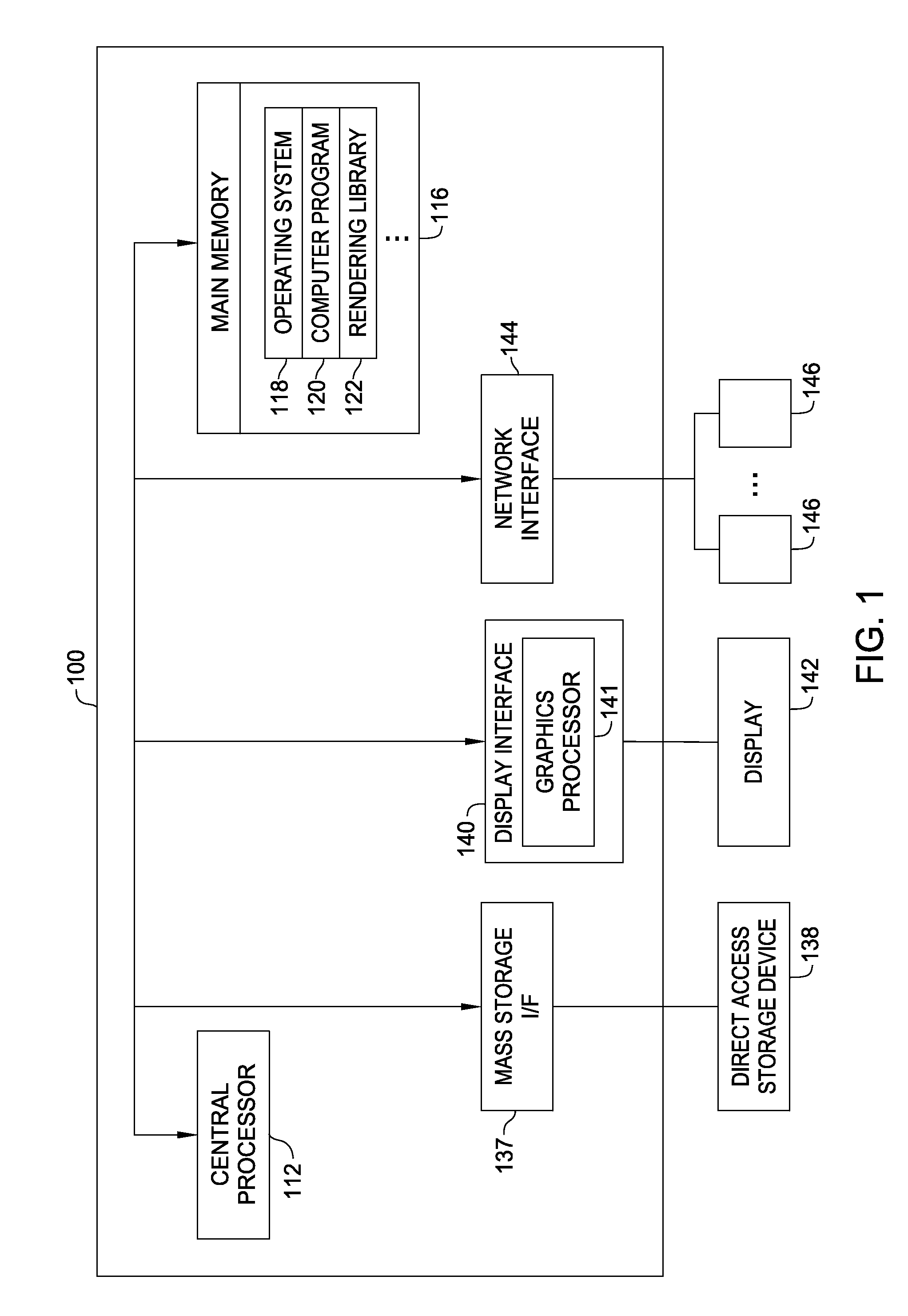
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1559 results about "Business rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
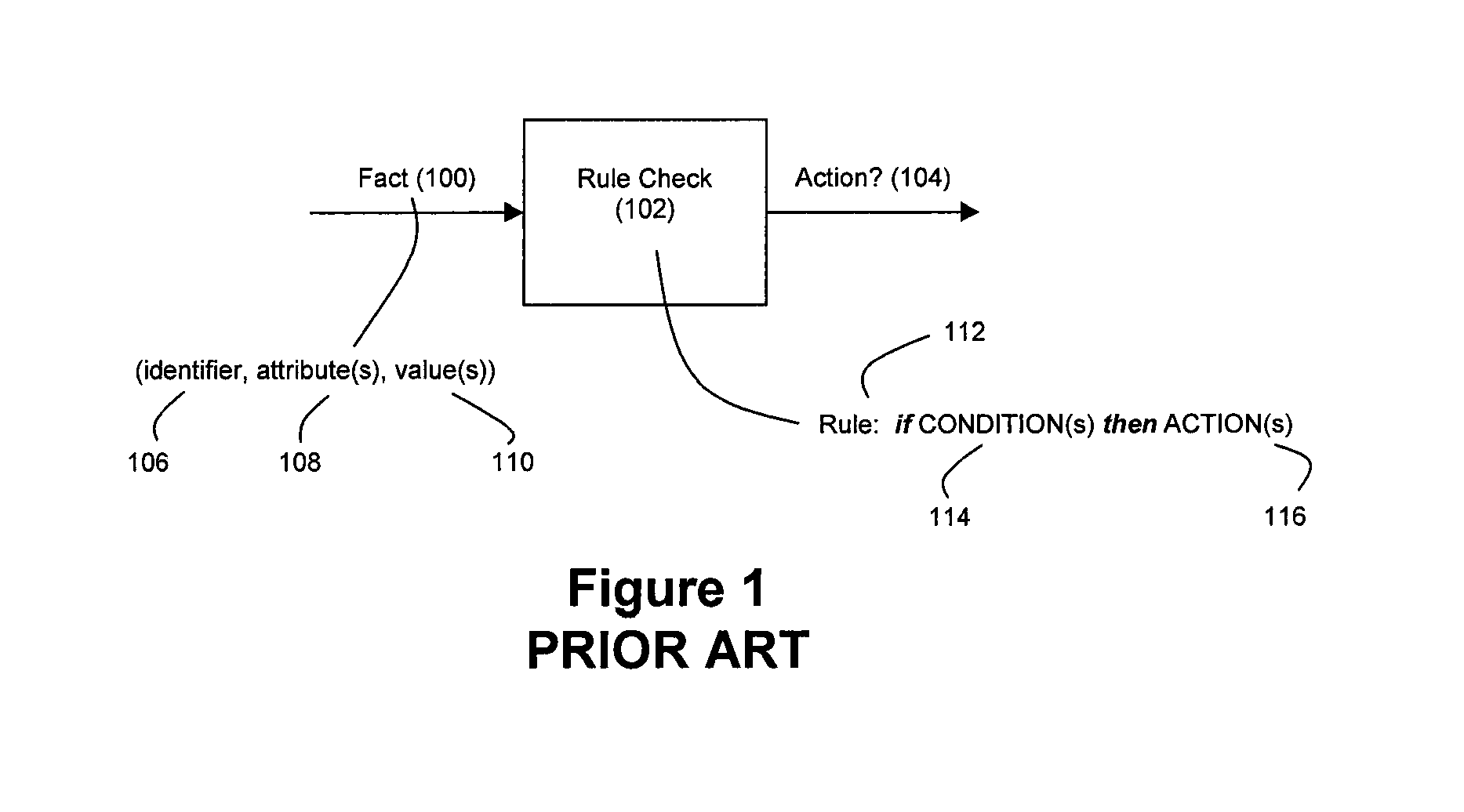
A business rule defines or constrains some aspect of business and always resolves to either true or false. It specifically involves terms, facts and rules. Business rules are intended to assert business structure or to control or influence the behavior of the business. Business rules describe the operations, definitions and constraints that apply to an organization. Business rules can apply to people, processes, corporate behavior and computing systems in an organization, and are put in place to help the organization achieve its goals. Even though a system of strategic processes govern business rules, business rules are not strategic themselves; they are directive.
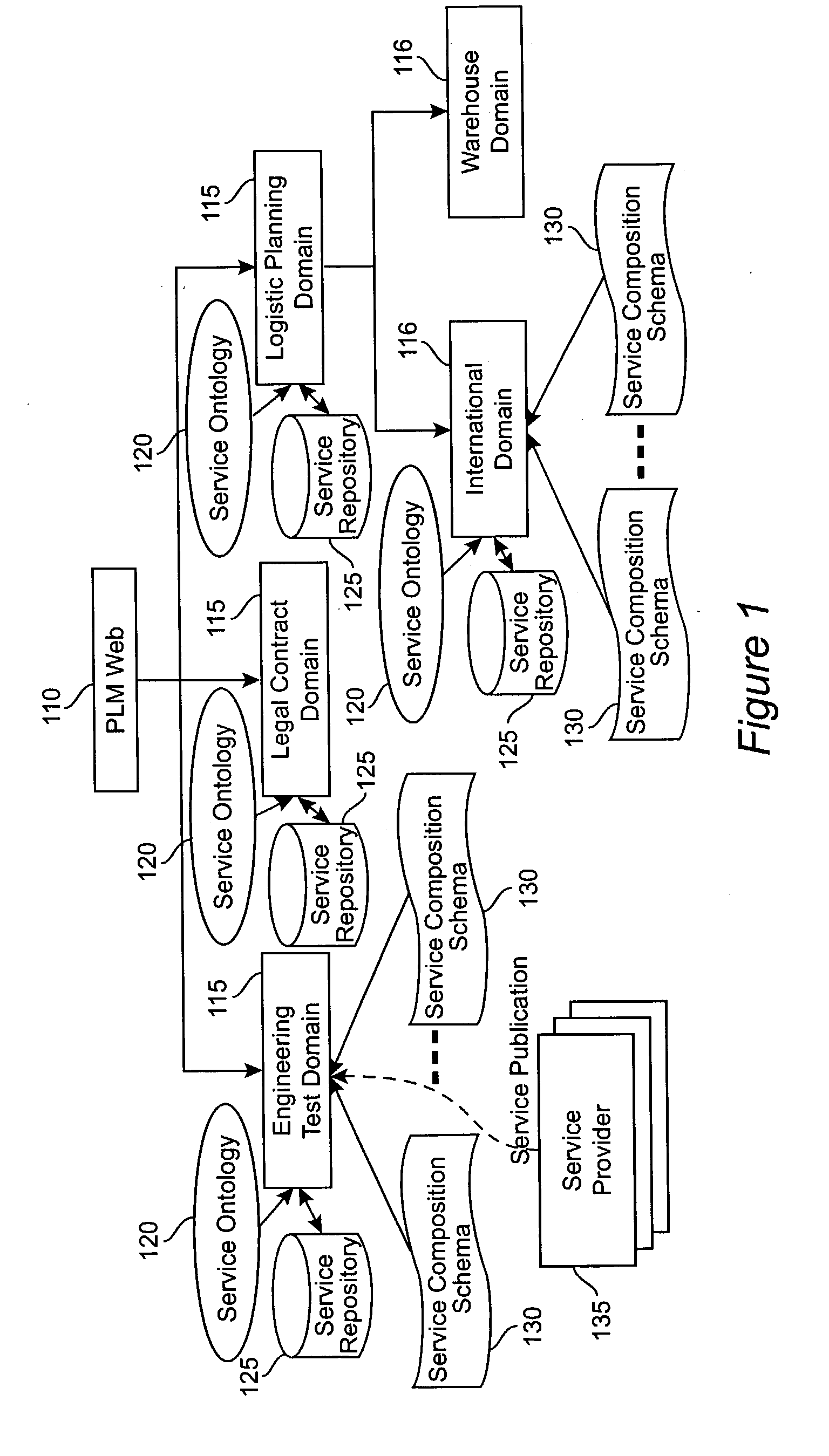
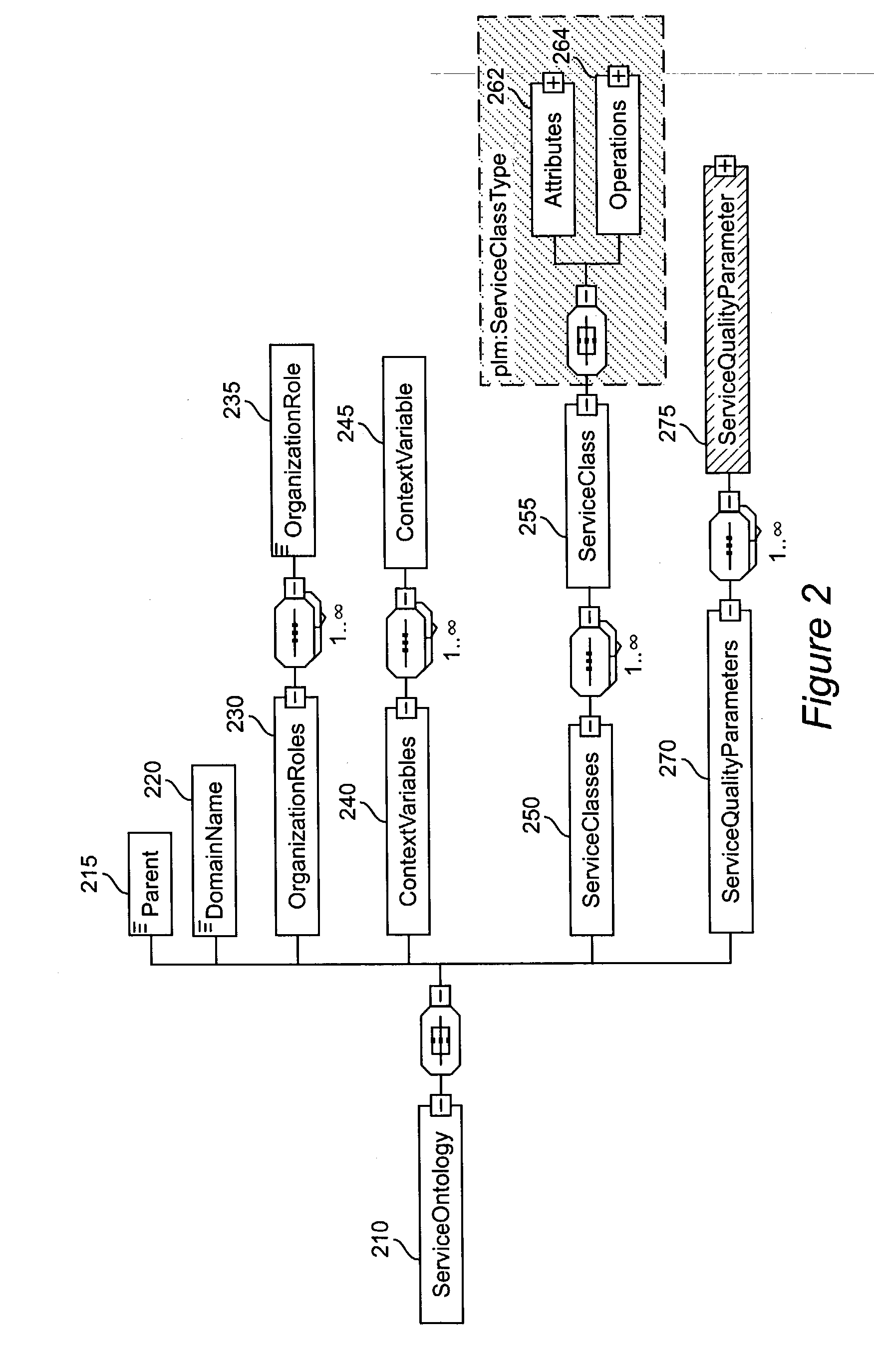
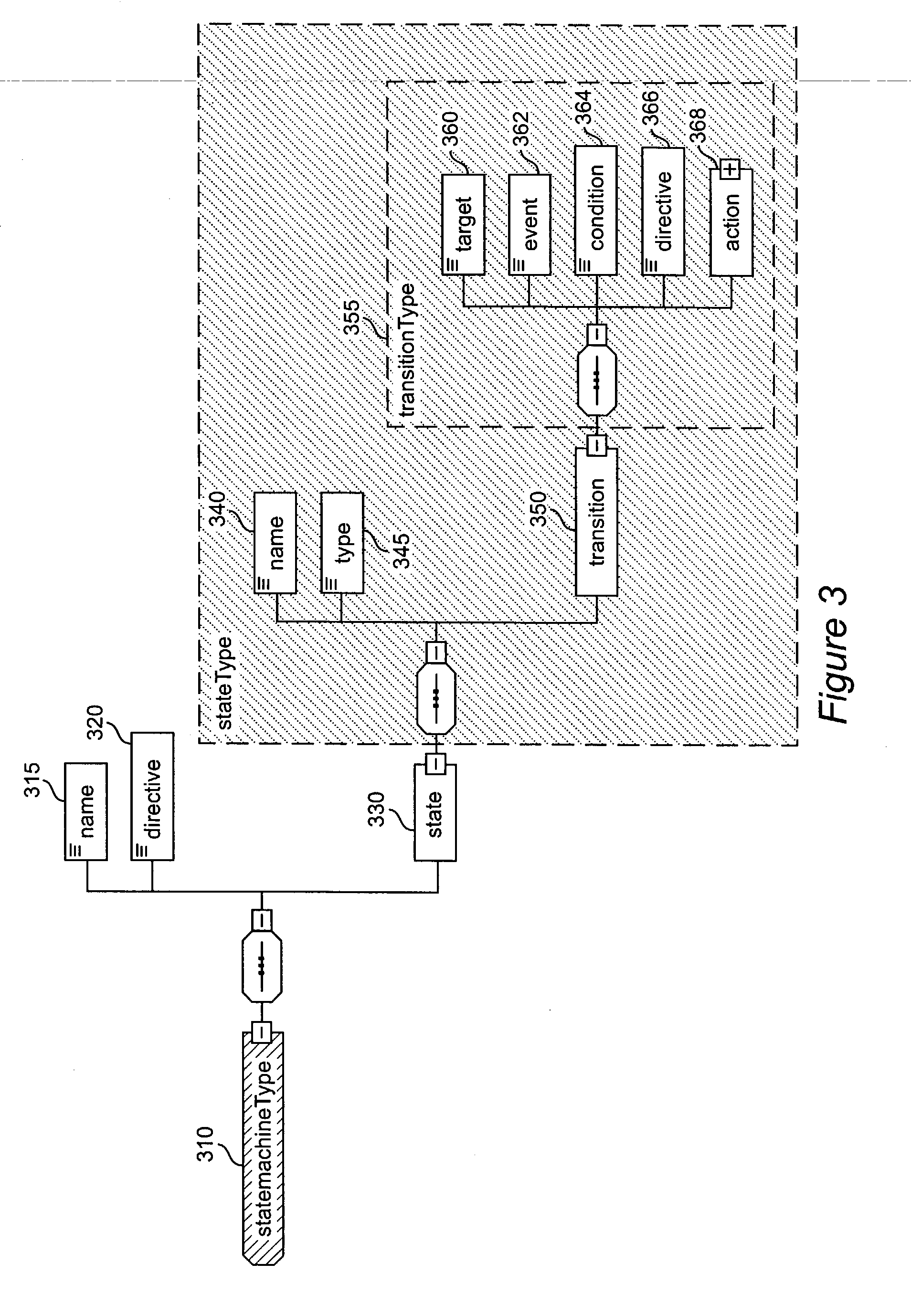
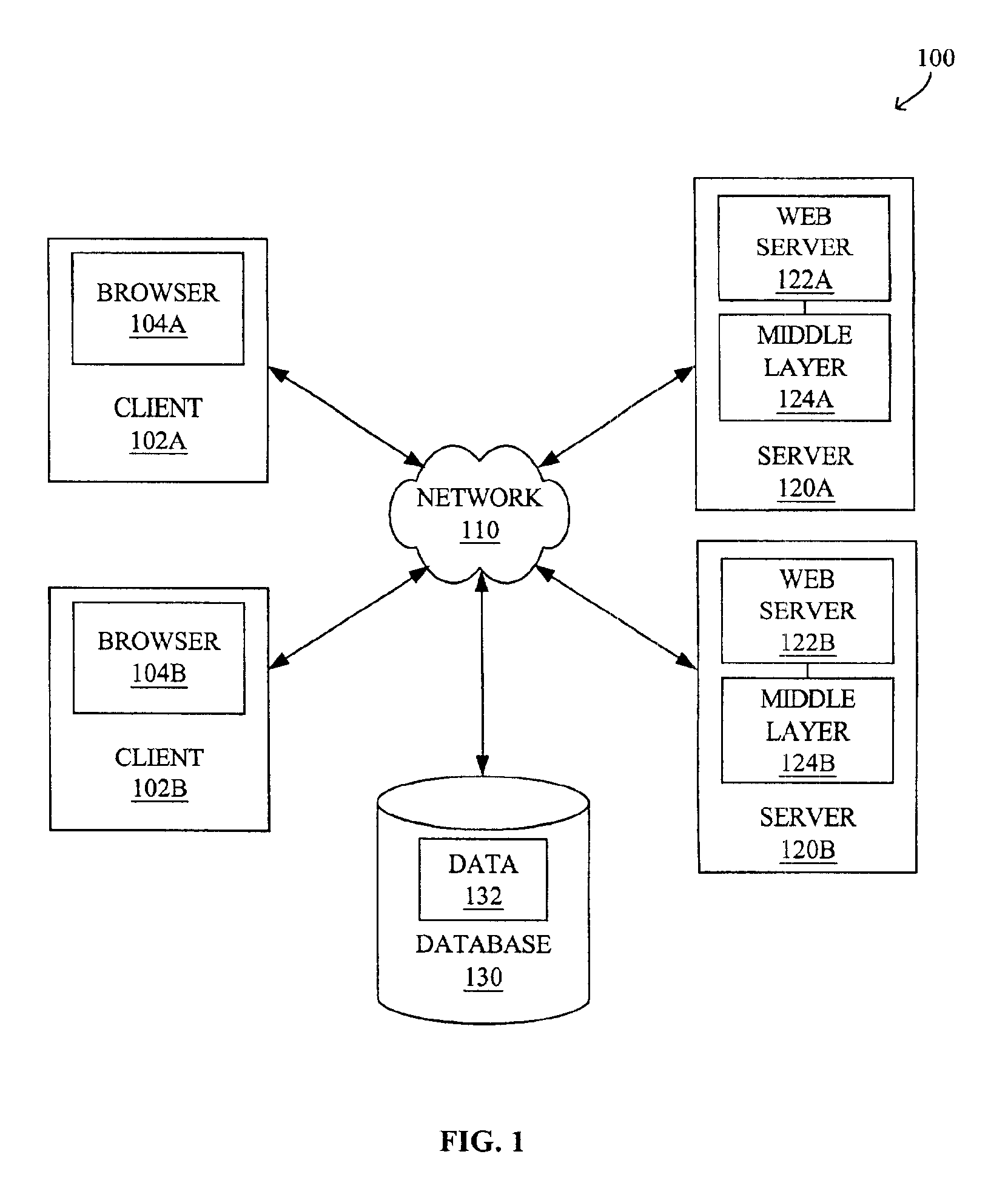
Method and apparatus for product lifecycle management in a distributed environment enabled by dynamic business process composition and execution by rule inference
InactiveUS20040162741A1Detect and resolve conflictOffice automationResourcesDistributed servicesNetwork topology
A system and method for supporting Product Lifecycle Management over a distributed service network topology that connects a hierarchy of functional domains, each domain having a service ontology and one or more service composition schemas defined by the service ontology. Each service composition schema models a business process in its domain. Descriptions of services provided to each domain are published to a service repository by providers of the services, in conformity with one of the service composition schemas. There is a business process proxy provided by the service provider for each service description, which encapsulates for public access the internal processes of the service provider. The invention makes use of an event messaging protocol that enables service collaboration and ad-hoc workflow composition. Each business process is implemented by an ad-hoc workflow comprised of one or more tasks connected by one or more business rules. For each business process there is a business flow manager that dynamically composes ad-hoc workflow prior to execution and dynamically modifies the ad-hoc workflow as the business process executes. The business flow manager uses backward-chain inferencing and then forward-chain inferencing to generate the ad-hoc workflows, based on user identification of a target task. The business flow manager is able to stop execution of the workflow and regenerate a workflow for remaining tasks in response to events received over the network from service providers, and is also able to detect conflicts in the workflows at composition time and at execution time.
Owner:IBM CORP
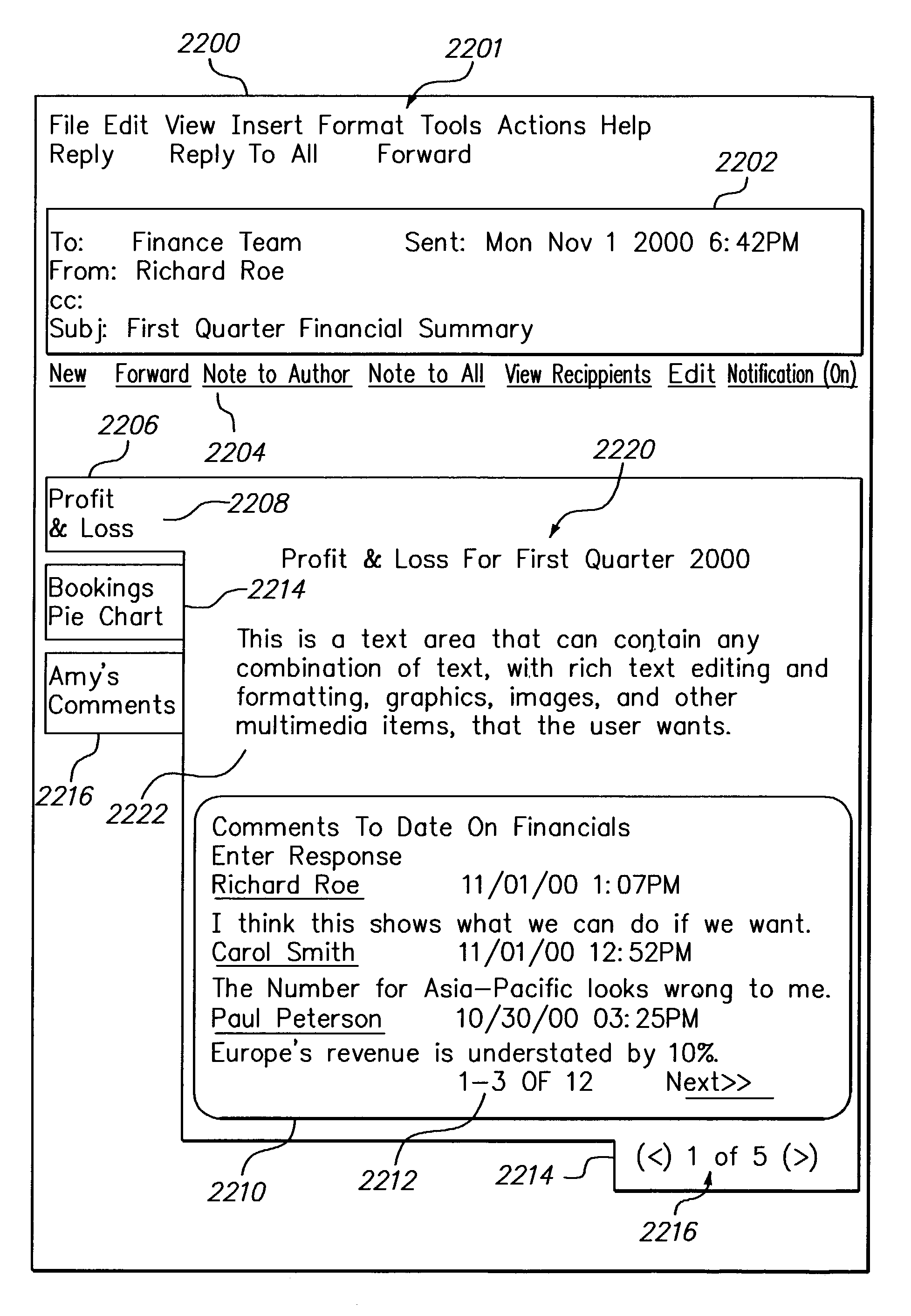
Methods and apparatus providing electronic messages that are linked and aggregated
InactiveUS7130885B2Promote collaborationAutomate quicklyMultiple digital computer combinationsOffice automationApplication softwareUser interface
A method for associating related electronic messages in computer storage. A first transportable application is created and stored. User input requesting creation of a link from the first transportable application to another transportable application is received. User input that selects a second transportable application from among a plurality of previously created transportable applications is received. A link from the first transportable application to the second transportable application is created and stored. As a result, transportable application may be inter-related in complex message webs. The message webs may also be inter-related in message web rings. Links may be generated manually or automatically, based on context, workflow processes, or other known relationships among applications. Recipient lists and data may propagate among fields of linked transportable applications, directly or according to abstract business rules. Further, multiple-part electronic messages are disclosed. A graphical user interface of an electronic messaging system displays a message in the form of one or more header portions and one or more body portions. Each of the body portions has a selection region. While one body portion is visible at a given time, all the selection regions are continuously visible in the user interface to facilitate selection of any of the body portions at a particular time. Selecting a selection region of a non-displayed body portion causes a server to generate a refreshed user interface that includes the entirety of the selected body portion, and that hides the previously viewed body portion. As a result, a large amount of associated information may be combined in a single message in a way that is clearly organized and easily accessible.
