Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
513 results about "Logical network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Logical Network. Definition - What does Logical Network mean? A logical network is a virtual representation of a network that appears to the user as an entirely separate and self-contained network even though it might physically be only a portion of a larger network or a local area network.
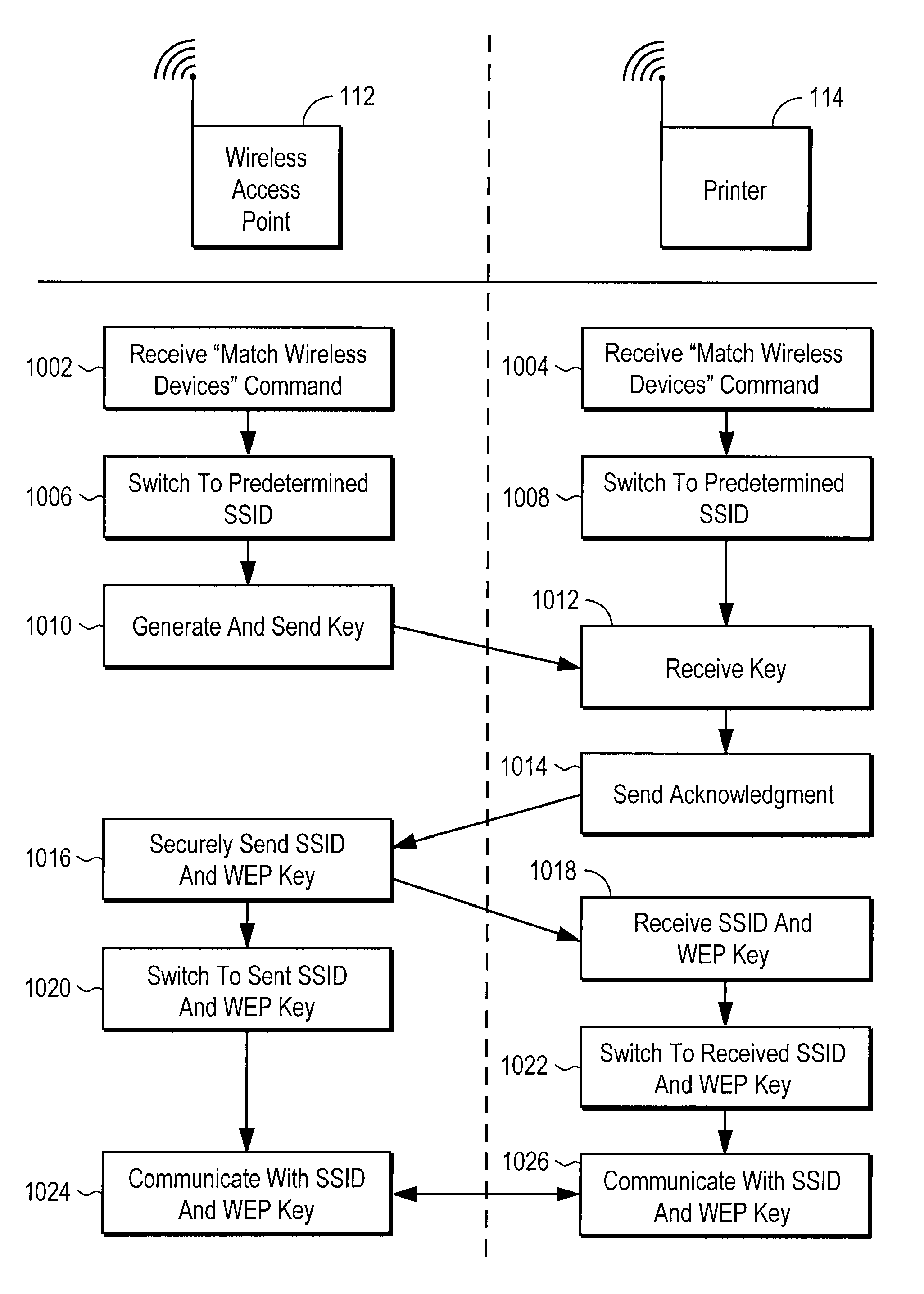
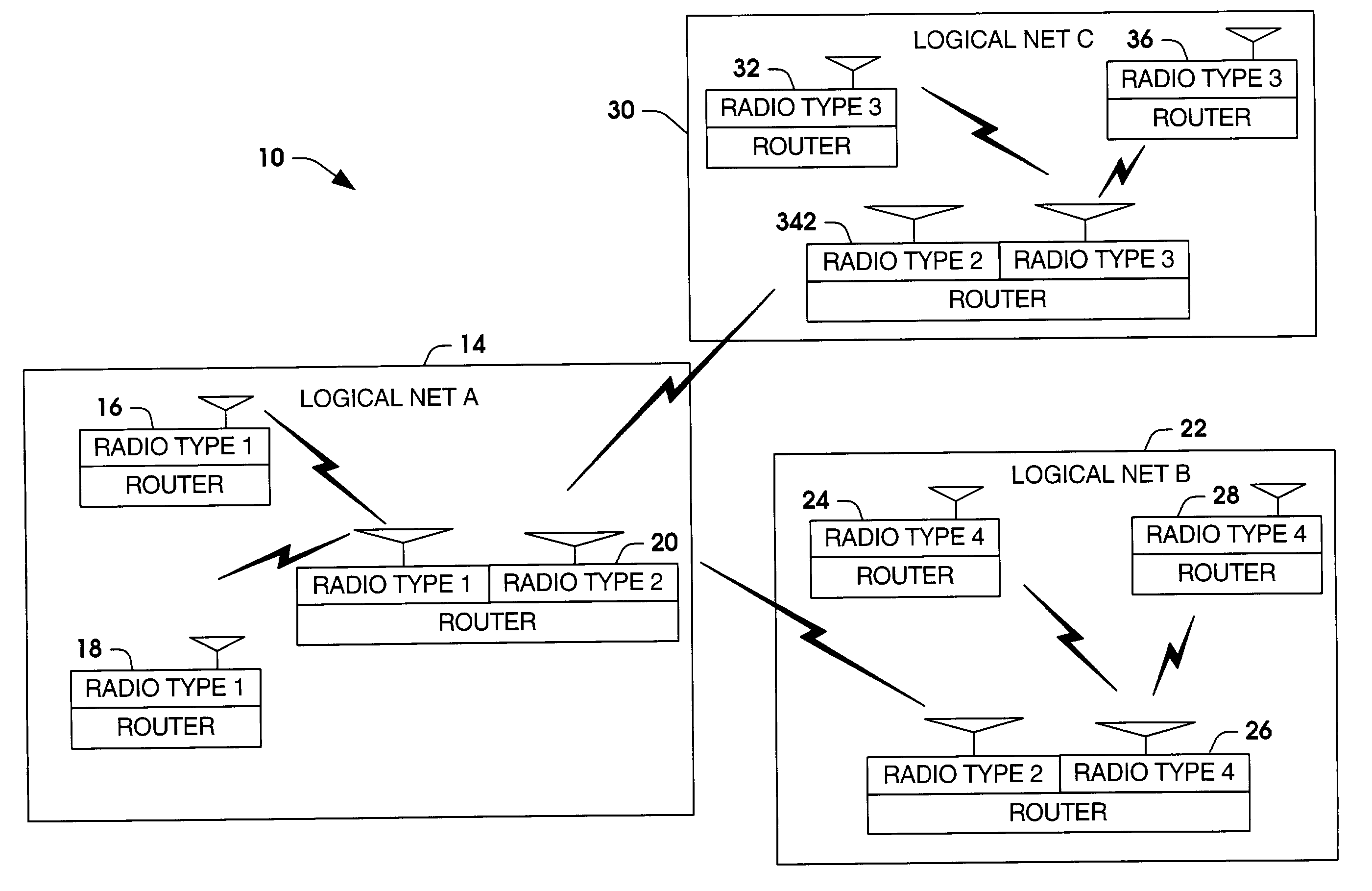
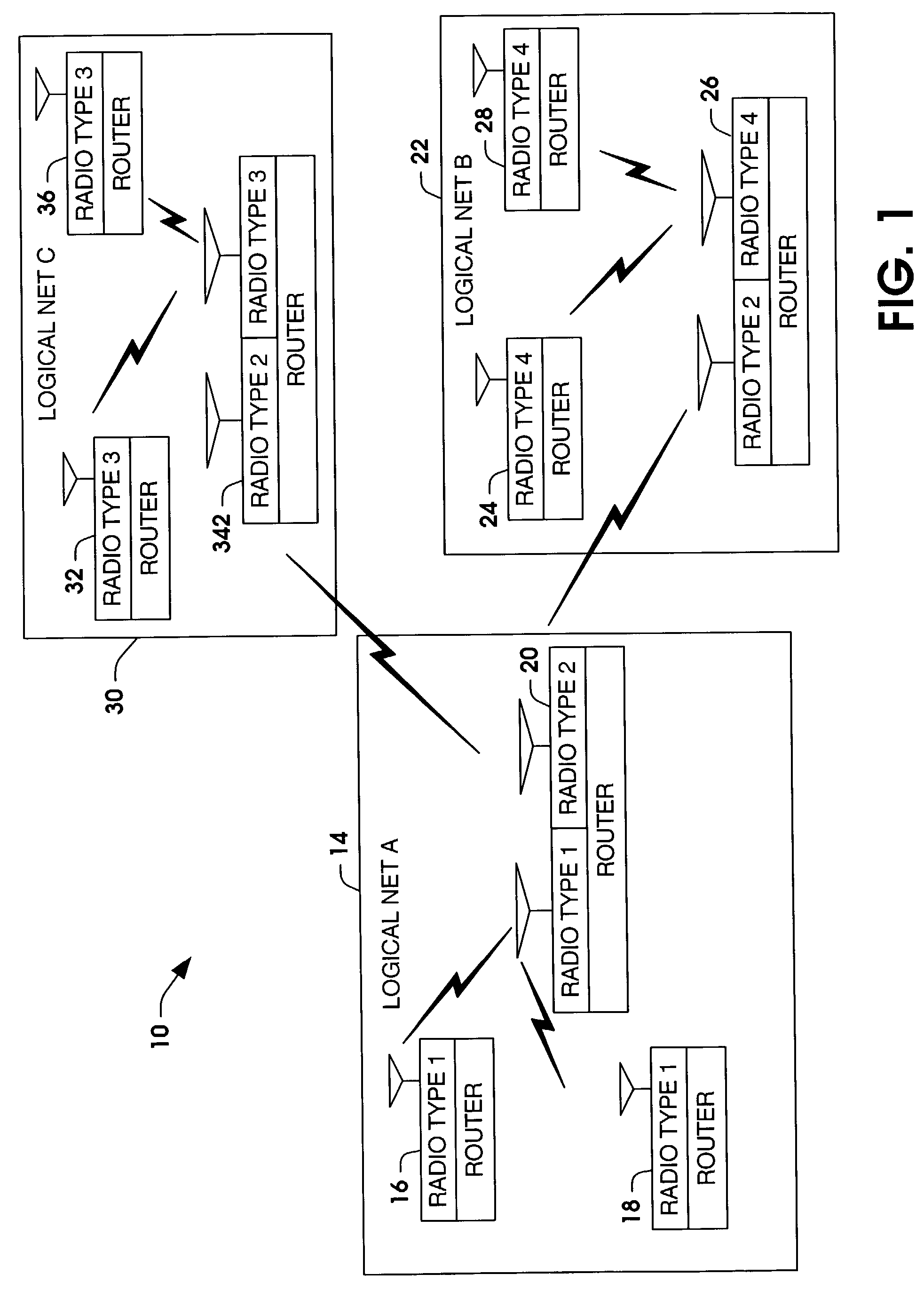
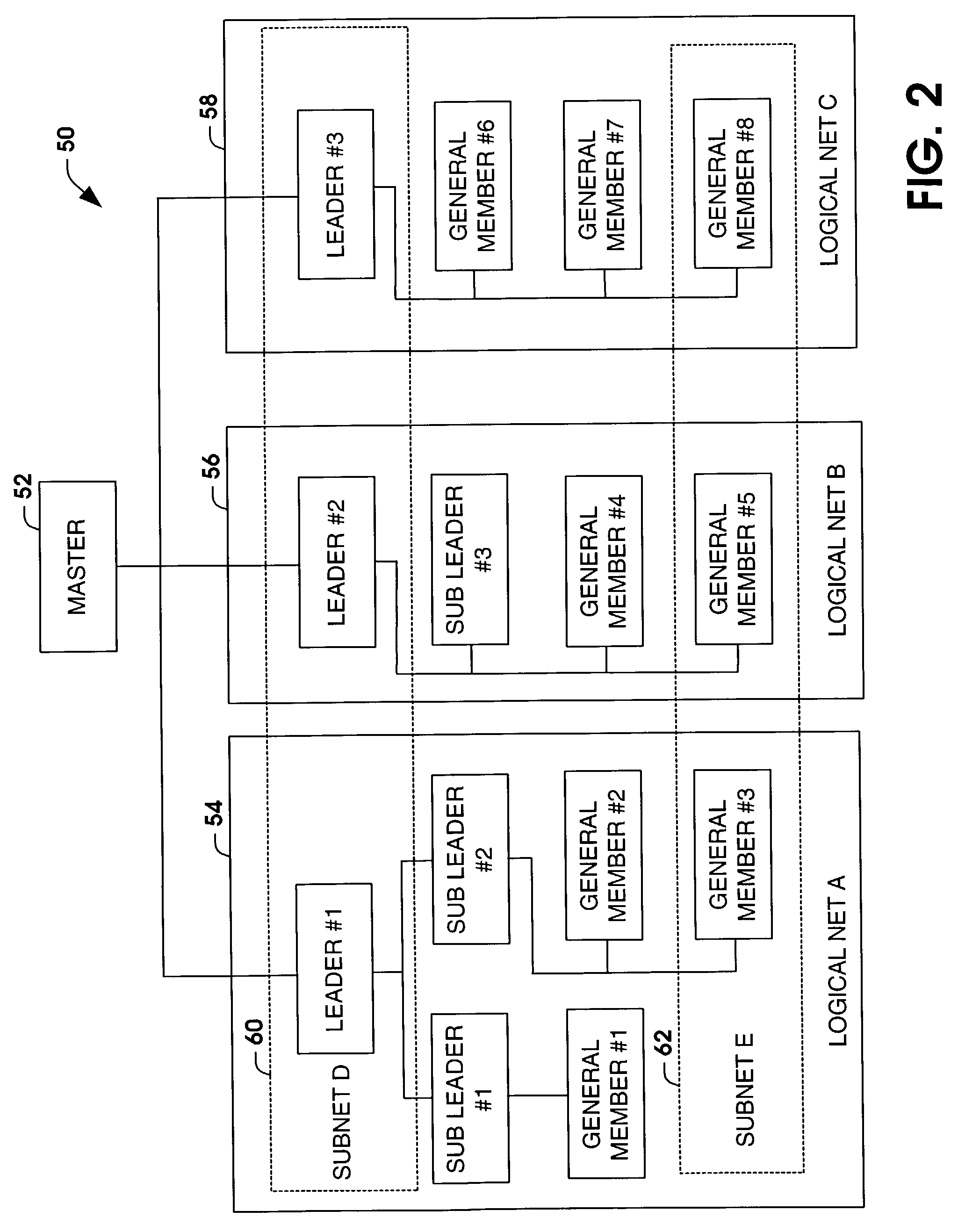
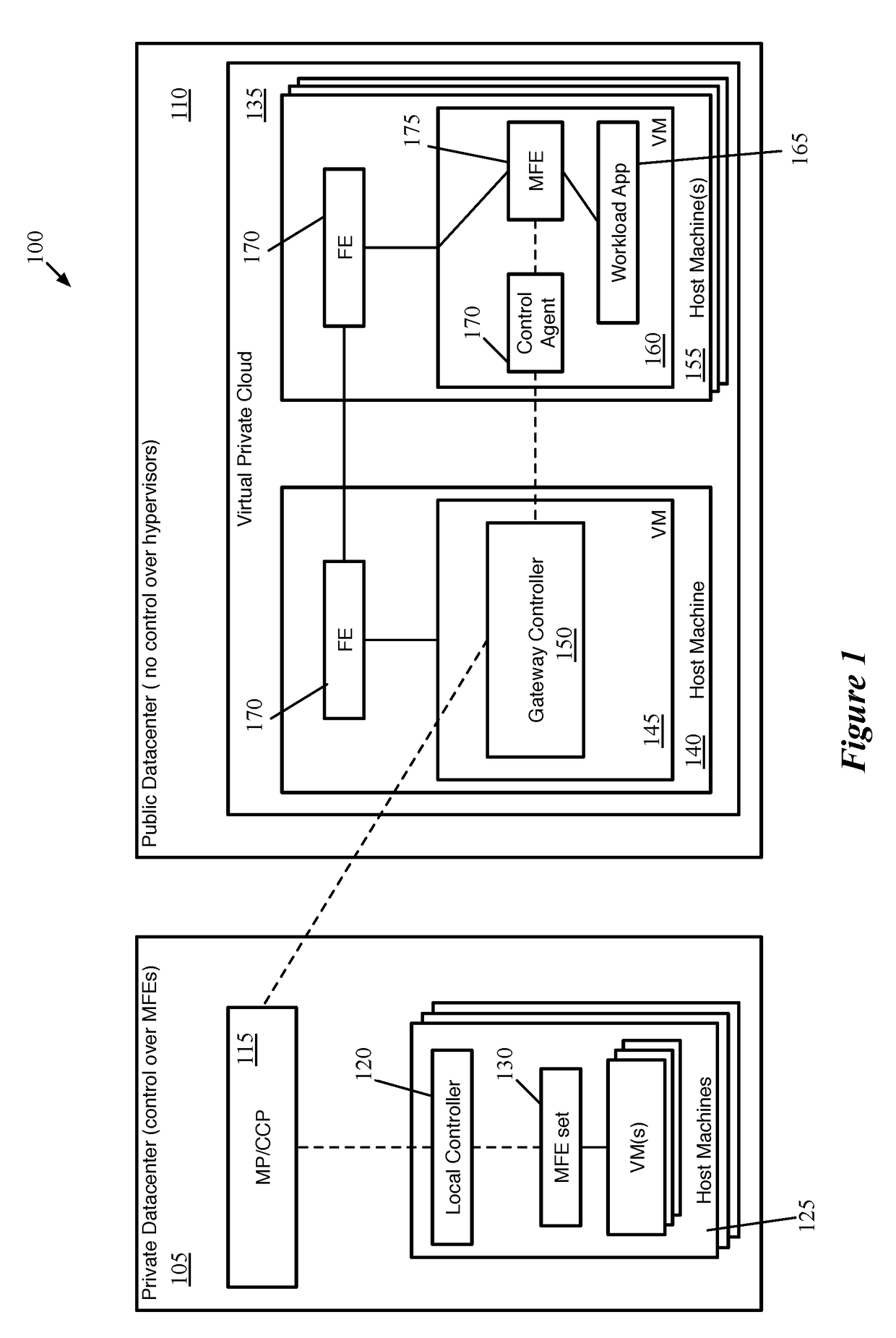
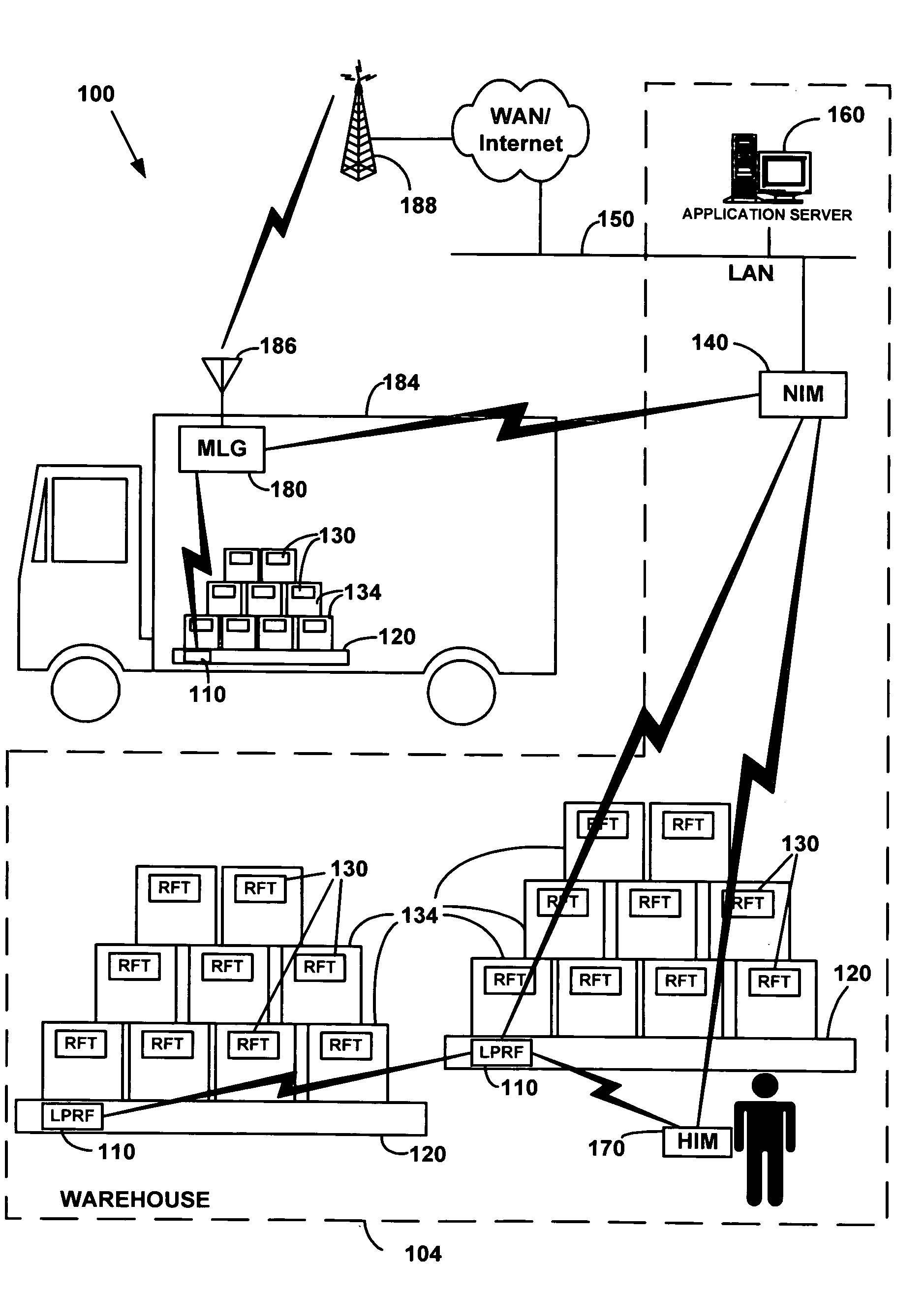
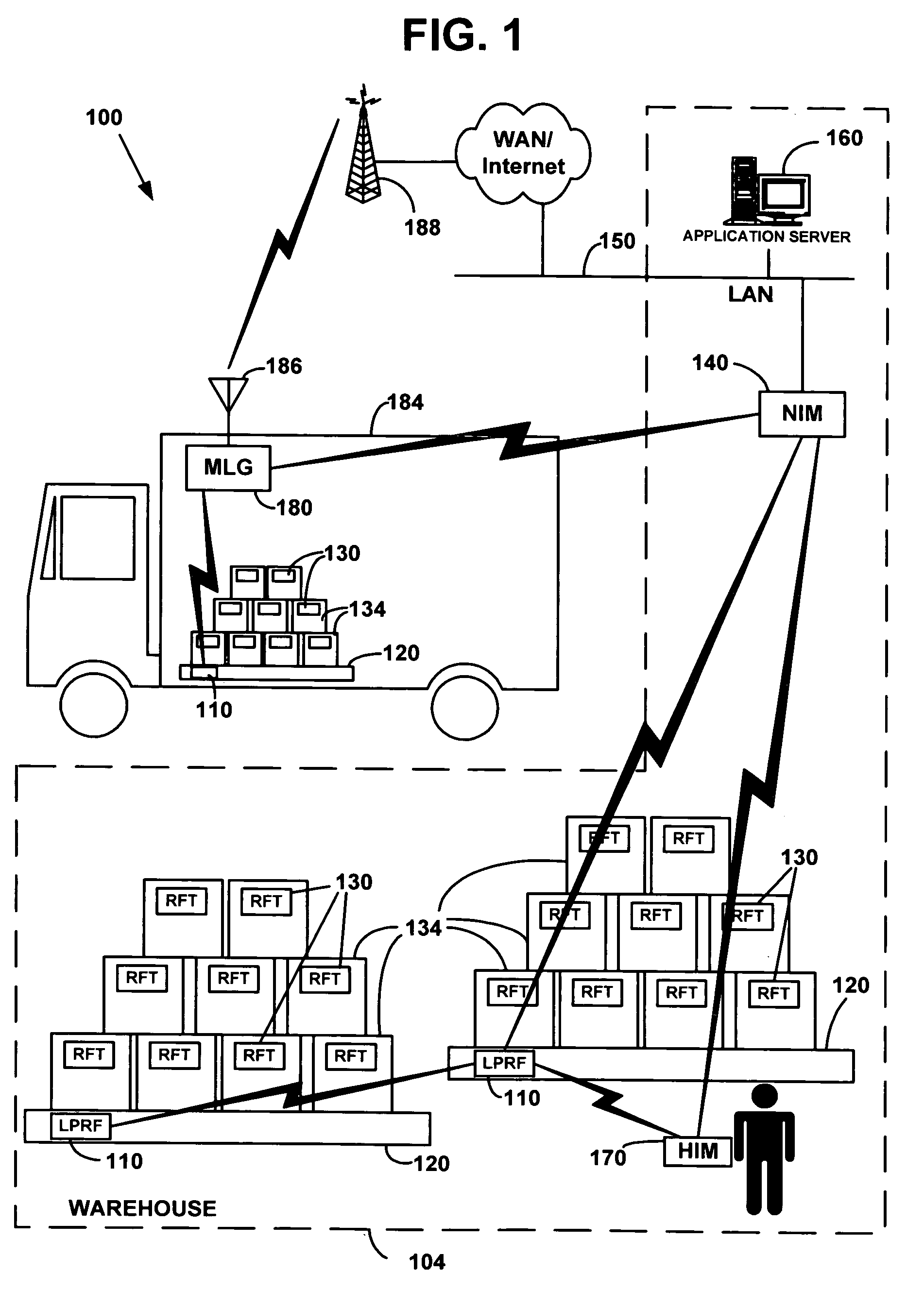
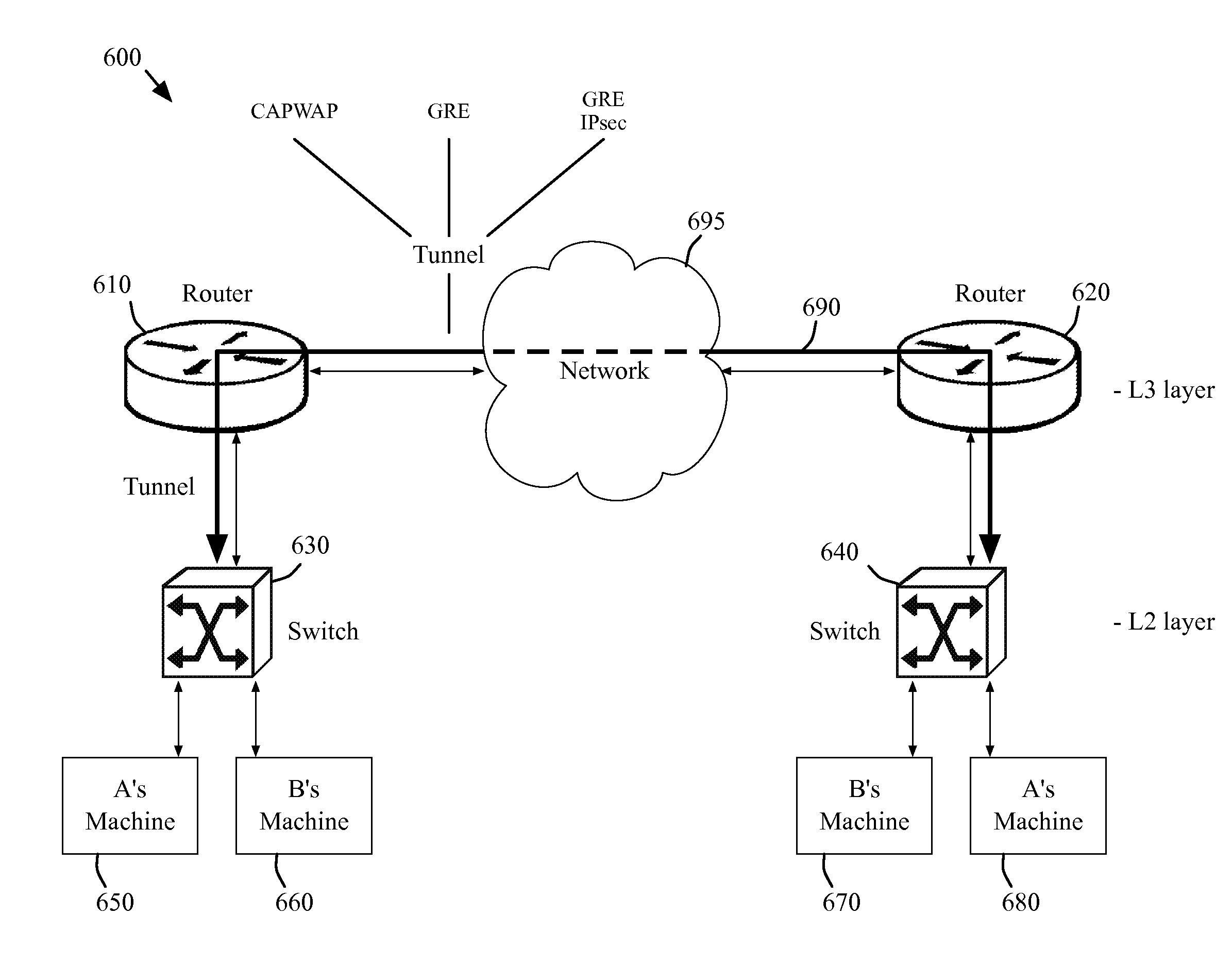
Simplified configuration and security for networked wireless devices
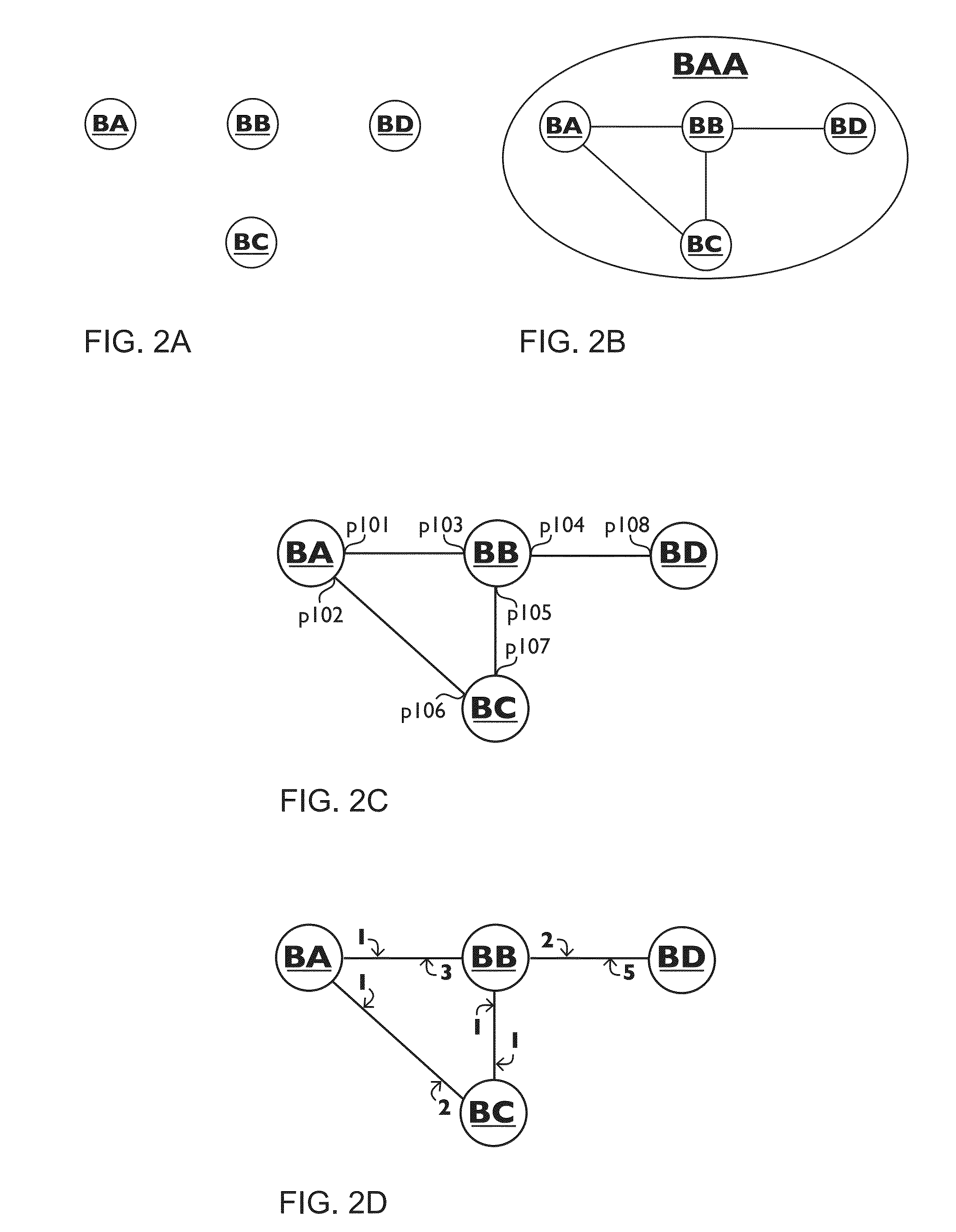
ActiveUS7356011B1Simple configurationEasy to implementSpecial service provision for substationNetwork traffic/resource managementLogical network
Wireless devices are easily configured with logical network and security settings. Configuration commands are received at master and slave wireless devices. The devices switch to predetermined logical network and security settings to allow communication between the master and slave devices. The master device selects a logical network and / or security setting and sends the setting(s) to the slave device. Both devices then switch to the selected setting(s) and use the setting(s) for future communications.
