Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
221 results about "Public environment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
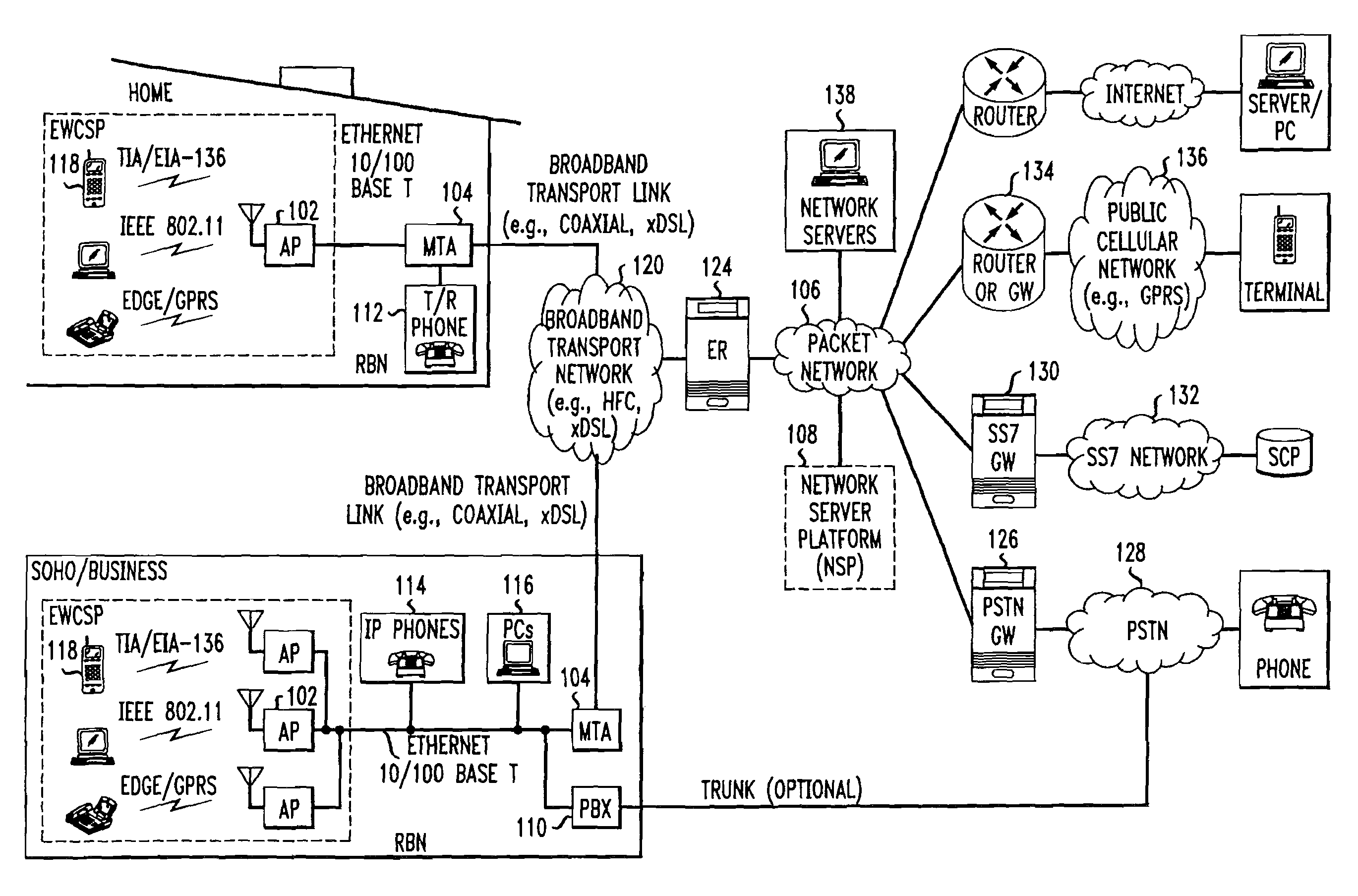
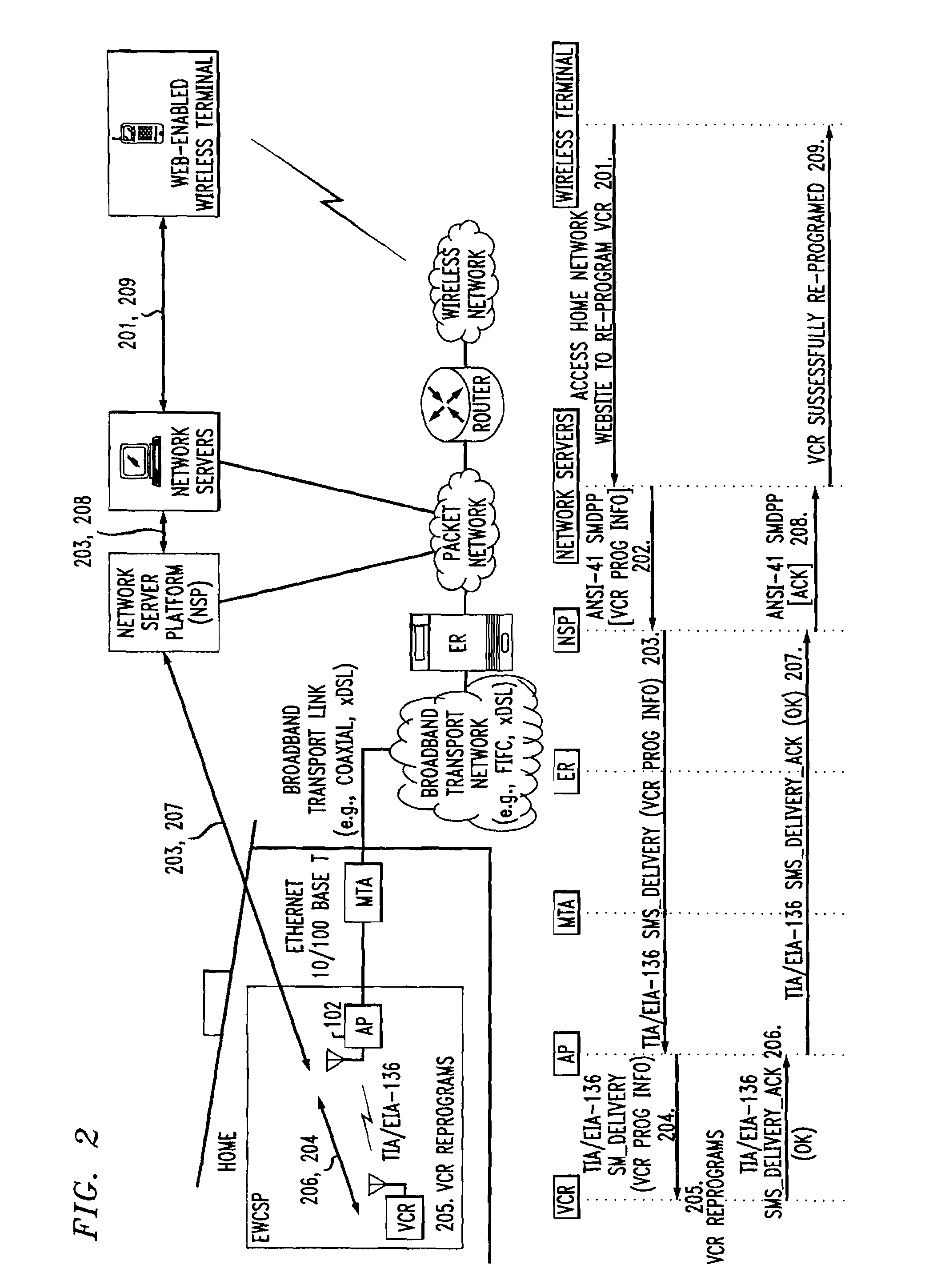
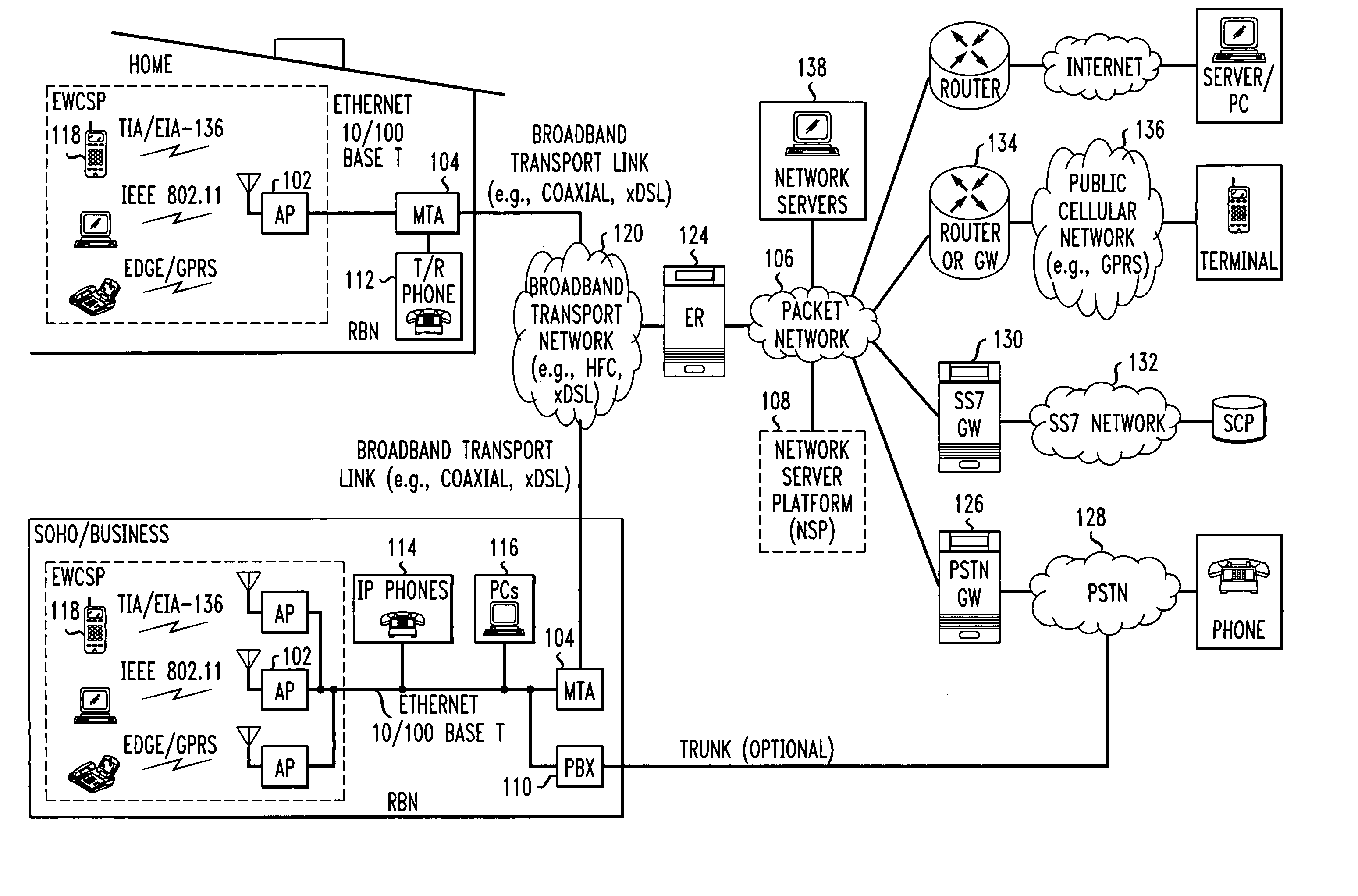
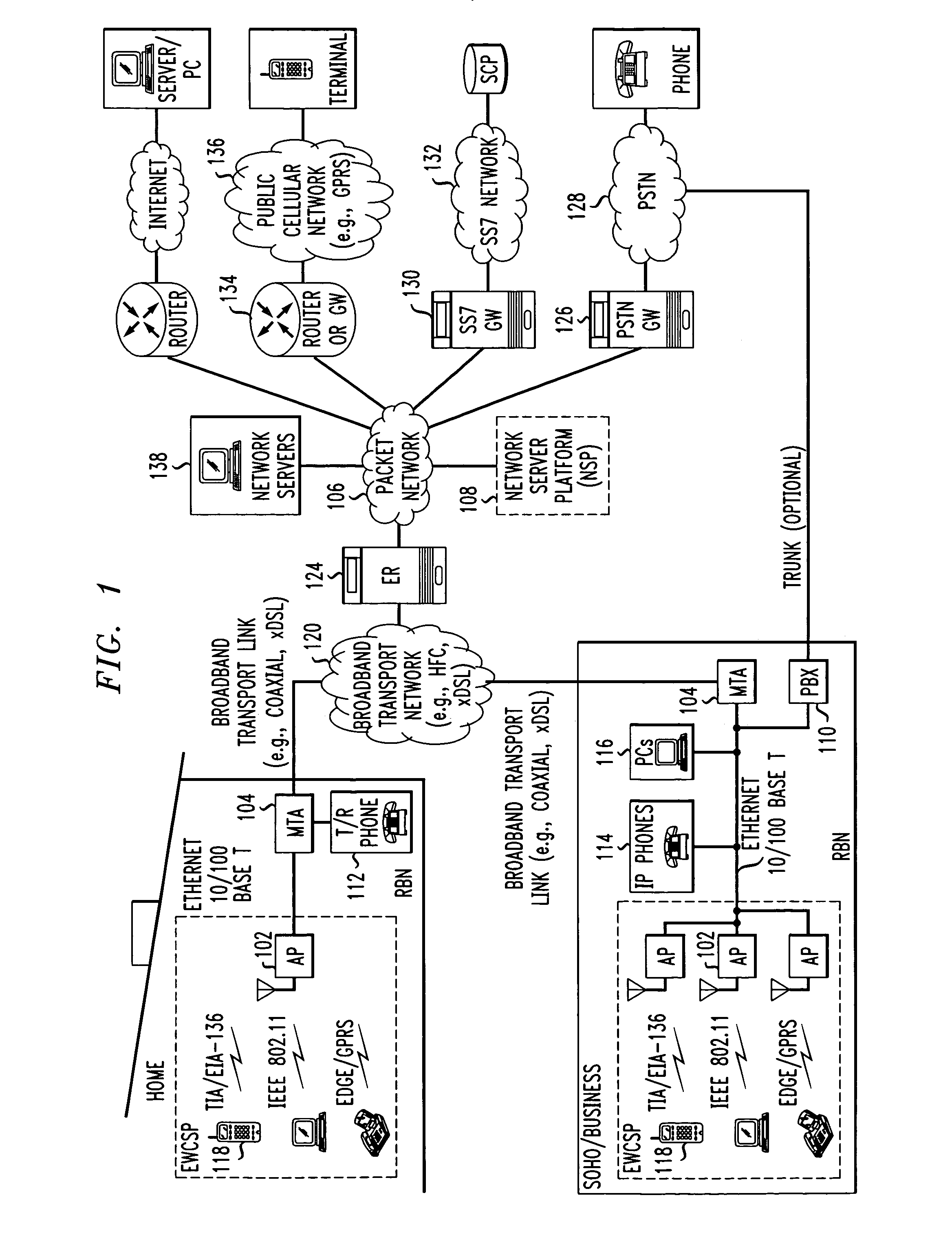
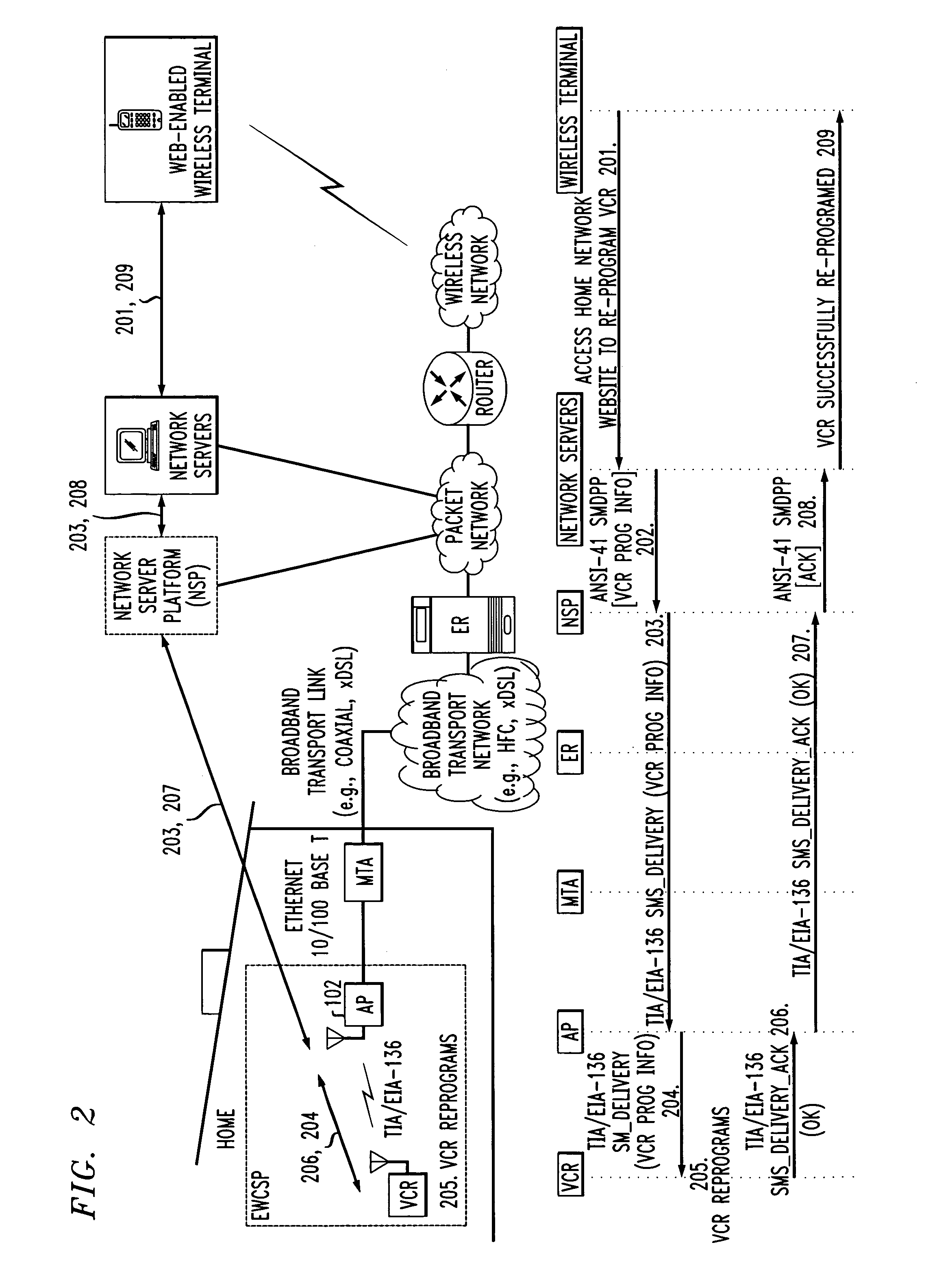
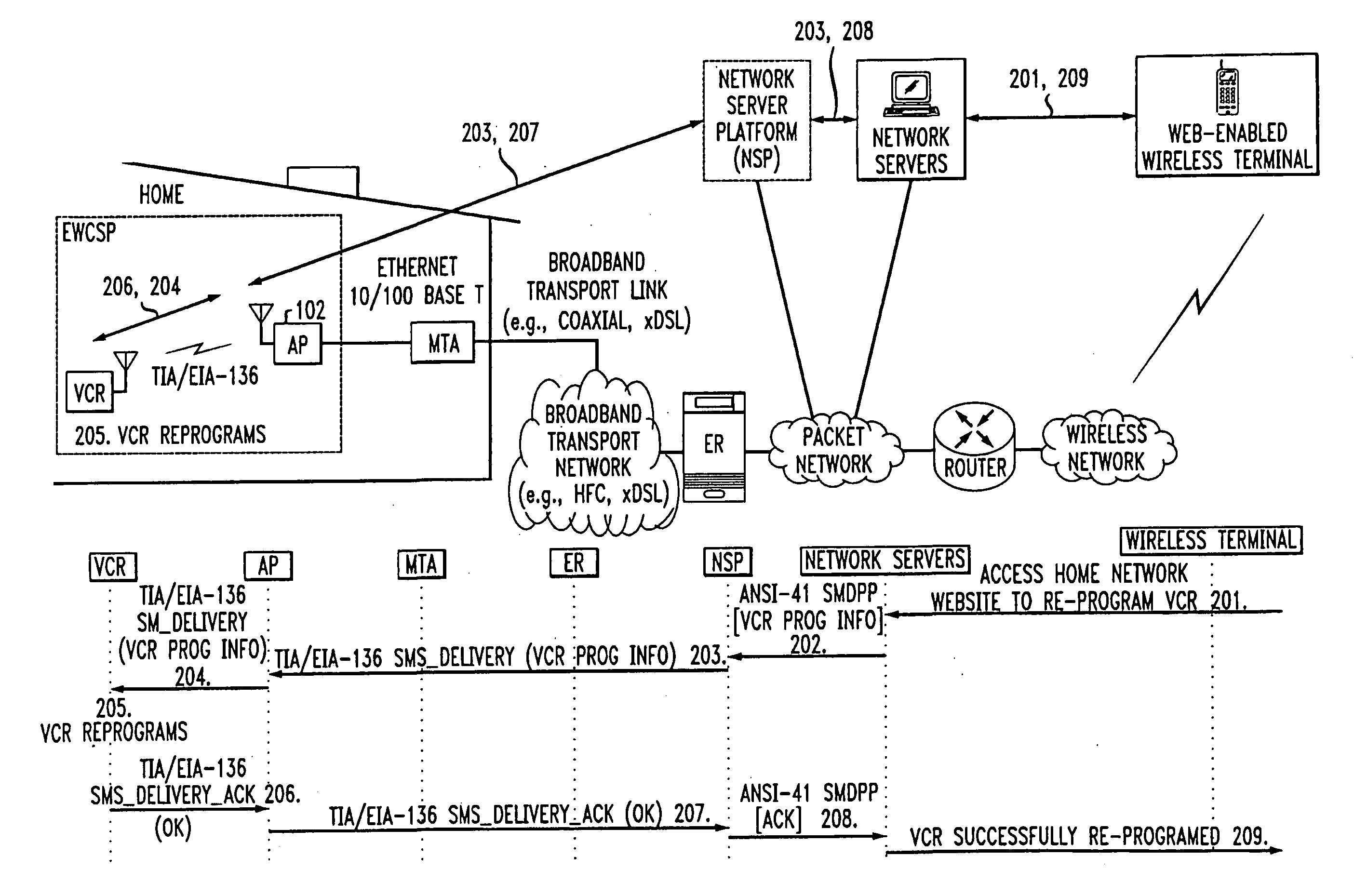
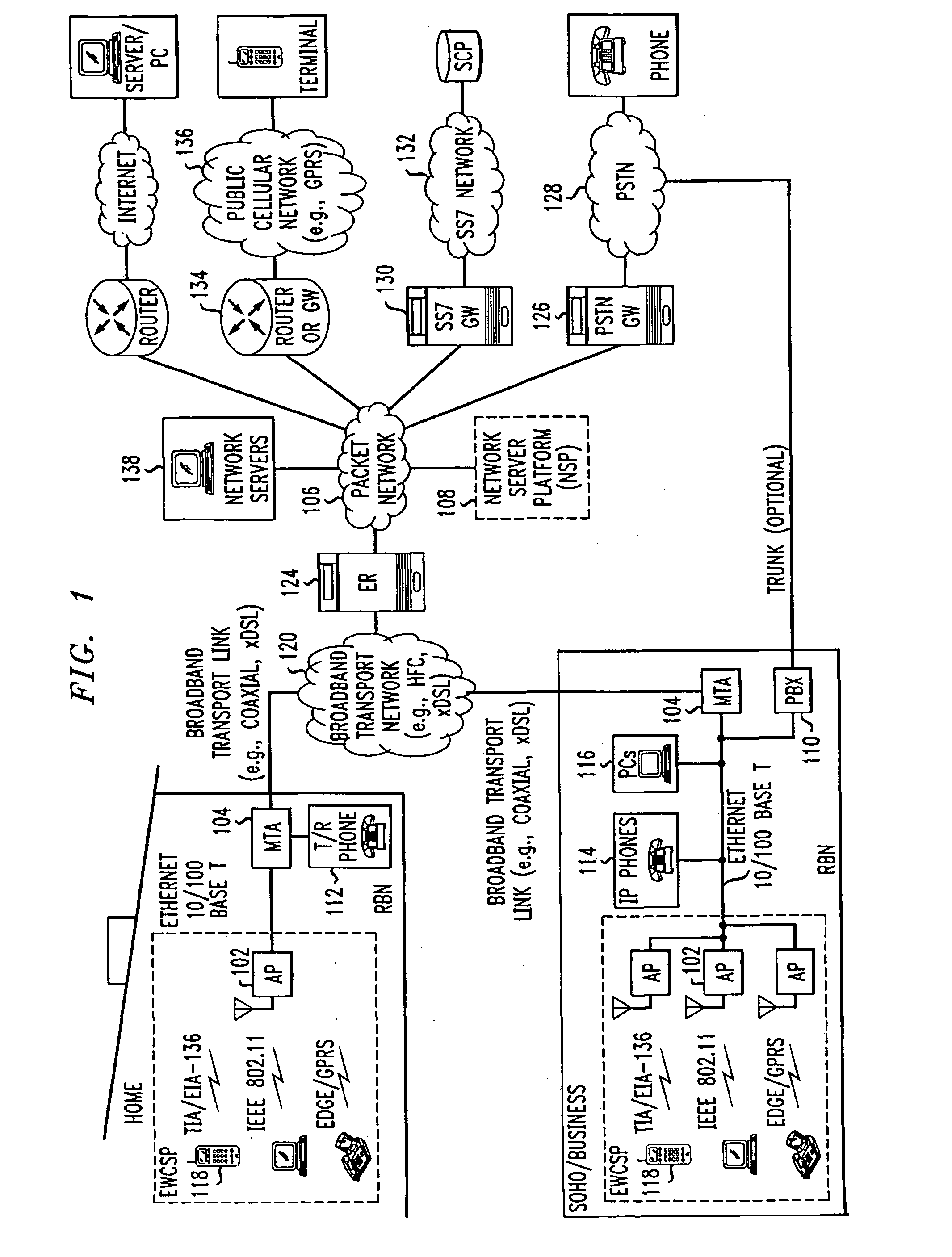
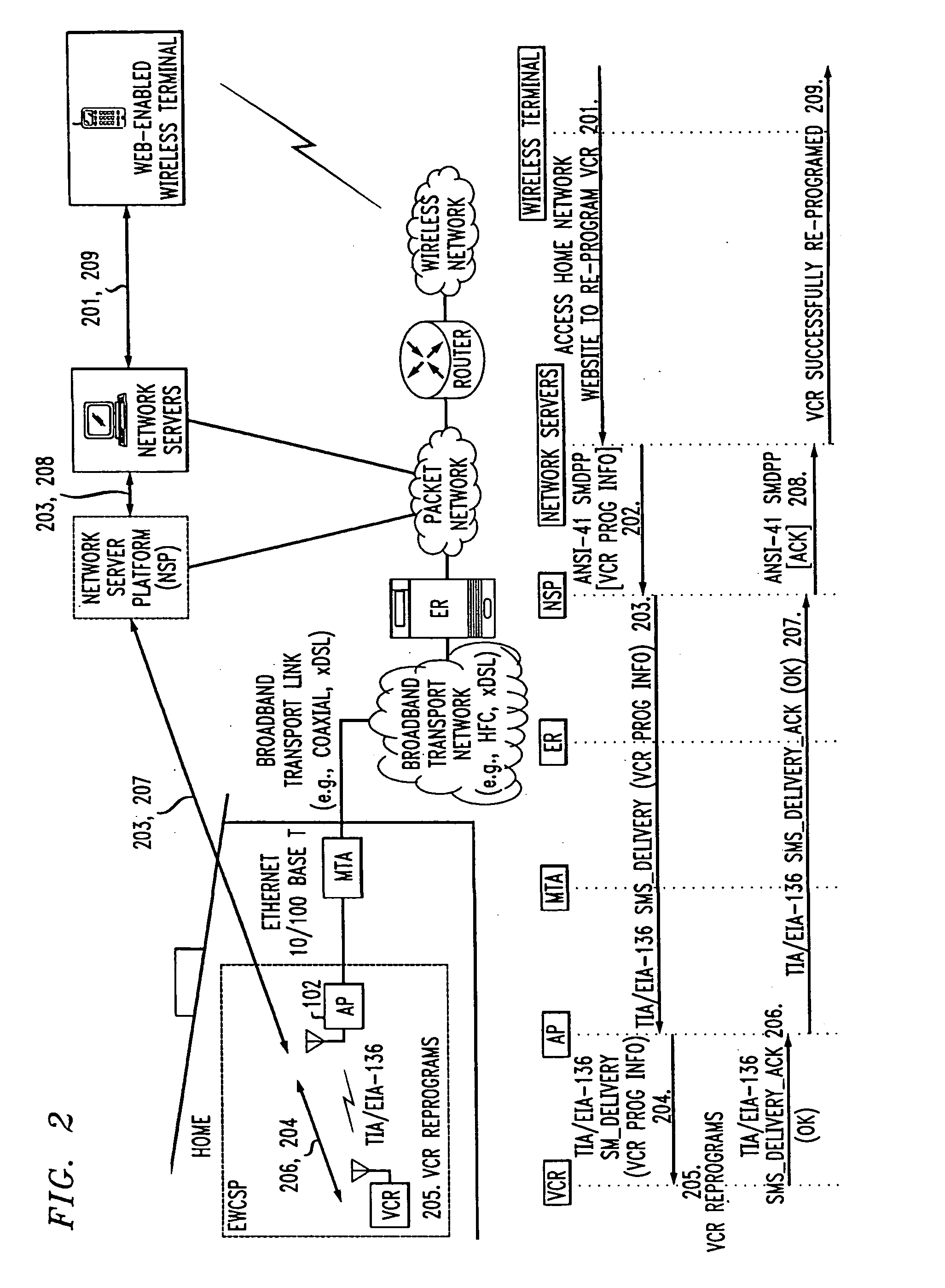
Computer readable medium with embedded instructions for providing communication services between a broadband network and an enterprise wireless communication platform within a residential or business environment
InactiveUS8155155B1Easy maintenanceCost-effectivelyError preventionFrequency-division multiplex detailsModem deviceBroadband transmission
The present invention sets forth computer-readable non-transitory medium having computer-executable instructions for providing network-centric service distribution method that integrates a wireless access system / service with conventional telecommunications services in the residence, SOHO, business or public environment through the use of a local broadband network, such as a Residential-Business Broadband Network (RBN). The RBN communicates with the service provider's broadband transport network and broadband packet network to facilitate end-to-end packet telecommunication services. Signals from a plurality of wireless devices are accepted and forwarded to an IEEE 802.11b interface for a wireless modem and / or to an Ethernet interface for a Voice over Internet Protocol (VOIP) / Ethernet Processor, where the forwarded signals comprise intranet telephony and data.
