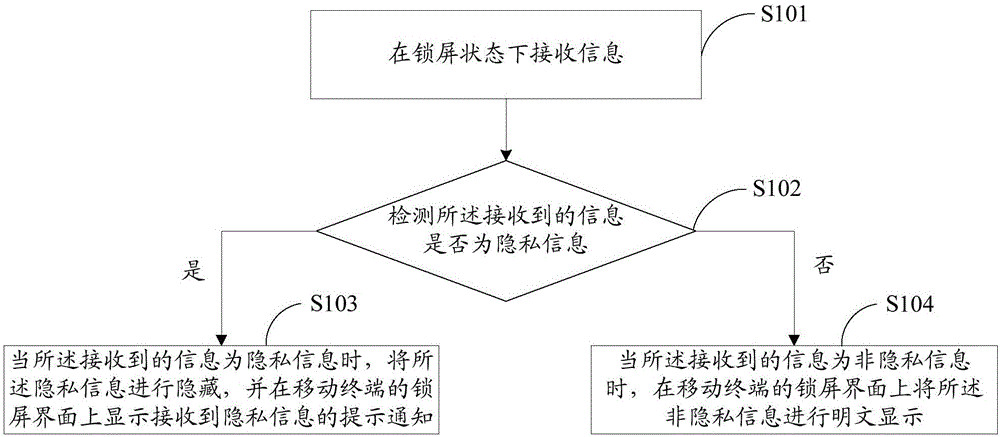
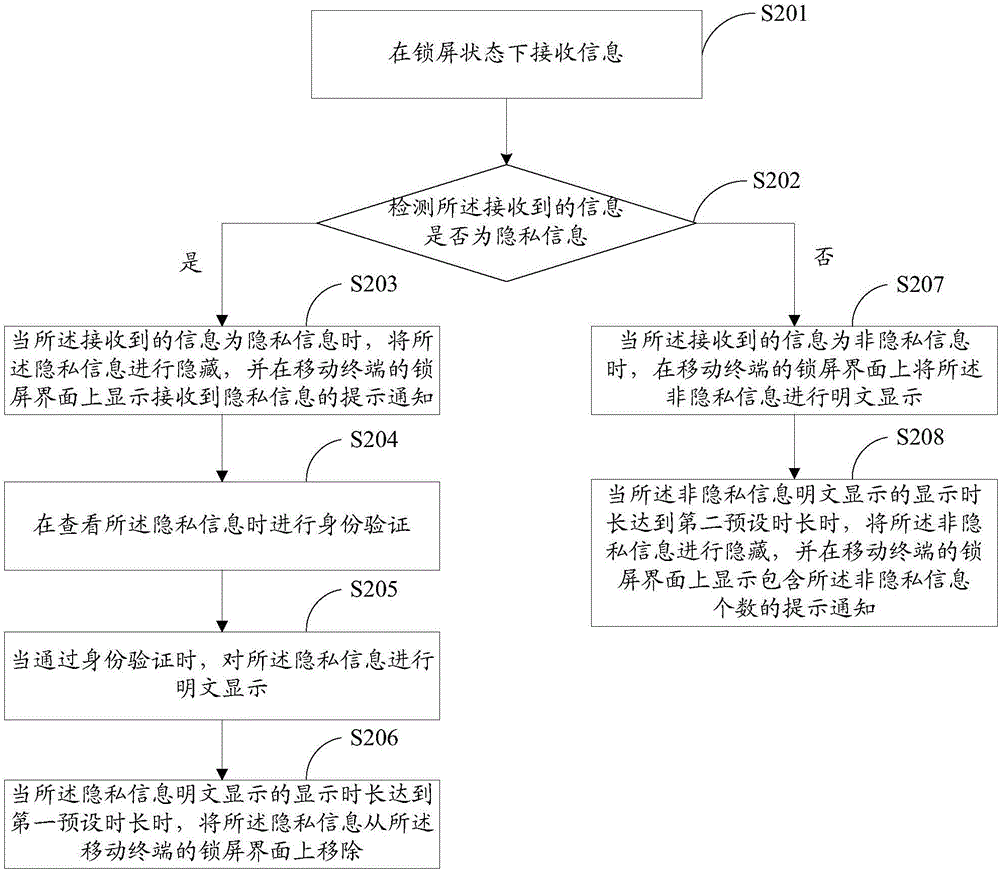
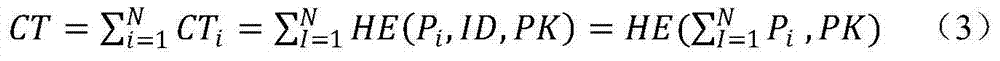Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
295results about How to "Prevent peeping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
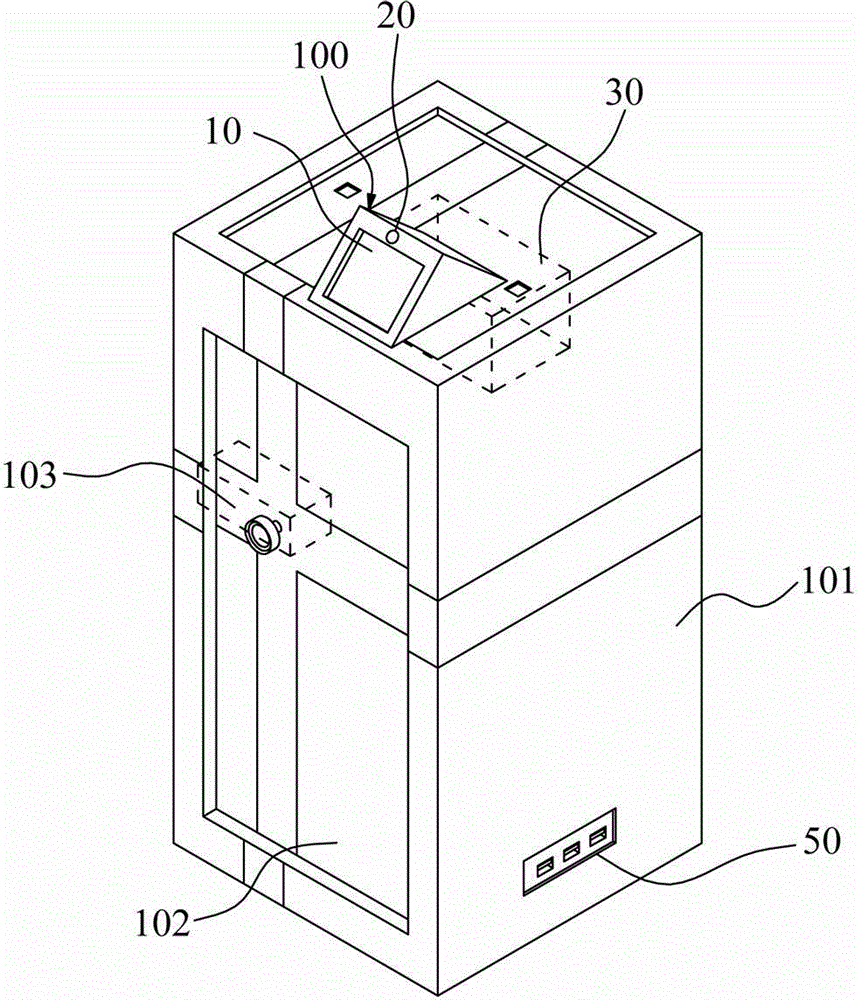
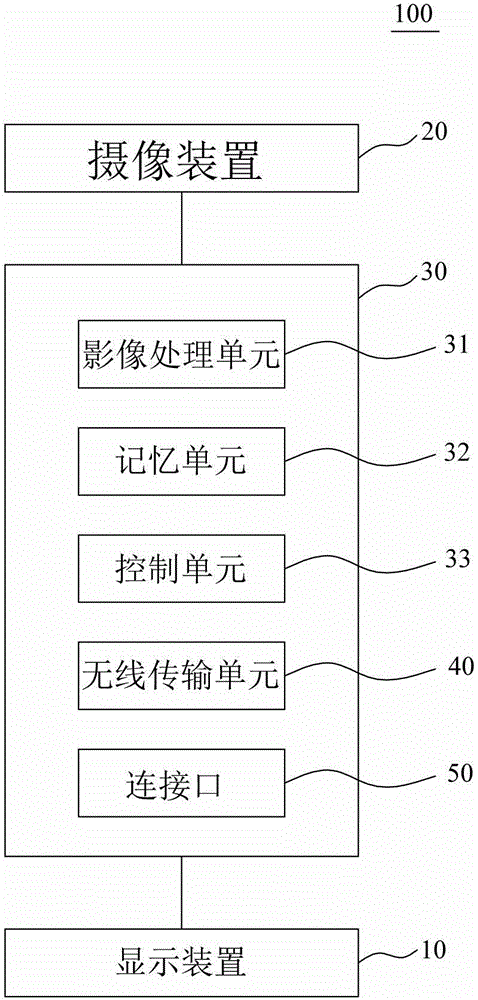
Eye-controlled password input apparatus, method and computer-readable recording medium
ActiveCN105320251AReduce complexityAvoid noiseInput/output for user-computer interactionCharacter and pattern recognitionImaging processingPassword
The present invention provides an eye-controlled password input apparatus, method and computer-readable recording medium. The apparatus comprises a display device to display a password menu, an image capturing device to capture an user's eye region image, a memory unit to store at least one preset password and a corresponding account number, a control unit to generate the password menu according to the preset password, and an image processing unit. The image processing unit obtains a plurality of reference objects from the eye image so as to recognize the eye movement direction and to confirm password input. After input a character of the password, the display device generates another password selection menu for the user to input another password character until the password input program is completed.
Owner:UTECHZONE CO LTD
Mobile terminal and anti-spy method thereof
ActiveCN103077361ADoes not restrict field of viewImprove experienceDigital data protectionInternal/peripheral component protectionComputer scienceField of view
The invention relates to a mobile terminal and an anti-spy method thereof. The method comprises the following steps of: detecting current content displayed by a screen of the mobile terminal; and when the content or an application with privacy properties is detected, displaying a mask in a preset zone of the current screen of the mobile terminal so as to protect the current content displayed by the screen of the mobile terminal. Through the application of the technical scheme of the invention, the screen content of the mobile terminal can be protected, the cost is low, few system resources are occupied, the vision of a user cannot be limited, and great experience is brought to the user.
Owner:DONGGUAN YULONG COMM TECH +1
Double-glazed with built-in shutters
The invention discloses an internally-arranged blind window with double layers of hollow glass, and belongs to the technical field of sunshade hollow glass products. The internally-arranged blind window comprises a window body, a shutter blind, a blind piece turnover adjusting control mechanism, a shutter blind lifting adjusting control mechanism, a shutter blind lifting and blind piece turnover transition mechanism, a blind piece turnover traction rope upper connecting mechanism, a blind piece turnover traction rope transition mechanism, a bottom strip traction rope transition mechanism and a blind piece turnover traction rope. The shutter blind comprises a bottom strip, a set of blind pieces, a bottom strip traction rope and a blind piece turnover rope. The internally-arranged blind window is characterized in that the blind pieces are of structures with cross section shapes tendency to S shapes, and the blind pieces are composed of large semicircular blind piece bodies and small semicircular blind piece bodies; arch directions of the small semicircular blind piece bodies is opposite to the arch directions of the large semicircular blind piece bodies, and the positions, located on the blind pieces, of traction rope recess holes are located on edge portions of sides, away from the small semicircular blind piece bodies, of the large semicircular blind piece bodies; the width of a closed gap between adjacent blind pieces and the degree of a maximum visual included angle alpha are obviously reduced, and a user is prevented from peeping at the interior from the exterior; and the privacy is protected, and safety is ensured.
Owner:CHANGSHU ZHONGQIN BUILDING MATERIAL
Method for preventing peep on computer and computer with method
InactiveCN101625716ALow costPrevent peepingCharacter and pattern recognitionInternal/peripheral component protectionComputer graphics (images)Display device
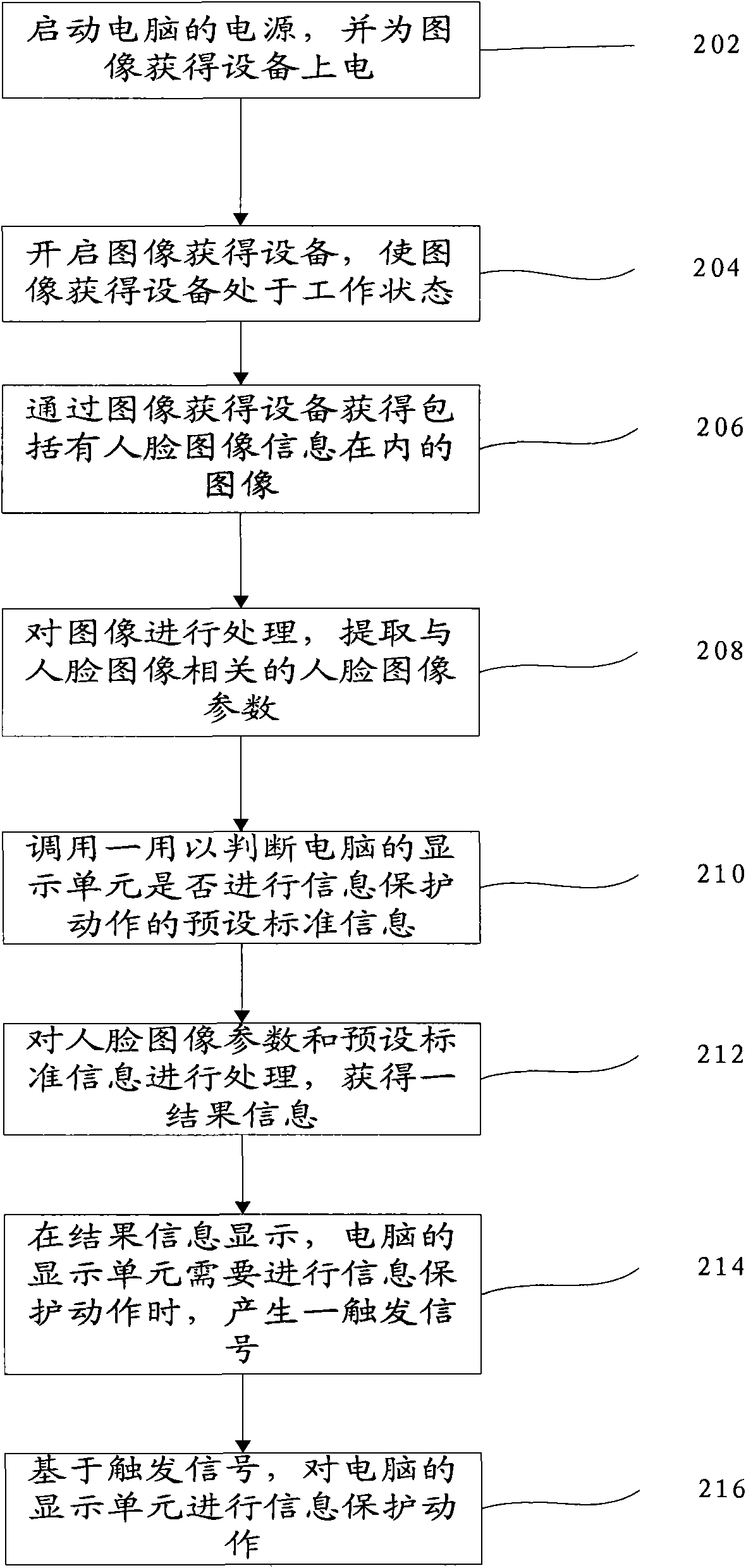
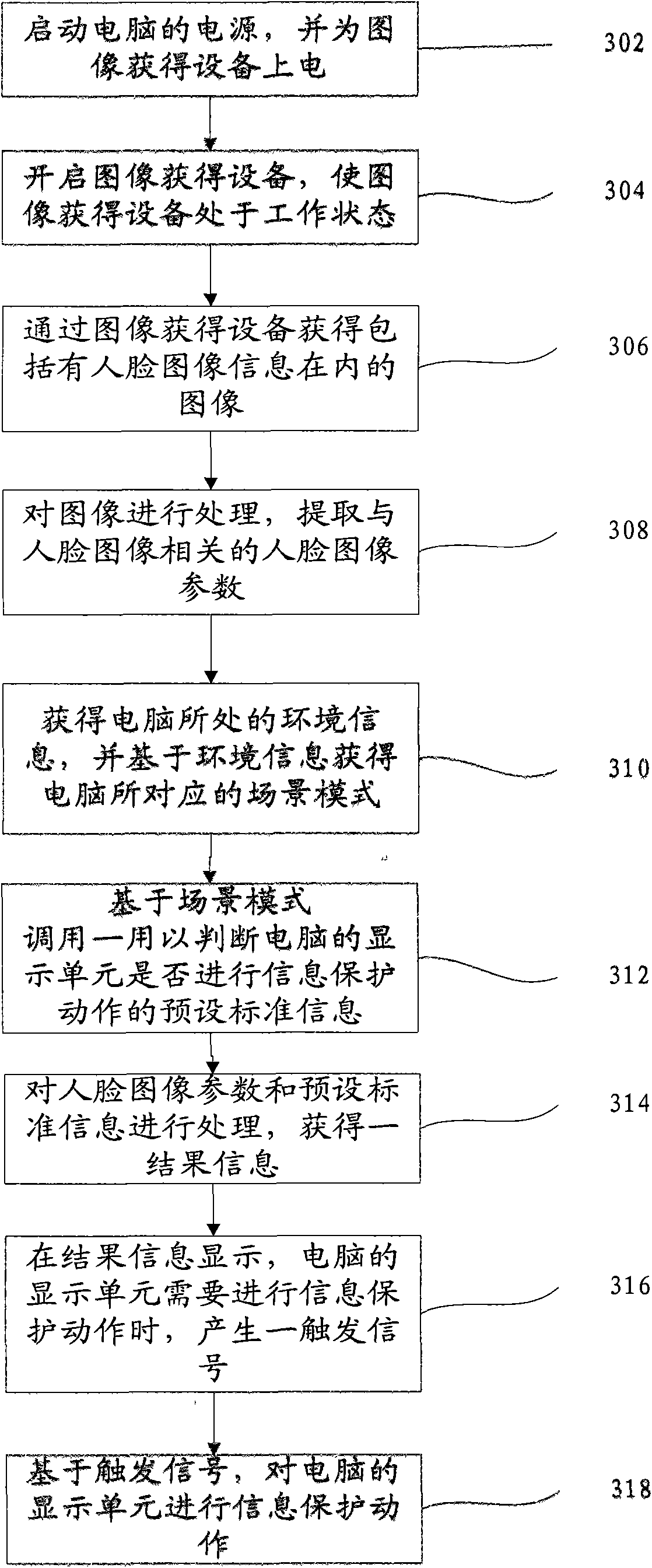
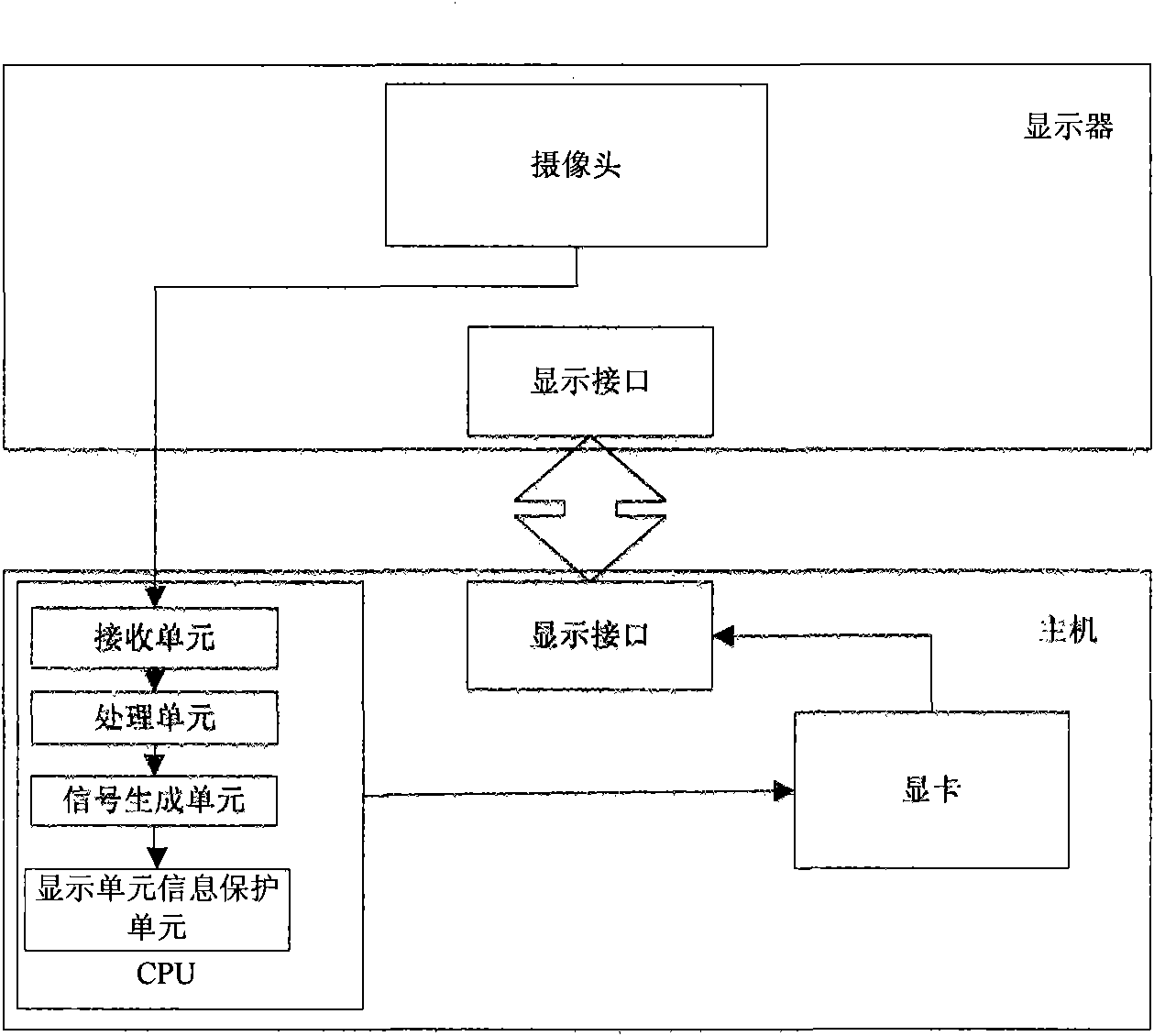
The invention provides a method for preventing the peep on a computer and the computer with the method. The method comprises the steps of: acquiring an image which is at a specific distance before a display unit (namely a screen of a display) and comprises human face image information through image acquisition equipment (namely the prior camera); extracting human face image parameters related to a human face image in the image; processing the human face image parameters and preset standard information for judging whether a display screen of a computer performs information protection action; and performing the information protection action on the display screen of the computer according to a processing result to prompt a user of the current peep of the content on the screen of the display by others. But no extra hardwares such as a polarizing film, a birefringent film and the like need to be added, which reduces the cost.
