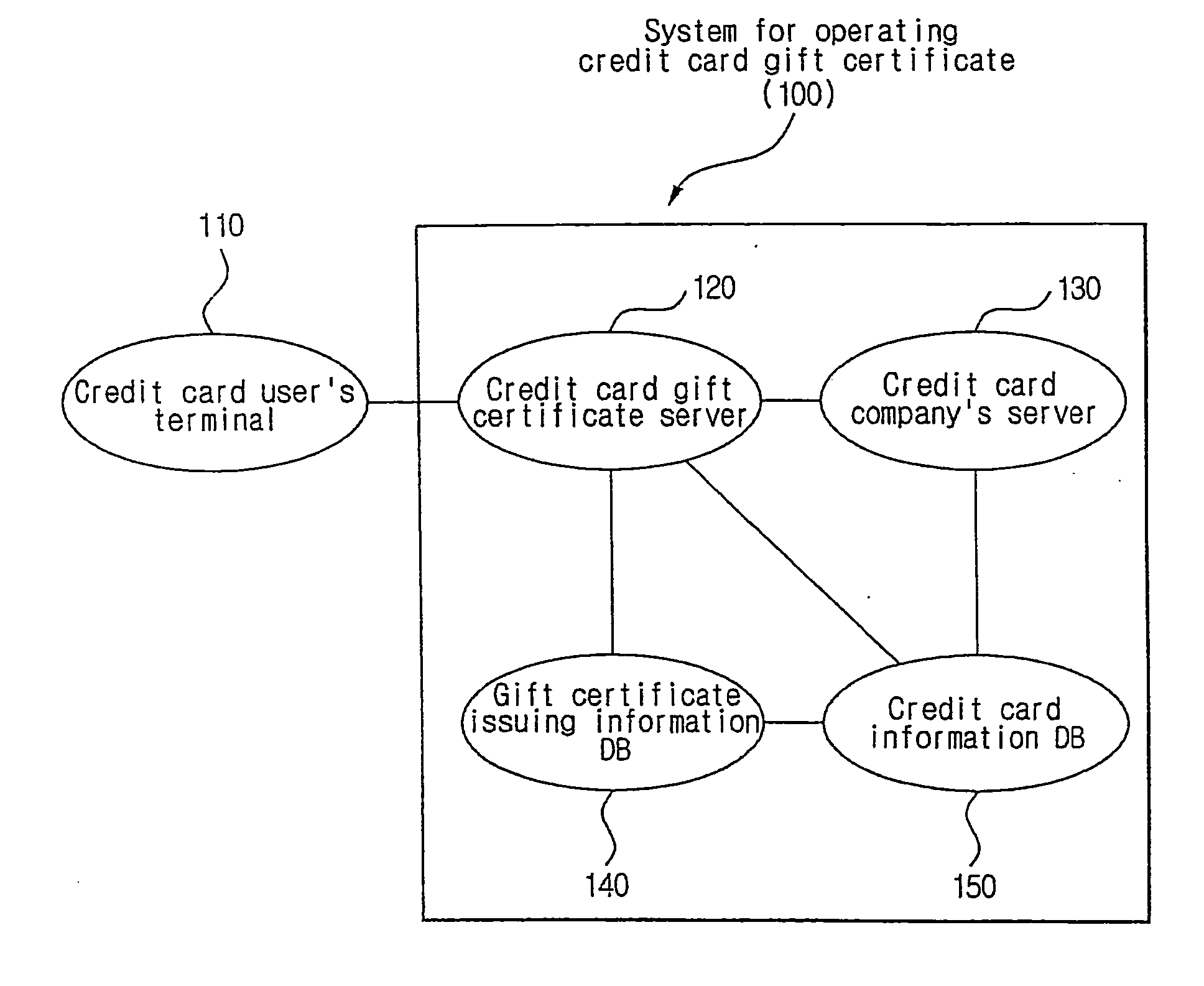
System and method for operating a gift certificate on the basis of credit card transactions
InactiveUS20050177493A1Reduce restrictionsTransaction were limitedCredit registering devices actuationFinanceCredit cardCertificate server
Disclosed are a system and method for operating a credit card gift certificate based on credit card transactions. According to the method for operating the credit card gift certificate, a credit card gift certificate server adds the limit of the credit card gift certificate corresponding to an amount of money printed on the credit card gift certificate to the transaction limit of a credit card of a credit card user, and the credit card user uses the amount of money of the gift certificate through the credit card transactions within the additionally configured limit of the credit card transaction. An amount obtained by subtracting the limit of the gift certificate from an amount paid by the credit card is determined as a payment amount to be paid by the user on a credit card bill that is sent to the user.
Owner:SIM WOO JIN
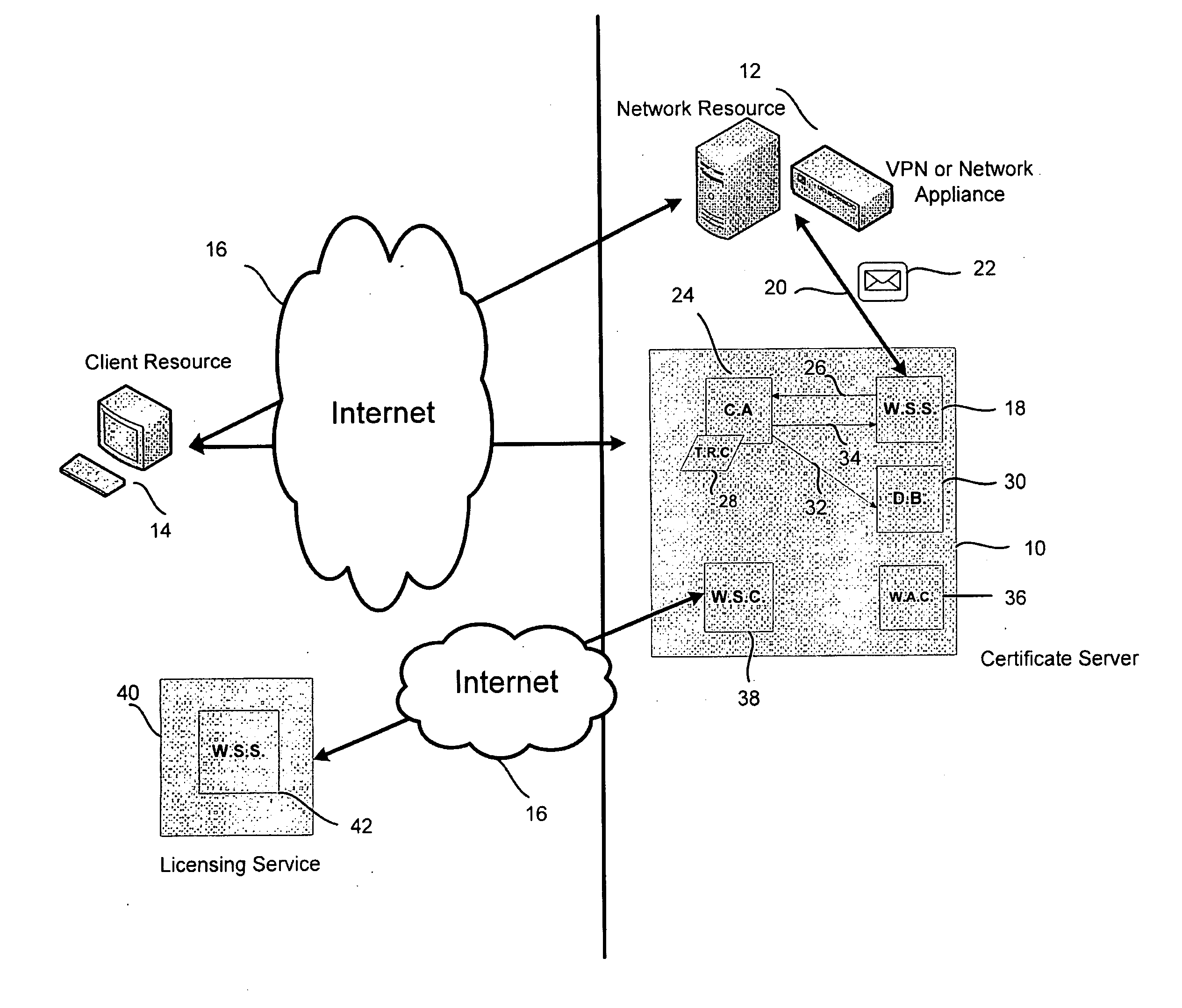
Method and system for generating digital certificates and certificate signing requests
InactiveUS20100138907A1Easy to trackDigital data processing detailsUser identity/authority verificationDigital signatureWeb service
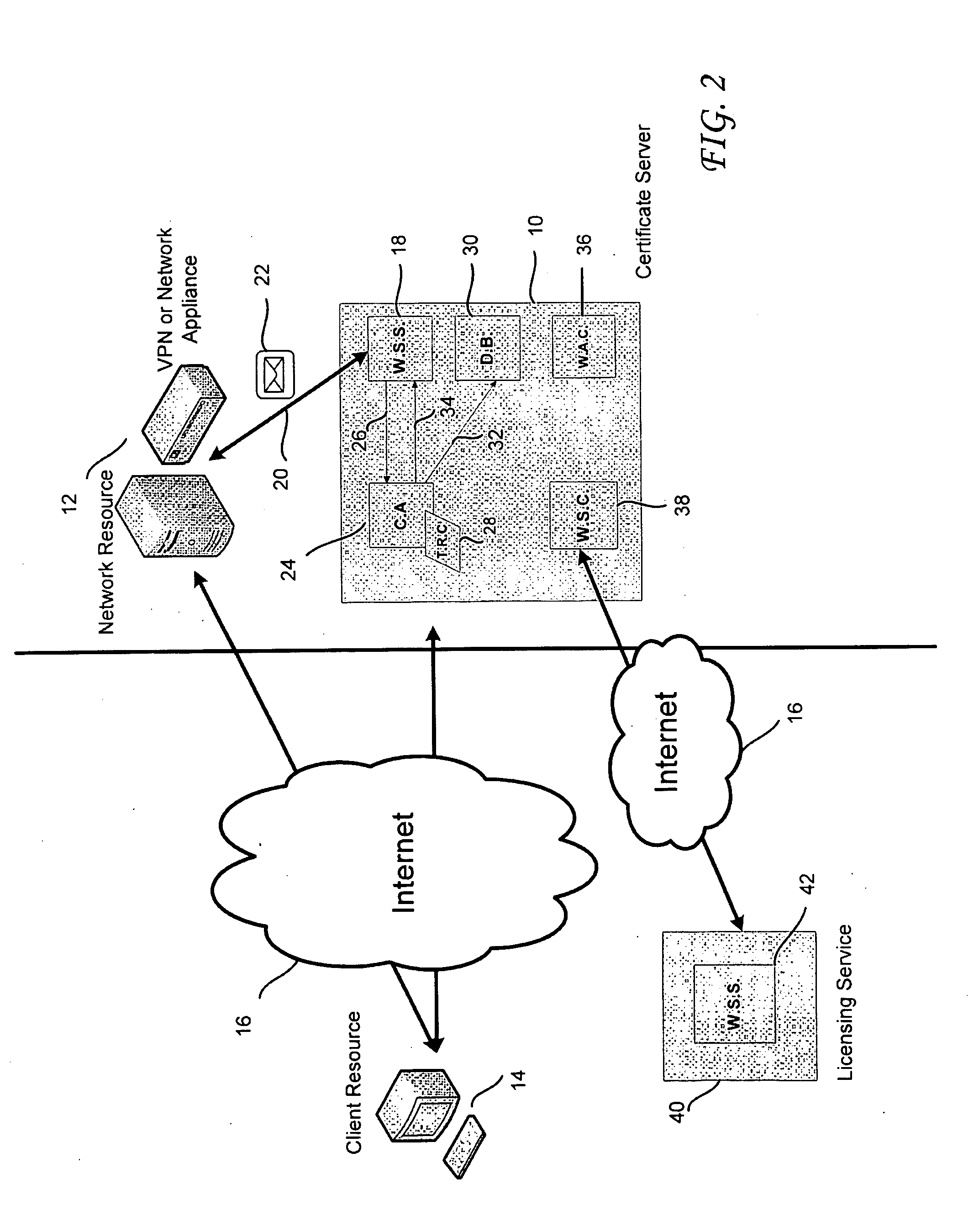
A certificate server is provided for issuing digital certificates to be used by a network resource and / or a client resource. The certificate server is configured to communicate with the network resource or the client resource to receive a certificate request. Upon receiving the certificate request, the certificate server may automate the process for authenticating the certificate request, validating the terms of the certificate request and digitally signing the certificate request. An authentication appliance may communicate with or be integrated within the certificate server. The certificate server includes a web service server, a certificate authority component, and a database that enable communication with either the network resource, client resource, or the authentication appliance to automate the administration process typically involved in receiving and signing a certificate request. The certificate authority component may sign the certificate request with a trusted root chain associated with the network resource.
