Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4144 results about "Recipient side" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
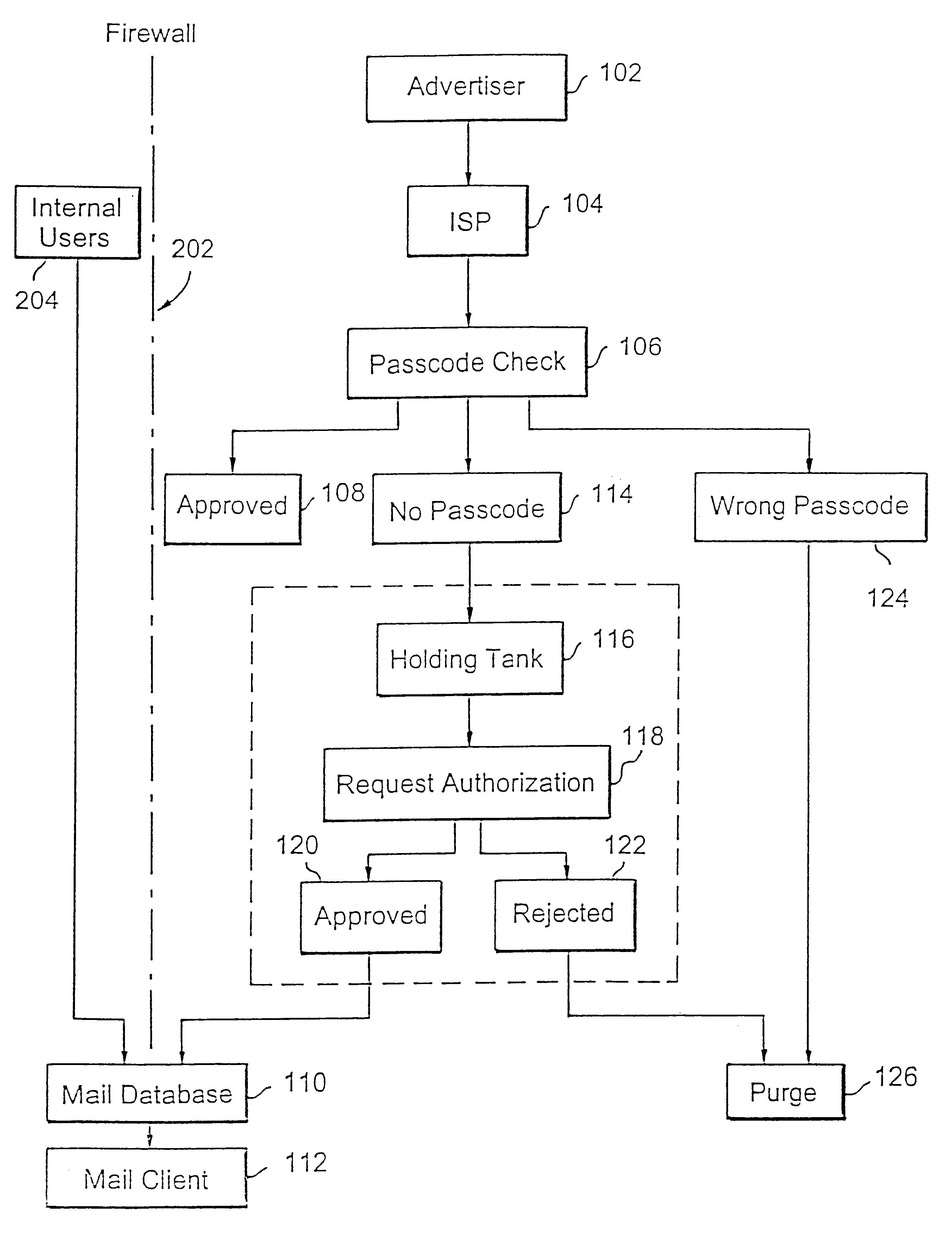
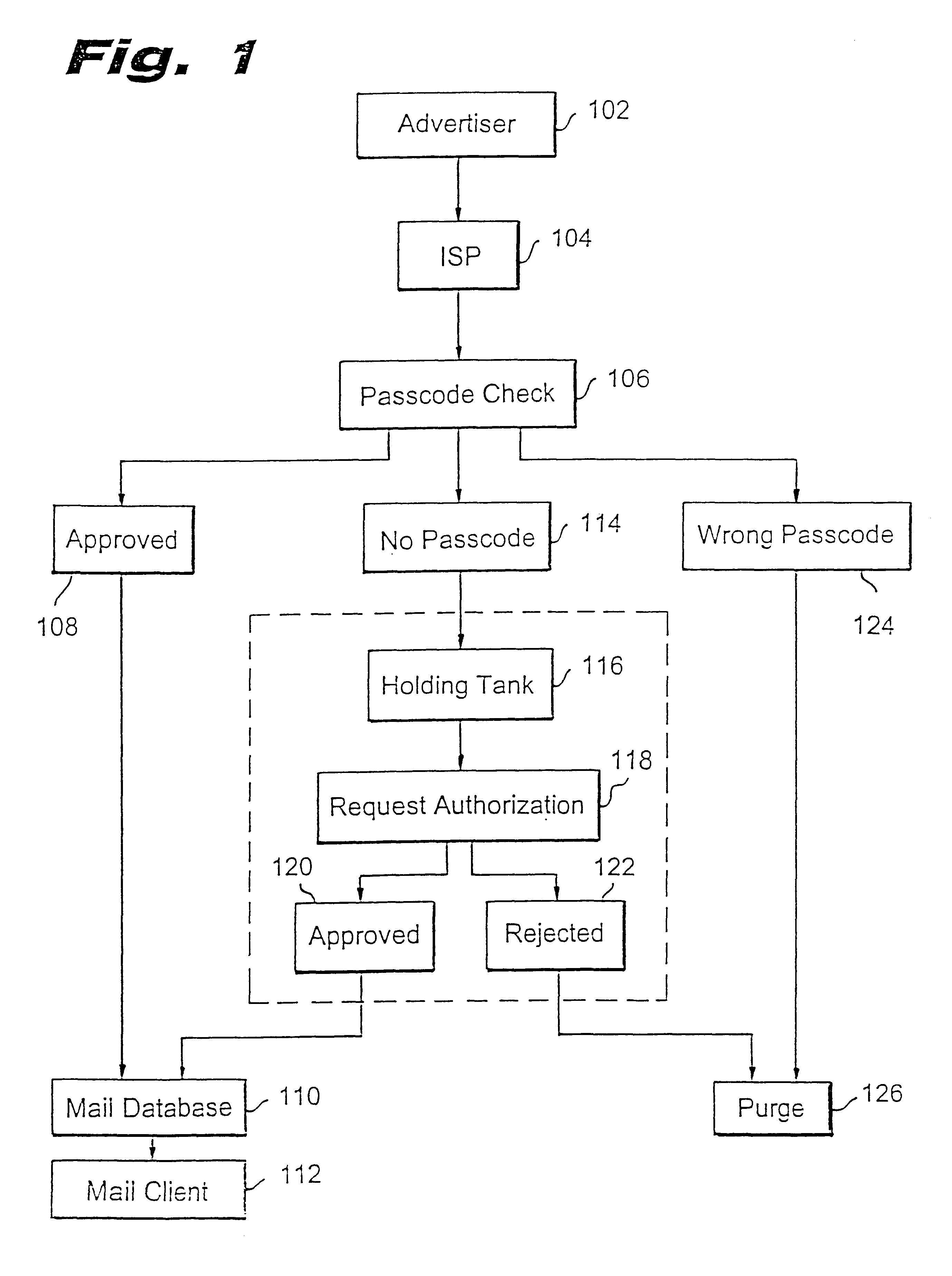
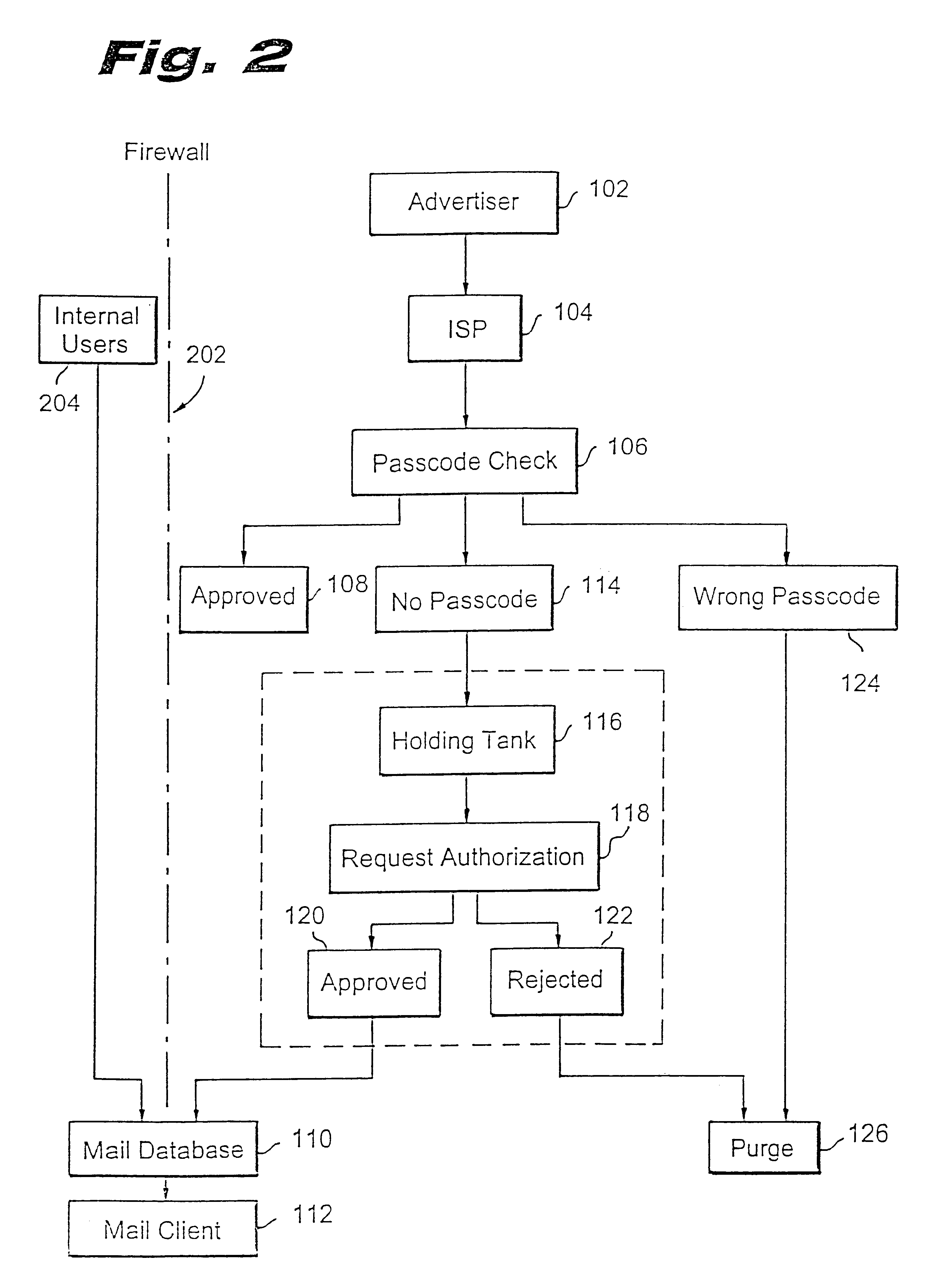
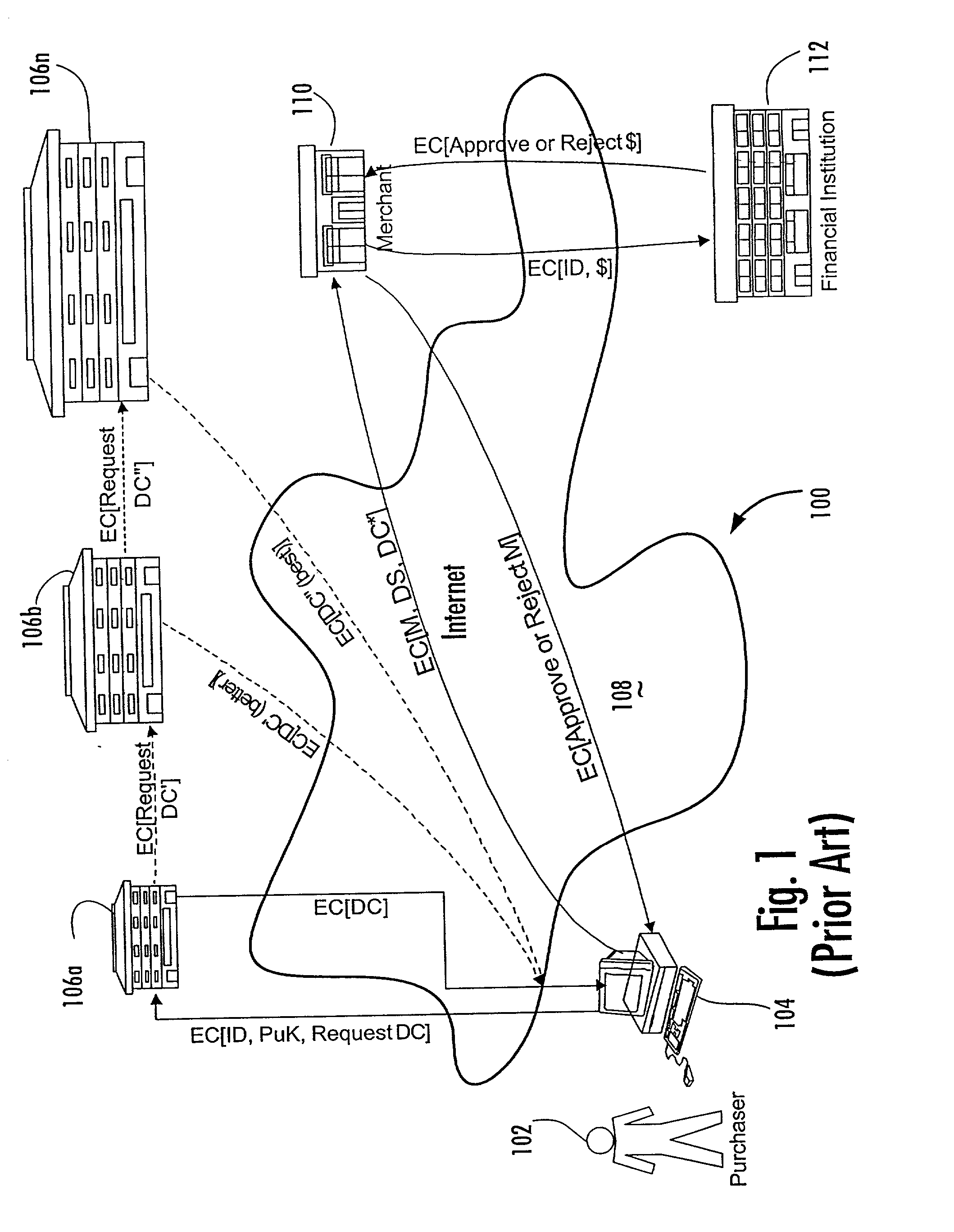
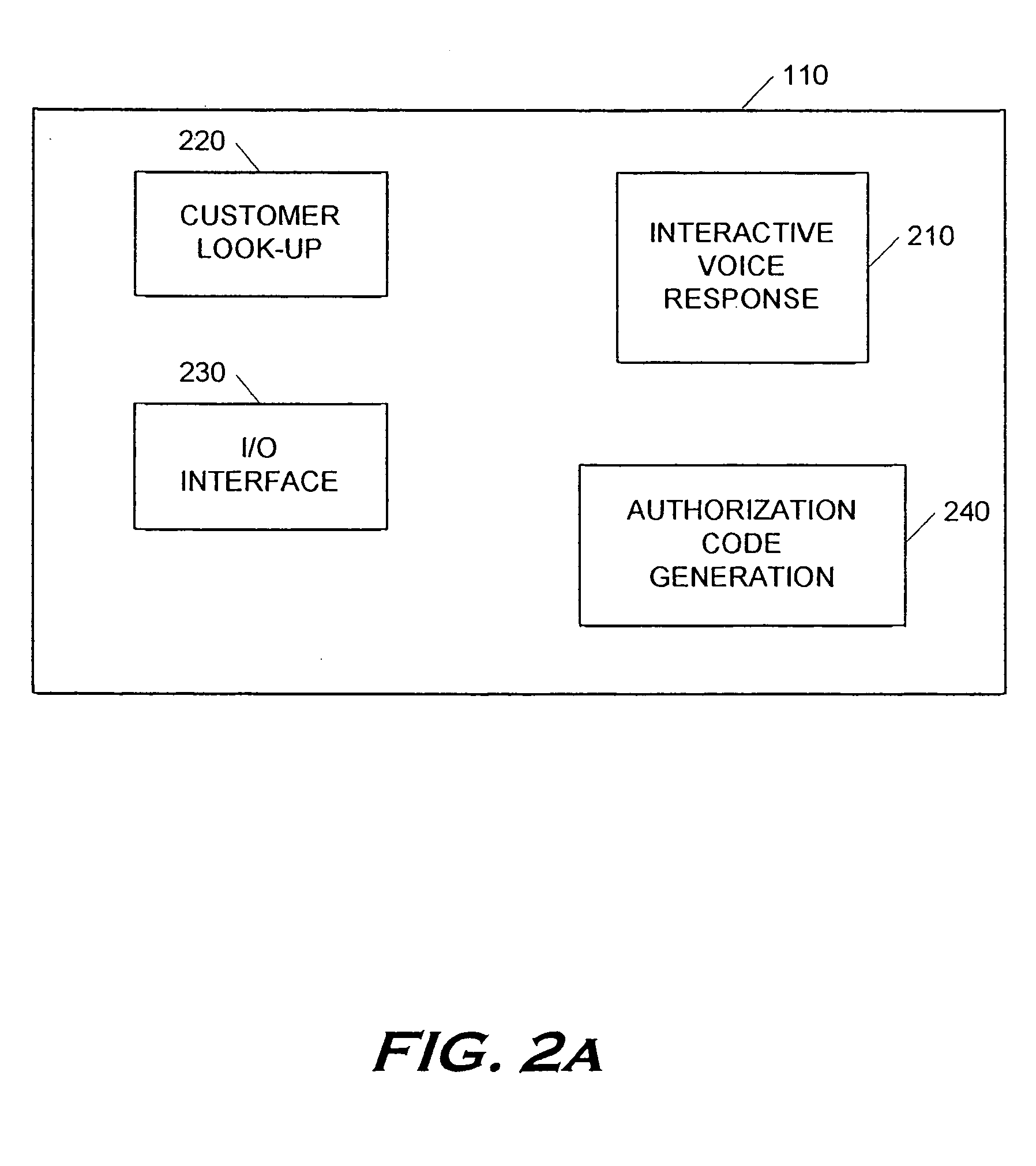
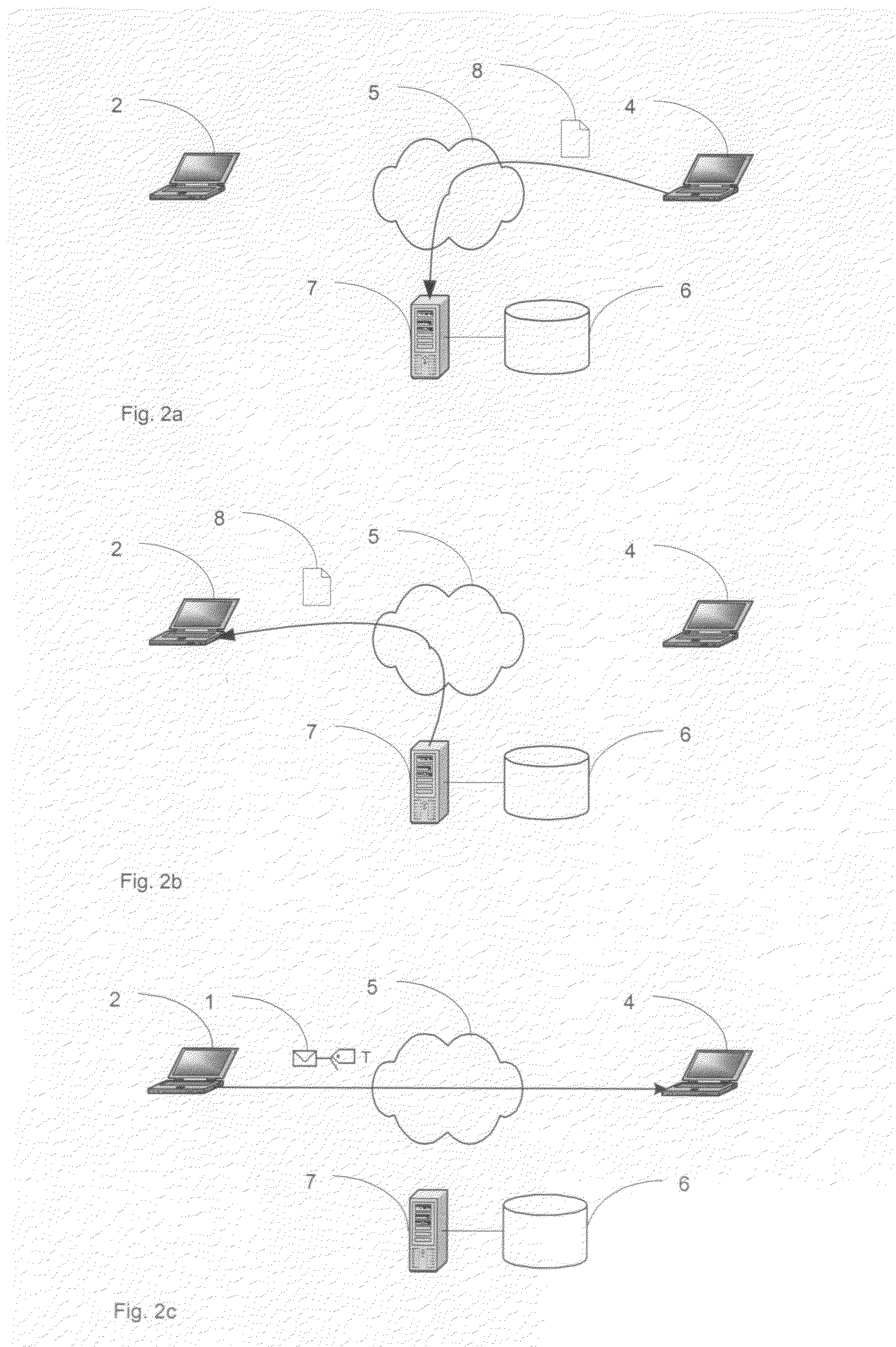
Method for blocking all unwanted e-mail (SPAM) using a header-based password
InactiveUS6266692B1Easy to sendEasy to solveOffice automationData switching networksEmail addressPassword
A method for blocking and / or filtering electronic mail. Selected senders are provided with a valid passcode associated with an e-mail address. When an e-mail is received at a mail server node, a field in a header of the e-mail is checked for a valid passcode associated with the destination e-mail address. If a valid passcode is detected, the e-mail is automatically sent to a receiver at the e-mail address. If an incorrect passcode is detected, the e-mail is automatically deleted at the server node and does not reach the receiver. If there is no passcode in the e-mail header, the e-mail is held temporarily, until the receiver approves to receive the e-mail. If the receiver rejects the e-mail, the e-mail is deleted. The present invention includes an additional capability for the senders of e-mails to request a passcode associated with a specific e-mail address in a lookup directory, before sending an e-mail to that address. Furthermore, the present invention enables firewall servers to block incoming e-mails only if they are received from the public Internet, thereby allowing all internal e-mails to reach the receiver without having to include valid passcodes.