Owner:METRICSTREAM
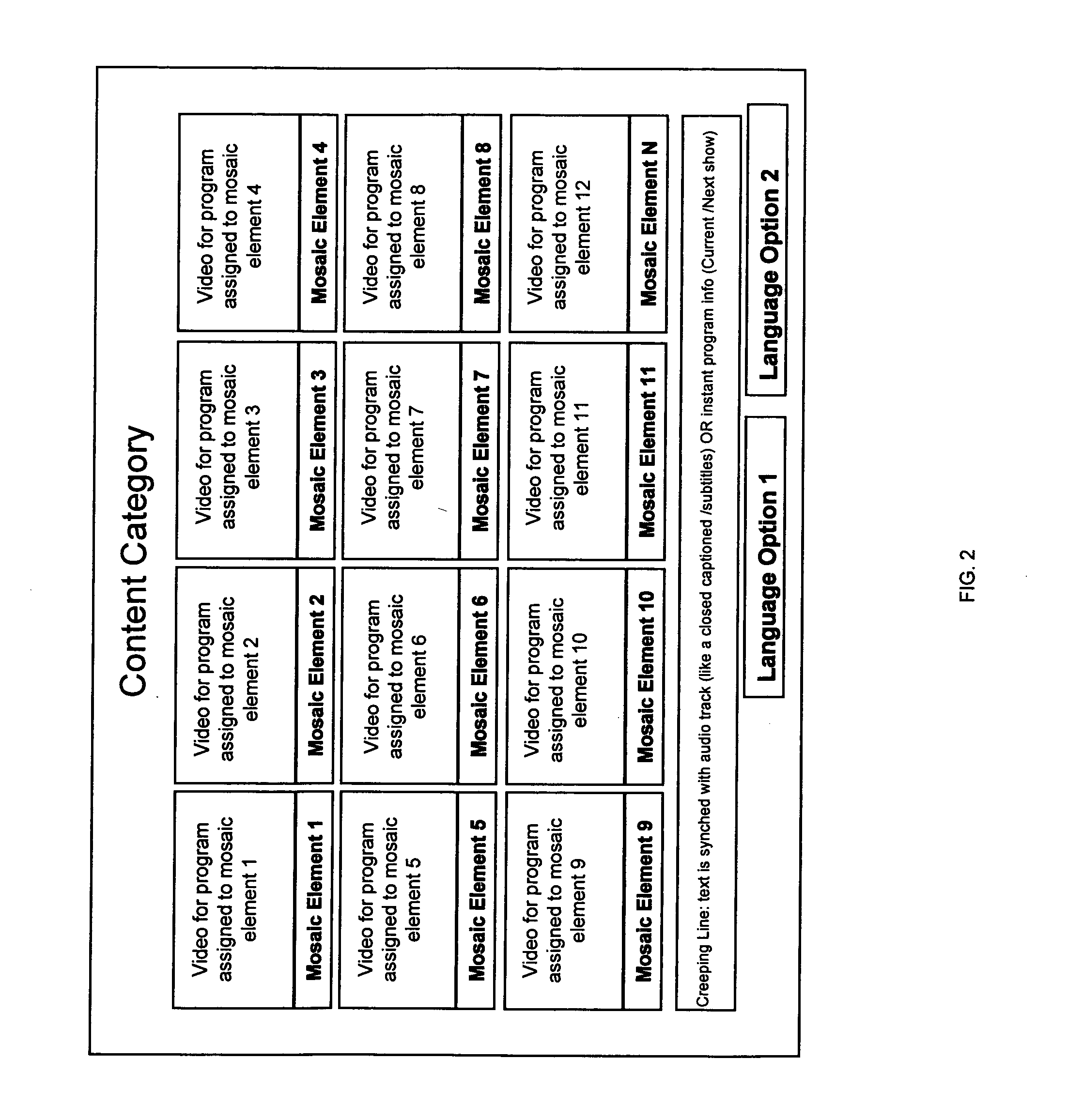
Dynamic mosaic extended electronic programming guide for television program selection and display
Owner:WEBTUNER CORP
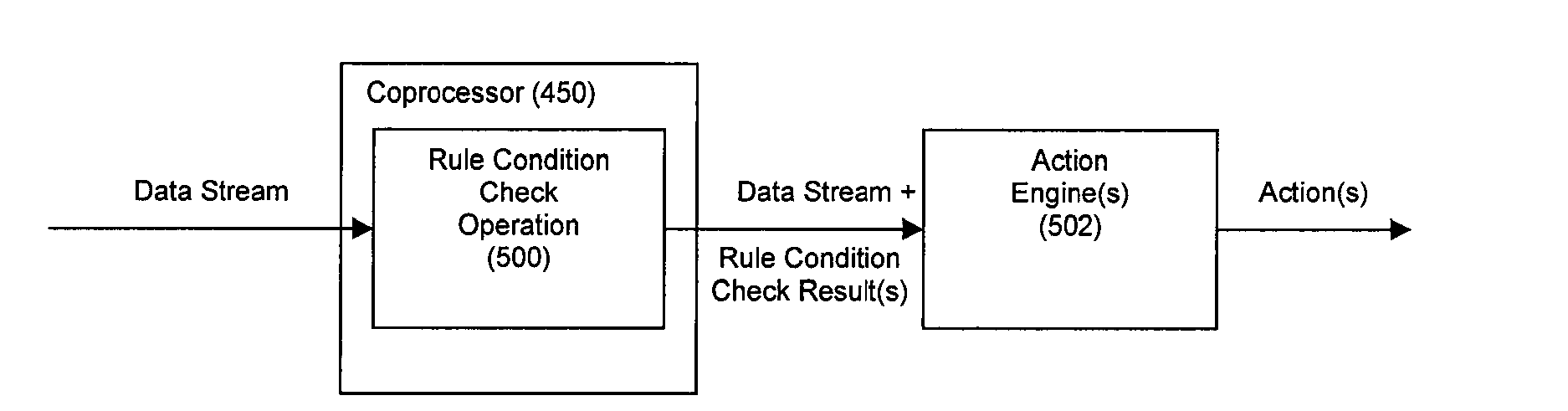
Method and System for Accelerated Stream Processing
ActiveUS20090287628A1Lower latencyImprove latencyDigital computer detailsCode conversionBusiness ruleEvent stream
Disclosed herein is a method and system for hardware-accelerating various data processing operations in a rule-based decision-making system such as a business rules engine, an event stream processor, and a complex event stream processor. Preferably, incoming data streams are checked against a plurality of rule conditions. Among the data processing operations that are hardware-accelerated include rule condition check operations, filtering operations, and path merging operations. The rule condition check operations generate rule condition check results for the processed data streams, wherein the rule condition check results are indicative of any rule conditions which have been satisfied by the data streams. The generation of such results with a low degree of latency provides enterprises with the ability to perform timely decision-making based on the data present in received data streams.
Owner:IP RESERVOIR
Deviation detection of usage patterns of computer resources
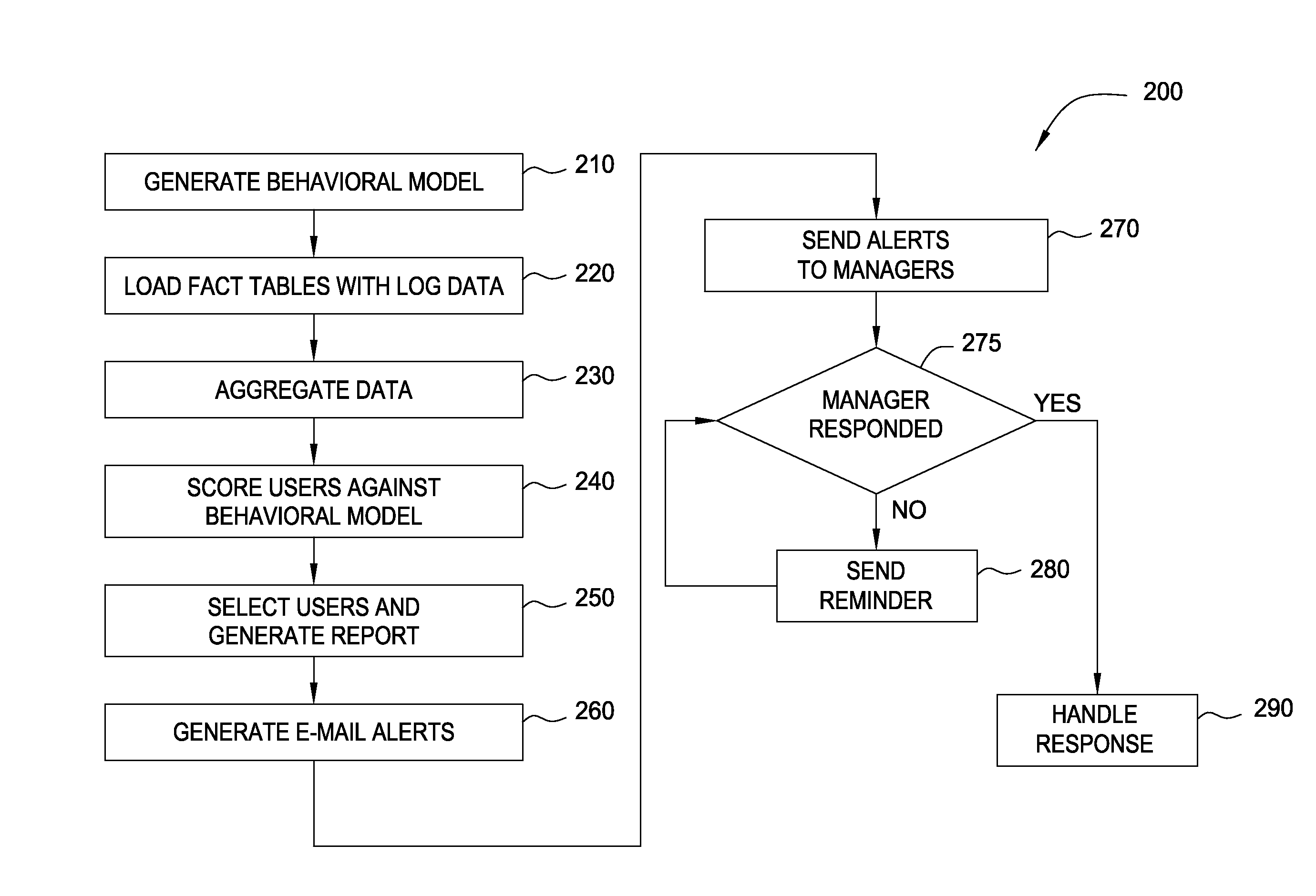
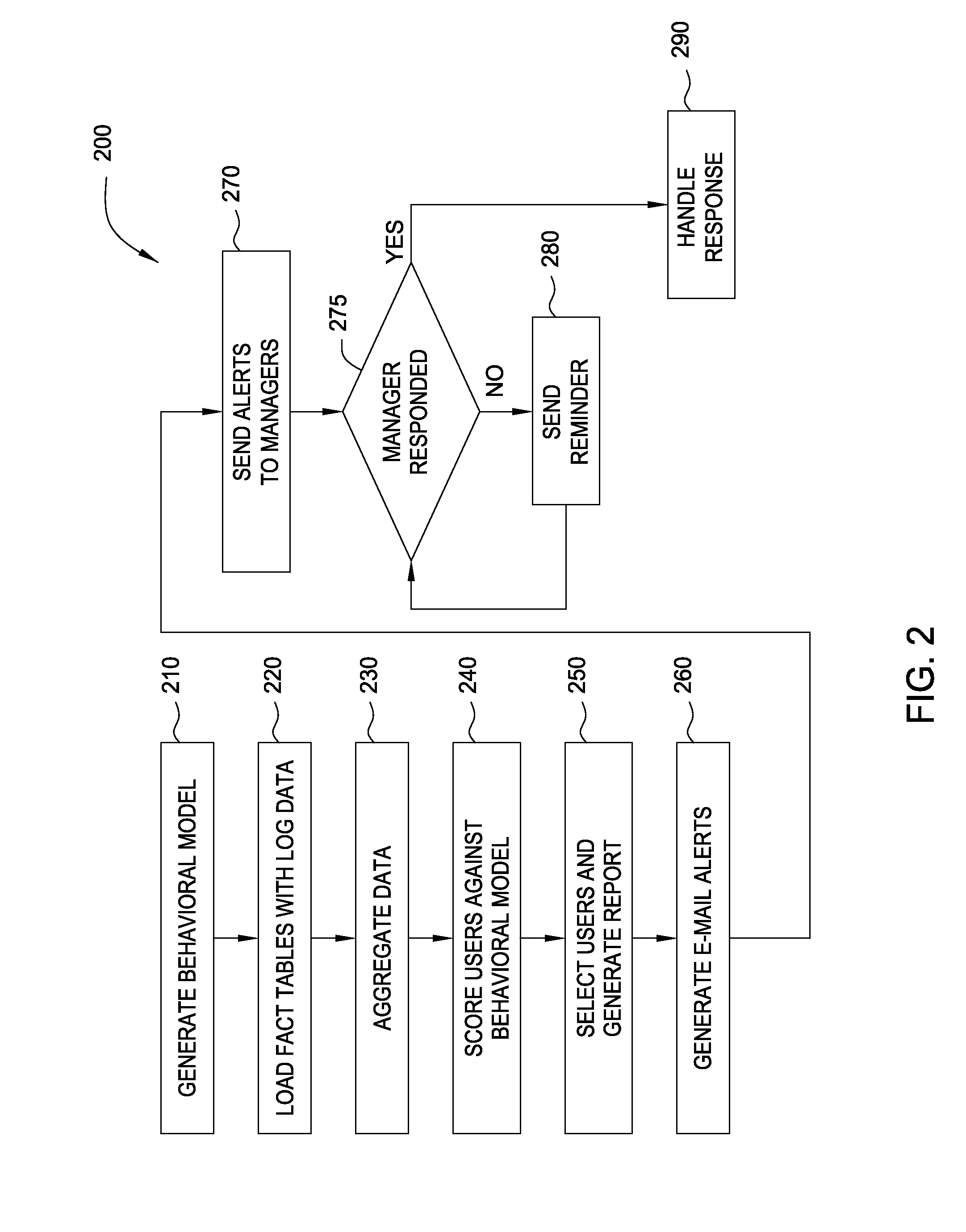
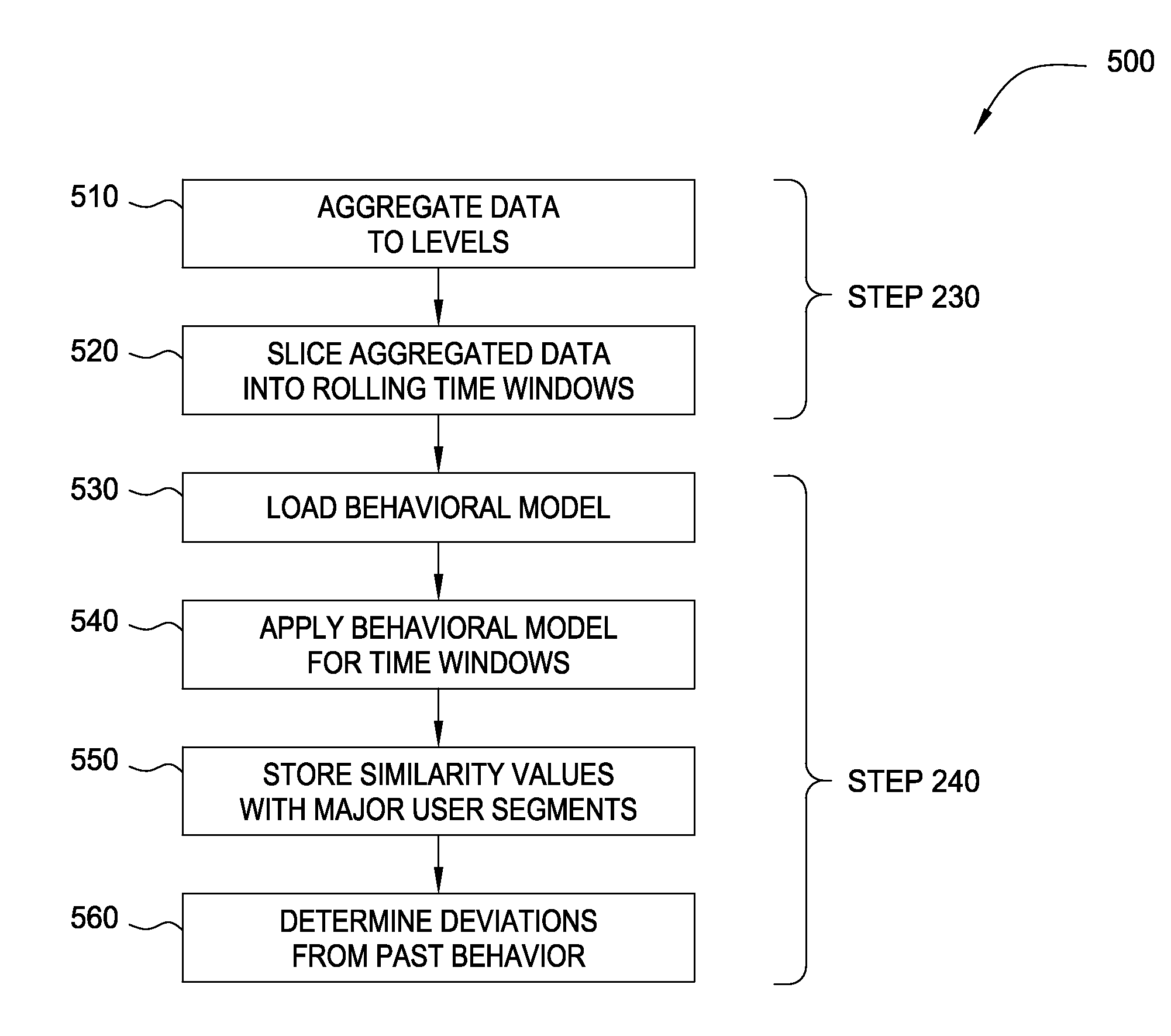
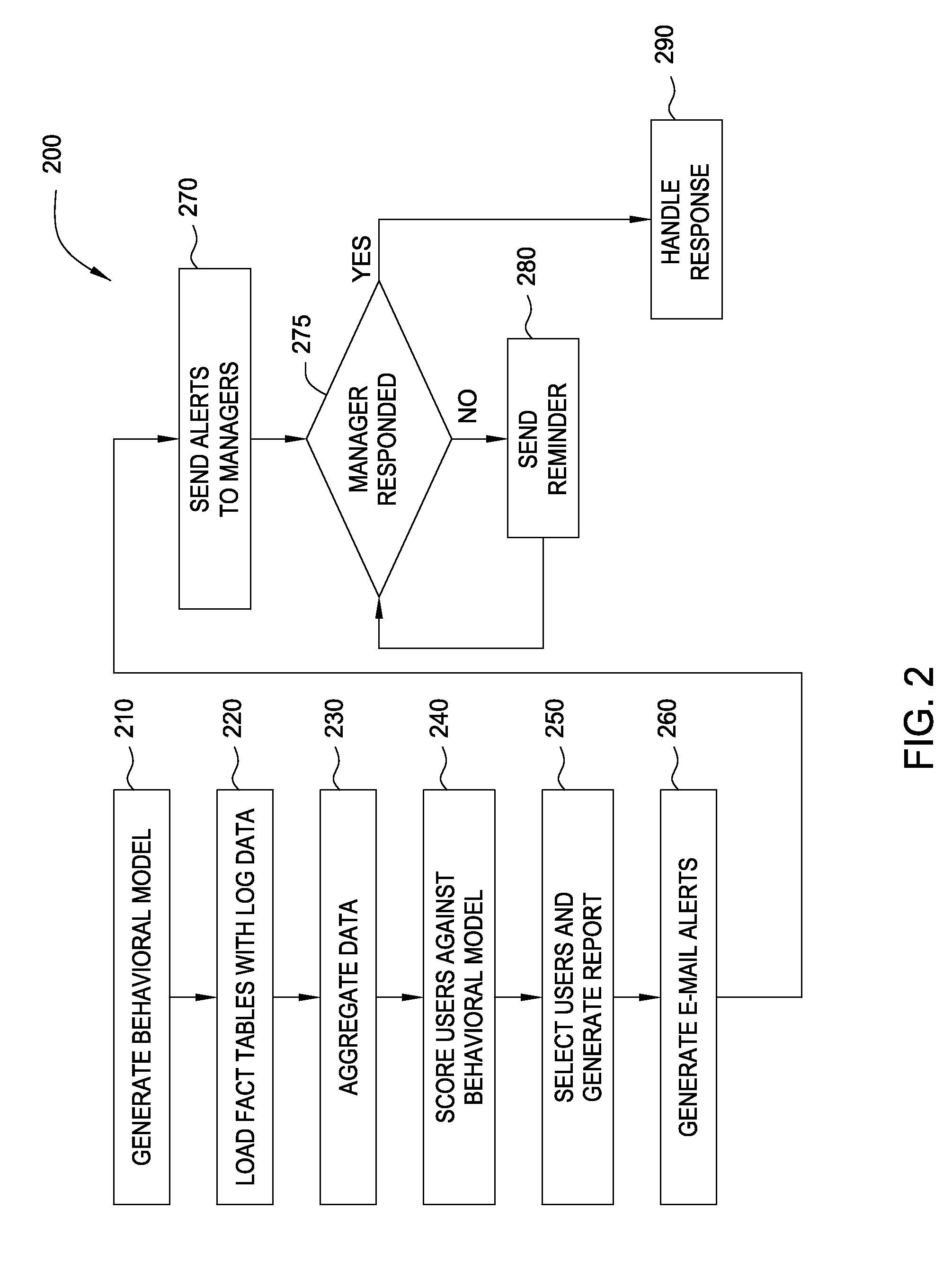
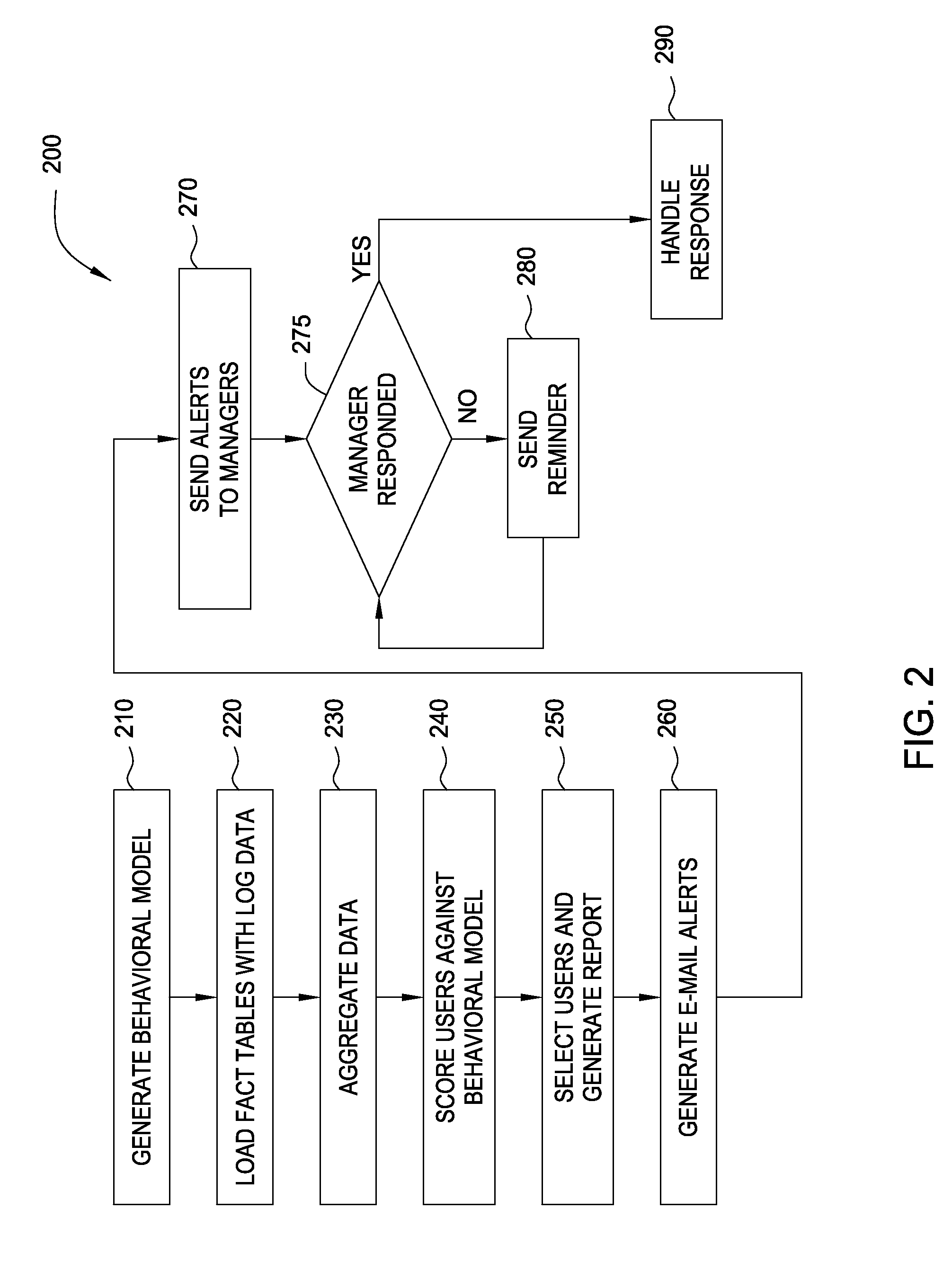
Embodiments of the invention provide a method for detecting changes in behavior of authorized users of computer resources and reporting the detected changes to the relevant individuals. The method includes evaluating actions performed by each user against user behavioral models and business rules. As a result of the analysis, a subset of users may be identified and reported as having unusual or suspicious behavior. In response, the management may provide feedback indicating that the user behavior is due to the normal expected business needs or that the behavior warrants further review. The management feedback is available for use by machine learning algorithms to improve the analysis of user actions over time. Consequently, investigation of user actions regarding computer resources is facilitated and data loss is prevented more efficiently relative to the prior art approaches with only minimal disruption to the ongoing business processes.
Owner:IBM CORP
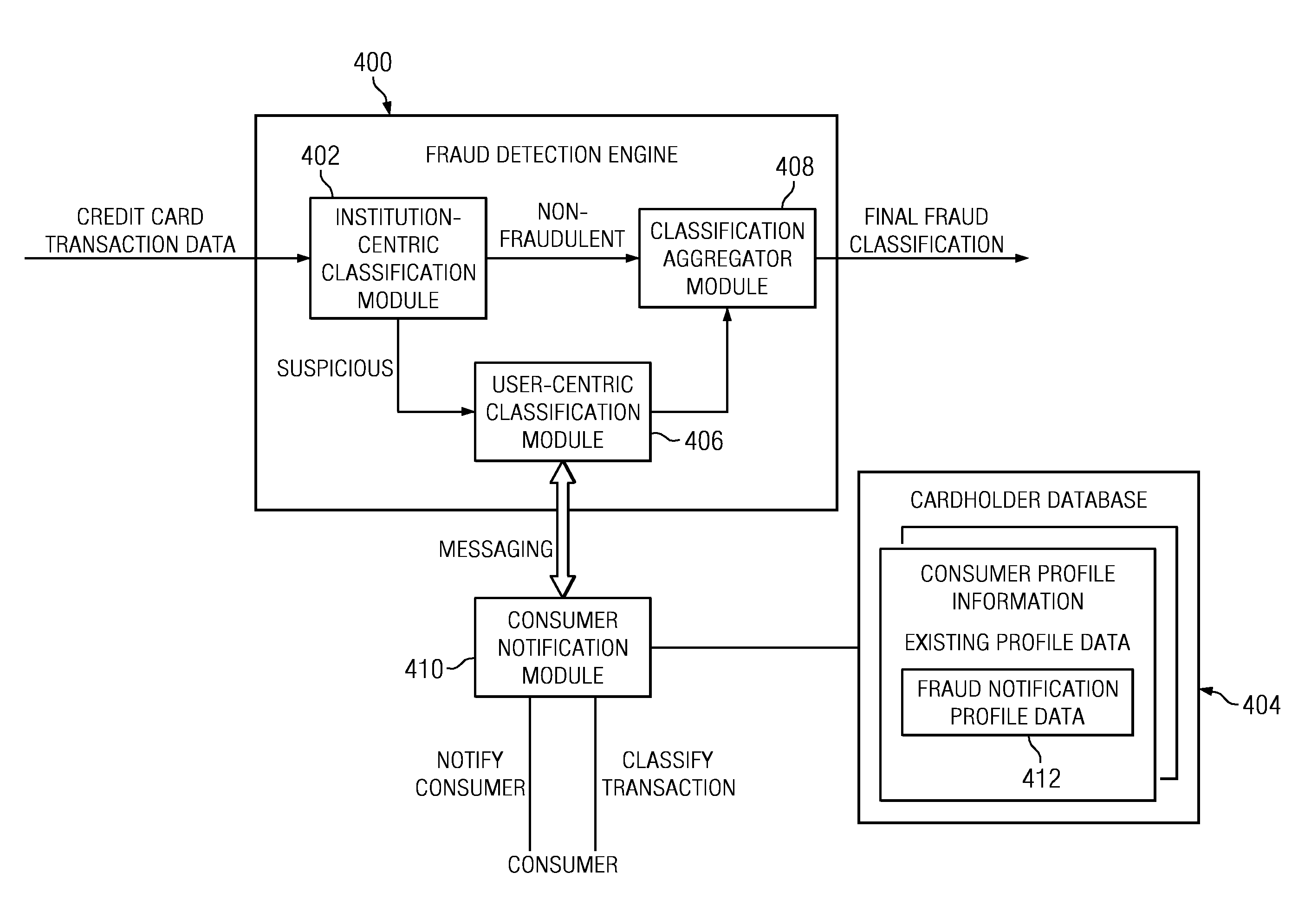
Method and System for Identification By A Cardholder of Credit Card Fraud
A method for fraud detection leverages an existing financial institution's fraud classification functionality, which produces a first level detection, with a “user-centric” classification functionality, which produces a “second” or more fine-grained detection regarding a potentially fraudulent transaction. After passing through an existing (“institution-centric”) fraud detection technique, a transaction that has been identified as potentially fraudulent is then subject to further analysis and classification at the “user” level, as it is the user is presumed to be the best source of knowledge of the legitimate credit card use. Information about the transaction is shared with the consumer, preferably via one or more near real-time mechanisms, such as SMS, email, or the like. Based on the user's response (or lack thereof, as the case may be), one or more business rules in the institution's fraud detection system can then take an appropriate action (e.g., no action, reverse the transaction if complete, deny the transaction if in-progress, or the like).
Owner:IBM CORP
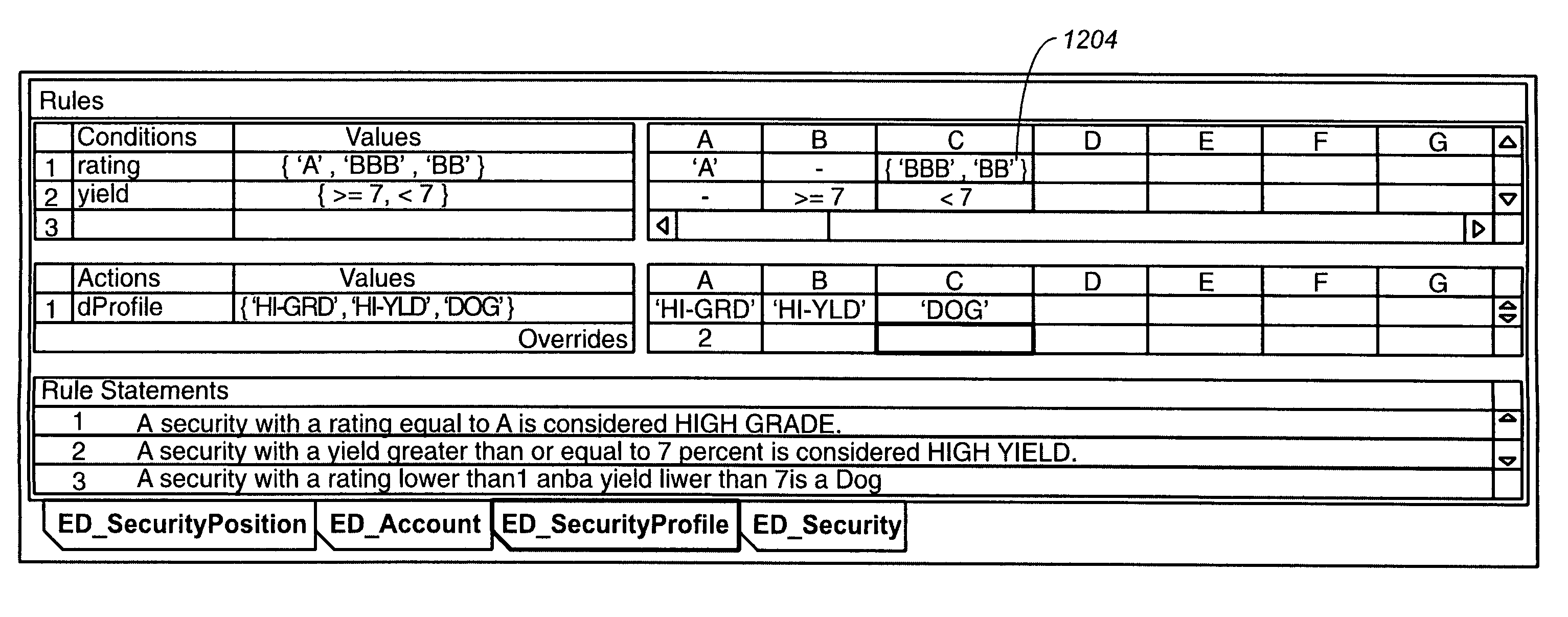
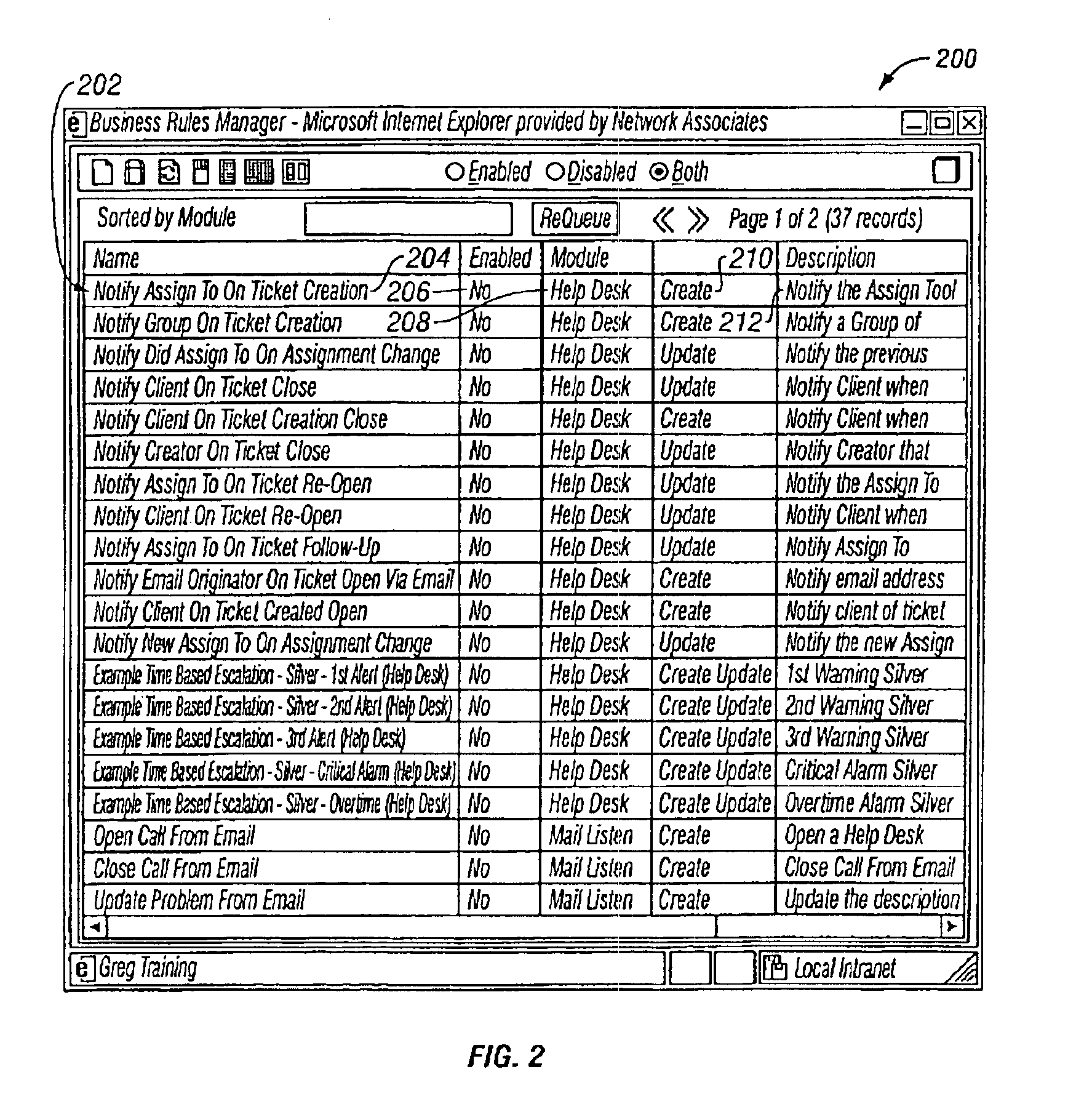
Business rules user interface for development of adaptable enterprise applications
ActiveUS7020869B2Reduce complexityMinimization requirementsTechnology managementVisual/graphical programmingApplication softwareDisplay list
Methods and apparatus, including computer program products, for interacting with a user to define business rules in a declarative manner. The invention operates to display a rule set as an editable list of conditions and an editable list of actions, the conditions and actions being linked to each other by the combination of an editable list of if-values and an editable list of then-values, wherein if-values and then-values are explicitly linked to each other, conditions and if-values are explicitly linked to each other, and then-values and actions are explicitly linked to each other in the displayed lists.
