Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2103 results about "Computer memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, memory refers to a device that is used to store information for immediate use in a computer or related computer hardware device. It typically refers to semiconductor memory, specifically metal-oxide-semiconductor (MOS) memory, where data is stored within MOSFET (MOS field-effect transistor) memory cells on a silicon integrated circuit chip. The term "memory" is often synonymous with the term "primary storage". Computer memory operates at a high speed, for example random-access memory (RAM), as a distinction from storage that provides slow-to-access information but offers higher capacities. If needed, contents of the computer memory can be transferred to secondary storage; a very common way of doing this is through a memory management technique called "virtual memory". An archaic synonym for memory is store.
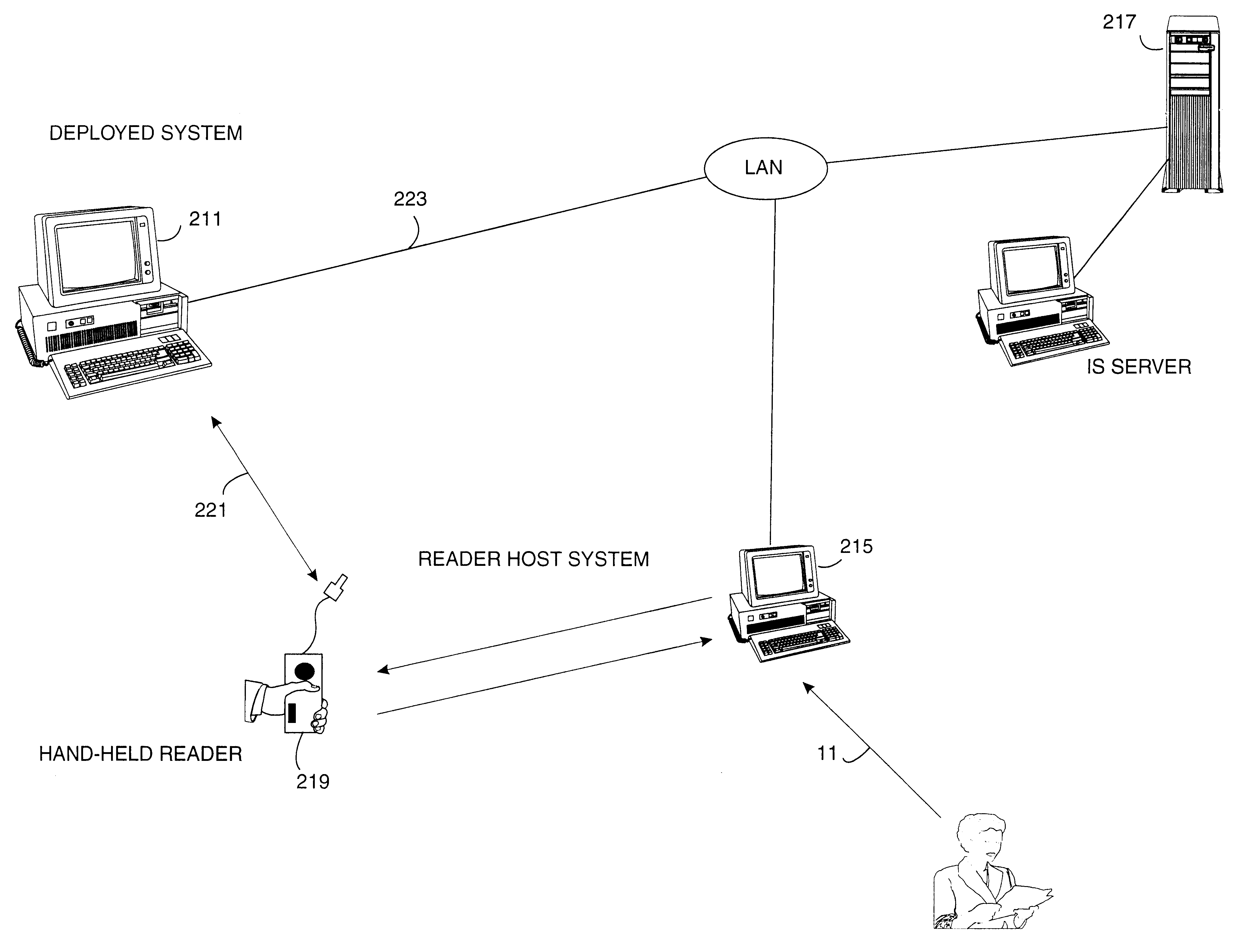
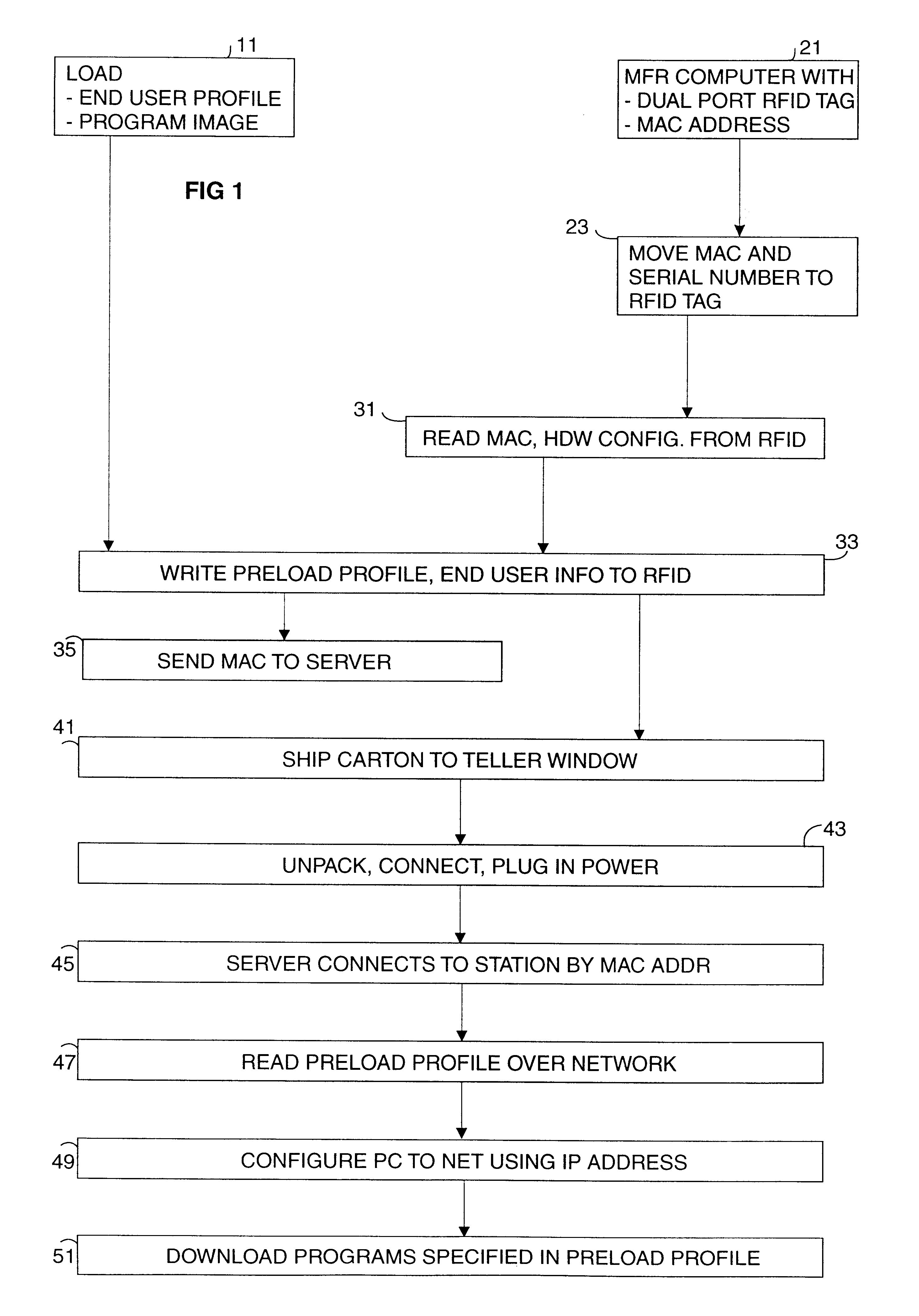
Method and economical direct connected apparatus for deploying and tracking computers
A method of asset control and workstation computer deployment that utilizes a dual port electronic memory identification RFID tag to hold serial number and hardware and software configuration profiles as well as user information. The RFID tag is mapped into the workstation computer memory space and can also be read and written by radio frequency signalling through a wired plug and access flap in a shipping carton. Serial numbers and MAC address is stored on the tag by the manufacturer. User information, workstation profile and software image information is stored onto the tag while the computer is being received for forwarding to the final workstation destination without the need to unpack and power up the computer. The information stored on the tag is used to allow automated system configuration and software downloading to the computer.
Owner:IBM CORP
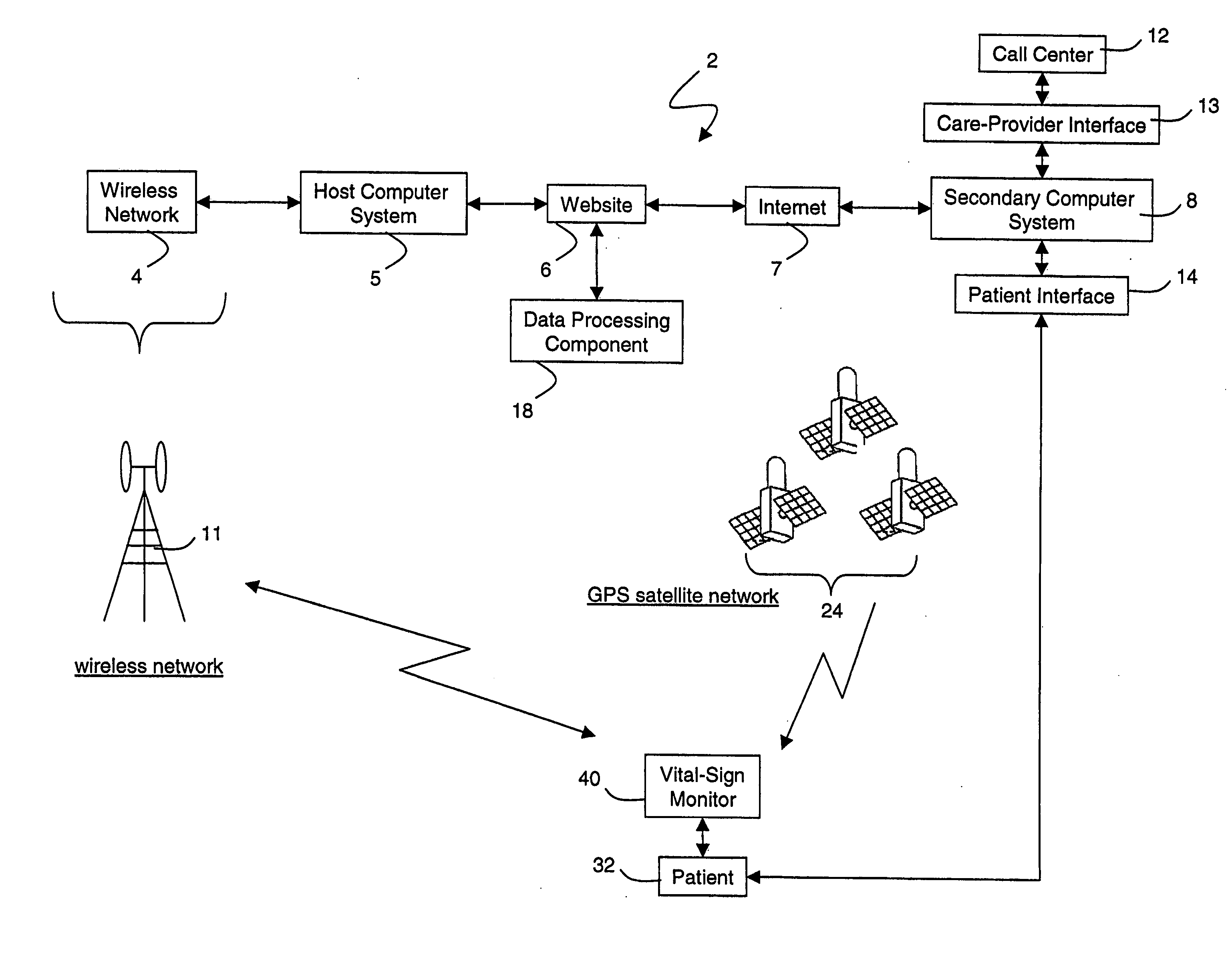
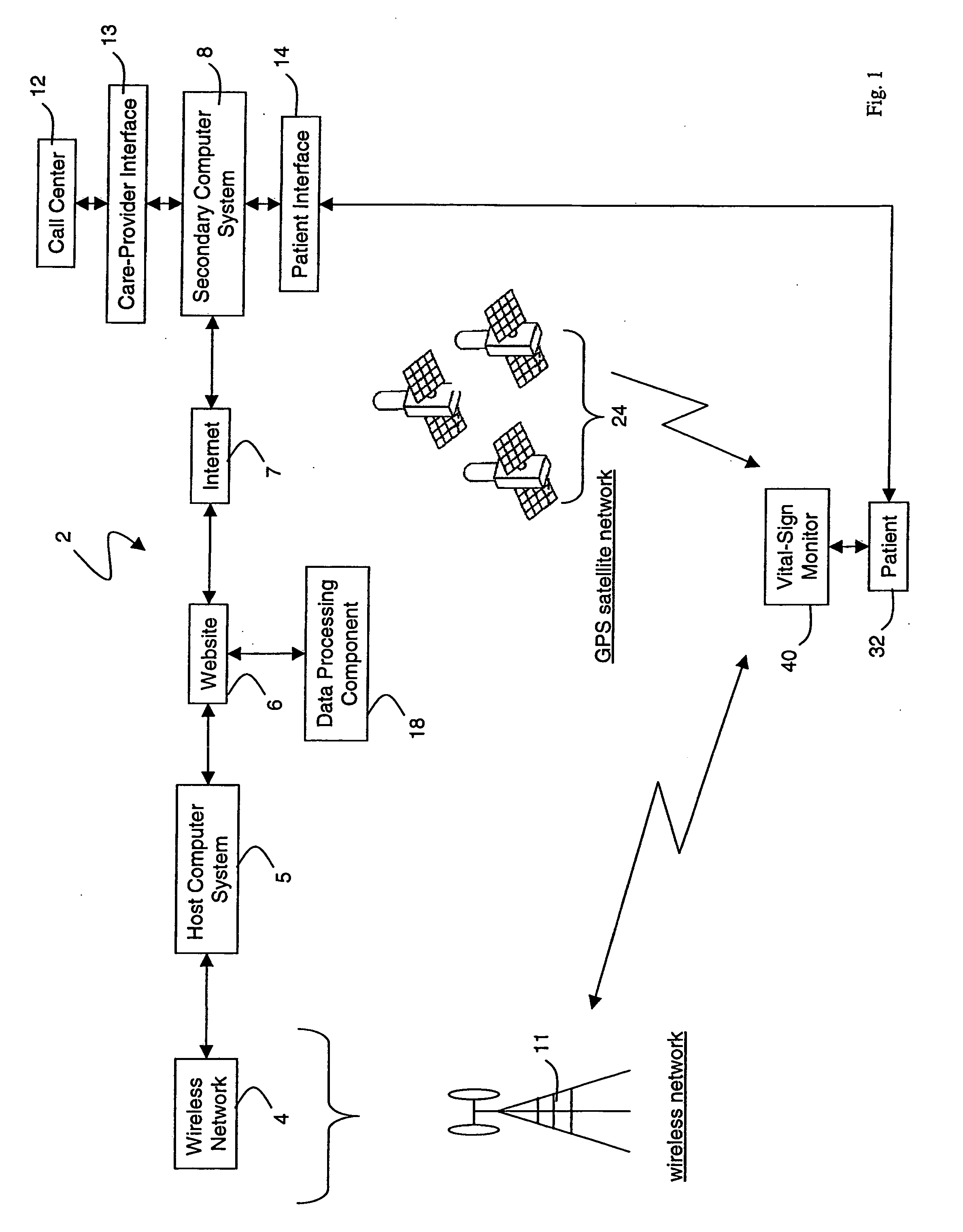
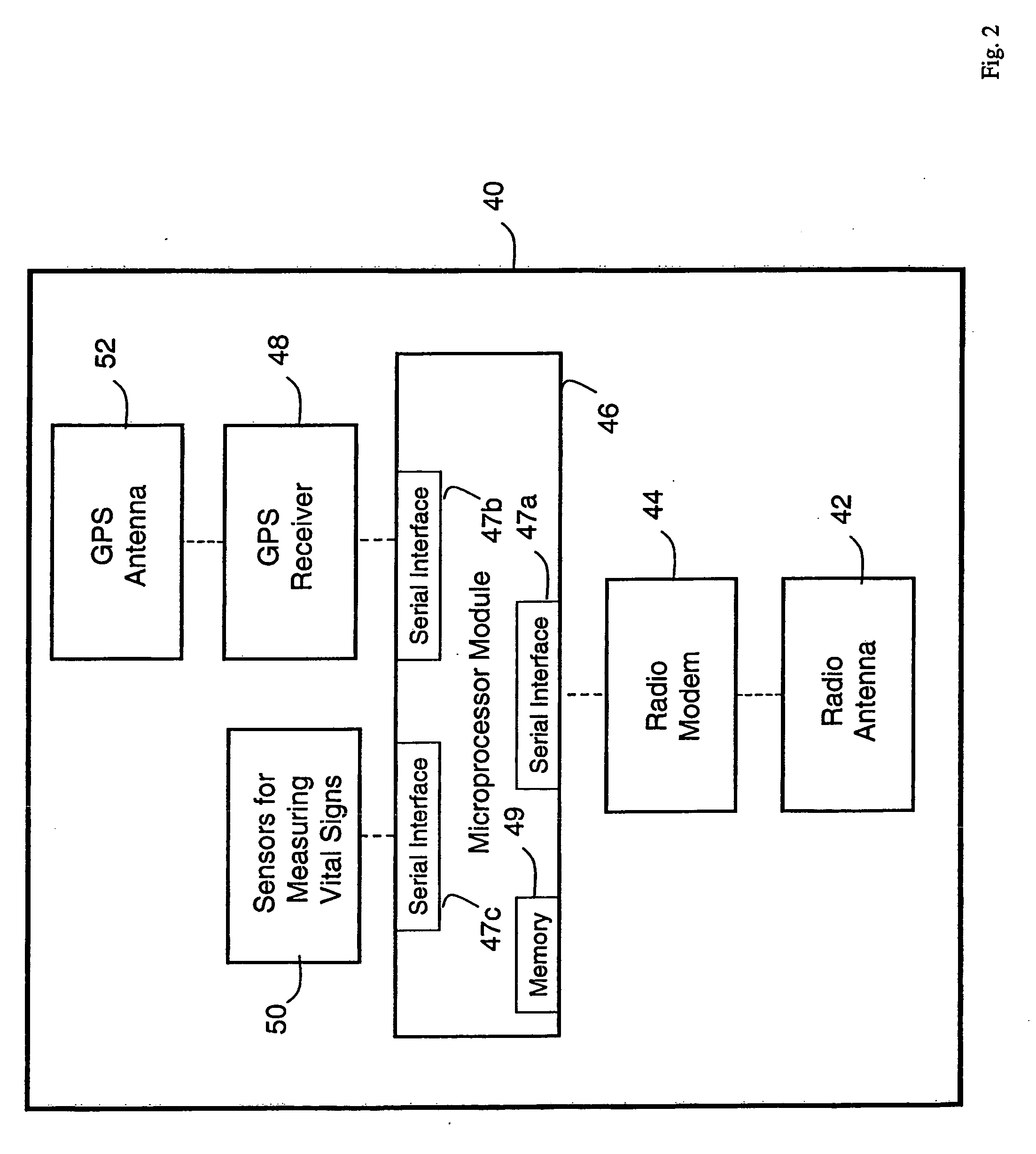
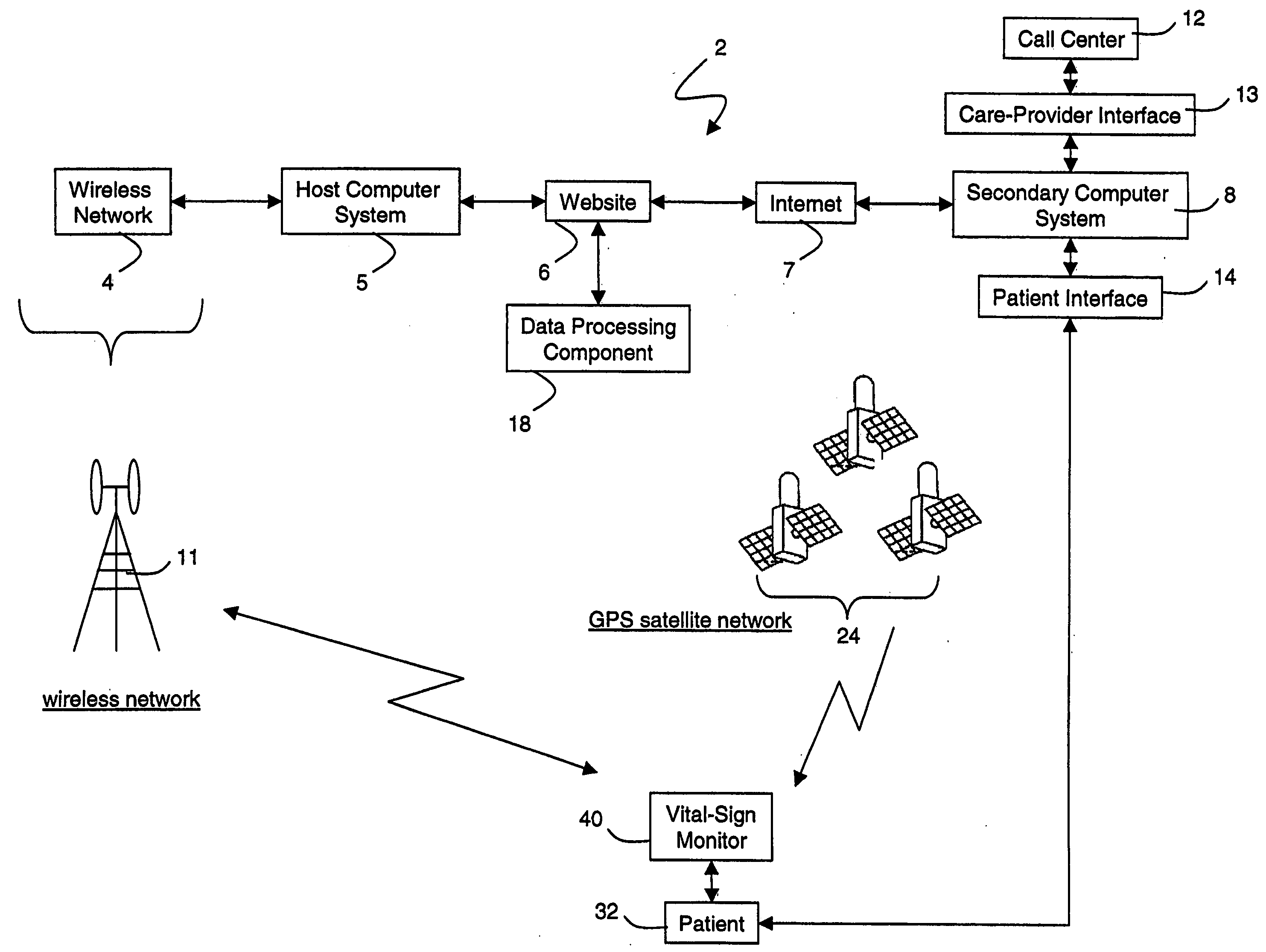
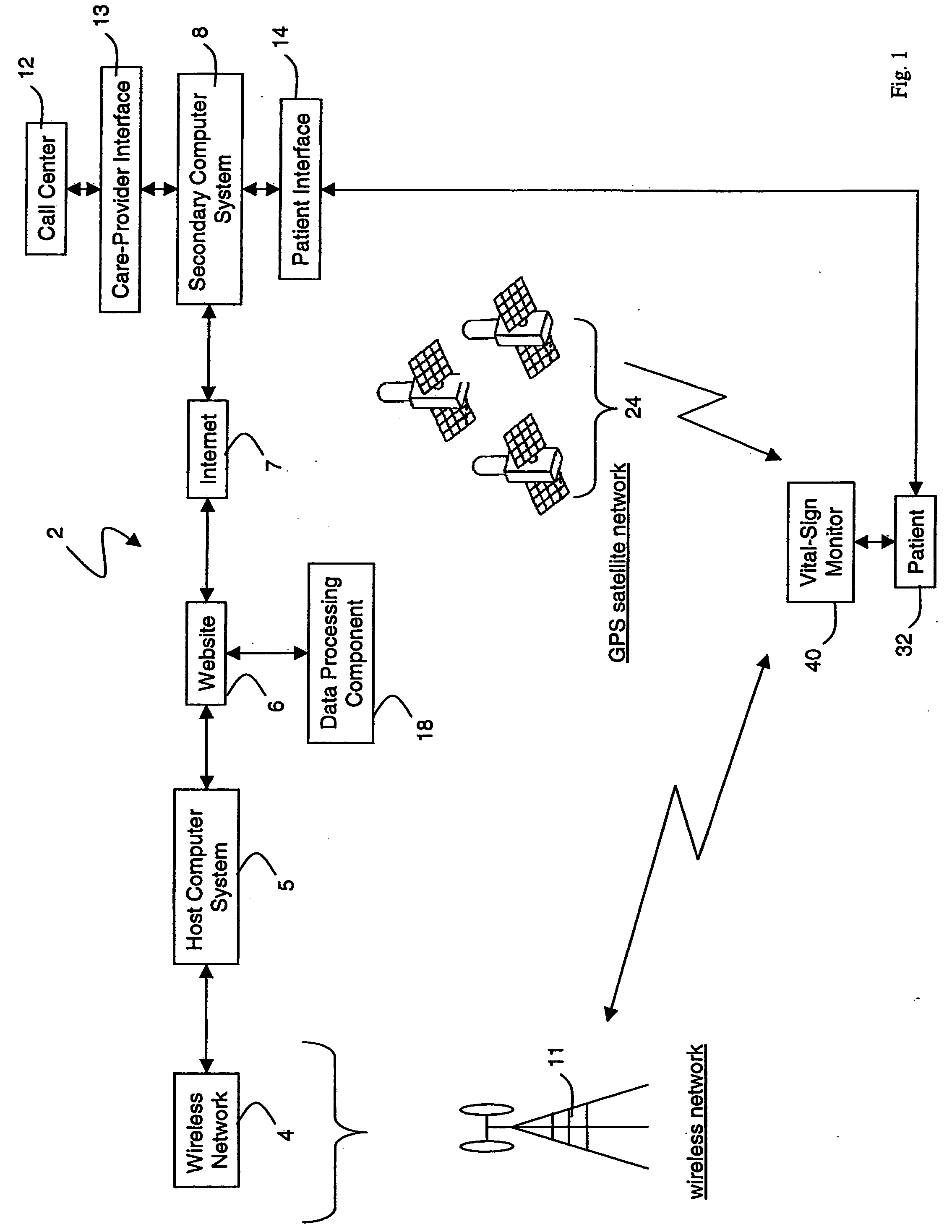
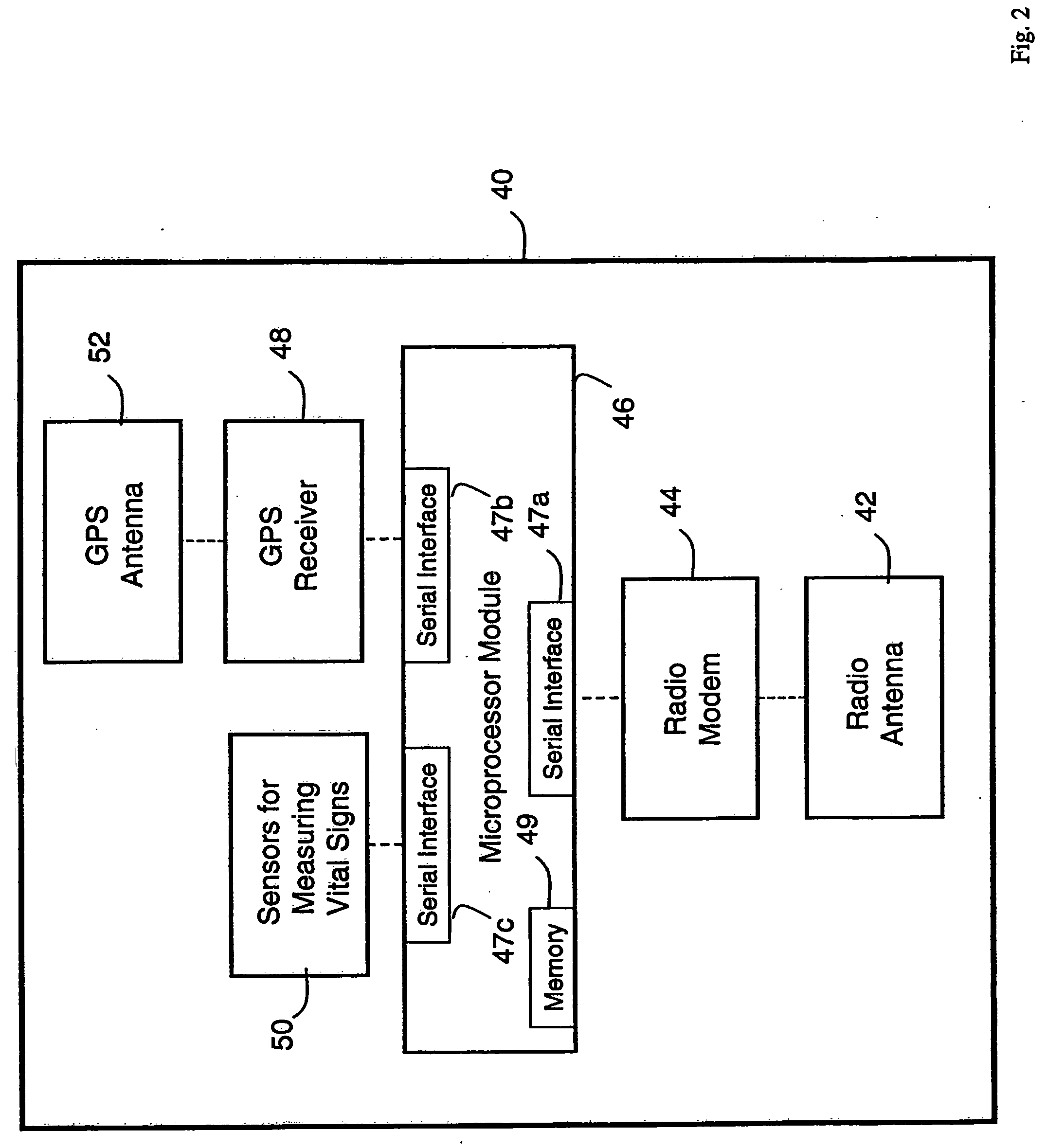
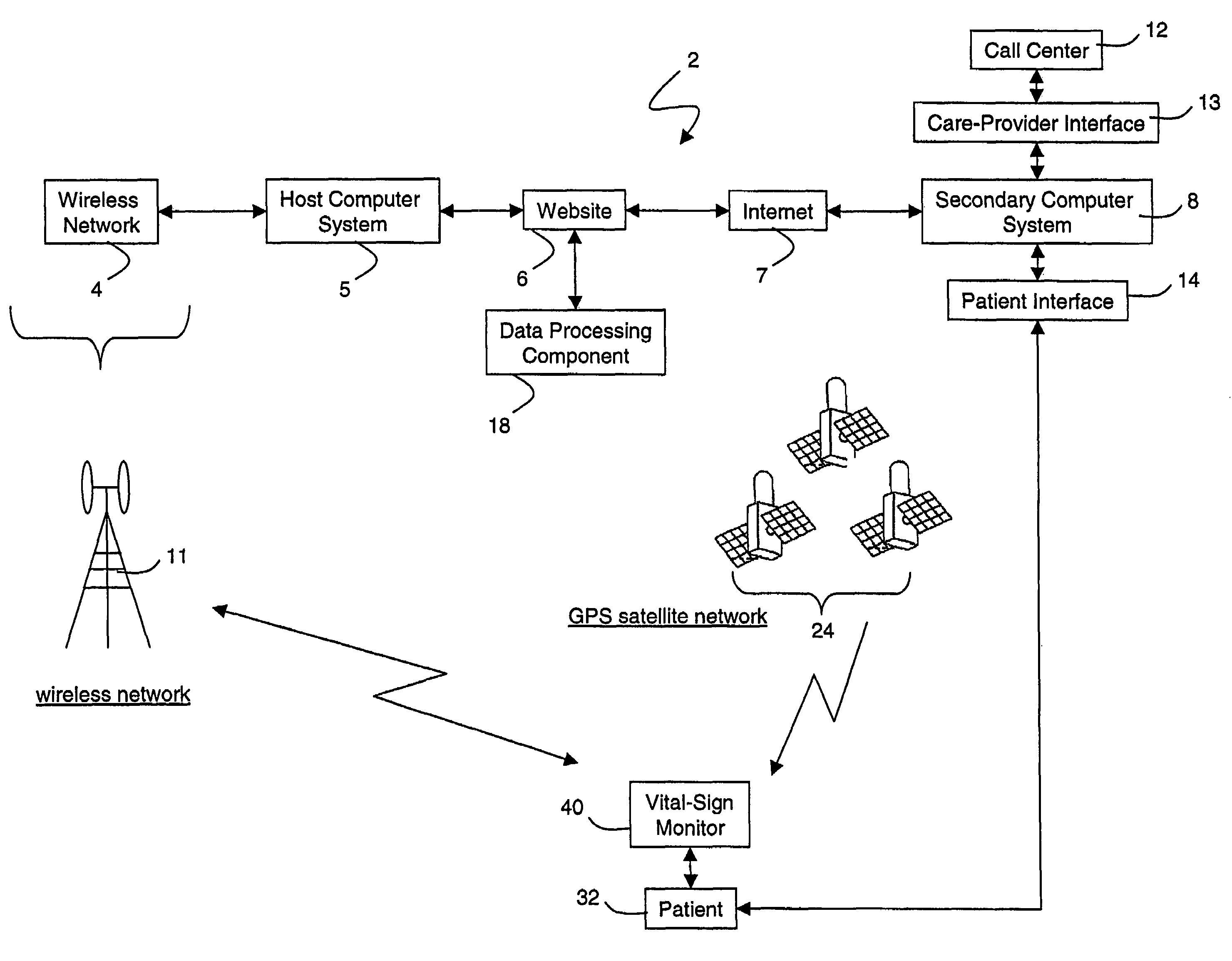
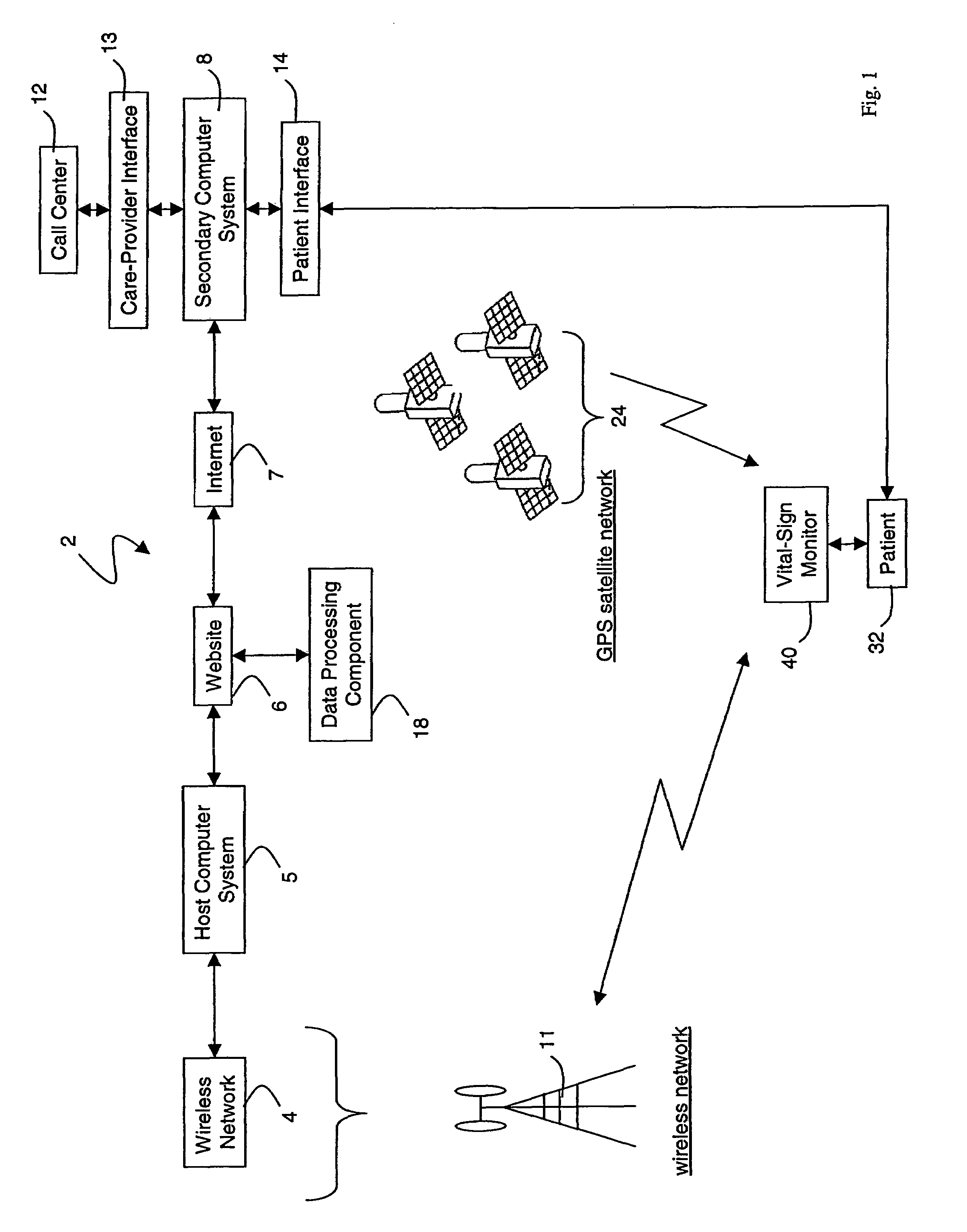
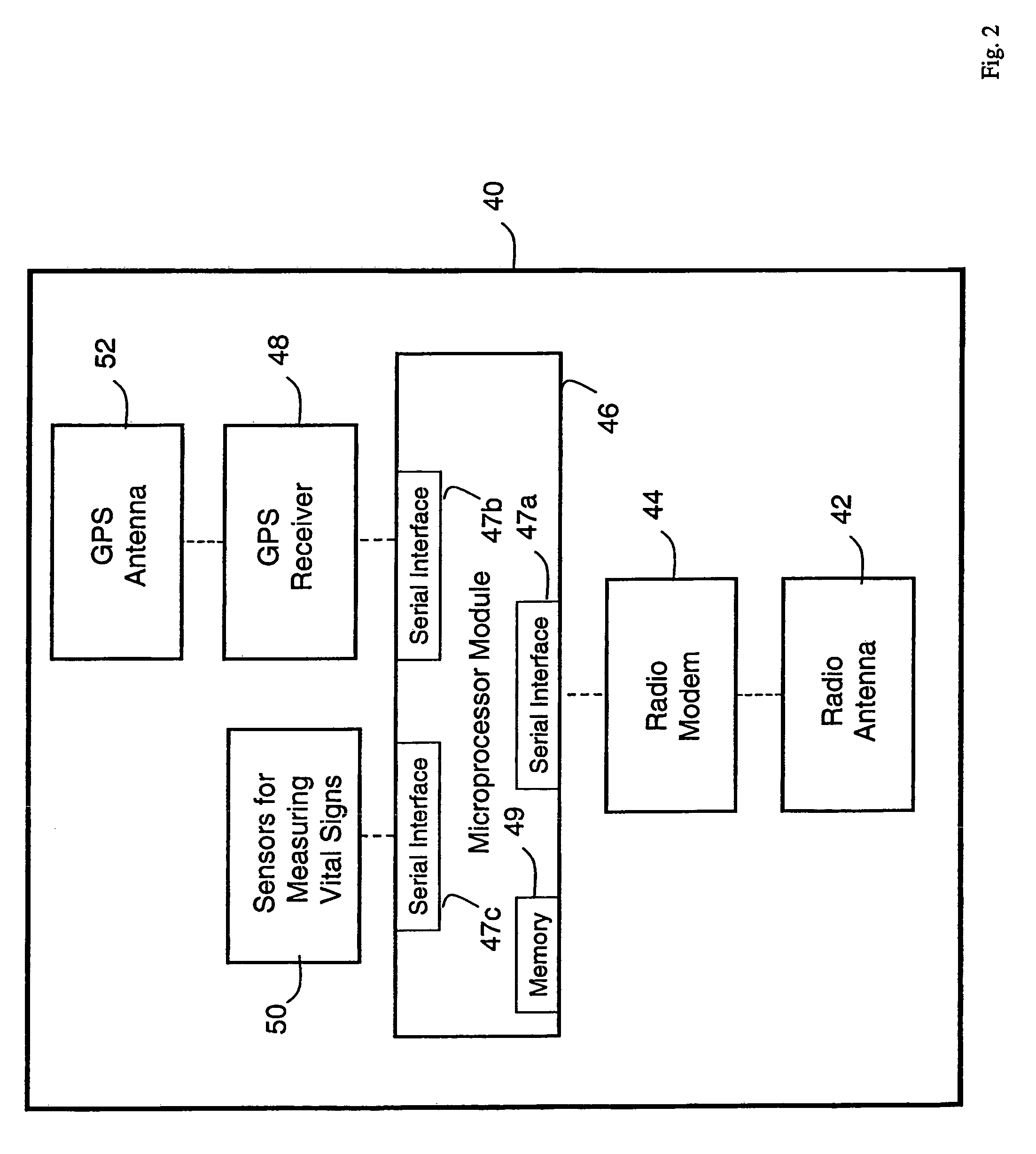
Wireless, internet-based medical-diagnostic system
ActiveUS20050010087A1Accurate diagnosisMinimize impactSurgeryCatheterGlobal Positioning SystemUser interface
A system for monitoring a patient's vital signs that features a vital-sign monitor including sensors for measuring from the patient at least one of the following vital-sign data: O2 saturation, blood pressure, electro-cardiogram, respirator rate, and blood glucose level. The system also includes a global positioning system that determines location-based data. A wireless transmitter, in electrical contact with the vital-sign monitor and global positioning system, receives the vital-sign and location-based data and wirelessly transmits these data through a conventional wireless network. A gateway software piece receives and processes the data from the wireless network and stores these data in a computer memory associated with a database software piece. The system also includes an Internet-based user interface that displays the vital sign data for both individual patients and care-providers.
Owner:SOTERA WIRELESS
Wireless, internet-based, medical diagnostic system
InactiveUS20060142648A1Accurate diagnosisMinimize impactRespiratory organ evaluationSensorsEmergency medicineGlobal Positioning System
A system for monitoring a patient's vital signs that features a vital-sign monitor including sensors for measuring from the patient at least one of the following vital-sign data: O2 saturation, blood pressure, electrocardiogram, respirator rate, and blood glucose level. The system also includes a global positioning system that determines location-based data. A wireless transmitter, in electrical contact with the vital-sign monitor and global positioning system, receives the vital-sign and location-based data and wirelessly transmits these data through a conventional wireless network. A gateway software piece receives and processes the data from the wireless network and stores these data in a computer memory associated with a database software piece. The system also includes an Internet-based user interface that displays the vital sign data for both individual patients and care-providers.
