Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
640results about How to "Avoid abuse" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Abuse-proofed dosage form
ActiveUS8114383B2Pulverisation of the dosage form is considerably more difficultComplicating or preventing the subsequent abuseOrganic active ingredientsPowder deliveryBreaking strengthPhysiology
The present invention relates to an abuse-proofed, thermoformed dosage form containing, in addition to one or more active ingredients with abuse potential optionally together with physiologically acceptable auxiliary substances, at least one synthetic or natural polymer with a breaking strength of at least 500 N and to a process for the production thereof.
Owner:GRUNENTHAL GMBH
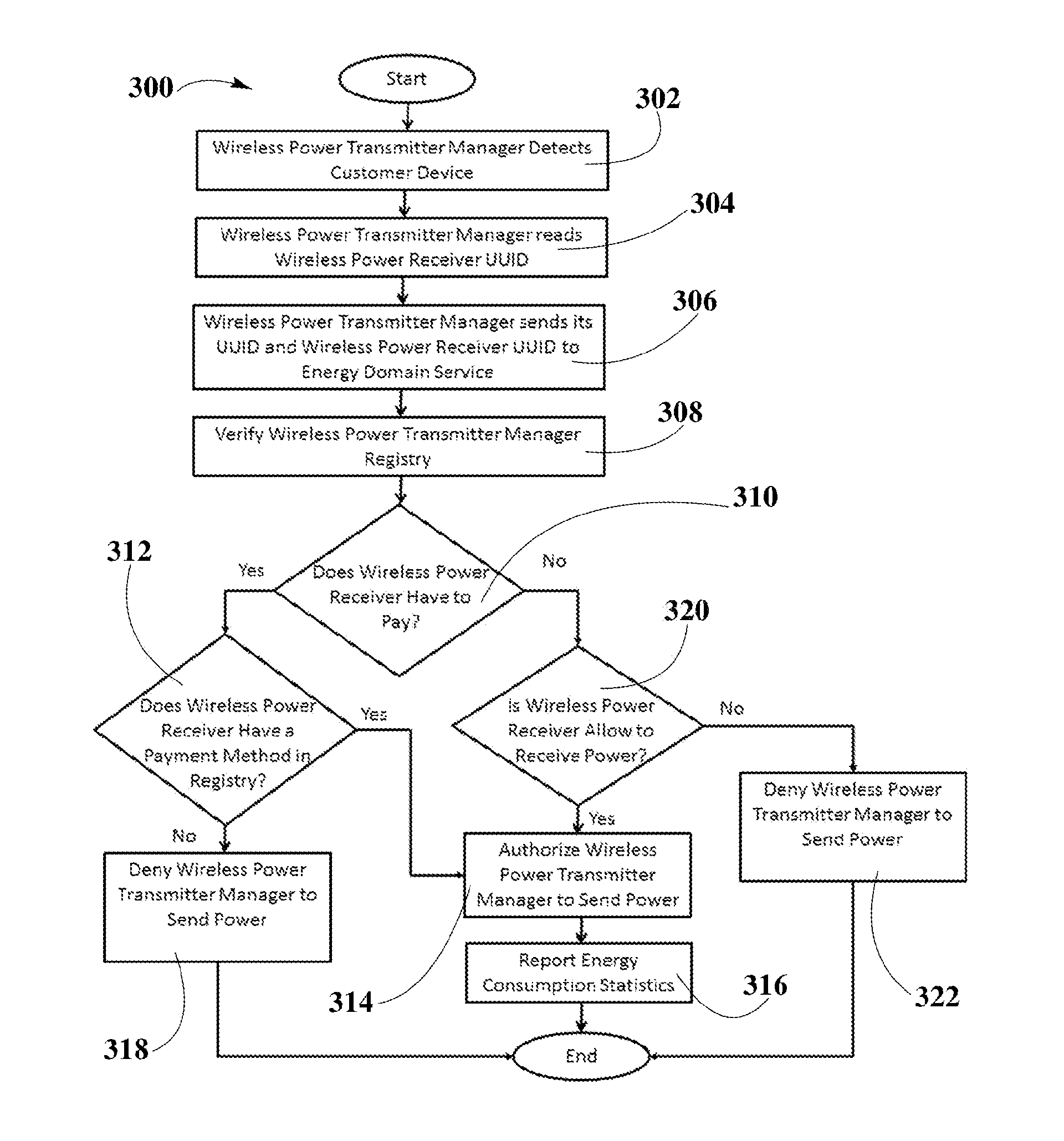
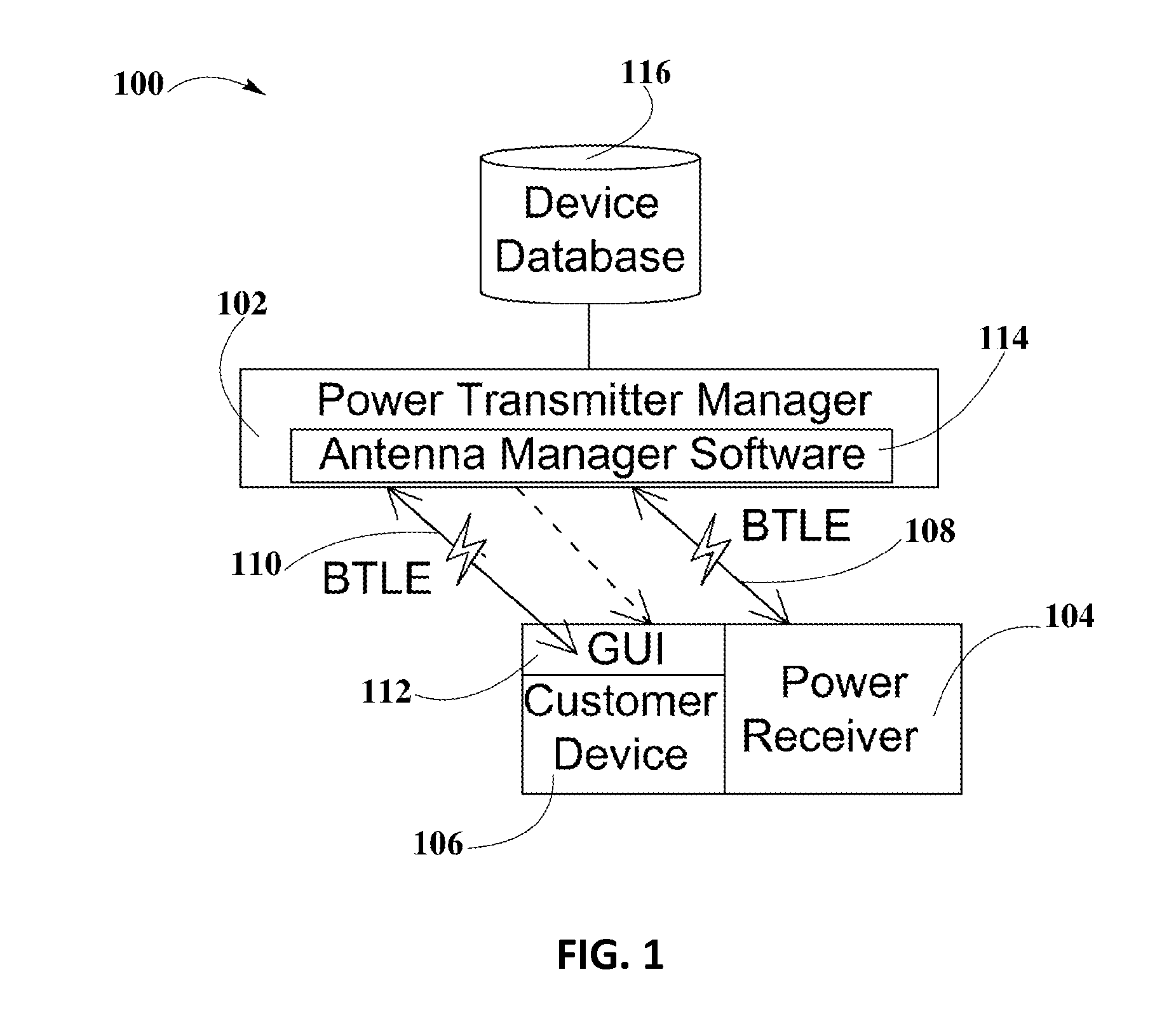
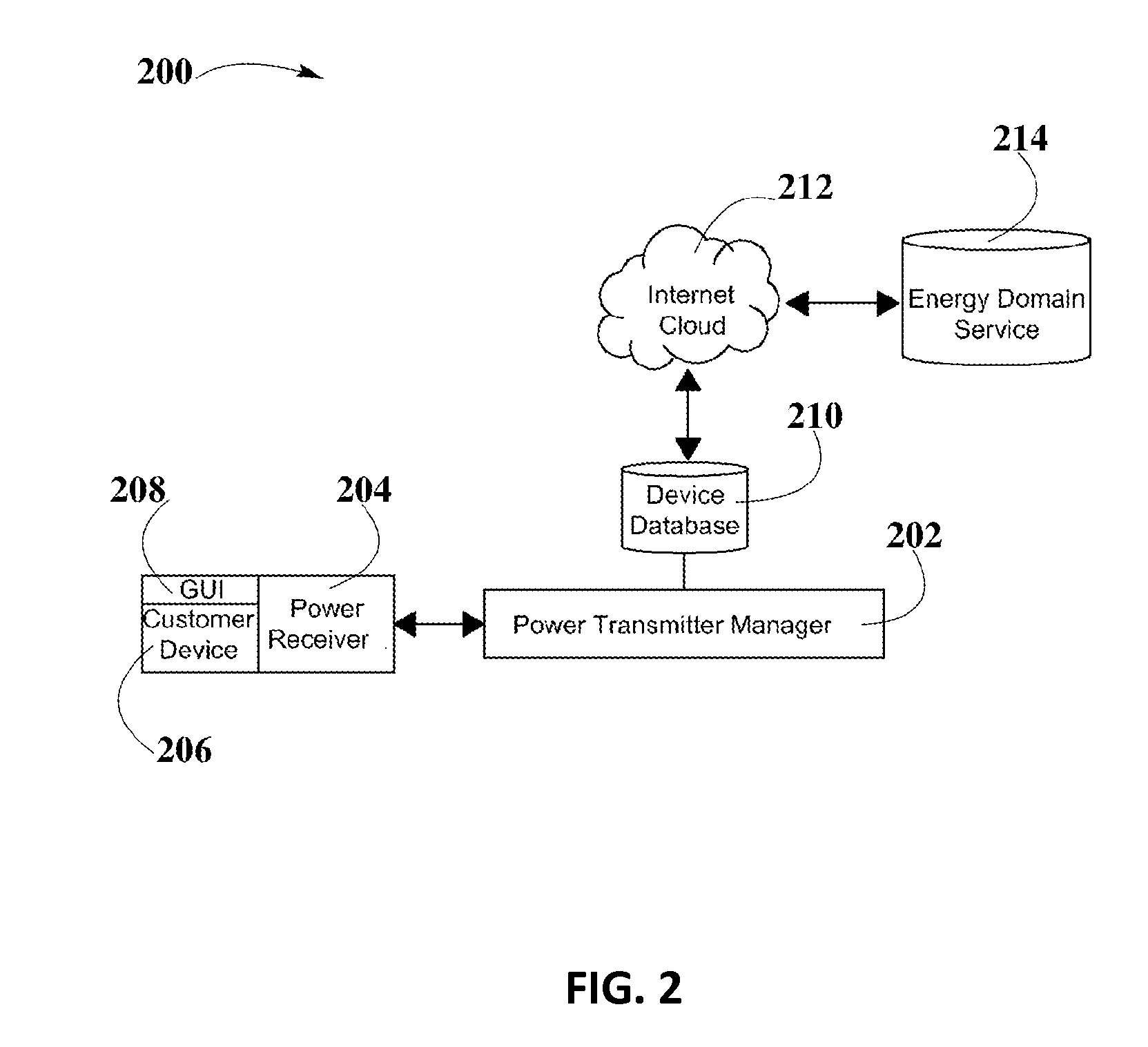
System and Method for Smart Registration of Wireless Power Receivers in a Wireless Power Network
ActiveUS20160020649A1Avoid abuseNear-field transmissionElectromagnetic wave systemElectric power transmissionUniversally unique identifier
A system and method for smart registration of wireless power receivers within a wireless power network is disclosed. Each wireless power device may include a universally unique identifier (UUID). Each wireless power device bought by a customer may be registered, at the time of purchase or later. The registry may be stored in an energy domain service, where energy domain service may be one or more cloud-based servers. The method for smart registration may include the steps of detecting a customer device; establishing a connection with a wireless power receiver to read its UUID; sending wireless power transmitter manager's UUID and wireless power receiver's UUID to energy domain service; inspecting wireless power transmitter manager registry; verifying wireless power receiver registry; authorizing power transfer to wireless power receiver; and reporting energy consumption for subsequent billing of customer depending on billing policy of wireless power transmitter manager specified within registry.
Owner:ENERGOUS CORPORATION
Abuse-safeguarded dosage form
A pharmaceutical dosage form that is safeguarded against abuse containing at least one active substance that is susceptible to abuse and at least two of the following constituents (a) through (d): (a) at least one substance that irritates the nasal and / or pharyngeal region; (b) at least one viscosity increasing agent that together with a required minimum quantity of an aqueous liquid forms a gel in an extract obtained from the dosage form, which gel can still be discerned after being introduced into an additional quantity of aqueous liquid; (c) at least one antagonist for the at least one active substance that is susceptible to abuse; and (d) at least one emetic.
Owner:GRUNENTHAL GMBH
Internet differentiated services service for transaction applications
InactiveUS6483805B1Avoid abuseError preventionTransmission systemsDifferentiated servicesTelecommunications network
A method of monitoring telecommunications network traffic comprising the steps of: receiving a packet stream comprising packets each identified as belonging to one of at least three classes; calculating a difference between the numbers of packets received identified as belonging to a first and a second of said classes; and deriving a measure of traffic load on the network responsive to said difference. The invention also relates to a method for admission control based on the above method of monitoring and a method for overcoming admission control avoidance. It also relates to apparatus embodying these methods.
Owner:AVAYA INC
Dosage Form with Impeded Abuse
InactiveUS20090004267A1Prevent crushingPrevent the subsequent abuseOrganic active ingredientsPowder deliveryWaxBreaking strength
A multiparticulate dosage form formulated to make misuse more difficult containing least one active substance with potential for misuse (A), at least one synthetic or natural polymer (C), optionally at least one natural, semi-synthetic or synthetic wax (D), at least one disintegrant (E) and optionally one or more additional physiologically compatible excipients (B), wherein the individual particles of the dosage form display a breaking strength of at least 500 N and a release of active substance of at least 75% after 45 minutes measured according to Ph.Eur. in the paddle mixer with sinker in 600 ml of aqueous buffer solution with a pH value of 1.2 at 37° C. and 75 rpm.
Owner:GRUNENTHAL GMBH
Mobile Payment Using Picture Messaging
ActiveUS20120054046A1Inexpensively incorporatePrevent abuseSpecial service for subscribersCash registersMessage passingMobile Web
Systems and methods are disclosed for mobile payment using picture messaging to deliver an image with an encoded payment key. A mobile device equipped with at least a display and an input is used to connect to a server on the mobile network. Upon authentication of a user of the mobile device, the server generates the payment key, encodes the key in an image, such as a bar code, and transmits the image to the mobile device. The user holds the display of the mobile device up to an optical scanner at a POS terminal. Logic on the POS terminal extracts the payment key from the image, and uses the payment key to bill the user. The POS terminal transmits the bill with the payment key to the server on the network. The server ensures that the key is active, and debits an account for the user based on the amount presented in the bill. The key is de-activated after a specified time period or one use, whichever occurs first.
Owner:AT&T INTPROP I L P
Abuse-proofed dosage form
A solid pharmaceutical dosage form that is safeguarded against abuse, comprising at least one active substance that is susceptible to abuse and at least one emetic that is spatially separate from the at least one active substance. The active substance or substances are present in the form of at least one sub-unit (a), and the at least one emetic is present in the form of at least one sub-unit (b), and the emetic from sub-unit (b) is not activated in the body if the dosage form has been correctly administered as prescribed.
Owner:GRUNENTHAL GMBH
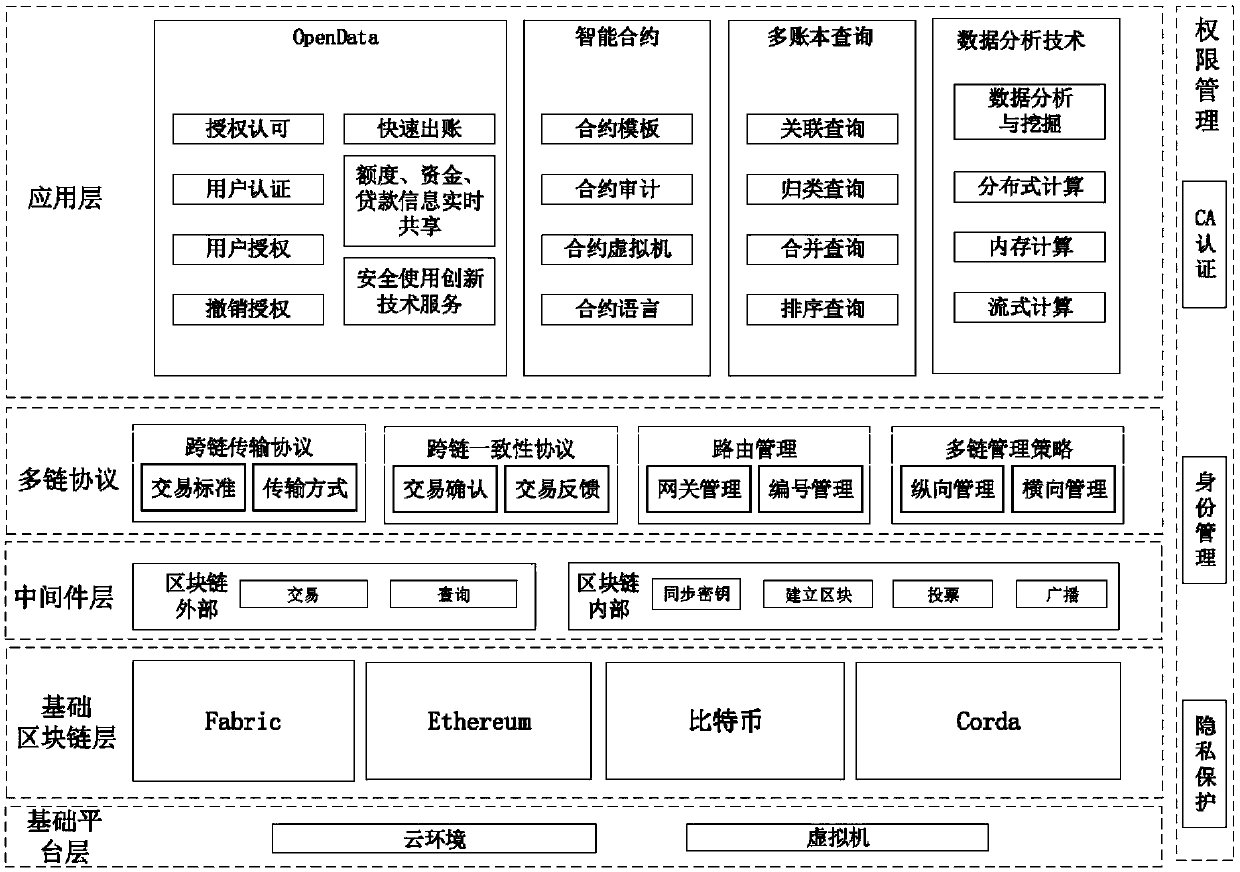
System architecture for cross-block-chain open data sharing under heterogeneous multi-chain architecture
ActiveCN108876370ASolve interconnection problemsQuality improvementPayment protocolsTransmission protocolOpen data
The invention provides a system architecture for cross-block-chain open data sharing under a heterogeneous multi-chain architecture. The system architecture comprises (1) an application layer, including an OpenData module, an intelligent contract module, a multi-account-book query module and a data analysis module; (2) a multi-chain protocol, including a cross-chain transmission protocol applied to a transaction standard and a transmission mode, a cross consistency protocol applied to transaction confirmation and transaction feedback, a heterogeneous block chain cross-chain data communicationand transaction protocol, routing management applied to gateway management and number management, and a multi-chain management strategy applied to longitudinal management and transverse management; (3) a middleware layer applied to transactions and query outside block chains and synchronous keys inside the block chains for establishing blocks and achieving voting and broadcast functions; (4) a basic block chain layer, including Fabric, Ethereum, Bitcoin and Corda; and (5) a basic platform layer based on a cloud environment and a virtual machine. The system architecture helps a user to securelyshare data and service provided by a third party, and the problem of "data splitting" is solved.