Owner:SECUREAUTH CORP
Method and system based on wireless terminal for applying digital certificate and wireless terminal
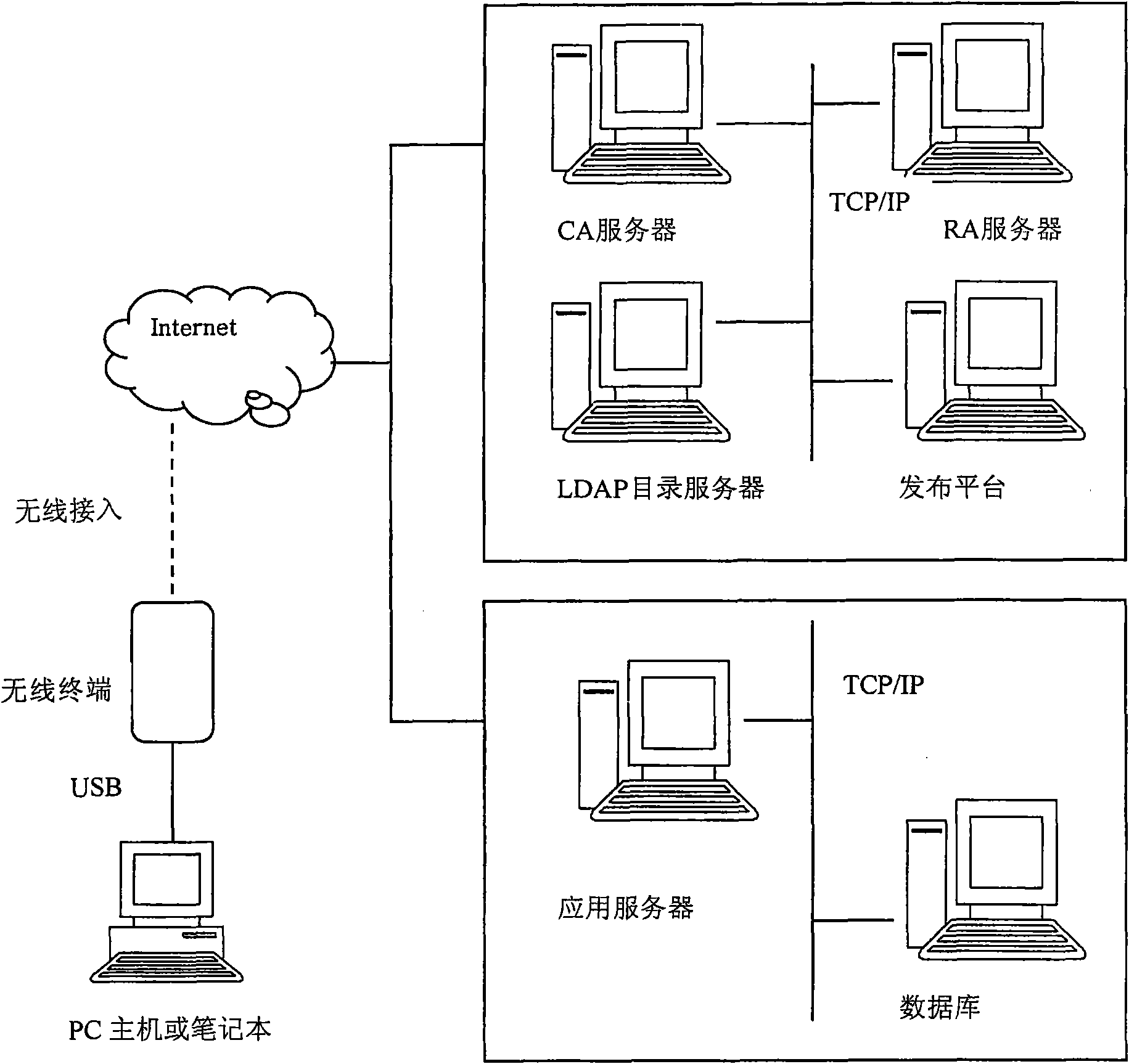
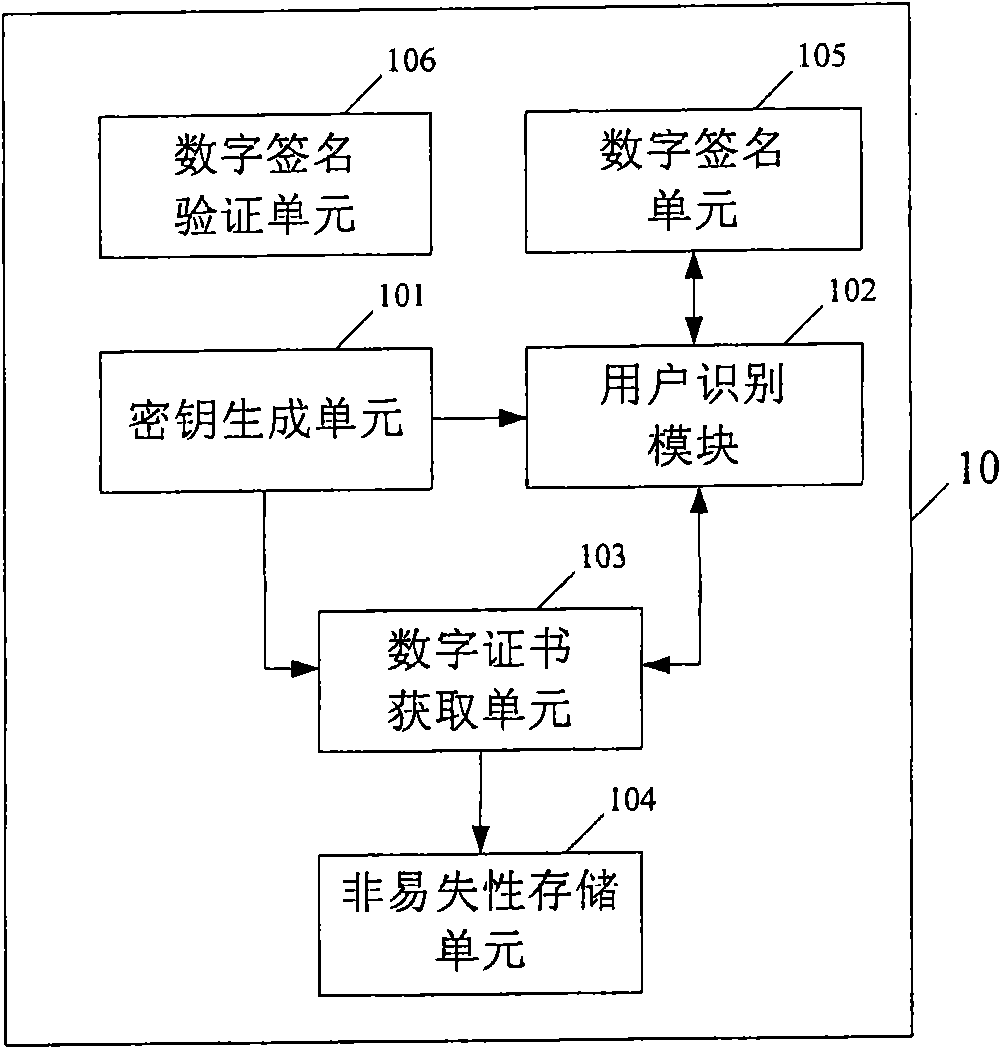
ActiveCN101777978AImprove securitySave storage spaceUser identity/authority verificationAuthentication serverCertificate server
The embodiment of the invention provides a method and a system based on a wireless terminal for applying a digital certificate and a wireless terminal. The method comprises the following steps: generating a key pair, a private key of the key pair is stored in a user identity module of the wireless terminal; sending a public key of the key pair, a user identity module number, application certificate information of user information to a certificate server; receiving a digital certificate issued by the certificate server; and storing the digital certificate into a nonvolatile storage of the wireless terminal. The technical scheme of the embodiment of the invention adopts the method separately storing the private key and the digital certificate to store the private key into an SIM card and store the digital certificate into a FLASH. Since the digital certificate can prove the hard core of a user ID to be the private key, the mode of storage can improve the safety of the private key.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
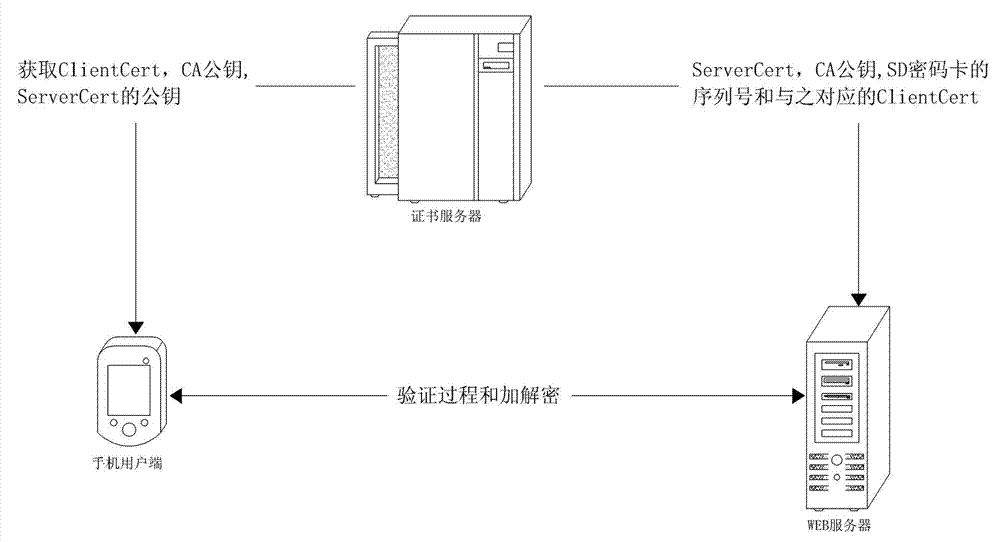
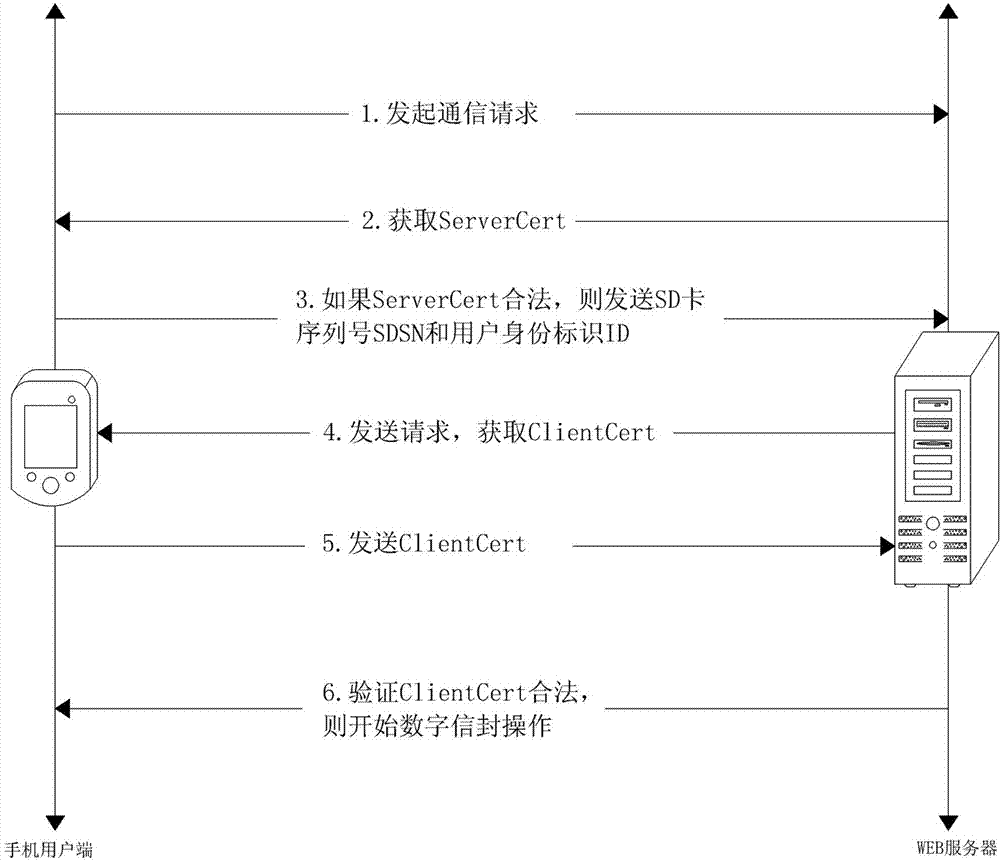
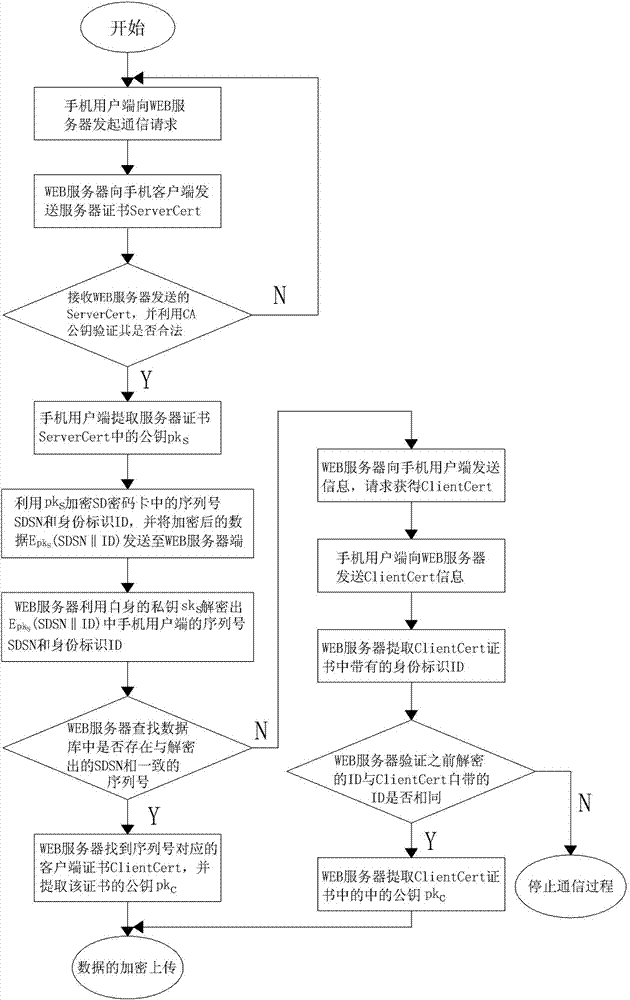
Secure digital (SD)-password-card-based Internet of things healthcare service system and secure communication method thereof
ActiveCN102882847AEnsure safetyImprove securityData processing applicationsUser identity/authority verificationWeb serviceMedical treatment
The invention discloses a secure digital (SD)-password-card-based Internet of things healthcare service system. The system comprises a server, a WEB server, a sensor and a client; and an SD password card stores a client certificate, a certificate authority (CA) public key and a public pks. The invention also discloses a secure communication method of the system. According to the method, an identity authentication