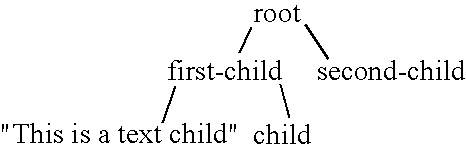Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5109 results about "Tree structure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
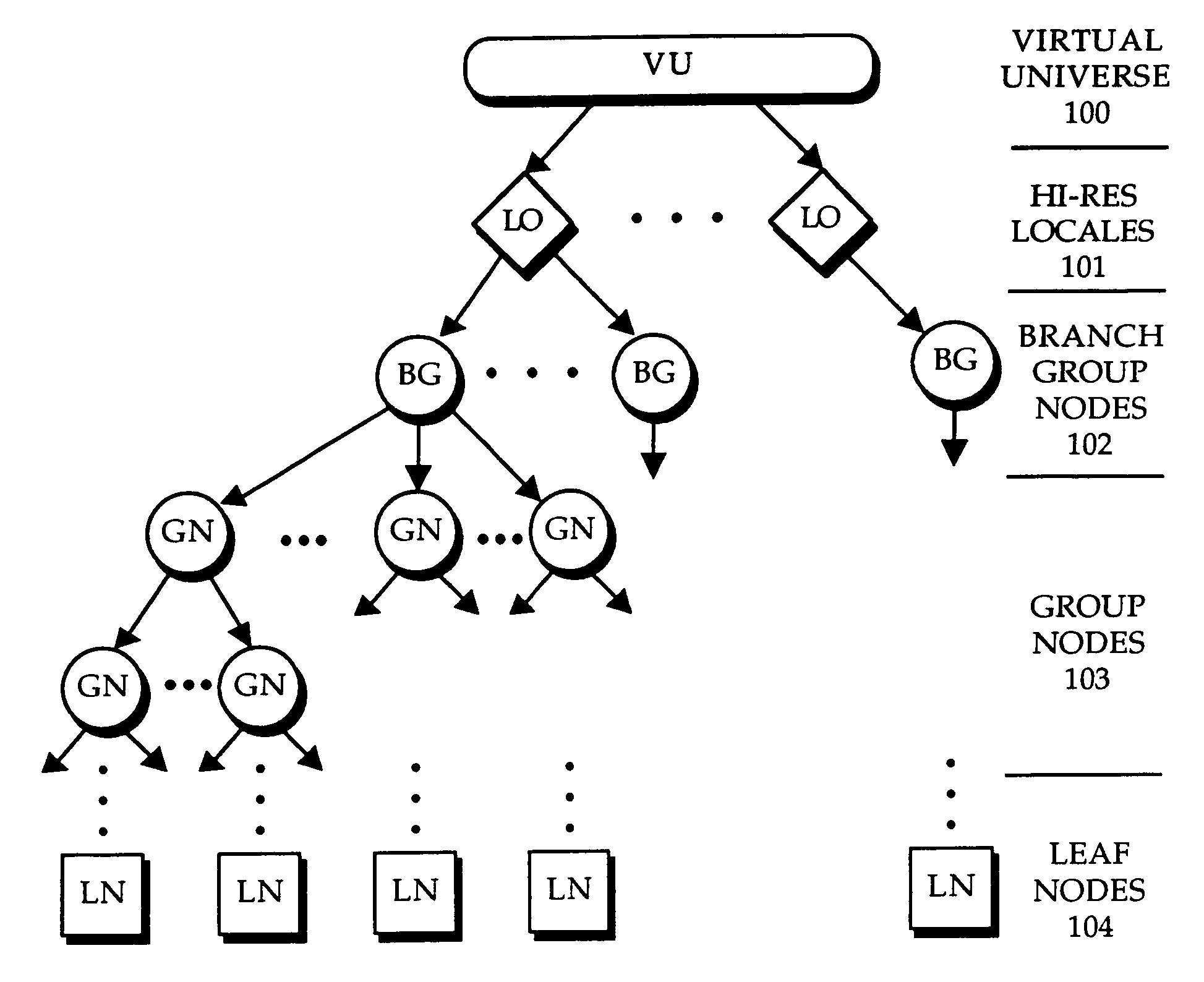
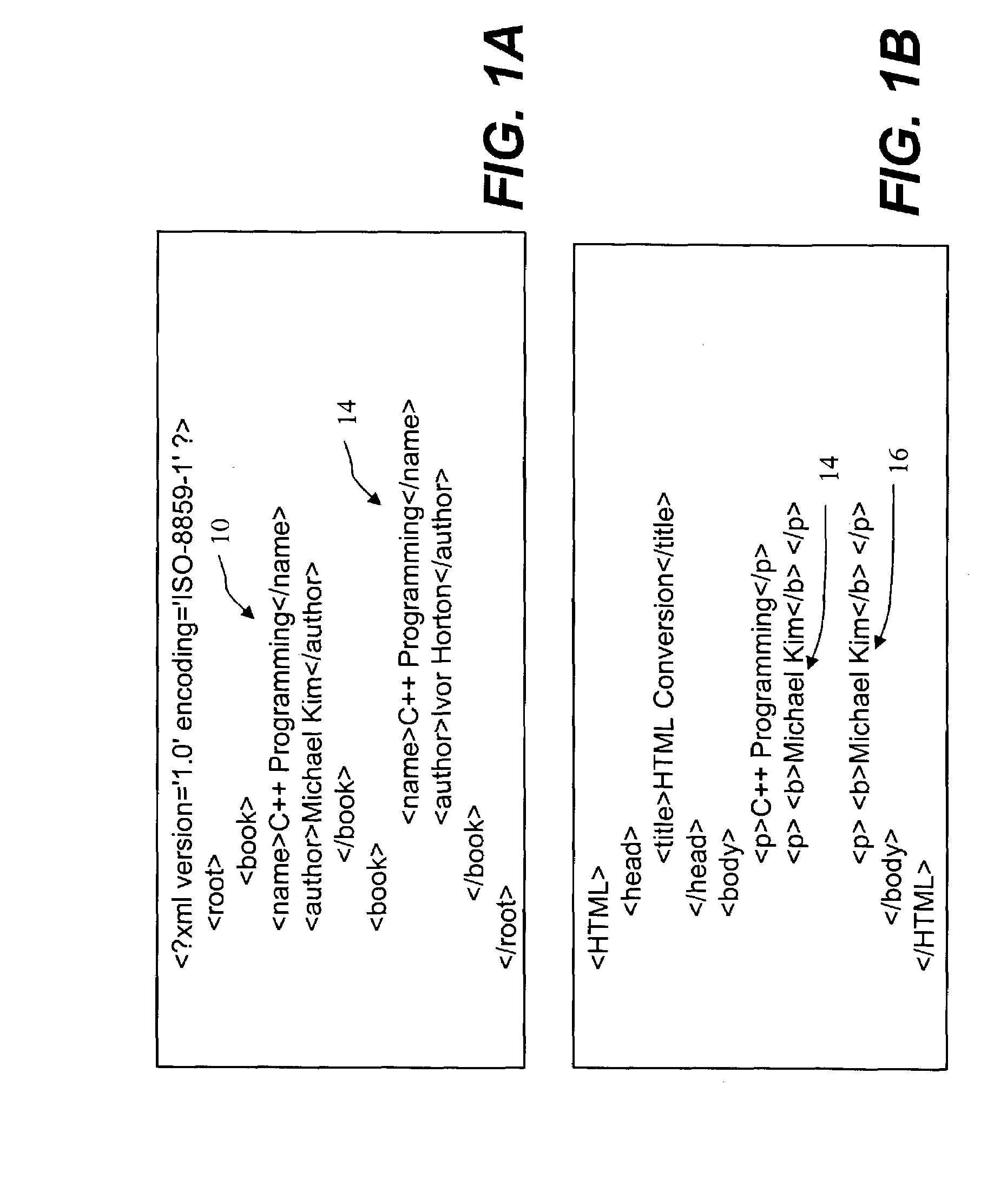
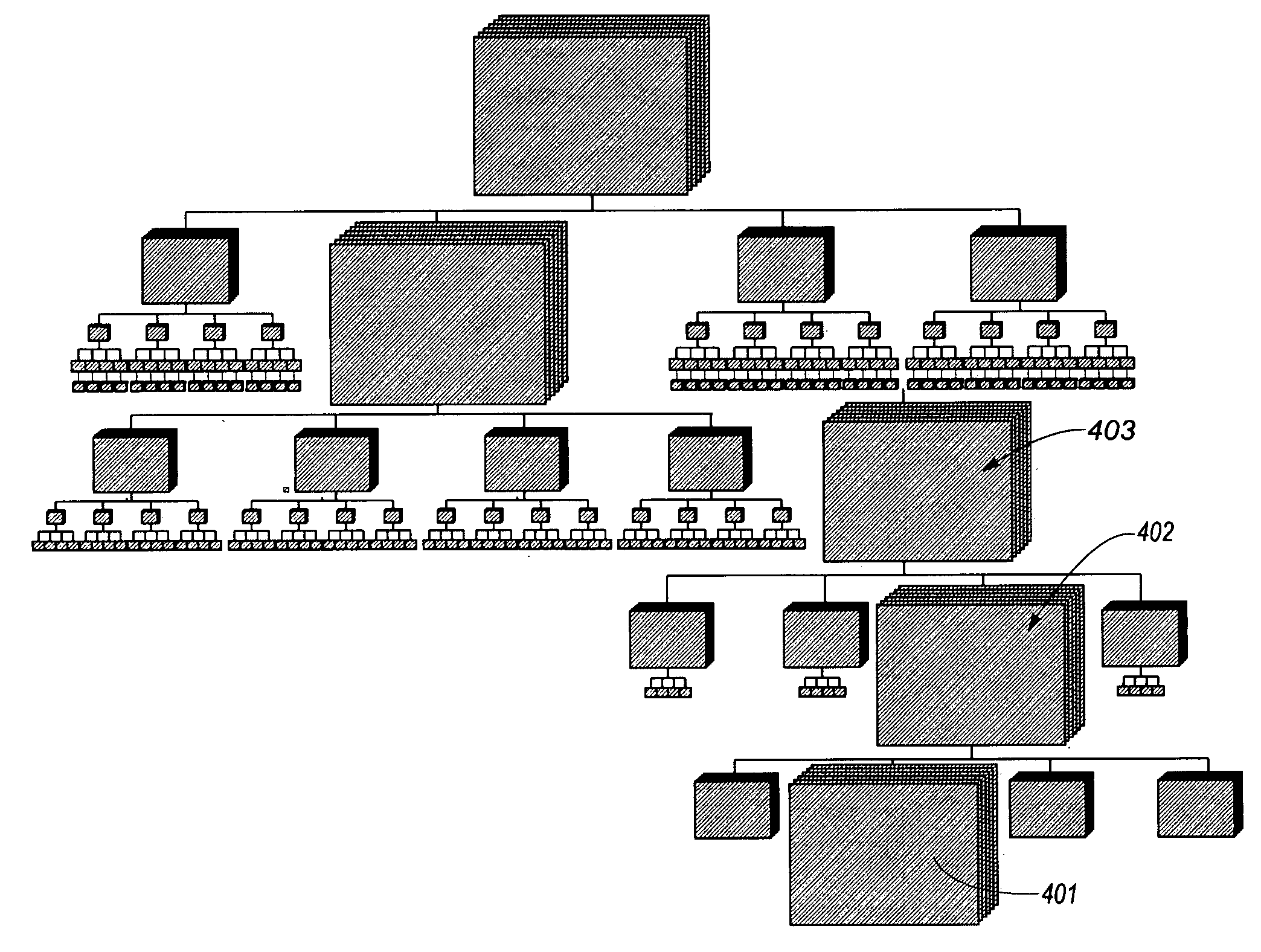
A tree structure or tree diagram is a way of representing the hierarchical nature of a structure in a graphical form. It is named a "tree structure" because the classic representation resembles a tree, even though the chart is generally upside down compared to an actual tree, with the "root" at the top and the "leaves" at the bottom.
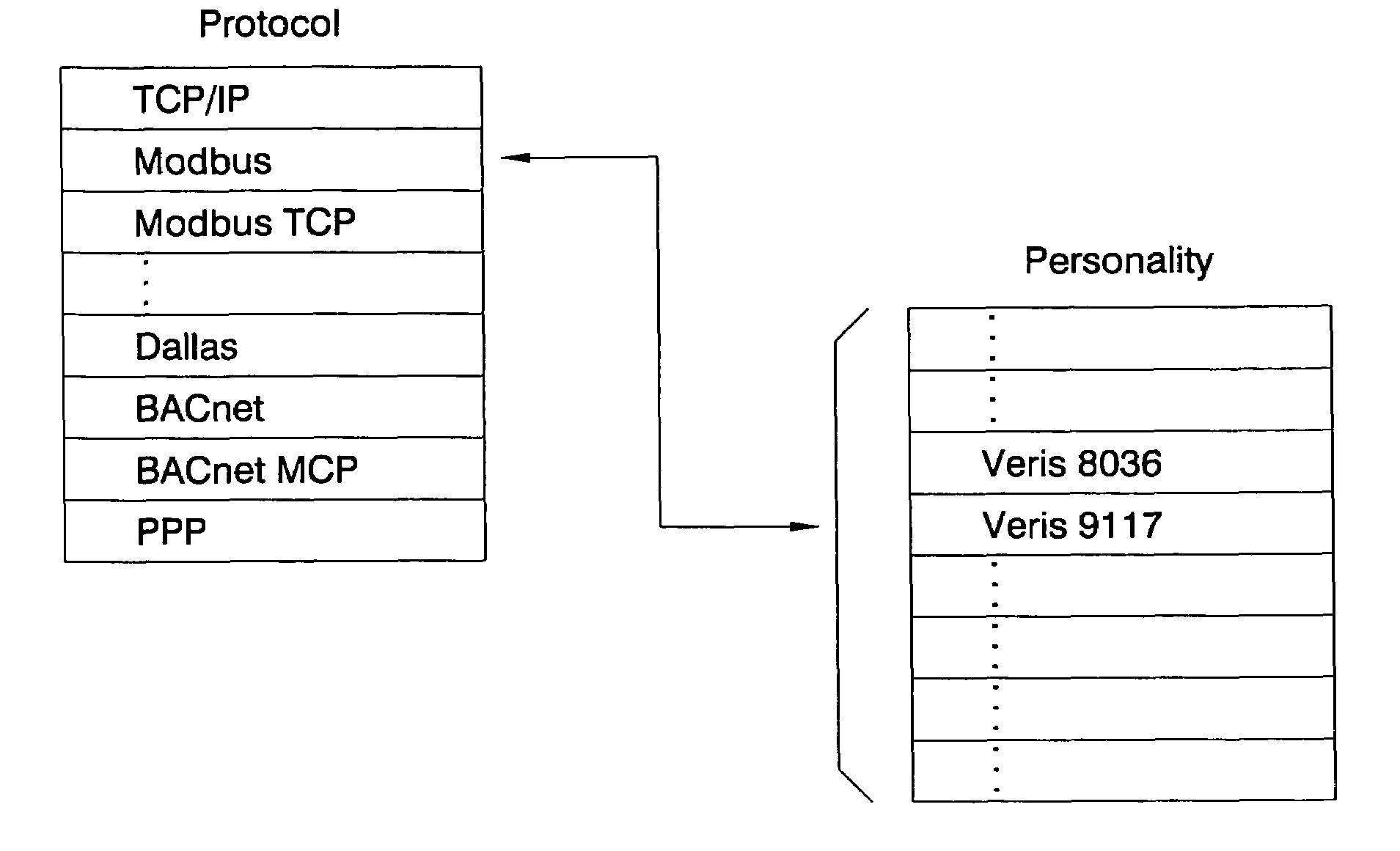
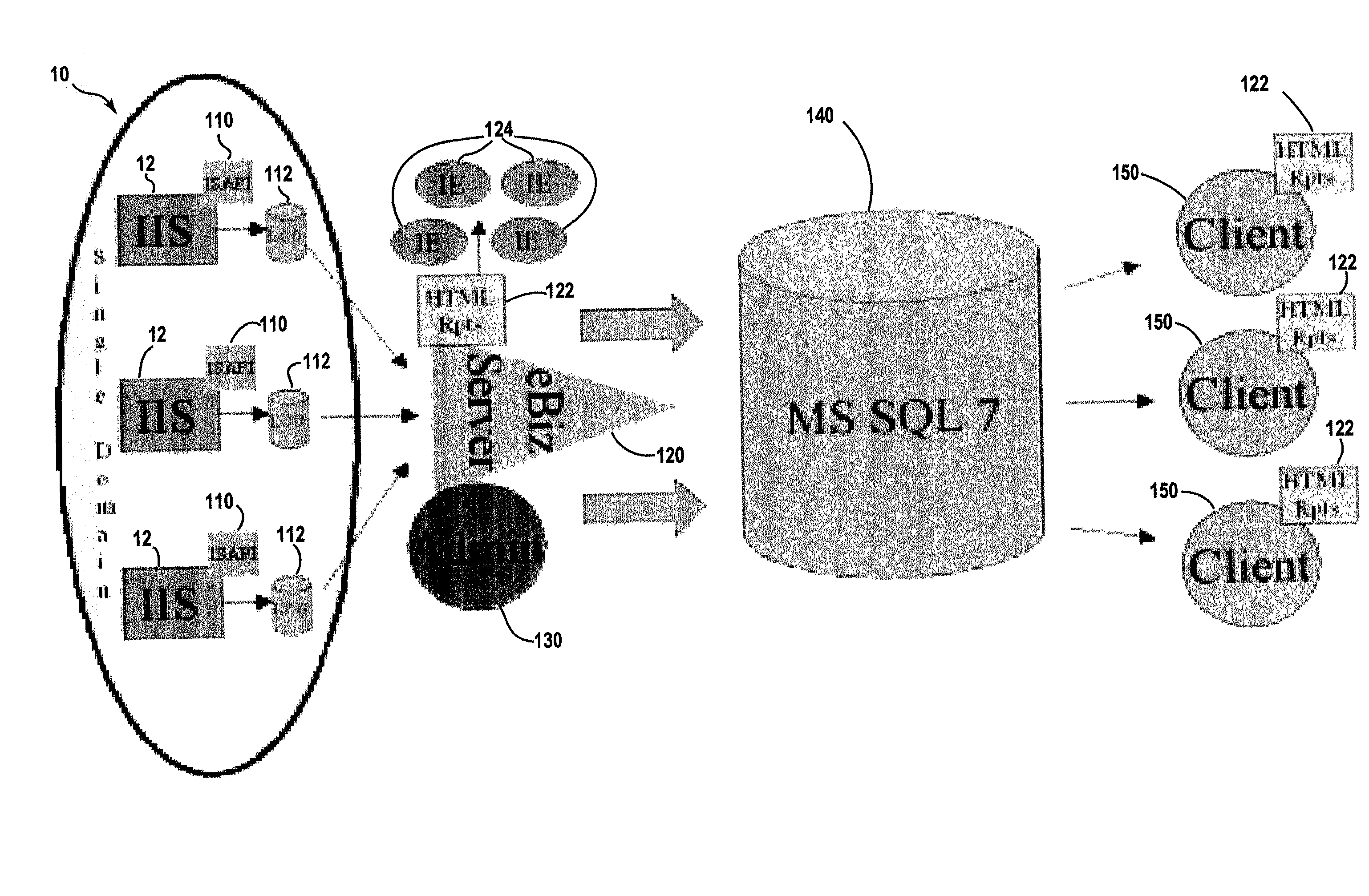
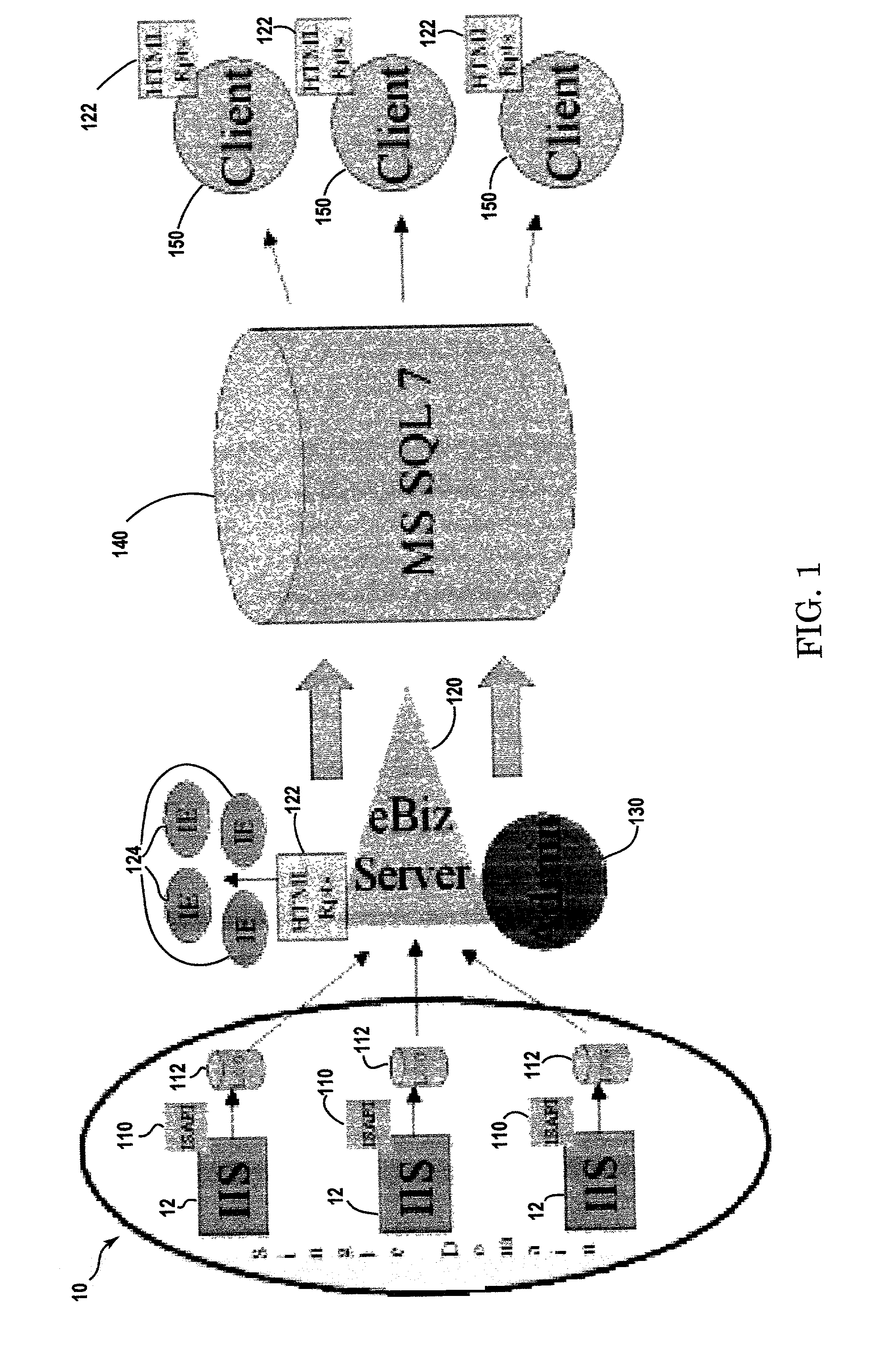
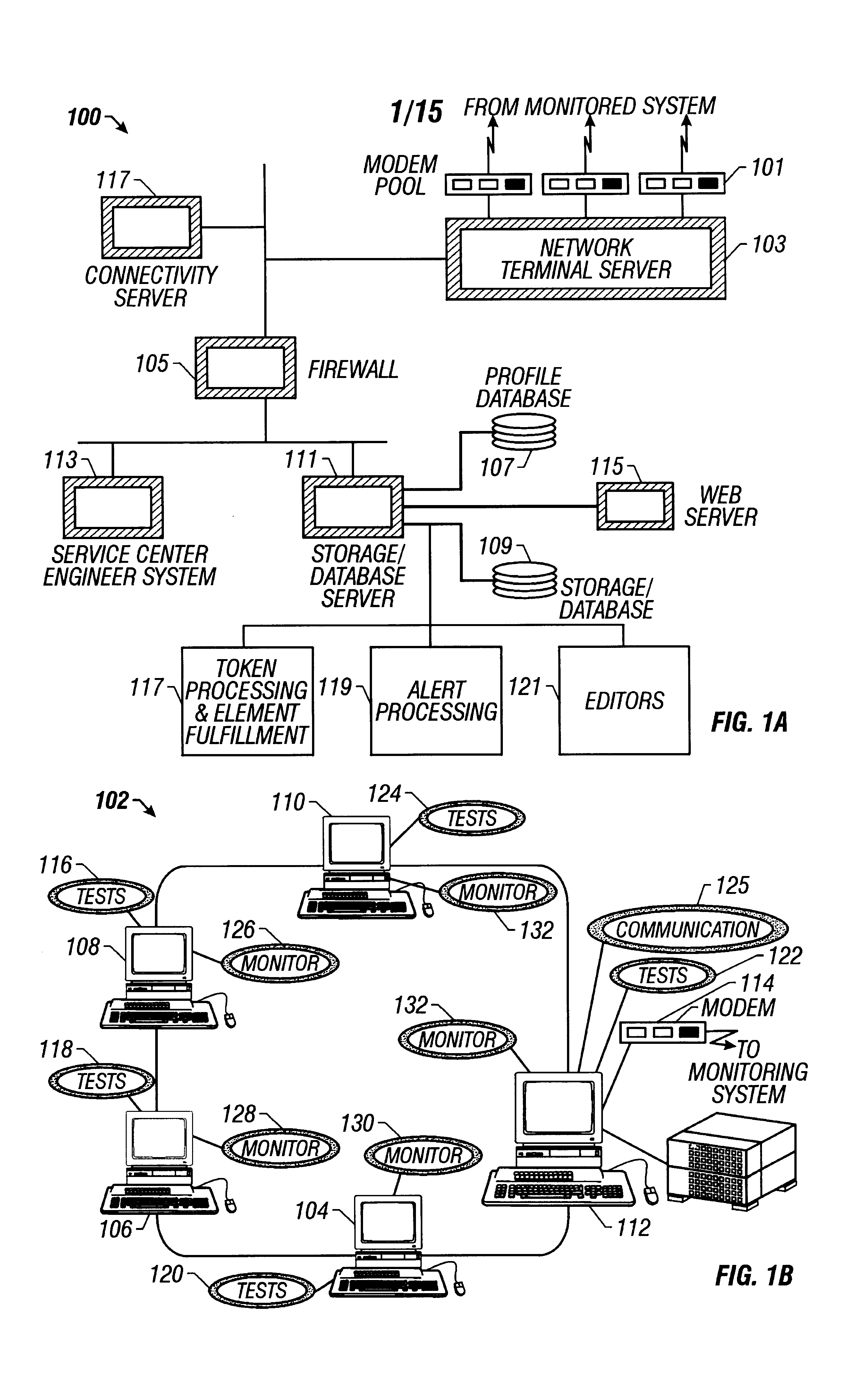
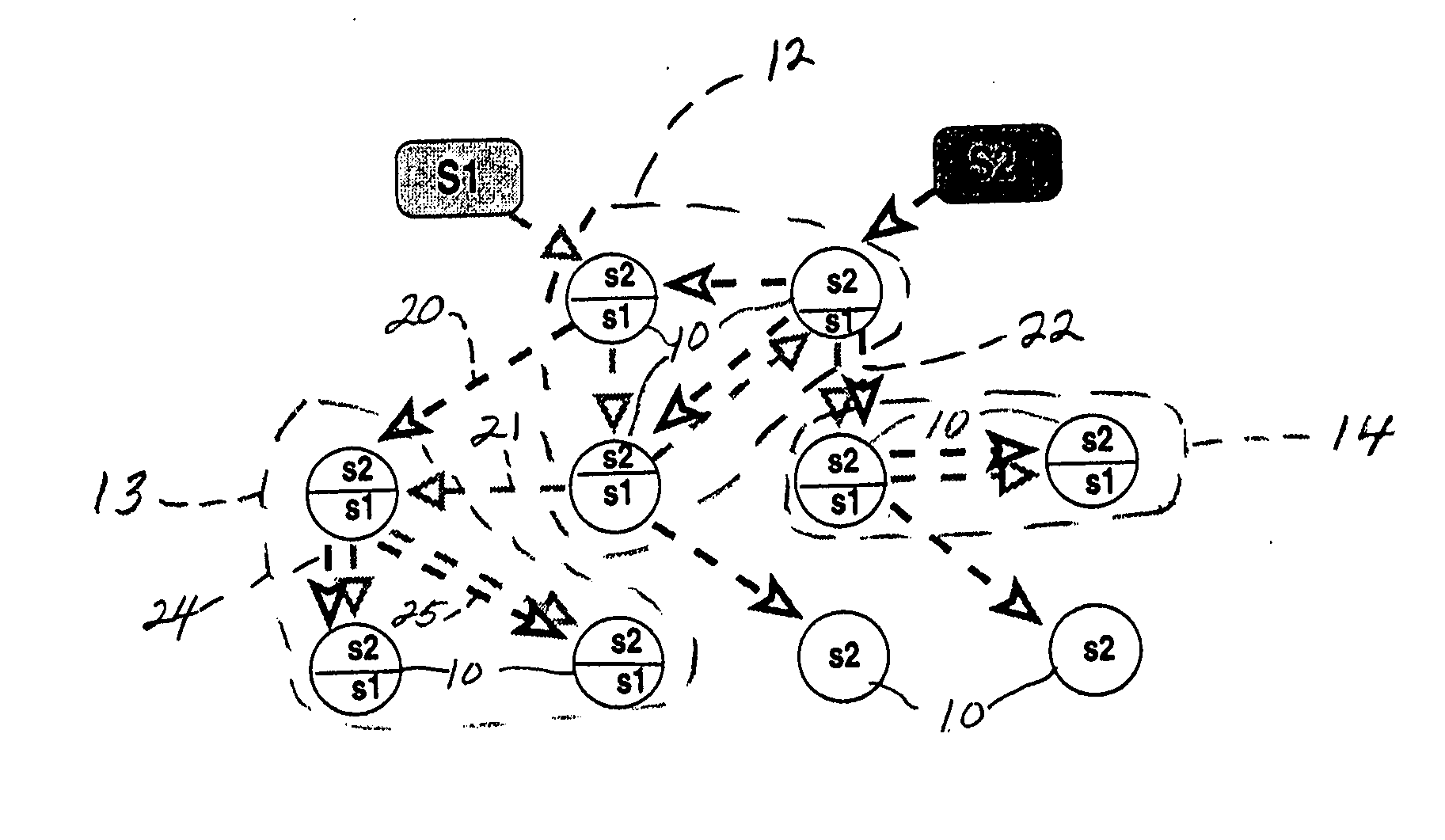
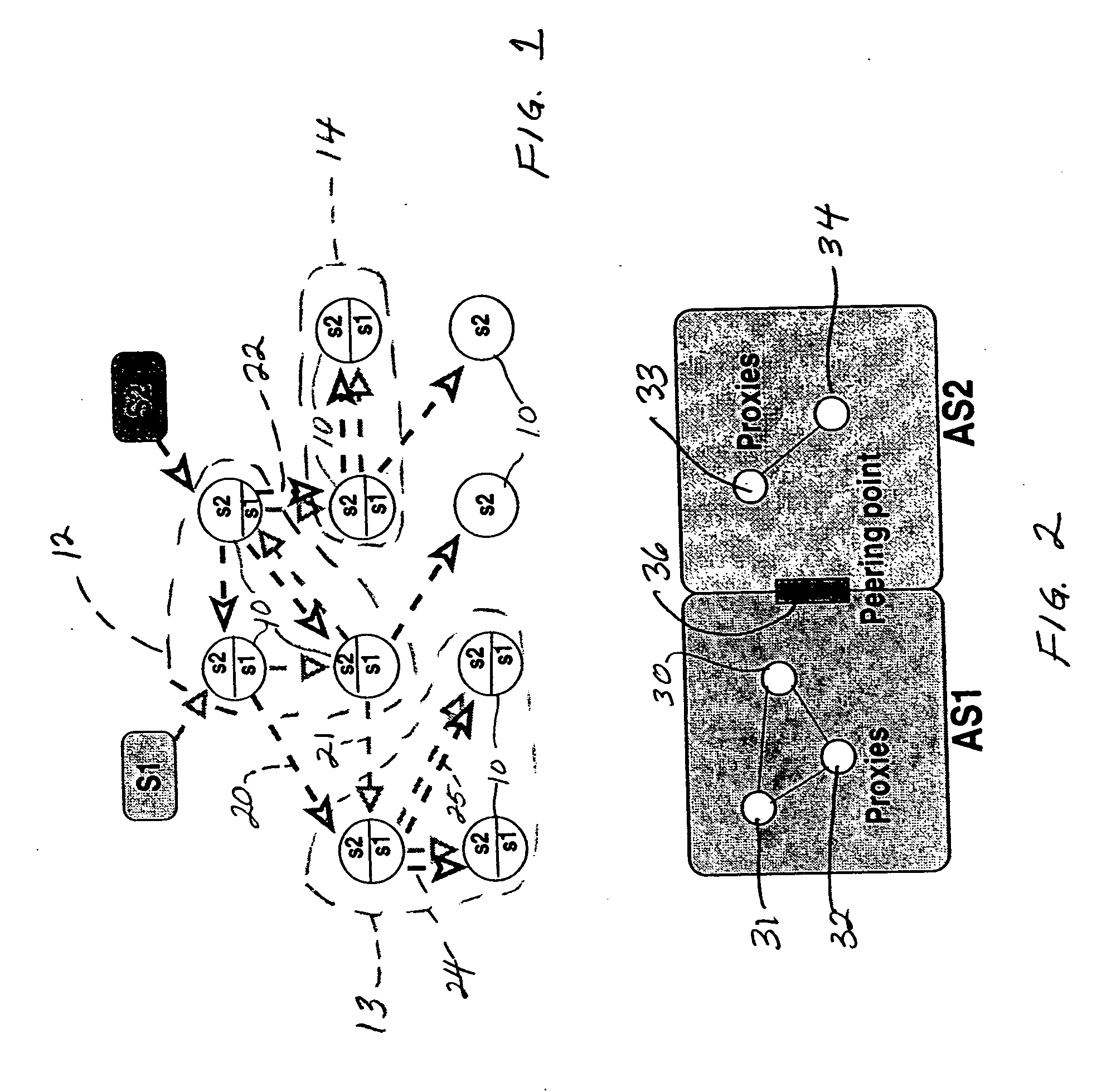
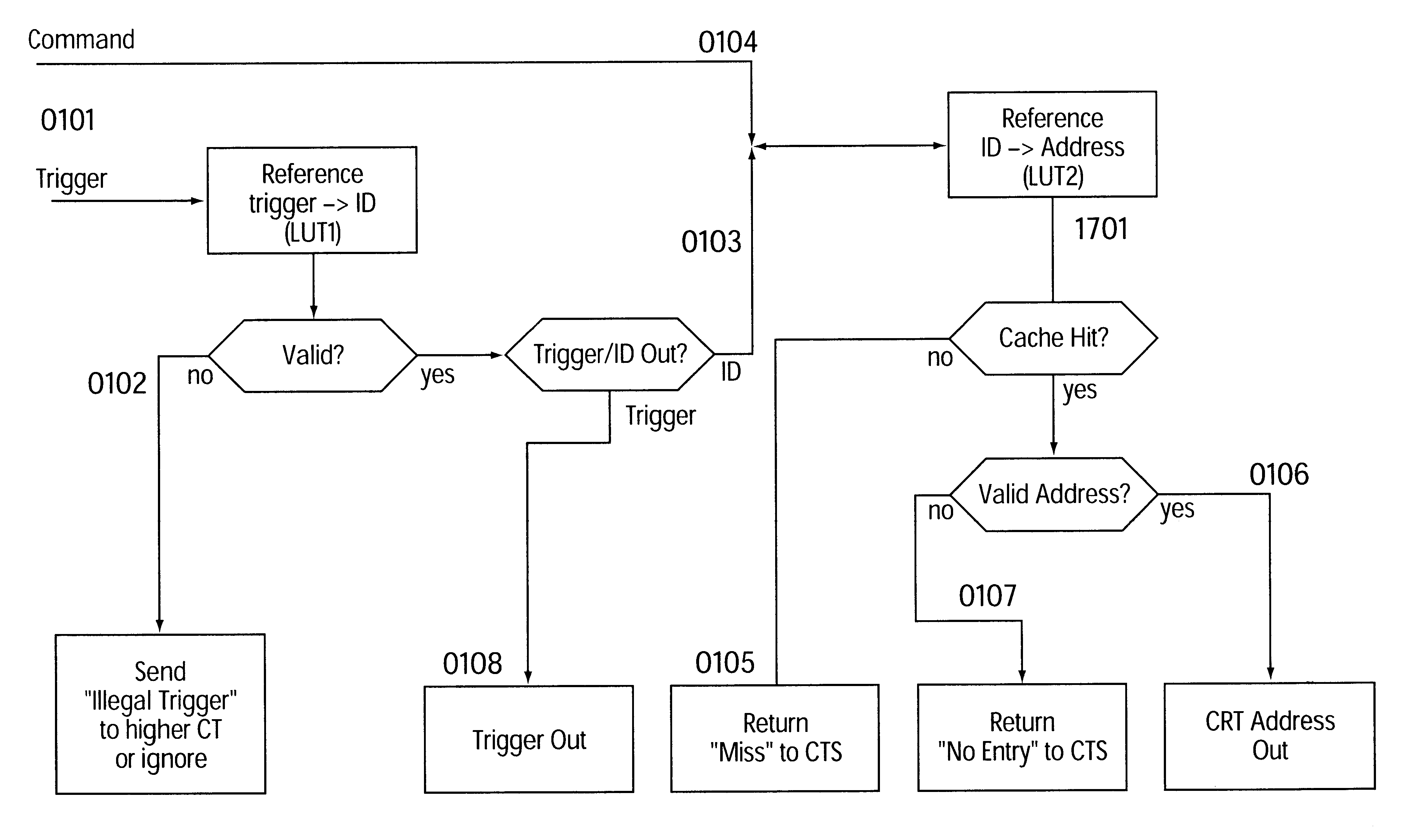
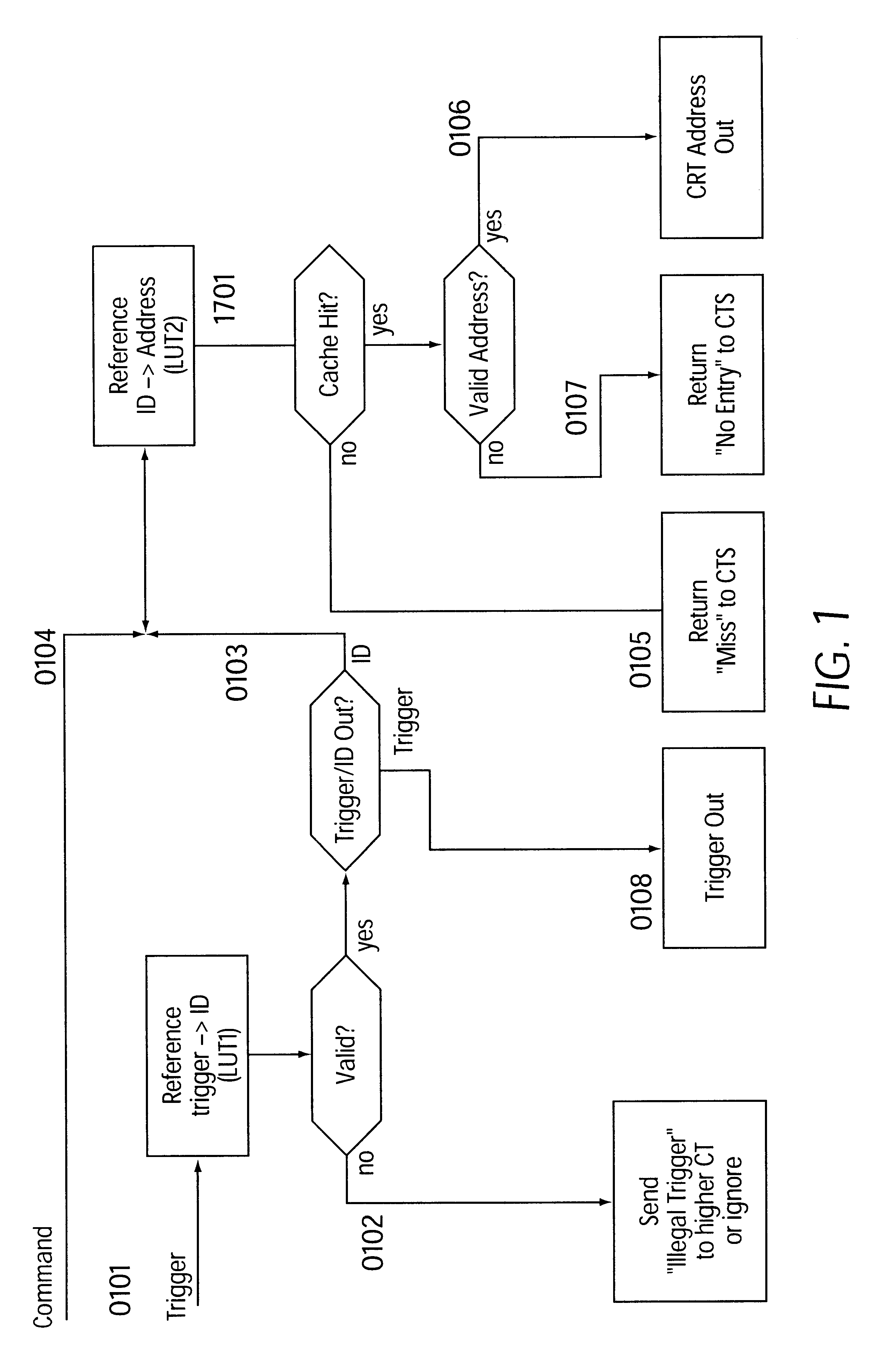
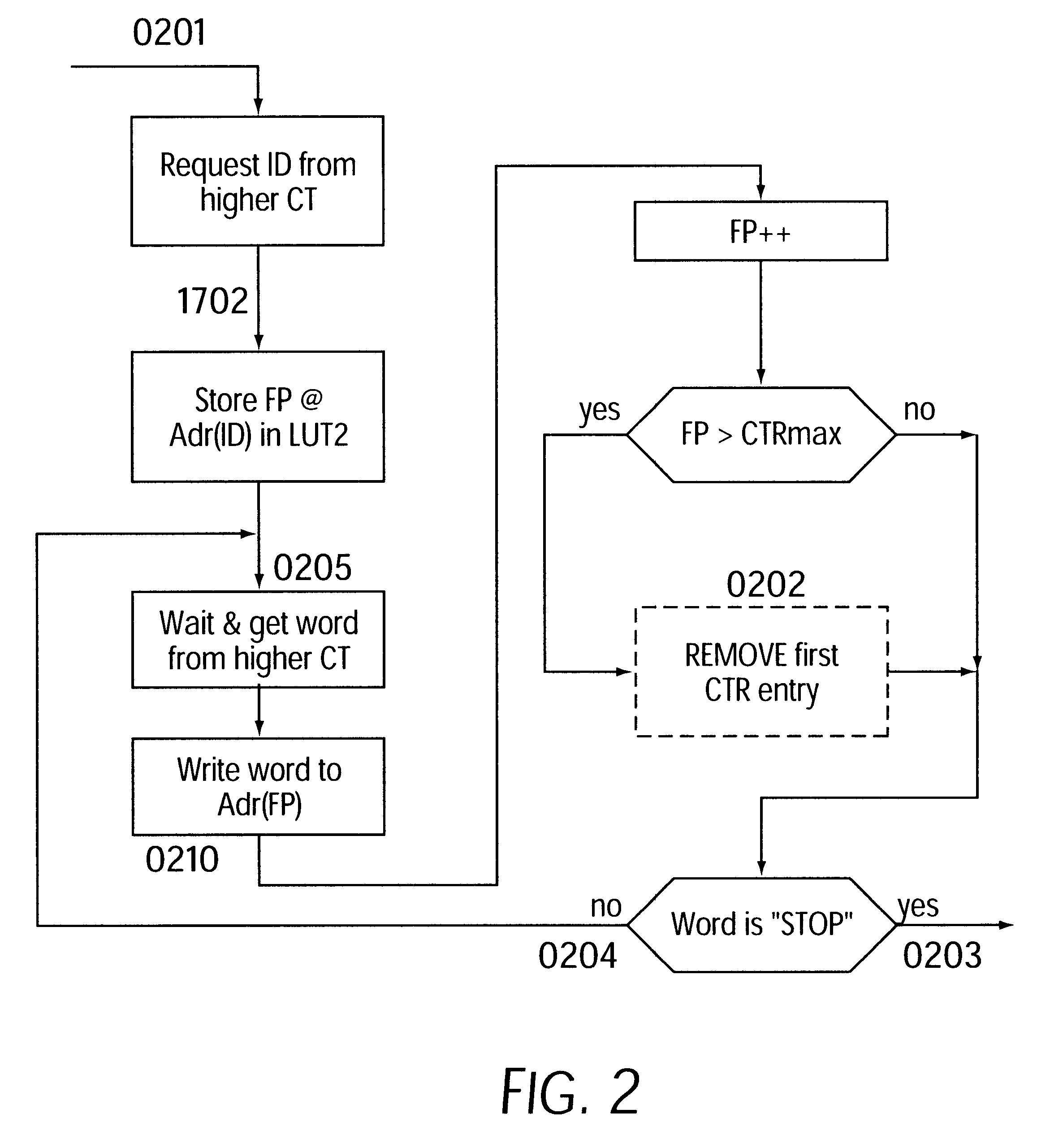
System and method for distributed facility management and operational control
ActiveUS7349761B1Programme controlSampled-variable control systemsControl systemEnvironmental control system
An environmental control system controls monitoring and operation of a multiplicity of disparate environmental control devices by determining an appropriate configuration for each control device and communicates corresponding monitoring and control commands to each device in accordance with its corresponding communication protocol over a selected I / O port. An operational instruction set includes a structural definition of an enterprise facility in which devices are defined by personality modules and communicate with a system host in accordance with a protocol defined in a protocol module. Facility implementation is defined by a node tree structure which collects suitable protocol nodes under a corresponding I / O interface port node. Device (personality) nodes are collected under corresponding protocol nodes, and data point nodes depend from their corresponding device nodes. Data points nodes are individually accessible by merely traversing the node tree using a URL-like notational structure, allowing off-site users to control and monitor environmental devices by issuing commands in the form of a URL.