Owner:LENOVO (BEIJING) LTD
Display system and control method
ActiveCN104732168APrevent peepingStatic indicating devicesInternal/peripheral component protectionControl signalComputer science
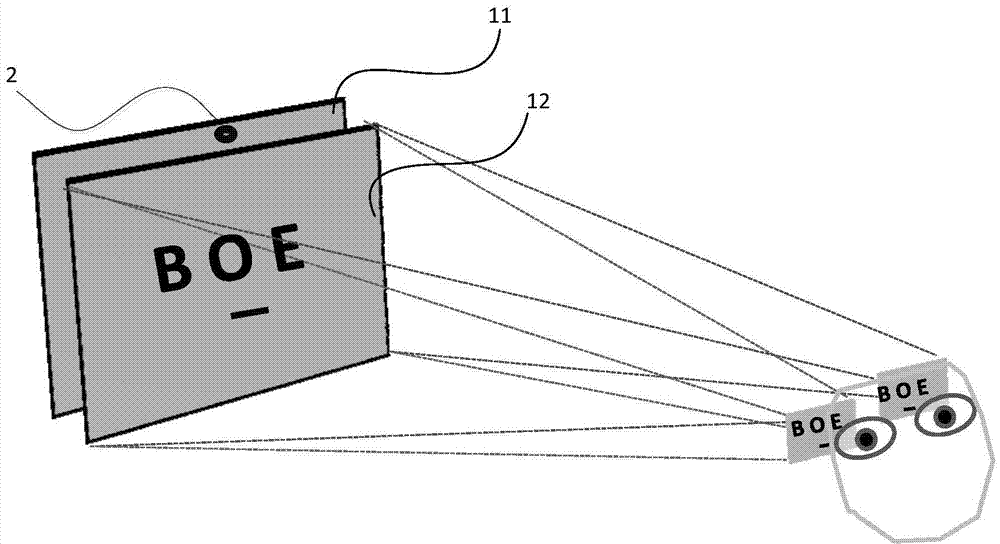
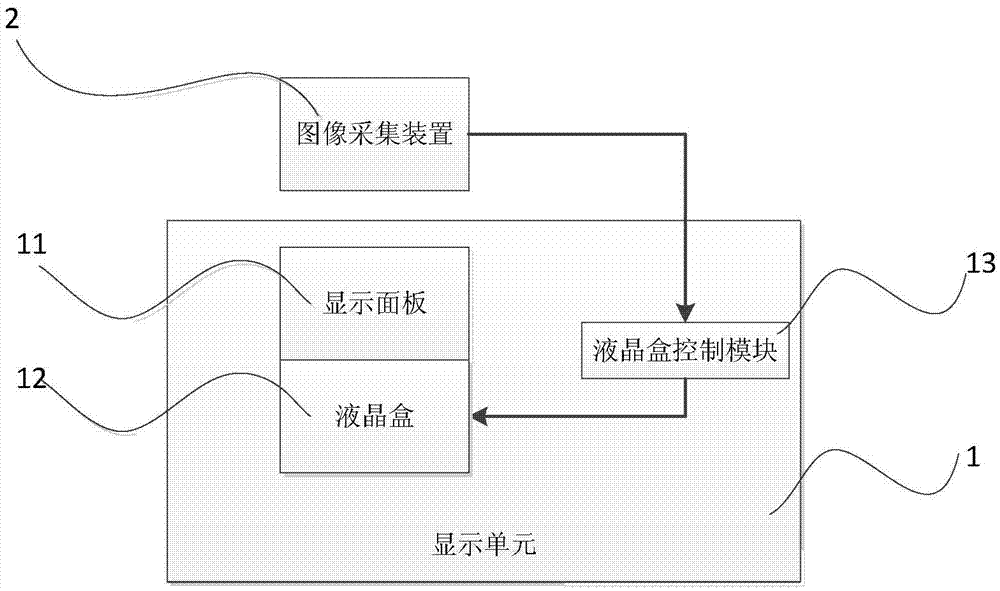
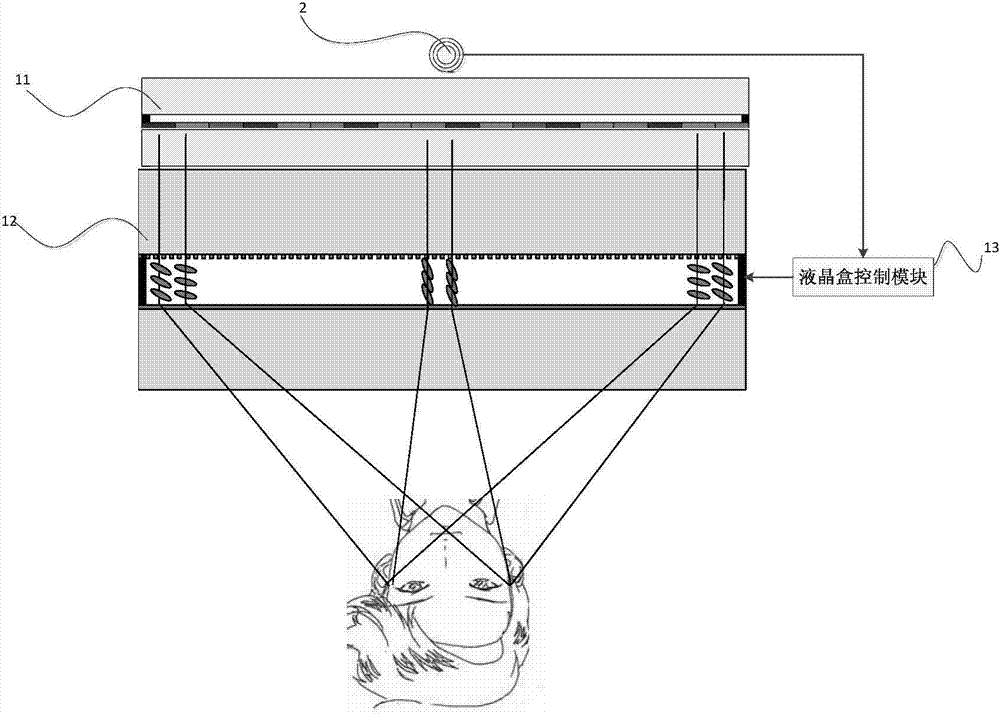
The invention discloses a display system and a control method. The display system comprises a display unit and an image collection device. The display unit comprises a display panel and a liquid crystal box arranged in the light emitting direction of the display panel. The display unit further comprises a liquid crystal box control module. The image collection device acquires an image in front of the display unit and transmits the image to the liquid crystal box control module. The liquid crystal box control module recognizes a reserved face in the image, determines a specific region where the reserved face is located according to the position of the reserved face in the image and outputs a control signal to the liquid crystal box according to the specific region, and the liquid crystal box controls light transmitting into the liquid crystal box from the display panel to be emitted to the specific region according to the control signal. The display system collects the image in front of the display unit, performs face recognition to determine the specific region where the reserved face is located and adjusts the direction of emergent light transmitting through the liquid crystal box, thereby enabling only the reserved face to see the displayed image, and preventing non-reserved objects in other regions from peeping at the image.
Owner:BOE TECH GRP CO LTD
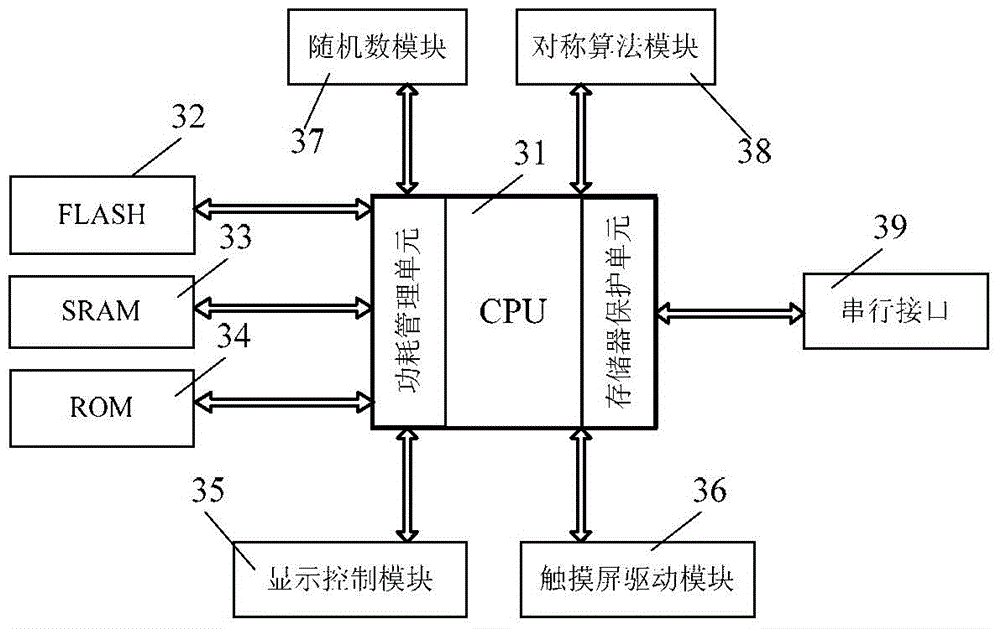
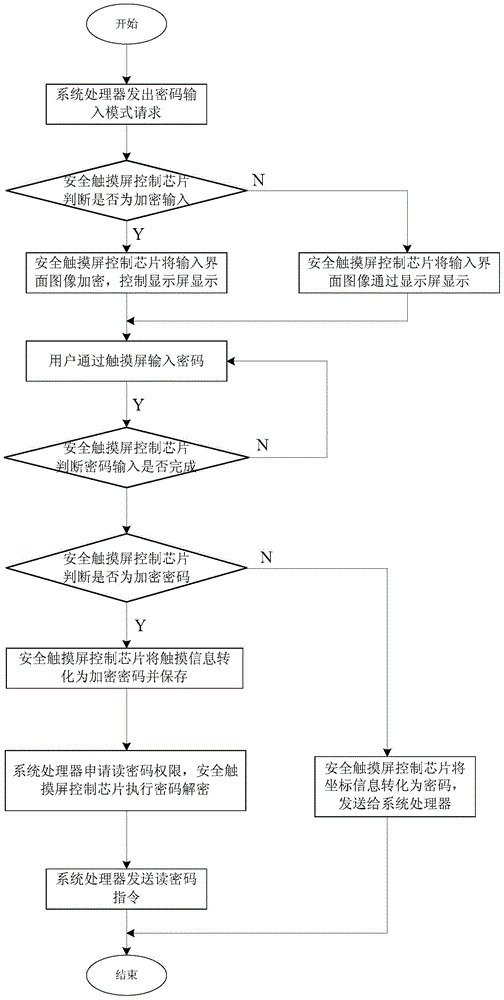
Security password input system and method based on security touch screen control chip
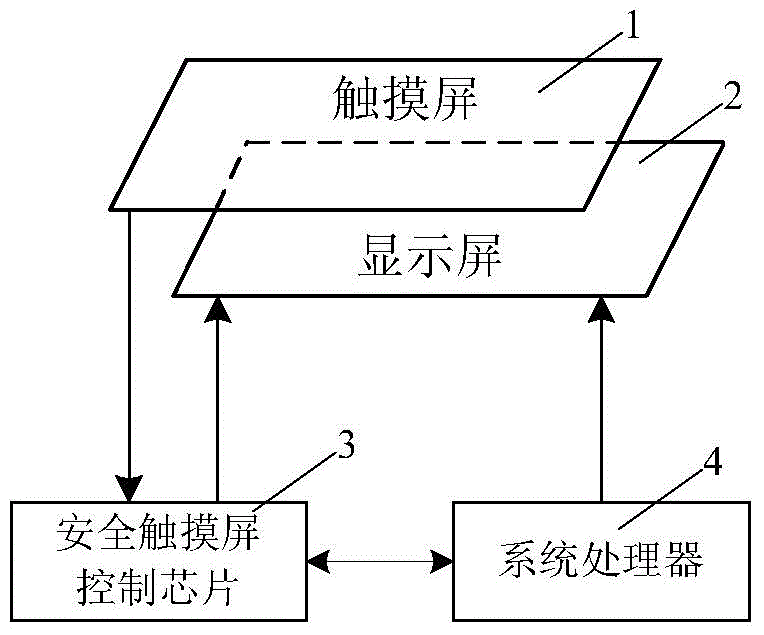
ActiveCN104156642AEasy to integratePrevent peepingDigital data authenticationInput/output processes for data processingStatic random-access memoryPassword
A security password input system based on a security touch screen control chip comprises a touch screen, a display screen, the security touch screen control chip and a system processor. The security touch screen control chip comprises a central processing unit. A FLASH memory, an SRAM (static random access memory), a display control module, a touch screen drive module, a random number module, a symmetric algorithm application module and a serial interface are connected to the central processing unit. The security touch screen control chip is used for encrypting an image of a password input interface, transmitting the image to the display screen for displaying, and encrypting and storing touch information generated by the touch screen; when the system processor sends out a command to read a password, the password is automatically decrypted and transmitted; the image of the password input interface is encrypted and decrypted both in the security touch screen control chip; the system processor is unable to acquire an encryption method of a password key pad, so that system Trojan programs still are unable to analyze the password through image recognition even after capturing the image of the password input interface.
Owner:HANGZHOU SYNOCHIP DATA SECURITY TECH CO LTD
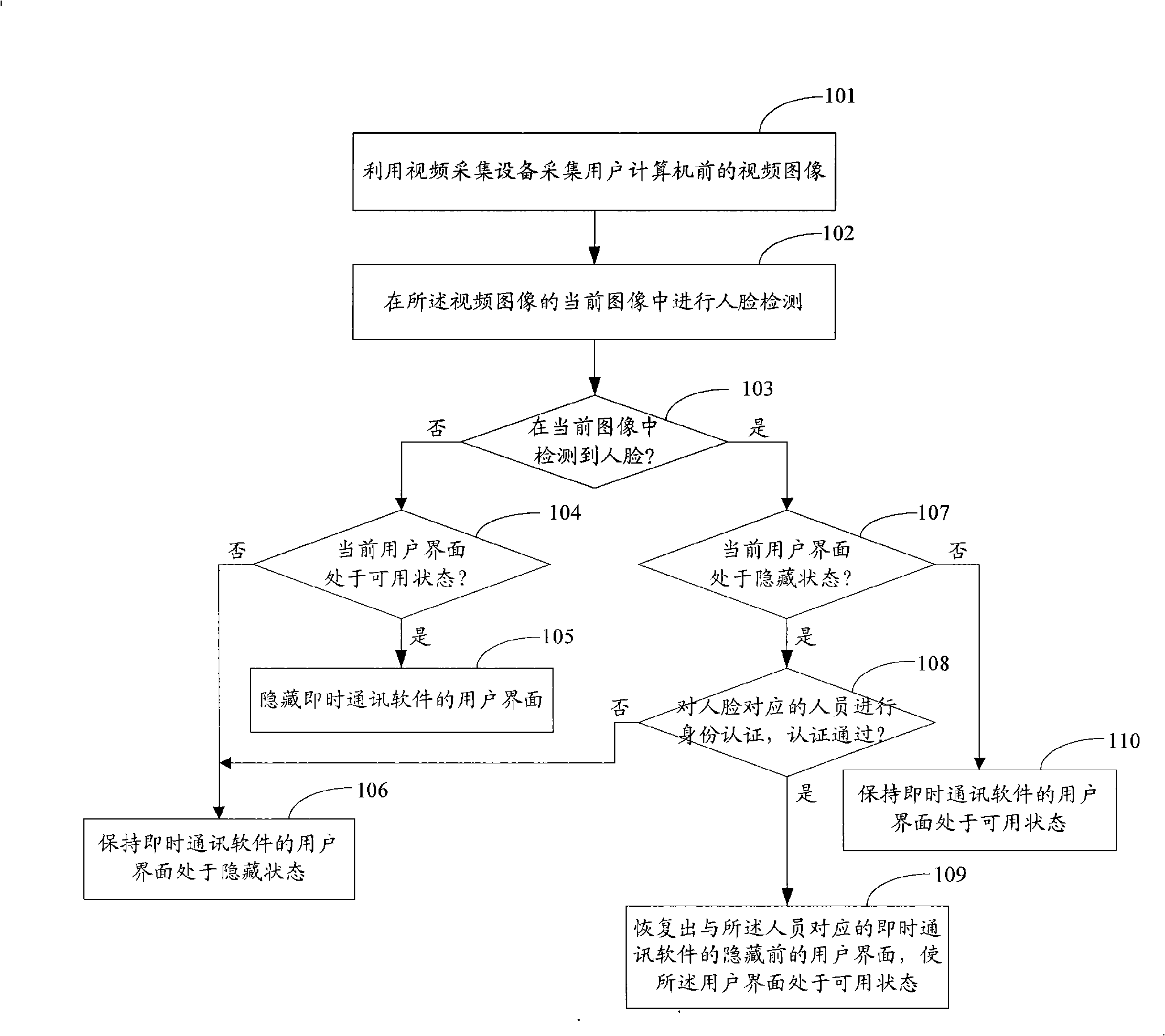
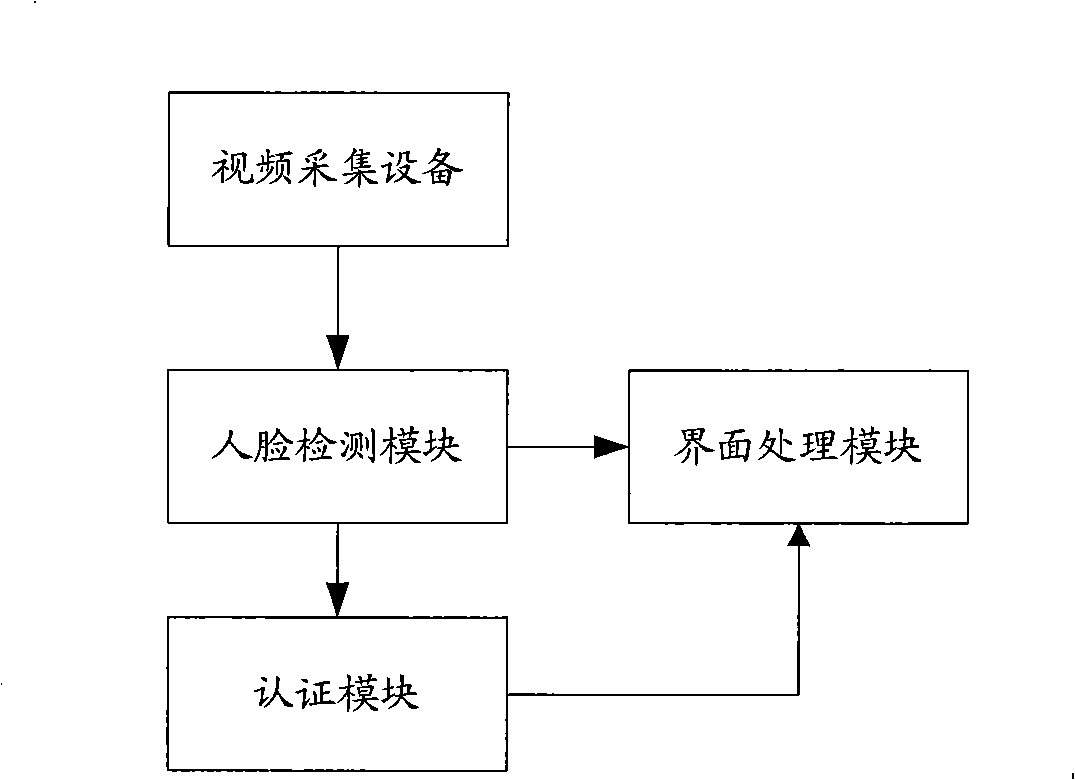
Method and system for controlling user interface of instant communication software
InactiveCN101325491AImprove securityPrevent peepingUser identity/authority verificationCharacter and pattern recognitionAcquisition apparatusCommunications software
The invention discloses a user status control method and system of an instant communication software. The method includes: detecting human face in the current image acquired by a video acquisition apparatus performing; if no face is detected in the current image and the current user interface of the instant communication software is at an operational state, cancelling the user interface; if face is detected in the current image and the current user interface of the instant communication software is at a cancelled state, recovering the cancelled user interface of the instant communication software corresponding the personnel, thereby the user interface is at an operational state. The technical scheme disclosed by the invention is capable of controlling the user interface of the instant communication software according to the use instance of users.