Owner:TRIAGE DATA NETWORKS
Wireless, internet-based medical-diagnostic system
ActiveUS7396330B2Accurate diagnosisMinimize impactSurgeryCatheterGlobal Positioning SystemUser interface
A system for monitoring a patient's vital signs that features a vital-sign monitor including sensors for measuring from the patient at least one of the following vital-sign data: O2 saturation, blood pressure, electro-cardiogram, respirator rate, and blood glucose level. The system also includes a global positioning system that determines location-based data. A wireless transmitter, in electrical contact with the vital-sign monitor and global positioning system, receives the vital-sign and location-based data and wirelessly transmits these data through a conventional wireless network. A gateway software piece receives and processes the data from the wireless network and stores these data in a computer memory associated with a database software piece. The system also includes an Internet-based user interface that displays the vital sign data for both individual patients and care-providers.
Owner:SOTERA WIRELESS
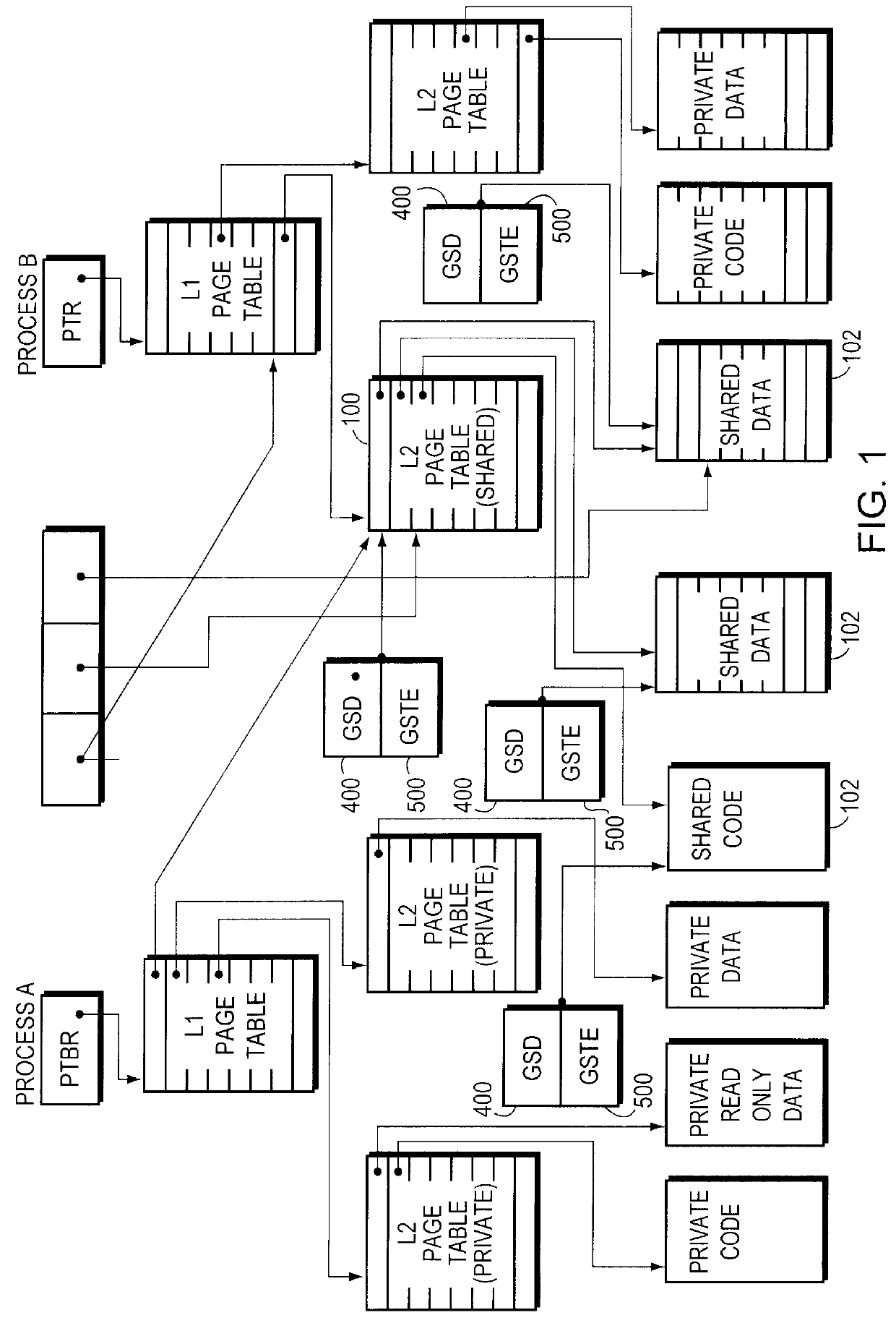
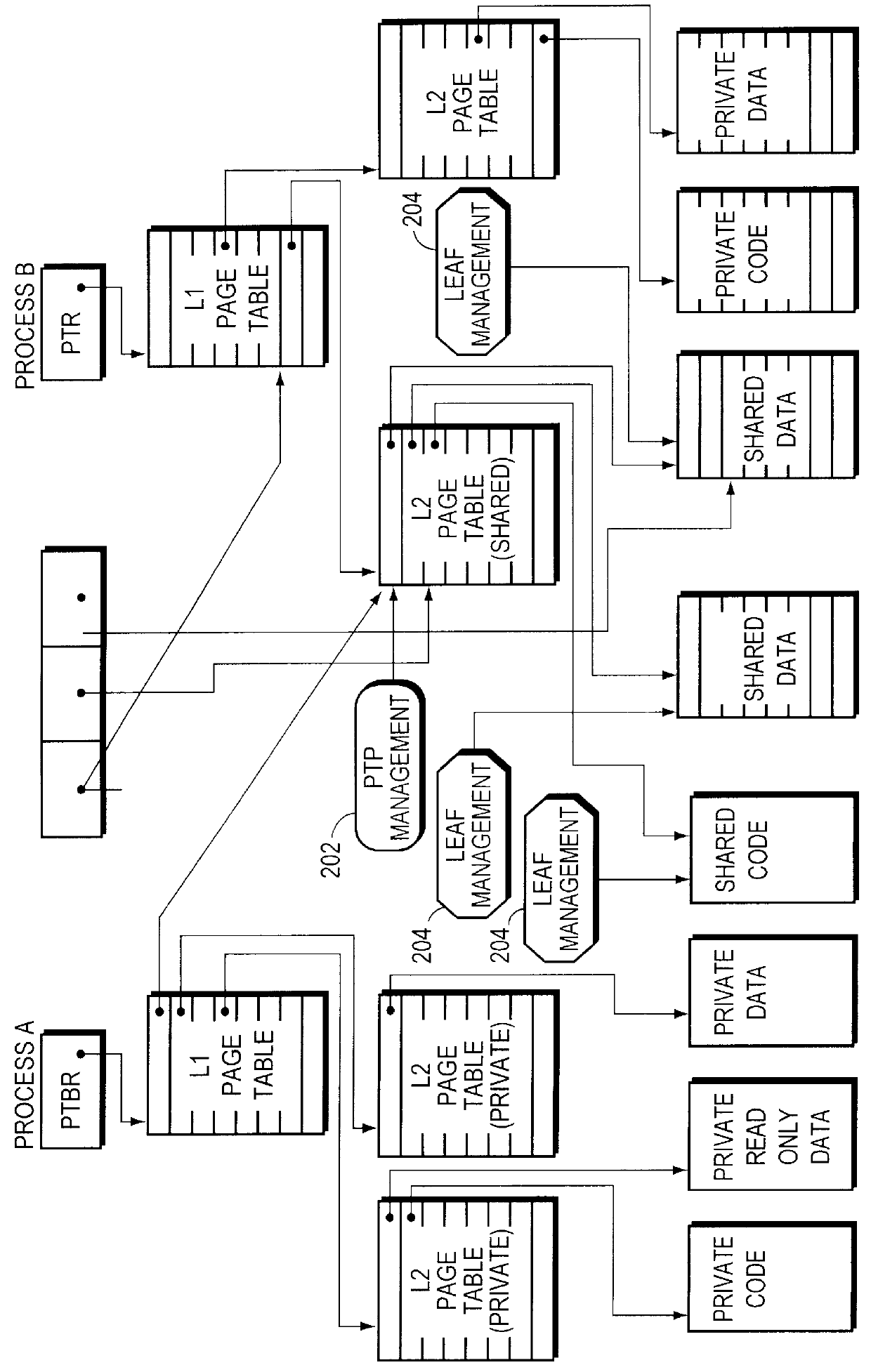
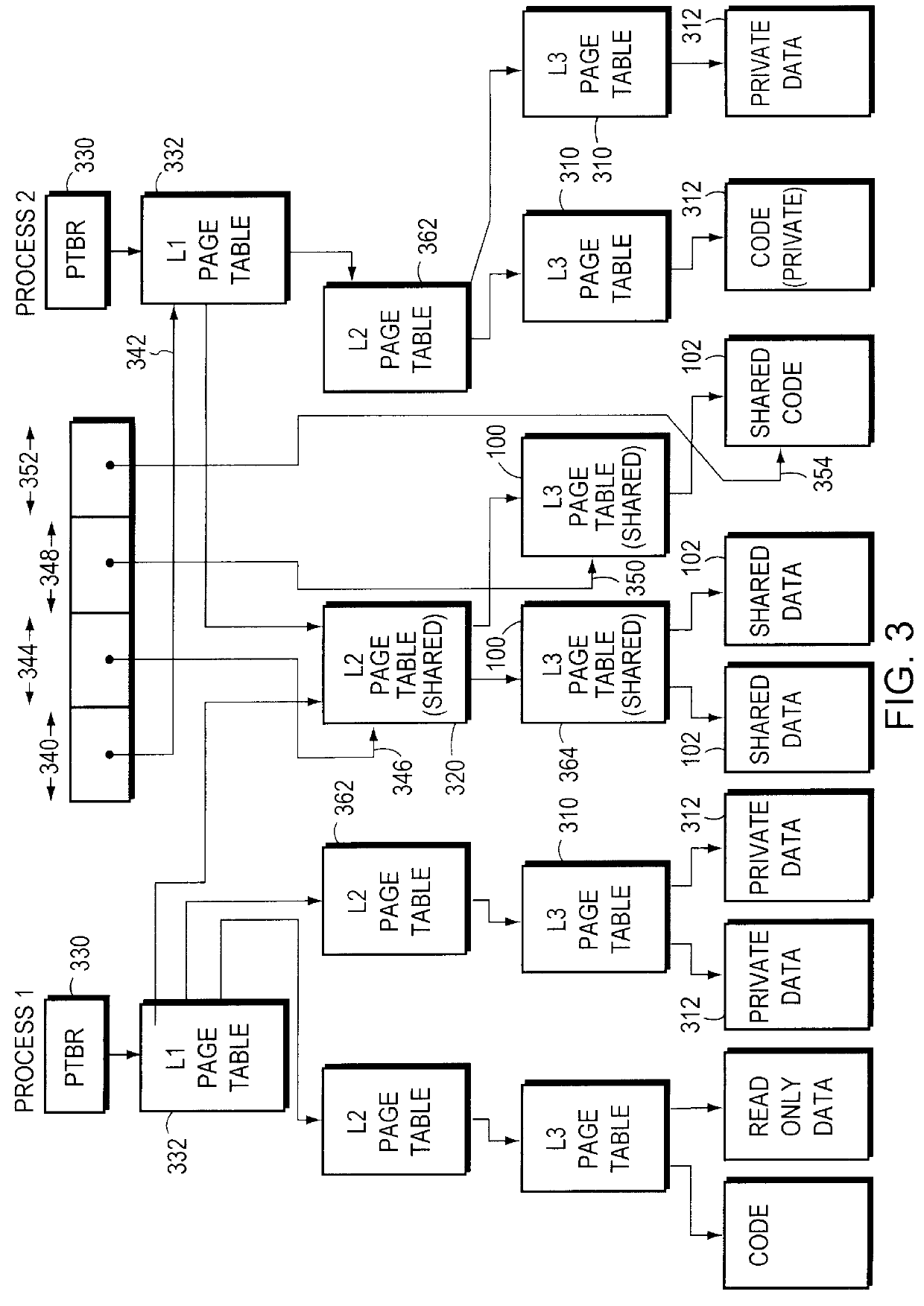
Sharing memory pages and page tables among computer processes
InactiveUS6085296AOptimizationReduce fragmentationMemory adressing/allocation/relocationMicro-instruction address formationPage tableComputer memory
A method of managing computer memory pages. The sharing of a program-accessible page between two processes is managed by a predefined mechanism of a memory manager. The sharing of a page table page between the processes is managed by the same predefined mechanism. The data structures used by the mechanism are equally applicable to sharing program-accessible pages or page table pages.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
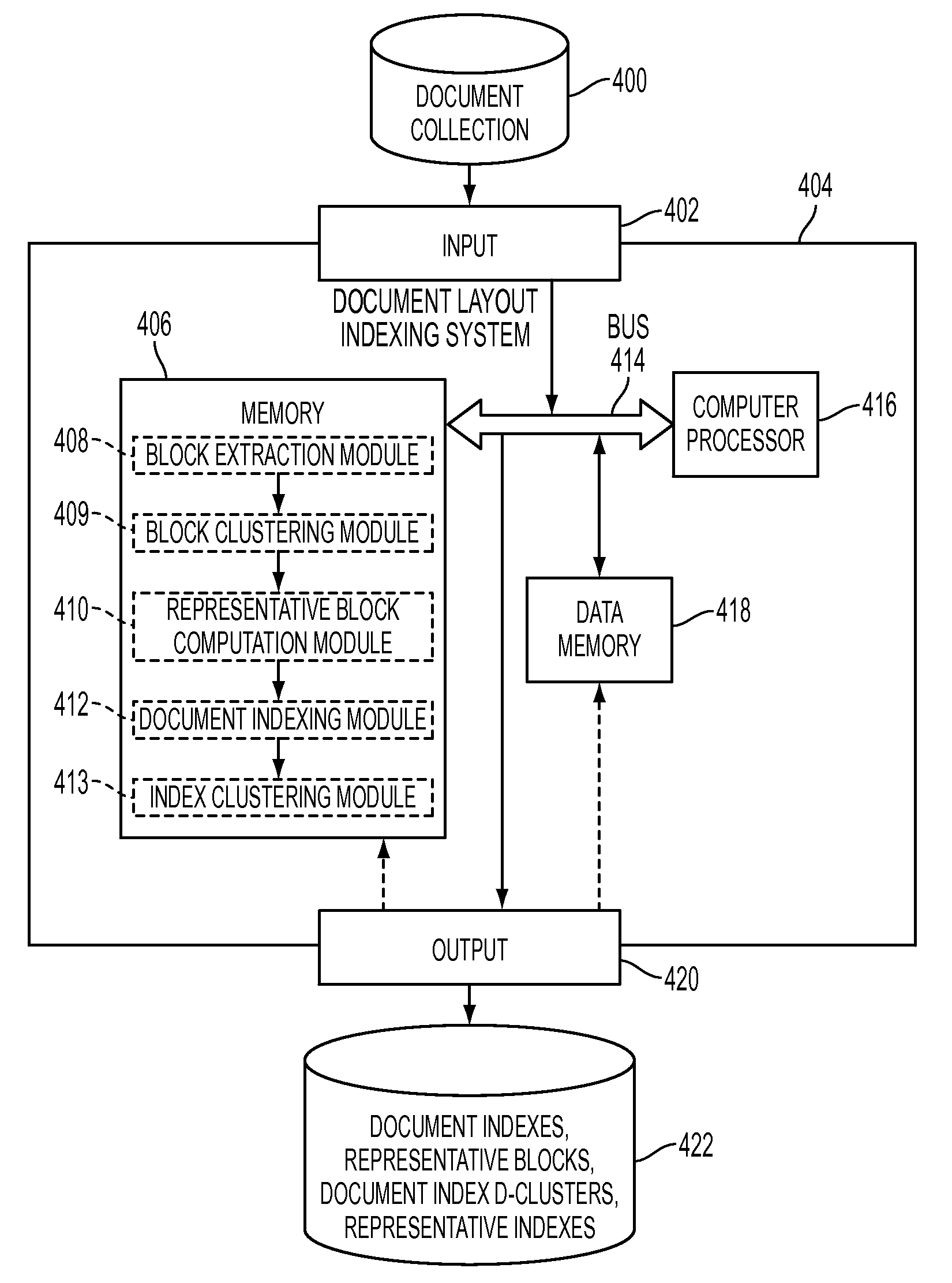
Scalable indexing for layout based document retrieval and ranking
InactiveUS7953679B2Digital data information retrievalDigital data processing detailsData miningDocumentation
A computer-based method and a system for indexing, querying, and ranking documents based on layout are provided. The method includes providing a plurality of documents to computer memory, extracting layout blocks from the provided documents, clustering the layout blocks into a plurality of layout block clusters, computing a representative block for each of the layout block clusters, generating a document index for each provided document based on the layout blocks of the document and the computed representatives blocks, clustering the created document indexes into a plurality of document index clusters, and generating a representative cluster index for each of the document index clusters. The indexes generated, together with the representative blocks and document index clusters, can be stored and used for retrieval of documents responsive to a layout query.
Owner:MAJANDRO LLC
User interface for a computing device
InactiveUS20140189608A1Available spaceEliminate needInput/output for user-computer interactionUnauthorised/fraudulent call preventionTablet computerHuman–computer interaction
There is disclosed a smartphone, tablet or other computing device comprising: (a) a touch sensitive display; (b) one or more processors; (c) computer memory; (d) one or more computer programs stored in the computer memory and configured to be executed by the one or more processors and including instructions for detecting a swipe in from one or more edges and then unlocking or making accessible the device from a screen in response to the detected swipe.
