Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
934results about How to "Effective resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
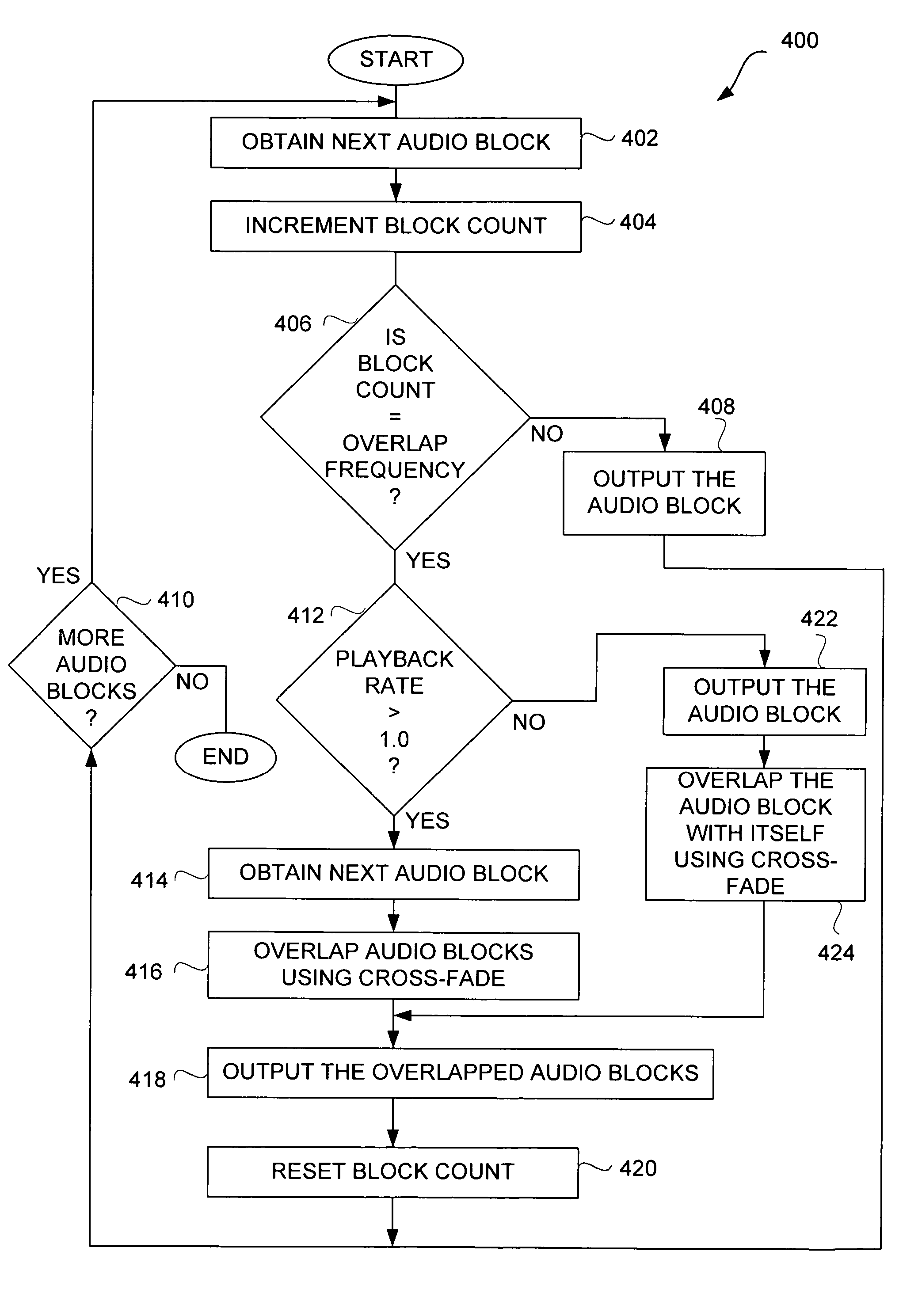
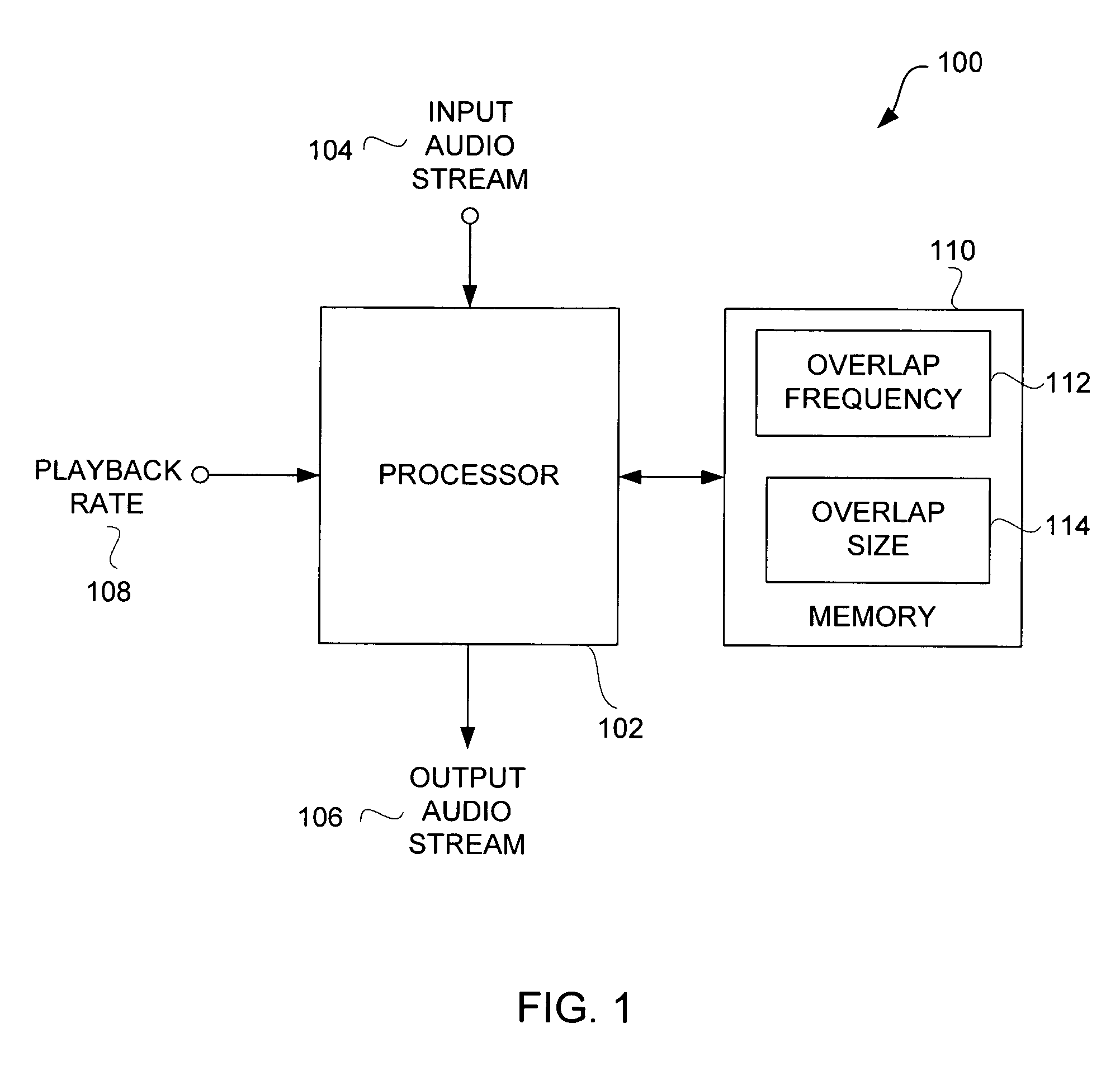
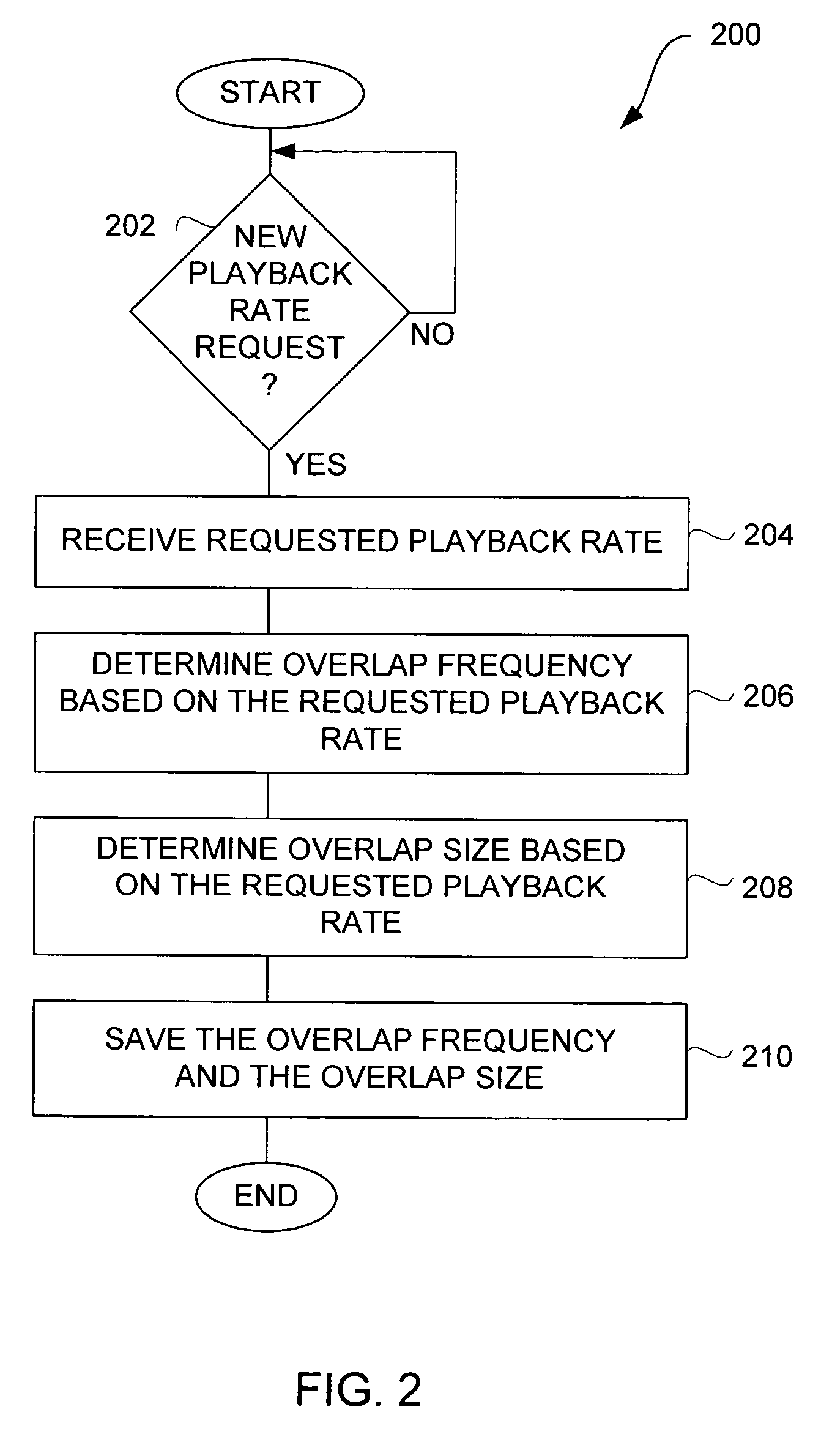
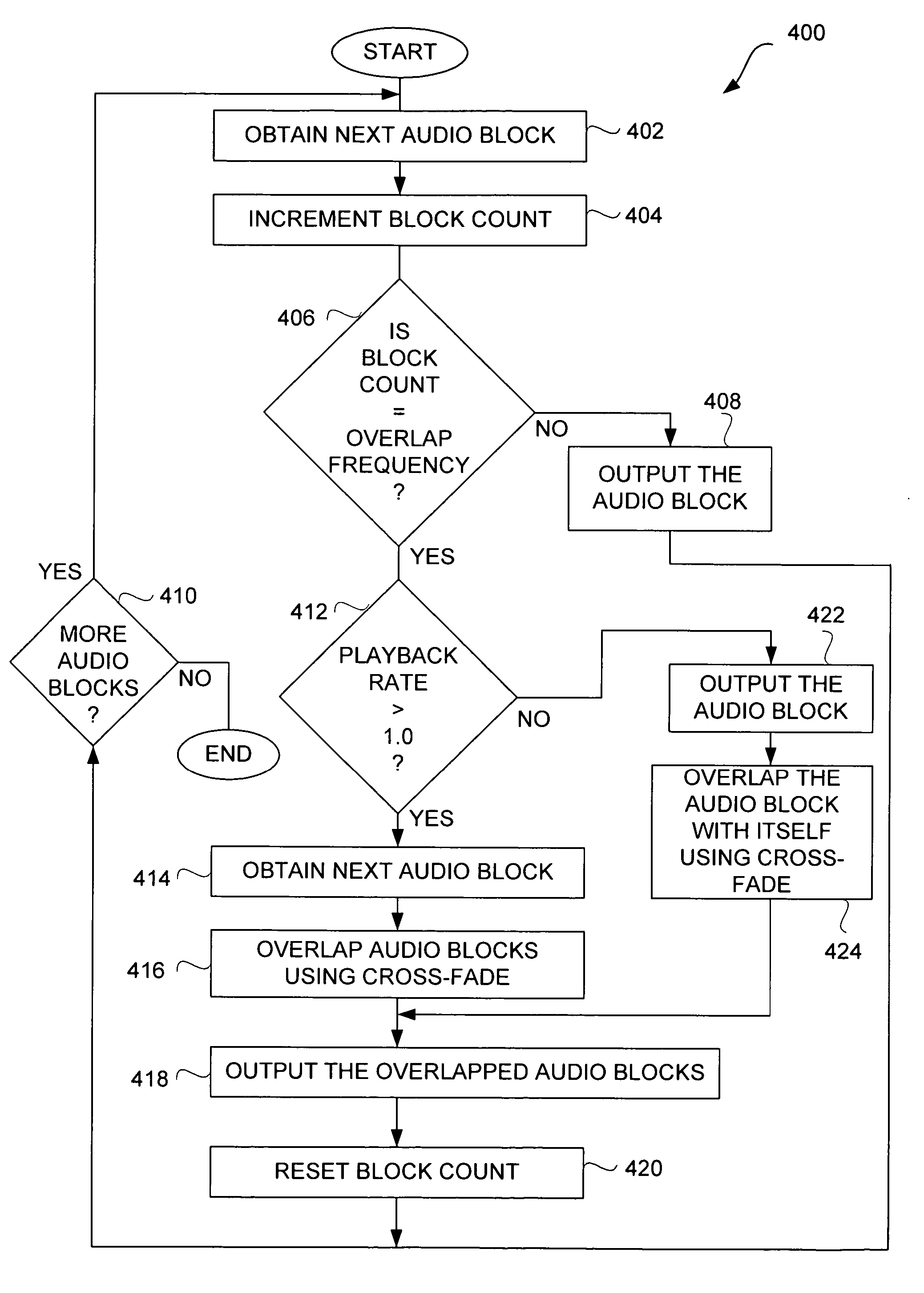
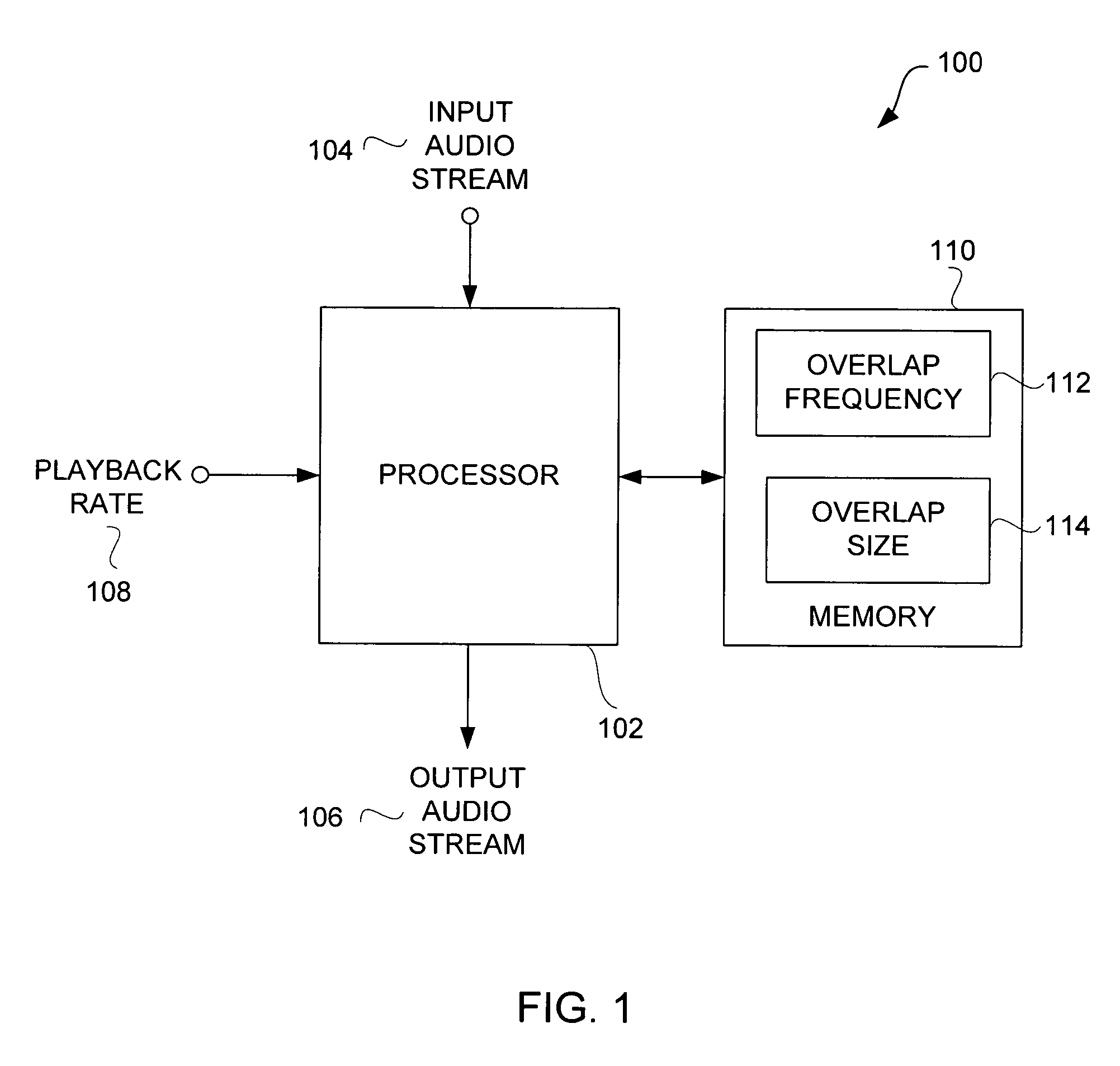
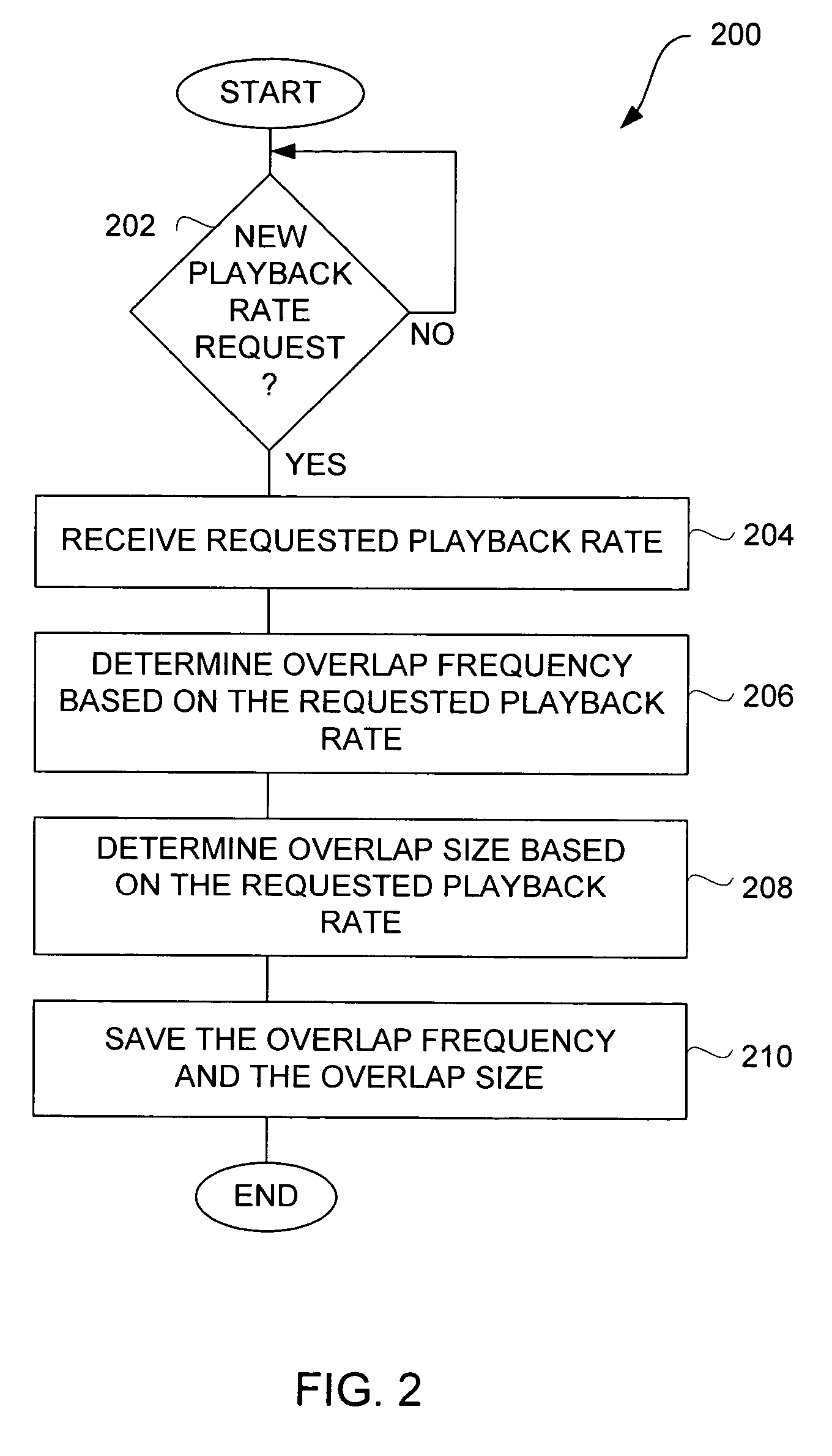
Efficient techniques for modifying audio playback rates
InactiveUS7664558B2Good choicePlayed back faster or slowerFilamentary/web record carriersSpeech analysisResource efficiencySpeech sound
Improved techniques for modifying a playback rate of an audio item (e.g., an audio stream) are disclosed. As a result, the audio item can be played back faster or slower than normal. The improved techniques are resource efficient and well suited for audio items containing speech. The resource efficiency of the improved techniques make them well suited for use with portable media devices, such as portable media players.
Owner:APPLE INC
Efficient techniques for modifying audio playback rates
InactiveUS20060221788A1Good choicePlayed back faster or slowerFilamentary/web record carriersSpeech analysisMediaFLOEngineering
Improved techniques for modifying a playback rate of an audio item (e.g., an audio stream) are disclosed. As a result, the audio item can be played back faster or slower than normal. The improved techniques are resource efficient and well suited for audio items containing speech. The resource efficiency of the improved techniques make them well suited for use with portable media devices, such as portable media players.
