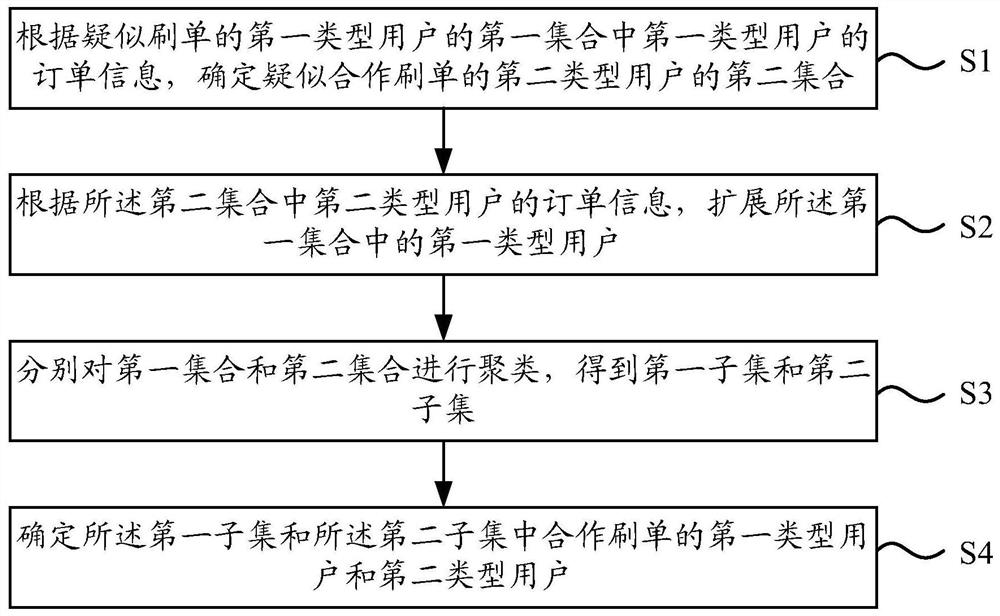
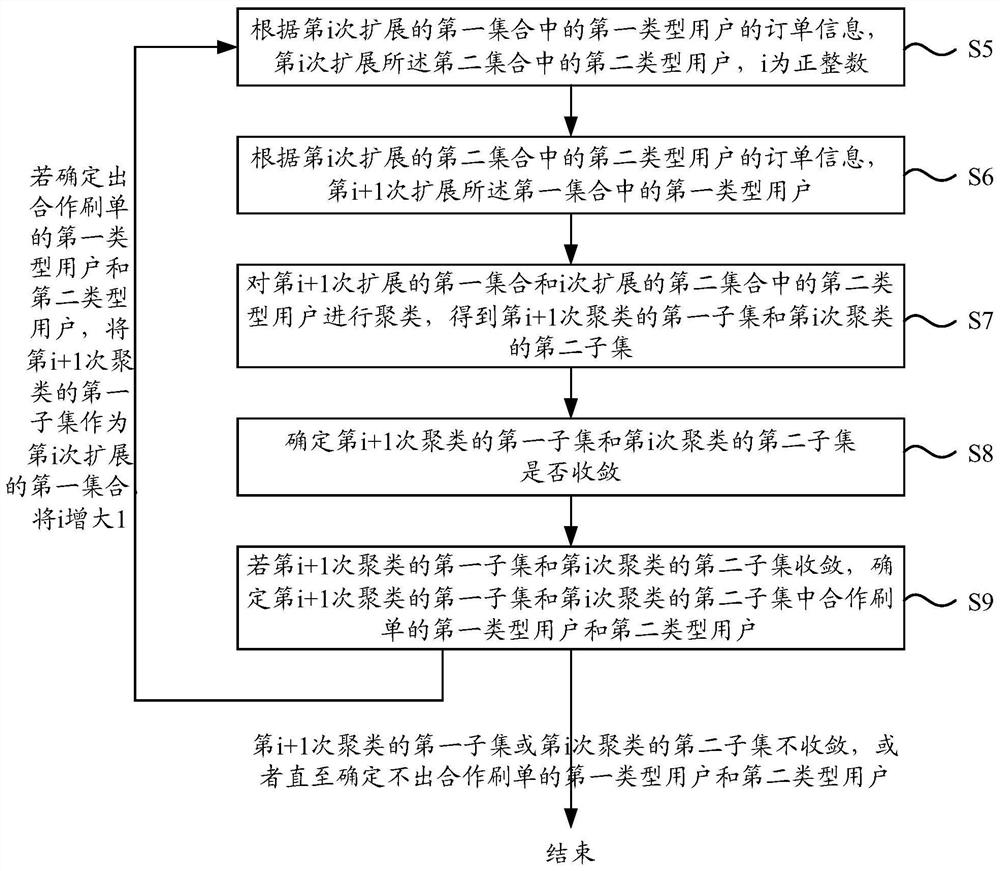
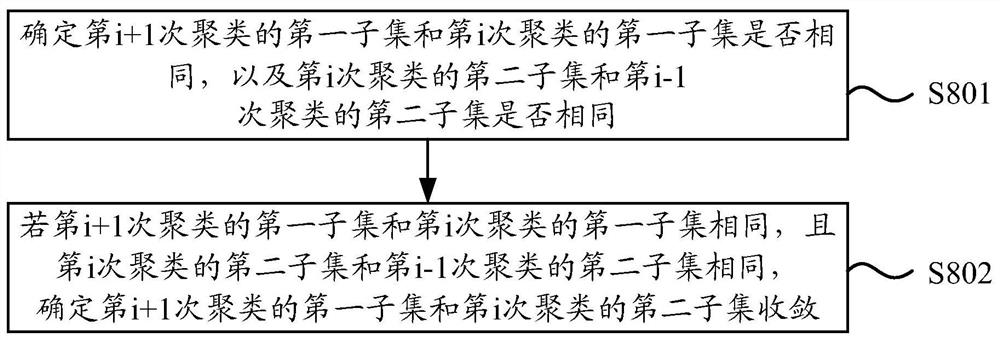
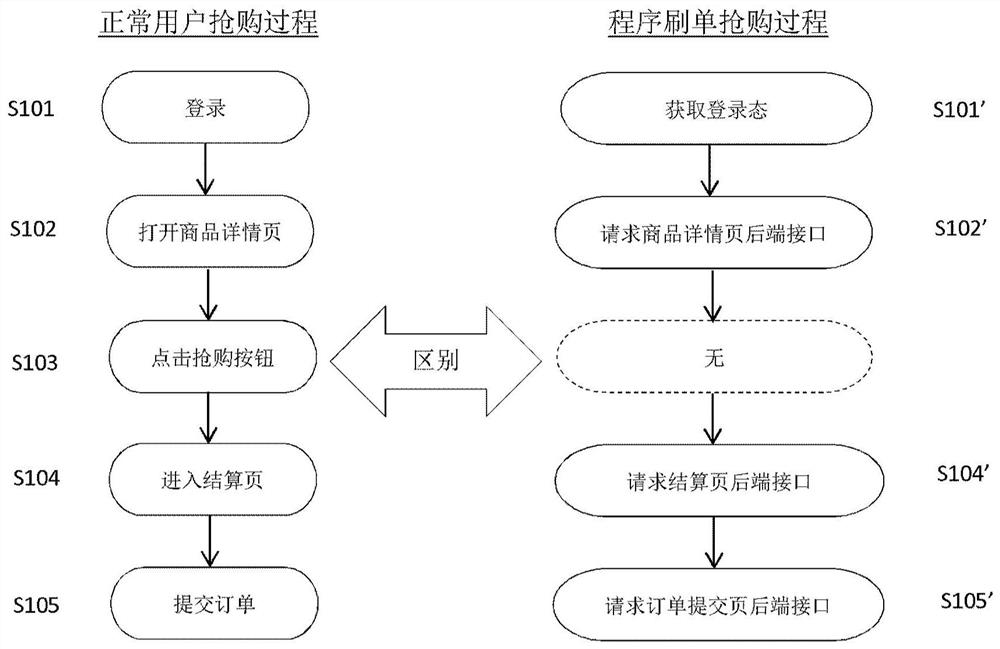
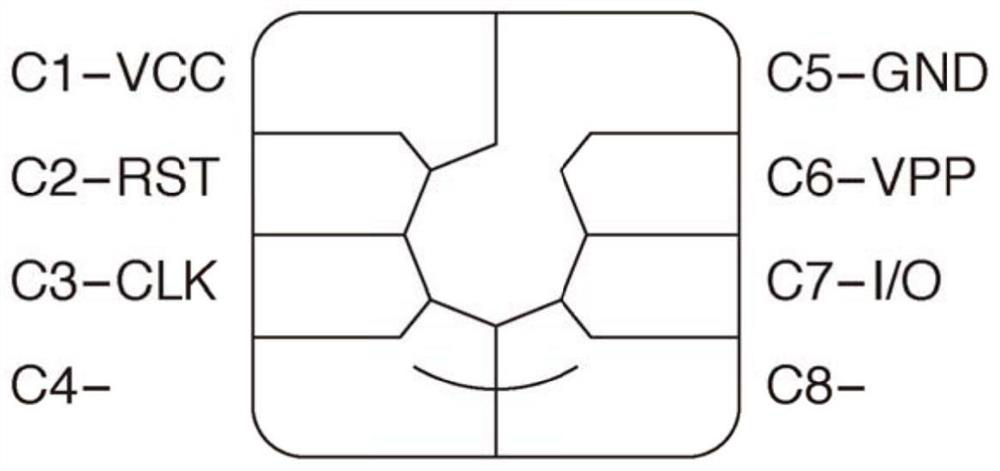
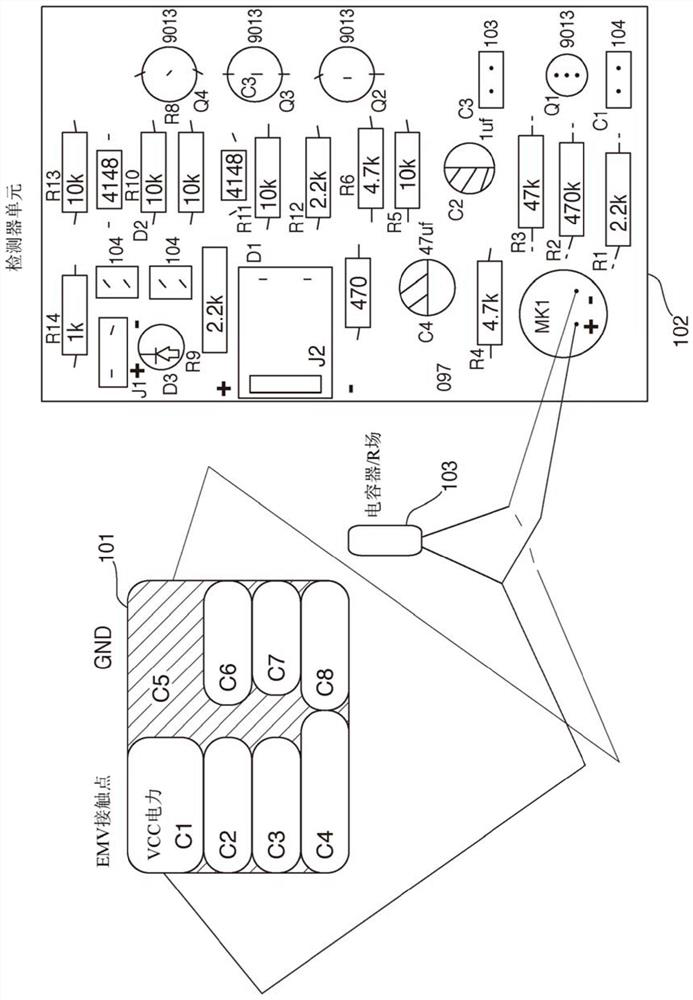
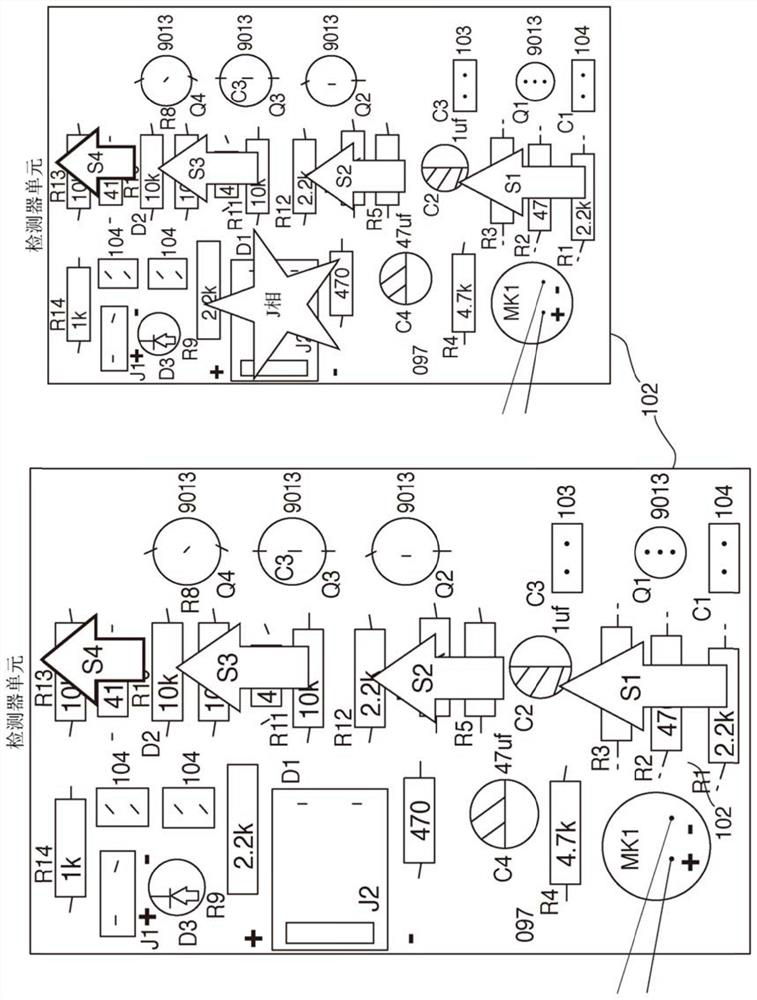
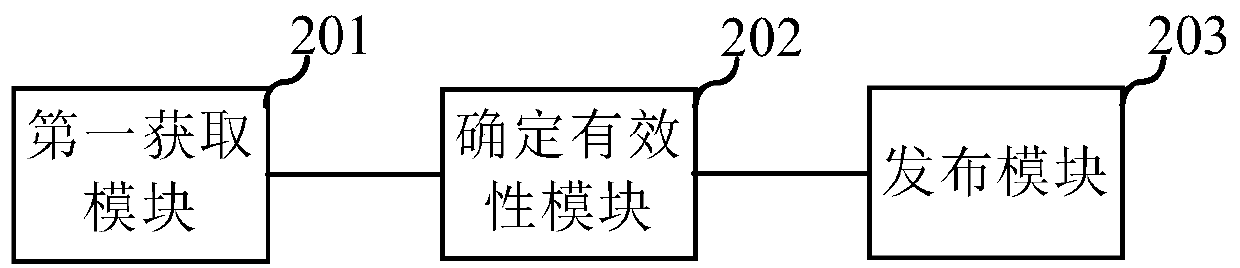
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41 results about "SwIPe" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The swIPe IP Security Protocol (swIPe) is an experimental Internet Protocol (IP) security protocol that was specified in 1993. It operates at the Internet Layer of the Internet Protocol Suite.