Owner:TREND MICRO INC
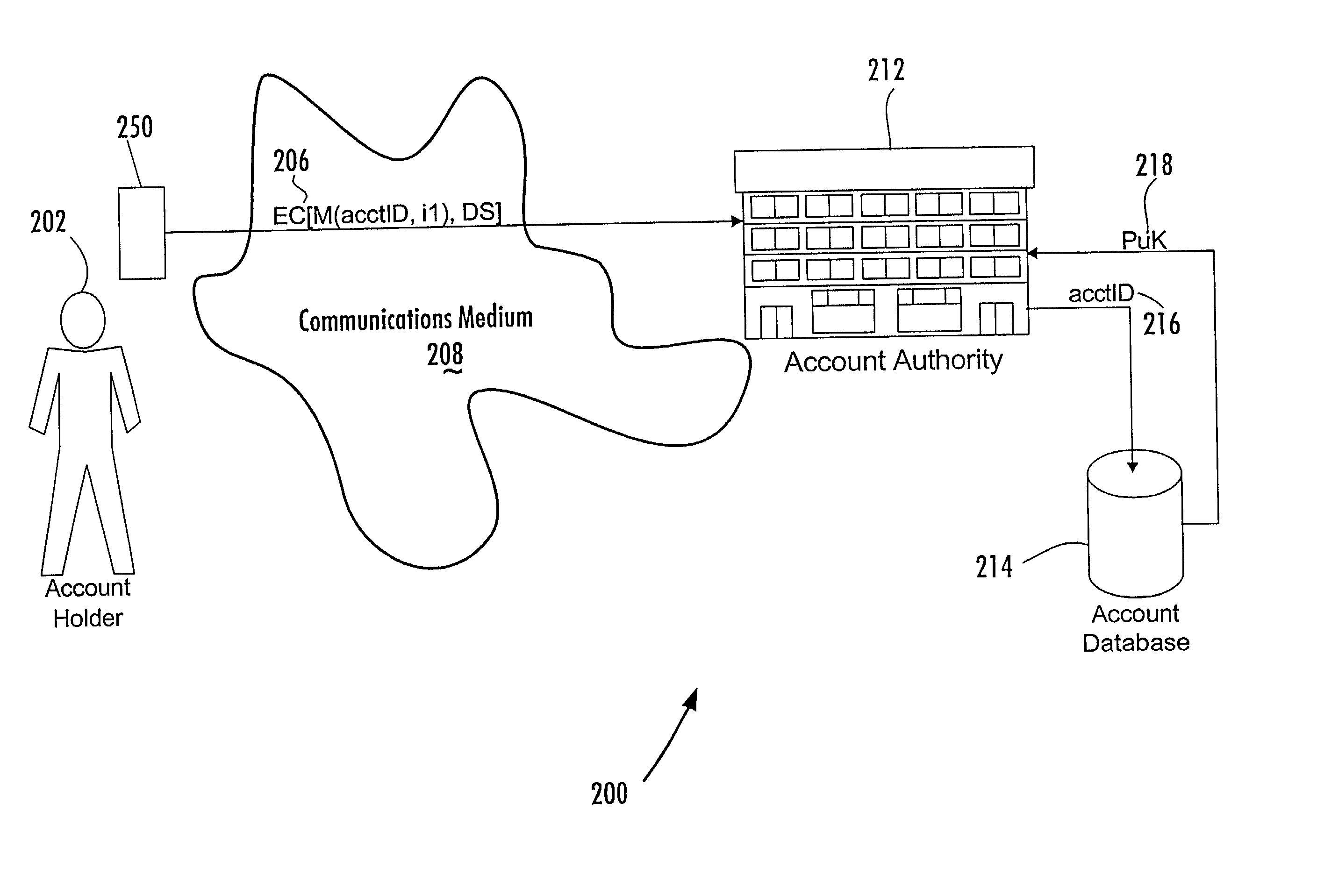
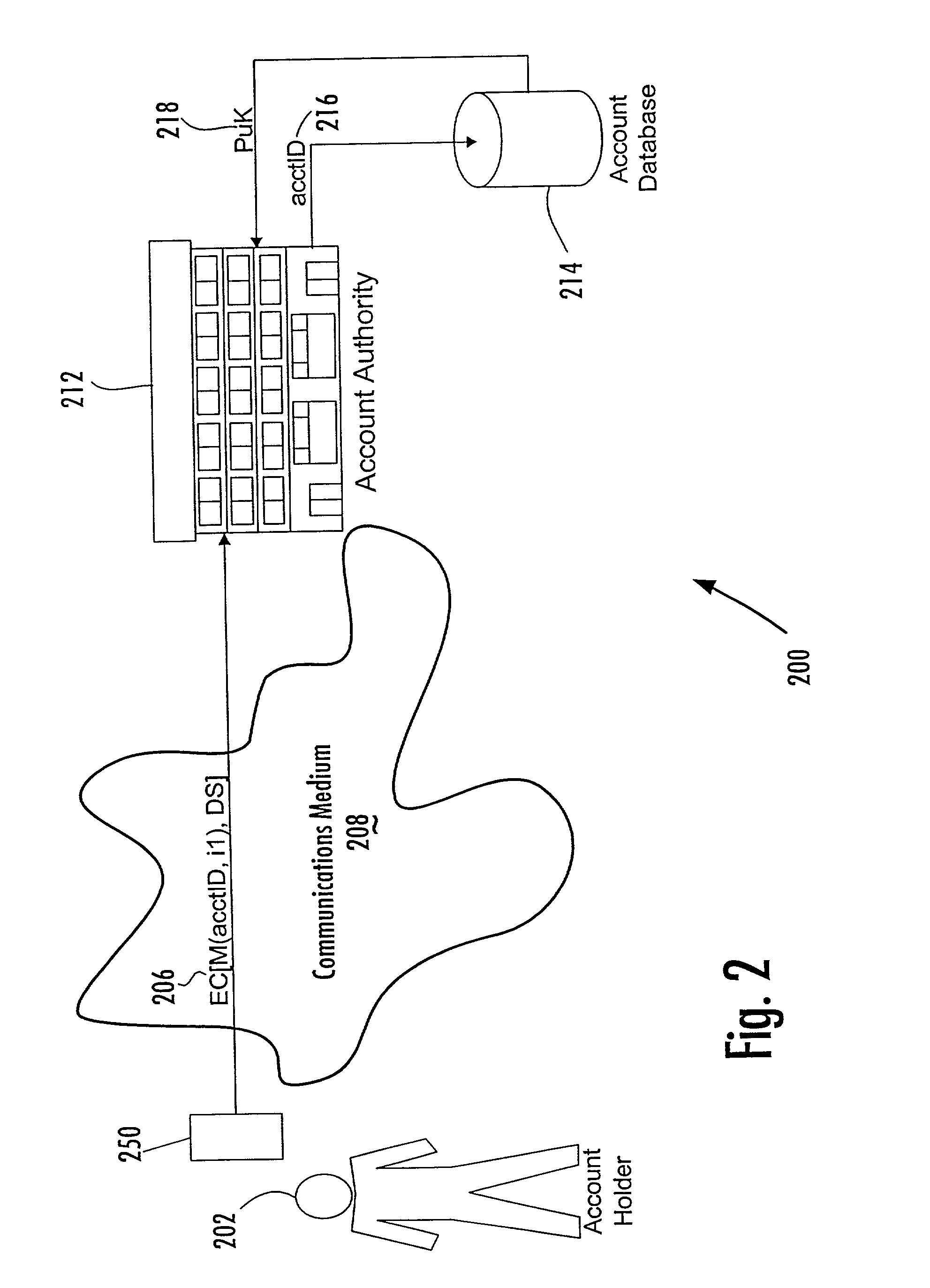
Account-based digital signature (ABDS) system
InactiveUS20020026575A1Key distribution for secure communicationFinanceDigital signatureElectronic communication
A method of authenticating an entity by a receiving party with respect to an electronic communication that is received by the receiving party and that includes both a unique identifier associated with an account maintained by the receiving party and a digital signature for a message regarding the account, consists of the steps of, before receipt of the electronic communication, first associating by the receiving party a public key of a public-private key pair with the unique identifier and, thereafter, only conducting message authentication using the digital signature received by the receiving party in the electronic communication and the public key associated with the account identifier.
Owner:FIRST DATA
Apparatus and method for facilitating money or value transfer
An apparatus and method for transferring money or value, using a wide range of interfaces to initiate a transfer and a wide range of options for receiving the transfer, including receiving the transferred sum directly to the communication device / account of the receiver. The receiver can use the transferred sum as an airtime credit, to obtain cash or to pay for other goods or services.
Owner:HIP CONSULT
Automatic deletion of electronic messages
InactiveUS20110213845A1Memory loss protectionError detection/correctionComputer hardwareElectronic information
A system and method are provided for automatically deleting messages such as e-mail upon consumption by the recipient. Consumption by the recipient may include viewing the message, forwarding or replying to the message, or archiving, saving, copying, or moving the message. An indicator is inserted in the message, for example in the message header or body, indicating that the message is to be deleted upon detection of a triggering consumption action. Upon receipt at the recipient's mail client, the client determines whether the indicator is present, and, upon detection of a triggering consumption action, automatically closes any views of the message displayed by the recipient's mail client and deletes the message. Optionally a warning is provided to the recipient prior to deletion.
Owner:BLACKBERRY LTD
Apparatus and method for facilitating money or value transfer
An apparatus and method for transferring money or value, using a wide range of interfaces to initiate a transfer and a wide range of options for receiving the transfer, including receiving the transferred sum directly to the communication device / account of the receiver. The receiver can use the transferred sum as an airtime credit, to obtain cash or to pay for other goods or services.
Owner:HIP CONSULT
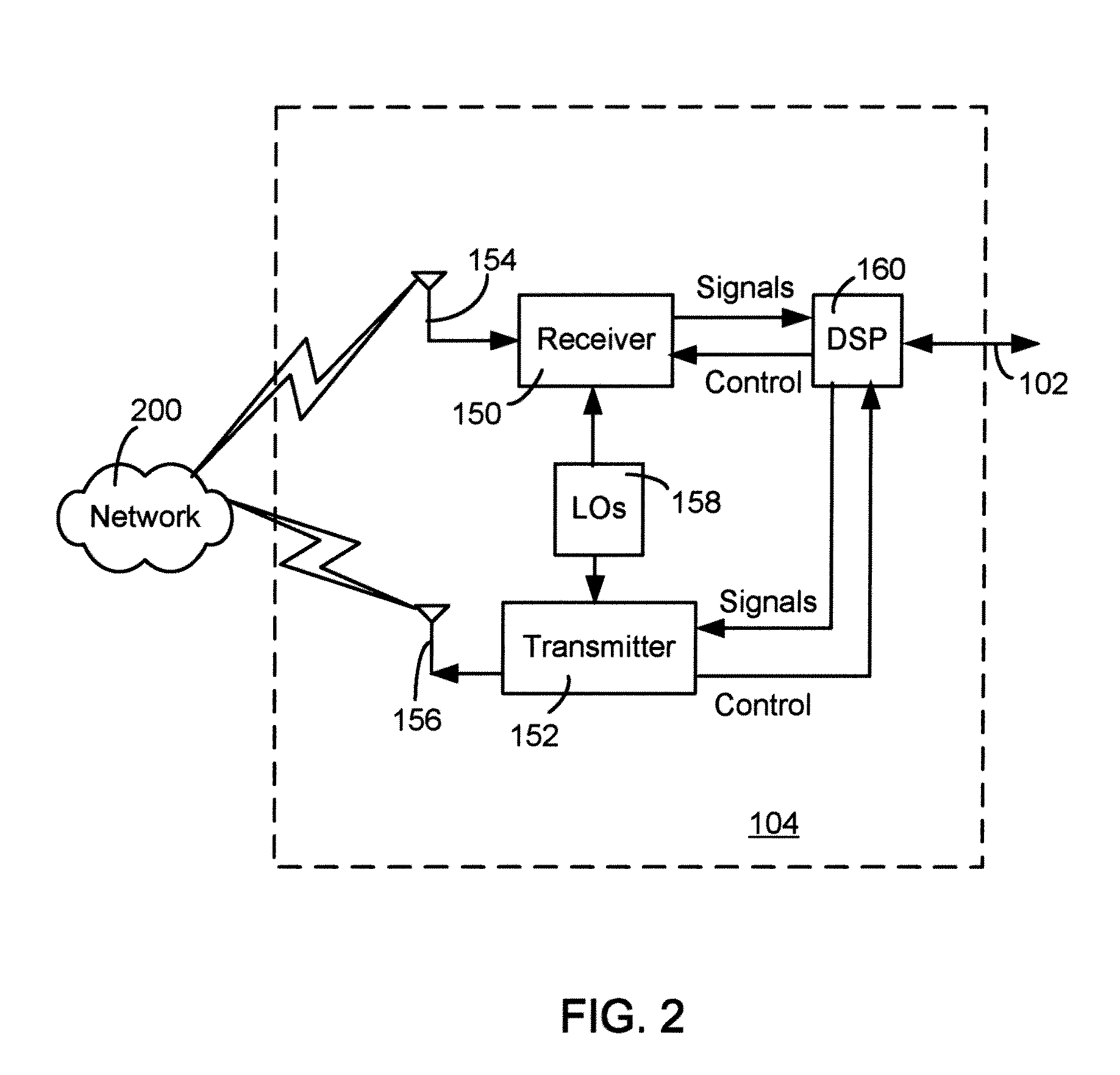
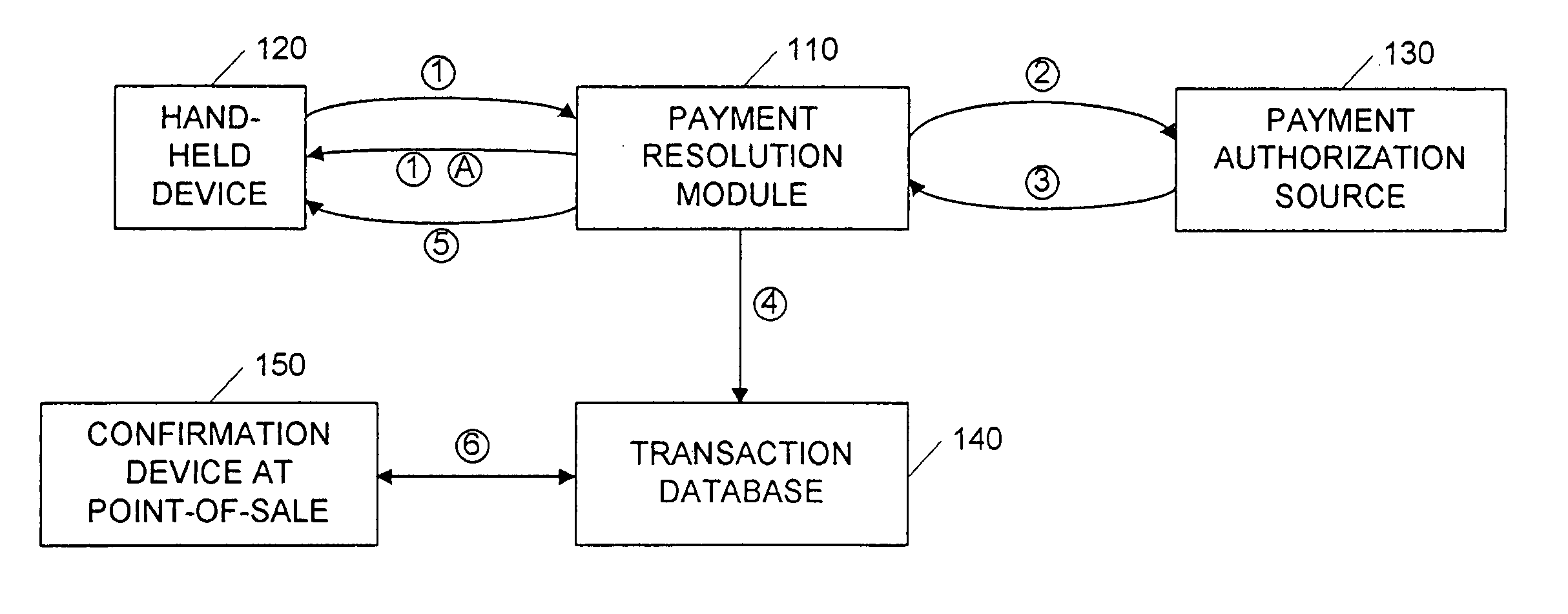
Secure money transfer between hand-held devices
A payment resolution module is configured to communicate with hand-held devices (such as mobile phones, PDA's, or computers) to allow secure transfer of funds between financial accounts associated with each of the hand-held devices. A user of a paying device may be identified as the owner of the device either by having the option to enter a personal identification code, or by using a biometric to identify himself, for example. Accordingly, only an authorized user of the hand-held device may use the hand-held device to transfer funds. A user of the recipient device may be identified by an identification code or a telephone number, for example, which is associated with a recipient financial account. After the payment resolution module receives authorization for a payment request to the recipient account, a payment transfer module transmits the requested amount from a payment source associated with the identified owner of the paying device to the recipient account.
Owner:XILIDEV
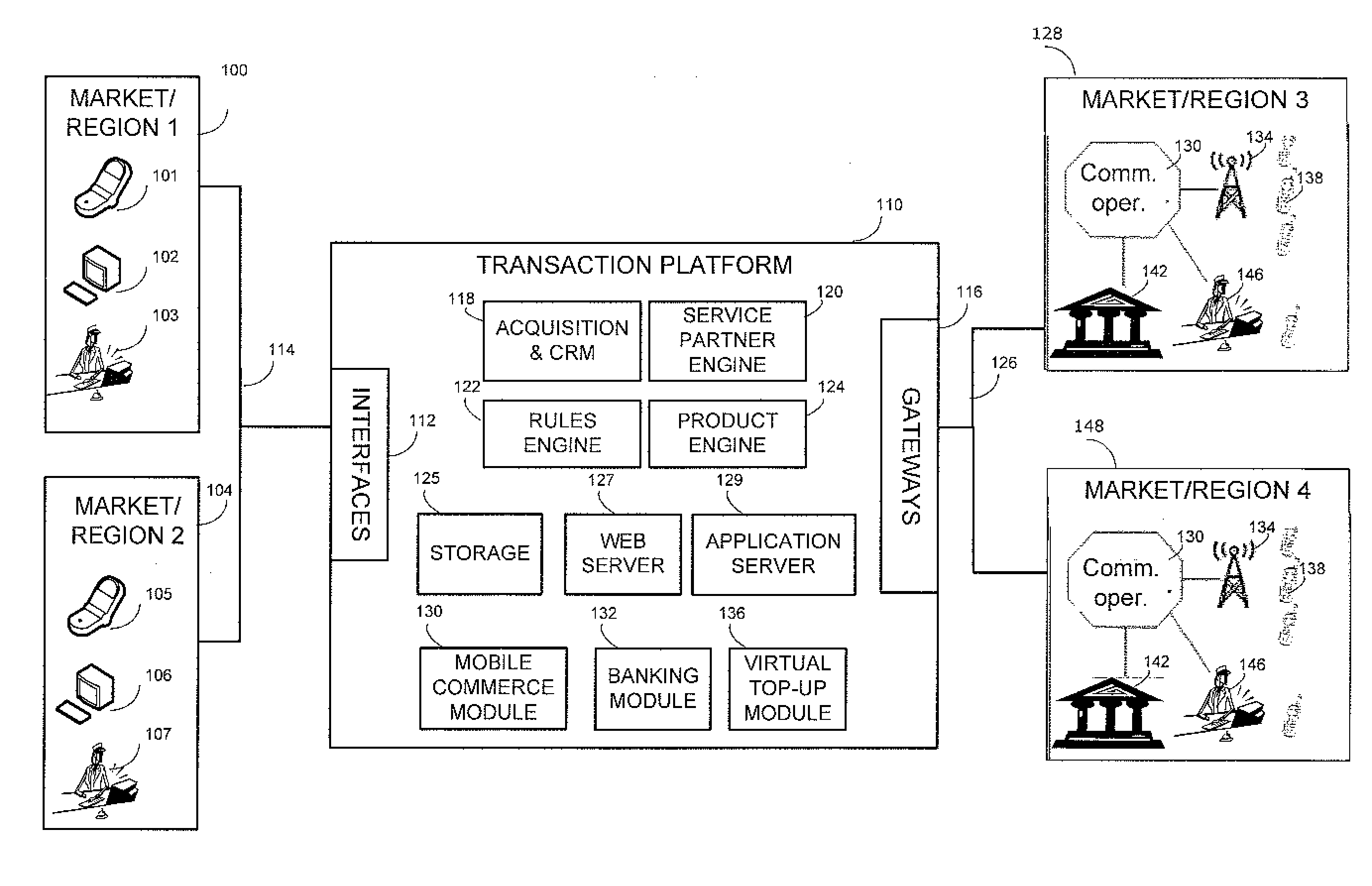
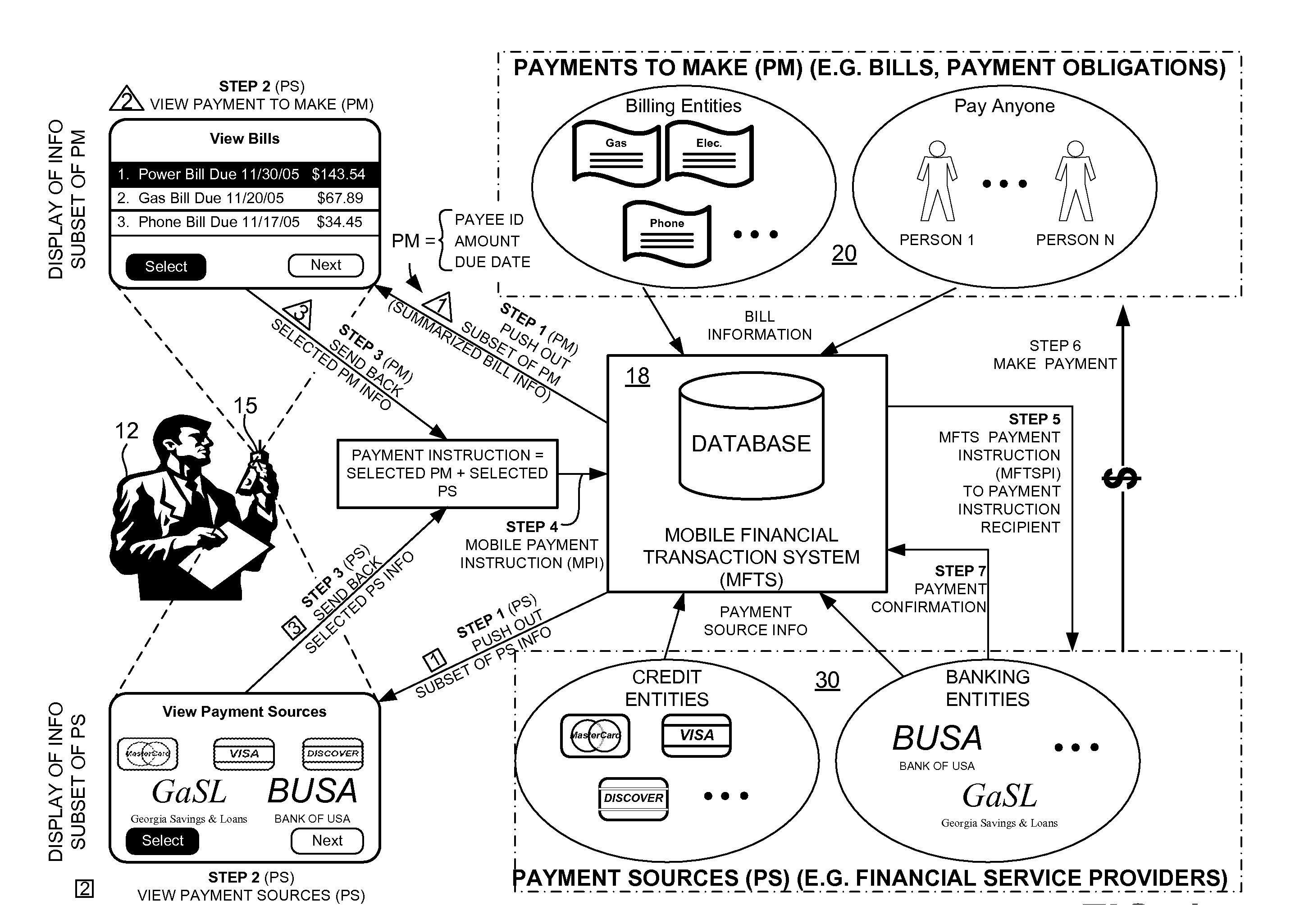
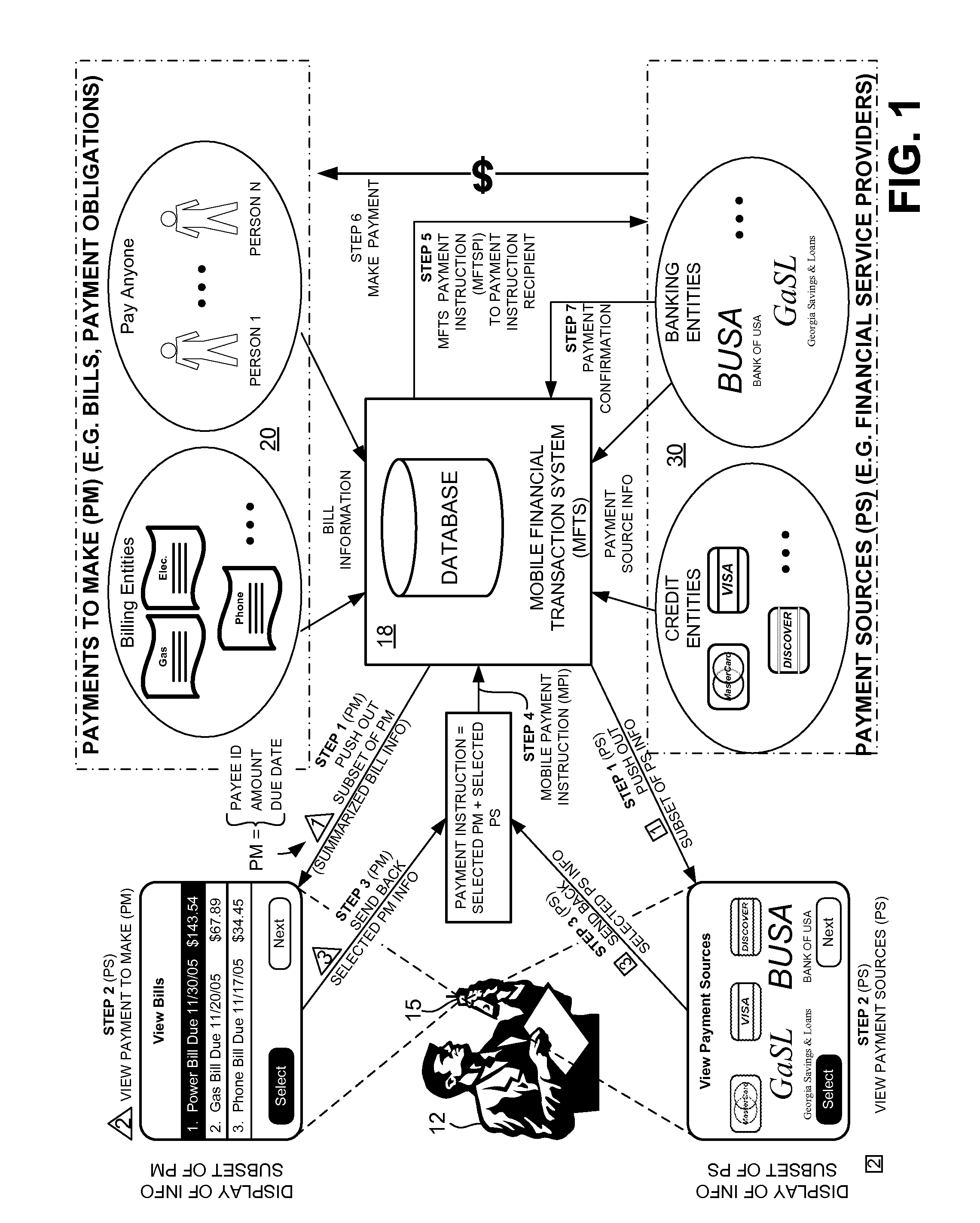
Methods and Systems For Payment Transactions in a Mobile Environment
ActiveUS20080010190A1Unprecedented convenienceUnprecedented flexibilityFinancePayment architecturePayment transactionFinancial transaction
Methods and systems for conducting financial transactions in a mobile environment utilizing a mobile device such as a mobile telephone or wireless connected personal digital assistant (PDA) that communicates with a mobile financial transaction system (MFTS) that stores user and transaction information. The MFTS receives information on behalf of a mobile device user corresponding to bills to pay or other payments to make. The MFTS also receives information corresponding to payment sources available for use in making payments. Selected payments information and payment source information are communicated to the mobile user via a wireless network and displayed for user selection. The user selects a payment to make and a payment source. A mobile payment instruction is generated and communicated to the MFTS. The MFTS instructs a payment instruction recipient to make a payment to an identified payee. Real-time updated account and payment balances are provided to the user's mobile device.