process comprises the following steps of: (a), initiating a request; (c), verifying whether ServerCert is legal; (d), encrypting and transmitting data; and (e), decrypting a secure digital serial number (SDSN) and an identity (ID); and (f) acquiring a public key pkc. And an uploading process comprises the following steps of: 1), generating a random number K; 2), signing the K; 3), encrypting the K; 5), verifying a signature; and 6), decrypting the K, wherein the K is used as a communication key. By the system and the method, the security of medical information is ensured, and the advantages of high speed, high security and convenience in management of a symmetrical encryption algorithm are realized, so that health data can be prevented from being stolen, destroyed, modified and unauthorizedly used.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Live broadcast stream media authentication method based on P2P network
InactiveCN101247409AFree data transferOpen Data DeliverySpecial service provision for substationIndexing ServiceUser authentication
The present invention provides authentication method based on P2Pnetwork living broadcast stream medium, first step: user terminal examines live program information from indexes server, and sends playing certain program demand when process flow starts; second step: indexes server provides connection information of program source provider and information of playing program required digital certificate to user terminal; third step: customer terminal software checks whether or not local installs required digital certificate, if digital certificate has already be mounted, application can be applied at digital certificate server of program provider according to required digital certificate information; four step: program provider executes user authentication according to user demand, and distributes digital certificate to legality user, at the same time executes authentication and management to user; five step: after obtaining digital certificate, user registers in P2Pnetwork for transmitting of living broadcast stream medium, receiving stream medium data for executing decipher, decoding and playing.