Malware warning
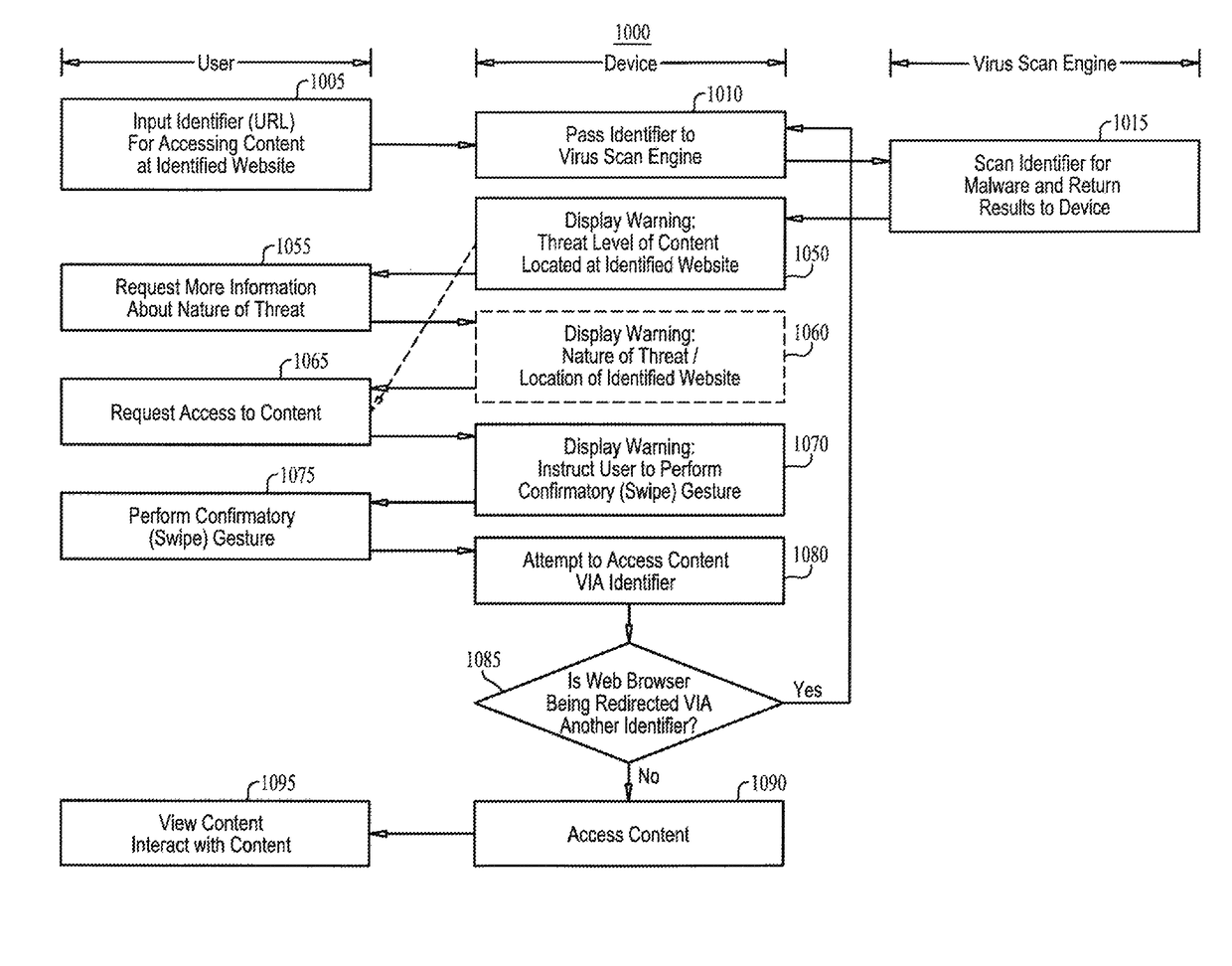
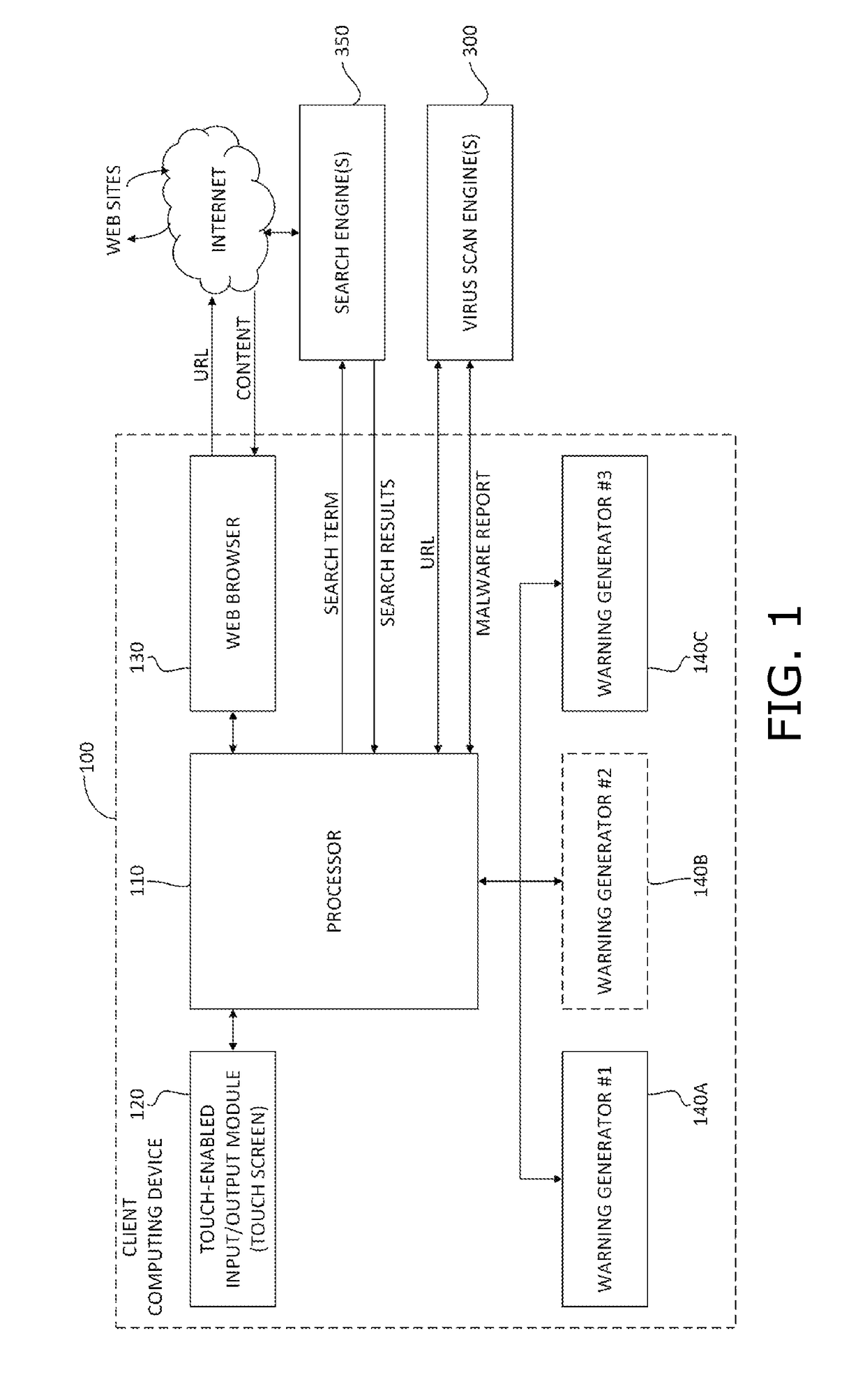
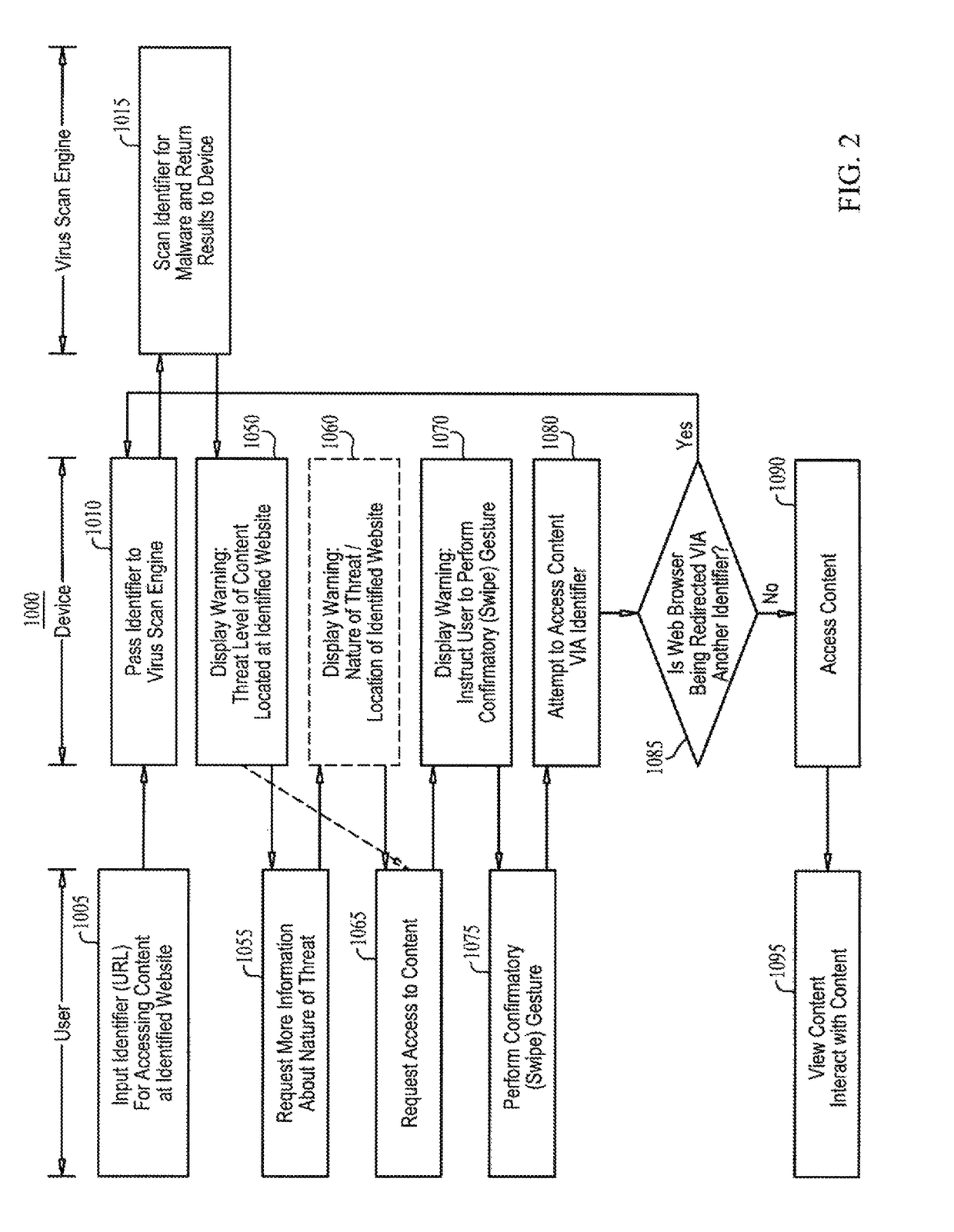
A malware warning system, including a client sending requests to and receiving replies from a server, and a server, including a first warning generator sending to the client a warning including a threat level of content located at a web site, in response to receiving from the client a URL for accessing content at the web site, a second warning generator sending to the client a warning including information about at least one of the nature of the threat of the content located at the web site and a location of the web site, in response to receiving from the client a request for more information about the nature of the threat, and a third warning generator, sending to the client a warning including an instruction to perform a swipe gesture to confirm a request to access the URL, in response to receiving that request from the client.