Owner:BEIHANG UNIV
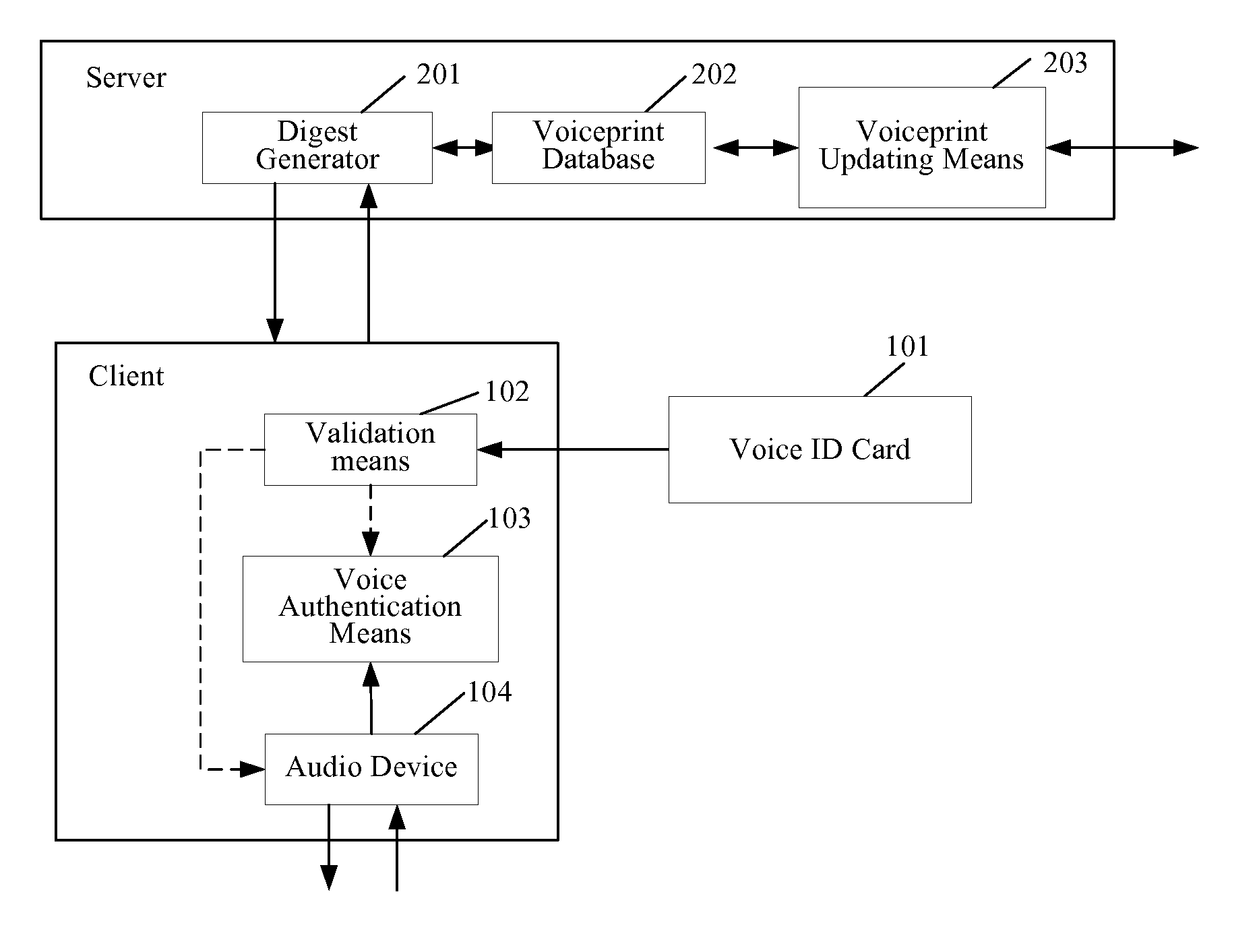
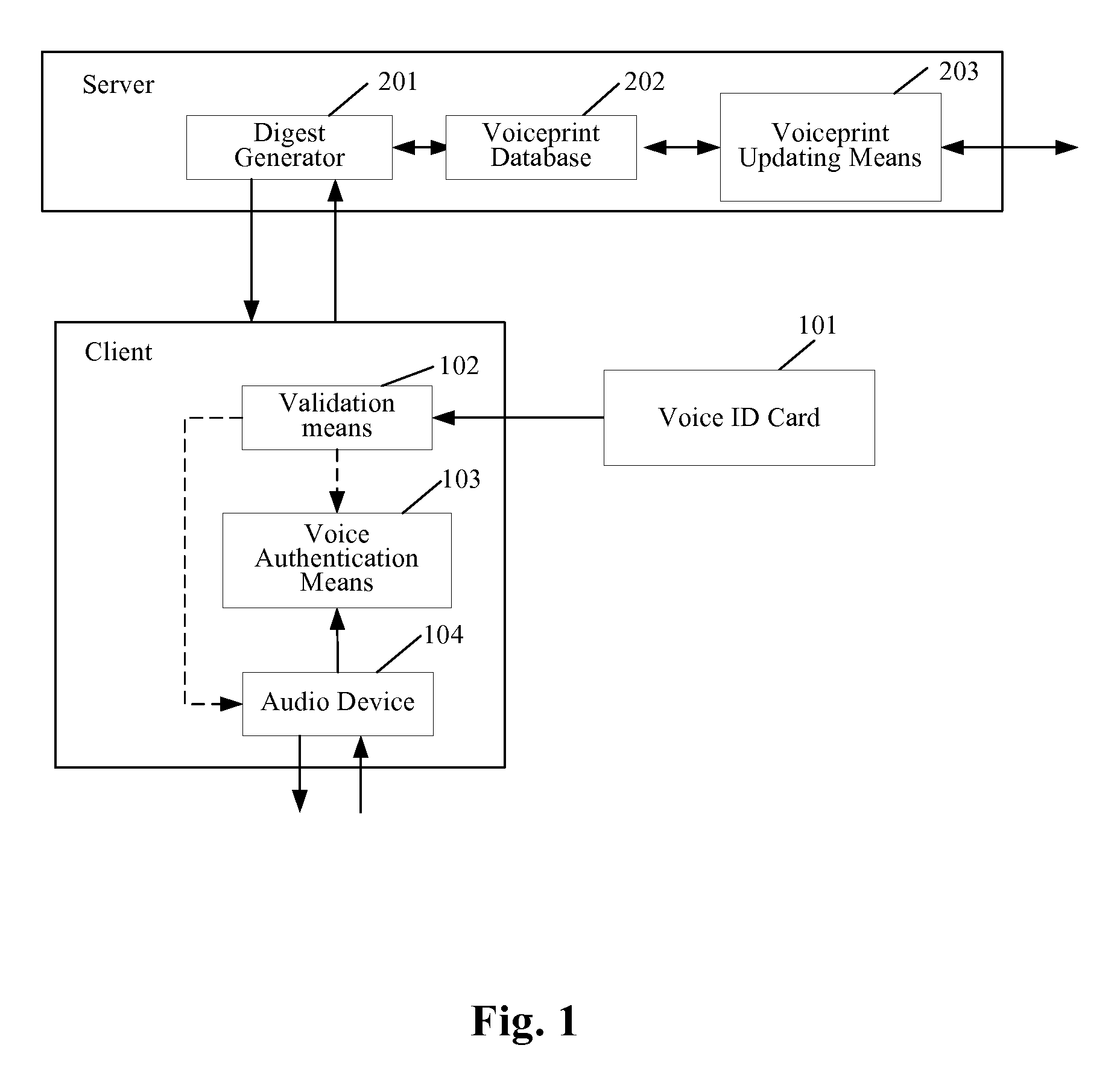
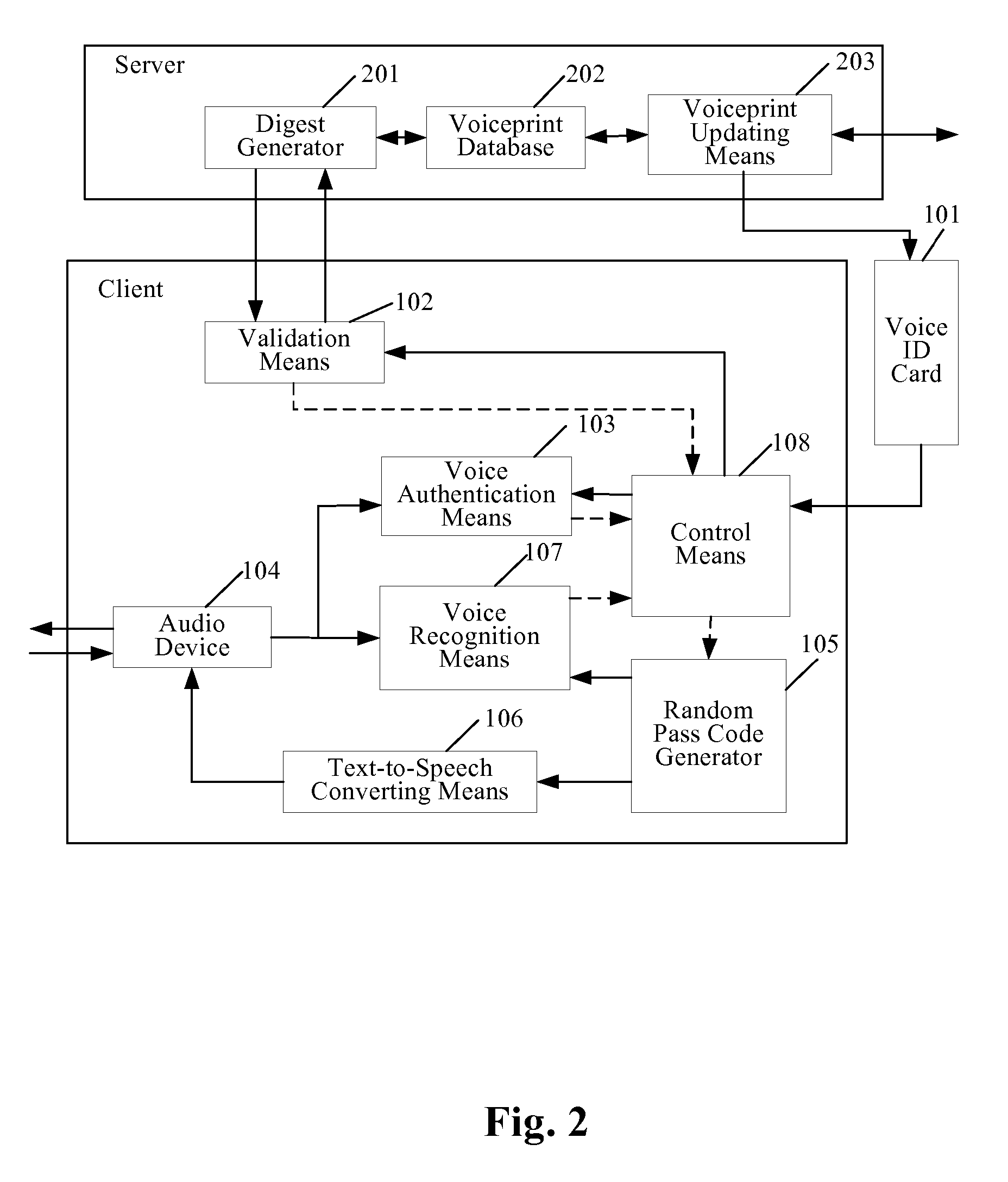
Voice authentication system and method using a removable voice id card
InactiveUS20070036289A1Avoid abuseImprove reliabilityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsClient-sideAuthentication system
A voice authentication system using a removable voice ID card comprises: at server side, a voiceprint database for storing the voiceprints of all authorized users; a voiceprint updating means for updating the voiceprints in said voiceprint database; and a voiceprint digest generator for generating a voiceprint digest according to a request from a client; at client side, a voice ID card for storing the voiceprint of an authorized user; a validation means for validating the voiceprint in the voice ID card on the basis of the voiceprint digest from the server; an audio device for performing voice interaction with a user; and a voice authentication means for determining whether the voiceprint from said voice ID card is of the same speaker as the voice from said audio device. The present invention can significantly avoid the abuse of a voice ID card when it is lost or stolen by using the voiceprint digest stored at server side to verify the voiceprint in the voice ID card.