Owner:APPLE INC
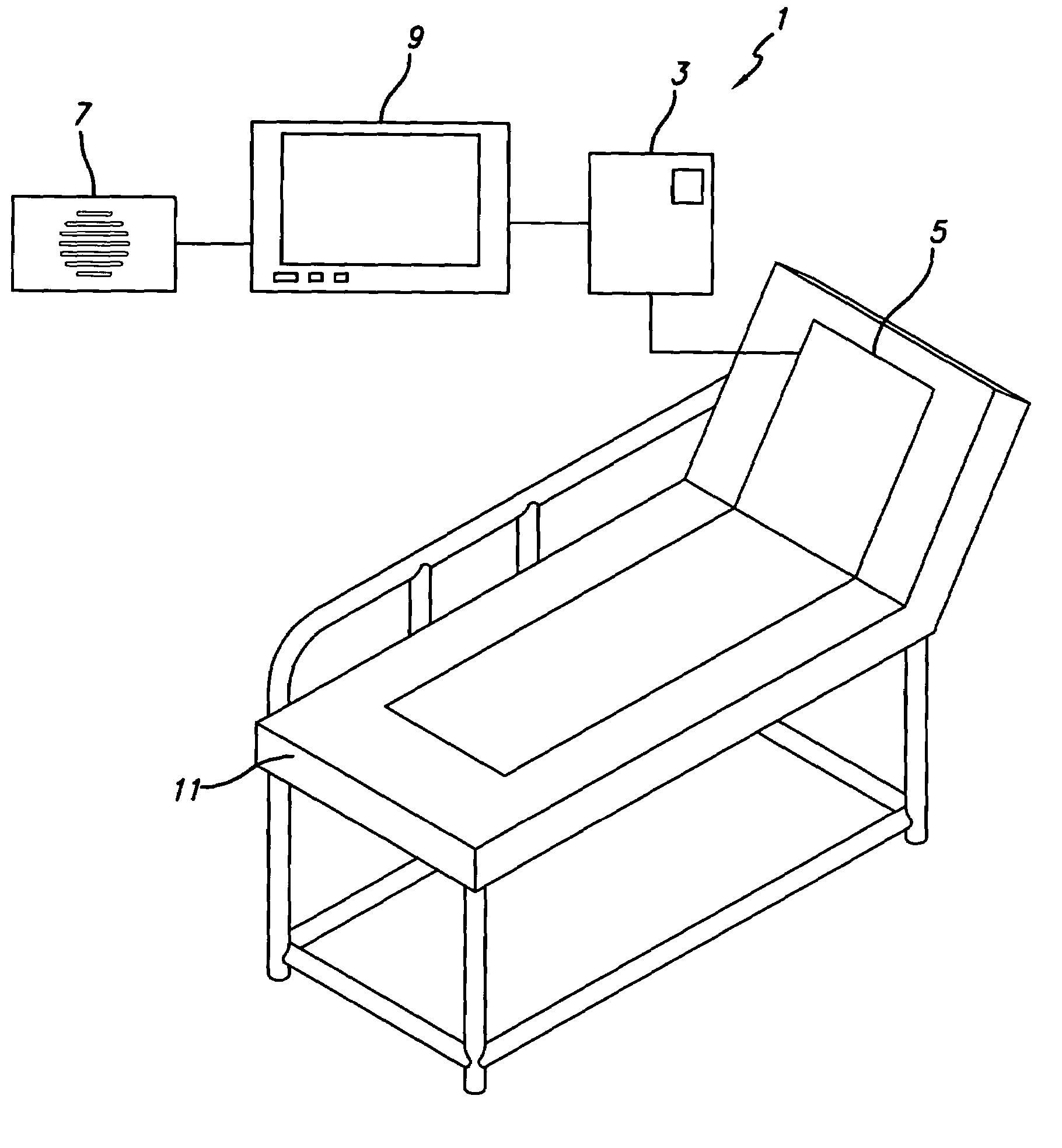
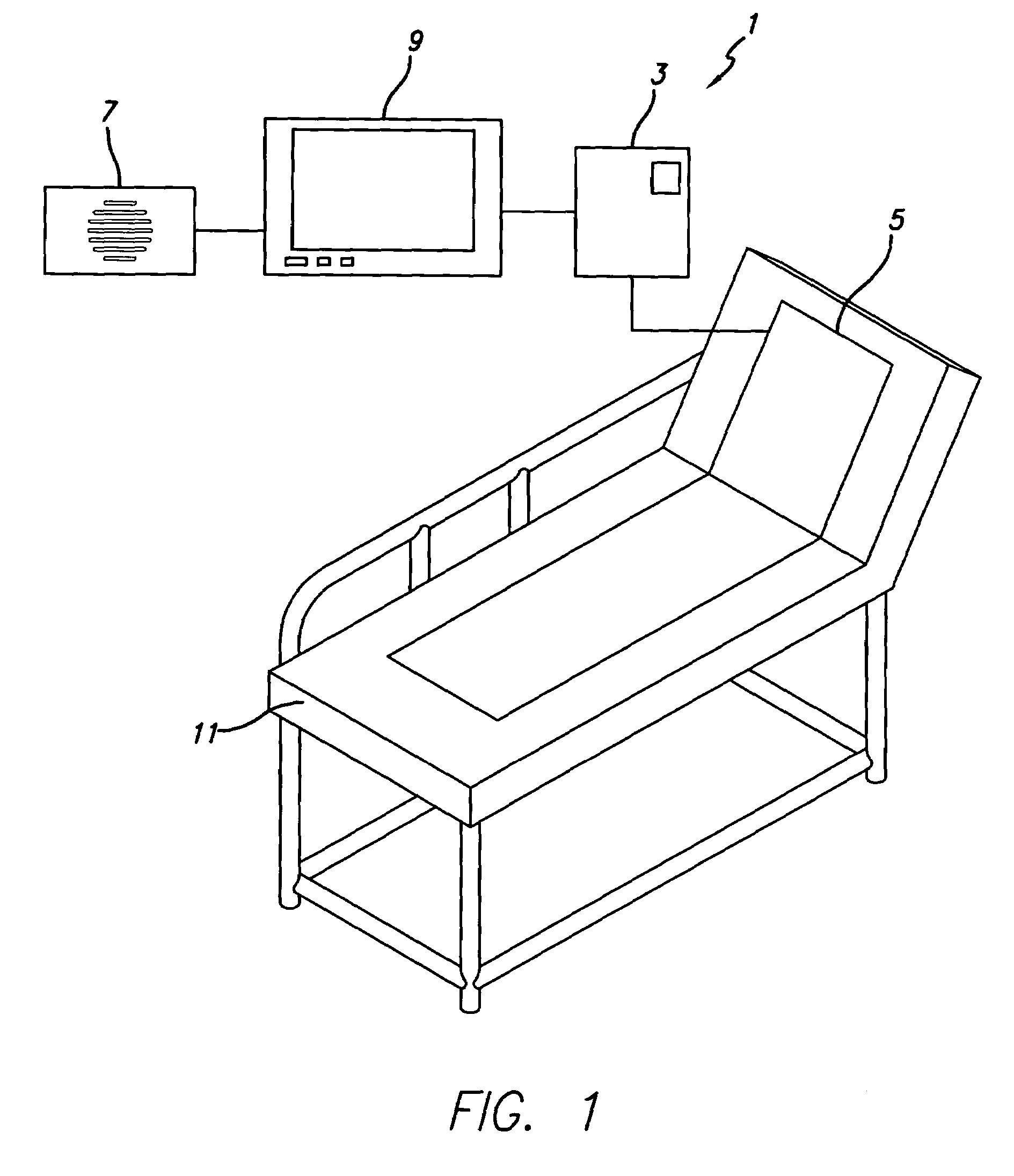
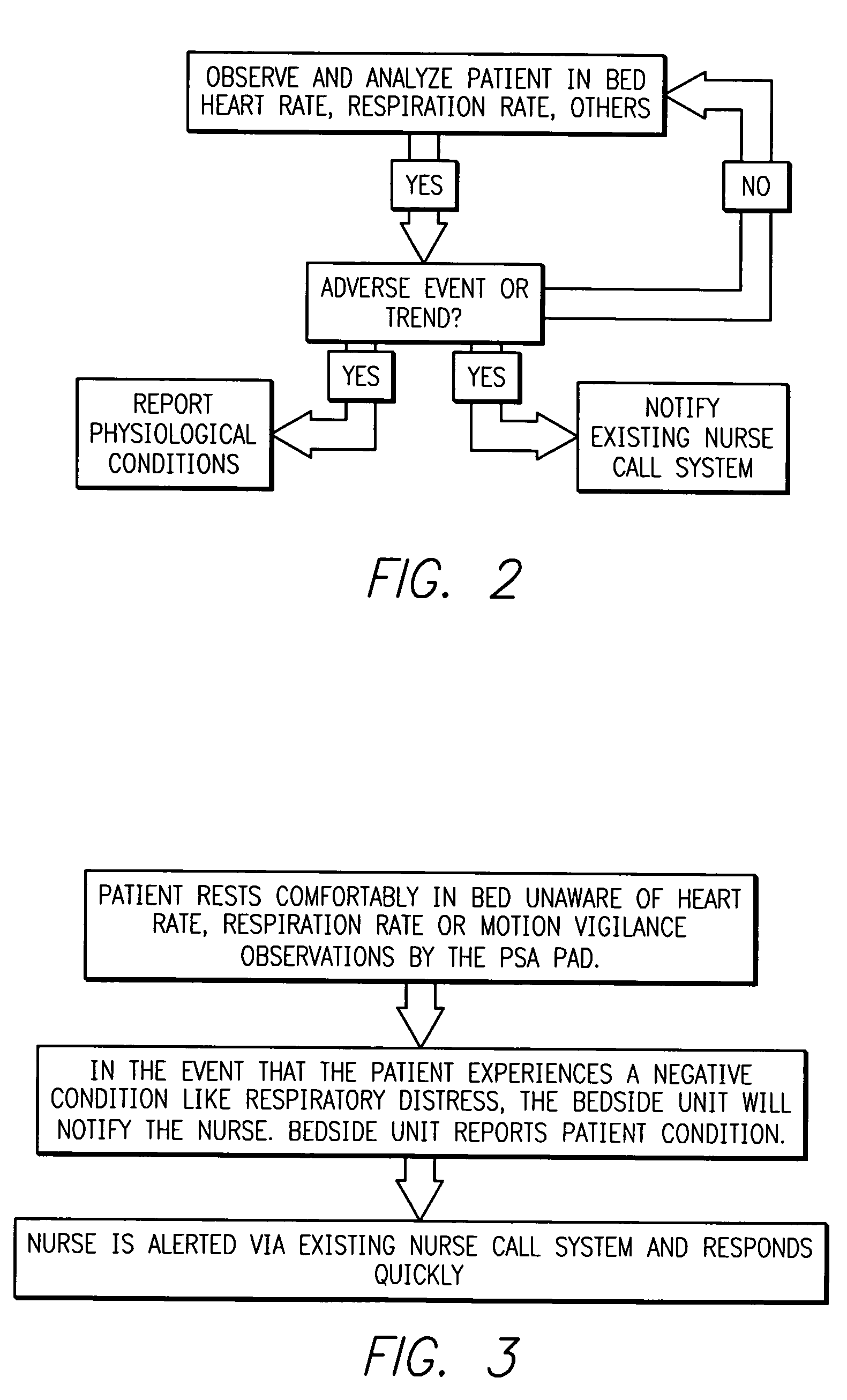
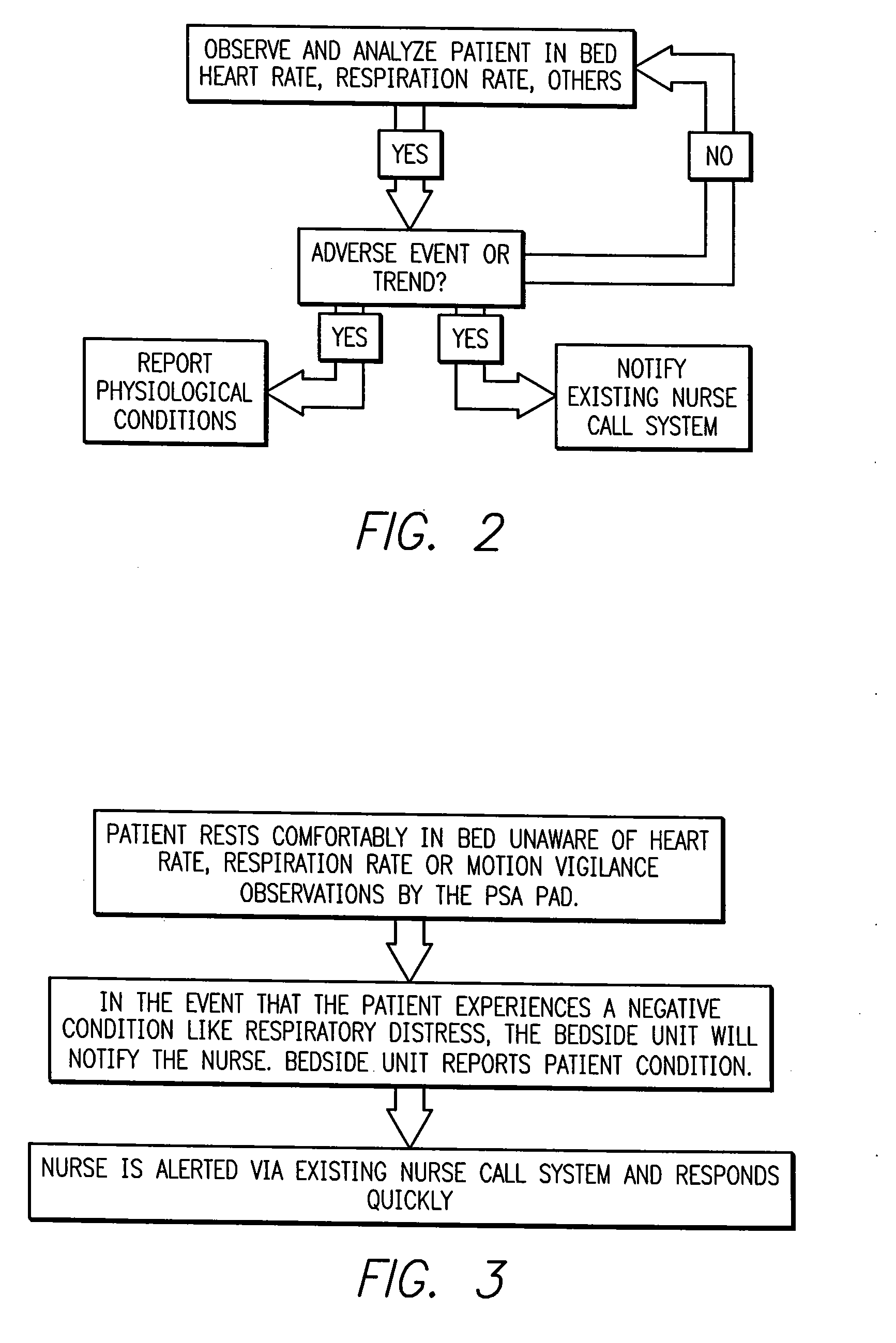
Intelligent medical vigilance system
InactiveUS7304580B2Improve abilitiesEffective resourcesAcoustic sensorsTelemedicineSensor arrayDisplay device
An intelligent medical vigilance system that observes and analyzes, and, only in the event of a clinically significant negative condition, notifies and reports the event to the care staff utilizing the hospital's existing nurse call system. The device includes a bedside unit connected to a pad or coverlet with a sensor array (placed under the patient) and also to an existing hospital nurse call system via an interface. Within the physical bedside unit are a signal processor and an alarm processor that measure data and evaluate whether a clinically significant event is occurring. The bedside unit is a wall-mounted unit with a display that becomes active when an alarm condition is enabled. The sensing pad or coverlet is a thin, piezoelectric film, or other similar sensing technology, with an array of sensors sheathed in soft padding and is not directly in contact with the skin of the patient. The nurse call feature is made up of hardware, software and cabling to connect to the nurse call system already installed in the hospital or care facility. The monitoring system can also be installed in vehicles to monitor operator physiological conditions.
Owner:HOANA MEDICAL
Techniques for discovering and managing security of applications
ActiveUS20170251013A1Minimizing security threatMinimizing riskTransmissionSafety management systemsData source
Techniques for discovery and management of applications in a computing environment of an organization are disclosed. A security management system discovers use of applications within a computing environment to manage access to applications for minimizing security threats and risks in a computing environment of the organization. The security management system can obtain network data about network traffic to identify unique applications. The security management system can perform analysis and correlation, including use of one or more data sources, to determine information about an application. The system can compute a measure of security for an application (“an application risk score”) and a user (“a user risk score”). The score may be analyzed to determine a threat of security posed by the application based on use of the application. The security system can perform one or more instructions to configure access permitted by an application, whether access is denied or restricted.
Owner:ORACLE INT CORP
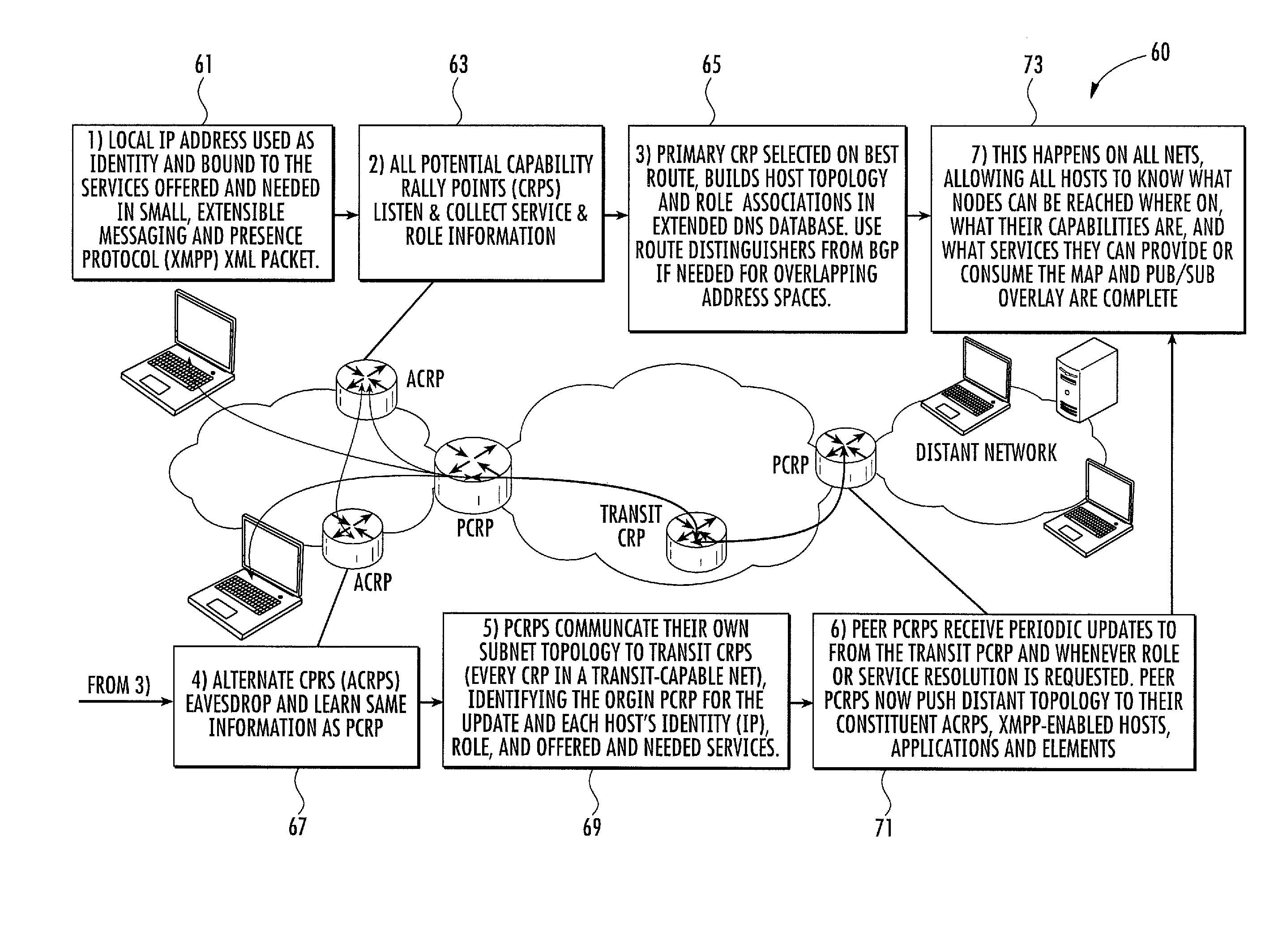
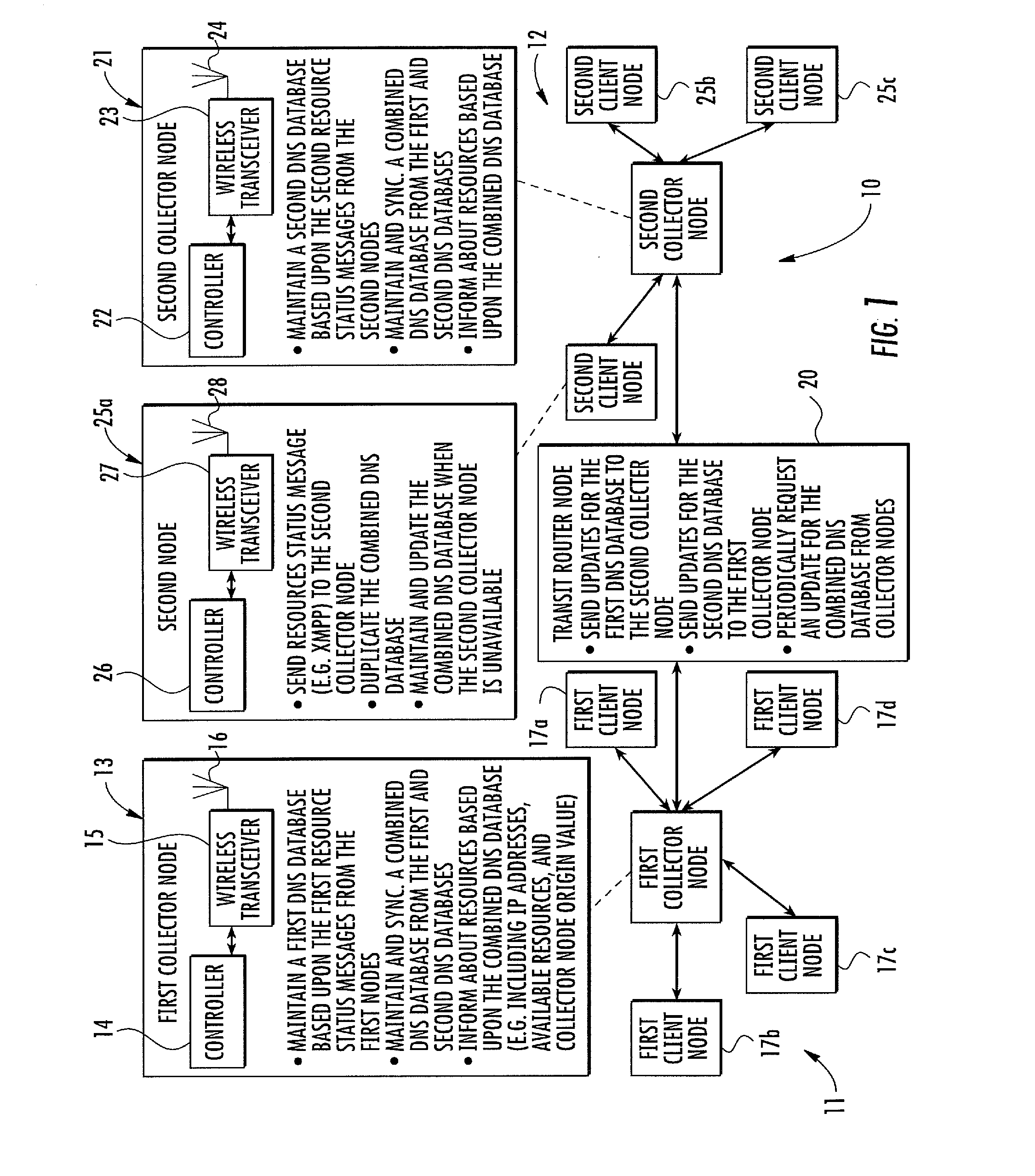
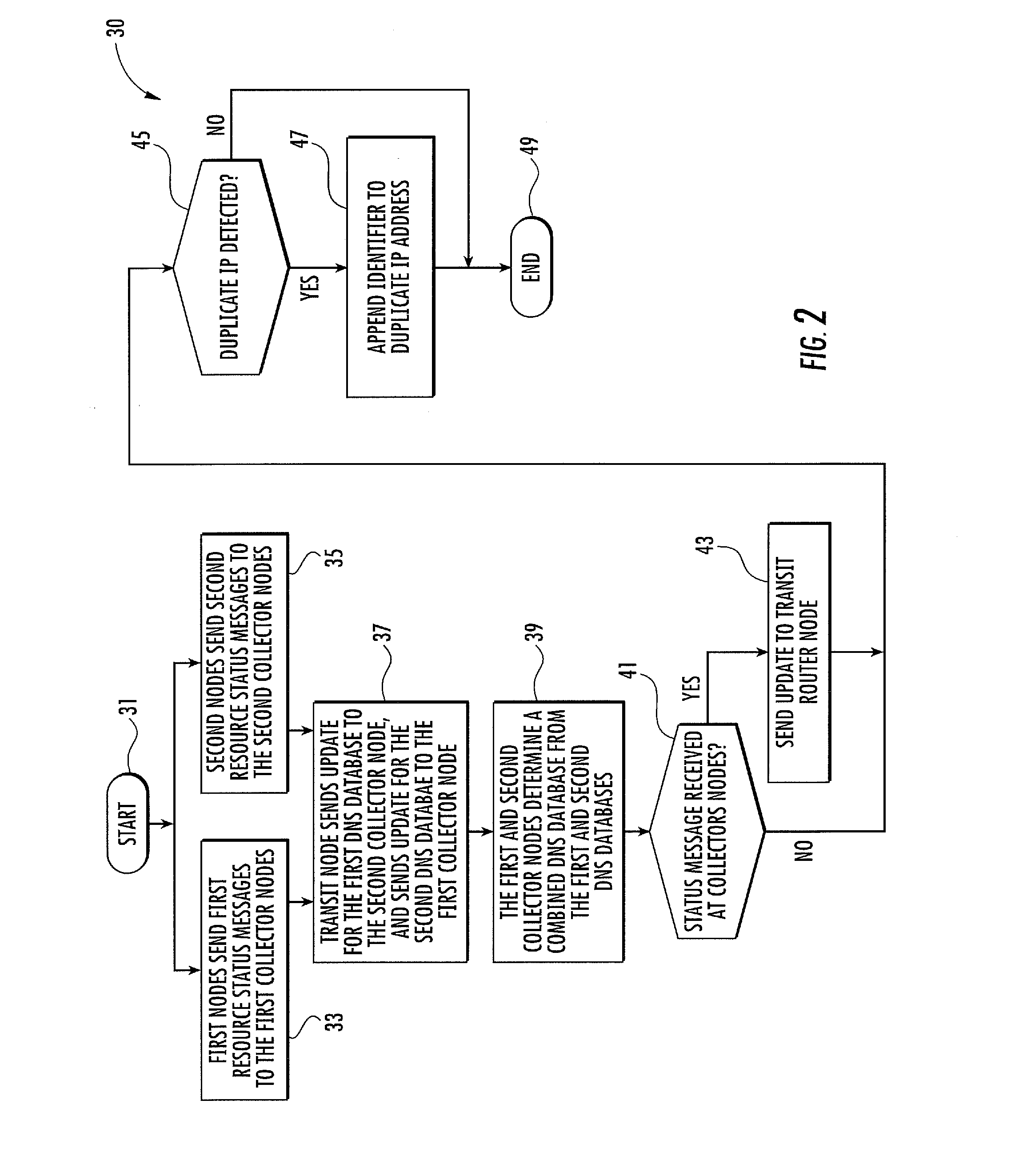
Manet with DNS database resource management and related methods
ActiveUS20130311661A1Effective resourcesEffective redirectingDigital computer detailsTransmissionEngineeringResource management
A network includes a first MANET subnet including a first collector node and first client nodes sending first resource status messages to the first collector node. The first collector node maintains a first DNS database based upon the first resource status messages. The network includes a second MANET subnet including a second collector node and second client nodes sending second resource status messages to the second collector node. The second collector node maintains a second DNS database based upon the second resource status messages. The network includes a transit router node sending updates from the first DNS database to the second collector node, and sending updates from the second DNS database to the first collector node. The first and second collector nodes each maintain and synchronize a combined DNS database from the first and second DNS databases, providing resource availability and status throughout the combined network to their respective clients.
Owner:STINGRAY IP SOLUTIONS LLC
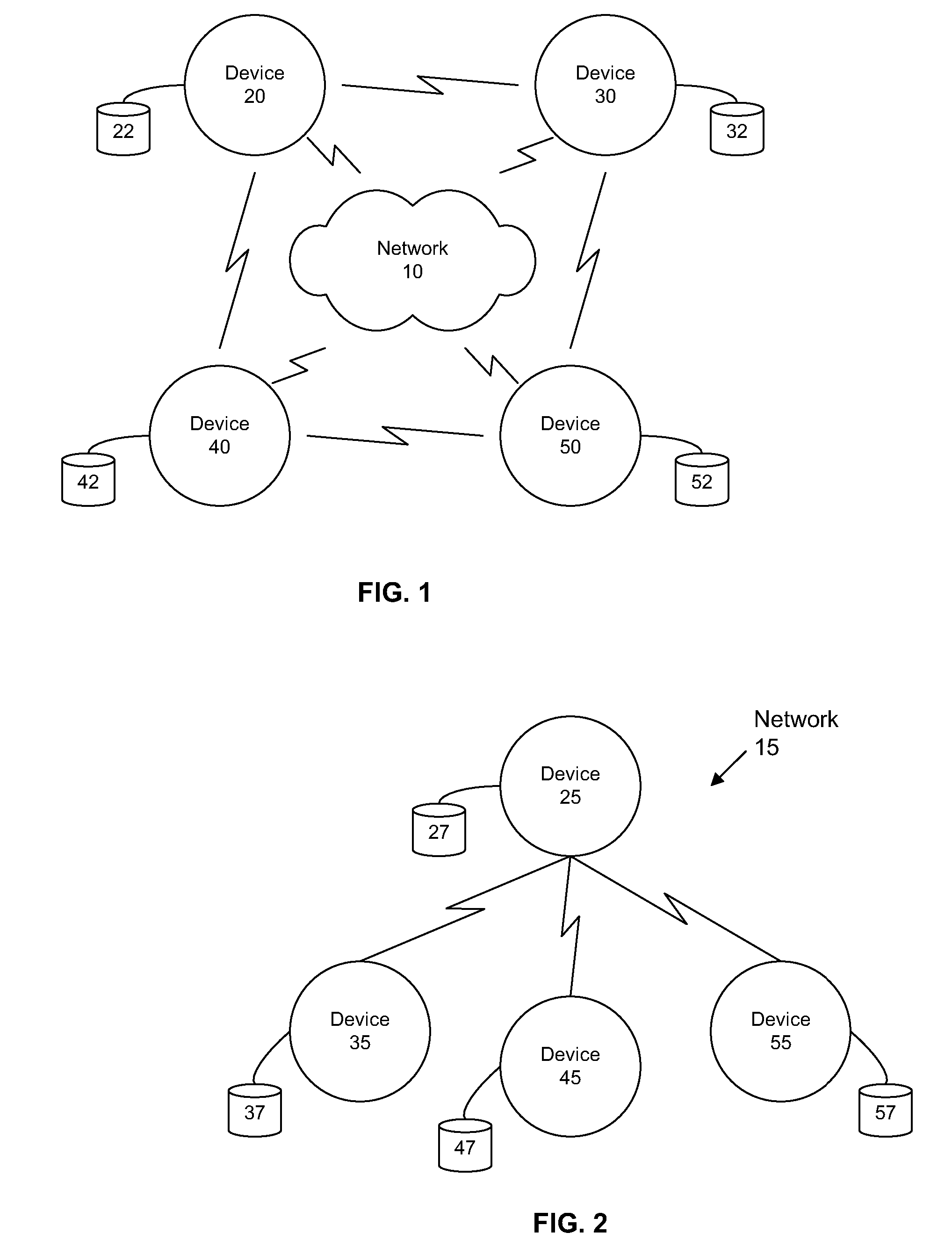
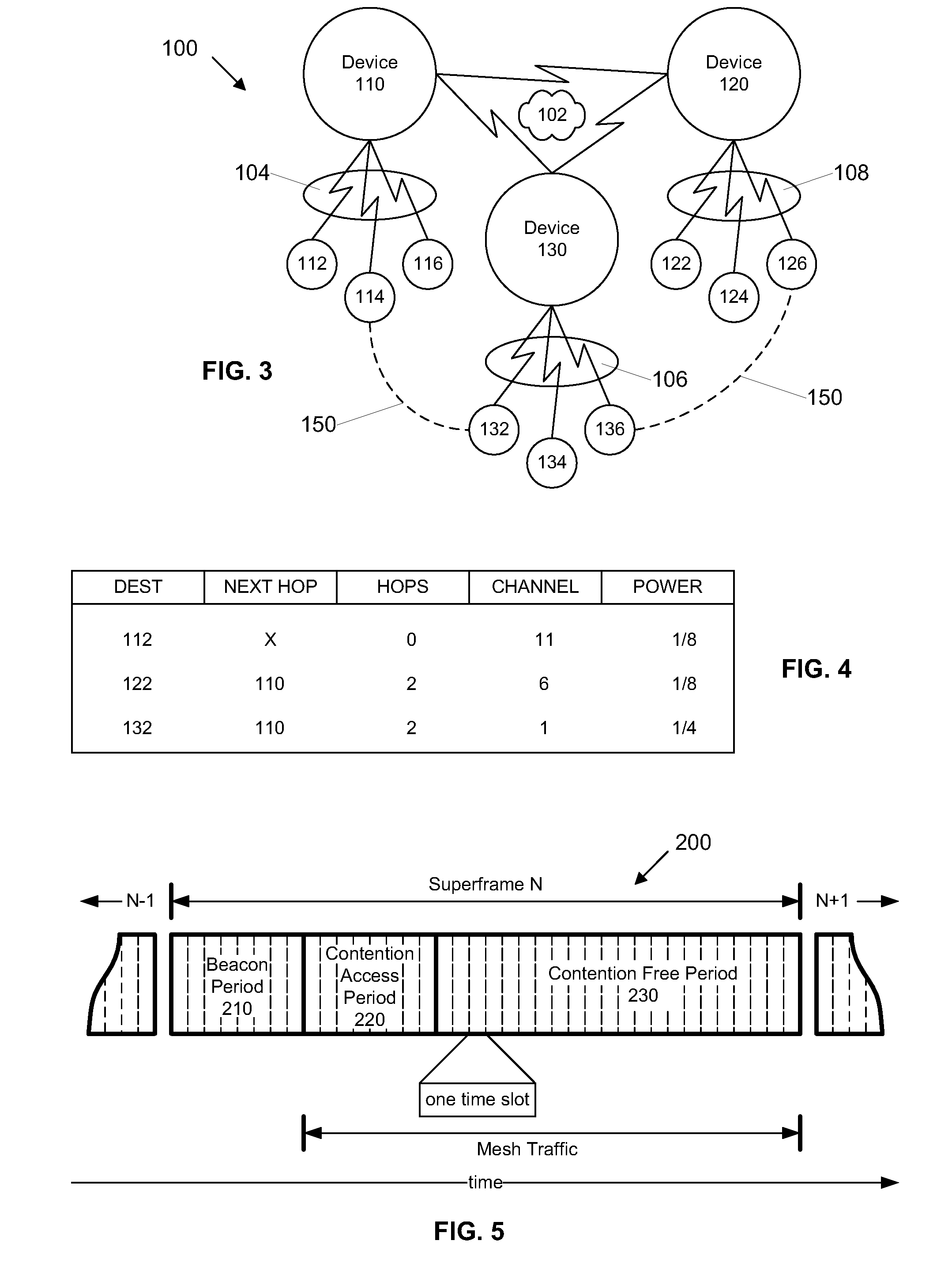
Multi-Hop Ultra Wide Band Wireless Network Communication
InactiveUS20070104215A1Avoid bandwidth reservation conflictImprove utilizationNetwork traffic/resource managementAssess restrictionFrequency spectrumCommunication device
A wireless communication system is provided that has at least three nodes arranged in a multi-hop ultra wide band (UWB) communication network such that communications from a first node destined for a third node pass through a second node. Each of the devices in the system includes a radio and a media access control (“MAC”) module that is configured to establish multi-hop UWB wireless communications between the three or more wireless communication devices that enables high bandwidth applications such as Voice Over Internet Protocol (“VoIP”); multiplayer gaming; Wireless High Definition Television; and Internet Protocol Television (“IPTV”) among others. The MAC module is configured to avoid bandwidth reservation conflicts so that network performance does not degrade as the number of hops or the number of nodes in the wireless communication system increases. The MAC also facilitates utilization of multiple channels to maximize the available spectrum and is further configured to dynamically switch between channels to maximize throughput and meet or exceed quality of service (“QoS”) requirements such that QoS is guaranteed and network resources are efficiently utilized.
Owner:UNWIRED BROADBAND INC
Distributed computing
InactiveUS20060195508A1Improve deploymentEasy to integrateResource allocationMultiple digital computer combinationsGraphicsGraphical user interface
A distributed computing system manages execution of jobs and their associated tasks. Multiple scheduling strategies respect job priority preferences. A graphical user interface allows viewing of job status information and on-the-fly modification of job priorities.