Owner:FINJAN MOBILE LLC
Method and Device to Reduce Swipe Latency
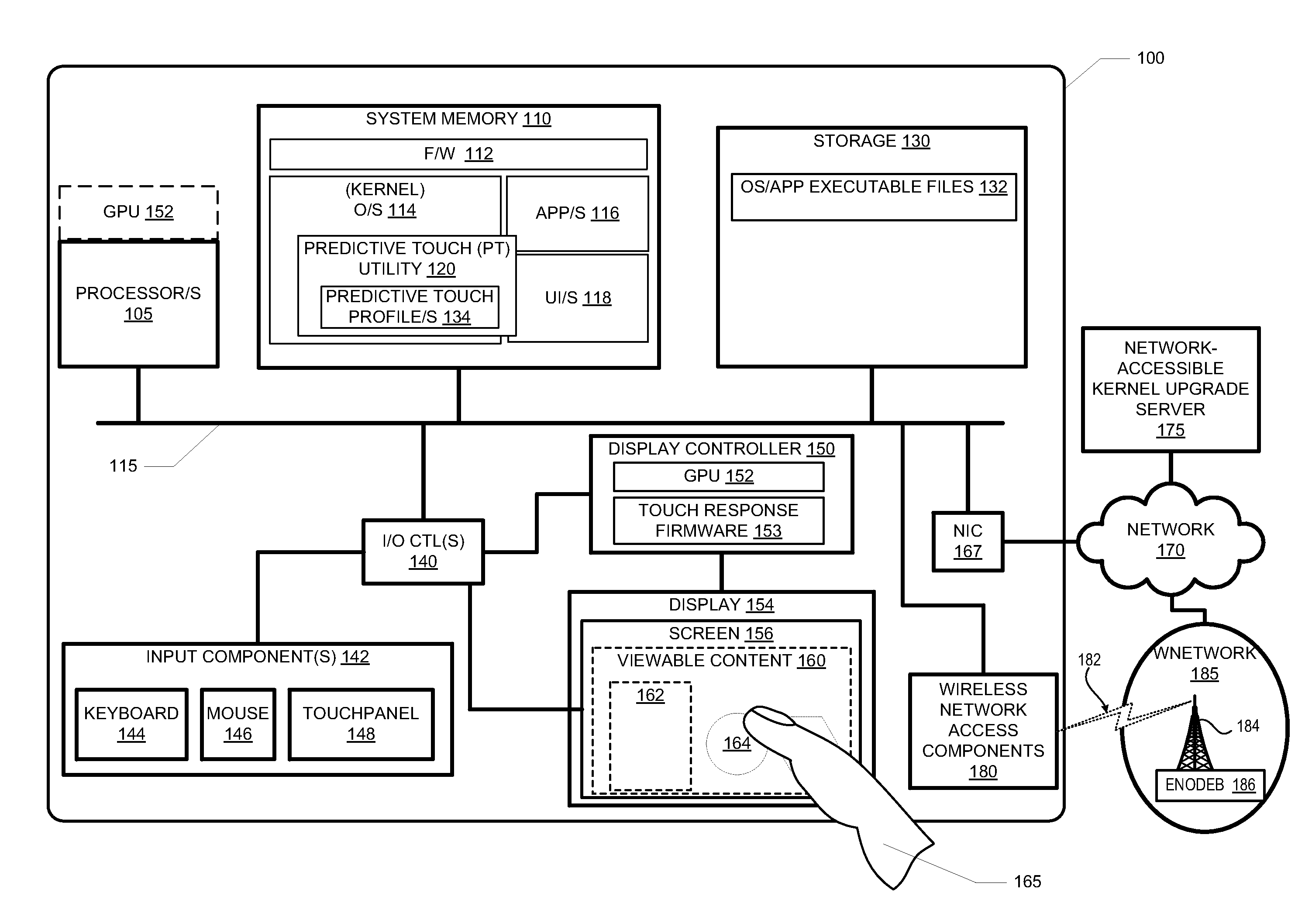
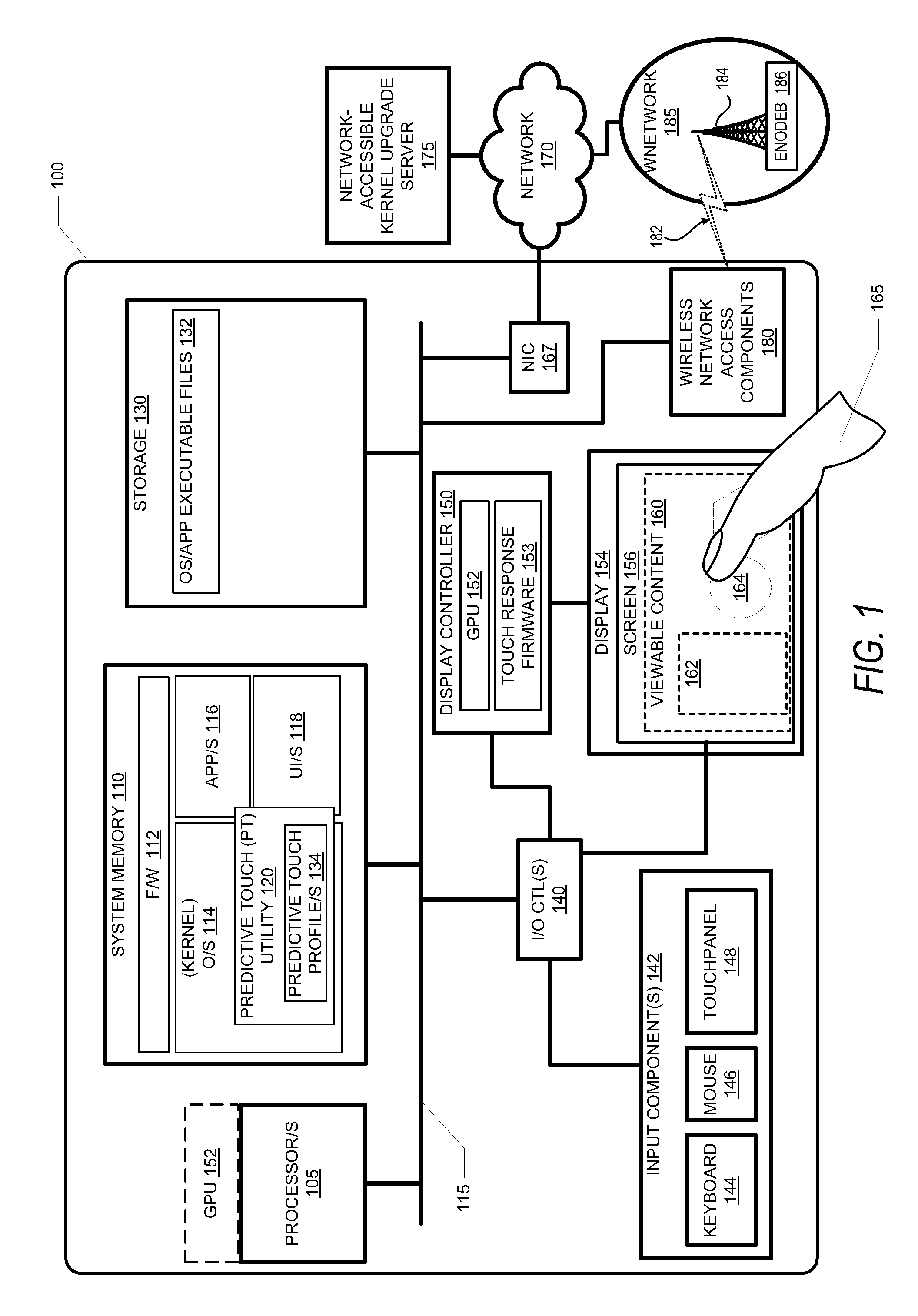
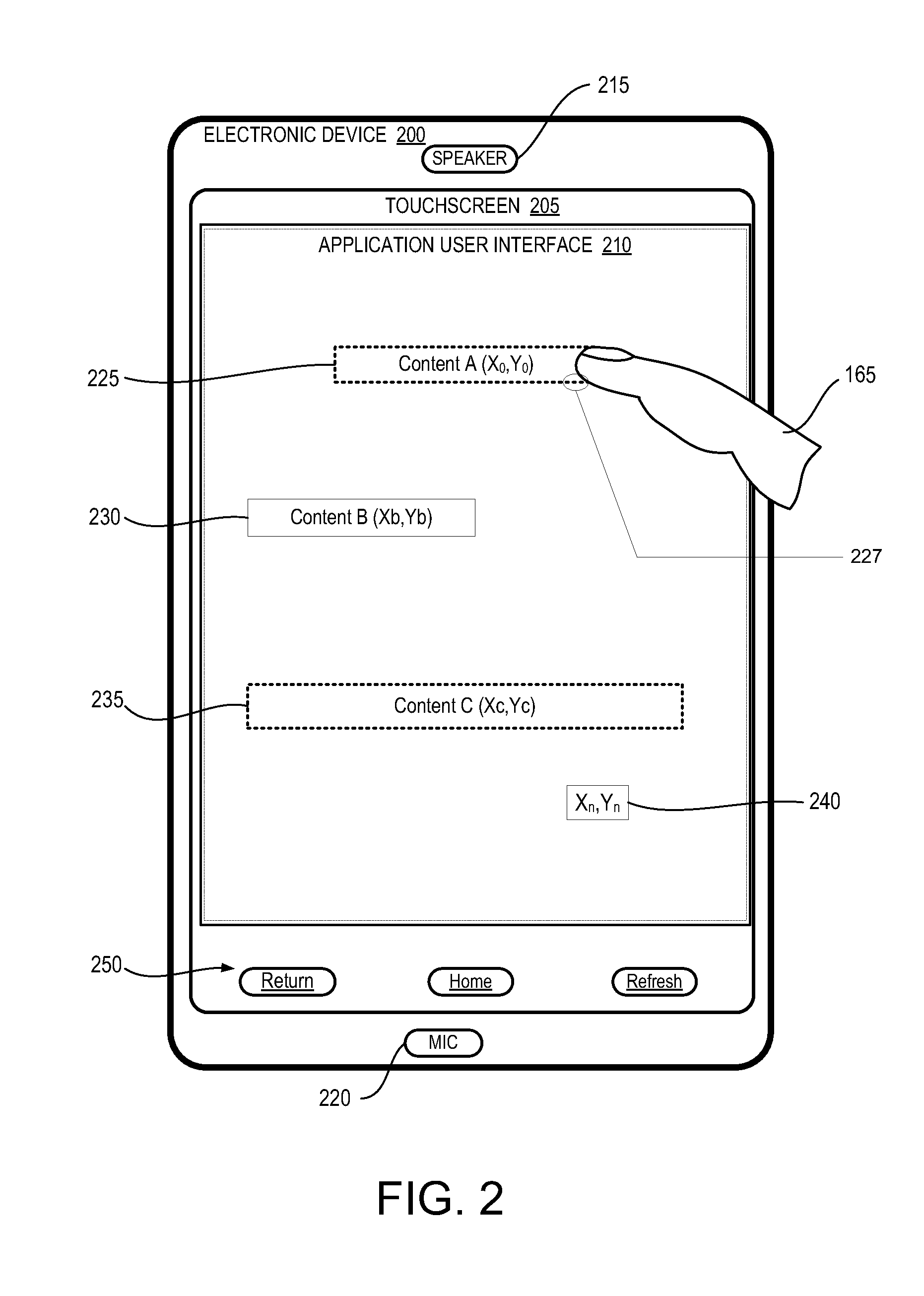
A plurality of methods 600-800 that collectively reduces touch swipe latency within a user interface (210) of an electronic device 100 / 200 includes: activating 610 a predictive touch utility 120; and in response to detecting 710 a sliding movement of an external manipulator 165 from a set of prior positions on a touchpanel 148 to a current position on the surface: dynamically computing 712 a predicted next position 392 based on the set of prior positions and the current position, before the external manipulator 165 arrives at an end position 240 while continuously touching the surface; and triggering 714 advancement of 536 the user interface 210 to a predicted next frame corresponding to the predicted next position 392. Activating the predictive touch utility 120 includes selecting and loading 612 a predictive touch profile 134 having a response curve 1500 / 1600 that correlates to gains applied to compute the predicted next position 392.
Owner:GOOGLE TECH HLDG LLC
Method and apparatus for displaying potentially private information
ActiveUS20150082446A1Unauthorised/fraudulent call preventionDigital data processing detailsInternet privacyDisplay device
Methods and apparatus for displaying potentially private information are disclosed. A computing device, that is showing a breathing view on its touch screen display, detects a peek request event, such as a swipe on the display. Before allowing the user to see potentially private information in response to the peek request, the computing device determines if the computing device is currently locked and if an increased privacy setting is enabled. If the computing device is not locked, or the increased privacy setting is not enabled (even though the computing device may be locked), the computing device shows a full peek view (e.g., some or all of the text from a recent text message). However, if the computing device is locked, and the increased privacy setting is enabled, the computing device shows a secure peek view (e.g., the number of new text messages, but no text from the messages).
