Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
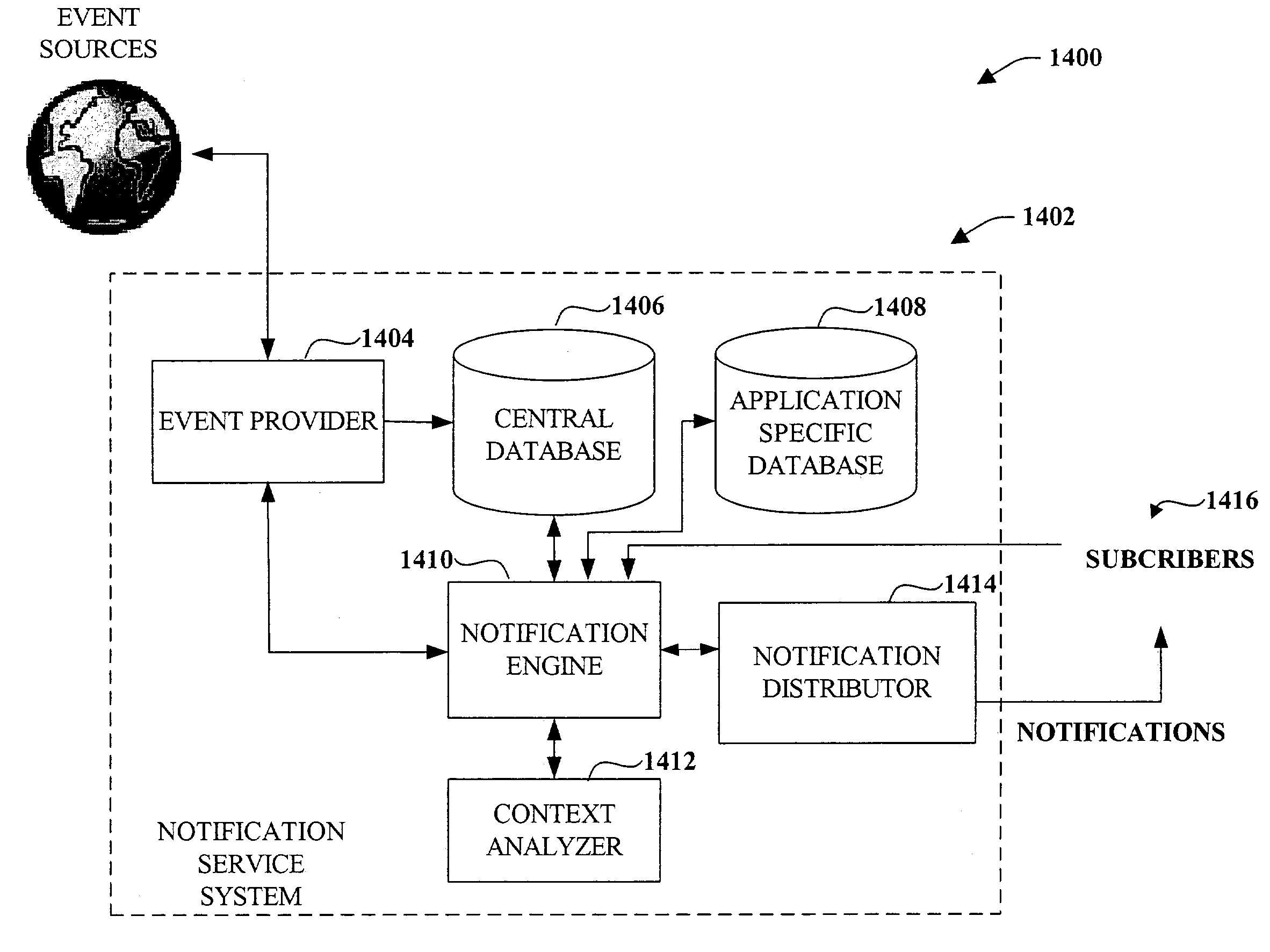
7169 results about "Current user" patented technology
Efficacy Topic
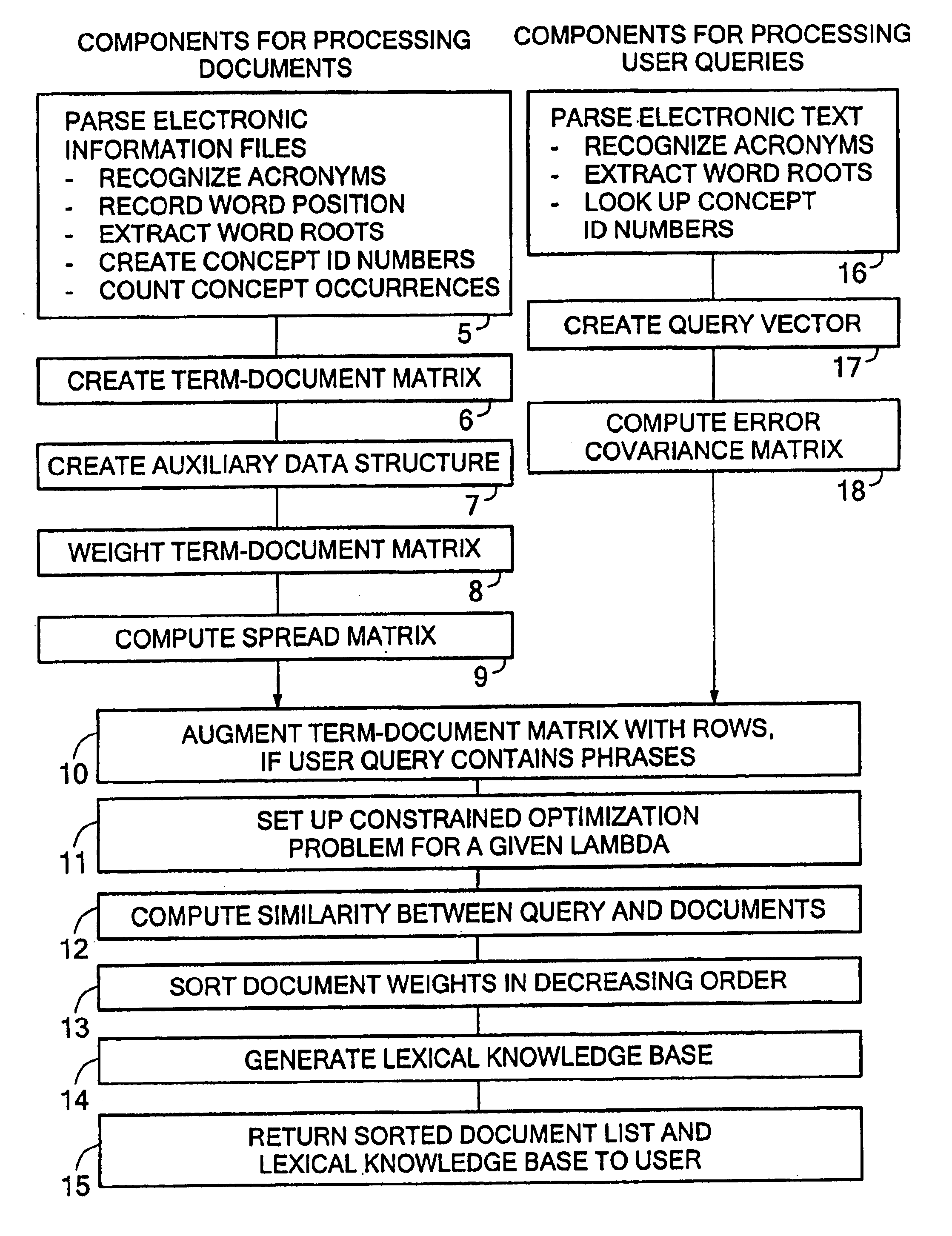
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
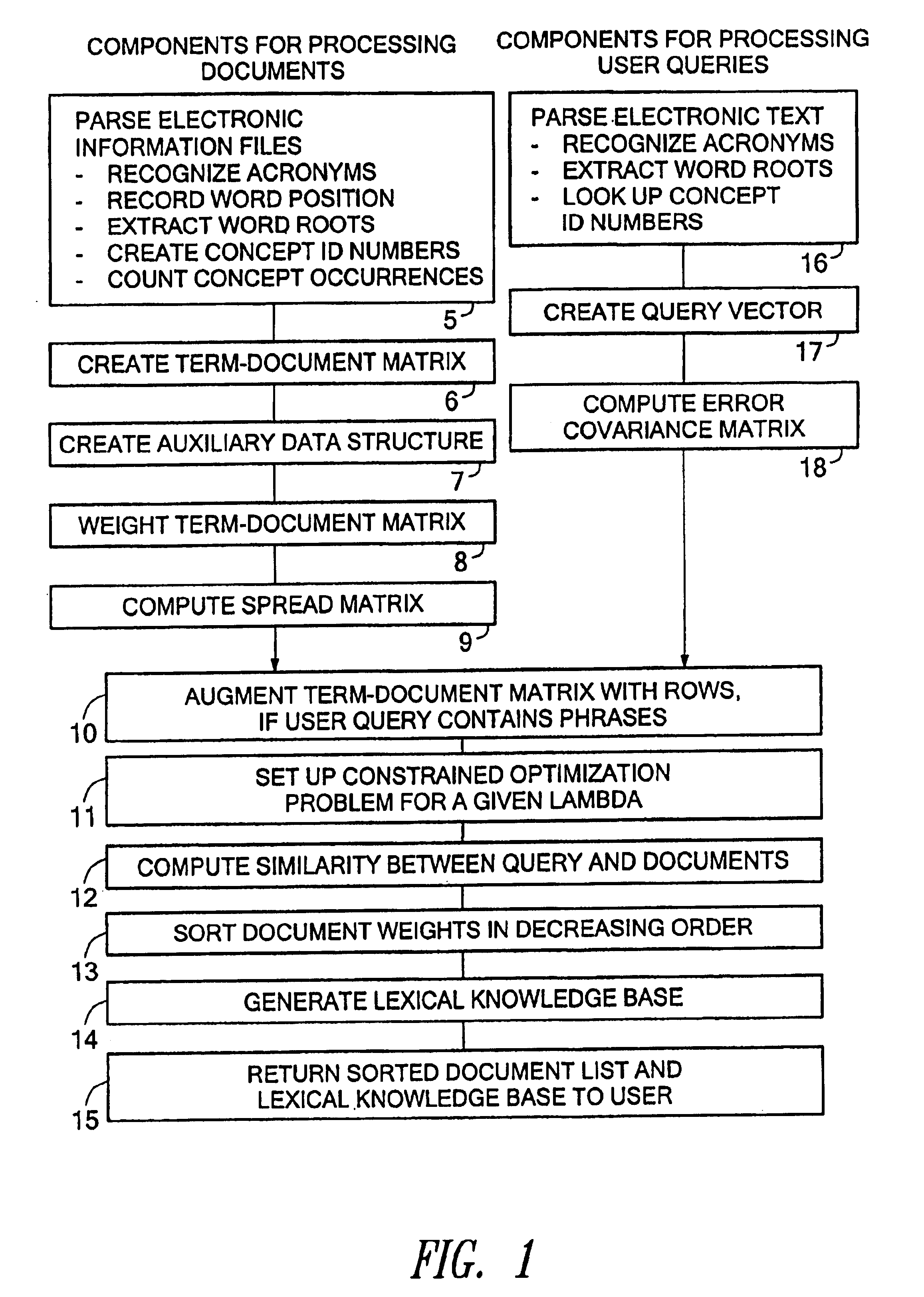
Current User is the User that is currently logged in into the System. In your case Both will be current user as they must have separate credentials and have different permission and role for that org. So the main point is that the logged in user will be current user.
Internet navigation using soft hyperlinks
InactiveUS6862710B1High degree of correlationHigh degreeData processing applicationsWeb data indexingNavigation systemDocument preparation
A system for internet navigation using soft hyperlinks is disclosed, in connection with an illustrative information retrieval system with which it may be used. The navigation tool provides freedom to move through a collection of electronic documents independent of any hyperlink which has been inserted within an HTML page. A user can click on any term in a document page, not only those that are hyperlinked. For example, when a user clicks on an initial word within the document, the disclosed system employs a search engine in the background to retrieve a list of related terms. In an illustrative embodiment, a compass-like display appears with pointers indicating the first four terms returned by the search engine. These returned terms have the highest degree of correlation with the initial search term in a lexical knowledge base that the search engine constructs automatically. The disclosed system allows the user to move from the current document to one of a number of document lists which cover different associations between the initial word clicked on by the user and other terms extracted from within the retrieved list of related terms. The disclosed system may further allow the user to move to a document that is considered most related to the initial word clicked on by the user, or to a list of documents that are relevant to a phrase or paragraph selection indicated by the user within the current page.
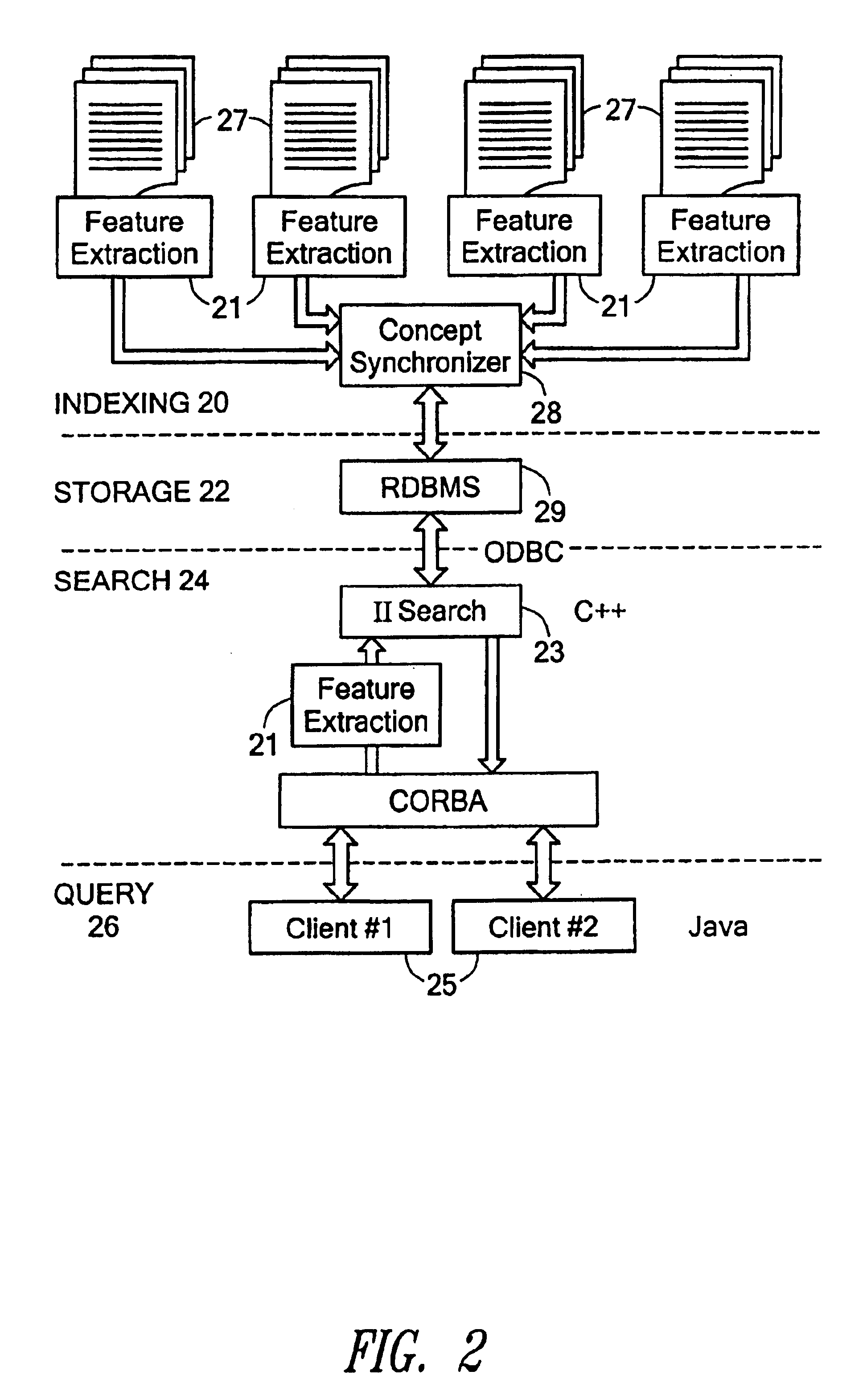
Owner:FIVER LLC
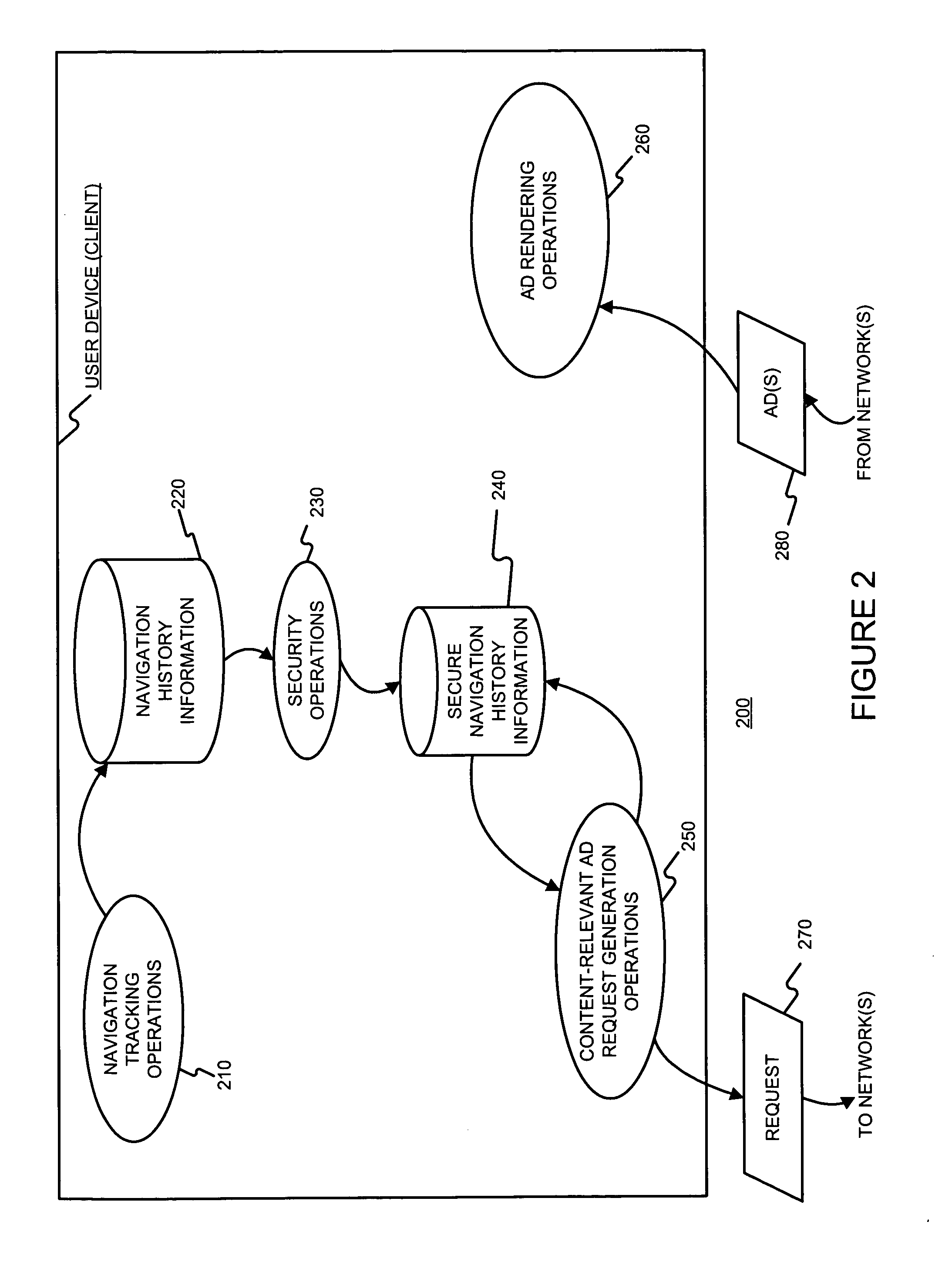
Determining advertisements using user behavior information such as past navigation information
Ads better targeted to individual users can be determined by using (recent) navigation history. User navigation (e.g., Web browsing) may be tracked, recorded and maintained. The navigation history information, and perhaps information about a current document, may be used to determine content-relevant and personalized ads. By doing so the ads seen by the user are more interesting and relevant to a current user interest inferred from their (recent) navigation.
Owner:GOOGLE LLC
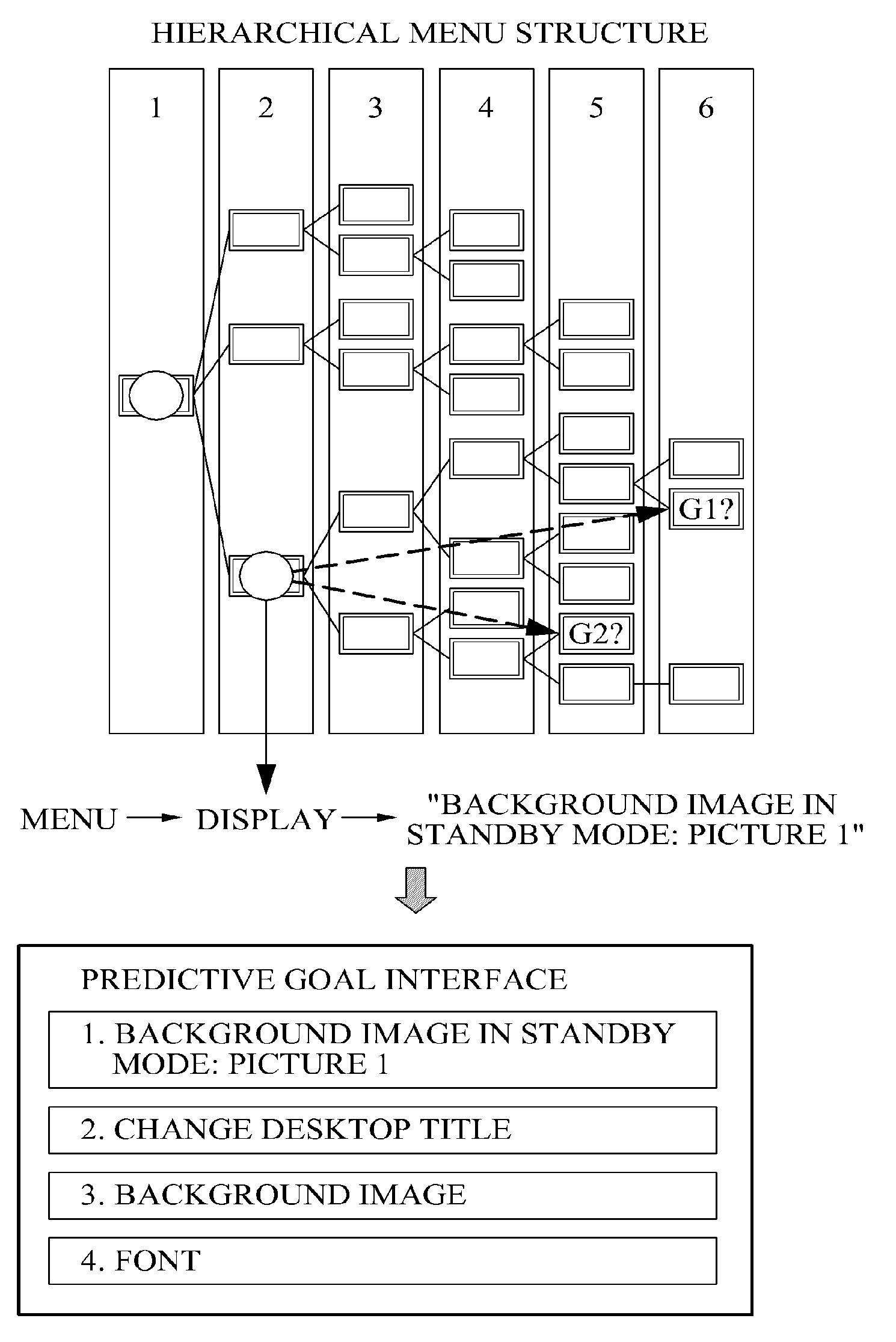
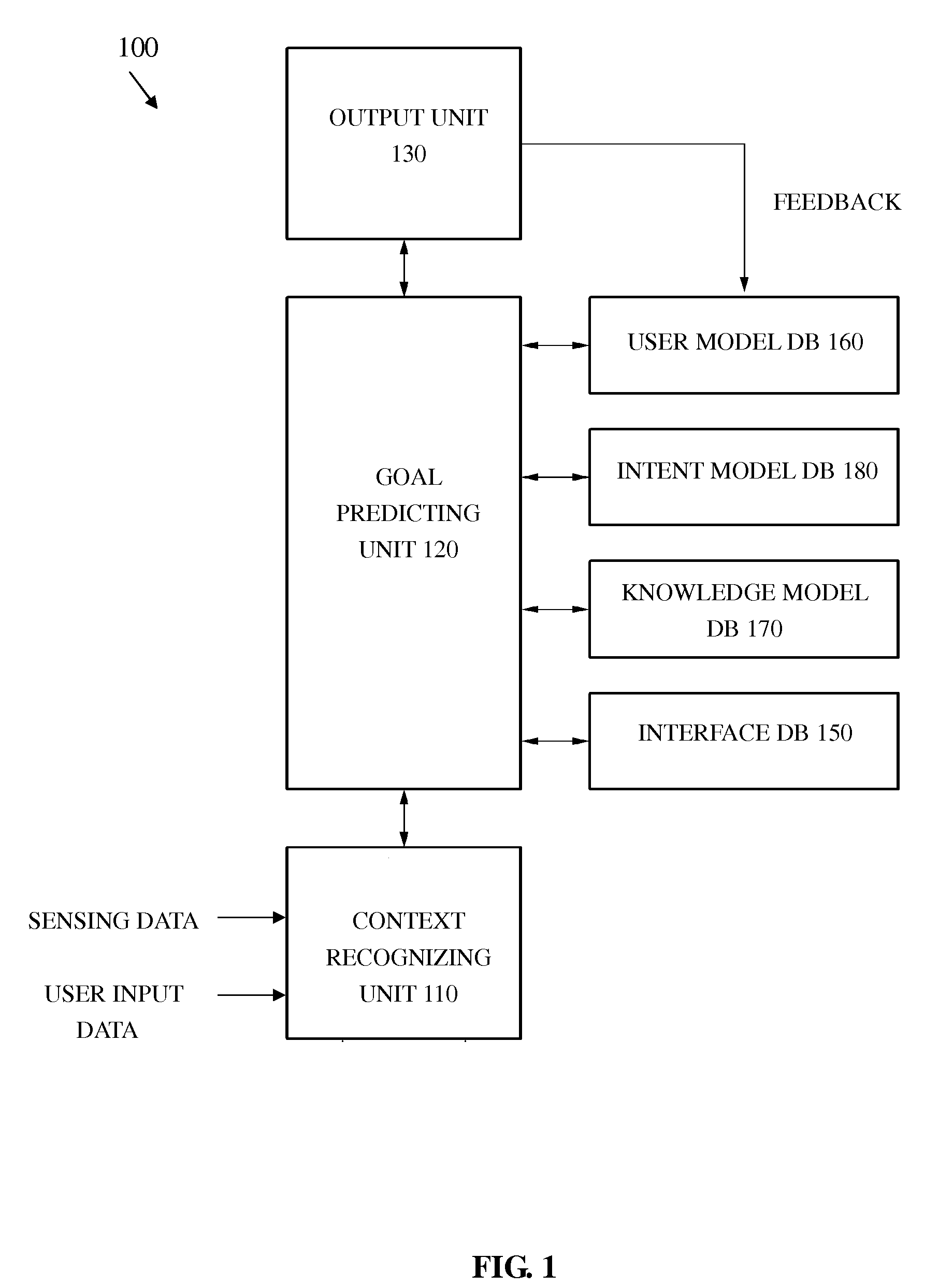
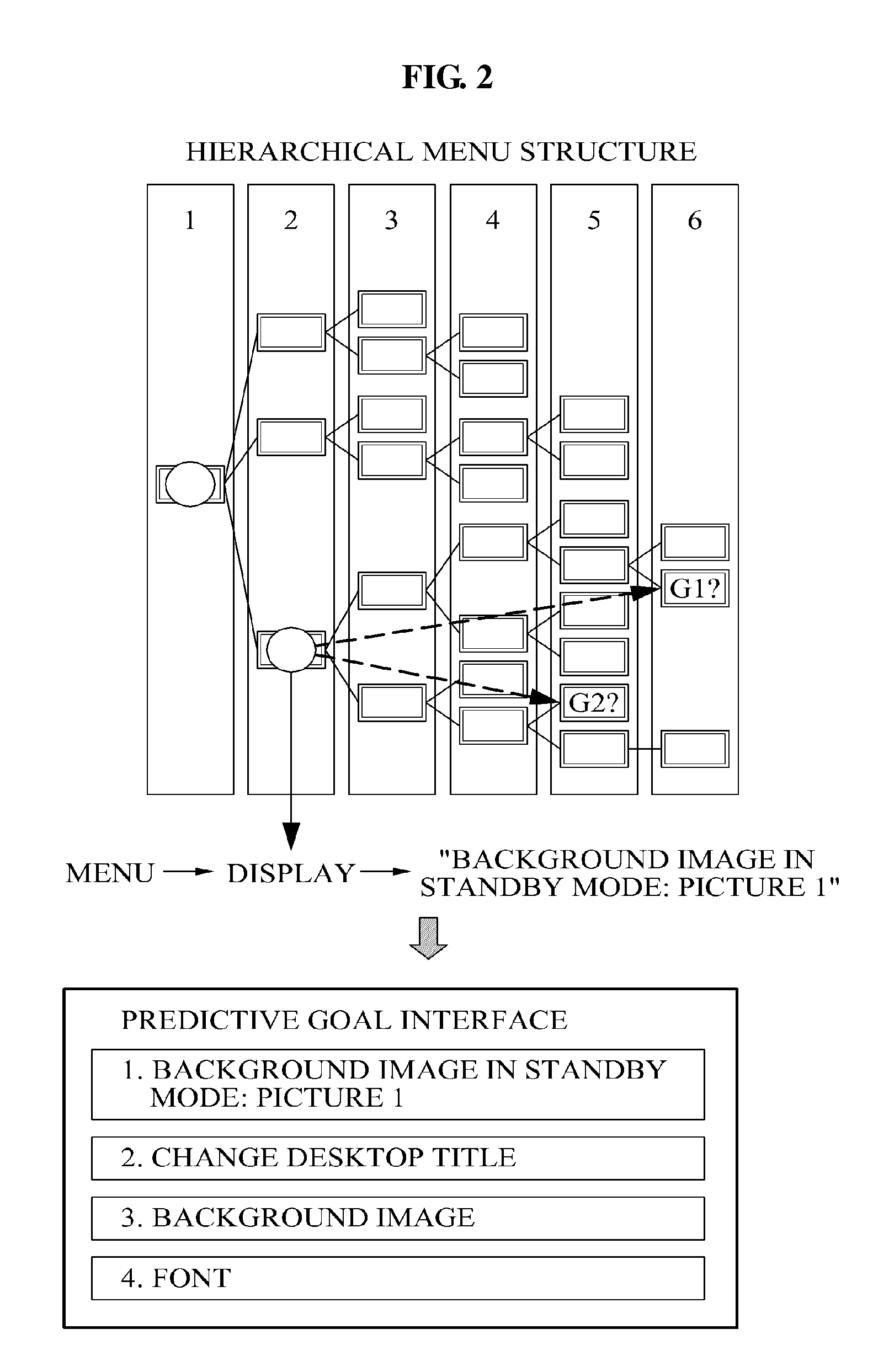
Apparatus and method for providing goal predictive interface
A predictive goal interface providing apparatus and a method thereof are provided. The predictive goal interface providing apparatus may recognize a current user context by analyzing data sensed from a user environment condition, may analyze user input data received from the user, may analyze a predictive goal based on the recognized current user context, and may provide a predictive goal interface based on the analyzed predictive goal.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for automating transcription services