Owner:CISCO TECH INC +1
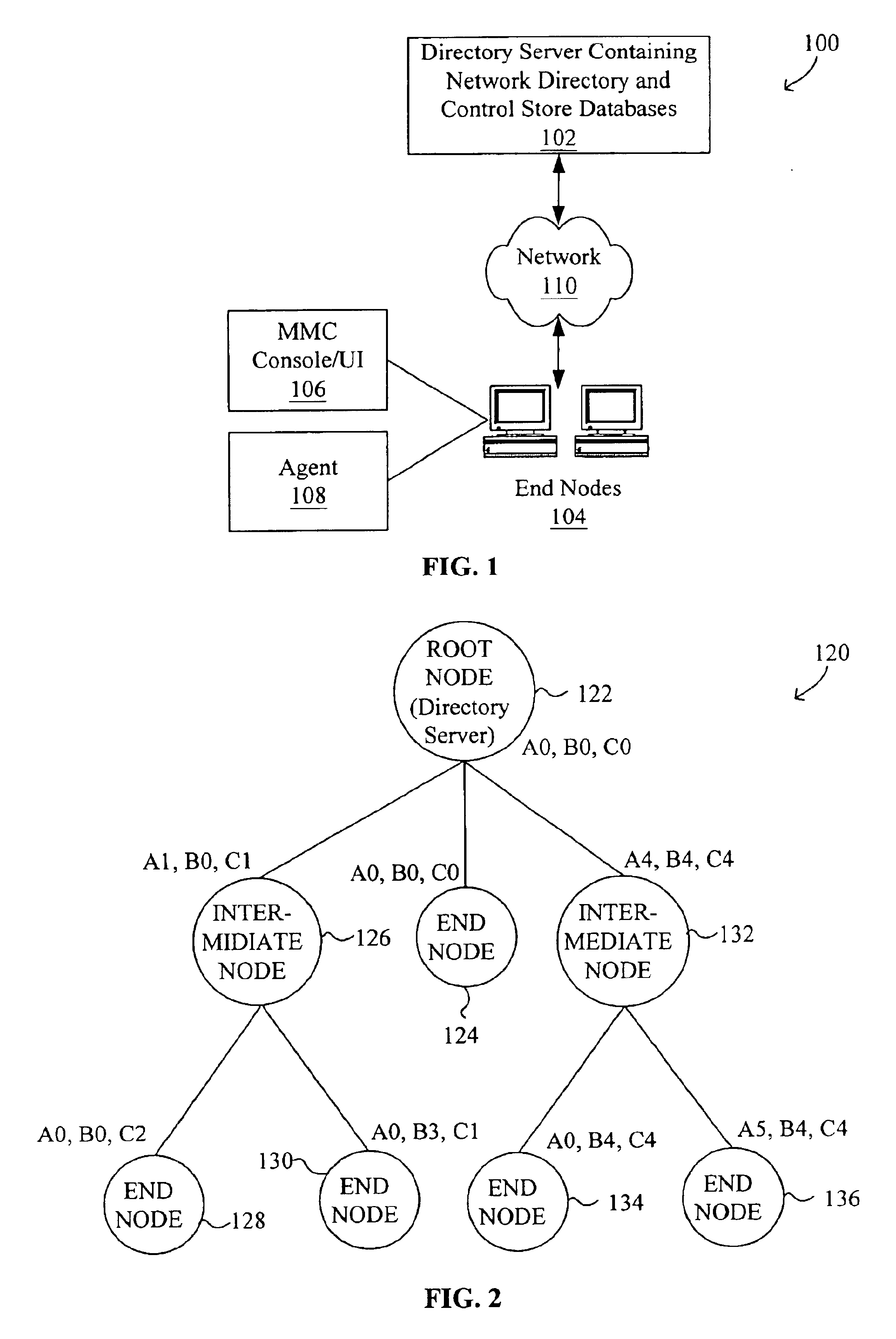
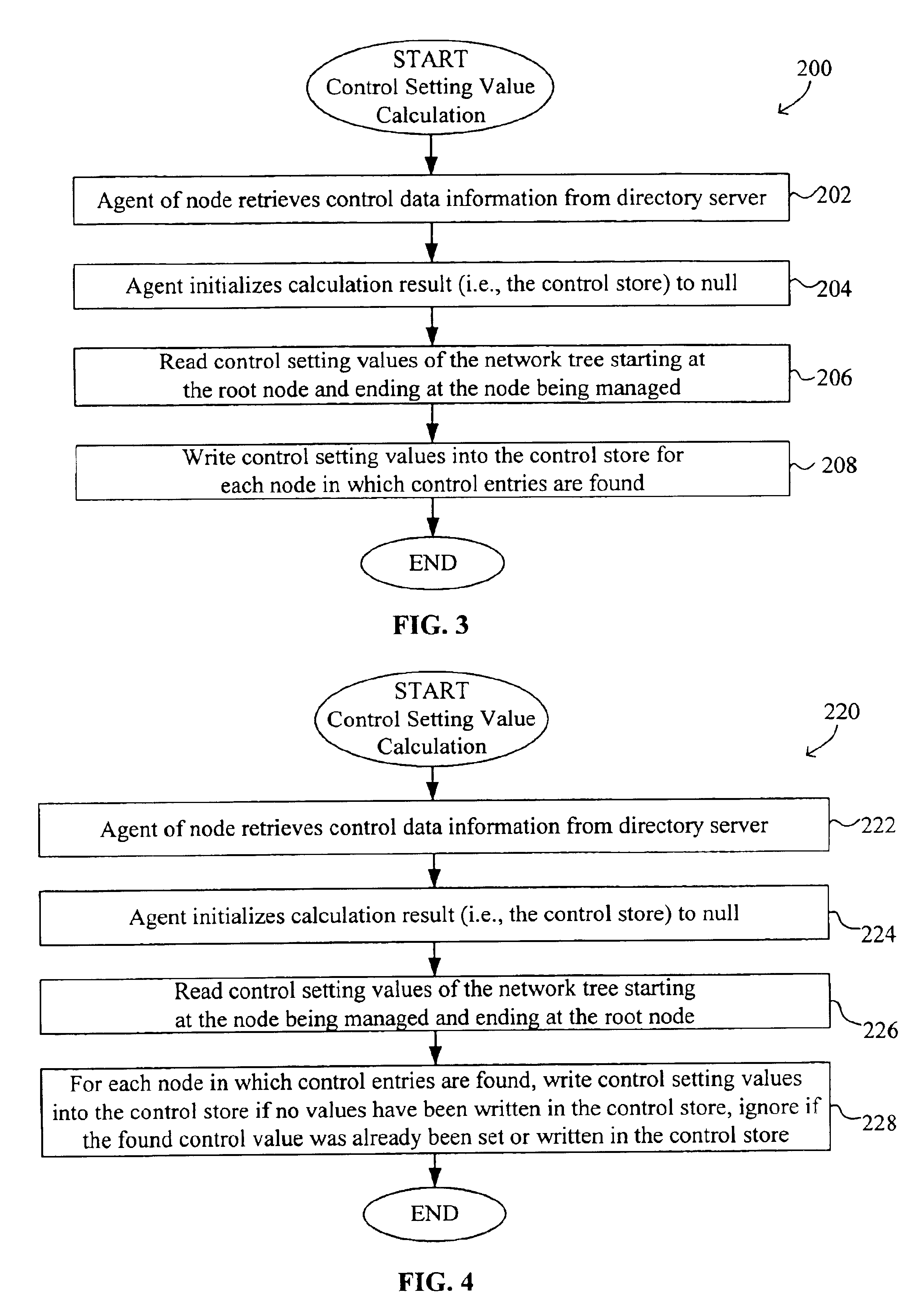
System and method for configuring computer applications and devices using inheritance
InactiveUS20020091819A1Multiple digital computer combinationsData switching networksStructure of Management InformationNetwork topology
A system and method using inheritance for the configuration, management, and / or monitoring of computer applications and devices via a computer network are disclosed. The method generally comprises determining a hierarchical tree structure based upon locations of devices in a network topology, each device being a node in the hierarchical tree structure, determining policies for each node in the hierarchical tree structure to be enforced by an agent corresponding to each node, the agent being in communication with the device and the resources corresponding to the device, and communicating the policy to the corresponding agent, wherein the policies corresponding to the resources of each device are selectively inherited along the hierarchical tree structure of the network directory.
Owner:MCAFEE INC
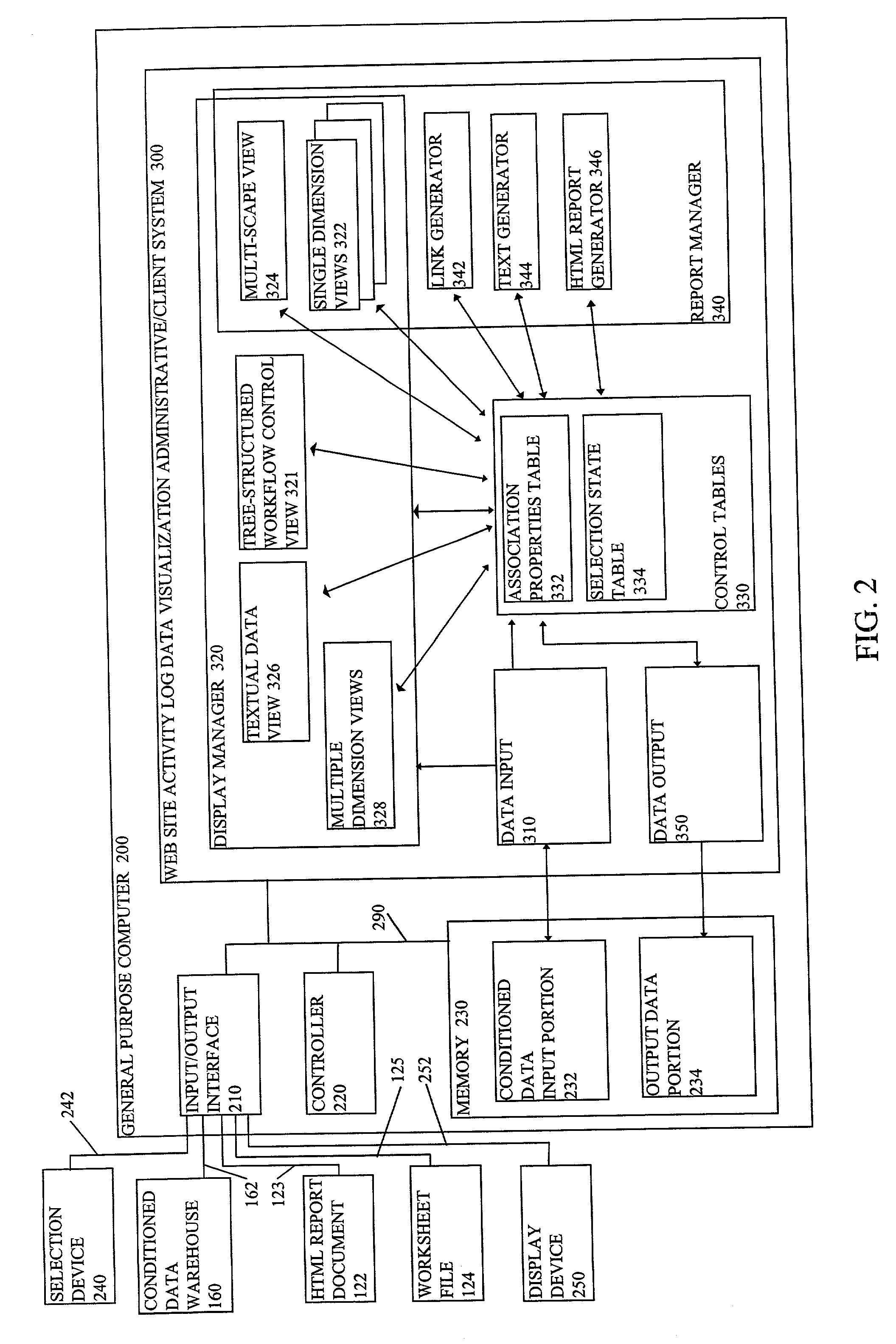
Systems and methods for visualizing and analyzing conditioned data
A tree-structured workflow control and a tree-structured report selection control allow users to easily display data and generate reports, without having to actively determine the various measures and dimensions to be displayed in various interactive views of the data and various simple and advanced reports. By linking predetermined sets of dimensions, measures and views to predetermined workflow control entries and report selection entries in a tree structure having labels on the branches and leaves that are logically related to the associated predetermined sets, the user can immediately obtain a data visualization perspective or a report without having to actively select the particular dimensions and measures for display, and without having to actively arrange the selected dimensions into a multi-dimensional view. The user can also alter the particular dimensions and / or measures being displayed and associate the user's selection with a new predetermined entry in the tree-structured workflow and report selection controls.