Owner:GOOGLE TECH HLDG LLC
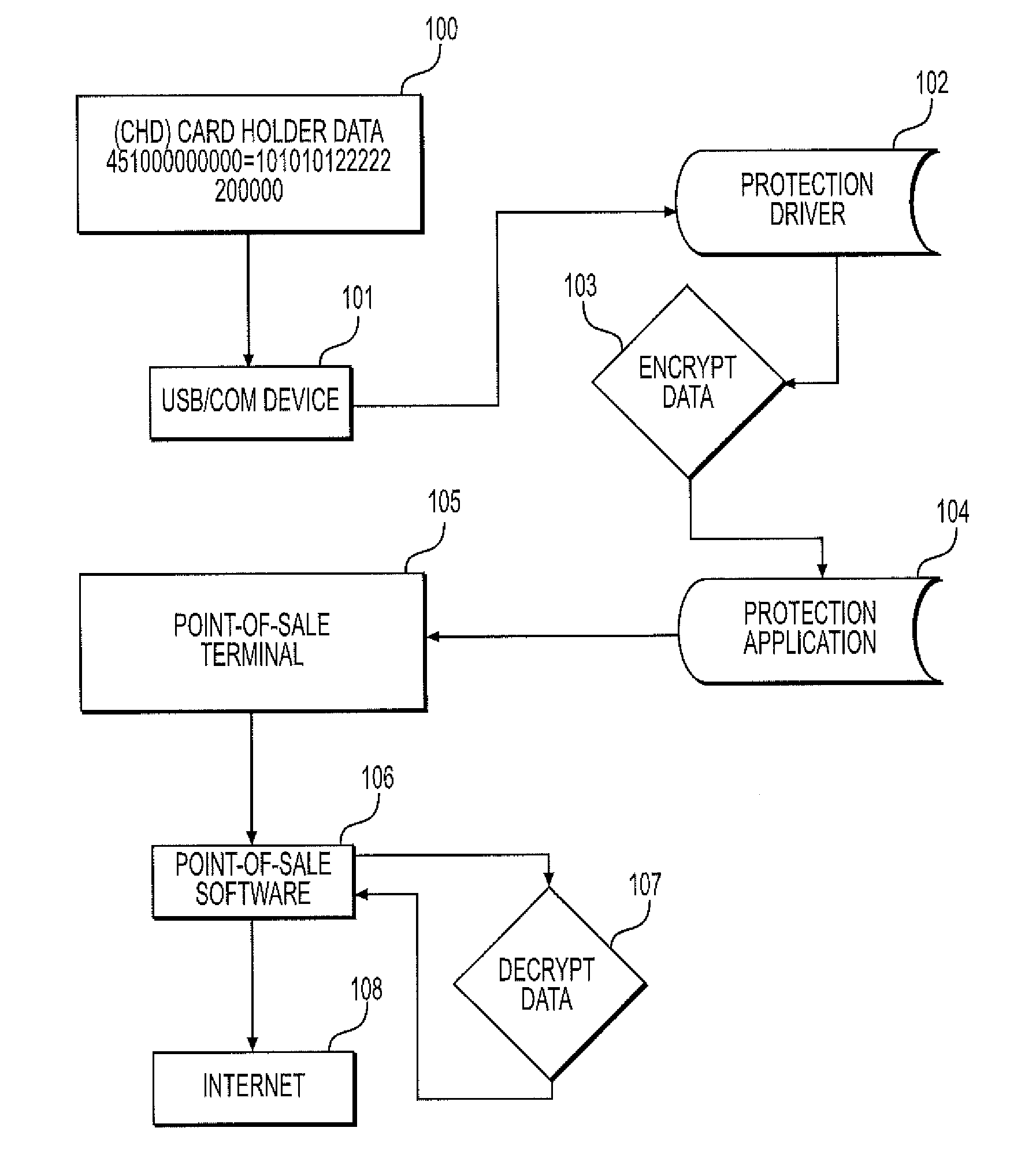
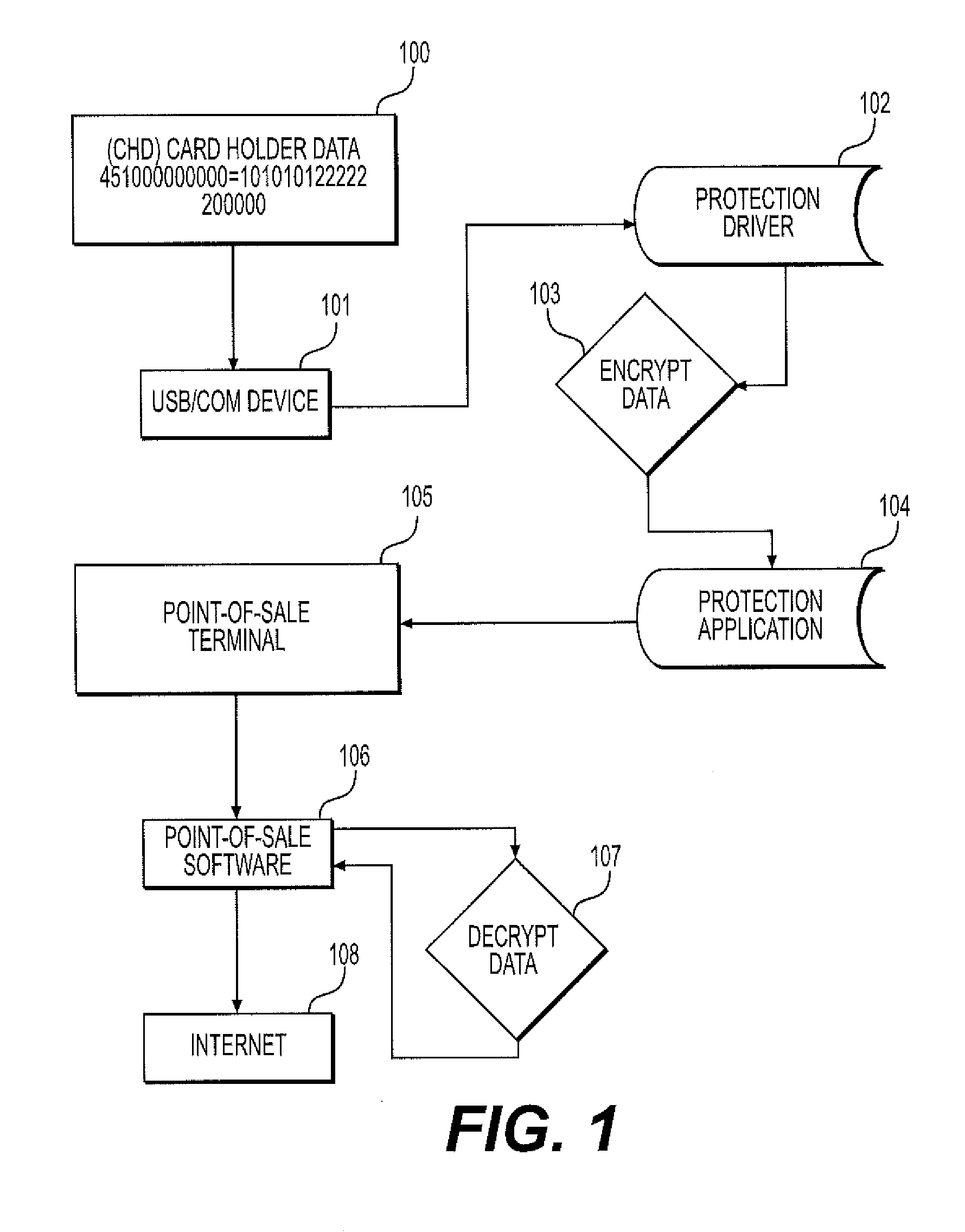
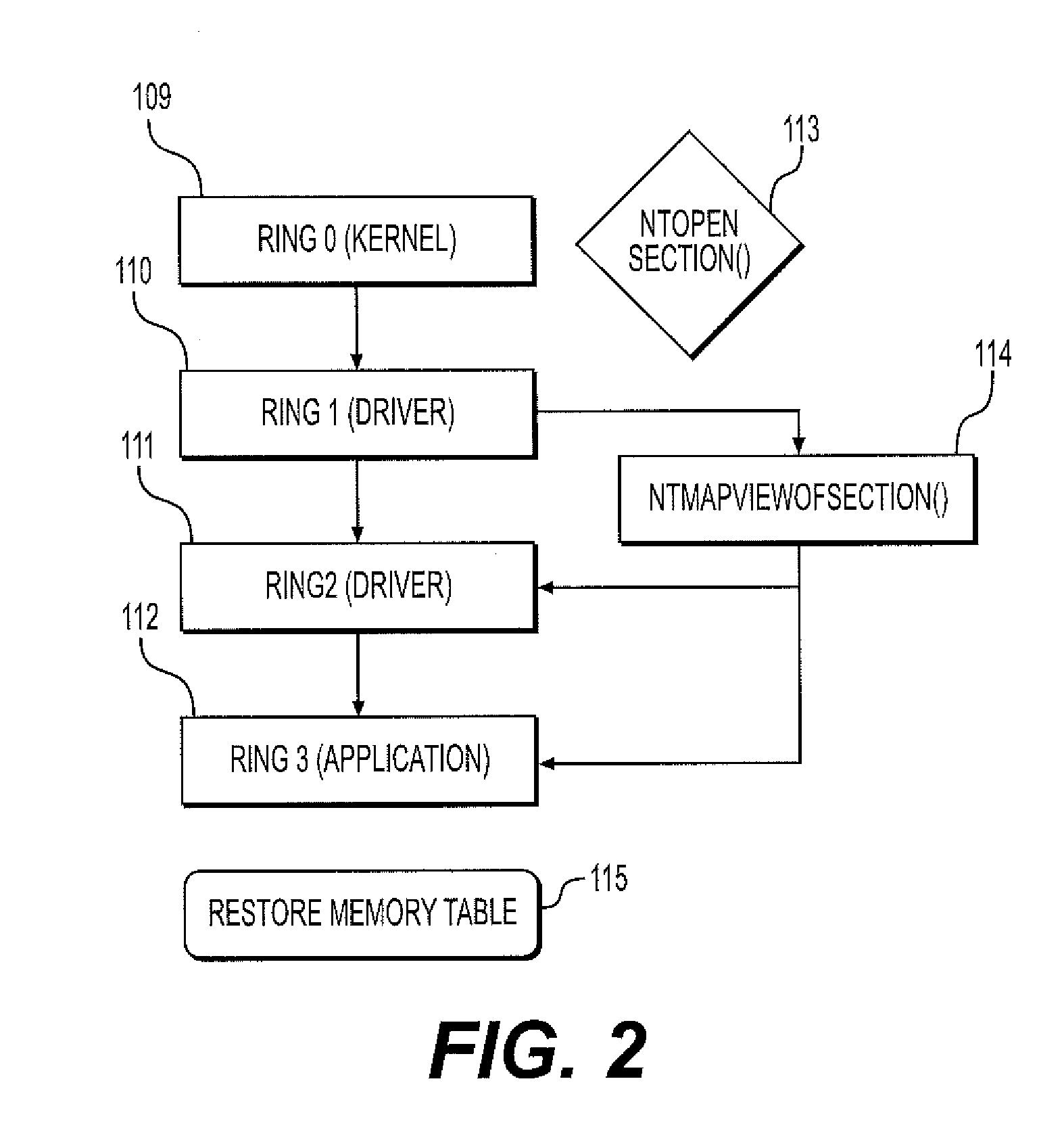
System and method for protecting against point of sale malware using memory scraping
A software, system and methodology for protecting against malware Point-of-Sale attacks that utilize, for example, memory scraping techniques. The application protects Point-of-sale hardware and its software against memory scraping malware attacks, and the loss of critical user credit card and confidential information often swiped at a terminal or stored in point of sale application databases. An embodiment of a method for blocking memory scraping attacks includes the following steps. Upon detecting a credit card swipe submission event from local hardware or comport event specific memory table events are flagged as unreadable, and immediately after allowing the data to be properly submitted, the system memory tables are cleared of data and specific memory processes are flagged as readable again. The method prevents memory scraping or point of sale malware from capturing swiped credit card data or input data, thereby protecting the user from theft of credit card data or other credentials.
Owner:TRUSTED KNIGHT CORP
Agent management system
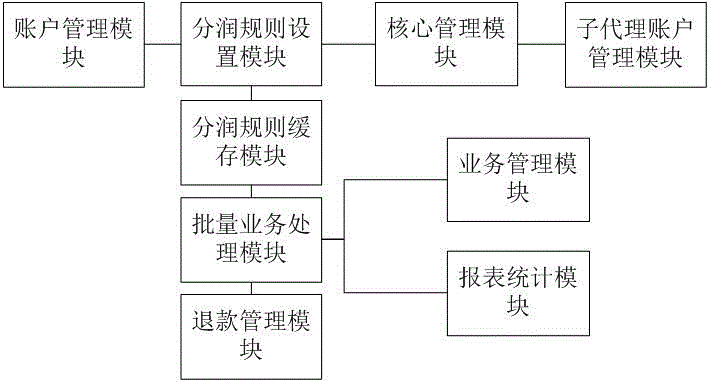
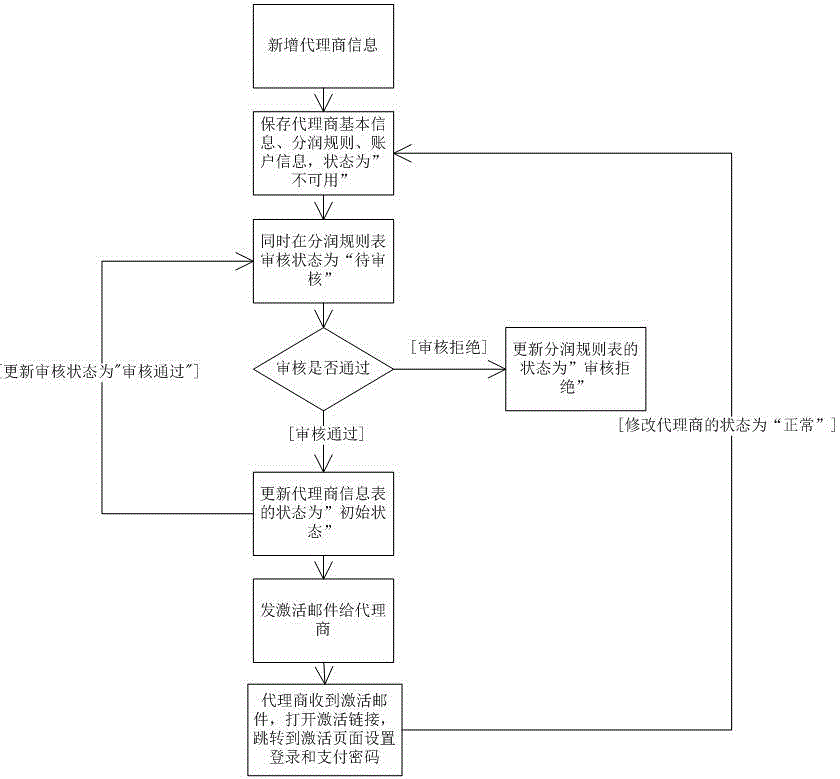
The invention belongs to the field of Internet application technologies, and particularly relates to a mobile card swiping device agent management system. The system comprises a batch task processing module, a profit distribution rule setting module, a profit distribution rule buffering module, a core management module, an account management module, a sub-agent account management module, a service management module, a refund management module, a report form statistics module and a database. For card wiping and collection agents and sub-agents belonging to the card wiping and collection agents, the service functions of conveniently and uniformly managing equipment, transactions, transaction profit distribution, sales information inquiry, equipment information inquiry, transaction information inquiry, sub-agent management, deposit withdrawal, profit distribution inquiry, contribution inquiry, refund inquiry, service configuration, advance fund account management, deposit withdrawal, terminal status inquiry, balance details, and agent product management are achieved.
Owner:SHANGHAI HANDPAY INFORMATION & TECH
Network access identity recognition system and method
InactiveCN103679887AEasy to useLow costIndividual entry/exit registersInternet privacyIdentity recognition
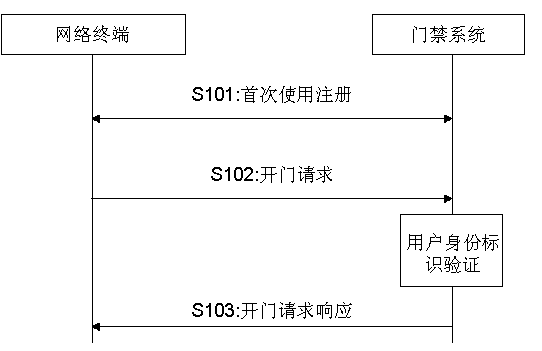
The invention relates to a network access identity recognition system. The network access identity recognition system consists of a network access identity recognition device and a communication terminal, wherein the communication terminal transmits user registration to the network access identity recognition device; after the registration passes, the network access identity recognition device transmits a user access identity marker to the communication terminal; the communication terminal transmits door-opening request to the network access identity recognition device; the network access identity recognition device receives the door-opening request, performs user access identity marker legality verification on the door-opening request and executes corresponding access permission operation after the user access identity marker verification passes. A user can use the network access system without swiping a card or other biological identity recognition methods; in particular, when a visitor comes, the user can open the door at the office, home or any places through the communication terminal, so that a user can use the network access identity recognition system conveniently and quickly; the network access identity recognition system can be mounted at any places near a door lock as the user contact operation is not required, so that the engineering arrangement is greatly facilitated.