Owner:PROGRESS SOFTWARE
Method and system for electronic settlement of checks
InactiveUS20080097899A1Efficiently clearingEfficiently settlingFinancePayment architectureChequeDatabase
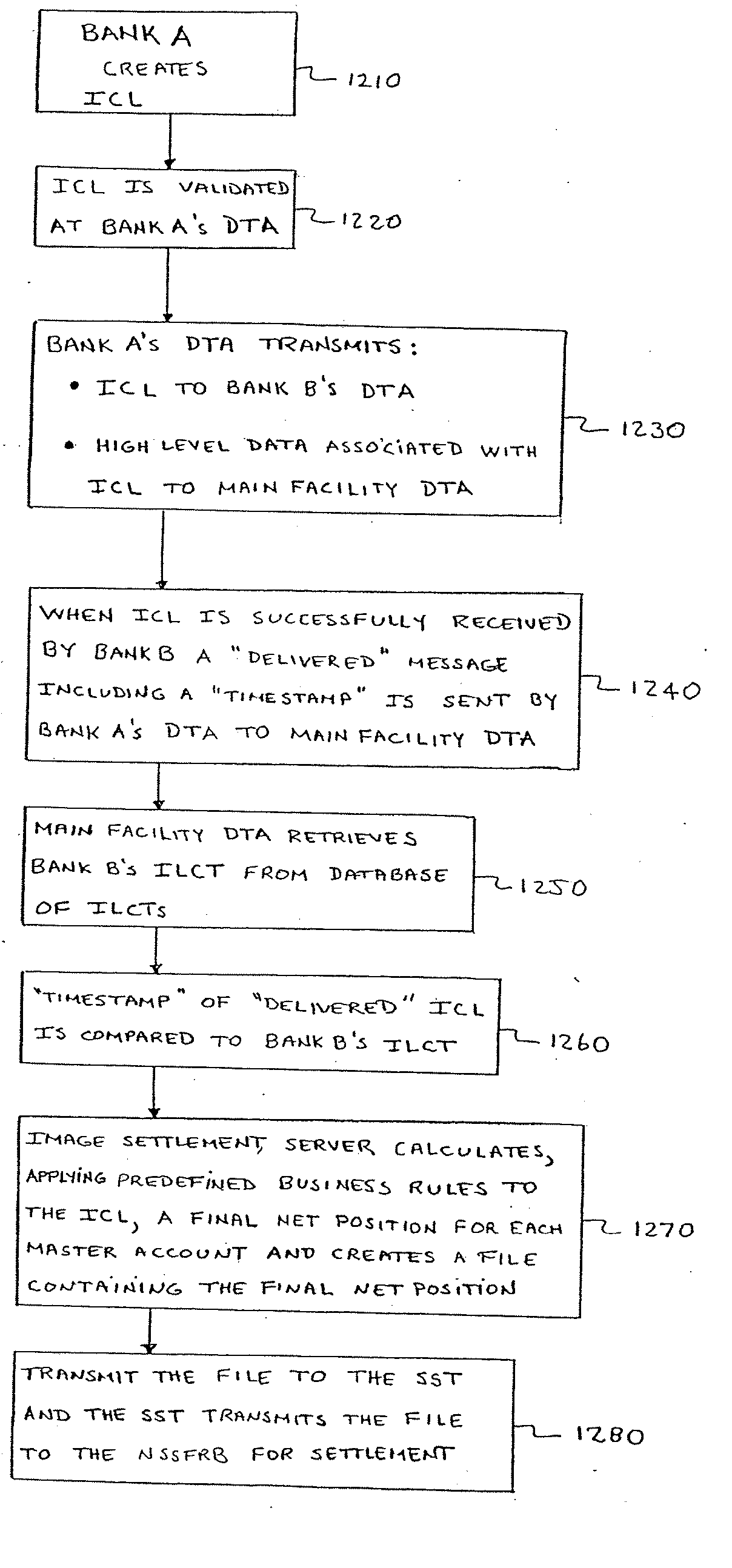
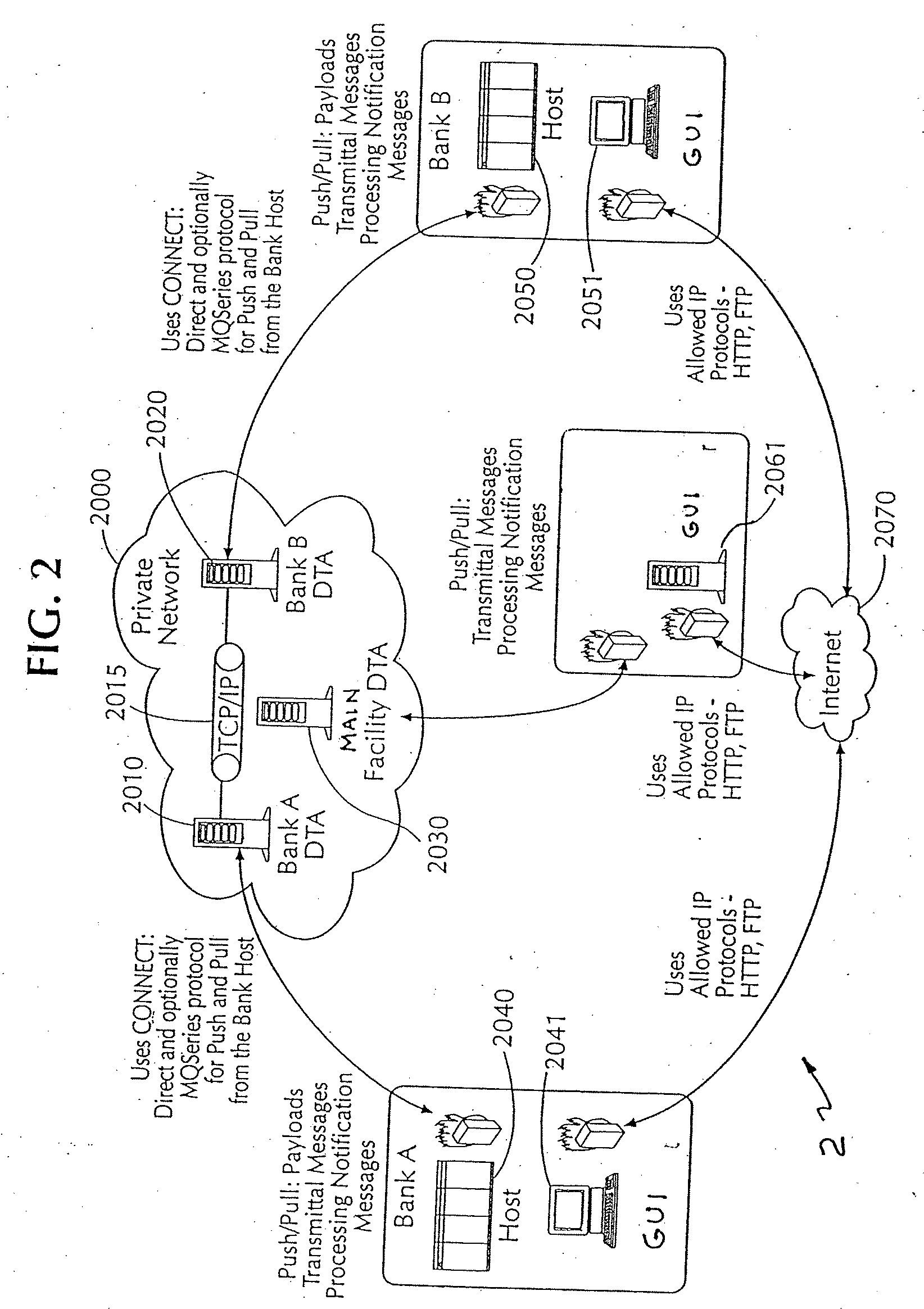
A system is provided for settling cash letters containing check images that are exchanged by banks connected to an image exchange system (IEX). Settlement amounts are computed and sent to the Federal Reserve Banks' National Settlement Service (FRBNSS) for settlement based upon business rules. Further, a method is provided for processing a financial check transaction between a plurality of financial institutions, including at least first and second institutions, the method including providing electronic check data, relating to at least one check to be paid by the second institution, from the first institution to the second institution to effect an automatic check presentment; and automatically performing an electronic settlement determination for the at least one check, based on the electronic check data and predetermined business rules.
Owner:THE CLEARING HOUSE PAYMENTS
Binding content to a domain
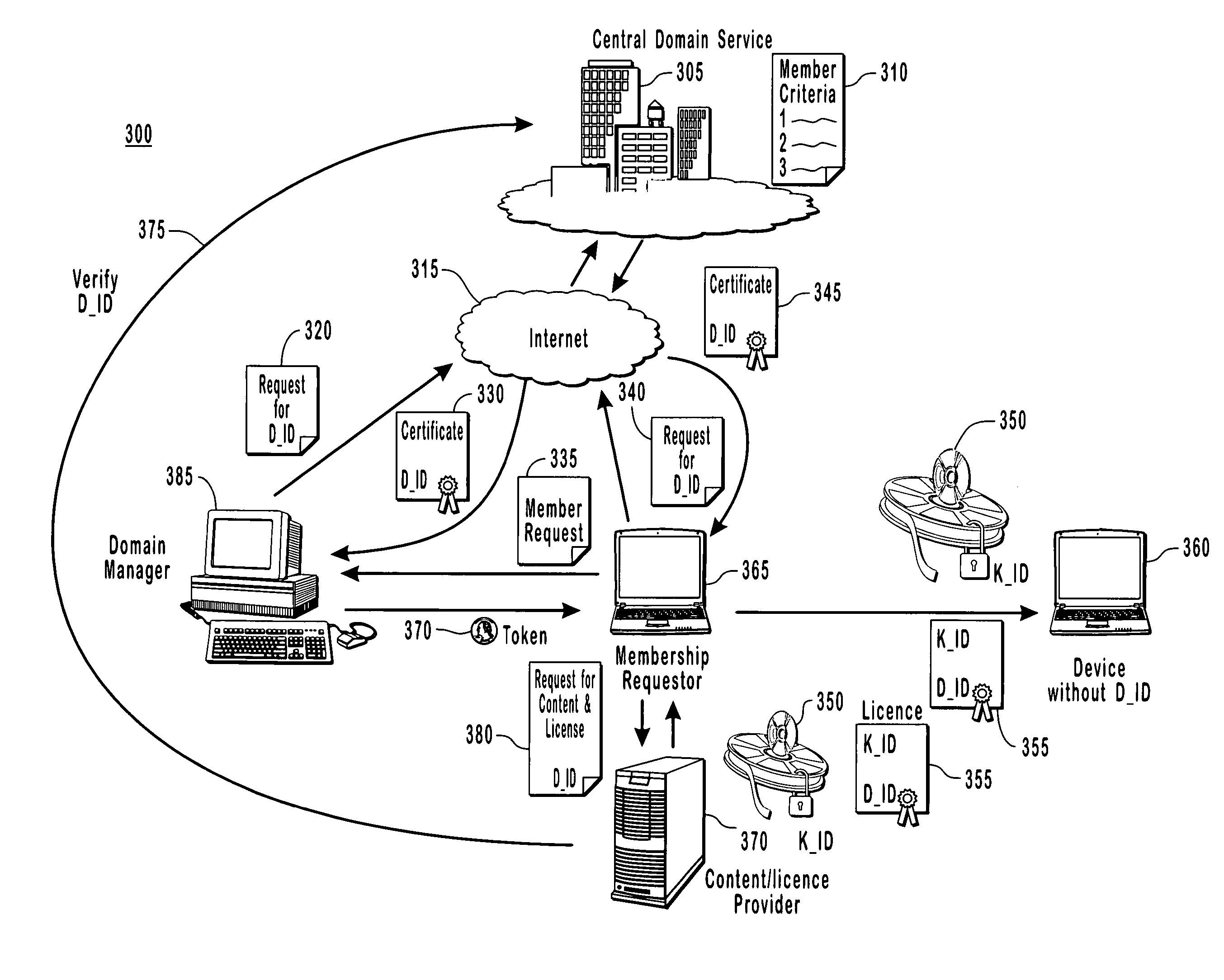
The present invention provides for a digital rights management system with a centralized domain service capable of creating and managing membership criteria for joining a domain in accordance with business rules defined by ac content owner. A domain identification is created that allows a content provider to uniquely bind content licenses to a domain. The content licenses include usage rights that define how content associated with the licenses may be consumed by one or more members of the domain. The centralized domain service can enforce digital rights by validating membership criteria including at least one of a domain proximity check for validating that a requestor is in close proximity to the domain, a total number of requestors, or the frequency that the requests have been made by various requesters to join the domain and unjoin from the domain.
Owner:ZHIGU HLDG
System and method for customizing and processing business logic rules in a business process system
Systems and methods for customizing business logic rules within a business process automation system and for processing business logic rules in a business process automation system are disclosed. The method for customizing business rules of a business logic application generally comprises serving a content page to a client browser of a client by a server that allows entering and modifying of data relating to a business logic rule, generating data by the server according to a predefined format such as a predefined XML format from information received via the content page, and automatically committing the generated data in the predefined format into a database. Preferably, a verification process such as by using DTDs (Document Type Definitions) is performed by the server prior to committing the data. The database stores data including data relating to business logic rules for implementing business logic as entries in the database and the generated data is committed into a corresponding entry in the database. Upon committing, the committed database business rule entry is ready for execution by the business logic application.
Owner:MCAFEE LLC
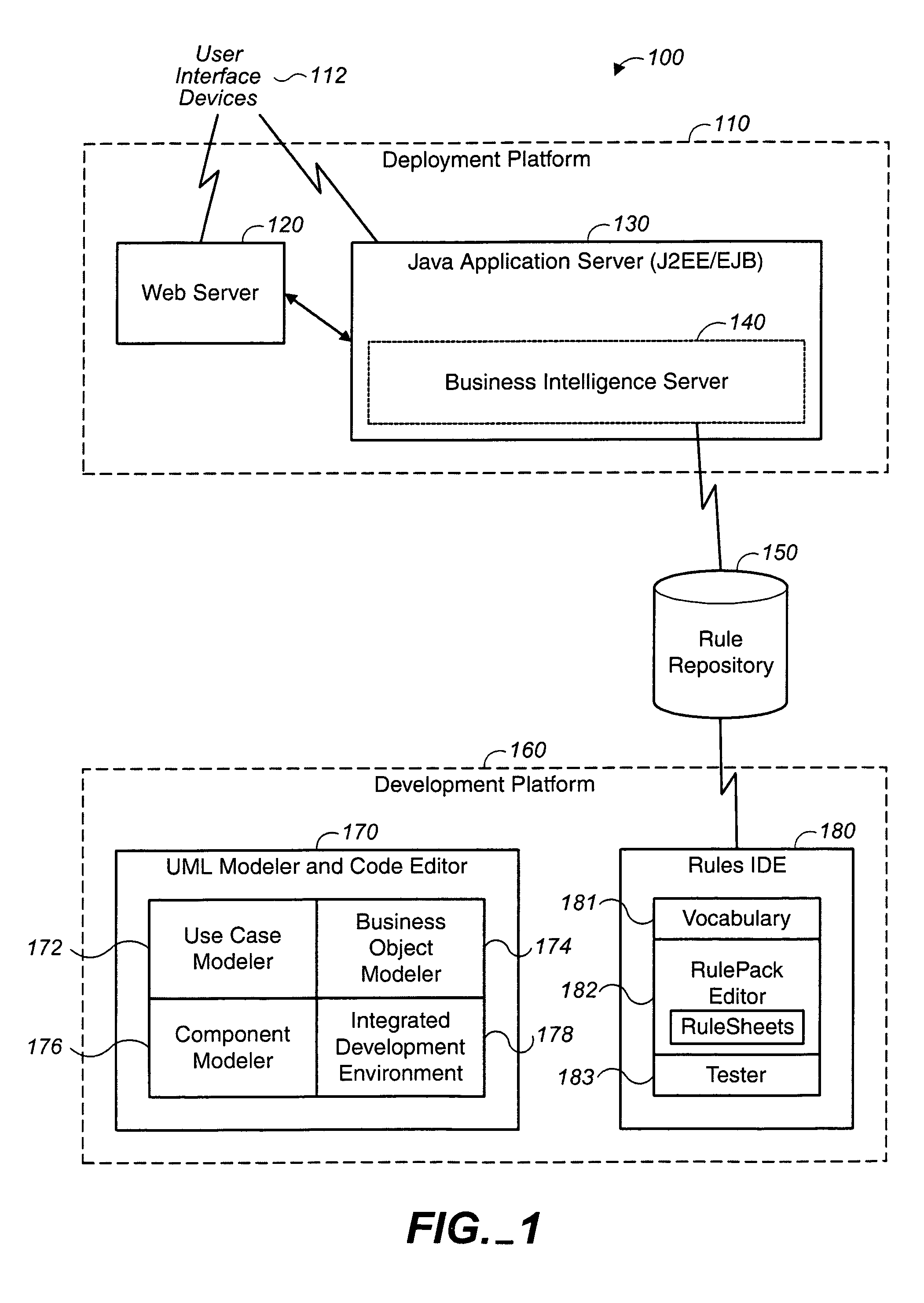
Integrated system for software application development
InactiveUS10001975B2Equally distributedProgram initiation/switchingVersion controlIntegrated softwareProject management
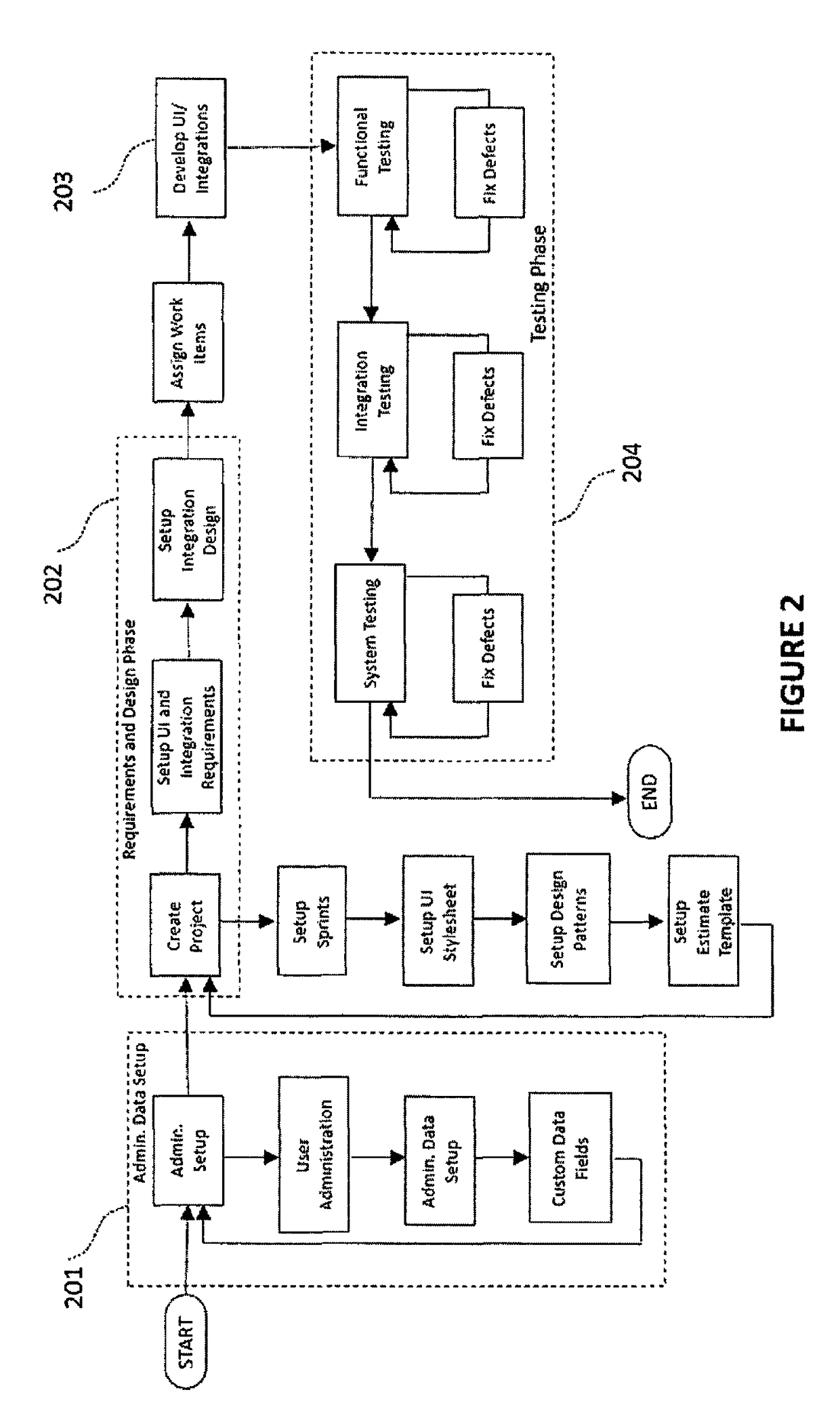
Methods and systems are disclosed for developing a software application through requirements specification, design, effort estimation, assigning and tracking work items, development, testing, collaboration and project management. The system is structured as an integrated software development system allowing for structured, systematic and user friendly set up of requirements specification (including workflow, user interface, business rules and integrations), technical design for UI features and integrations using design patterns, automated effort estimation, automated story card and task creation. The system also provides a novel, audio-video playback capability for workflow visualization. Further, the system provides visual depiction of defects and changed items side-by-side with requirements, as well as predictive modeling of defects that allows for forecasting of defect completion rate. In the preferred embodiment, the system is delivered as a multi-tenant Software as a Service.
Owner:BHARTHULWAR SHRIDHAR V
Modeling user access to computer resources
ActiveUS20090292743A1Memory loss protectionDigital data processing detailsComputer resourcesData loss
Embodiments of the invention provide a method for detecting changes in behavior of authorized users of computer resources and reporting the detected changes to the relevant individuals. The method includes evaluating actions performed by each user against user behavioral models and business rules. As a result of the analysis, a subset of users may be identified and reported as having unusual or suspicious behavior. In response, the management may provide feedback indicating that the user behavior is due to the normal expected business needs or that the behavior warrants further review. The management feedback is available for use by machine learning algorithms to improve the analysis of user actions over time. Consequently, investigation of user actions regarding computer resources is facilitated and data loss is prevented more efficiently relative to the prior art approaches with only minimal disruption to the ongoing business processes.
Owner:DAEDALUS BLUE LLC
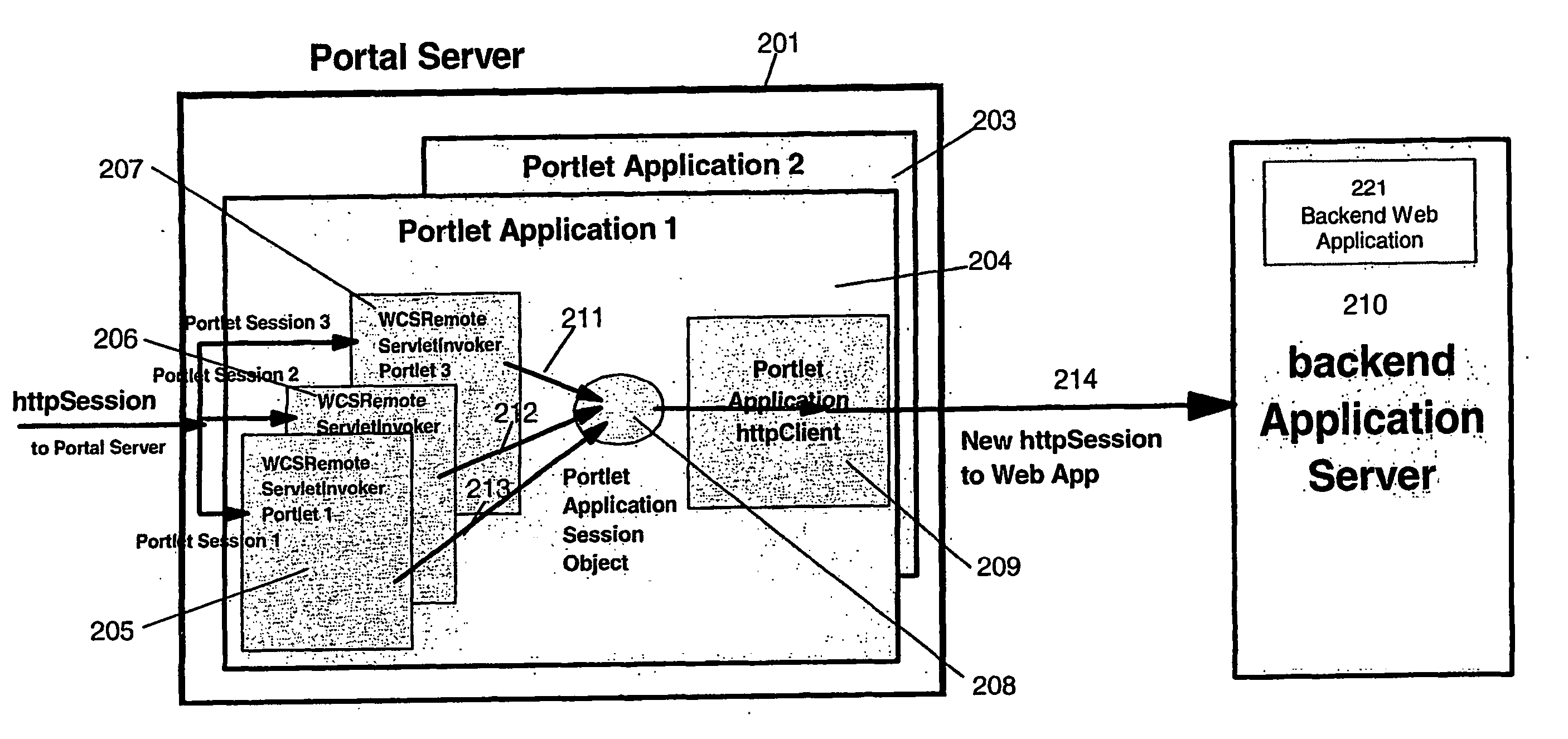
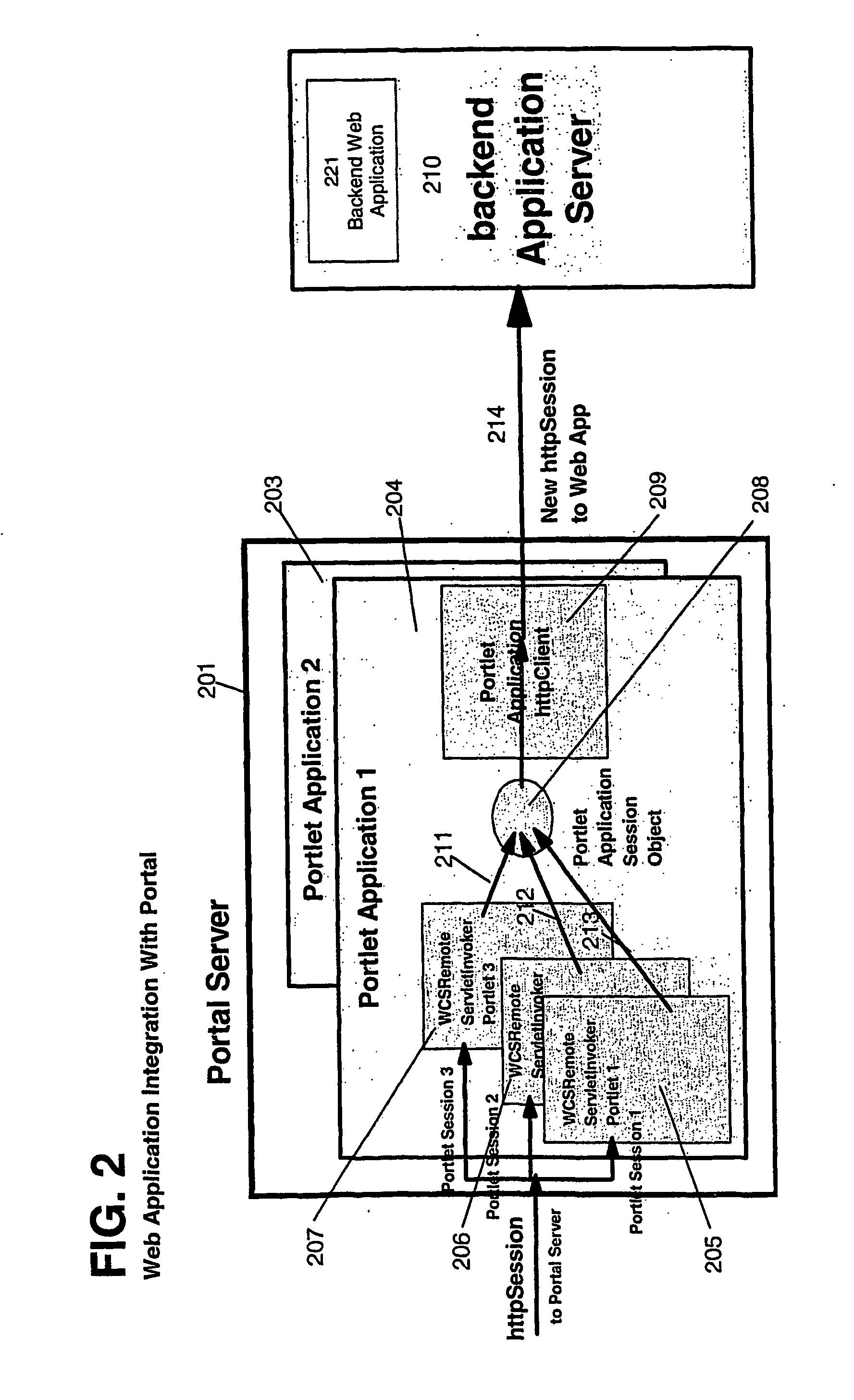
Method and apparatus for using business rules or user roles for selecting portlets in a web portal
InactiveUS20060235935A1Improve the level ofDigital data protectionMultiple digital computer combinationsPortletApplication software
An embodiment of the invention includes means to select portal resources (portlets, page and page groups) as displayed to a user based on pluggable rules engine; a rules database; and a portlet application aggregation engine which applies rules to select and display selected portlets, pages and page groups to a user.
