Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
447results about How to "Avoid identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Privacy firewall
ActiveUS9665722B2Protect normal useAvoid identificationRelational databasesDigital data protectionSupplicantInternet privacy
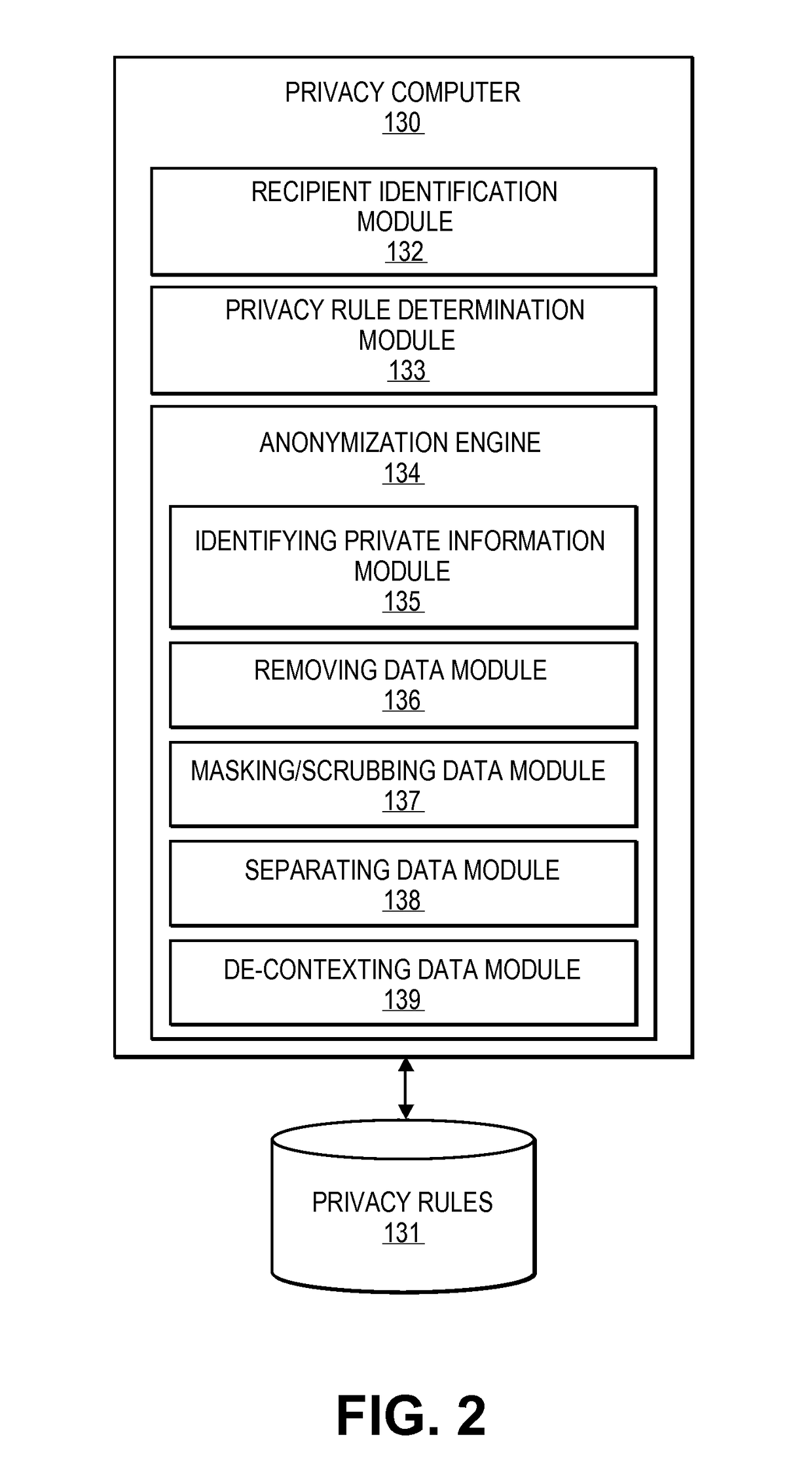
Embodiments of the invention relate to systems and methods for providing an anonymization engine. One embodiment of the present invention relates to a method comprising receiving a message directed at a recipient computer located outside a secure area by a privacy computer located within a secure area. The privacy computer may identify private information using a plurality of privacy rules and anonymize the message according to the plurality of privacy rules. Another embodiment may be directed to a method comprising receiving a request for sensitive data from a requesting computer. An anonymization computer may determine a sensitive data record associated with the request and may anonymize the sensitive data record by performing at least two of: removing unnecessary sensitive data entries from the sensitive data record, masking the sensitive data entries to maintain format, separating the sensitive data entries into associated data groupings, and de-contexting the data.
Owner:VISA INT SERVICE ASSOC
Systems and methods for detecting obstructions in a camera field of view
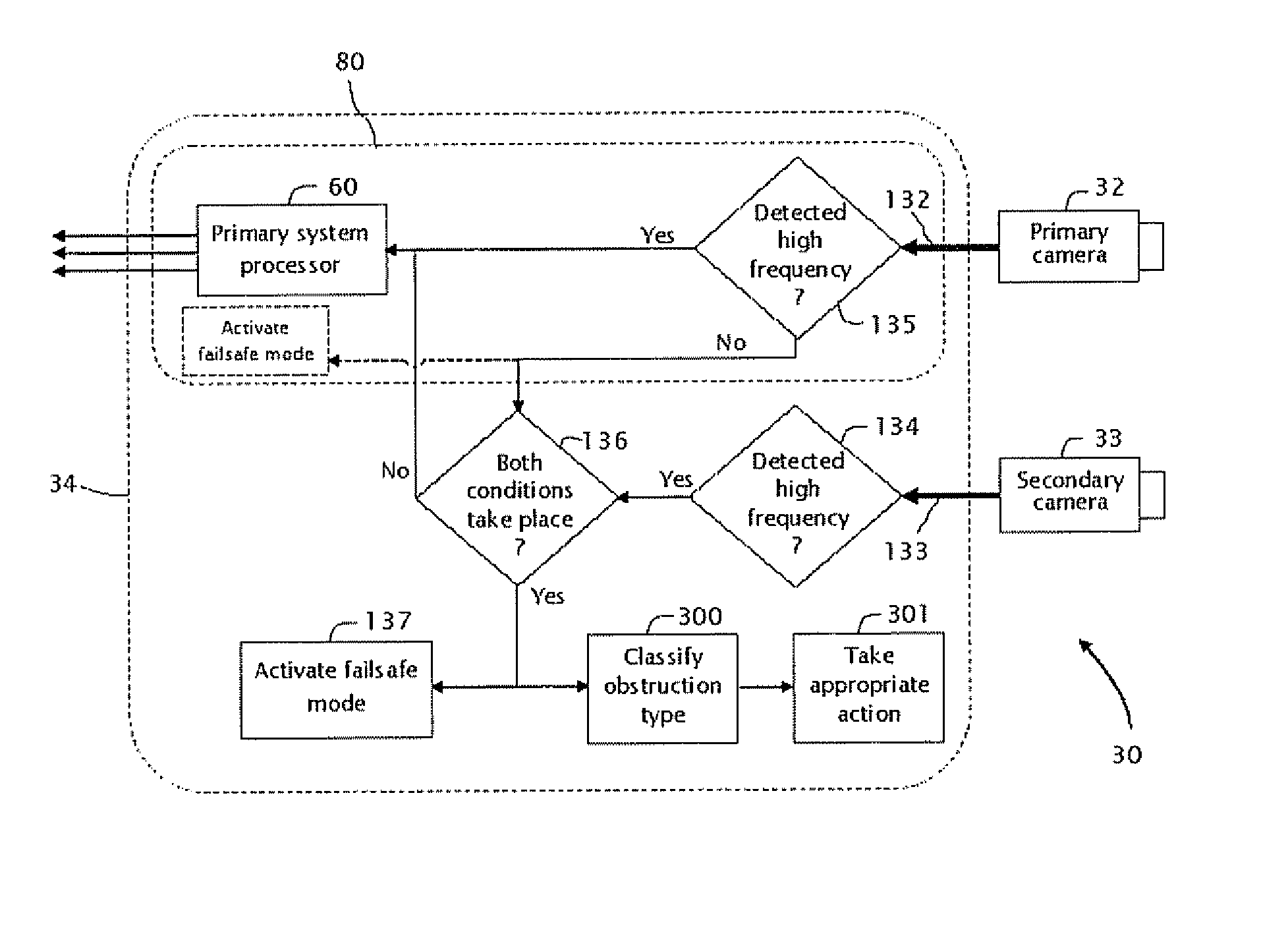
ActiveUS8553088B2Avoid identificationIncrease blockingVehicle headlampsCharacter and pattern recognitionField of viewImaging data
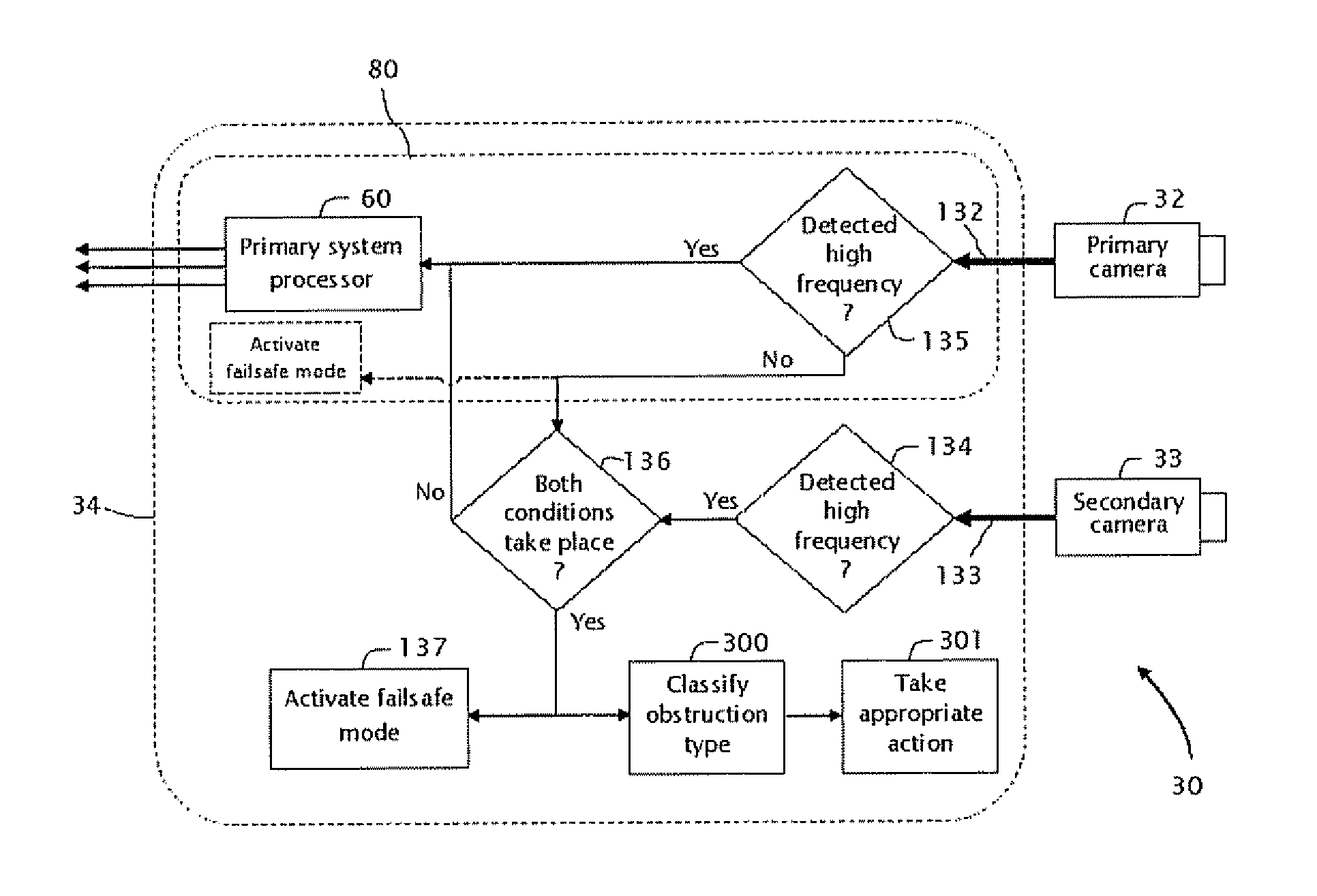
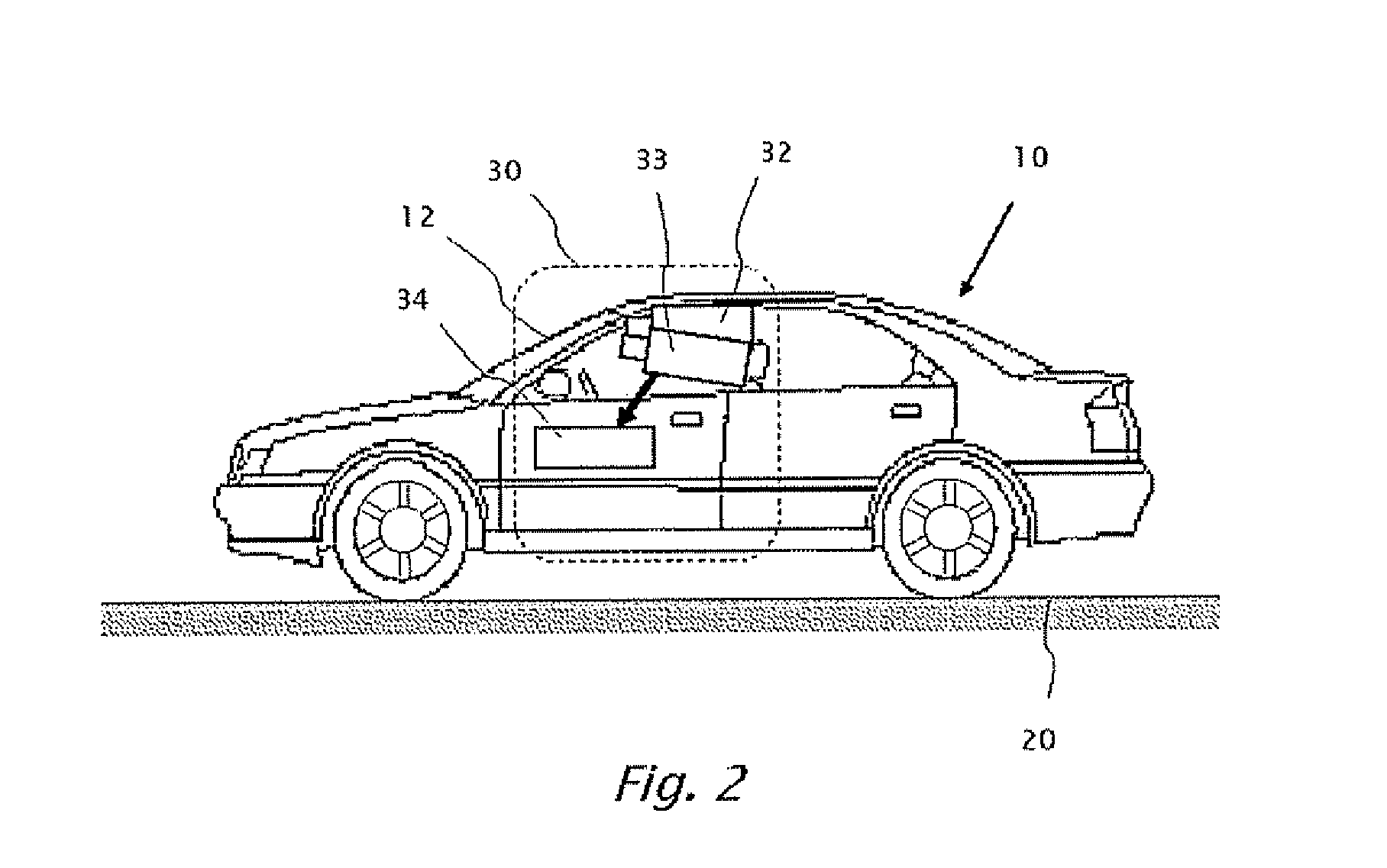
A system mounted on a vehicle for detecting an obstruction on a surface of a window of the vehicle, a primary camera is mounted inside the vehicle behind the window. The primary camera is configured to acquire images of the environment through the window. A secondary camera is focused on an external surface of the window, and operates to image the obstruction. A portion of the window, i.e. window region is subtended respectively by the field of view of the primary camera and the field of view of the secondary camera. A processor processes respective sequences of image data from both the primary camera and the secondary camera.
Owner:MOBILEYE VISION TECH LTD
Systems and methods for detecting obstructions in a camera field of view
ActiveUS20070115357A1Avoid identificationIncrease blockingVehicle headlampsCharacter and pattern recognitionField of viewImaging data
A system mounted on a vehicle for detecting an obstruction on a surface of a window of the vehicle, a primary camera is mounted inside the vehicle behind the window. The primary camera is configured to acquire images of the environment through the window. A secondary camera is focused on an external surface of the window, and operates to image the obstruction. A portion of the window, i.e. window region is subtended respectively by the field of view of the primary camera and the field of view of the secondary camera. A processor processes respective sequences of image data from both the primary camera and the secondary camera.