Owner:QUALCOMM INC
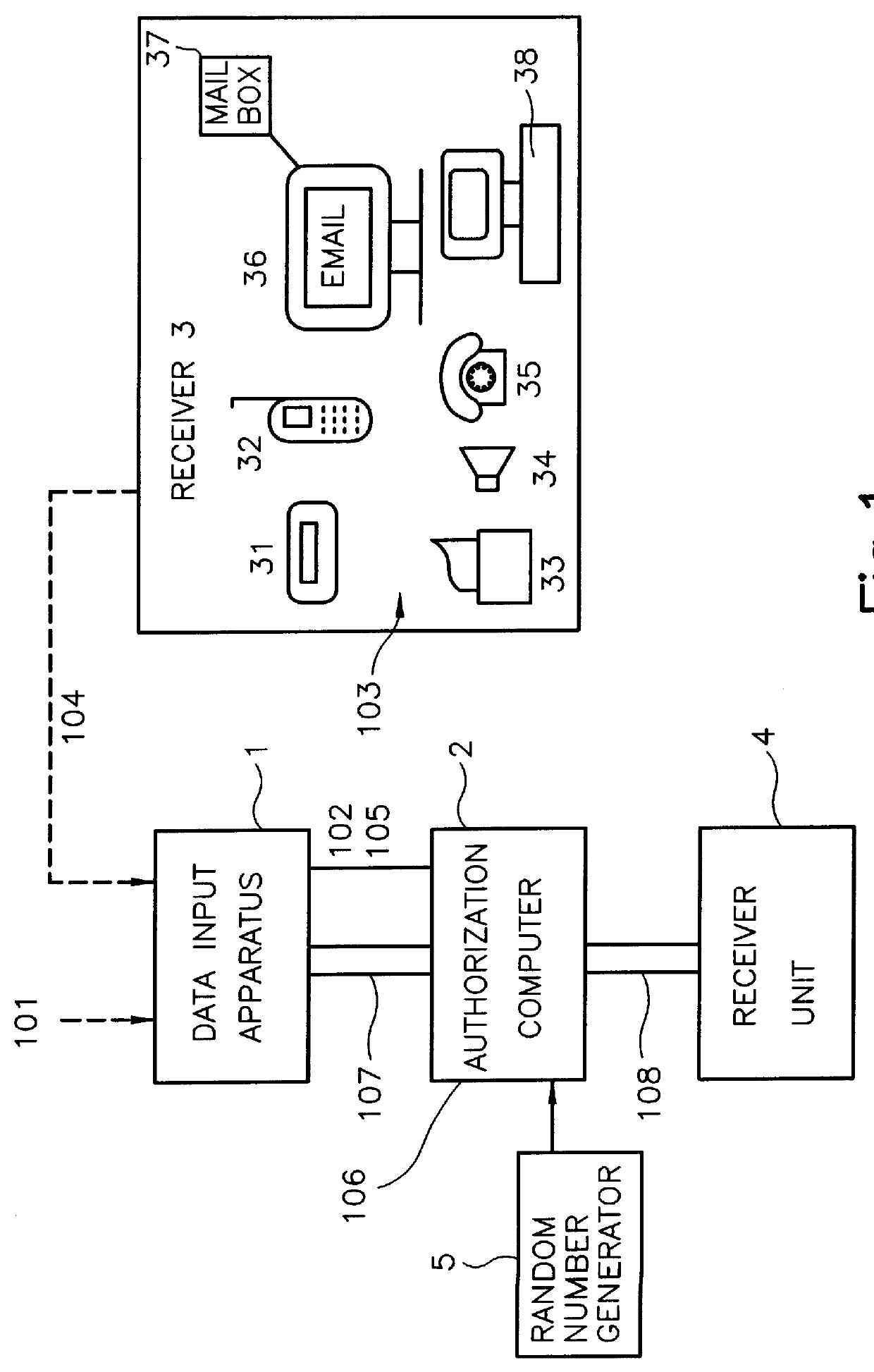
Method for authorizing in data transmission systems
InactiveUS6078908ALow costFacilitate communicationLock applicationsDigital data processing detailsPasswordPager
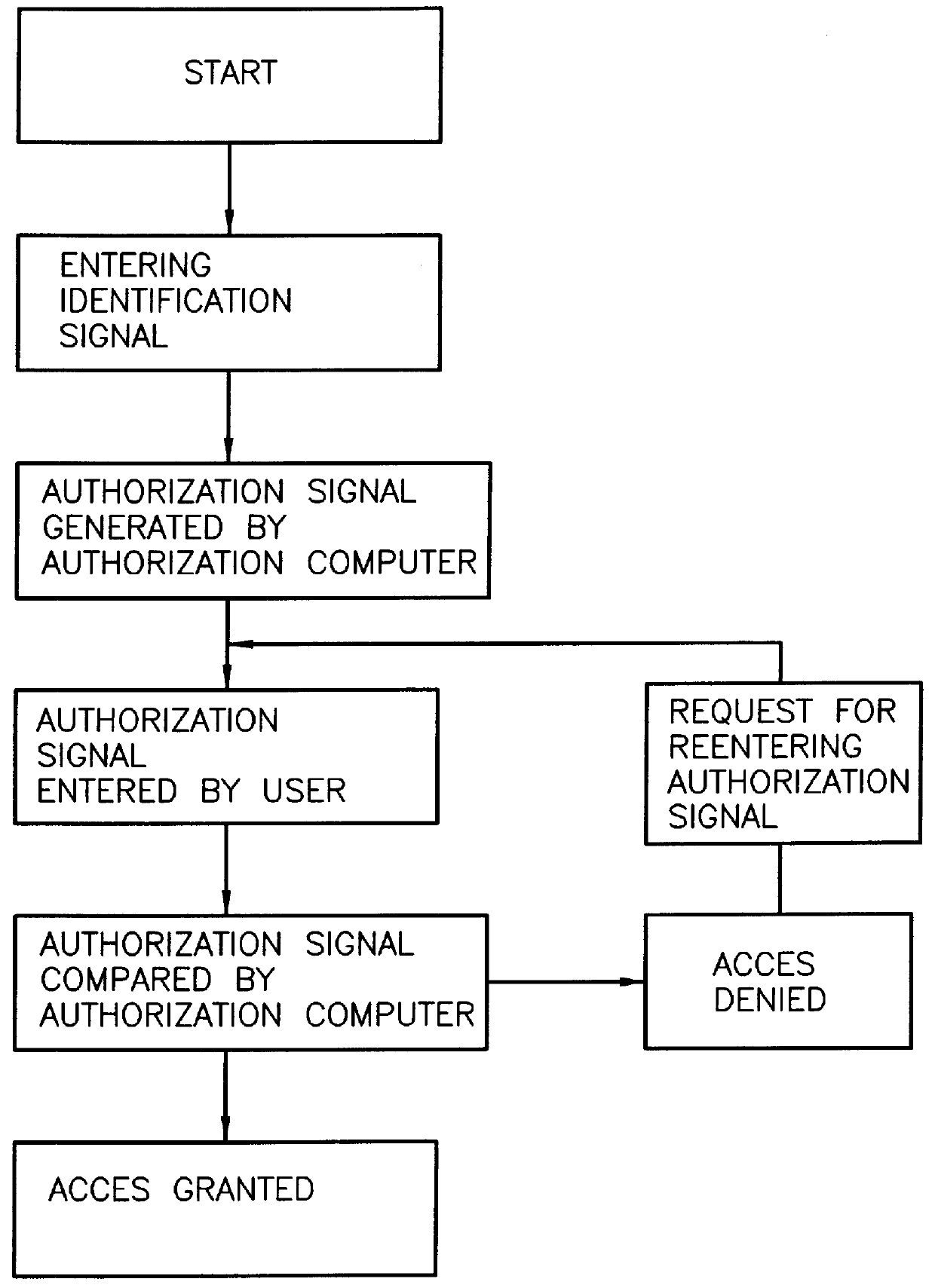
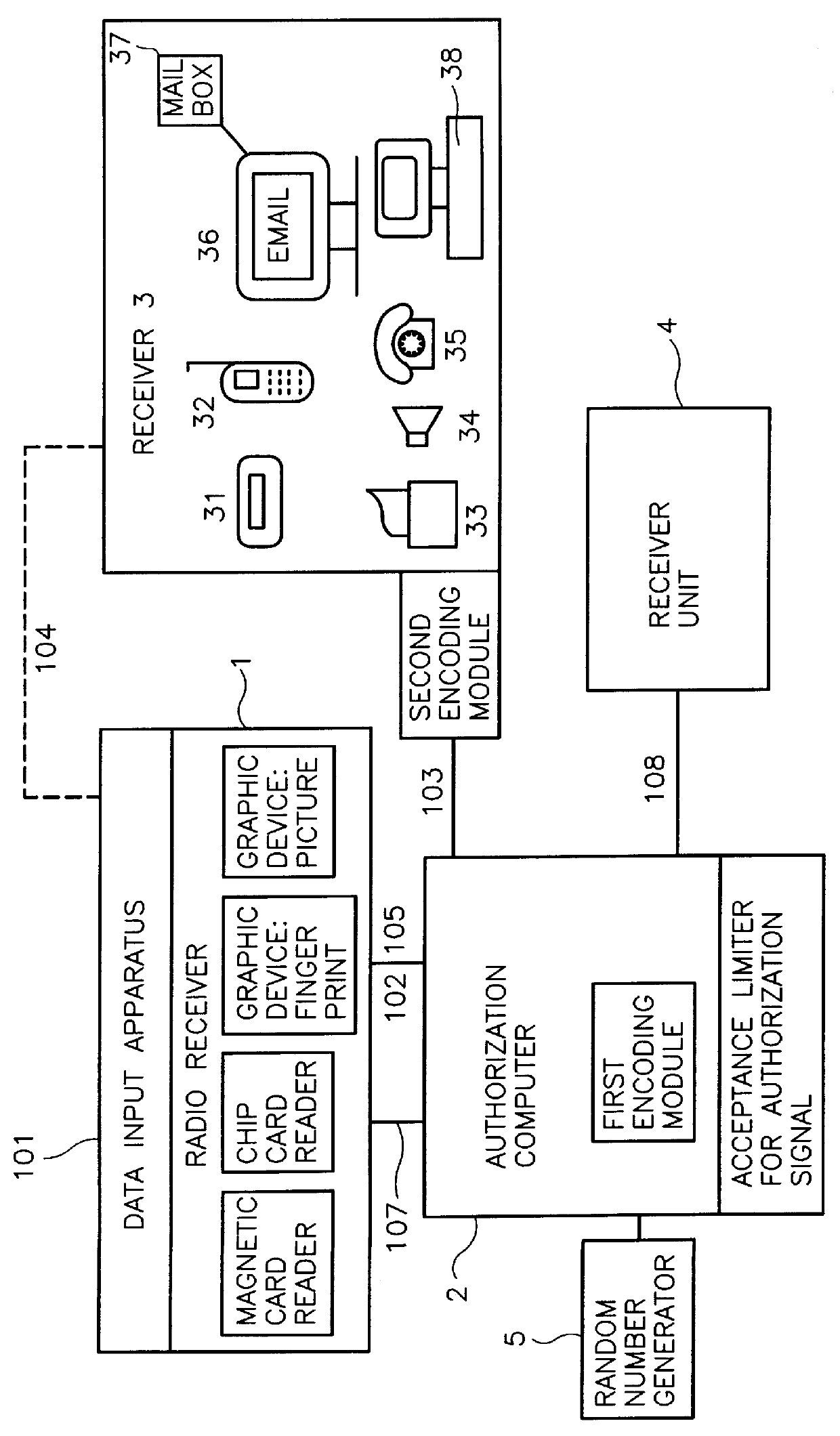
The invention relates to a method and to a device for the authorization in data transmission systems employing a transaction authorization number (TAN) or a comparable password. According to a first step, the user sends a qualifying identification of the data input apparatus together with a request for the generation or for the selection of a transaction authorization number TAN or of comparable password from a data file from the data input apparatus to an authorization computer. In a second step the authorization computer generates the transaction authorization number TAN or the comparable password or selects them form a data file. According to a third step, the authorization computer sends the transaction authorization number TAN or the comparable password over a second transmission path different from the first transmission path to a monitor, for example a pager. According to a fourth step, the user reads this transaction authorization number TAN or the comparable password from the receiver and enters the transaction authorization number TAN or the comparable password into the data input apparatus. According to a fifth step, this transaction authorization number TAN or the comparable password is transmitted to the authorization computer. According to a sixth step, the authorization computer verifies the validity of the transaction authorization number TAN or of the comparable password in order to establish or switch free, according to a seventh step, a connection between the data input apparatus and the receiver unit.
Owner:SCHMITZ KIM
Privacy firewall
ActiveUS9665722B2Protect normal useAvoid identificationRelational databasesDigital data protectionSupplicantInternet privacy
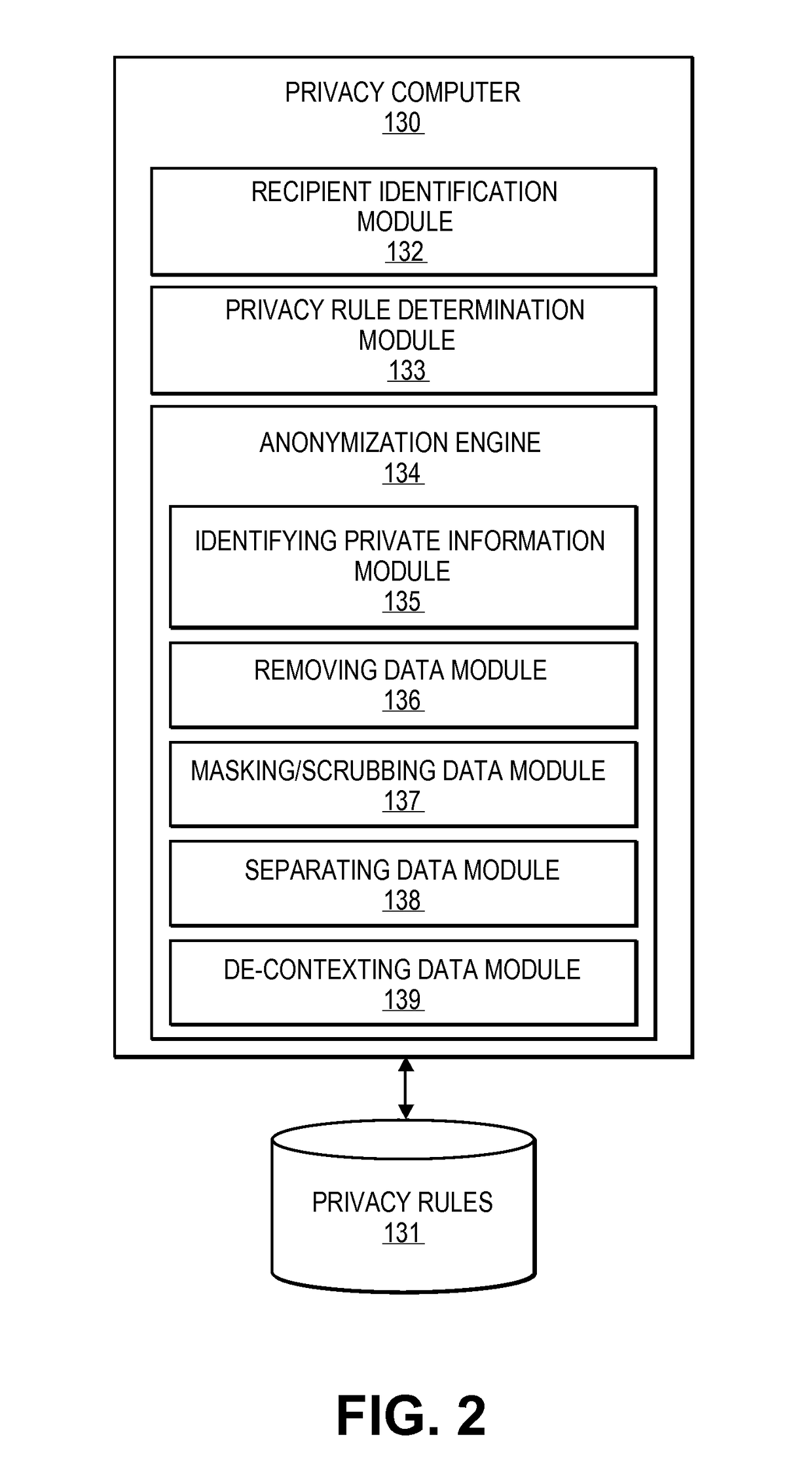
Embodiments of the invention relate to systems and methods for providing an anonymization engine. One embodiment of the present invention relates to a method comprising receiving a message directed at a recipient computer located outside a secure area by a privacy computer located within a secure area. The privacy computer may identify private information using a plurality of privacy rules and anonymize the message according to the plurality of privacy rules. Another embodiment may be directed to a method comprising receiving a request for sensitive data from a requesting computer. An anonymization computer may determine a sensitive data record associated with the request and may anonymize the sensitive data record by performing at least two of: removing unnecessary sensitive data entries from the sensitive data record, masking the sensitive data entries to maintain format, separating the sensitive data entries into associated data groupings, and de-contexting the data.
