Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
369 results about "Human operator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
"The Human Operators" is the seventh episode of season five of the revived American science fiction television series The Outer Limits. It is based on a science fiction short story by Harlan Ellison and A. E. van Vogt, first published in the January 1971 issue of The Magazine of Fantasy and Science Fiction.
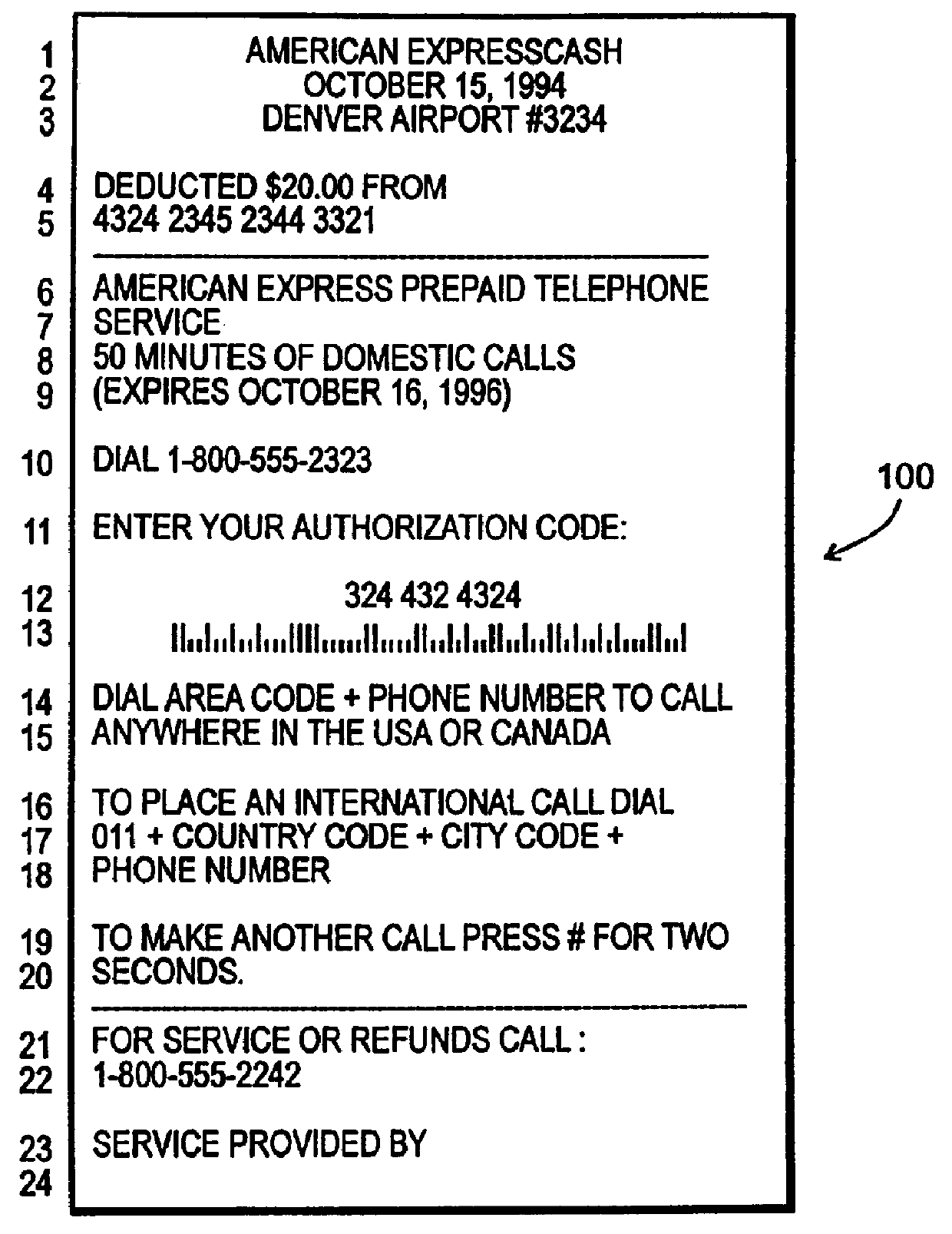
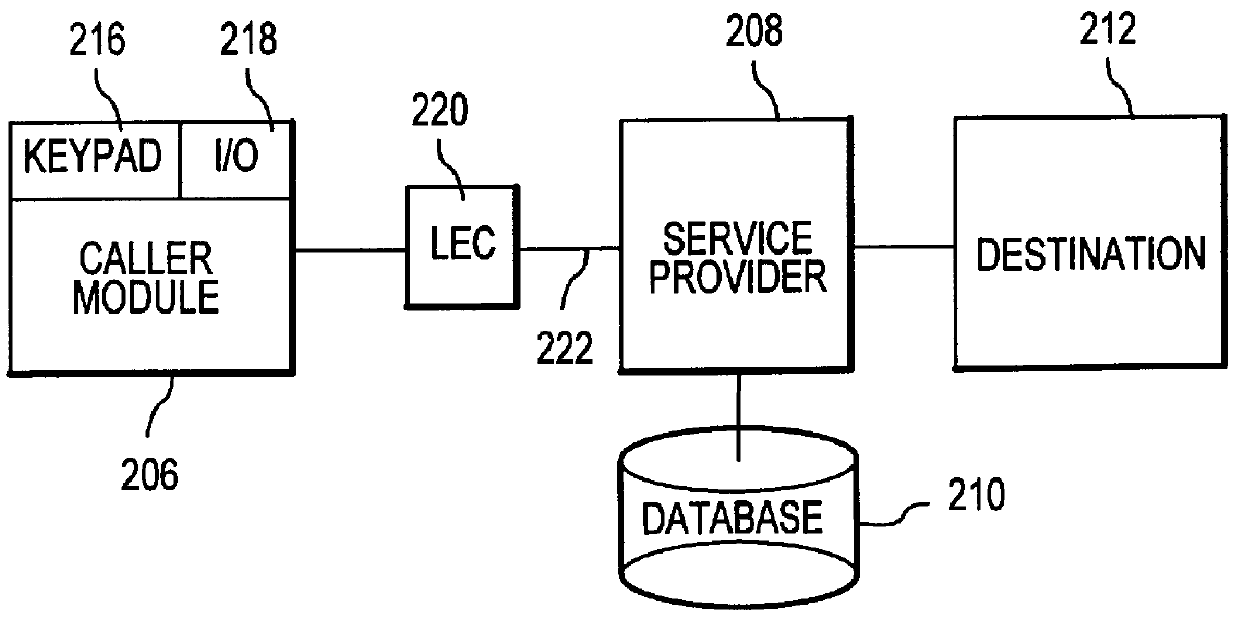
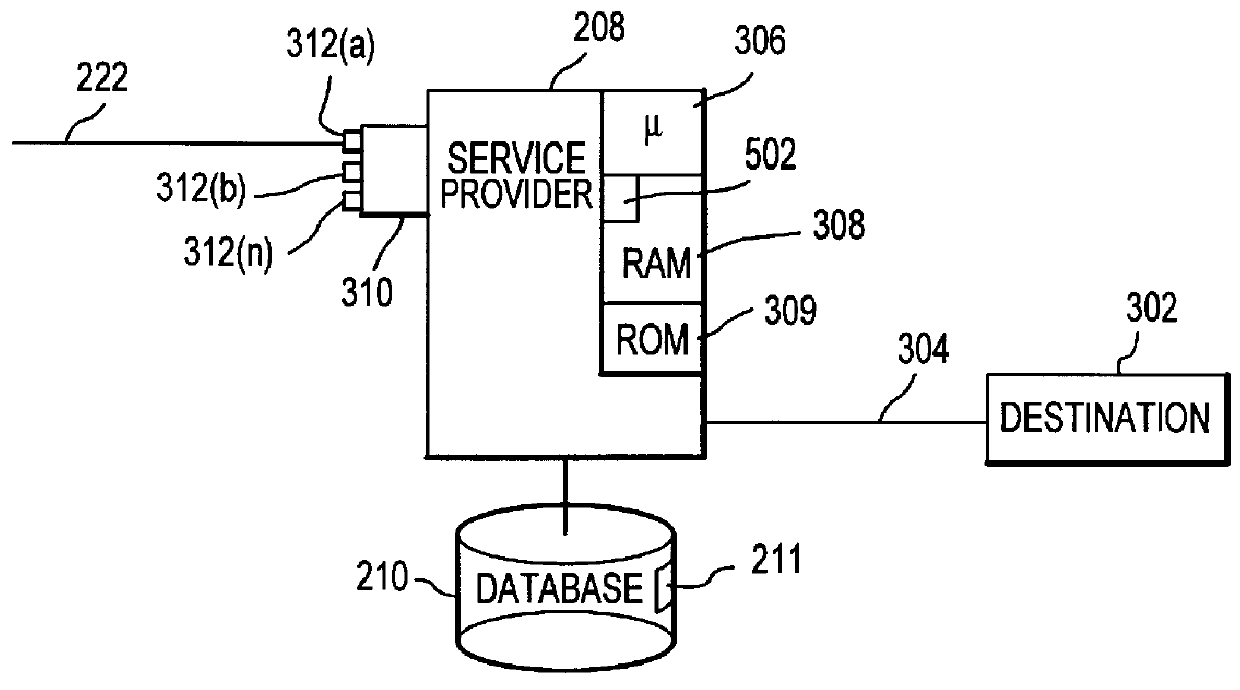
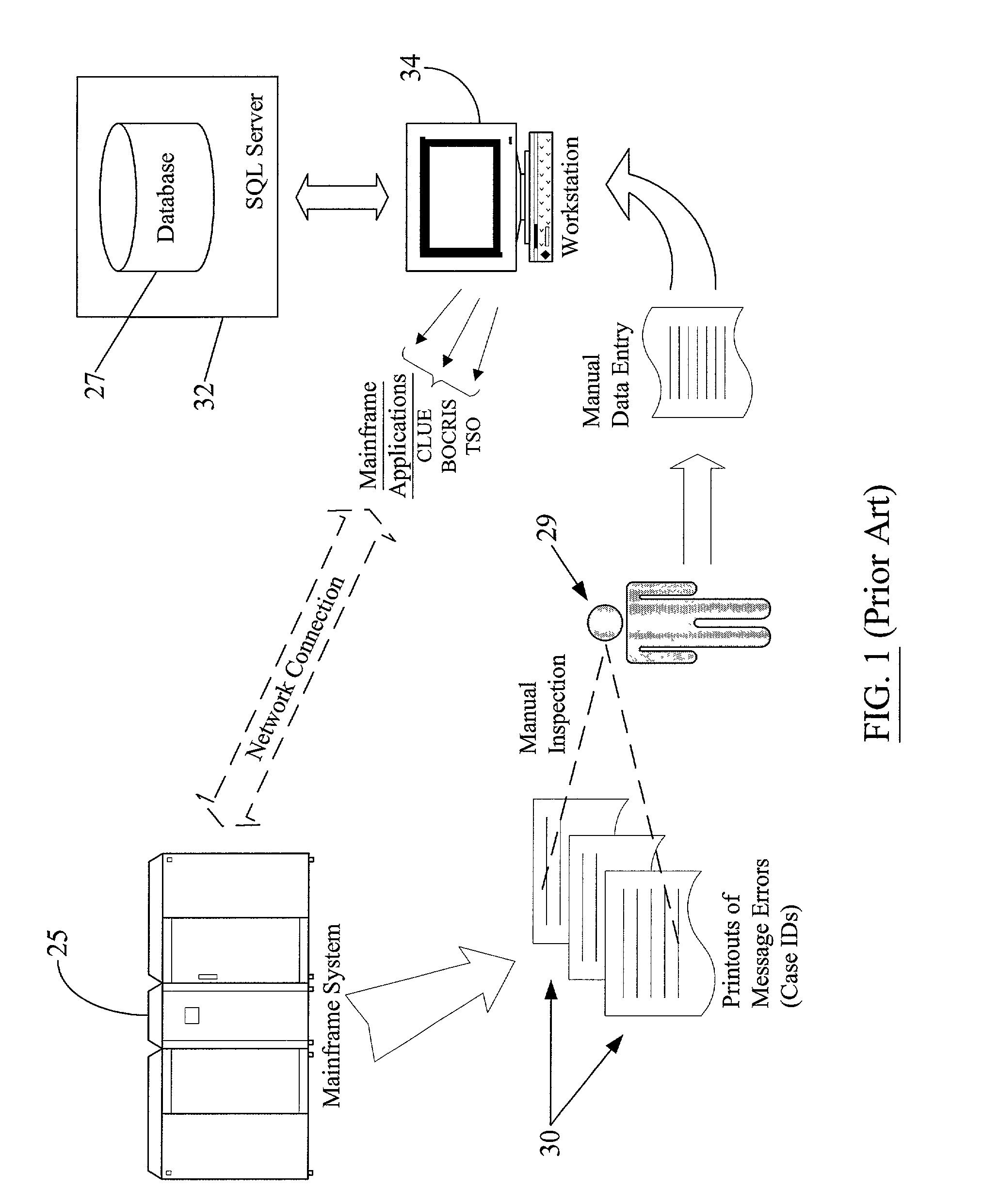
Method and apparatus for summaries of prepaid instrument transaction activity
InactiveUS6115458AConveniently and efficiently generatingConveniently and efficiently and transmittingPayment circuitsVerifying markings correctnessCredit cardSummary data
A system for generating and transmitting summary transaction data includes a computer database from which information is compiled and forwarded to a requesting party automatically, i.e., without the need to interface with a human operator. A party having access to a prepaid transaction account number may access the host computer from a remote location and interactively request transaction information pertaining to the account using virtually any communication modality. The computer is suitably configured to communicate with one or more of the foregoing communication modalities and to automatically compile and transmit the summary data to a requested destination, for example, to a PC. The computer may further be configured to allow the requesting party to select among various formats to configure the form of the summary data. Summary transaction data may be generated and transmitted for virtually any type of prepaid transaction card, including phone cards, travel, credit cards, stored value (e.g., smart cards) cards, and the like.
Owner:LIBERTY PEAK VENTURES LLC +1
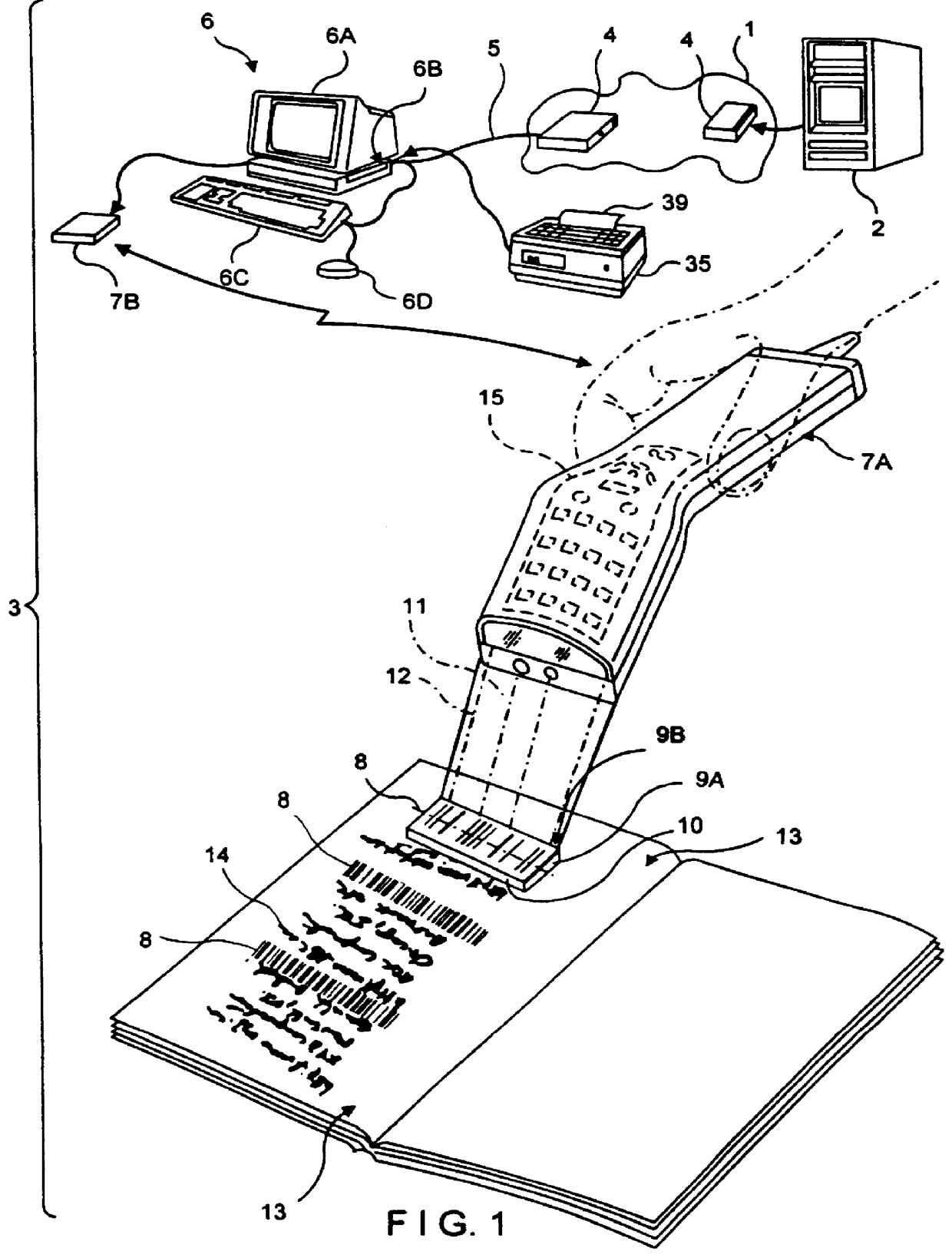
System for storing, accessing and displaying html encoded
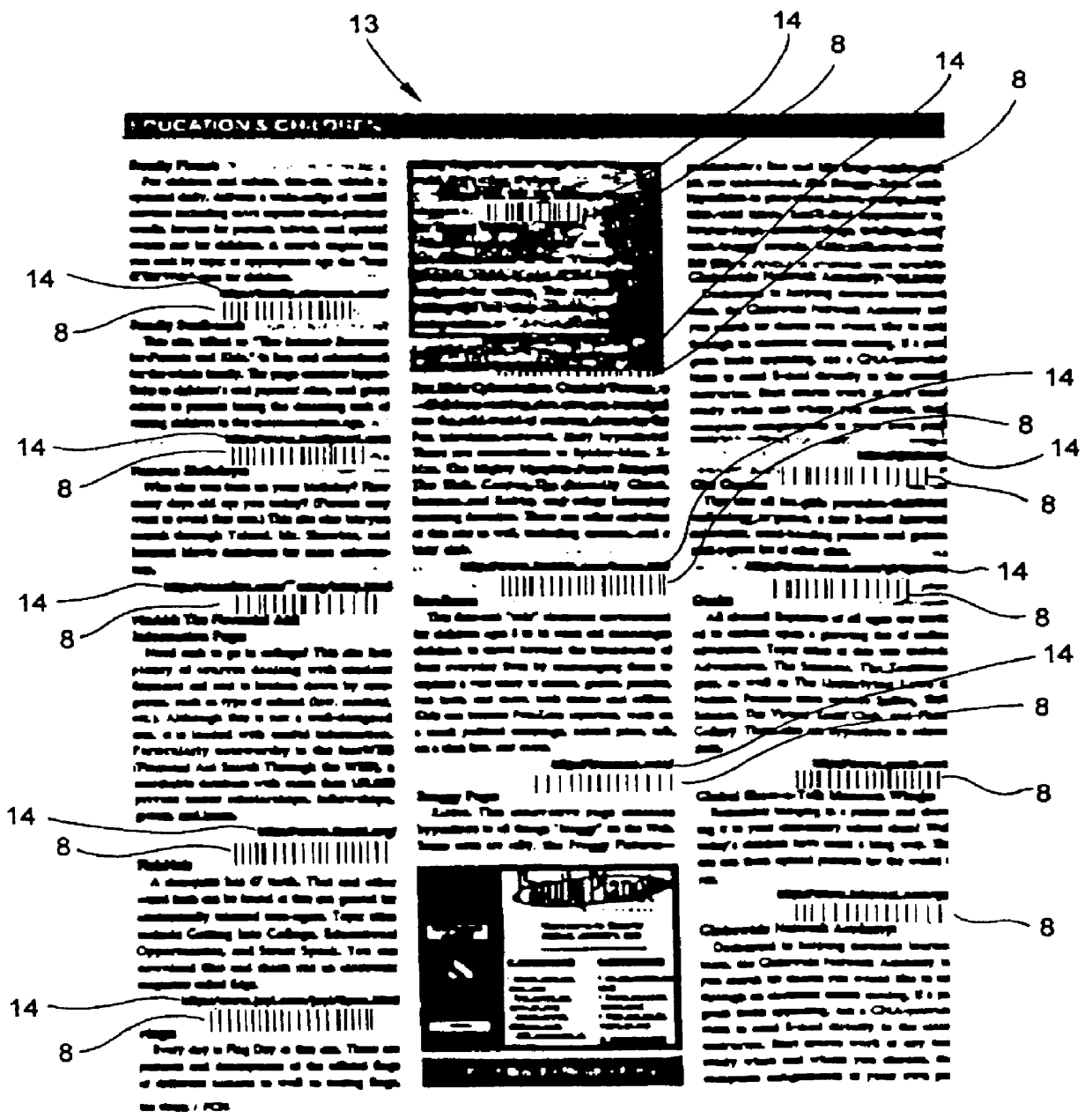
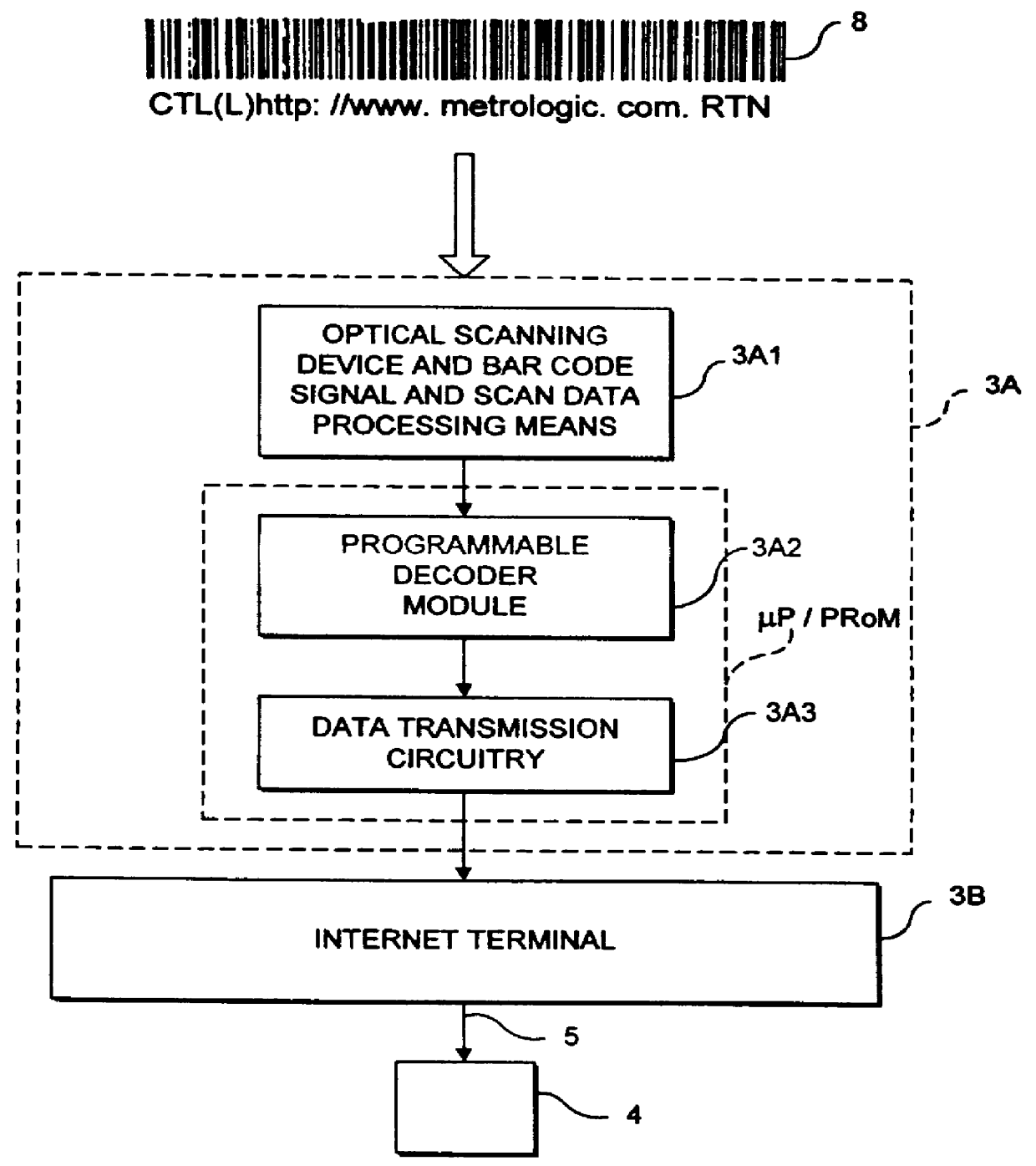
InactiveUS6152369AEasy accessDigital data information retrievalCharacter and pattern recognitionObject pointDisplay device
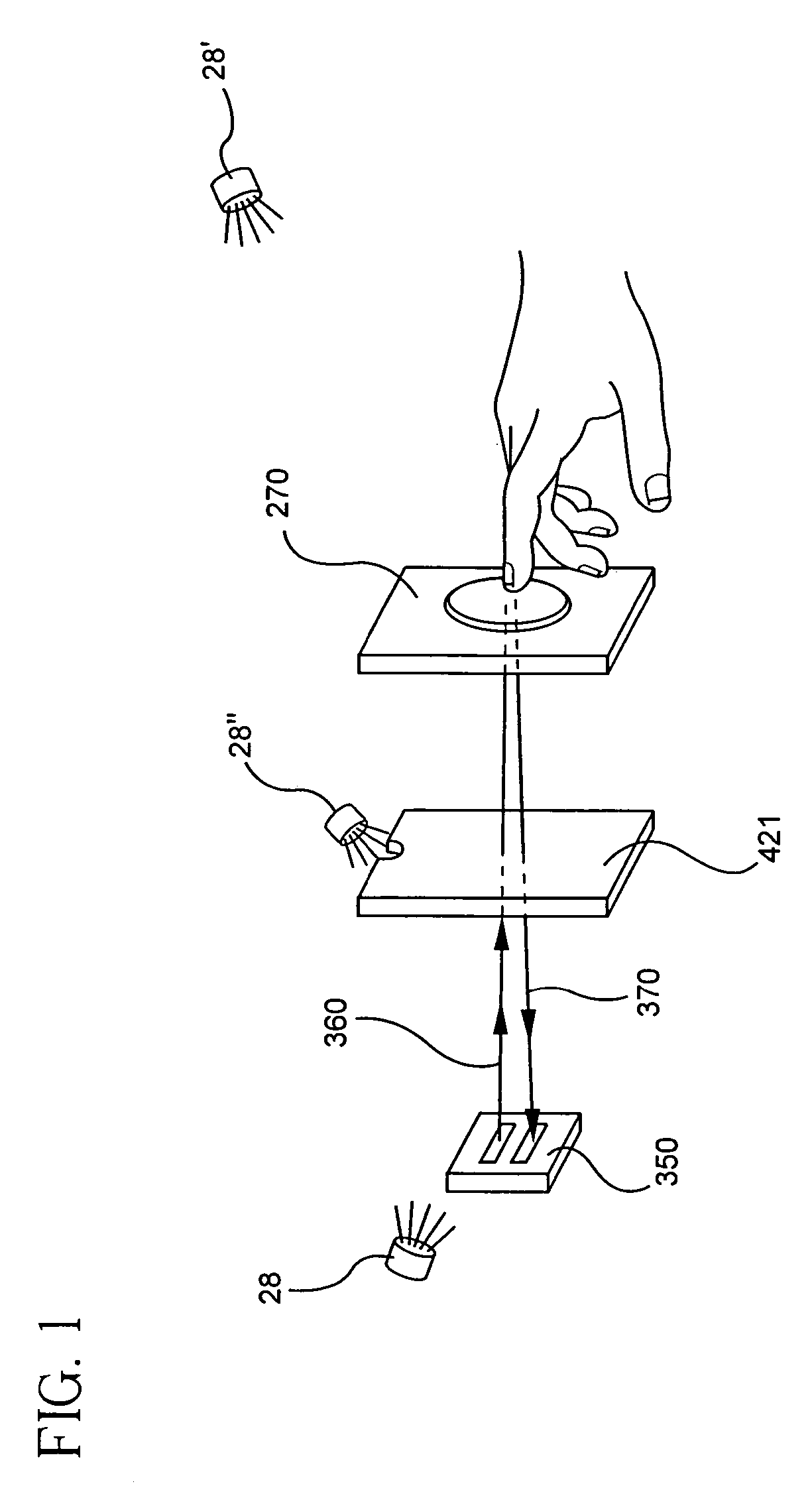
A system for storing, accessing and displaying HTML-encoded documents relating to an object being worked upon in a work environment by a human operator. The human operator wears a body-wearable http-enabled client system equipped with a code symbol reader programmed to read a URL-encoded symbol on the object pointing to a HTML-encoded document stored on one or more http-enabled information servers. The http-enabled client system is connected to the information network by a two-way wireless telecommunication link. The code symbol reader is programmed for reading the URL-encoded symbol affixed to the object and automatically produces symbol character data representative of the read code symbol and the URL encoded therewithin. The http-enabled client system also includes a network accessing mechanism and a display device. The network accessing mechanism is programmed for automatically accessing one or more of the HTML-encoded documents from one or more of the http-enabled information servers in response to symbol character data being produced by the code symbol reader. The display device is operably connected to the network accessing mechanism, for visually displaying HTML-encoded documents accessed from the http-enabled information servers in response to symbol character data being produced by the code symbol reader. As a result of the present invention, the human operator is enabled to freely review the HTML-encoded documents displayed on the display device while working with the object in diverse work environments involving, for example, inventory management, assembly-line and / or plant inspection, and craft or vehicle inspection and / or repair.
Owner:METROLOGIC INSTR
Data processing and feedback method and system
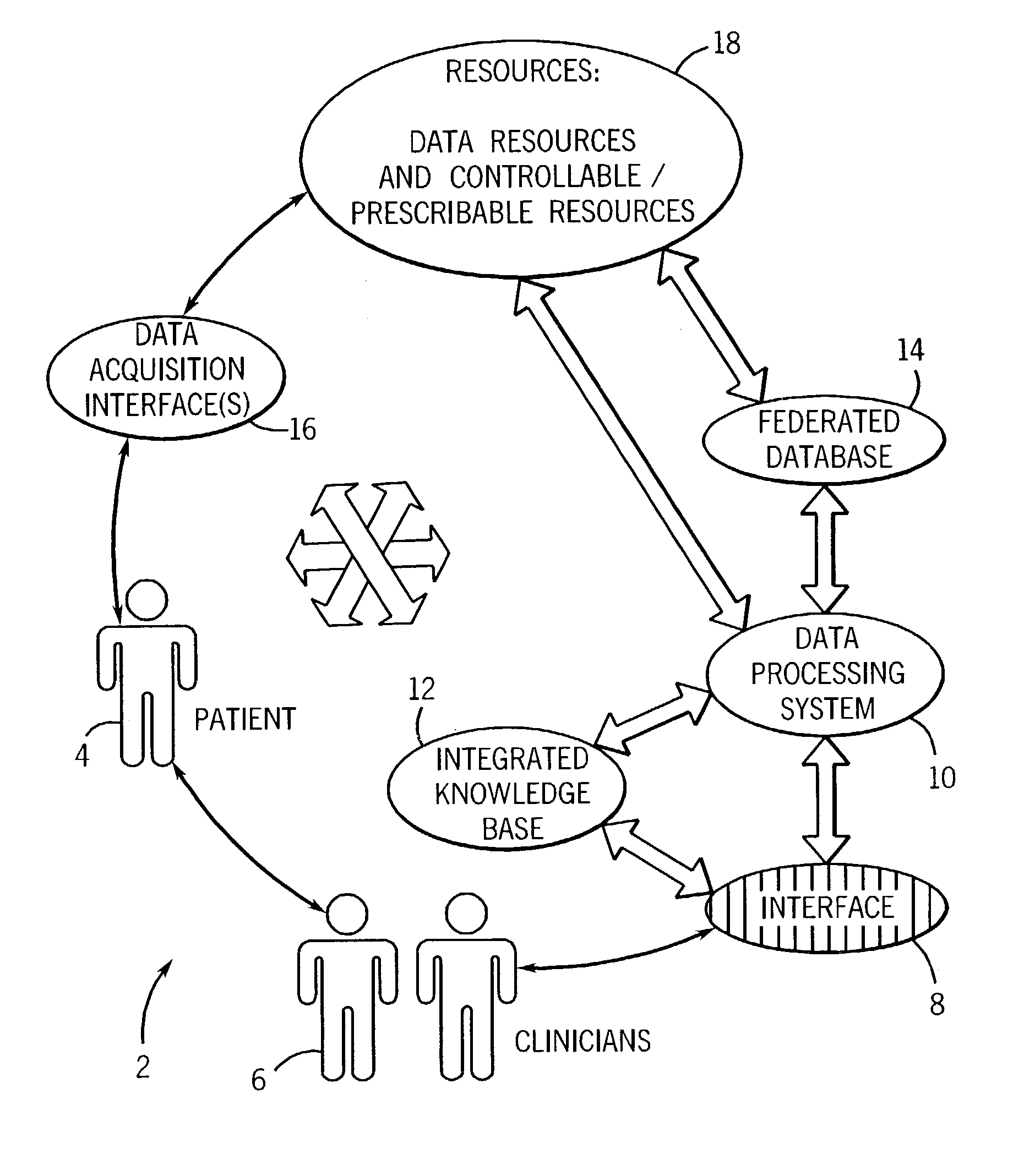
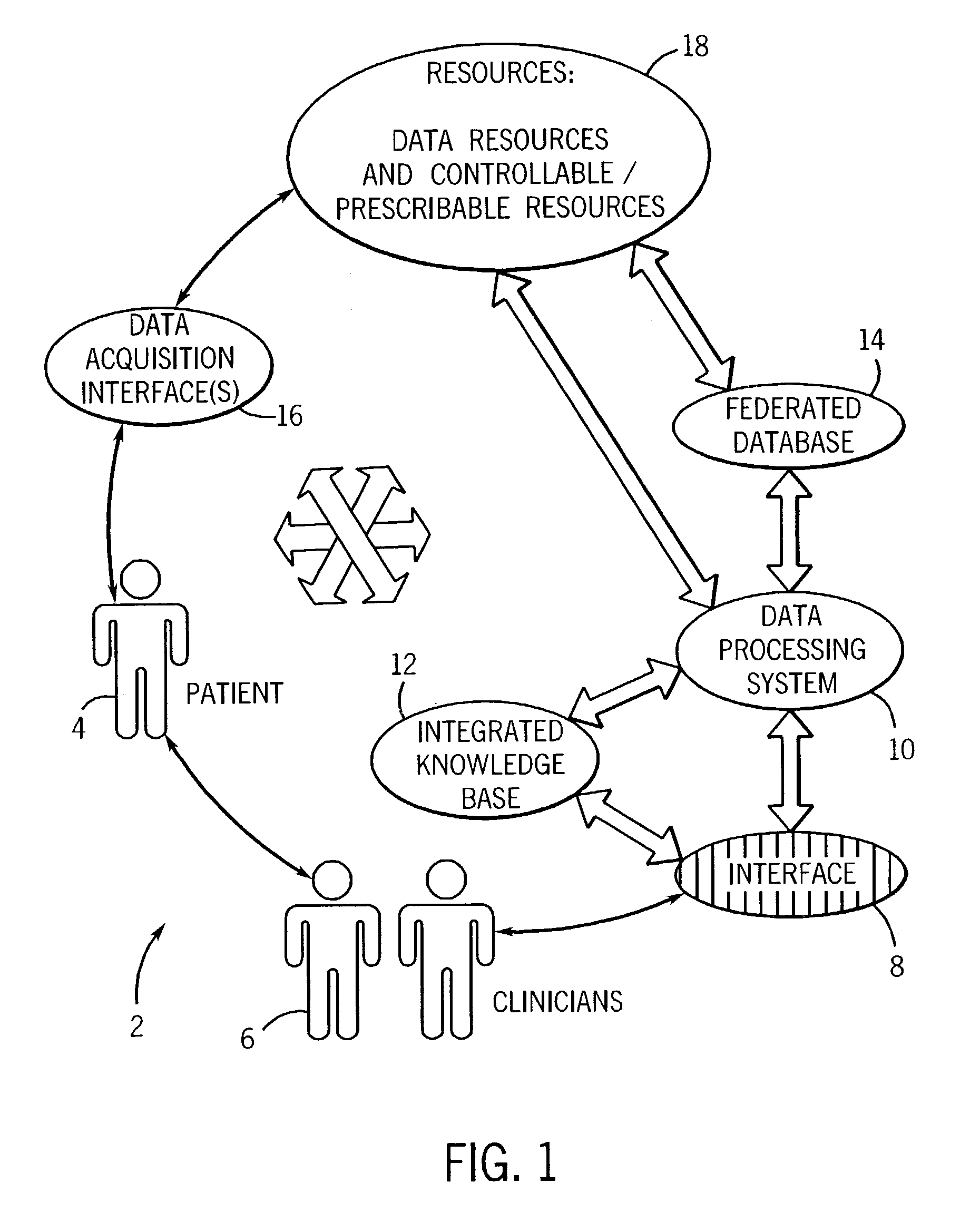
ActiveUS7187790B2Patient care can be improvedQuick identificationCharacter and pattern recognitionOffice automationComputer-aidedHuman operator
A technique is provided for offering feedback, including feedback for patient care and for training purposes for medical professionals and human operators. The technique includes accessing data, such as image data, for evaluation by a human operator. The data is then analyzed via a computer-assisted data operating algorithm, and the analysis may further include analysis of supplemental data accessed from an integrated knowledge base. Based upon the analysis feedback is provided to the operator, such as for completing or complementing the evaluation, correcting analysis by the human operator, or otherwise informing the human operator of similarities or differences between the analyses.
