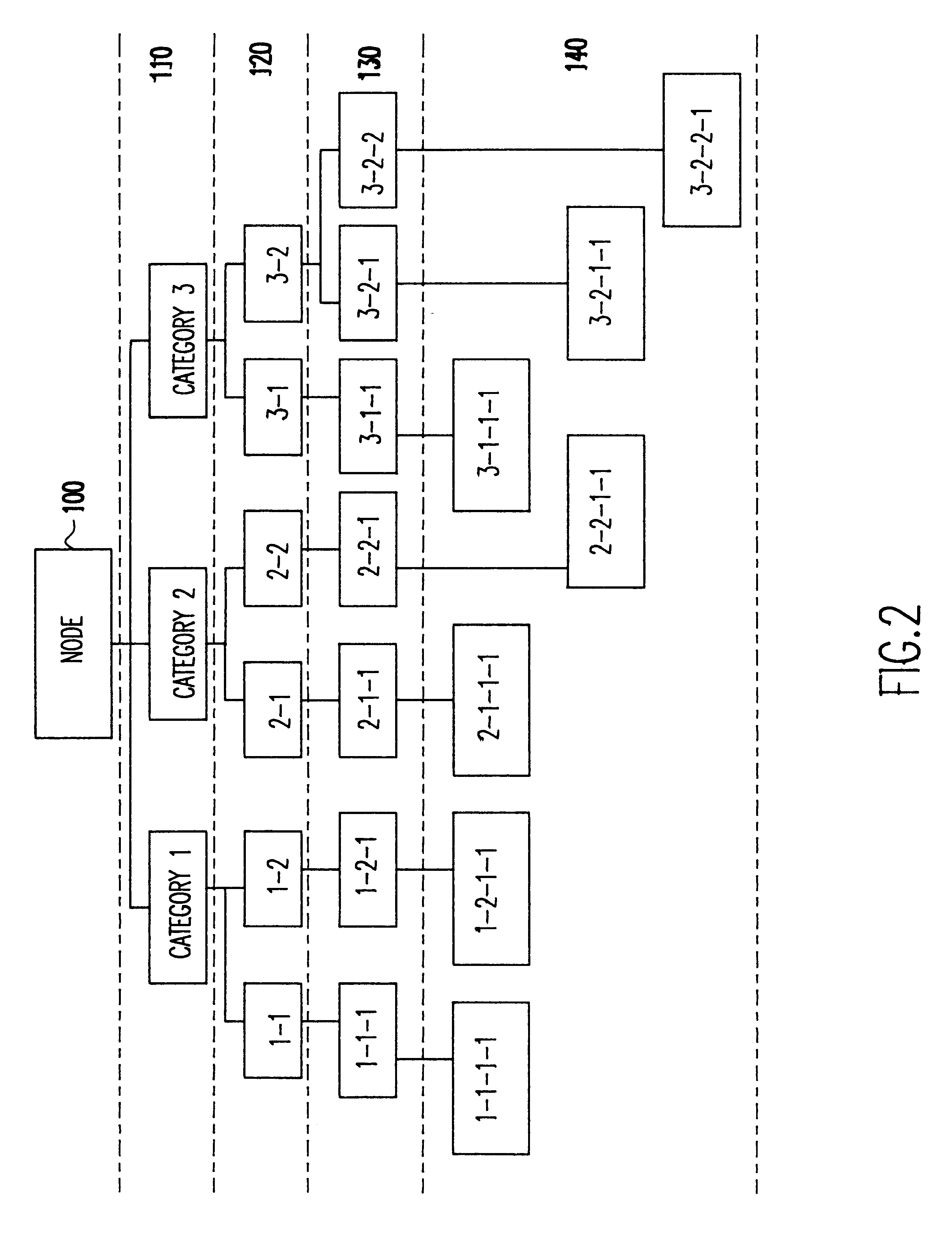
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5345 results about "Electronic information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
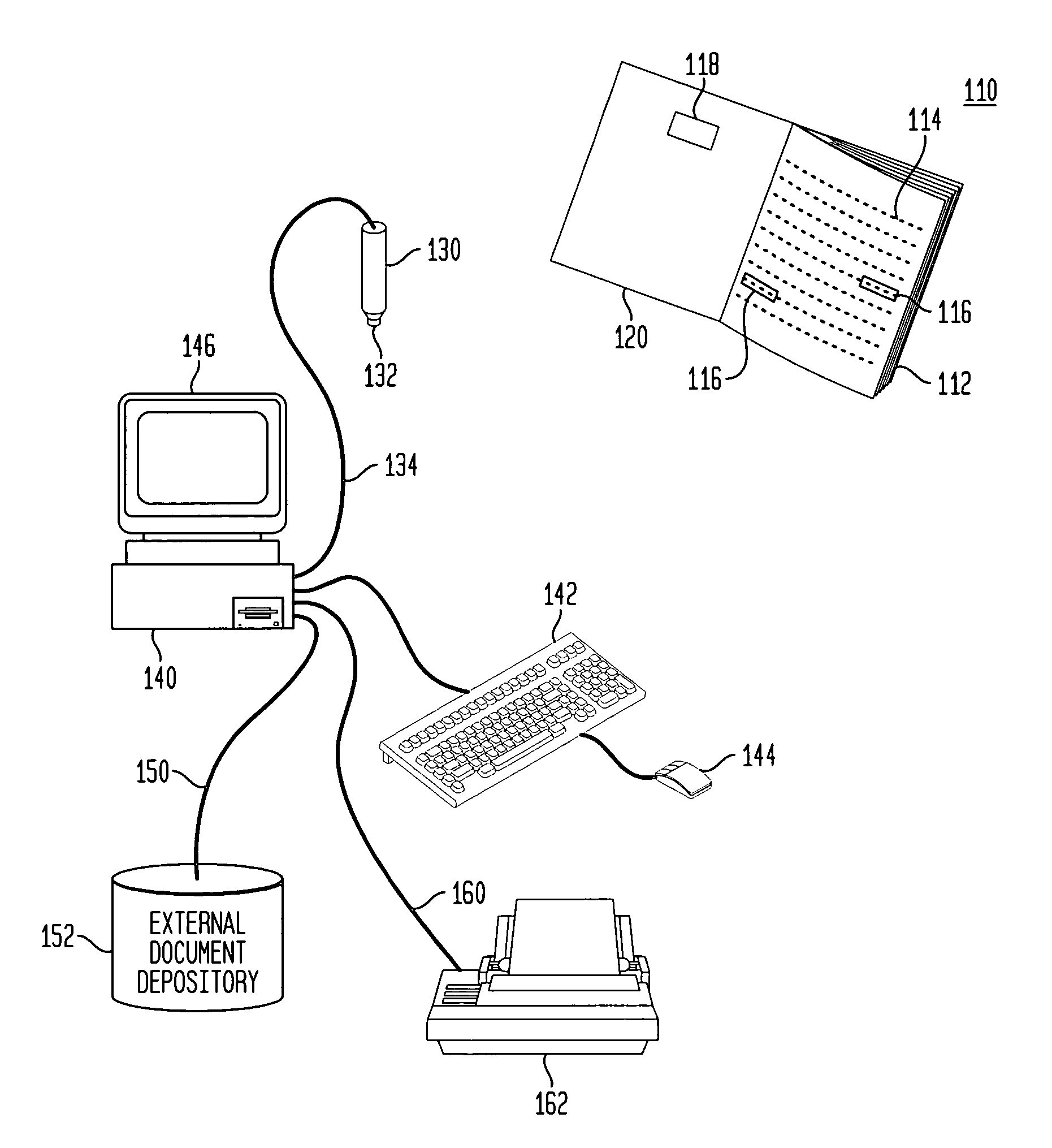
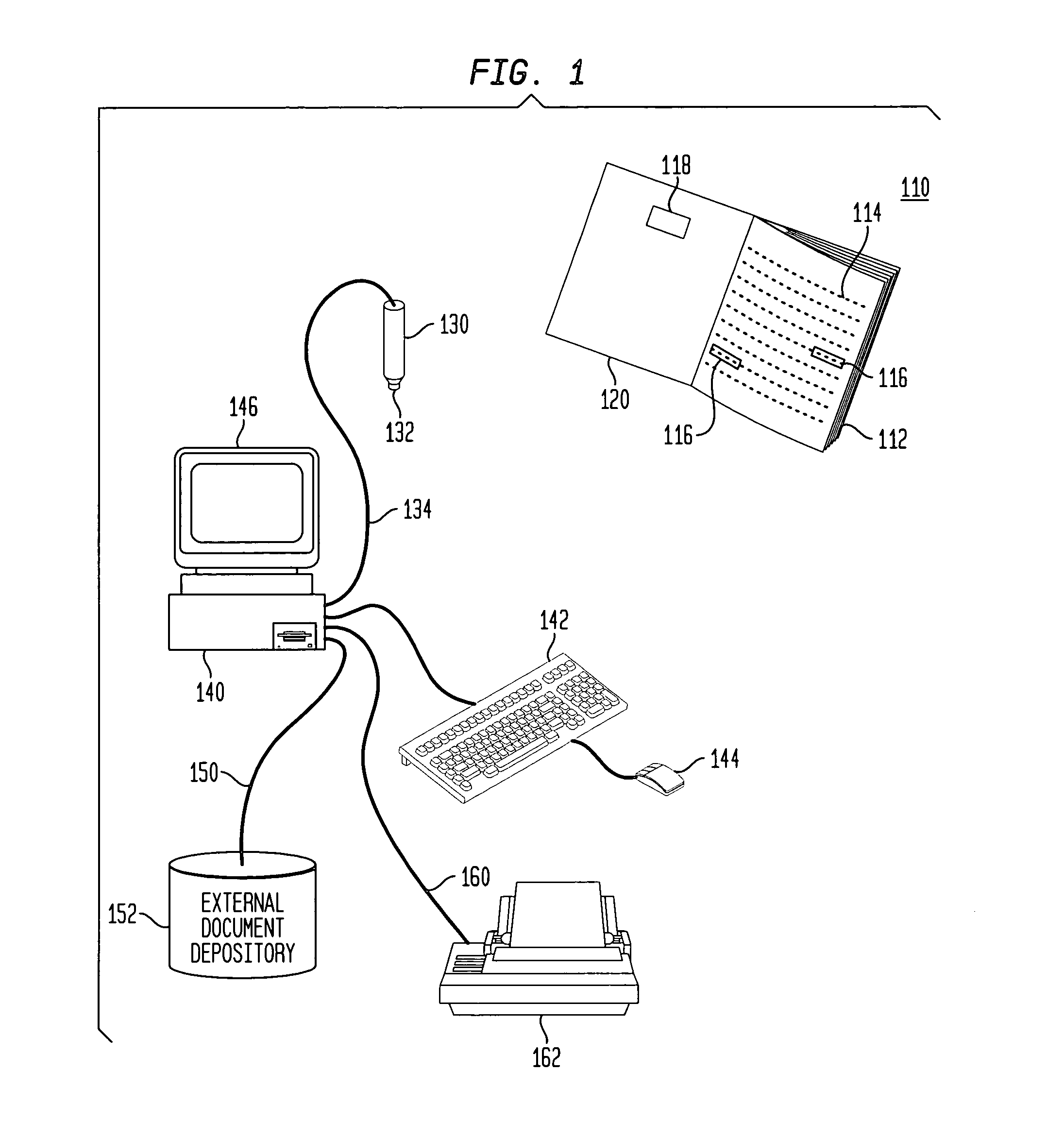
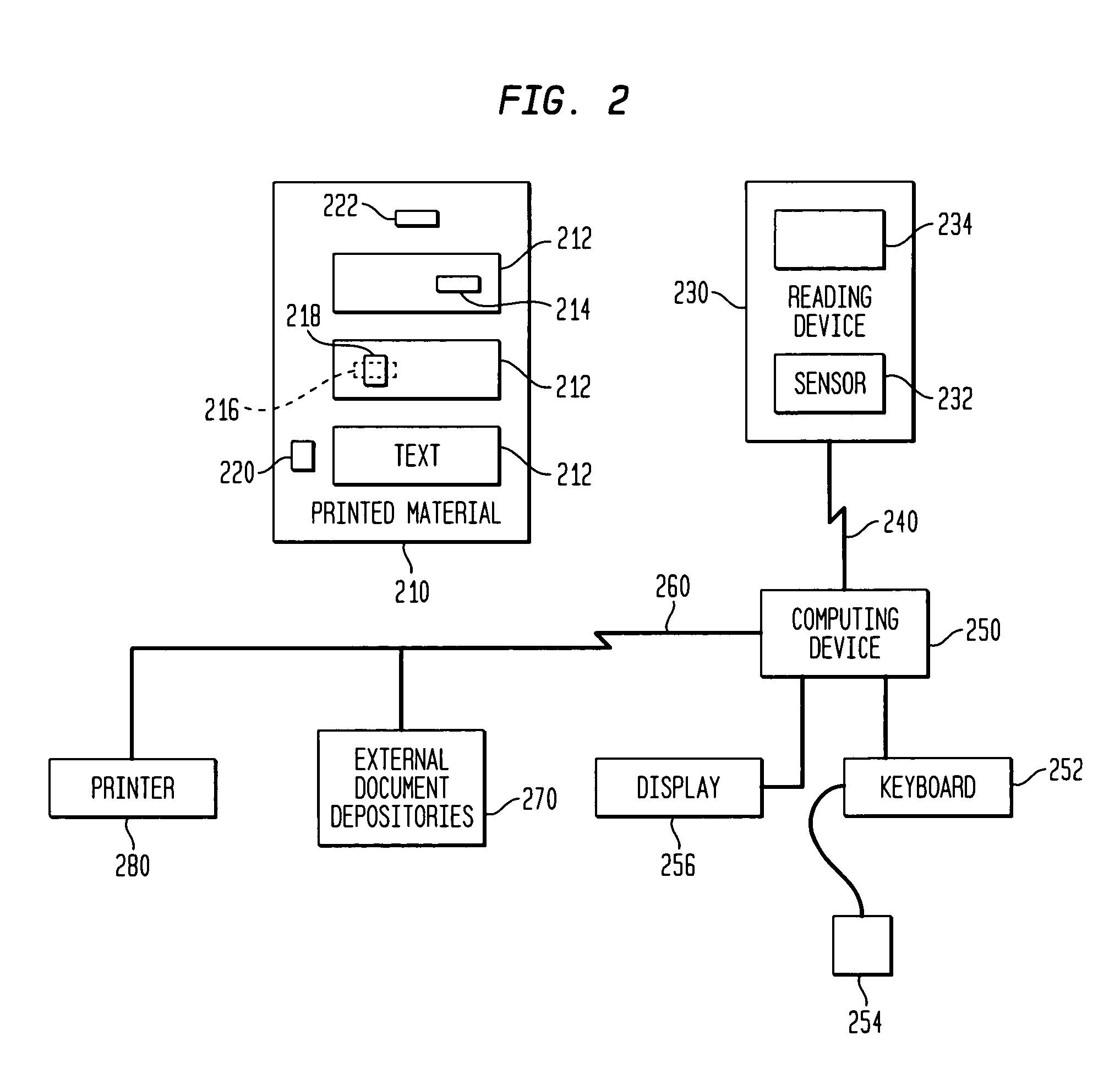
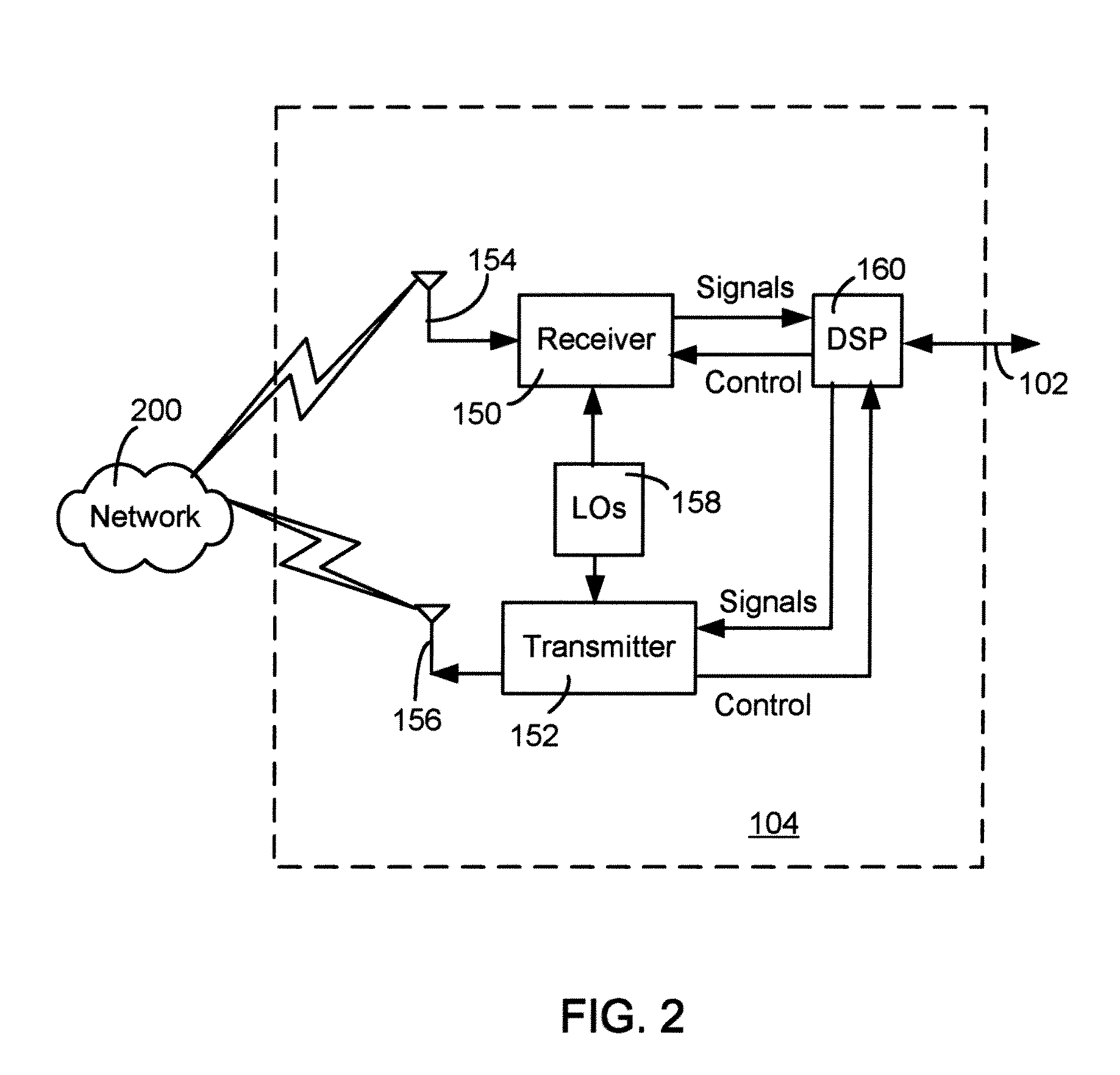
Retrieval and manipulation of electronically stored information via pointers embedded in the associated printed material
InactiveUS6964374B1Facilitates retrieval and manipulationDigital data information retrievalCharacter and pattern recognitionGraphicsElectronic information
A method of retrieving and manipulating electronic information that relates to a printed document. Each printed document contains an initialization marking that is recognizable by an external sensory device and unique to the printed document. When a reader of the printed document desires to retrieve and manipulate electronic information that relates to the printed document, the reader initializes the system by using the sensory device to recognize the initialization marking. The sensory device transfers a code embedded in the initialization marking to a computing device. This configures the computing device to access the stored data and instruction sets associated with the printed document. In addition to the initialization marking, areas throughout the printed document (e.g., text, tables, figures, etc.) also contain markings that are recognizable by the external sensory device. The reader of the printed document uses the sensory device to recognize the markings and transfer the code embedded in the markings to the computing device. The computing device uses the code to retrieve and display the electronic information that relates to that area of the printed document.
Owner:WSOU INVESTMENTS LLC +1
Automatic deletion of electronic messages
InactiveUS20110213845A1Memory loss protectionError detection/correctionComputer hardwareElectronic information
A system and method are provided for automatically deleting messages such as e-mail upon consumption by the recipient. Consumption by the recipient may include viewing the message, forwarding or replying to the message, or archiving, saving, copying, or moving the message. An indicator is inserted in the message, for example in the message header or body, indicating that the message is to be deleted upon detection of a triggering consumption action. Upon receipt at the recipient's mail client, the client determines whether the indicator is present, and, upon detection of a triggering consumption action, automatically closes any views of the message displayed by the recipient's mail client and deletes the message. Optionally a warning is provided to the recipient prior to deletion.
Owner:BLACKBERRY LTD
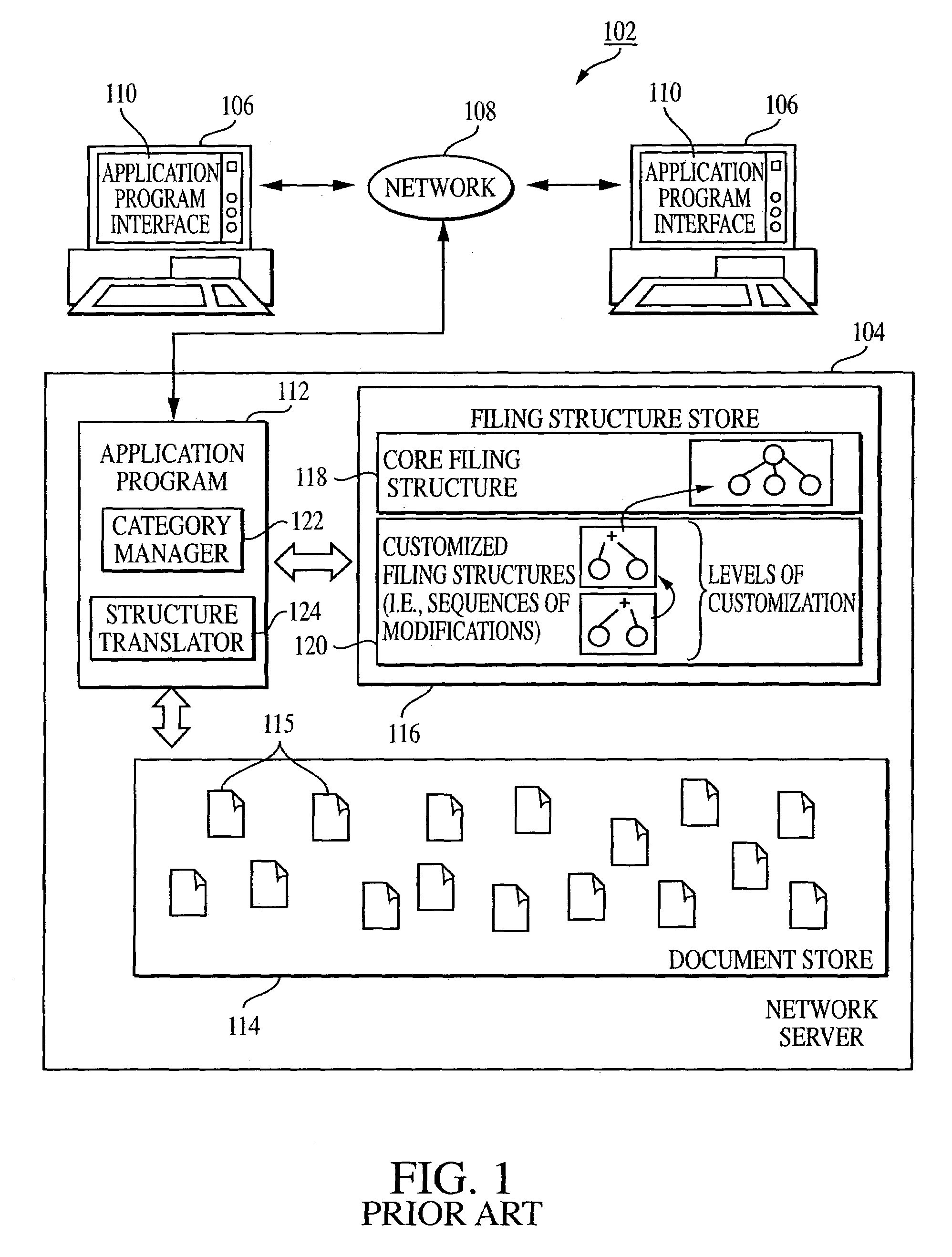
Computer assisted and/or implemented method for group collarboration on projects incorporating electronic information
InactiveUS7386535B1Reduce deficiencyEfficient and effective filingOffice automationResourcesComputer-aidedApplication software
A method, system, and computer program device manages group collaboration on projects, where the projects incorporate associatively filed electronic information. A team of users associated with the project is optionally dynamic and re-definable. A plurality of items are associated with a project; the present invention provides for automatic integration with different native applications supporting the items. Items and / or projects can be associated with more than one project. One or more embodiments of the present invention provide, for example, that a team member can send messages automatically addressed to other team members on the project. Optionally, team members can also attach items in the project to emails to be sent to individuals not on the team.
Owner:STEVENS TEK
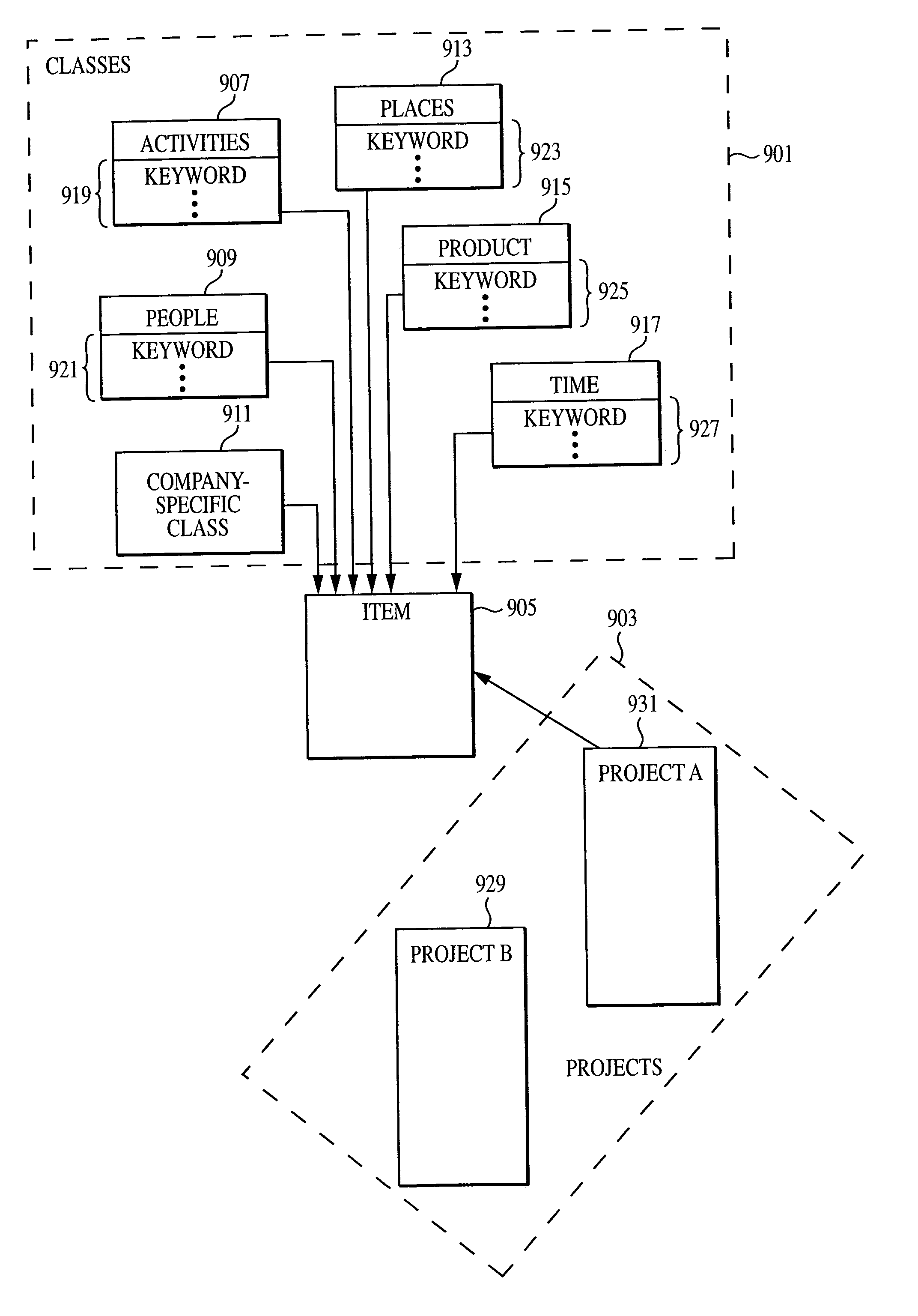
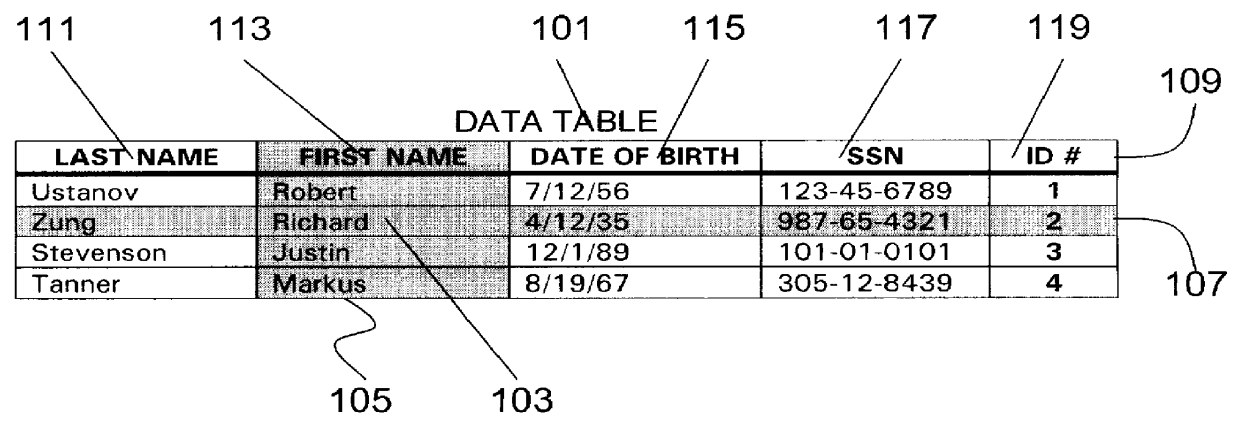
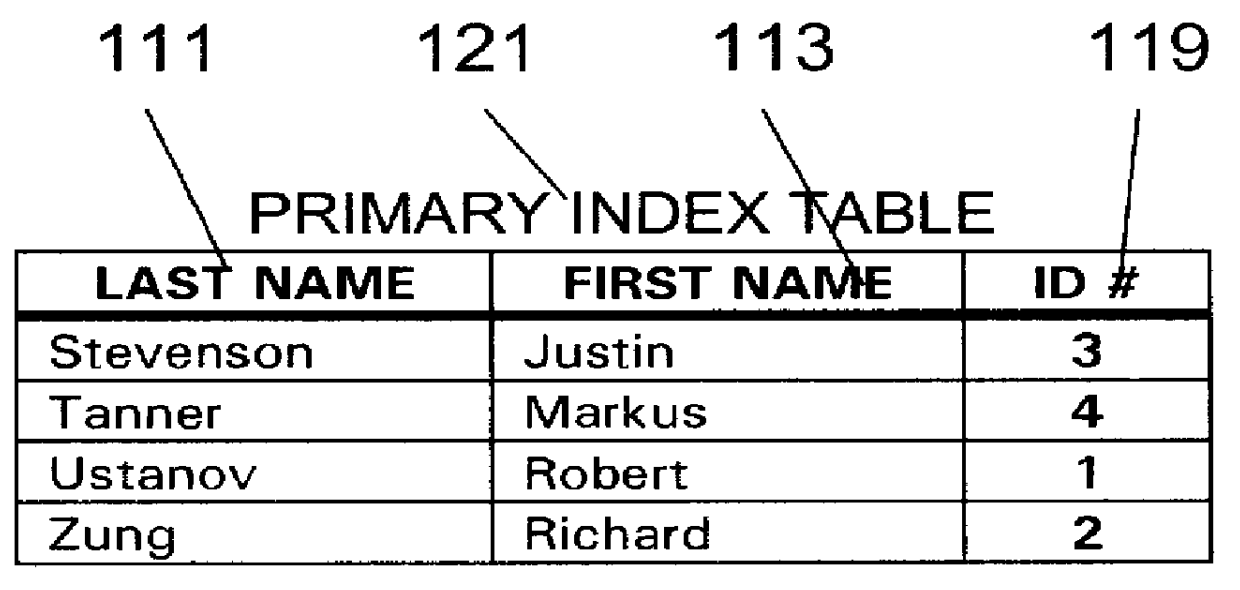
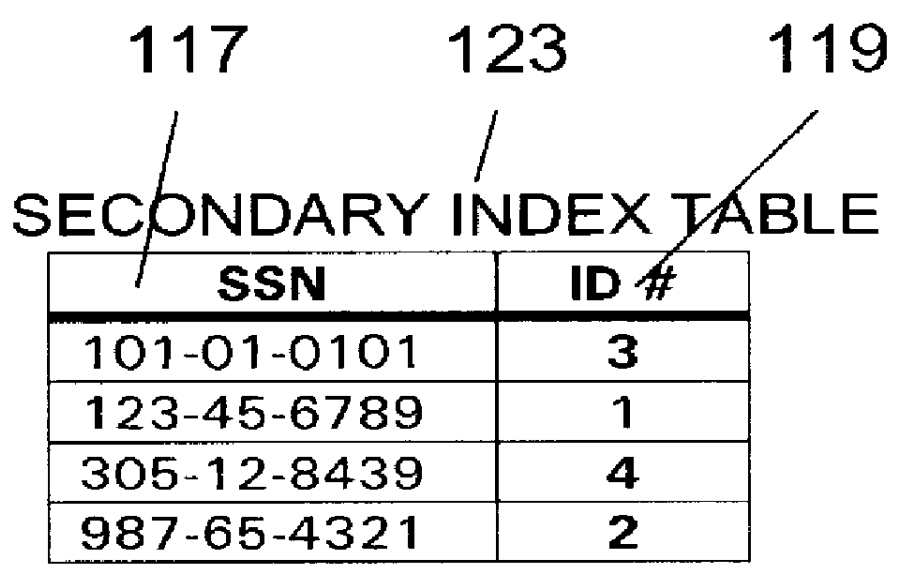
Associative database model for electronic-based informational assemblies
InactiveUS6112209AHigh degree of orderData processing applicationsRelational databasesData setData field
An indexing system and linking method for an assembly of electronic-based informational items stored in and ordered by a plurality of records uniquely identified over a plurality of relational data tables making up a data set wherein each table is assigned a unique domain of unique alphanumeric indicia for assignment and storage in the records. The records are ordered by the alphanumeric indicia whereby each data table acts as its own primary key. The records are bi-directionally linked to each other via a plurality of separate, central linking table indexes wherein each index record is structured with a plurality of linking fields defined to store sets of two or more alphanumeric indicia belonging to a plurality of records in the data set. Each record is further structured to include an internal set of unique indicum for each data field whereby the combination of the unique record indicum and the unique field indicum uniquely identify each record-field over the plurality of relational data tables making up the data set such that each record field may be linked to a plurality of other record-fields or records via the plurality of separate, central linking table indexes. Each central linking table indexes is further generalized to provide multiple arrays of linking indicia in a plurality of indexing fields such that a plurality of the records from a plurality of the data tables may be linked together as a data cluster. The linking values stored in the central linking table indexes may be predefined to automatically structure and link a plurality of unspecified data and changes in the data may alter the linking structure to provide further capabilities.