Owner:CANONICAL LTD
System and Method to Control a Wireless Power Transmission System by Configuration of Wireless Power Transmission Control Parameters
ActiveUS20160056966A1Preventing contradictory configurationNetwork topologiesHybrid transportElectric forceWeb browser
A system and method to control a wireless power transmission system by configuration of wireless power transmission control parameters is disclosed. The configuration of the system may be performed by an operator using a standard web browser on a computing device where the system configuration GUI presented to the operator may be functionally identical regardless of the computing device running the browser. The system configuration GUI may be connected to system through a system configuration API. According to some aspects of this embodiment, a method to control wireless power transmission system by configuration of wireless power transmission control parameters may include accessing the system configuration GUI, displaying operational or other parameter to configure the system, selecting an operational parameter, configuring the selected operational parameter, and then continuing to configure others operational parameter if needed, storing configuration parameters in the computer memory, and communicating configuration parameters to others system computers.
Owner:ENERGOUS CORPORATION
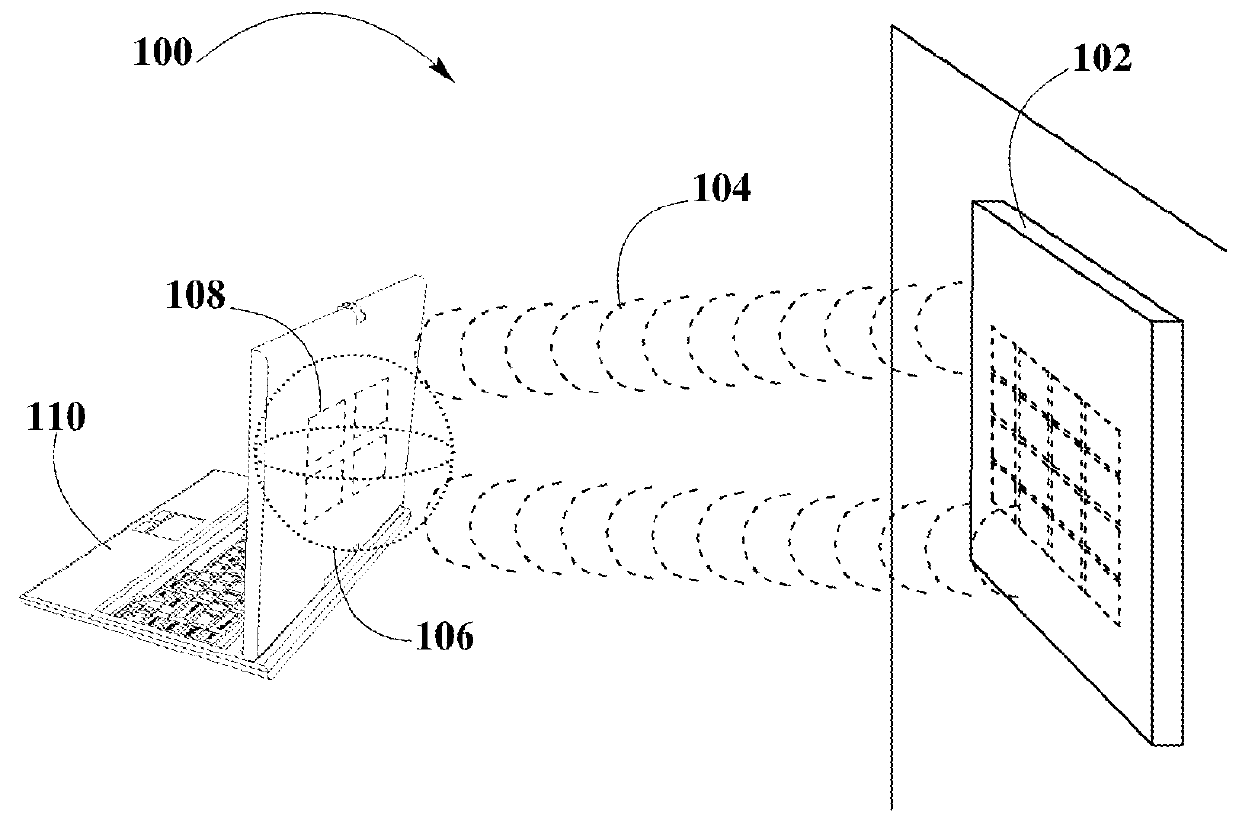
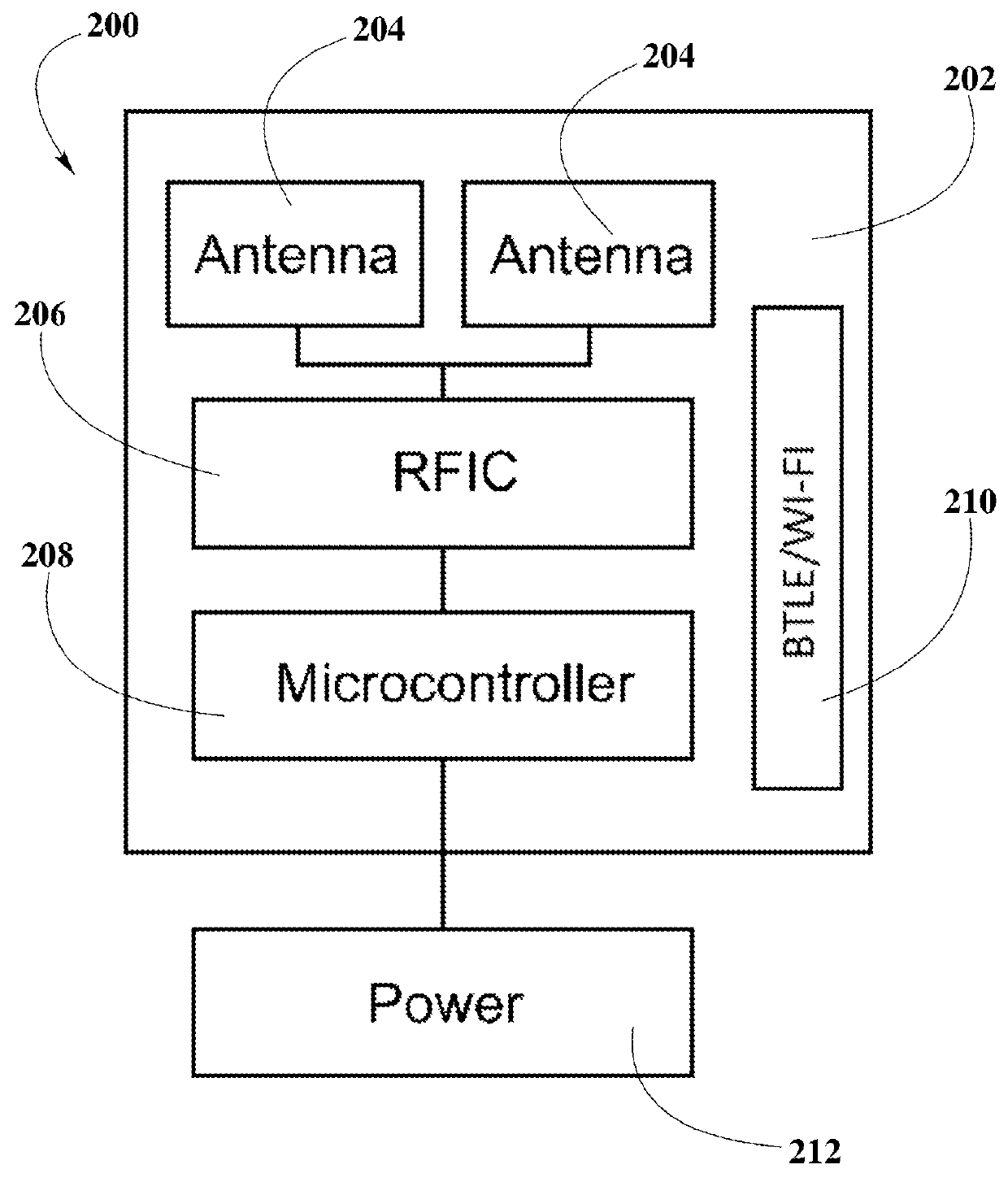
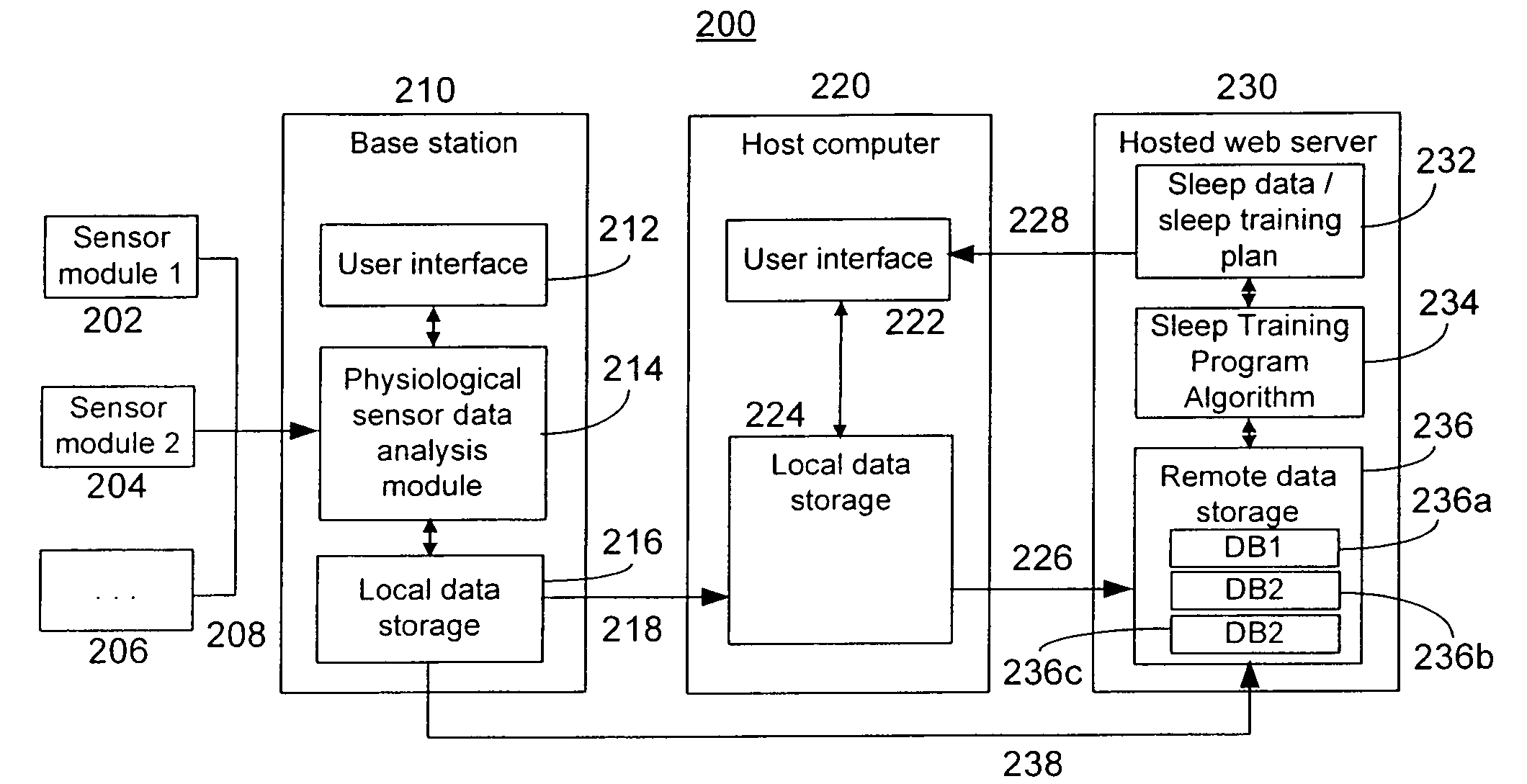
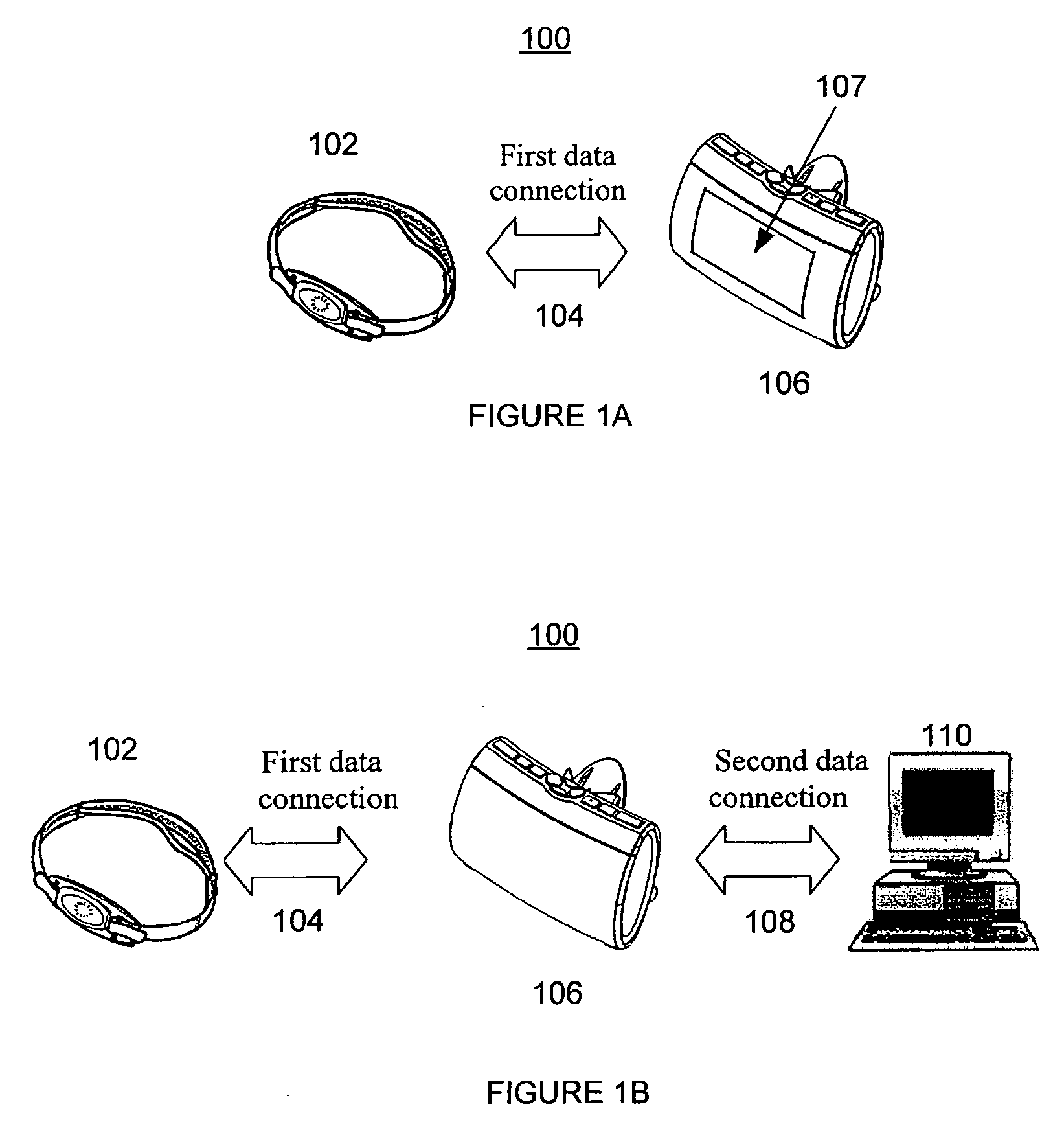
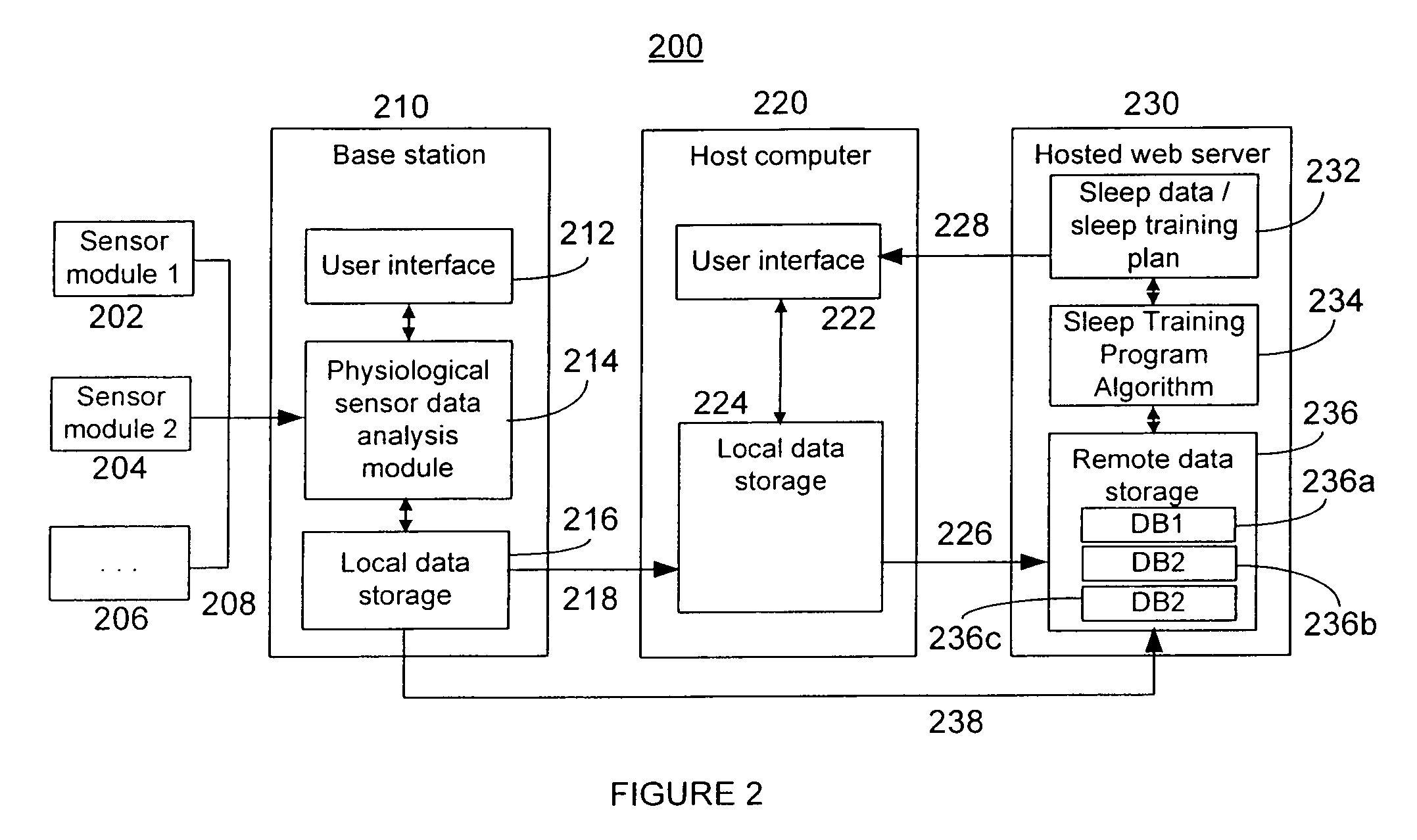
Data-driven sleep coaching system
InactiveUS20100099954A1Improving user sleep satisfactionEfficient use ofElectroencephalographyMedical automated diagnosisComputer memoryData-driven
System and method for a user to monitor and / or modify his or her sleep. In one embodiment, the sleep coaching system comprises a sensor for sensing a physiological signal of a sleeping user such as an EEG, computer memory databases for storing user and sleep-related data and advice, and a processor that generates a set of advice to improve user sleep satisfaction based on the user and sleep-related data. The advice to improve user sleep satisfaction, which may be communicated to the user, may comprise a sleep coaching plan, which may include one or more sleep coaching workshops that the user may undertake.
Owner:RESMED SENSOR TECH
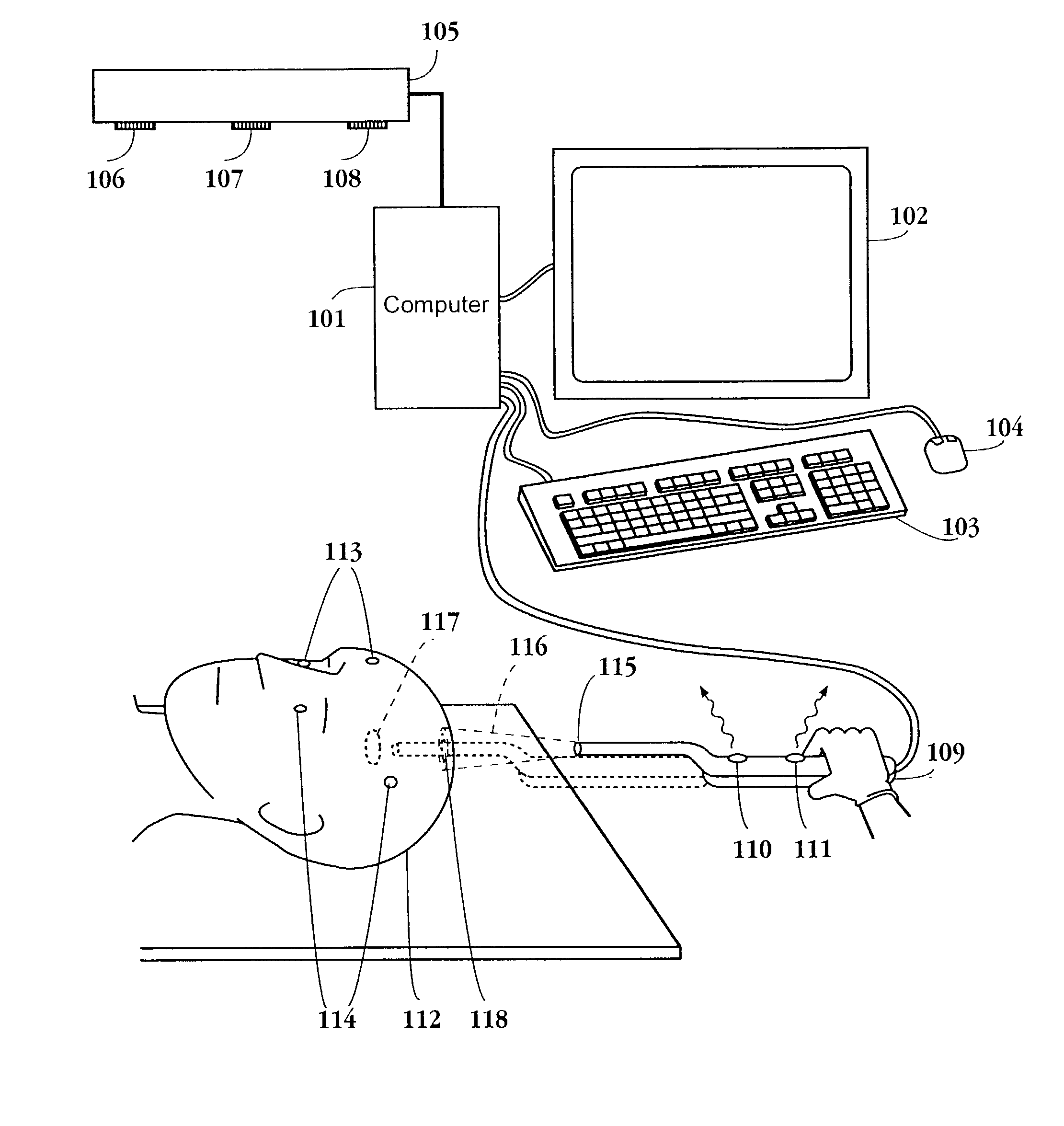
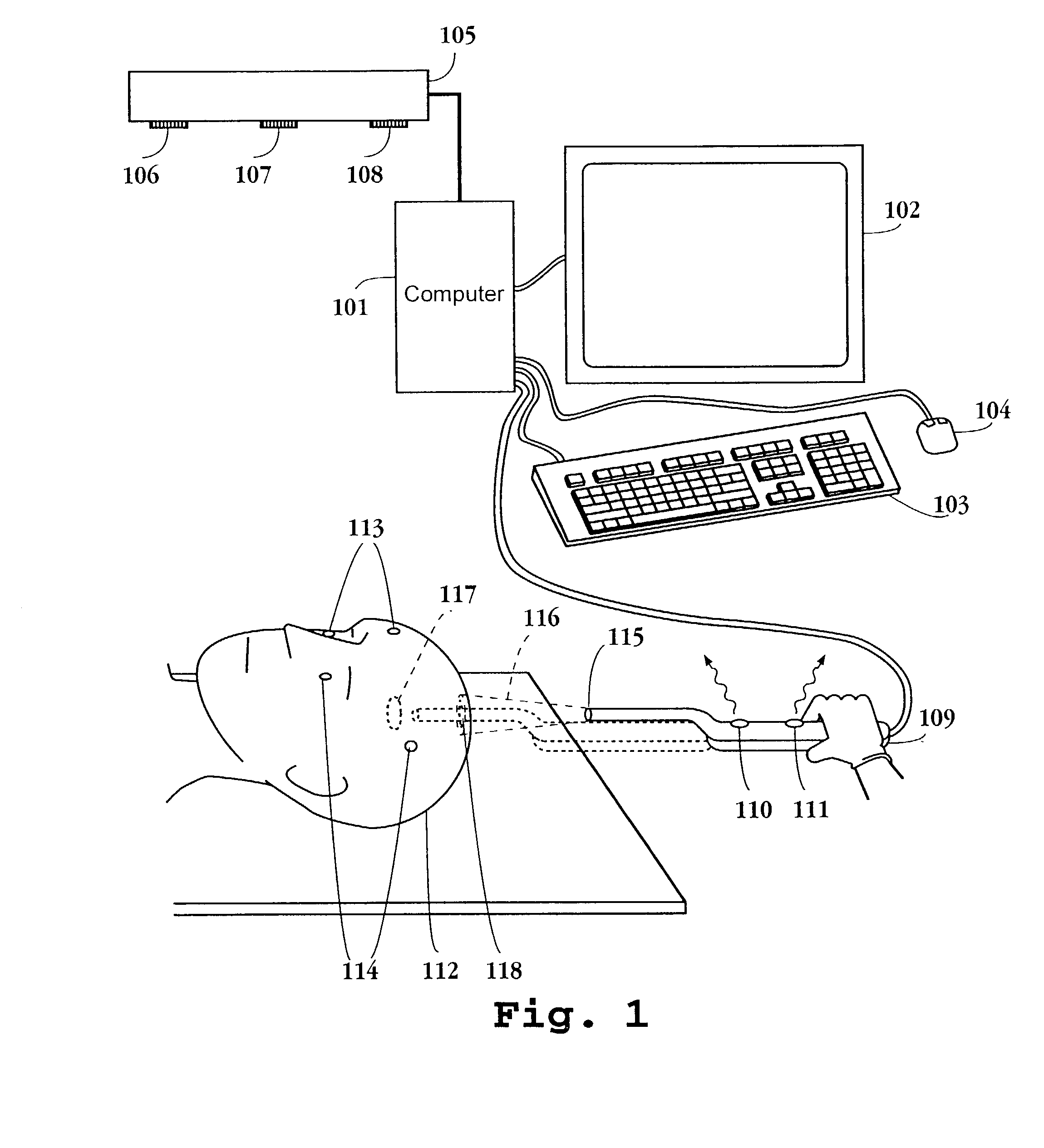
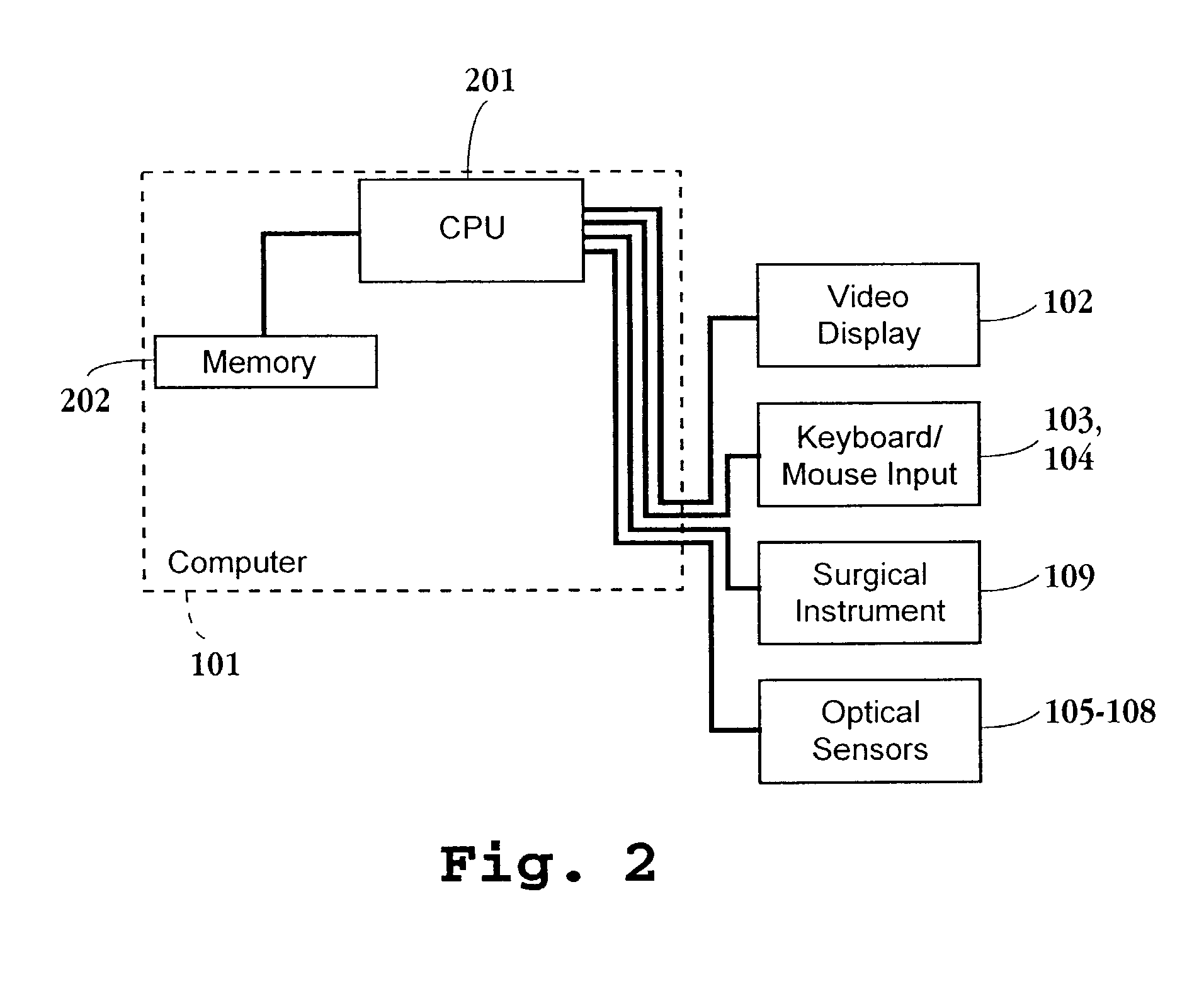
Method and apparatus for volumetric image navigation
InactiveUS7844320B2Effectively “ seeUltrasonic/sonic/infrasonic diagnosticsSurgical navigation systemsUltrasonic sensorViewpoints
A surgical navigation system has a computer with a memory and display connected to a surgical instrument or pointer and position tracking system, so that the location and orientation of the pointer are tracked in real time and conveyed to the computer. The computer memory is loaded with data from an MRI, CT, or other volumetric scan of a patient, and this data is utilized to dynamically display 3-dimensional perspective images in real time of the patient's anatomy from the viewpoint of the pointer. The images are segmented and displayed in color to highlight selected anatomical features and to allow the viewer to see beyond obscuring surfaces and structures. The displayed image tracks the movement of the instrument during surgical procedures. The instrument may include an imaging device such as an endoscope or ultrasound transducer, and the system displays also the image for this device from the same viewpoint, and enables the two images to be fused so that a combined image is displayed. The system is adapted for easy and convenient operating room use during surgical procedures.