Owner:VISA INT SERVICE ASSOC
Network configured for delivery of content for download to a recipient
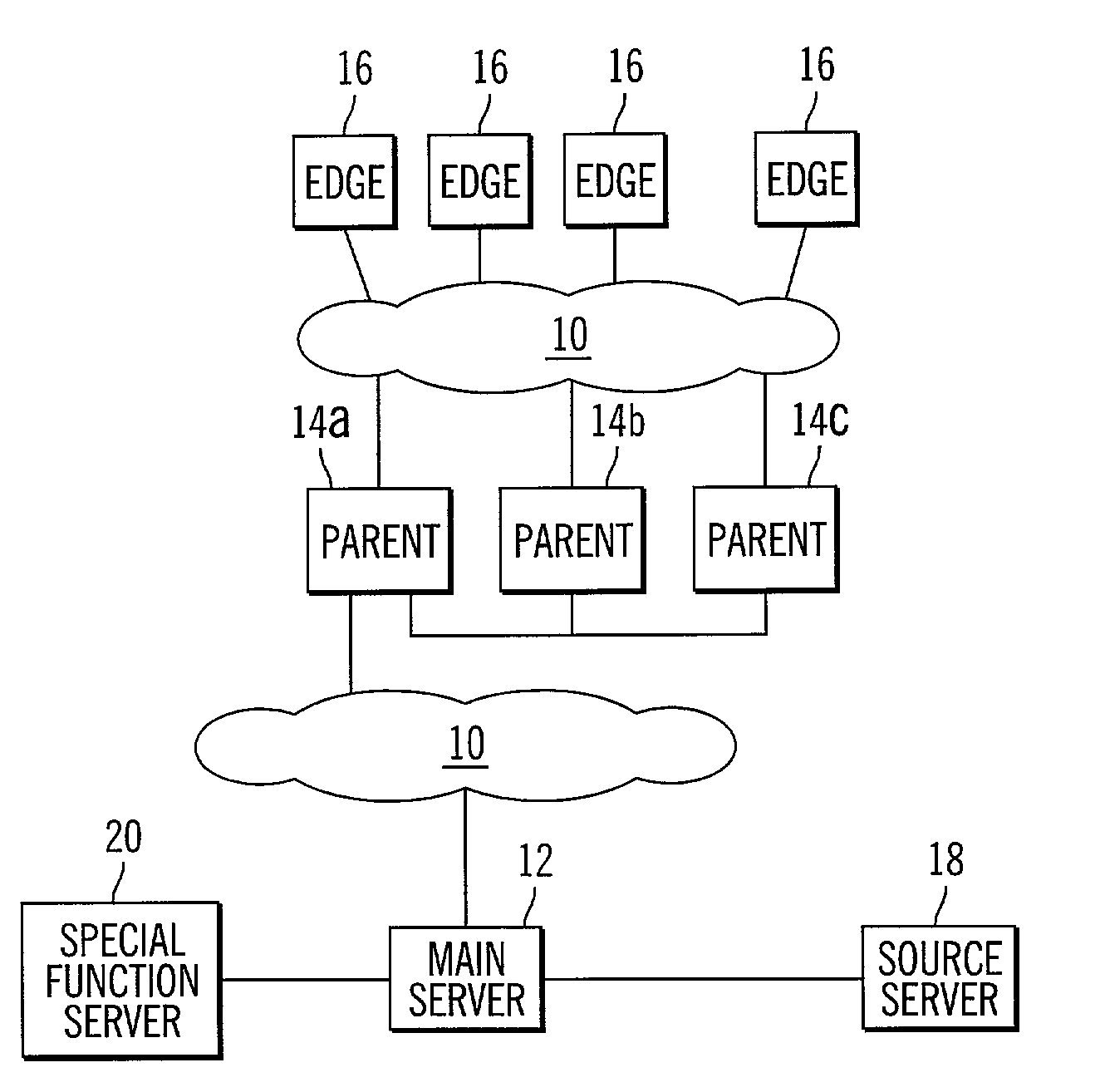
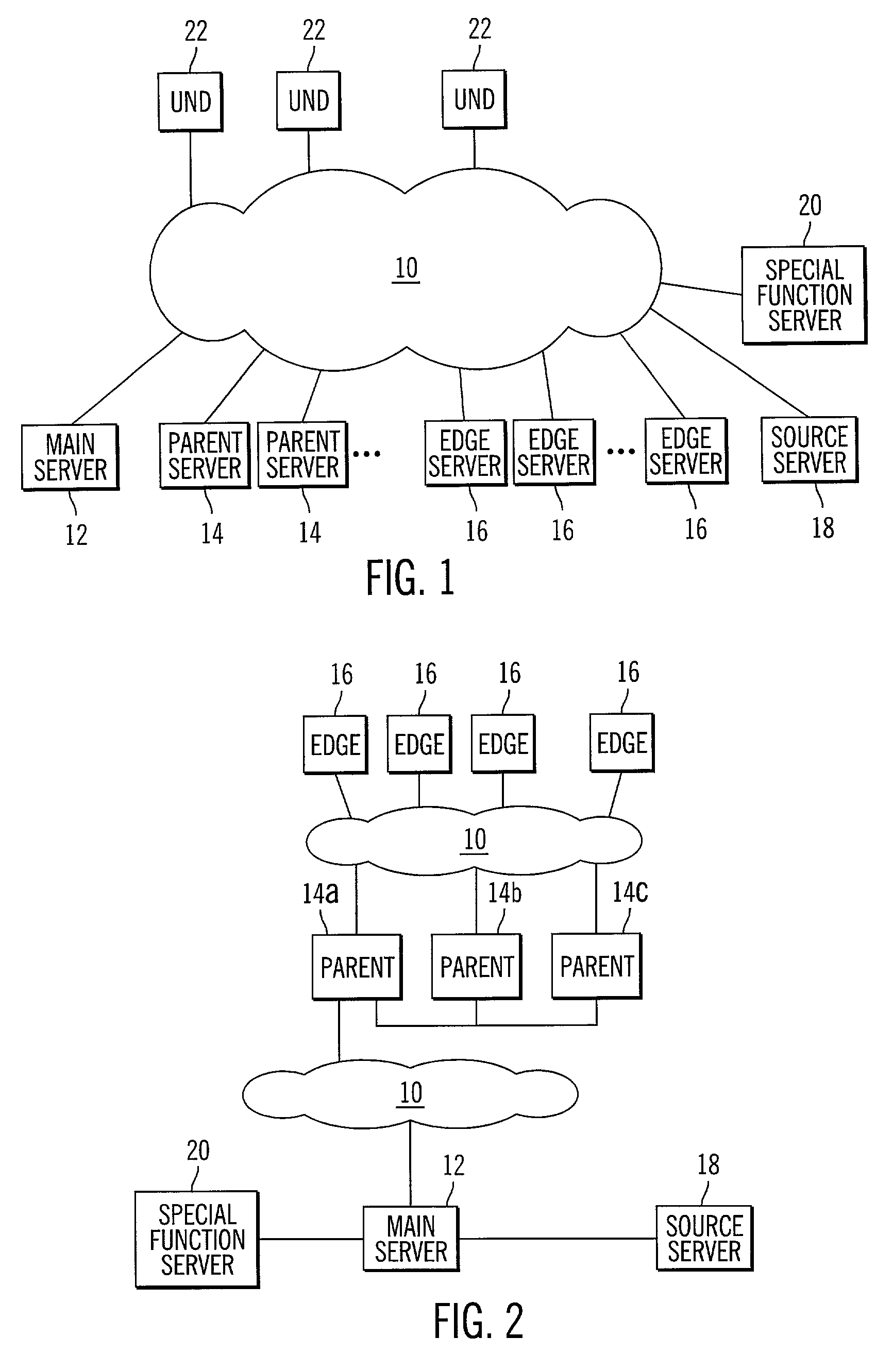
InactiveUS7024466B2Increase speed and efficiencyEffective controlMultiprogramming arrangementsMultiple digital computer combinationsEdge serverNetwork architecture
Owner:BLOCKBUSTER LLC
Method and apparatus for improving file access performance of distributed storage system
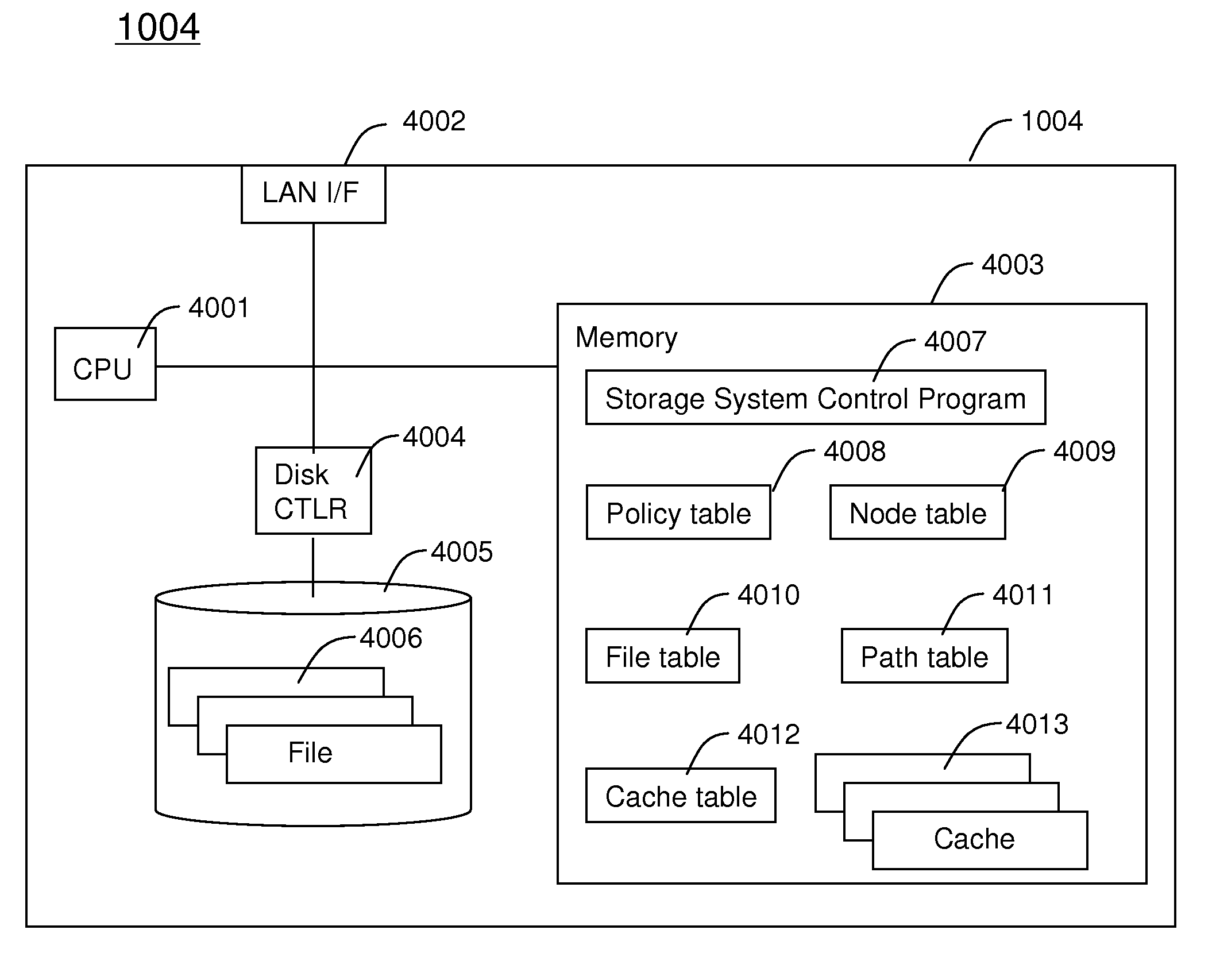
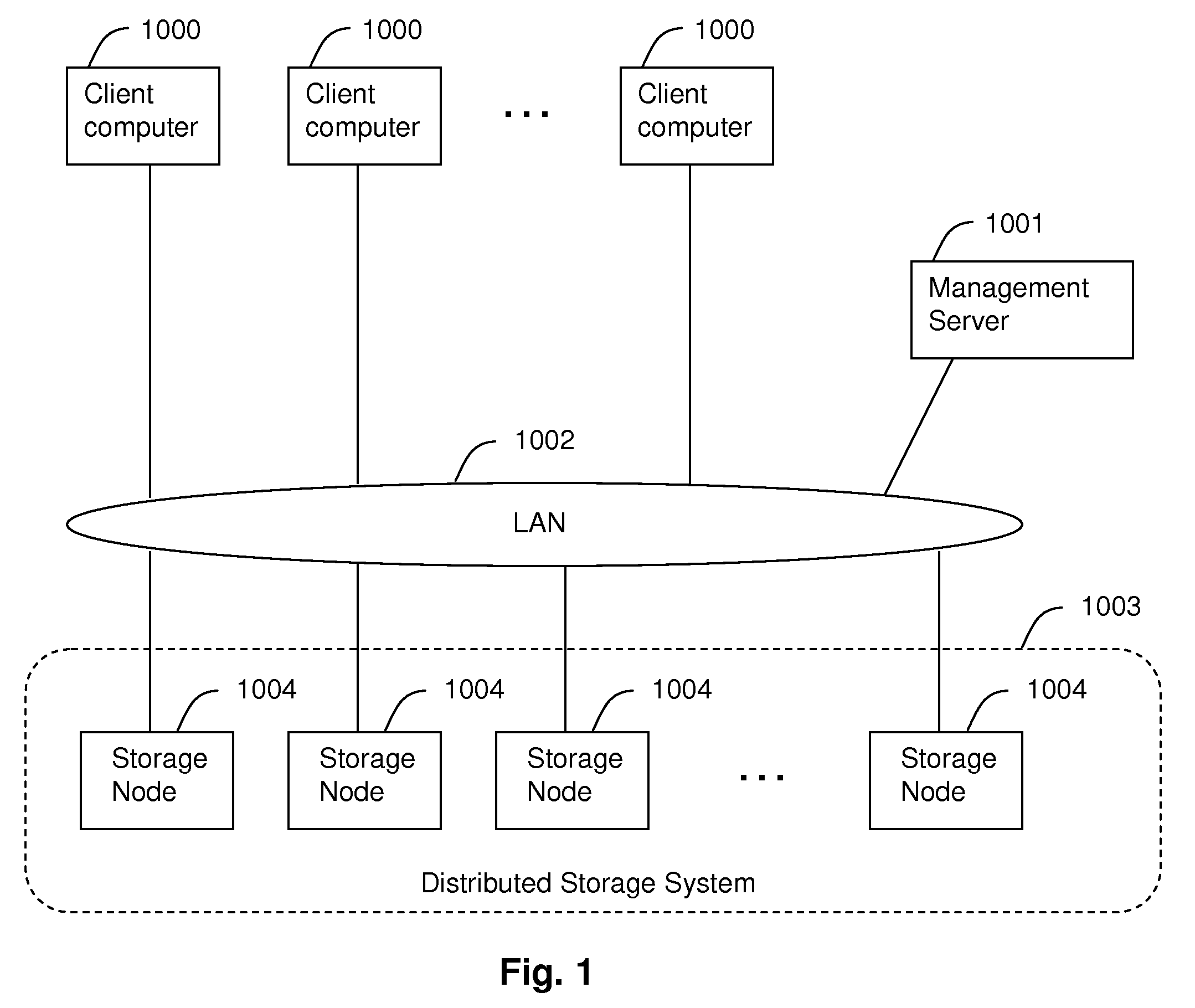
InactiveUS8086634B2Improve performanceReduce overheadDigital data information retrievalDigital data processing detailsNetwork connectivityDistributed memory systems
Embodiments of the invention provide methods and apparatus for improving the performance of file transfer to a client from a distributed storage system which provides single name space to clients. In one embodiment, a system for providing access to files in a distributed storage system comprises a plurality of storage nodes and at least one computer device connected via a network. Each storage node is configured, upon receiving a file access request for a file from one of the at least one computer device as a receiver storage node, to determine whether or not to inform the computer device making the file access request to redirect the file access request to an owner storage node of the file according to a preset policy. The preset policy defines conditions for whether to redirect the file access request based on at least one of file type or file size of the file.
Owner:HITACHI LTD
Ppdu receiving method and apparatus based on the MIMO technique in a WLAN system
ActiveUS20120327915A1Improve throughputBottleneck phenomenon can be decreasedError preventionTransmission path divisionMulti inputTelecommunications
Provided is a method of receiving a physical layer convergence procedure (PLCP) protocol data unit (PPDU) by an access point (AP) in a wireless local area (LAN) system. The method includes: allocating a first transmission channel bandwidth to a first station (STA) which is multiple input multiple output (MIMO)-paired with the AP; allocating a second transmission channel bandwidth to a second STA which is MIMO-paired with the AP; transmitting to the first STA and the second STA a sync trigger for determining a time point at which the first STA transmits a first PPDU and a time point at which the second STA transmits a second PPDU; and receiving simultaneously the first PPDU and the second PPDU from the first STA and the second STA.
Owner:LG ELECTRONICS INC
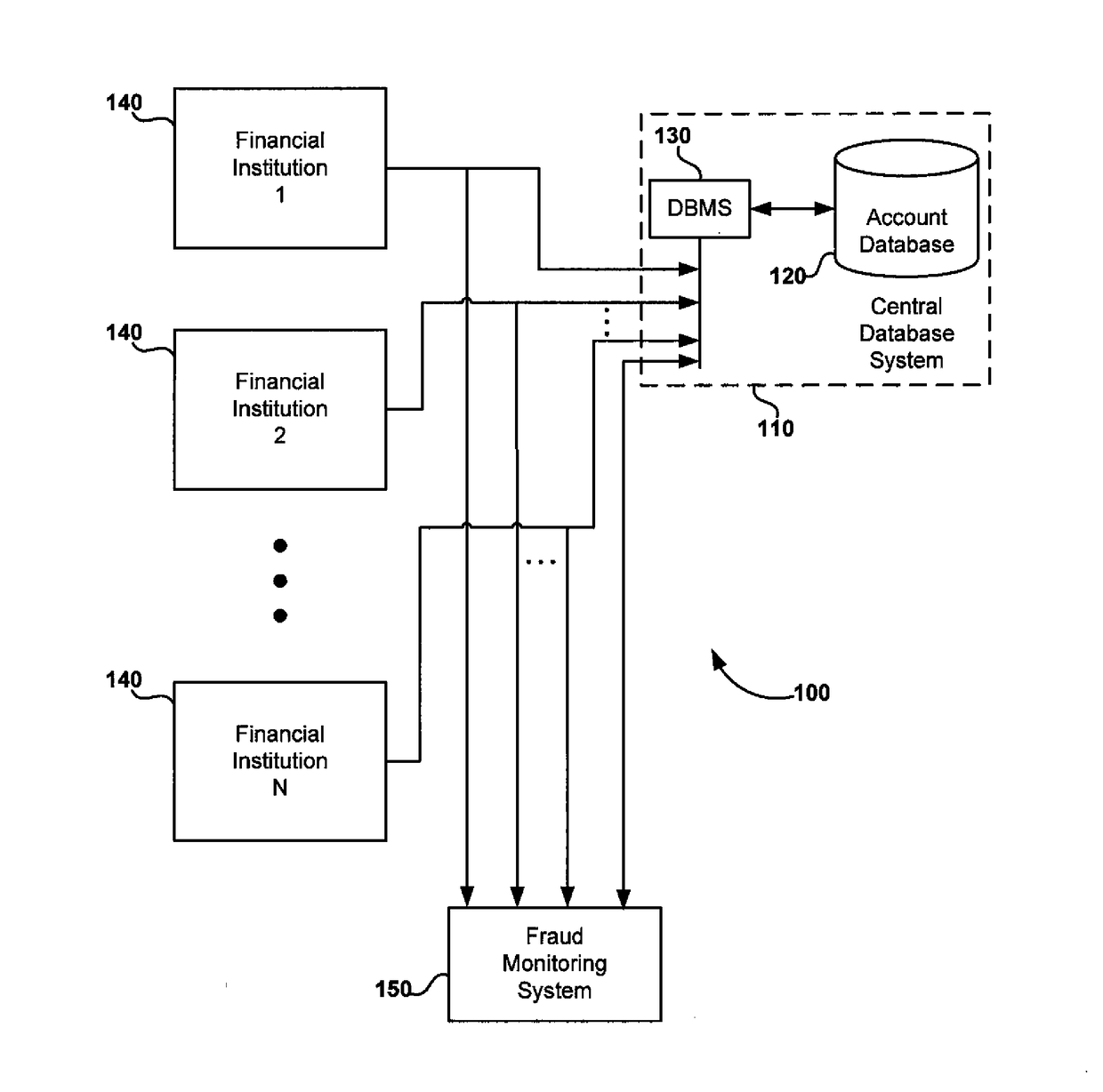
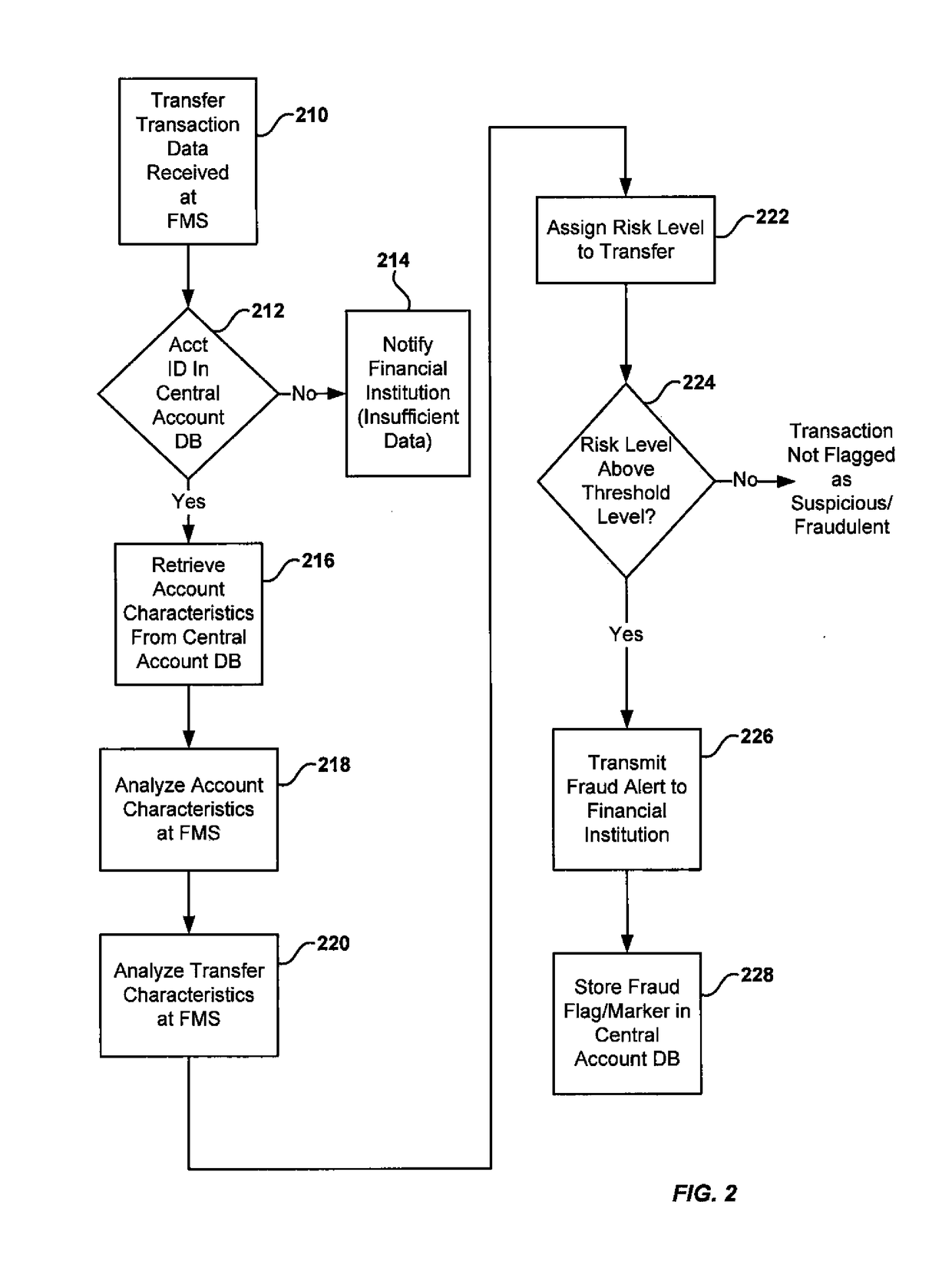
System and method for detecting fraudulent account access and transfers
Transfers of money into a recipient account are analyzed for risk of fraud by using a fraud monitoring system to analyze characteristics of the recipient account. The recipient account characteristics are stored in a central database, which has account data (for recipient accounts) contributed from a plurality of financial institutions that maintain such accounts. When a transfer is made or attempted, the stored characteristics of the recipient account are analyzed and a risk score is assigned to the transfer based on the recipient account. If the risk score indicates a suspicious or fraudulent transaction, an alert is provided. In an alternative embodiment, the risk analysis may be supplemented by analysis of transaction data association with the transfer.
Owner:EARLY WARNING SERVICES
Technique for enabling traffic engineering on CE-CE paths across a provider network
ActiveUS20070133406A1Create efficientlyReduce needError preventionTransmission systemsPrivate networkDistributed computing
A technique enables Traffic Engineering (TE) on paths between customer edge devices (CEs) across a provider network (“CE-CE paths”) in a computer network. According to the novel technique, TE is configured on a link from a sending provider edge device (PE) to a first CE (“PE-CE link”), e.g., a CE of one or more virtual private networks (VPNs). The sending PE conveys TE information of the PE-CE link to one or more receiving PEs in the provider network. Upon receiving the TE information, each receiving PE expands a TE database (TED) for information regarding the provider network (i.e., a “core TED”) to include TE-configured PE-CE links, e.g., by updating one or more corresponding VPN TEDs (VTEDs) for each VPN maintained by the receiving PE. Once the receiving PEs have the TE information for configured PE-CE links from the provider network, one or more TE techniques may be applied to paths from a second CE of the receiving PE to the first CE (a CE-CE path) to thereby facilitate, e.g., establishment of TE-LSPs along CE-CE paths.
Owner:CISCO TECH INC
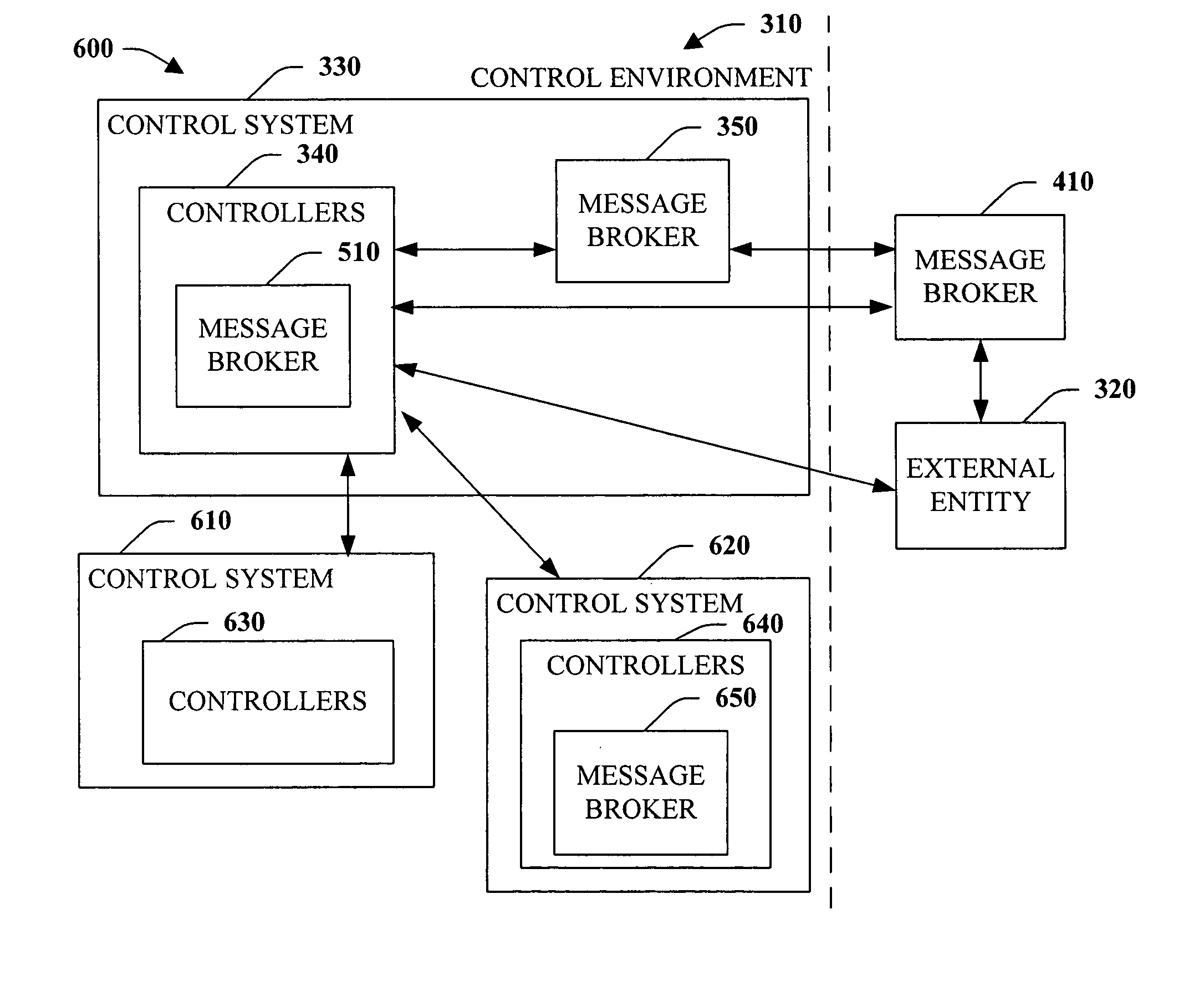
Reliable messaging instruction
ActiveUS20060209868A1Mitigate the aforementioned deficienciesReduce overheadComputer controlElectric controllersReliable messagingMessage passing
The subject invention provides reliable messaging with and within a control environment. The systems and methods utilize a message broker that facilitates message exchange. The message broker can be located within an industrial controller, as a dedicated entity within a control environment and / or an entity external to the control environment. Messages transmitted from an industrial controller and / or the external entity can be routed through the message broker prior to reaching a destination, wherein the message can be stored in the message broker and subsequently obtained by a recipient. The message broker decouples the message sender (e.g., an industrial controller, an external entity . . . ) from the message recipient (e.g., an industrial controller, an external entity . . . ) such that messages can be successfully transmitted (to the message broker) regardless of a state of the recipient, and messages can be retrieved (from the message broker) regardless of a state of the sender.