Owner:深圳市呤云科技有限公司
Authority management method and system for access control system
InactiveCN106530458AIncrease flexibilityImprove practicalityIndividual entry/exit registersAccess control matrixComputer terminal
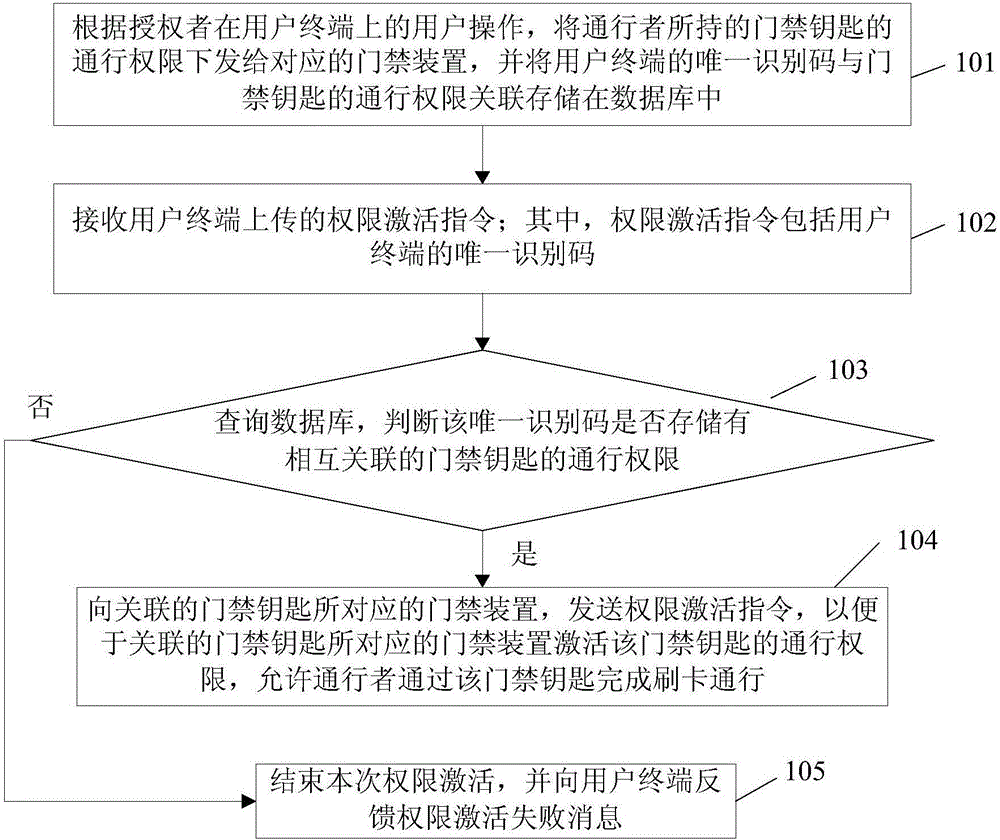
The invention discloses an authority management method and system for an access control system. The method comprises the steps that passing authority of an access control key held by a passer is issued to a corresponding access control device according to a user operation of an authorizer on a user terminal, and a unique identification code of the user terminal and the passing authority of the access control key are stored in a database in an associated mode; an authority activation instruction uploaded by the user terminal is received, wherein the authority activation instruction comprises the unique identification code; the database is inquired, and whether the passing authority of the access control key associated with the unique identification code is stored in the unique identification code or not; if yes, the authority activation instruction is sent to the access control device corresponding to the associated access control key, so that the access control device corresponding to the associated access control key activates the passing authority of the access control key, and the passer is allowed to swipe a card for passing through the access control key. By means of the authority management method and system for the access control system, remote one-key authorization and activation can be achieved, and the authority management flexibility and practicability of the access control system can be improved.
Owner:广东鑫际物联网科技有限公司
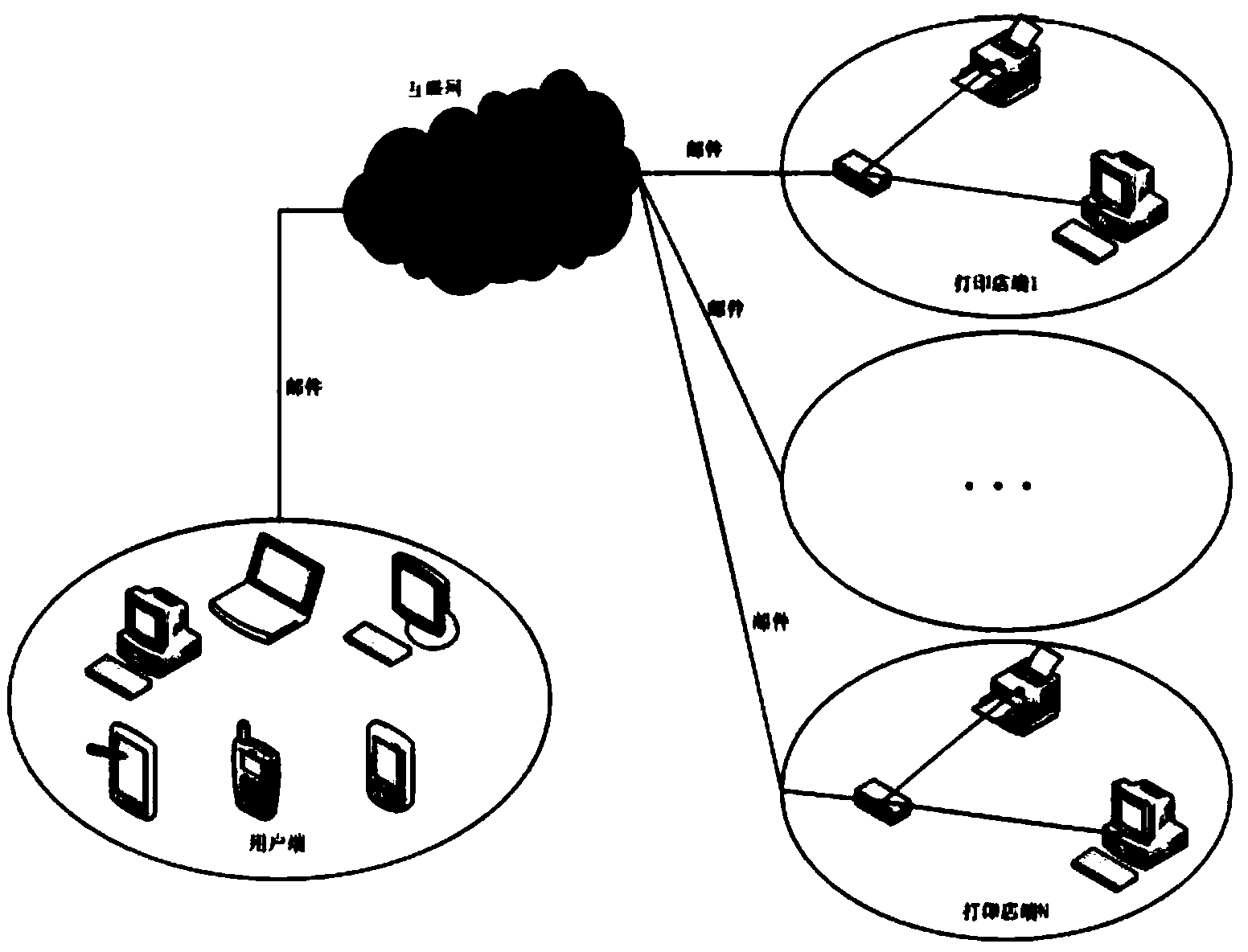
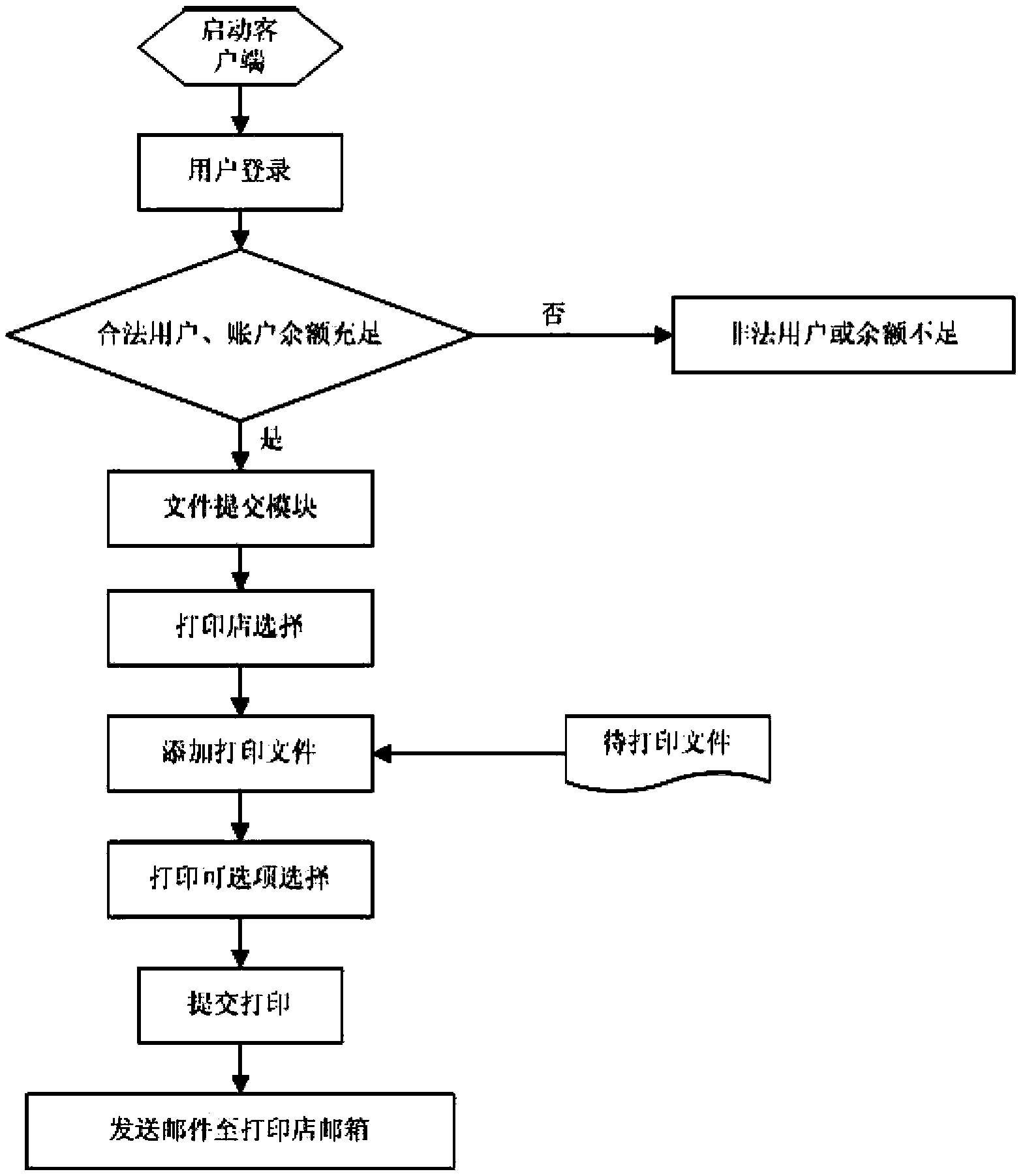
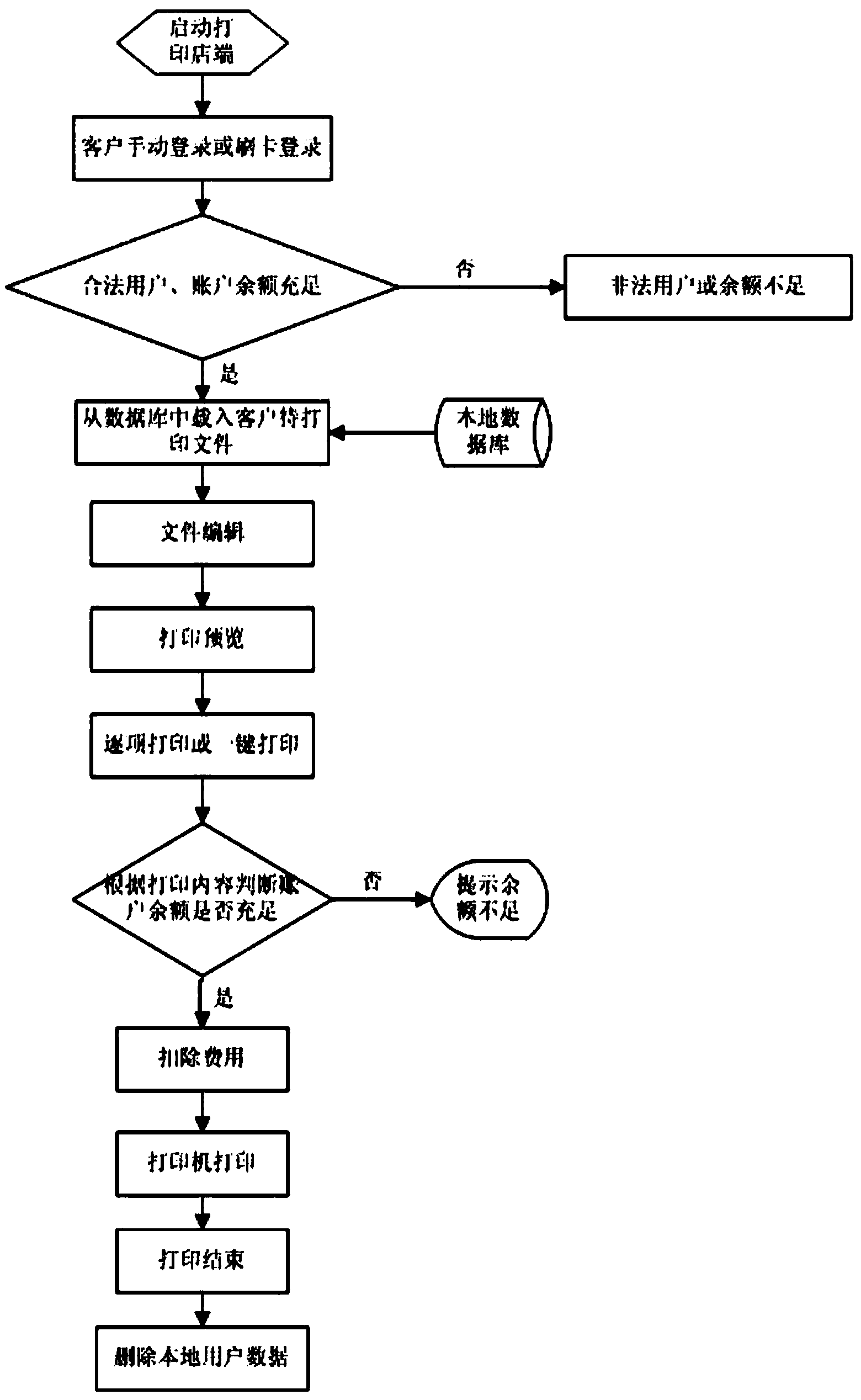
Campus shared printing service system and method based on cloud computing
InactiveCN104299327AReduce erectionIncrease speedApparatus for meter-controlled dispensingTransmissionPaymentClient-side
The invention relates to the technical field of cloud computing, in particular to a campus shared printing service system and method based on cloud computing. According to the campus shared printing service system and method, an IP network is used for realizing cloud sharing and self-help printing service, and a student or a teacher can submit a printing request to any networked device and then swipe a card for payment in a printing shop after the printing request is confirmed to obtain a printed document. The system comprises two parts, wherein one part is a client-side and the other part is a printing shop terminal system. By means of the printing client-side of the system, only one networked device is needed for submitting the printing request, and then the user can call out the document to be printed by swiping the card in the printing shop; moreover, payment by swiping the card is quite convenient, so that time and cost are saved; besides, jump-a-queue printing is supported, the queue is jumped at a backstage, and therefore convenience is provided to the user who wants to take a printing result immediately.