Owner:BERNARDIN JAMES +1
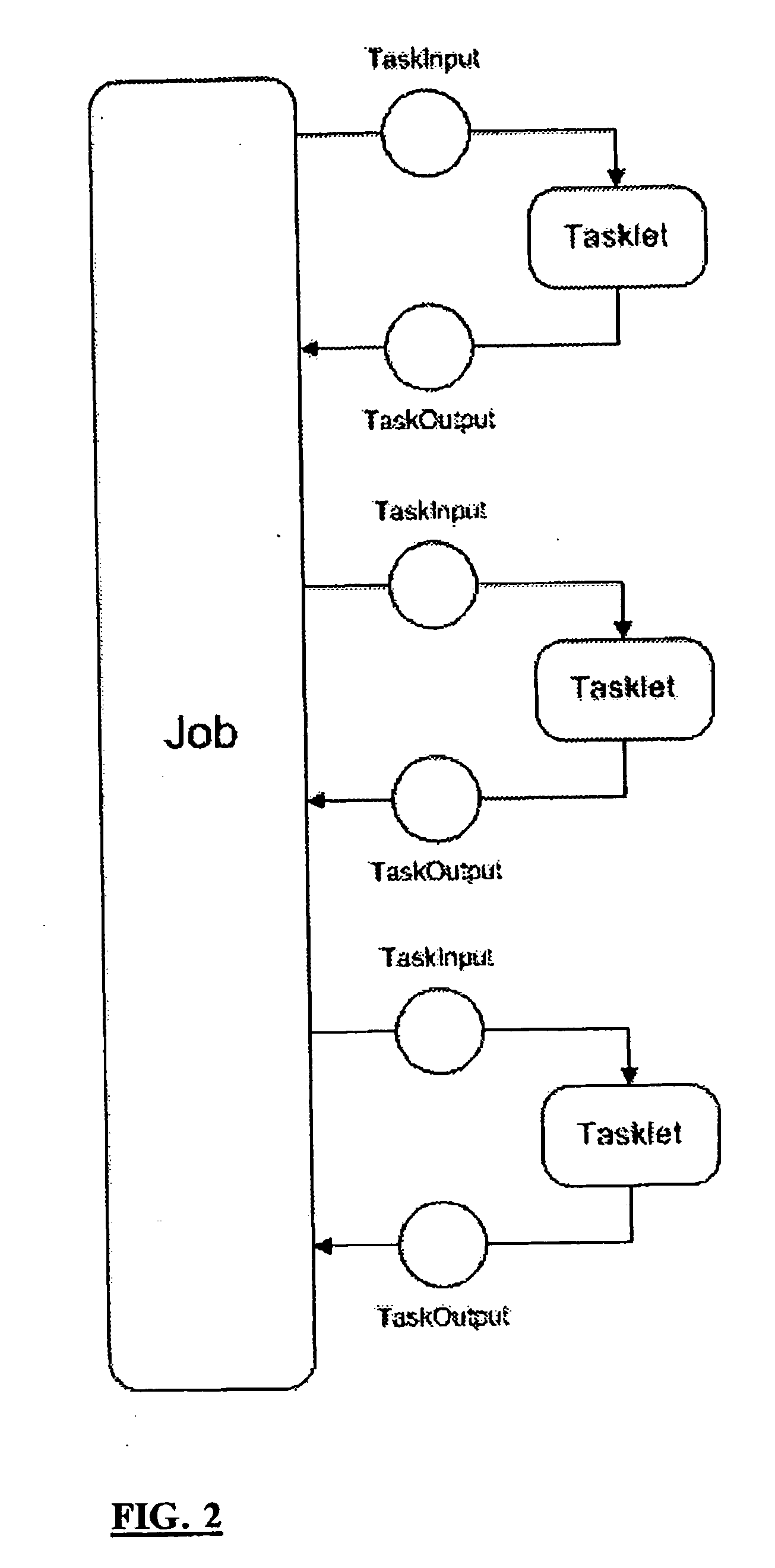
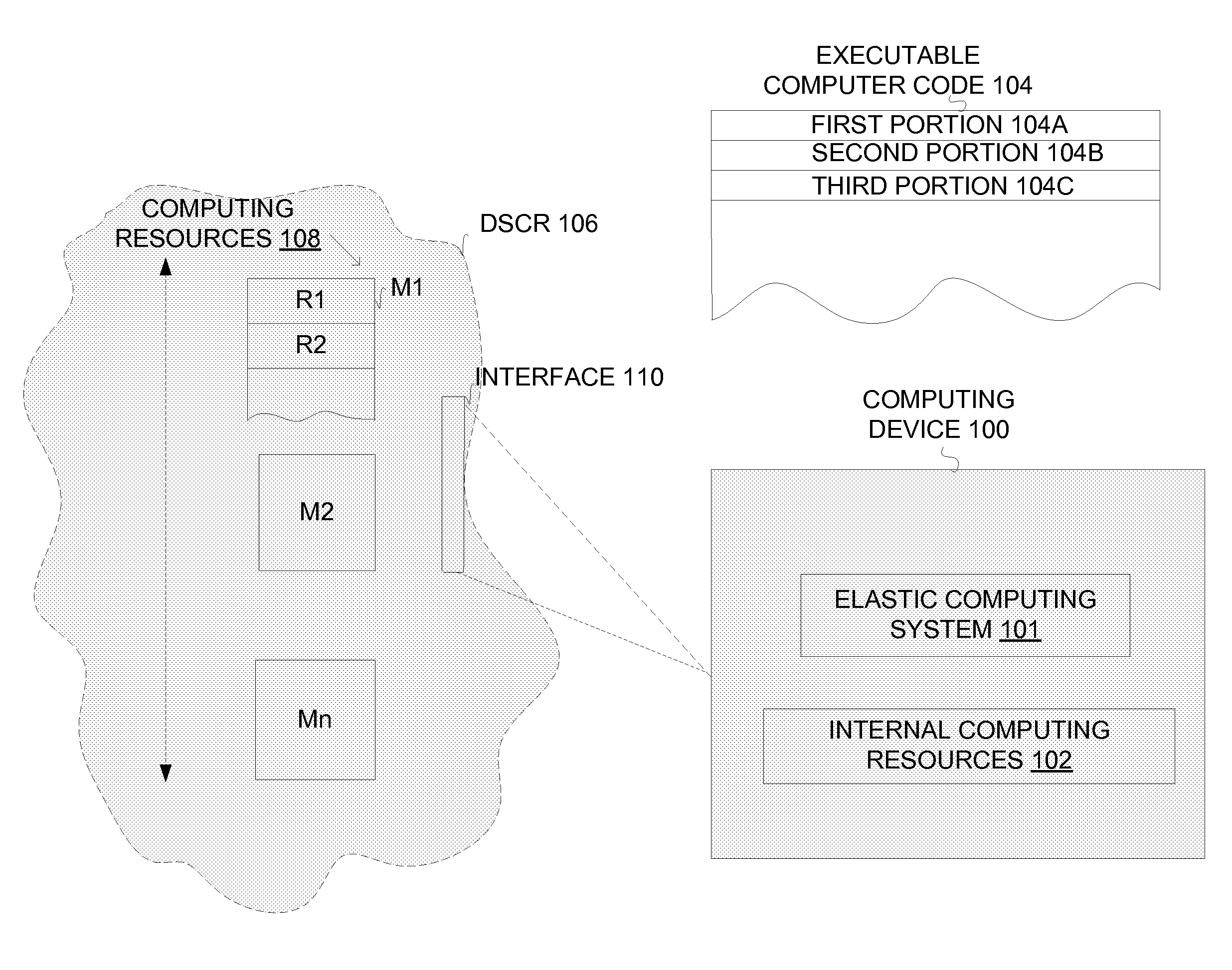
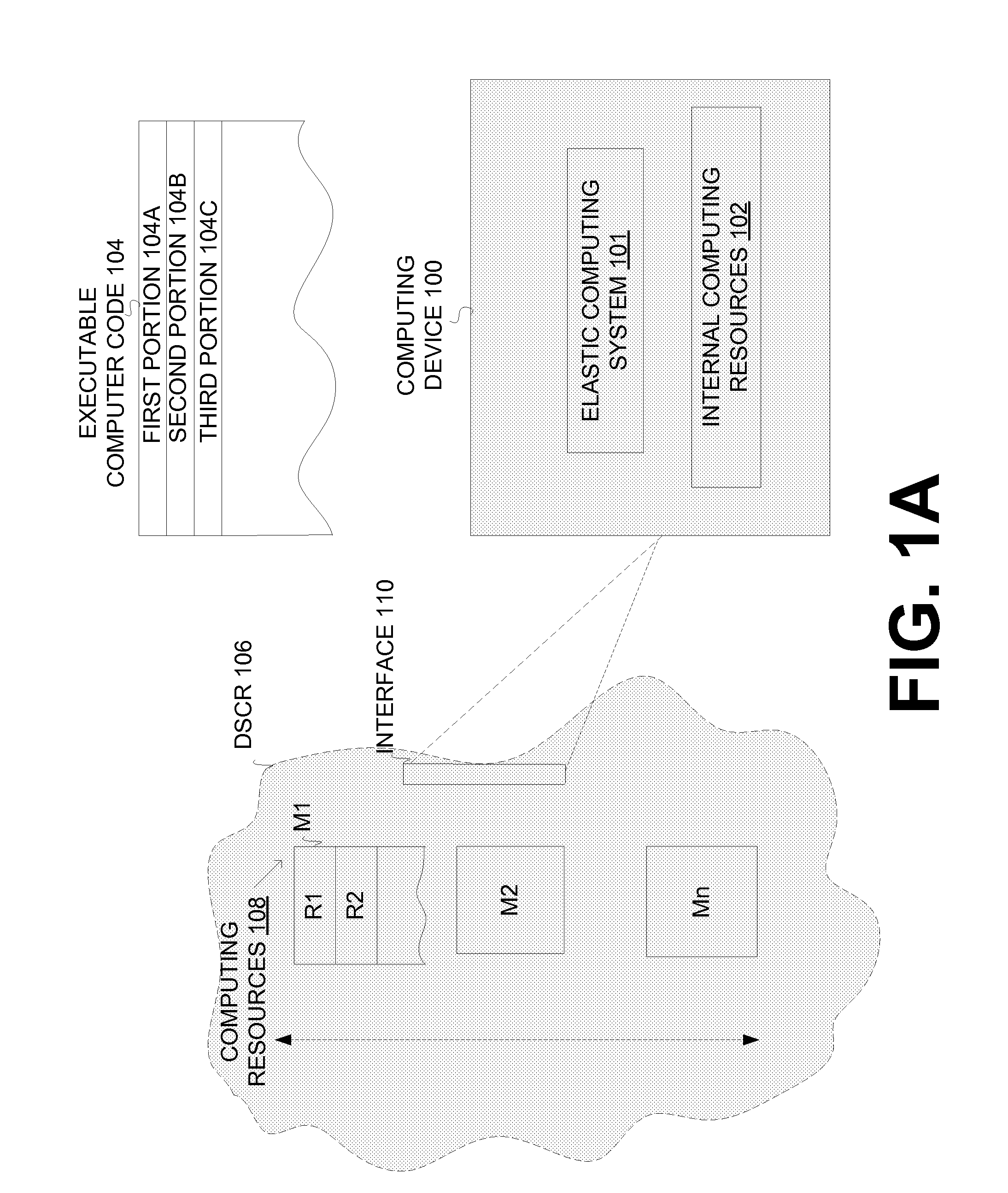
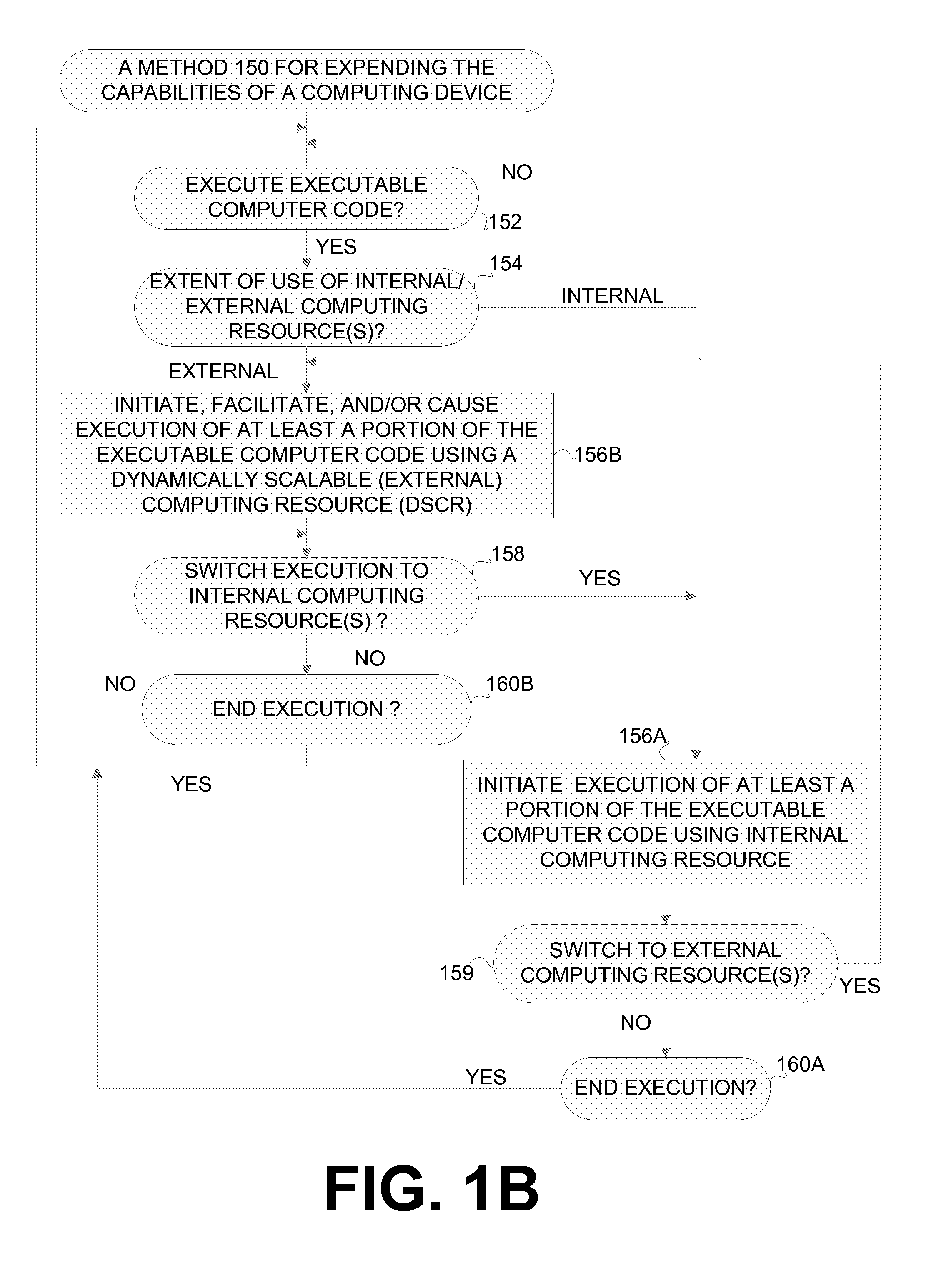
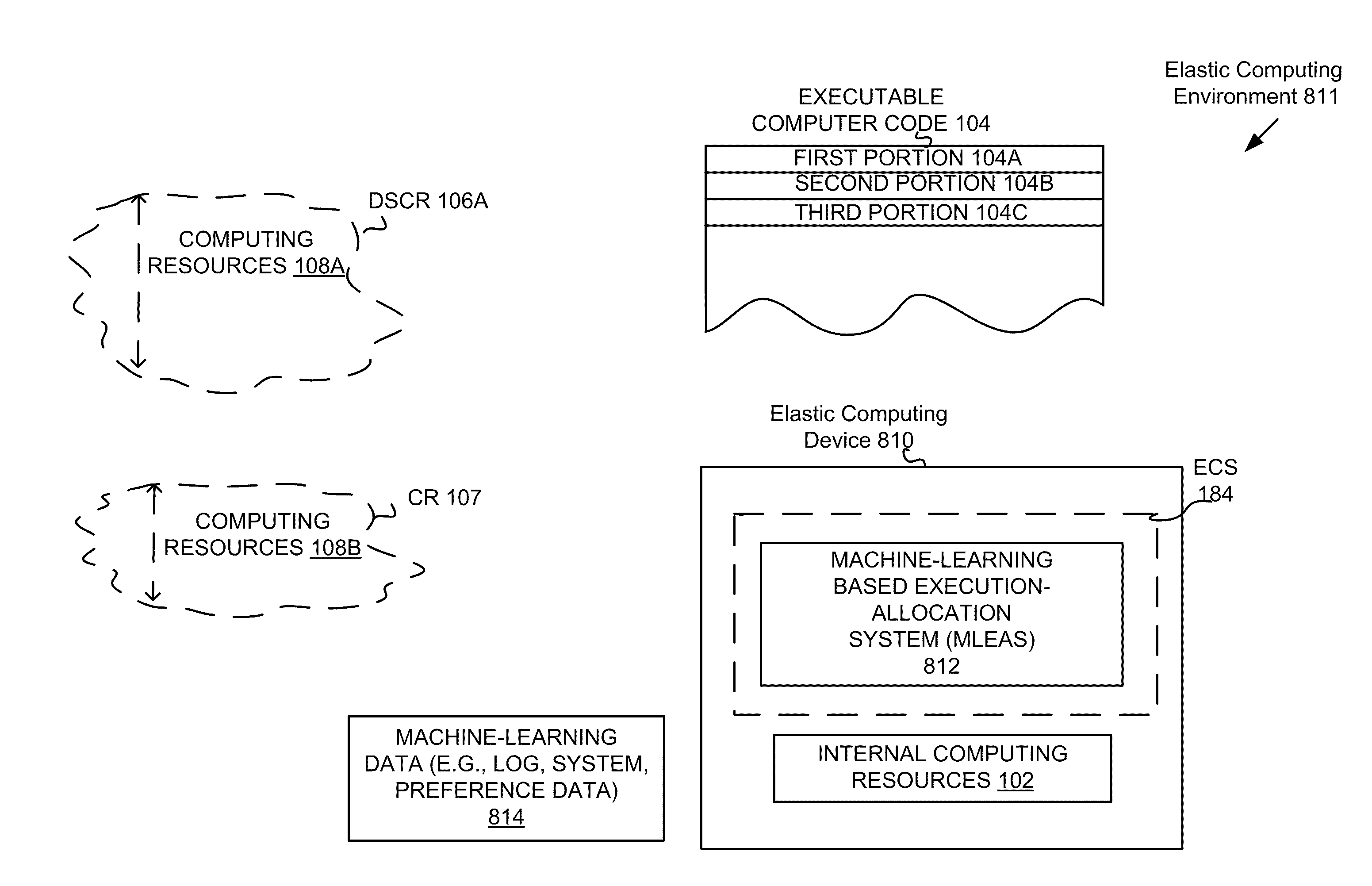
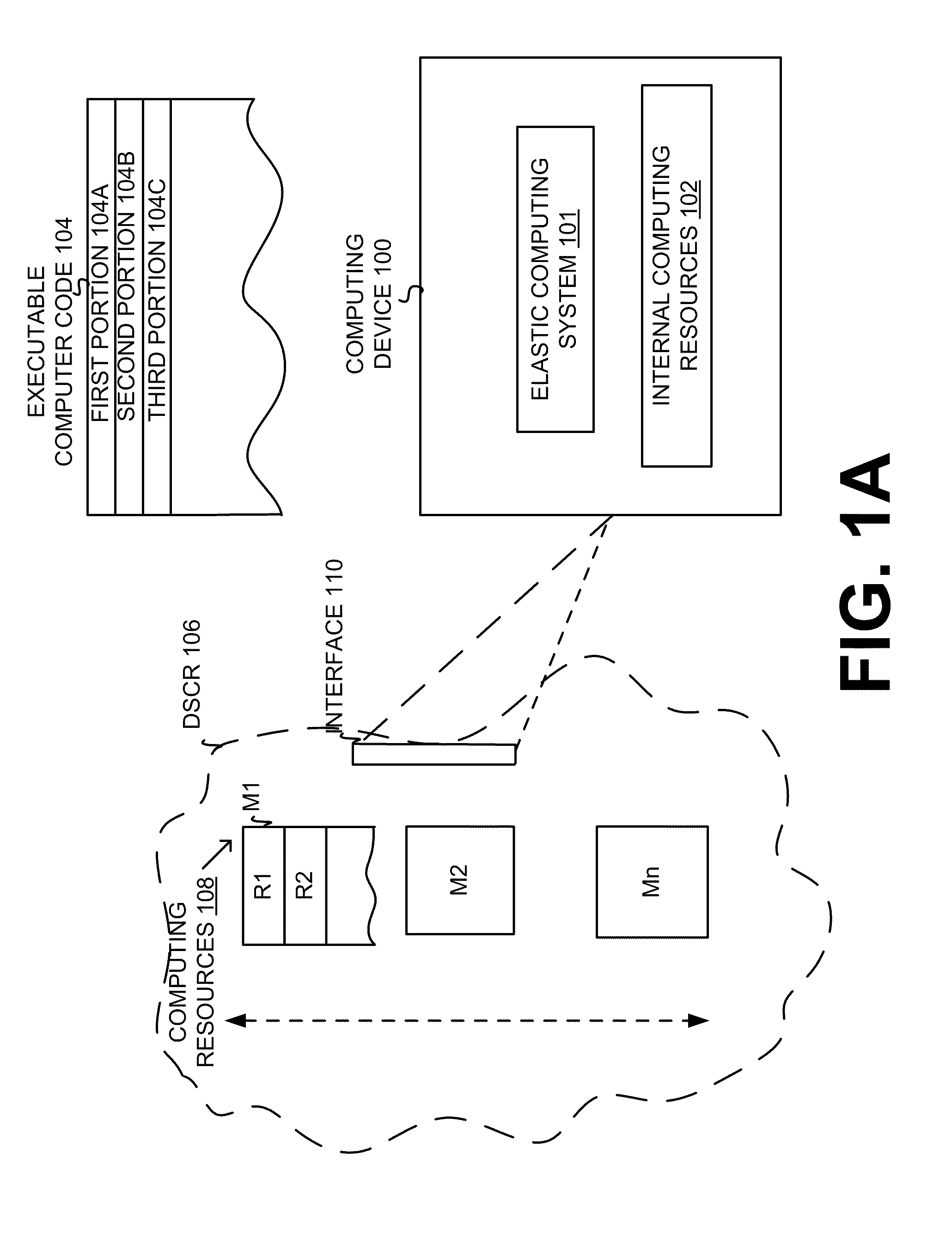
Extending the capability of computing devices by using dynamically scalable external resources
InactiveUS20100131590A1Limited and/or reduce computing resourceEffective migrationResource allocationMultiple digital computer combinationsDynamic ExtensionOn demand
Techniques for extending the capabilities of computing environments and / or systems are disclosed. A scalable and dynamic external computing resource can be used in order to effectively extend the internal computing capabilities of a computing environment or system. The scalable and dynamic external computing resource can provide computing resources that far exceed the internal computing resources, and provide the services as needed, and in a dynamic manner at execution time. As a result, a computing device may function with relatively limited and / or reduced computing resources (e.g., processing power, memory) but have the ability to effectively provide as much computing services as may be needed, and provide the services when needed, on demand, and dynamically during the execution time.
Owner:SAMSUNG ELECTRONICS CO LTD
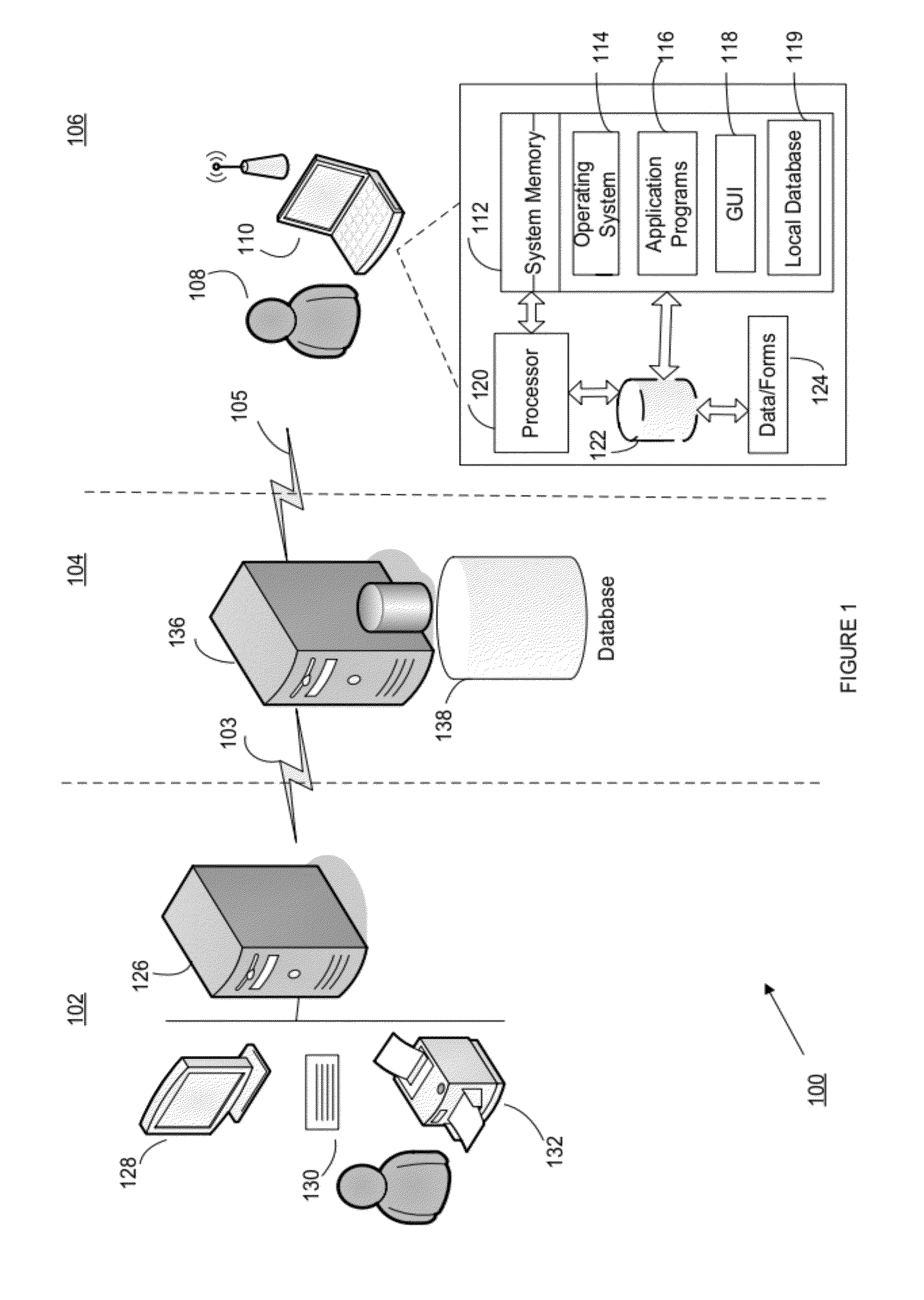
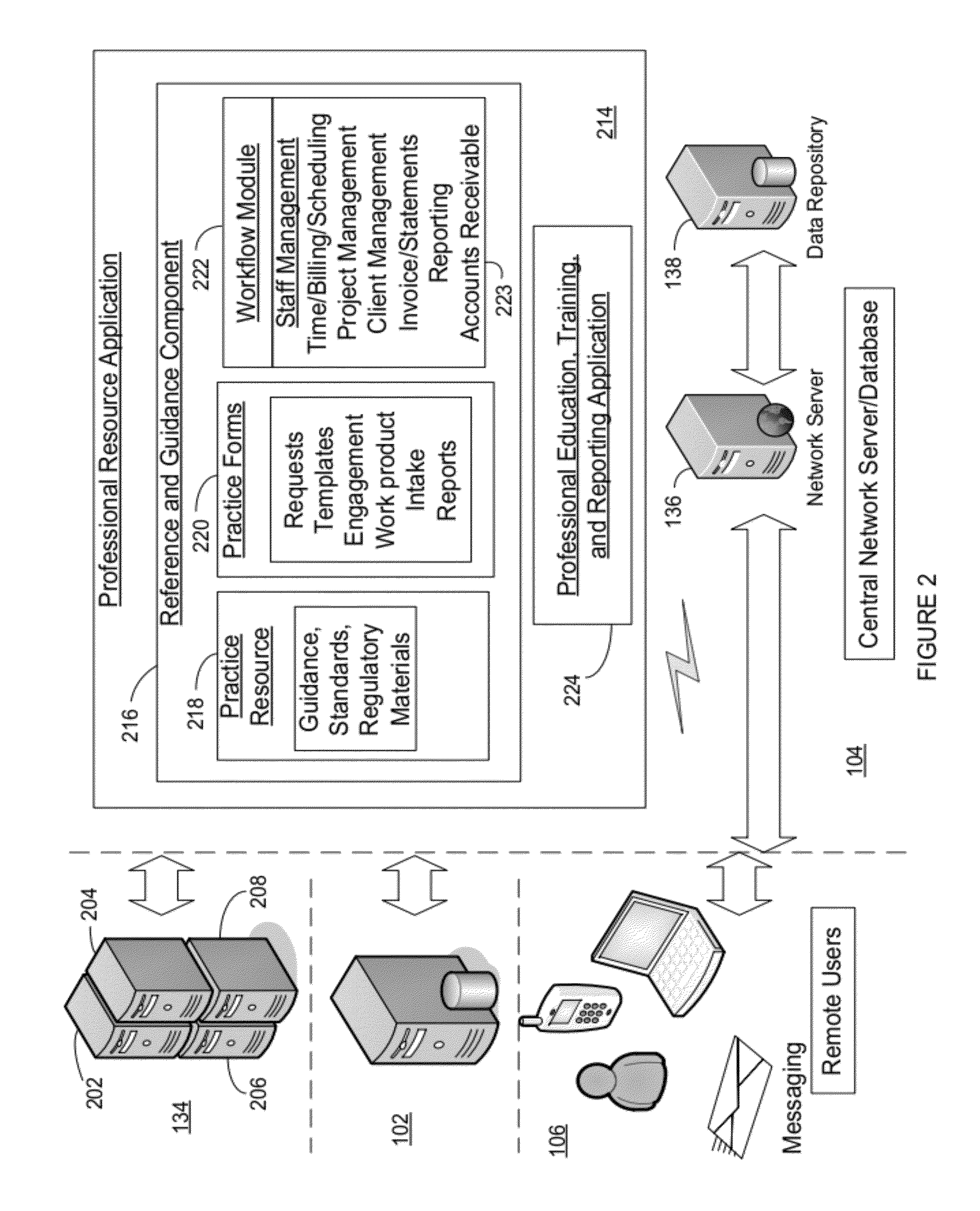
Method and system for implementing workflows and managng staff and engagements
ActiveUS20120215578A1Long unmet needEffectively and efficiently allocateOffice automationResourcesKnowledge managementSoftware modules
The present invention relates to software and a method of use for implementing workflows and managing engagements and staff. More particularly, the present invention relates to a software module tracking data of staff, engagements and workflows and a method of using such data in the management of staff and assignment of tasks. Information concerning employees is input into a database by the manager and the employees, and is tracked therein. The information concerning an employee includes an employee's availability, ability and experience. Workflow / Task information is input into the database when either a client makes a request for service of the business, or a workflow / task internal to the business is needed to be performed. Task information includes the nature of the work and deadlines. Task information is compared to the employee information. A list is automatically generated naming the employees best suited to the mandate of the task. The manager then chooses a name from the top of the list and assigns the task to that employee.