Owner:IBM CORP
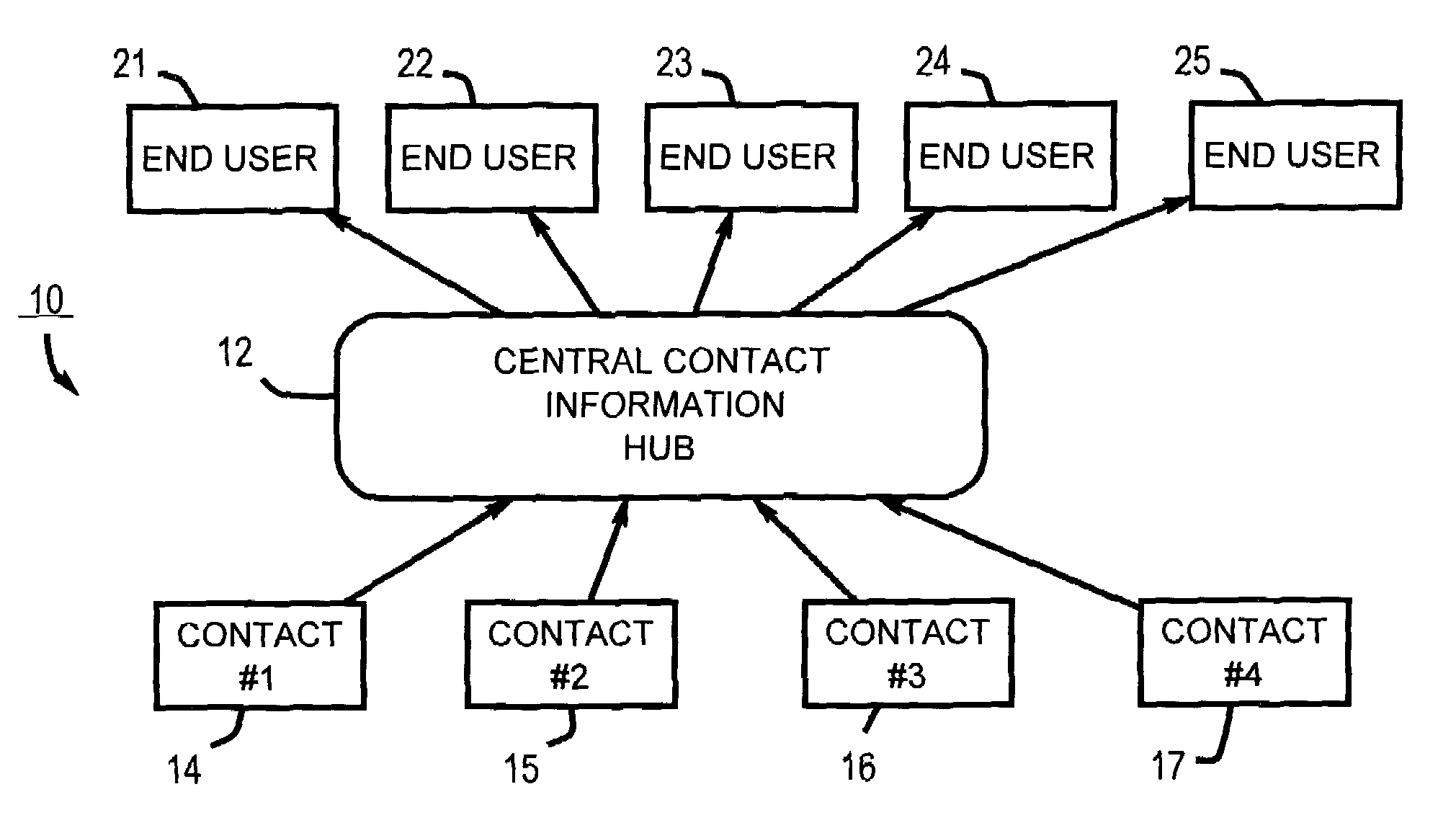
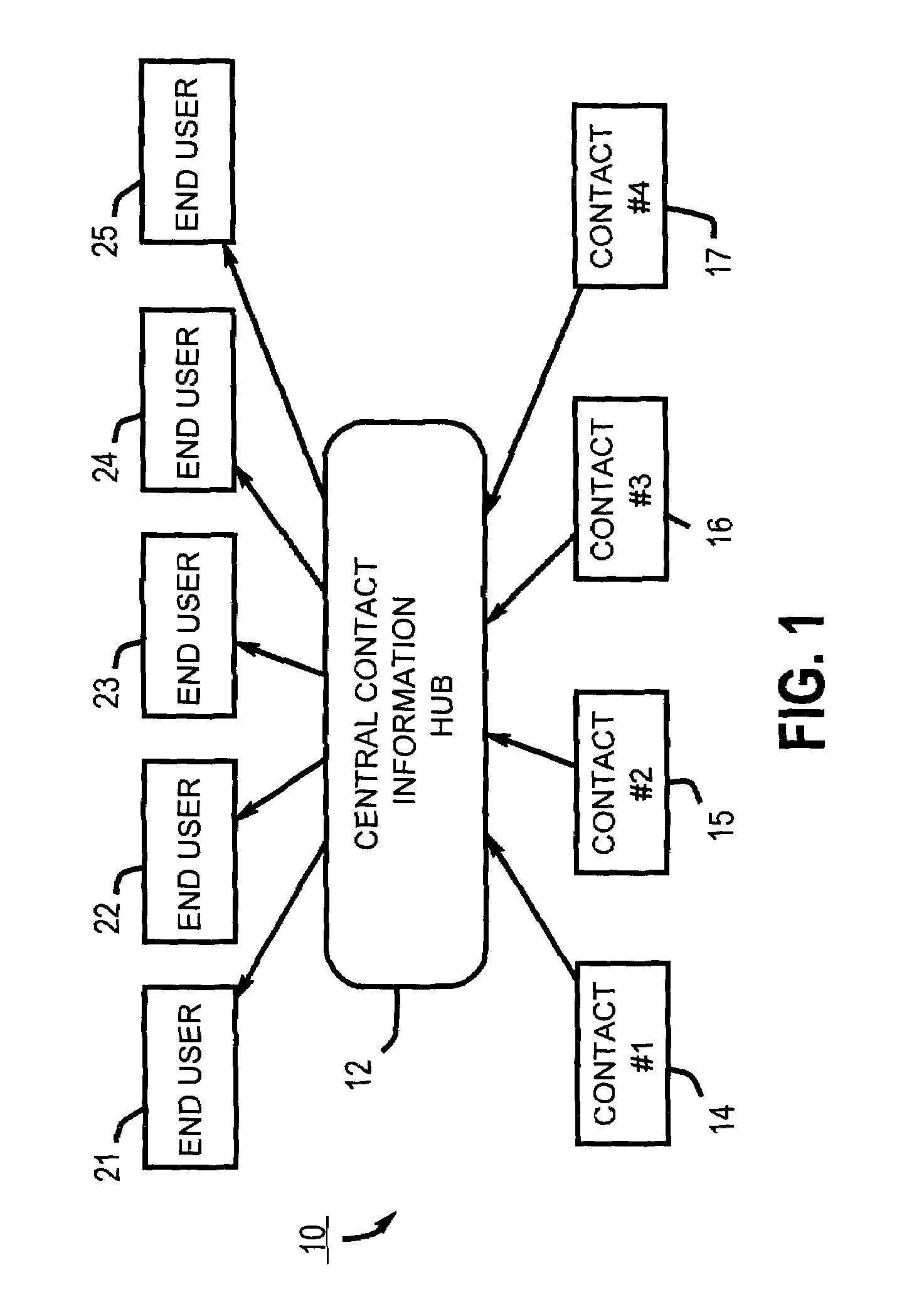
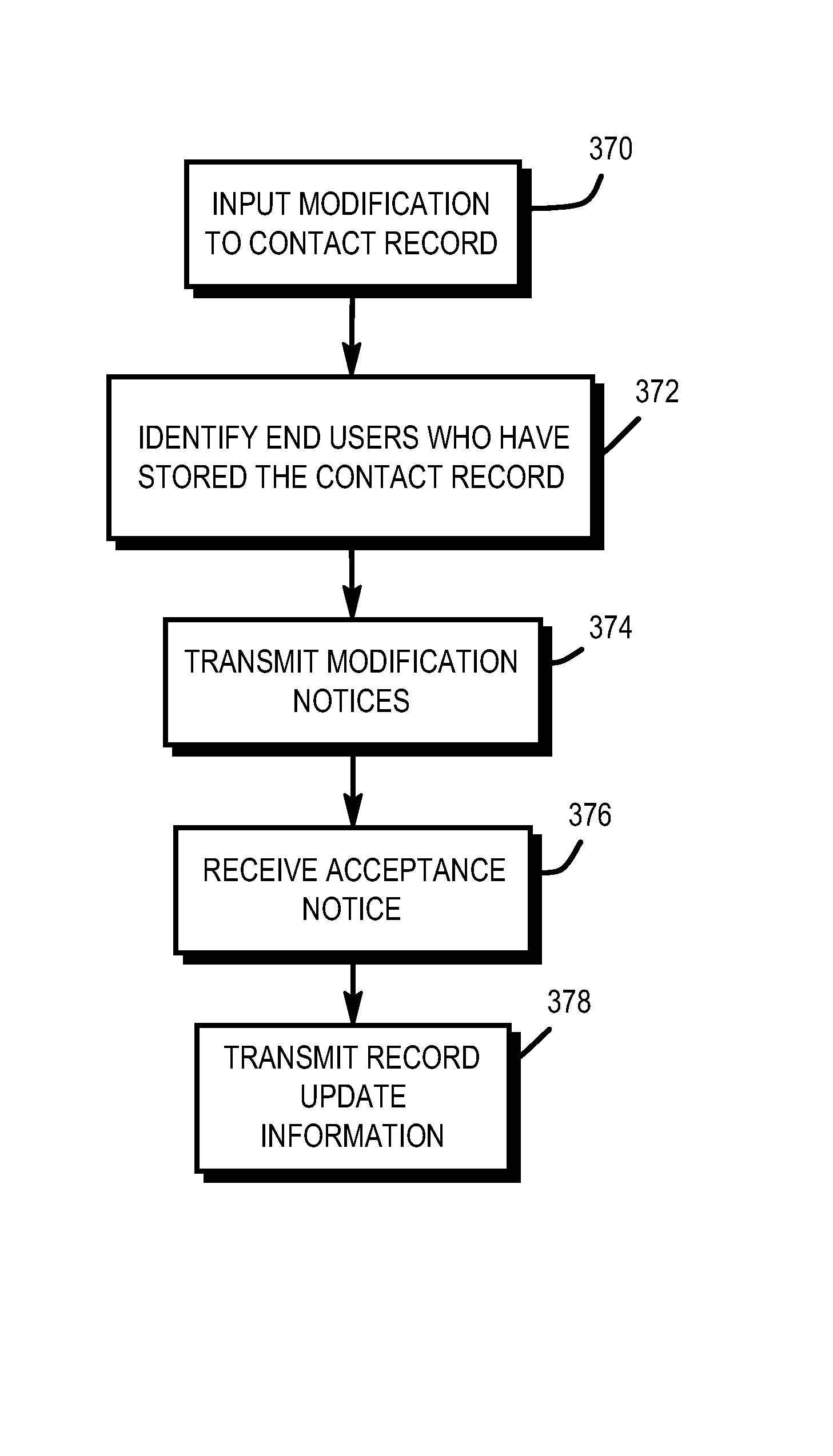
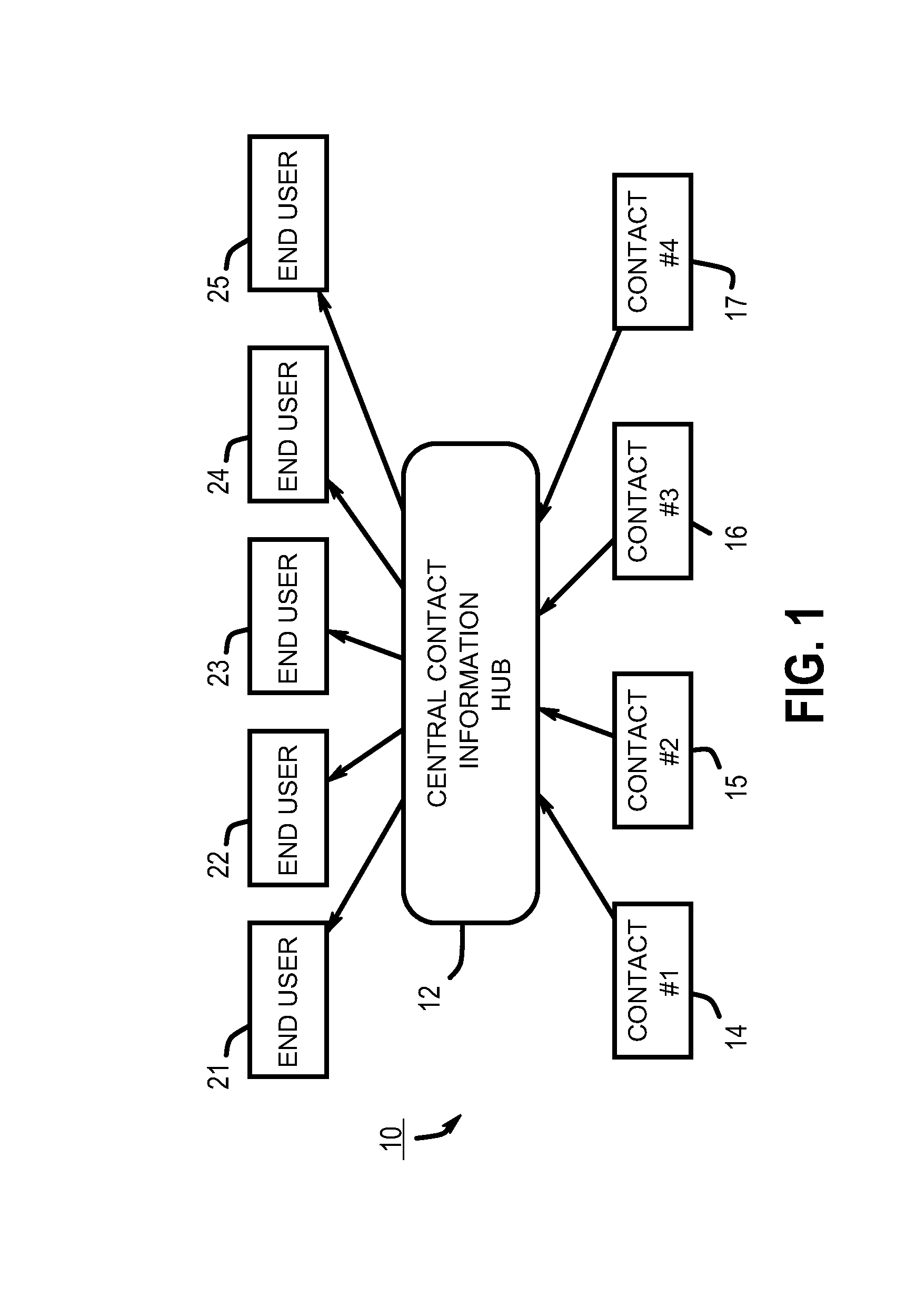
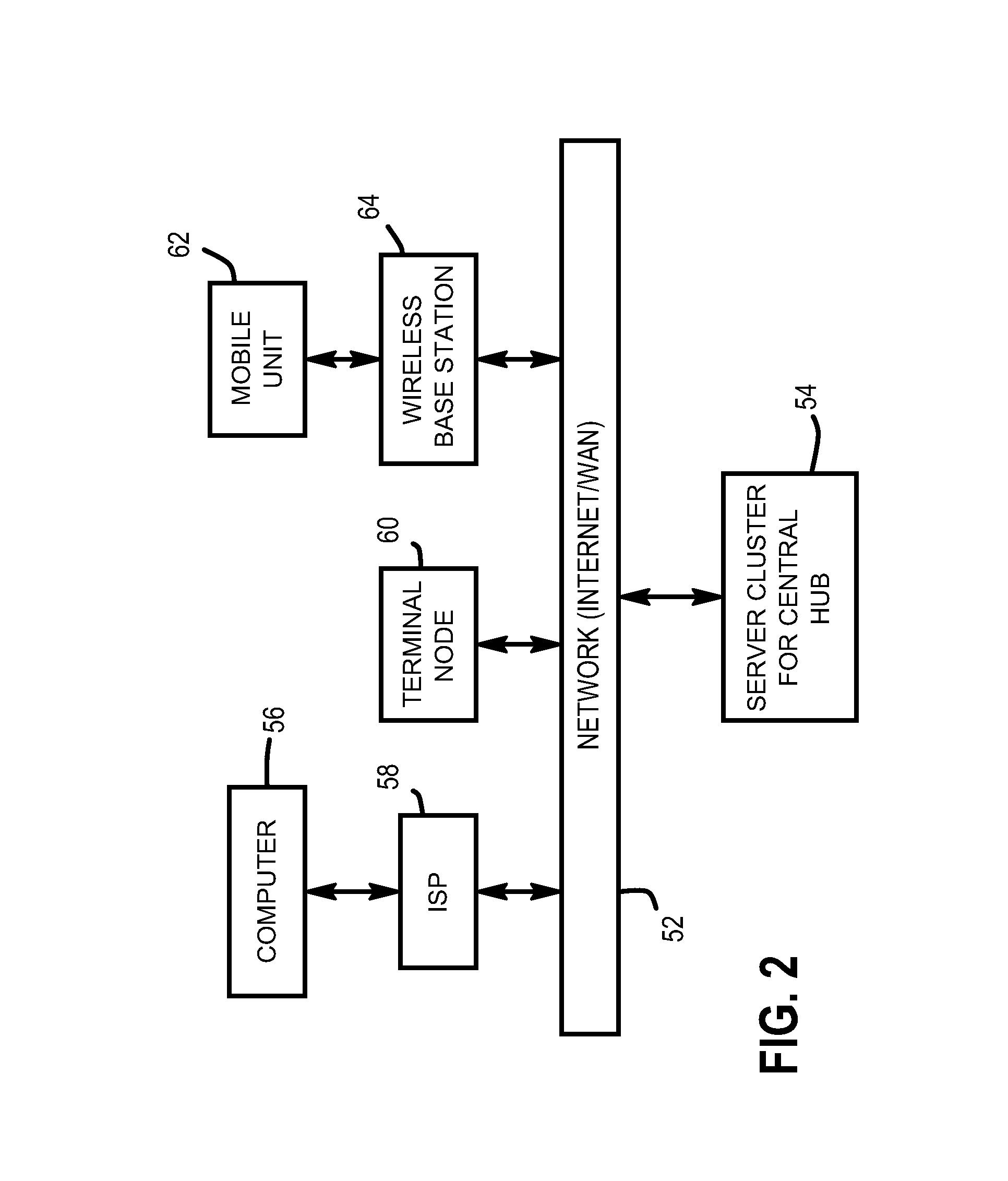
Apparatuses for requesting, retrieving and storing contact records
InactiveUS7440746B1Hard costSignificant and costly problemData processing applicationsSpecial service for subscribersThe InternetCentral database
Provided are wireless and standalone handheld devices, such as PDAs and wireless telephones, that are configured for inputting a unique contact identifier that uniquely identifies a desired contact record, querying a central database of contact information to obtain the desired contact record, receiving the record and storing it, In various embodiments, such requests can be made directly over a wireless network or indirectly when synchronizing the handheld device with a computer connected to the Internet or to another network.