Owner:GUSACK MARK DAVID
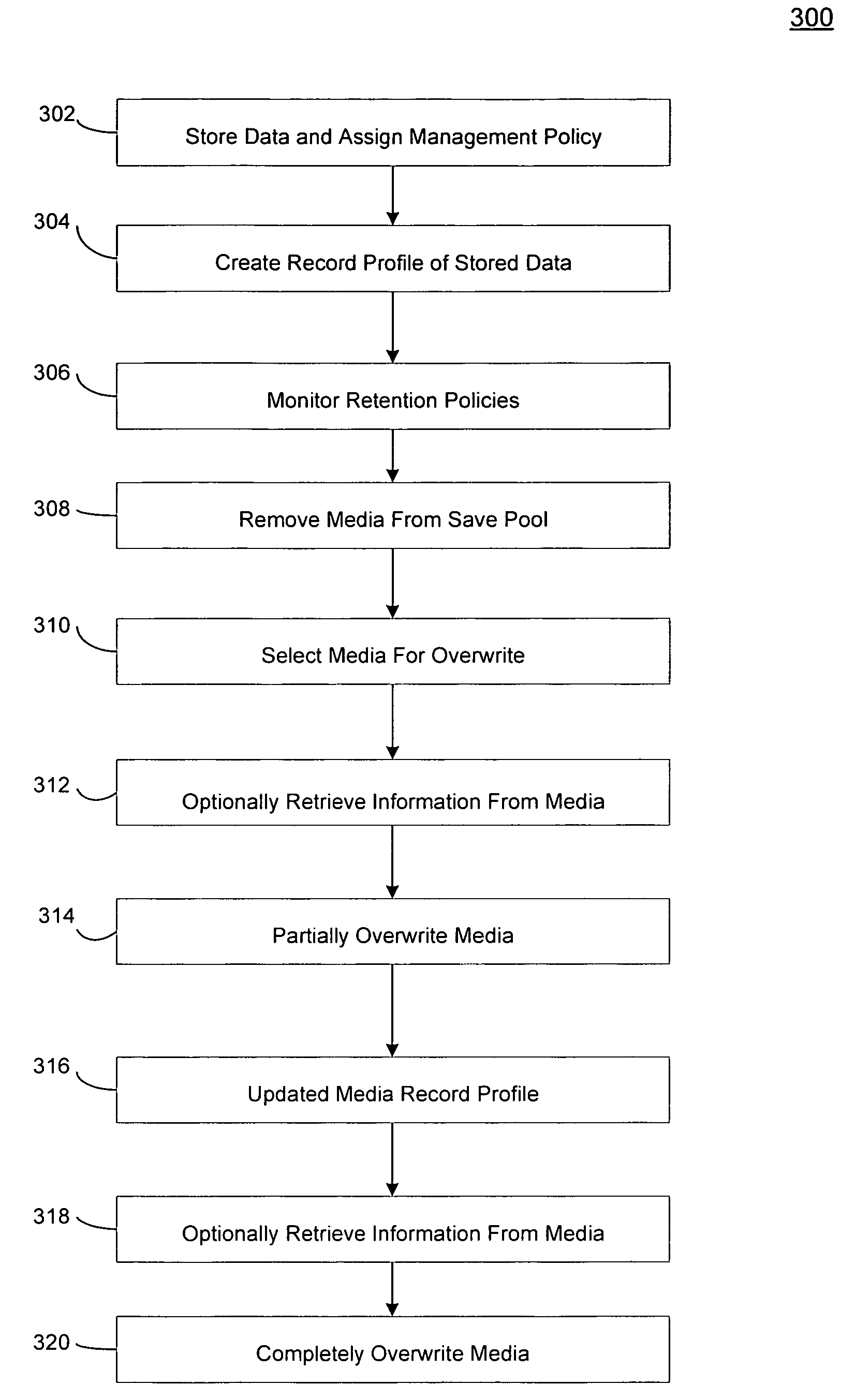
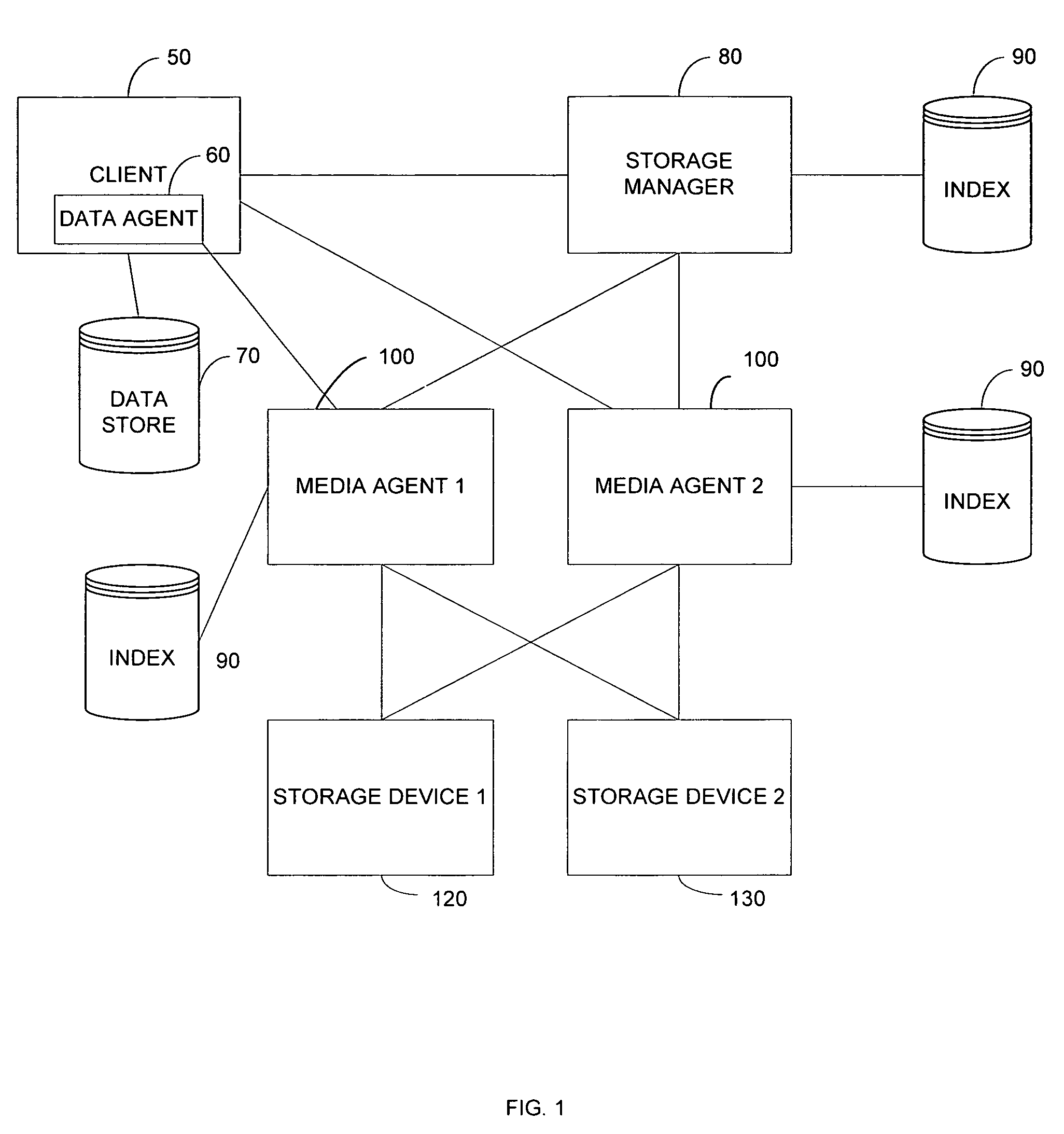
Systems and methods for recovering electronic information from a storage medium
ActiveUS7472238B1Error detection/correctionMemory adressing/allocation/relocationSystems managementEngineering
In one embodiment of the invention, a method is provided for retrieving certain electronic information previously stored on certain storage media after a threshold set in the storage retention criteria has been exceeded in an electronic information storage system that stores electronic information on storage media in accordance with a storage retention criteria is provided. The method includes storing a record in a memory associated with a system manager that assigns the storage retention criteria to the certain electronic data, designating the storage media available for overwrite after the threshold set in the storage retention policy has been exceeded, identifying the certain storage media available for overwrite, and retrieving information from the certain media after the threshold set in the storage retention policy has been exceeded.
Owner:COMMVAULT SYST INC
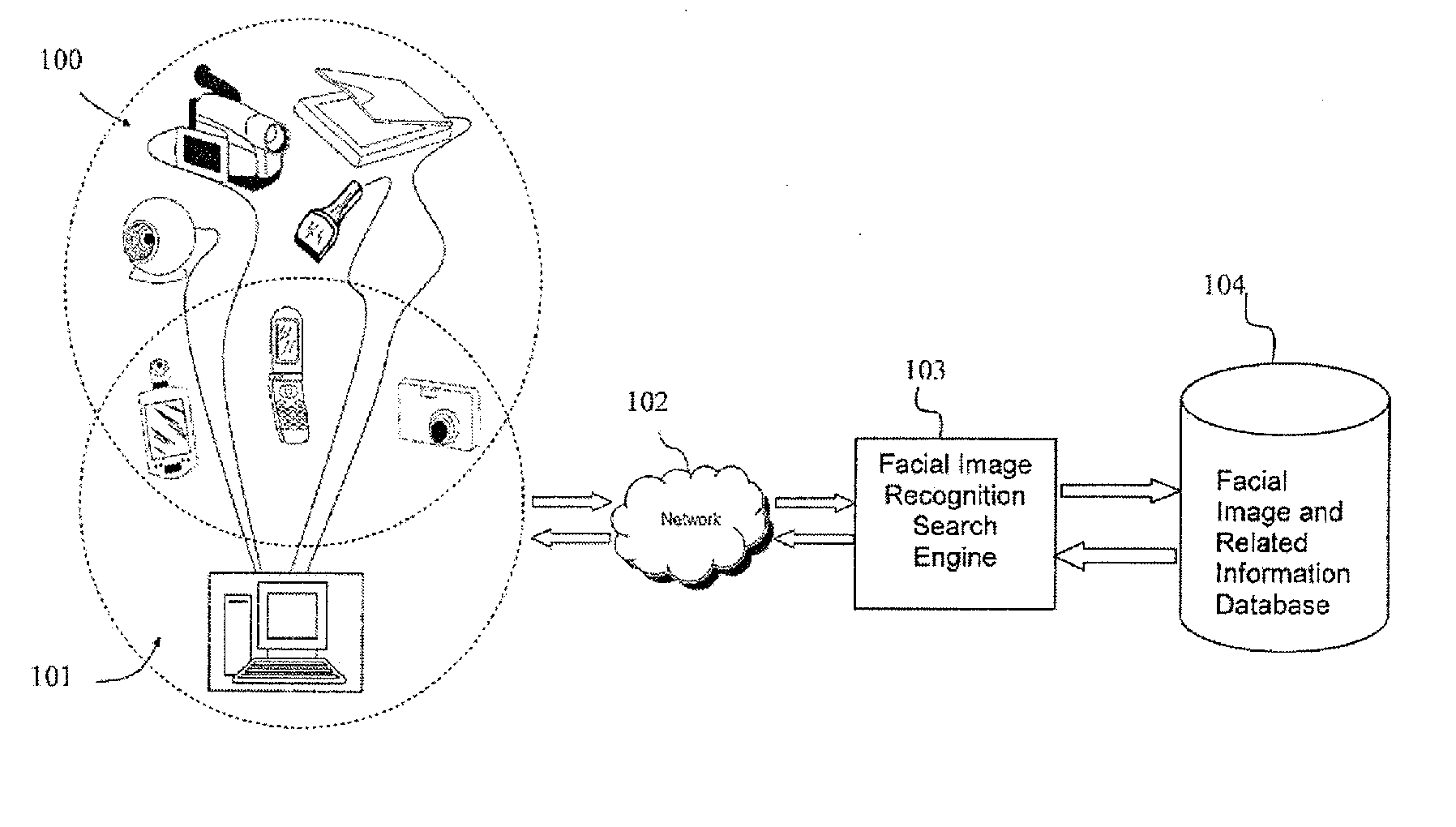
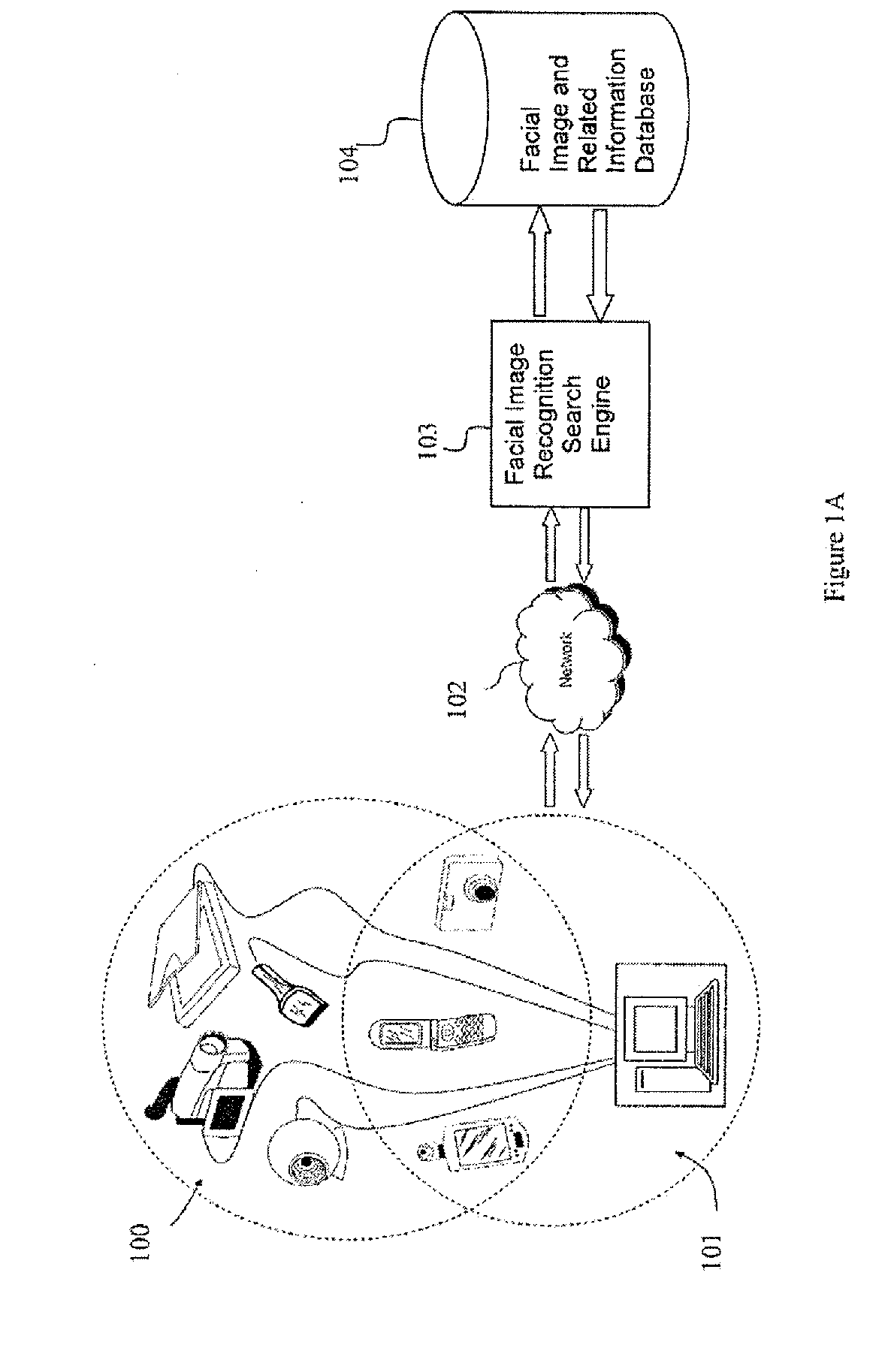
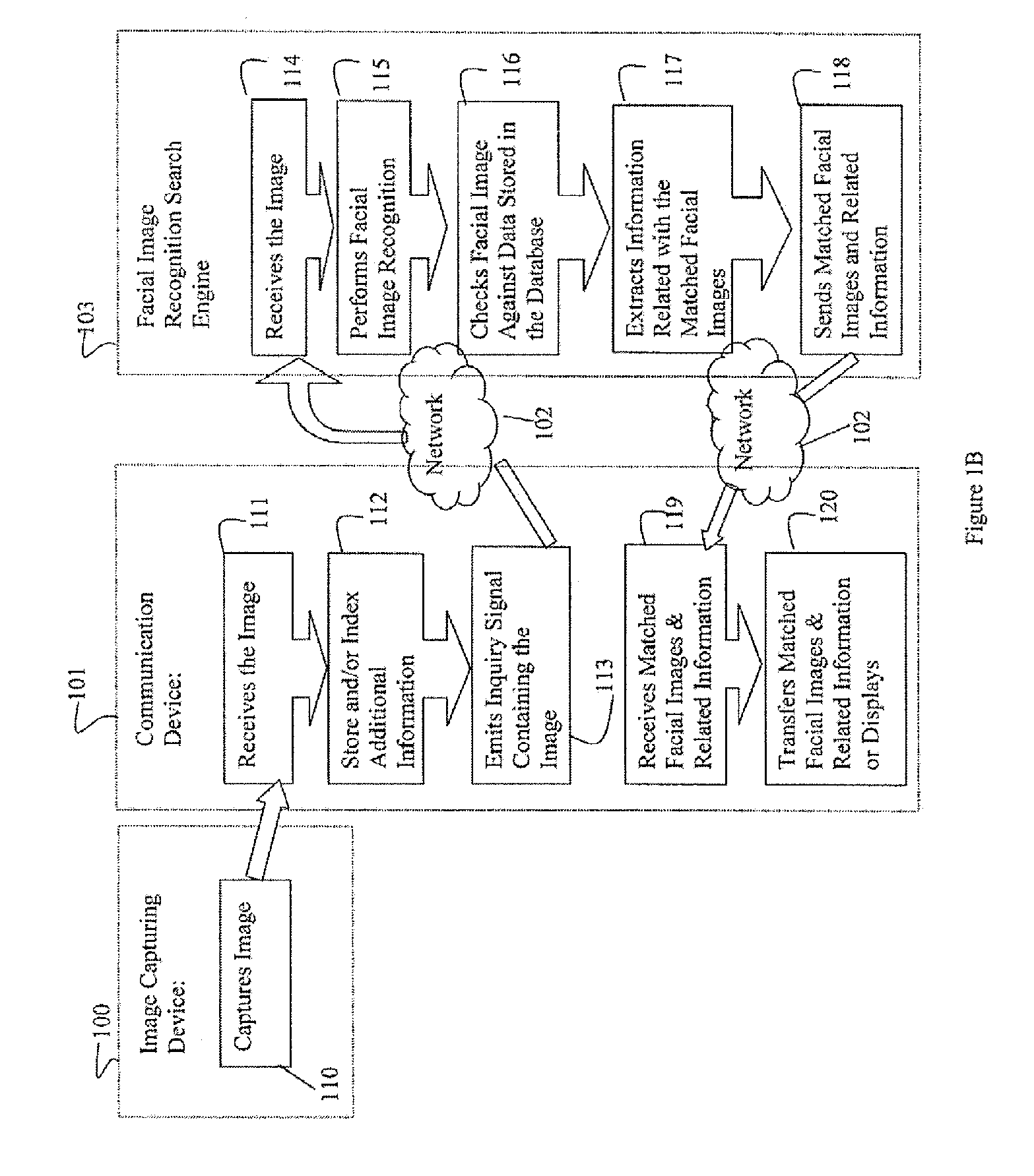
Photo Automatic Linking System and method for accessing, linking, and visualizing "key-face" and/or multiple similar facial images along with associated electronic data via a facial image recognition search engine
ActiveUS20070172155A1Quick searchEnhanced and improved organization, classification, and fast sorts and retrievalDigital data information retrievalCharacter and pattern recognitionHealth professionalsWeb crawler
The present invention provides a system and method for input of images containing faces for accessing, linking, and or visualizing multiple similar facial images and associated electronic data for innovative new on-line commercialization, medical and training uses. The system uses various image capturing devices and communication devices to capture images and enter them into a facial image recognition search engine. Embedded facial image recognition techniques within the image recognition search engine extract facial images and encode the extracted facial images in a computer readable format. The processed facial images are then entered for comparison into at least one database populated with facial images and associated information. Once the newly captured facial images are matched with similar “best-fit match” facial images in the facial image recognition search engine's database, the “best-fit” matching images and each image's associated information are returned to the user. Additionally, the newly captured facial image can be automatically linked to the “best-fit” matching facial images, along with comparisons calculated, and / or visualized. Key new use innovations of the system include but are not limited to: input of user selected facial images for use finding multiple similar celebrity look-a-likes, with automatic linking that return the look-a-like celebrities' similar images, associated electronic information, and convenient opportunities to purchase fashion, jewelry, products and services to better mimic your celebrity look-a-likes; health monitoring and diagnostic use by conveniently organizing and superimposing periodically captured patient images for health professionals to view progress of patients; entirely new classes of semi-transparent superimposed training your face to mimic other similar faces, such as mimic celebrity look-a-like cosmetic applications, and or facial expressions; intuitive automatic linking of similar facial images for enhanced information technology in the context of enhanced and improved organization, classification, and fast retrieval objects and advantages; and an improved method of facial image based indexing and retrieval of information from the web-crawler or spider searched Web, USENET, and other resources to provide new types of intuitive easy to use searching, and / or combined use with current key-word searching for optimized searching.
Owner:VR REHAB INC +2
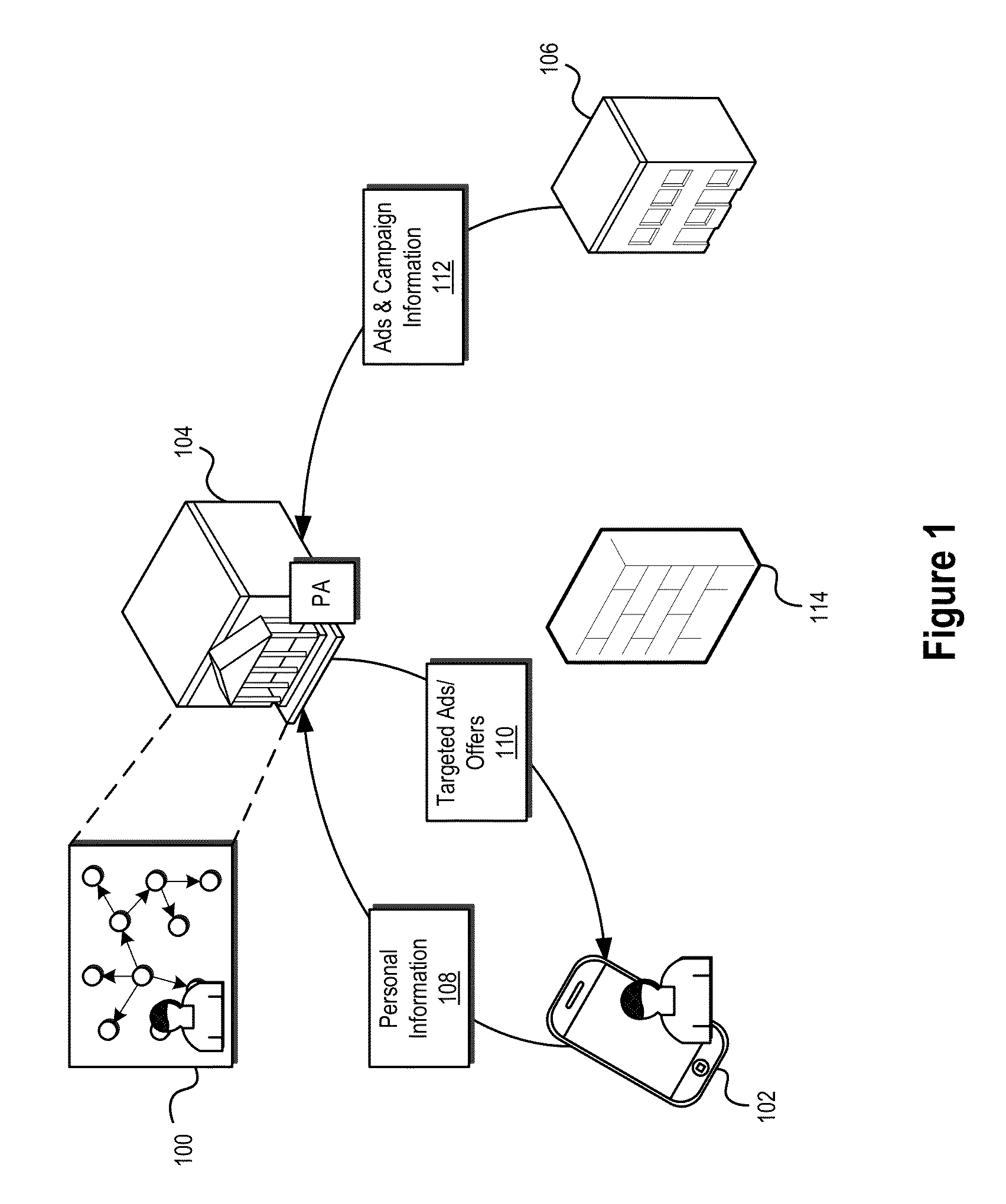
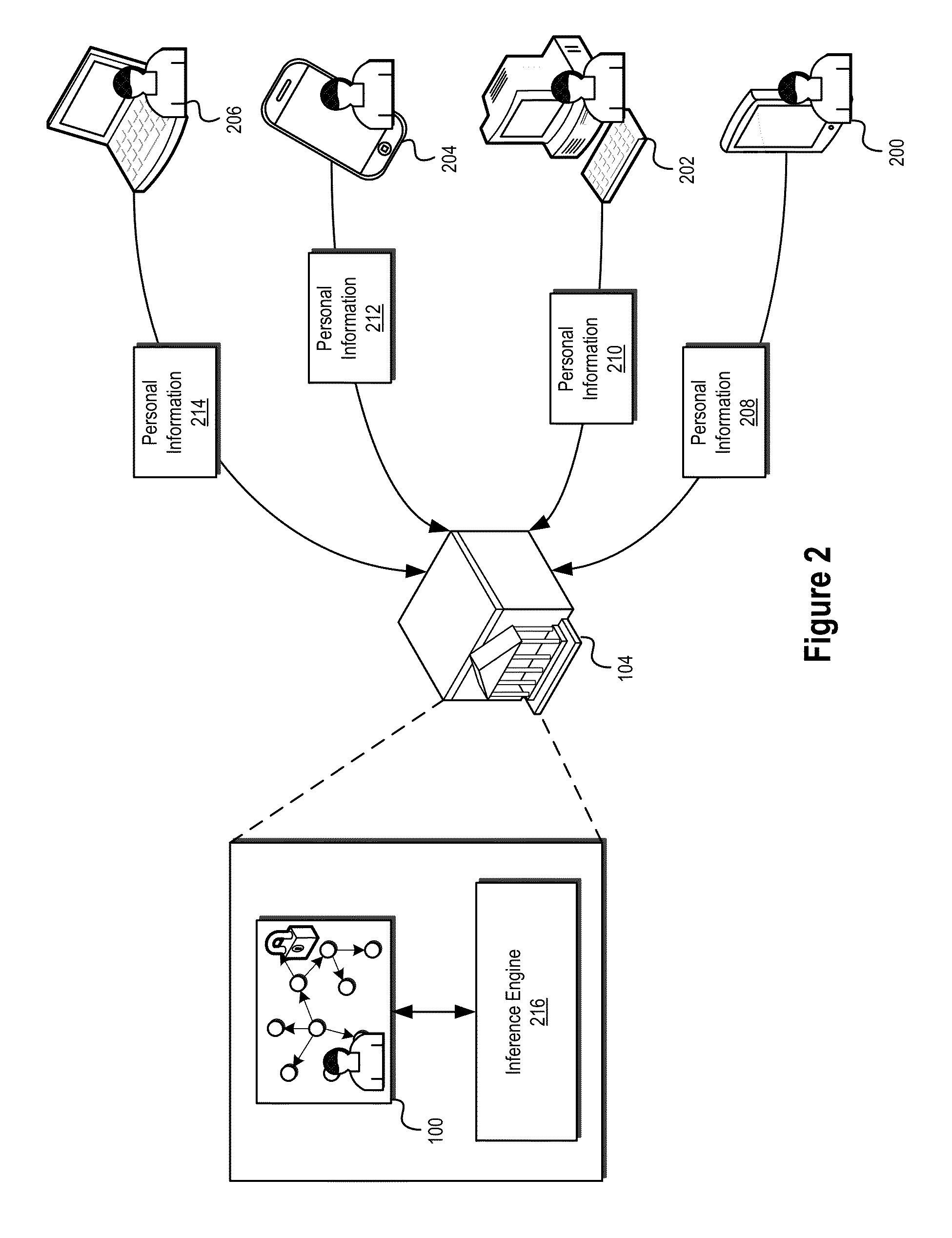
Information targeting systems and methods
ActiveUS9355157B2Facilitate secure collection and use and management and distributionConvenient and effective positioningDigital data information retrievalSpecial data processing applicationsInternet privacyElectronic information
The present disclosure relates generally to systems and methods for the secure management of electronic information relating to a user. In certain embodiments, systems and methods disclosed herein may allow for personal information related to a user to be used in connection with information targeting systems and methods configured to match and / or target information for delivery to a user based on the user's interests. In some embodiments, personal information relating to a user may be stored and / or managed in a personal ontology graph or other data structure including, among other things, various inferred interests of the user derived from available personal information.