Owner:ADVIZOR SOLUTIONS
Self-healing hierarchical network management system, and methods and apparatus therefor
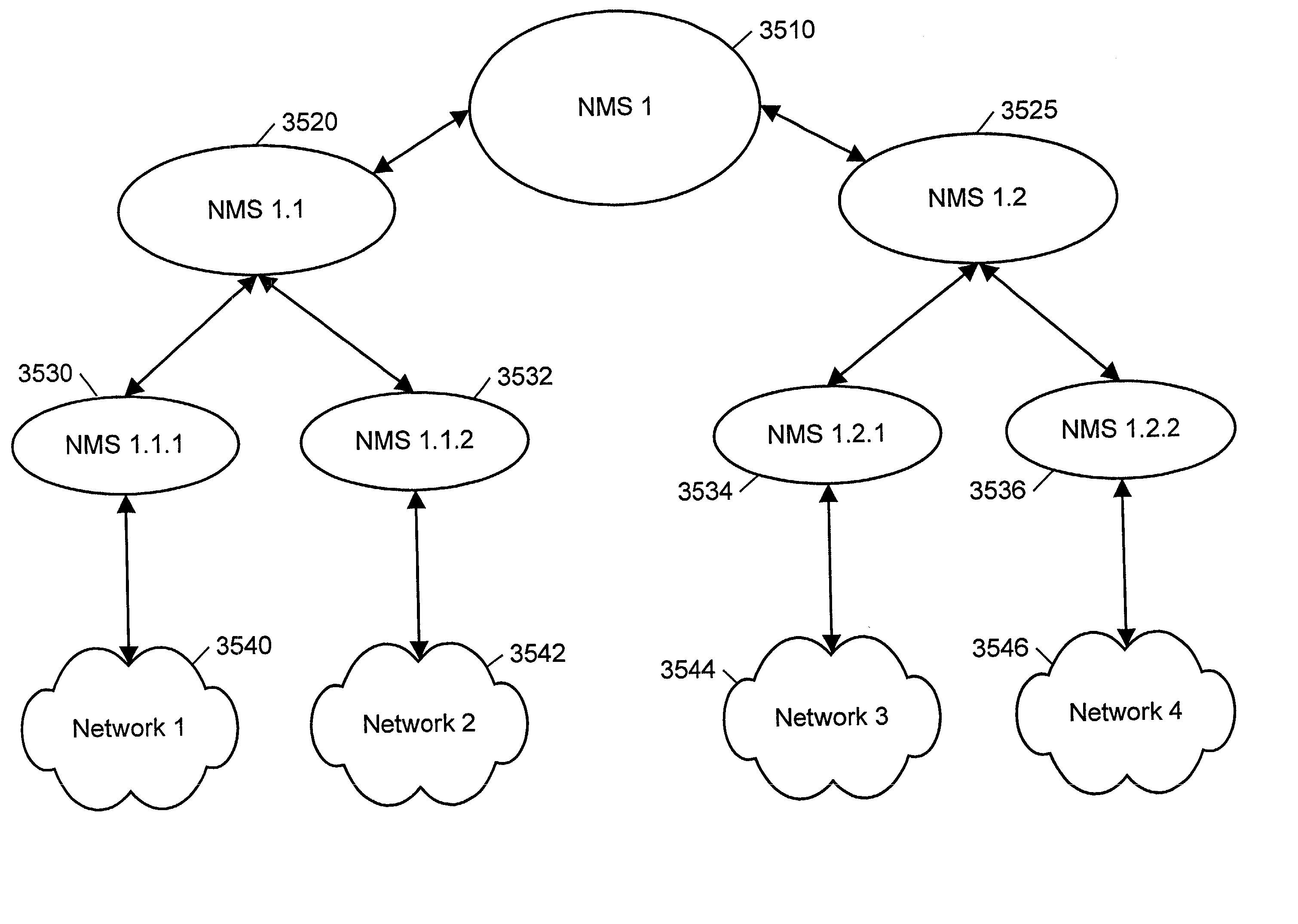
InactiveUS20020174207A1Multiplex system selection arrangementsWavelength-division multiplex systemsSelf-healingNetwork management
A hierarchical network management system (NMS) in which a plurality of NMS managers, each responsible for different portions or aggregations of a communications network, are logically arranged in a tree structure. The NMS managers are further organized into various sub-groups. The NMS managers within each sub-group monitor the status of one another in order to detect when one of them is no longer operational. If this happens, the remaining operational NMS managers of the sub-group collectively elect one of them to assume the responsibility of the non-operational NMS manager. The NMS is thus "self-healing" in the sense that one NMS manager can dynamically, without operator intervention, assume the responsibilities for another NMS manager.
Owner:FIRSTWAVE SECURE INTELLIGENT OPTICAL NETWORKS
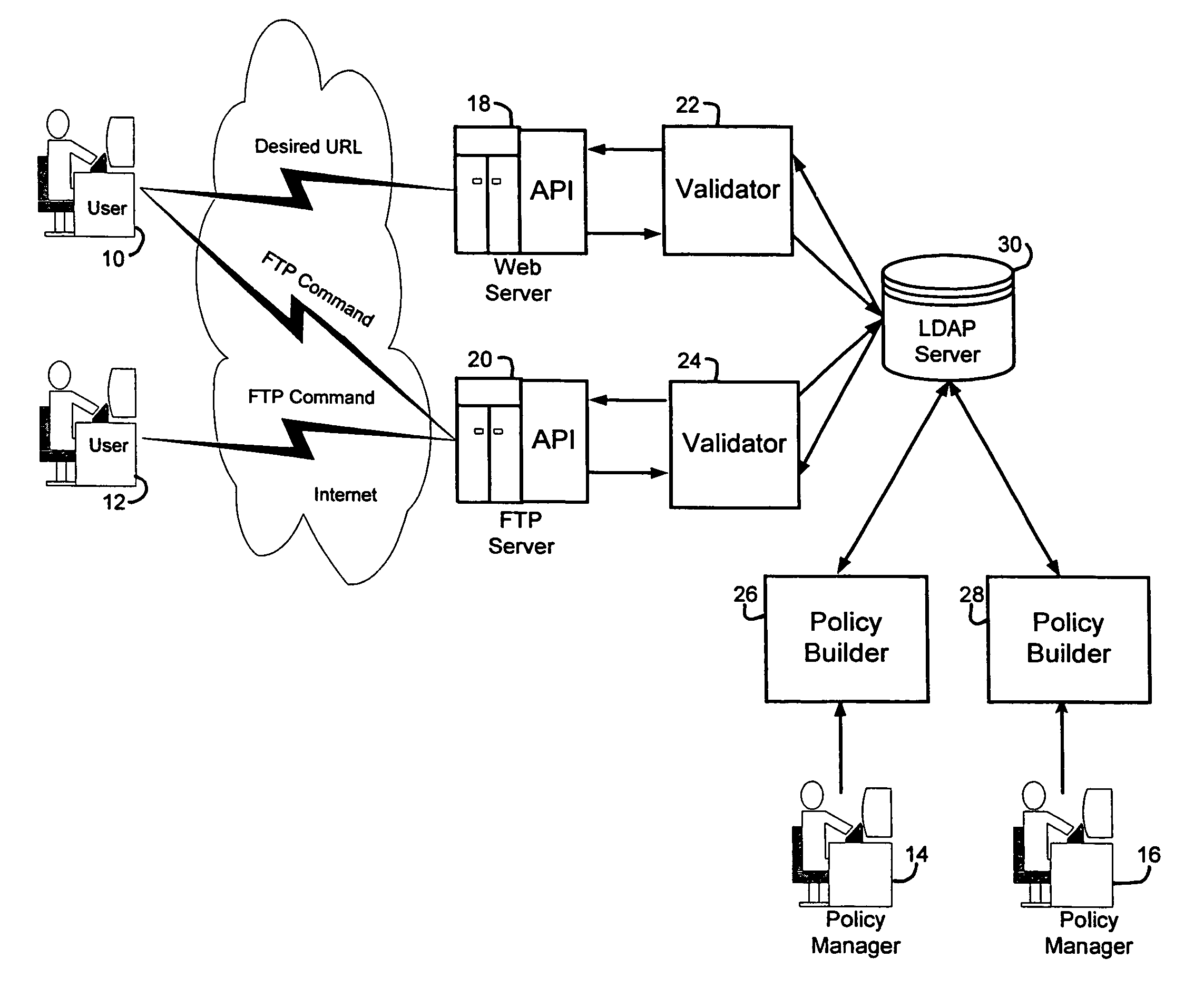
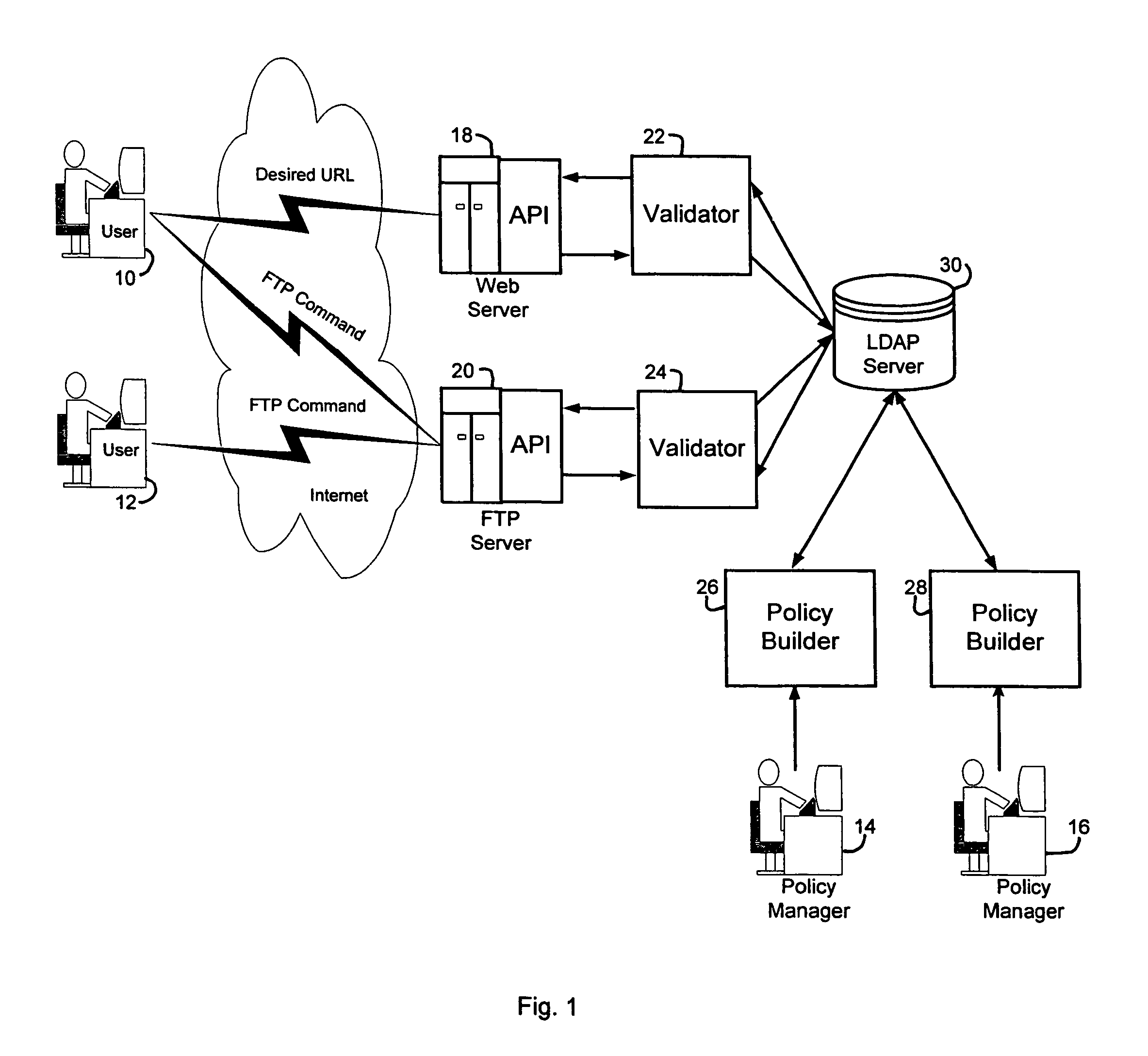
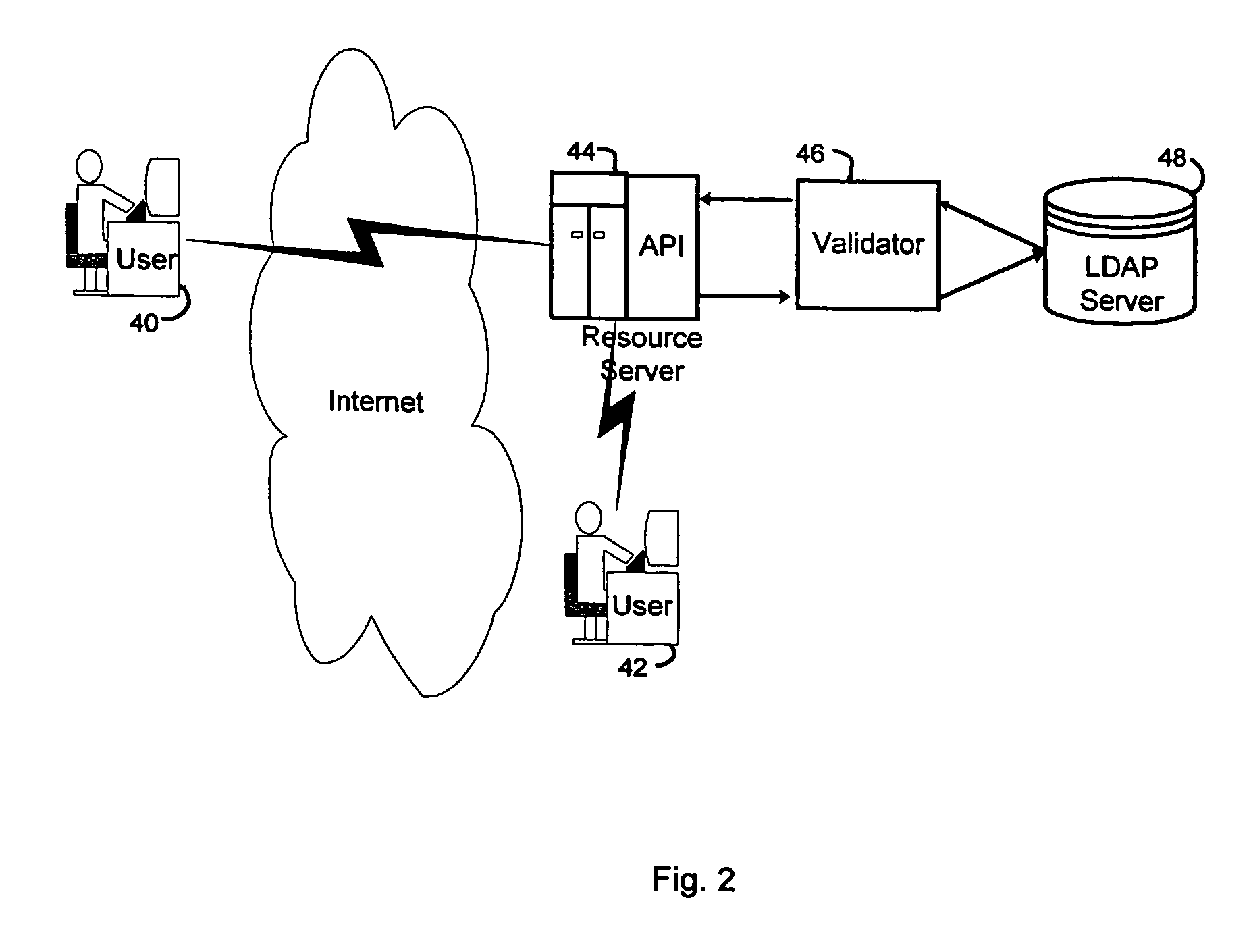
Computer system security service
A security service of computer networks having a policy builder, an LDAP-compliant database, a validator and an API. The policy builder component provides a graphical user interface to be used by a policy manager to define access policies for users seeking to access network services and resources. The graphical user interface has a grid of nodes representing access policies. The grid is arranged to correspond to a defined tree structure representing services and resources and a business relationship tree structure representing users. The graphical user interface permits the policy manager to define policy builder plug-ins for access policy customization. The LDAP-compliant database maintains the policy builder plug-ins. The validator component receives requests from users and queries the LDAP-compliant database to obtain relevant access policies as defined by the policy manager. The system provides for double inheritance of access policies such that where there is no express definition of an access policy for a node, the access policies are propagated according to the hierarchical structures of the data. The validator includes validator plug-ins for carrying out access policies corresponding to the access policies defined by policy builder plug-ins.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
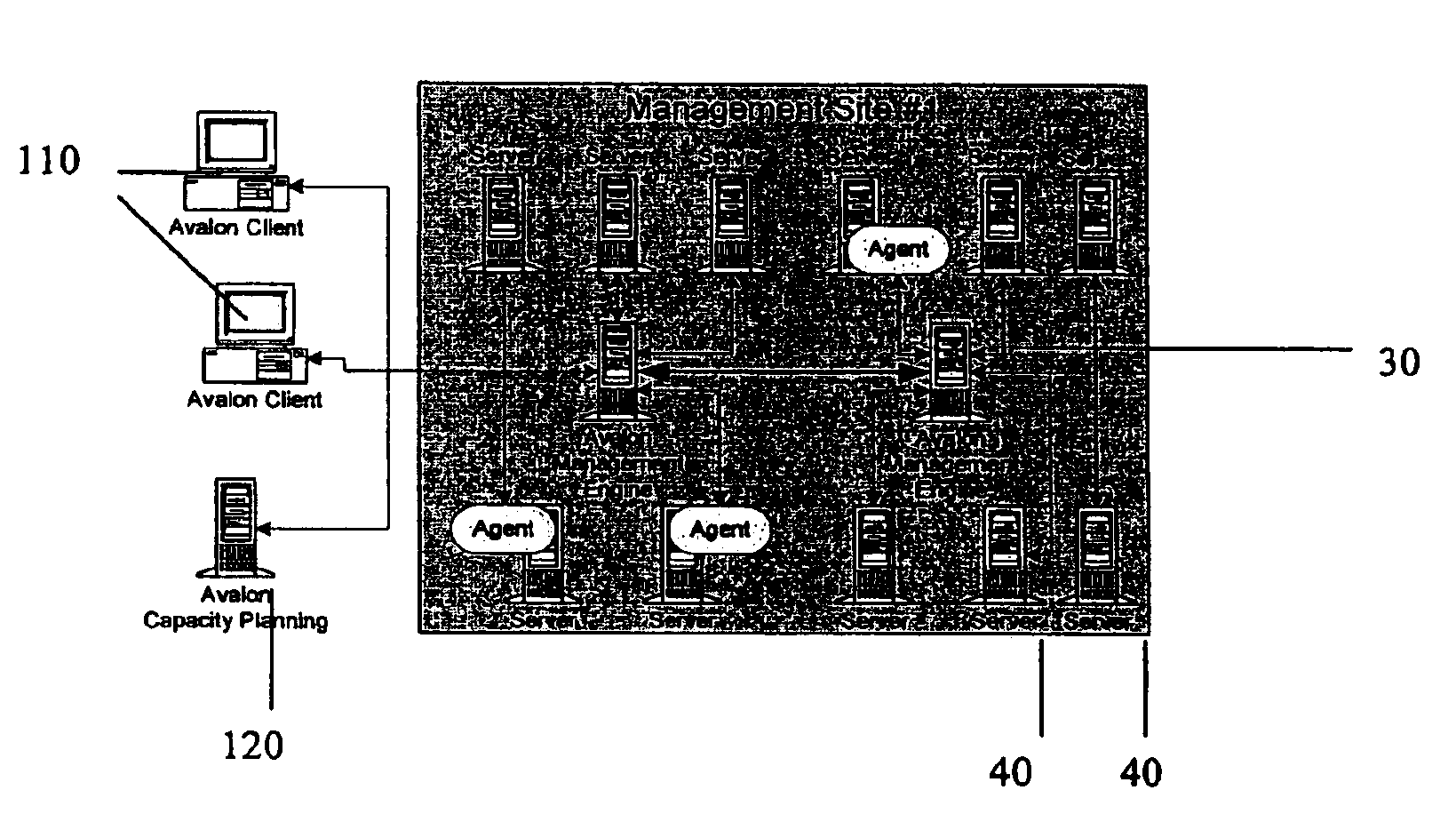
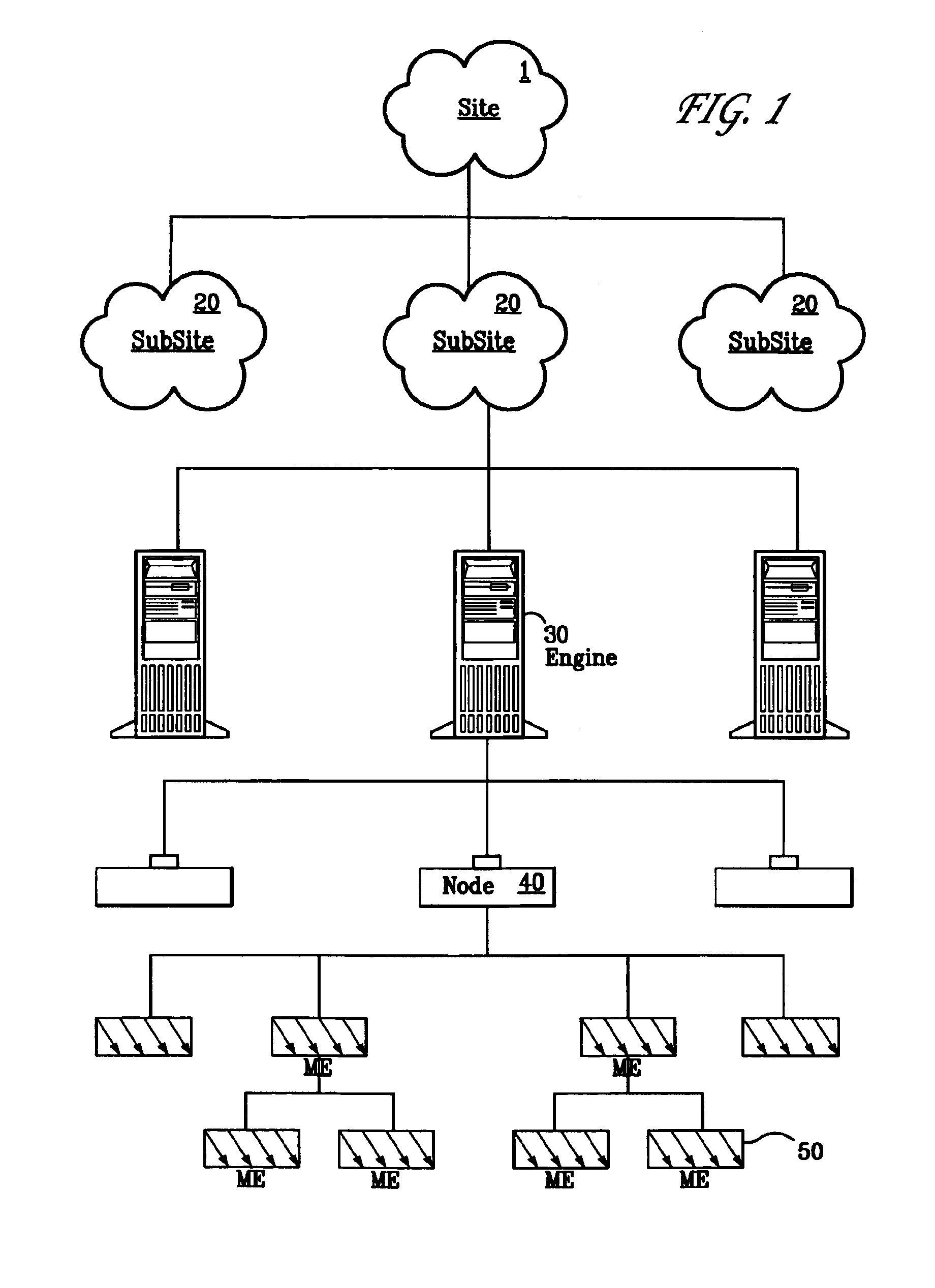
Enterprise management system
InactiveUS6983317B1Improve availabilityImprove robustnessDigital computer detailsTransmissionRoot cause analysisAccess management
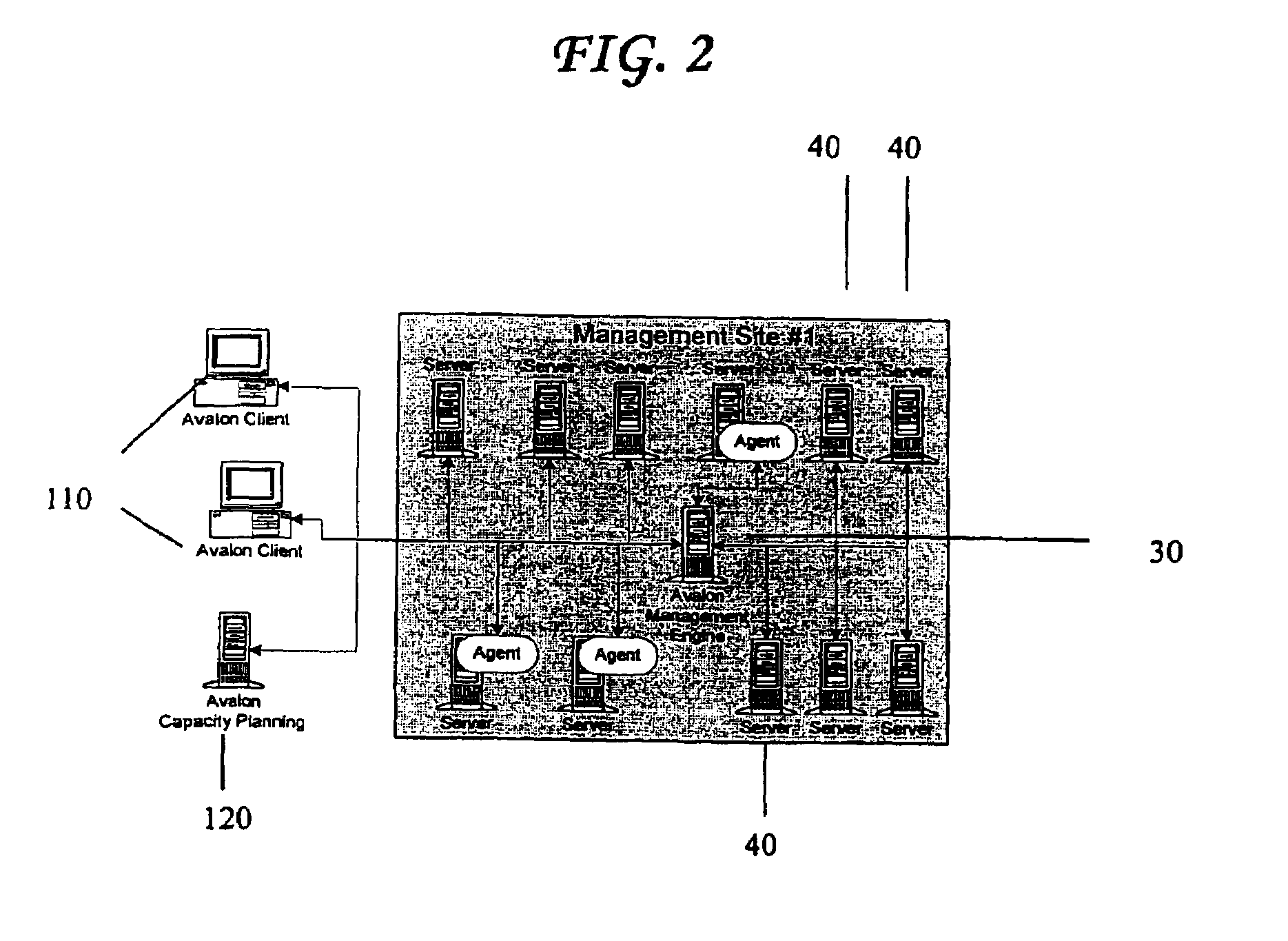
A Managed Site (10), a logical network entity, is composed of a number of Sub Sites (20) in a one to many relationship. A Sub Site (20) is a logical component, which is composed of a number of Engines (30). Nodes (40) similarly relates to their Engine (30) in a many to one relationship. A Node (40) is a collection of Managed Elements (ME's) (50) (while being an ME (50) itself), which represent network state information. The subsite (20) consists of the engine (30) connected to server nodes (40). One or more clients (110) are connected to the management engine (30) and access management engine (30) information relating to managed elements (50) including nodes (40). The connected manager engines may communicate with one another so that, for example, in the event of a failure, one of the manager engines remaining on line commences monitoring of manage elements assigned to the failed manager engine. Upon accessing the manager engine (30), the client interface displays relationships among managed elements (50) using meaningful connectors and tree-like structures. In addition to basic managed element state monitoring functionality, the manager engine (30) provides a variety of automated tasks ensuring the health of the network and optimal failure correction in the event of a problem. For example, the manager engine (30) performs root cause analysis utilizing an algorithm tracing through manged element (50) relationships and indicating the source of the failure.