InactiveUS6122614AMinimize the numberSimple meansSpeech recognitionSpeech synthesisAcoustic modelSpeech identification
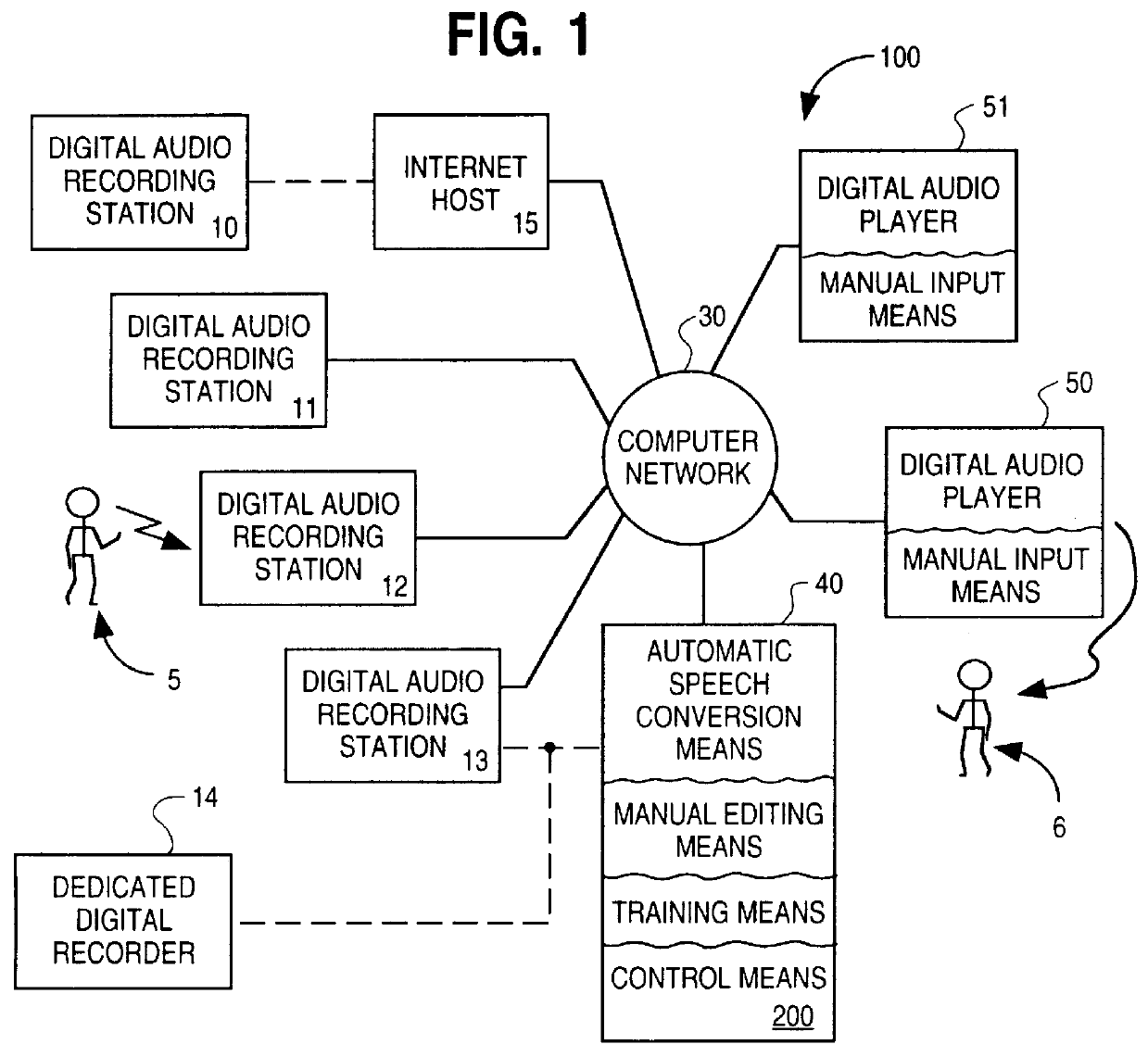
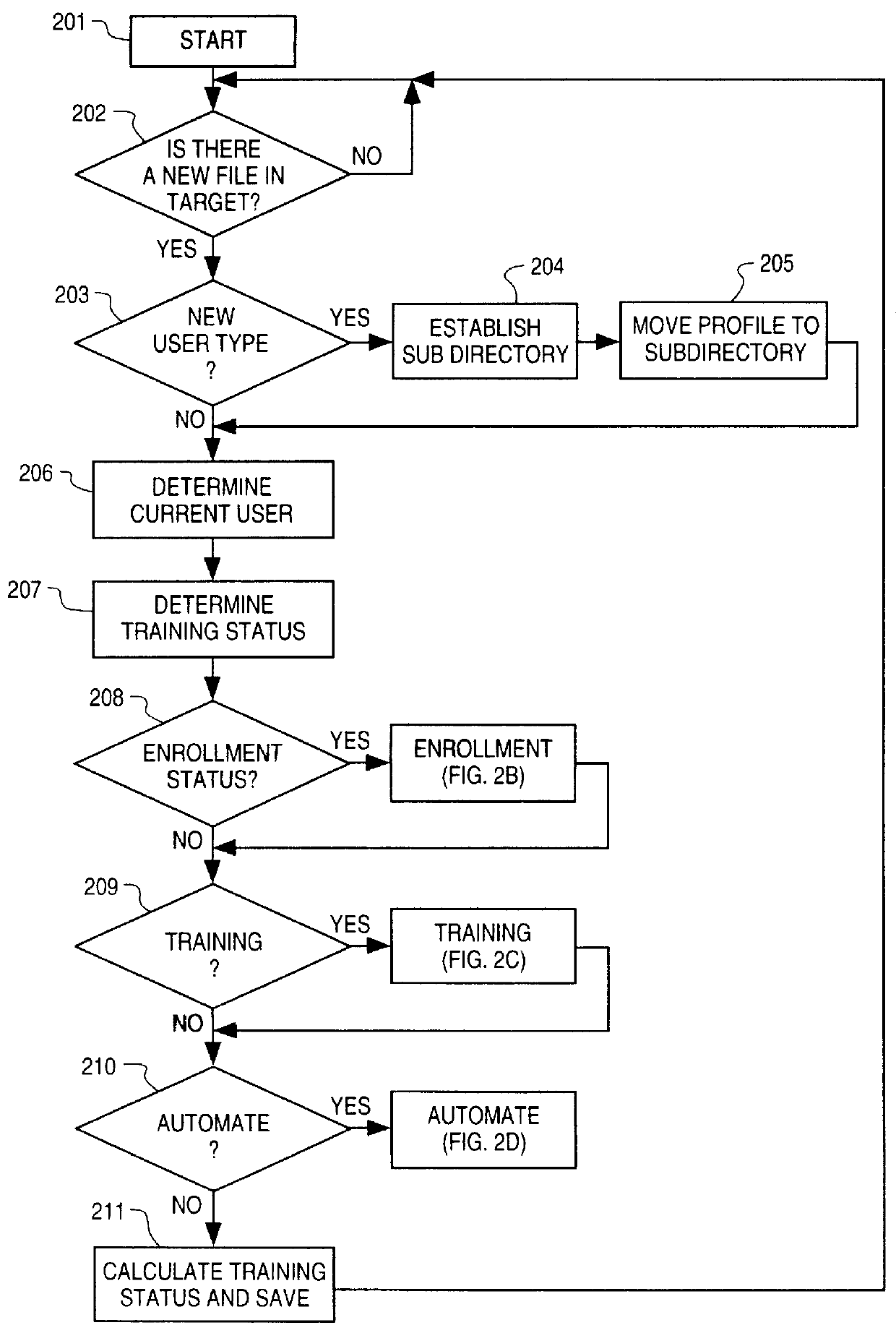
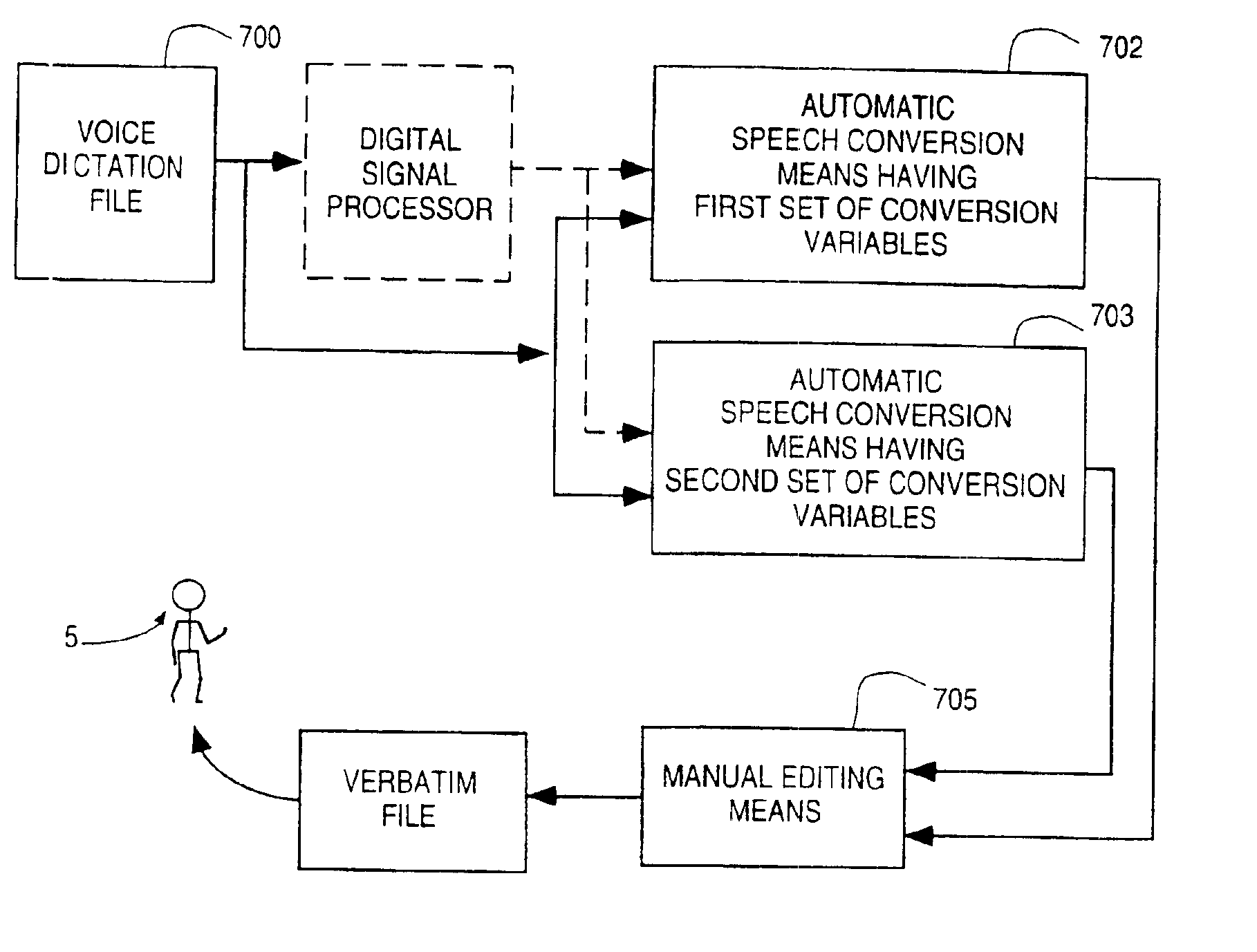
A system for substantially automating transcription services for multiple voice users including a manual transcription station, a speech recognition program and a routing program. The system establishes a profile for each of the voice users containing a training status which is selected from the group of enrollment, training, automated and stop automation. When the system receives a voice dictation file from a current voice user based on the training status the system routes the voice dictation file to a manual transcription station and the speech recognition program. A human transcriptionist creates transcribed files for each received voice dictation files. The speech recognition program automatically creates a written text for each received voice dictation file if the training status of the current user is training or automated. A verbatim file is manually established if the training status of the current user is enrollment or training and the speech recognition program is trained with an acoustic model for the current user using the verbatim file and the voice dictation file if the training status of the current user is enrollment or training. The transcribed file is returned to the current user if the training status of the current user is enrollment or training or the written text is returned if the training status of the current user is automated. An apparatus and method is also disclosed for simplifying the manual establishment of the verbatim file. A method for substantially automating transcription services is also disclosed.
Owner:CUSTOM SPEECH USA +1
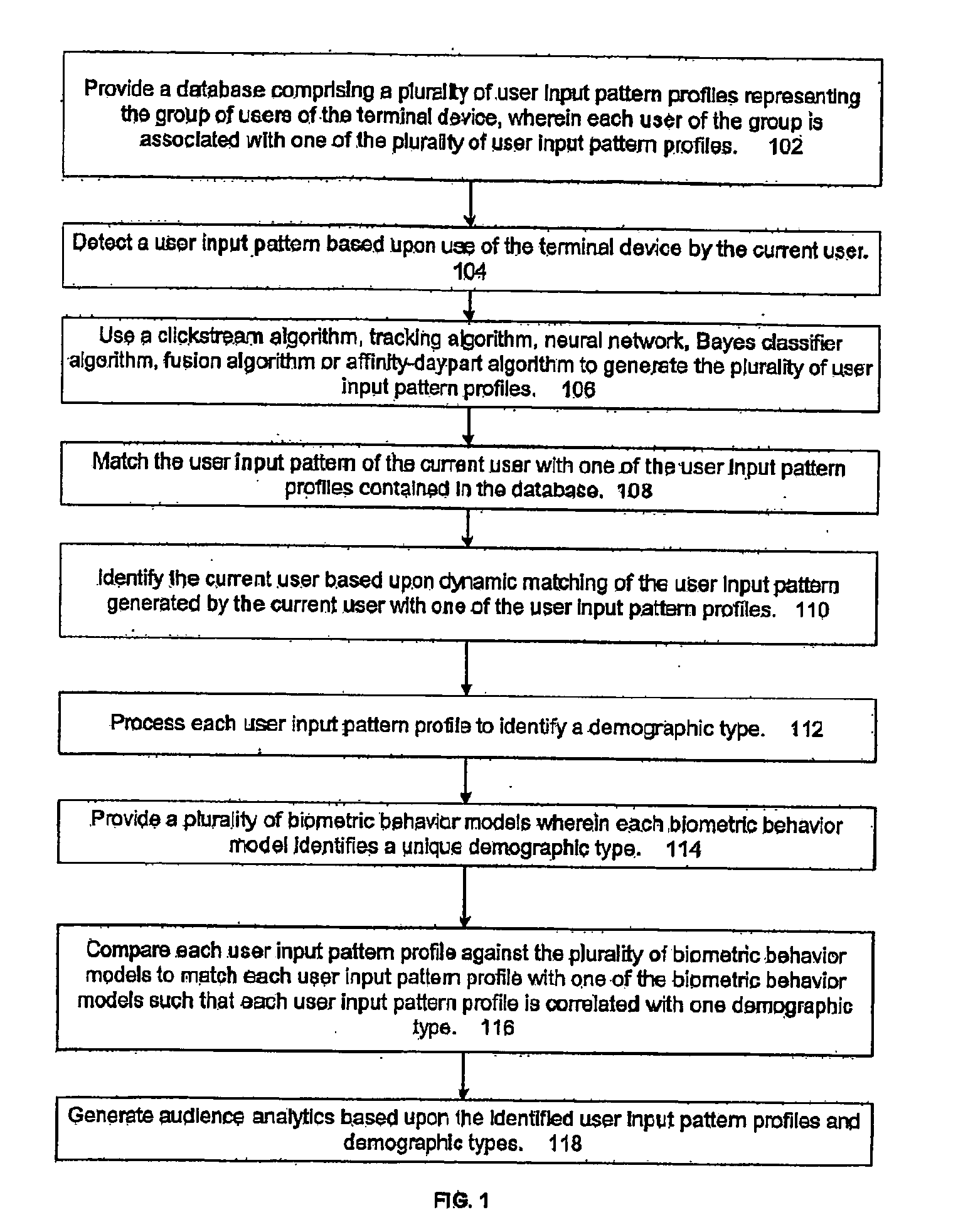
Generating audience analytics
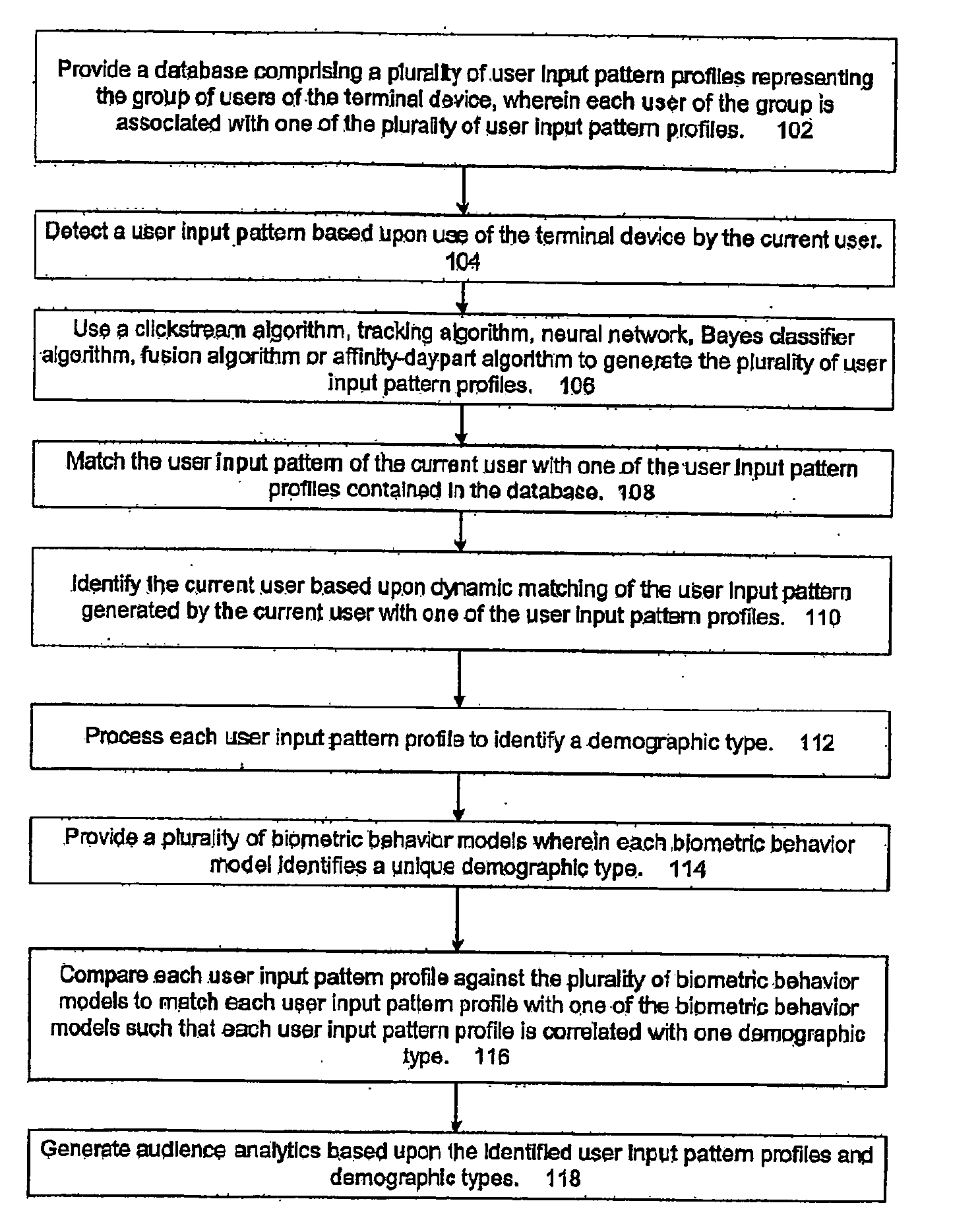
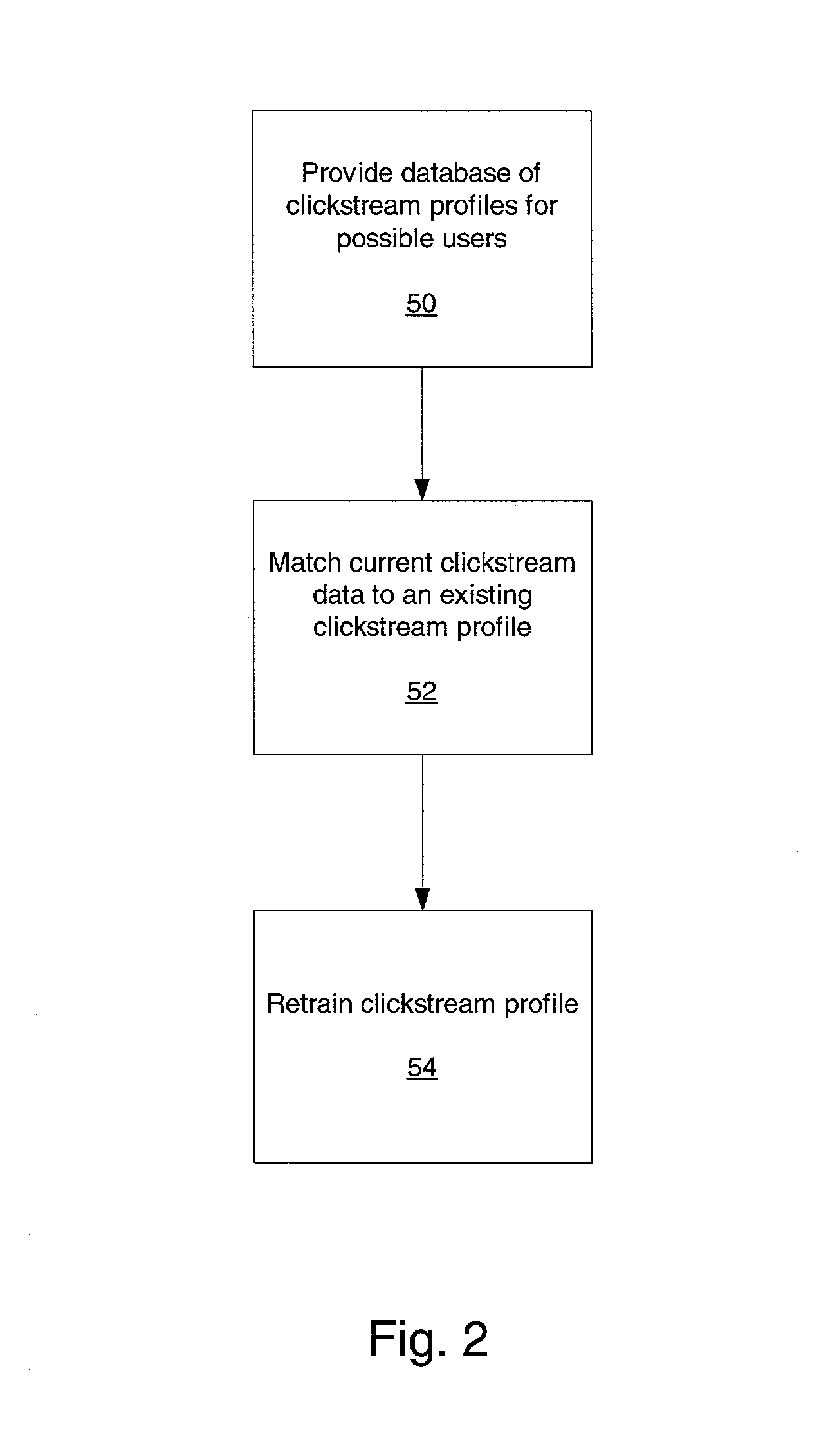
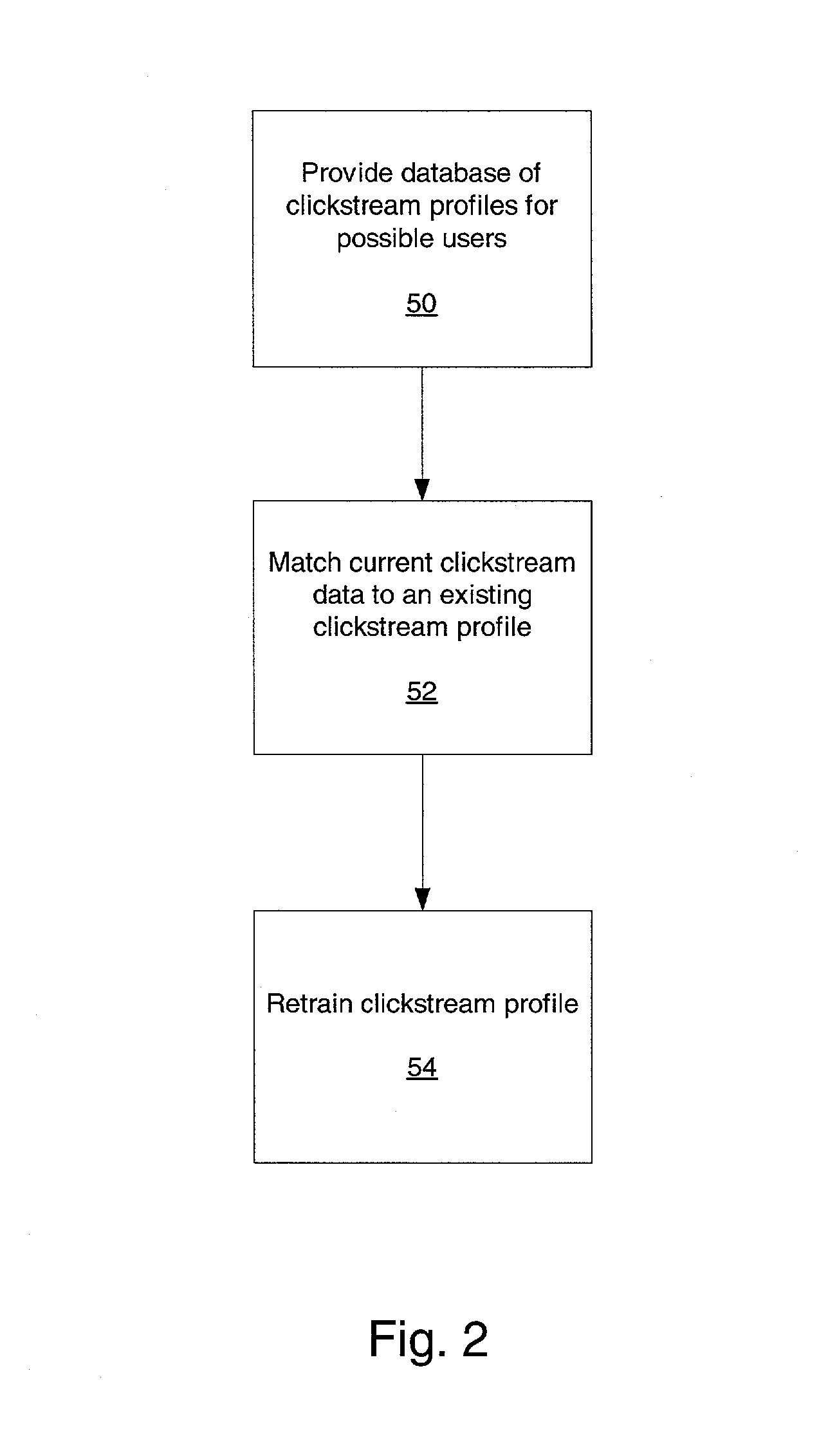
The present invention is directed to generating audience analytics that includes providing a database containing a plurality of user input pattern profiles representing the group of users of terminal device, in which each user of the group is associated with one of the plurality of user input pattern profiles. A clickstream algorithm, tracking algorithm, neural network, Bayes classifier algorithm, or affinity-day part algorithm can be used to generate the user input pattern profiles. A user input pattern is detected based upon use of the terminal device by the current user and the user input pattern of the current user is dynamically matched with one of the user input pattern profiles contained in the database. The current user is identified based upon dynamic matching of the user input pattern generated by the current user with one of the user input pattern profiles. The present invention processes each user input pattern profile to identify a demographic type. A plurality of biometric behavior models are employed to identify a unique demographic type. Each user input pattern profile is compared against the plurality of biometric behavior models to match each user input pattern profile with one of the biometric behavior models such that each user input pattern profile is correlated with one demographic type. Audience analytics are then based upon the identified demographic types.