Owner:VIMICRO CORP
Method and device for tracking positioning of mobile terminal device and mobile terminal device thereof
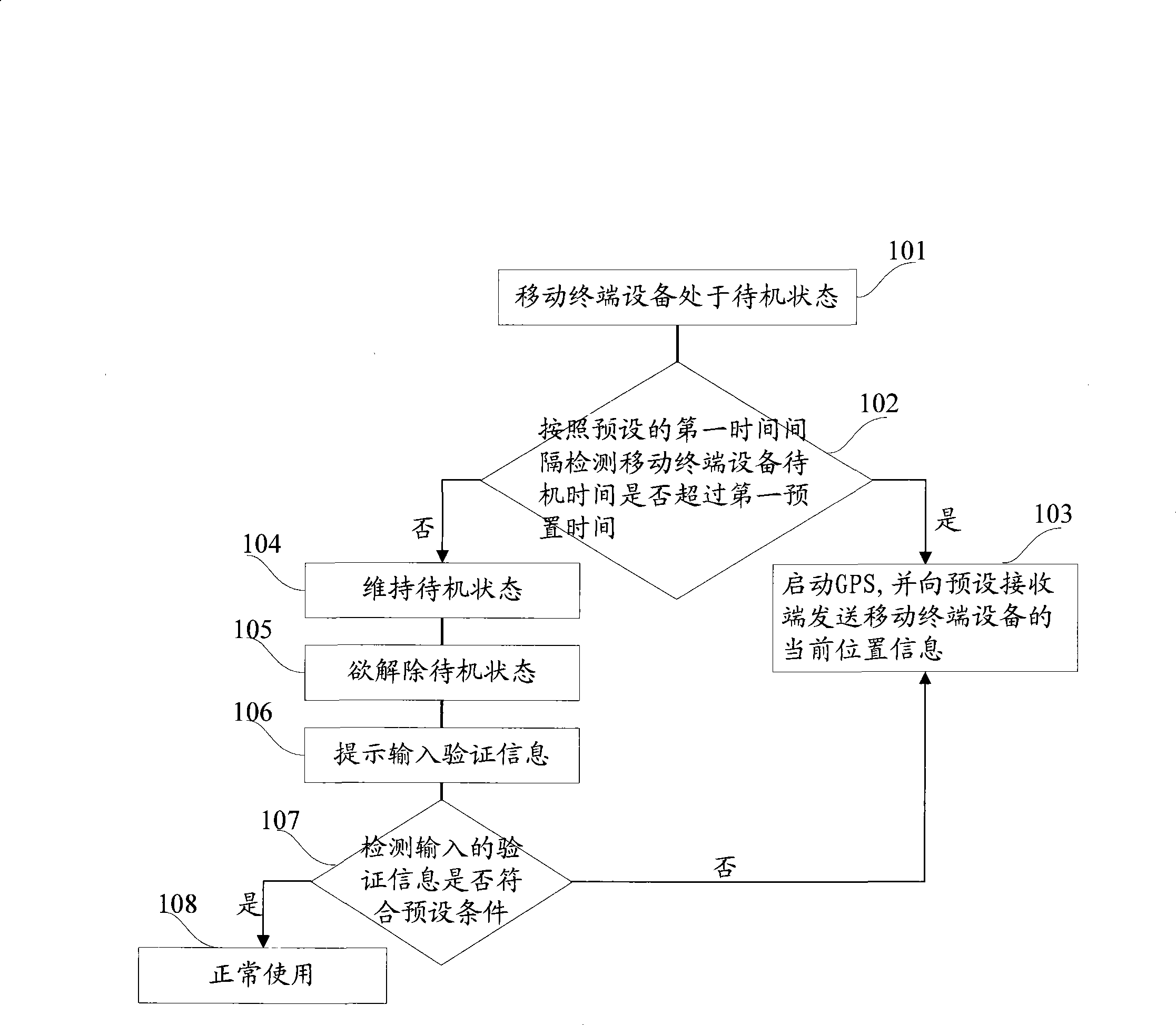
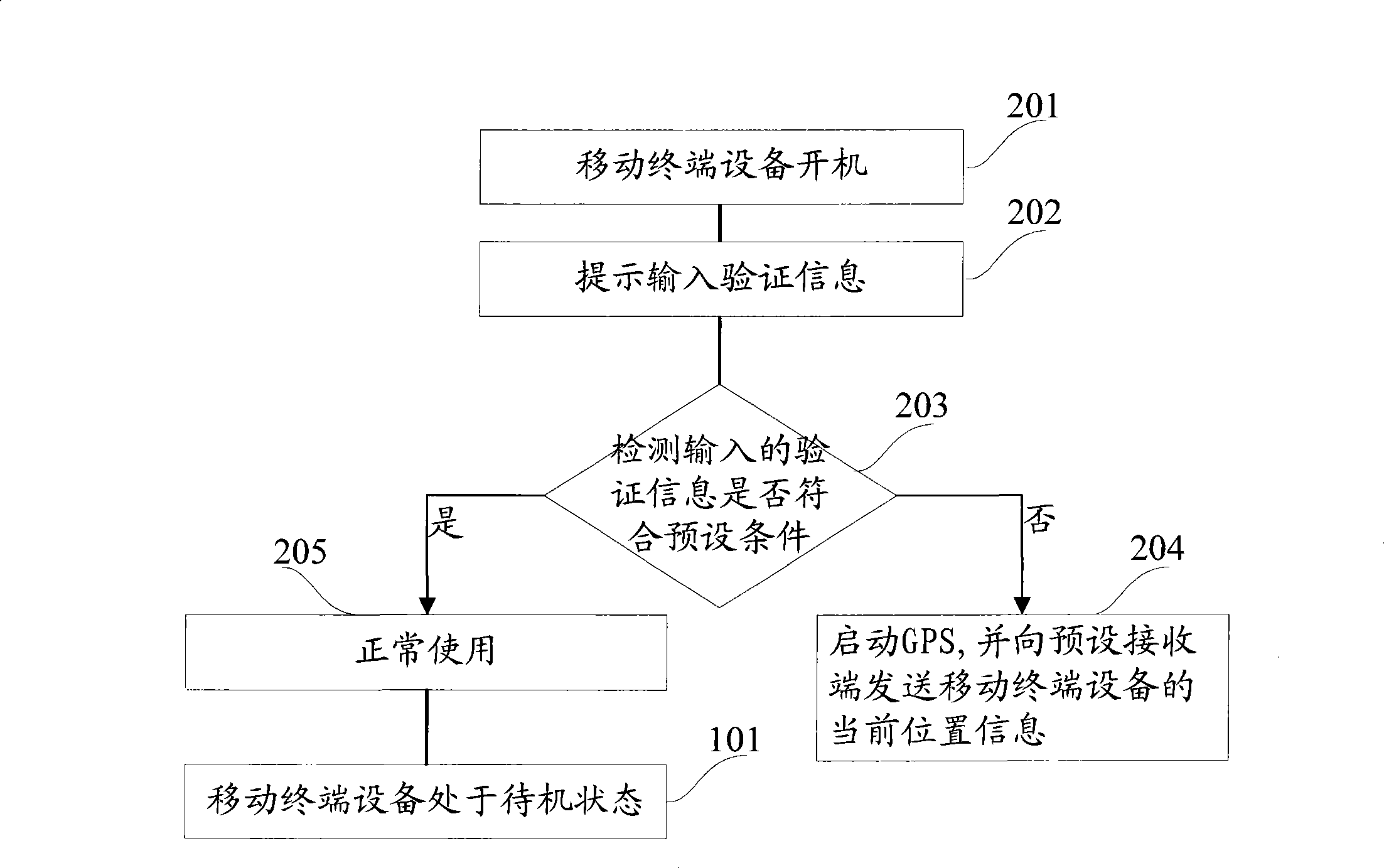
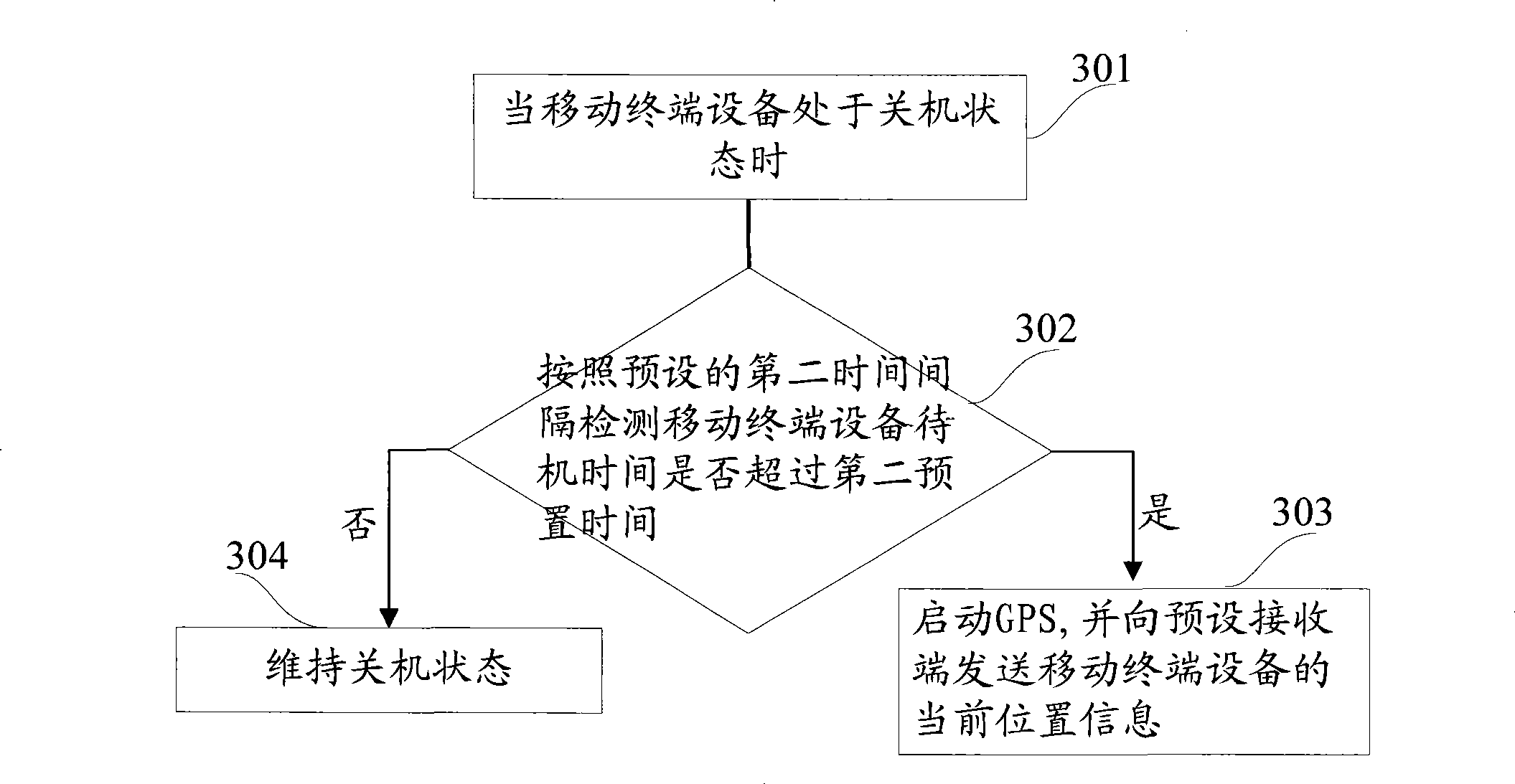
InactiveCN101399881ASave powerProtect the owner's private informationSubstation equipmentWireless communicationEngineeringTerminal equipment
The invention provides a method and a device for tracing and locating a movable terminal. The method includes: when the movable device is arranged in a standby state, whether the standby time of the movable terminal device exceeds a first preset time or not is detected according to a preset first time interval; if not, then GPS is started and the current position information of the movable terminal device is transmitted to a preset receiving terminal; if not, then maintaining the standby state; when the standby state is released, then the movable terminal device indicates to input verification information; if the input verification information meets a preset condition, then the movable terminal device is normally used; if not, then the GPS is started and the current position information of the movable terminal device is transmitted to the preset receiving terminal.
Owner:VIMICRO CORP
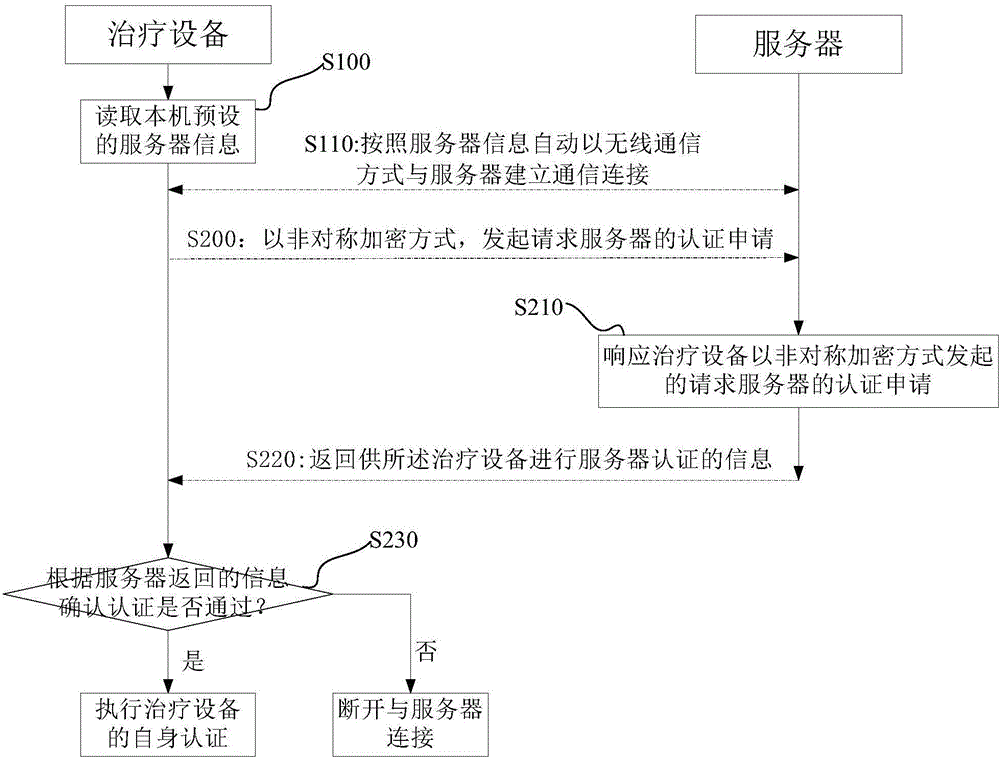
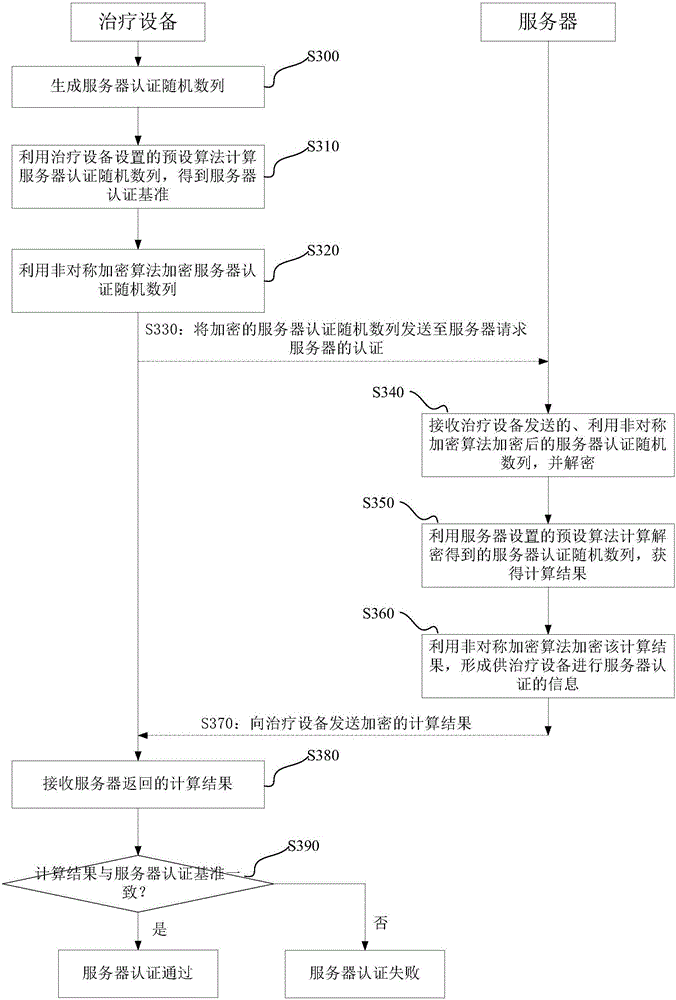
Authentication method, authentication device, authentication system and treatment equipment
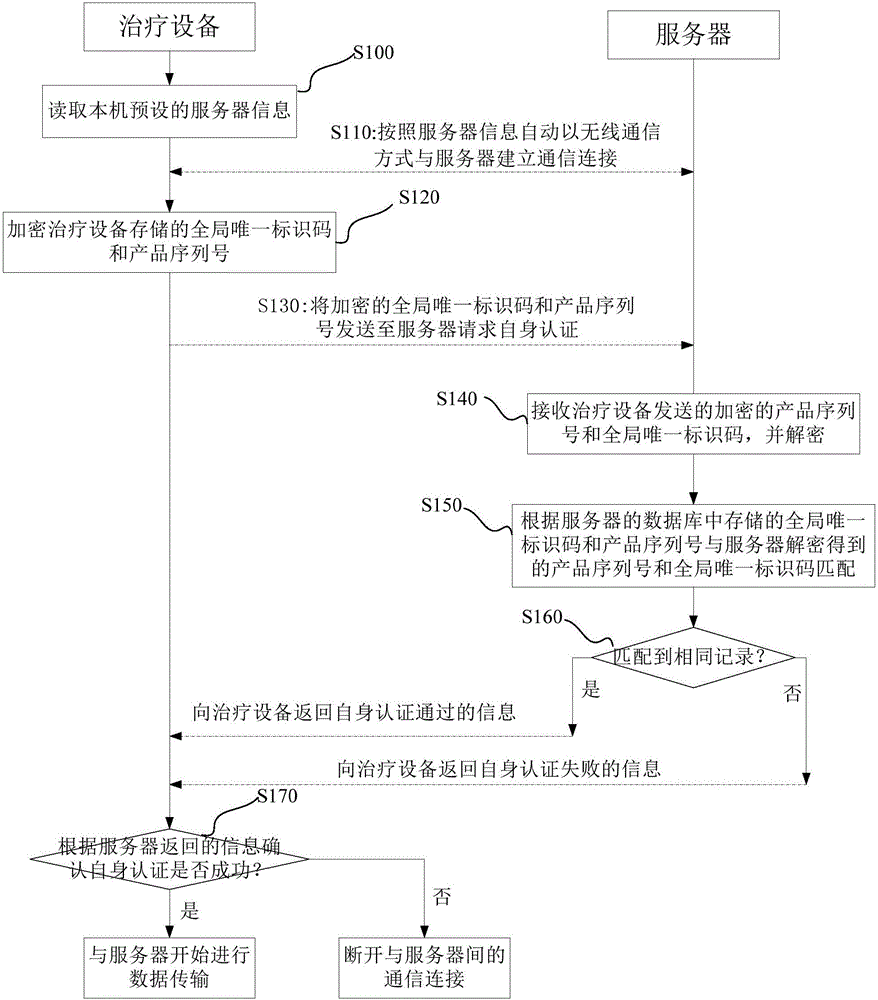
ActiveCN105871857AAvoid same-identity situationsPrevent peepingTransmissionData transmissionAuthentication system
The invention discloses an authentication method, an authentication device, an authentication system and treatment equipment. The authentication method comprises the steps of reading server information which is preset by a local machine, automatically establishing communication connection according to the server information in a wireless communication manner; and initiating self authentication by the treatment equipment, wherein self authentication comprises reading a global unique identification code and a product serial number which are pre-stored by the local machine; encrypting the global unique identification code and the product serial number which are stored in the treatment equipment, and transmitting the encrypted global unique identification code and the product serial number to a server for requesting self authentication; confirming a self authentication result according to information which returns from the server; if self authentication passes, starting data transmission with the server; and if self authentication fails, disconnecting communication connection with the server. The authentication method, the authentication device, the authentication system and the treatment equipment reduce operation difficulty and complexity in identity authentication.
Owner:BMC MEDICAL
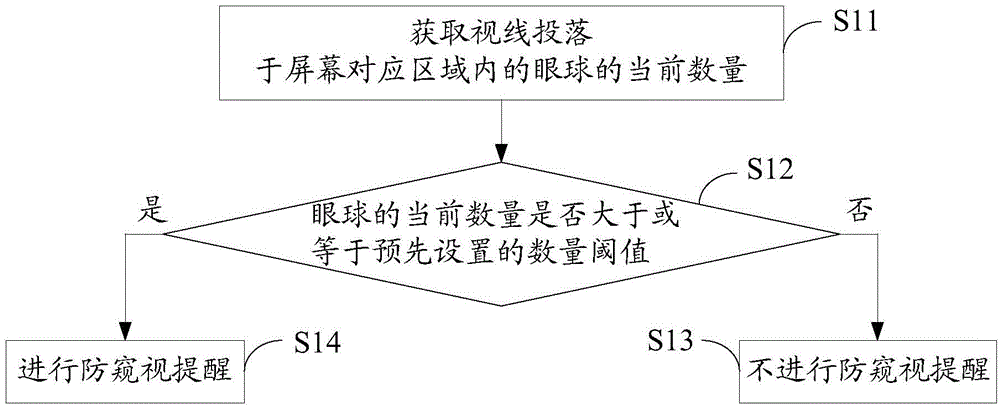
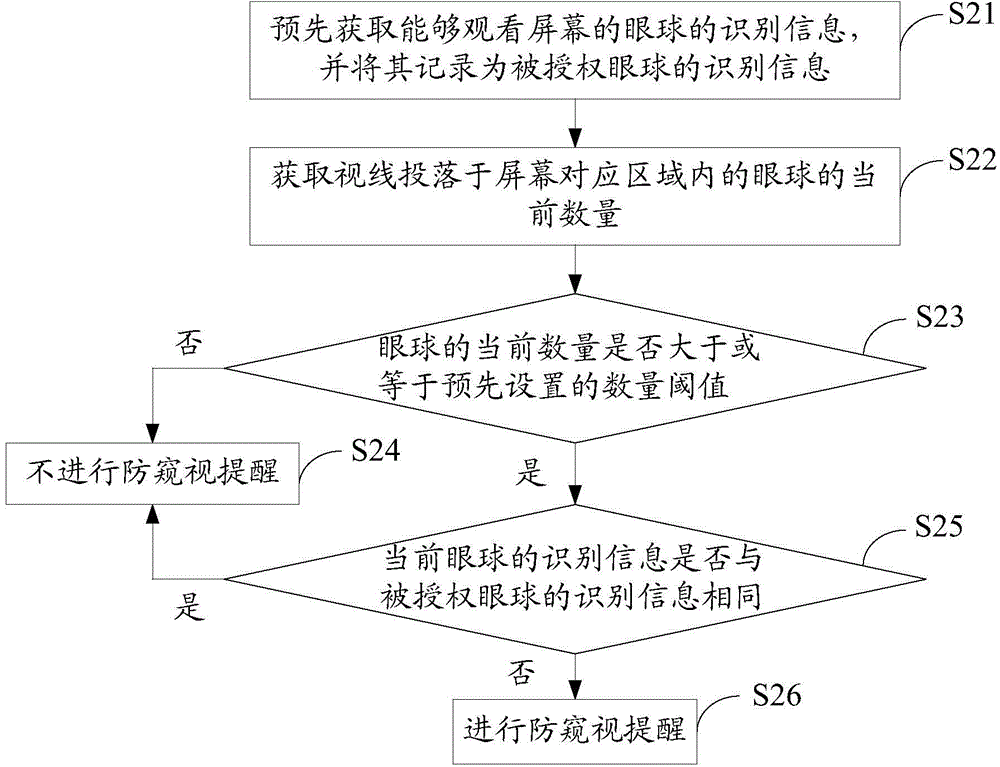
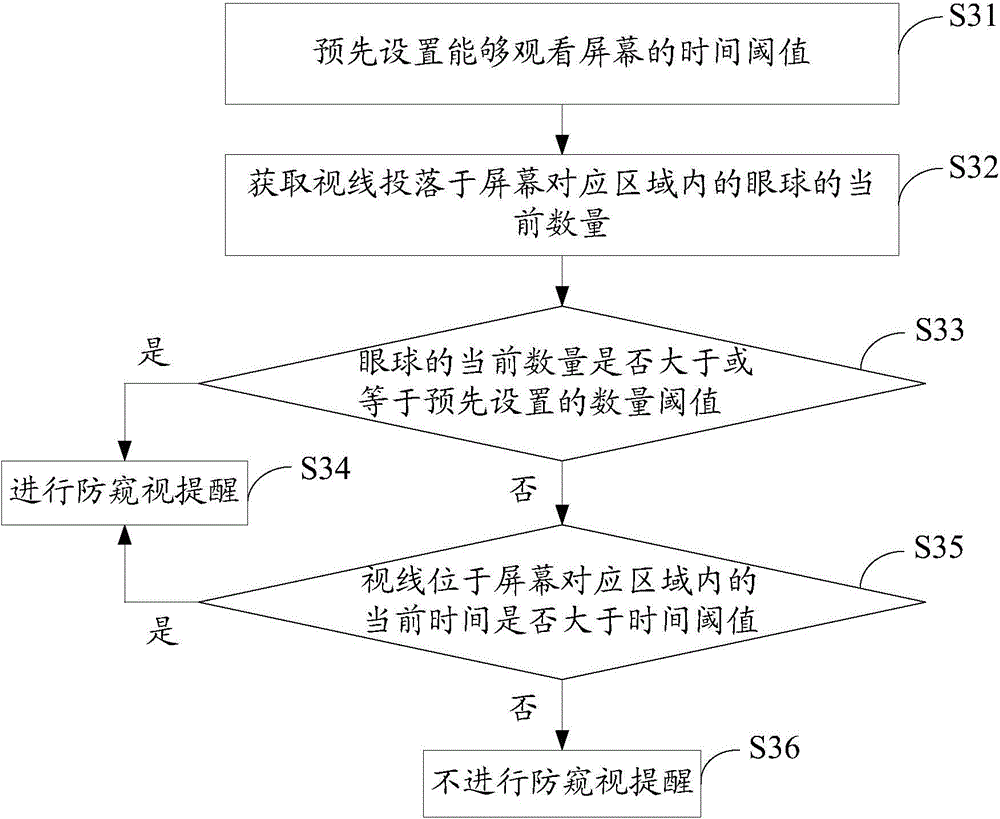
Peep prevention method and device for screen
InactiveCN104463041AProtect personal privacyPrevent peepingInternal/peripheral component protectionEmergency medicineComputer terminal
The invention provides a peep prevention method and device for a screen. The peep prevention method for the screen includes the steps that the current number of eyeballs with the sight lines falling into a corresponding area of the screen is acquired; whether the current number is larger than a preset number threshold value or not is judged, and the number threshold value represents the number of the eyeballs capable of watching the screen when the privacy is protected; if the current number is larger than the number threshold value, peep prevention reminding can be conducted. By the adoption of the mode, the ambient environment of a display terminal can be monitored, peep prevention reminding can be conducted when it is monitored that the content displayed by the screen of the display terminal is likely to be peeped, and therefore the personal privacy can be effectively protected.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
Privacy protection method during text display and communication terminal
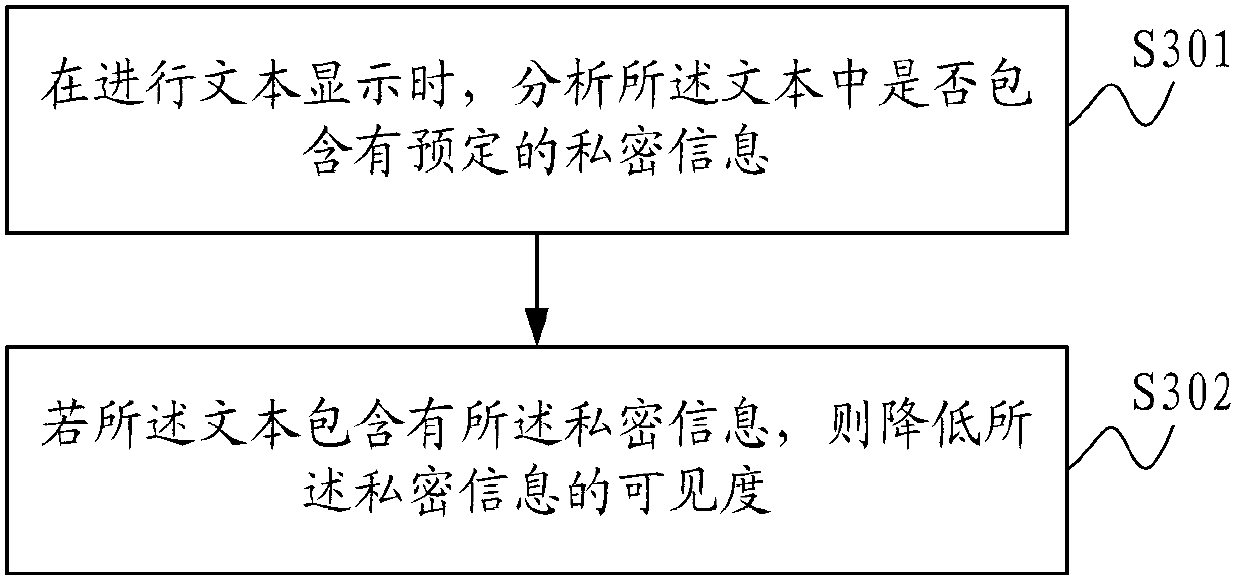
ActiveCN103218568APrevent peepingPlay a privacy protection effectDigital data protectionInternal/peripheral component protectionVisibilityText display
The invention is applicable to the technical field of communication, and provides a privacy protection method during text display. The method comprises the following steps that during the text display, whether preset privacy information is contained in the text or not is analyzed; and if the privacy information is contained in the text, the visibility of the privacy information is reduced for preventing the privacy information from being peeped by others. Correspondingly, the invention also provides a communication terminal. Therefore, the effective privacy protection can be realized on the privacy information of users.