Owner:MICROSOFT TECH LICENSING LLC
Core assisted mesh protocol for multicast routing in ad-hoc Networks
InactiveUS6917985B2Enrich connectivityStay connectedSpecial service provision for substationError preventionIP multicastBroadcasting
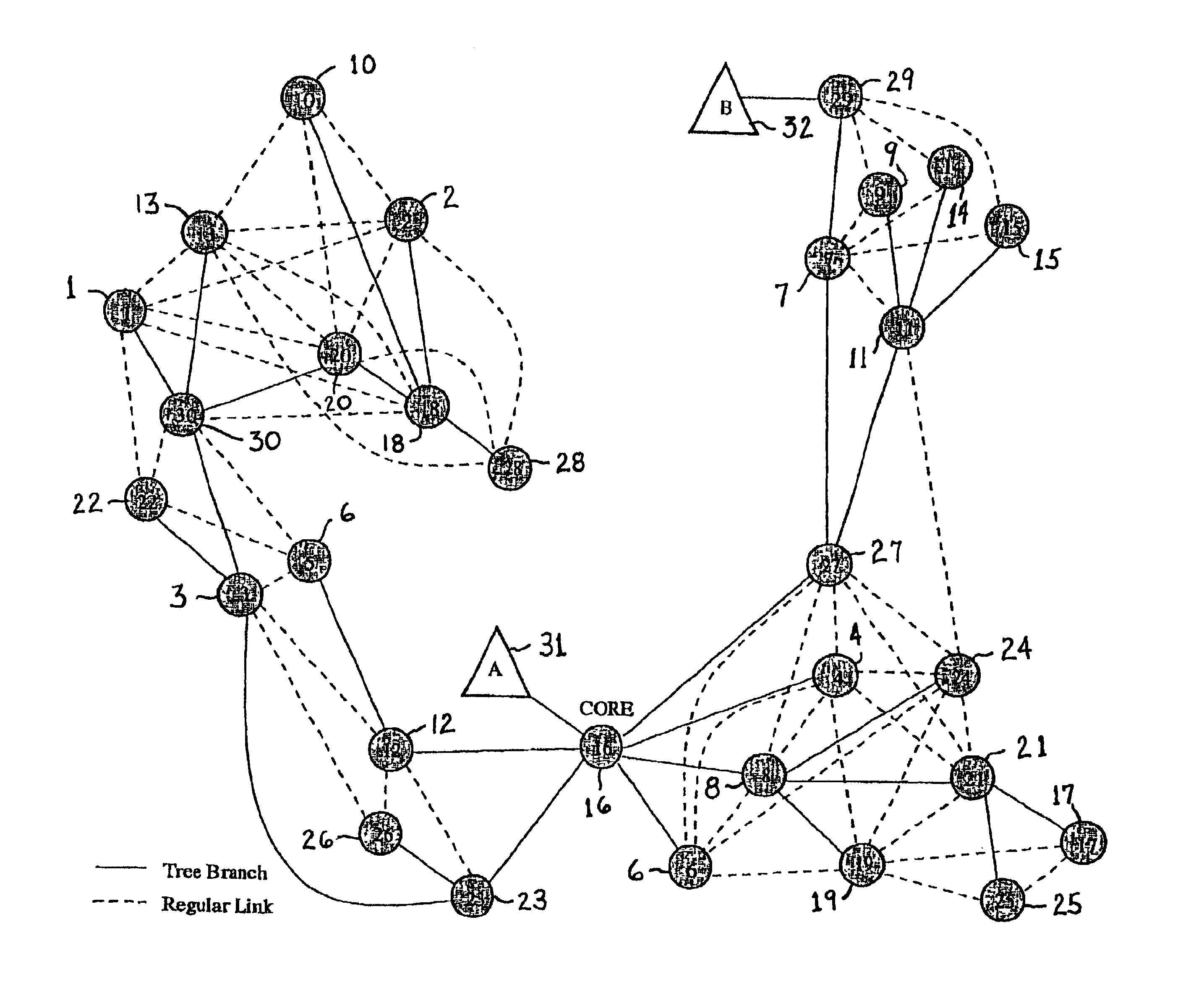
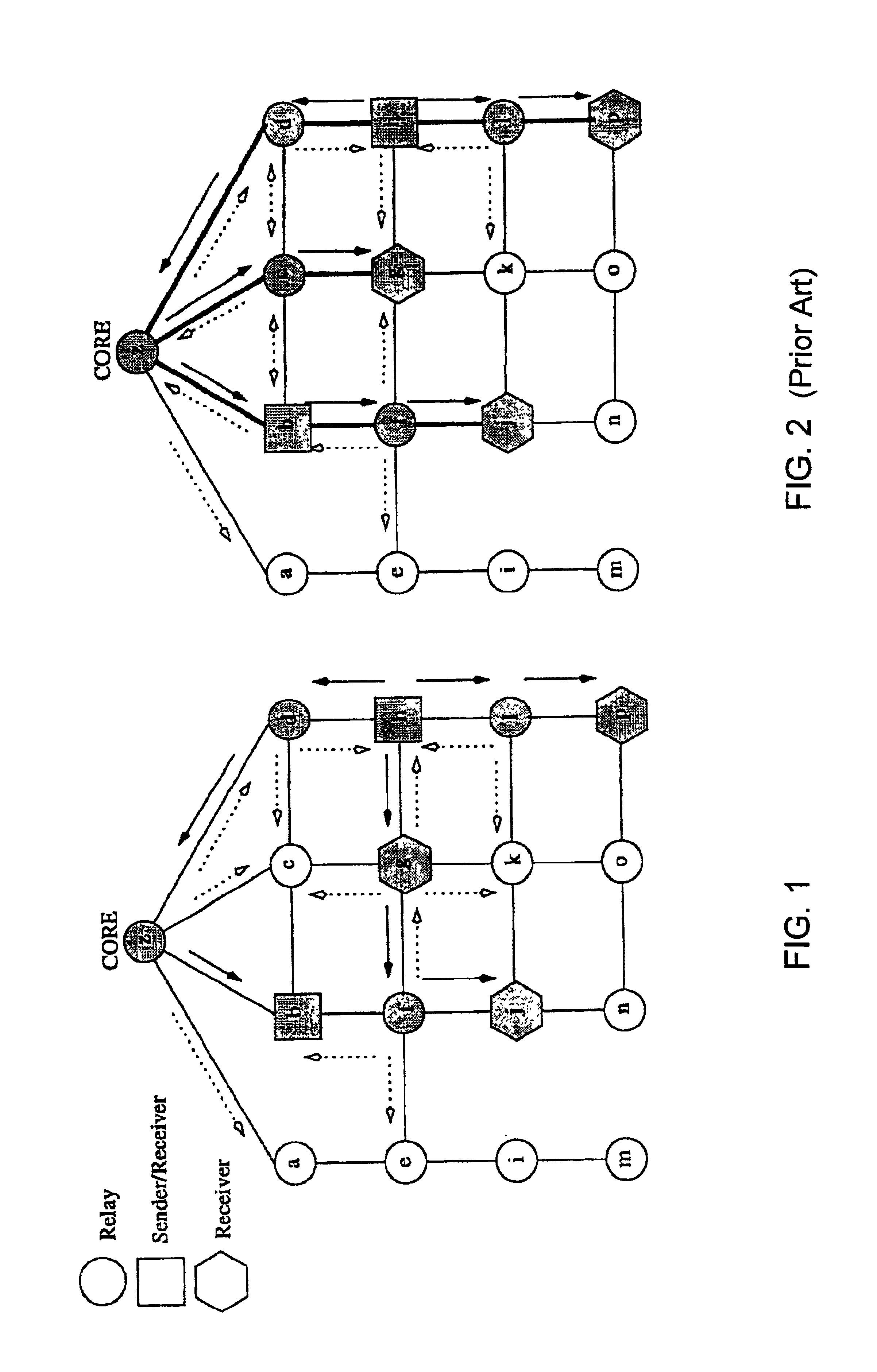
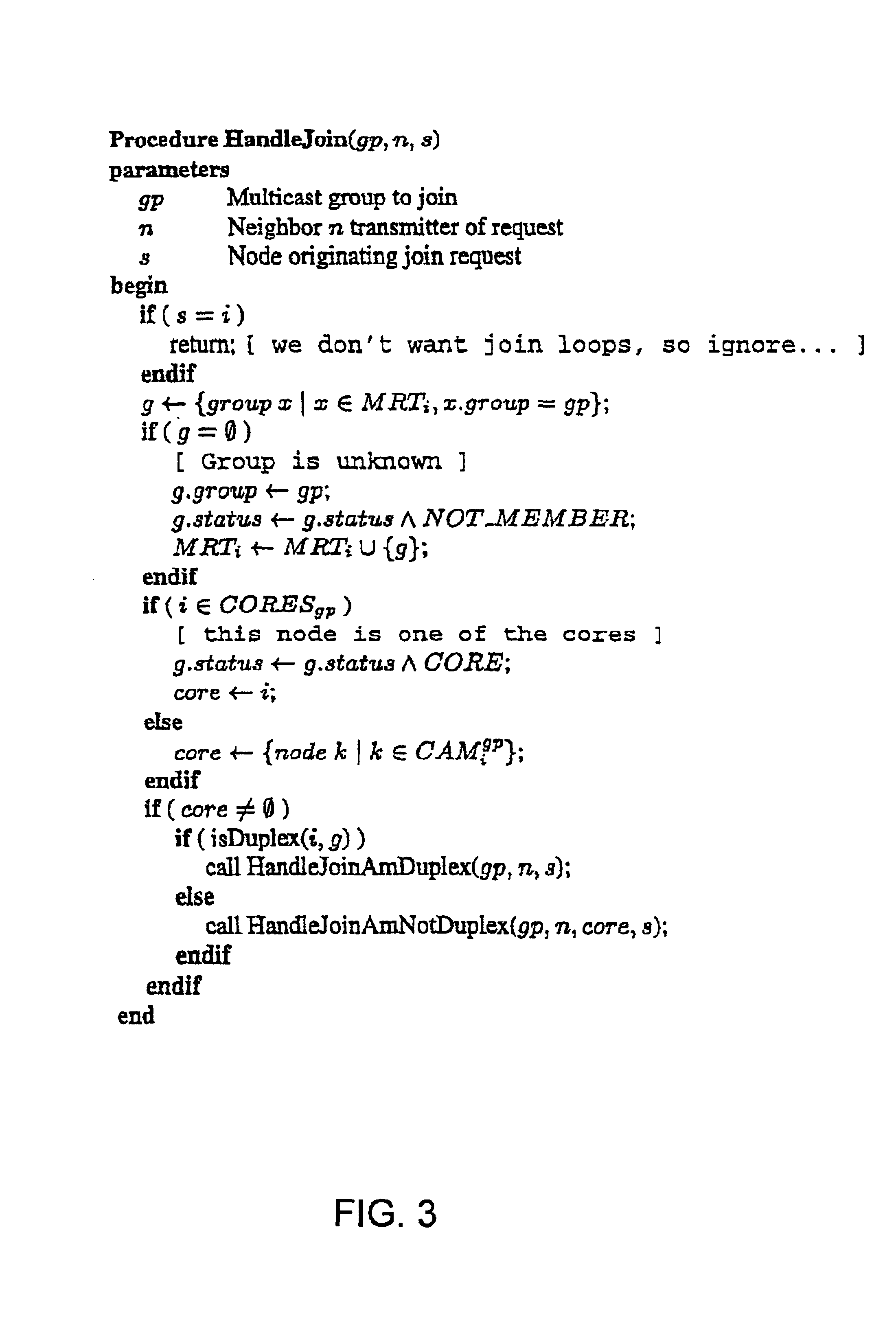
A method of providing multicast routing for use in ad hoc broadcast networks, such as wireless and mobile networks. The method is described within a protocol referred to as core-assisted mesh protocol, or CAMP. The method departs from traditional tree-structured multicast protocols and utilizes multicast meshes in which the network need not be flooded with control or data packets to establish routing paths. Each router configured for CAMP is capable of accepting unique packets arriving from any neighbor in the mesh, wherein packets are forwarded along reverse shortest paths to the receiver. Multiple cores may be defined for a group wherein the loss of a single core does not prevent packet flow. Routers for sender-only hosts are allowed to join the multicast mesh in simplex mode, and in certain cases may join without the sending of a join request.
Owner:RGT UNIV OF CALIFORNIA
Usage based methods of traversing and displaying generalized graph structures
InactiveUS6509898B2Data processing applicationsDrawing from basic elementsRankingTheoretical computer science
A method for generating a tree structure representation of a generalized graph structure for display includes the more important links in the representation. Usage parameters are referenced in generating the tree structure from the generalized graph structure. Frequency, recency, spacing of accesses, and path information are exemplary types of usage parameters. A breadth-first or depth-first traversal of the graph references usage parameters associated with each node or link. The usage parameters which are associated with each node are referenced in order to determine the visitation order. The visitation order is determined by visiting the highest used nodes or links first. A method of displaying the tree structure references the usage parameters to determine the positioning of the nodes in the layout of the tree structure. In a preferred embodiment, the root node is positioned in the center of the layout. In one example, sibling nodes are spread out on links which emanate radially about their parent. The highest-used sibling nodes can be placed farthest apart from each other so as to achieve optimal separation so that they have the most growth space. The lowest-used nodes are then placed in the remaining space between the high-usage nodes. In another example, sibling nodes are positioned at the same radius from the root node. Each leaf node in the hierarchy is assigned the same amount of angular space. The layout angle of each node is a function of the ranking of the node's usage parameter relative to its siblings. Derived usage parameters such as need probability, cocitation clustering, or functions of both node and link usages can alternatively be referenced.
Owner:GOOGLE LLC
Method and apparatus for creating and deploying applications from a server application
ActiveUS7139821B1Multiple digital computer combinationsMemory systemsCommunication interfaceSecure communication
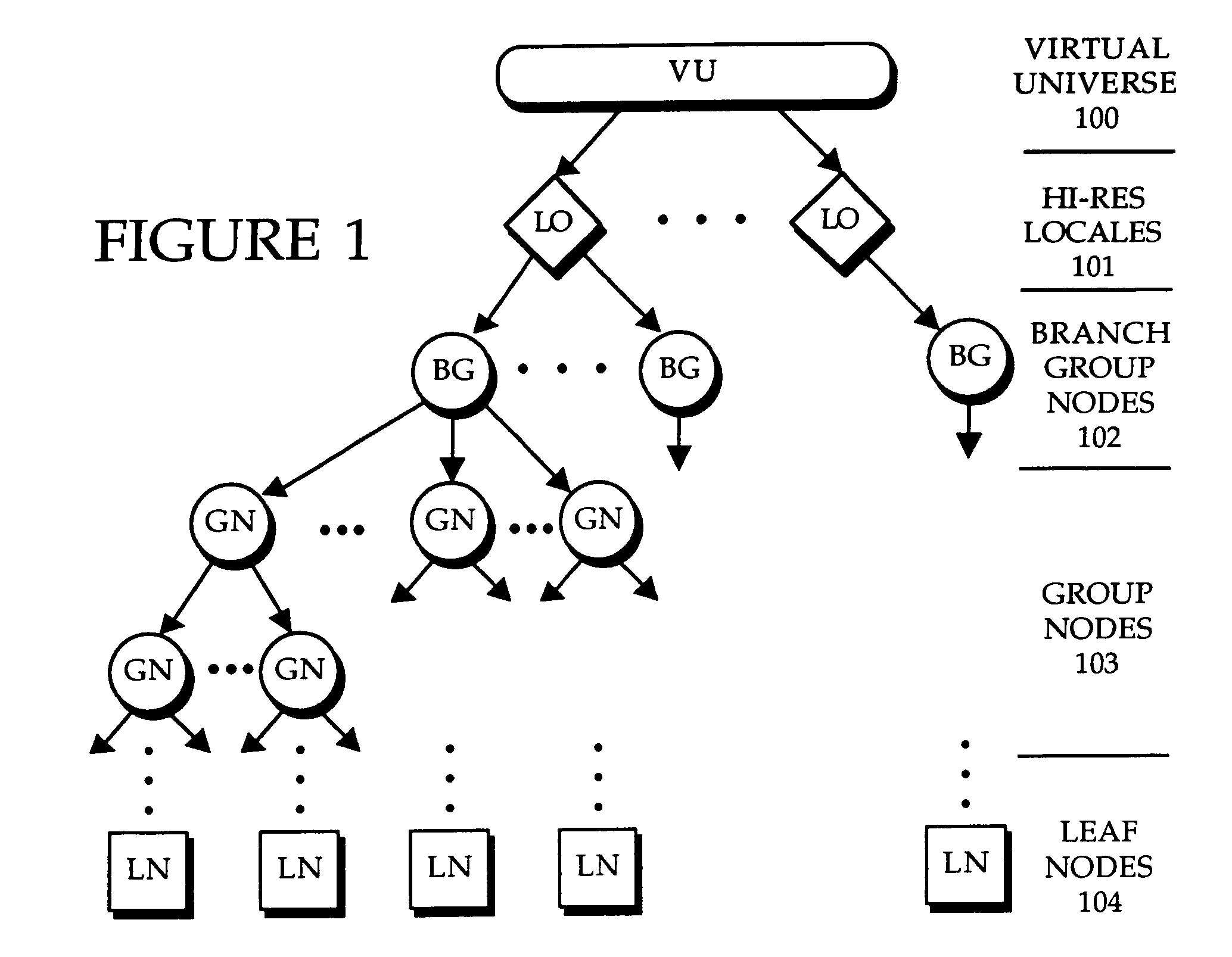
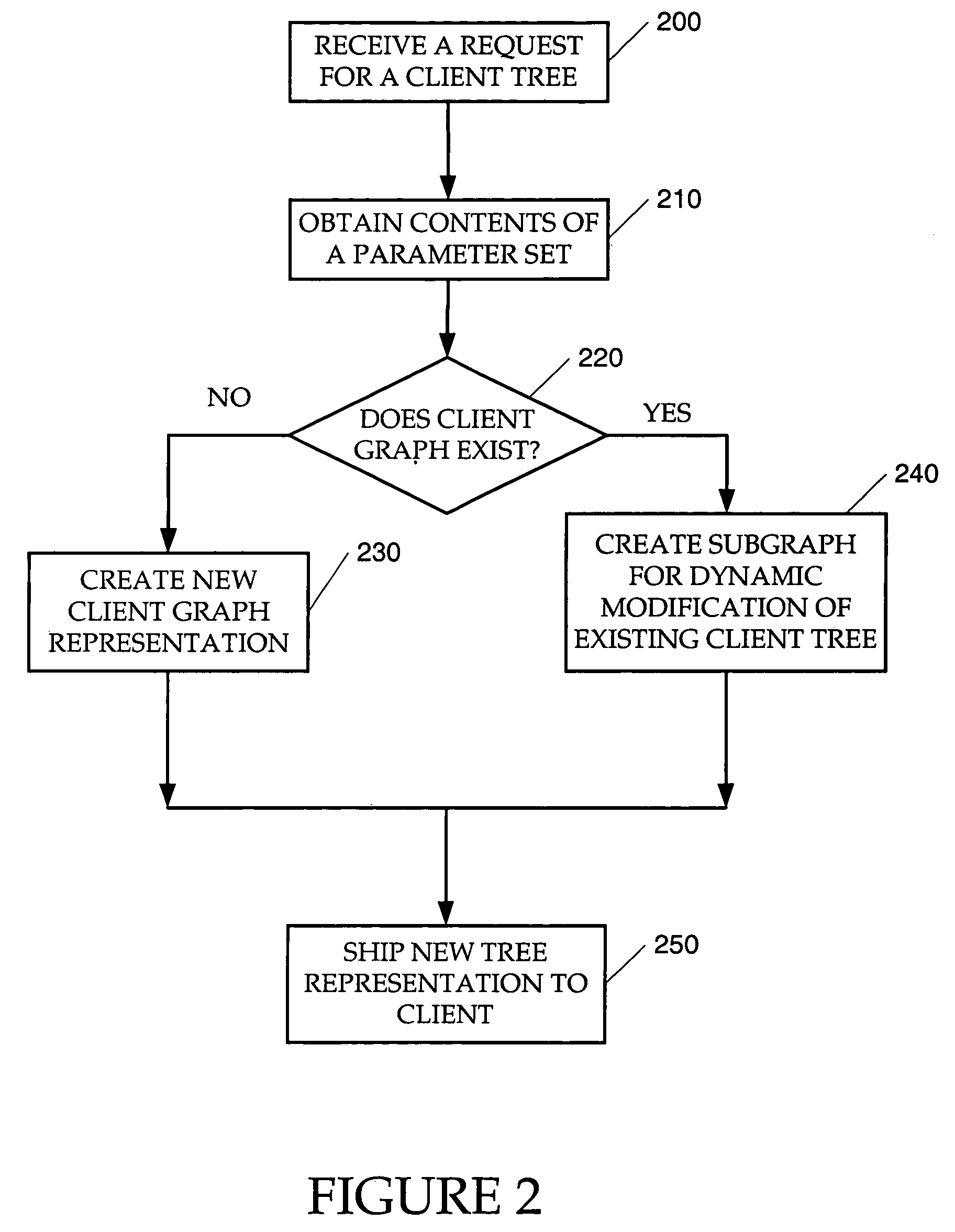
In a system where client and server components (or actors) of an application are organized as complementary hierarchical graphs, a method and apparatus for creating server applications and dynamically deploying server applications on a client system are described. The server graph comprises, as a minimum, server nodes corresponding to the union of all possible client nodes, whereas each client graph corresponds to a subset of the related server nodes. The server graph is a compound tree from which all possible combinations of client trees can be dynamically created. At a desired time, for example, when the client requests for a client tree representation, the server creates the client tree representation using a peeling process to determine which nodes in the server actor tree should be included in the client tree representation. The peeling process involves determining the server actor nodes that meet a set of criteria for the particular client. The generated client tree structure contains objects that are shipped via a secured communication interface to the client in a tree structure.
Owner:ORACLE INT CORP
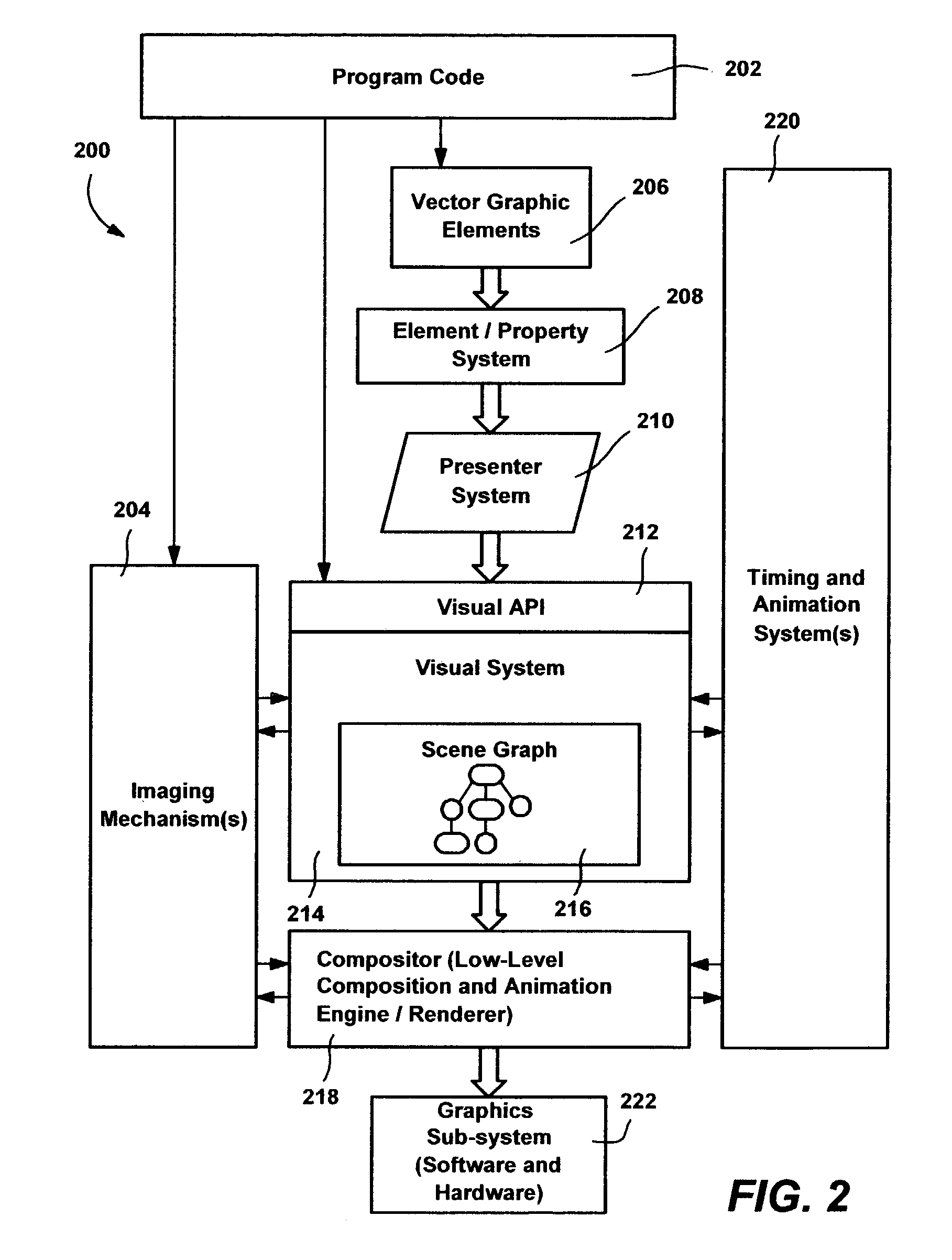
System and method for managing visual structure, timing, and animation in a graphics processing system
InactiveUS7088374B2Smooth animationDrawing from basic elementsCathode-ray tube indicatorsGraphicsAnimation
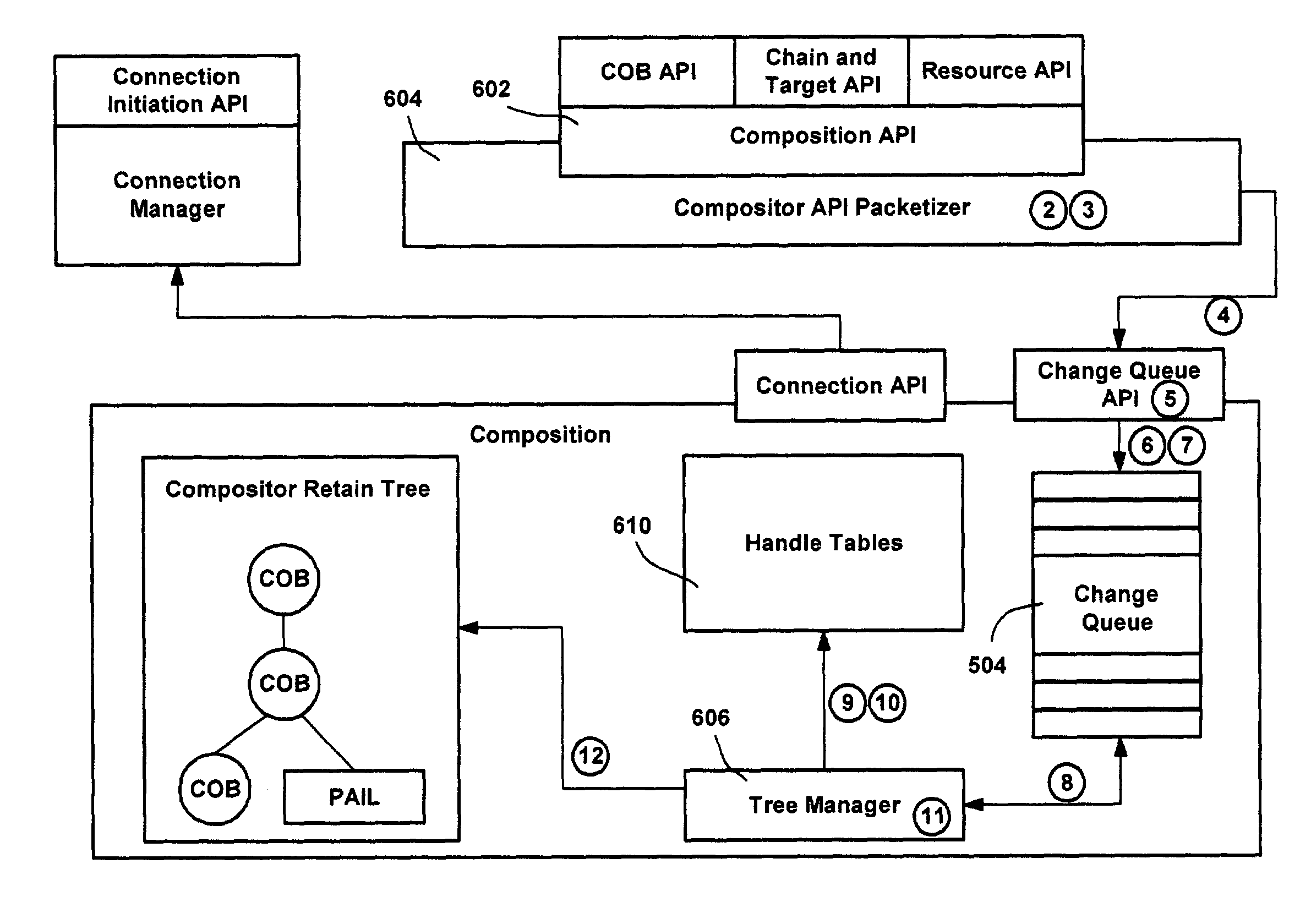
A visual tree structure as specified by a program is constructed and maintained by a visual system's user interface thread. As needed, the tree structure is traversed on the UI thread, with changes compiled into change queues. A secondary rendering thread that handles animation and graphical composition takes the content from the change queues, to construct and maintain a condensed visual tree. Static visual subtrees are collapsed, leaving a condensed tree with only animated attributes such as transforms as parent nodes, such that animation data is managed on the secondary thread, with references into the visual tree. When run, the rendering thread processes the change queues, applies changes to the condensed trees, and updates the structure of the animation list as necessary by resampling animated values at their new times. Content in the condensed visual tree is then rendered and composed. Animation and a composition communication protocol are also provided.