Owner:THOMSON REUTERS ENTERPRISE CENT GMBH
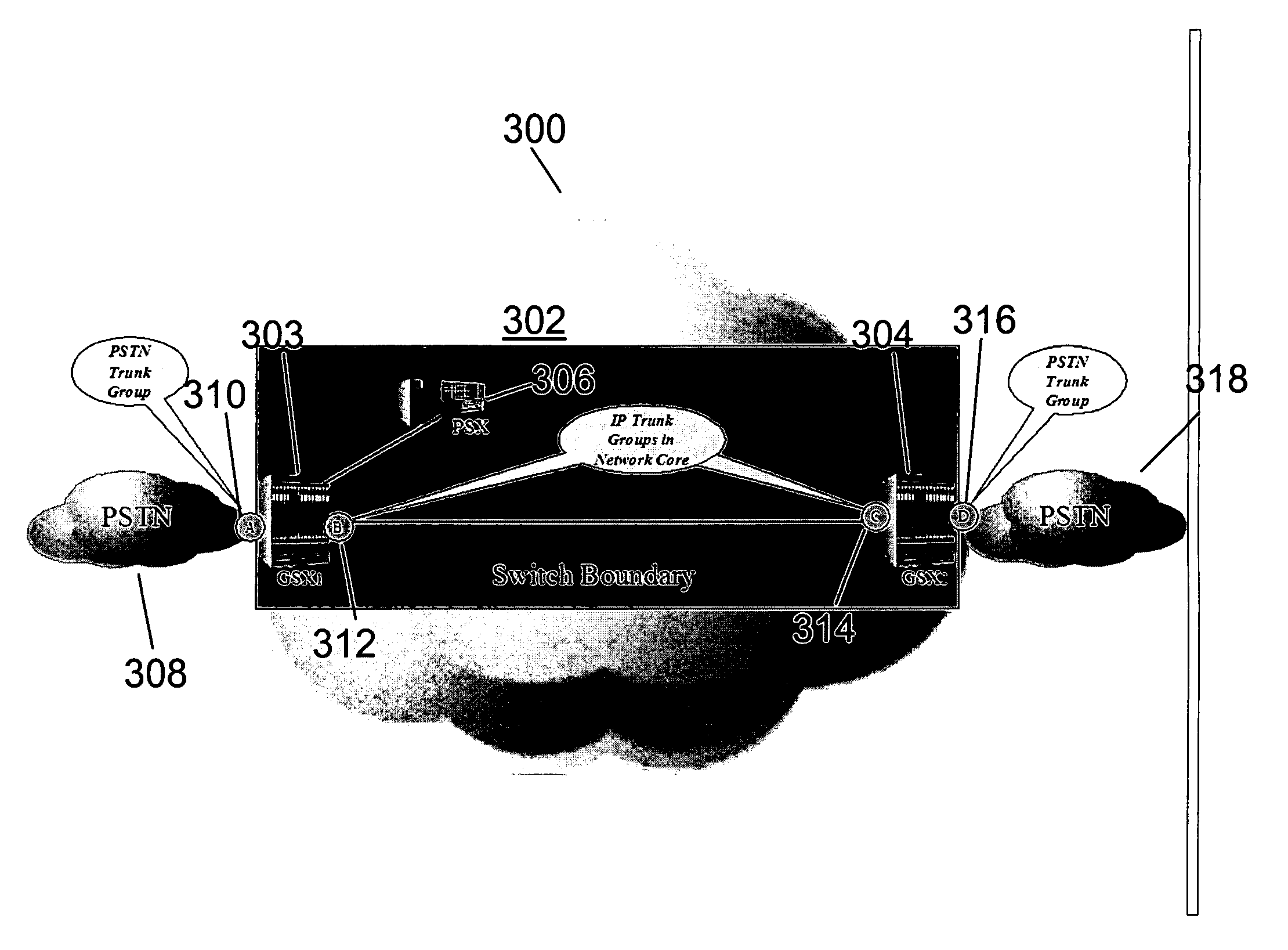
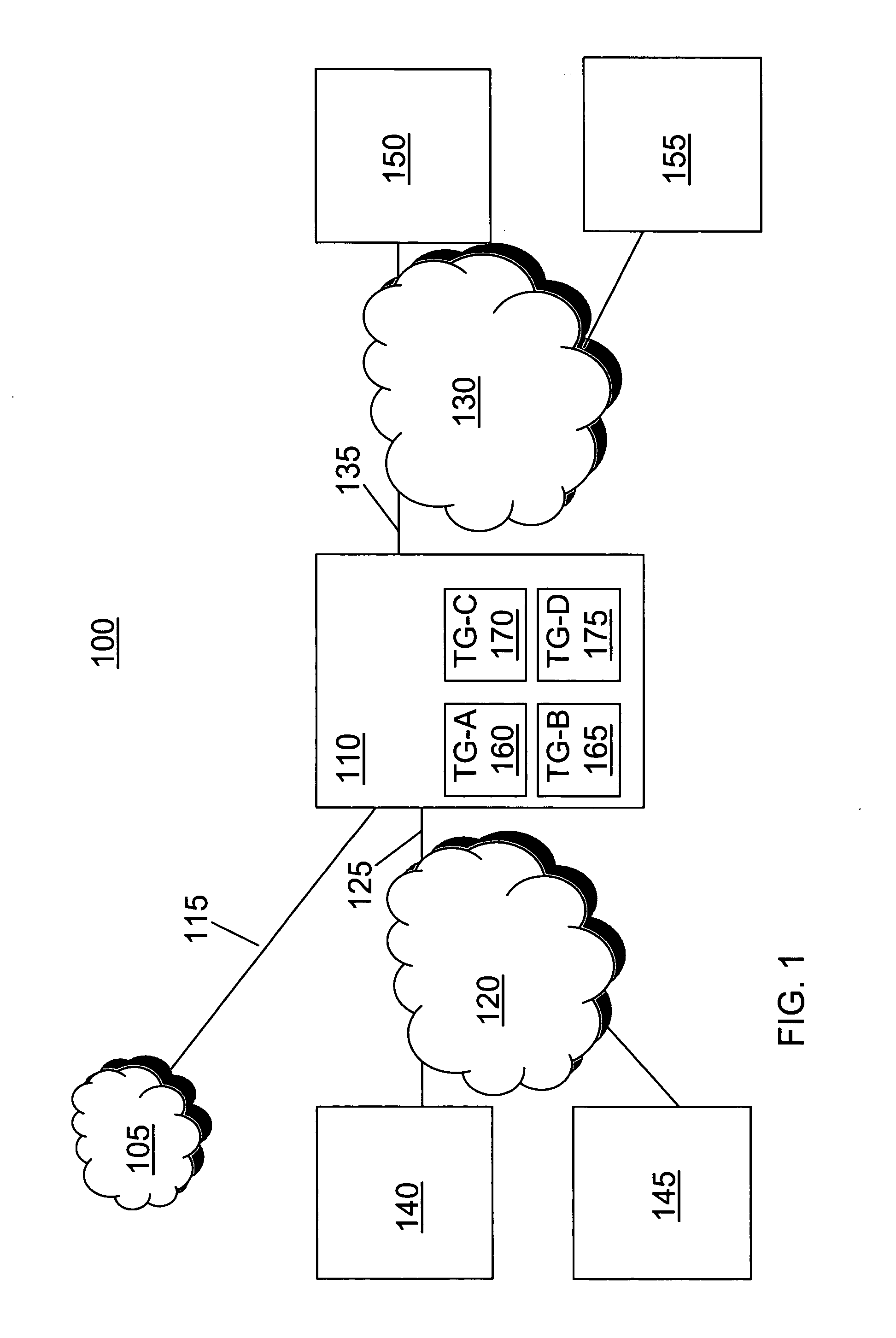
Defining logical trunk groups in a packet-based network
InactiveUS20060072555A1Improve scalabilityEasy to handleEnergy efficient ICTInterconnection arrangementsNetwork packetDistributed computing
Described are methods and apparatus, including computer program products, for defining logical trunk groups in a packet-based network. A plurality of logical trunk groups are defined for a first media gateway in communication with a packet-based network. Each of the plurality of logical trunk groups is associated with one or more media gateways in communication over the packet-based network with the first media gateway. Data associated with a call that is received or transmitted by the media gateway is associated with a first logical trunk group of the plurality of logical trunk groups.
Owner:SONUS NETWORKS
Using execution statistics to select tasks for redundant assignment in a distributed computing platform
InactiveUS7093004B2Minimizes unnecessary network congestionImprove deploymentResource allocationMultiple digital computer combinationsOff the shelfSelf adaptive
The invention provides an off-the-shelf product solution to target the specific needs of commercial users with naturally parallel applications. A top-level, public API provides a simple “compute server” or “task farm” model that dramatically accelerates integration and deployment. A number of described and claimed adaptive scheduling and caching techniques provide for efficient resource and / or network utilization of intermittently-available and interruptible computing resource in distributed computing systems.
Owner:DATASYNAPSE
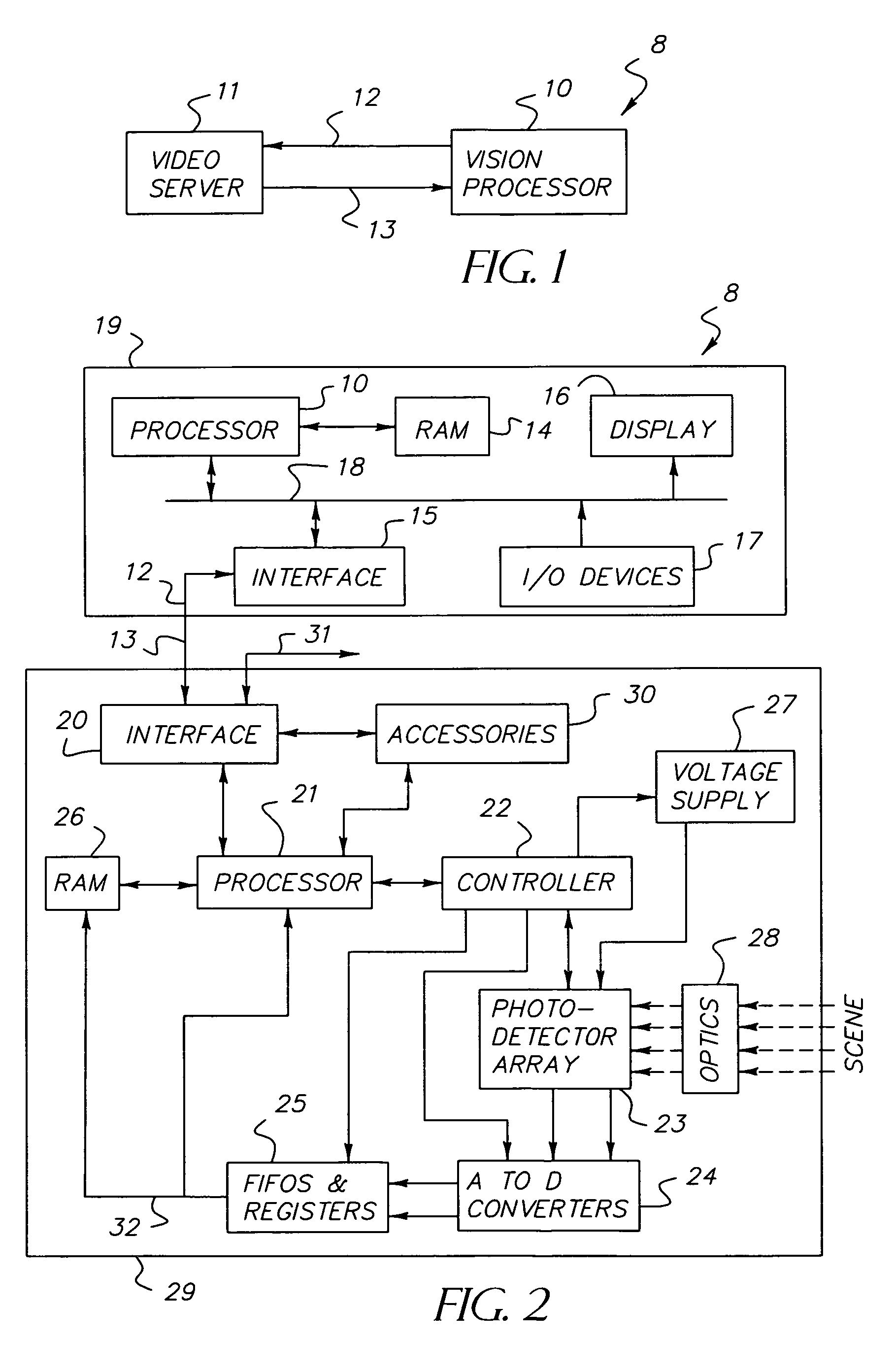
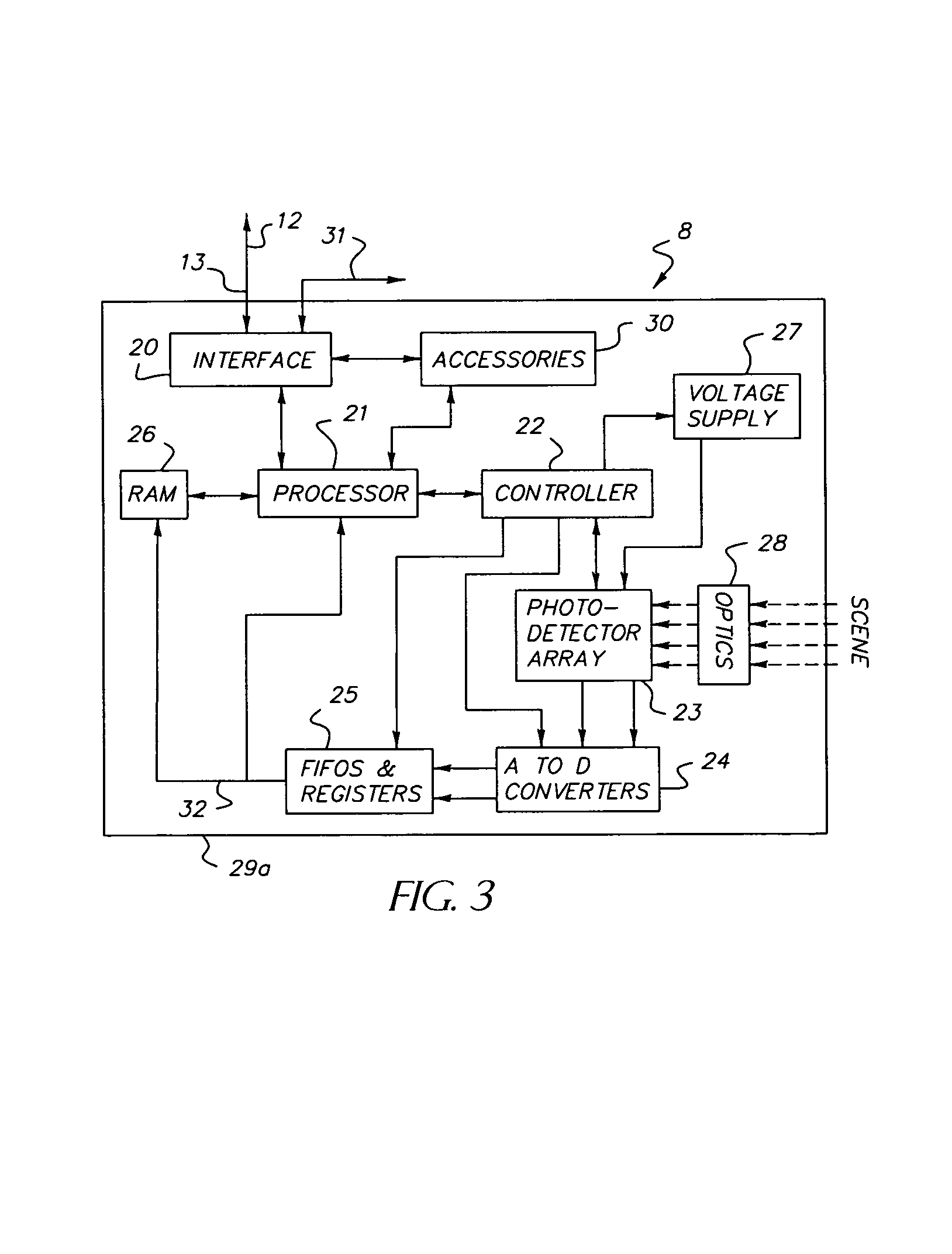
Dynamically reconfigurable vision system
InactiveUS7106374B1Efficiently usEffective resourcesTelevision system detailsTelevision system scanning detailsVision processingPhotodetector
A closed-loop vision system is disclosed that utilizes a concept known as Dynamically Reconfigurable Vision (DRV), which is adaptive image sensing driven by a computer or human operator's response to changing scenery. The system reduces the amount of irrelevant video information sensed and thus achieves more effective bandwidth and computational resource utilization, as compared to traditional vision systems. One or more reconfigurable photodetector arrays sensitive to either visible, infrared or ultraviolet radiation are present in the DRV system. These photodetector arrays feature on-chip means for spatial and temporal data reduction implemented through multiple independently controllable, time-correlated, frequently overlapping windows on the photodetector array that may be programmed according to their size, location, resolution, integration time, and frame rate. All photodetector array windows are dynamically reconfigurable in real time on a frame-by-frame basis. Furthermore, a DRV system is constructed in a client-server architecture in which a vision processor client passes window request command messages to the reconfigurable photodetector array server, which in turn delivers the requested video back to the client processor. The ability to simultaneously reconfigure, integrate, process, and readout multiple photodetector array video windows is an important characteristic of the DRV system.
Owner:COMPTEK AMHERST SYST INC
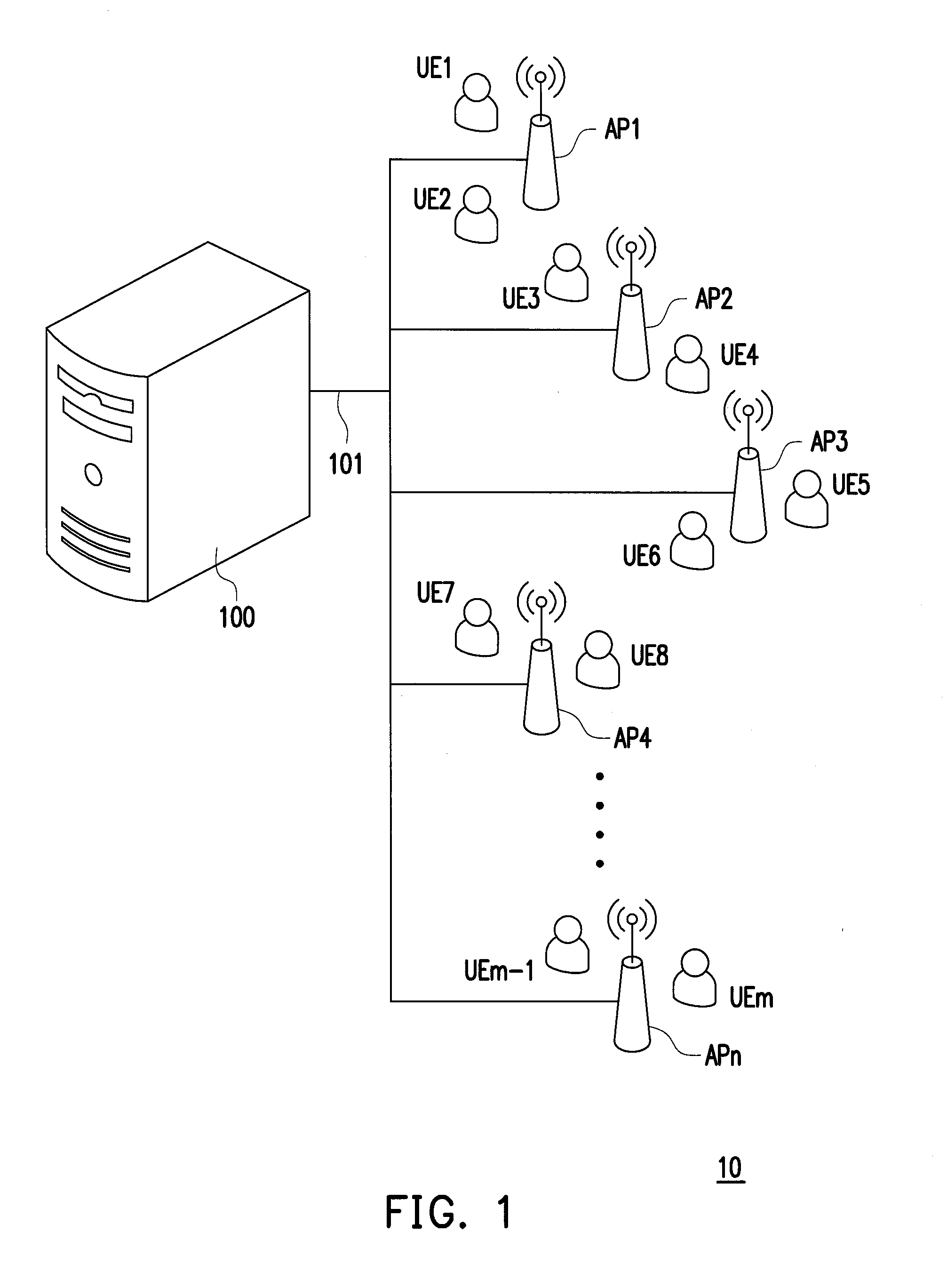
Access point and communication system for resource allocation
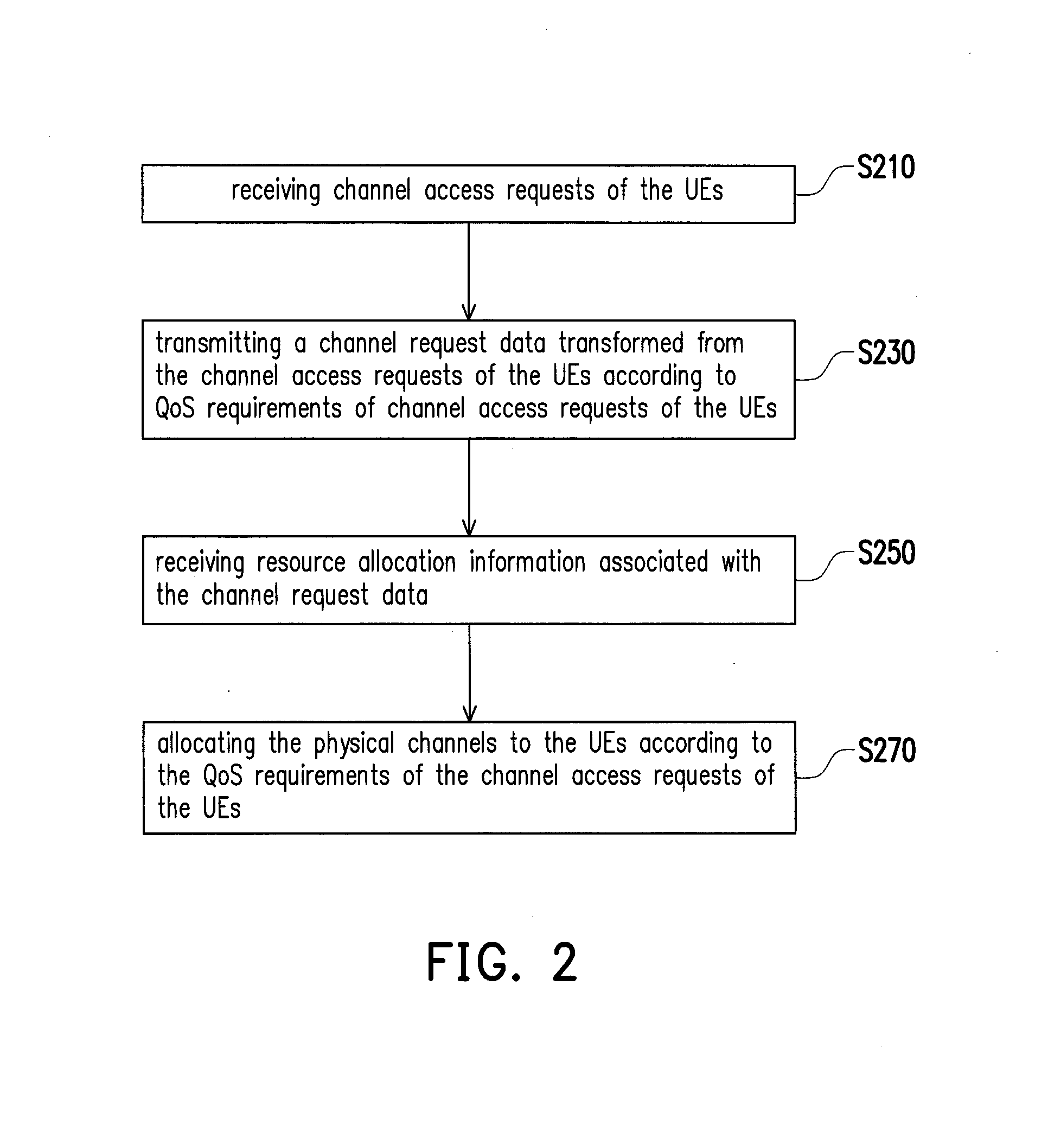
ActiveUS20150055633A1Efficient use of resourcesGuaranteed data transmission efficiencyPower managementNetwork traffic/resource managementCommunications systemTransceiver
An access point (AP) and a communication system are provided. The access point comprises at least but not limited to a transceiver, a network connection unit, and a processing circuit. The processing circuit is configured for the following steps. The AP receives channel access requests of the user equipments (UEs) from the UEs. Next, the AP transmits a channel request data according to QoS requirements of plurality of channel access requests of the UEs to the server. Afterward, the AP receives resource allocation information associated with the channel request data from the server, wherein the resource allocation information comprises an allocated result of physical channels and transmission power configurations. Subsequently, the AP allocates the physical channels to the UEs according to the QoS requirements of the channel access requests of the UEs and the resource allocation information.