Owner:CICAS IP LLC
Security System And Method For Computer Operating Systems
InactiveUS20080104348A1Prevent unauthorized accessDigital data processing detailsUser identity/authority verificationOperational systemData access
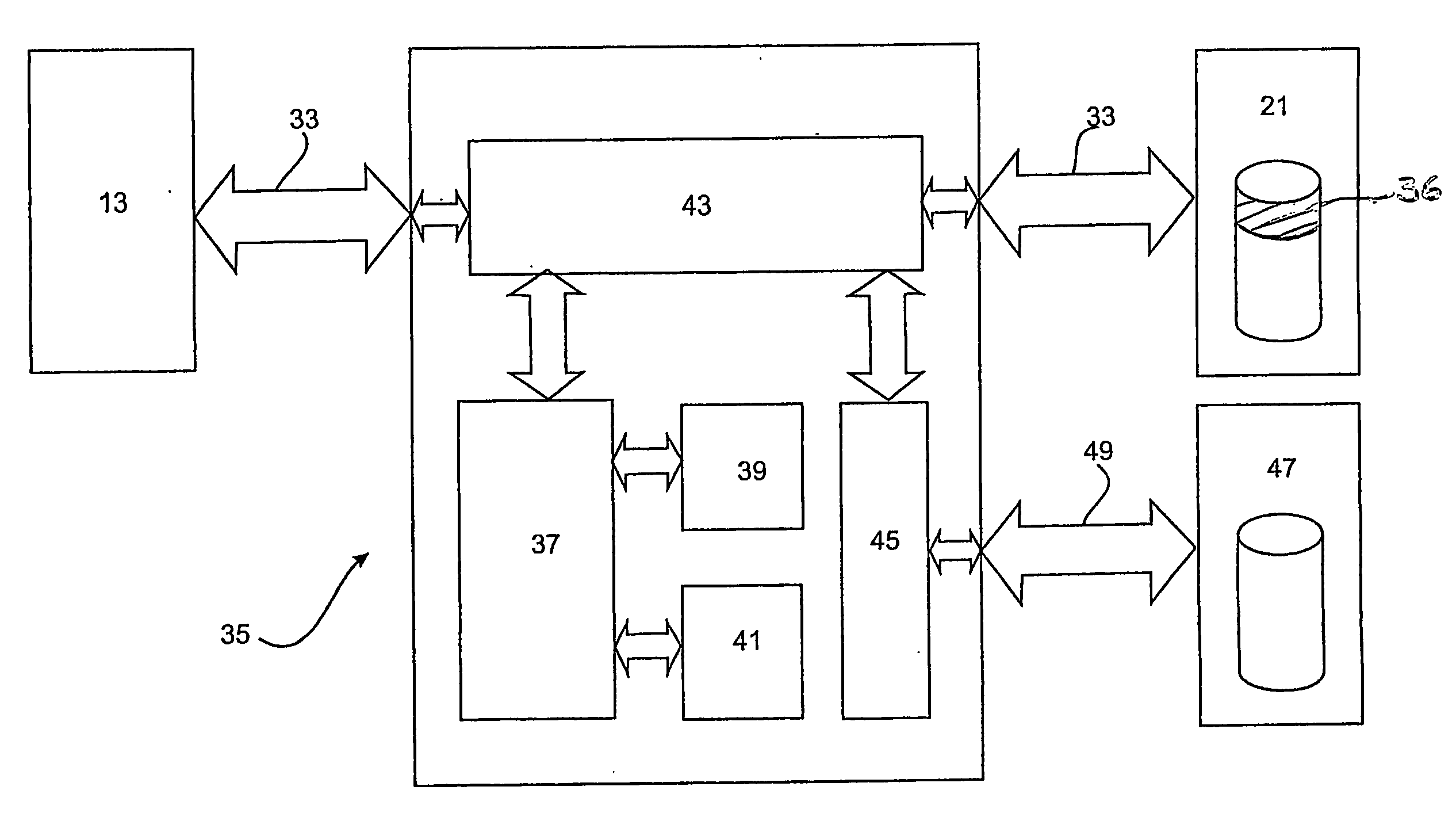
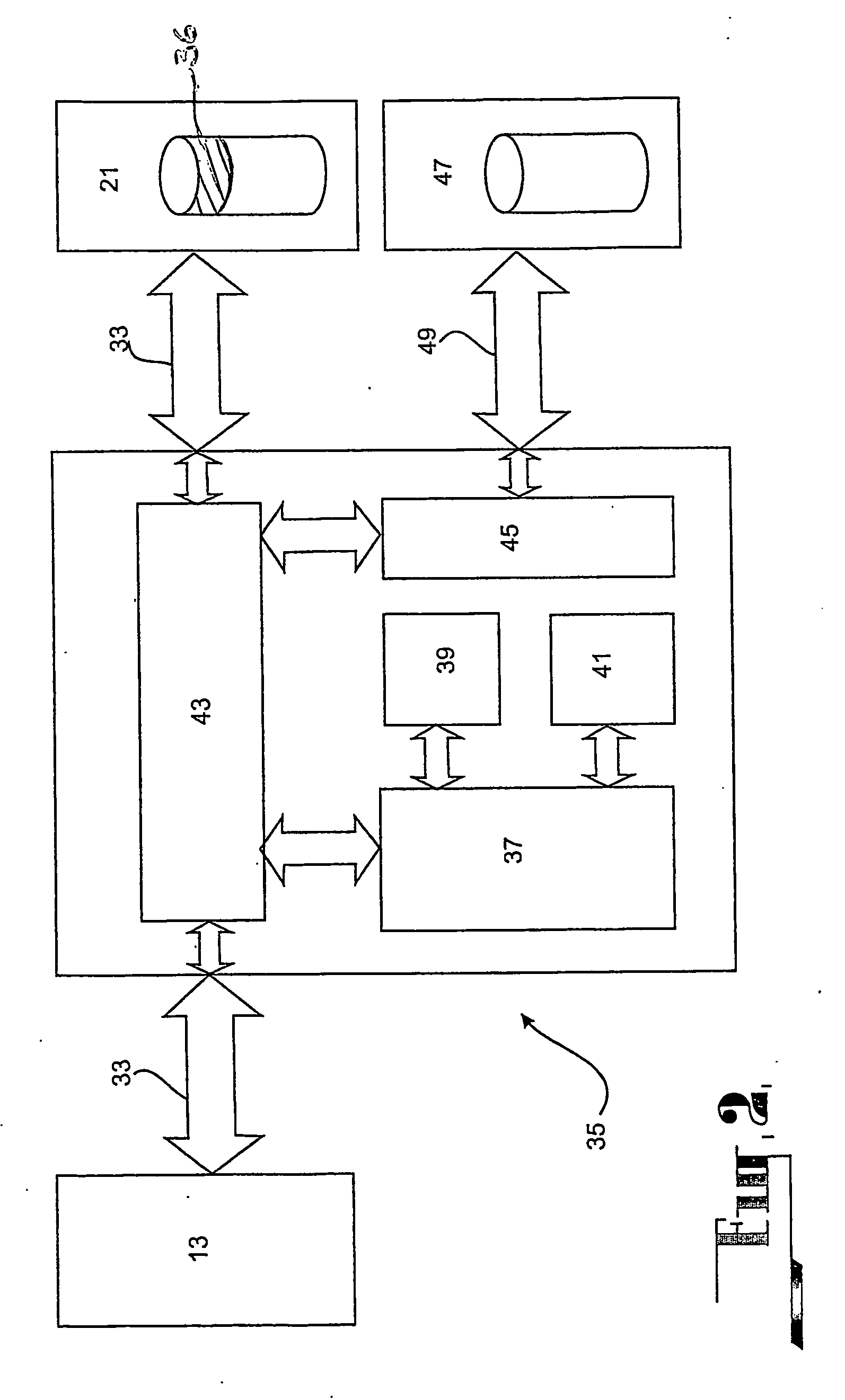
A security system for a computer operating system comprising a processor (37) that is independent of the host CPU (13) for controlling access between the host CPU (13) and a security partition formed in the storage device (21) for storing the operating system. A program memory (41) that is independent of the computer memory and the storage device (21) unalterably stores and provides computer programs for operating the processor (37) in a manner so as to control access to the security partition in the storage device (21). All data access by the host CPU (13) to the data storage device (21) is blocked before initialisation of the security system and is intercepted immediately after the initialisation under the control of the processor (37). The processor (37) effects independent control of the host CPU (13) and configuration of the computer (11) to prevent unauthorised access to the security partition on the storage device (21) during the interception phase. All users of the computer (11) are authenticated with a prescribed profile of access to the operating system files in the security partition on the storage device (21) and data access to the storage device remains blocked until a user of the computer (11) is correctly authenticated.
Owner:SECURE SYST LTD
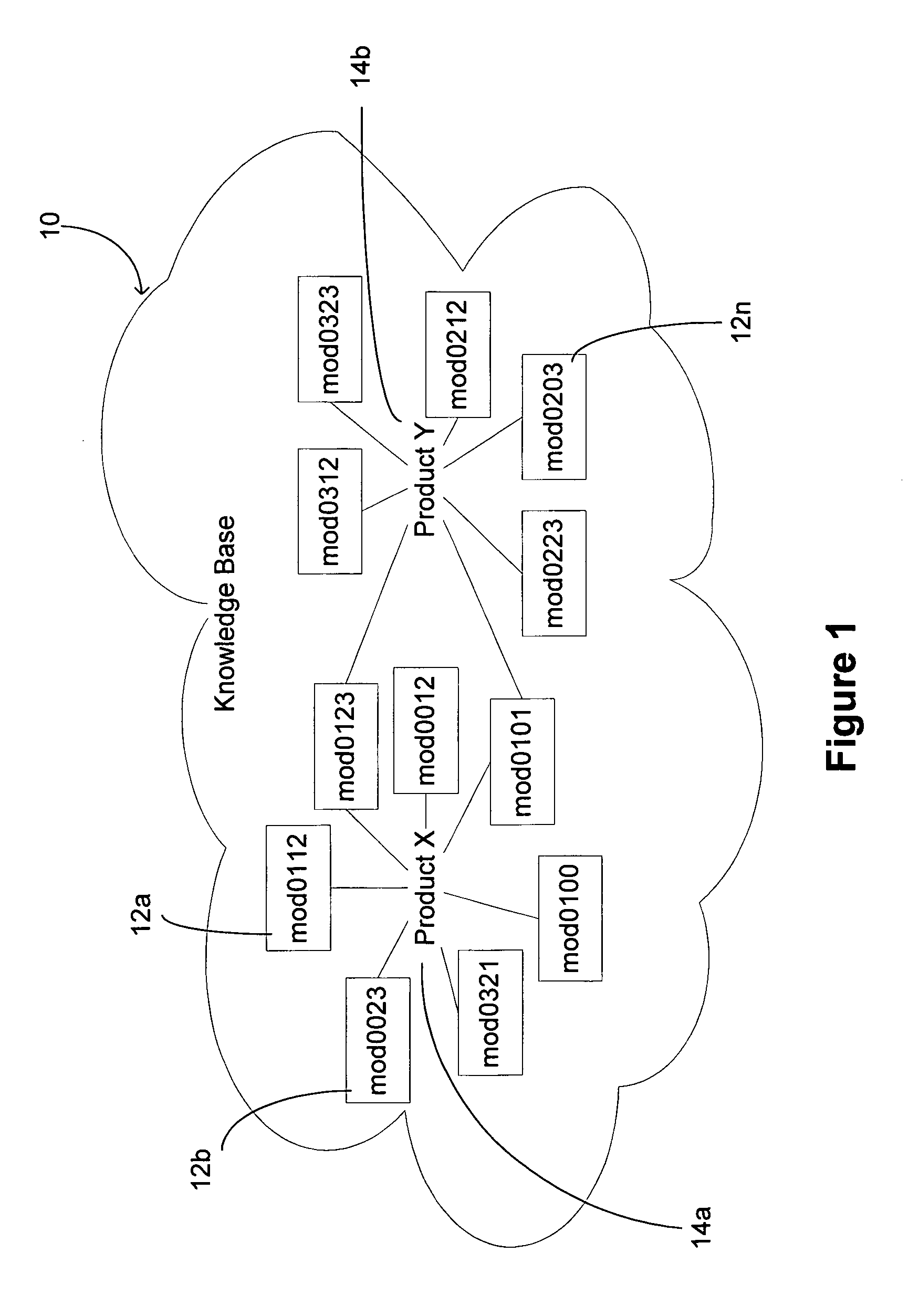
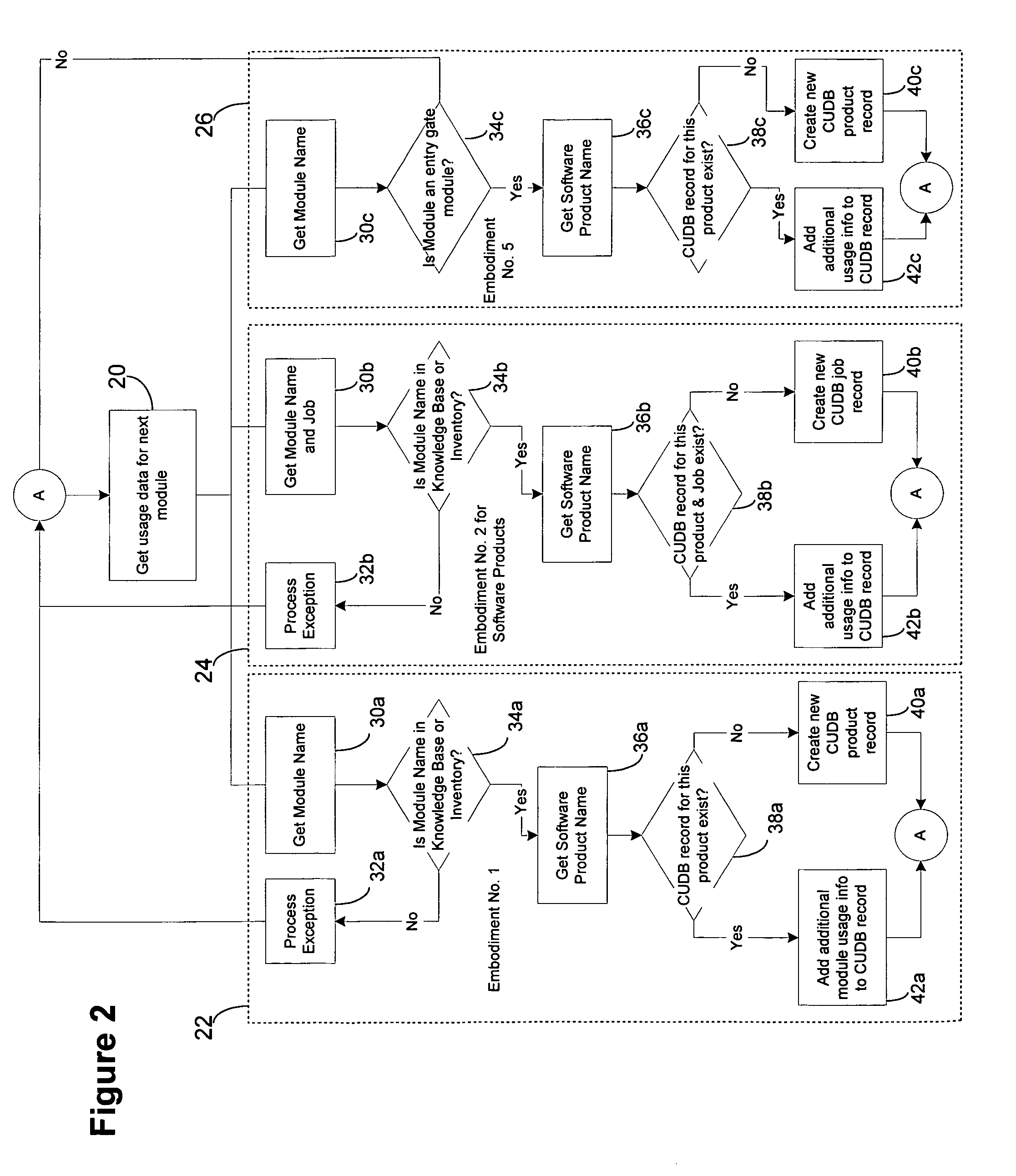
Consolidation and reduction of usage data
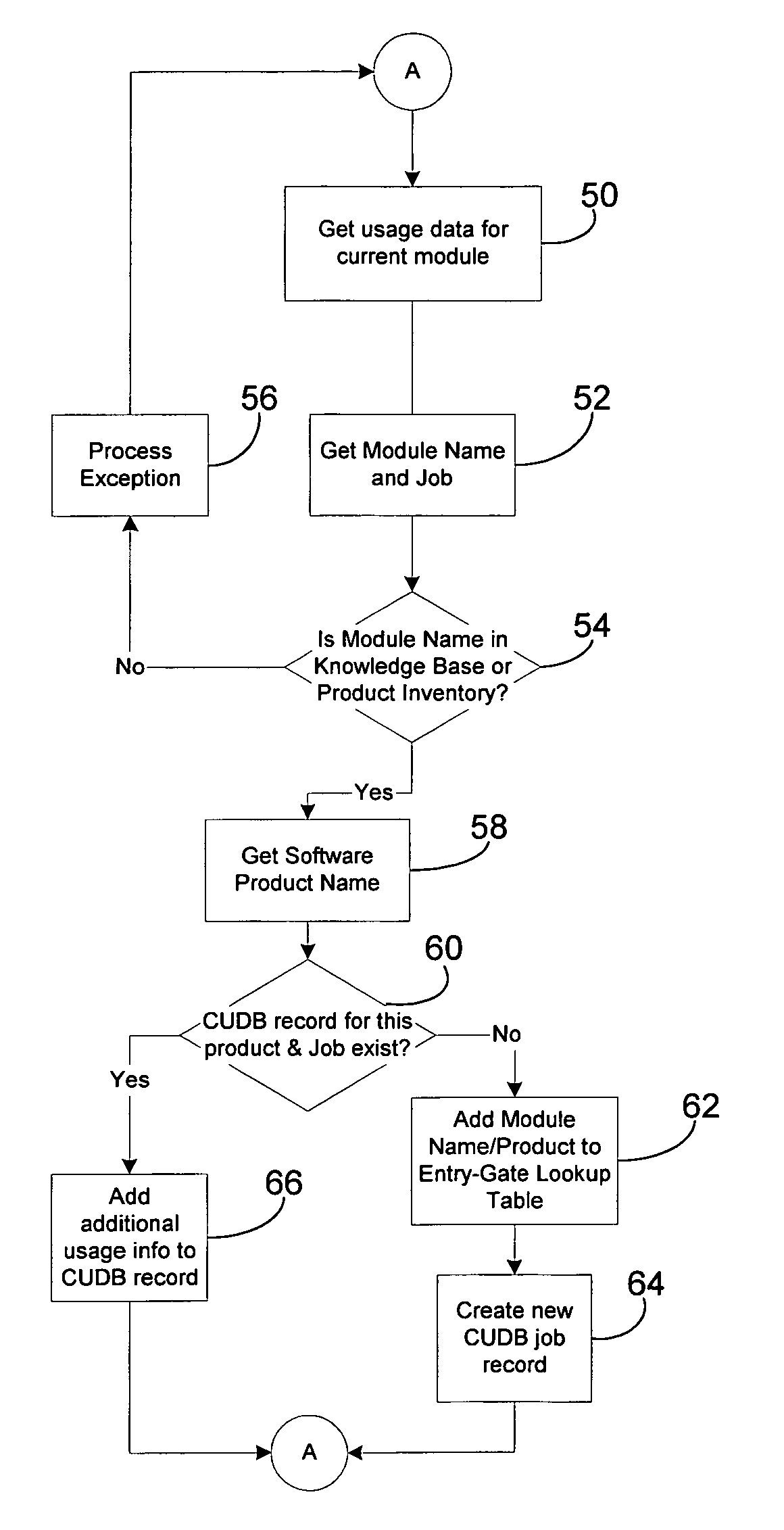
InactiveUS6996807B1Quantity minimizationHardware monitoringSpecific program execution arrangementsReducerComputer memory
A software monitoring and auditing system which determines the inventory of software products on a computer includes data reducer software which processes detailed software usage data gathered by a monitoring component of the software to create a condensed usage database. The reducer software contemporaneously converts the data records in a manner which reduces the amount of data records by at least a factor of 100, consuming less computer memory and allowing users of the software monitoring and auditing system to review usage data on a desktop PC or the like.
Owner:IBM CORP
Method and apparatus for accessing electronic data via a familiar printed medium
InactiveUS6866196B1Low costTelevision system detailsAnalogue secracy/subscription systemsOutput deviceComputer memory
Owner:MARSHALL FEATURE RECOGNITION
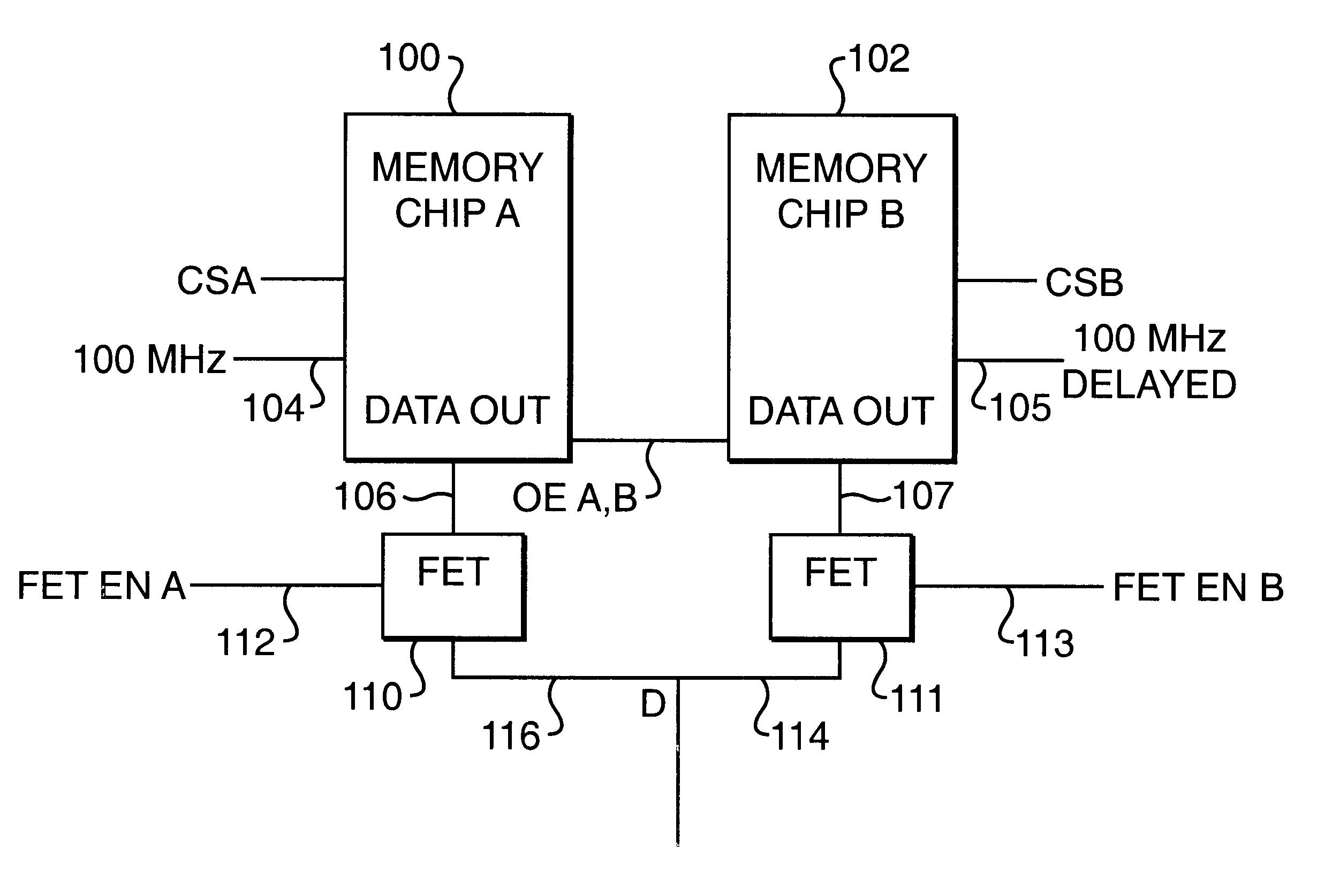
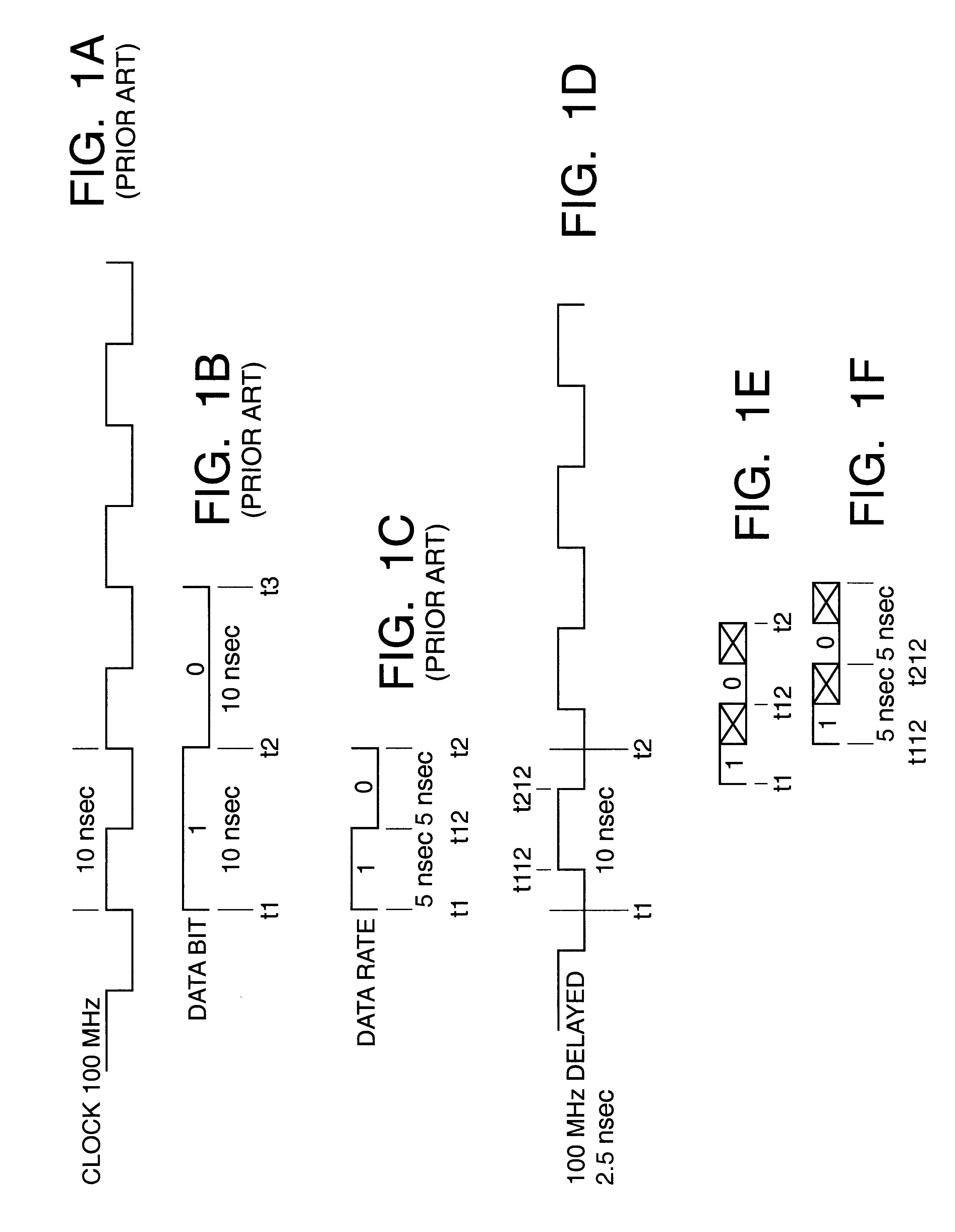
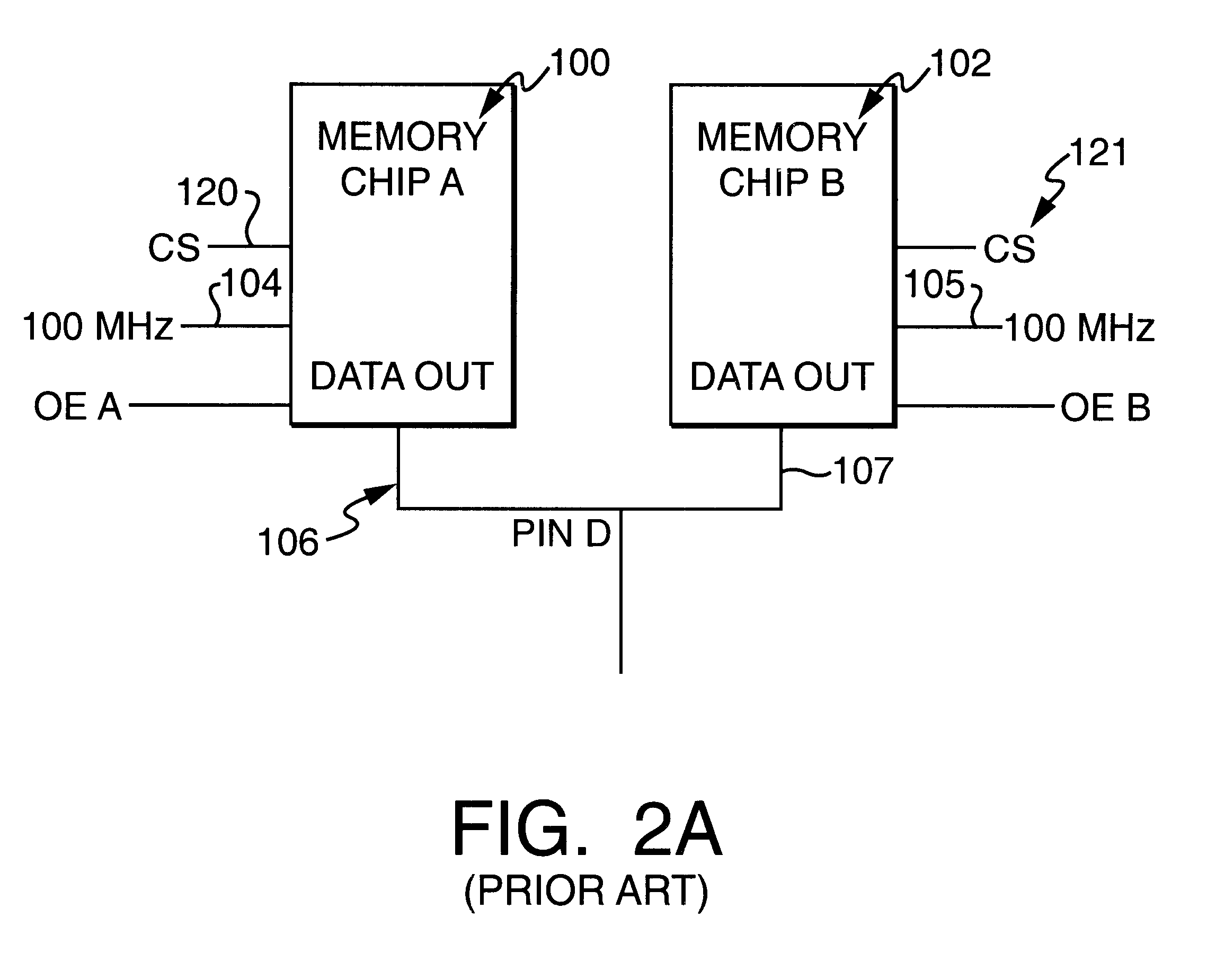
Memory system using FET switches to select memory banks
A computer memory system provides a double data rate (DDR) memory output while requiring memory chips with only half the frequency limit of the prior art DDR memory chips. The system contains a first memory bank having data lines and a second memory bank having data lines. The first and second memory banks are associated with first and second clock signals, respectively, where the second clock signal is delayed from the first clock signal such that the data lines of the first memory bank are connected to a data bus in synchronism with the first clock signal while the data lines of the second memory bank are connected with the data bus in synchronism with the second clock signal. In one embodiment, a first FET switch connects the data lines of the first memory bank with the data bus and a second FET switch connects the data lines of the second memory bank with the data bus. The second FET switch is connected to the data bus at a time delayed from the beginning after the start of each clock cycle of the second clock signal. As a result, the data bus is never connected to the data lines of both memory banks at the same time, but rather, the data bus is alternately connected with the first memory bank and then the second memory bank.