Owner:SWAN JOSEPH G
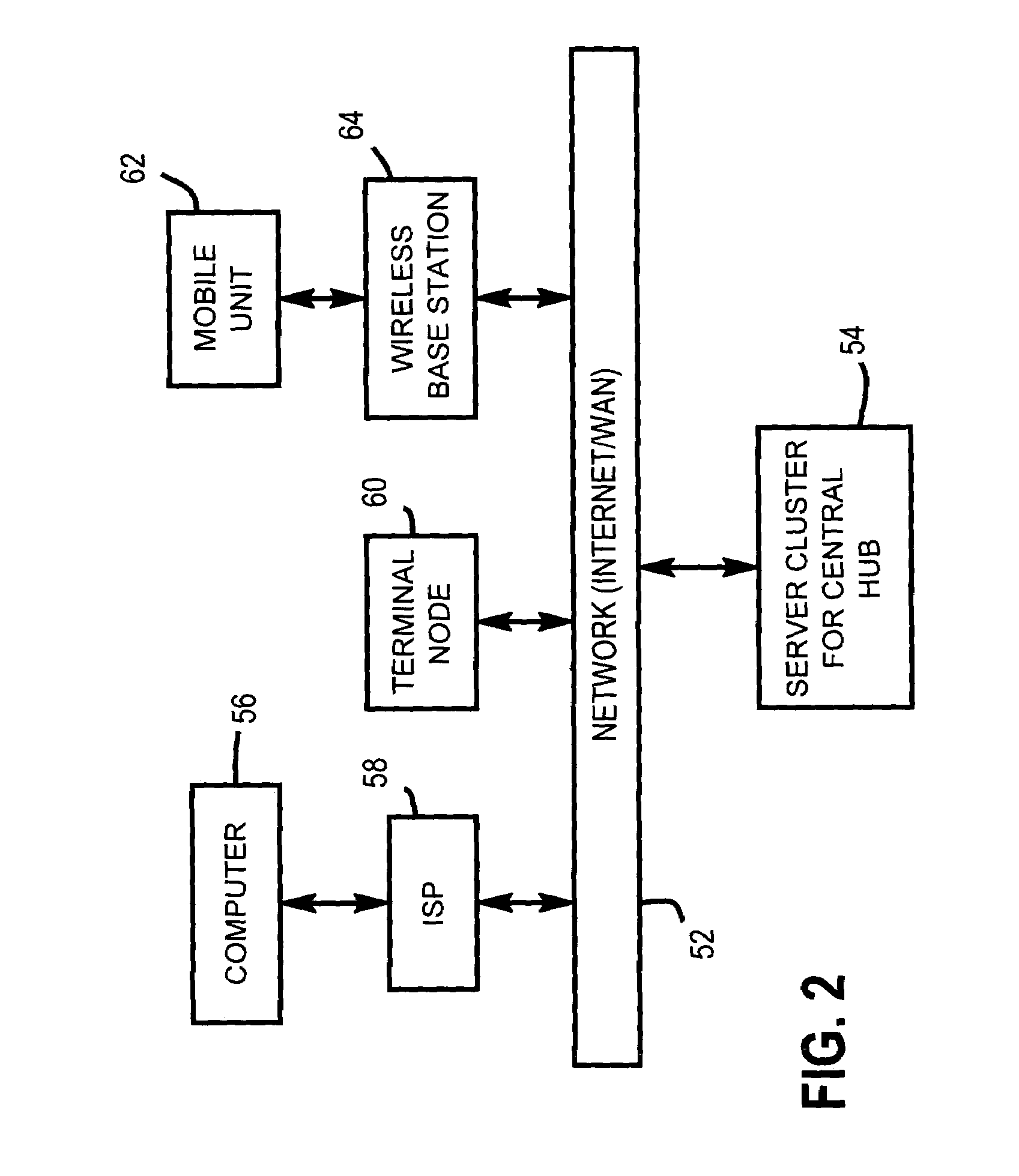
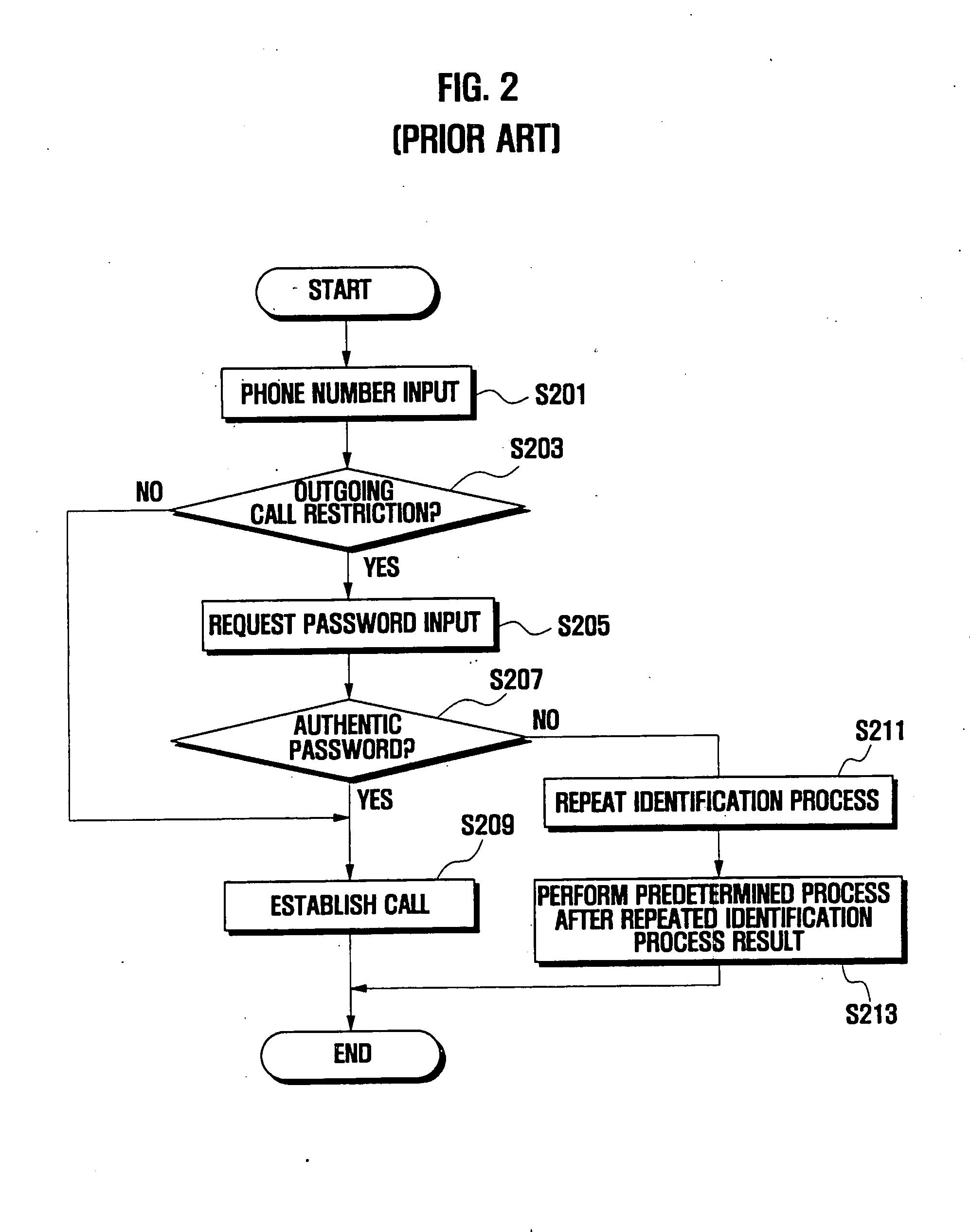
Service restriction apparatus and method for portable communication device
InactiveUS20070238449A1Effectively controlling usageEffectively managing utilizationAssess restrictionSpecial service for subscribersOperating systemPortable communications device
A service restriction apparatus and method for a portable phone. A utilization restriction method for a portable communication device includes determining whether a service restriction function is activated when an incoming or outgoing call request is detected; determining whether a phone number of the incoming or outgoing call is registered in a communication-allowed phone number list if a service restriction function is activated; attempting to process the incoming or outgoing call if the phone number is registered in the communication-allowed phone number list; and blocking the incoming or outgoing call if the phone number is not registered in the communication-allowed phone number list.
Owner:SAMSUNG ELECTRONICS CO LTD
Virtual account convenient application system based on mobile terminal and achieving method thereof
InactiveCN103268550AReduce operating costsAvoid abuseProtocol authorisationOperational costsComputer terminal
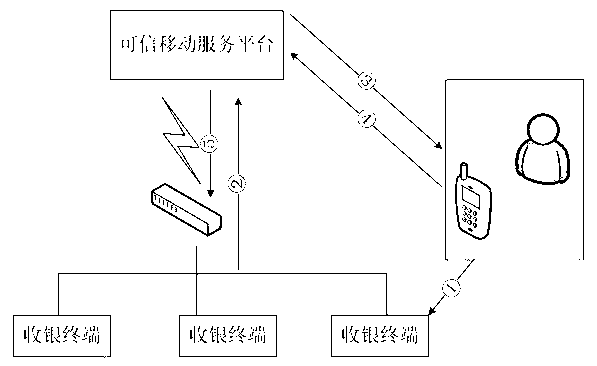
The invention discloses a virtual account convenient application system based on a mobile terminal and an achieving method thereof. The mobile terminal of a user serves as a carrier, and the mobile terminal is connected with a cash terminal and a reliable mobile service platform of a merchant through the internet or a communication network. Based on the binding relation of a cell phone account of the mobile terminal and a virtual account, the reliable mobile service platform utilizes cell phone hardware to serve as an important medium for identification to achieve a basis of identification verification and trading monitoring, and provides various consumption modes regarding mobile payment consumption movements of a series of virtual accounts for each user in various application places. With the development of popularization of intelligent cell phones and the mobile internet, by the adoption of the technical scheme of the virtual account convenient application system, transaction safety is ensured, manufacturing cost of a financial practical card is reduced, and abuse of a false card is thoroughly eradicated, operation cost of mobile payment is reduced, and safety and low cost of the virtual account convenient application system based on the mobile terminal further facilitate popularization.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
Provisioning quality of service in home networks using a proxy interface
InactiveUS20050165899A1Avoid abuseReduce usageMultiple digital computer combinationsElectric digital data processingQuality of serviceWeb browser
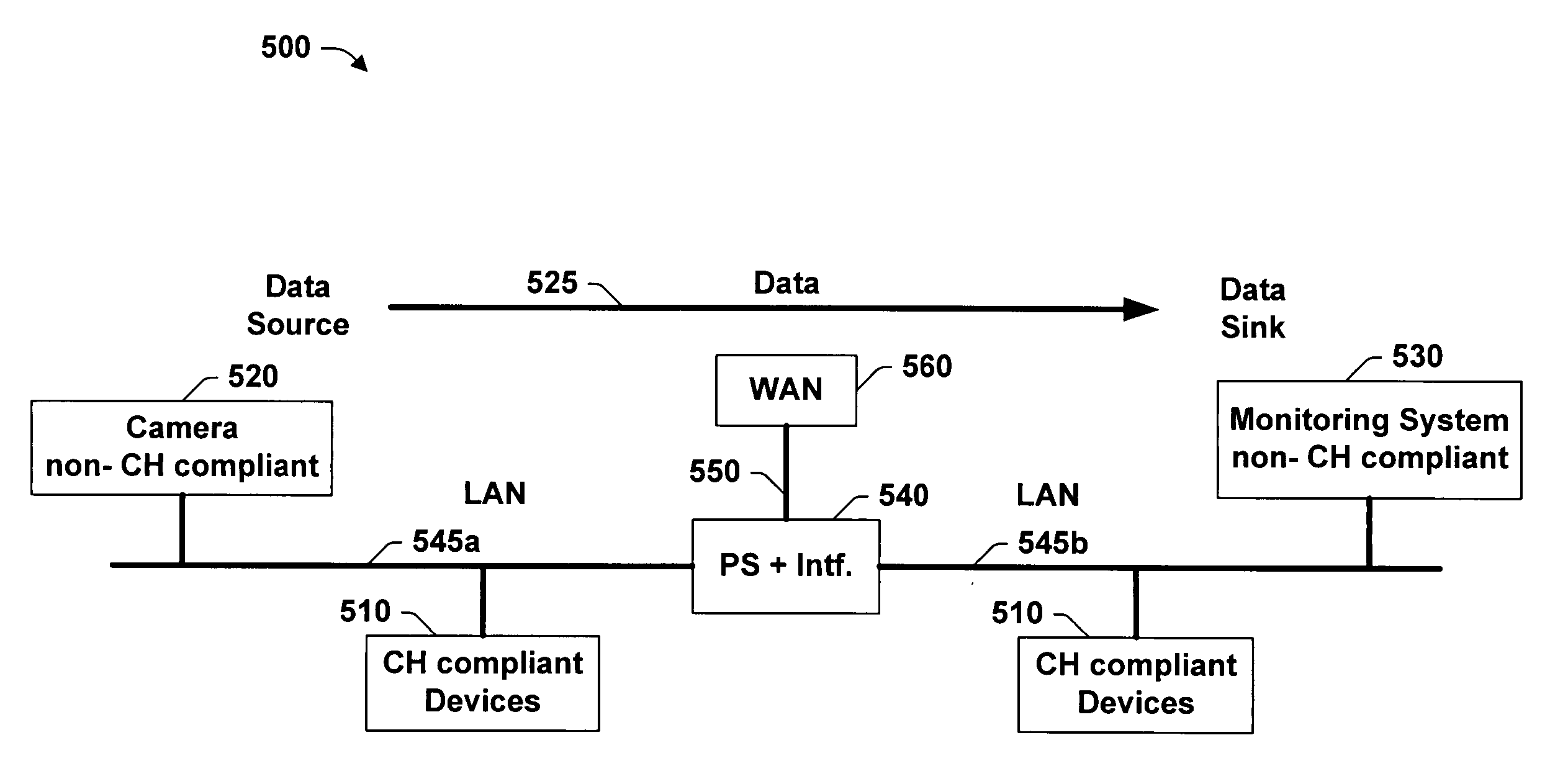