Owner:MICROSOFT TECH LICENSING LLC
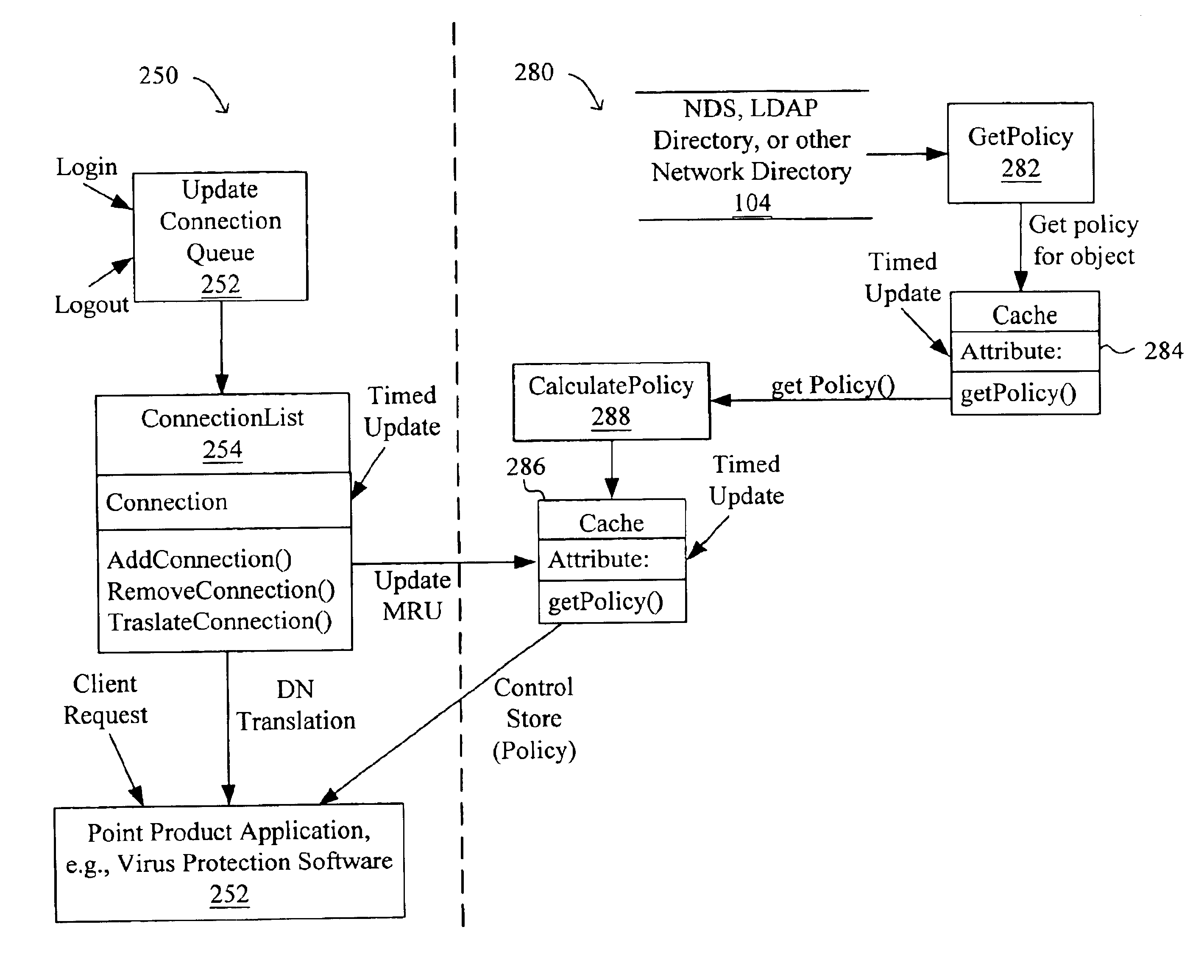
System and method for configuration, management, and monitoring of a computer network using inheritance
InactiveUS6834301B1Data processing applicationsDigital data processing detailsTree structureOperating system
A system and method using inheritance for the configuration, management, and / or monitoring of computer applications and devices via a computer network are disclosed. The method generally comprises calculating control settings to be enforced by an end node corresponding to a device of the network of devices, the control settings being calculated by the corresponding device. The control settings to be enforced by the end node are applicable to the device and the resources of the device. The calculation is performed by the end node or device by accessing data stored in a network directory defining a hierarchical tree structure containing nodes corresponding to the network of devices and defining control settings corresponding to and to be enforced upon the resources available to the devices. The control settings corresponding to the resources of each device are selectively inherited down the hierarchical tree structure of the network directory.
Owner:MCAFEE INC
Method and system for collecting data on a wireless device
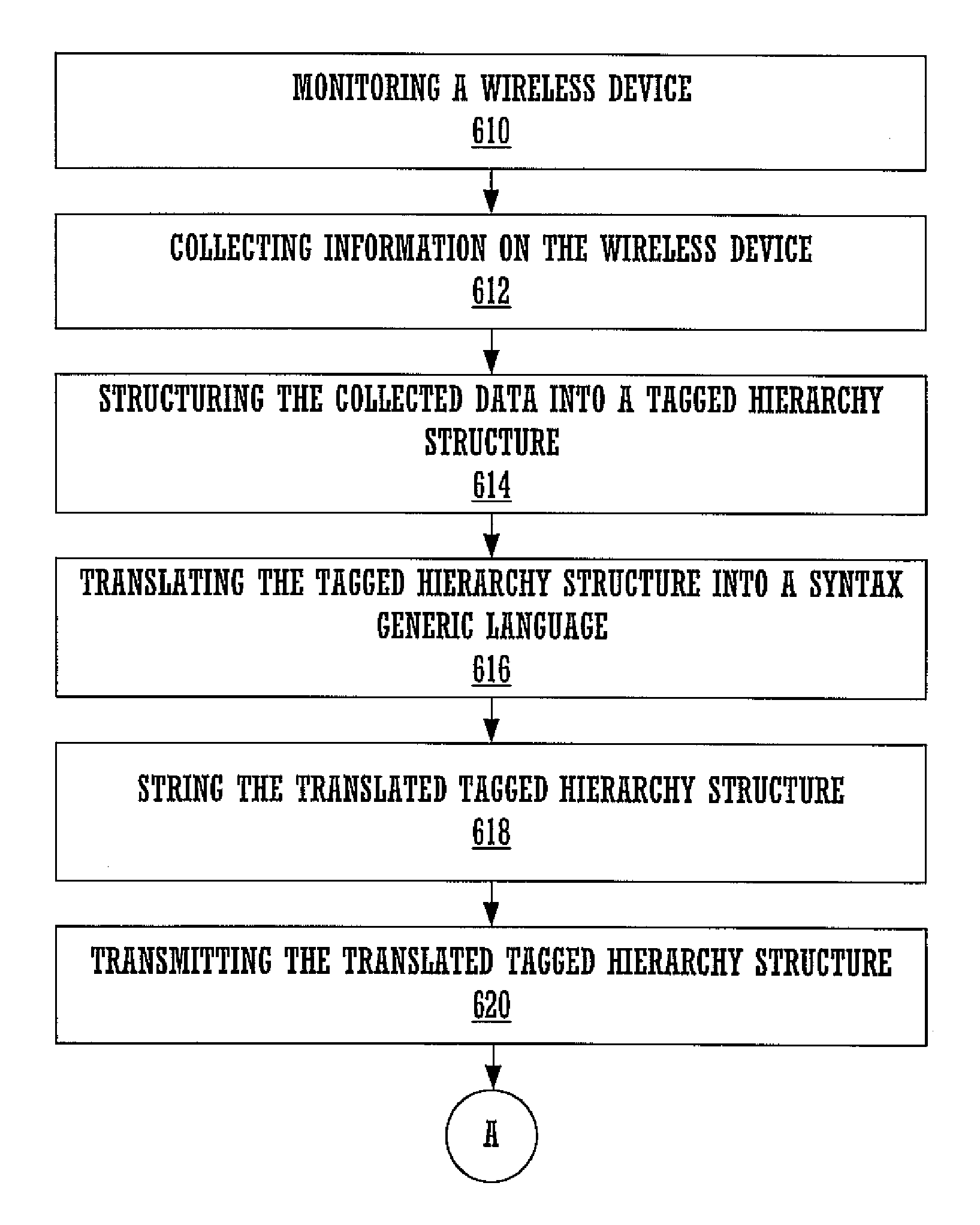
ActiveUS8321556B1Easy to addEasy to monitorDigital data processing detailsDigital computer detailsData transformationStatistical analysis
A method of storing collected data on a wireless device. User interaction with a wireless device and / or the performance of the wireless device is monitored and data related thereto collected. The collected data may be structured into a tagged hierarchical structure comprising a plurality of events that are separate and independent from one another. Each event may describe a specific application with a plurality of attributes. The tagged hierarchical structure formed as a tree structure is translated into a syntax generic language. The result may be formed into a compact format using a zipped format and / or a binary-equivalent format and then stored and transmitted to a central location (e.g., a server) for statistical analysis processing. The server transforms the received data into expanded format and forms a hierarchical tree structure for each event and its attributes. The result is processed for producing a statistical analysis of the collected data.
Owner:THE NIELSEN CO (US) LLC
System, method and technique for searching structured databases
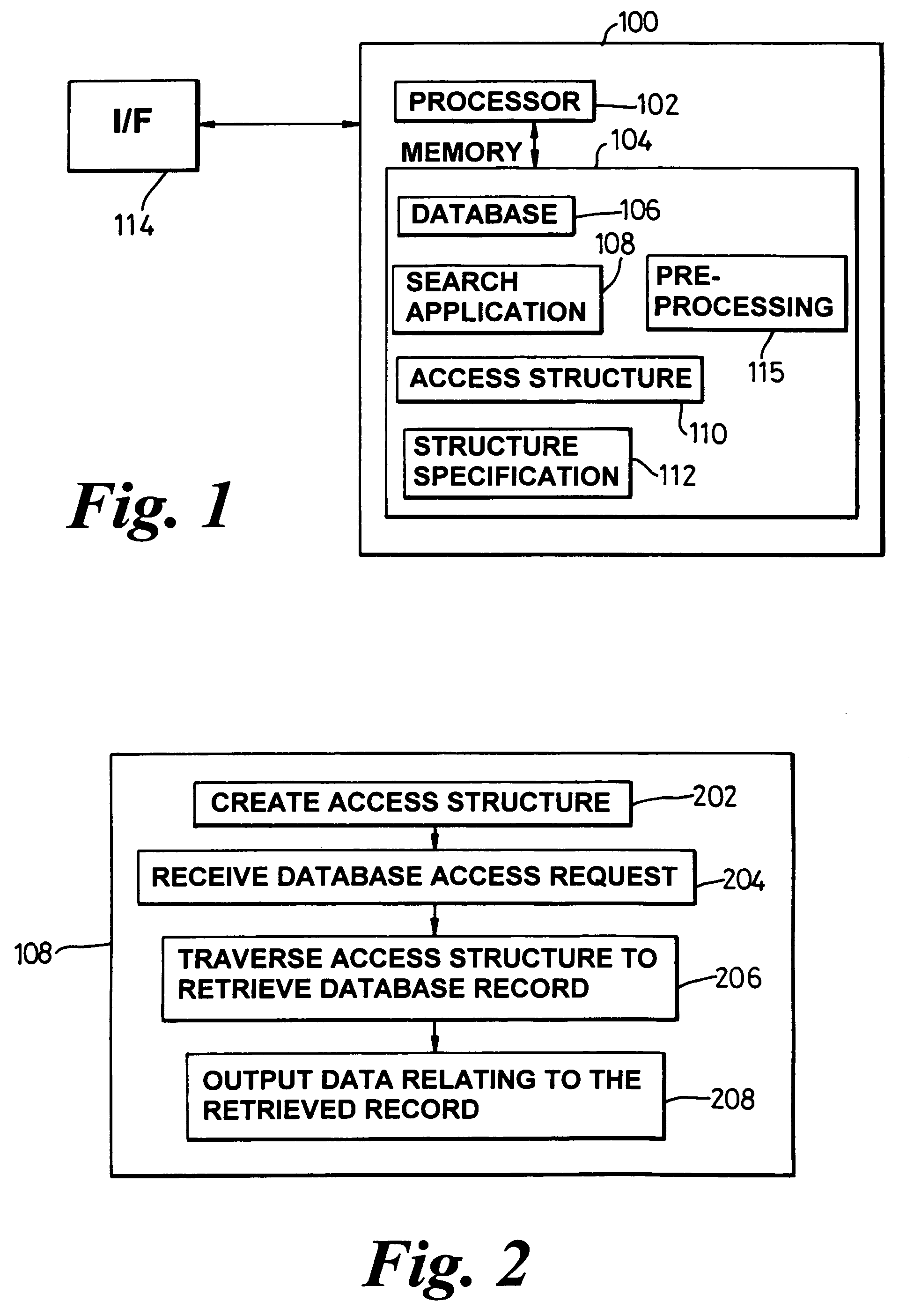
ActiveUS7403941B2Reliable resultsData processing applicationsDigital data information retrievalAccess structureTree (data structure)
Owner:APPLE INC
Indexing XML datatype content system and method
InactiveUS20050091188A1Data processing applicationsDigital data processing detailsPaper documentDocument preparation
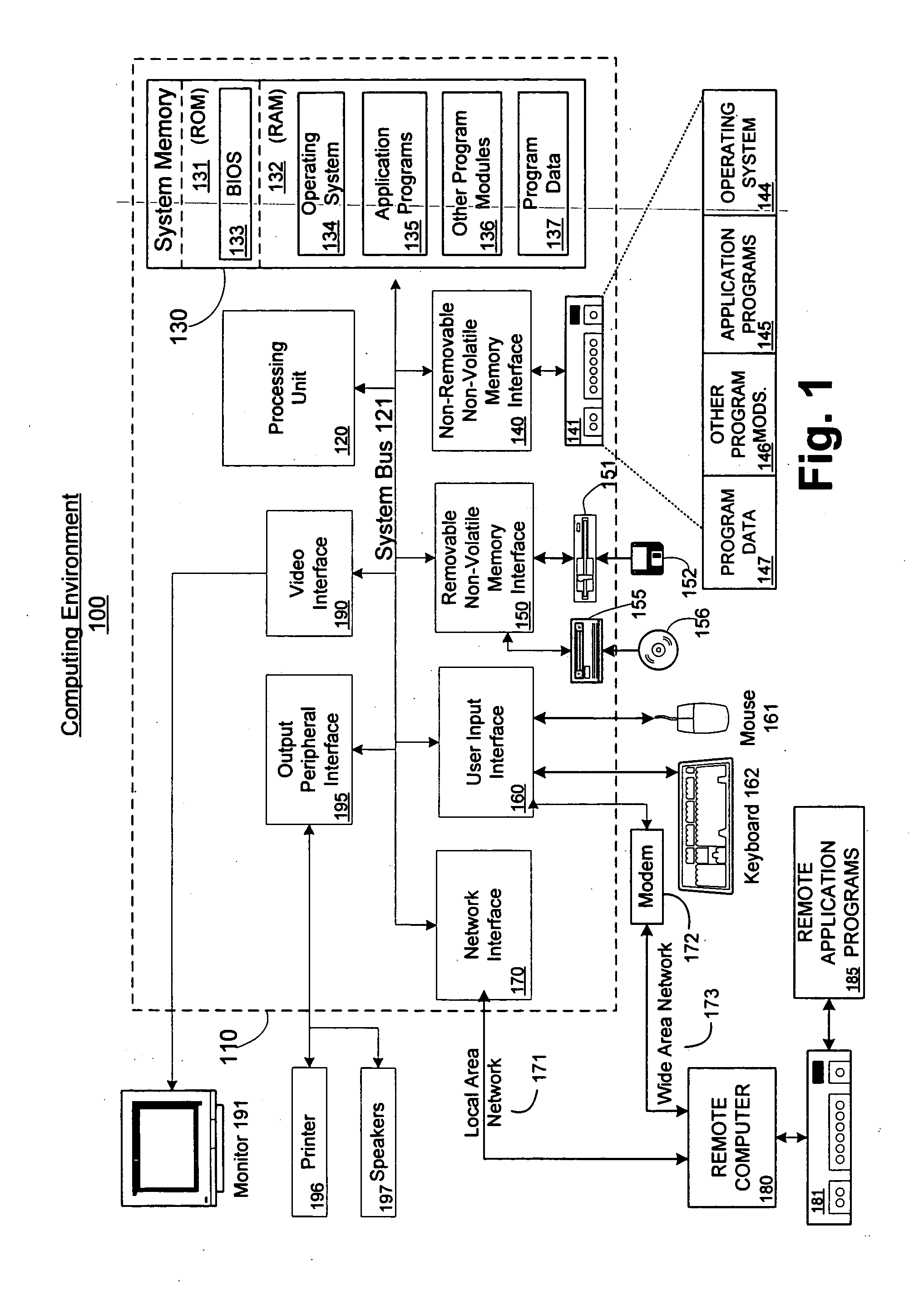
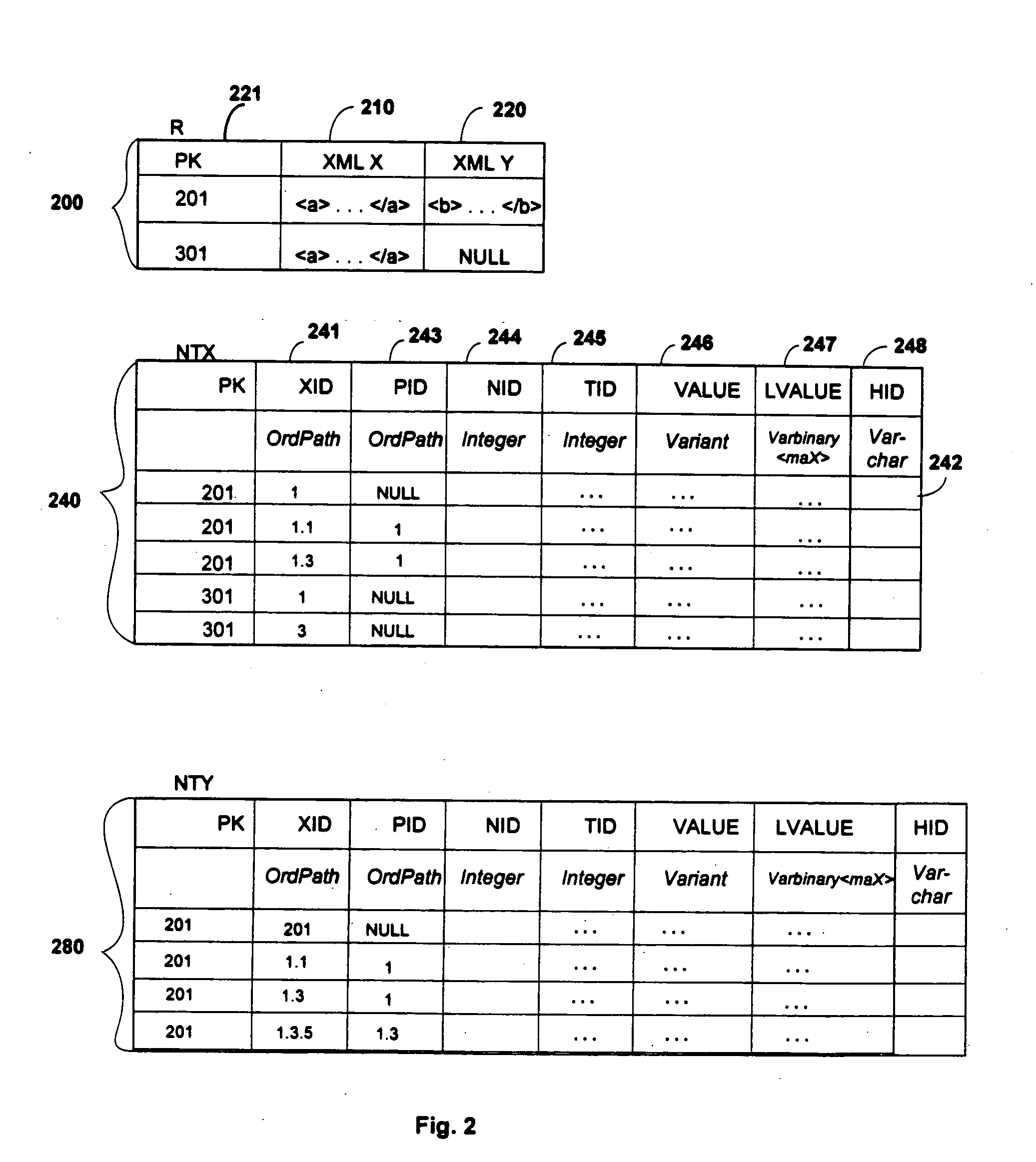
Storing and querying XML data in a primary table or document utilizes an index of XML data and includes creating a primary table structure, creating a primary XML index commensurate with the primary table structure, populating the primary table and the primary XML index, and running a query on the XML data in a primary table by utilizing the XML index. The XML index can be implemented as a node table. The node table may have a B+-tree structure and be populated by shredding the XML values in the primary table. The XML data may be stored as binary large objects in an XML column of the primary table. Secondary XML indexes may be created to assist in the search and retrieval of XML data stored in the primary table. Both the primary XML index and the secondary XML index tables may be created using data definition language statements.
Owner:MICROSOFT TECH LICENSING LLC
Method, system, program, and data structure for a dense array storing character strings
InactiveUS6470347B1Reduce in quantityLess storage spaceData processing applicationsDigital data information retrievalArray data structureTheoretical computer science
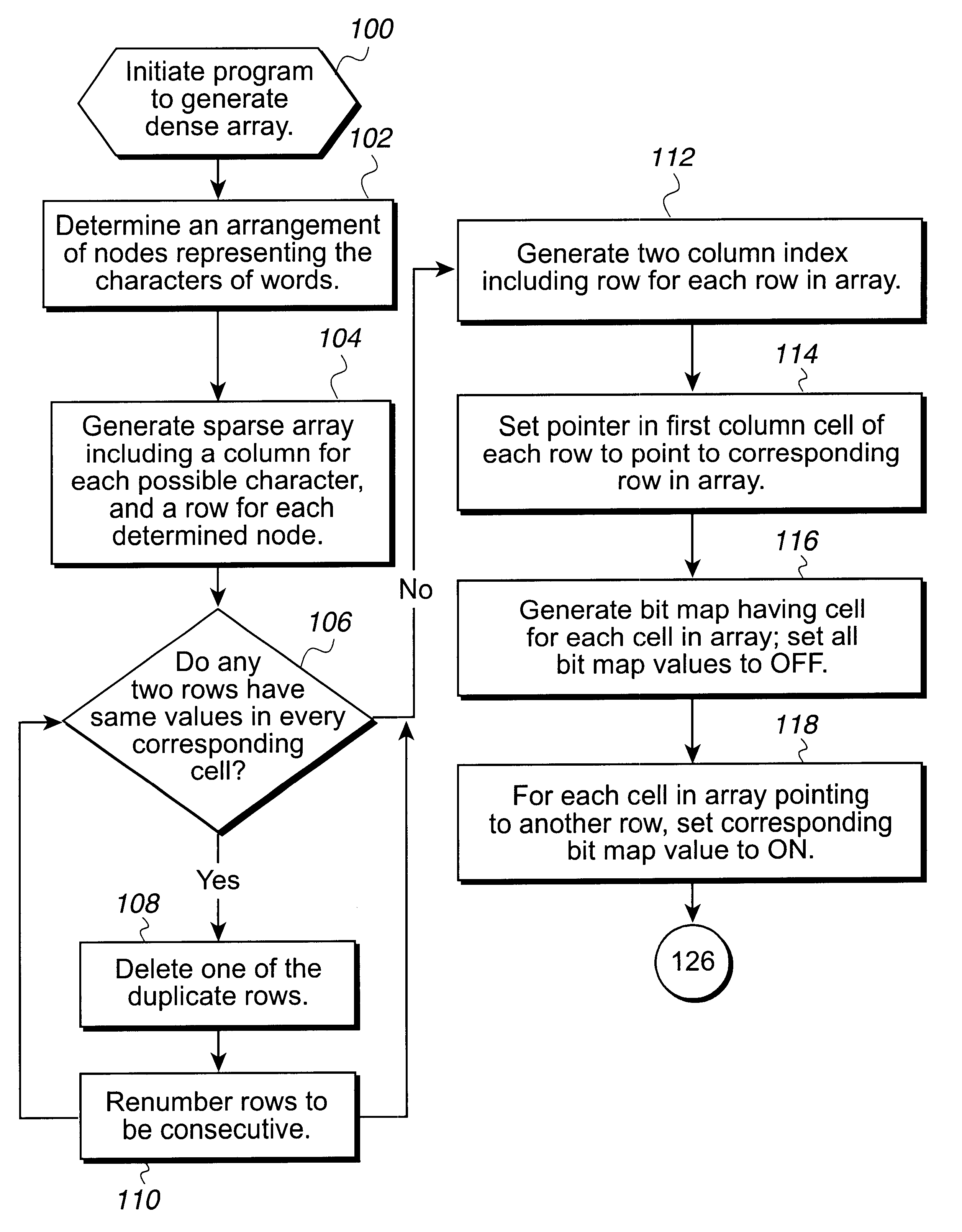
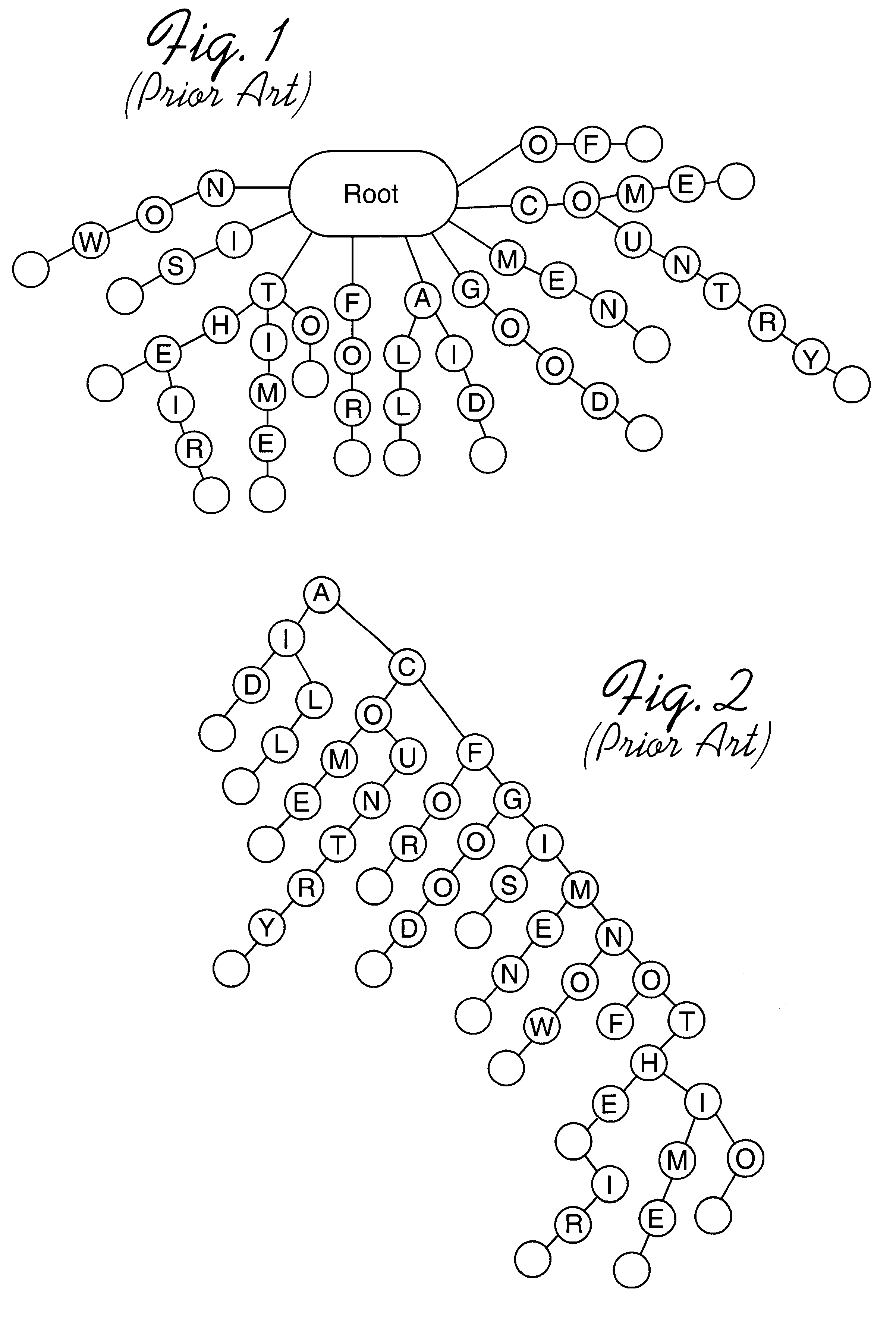
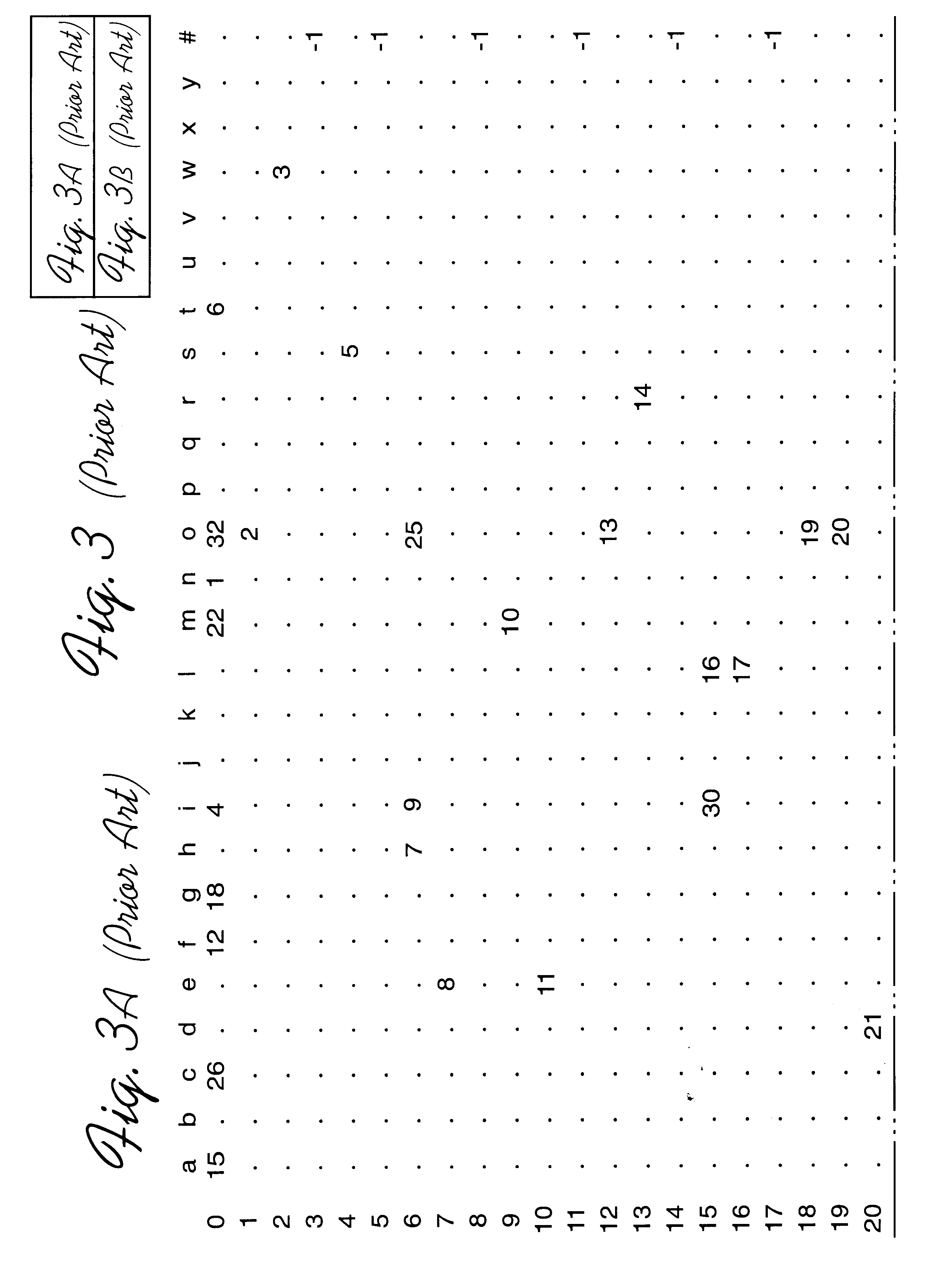
Disclosed is a system, method, and program for generating a data structure in computer memory for storing strings, such as words in a dictionary. Each string includes at least one character from a set of characters. An arrangement of nodes is determined to store the characters such that the arrangement of the nodes is capable of defining a tree structure. An array data structure is generated to store the nodes. The array includes a row for each node and a column for each character in the set of characters. A non-empty cell identifies a node for the character indicated in the column of the cell that has descendant nodes in the row indicated in the cell content for the node. The array data structure is processed to eliminate at least one row in the array data structure to reduce a number of bytes needed to represent the array data structure. In this way, the array data structure following the processing requires less bytes of storage space then before the processing.