Owner:DONGGUAN YULONG COMM TECH +1
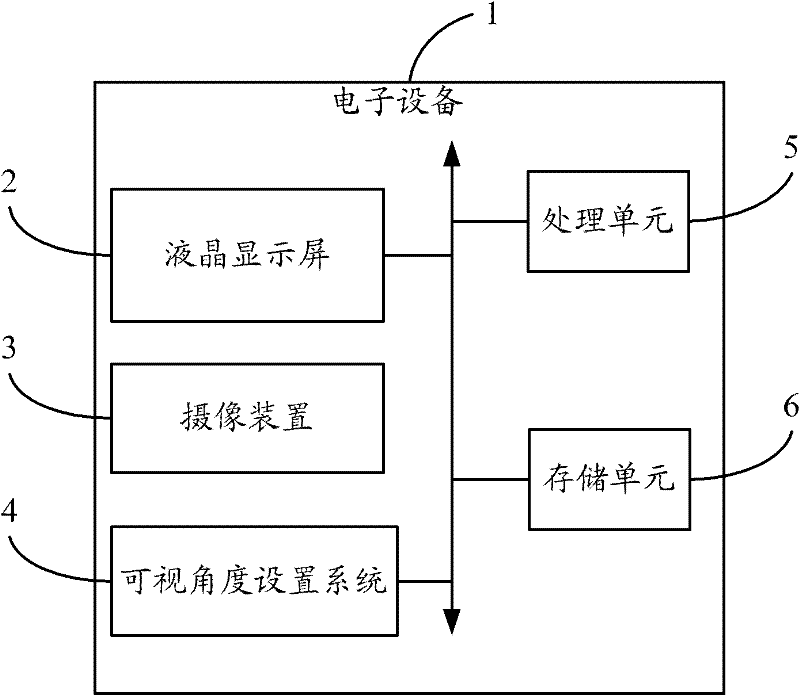
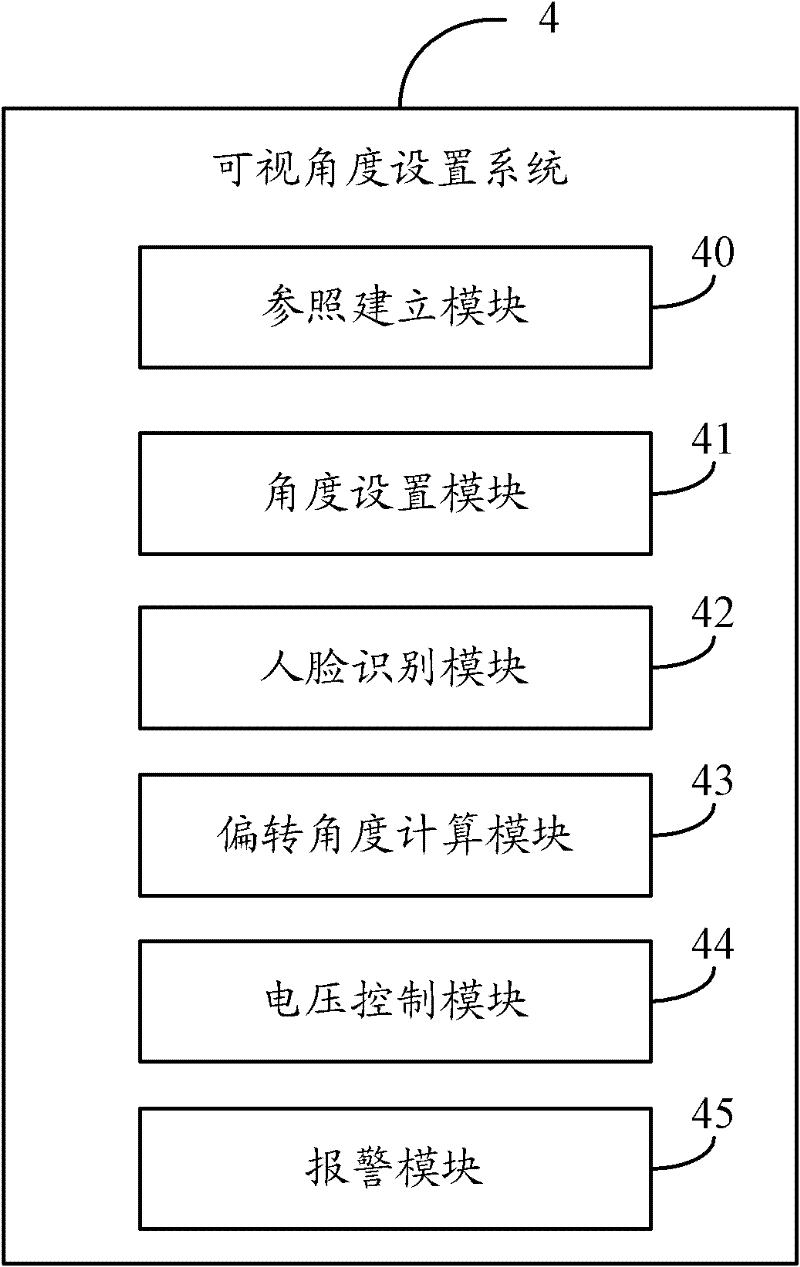
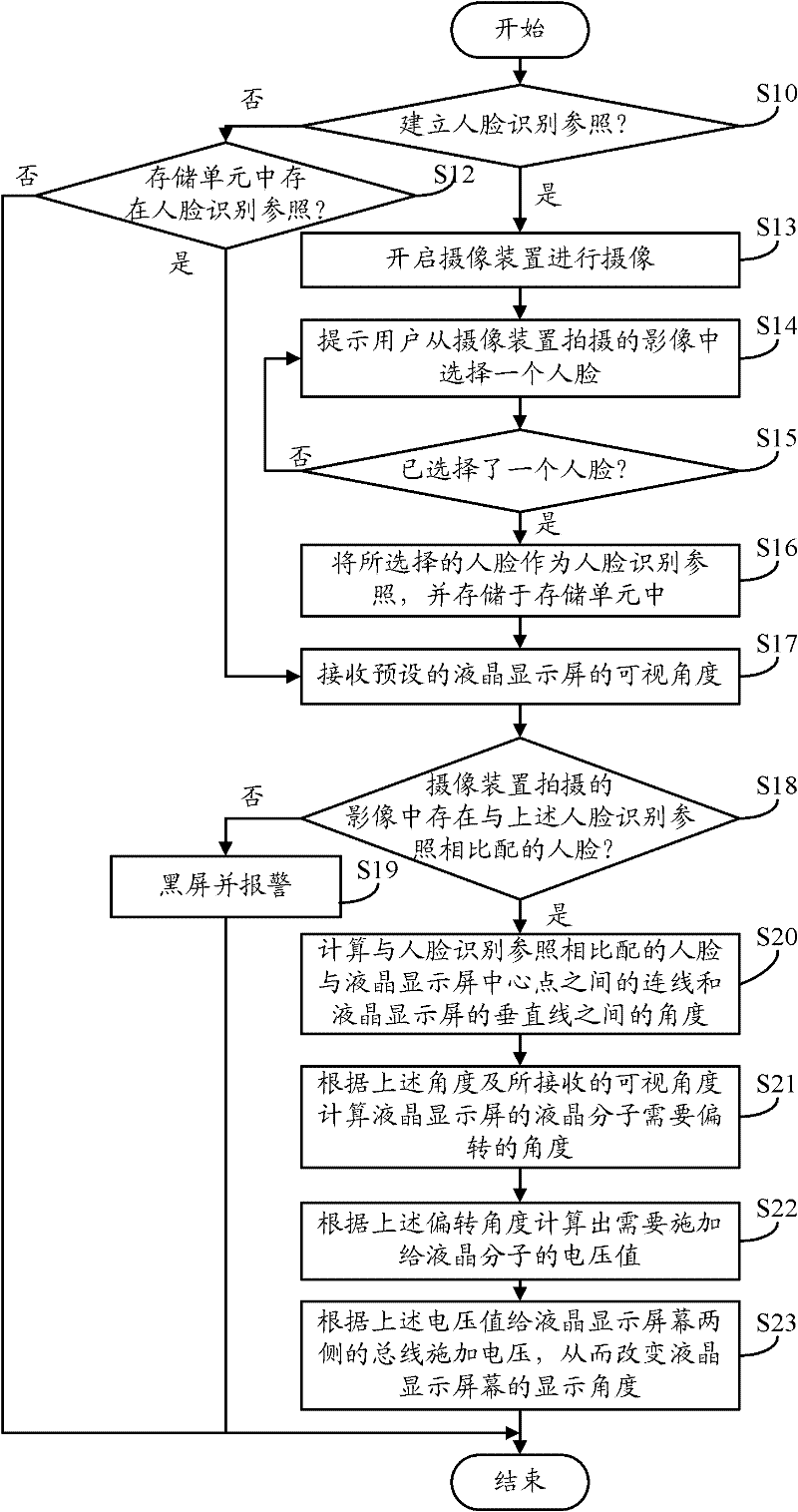
Visual angle setting system and method for liquid crystal display screen
InactiveCN102237020AChange viewing angleImprove information securityMeasurement devicesCharacter and pattern recognitionComputer scienceVoltage
The invention provides a visual angle setting method for setting the visual angle of a liquid crystal display screen of electronic equipment. The method comprises the following steps of: acquiring a face identification reference; receiving a preset visual angle of the liquid crystal display screen; identifying a face matched with the face identification reference in a current image shot by a pickup device of the electronic equipment; calculating the angle between a connecting line of the central point of double eyes of the identified face and the central point of the liquid crystal display screen and the vertical line of the liquid crystal display screen; calculating the deflecting angle of liquid crystal molecules of the liquid crystal display screen according to the angle and the received visual angle; calculating a voltage value applied to the liquid crystal molecules of the liquid crystal display screen according to the deflecting angle; and applying voltage to buses at two sides of the liquid crystal display screen according to the voltage value so as to change the visual angle of the liquid crystal display screen. The invention also provides a visual angle setting system. According to the method and the system disclosed by the invention, the visual angle of the liquid crystal display screen can be set according to the personalized requirements of a user.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
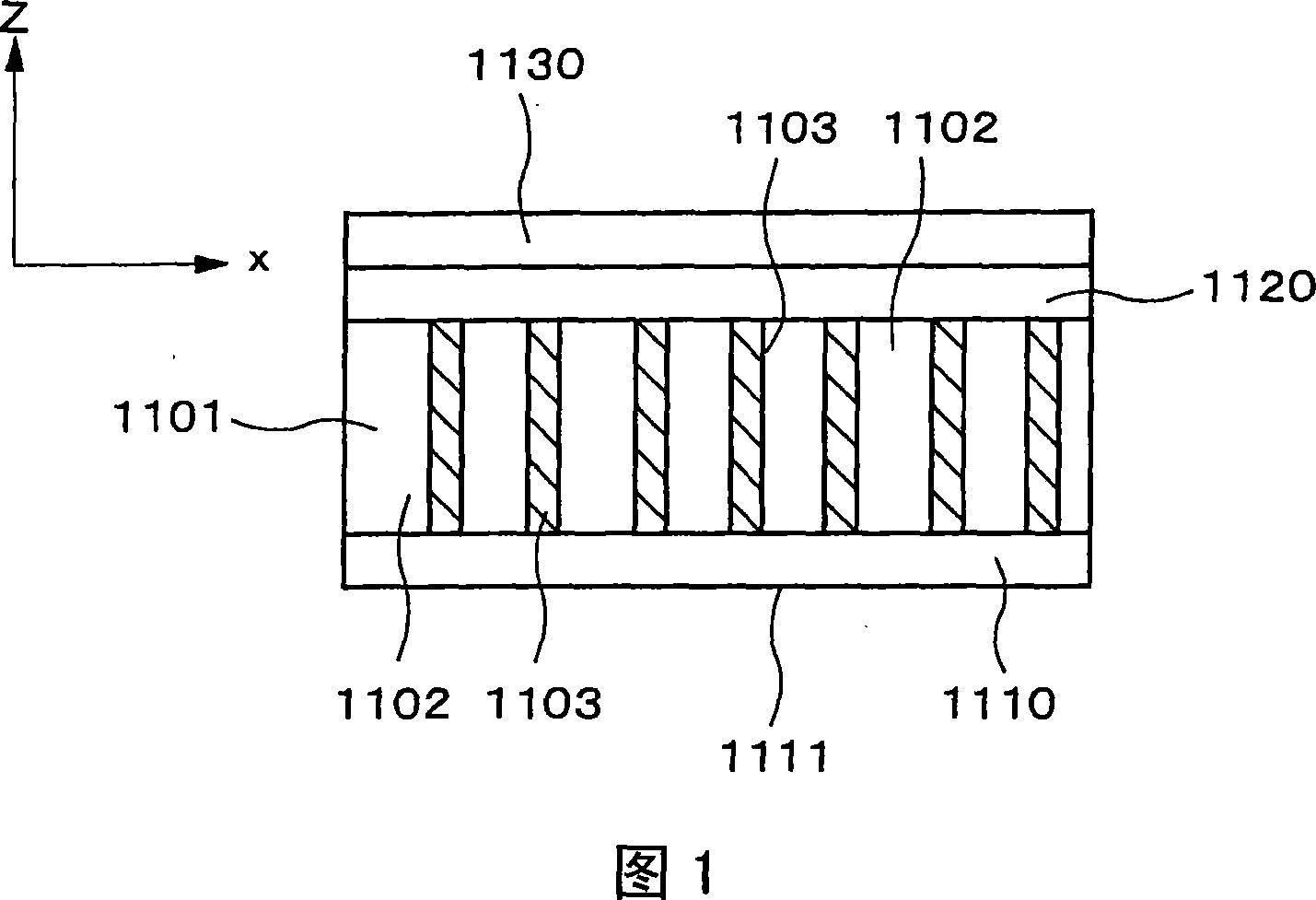
Optical element, display device, and terminal device
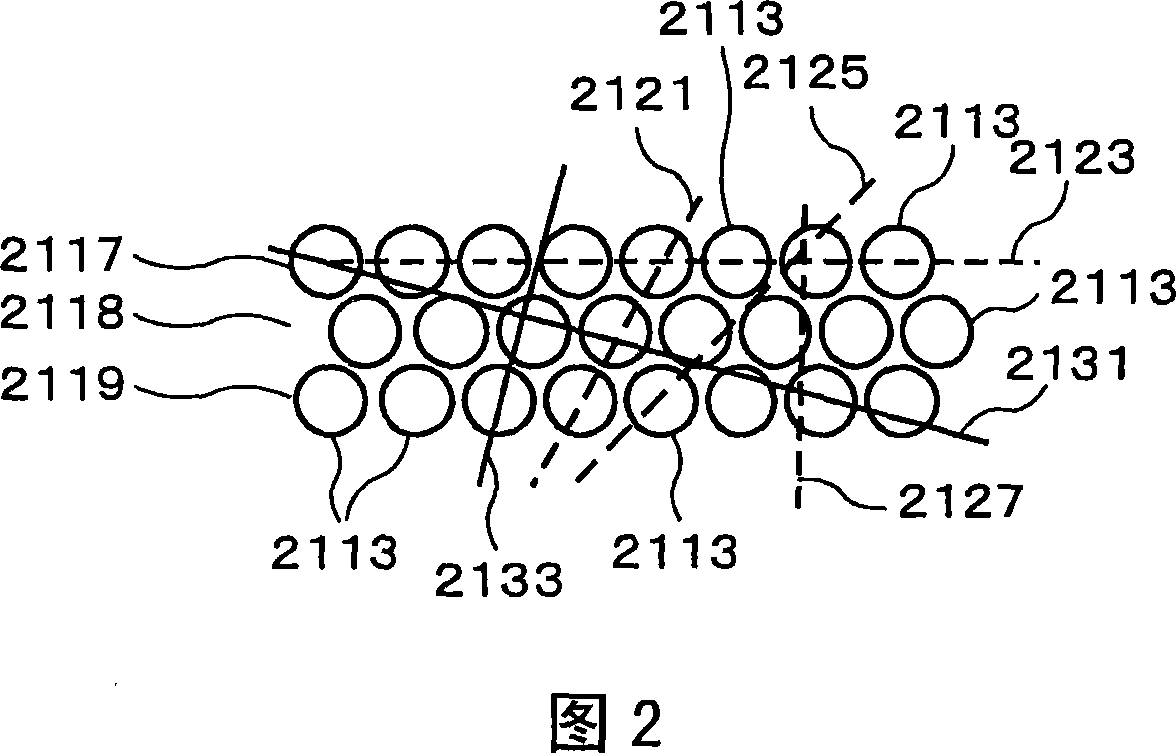
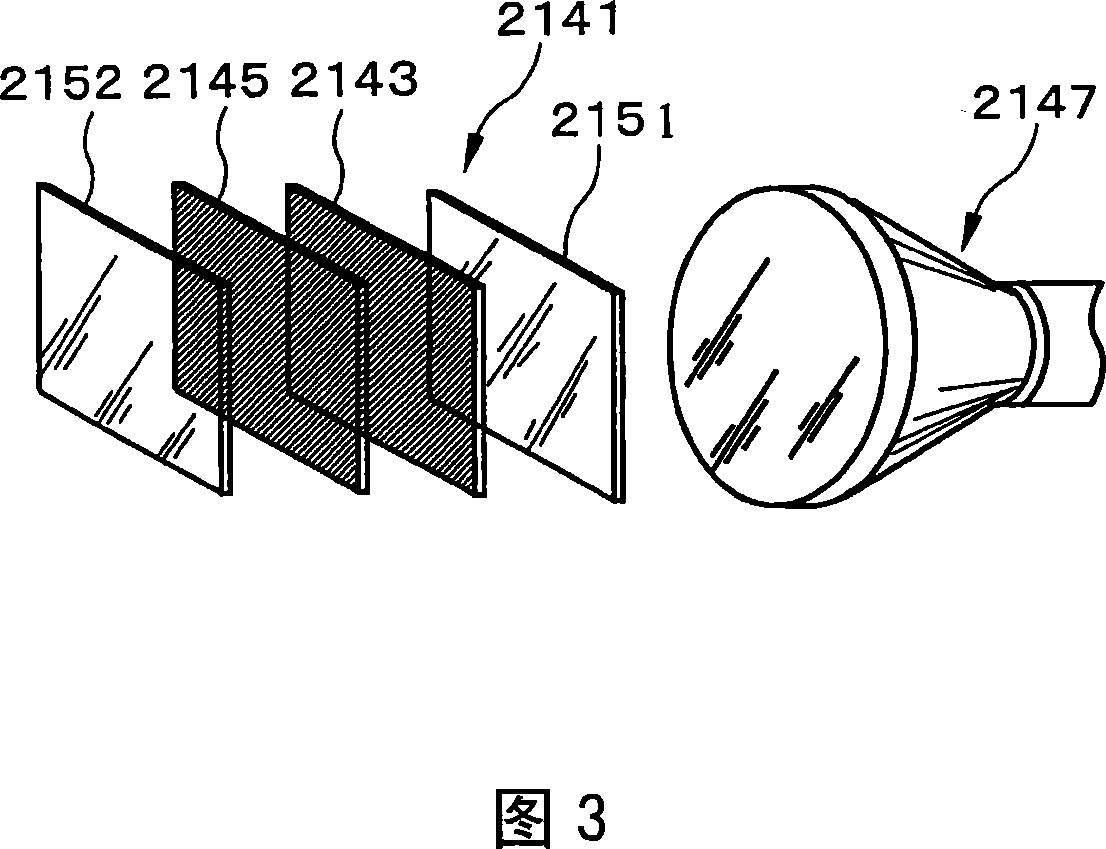
ActiveCN101042490APrevent peepingImprove directionalityTelephone set constructionsNon-linear opticsDisplay deviceTerminal equipment
A plurality of pixels is arranged periodically in the x-axis direction and the y-axis direction in the display panel of a display device, and because light is blocked by the portion other than the open part in each pixel, the display panel has a two-dimensional lattice structure. The pixels are rectangular, and the length Px of the long edges in the x direction is larger than the length Py of the short edges in the y direction. A louver, in which transparent regions and non-transparent regions are arranged periodically in a one-dimensional direction, is provided on the display panel, and the angle formed by the x axis and the one-dimensional period direction of the louver is 45 degrees or less, and preferably 10 degrees or less. This configuration makes it possible to obtain an optical element having high directivity, reduced moire, and high transmittance. It is also possible to obtain a display device having excellent display quality into which the optical element is incorporated.