An engineering model is described for a home gateway and interface system and method for providing quality of service to a home LAN device on a home network that is not QoS capable. The gateway comprises a modem (e.g., cable, DSL modem) and a portal service proxy interface. The modem is connected between the home network and a WAN cable network, and is operable to bridge traffic between the home LAN of the home network and the WAN cable network. The portal service interface is connected to the modem and is utilized as a proxy for QoS reservations and data communications between the home LAN devices on the home network. The portal interface acts on behalf of a client to make requests of the non-QoS capable home LAN devices and communicate these QoS needs to the QoS capable devices. The portal service interface is operable to manually input and obtain a set of QoS requirements of a client or user, for example, using a protocol such as the HTTP or Telnet protocol on a web browser. The QoS requirements are then utilized in the gateway and communicated to the home LANs thru the modem for selectively transmitting or receiving the data between the devices, based on the QoS needs of each home LAN device obtained from the client.
Owner:TEXAS INSTR INC
Abuse-Resistant Dosage Form
A solid pharmaceutical dosage form that is safeguarded against abuse, comprising at least one active substance that is susceptible to abuse and at least one emetic that is spatially separate from the at least one active substance. The active substance or substances are present in the form of at least one sub-unit (a), and the at least one emetic is present in the form of at least one sub-unit (b), and the emetic from sub-unit (b) is not activated in the body if the dosage form has been correctly administered as prescribed.
Owner:GRUNENTHAL GMBH
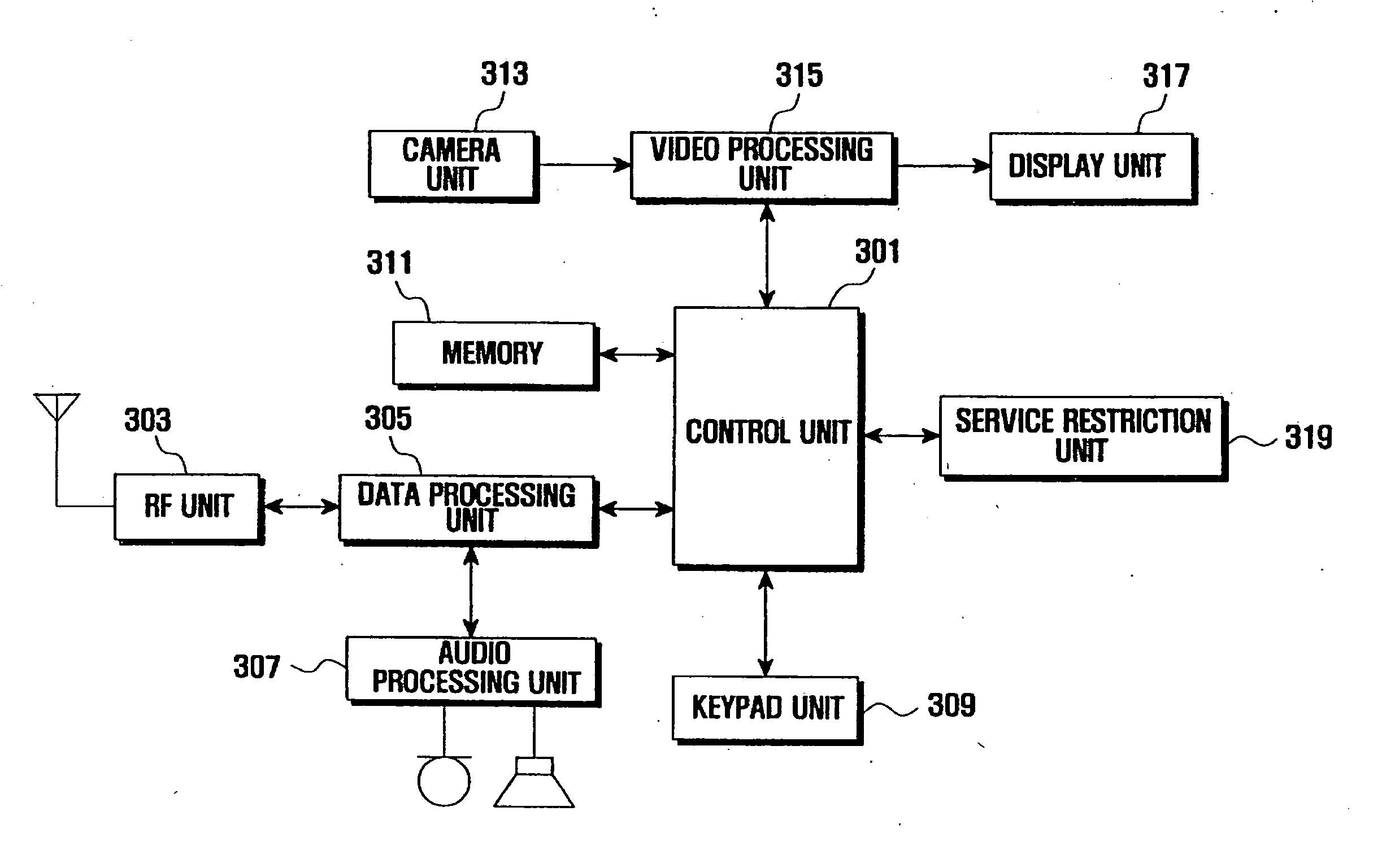
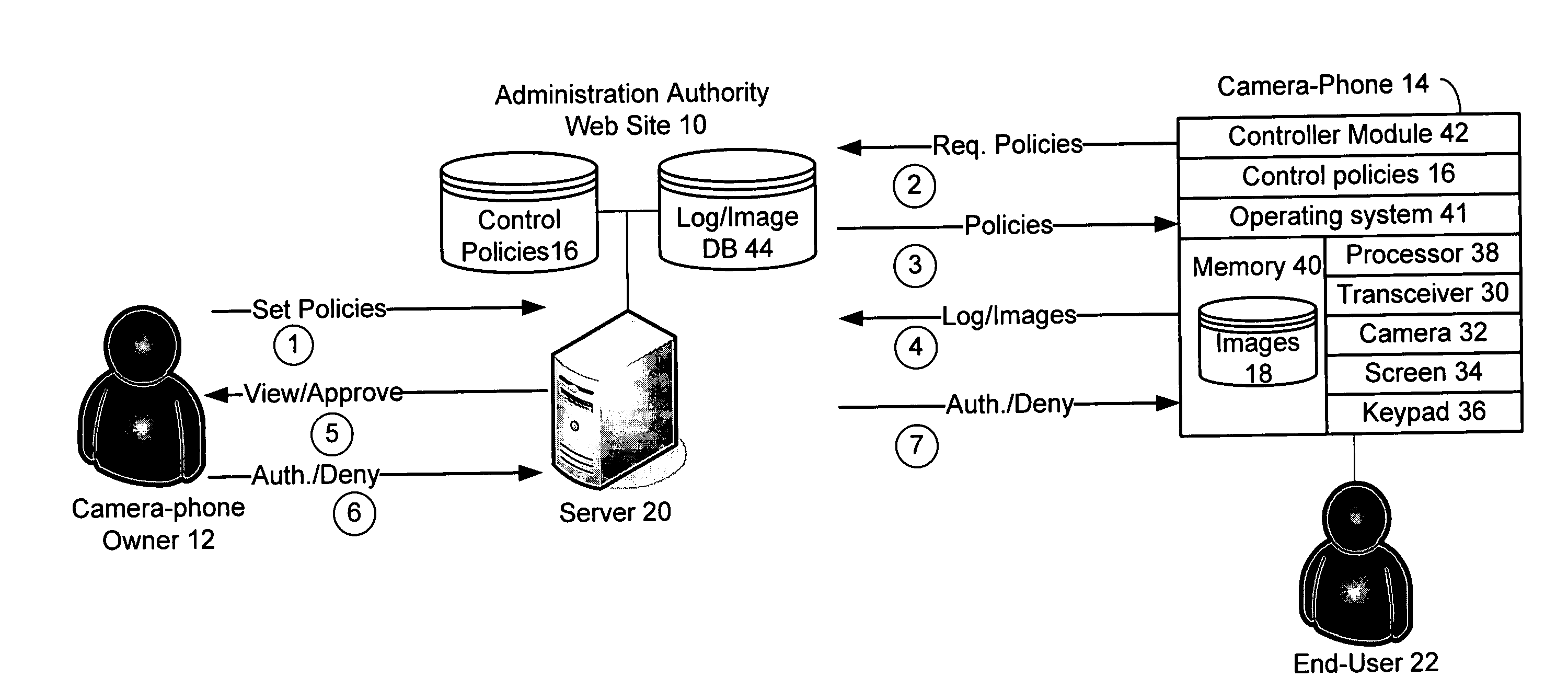
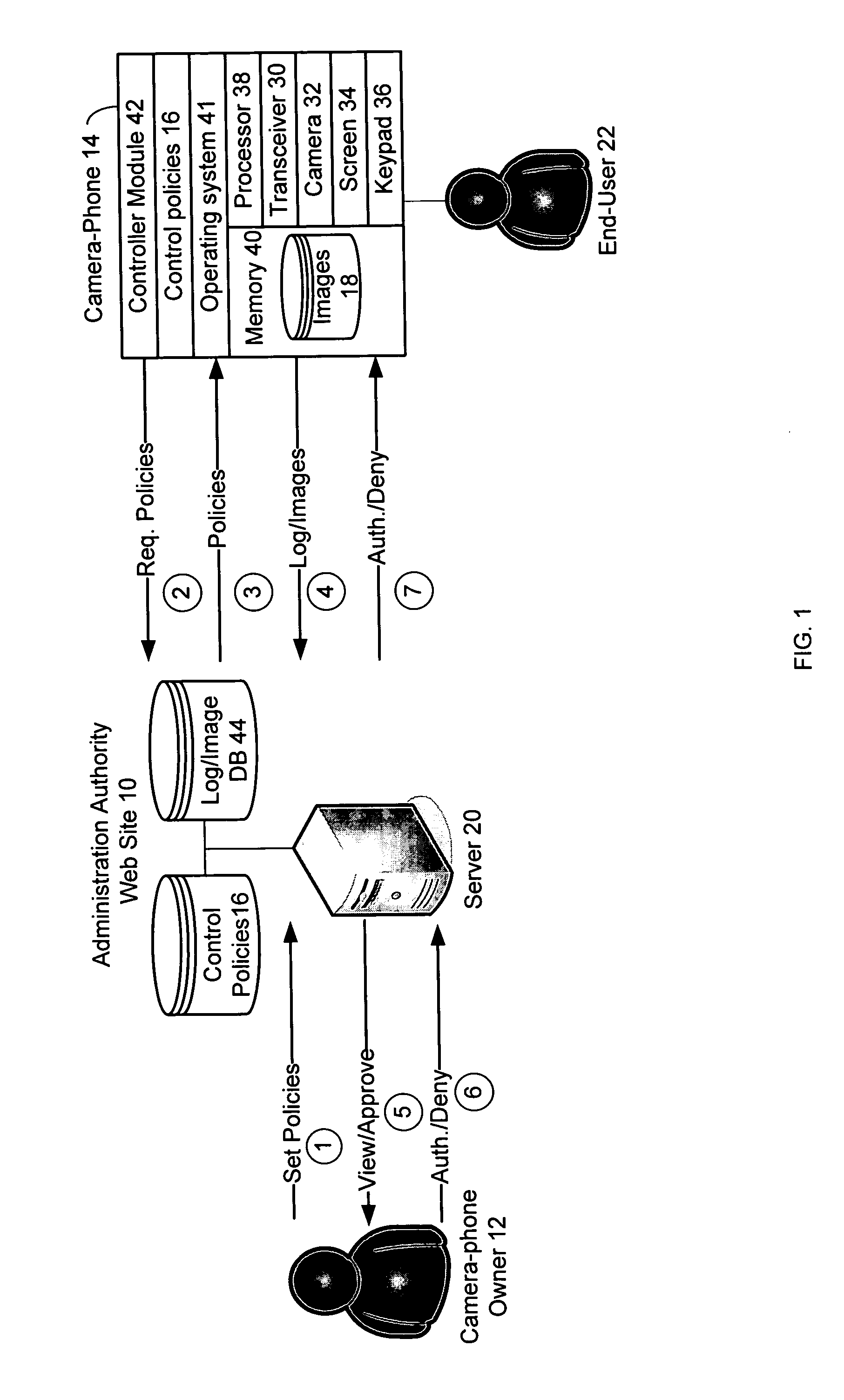
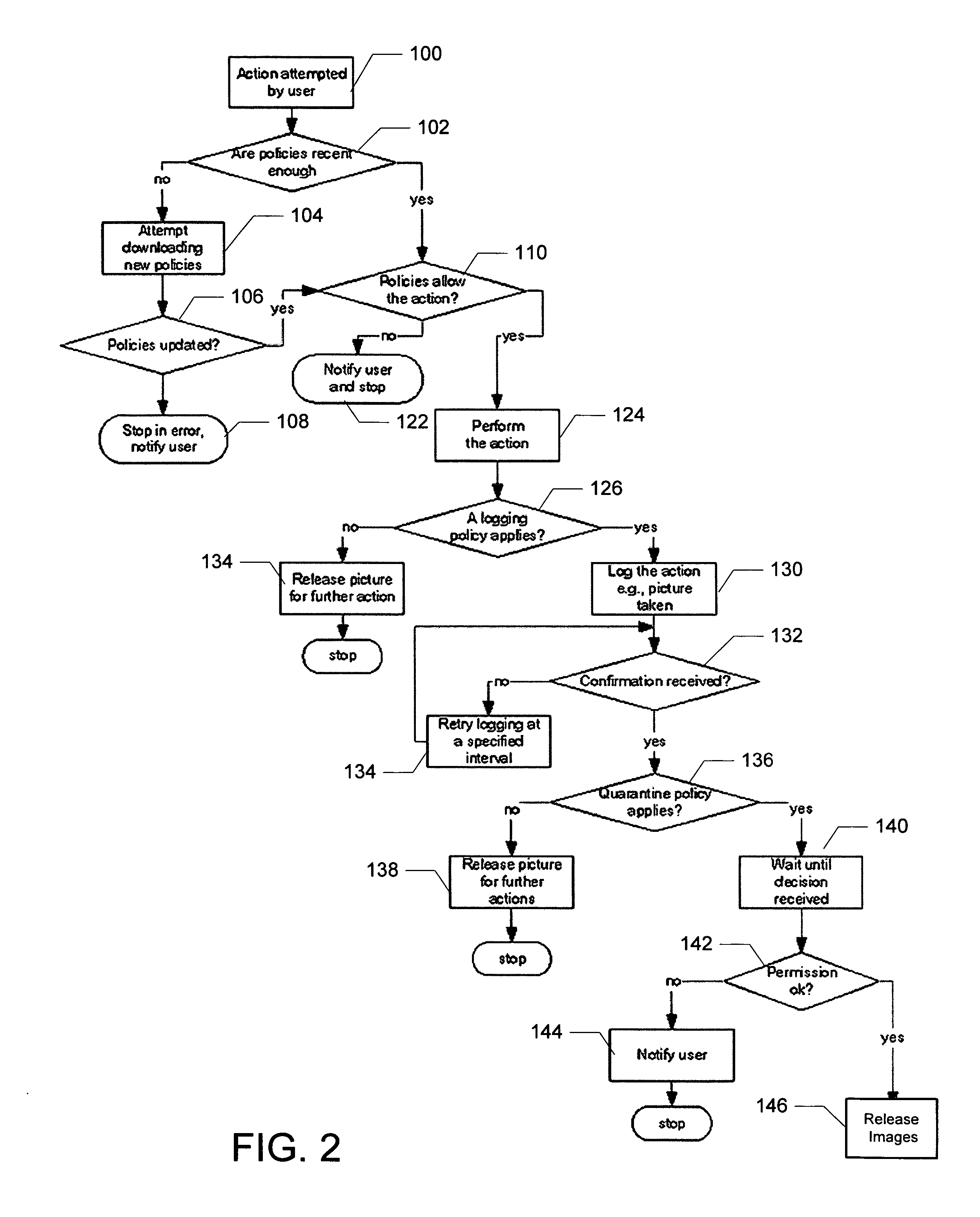
Parental and corporate controls for camera-phones
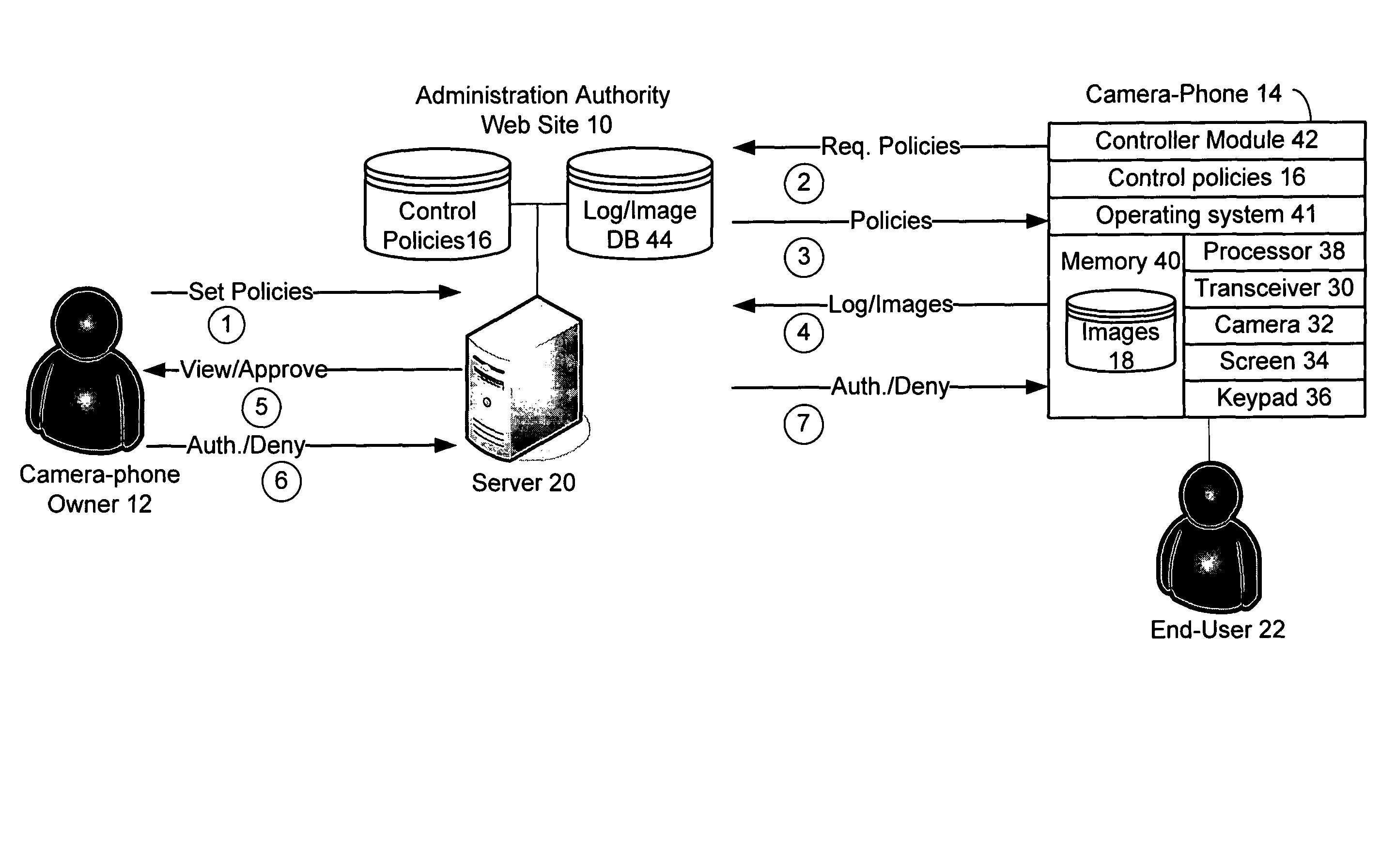
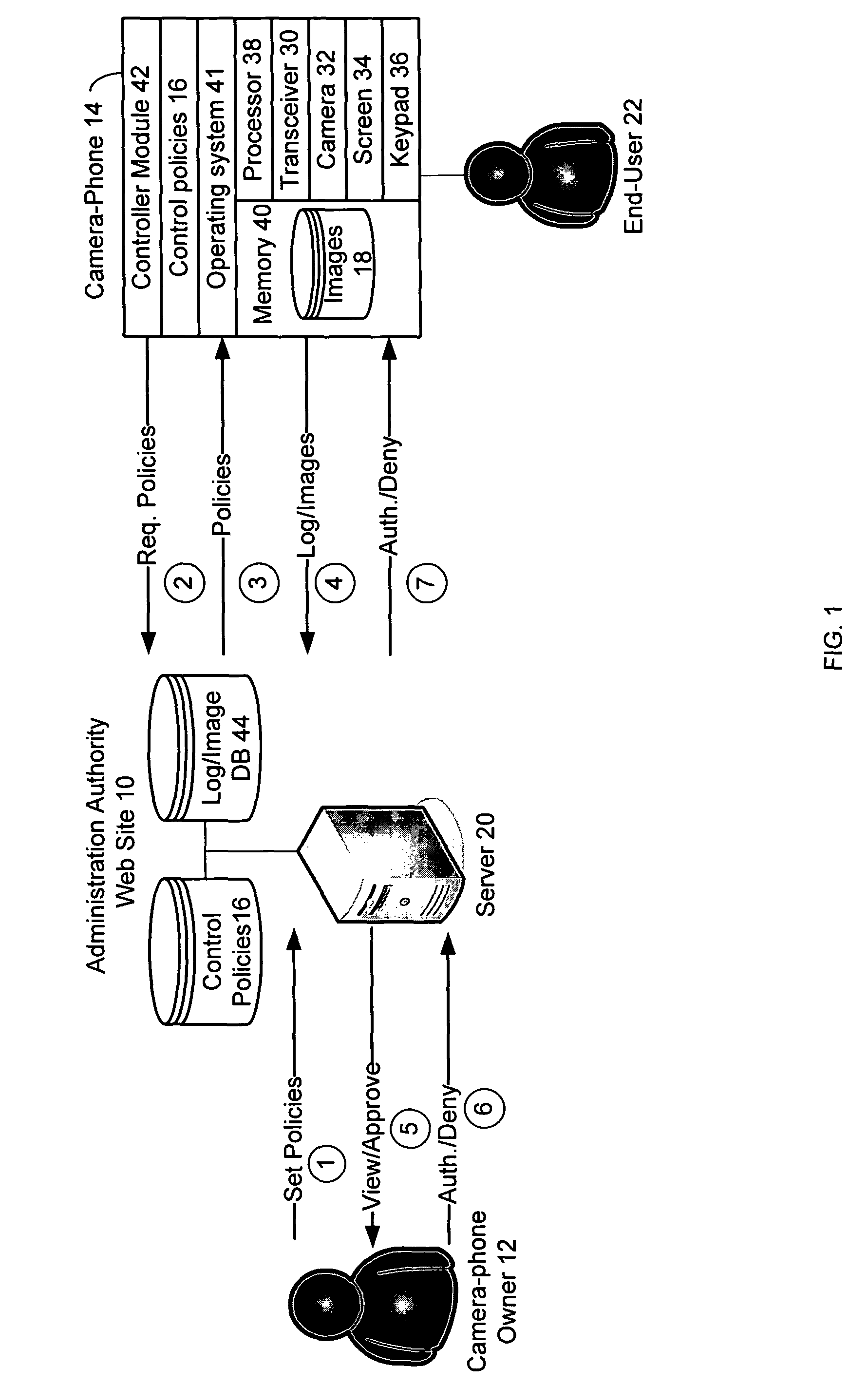
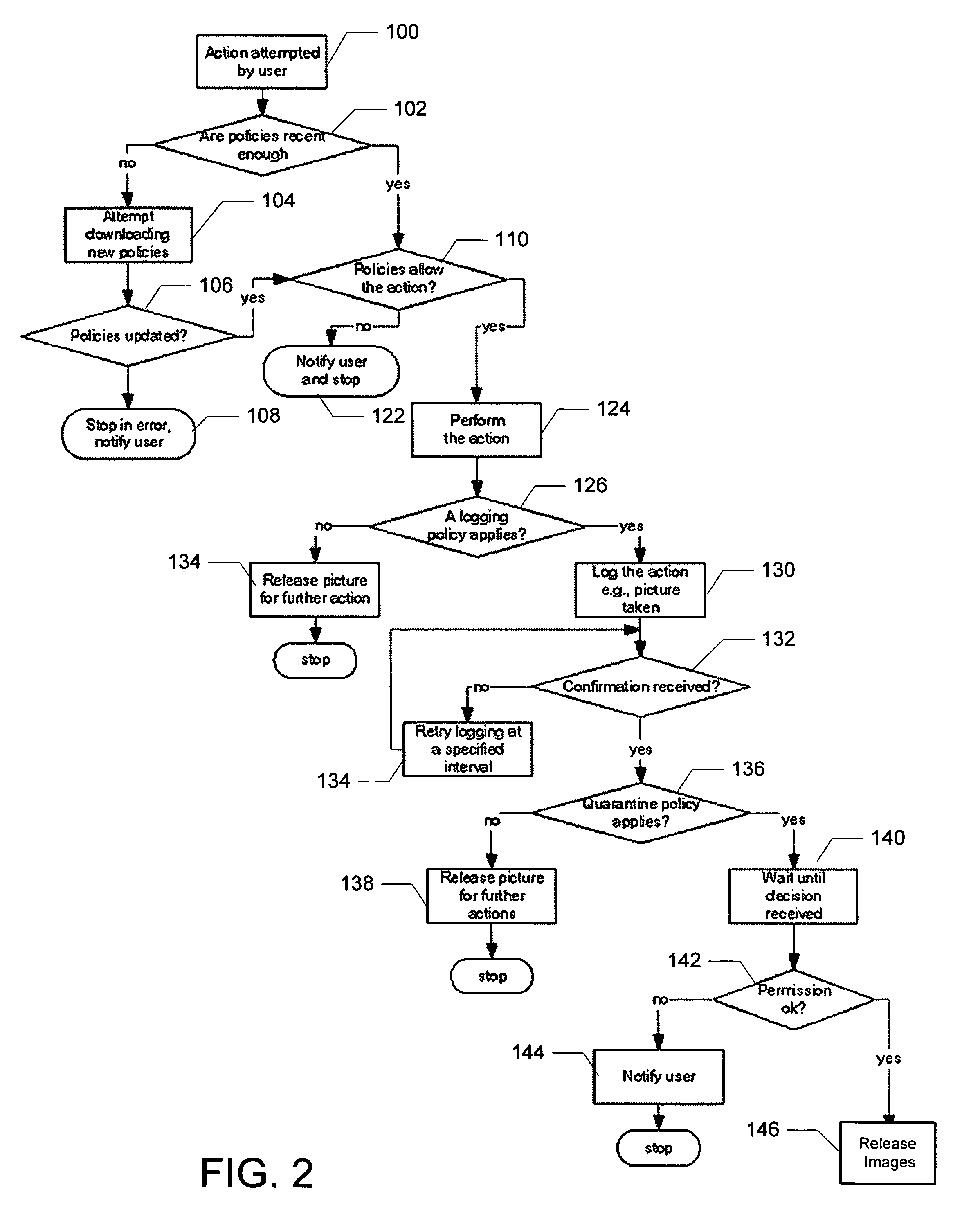
A system and method of the present invention provide parental and corporate control for a camera-phone. An administration authority web site is provided that enables an owner of a camera-phone to log into a server and establish a set of control policies that specify what actions on the phone are authorized for what user. The control policies that affect behavior of the camera-phone are downloaded to the camera-phone, and the camera-phone is then operated such that a user of the camera-phone is only able to perform actions authorized by the control policies. In a further embodiment, a control policy is provided that requires the camera-phone to upload captured images to the server for review by the camera-phone owner. In addition, the images may be quarantined until the camera-phone owner authorizes their release to the user.