Owner:AT & T INTPROP II LP
Broadband network with enterprise wireless communication method for residential and business environment
InactiveUS7010002B2Easy to optimizeCost-effective deploymentMultiplex system selection arrangementsTelephone data network interconnectionsModem deviceBroadband transmission
The present invention sets forth a network-centric service distribution architecture and method that integrates a wireless access system / service in the residence, SOHO, business or public environment through the use of a local broadband network, such as a Residential-Business Broadband Network (RBN), to the service provider's broadband transport network and to a service provider's broadband packet network that facilitates end-to-end packet telecommunication services. Access functions for connecting said service provider's broadband packet network to the RBN via said service provider's broadband transport network are provided. Call and service termination functions to a plurality of local RBN devices are also provided. Signals from a plurality of wireless devices are accepted and forwarded to an IEEE 802.11b interface for a wireless modem and / or to an Ethernet interface for a Voice over Internet Protocol (VOIP) / Ethernet Processor, where the forwarded signals comprise intranet telephony and data. Voice signals are also accepted from a plurality of tip / ring interfaces and forwarded to a broadband transport interface for back haul of data and voice packets. A service provider can deploy services in an integrated voice, data and multimedia environment cost-effectively based on one broadband packet network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
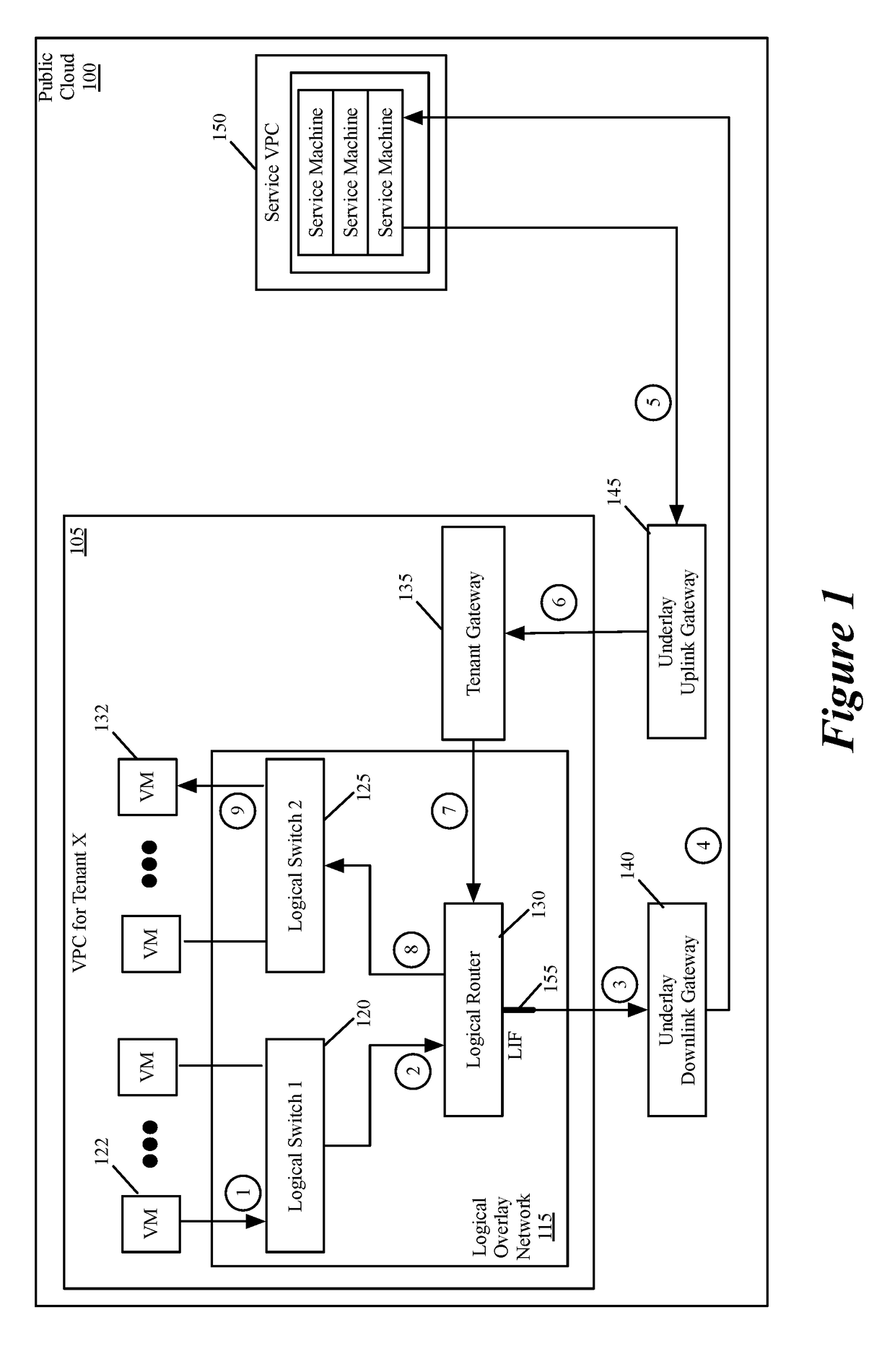
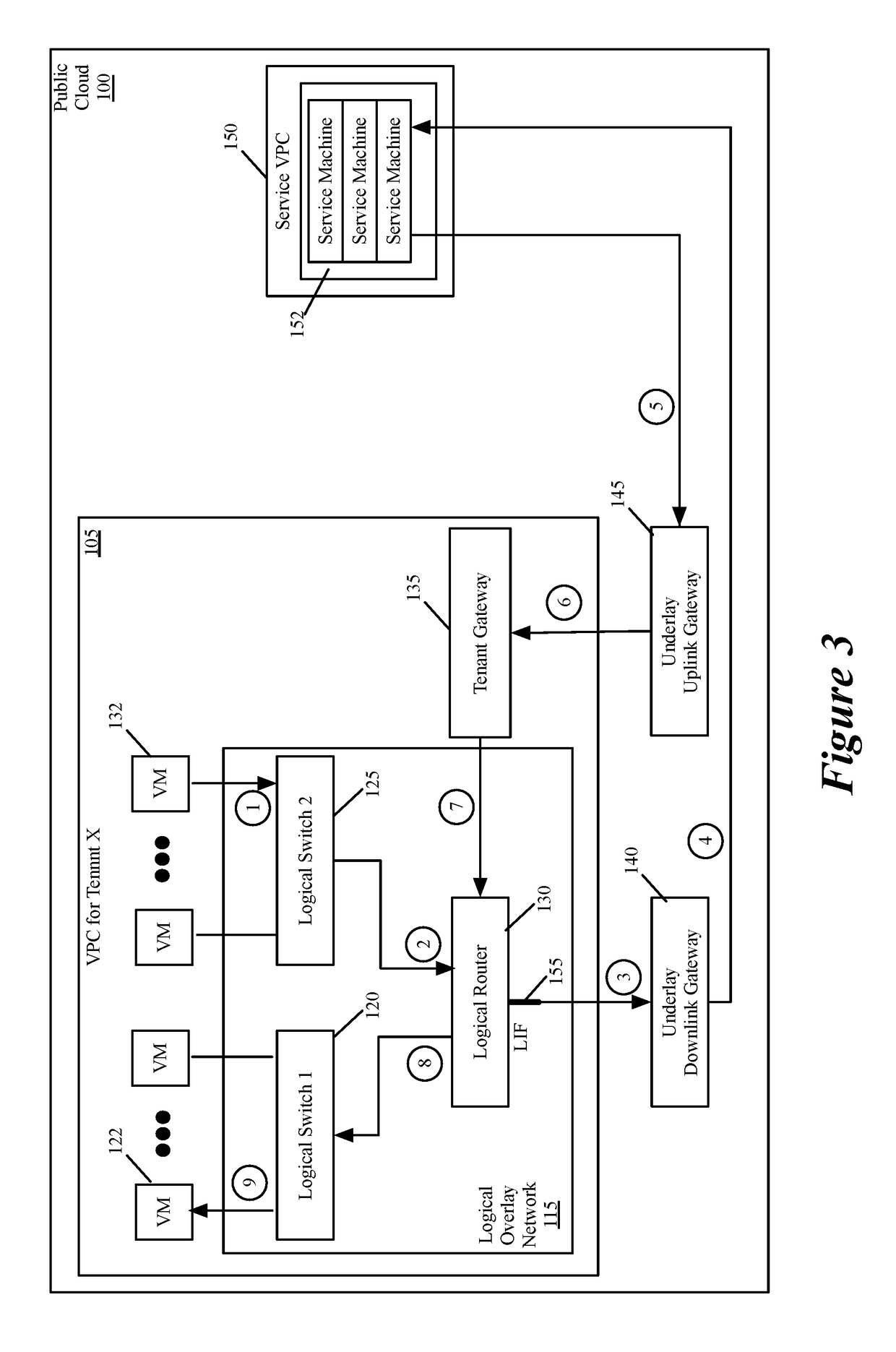
Performing in-line service in public cloud
Some embodiments provide a novel way to insert a service (e.g., a third party service) in the path of a data message flow, between two machines (e.g., two VMs, two containers, etc.) in a public cloud environment. For a particular tenant of the public cloud, some embodiments create an overlay logical network with a logical overlay address space. To perform a service on data messages of a flow between two machines, the logical overlay network passes to the public cloud's underlay network the data messages with their destination address (e.g., destination IP addresses) defined in the logical overlay network. The underlay network (e.g., an underlay default downlink gateway) is configured to pass data messages with such destination addresses (e.g., with logical overlay destination addresses) to a set of one or more service machines. The underlay network (e.g., an underlay default uplink gateway) is also configured to pass to the particular tenant's public cloud gateway the processed data messages that are received from the service machine set and that are addressed to logical overlay destination addresses. The tenant's public cloud gateway is configured to forward such data messages to a logical forwarding element of the logical network, which then handles the forwarding of the data messages to the correct destination machine.
Owner:NICIRA
Broadband network with enterprise wireless communication system for residential and business environment
InactiveUS20060209795A1Easy maintenanceCost-effectivelyInterconnection arrangementsBroadband local area networksBroadband transmissionEngineering
The present invention sets forth a network-centric service distribution architecture that integrates a wireless access system in the residence, SOHO, business or public environment through the use of a local broadband network, such as a Residential-Business Broadband Network (RBN), to the service provider's broadband transport network and to a service provider's broadband packet network. The system includes Media Terminal Adapter is coupled via the RBN to the access port(s) and via the service provider's broadband transport network to the service provider's broadband packet network. The access port is coupled to the Media Terminal Adapter via either a RBN (e.g., a Local Area Network—LAN) or simply via a traditional POTS line interface. The access port receives and sends wireless signals to a plurality of RBN devices, allowing the user to control theses devices remotely from the residence, business, SOHO or public environments. The integration of an RBN to a service provider's broadband packet network allows a subscriber to communicate at home and at the office with one communication device anytime anywhere.
Owner:AT&T PROPERTIES LLC
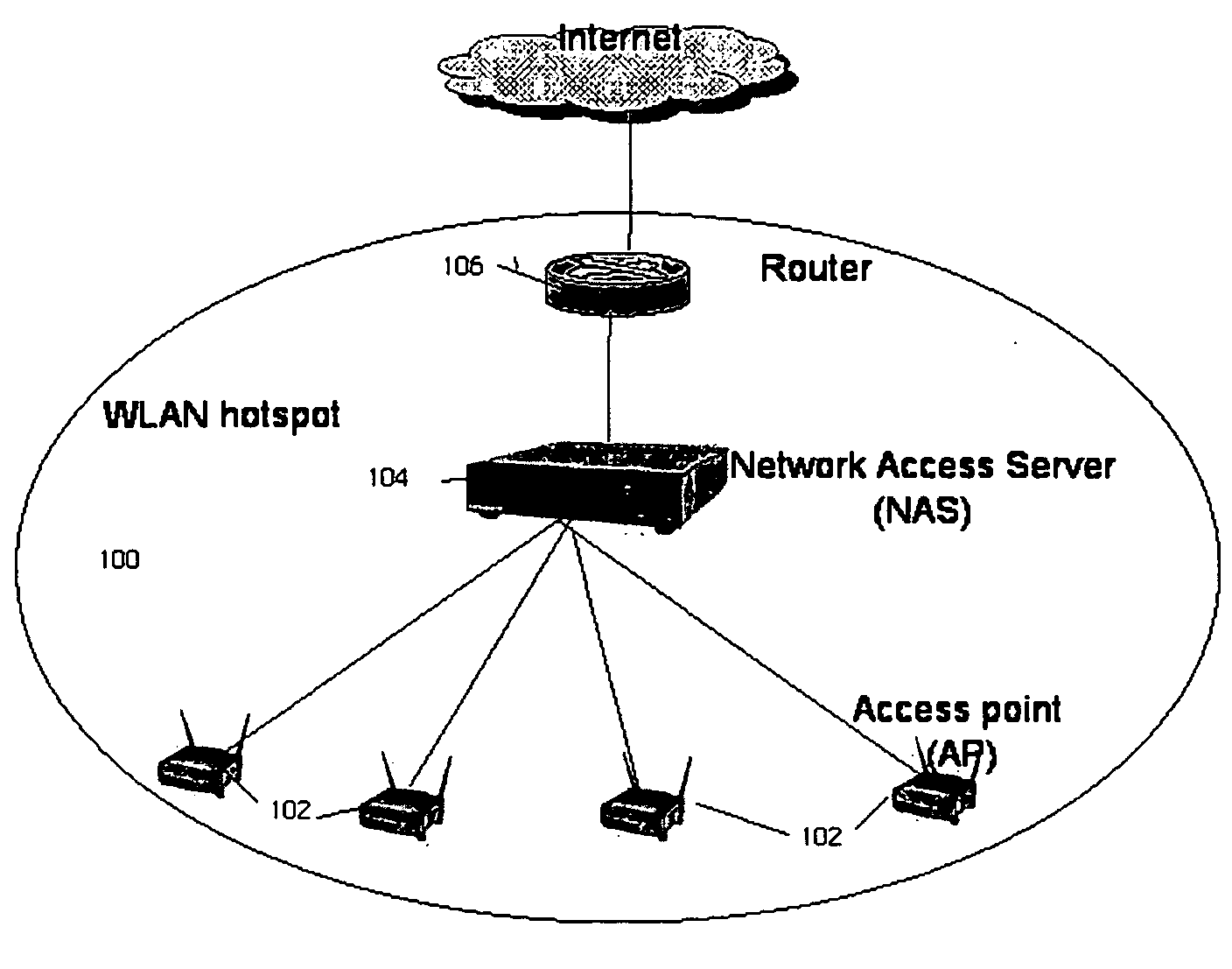
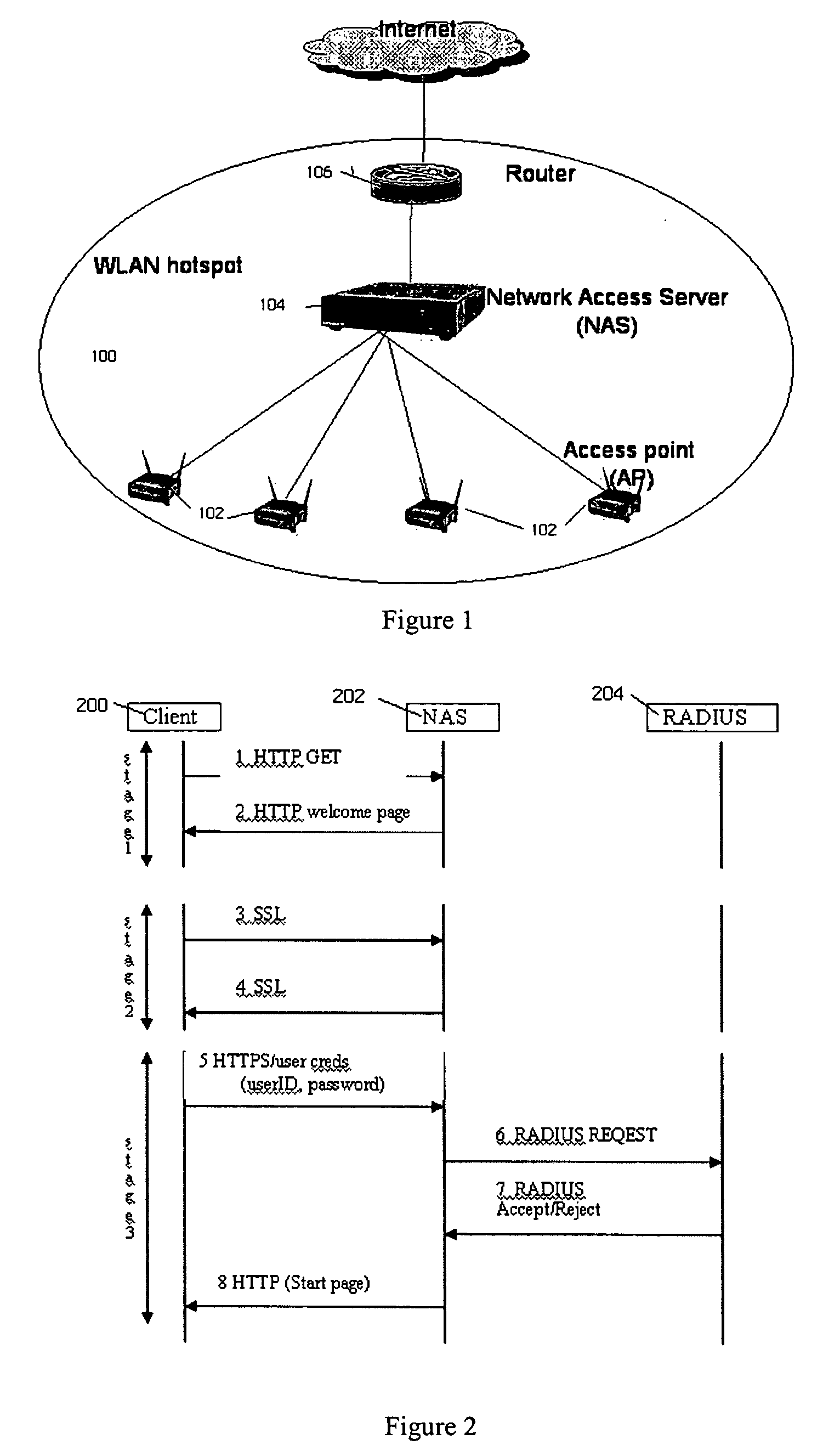
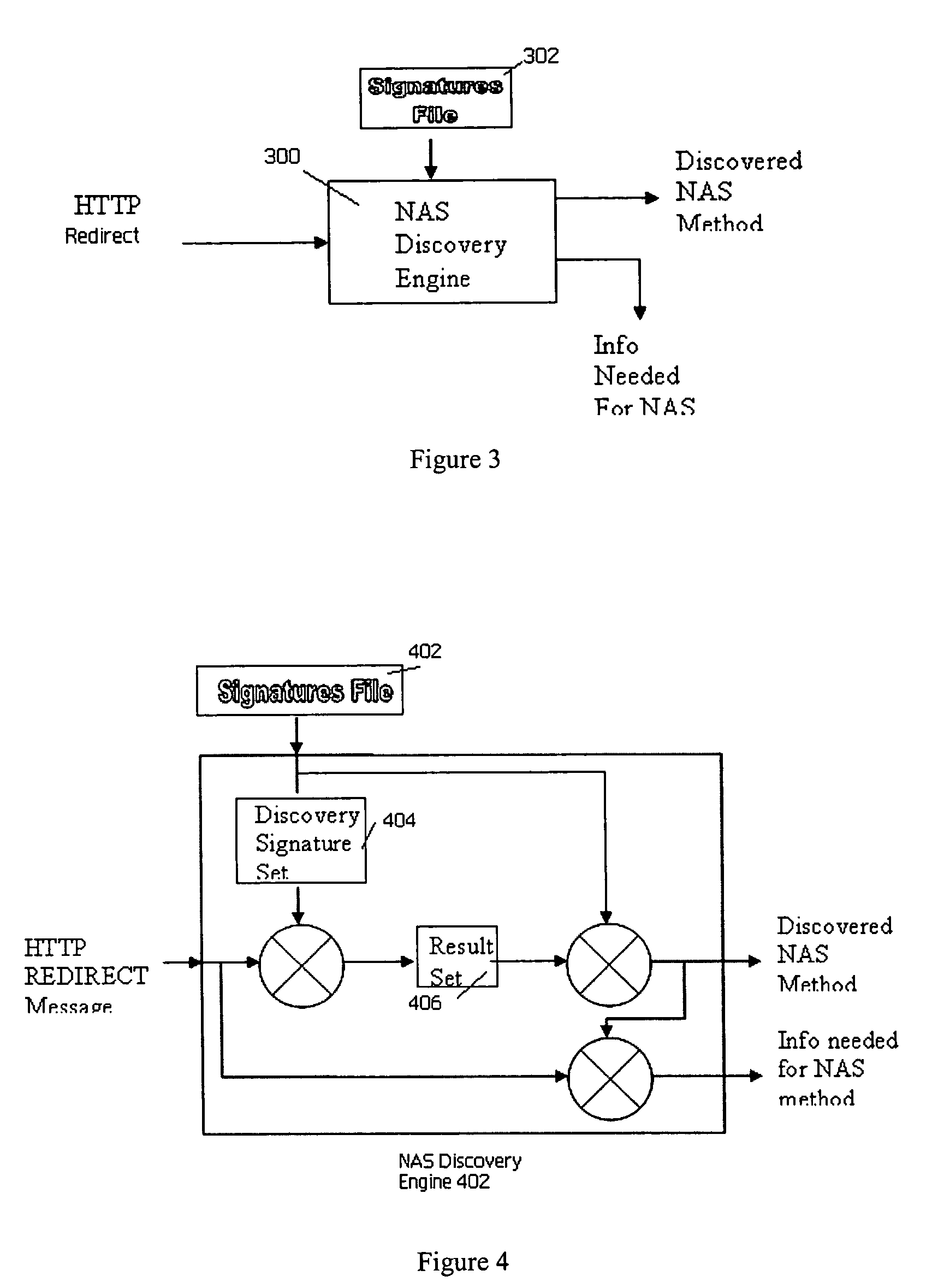
Network access server (NAS) discovery and associated automated authentication in heterogenous public hotspot networks
InactiveUS20060174127A1User identity/authority verificationNetwork topologiesPublic environmentNetwork access server
Automated HTTP-based user authentication in a public WLAN environment is facilitated across heterogeneous network access servers (NASs). Each of a set of network access servers has a given authentication protocol, and these protocols typically differ from one another. According to the invention, each authentication protocol has a unique “signature.” According to the invention, a “smart” client that is executable on a given wireless device seeking access to the public WLAN environment is provided with a set of signatures. These signatures are used by the client to determine the appropriate access protocol to use with respect to a given NAS that is controlling access to the WLAN. The client may also have the capability of discovering an unknown authentication protocol “on-the-fly” as it attempts to obtain wireless access. The set of signatures is updated in the client from time-to-time without requiring the client software to be recompiled. The present invention thus provides a generic mechanism by which a client can work with any NAS.