Owner:GE MEDICAL SYST GLOBAL TECH CO LLC
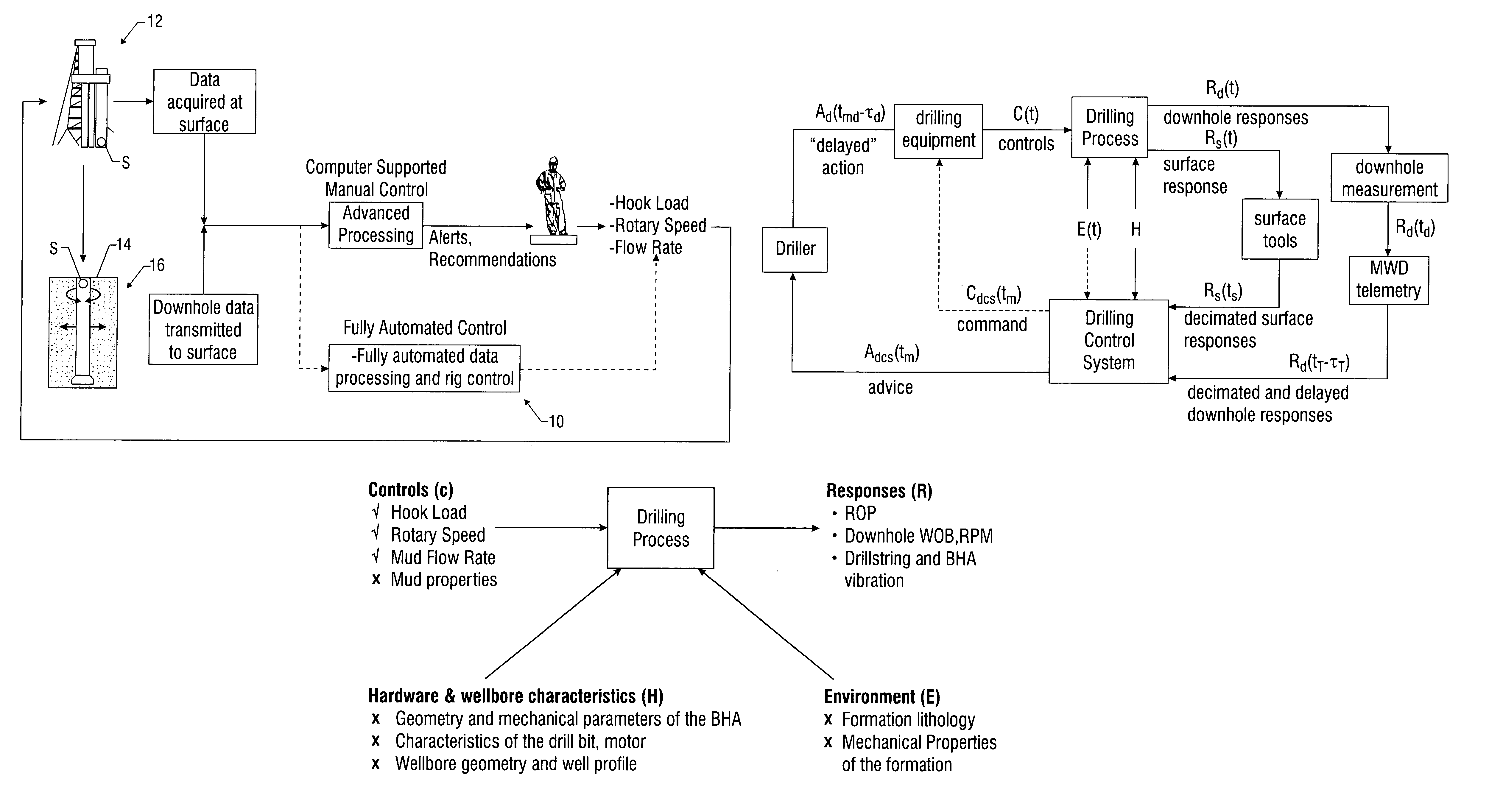
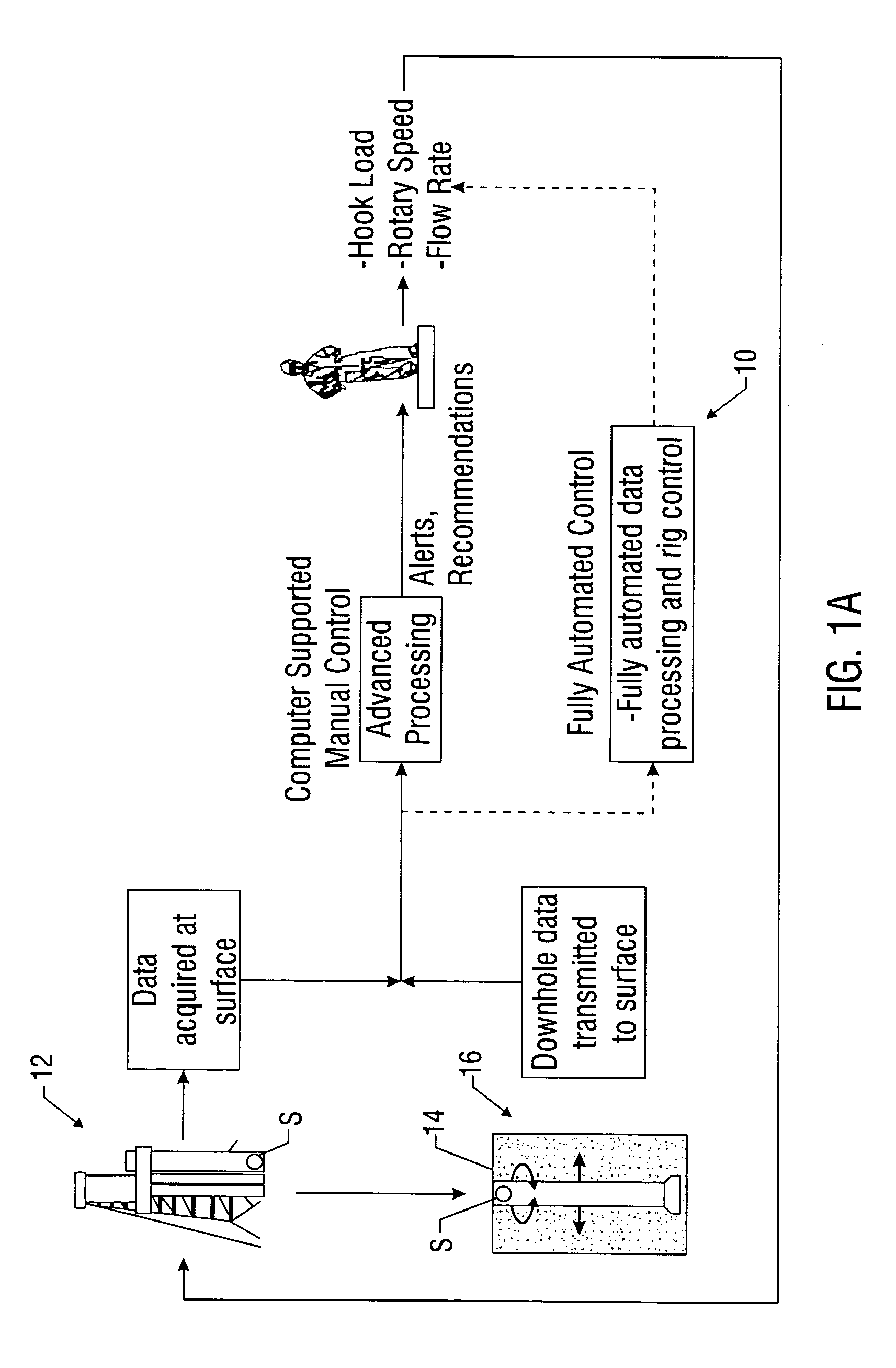
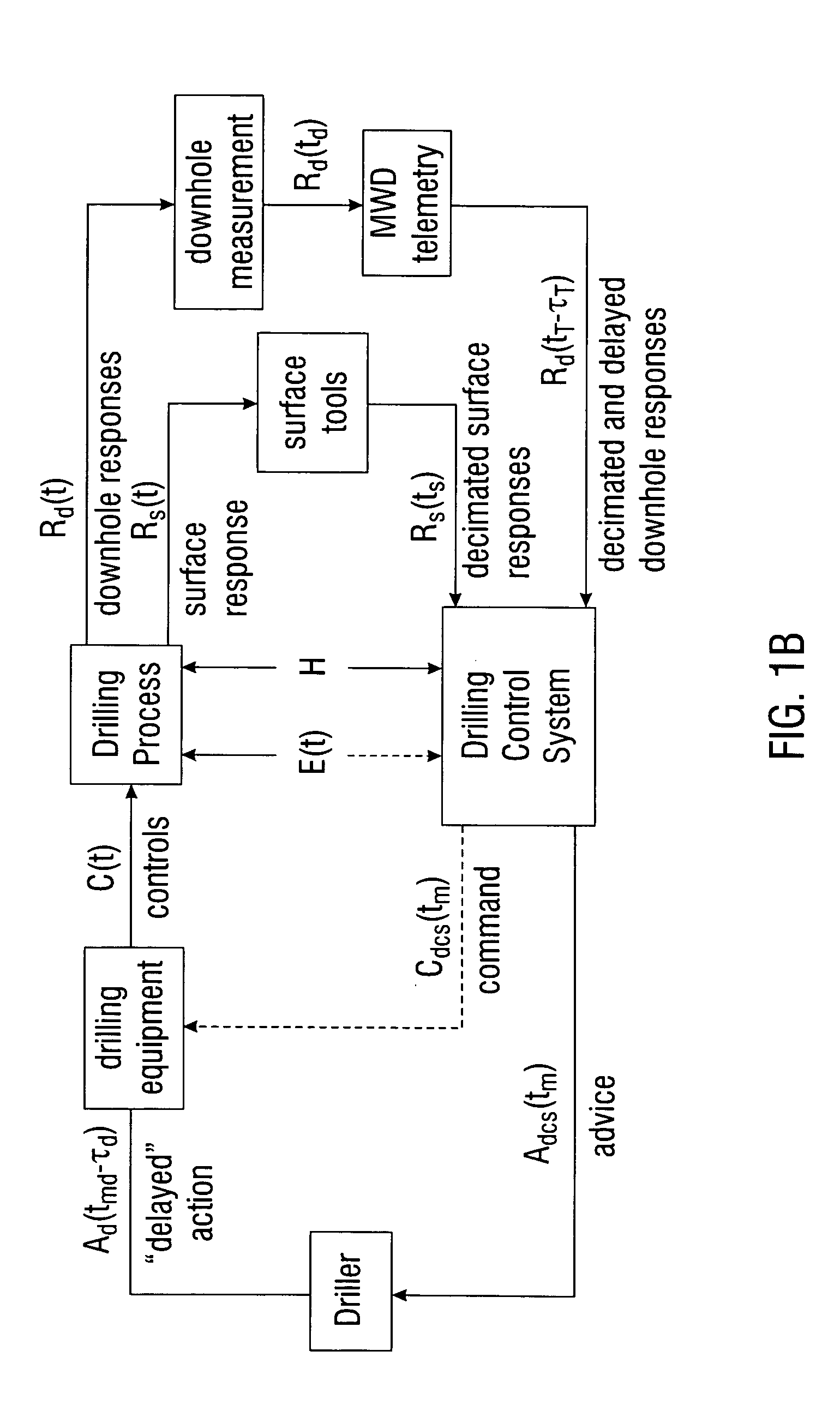
Real-time drilling optimization based on MWD dynamic measurements
A drilling control system provides, in one aspect, advisory actions for optimal drilling. Such a system or model utilizes downhole dynamics data and surface drilling parameters, to produce drilling models used to provide to a human operator with recommended drilling parameters for optimized performance. In another aspect, the output of the drilling control system is directly linked with rig instrumentation systems so as to provide a closed-loop automated drilling control system that optimizes drilling while taking into account the downhole dynamic behavior and surface parameters. The drilling models can be either static or dynamic. In one embodiment, the simulation of the drilling process uses neural networks to estimate some nonlinear function using the examples of input-output relations produced by the drilling process.
Owner:BAKER HUGHES INC
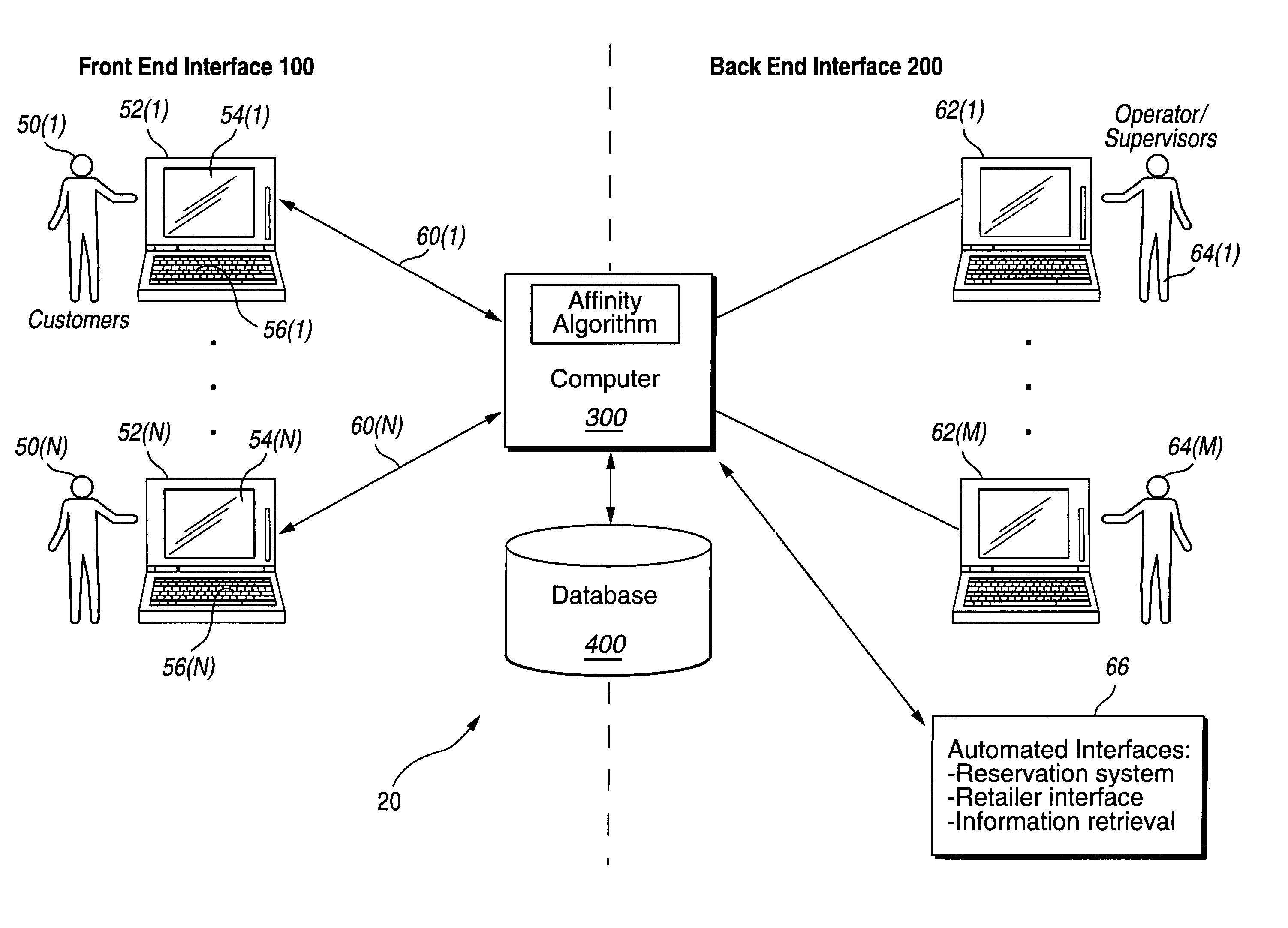
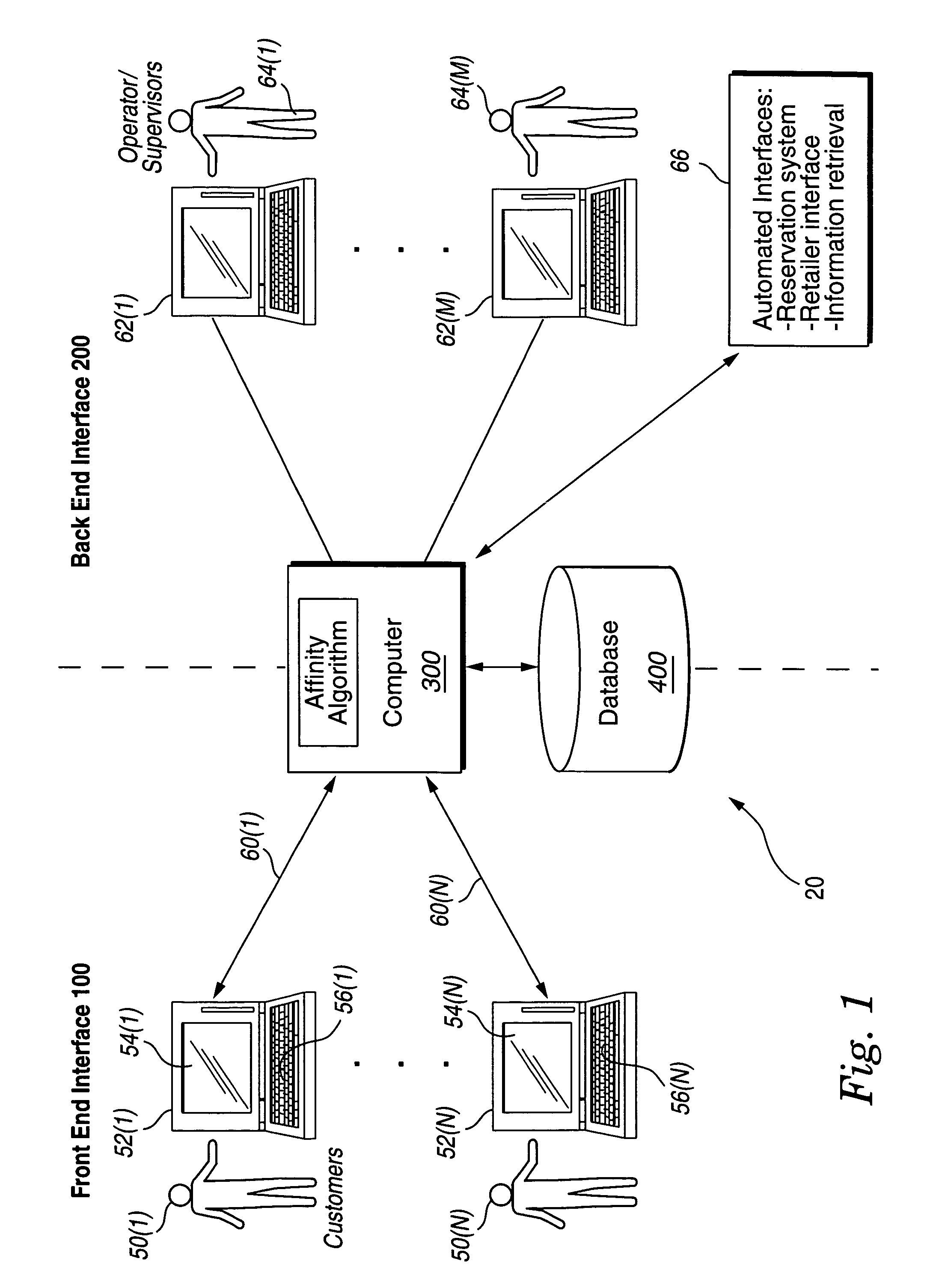
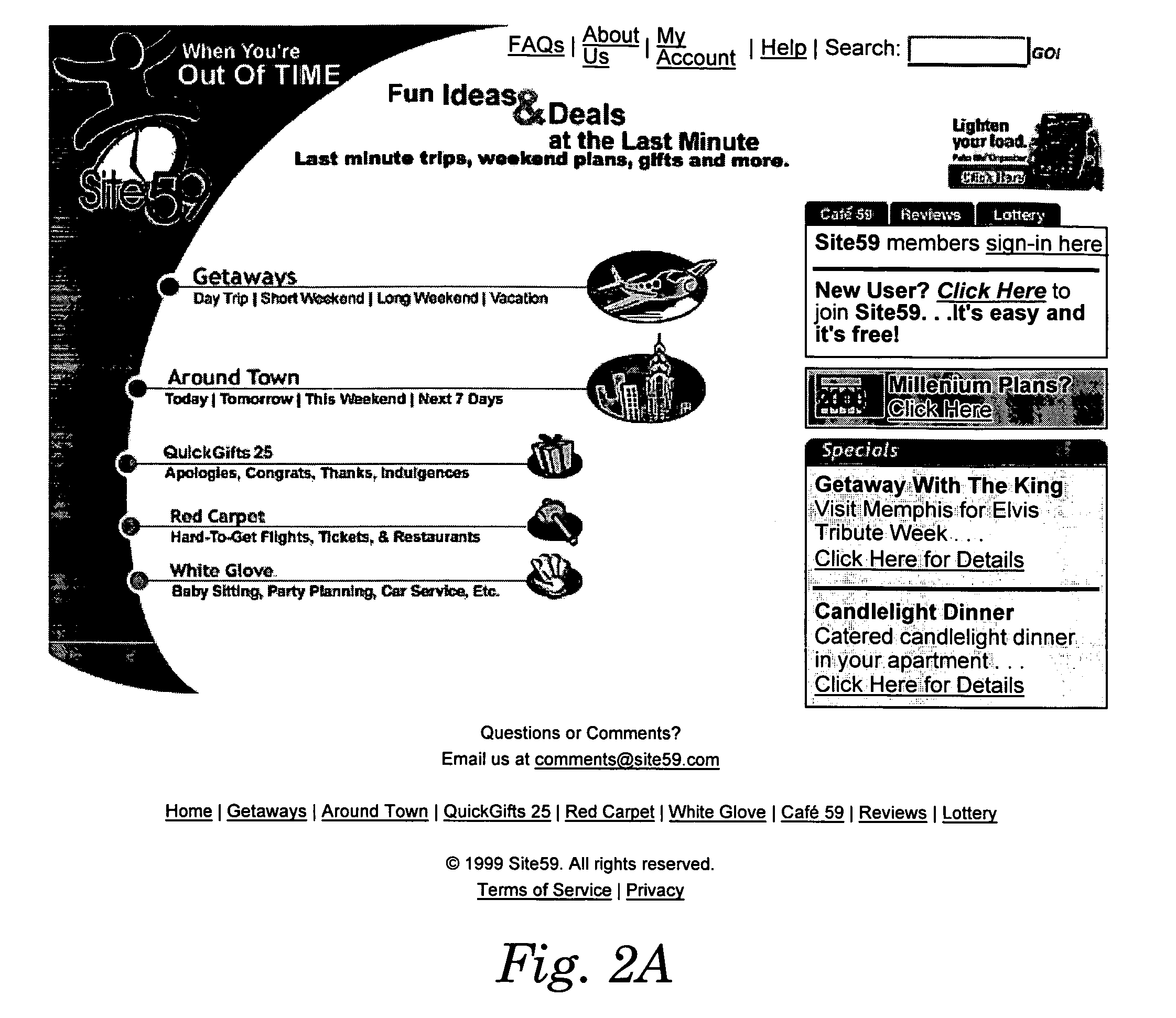
System and method for grouping and selling products or services
InactiveUS7092892B1Less free timeImprove permeabilityFinanceReservationsService provisionComputerized system
A system and method for grouping and selling products or services using a computer system, potentially connected to a network. The computer system includes a computer with multiple terminals, potentially instantiated as a server computer or computers and distributed client computers. The computer system presents a sales interface on some terminals. The sales interface shows products or services and groups of products and / or services that are for sale. The computer system presents a back end interface on some terminals, which can be used to enter new products, services and groupings of products and / or services to be offered for sale on the sales interface. Descriptions of the products or service offerings are entered into the computer system either by data entry operators using the back end interface or by a program reading product or service descriptions from external computer systems. The method groups these products or services according to an affinity algorithm. The groupings may then potentially be reviewed and approved or selected by human operators using the back end interface before being offered for sale on the sales interface. One advantageous application is the dynamic packaging of perishable items such as travel goods and services (e.g., airline tickets, rental cars, hotel rooms, entertainment opportunities, etc.).
Owner:SITE59
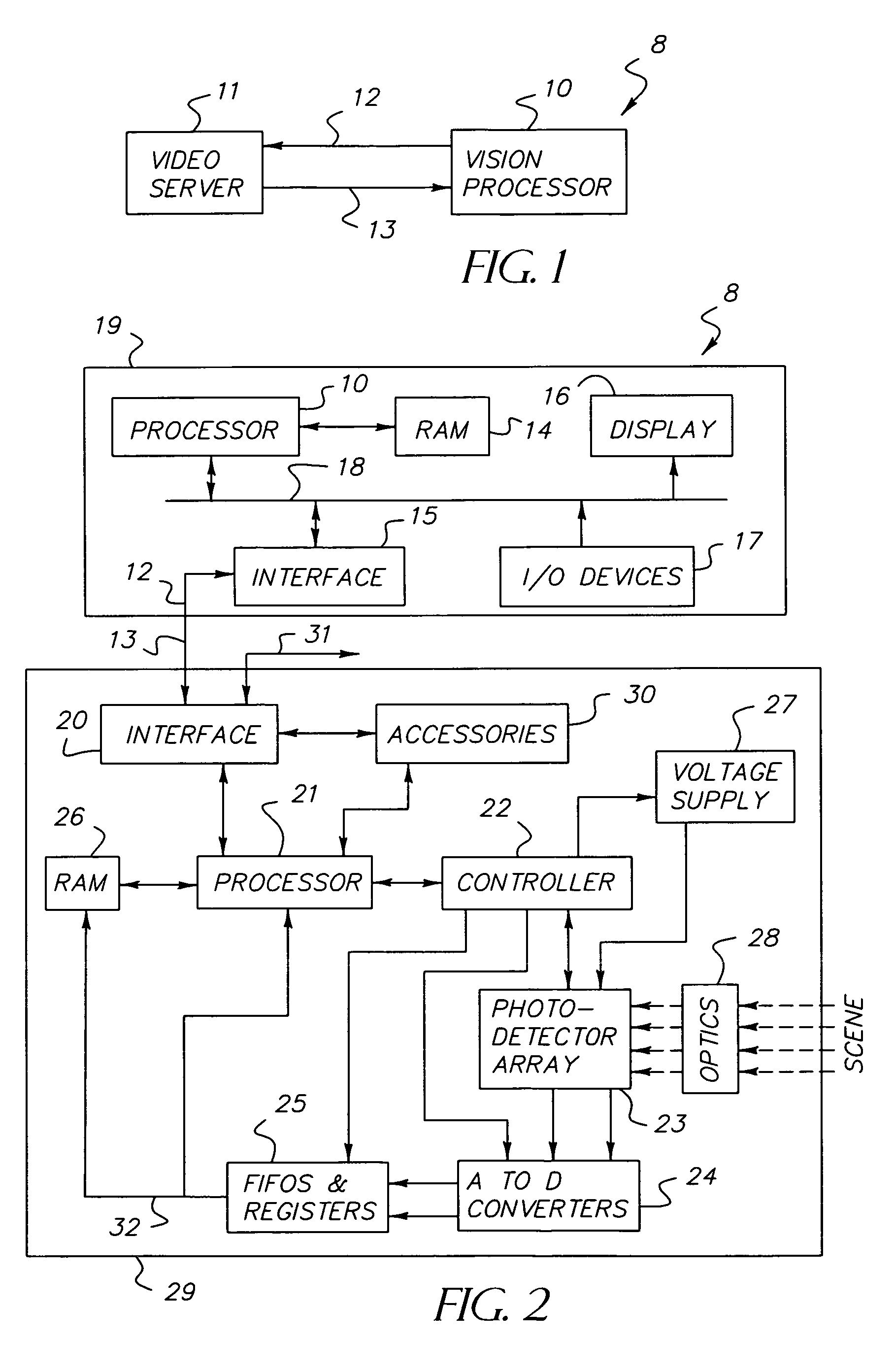
Dynamically reconfigurable vision system
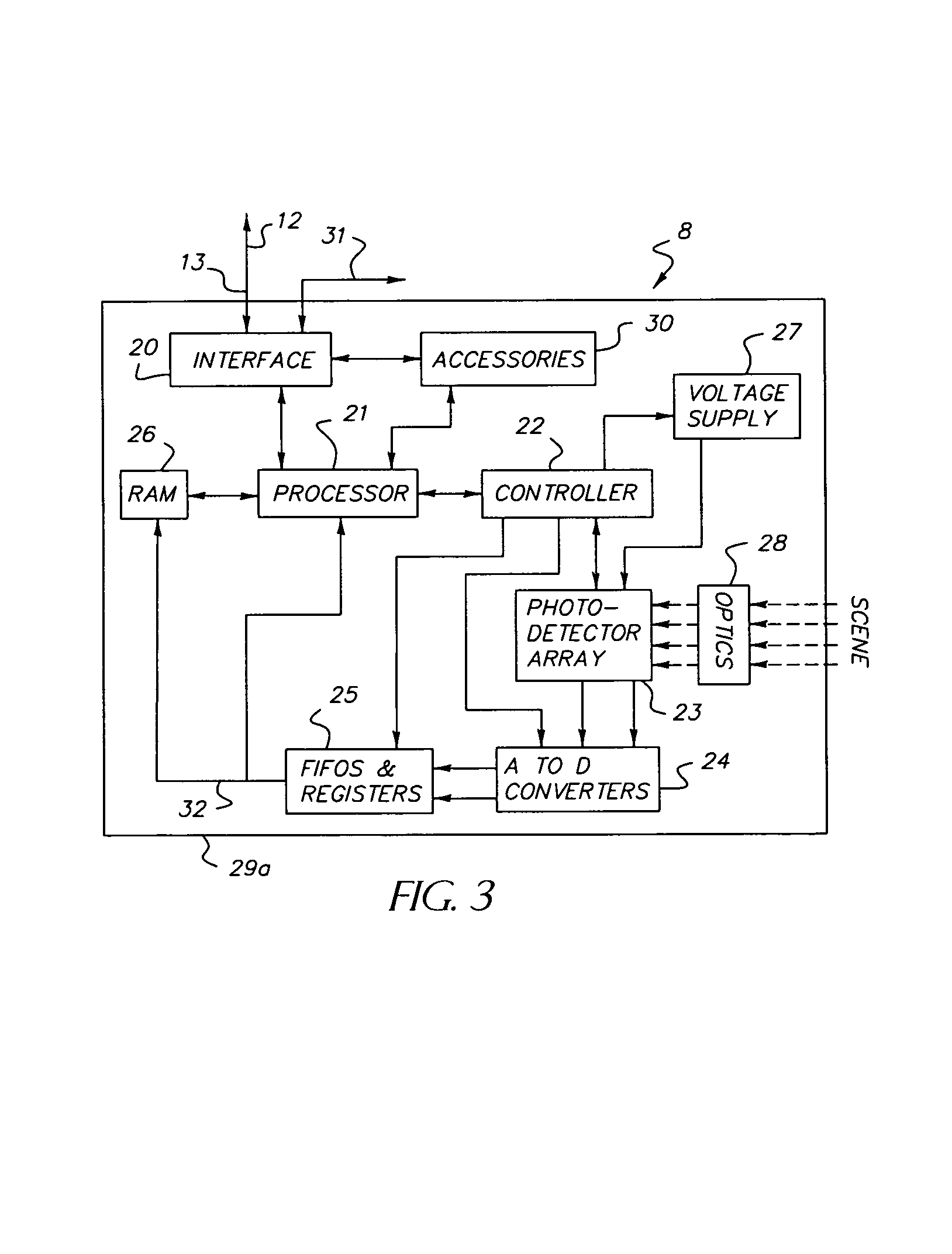
InactiveUS7106374B1Efficiently usEffective resourcesTelevision system detailsTelevision system scanning detailsVision processingPhotodetector
A closed-loop vision system is disclosed that utilizes a concept known as Dynamically Reconfigurable Vision (DRV), which is adaptive image sensing driven by a computer or human operator's response to changing scenery. The system reduces the amount of irrelevant video information sensed and thus achieves more effective bandwidth and computational resource utilization, as compared to traditional vision systems. One or more reconfigurable photodetector arrays sensitive to either visible, infrared or ultraviolet radiation are present in the DRV system. These photodetector arrays feature on-chip means for spatial and temporal data reduction implemented through multiple independently controllable, time-correlated, frequently overlapping windows on the photodetector array that may be programmed according to their size, location, resolution, integration time, and frame rate. All photodetector array windows are dynamically reconfigurable in real time on a frame-by-frame basis. Furthermore, a DRV system is constructed in a client-server architecture in which a vision processor client passes window request command messages to the reconfigurable photodetector array server, which in turn delivers the requested video back to the client processor. The ability to simultaneously reconfigure, integrate, process, and readout multiple photodetector array video windows is an important characteristic of the DRV system.