Owner:COX COMMUNICATIONS
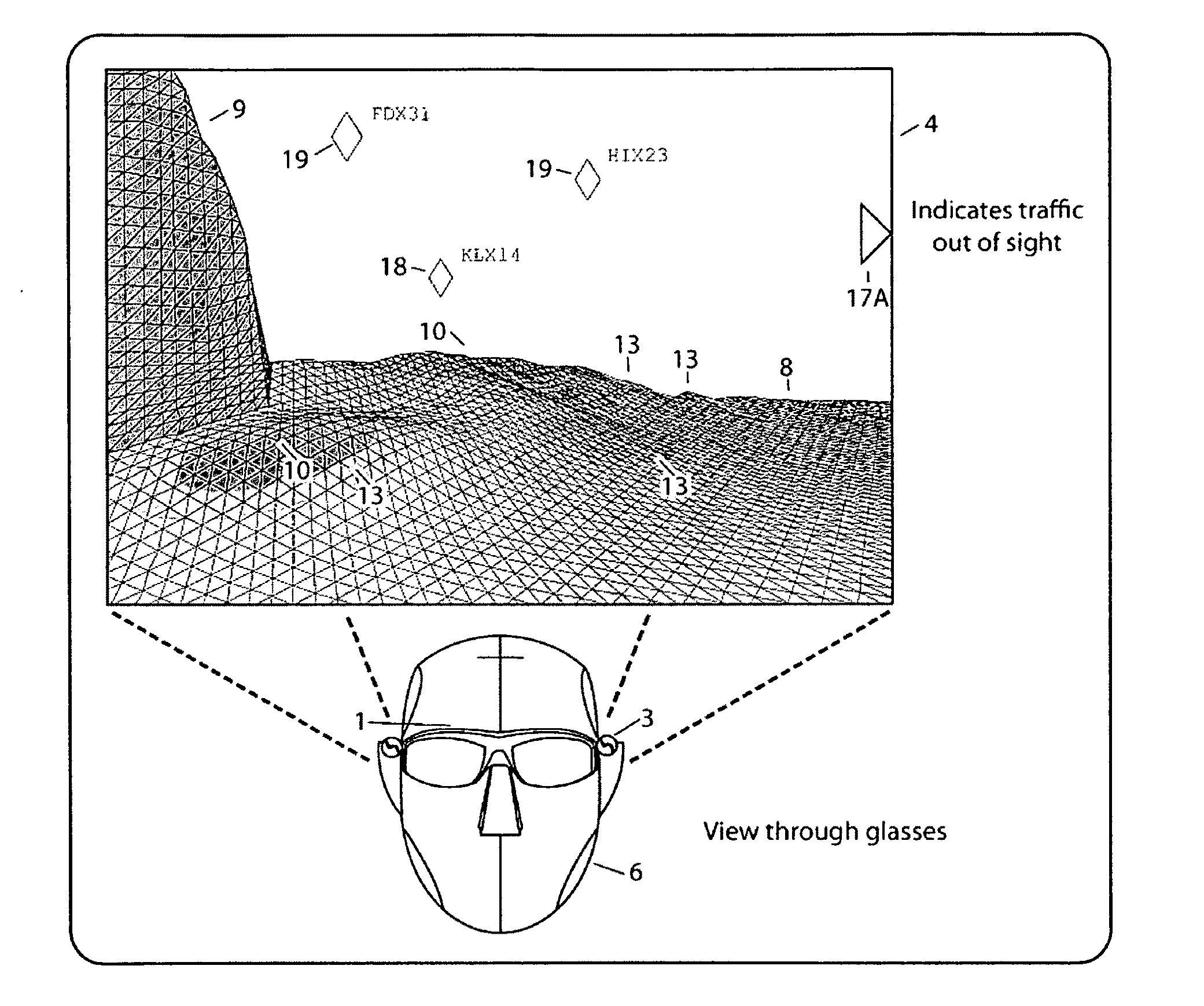
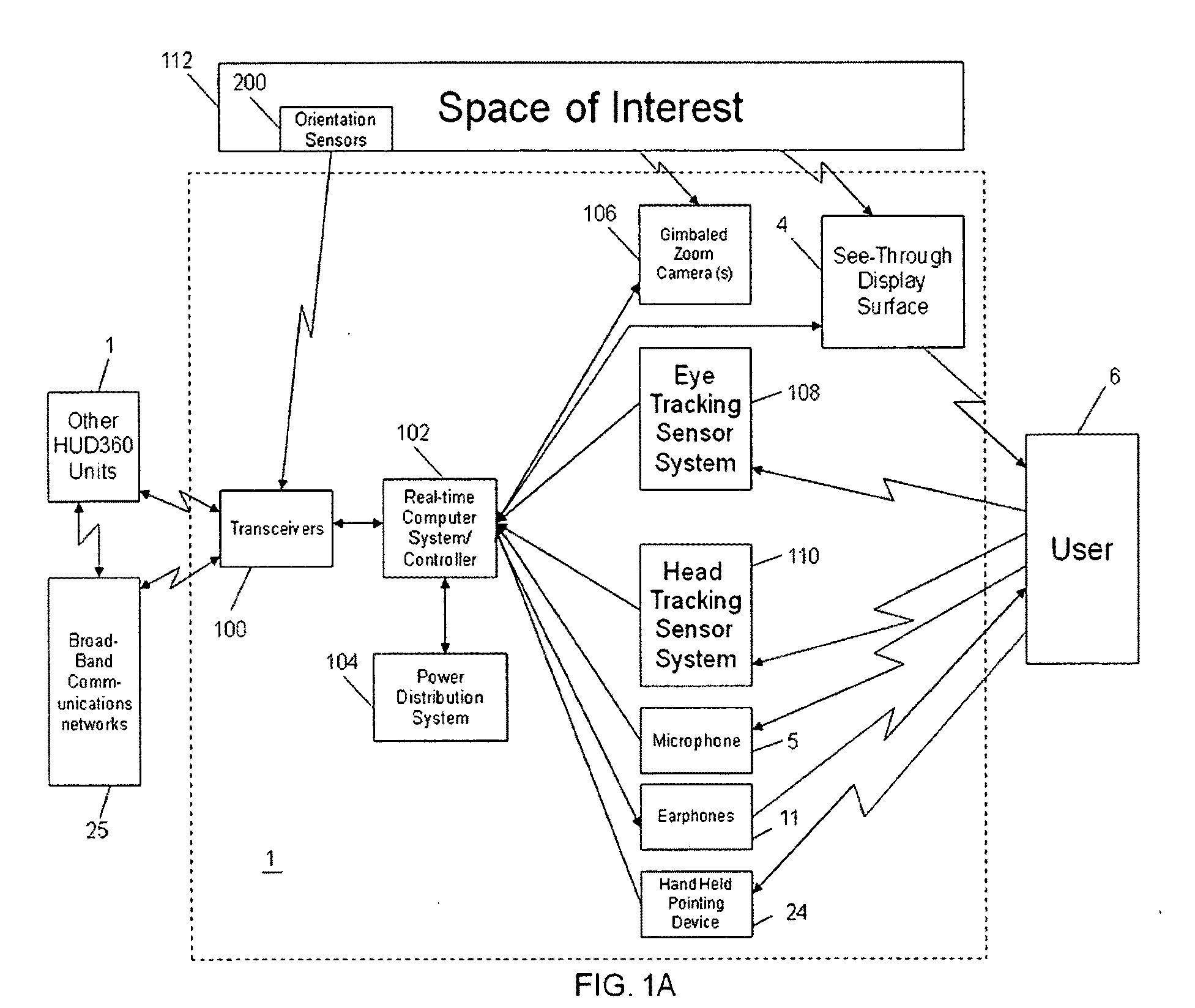
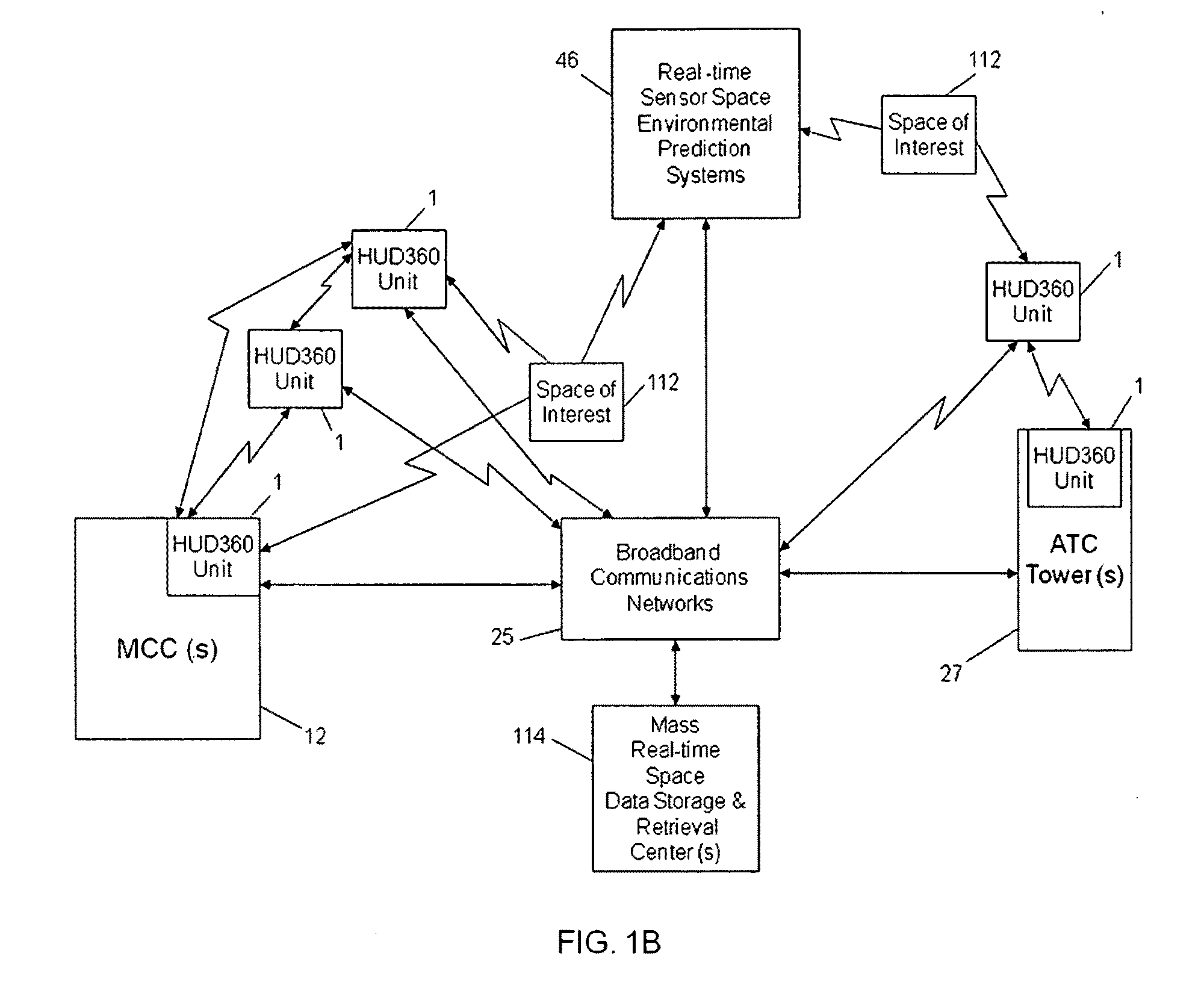
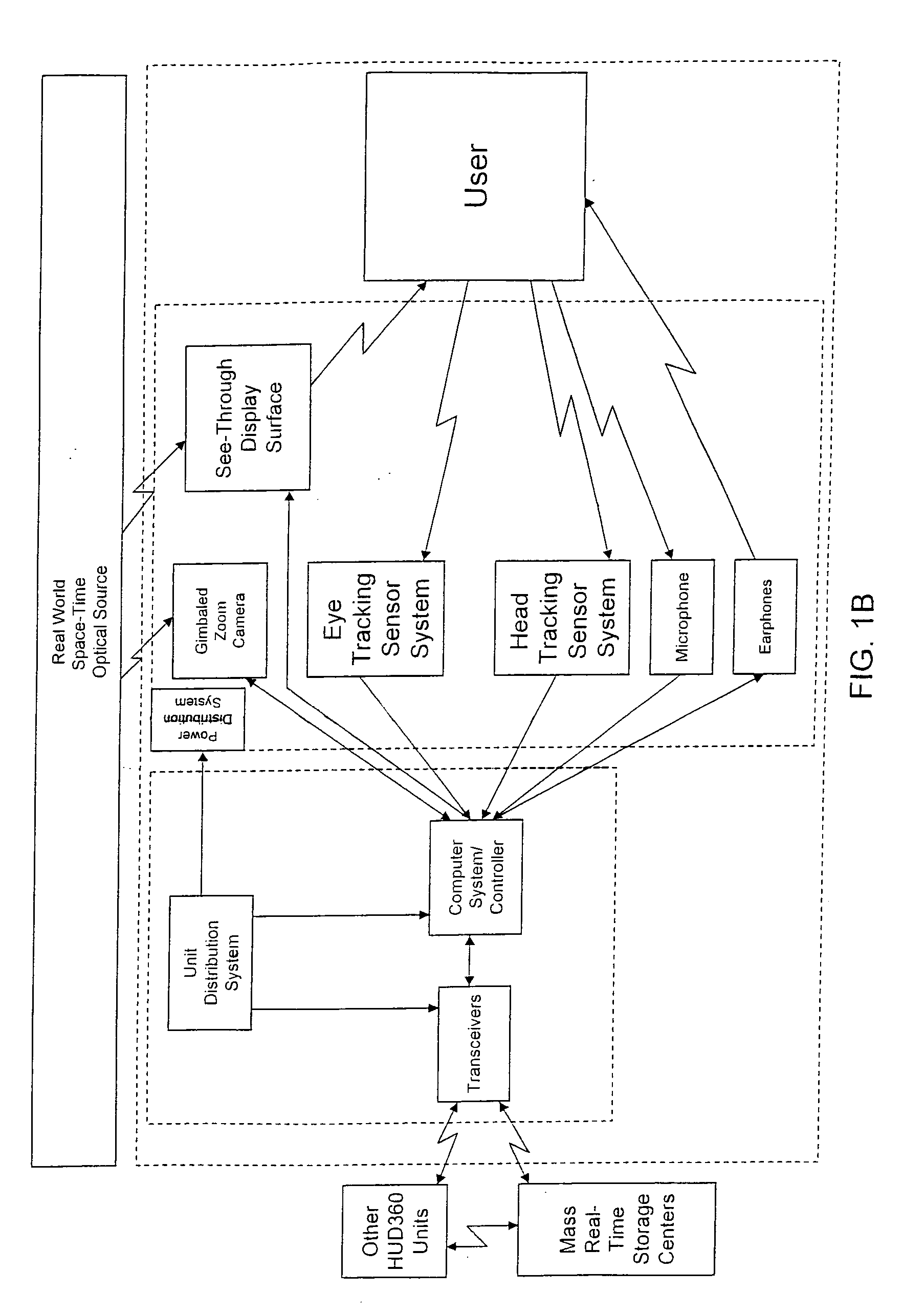
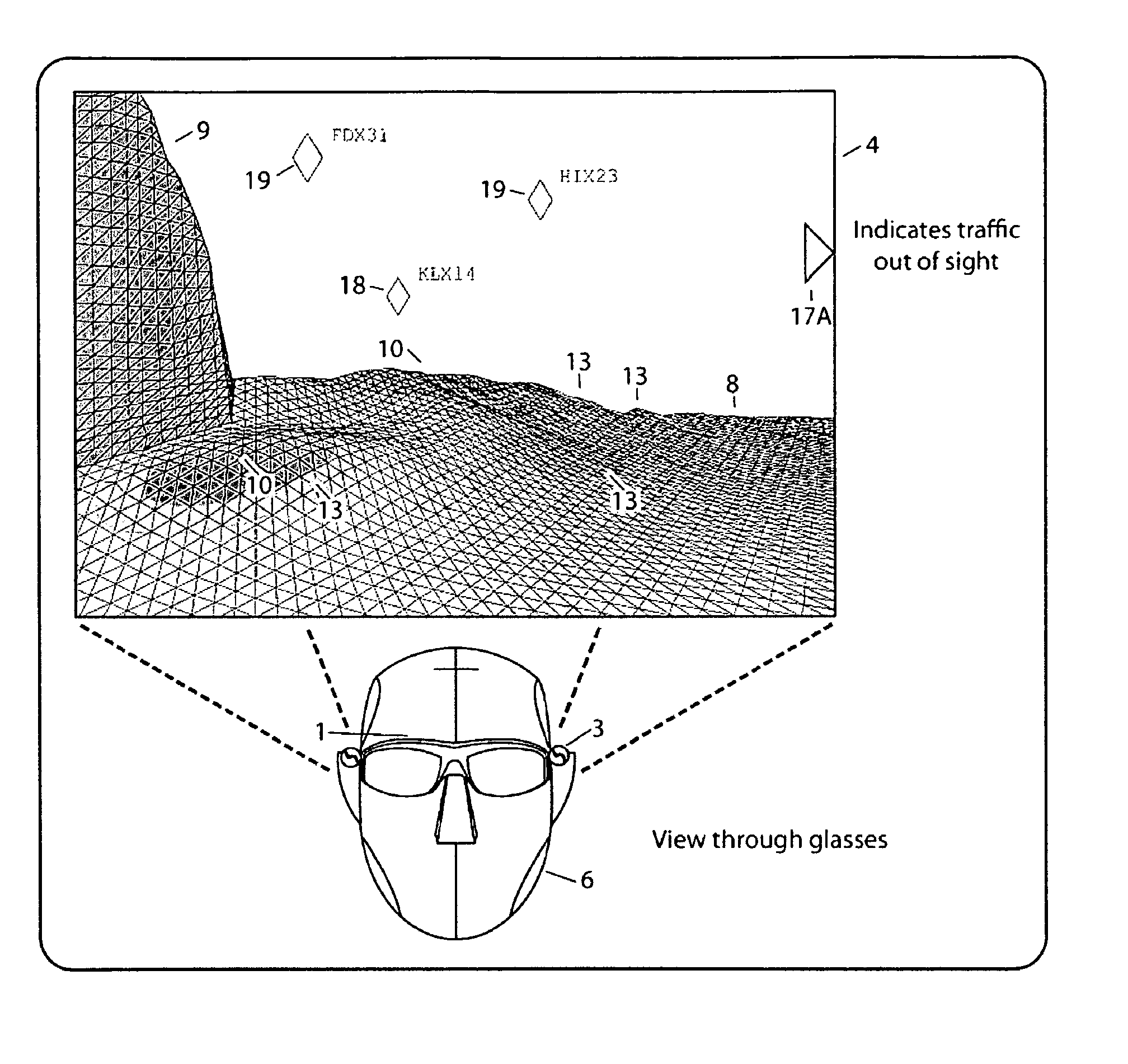
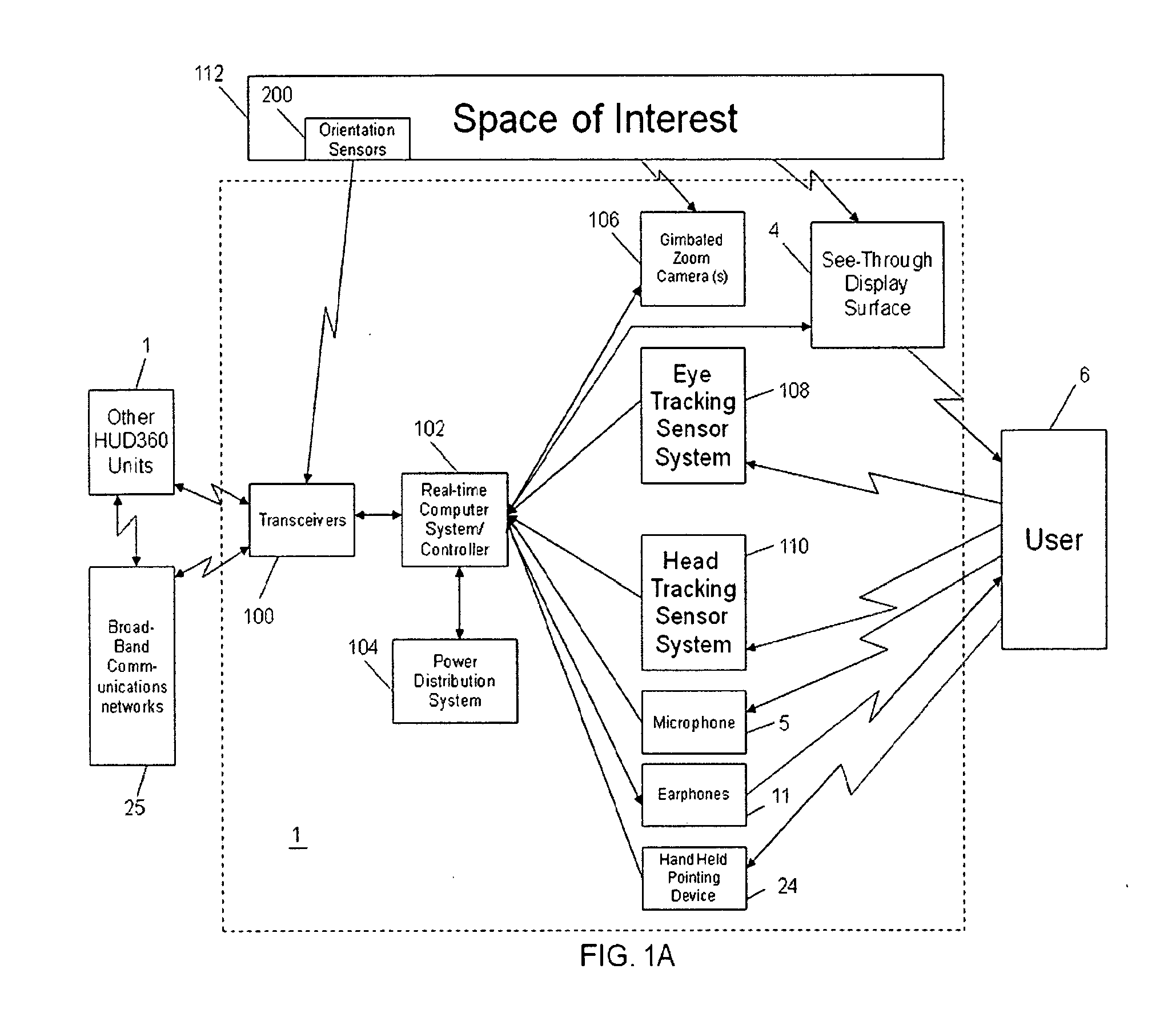
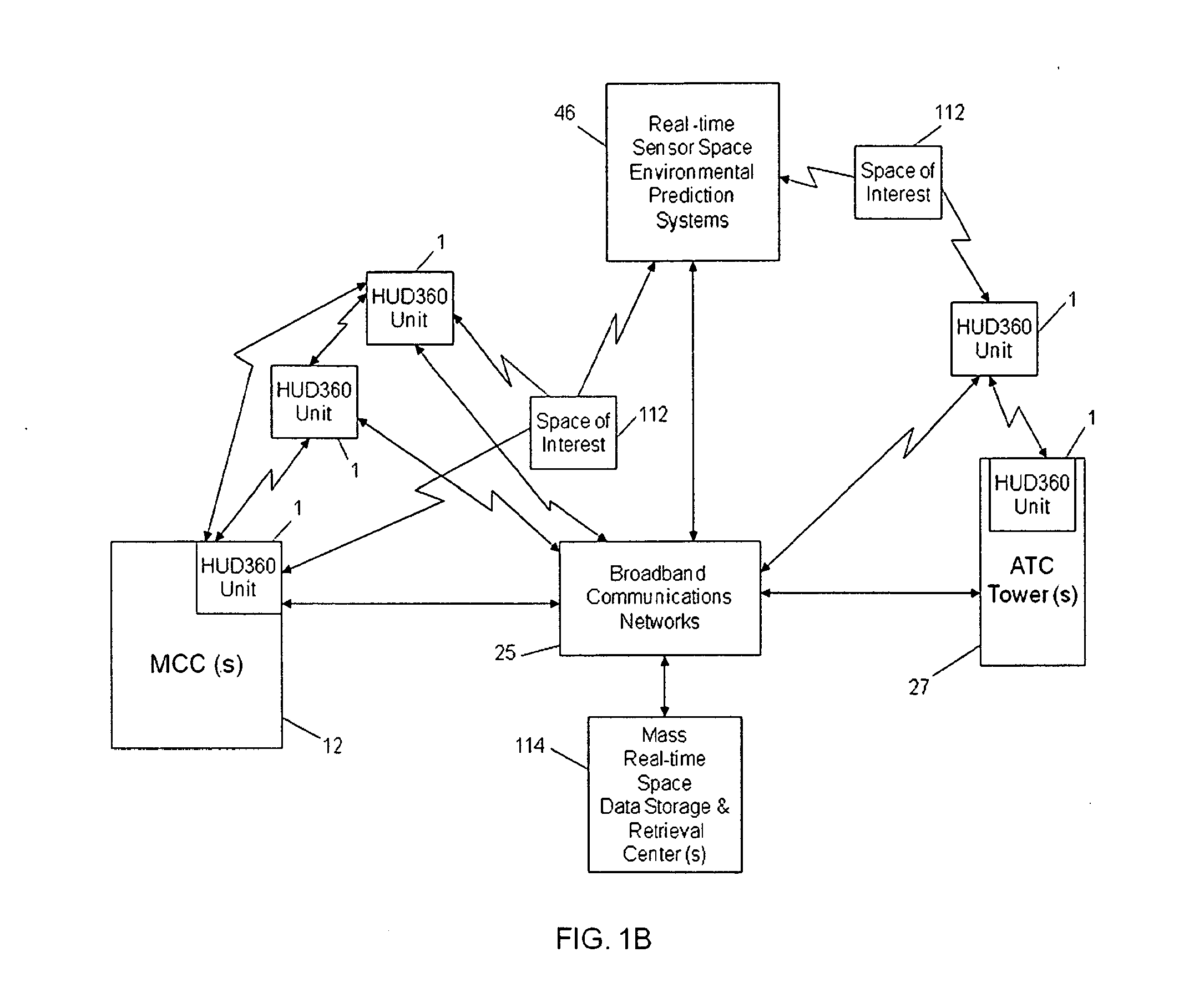
Computer-aided system for 360º heads up display of safety/mission critical data
InactiveUS20100238161A1Improve assessmentSatisfy safety performance requirementsCathode-ray tube indicatorsInput/output processes for data processingHead-up displayDisplay device
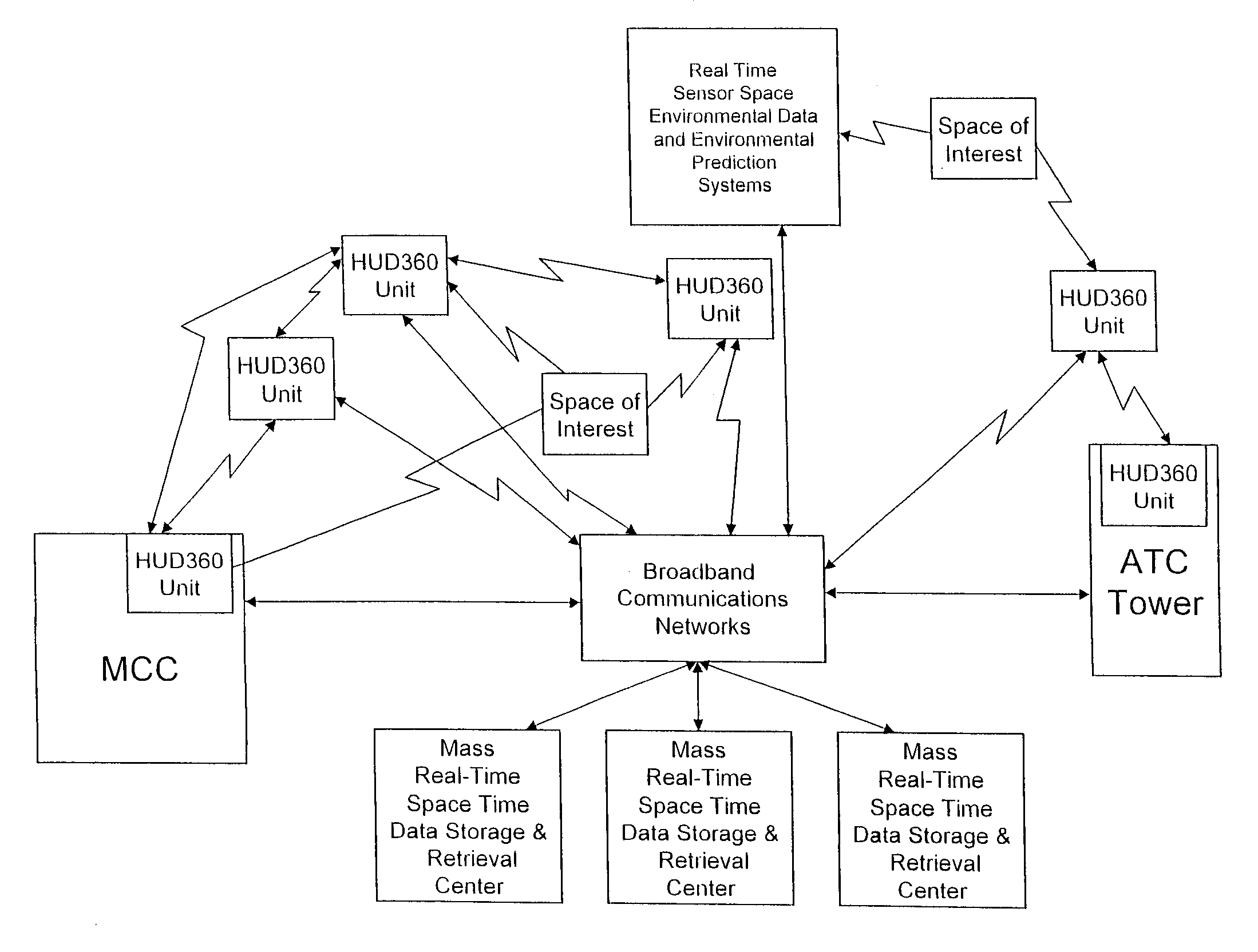
A safety critical, time sensitive data system for projecting safety / mission critical data onto a display pair of Commercial Off The Shelf (COTS) light weight projection glasses or monocular creating a virtual 360° HUD (Heads Up Display) with 6 degrees of freedom movement. The system includes the display, the workstation, the application software, and inputs containing the safety / mission critical information (Current User Position, Total Collision Avoidance System—TCAS, Global Positioning System—GPS, Magnetic Resonance Imaging—MRI Images, CAT scan images, Weather data, Military troop data, real-time space type markings etc.). The workstation software processes the incoming safety / mission critical data and converts it into a three dimensional space for the user to view. Selecting any of the images may display available information about the selected item or may enhance the image. Predicted position vectors may be displayed as well as 3D terrain.