Owner:MOBILEYE VISION TECH LTD
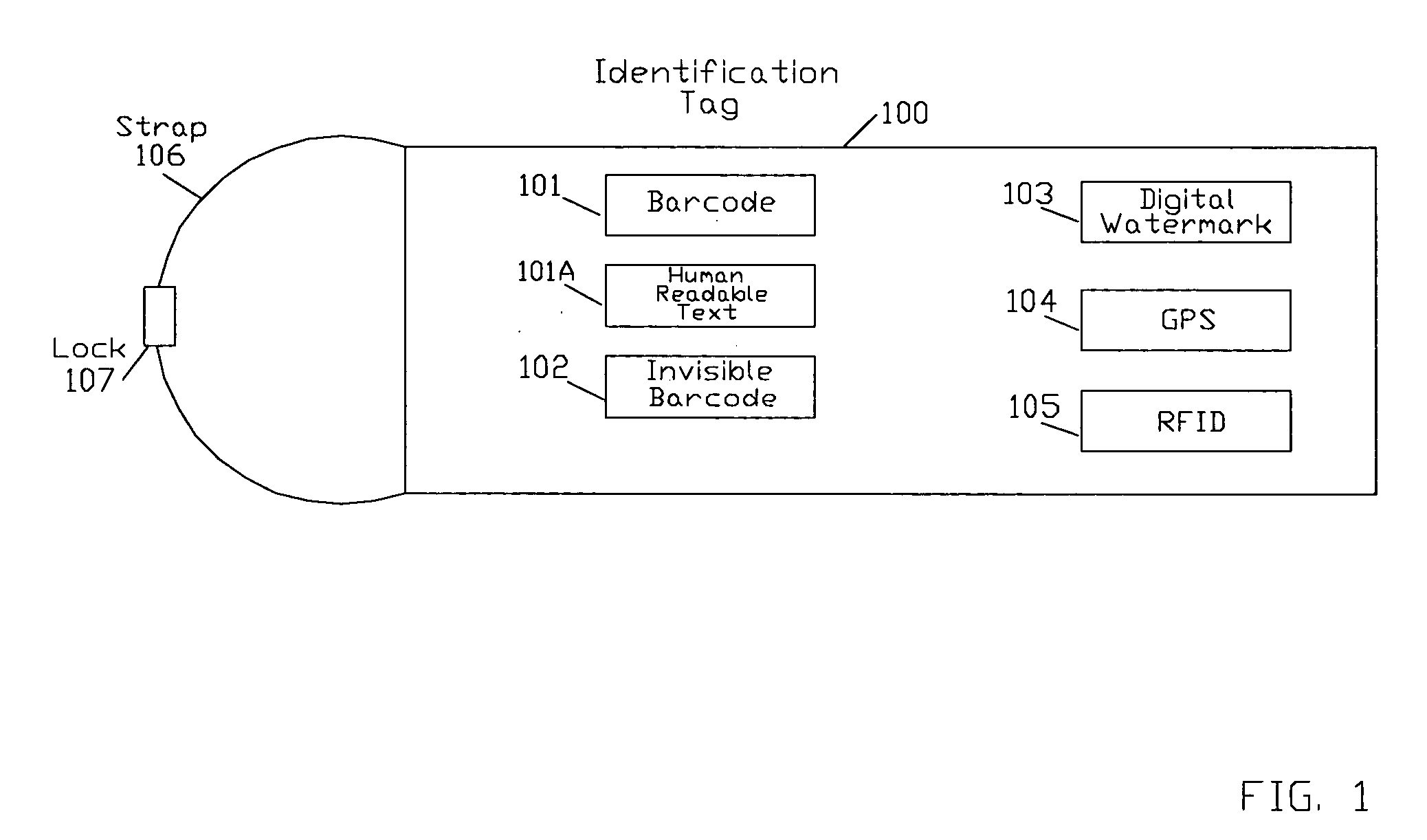
System, method, and apparatus for identifying and authenticating the presence of high value assets at remote locations
InactiveUS20040177032A1Avoid identificationPrevent fraudFinanceCo-operative working arrangementsOperating systemEngineering
A system, method, and apparatus for identifying and authenticating the presence of high value assets at remote location includes associating an identification tag with the asset. The identification tag includes identification information that can be electronically read and sent to a remote location for verifying the authenticity of the asset.
Owner:THE TB GROUP
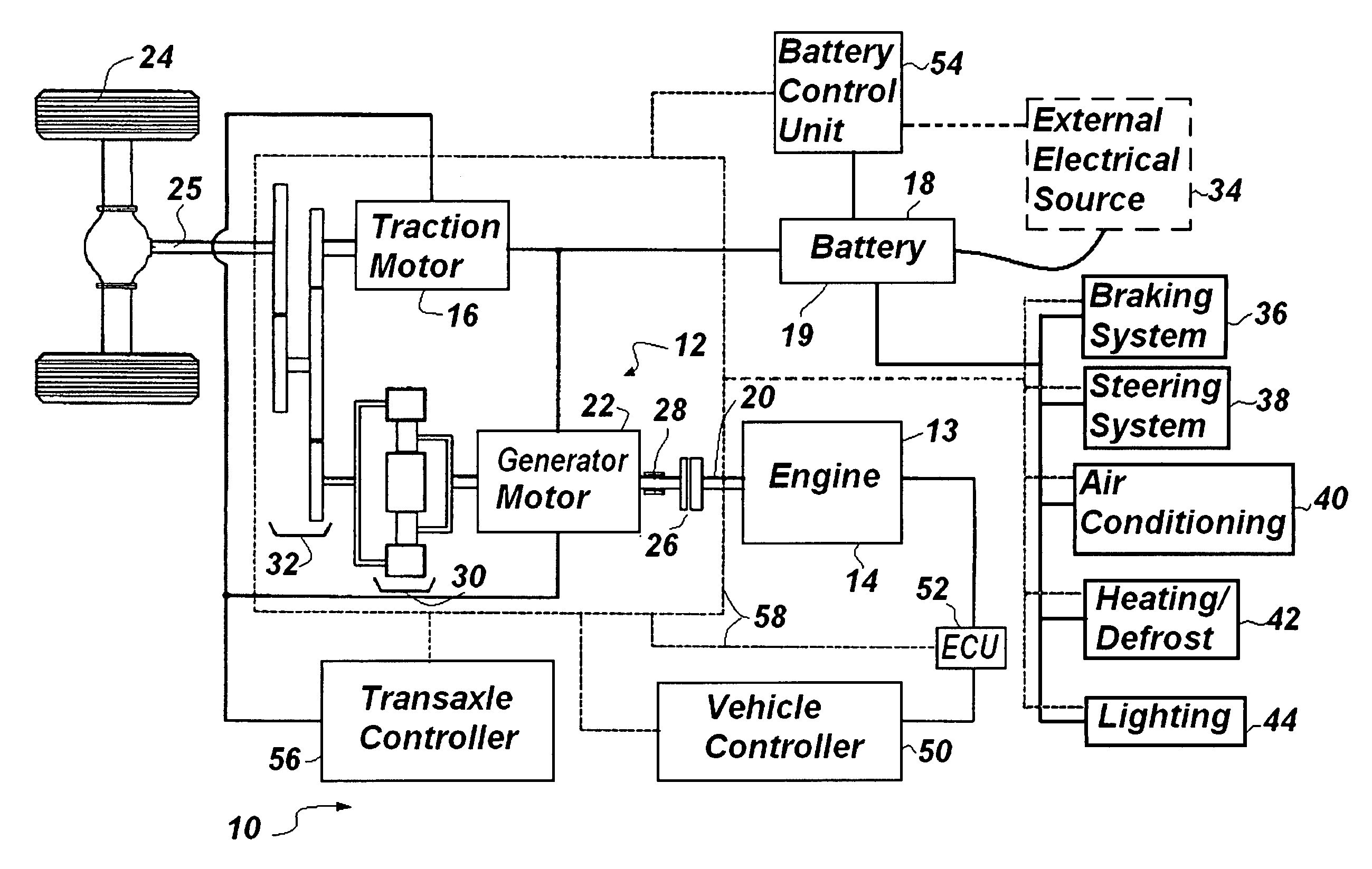
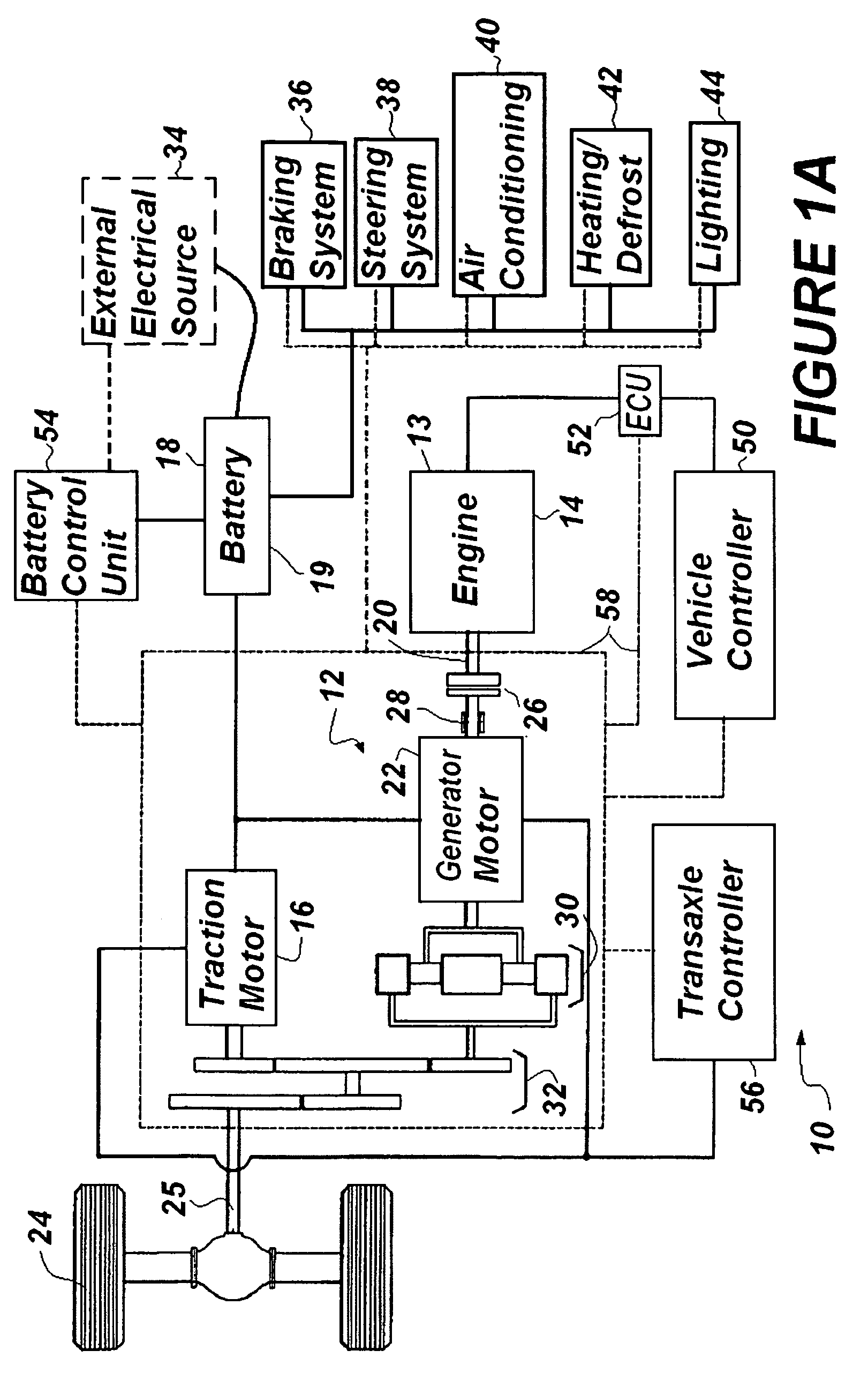
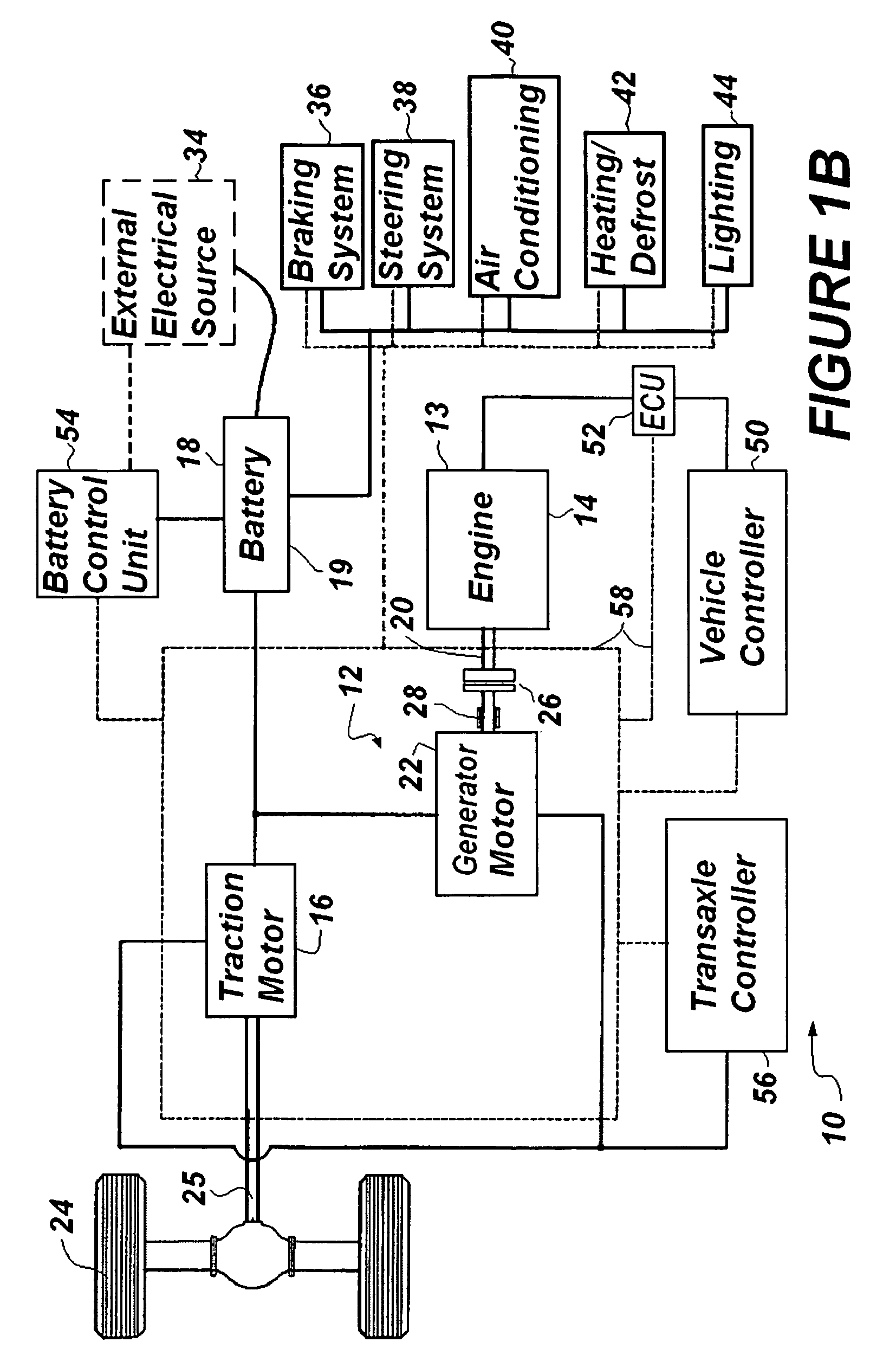
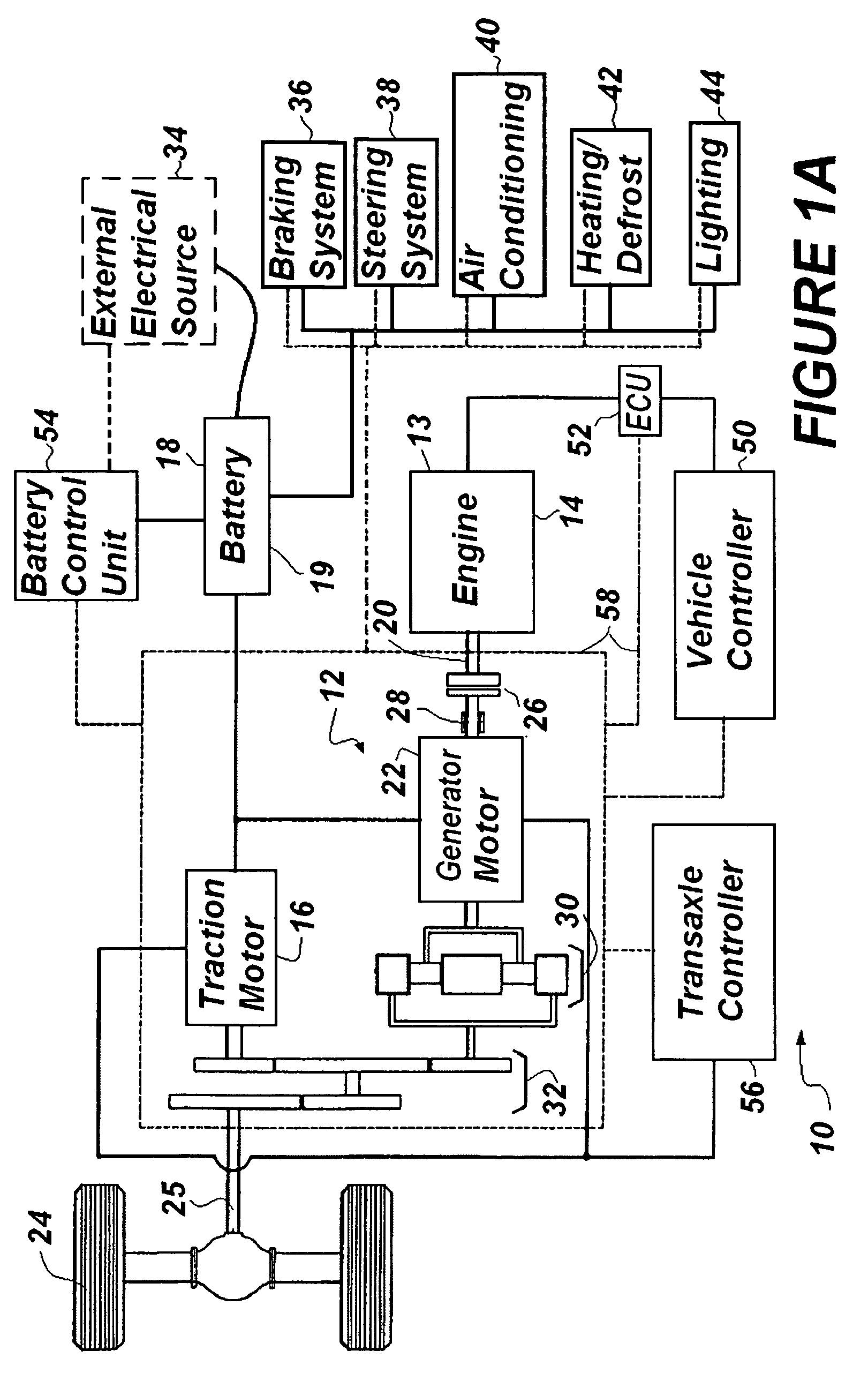
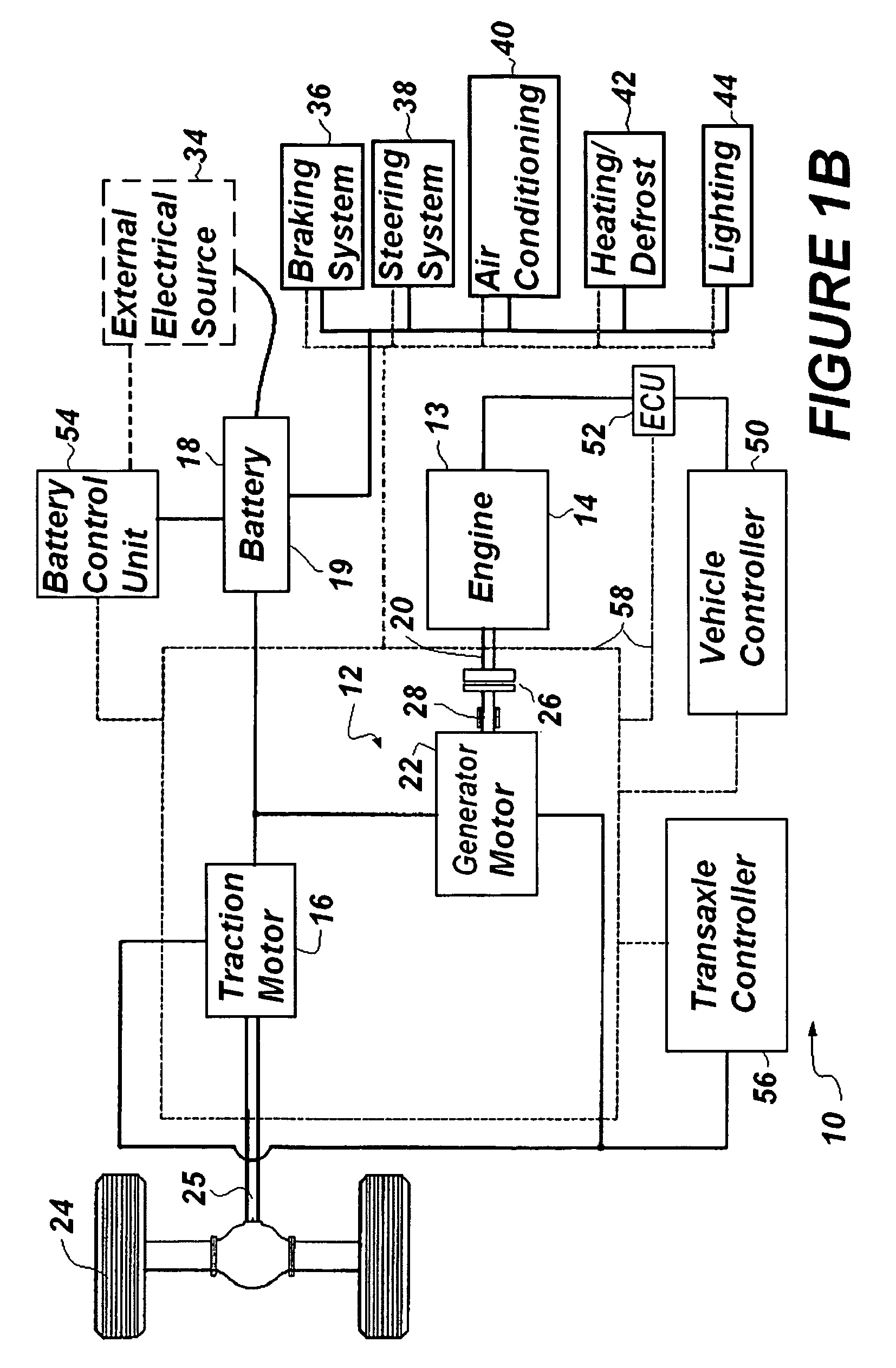
Self-learning control system for plug-in hybrid vehicles
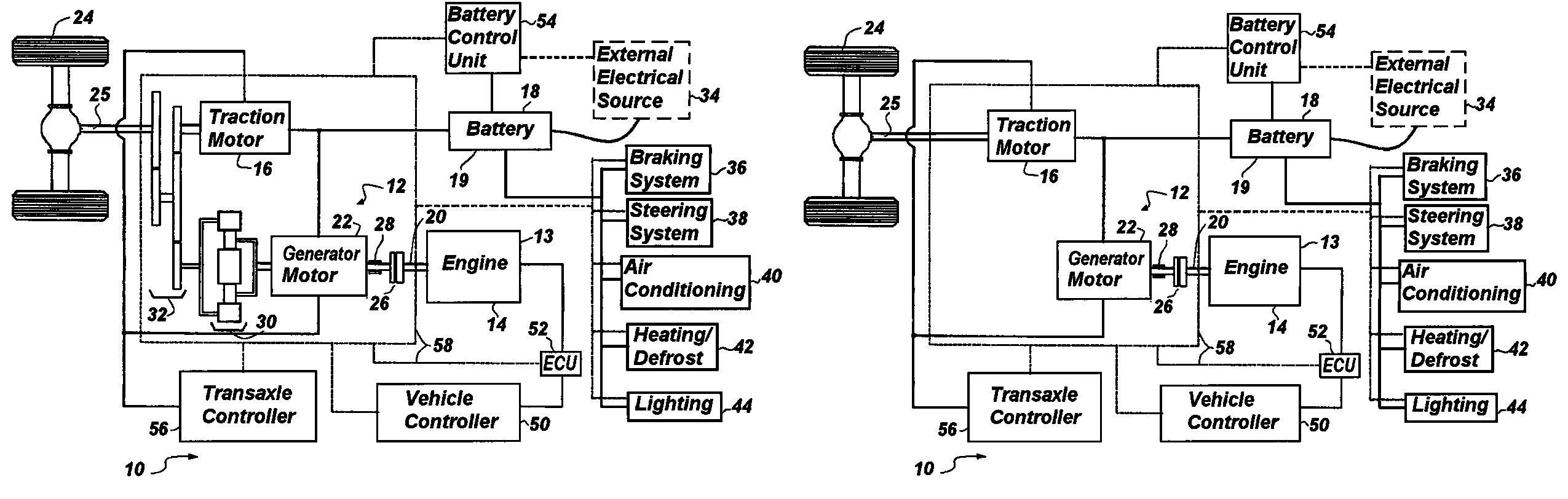
InactiveUS20090114463A1Improve powerMaximize recharge energyDigital data processing detailsExternal condition input parametersControl systemState of charge
A system is provided to instruct a plug-in hybrid electric vehicle how optimally to use electric propulsion from a rechargeable energy storage device to reach an electric recharging station, while maintaining as high a state of charge (SOC) as desired along the route prior to arriving at the recharging station at a minimum SOC. The system can include the step of calculating a straight-line distance and / or actual distance between an orientation point and the determined instant present location to determine when to initiate optimally a charge depleting phase. The system can limit extended driving on a deeply discharged rechargeable energy storage device and reduce the number of deep discharge cycles for the rechargeable energy storage device, thereby improving the effective lifetime of the rechargeable energy storage device. This “Just-in-Time strategy can be initiated automatically without operator input to accommodate the unsophisticated operator and without needing a navigation system / GPS input.
Owner:UT BATTELLE LLC
Dynamically and customizably managing data in compliance with privacy and security standards
InactiveUS9049314B2Preserving professional confidencesAvoid identificationDigital data protectionOffice automationDocumentation procedureRecordset
Owner:VERISMA SYST
Computer resource distribution method based on prediciton