Owner:ZHENGZHOU XUESHENGBAO ELECTRONICS SCI & TECH
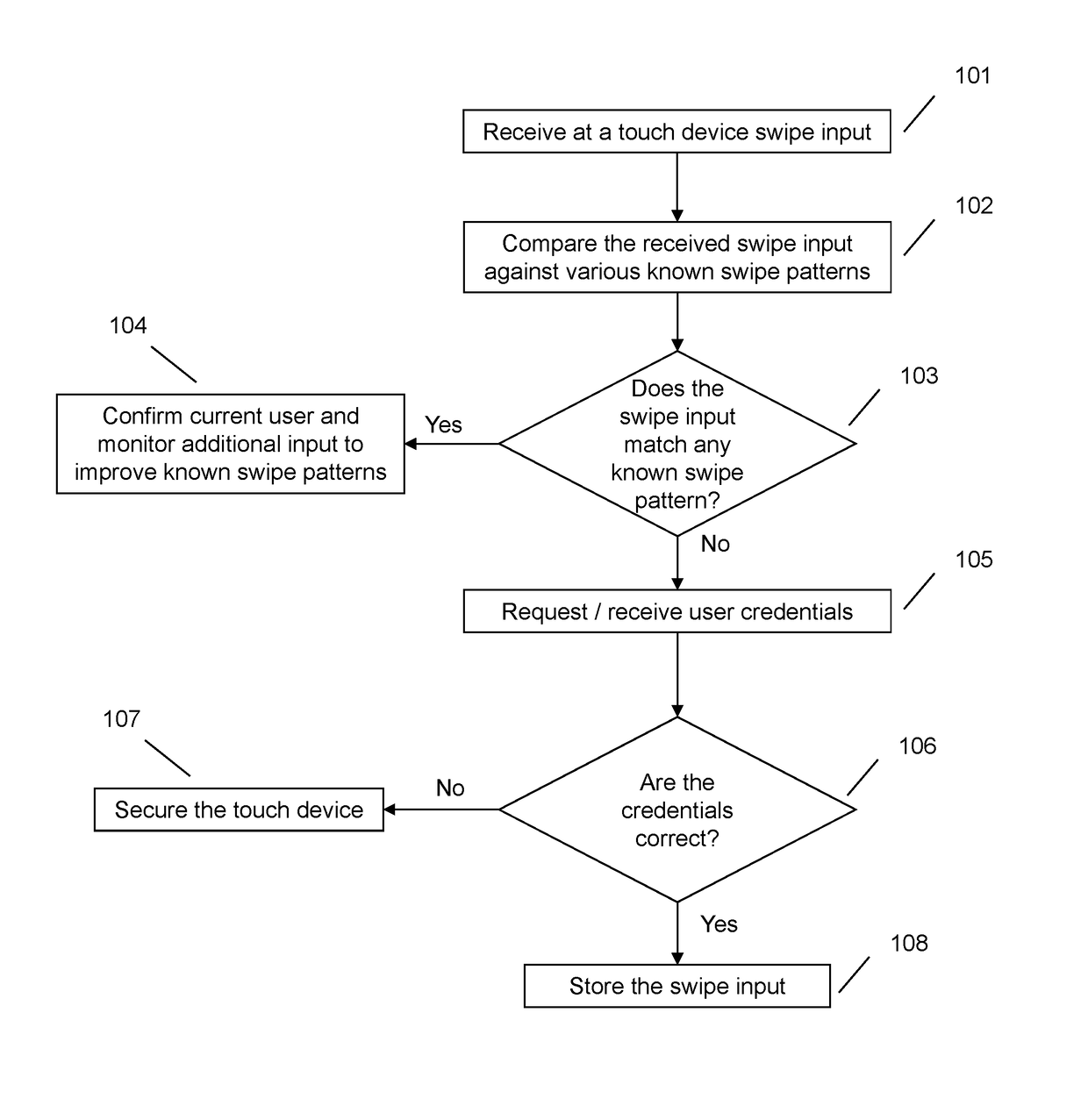
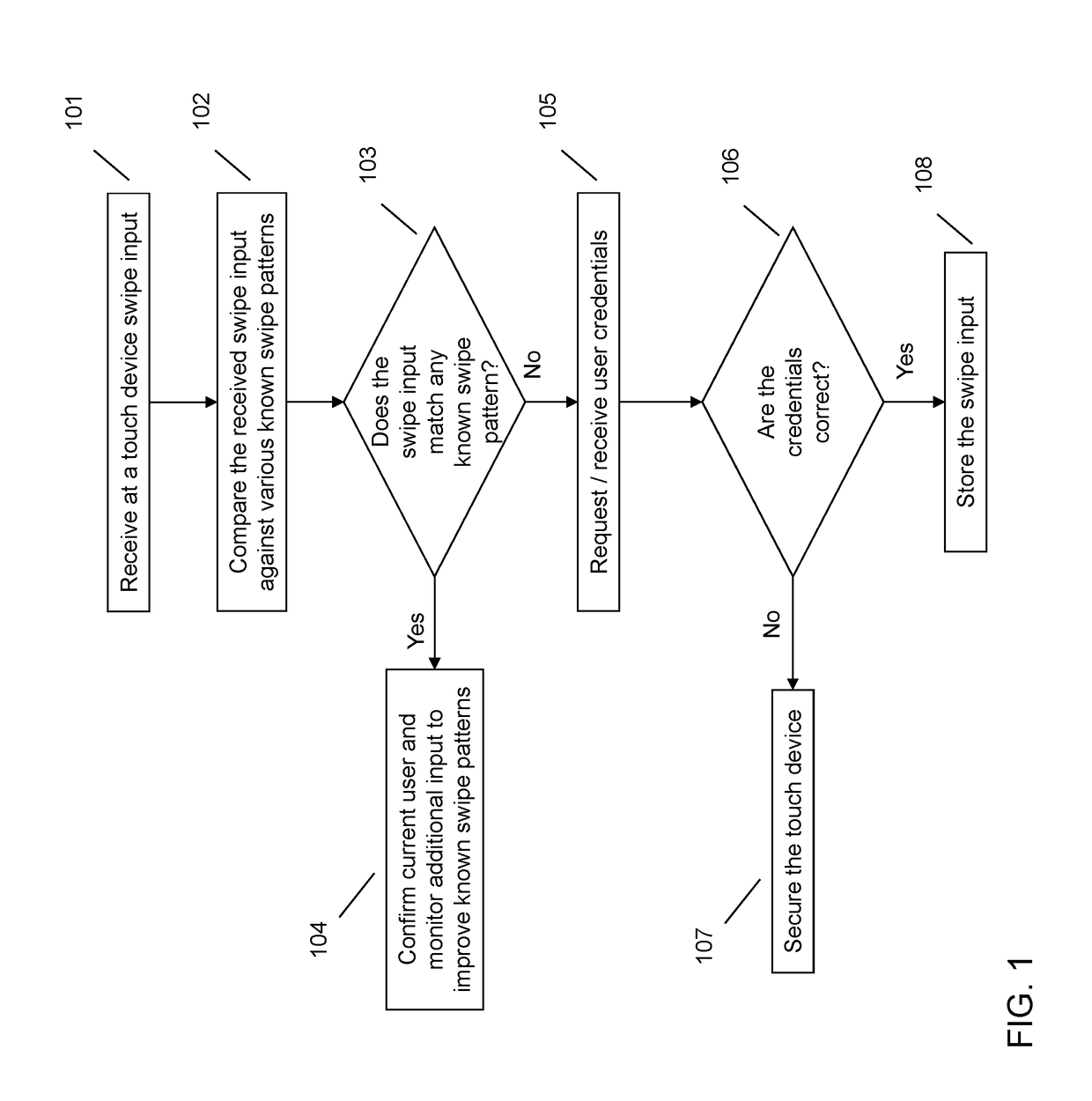
Device security via swipe pattern recognition
One embodiment provides a method for ensuring device security via swipe pattern recognition, the method comprising: utilizing at least one processor to execute computer code that performs the steps of: receiving, using a touch device, at least one swipe input of a user; determining, using the at least one processor, if the at least one swipe input matches a known swipe pattern of the user, the match requiring exceeding a match confidence level; and responsive to said determining, executing an action associated with the touch device. Other aspects are described and claimed.
Owner:IBM CORP
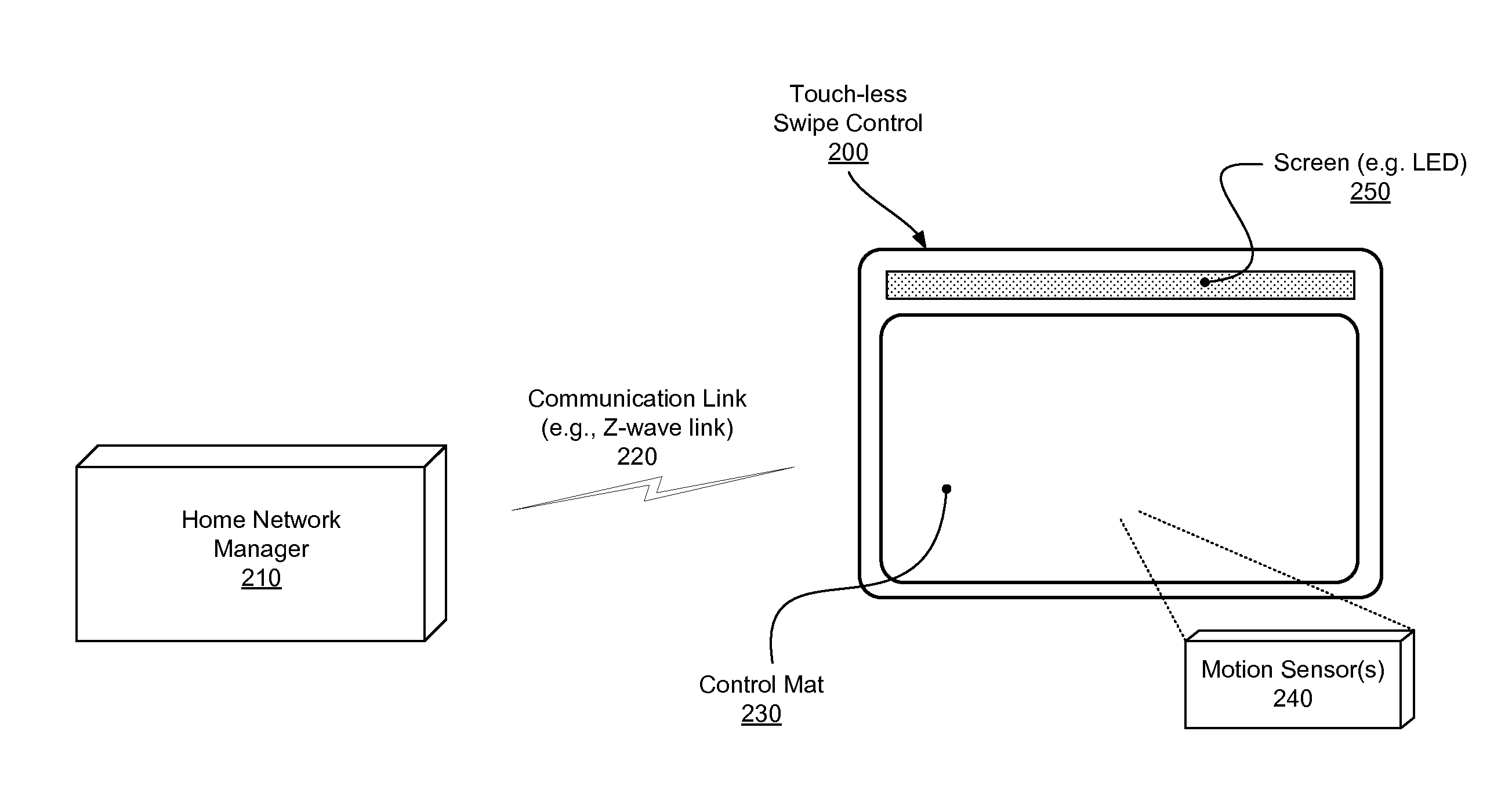
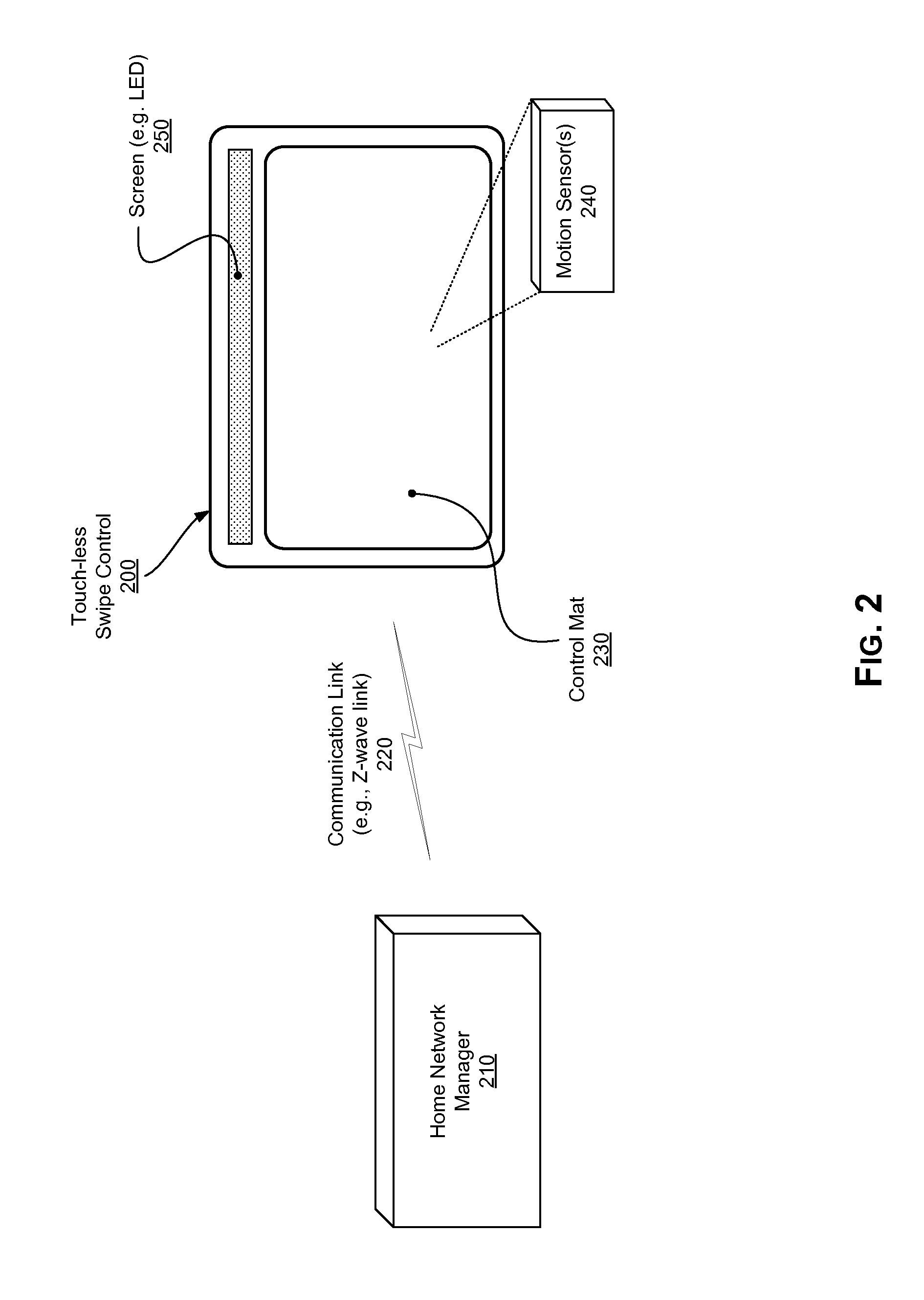
Touch-less swipe control
InactiveUS20150088282A1Programme controlInput/output for user-computer interactionComputer hardwareTransceiver
A touch-less swipe control system for use with a network to control a device of the network. The touch-less swipe control system may include a control mat to detect a touch-less gesture, and a processor coupled to the control mat to receive data indicative of the touch-less gesture, wherein the processor may be configured to recognize if the received data is associated with a control of the device. The touch-less swipe control system may include a communication transceiver to communicate the control to the device in response to having recognized that the received data is associated with a control of the device.