Owner:SMITH MICRO SOFTWARE INC
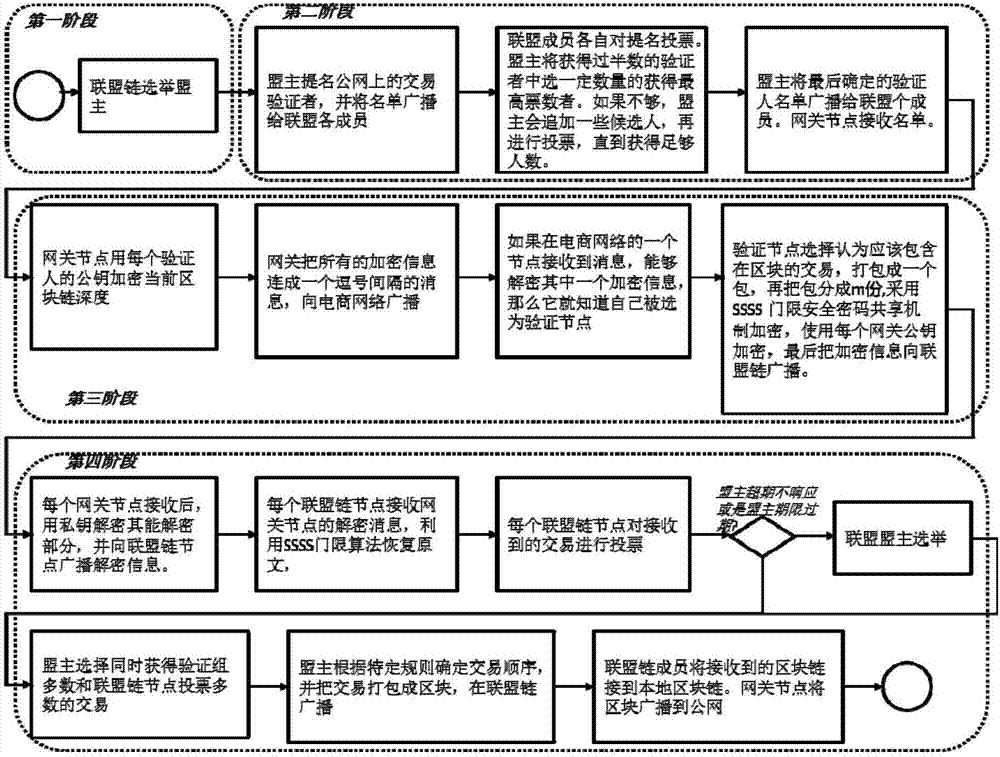
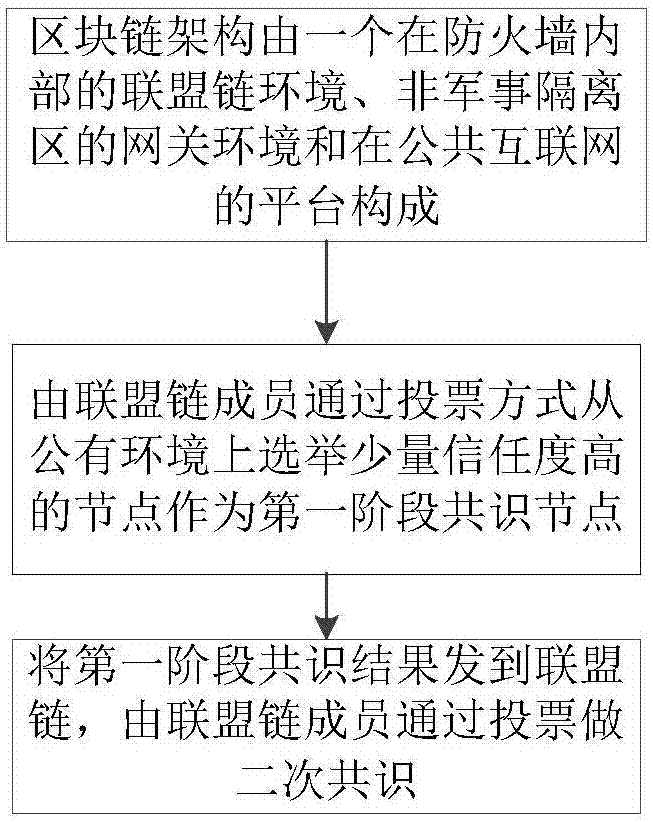
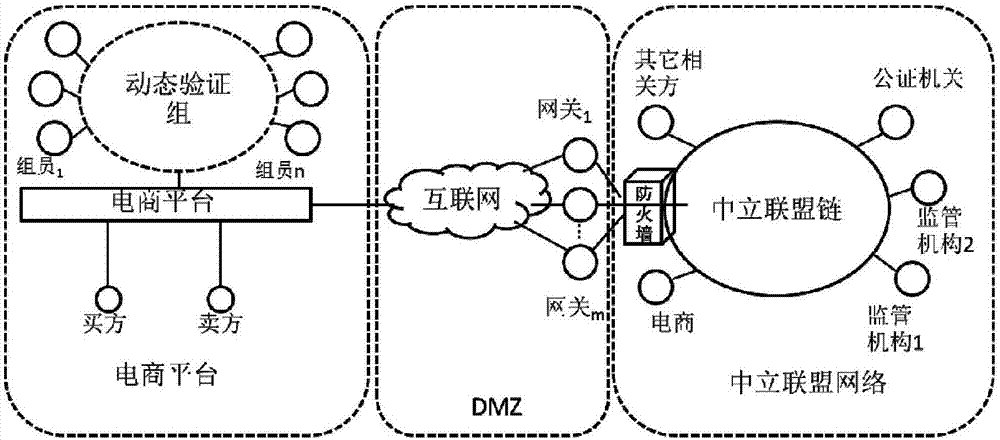
Credit-based blockchain consensus method for large-scale e-commerce
ActiveCN107395403APerformance is not affectedImprove consensus efficiencyFinanceData switching networksPublic environmentThe Internet
The invention discloses a credit-based blockchain consensus method for large-scale e-commerce. According to the method, by applying a blockchain to the large-scale e-commerce application scene, the scalability needed by the large-scale e-commerce scene can be achieved, millions of nodes can be supported, the consensus requirement that the service speed of the e-commerce is ten millions per second can be met, energy consumption such as Bitcoins is not needed, and the problem that a blockchain adopting proof of stake (POS) is lack of security guarantee is solved. The method comprises the steps that 1, the structure of the blockchain is composed of an alliance chain environment in a firewall, a gateway environment in a non-military isolation area and a platform in the public Internet; 2, alliance chain members elect a few nodes with a high trust degree from a public environment to serve as first-stage consensus nodes; and 3, a first-stage consensus result is sent to a alliance chain, the alliance chain members perform secondary consensus through voting to ensure the accuracy of the consensus result from the public environment, and then the security requirement is met.
Owner:北京区块链云科技有限公司
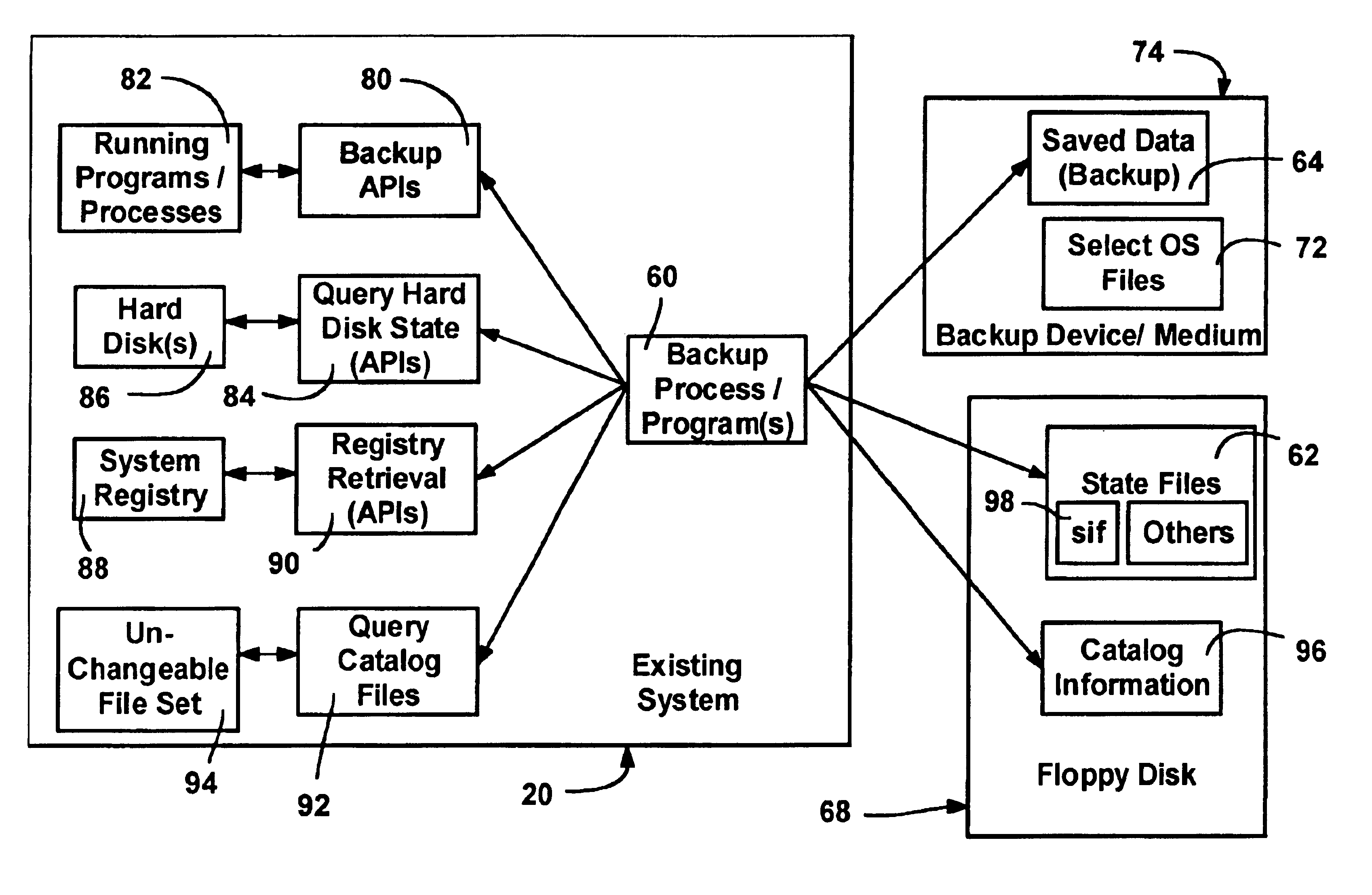
Extensible system recovery architecture
A system recovery method and framework for backing up and restoring a system that cannot reboot. The framework defines a common process, environment, and syntax, whereby backup programs integrate with this framework by collecting and writing appropriate information to be used during system recovery in the proper format. The format is a System Information File, a text file that specifies the hard disk state of the system and the location of key partitions where key components of the operating system are located. The file also includes instructions for specifying programs to launch during