Owner:INTERTRUST TECH CORP
Method and system for automated intelligent electronic advertising
ActiveUS20050289113A1Web data indexingDigital data processing detailsElectronic informationSearch engine query
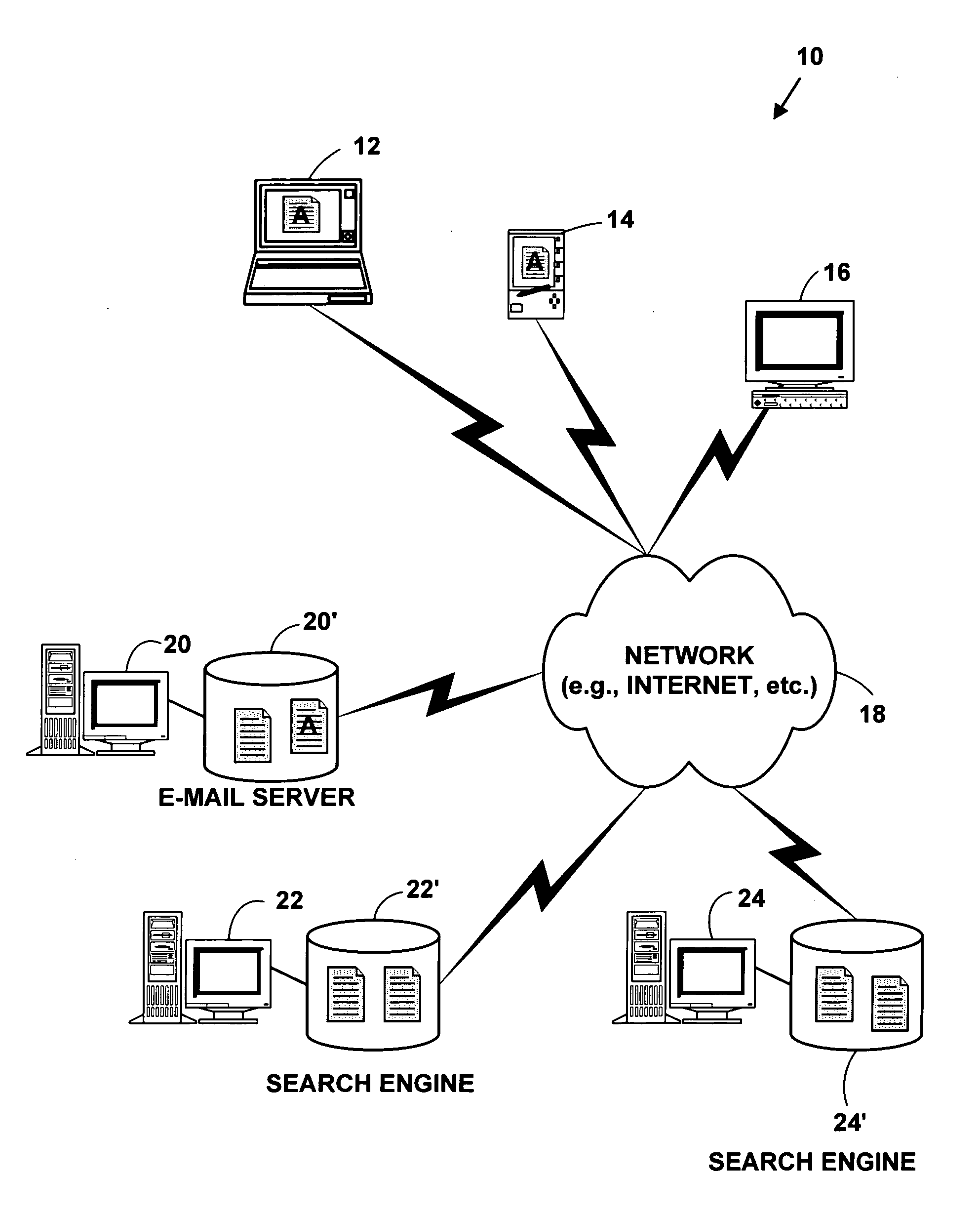
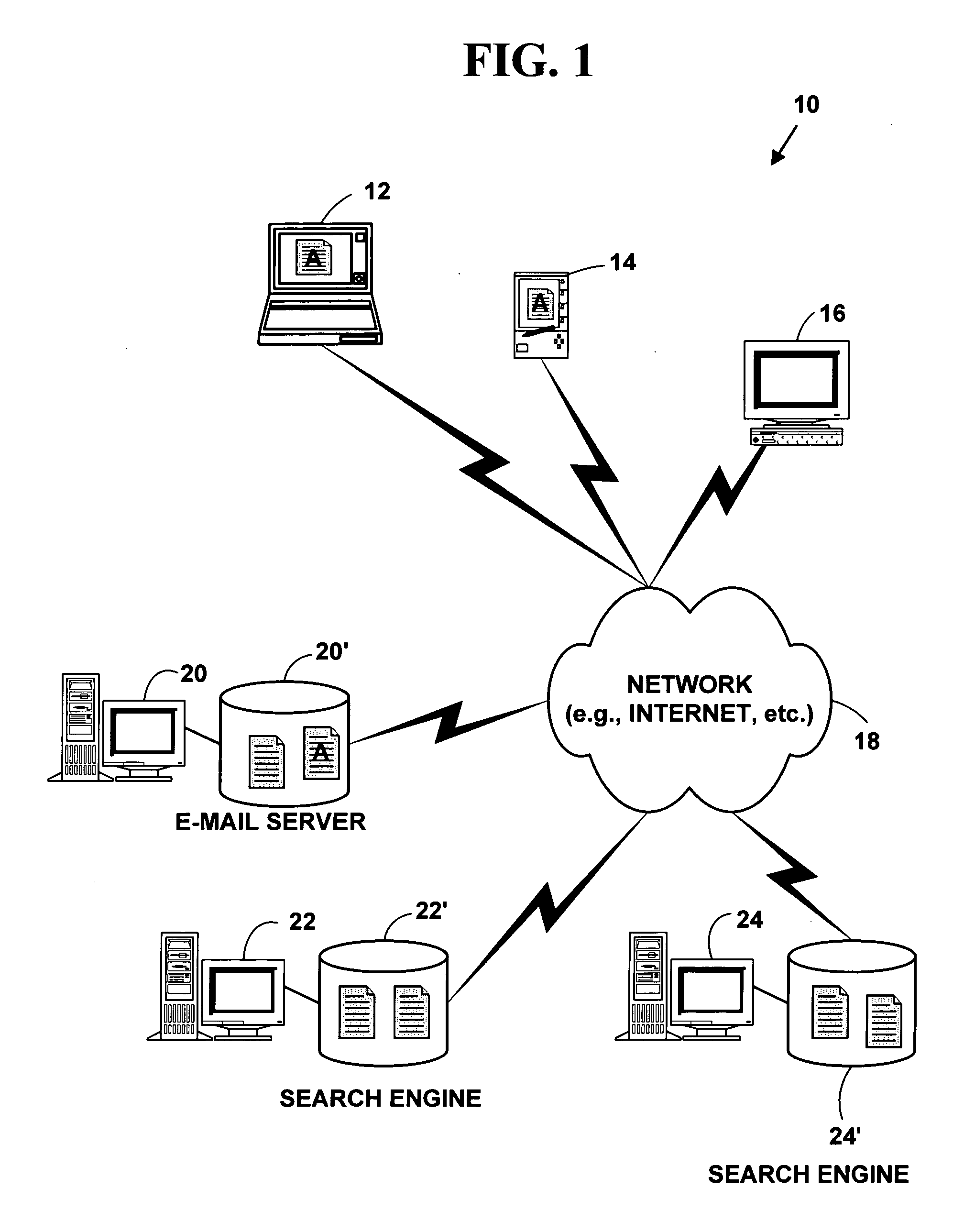
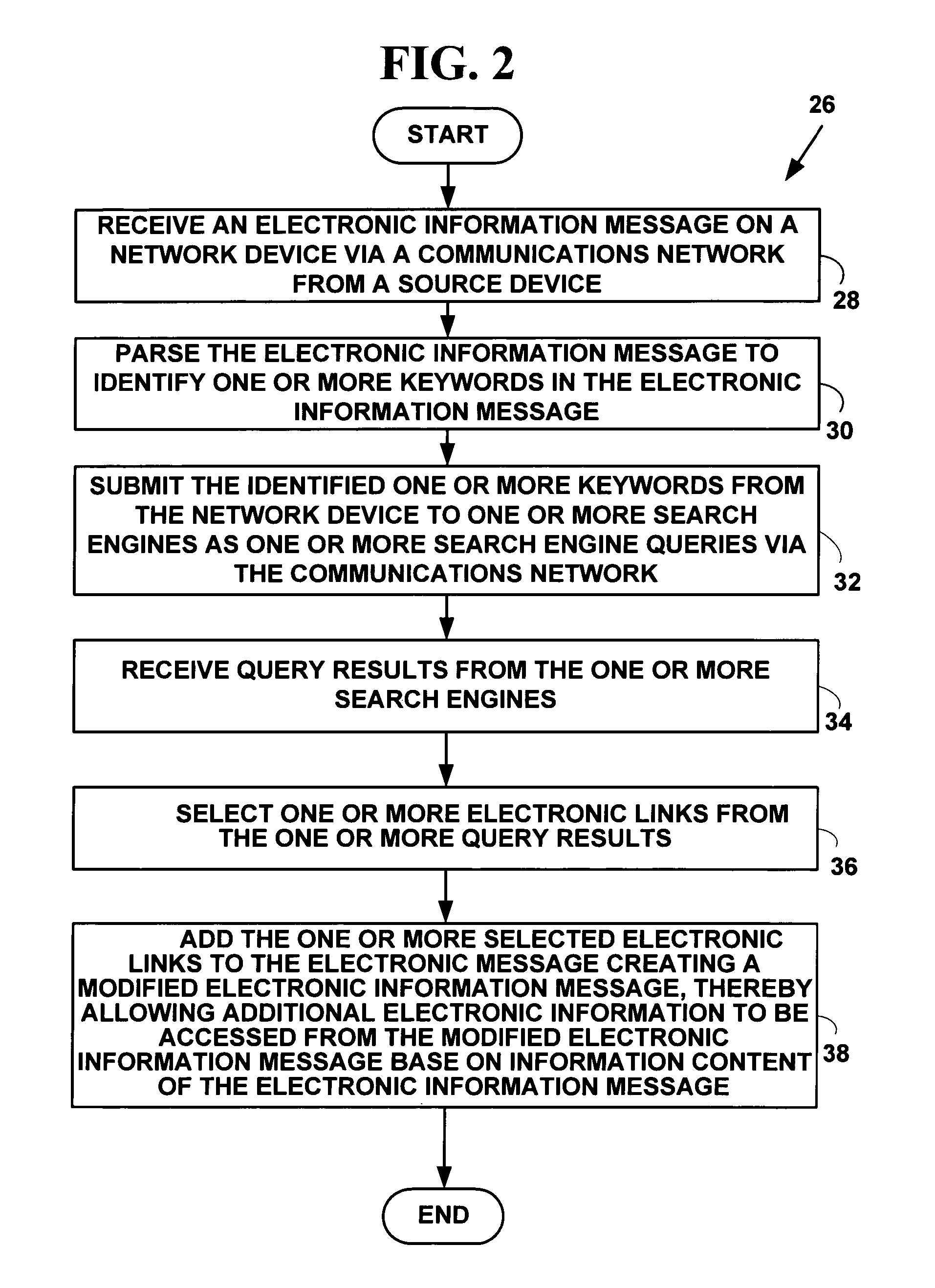
A method and system for automated intelligent electronic advertising. The method and system parse electronic information messages (e.g., e-mail messages, instant messages, etc.) for keywords and make search engine queries or database queries for electronic links based on the identified keywords. The electronic links returned from search engine queries or database queries are added to the electronic information messages creating a modified electronic information message. This allows additional electronic information to be accessed from the modified electronic information message based on information content of the original electronic information message.
Owner:BOOKSTAFF BLAKE
Networked personal customized information and facility services
InactiveUS6055512AMultiple digital computer combinationsBuying/selling/leasing transactionsData displayPersonal details
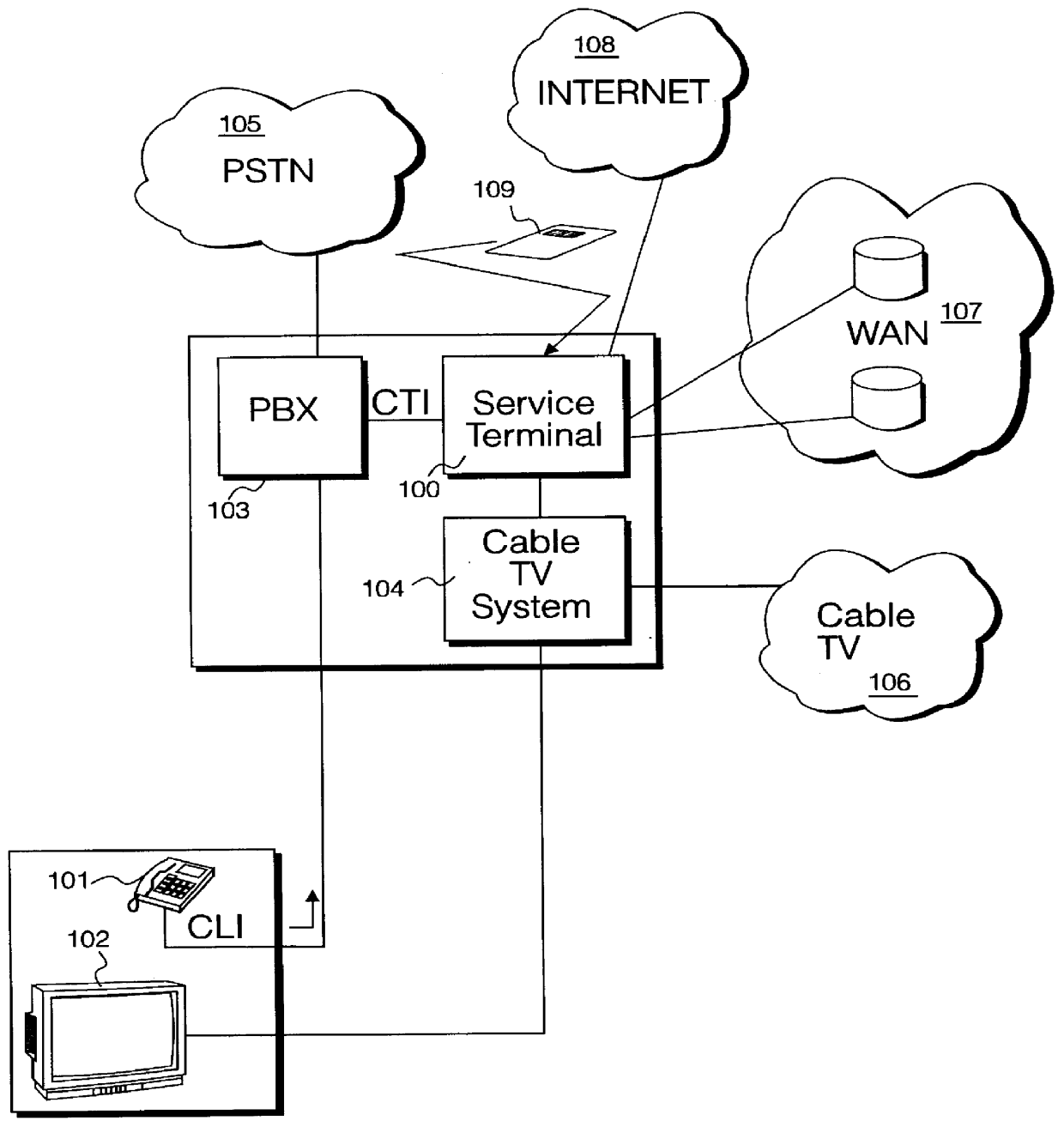
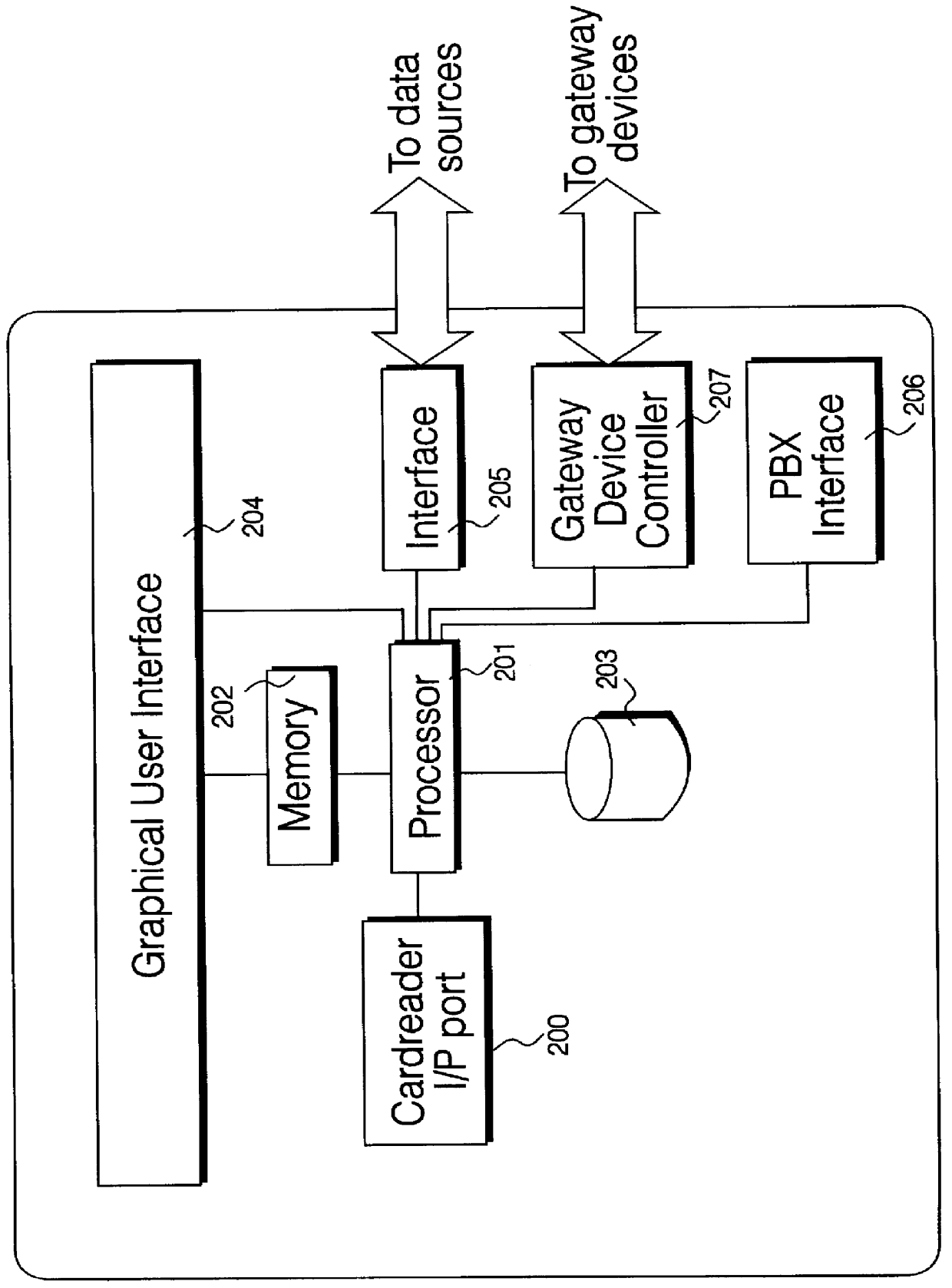
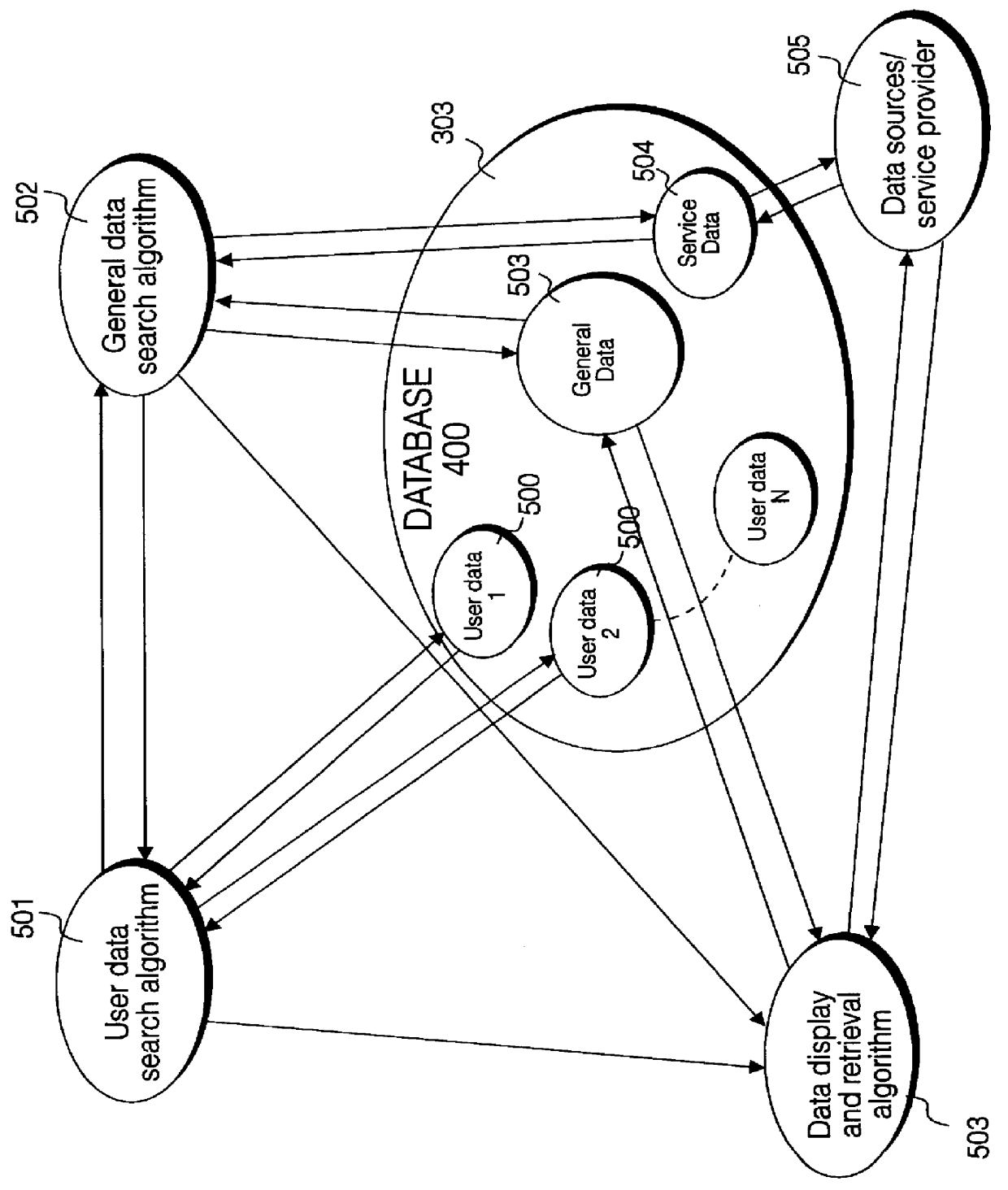
A service terminal facility is provided at a public access location, for example in a hotel, hospital or airport, the service terminal facility available for providing electronic information services to users, in response to input of a portable data storage medium, for example a smart card or the like. A smart card contains stored data describing user specified information such as contacts names, personal details and medical information and personal interest information. The service terminal comprises a search engine for searching the user data and comparing data types within the user data with general data stored locally at the service terminal. The service terminal selects data corresponding to data types specified in the user data and displays these on the graphical user interface at the service terminal, or at a user interface connected with the service terminal. The user data may specify one or more data sources or service providers from which electronic data services of interest to the user can be obtained. The service terminal may obtain listings of data from remote data sources and / or service providers and display these on the graphical user interface and / or user interface. The user may instruct downloading of electronic data or electronic information services from remote data sources or service providers from the service terminal for delivery to the graphical user interface or the user interface.
Owner:NORTEL NETWORKS LTD
Resolving queries based on automatic determination of requestor geographic location
InactiveUS7774342B1Web data indexingDigital data processing detailsGeolocationElectronic information
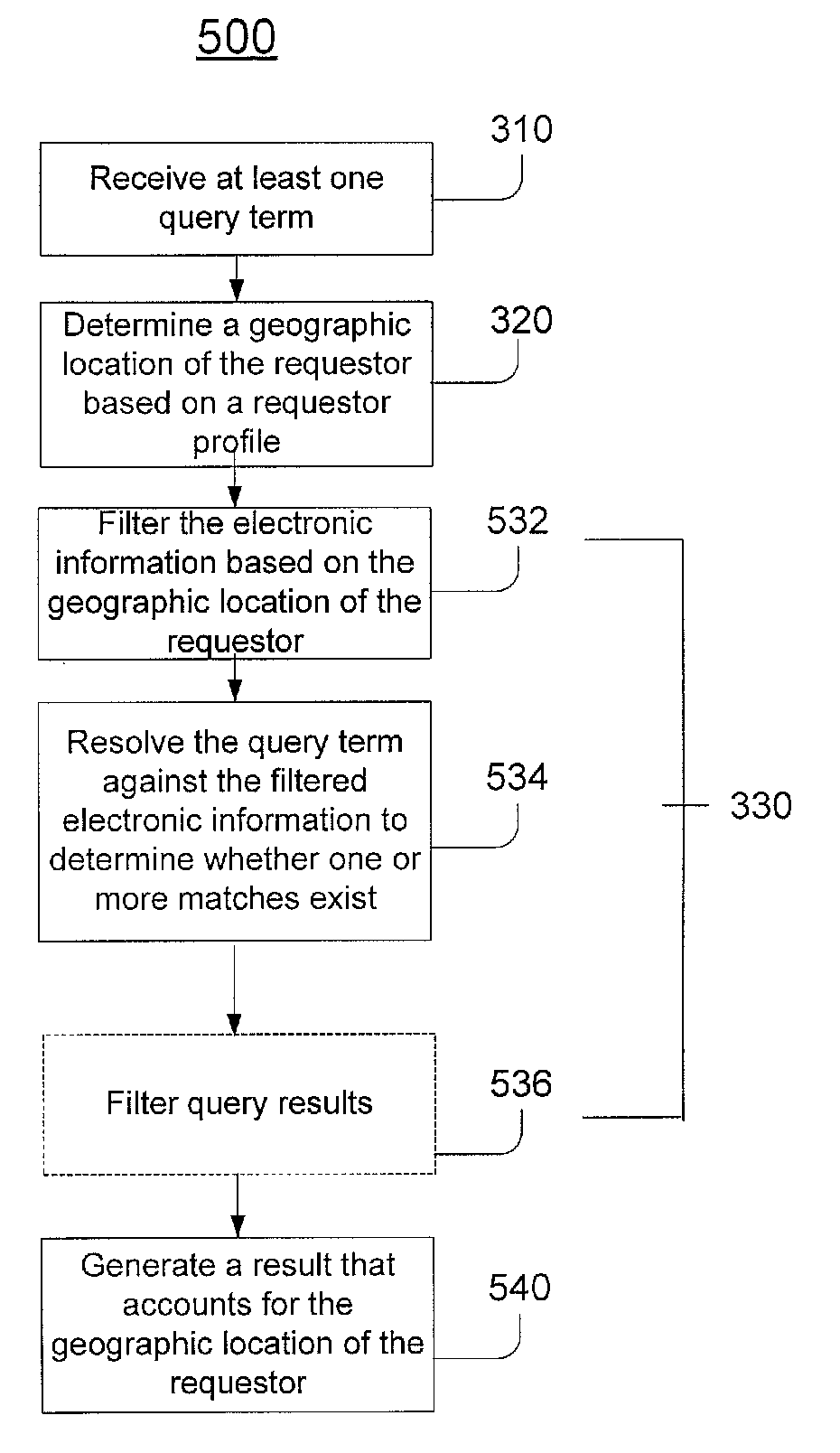
Resolving a query term includes receiving at least one query term from a requestor and determining a geographic location of the requestor. The geographic location of the requestor may be determined by accessing an electronic information store containing a requestor profile including geographic information about the requestor, where the requestor profile is used by more than one program. The query term is resolved against electronic information within at least one electronic information store to determine whether one or more matches exist and a result is generated that accounts for the geographic location of the requestor.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for manipulating electronic information using a three-dimensional iconic representation
InactiveUS7266768B2Efficient and convenient document managementEfficient and convenient and organizationDigital computer detailsNatural language data processingGraphicsGraphical user interface
Embodiments of the present invention relate to methods and systems for editing, creating and modifying documents through the use of multiple function icons in a graphical user interface environment. Icons comprising a series of object images may represent documents and the pages thereof. Manipulation of the object images and their parts through user input with a pointing device or other input device causes document modification to occur.
Owner:SHARP KK
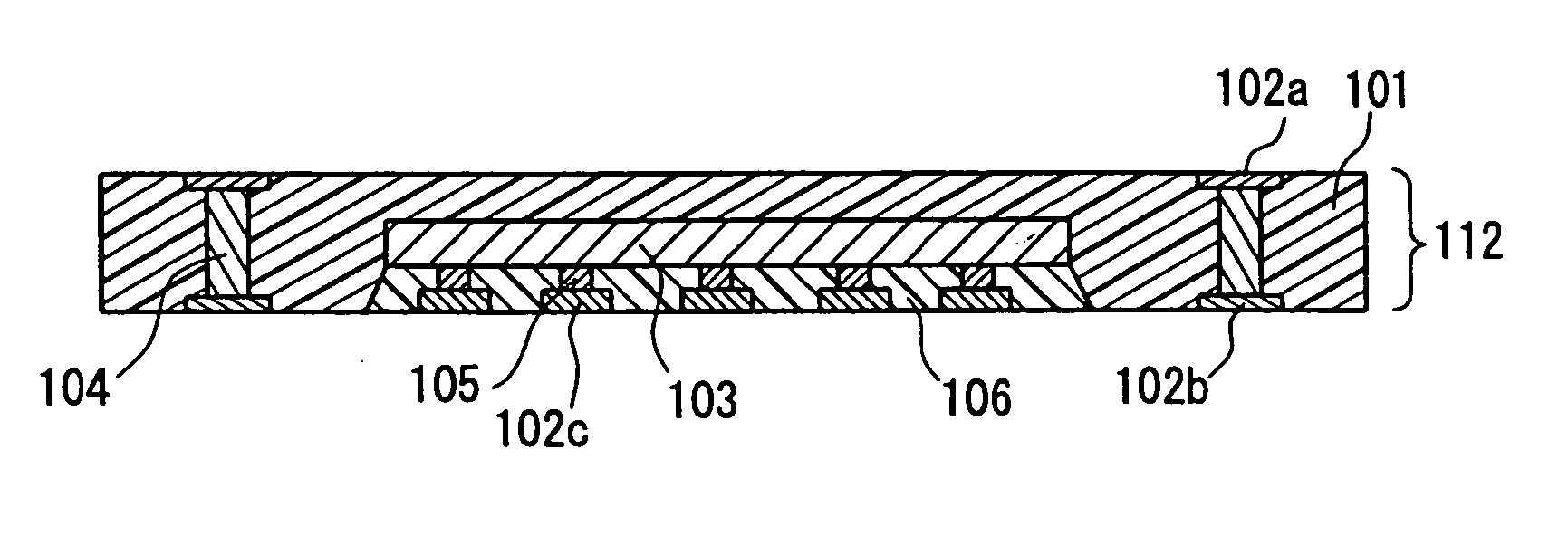
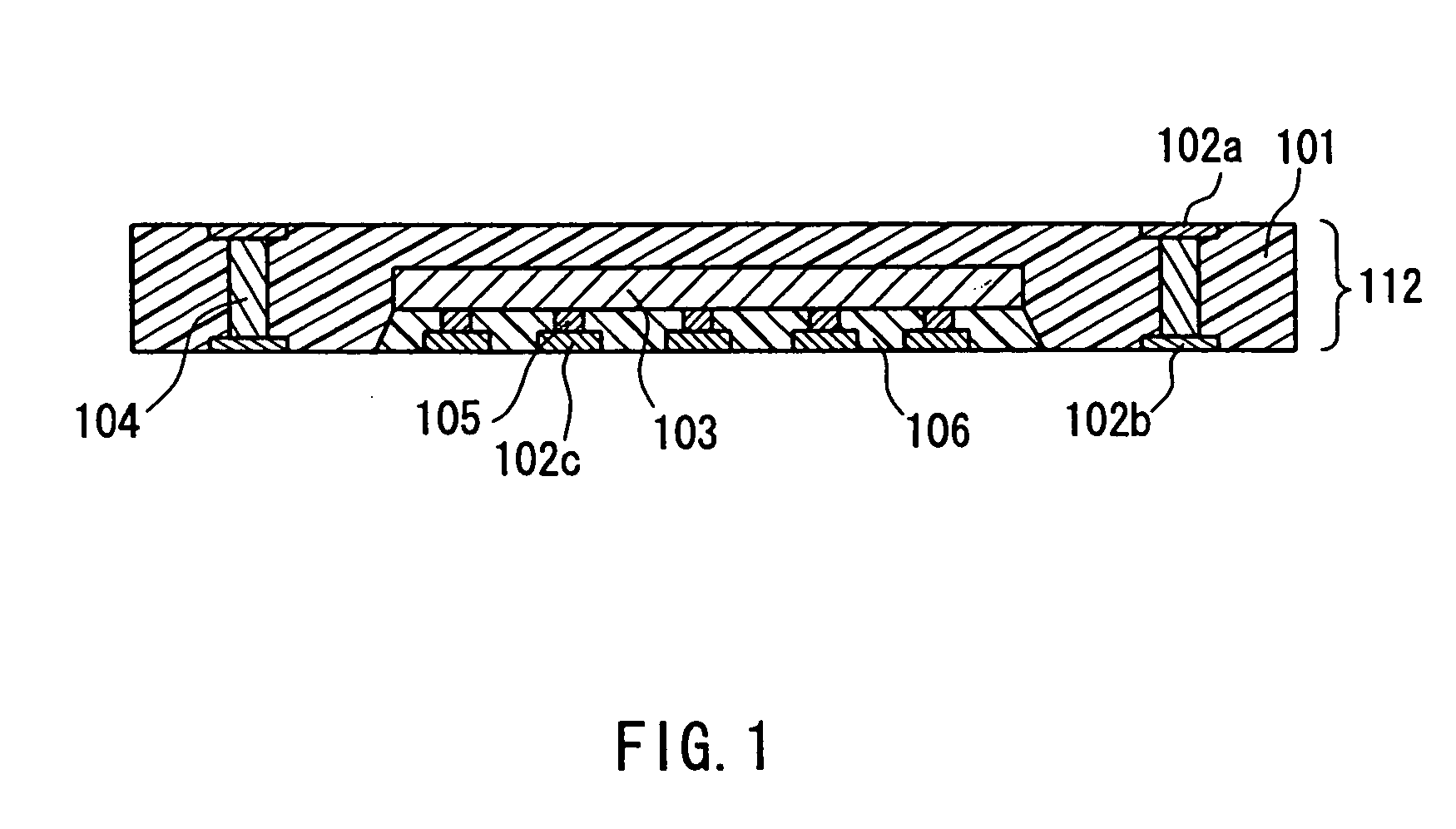
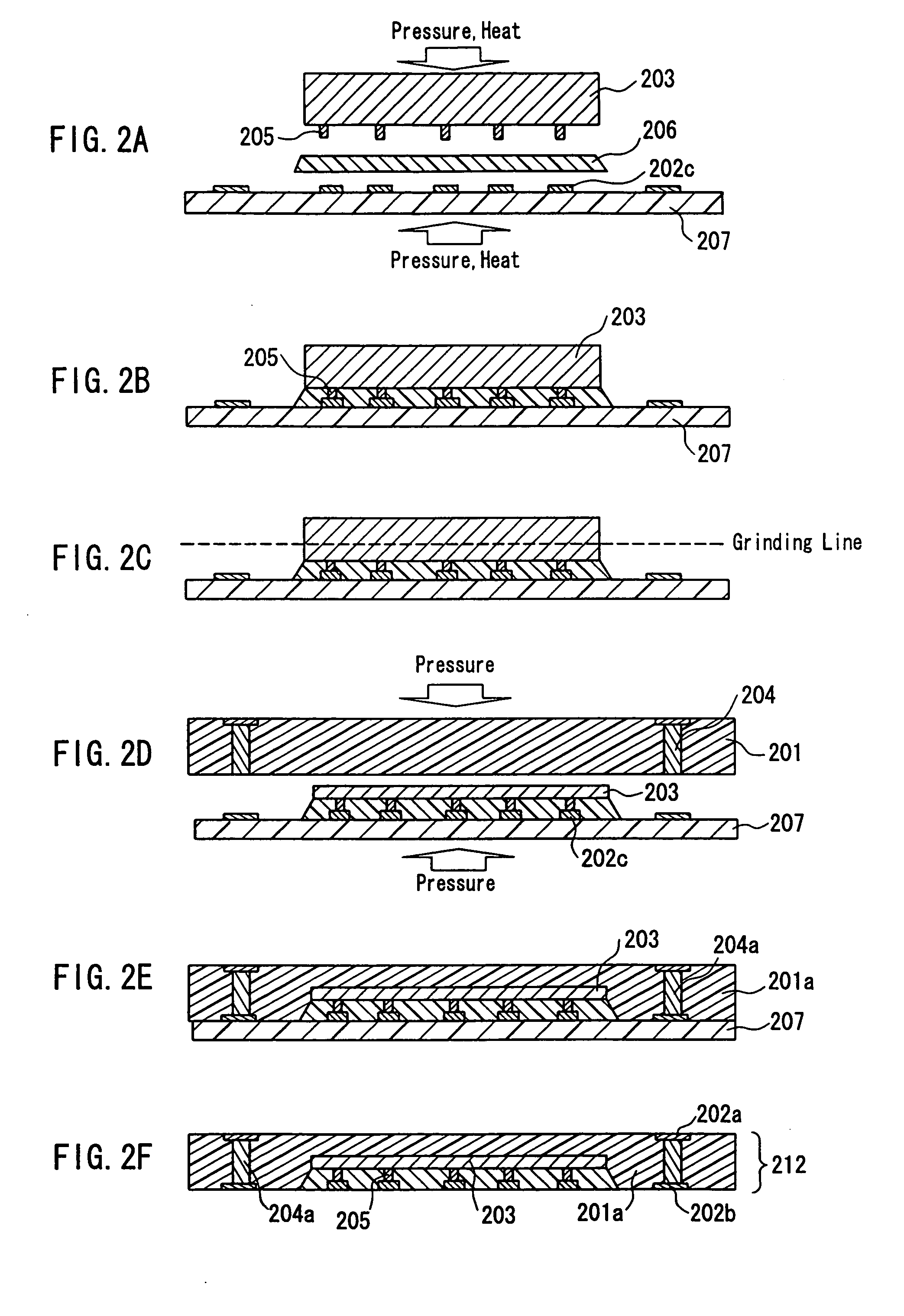
Circuit component built-in module with embedded semiconductor chip and method of manufacturing
InactiveUS20040145044A1Improve Noise PerformanceSemiconductor/solid-state device detailsSolid-state devicesHigh densityMiniaturization
A circuit component built-in module includes: a first electrical insulating substrate made of a mixture containing an inorganic filler and a thermosetting resin; a plurality of wiring patterns formed at least on a principal surface of the first electrical insulating substrate; a semiconductor chip incorporated in the first electrical insulating substrate and connected electrically with the wiring patterns; and inner vias electrically connecting the plurality of wiring patterns with one another, the inner vias passing through the first electrical insulating substrate. In the circuit component built-in module, the semiconductor chip has a thickness of not less than 30 mum and not more than 100 mum, and has a non-wired surface ground, and the circuit component built-in module has a thickness in a range of not less than 80 mum and not more than 200 mum. With this configuration, the high-performance and compact-size circuit component built-in module in which circuit components are mounted at a high density is provided so as to be used suitably in various types of electronic information devices.