Owner:NAT CHIAO TUNG UNIV
Method for dynamically reprovisioning applications and other server resources in a computer center in response to power and heat dissipation requirements
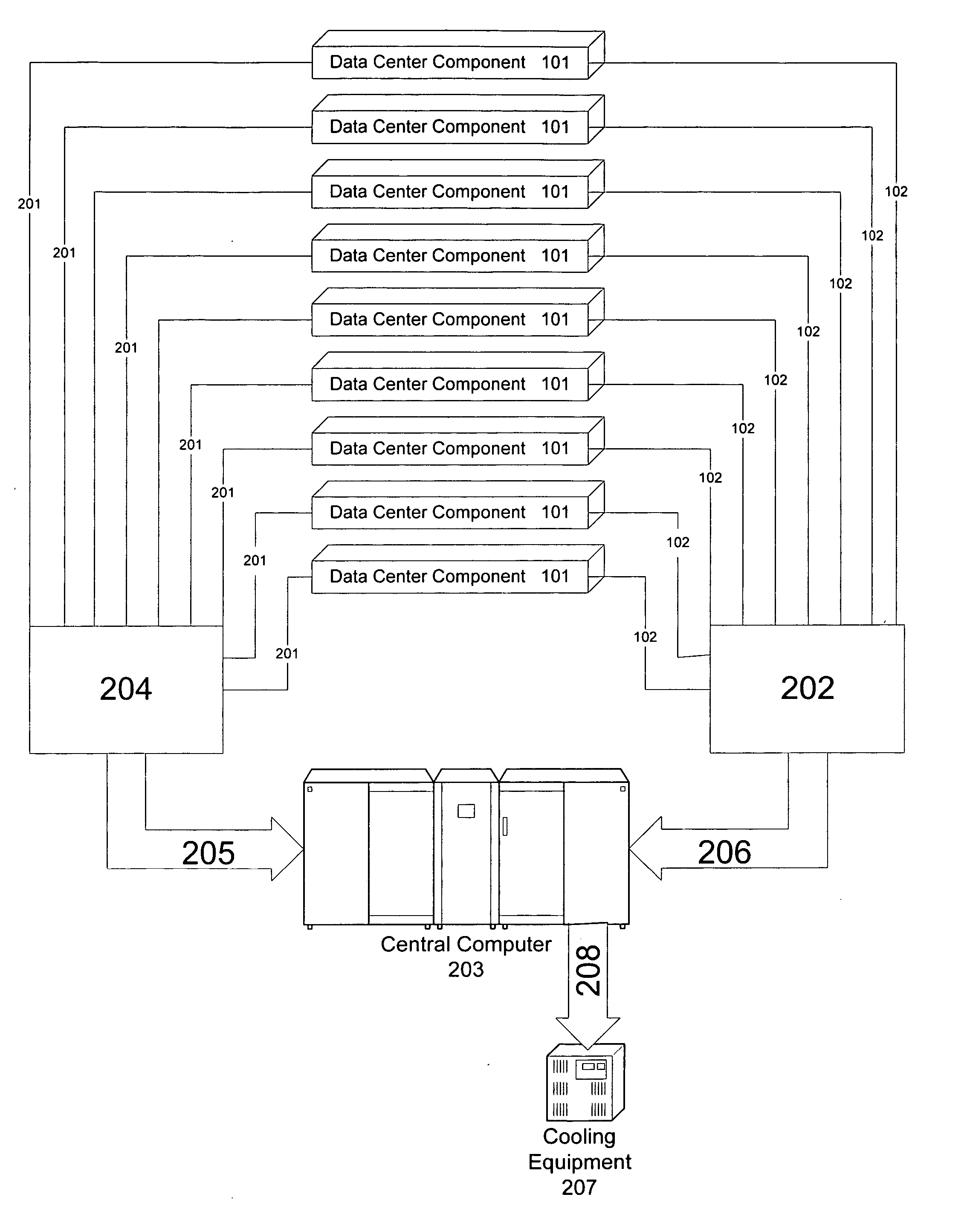
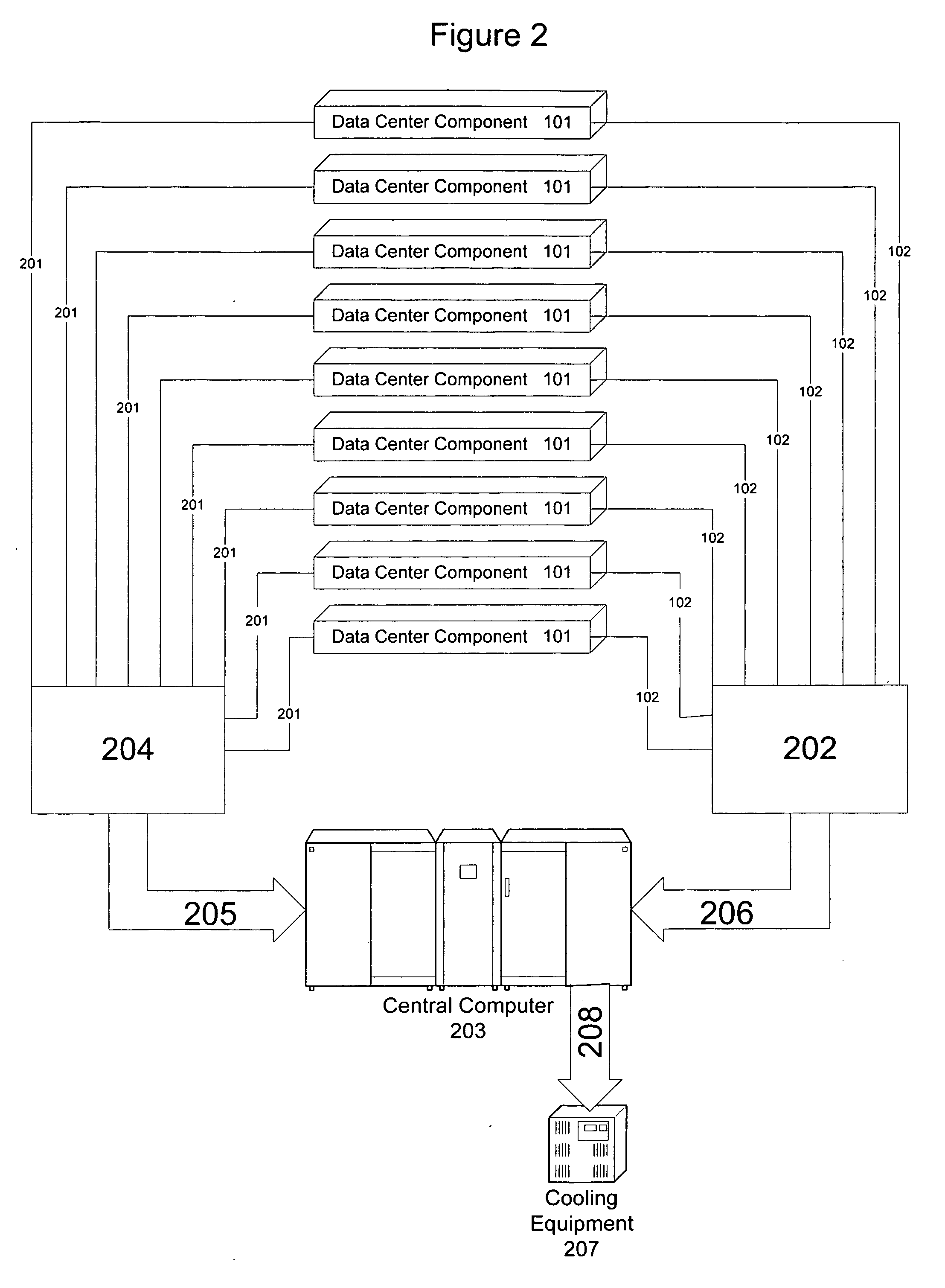
InactiveUS20060112286A1Improve it internal algorithm and modelEffective resourcesEnergy efficient ICTVolume/mass flow measurementMultiple applicationsApplication software
Applications and other server resources in a computer center are dynamically reprovisioned in response to power consumption and heat dissipation loads. Power consumption and temperature of each of a plurality of data center components which comprise the computer center are monitored. Based on the monitored power consumption and temperature, one or more applications from one or more data center components are relocated to other data center components of the computer center as needed to change power consumption and heat dissipation loads within the computer center. Also, based on the monitored power consumption and temperature, one or more applications running on one or more data center components of the computer center may be rescheduled as needed to change power consumption and heat dissipation loads within the computer center. Cooling devices within the computer center may also be controlled as needed to change heat dissipation loads within the computer center.
Owner:IBM CORP
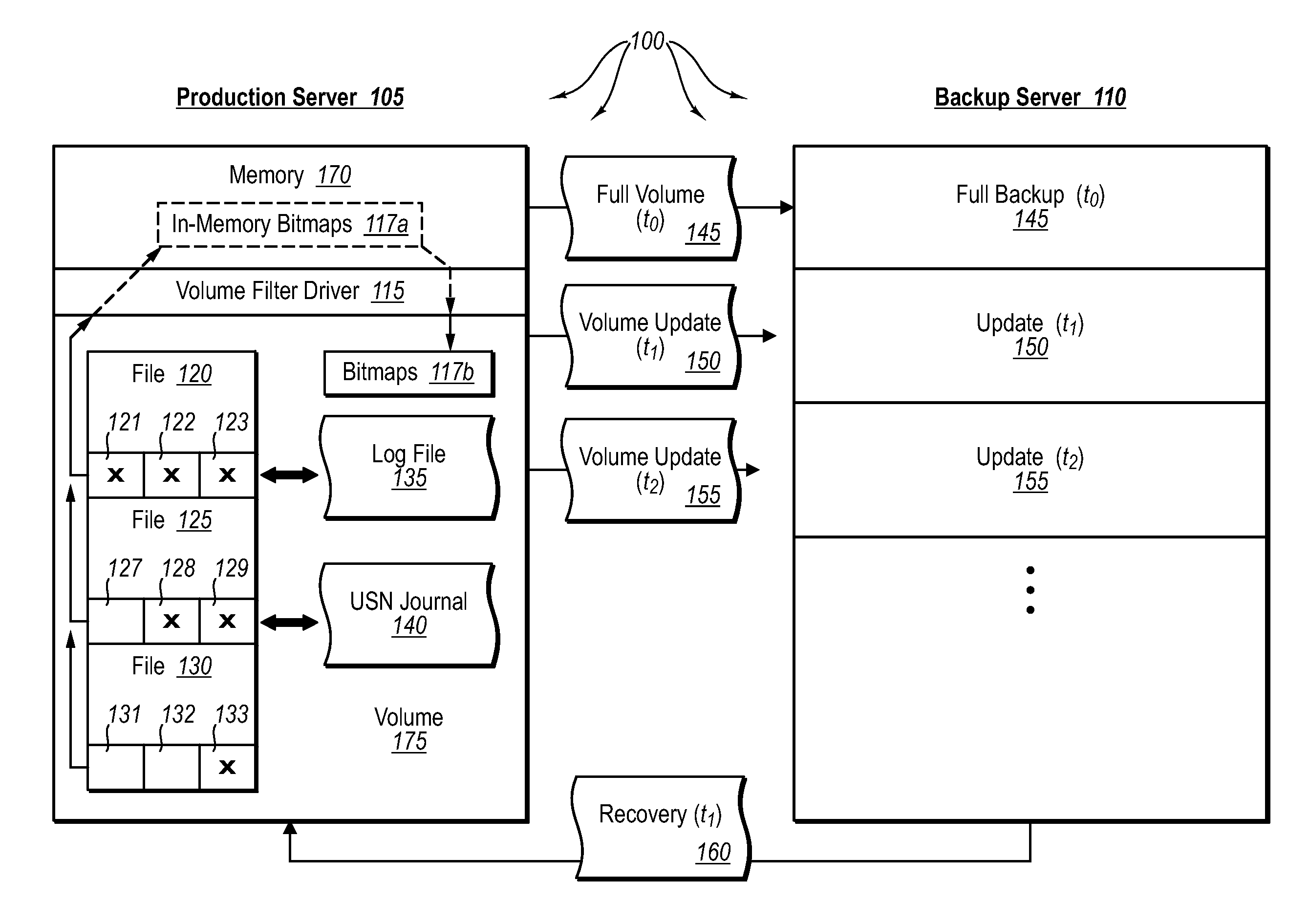
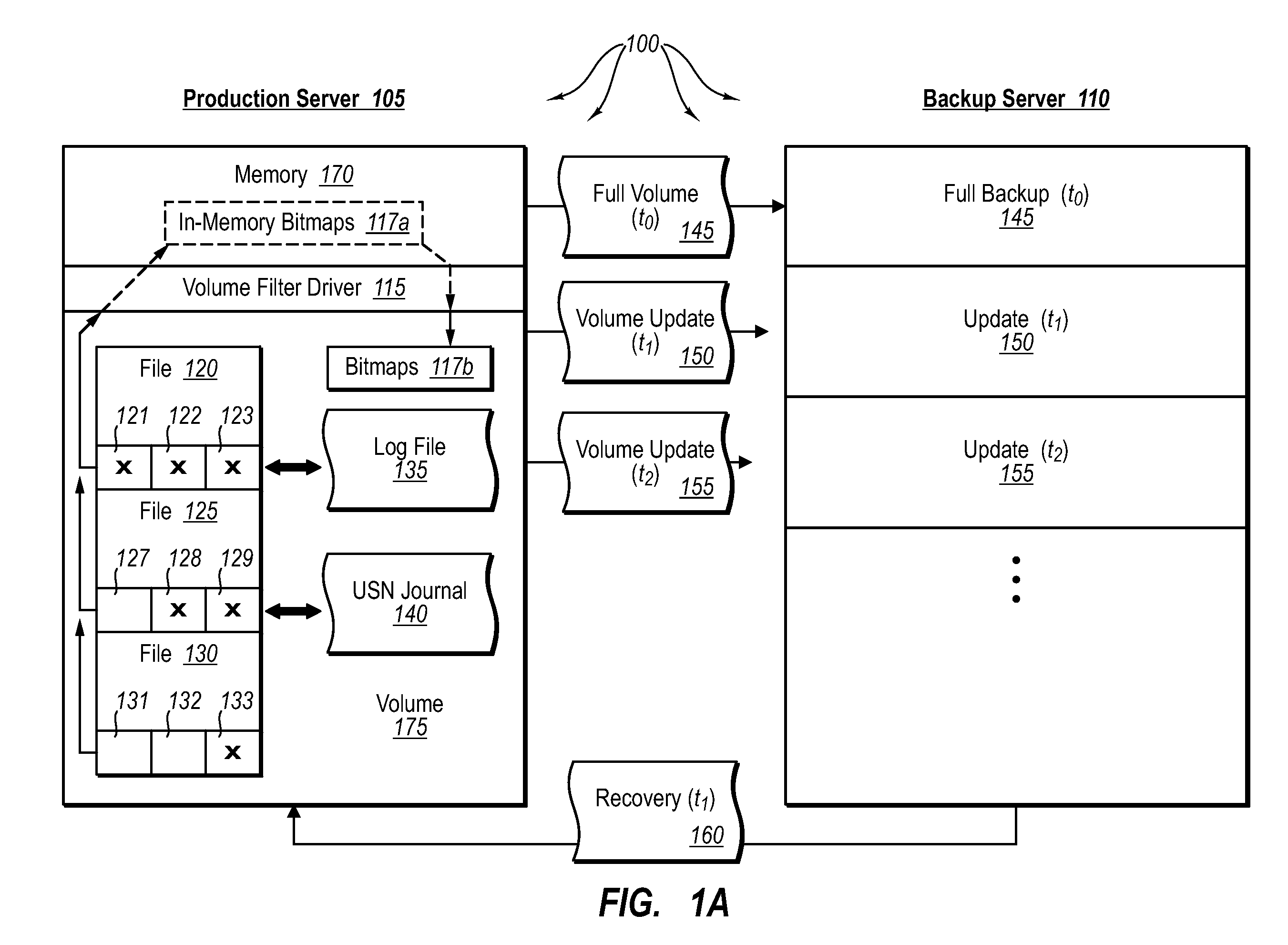
Creating frequent application-consistent backups efficiently
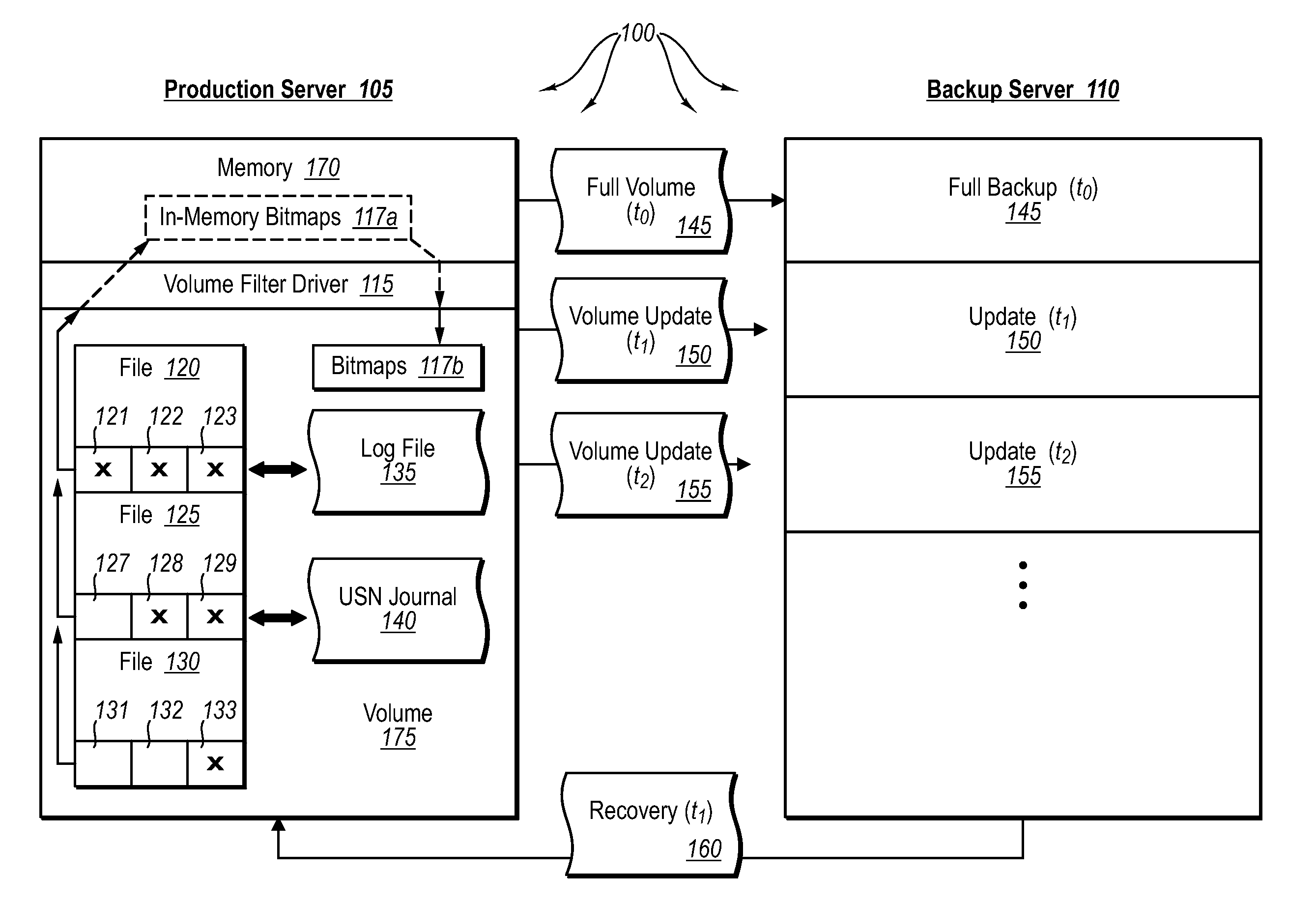
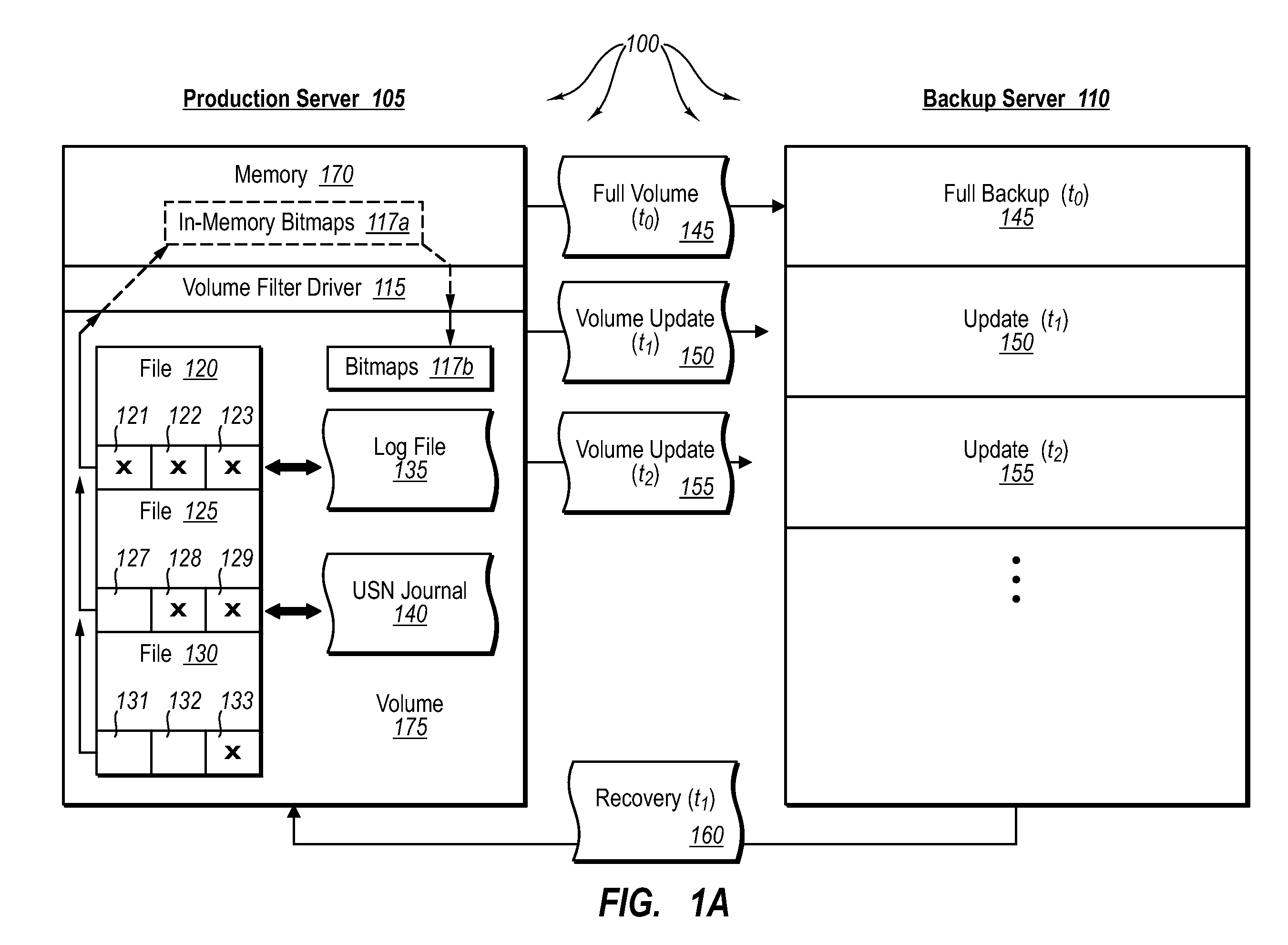
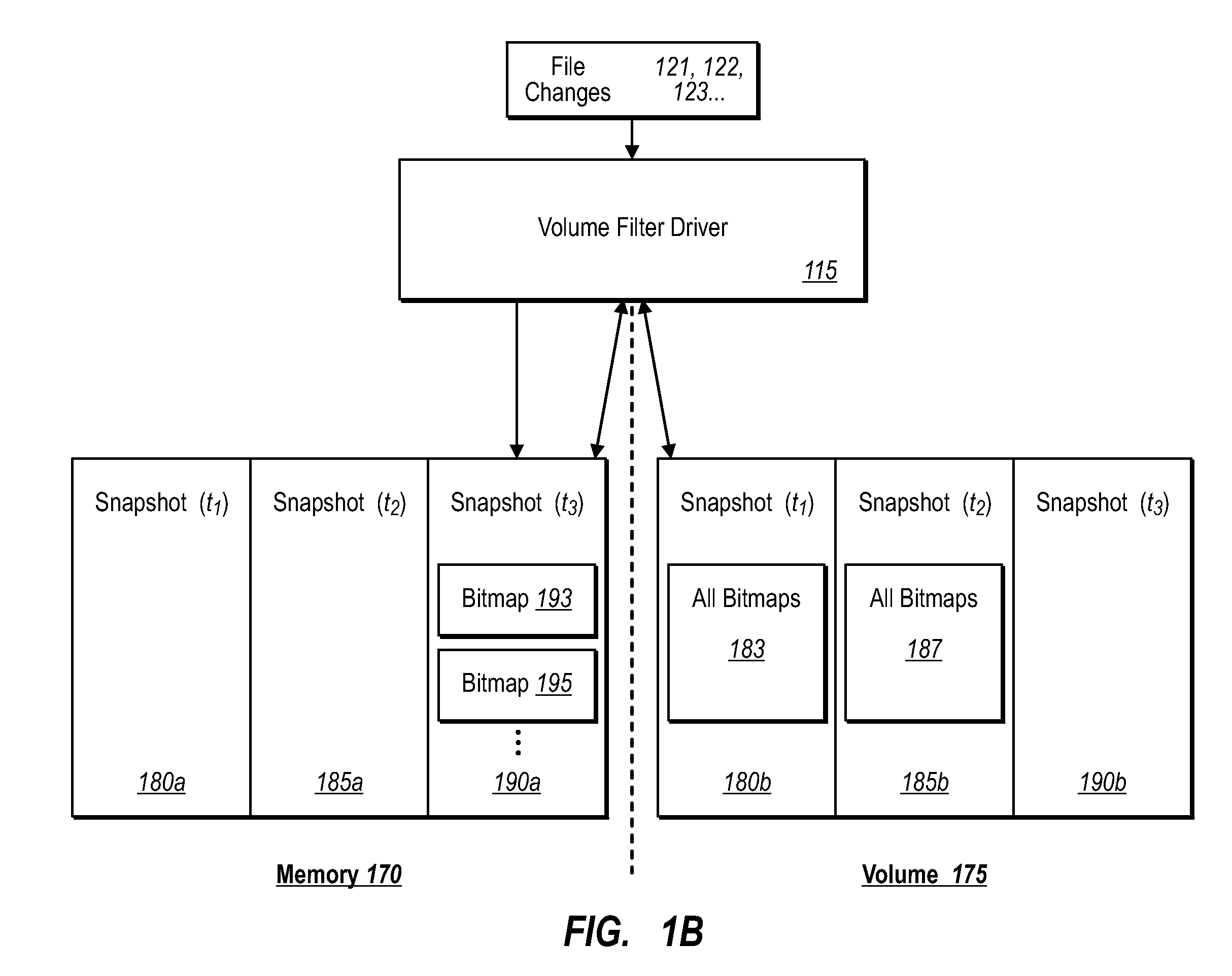
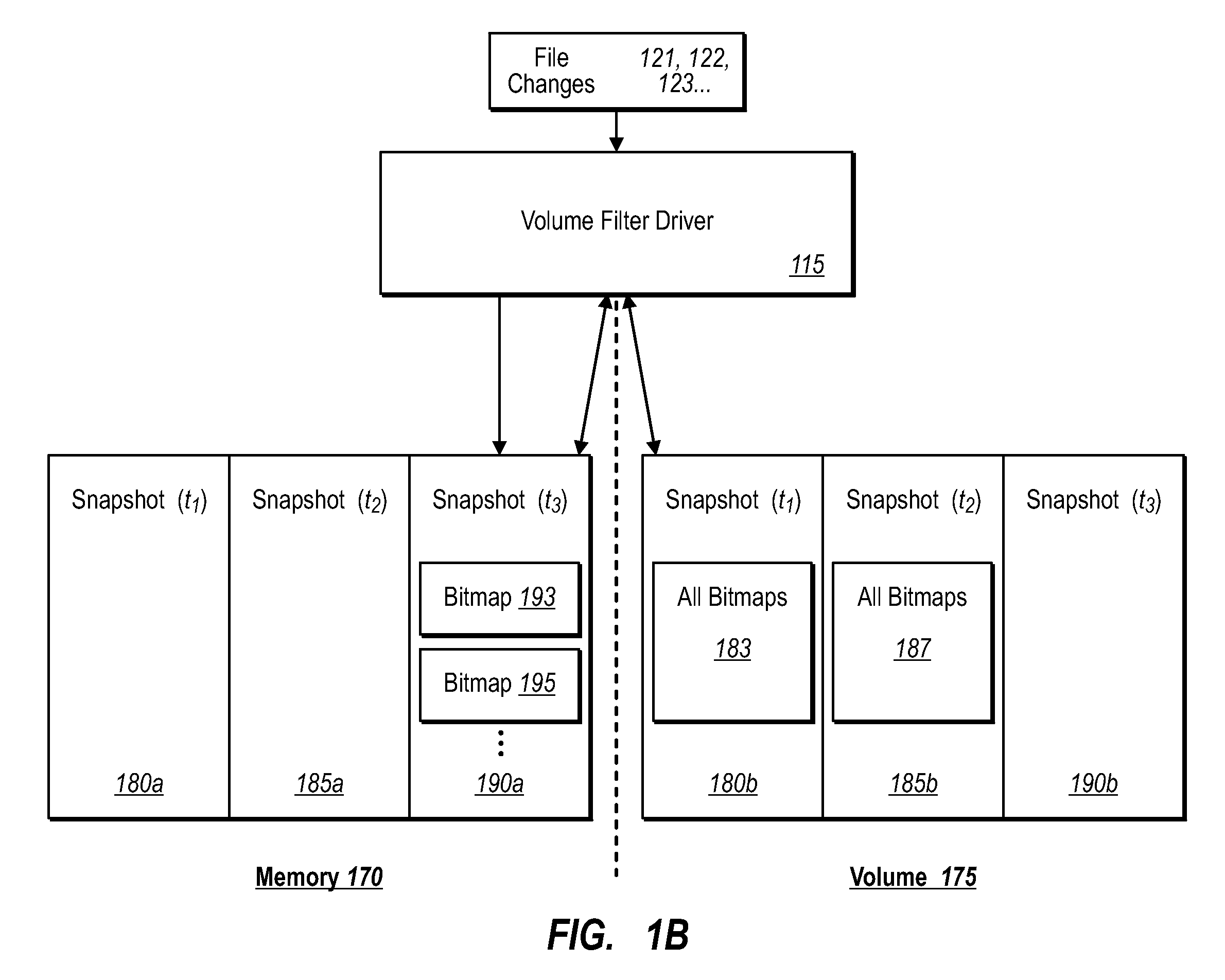
ActiveUS20070276885A1Save resourcesProduction serverData processing applicationsMemory loss protectionApplication softwareBitmap
Data can be protected at a production server in a virtually continuous fashion, without necessarily imposing severe constraints on the source application(s). For example, a production server can create an application-consistent backup of one or more volumes, the backups corresponding to a first instance in time. A volume filter driver can monitor data changes in each volume using an in-memory bitmap, while a log file and / or update sequence number journal can keep track of which files have been added to or updated. The volume updates are also consistent for an instance (later) in time. At the next replication cycle, such as every few minutes (however configured), the volume filter driver passes each in-memory bitmap to the physical disk on the production server. The production server then sends the updates to the backup server, which thus stores application-consistent backups for the volume for multiple instances of time.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for intelligent medical vigilance
InactiveUS20070156031A1Improve abilitiesEffective resourcesCatheterRespiratory organ evaluationSensor arrayDisplay device
An intelligent medical vigilance system that observes and analyzes, and, only in the event of a clinically significant negative condition, notifies and reports the event to the care staff utilizing the hospital's existing nurse call system. The device includes a bedside unit connected to a pad or coverlet with a sensor array (placed under the patient) and also to an existing hospital nurse call system via an interface. Within the physical bedside unit are a signal processor and an alarm processor that measure data and evaluate whether a clinically significant event is occurring. The bedside unit is a wall-mounted unit with a display that becomes active when an alarm condition is enabled. The sensing pad or coverlet is a thin, piezoelectric film, or other similar sensing technology, with an array of sensors sheathed in soft padding and is not directly in contact with the skin of the patient. The nurse call feature is made up of hardware, software and cabling to connect to the nurse call system already installed in the hospital or care facility. The monitoring system can also be installed in vehicles to monitor operator physiological conditions. Vigilance alarms are suspended if a patient is detected out of bed. An unable-to-measure alert is provided if the system is unable to reliably monitor. Bed exit alarms can be placed into a pause mode for supervised bed exit of patients on bed restriction. An alert message is generated and maintained on the display screen to inform a responding caregiver of the time and reason for any alarm.