the restore phase, and any commands that need to be run in error handling cases. The file also includes or references any additional drivers or files to copy to assist in the restore process. A framework for restoring is also provided, and includes reading the file to restore the disk partition state, creating a common environment, and configuring (initializing) the common environment. When the environment is configured, the programs specified in the file are run to restore the remainder of the system.
Owner:MICROSOFT TECH LICENSING LLC
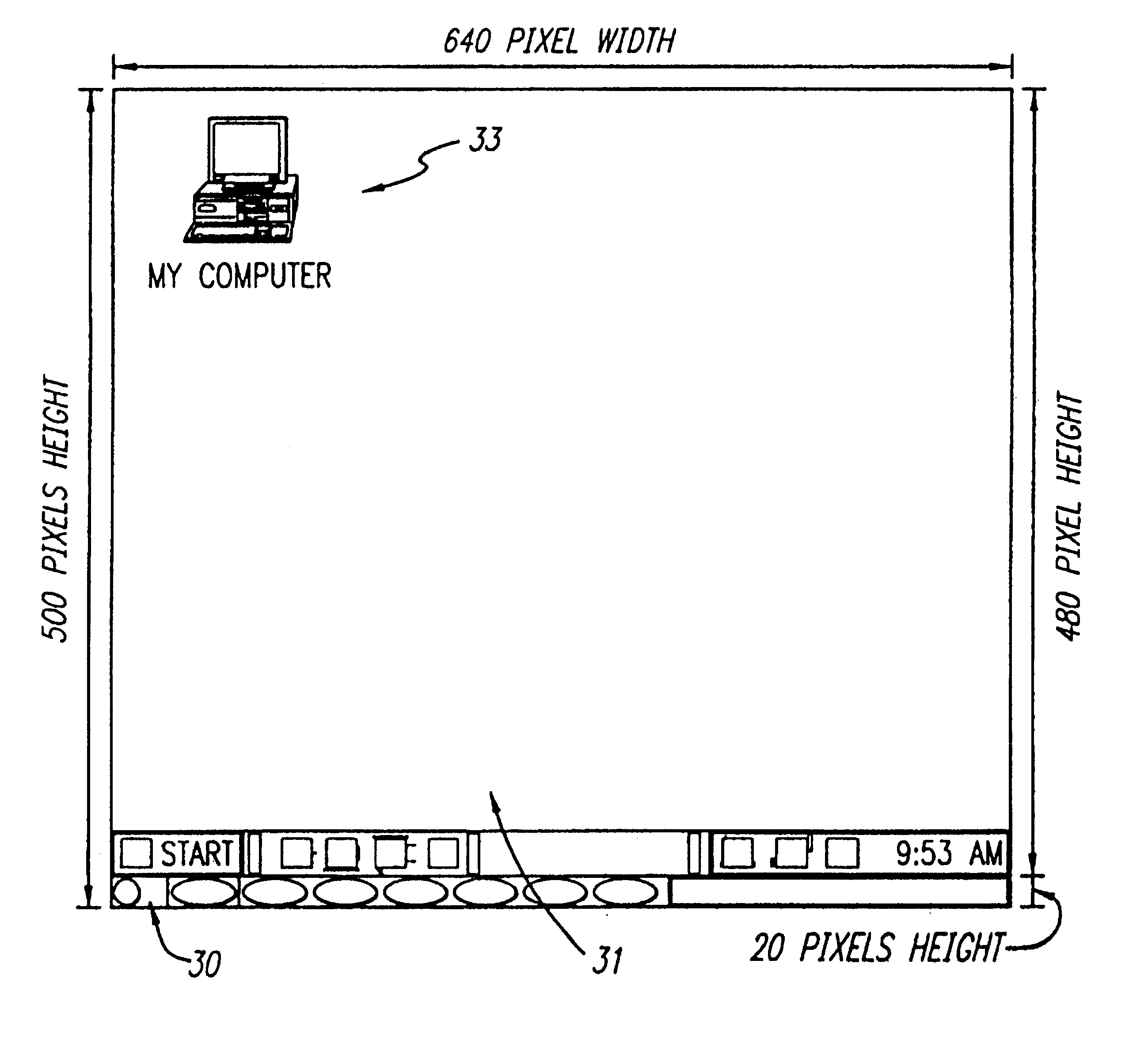
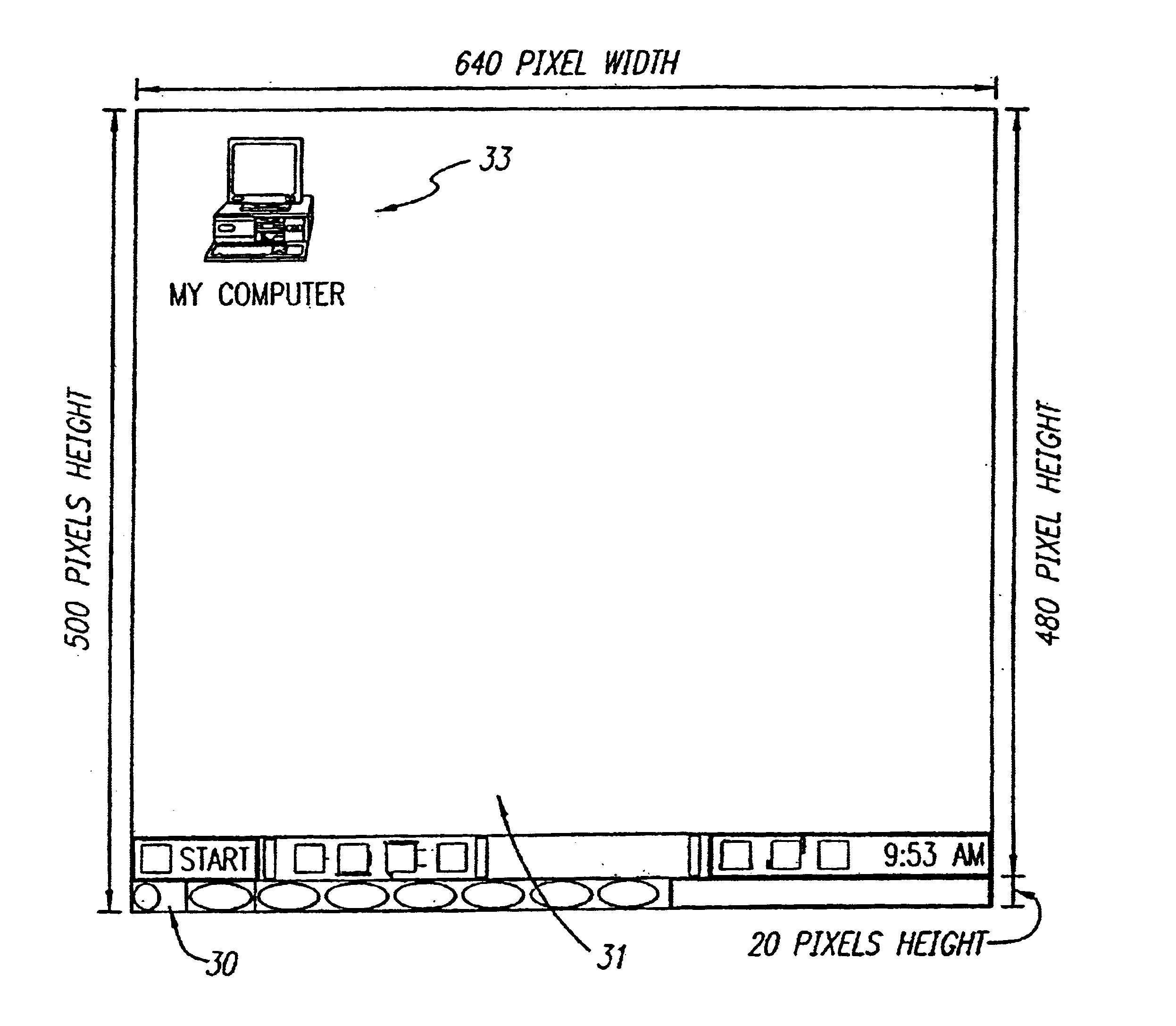
Secondary user interface
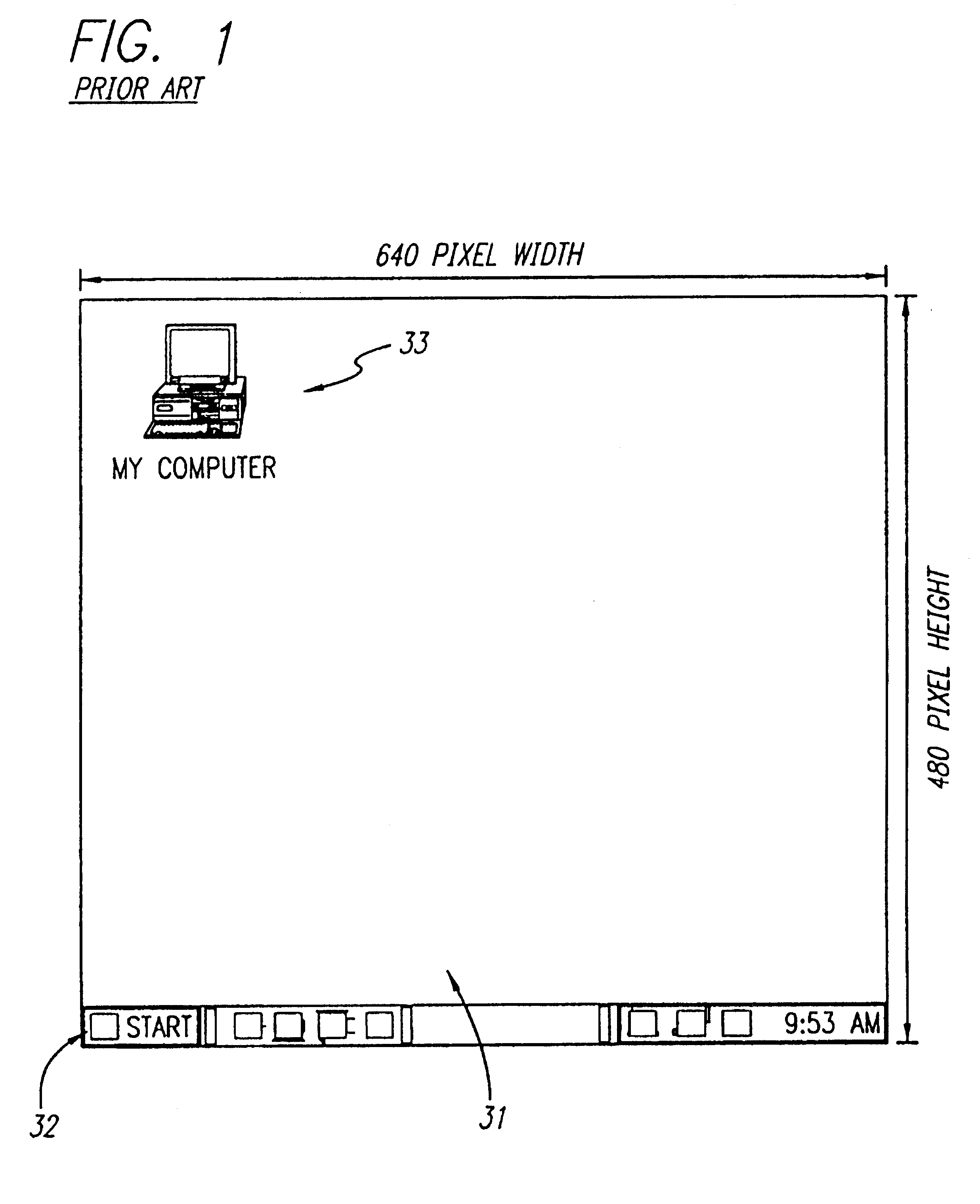
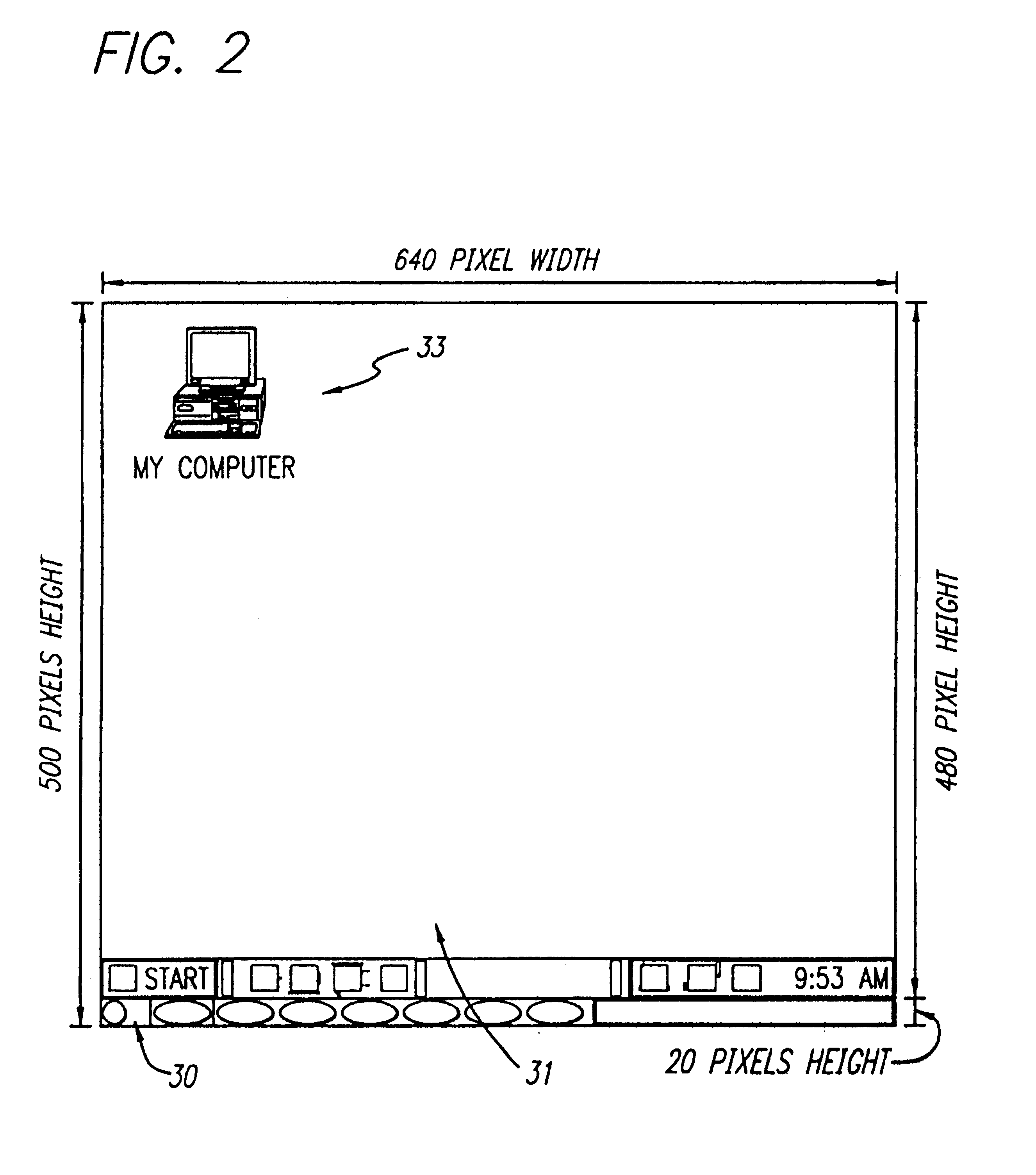
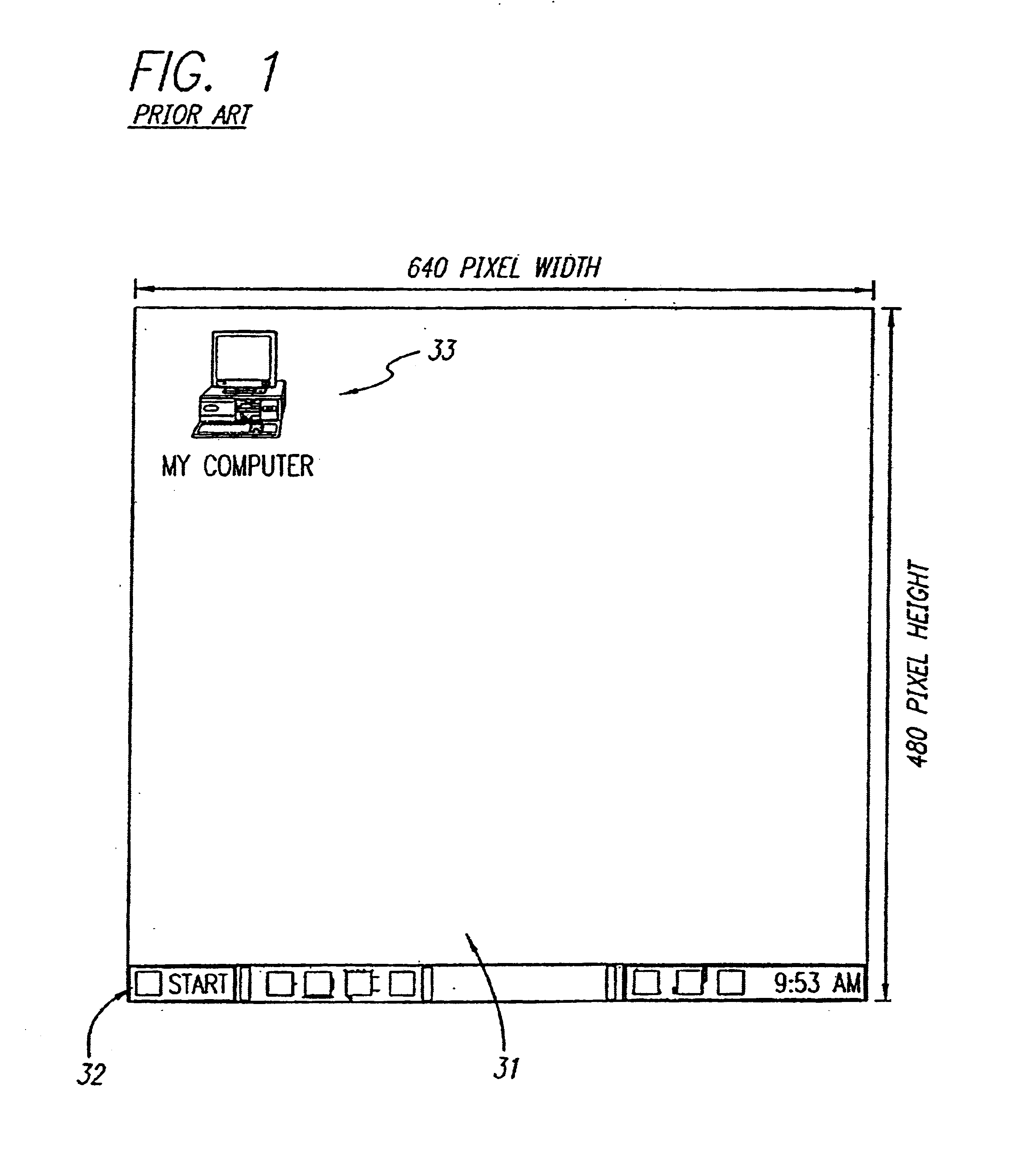
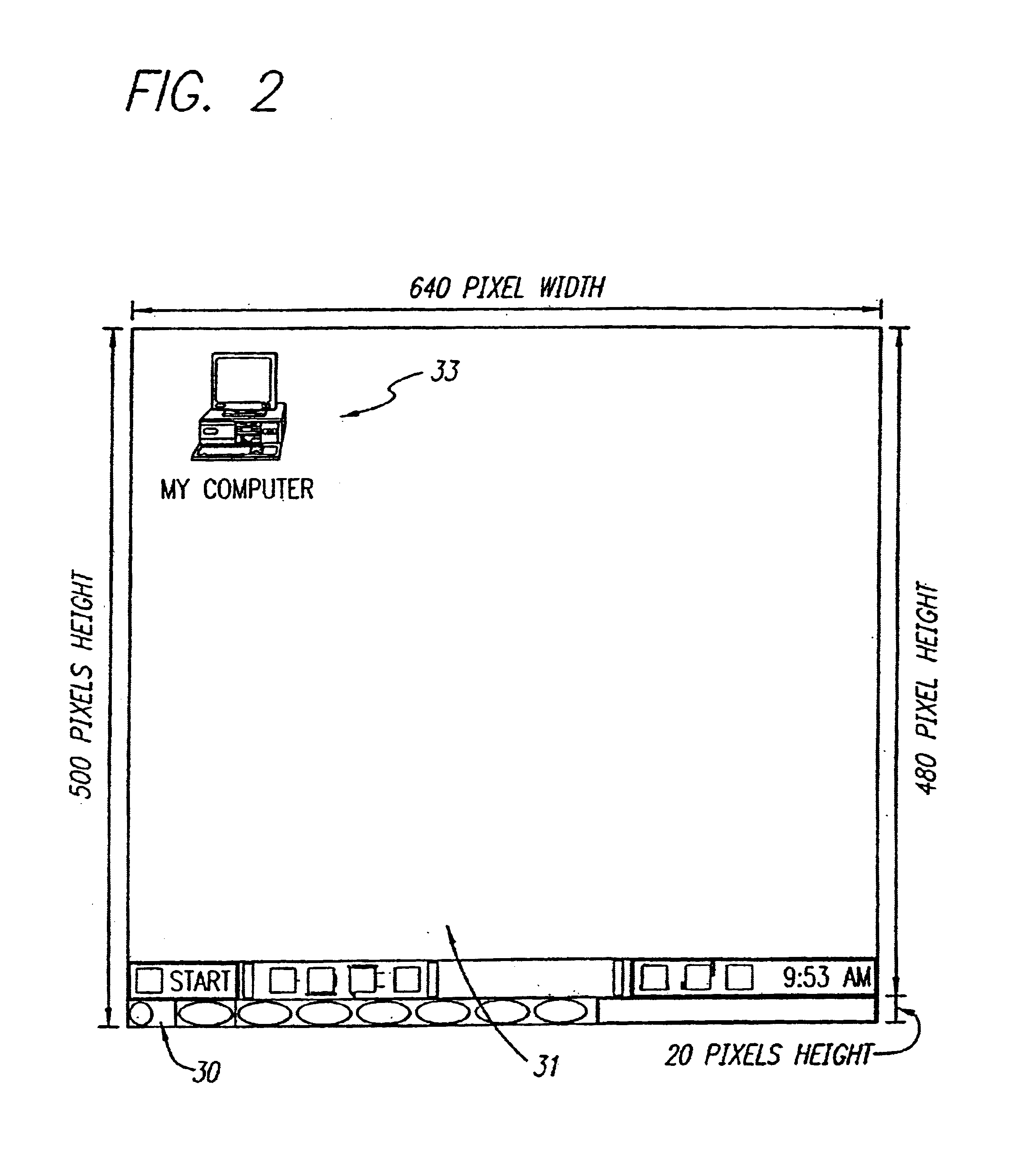
A method for creating and accessing a graphical user interface in the overscan area outside the area of the display normally utilized by the common operating systems. This normal display area is generally known as the "desktop". The desktop serves as a graphical user interface to the operating system. The desktop displays images representing files, documents and applications available to the user. The desktop is restricted in the common environments to a predetermined set of resolutions (e.g., 640x480, 800x600, 1024x768) as defined by VGA and SVGA standards. Displayable borders outside this area are the overscan area.
Owner:OSTENDO TECH INC
Method for automatic device monitoring by a central computer
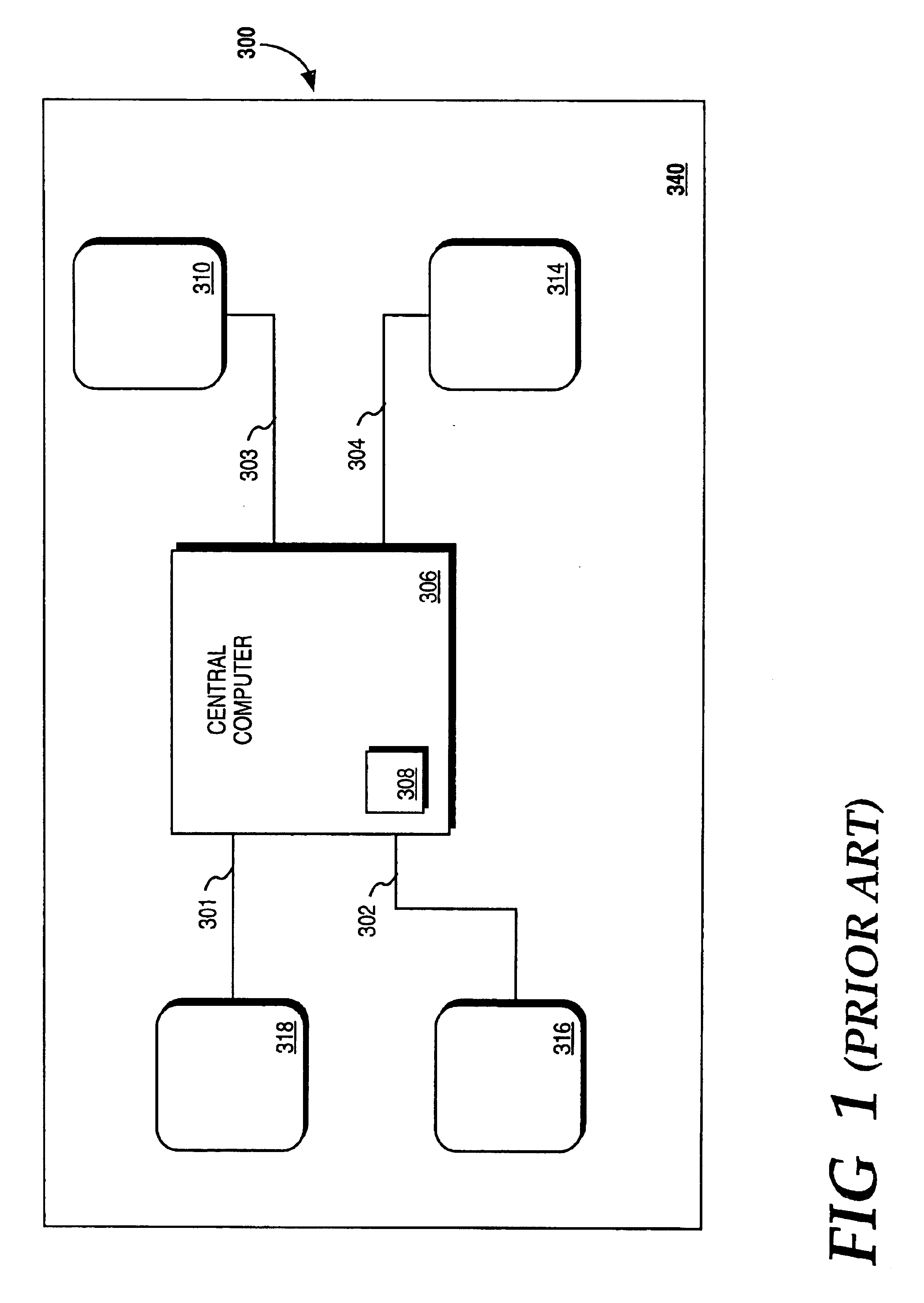
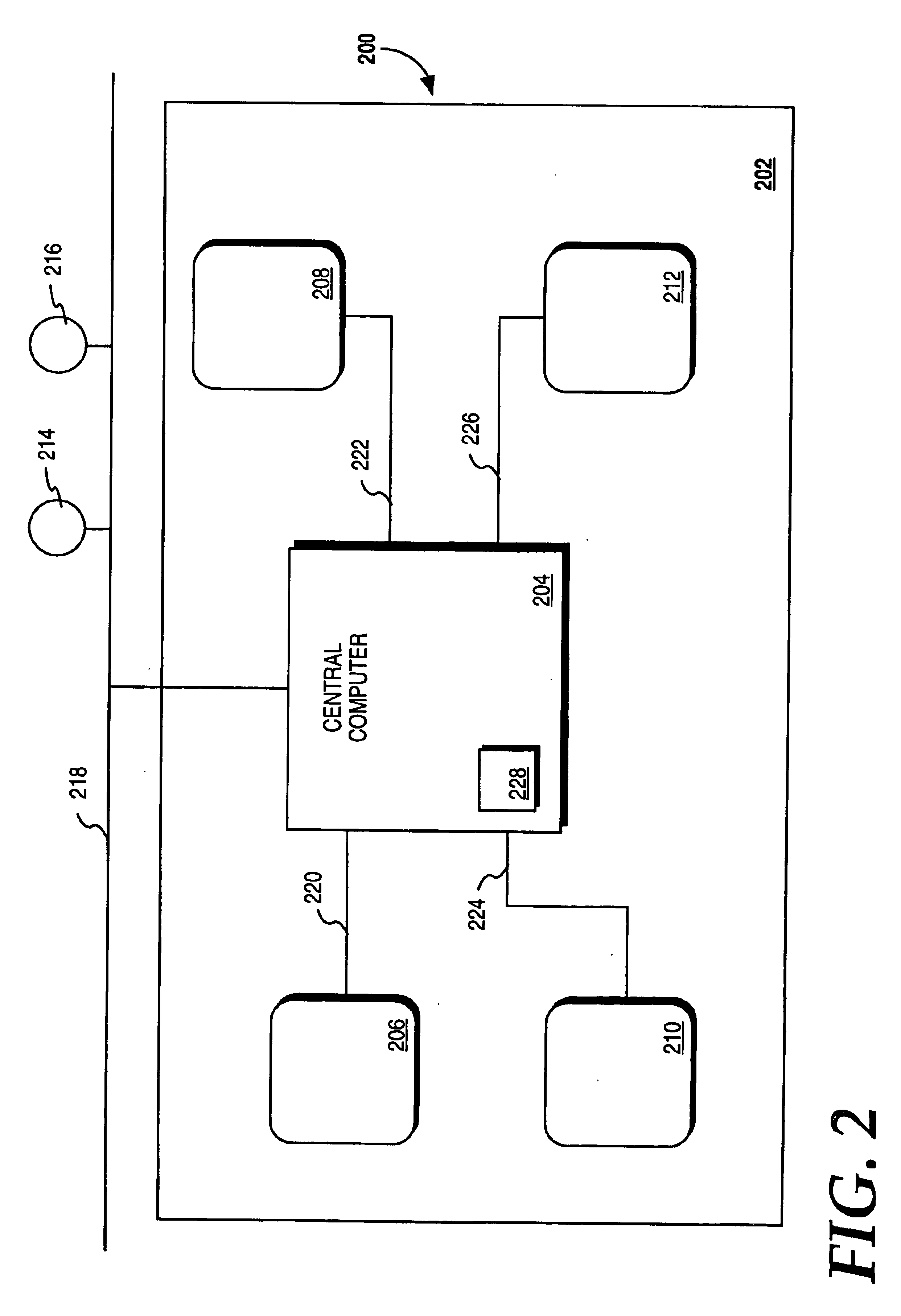
A method for monitoring a plurality of devices in a common environment. The method comprises the steps of receiving usage information from one of the devices and storing the usage information on a memory device of a computer. The method further comprises the steps of using the computer to automatically access a remote database containing information regarding the device and transmitting the stored usage information to the remote database. The information is received from the remote database and an action to be taken by the device is generated using the information from the remote database and the stored usage information.