Owner:COMPTEK AMHERST SYST INC
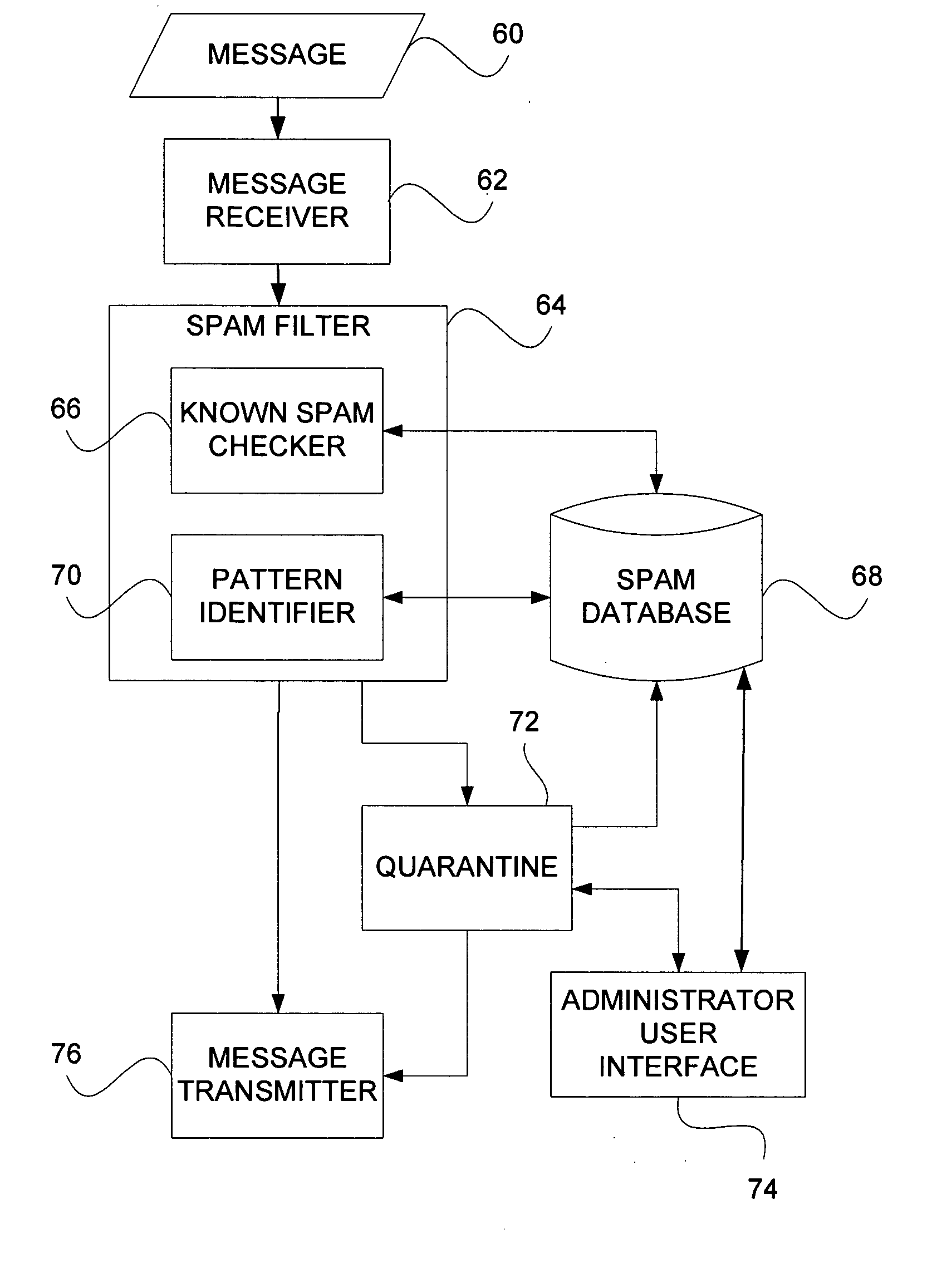
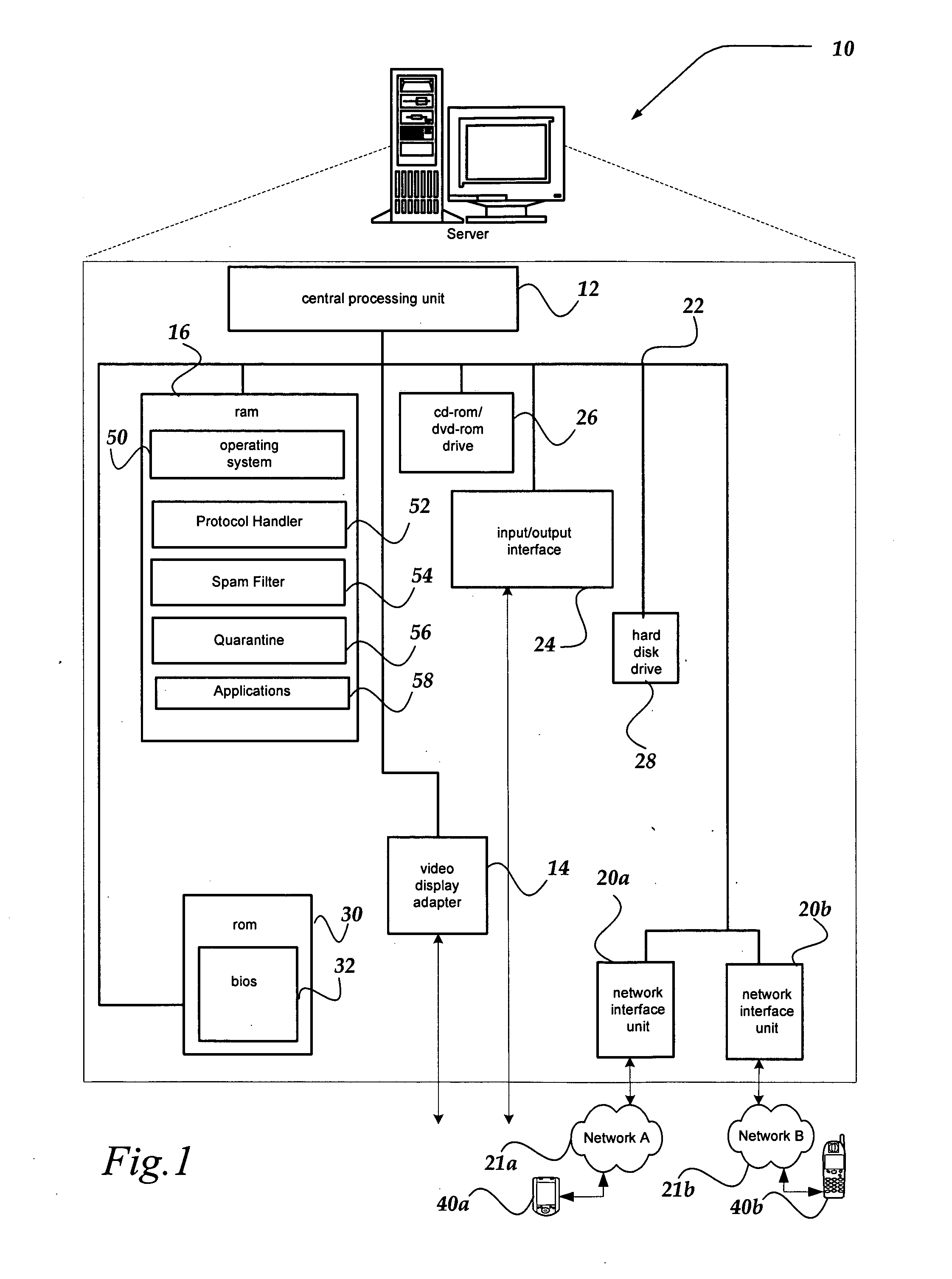
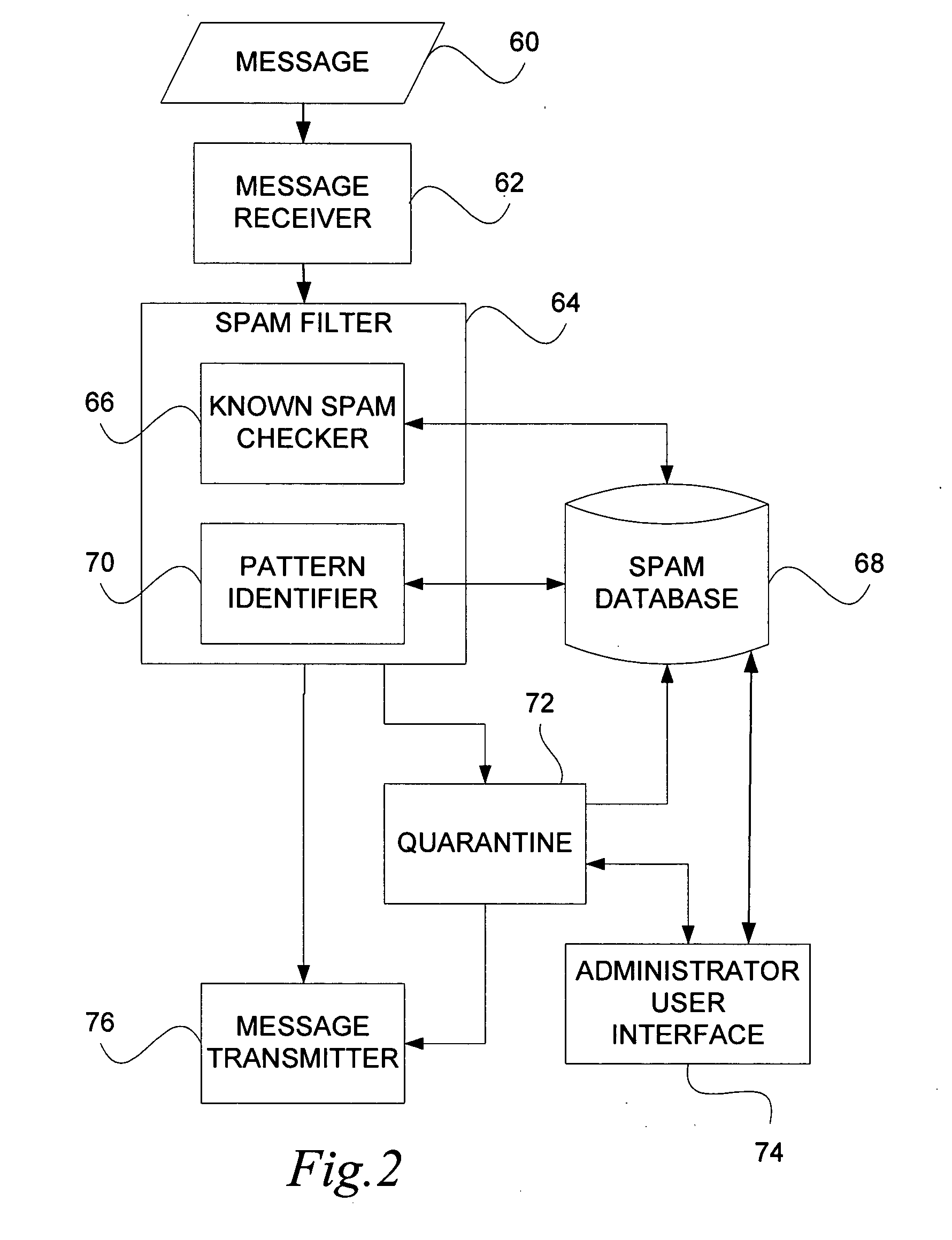
Messaging spam detection
InactiveUS20060026242A1Multiple digital computer combinationsData switching networksEmail addressTelecommunications
Detecting unsolicited messages (spam) by aggregating information across multiple recipients and / or across the same or differing messaging protocols. Multiple messages are analyzed to detect a call to action pattern that specifies a target communication address with which the recipients are requested to communicate, such as an email address, an Internet address, a telephone number, and the like. Once a frequency threshold of messages containing the call to action pattern is reached, subsequent messages are temporarily quarantined for evaluation by a human operator. If the human determines that the messages are not spam, the human can release the quarantined messages, and indicate that future messages with the call to action pattern are not to be delayed. Conversely, if the human determines that the messages are spam, the human can delete the messages in quarantine, and indicate that all future messages with that call to action pattern are to be deleted automatically.
Owner:WIRELESS SERVICES CORP
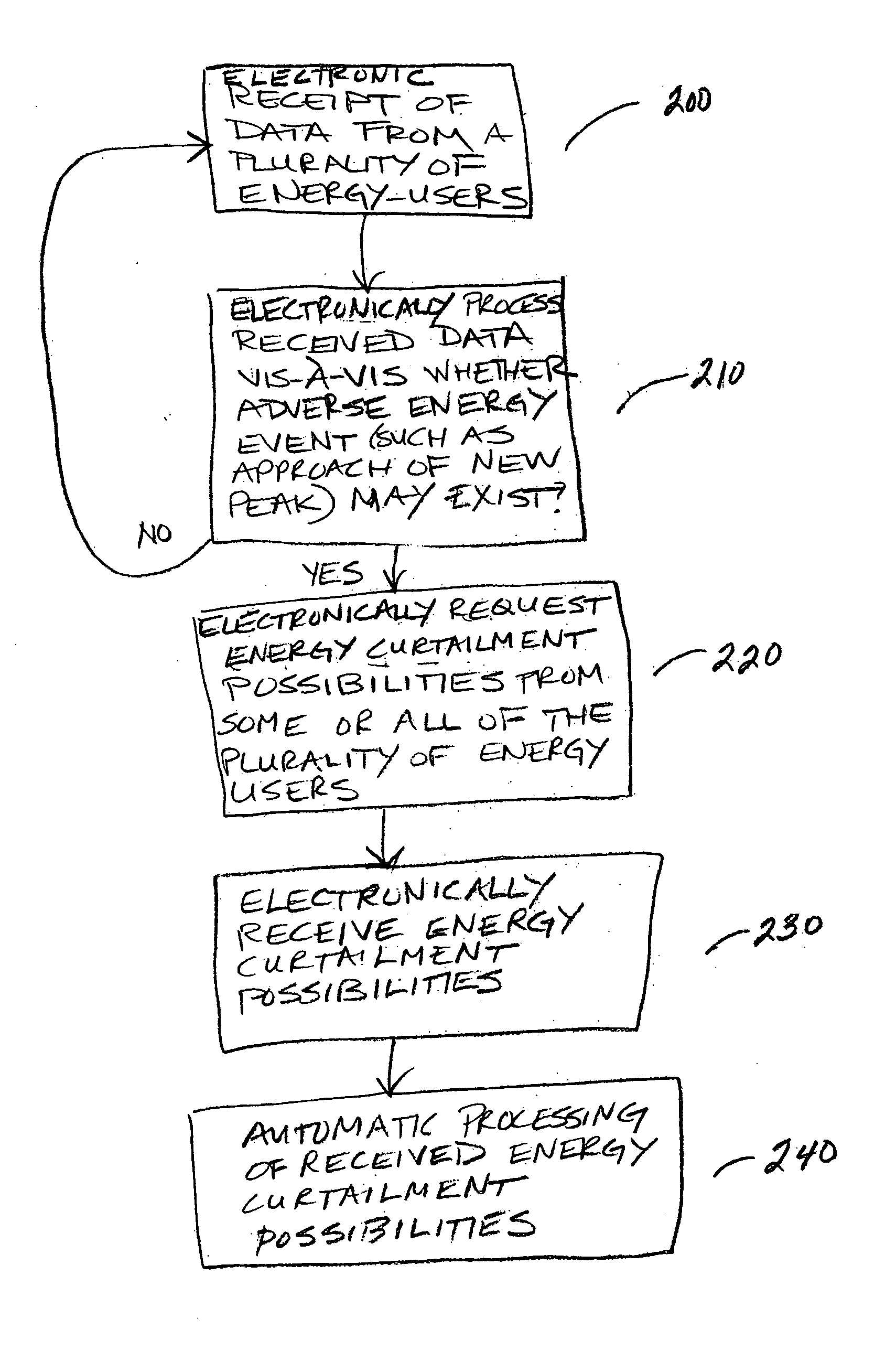
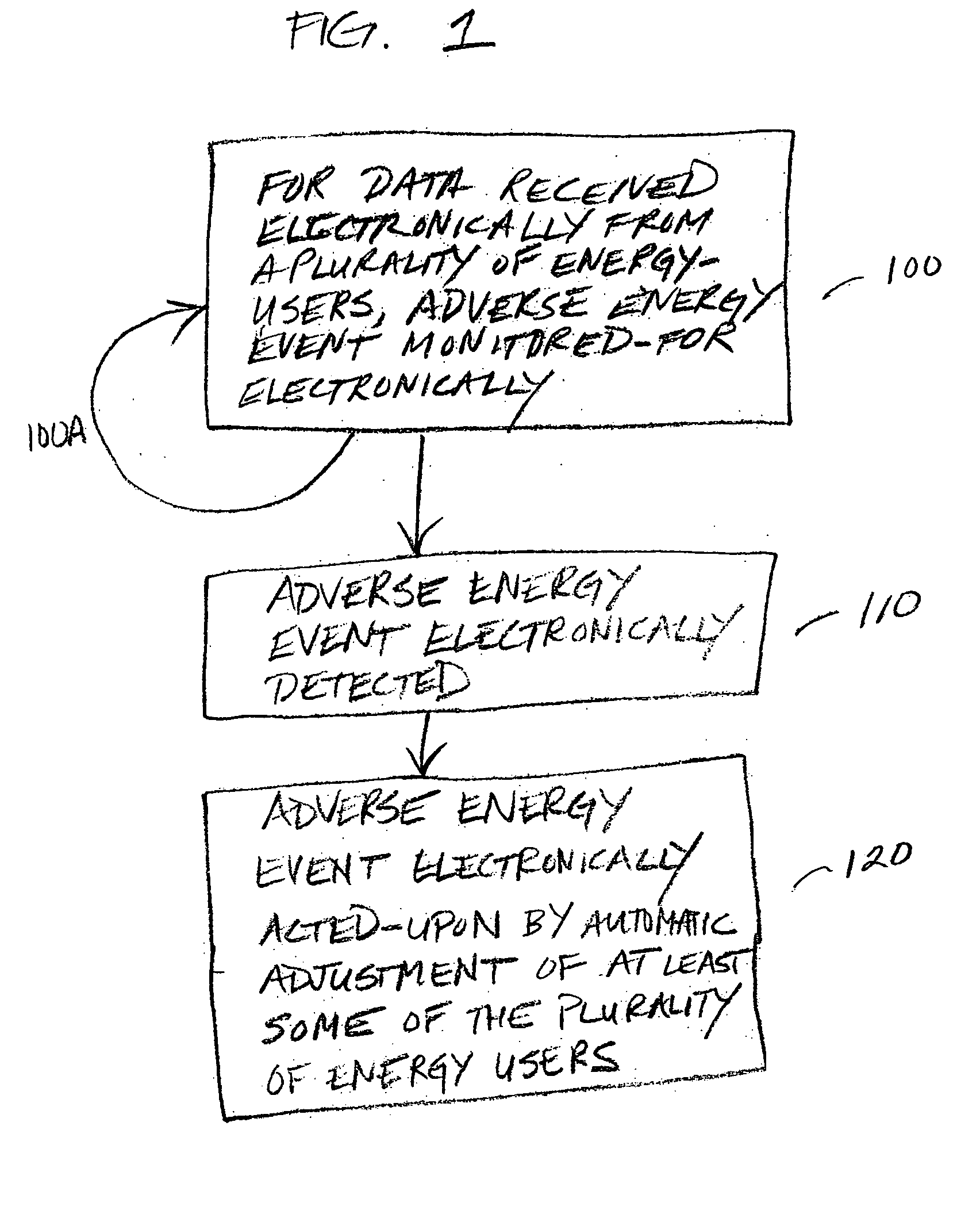
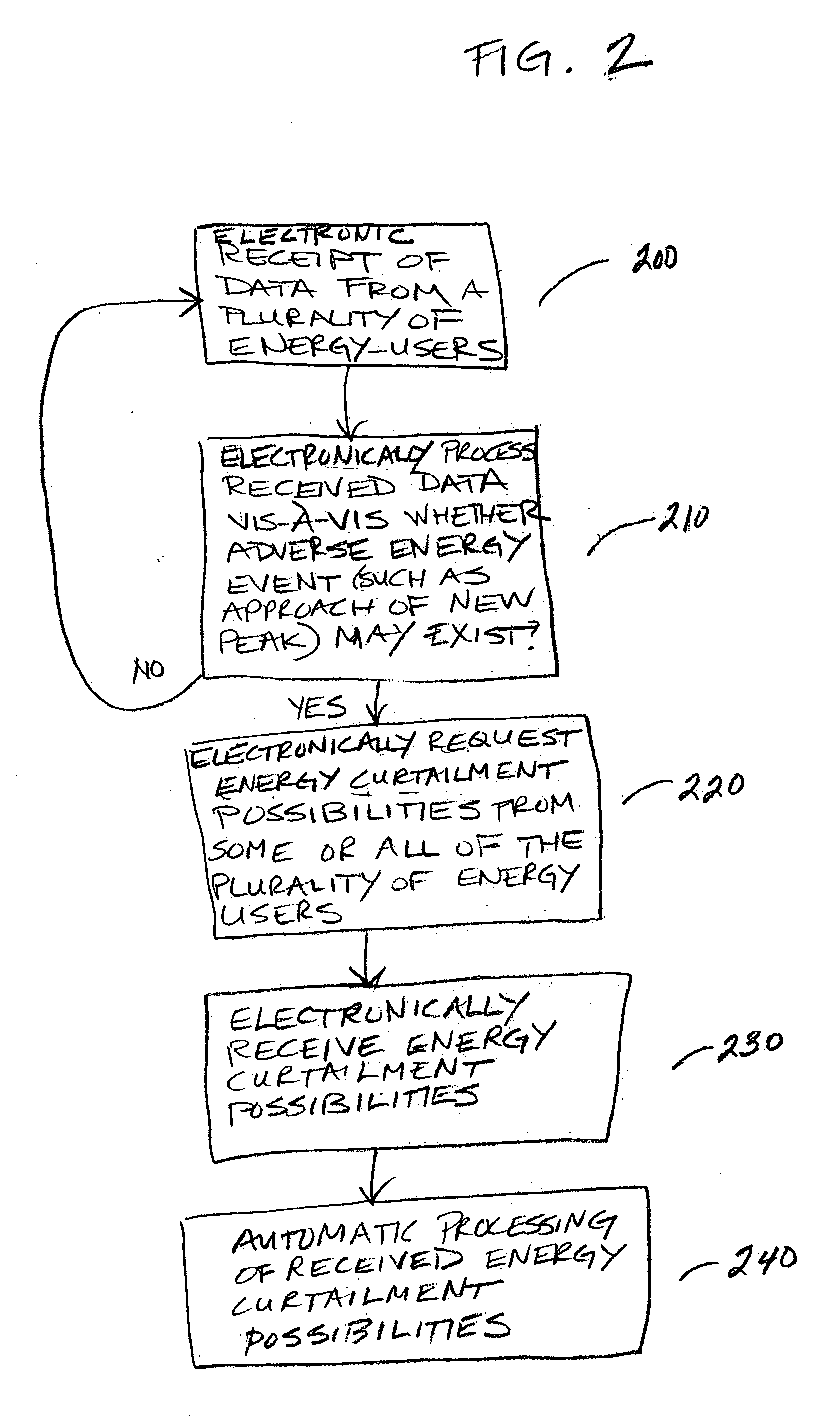
Automatic energy management and energy consumption reduction, especially in commercial and multi-building systems
InactiveUS20050038571A1Minimal impactLevel controlLoad forecast in ac networkReal time analysisNerve network
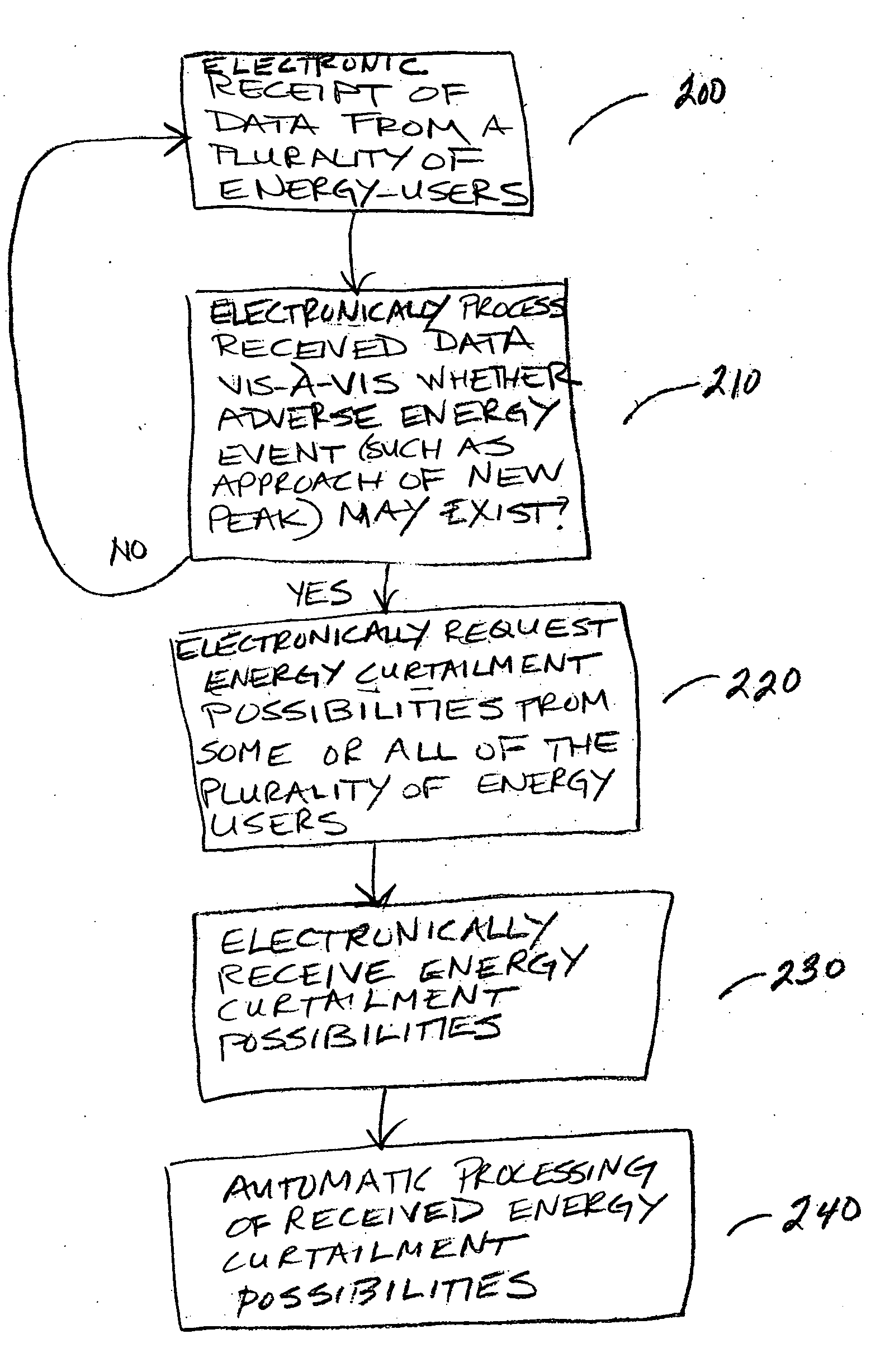
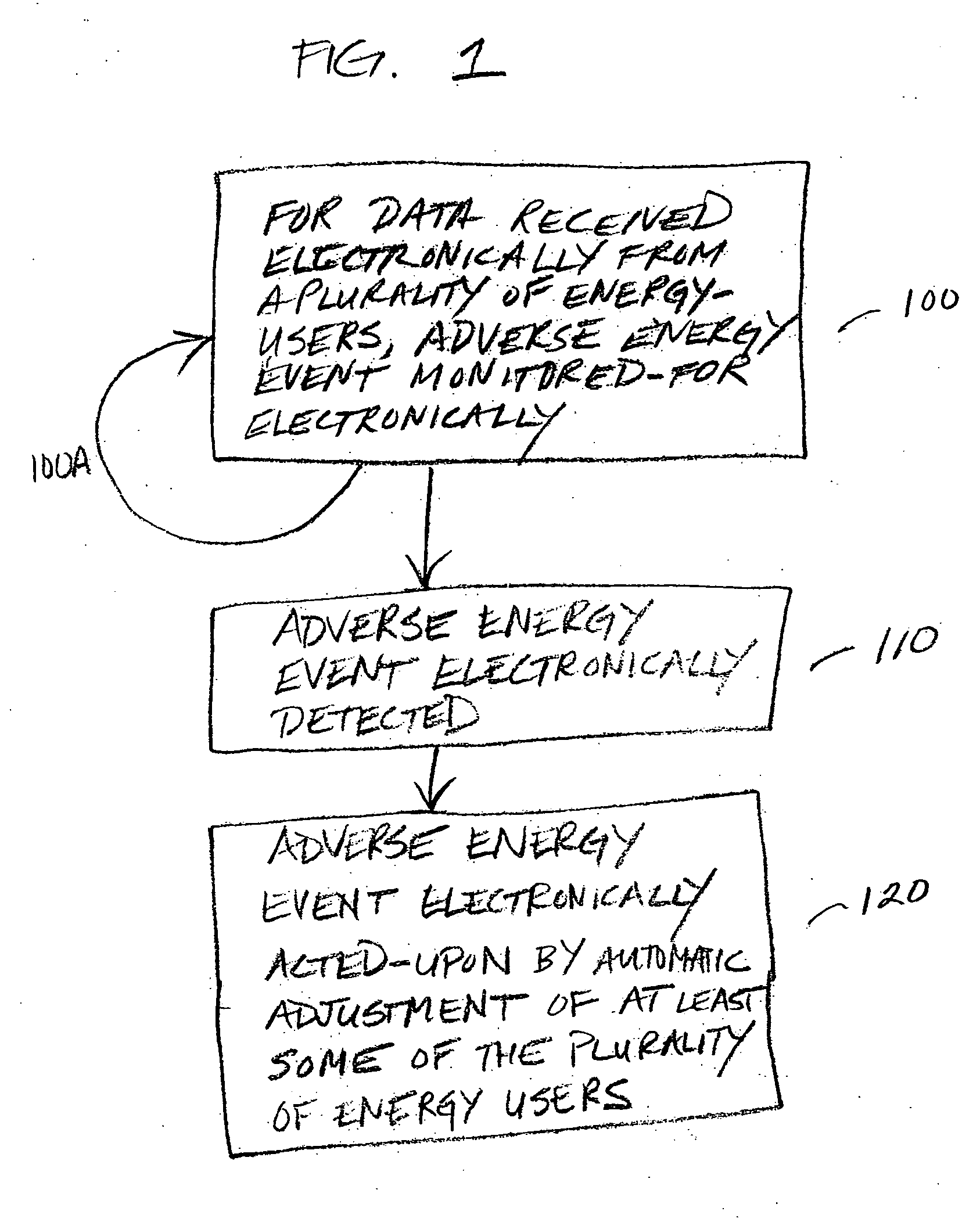
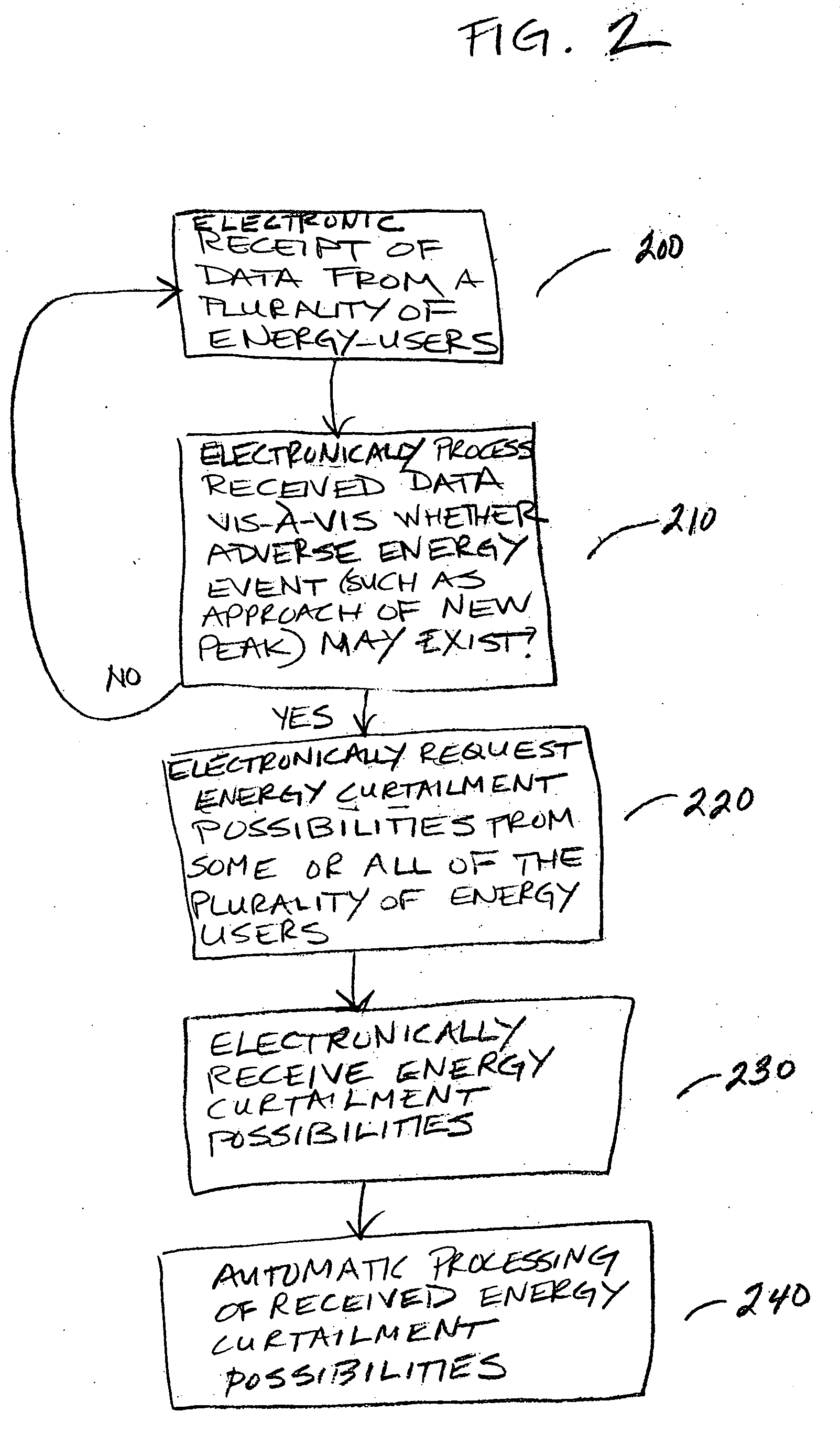
Automatic energy management is provided, in even the most complex multi-building system. The necessity of a human operator for managing energy in a complex, multi-building system is reduced and even eliminated. Computer-based monitoring and computer-based recognition of adverse energy events (such as the approach of a new energy peak) is highly advantageous in energy management. Immediate automatic querying of energy users within a system of buildings for energy curtailment possibilities is provided. Such immediate, automatic querying may be answered by the energy users through artificial intelligence and / or neural network technology provided to or programmed into the energy users, and the queried energy users may respond in real-time. Those real-time computerized responses with energy curtailment possibilities may be received automatically by a data processing facility, and processed in real-time. Advantageously, the responses from queried energy users with energy curtailment possibilities may be automatically processed into a round-robin curtailment rotation which may be implemented by a computer-based control system. Thus, impact on occupants is minimized, and energy use and energy cost may be beneficially reduced in an intelligent, real-time manner. The invention also provides for early-recognition of impending adverse energy events, optimal response to a particular energy situation, real-time analysis of energy-related data, etc.