Owner:IBM CORP
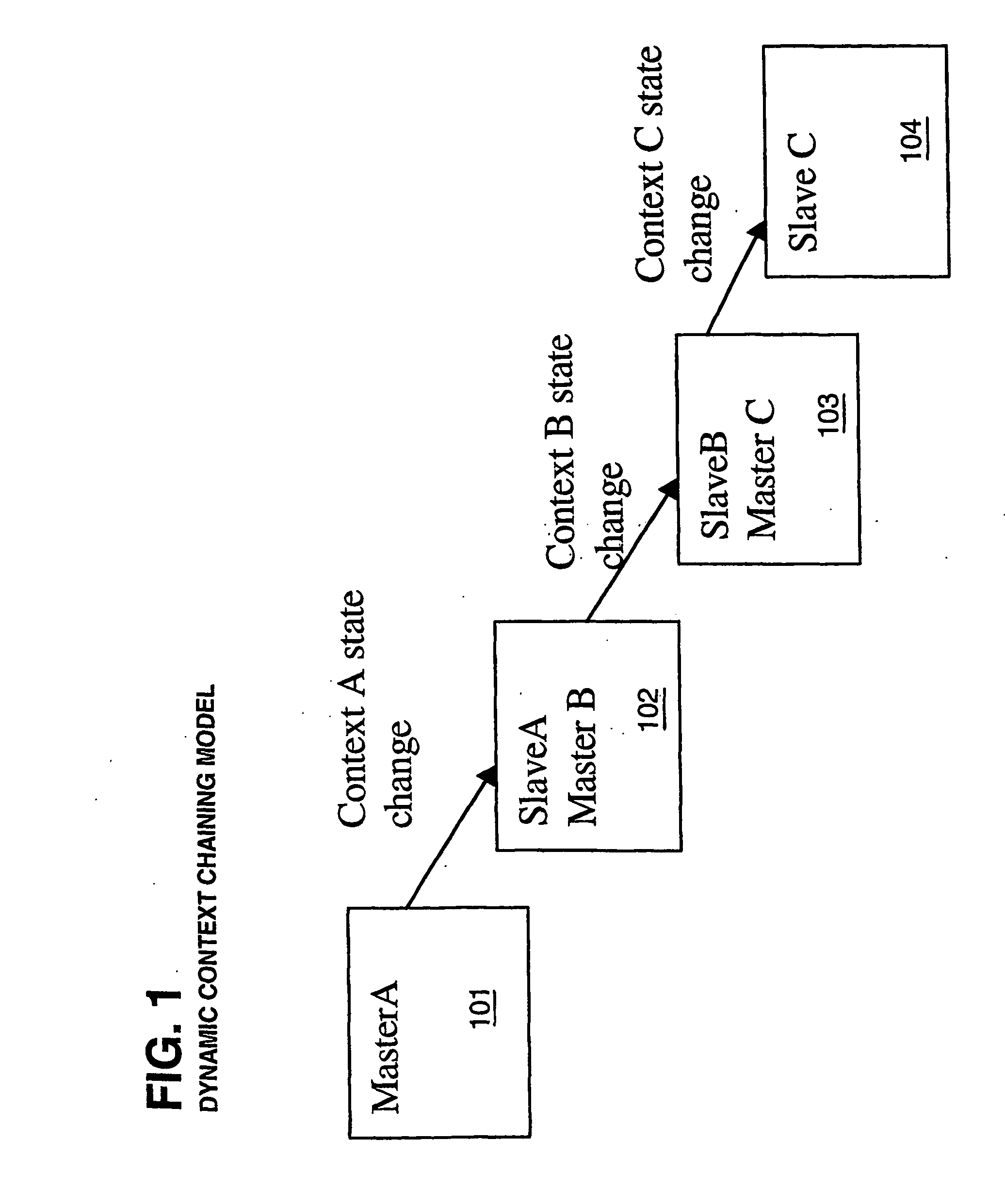
Cross-domain authentication
InactiveUS20050204041A1Overcome deficienciesAvoid the needDigital data processing detailsDigital computer detailsService provisionClient-side
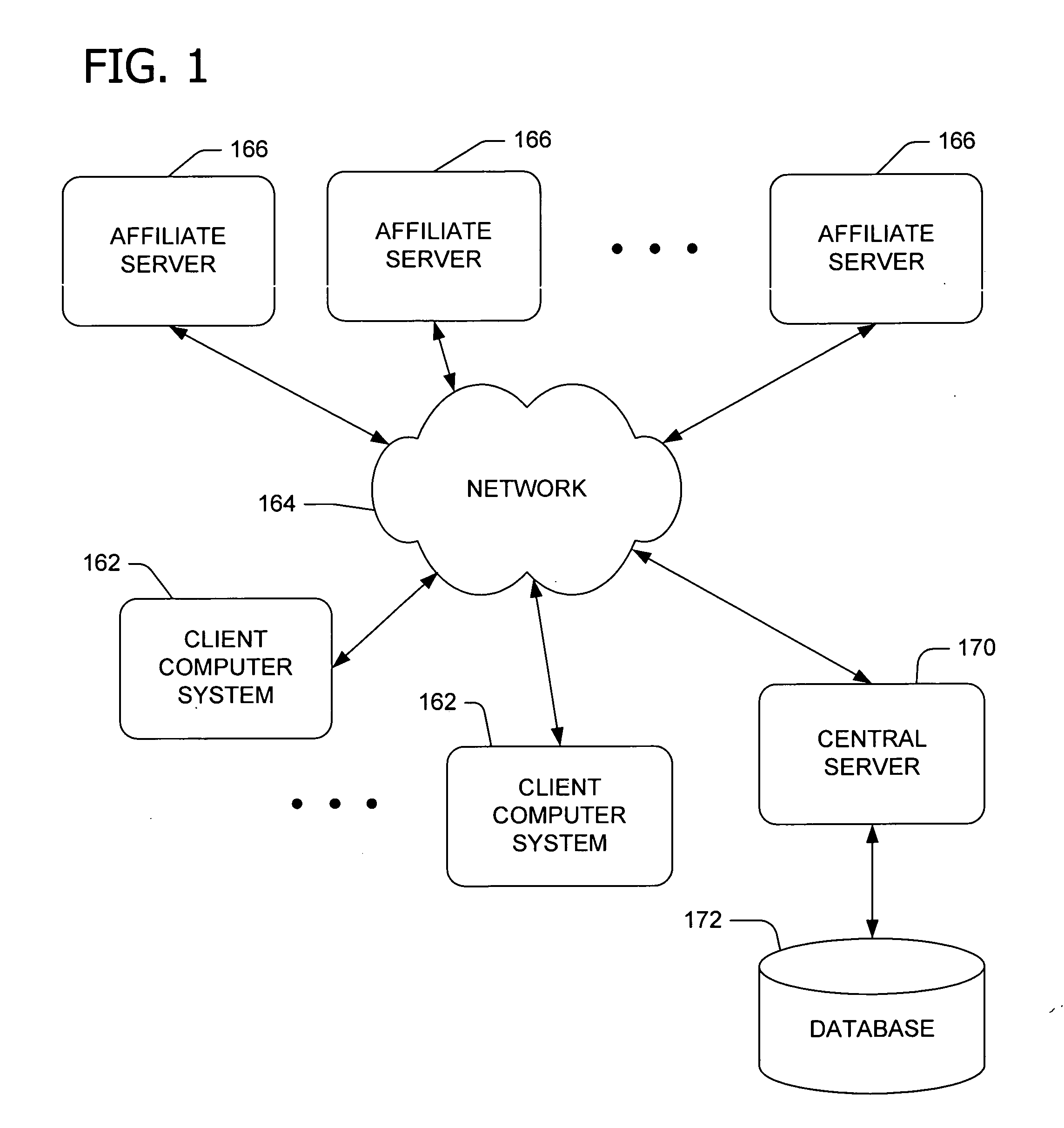
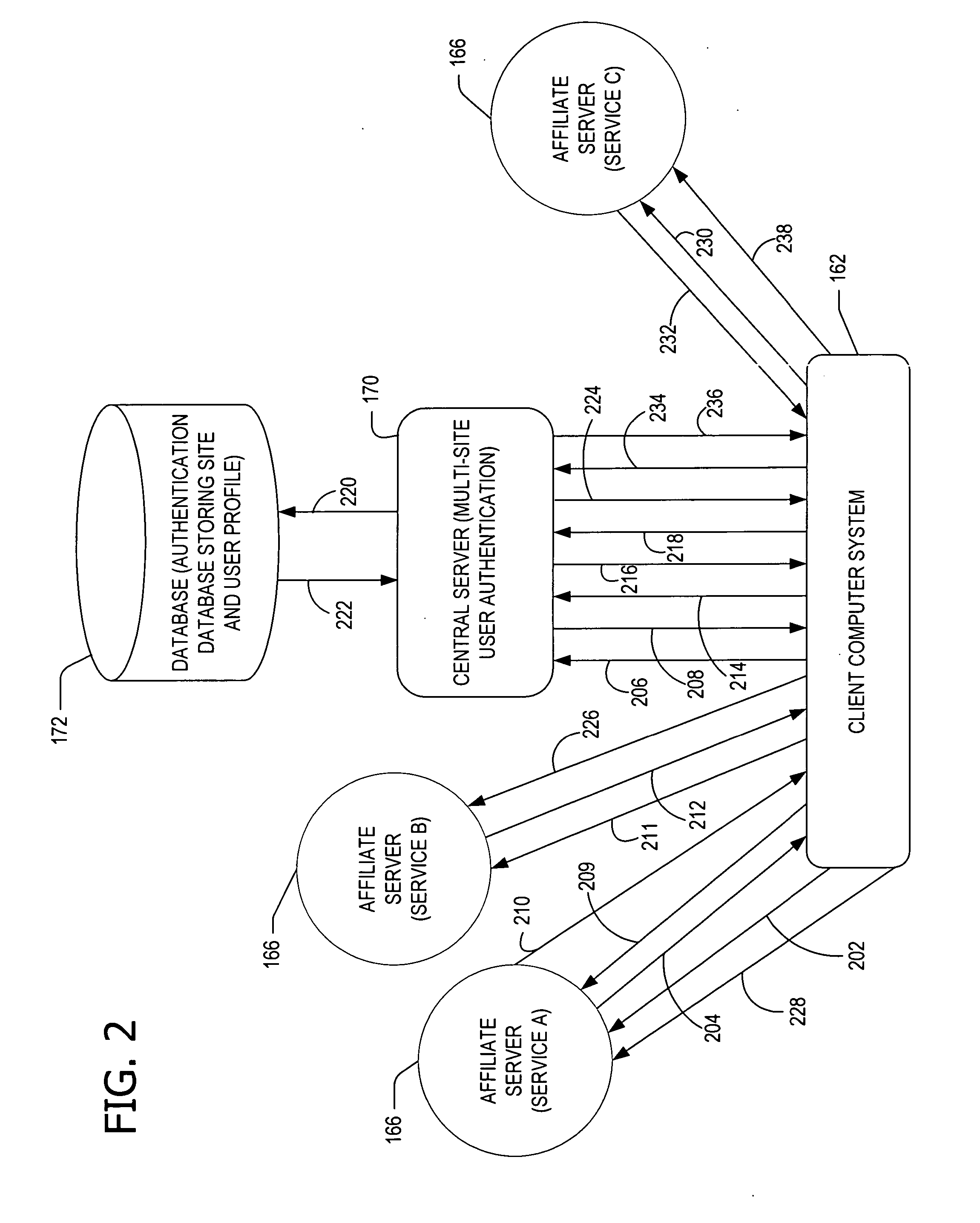
Providing services within a network of service providers sharing an authentication service and a set of business rules. A central server receives a first request from a first server to provide a first service to a user via a client without forcing the user to present credentials. In response to the received first request, the central server stores data identifying the first service on the client. The central server further receives a second request from a second server to provide a second service to the user via the client after the user presents the credentials to the second service. After receiving the second request and the presented credentials, the central server allows the user access to the second service. In response to allowing the user access to the second service, the central server further allows the user access to the first service as a result of the stored data.
Owner:MICROSOFT TECH LICENSING LLC
System and method of dynamic service composition for business process outsourcing
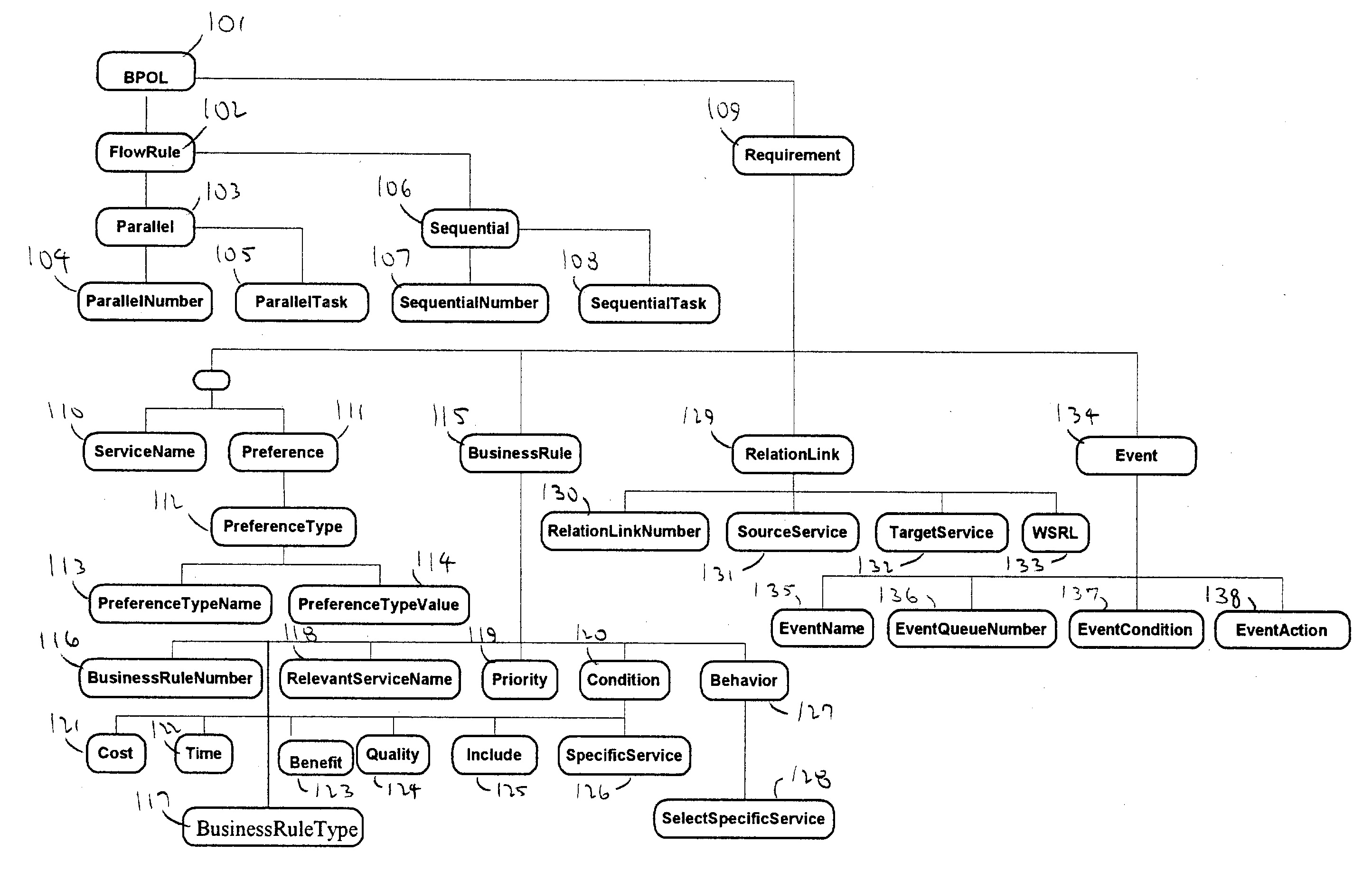
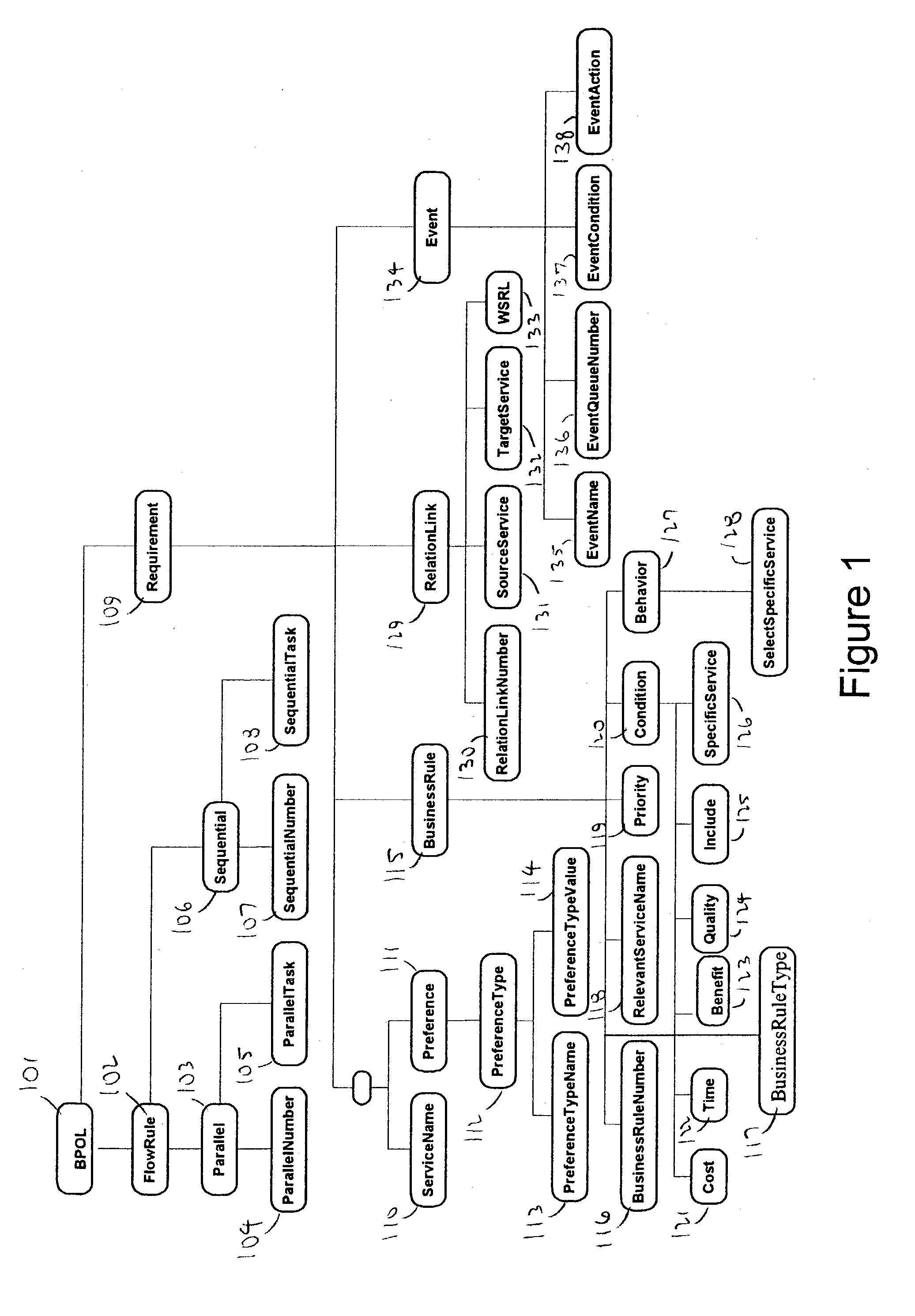
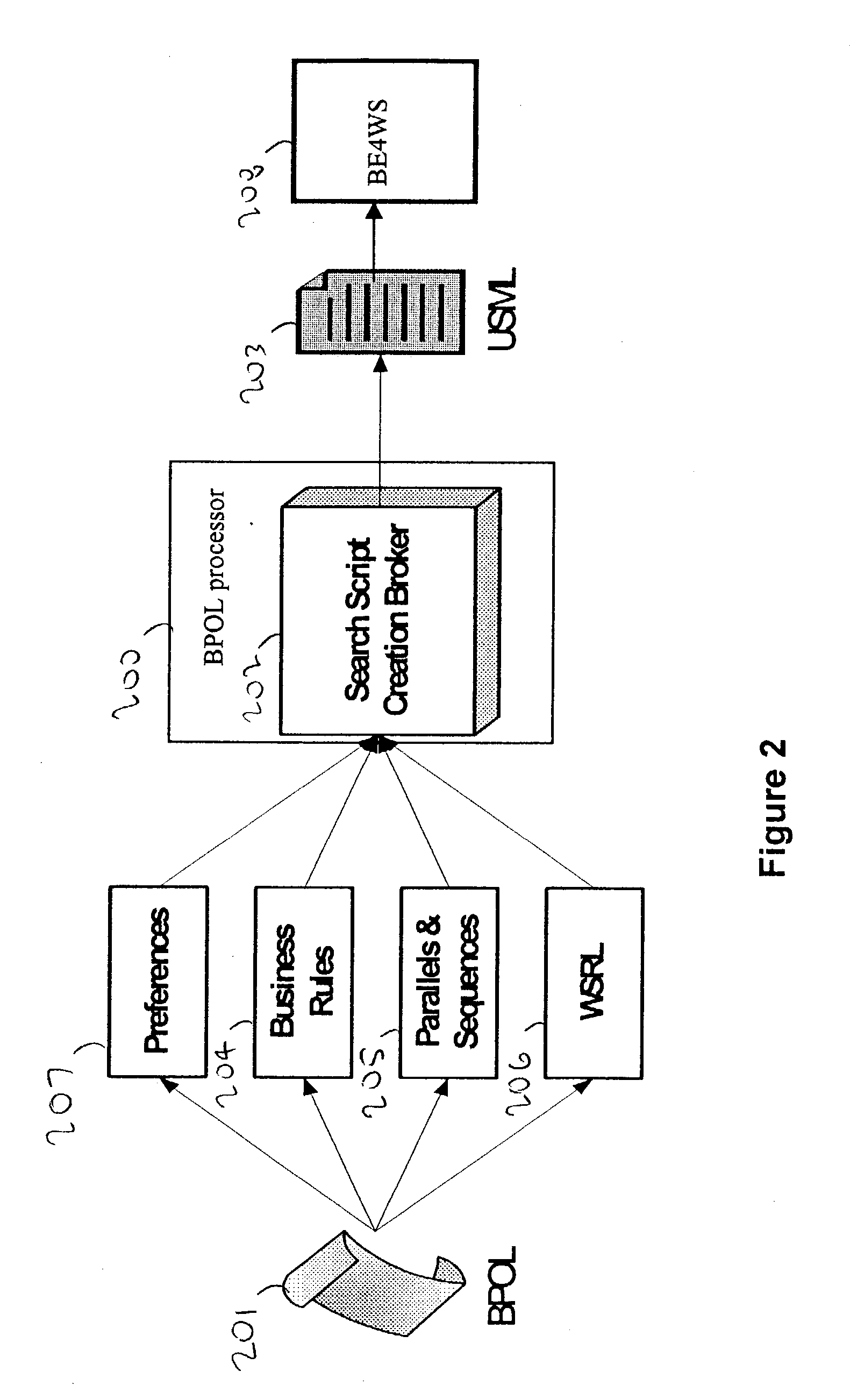
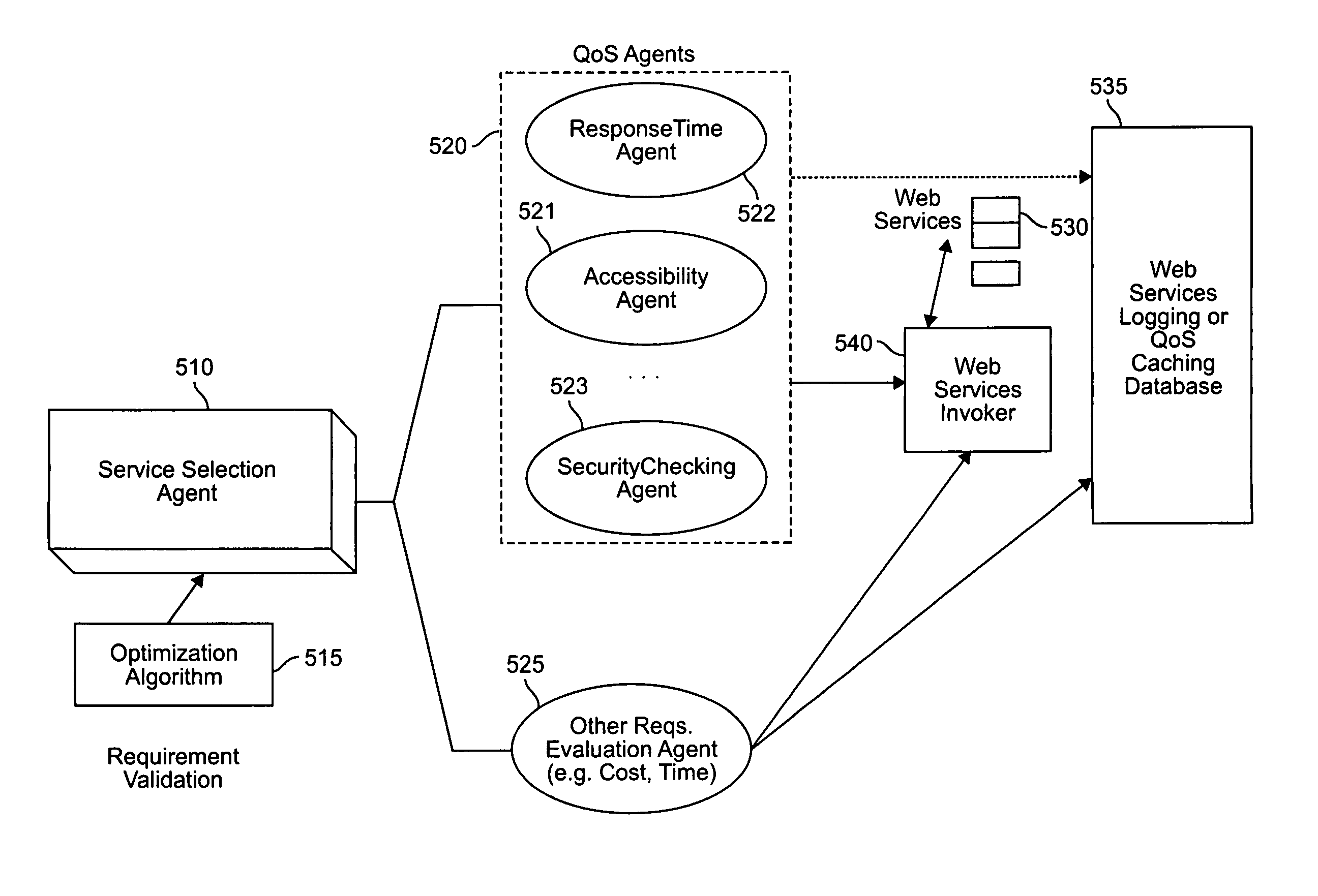
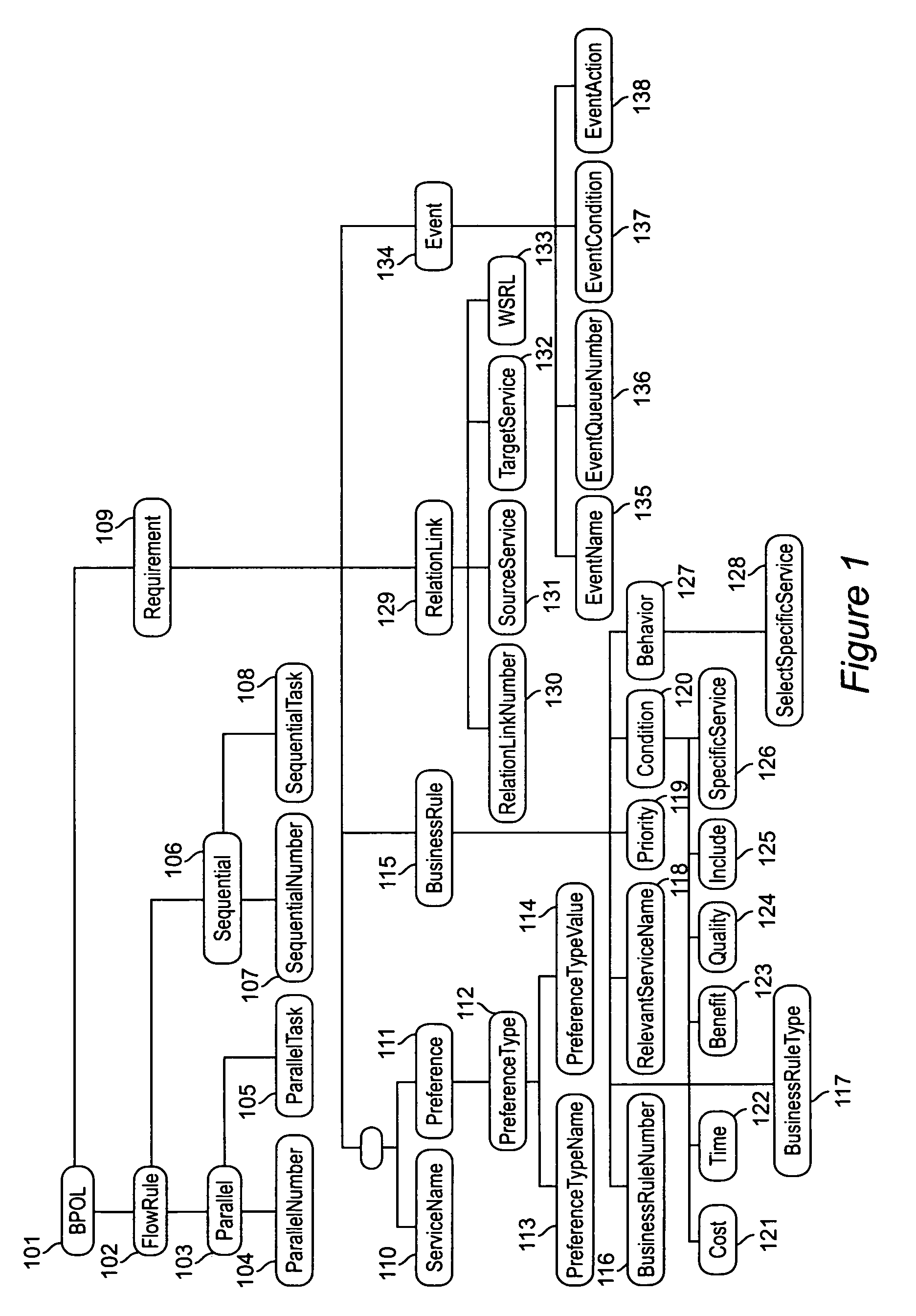
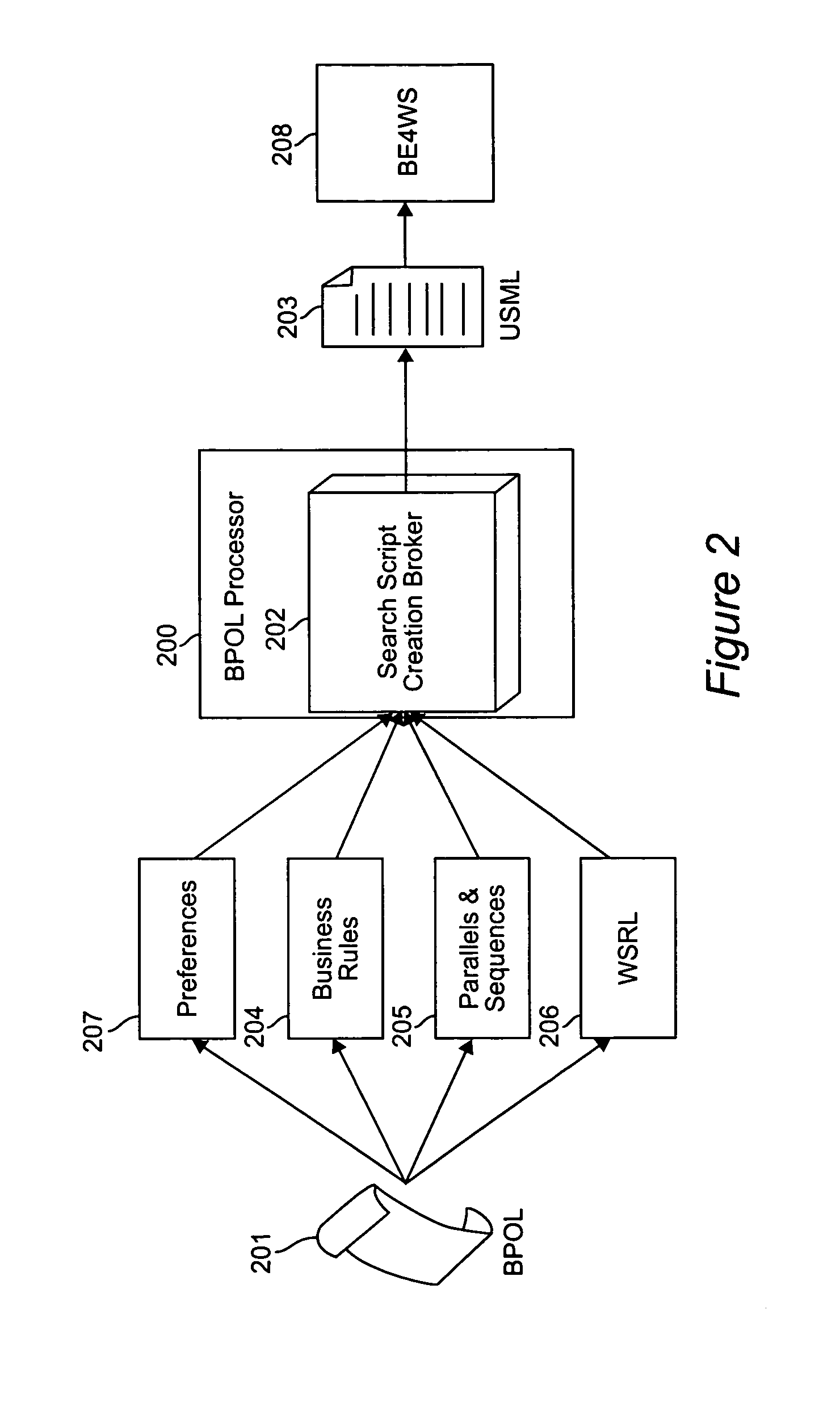
A system and method for capturing a plurality of business requirements using a Business Process Outsourcing Language (BPOL), an XML representation for expressing business process flow rules, preferences, business rules and event-action mappings as well as service links, to automate the process of generating business processes for use with Web services. BPOL is used to dynamically construct a search script for an advanced Web services discovery engine to find Web services from both UDDI registries and Web services Inspection Language (WSIL) documents and then create a qualified service list. Then a service selection problem is mapped into a solution space {0,1} for use by an optimization algorithm that performs second level service selection of the best set of services based on the requirements.