Owner:MAYFIELD XI +9
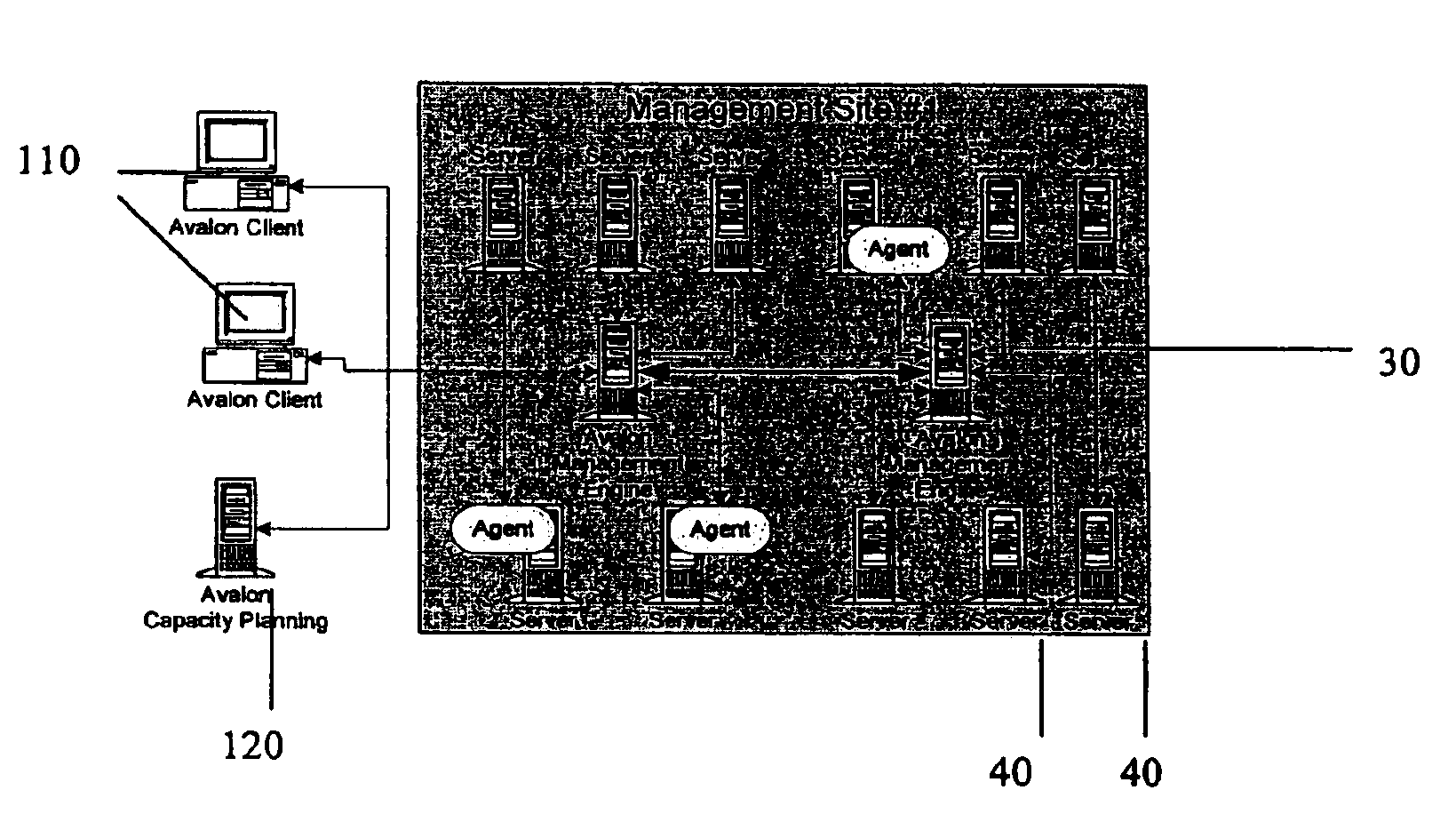
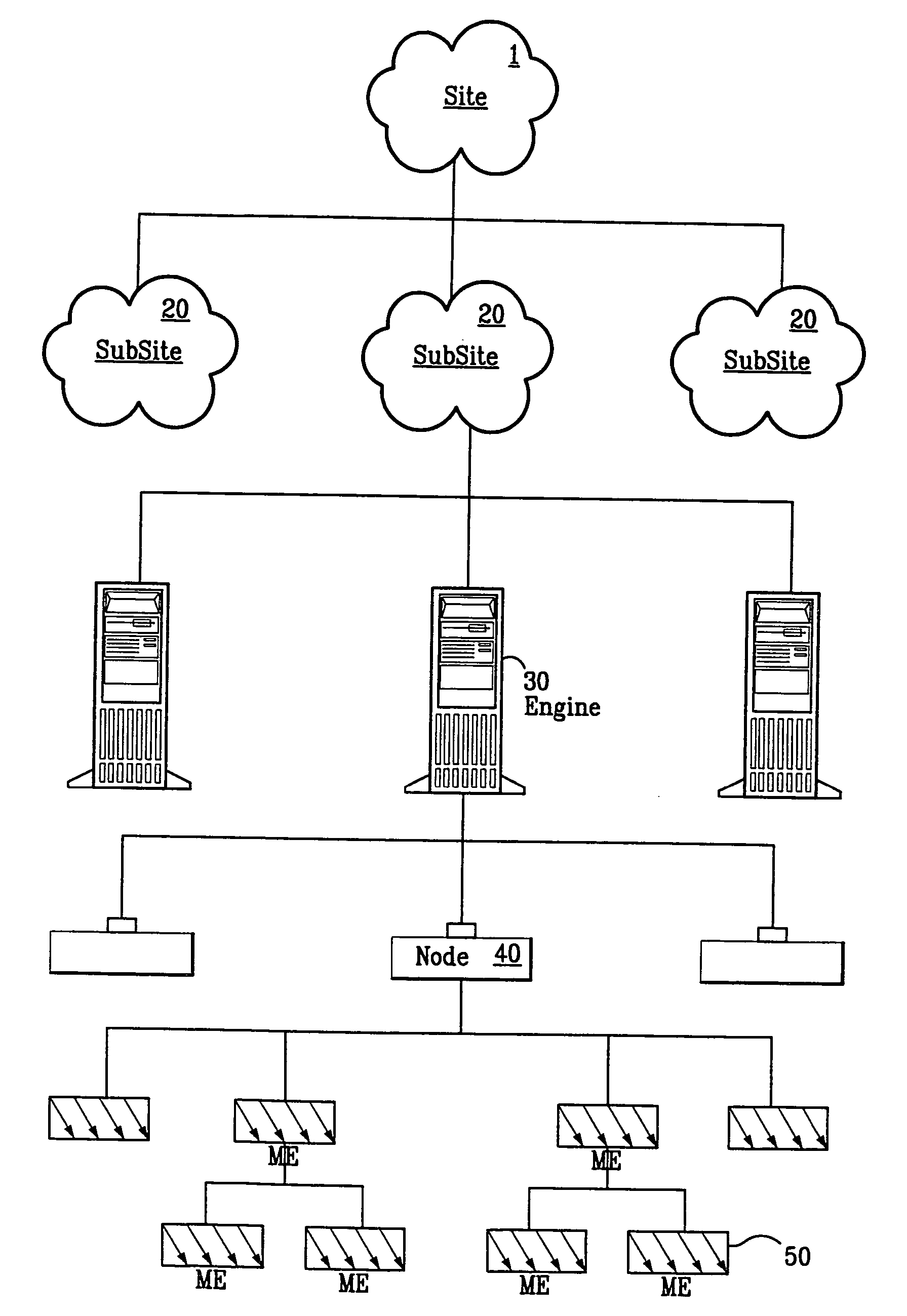
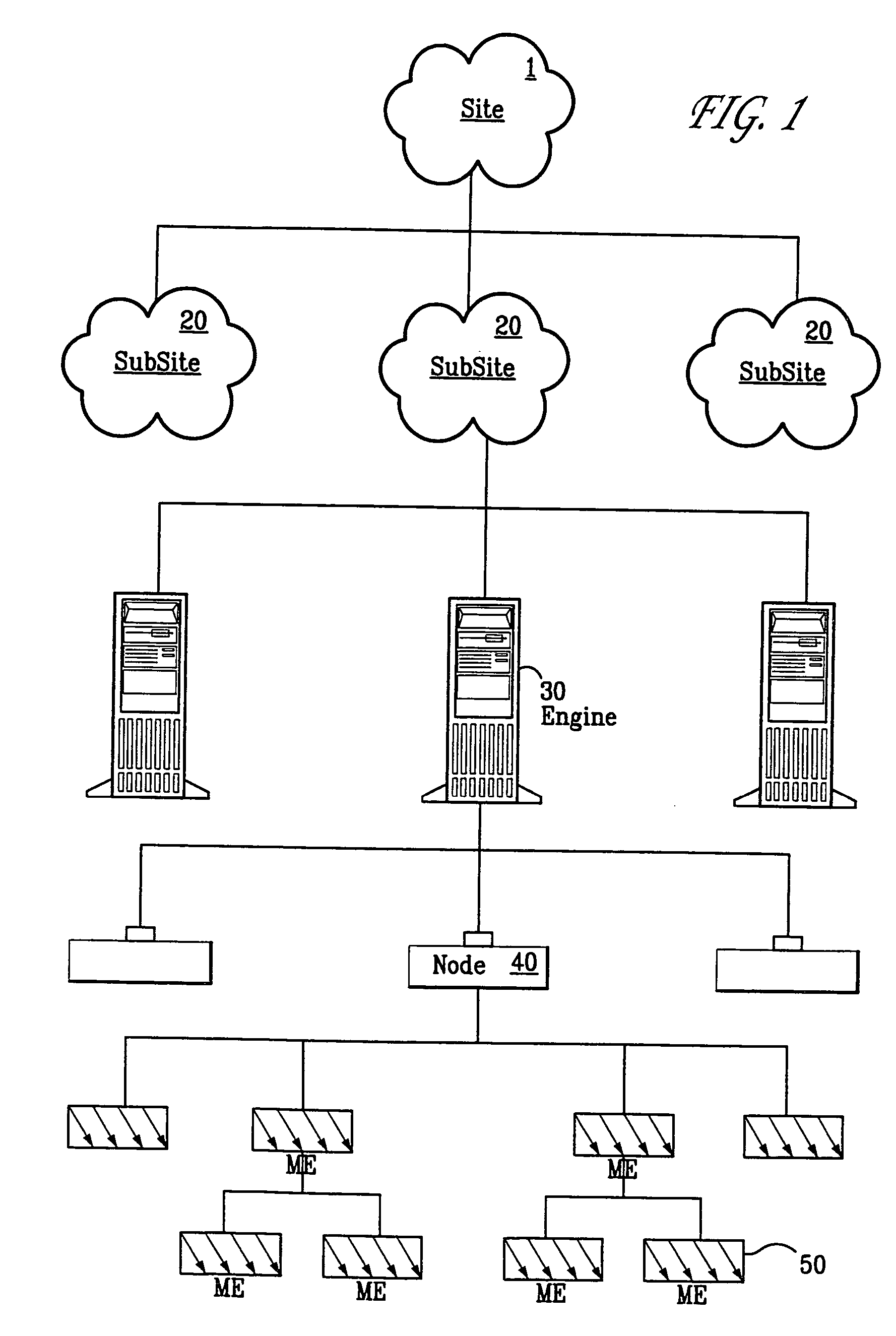
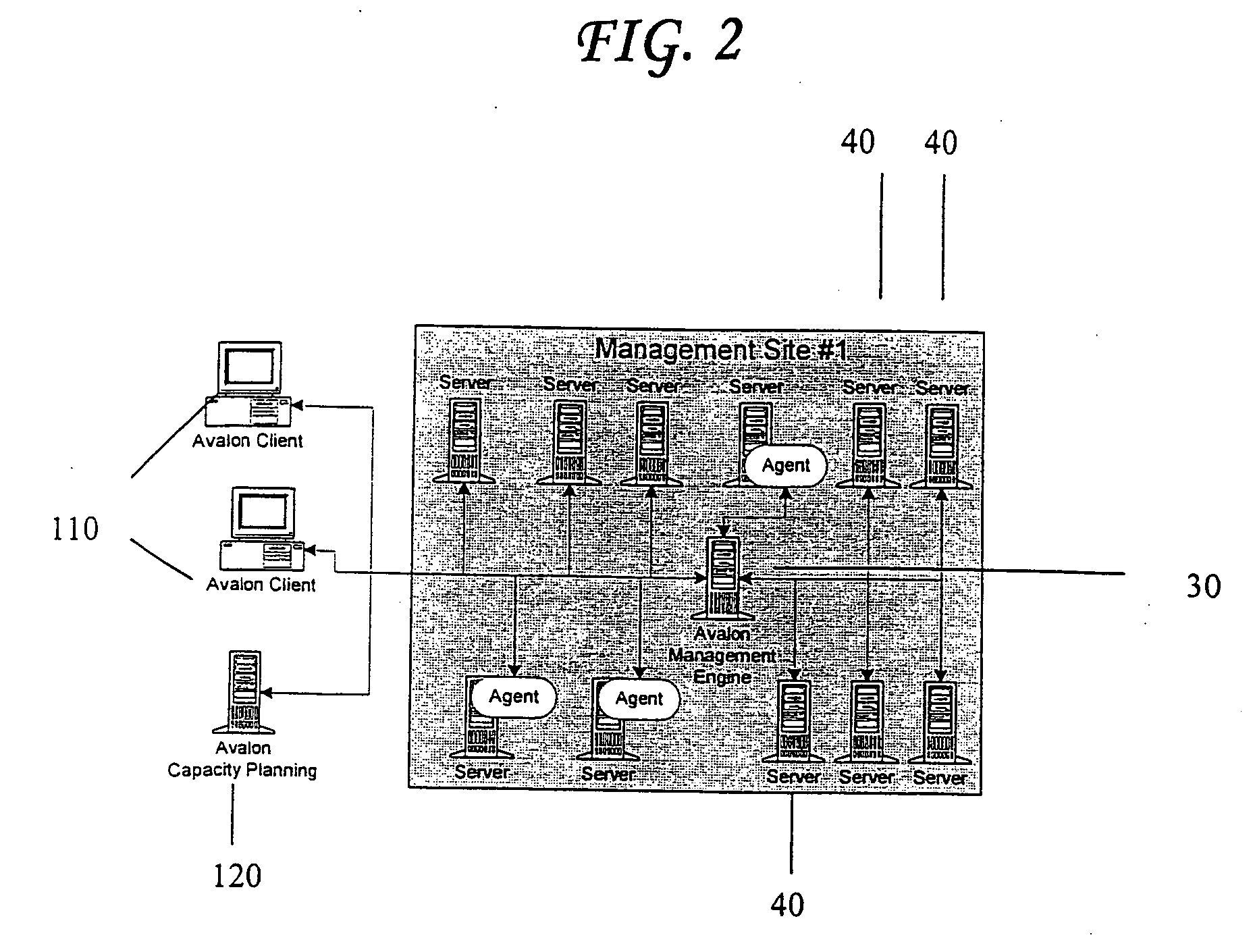
Enterprise management system
InactiveUS6983317B1Improve availabilityImprove robustnessDigital computer detailsTransmissionRoot cause analysisAccess management
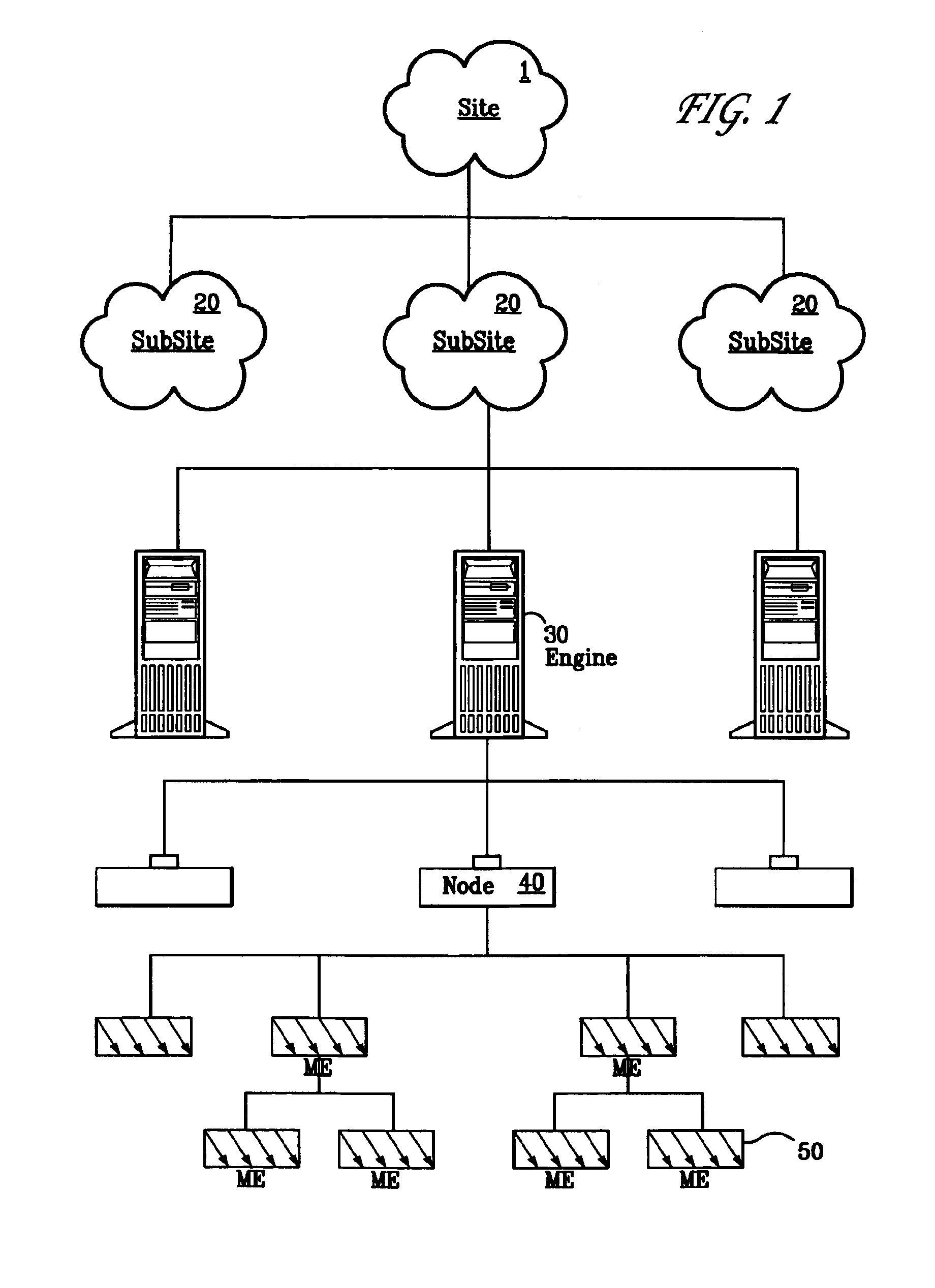
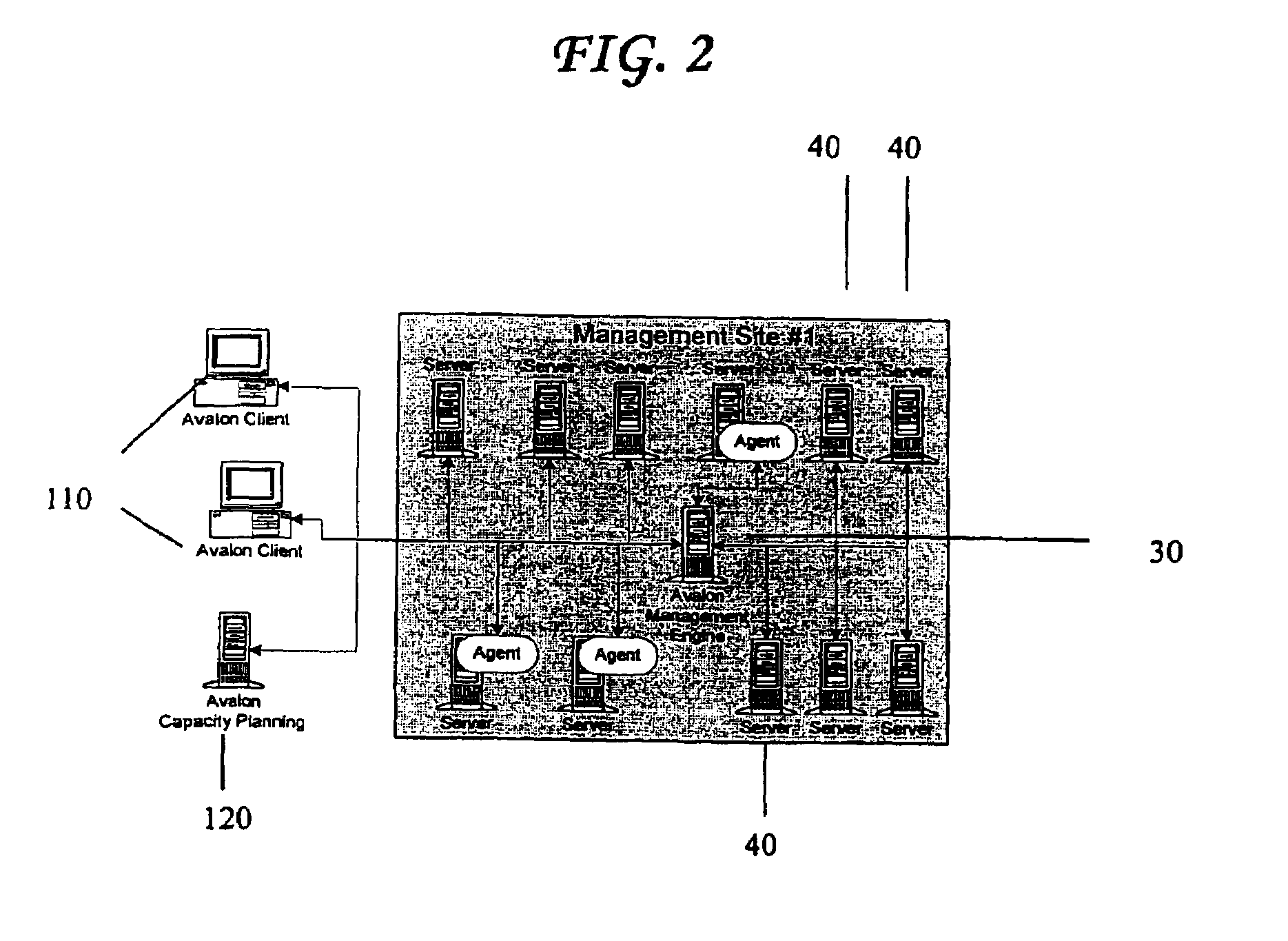
A Managed Site (10), a logical network entity, is composed of a number of Sub Sites (20) in a one to many relationship. A Sub Site (20) is a logical component, which is composed of a number of Engines (30). Nodes (40) similarly relates to their Engine (30) in a many to one relationship. A Node (40) is a collection of Managed Elements (ME's) (50) (while being an ME (50) itself), which represent network state information. The subsite (20) consists of the engine (30) connected to server nodes (40). One or more clients (110) are connected to the management engine (30) and access management engine (30) information relating to managed elements (50) including nodes (40). The connected manager engines may communicate with one another so that, for example, in the event of a failure, one of the manager engines remaining on line commences monitoring of manage elements assigned to the failed manager engine. Upon accessing the manager engine (30), the client interface displays relationships among managed elements (50) using meaningful connectors and tree-like structures. In addition to basic managed element state monitoring functionality, the manager engine (30) provides a variety of automated tasks ensuring the health of the network and optimal failure correction in the event of a problem. For example, the manager engine (30) performs root cause analysis utilizing an algorithm tracing through manged element (50) relationships and indicating the source of the failure.
Owner:MICROSOFT TECH LICENSING LLC
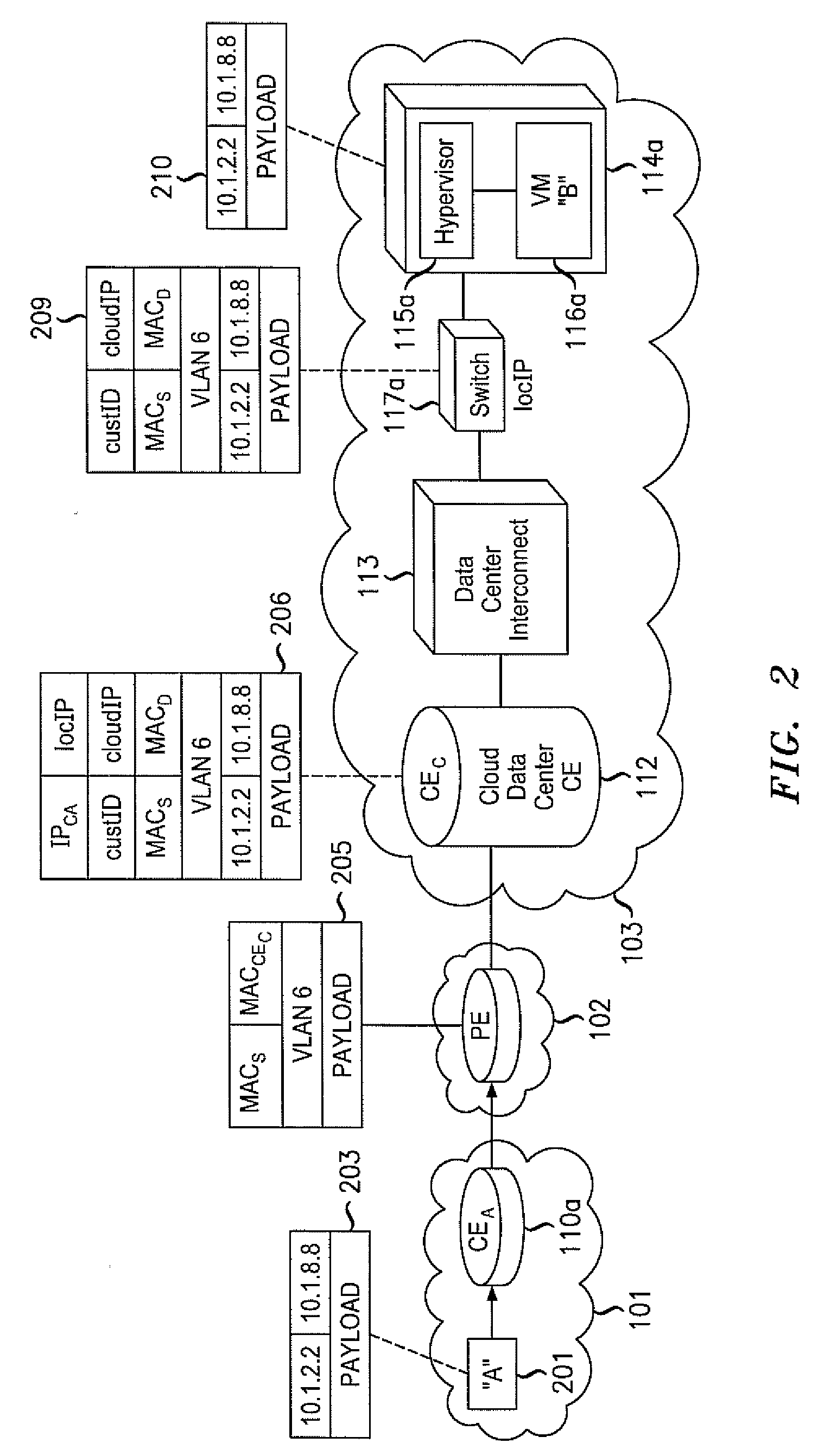
Layer 2 seamless site extension of enterprises in cloud computing
ActiveUS20110075667A1Ensure safetyHighly-dynamic scalability of cloud resourcesMultiple digital computer combinationsNetworks interconnectionNetwork packetIp address
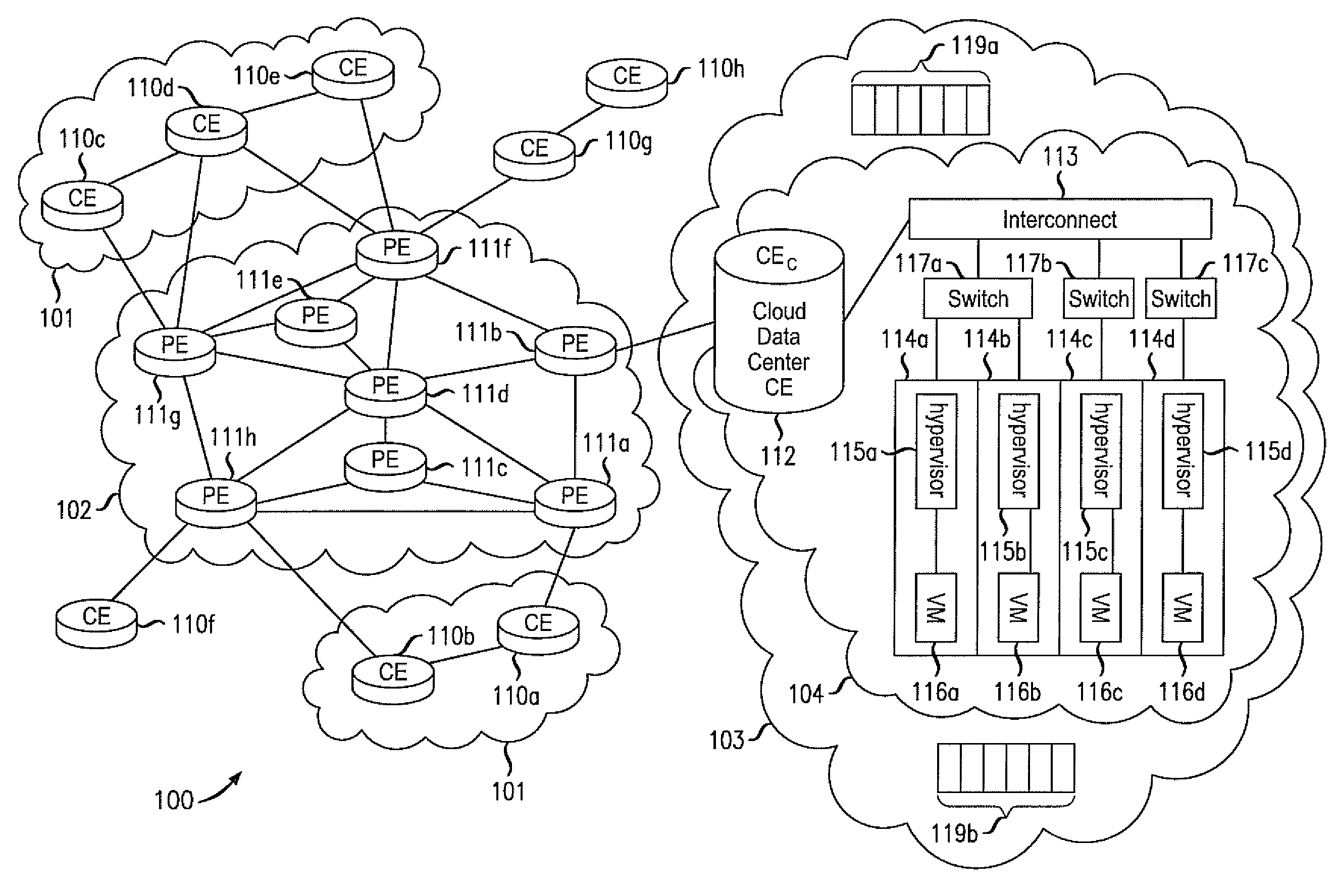
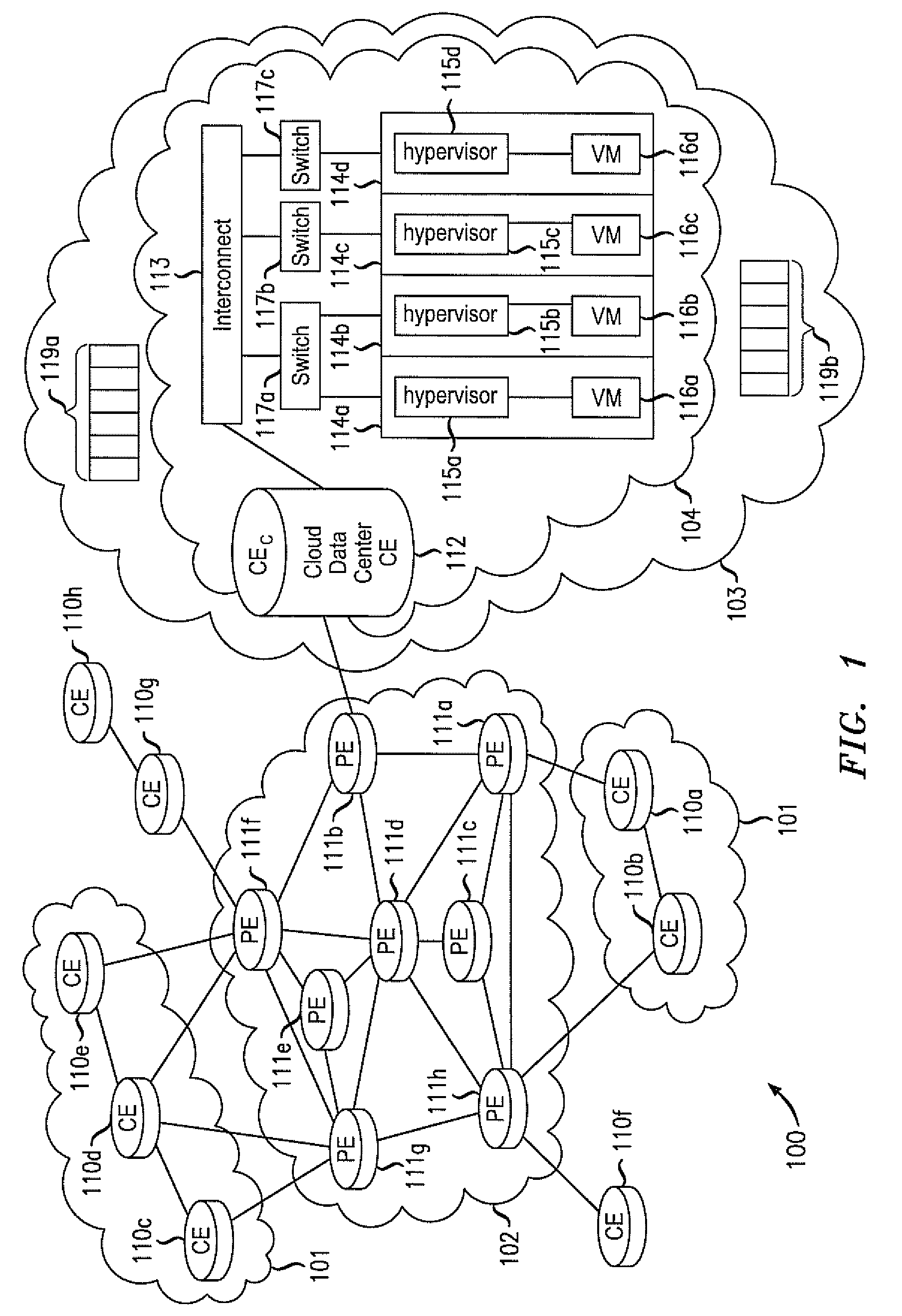
Various embodiments relate to a Cloud Data Center, a system comprising the Cloud Data Center, and a related method. The Cloud Data Center may include a logical customer edge router to send packets between addresses in a private enterprise network and addresses in a logical network within a cloud network using Layer 2 protocol and MAC addressing. The logical network may have resources, known as virtual machines, allocated to the private enterprise network and may share a common IP address space with the private enterprise network. A directory at the Cloud Data Center may correlate the enterprise IP addresses of virtual machines with a MAC address, cloud IP address, and a location IP address within the logical network. The Cloud Data Center may double encapsulate packets with MAC, cloudIP, and locIP headers, when sending a packet to a destination in the logical network.