Owner:INTERCAP CAPITAL PARTNERS
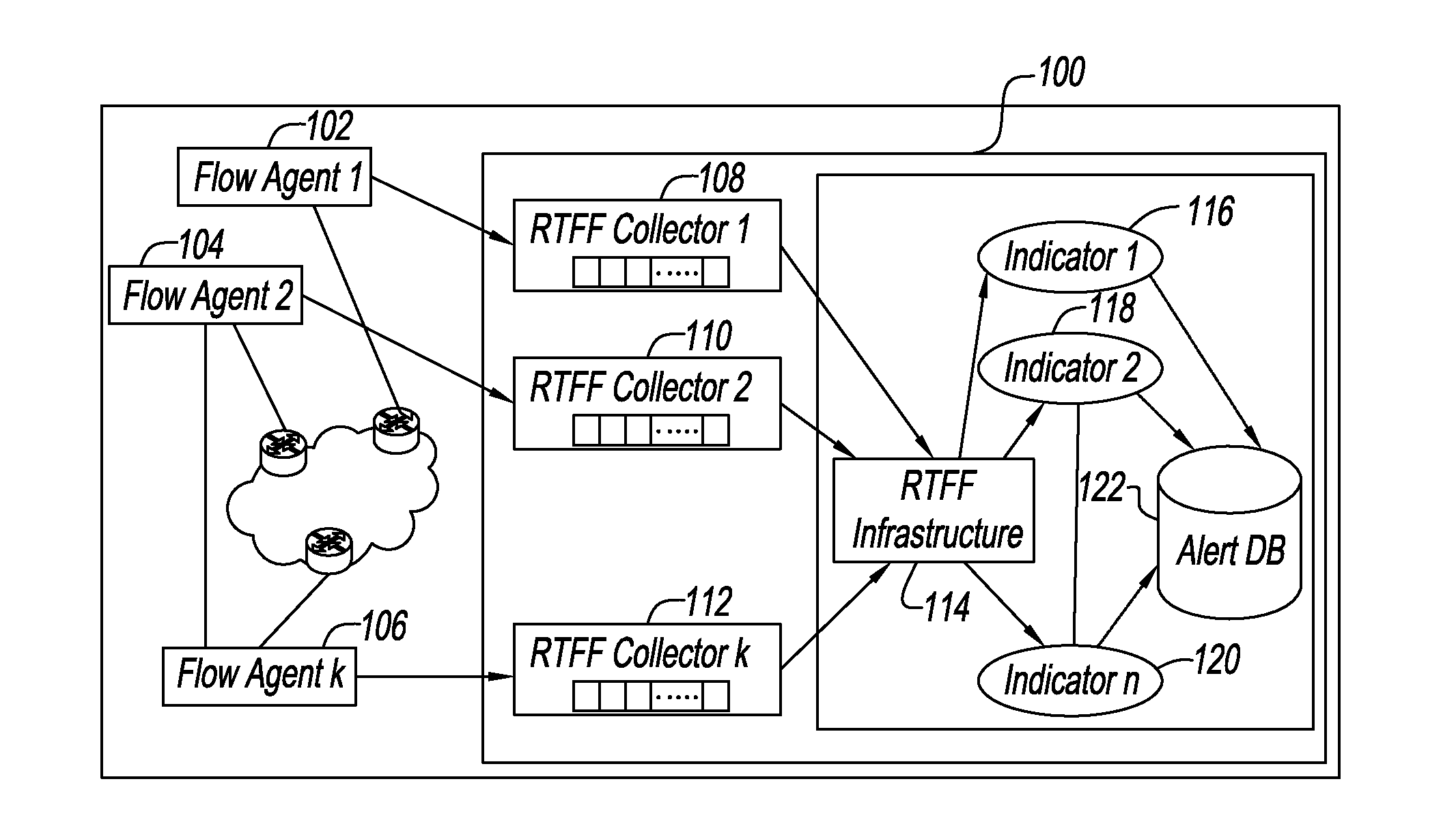
System and method for correlating historical attacks with diverse indicators to generate indicator profiles for detecting and predicting future network attacks
InactiveUS20140082730A1Reduce detectionAccurately detect and predictMemory loss protectionError detection/correctionTraffic characteristicAnomalous behavior
An apparatus and method predict and detect network attacks by using a diverse set of indicators to measure aspects of the traffic and by encoding traffic characteristics using these indicators of potential attacks or anomalous behavior. The set of indicators is analyzed by supervised learning to automatically learn a decision rule which examines the temporal patterns in the coded values of the set of indicators to accurately detect and predict network attacks. The rules automatically evolve in response to new attacks as the system updates its rules periodically by analyzing new data and feedback signals about attacks associated with that data. To assist human operators, the system also provides human interpretable explanations of detection and prediction rules by pointing to indicators whose values contribute to a decision that there is an existing network attack or an imminent network attack. When such indictors are detected, an operator can take remediation actions.
Owner:PERSPECTA LABS INC +1
Holographic human-machine interfaces
ActiveUS7054045B2Reduced weight and size and power consumptionImprove smoothnessInput/output for user-computer interactionElectronic switchingHuman–machine interfaceSignal generator
Owner:HOLOTOUCH
Automatic energy management and energy consumption reduction, especially in commercial and multi-building systems
InactiveUS20050043862A1Minimal impactMechanical power/torque controlLevel controlReal time analysisNew energy
Automatic energy management is provided, in even the most complex multi-building system. The necessity of a human operator for managing energy in a complex, multi-building system is reduced and even eliminated. Computer-based monitoring and computer-based recognition of adverse energy events (such as the approach of a new energy peak) is highly advantageous in energy management. Immediate automatic querying of energy users within a system of buildings for energy curtailment possibilities is provided. Such immediate, automatic querying may be answered by the energy users through artificial intelligence and / or neural network technology provided to or programmed into the energy users, and the queried energy users may respond in real-time. Those real-time computerized responses with energy curtailment possibilities may be received automatically by a data processing facility, and processed in real-time. Advantageously, the responses from queried energy users with energy curtailment possibilities may be automatically processed into a round-robin curtailment rotation which may be implemented by a computer-based control system. Thus, impact on occupants is minimized, and energy use and energy cost may be beneficially reduced in an intelligent, real-time manner. The invention also provides for early-recognition of impending adverse energy events, optimal response to a particular energy situation, real-time analysis of energy-related data, etc.
Owner:INTERCAP CAPITAL PARTNERS
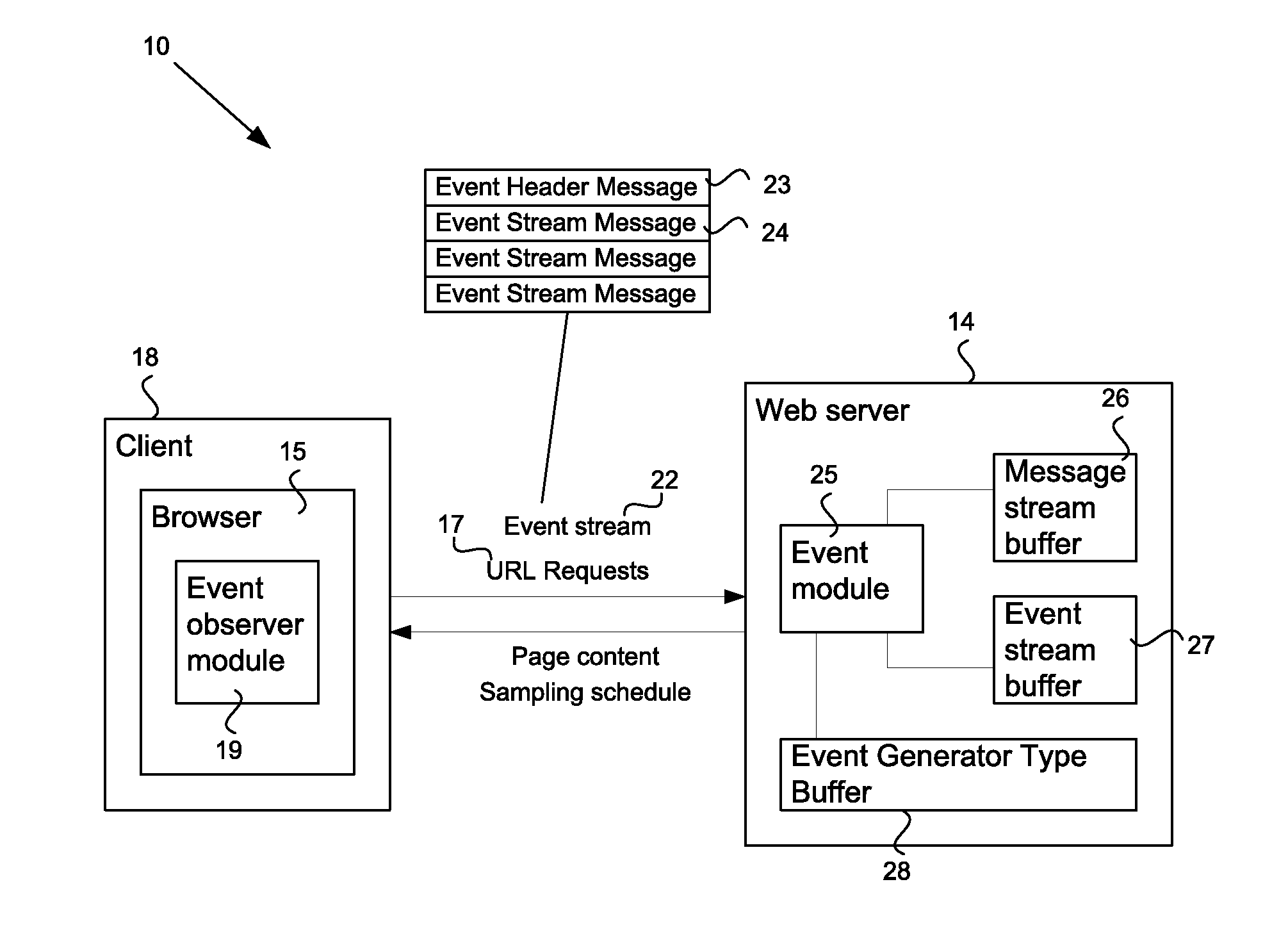
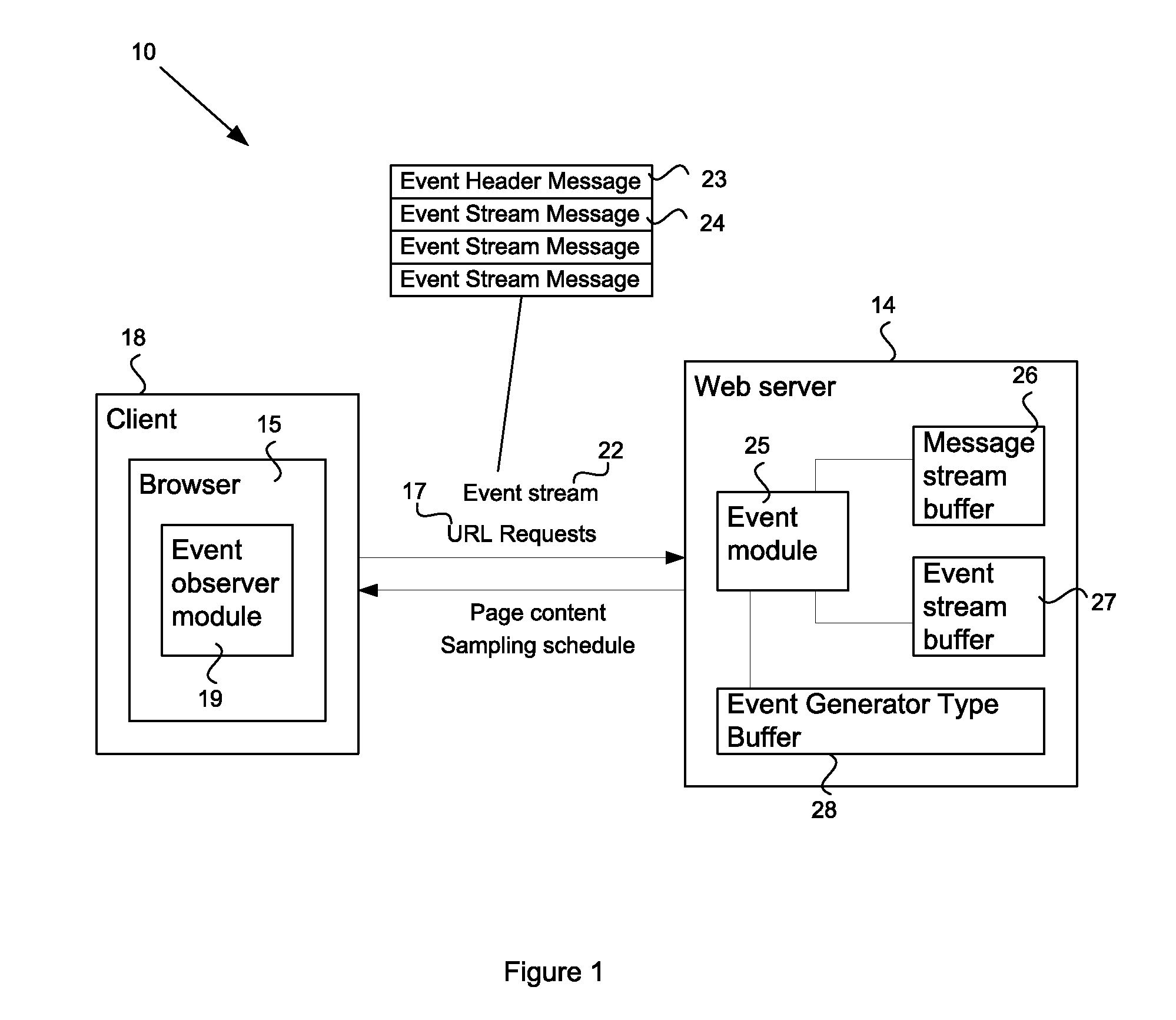
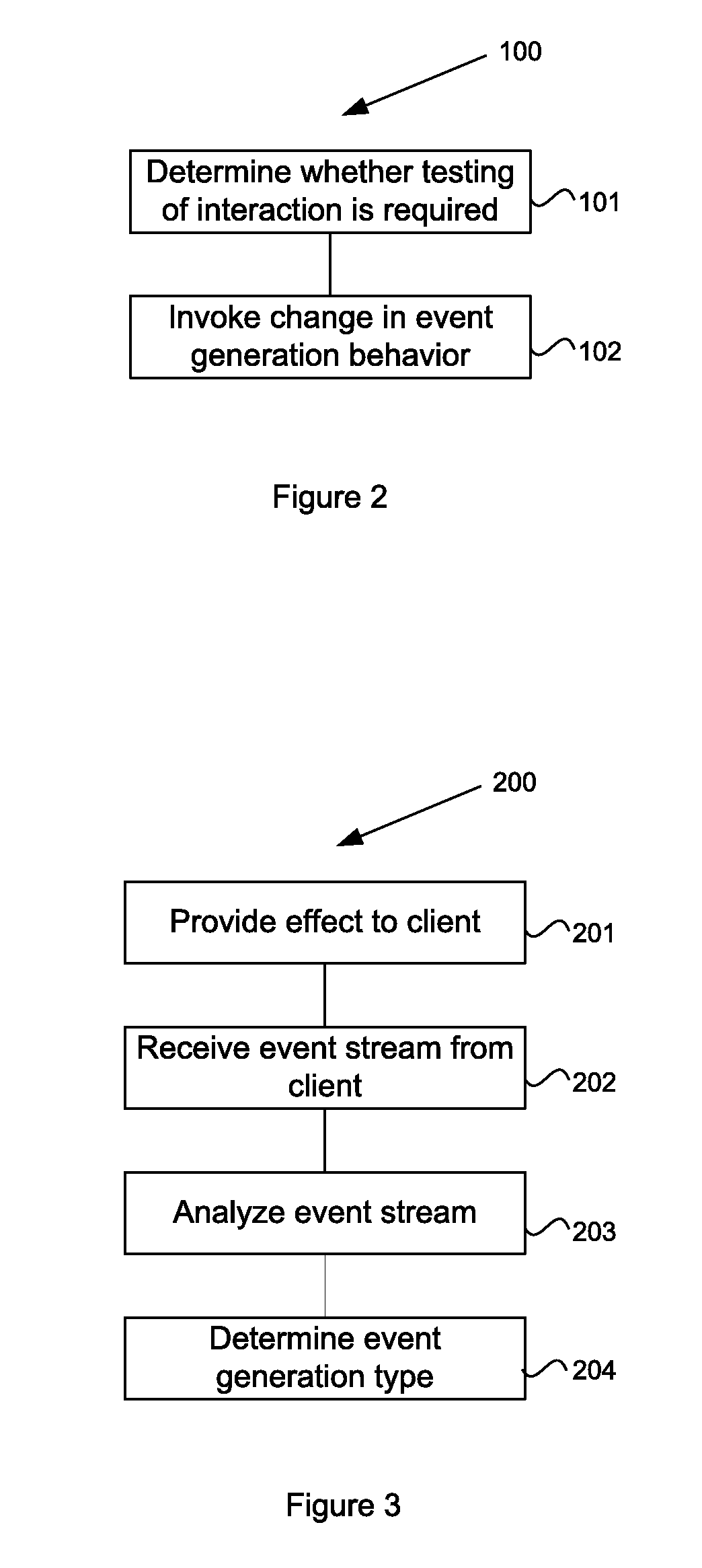
System and method for processing user interface events
ActiveUS20100287229A1Multiple digital computer combinationsDigital data authenticationHuman behaviorHuman interaction
A system and method to detect and prevent non-human interaction between a client and a web server invokes an effect to change the event generation behavior at the client. Subsequent event streams from the client to the server are analyzed to determine whether the event streams contain events corresponding to expected reactions of a human operator at the client to the effect. Indications of non-human behavior may invoke more direct human testing, for example using a dynamic CAPTCHA application, or may cause a termination of the client / URL interaction.
Owner:ORACLE INT CORP
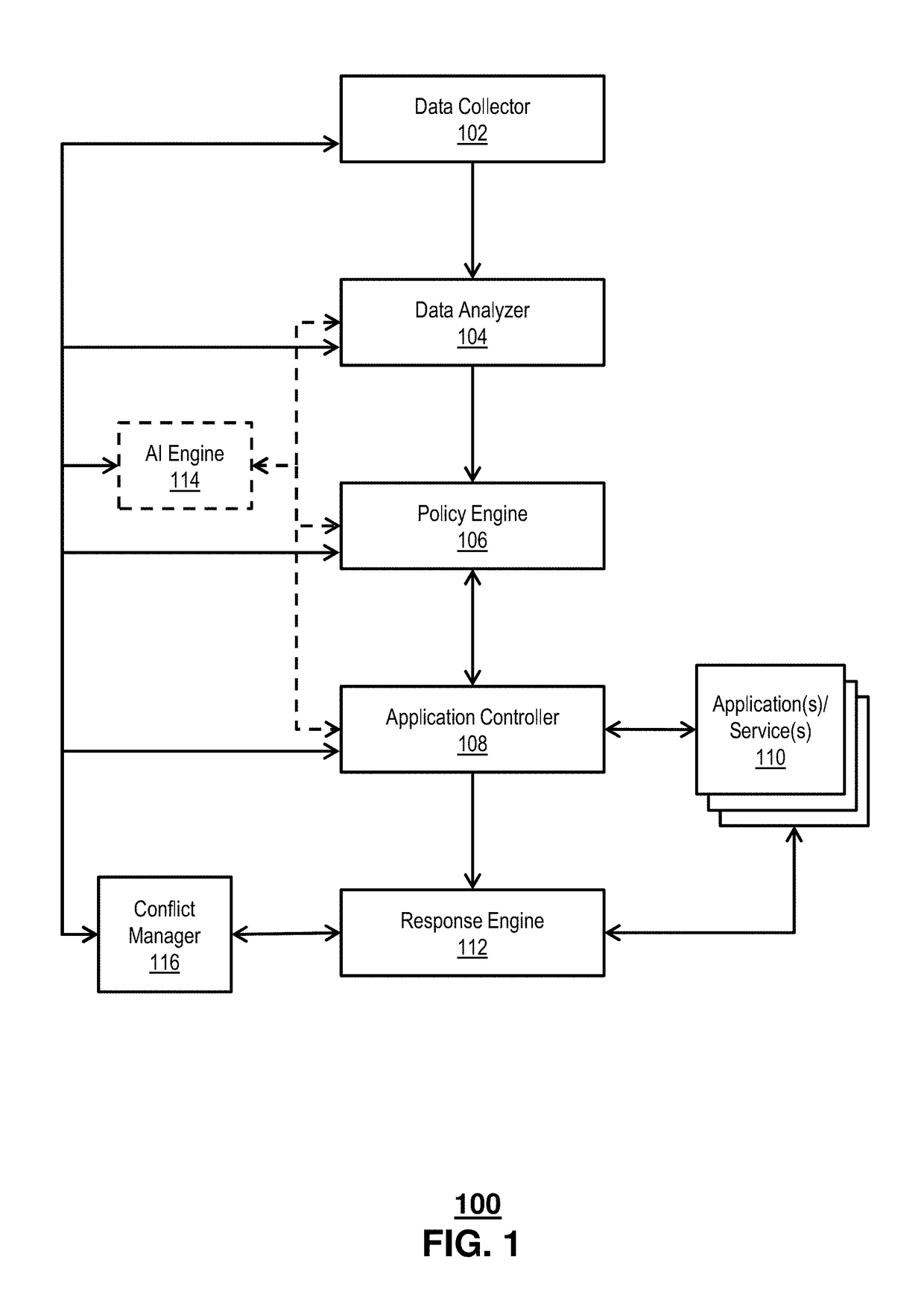
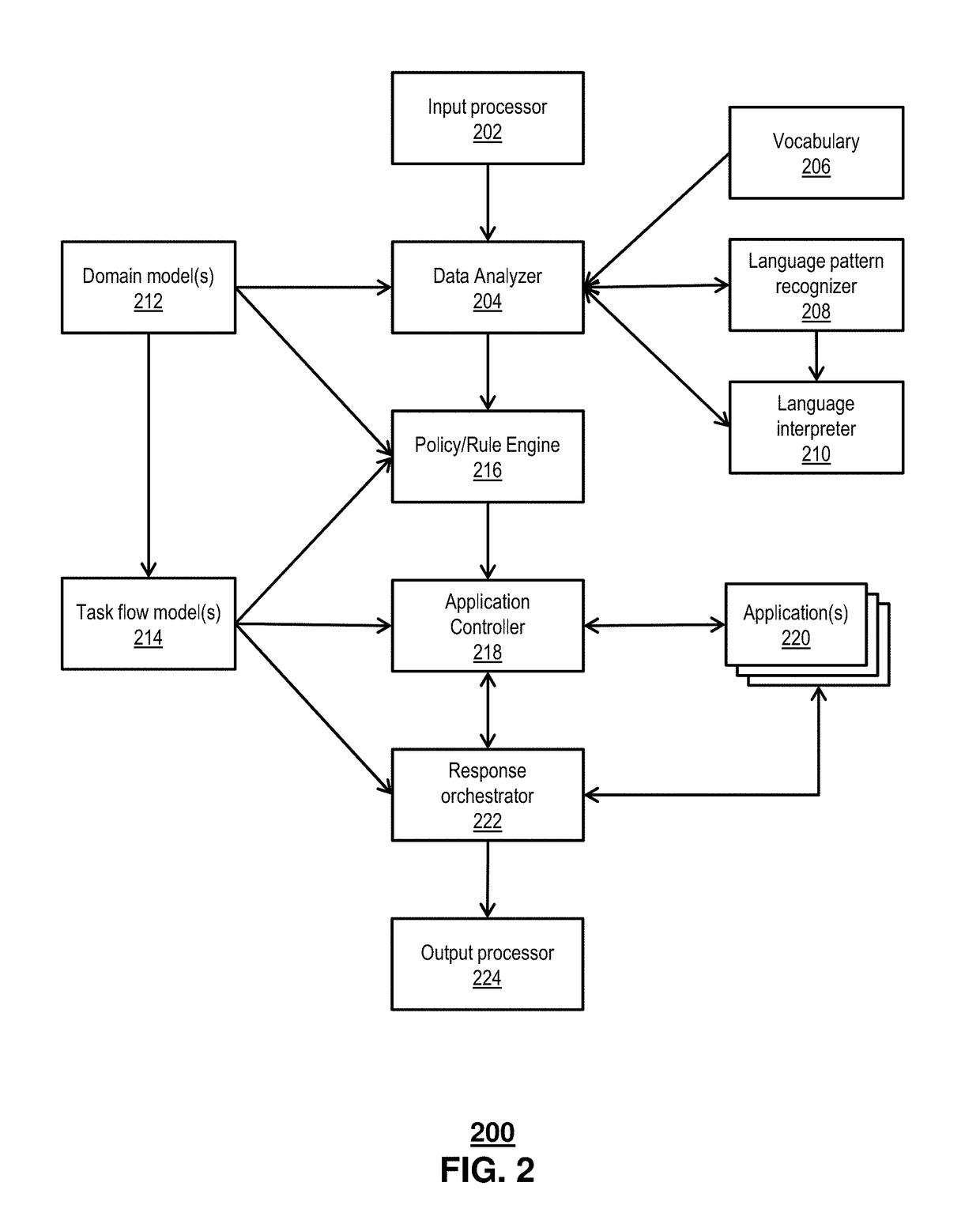
Asynchronous virtual assistant
Aspects of the subject disclosure may include, for example, obtaining an input, e.g., from a human operator, comprising a request. A number of activities are identified, e.g., by a virtual assistant, based on the request. Performance of the number of activities is facilitated, e.g., by the virtual assistant. A result is determined, e.g., by the virtual assistant, based on the performance of the number of activities, wherein a response to the request is based on the result. Other embodiments are disclosed.
Owner:AT&T INTPROP I L P
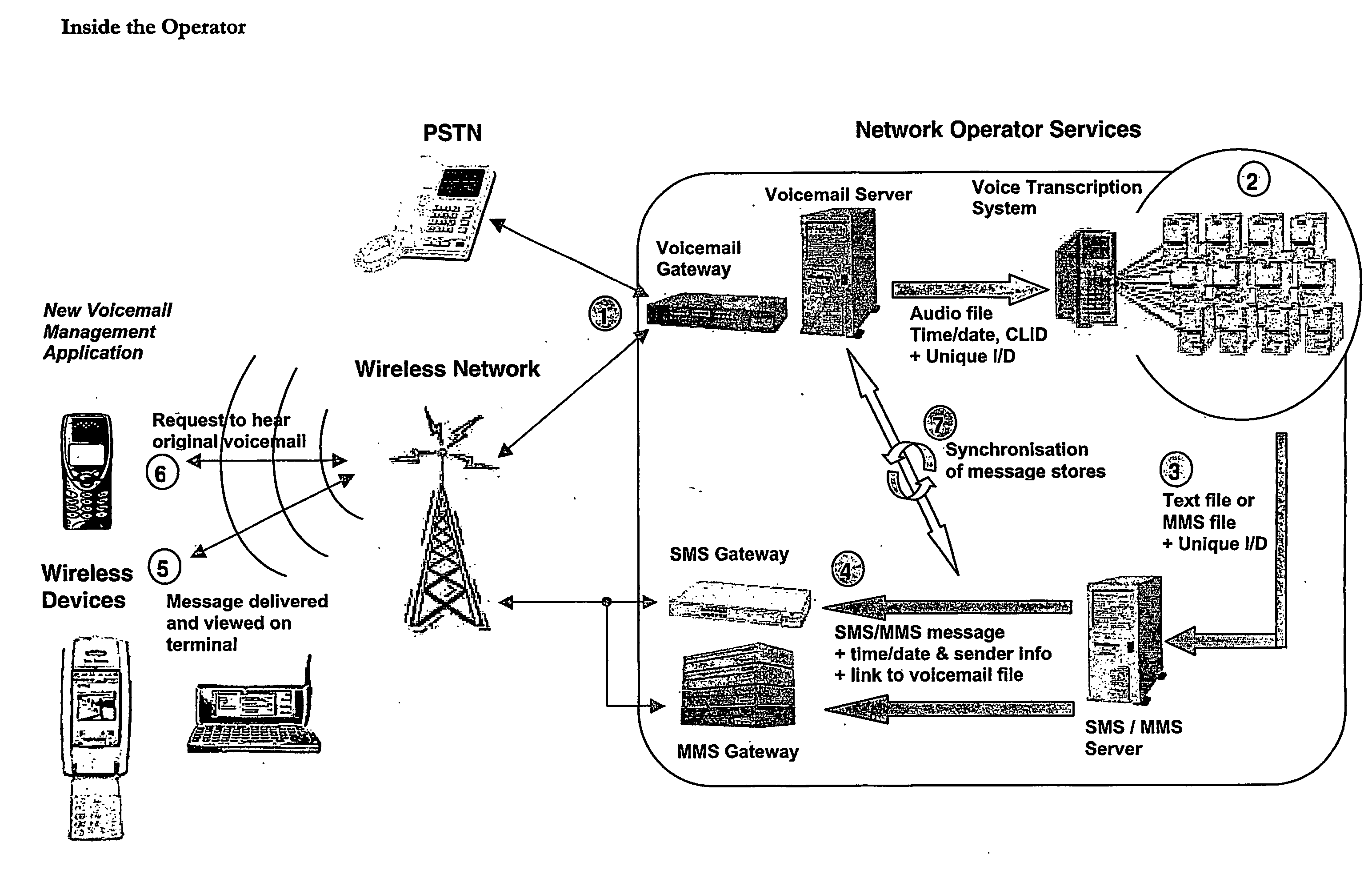
Method of providing voicemails to a wireless information device
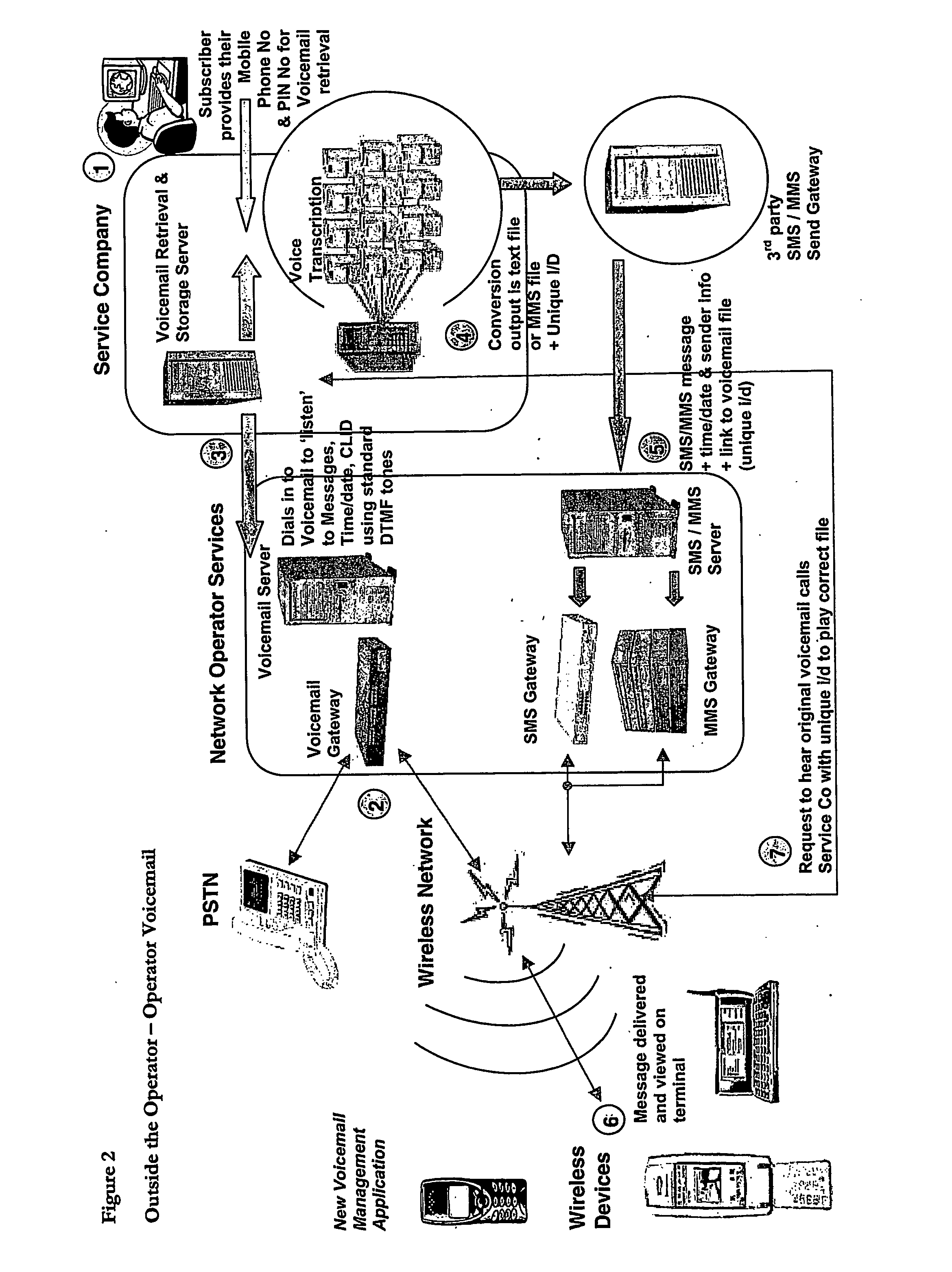
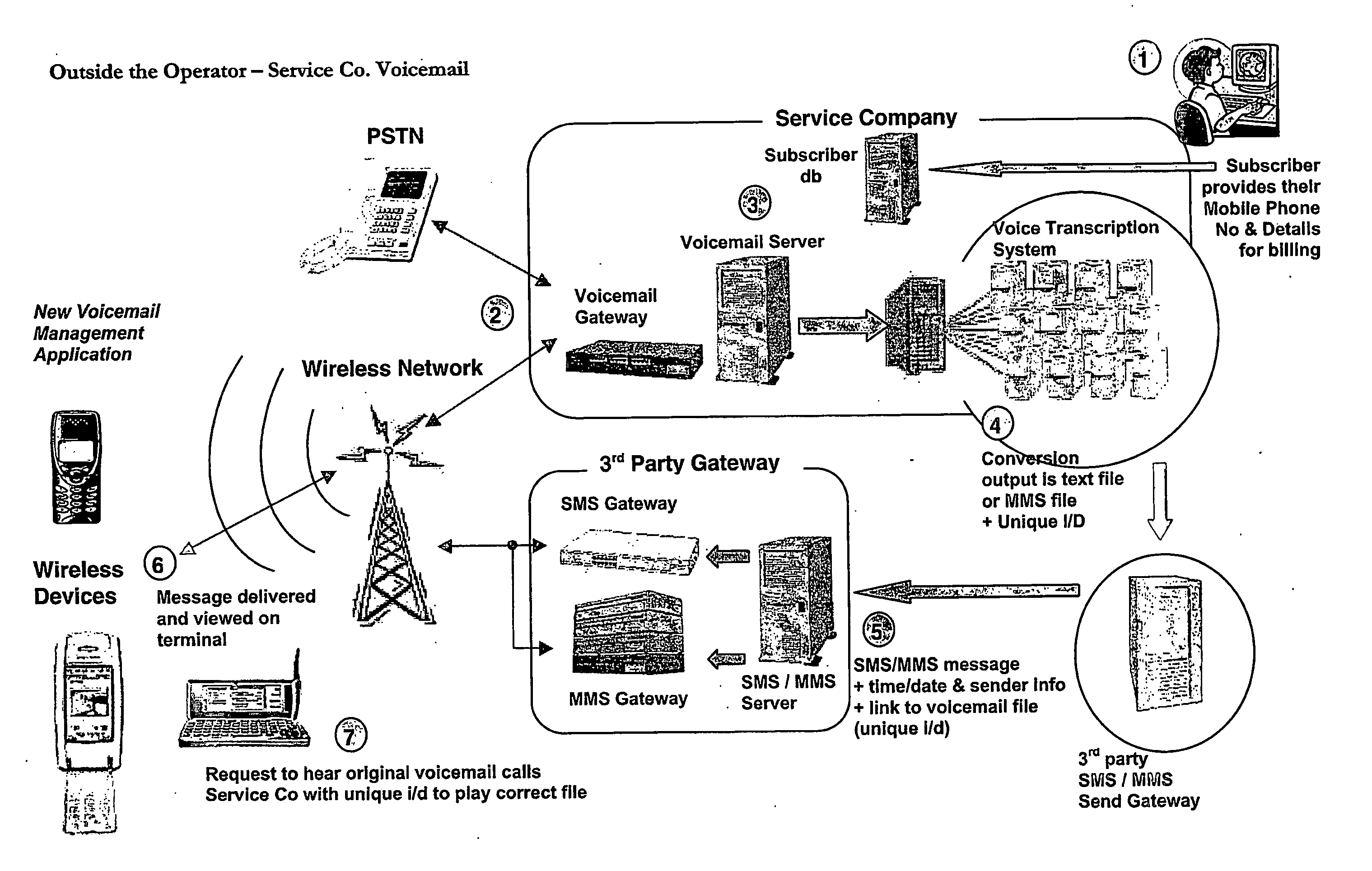
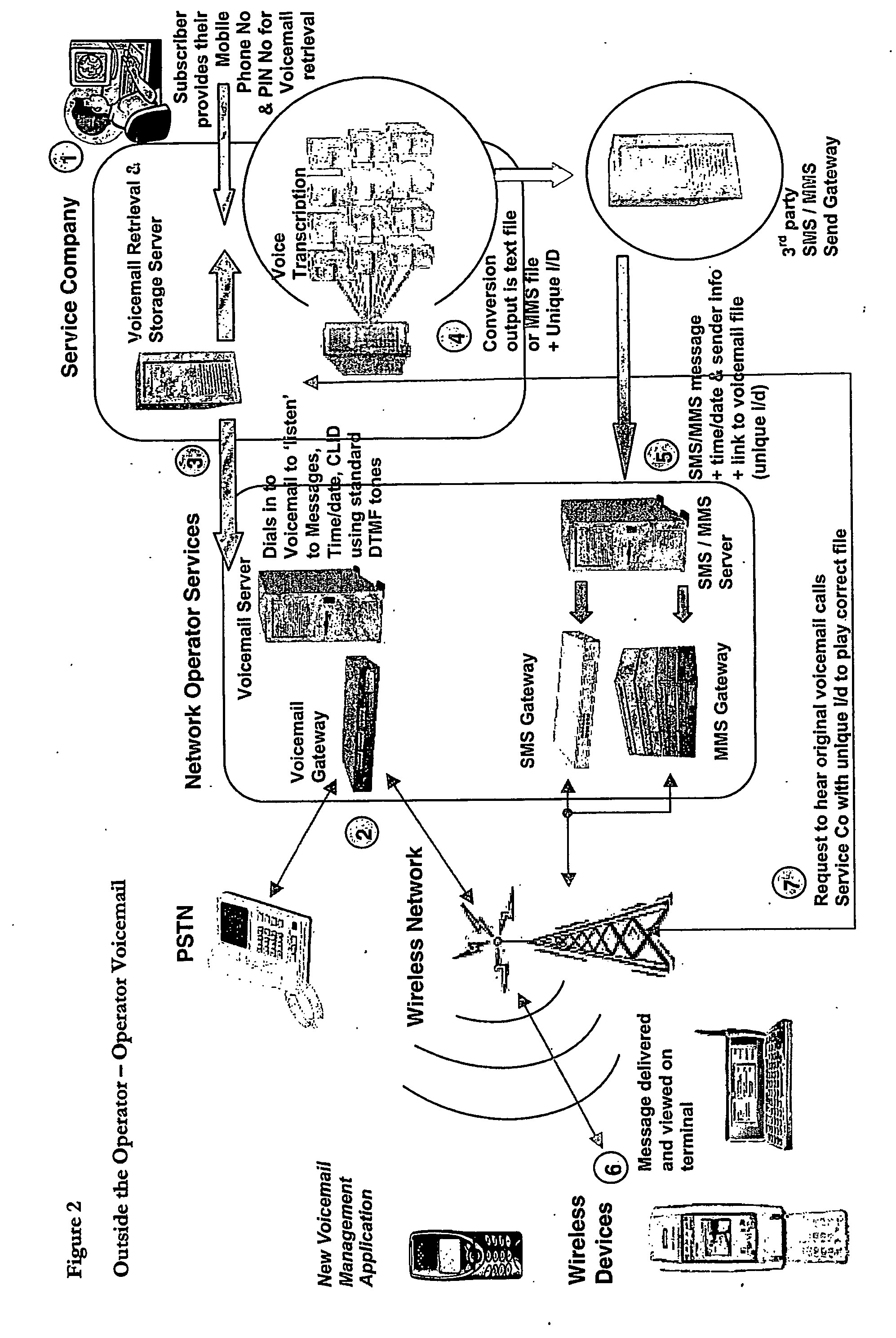
InactiveUS20060223502A1Save expensive costsEncourages some commitmentInformation formatDevices with voice recognitionInformation deviceHuman operator
Voicemail is received at a voicemail server and converted to an audio file format; it is then sent or streamed over a wide area network to a voice to text transcription system comprising a network of computers. One of the networked computers plays back the voice message to an operator and the operator intelligently transcribes the actual message from the original voice message by entering the corresponding text message (actually a succinct version of the original voice message, not a verbose word-for-word conversion) into the computer to generate a transcribed text message. The transcribed text message is then sent to the wireless information device from the computer. Because human operators are used instead of machine transcription, voicemails are converted accurately, intelligently, appropriately and succinctly into text messages (SMS / MMS).