Owner:INTEL CORP
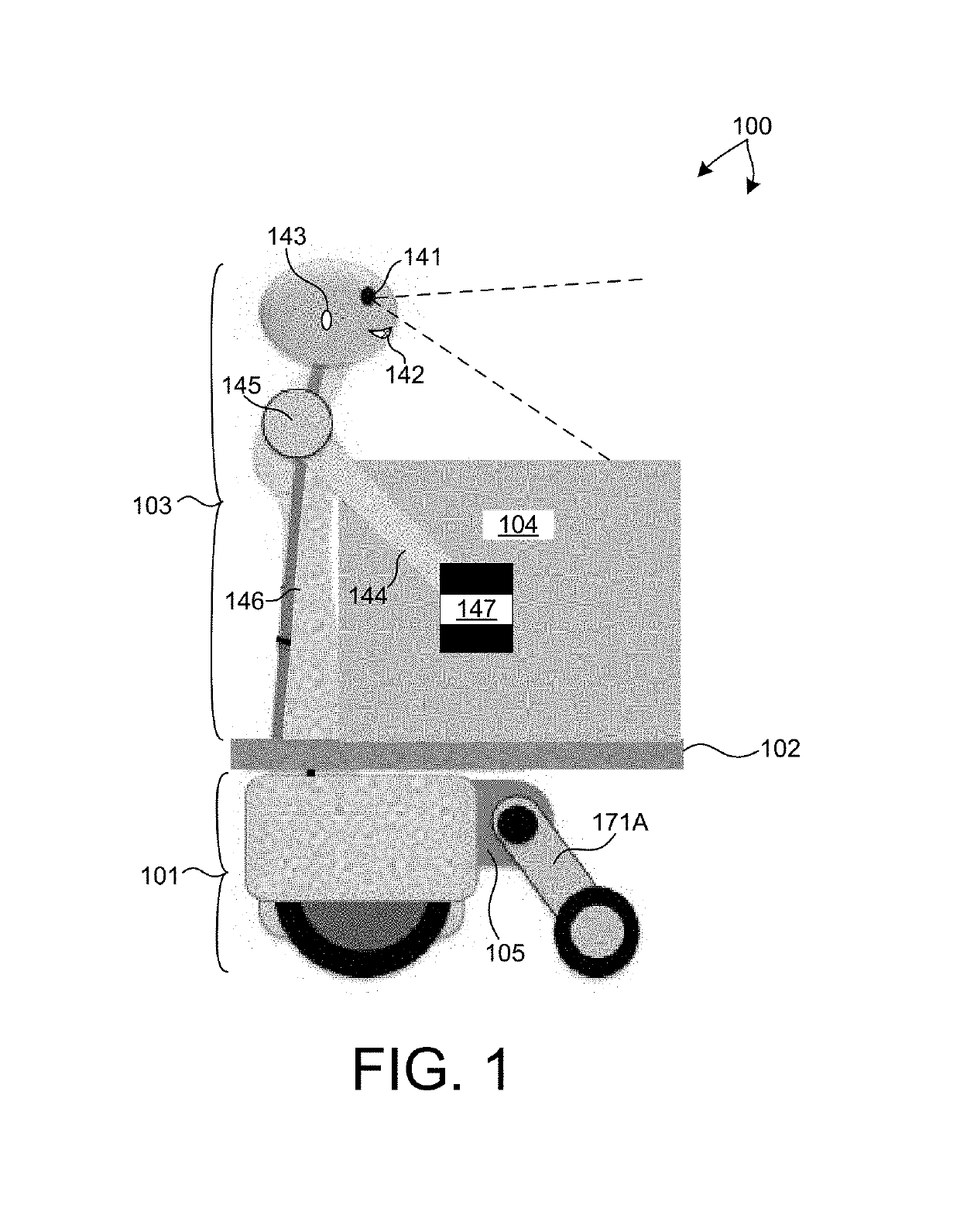
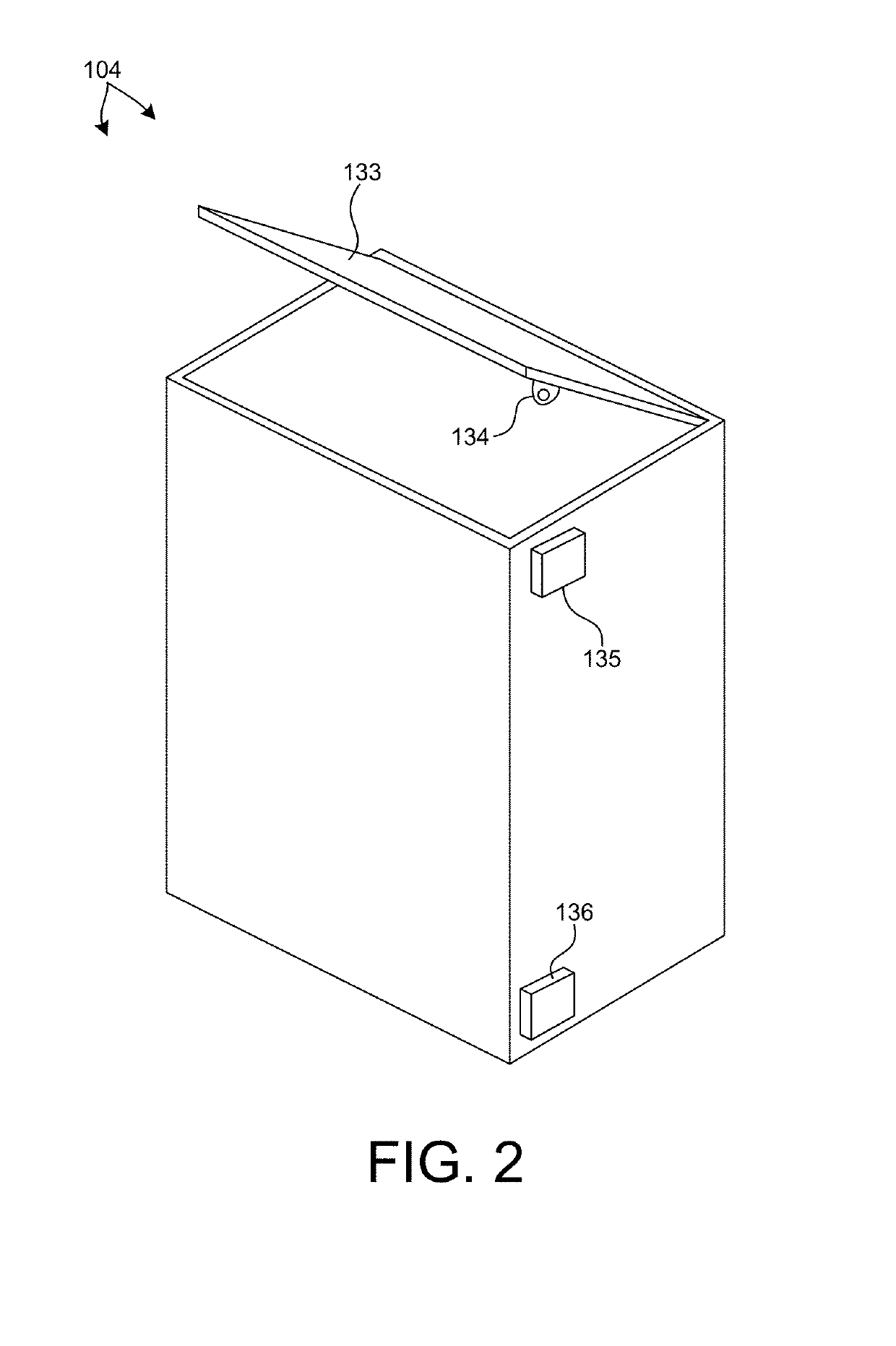
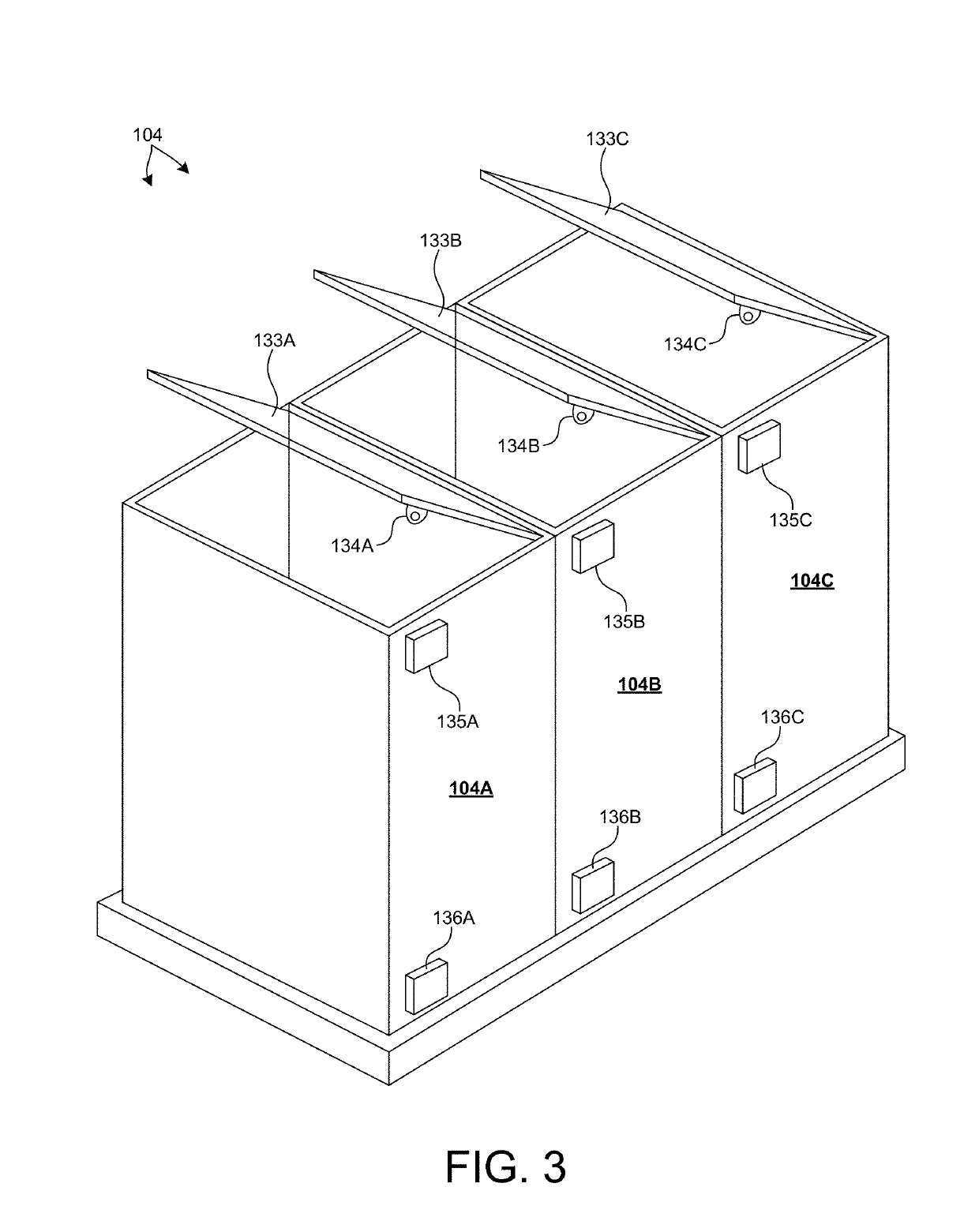
Autonomous robotic vehicles for mobile storage and trash collection applications
ActiveUS10286558B1Increase speedMaintain vehicle stabilityRefuse receptaclesNavigation instrumentsPublic environmentPayment
Methods and systems for autonomously interacting with persons in a public environment to store and transport their personal material items are described herein. A service robot includes one or more secure storage cells, and is configured to collect items such as personal belongings, refuse, etc., from users and transport the collected items to different locations. The service robot maneuvers through a crowded environment autonomously, avoiding collisions with people and objects, and minimizing disturbances to traffic flow. Users indicate a desire to store and transport items to a desired location. In response, the service robot unlocks a lid of a storage cell, and the user is able to load material items. In some examples, access to the storage cell is controlled based on access codes. In some examples, access to the storage cell is controlled based on receipt of an electronic payment.
Owner:BOSTON INCUBATOR CENT LLC +1
Method and system for displaying data in a second display area
InactiveUS6966036B2High speedIncreased accessible areaMultiprogramming arrangementsCathode-ray tube indicatorsPublic environmentGraphics
A method for creating and accessing a graphical user interface in the overscan area outside the area of the display normally visible to users of the common operating systems. This normal display area is generally known as the “desktop”. The desktop serves as the graphical user interface to the operating system. The desktop displays images representing documents and applications available to the user (icons). The desktop is restricted in the common environments to a predetermined set of resolutions (e.g., 640×480, 800×600, 1024×768) as defined by VGA and SuperVGA standards. Displayable borders outside this area are the overscan.
Owner:OSTENDO TECH INC
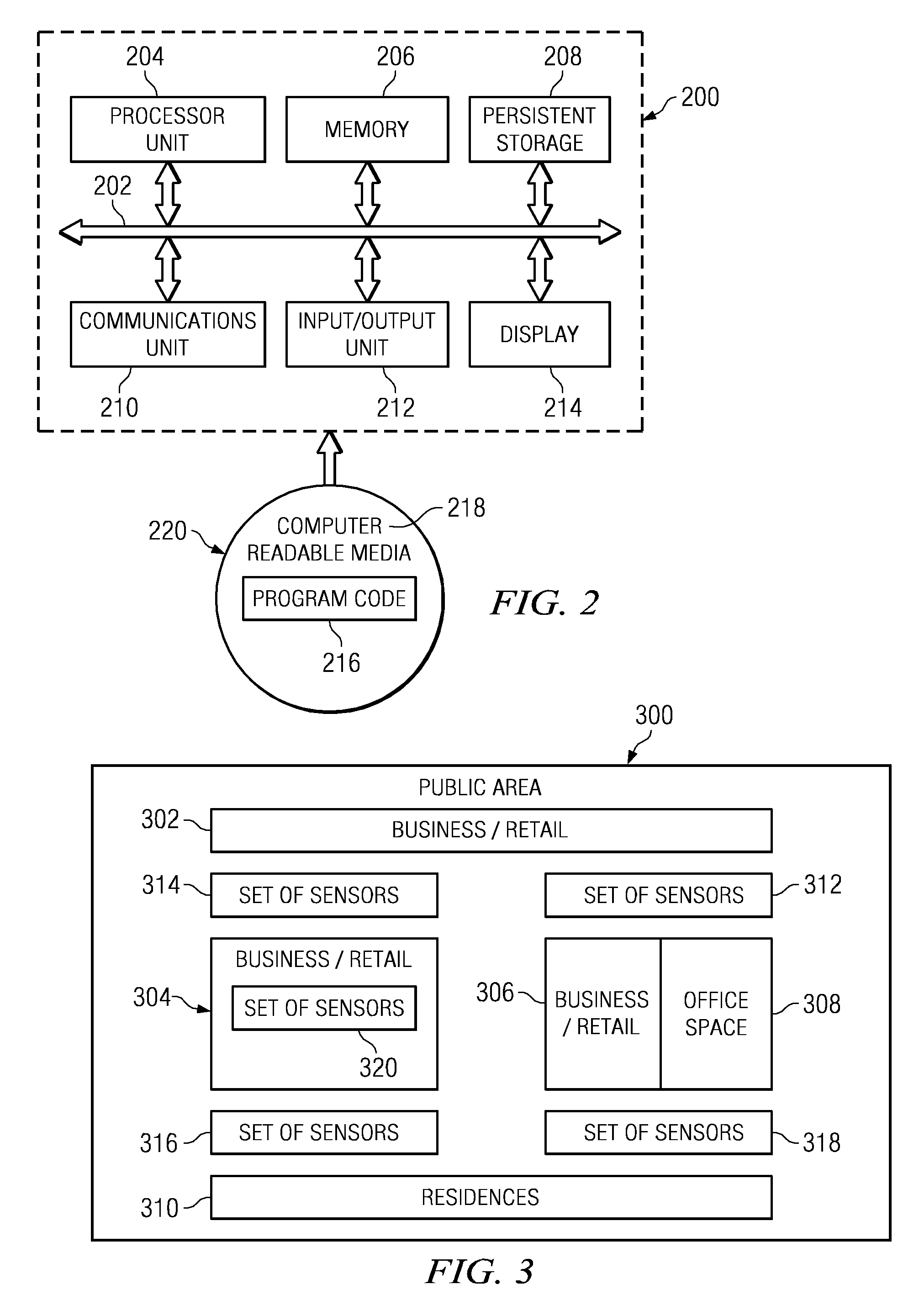
Unique cohort discovery from multimodal sensory devices
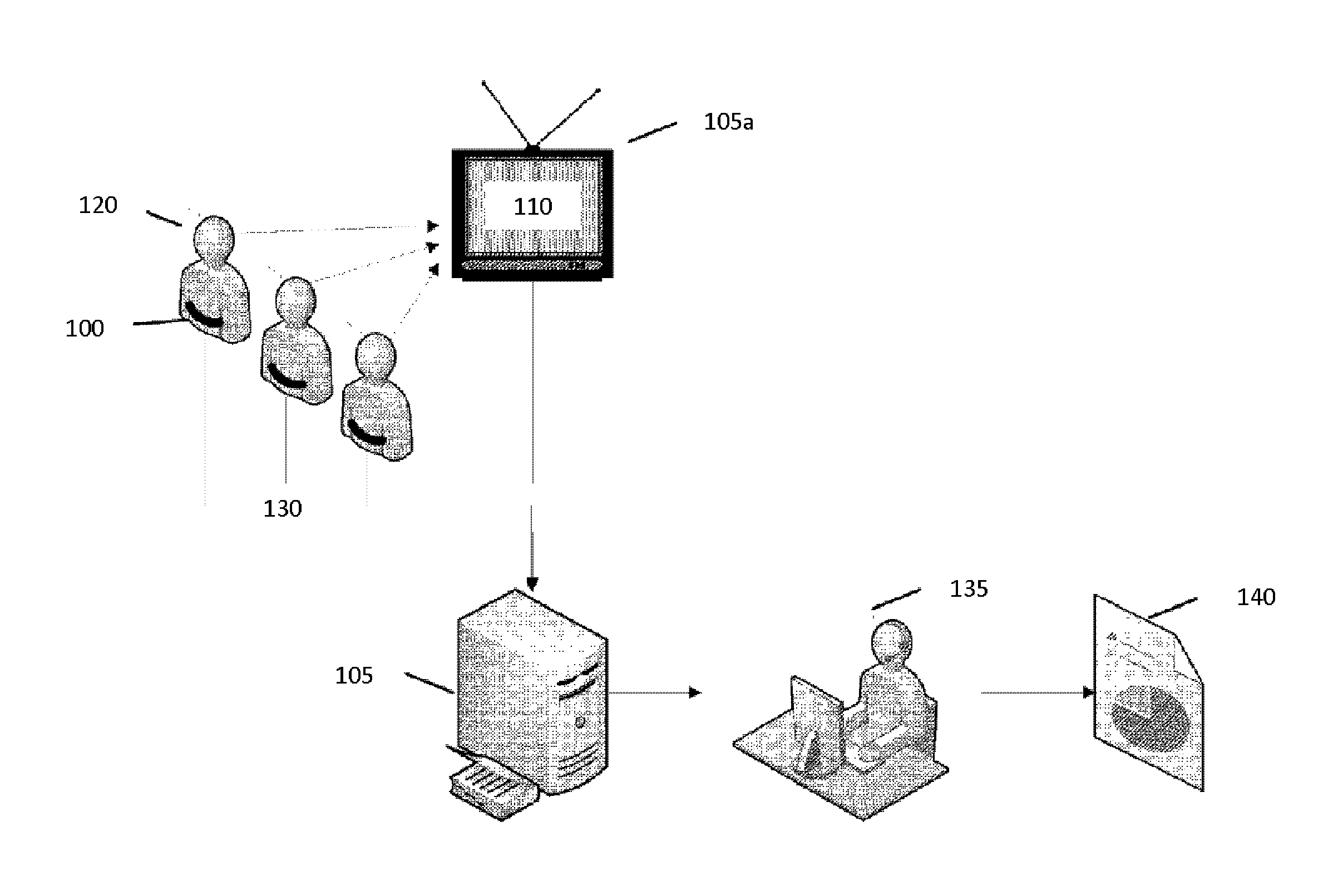
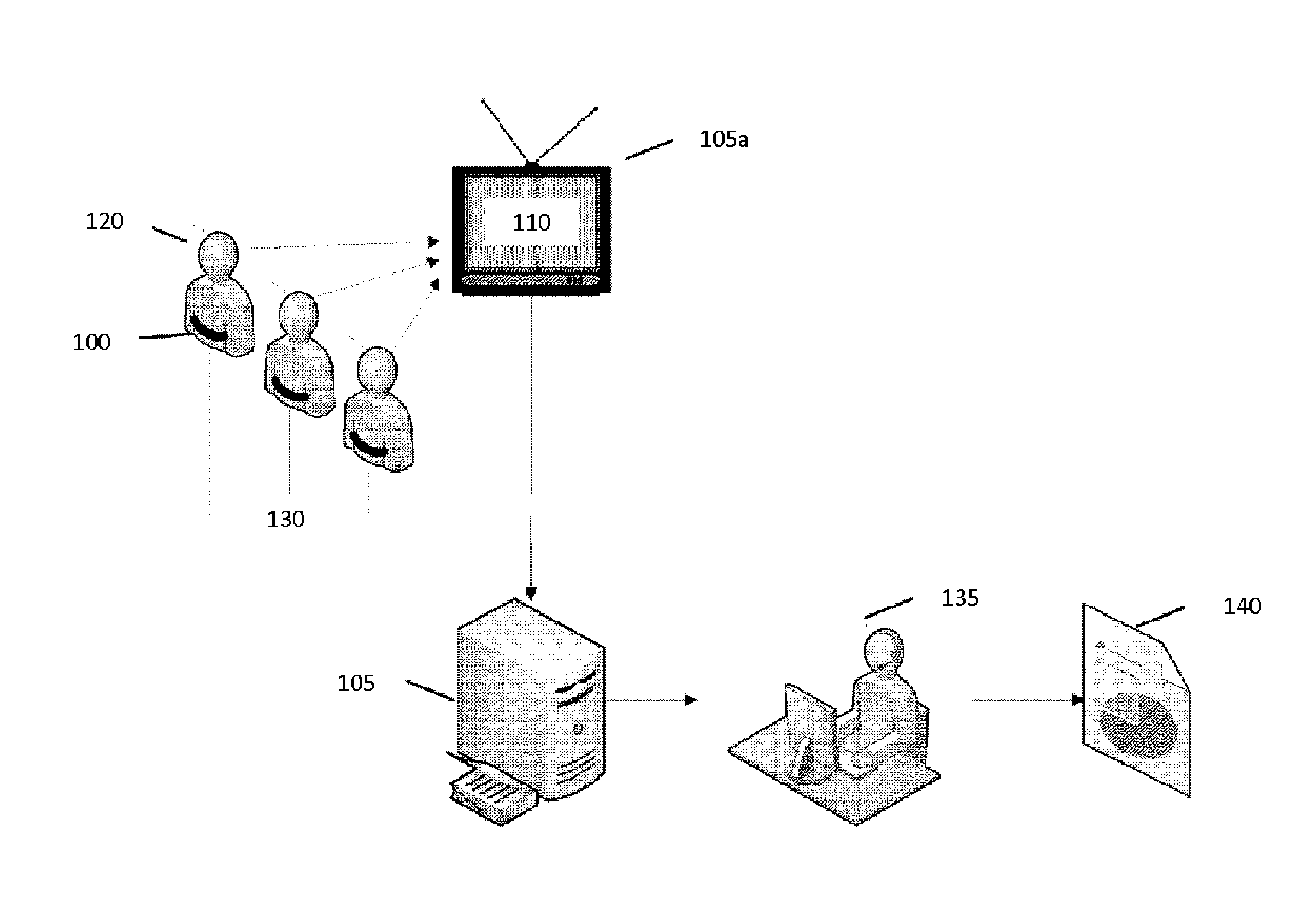
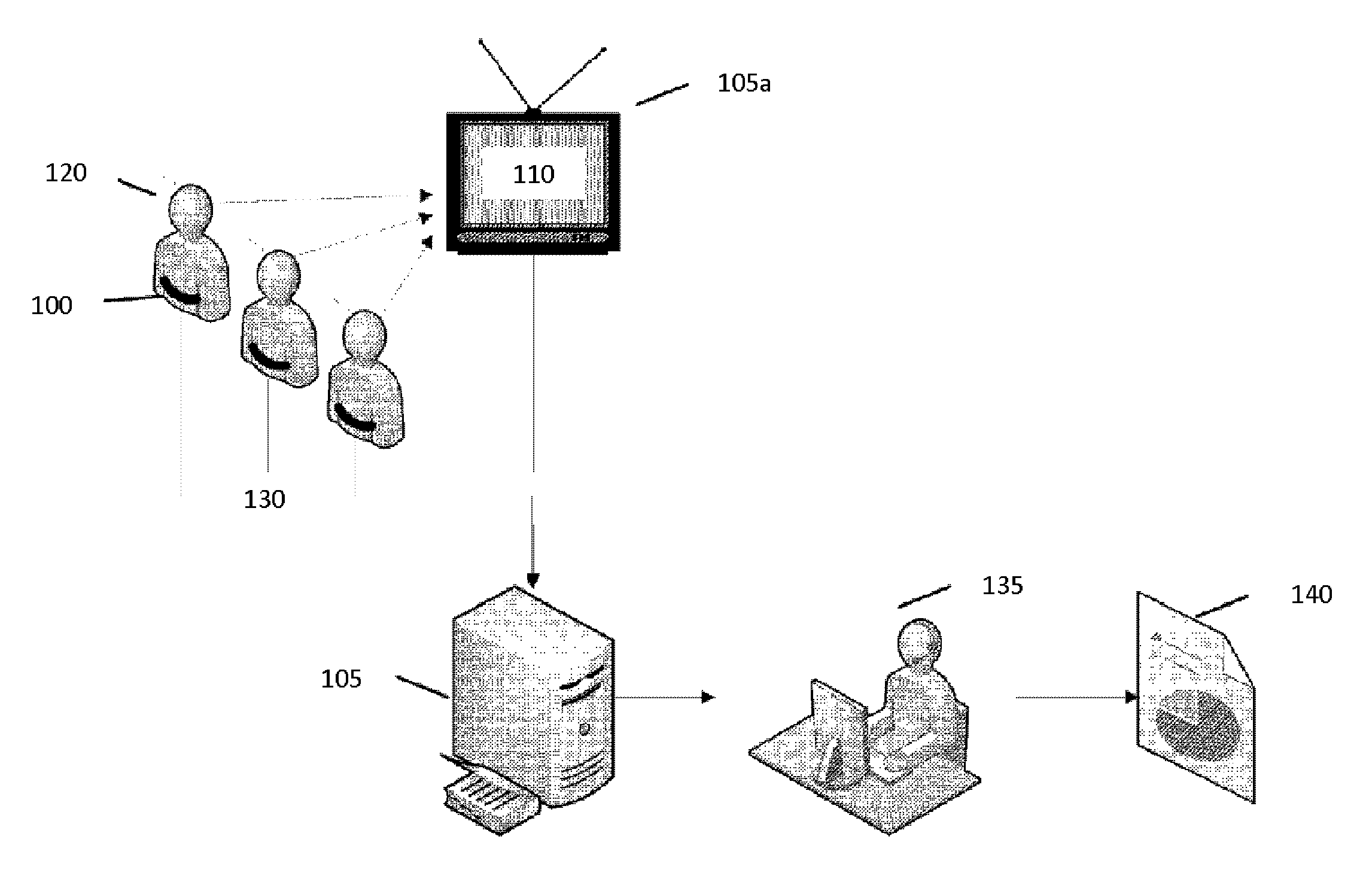
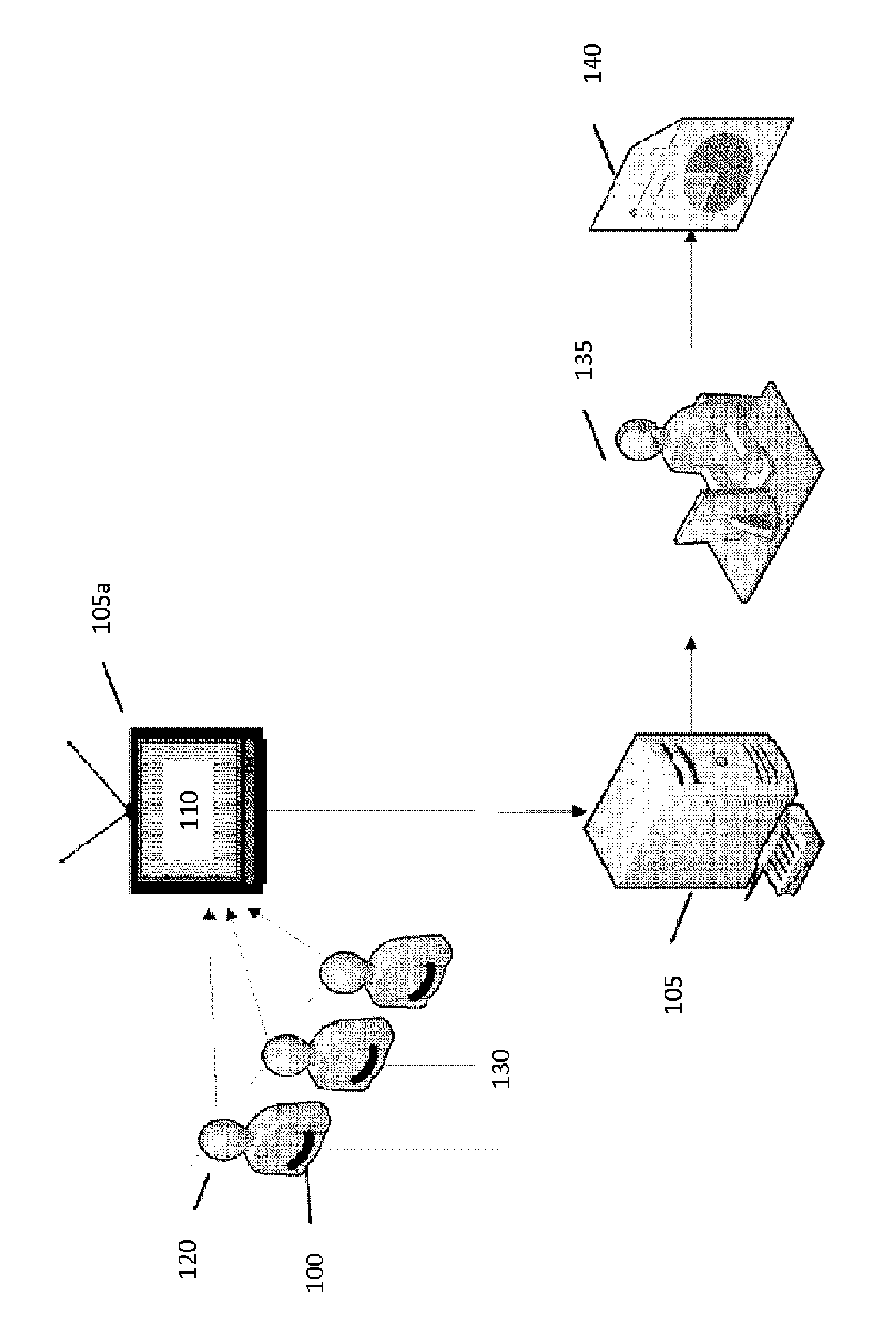
InactiveUS20090240695A1Television system detailsVideo data clustering/classificationPublic environmentMultimedia
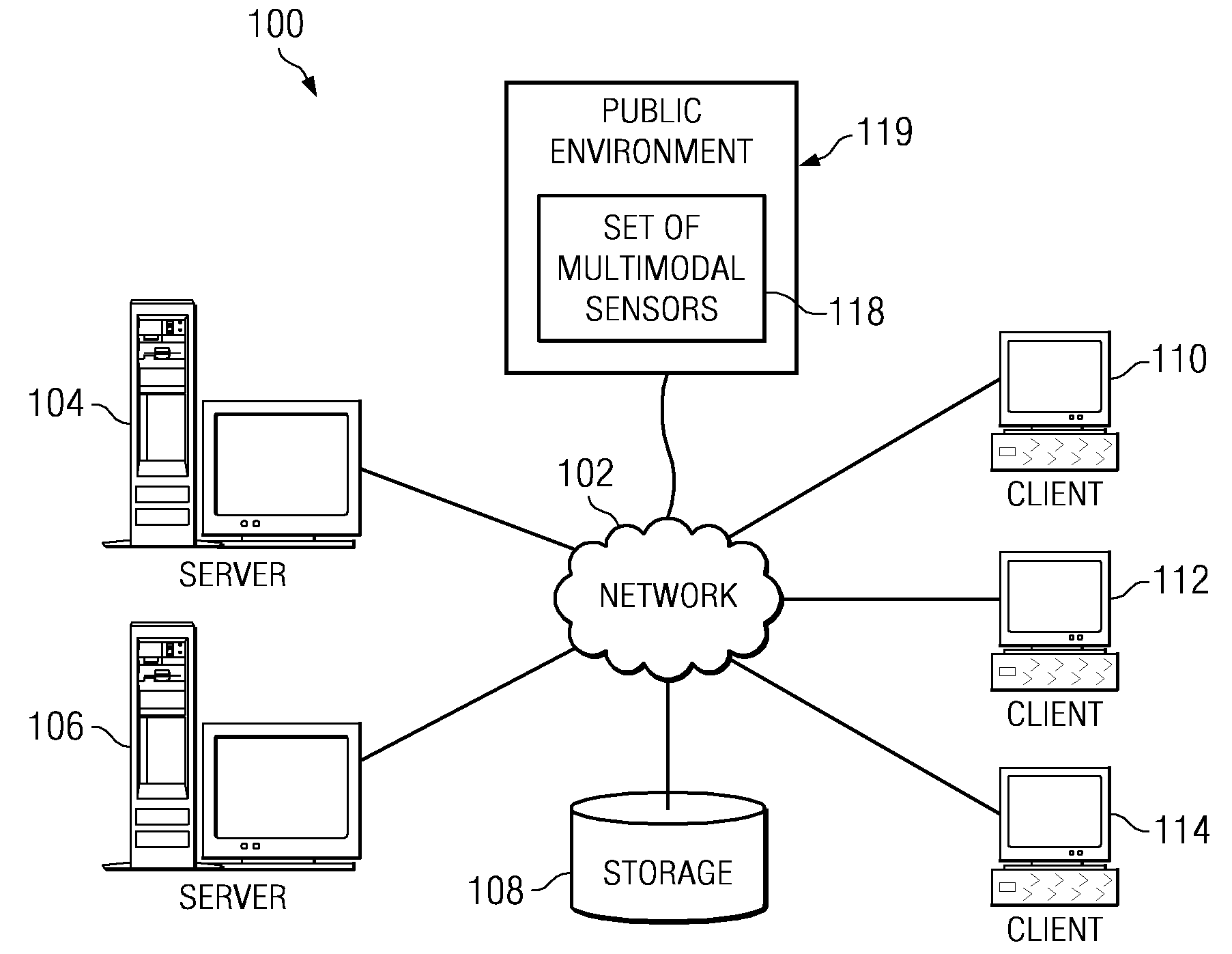
According to one embodiment of the present invention, a computer implemented method, apparatus, and computer-usable program product for generating unique cohort groups using multimodal sensory device. Multimodal sensory data is received from a set of multimodal sensors in a public environment. The set of multimodal sensors are associated with a network. The multimodal sensory data is received from the set of multimodal sensors over the network. The multimodal sensory data is processed to generate a plurality of attributes to form cohort attributes. A plurality of unique cohort groups is generated using the cohort attributes and the multimodal sensory data. Each member of the cohort group shares at least one common attribute.
Owner:IBM CORP
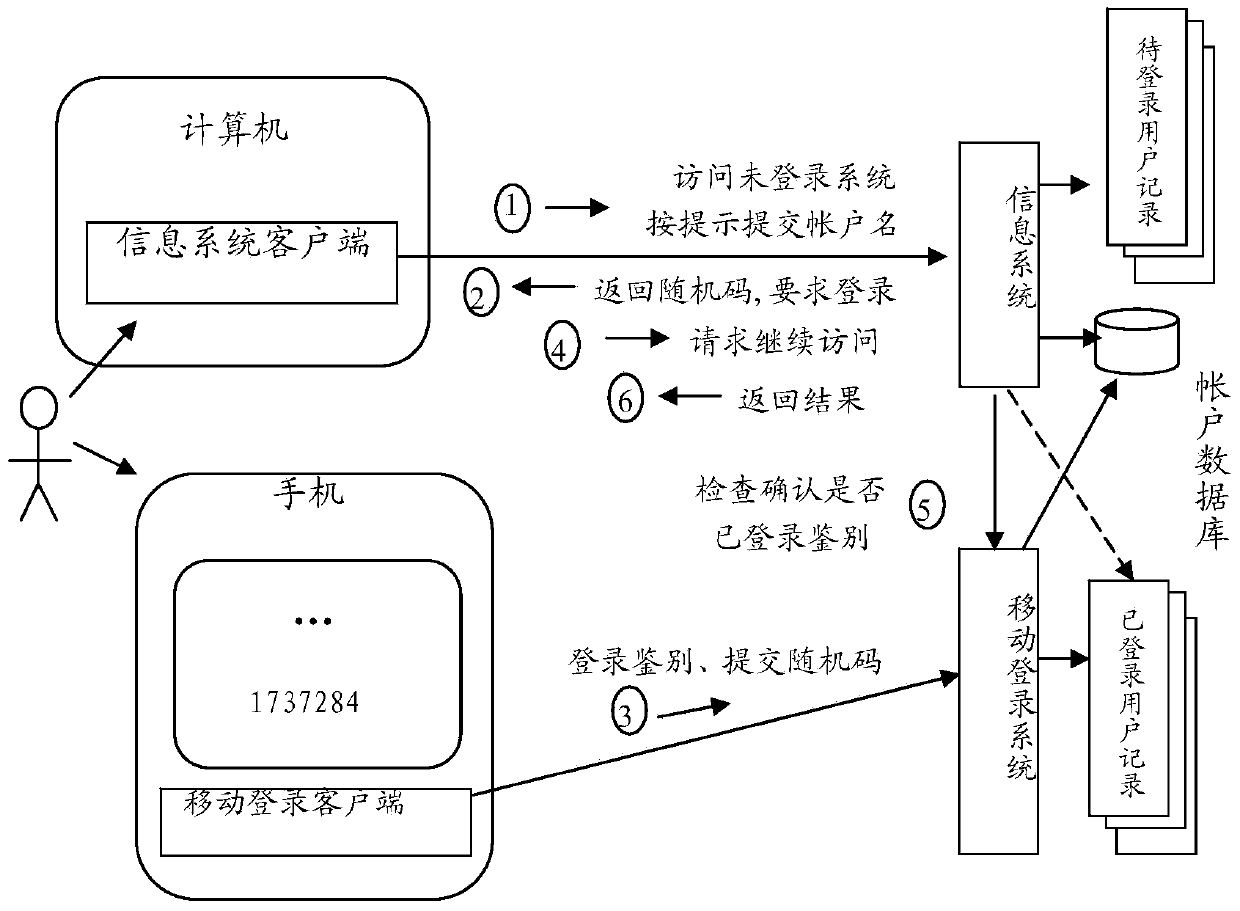
System for login based on mobile phone and login method
ActiveCN104202162ANo chance of theftImprove securityUser identity/authority verificationPublic environmentClient-side