InactiveUS20090113056A1Reduce in quantityReduce maintenance costsResource allocationDigital computer detailsComputer resourcesDistribution method
Owner:HITACHI LTD
Self-learning control system for plug-in hybrid vehicles
InactiveUS7849944B2Improve powerMaximize recharge energyDigital data processing detailsExternal condition input parametersControl systemState of charge
A system is provided to instruct a plug-in hybrid electric vehicle how optimally to use electric propulsion from a rechargeable energy storage device to reach an electric recharging station, while maintaining as high a state of charge (SOC) as desired along the route prior to arriving at the recharging station at a minimum SOC. The system can include the step of calculating a straight-line distance and / or actual distance between an orientation point and the determined instant present location to determine when to initiate optimally a charge depleting phase. The system can limit extended driving on a deeply discharged rechargeable energy storage device and reduce the number of deep discharge cycles for the rechargeable energy storage device, thereby improving the effective lifetime of the rechargeable energy storage device. This “Just-in-Time strategy can be initiated automatically without operator input to accommodate the unsophisticated operator and without needing a navigation system / GPS input.
Owner:UT BATTELLE LLC
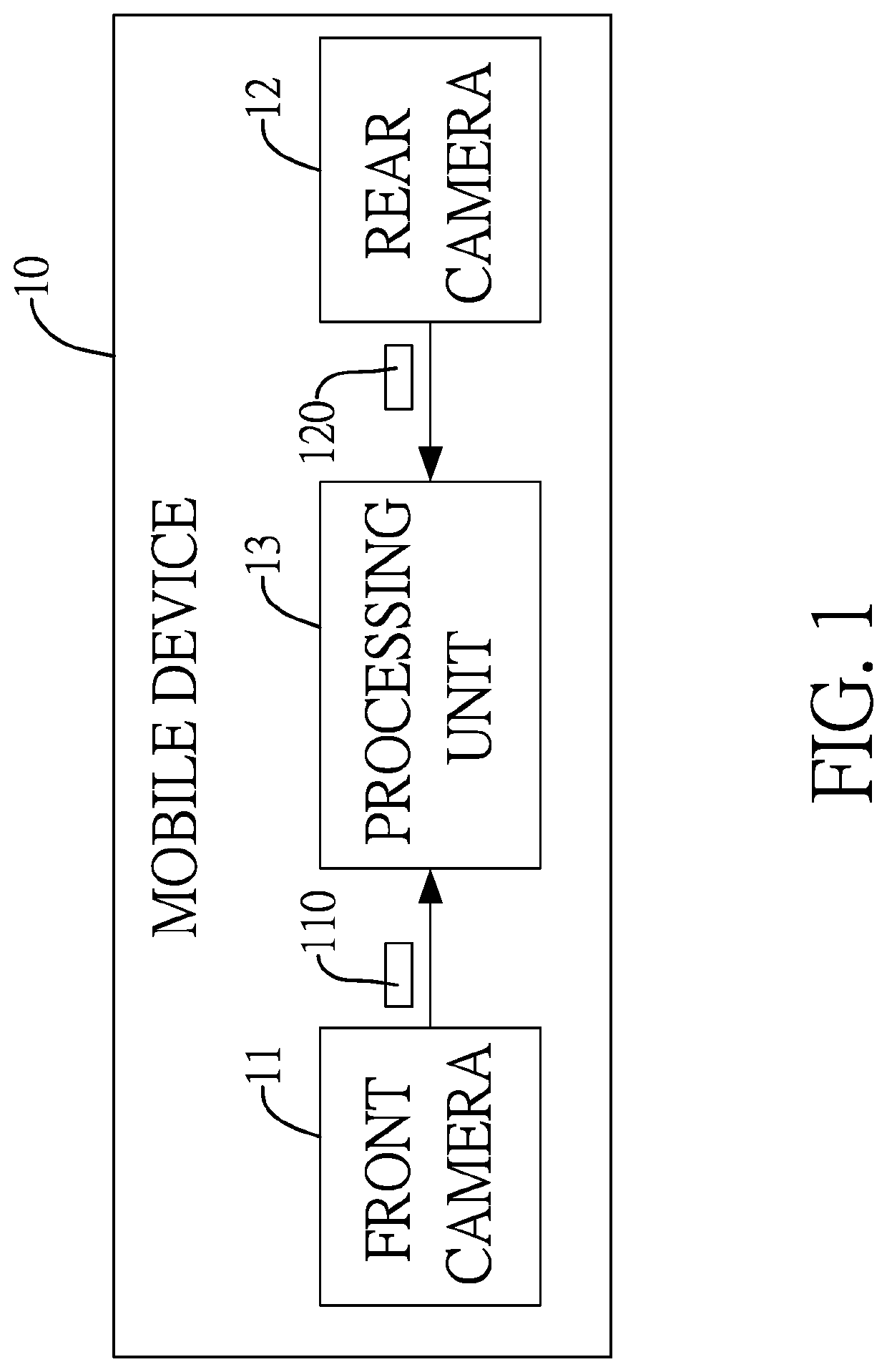
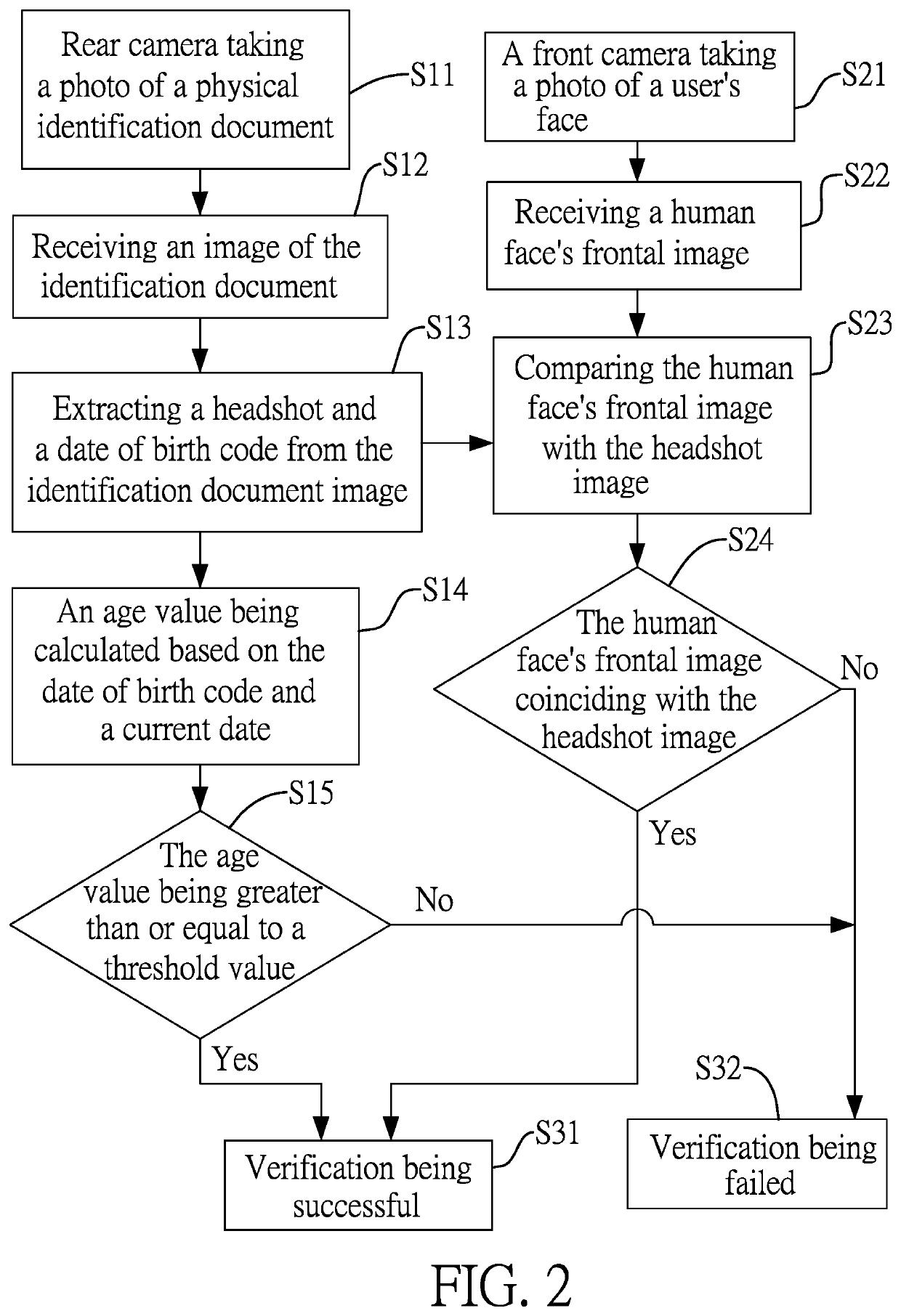
Method for verifying user identity and age
InactiveUS20190362169A1Prevent fraudAvoid identificationBuying/selling/leasing transactionsMultiple biometrics useComputer visionDate of birth
A method for verifying user identity and age includes: using a front camera to receive a frontal image of a human face; using a rear camera to receive an image of an identification document, from which a headshot and a date of birth code are extracted; determining whether there is a coincidence or not by comparing the face image and the headshot; determining whether an age value, calculated by comparing the date of birth code and a current date, is greater than or equal to a threshold value; when the face image coincides the headshot and the age value is larger than or equal to the threshold value, the verification is passed and an online transaction proceeds; when the face image is not consistent with the headshot or the age value is smaller than the threshold value, the verification fails and the online transaction is terminated.