Owner:ROCKWELL AUTOMATION TECH
Digital Content Protection Method and Apparatus
InactiveUS20020099948A1Improve securityMinimizes probabilityKey distribution for secure communicationDigital data processing detailsDigital signatureDigital content
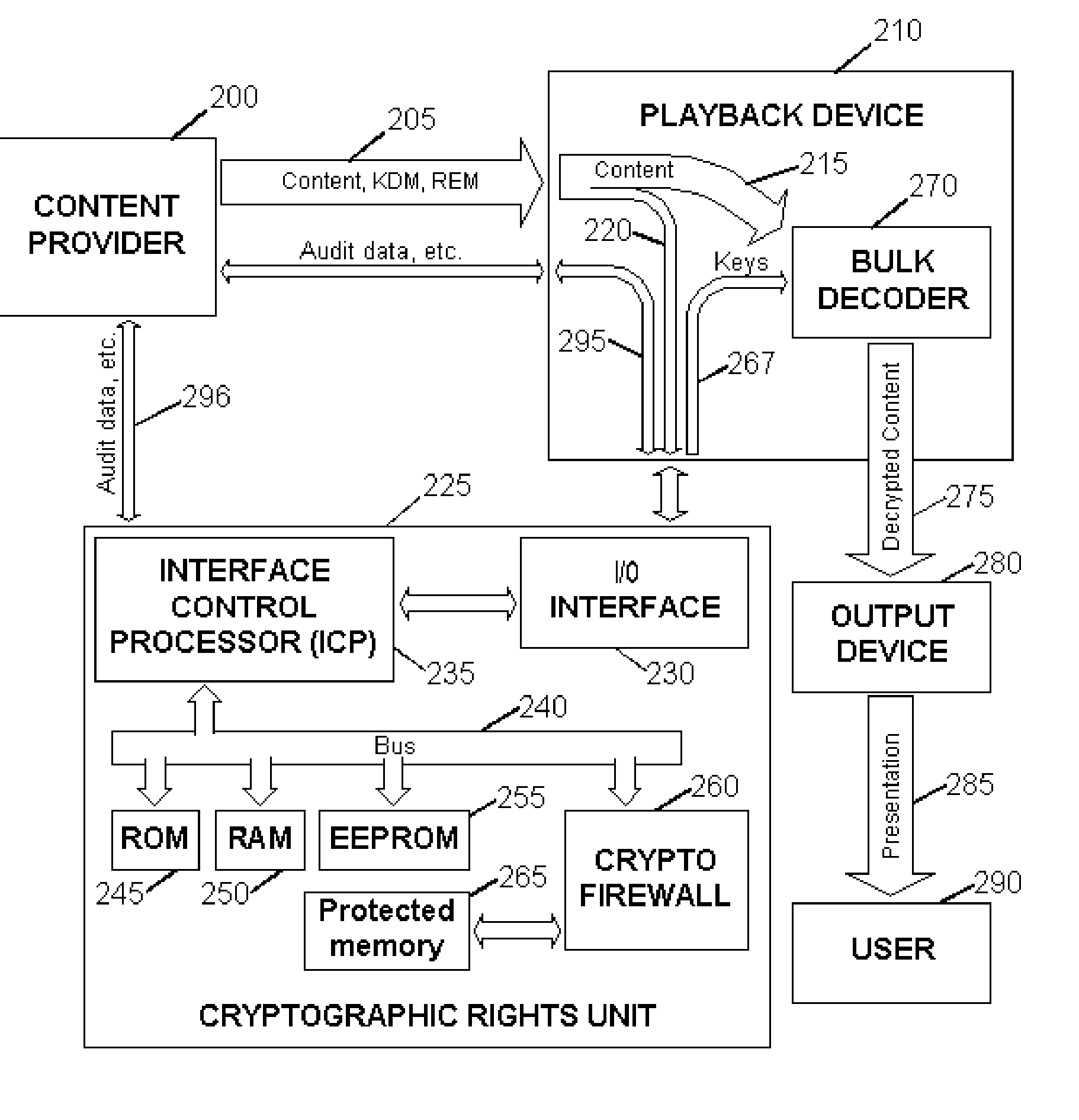
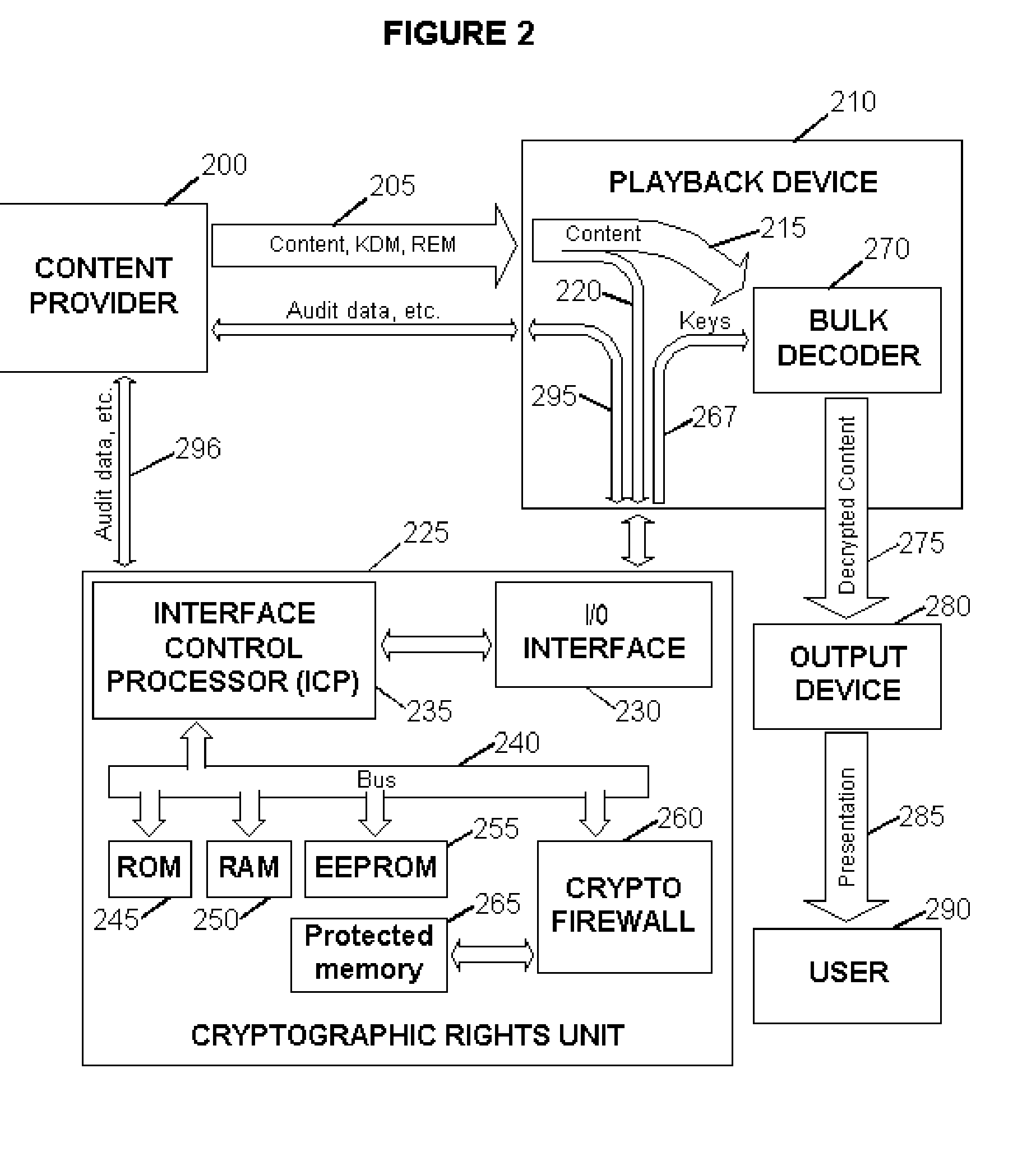
<heading lvl="0">Abstract of Disclosure< / heading> Before use, a population of tamper-resistant cryptographic enforcement devices is partitioned into groups and issued one or more group keys. Each tamper-resistant device contains multiple computational units to control access to digital content. One of the computational units within each tamper-resistant device communicates with another of the computational units acting as an interface control processor, and serves to protect the contents of a nonvolatile memory from unauthorized access or modification by other portions of the tamper-resistant device, while performing cryptographic computations using the memory contents. Content providers enforce viewing privileges by transmitting encrypted rights keys to a large number of recipient devices. These recipient devices process received messages using the protected processing environment and memory space of the secure unit. The processing result depends on whether the recipient device was specified by the content provider as authorized to view some encrypted digital content. Authorized recipient devices can use the processing result in decrypting the content, while unauthorized devices cannot decrypt the content. A related aspect of the invention provides for securing computational units and controlling attacks. For example, updates to the nonvolatile memory, including program updates, are supported and protected via a cryptographic unlocking and validation process in the secure unit, which can include digital signature verification.
Owner:CRYPTOGRAPHY RESEARCH
Messaging communication application
InactiveUS20120114108A1Solve the real problemAvoid problemsAutomatic exchangesMessaging/mailboxes/announcementsNotification ReceiverTelecommunications
A messaging application that includes a transmit module configured to progressively transmit time-based media of a message to a recipient as the media is created. The transmit module transmits the message in either a messaging mode where the time-based media of the message is transmitted before a delivery route to the recipient is completely discovered or a call mode where the transmission occurs after providing a notification requesting synchronous communication and receiving a confirmation that the recipient would like to engage in synchronous communication. In response to the notification, the recipient has the option of rendering the incoming message in either a real-time mode as the time-based media of the message is received or a time-shifted mode by rendering the time-based media of the message at an arbitrary later time after it was received.
Owner:VOXER IP
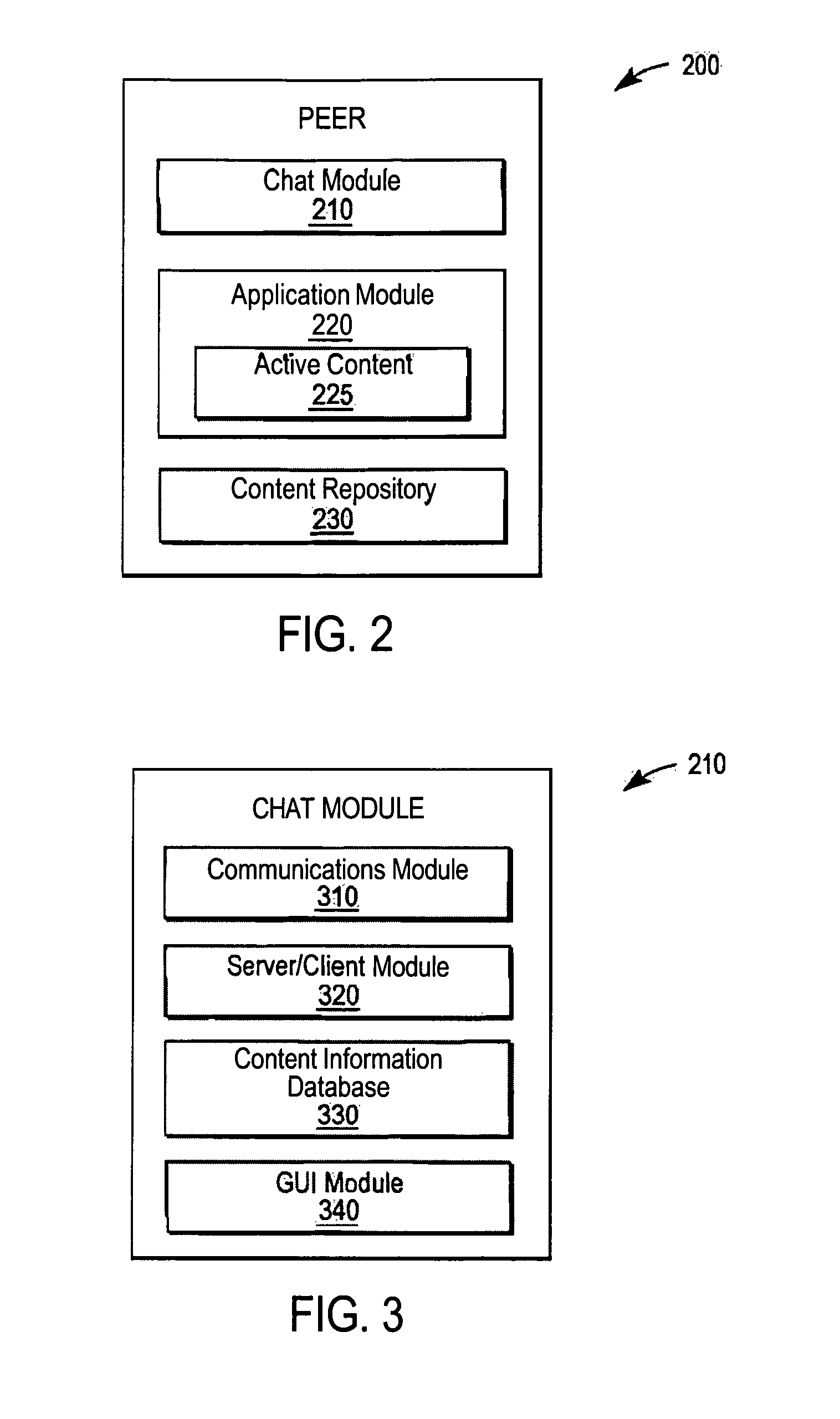
Peer-to-peer active content sharing
ActiveUS8001187B2Special service provision for substationMultiple digital computer combinationsContent sharingRecipient side
Owner:APPLE INC
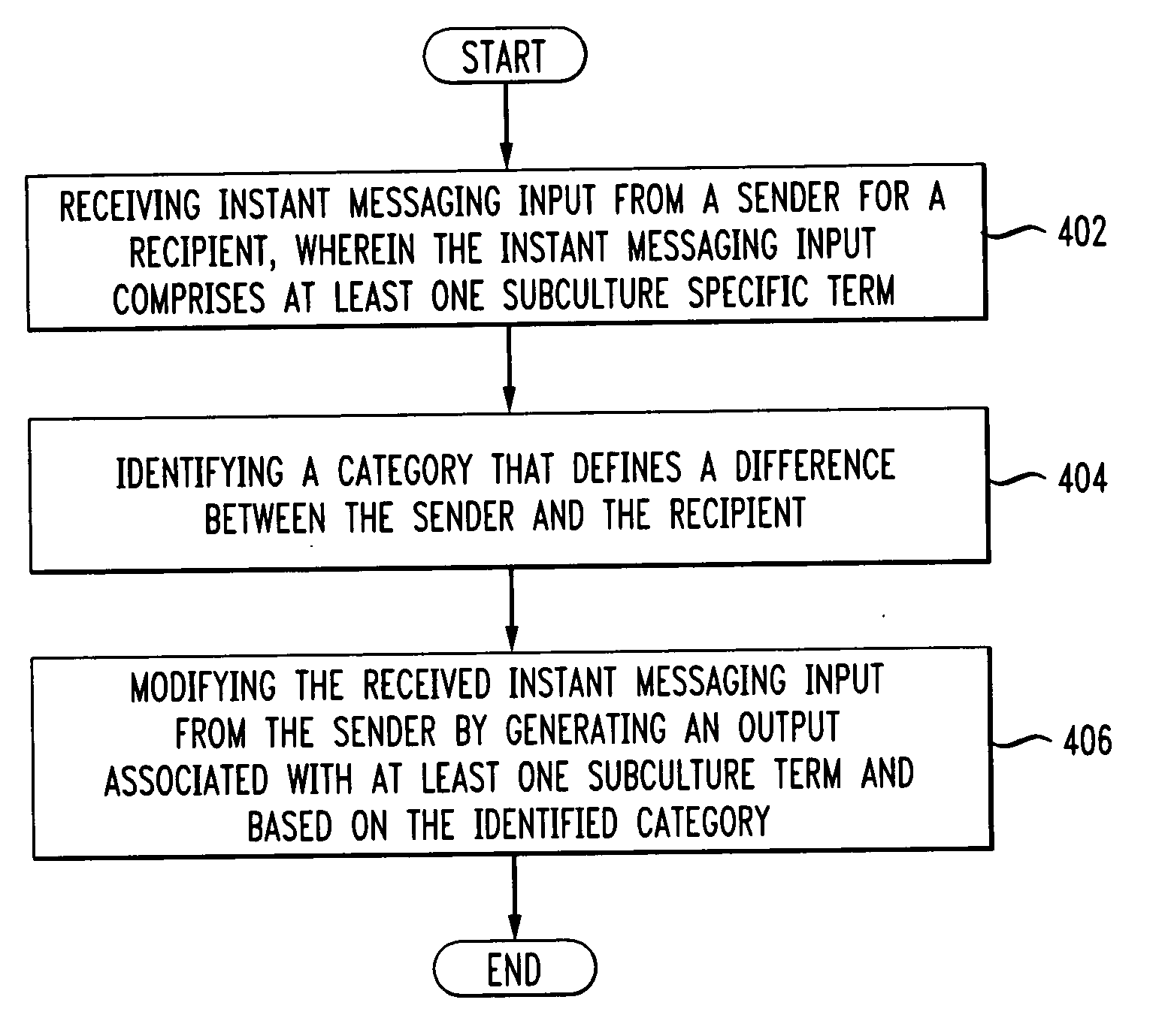
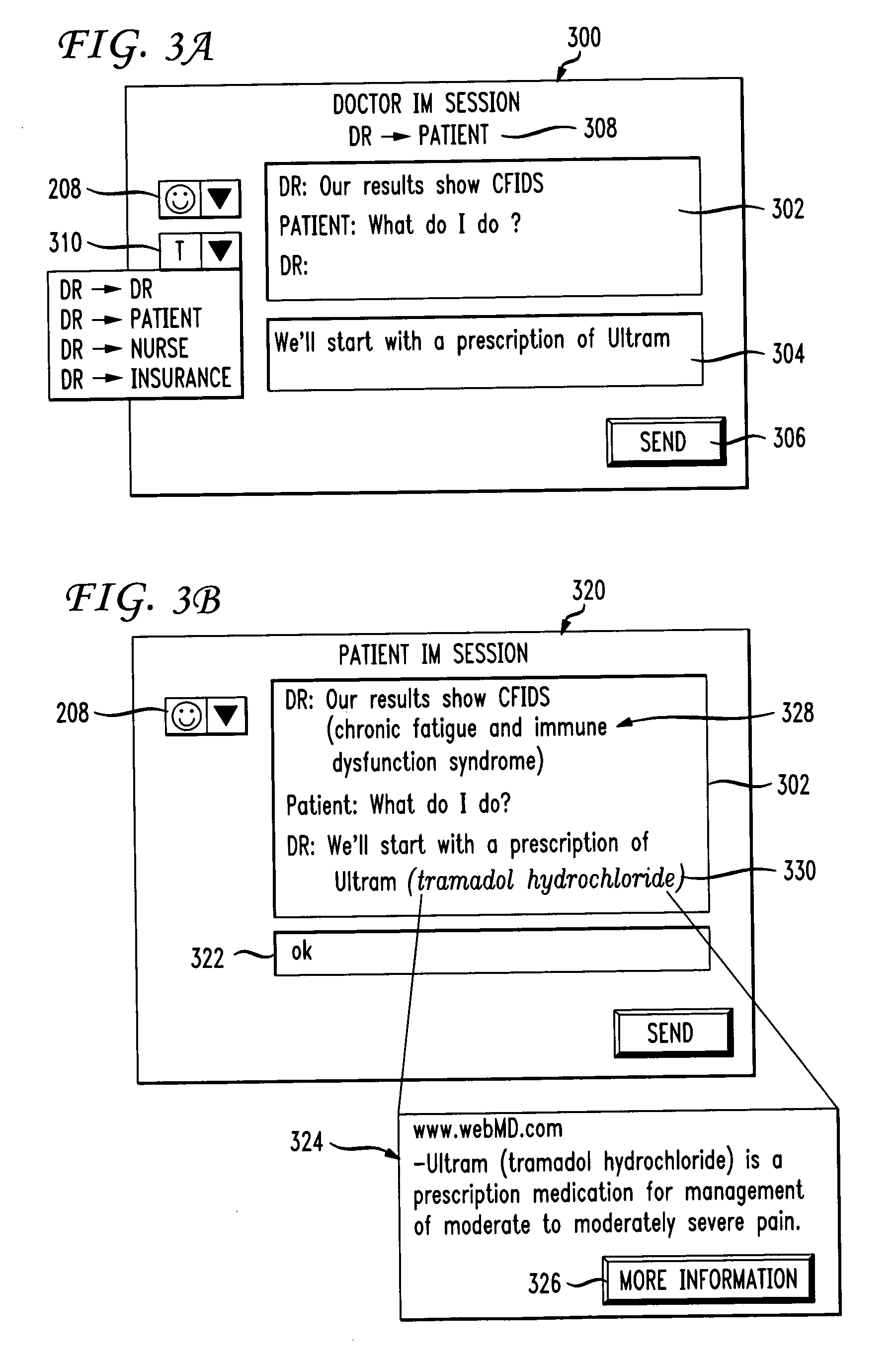
System and method for text translations and annotation in an instant messaging session
ActiveUS20060167992A1Natural language translationMultiple digital computer combinationsMessage passingRecipient side
A system and method for translating received input from a sender to recipient in an instant messaging dialog is disclosed. The method comprises receiving instant messaging input from a sender for recipient, wherein the instant messaging input comprises at least one subculture specific term. A category is identified the defines a difference between the sender and the recipient and the received instant messaging input is modified from the sender by generating an output associated with the least one subculture specific term and based on the identified category. Multiple recipients in a chat session may also each receive a translated or annotated message according to characteristics of each individual recipient.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Traffic information providing system,traffic information expression method and device
InactiveUS20060082472A1Low accuracyImprove accuracyAnalogue computers for vehiclesArrangements for variable traffic instructionsComputer scienceRecipient side
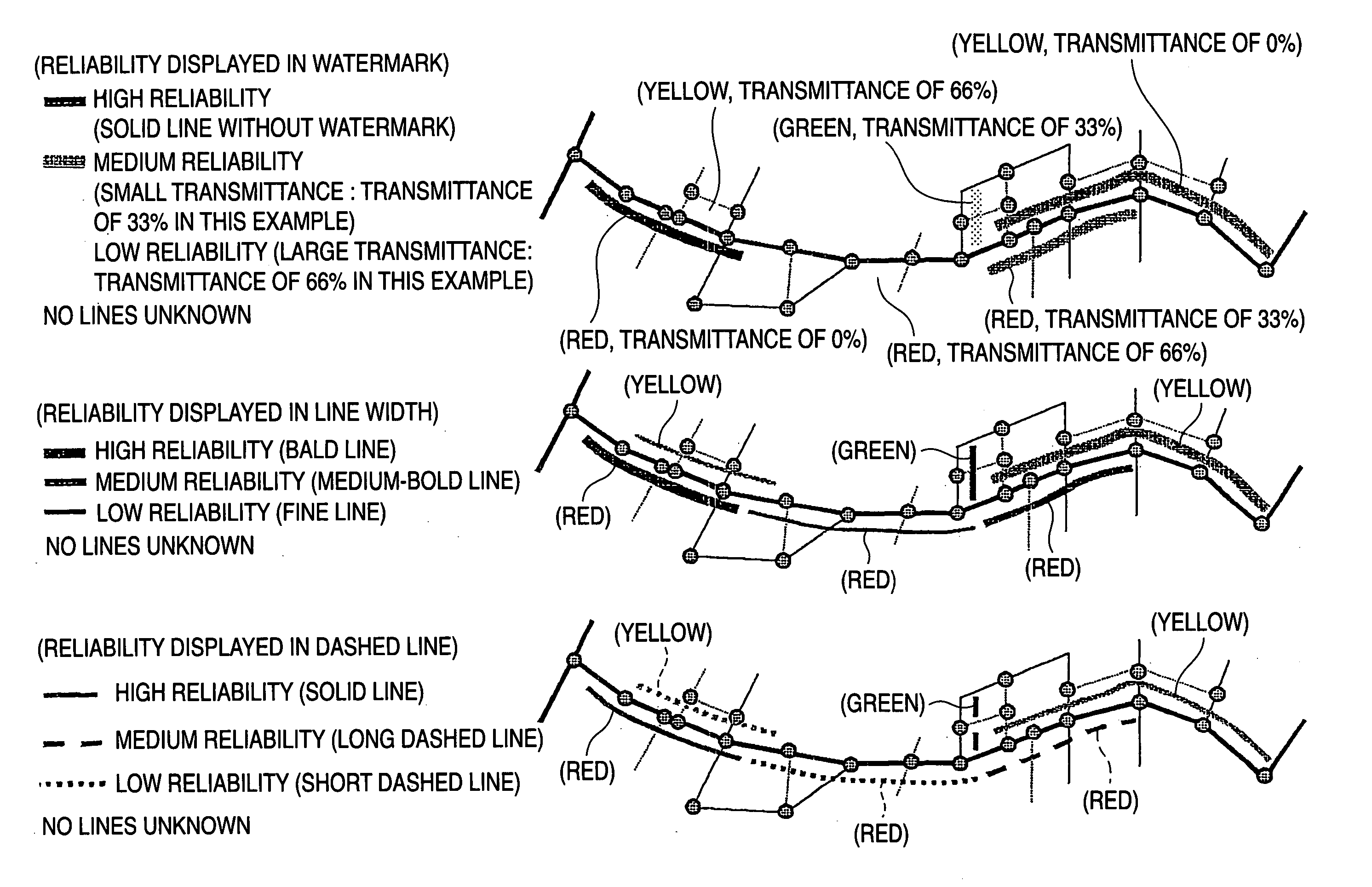
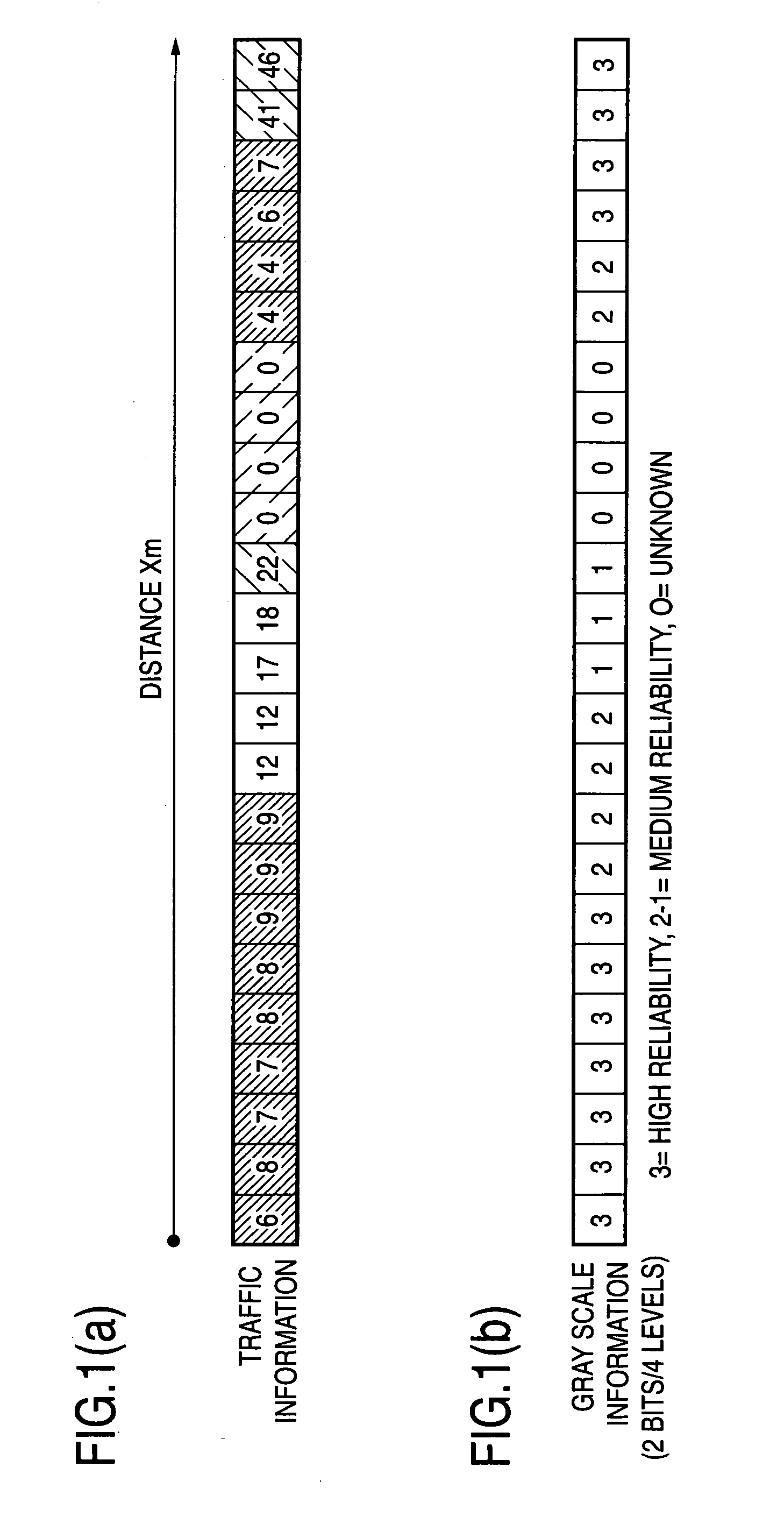