Owner:REALTIME
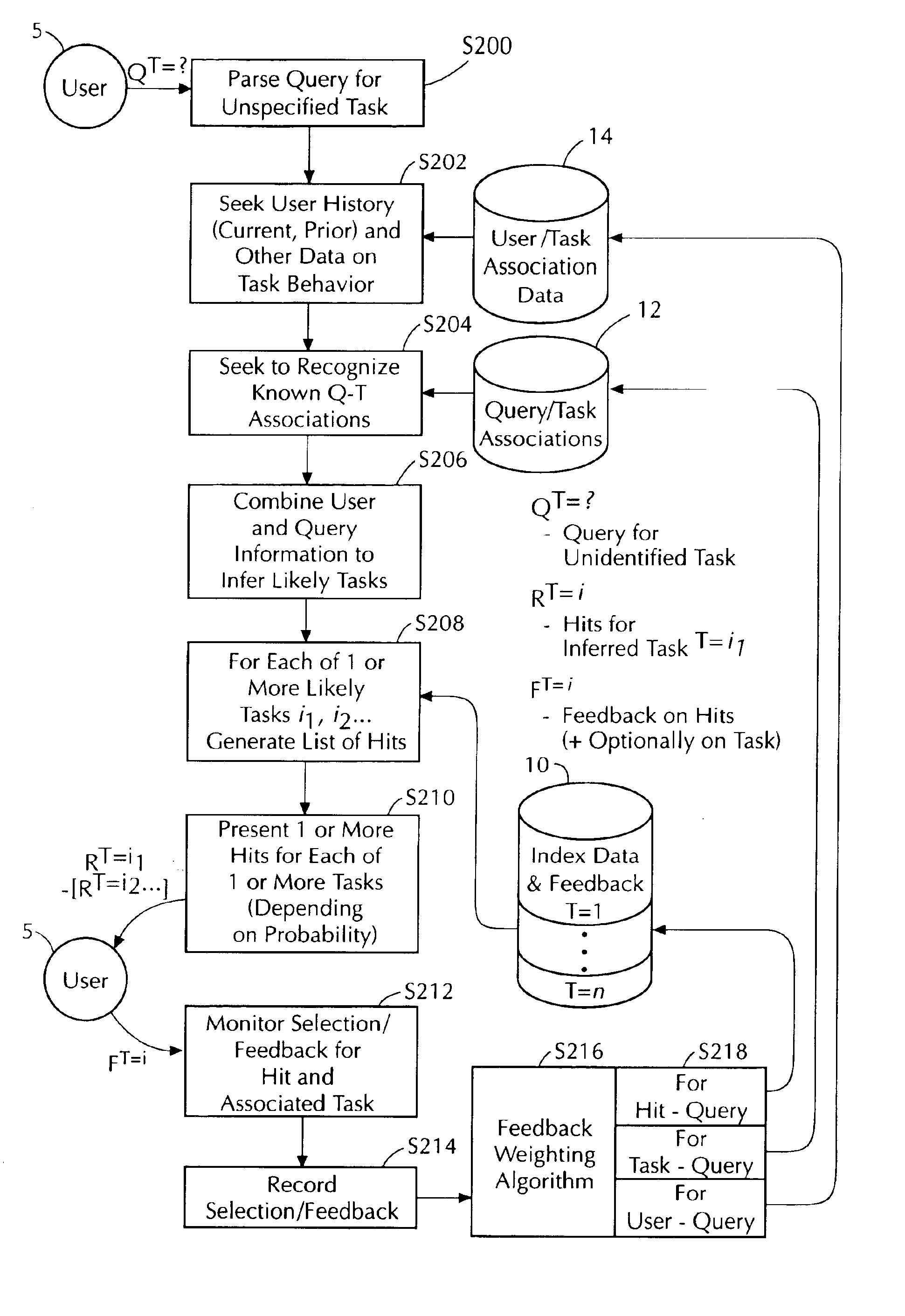
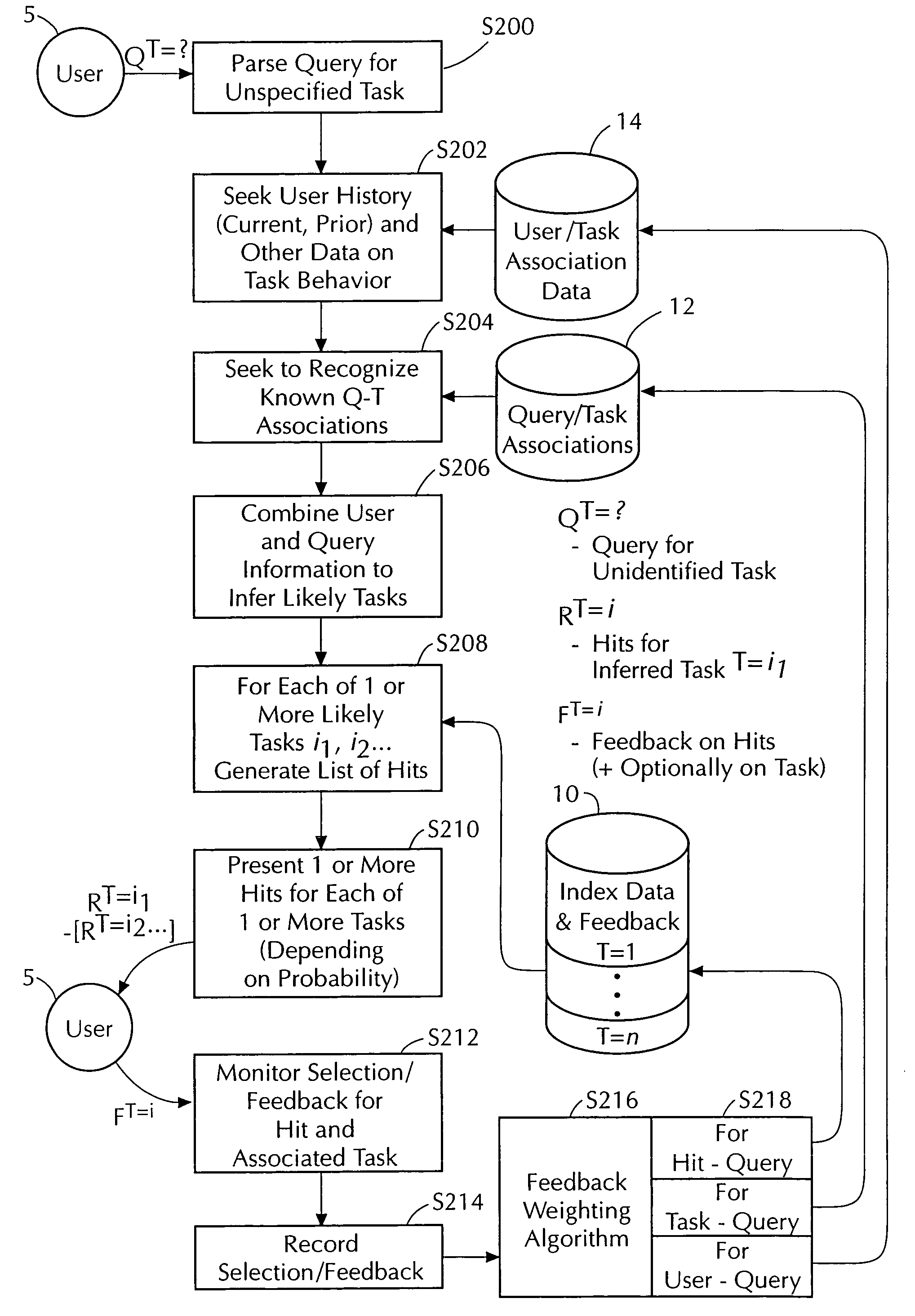
Task/domain segmentation in applying feedback to command control
InactiveUS6954755B2Reduced extraneous “ noise ” informationFurther focus the searchData processing applicationsWeb data indexingCommunication interfaceCommand and control
An apparatus for responding to a current user command associated with one of a plurality of task / domains includes: a digital storage device that stores cumulative feedback data gathered from multiple users during previous operations of the apparatus and segregated in accordance with the plurality of task / domains; a first digital logic device that determines the current task / domain with which the current user command is associated; a second digital logic device that determines a current response to the current user command on the basis of that portion of the stored cumulative feedback data associated with the current task / domain; a first communication interface that communicates to the user the current response; and a second communication interface that receives from the user current feedback data regarding the current response. The current feedback data is added to the cumulative feedback data stored in the digital storage device and associated with the current task / domain.
Owner:OPEN TV INC +1
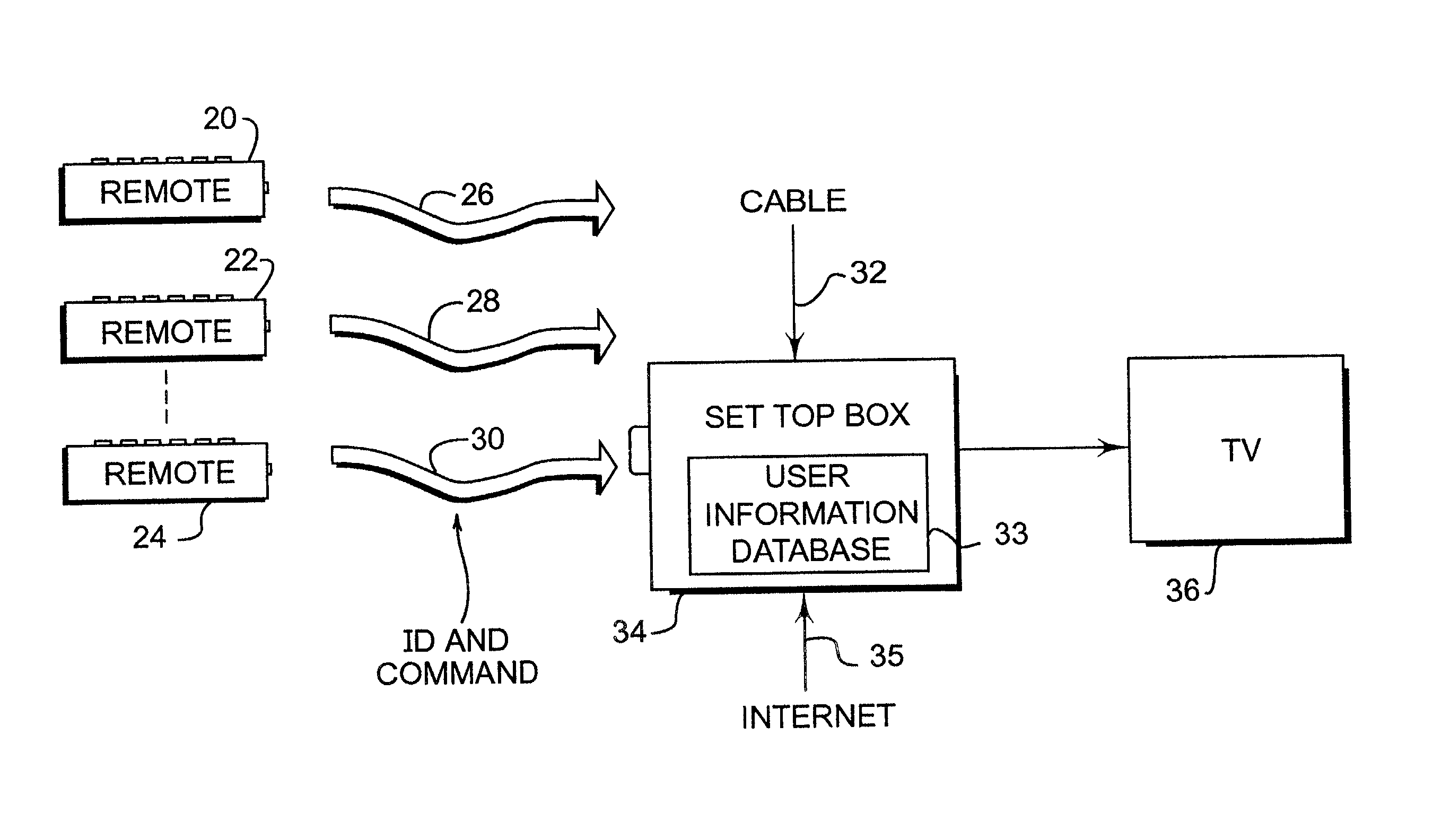
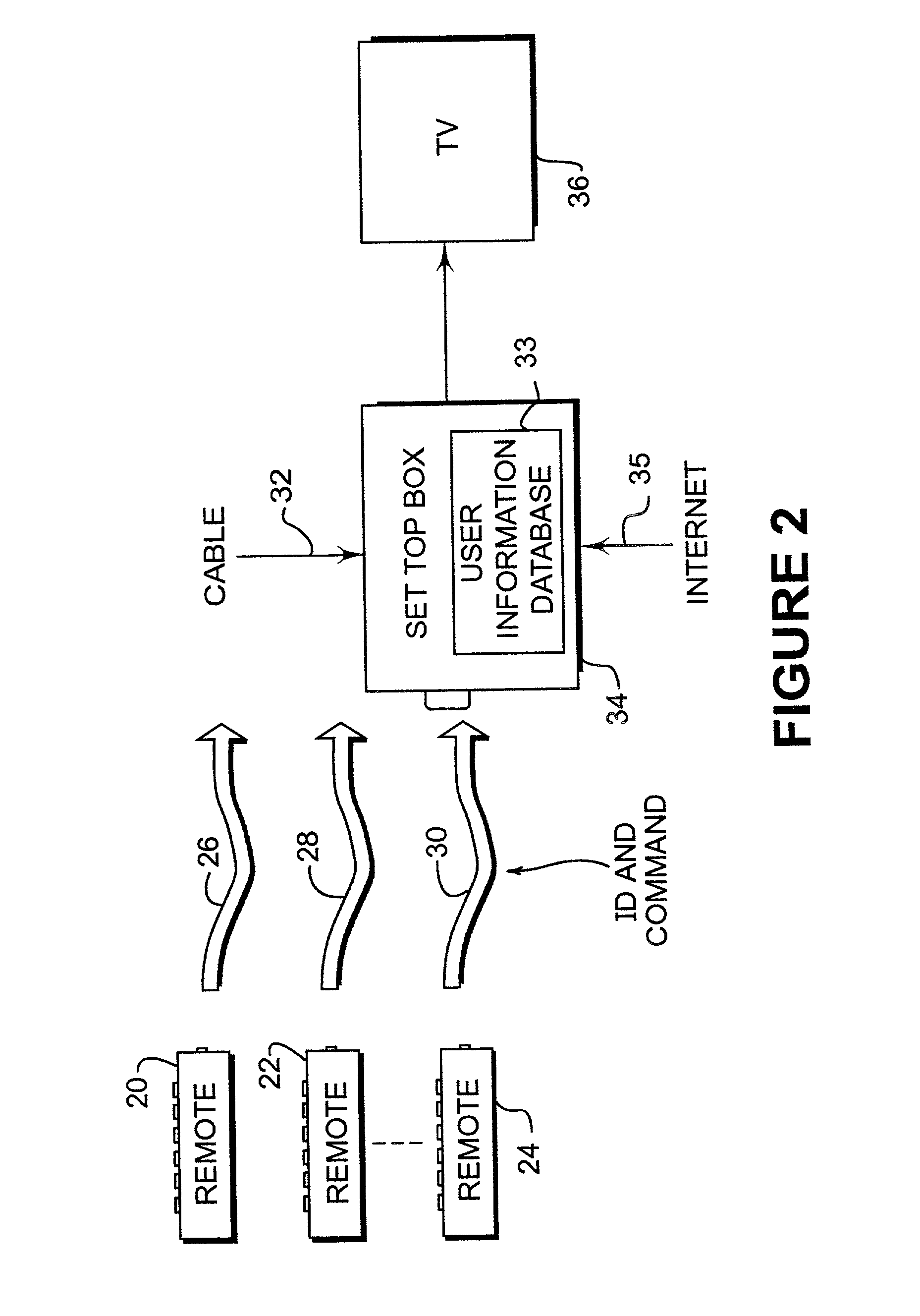
Personalized remote control
InactiveUS20020059588A1Television system detailsAnalogue secracy/subscription systemsPersonalizationRemote control
Disclosed is a remote control device that interacts with a set-top box to provide selective programming and / or enhanced content based upon the identity of the user of the remote control. The present invention utilizes preference and profile data corresponding to the current user to control the video output and / or enhanced content of the display. The present invention can also select or exclude video or enhanced content based upon tags that describe video content and the identity of the user based upon the use of a personalized remote control. The present invention can employ recognition techniques, such as word recognition, image recognition and sound recognition to restrict or select video content based upon the identity of the user of a personalized remote control device.
Owner:INTELLOCITY USA
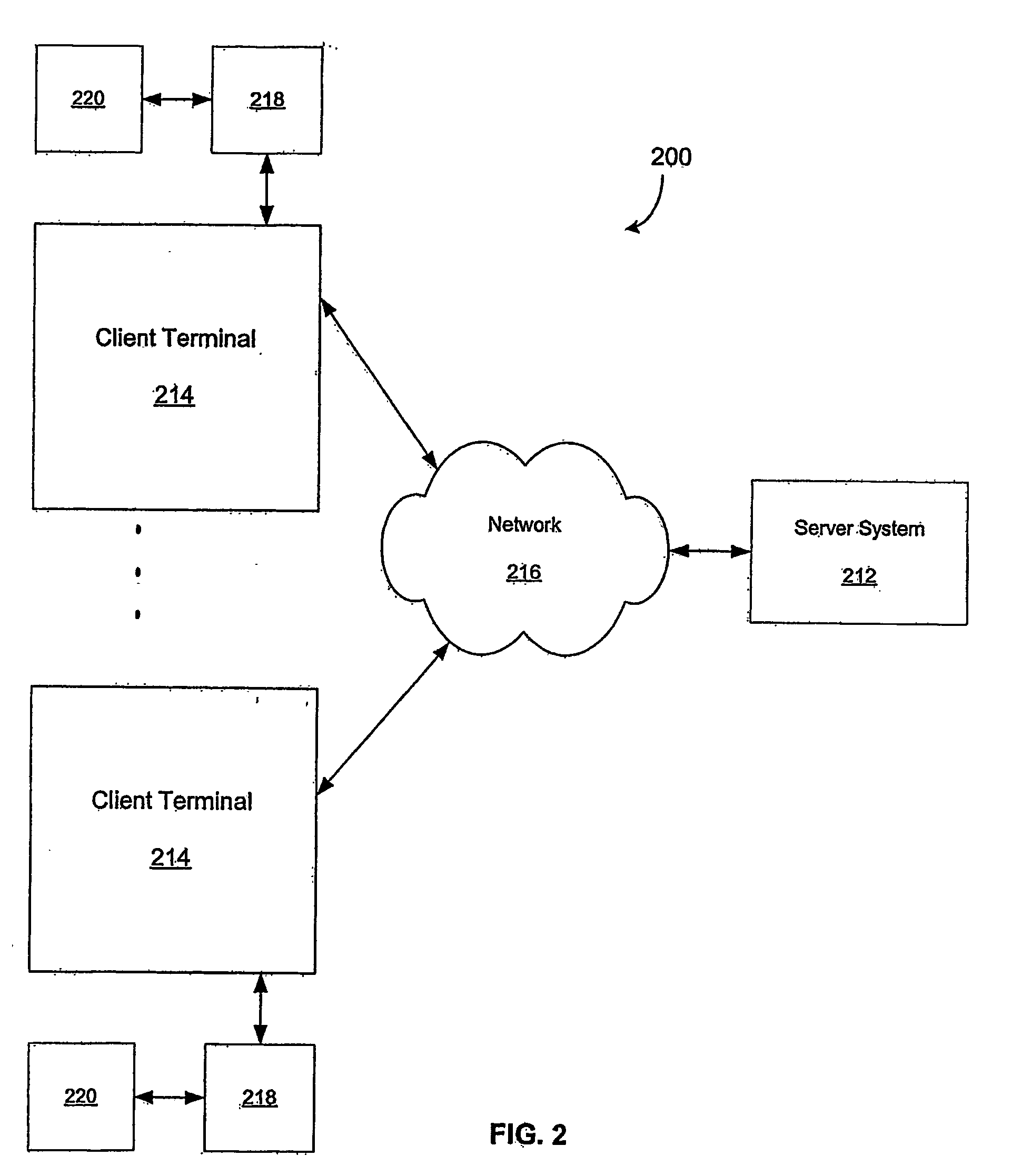
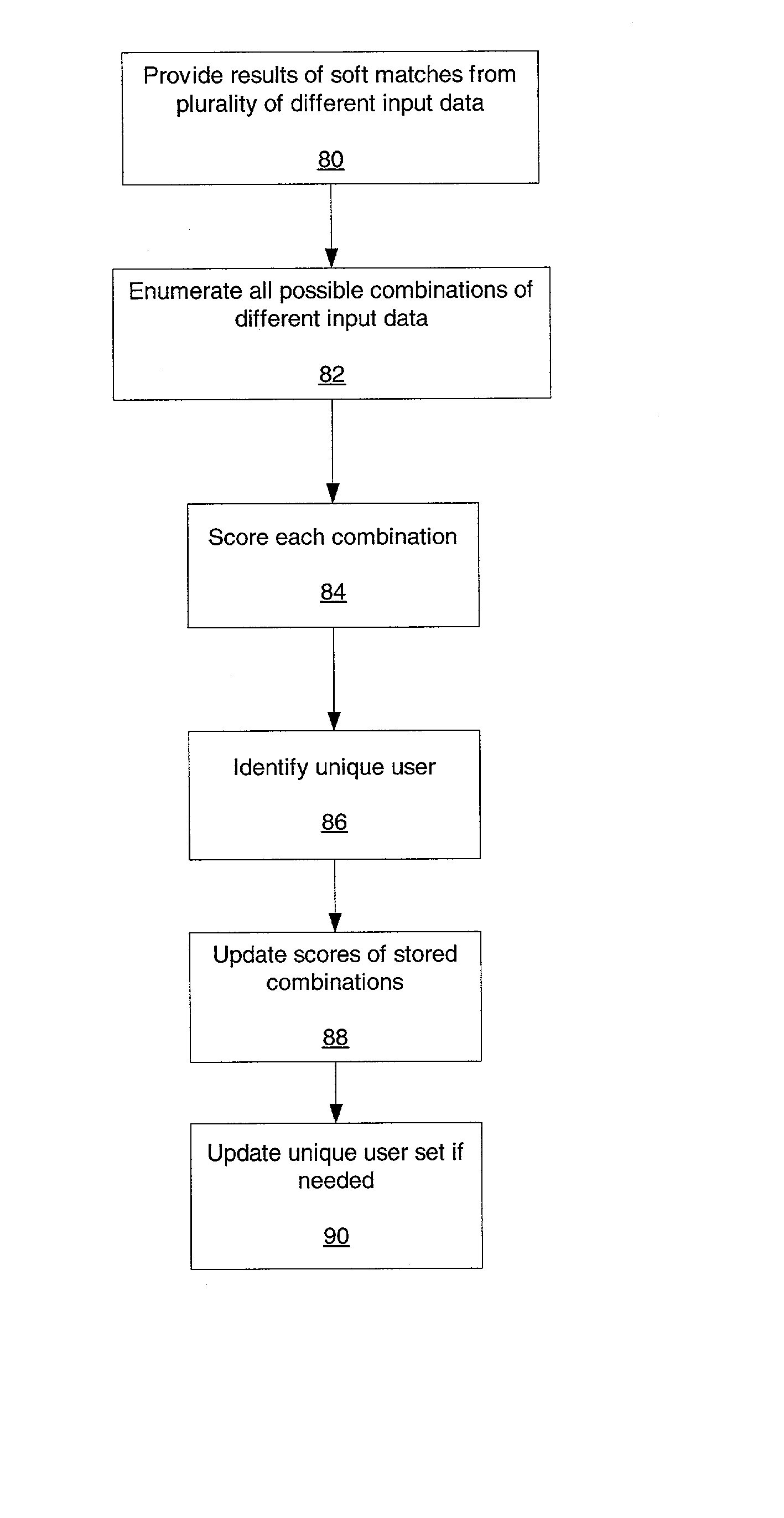
Method and apparatus for identifying unique client users from user behavioral data
ActiveUS7092926B2Digital computer detailsAnalogue secracy/subscription systemsUser inputTerminal equipment
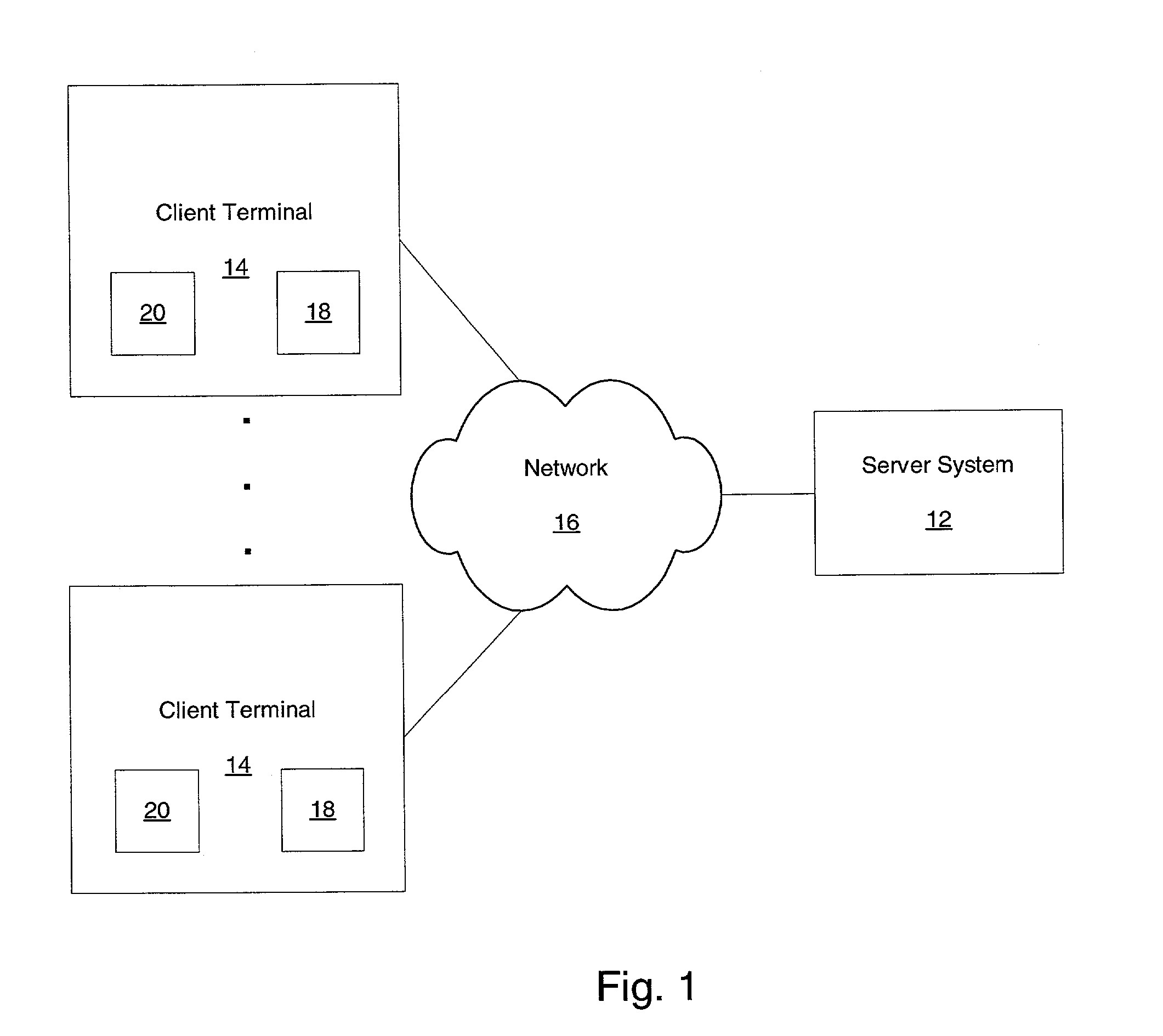
A method and system are provided for identifying a current user of a terminal device from a group of possible users. The method includes providing a database containing multiple user input pattern profiles of prior user inputs to the terminal device. Each of the possible users of the group are associated with at least one of the user input pattern profiles. Current input patterns from use of the terminal device are detected. The current input patterns are combined and then dynamically matched with one of the user input pattern profiles, and the possible user associated with the matched user input pattern profile is selected as the current user. The system for identifying a current user of a terminal device from a group of possible users includes a database containing multiple user input pattern profiles of prior user inputs to the terminal device. Each of the possible users is associated with at least one of the user input pattern profiles. The system detects current input patterns from use of the terminal device, and then combines the patterns and dynamically matches the patterns with one of the user input pattern profiles. The system selects the possible user associated with the matched user input pattern profiles as the current user.
Owner:COX COMMUNICATIONS
Computer-aided system for 360 degree heads up display of safety/mission critical data
InactiveUS20100240988A1Satisfy safety performance requirementsGuaranteed uptimeCathode-ray tube indicatorsDiagnostic recording/measuringHead-up displayDisplay device
A safety critical, time sensitive data system for projecting safety / mission critical data onto a display pair of Commercial Off The Shelf (COTS) light weight projection glasses or monocular creating a virtual 360° HUD (Heads Up Display) with 6 degrees of freedom movement. The system includes the display, the workstation, the application software, and inputs containing the safety / mission critical information (Current User Position, Total Collision Avoidance System—TCAS, Global Positioning System—GPS, Magnetic Resonance Imaging—MRI Images, CAT scan images, Weather data, Military troop data, real-time space type markings etc.). The workstation software processes the incoming safety / mission critical data and converts it into a three dimensional space for the user to view. Selecting any of the images may display available information about the selected item or may enhance the image. Predicted position vectors may be displayed as well as 3D terrain.