Owner:FOOTHILLS IP LLC
Product registration and tracking system
InactiveUS20130080251A1Convenient registrationCustomer relationshipMarketingApplication softwareComputer memory
A server for registration of products may include a processor and computer storage. The processor may be configured to receive, via a network, a communication from a product application executed on a computing device, the communication including a product identification (ID) associated with a product and an indication of registration of the product by a user of the product application. The processor may further be configured to register the product at least by storing, in the computer storage, the product ID and a relationship between the product and an identification of the user of the product application. The processor may further be configured to send a subsequent communication to the product application on the computing device based on the registration of the product.
Owner:ACCENTURE GLOBAL SERVICES LTD
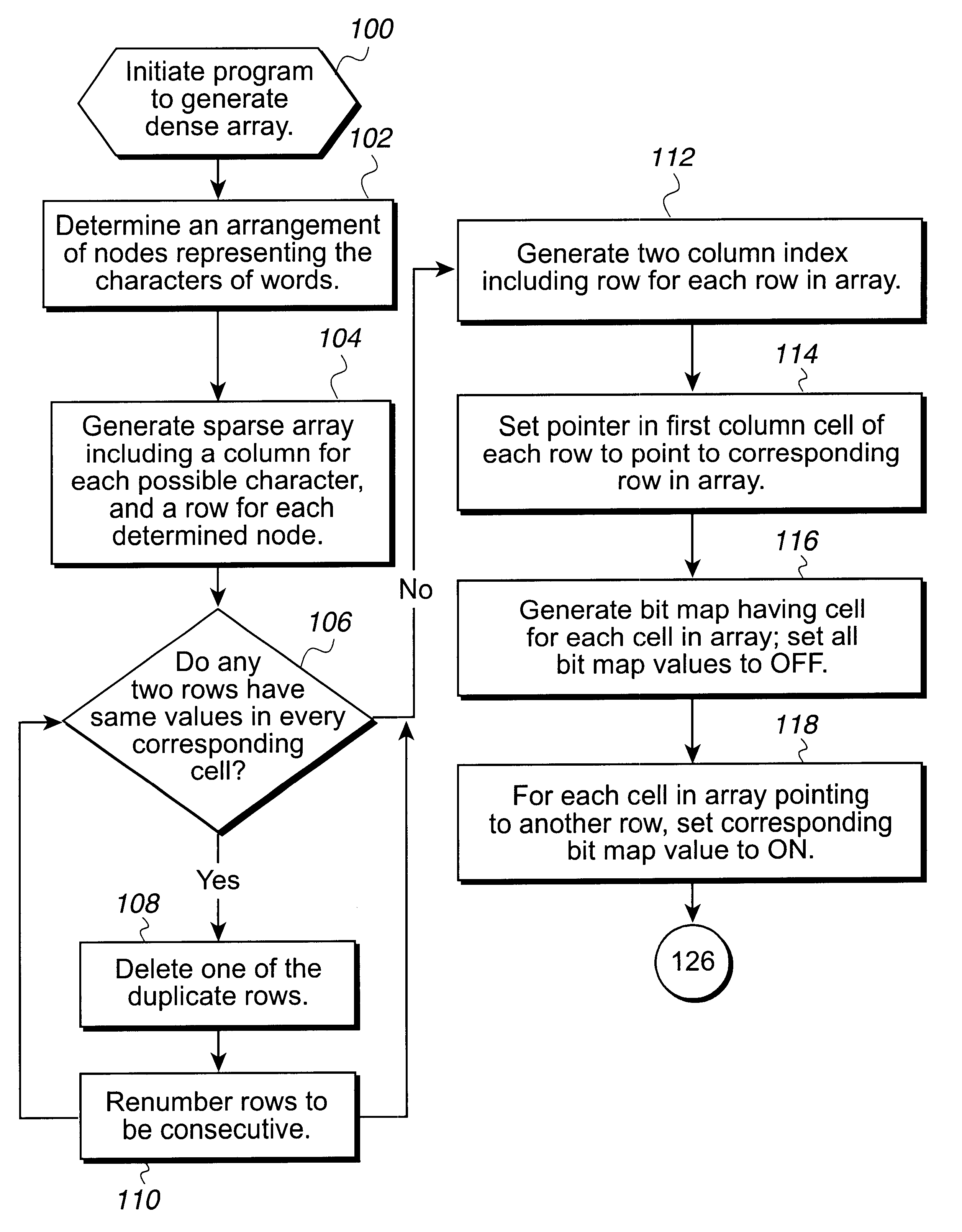
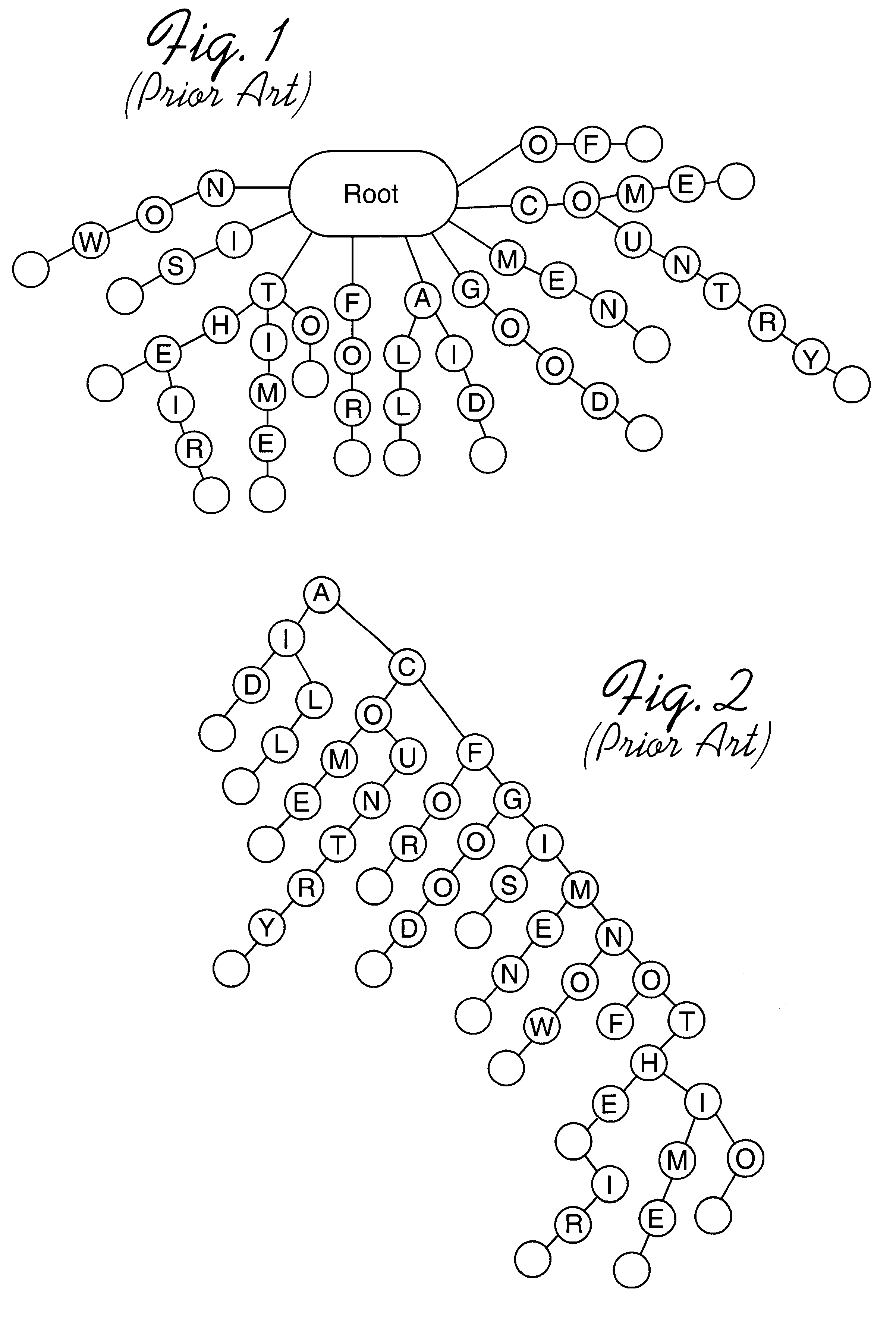
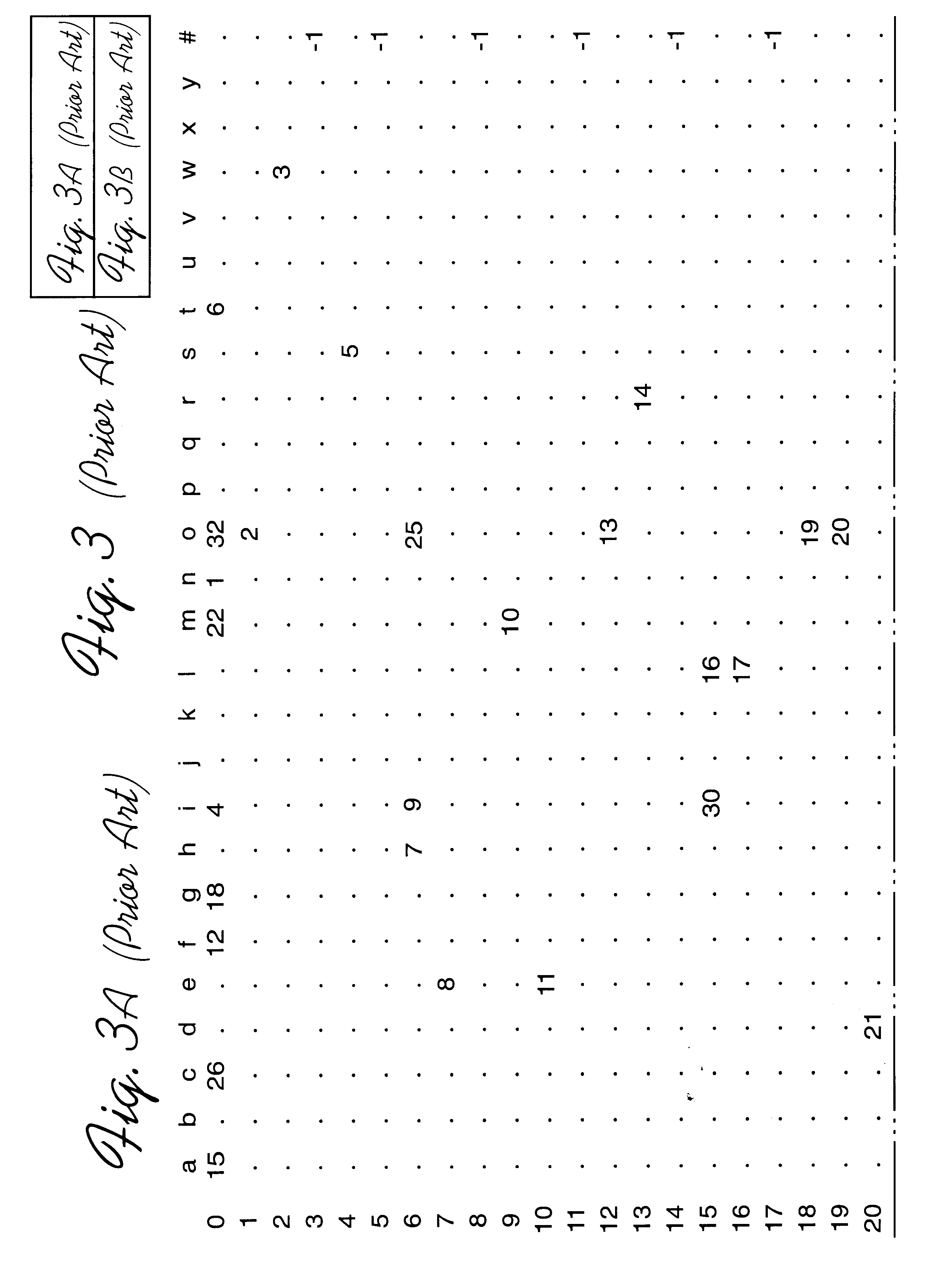
Method, system, program, and data structure for a dense array storing character strings
InactiveUS6470347B1Reduce in quantityLess storage spaceData processing applicationsDigital data information retrievalArray data structureTheoretical computer science
Disclosed is a system, method, and program for generating a data structure in computer memory for storing strings, such as words in a dictionary. Each string includes at least one character from a set of characters. An arrangement of nodes is determined to store the characters such that the arrangement of the nodes is capable of defining a tree structure. An array data structure is generated to store the nodes. The array includes a row for each node and a column for each character in the set of characters. A non-empty cell identifies a node for the character indicated in the column of the cell that has descendant nodes in the row indicated in the cell content for the node. The array data structure is processed to eliminate at least one row in the array data structure to reduce a number of bytes needed to represent the array data structure. In this way, the array data structure following the processing requires less bytes of storage space then before the processing.
Owner:IBM CORP
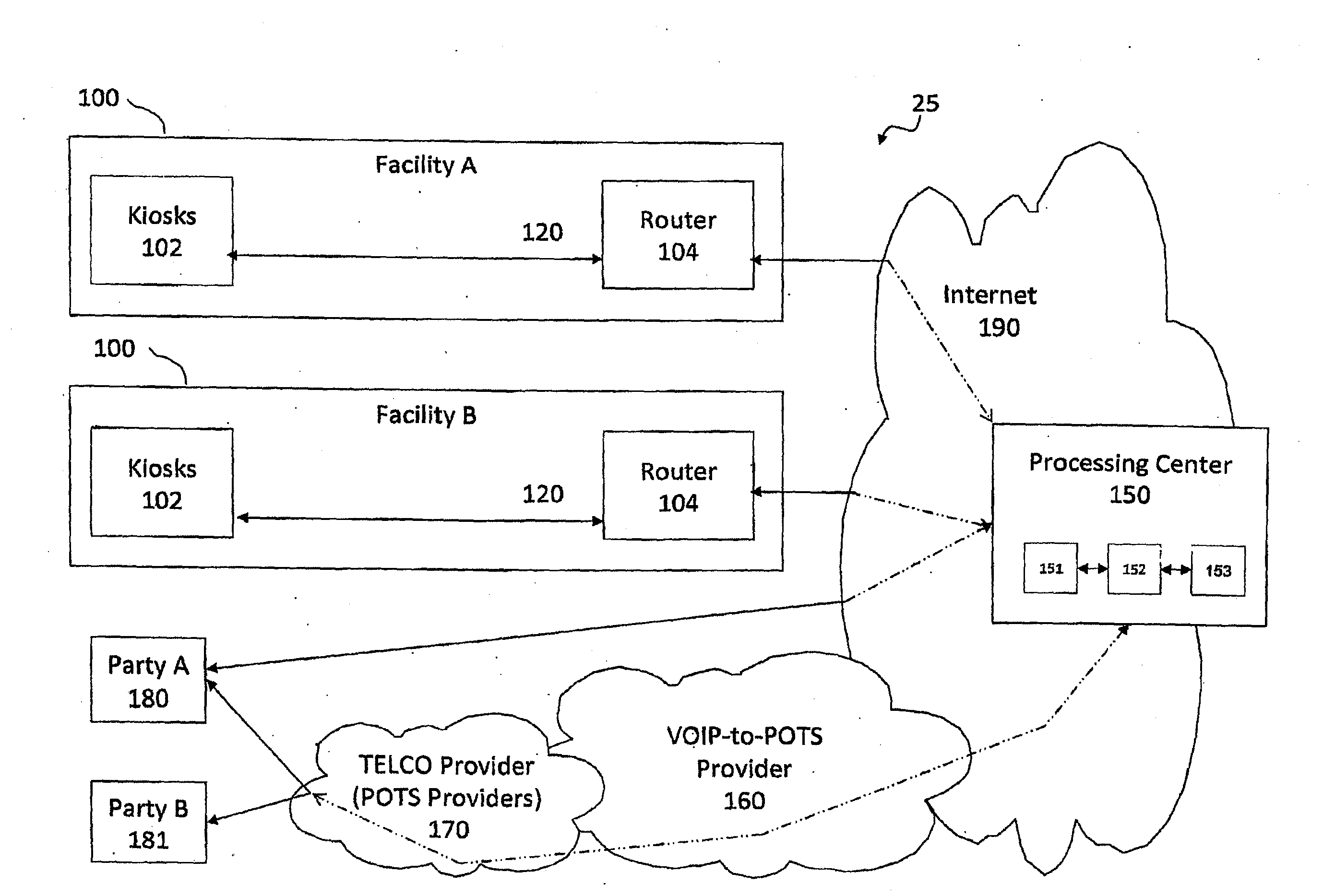
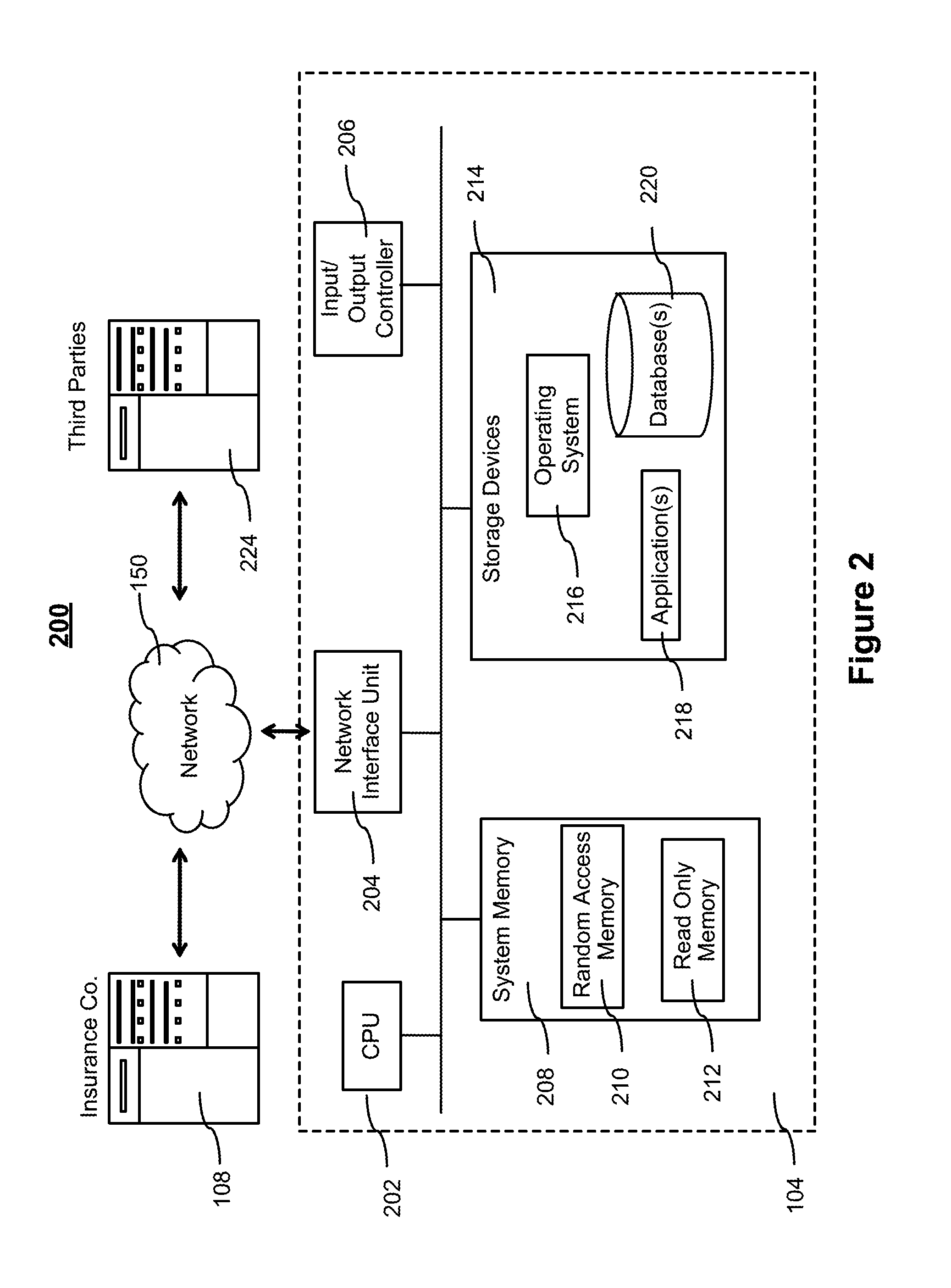
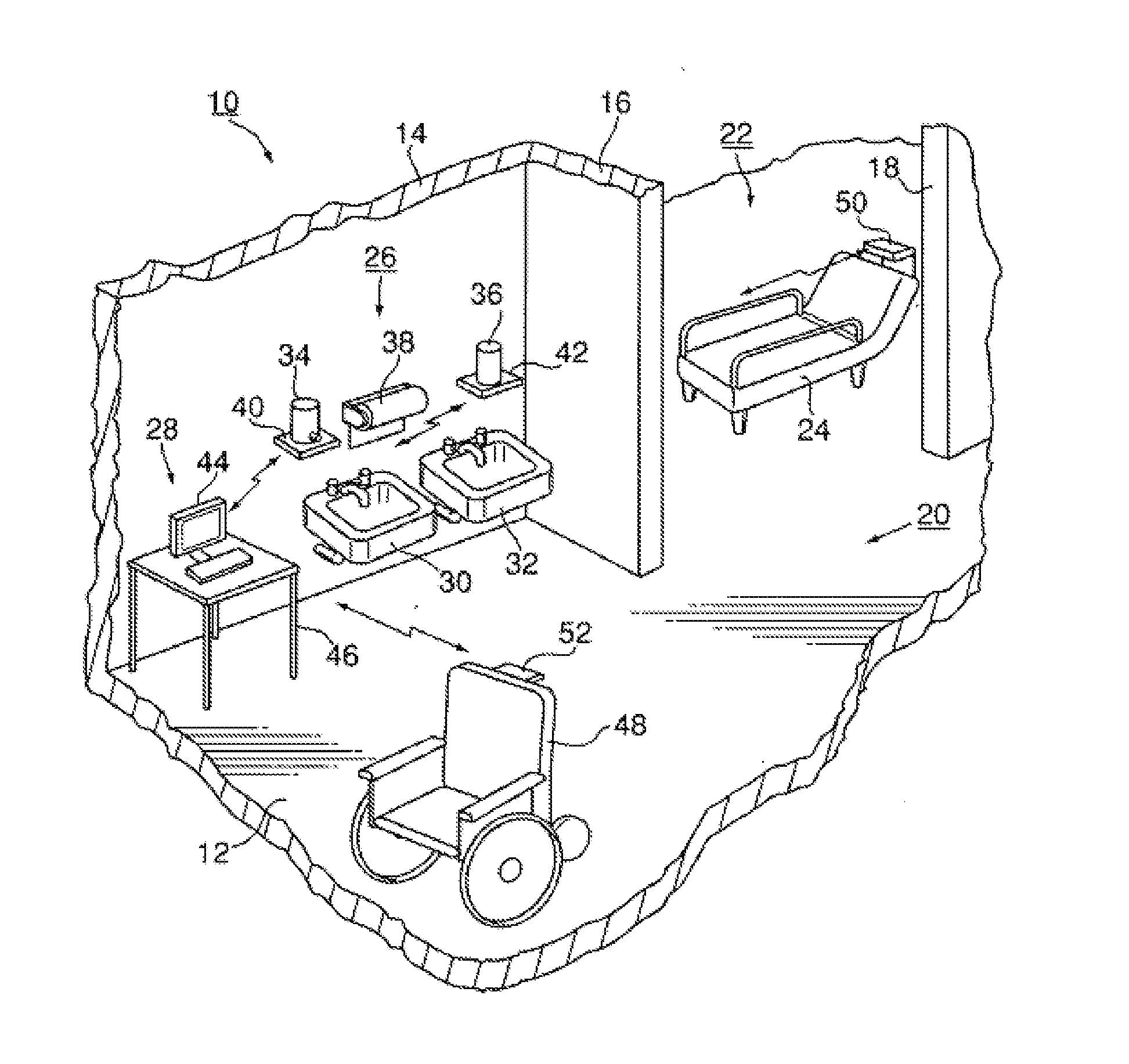
Interactive audio/video system and device for use in a secure facility
ActiveUS20120262271A1Electric signal transmission systemsImage analysisDisplay deviceMessage passing
A system and device for providing services to a secure facility. The system includes a kiosk with a processor, display, speaker, microphone, and a camera, and the kiosk communicates with a server that includes a server processor, a network interface unit, and a computer memory. The kiosk receives communications and transmits audio and video of the communications to the server via an internet connection, and the server records the audio and video and transmits the audio and video to a destination. The kiosk is configured to authenticate the identity of a user by verifying a personal identification number entered by the user and also performing one or more of a facial recognition via the camera or a biometric voice recognition via the microphone. The kiosk provides access to services including internet services, text-based messaging, tele-medical services, religious and educational materials, commissary ordering, and entertainment.
Owner:GLOBAL TELLINK
Respiratory control by means of neuro-electrical coded signals
A method and device for respiratory control. The method comprises selecting neuro-electrical coded signals from a storage area that are representative of body organ function. The selected neuro-electrical coded signals are then transmitted to a treatment member, which is in direct contact with the body, and which then broadcasts the neuro-electrical coded signals to a specific body respiration nerve or organ to modulate the body organ functioning. A control module is provided for transmission to the treatment member. The control module contains the neuro-electrical coded signals which are selected and transmitted to the treatment member, and computer storage can be provided for greater storage capacity and manipulation of the neuro-electrical coded signals.
Owner:ORTIZ & LOPEZ PLLC
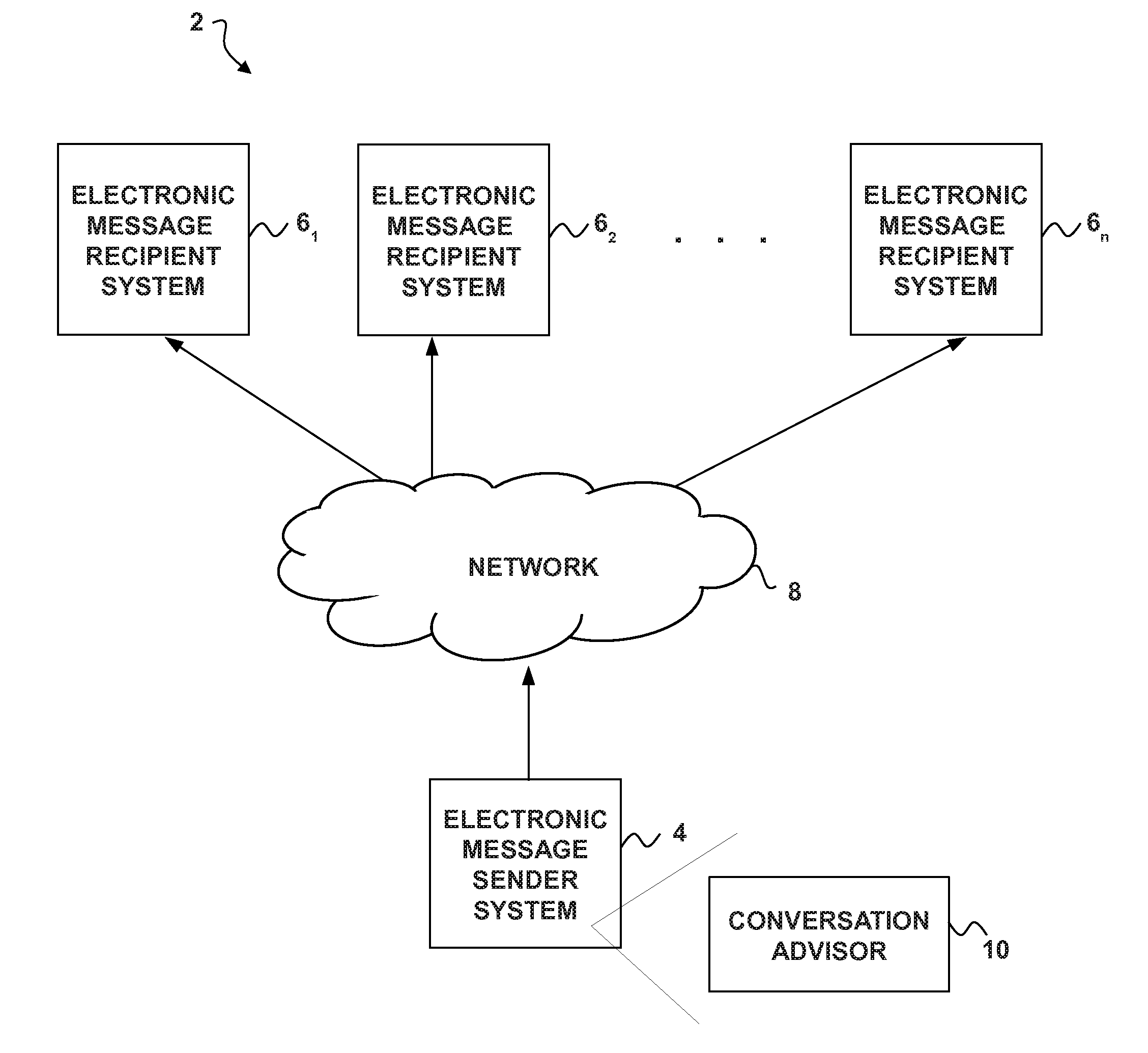
Conversation Advisor
A method, system and computer program product for assisting the authoring of electronic messages are disclosed. Operations performed according to an example embodiment may include:accessing an electronic message stored in digital form in a computer memory;inspecting the electronic message to identify intended recipients of the electronic message;gathering and analyzing historical data stored in digital form in a computer memoryrelating to a conversation history that links an author of the electronic message to the intended recipients;performing semantic analysis on the electronic message to extract words and phrases representing recipient fitness information that is indicative of whether the electronic message is appropriate for the intended recipients;generating a fitness result for the electronic message by comparing the recipient fitness information to the historical data and identifying inconsistencies; andoutputting the fitness result for viewing on an electronic display device associated with the author of the electronic message.