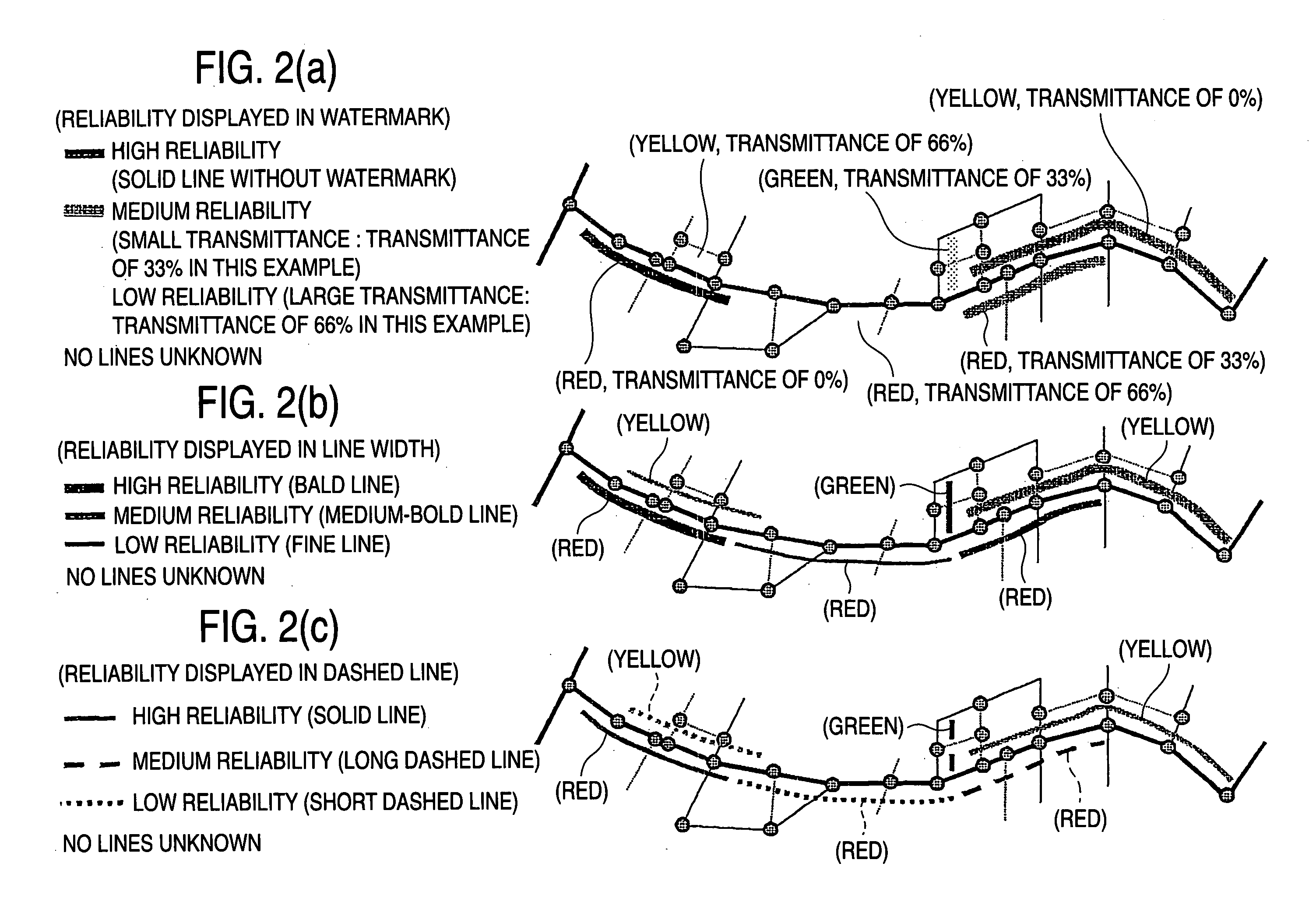
The invention provides a traffic information display method which presents traffic information so as to quantatively indicate the reliability and superiority of traffic information. The invention also provides a traffic information providing system which clearly communicates an “unknown” section to the receiving party. The invention represents the state volume of traffic information by the state volume of each sampling point set by segmenting a target road and represents traffic information by using the state volume of traffic information and gray scale information which displays the reliability of the state volume in multiple levels. The user thus understands how reliable the traffic information is and properly evaluates the traffic information. The traffic information may be used to perform a high-accuracy path search and provide traffic information at a reasonable cost. The traffic information providing system of the invention includes traffic information providing apparatus for providing, as traffic information, the state volume of traffic information of each distance quantization unit set by segmenting a target road and mask bit information indicating that the state volume is valid or invalid, and traffic information utilization apparatus for reproducing a valid state volume by using the mask bit information. In the traffic information providing system, the receiving party clearly recognizes, based on the mask bit information, an “unknown” section enclosed by an ellipse:
Owner:PANASONIC CORP
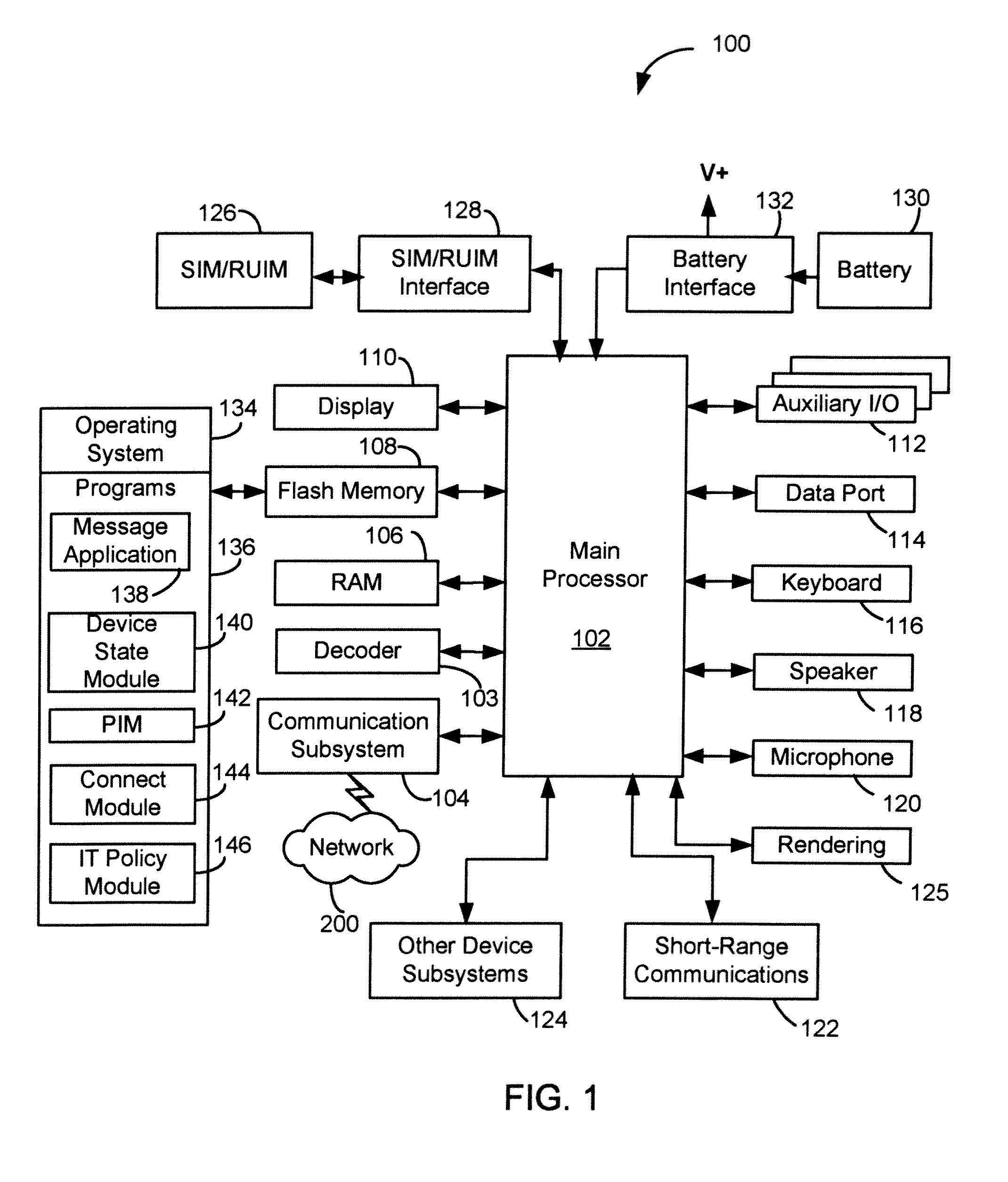
Method and system for enhanced electronic mail processing
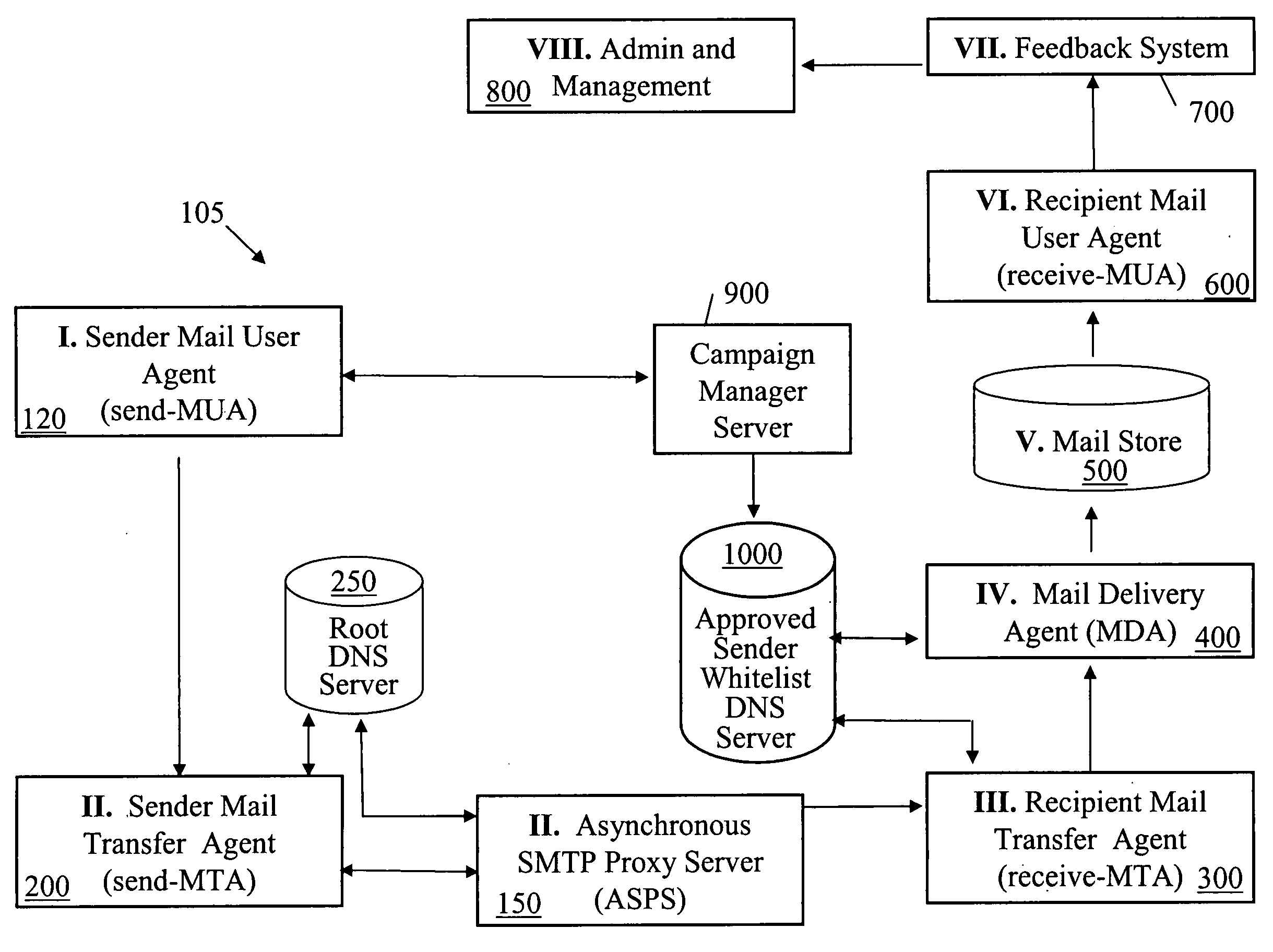
InactiveUS20060168057A1Improved electronic mail deliverabilityMultiple digital computer combinationsData switching networksProxy serverTransfer agent
An asynchronous proxy server system interposed between sender and recipient mail transfer agents, or other agent on the sender side, is configured to classify outgoing mail. Message and message header information is processed and compared against a set of business rules. The message header is modified to reflect an assertion based on an outcome of the comparison. The modified outgoing message is then routed to its destination.
Owner:HABEAS
Systems and methods for providing and updating a unified client
InactiveUS20110126192A1Improved end user experienceImprove experienceProgram loading/initiatingMemory systemsClient-sideReceipt
The present invention is directed towards systems and methods for more efficiently managing installation of a plurality of application plug-ins for a client device. A client device executes, upon startup, a receiver application. The receiver application may manage installations of application plug-ins for a user of the client device. The receiver application may receive from an update server a delivery of application plug-ins to install on the client device. Upon receipt of the delivery, the receiver application may automatically install each of the application plug-ins on the client device transparently to the user of the client device. The receiver application may automatically start each of the application plug-ins.
Owner:CITRIX SYST INC
Digital telecommunication system with selected combination of coding schemes and designated resources for packet transmission based on estimated transmission time
InactiveUS6363425B1Quantity minimizationAir interface efficientlyError prevention/detection by using return channelCode conversionForward error correctionMajorization minimization
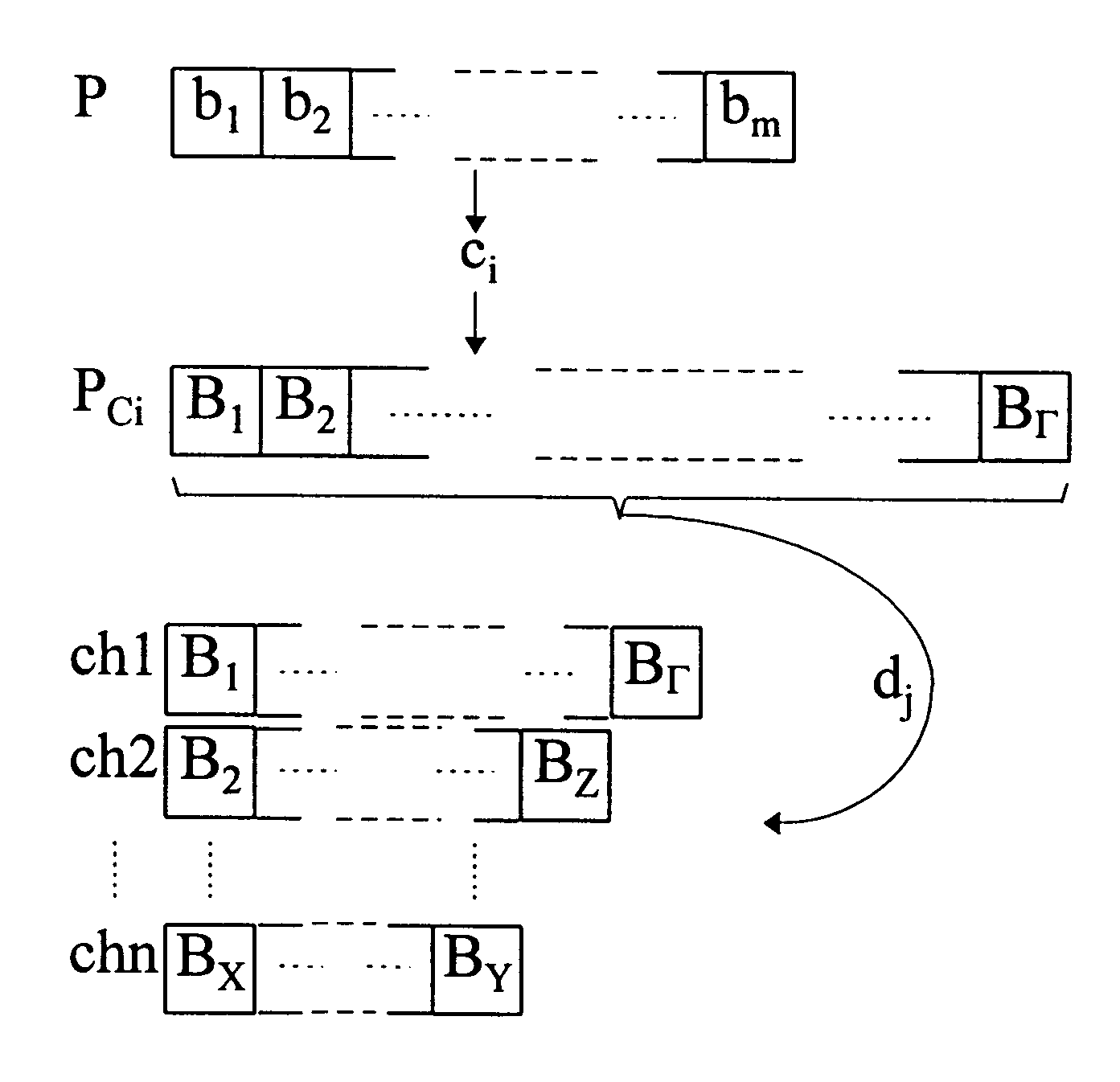
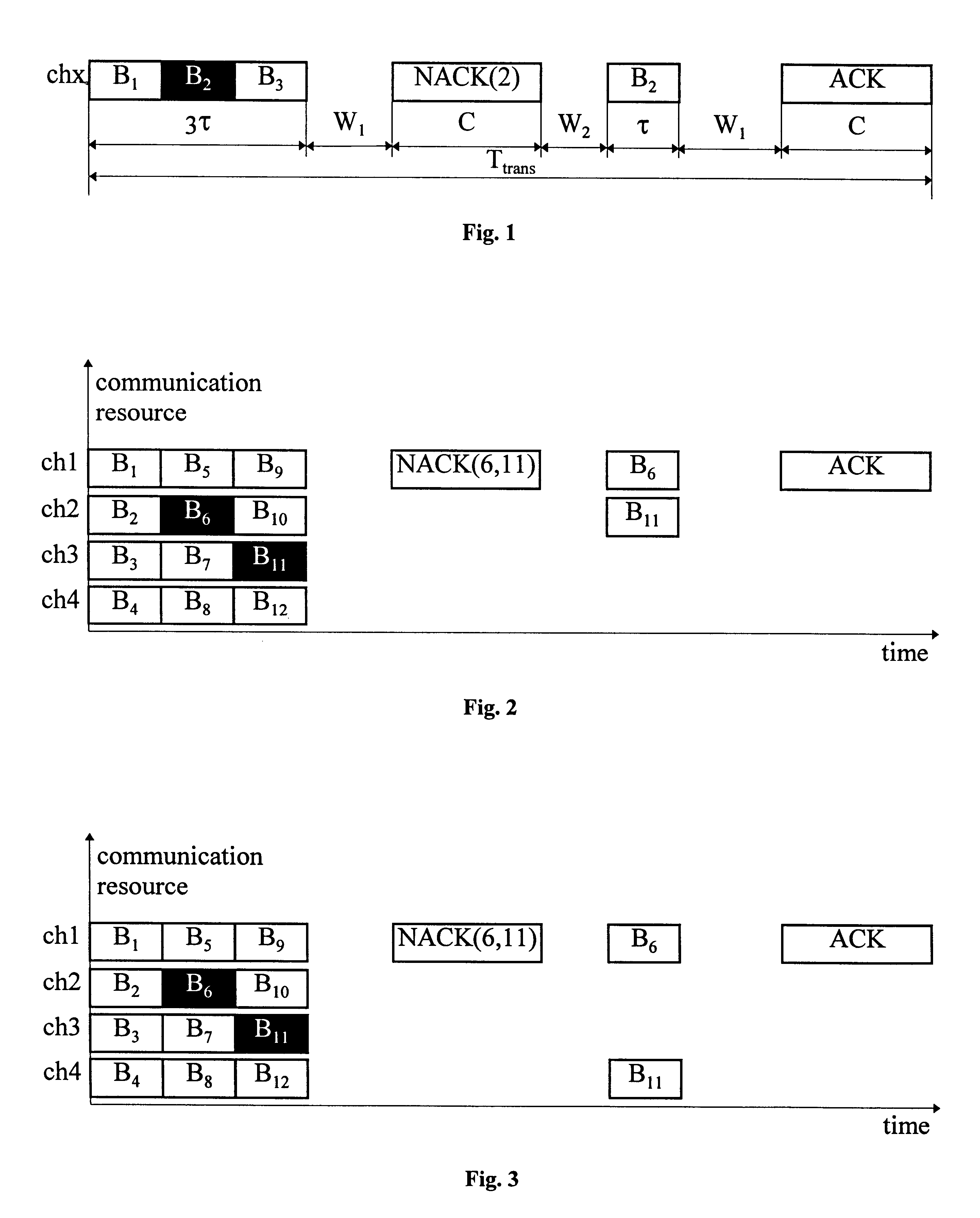
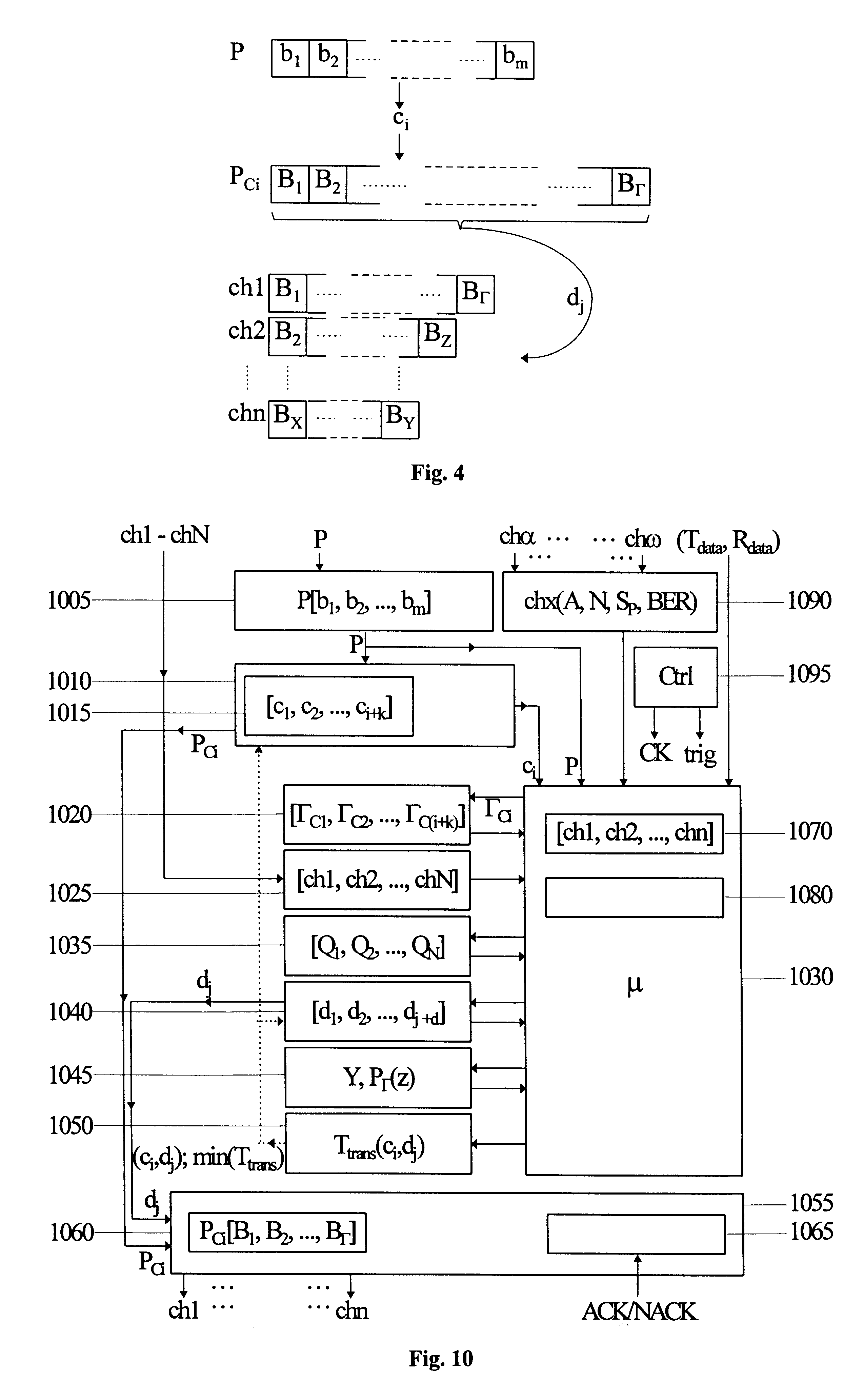
The present invention relates to a method and an arrangement for communicating packet information in a digital telecommunications system. Through the invention is selected a set of designated communication resources (ch1-chn) from an available amount of resources. Every packet (P) is forward error correction encoded into an encoded packet (Pci), via one of at least two different coding schemes (ci), prior to being transmitted to a receiving party, over the designated communication resources (ch1-chn). An estimated transmission time is calculated for all combinations of coding scheme (ci) and relevant distribution (dj) of the encoded data blocks (B1-BΓ), in the encoded packet (Pci) over the set of designated communication resources (ch1-chn), and the combination (ci,dj) is selected, which minimises the estimated transmission time.