Owner:SPINVOX LTD
Apparatus and methods for a human de-amplifier system
InactiveUS6084371AProgramme-controlled manipulatorMicromanipulatorOperational systemAudio power amplifier
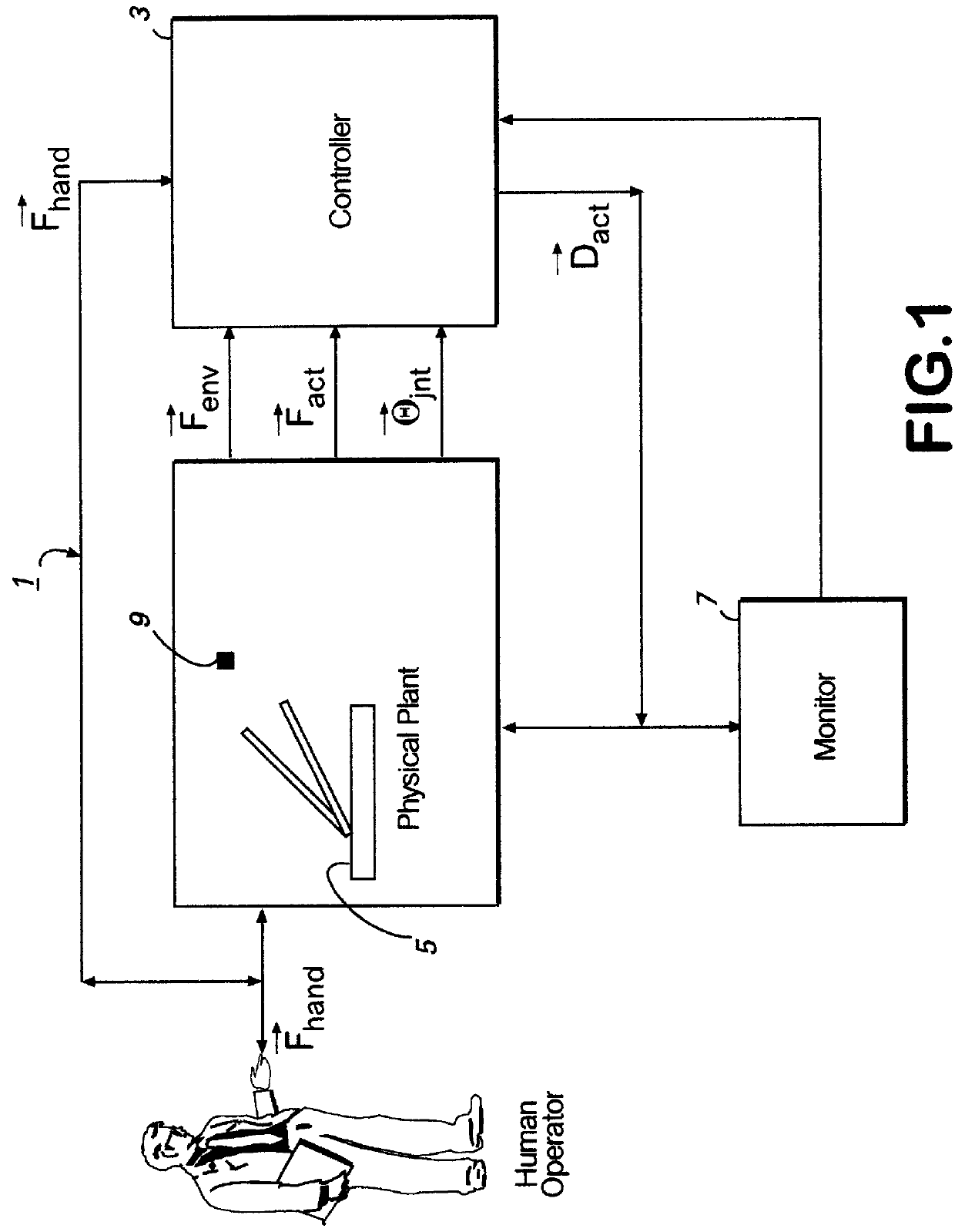
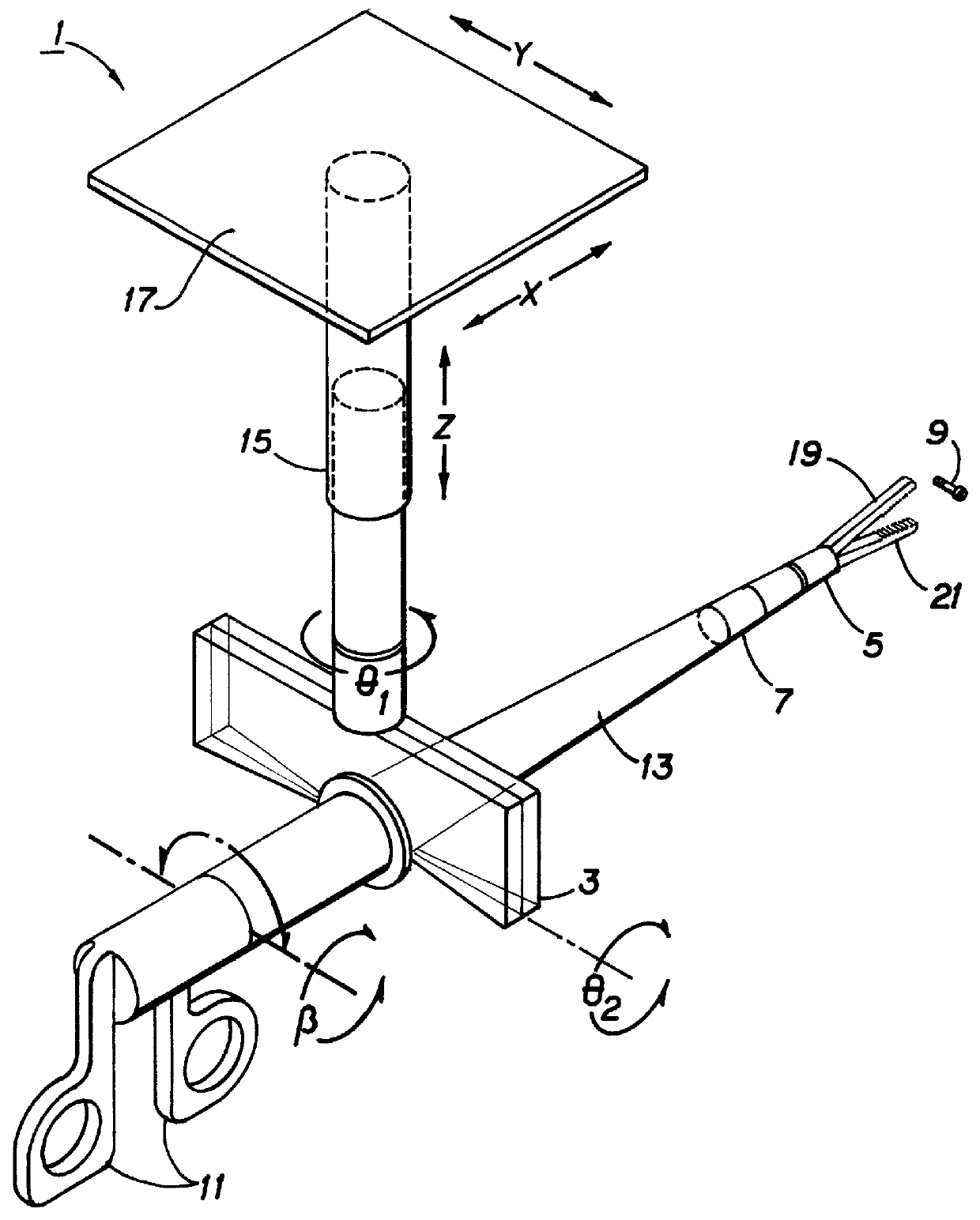
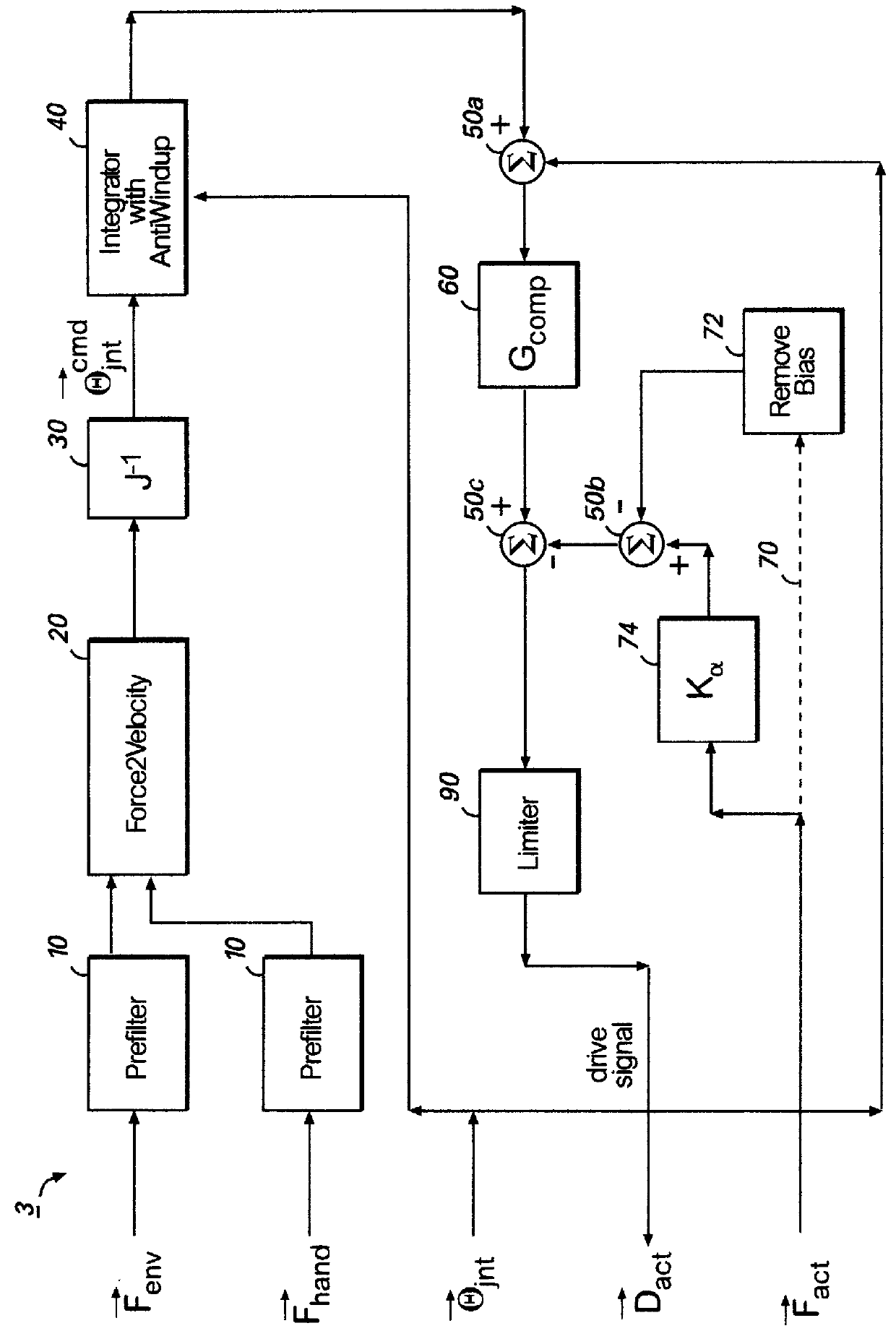
A human de-amplifier system for interfacing a human operator and a physical object through a physical plant, wherein the physical object has dimensions in the range of 1 micrometer to 1 mm. The human de-amplifier system uses an inner-feedback loop to increases the equivalent damping of the operating system to stabilize the system when it contacts with the environment and reduces the impact of the environment variation by utilizing a high feedback gain, determined by a root locus sketch. Because the stability of the human de-amplifier system of the present invention is greatly enhanced over that of the prior art, the de-amplifier system is able to manipulate the physical object has dimensions in the range of 1 micrometer to 1 mm with high stability and accuracy. The system also has a monitoring device to monitor the motion of the physical object under manipulation.
Owner:LOCKHEED MARTIN ENERGY SYST INC
Building and Using Intelligent Software Agents For Optimizing Oil And Gas Wells
A system and method for monitoring processes in the production of oil and gas uses intelligent software agents employing associative memory techniques that receive data from sensors in the production environment and from other sources and perform pattern matching operations to identify normal and abnormal behavior of the well production. The agents report the behaviors to human operators or other software systems. The abnormal behavior may consist of any behavior of the production processes that is other than the desired behavior of the well. The intelligent software agents are trained to identify both specific behaviors and behaviors that have never before been observed and recognized in the well.
Owner:LAFFERTY CHAD +3
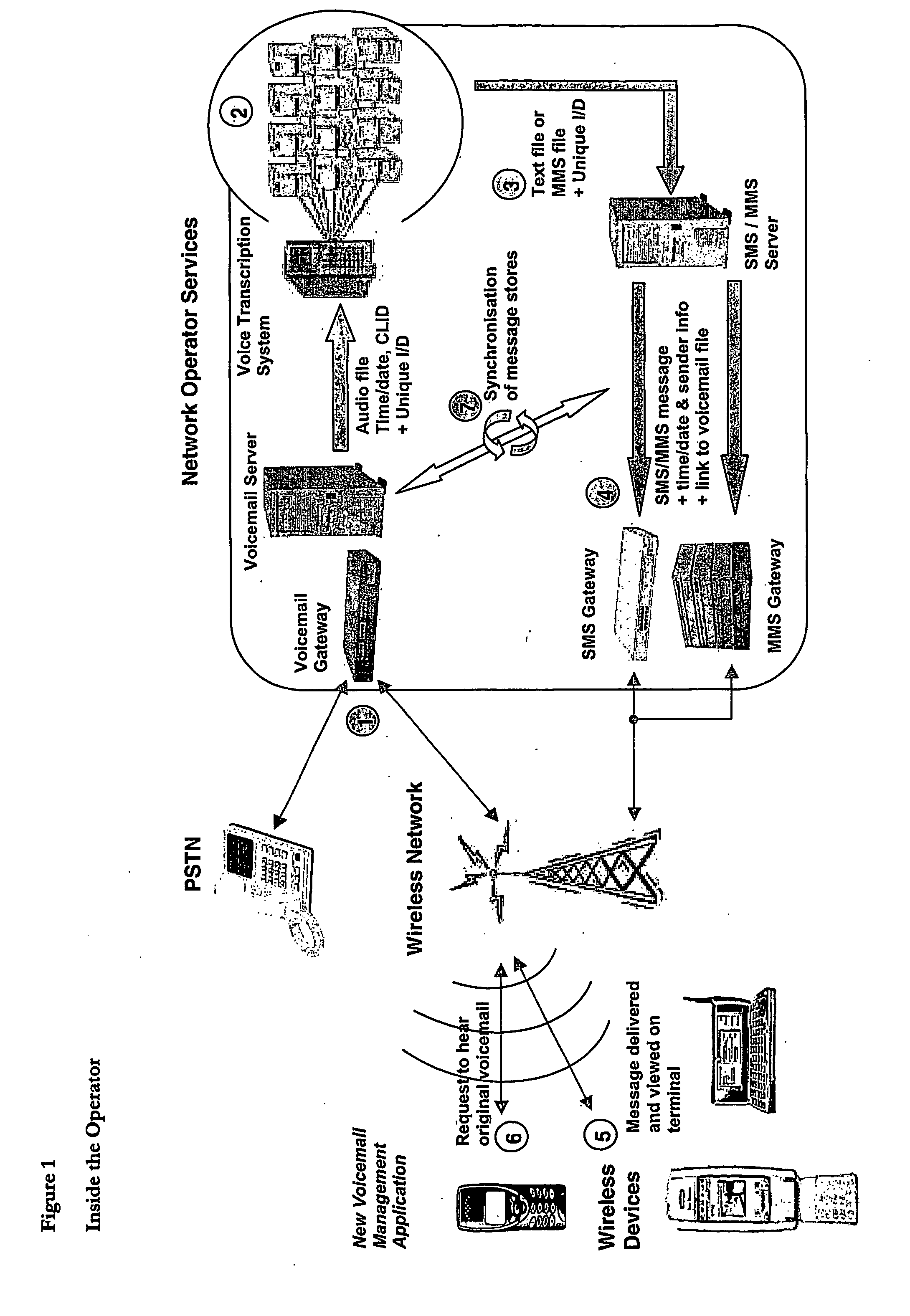
Method of generating a sms or mms text message for receipt by a wireless information device
InactiveUS20070054678A1Save expensive costsEncourages some commitmentRadio/inductive link selection arrangementsAutomatic exchangesInformation deviceHuman operator
A spoken message that a user wishes to have converted to a SMS or MMS message is received at a voicemail server and converted to an audio file format; it is then sent or streamed over a wide area network to a voice to text transcription system comprising a network of computers. One of the networked computers plays back the voice message to an operator and the operator intelligently transcribes the actual message from the original voice message by entering the corresponding text message (actually a succinct version of the original voice message, not a verbose word-for-word conversion) into the computer to generate a transcribed text message. The transcribed text message is then sent to the wireless information device from the computer as a SMS or MMS text message. Because human operators are used instead of machine transcription, voicemails are converted accurately, intelligently, appropriately and succinctly into text messages (SMS / MMS).
Owner:SPINVOX LTD
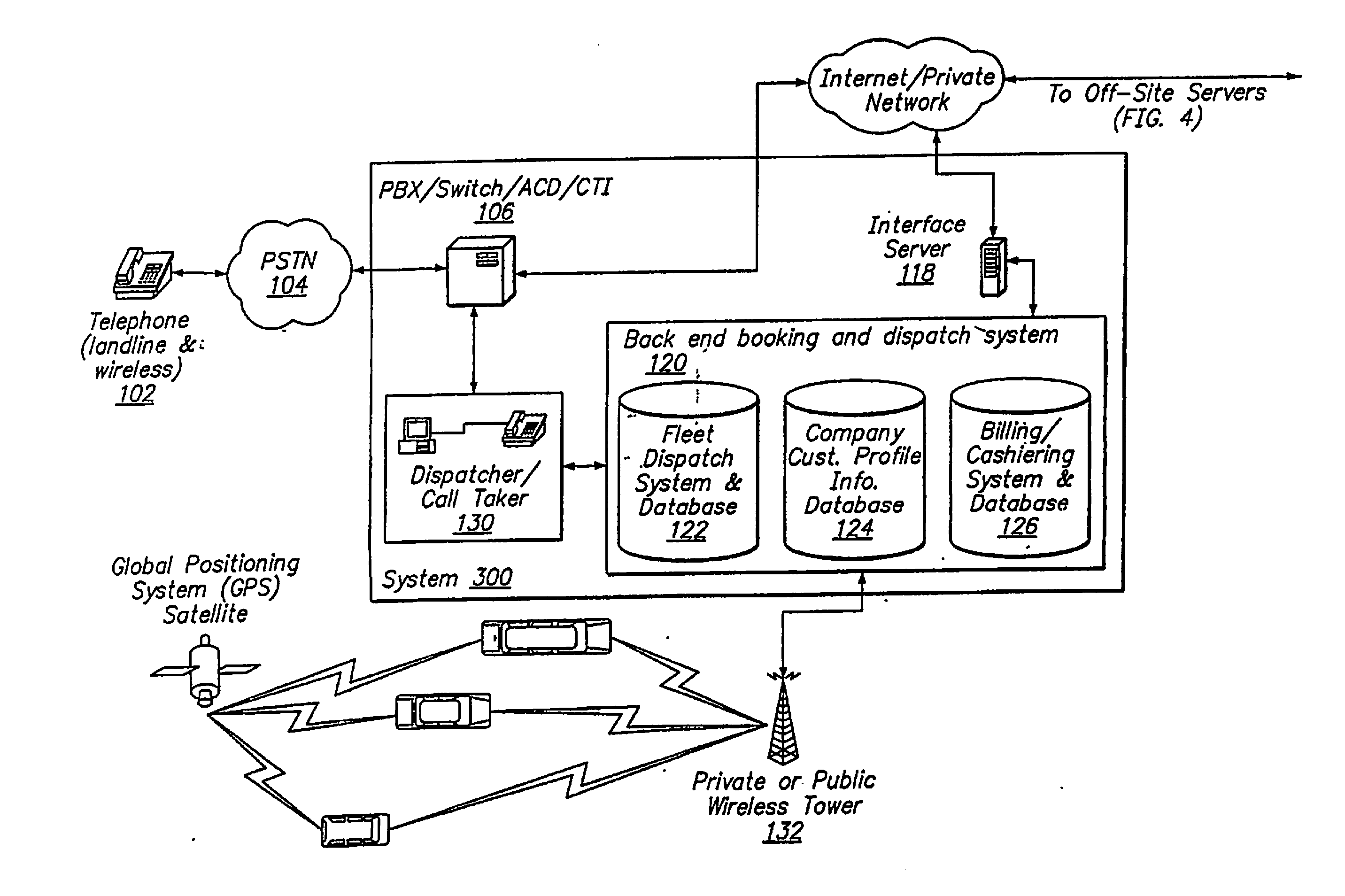
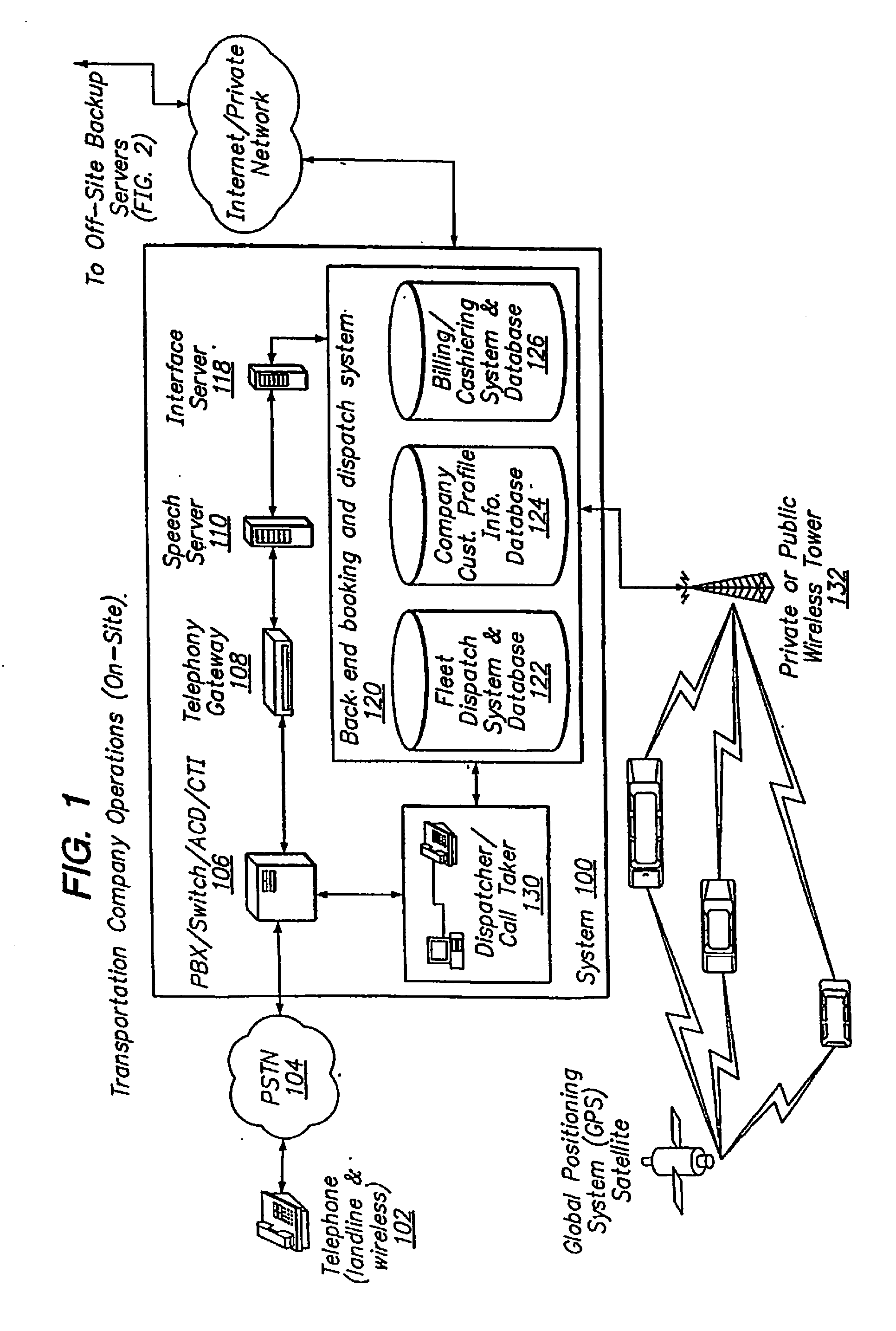
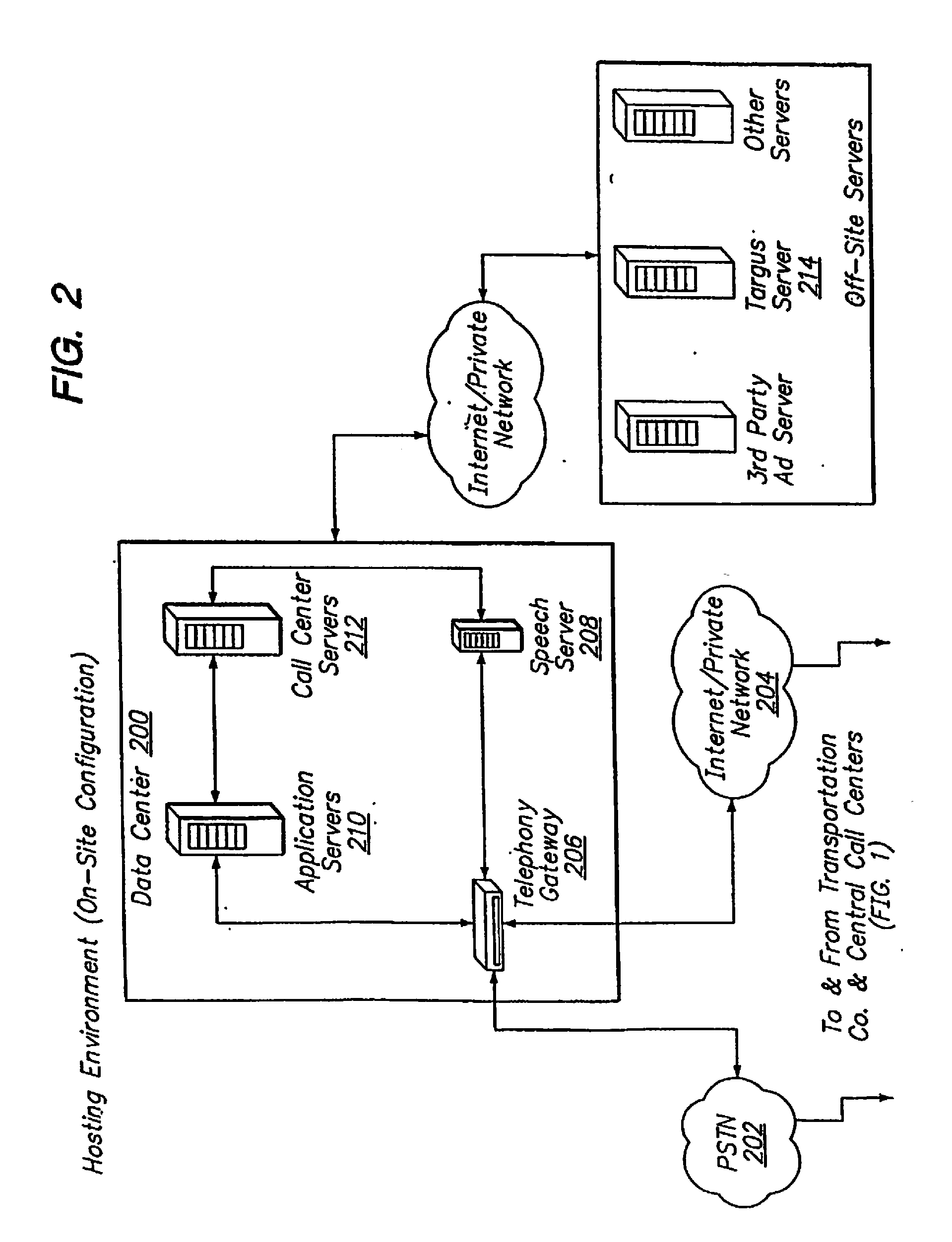
Automated Transportation Call-Taking System
An automated, scalable call-taking system integrates with existing telephony infrastructures and enables, through use of speech recognition, DTMF detection, text-to-speech (TTS), and other related software or hardware, the inputting, access, and retrieval of information to and from multiple back-end dispatch and booking systems without the need for a human operator.