Owner:CHEMTRON RES
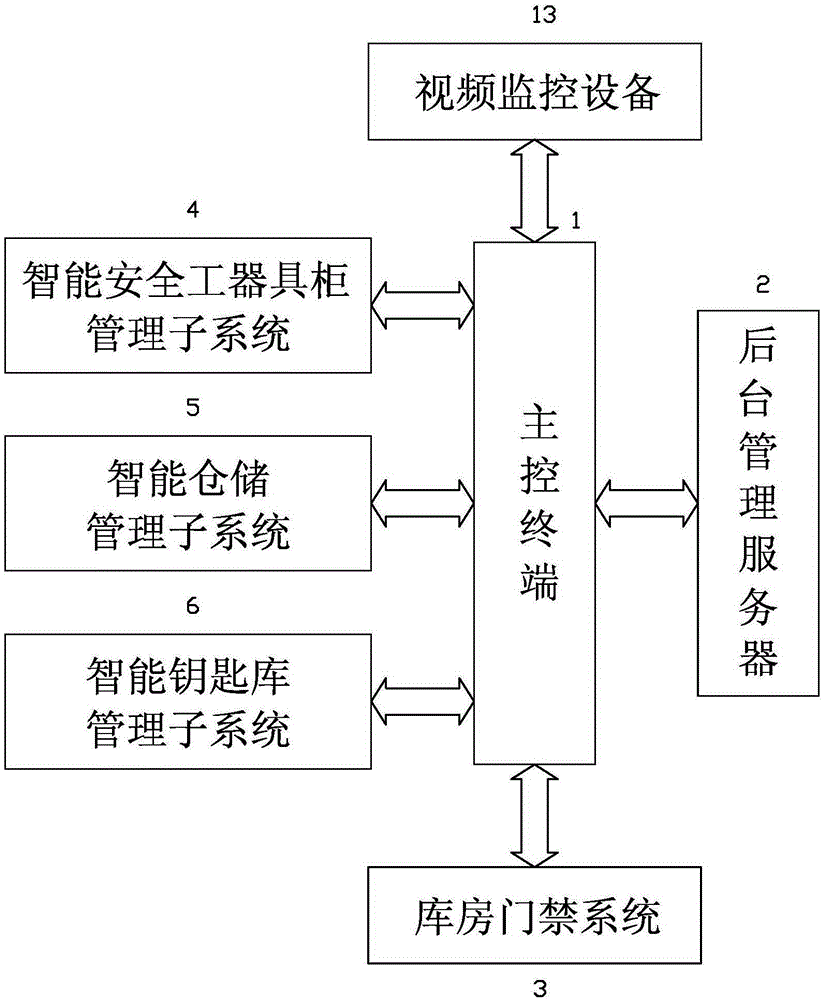
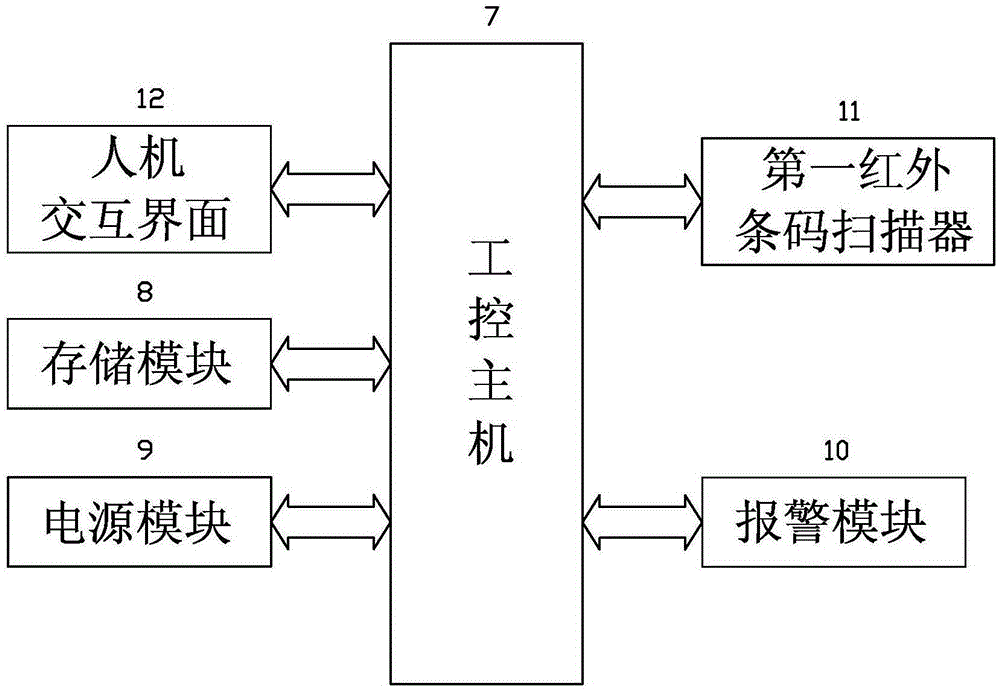
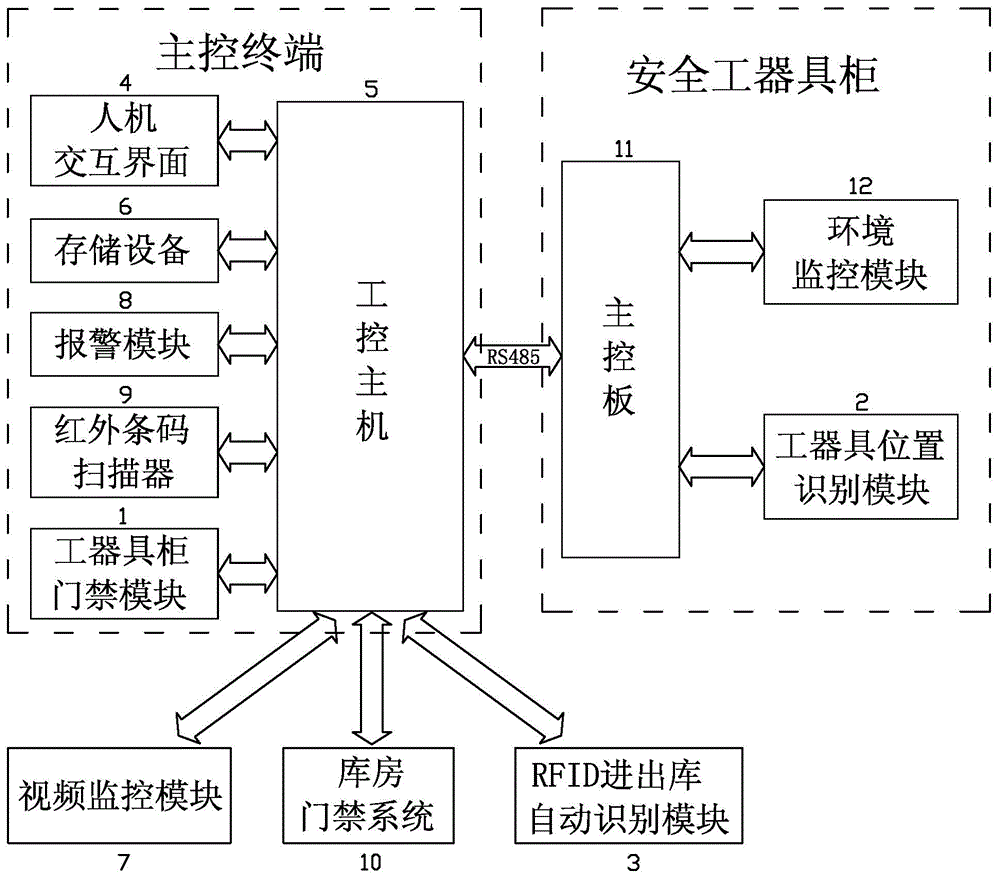
Intelligent power supply station storeroom management system and method based on internet of things
ActiveCN105160748ALearn about usageAvoid abuseData processing applicationsIndividual entry/exit registersThe InternetEngineering
The invention provides an intelligent power supply station storeroom management system and method based on the internet of things. The intelligent power supply station storeroom management system comprises a master control terminal, a background management server connected to the master control terminal, an intelligent security tool cabinet management sub system capable of being connected to the master control terminal in a communication mode, an intelligent warehouse management sub system and an intelligent key library management sub system. The master control terminal is internally provided with intelligent security tool cabinet management system software, intelligent warehouse management software and intelligent key library management system software. A three-in-one comprehensive management model of real-time voice, data and images is adopted for the system, use of a security tool, consumption of spare parts and borrowing of keys are managed through an intelligent means, the failure repair time of a response field can be effectively shortened, the failure reaction speed is increased, the agricultural distribution network construction, overhauling and repairing work efficiency is improved, the work procedure of operation personnel is standardized, the safe production awareness is enhanced, a novel intelligentized power supply station storeroom based on a technology of the internet of things is constructed, and powerful guarantee is provided for safe production of a power enterprise.
Owner:STATE GRID FUJIAN JINJIANG POWER SUPPLY
Process for the production of an abuse-proofed dosage form
InactiveUS20080311197A1Intense negative effectAvoid formingBiocideNervous disorderBreaking strengthMedicine
The present invention relates to a process for the production of an abuse-proofed dosage form containing, apart from one or more active ingredients with potential for abuse and optionally physiologically acceptable auxiliary substances, at least one synthetic or natural polymer (C) with a breaking strength of at least 500 N, wherein the formulation mixture is combined with a solvent for the polymer (C) at least in quantities such that the formulation mixture is at least uniformly moistened, the at least moistened composition is optionally divided into sub-portions, dried and shaped to yield the dosage form.
Owner:GRUNENTHAL GMBH
Man-machine identification method and system
ActiveCN104036780AAvoid abuseImprove experiencePayment architectureDigital data authenticationMan machineDeclassification
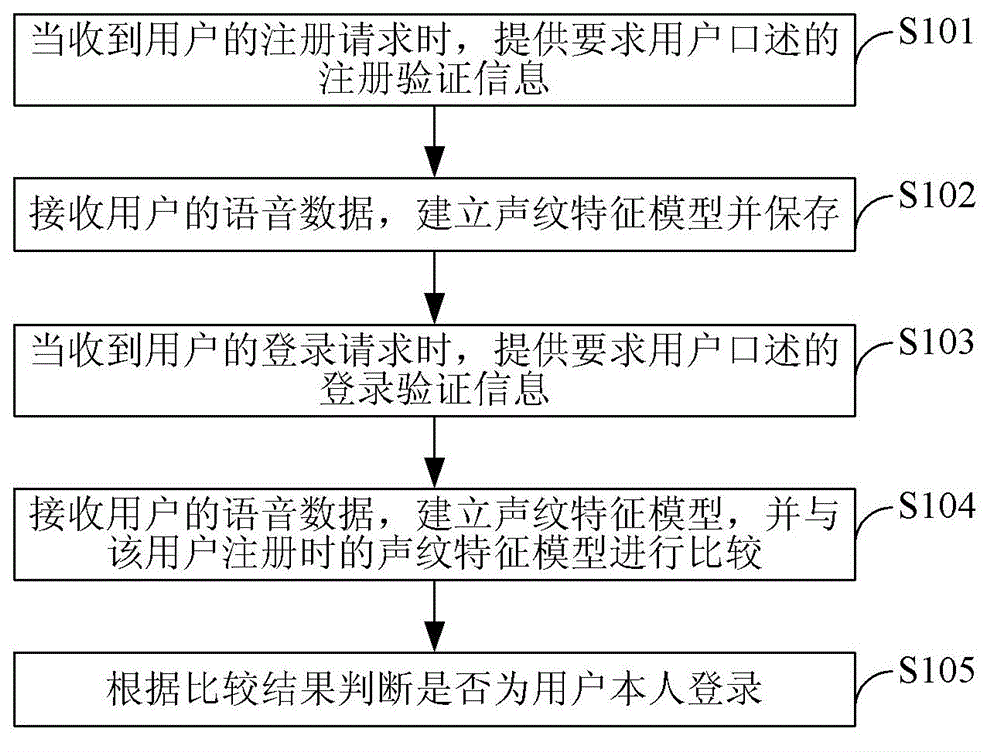
The invention discloses a man-machine identification method and system. The method comprises: when a registration request of a user is received, providing registration verification information which the user is requested to orally state; receiving voice data of the user, and establishing a voiceprint characteristic model for storage; when a login request of the user is received, providing login verification information which the user is requested to orally state; receiving voice data of the user, and establishing a voiceprint characteristic model, and comparing with the voiceprint characteristic model during registration of the user; and according to a comparison result, determining whether the user himself logs in. The man-machine identification method and system can improve declassification difficulties in man-machine identification.
Owner:ALIBABA GRP HLDG LTD
Pharmaceutical Formulation Containing Opioid Agonist, Opioid Antagonist and Gelling Agent
InactiveUS20150031718A1Avoid abuseReduce releaseBiocidePharmaceutical non-active ingredientsOpioid antagonistPharmaceutical formulation
Disclosed in certain embodiments is an oral dosage form comprising a therapeutically effective amount of an opioid analgesic, an opioid antagonist and one or more pharmaceutically acceptable excipients; the dosage form further including a gelling agent in an effective amount to impart a viscosity unsuitable for administration selected from the group consisting of parenteral and nasal administration to a solubilized mixture formed when the dosage form is crushed and mixed with from about 0.5 to about 10 ml of an aqueous liquid.
Owner:PURDUE PHARMA LP
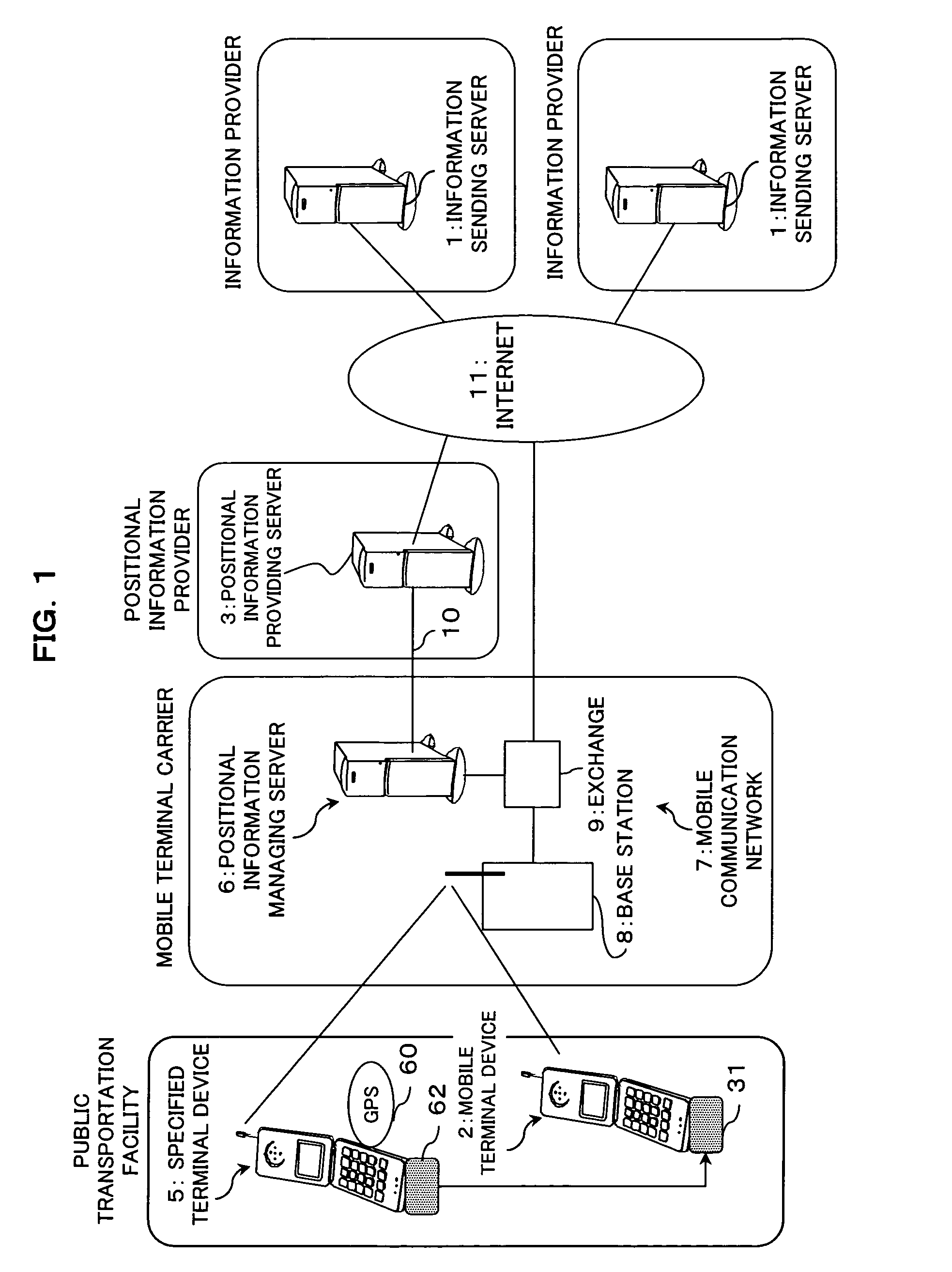
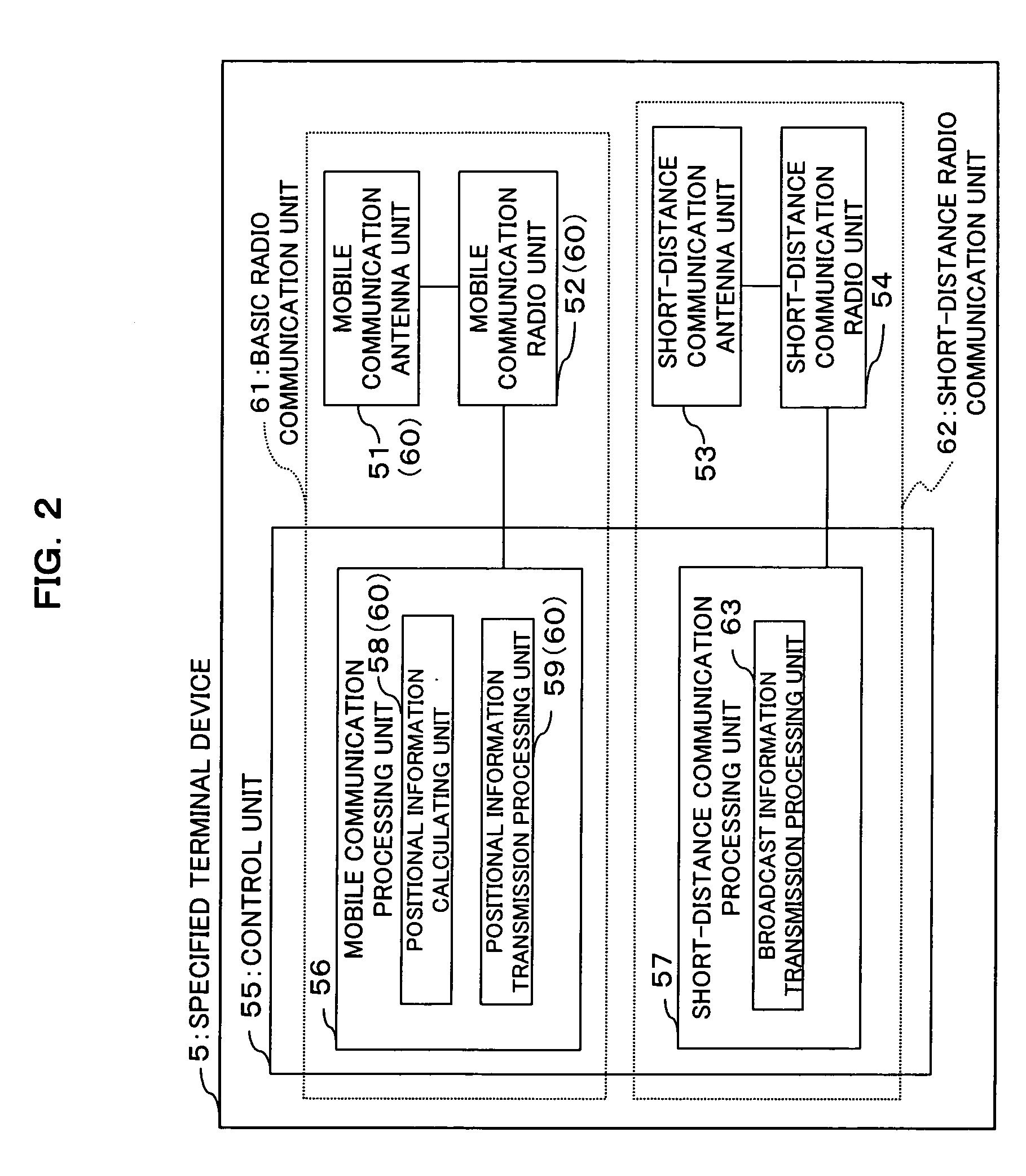
Positional information providing method and positional information providing system
InactiveUS20050032529A1Privacy protectionAvoid abuseInstruments for road network navigationNetwork topologiesTerminal equipmentLibrary science
In a positional information providing method, an information sending server transmits desired decision positional information and unique information on a designated mobile terminal device to a positional information providing server, and a mobile terminal device transmits unique information thereon to the positional information providing server, and when the designated unique information and the unique information agree with each other, the positional information providing server makes a decision as to whether or not there is a point of agreement between the decision positional information and the positional information on the mobile terminal device and, when the decision indicates that there is a point of agreement between the decision positional information and the positional information on the mobile terminal device, the positional information providing server notifies the decision result through a network to the information sending server, thereby providing the positional information.