Owner:NEC LCD TECH CORP
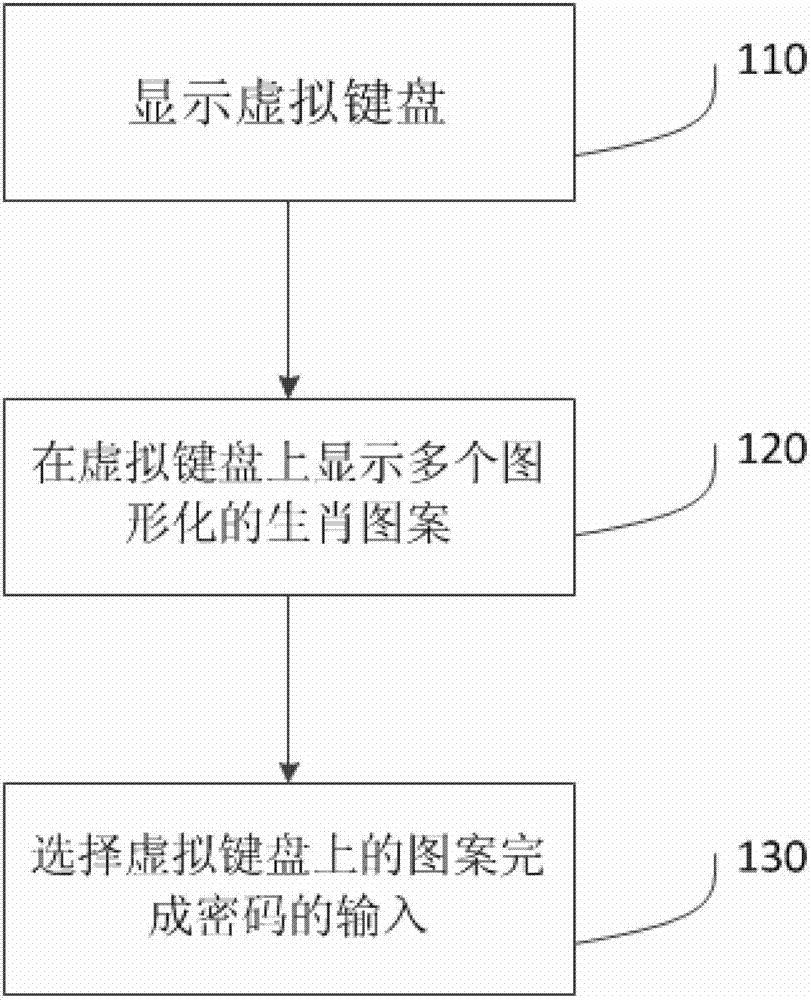
Random password generation method and device
ActiveCN103034798AEasy to rememberPrevent peepingDigital data authenticationSubstation equipmentPersonalizationAlgorithm
The invention discloses a random password generation method and device. The random password generation method comprises the following steps of: A, displaying a virtual keyboard; B, generating a plurality of graphic Chinese zodiac patterns on the virtual keyboard; and C, selecting the patterns on the virtual keyboard to finish input of passwords. Therefore, according to the method and the device, multiple or all of personalized 12 Chinese zodiac patterns can be arranged on the virtual keyboard, and the password input is finished by selecting the appropriate Chinese zodiac patterns; and meanwhile, the passwords can further comprise digits and letters except the Chinese zodiac patterns and can be displayed randomly. Therefore, convenience is provided for a user to well memorize the passwords, and a peeper is prevented from memorizing the passwords input by the user.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Display device, control method thereof, electronic device including display device
InactiveCN1834976APrevent peepingNo effortComplete banking machinesImage analysisComputer hardwareMarine engineering
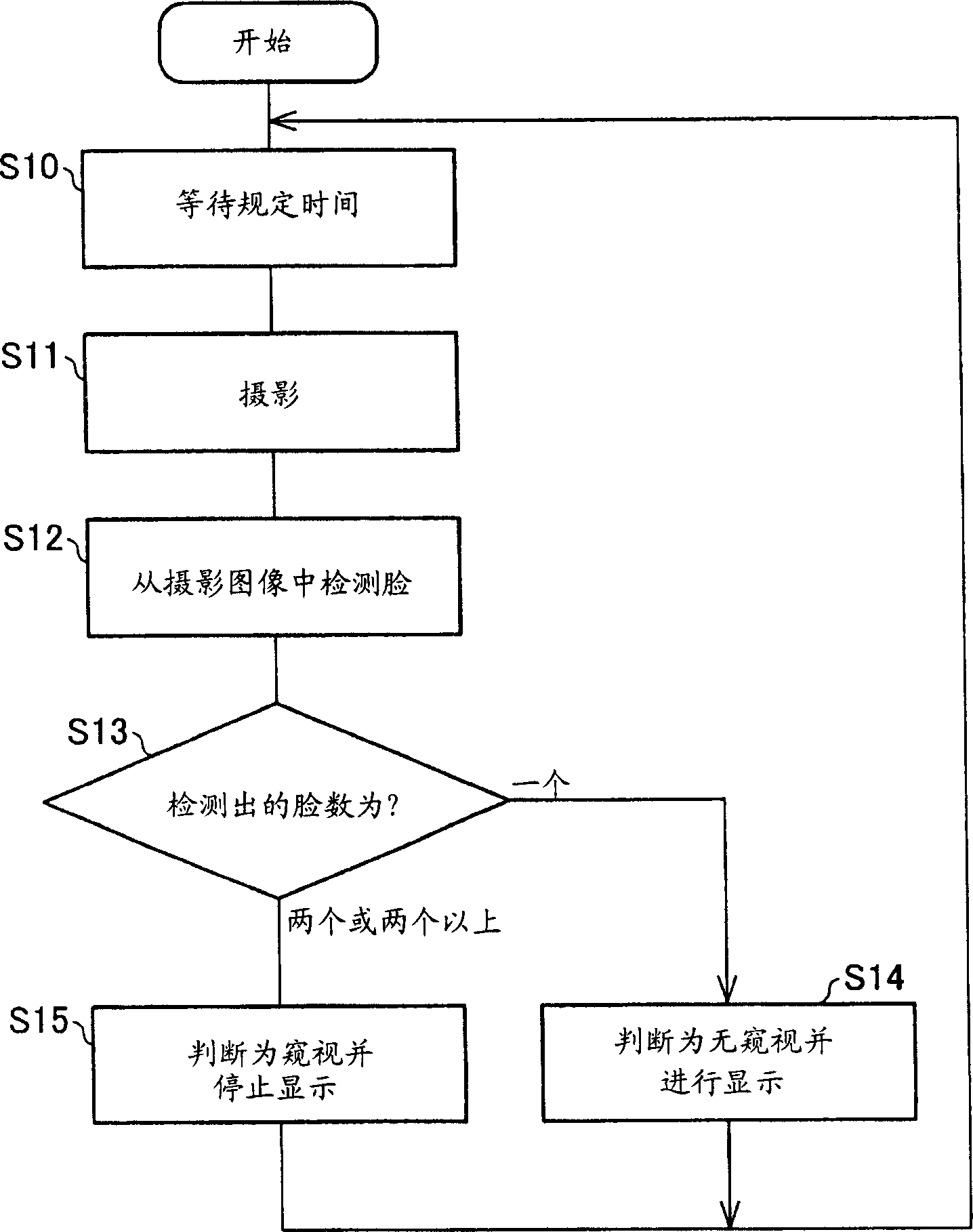
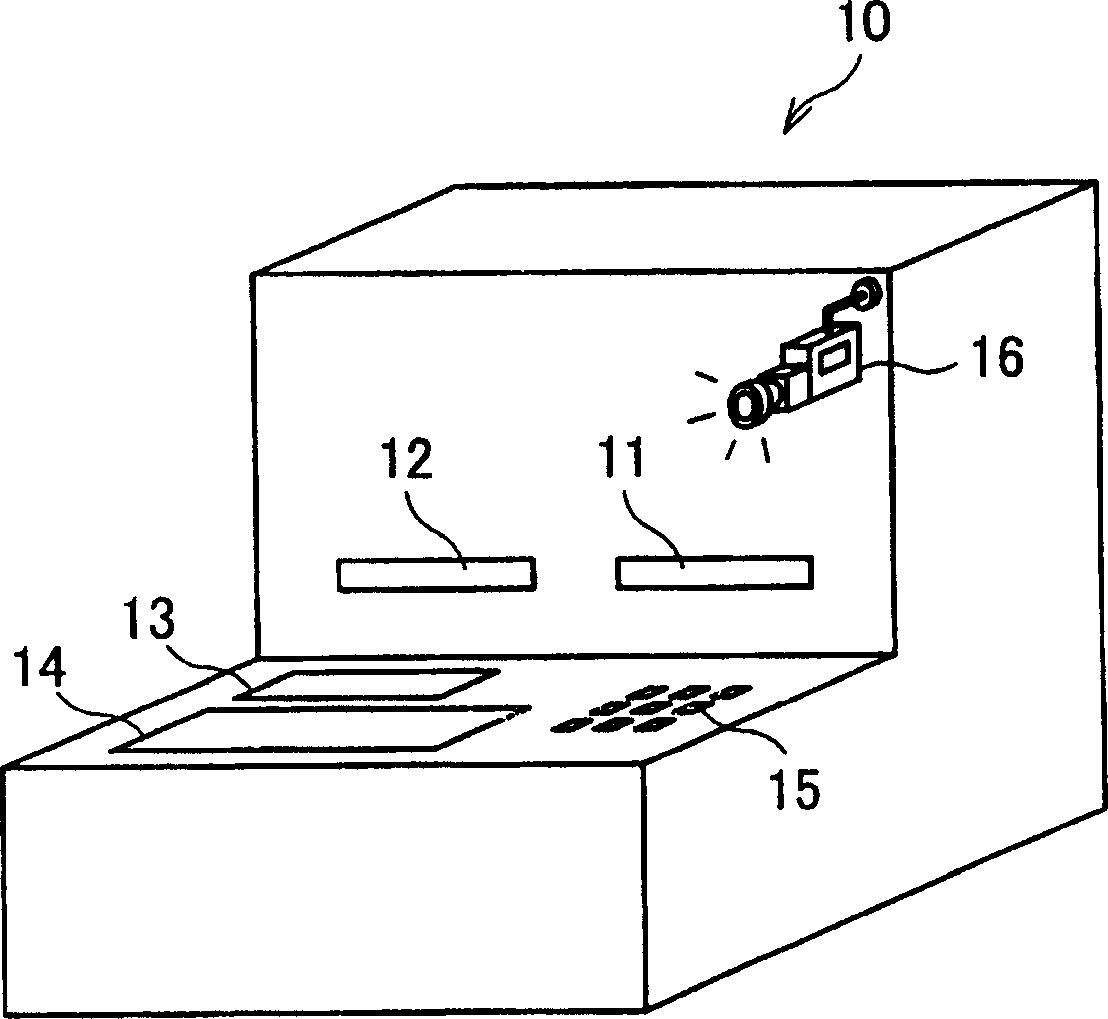
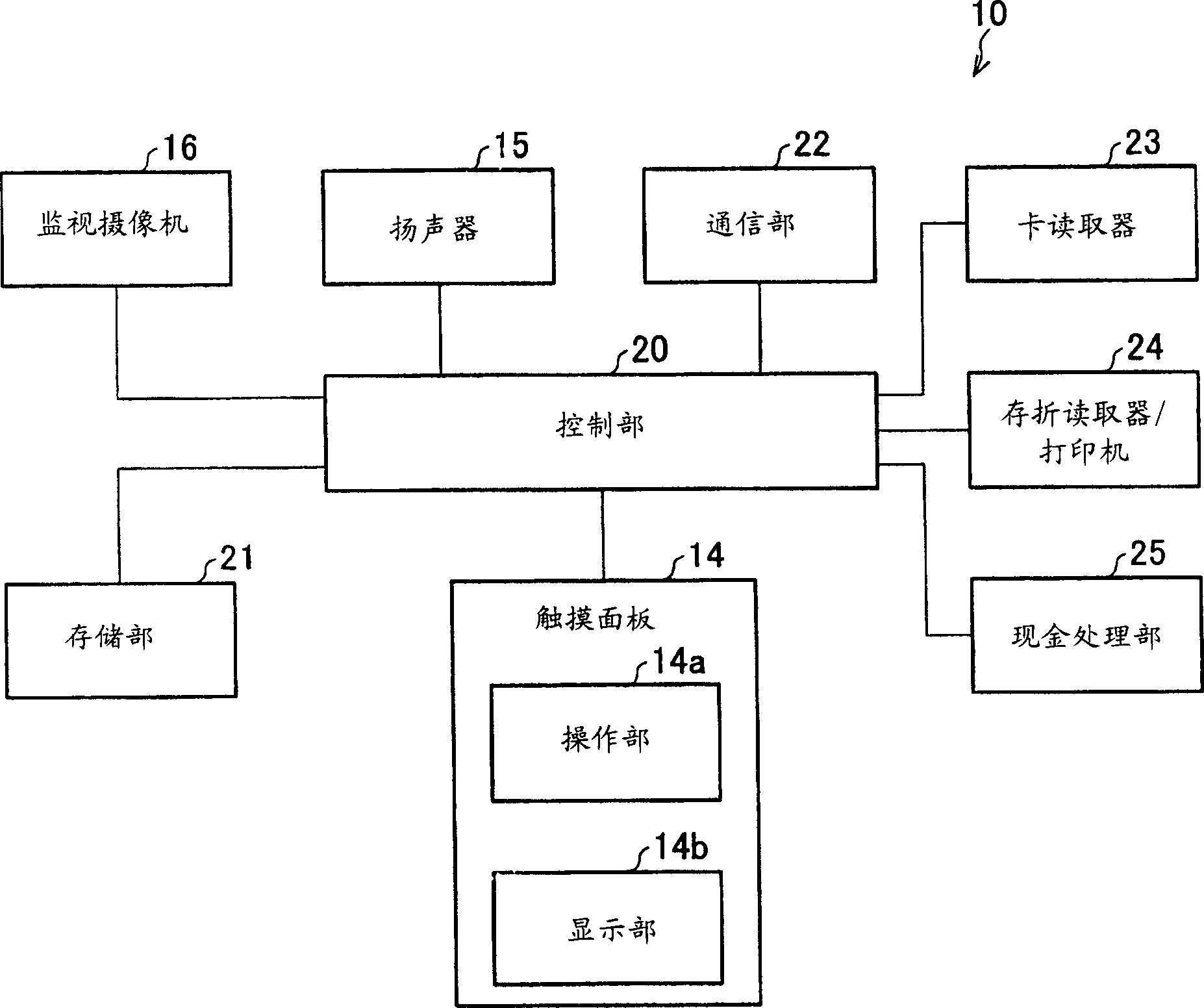
An ATM has a display section of a touch panel and a security camera that takes an image of at least an area from which display information on the display section is viewable. After a predetermined waiting time, the security camera takes an image. From the taken image, human faces are detected, and how many human faces are detected is counted. If the number of human faces is one, the display is carried out as peeping is not underway according to the judgment. Meanwhile, if a plurality of human faces are detected, the display is stopped as peeping is underway according to the judgment.
Owner:ORMON CORP
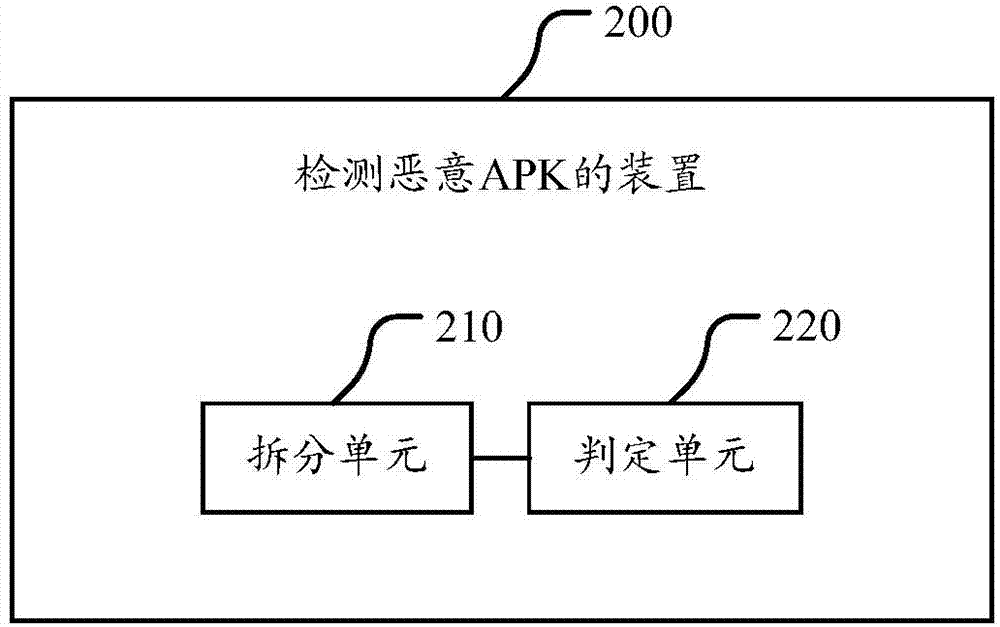
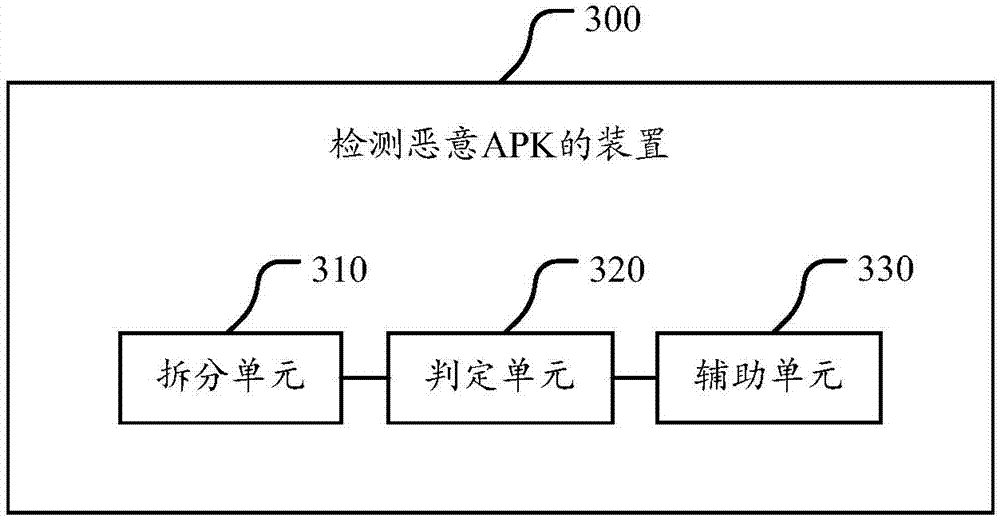
Method, device, client and server for detecting malicious APK
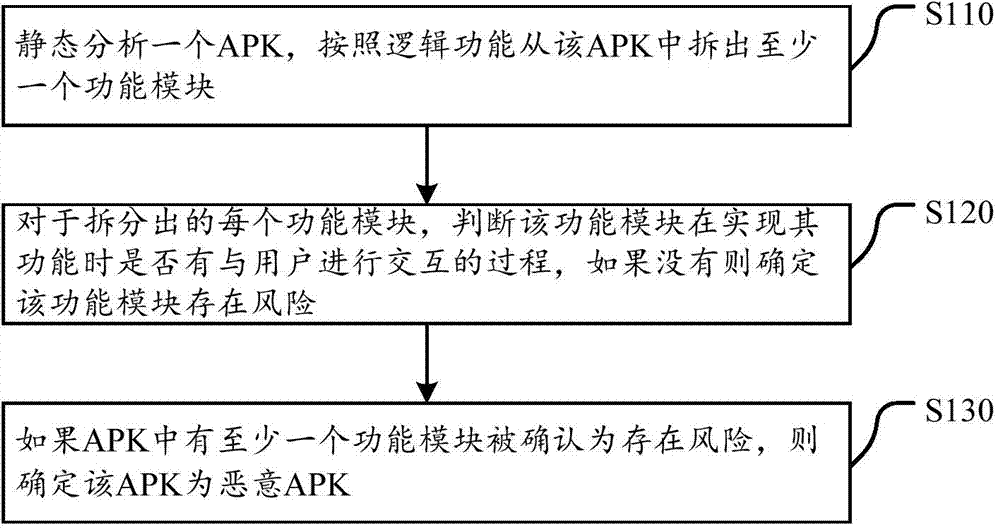
ActiveCN104517054AImprove experiencePrevent peepingPlatform integrity maintainanceFunctional moduleStatic analysis
The invention discloses a method, a device, a client and a server for detecting a malicious APK. The method comprises the following steps: statically analyzing one APK; disassembling at least one functional module from the APK according to a logic function; with regard to the functional module, judging whether the functional module has a process of interacting with a user or not when realizing the function; if not, determining that the functional module has risks; and if so, determining that at least one functional module in the APK has risks, namely determining the APK to be the malicious APK. The operation rule is carried out based on the malicious APK under the condition that a user does not know the condition, and whether each functional module of the APK is interacted with the user or not is judged so as to determine the safety grade of the APK. The method, which can be used for heuristically and directly detecting the malicious APK, is provided, and the detection of the unknown APK can be realized.
Owner:三六零数字安全科技集团有限公司
Safety payment method capable of realizing multi-screen disturbance display of mobile terminal
InactiveCN108171509AReflect the degree of influenceExclusively conform to the real parameter situationPayment architecturePaymentDistraction
The invention relates to a safety payment method capable of realizing multi-screen disturbance display of a mobile terminal. By obtaining screen illumination response index of the mobile terminal forillumination intensity and screen brightness disturbance index of the mobile terminal itself, the subsequent mobile terminal can be helped to get a disturbance display scheme according with real parameter information of its screen; by calculating energy distraction index and payment operation mood relaxation index of a legal user of the mobile terminal during payment operation, the mobile terminalcan be helped in many ways to accurately identify whether its legal user is carrying out payment operation, and thus, payment information safety of the legal user of the mobile terminal is further ensured; by obtaining payment disturbance flash frequency of each screen disturbance display image, normal payment operation of the legal user of the mobile terminal can be guaranteed effectively; and peep of payment information of the user by illegal users can be prevented by utilizing flash frequency display of the screen, thereby greatly improving payment information safety of the legal user of the mobile terminal.