The invention relates to a system for login based on a mobile phone and a login method. The login method comprises the following steps that when a user utilizes a client to visit an information system which is not logged in, the information system returns a random code to the client of the user; the user starts a mobile login client in the mobile phone to utilize an identity credential in the information system and / or the returned random code to complete login authentication for the information system on the mobile login system; after the login authentication is completed, the user utilizes the client to continue visiting the information system; and the information system affirms whether the user completes the login authentication for login of the information system through searching the mobile login system, if yes, the user is allowed to visit the information system, and otherwise, the user is required to log in. In addition, the random code is divided into two parts to be respectively returned to the client and transmitted to the mobile phone, so that safety of the method is further improved. Through the system for login based on the mobile phone and the login method, the user can safely log in the information system in the public environment, such as an Internet bar, by utilizing a computer.
Owner:WUHAN UNIV OF TECH
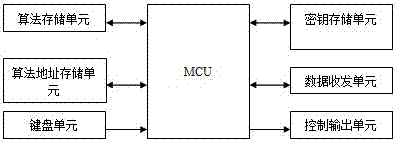
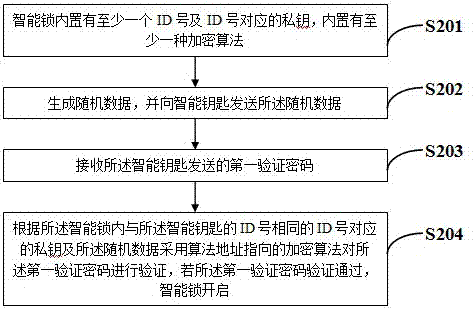
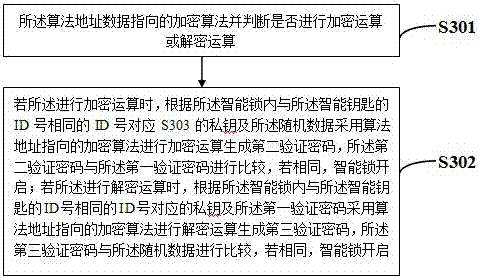
Smart lock and smart key thereof
InactiveCN107578511ASolve the inconvenience of carryingImprove securityIndividual entry/exit registersPublic environmentIdentity recognition
The invention provides a control scheme of a smart lock and a smart key thereof. Identity (ID) numbers are used for identity recognition of the smart lock and the smart key thereof, and security openverification is carried out by means of a private key, random data and an algorithm address pointed encryption algorithm. In a verification process, the private key is not transmitted in a public environment and the used encryption algorithm is selected and changed by a user, so that the fact that a cracking mechanism is established according to the encryption algorithm for cracking products in batches is prevented, and the security of an intelligent lock system is improved.
Owner:林海航
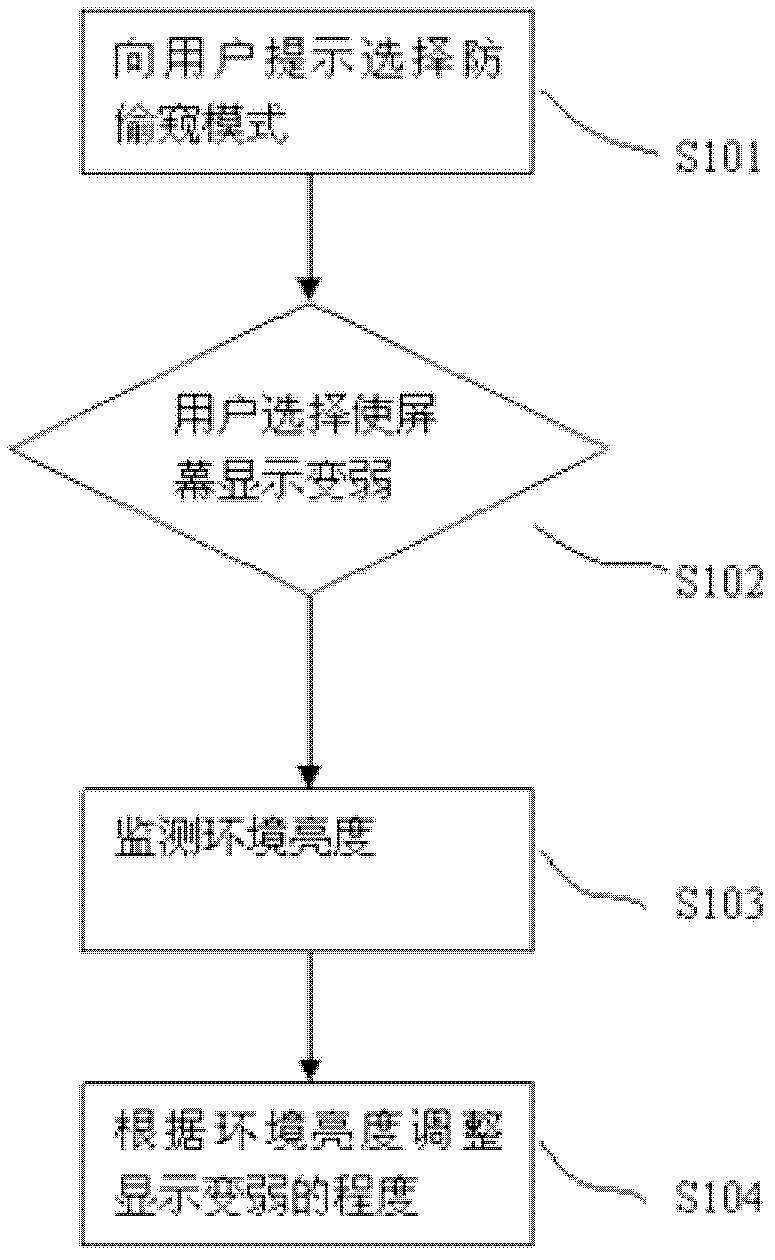
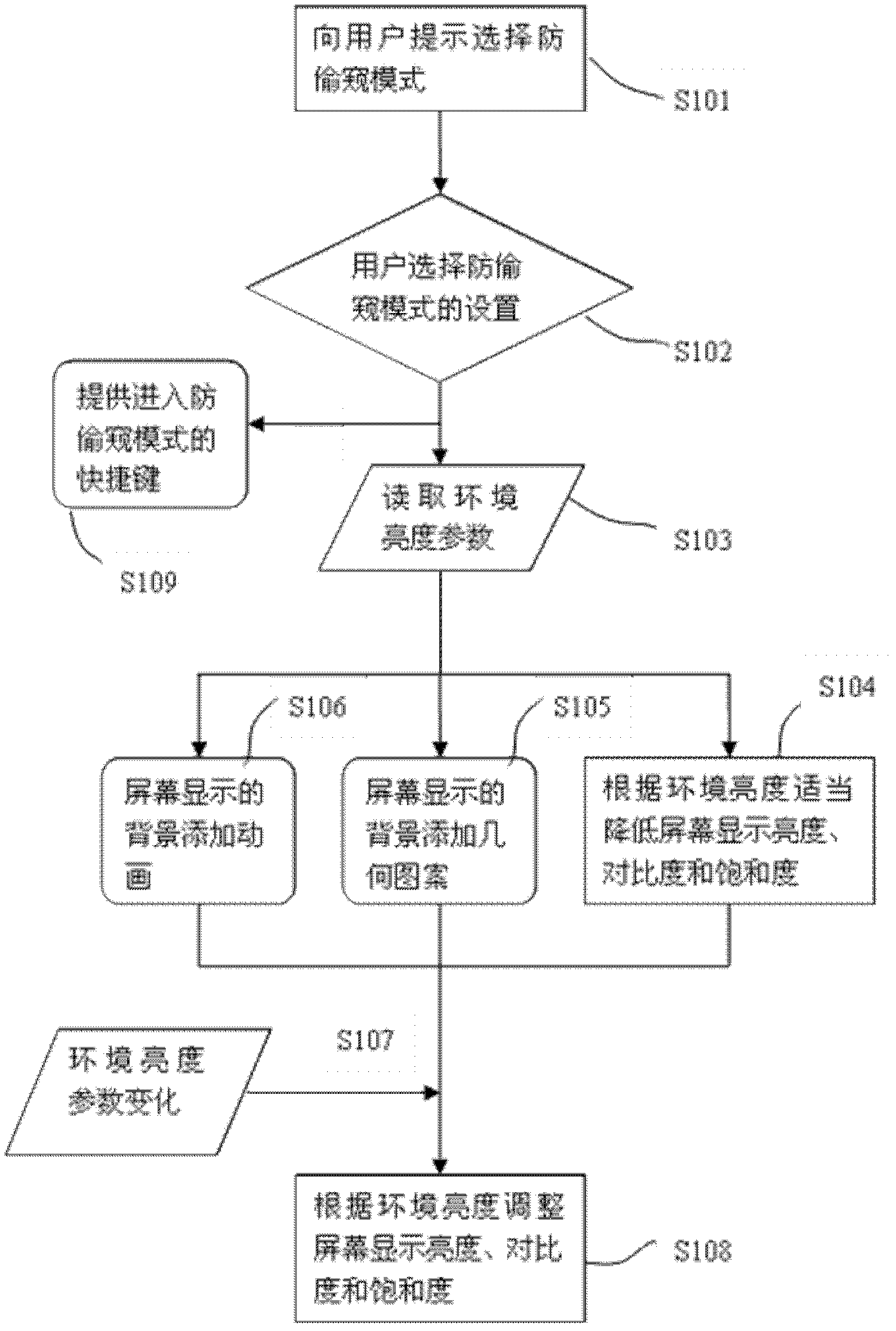
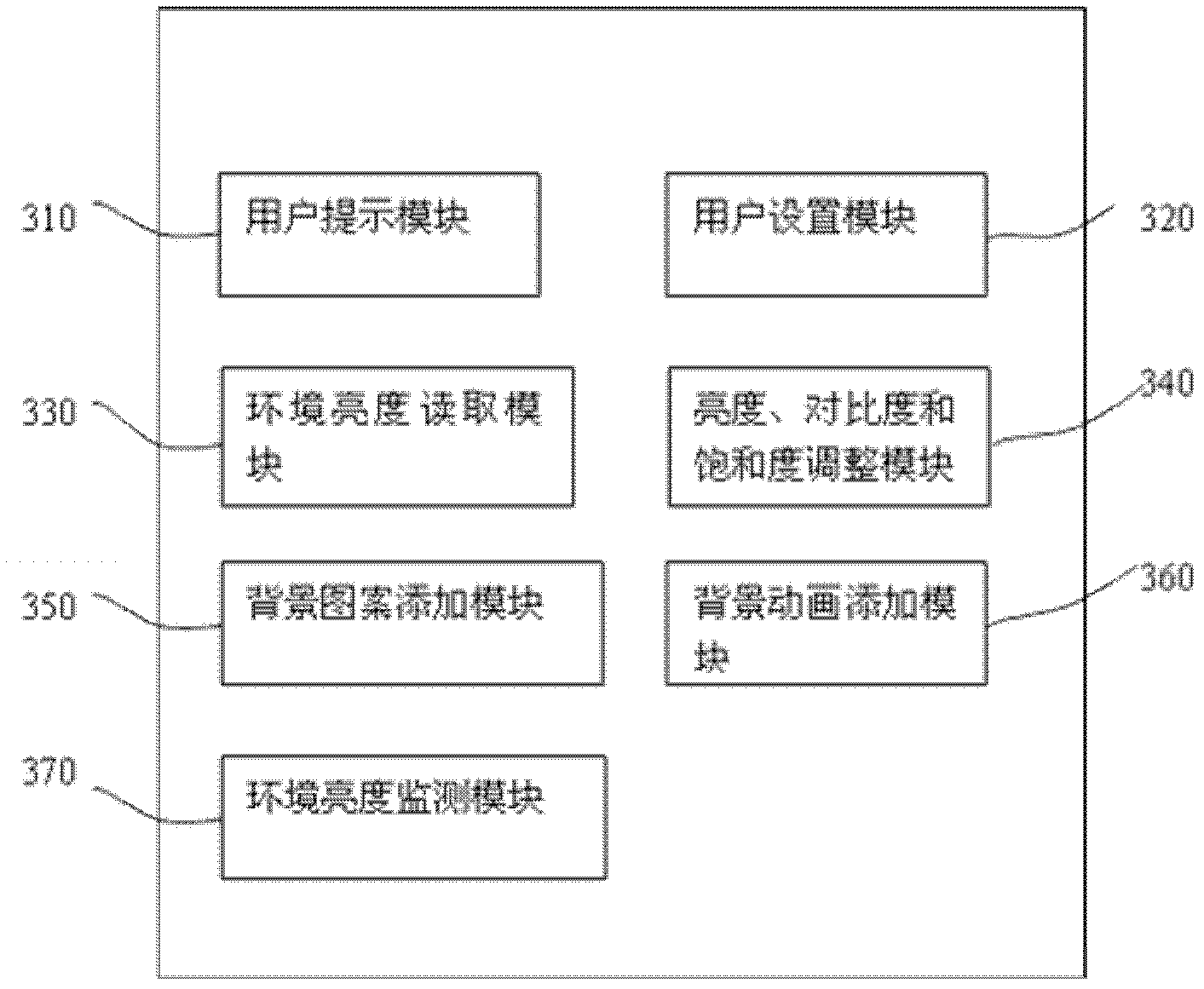
Method and system for preventing mobile device screen display from being peeped
InactiveCN102855453AIncrease brightnessReduce brightnessInternal/peripheral component protectionPublic environmentMobile device
The invention provides a method and a system for preventing mobile device screen display from being peeped. The method includes: prompting a user to select a peep-preventing mode, adjusting one or more of background luminance, background color, character contrast ratio or refresh frequency of mobile device display according to selection of the user to enable the display to be weakened, and adjusting one or more of the background luminance, the background color, the character contrast ratio or the refresh frequency of the display according to ambient luminance so that the weakened degree adapts to the ambient luminance. The method and the system have the advantage that mobile device display which is weakened in crowded public environments prevents personal information from being peeped.