Owner:UNIFIED DISPATCH
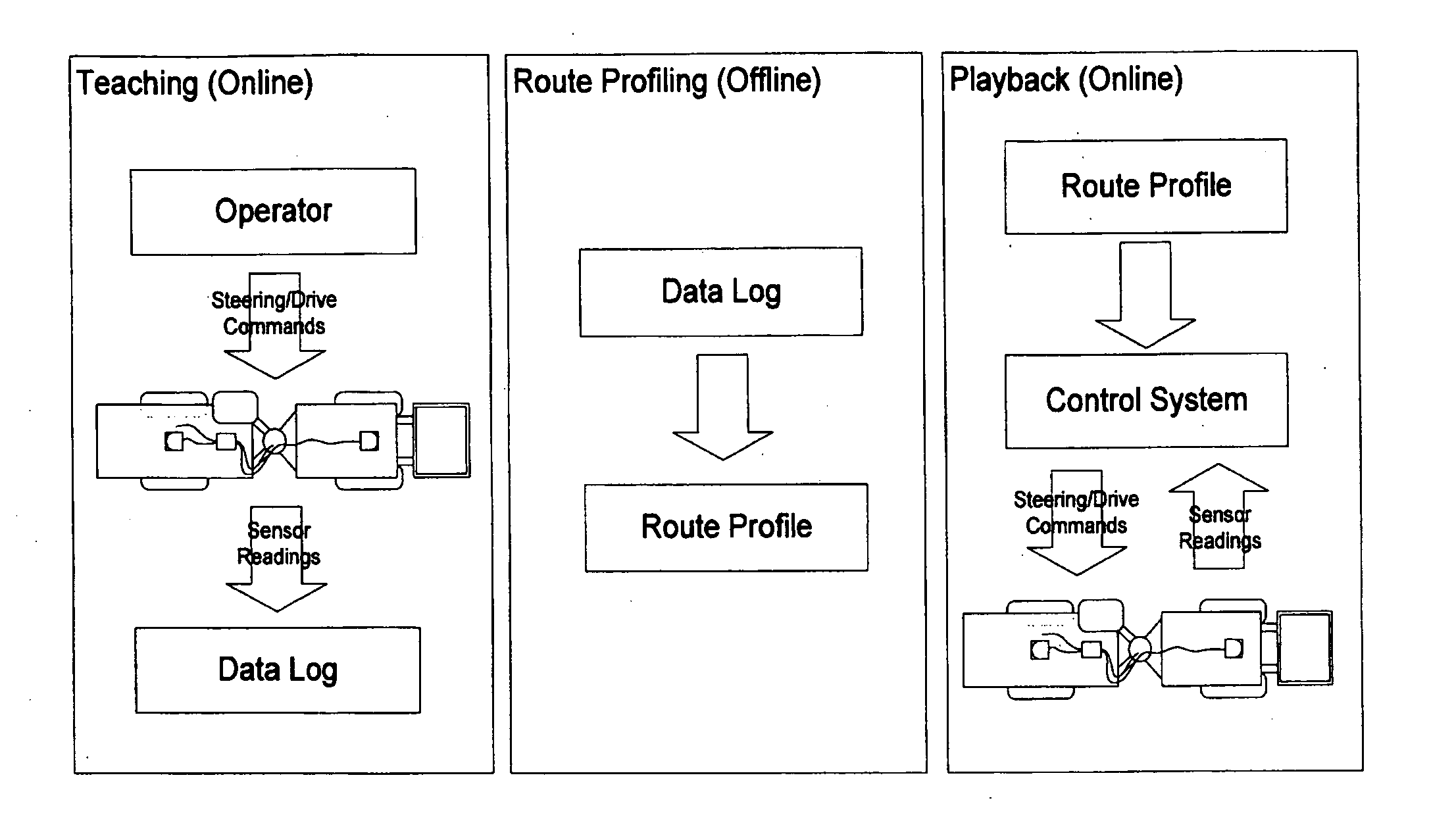
Guidance, Navigation, and Control System for a Vehicle
The present invention provides a guidance, navigation, and control method and system for an underground mining vehicle that allow said vehicle to be taught a route by a human operator and then have it automatically drive the route with no human intervention. The method works in three steps: teaching, route profiling, and playback. In the teaching step the vehicle is manually driven by a operator (or using tele-operation whereby the operator views a screen displaying live views from vehicle-mounted cameras and using remote controls) along a route which can consist of an arbitrary sequence of maneuvers including tramming forwards, switching directions, tramming backwards, turning, or pausing movement. During this phase raw data from vehicle-mounted sensors including odometric sensors and rangefinders are logged to a file throughout teaching for later processing. During the (offline) route profiling step, the raw data in the log file are processed into a route profile including a vehicle path, a sequence of local metric submaps located along the path, and a profile of desired speed as a function of distance along the path. During the playback step, the vehicle automatically repeats the route that was taught during the teaching phase, as represented by the route profile. This is accomplished by first determining where the vehicle is on the route using a localization method which uses the odometric and laser rangefinder sensors and the local metric maps to determine the vehicle location. A steering control method adjusts the vehicle's steering to ensure it tracks the intended path. A drive control method adjusts the vehicle's speed accordingly and safety method ensures the vehicle stops in the event that an obstruction is on the vehicle's intended path.
Owner:MACDONALD DETTWILER & ASSOC INC
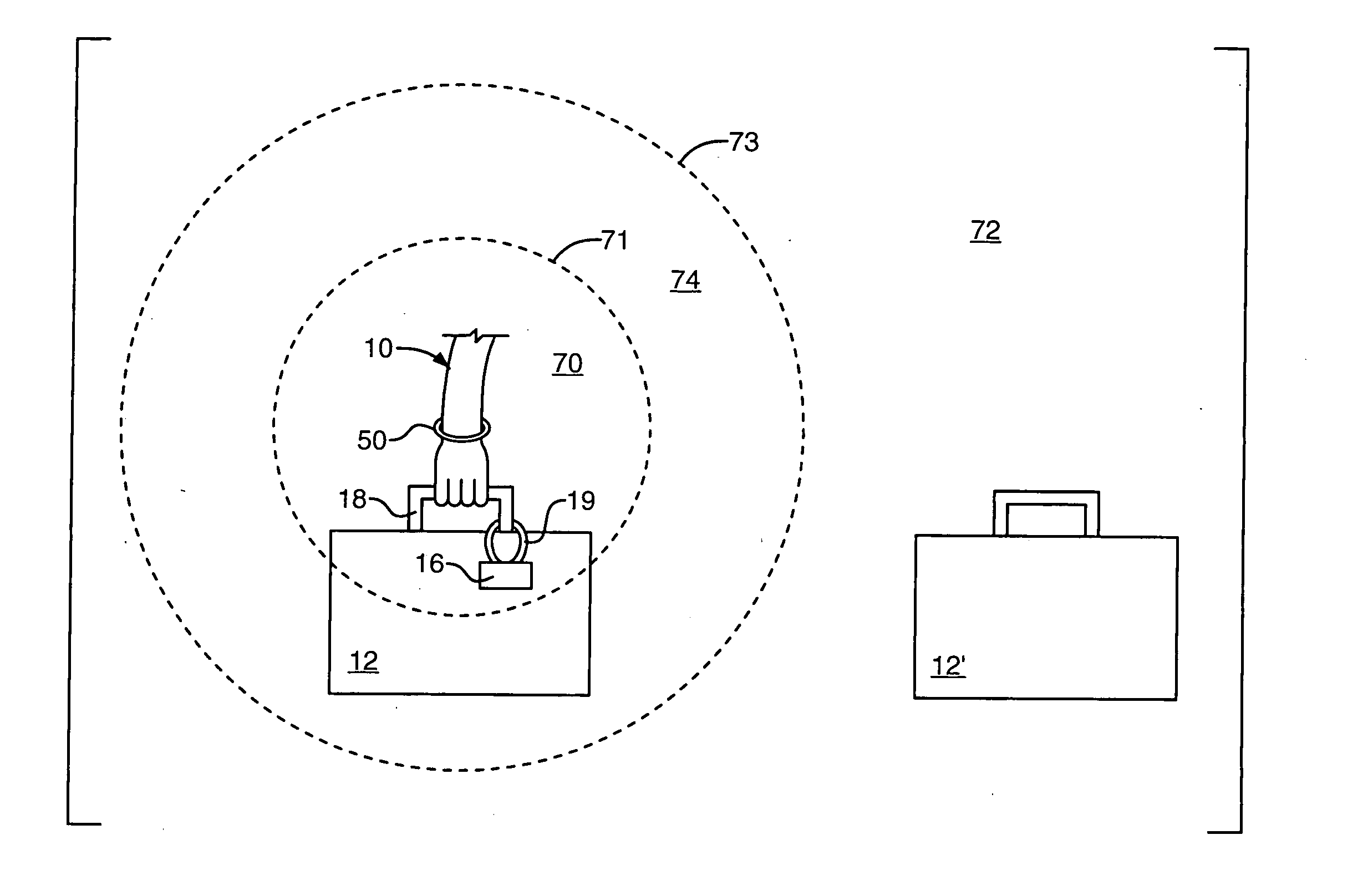
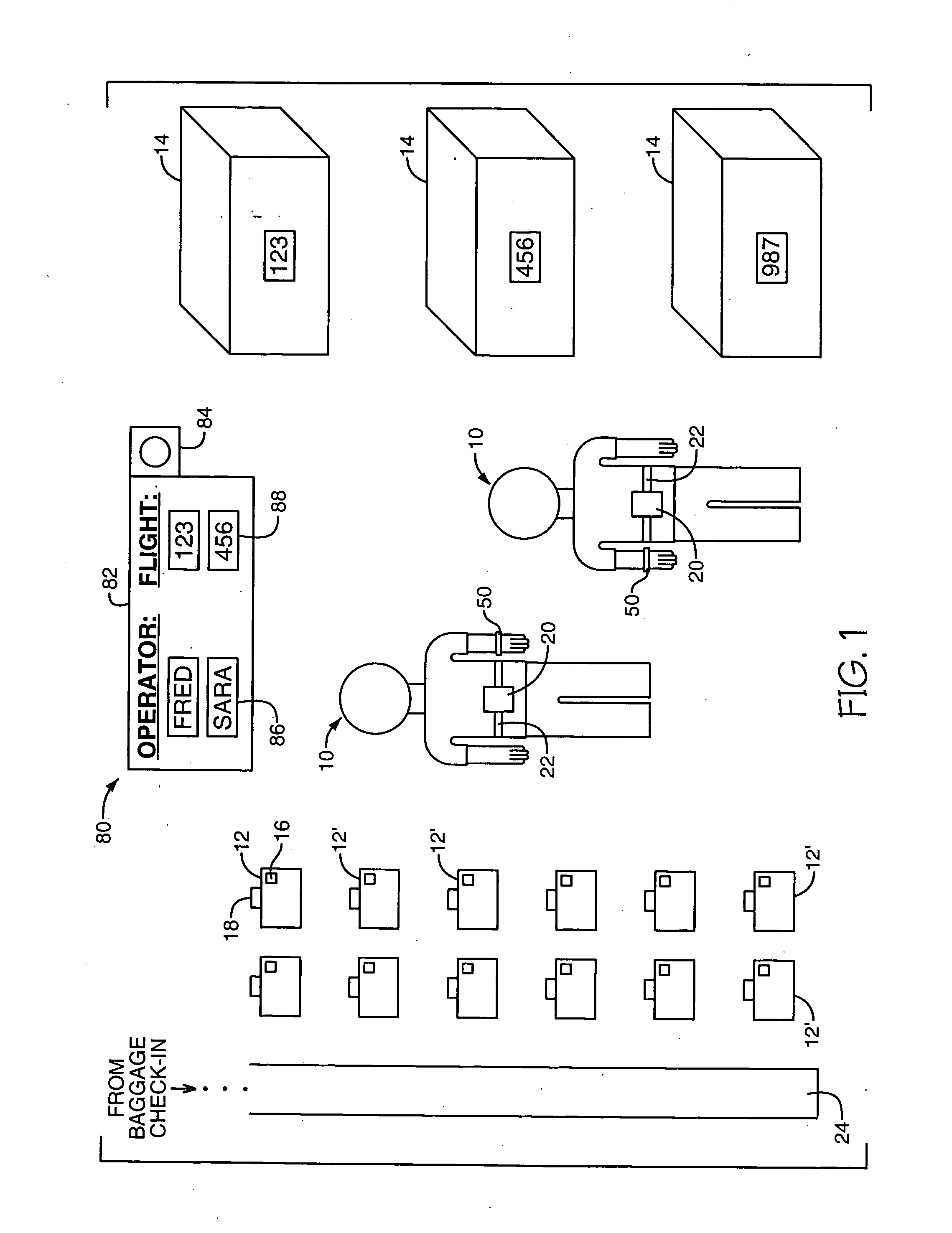
RF identification system with restricted range
InactiveUS20050040961A1Reduced communication rangeMinimize the possibilityAntenna supports/mountingsRadiating elements structural formsTransceiverHuman operator
A method of adjusting the 2-way communication range of an RFID system to assist a human operator to individually handle and interrogate a plurality of tagged objects, such as suitcases, that each include an RFID tag transceiver. An RFID interrogator transceiver is mounted on the human operator. The 2-way communication range between the interrogator transceiver and the tag transceivers is adjusted to only slightly exceed the closest distance between the interrogator and the tag while the operator is handling the tagged object. Preferably, the 2-way communication range is short enough that other tagged objects will remain outside the communication range and will not respond to messages from the interrogator. Another aspect of the invention is a method of verifying whether an object to be transported has reached its intended destination. In this aspect, an interrogator transceiver at a first destination interrogates an RFID tag transceiver on the object, and in response the tag transmits its intended destination.
Owner:ROUND ROCK RES LLC
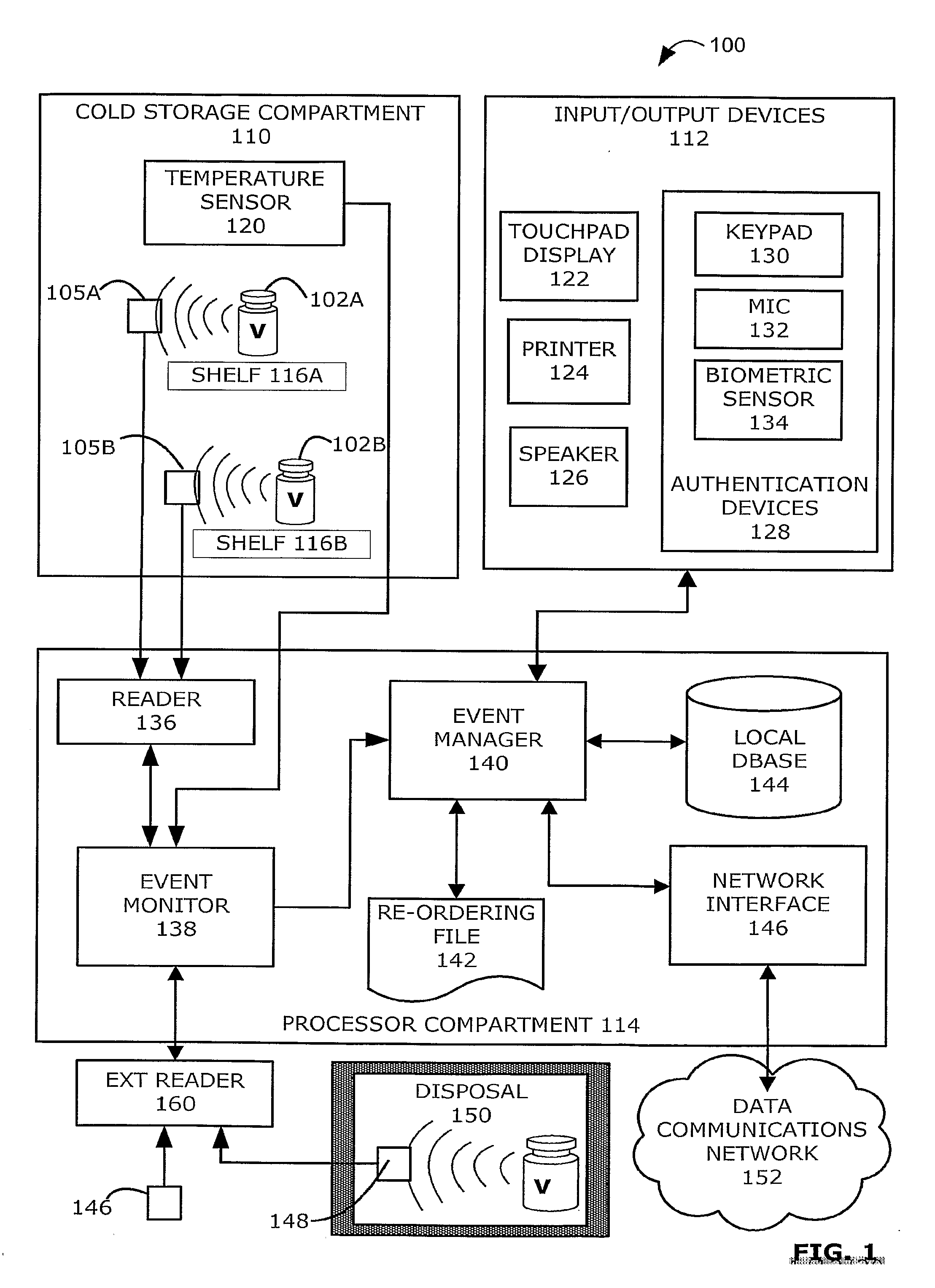
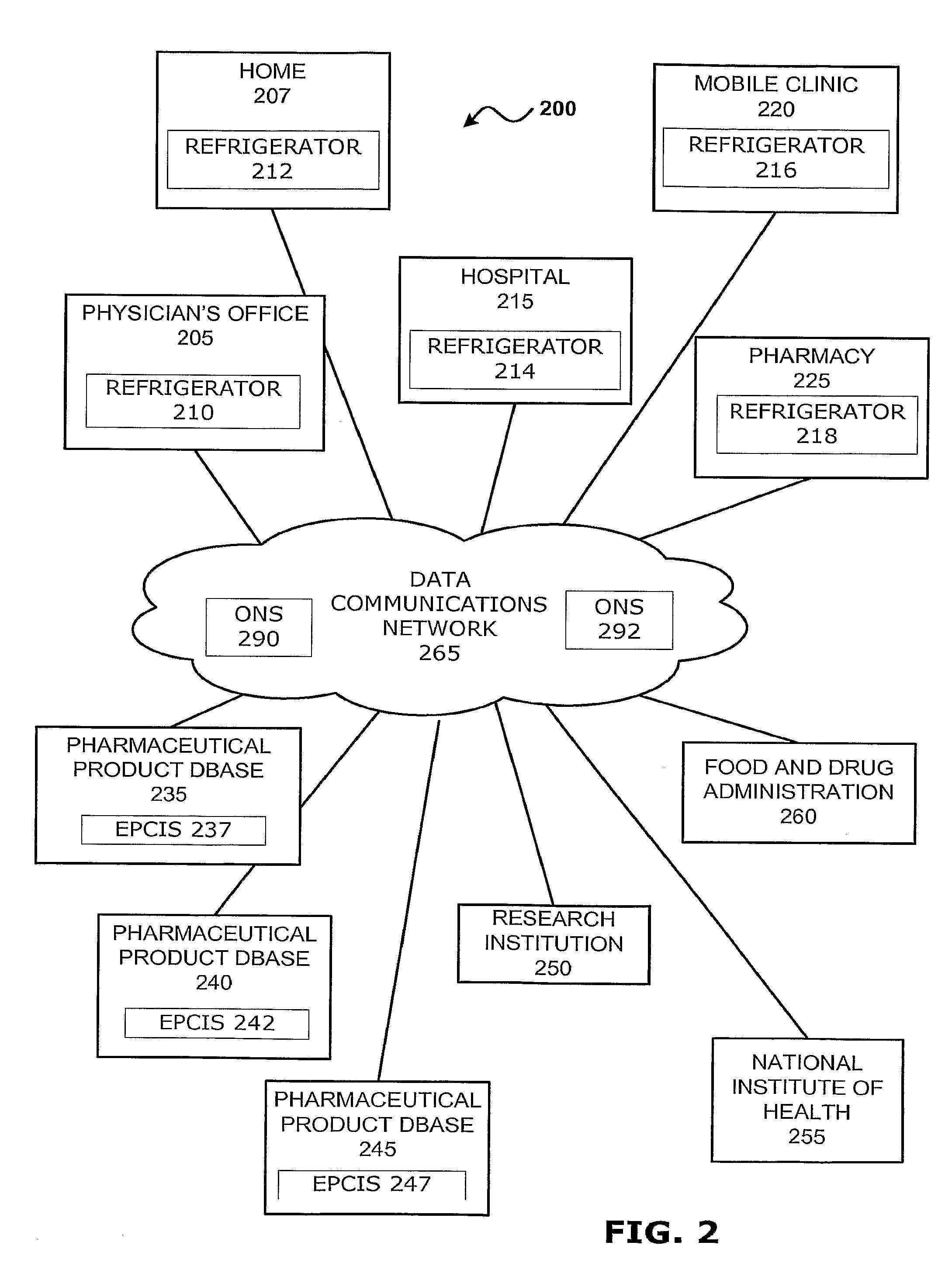
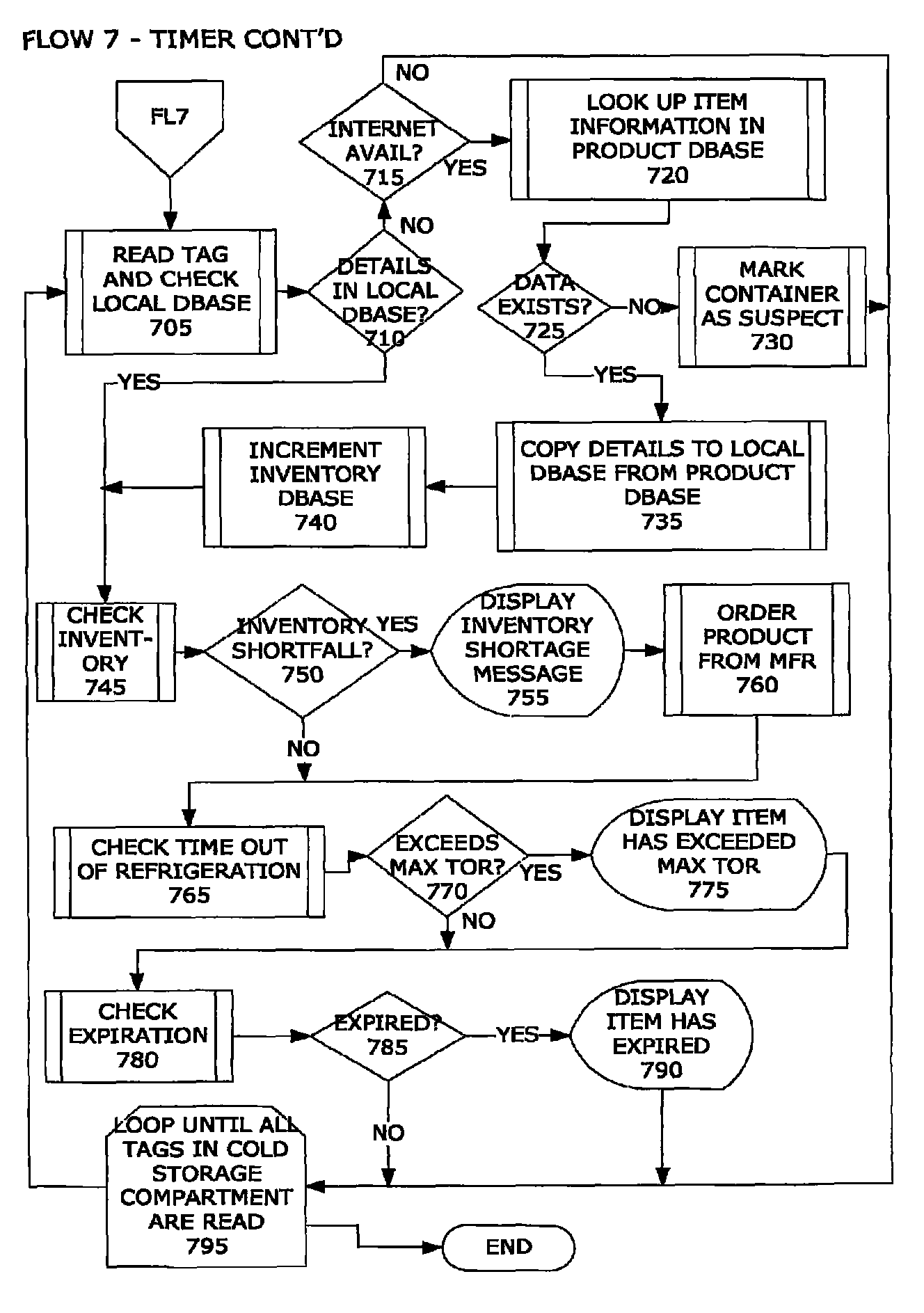
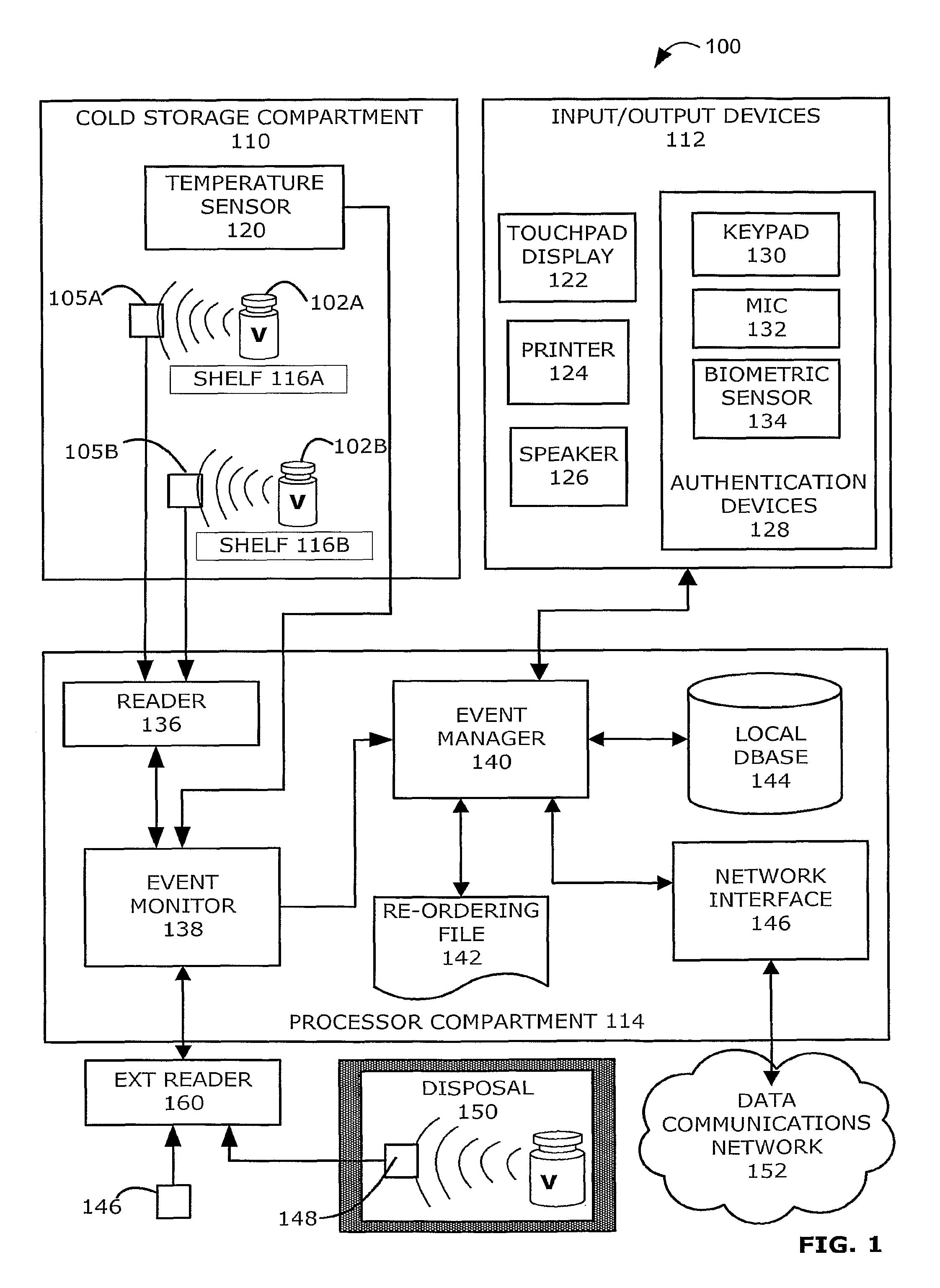
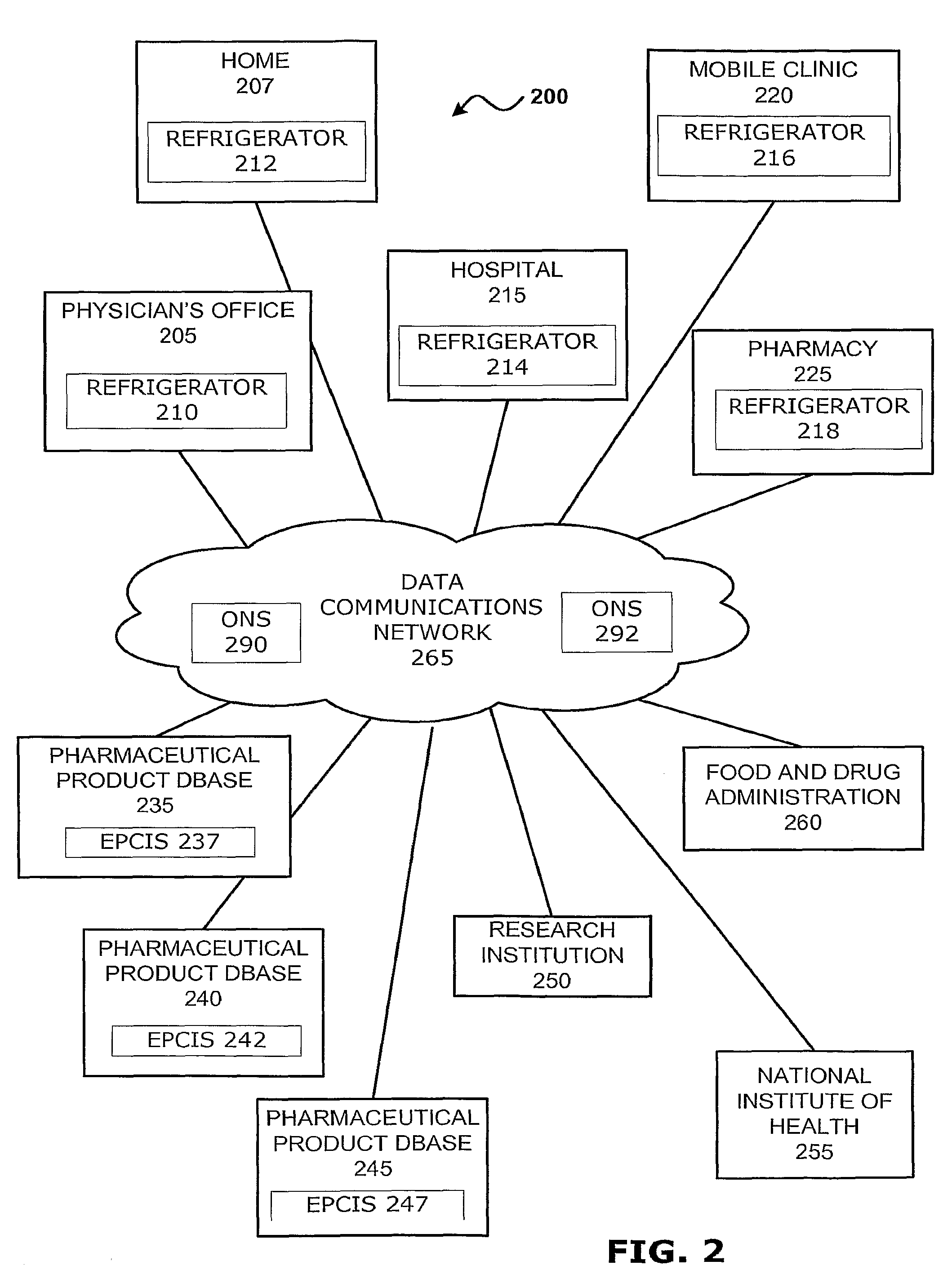
Intelligent Refrigerator for Storing Pharmaceutical Product Containers
Intelligent refrigerator system for storing pharmaceutical product containers, such as vials, ampules, syringes, bottles, medication tubes, blister packs and cartons, at the point of dispensing. Embodiments of the invention use product identification technology, such as radio-frequency identification (RFID) tags and readers, to uniquely identify containers as they are added to or removed from the cold storage compartment of the refrigerator, and automatically retrieve from a local or remote database a variety of details associated with the containers and their contents, such as manufacturing data, expiration dates, time out of refrigeration, inventory levels, safety information, usage statistics, known contraindications and warnings, etc. If the details indicate that there is a problem with a particular pharmaceutical (e.g., that it is counterfeit, expired, suspect, spoiled, recalled or almost depleted), then a message or warning is automatically delivered to a human operator via an attached output device, such as a display screen, speaker or printer. Embodiments of the invention may also be configured to monitor and report temperature faults, power failures and other anomalies associated with the refrigerator or cold storage compartment.