Owner:INST OF ELECTRICAL ENG CHINESE ACAD OF SCI
Method and system for managing certificates
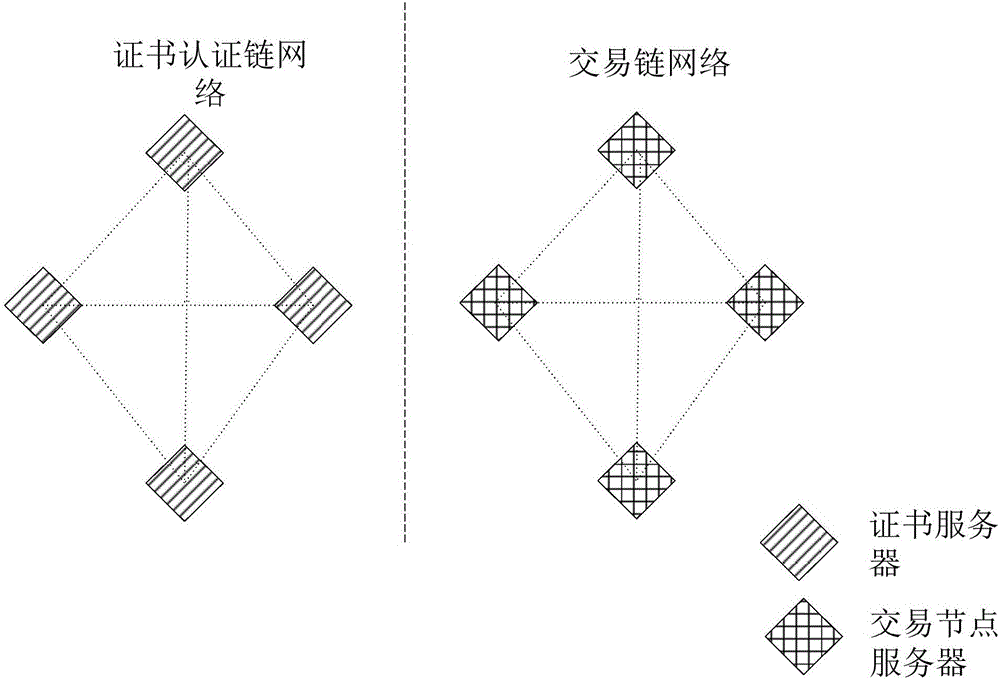
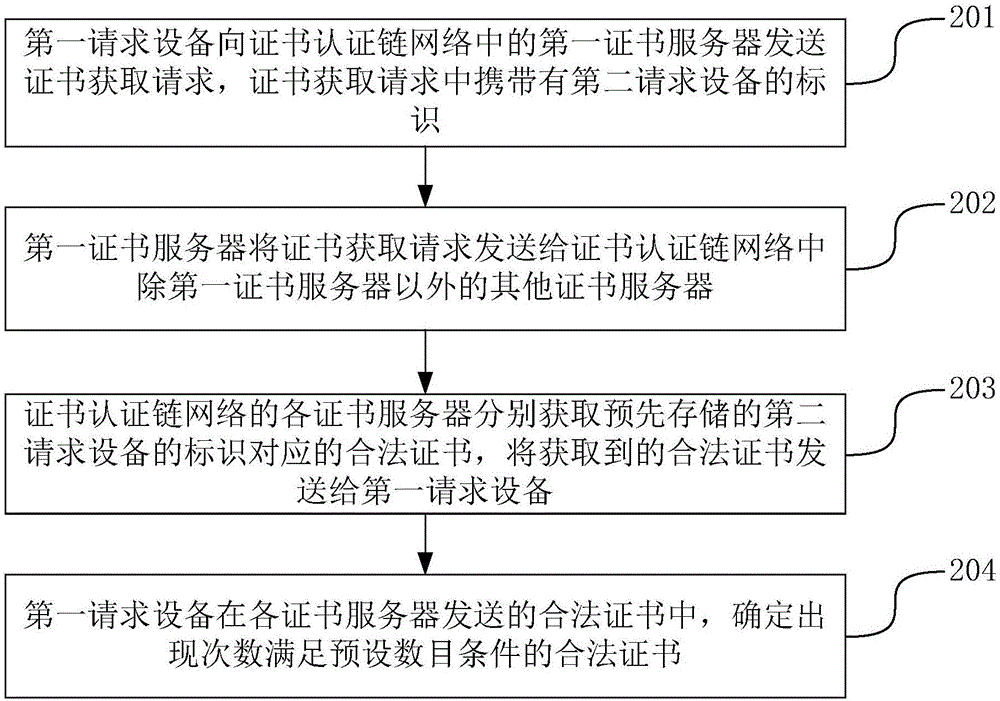
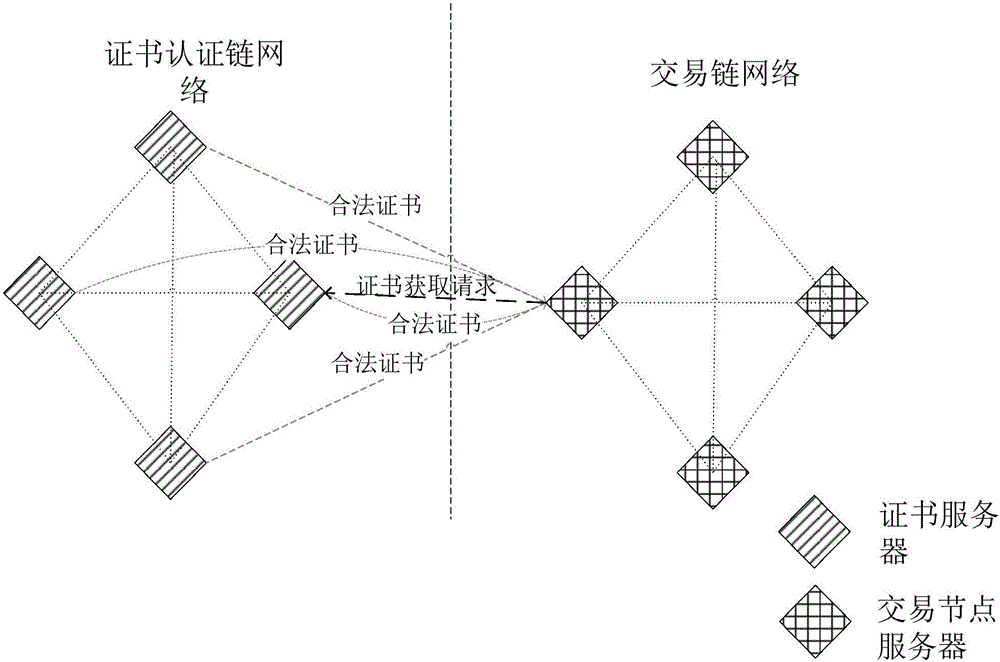
ActiveCN106789089ANormal transactionUser identity/authority verificationChain networkCertificate server
The invention discloses a method and system for managing certificates, and belongs to the technical field of computers. The method comprises the following steps that a certificate obtaining request sent by first requesting equipment is received, wherein the certificate obtaining request carries with an identifier of second requesting equipment; the certificate obtaining request is sent to other certificate servers in a certificate authentication chain network, a legal certificate corresponding to the prestored identifier of the second requesting equipment is obtained, the obtained legal certificate is sent to the first requesting equipment, and the first requesting equipment determines the legal certificates of which the occurrence numbers meet the preset number conditions in the legal certificates sent by the certificate servers. By adopting the method and system for managing the certificates, transactions in a block chain can be normally operated.