Owner:HOANA MEDICAL
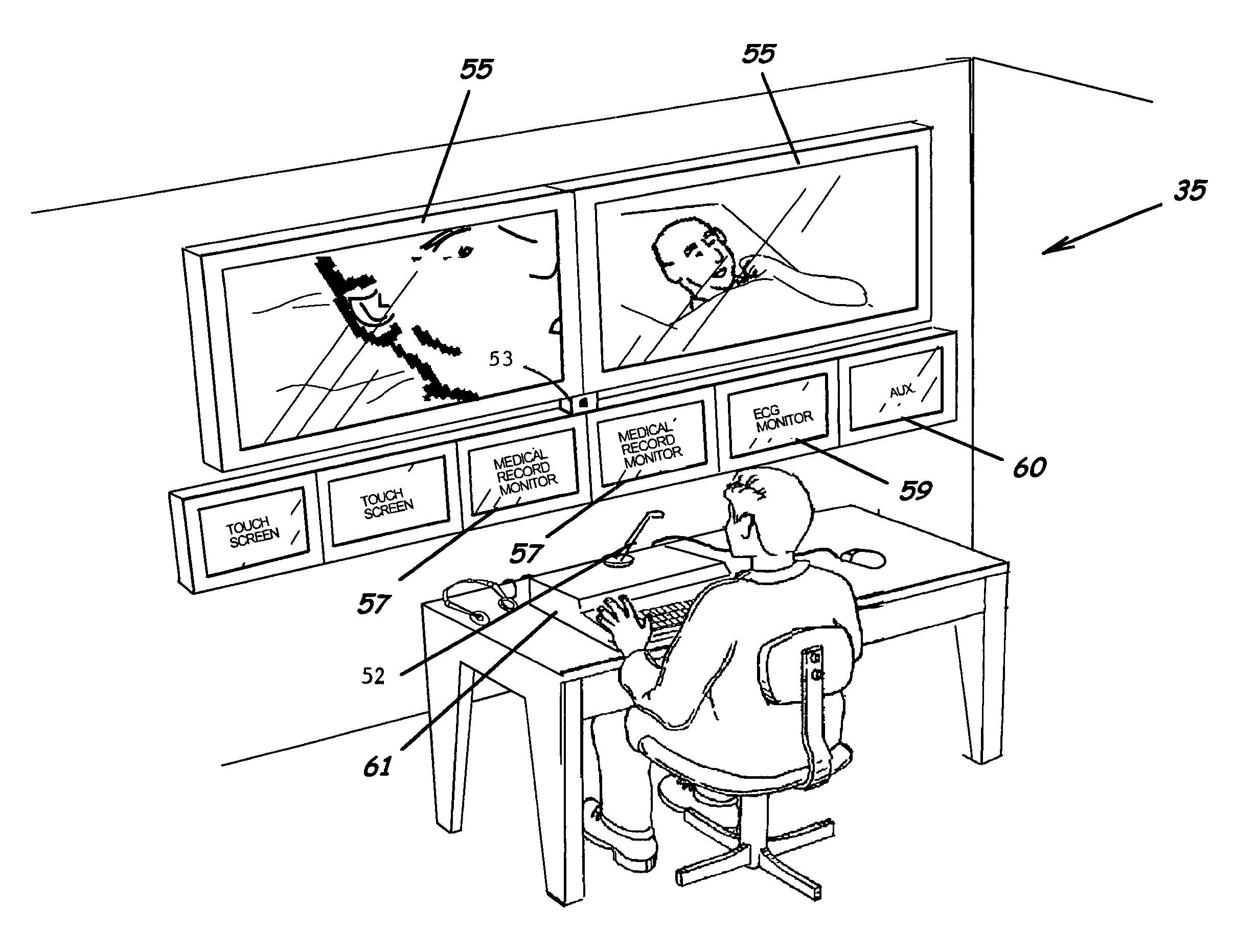
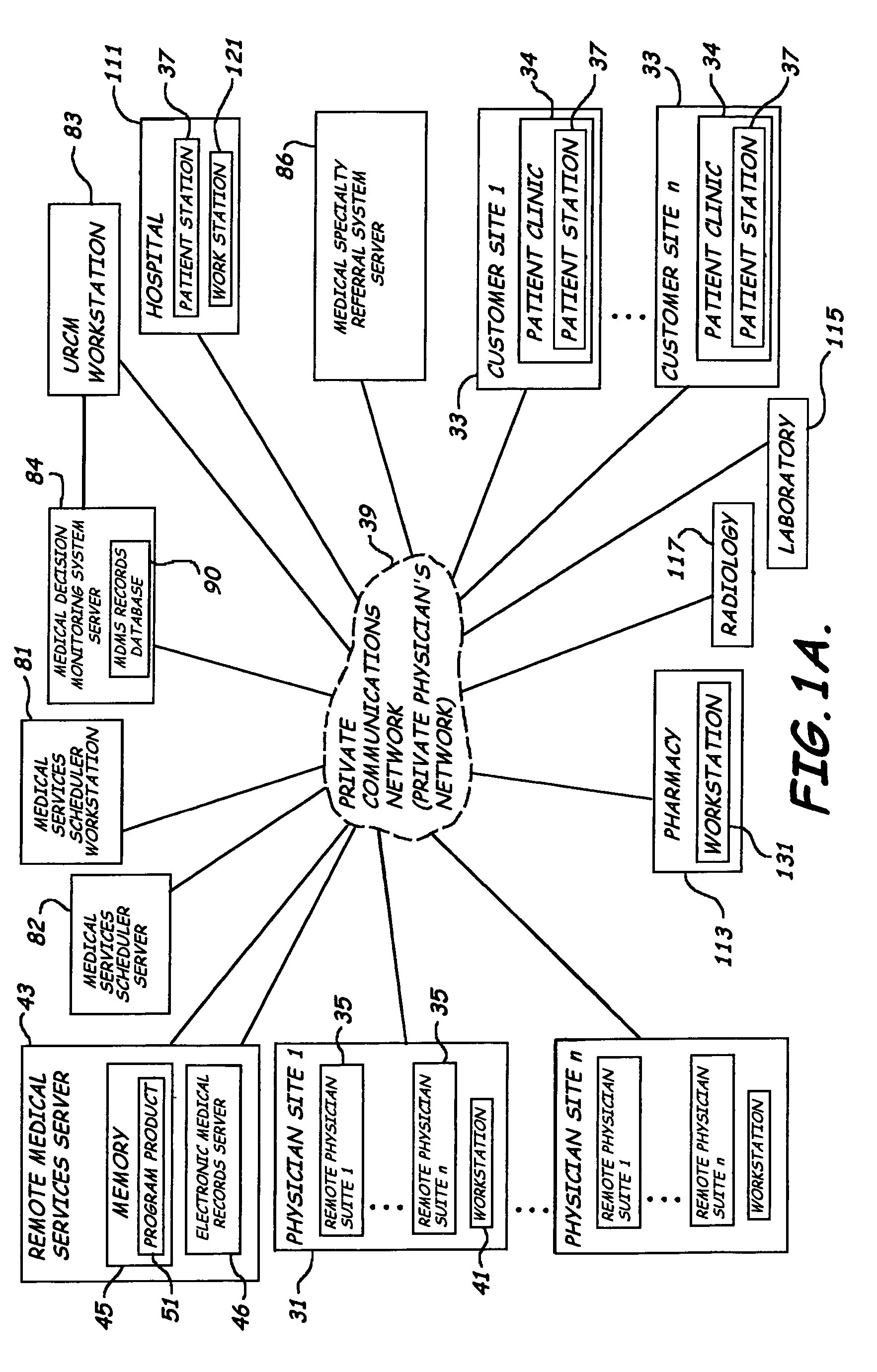
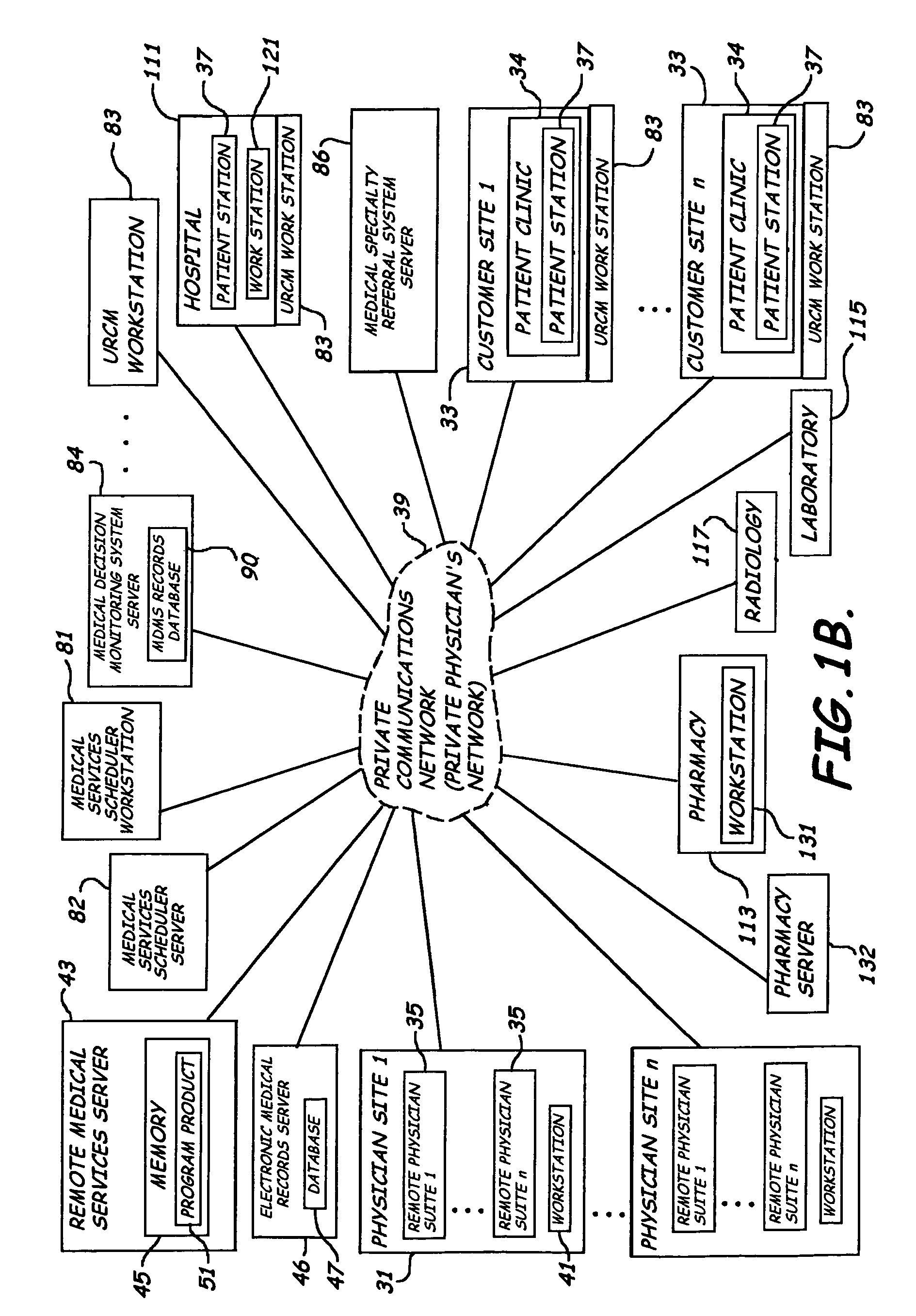
System, method and program product for delivering medical services from a remote location
ActiveUS7912733B2Enhanced medical service deliveryEffective resourcesMedical communicationData processing applicationsMedical recordDelivery suite
A system, program product, and methods related to enhanced medical services delivery to geographically distributed patient populations by remotely located physicians are provided. An embodiment of the system includes a remote medical services server, a plurality of patient electronic medical records stored in the memory of the remote medical services server, and a remote medical services program product stored in the memory of the remote medical services server adapted to access the plurality of patient electronic medical records to thereby allow display of and data entry in a selected patient electronic medical record. A patient medical service delivery station captures patient video images and displays remote physician video images. A remote physician medical service delivery suite in communication with the patient medical service delivery station through the communications network captures remote physician video images and displays patient video images and patient electronic medical records, to allow the remote physician to perform remote patient medical service delivery.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
Distributed processing of high level protocols, in a network access server
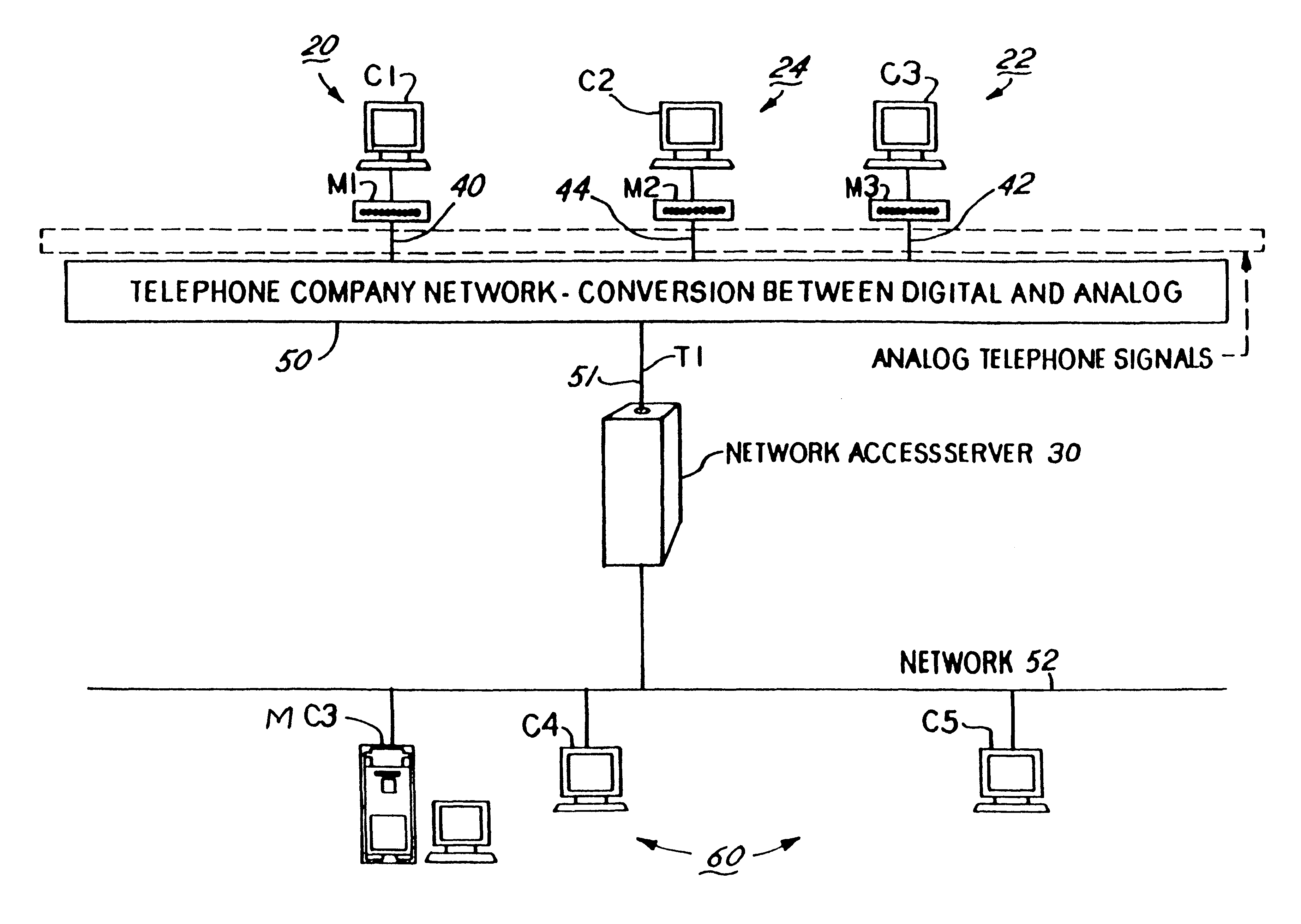
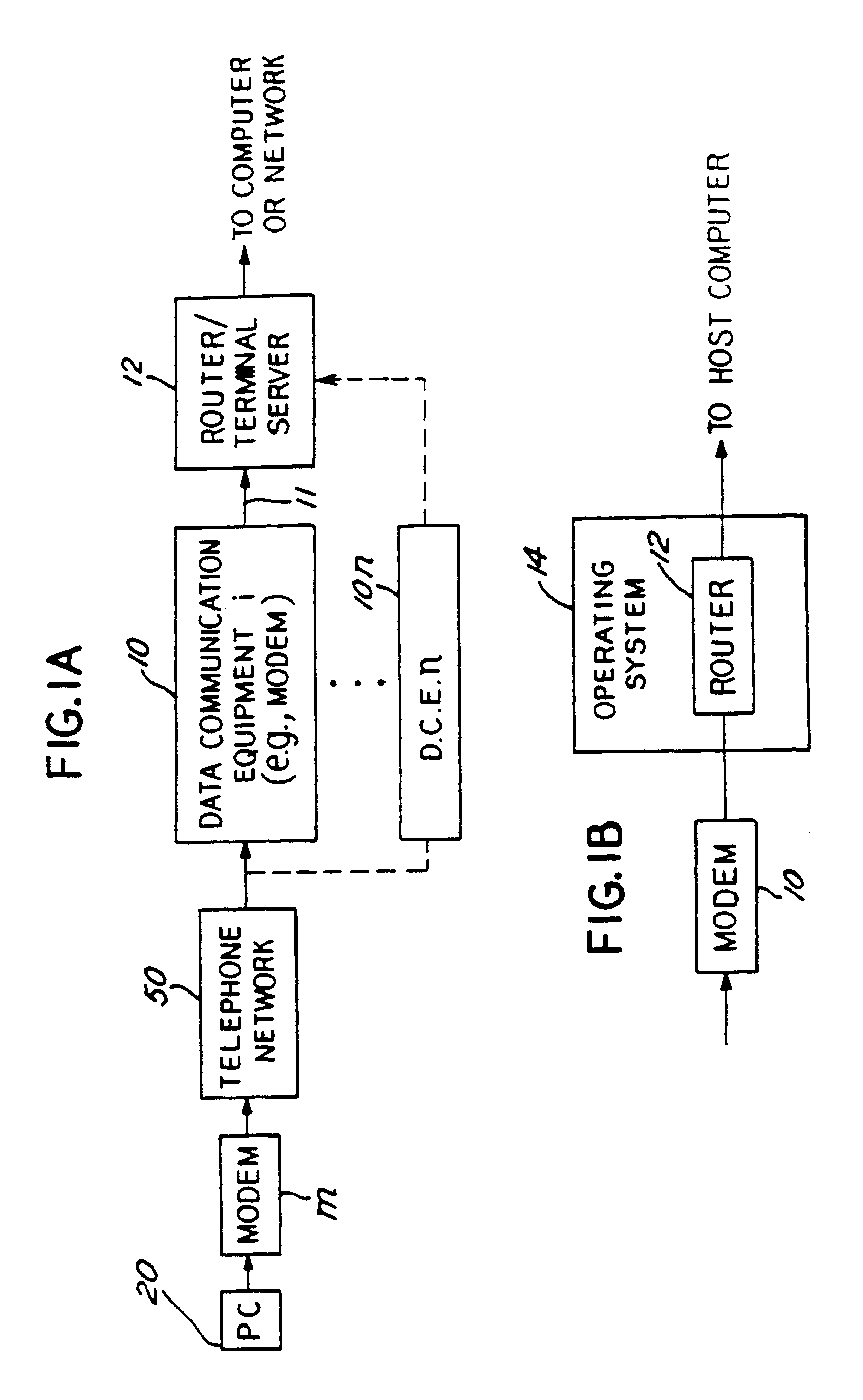
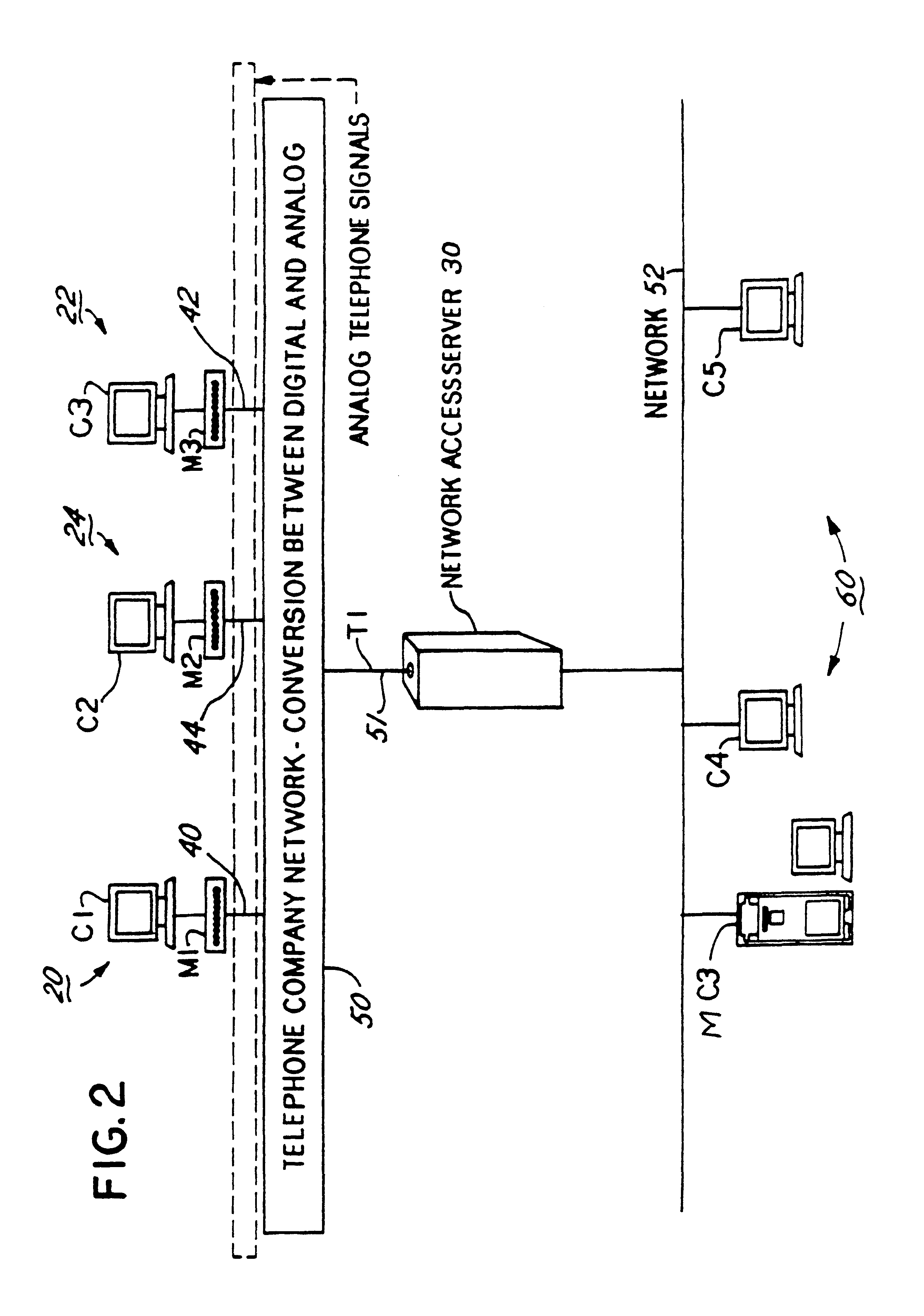
InactiveUS6304574B1Introduces latency and delayHeavy loadTelephone data network interconnectionsTime-division multiplexNetwork access serverModem device
A method and apparatus for distributing protocol processing among a plurality of computing platforms. Data communications equipment such as Remote Access Devices, Communication Servers, Terminal Servers, and Dial-up Routers provide single user or large-scale multiple user communication access to various computing environments. The equipment costs and performance of such access equipment is related to the amount of CPU processing capability and memory required to support the desired number of serial communication links. It is common to use protocols that terminate in their entirely in the same processing machine. This invention encompasses methods developed to increase the cost / performance capabilities of the communication equipment that supports these serial links, primarily by means of distributing the protocol processing for higher level protocols across multiple computing platforms, including devices such as modems. Examples of such higher level protocols include PPP, SLIP and RTP.
Owner:UTSTARCOM INC
Demand responsive method and apparatus to automatically activate spare servers
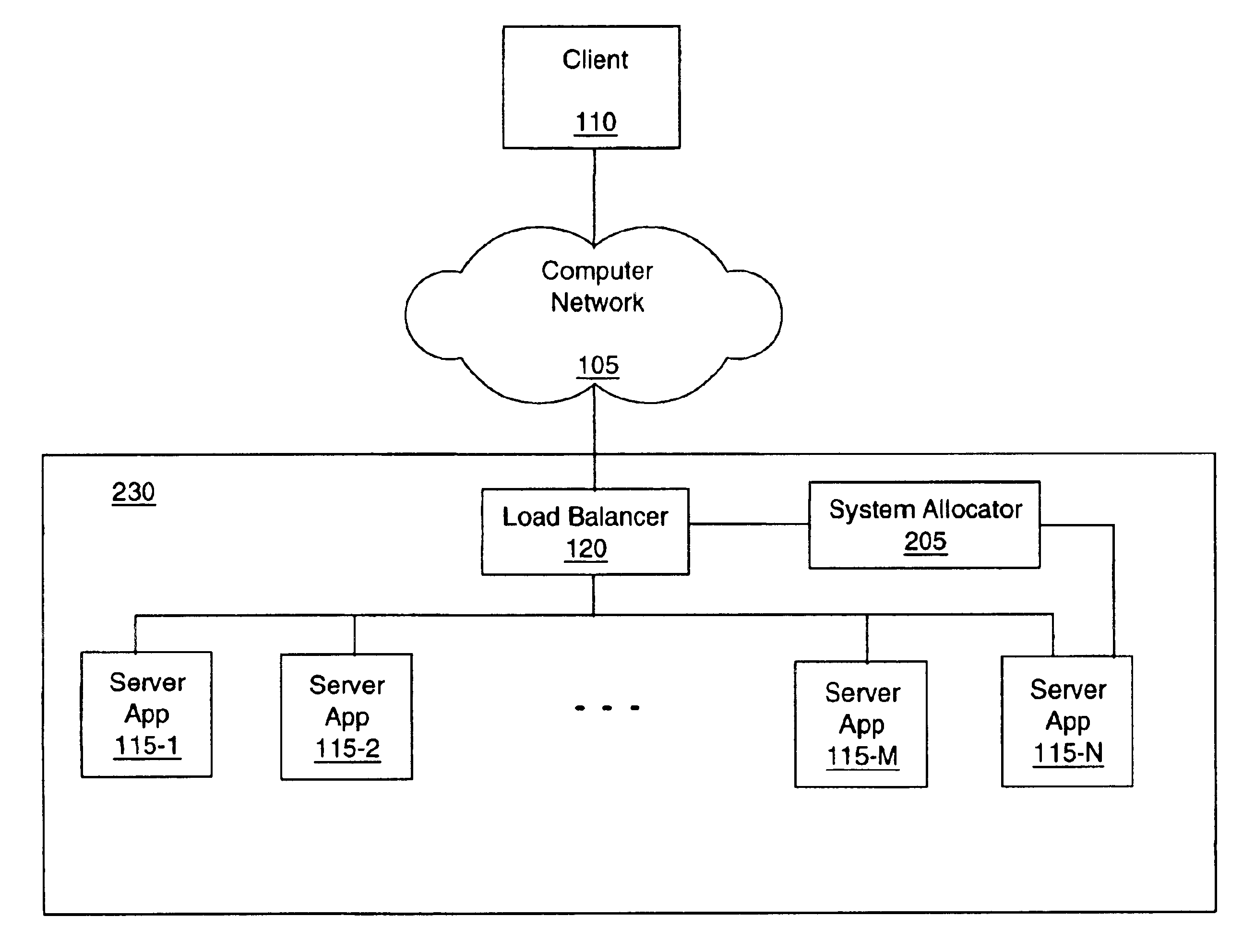
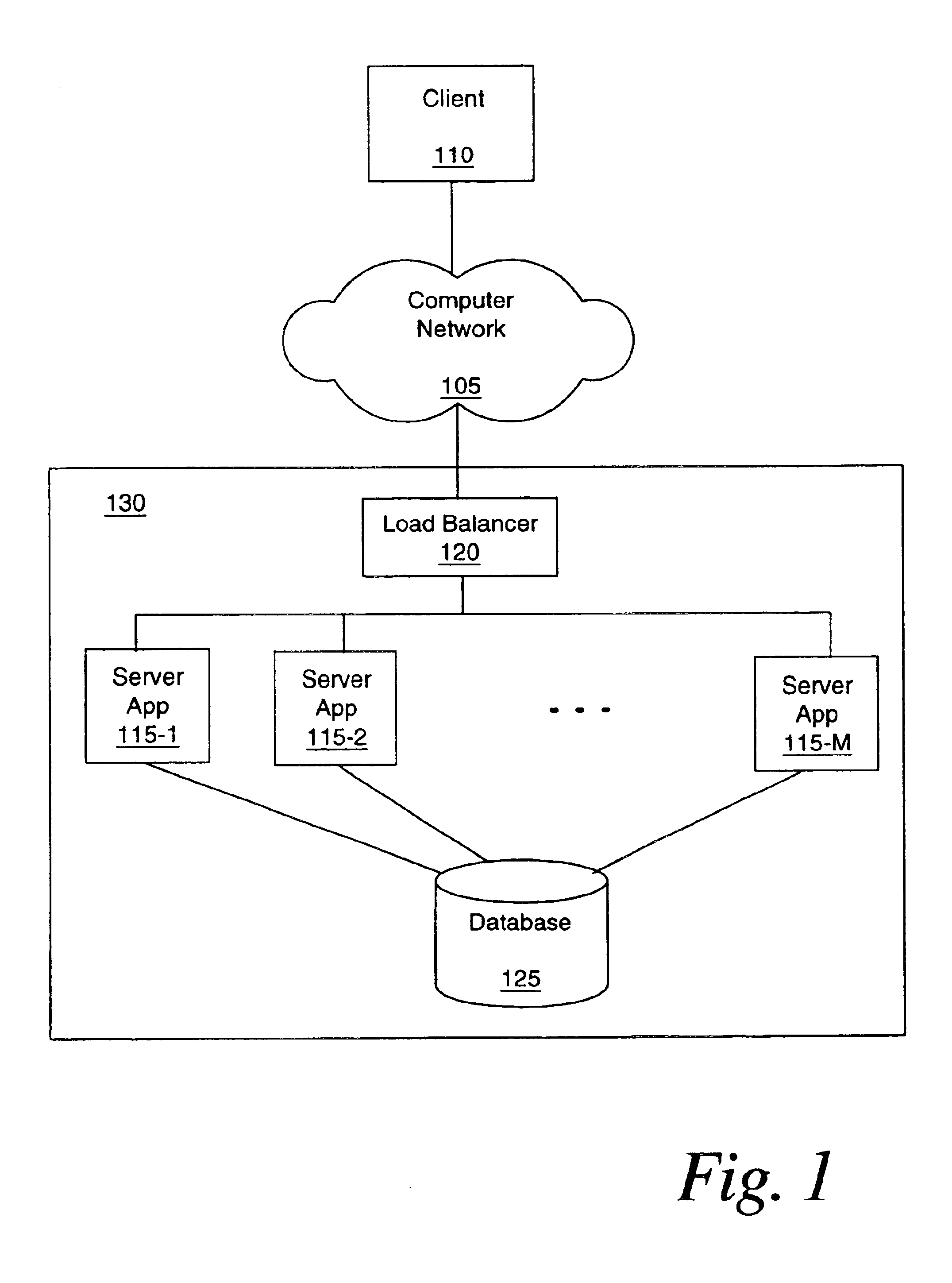
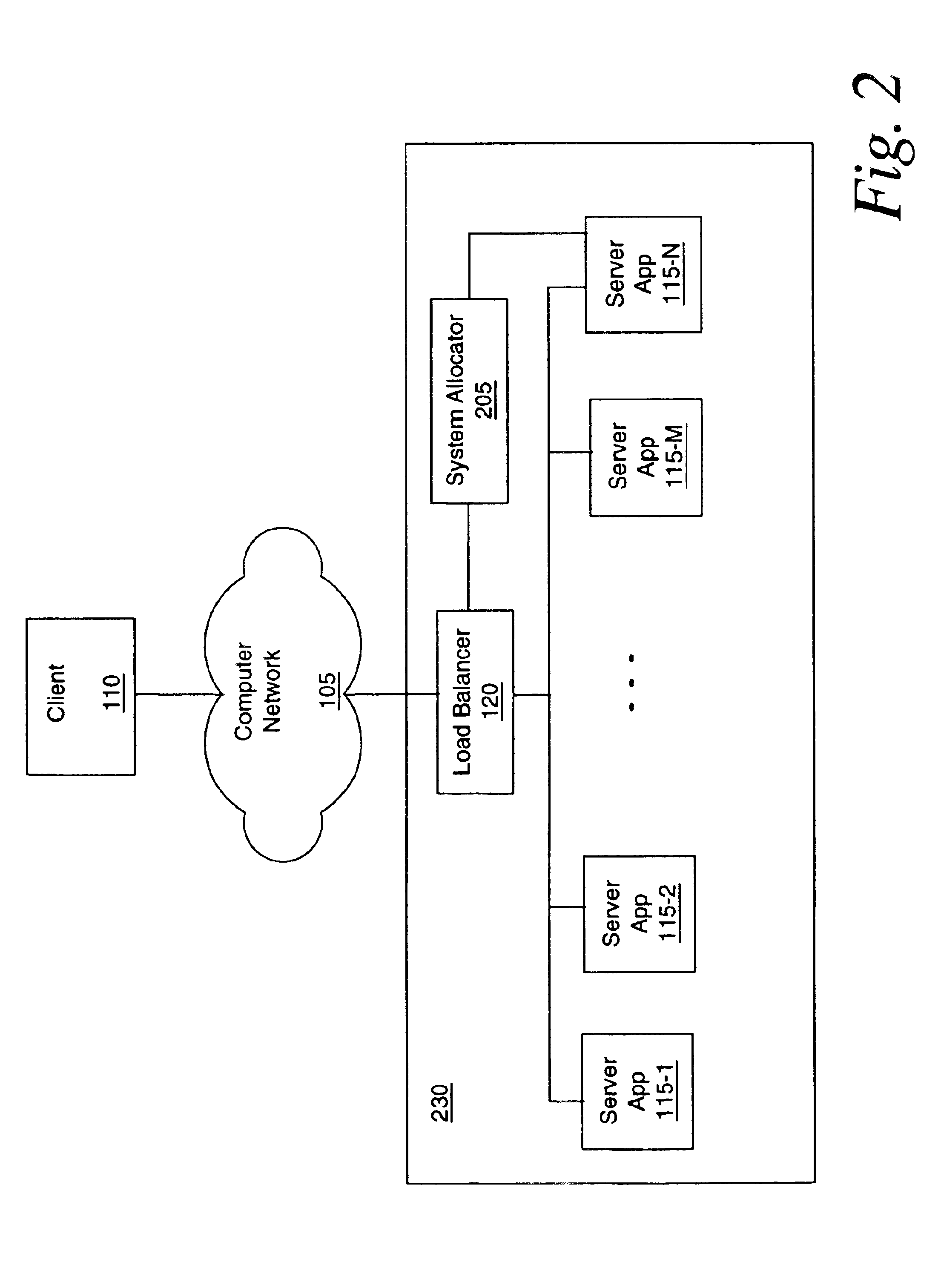
InactiveUS6880156B1Minimize durationSurges in server demand can be accommodated quicklyResource allocationMultiple digital computer combinationsApplication softwareDemand response
A server and method of its operation adapt the number of server applications within the server. The server is connected to a computer network. The server comprises one or more active server applications, a load detector, an inactive additional server application and an allocator. The load detector, which may be part of a load balancer, is connected to the one or more server applications and the computer network. The allocator is connected to the load detector and the additional server application. The allocator causes the additional server application to activate in response to a load condition. The method measures a load on the server, detects when the load exceeds a threshold and, in response thereto, activates an additional server application on the server. Optionally, the method also detects when the load is less than a deactivation threshold, and in response thereto, deactivates the additional server application. Also disclosed is a system comprising a plurality of computers, one or more connections to one or more servers, and a module. Each of the computers is capable of hosting a server application. The module is connected to the: computers and the connection(s). The module receives a request for an additional server application from one of the servers. Such a request may, for example, be generated when the server is experiencing a surge. In response to the request, the module activates the server application on one or more of the computers so as to support the requesting server.