Owner:REALTIME
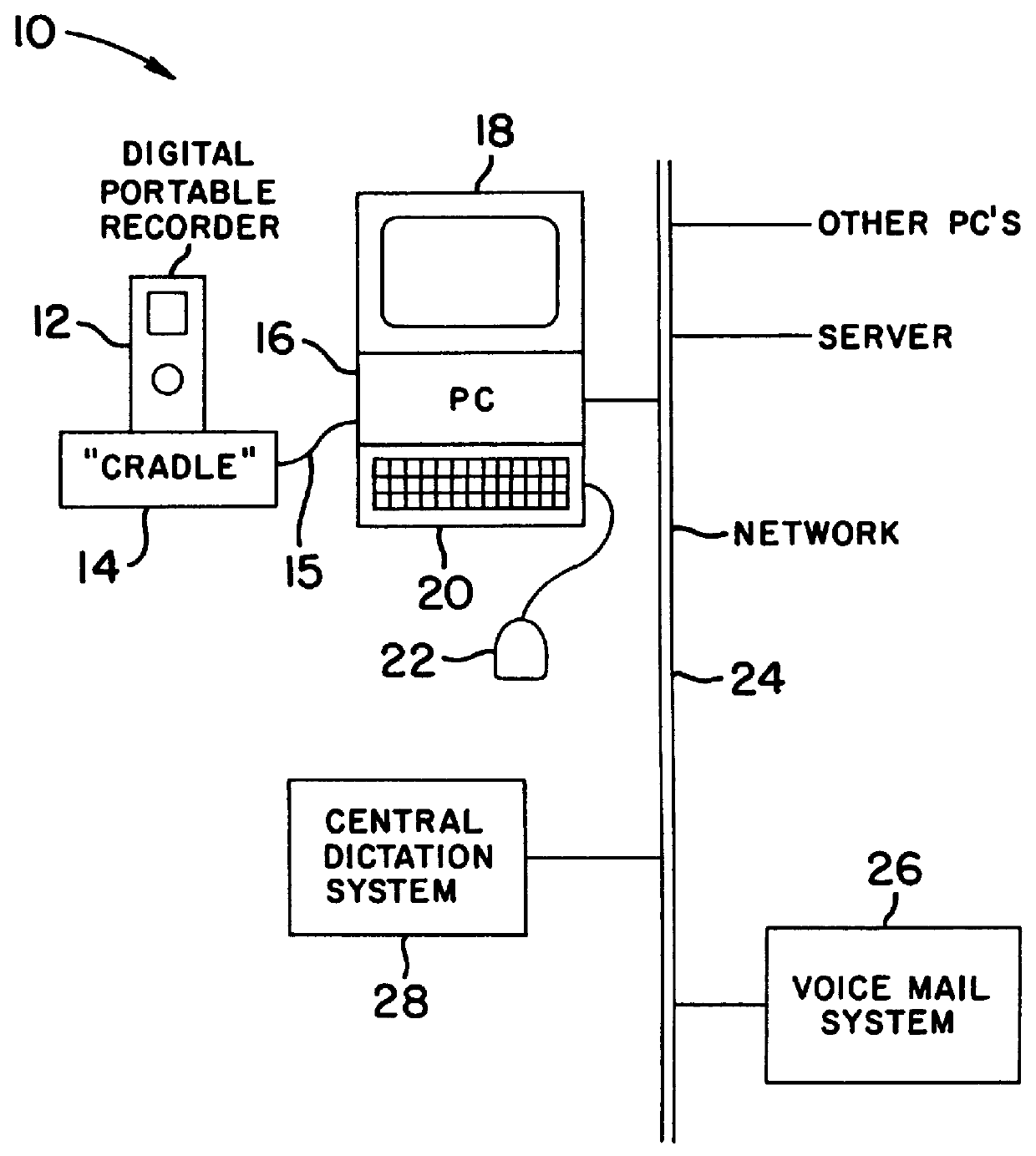
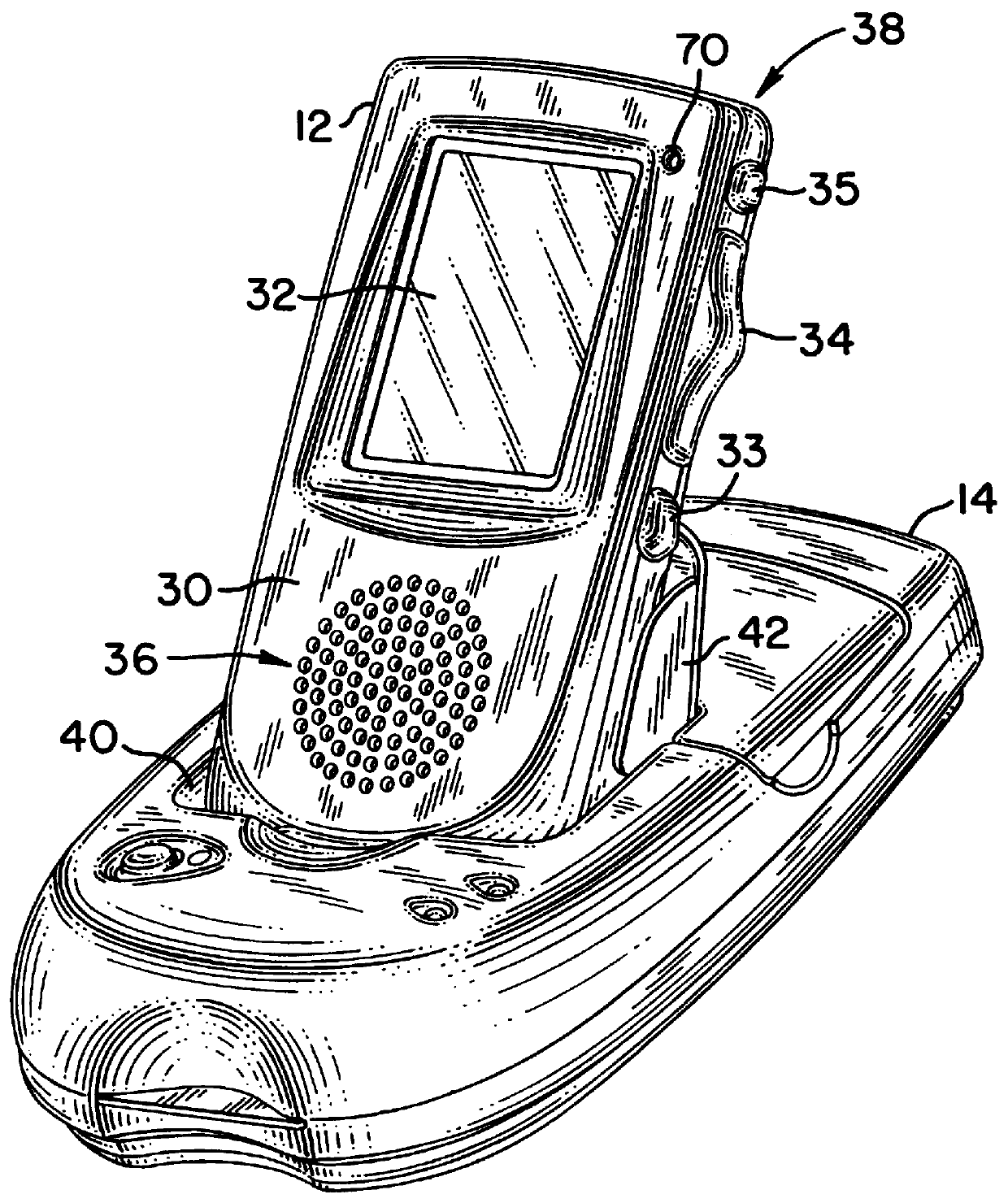
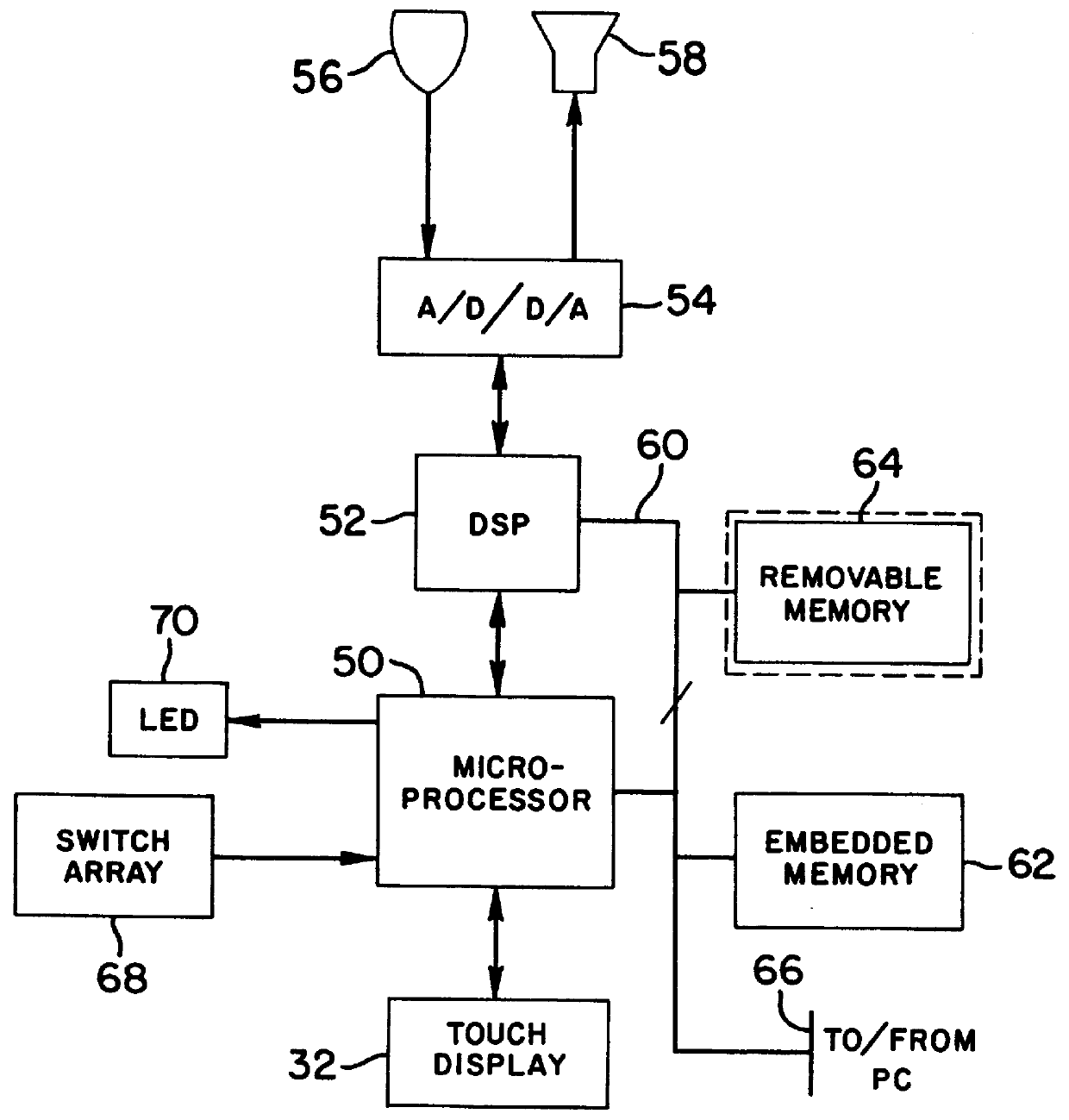
Portable digital audio recorder with adaptive control configurations
InactiveUS6038199AEasy to shareEasy to manageDriving/moving recording headsSpecial service for subscribersComputer hardwareSelf adaptive
A portable digital audio recorder provides a first set of control or editing options with respect to a first category of voice data files stored in the recorder, and provides a different set of control or editing options with respect to a second category of voice data files stored in the recorder. The recorder may also be conveniently shared among a number of users and adapts various operating parameters to the preferences of the current user.
Owner:NUANCE COMM INC
Automated transcription system and method using two speech converting instances and computer-assisted correction
InactiveUS6961699B1Improve accuracyNatural language data processingSpeech recognitionComputer-aidedVoice transformation
A system for automating transcription services for one or more users. This system receives a voice dictation file from a current user, which is automatically converted into a first written text based on a set of conversion variables. The same voice dictation file is automatically converted into a second written text based on a second set of conversion variables. The first and second sets of conversion variables have at least one difference, such as different speech recognition programs, different vocabularies, and the like. The system further includes a program for manually editing a copy of the first and second written text to create a verbatim text of the voice dictation file. This verbatim text can be delivered to the current user as transcribed text. The verbatim text can also be fed back into each speech recognition instance to improve the accuracy of each instance with respect to the human voice in the file.
Owner:CUSTOM SPEECH USA
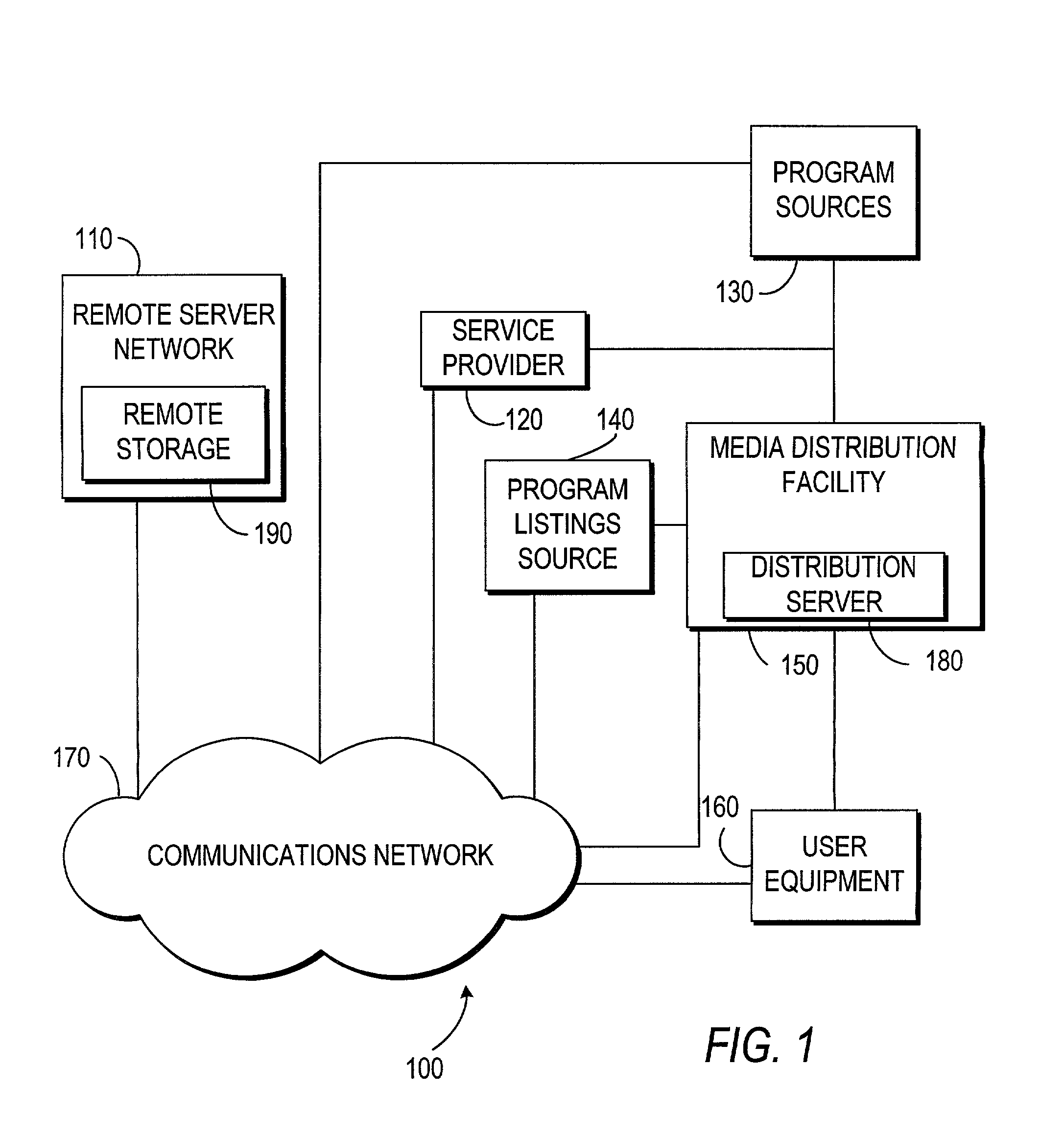
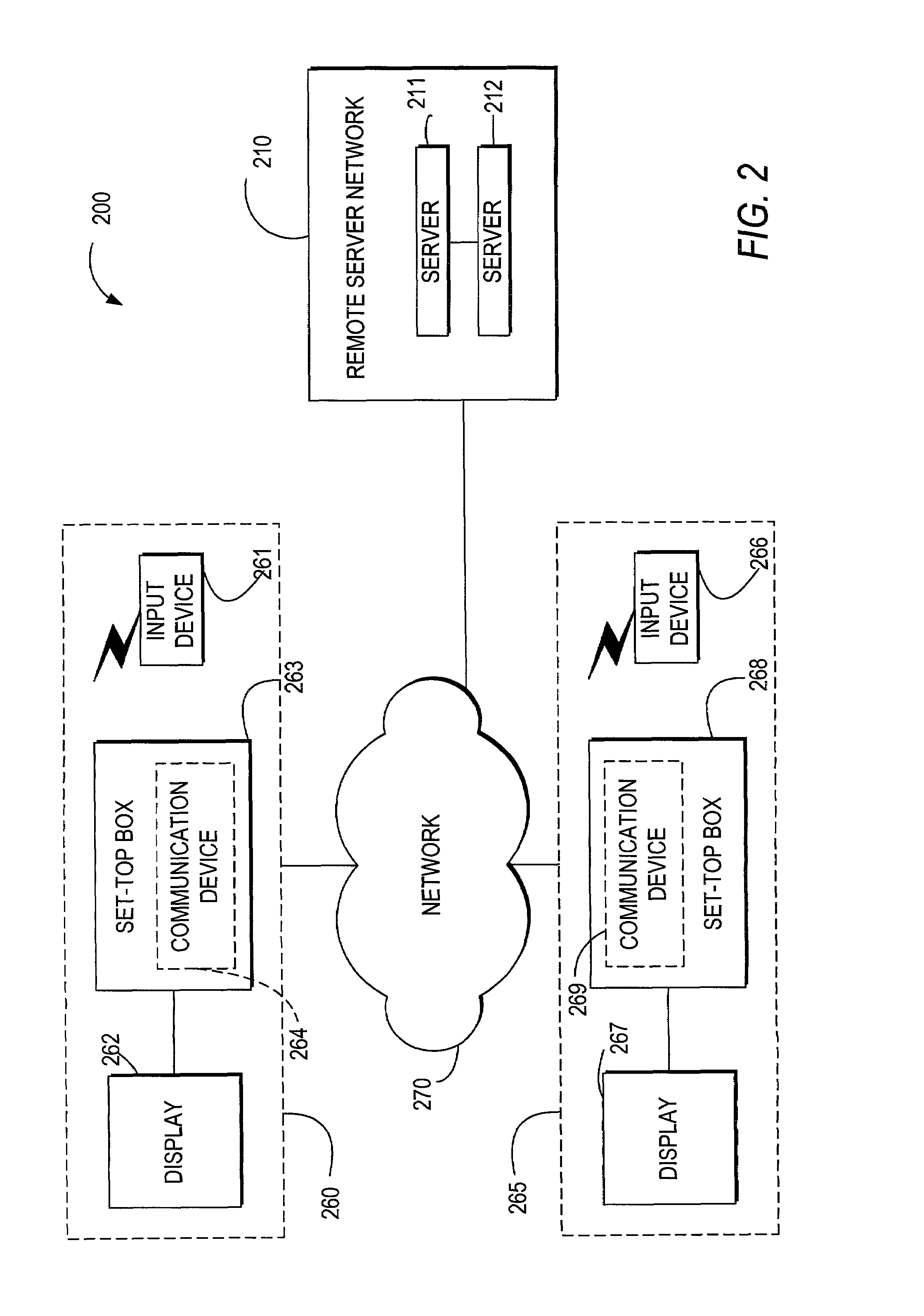
Systems and methods for providing storage of data on servers in an on-demand media delivery system
ActiveUS7650621B2Television system detailsAnalogue secracy/subscription systemsFile allocationData storing
A system and method may be provided that allows users to store, retrieve, and manipulate on-demand media content and data stored on a remote server network in an on-demand media delivery system. More particularly, the system may allow a user to access his or her on-demand media account from user equipment in different locations as long as the current user equipment can communicate with a remote server that stores user-specific information. The system upon user selection may freeze the delivery of on-demand media at a particular point and allow the user to resume the media at a later time from some other network location in system. Users may upload personal images or files to an on-demand delivery server for later retrieval and display. Users may be permitted to assign access rights to the uploaded files.
Owner:ROVI GUIDES INC
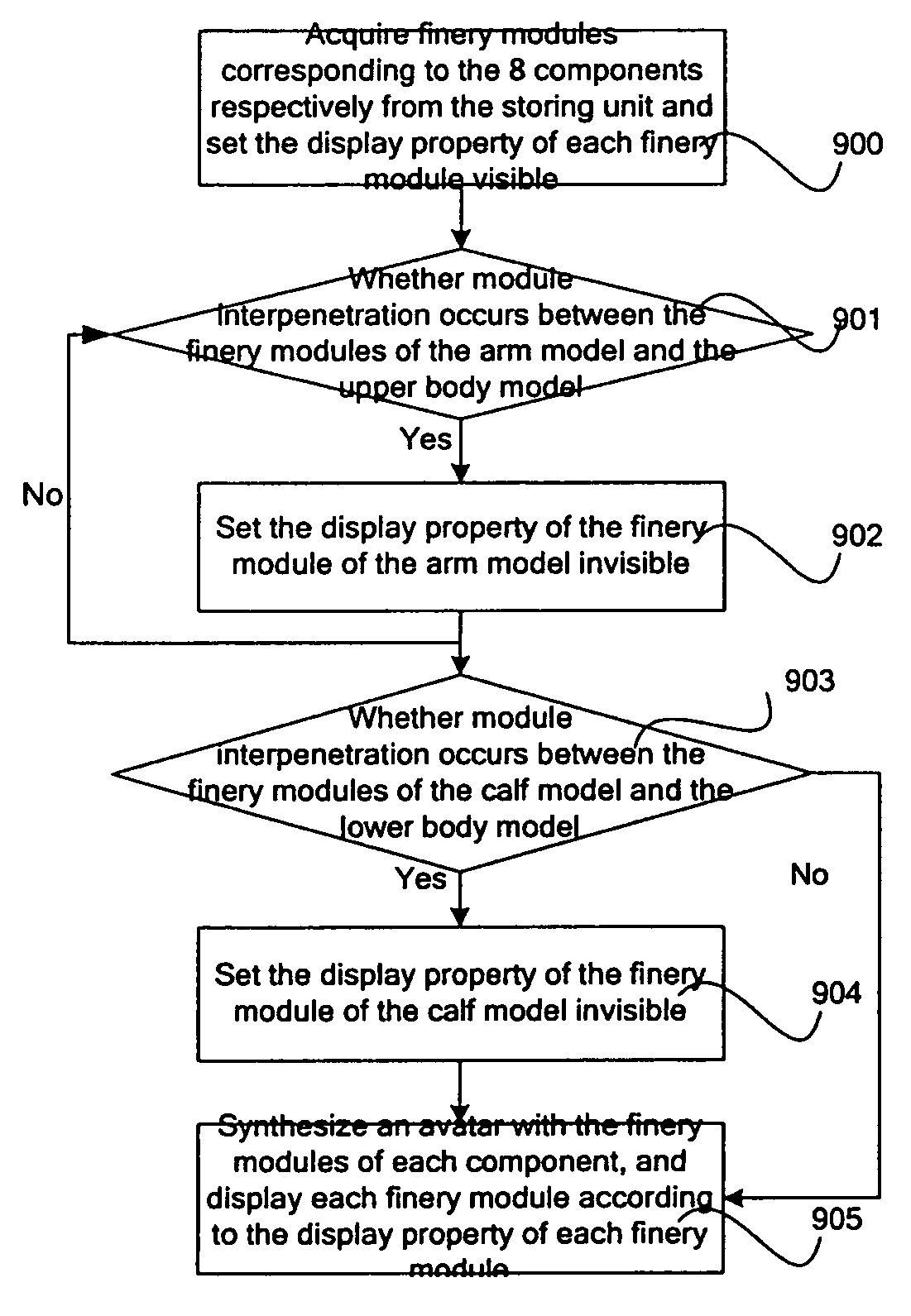
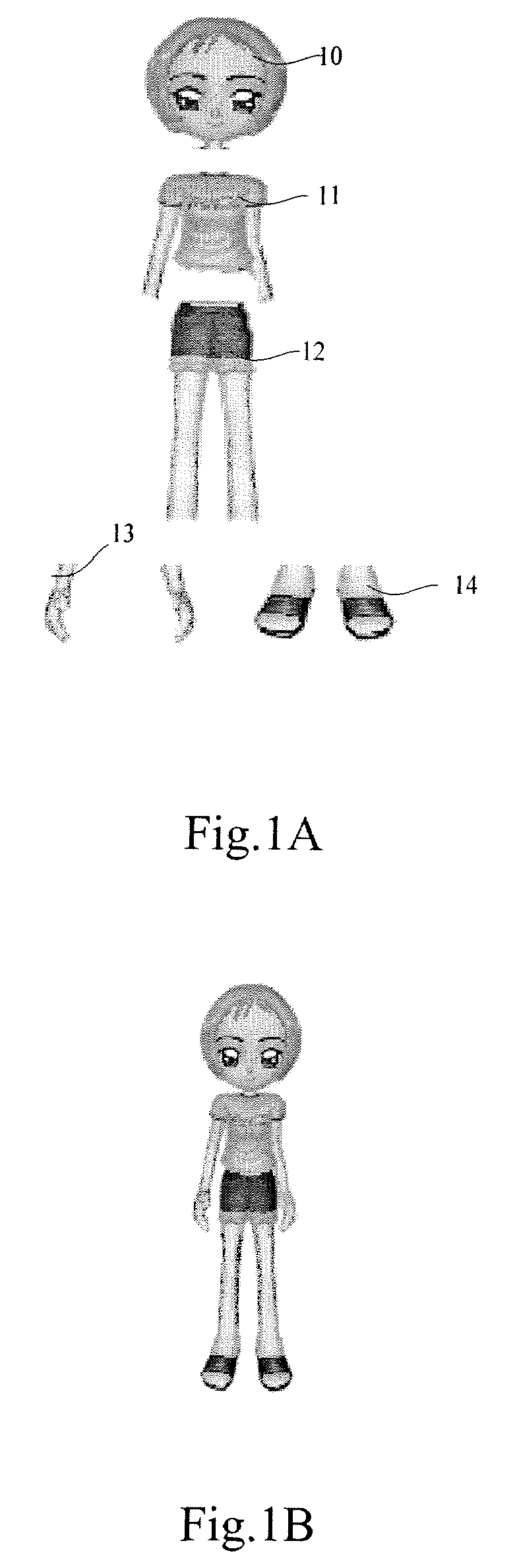
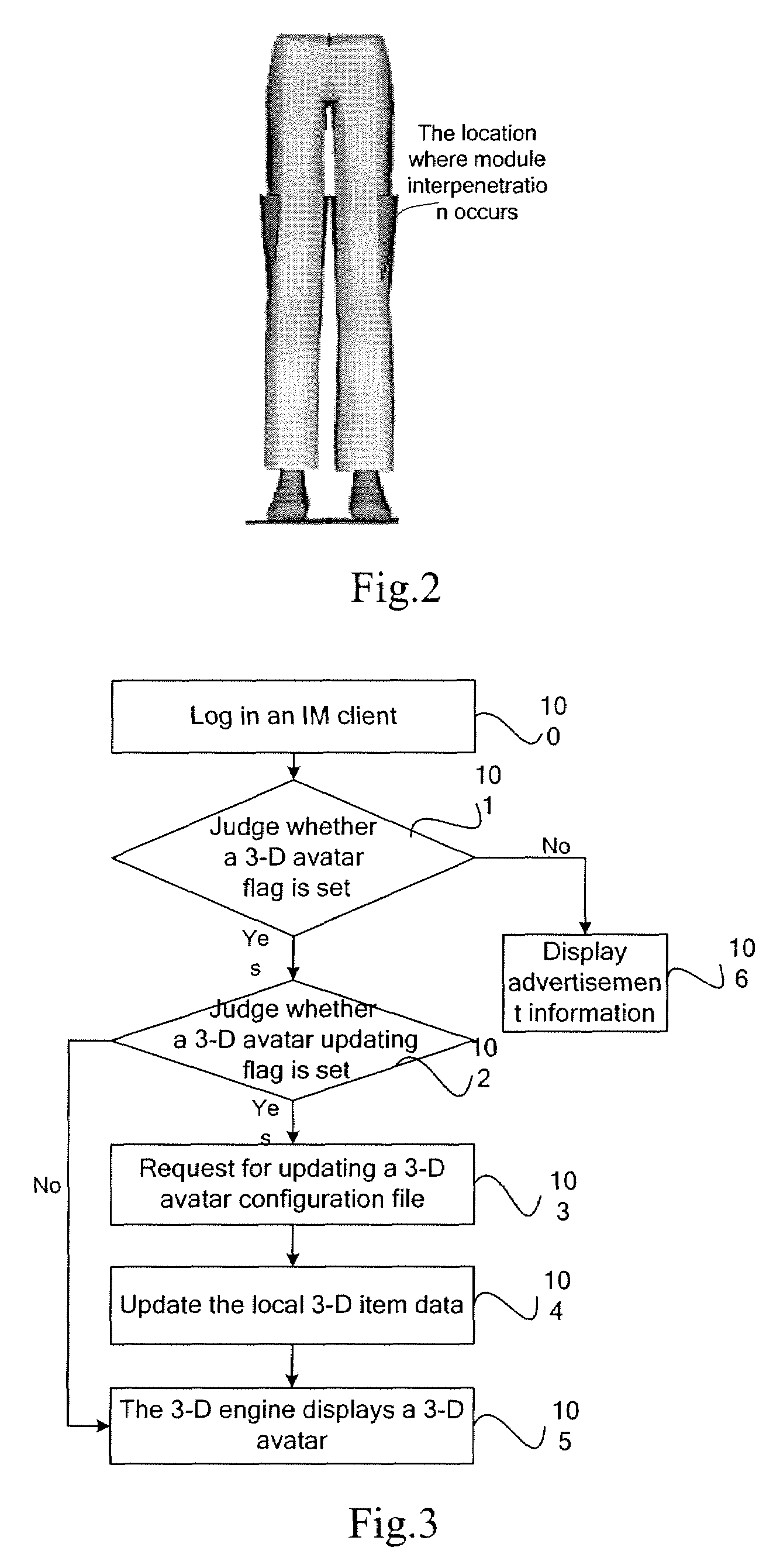
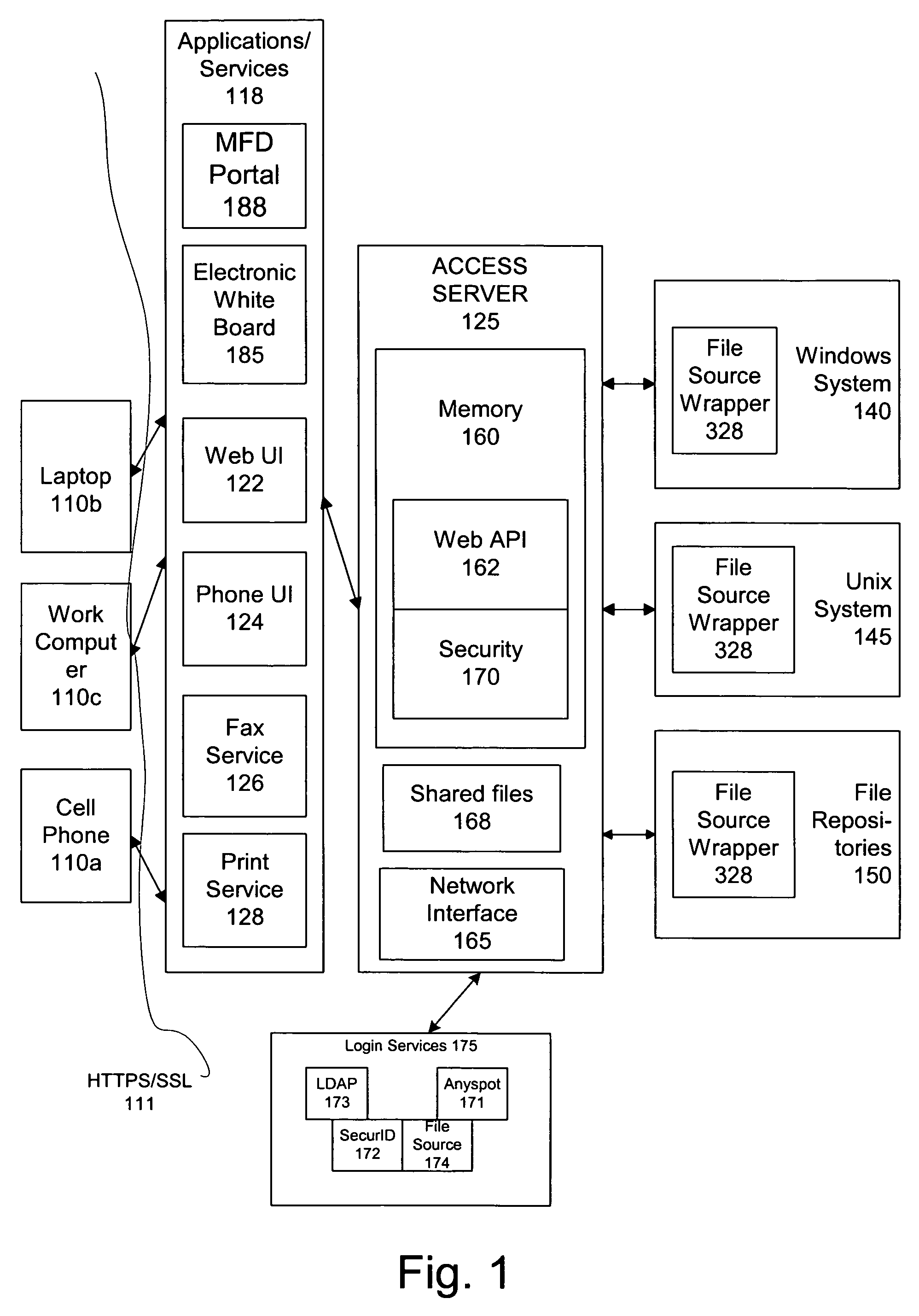
Method of displaying 3-D avatar and system thereof
A method of displaying a 3-D avatar provided includes acquiring a 3-D avatar configuration file for a current user; acquiring at least one 3-D item suite indicated by the 3-D avatar configuration file; displaying the at least one 3-D item suite according to the 3-D avatar configuration file. An instant messaging client, a server and a system of displaying a 3-D avatar are also provided. With the above technical solutions, a 3-D avatar is displayed in an IM client, with which a user can exhibit different personal images by freely choosing different 3-D item suite.