Owner:TELEFON AB LM ERICSSON (PUBL)
Technique for ethernet access to packet-based services
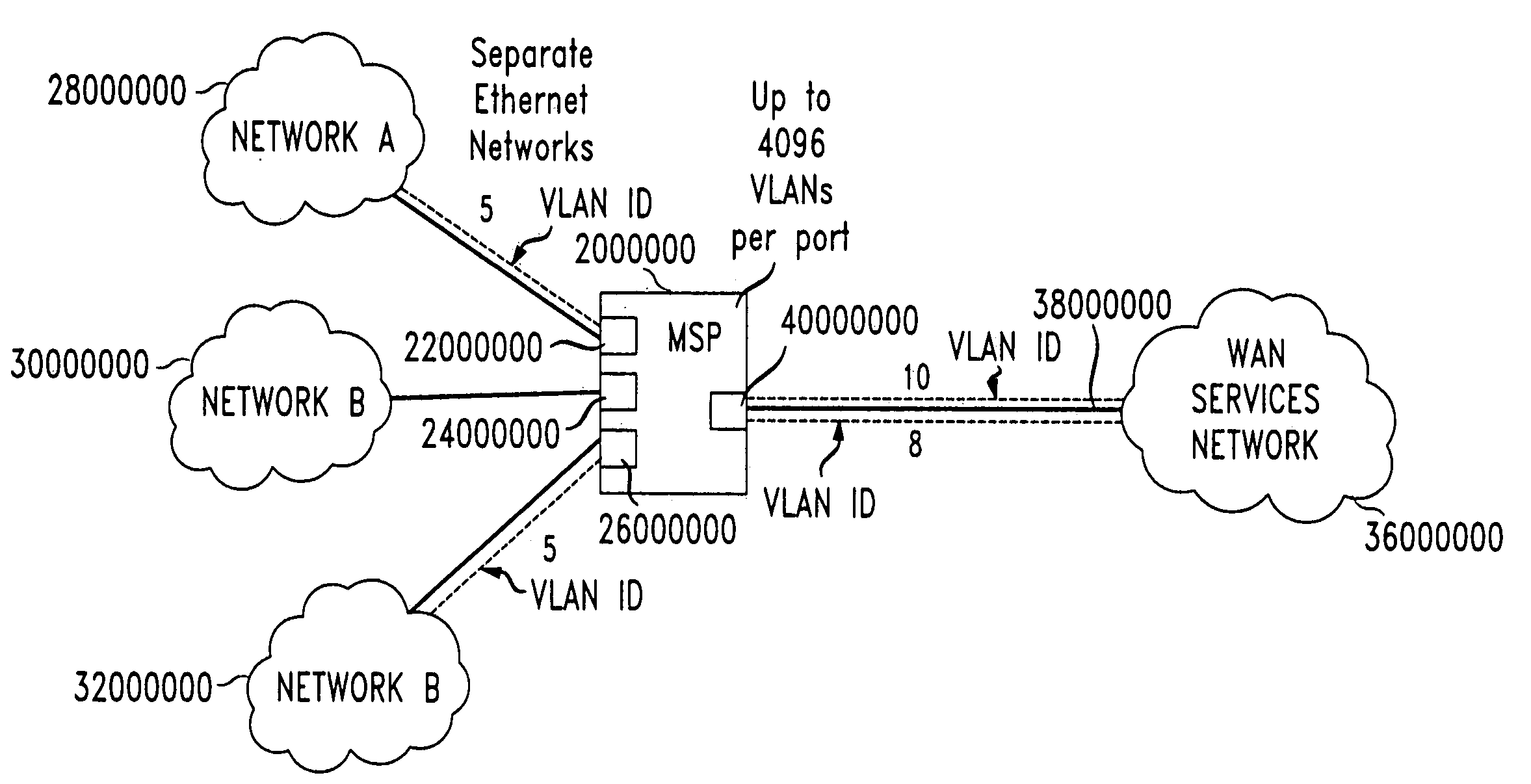
ActiveUS7092389B2Convenient and efficientThe process is convenient and fastNetworks interconnectionMetropolitian area networksTraffic volumeReceipt
An Ethernet Metropolitan Area Network (10) provides connectivity to one or more customer premises (161,162,163) to packet-based services, such as ATM, Frame Relay, or IP, while advantageously providing a mechanism for assuring security and regulation of customer traffic. Upon receipt of each customer-generated information frame (20), an ingress Multi-Service Platform (MSP) (122) “tags” the frame with a customer descriptor (22′) that specifically identifies the recipient customer. In practice, the MSP tags each frame by overwriting the Virtual Local Area Network (VLAN) identifier (22) with the customer descriptor. Using the customer descriptor in each frame, a recipient Provider Edge Router (PER) (18) or ATM switch can map the information as appropriate to direct the information to the specific customer at its receiving site. In addition, the customer descriptor (22′) may also include Quality of Service (QoS) information, allowing the recipient Provider Edge Router (PER) (18) or ATM switch to afford the appropriate QoS level accordingly. Each Ethernet switch may advantageously overwrite the VLAN identifier at an incoming port with a second tag associated with an egress port to increase the scale associated with single switch.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Transaction system for business and social networking
ActiveUS20130276140A1Digital data processing detailsServices signallingComputer networkService provision
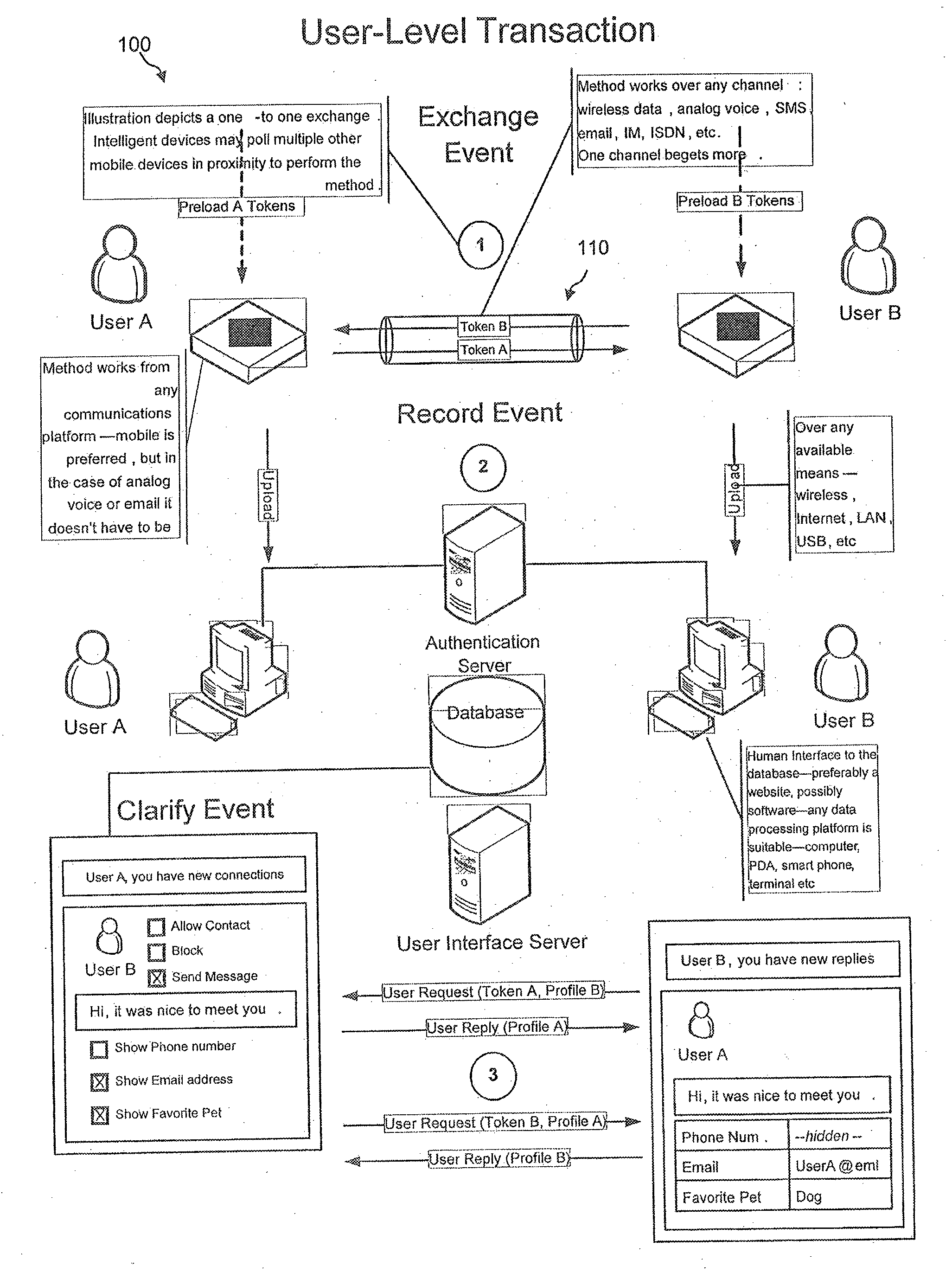
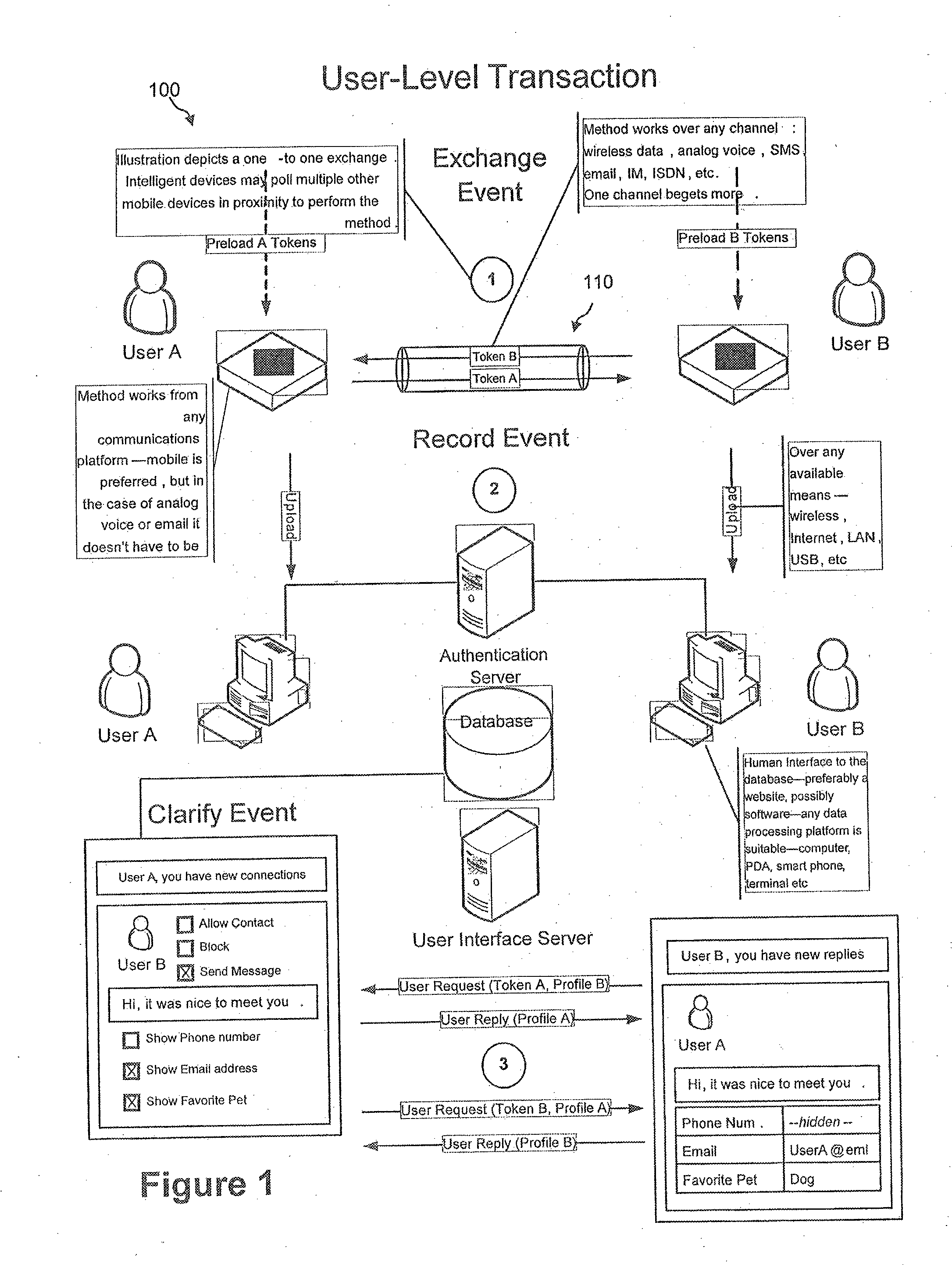
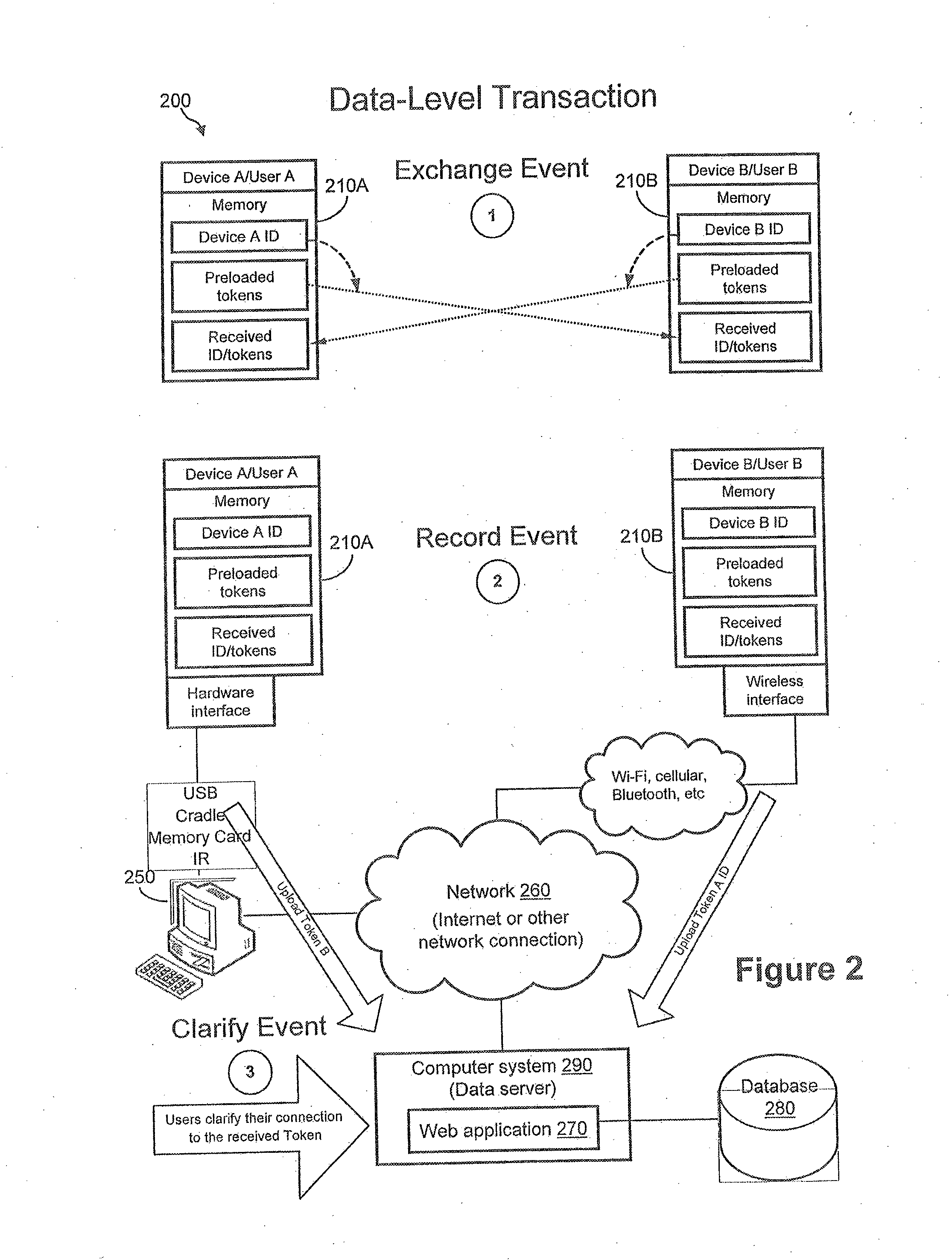
A wireless face-to-face bilateral communication method between at least two users of a service provider, each having a token device, and at least one having a user-defined profile, comprising: between a sending token device and a receiving token device, transmitting unique electronic transaction tokens between a consenting sending party and a consenting or optionally consenting receiving party wherein said transaction tokens may be used for single use, party-approved after-contact, computer-network facilitated access to each other's profile.
Owner:COFFING DAN +1
Email enhancement
InactiveUS20080147818A1Improve efficiencyFacilitate prioritizationMultiple digital computer combinationsRecipient categoryRecipient side
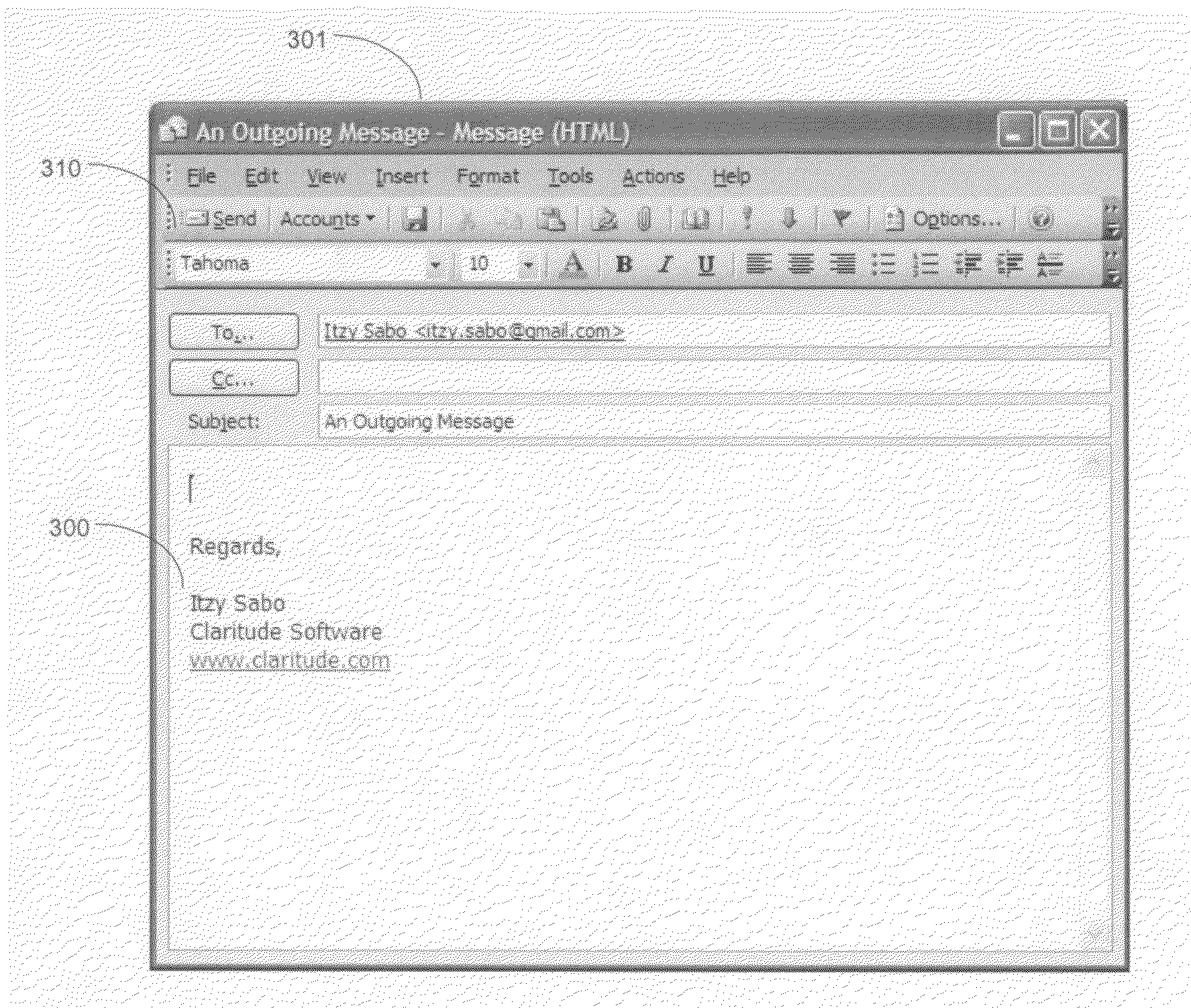
A method of improved handling of an email by a recipient email program comprising the steps of: (a) displaying a dialog to a sender of the email in response to the sender attempting to send the email to the recipient, wherein the dialog allows the sender to select tags for tagging the email, said tags being predetermined by the recipient; (b) sending the email together with tags selected by the sender from list of tags offered by the recipient, and (c) using the selected tags to prioritize the incoming email in accordance with recipient categories.