Owner:IBM CORP
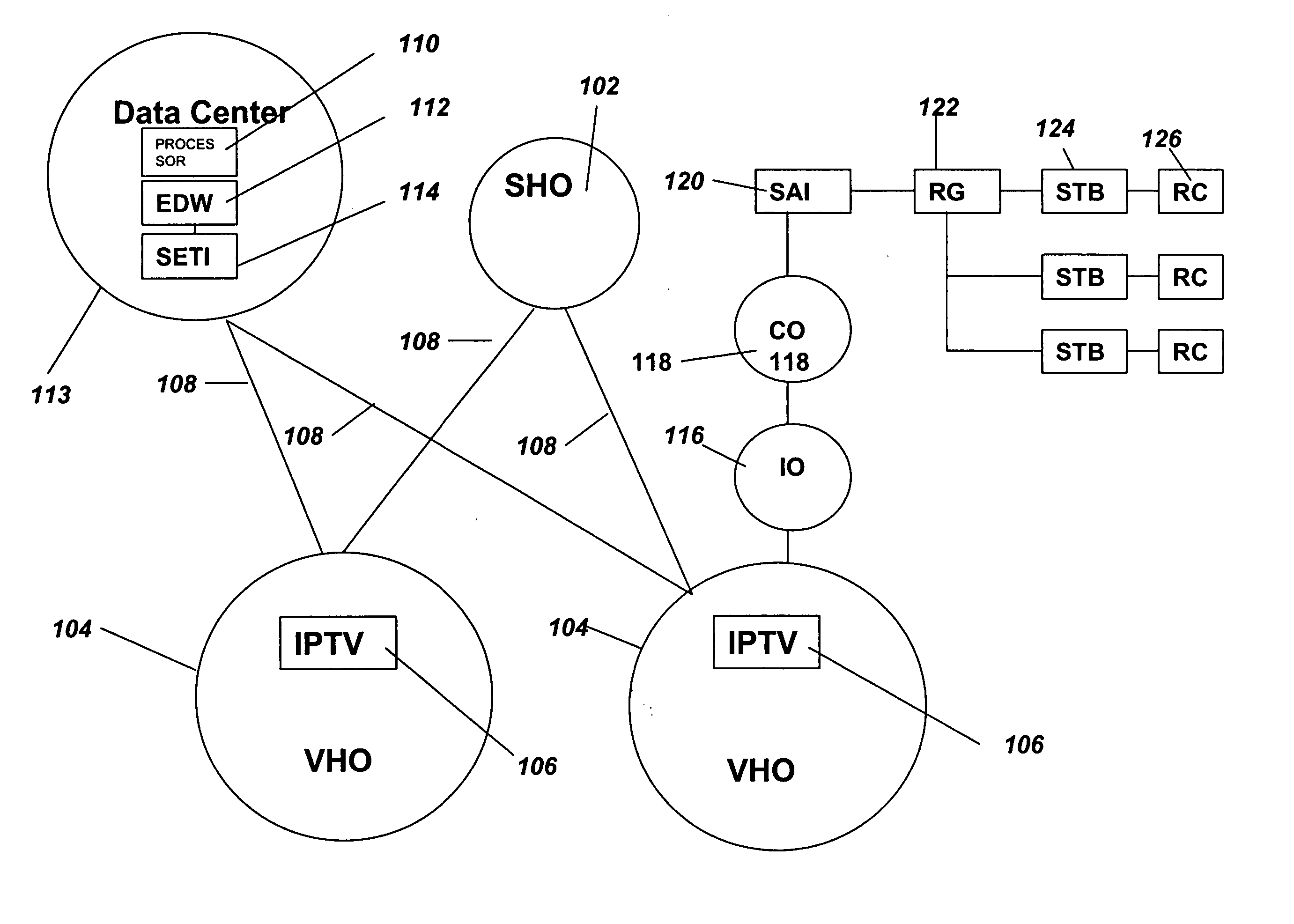
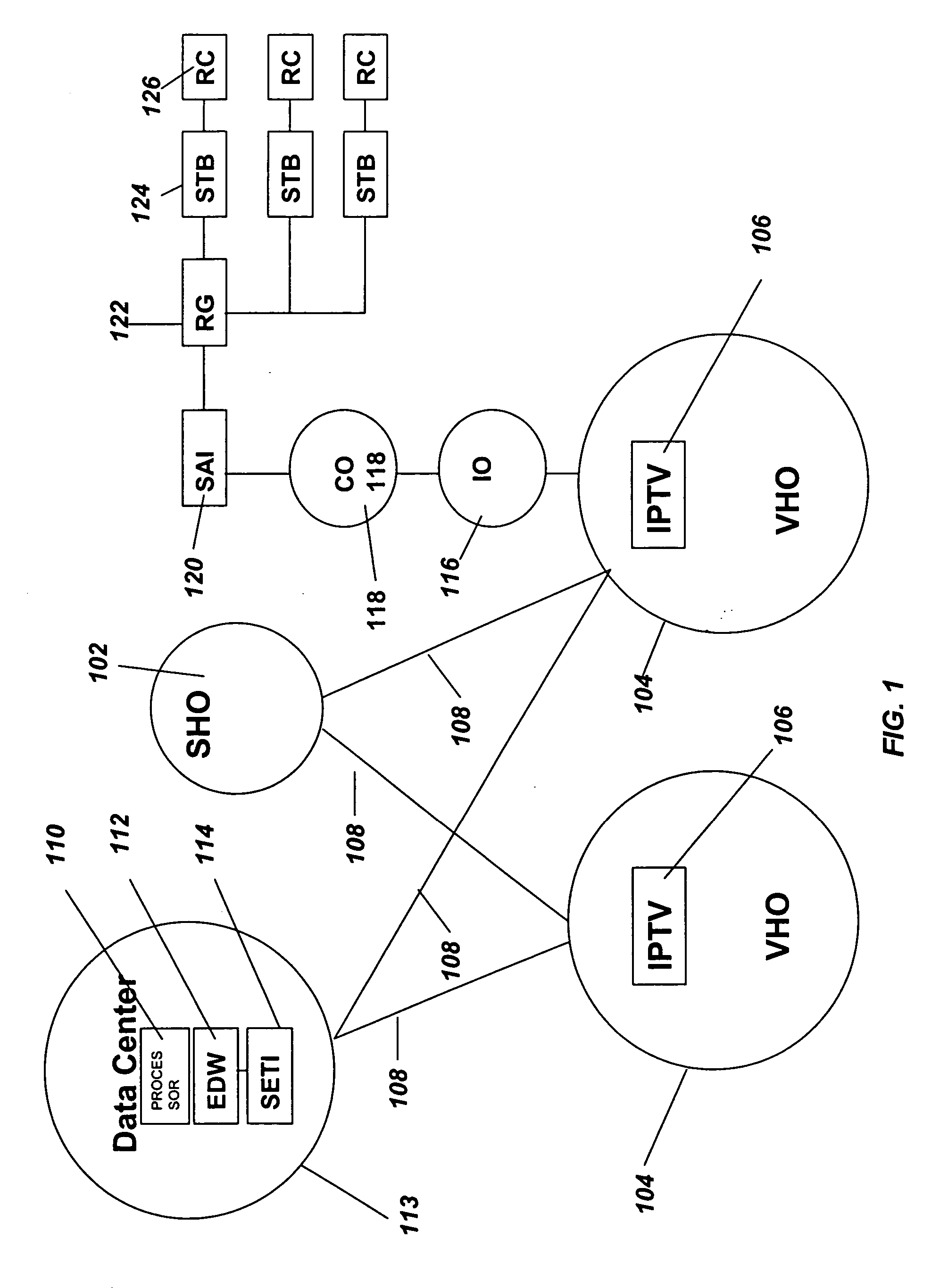
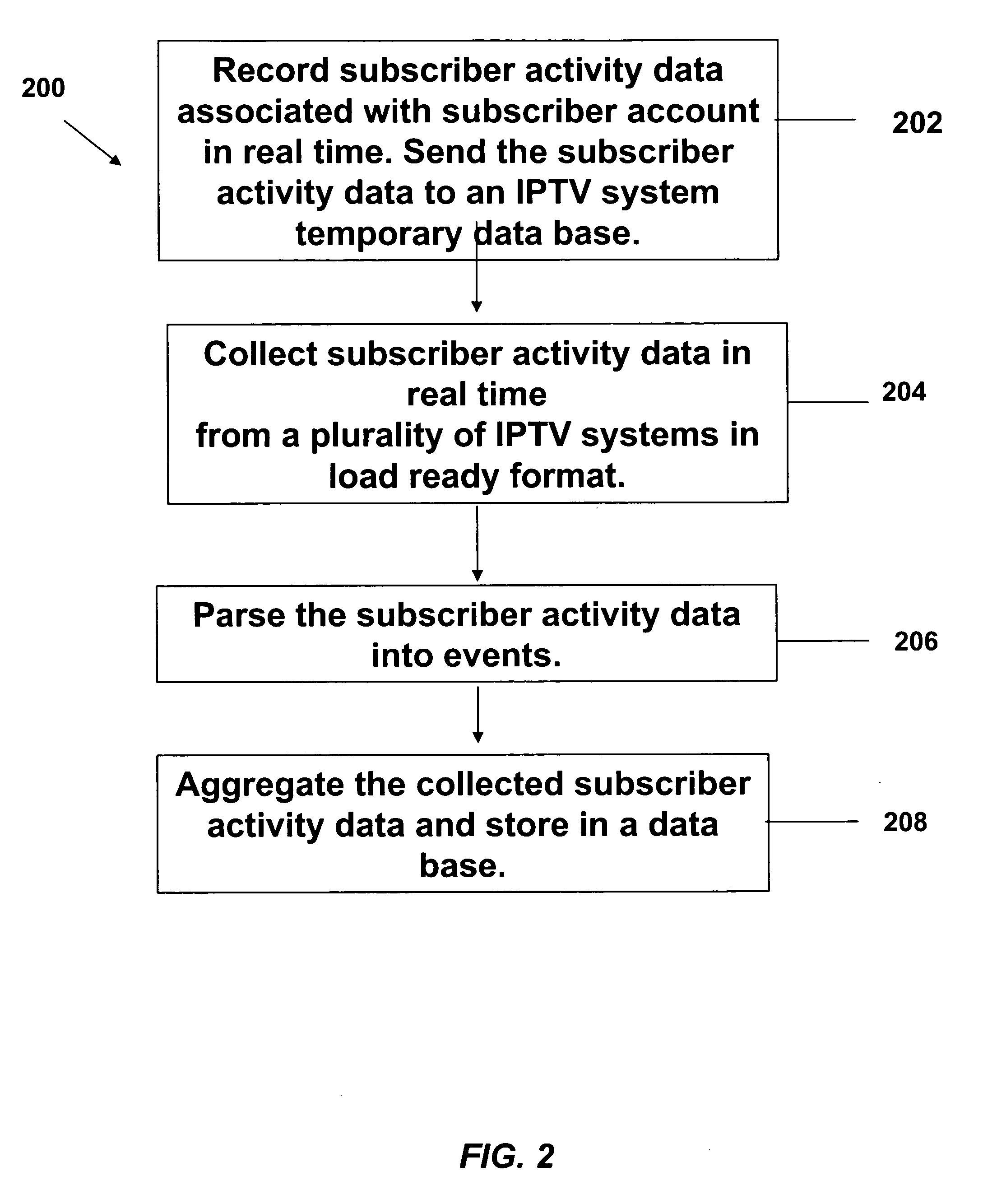
Data collection and analysis for internet protocol television subscriber activity
InactiveUS20070074258A1Easy to understandTwo-way working systemsSelective content distributionCyber operationsSummary data
A method and apparatus are provided that interact with an IPTV product deployed in a communication network. The method and apparatus of the present invention collects subscriber activity data, such as channel changes generated by the subscriber while watching video or TV in an IPTV system. The system and method of the present invention collects, parses and processes this consumer activity data. The method and apparatus of the present invention collects and aggregates the IPTV consumer activity data from multiple IPTV consumer activity data collection systems. The aggregated data, collected over a national or global basis can then be used to generate metrics. The metrics are then analyzed by business rules to generate marketing data reports that can be used as an strategic analysis tool for communication network operators, content providers and advertisers to determine consumer usage of the IPTV systems and viewing of programming and advertising.
Owner:SBC KNOWLEDGE VENTURES LP
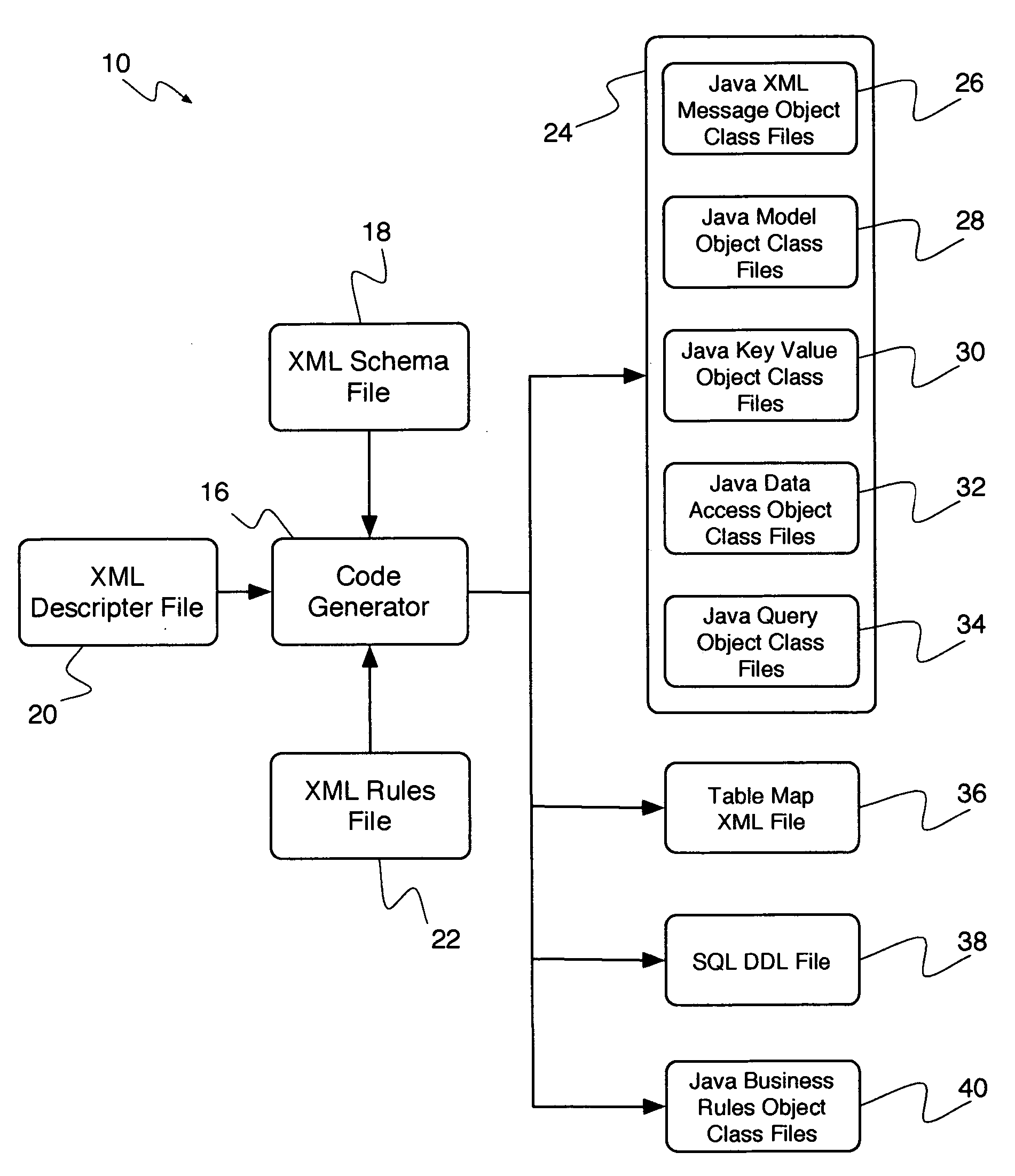
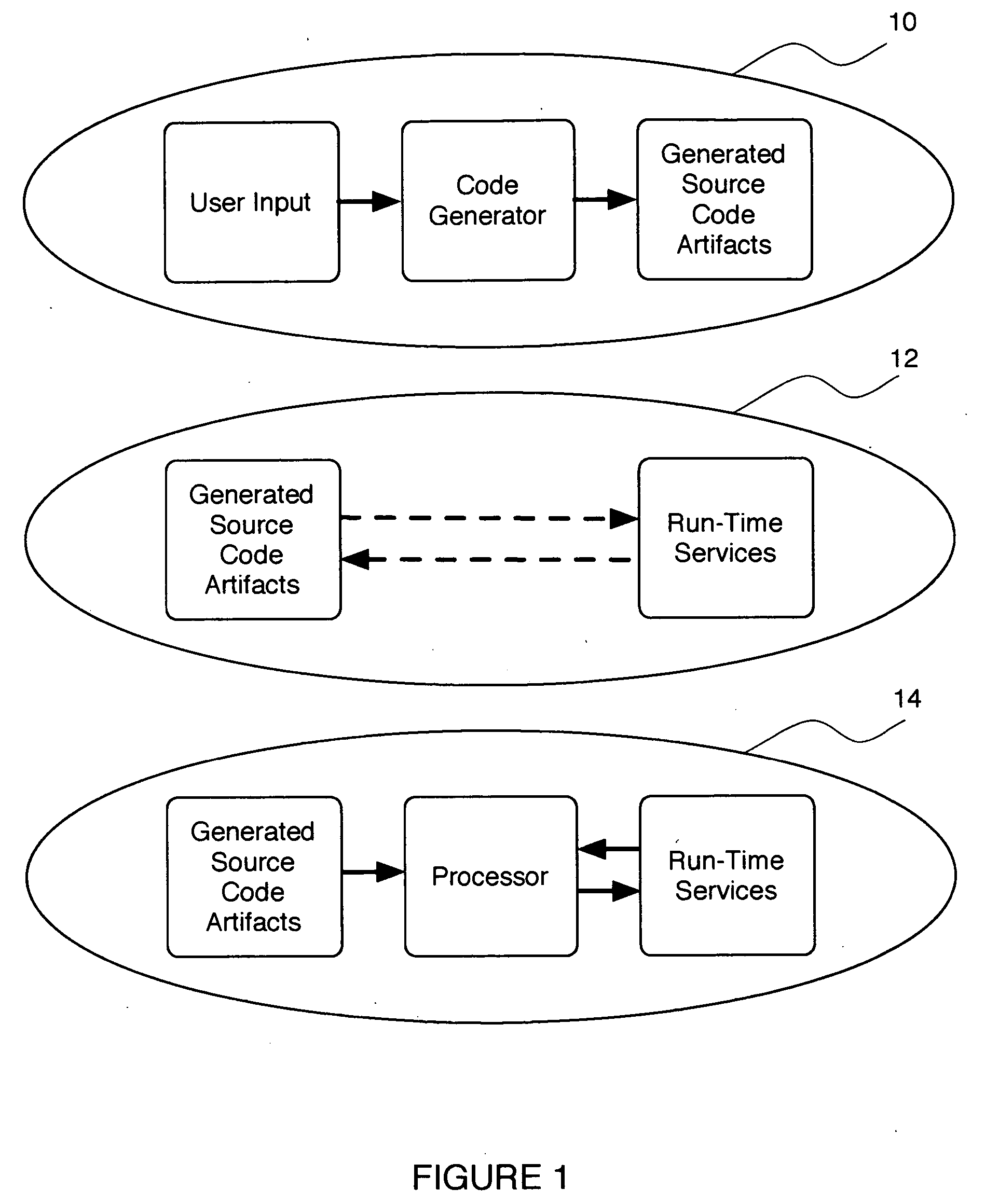
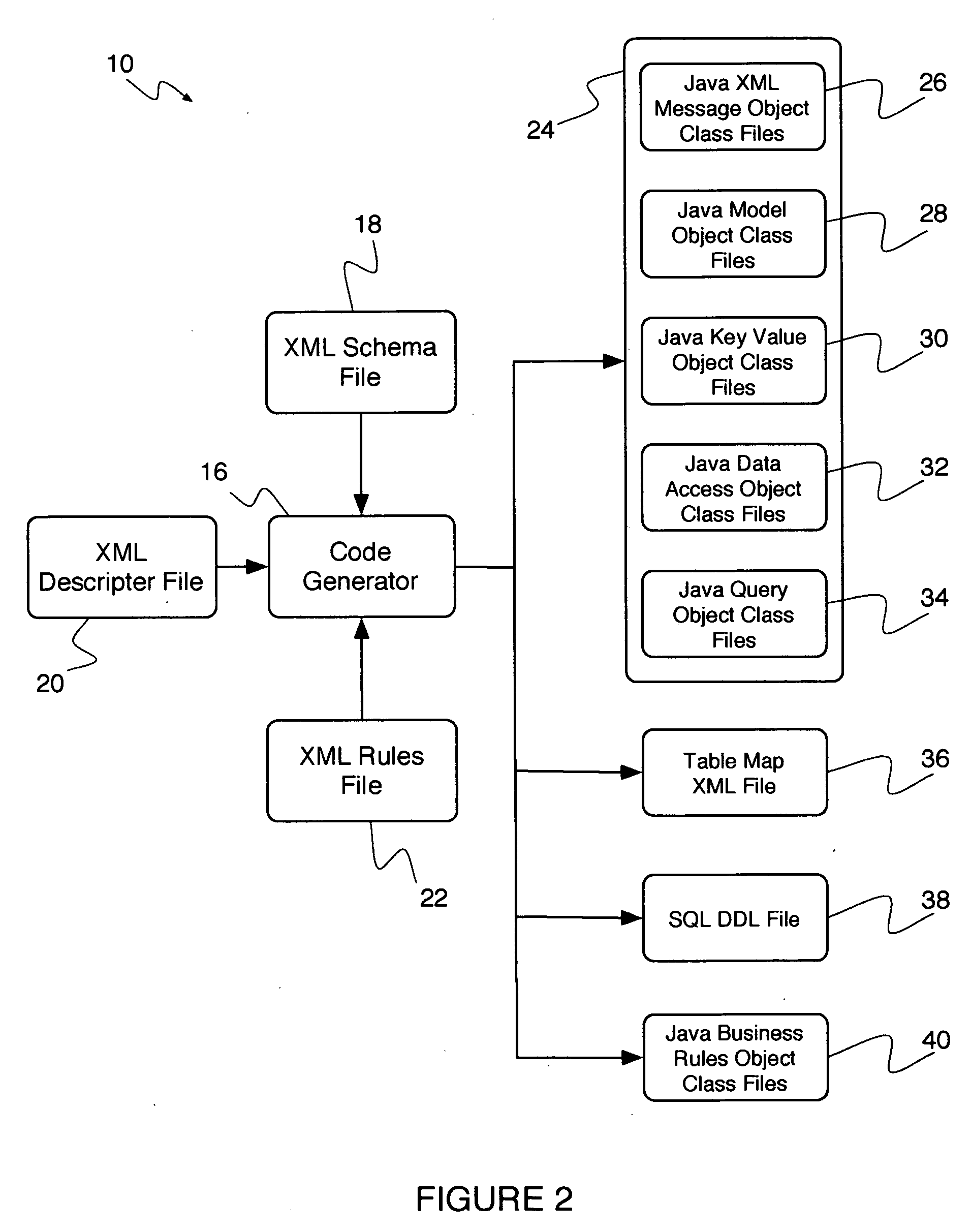
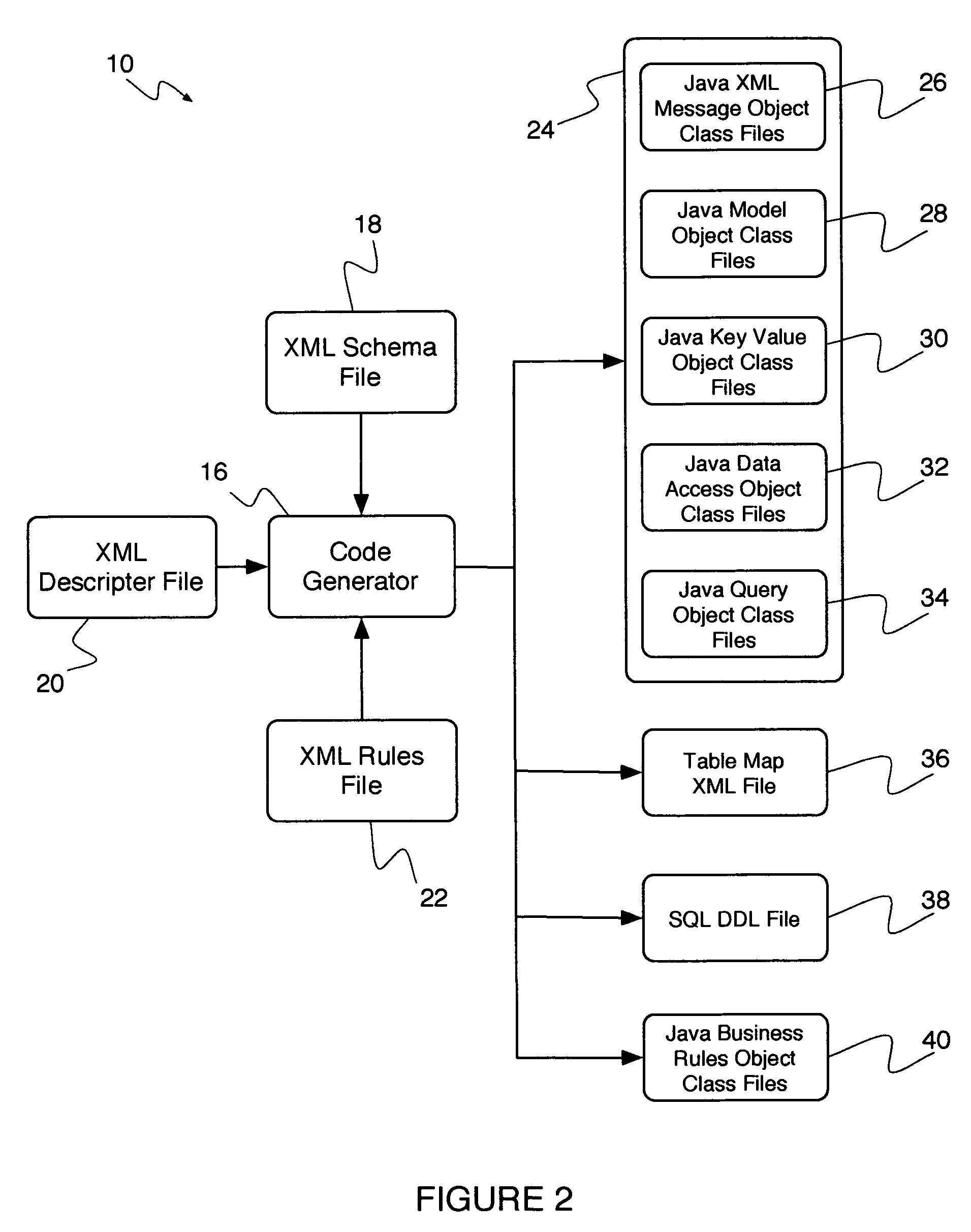
System and method for automating the development of web services that incorporate business rules
ActiveUS20060129605A1Reduces and eliminates disadvantageQuality improvementSoftware designSpecial data processing applicationsWeb serviceRunning time
A system and method for developing web services that incorporate business rules. The system and method includes three frameworks: a Design Time Framework, an Object-Service Framework, and a Run Time Framework. In the Design Time Framework, the system and method includes receiving a business rule in a descriptive markup language from a user and generating source code artifacts in an object oriented programming language based on the business rule. In the Object-Service Framework, the system and method includes relating the generated source code artifacts to a pre-built Business Rules service. Finally, in the Run Time Framework, the system and method includes providing the Business Rules service, wherein the Business Rules service interacts with the generated source code artifacts through the relationship defined by the Object-Service Framework.