Owner:IBM CORP
Live migration of virtual machine during direct access to storage over sr iov adapter
ActiveUS20120042034A1Digital computer detailsComputer security arrangementsComputer memoryVirtual machine
A method is provided to migrate a virtual machine from a source computing machine to a destination computing machine comprising: suspending transmission of requests from a request queue disposed in source computing machine memory associated with the VM from the request queue to a VF; while suspending the transmission of requests, determining when no more outstanding responses to prior requests remain to be received; in response to a determination that no more outstanding responses to prior requests remain to be received, transferring state information that is indicative of locations of requests inserted to the request queue from the VF to a PF and from the PF to a memory region associated with a virtualization intermediary of the source computing machine. After transferring the state information to source computing machine memory associated with a virtualization intermediary, resuming transmission of requests from locations of the request queue indicated by the state information to the PF; and transmitting the requests from the PF to the physical storage.
Owner:VMWARE INC
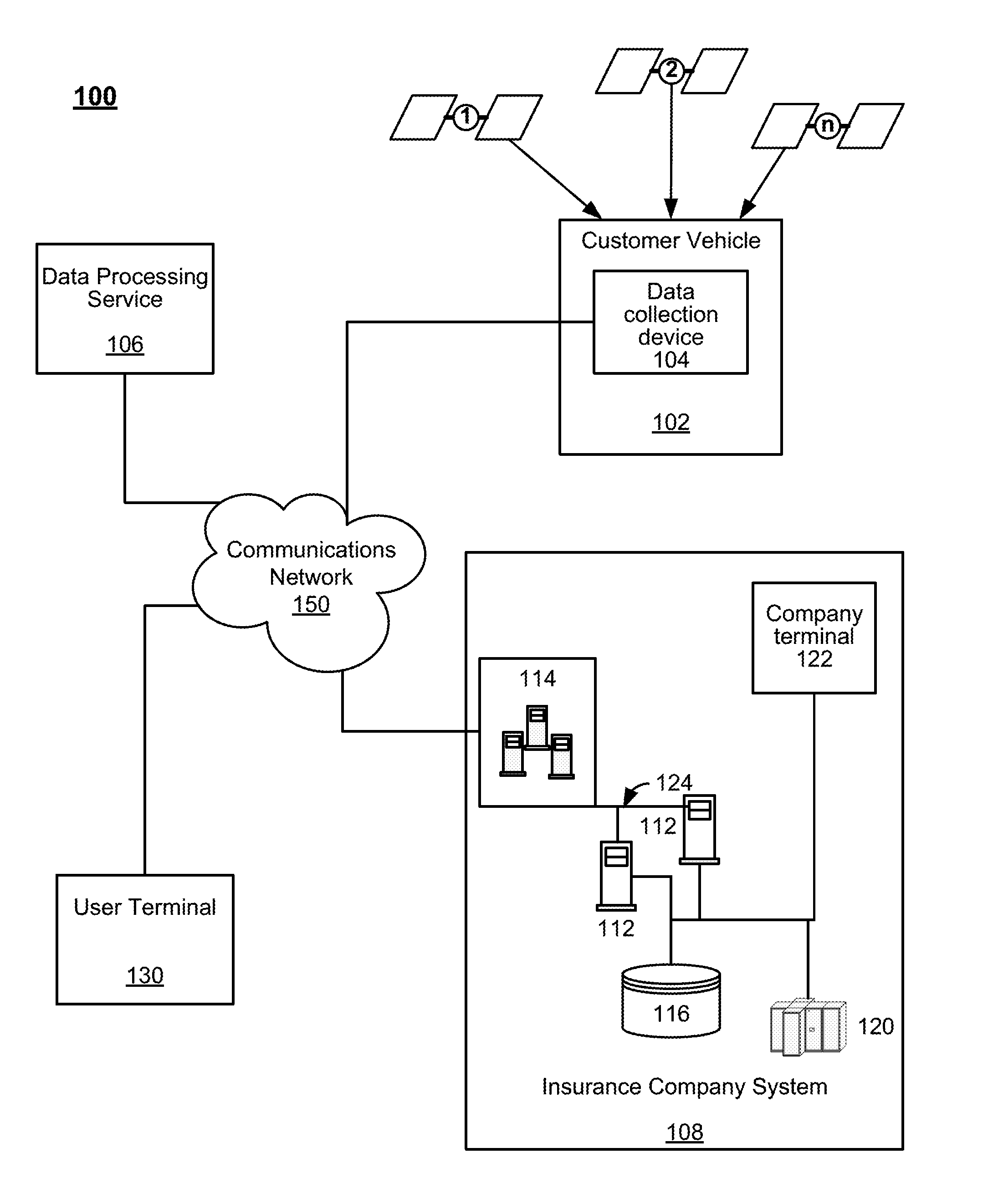
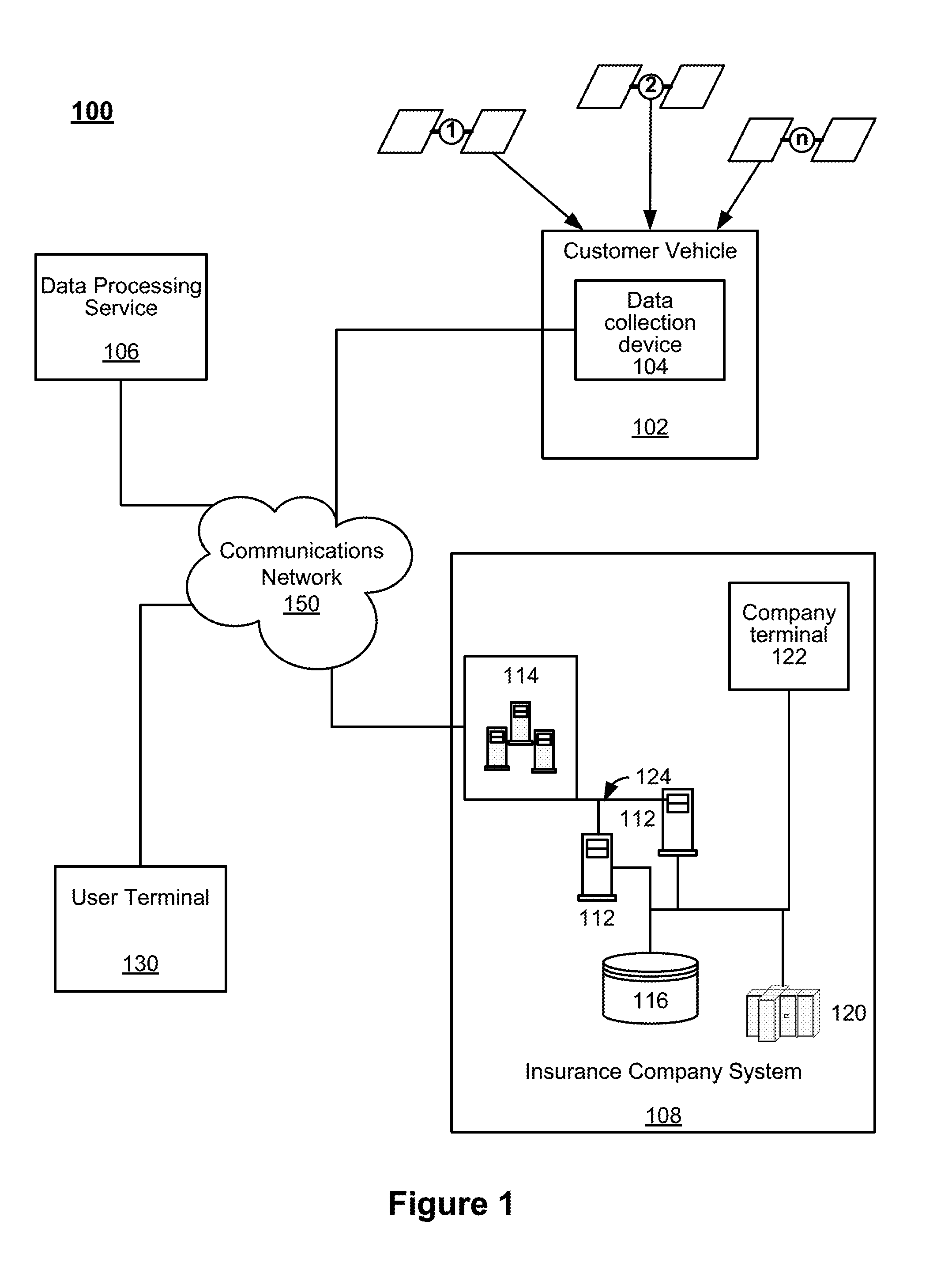
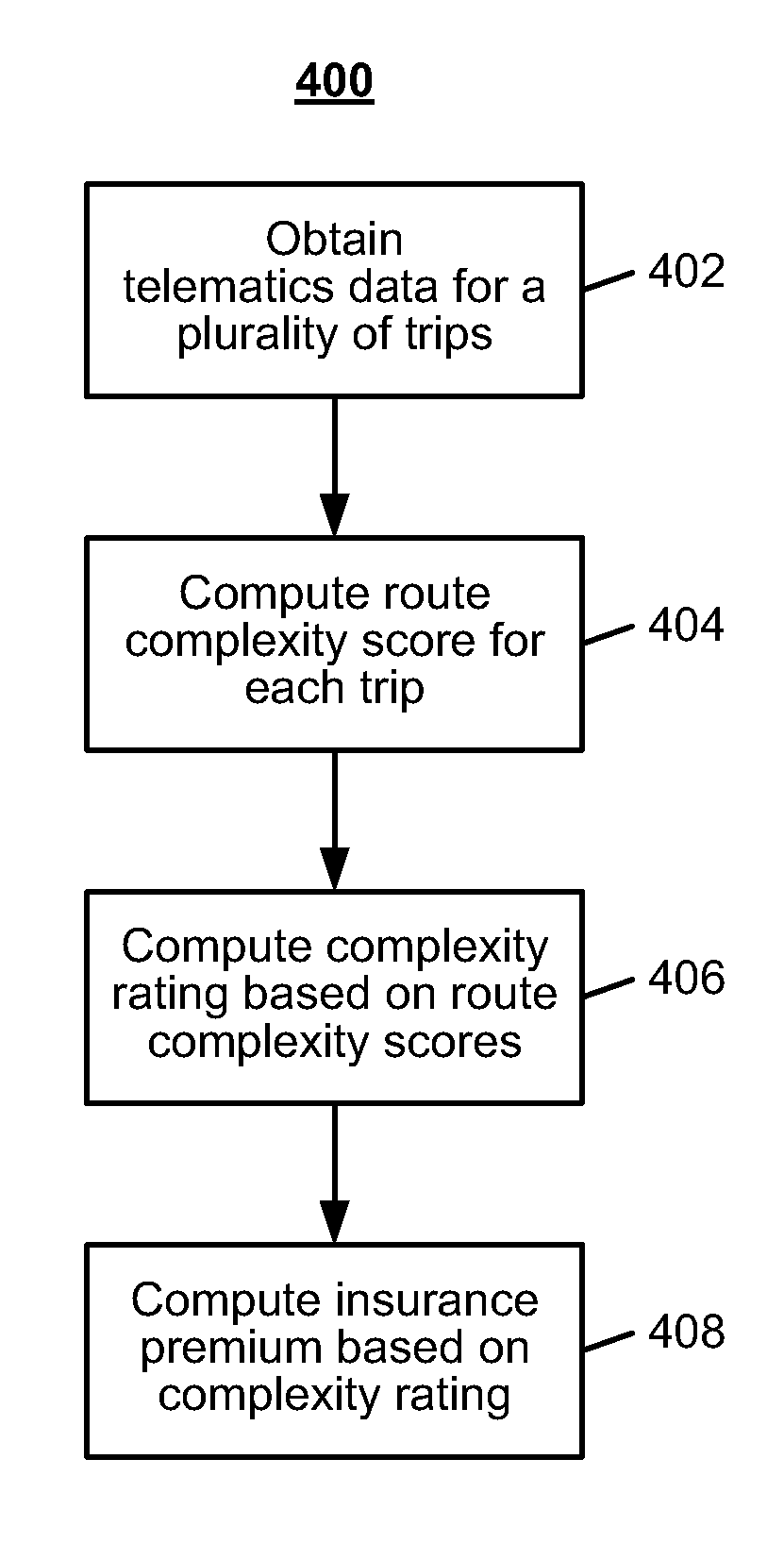
System and method for determining an insurance premium based on complexity of a vehicle trip
Systems and methods are disclosed herein for pricing an insurance premium based on route complexity. The system includes a computer memory and a processor in communication with the computer memory. The computer memory stores telematics data received from a sensor within a vehicle. The telematics data includes at least one of geo-position information of the vehicle and vehicle kinematics data. The processor is configured to compute a complexity score of the trip based on the telematics data. The processor is also configured to determine a price for automobile insurance for the driver based on the complexity score of the at least one trip.
Owner:HARTFORD FIRE INSURANCE
Optical position determination on any surface
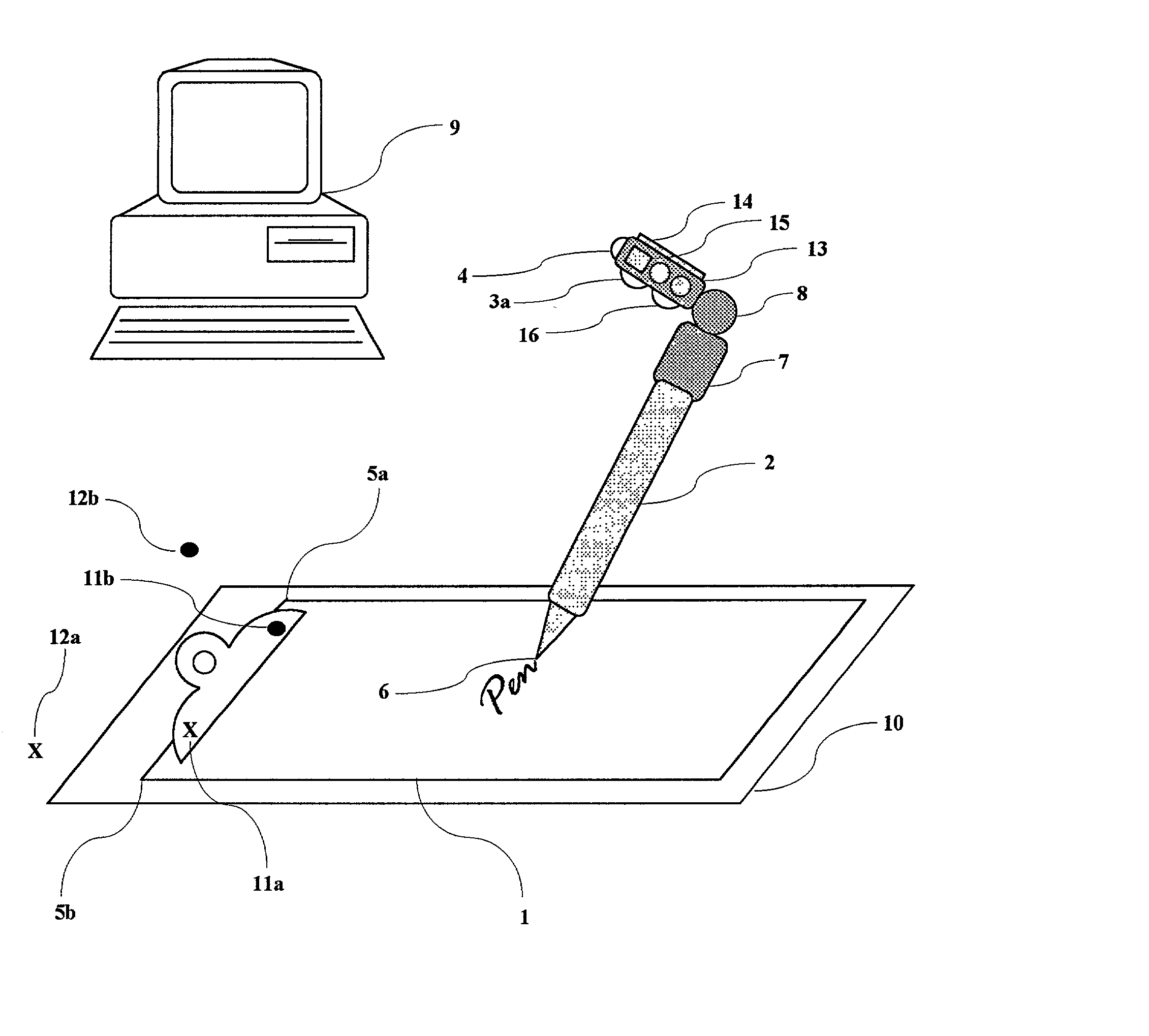
InactiveUS20020163511A1Eliminate needOvercome disadvantagesCathode-ray tube indicatorsInput/output processes for data processingMicrocomputerComputer graphics (images)
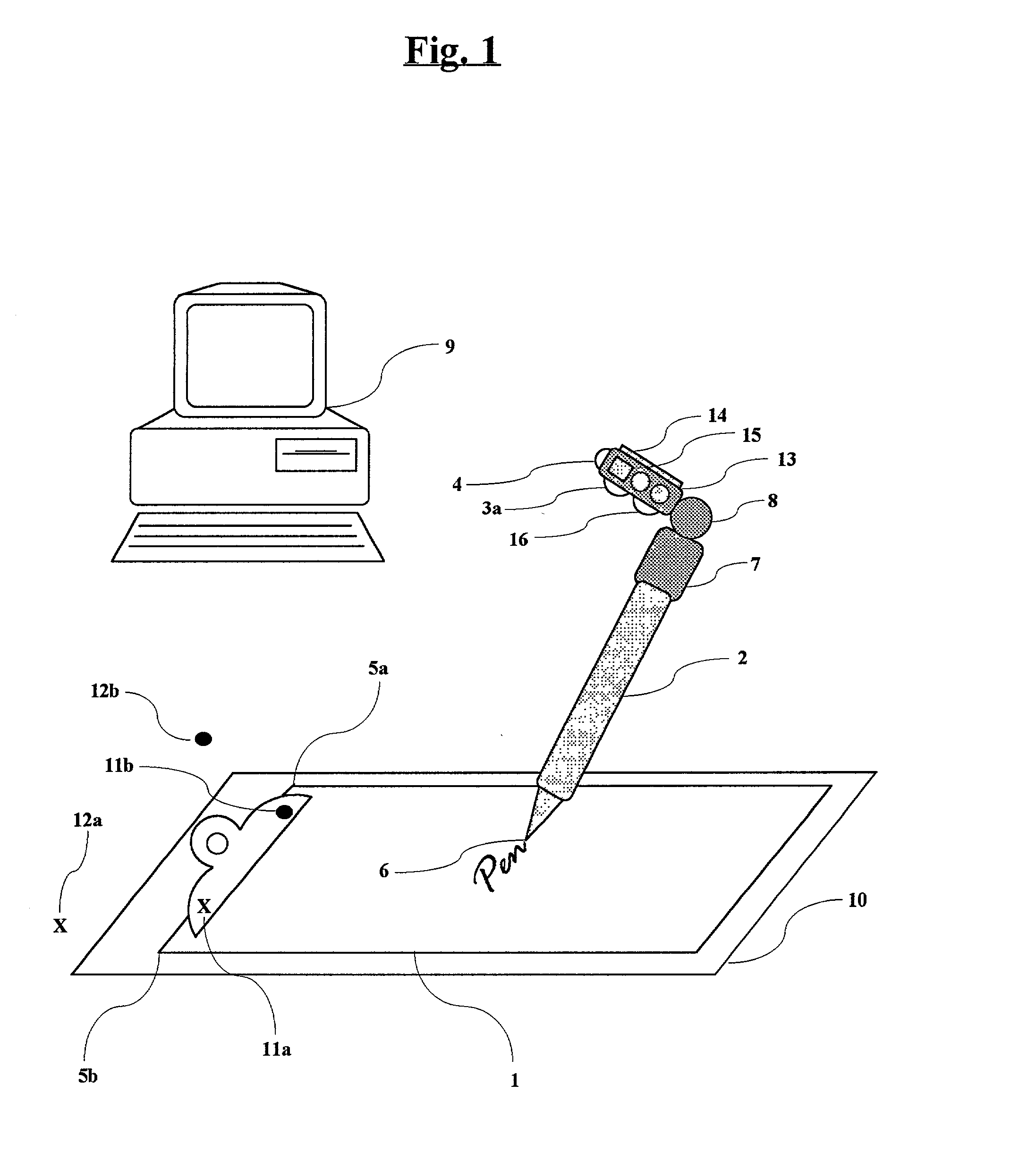
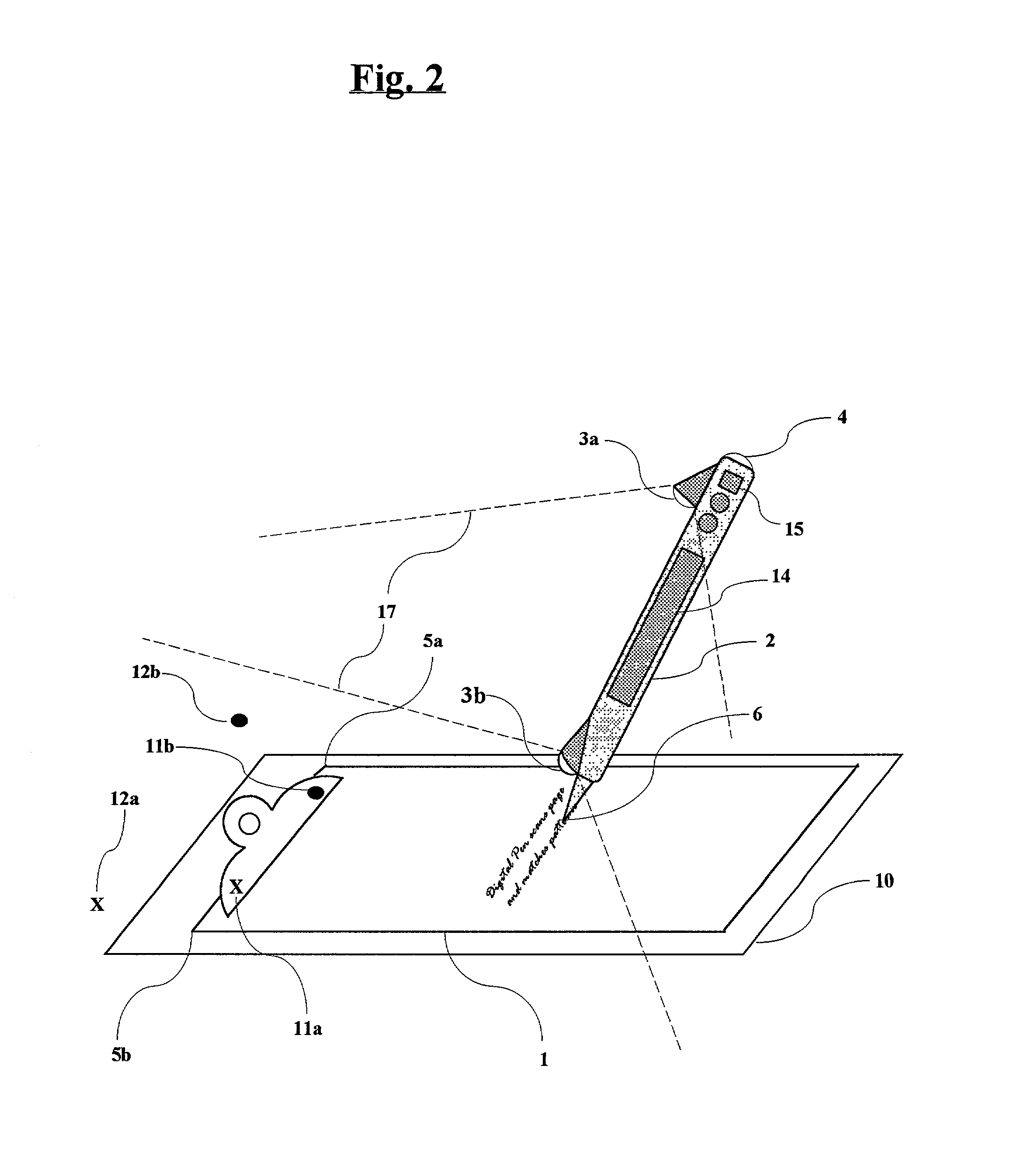
The present invention proposes the use of a surface or writing surface such as paper and a moveable element such as a pen or a stylus. The stylus comprises an input means such as a charge-coupled device (CCD) or digital camera, a microcomputer, memory, power supply, and a communications device, whereby the digital camera scans the surface for position-related information to determine the position and / or movement of the stylus relative to the surface. The path of stylus is determined by detecting a sequence of position-related information. An output signal from the digital camera or array of light sensitive elements is sent to a computer or processor and finally output to the user. The output can be in various forms including an image on a computer display or a computer printout. When writing on the surface, handwriting recognition software can be used to convert the handwritten text into a "keyboard-typed" representation.