Owner:GOOD COURAGE LTD
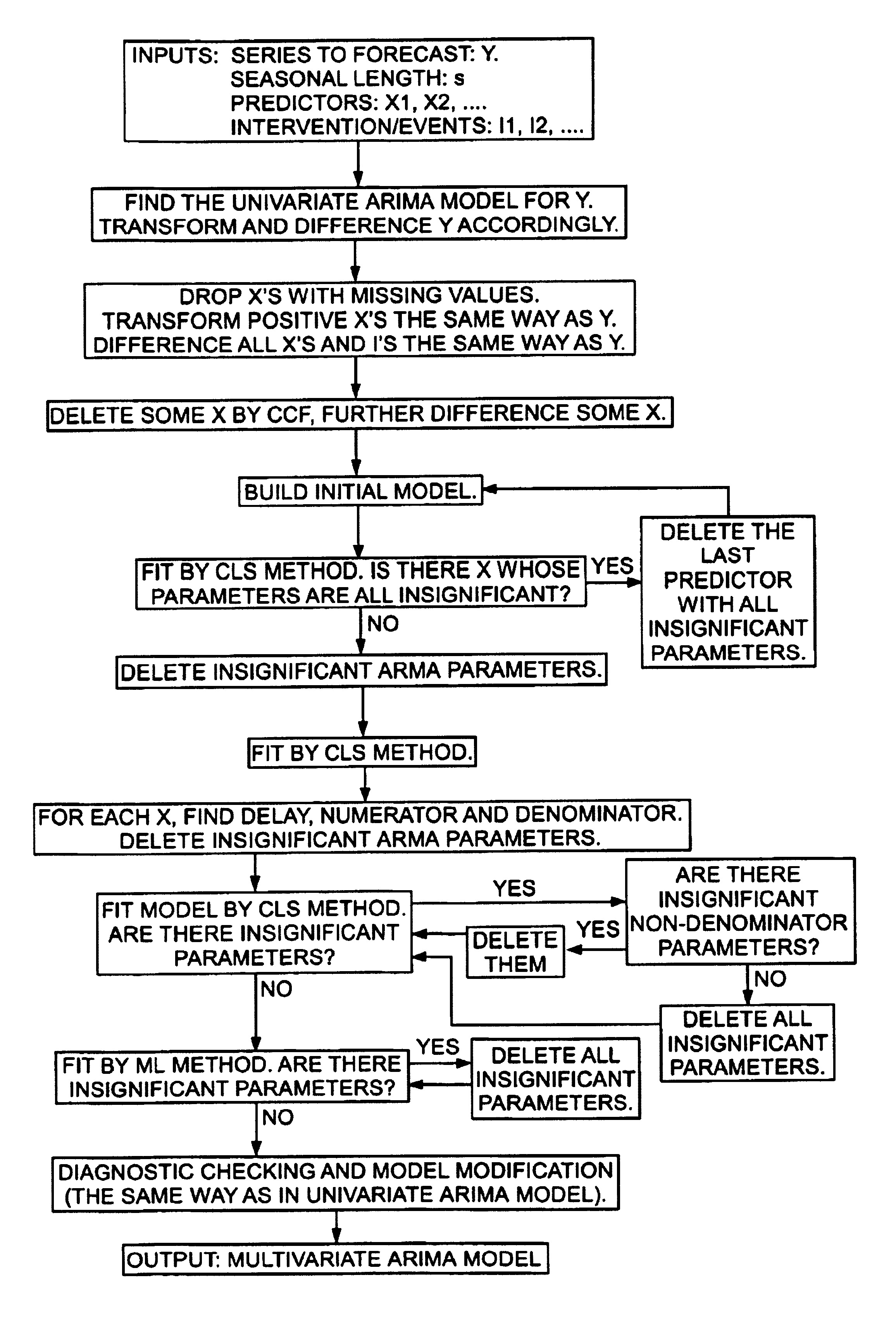
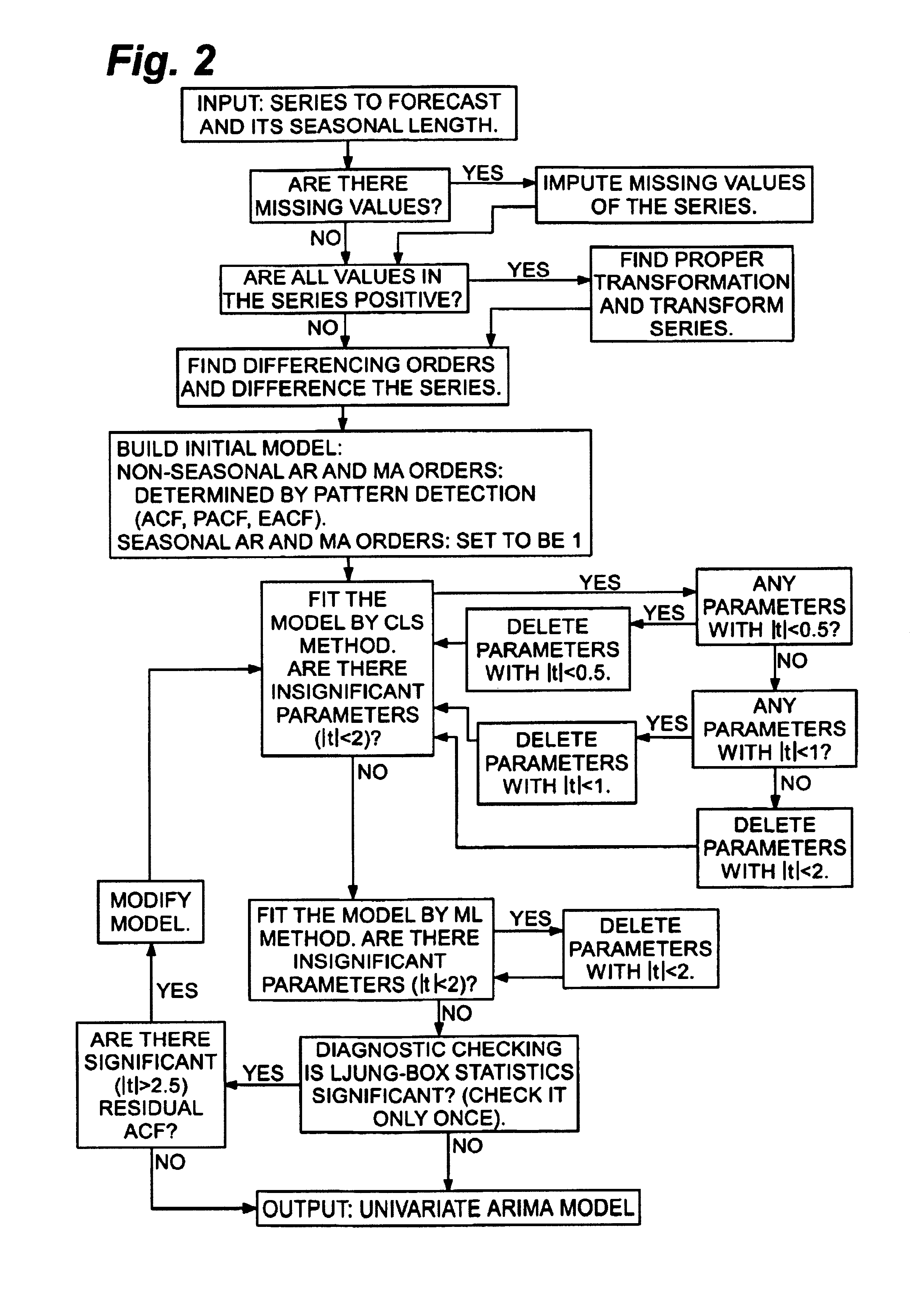
System and method for building a time series model
InactiveUS6928398B1Parameter estimates more accurateAvoid identificationComputation using non-denominational number representationResourcesAlgorithmPattern detection
A method and computer system is provided for automatically constructing a time series model for the time series to be forecasted. The constructed model can be either a univariate ARIMA model or a multivariate ARIMA model, depending upon whether predictors, interventions or events are inputted in the system along with the series to be forecasted. The method of constructing a univariate ARIMA model comprises the steps of imputing missing values of the time series inputted; finding the proper transformation for positive time series; determining differencing orders; determining non-seasonal AR and MA orders by pattern detection; building an initial model; estimating and modifying the model iteratively. The method of constructing a multivariate ARIMA model comprises the steps of finding a univariate ARIMA model for the time series to be forecasted by the method of constructing a univariate model; applying the transformation found in the univariate model to all positive time series including the series to be forecasted and predictors; applying differencing orders found in the univariate model to all time series including the series to be forecasted, predictors, interventions and events; deleting selected predictors and further differencing other predictors; building an initial model wherein its disturbance series follows an ARMA model with AR and MA orders found in the univariate model; estimating and modifying the model iteratively.
Owner:IBM CORP
System and method for inhibiting the decryption of a nucleic acid probe sequence used for the detection of a specific nucleic acid
InactiveUS20060073487A1Reduce or impede a person's ability to designAvoid identificationSugar derivativesMicrobiological testing/measurementGenetic AnomalyNucleic Acid Probes
Sequence-specific nucleic acid hybridization assays are used for the detection of specific genetic sequences as indicators of genetic anomalies, mutations, and disease propensity. In addition, they are used for the detection of various biological agents and infectious pathogens. Because a complementary probe or nucleic acid sequence is required to detect a sequence of interest in a hybridization-based assay, nucleic acid sequencing techniques can rapidly determine the specific probe sequence being used for detection. This allows reverse engineered assays to be produced rapidly. In addition, it enables the circumvention of hybridization-based assays for biological agent or infectious pathogen detection by providing the information necessary to create or alter nucleic acid sequences to produce false positives or false negatives. The present invention provides methods and compositions for inhibiting the identification of specific detection sequences. More specifically, the invention provides masking sequences that mask the identity of specific detection sequences.
Owner:RADIX BIOSOLUTIONS
Monitoring system, monitoring module apparatus and method of monitoring a volume
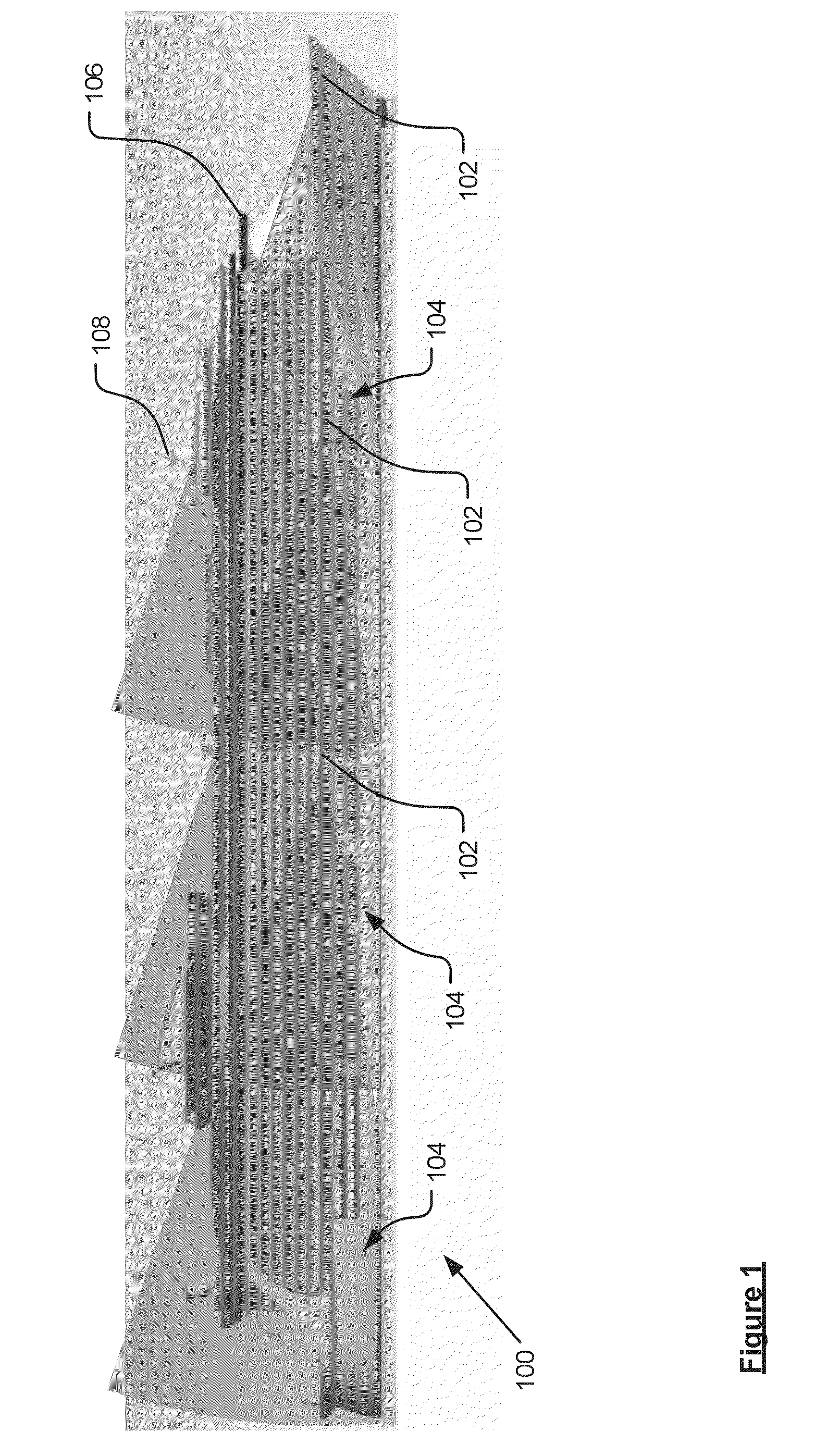
ActiveUS20130169809A1Quick and accurate responseMinimize occurrenceColor television detailsClosed circuit television systemsImage resolutionReal-time computing
A monitoring system for a periphery of a structure (100) comprises a monitoring module (102) having a detection and ranging system (304, 308) arranged to support monitoring of a portion of the periphery in order to detect passage of a body beyond the periphery. The detector (304, 308) has an imaging resolution that prevents conclusive visual identification by a human operator of the nature of the body. The monitoring module also comprises a video capture apparatus (312, 314) arranged to provide video data. The system also comprises a monitoring station apparatus (200) arranged to receive data from the monitoring module (102). In response to detection of the passage of the body by the detection system (304, 308), the monitoring station (200) enables the operator to review the video data. The video data enables the operator to identify readily the nature of the body detected and thereby to provide confirmatory visual evidence when the body is human.
Owner:FLIR SYST LTD
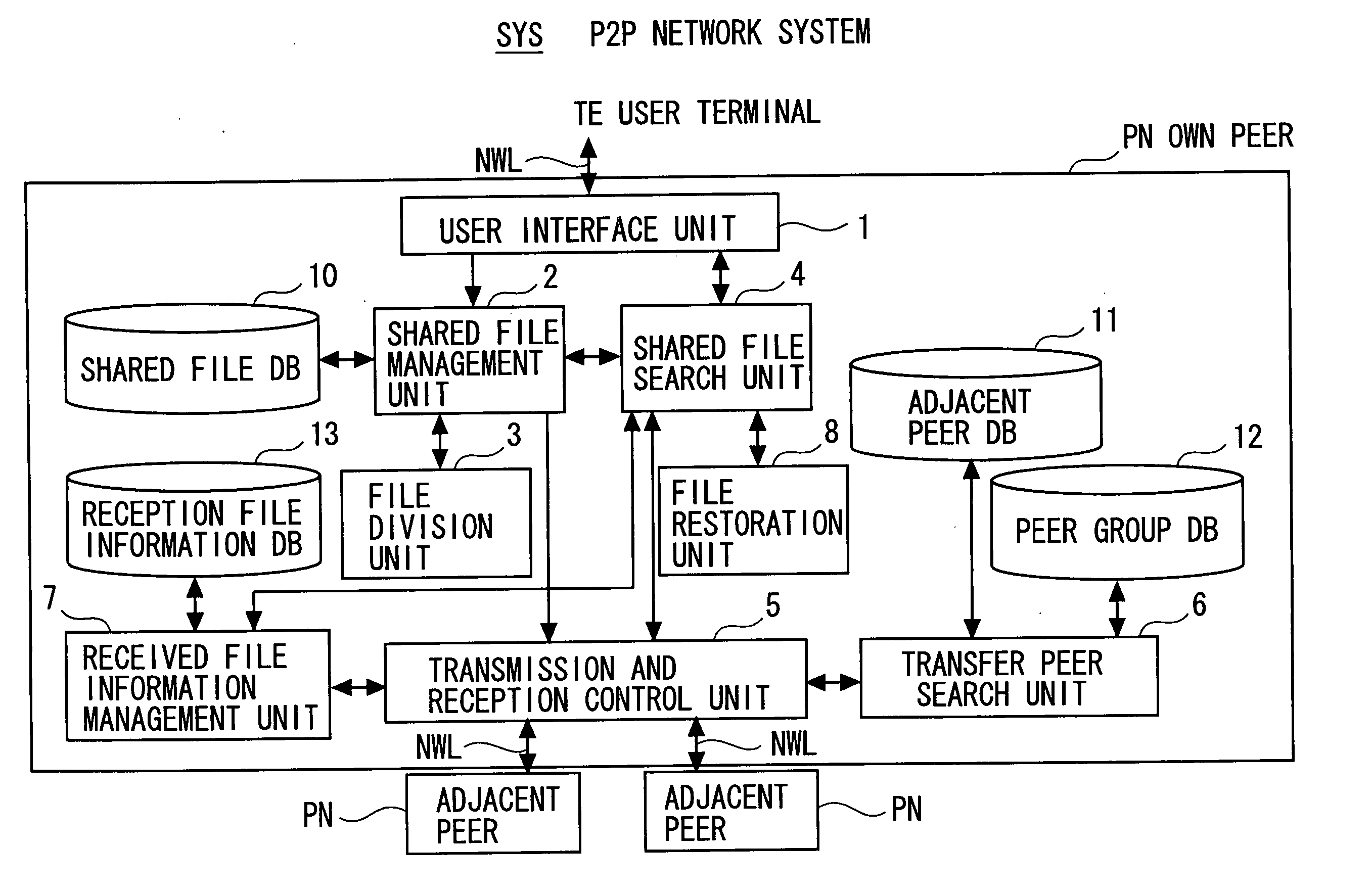
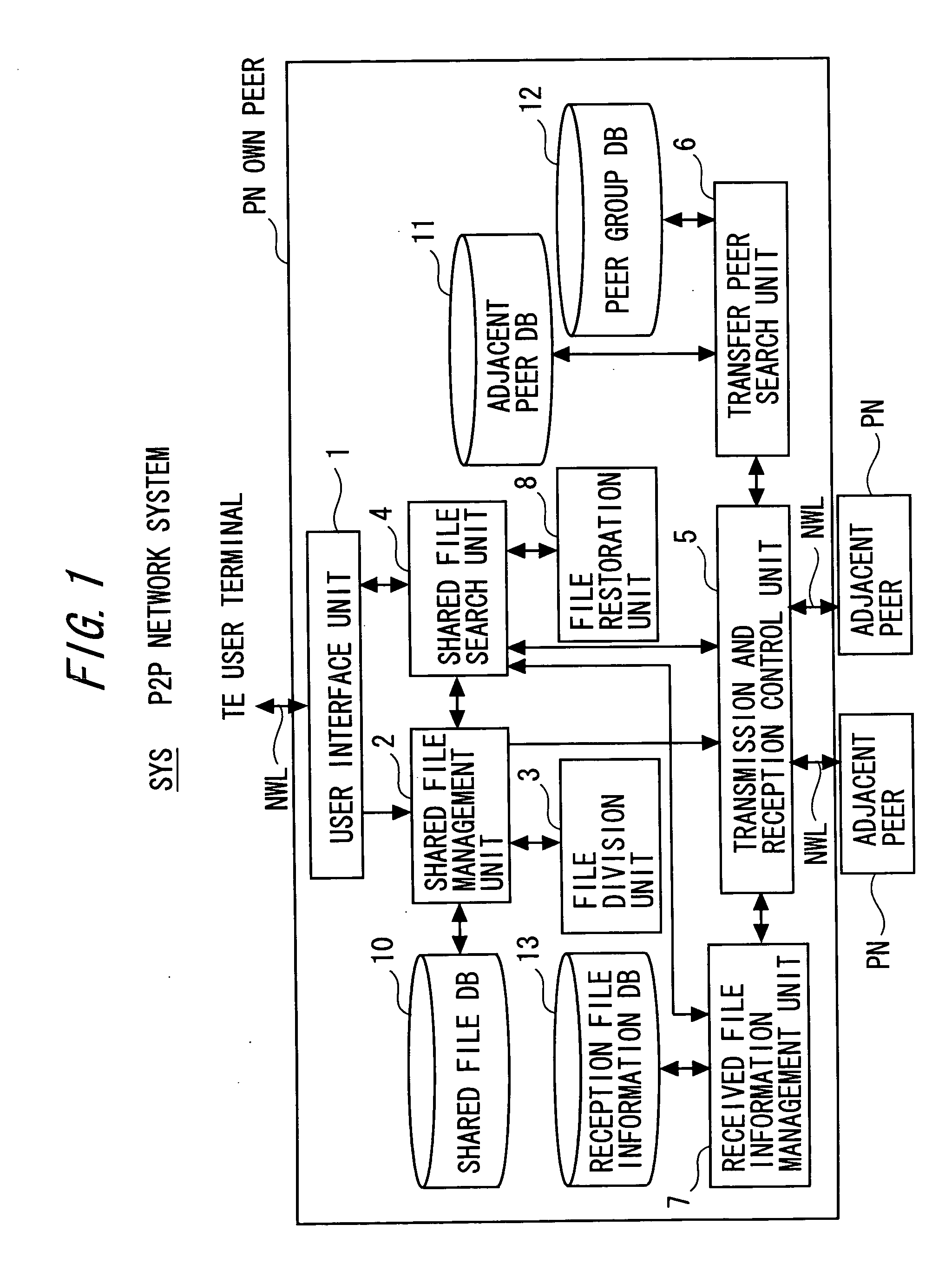
P2P network system
InactiveUS20050216473A1Prevent unauthorized accessInhibitory contentDigital data information retrievalDigital data processing detailsInformation sharingComputer science
A peer node according to the present invention relates to a peer node for constructing a peer-to-peer (P2P) network allowing P2P type communication. The peer node includes a unit dividing a share target file for information sharing through the P2P network into a plurality of divided files in a form where contents of each divided file makes no sense by itself; a unit distributing and arranging the plurality of divided files to and in a plurality of peer nodes including the own peer node and at least one other peer node constituting the P2P network; and a unit moving each of the divided files of distribution and arrangement between the plurality of peer nodes at a certain period of time.