Owner:ALCATEL LUCENT SAS
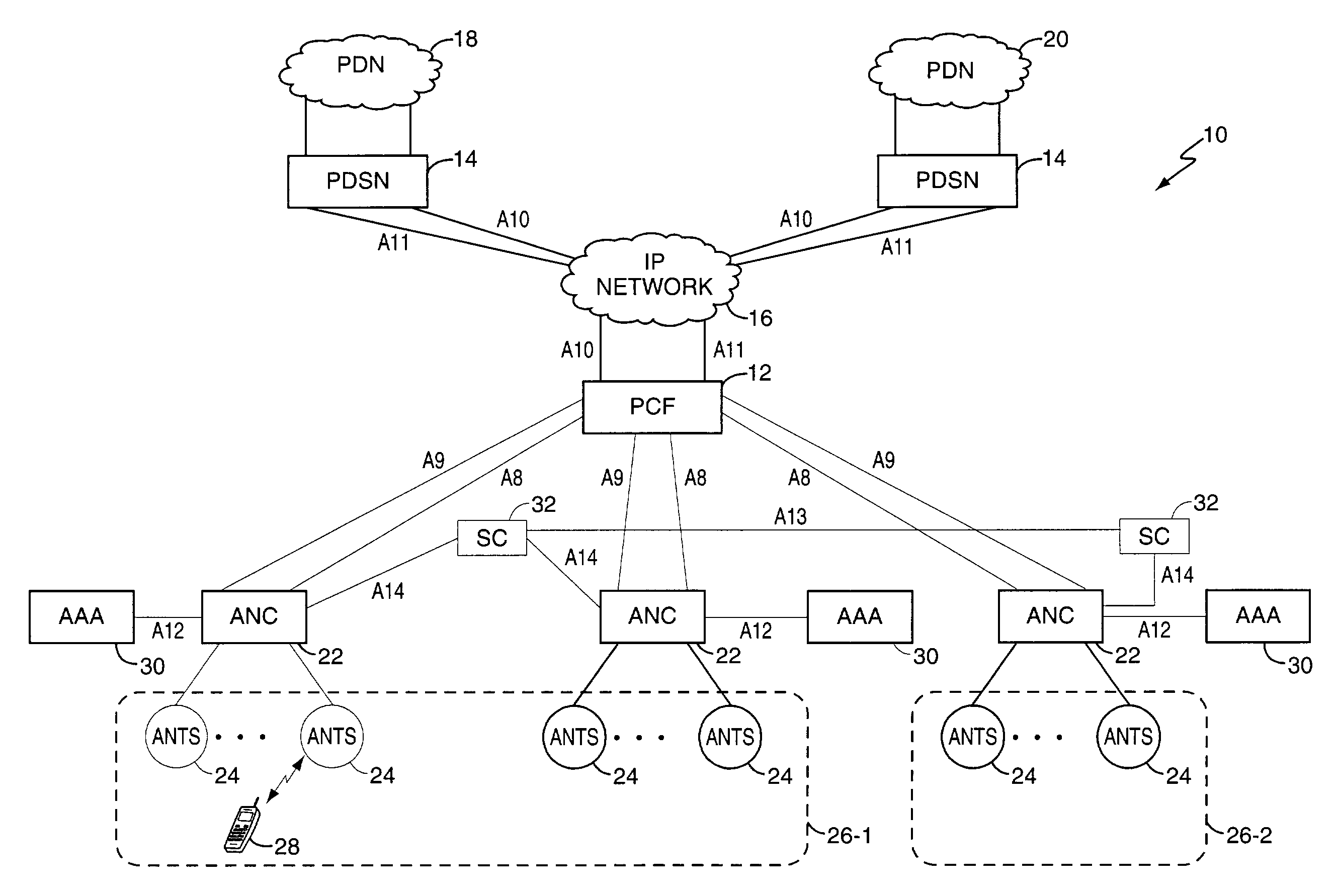
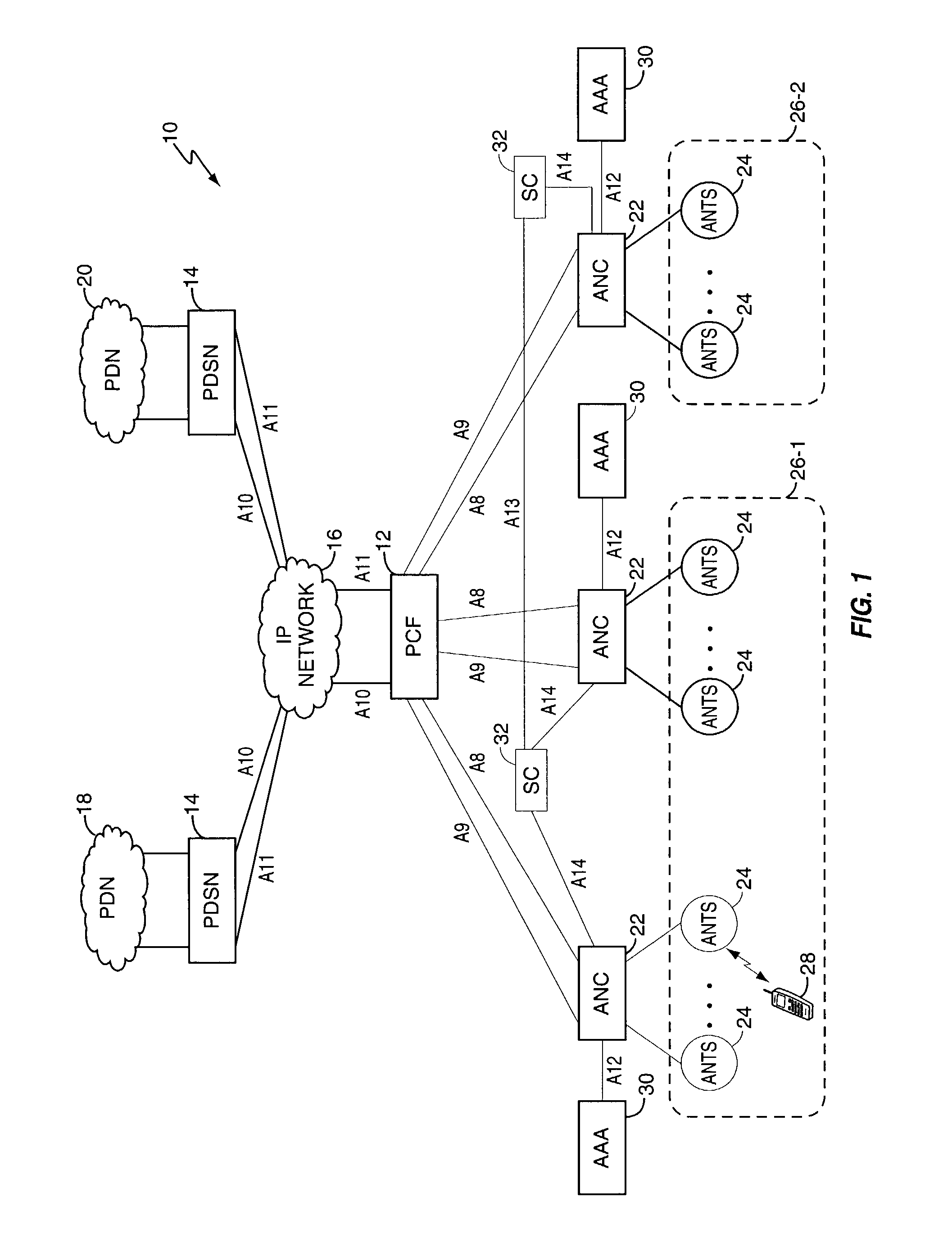
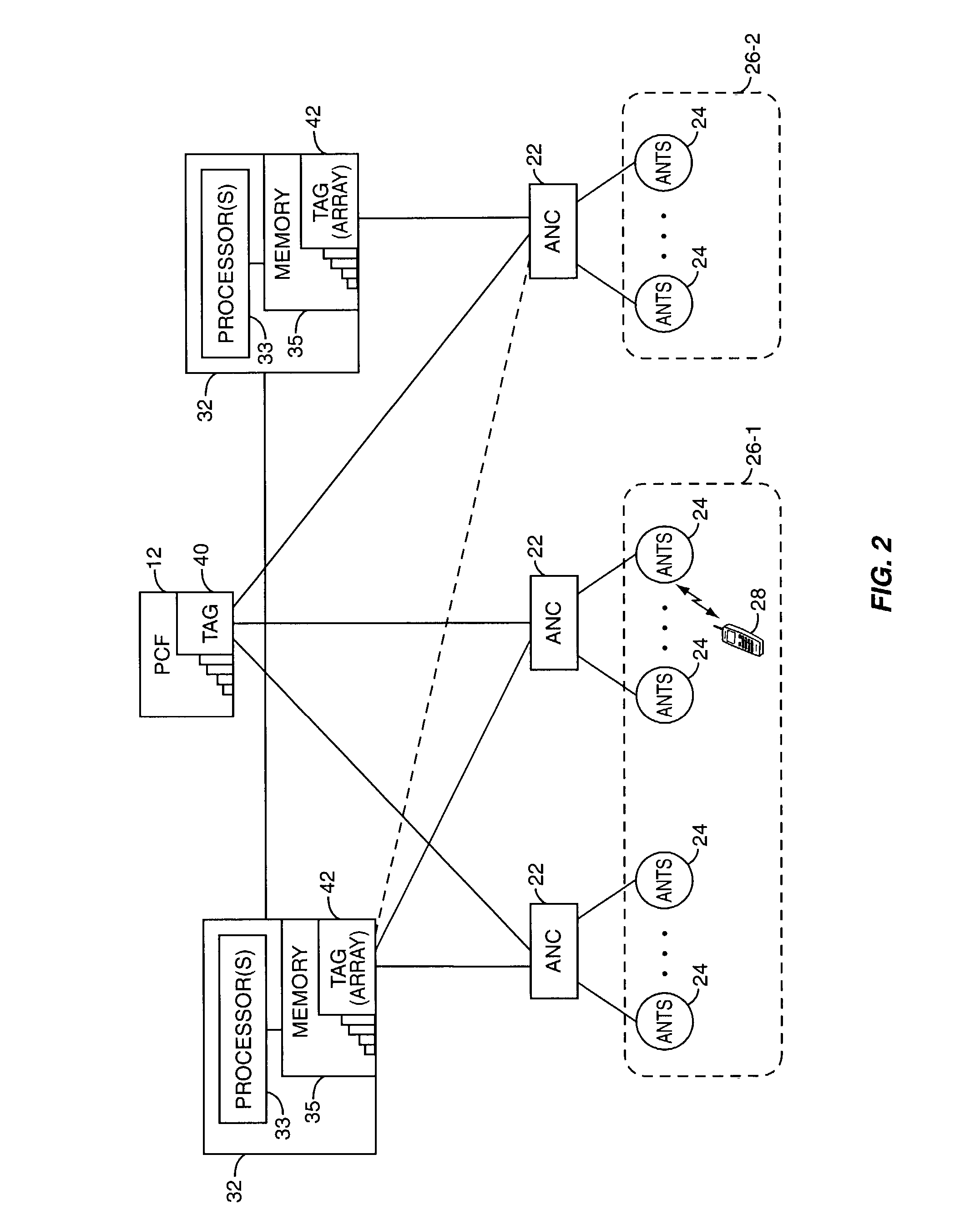
Mobility management entity for high data rate wireless communication networks
ActiveUS7457265B2Reduce amountEasy to manageTime-division multiplexData switching by path configurationSession controlGranularity
A session controller provides mobility management support in a 1xEVDO wireless communication network, such as one configured in accordance with the TIA / EIA / IS-856 standard. Operating as a logical network entity, the SC maintains location (e.g., a pointing tag) and session information at an access network controller (ANC) granularity, thus allowing it to track access terminal (AT) transfer between ANCs but within subnet boundaries, where a network subnet comprises one or more ANCs. This allows a packet control function (PCF) to maintain location information at a packet zone granularity, thereby reducing mobility management overhead at the PCF. The SC provides updated tag and session information to PCFs, ANCs, and other SCs as needed. Information exchange with other SCs arises, for example, when two or more SCs cooperate to maintain or transfer routing and session information across subnets.
Owner:TELEFON AB LM ERICSSON (PUBL)
Extension of logical networks across layer 3 virtual private networks
ActiveUS20130287026A1Increase heightGood serviceData switching by path configurationPrivate networkLogical network
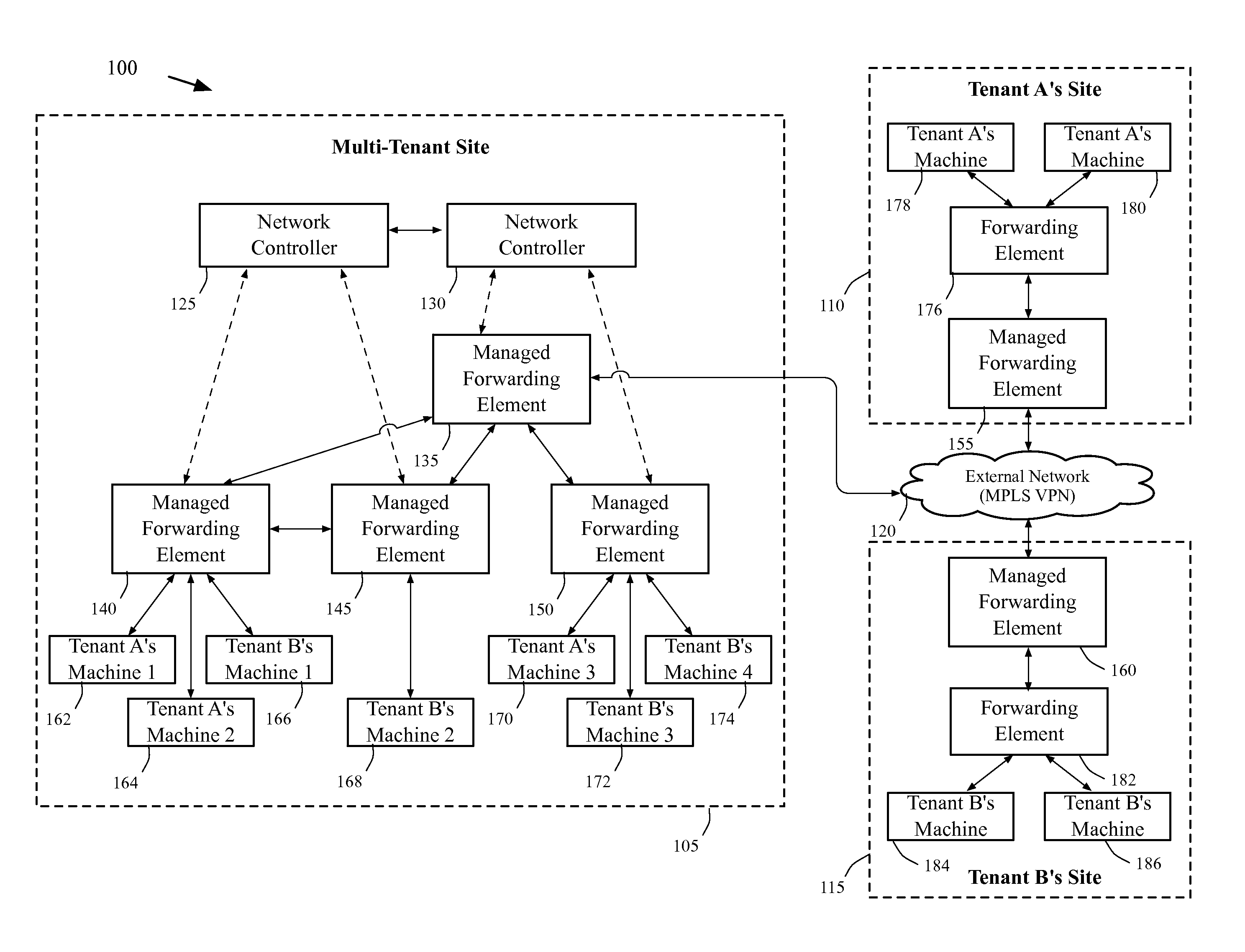
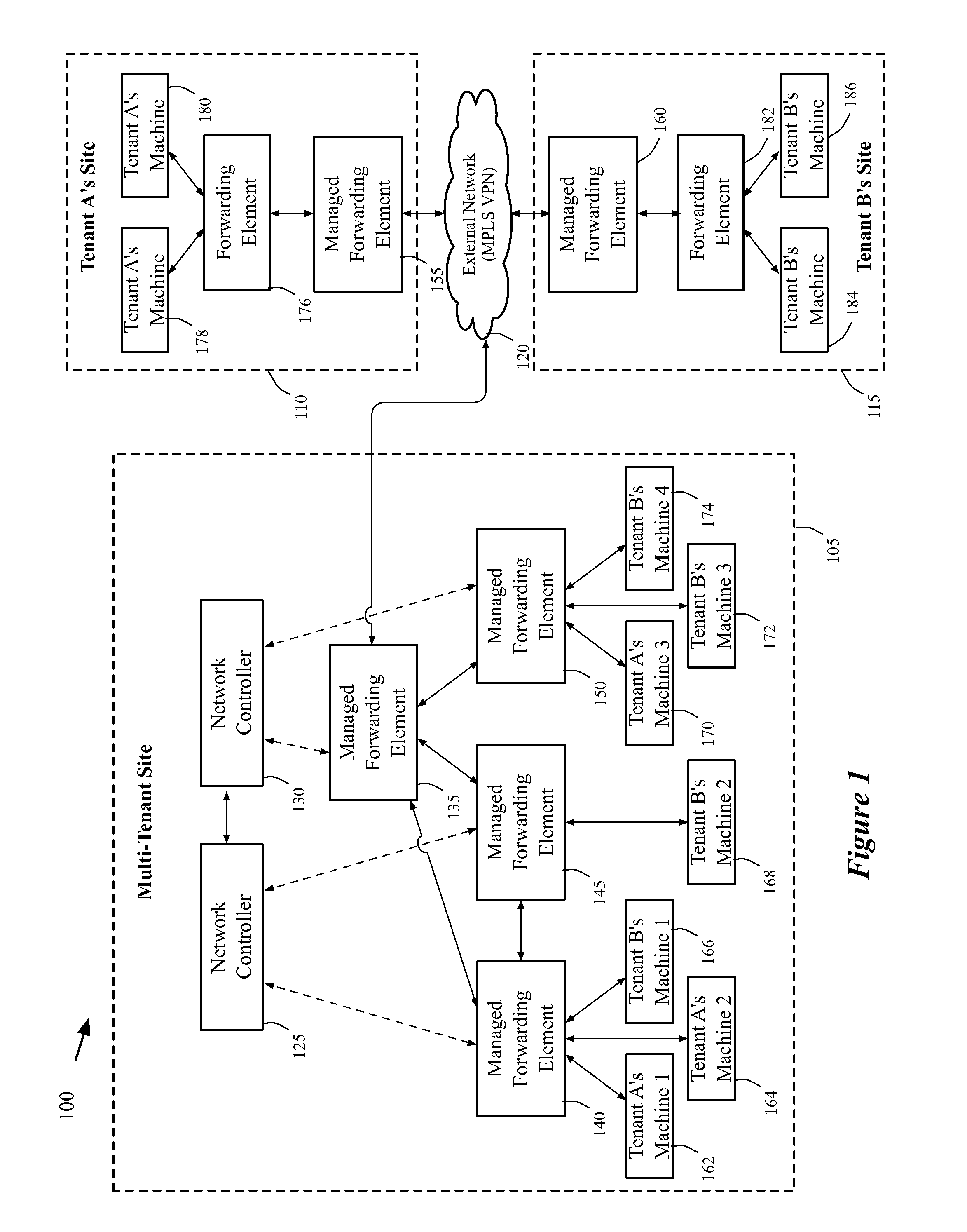
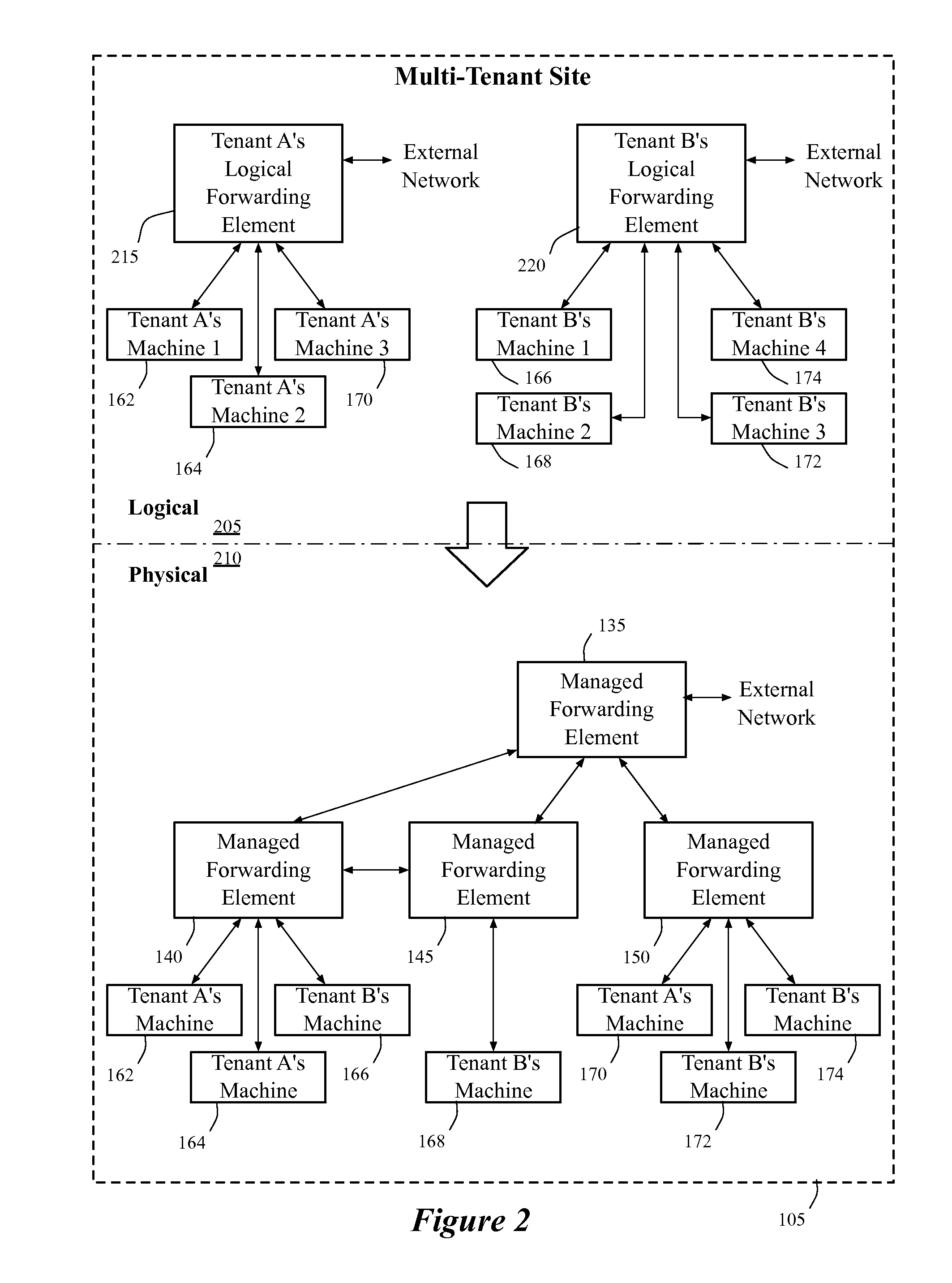
A method of manages a set of managed forwarding elements that forward data between machines. The method configures (1) a first managed forwarding element to operate in a first network that uses first and second address spaces that at least partially overlap with each other, (2) a second managed forwarding element to operate in a second network that uses the first address space, and (3) a third managed forwarding element to operate in a third network that uses the second address space. A machine in the second network and a machine in the third network have an identical address that belongs to both the first and second address spaces. The method directs the first managed forwarding element to connect to the second and third managed forwarding elements in a manner that enables the first managed forwarding element to forward data from a machine in the first network to the machine in the second network via the second managed forwarding element.
Owner:NICIRA
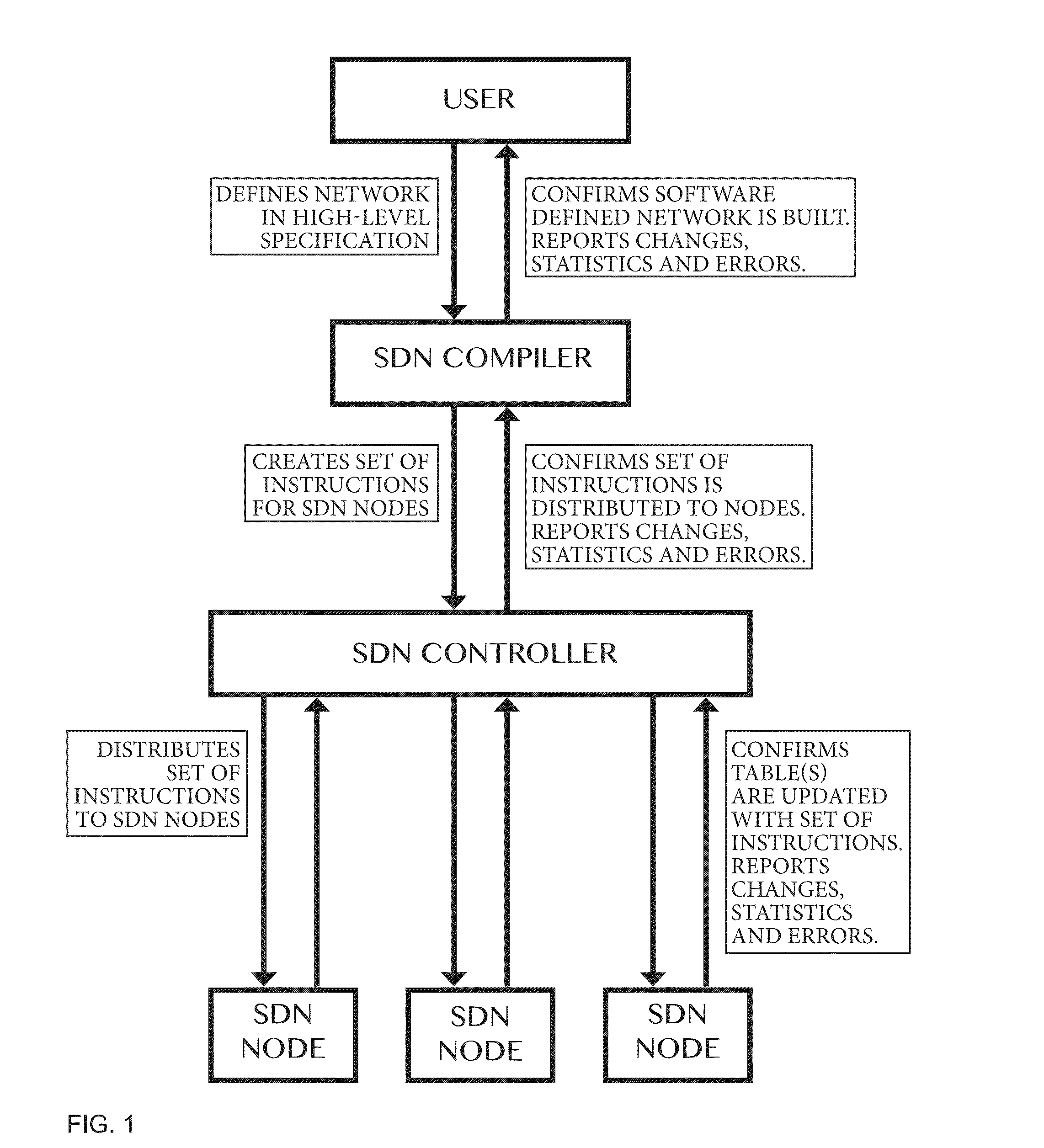
Compiler for and method for software defined networks
ActiveUS20160173338A1Small sizeSpeed up the calculation processDigital computer detailsData switching networksLogical networkSoftware define network
Method of and a compiler for controlling a network based on a logical network model. The network has physical nodes and virtual nodes. The physical nodes are interconnected by physical links in accordance with a physical network layout. The logical network model has logical nodes indicated with a logical node name which refers to at least one physical or at least one virtual node in the network. The method uses a physical forwarding point-of-attachment relation defining physical paths of the physical network in dependence on a physical forwarding policy, a first mapping relation defining how the virtual nodes and the physical nodes are mapped to one another, and a second mapping relation defining how the logical nodes are mapped to the physical nodes and the virtual nodes. The method also includes transforming paths in the physical network to paths between the physical nodes and the virtual nodes.