Owner:TENCENT TECH (SHENZHEN) CO LTD
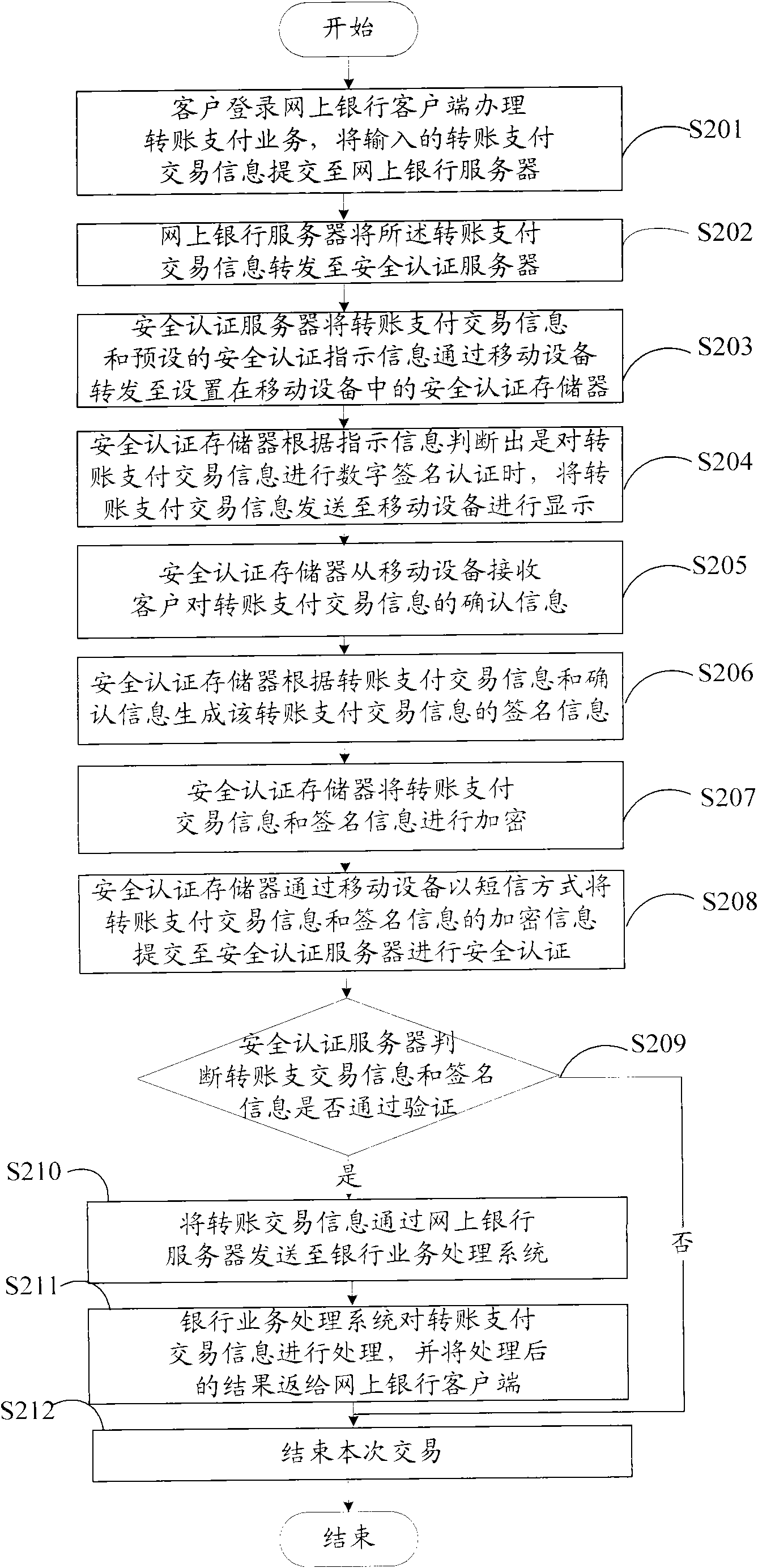
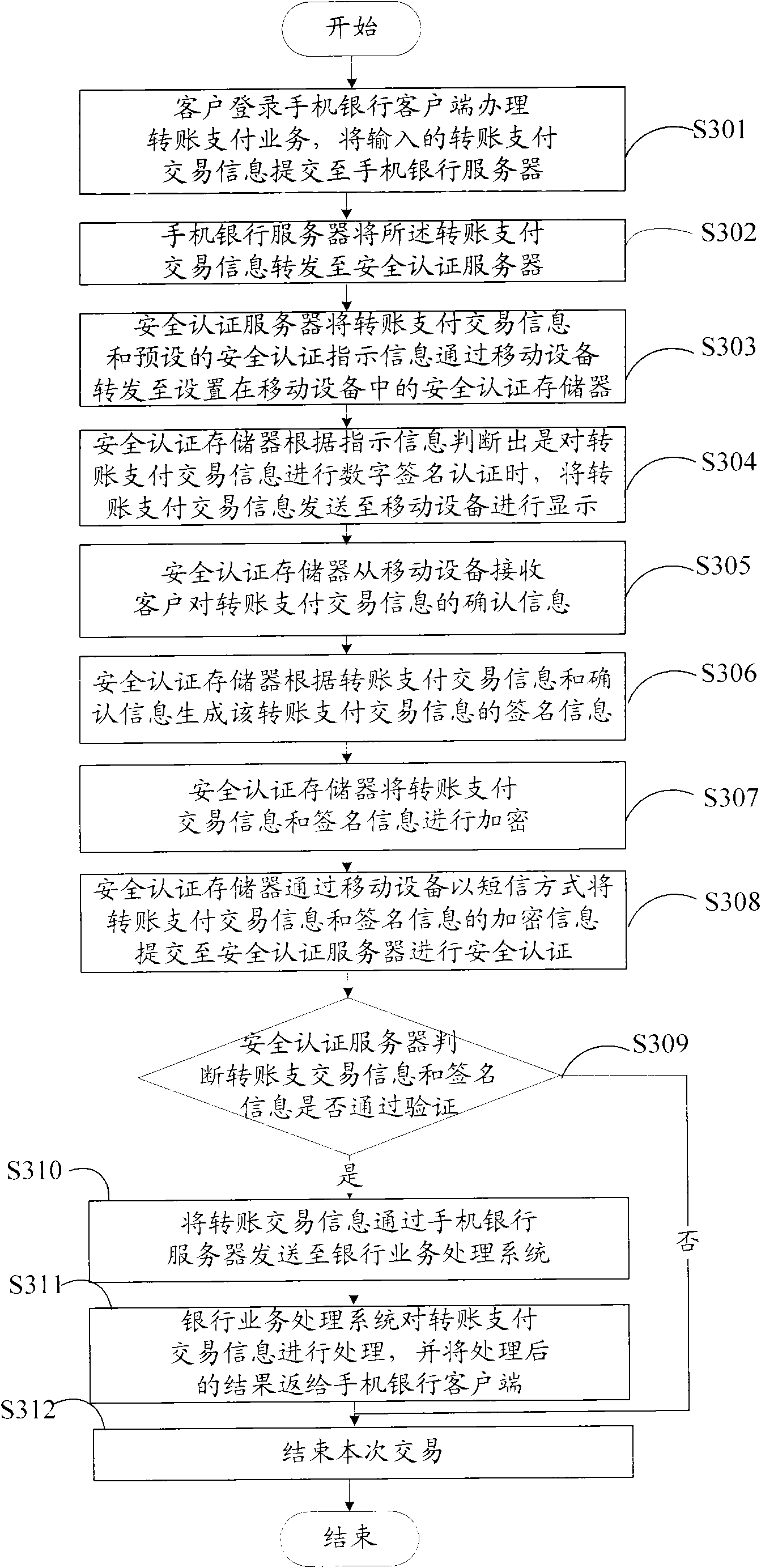
Electronic bank safety certificating method and system based on mobile equipment
The invention provides an electronic bank safety certificating method based on mobile equipment, which comprises the following steps of: sending transaction information of payment by the transfer of accounts at a bank client to a safety certificating server by utilizing an electronic bank server; sending the transaction information of payment by the transfer of accounts and the preset safety certificating indication information to a safety certificating memory arranged on the mobile equipment by utilizing the safety certificating server through the mobile equipment; judging whether digital signature certification or dynamic command certification is carried out on the transaction information of payment by the transfer of accounts by utilizing the safety certificating memory according to the safety certificating indication information, if so, carrying out digital signature certification on the transaction information of payment by the transfer of accounts, if not so, carrying out dynamic command certification on the transaction information of payment by the transfer of accounts. The invention also provides an electronic bank safety certificating device based on the mobile equipment. The invention can provide unified safety certification for multi-channel electronic transactions. The device has the characteristics of convenience for carrying, good custom experience and the like.
Owner:CHINA CONSTRUCTION BANK
Electronic document automatic signing system and method
InactiveCN101127107APrevent forgeryUser identity/authority verificationComputer security arrangementsElectronic documentUser authentication
The utility model relates to a system and a method for electronic document automatic signature; wherein, the method comprises the following steps: an electronic document used for electronic signature is generated and then the signature information is sent to a user end computer and the user is informed to carry out the operation of electronic signature; the operation of electronic signature is confirmed by the user; a digital certificate of the user is obtained from the database of a certificate server; the identity of the user is verified