Owner:PANASONIC CORP
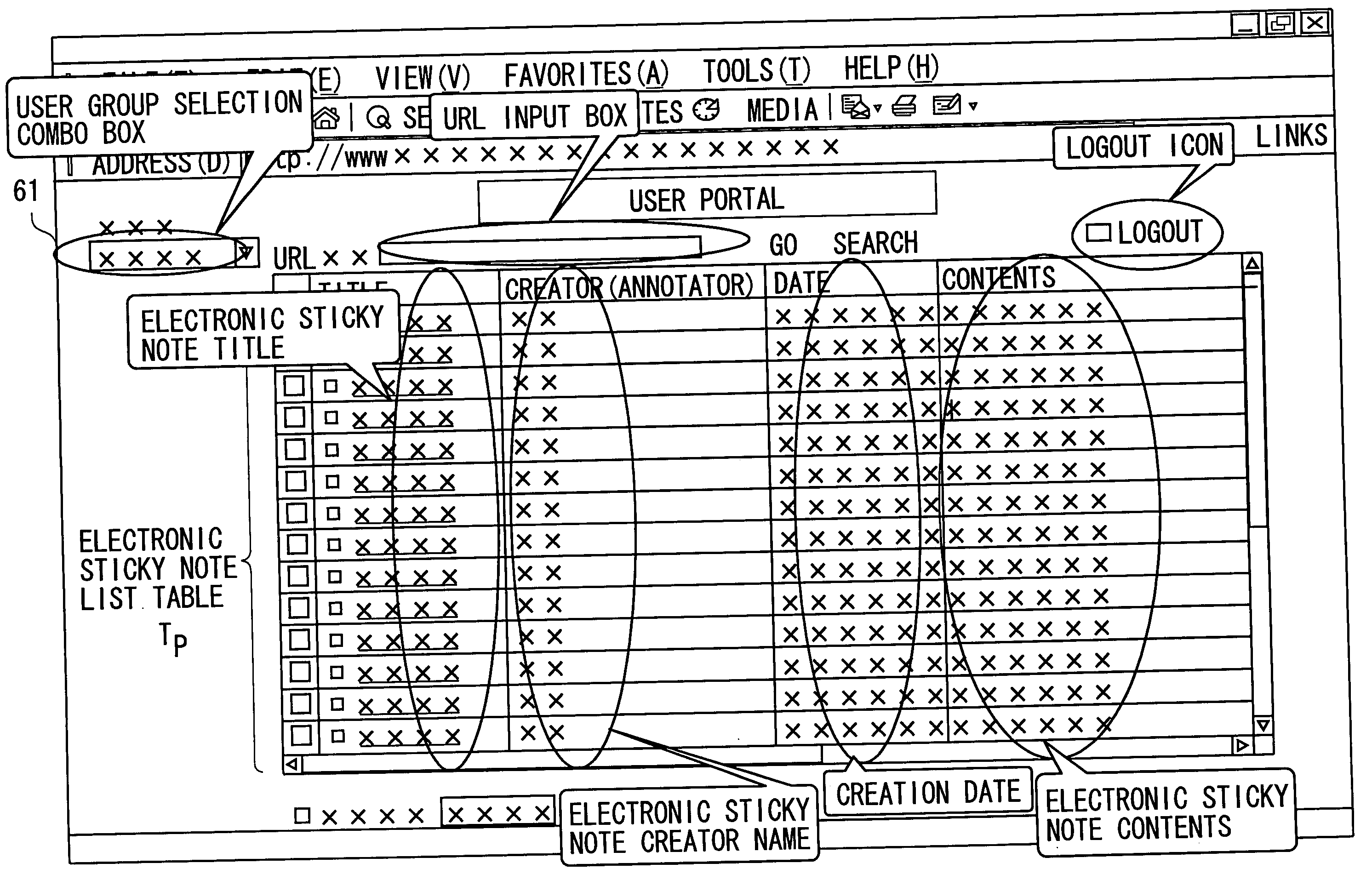
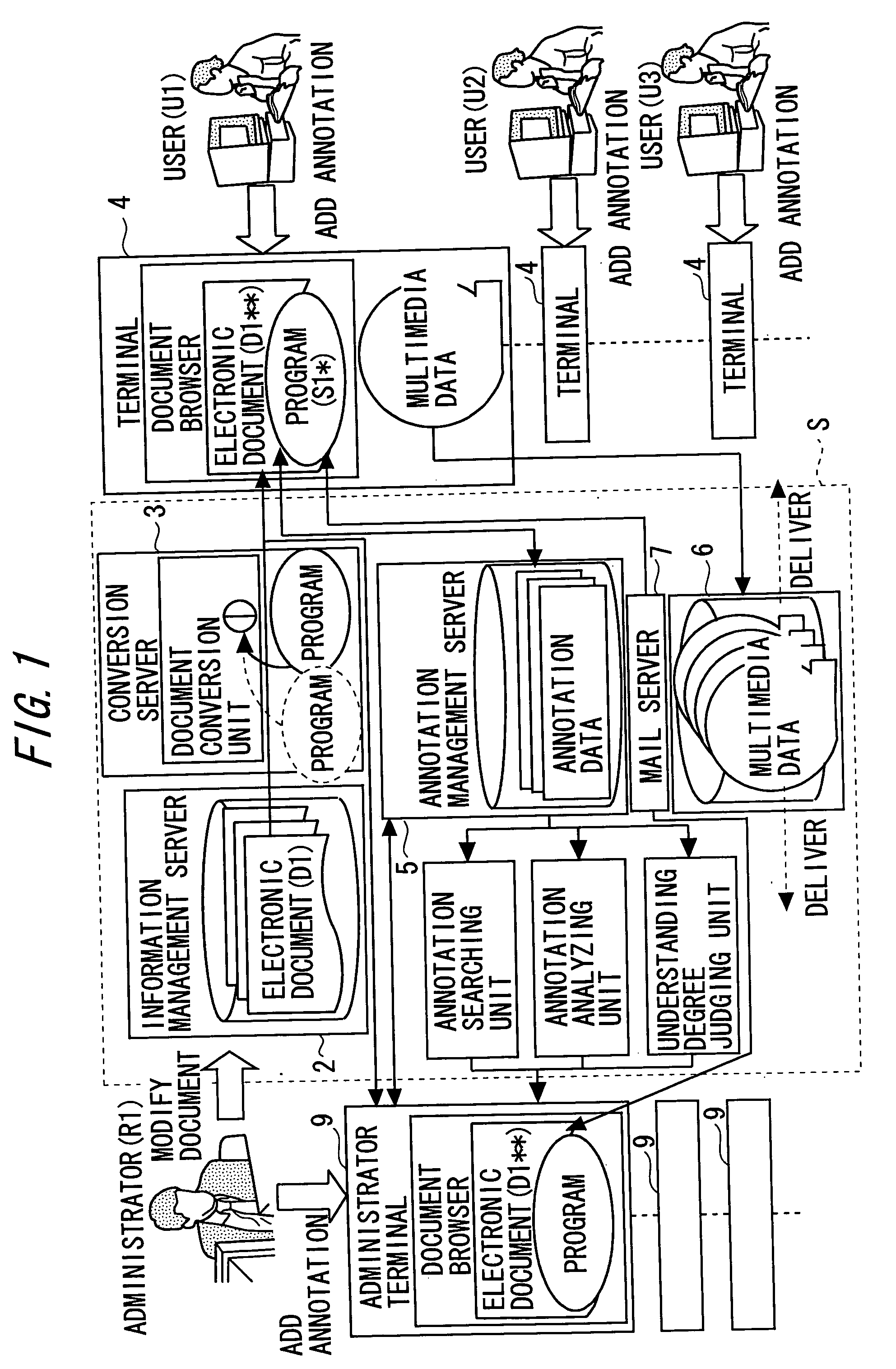
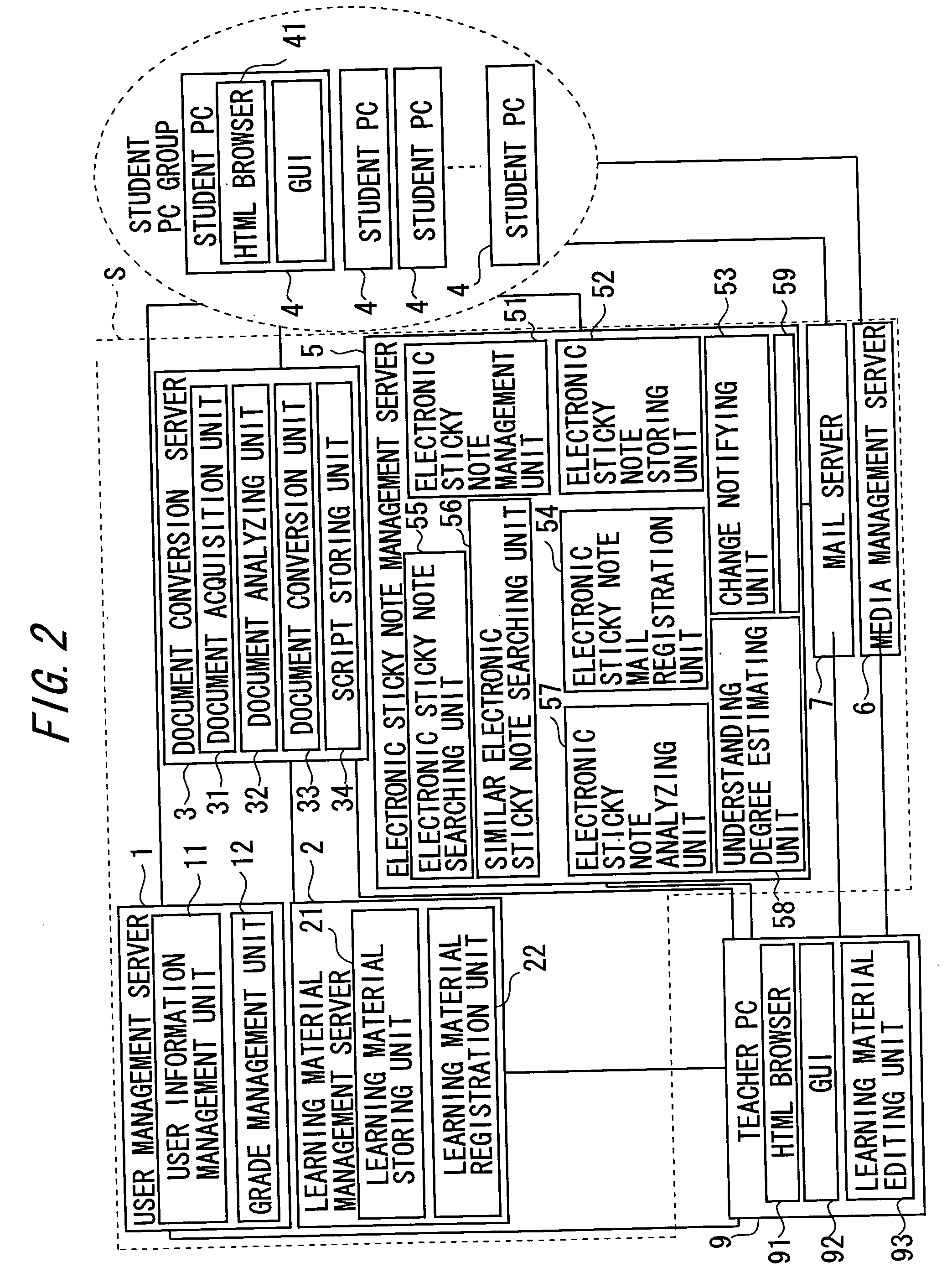
Information sharing device and information sharing method
InactiveUS20050223315A1Easy to understandNatural language data processingElectrical appliancesElectronic documentInformation sharing
A technique is provided which enables users to add, with ease, annotation information to an electronic document on a network and to share the annotation information within a disclosure range set to the annotation information. An electronic information is provided in a state that allows the electronic information to have annotation in formation attached, annotation information to be attached to the electronic information is stored, attribute information indicating the disclosure range of the annotation information is stored and, when a user requests to provide annotation information, annotation information available to the user is provided to a terminal of the user by consulting the attribute information.
Owner:FUJITSU LTD
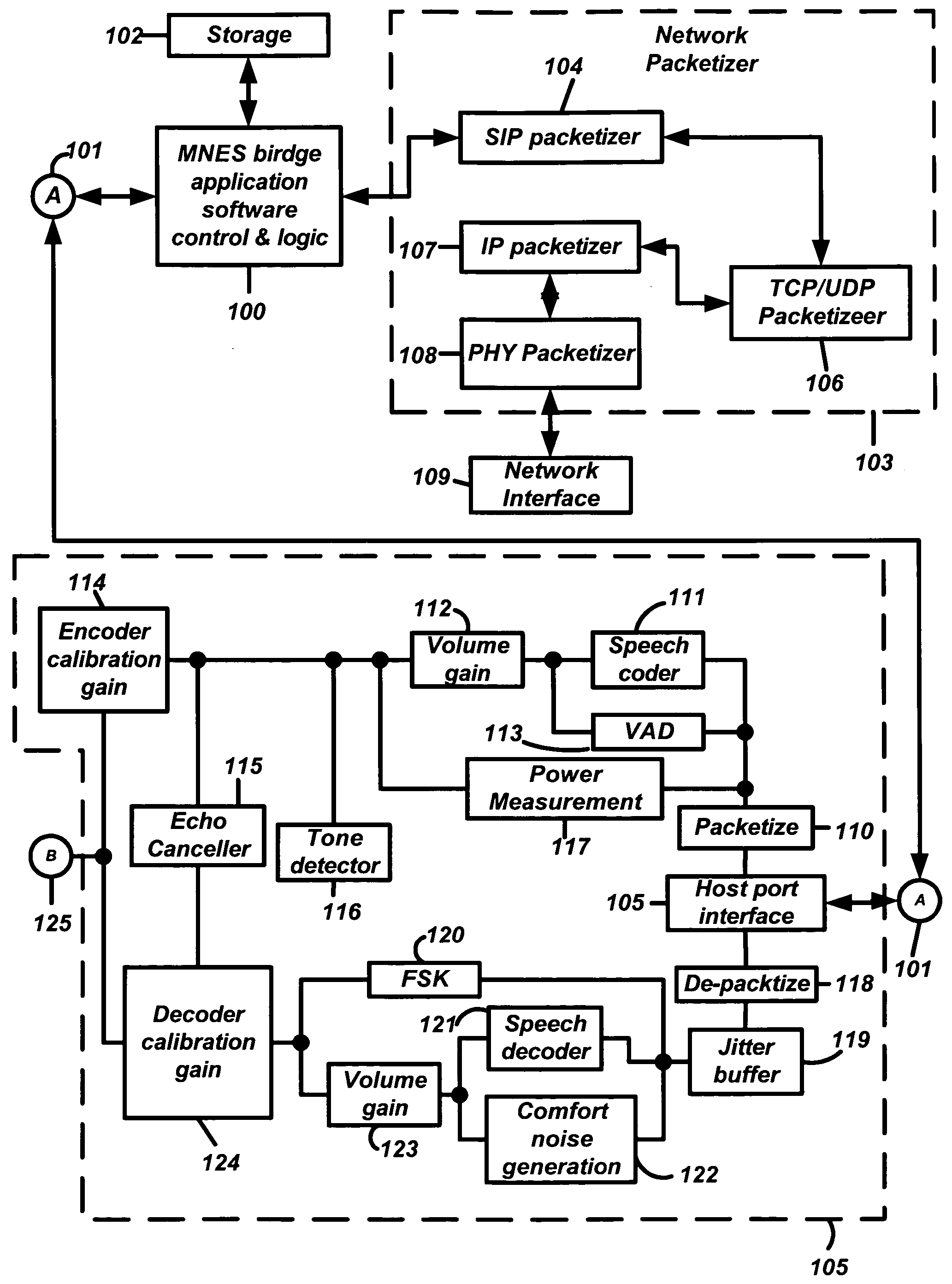
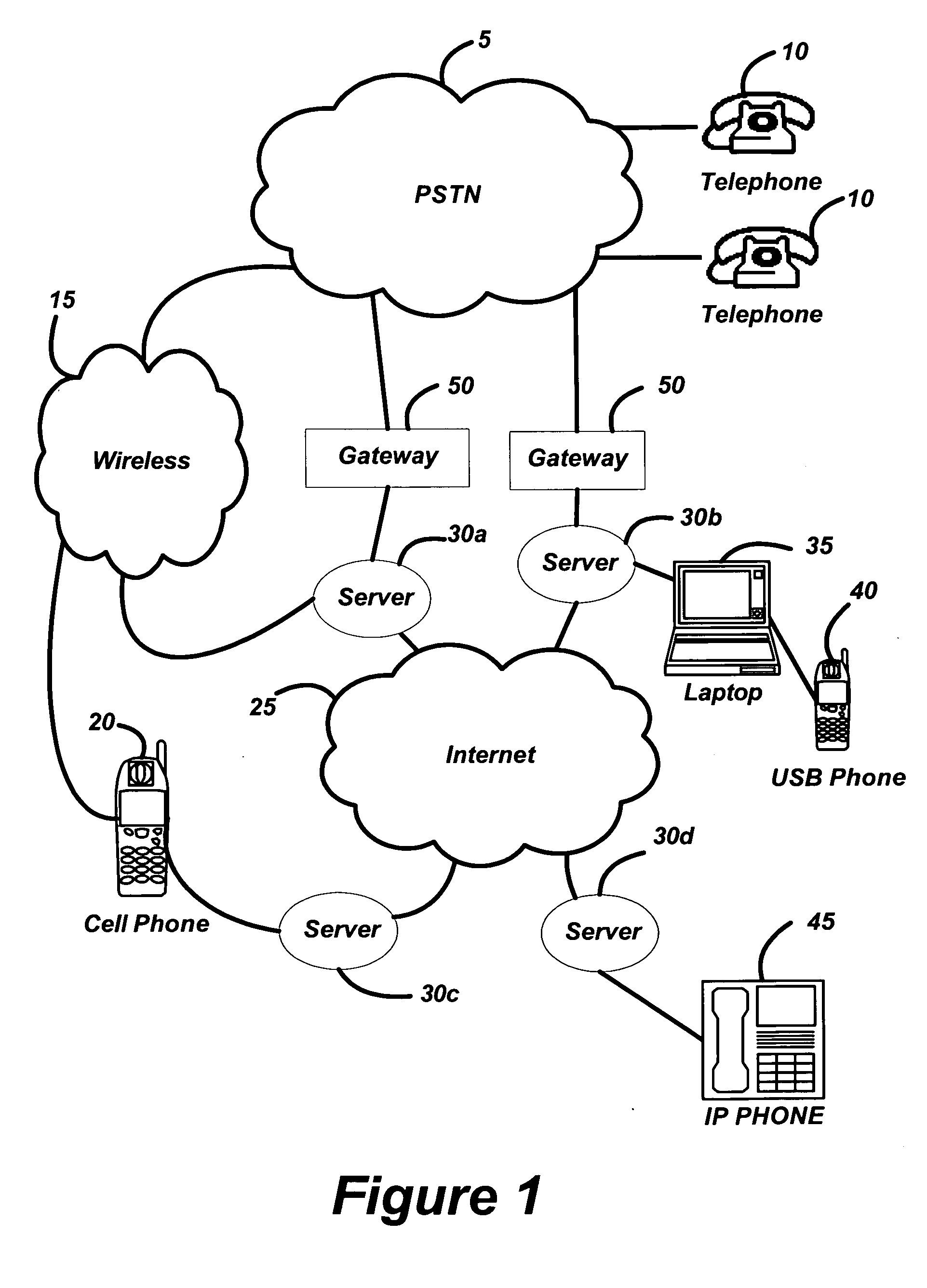
Multi-network exchange system for telephony applications
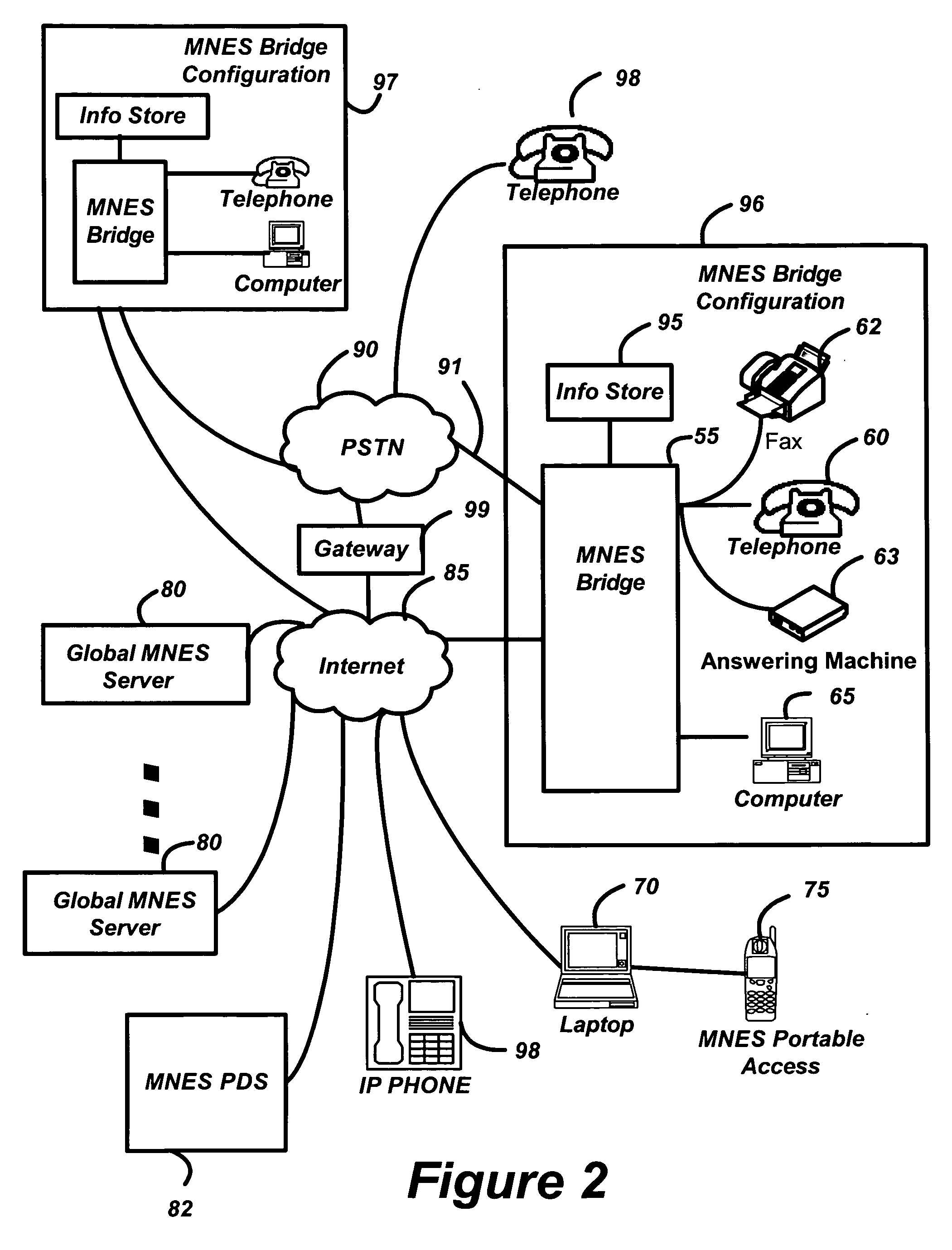
InactiveUS20050091407A1Protect data securityEasy transferInterconnection arrangementsError preventionThe InternetElectronic information
A multi-network exchange system has a first type network (PSTN) and a second type network (Internet) and a multi-network exchange bridge in communication with the first and second type networks for the transfer of electronic information signals (telephone calls) between the first and second type networks. The multi-network exchange bridge apparatus facilitates transfer of electronic information signals to a portable access device or a gateway portal in communication with a node of one of second type networks from the first network. The multi-network exchange bridge has at least one multi-network instantiation device that enables the portable access device to function as a remote extension of the multi-network exchange bridge. A fixed address translation device provides conversion of a first address fixedly describing a node of the first type network to a second address or third address virtually describing nodes of the second type network
Owner:EMERJ
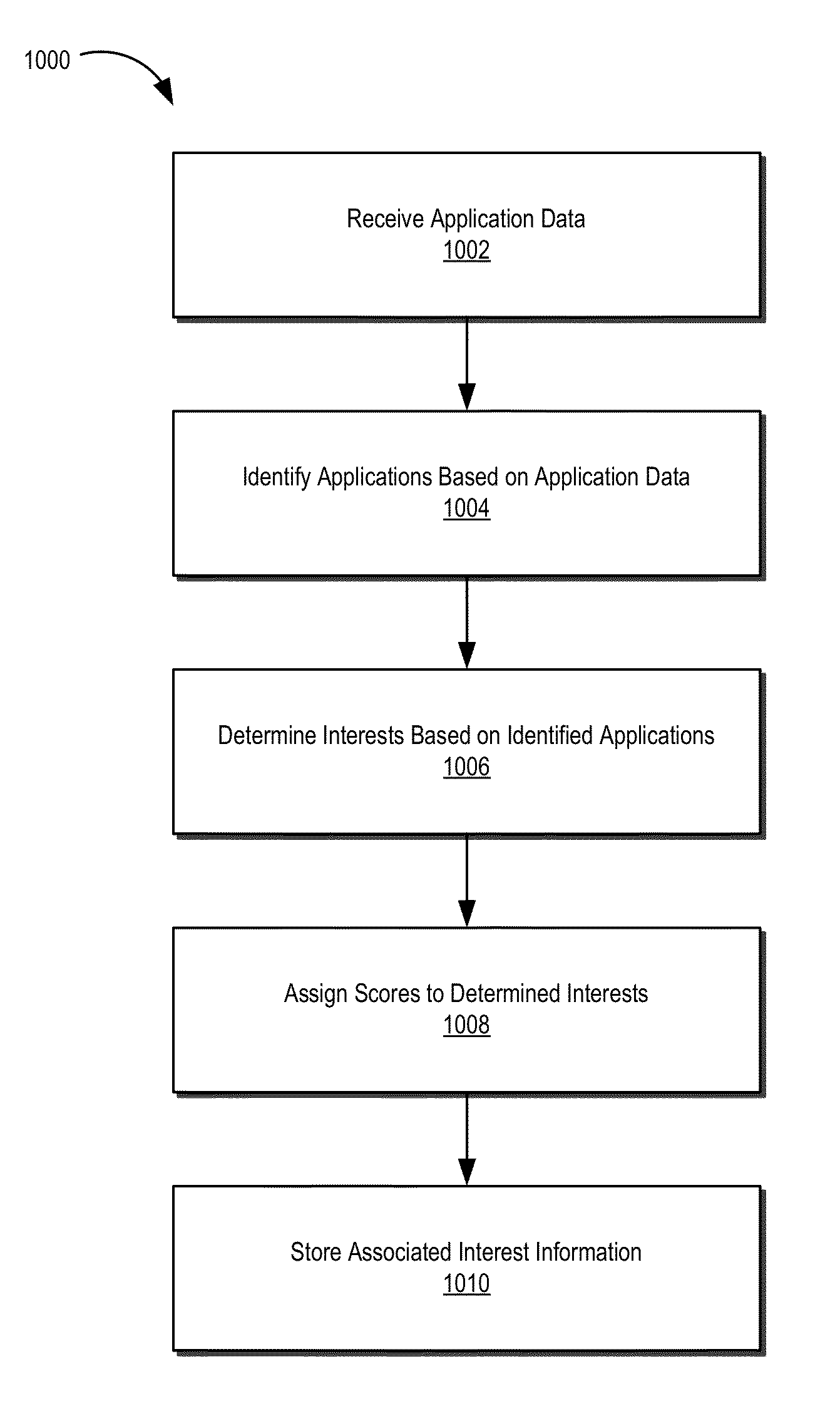
Method of creating data streams for user-specific usage data gathering systems
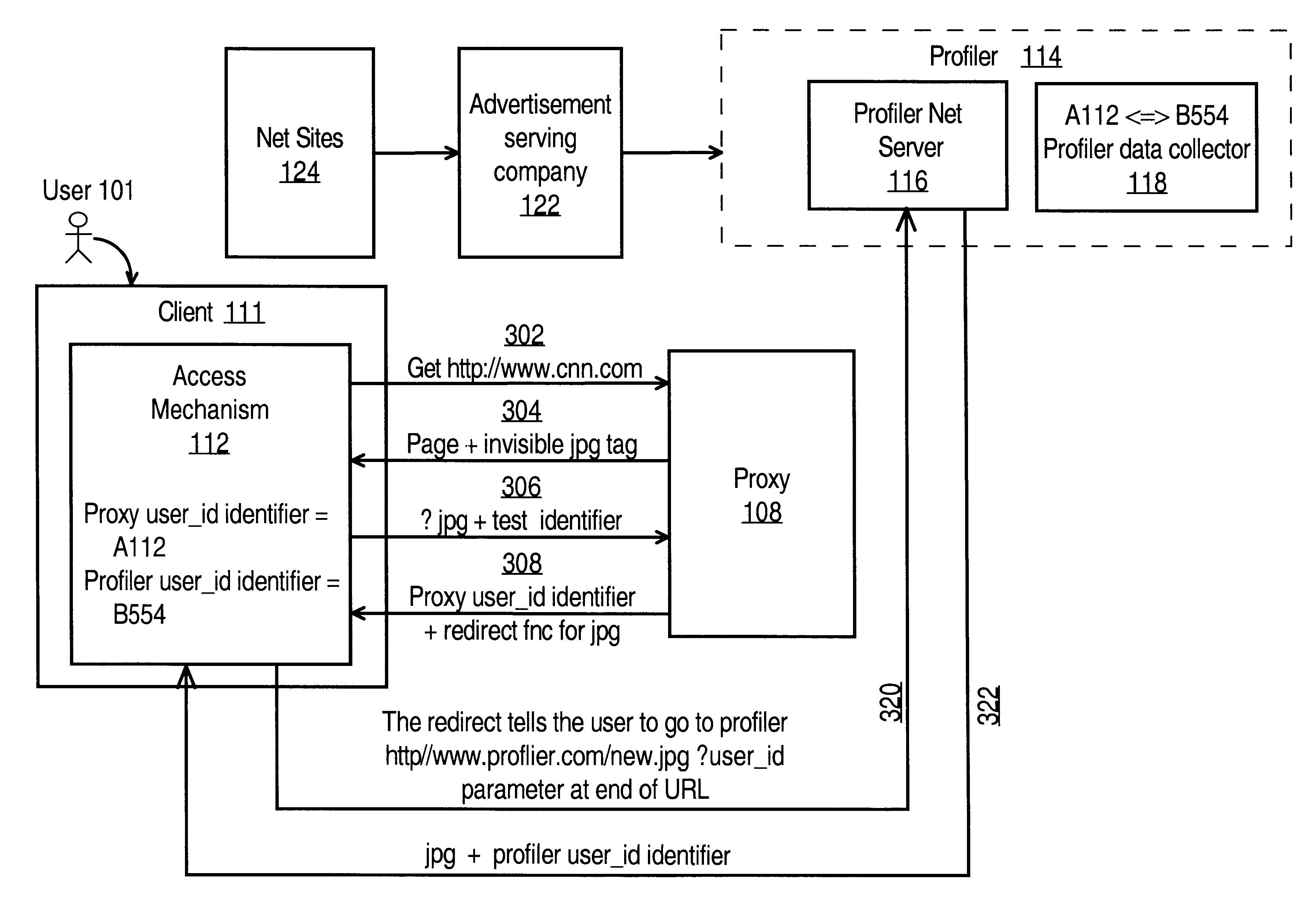
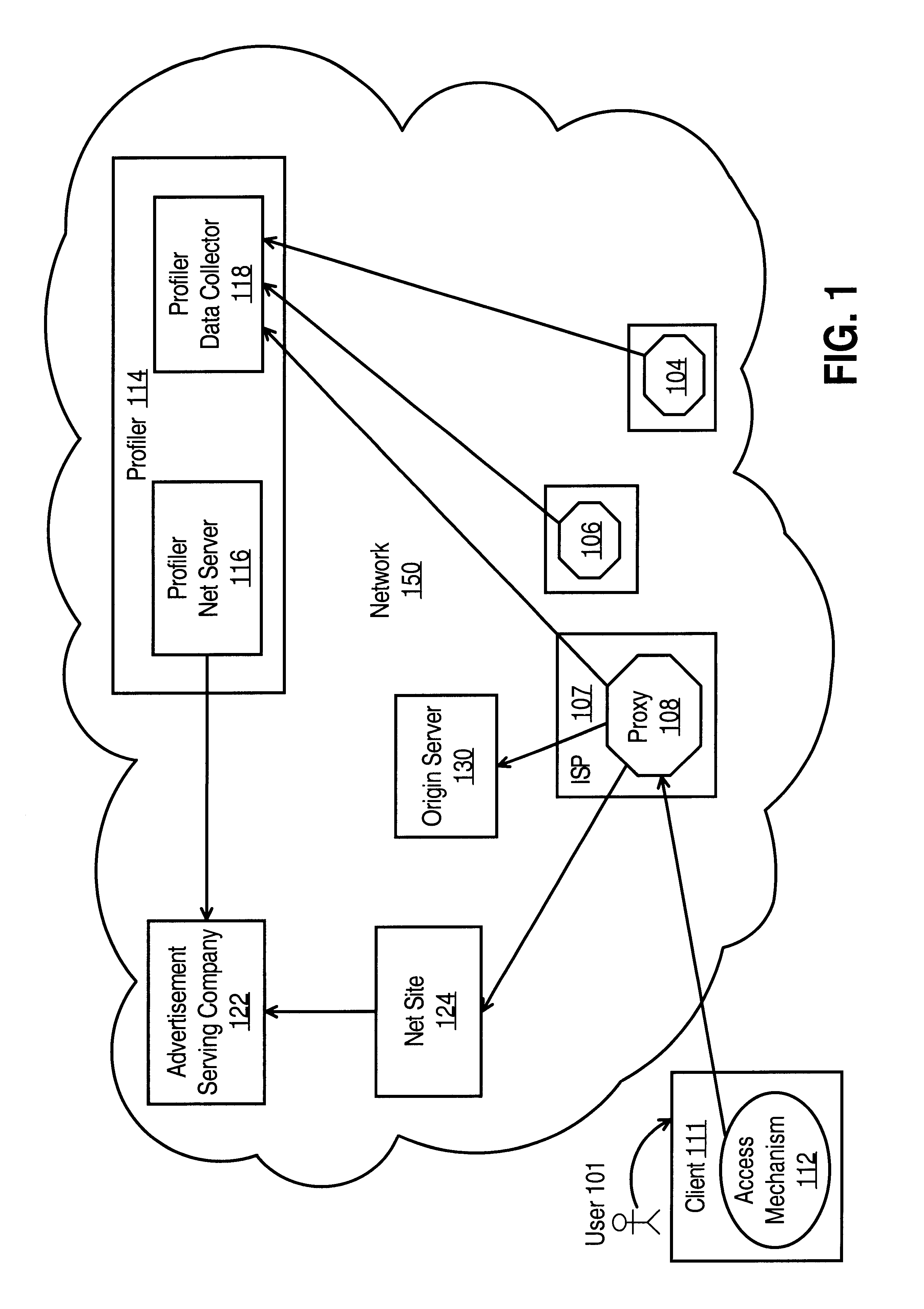
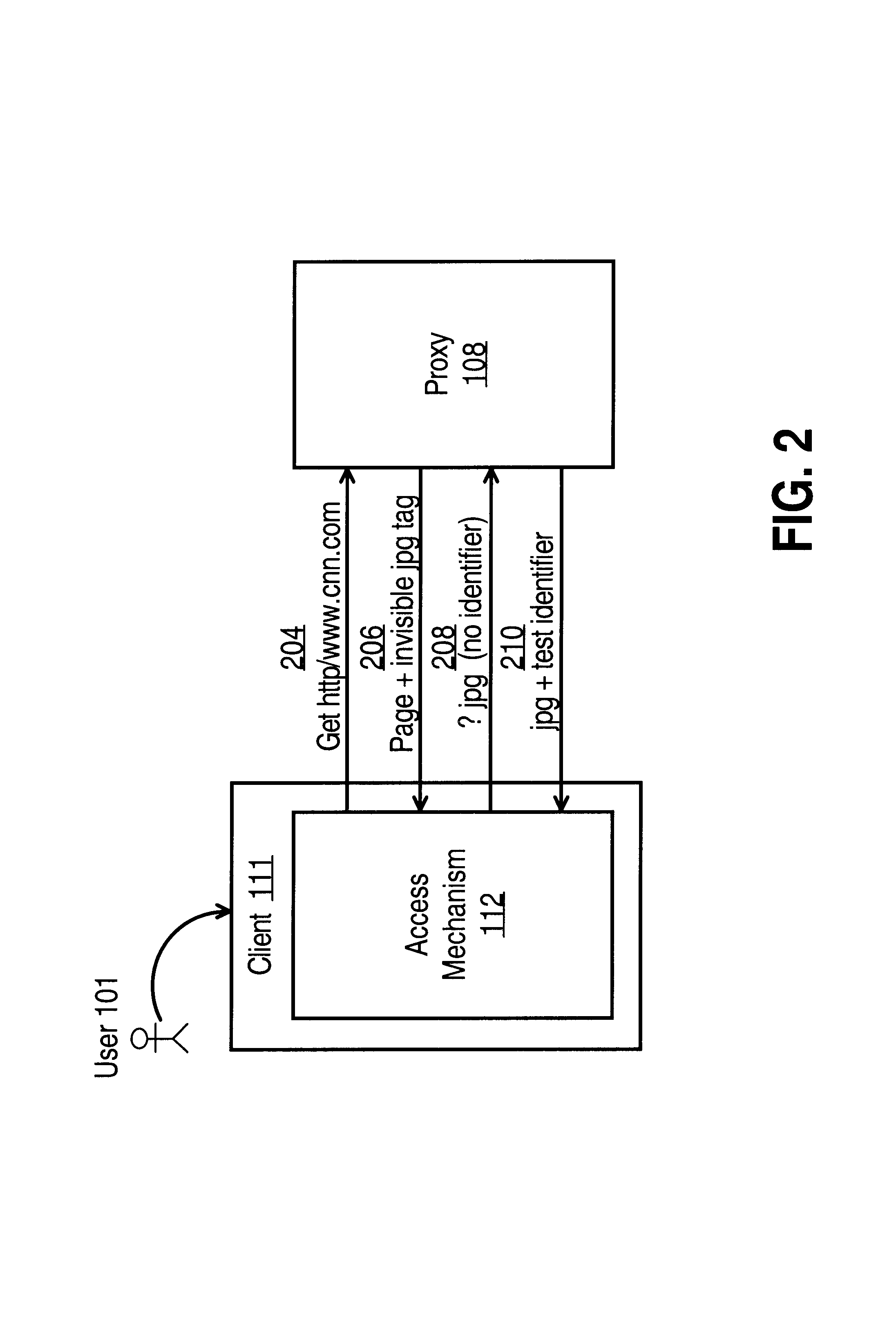
InactiveUS6993590B1Error detection/correctionMultiple digital computer combinationsData streamElectronic information
A method and apparatus are provided for capturing and managing user-specific data, where the user-specific data contains information on the user's interaction with the Net. The method generally involves using a proxy to capture or cause to capture the user-specific data and then storing the user-specific data. The user-specific data may be used to customize the contents of electronic information delivered to the particular user.