Owner:FUJITSU LTD
System, method and computer program product for enabling access to a resource of a multi-tenant on-demand database service utilizing a token
ActiveUS20130198236A1Avoid identificationUnwanted useWeb data indexingDigital data processing detailsDatabase servicesOn demand
In accordance with embodiments, there are provided mechanisms and methods for enabling access to a resource of a multi-tenant on-demand database service utilizing a token. These mechanisms and methods for enabling access to a resource of a multi-tenant on-demand database service utilizing a token can be utilized to prevent identification of a user attempting to access the resource, and thus unwanted use of the user's identity.
Owner:SALESFORCE COM INC
Computer resource distribution method based on prediction
InactiveUS7500001B2Reduce in quantityReduce maintenance costsResource allocationDigital computer detailsComputer resourcesDistribution method
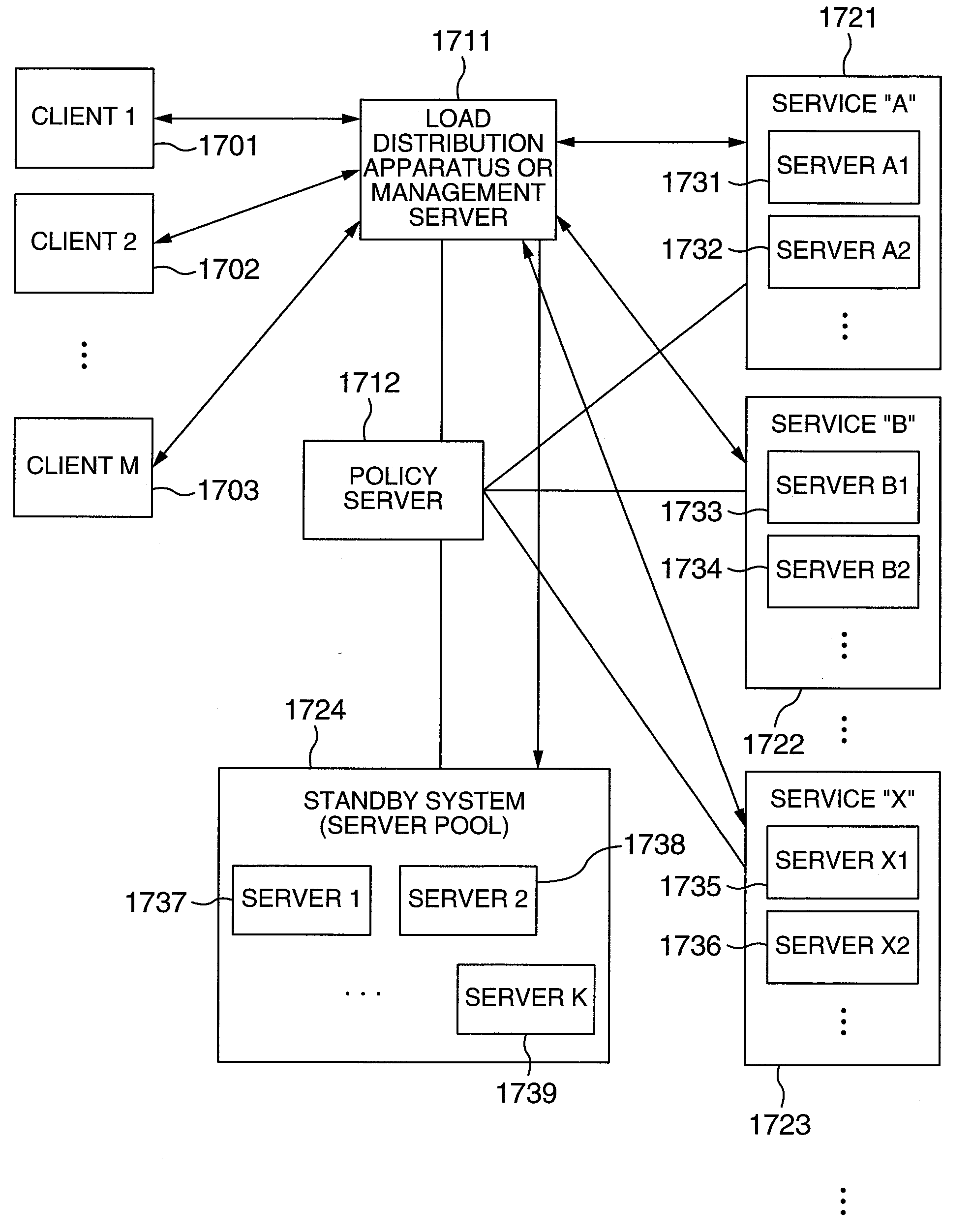
A resource distribution method capable of lending surplus resources among a plurality of services and reducing the maintenance cost of the surplus resources is provided. Computer resources in the standby system have a dead standby state in which at least an application is not installed. A plurality of services or a plurality of users share the computer resources in the standby system. As a result, improvement of the utilization factor of idle computer resources and server integration are implemented, and the cost required to maintain the computer resources is reduced. Furthermore, load prediction is conducted as regards individual services by using past operation history. Idle computer resources secured from services having surplus and maintained are thrown in according to a result of the prediction.
Owner:HITACHI LTD
Use of nano structured lipid carrier drug feeding system
InactiveCN101129335AIncrease intakeGood curative effectPowder deliveryOrganic active ingredientsLipid formationMonoglyceride
The invention discloses an application of nanometer structure lipid carrier administration system in the antineoplastic drug to reverse the multiple-drug tolerance of tumour cell, which comprises the following parts: solid lipid material, liquid lipid material and antineoplastic drug, wherein the rate of the liquid lipid (such as oleic acid) is 0-30wt%; the solid lipid is selected from monoglyceride; the liquid lipid is oleic acid; the antineoplastic drug is Paclitaxel or adriablastina. The invention has highly effective cell uptaking and cytolymph condensing function with packing molecular target in the antineoplastic drug of cell, which avoids P-glucoprotein in the drug tolerant cytolymph from identifying the antineoplastic drug to reduce exclusion.
Owner:ZHEJIANG UNIV
Pattern recognition method of substation switch based on infrared detection
ActiveCN102289676AImprove match stabilityImprove noise immunityCircuit arrangementsCharacter and pattern recognitionPattern recognitionSmart substation
The invention discloses a method for identifying the mode of a switch of a substation based on infrared detection. The method comprises the following steps of: 1, inputting an image to be identified, acquiring a switch area of the image by image registration, and sequentially graying, binarizing and thinning the switch area; 2, linearly detecting the image of the thinned switch area by using a Hough transformation algorithm; and 3, determining a detection result, and identifying the state of the switch by using a switch state determination condition. An H matrix between two images is obtainedby matching of the features of scale invariant feature transform (SIFT), the switch area in the image is found, and then the state of the switch is identified. Experiments show that: by the method, the problem of identification of a power switch can be effectively solved; an important significance is provided for automatic monitoring of the power equipment of an intelligent substation; the burdens on an inspector of the substation can be reduced; and detection efficiency is greatly improved.
Owner:STATE GRID INTELLIGENCE TECH CO LTD
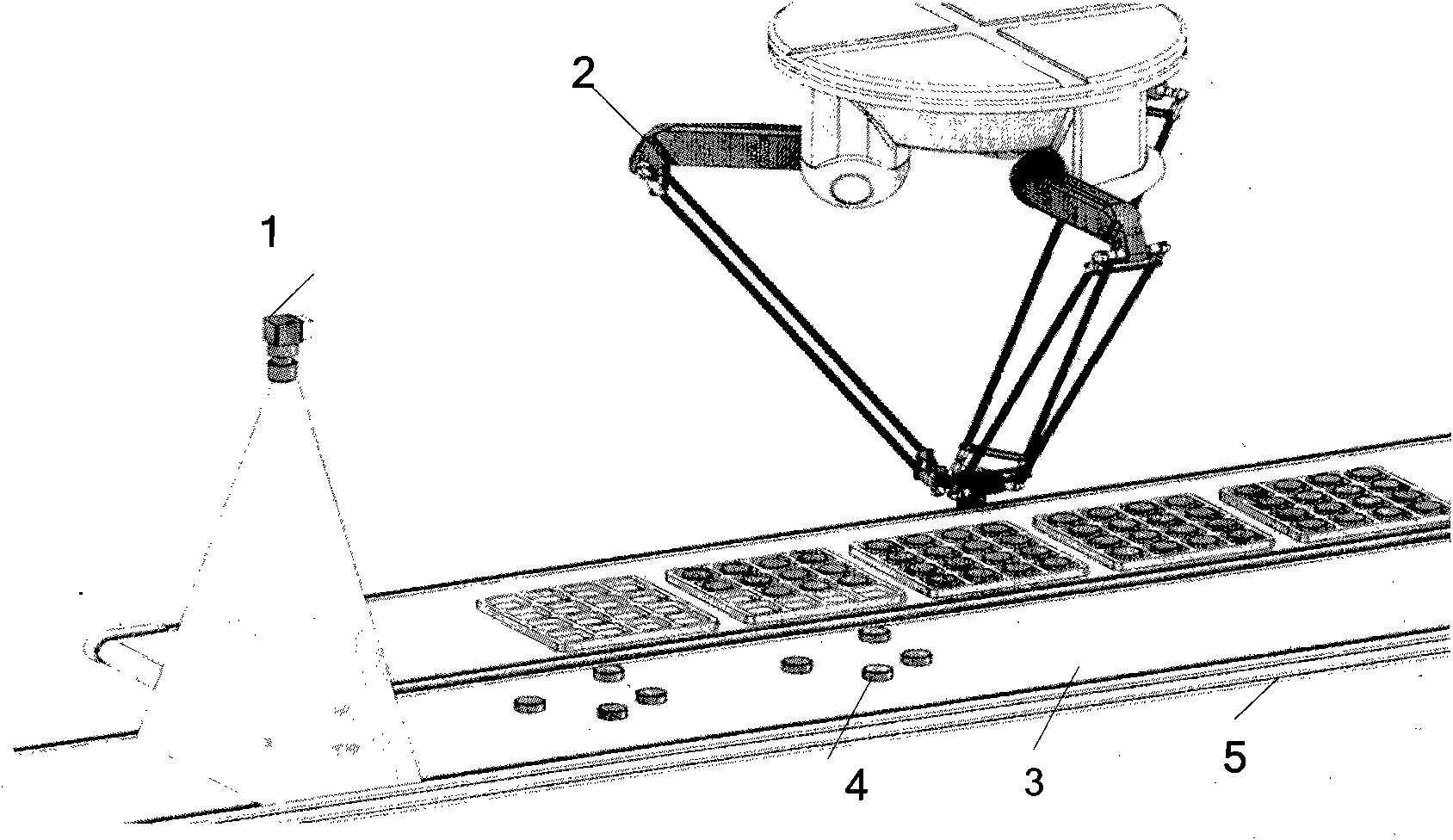
Method for tracking moving object on production line
InactiveCN101872423AAvoid identificationAvoid the situationProgramme-controlled manipulatorImage analysisProduction lineMotor control
The invention discloses a method for tracking a moving object on a production line, and belongs to the field of automatic devices. The method comprises the following steps that: a visual sensor acquires an image of the moving object and transmits the image to a computer; a servo motor controls the operating speed of a conveying belt and acquires displacement information of the conveying belt; the computer receives the image and identifies position information of the moving object; the computer eliminates the situations of missing and repeated identification of the moving object according to the image, the position information, a first decision making condition and a second decision making condition and acquires effective position information of the moving object; the computer acquires position coordinates of the moving object according to the effective position information and the displacement information and stores the position coordinates in a grasped moving object database; and parallel mechanical hands sequentially extract the position coordinates of the moving objects from the grasped moving object database and perform the grasping operation. The method can meet the requirement that the parallel mechanical hands grasp the scattered moving objects at a high speed in real time.
Owner:TIANJIN UNIV
Display panel, control method thereof, display device and display system for anti-peeping display
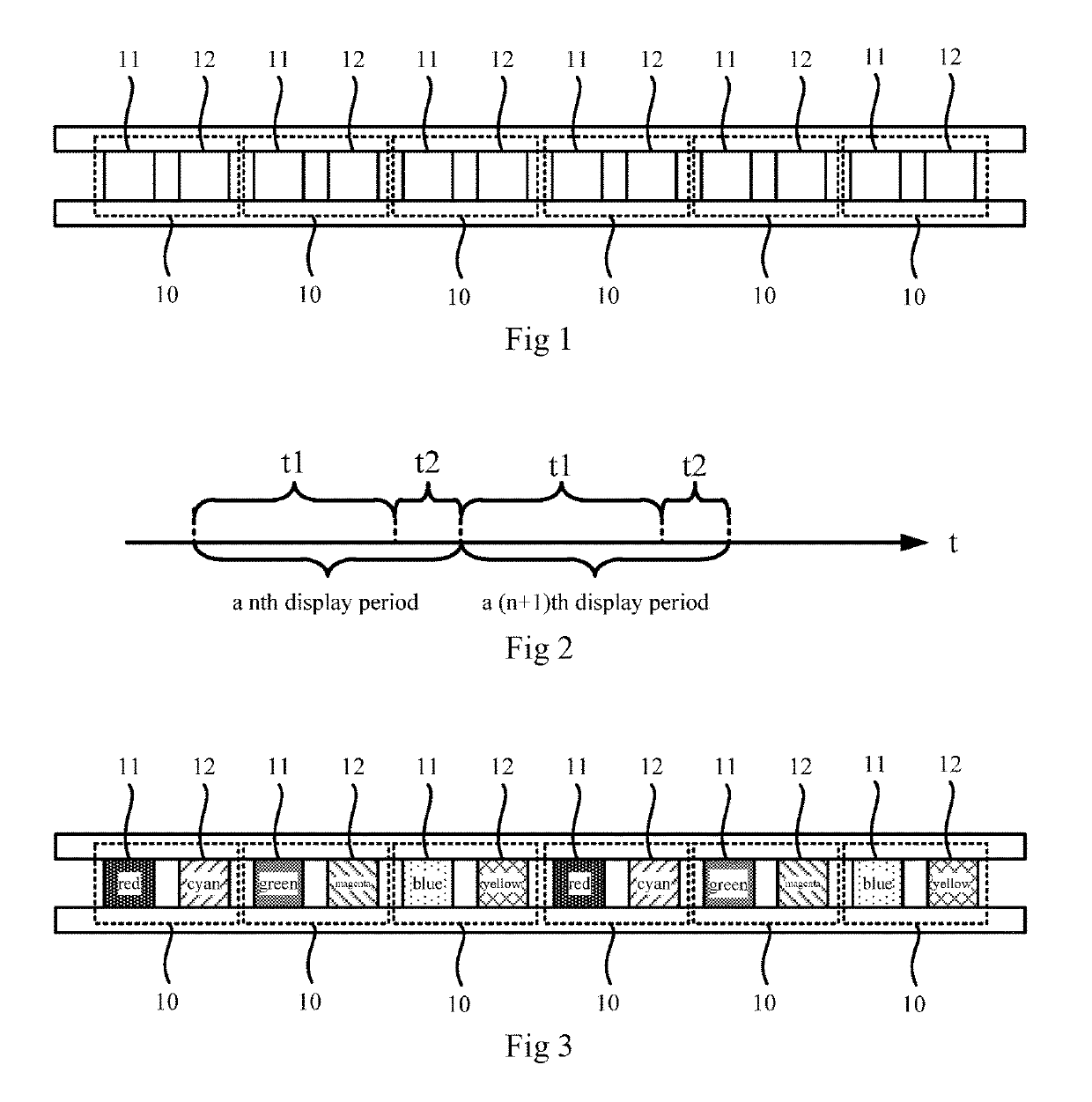
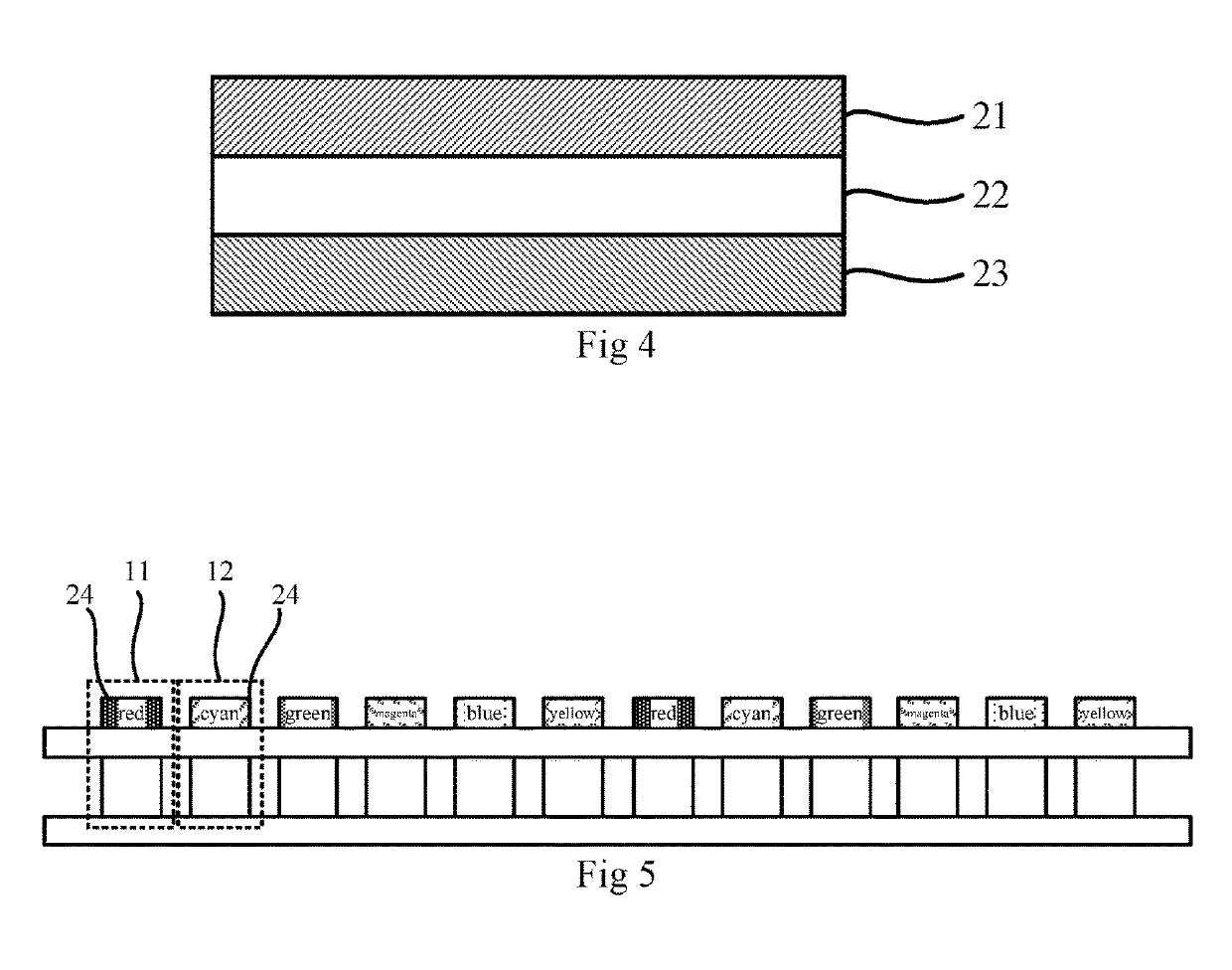
ActiveUS10504437B2Improve privacyAvoid identificationStatic indicating devicesSolid-state devicesDisplay deviceComputer science
This disclosure relates to a display panel, a control method thereof, a display device and a display system comprising such a display panel. The display panel includes a plurality of pixel units. Each pixel unit has a plurality of subpixels Each subpixel has a display subpixel and an interference subpixel. Additionally, the interference subpixel and the display subpixel are different in at least one of color and gray scale. The display panel also includes a first control unit configured to control the display subpixel to be switched on during a first period of time in each display period, and to control the interference subpixel to be switched off during the first period of time in each display period and switched on during a second period of time in each display period.