according to the digital certificate; after the verification of the identity of the user, a summary of the electronic document is generated; according to the private key of the digital certificate, the summary of the electronic document is encrypted, thus an electronic signature of the electronic document is obtained. With the utility model, the identity of the signer can be verified before the generation of the electronic signature, thus the electronic signature from forging is effectively prevented.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
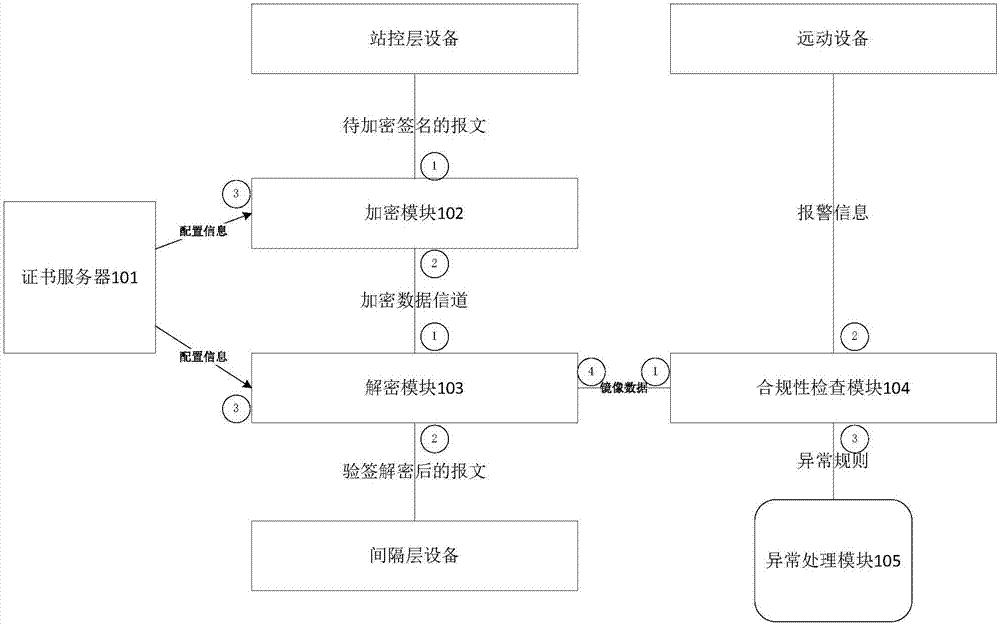
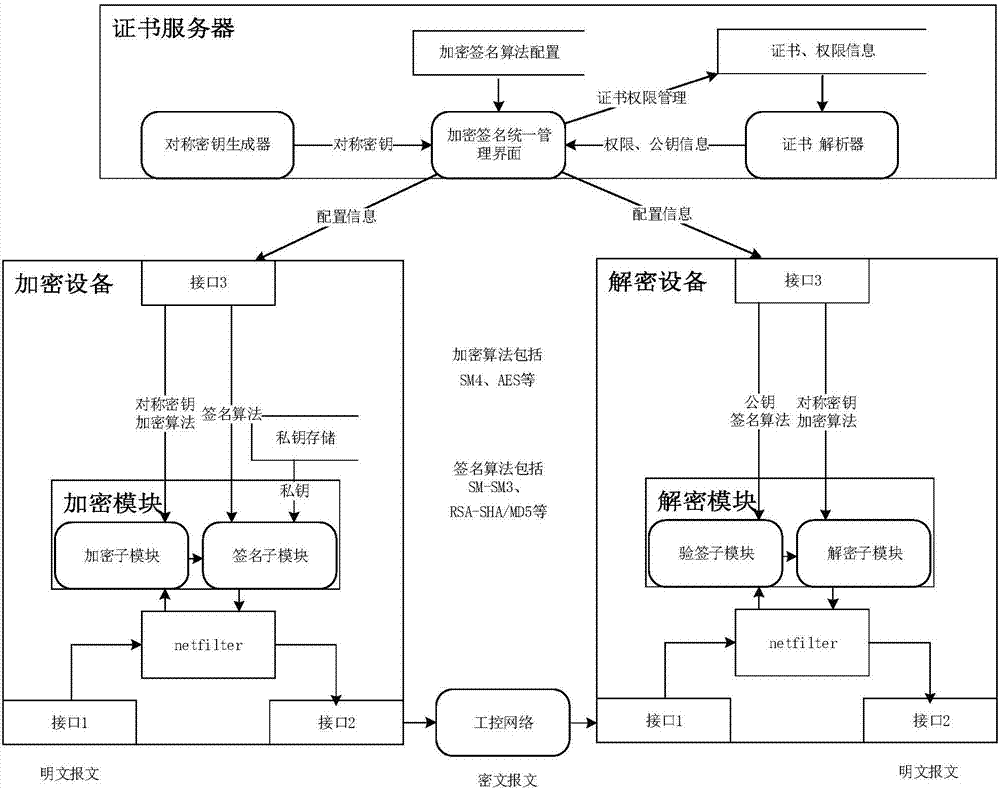
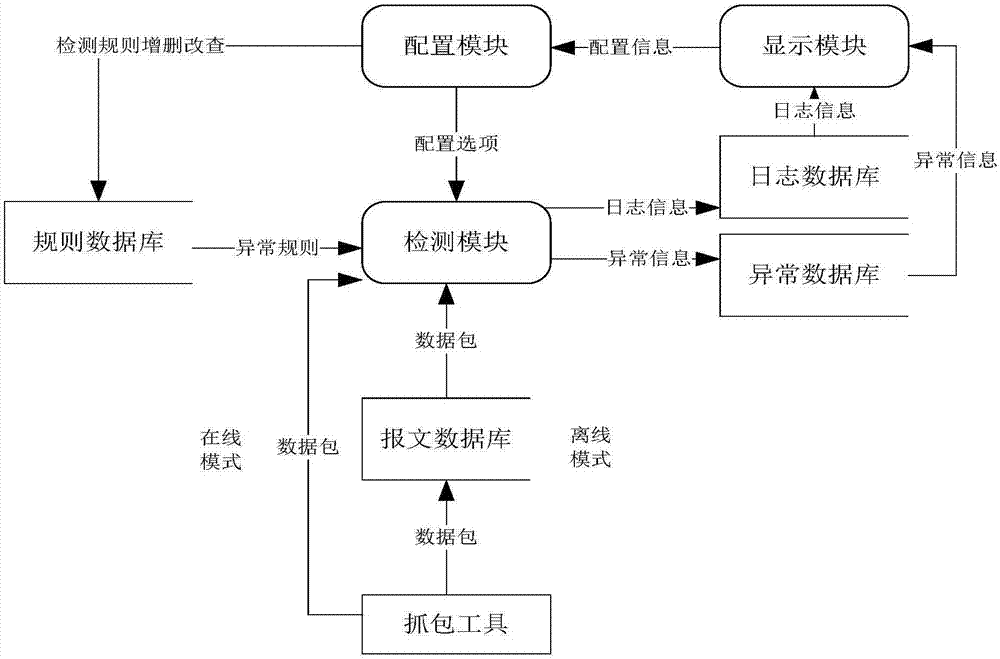
Smart grid information transmission safety protection device and safety protection method
ActiveCN107483444AEasy to deployReduce maintenance costsUser identity/authority verificationPlaintextInformation transmission
The invention discloses a smart grid information transmission safety protection device and a safety protection method, which relate to the technical field of smart grid information transmission safety. The device comprises a certificate server, an encryption and decryption module, a compliance check module and an exception handling module, wherein the encryption and decryption module is wholly serially connected between a station level and a bay level for carrying out encryption signature and signature verification decryption functions on original transparently-transmitted data; the compliance check module grabs a plaintext data packet in an offline or online mode and submits the plaintext data packet to the detection module for compliance check, and as for a compliance message, an analysis result is stored to a log database in a log format; and exception information is independently stored in an exception database through the exception handling module, and an administrator is notified. In the case of permissible delay in the smart grid, the encryption and decryption module together protects the internal information of the smart grid, behaviors that the internal data are tampered and destructed in the case of transmission are resisted, and the safety of the grid is further improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
System and method for issuing digital certificate using encrypted image
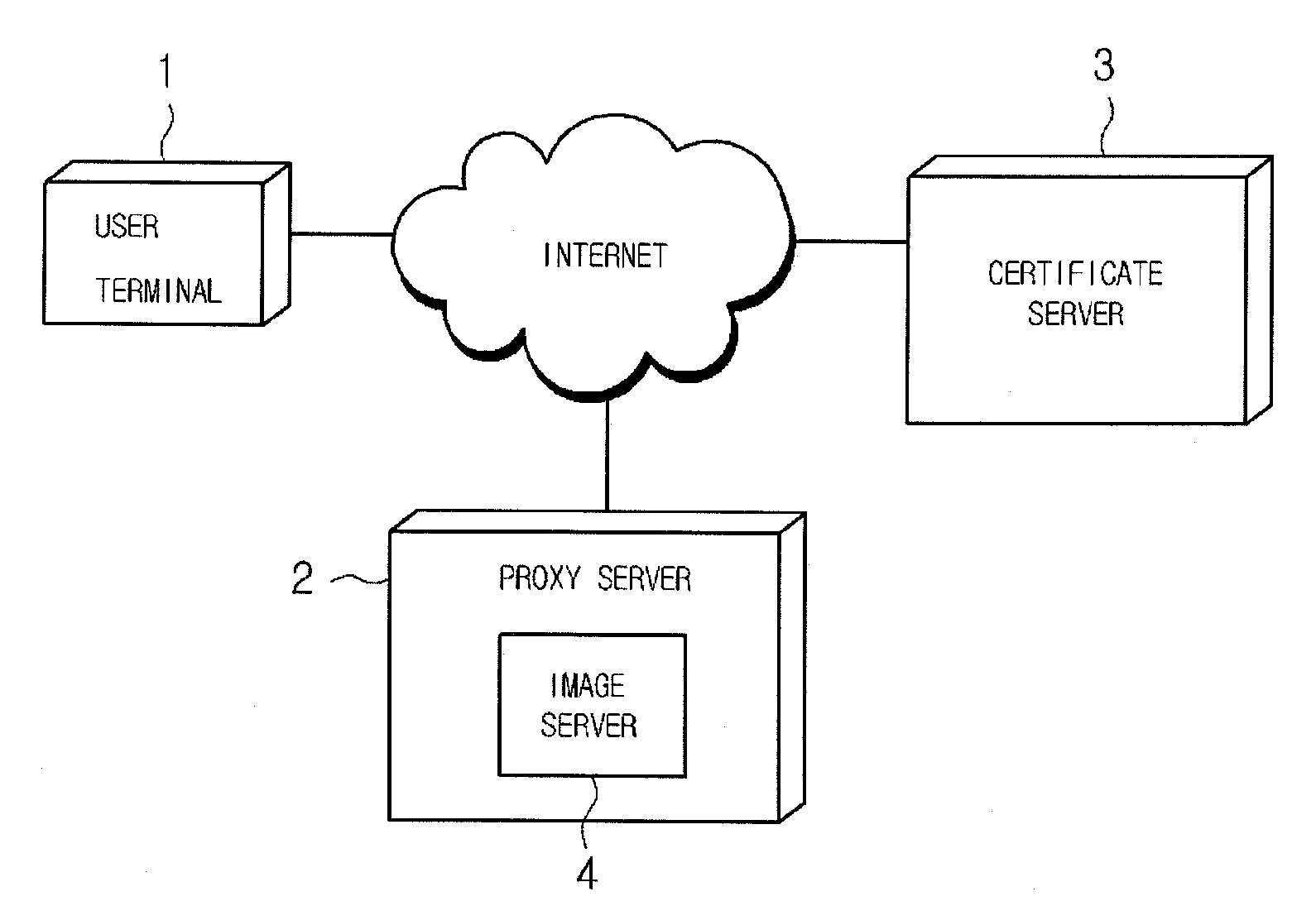