Owner:EOS SOFTWARE
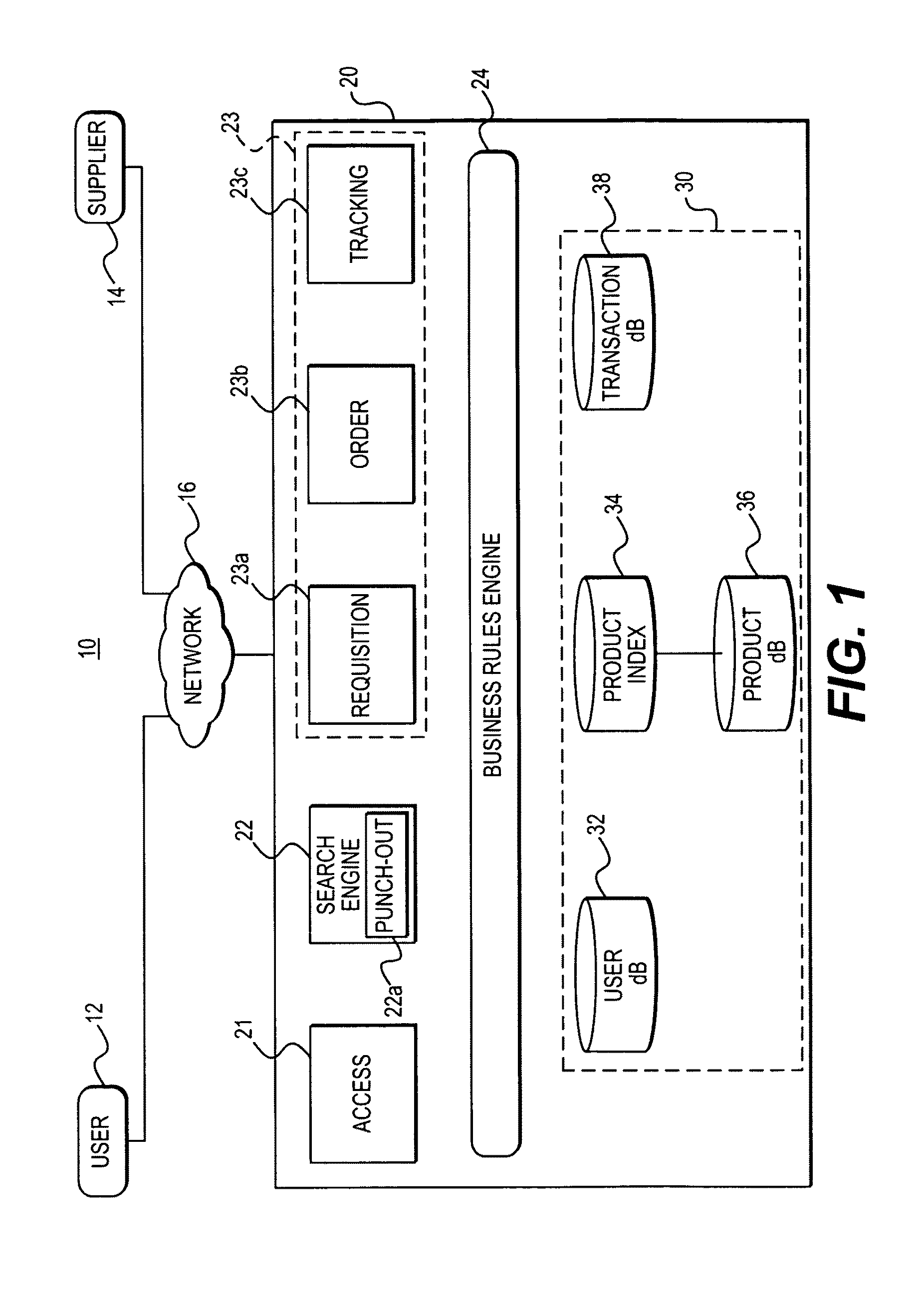
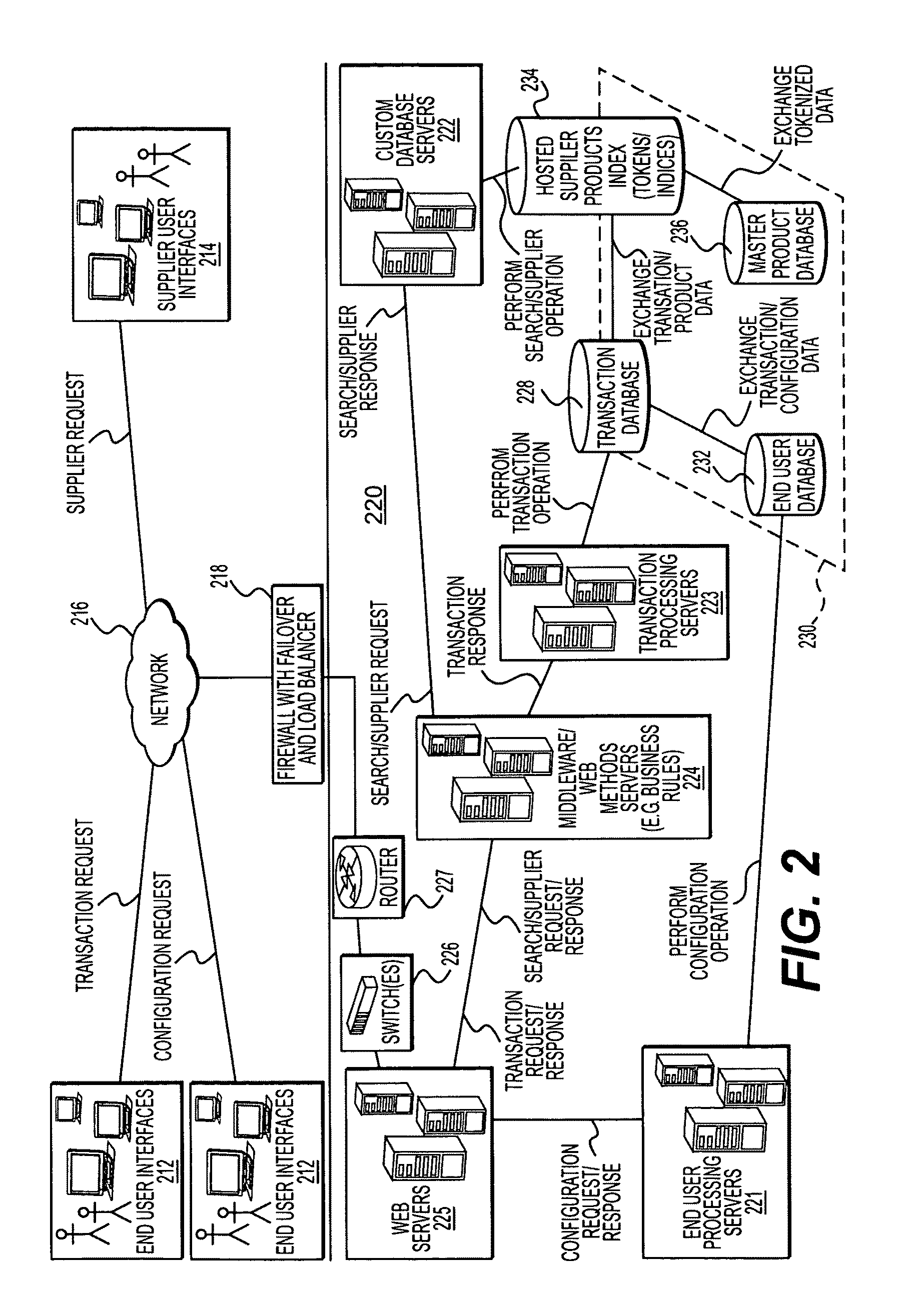
Multi-constituent attribution of a vendor's product catalog
A single instance, multi-tenant procurement system, includes an access module to provide access to a plurality of end users associated with an organization to their respective accounts, each account being customized by a super user of the organization, a search engine to execute searches for products offered by one or more suppliers, a transaction module to process and track one or more requisitions generated by the plurality of end users, a business rules module to apply business rules established between the organization and the one or more suppliers to process the requisitions, and a data repository to store data generated on the system.
Owner:SCIQUEST
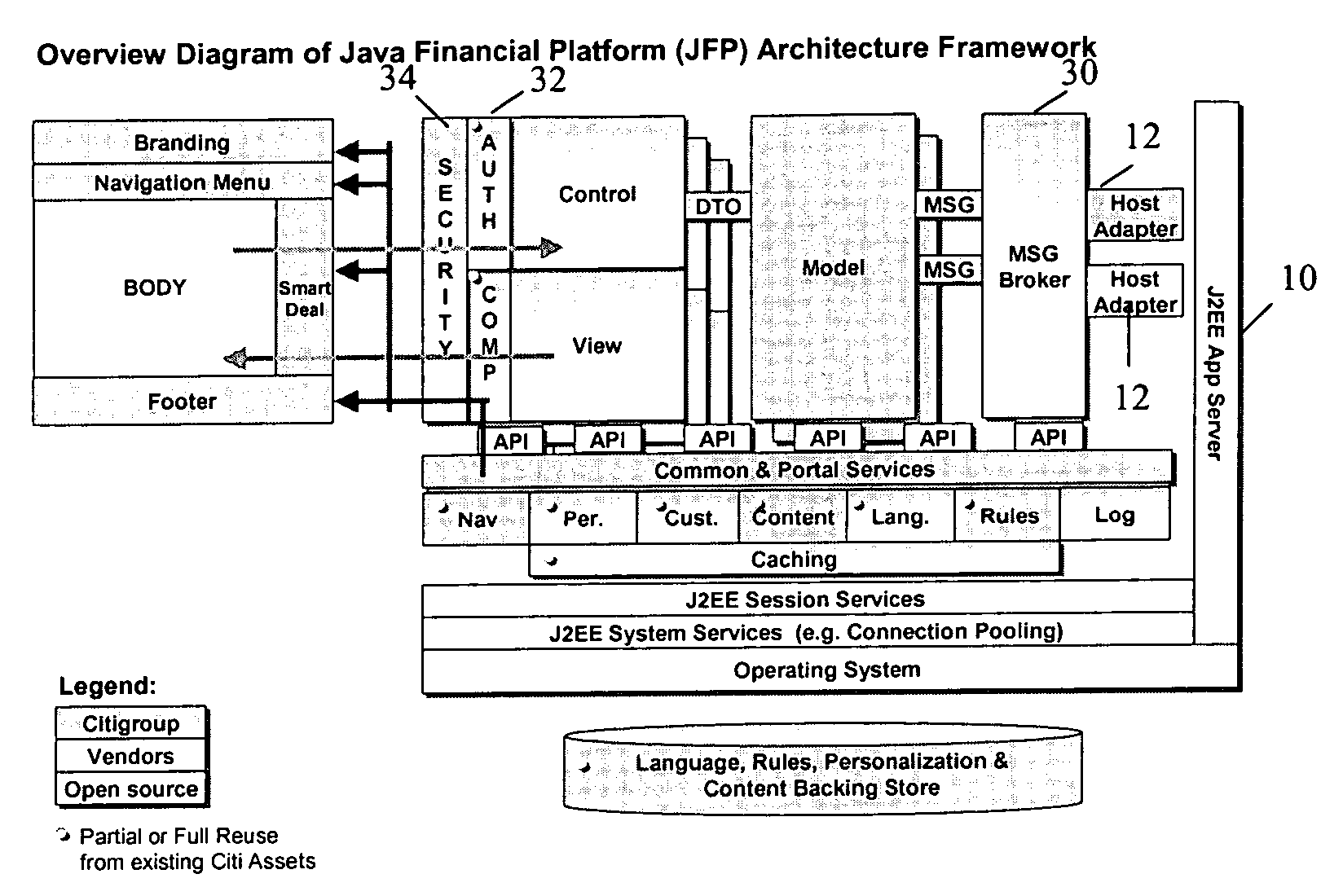
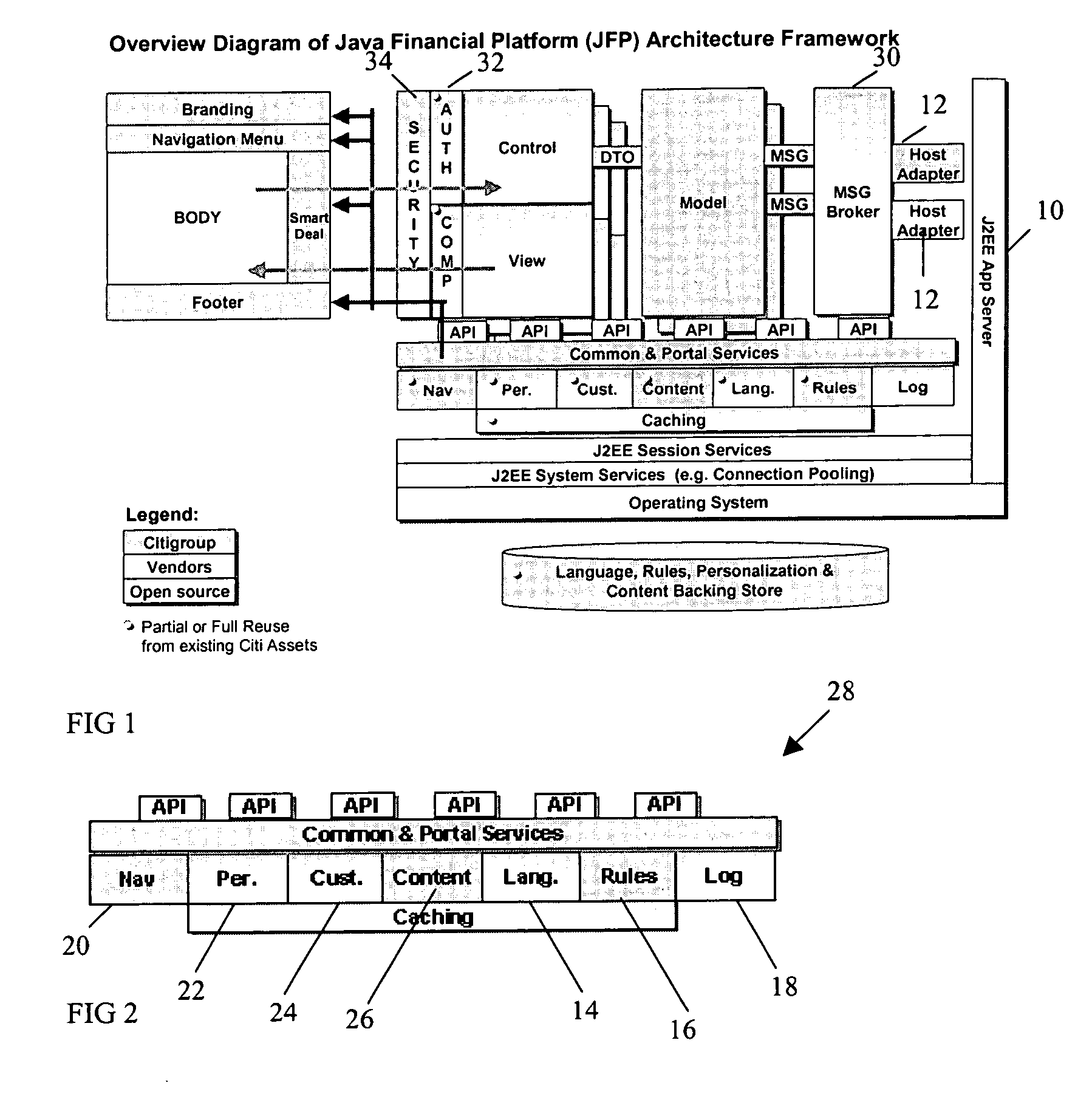
Methods and systems for implementing on-line financial institution services via a single platform
ActiveUS20060195816A1Eliminate database accessShort response timeFinanceSpecific program execution arrangementsApplication serverApplication software
A method and system for implementing on-line financial institution services via a single physical and logical platform deploys global online banking applications in an environment in which the applications are built from a single source base and adapted to various business rules and languages associated with different regions, countries and businesses. Separate web apps are created for each individual business according to contextual attributes, and application servers running the context dependent web apps provide the interface between customers and banking functionality. The platform relies in part on reuse of appropriate components to achieve integration, as well as sharing of core services. As a result of the independent nature of business specific components, each business may require different versions of application software and may update or implement new components without affecting existing business components.
Owner:CITICORP CREDIT SERVICES INC (USA)
System and method for performing dwelling maintenance analytics on insured property
A computer device and method for processing maintenance related data for performing maintenance analytics on insured property. Informatic data is received from one or more sensor devices relating to a property covered by an insurance policy. Analysis is performed on the received informatic data to determine one or more conditions associated with the property. Predefined business rules are applied using the determined one or more conditions associated with the property to determine a maintenance profile for the property indicating one or more of maintenance history and repair or maintenance requirements for the property.
Owner:HL ACQUISITION INC +1
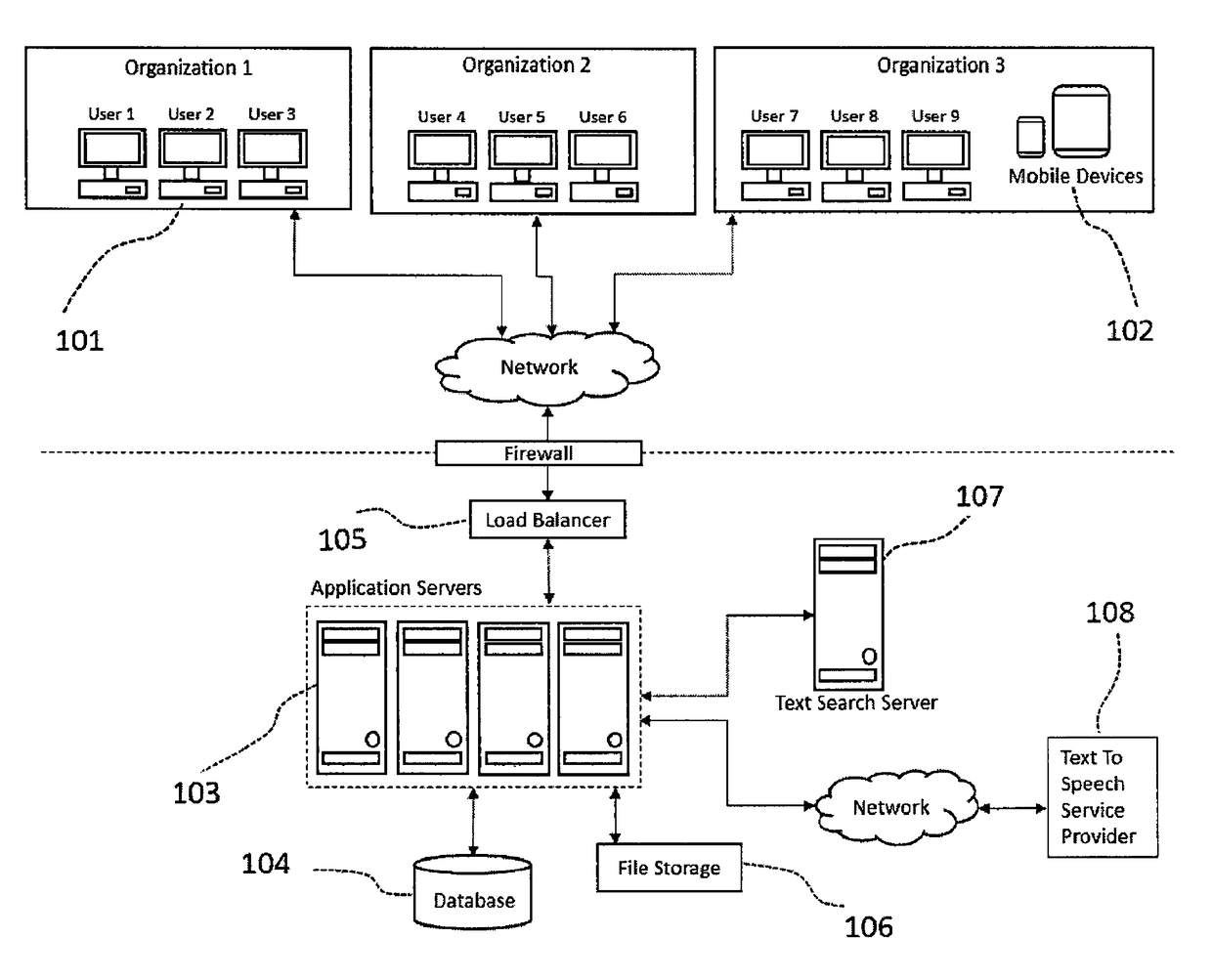
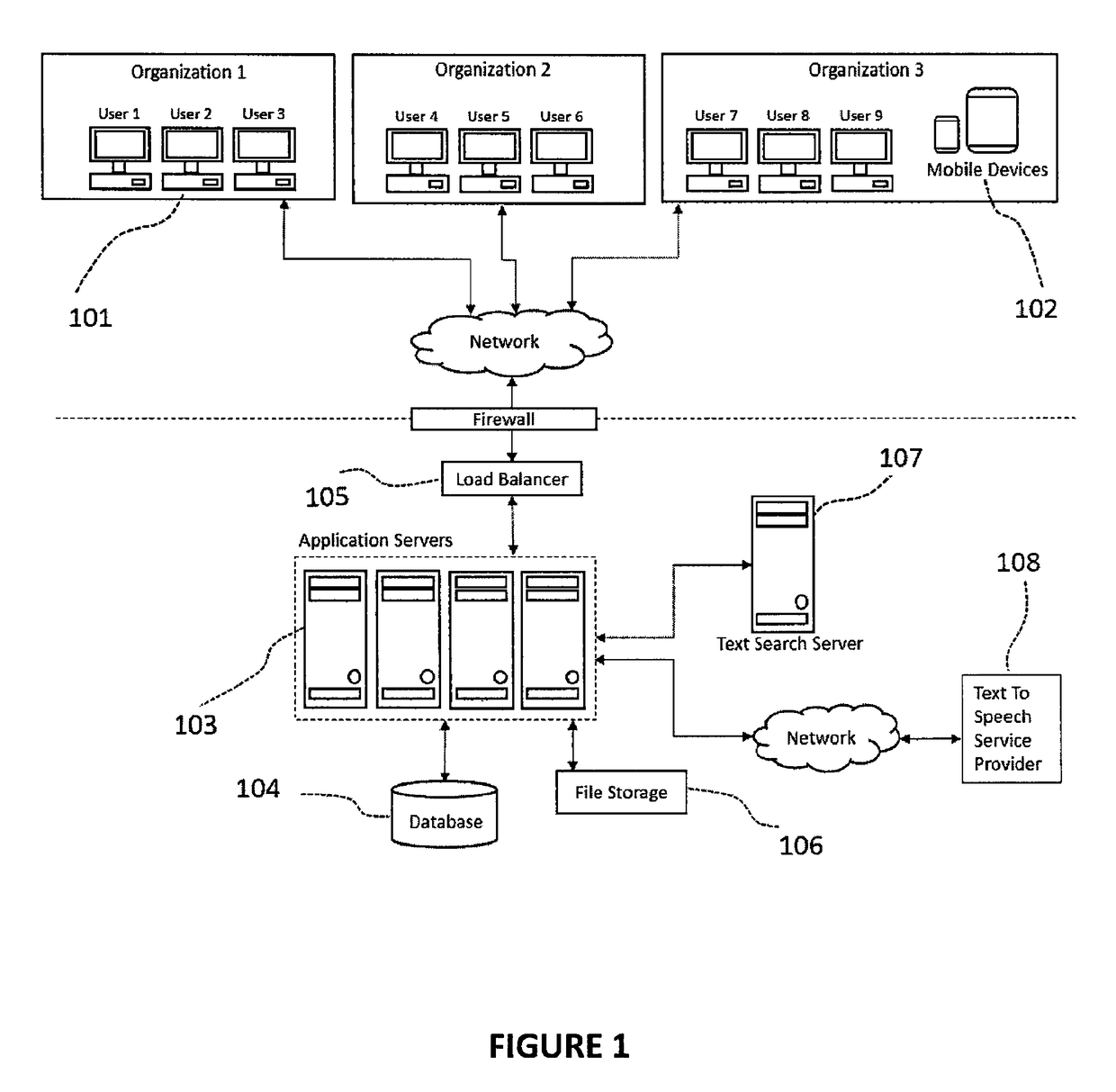
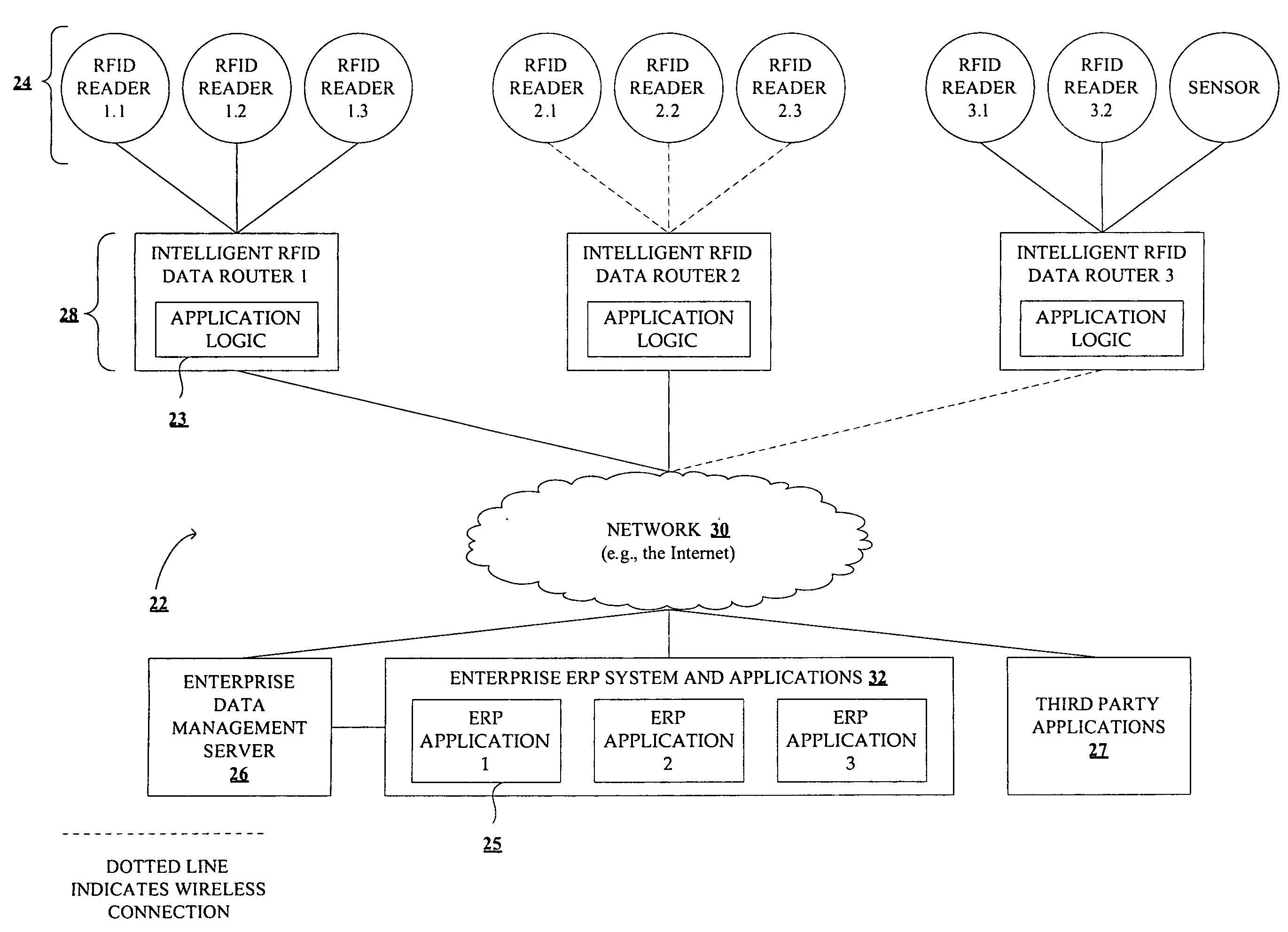
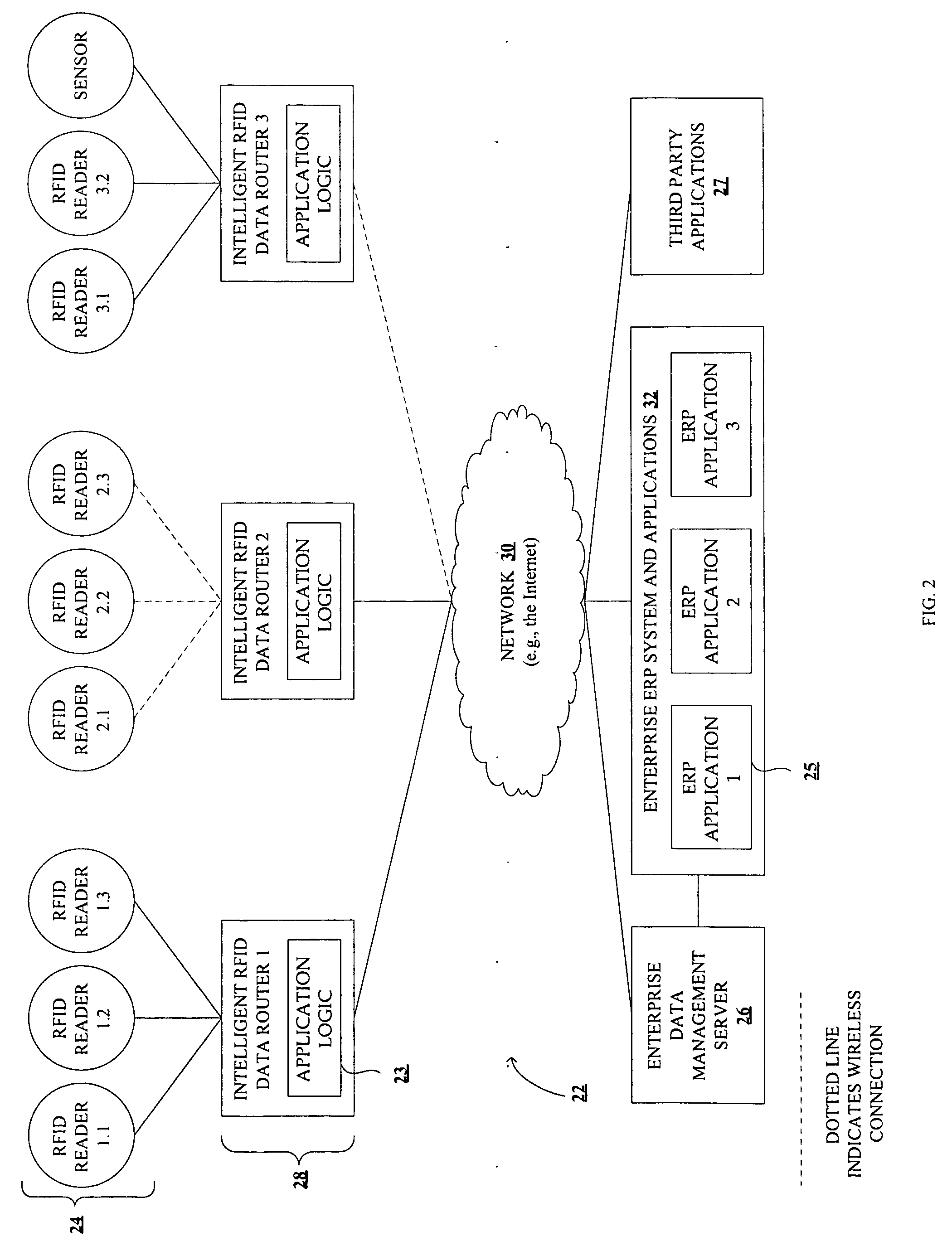
Method and system for sensor data management
InactiveUS20060143439A1Network topologiesSubscribers indirect connectionData managementReal time management
Methods and systems for real-time management of sensor data, based on application level logic made available at the edge of the enterprise are disclosed. According to an embodiment of the invention, an intelligent data router is communicatively coupled to one or more data sensors and a data management server. In one embodiment, the intelligent data router executes application level logic encapsulating business rules to make real-time enterprise data decisions and execute business transactions.