Owner:TENCENT TECH (SHENZHEN) CO LTD
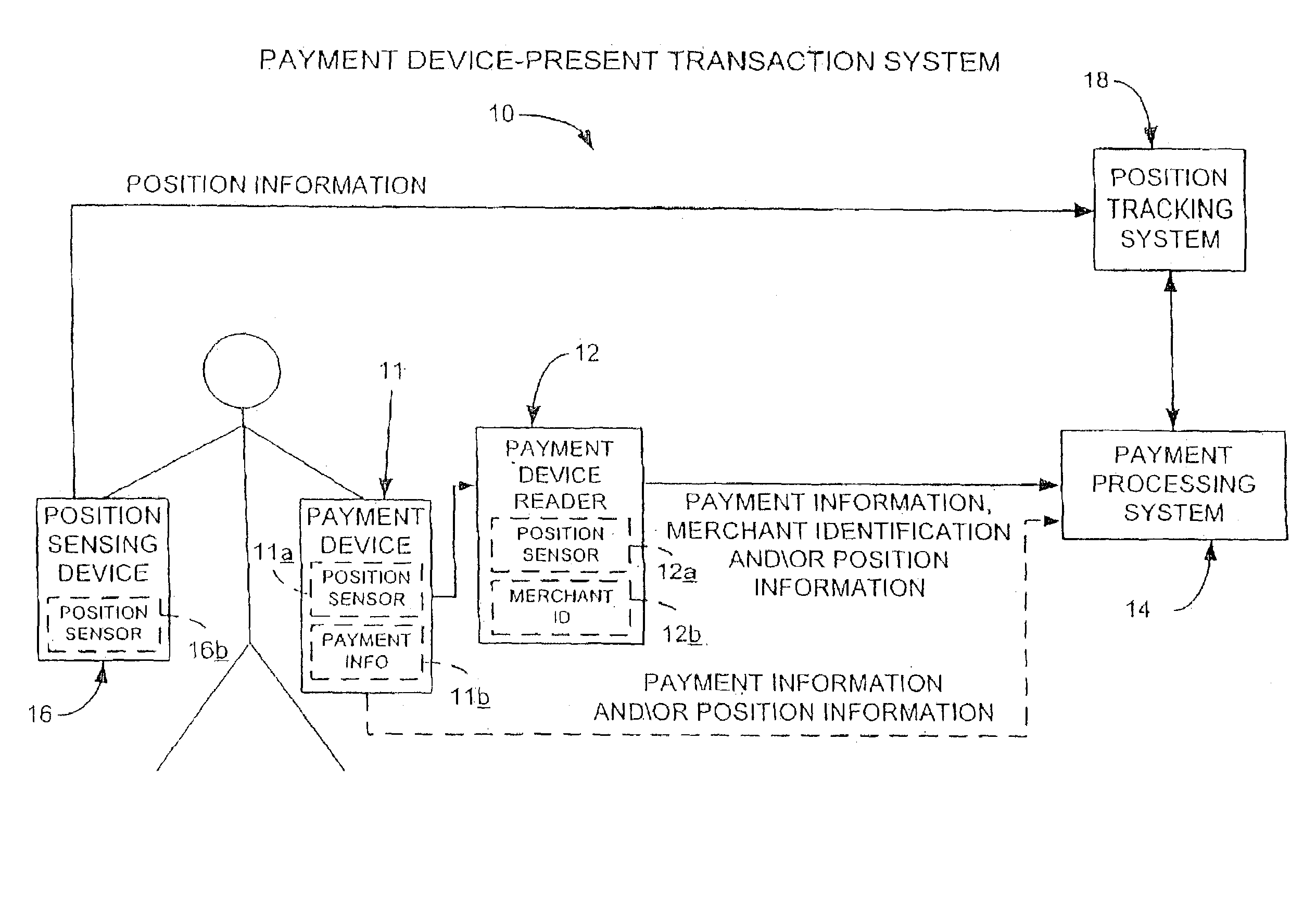
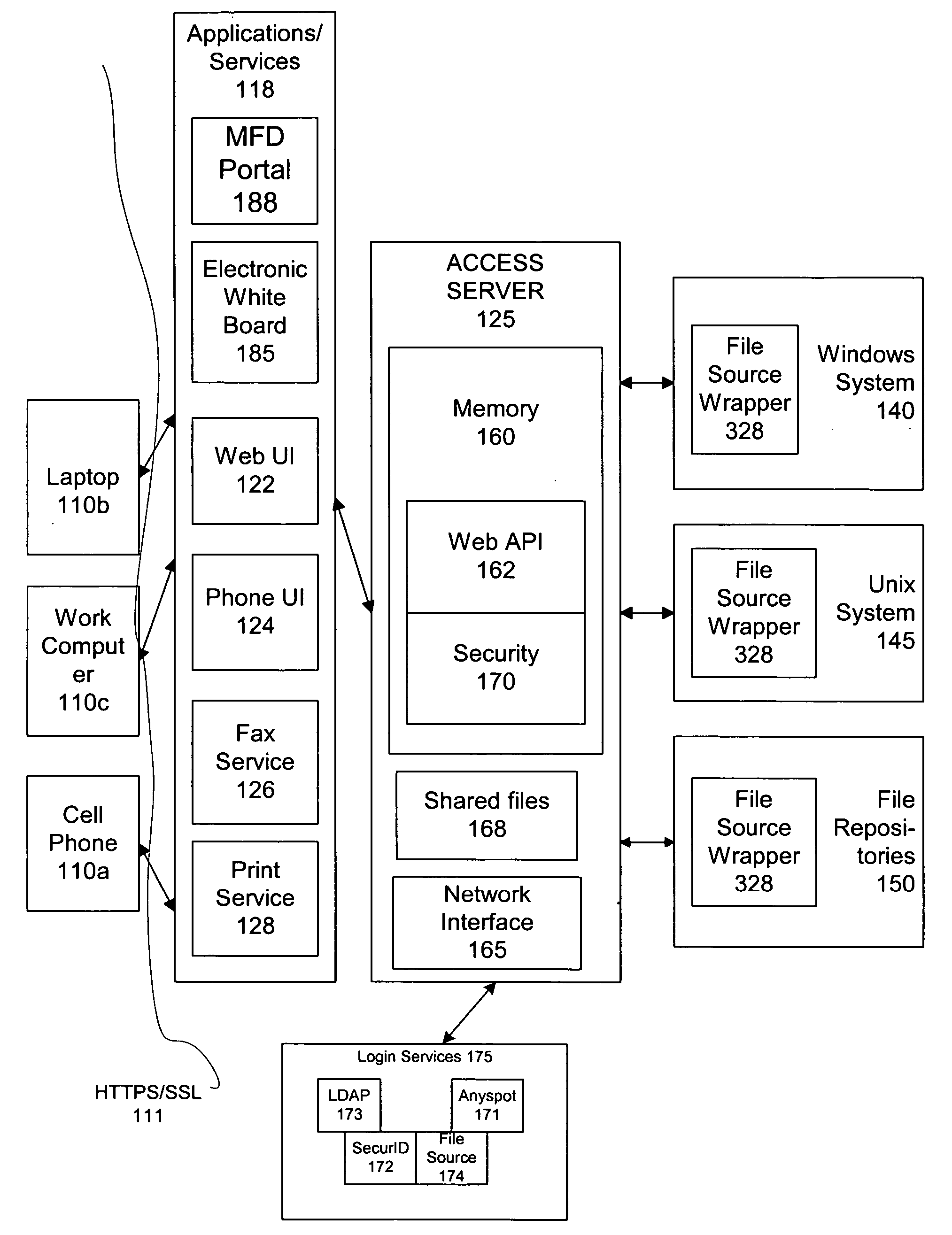
Remote file management using shared credentials for remote clients outside firewall
InactiveUS7412447B2Data processing applicationsMetadata multimedia retrievalEmail attachmentClient-side
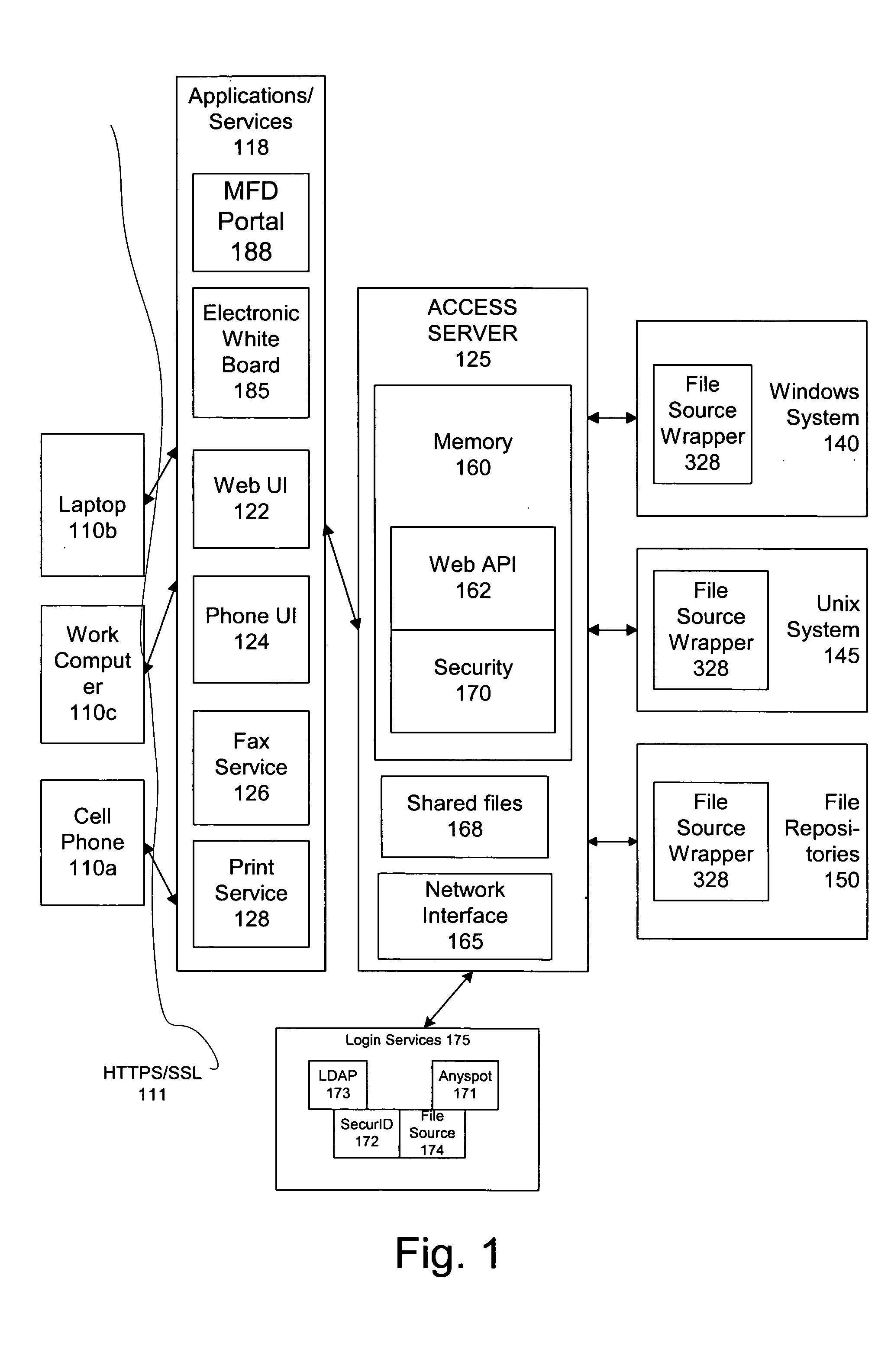
An access server allows secure access to commonly used files stored on multiple file sources from a variety of client devices. The access server extracts a list of file sources associated with the user, and accesses each of those sources. The server is then configured to extract a list of most recently used files by the current user as well as information associated with those files. The access server also processes electronic mail attachments. The access server intercepts electronic mail messages containing attachments, and transmits the attachments to a file server.
Owner:FUJIFILM BUSINESS INNOVATION CORP
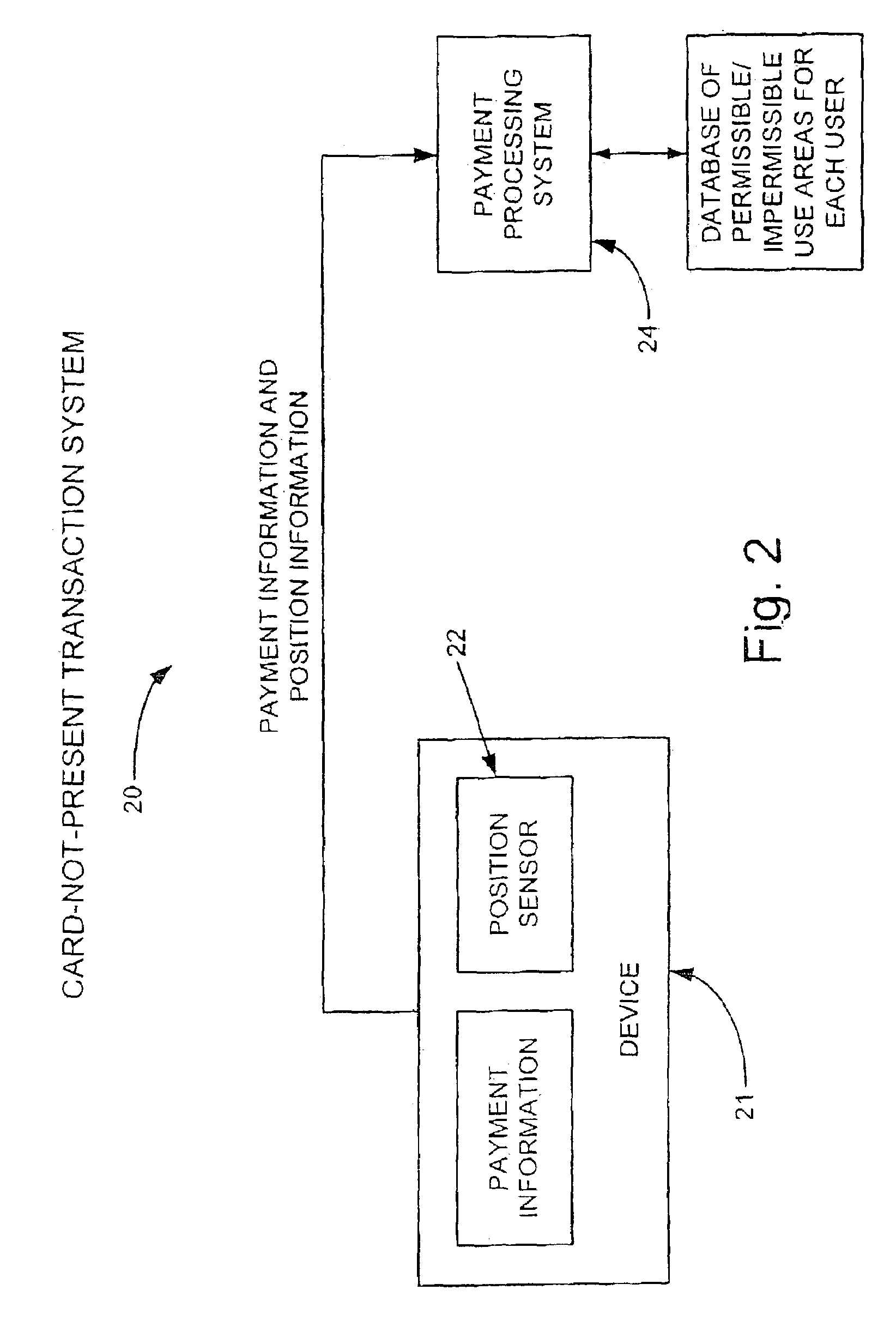
Location based fraud reduction system and method
ActiveUS7376431B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCredit cardTelecommunications
Likelihood of fraud is reduced by having at least one of an identifier of a location from where a request is submitted or information that can lead to identification of the location, submitted with or in addition to a request. Then, determination is made to whether to service the request, based at least in part on the location from where the request is submitted. In various embodiments, the location may be compared against predetermined permissible location(s) or a current user location. The request may be a request to charge an amount against an account, such as a credit card account, a request to access a physical resource, such as a VPN, or an informational resource, such as account information, or a request to access a secured area.
Owner:BLOCK INC
Computer-aided system for 360° heads up display of safety/mission critical data
InactiveUS20140240313A1Input/output for user-computer interactionCathode-ray tube indicatorsTerrainHead-up display
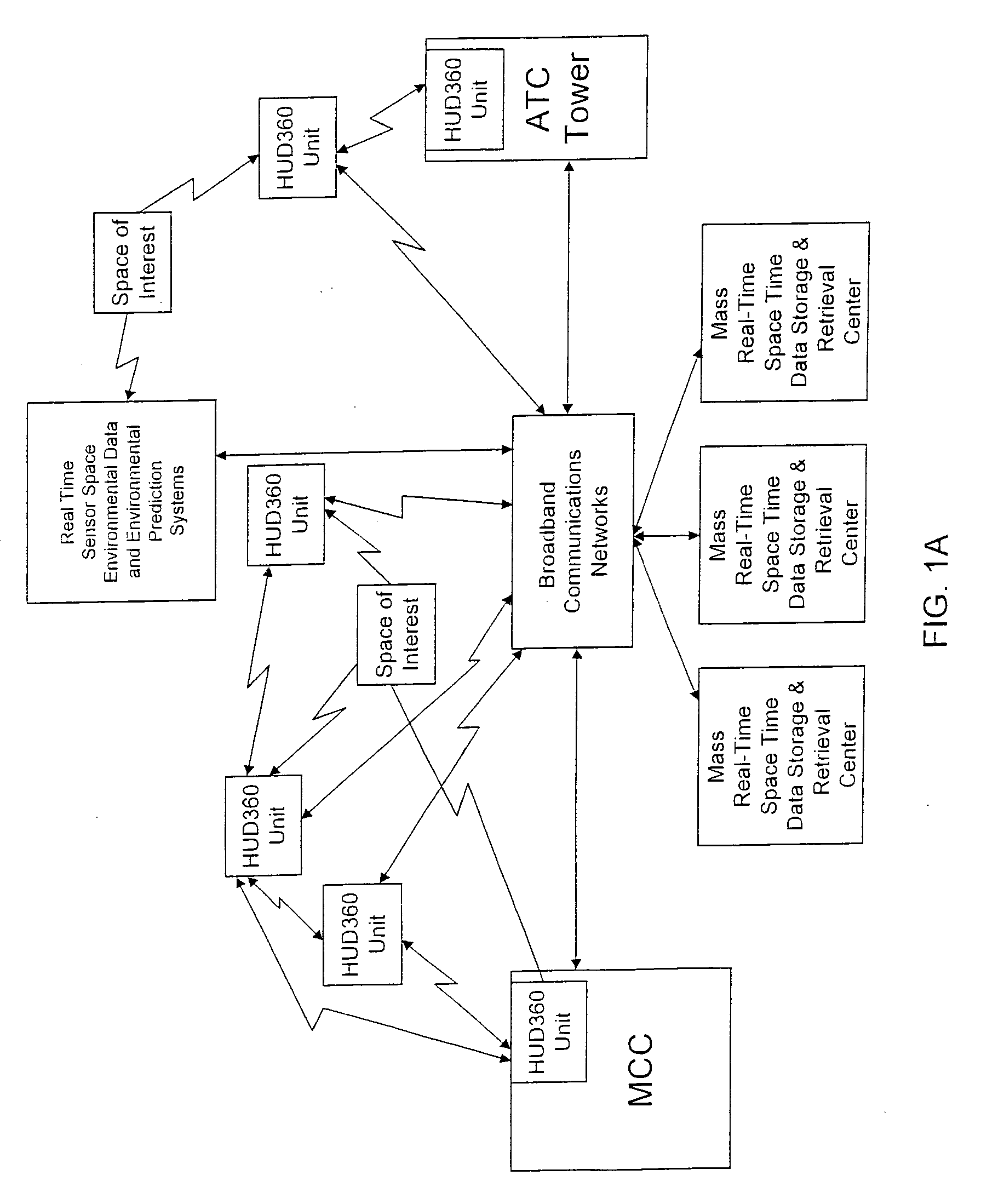
A Heads-Up-Display (“HUD”) system for projecting safety / mission critical data onto a display pair of light weight projection glasses or monocular creating a virtual 360 degree is disclosed. The HUD system includes a see-through display surface, a workstation, application software, and inputs containing the safety / mission critical information (Current User Position, Total Collision Avoidance System—TCAS, Global Positioning System—GPS, Magnetic Resonance Imaging—MRI Images, CAT scan images, Weather data, Military troop data, real-time space type markings etc.). The workstation software processes the incoming safety / mission critical data and converts it into a three-dimensional stereographic space for the user to view. Selecting any of the images may display available information about the selected item or may enhance the image. Predicted position vectors may be displayed as well as three-dimensional terrain.
Owner:REALTIME
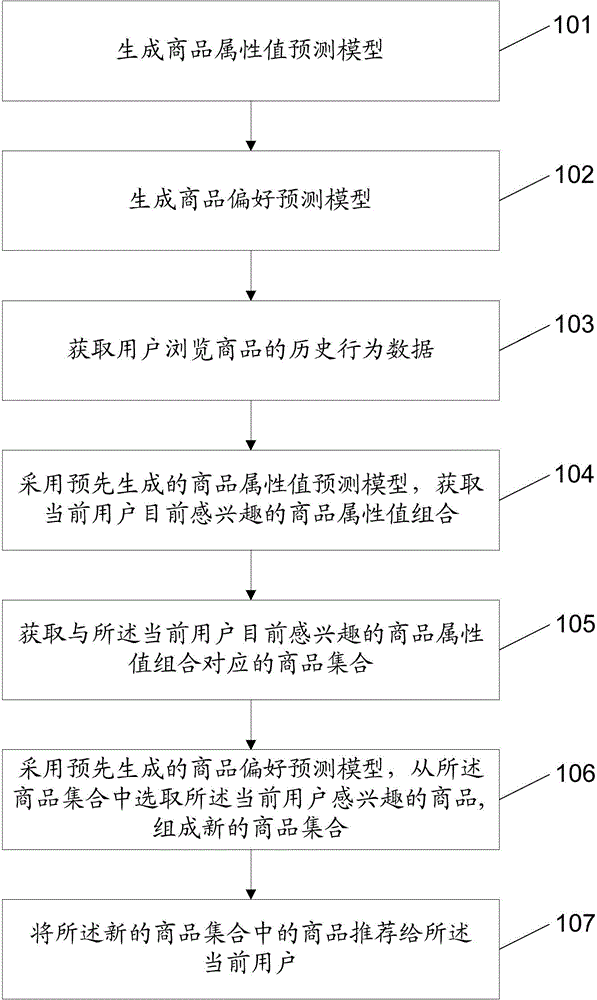
Commodity recommendation method and device
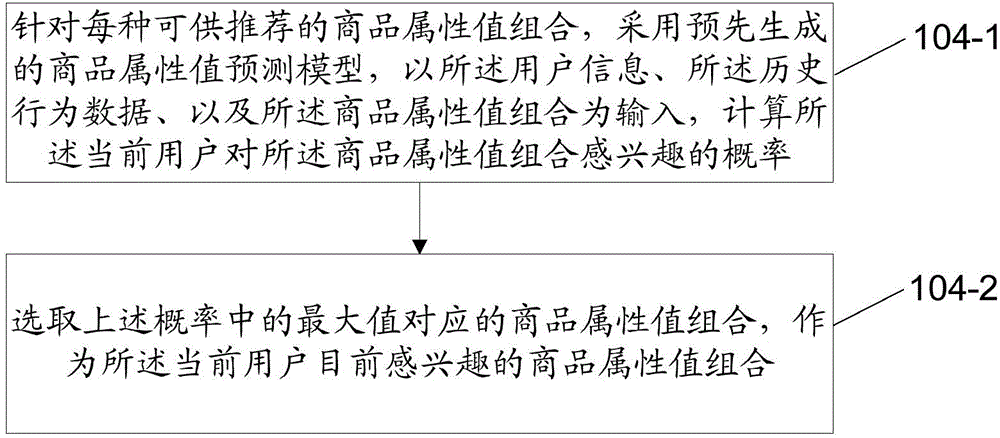
The invention discloses a commodity recommendation method which comprises a step of obtaining the historical behavior data of a user browsing commodity, a step of using a pre-generated commodity attribute value prediction model to obtain the currently interested commodity attribute value combination of a user according to the user information of a current user, the historical behavior data and a recommended commodity attribute value combination, and a step of obtaining the commodity set corresponding to the currently interested commodity attribute value combination of the user and recommending at least a part of the commodity in the commodity set to the current user. The invention also discloses a commodity recommendation device. By using the method provided by the invention, the currently interested commodity information can be accurately recommended to the user who browses the commodity at present in real time, the time of browsing the commodity of the user can be saved, the user experience can be effectively improved, and the commodity sale volume of a site can be improved.
Owner:ALIBABA GRP HLDG LTD
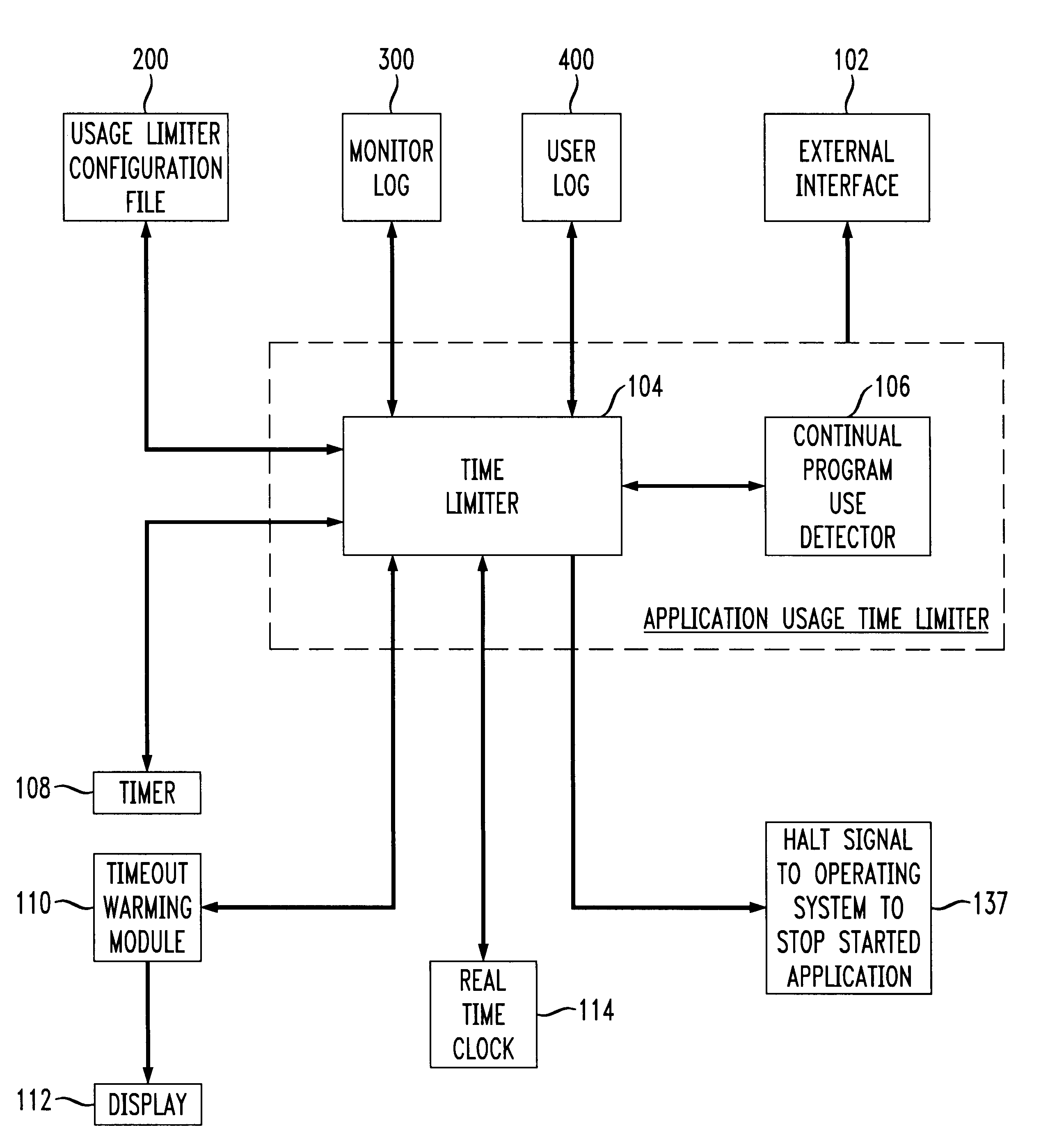
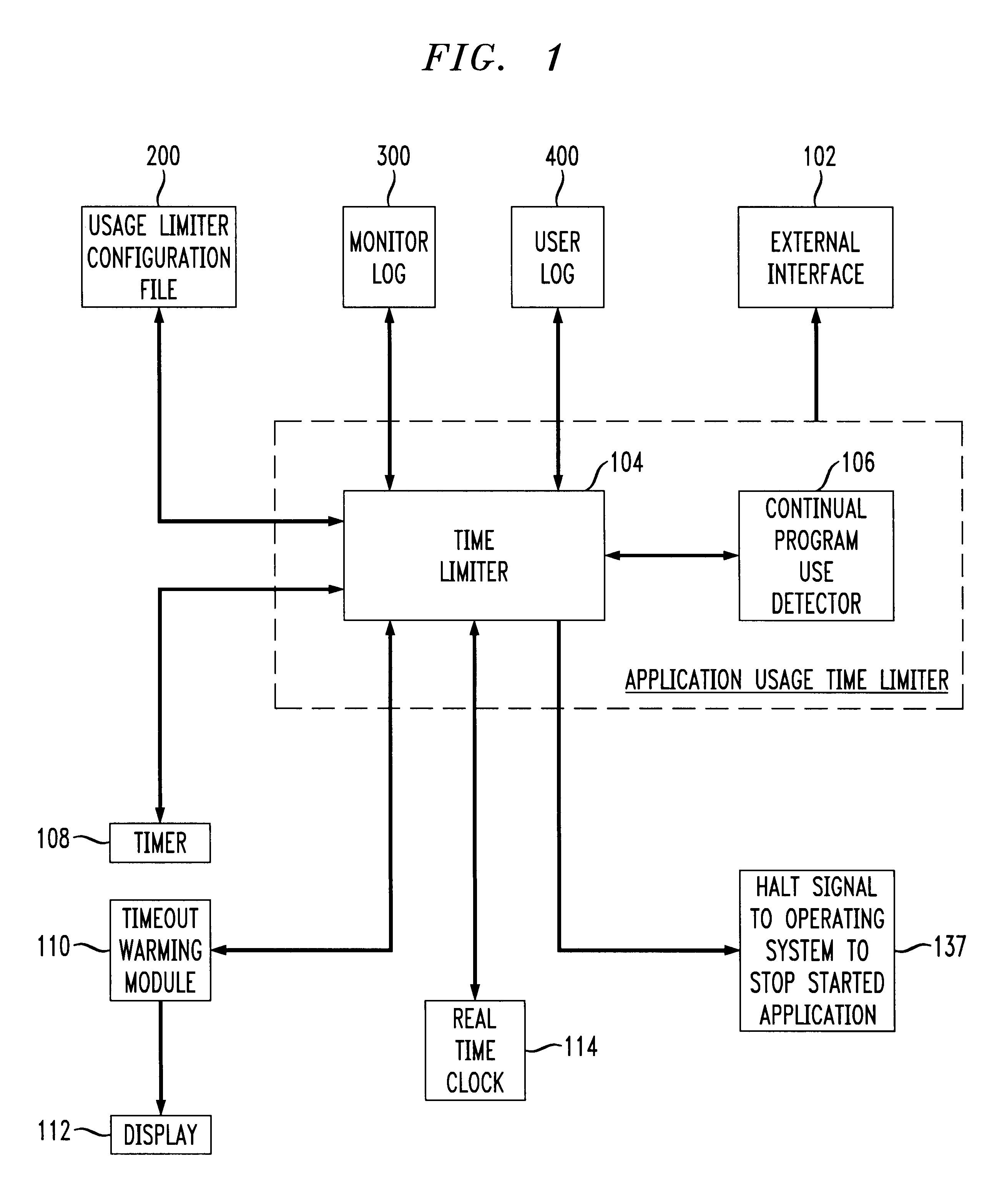
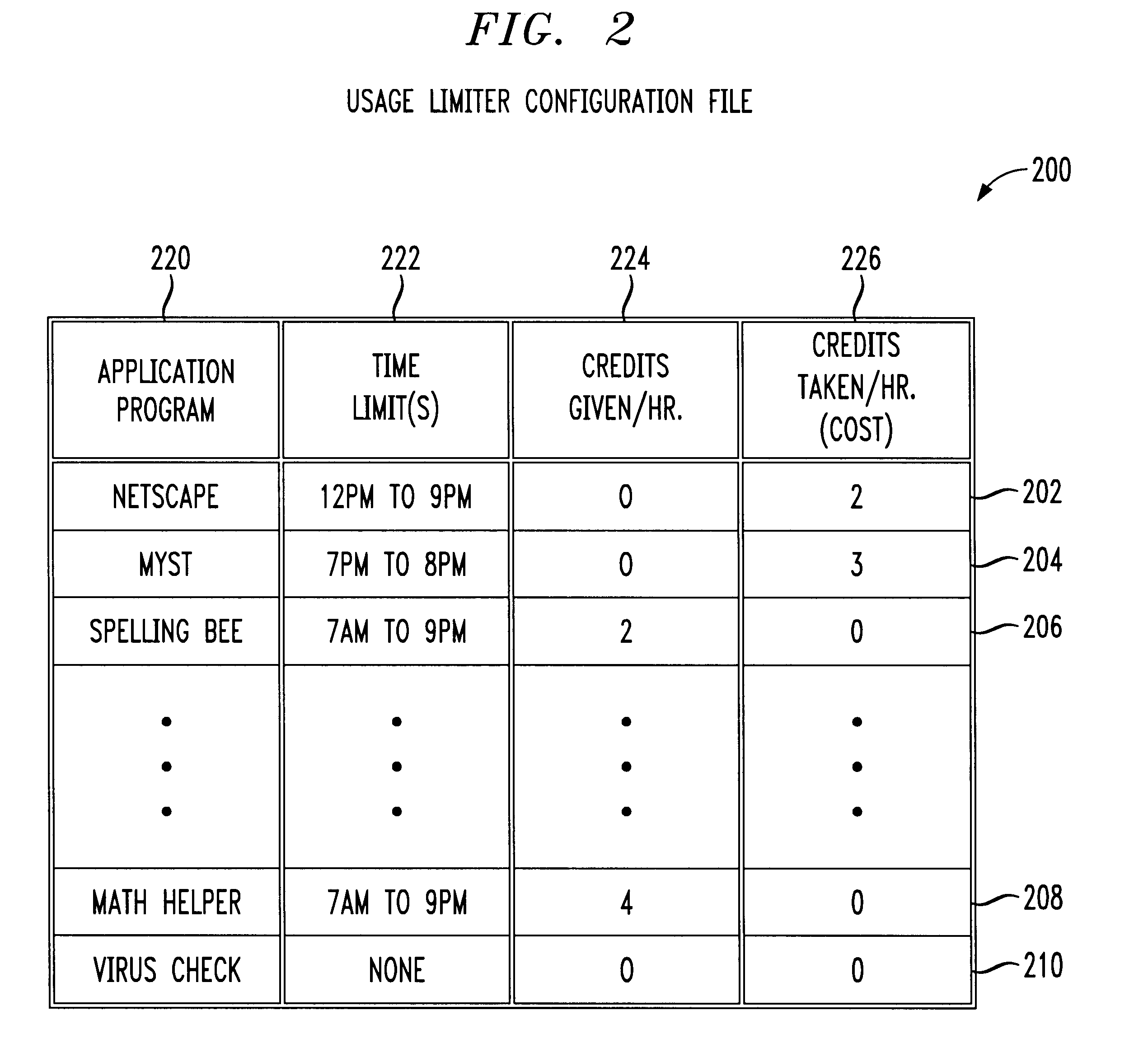
Application usage time limiter
An application usage time limiter monitors certain pre-configured application programs when opened or otherwise executed on a computer (e.g. a PC). The application usage time limiter is itself a program running either as a front end to various selected programs for monitoring, or as a separate program running in a time-sharing operating system environment. Pre-configurable options in a usage limiter configuration file or other memory area are set to limit real time ranges that particular application programs on a particular computer can be started and run, and a limit to a length of time that a specific program (or category of programs-an be operated given a number of available credits for a current user. The user is given credits at a pre-configured rate per hour of usage of an application program designated in the usage limiter configuration file as being beneficial, and the user gives back (or looses) credits at a pre-configured rate per hour of usage for use of programs designated as non-beneficial. Preferably, continued usage of beneficial programs is detected, e.g., by keystrokes. Application programs selected for monitoring in the usage limiter configuration file can be identified on an application by application basis, as a specific category of applications identifiable when the particular application is started, or as being stored in a specific directory (e.g., folder in a Windows(TM) operating system). A credit-giving (i.e., beneficial program) must be run by a particular user to earn credits before a credit-taking (i.e., non-beneficial program) can be run by that user. Up front credits may be provided to a particular user in a user log.