Owner:VL COLLECTIVE IP LLC
System, method and apparatus for organizing groups of self-configurable mobile robotic agents in a multi-robotic system
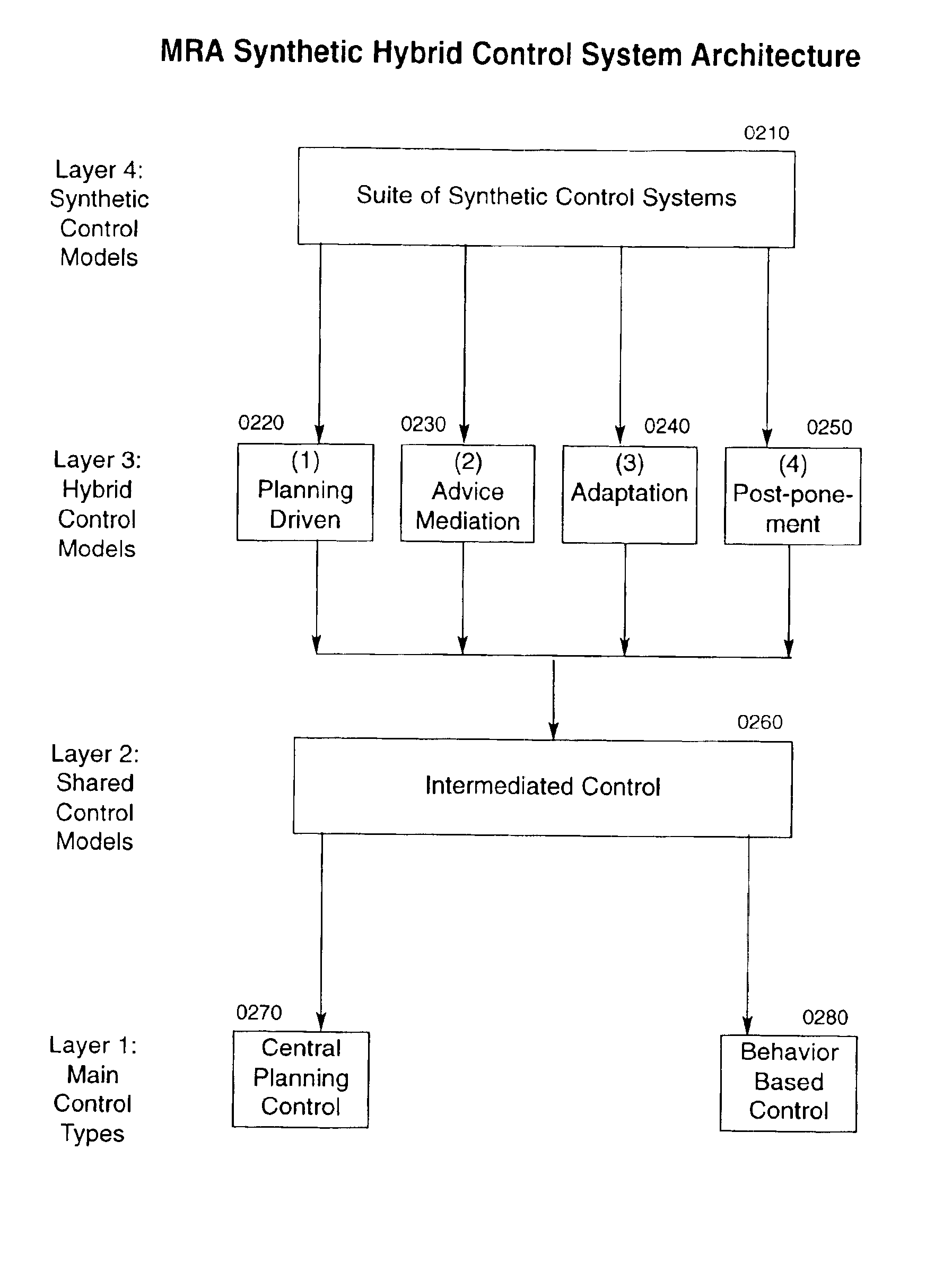
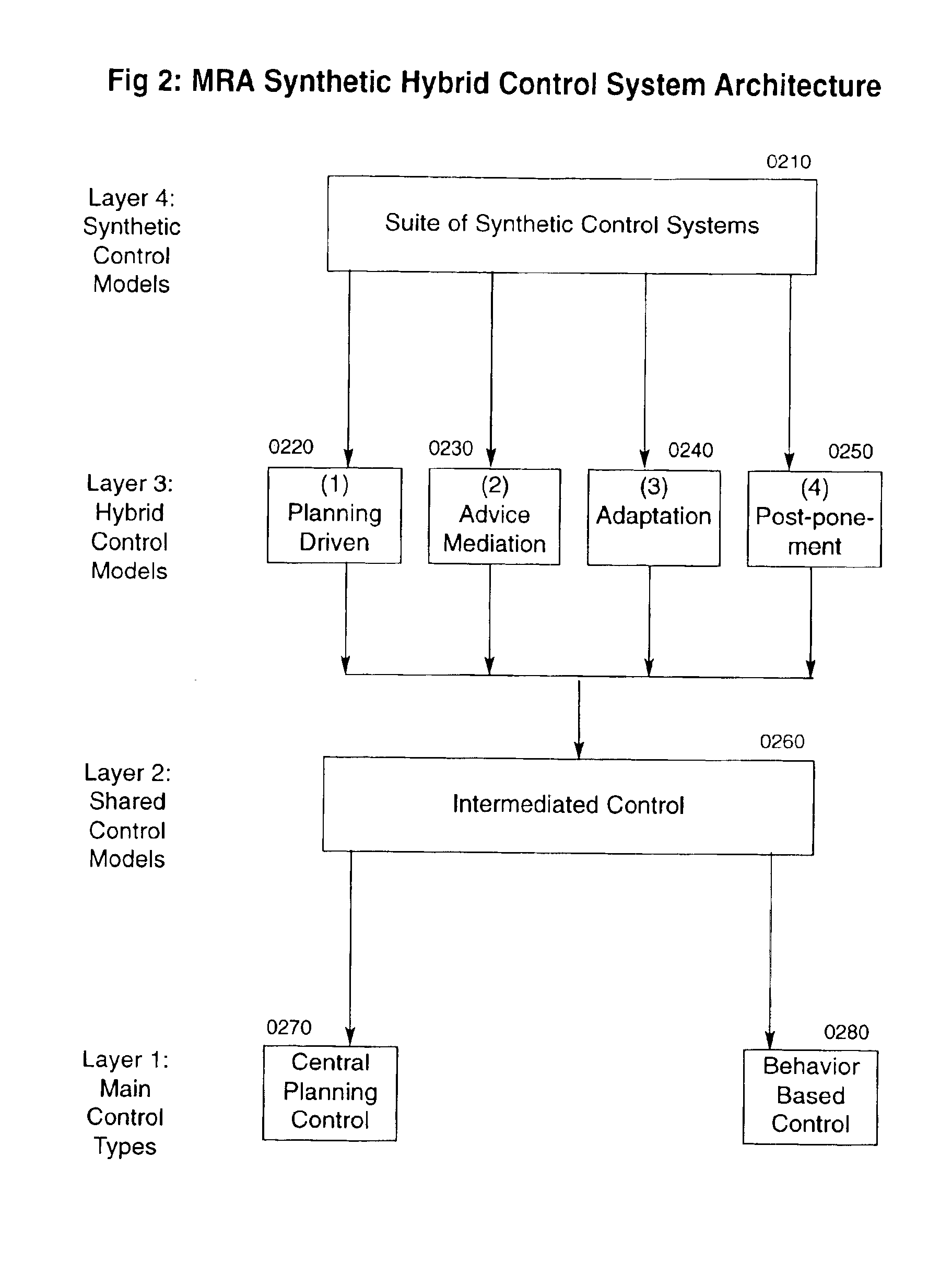
InactiveUS6904335B2Severe resource restrictionComplex behaviorProgramme-controlled manipulatorAutonomous decision making processRobotic systemsMultirobot systems
A system of self-organizing mobile robotic agents (MRAs) in a multi-robotic system (MRS) is disclosed. MRAs cooperate, learn and interact with the environment. The system uses various AI technologies including genetic algorithms, genetic programming and evolving artificial neural networks to develop emergent dynamic behaviors. The collective behaviors of autonomous intelligent robotic agents are applied to numerous applications. The system uses hybrid control architectures. The system also develops dynamic coalitions of groups of autonomous MRAs for formation and reformation in order to perform complex tasks.
Owner:SOLOMON RES
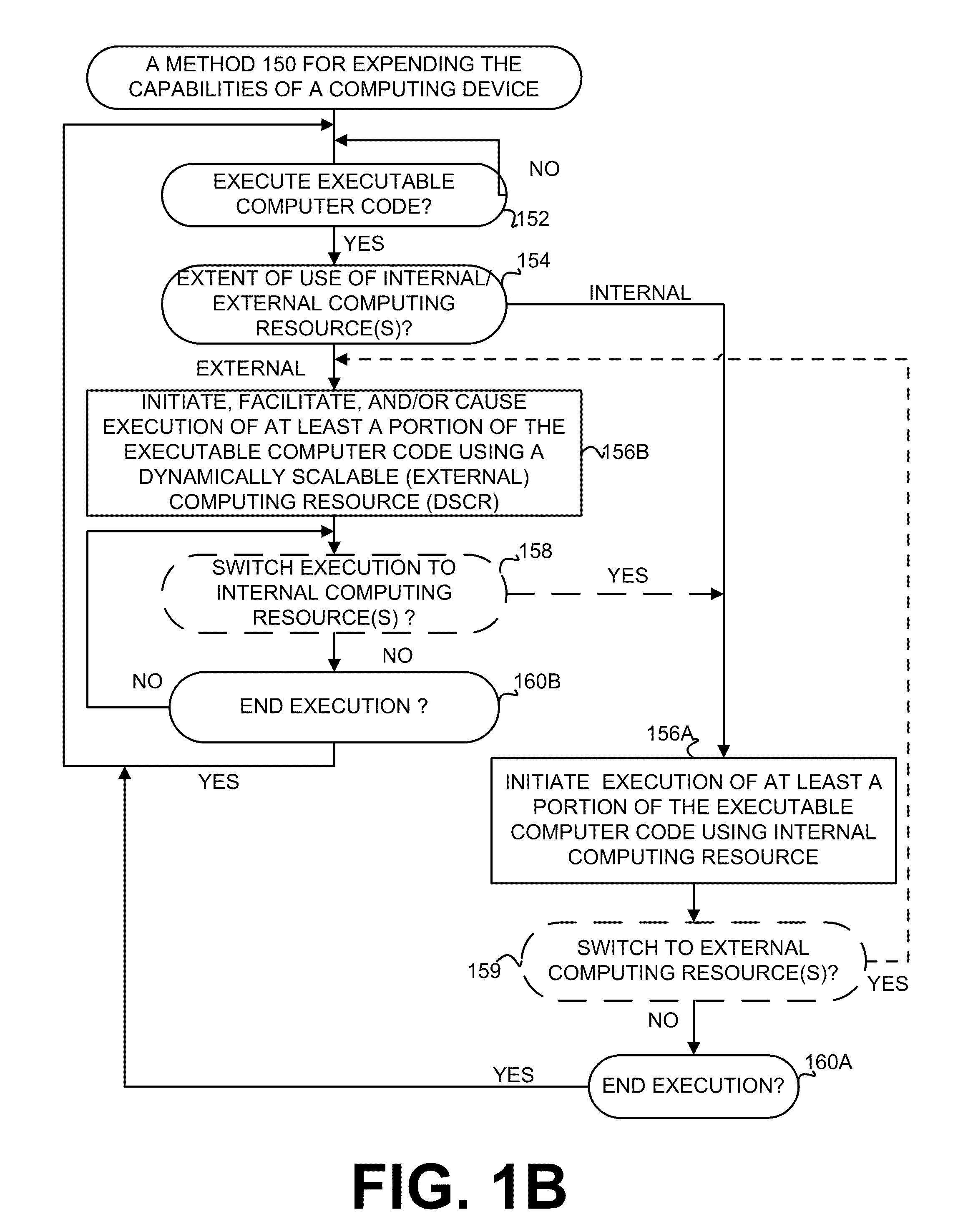
Execution allocation cost assessment for computing systems and environments including elastic computing systems and environments
InactiveUS20110004574A1Computing capabilities of a computing systemEffective resourcesResource allocationDigital computer detailsScalable computingParallel computing
Techniques for allocating individually executable portions of executable code for execution in an Elastic computing environment are disclosed. In an Elastic computing environment, scalable and dynamic external computing resources can be used in order to effectively extend the computing capabilities beyond that which can be provided by internal computing resources of a computing system or environment. Machine learning can be used to automatically determine whether to allocate each individual portion of executable code (e.g., a Weblet) for execution to either internal computing resources of a computing system (e.g., a computing device) or external resources of an dynamically scalable computing resource (e.g., a Cloud). By way of example, status and preference data can be used to train a supervised learning mechanism to allow a computing device to automatically allocate executable code to internal and external computing resources of an Elastic computing environment.
Owner:SAMSUNG ELECTRONICS CO LTD
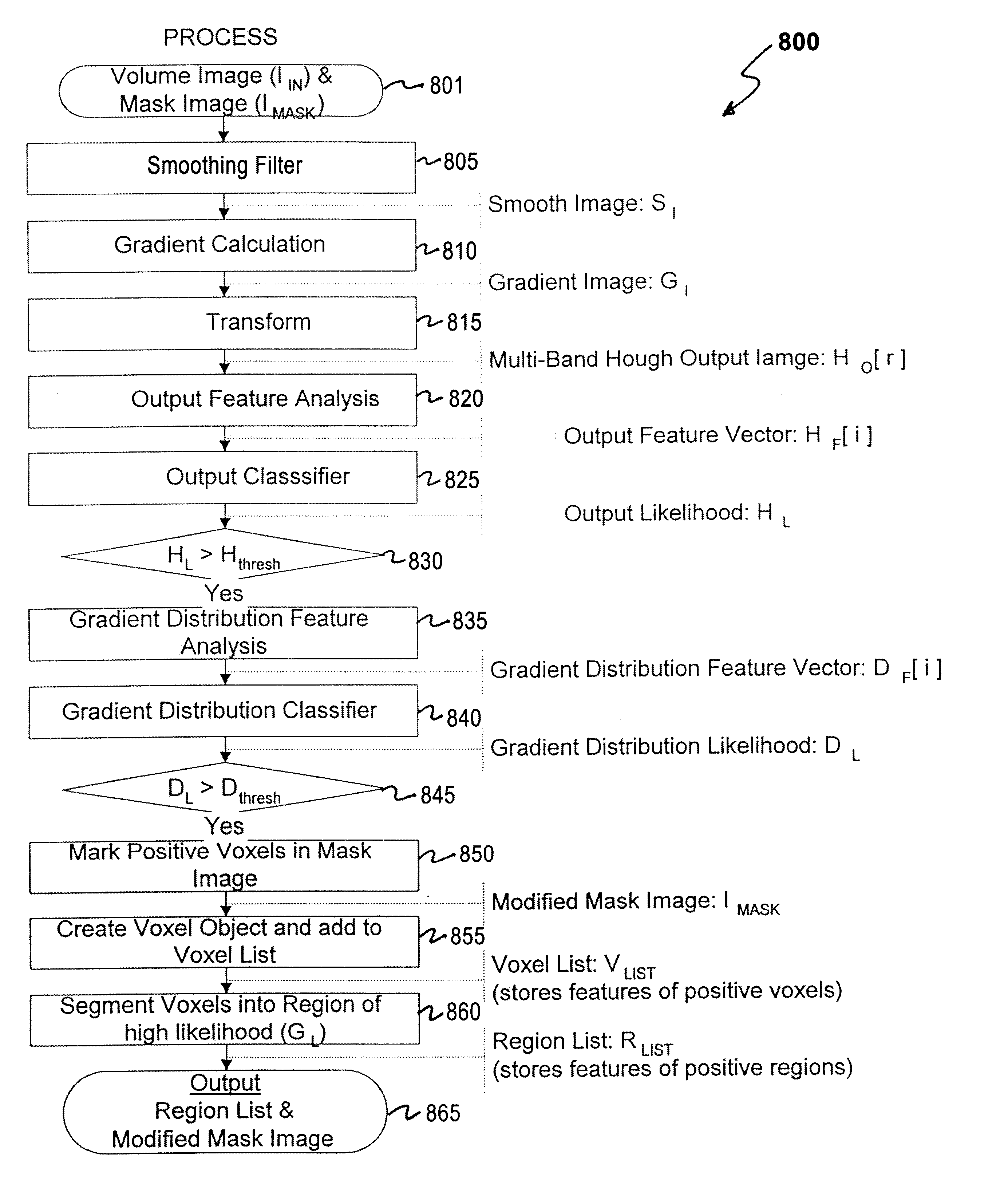
Density nodule detection in 3-D digital images
InactiveUS6909797B2Quickly highlightReduce sensitivityMaterial analysis using wave/particle radiationImage analysisVoxelRapid scan
An algorithm is quickly scans a digital image volume to detect density nodules. A first stage is based on a transform to quickly highlight regions requiring further processing. The first stage operates with somewhat lower sensitivity than is possible with more detailed analyses, but operates to highlight regions for further analysis and processing. The transform dynamically adapts to various nodule sizes through the use of radial zones. A second stage uses a detailed gradient distribution analysis that only operates on voxels that pass a threshold of the first stage.
Owner:MEVIS MEDICAL SOLUTIONS
Methods and Systems for Script Operations Management
Systems and methods for detecting, reporting and repairing of damaged scripts used to obtain financial account information from financial institutions are described, along with systems and methods for improved communications to users of financial software of the status of repair efforts. The systems and methods provide for improved speed in repairing script errors. In some embodiments, the script errors may be detected and repaired before a user even notices and / or reports the script error. In addition, the systems and methods provide for automatic detection and prioritization of script errors in conjunction with enhanced response times to script errors reported by users of financial software. Benefits are provided to the user experience, as well as to the efficiency of and resources required of service providers to repair broken scripts.
Owner:IN2M CORP
Creating frequent application-consistent backups efficiently
ActiveUS7613750B2Save resourcesProduction serverData processing applicationsMemory loss protectionApplication softwareBitmap
Data can be protected at a production server in a virtually continuous fashion, without necessarily imposing severe constraints on the source application(s). For example, a production server can create an application-consistent backup of one or more volumes, the backups corresponding to a first instance in time. A volume filter driver can monitor data changes in each volume using an in-memory bitmap, while a log file and / or update sequence number journal can keep track of which files have been added to or updated. The volume updates are also consistent for an instance (later) in time. At the next replication cycle, such as every few minutes (however configured), the volume filter driver passes each in-memory bitmap to the physical disk on the production server. The production server then sends the updates to the backup server, which thus stores application-consistent backups for the volume for multiple instances of time.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for transmitting and receiving data over a shared access carrier network
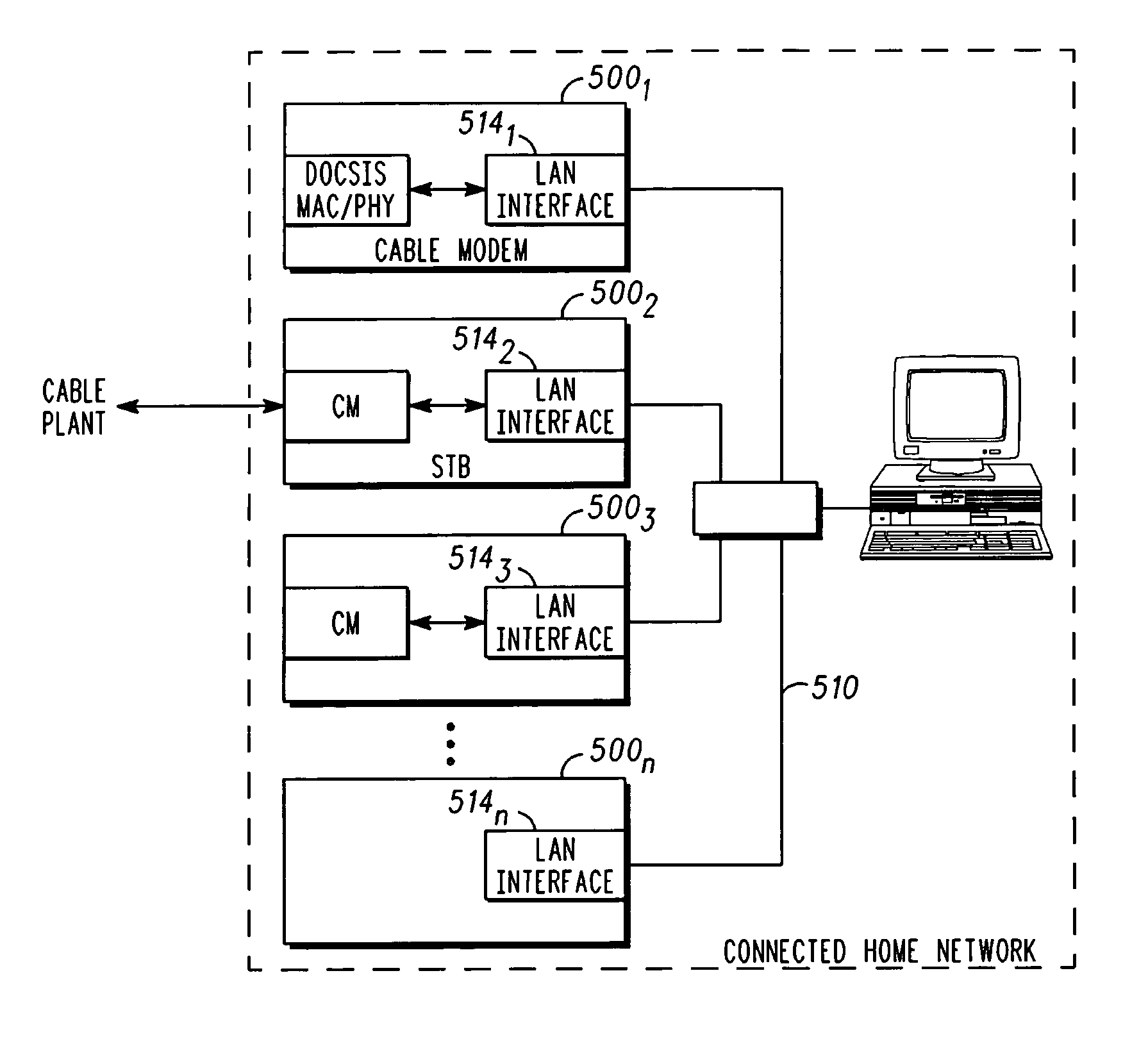
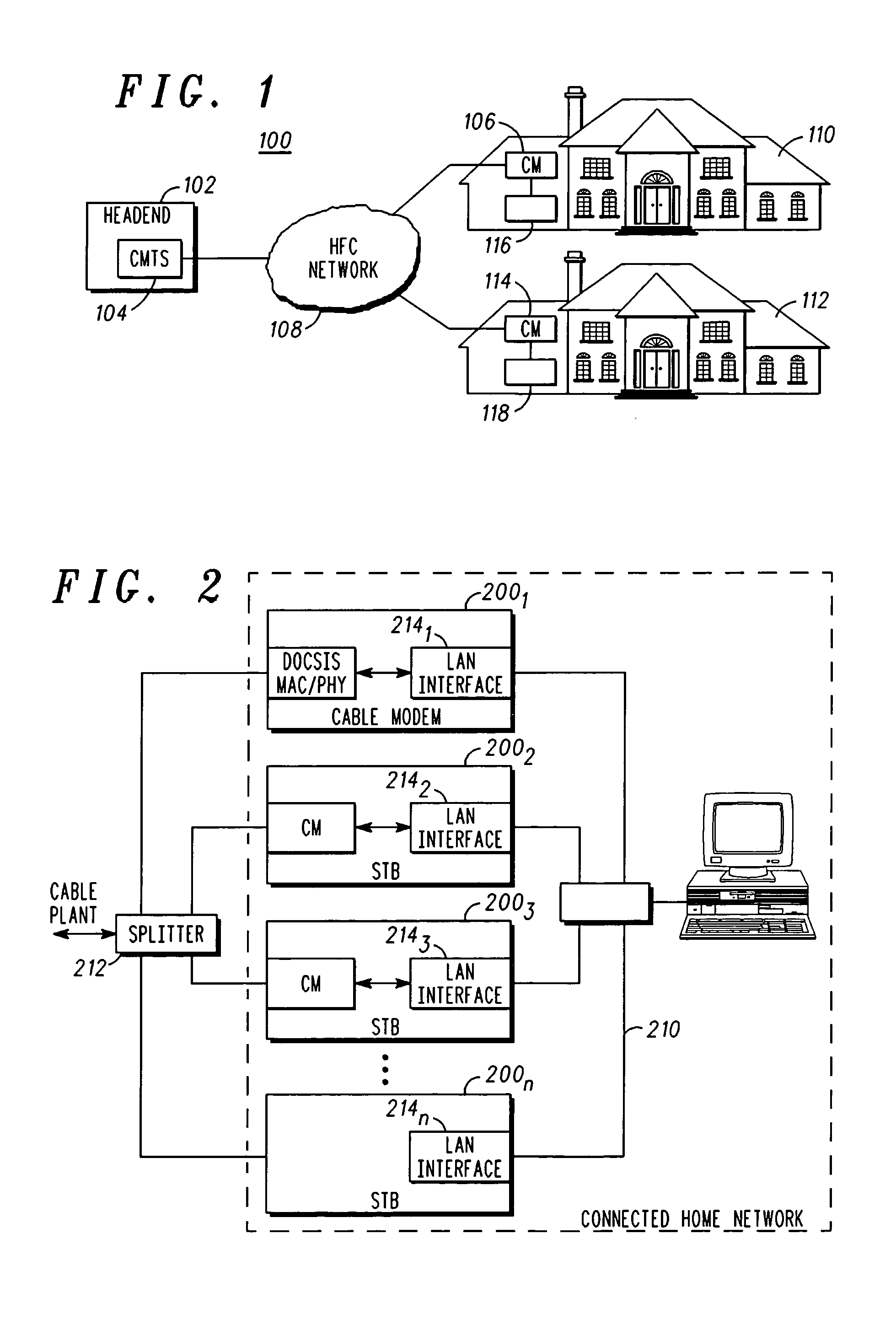
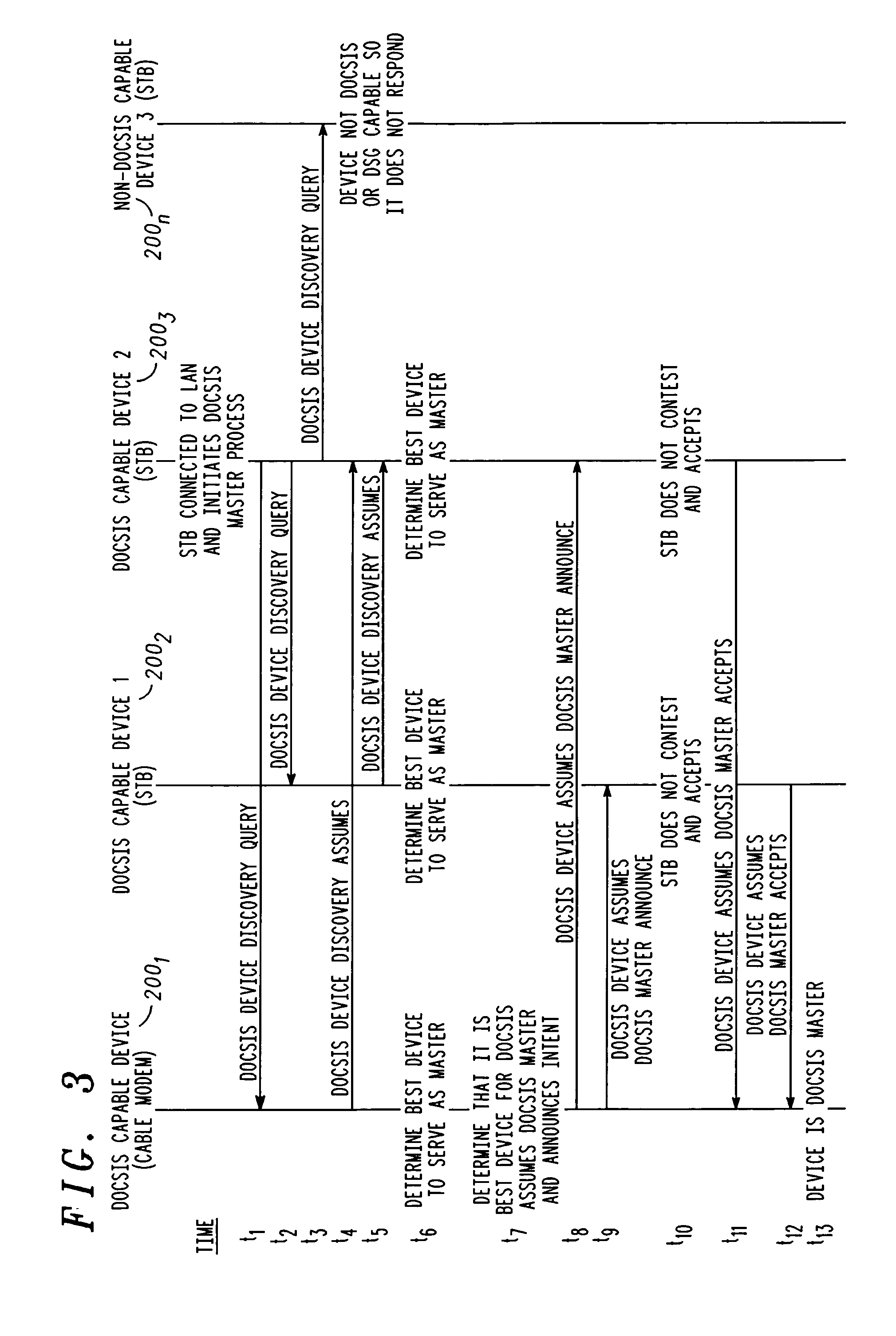
ActiveUS20060280197A1Effective resourcesReduce in quantityError preventionBroadband local area networksUser deviceModem device
A method for transmitting and receiving data over a shared access carrier network with a plurality of user devices is provided. The user devices each have a modem associated therewith and a network interface for communicating over a local network. The method begins by transmitting a query from each one of the user devices over the local network requesting remaining ones of the plurality of user devices to specify available resources pertaining to shared access carrier network connectivity capabilities of the modem associated therewith. A reply is received over the local network in response to the query from each of the remaining user devices. Based on the replies from each of the remaining user devices, at least one of the user devices is selected to serve as a master device that provides connectivity to the shared access carrier system through which the other of the plurality of user devices transmit and receive data.