Owner:XPASEO
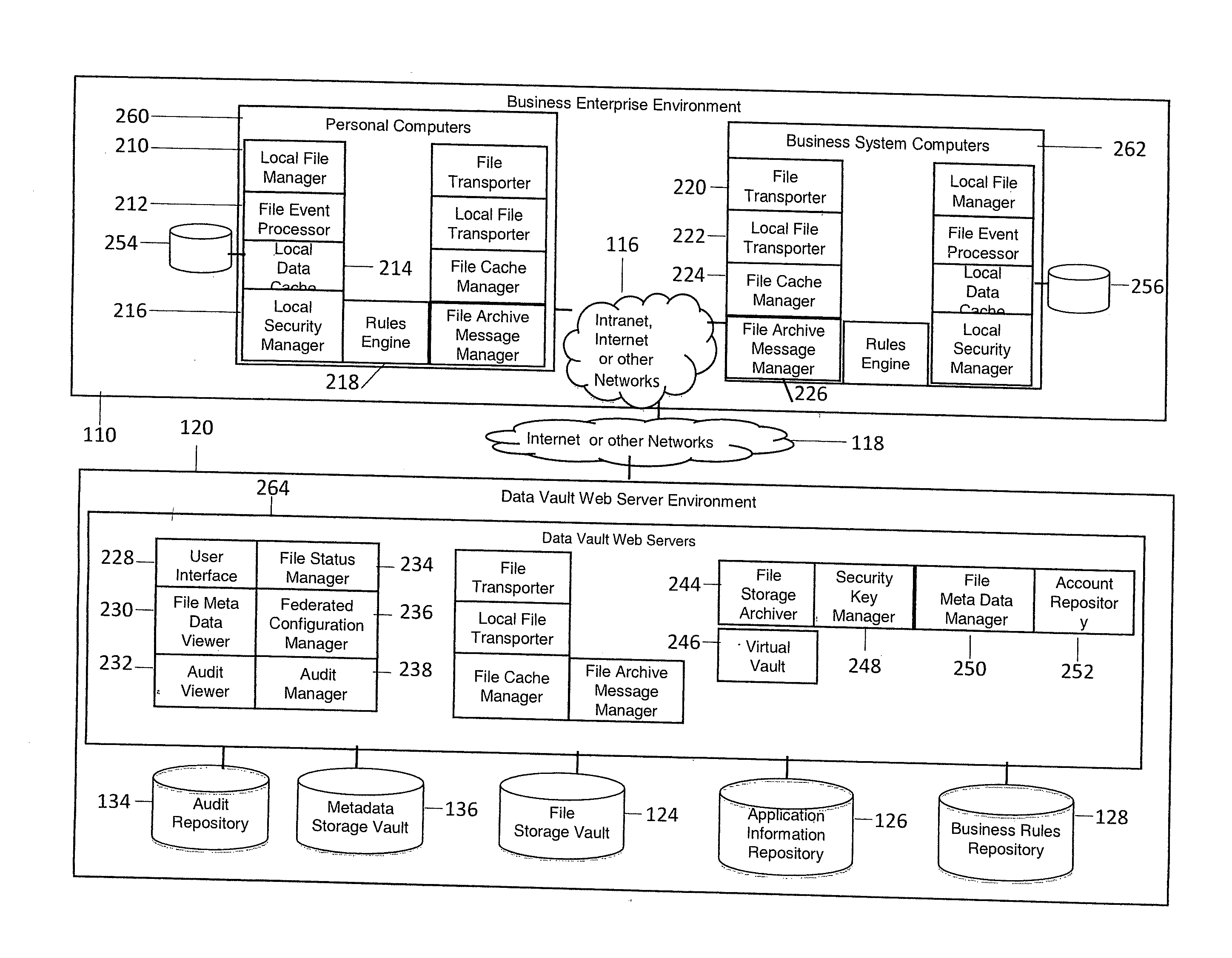
System and method for providing automated electronic information backup, storage and recovery
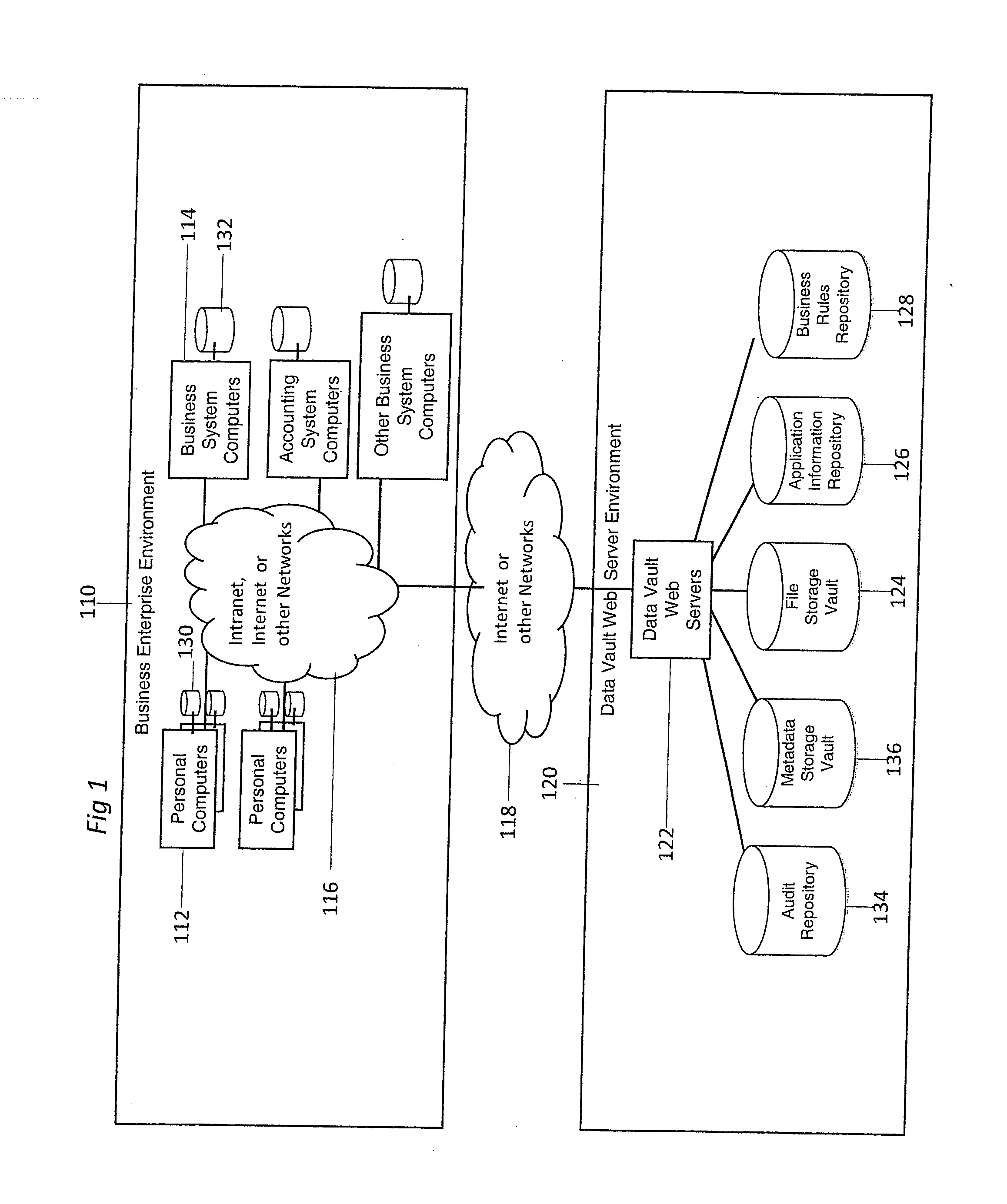
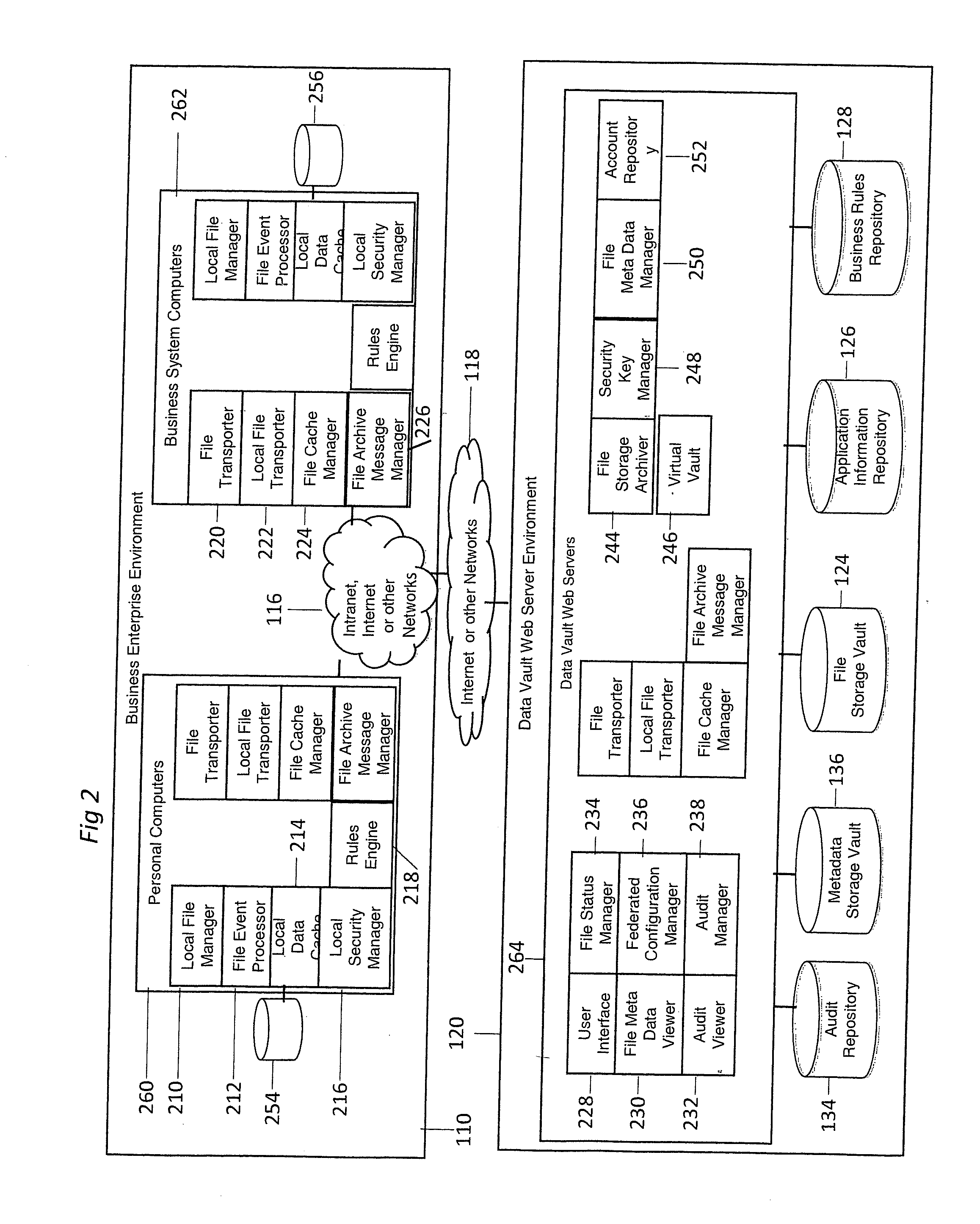
InactiveUS20100293147A1Avoid dataAvoid redundancyDigital data processing detailsSpecial data processing applicationsInformation repositoryApplication software
An automated electronic information backup, storage migration, and recovery system includes techniques for automatically observing all file events over a plurality of computing devices. The observed file events are mapped to the applications producing them. A relevancy of those file events are determined based on an application information repository. Business rules are produced based on this information to automatically backup all relevant file event changes and restore or migrate backed up information when necessary.
Owner:HIPAA BOX
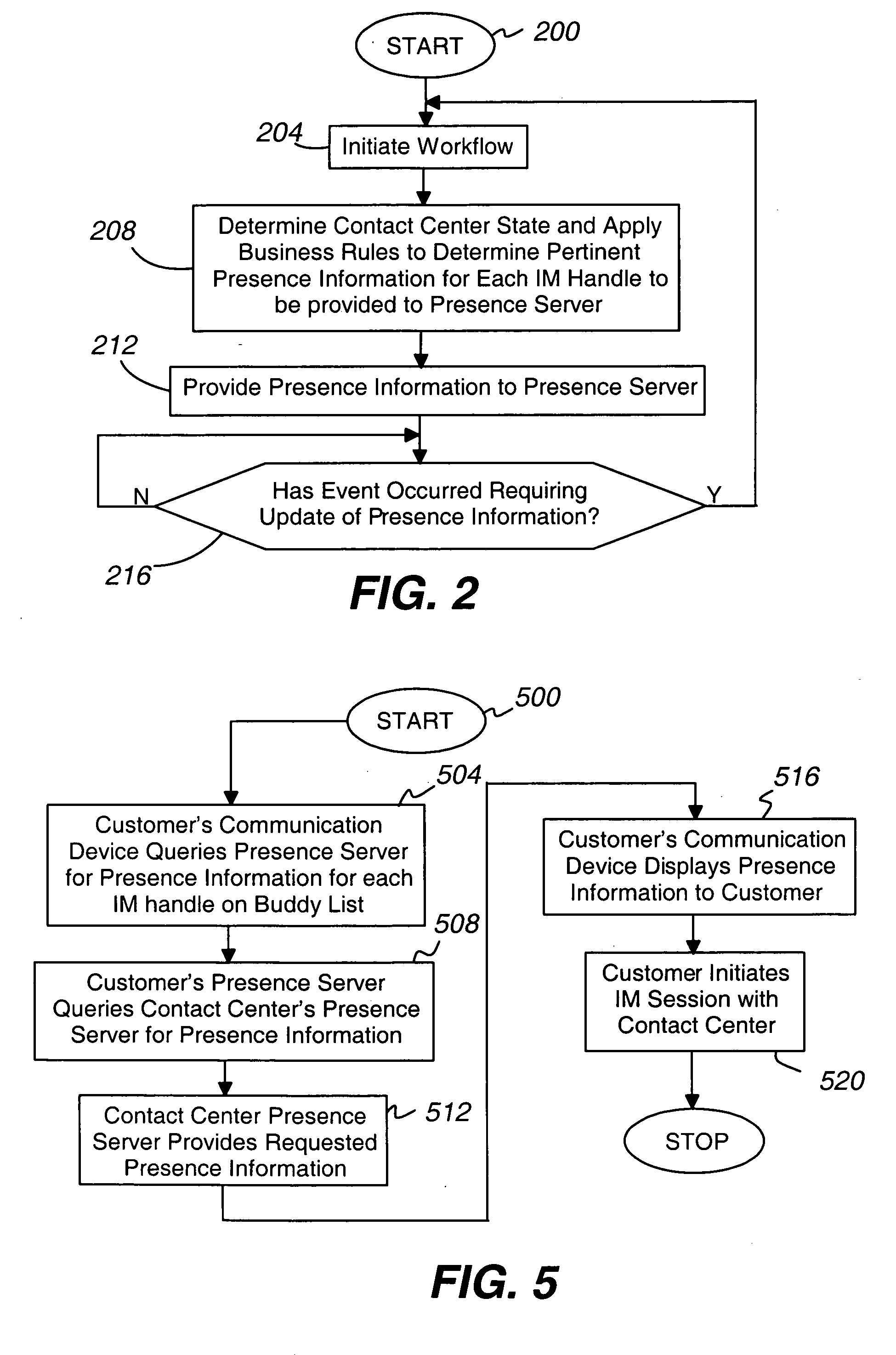
Using business rules for determining presence
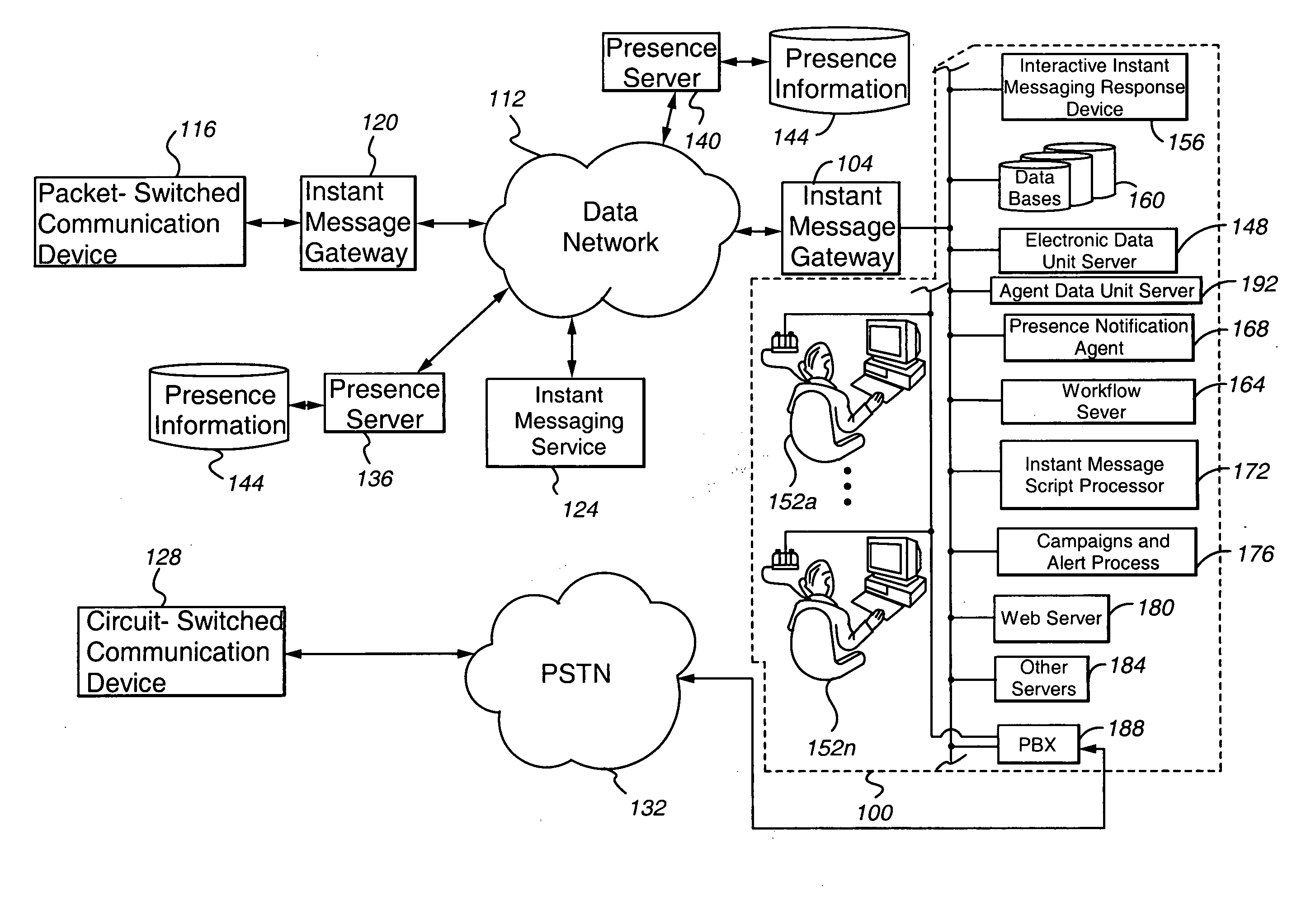
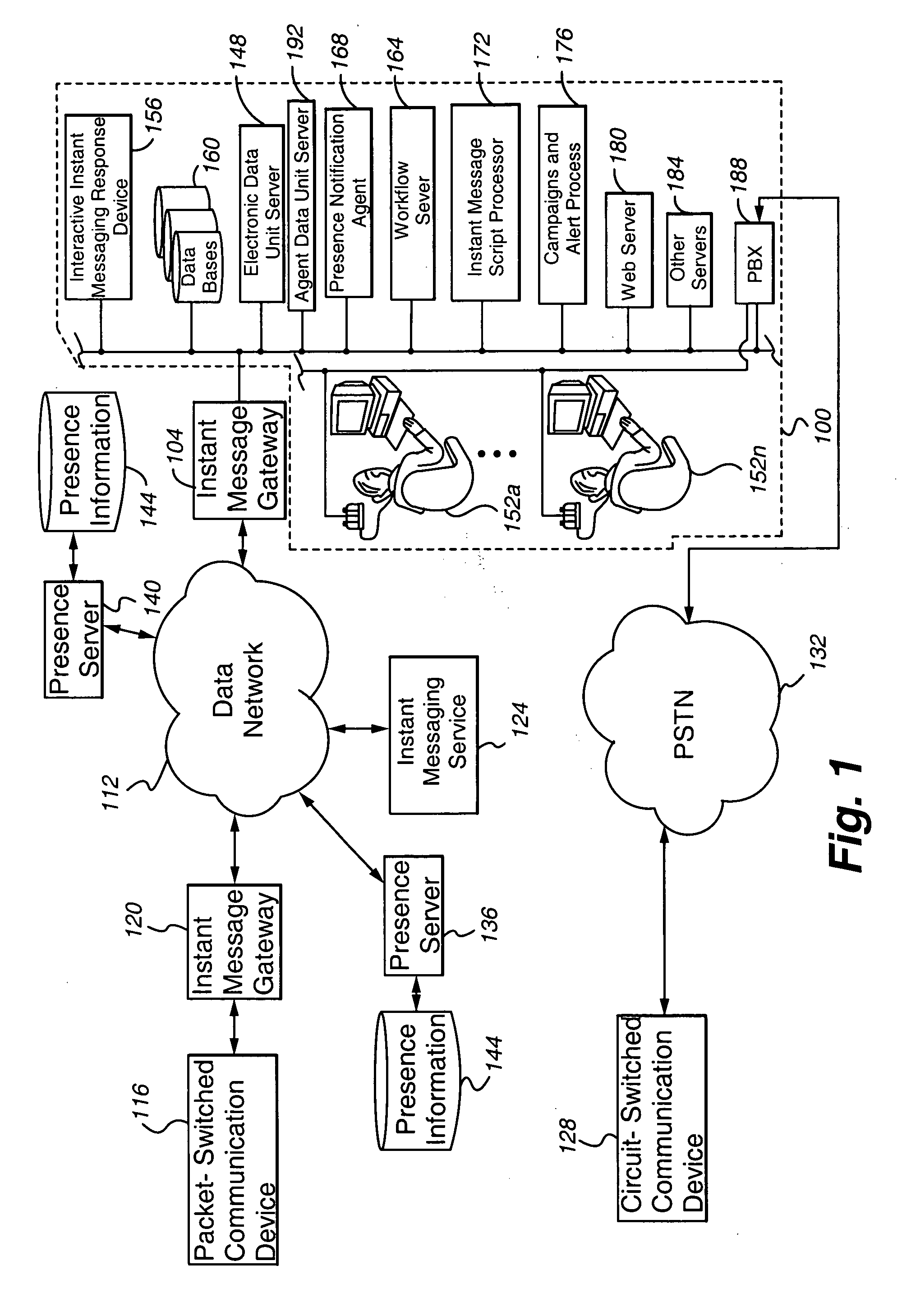
ActiveUS20050187781A1Reduce expensesEfficient and customer attractiveSpecial service for subscribersData switching networksMessage passingBusiness rule
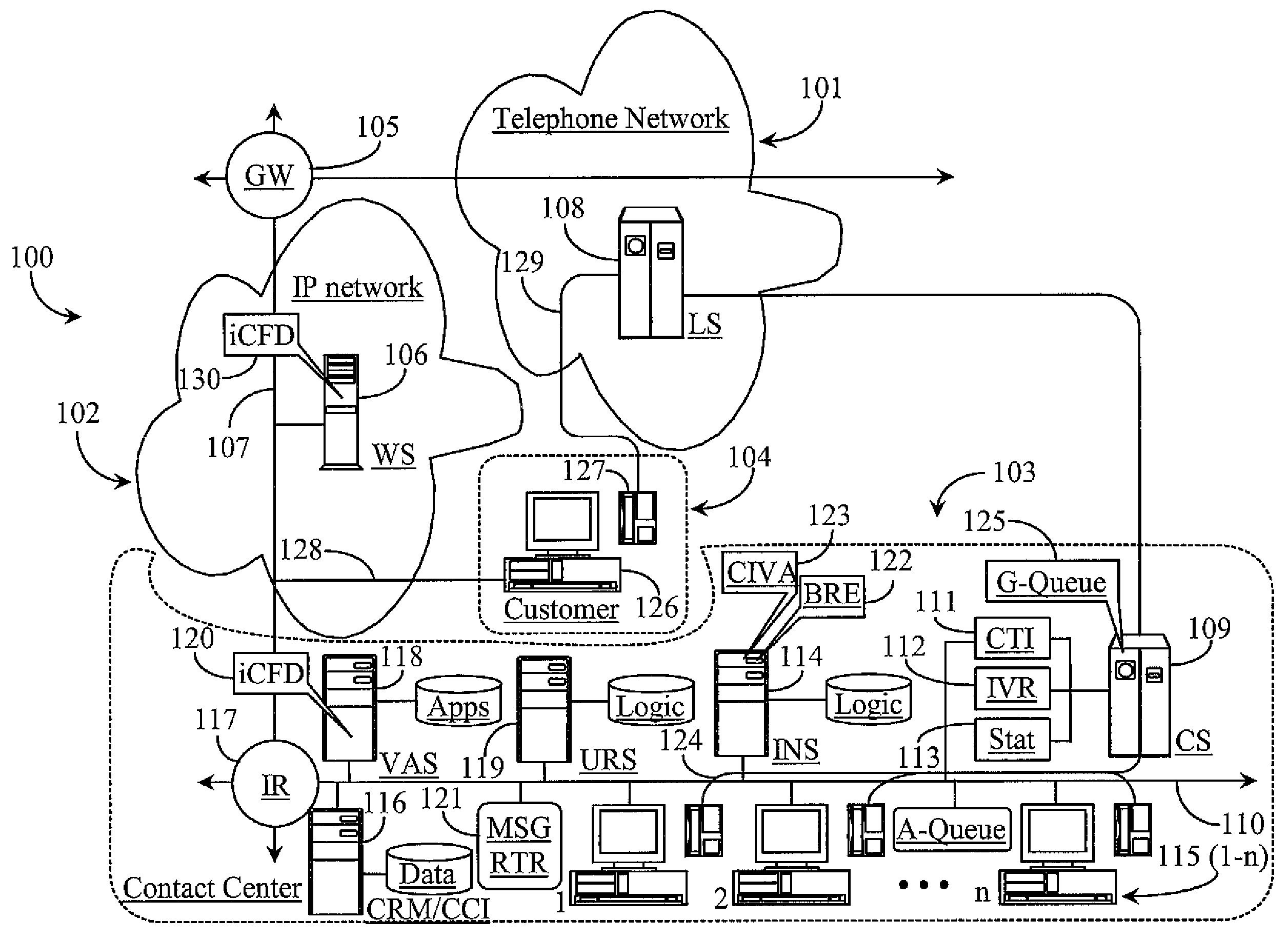
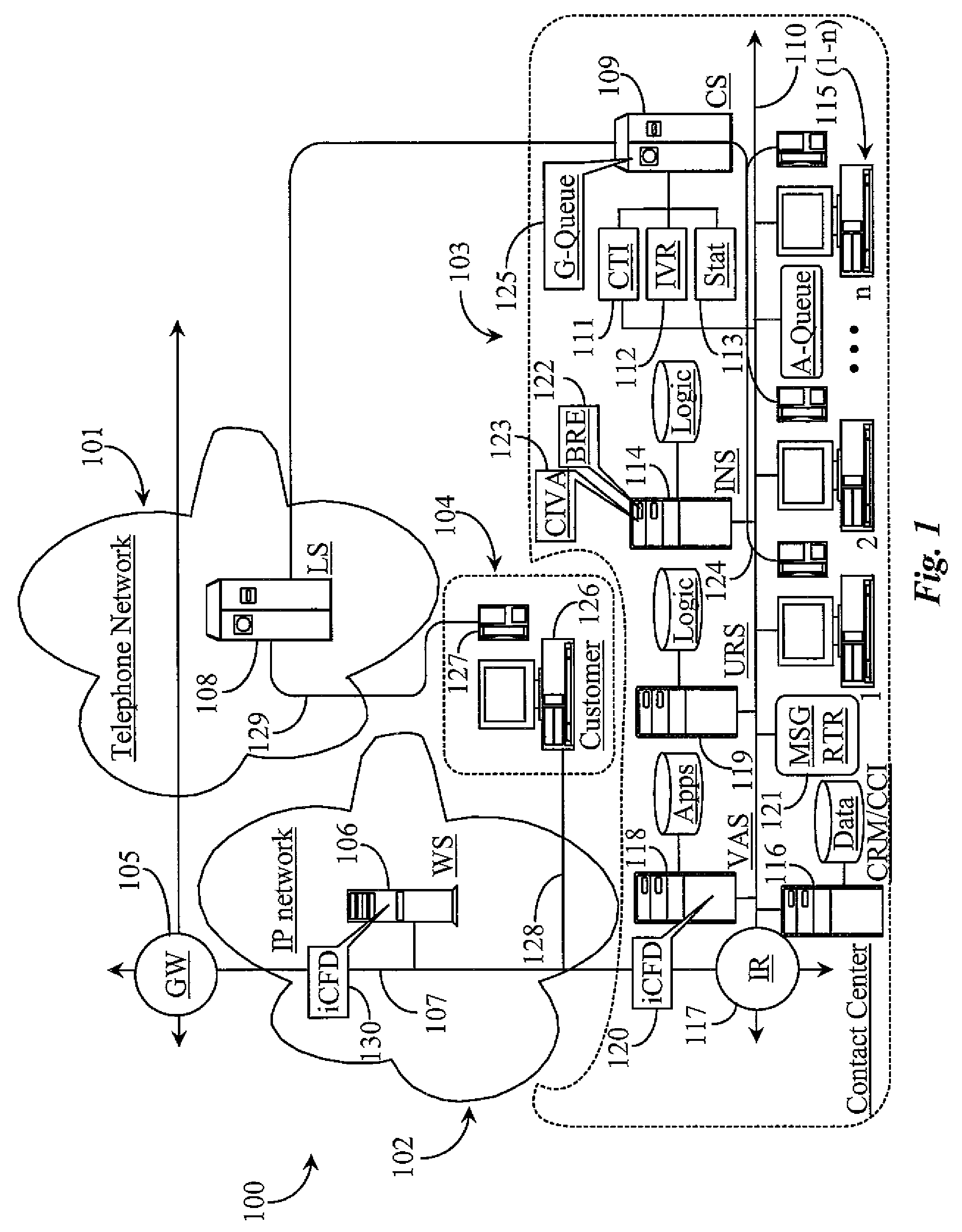
The present invention provides various contact center embodiments for interacting with customers using instant messaging. In one embodiment, the contact center is configured to receive instant message notifications from a customer when the customer is available for contact by instant messaging. In another embodiment, the contact center is configured to route sessionless instant messages only to a selected agent for a specified period of time. In another embodiment, the contact center is configured to provide to customers presence information for administered instant message addresses before the customers contact the contact center. In another embodiment, the contact center is configured to perform an outbound instant messaging campaign or alert with customers.