Owner:IBM CORP
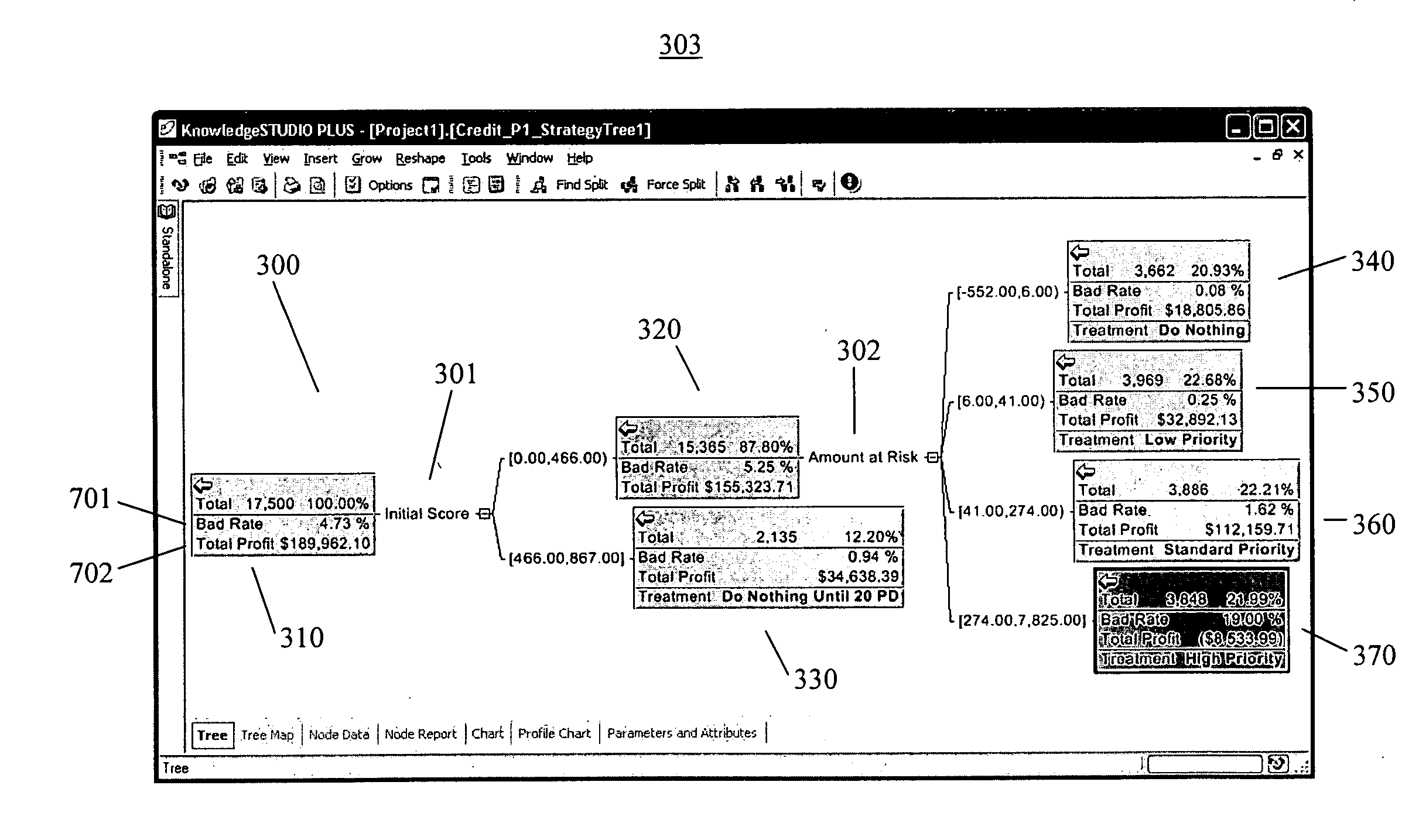
Strategy trees for data mining
ActiveUS20070094060A1Problem can be addressedDigital data information retrievalSpecific program execution arrangementsGraphicsData set
A method for applying a strategy to a dataset in a data mining system to address a business problem, comprising: receiving at least one conditional expression defining the strategy from a user through a graphical user interface (“GUI”) displayed on a display screen of the data mining system; applying the conditional expression to the dataset to split the dataset into segments; displaying the segments as nodes in a tree structure on the display screen; receiving a calculation expression for operating on one or more values in one or more of the segments; applying the calculation expression to one or more of the segments to generate one or more respective calculated values; displaying the one or more calculated values in respective nodes of the tree structure; receiving a treatment expression for operating on the calculated values; applying the treatment expression to one or more of the calculated values to generate respective responses to the business problem; and, displaying the responses in respective nodes of the tree structure to thereby address the business problem.
Owner:ANGOSS SOFTWARE CORP
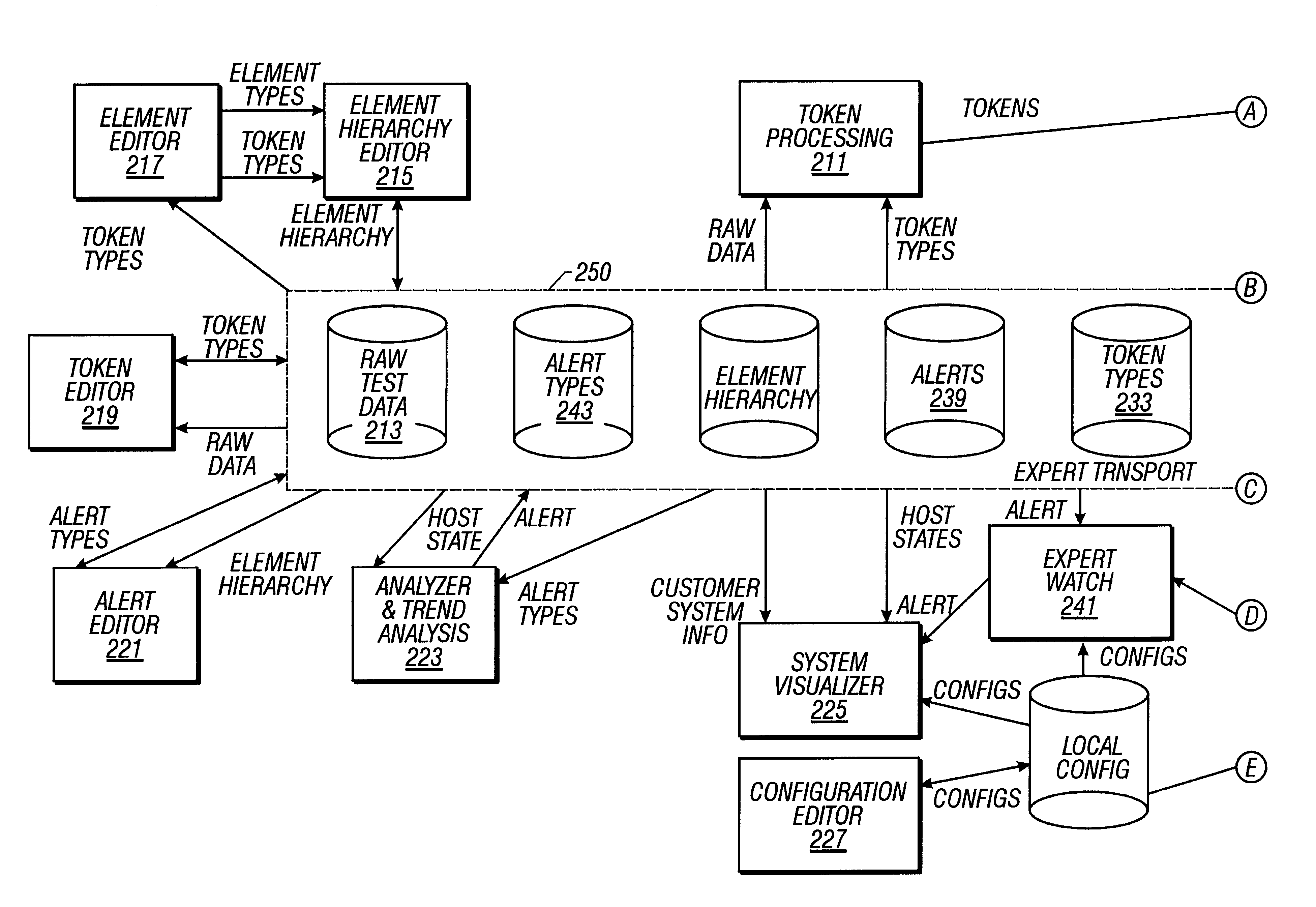
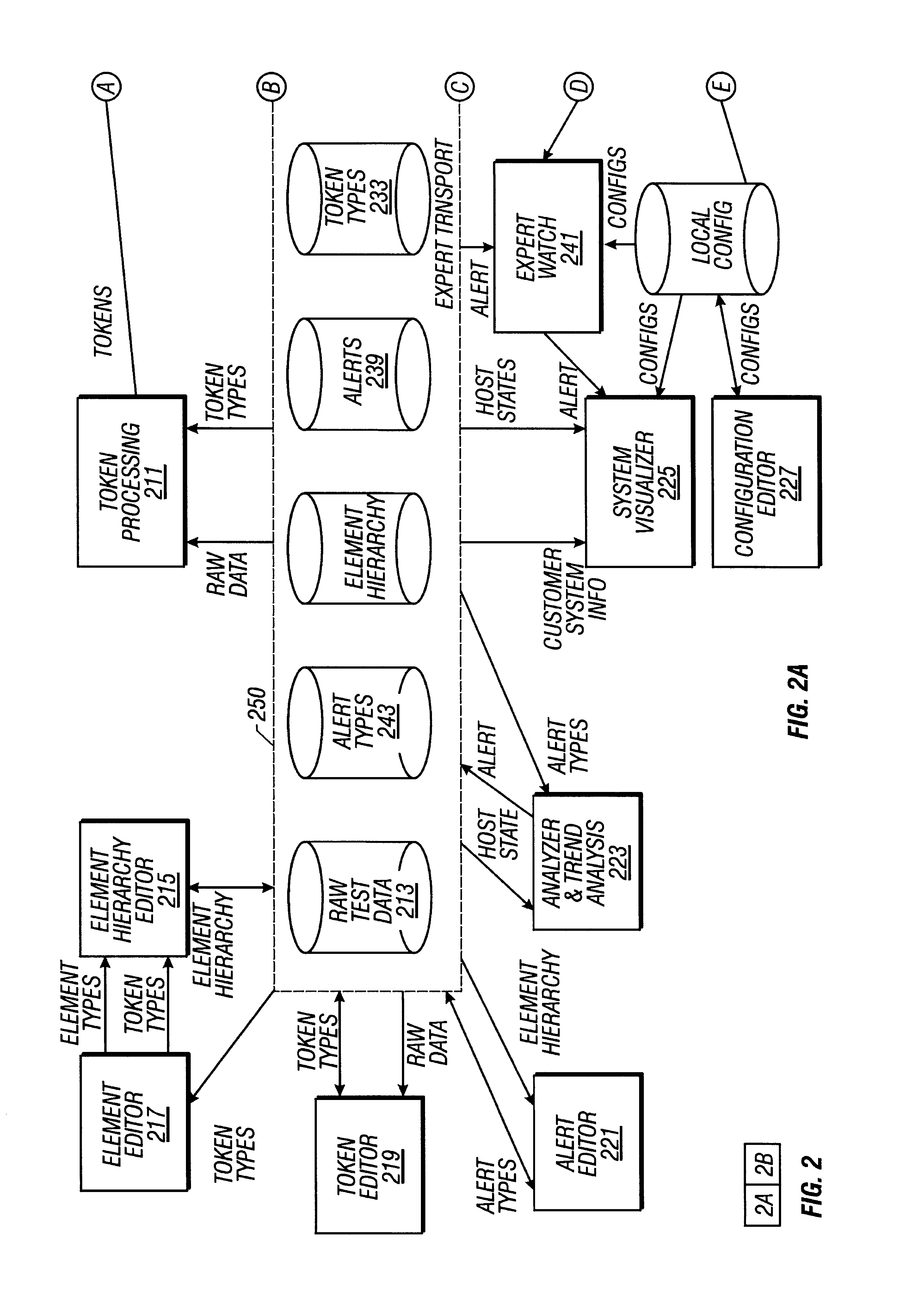
Remote alert monitoring and trend analysis
InactiveUS6182249B1Easy to detectProactive monitoringHardware monitoringData switching networksDiagnostic dataComputer hardware
A monitoring system generates alerts indicating predefined conditions exist in a computer system. Alerts are generated by comparing alert definitions to a host state representing the state of the hardware and software components of a computer system. to determine if conditions defined in the alert definitions exist in the host state; and generating alerts accordingly. The host state is a static tree structure including elements in a fixed hierarchical relationship, the elements being given value by associated tokens, the elements and associated tokens representing the hardware and software components of the computer system. The alert definitions generate alerts according to the values of at least one token, at least one alert or a combination of various tokens and / or alerts. The host state is created by providing a static tree structure representing a general computer system. Component information indicating hardware and software components of the computer system is extracted from diagnostic data of the computer system. The host state is generated according to the static tree structure and the component information.
Owner:ORACLE INT CORP
Extensible stylesheet designs in visual graphic environments
ActiveUS7080083B2Easy to useData processing applicationsDigital data processing detailsGraphicsGraphical user interface
Owner:CHARTOLEAUX
Concurrency control for B-trees with node deletion
InactiveUS20050171960A1Highly concurrent access of dataEasy to solveData processing applicationsDigital data information retrievalConcurrency controlTree (data structure)
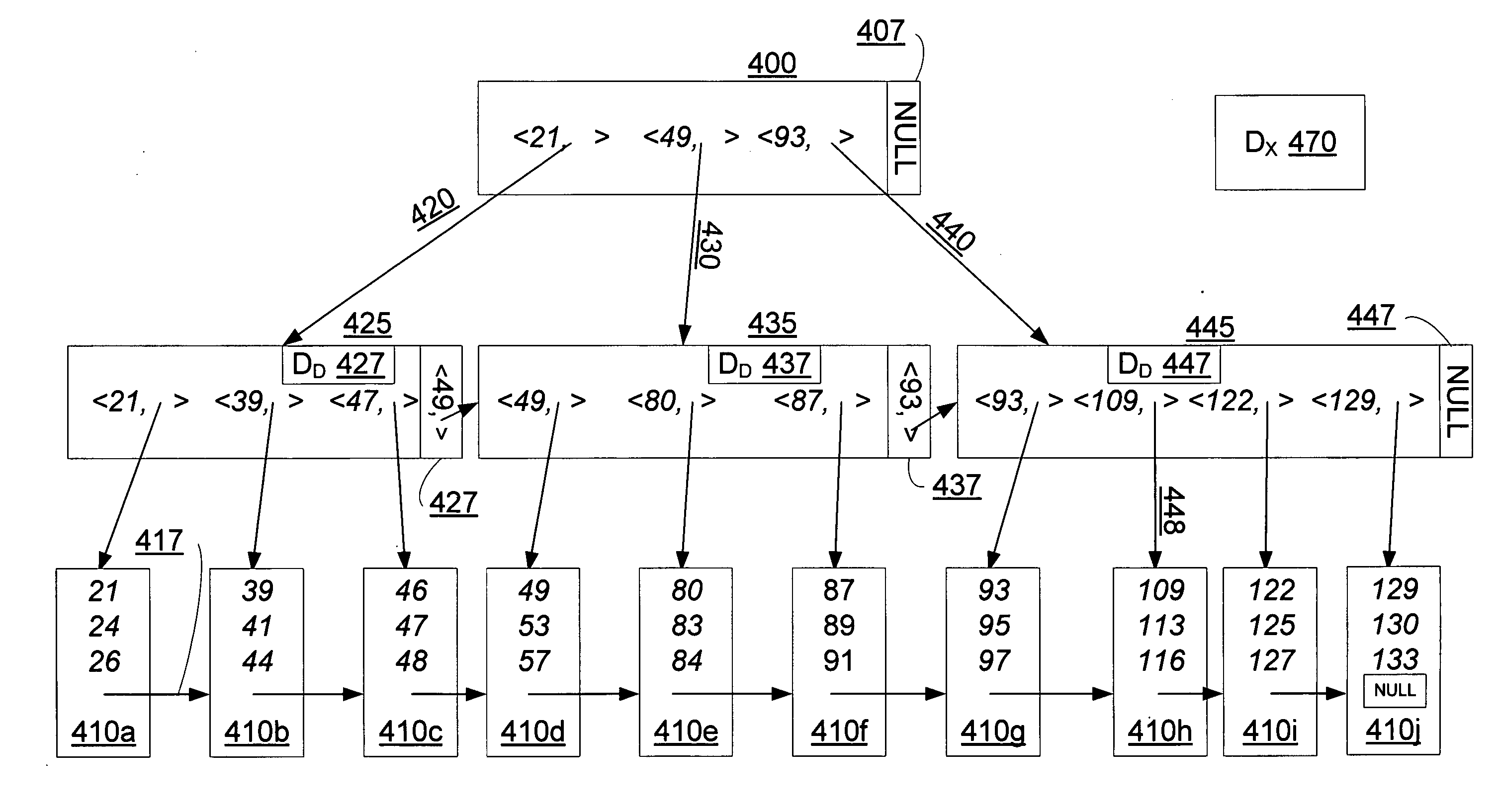
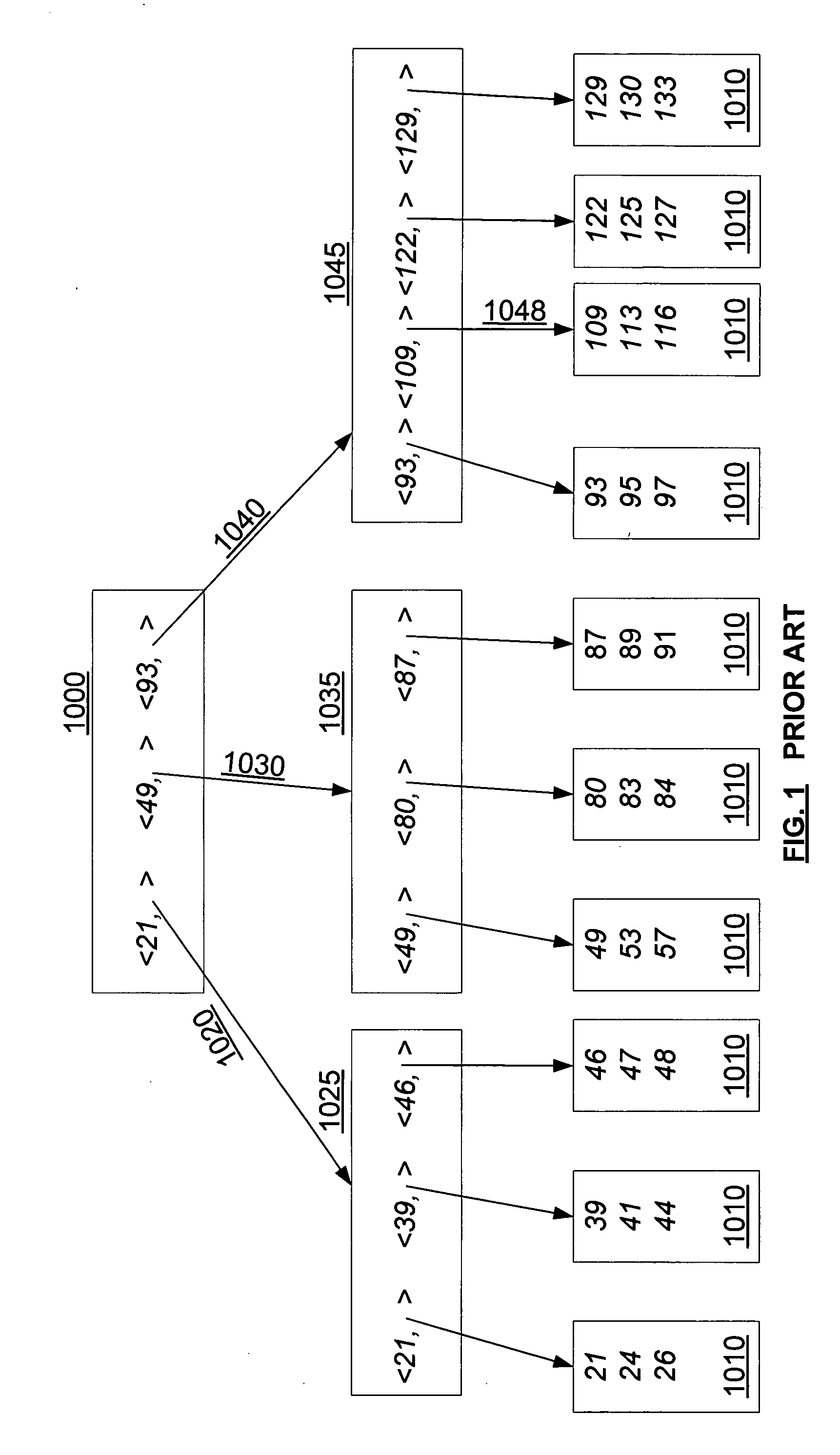
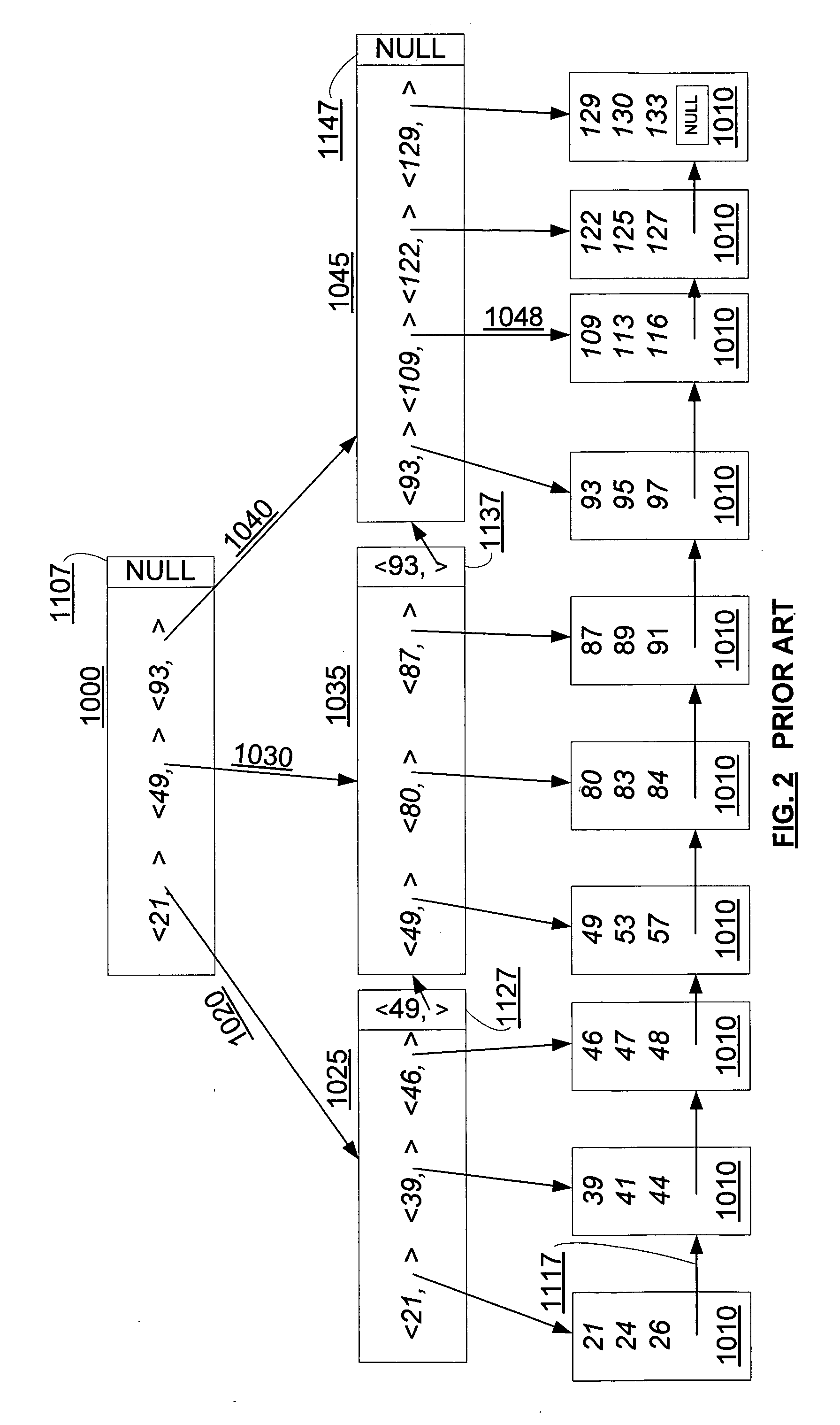
A data structure, added to a modified form of the Blink-tree data structure, tracks delete states for nodes. The index delete state (DX) indicates whether it is safe to directly access an index node without re-traversing the B-tree. The DX state is maintained globally, outside of the tree structure. The data delete state (DD) indicates whether it is safe to post an index term for a new leaf node. A DD state is maintained in each level 1 node for its leaf nodes. Delete states indicate whether a specific node has not been deleted, or whether it may have been deleted. Delete states are used to remove the necessity for atomic node splits and chains of latches for deletes, while not requiring retraversal. This property of not requiring a retraversal is exploited to simplify the tree modification operations.