Owner:R2 SOLUTIONS
Methods, software programs, and systems for electronic information security
InactiveUS7395436B1Digital data processing detailsUser identity/authority verificationConfidentialityDigital signature
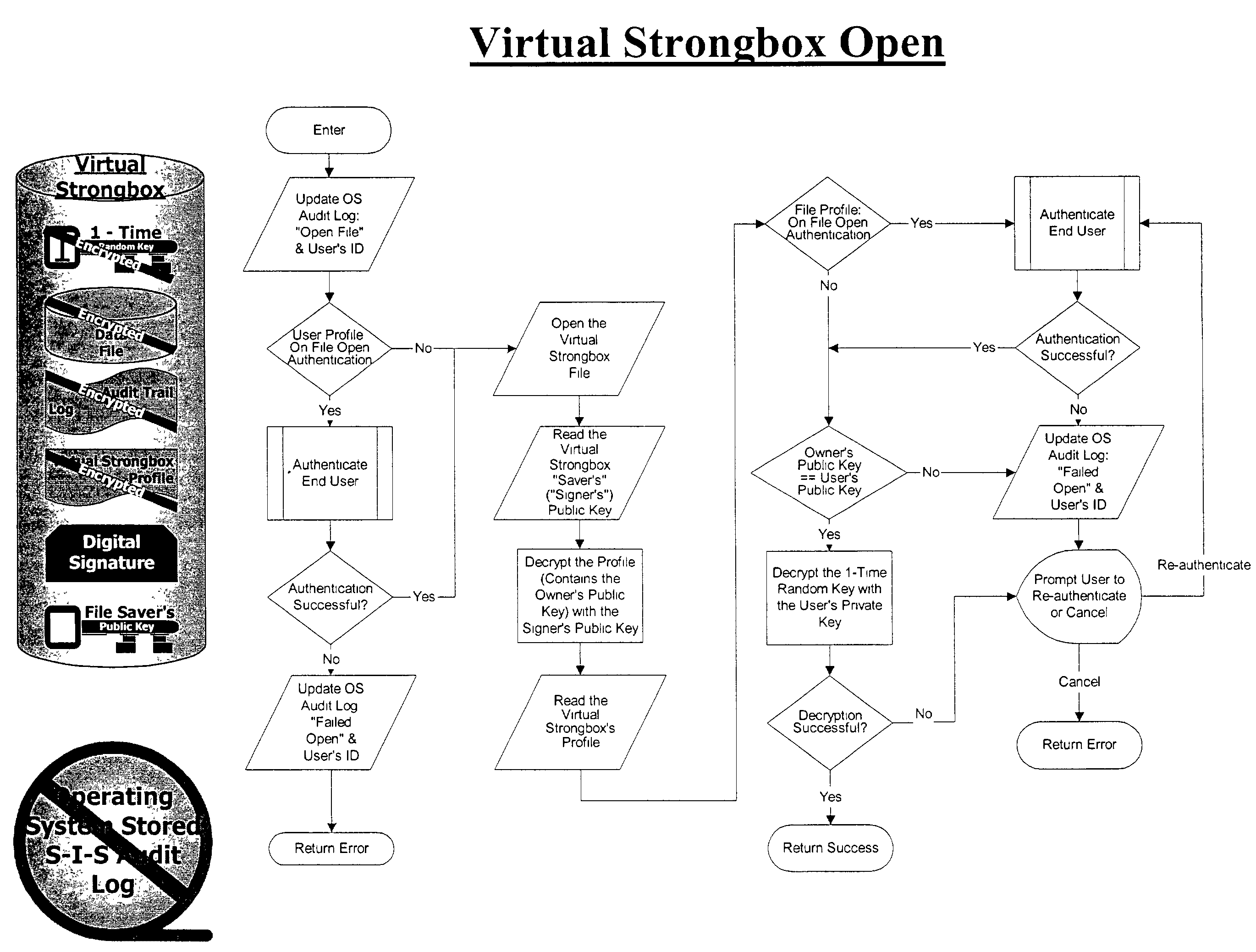
The present invention relates to various methods, software programs, and systems for electronic information security. More particularly, these various methods, software programs, and systems may serve to protect information security by providing an integrated system that helps ensure confidentiality, integrity, accountability, and ease of use. Certain embodiments of the present invention relate to methods, software programs, and systems for electronic information security utilizing a file container for storing: (a) a data file, which data file is encrypted with a one-time random encryption key; (b) the one-time random encryption key, which one-time random encryption key is encrypted with a public key portion of a public key / private key pair associated with an owner of the file container; (c) an audit trail log of the history of the file container, which audit trail log is encrypted with the one-time random encryption key with which the data file is encrypted; (d) a digital signature based upon a hash of the combined data file and the audit trail log, which hash is encrypted with a private key portion of a public key / private key associated with a writer / creator of the file container; and (e) a profile associated with the file container. Additional embodiments of the present invention relate to methods, software programs, and systems for electronic information security utilizing a fully integrated system for user authentication, virus scanning, time / date certification, encryption / decryption, digital signatures, stored document protection, transmitted document protection, and delivery verification.
Owner:KENEISYS
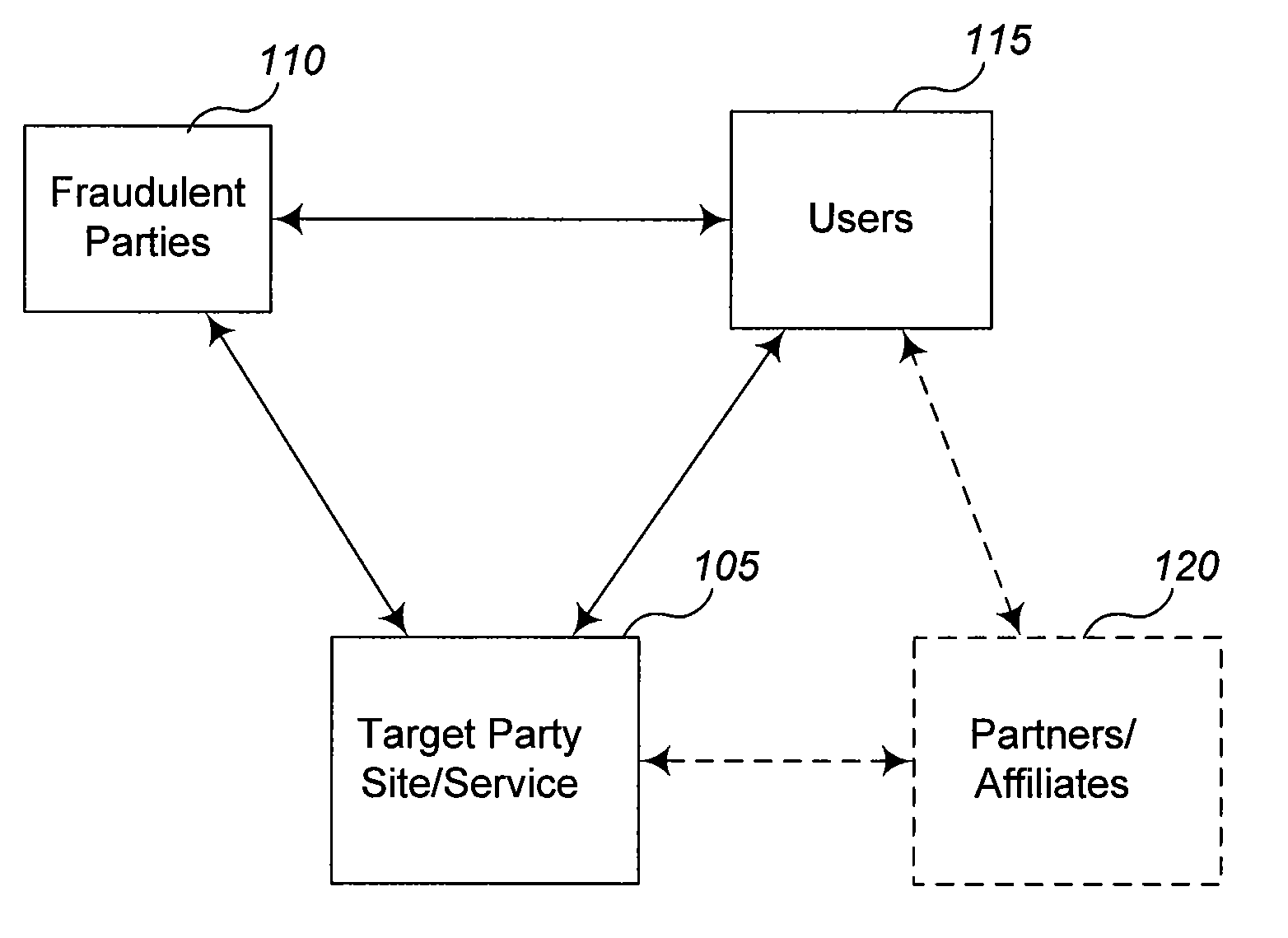
Detecting fraudulent activity by analysis of information requests
Techniques are described for use in inhibiting attempts to fraudulently obtain access to confidential information about users. In some situations, the techniques involve automatically analyzing at least some requests for information that are received by a Web site or other electronic information service, such as to determine whether they likely reflect fraudulent activities by the request senders or other parties that initiate the requests. For example, if a request is being made to a Web site based on a user's interaction with a third-party information source (e.g., another unaffiliated Web site) that is not authorized to initiate the request, the third-party information source may be a fraudulent phishing site or engaging in other types of fraudulent activity. If fraudulent activity is suspected based on analysis of one or more information requests, one or more actions may be taken to inhibit the fraudulent activity.
Owner:AMAZON TECH INC
Flexible display device for displaying electronic information
InactiveUS20060209218A1Reduce wearFlexible display is not easily lostElectric indicationElectronic time-piece structural detailsDisplay deviceElectronic information
A flexible display device for displaying electronic information has a main body, a small screen, a reel mechanism, a scrolling display and a wrist strap. The screen is disposed on the main body for displaying information. The reel mechanism is disposed on the main body. The scrolling display is rolled and hidden in the main body by the reel mechanism for displaying information, wherein the scrolling display is a CLC display or an OLED display. The wrist strap connects with the main body for securing the main body around a wearer. The scrolling display has a screen puller connected to one side thereof for pulling out the scrolling display. The flexible display device is portable, and usable in a fixed state. In addition, the flexible display is not easily to get lost and lessens abrading of the monitor's surface of the scrolling display from usual wear and tear.
Owner:IND TECH RES INST
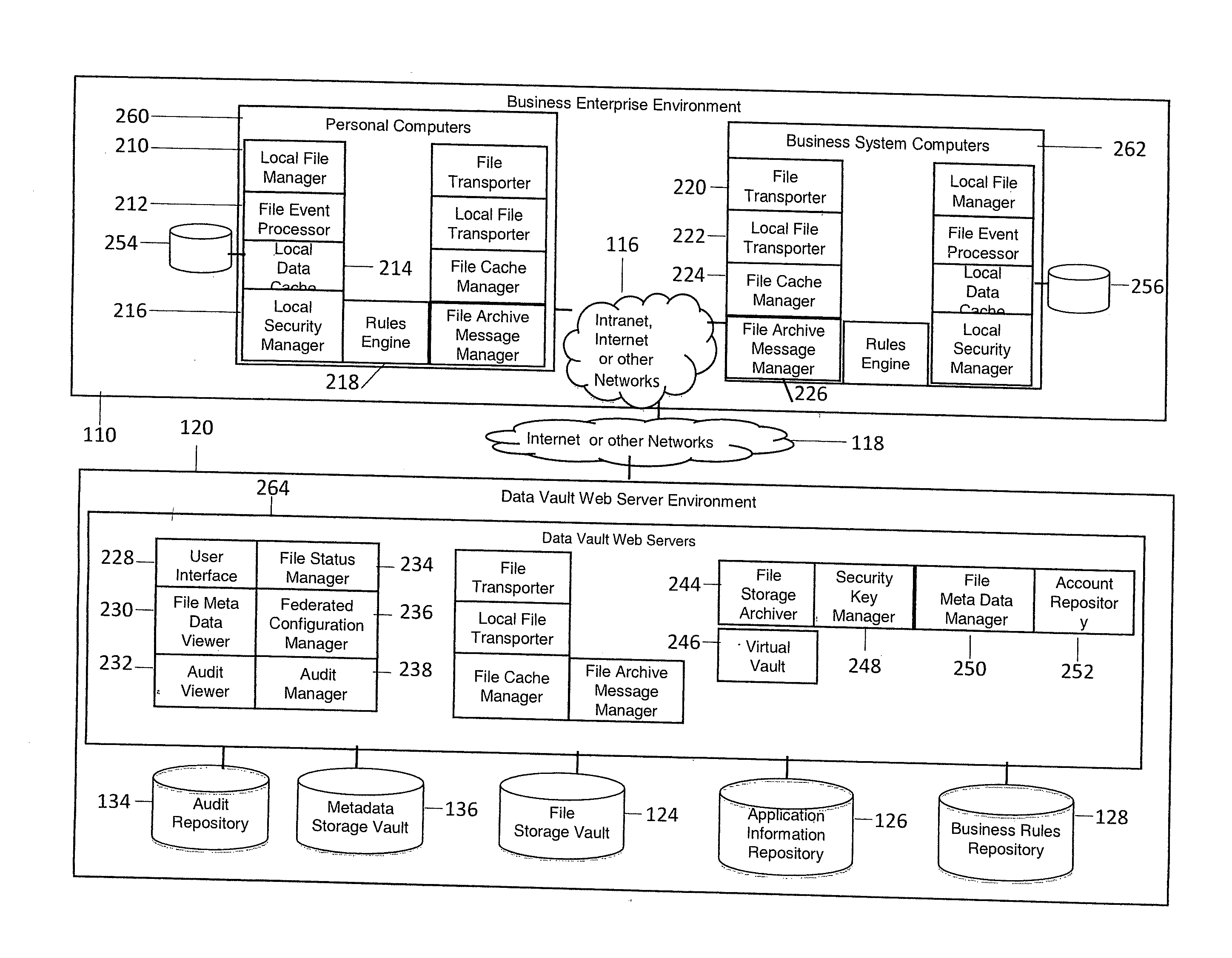
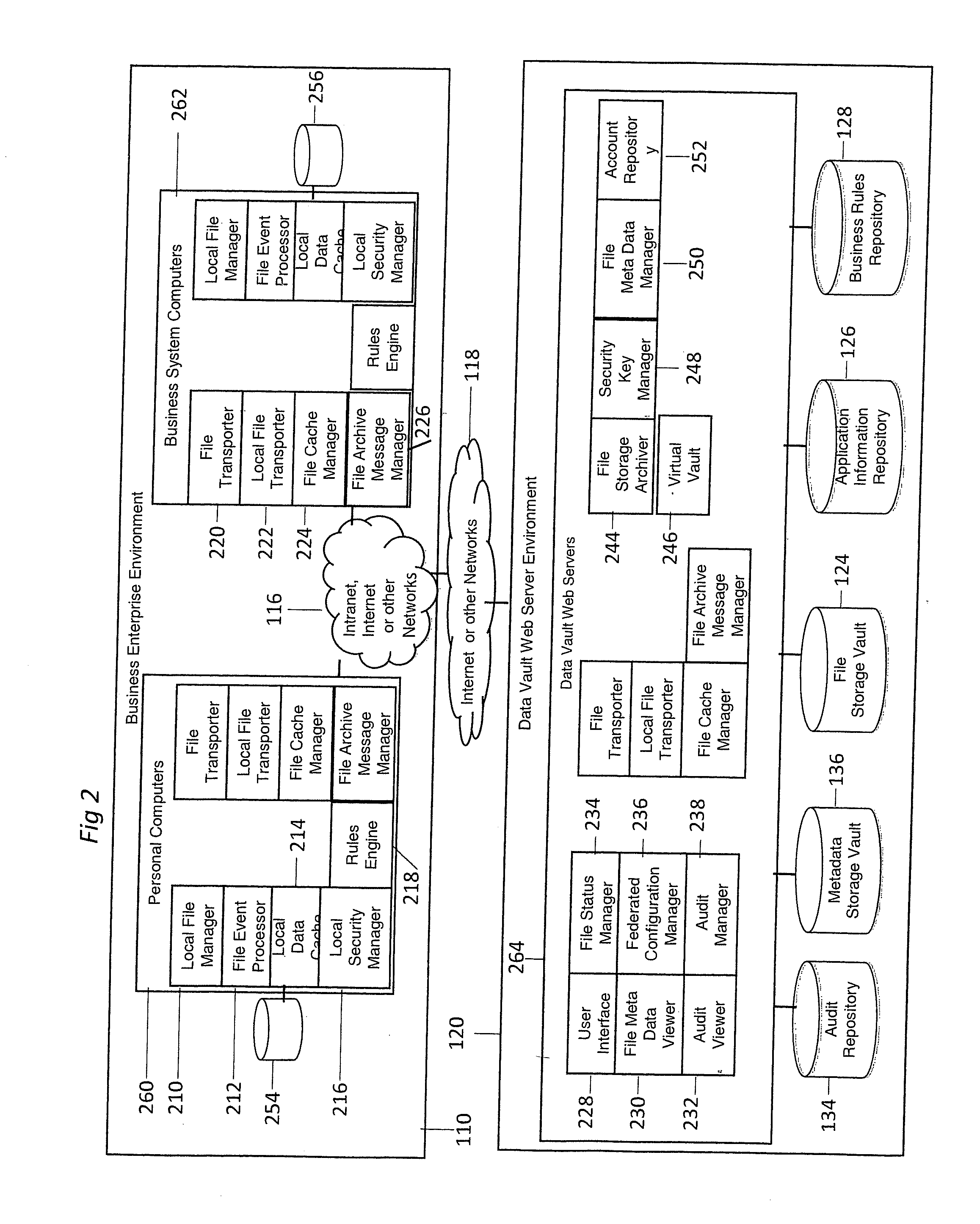
System and method for providing automated electronic information backup, storage and recovery
InactiveUS20100293147A1Avoid dataAvoid redundancyDigital data processing detailsSpecial data processing applicationsInformation repositoryApplication software
An automated electronic information backup, storage migration, and recovery system includes techniques for automatically observing all file events over a plurality of computing devices. The observed file events are mapped to the applications producing them. A relevancy of those file events are determined based on an application information repository. Business rules are produced based on this information to automatically backup all relevant file event changes and restore or migrate backed up information when necessary.
Owner:HIPAA BOX
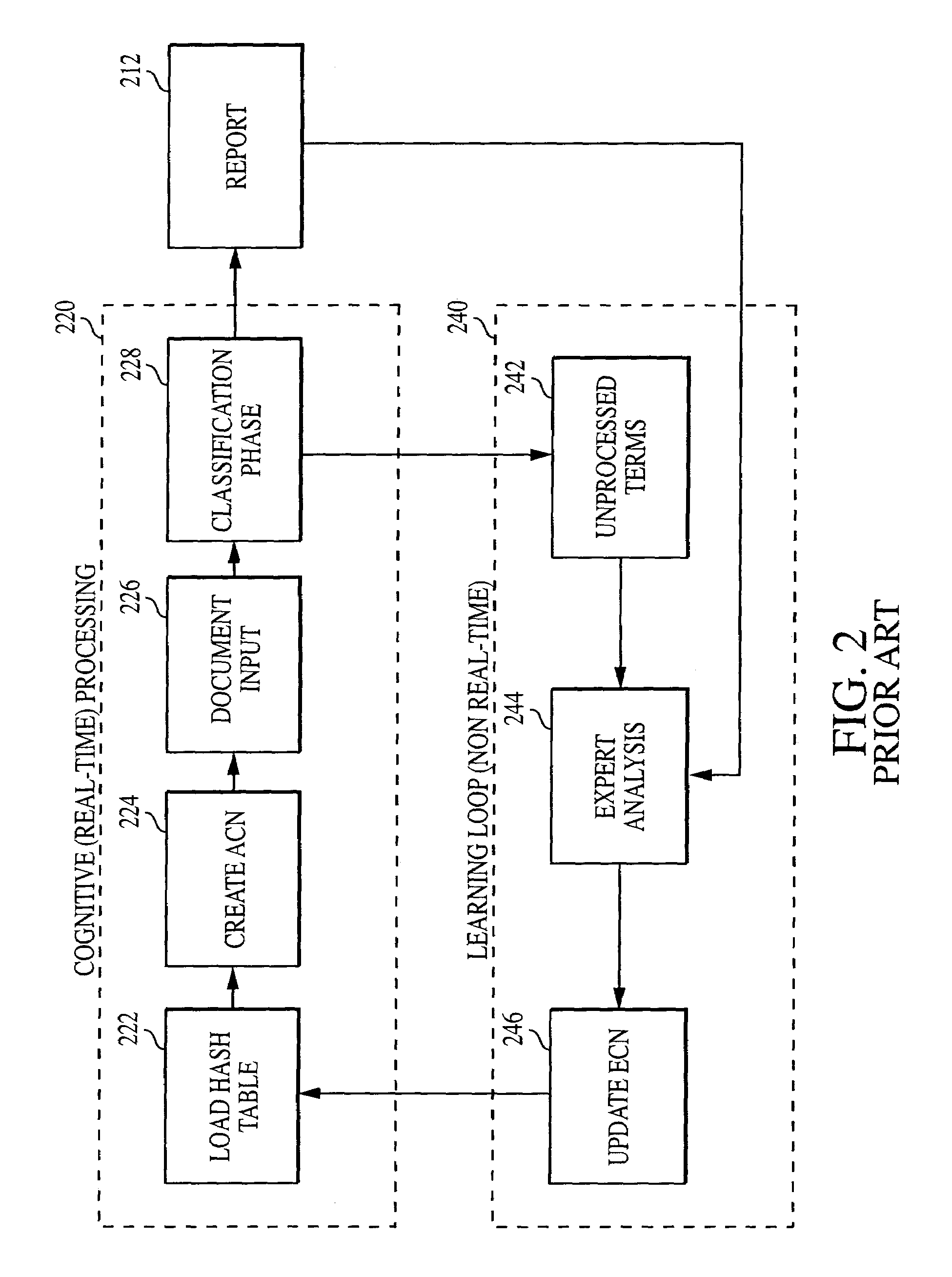
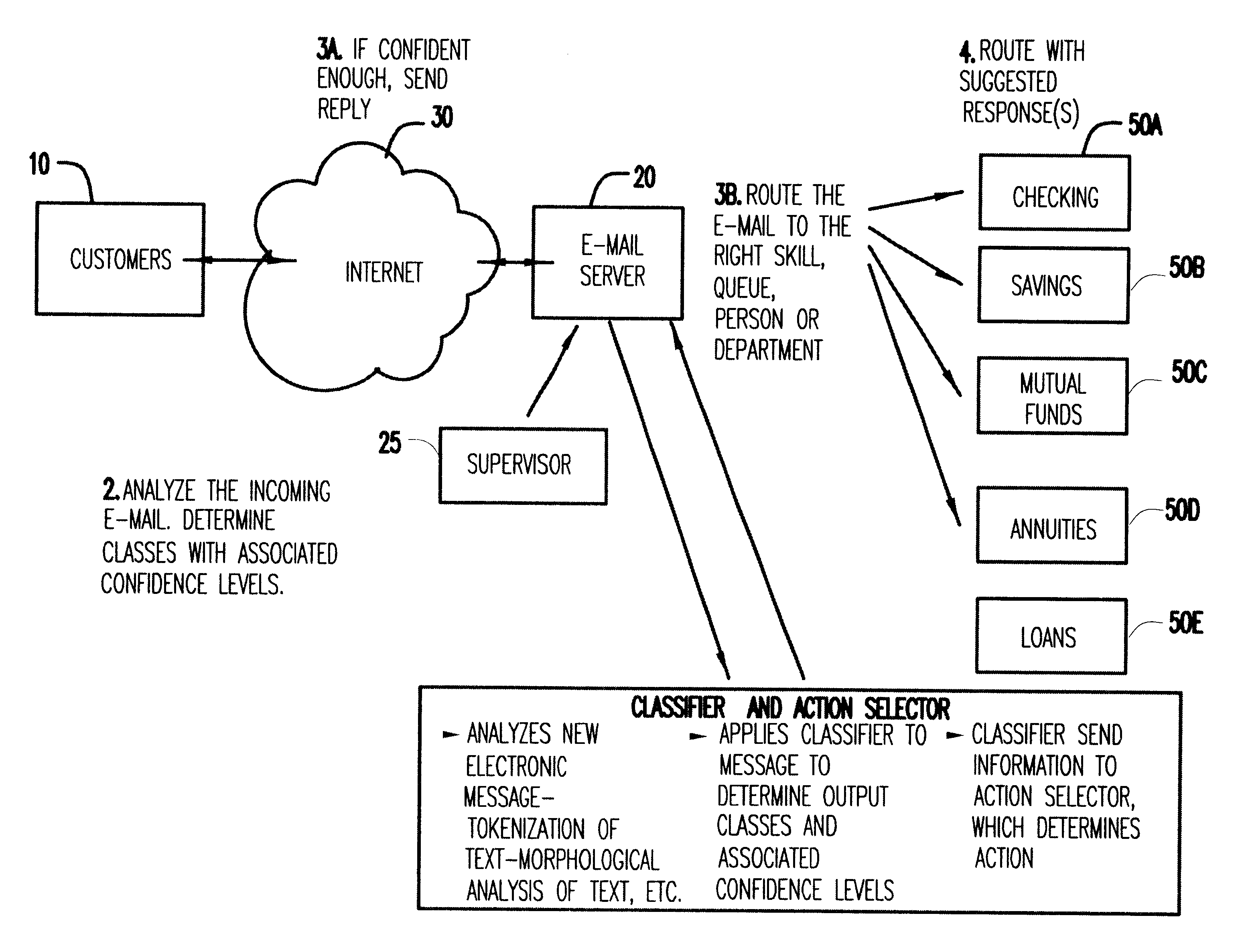
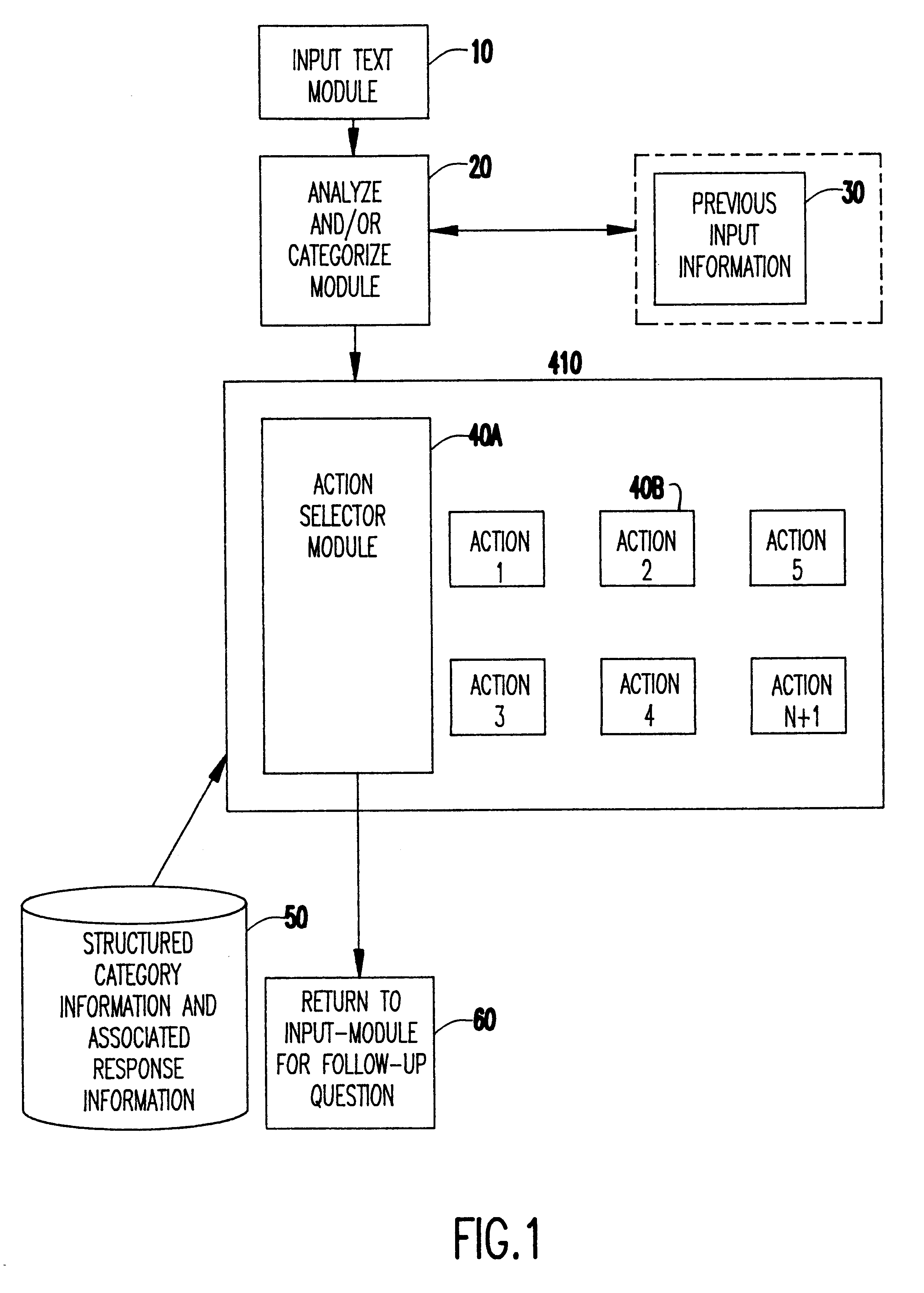
Machine learning based electronic messaging system
InactiveUS6424997B1Natural language data processingMultiple digital computer combinationsLearning basedComputer module
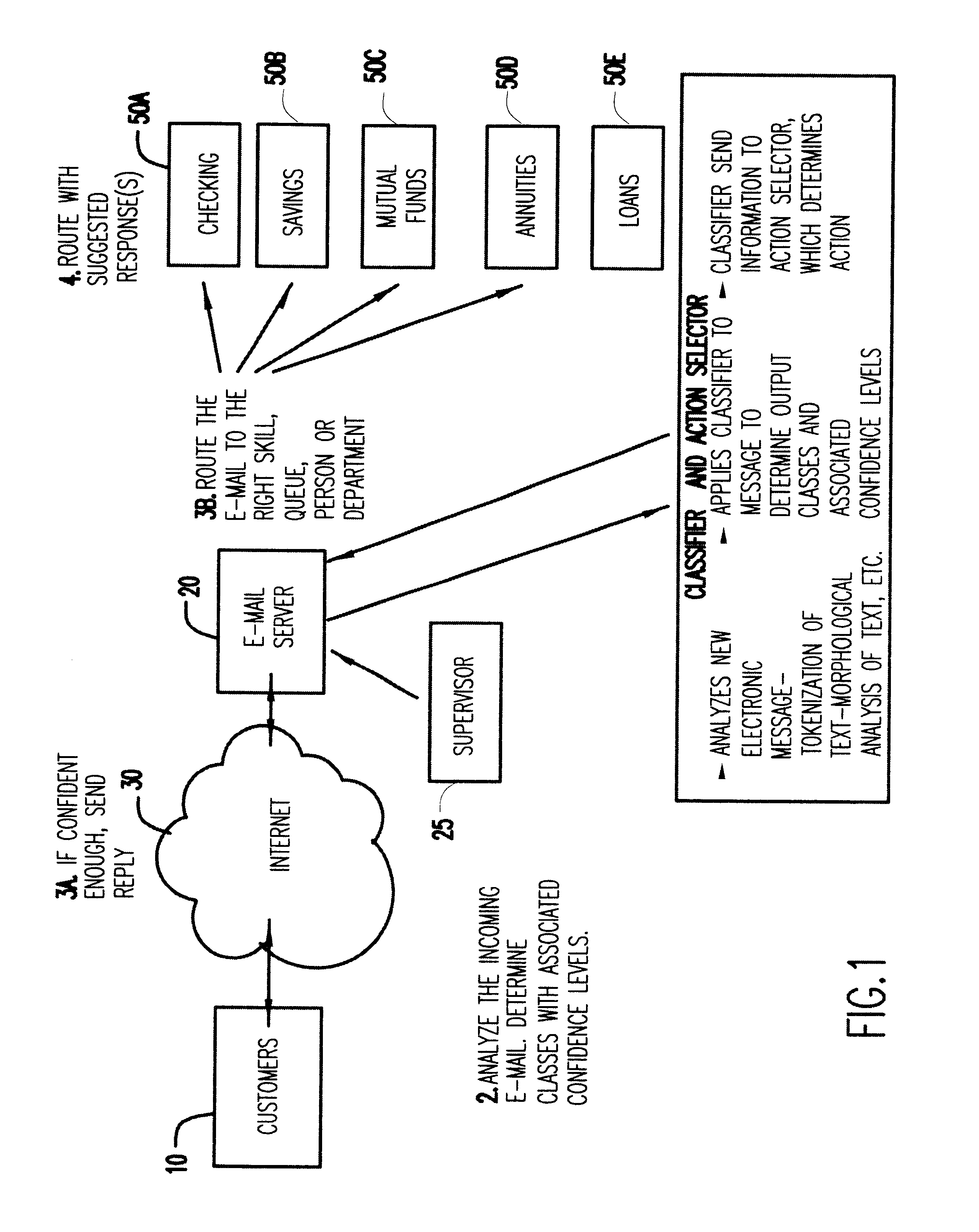
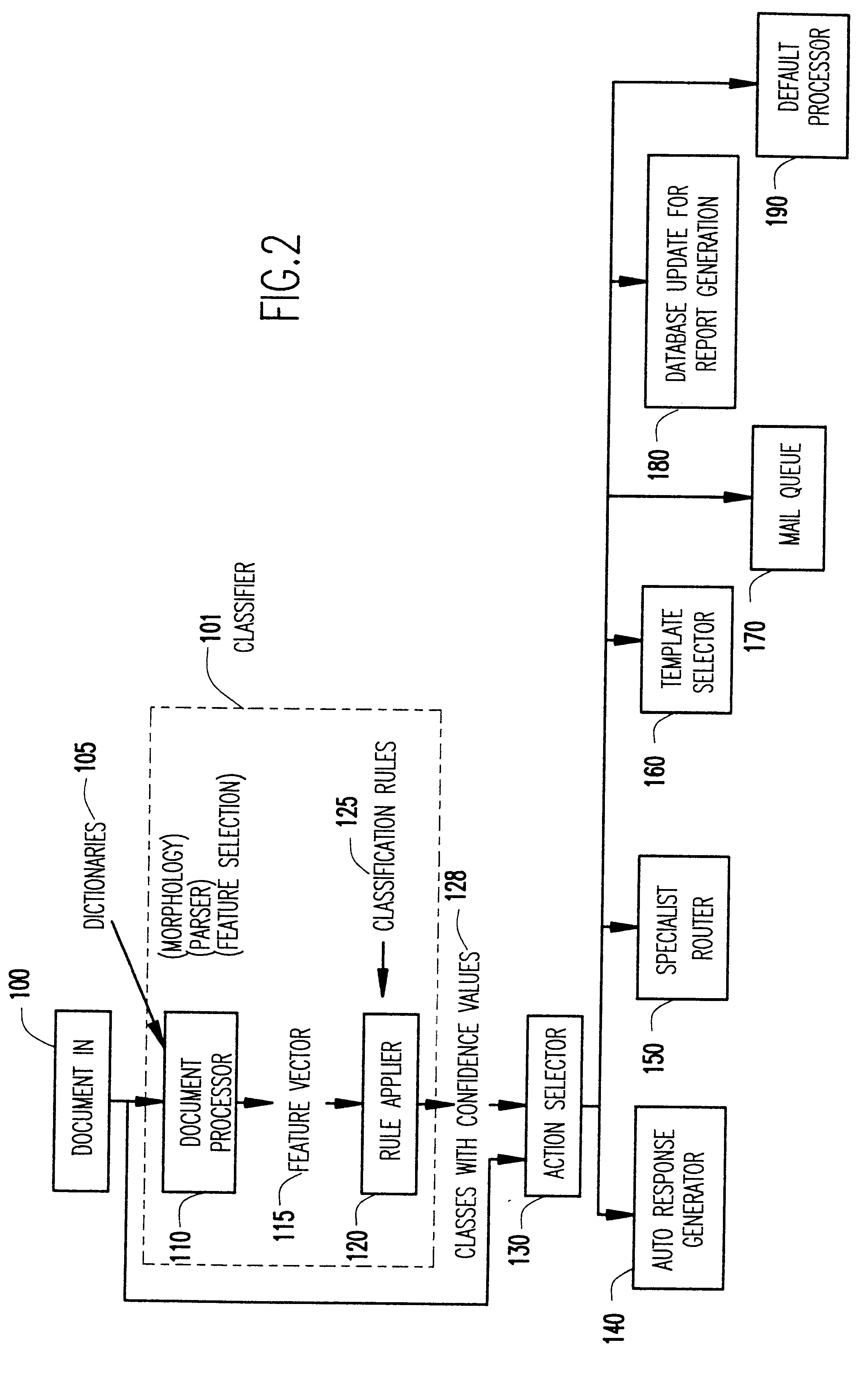
A machine learning based electronic mail system. A classifier and action selection module analyzes the incoming message and classifies the messages with associated confidence levels, which may include analyzing the electronic message by tokenization of the text, morphological analysis of the text, and other well known processes. The classifier and action selection module then determines the appropriate action or actions to effect on the message.