Owner:SABO ITZCHAK
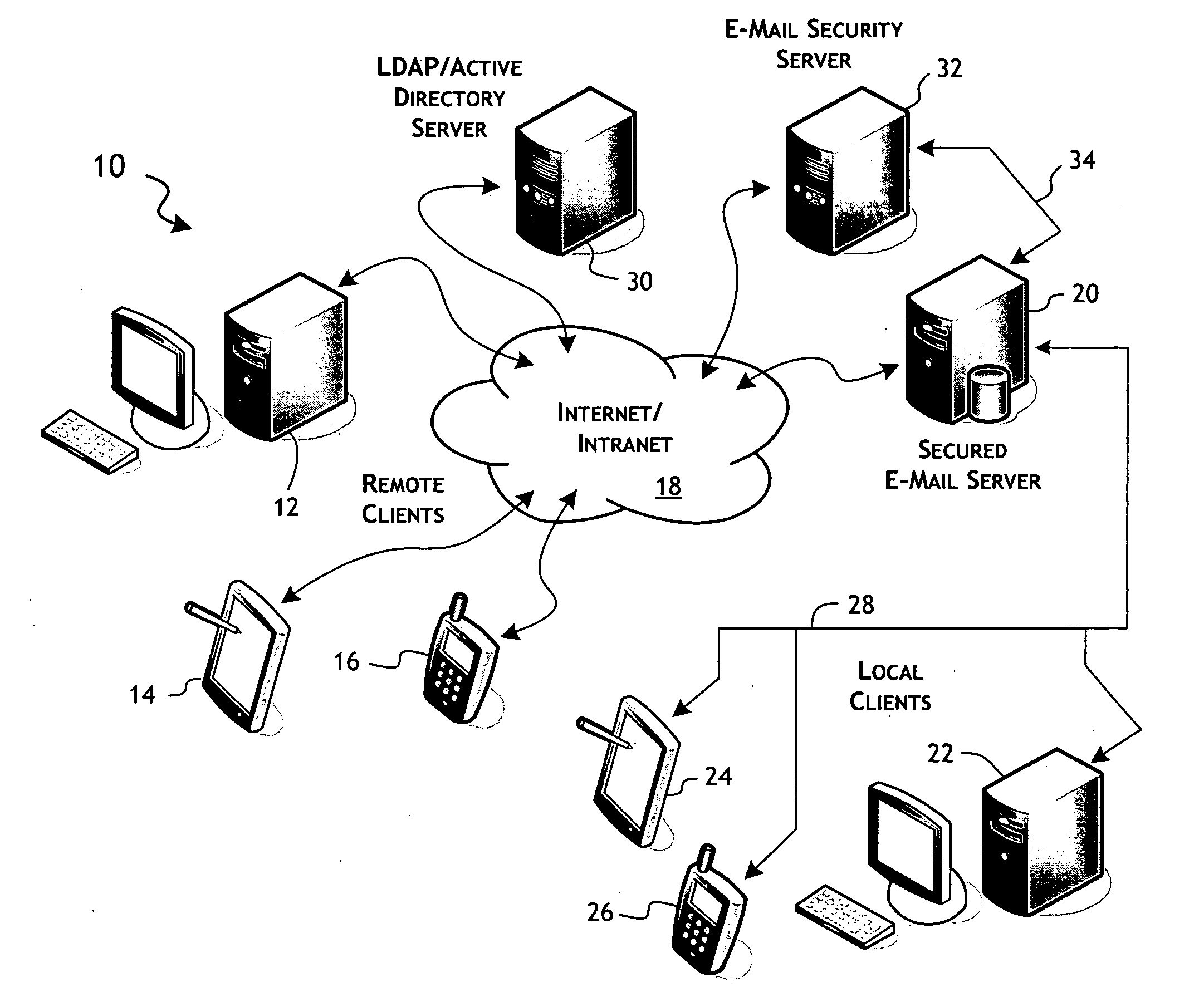
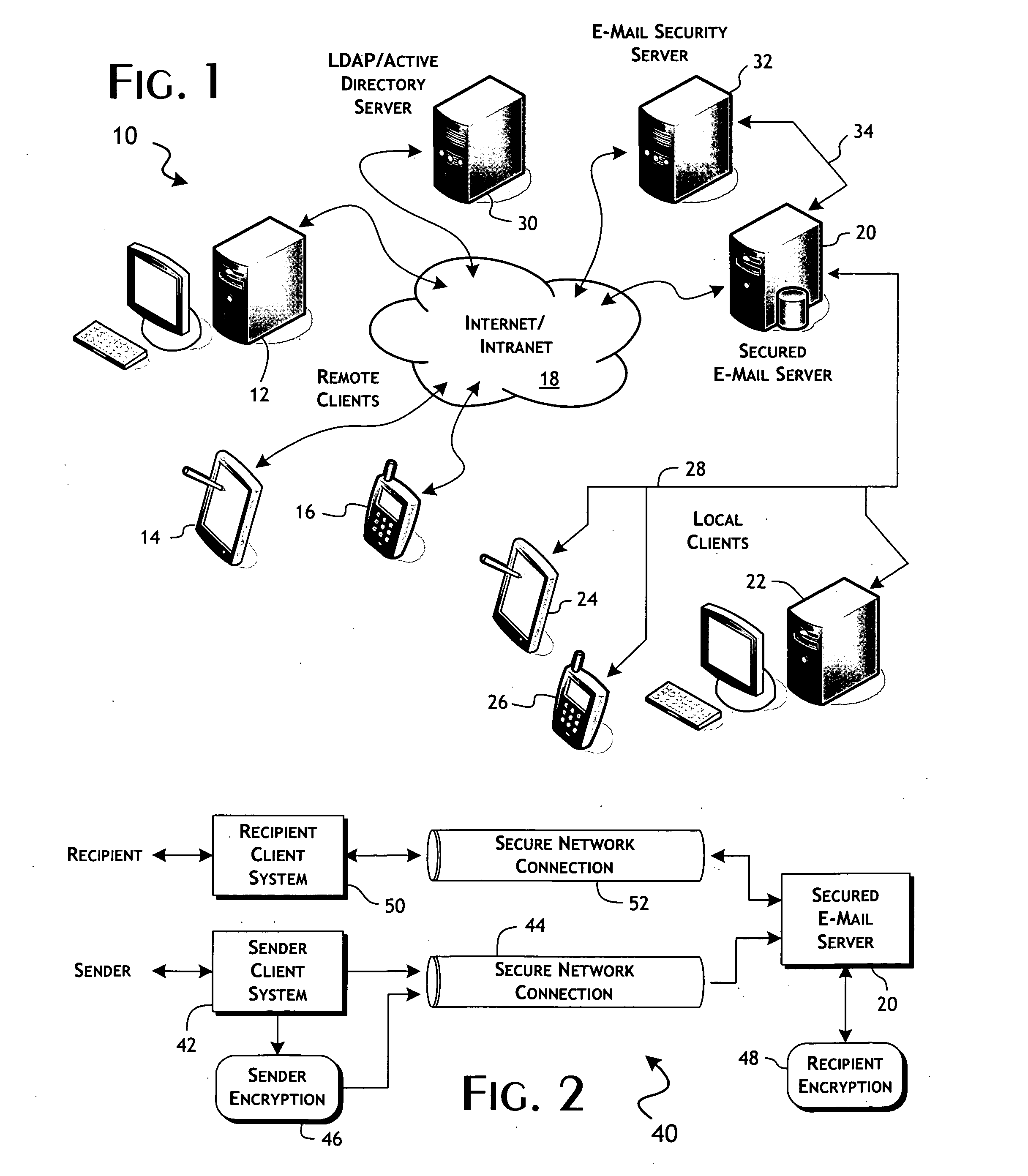
Secure e-mail services system and methods implementing inversion of security control
InactiveUS20080098237A1Digital data processing detailsUser identity/authority verificationComputerized systemRecipient side
A secure e-mail service, executable on a recipient e-mail server or associated computer system, implements inverted security control over recipient content stored by the recipient e-mail server. Recipient content is received in conjunction with e-mail messages transmitted directed to recipients from sender computer systems unassociated with the secure e-mail service. The secure e-mail service includes a policy engine that operates on e-mail messages, as received from a communications network, to evaluate metadata features of the message and select a corresponding encryption key. The service further includes a content processing engine that operates to encrypt a portion of the message in a manner that allows subsequent decryption of said portion using the selected encryption key. A service interface enables transfer of the e-mail message, including the portion as encrypted, to the recipient e-mail server, which supports access by the recipients.
Owner:DUNG TRUNG T +2
Methods and systems for detecting, locating and remediating a congested resource or flow in a virtual infrastructure
InactiveUS20140215077A1Well formedDigital computer detailsData switching networksRemedial actionDistributed computing
Once a potential bottleneck is identified, the system provides a methodology for locating the bottleneck. The methodology involves checking in order each of the application, transport and network layers of a sender and receiver nodes for performance problems. Conditions are defined for each of the layers at the sender and receiver nodes that are indicative of a particular type of bottleneck. When the conditions are met in any one of the layers, the system can be configured to stop the checking process and output a message indicating the presence of a bottleneck in the layer and its location. In addition, the system can be configured to generate and output a remedial action for eliminating the bottleneck. The system can be configured to perform the action automatically or after receiving a confirmation from the user.
Owner:F5 NETWORKS INC
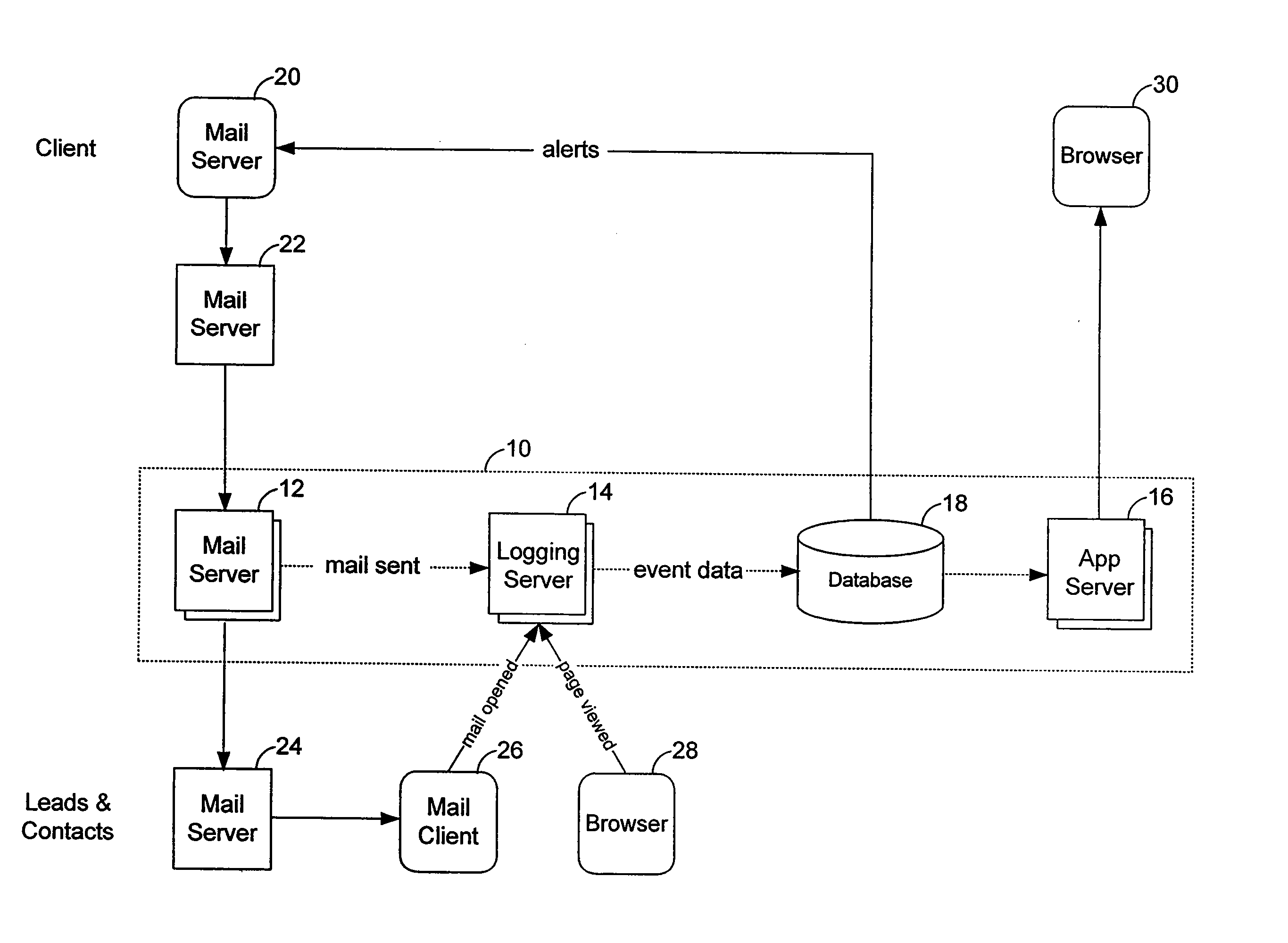
Method and system for monitoring email and website behavior of an email recipient
ActiveUS20070005762A1Interference be notMultiple digital computer combinationsData switching networksHyperlinkWeb site
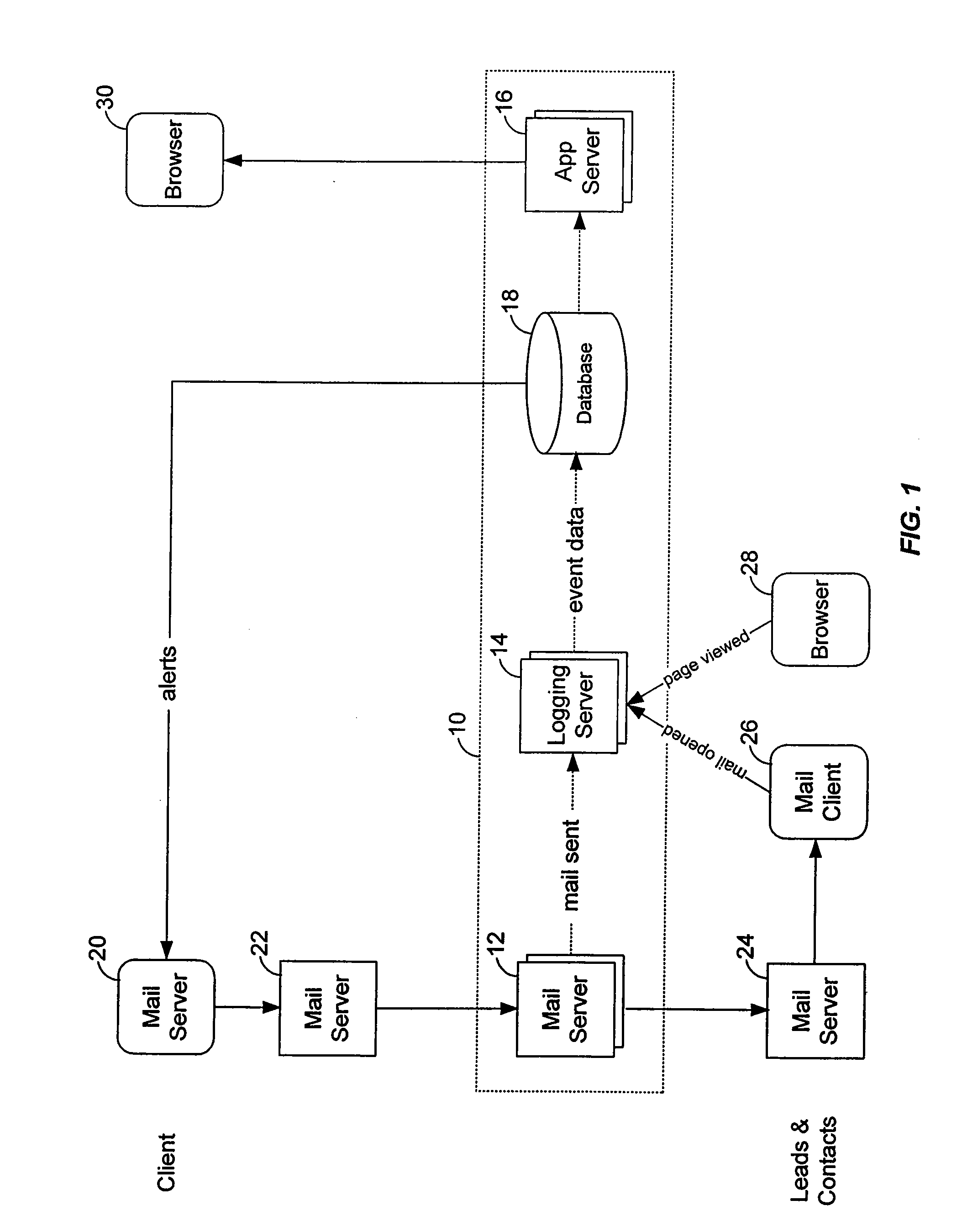
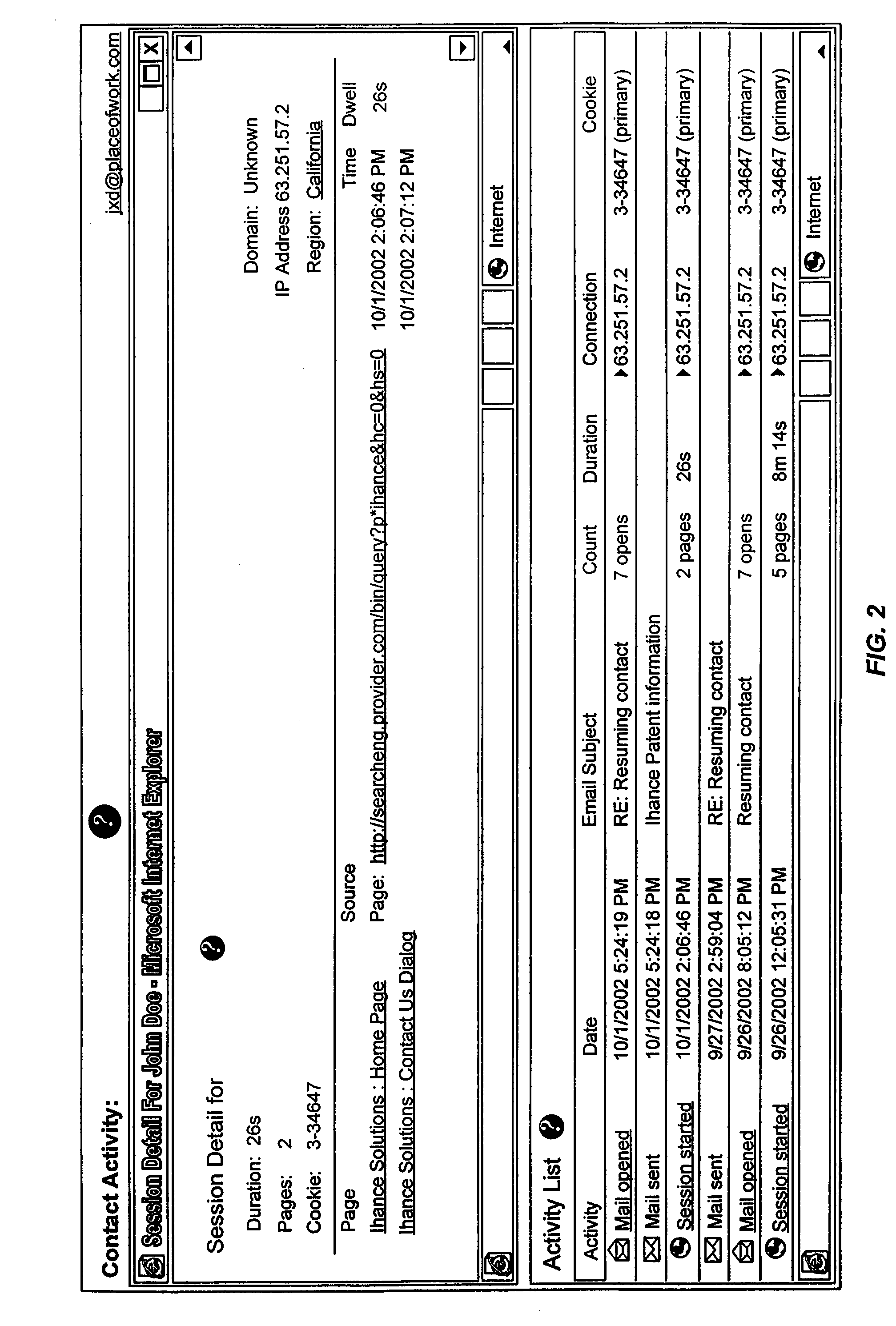
A system for monitoring email and website behavior of an email recipient is provided. According to one exemplary embodiment, the system includes a mail enhancement server and a logging server. The mail enhancement server is configured to intercept all outgoing emails from a mail server. The mail enhancement server then modifies each outgoing email to include a tracking code. The tracking code is embedded in an image call which in turn is also inserted into the outgoing email. If the outgoing email contains hyperlinks, each hyperlink is also modified to include the tracking code. The tracking code is uniquely associated with the outgoing email. The image call (and the tracking code) is used to detect when the recipient of the outgoing email has opened that email. The tracking code, when embedded in a hyperlink, is also used to monitor whether the recipient has opened the email and / or clicked through on one or more of the hyperlinks in the email. The logging server associates a cookie with the recipient of the outgoing email. When the logging server receives an image call, the corresponding image and the cookie are concurrently delivered to the recipient. The cookie is used to monitor the behavior of the recipient at a website, regardless of how the recipient arrives at that website, be it through a click-through from the email or otherwise. The logging server is configured to capture and store relevant information relating to the outgoing email thereby allowing the sender of the outgoing email and the recipient to be linked and the behavior of the recipient to be monitored via the tracking code, the image call and the cookie.
Owner:XANT INC
Packet format
InactiveUS20050249244A1Reception robustReduce power consumptionTime-division multiplexData switching by path configurationAccess networkWireless lan
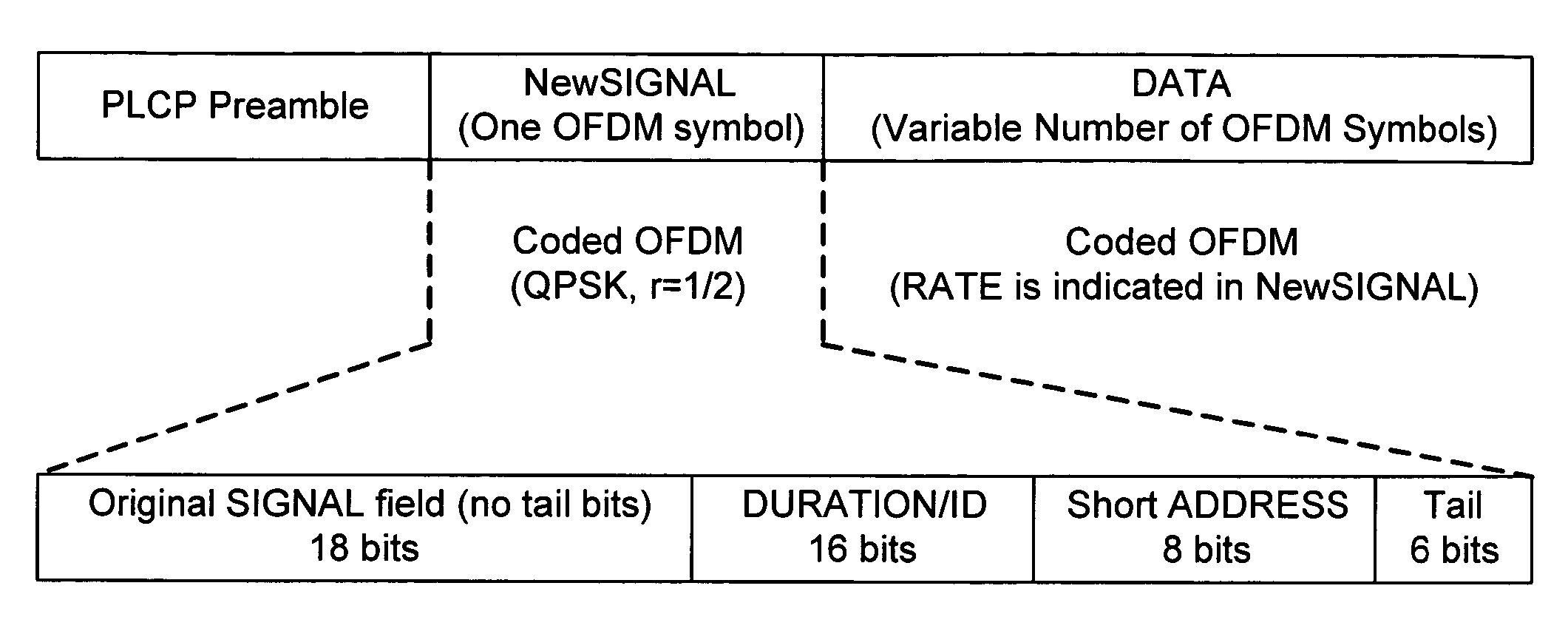
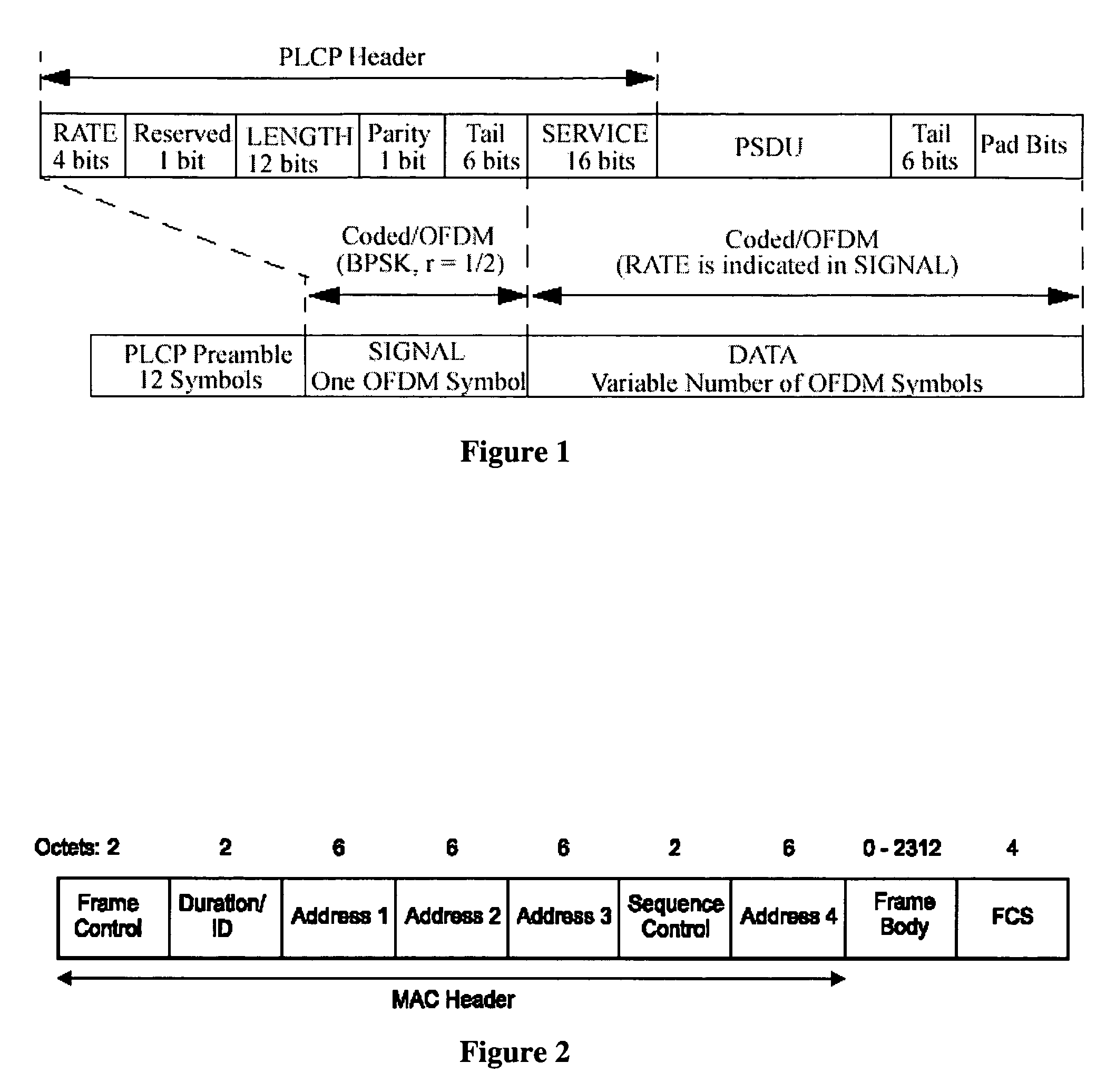
The present invention relates to packet construction of format for communications across multiple access networks such as wireless local area networks (WLAN). The present invention provides a device for use in a wireless network and comprising means for generating a packet comprising a first portion having a destination address and preferably a network duration identifier for a recipient device in the network, and a second portion; and means for transmitting the first portion at a predetermined coding and / or modulation rate, and means for transmitting the second portion at a higher coding and / or modulation rate.
Owner:KK TOSHIBA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com