Owner:网秦无限(北京)科技有限公司
Data collection system for aggregating biologically based measures in asynchronous geographically distributed public environments
ActiveUS20130226464A1ElectroencephalographyAcceleration measurementPublic environmentAudience response
The present invention relates to biologically and behaviorally based systems and methods for measuring audience response to a target stimulus. The systems and methods are deployable in multiple locations and may display stimuli based on location, target demographics, and combinations thereof.
Owner:NIELSEN CONSUMER LLC
System simulation and graphical data flow programming in a common environment using wire data flow
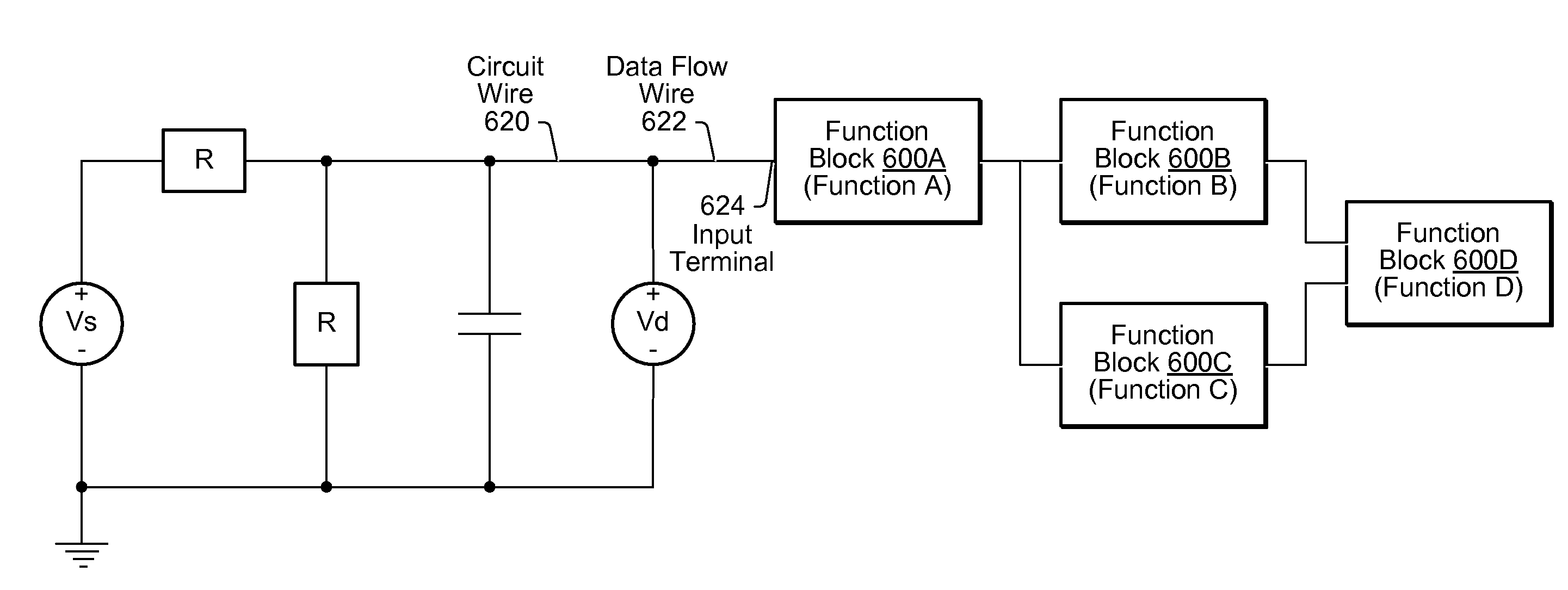
ActiveUS7568178B2Detecting faulty computer hardwareComputer programmed simultaneously with data introductionData flow programmingPublic environment
Owner:NATIONAL INSTRUMENTS
Peeping prevention method, device and mobile terminal
The invention discloses a peeping prevention method, a peeping prevention device and a mobile terminal. The method and the device are used for the information security protection of the mobile terminal. The peeping prevention method comprises the following steps of controlling image acquisition equipment of the mobile terminal to acquire a peripheral image of the mobile terminal; detecting whether the peripheral image comprises faces besides that of a user of the mobile terminal; when the peripheral image is detected to comprise the faces besides that of the user, transmitting a prompting signal to the user to prevent information in the mobile terminal from being peeped. Due to the adoption of the technical scheme, the secure use of the mobile terminal in a complex or public environment can be ensured, and the information of the user in the mobile terminal can be prevented from being peeped.
Owner:LENOVO MOBILE COMM TECH
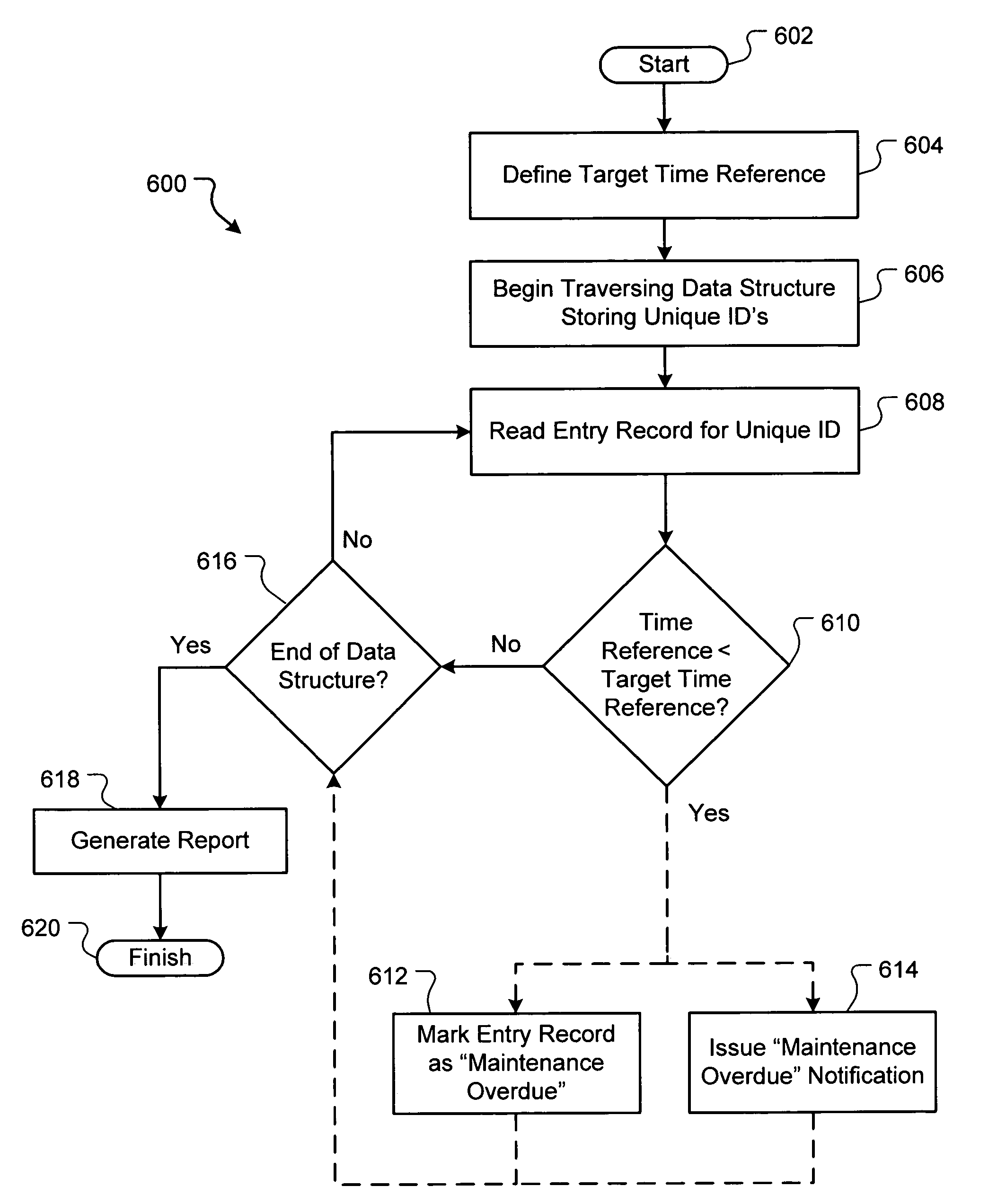
Managing maintenance of serviceable items based on unique identification labeling
ActiveUS20060217995A1Avoid flowAvoid pollutionCharacter and pattern recognitionVisual presentationPublic environmentUnique identifier
A system and method for tracking and managing maintenance of serviceable items based on unique identification labeling affixed to the items is disclosed. The serviceable items are described as filters within a common environment that require routine maintenance to adhere to certain expectations relative to the operability of the items. Such operability may relate to any type of filtering of contaminants from a liquid or gaseous substance that flows through the filters. A unique identifier (ID) label is affixed to each filter. The unique ID label represents a unique filter ID that uniquely identifies the filter relative to all other filters in the common environment. A handheld computing device communicatively connected to a local computer reads the unique ID label of each filter following maintenance of the filter to track maintenance of the filters over time.
Owner:ECOLAB USA INC
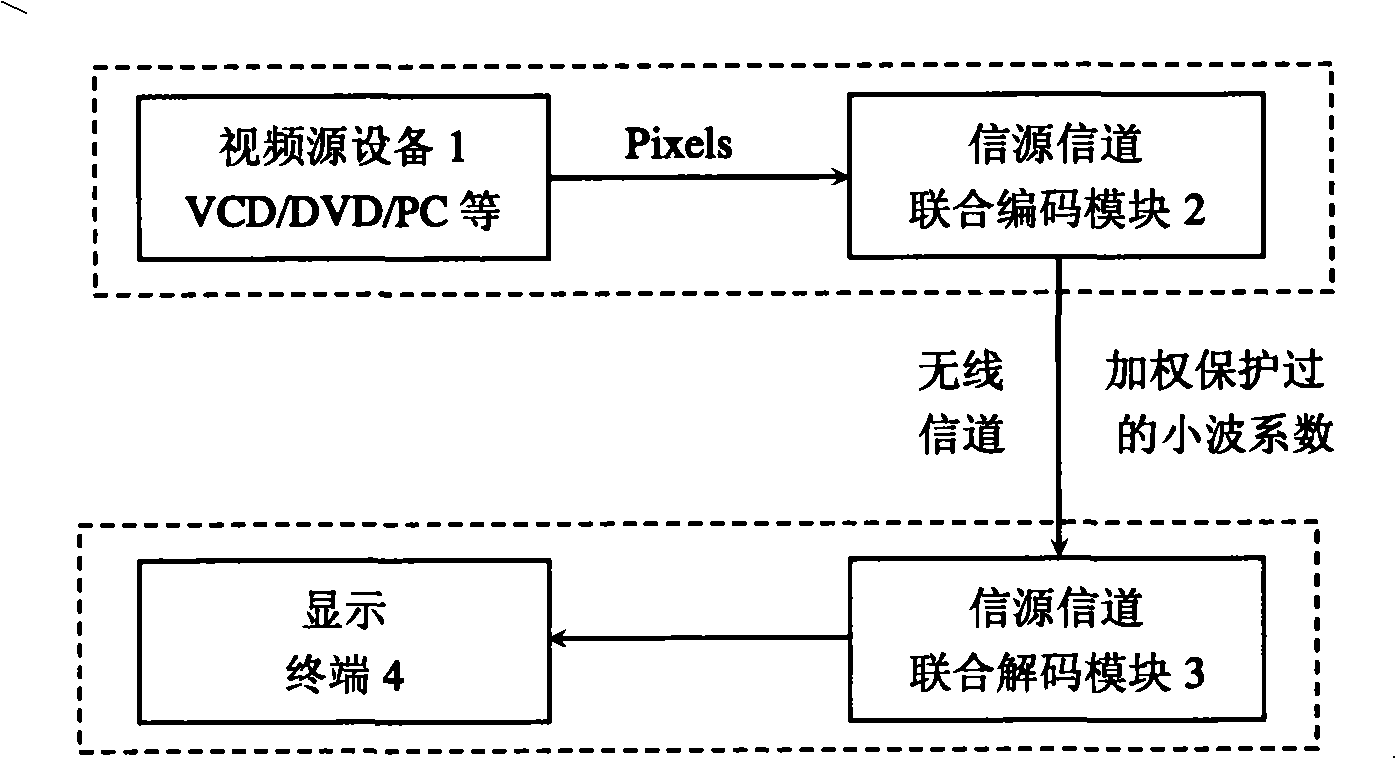
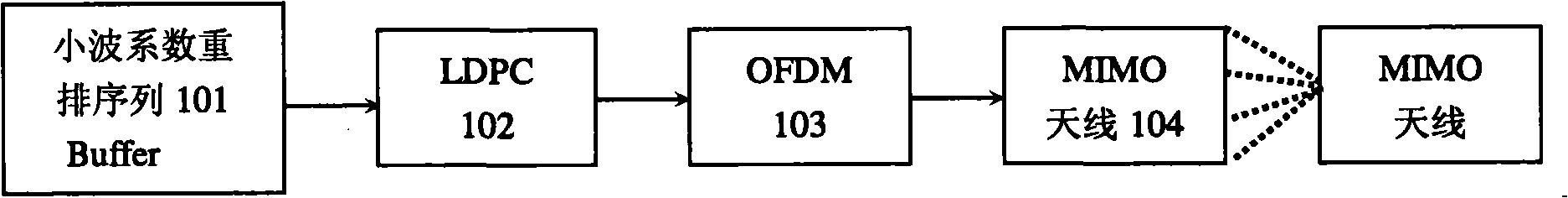
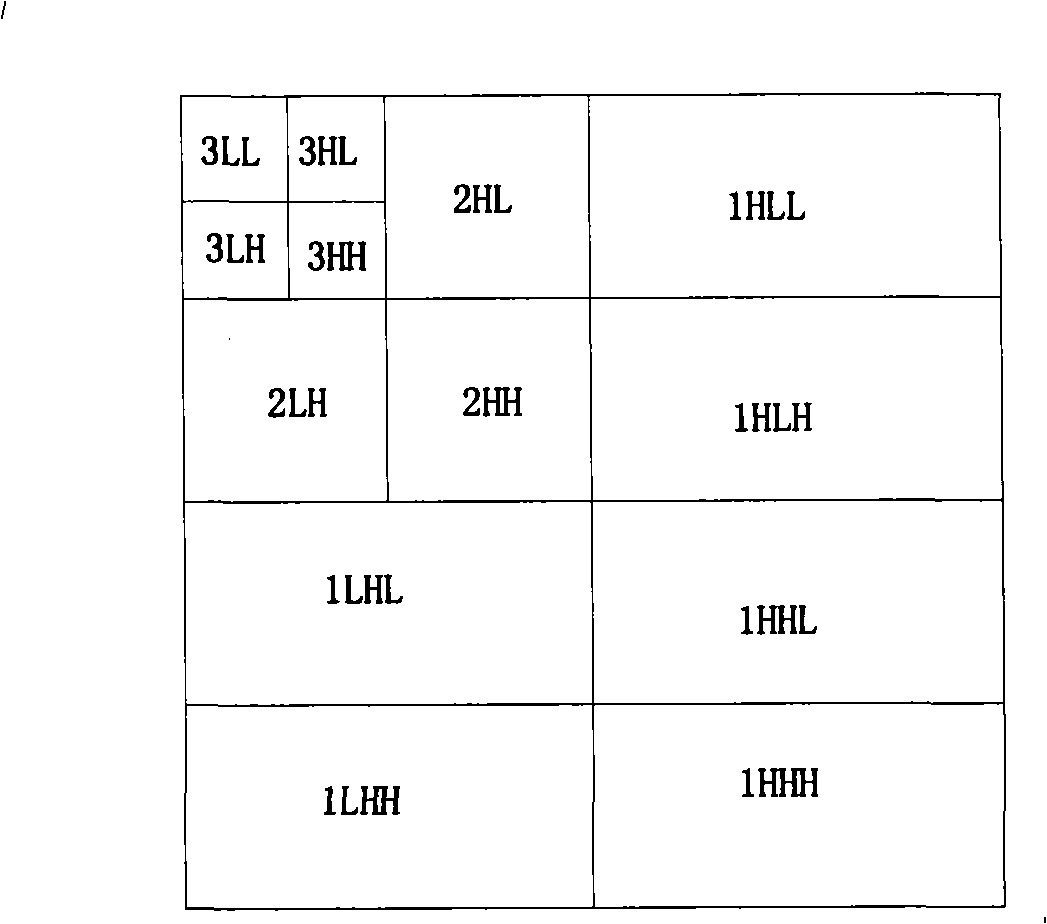
Non-compression high definition video signal wireless transmission method based on wavelet conversion characteristics
InactiveCN101494774AProtect image qualityEasy to useColor television with pulse code modulationPulse modulation television signal transmissionImaging qualityTelevision equipment
The invention discloses a non-compressed high-definition video signal wireless transmission method based on wavelet transform characteristics, which adds a source-channel combined decoding module of images on the wireless channel between the video source equipment and the television, wherein, the transmitting end reads the original image frame in the external buffer through the source-channel combined decoding module, performs coding protection processing according to the image characteristic and based on wavelet transform, and uses the MIMO channel to expand the transmission band-width for transmitting high-definition video signals; the flow path of the receiving end is reverse. Using the method of the present invention not only eliminates the signal line so that the television equipment is more simple, but also can greatly protect the image quality even in poor channel conditions (such as airports, bus stations and other public environments), showing superiority of supporting the high-definition picture quality of the high-definition digital television.
Owner:XIAMEN OVERSEAS CHINESE ELECTRONICS ENTERPRISE
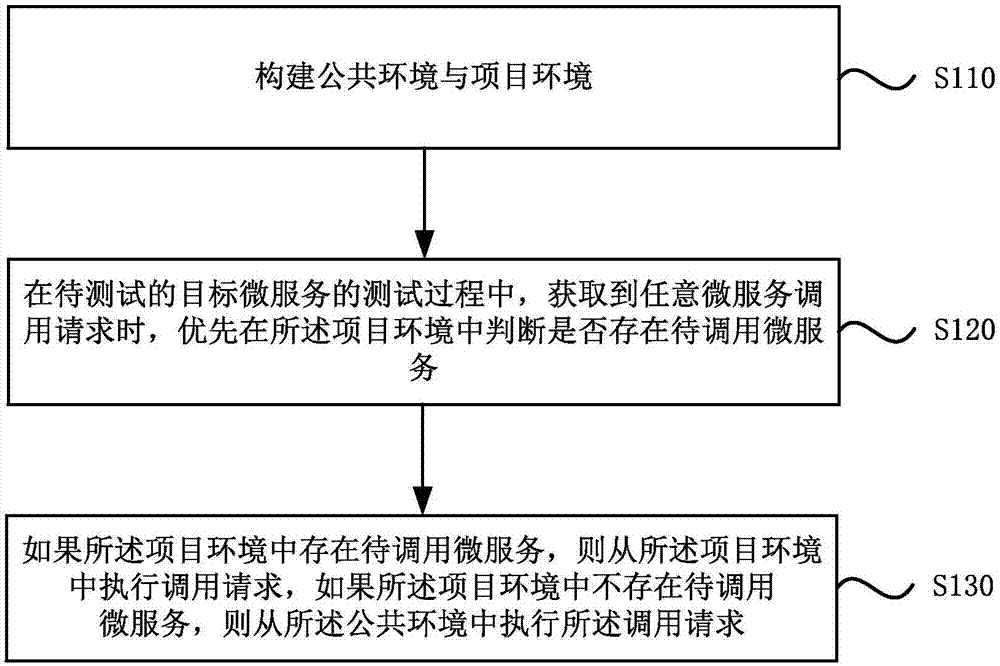
Micro-service test method and device
ActiveCN107979508AGuaranteed stabilityImprove test efficiencySoftware testing/debuggingData switching networksTest efficiencyPublic environment
The embodiment of the invention discloses a micro-service test method and device. The method comprises the steps of establishing a public environment and project environments, wherein the public environment comprises a current version of at least one piece of micro-service, and the project environments comprise an updating version of the at least one piece of micro-service; preferentially judgingwhether to-be-called micro-service exists in the project environments or not when any micro-service calling request is acquired in a test process of to-be-tested target micro-service; and performing the calling request from the project environments if the to-be-called micro-service exists in the project environments, and performing the calling request from the public environment if the to-be-called micro-service does not exist in the project environments. According to the embodiment of the invention, the target micro-service can be rapidly tested, and the test efficiency of the micro-service can be improved.
Owner:上海云犀信创网络科技有限公司
Vigorous air machine
InactiveCN106066066AEasy to usePurify Filtration Volume EnergyMechanical apparatusSpace heating and ventilation safety systemsAnti virusEngineering
A vigorous air machine is used for achieving a circulation positive pressure breathing air conditioner, outdoor aerobic air is subjected to washing filtering and dust falling and removing, and virus removing and sterilizing are synchronously conducted. Anti-virus sterilization Chinese and western medicine materials are added in filter hydrolysate so as to achieve the using function of the vigorous air technology, the vigorous air is guided into the relatively fixed working and using area through assistance of a pipeline draught fan, and accordingly the vigorous air machine is applicable to workers in market business and service areas, workers beside public environment office tables or indoor workers, machine tool and assembly line operators, students, old people, pregnant women and infants living in relatively fixed areas for constant-temperature air blowing and vigorous air exhalation, and then the vigorous air is guided in for positive pressure breathing usage. Positive pressure breathing usage is different from indoor usage under the closed condition but can also achieve the same safe and actual breathing health protection function and effect, the working and living groups do not inhale virus gas or inhale little harmful gas under the relative indoor and outdoor harmful gas work environment, and working and living breathing safety and health of people are protected.