Owner:LINKEDIN
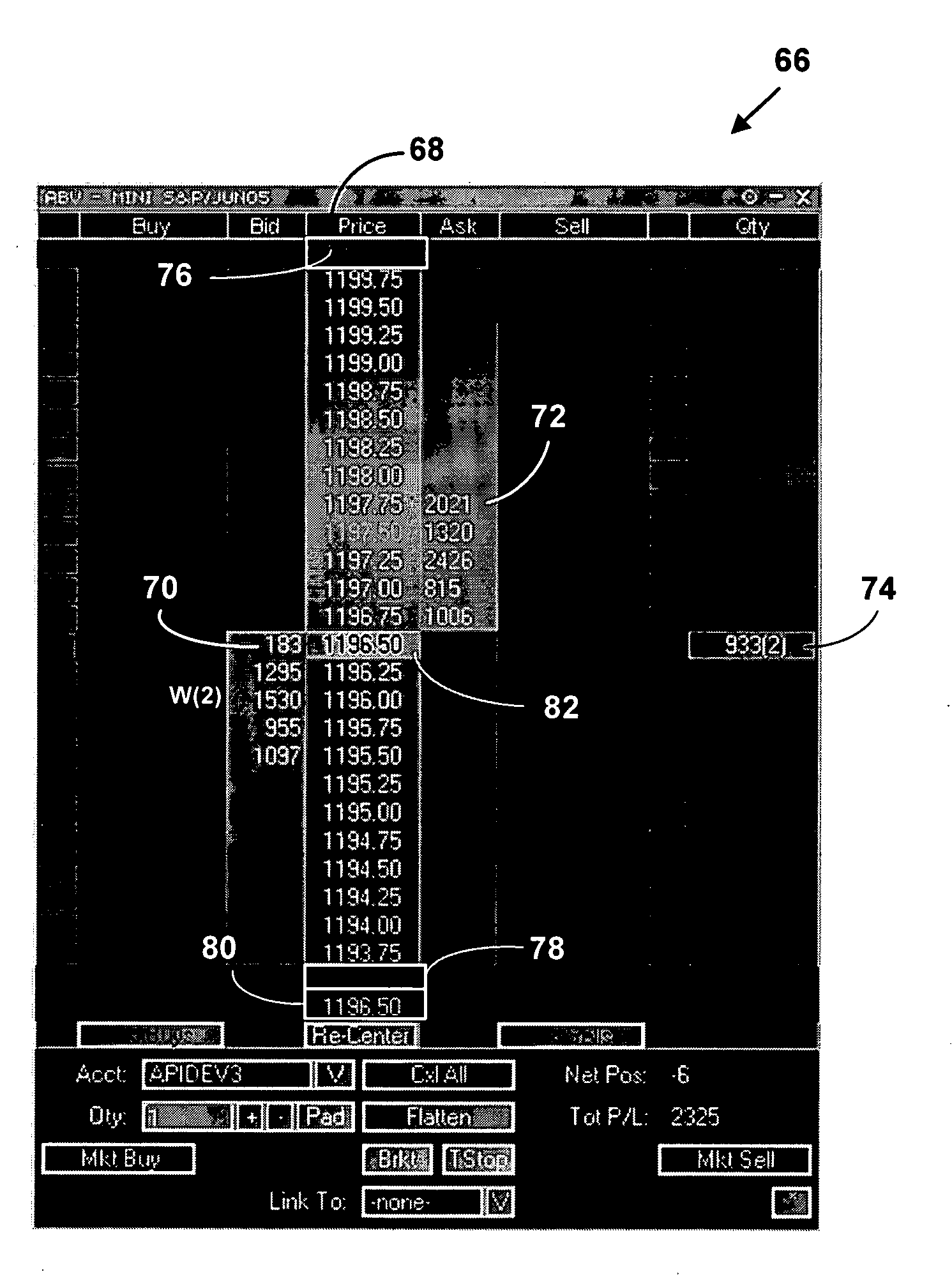
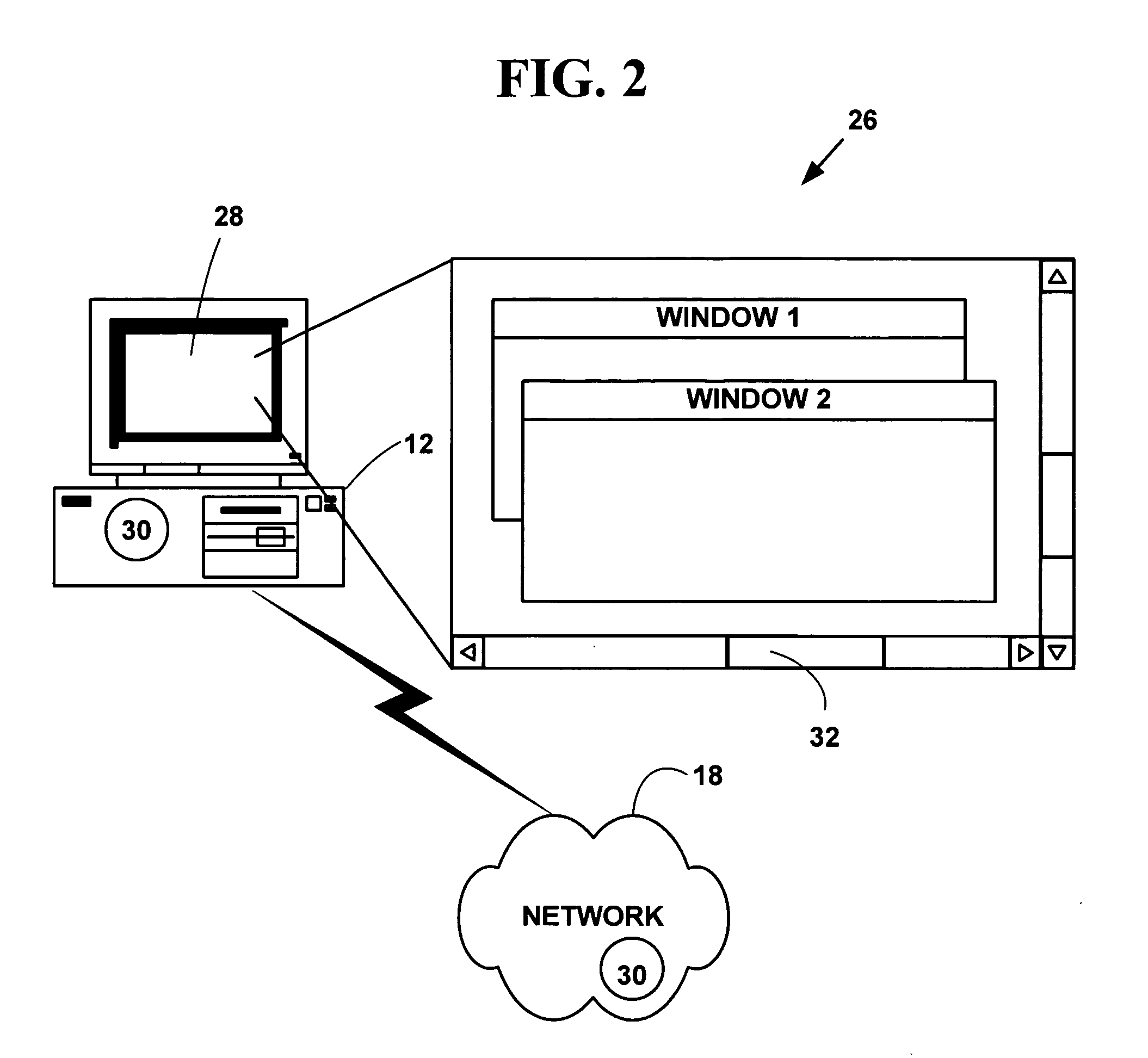
Method and system for providing a graphical user interface for electronic trading
A method and system for providing a graphical user interface for electronic trading. Electronic trading information is obtained on an application on a target device from one or more electronic trading exchanges. The trading electronic information is processed electronic trading information is displayed on a multi-windowed graphical user interface (GUI) where it is used to automatically executed automatic trades. The method and system may improve multiple types of electronic information that can be selectively displayed on a GUI by a user and used to automatically execute plural different pre-determined types of electronic trading strategies.
Owner:ROSENTHAL COLLINS GROUP
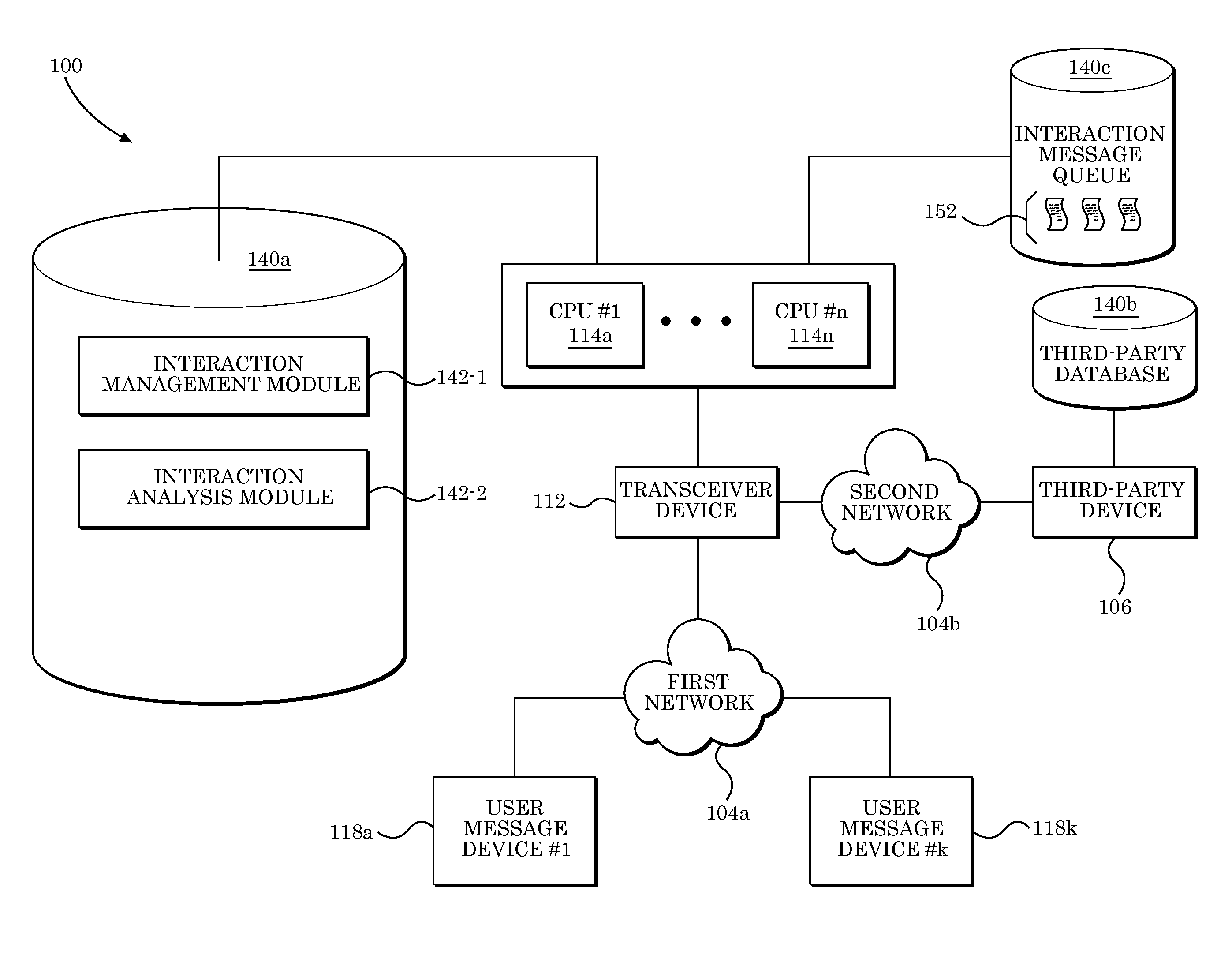
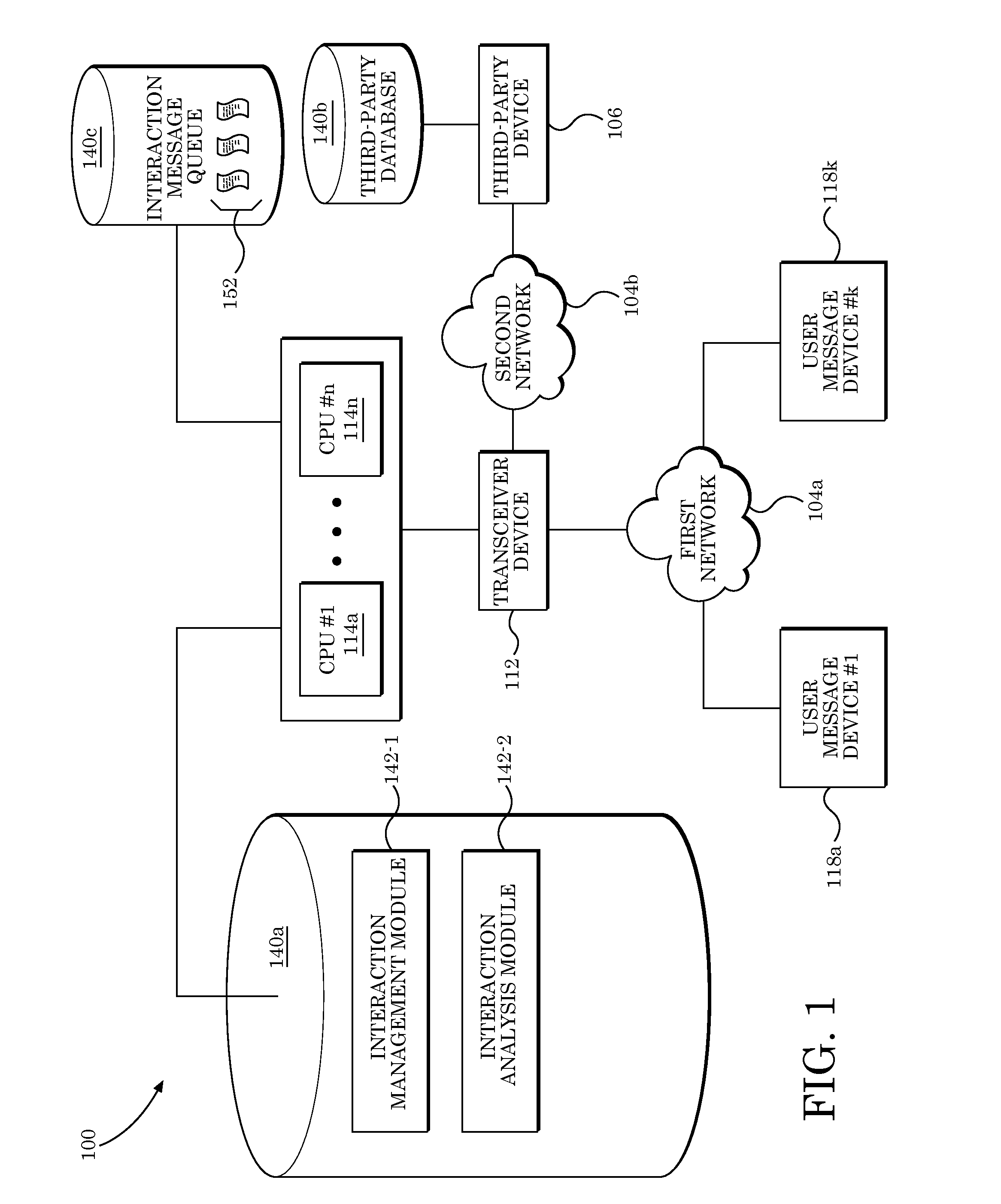
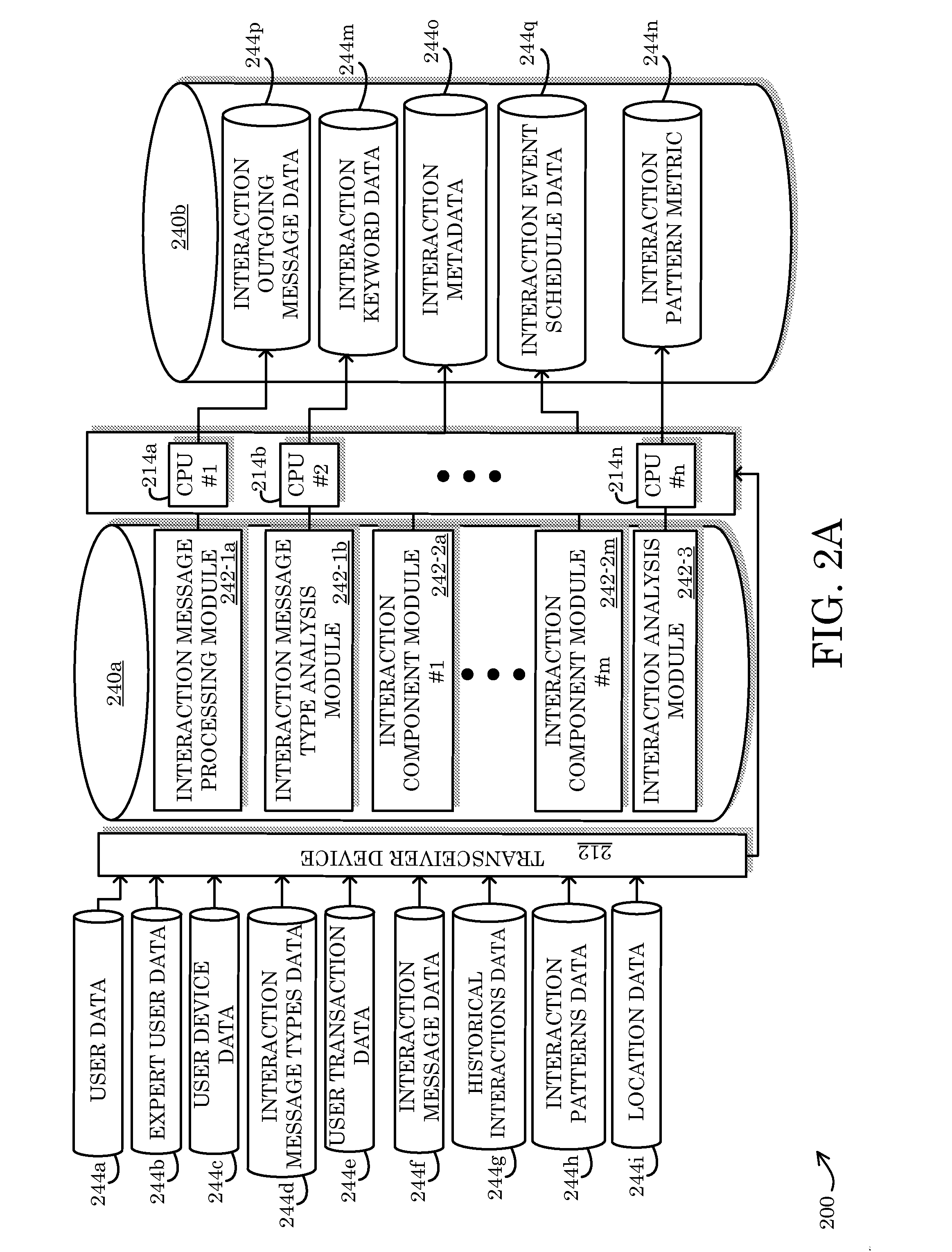
Predictive electronic message management systems and controllers
Systems, methods, and articles of manufacture provide for interaction management (IM) data processing that allows for automated analysis of, response to, and / or identification of patterns in electronic messages (e.g., emails, text messages), via specially-programmed data processing modules configured to be executed in a communications system environment.