Owner:MICROSOFT TECH LICENSING LLC
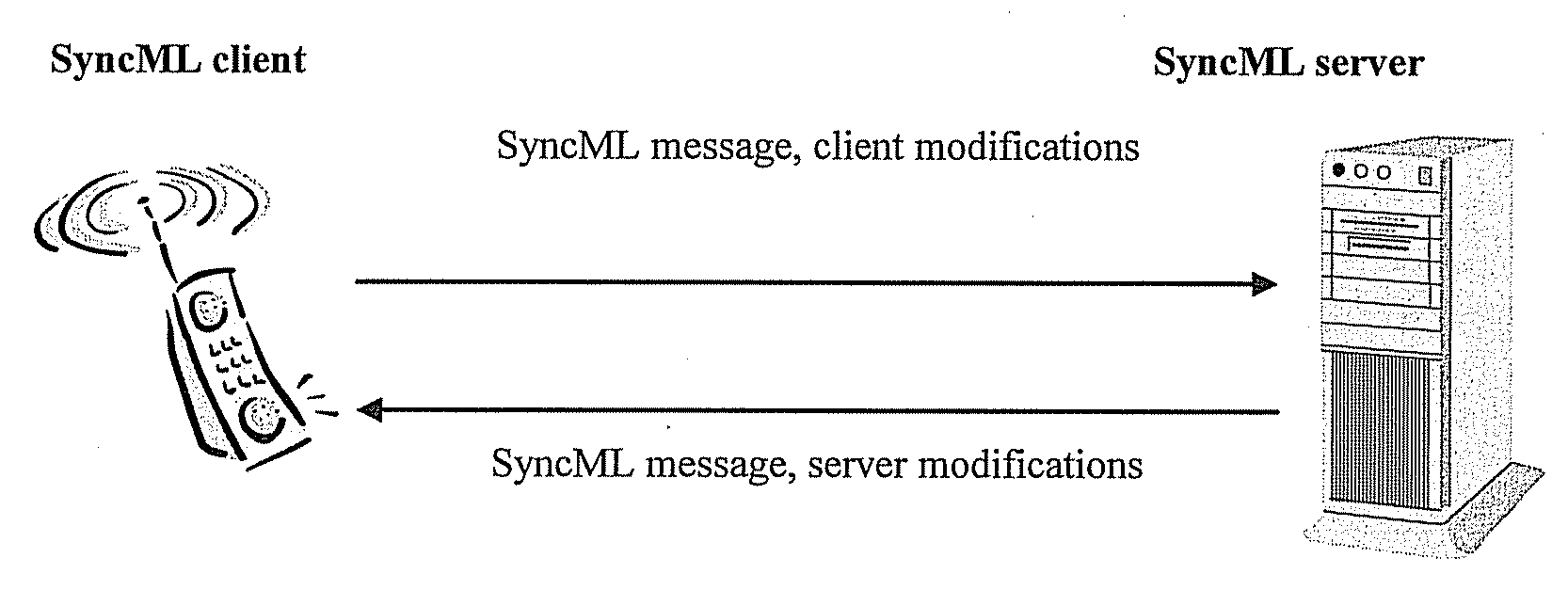
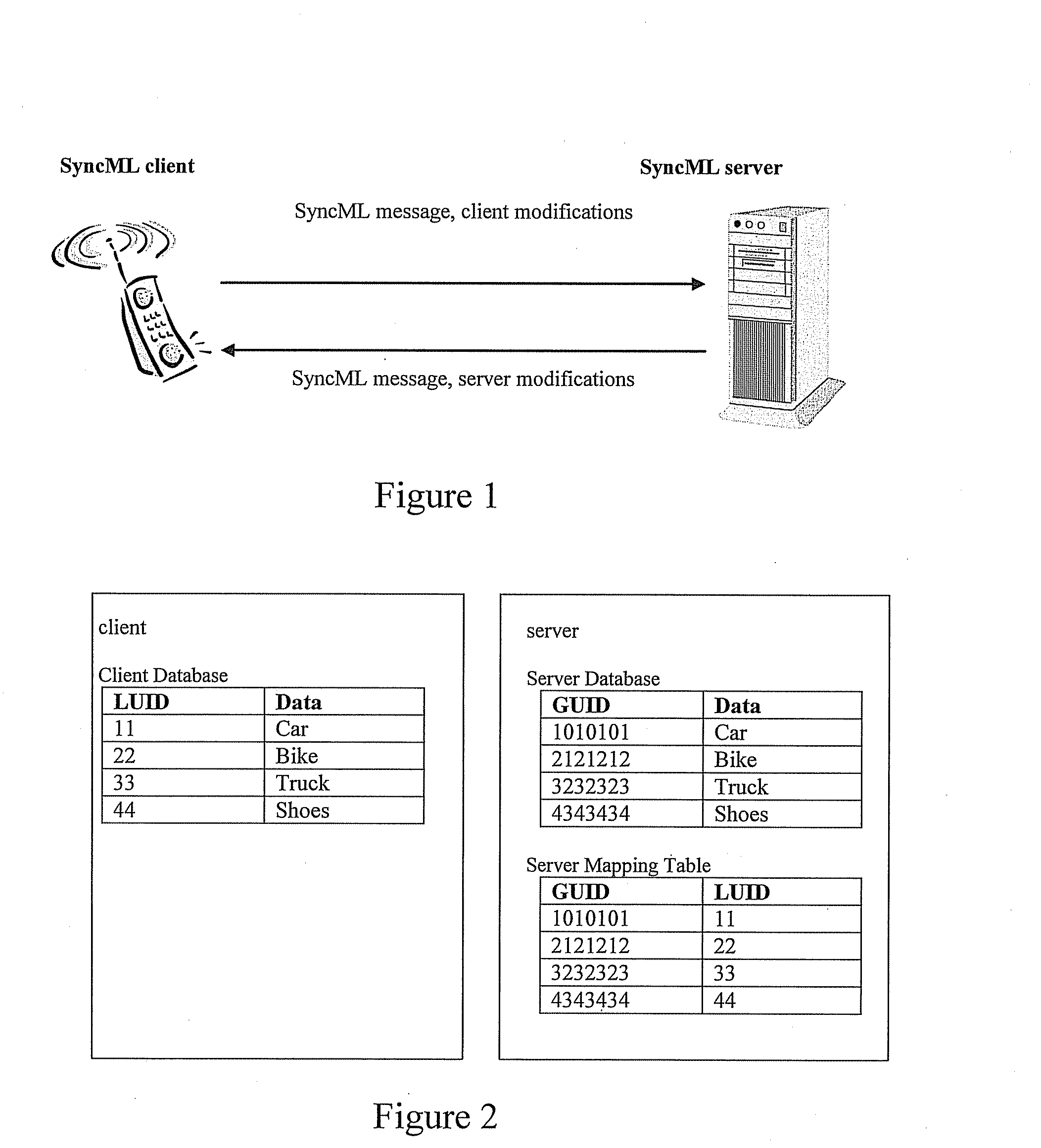
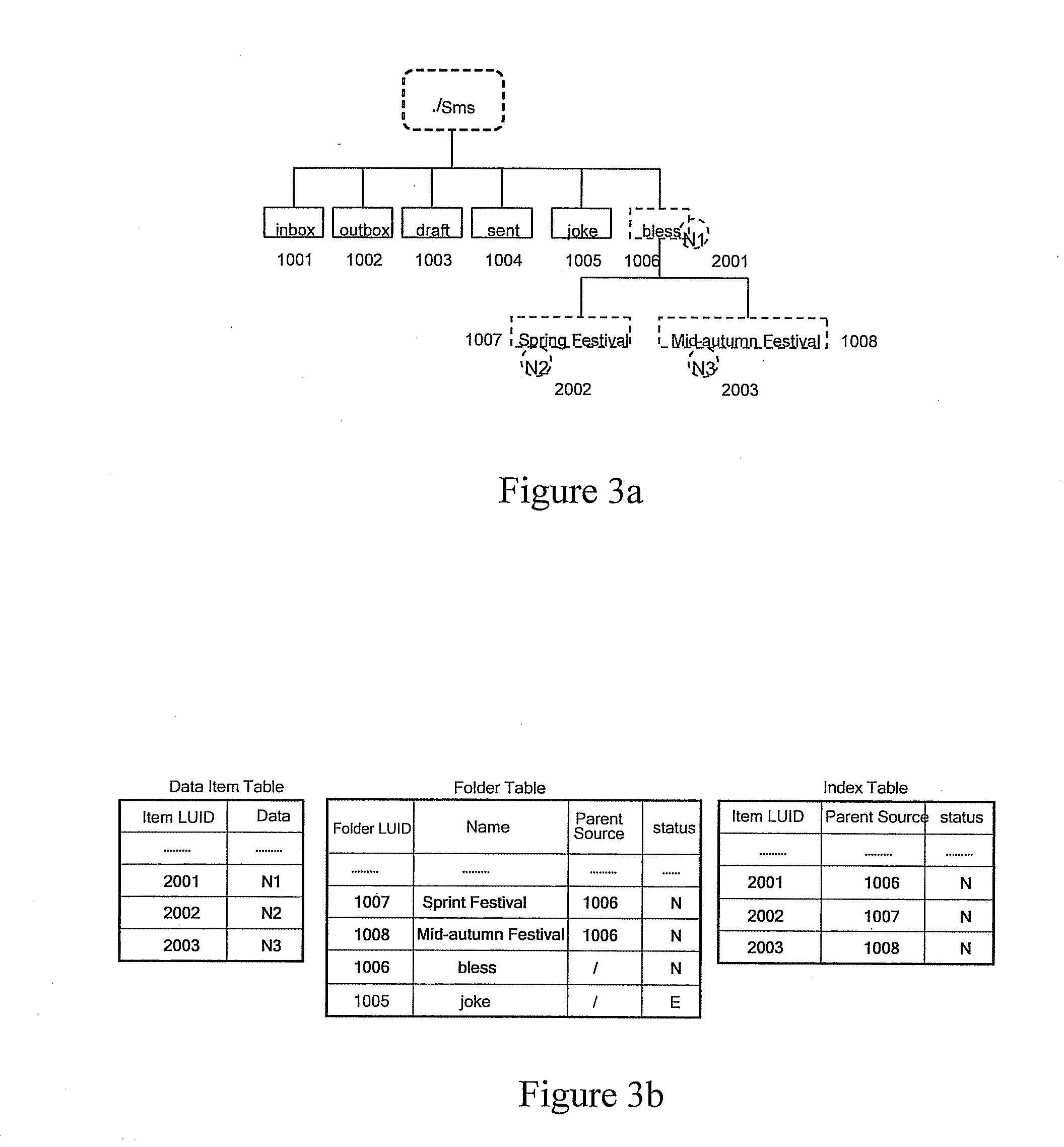
Method, system, client and server for implementing data sync
ActiveUS20080104277A1Improve data synchronization efficiencySave system resourcesMultiple digital computer combinationsTransmissionData synchronizationClient-side
This invention discloses a method for synchronizing a plurality of devices, including: obtaining, by a first device, an extended address of an informational node of a plurality of informational nodes of a second device, the plurality of informational nodes arranged in a hierarchical tree structure; and utilizing the extended address to locate the informational node amongst the tree structure to enable synchronization of the informational node; wherein the extended address includes a hierarchical location of the informational node. This invention further discloses a system, client and server for data sync, and the folder-level data sync can be implemented by using the method of this invention.
Owner:HUAWEI TECH CO LTD
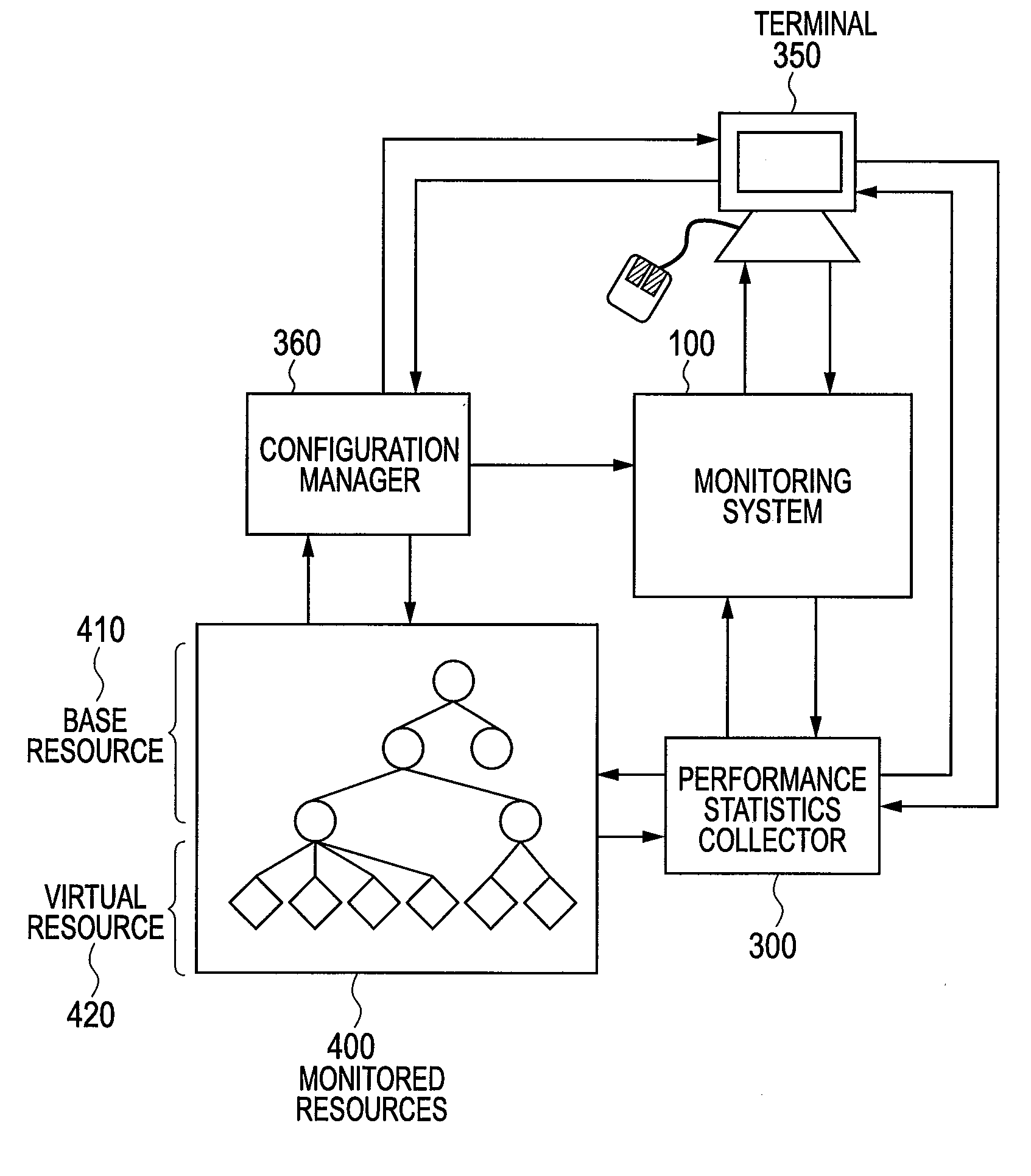
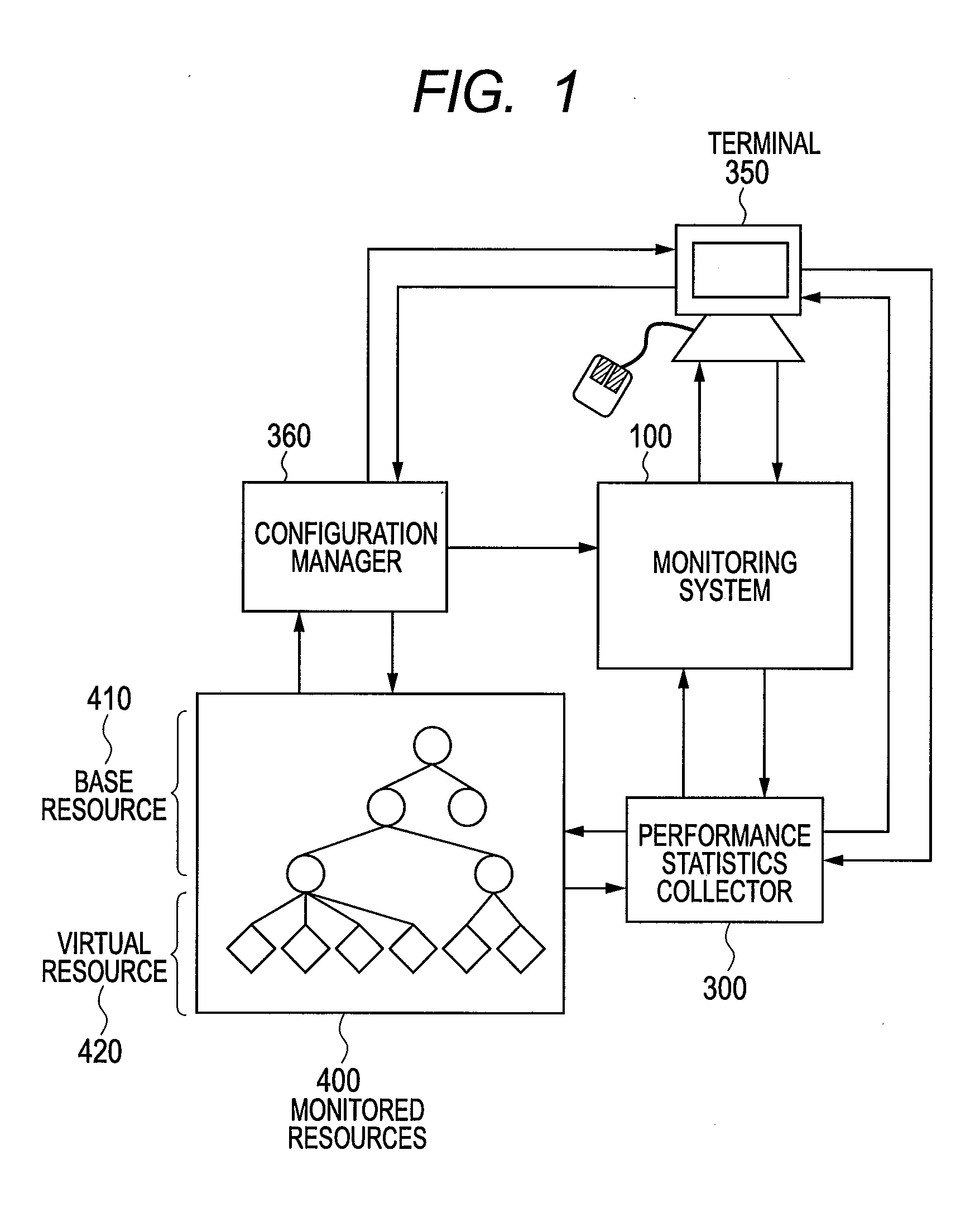
Monitoring system of computer and monitoring method
InactiveUS20120117226A1Low costEasy to analyzeDigital computer detailsProgram controlVirtualizationComputer resources
There is provided a monitoring system capable of representing relationships of computer resources that virtual servers use in a tree structure and aggregating the performance statistics of the virtual resources sharing physical resources. The monitoring system has: a virtualization module that makes virtual computers operate; and a monitoring module for monitoring the physical computers and components of the virtual computers. The monitoring module designates the physical computer and the components of the virtualizing module as base resources, manages the components of the virtual computers as virtual resources, generates a platform tree by extracting a tree structure from the virtual resources and the components of the base resources for predetermined platforms, generates a service provision tree by extracting a tree structure having the base or virtual resources as starting points, and establishes a reference relationship for the components contained in the platform tree and also contained in the service provision tree.
Owner:HITACHI LTD
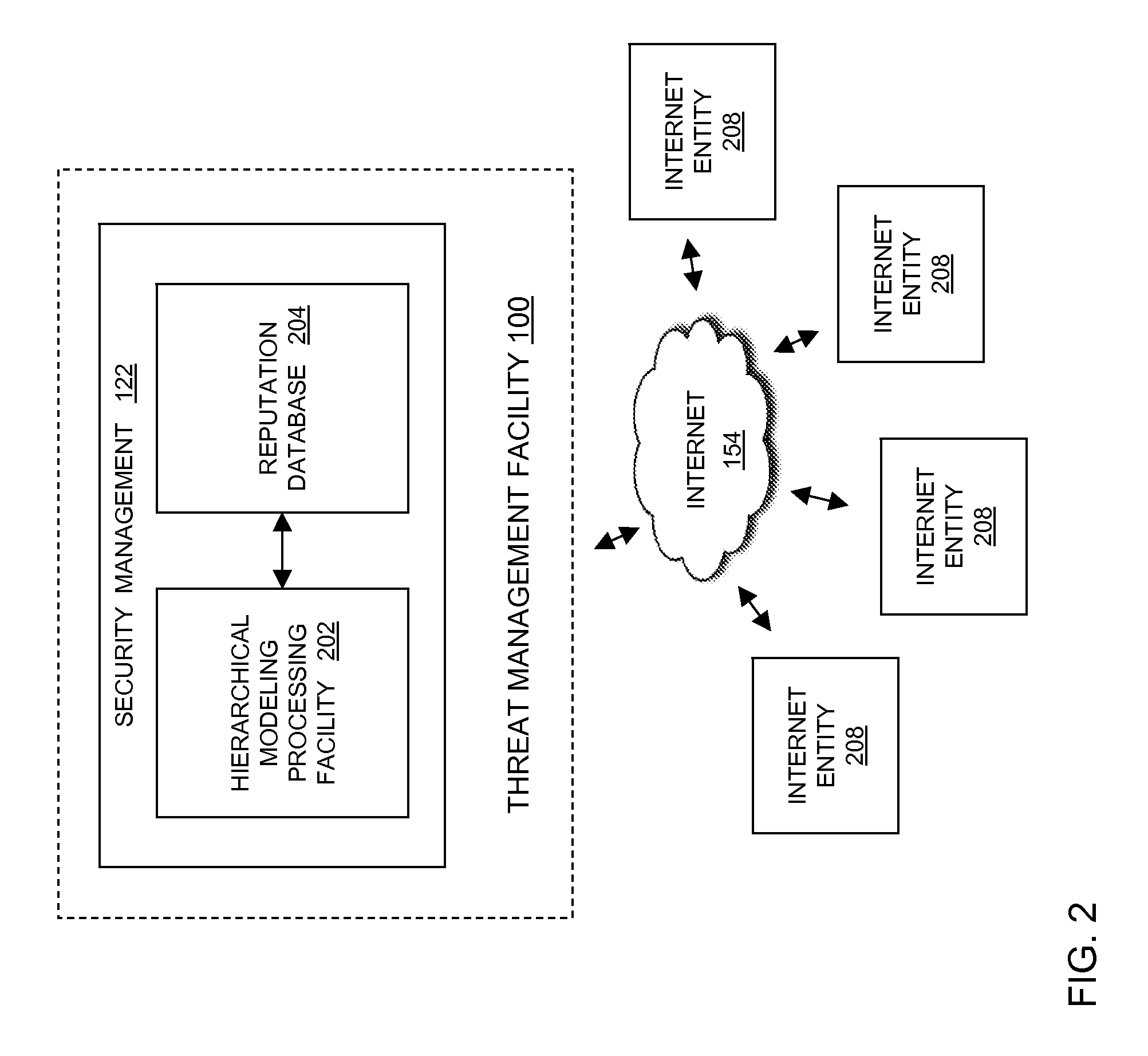
Hierarchical statistical model of internet reputation
ActiveUS20110055923A1Improve securityMemory loss protectionError detection/correctionEmail addressIp address
Owner:SOPHOS
Integrated web-based workspace with curated tree-structure database schema
InactiveUS20120096389A1Streamlining actionStreamlining flowWebsite content managementSpecial data processing applicationsDocumentation procedureDocument preparation
A virtual web-based computing platform combining a particular network database hierarchy, graphical user interface, and integrated suite of computational tools accessible on demand, by which users gain access to an integrated Virtual Workspace for organizing emails, contacts, bookmarks, tasks, documents, notes, and all other relevant information. The network database hierarchy employs unique data structure and methods, allowing the user to centrally store and manage all data, regardless of type, as well as activities (actions taken and documented by the user). Nevertheless, the interface to said database offers a familiar folder / sub-folder “look and feel” using a tree data hierarchy, which gives a common, centralized and unified approach for storing, managing, displaying, and various types of data, regardless of object- and data-types.