Owner:MERCK SHARP & DOHME LLC
Method of compression for wide angle digital video
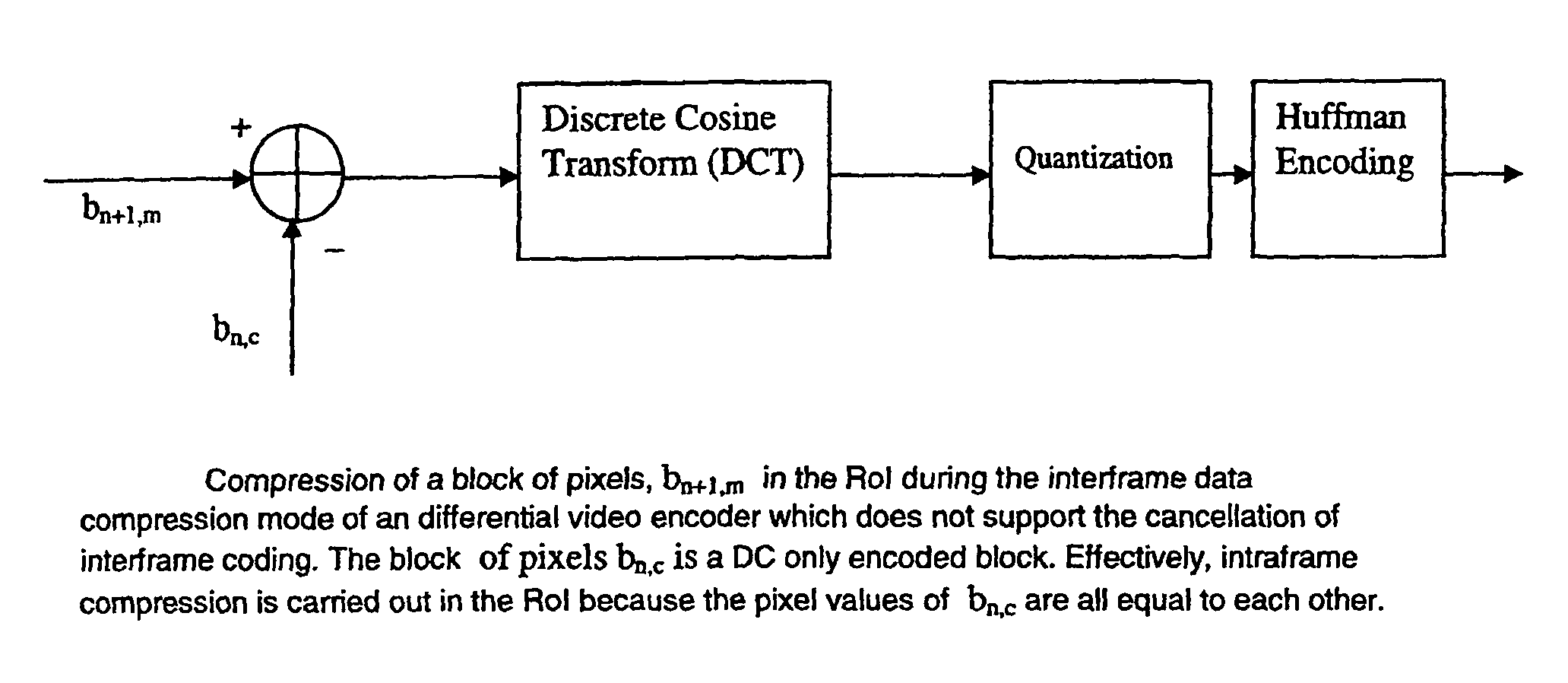
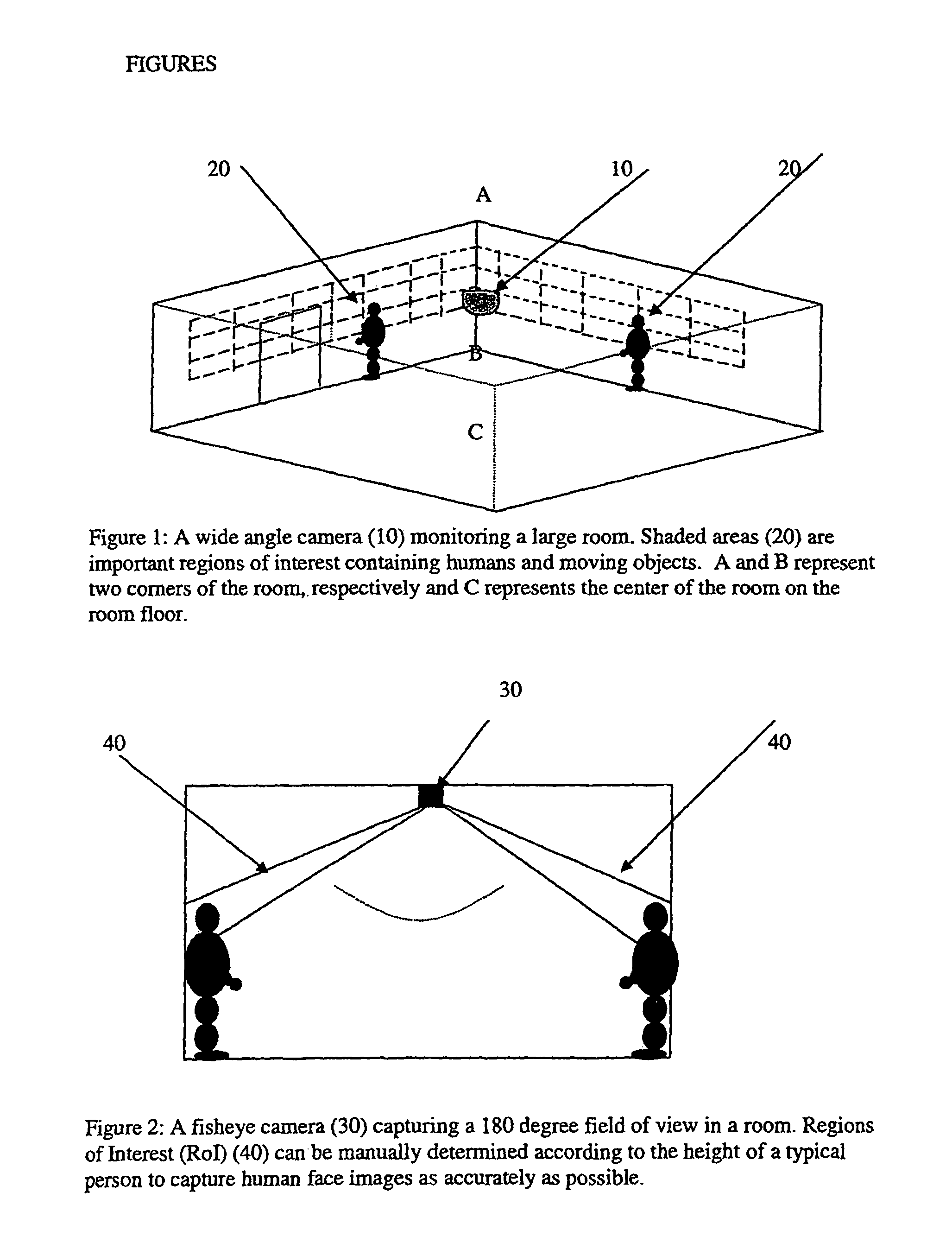
InactiveUS7894531B1Small sizeEncoding can be losslessColor television with pulse code modulationColor television with bandwidth reductionDigital videoLevel of detail
A system and method for varying the level of detail encoded in a video. In a preferred embodiment, some regions of a wide-angle video scene are encoded in an almost lossless manner, while other regions are encoded with less detail. Regions of interest can be determined in many ways, including a priori, automatically in real time, or by the selection of human operators.
Owner:GRANDEYE
Automatic provisioning of network address translation data
InactiveUS20050053063A1Multiple digital computer combinationsNetworks interconnectionPrivate IPNetwork address translation
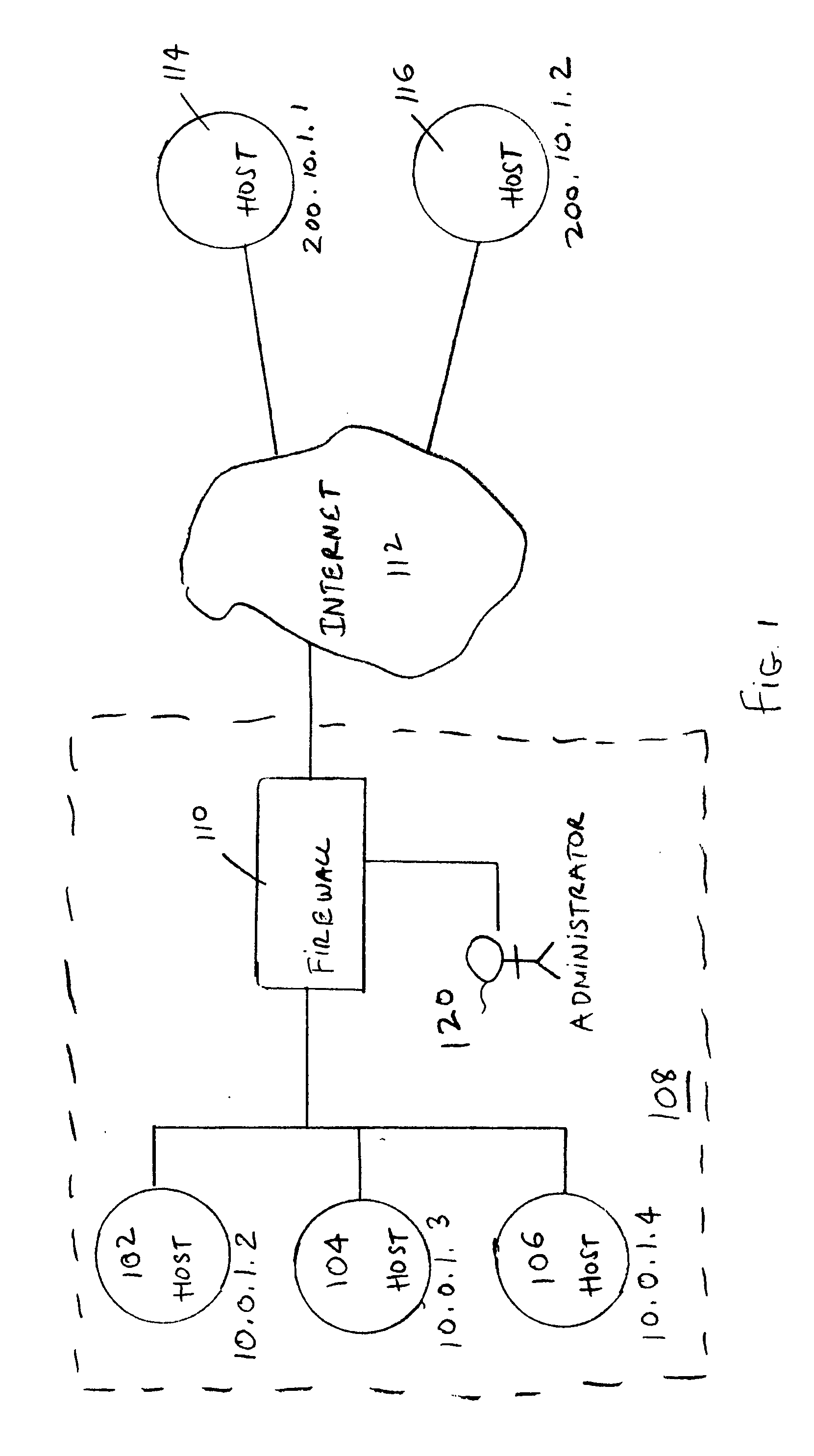
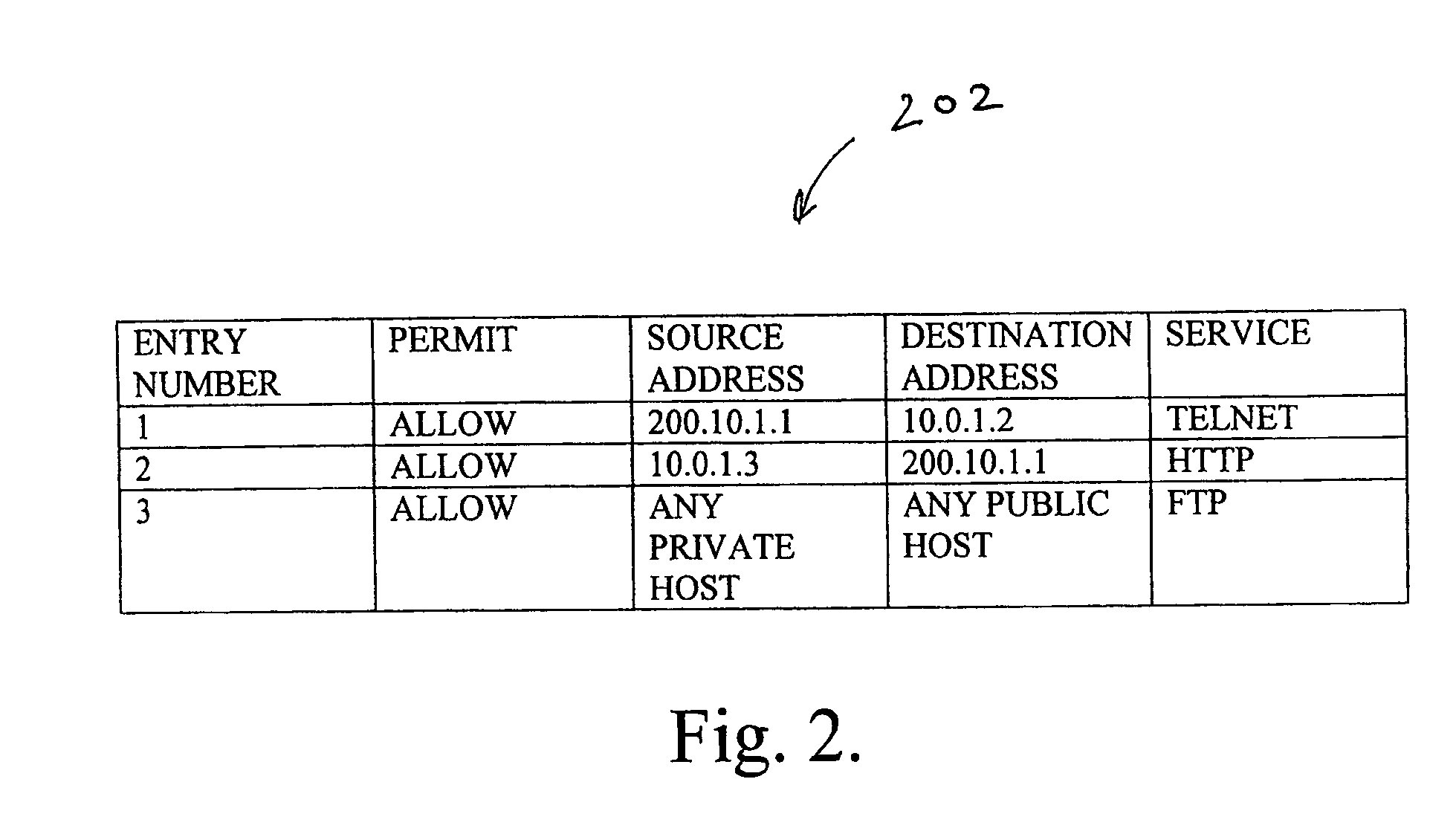
A method for automatically generating network address translation (NAT) data to enable a private host having a private IP address to communicate with a public host having a first public IP address. The method includes providing automated NAT provision software which, responsive to a message initiated by one of the private host and the public host, consults a security policy associated with the private host to determine whether the communication between the private host and the public host is permissible. The method further includes provisioning automatically using the software and without a human operator intervention after the consulting, if the consulting indicates that the communication between the private host and the public host is permissible, in a database a second public IP address for address translation between the private IP address and the second public IP address.
Owner:HEWLETT PACKARD DEV CO LP
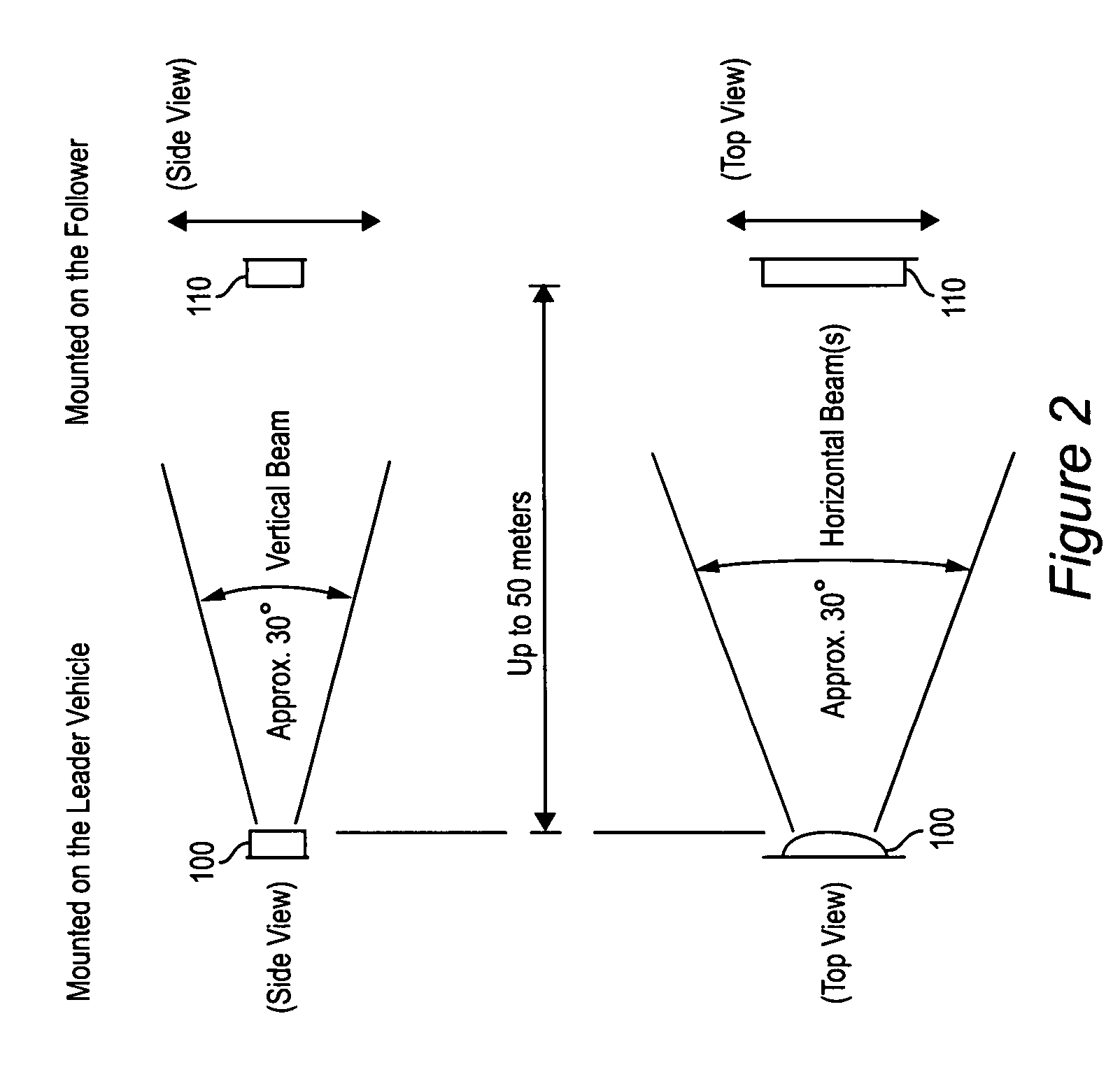
Automatic homing systems and other sensor systems
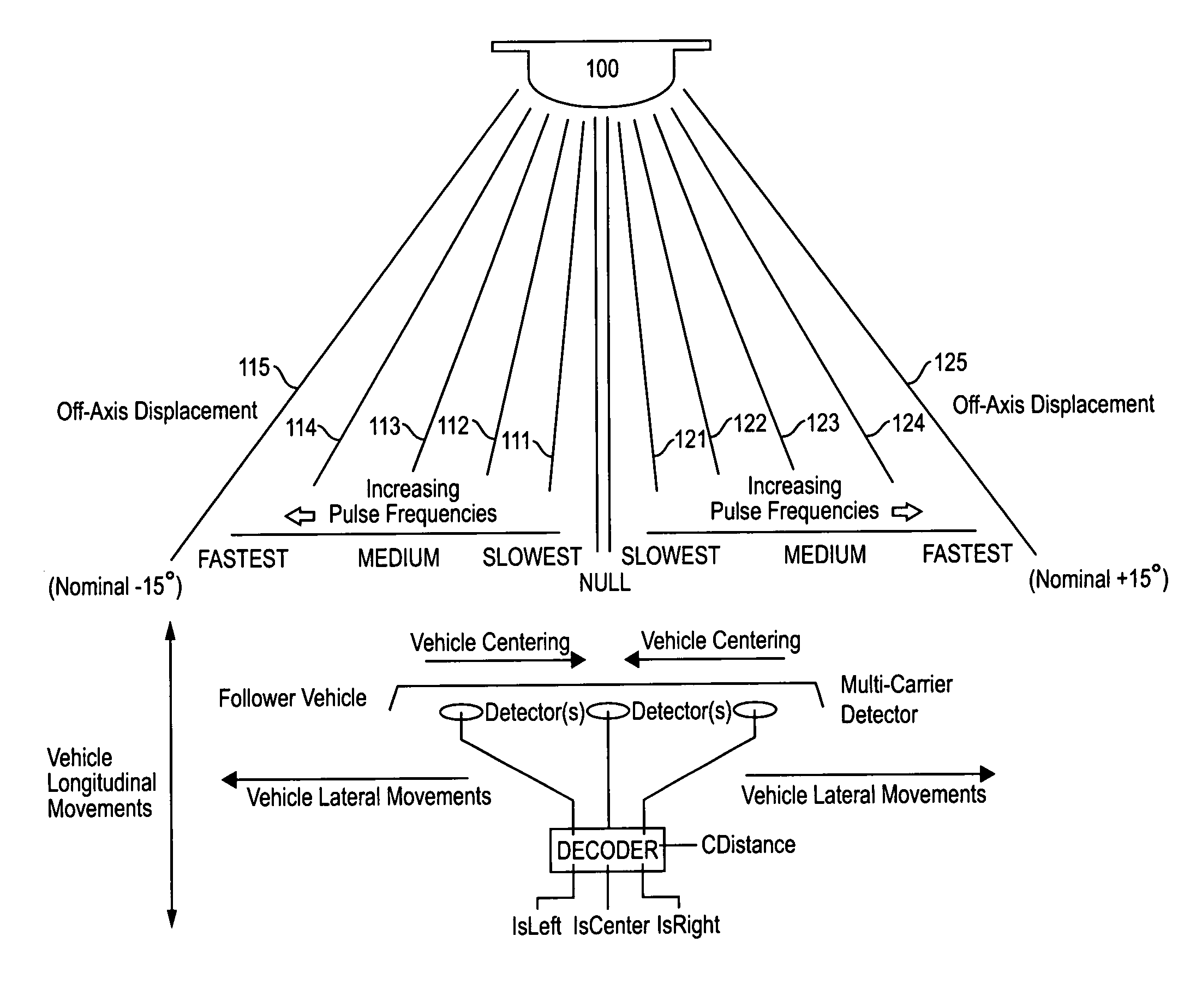
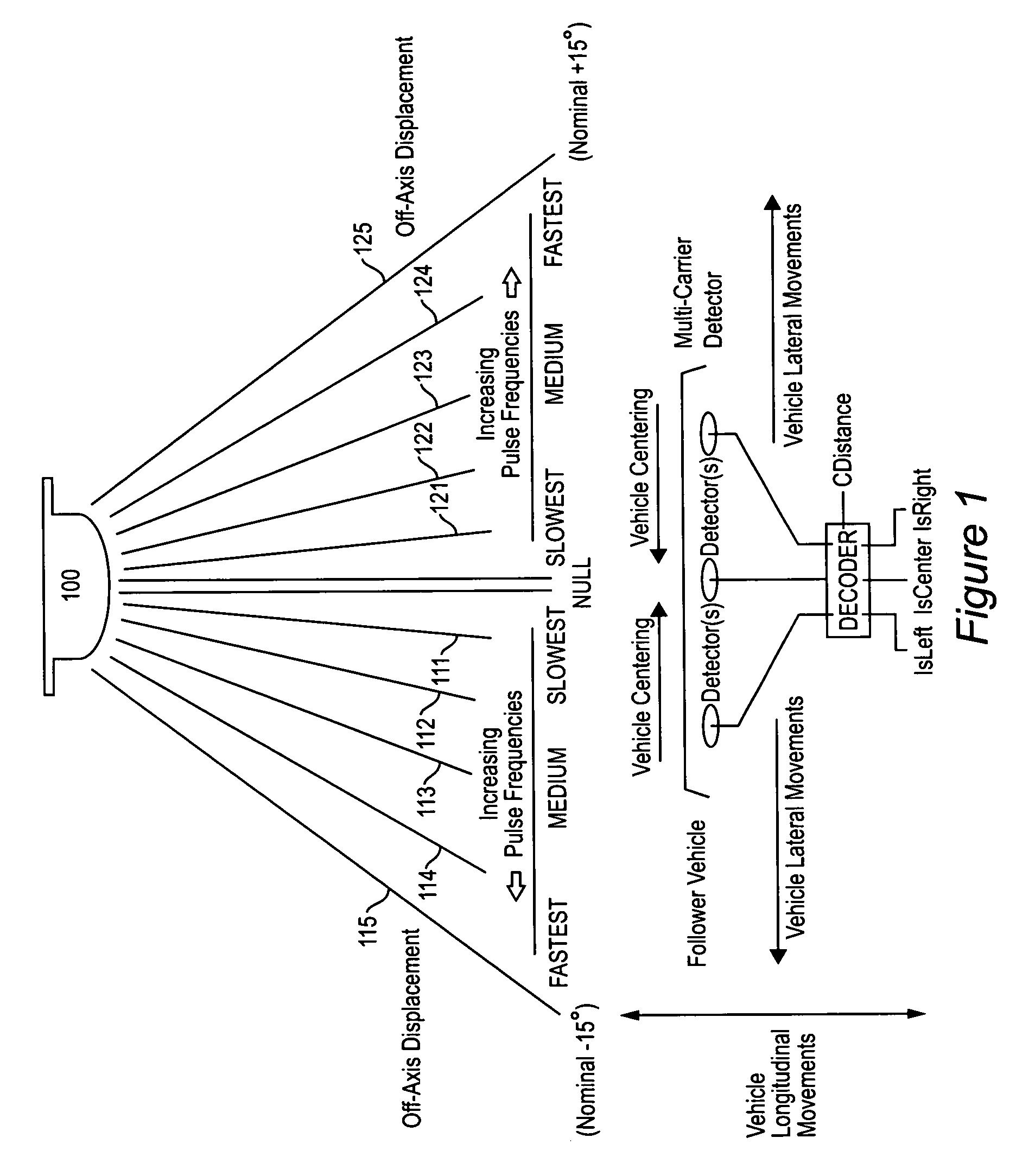
Automatic homing systems are disclosed, operable between pairs of objects. One or both of the objects in the pair may be moving and / or unmanned. Examples of a pair of objects between which the inventive automatic homing systems may be operated are ground vehicles in leader-follower configuration, as well as aircraft, spacecraft, watercraft. The automatic homing systems are based on a relatively simple, elegant concept of rightness / leftness and a line-of-sight link between a respective leader vehicle and follower vehicle. Complex EO / IR cameras, LIDAR, RADAR, and / or SONAR-based sensor systems can be avoided. Convoys of vehicles in leader-follower configuration advantageously may be operated without needing human operators in the follower vehicles.
Owner:SRS TECH
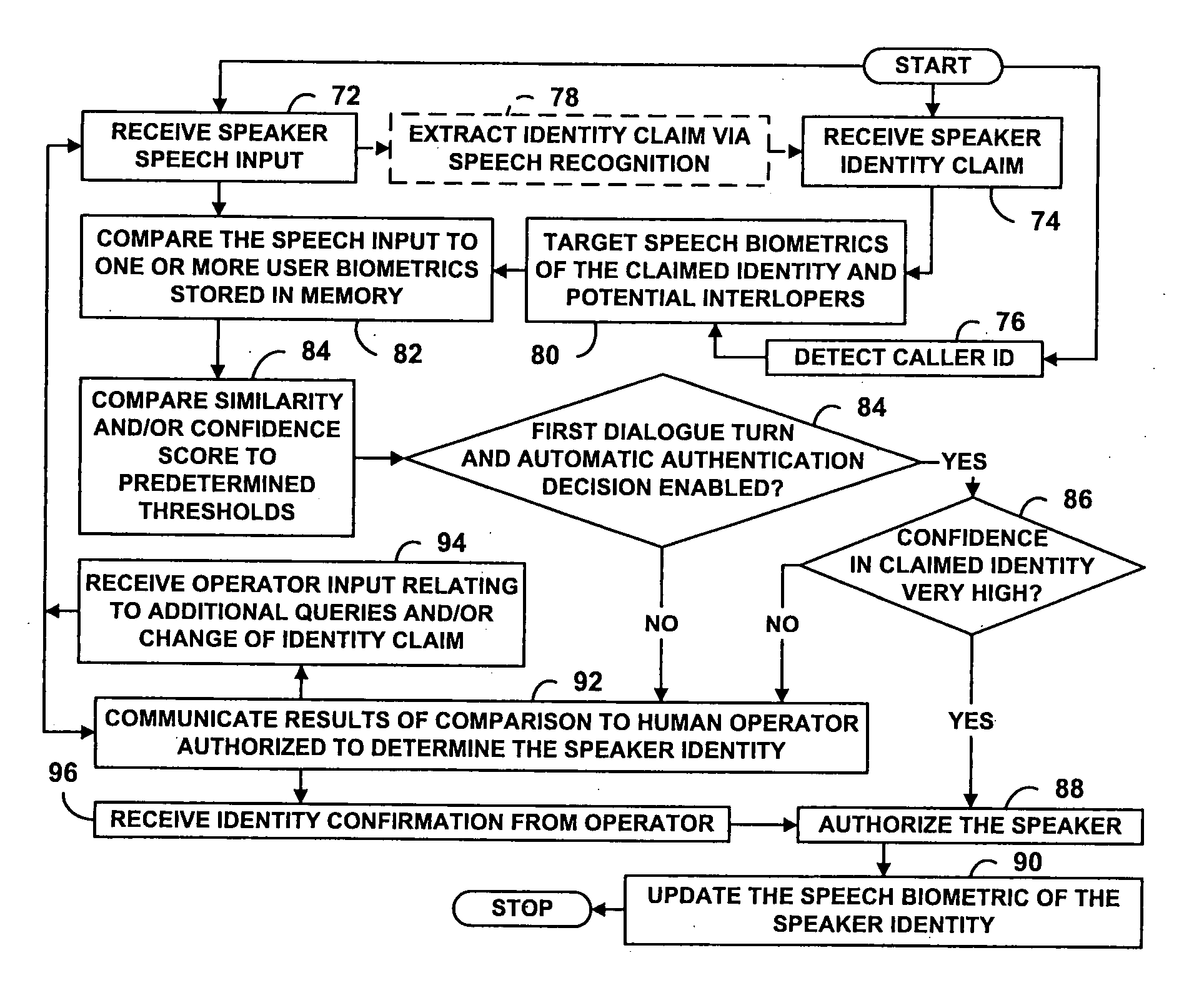
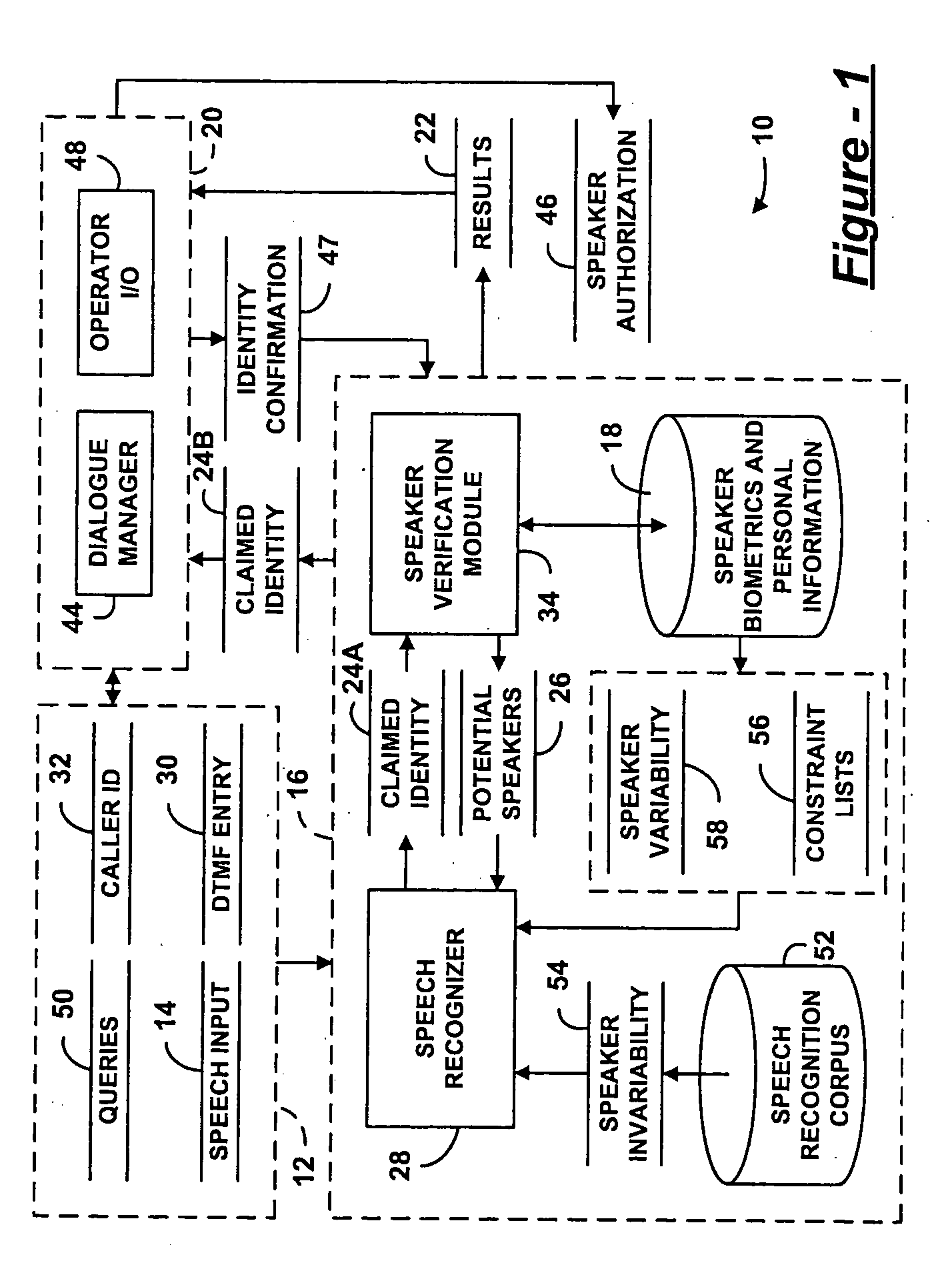
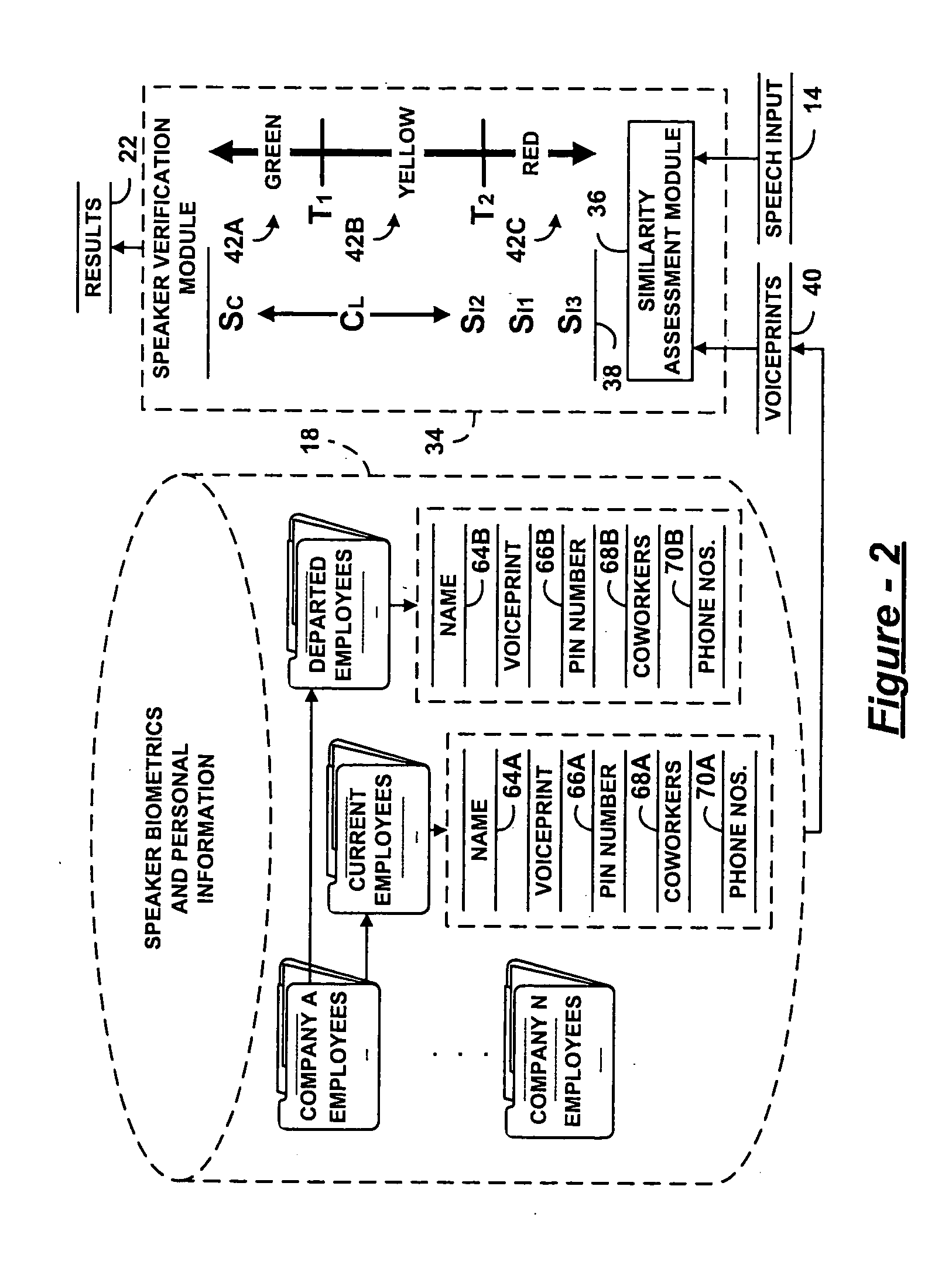
Speaker verification for security systems with mixed mode machine-human authentication
The central concept underlying the invention is to combine the human expertise supplied by an operator with speaker authentication technology installed on a machine. Accordingly, a speaker authentication system includes a speaker interface receiving a speech input from a speaker at a remote location. A speaker authentication module performs a comparison between the speech input and one or more speaker biometrics stored in memory. An operator interface communicates results of the comparison to a human operator authorized to determine identity of the speaker.