Owner:WOLTING HLDG
Secure network-routed voice multicast dissemination
InactiveUS20040095900A1Efficient processTime-division multiplexData switching by path configurationVoice communicationMobile communication systems
Systems and methods are provided for routing voice communications to groups in a voice communication system. The voice communication system can be a mobile communication system having a plurality of members grouped as logical networks and / or unit task organizations. One or more routers are provided in the system. The one or more routers extract routing information from received voice messages. The routing information is used with a router database to determine which identified group to route the digitized voice packets. The one or more routers can be adapted to receive and route voice communications to different radio types across different logical networks.
Owner:NORTHROP GRUMMAN SYST CORP
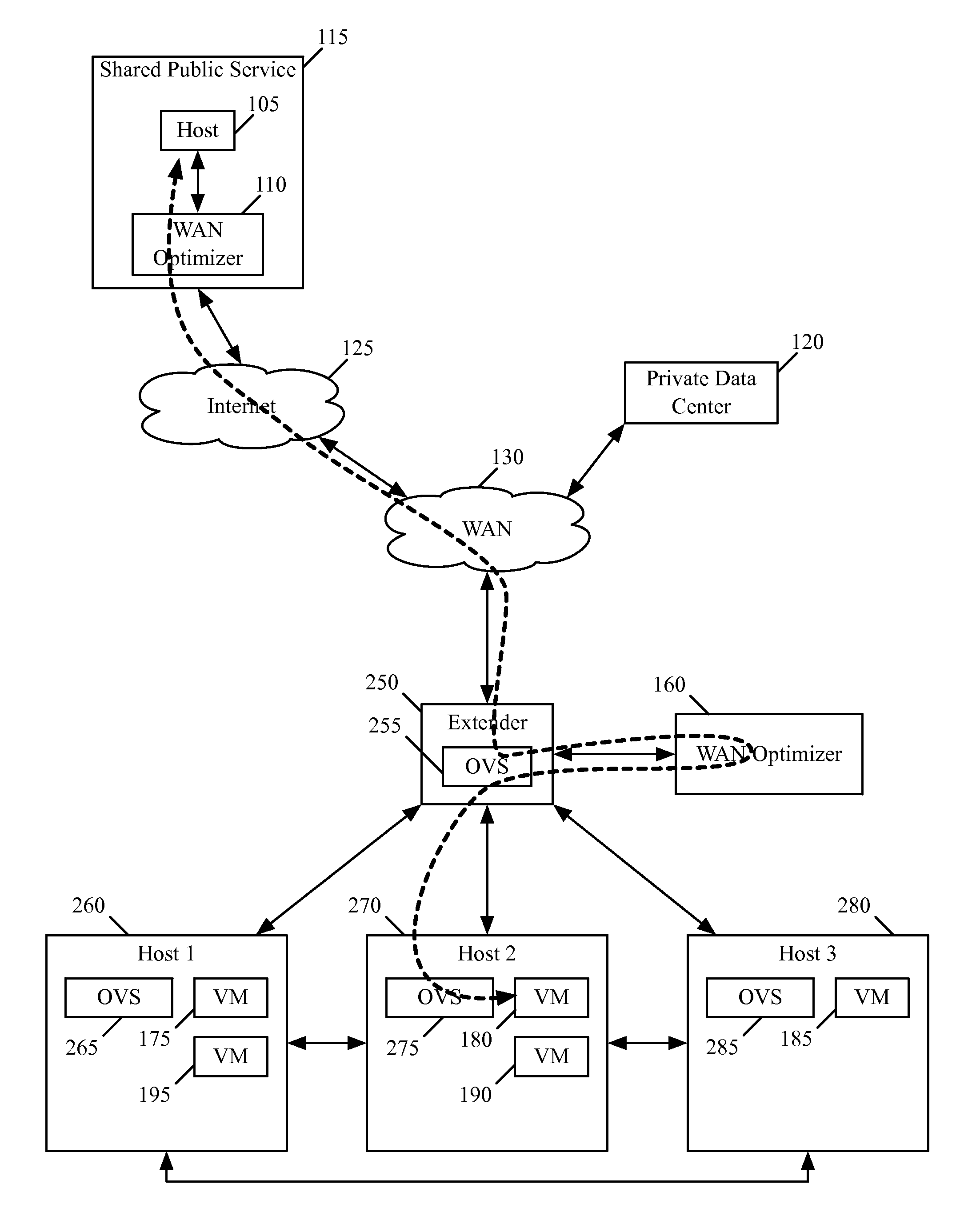
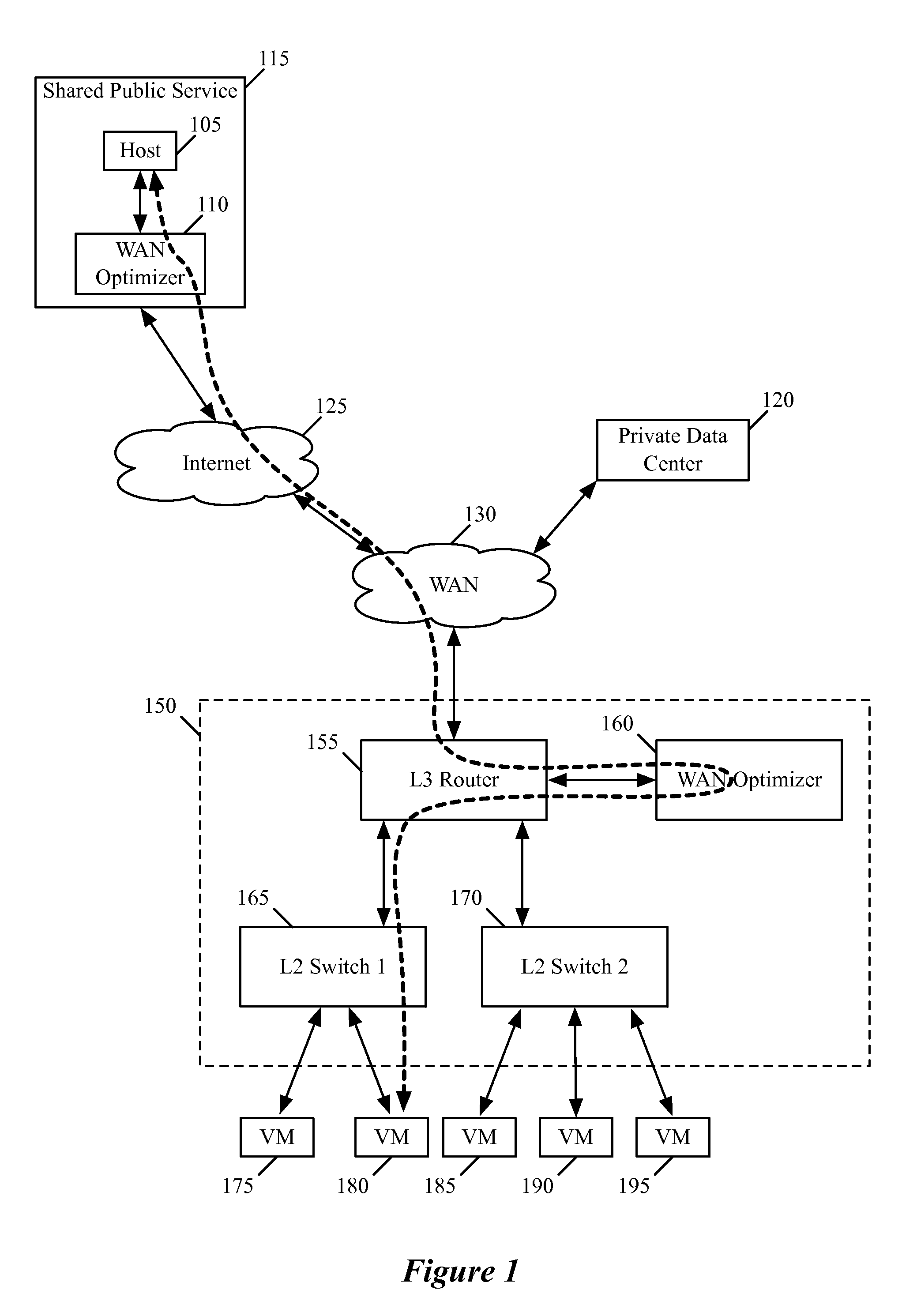
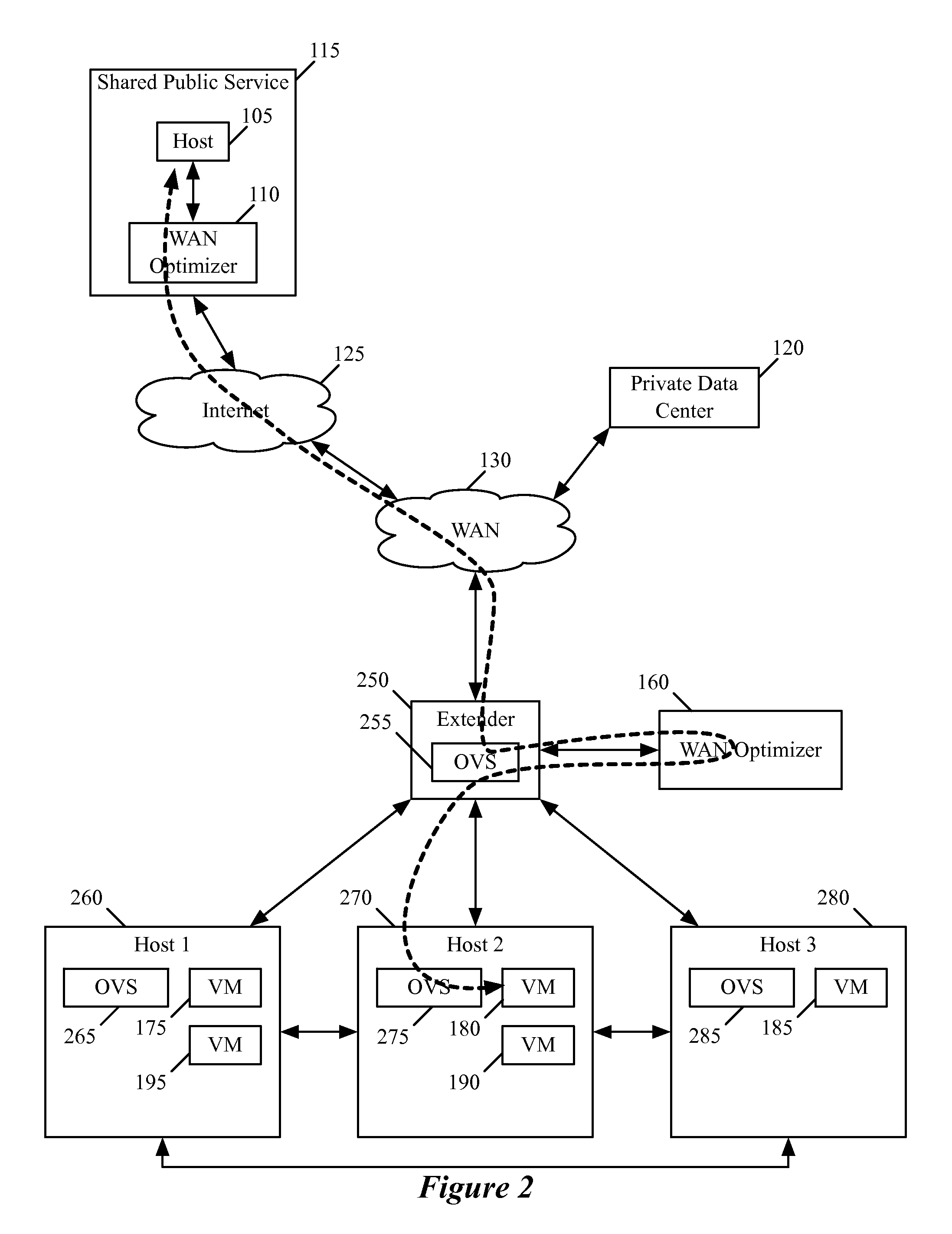
Wan optimizer for logical networks
ActiveUS20130121209A1Digital computer detailsData switching by path configurationControl systemNetwork control
Some embodiments provide a non-transitory machine readable medium of a controller of a network control system for configuring a wide area network (WAN) optimizer instance to implement a WAN optimizer for a logical network. The controller receives a configuration for the WAN optimizer to optimize network data from the logical network for transmission to another WAN optimizer. The controller identifies several other controllers in the network control system on which to implement the logical network. The controller distributes the configuration for implementation on the WAN optimizer.
Owner:NICIRA
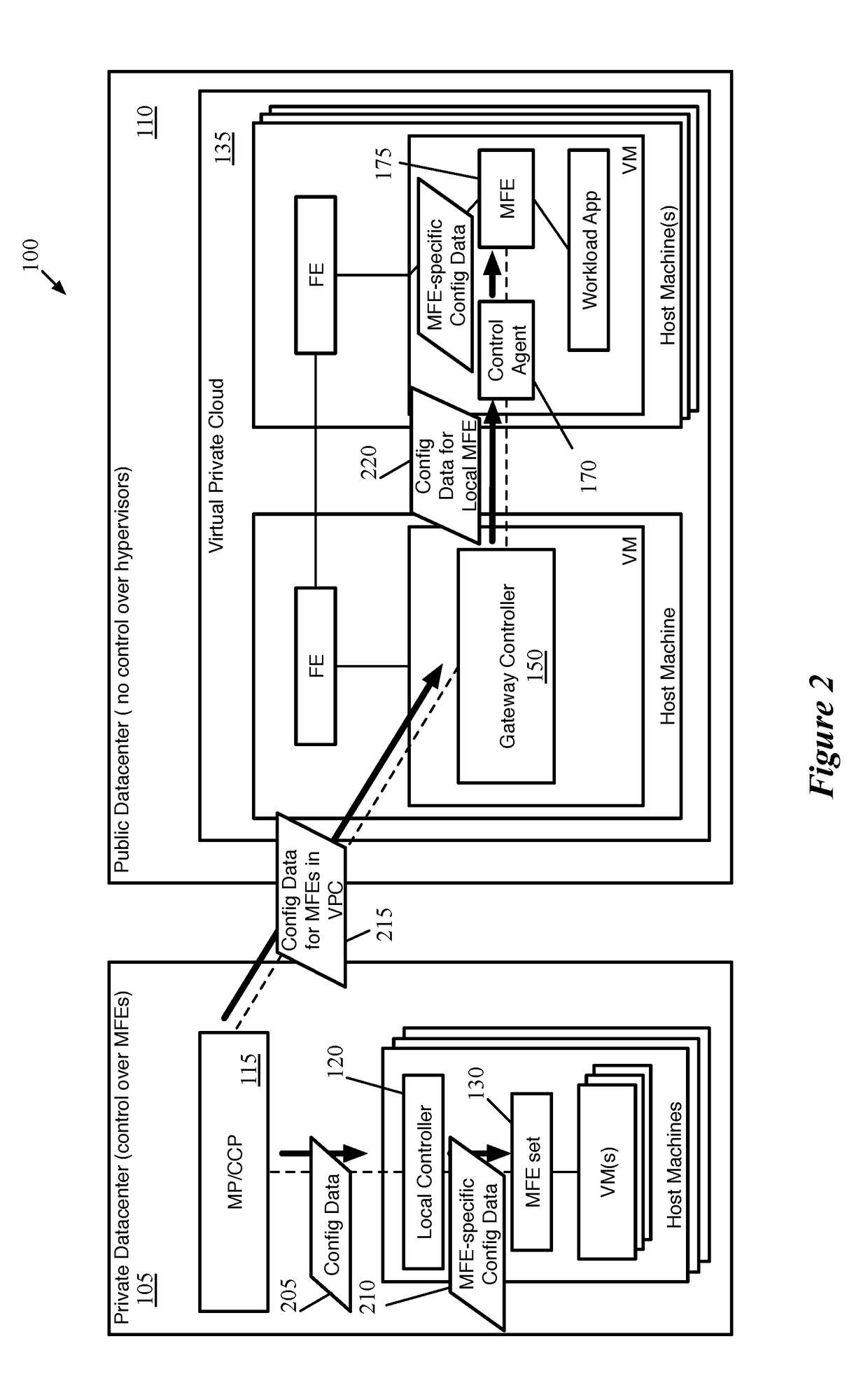
Distributed Network Encryption for Logical Network Implemented in Public Cloud
ActiveUS20180063193A1Key distribution for secure communicationUser identity/authority verificationKey distributionKey storage
Some embodiments provide a method for a first data compute node (DCN) operating in a public datacenter. The method receives an encryption rule from a centralized network controller. The method determines that the network encryption rule requires encryption of packets between second and third DCNs operating in the public datacenter. The method requests a first key from a secure key storage. Upon receipt of the first key, the method uses the first key and additional parameters to generate second and third keys. The method distributes the second key to the second DCN and the third key to the third DCN in the public datacenter.
Owner:NICIRA
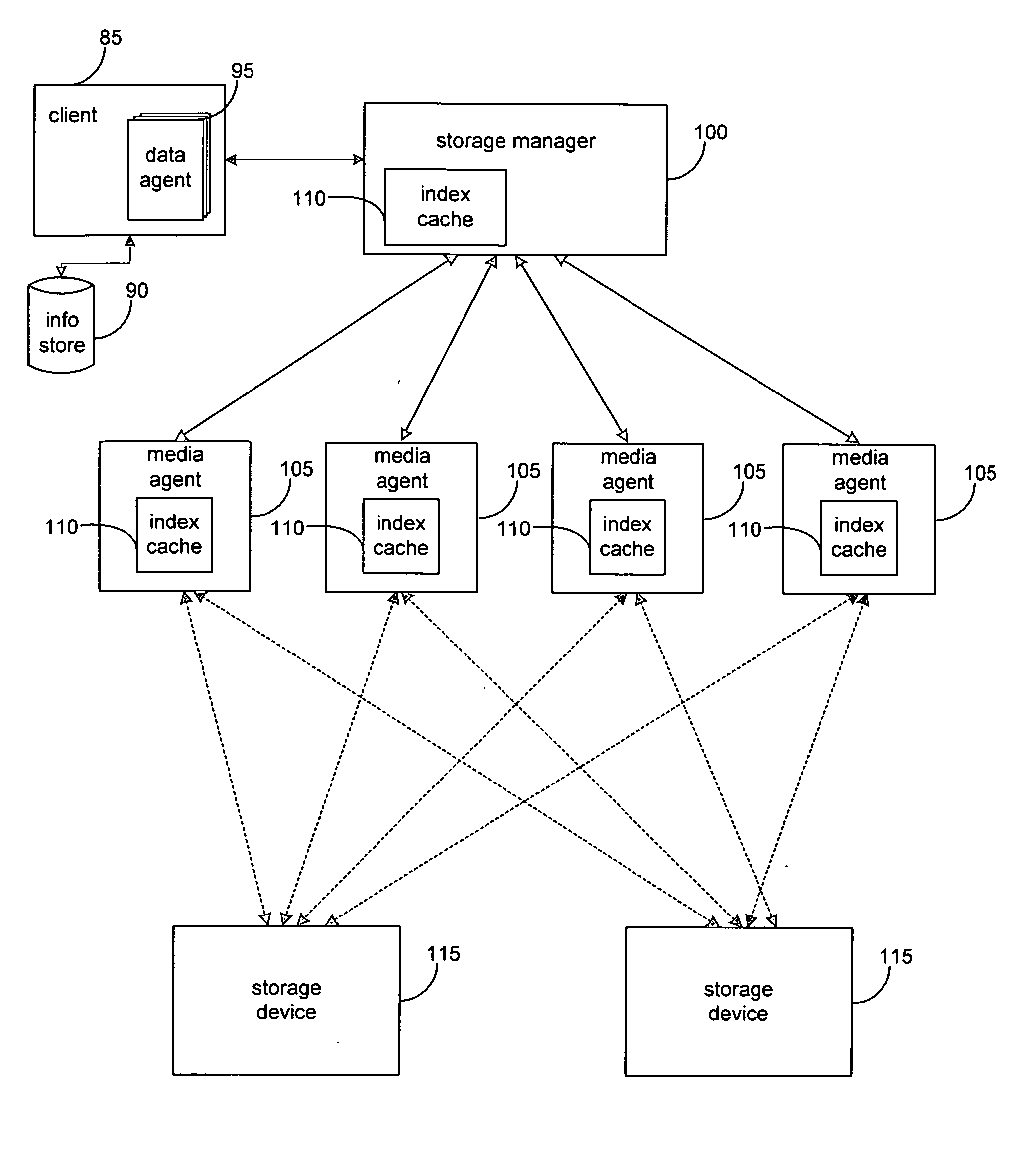
System and method for dynamically performing storage operations in a computer network
ActiveUS20050044114A1Data processing applicationsInput/output to record carriersLogical networkOperating system
Methods and systems are described for performing storage operations on electronic data in a network. In response to the initiation of a storage operation and according to a first set of selection logic, a media management component is selected to manage the storage operation. In response to the initiation of a storage operation and according to a second set of selection logic, a network storage device to associate with the storage operation. The selected media management component and the selected network storage device perform the storage operation on the electronic data.
Owner:COMMVAULT SYST INC
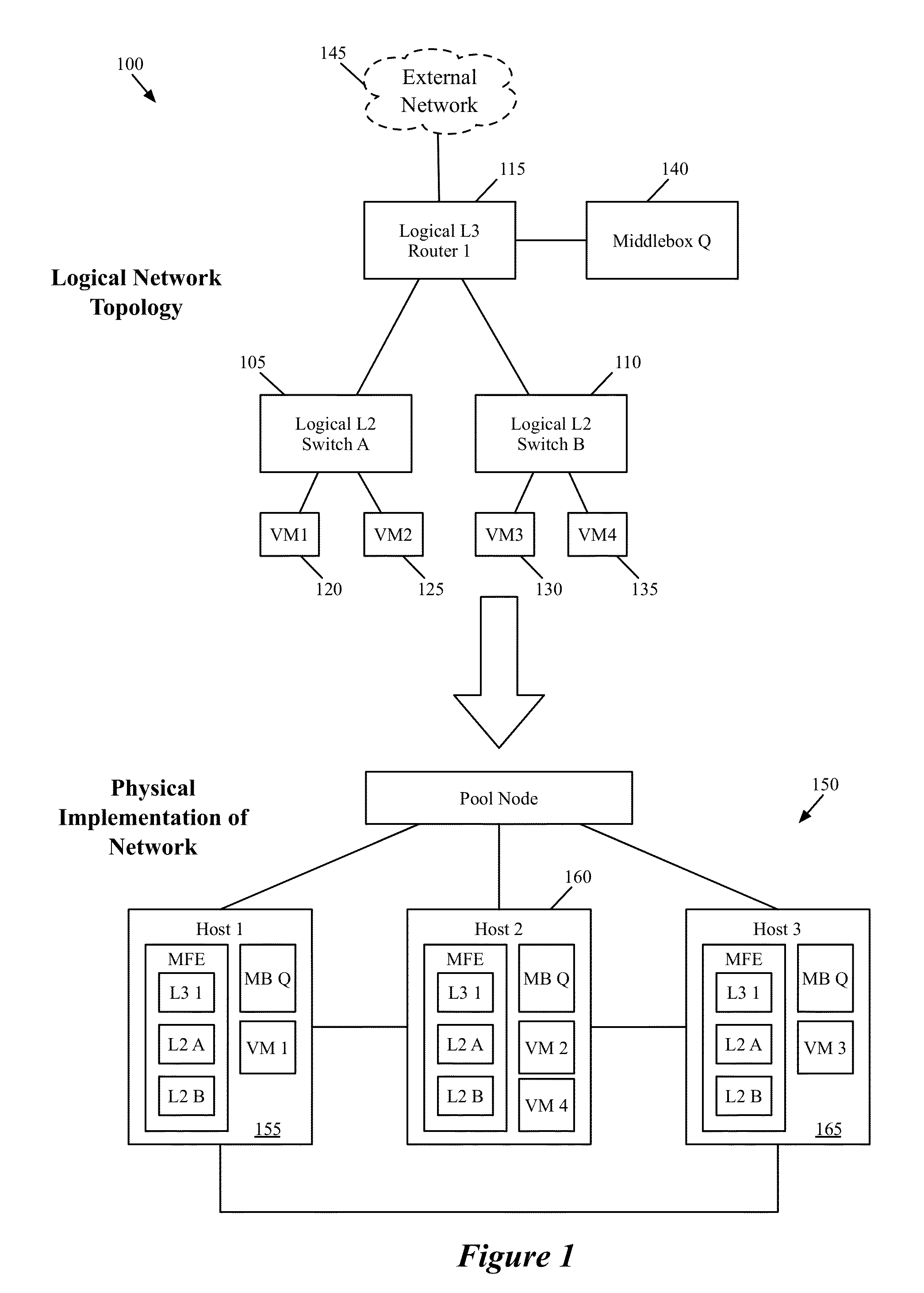
Multiple levels of logical routers
Some embodiments provide a managed network for implementing a logical network for a tenant. The managed network includes a first set of host machines and a second set of host machines. The first set of host machines is for hosting virtual machines (VMs) for the logical network. Each of the first set of host machines operates a managed forwarding element that implements a first logical router for the tenant logical network and a second logical router to which the first logical router connects. The implementation of the second logical router is for processing packets entering and exiting the tenant logical network. The second set of host machines is for hosting L3 gateways for the second logical router. The L3 gateways connect the tenant logical network to at least one external network.