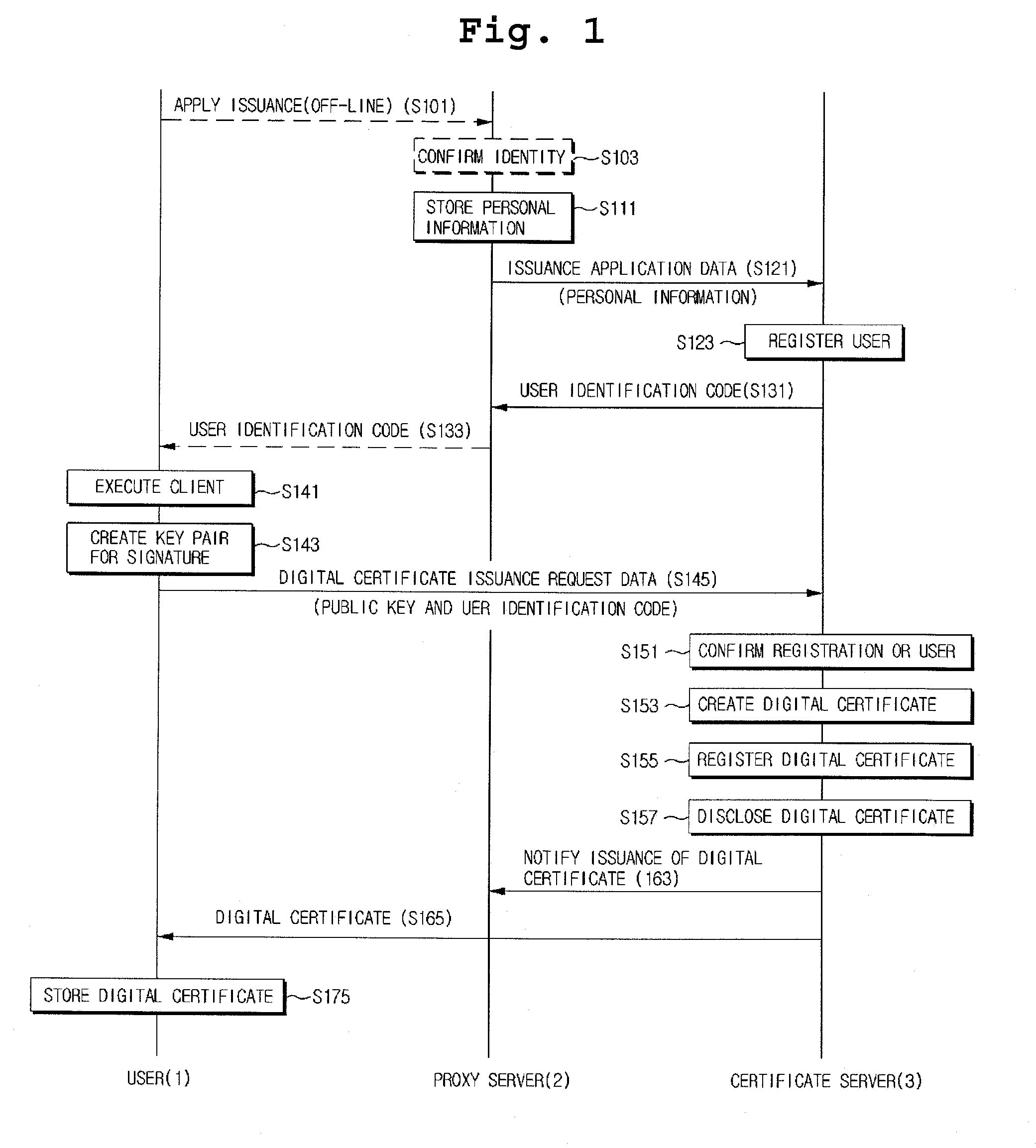
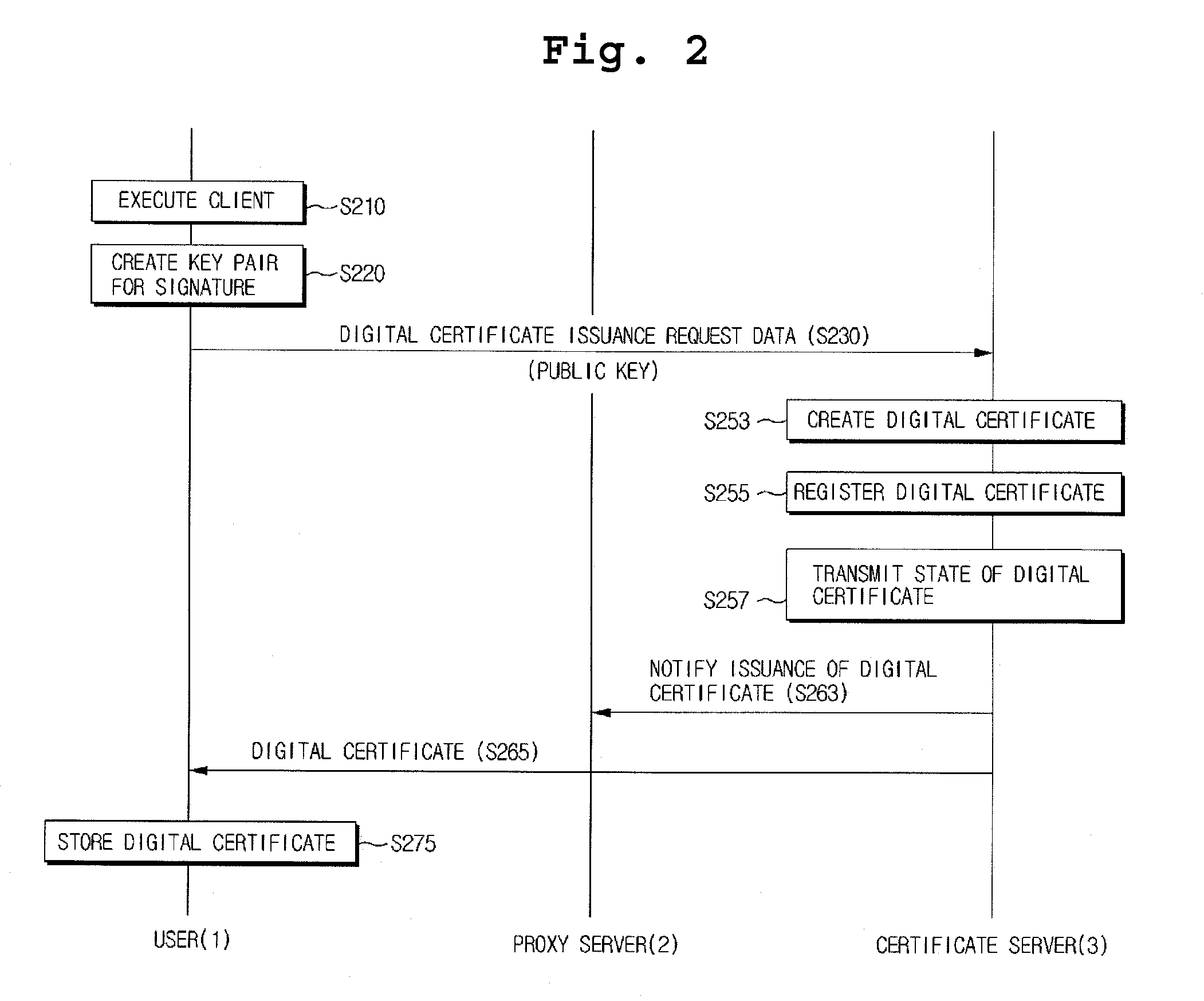
ActiveUS20100088507A1Avoid abuseEasy to identifyDigital data processing detailsMultiple digital computer combinationsProxy serverCertificate server
The present invention relates to a system and method for issuing a digital certificate using an encrypted image, in which a digital certificate is sealed in a digital envelope image so as to protect a digital certificate user from damages caused by hacking, phishing attacks and the like in the course of issuance, update and re-issuance of the digital certificate, and the method for issuing a digital certificate comprises the steps of: storing a user select image for issuing the digital certificate, by a proxy server or a certificate server; and requesting the certificate server to issue the digital certificate and, if the digital certificate is issued, creating a sealed digital envelope image by combining the digital certificate with the user select image and transmitting the digital envelope image to a user terminal.
Owner:OLCORPS
Electronic currency transfer payment system and method
ActiveCN105096118ASolve problems with application limitationsMeet diverse needsProtocol authorisationComputer terminalCertificate server
The invention relates to an electronic currency transfer payment system and method. The system includes a digital certificate server end, an intelligent mobile terminal, security intelligent hardware and a currency trusteeship server end. With the system adopted, transfer payment operation of electronic currencies can be realized, wherein the transfer payment operation of the electronic currencies includes various types of transfer payment operation, for example, recharging electronic currencies in the security intelligent hardware and carrying out online payment through utilizing the electronic currencies in the security intelligent hardware; and other types of transfer payment operation of the electronic currencies can be also carried out; and the security of the transfer payment operation of the electronic currencies can be protected through the security intelligent hardware. With the electronic currency transfer payment system and method of the invention adopted, various kind of transfer payment operation of electronic currencies can be realized, and therefore, diverse needs of users can be satisfied.