Owner:BOE TECH GRP CO LTD +1
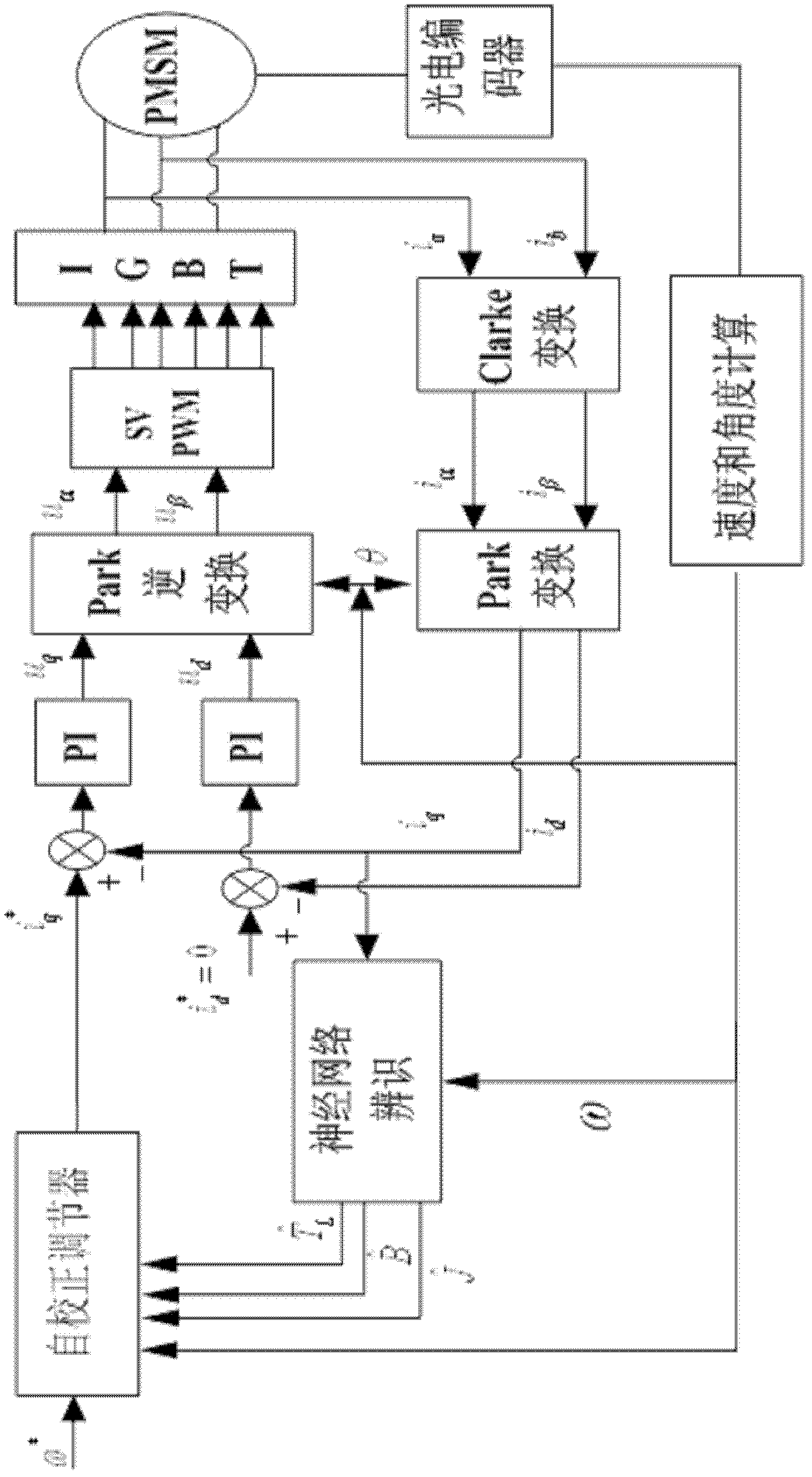
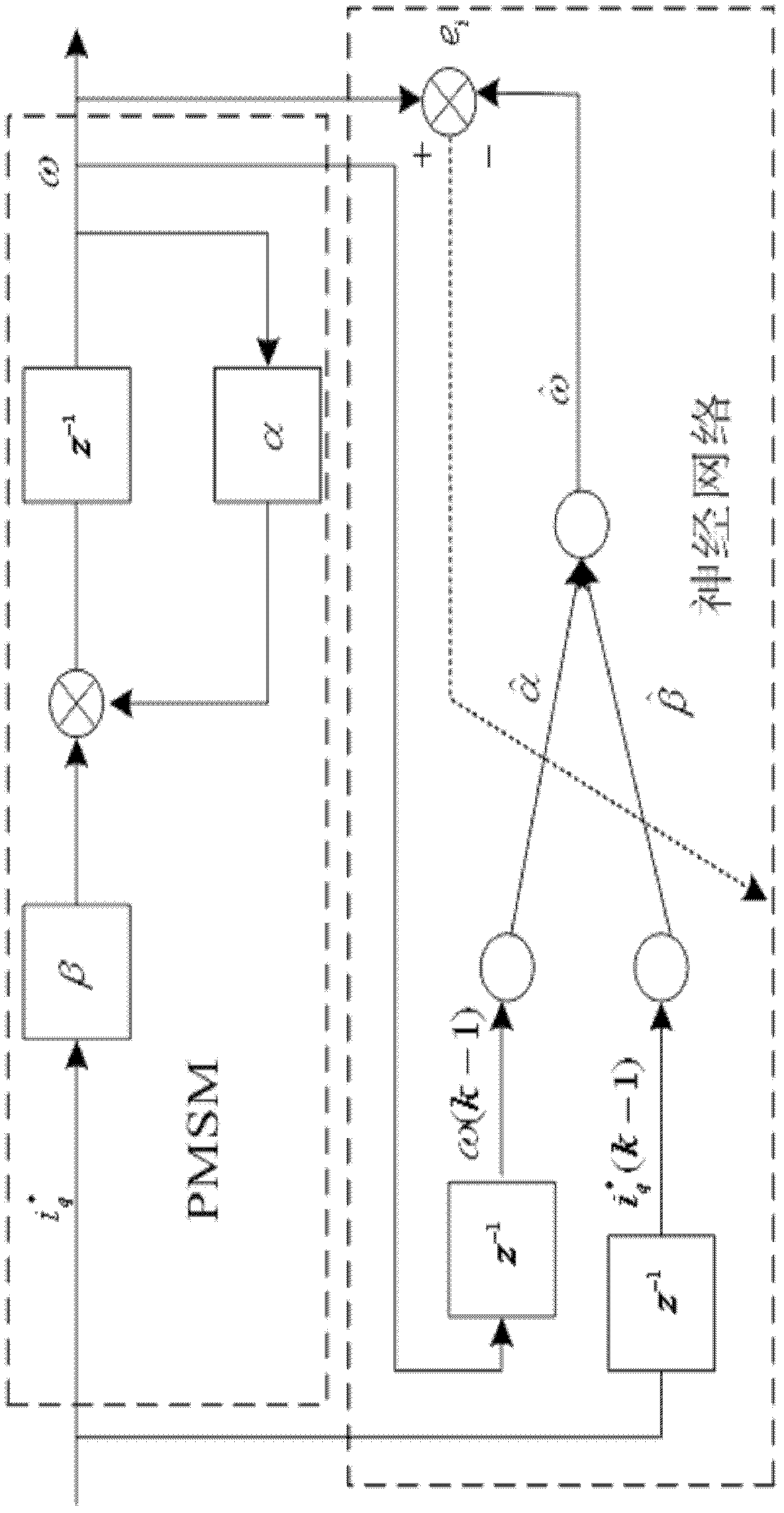
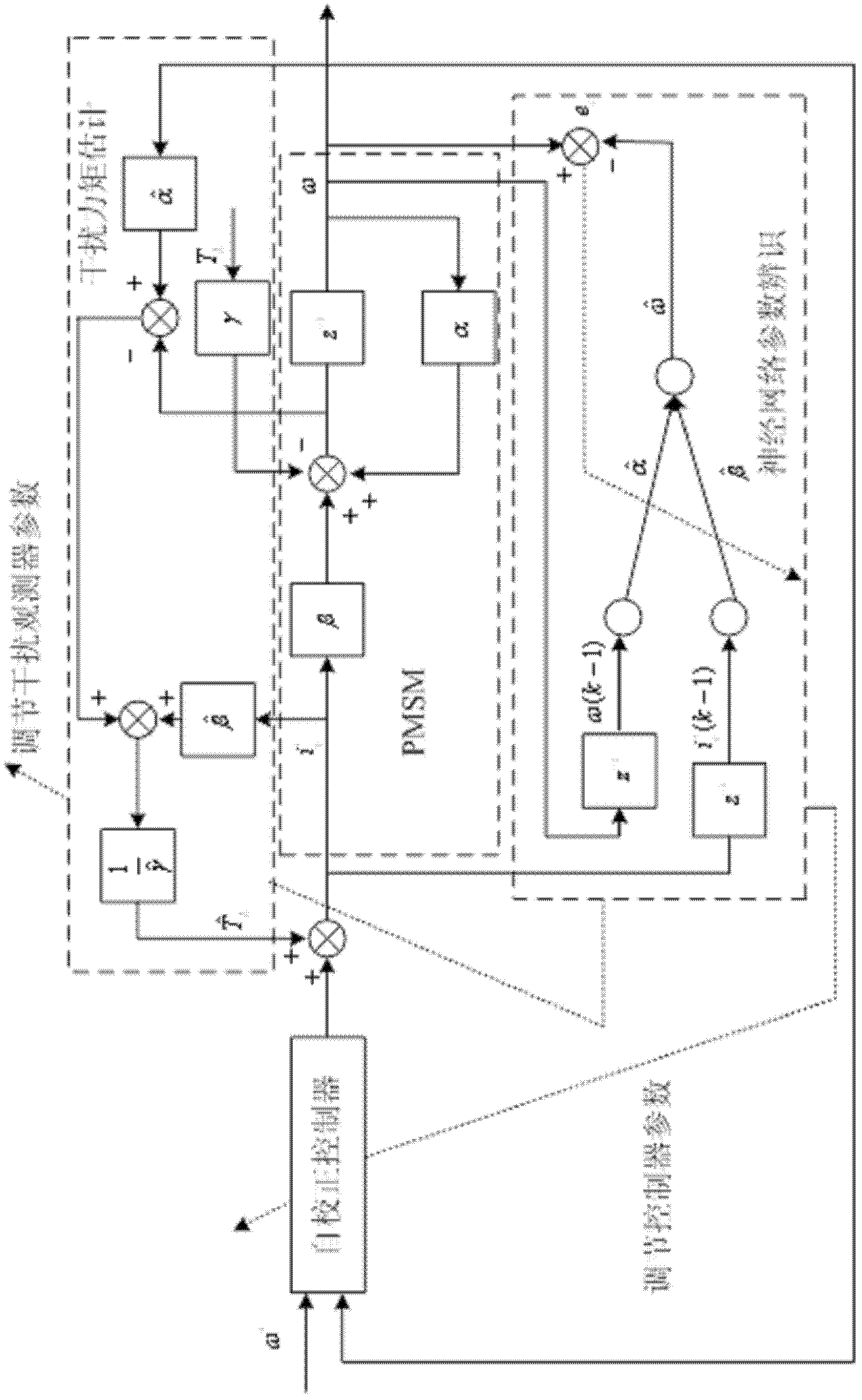
Neural-network self-correcting control method of permanent magnet synchronous motor speed loop
ActiveCN102497156AAdaptableSimple structureElectronic commutation motor controlVector control systemsPower flowLoad torque
The invention discloses a neural-network self-correcting control method of a permanent magnet synchronous motor speed loop. The method is characterized by: taking a current loop and a motor as generalized objects; firstly, collecting information, such as a rotating speed, a current and the like; using an adaptive linear time-delay neural network to carry out off-line parameter identification to the motor; then, taking a weight obtained through off-line learning as an initial value of on-line learning; finally, carrying out on-line parameter identification to the system, calculating a load torque of the motor according to the identified parameter; designing a neural-network self-correcting control law according to the obtained parameter value and a load disturbance value, adjusting the network weight on line according to an error between a controlled object and an identification model, and then setting the parameter of the neural-network self-correcting controller on line so as to realize online adjustment of the controller parameter. Uncertainty of the system and influence brought by the external disturbance can be eliminated. Dynamic performance and an anti-disturbance ability of a servo system can be improved.
Owner:SOUTHEAST UNIV +1
Vehicle identification means detection and evasion system
InactiveUS7076349B2Avoid identificationRoad vehicles traffic controlDigital data processing detailsDriver/operatorEngineering
A system for detecting and evading vehicle identification means (VIM), comprising: locating means, control means having a plurality of I / O channels, each adapted to receive or transmit serial or parallel data, processing means, electronic storage means comprising at least one database of known VIM coordinates and identification prevention device (IPD) adapted to automatically prevent identification of the vehicle's license plate number, owner or driver.
Owner:DAVIDSON RON YAACOV
Memory data protecting device and LSI for IC card
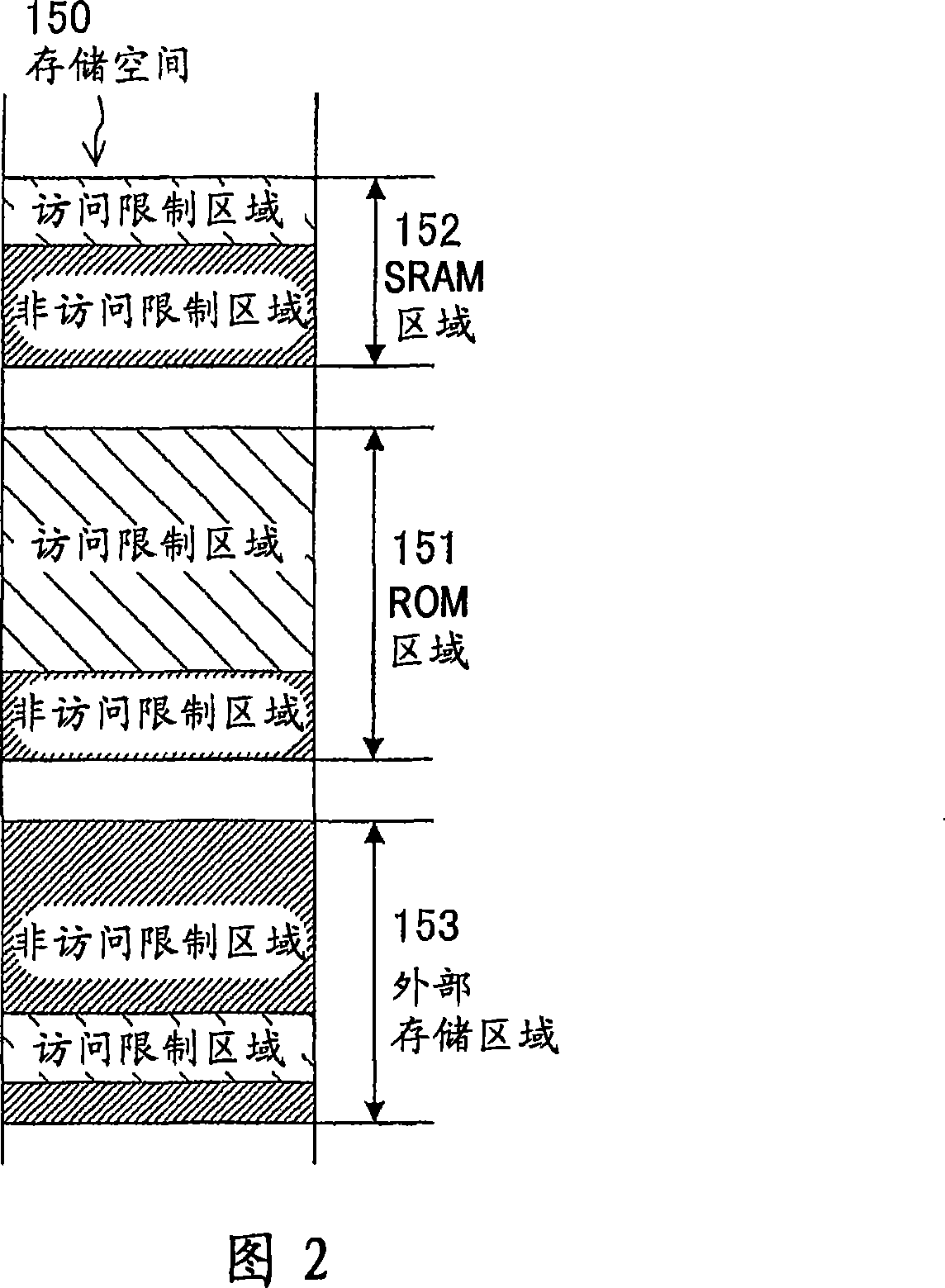
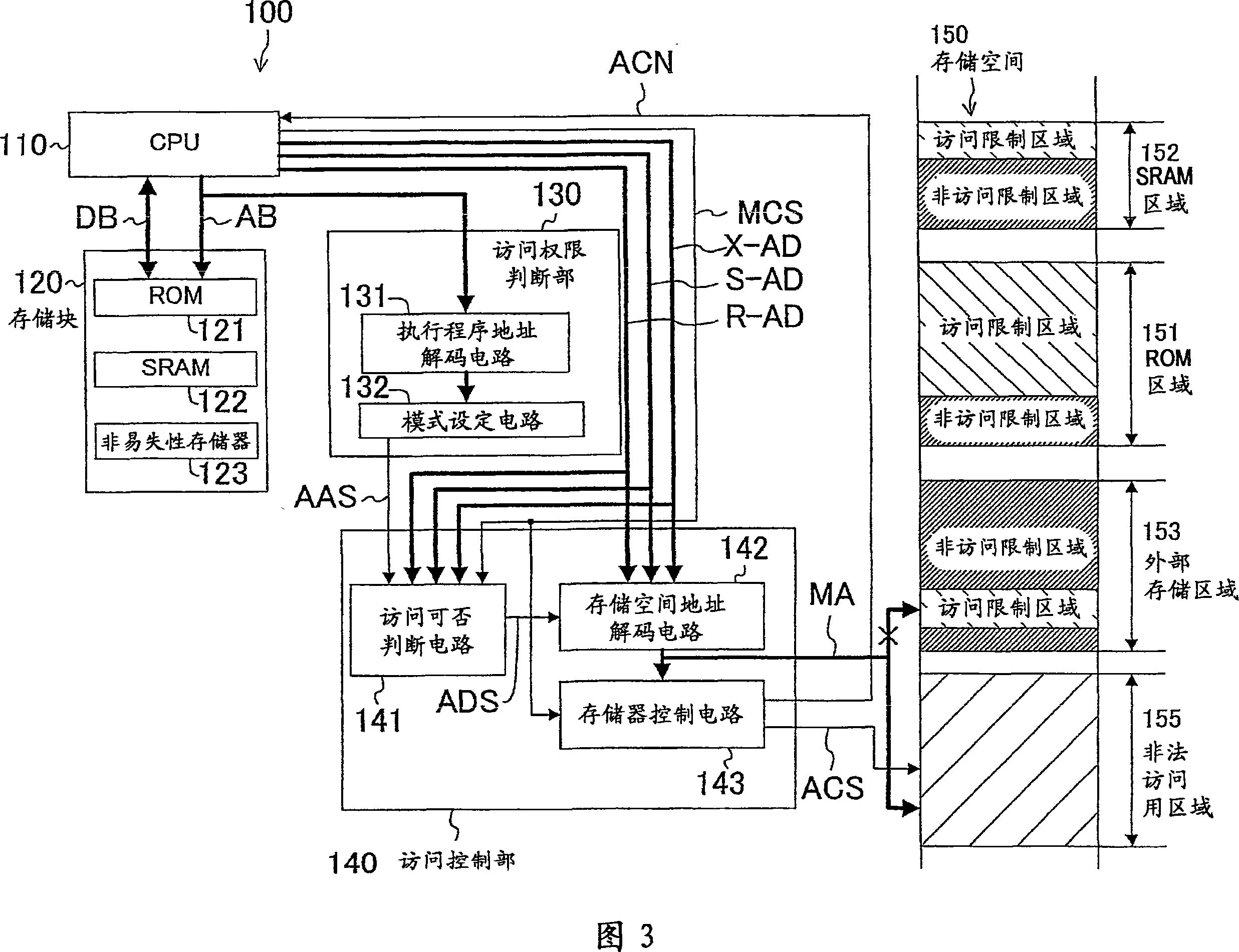
InactiveCN101082886AAvoid identificationReliable access controlUnauthorized memory use protectionDigital data protectionInternet privacyEngineering
The present invention provides a data protecting device for the storing device, which sets illegal visiting used area in the memory space, and allocates physical addresses to the illegal visiting used area. In the visiting authority judging part and the visiting judging circuit, it judges the visiting to the safe data which is to be executed by the CPU is normal visiting or illegal visiting. When the visiting is judged to be illegal visiting, it modifies the logical address mapping of the safe data which is to be visited to the physical address of the illegal visiting used area. Afterwards, it does data treatment to the illegal visiting used area when the mapping is modified. Therefore, when illegal visiting happens, the location of the important area where the safety data is stored is not identified, and thereby it can protect the safety data.