Owner:LUCENT TECH INC
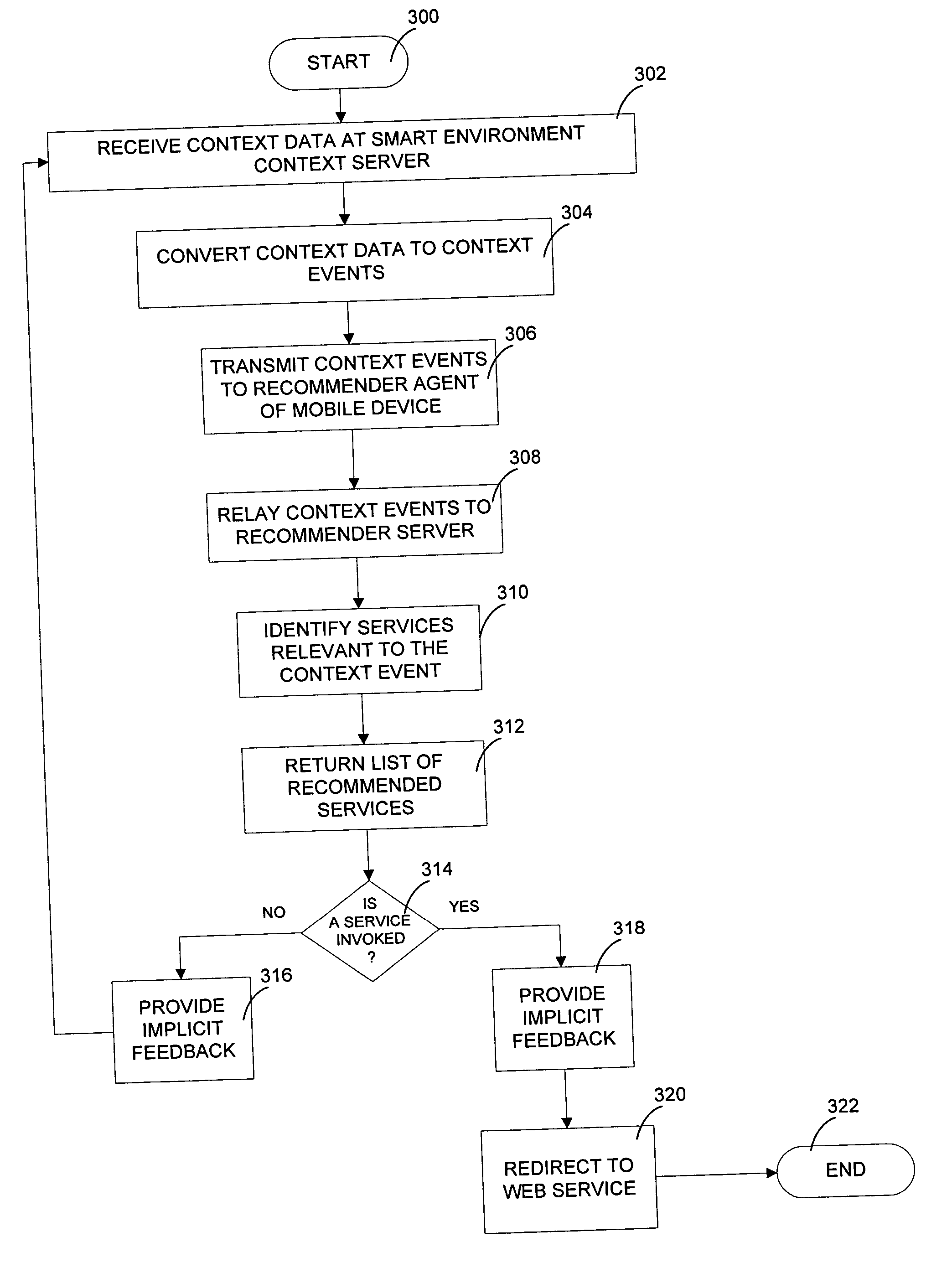
Method and system for pushing services to mobile devices in smart environments using a context-aware recommender
InactiveUS20040153373A1Buying/selling/leasing transactionsMarketingContext-aware servicesIntelligent environment
A context-aware service recommender system receives current user context and recommends a list of browser-based services to a user on a mobile devices. A user's mobile device receives context events from smart environments in which the mobile device is operating. Data about the context events is relayed to a service recommendation server. The server develops recommendations based on the context and other factors, and relays information about the recommended services to the mobile device. As each recommended service is selected or ignored by the user of the mobile device, the device sends implicit feedback with this information to the service recommendation server for use in subsequent recommendations.
Owner:NTT DOCOMO INC
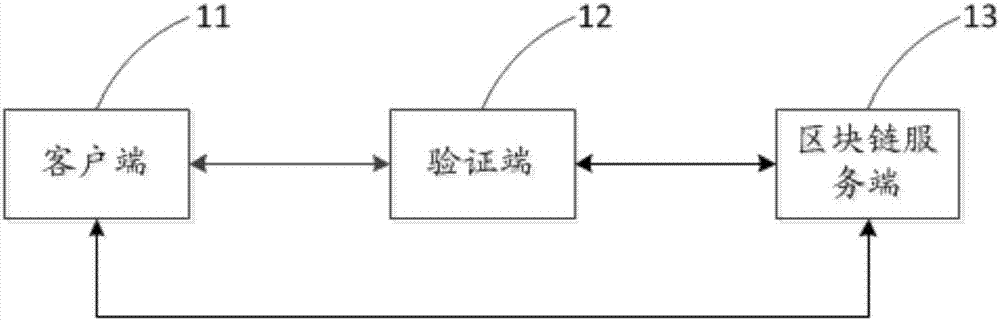
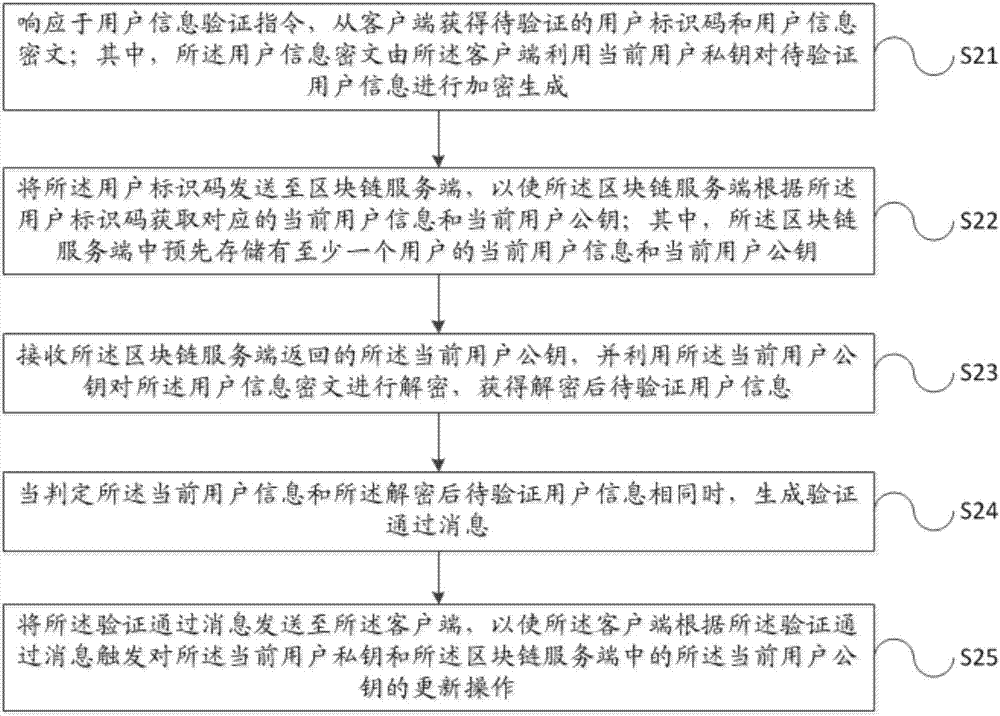
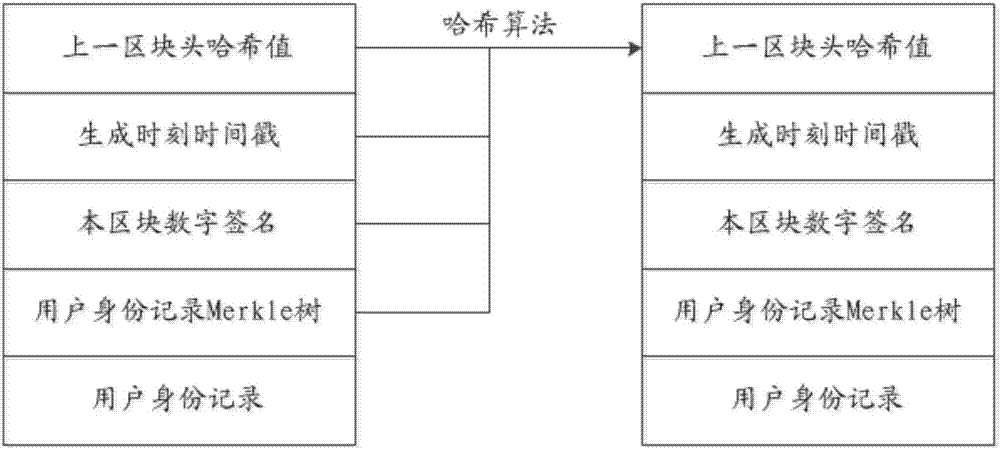
User identity verification method, apparatus and system based on block chain
InactiveCN107579817AImprove securityImprove accuracyKey distribution for secure communicationUser identity/authority verificationCiphertextUser authentication
The invention discloses a user identity verification method, apparatus and system based on a block chain. The user identity verification method comprises the following steps: obtaining a user identification code and a user information ciphertext from a client, wherein the user information ciphertext is generated by encrypting to-be-verified user information by using a current user private key; sending the user identification code to a block chain server, so that the block chain server obtains corresponding current user information and a current user public key; decrypting the user informationciphertext by using the current user public key returned by the block chain server to obtain decrypted to-be-verified user information; when it is judged that the current user information is the sameas the decrypted to-be-verified user information, generating a verification pass message; and triggering the updating operation of the current user private key and the current user public key according to the verification pass message by the client. By adoption of the user identity verification method, apparatus and system, the security of user identity verification process can be improved, and the accuracy of a user identity verification result can be improved.
Owner:GRG BAKING EQUIP CO LTD
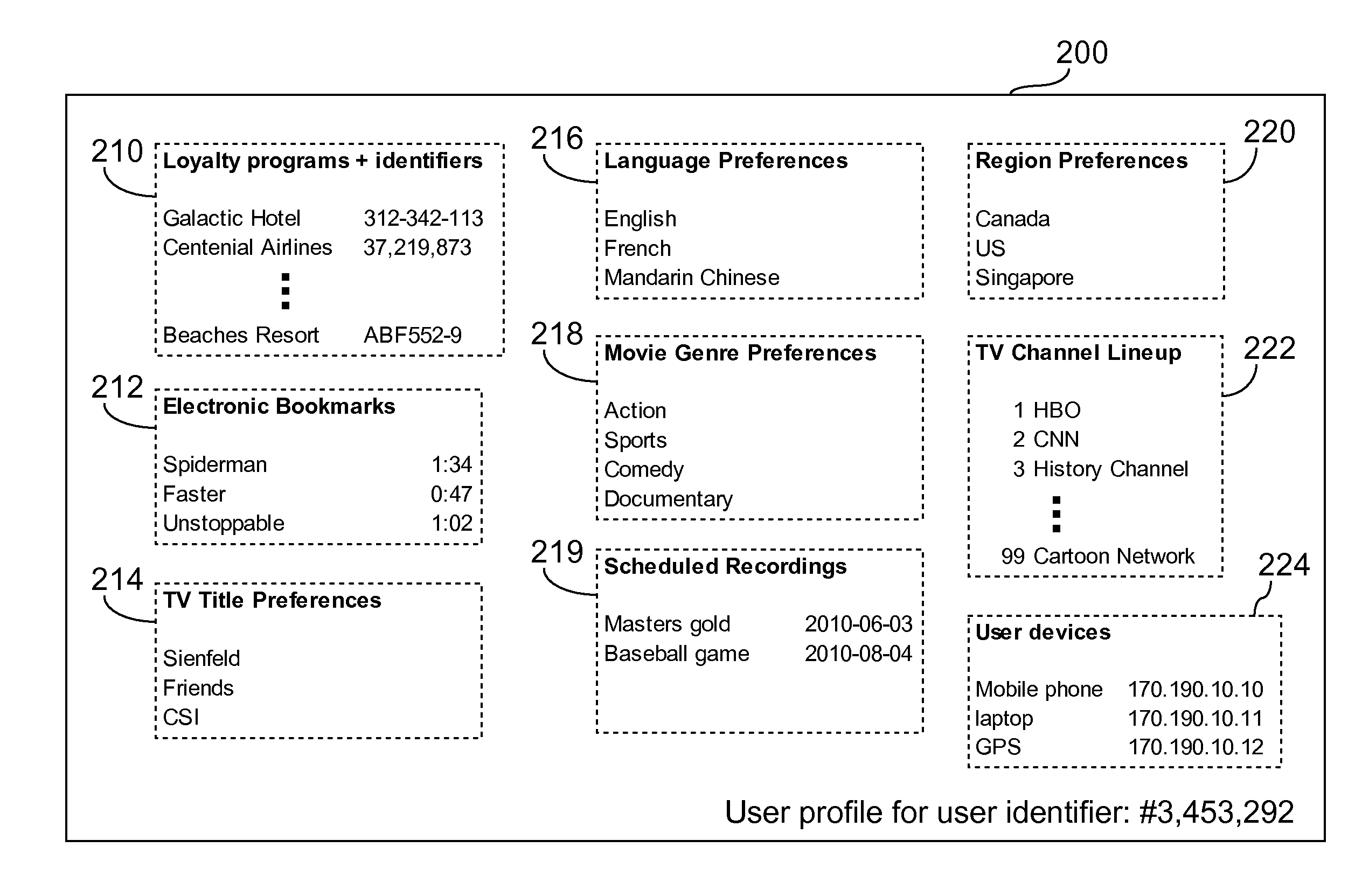
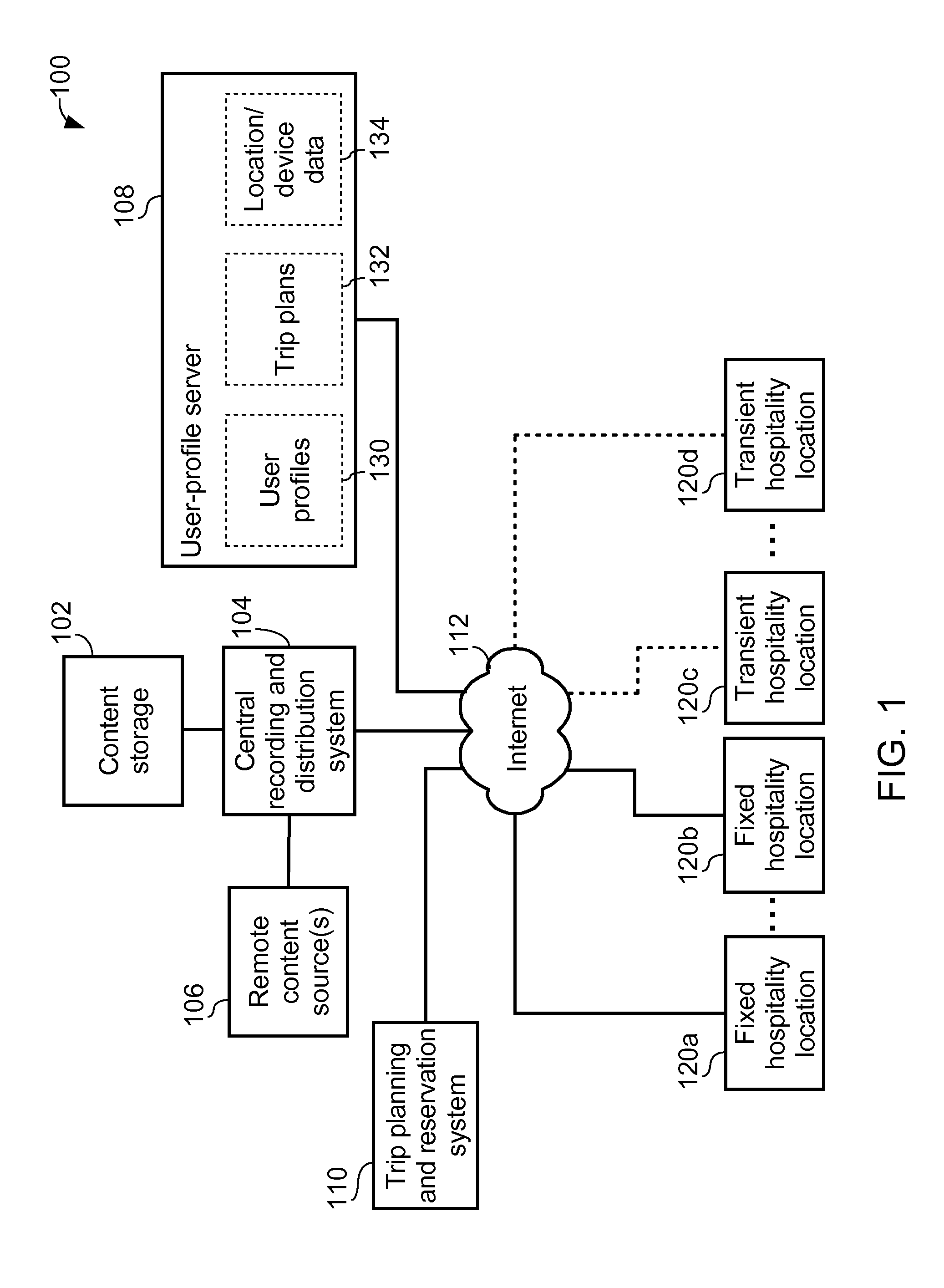
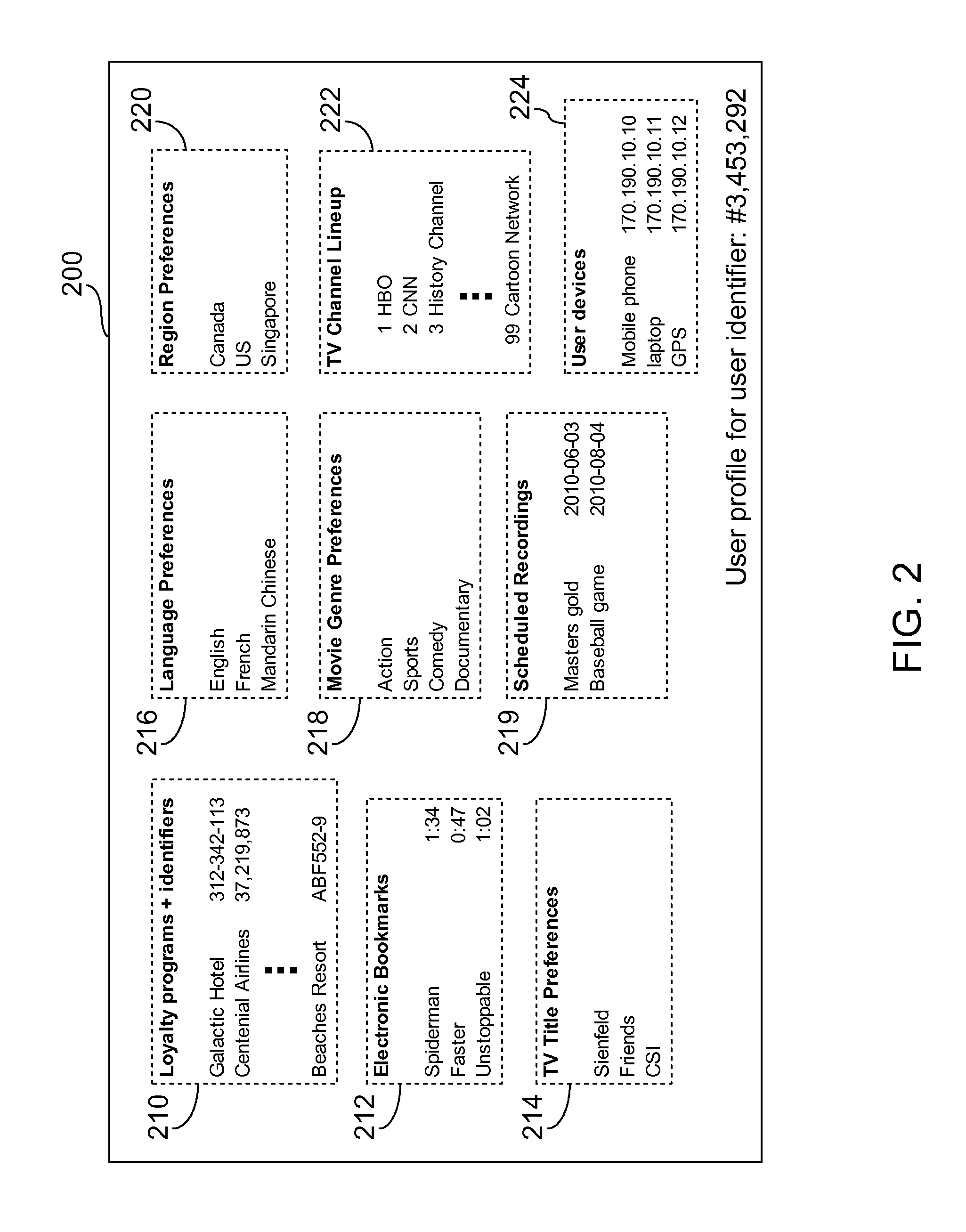
Method of providing user-tailored entertainment experience at hospitality location and hospitality media system thereof
A hospitality media system includes a plurality of entertainment devices installed at a hospitality location and a content selector. The content selector is configured to retrieve a plurality of user profiles corresponding to current users of the hospitality location, and automatically adjust content made available on each of the entertainment devices at the hospitality location according to information stored in the user profiles.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
Task/domain segmentation in applying feedback to command control
InactiveUS7062488B1Further focus the searchReduced extraneous “ noise ” informationData processing applicationsWeb data indexingCommunication interfaceCommand and control
An apparatus for responding to a current user command associated with one of a plurality of task / domains. The apparatus comprises: a digital storage device that stores cumulative feedback data gathered from multiple users during previous operations of the apparatus and segregated in accordance with the plurality of task / domains; a first digital logic device that determines the current task / domain with which the current user command is associated; a second digital logic device that determines a current response to the current user command on the basis of that portion of the stored cumulative feedback data associated with the current task / domain; a first communication interface that communicates to the user the current response; and a second communication interface that receives from the user current feedback data regarding the current response. The current feedback data is added to the cumulative feedback data stored in the digital storage device and associated with the current task / domain.