Owner:ARRIS ENTERPRISES LLC
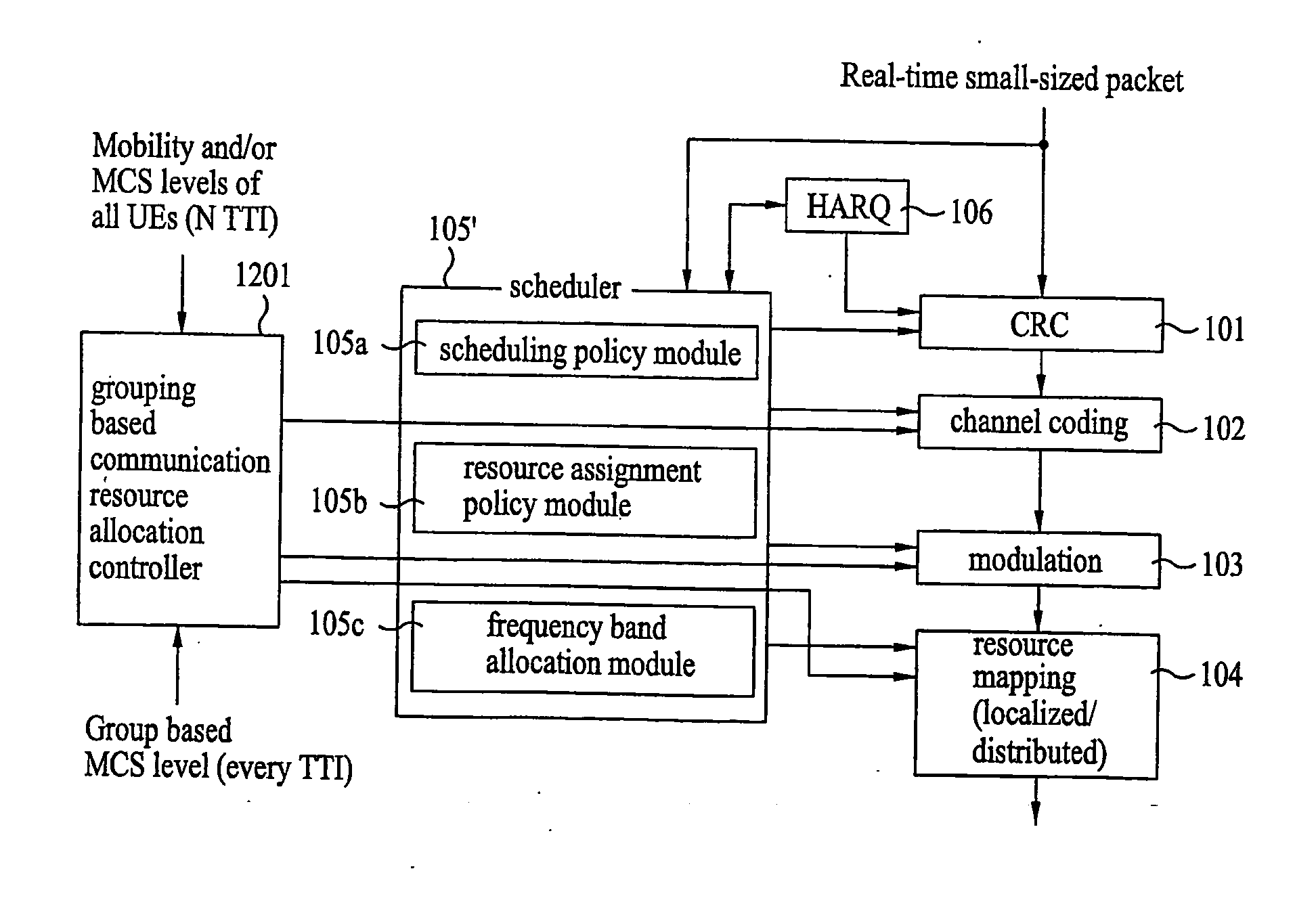
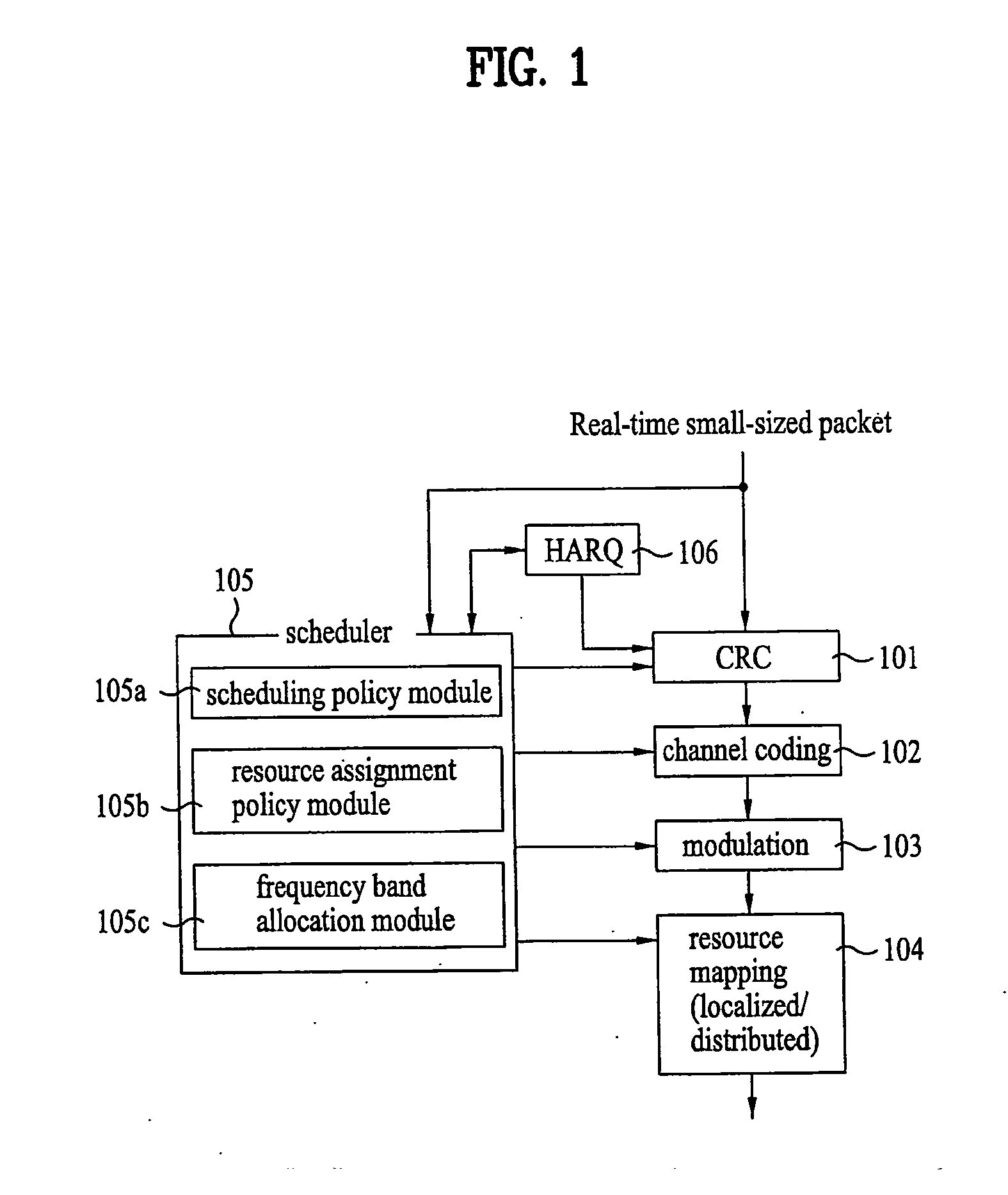
Grouping based resource allocation method, method for transmitting signal using the same, and grouping based resource allocation controller
InactiveUS20100177717A1Quantity minimizationReduce control signaling overheadWireless commuication servicesComputer scienceResource allocation
A grouping based resource allocation method, a method for transmitting a signal using the same, and a grouping based resource allocation controller are disclosed. That is, the method including grouping a plurality of user equipments (UEs) to a predetermined number of groups using feedback information received from the plurality of UEs and dynamically allocating communication resources to the UEs included in the groups according to the group based feedback information and the method for transmitting the signal using the same are disclosed. In addition, a grouping based resource allocation controller including a grouping module and control module for performing the above-described method in a base station is disclosed.
Owner:LG ELECTRONICS INC
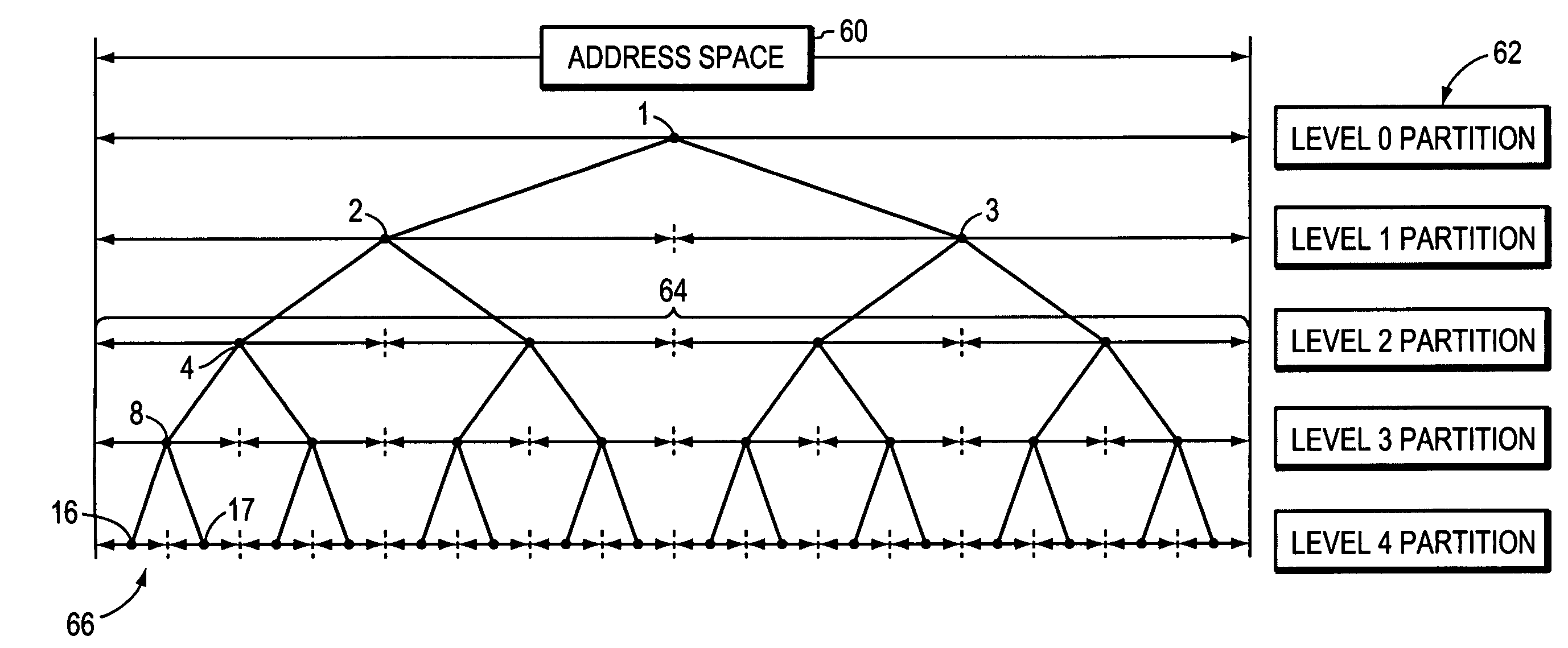
Method and apparatus for determining if stored memory range overlaps key memory ranges where the memory address space is organized in a tree form and partition elements for storing key memory ranges
ActiveUS7251663B1Efficient of system resourceEffective timeData processing applicationsDigital data processing detailsMemory addressTheoretical computer science
An efficient method and apparatus for storing and retrieving memory ranges is disclosed. A key range that is stored or to be stored is associated with a node in the tree hierarchy encompassing the entire memory address space. All previously stored ranges are listed or otherwise associated with each node, and all possible nodes that may contain ranges that overlap the key range, regardless of starting or ending locations or range length, are found. Partitions are developed in the tree structure of the available address space and the width of the key range (w), the widths of the partitions (d), and the range of offsets in the starting location of the key range with respect to a partition (o) are used to develop a formula that finds a partition suitable for storing the key range. Hashing and dynamic tree building may be used.
Owner:NETWORK APPLIANCE INC
Packet transfer device
InactiveUS20060092971A1Improve service qualityEffective resourcesError preventionTransmission systemsNetwork interfaceComputer science
A router with a server incorporated to provide services has a problem in that the server's resource cannot be allocated dynamically according to user requests. Service request packets received at a plurality of network interfaces are controlled such that the total bandwidth of the service request packets does not exceed a preset threshold. This makes it possible to process as many service requests from users as possible while limiting a server resource occupied by one service to a fixed amount. The network interfaces are notified of how much of a server resource is occupied by each service. In the case where one service consumes less than its allocated resource amount, the resultant surplus resource is made available to other services by easing the bandwidth control on other services. The above problem is thus solved.
Owner:HITACHI LTD
Radio communications apparatus, radio communications system, and base station equipment
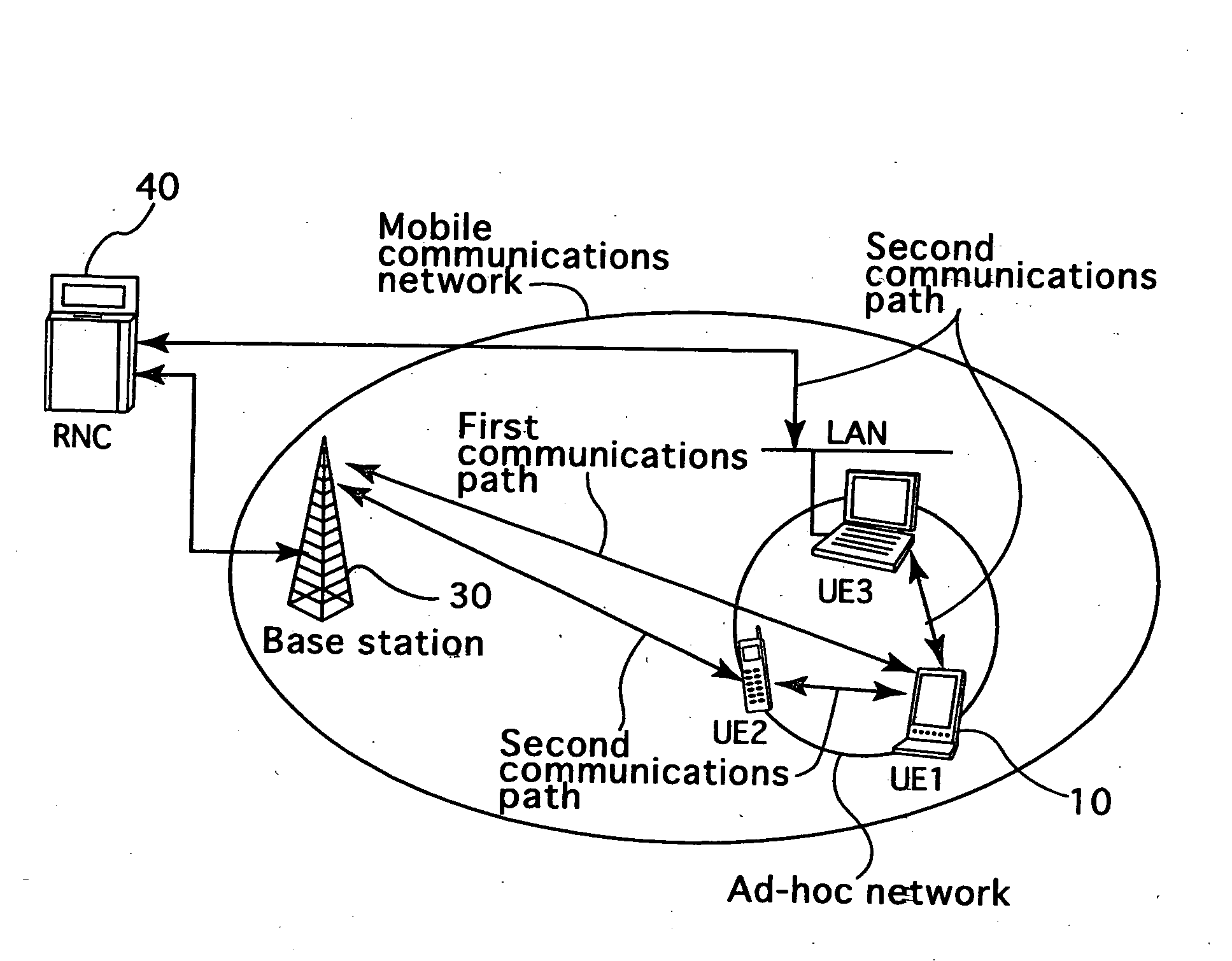
InactiveUS20060205408A1Promote network efficiencyEasy to optimizeData switching by path configurationRadio/inductive link selection arrangementsCommunications systemRadio communications
Radio communications apparatus, radio communications system, and base station equipment that effectively utilize the network resources of both an ad-hoc network and a mobile communications network to increase the efficiency of and optimize the networks, thereby improving the communication capacity and throughput of the networks as a whole. The radio communications apparatus (UE1) employs TDD-CDMA system for communications with a base station (30) of the mobile communications network, and also employs the TDD-CDMA system, which is common to the base station, for communications with other radio communications apparatuses in the ad-hoc network, while using the same frequency band. Communications paths for communicating with the base station equipment include a first communications path for directly communicating with the base station and a second communications path for communicating with the base station equipment via another radio communications apparatus (UE2, UE3 or the like) in the ad-hoc network. The radio communications apparatus (UE1) uses one of those communications paths, which is designated by the base station equipment, to communicate with the base station equipment.
Owner:KEIO UNIV +1
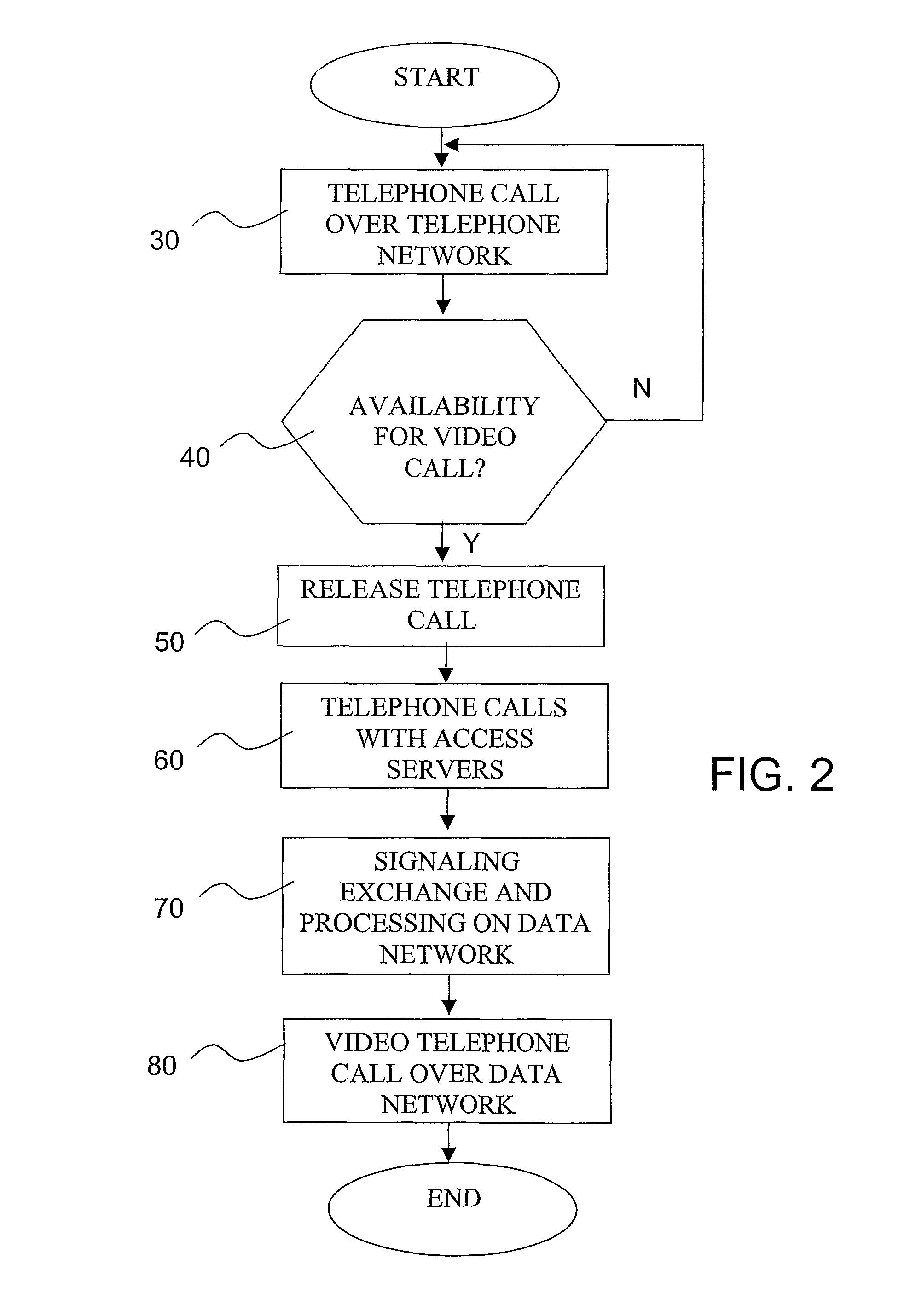
Method and system for video telephone communications set up, related equipment and computer program product
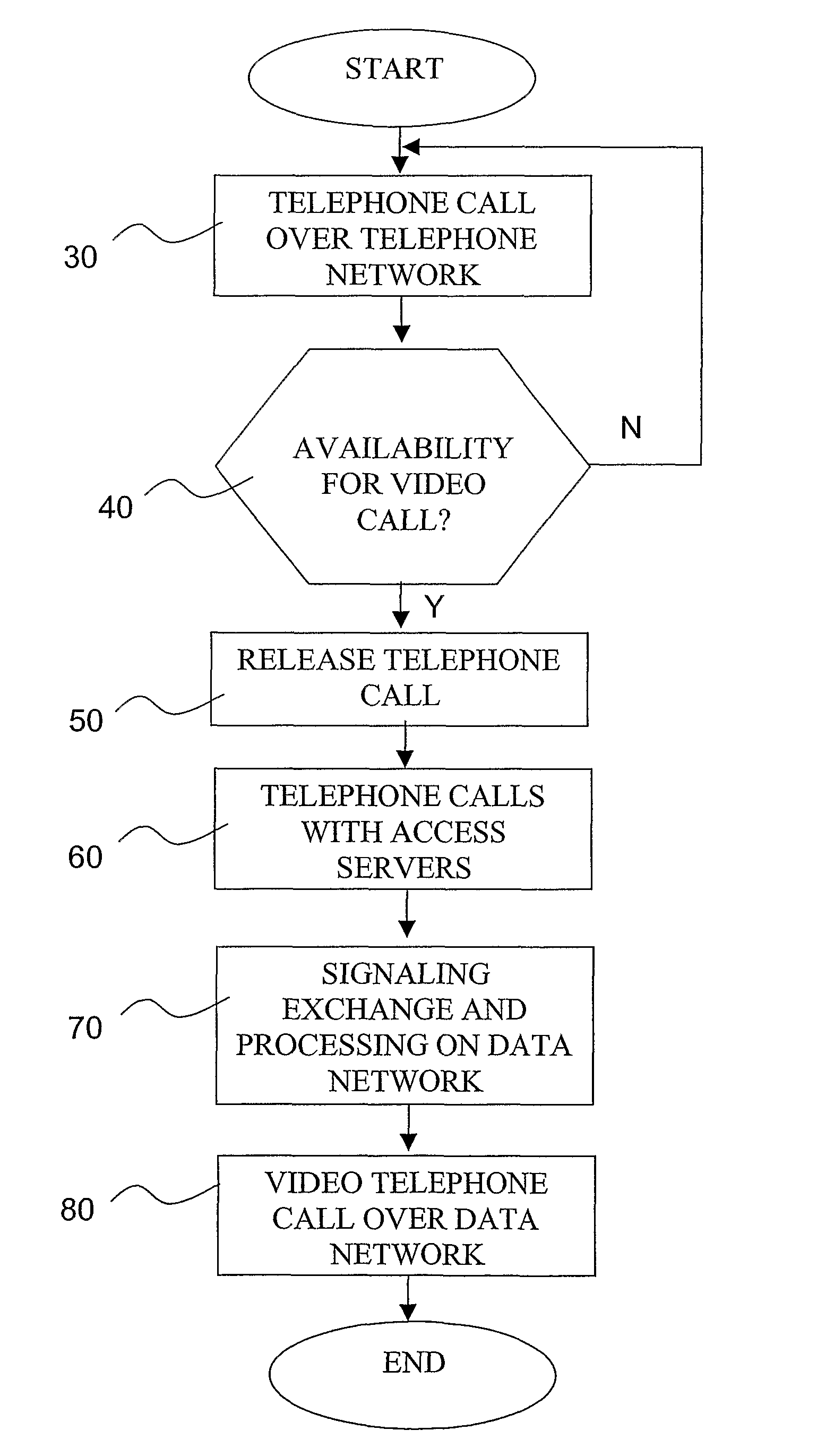
ActiveUS8488591B2Efficiently establishedEfficient use ofInterconnection arrangementsSpecial service for subscribersComputer terminalTelephone terminal
A method of setting up a video telephone call between a first video telephone terminal and a second video telephone terminal on a data network includes the steps of: establishing a telephone call over a telephone network between the first and second terminals; exchanging between the first and second terminals during the telephone call availability signals to seek availability to hold a video telephone call; if the availability is confirmed, releasing the telephone call; establishing respective telephone calls between each of the first and second terminals and a corresponding access server of the data network, for achieving connection of the first and second terminals to the data network; establishing a signalling exchange between the first and second terminals through a service center of the data network to achieve the set up of the video telephone call; and establishing a peer-to-peer video telephone call between the first and second terminals over the data network.
Owner:TELECOM ITALIA SPA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com