Owner:FIBAR GRP
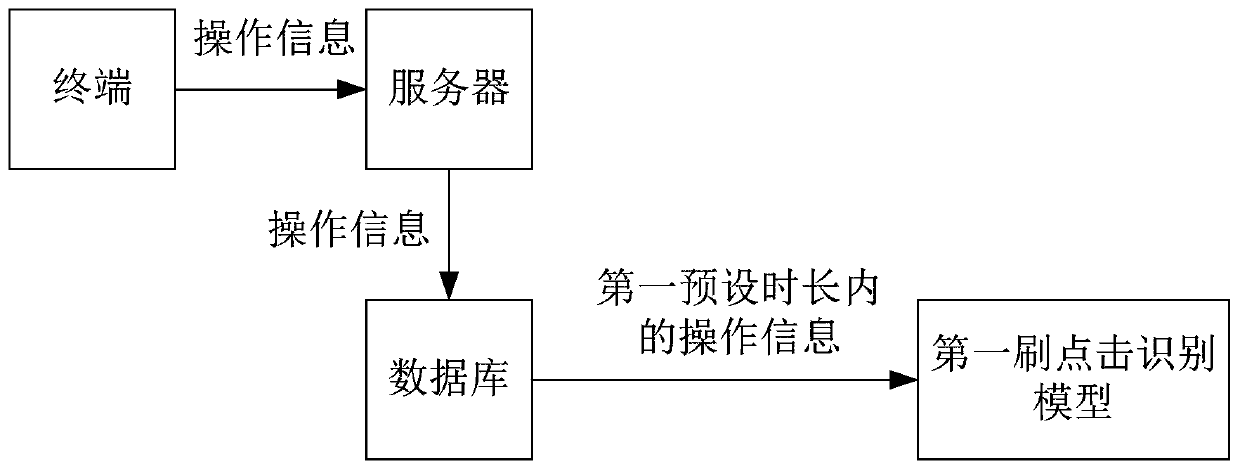
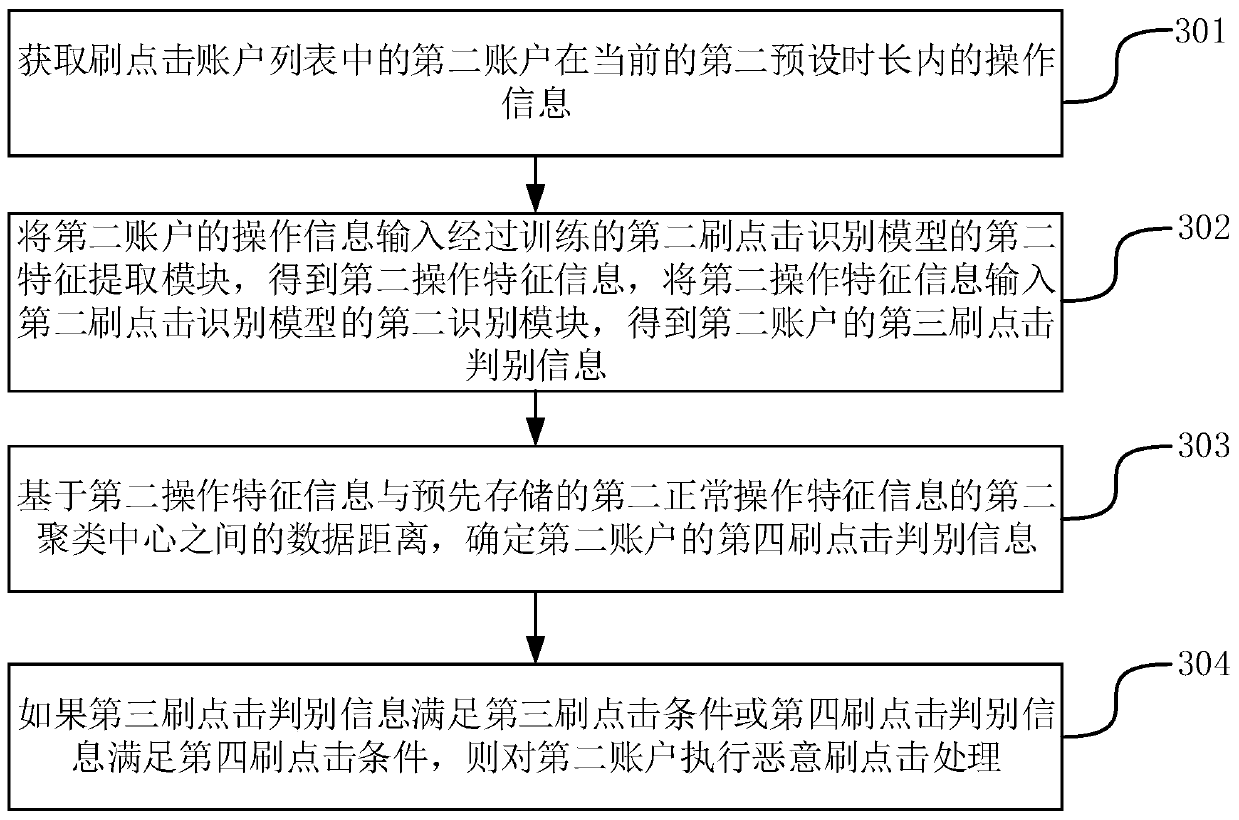
Method, device and equipment for detecting malicious click refreshing operation, and storage medium
ActiveCN111177725AEasy to identifyPlatform integrity maintainanceMachine learningFeature extractionThe Internet
The invention discloses a method, a device and equipment for detecting malicious click refreshing operation, and a storage medium, and belongs to the technical field of the Internet. The method comprises the steps of obtaining operation information of a first account within a first preset duration; inputting the operation information of the first account into a first feature extraction module of atrained first swipe click recognition model to obtain first operation feature information, and inputting the first operation feature information into a first recognition module of the first swipe click recognition model to obtain first swipe click discrimination information of the first account; based on a data distance between the first operation feature information and a first clustering centerof pre-stored normal operation feature information, determining second brushing and clicking discrimination information of the first account; and if the first click refreshing judgment information meets the first click refreshing condition or the second click refreshing judgment information meets the second click refreshing condition, executing malicious click refreshing processing on the first account. By the adoption of the scheme, whether malicious click refreshing operation behaviors exist in the account can be effectively detected.
Owner:GUANGZHOU BAIGUOYUAN INFORMATION TECH CO LTD
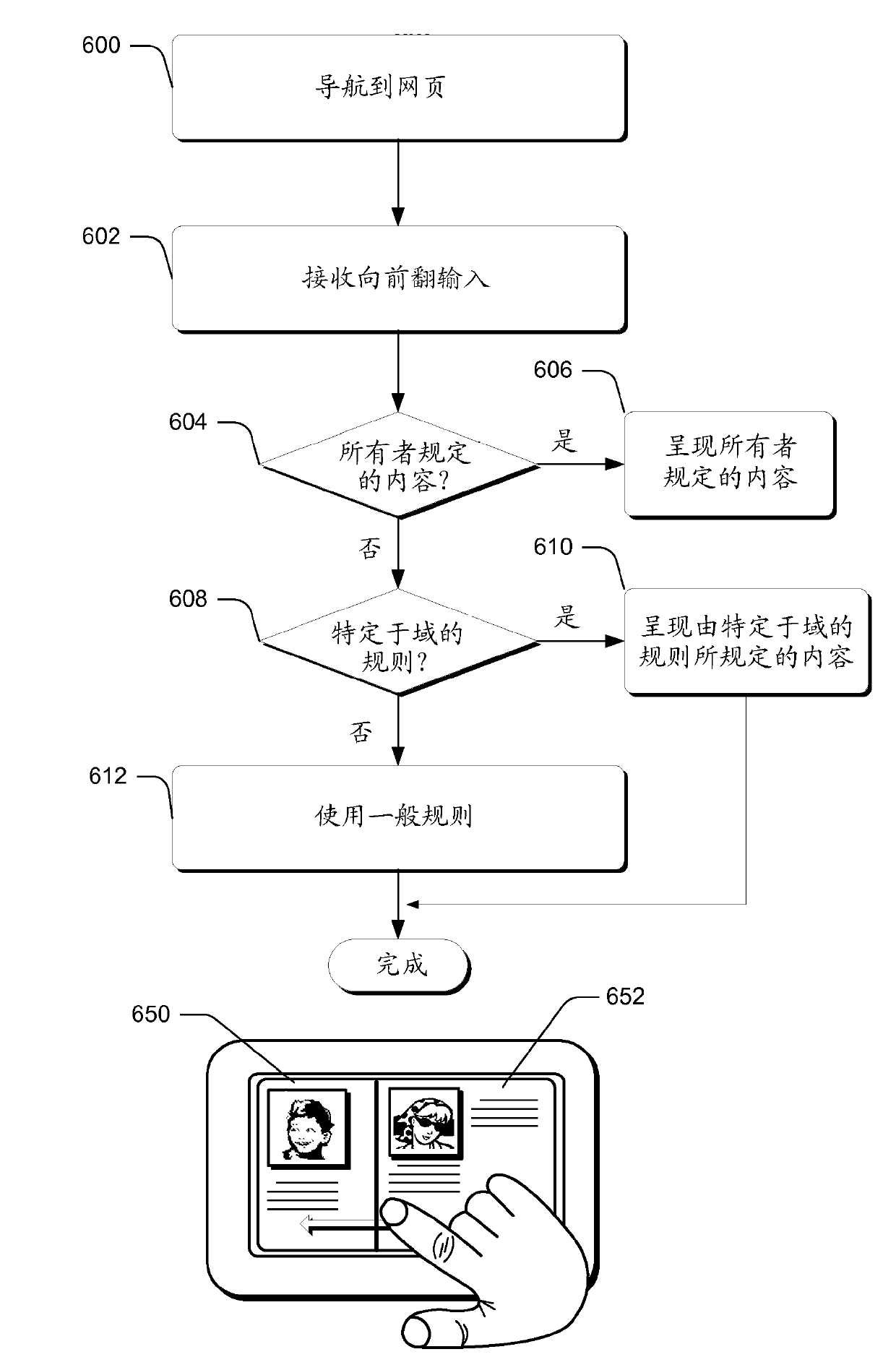
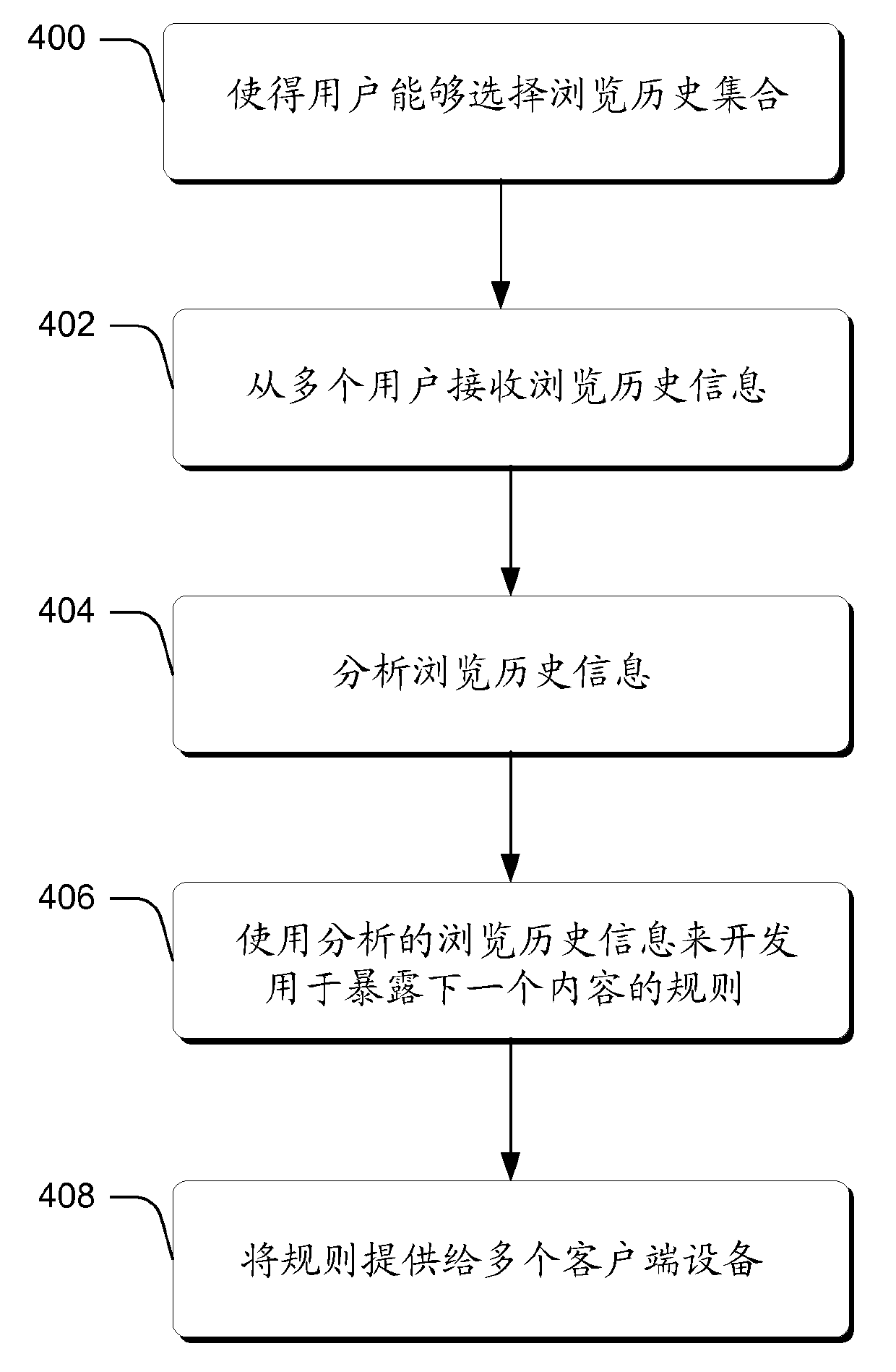
Flip ahead
In one or more embodiments, a flip ahead input, such as a gesture, provides touch users with an ability to easily navigate various websites. The flip ahead input can be utilized to advance to the next portion of relevant content. In at least some embodiments, the flip ahead input resides in the form of a forward swipe. In one or more embodiments, the flip ahead input is configured to be utilized in association with an aggregated browsing history from multiple users. The aggregated browsing history is analyzed to generate rules that are then downloaded to a client device and used by a suitably-configured web browser to ascertain the next portion of content when a flip ahead input is received.