Owner:NINGBO UNIV
Electronic equipment and display screen peeping-prevention method thereof
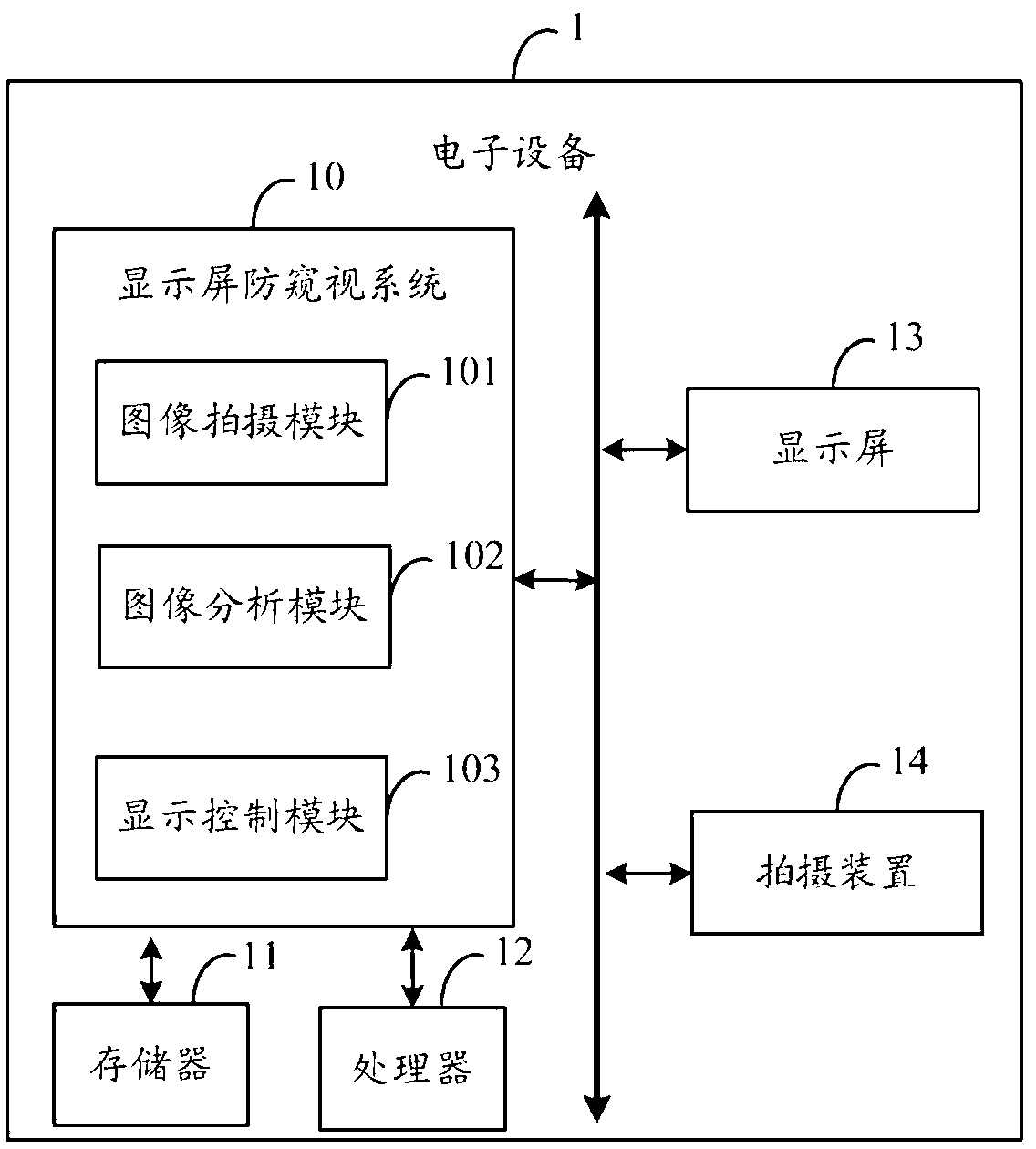
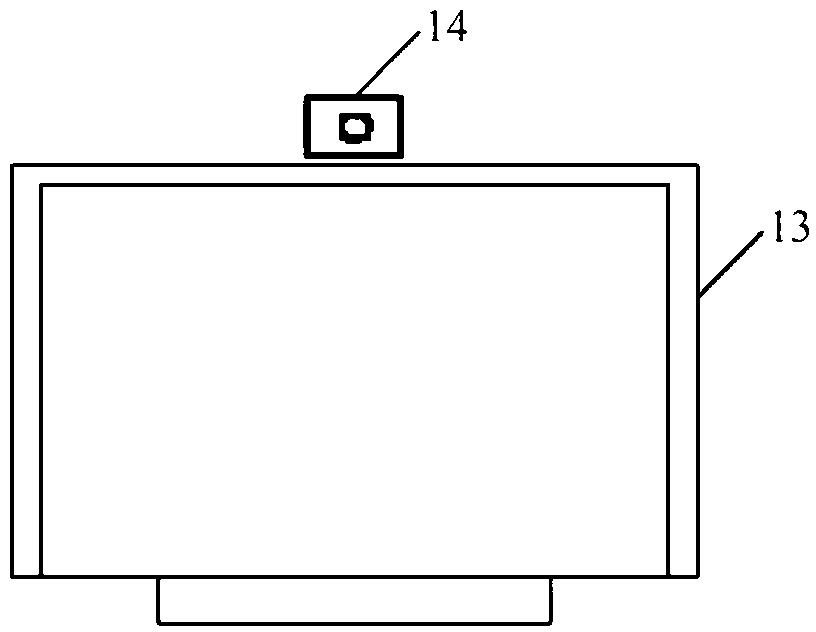
InactiveCN103324899APrevent peepingAvoid embarrassmentInternal/peripheral component protectionDigital data authenticationComputer hardwareComputer graphics (images)
The invention provides a display screen peeping-prevention system of electronic equipment. The system comprises an image shooting module, an image analysis module and a display control module, wherein the image shooting module is used for controlling a shooting device to continuously shoot images in front of a display screen; the image analysis module is used for utilizing the human face recognition technology to perform image analysis and processing on each image, and judging whether the display screen is currently in a state of being peeped or not, and the display control module is used for controlling the display screen to display a preset peeping prevention picture when the display screen is judged to be in the state of being peeped currently. The invention further provides a display screen peeping prevention method. According to the invention, the display screen of the electronic equipment can be effectively prevented from being peeped.
Owner:FU TAI HUA IND SHENZHEN +1
Privacy protection method and apparatus for video chatting
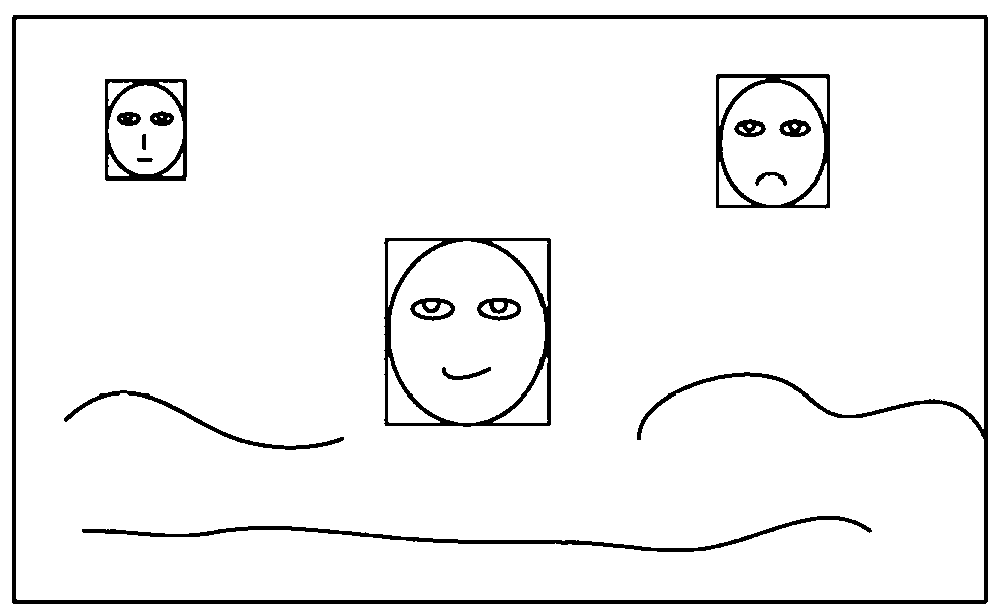
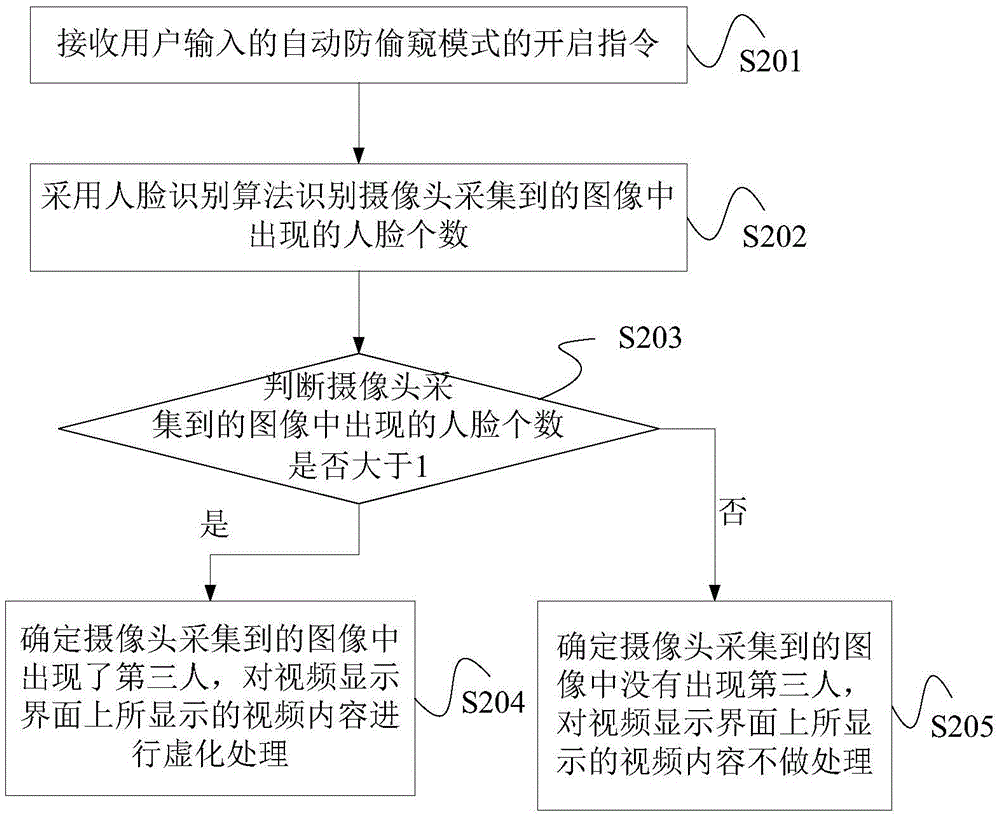
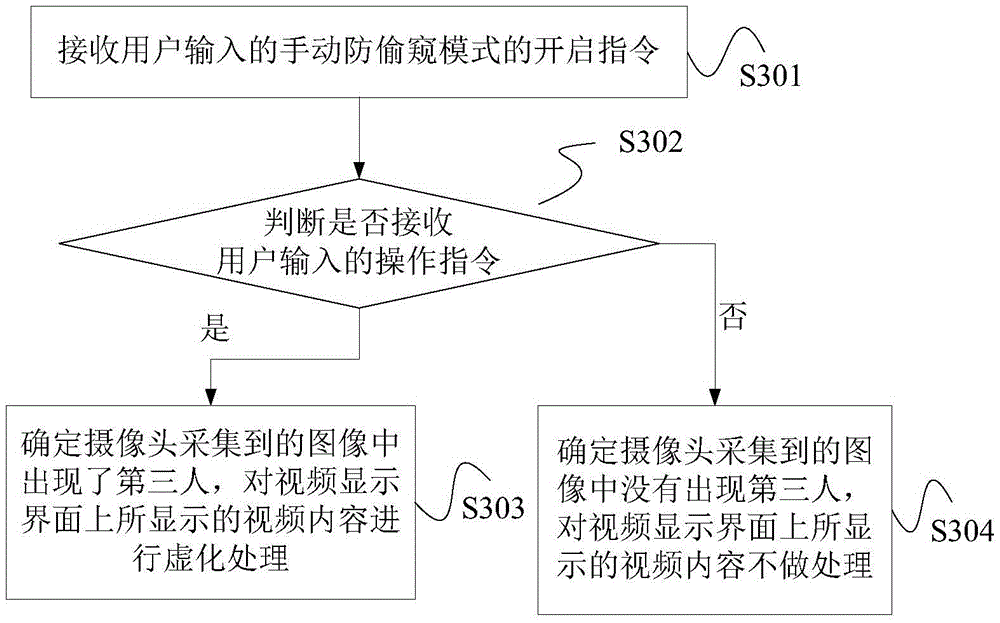
InactiveCN105472303APrevent peepingTwo-way working systemsComputer graphics (images)Privacy protection
The disclosure relates to a privacy protection method and apparatus for video chatting. The method comprises: during a video chatting process, whether a third person except video chatting participants occurs in an image collected by a camera is detected; and if so, grammaticalization processing is carried out on a video content displayed on a video display interface. According to the method, whether the third person except video chatting participants occurs in the image collected by the camera is detected; and if so, grammaticalization processing is carried out on the video content displayed on the video display interface, thereby protecting the video content from being peeped.
Owner:XIAOMI INC
Hand-held electronic equipment and display method
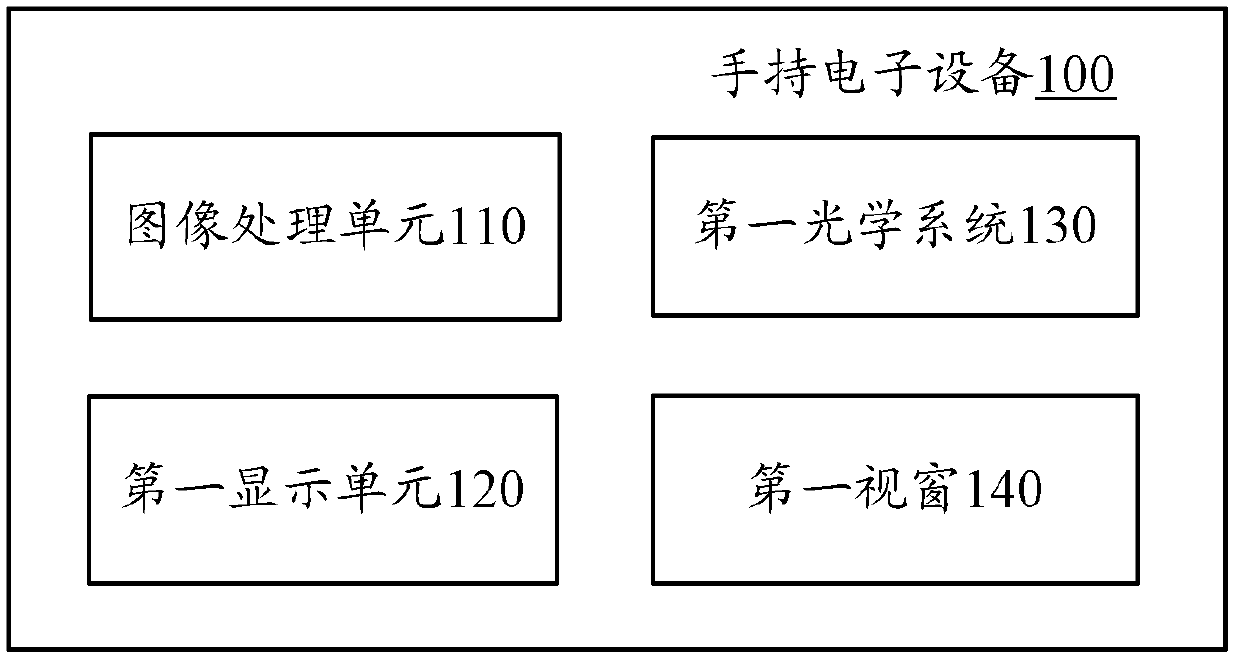
InactiveCN103309039AReduce power consumptionPrevent peepingOptical elementsImaging processingHand held
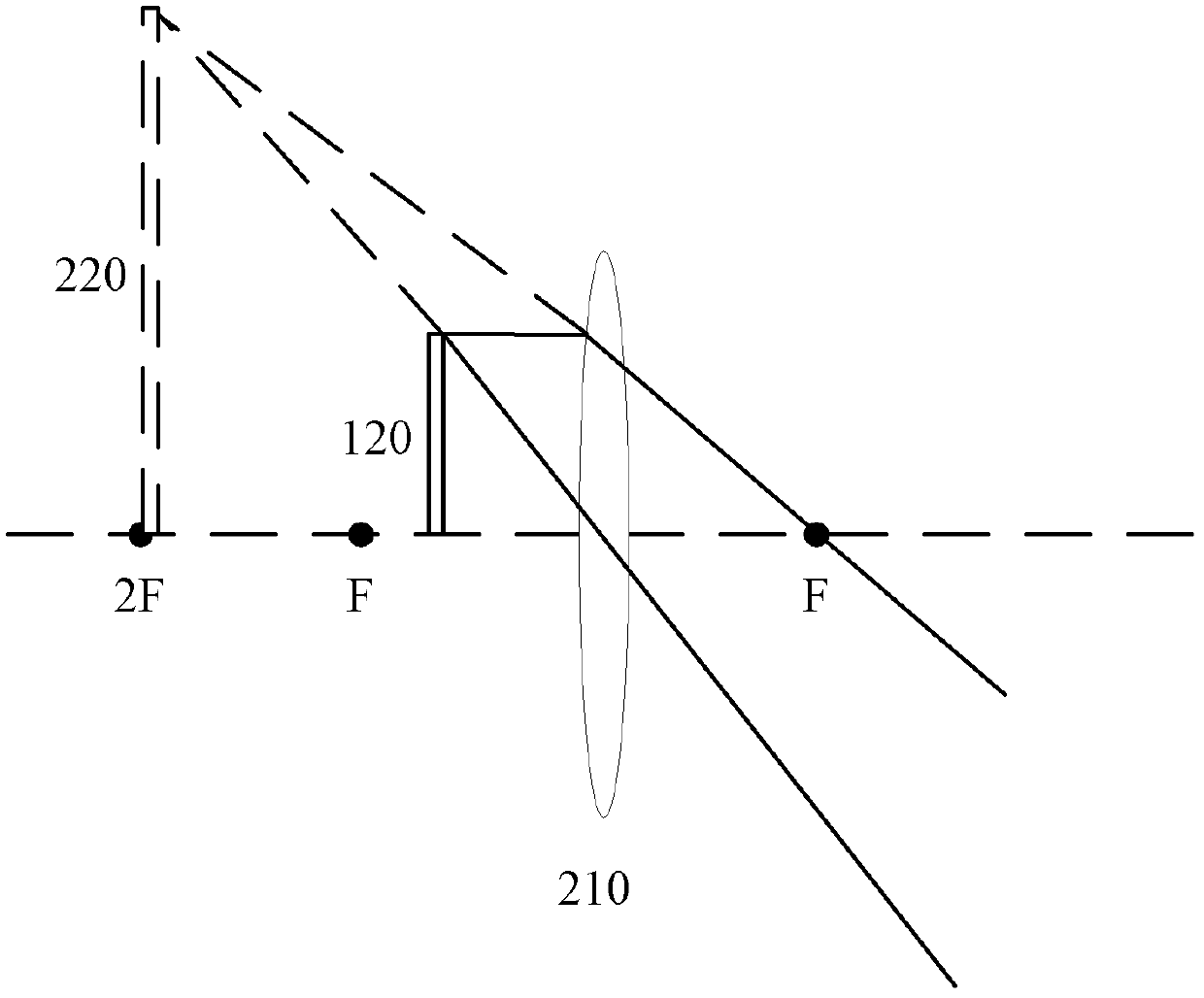
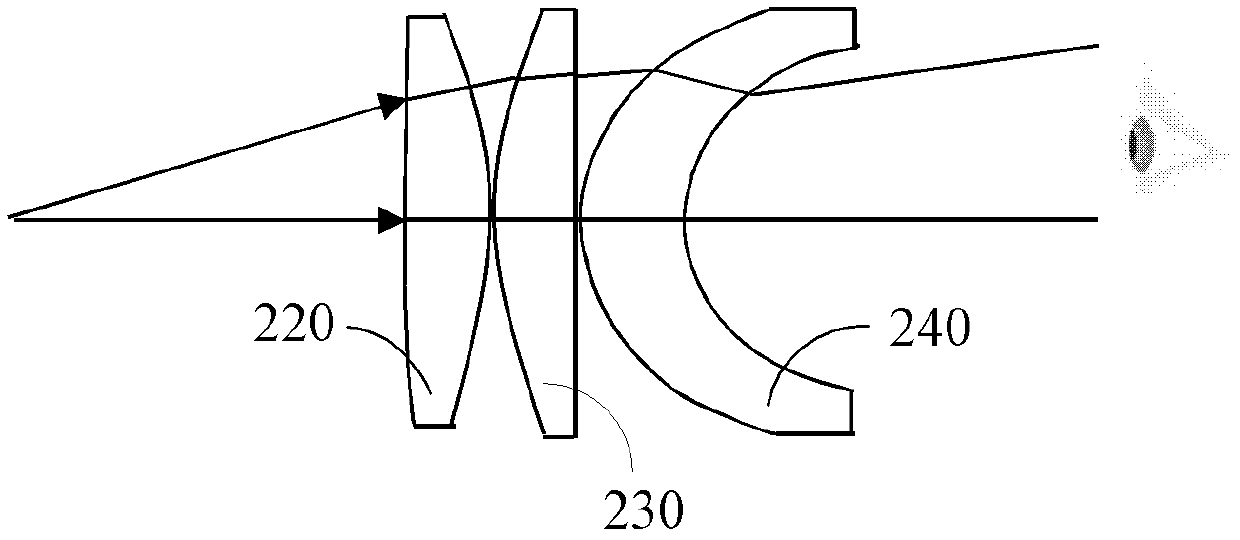
An embodiment of the invention provides hand-held electronic equipment and a display method. The hand-held electronic equipment comprises: an image processing unit which is configured to provide a first image; a first display unit which is configured to display the first image; a first optical system which is configured to receive light rays emitted from the first display unit and to switch the light path of the light rays emitted from the first display unit so as to form a first amplification virtual-image, wherein the length of the light path between the first optical system and the first display unit is less than the focal length of the first optical system; a first window which is arranged on a first outer surface of the hand-held electronic equipment so that viewers can see the first amplification virtual-image through the first optical system when the viewers are close to the first outer surface.