Owner:NICIRA
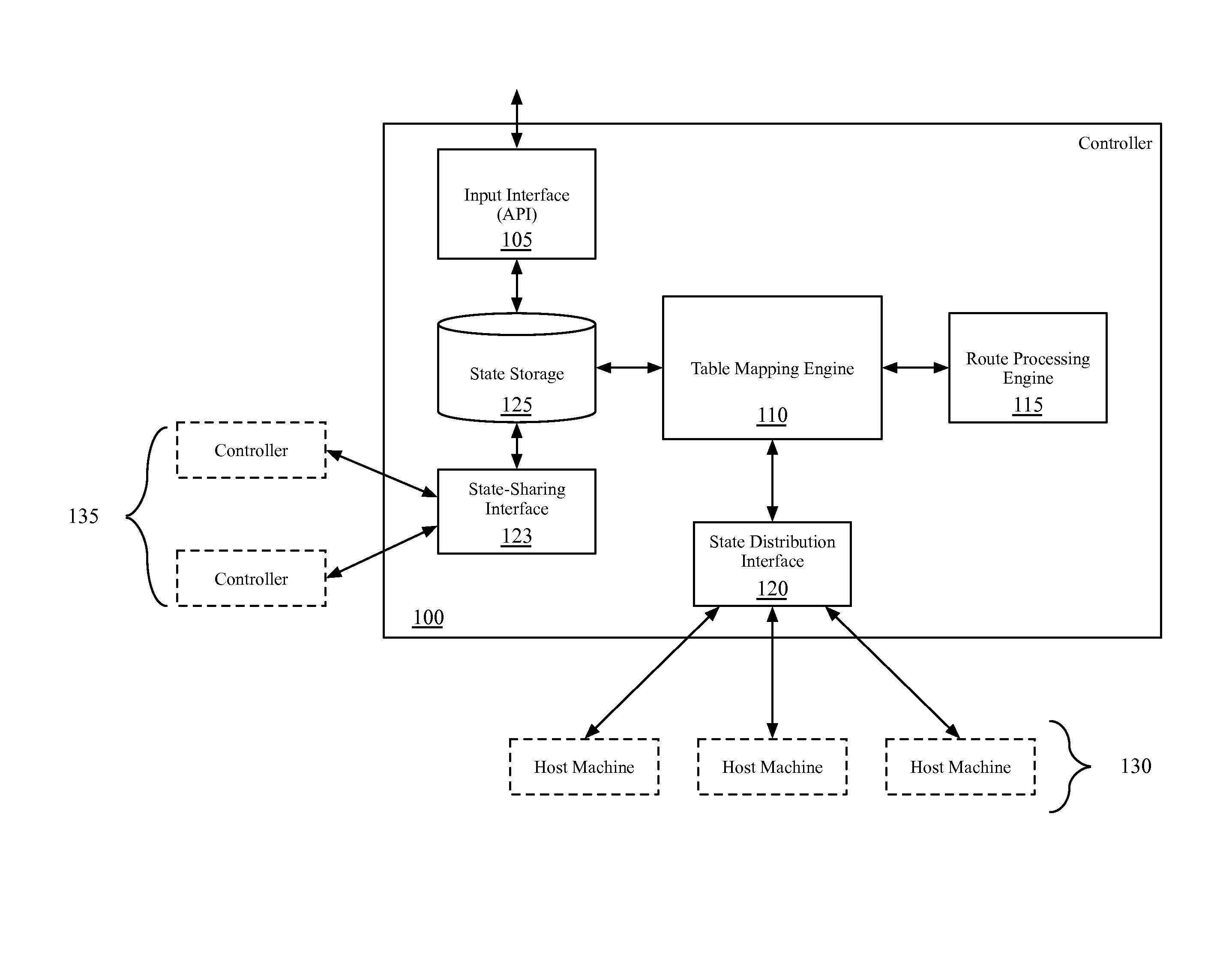
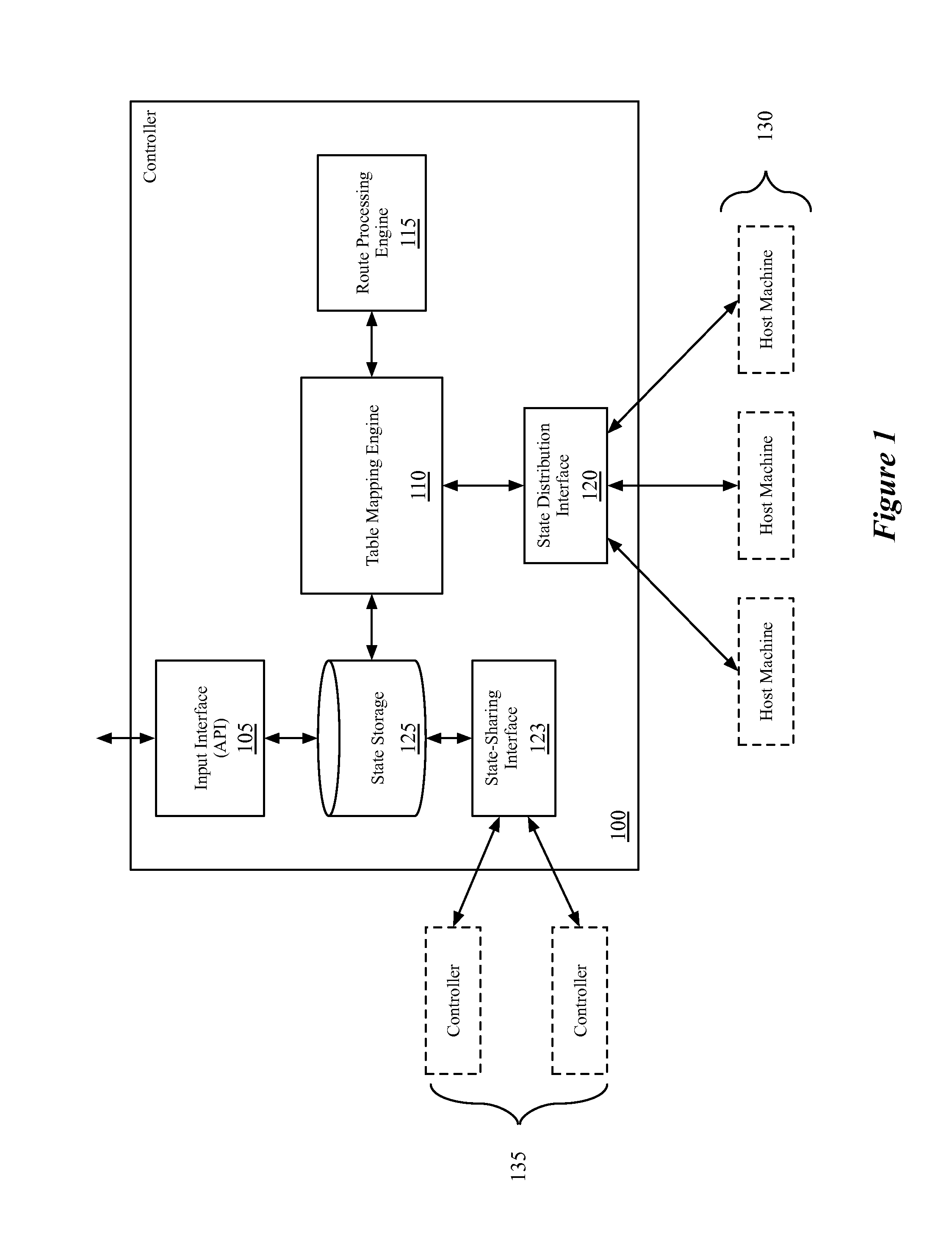
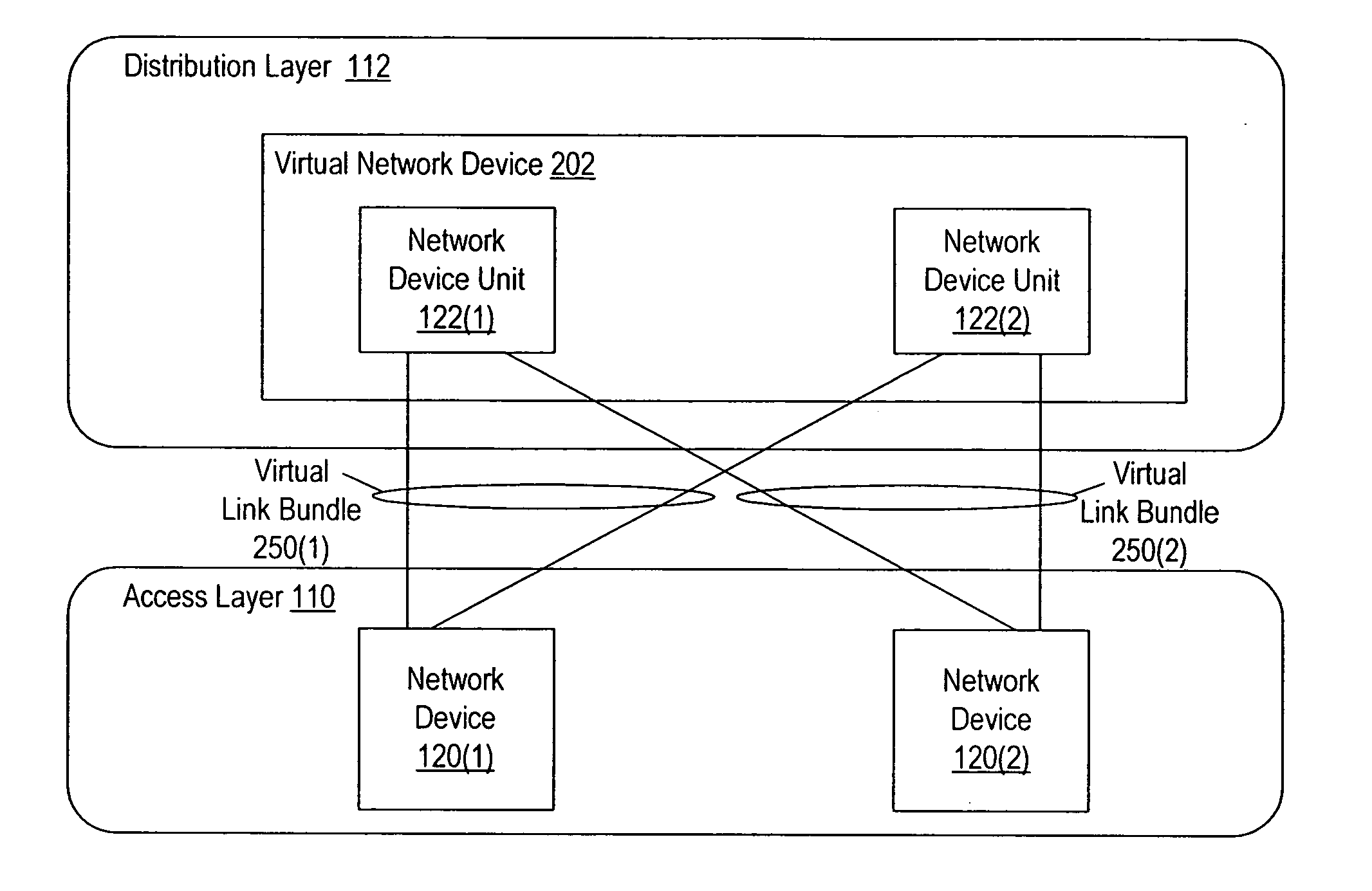
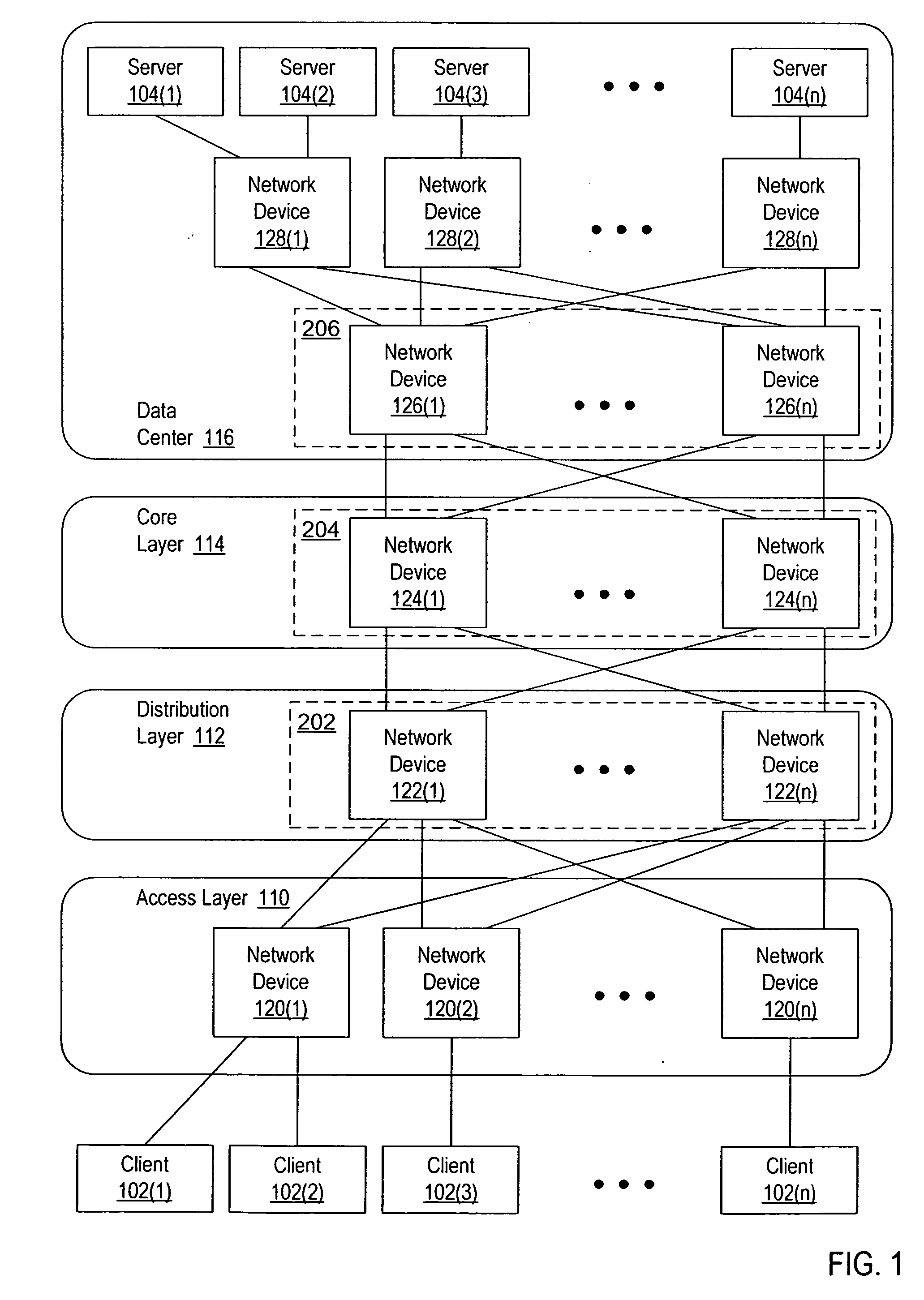
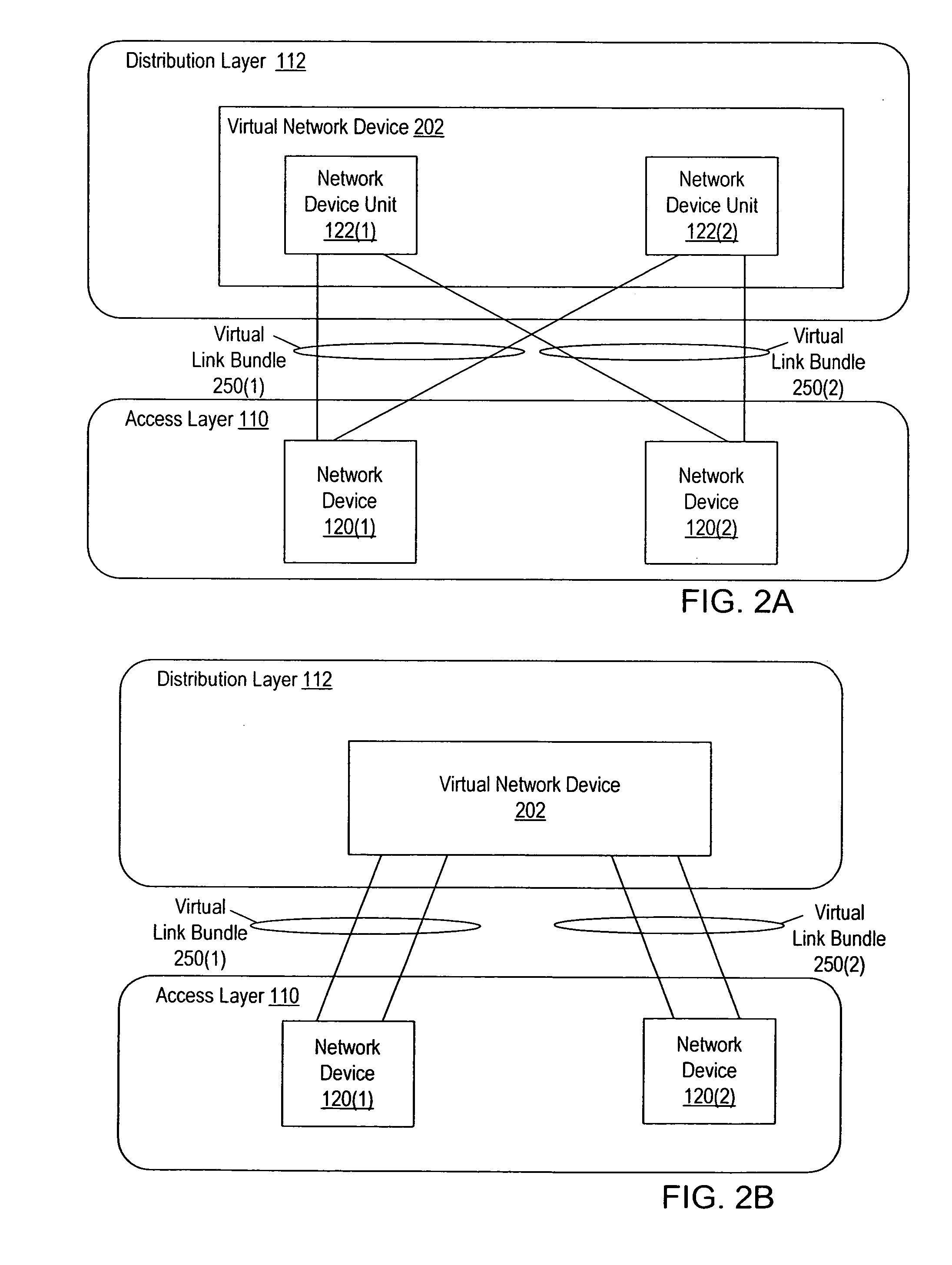
Interface bundles in virtual network devices
A virtual network device includes several different virtual network device sub-units, which collectively operate as a single logical network device. An interface bundle includes interfaces in more than one of the different virtual network device sub-units included in the virtual network device. The interface bundle is coupled to a virtual link bundle, which connects the virtual network device to another device. The interface bundle is managed as a single logical interface.
Owner:CISCO TECH INC
Communications within population of wireless transceivers based on common designation
InactiveUS7221668B2High sensitivityIncrease rangeEnergy efficient ICTPosition fixationWireless transceiverTransceiver
Owner:GOOGLE LLC
Information Exchange Among Members of a Group of Communication Device Users
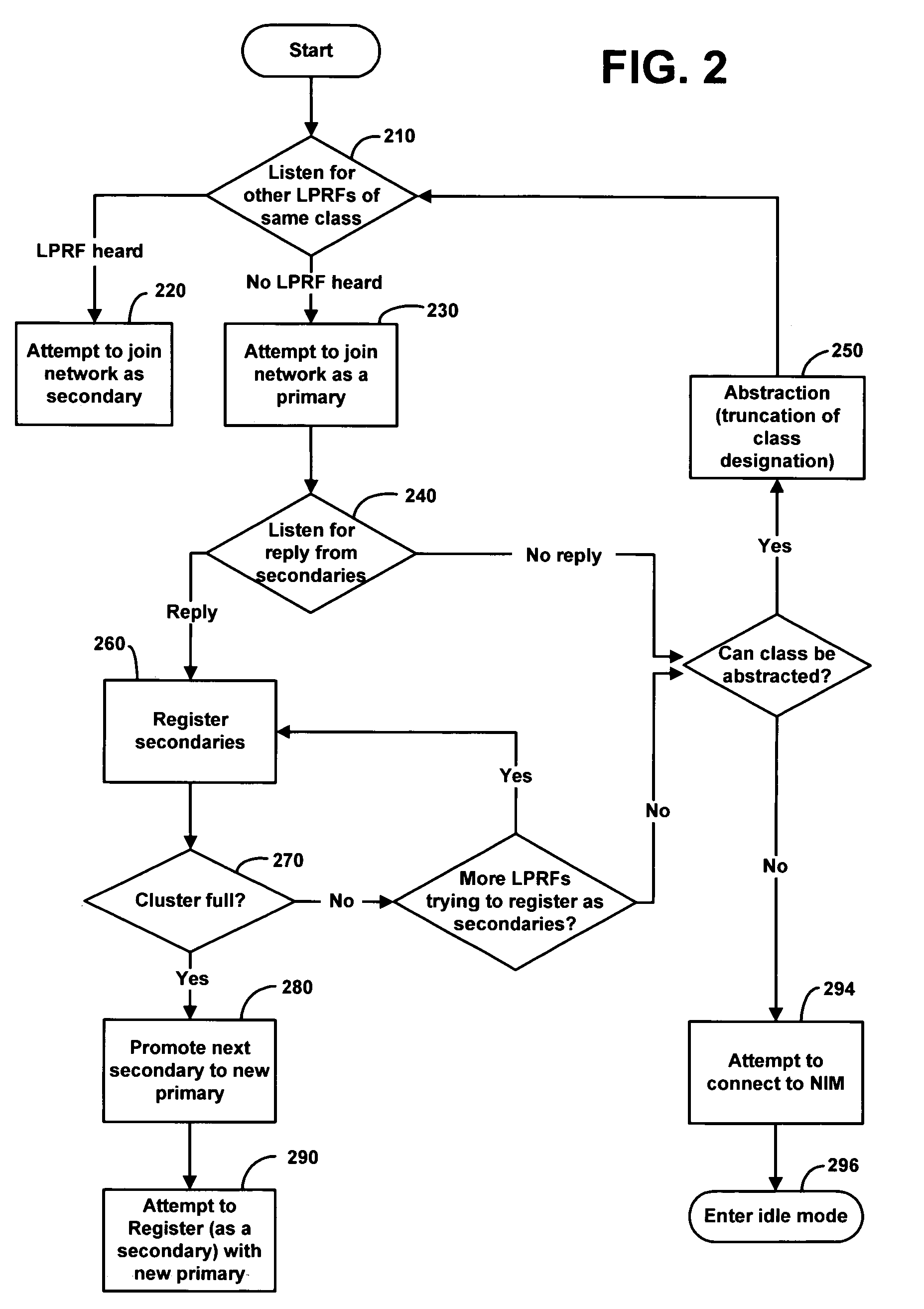
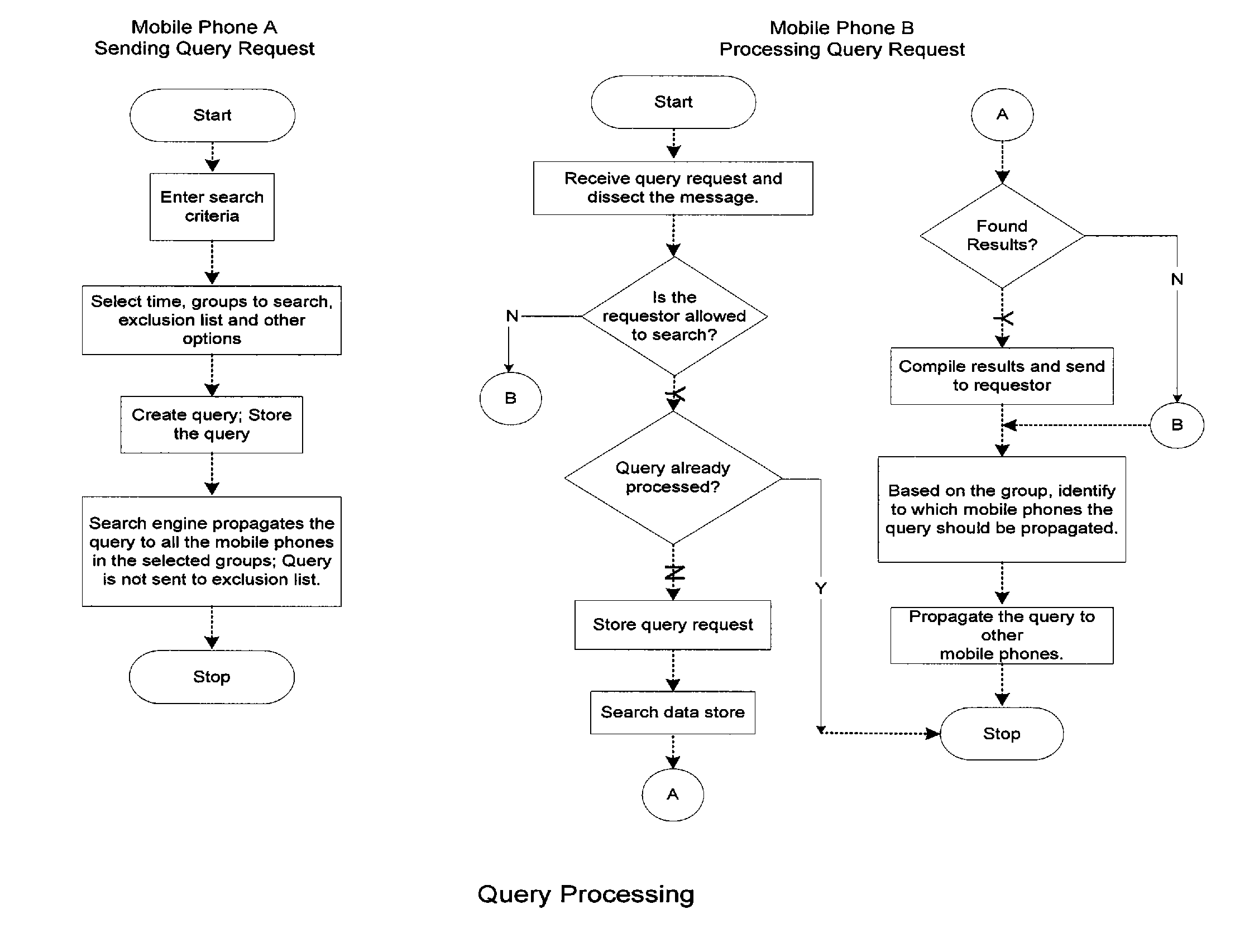
InactiveUS20070271234A1More dataFacilitate transmission and receptionDigital data information retrievalSpecial data processing applicationsLogical networkCommunication device
A method, system, and apparatus for controlling transmission and reception of communications between a plurality of telecommunication devices in a group to allow searching of stored resources is provided. The invention includes a group management module for creating and maintaining association links for each of the plurality of telecommunication devices representing a logical network of devices. The invention also includes a search engine for transmission and reception of communications between the devices in a group, the search engine configured to route a search query from an originating device along the association links to all devices in the group, search stored resources in all devices in the group, and return results of the search query to the originating device, thereby allowing searching of stored resources on all the plurality of telecommunication devices without relying on a centralized server or physical network or wireless network for storing resources.
Owner:RAVIKIRAN CHICKMANGALORE N
Method and apparatus for medium access control in powerline communication network systems
InactiveUS6854059B2Backward compatibilityKey distribution for secure communicationPower distribution line transmissionNetworked systemMedia access control
An inventive Medium Access Control (MAC) protocol for powerline networking systems is described. The inventive MAC protocol controls access to and use of a physical medium (power lines) in a powerline networking system. The MAC protocol method and apparatus includes a method of providing “blanking intervals” in which devices using newer versions of the protocol “clear out” earlier version devices. The use of blanking intervals greatly eases backward compatibility of the network when the protocol is upgraded with new versions. The method of using blanking intervals is closely coupled to a technique of using “beacons.” The beacons are used to propagate blanking interval information throughout the network. The beacons also include a mechanism for informing devices of the expiration of blanking information. The MAC also includes a method of establishing and maintaining “virtual circuit” connections between selected devices on the network. The virtual circuits can be established in powerline networking systems not having a central controller. A method of assigning unique Logical Network Identifiers (LNIs) to logical networks in the powerline networking system is also described. The LNIs uniquely identify each of the logical networks in the network. A means for creating, managing and distributing network encryption keys is also described. The encryption keys are used by the devices in the powerline networking system to prevent data from being shared with unauthorized users.
Owner:CONEXANT SYST INC
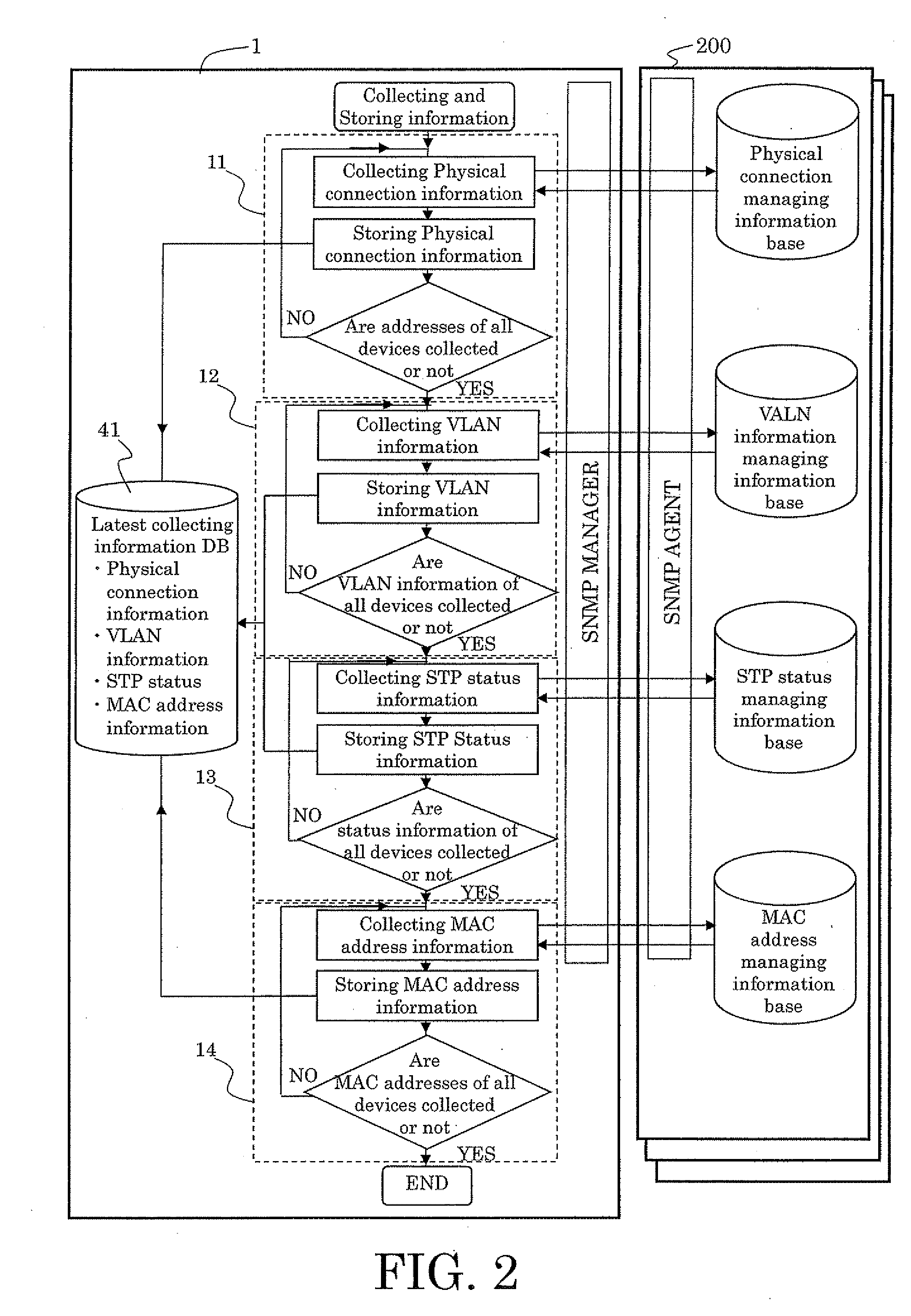
Network management method
InactiveUS20070274234A1Reliable monitoringGood estimateData switching by path configurationNetwork managementLogical network
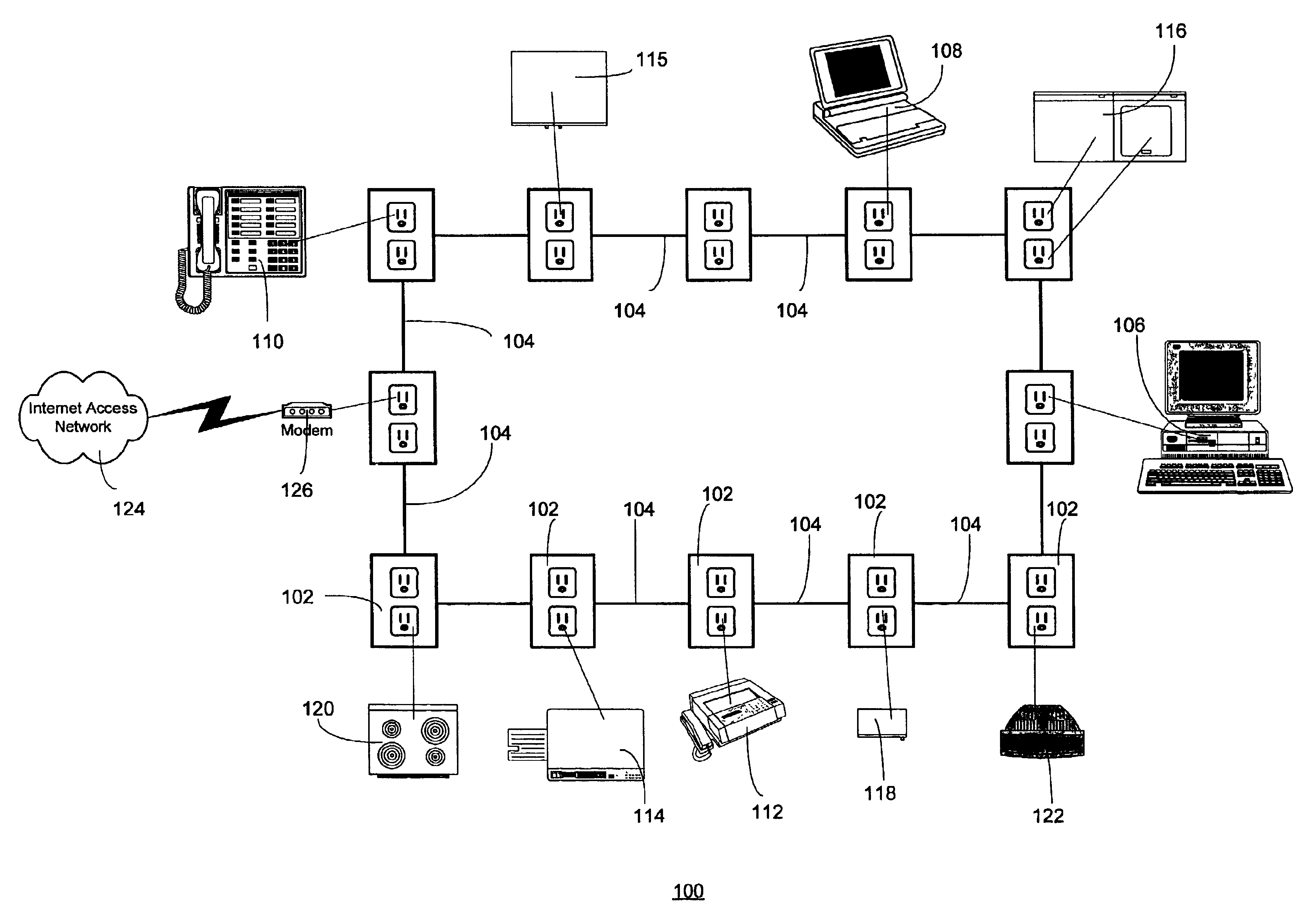
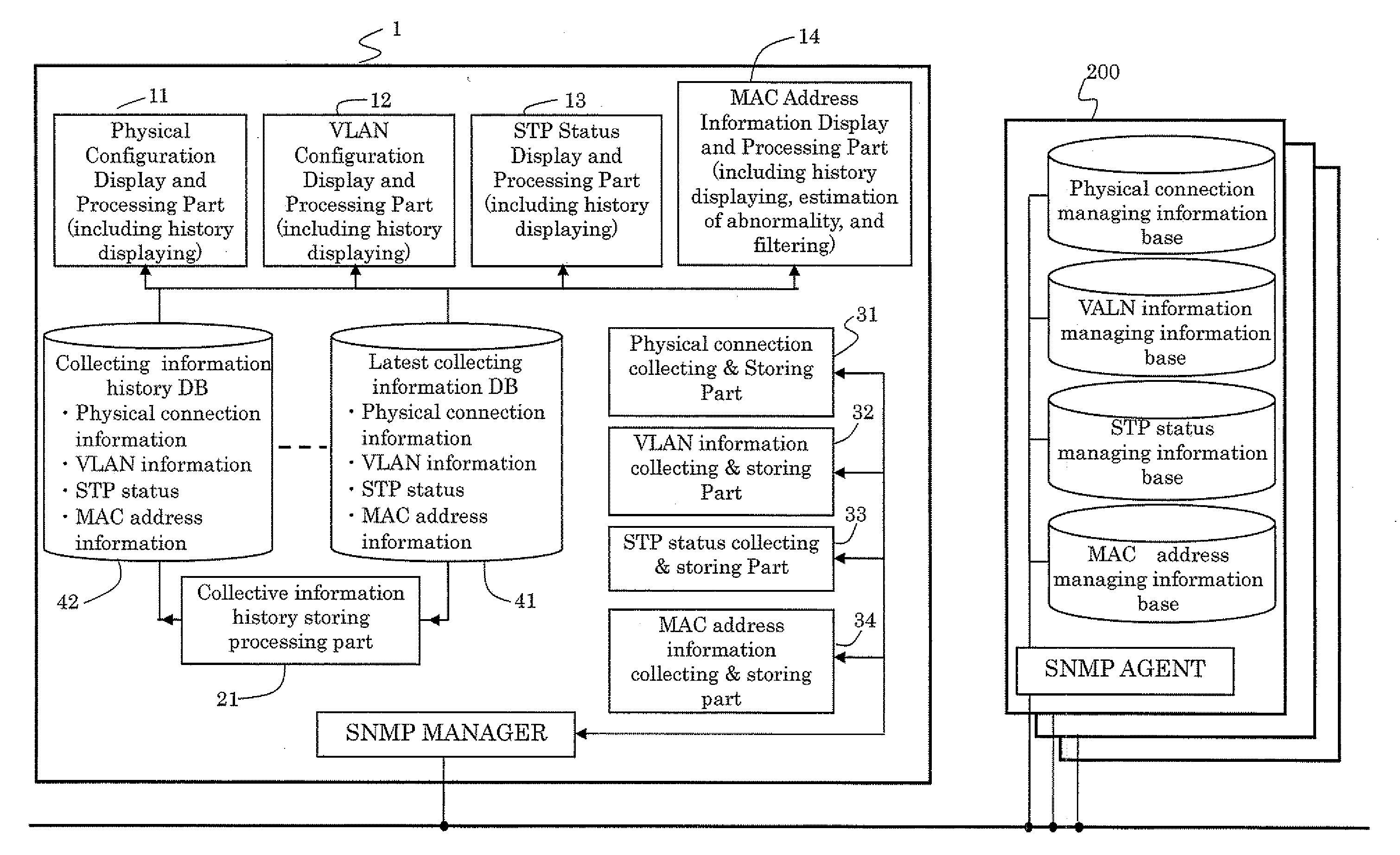
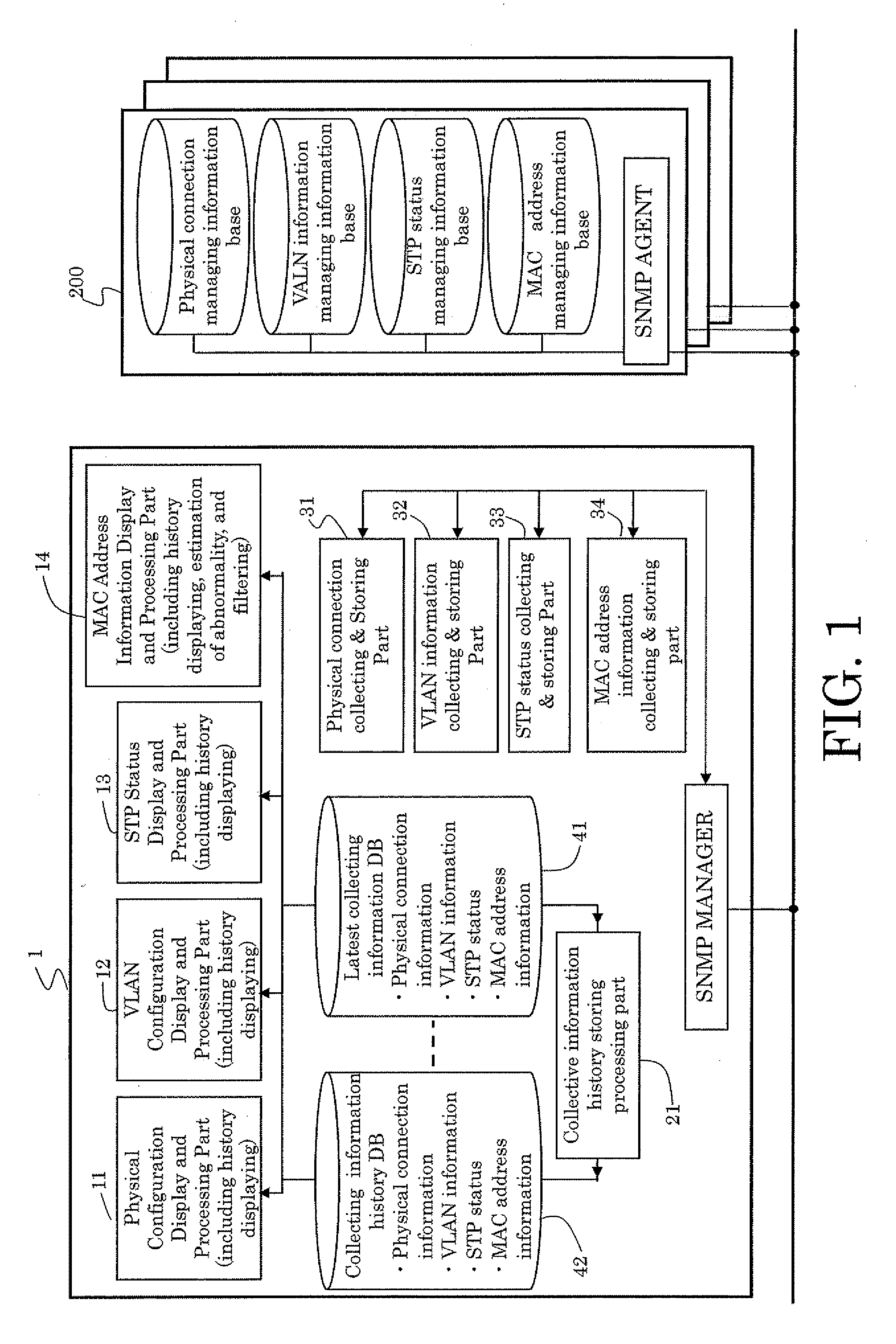
The present invention provides a method in which the physical connection information and the logical network configuration information are kinked to the status of spanning tree, and the status of spanning tree is displayed with the physical connection and the logical network configurations. The method can provide the better recognition about not only intended the physical and logical configurations but the status of spanning tree to a network administrator. Therefore, the network administrator can integrally recognize the status of the network and the failure in the network will be analyzed easily to recover the network to normal state in shorter time.