Owner:AVAYA INC
System and method for automating the development of web services that incorporate business rules
ActiveUS8615731B2Reduces and eliminates disadvantageQuality improvementSoftware designSpecial data processing applicationsWeb serviceSource code
A system and method for developing web services that incorporate business rules. The system and method includes three frameworks: a Design Time Framework, an Object-Service Framework, and a Run Time Framework. In the Design Time Framework, the system and method includes receiving a business rule in a descriptive markup language from a user and generating source code artifacts in an object oriented programming language based on the business rule. In the Object-Service Framework, the system and method includes relating the generated source code artifacts to a pre-built Business Rules service. Finally, in the Run Time Framework, the system and method includes providing the Business Rules service, wherein the Business Rules service interacts with the generated source code artifacts through the relationship defined by the Object-Service Framework.
Owner:EOS SOFTWARE
System and method of dynamic service composition for business process outsourcing
ActiveUS7114146B2Dynamic configurationFinanceDigital data processing detailsService compositionDocumentation procedure
A system and method for capturing a plurality of business requirements using a Business Process Outsourcing Language (BPOL), an XML representation for expressing business process flow rules, preferences, business rules and event-action mappings as well as service links, to automate the process of generating business processes for use with Web services. BPOL is used to dynamically construct a search script for an advanced Web services discovery engine to find Web services from both UDDI registries and Web services Inspection Language (WSIL) documents and then create a qualified service list. Then a service selection problem is mapped into a solution space {0,1} for use by an optimization algorithm that performs second level service selection of the best set of services based on the requirements.
Owner:IBM CORP
Modeling user access to computer resources
Embodiments of the invention provide a method for detecting changes in behavior of authorized users of computer resources and reporting the detected changes to the relevant individuals. The method includes evaluating actions performed by each user against user behavioral models and business rules. As a result of the analysis, a subset of users may be identified and reported as having unusual or suspicious behavior. In response, the management may provide feedback indicating that the user behavior is due to the normal expected business needs or that the behavior warrants further review. The management feedback is available for use by machine learning algorithms to improve the analysis of user actions over time. Consequently, investigation of user actions regarding computer resources is facilitated and data loss is prevented more efficiently relative to the prior art approaches with only minimal disruption to the ongoing business processes.
Owner:DAEDALUS BLUE LLC
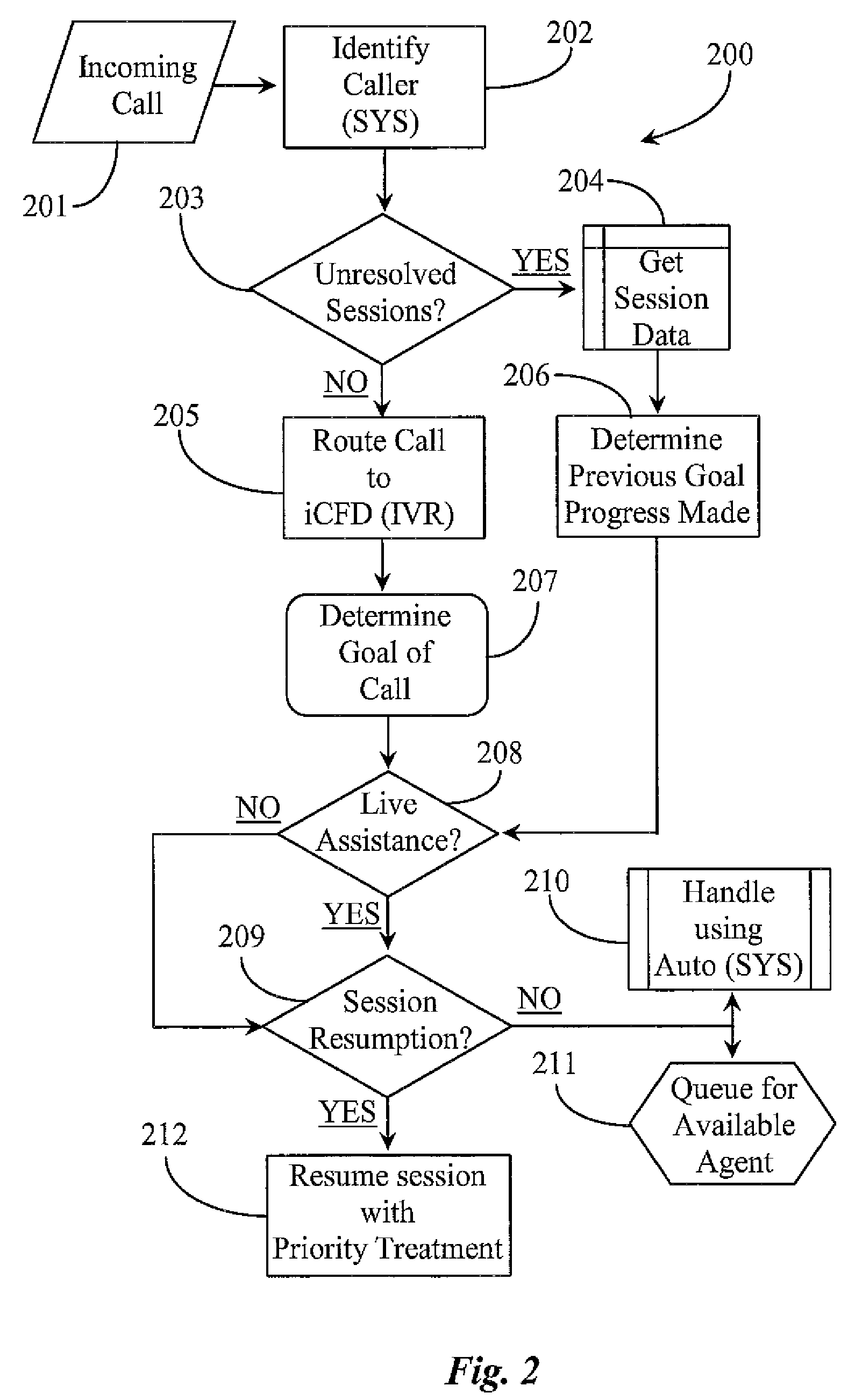
System and Methods for Tracking Unresolved Customer Involvement with a Service Organization and Automatically Formulating a Dynamic Service Solution
ActiveUS20100158236A1Increase in generated revenueImprove customer satisfactionManual exchangesAutomatic exchangesCustomer engagementContact center
A system for managing customer involvement with a contact center involves one or more monitoring applications executing on one or more computerized servers associated with the contact center, the applications monitoring communications between individual customers and the center; and a rules engine executing on the one or more computerized servers, the rules engine accessible to the monitoring application, the rules engine enabled to generate and implement business rules. Upon detection by one of the monitoring applications of an instance of unsuccessful or incomplete interaction between a customer and the contact center, session data determined during monitoring is used by the rules engine to determine contact center-initiated activity to be implemented to establish new communication with the customer to resolve issues related to the unsuccessful or incomplete interaction.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
Creating, distributing and enforcing relational and business rules at front-end application
InactiveUS20020147726A1Ensure consistencyLittle or no reuseDigital data processing detailsOffice automationProcessing InstructionOff the shelf
A method and system and computer readable medium for: (1) the creation and representation of business rule definitions, (2) the creation and representation of enforcing rule handlers, (3) the creation and representation of a framework to check the existence of rules then, apply the appropriate handler, (4) and the distribution of the rule definitions and handlers to clients. The present invention defines a rule language and provides a framework that separates the definition of the rules, the enforcing handler, the system at which rules are generated and the system at which rules are enforced. Further, in one embodiment, the present invention uses standard XML notations to define rules and standard XSL and XSLT processing instructions to enforce rules. Using standard XML, XSL and SXLT allows clients to use off-the-shelf XML parser and XSL processors in lieu of developed code or rule based engines.
Owner:PARTNERCOMMUNITY
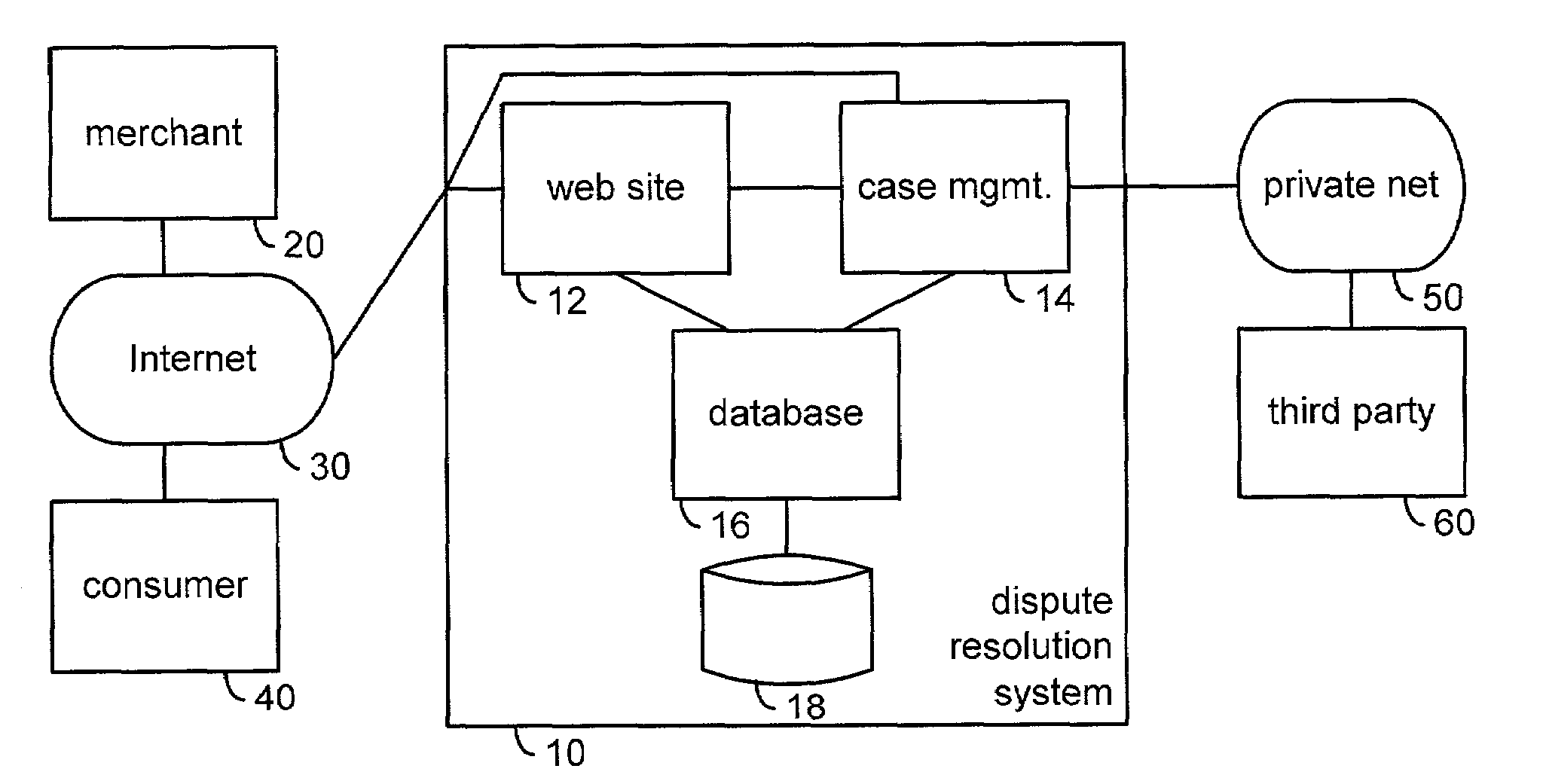
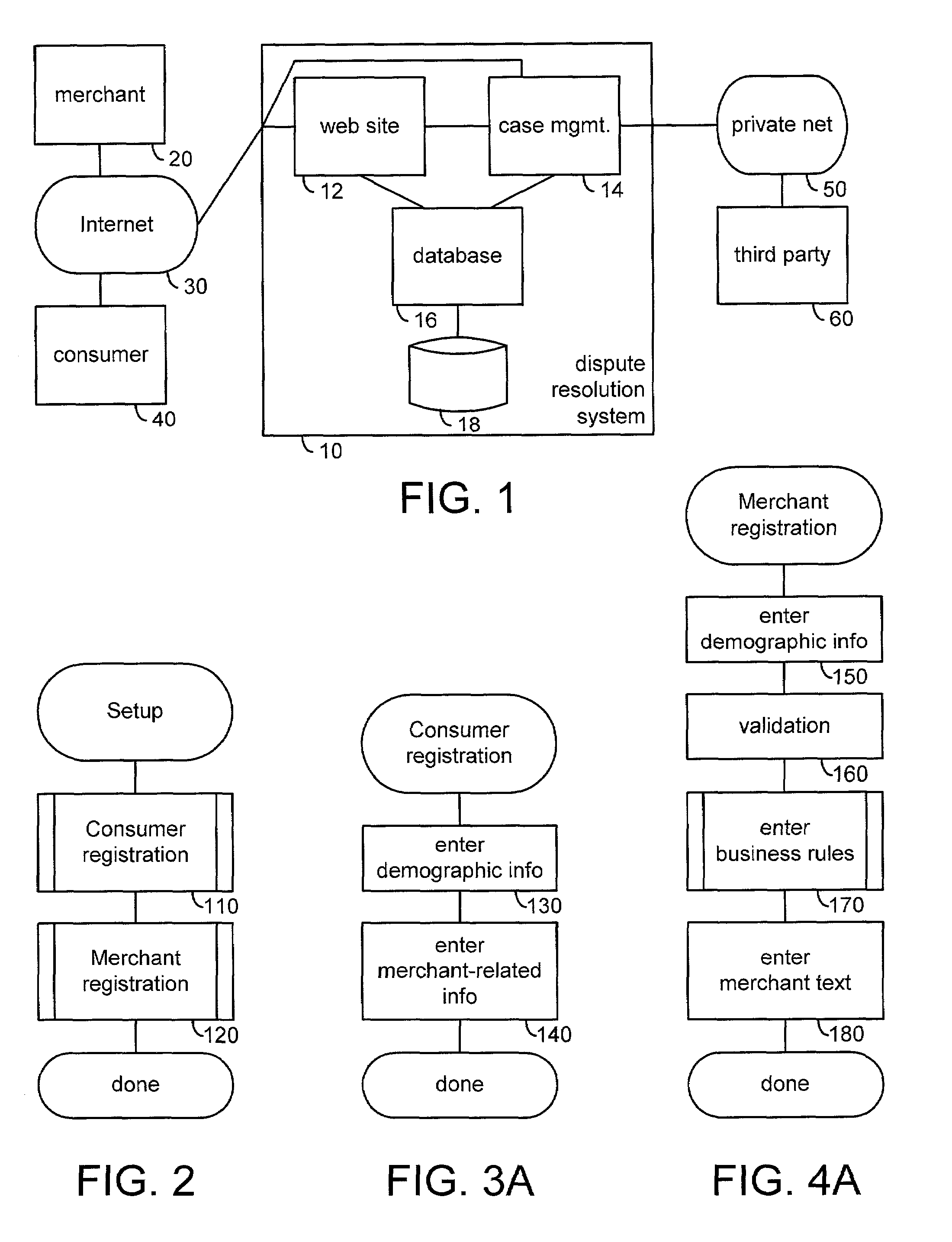
Automated complaint resolution system
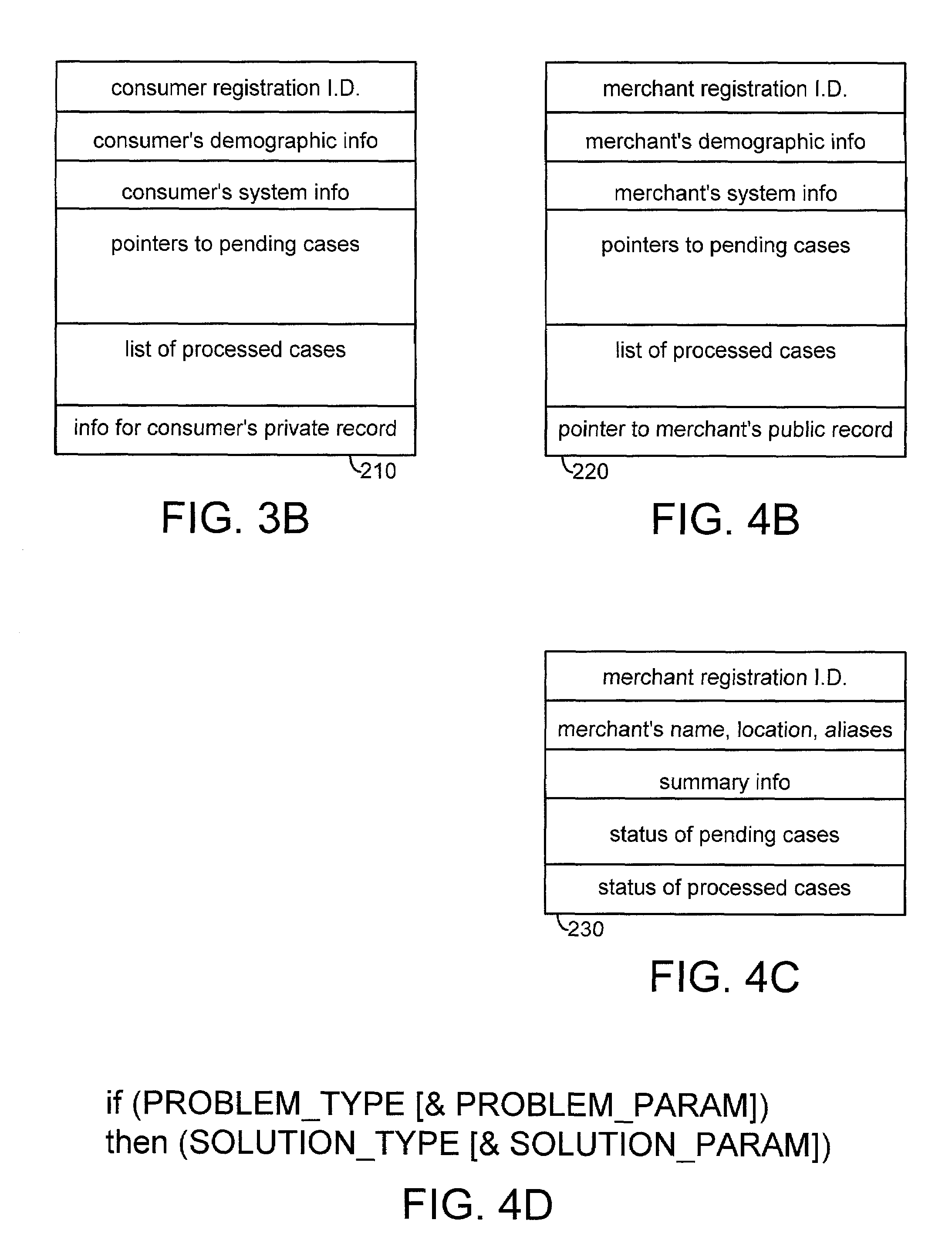
A complaint resolution system, also referred to as a disputes system, enables registered consumers to file a complaint against a merchant. During complaint preparation, the disputes system advises the consumer of relevant cases and other information, allows the consumer to vent their emotions, and prepares a well-formed complaint on behalf of the consumer. After the consumer approves filing of the complaint, the complaint is compared with the merchant's stored business rules. If the merchant's solution for the problem and the consumer's desired solution match, then the disputes system automatically forms an agreement. The disputes system monitors compliance with the agreement by the merchant and consumer. If the merchant has specified a business rule for the problem, but the merchant's solution for the problem and the consumer's desired solution differ, then the disputes system initiates automated mediation, automatically preparing an Answer comprising the solution from the merchant's business rule as the merchant's starting negotiating position. If the merchant has not specified a business rule for the consumer's problem, then the disputes system initiates automated mediation, asking the merchant for his or her Answer to the consumer's complaint. During processing of the consumer's complaint, the disputes system maintains and updates a detailed case record. At the conclusion of the case, the disputes system automatically prepares an anonymized case summary, and adds the anonymized case summary to a database of anonymized case summaries.
Owner:POMERANCE BRENDA
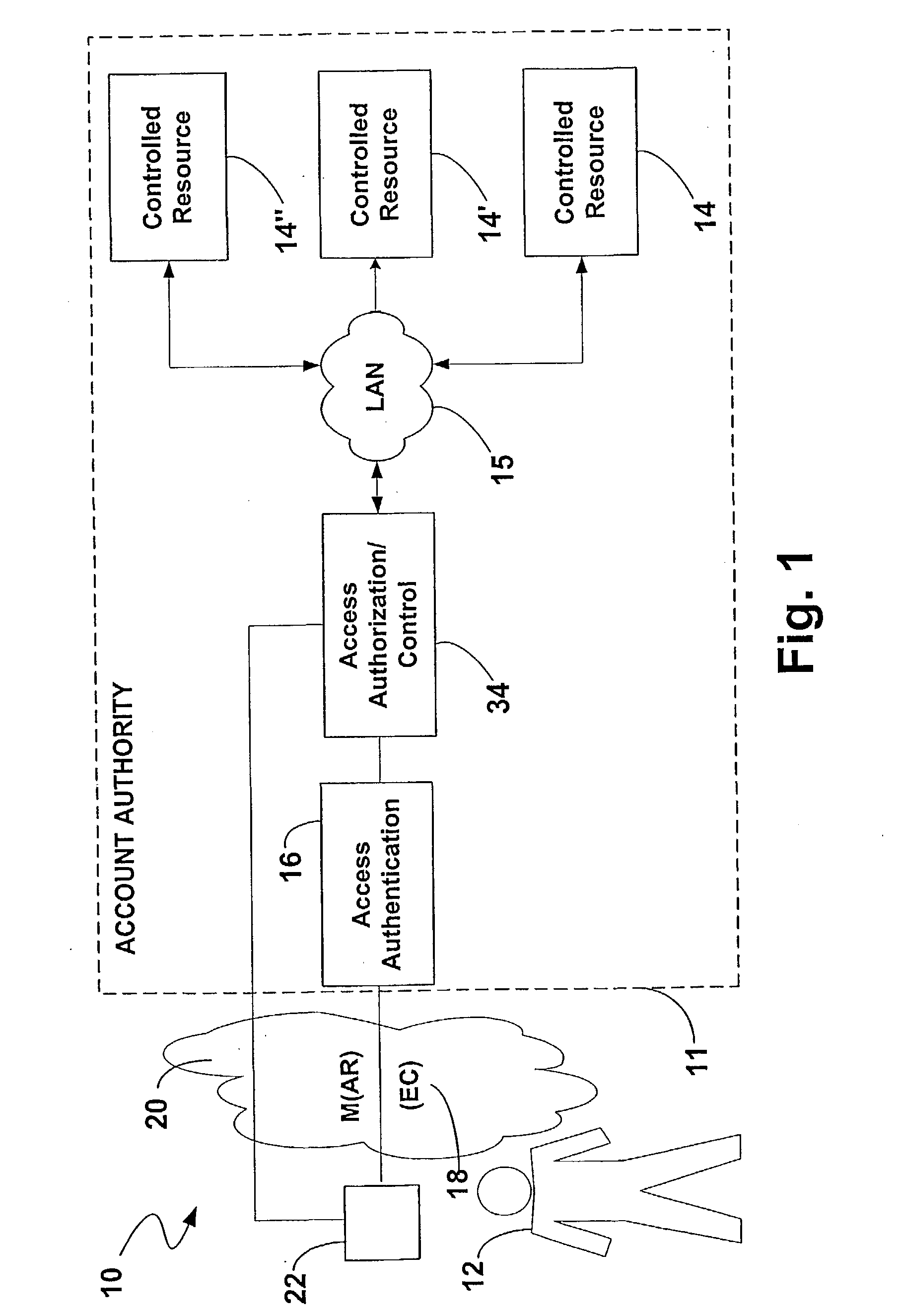
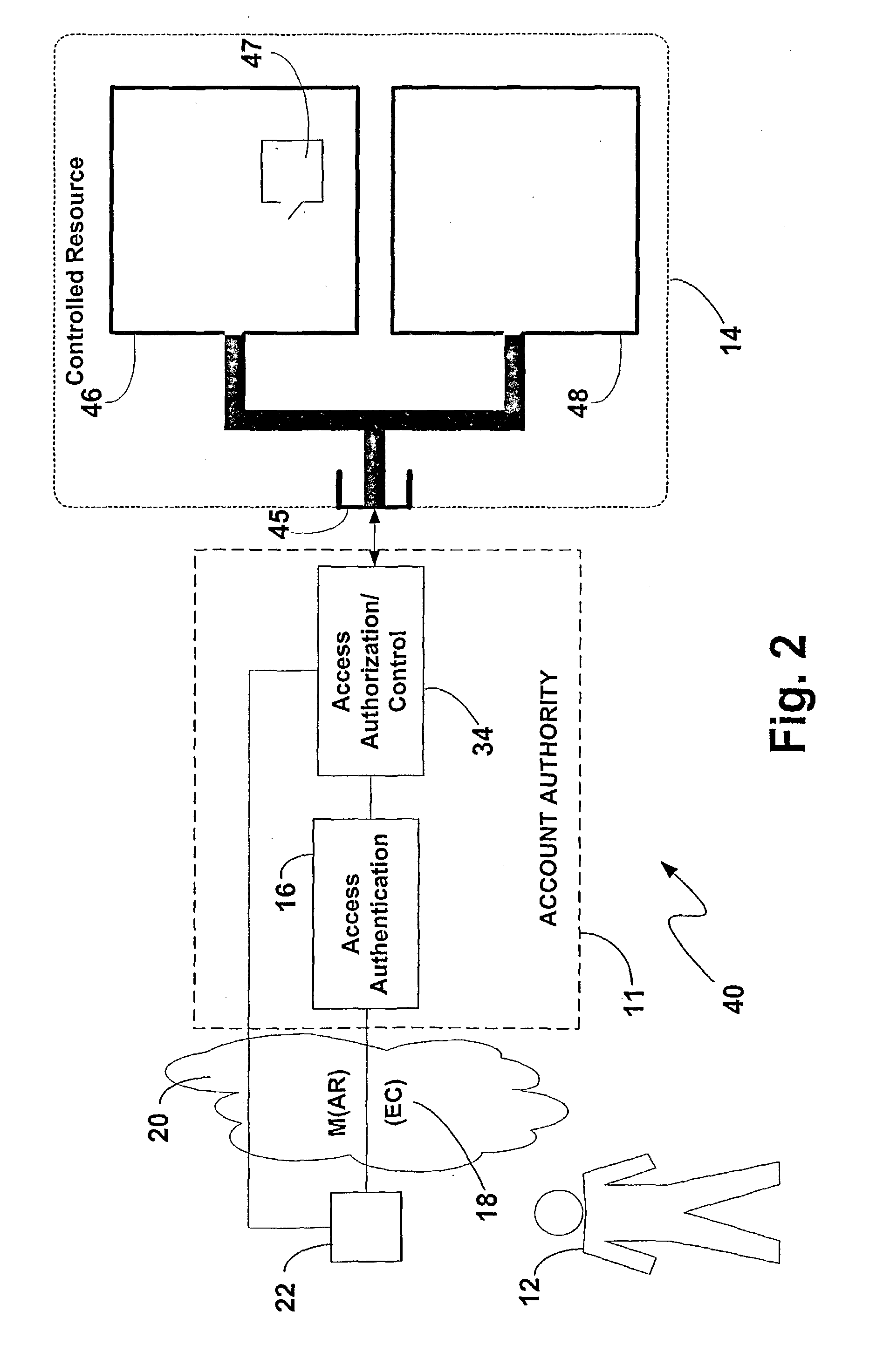
Method and apparatus for access authentication entity
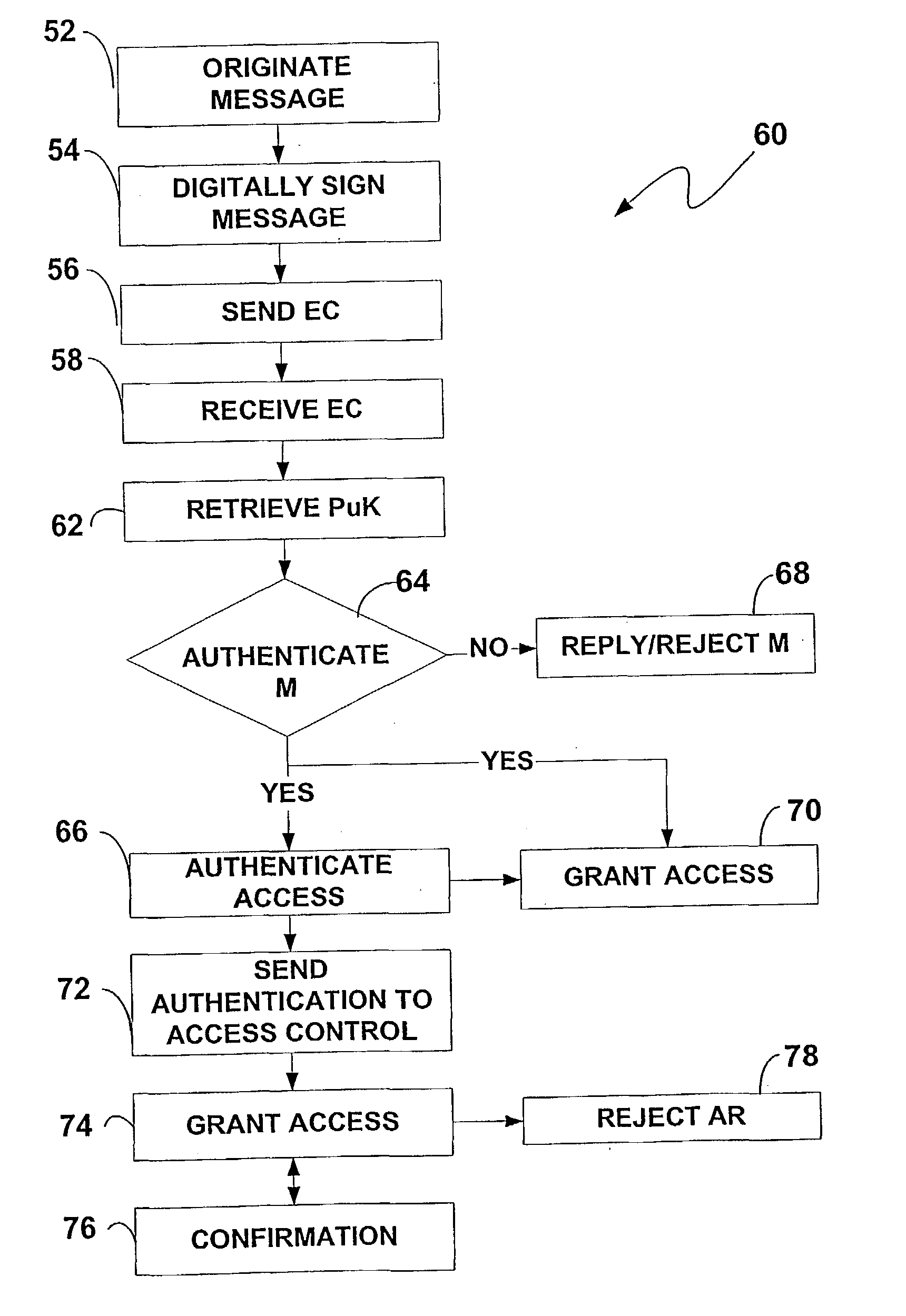
InactiveUS20040128508A1User identity/authority verificationMultiple digital computer combinationsResubmissionDigital signature
A system for authenticating a requesting entity for access to a controlled resource using one or more authentication factors communicated electronically regarding a security account record in an access authentication component (11). Each record being retrievable based on a unique identifier associated with the requesting entity (30) and a public key of a respective public-private key pair of the requesting entity. The requesting entity originates a digitally signed electronic message including an access request and the unique identifier. The access authentication component (34) retrieves the public key by using the unique identifier to authenticate the electronic message. An access authentication signal can be used for granting access to the requesting entity. The message authentication can include authenticating a security profile of a device and one or more types of verification data of the requesting entity and combinations thereof (24). Business rule can be established to require a reconfirmation of the security profile or resubmission of the verification status or a new / different verification status for a new transaction during a session or following a perset session expiration period.
Owner:FIRST DATA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com