Owner:LENOVO (BEIJING) LTD
Information display method and device and terminal
ActiveCN106534572AImprove securityPrevent peepingUnauthorised/fraudulent call preventionInternet privacyComputer terminal
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
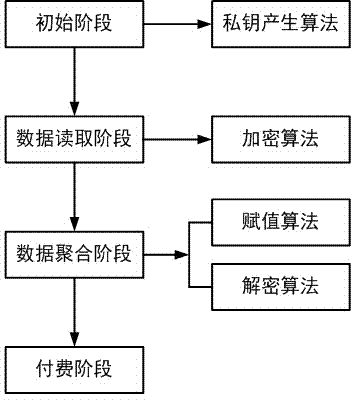
Charging method with privacy protection in smart power grid
InactiveCN104125074AEnsure safetyPrevent peepingUser identity/authority verificationApparatus for hiring articlesPlaintextCiphertext
The invention discloses a charging method with privacy protection in a smart power grid. The charging method comprises the following steps that: a smart electric meter records the electric quantity used by a user in real time, encrypts the recorded data by means of co-state encryption, and sends ciphertexts to a polymerizer; after a time period, the polymerizer summates the collected ciphertexts about the electric quantity used by the user, and then decrypts the ciphertexts to obtain the plaintext of the electric quantity sum used by the user during the time period; finally the polymerizer sends the plaintext to a charging department, and the charging department calculates to obtain the electric utilization charge of the user. In the charging method disclosed by the invention, the electric quantity condition consumed by the user cannot be obtained by any department except the polymerizer, and the consumption details cannot be known, thus furthest ensuring the security of user information, and effectively preventing the user information from being peeped.
Owner:STATE GRID CORP OF CHINA +3
Liquid crystal display device
InactiveUS20070036917A1Narrow viewing angleIncrease brightnessLiquid crystal compositionsThin material handlingPolarizerEngineering
A liquid crystal display device comprising a liquid crystal cell containing a nematic liquid crystal material aligned nearly in parallel to the surfaces of the cell at the time of no voltage application thereto, and two polarizers disposed on both outer sides of the liquid crystal cell, wherein the optically anisotropic layer comprising a hybrid-aligned compound is disposed between the liquid crystal cell and one of the polarizers and the alignment control direction of the hybrid-aligned compound is nearly in parallel to absorption axis of any one of the polarizers.
Owner:FUJIFILM CORP
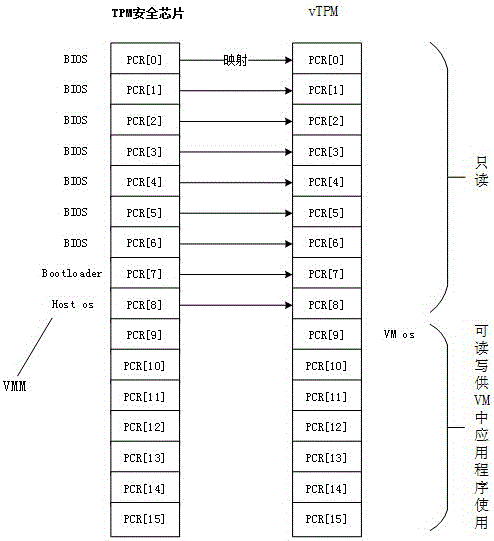
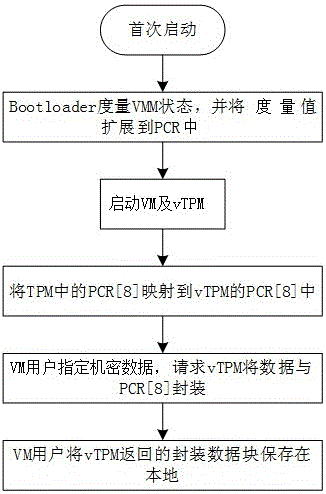
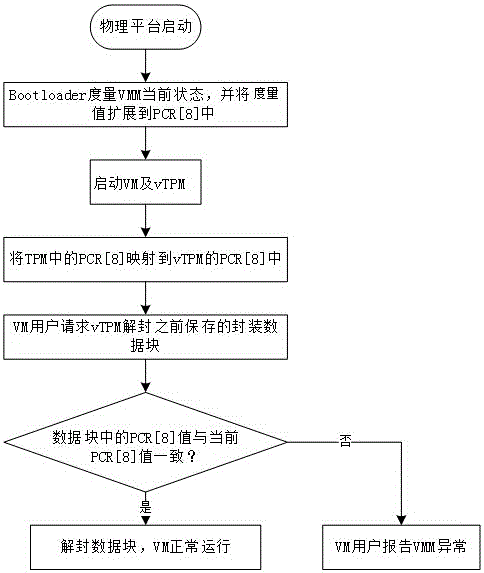
Virtual machine monitor local integrity detection system and implementation method
InactiveCN105930199AEnsure safe productionPrevent peepingPlatform integrity maintainanceSoftware simulation/interpretation/emulationInformation securityVirtual machine
The invention discloses a virtual machine monitor local integrity detection system and an implementation method and belongs to the field of information security. The invention is aimed at solving the technical problem that how to realize verifying a VM operation bottom layer environment of a user's own and guarantee safety production of VM. The technical scheme is described below: (1) a virtual machine monitor local integrity detection system comprises a physical platform and VMs, wherein the physical platform is provided with a TPM chip or a TCM chip, and a vTPM corresponding to each VM is virtualized on the physical platform. (2) an implementation method for virtual machine monitor local integrity detection comprises two stages which are the standard PCR value packaging stage and the PCR value comparing and de-packaging stage.
Owner:INSPUR GROUP CO LTD
Window structure
InactiveUS20150219830A1Prevent peepingIncreased durabilityMechanical apparatusMirrorsLight emitterPhysics
To realize a window structure that can ensure that scenery can be viewed from an indoor space during the daytime and prevent peeping from outdoors regardless of whether it is daytime or nighttime.A window structure including a translucent planar light emitter in which a half mirror layer is provided on the inside thereof, and glass panels provided on an inside and an outside of the planar light emitter. The planar light emitter includes a translucent resin panel, a light-emitting element provided on an end surface of the resin panel, and a light diffusing layer provided on a surface of the translucent resin panel. A surface of the planar light emitter emits light when light of the light-emitting element enters from the end surface of the resin panel, is reflected by the half mirror layer, and is diffused by the light diffusing layer.
Owner:MIRAI KIKAKU
Password protection apparatus and method and cipher keyboard
InactiveCN101290647APrevent peepingReduce manufacturing costComplete banking machinesInternal/peripheral component protectionPassword protectionDigital signal
The invention relates to a password protection device which is connected to a host system, the password protection device comprises a password keyboard with numeric keys and an enter key which is used for responding to the operation of a user and generating corresponding digital signal and acknowledge signal. The password protection device further comprises a random number generation unit and a processor, the password keyboard further comprises a display unit, the random number generation unit is used for generating random numbers, the display unit is used for displaying the random numbers, the processor is used for calculating password data according to the random numbers and a digital signal which is input by the user through the numeric keys and sending to the host system for a password validation, so that the input orders of any password on the keyboard are random while the user enters different numeric keys according to the different random numbers on the display unit, thereby effectively prevent password from being peeped. The invention also provides a corresponding password keyboard and a password protection method.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Peeping-preventing electronic device and peeping-preventing method
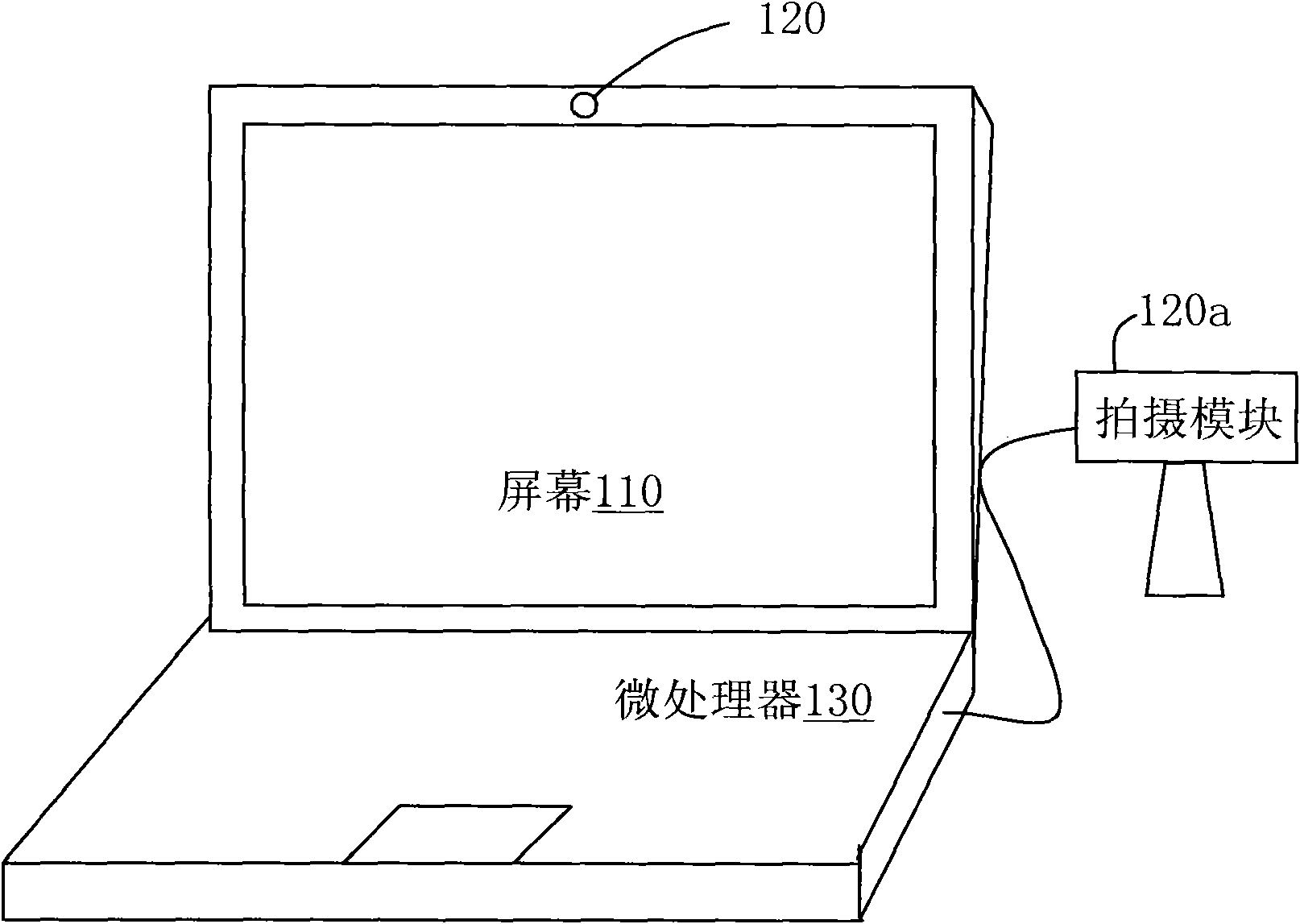
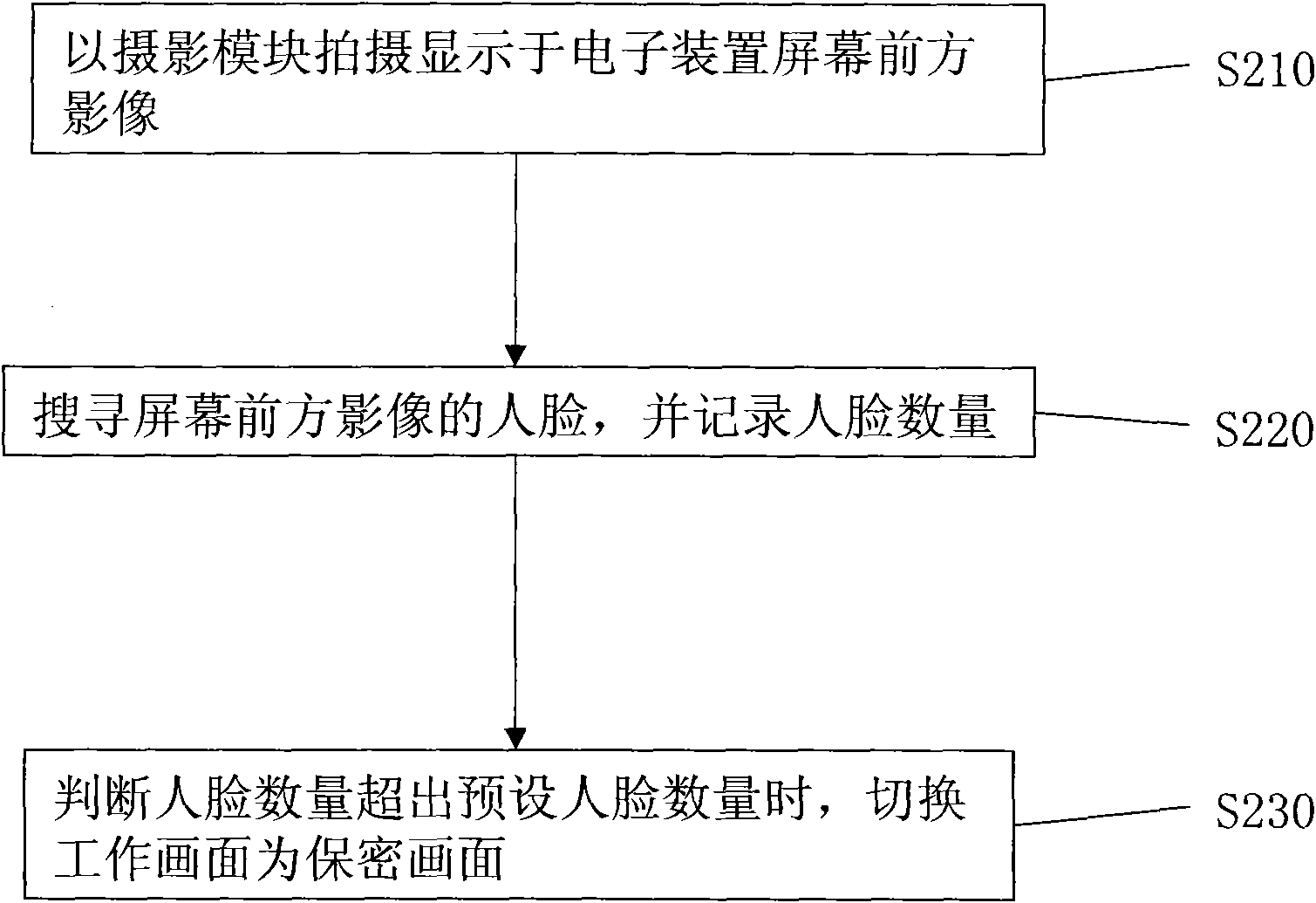
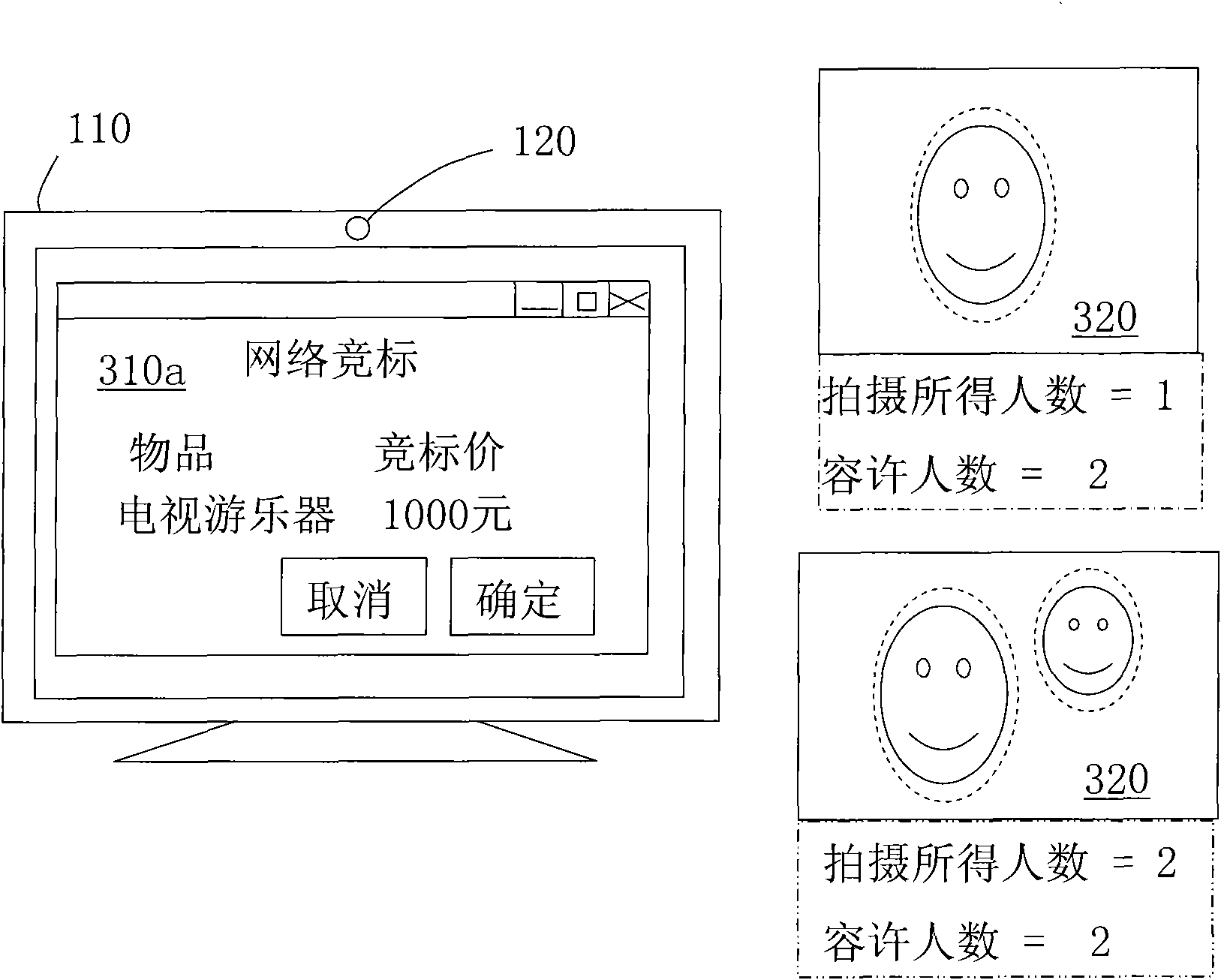
InactiveCN101576943APrevent peepingHardware monitoringInternal/peripheral component protectionComputer graphics (images)Camera module
The invention discloses a peeping-preventing electronic device and a peeping-preventing method. The peeping-preventing electronic device is used for an electronic device and comprises a screen, a camera module, a microprocessor, and the like. Firstly, the camera module shoots an image in front of the screen of the electronic device, researches faces of people of the image in the front of the screen, and records the number of the faces. When the number of the faces exceeds the preset face number, a working picture of the screen is switched into a preset picture so as to prevent the working picture from being peeped.