Owner:FUJITSU LTD
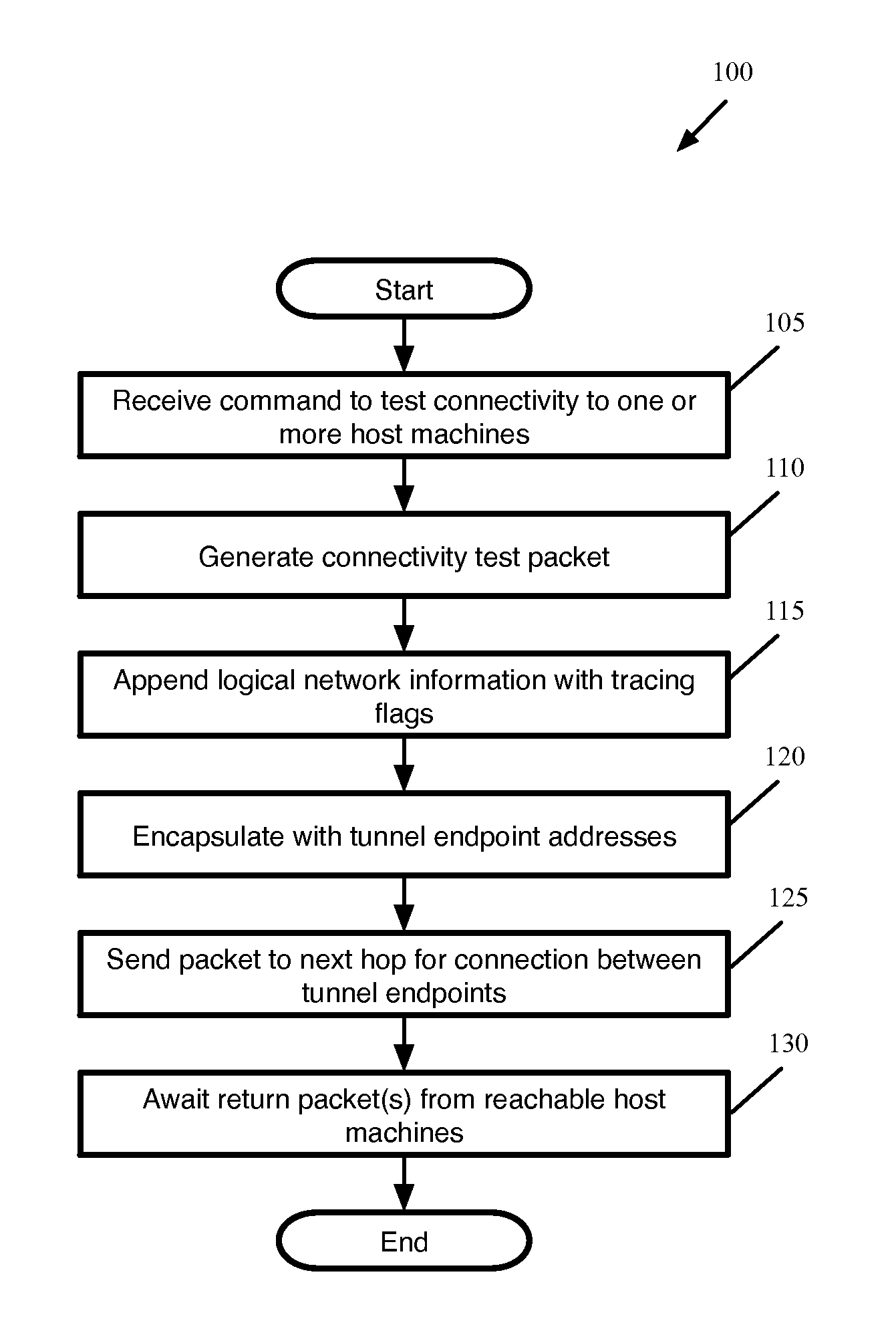
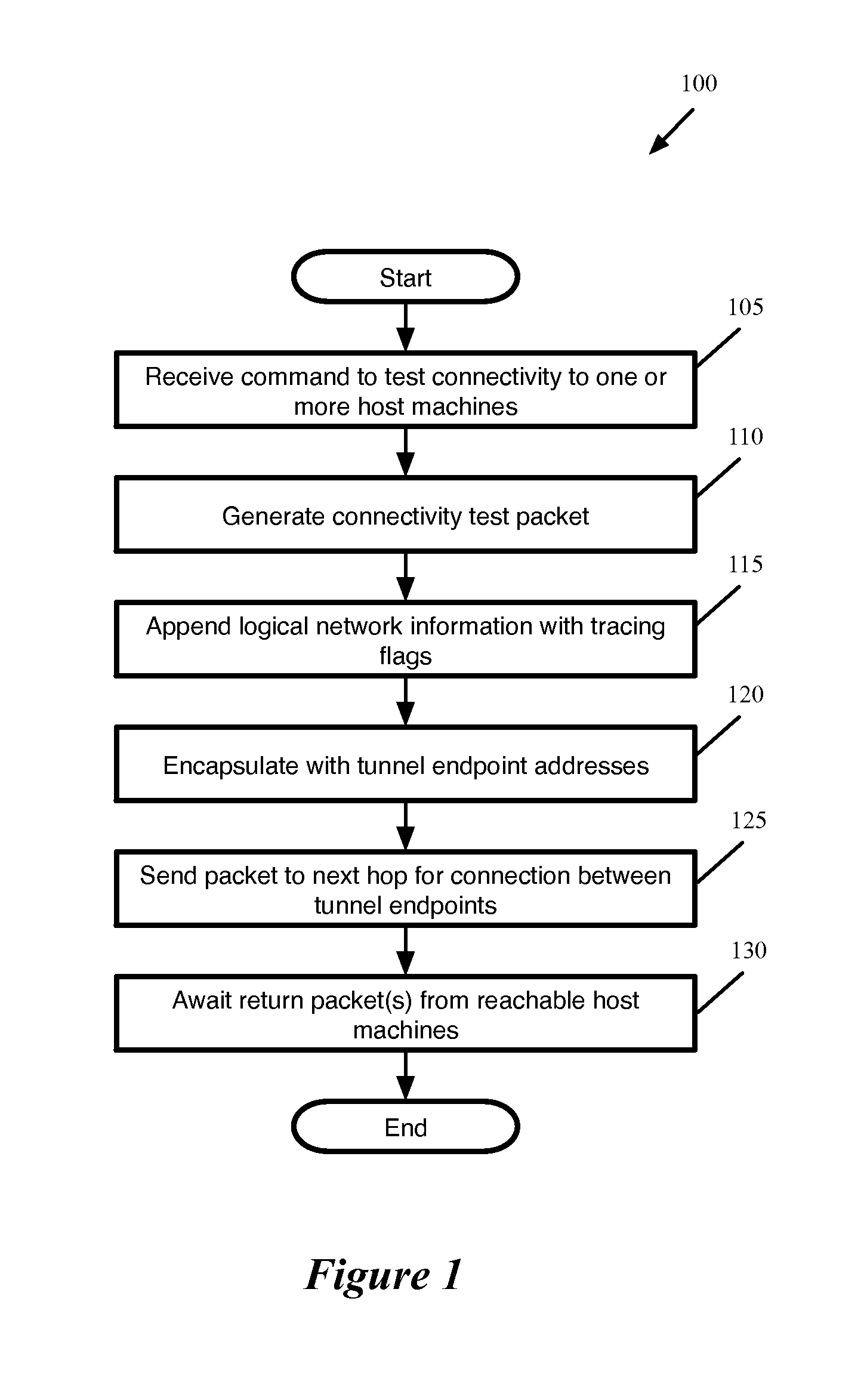
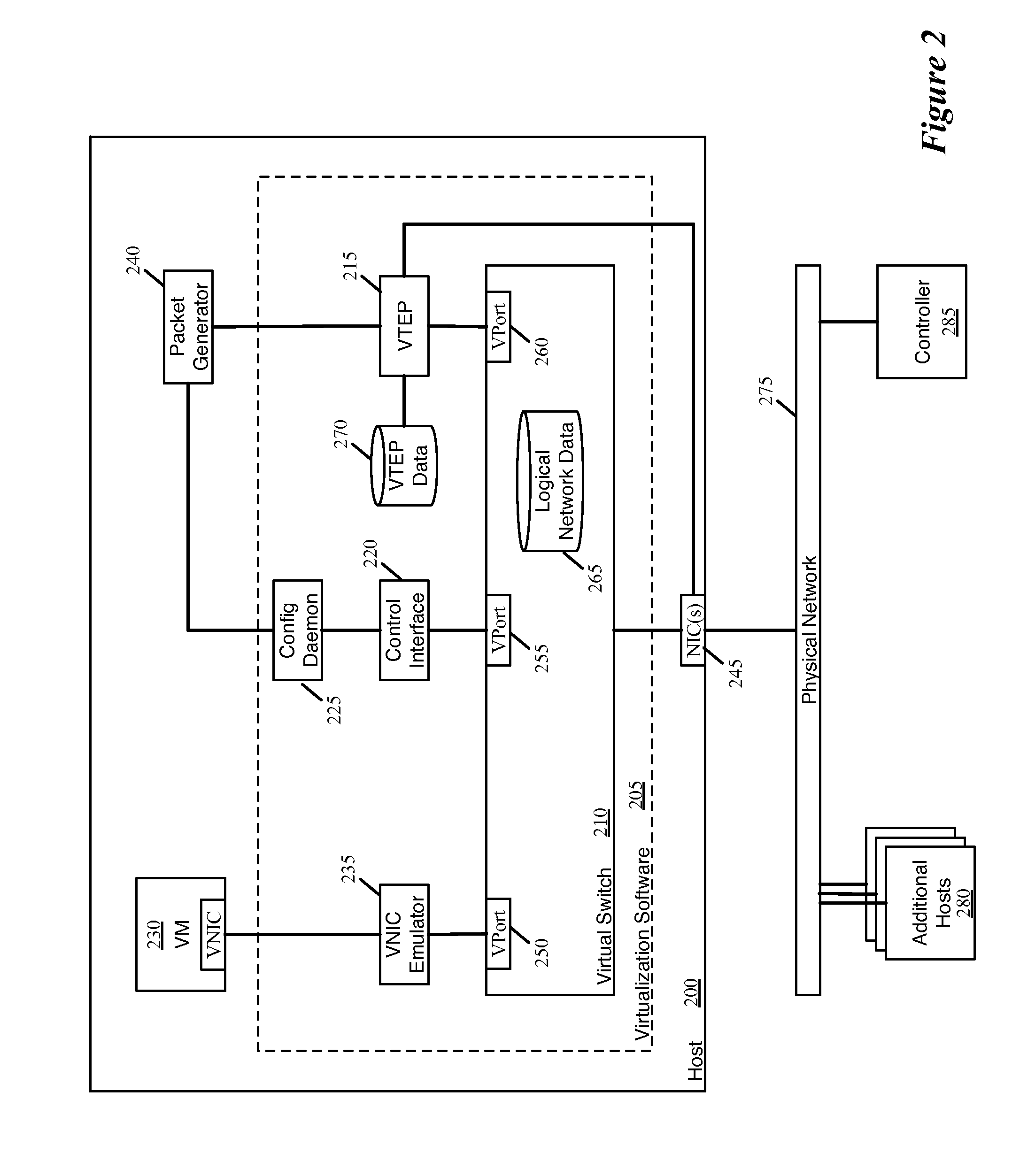
Tracing Host-Originated Logical Network Packets
Some embodiments provide a method for a first host machine that hosts a virtual machine connected to a particular logical network. The method receives a command to test connectivity between the first host machine and a set of at least one additional host machine that also host virtual machines on the particular logical network. At the first host machine, the method generates a packet for sending to the set of additional host machines in order to test the connectivity. The method appends to the generated packet (i) information that identifies the particular logical network and (ii) a flag indicating that the packet is for connectivity testing. The method encapsulates the generated packet with tunnel endpoint addresses, including a tunnel endpoint located at the first host machine. The method sends the encapsulated packet from the first host machine to the set of additional host machines according to the tunnel encapsulation.
Owner:NICIRA
Forming ad hoc RSI networks among transceivers sharing common designation
InactiveUS7200132B2High sensitivityIncrease rangeEnergy efficient ICTPosition fixationWireless transceiverTransceiver
A method of forming ad hoc RSI hierarchical communication networks among pluralities of wireless transceivers includes assigning to each of the transceivers one or more common designations. A network organization routine of the transceivers operates to establish hierarchical networks based on the transceivers' common designations, resulting in a logical network organization that provides efficiencies for acquiring information from particular transceivers that share a common designation. Each transceiver's common designation is used by a digital processor of the transceiver to selectively receive data packets that are intended for receipt by transceivers sharing the particular common designation. Such a “common designation” network reduces power consumption and signal interference thereby increasing battery life. Each transceiver may include a sensor interface a query handling routine in communication with a memory of the transceiver for serving as a dynamic distributed hierarchical database system of information such as, for example, sensor-derived information and time-sensitive information.
Owner:GOOGLE LLC
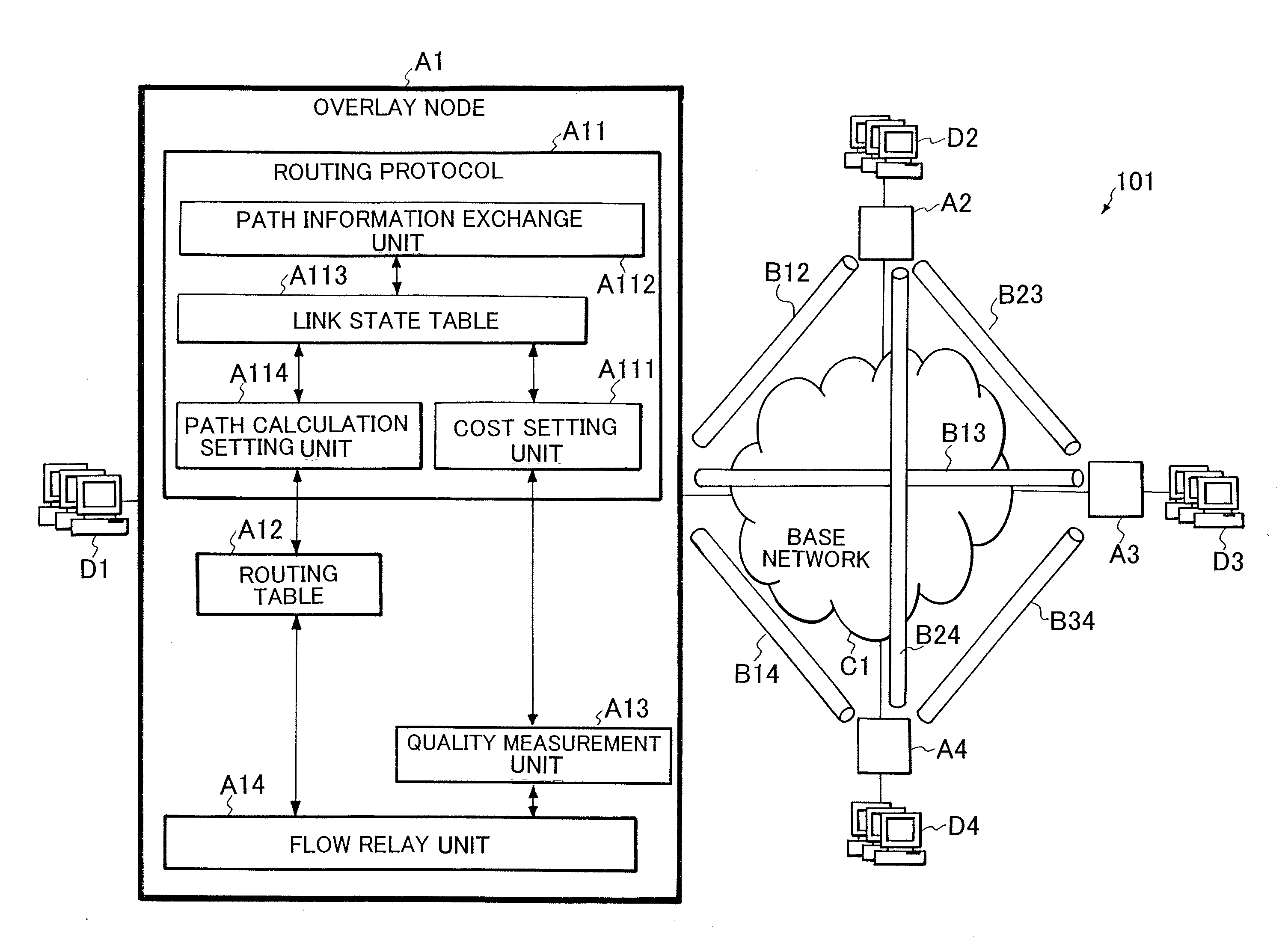
QoS ROUTING METHOD AND QoS ROUTING APPARATUS
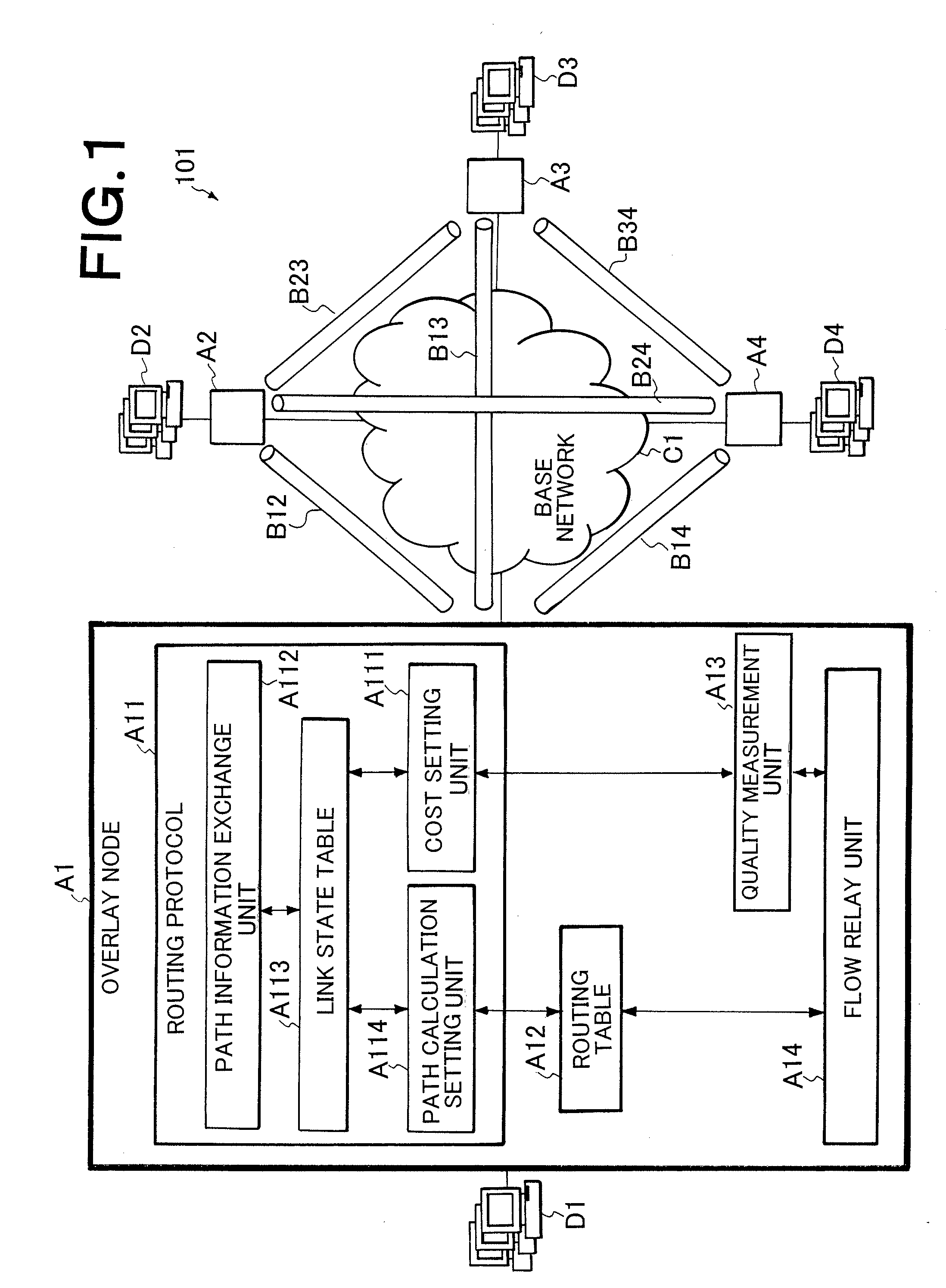
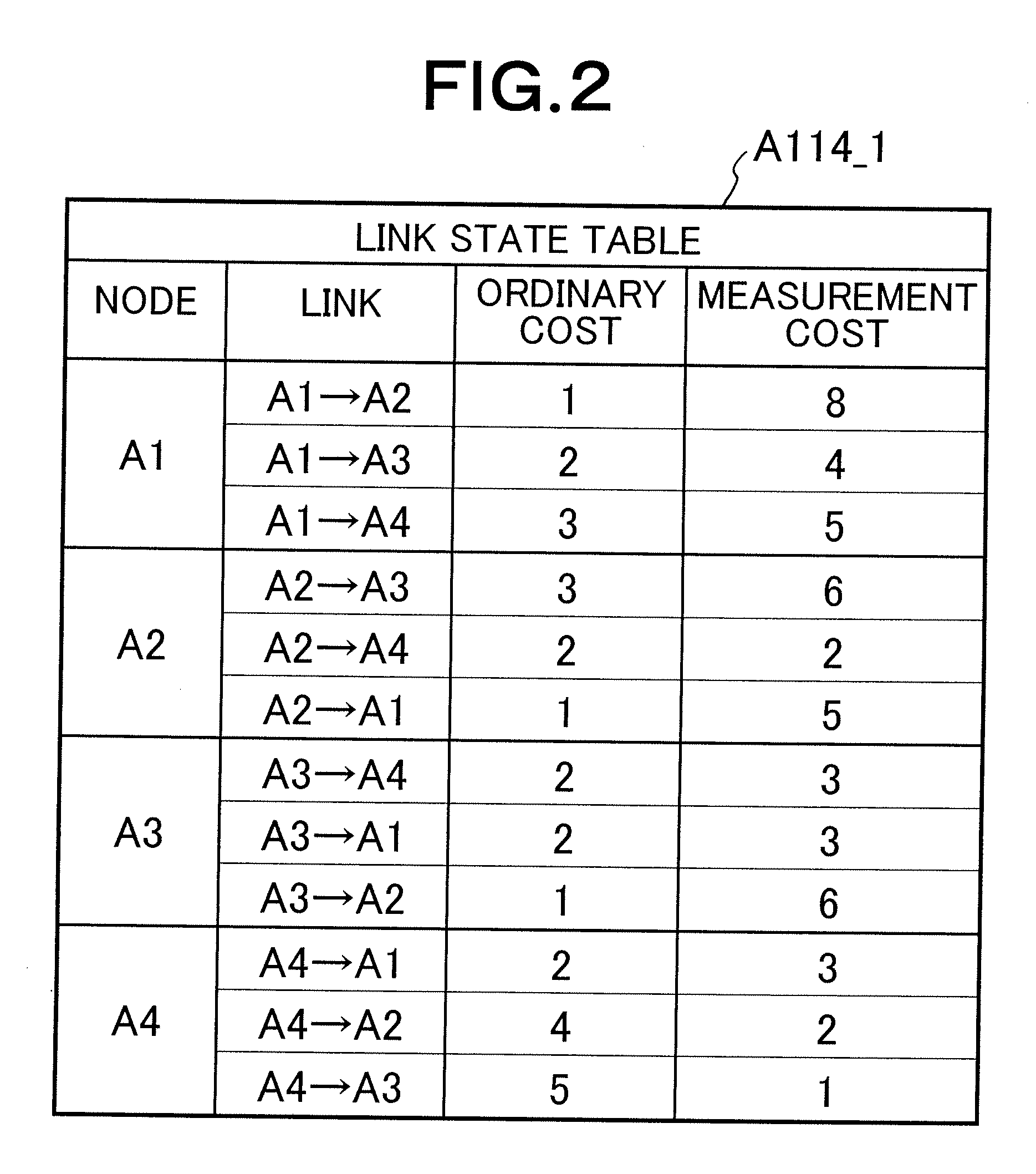
ActiveUS20080101227A1Reduced measurement accuracyHigh measurement accuracyError preventionFrequency-division multiplex detailsData packPathPing
A QoS routing apparatus as a node of a logical network to transmit data communicated between user's terminals comprises a relay unit discriminating whether or not flows of received data are measurement flows and transmitting said received data, a quality measurement unit measuring communication quality of links connected the own apparatus using the measurement flows, a quality accuracy setting unit determining measurement accuracy of the communication qualities of the respective links and a path setting unit prescribing transmission amounts of the measurement flows to the respective links. When the path setting unit prescribes the transmission amounts of the measurement flows, it applies a higher rate to a link which has been determined a lower measurement accuracy.