Owner:廖小谦
Network Device and Computer Readable Medium Therefor
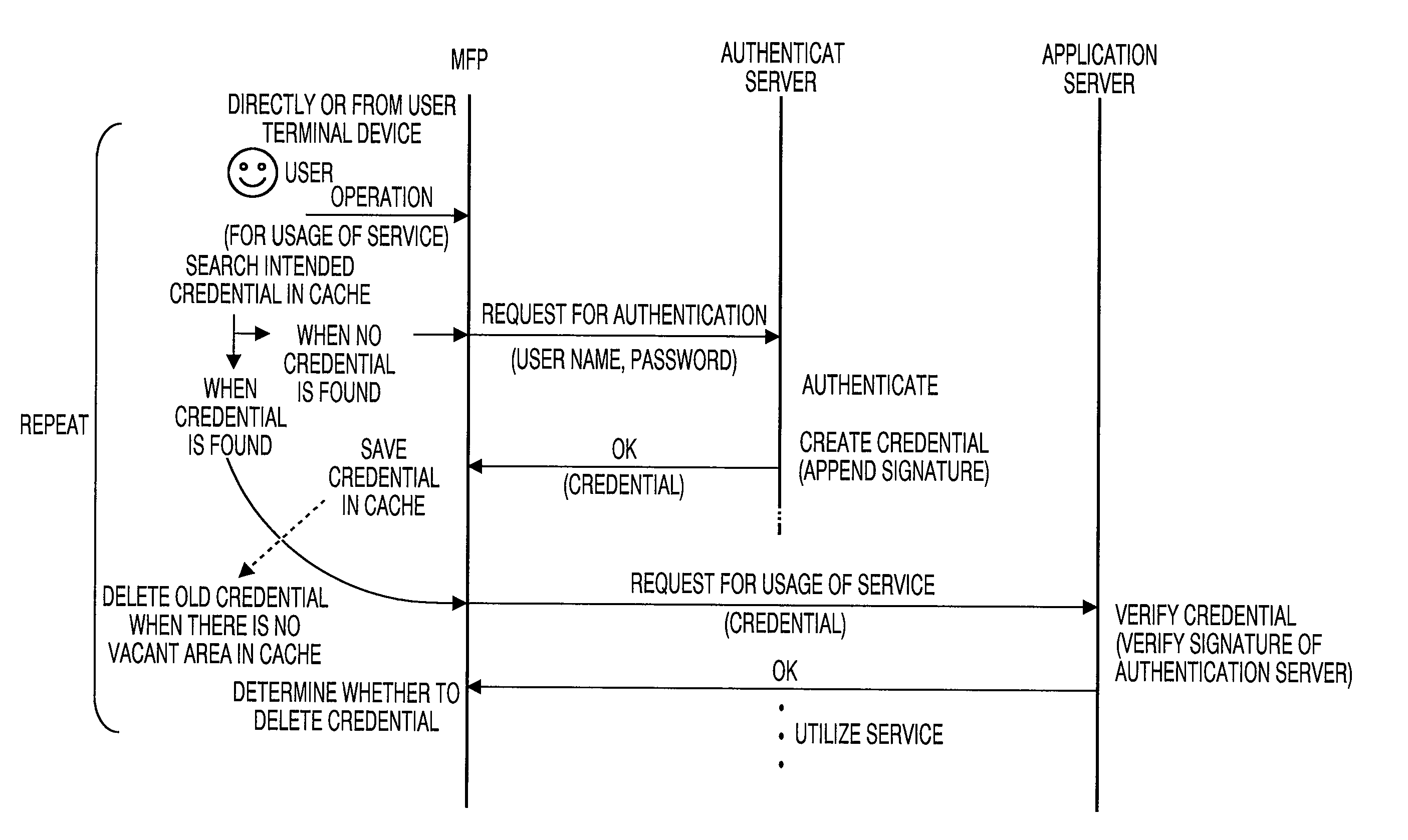
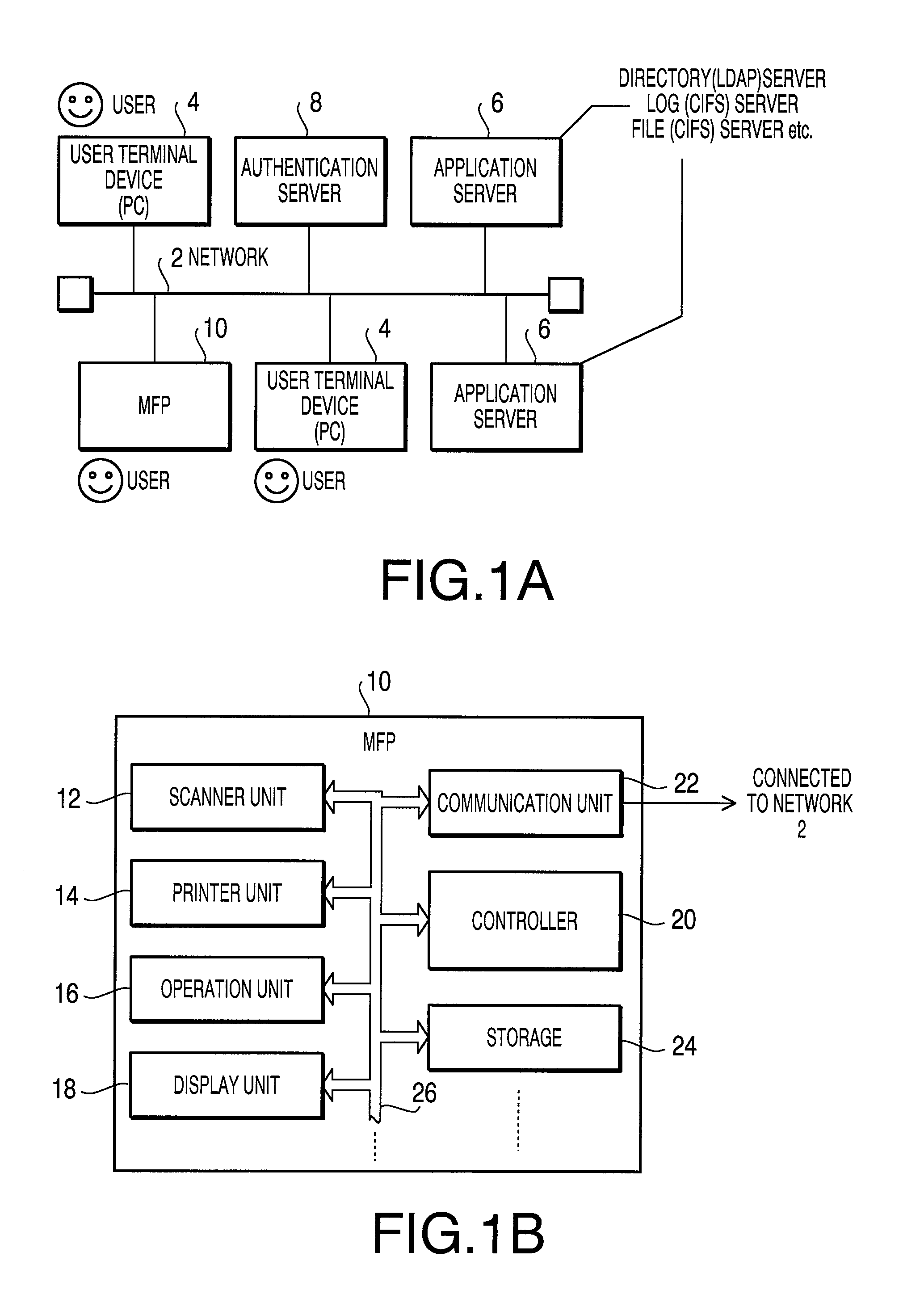
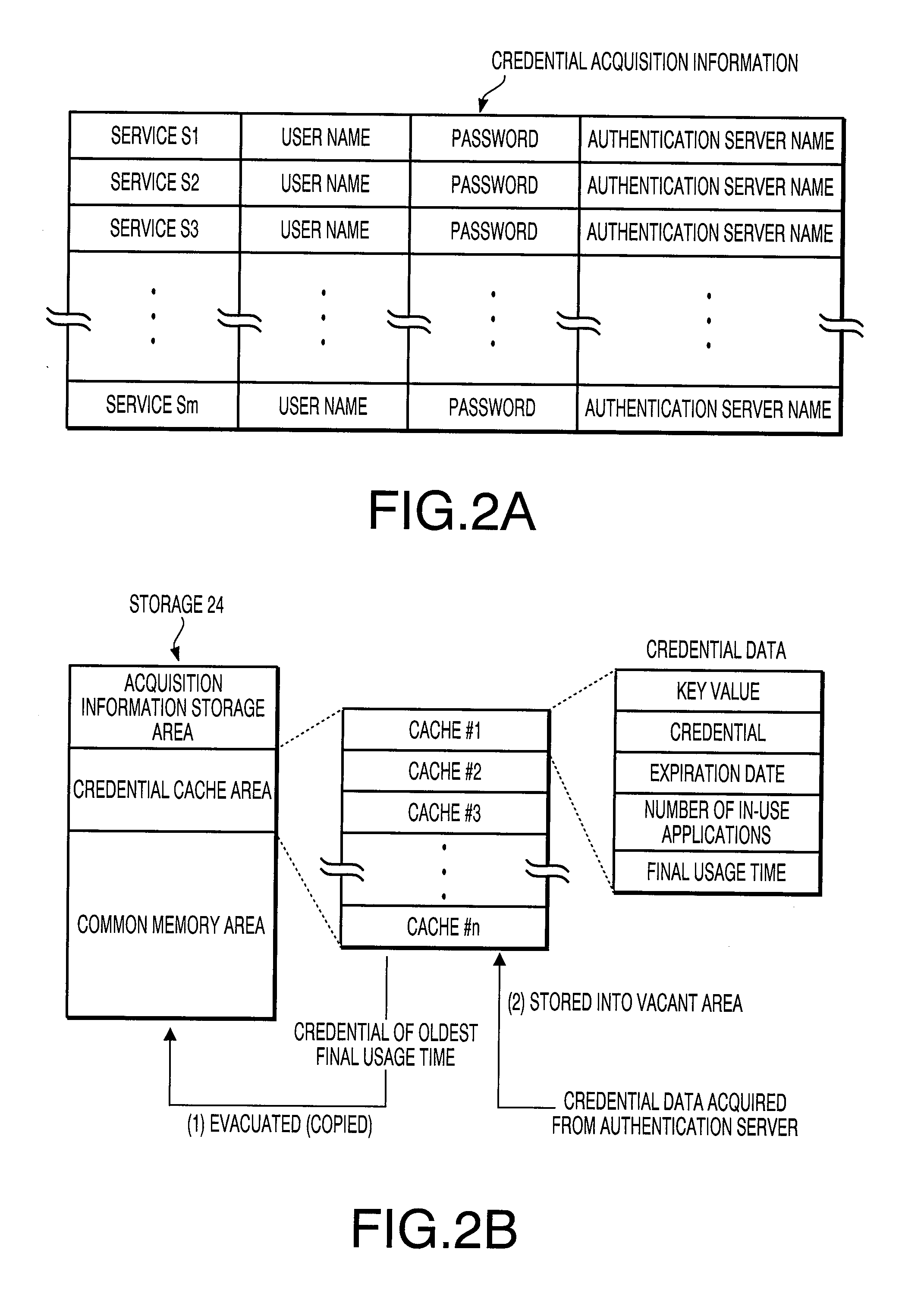
ActiveUS20100115268A1Improve user friendlinessEasy to useDigital data processing detailsMultiple digital computer combinationsNO storageAuthentication server
A network device, connectable with a service providing server and an authentication sever via a network, includes an acquisition information storage storing acquisition information for acquiring a certificate corresponding to each of services the service providing server provides, a certificate storage storing certificates acquired from the authentication server, a determining unit that, in response to acceptance of a request for utilizing a service, determines whether a certificate necessary for utilizing the requested service is stored in the certificate storage, and a controller that, when the necessary certificate is not stored, reads out acquisition information for the necessary certificate from the acquisition information storage, makes a certificate acquiring unit acquire the necessary certificate from the authentication server using the acquisition information, and stores the necessary certificate into the certificate storage. When the necessary certificate is stored, the controller makes the certificate acquiring unit acquire the necessary certificate from the certificate storage.
Owner:BROTHER KOGYO KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com