Owner:INVENTEC CORP
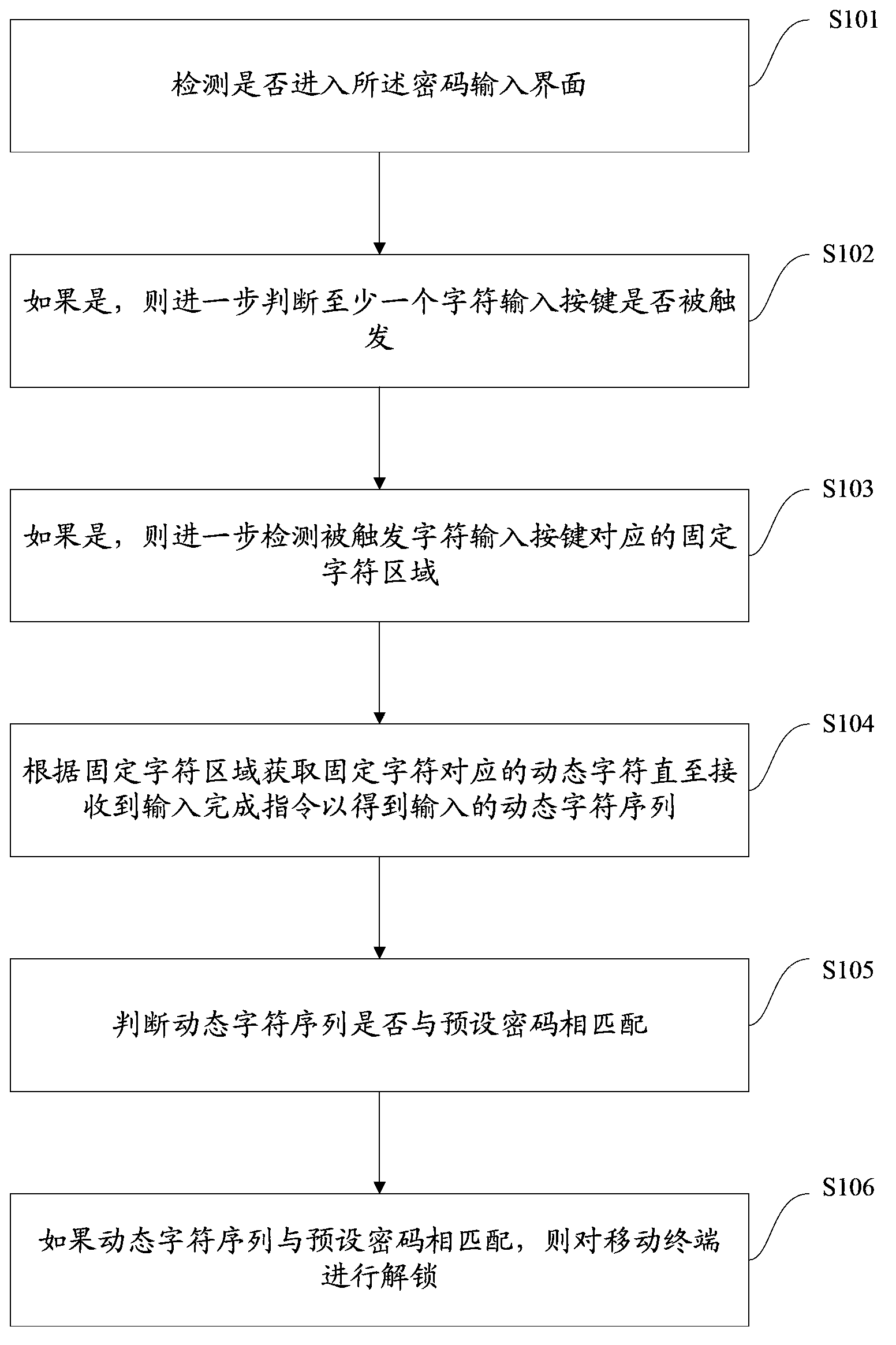
Dynamic decryption method used for mobile terminal, and mobile terminal
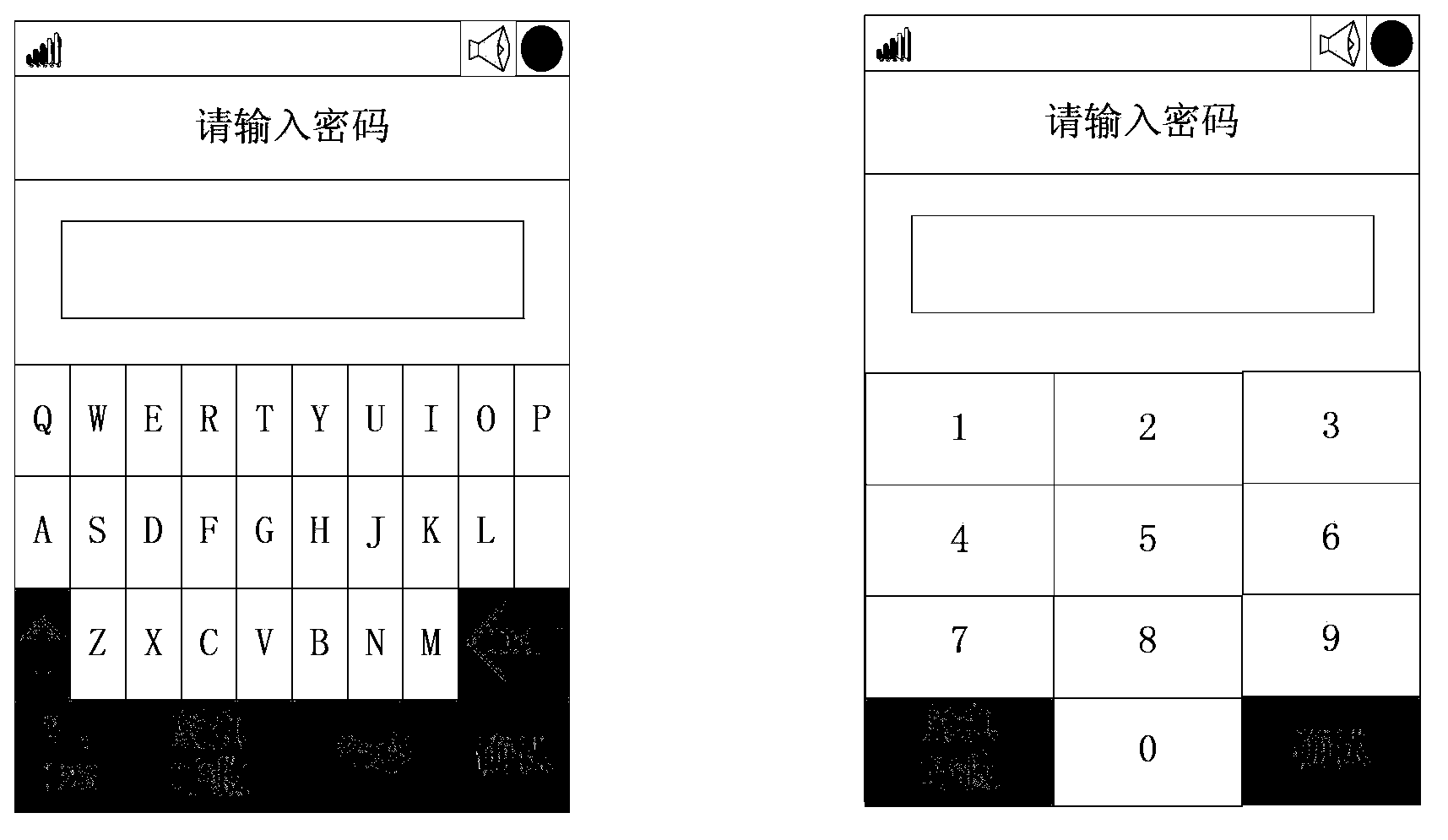
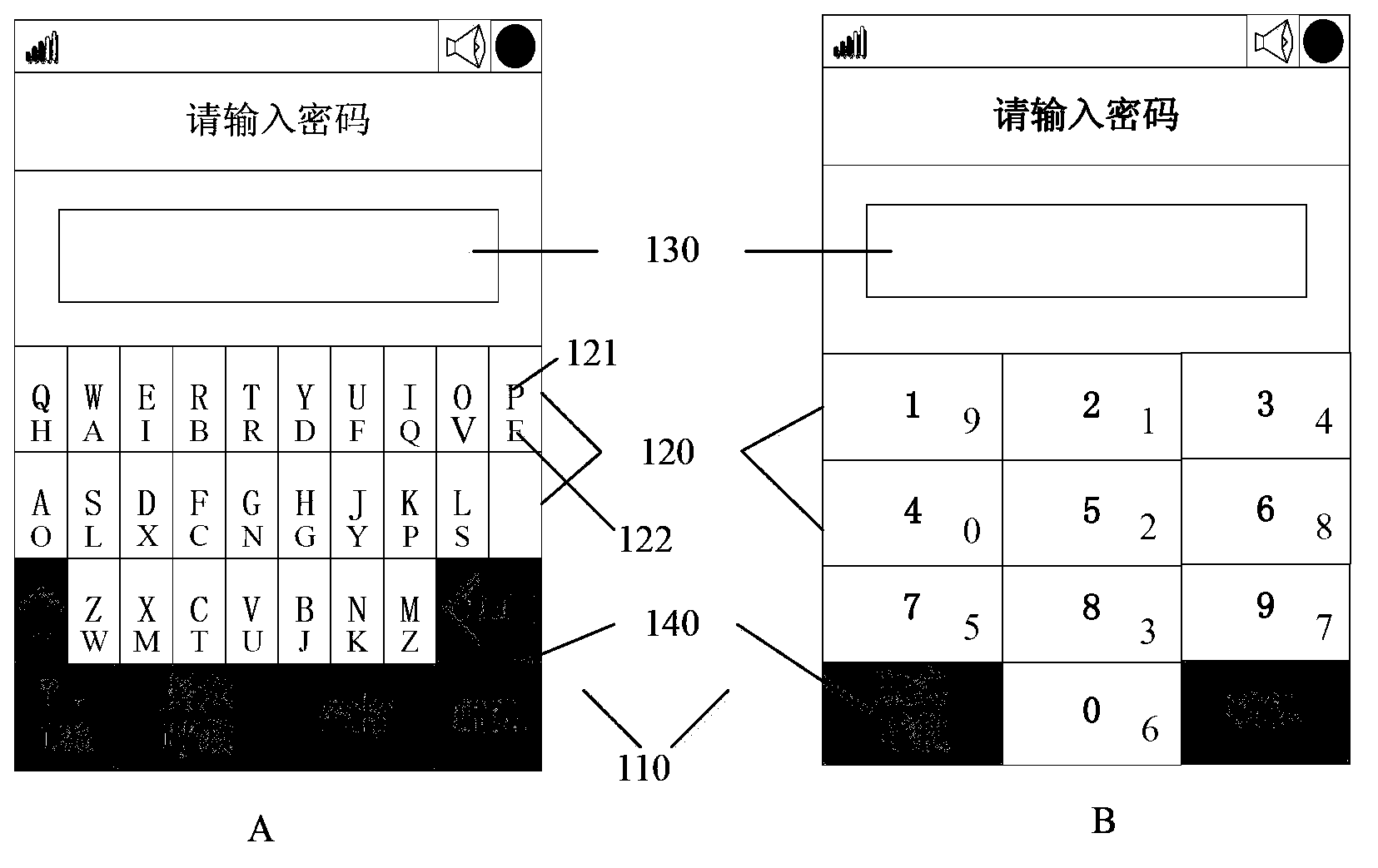
The invention proposes a dynamic decryption method used for a mobile terminal. The method includes the following steps: detecting whether a password input interface is entered; if so, further judging whether at least one character input button is triggered; if so, further detecting a fixed-character region corresponding to the triggered character input button; obtaining dynamic characters corresponding to fixed characters according to the fixed-character region until an input completion instruction is received so as to obtain an input dynamic-character sequence; judging whether the dynamic-character sequence matches a preset password; and if the dynamic-character sequence matches the preset password, unlocking the mobile terminal. The dynamic decryption method used for the mobile terminal is capable of preventing effectively that the password is peeped by others so that password leakage is prevented and thus the security of the mobile terminal is improved. The invention also proposes the mobile terminal.
Owner:BYD CO LTD
Portable electronic device and automatic unlocking method thereof
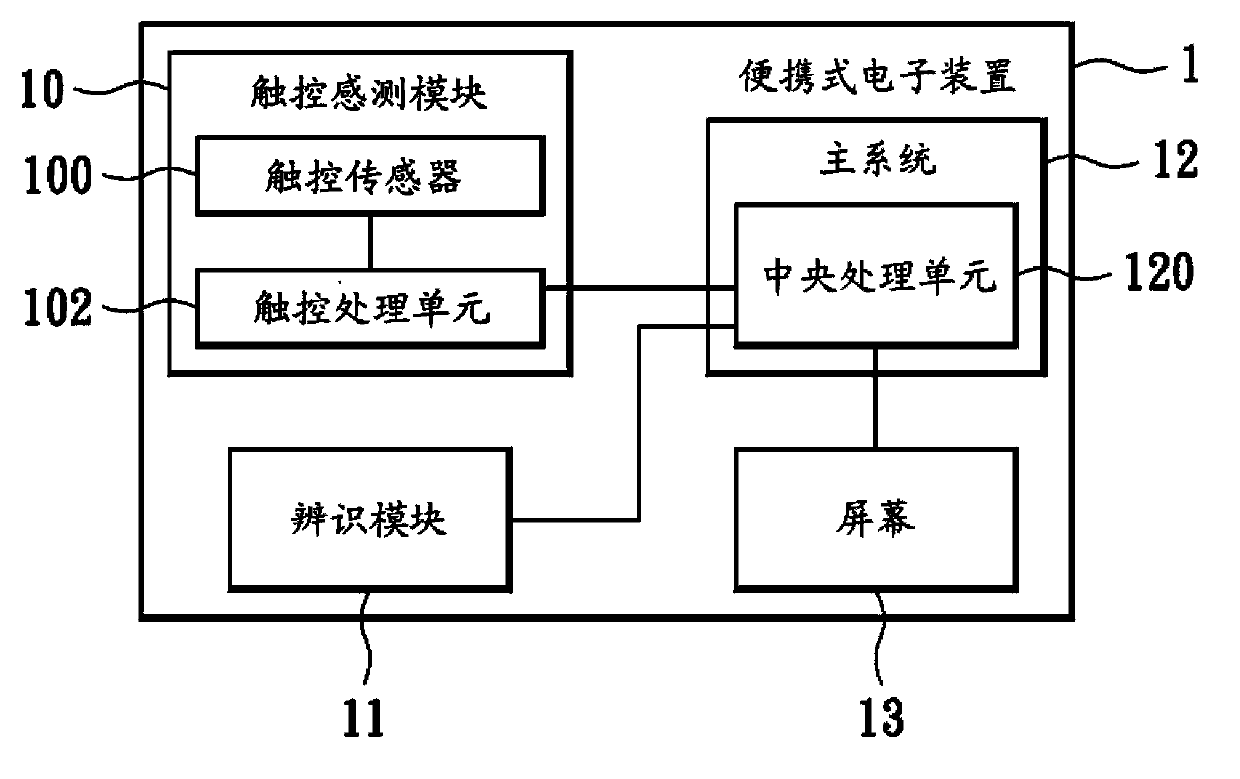
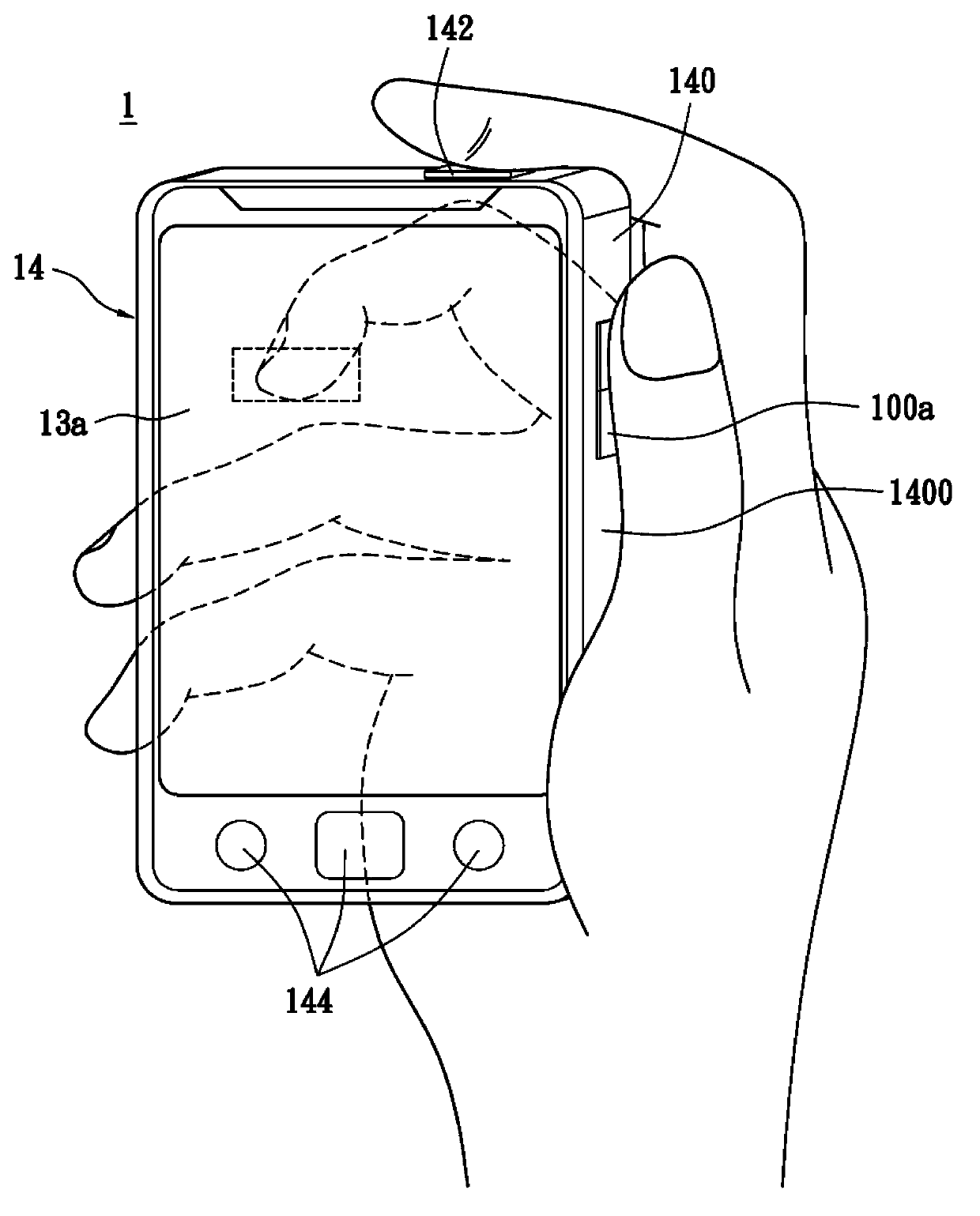
InactiveCN103631508AEliminate manual entryPrevent peepingPower managementUnauthorised/fraudulent call preventionTouch SensesHuman–computer interaction
Owner:WISTRON CORP
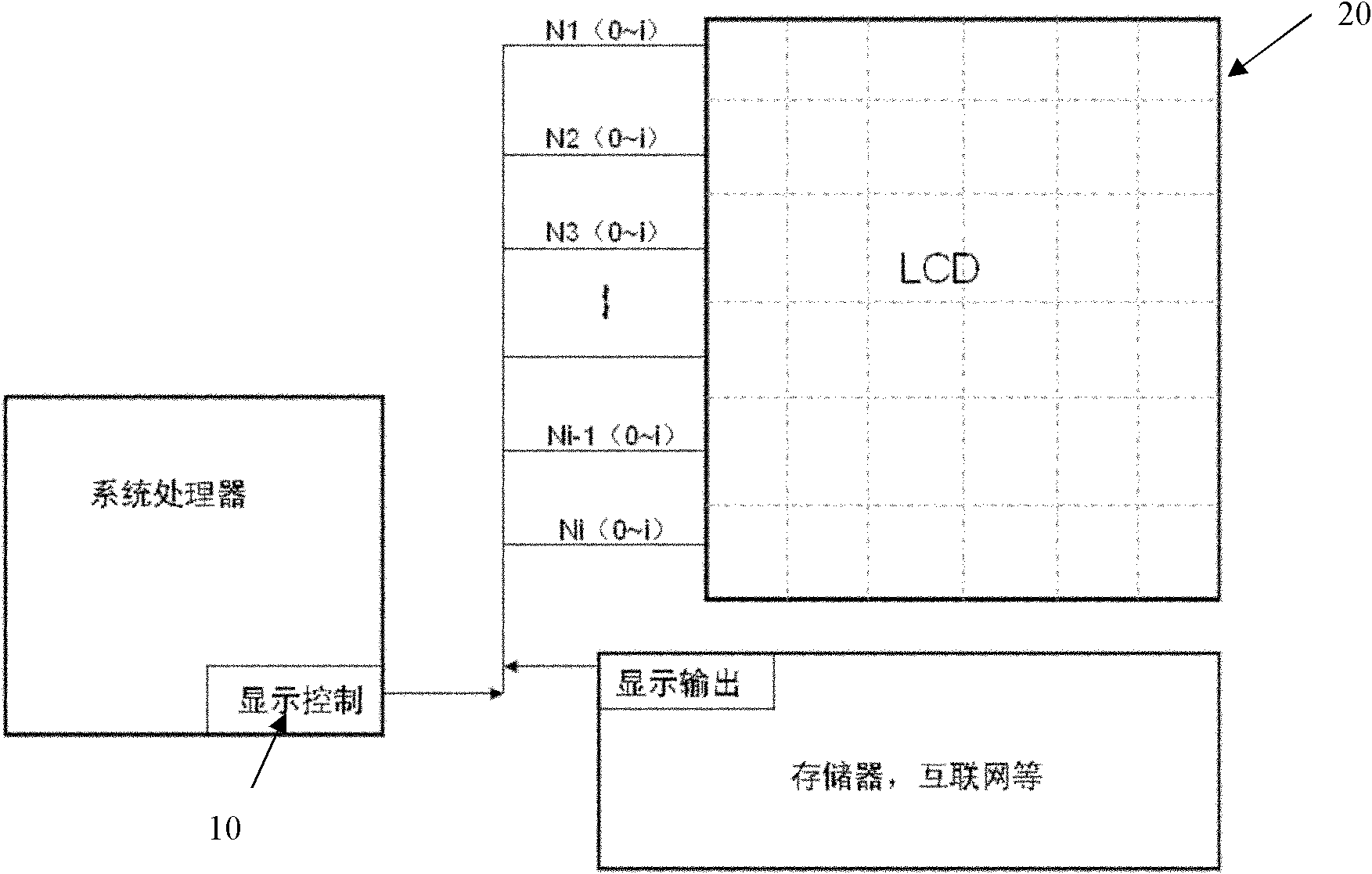
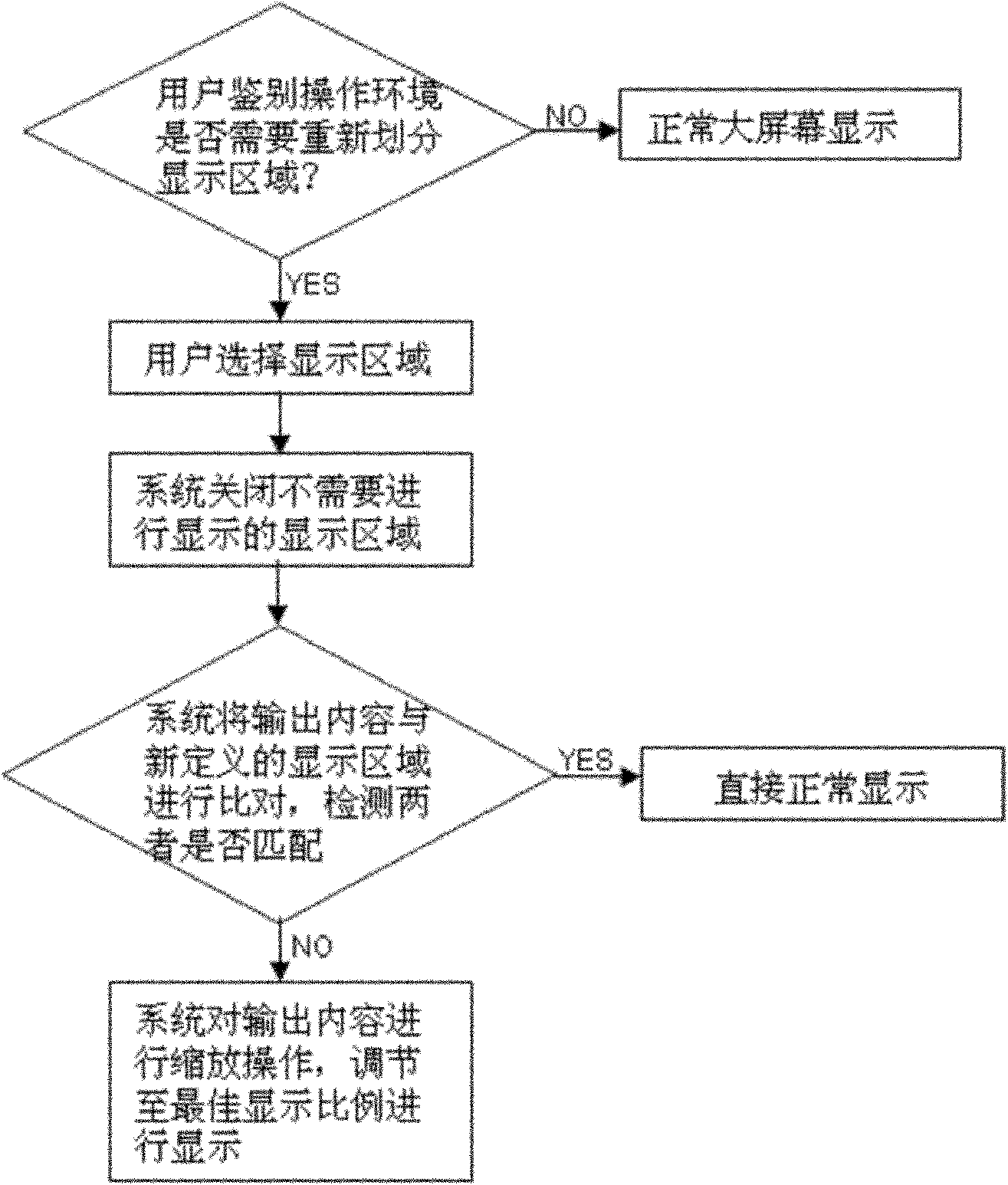
Method for supporting display of a plurality of sub display screens on mobile phone display screen
InactiveCN102123208AIncrease battery lifeZoom outSubstation equipmentHigh level techniquesPower savingOperating environment
The invention relates to a method for supporting the display of a plurality of sub display screens on a mobile phone display screen. The method comprises the following steps of: 1, adopting a display screen which can be divided as the mobile phone display screen; 2, in a system processor, dividing the mobile phone display screen into a plurality of sub display screens, wherein the working states of the sub display screens can be independently controlled; S3, setting an interface in a system to perform display control on the sub display screens; S4, setting a corresponding interface convenient for a user to operate on the mobile phone display screen. By the method, a user can enter a power-saving mode by closing the plurality of sub display screens under an operation environment that large-screen display is not needed, and the power endurance of a mobile phone is prolonged.
Owner:SHENZHEN SANG FEI CONSUMER COMM CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com