Owner:THE TRAVELERS INDEMNITY
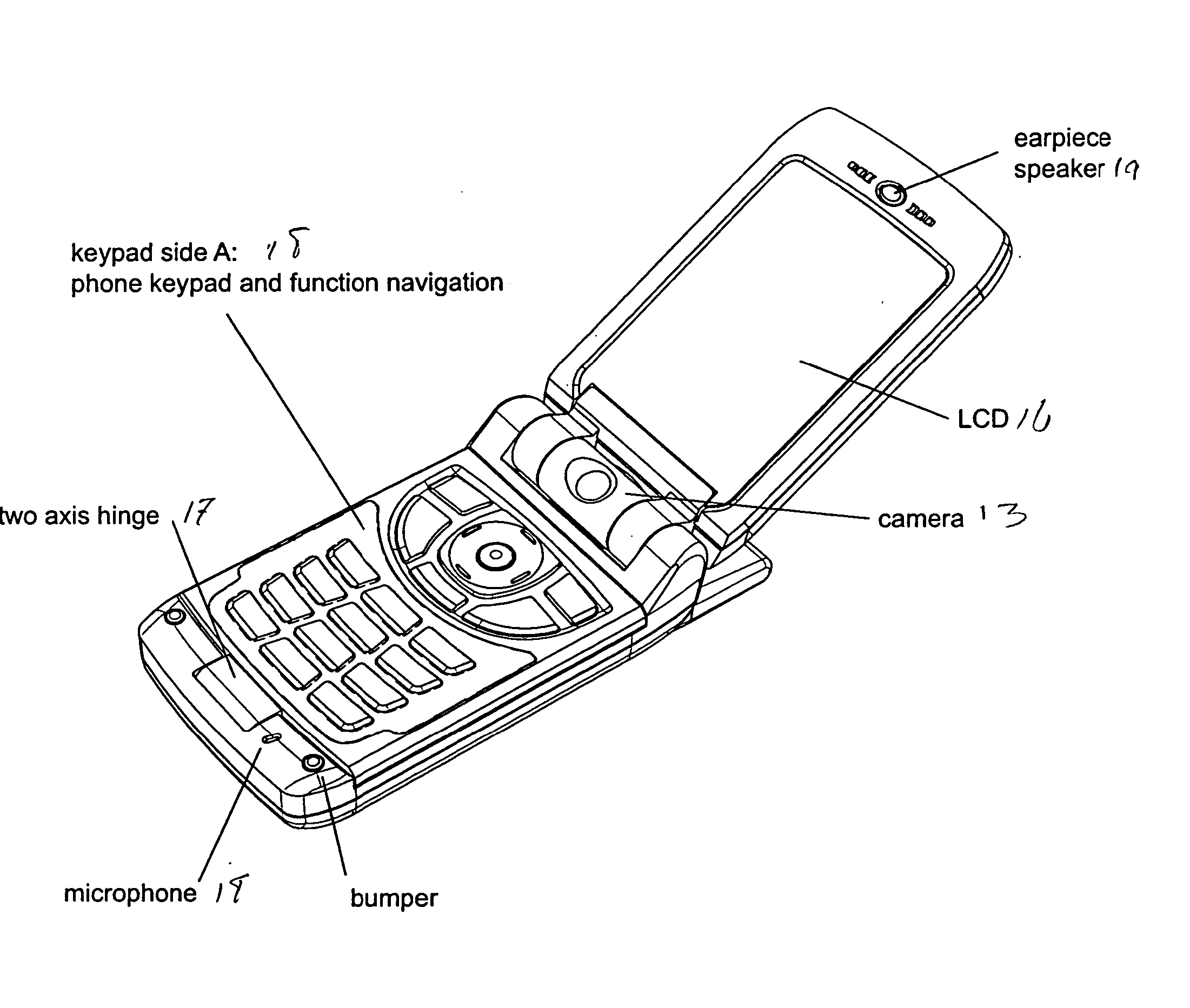
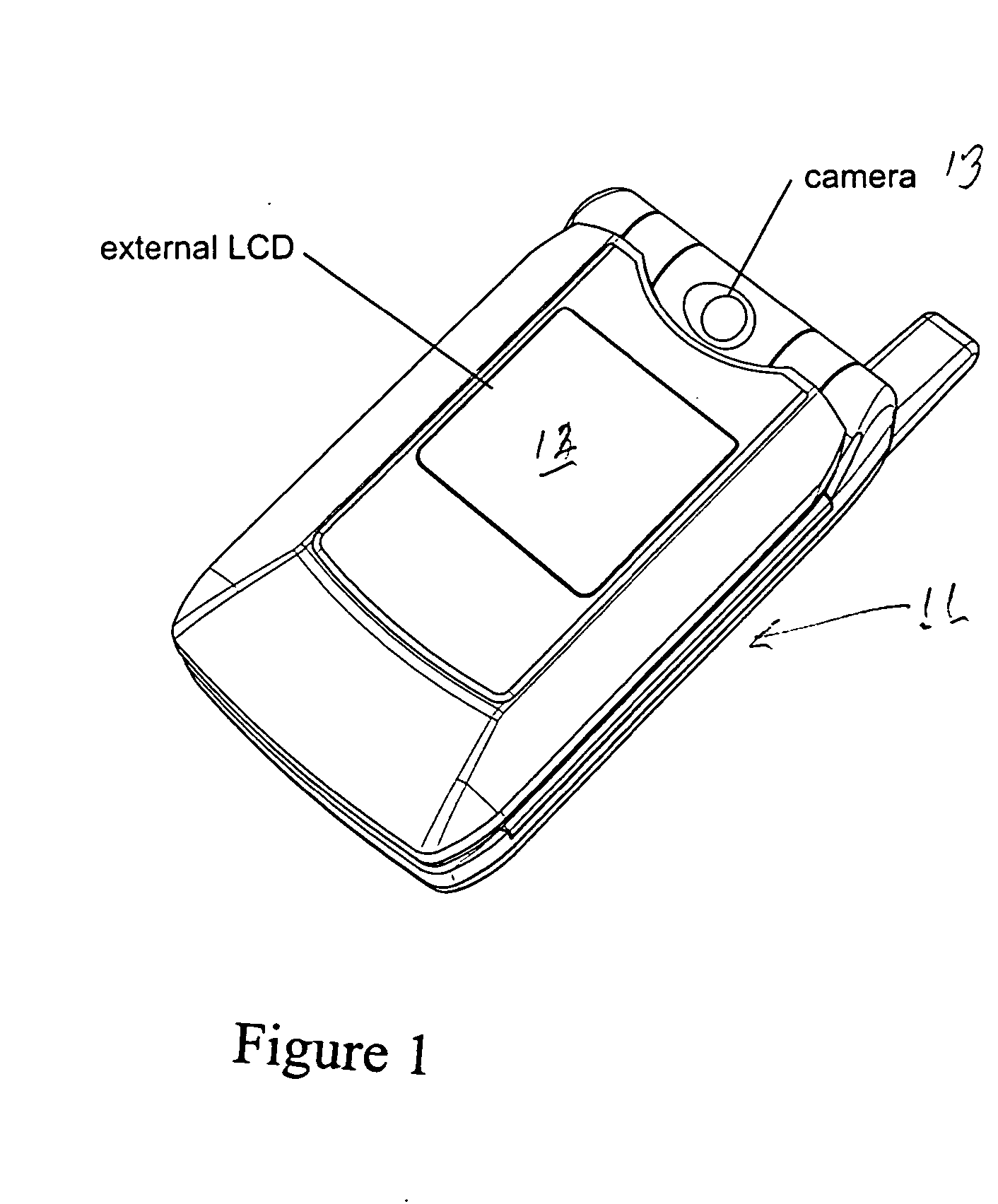
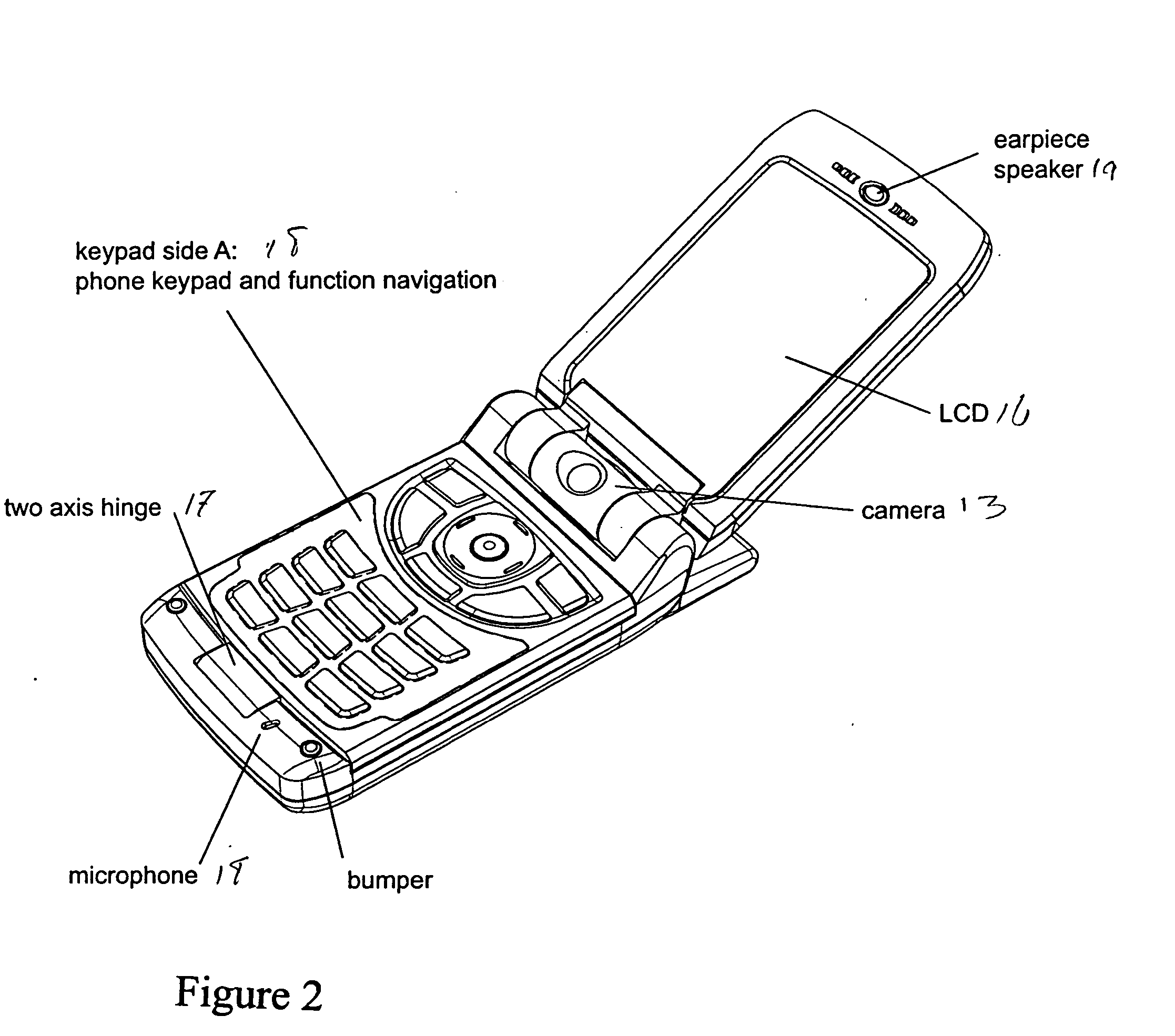
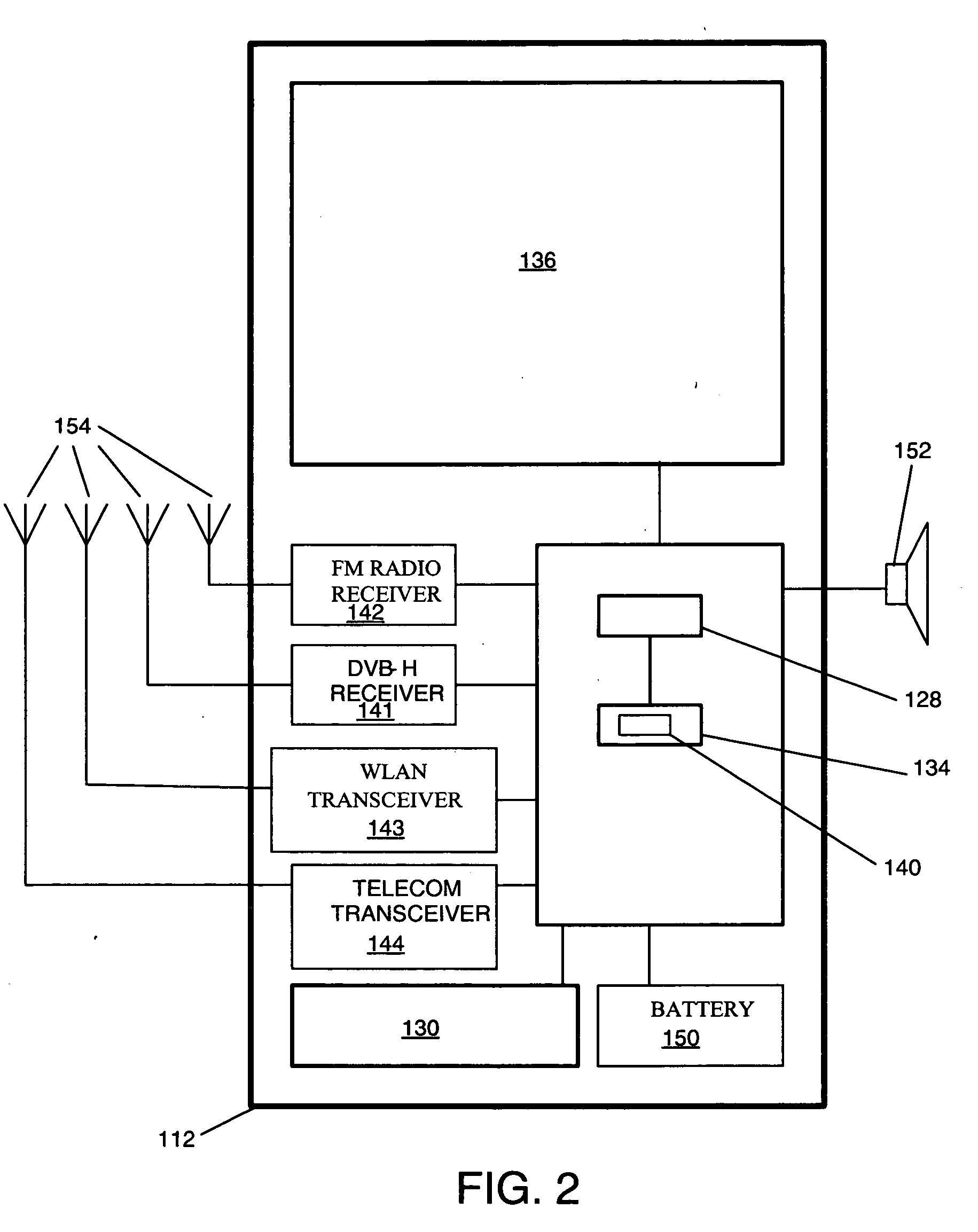
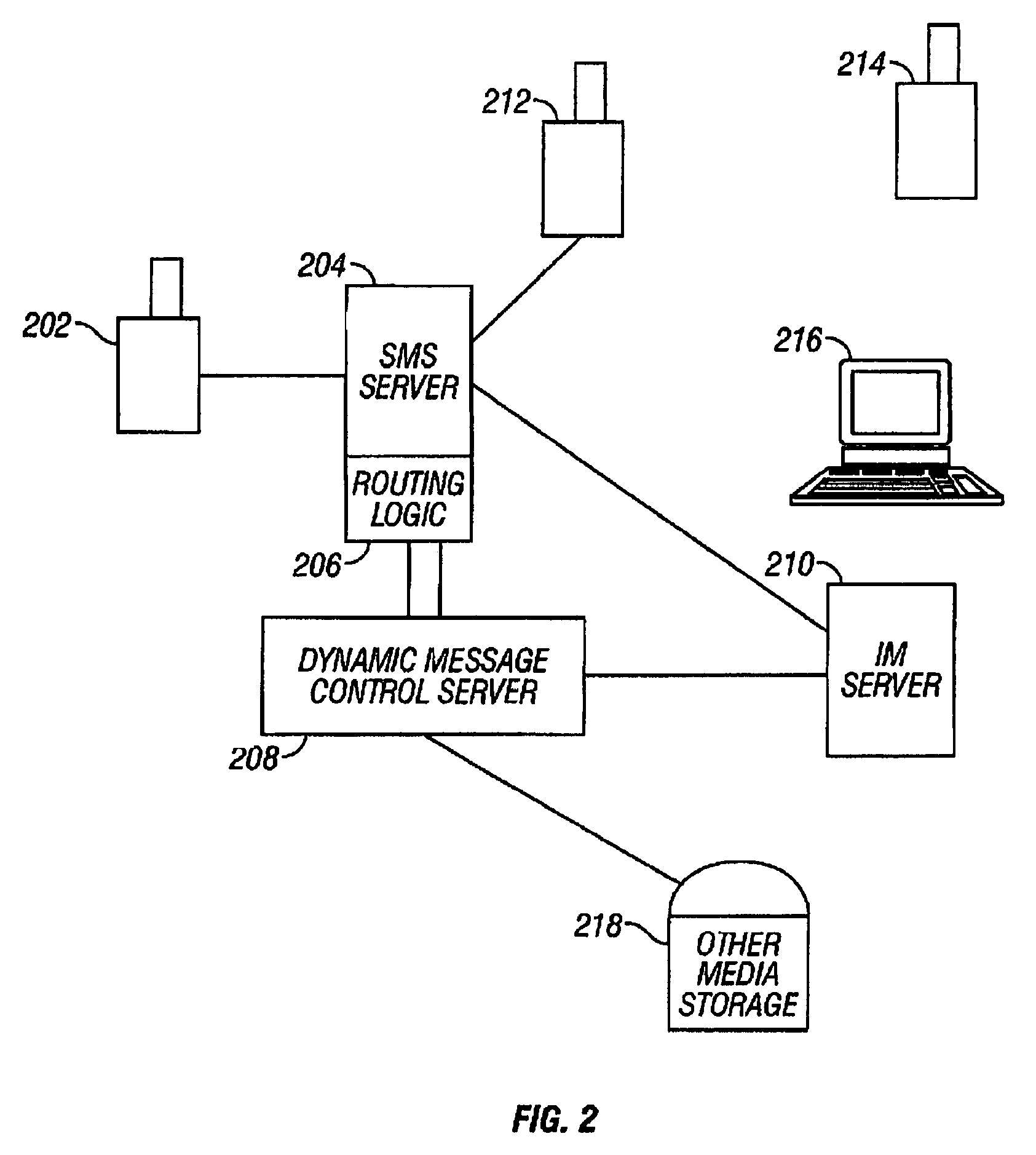
Wireless cell phone
InactiveUS20040142734A1Devices with multiple keyboard unitsDevices with multiple display unitsDisplay deviceElectronic information
A wireless cell phone comprising a handset, a keypad assembly rotatably coupled to the handset, and a handset cover rotatably coupled to the handset. The keypad assembly is rotatable about at least two axes, and removable from the handset. The keypad assembly has a first side for a telephone keypad and a second side for a data communication keypad. The handset cover is rotatably coupled to the handset and includes an exterior display and an interior display. The exterior display is capable of displaying electronic information when the handset cover is in a folded position with respect to the handset.
Owner:SAMSUNG ELECTRONICS CO LTD
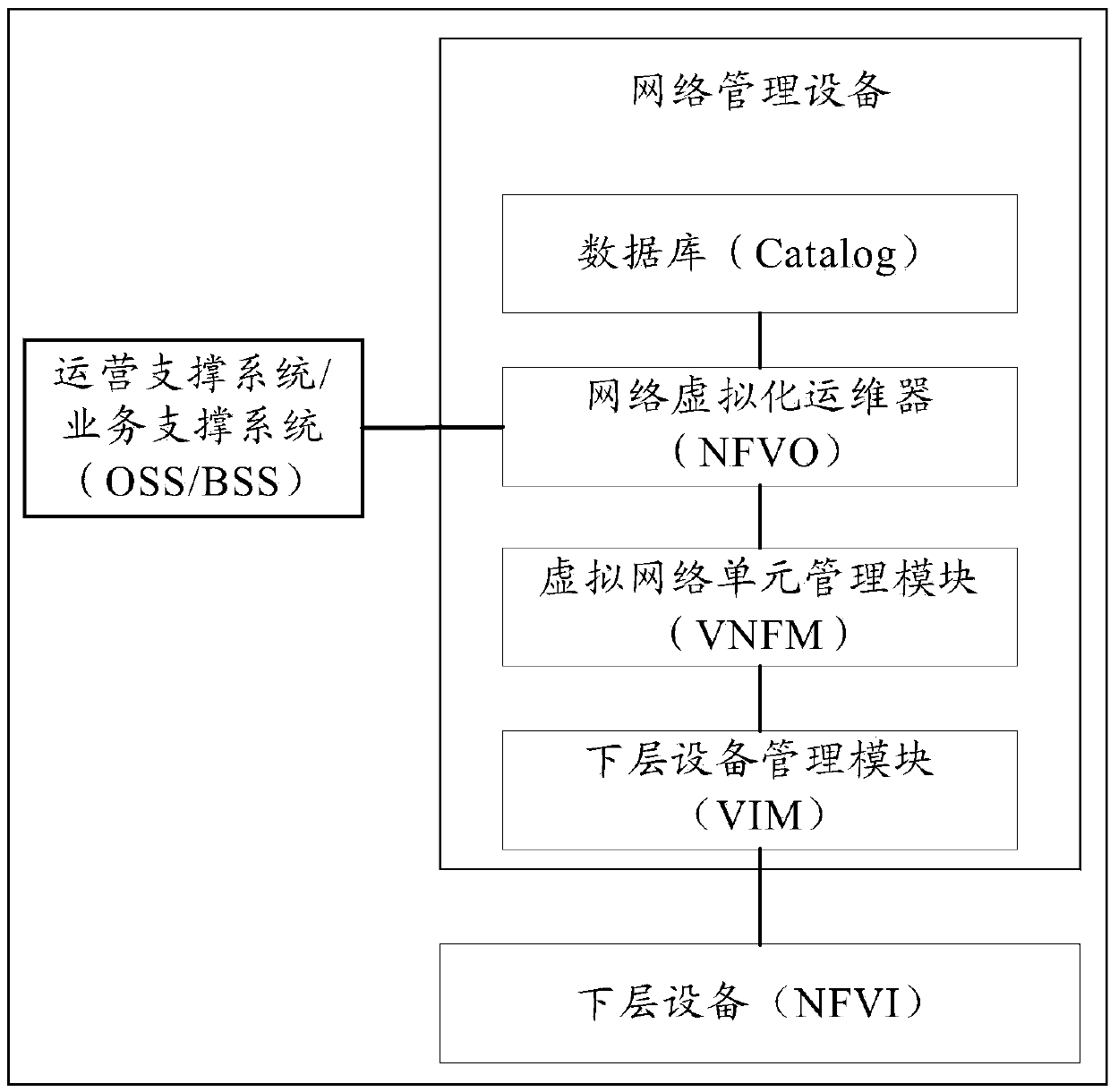
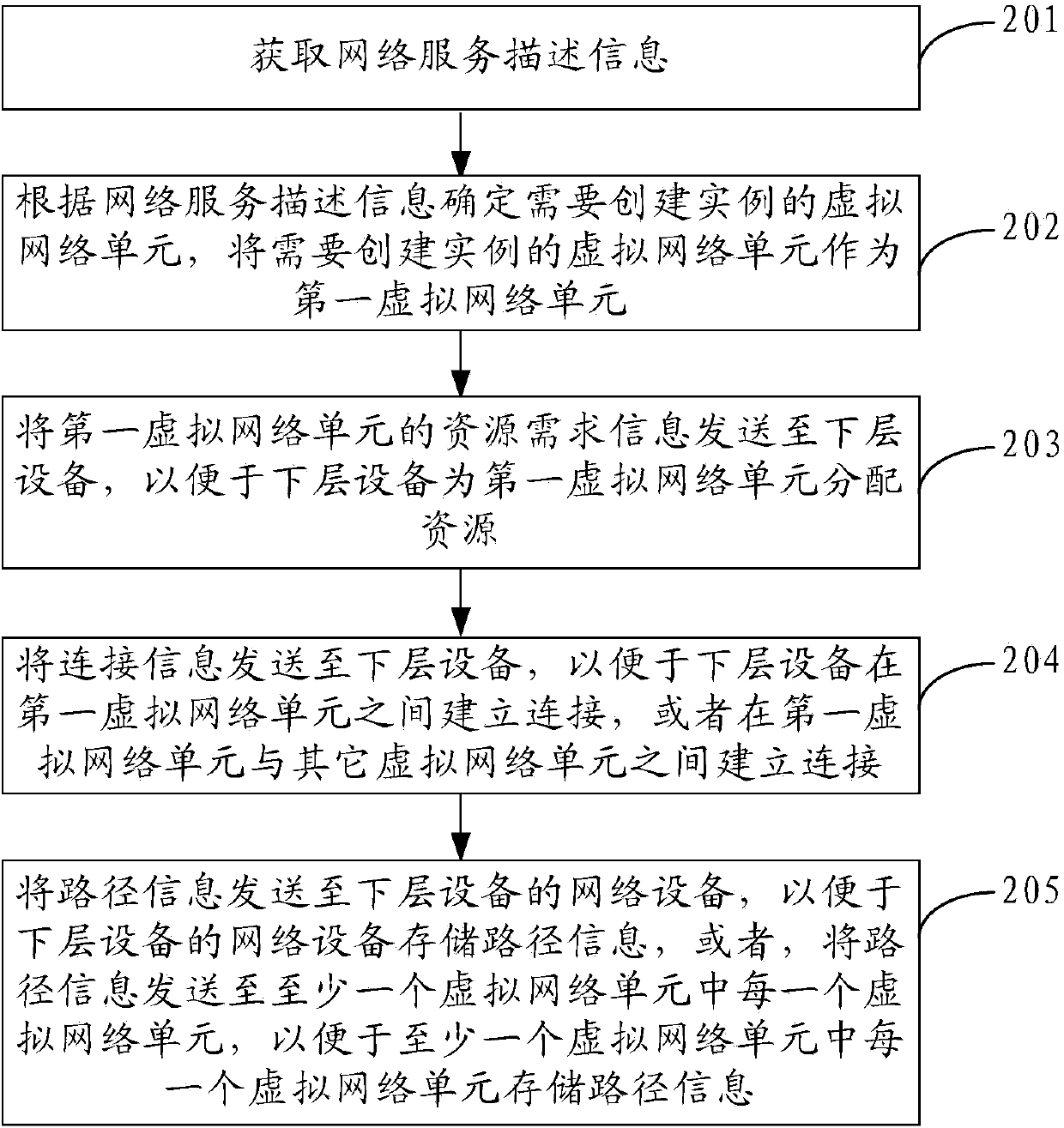
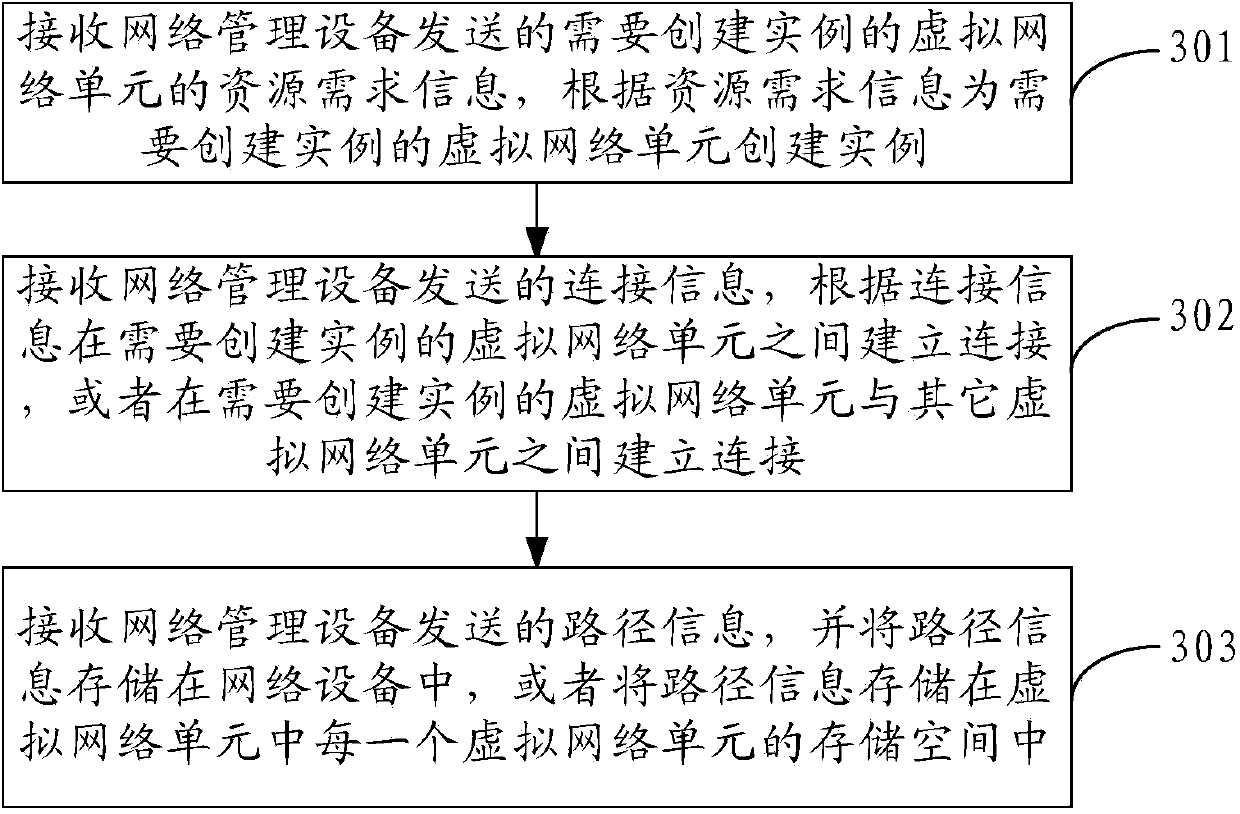
Creation method and device of virtual network instance
The invention discloses a creation method of a virtual network instance, relates to the field of electronic information and aims to solve the problem that when multiple paths among internal virtual network units in a network service are available for data, the failure of determining one of the paths for transmission causes service interruption. According to a specific scheme, the method includes: acquiring network service descriptive information, determining virtual network units with expected instance creation according to the network service descriptive information, transmitting resource request information and connection information of the virtual network units with expected instance creation to a lower-layer device, transmitting path information to a network device of the lower-layer device, or transmitting the path information to each one of the virtual network units, and selecting the transmission path according to the path information when the data is under transmission among the virtual network units. The creation method is applied to creation of the virtual network instances.
Owner:HUAWEI TECH CO LTD
Advertising based on widgets
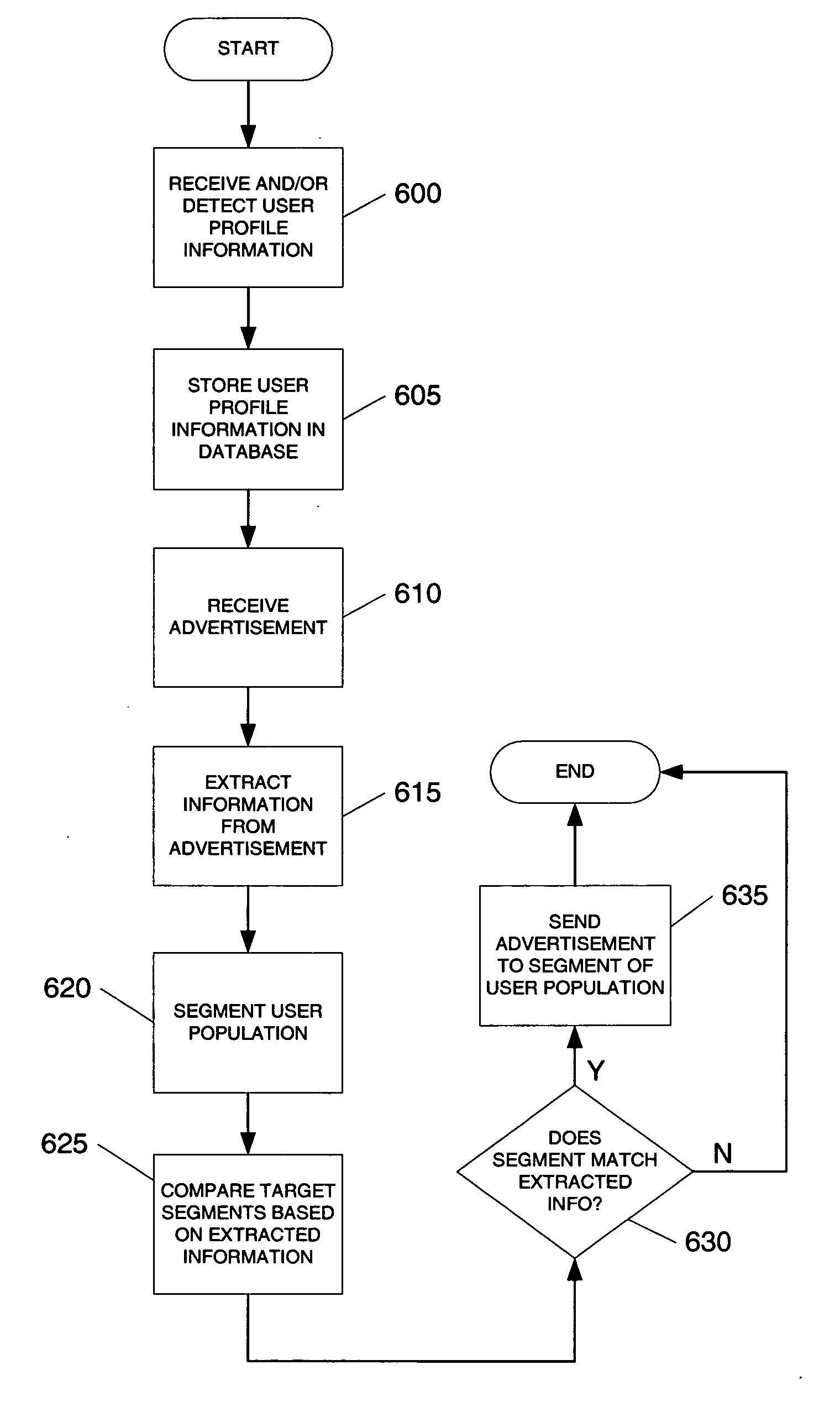
ActiveUS20080010133A1Improve segmentationImprove protectionCommerceSpecial data processing applicationsUser inputElectronic information
Electronic advertisements and other types of electronic information are distributed based on user profiles and in particular, collections of widgets. User profiles may be generated based on a combination of user entered information and information inferred or derived from user behavior and interaction patterns. The use and collection of various widgets may also be recorded by a user profile to determine a user's preferences and interests. An advertisement may be distributed by segmenting a user population according to user profile information and one or more attributes of the advertisement. Users may further interact with the widgets in a variety of ways including requesting additional information about the advertised product or service and / or requesting communications with an advertiser without compromising their privacy.
Owner:NOKIA TECHNOLOGLES OY
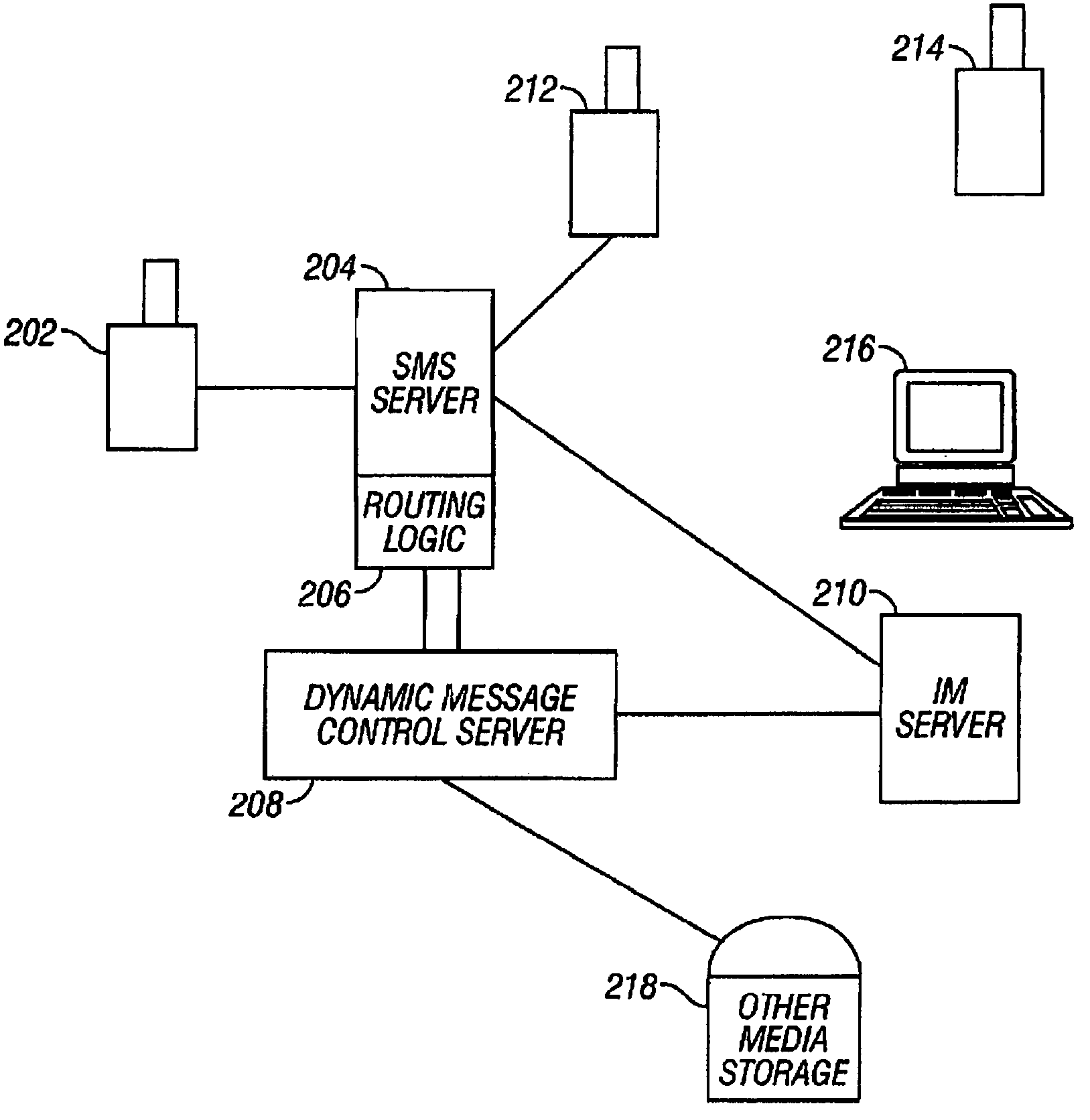
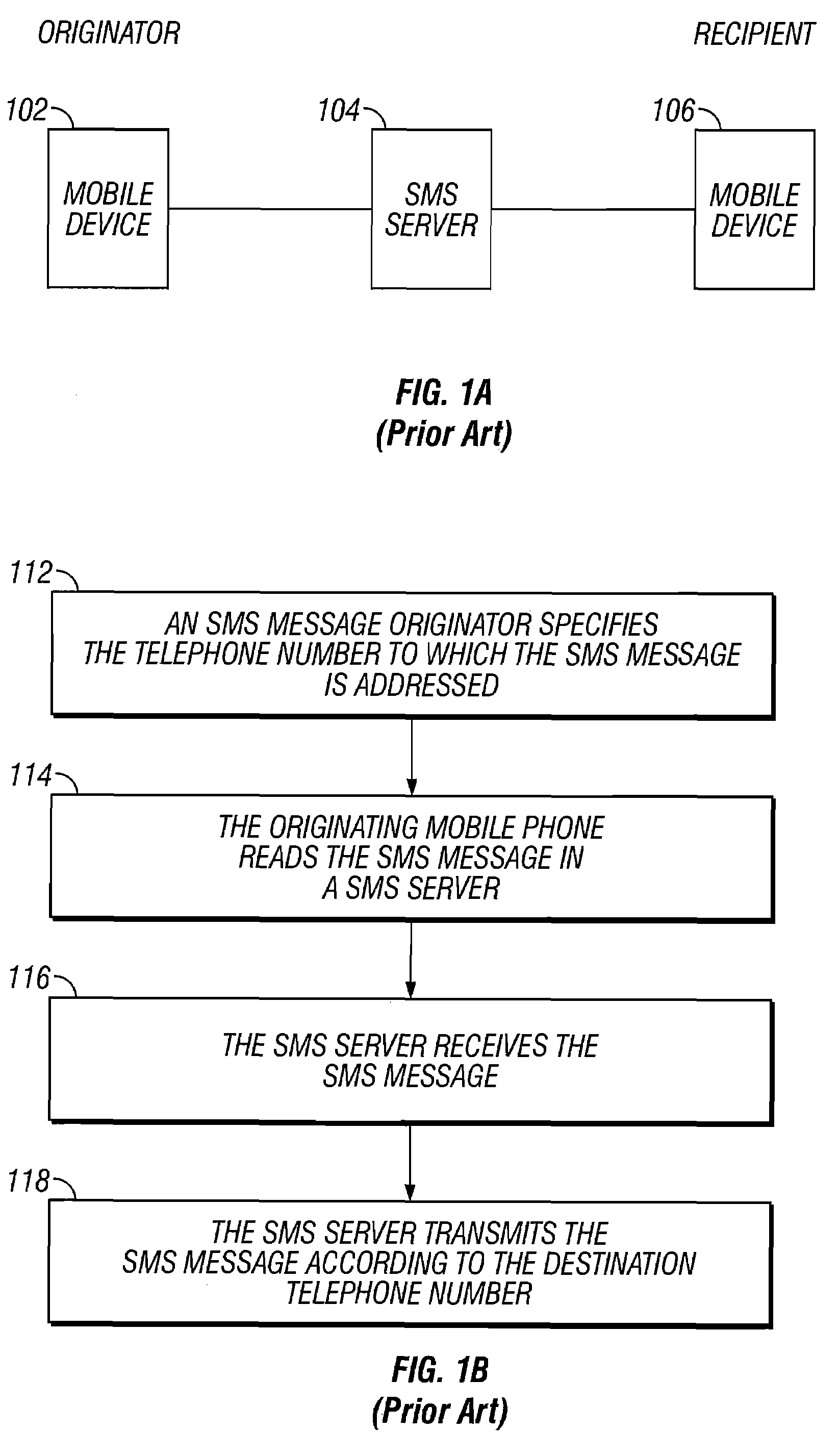
Electronic message forwarding
InactiveUS7428580B2Data processing applicationsMultiple digital computer combinationsMobile deviceComputer science
The invention provides a method of transmitting electronic messages in a computer environment. The preferred embodiment receives an electronic message addressed to a telephone number and determines an instant message identifier associated with the telephone number. In response to the determination that an instant message identifier associates with the telephone number, it is further determined whether an instant message receiver is available to receive messages addressed to the instant message identifier. In response to a determination that an instant message receiver is available to receive instant messages addressed to the instant message identifier, the electronic message is forwarded as an instant message addressed to the instant message identifier. In response to a determination that an instant message receiver is available to receive instant message addressed to the instant message identifier, electronic message is sent to a mobile device at the telephone number in response to a determination that no instant message receiver is available to receive instant messages addressed to the instant message identifier.