Owner:OPEN TV INC +1
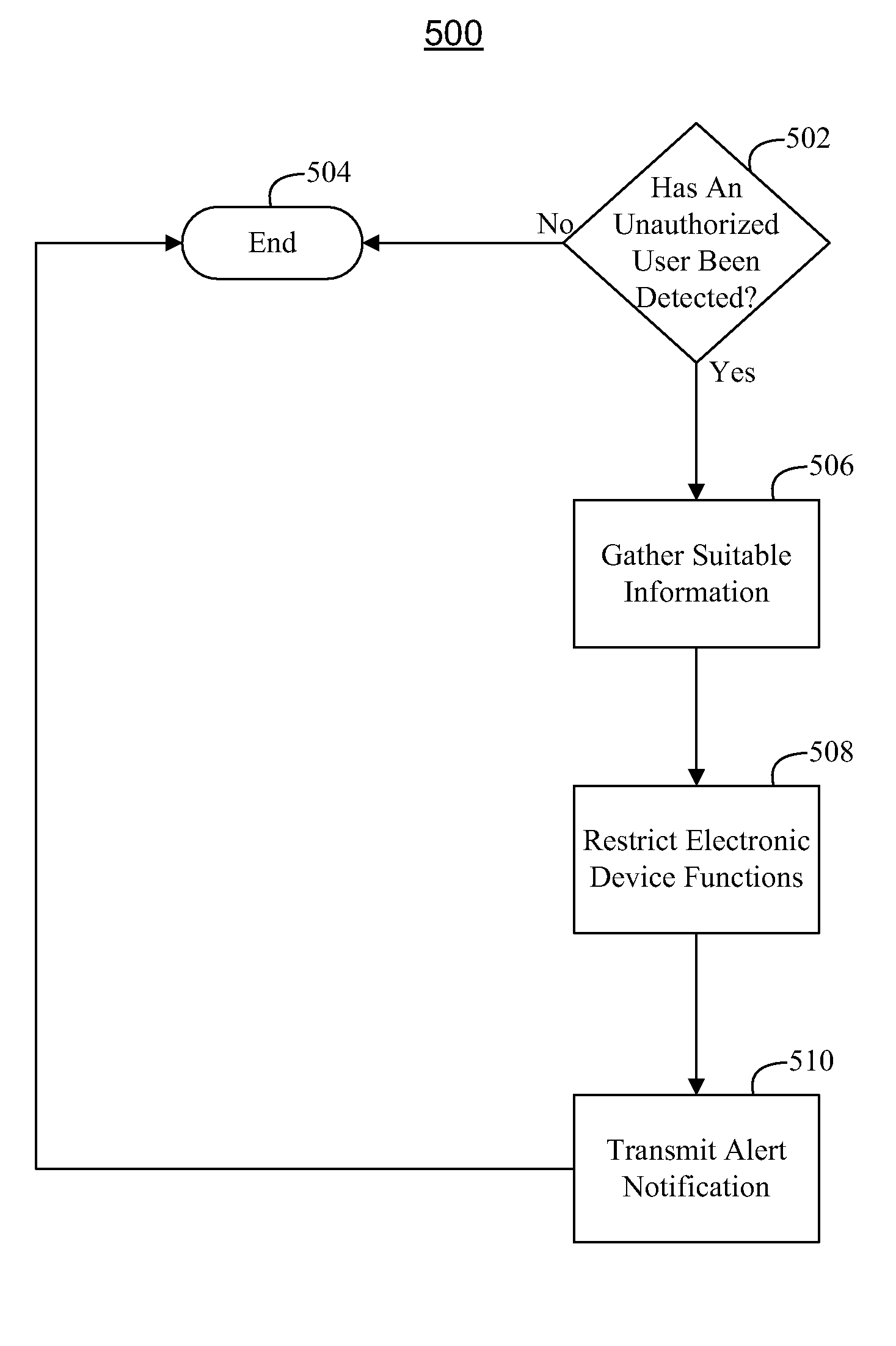
Systems and methods for identifying unauthorized users of an electronic device
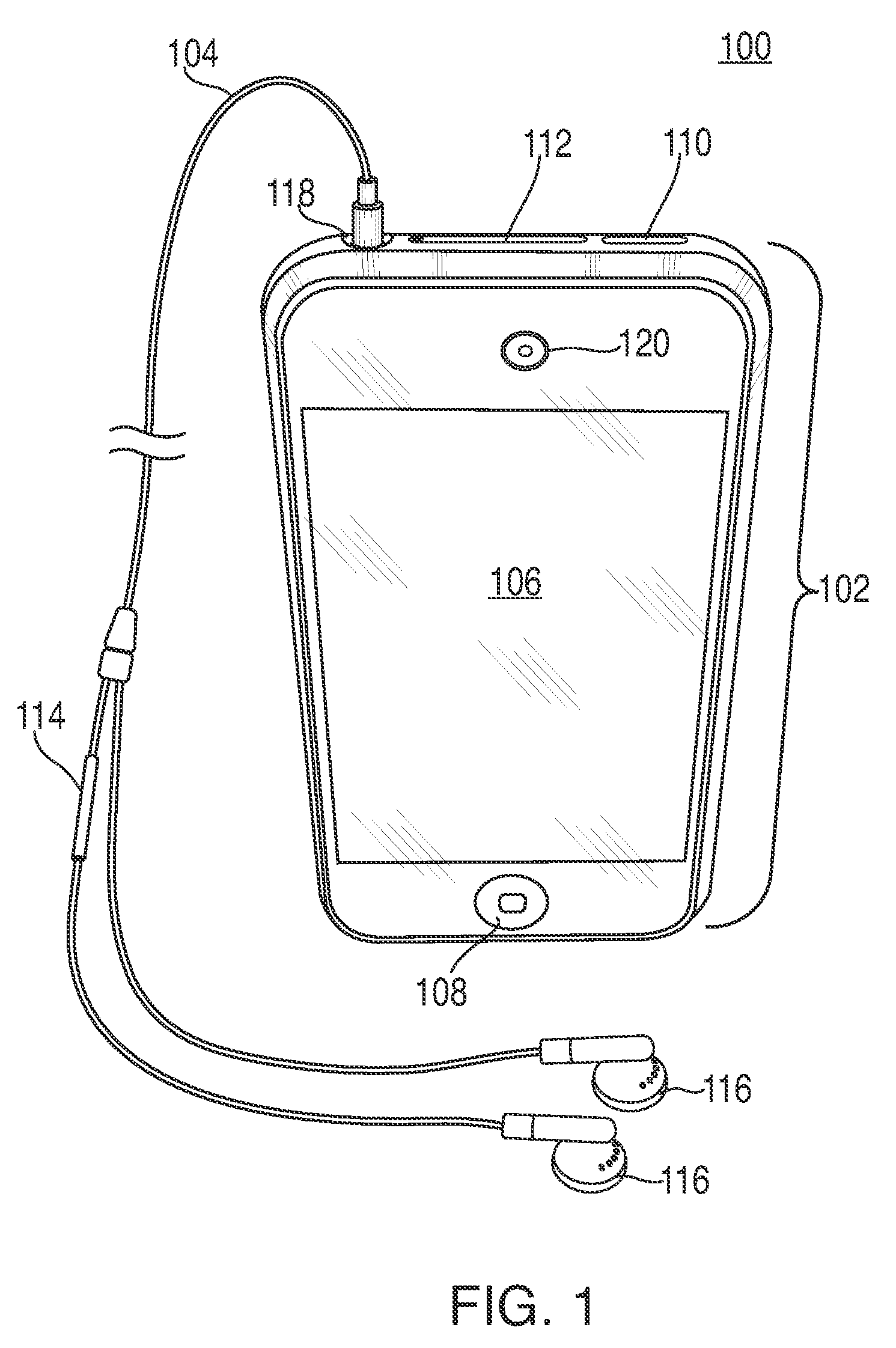
ActiveUS20100207721A1Electric signal transmission systemsMultiple keys/algorithms usageElectronic mailCurrent user
This is generally directed to identifying unauthorized users of an electronic device. In some embodiments, an unauthorized user of the electronic device can be detected by identifying particular activities that may indicate suspicious behavior. In some embodiments, an unauthorized user can be detected by comparing the identity of the current user to the identity of the owner of the electronic device. When an unauthorized user is detected, various safety measures can be taken. For example, information related to the identity of the unauthorized user, the unauthorized user's operation of the electronic device, or the current location of the electronic device can be gathered. As another example, functions of the electronic device can be restricted. In some embodiments, the owner of the electronic device can be notified of the unauthorized user by sending an alert notification through any suitable medium, such as, for example, a voice mail, e-mail, or text message.
Owner:APPLE INC
Interactive Marketing, Product/Market Research, Contact Access and Usage Tracking for Wireless
A method and system for requesting and delivering mobile marketing interactions, controlling access and tracking usage for wireless device applications directly from a wireless device is disclosed. Upon starting an application on a wireless device, the application connects to a server and posts information about the application, the user of the application, device specific data and any cached marketing interactions. This information is processed by the server. Application usage statistics, marketing interactions and any device changes are stored in a database at the server. Real-time processing and business rule checks on the information sent from the wireless device application is performed by the server to determine content access rights by the user as well as current marketing interactions that will be displayed within the application. Content access rights and marketing information is returned to the wireless device application from the server which configures the current user experience of the wireless device application.
Owner:LOCATION LABS
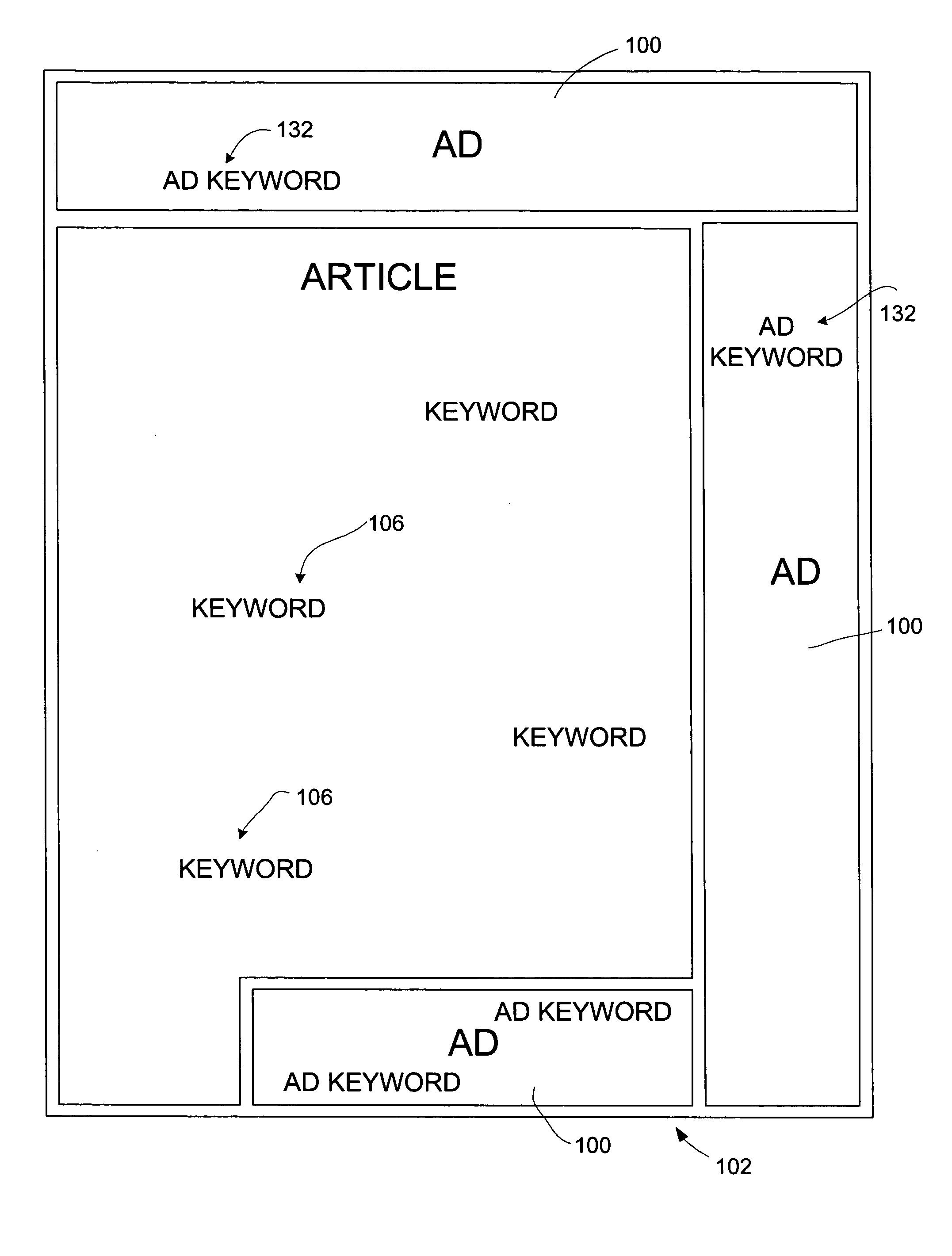
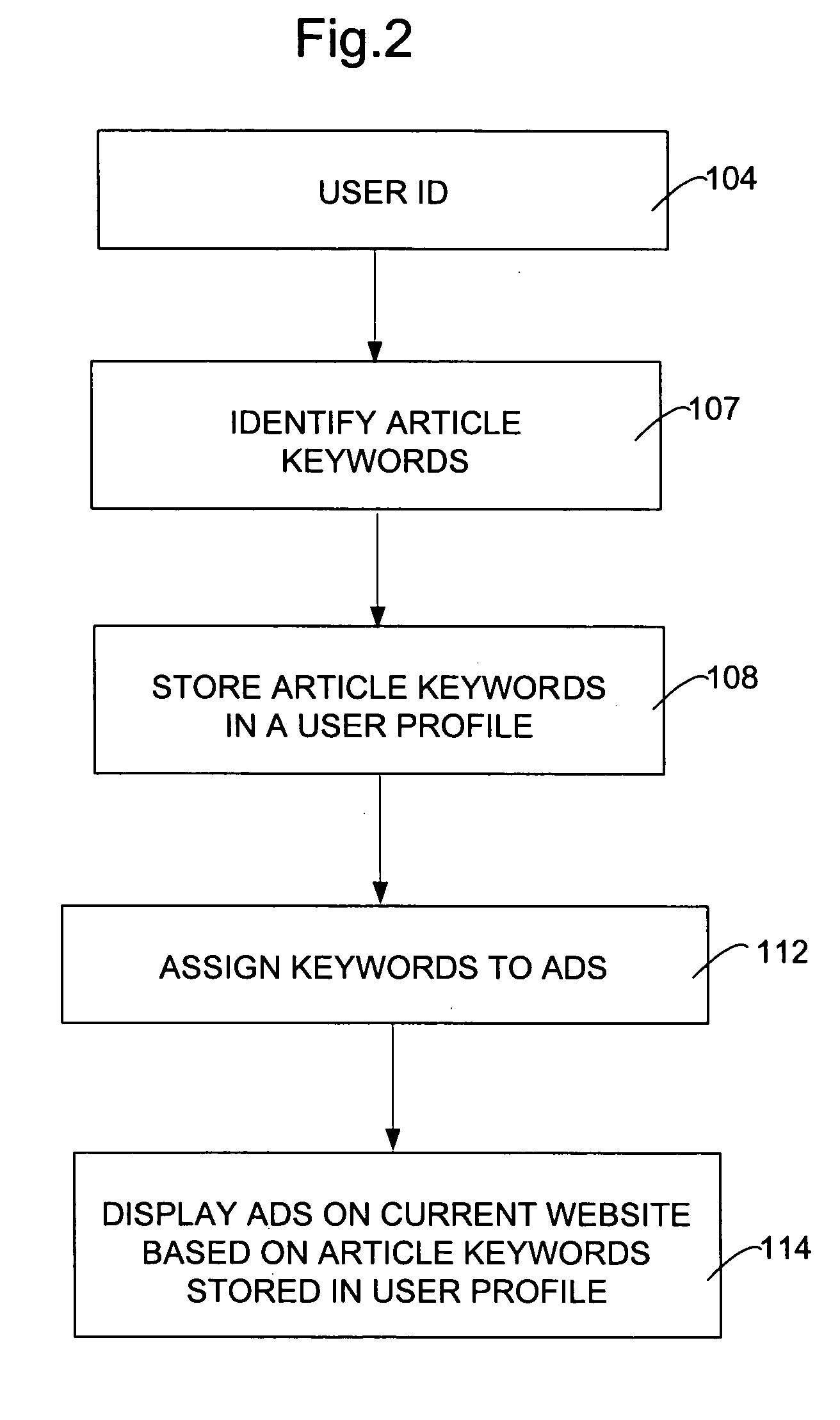
Assigning textual ads based on article history
A method of selecting textual advertisements for display on a web page based on user history. In the method, a user accessing a web site is identified. Keywords in articles displayed on web pages viewed by the user are identified and stored in a user profile. The advertisements displayed on a current user selected web page are based on keywords from the articles viewed by the user in the past that are stored in the user profile.
Owner:MICROSOFT TECH LICENSING LLC
Automatic update of online social networking sites
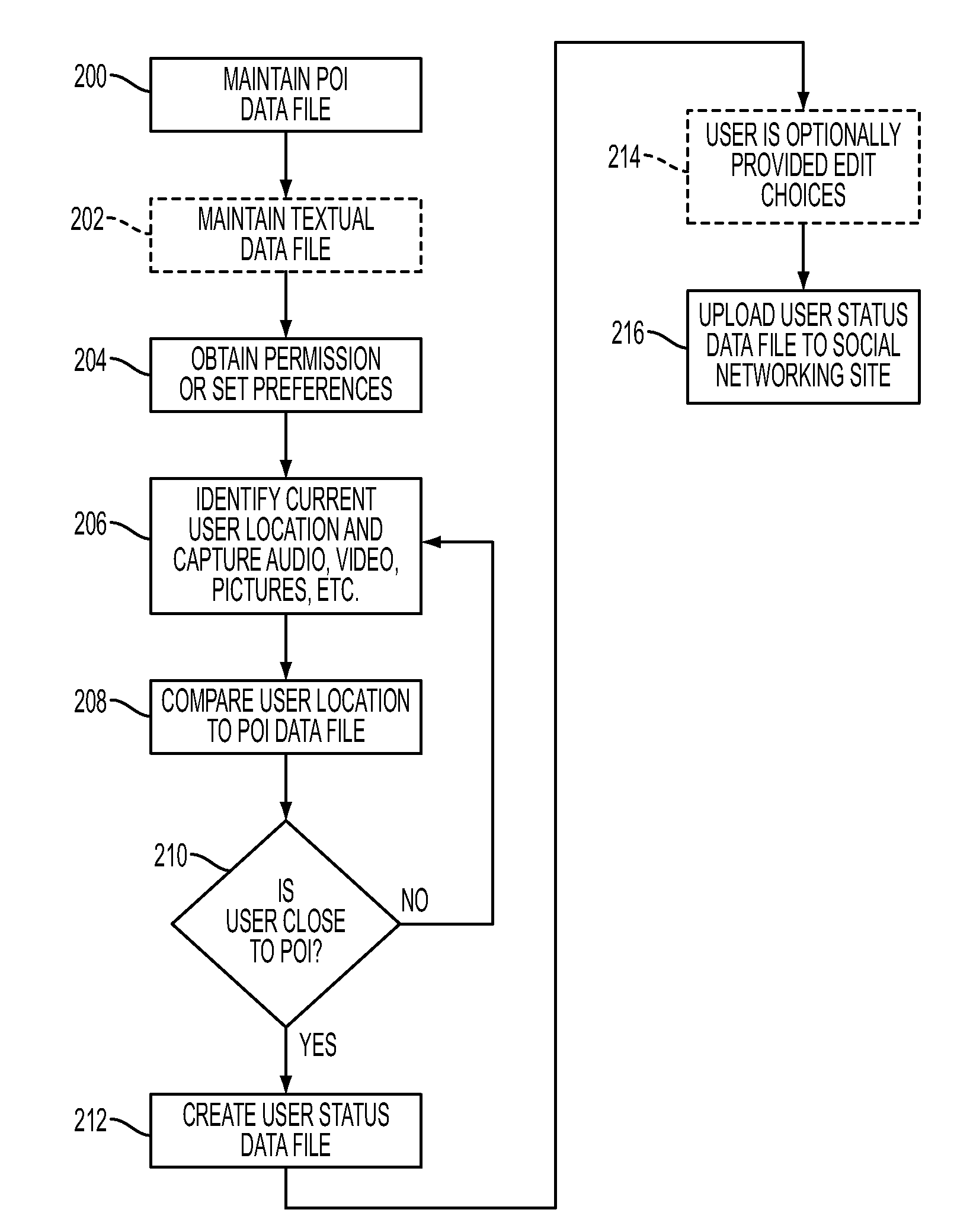
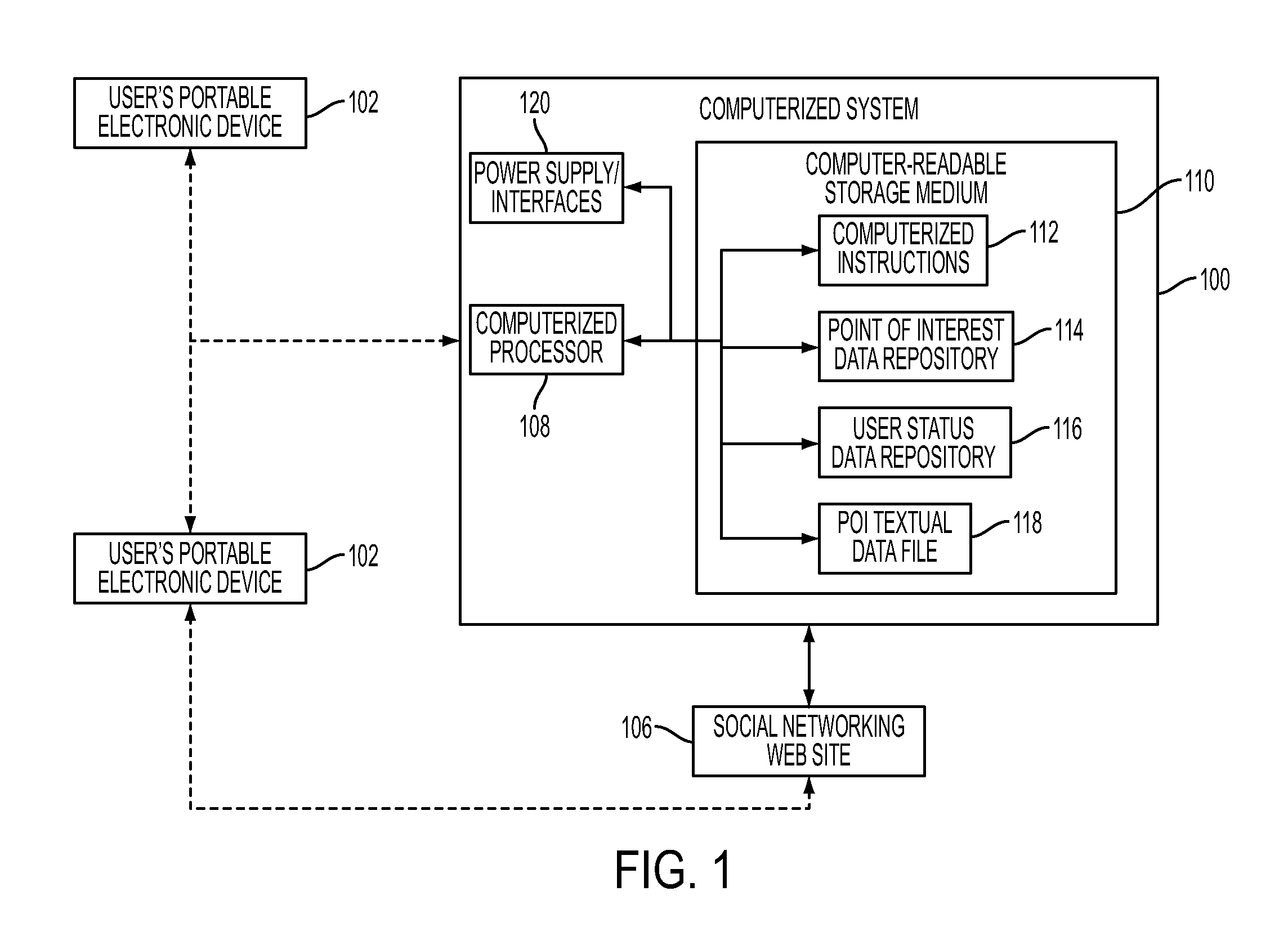
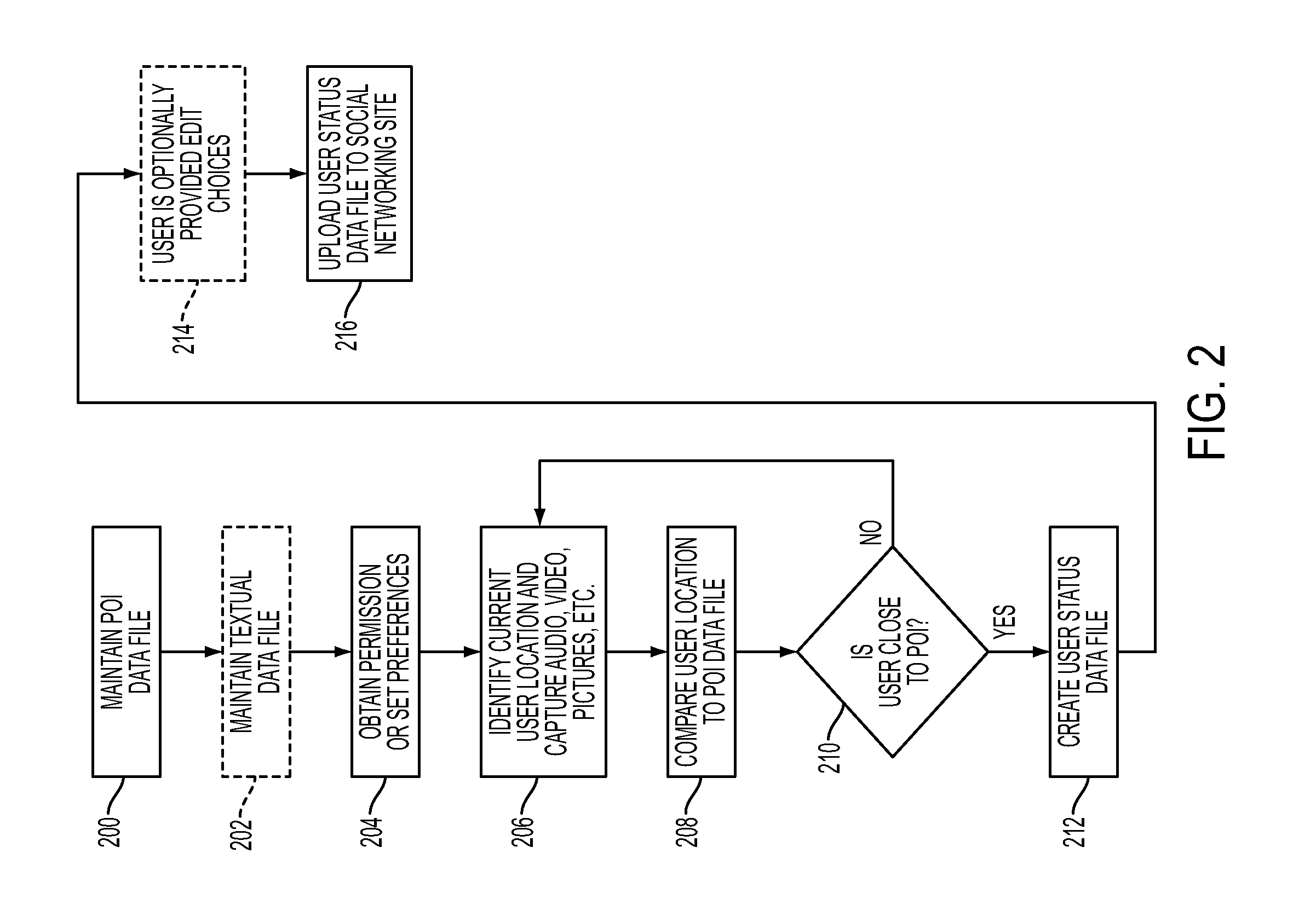
ActiveUS20110047182A1Cumbersome nature is reducedFrequent updateDigital data processing detailsOffice automationWeb siteGeotargeting
Systems and methods maintain at least one point of interest data file within a computer-readable storage medium and automatically identify a current user location of a user based on a geographic positioning feature of a portable electronic device that is maintained within a first predetermined distance from the user. The systems and methods automatically compare the current user location with the point of interest data file to identify whether the user is located within a second predetermined distance of a point of interest maintained within the point of interest data file. If the user is within the second predetermined distance of a point of interest, the systems and methods automatically create a user status data file. The user status data comprises data identifying that the user is currently at the point of interest. The user status data file is comprised of, but is not limited to, video, still pictures, and audio captured at the current user location as well as textual description of the user's participation at the point of interest. The systems and methods automatically upload the user status data file to a social networking web site associated with the user as an activity post associated with the user.
Owner:III HLDG 6
Expression and flexibility framework for providing notification(s)
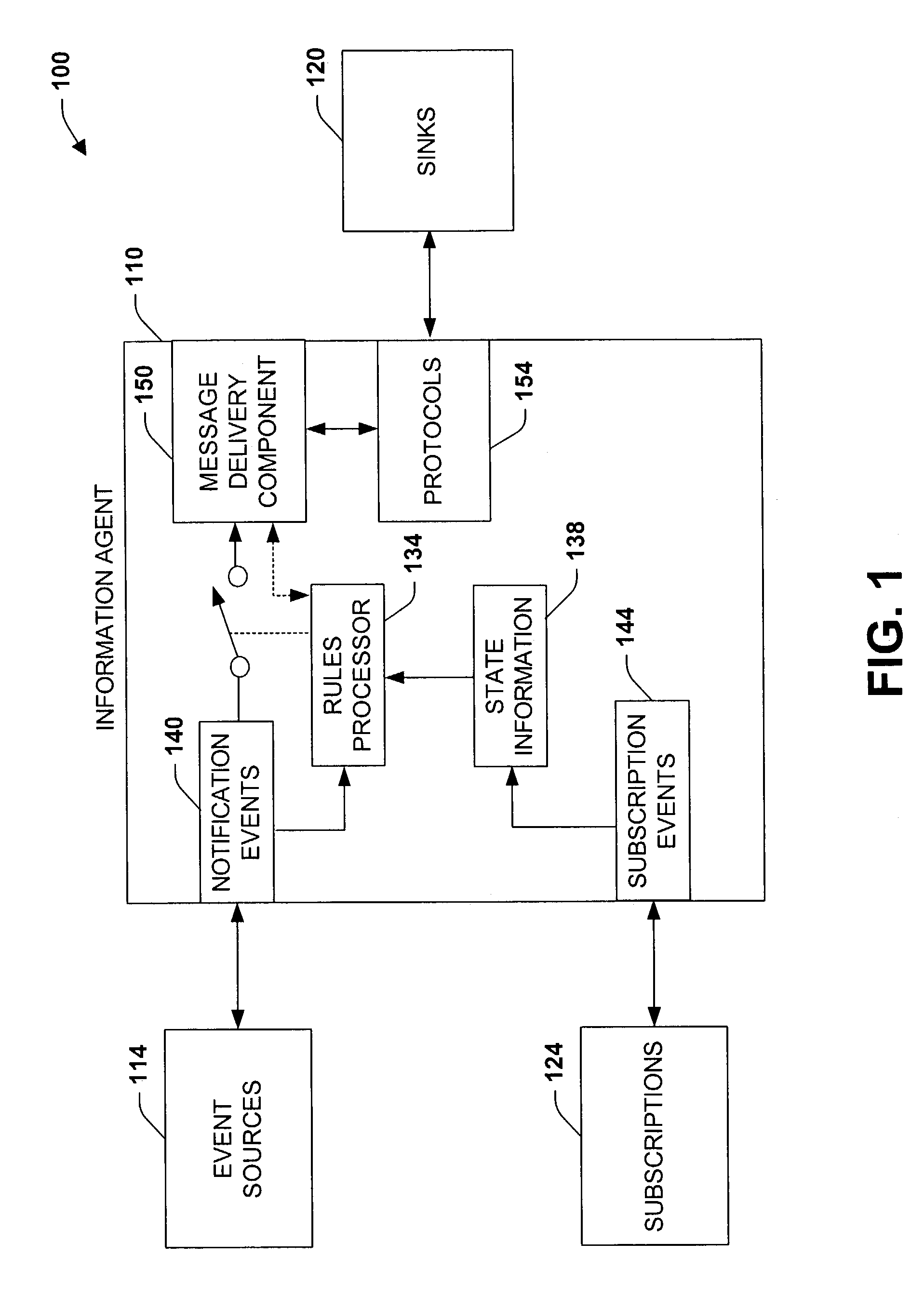
InactiveUS7209916B1Reduce unnecessary distractionsFacilitate efficient deliveryData processing applicationsDigital data processing detailsData centerApplication software
The present invention relates to a system and methodology to facilitate timely delivery of notifications and performance of automated actions for users in the framework of an ad-hoc rules processing environment. An information agent operates as a distributed application to perform automated actions for users in accordance with user preferences and context. Various rules can be executed to delay, inhibit, and / or enable an action such as sending notifications according to the preferences and current user states as determined from the context. The rules can include data centric matching logic, set-oriented execution rules, rule ordering / interaction hierarchies, and ad-hoc Boolean combinations, for example.
Owner:MICROSOFT TECH LICENSING LLC
Remote file management
InactiveUS20050192966A1Data processing applicationsMetadata multimedia retrievalClient-sideFile server
An access server allows secure access to commonly used files stored on multiple file sources from a variety of client devices. The access server extracts a list of file sources associated with the user, and accesses each of those sources. The server is then configured to extract a list of most recently used files by the current user as well as information associated with those files. The access server also processes electronic mail attachments. The access server intercepts electronic mail messages containing attachments, and transmits the attachments to a file server.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Method and apparatus for identifying unique client users from user behavioral data
ActiveUS20020178257A1Digital computer detailsAnalogue secracy/subscription systemsUser inputTerminal equipment
A method and system are provided for identifying a current user of a terminal device from a group of possible users. The method includes providing a database containing multiple user input pattern profiles of prior user inputs to the terminal device. Each of the possible users of the group are associated with at least one of the user input pattern profiles. Current input patterns from use of the terminal device are detected. The current input patterns are combined and then dynamically matched with one of the user input pattern profiles, and the possible user associated with the matched user input pattern profile is selected as the current user. The system for identifying a current user of a terminal device from a group of possible users includes a database containing multiple user input pattern profiles of prior user inputs to the terminal device. Each of the possible users is associated with at least one of the user input pattern profiles. The system detects current input patterns from use of the terminal device, and then combines the patterns and dynamically matches the patterns with one of the user input pattern profiles. The system selects the possible user associated with the matched user input pattern profiles as the current user.
Owner:COX COMMUNICATIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com