Owner:ANOTO AB
Electronic gaming apparatus and method
InactiveUS6053813AEasy to useEasy to calculateRoulette gamesApparatus for meter-controlled dispensingTheoretical computer scienceEngineering
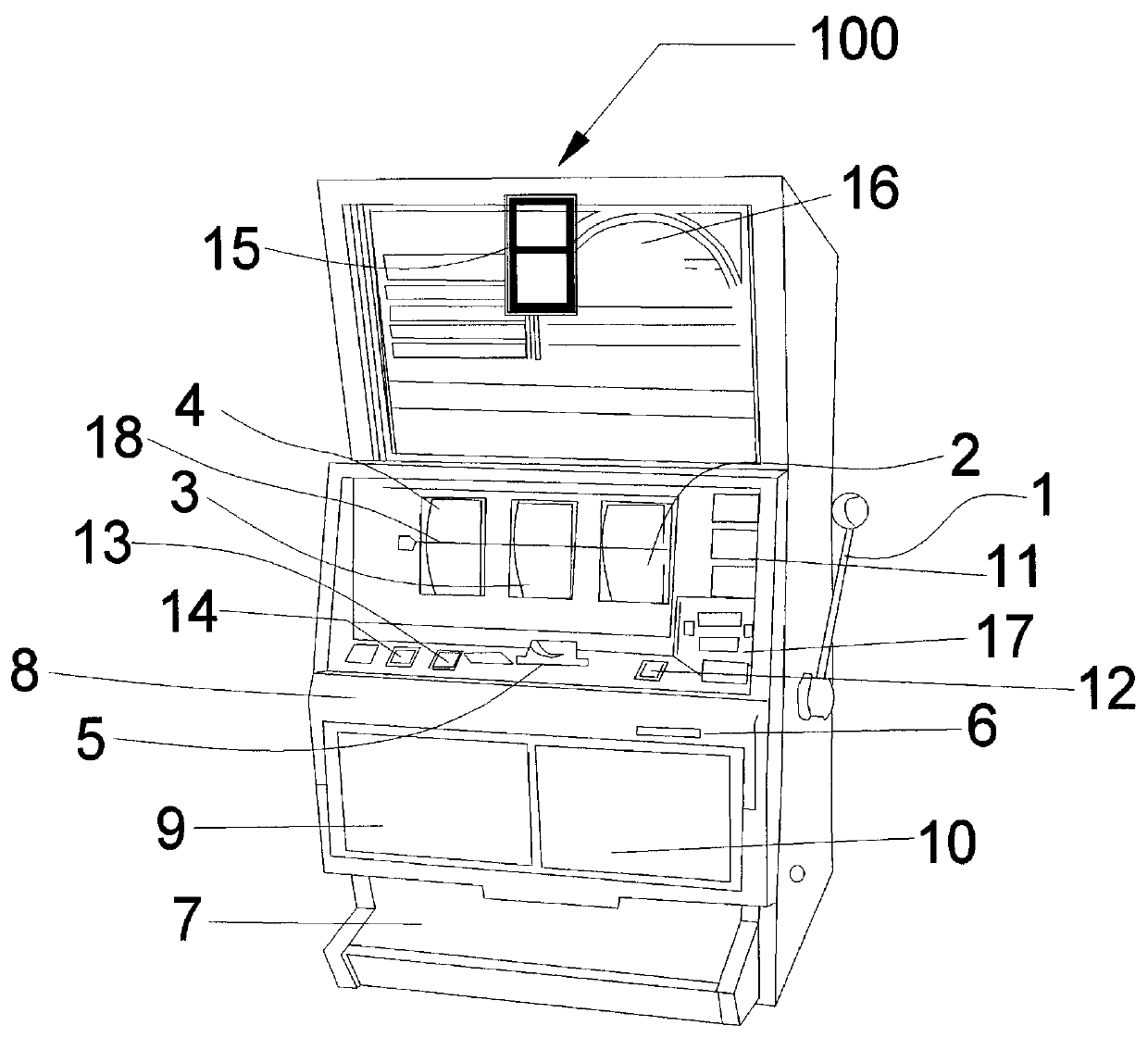
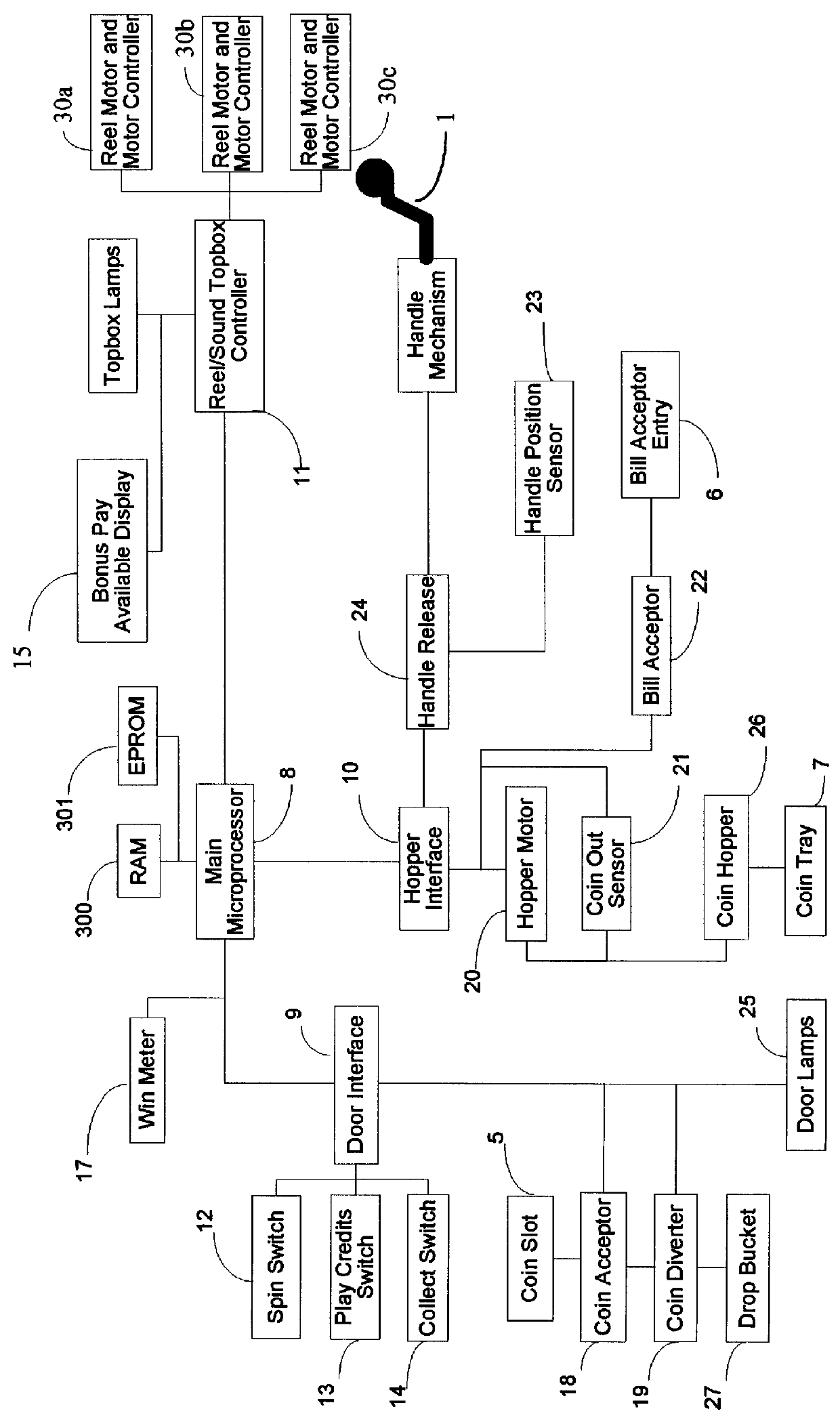
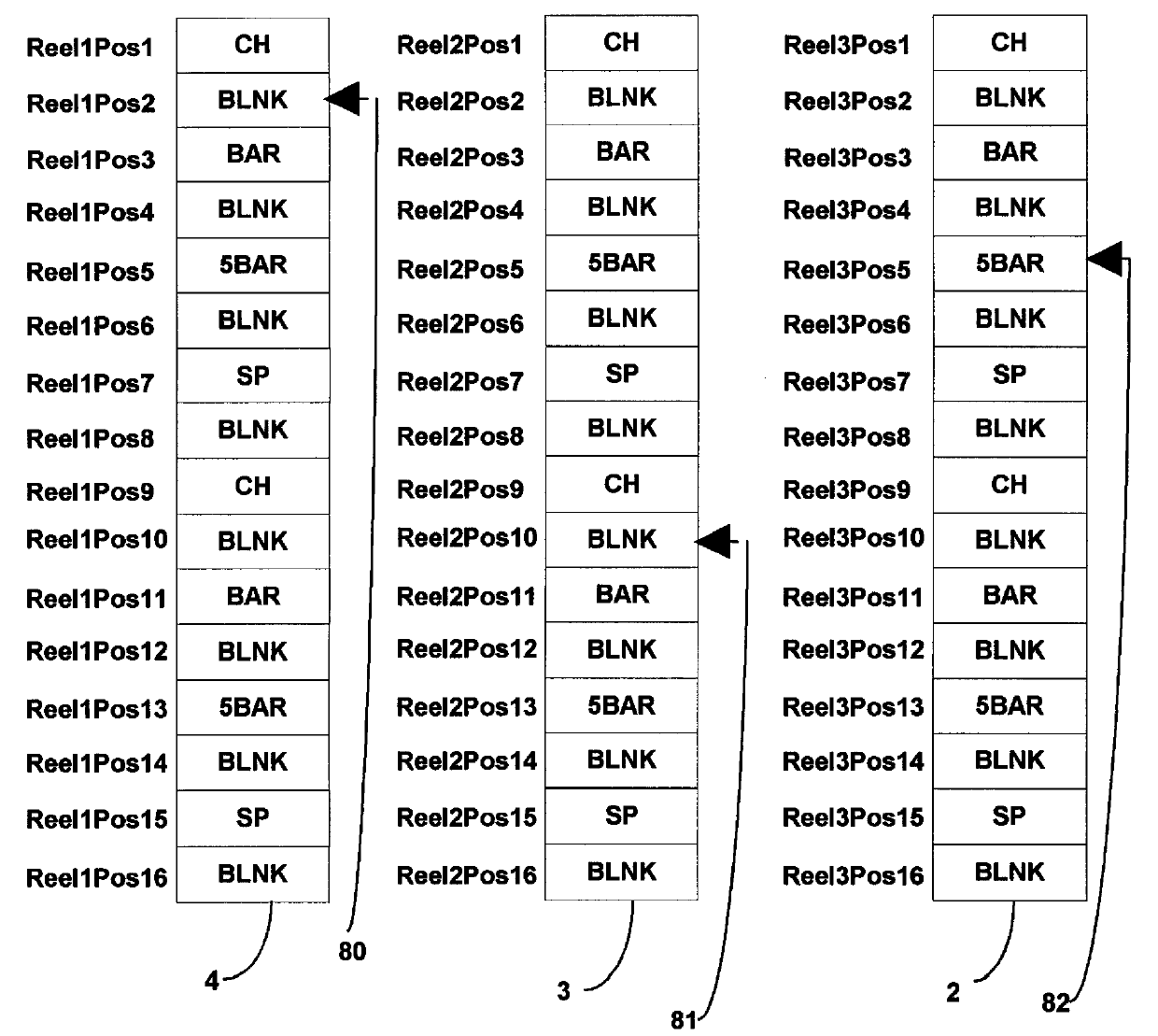
A method for operating a microprocessor controlled, reel type slot machine in which payoff is determined before a final game outcome is displayed to a player. A pre-defined count of random numbers is generated and presented to a digital filter having tap outputs which correspond to paytable payline equations. The minimum number of payline equations is equal to the number of distinct paylines in the paytable plus one. Any changes in game outcome are taken into account by modifying variables in computer memory and as such do not require a change in tables stored in computer memory. Several features for attracting players to the apparatus and increasing the enjoyment of playing a game are included.
Owner:MATHIS RICHARD M
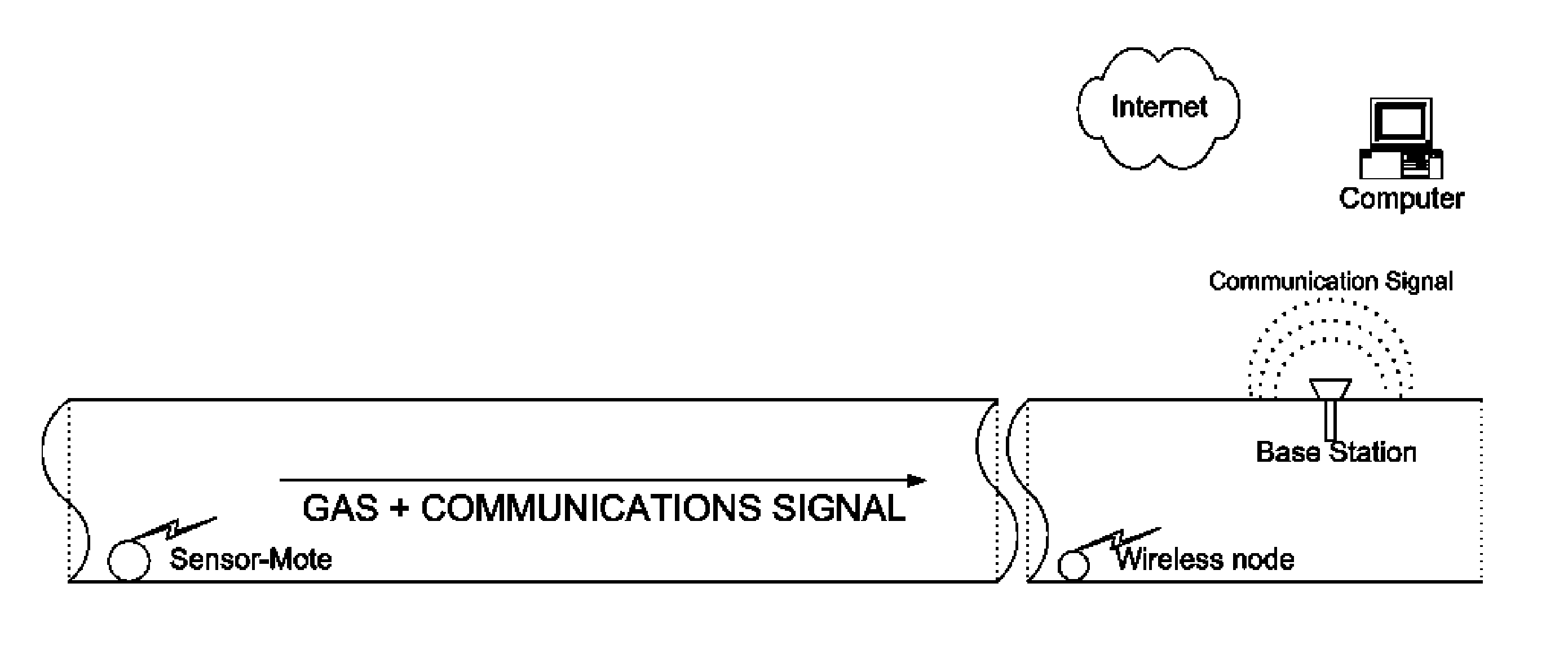
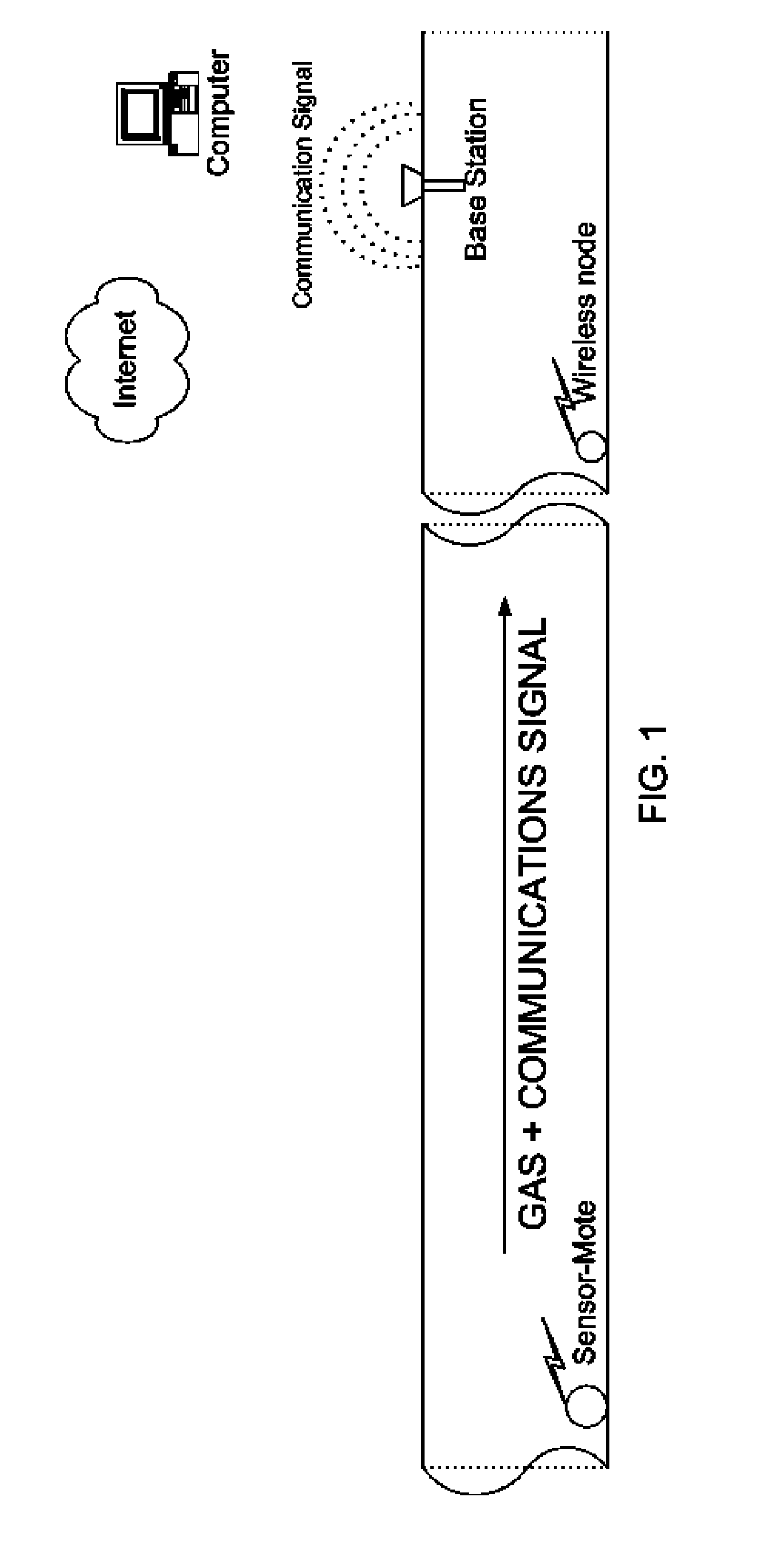
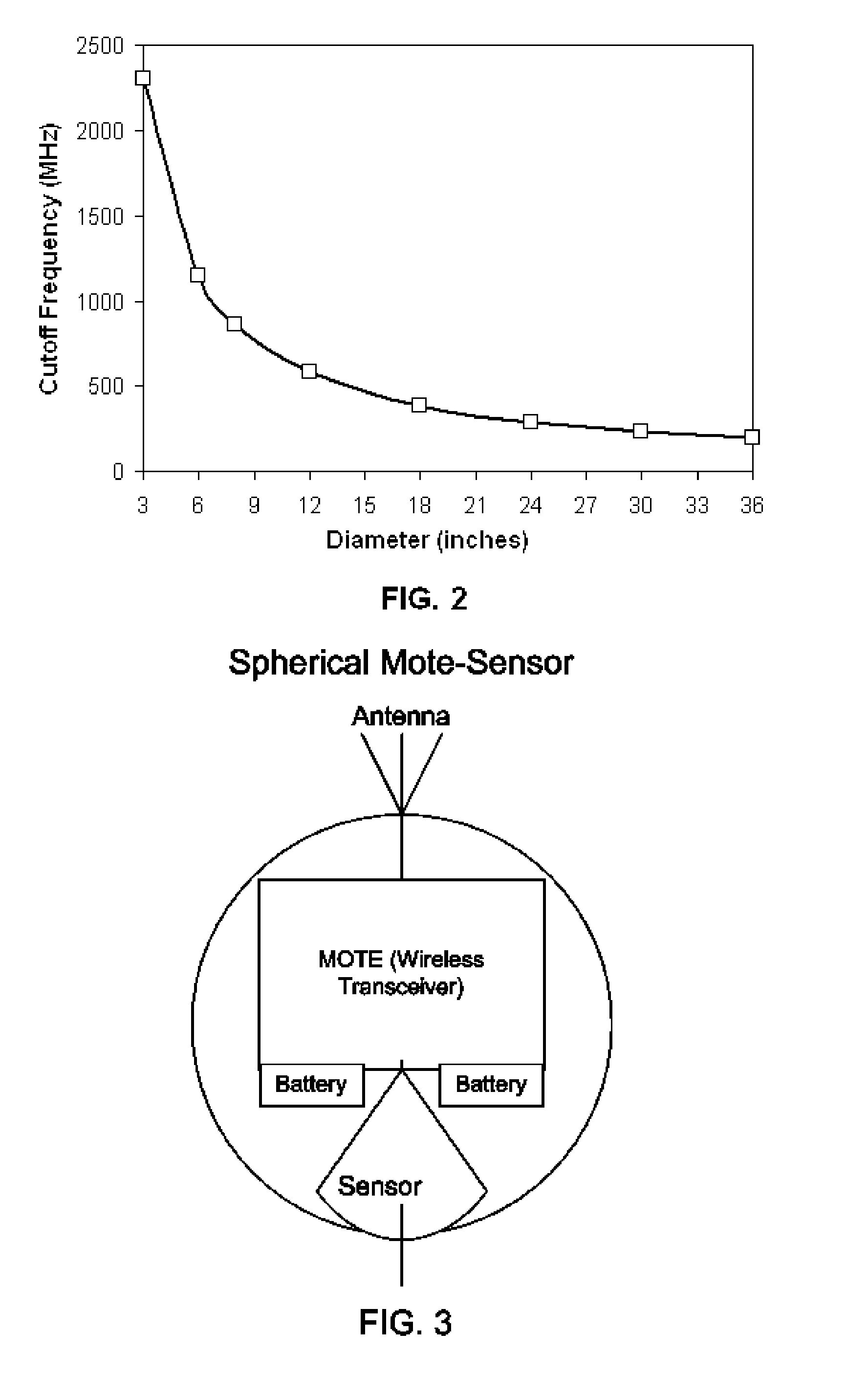
Remote Monitoring of Pipelines using Wireless Sensor Network
InactiveUS20050145018A1Low costLittle powerVehicle testingDetection of fluid at leakage pointLine sensorWireless transceiver
A wireless sensor system is installed inside pipelines using sensors and wireless transceivers that are small, low-cost, and rugged. The objective is monitoring the pipeline and recommending maintenance and repair at specific locations in the pipeline. Maintenance includes detection of leaks and prevention of catastrophic failures as a result of internal corrosion or other damage, such as third party mechanical damage, using multitude of sensors. After establishing the wireless sensor network the network is activated so the sensor can make measurements periodically or continuously using instructions transmitted via the base station. The sensor data from the various sensors are transmitted inside the pipe and extracted to access points in the pipeline to a remote computer that stores the data within the computer memory. The sensed information can be used for monitoring as well as analysis using a recommendation engine to provide maintenance and repair alerts.
Owner:SOUTHWEST RES INST
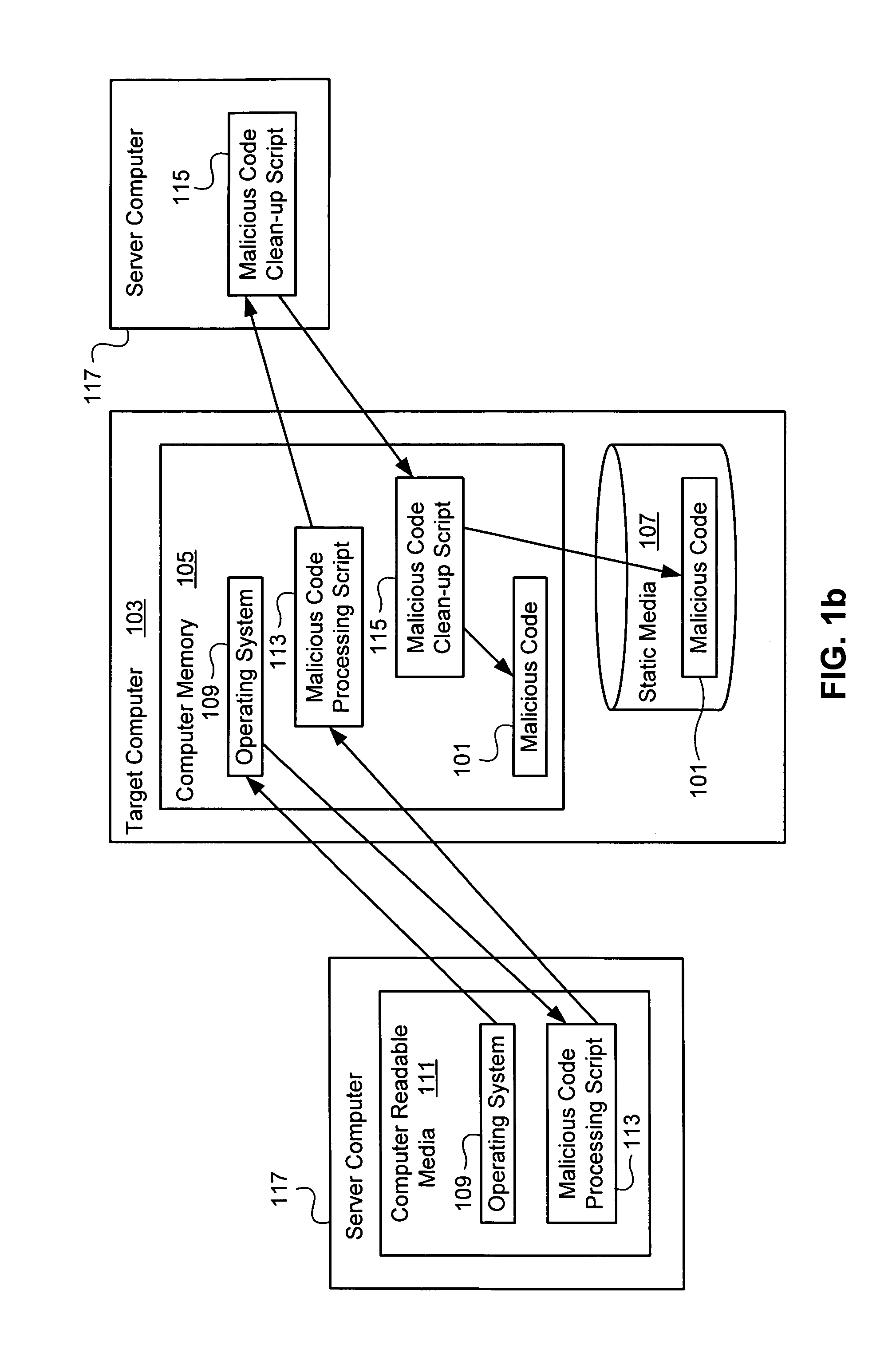
Automated identification and clean-up of malicious computer code
ActiveUS7546638B2Memory loss protectionUser identity/authority verificationOperational systemComputer memory
Malicious computer code (101) is automatically cleaned-up from a target computer (103). An operating system (109) automatically boots (201) in the computer memory (105) of the target computer (103). The booted operating system (109) automatically runs (203) a malicious code processing script (113) in the computer memory (105) of the target computer (103), under control of the booted operating system (109). The malicious code processing script (113) automatically copies (205) and runs (207) at least one malicious code clean-up script (115). At least one malicious code clean-up script (115) automatically cleans-up (209) malicious code (101) from the target computer (103).
Owner:NORTONLIFELOCK INC
System and method for computing and scoring the complexity of a vehicle trip using geo-spatial information
Systems and methods are disclosed herein for pricing an insurance premium based on route complexity. The system includes a computer memory and a processor in communication with the computer memory. The computer memory stores telematics data received from a sensor within a vehicle. The telematics data includes at least one of geo-position information of the vehicle and vehicle kinematics data. The processor is configured to compute a complexity score of the trip based on the telematics data. The processor is also configured to determine a price for automobile insurance for the driver based on the complexity score of the at least one trip.
Owner:HARTFORD FIRE INSURANCE
Knowledge driven composite design optimization process and system therefor
InactiveUS7010472B1Easy to understandFacilitates later update of knowledge baseConstraint-based CADSpecial data processing applicationsGeneral purpose computerInterconnection
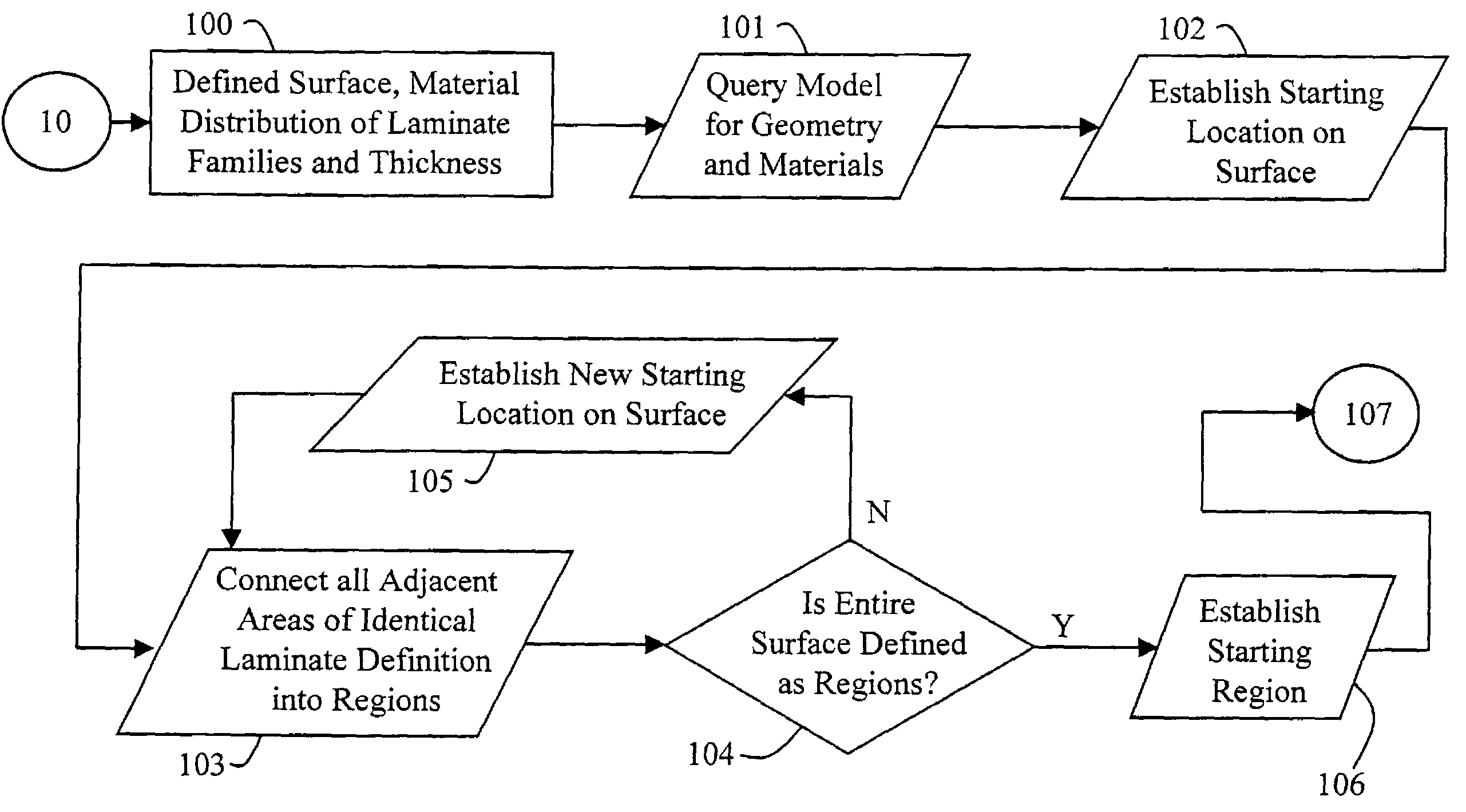
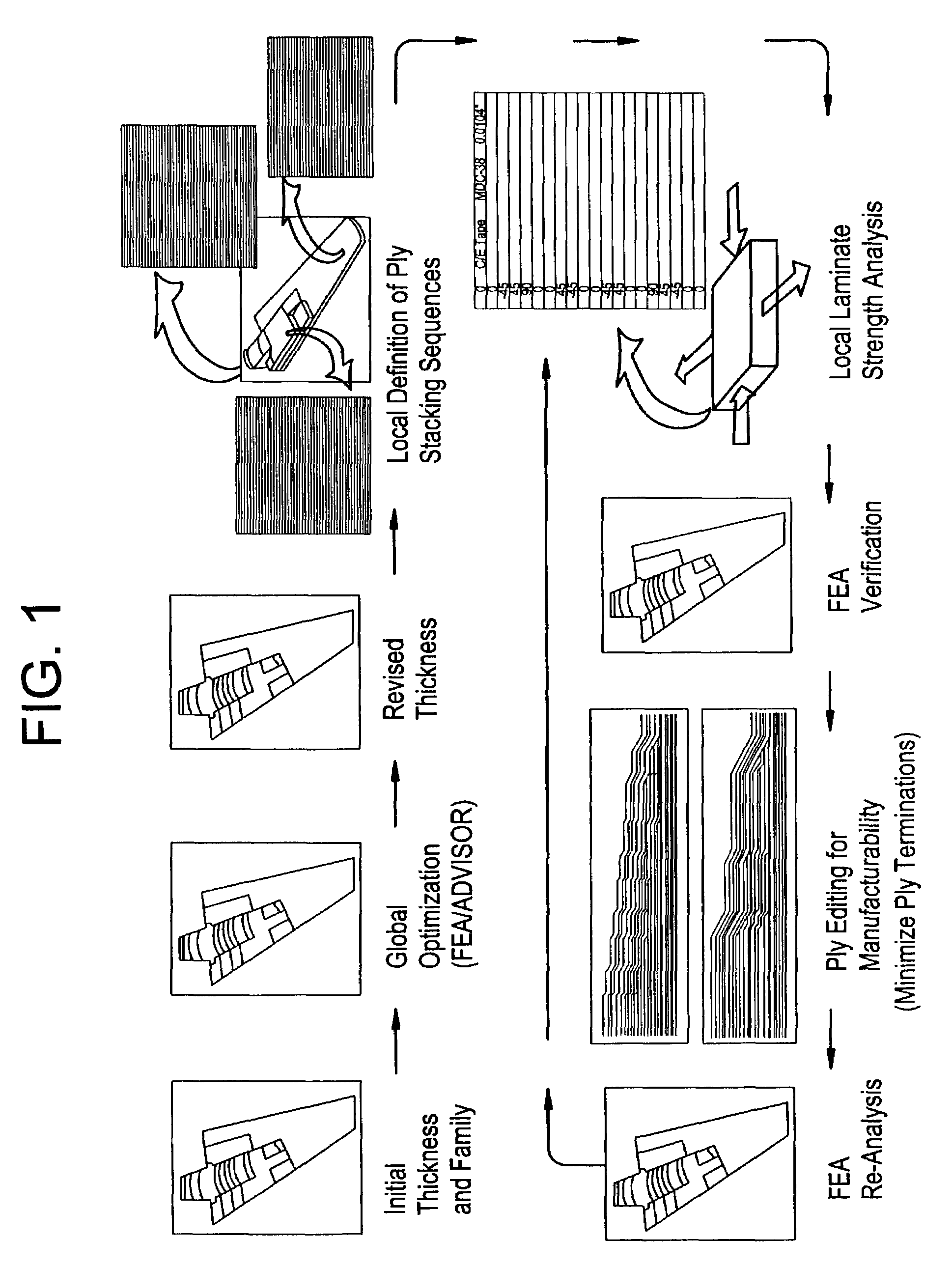
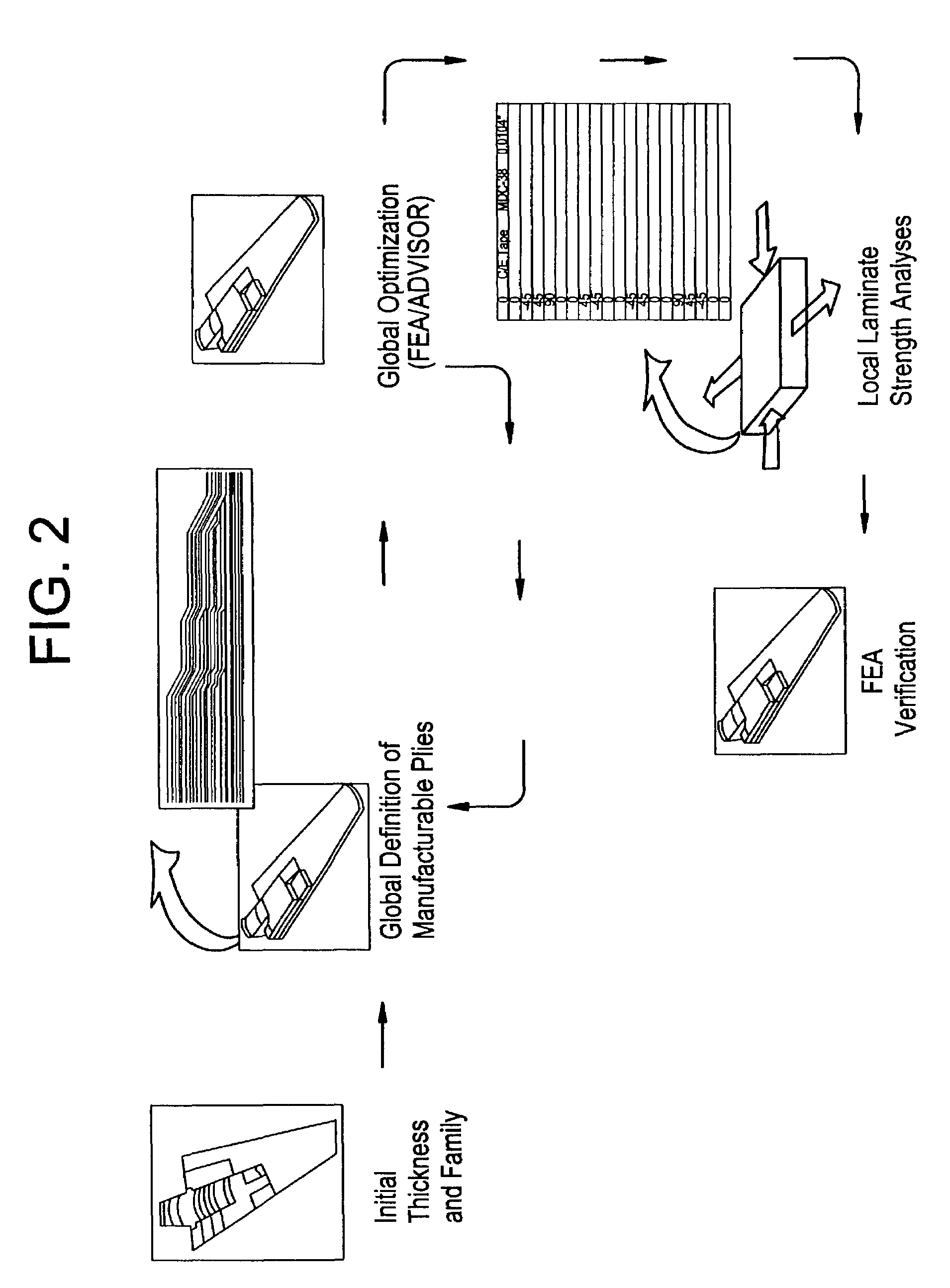
A knowledge driven composite design optimization process for designing a laminate part includes steps for generating a globally optimized 3-D ply definition for a laminate part, and modifying the 3-D ply definition to include features of the laminate part, where the generating and modifying steps are parametrically linked to one another and are performed in the recited order. Preferably, the generating step includes substeps for determining connectivity between a plurality of regions defining the laminate part, subsequently generating ramp features detailing interconnection of the regions defining the laminate part, and displaying views and corresponding tabular data describing the laminate part and illustrating both inter-region connectivity and the ramp features as specified by a user. A knowledge driven composite design optimization system and associated computer memory for operating a general purpose computer as a knowledge driven composite design optimization system are also described.