Owner:PANASONIC CORP
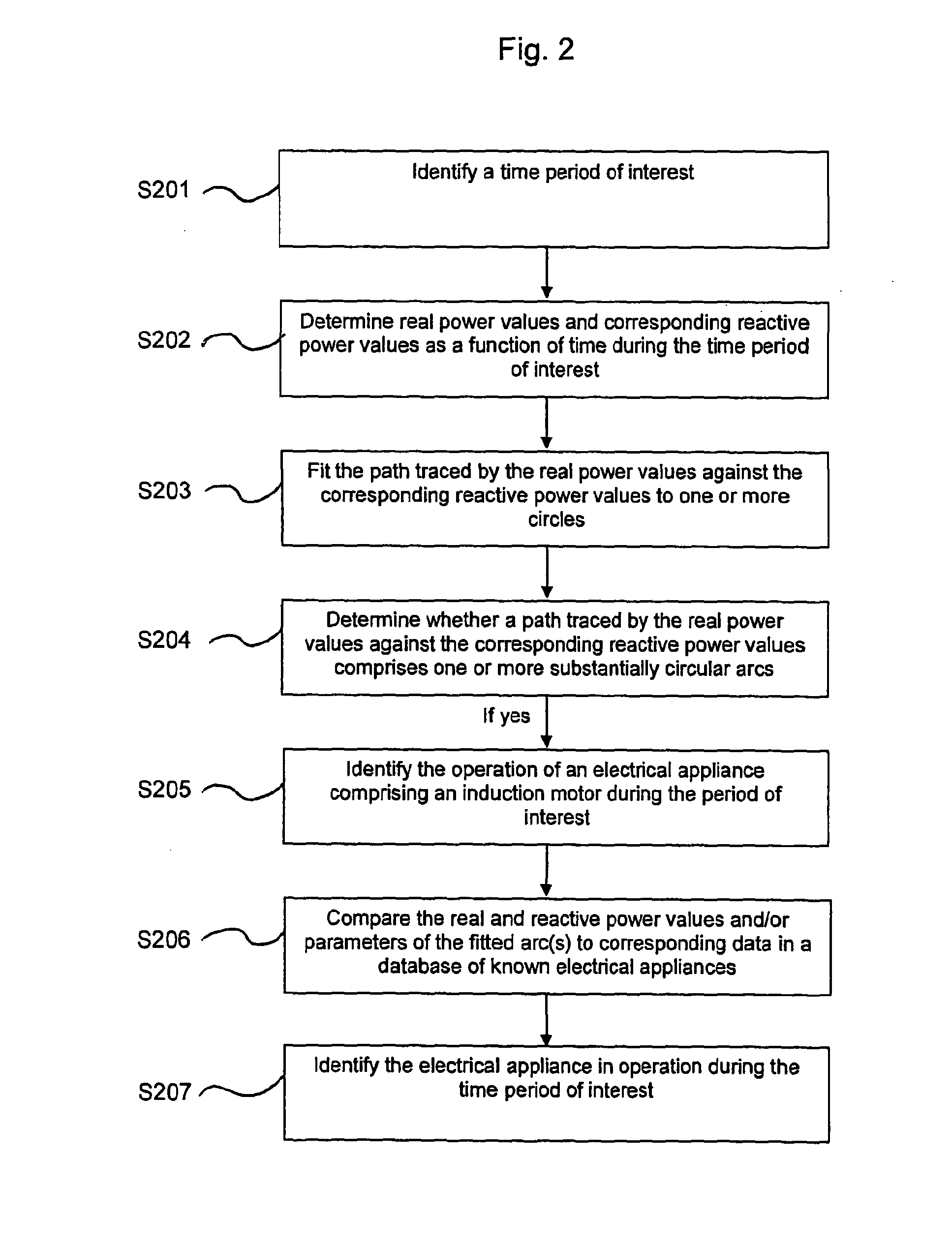
Identifying the operation of a specified type of appliance
ActiveUS20120136593A1Avoid identificationReduce in quantityElectric devicesTariff metering apparatusEffective powerElectricity
A method of identifying the operation of an electrical appliance comprising an induction motor is described. The method comprises identifying the operation of an electrical appliance comprising an induction motor when a path traced by real power values against corresponding reactive power values over a time period of interest comprises one or more substantially circular arcs. The real power values are related to the total real power supplied to one or more electrical appliances as a function of time, and the reactive power values are related to the total reactive power supplied to the one or more electrical appliances as a function of time.There is also described a related method of identifying the operation of a specified type of appliance, in which the operation of said specified type of appliance is dependent on a supply of at least one utility such as electricity, natural gas or water. Corresponding computer programs, computer-readable mediums, computer program products and apparatuses are also described.
Owner:SENSUS USA
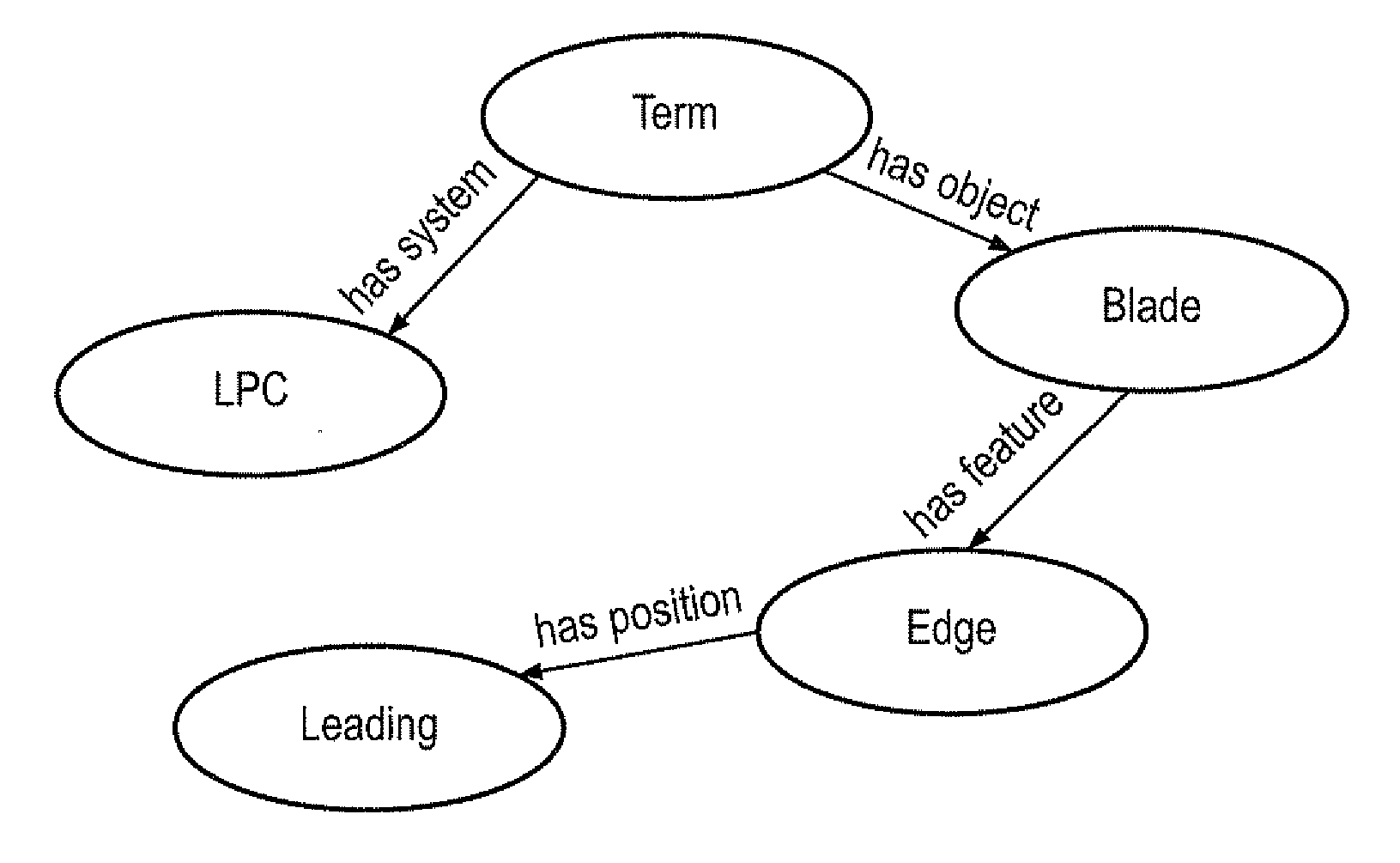
Entity recognition
ActiveUS20110320186A1Reduce overheadLow costDigital data information retrievalNatural language data processingNamed-entity recognitionDocument preparation
The invention relates to a method of querying technical domains that recognises the concepts represented by strings of characters, rather than merely comparing strings. It can be used to compute conceptual similarity between terms. The method employs string distance metrics and a cyclic progression of lexical processing to recognise constituent term concepts that are then combined to form full-term concepts by means of a grammar. Terms can be extracted and identified as being conceptually similar (or dissimilar) to other terms even if they have never previously been encountered.A key advantage is the ability to extract terms from documents based on the combination of a limited number of sub-concepts. This avoids the need for the prior identification of all possible terms that current methods require. A second key advantage is the ability to introduce or remove concepts and synonyms individually without the need to alter terms which the concept or synonym constitutes.
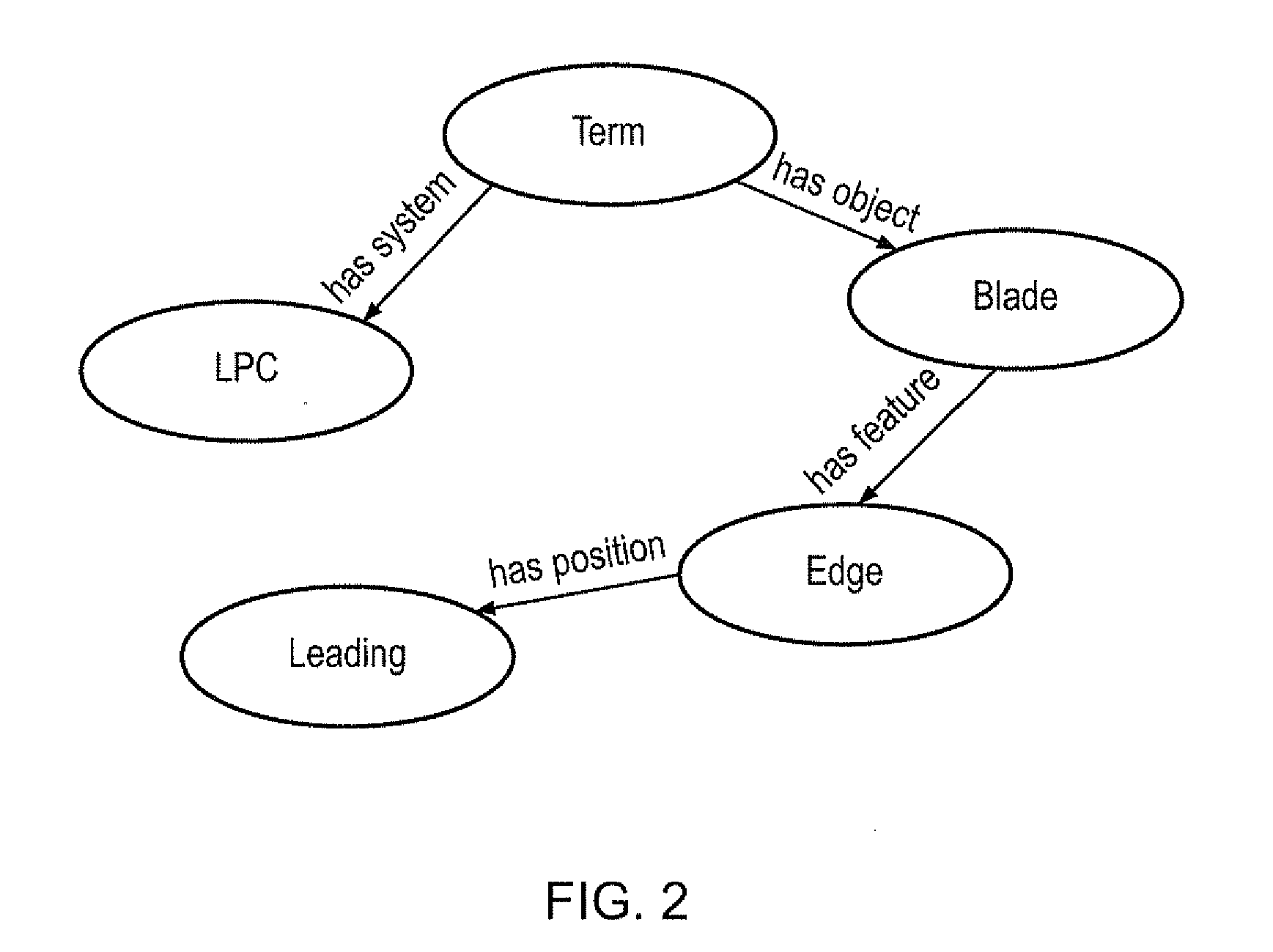
Owner:ROLLS ROYCE PLC
Face capturing and recognition method based on face quality evaluation
InactiveCN109117797AReduce computational complexitySave time and costCharacter and pattern recognitionNeural learning methodsData setRecognition algorithm
The invention discloses a face capture recognition method based on face quality evaluation. The invention adopts depth learning to carry out face quality evaluation score regression training on threetypical data sets with quality grade difference, acquisition of Face Quality Evaluation Model, the model is applied to face capture system, In order to reduce the system load without losing accuracy,the real-time received video stream is divided into several capture cycles according to the fixed number of frames, and the capture quality conditions are dynamically adjusted in each capture cycle, and the highest quality face in a period of time is output for face recognition algorithm to recognize. The invention adopts the technology of depth learning to score face quality, cooperates with facecapture to carry out low-quality face filtering and optimal face selection, thereby better serving the face recognition system, and realizes lower system hardware resource occupancy and higher face recognition rate at the same time.