Owner:FUJITSU LTD
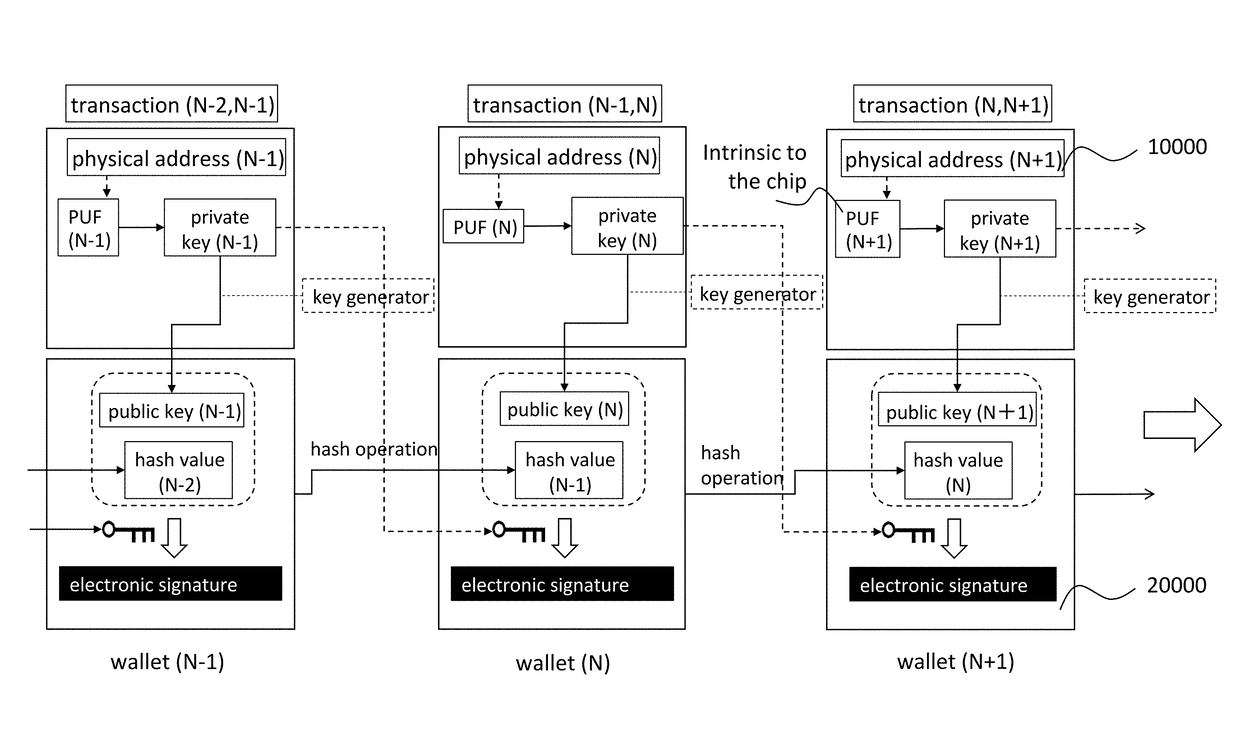
Network without Abuse of a Private Key
ActiveUS20180076957A1Avoid abuseAbuse of the private keys can be preventedKey distribution for secure communicationDigital data processing detailsSemiconductor chipLogical network
A network includes a logical network and a physical network. The logical network includes a plurality of logical nodes. Each logical node is connected to a respective identification core. Each identification core includes at least one semiconductor chip having a physical randomness. Each semiconductor chip generates one of a plurality of pairs of private keys and public keys based on the physical randomness thereof according to an input received by the one of the at least one semiconductor chip under a public key cryptography. One of the public keys is regarded as a logical address of one of the logical nodes, which is connected to one of the identification cores. The physical network includes a plurality of physical nodes. Each identification core is one of components in each physical node. The logical network is uniquely linked to the physical network by the pairs of private keys and public keys.
Owner:WATANABE YUKIKO
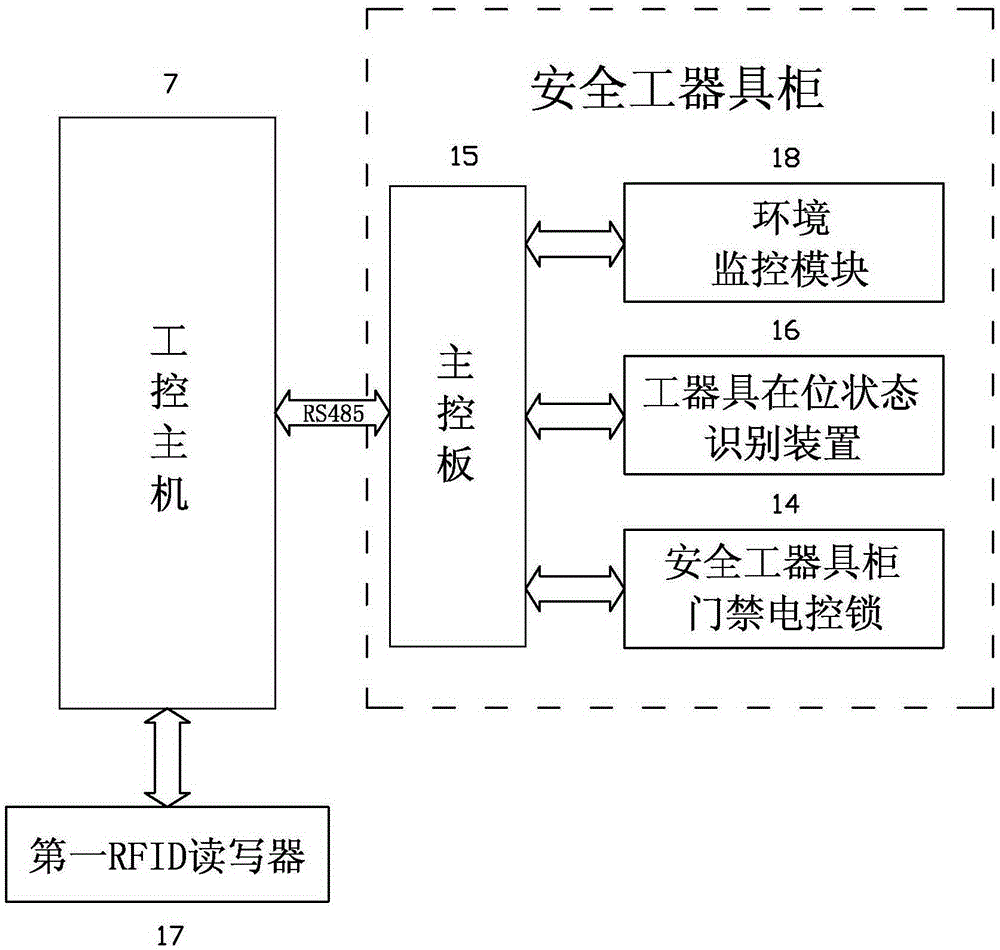
Power supply station safety apparatus cabinet warehouse intelligent management system and method
InactiveCN105117855APrevent mistakingAvoid misplacementIndividual entry/exit registersResourcesComputer moduleIntelligent management
The invention relates to a power supply station safety apparatus cabinet warehouse intelligent management system. The power supply station safety apparatus cabinet warehouse intelligent management system includes a safety apparatus cabinet, an apparatus cabinet access control module, an apparatus position identification module, an RFID warehouse entering and exiting automatic identification module, a main control terminal and a man-machine interaction interface, wherein the main control terminal can be in communication connection with the apparatus position identification module, the RFID warehouse entering and exiting an automatic identification module and the man-machine interaction interface. According to the power supply station safety apparatus cabinet warehouse intelligent management system of the invention, specific unique positions where apparatuses are stored are determined through the apparatus position identification module, and the unique identities of the apparatuses are marked through the RFID warehouse entering and exiting automatic identification module, and therefore, when the apparatus position identification module and the RFID warehouse entering and exiting automatic identification module are used in combination, wrong taking and wrong arrangement of the apparatuses can be effectively prevented; the power supply station safety apparatus cabinet warehouse intelligent management system can be connected with an original GPMS through a GPMS interface, so that the power supply station safety apparatus cabinet warehouse intelligent management system and a two-ticket system can form a locking linkage management mode, so that a management layer can effectively and quickly understand the use situation of the safety apparatuses, and the abuse and non-standard use of the safety apparatuses can be completely eradicated, and the apparatuses can be managed and monitored more safely, and the intelligent monitoring and management of an apparatus warehouse can be realized.
Owner:STATE GRID FUJIAN JINJIANG POWER SUPPLY
Retrieving and storing updated contact records
InactiveUS7933587B1Easy to storeLimited in numberData processing applicationsMultiple digital computer combinationsComputer networkThe Internet
Owner:SWAN JOSEPH G
Policy-based controls for wireless cameras
A system and method of the present invention provide parental and corporate control for a camera-phone. An administration authority web site is provided that enables an owner of a camera-phone to log into a server and establish a set of control policies that specify what actions on the phone are authorized for what user. The control policies that affect behavior of the camera-phone are downloaded to the camera-phone, and the camera-phone is then operated such that a user of the camera-phone is only able to perform actions authorized by the control policies. In a further embodiment, a control policy is provided that requires the camera-phone to upload captured images to the server for review by the camera-phone owner. In addition, the images may be quarantined until the camera-phone owner authorizes their release to the user.
Owner:CHEMTRON RES
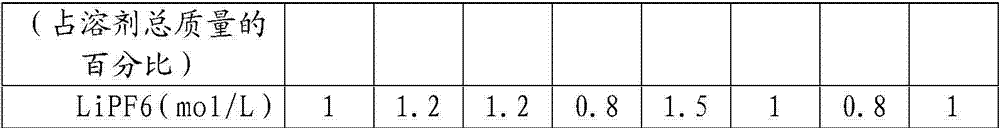
Non-aqueous electrolyte for high-voltage lithium ion batteries
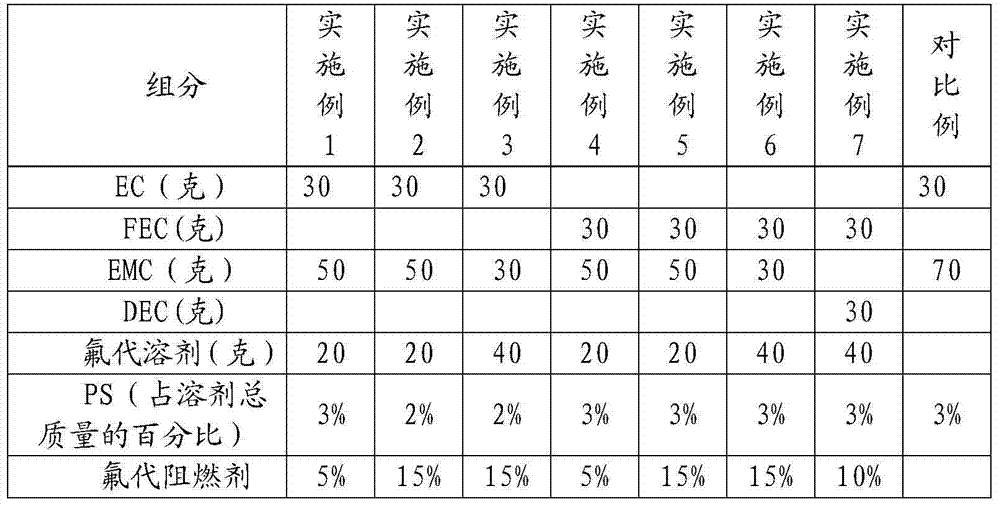
ActiveCN103579676AImprove flame retardant performanceAvoid abuseSecondary cellsOrganic electrolytesSolventLithium-ion battery
The invention discloses a non-aqueous electrolyte for high-voltage lithium ion batteries, which is composed of a solvent, lithium salts, a fluorinated flame retardant and a film-forming additive, wherein cyclic carbonates and / or chain carbonates account for 30-95 wt% of the solvent, the fluorinated solvent accounts for 5-70 wt% of the solvent, the mol concentration of the lithium salts in a mixed solution formed by the fluorinated solvent and the cyclic carbonates and / or chain carbonates is 0.8-1.5 mol / L; the fluorinated flame retardant accounts for 1-30 wt% of the solvent; and the film-forming additive accounts for 1-8 wt% of the solvent. The high-flash-point no-flash-point fluorinated solvent can obviously enhance the flash point of the electrolyte solvent; and the fluorinated solvent and the fluorinated flame retardant can synergically improve the flame-retardant effect of the lithium battery under high voltage, thereby thoroughly preventing misuse of batteries, and avoiding fire, combustion, explosion and other potential safety hazards caused by overcharging.
Owner:ZHUHAI SMOOTHWAY ELECTRONICS MATERIALS
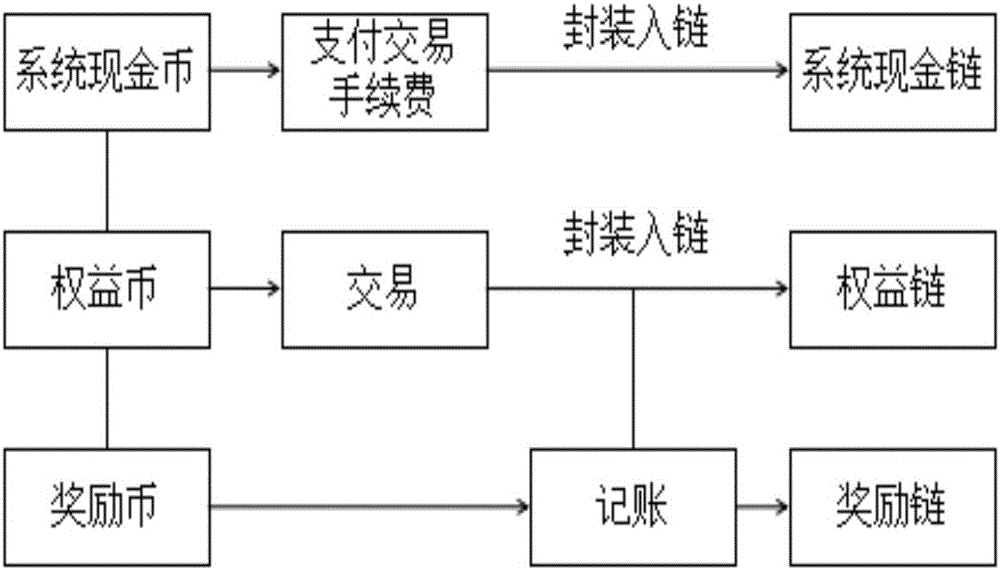
Block chain consensus mechanism
InactiveCN106530072AAvoid Double Spending AttacksAvoid abuseFinanceElectronic credentialsProof-of-stakeDistributed computing
The invention belongs to the technical field of block chains, and provides a block chain consensus mechanism. The block chain consensus mechanism is based on a right and interest certificate consensus mechanism, and comprises a right and interest chain, a system cash chain and an award chain, wherein the right and interest chain is used for recording ins and outs of rights and interests; the system cash chain is used for recording and paying the commission charge when the rights and interests are transferred; and the award chain is used for recording an award for distributing a packaging block and loading the block to the chain. Adoption of the consensus mechanism not only solves a problem of double-spend attacks, but also solves problems that account keeping becomes more and more centralized and that general right and interest award mechanisms are inconsistent in the real world.