Owner:META PLATFORMS INC
Authentication System
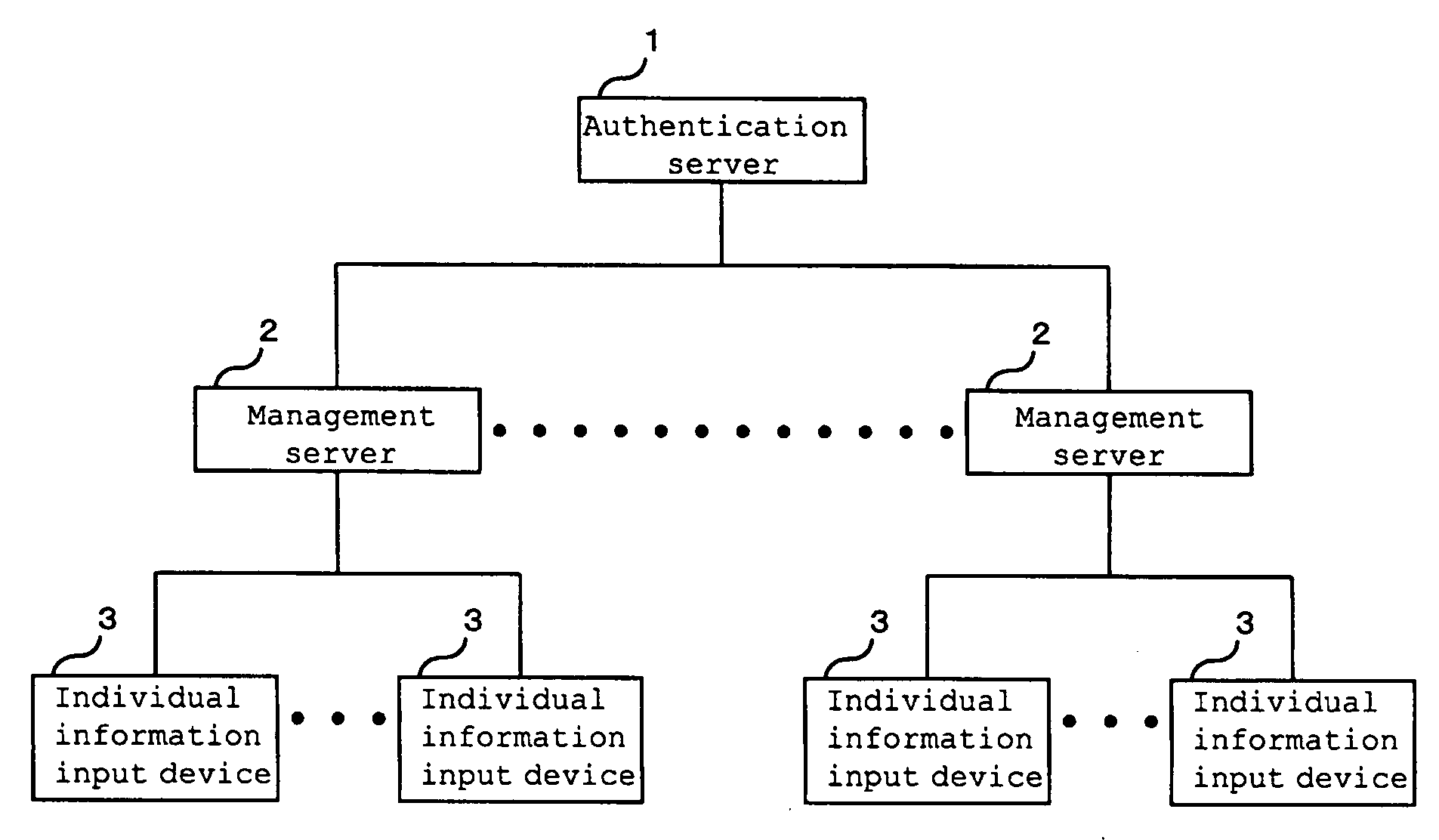
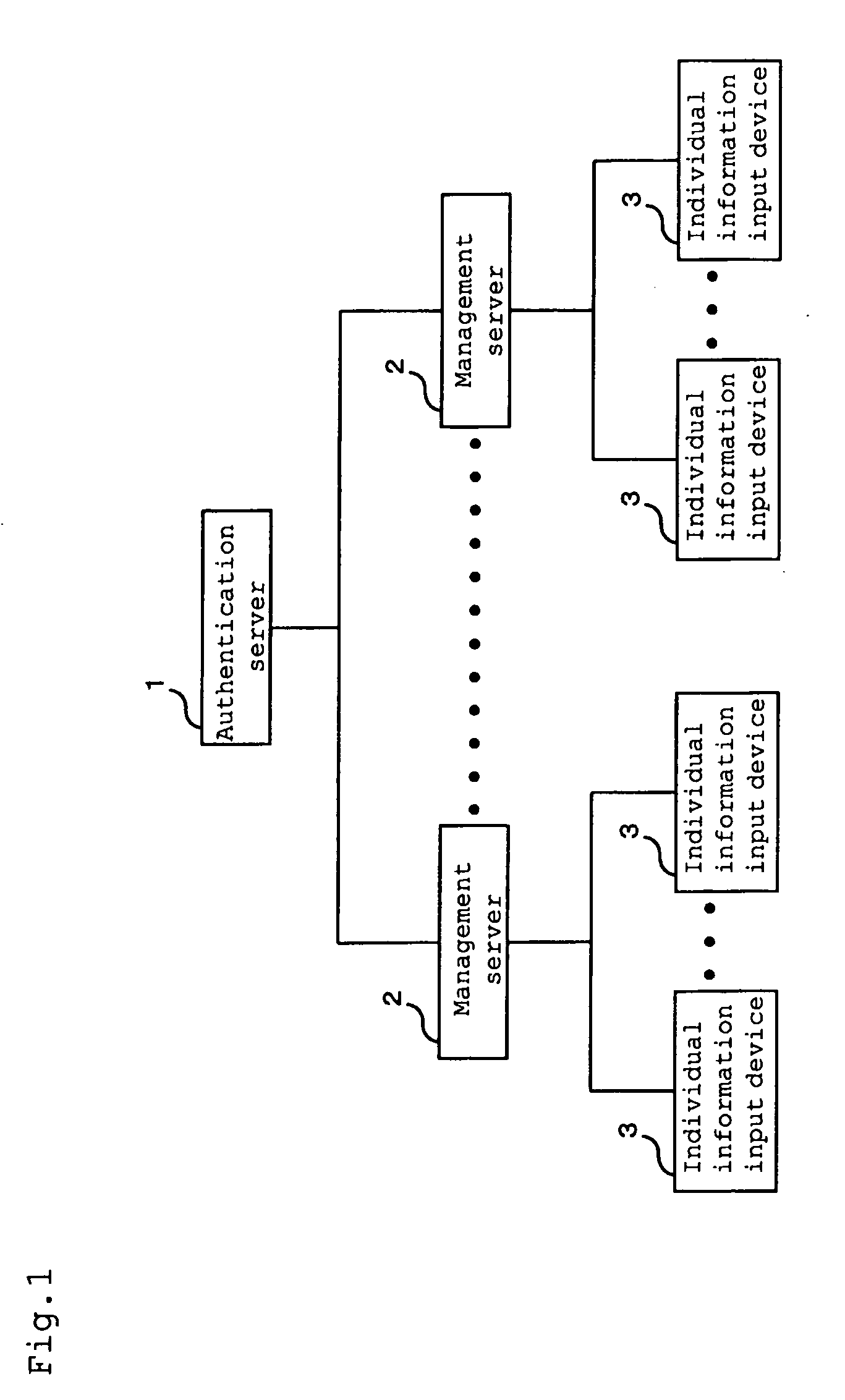
InactiveUS20090189736A1Easy to findImprove securityProgramme controlElectric signal transmission systemsAuthentication serverElectronic information
[Problems] To provide an authentication system improving authentication accuracy of existence of a registered person and easily find an unauthorized act to improve the security in a system by performing authentication using coincidence / non-coincidence of biometrics information and temporal / spatial authentication when performing individual authentication via a network by using electronic information which is easily tampered, easily leaks out, and is easily stolen.[Means for Solving Problems] An authentication server (1) includes a database for managing individual information on a registered person to be authenticated. Moreover, the authentication server (1) is connected to a plurality of management servers (2) via a communication network and correlates the individual information transmitted from an individual information input device (3) via the management server (2) with the individual information in the database, thereby authenticating the existence of the registered person.
Owner:IHC CORP
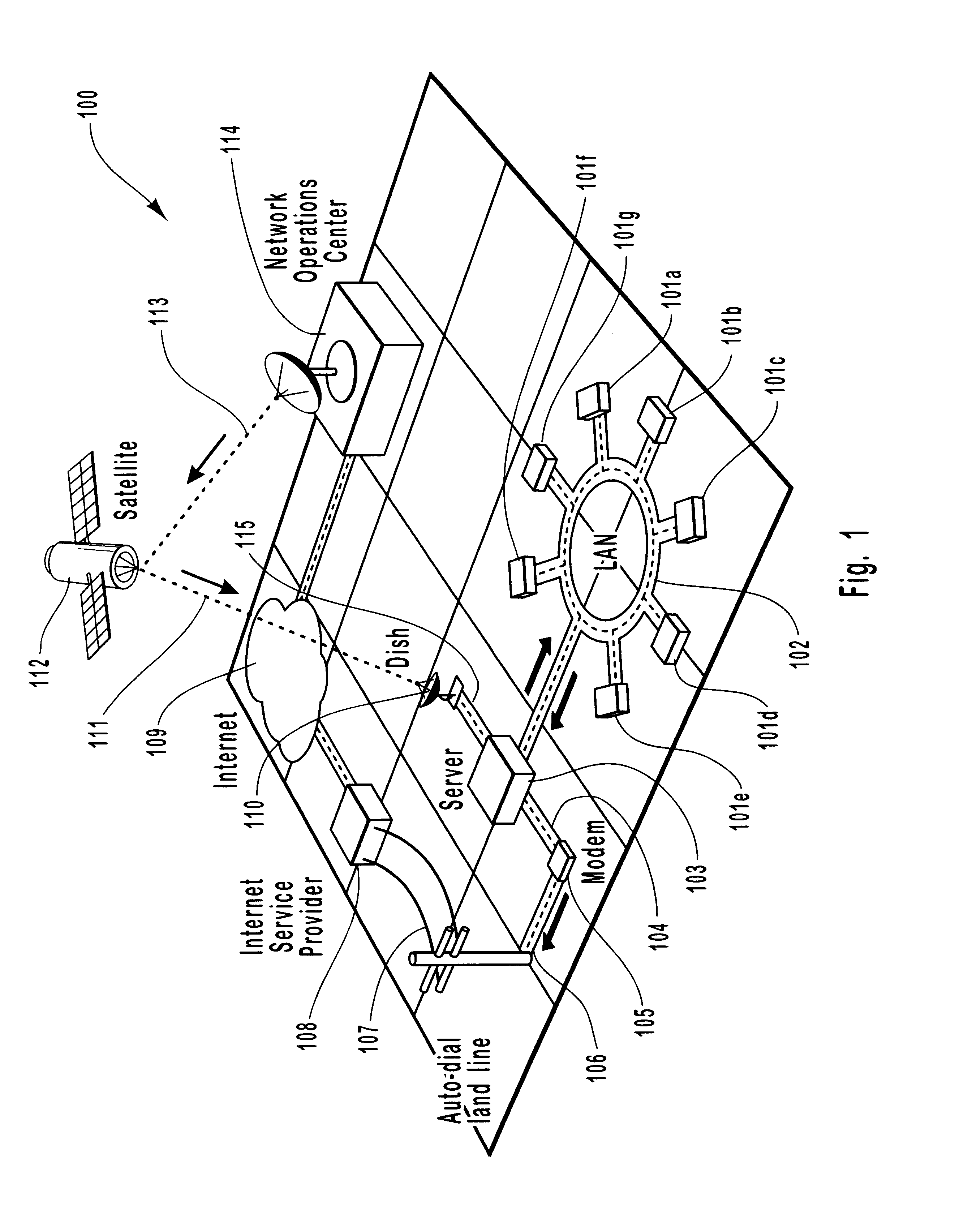
Method and system for asymmetric satellite communications for local area networks
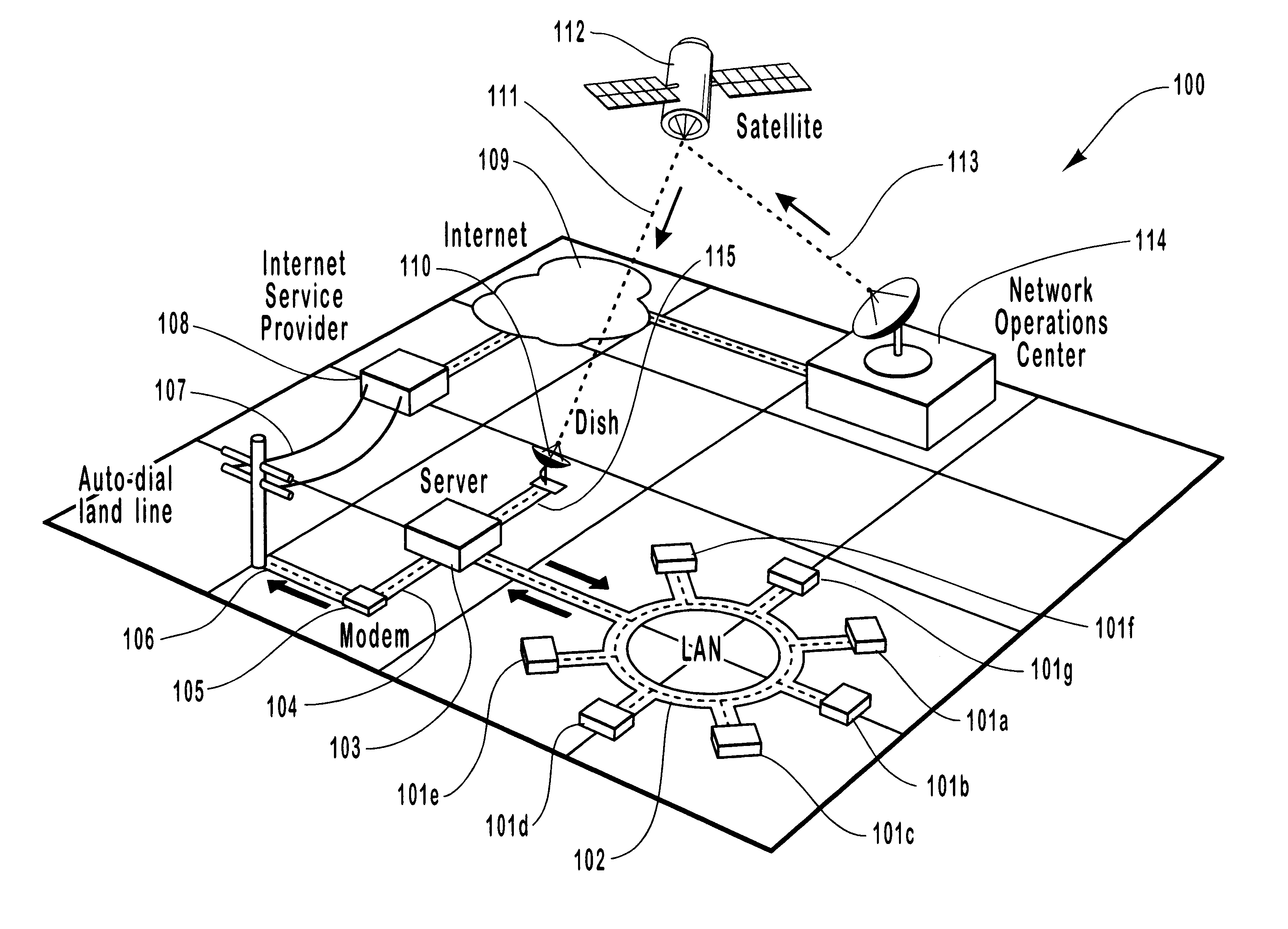
InactiveUS6205473B1Efficient communicationIncrease speedError preventionTransmission systemsNon symmetricLow speed
A method and system for providing high-speed, satellite-based information delivery is described. Improved communication channel efficiency is accomplished by employing an asymmetric data flow. The high bandwidth channel capacity of digital satellite systems is used for the download of large volumes of data. While relatively low speed communication channels are used for upstream data requests. The use of separate channels for upstream data and downloaded data provides an increased efficiency of use for typical internet and other electronic information service subscribers. A typical user in such systems generally makes relatively short information requests. These requests are then followed by large amounts of information being transferred to the user's computer in response to the request. The volume of data being downloaded often causes a capacity overload of typically used land lines. This invention solves this problem, without becoming prohibitively expensive, by employing digital satellite dish receivers to receive the high volume of downloaded data and using the relatively low speed communication channels low volume upstream requests. Moreover, this invention is designed to interface with all common communication devices as well as being designed to operate on and with all common computing platforms.
Owner:HUGHES NETWORK SYST
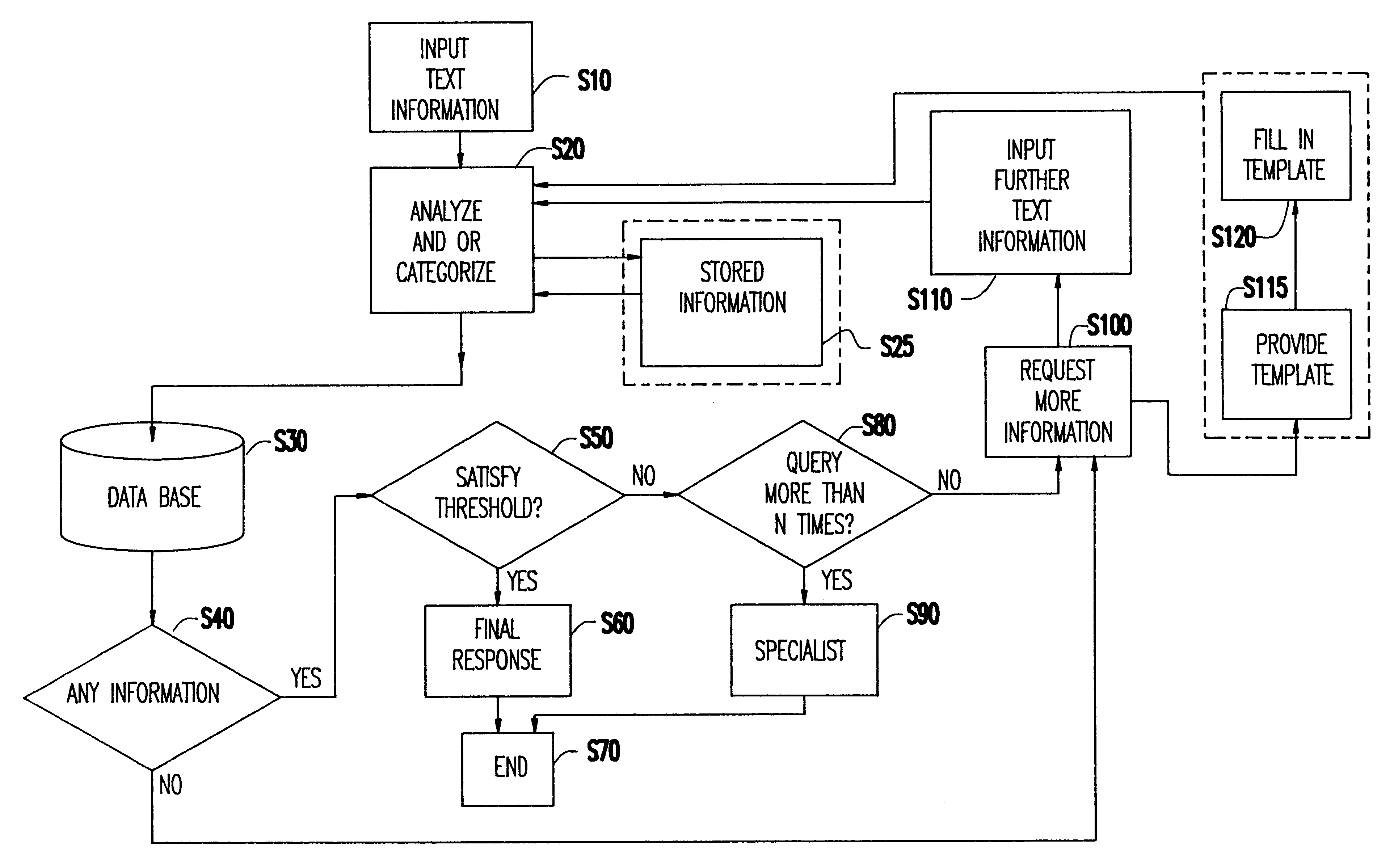
Interactive electronic messaging system
InactiveUS6477551B1Data processing applicationsNatural language data processingConfidence intervalElectronic information
A method and apparatus for interacting with incoming text information, e.g., a user query. The method of the present invention categorizes the incoming text information, and may also provide associated confidence levels with the categorization feature. The categorized information is used to query a database having associated category information with associated threshold values. The confidence levels may also be used when querying the database. The categorized information and corresponding confidence levels are then compared to the threshold value. If the categorized information and corresponding confidence levels equals or exceeds the threshold value then a response is provided by the system and method of the present invention. If the categorized information and corresponding confidence levels does not equal or exceed the threshold value then the system of the present invention will request further information of the user, and the method will repeat until (i) the categorized information and corresponding confidence levels equals or exceeds the threshold value or (ii) the system of the present invention times out.
Owner:IBM CORP
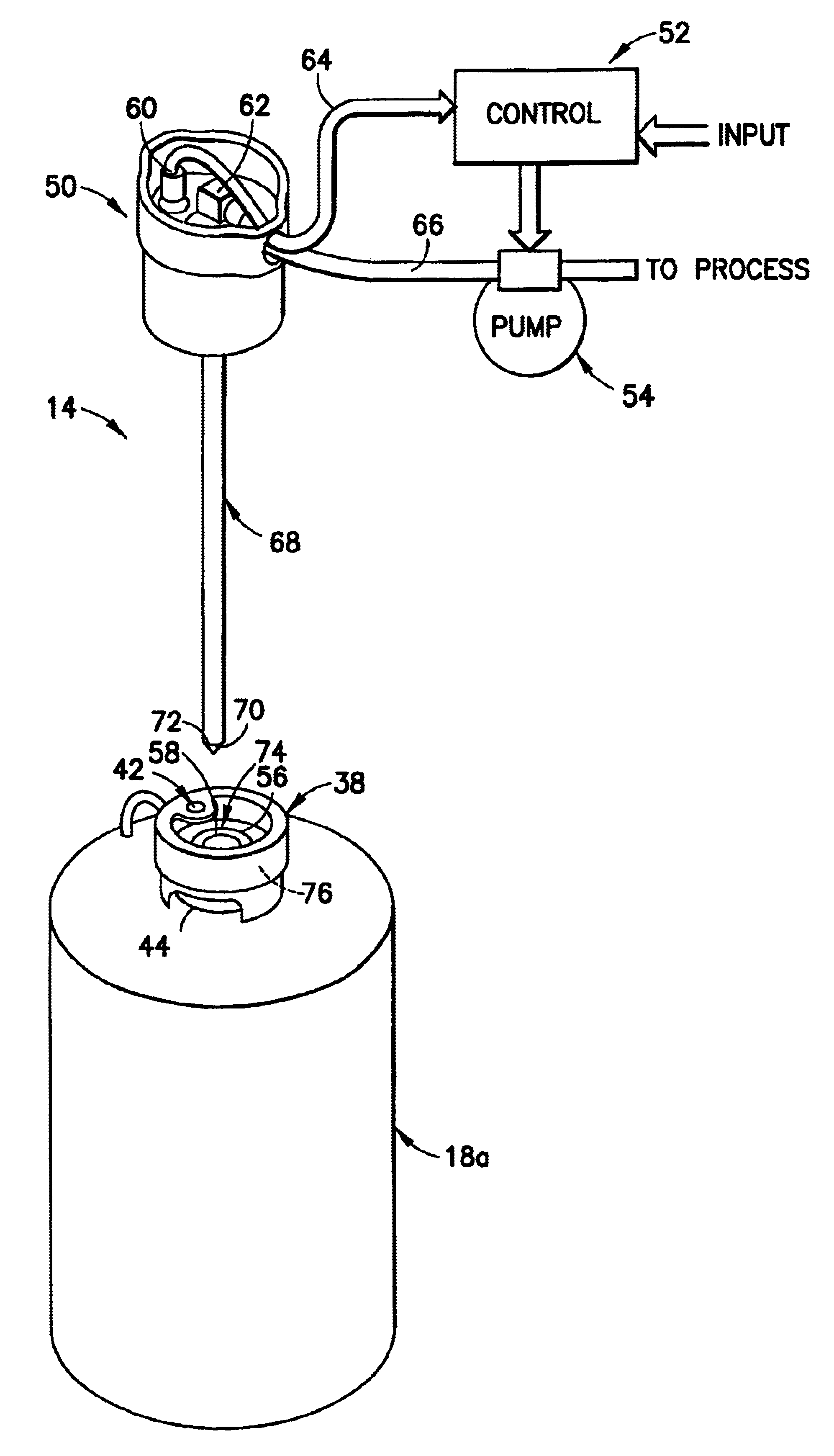
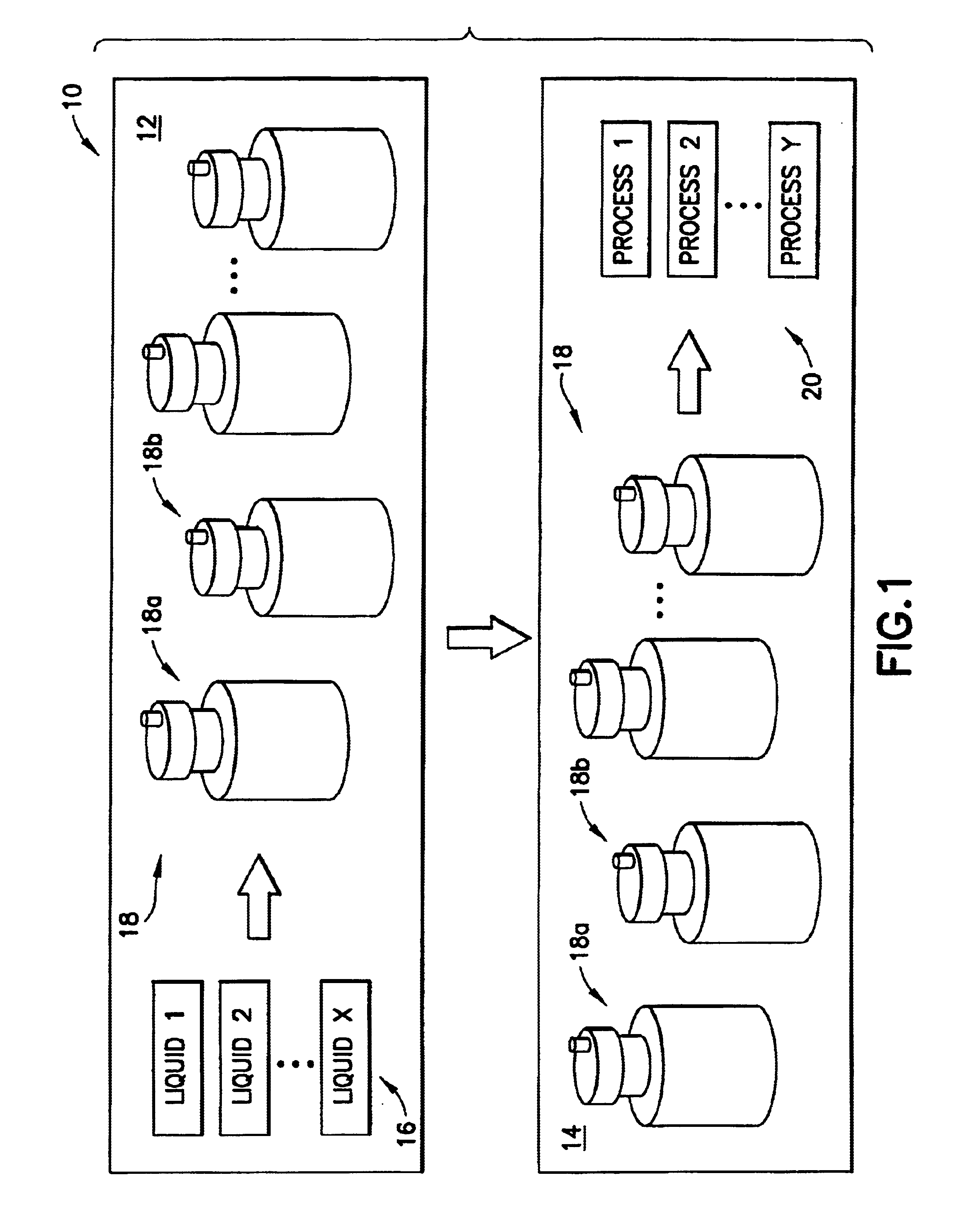
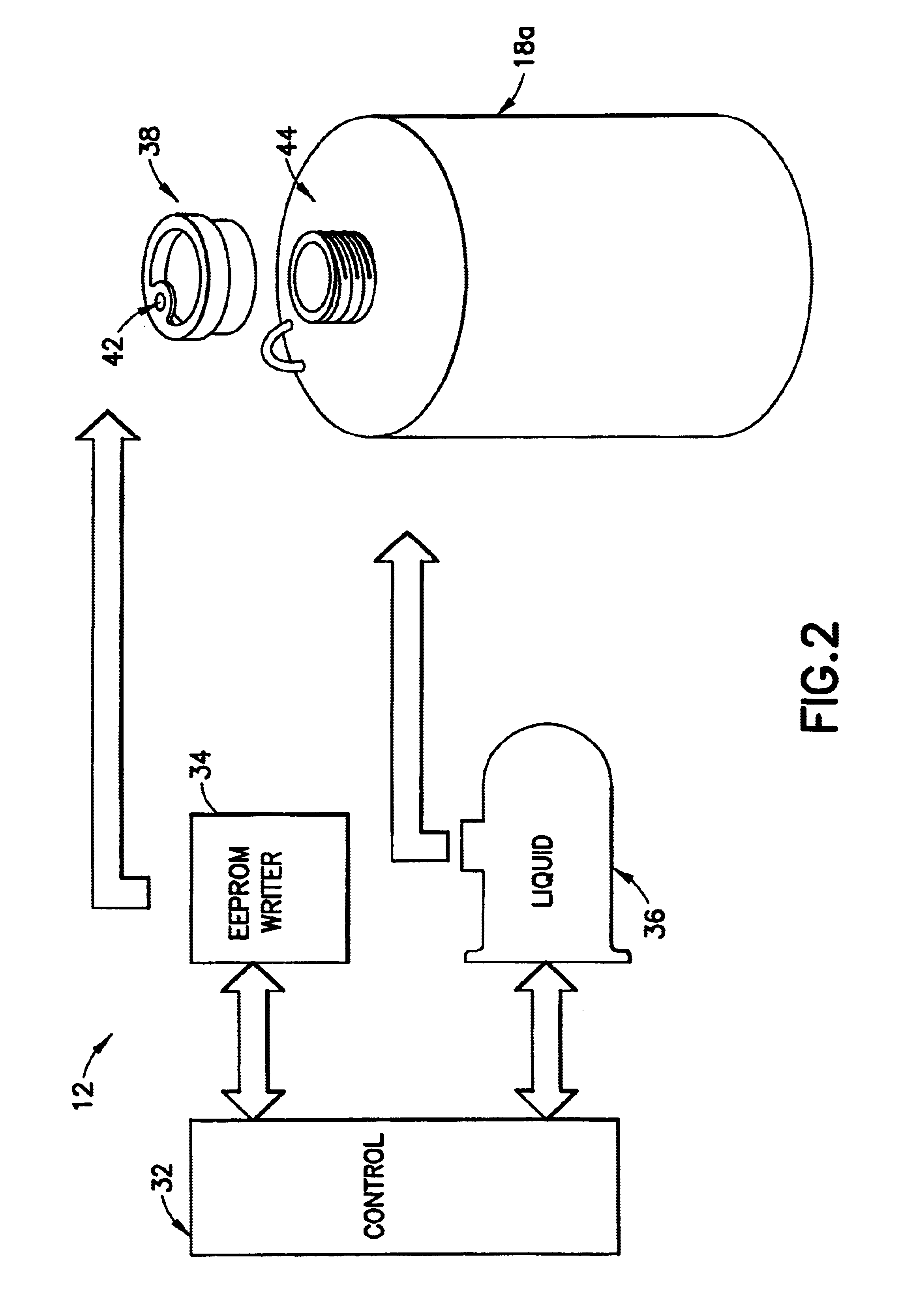
Liquid handling system with electronic information storage
The present invention is a system for handling liquid and a method for the same. The system has a container capable of holding a liquid. An electronic storage device is coupled with the container for electronically storing information relating to the liquid stored in the container. The system also has an antenna, for storing information to and reading information from the electronic storage device. Finally, the system has a microprocessor-based controller, coupled with the antenna, for controlling processing of the liquid based on information read from the electronic storage device by the antenna.
Owner:ENTEGRIS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com