Owner:MCDONNELL DOUGLAS
Personnel location and monitoring system and method for enclosed facilities
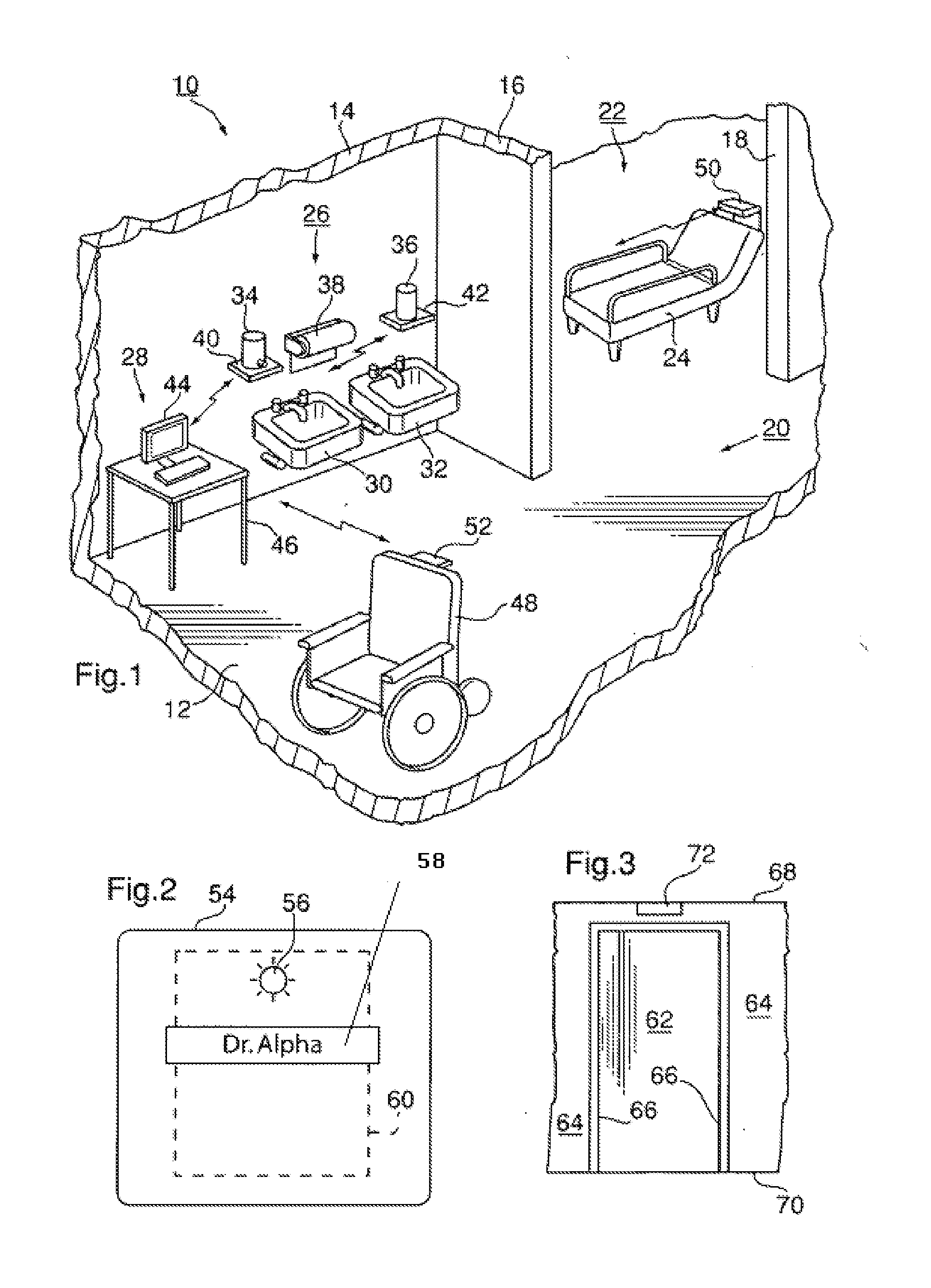
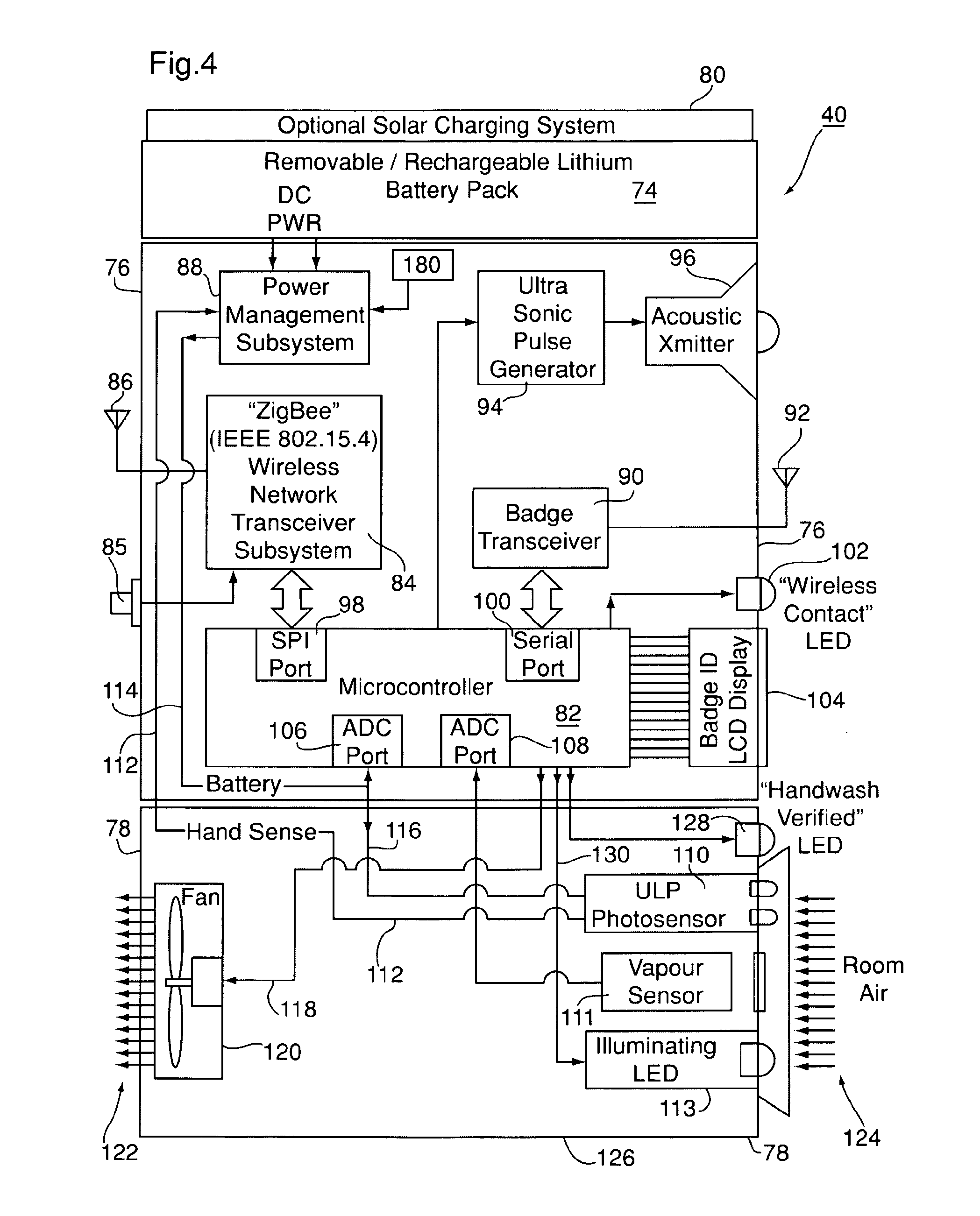
InactiveUS20110227740A1Limit power usageMeet growth requirementsRegistering/indicating time of eventsPosition fixationMotion detectorMonitoring system
A wireless time-of-flight distance measurement device a motion detector is used at each of a plurality of stations in a wireless network in an enclosed facility to accurately locate a badge-wearing person near the station. The location, badge number and time of detection are transmitted through the network and stored in a computer memory. In a healthcare facility, hand washing detectors are located at some of the stations and caused to energize a hand wash status indicator light on the badge when the wearer has washed his or her hands. The light remains “on” for only a certain length of time, but will be extinguished sooner by a monitor device near each patient when the healthcare worker leaves the vicinity of the patient. These events also are transmitted and stored so that a timed record of each worker's hand washing and visits to patients is created.
Owner:XHALE
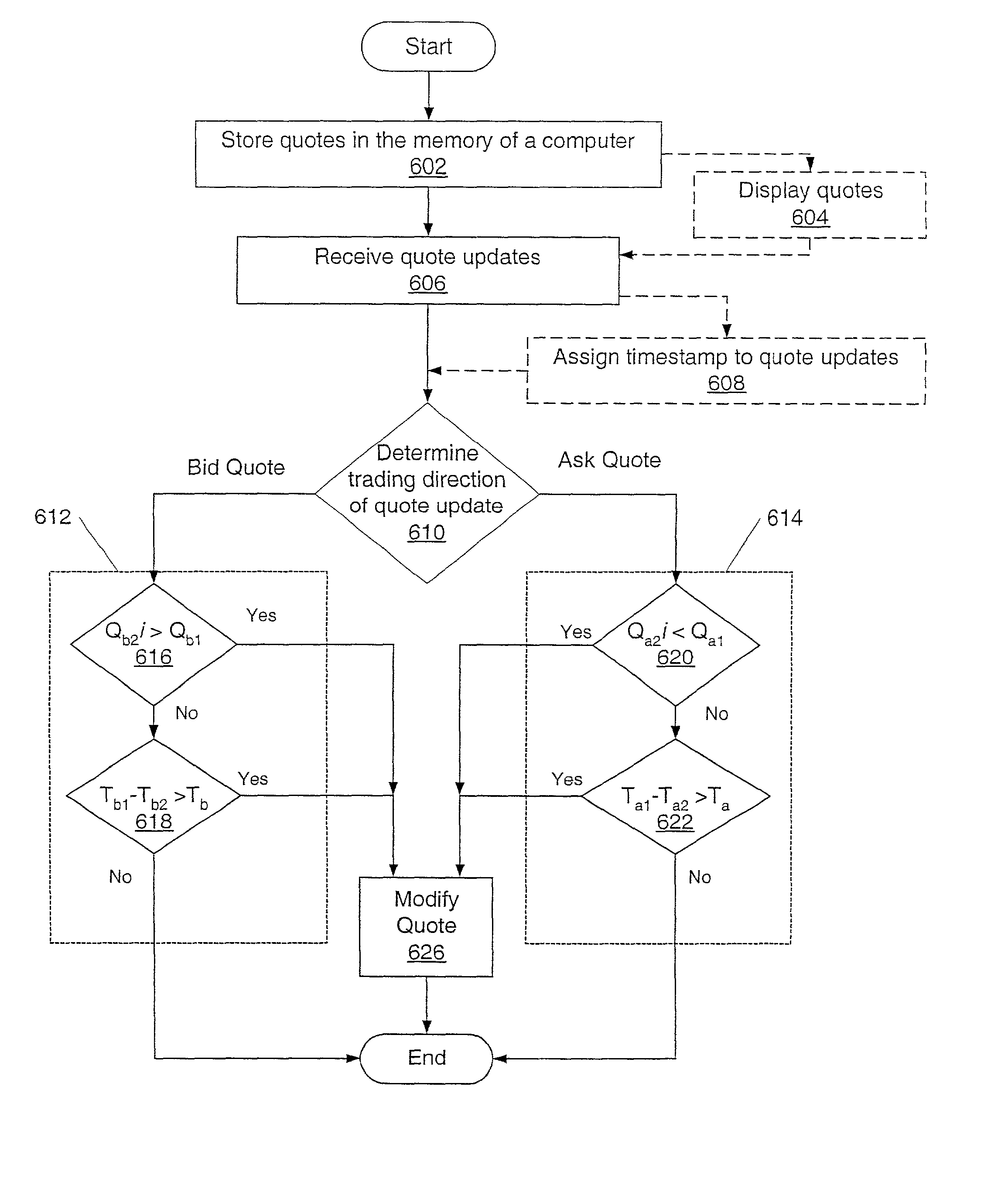
Methods and systems for suppression of stale or invalid data in a securities quotation display
Methods and systems for displaying information related to securities to a user are provided. In an embodiment, a method may include storing securities quotes in a memory of a computer. The method may include receiving quote updates information. The received quote update information and the quotes stored in the memory of the computer may be compared via one or more criteria. For bid quotes, a first criterion may include determining if a quote stored in the memory of the computer is greater than the price of a quote update. For ask quotes, the first criterion may include determining if a quote stored in the memory of the computer is less than the price of a quote update. A second criterion may include determining if a timestamp associated with the quote update minus a timestamp associated with the quote stored in the memory of the computer is greater than a predetermined threshold time. If one or more of the criteria are met, the method may modify the quote in the memory of the computer. Modifying the quote may include, but is not limited to: changing a display color, changing a font style, inhibiting the quote from being displayed, and deleting the quote from the memory of the computer.
Owner:INSTINET GRP INC +2
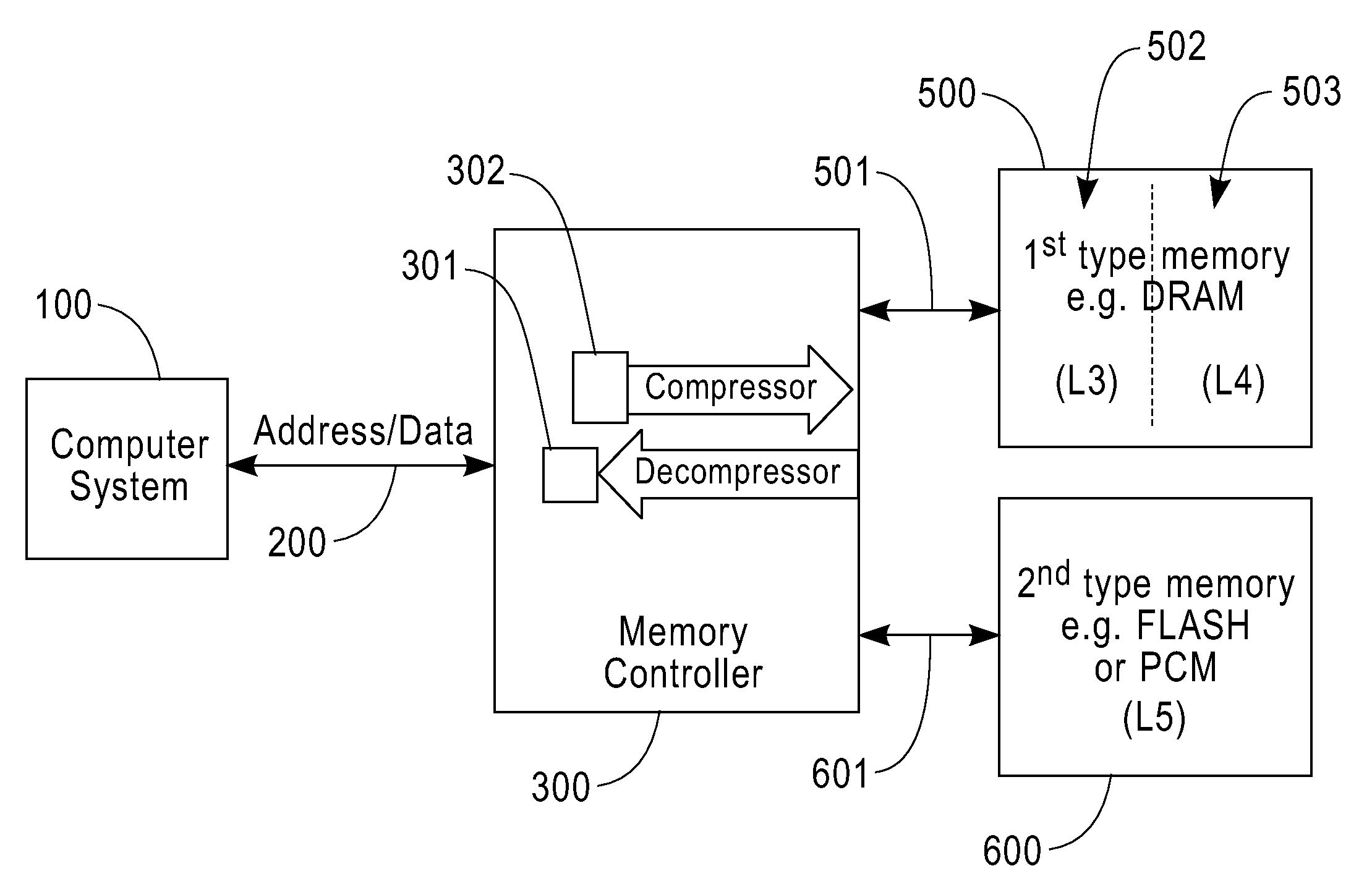
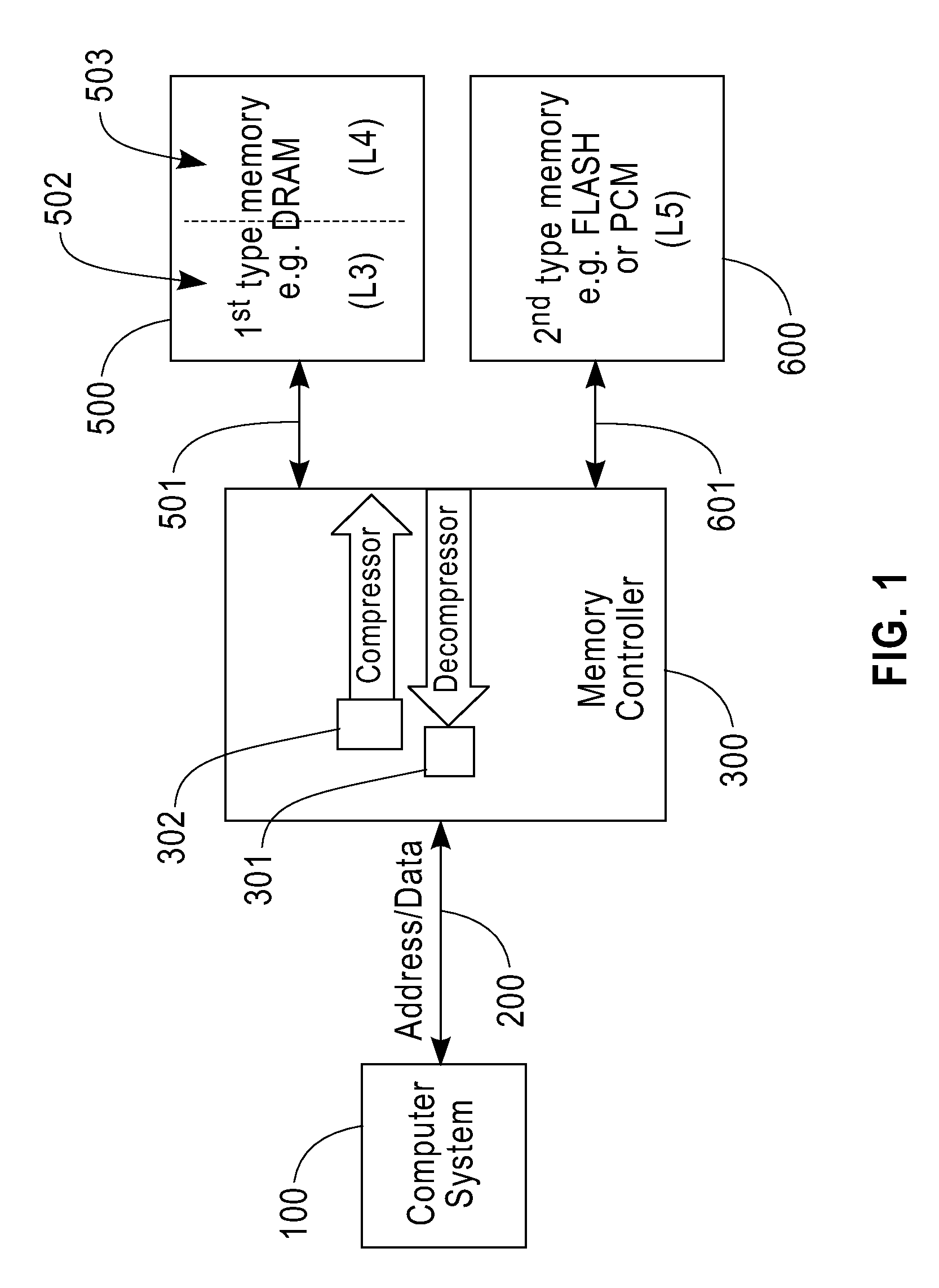
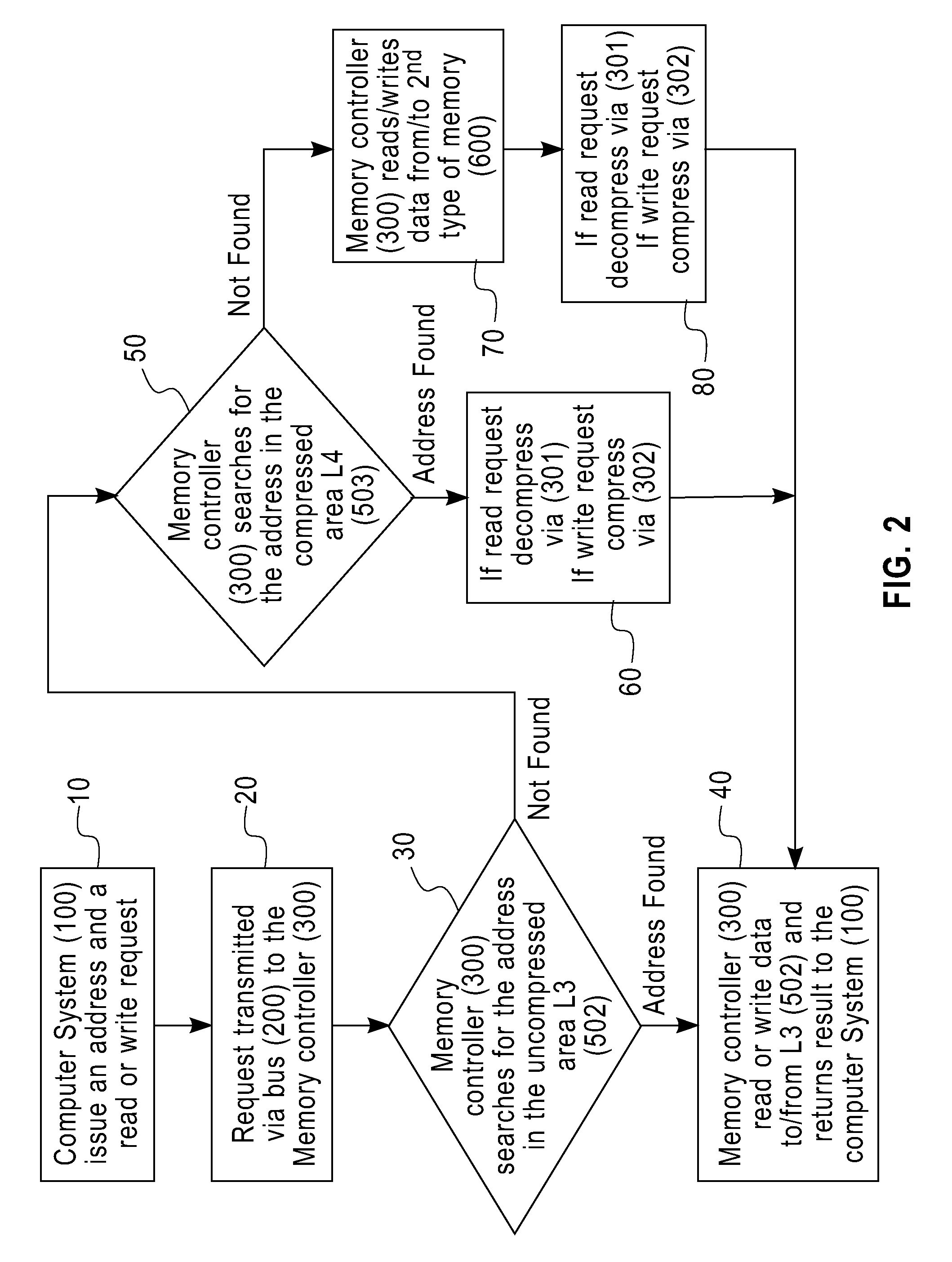
Bus attached compressed random access memory
InactiveUS20090254705A1Eliminate the problemLow costMemory architecture accessing/allocationMemory adressing/allocation/relocationThree levelMemory hierarchy
A computer memory system having a three-level memory hierarchy structure is disclosed. The system includes a memory controller, a volatile memory, and a non-volatile memory. The volatile memory is divided into an uncompressed data region and a compressed data region.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com