Owner:IQTELL COM
Resource-aware adaptive multicasting in a shared proxy overlay network
InactiveUS20050091399A1Easy to handleFacilitates adaptively shifting loadDigital computer detailsTransmissionResource basedDatapath
Owner:NEC LAB AMERICA
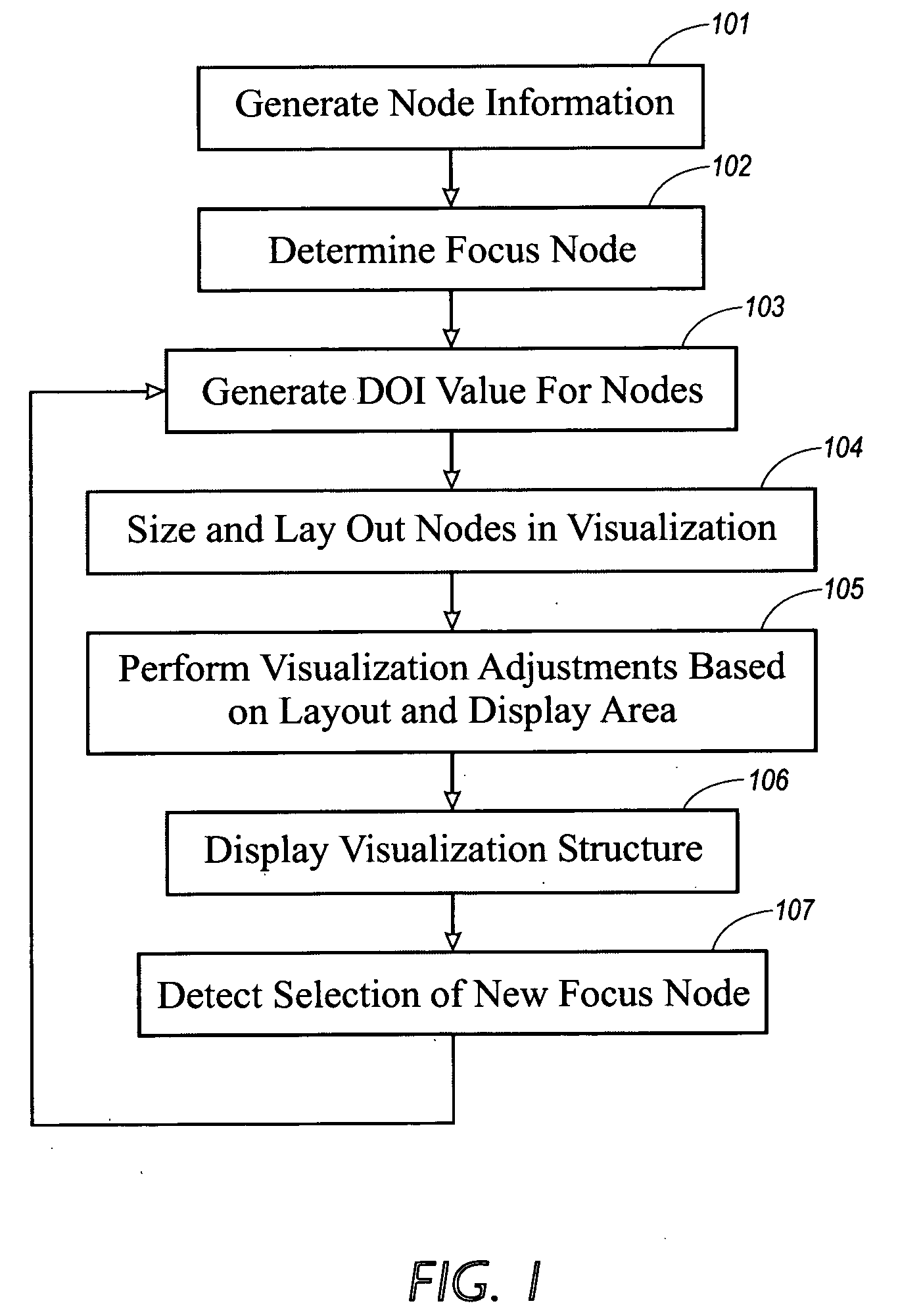
System and method for browsing hierarchically based node-link structures based on an estimated degree of interest
InactiveUS20050273730A1Drawing from basic elementsWeb data navigationDisplay deviceArtificial intelligence
Owner:XEROX CORP
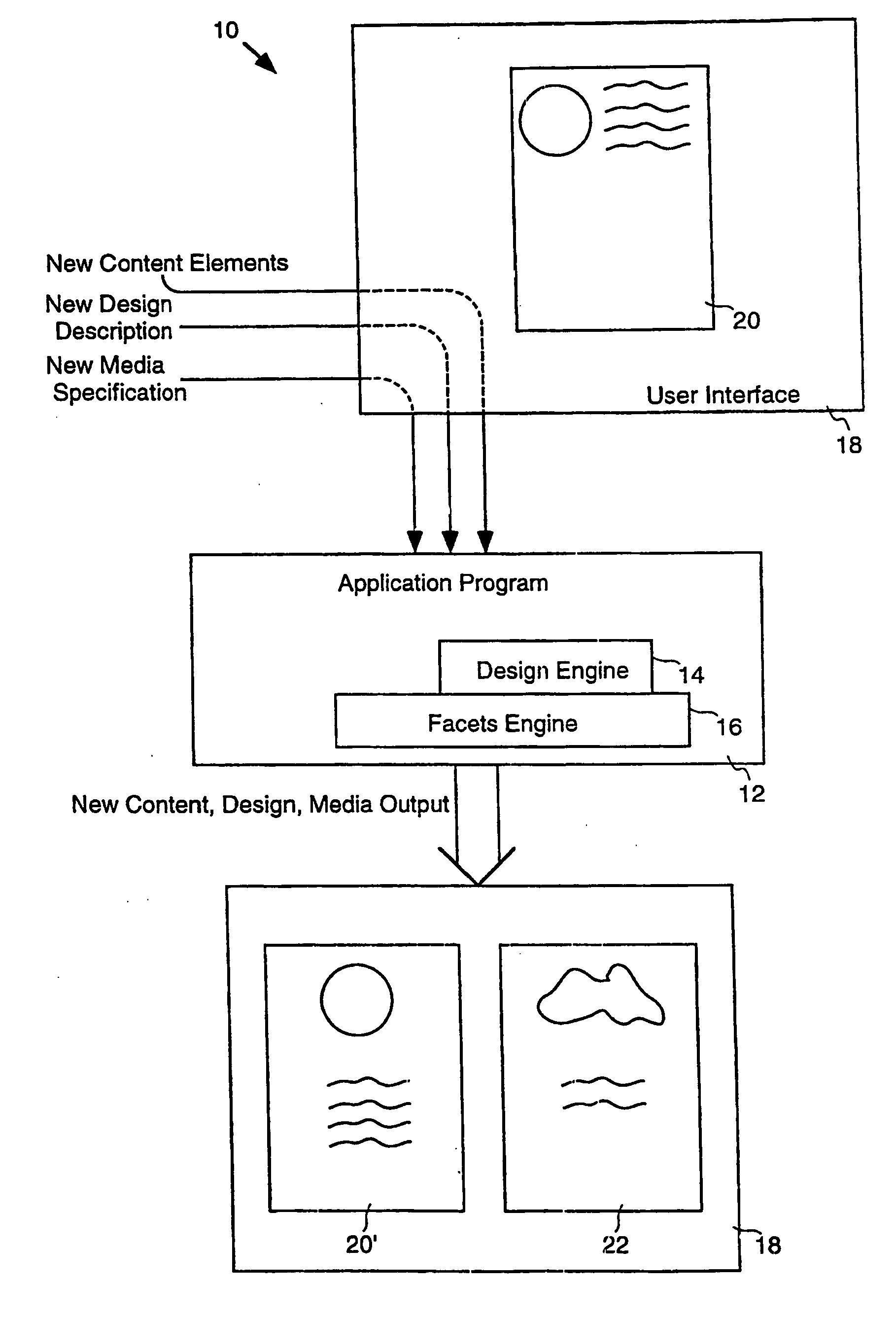
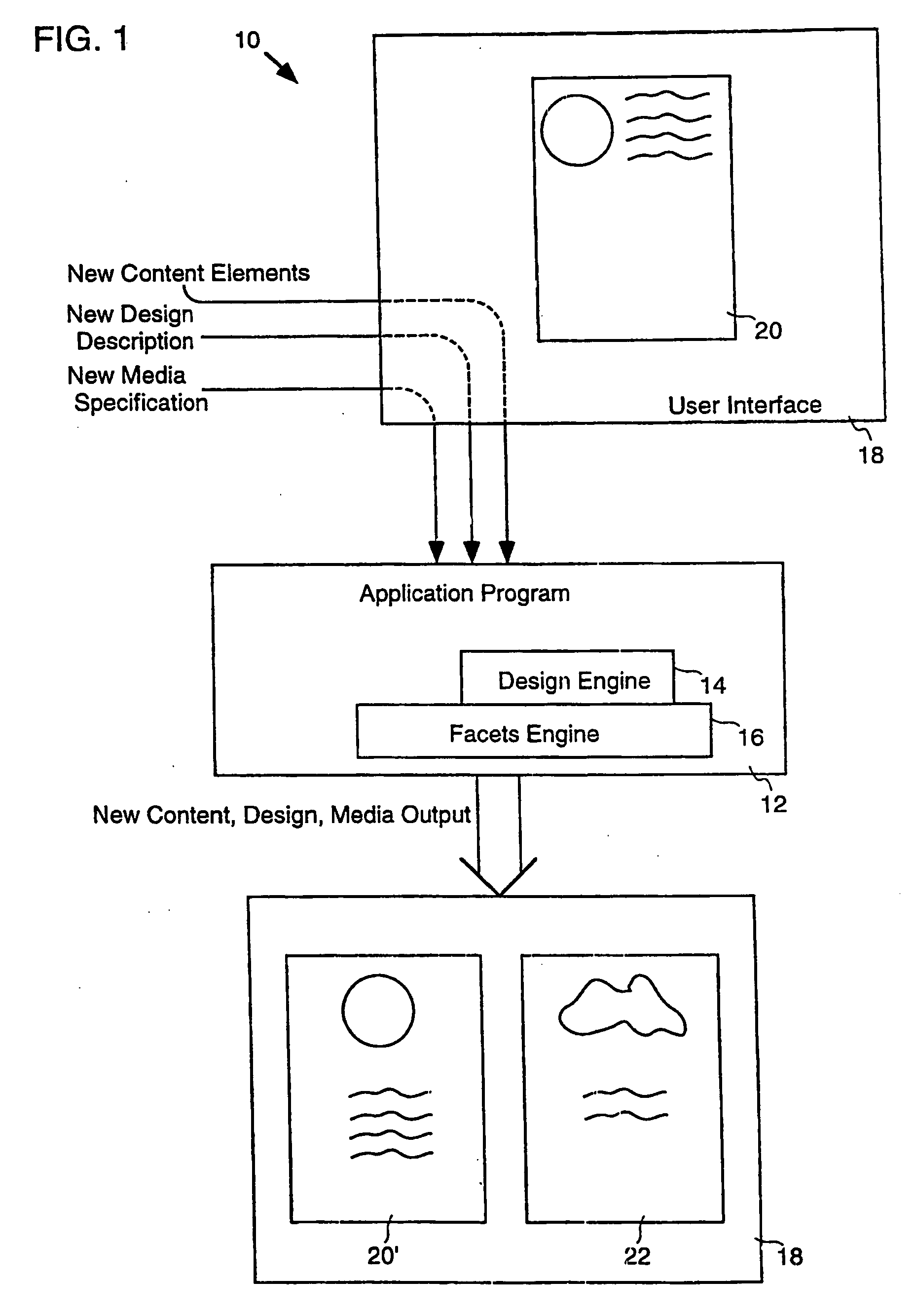
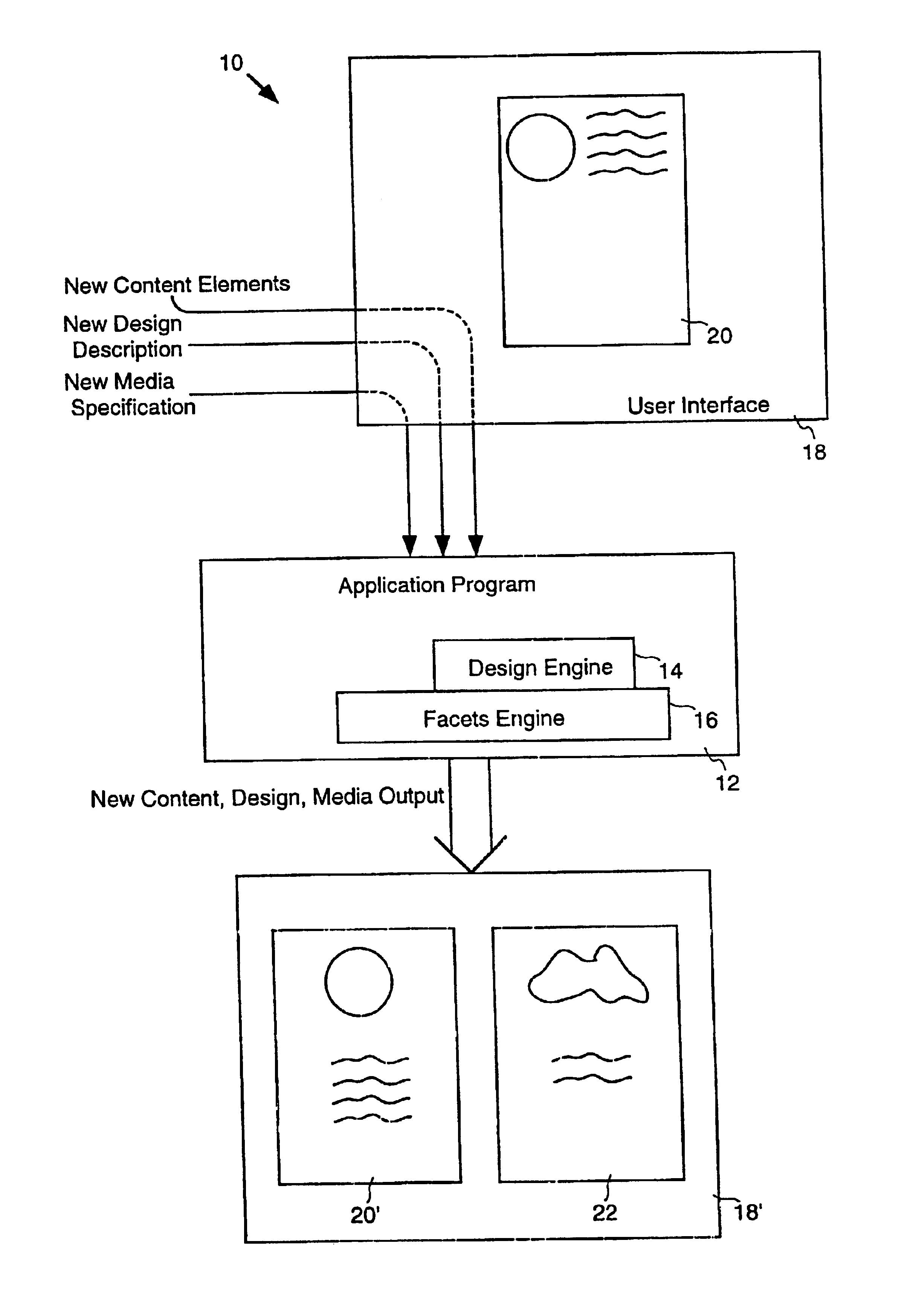
Automatic layout of content in a design for a medium
InactiveUS20050223320A1Stable supportNatural language data processingTransmissionMultiple formsTheoretical computer science
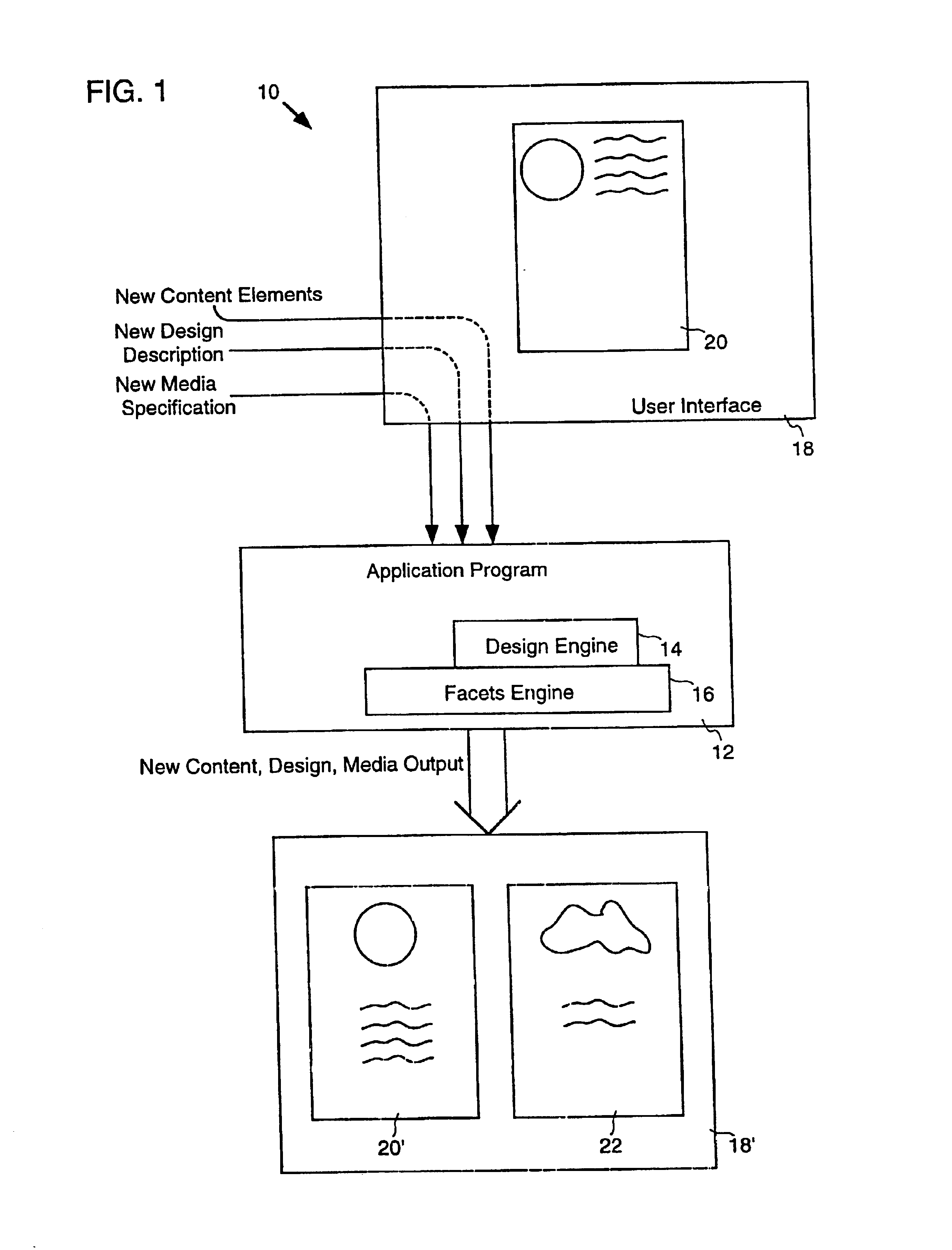
A three-way separation of information in a document includes content, design and media aspects. This division supports automatic rendering to multiple forms of media such as print, Intranet, Internet, and OLE embedding. In a particular embodiment, the document is separated into its content, design and media aspects. Content, design, a medium specification are identified and layout is performed as per the three aspects. In one embodiment, an information data structure is provided that includes three tree structures: a design tree, a content tree and a media tree. A media division data structure is associated with a parent component in a composition. The parent component has a parent region in a medium and has child components. Each child component is associated with a child region of the medium. The media division data structure provides rules, properties and values for performing layout in a particular region of the medium. Layout may be performed on a server.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for providing differentiated services within a network communication system
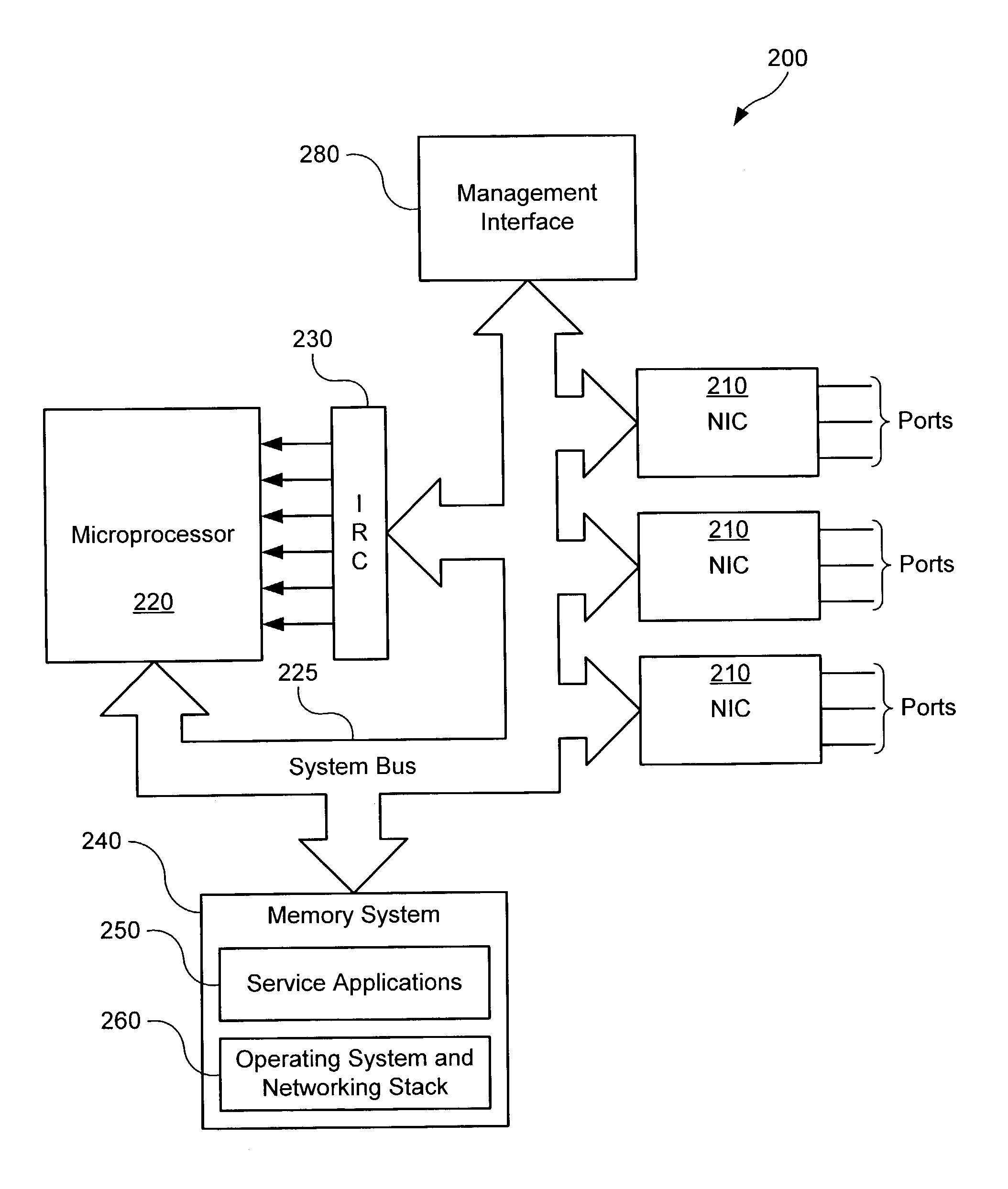
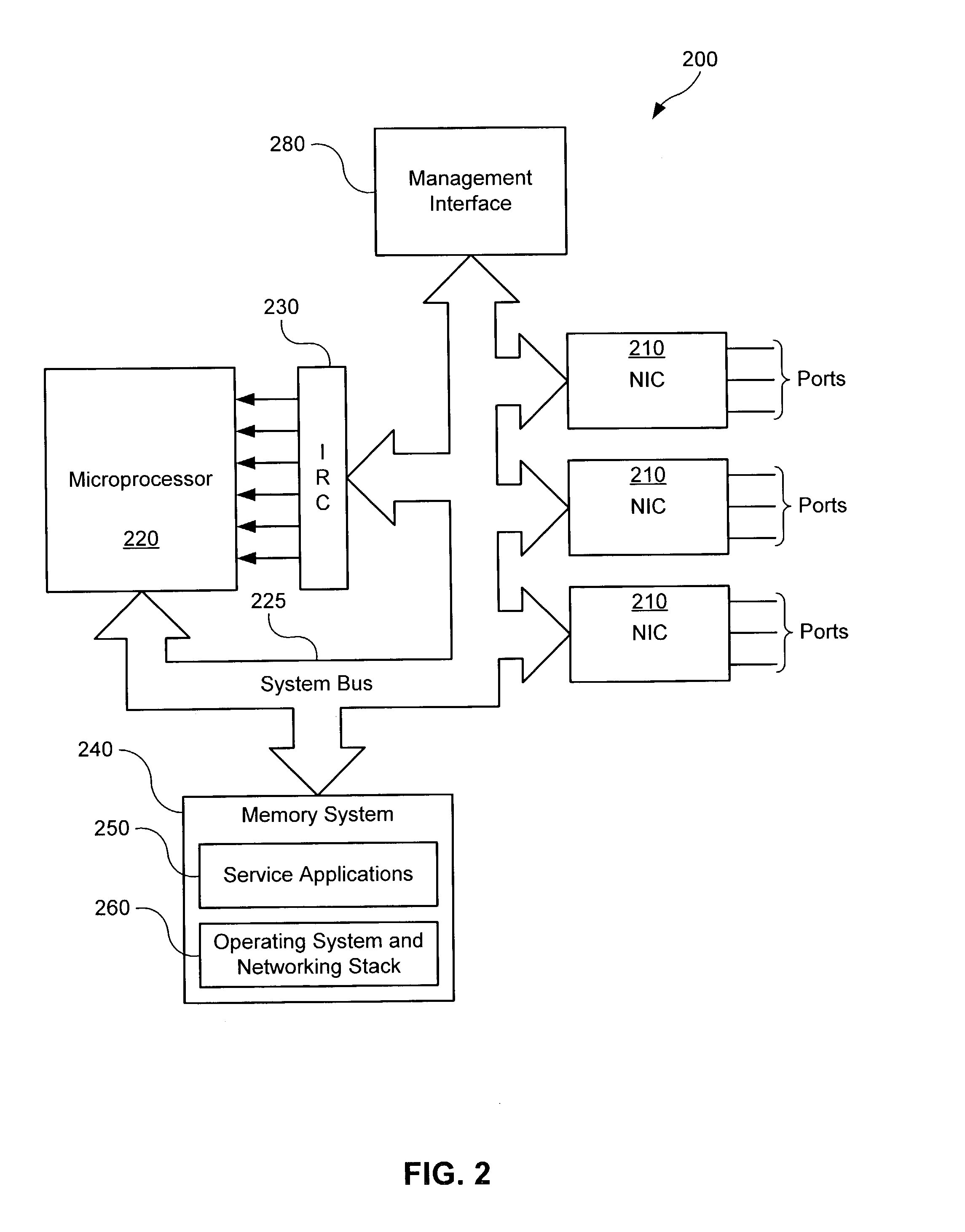
ActiveUS7031314B2Lower performance requirementsEfficient managementData switching by path configurationNetwork connectionsDifferentiated servicesCommunications system
A service module incorporated within the network infrastructure intercepts packets communicated between a client and a server to determine whether the connection corresponds to one of a plurality of service applications that may supported by the service module. If so, the service module breaks the connection by terminating the connection with the client at the service module and opening a separate connection between the service module and the server. The service application may then perform application-specific process of the data communicated between the client and server. In order to increase processing efficiency associated with classifying the connection between the client and the server, the service module stores classification rules in a plurality of hashing tables, with hash conflicts arranged as an m-ary tree structure. This arrangement enables the service module to efficiently search for classification rules and resolve hash conflicts without imposing a significant processing penalty.
Owner:OPTIMORPHIX INC
Method for hierarchical caching of configuration data having dataflow processors and modules having two-or multidimensional programmable cell structure (FPGAs, DPGAs, etc.)--
InactiveUS6480937B1Improve performanceEasy transferMemory adressing/allocation/relocationProgram controlData stream processingComputer module
A method of caching commands in microprocessors having a plurality of arithmetic units and in modules having a two- or multidimensional cell arrangement is provided. The method includes combining a plurality of cells and arithmetic units to form a plurality of groups, assigning a cache unit to a group, and connecting the cache unit to a higher level unit via a tree structure. The cache unit may send requests for required commands to the higher level cache unit, which may return a command sequence including the required command, if the higher level cache unit holds the first command sequence including the required command in the higher level cache unit's local memory.
Owner:SCIENTIA SOL MENTIS AG +1
Automatic layout of content in a design for a medium
InactiveUS6928610B2Stable supportDigital data information retrievalDigital computer detailsMultiple formsTheoretical computer science
A three-way separation of information in a document includes content, design and media aspects. This division supports automatic rendering to multiple forms of media such as print, Intranet, Internet, and OLE embedding. In a particular embodiment, the document is separated into its content, design and media aspects. Content, design, a medium specification are identified and layout is performed as per the three aspects. In one embodiment, an information data structure is provided that includes three tree structures: a design tree, a content tree and a media tree. A media division data structure is associated with a parent component in a composition. The parent component has a parent region in a medium and has child components. Each child component is associated with a child region of the medium. The media division data structure provides rules, properties and values for performing layout in a particular region of the medium. Layout may be performed on a server.
Owner:MICROSOFT TECH LICENSING LLC
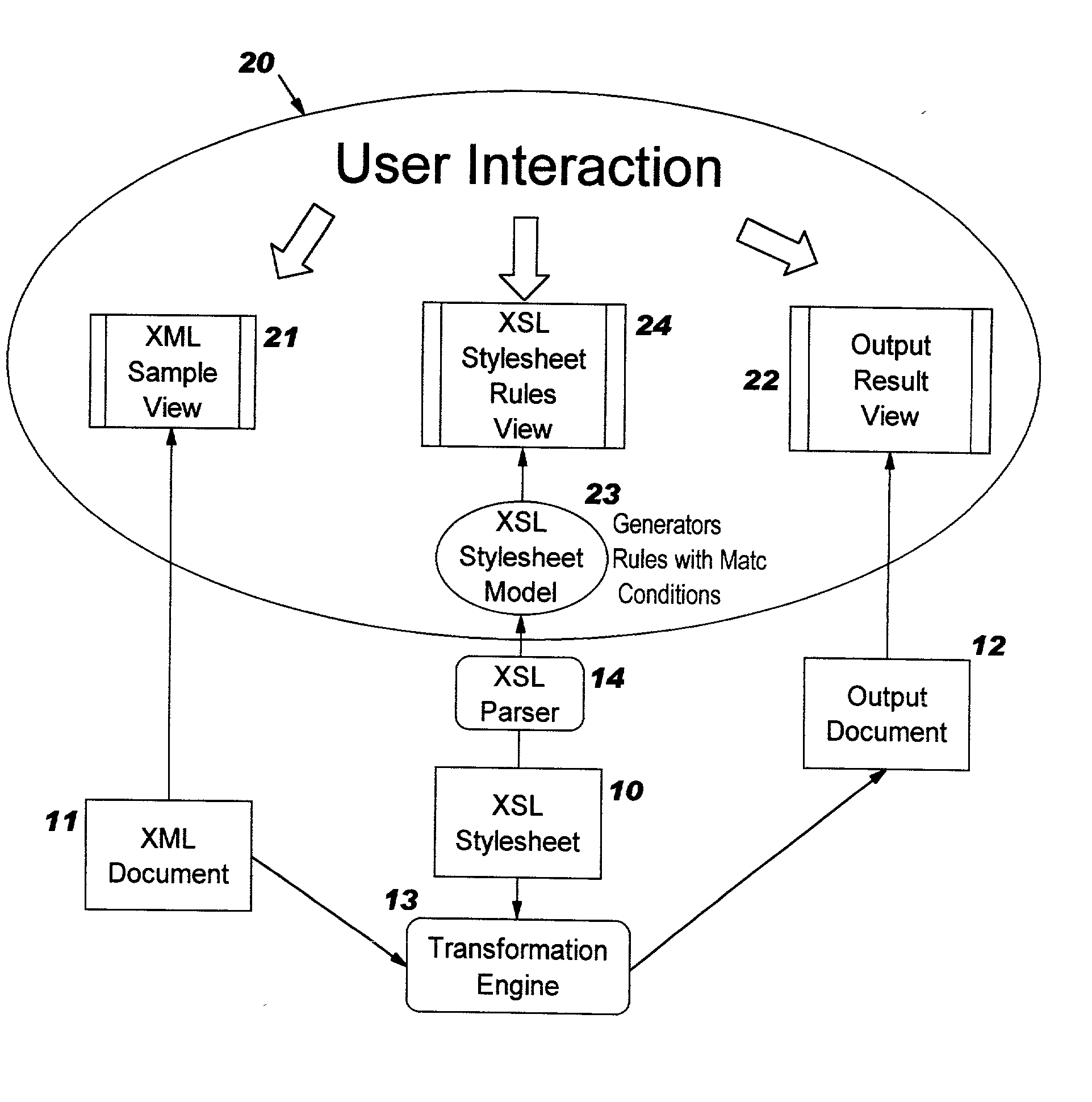
Method and system for stylesheet-centric editing
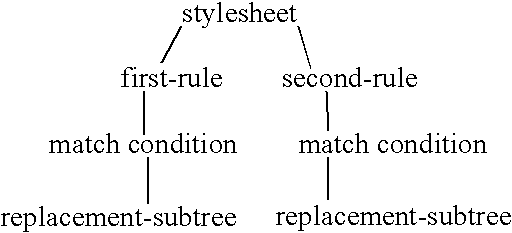
InactiveUS20040205571A1Natural language data processingSpecial data processing applicationsTemplate basedTree structured data
A method (and structure) for enacting changes to a document containing a template-based program that transforms tree-structured data from a first tree-structured data into a second tree-structured data, including providing an interface to permit selection of a document containing the template-based program, constructing a model of the template-based program in the selected document by parsing elements of the template-based program into a corresponding logical construct having a match condition and at least one generator, where the match condition determines whether an element in the first tree-structure data is to be processed by one or more of the at least one generator, and displaying a representation of the model to the user.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com