Owner:NEC CORP
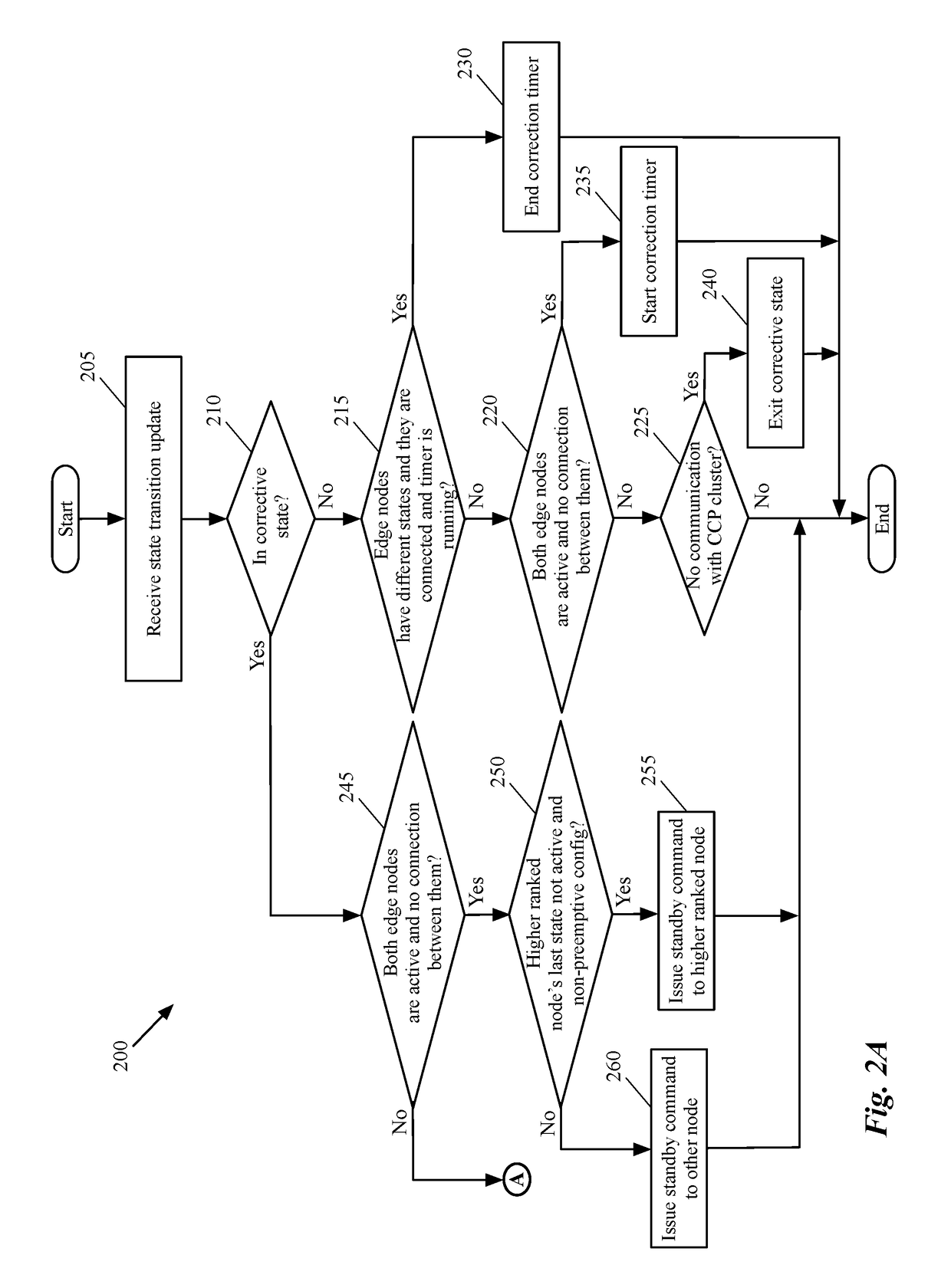
Dynamic recovery from a split-brain failure in edge nodes
ActiveUS20180176073A1Reduce the possibilityIncrease the number ofError detection/correctionSignal allocationActive edgeLoad Shedding
Some embodiments provide a method for employing the management and control system of a network to dynamically recover from a split-brain condition in the edge nodes of the network. The method of some embodiments takes a corrective action to automatically recover from a split-brain failure occurred at a pair of high availability (HA) edge nodes of the network. The HA edge nodes include an active machine and a standby machine. The active edge node actively passes through the network traffic (e.g., north-south traffic for a logical network), while the standby edge node is synchronized and ready to transition to the active state, should a failure occur. Both HA nodes share the same configuration settings and only one is active until a path, link, or system failure occurs. The active edge node also provides stateful services (e.g., stateful firewall, load balancing, etc.) to the data compute nodes of the network.
Owner:NICIRA
Forming communication cluster of wireless AD HOC network based on common designation
InactiveUS7209468B2High sensitivityIncrease rangeEnergy efficient ICTPosition fixationWireless transceiverTransceiver
A method of forming an ad hoc hierarchical communication network among a plurality of wireless transceiver includes assigning to each of the transceivers one or more common designations. A network organization routine of the transceivers operates to establish hierarchical networks based on the transceivers' common designations, resulting in a logical network organization that provides efficiencies for acquiring information from particular transceivers that share a common designation. Each transceiver's common designation is used by a digital processor of the transceiver to selectively receive data packets that are intended for receipt by transceivers sharing the particular common designation. Such a “common designation” network reduces power consumption and signal interference, which increases battery life in the transceivers. The transceivers may include a query handling routine in communication with a memory of the transceiver for serving as a dynamic distributed hierarchical database system of information such as, for example, sensor-derived information and time-sensitive information.
Owner:GOOGLE LLC
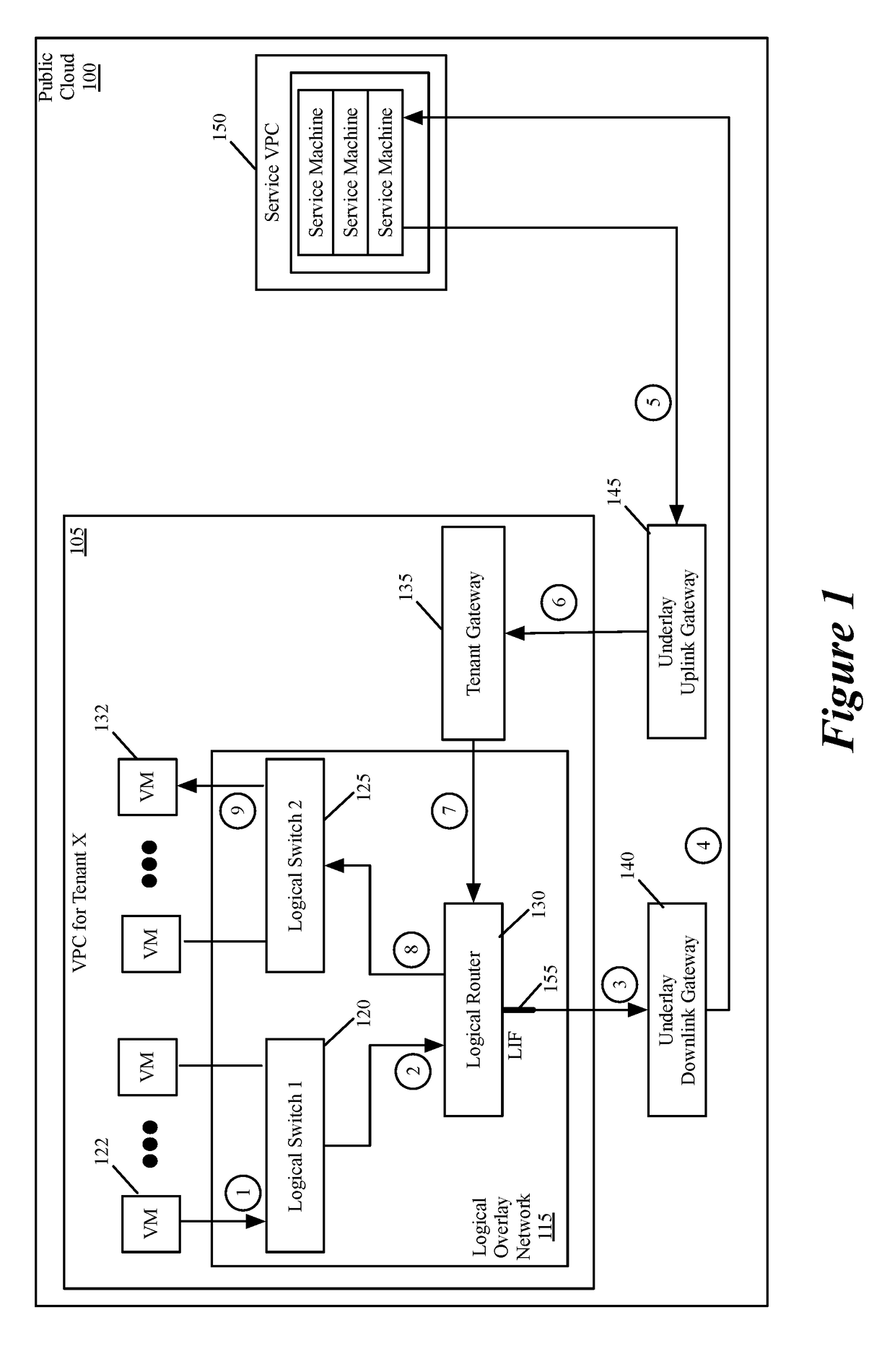
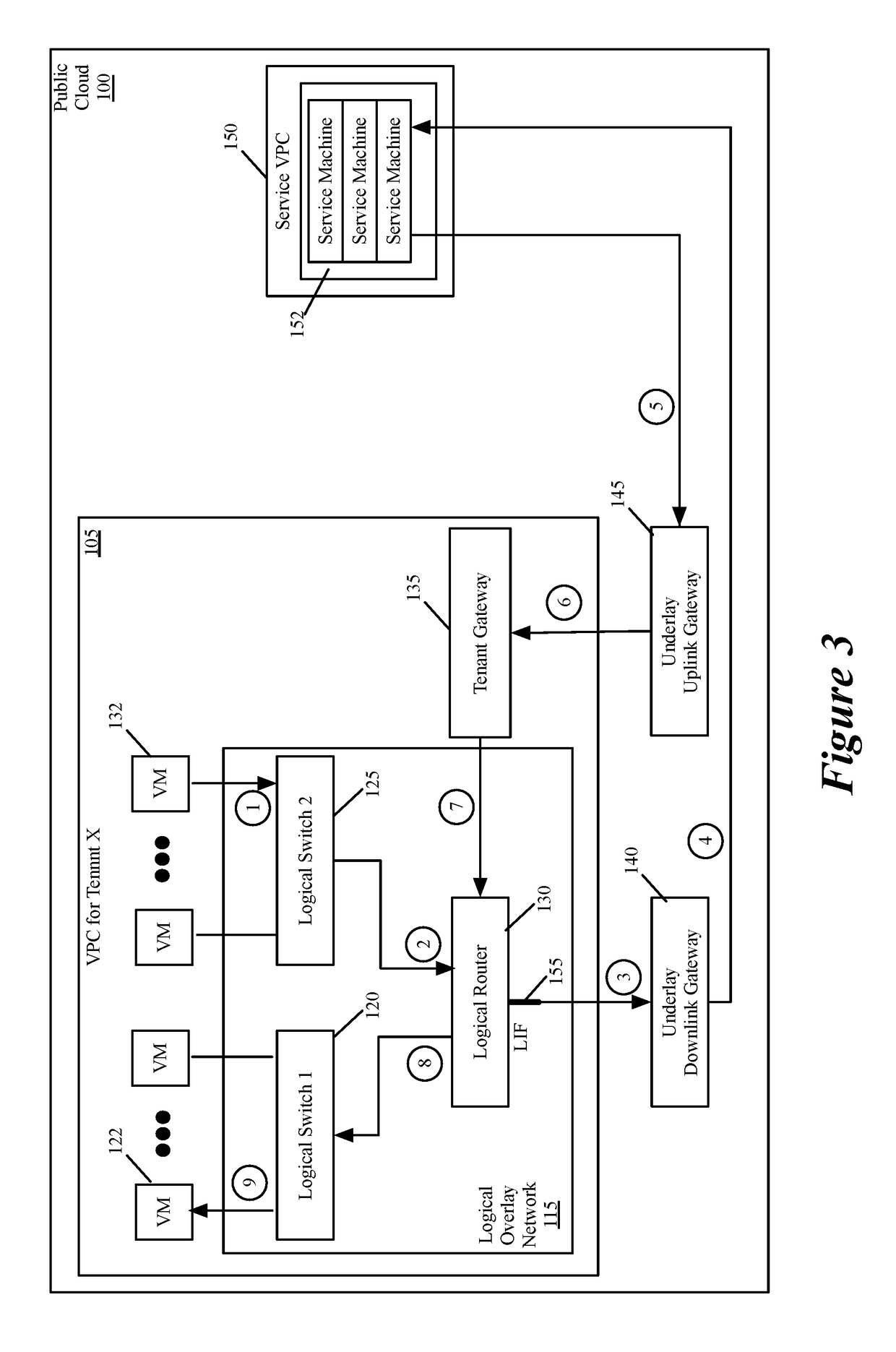
Performing in-line service in public cloud
Some embodiments provide a novel way to insert a service (e.g., a third party service) in the path of a data message flow, between two machines (e.g., two VMs, two containers, etc.) in a public cloud environment. For a particular tenant of the public cloud, some embodiments create an overlay logical network with a logical overlay address space. To perform a service on data messages of a flow between two machines, the logical overlay network passes to the public cloud's underlay network the data messages with their destination address (e.g., destination IP addresses) defined in the logical overlay network. The underlay network (e.g., an underlay default downlink gateway) is configured to pass data messages with such destination addresses (e.g., with logical overlay destination addresses) to a set of one or more service machines. The underlay network (e.g., an underlay default uplink gateway) is also configured to pass to the particular tenant's public cloud gateway the processed data messages that are received from the service machine set and that are addressed to logical overlay destination addresses. The tenant's public cloud gateway is configured to forward such data messages to a logical forwarding element of the logical network, which then handles the forwarding of the data messages to the correct destination machine.
Owner:NICIRA
Use of tunnels to hide network addresses
ActiveUS20130058351A1Data switching by path configurationSecuring communicationNetwork addressingNetwork address
For a managed network including first and second managed switching elements that implement logical data path sets, some embodiments provide a method that establishes, from the first managed switching element, a network tunnel through a network to the second managed switching element. The network includes a set of unmanaged switching elements. Through the network tunnel, the network forwards logical network data to the set of unmanaged switching elements for the set of unmanaged switching elements to forward to the second managed switching element. The logical network is hidden from the set of unmanaged switching elements when the logical network data is forwarded through the tunnel.
Owner:NICIRA
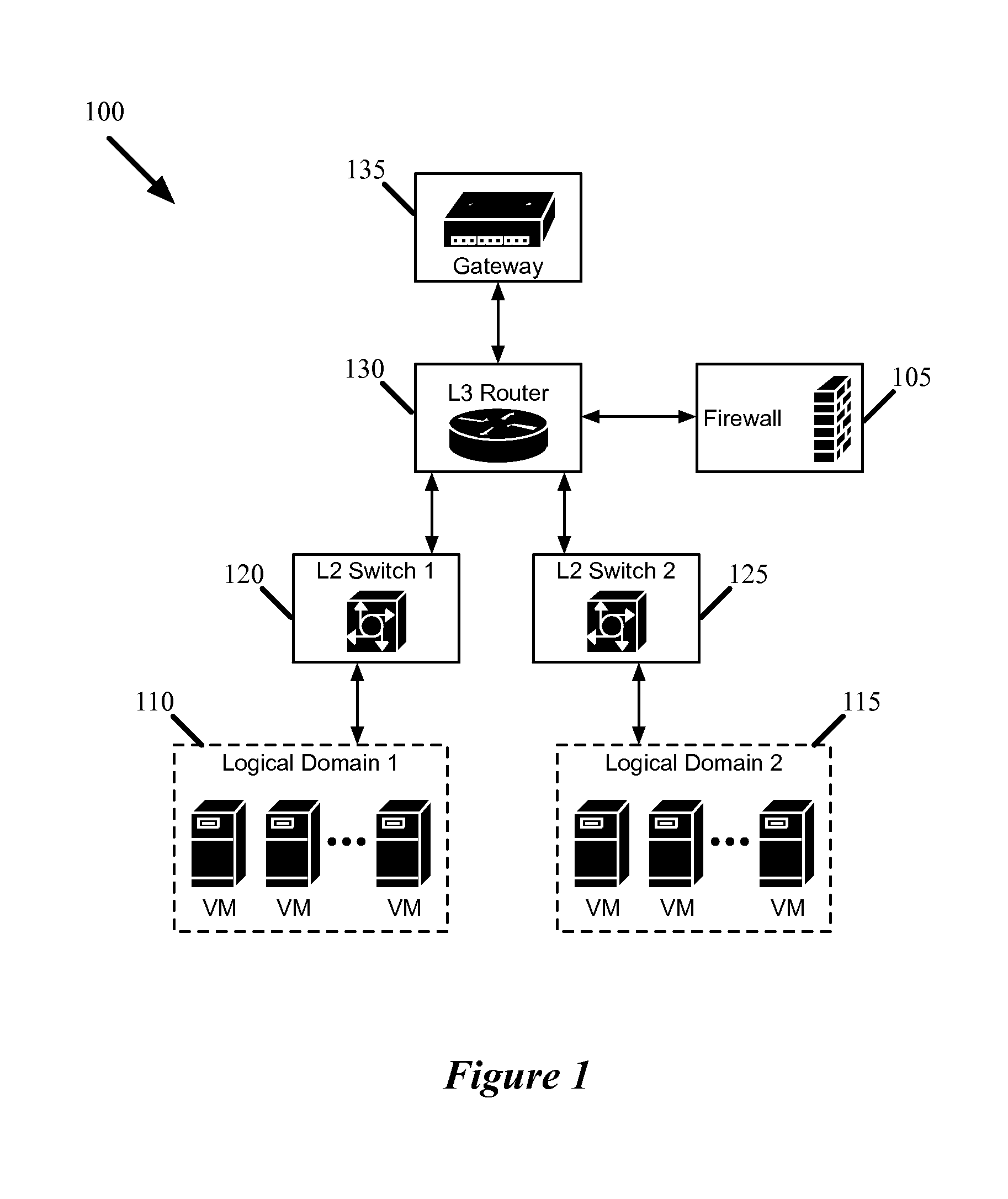
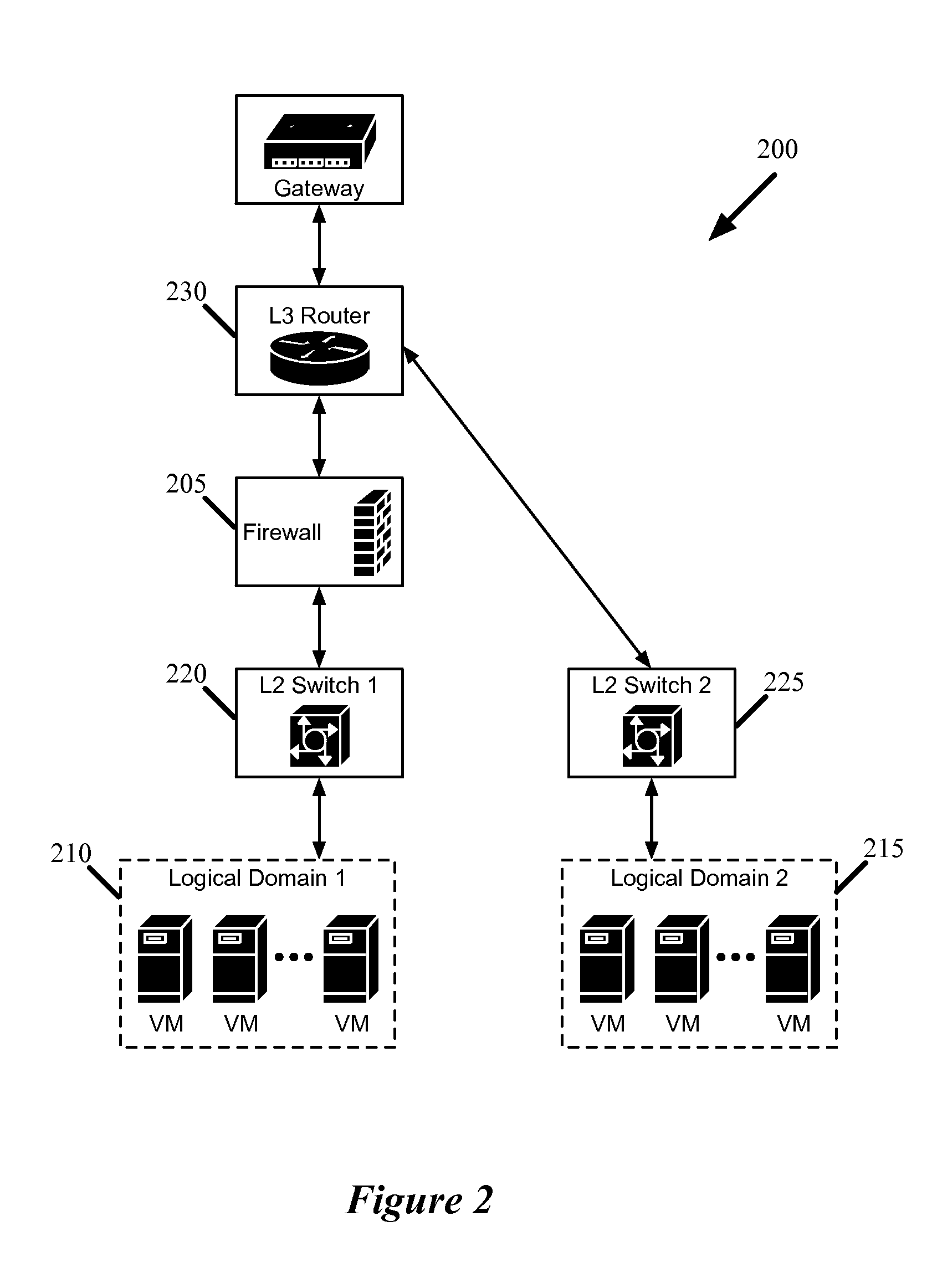
Firewalls in logical networks
ActiveUS20130125230A1Faster packet processing decisionEasy to handleMultiple digital computer combinationsData switching networksLogical networkSoftware
Some embodiments provide a method for configuring a logical firewall in a hosting system that includes a set of nodes. The logical firewall is part of a logical network that includes a set of logical forwarding elements. The method receives a configuration for the firewall that specifies packet processing rules for the firewall. The method identifies several of the nodes on which to implement the logical forwarding elements. The method distributes the firewall configuration for implementation on the identified nodes. At a node, the firewall of some embodiments receives a packet, from a managed switching element within the node, through a software port between the managed switching element and the distributed firewall application. The firewall determines whether to allow the packet based on the received configuration. When the packet is allowed, the firewall the packet back to the managed switching element through the software port.
Owner:NICIRA
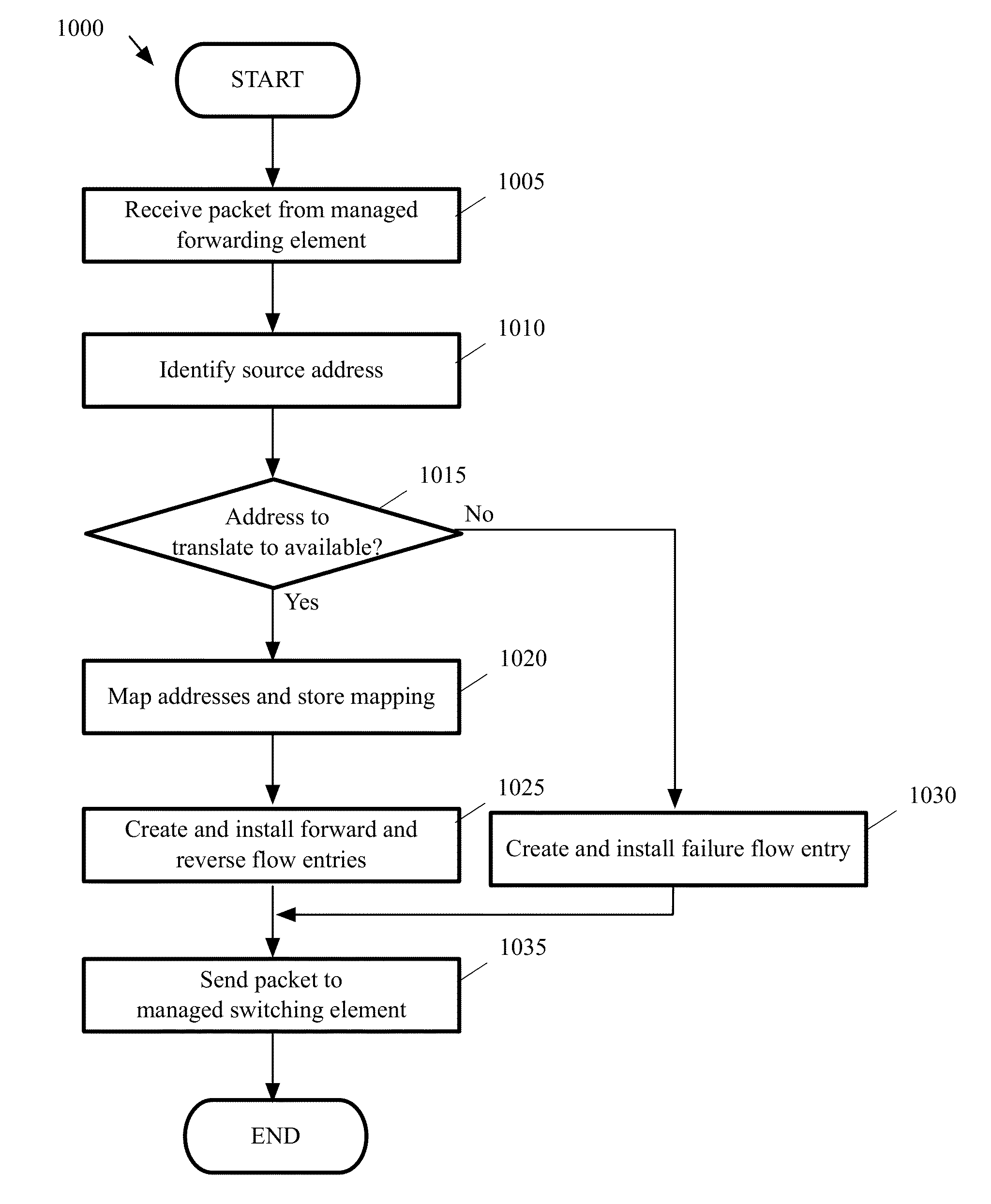
Dynamic Generation of Flow Entries for Last-Hop Processing
Some embodiments provide a method for a first managed forwarding element that implements logical forwarding elements of a logical network. The method receives a first packet from a second managed forwarding element. The first packet includes context information that indicates a logical network destination that maps to a physical destination connected to the first managed forwarding element. At the first managed forwarding element, the method dynamically generates a flow entry for processing subsequent packets received by the first managed forwarding element from the physical destination and sent to a source of the first packet. The method processes a second packet received by the first managed forwarding element from the physical destination with the dynamically generated flow entry. The dynamically generated flow entry specifies to send the second packet to the second managed forwarding element before logically forwarding the second packet through the logical network.
Owner:NICIRA
Method for geolocating logical network addresses
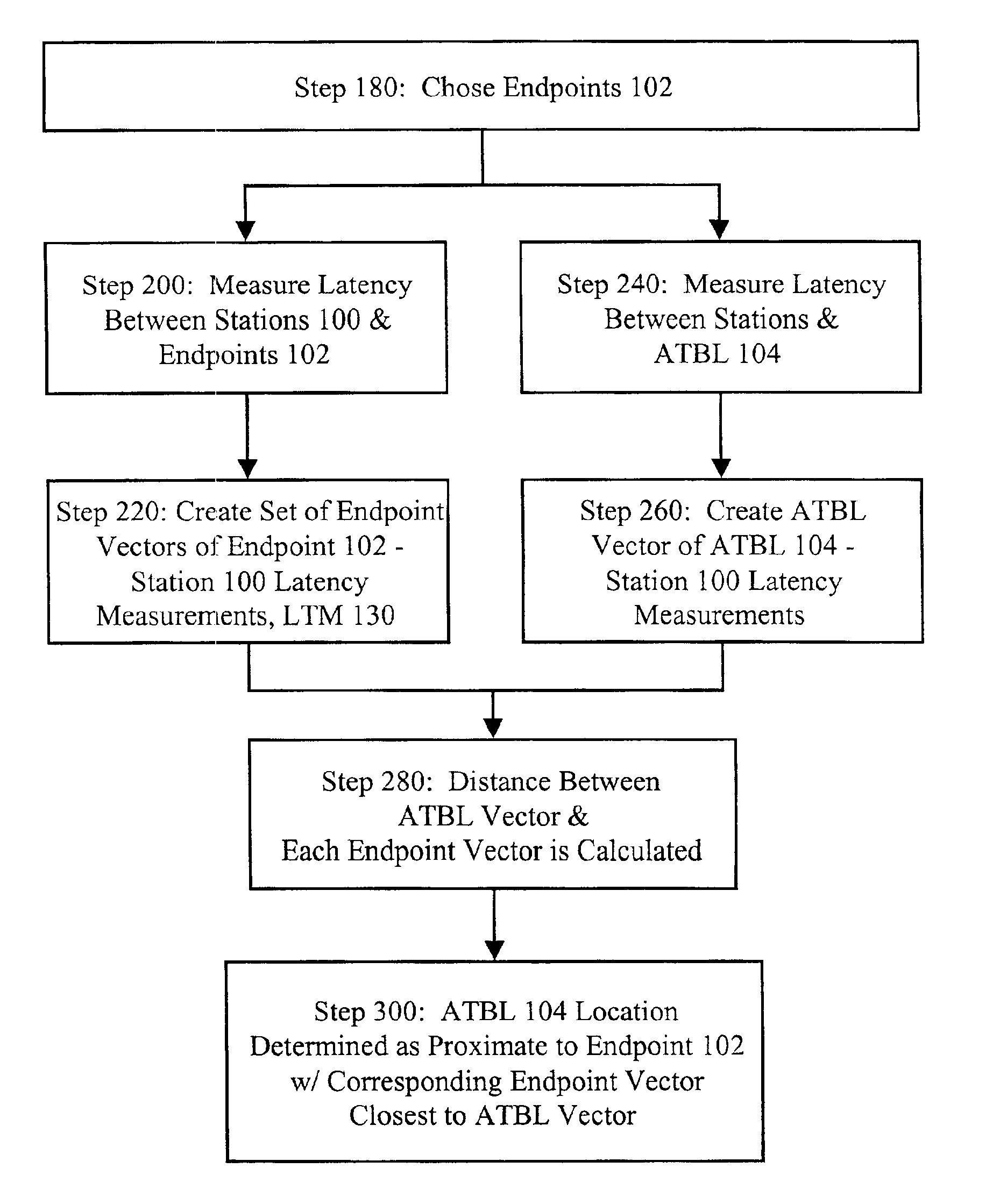
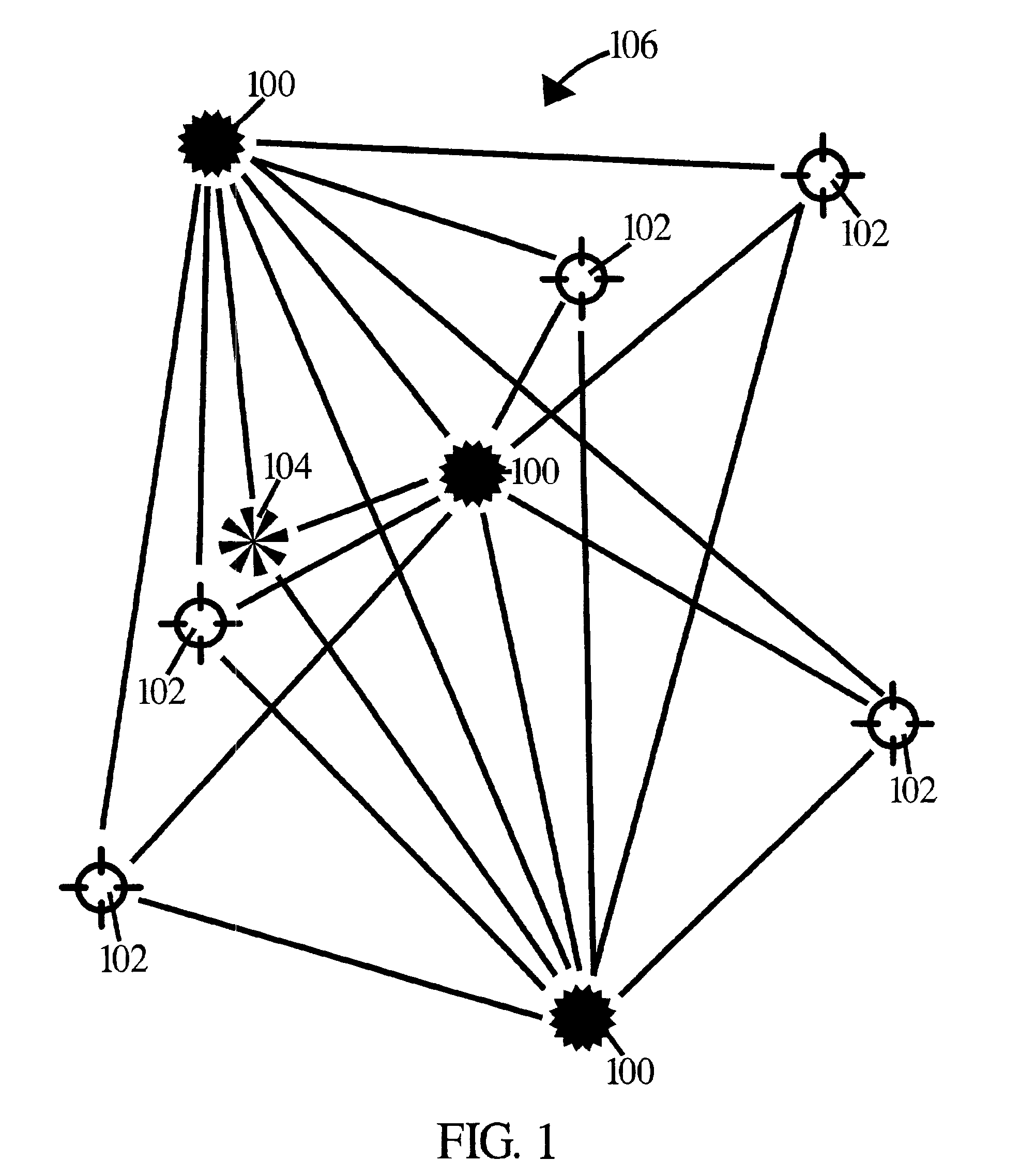
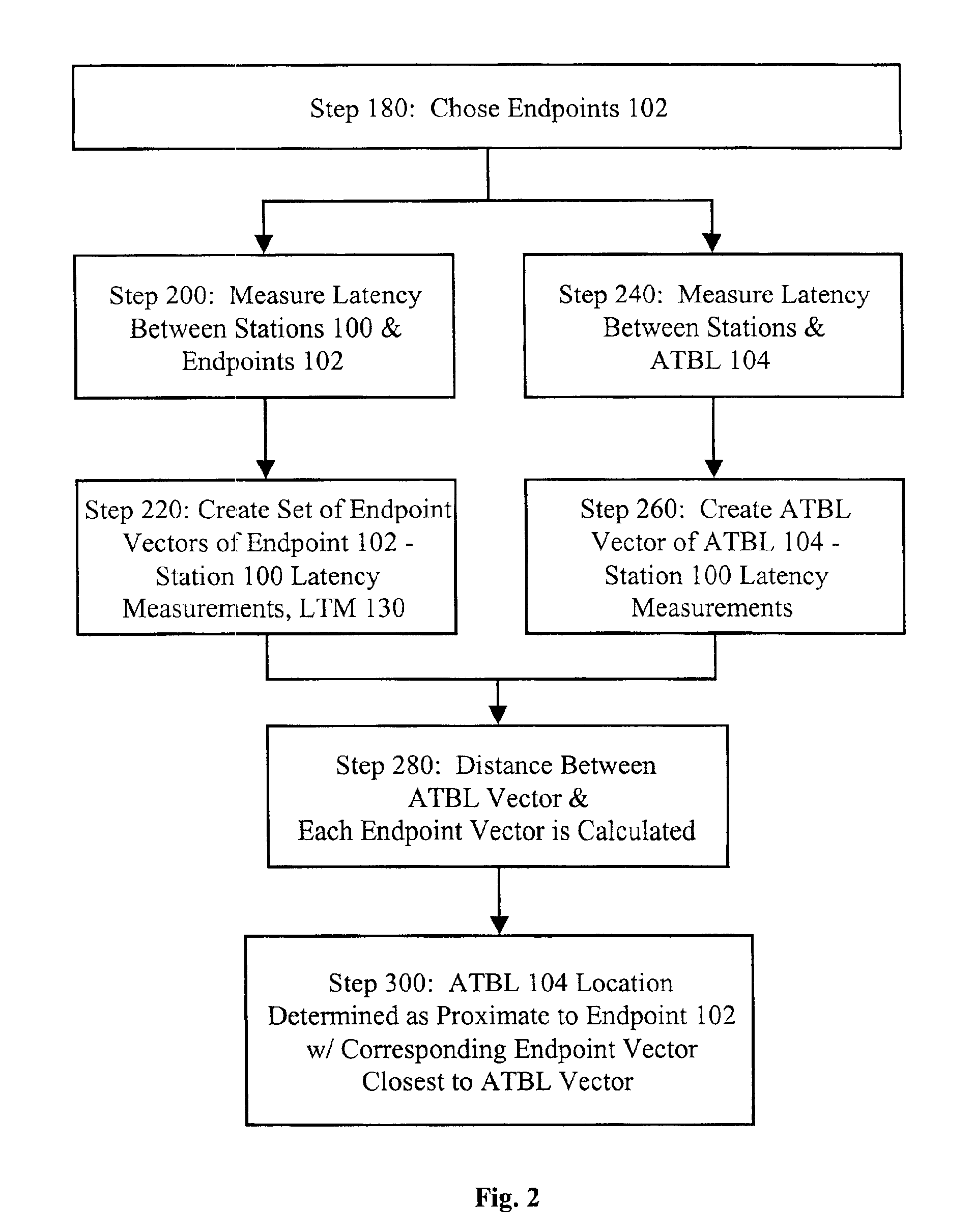
InactiveUS6947978B2High resolutionHigh densityMultiple digital computer combinationsLoop networksGeotargetingNetwork addressing
Method for geolocating logical network addresses on electronically switched dynamic communications networks, such as the Internet, using the time latency of communications to and from the logical network address to determine its location. Minimum round-trip communications latency is measured between numerous stations on the network and known network addressed equipment to form a network latency topology map. Minimum round-trip communications latency is also measured between the stations and the logical network address to be geolocated. The resulting set of minimum round-trip communications latencies is then correlated with the network latency topology map to determine the location of the network address to be geolocated.