Owner:TIANJIN MIYOU TECH
Dosage form with impeded abuse
InactiveUS8722086B2Prevent crushingPrevent the subsequent abuseOrganic active ingredientsPill deliveryWaxBreaking strength
A multiparticulate dosage form formulated to make misuse more difficult containing least one active substance with potential for misuse (A), at least one synthetic or natural polymer (C), optionally at least one natural, semi-synthetic or synthetic wax (D), at least one disintegrant (E) and optionally one or more additional physiologically compatible excipients (B), wherein the individual particles of the dosage form display a breaking strength of at least 500 N and a release of active substance of at least 75% after 45 minutes measured according to Ph.Eur. in the paddle mixer with sinker in 600 ml of aqueous buffer solution with a pH value of 1.2 at 37° C. and 75 rpm.
Owner:GRUNENTHAL GMBH
System for inductively charging vehicles, comprising an electronic positioning aid
InactiveCN102741083AImprove convenienceFrequent connectionCharging stationsOperating modesElectricityDriver/operator
The present invention relates to a system that ensures a self-guiding, electronic positioning of a secondary coil at a vehicle side, without the aid of indicators or kinematic or mechanical aids, in relation to a primary coil that is fixed at a a ground side, in order to guarantee a transfer of energy with over 90% efficiency without the disadvantages of moving, frictional and elastic components in terms of energy consumption, functional safety and wear. To achieve this aim, the coil housing at the ground side fulfils the role of an electronics housing, reflective element and cooling element thanks to the choice of material used, the surface and the inner supports and can thus be retrofitted, as a single installation at the ground side in the form of an operation-ready complete package, to any flat base with an electric connection. The vehicle can be used both for transporting passengers and loads and can be steered by a vehicle driver or can be operated without a driver, for example for cleaning areas, for natural protection or for intralogistics.
Owner:CONDUCTIX WAMPFLER
Terminal device and terminal device operation management system and operation management method
InactiveUS7013128B2Avoid abuseAvoid dataUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyTelecommunications
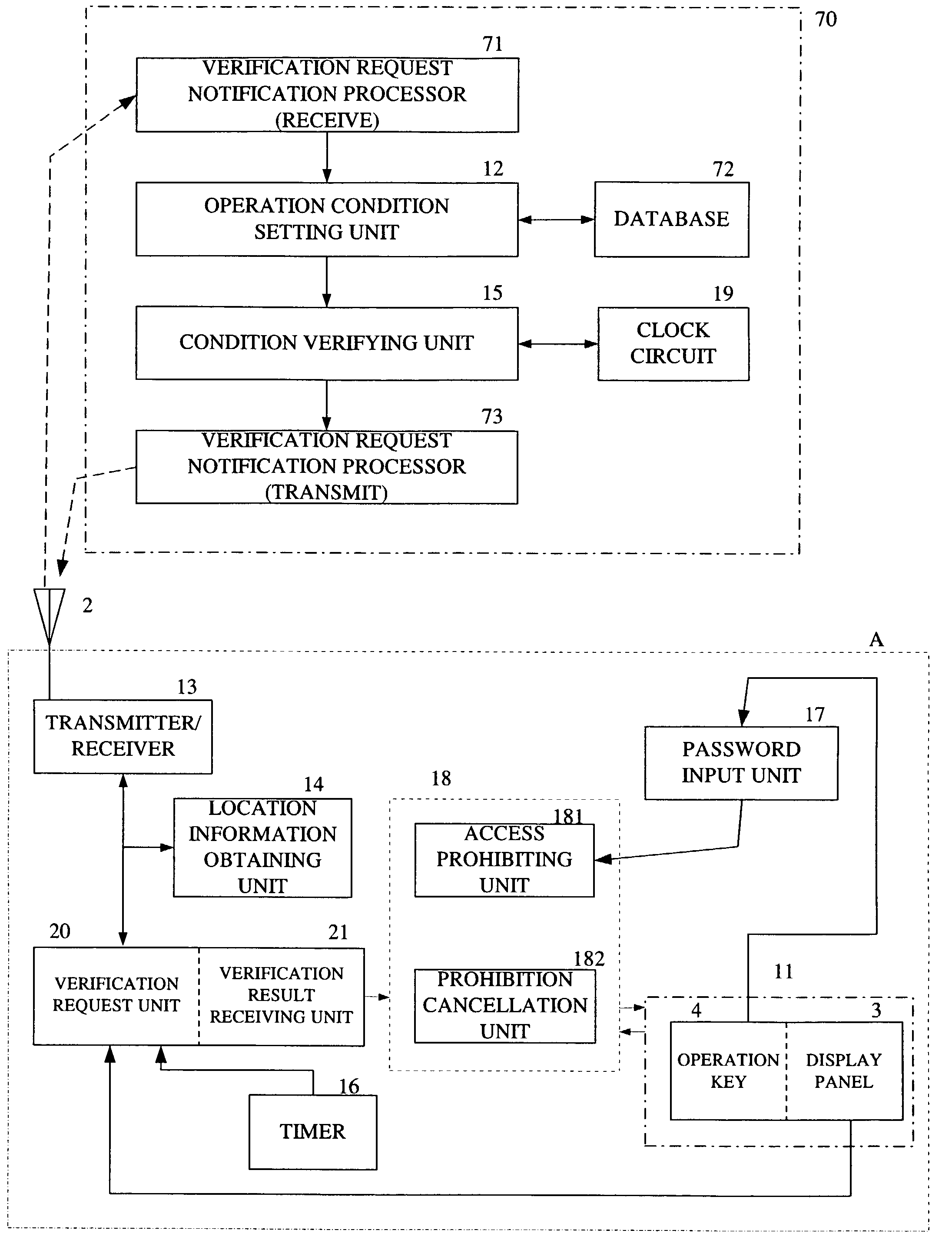
A portable terminal includes a function to detect its own location. The owner of such terminal registers in advance an area in which he expects to be for a given time slot as conditions for operation. The portable terminal verifies its location with respect to the operation conditions set by the owner, and where it is determined that the operation conditions are not met, the portable terminal disables itself, prohibiting its use. Where a pre-registered password is subsequently input, the portable terminal cancels this prohibition. Consequently, if the owner loses the portable terminal while away from home or the office, for example, a third party cannot operate the portable terminal, and moreover, unless the owner-registered password is input, the prohibition is not cancelled, thereby preventing disclosure of the data and other information stored in the portable terminal.
Owner:MINOLTA CO LTD
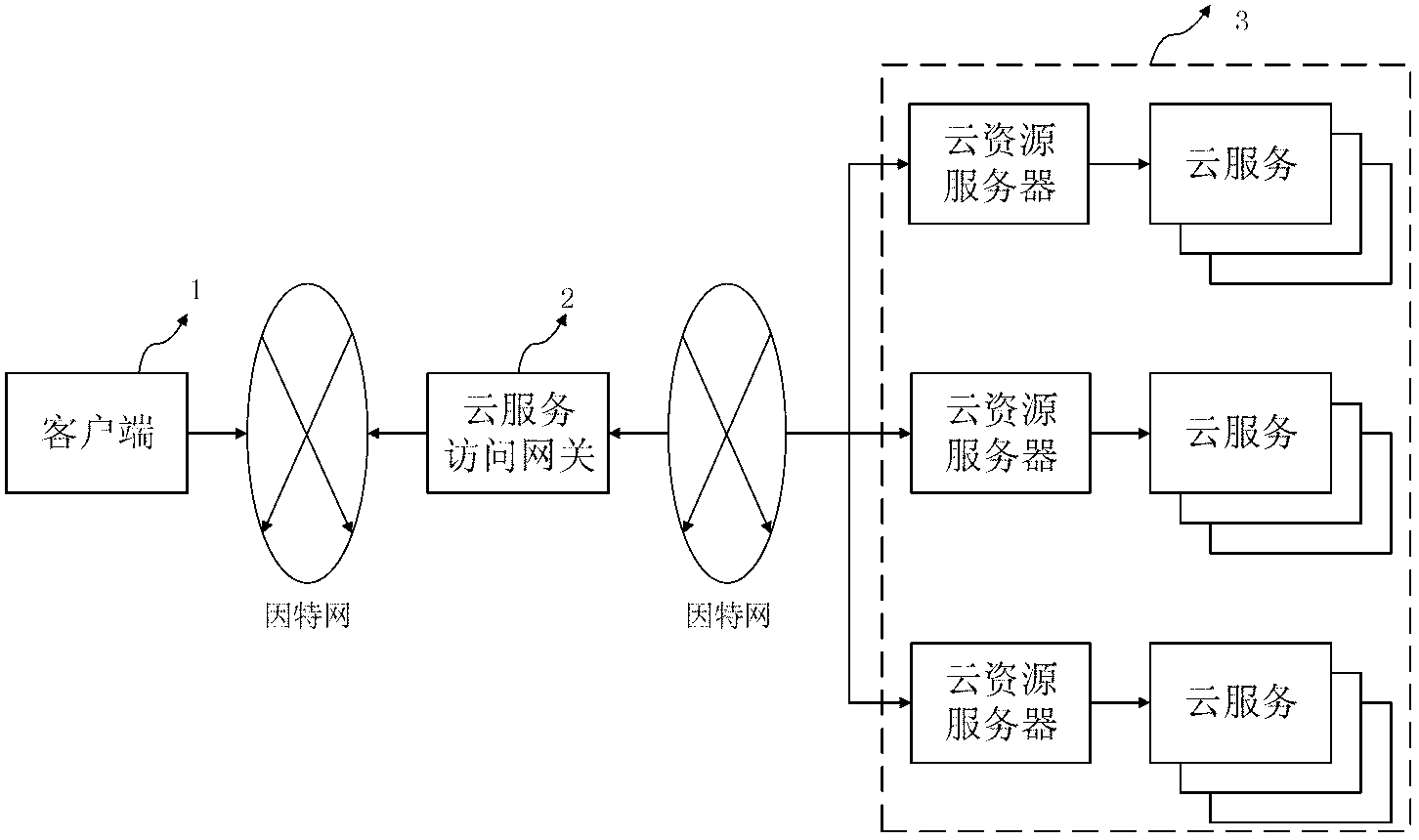
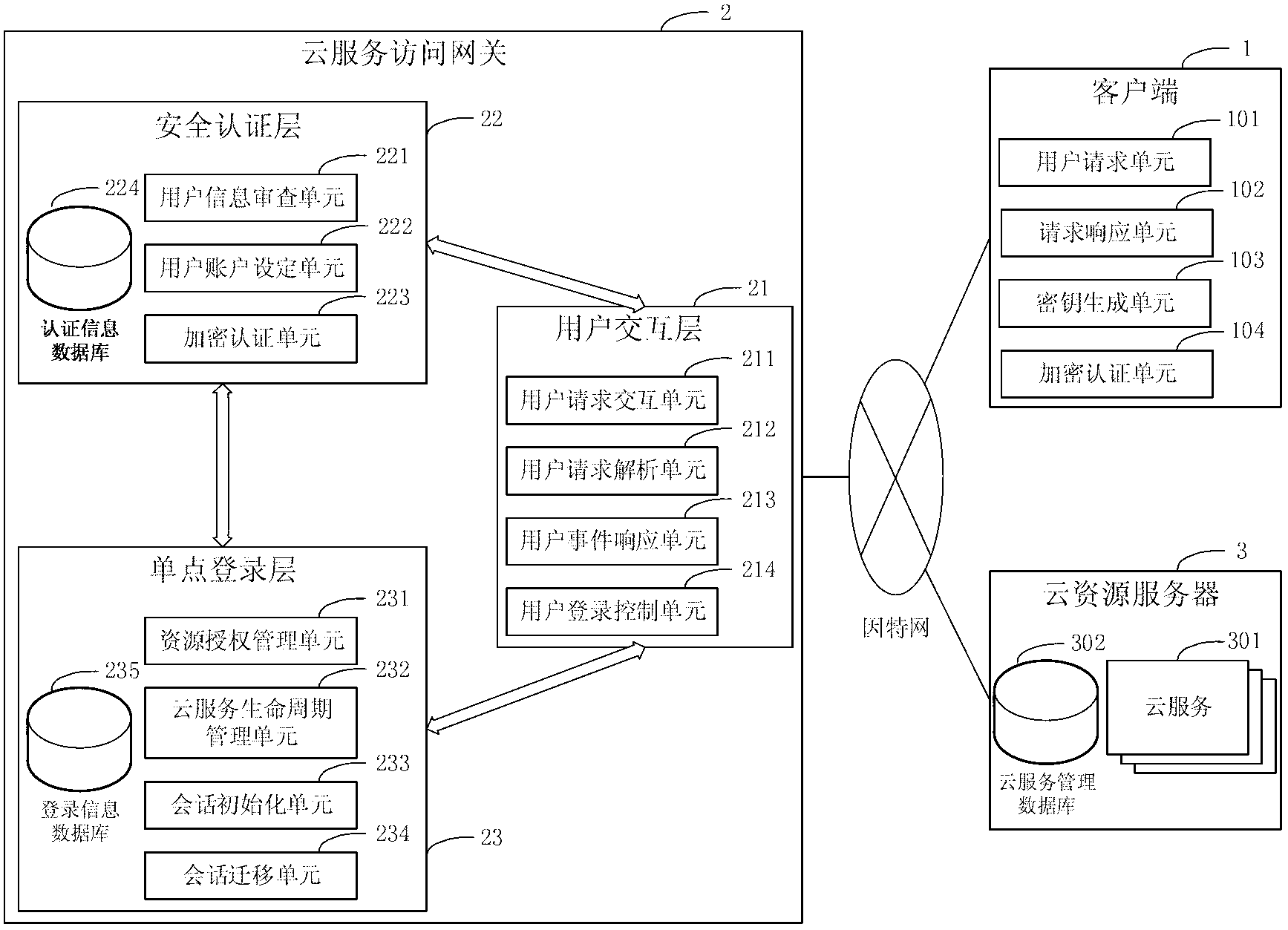
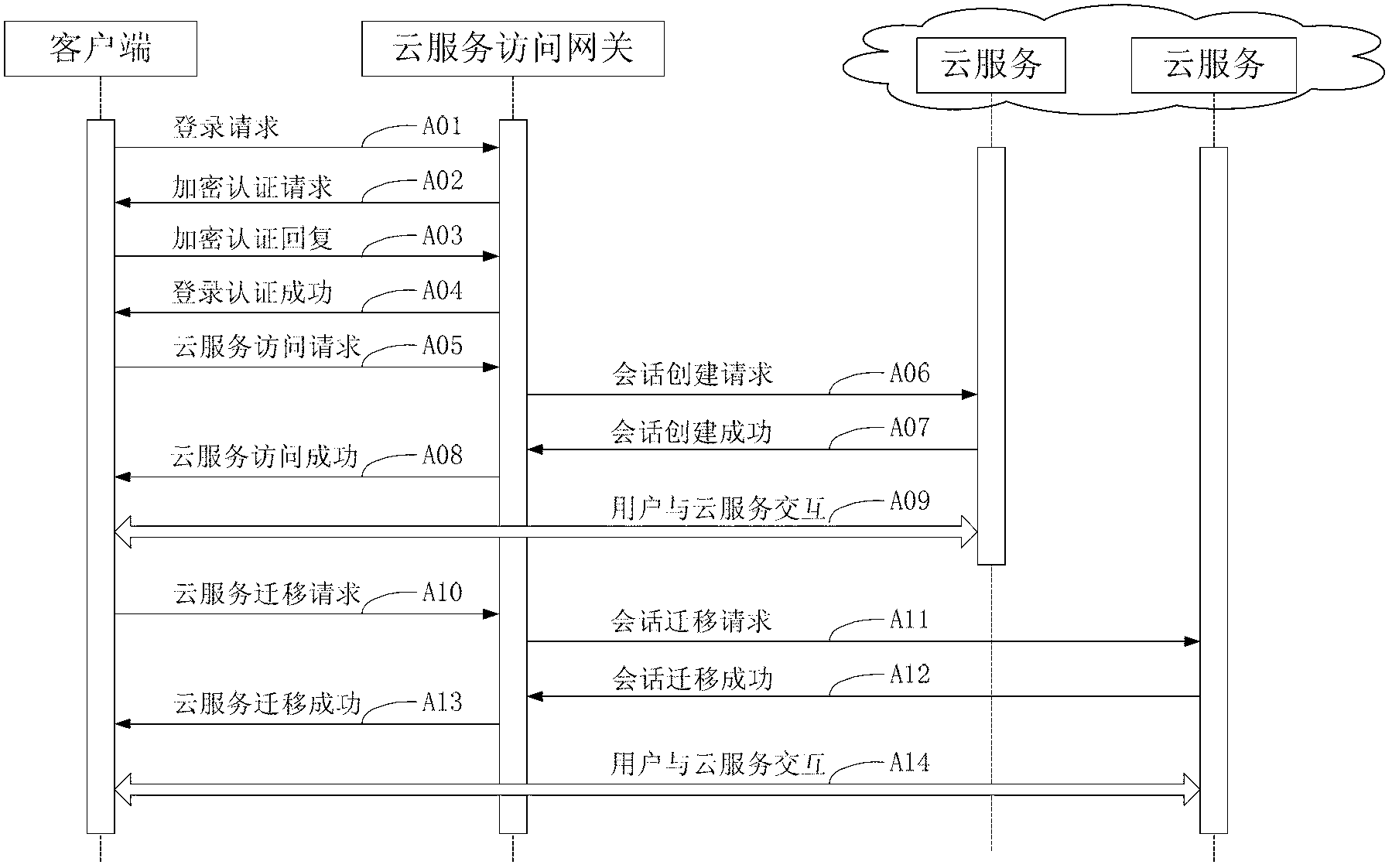
Gateway system and gateway method for Cloud service accounting management
ActiveCN103236969AProtection securityProtect SimplicityMetering/charging/biilling arrangementsNetwork connectionsInteraction layerInformation processing
The invention discloses a gateway system and a gateway method for Cloud service accounting management. The gateway system comprises a client side, a Cloud service access gateway, and a Cloud source server. The Cloud service access gateway comprises a user interaction layer, a safety authentication layer and a single sign-on layer. According to requirements of system security and management of the Cloud service access gateway, frequent data transmission and synchronous information processing are performed with the client side and the Cloud source server to realize coordination action of cryptographic authentication and single sign-on. The method includes starting; logging in Cloud gateway; logging in Cloud service to start charging; migrating the Cloud service along with charging migration; logging out the Cloud service with end of charging; and ending with charging requests. In the method, interaction of a user and the Cloud service is realized in the client side, and technological means of interactive transmission in three functional layers can be used for achieving execution efficiency and safety of the gateway system of the Cloud service accounting management.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com