Owner:PANASONIC CORP
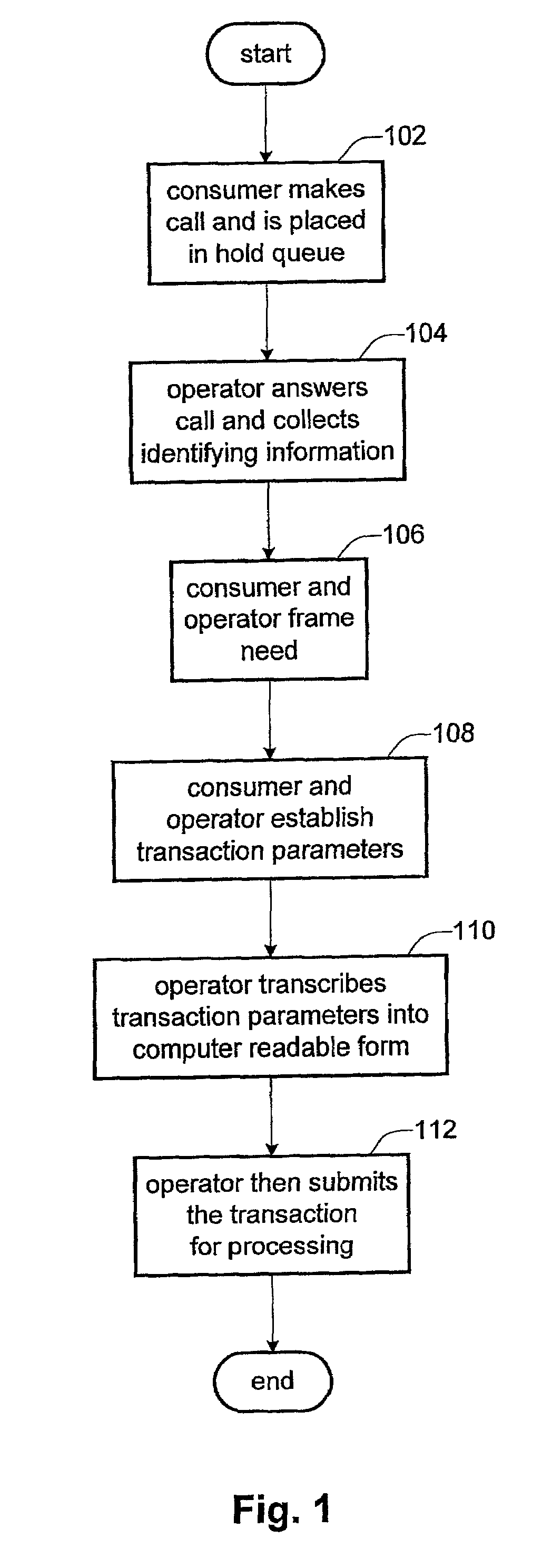
Automated transaction management system and method
InactiveUS6862573B2Reduce errorsReduce labor costsOffice automationResourcesHard codingHuman operator
An automated knowledge dependent transaction management system for processing both the front-end and back-end of a transaction is provided. The system contains hard-coded transaction management module to support the processing of deterministic manual work independent of the specific transactions. According to the invention, the hard-coded module is separated from the business logic that comprise the definition and configuration of the transaction specific data models, business rules and process steps which drive the manual work of human operators. Such separation of code and business logic allows any ordinary business administrator without any computer programming experience to quickly develop the business logic through a simple GUI. Further, any change in the business logic can be implemented quickly using the GUI by the ordinary administrator to accommodate changes in the business environment without relying on computer programmers.
Owner:VERSATA
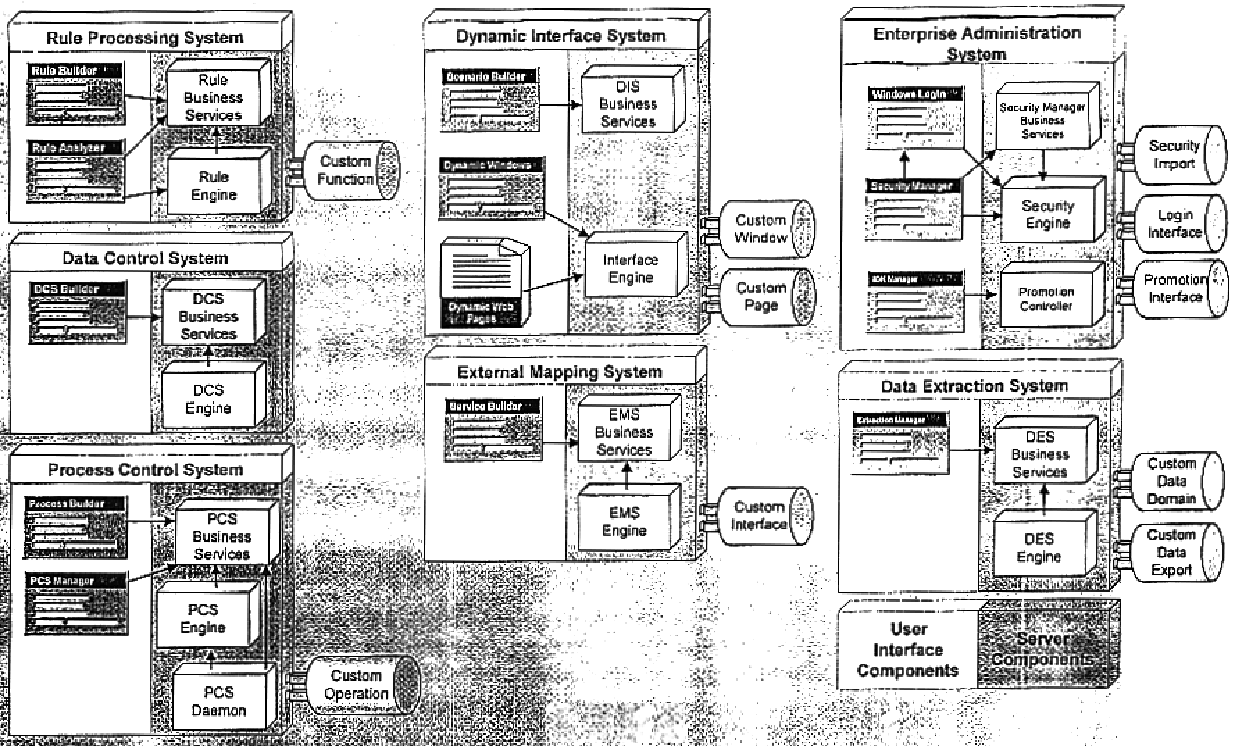
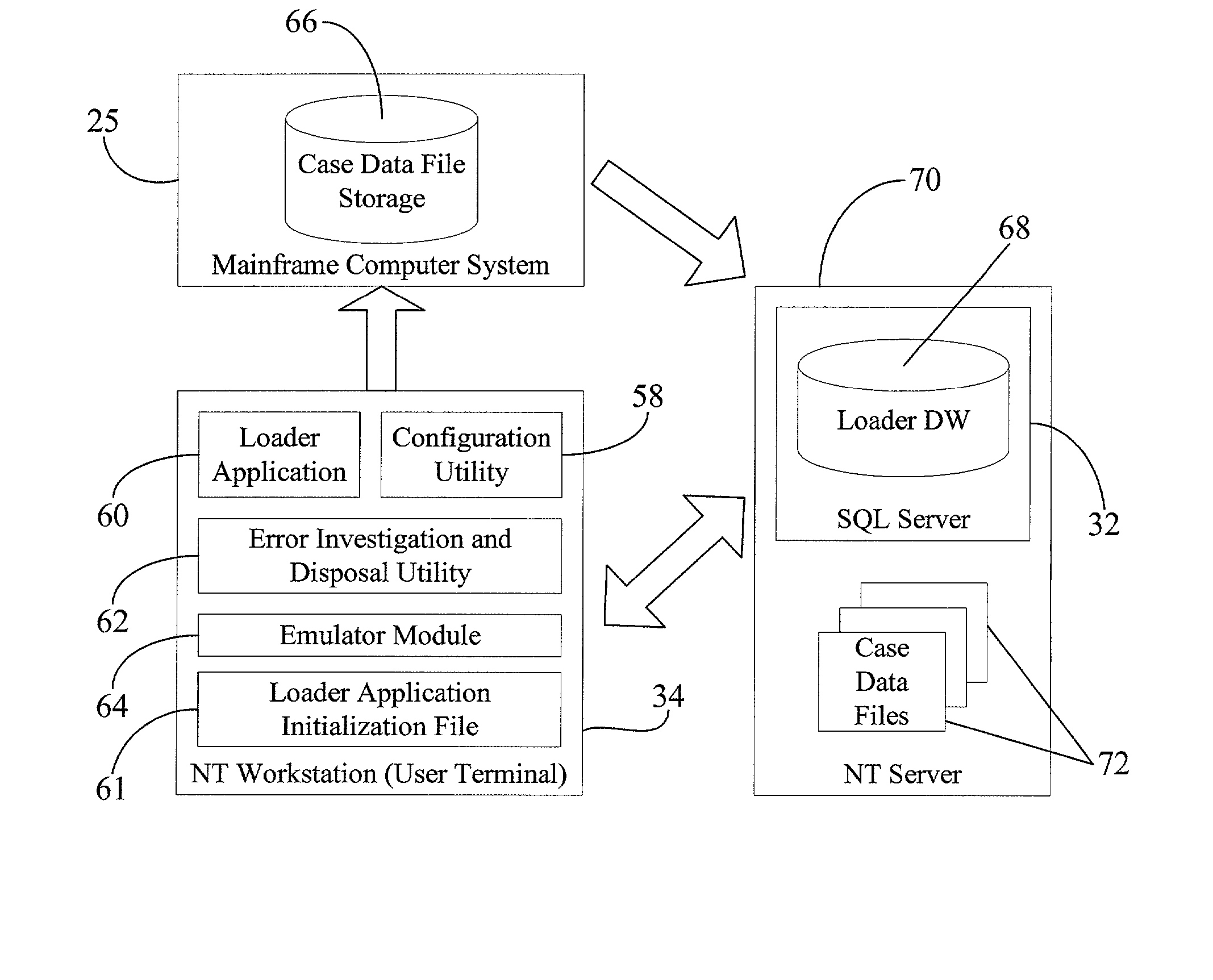
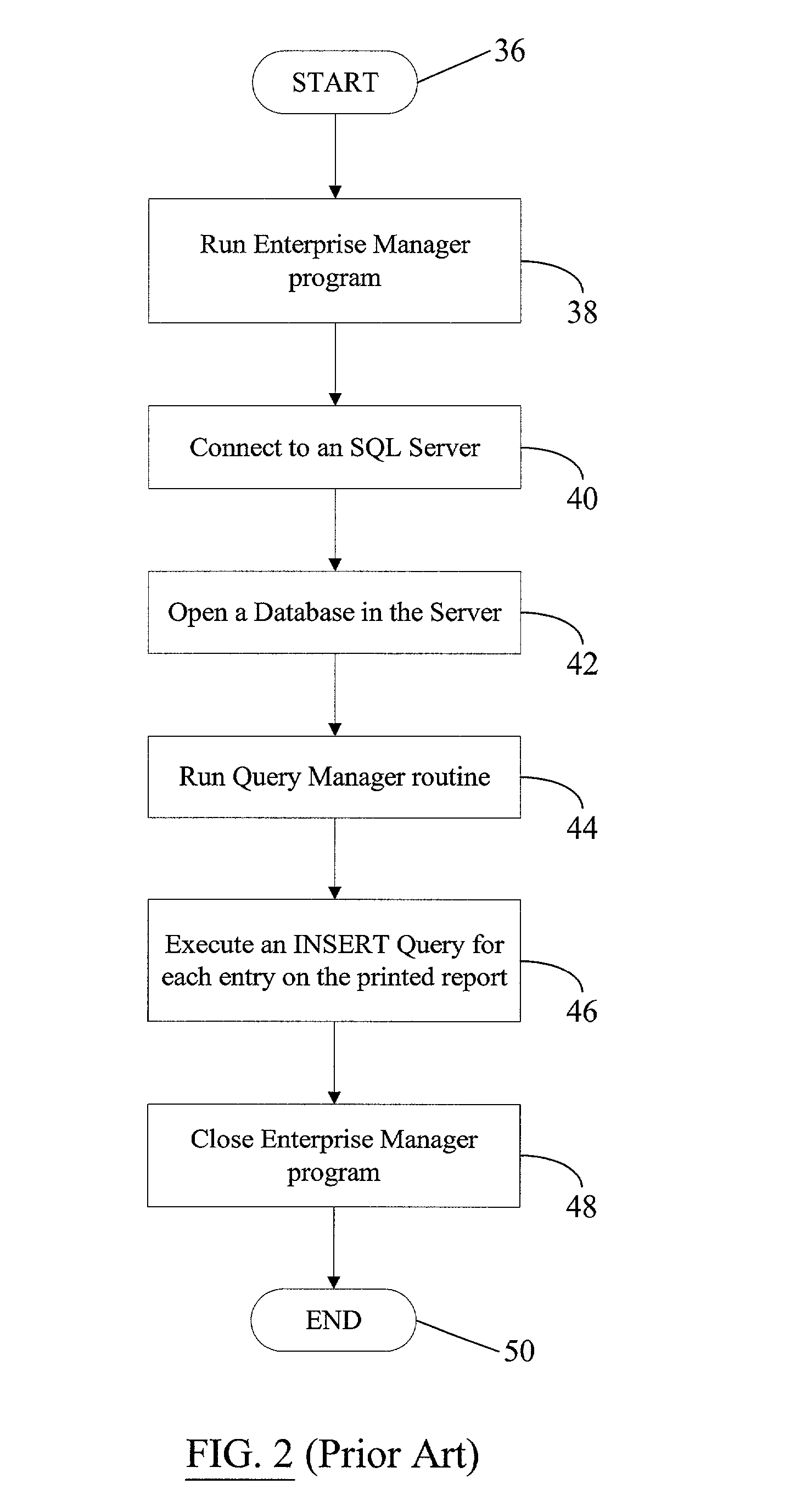
Error usage investigation and disposal system
InactiveUS20020129039A1Reduce errorsFacilitates electronic investigationDatabase management systemsDigital data processing detailsError processingData error
As part of electronically handling a large amount of data (e.g., error messages) generated within, for example, a telephone service provider's billing network, a configuration utility software allows a user to electronically change or update various configuration parameters for another software application, e.g., a loader application, and also to access the performance data generated by the loader application so as to optimize the performance of the loader application in varying data transfer situations. The loader application, in turn, is a computer-based data transfer application that electronically loads a large volume of data, e.g., telecommunication billing data, from one computer into another computer. The loader application thus substantially reduces human involvement during transfers of large amount of data, and thereby also reduces errors typically associated with manual data entries by human data operators. After completion of data transfers, an error handler program facilitates electronic investigation and disposal of errors in the received data, thereby minimizing participation of human operators in the data error rectification process. The reduced reliance on manual identification and correction of data errors thus results in increased accuracy and efficiency in the overall network data management and customer billing operations.
Owner:BELLSOUTH INTPROP COR
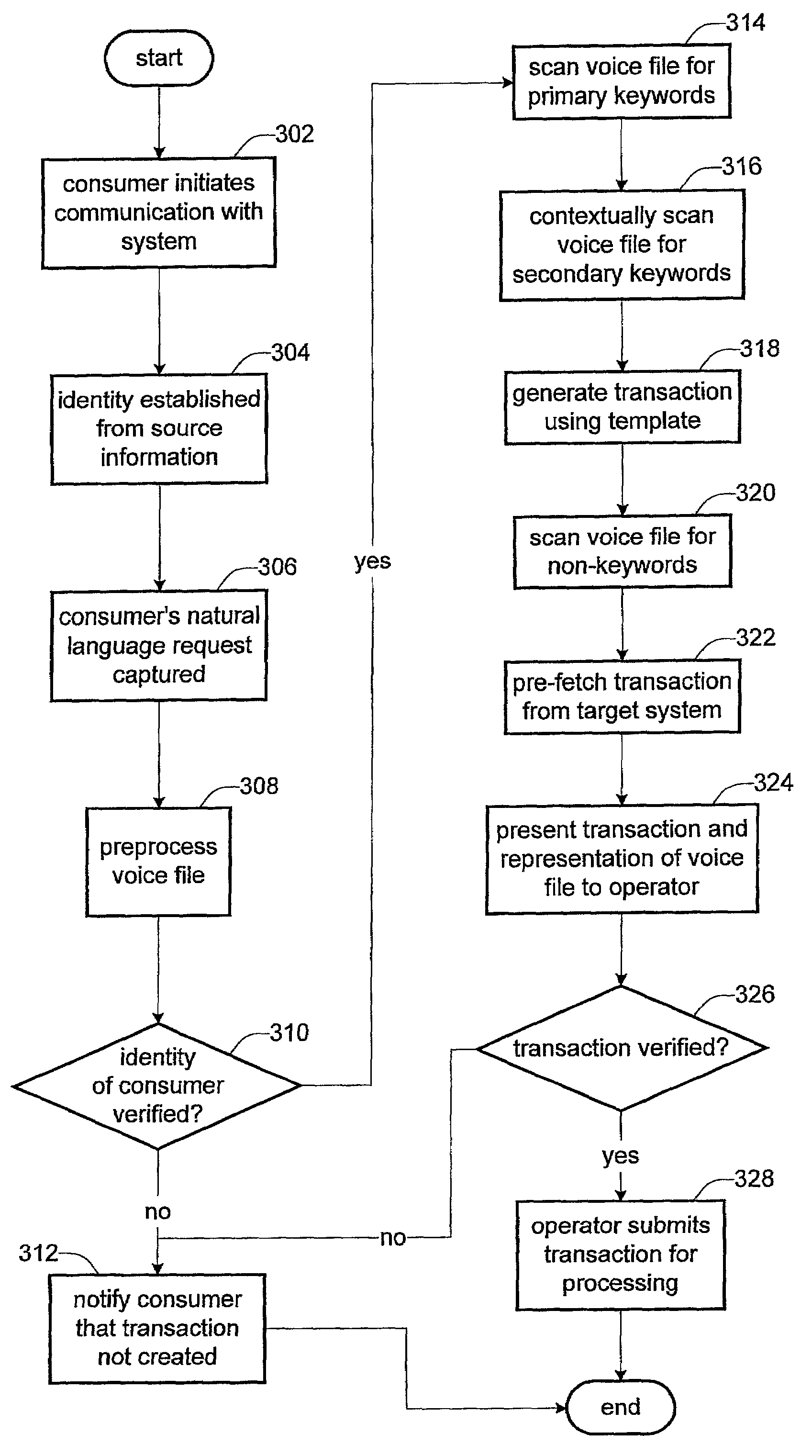
Syntax-driven, operator assisted voice recognition system and methods
ActiveUS7136814B1Buying/selling/leasing transactionsSpeech recognitionSpeech identificationContext based
Methods and apparatus are described for effecting a computer transaction using speech as a primary input. The speech is captured using a speech recognition program. A context associated with the captured speech is determined. Where the context has been determined, the computer transaction is built based on the context and at least a portion of the captured speech. A representation of the computer transaction is presented to a human operator for verification. The computer transaction is effected upon verification by the human operator.
Owner:THE PROCTER & GAMBLE COMPANY
Intelligent refrigerator for storing pharmaceutical product containers
Intelligent refrigerator system for storing pharmaceutical product containers, such as vials, ampules, syringes, bottles, medication tubes, blister packs and cartons, at the point of dispensing. Embodiments of the invention use product identification technology, such as radio-frequency identification (RFID) tags and readers, to uniquely identify containers as they are added to or removed from the cold storage compartment of the refrigerator, and automatically retrieve from a local or remote database a variety of details associated with the containers and their contents, such as manufacturing data, expiration dates, time out of refrigeration, inventory levels, safety information, usage statistics, known contraindications and warnings, etc. If the details indicate that there is a problem with a particular pharmaceutical (e.g., that it is counterfeit, expired, suspect, spoiled, recalled or almost depleted), then a message or warning is automatically delivered to a human operator via an attached output device, such as a display screen, speaker or printer. Embodiments of the invention may also be configured to monitor and report temperature faults, power failures and other anomalies associated with the refrigerator or cold storage compartment.
Owner:MERCK SHARP & DOHME LLC
Operator safety device for a machine having sharp implements
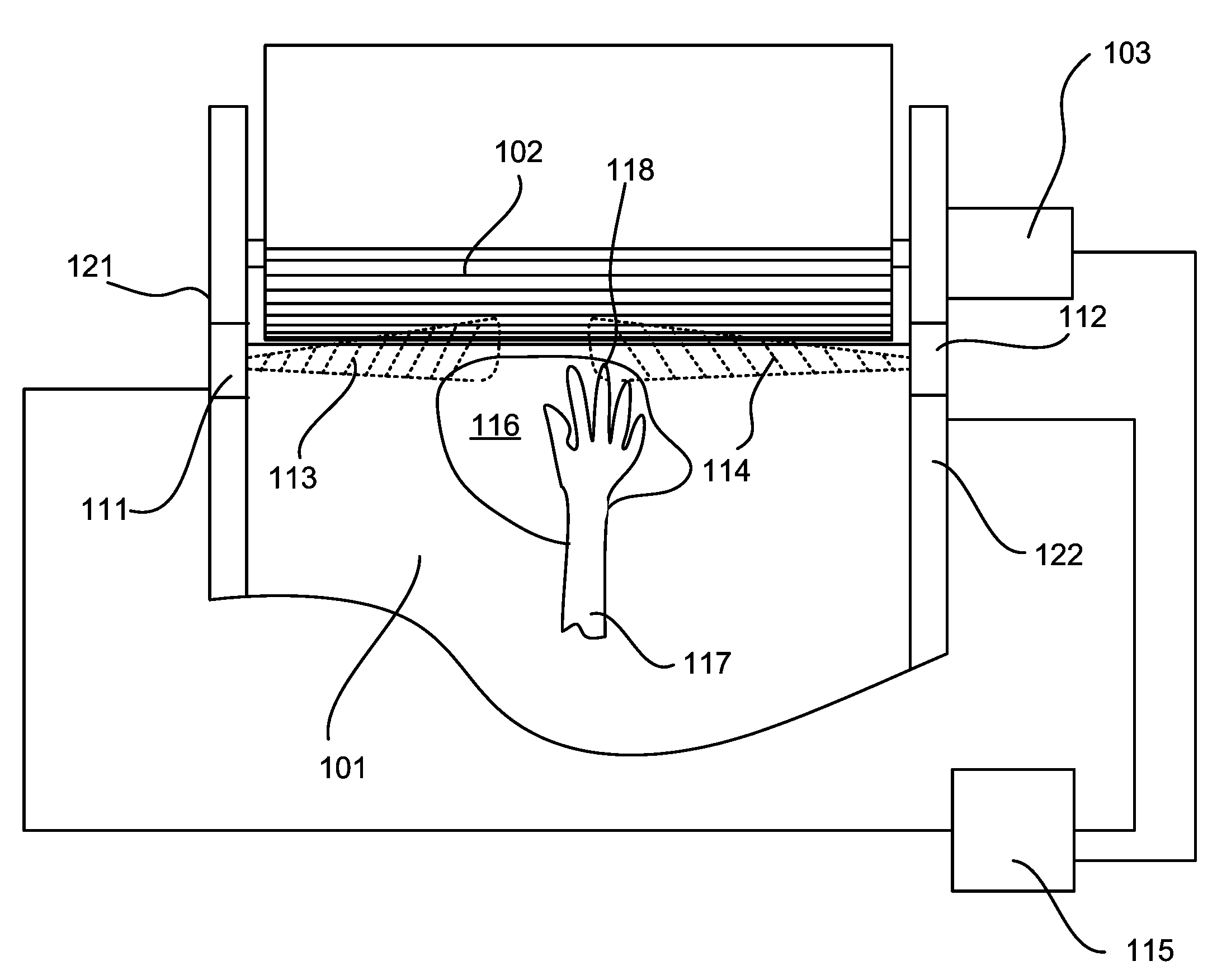
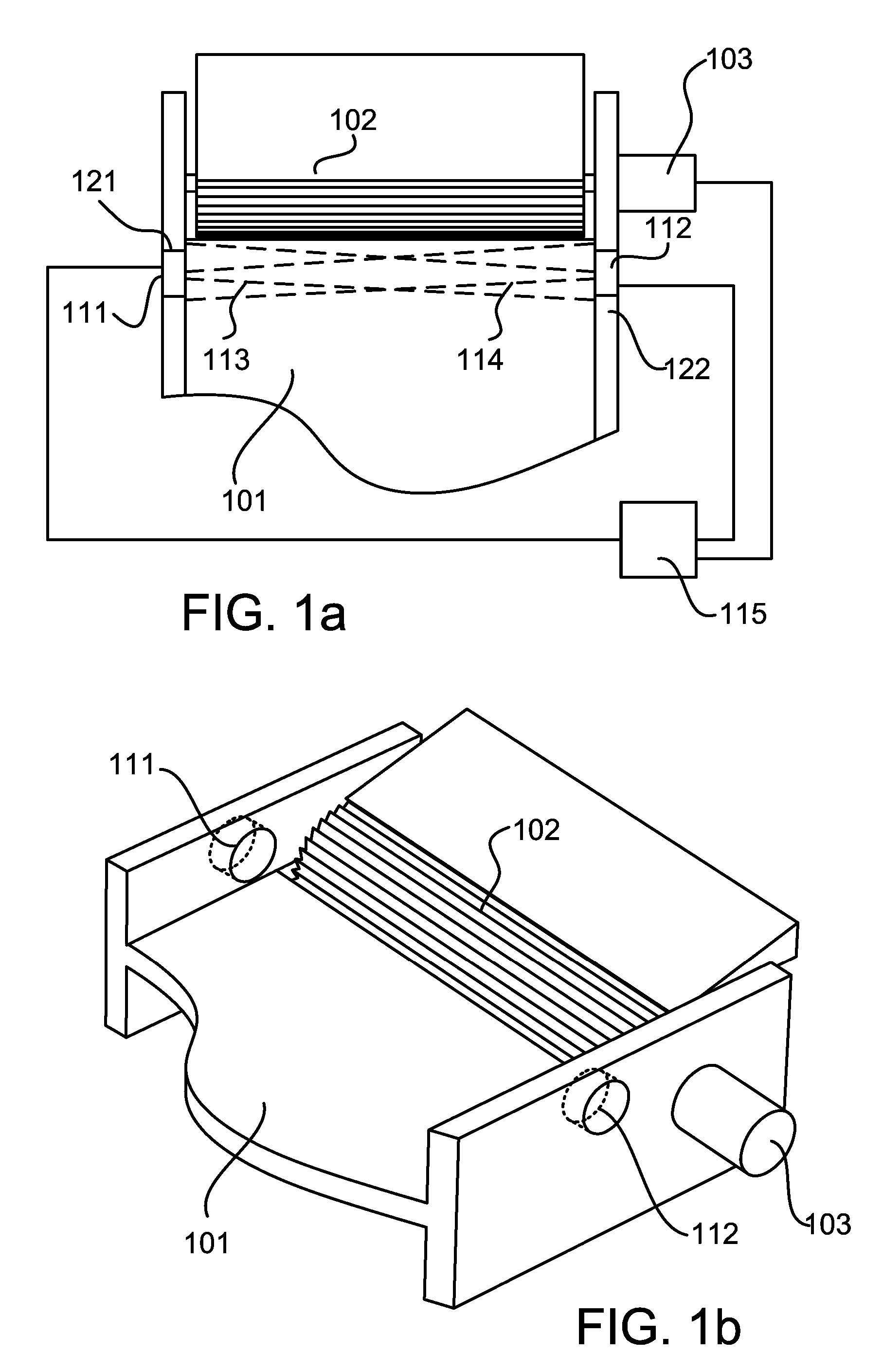
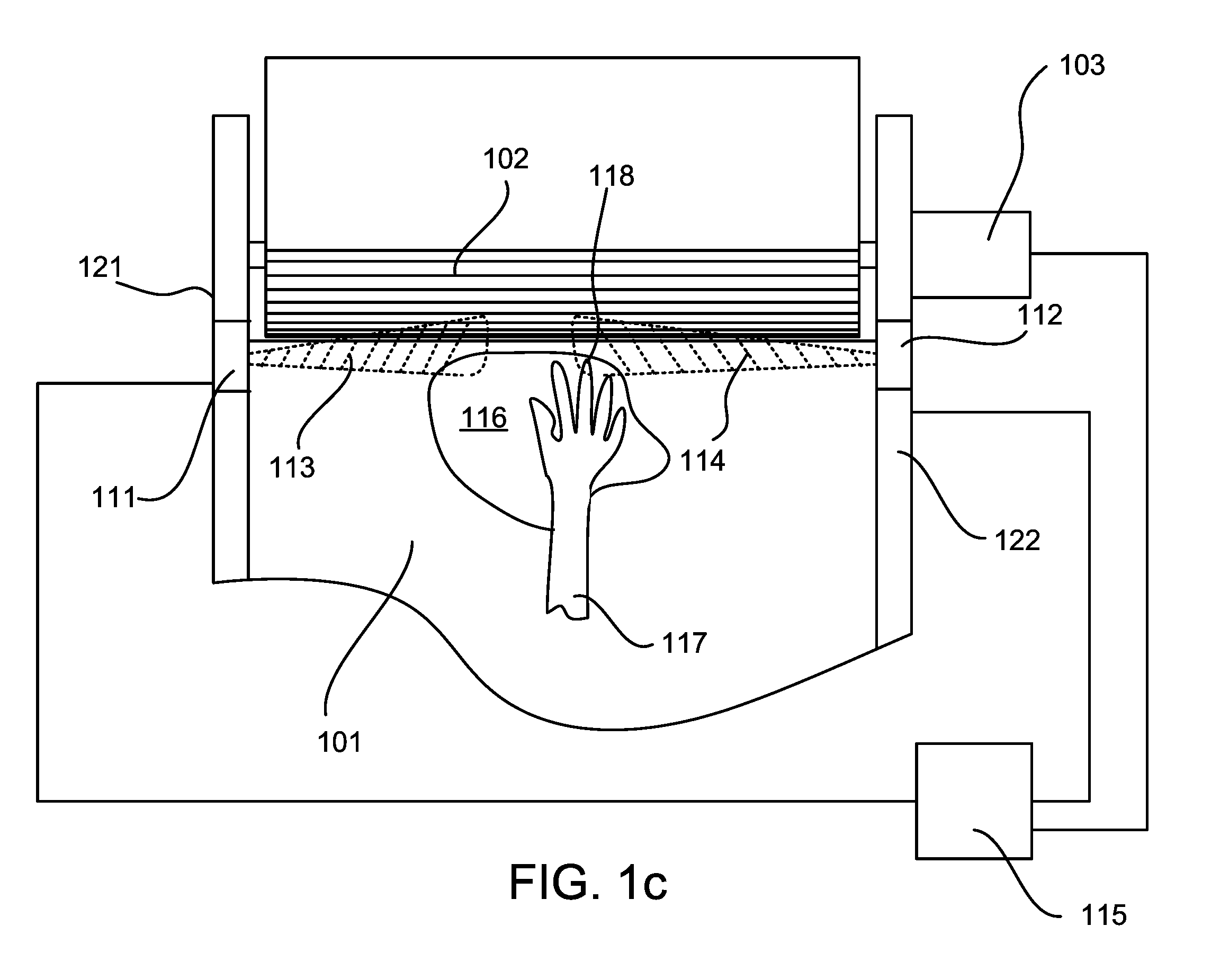
InactiveUS20060197020A1Providing operator safetySafer for operatorRadiation pyrometryMaterial analysis by optical meansEngineeringHuman operator
A novel human operator safety device is disclosed for use with motorized machines that have a danger zone that includes sharp cutting implements that can potentially cause operator harm. The operator safety device includes an optical or thermal sensor for either processing optically derived information to determine whether an extremity of an operator is within a predetermined proximity of the danger zone of the machine and processing thermal information to determine whether an extremity of an operator is within a predetermined proximity of the danger zone of the machine. If a presence is detected, at least a portion of the machine what may cause operator harm is stopped. For example, a thermal camera, an optical camera, laser or thermal sensor is used for determining whether an extremity of an operator is within a predetermined proximity of the danger zone.
Owner:TRZECIESKI MICHAEL A +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com