Owner:常州市利众环保科技有限公司
Data collection system for aggregating biologically based measures in asynchronous geographically distributed public environments
ActiveUS9292858B2ElectroencephalographyRespiratory organ evaluationPublic environmentAudience response
The present invention relates to biologically and behaviorally based systems and methods for measuring audience response to a target stimulus. The systems and methods are deployable in multiple locations and may display stimuli based on location, target demographics, and combinations thereof.
Owner:NIELSEN CONSUMER LLC
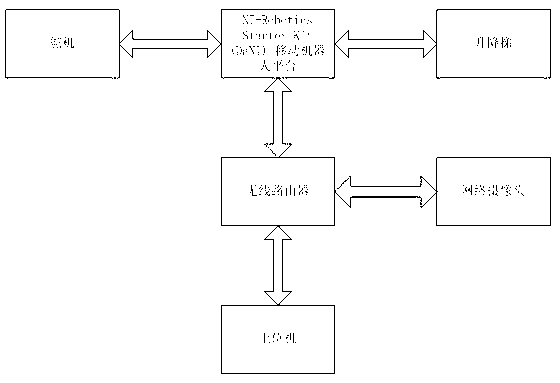
Intelligent safety patrol system based on DaNI mobile robot platform
InactiveCN102799185AReduce work stressImprove securityTelevision system detailsColor television detailsElectricityWireless router
The invention discloses an intelligent safety patrol system based on a DaNI mobile robot platform. The intelligent safety patrol system comprises a DaNI mobile robot platform, a wireless router, an elevator, a steering engine, a power supply, a network camera, an upper computer and the like, wherein the power supply is used for supplying power for the wireless router, the elevator, the network camera and the steering engine; the steering engine, the elevator and the wireless router are all electrically connected with the DaNI mobile robot platform; the elevator is fixed on the DaNI mobile rotor platform; the steering engine is fixed on the top of the elevator; the steering engine is fixed on the top of the elevator; the network camera is arranged on the steering engine; the network camera is connected with the wireless router; the wireless router is arranged at the bottom of the DaNI mobile robot platform; and the wireless router wirelessly communicates with the upper machine. The intelligent safety patrol system disclosed by the invention is adopted for safety patrol, so that the work stress of security personnel can be relieved, the safety of public environments is enhanced, the social life quality is promoted and the security cost is lowered.
Owner:ZHEJIANG UNIV
Image display method and terminal
ActiveCN103970501AGuaranteed privacyEnsure safetyCathode-ray tube indicatorsSubstation equipmentPublic environmentComputer graphics (images)
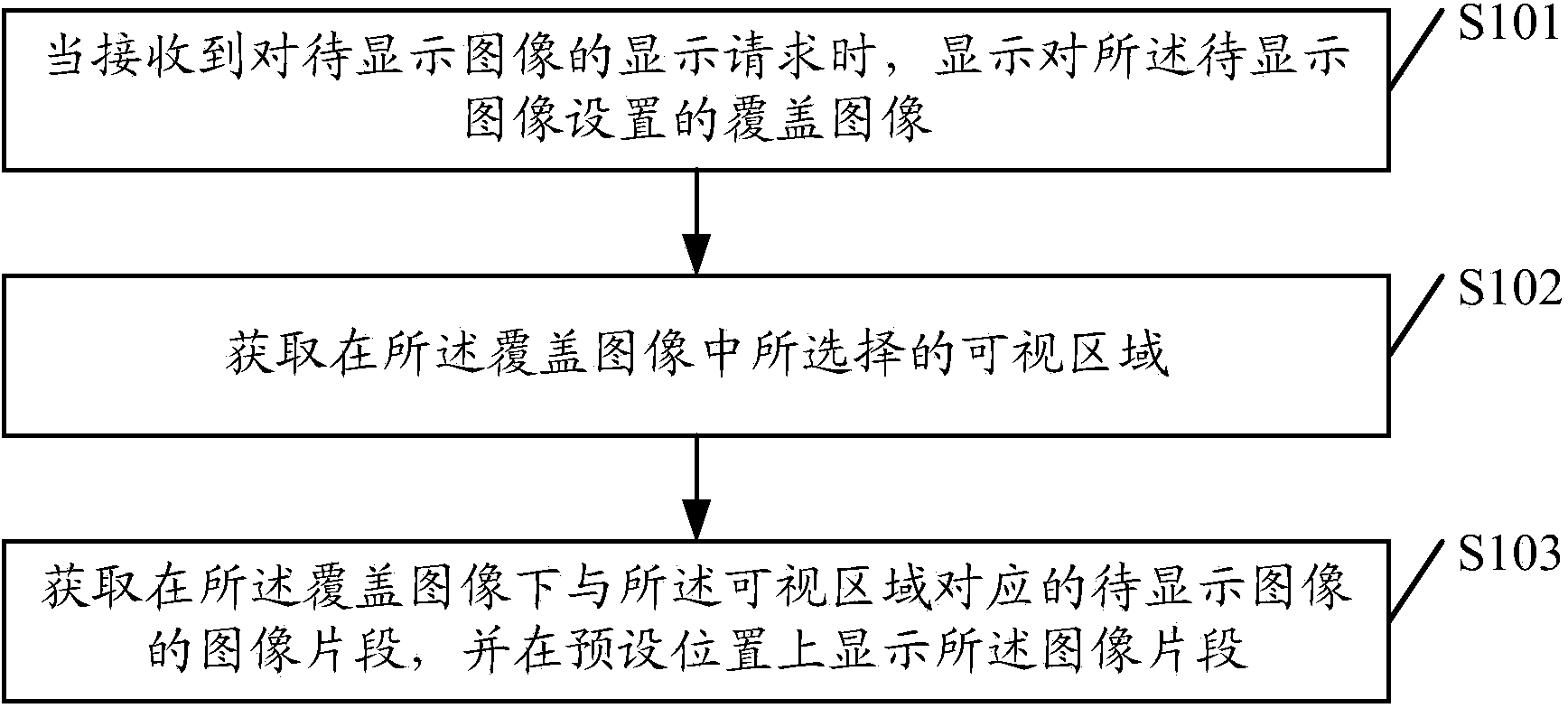
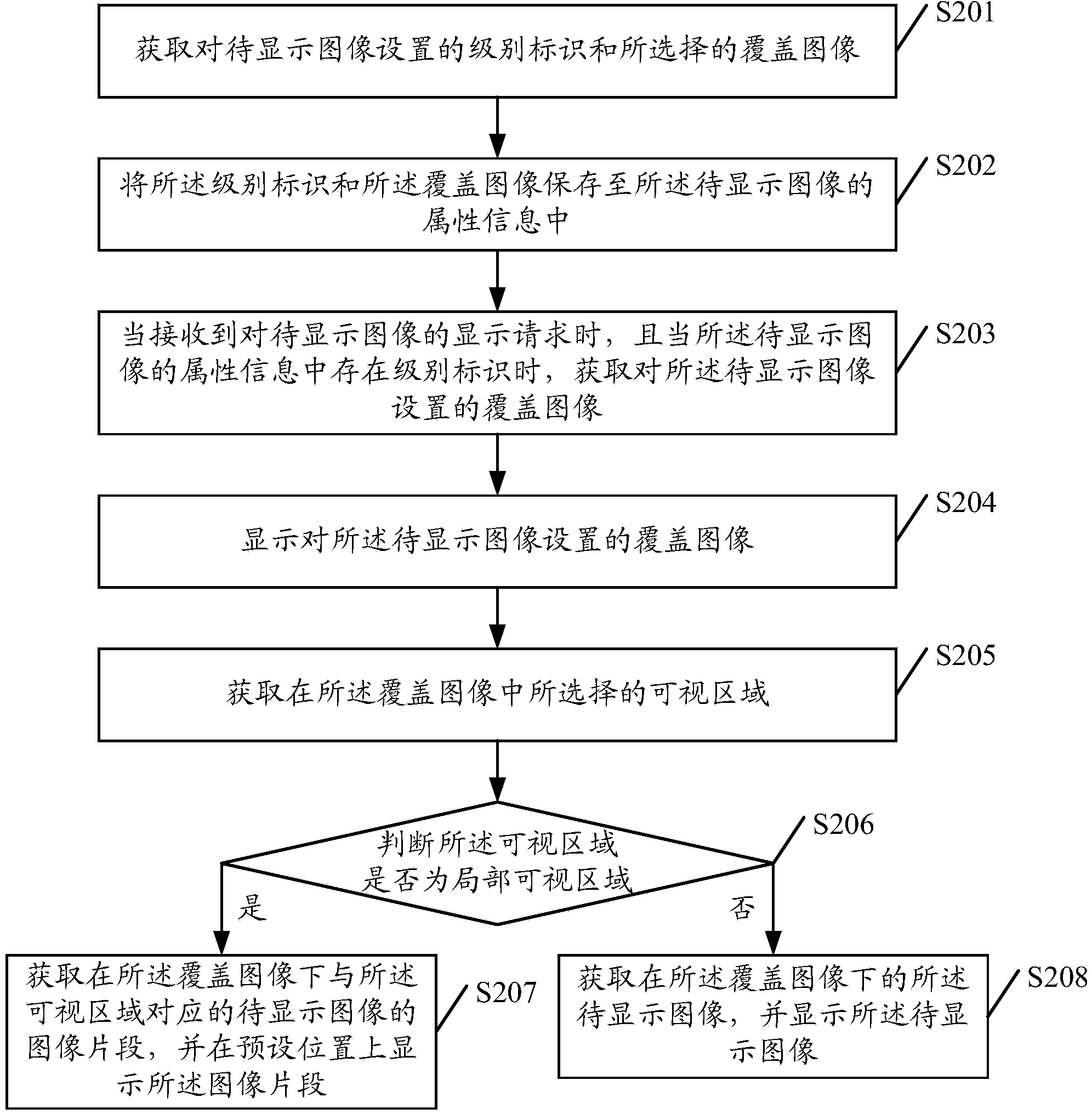
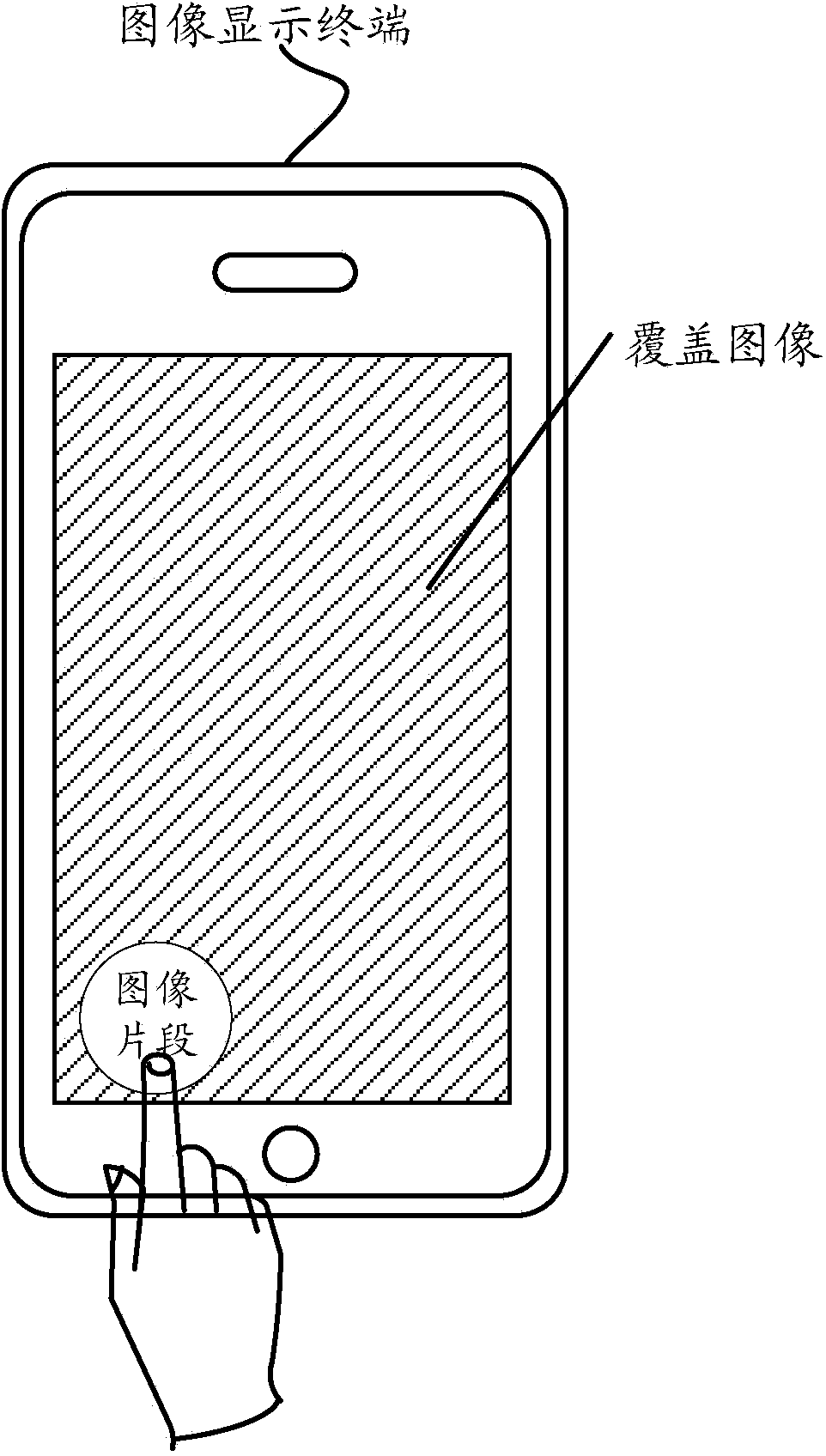
The embodiment of the invention discloses an image display method and terminal. The method includes the following steps that when a display request of an image to be displayed is received, a cover image set for the image to be displayed is displayed; a visual area selected in the cover image is obtained; an image section of the image to be displayed and corresponding to the visual area is obtained in the cover image, and the image section is displayed on a preset position. According to the image display method and terminal, privacy and safety of the image can be guaranteed, and influences of public environment factors on image browsing are reduced.
Owner:VOVIV TECH SHENZHEN
Water pricing system
ActiveCN105551146ARealize on-off controlLow input costApparatus for hiring articlesPublic environmentIntelligent control
The invention belongs to the technical field of water supply devices, and discloses a water pricing system which comprises a water metering terminal, a mobile control terminal and a background server. When water pricing operation is executed, the mobile control terminal and the water metering terminal are in communication, water start and stop operation is controlled, and water data is recovered; meanwhile, the mobile terminal is connected with the background server, and the water data is transmitted back to the background server; the background server calculates the water price according to the water data and transmits the water price to the mobile control terminal. By establishing the wireless connection of a mobile intelligent control end, the site water metering terminal and a background system, intelligent pricing and deducting operation is achieved, water pricing operation in the public environment is greatly simplified, and meanwhile cost input is reduced.
Owner:WUHAN KUANFAN ENERGY TECH
Universal microorganism bacterial agent
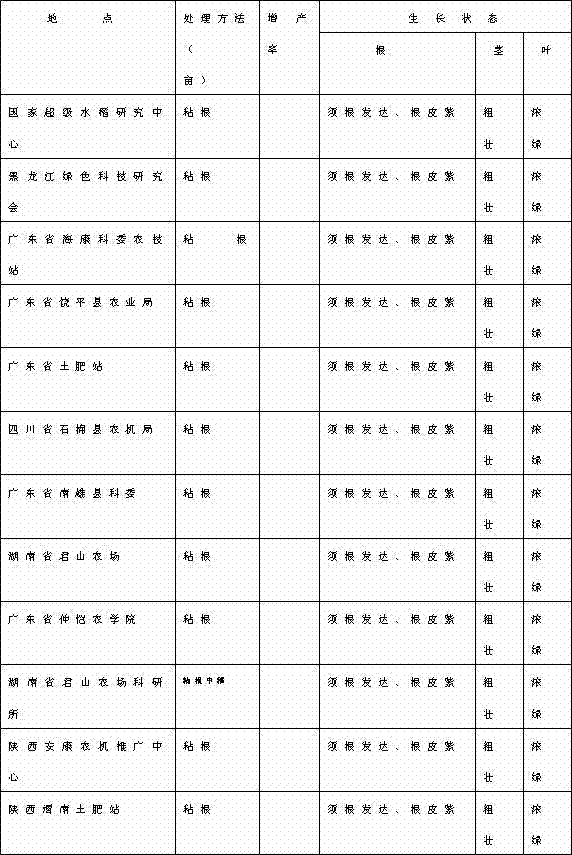
The invention discloses a universal microorganism bacterial agent which is characterized by comprising one or more of bacillus, pseudomonas, composite azotobacter, photosynthetic bacteria, yeast, fusarium oxysporum, actinomycetes, potassium bacteria, phosphate solubilizing bacteria, bifidobacterium, lactic acid bacteria, the bacteria are activated, and meanwhile, the viable count of the bacteria is not less than 10<8> / ml, and the infectious microbe rate is not greater than 3%. According to different applications and characteristics of the bacteria, special proportion and activation are adopted for different amounts for composite culture so as to make the agent into different special dosage forms, functions and effects of single aspect are highlighted, non-leguminous crops are enabled to have the nitrogen fixation function, the functions in cultivation, breeding, environment-friendliness, mariculture, biological preservation and the like are outstanding, and the agent has important significance in prompting animal and vegetable growth, improving product quality, improving product mass, eliminating public environment pollution and the like.
Owner:云南晋企生物科技有限公司
Anticipating merchandising trends from unique cohorts
A computer implemented method, apparatus, and computer-usable program product for identifying marketing trends in unique cohort groups. Information describing a plurality of unique cohort groups associated with a public environment is retrieved. Each member of a cohort group in the plurality of unique cohort groups shares at least one common attribute. Sets of attributes associated with the plurality of unique cohort groups are identified. The sets of attributes are analyzed by a cohort trend detection engine to identify attribute trends associated with the sets of attributes and a frequency of occurrence of the attribute trends in the plurality of unique cohort groups to form current attribute trends. In response to a query to an inference engine requesting inferences associated with the marketing trends, inferences describing future occurrences of the attributes in the plurality of cohort groups are received to form a set of future attribute trends. A set of marketing trends are generated using the current attribute trends and the set of future attribute trends. The set of marketing trends describes probable future marketing trends in the given environment.
Owner:IBM CORP
Method and system for preventing overhearing of private conversations in public places
InactiveUS20110188666A1Mitigate, alleviate or eliminate onePreventing overhearing of private conversations in public placesSpeech analysisCommunication jammingPublic environmentPublic place
A method for preventing overhearing of private conversations in public spaces is disclosed. The method comprises detecting the social activity of the people in the public space and assessing the social situation and adapting the degree of sound masking and / or sound absorption at the desired locations to suit the assessed social situation. The method can be useful in public environments such as airports, city centers, club, bars, cafes and shopping centers where it is required to prevent over-hearing of private conversations.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Infectious medical waste treatment system
InactiveCN108662589AConvenient high temperature and high pressure disinfectionSuspended high temperature and high pressure disinfection thoroughlyIncinerator apparatusPublic environmentCombustion chamber
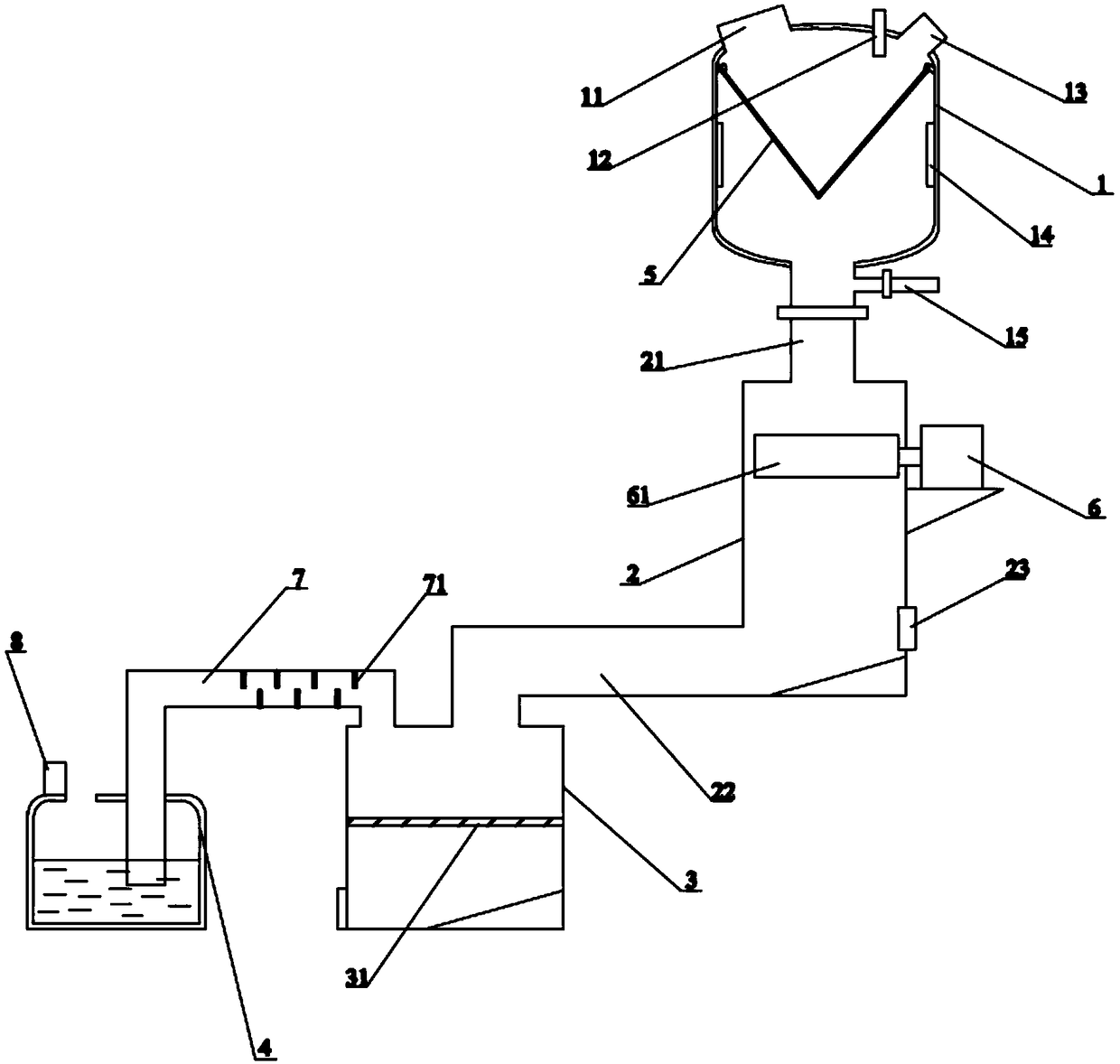
The invention belongs to the technical field of waste treatment equipment, and particularly relates to an infectious medical waste treatment system. The infectious medical waste treatment system comprises a disinfection tank, a smashing tower, a combustion chamber and a waste gas purification chamber which are connected in sequence; the top of the disinfection tank is provided with a feeding port,a thermometer and a pressure meter; the bottom of the disinfection tank communicates with the top of the smashing tower through a feeding pipeline; the bottom of the outer wall of the smashing towercommunicates with the top of the combustion chamber through a transporting pipeline; the side, opposite to a pipe port of the transporting pipeline, on the outer wall of the smashing tower is providedwith a fan; a filter screen is arranged in the combustion chamber in the transverse direction; the lower end of the outer wall of the combustion chamber is provided with an ash discharging port; andthe top of the combustion chamber communicates with the top of the waste gas purification chamber through an exhausting pipeline. Due to the treatment system, infectious medical waste is sequentiallysubjected to high temperature and high pressure sterilization and disinfection, drying, physical smashing and high-temperature combustion, waste gas after combustion is discharged into the atmosphereafter being purified, no toxic pollutants are generated in the whole process, and the public environment is protected.
Owner:THE FIRST AFFILIATED HOSPITAL OF HENAN UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com