Owner:ZHEJIANG ICARE VISION TECH
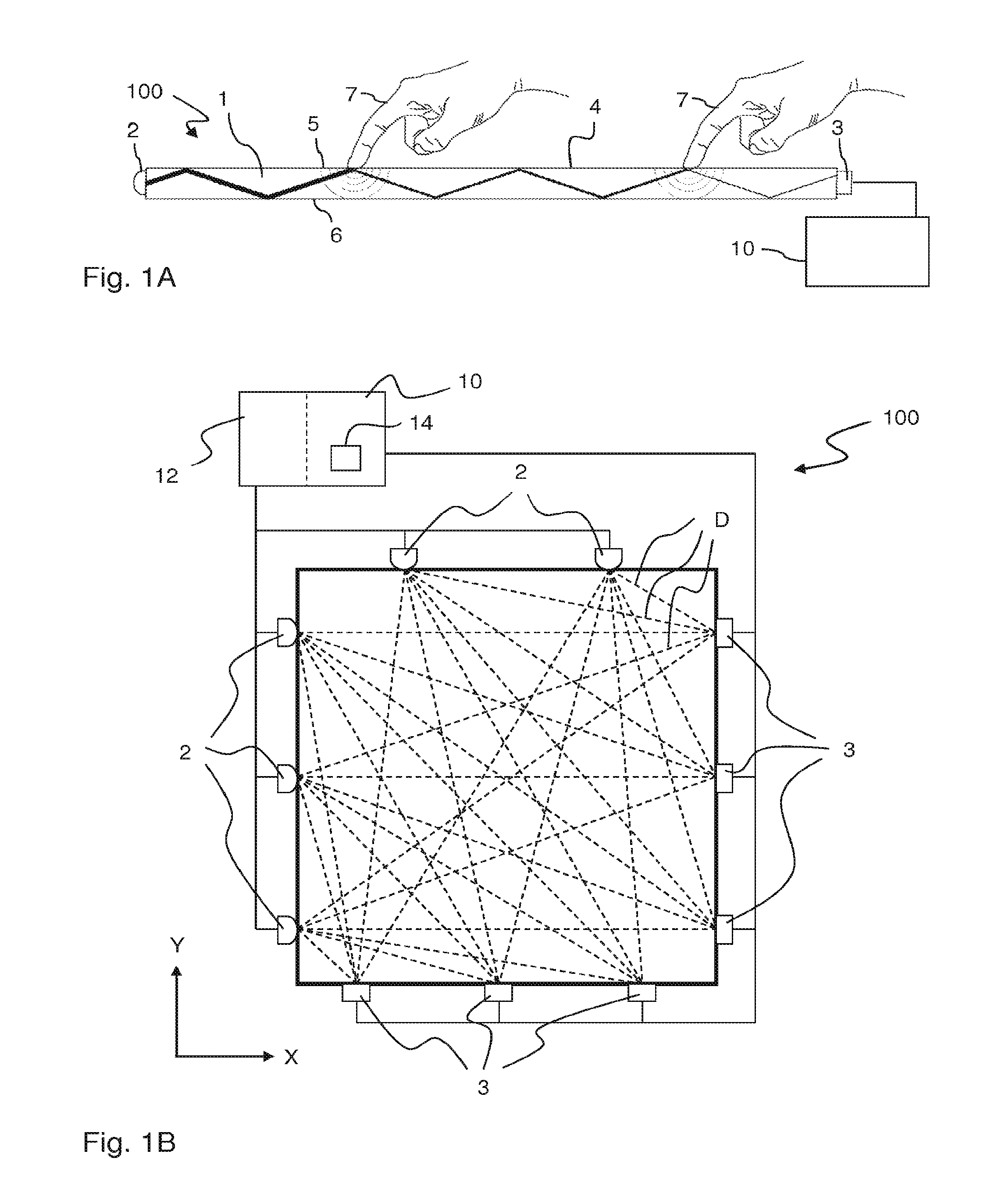
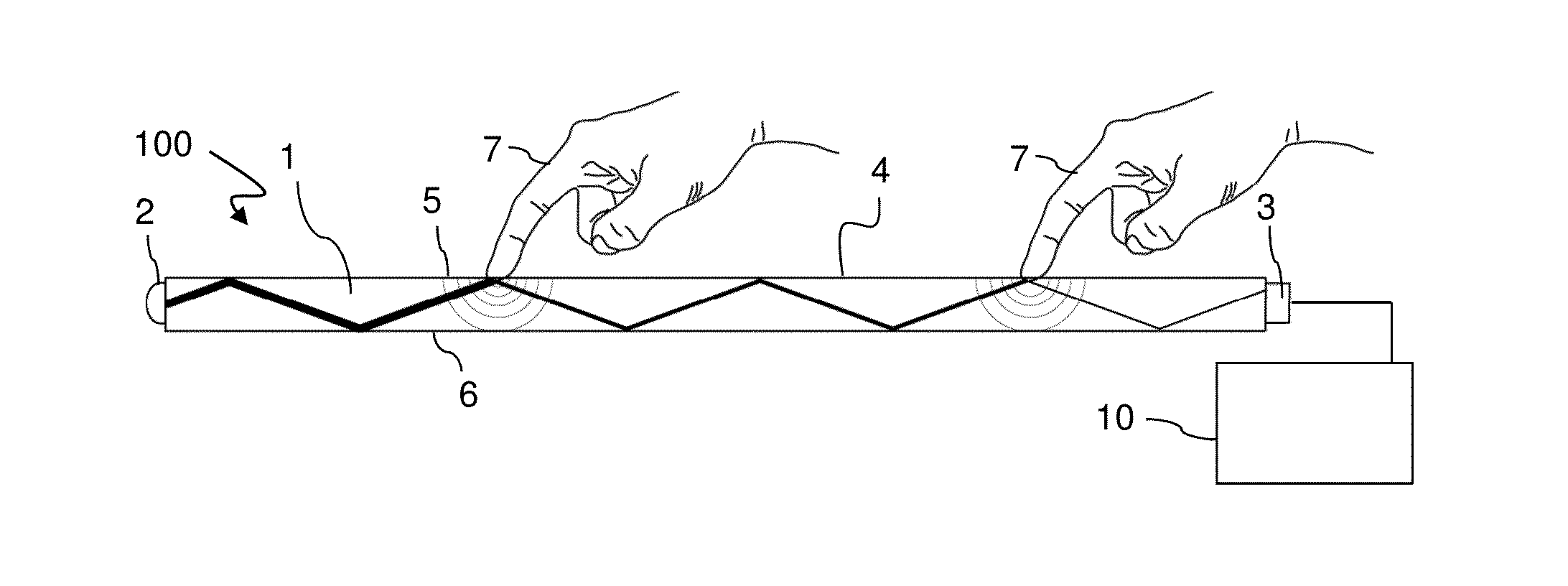
Tracking objects on a touch surface
ActiveUS9317168B2Errors introduced into the movement trajectories may propagateReduce in quantityInput/output processes for data processingHuman–computer interaction
Owner:FLATFROG LAB
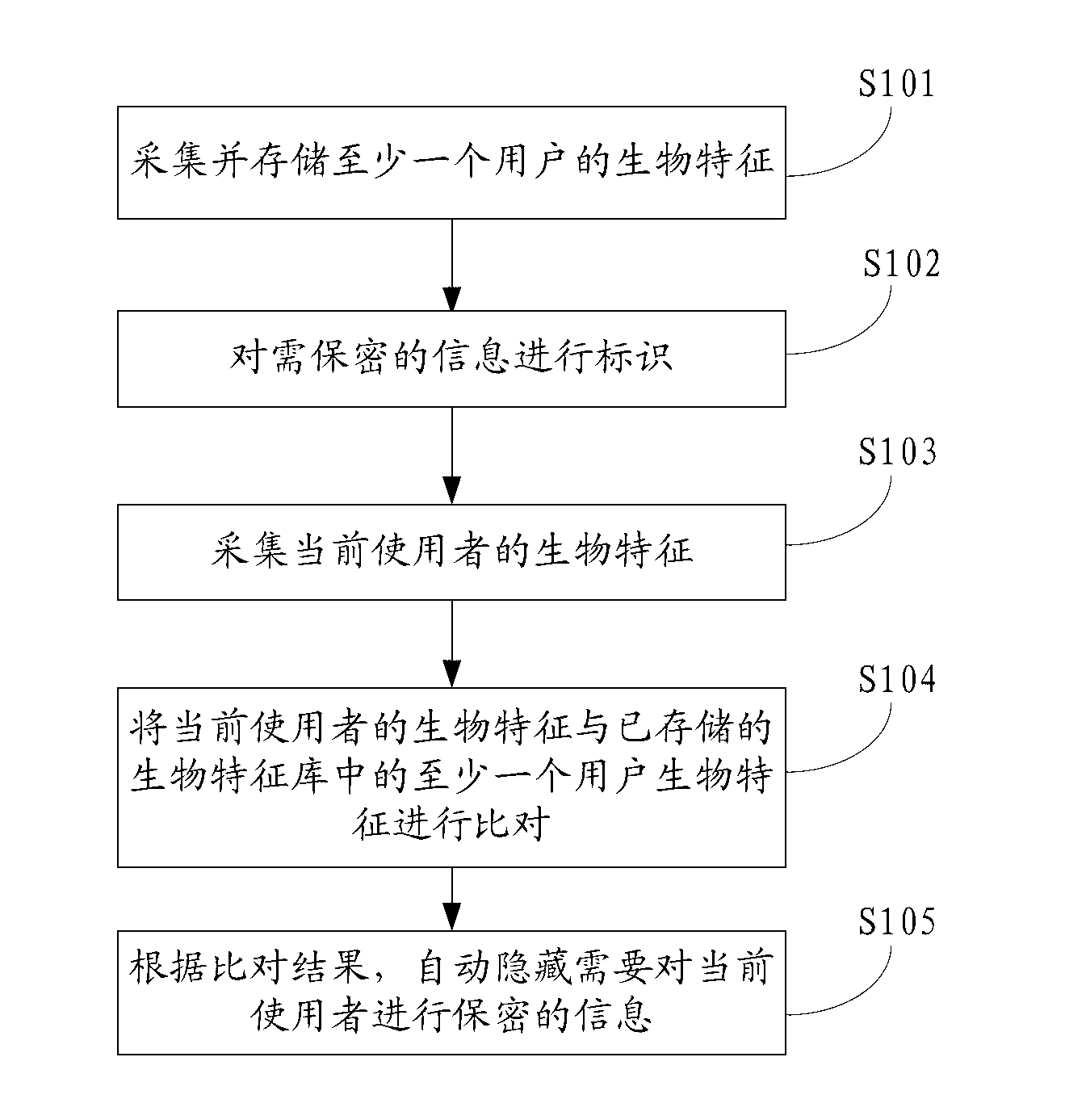
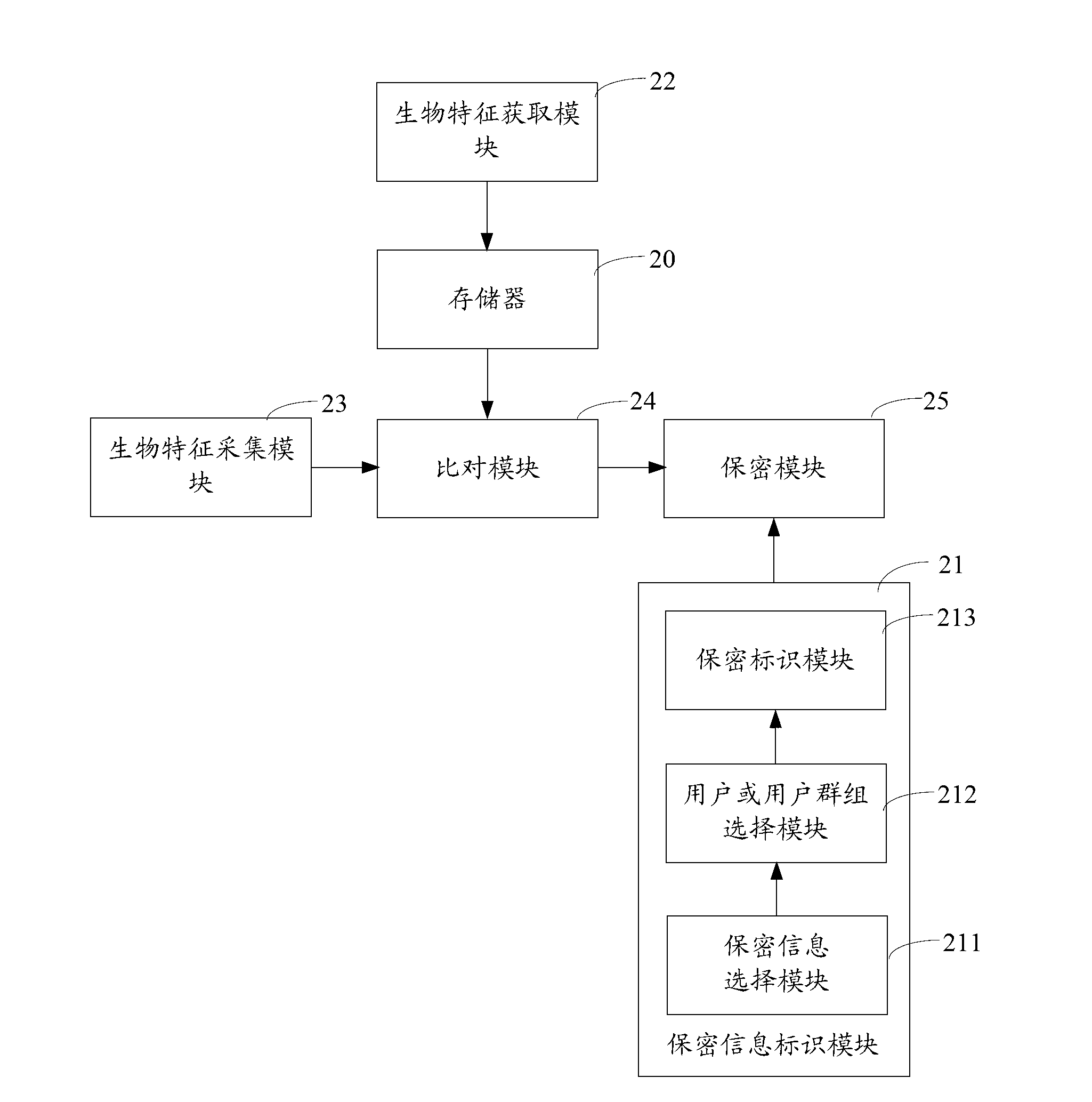
Information privacy method and electronic terminal
InactiveCN103177206AAvoid identificationConfidentiality is concealedDigital data protectionDigital data authenticationComputer terminalInformation confidentiality
The invention belongs to the field of communication and provides an information privacy method and an electronic terminal. The information privacy method includes the following steps. Biological characteristics of a current user are collected. The biological characteristics of the current user are compared with at least one user biological characteristic stored in a biological characteristic base. The user biological characteristic is correlated with operation authority of information privacy. According to a comparison result, information that the current user is not supposed to know is automatically hidden. The biological characteristics of the current user are collected and compared with the stored biological characteristics. Based on the comparison result, the information that the current user is not supposed to know is automatically hidden. Thus, automatic identification can be performed without tedious log-in and code entering. Private information can be automatically hidden and a privacy manner is invisible and not easily observed by people.
Owner:NUBIA TECHNOLOGY CO LTD
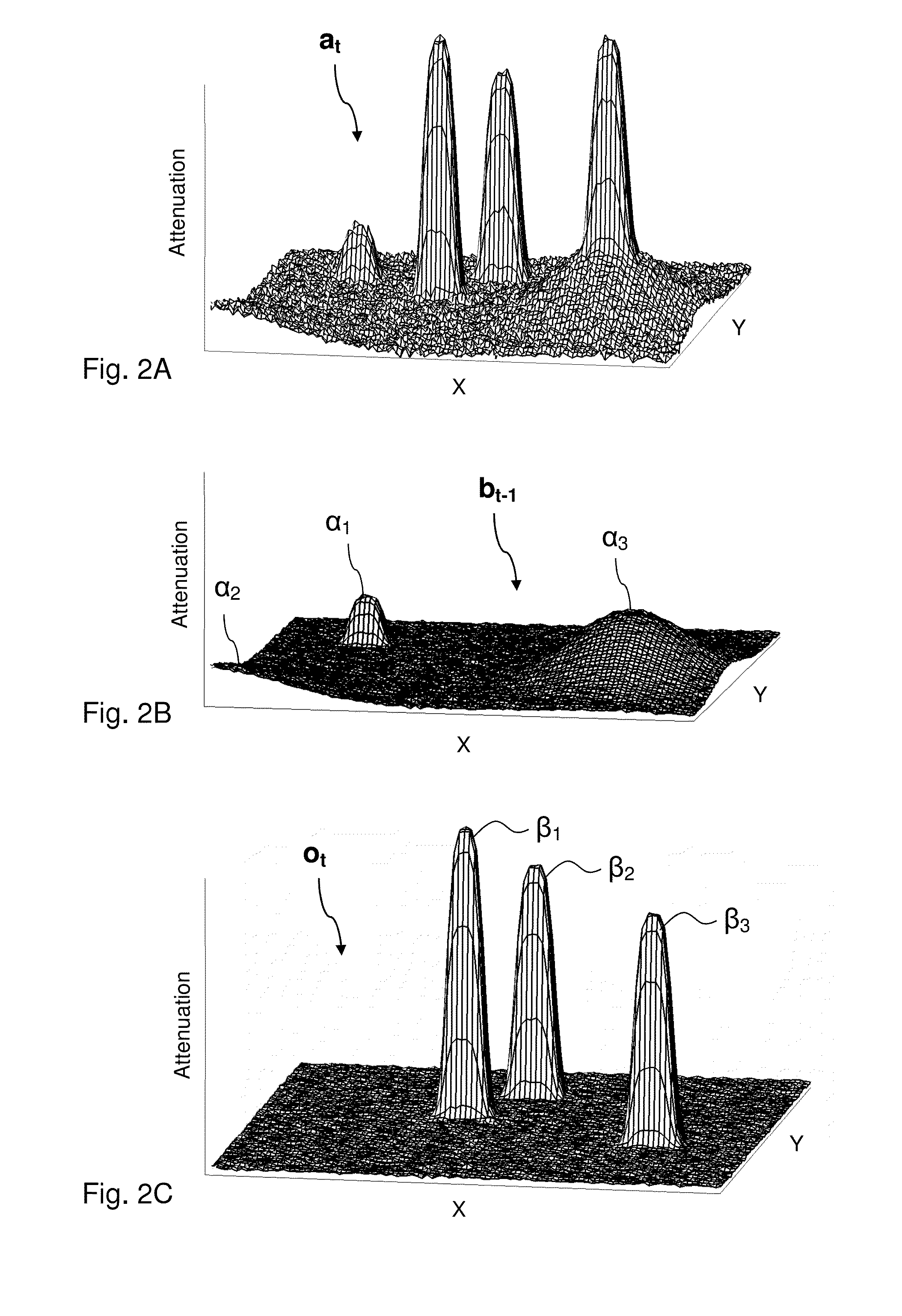
Tracking objects on a touch surface
InactiveUS20160202841A1Improve accuracyErrors introduced into the movement trajectories may propagateImage enhancementImage analysisNegative peakHuman–computer interaction
A device implements a method of tracking objects on a touch surface of an FTIR based touch-sensitive apparatus. An interaction map is generated that indicates local changes in interaction on the touch surface. The interaction map is processed for identification of positive and negative peaks that represent a locally increased and decreased interaction in the interaction map, respectively. To suppress the impact of interferences, a dedicated first heuristic and / or second heuristic is applied to identify potentially false peaks among the positive peaks. The first heuristic designates a positive peak as a potentially false peak when the positive peak is deemed to be associated with one or more of the negative peaks. The second heuristic designates a positive peak as a potentially false peak when the positive peak is deemed to be located along one of the movement trajectories. Movement trajectories of all objects deemed to exist on the touch surface at a preceding time point are then updated while taking the potentially false peaks into account.
Owner:FLATFROG LAB
Tracking objects on a touch surface
ActiveUS20140375607A1Improve accuracyErrors introduced into the movement trajectories may propagateInput/output processes for data processingHuman–computer interaction
Owner:FLATFROG LAB
System, method, and apparatus for identifying and authenticating the presence of high value assets at remote locations
InactiveUS7774268B2Avoid identificationPrevent fraudFinanceCo-operative working arrangementsOperating system
A system, method, and apparatus for identifying and authenticating the presence of high value assets at remote location includes associating an identification tag with the asset. The identification tag includes identification information that can be electronically read and sent to a remote location for verifying the authenticity of the asset.
Owner:THE TB GROUP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com