Owner:GOVERNMENT OF THE UNITED STATES AS REPRESENTED BY THE DIRECTOR NAT SECURITY AGENCY
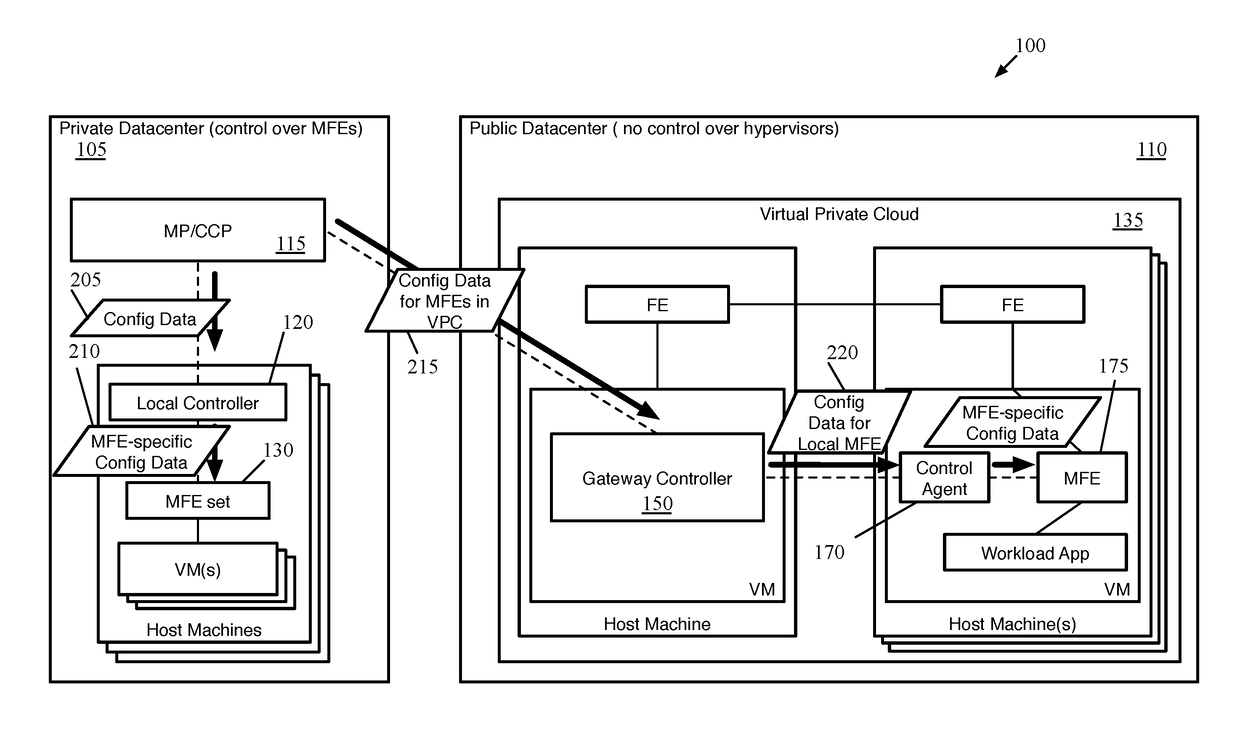
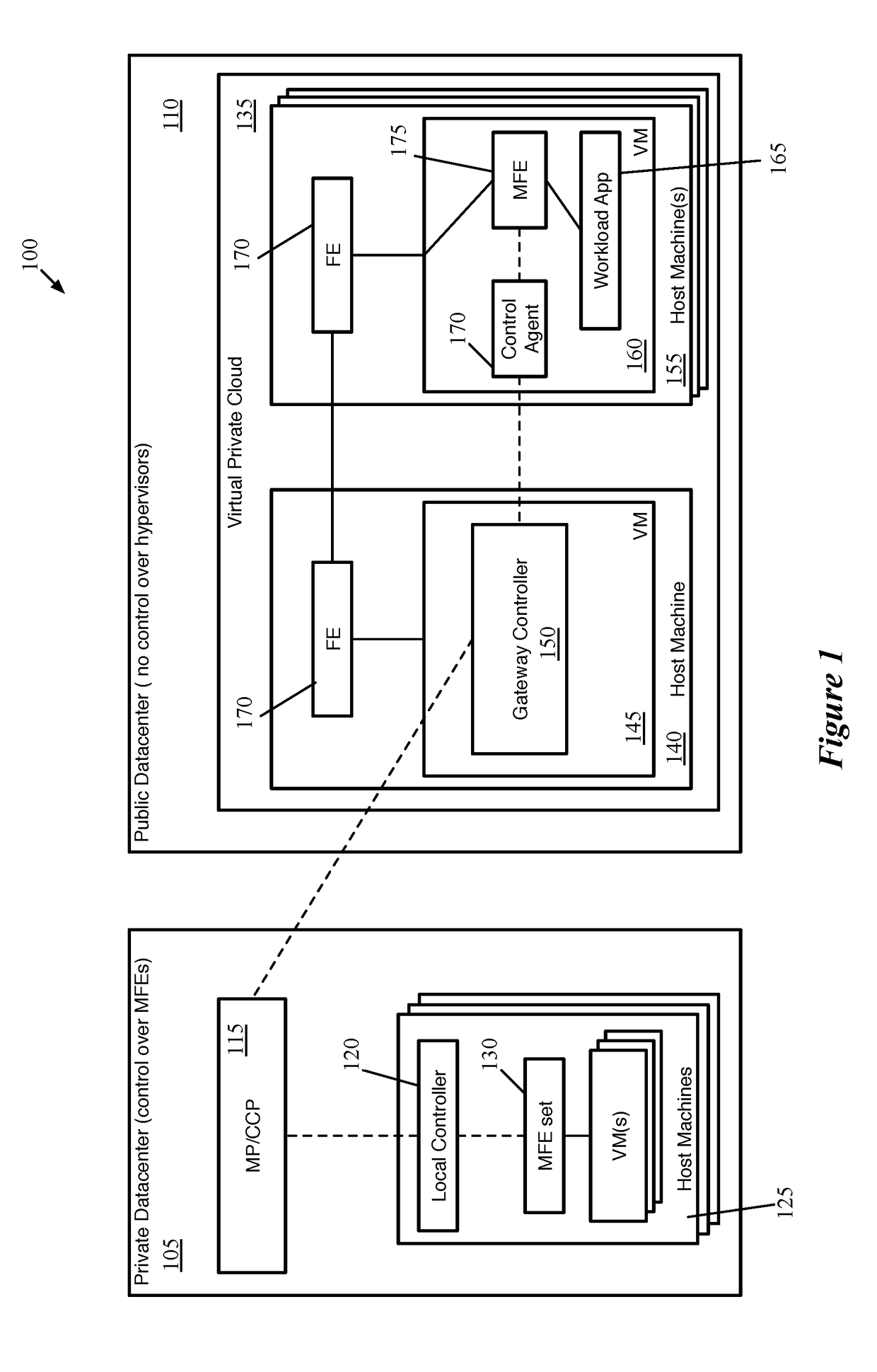
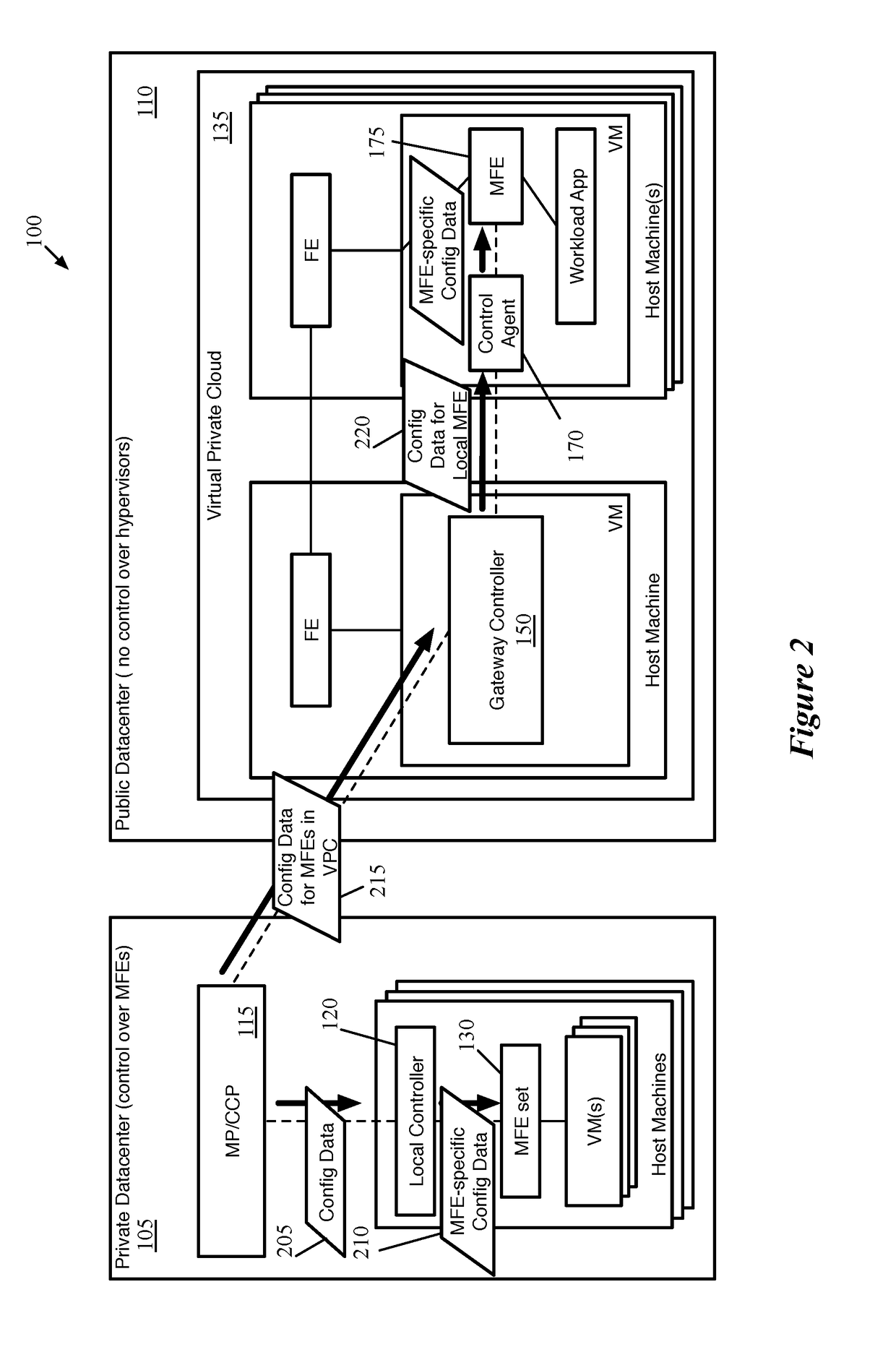
Extension of network control system into public cloud
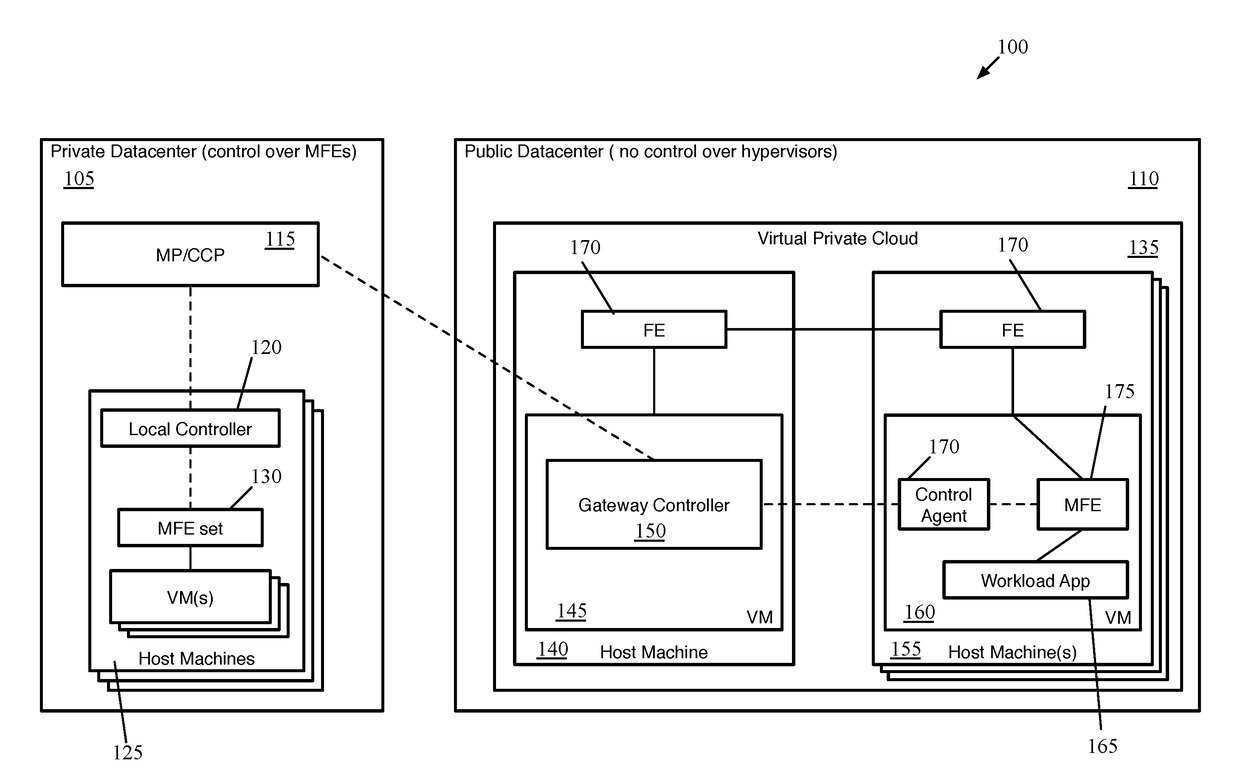
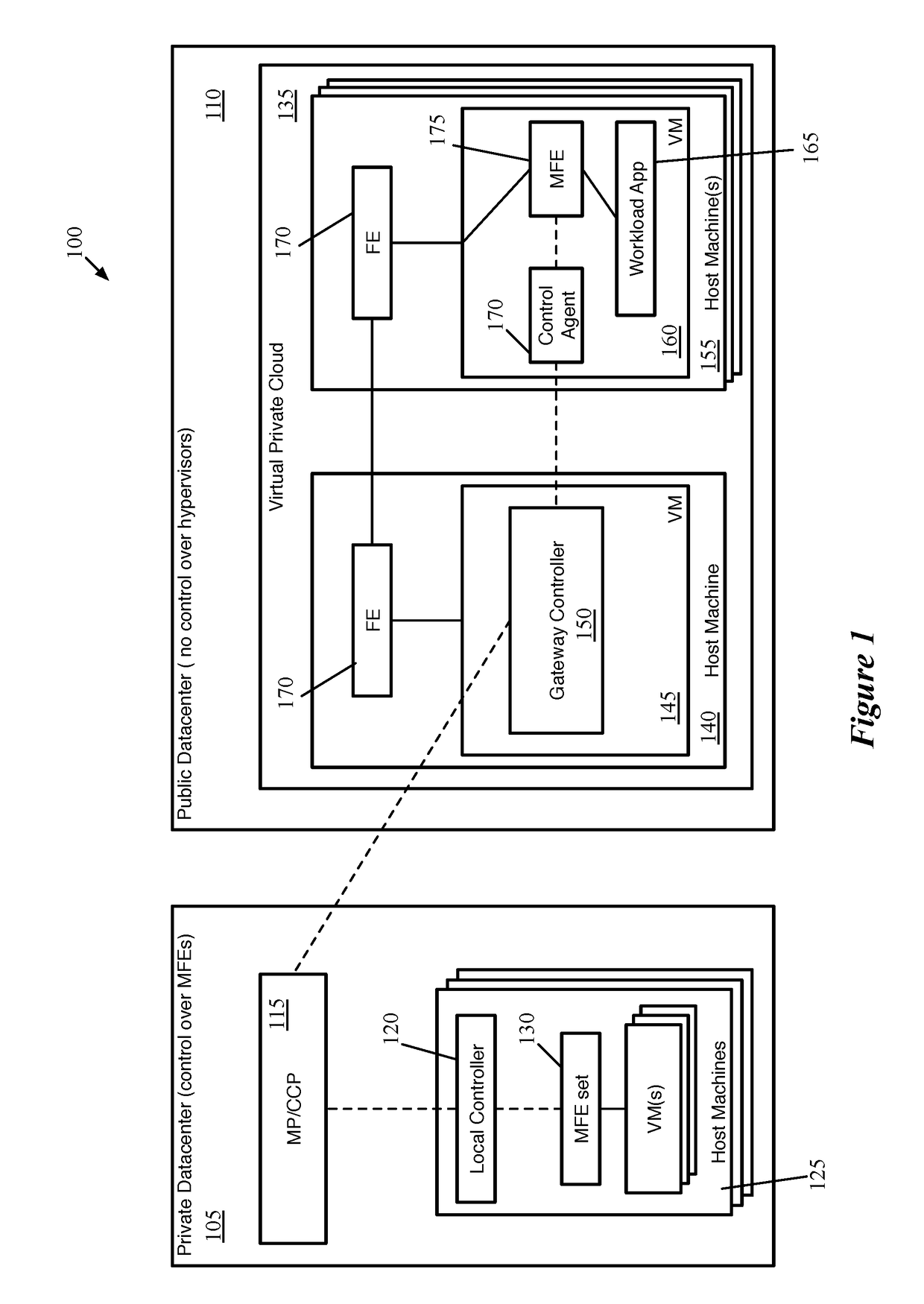
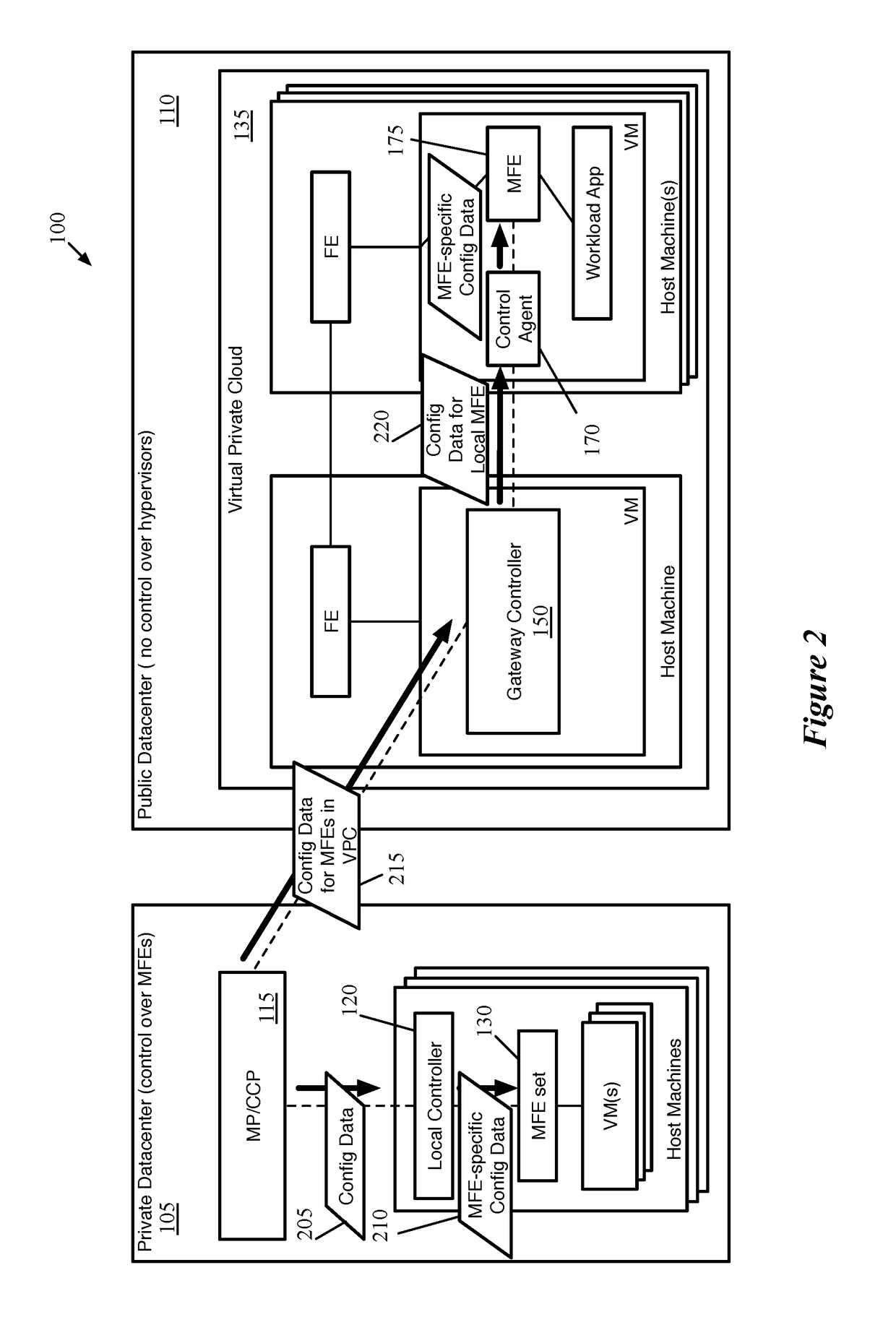
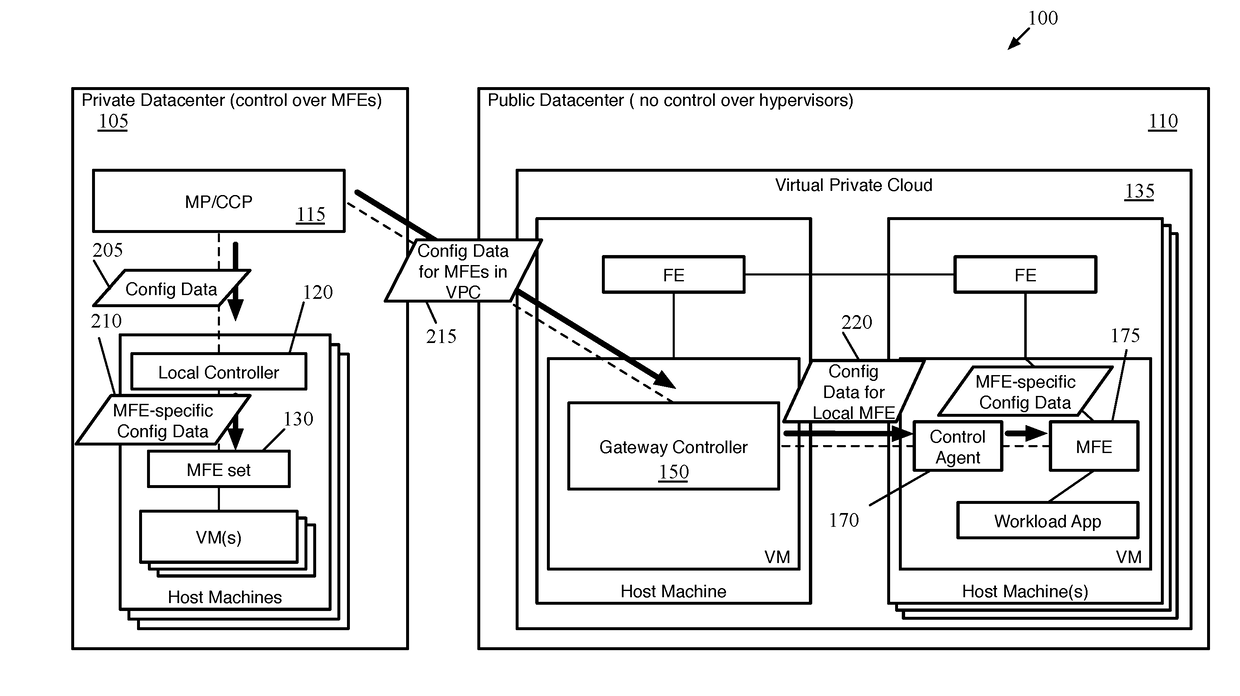
ActiveUS20180062917A1Digital computer detailsReliability/availability analysisData setControl system
Some embodiments provide a method for a first network controller that manages a logical network implemented in a datacenter including forwarding elements to which the first network controller does not have access. The method identifies a first data compute node (DCN) in the datacenter configured to execute a second network controller. The method distributes configuration data defining the logical network to the first DCN. The second network controller distributes sets of the configuration data to local agents executing on additional DCNs in the datacenter that send and receive messages through the logical network. Both managed forwarding elements and the local agents execute on each of the additional DCNs. Each local agent on a particular DCN is for receiving a set of configuration data from the second network controller and configuring the managed forwarding element on the particular DCN to implement the logical network according to the set of configuration data.
Owner:NICIRA
Enterprise management system
InactiveUS20060041660A1Improve availabilityImprove robustnessMultiple digital computer combinationsTransmissionRoot cause analysisFailure management
A Managed Site (10), a logical network entity, is composed of a number of Sub Sites (20) in a one to many relationship. A Sub Site (20) is a logical component, which is composed of a number of Engines (30). Nodes (40) similarly relates to their Engine (30) in a many to one relationship. A Node (40) is a collection of Managed Elements (ME's) (50) (while being an ME (50) itself), which represent network state information. The subsite (20) consists of the engine (30) connected to server nodes (40). One or more clients (110) are connected to the management engine (30) and access management engine (30) information relating to managed elements (50) including nodes (40). The connected manager engines may communicate with one another so that, for example, in the event of a failure, one of the manager engines remaining on line commences monitoring of manage elements assigned to the failed manager engine. Upon accessing the manager engine (30), the client interface displays relationships among managed elements (50) using meaningful connectors and tree-like structures. In addition to basic managed element state monitoring functionality, the manager engine (30) provides a variety of automated tasks ensuring the health of the network and optimal failure correction in the event of a problem. For example, the manager engine (30) performs root cause analysis utilizing an algorithm tracing through manged element (50) relationships and indicating the source of the failure.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic recovery from a split-brain failure in edge nodes
ActiveUS10237123B2Reduce the possibilityIncrease the number ofSignal allocationData switching networksNODALTraffic capacity
Some embodiments provide a method for employing the management and control system of a network to dynamically recover from a split-brain condition in the edge nodes of the network. The method of some embodiments takes a corrective action to automatically recover from a split-brain failure occurred at a pair of high availability (HA) edge nodes of the network. The HA edge nodes include an active machine and a standby machine. The active edge node actively passes through the network traffic (e.g., north-south traffic for a logical network), while the standby edge node is synchronized and ready to transition to the active state, should a failure occur. Both HA nodes share the same configuration settings and only one is active until a path, link, or system failure occurs. The active edge node also provides stateful services (e.g., stateful firewall, load balancing, etc.) to the data compute nodes of the network.
Owner:NICIRA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com