Owner:MICROSOFT TECH LICENSING LLC
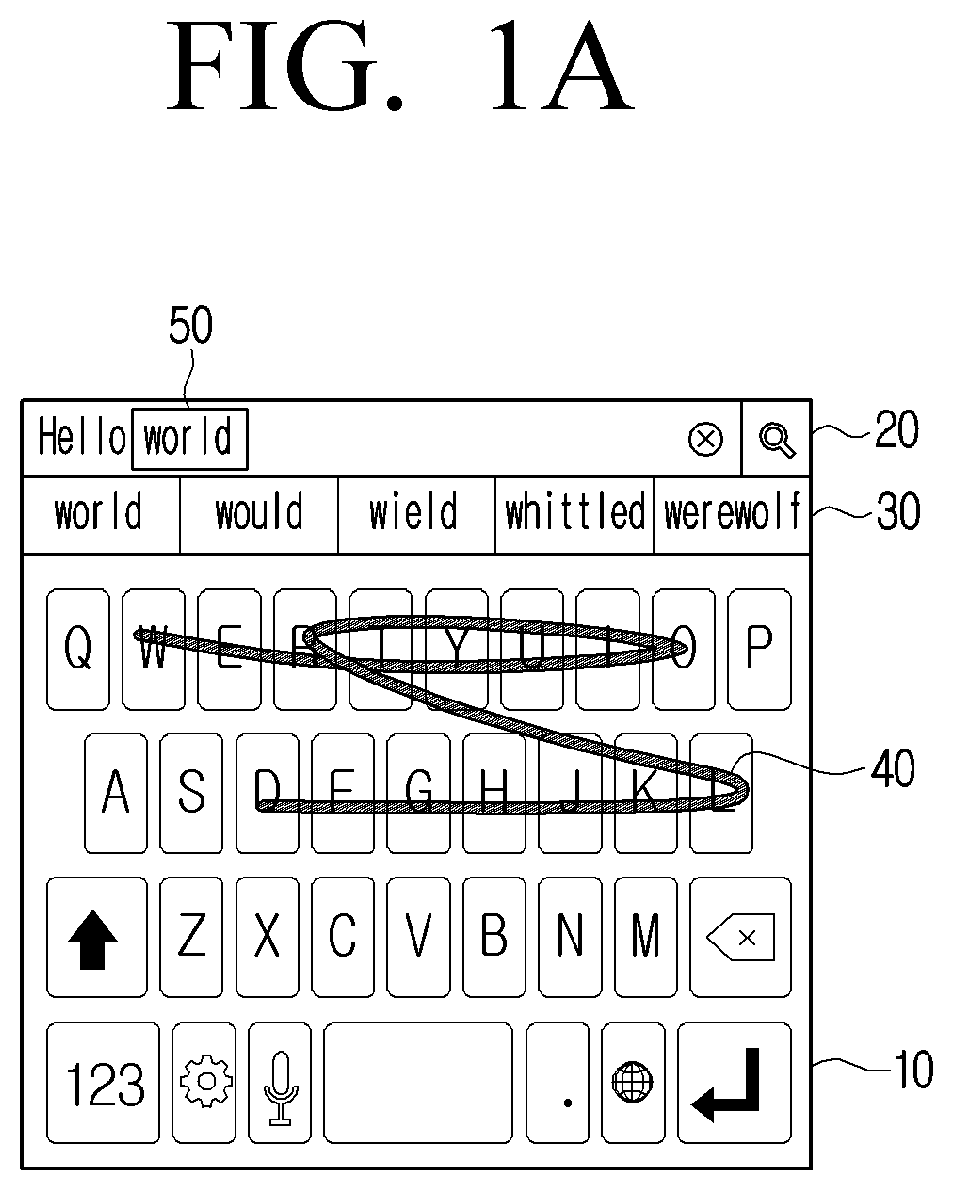
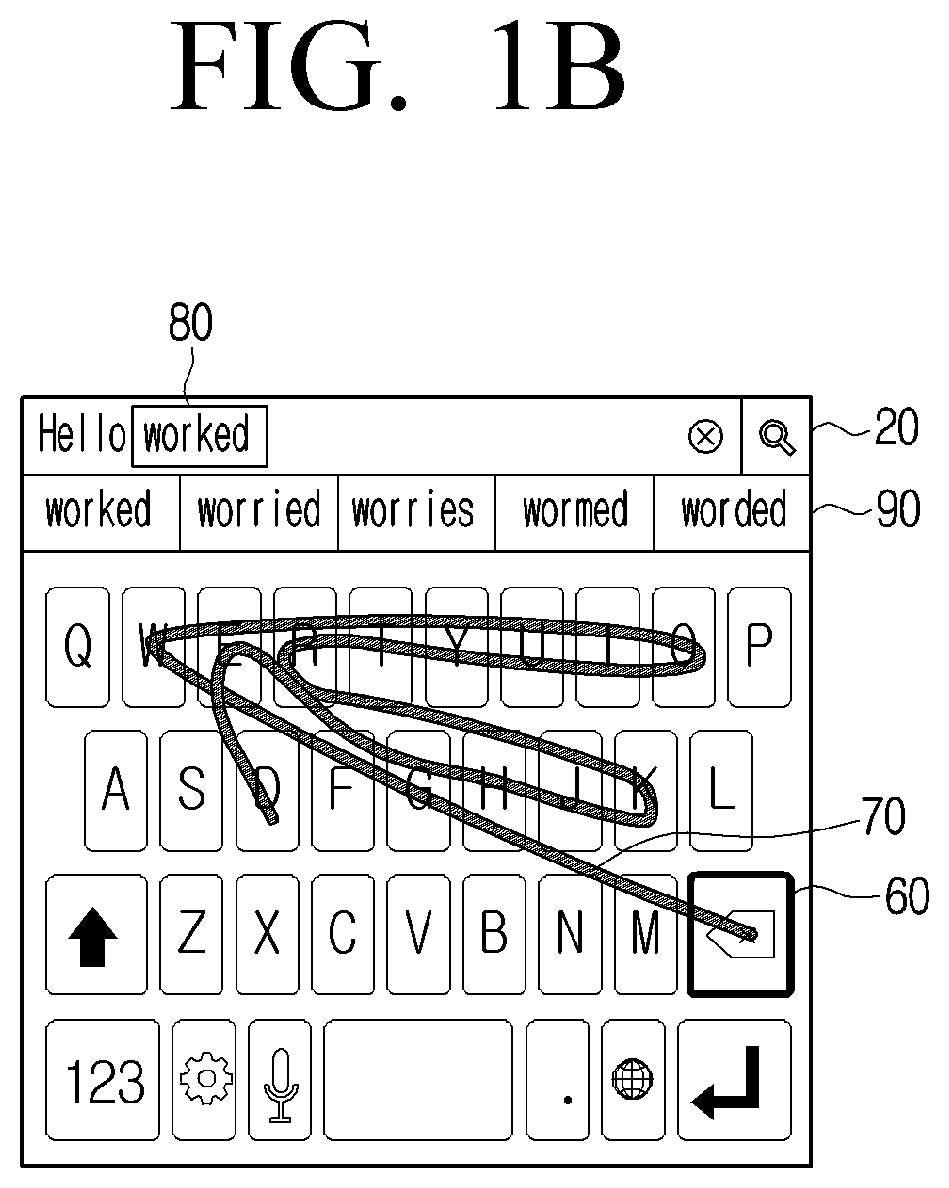
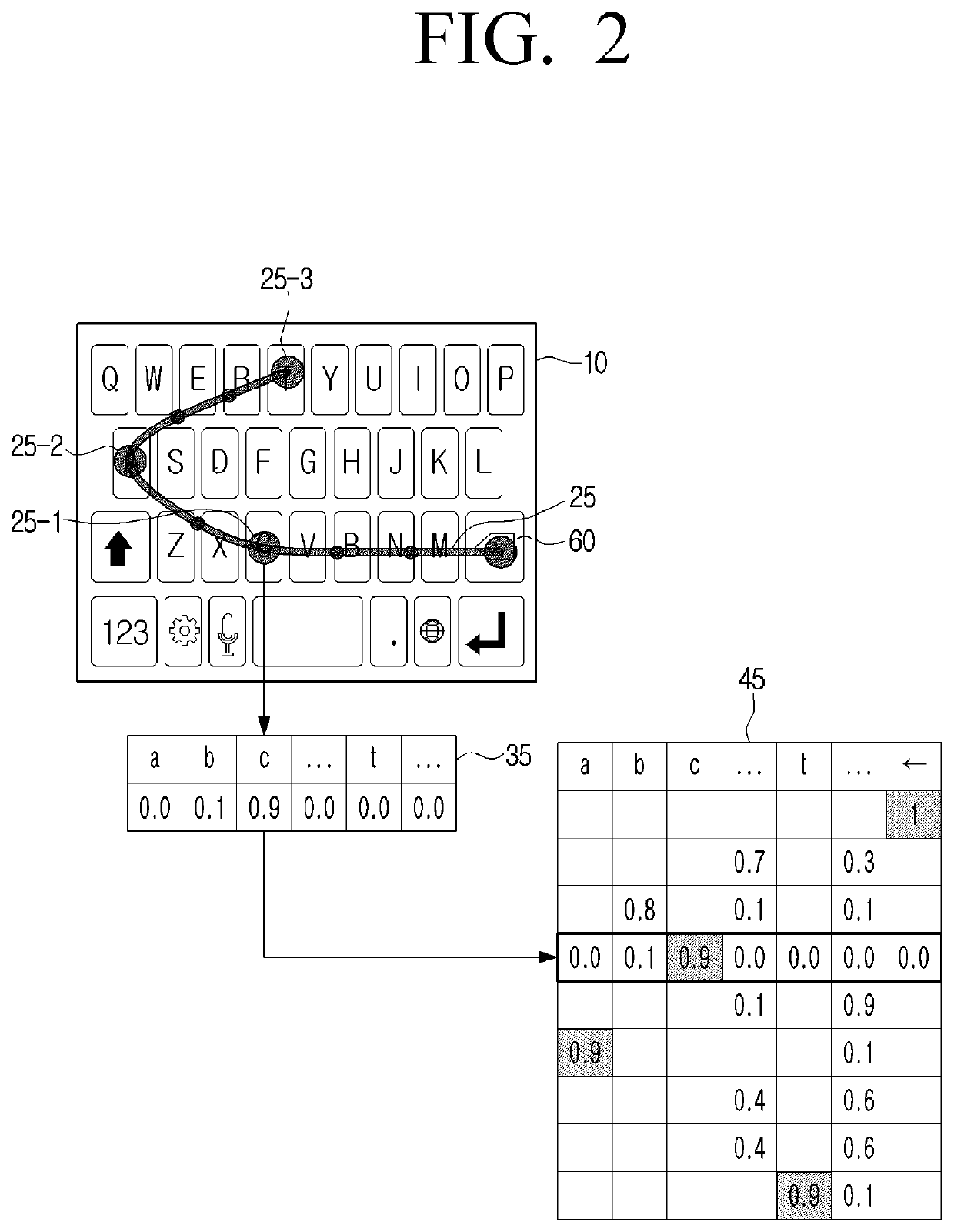
Electronic apparatus for recommending words corresponding to user interaction and controlling method thereof
PendingUS20220035999A1Efficient inputReduced scoreNatural language data processingInput/output processes for data processingComputer hardwareDisplay device
An electronic apparatus and a controlling method thereof are provided. The electronic apparatus includes a memory storing an artificial intelligence model, a display configured to display a keypad screen, and a processor configured to, based on a swipe interaction contacting a first key and connecting a plurality of keys being on the keypad screen, remove from the input window, a first word that is pre-input to the input window, obtain a word candidate list corresponding to the swipe interaction by inputting information regarding a trajectory of the swipe interaction to an artificial intelligence model, and control the display to display, in the input window, a second word having a highest score in the word candidate list.
Owner:SAMSUNG ELECTRONICS CO LTD
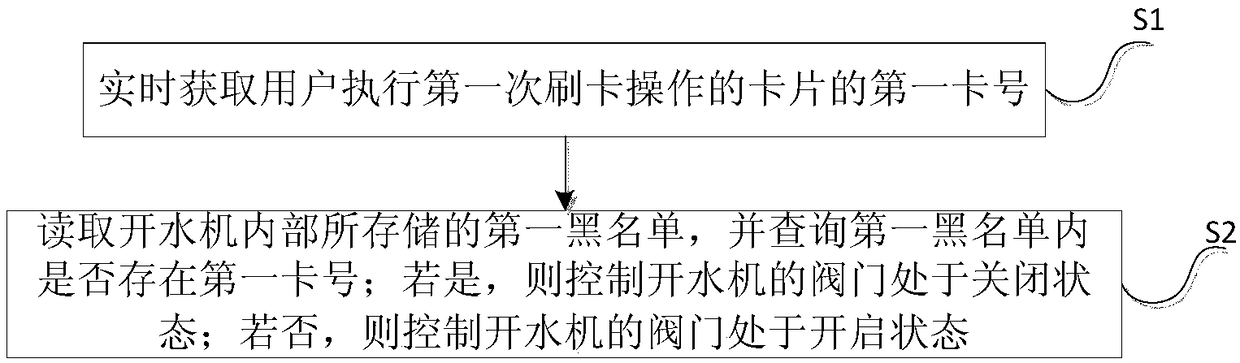
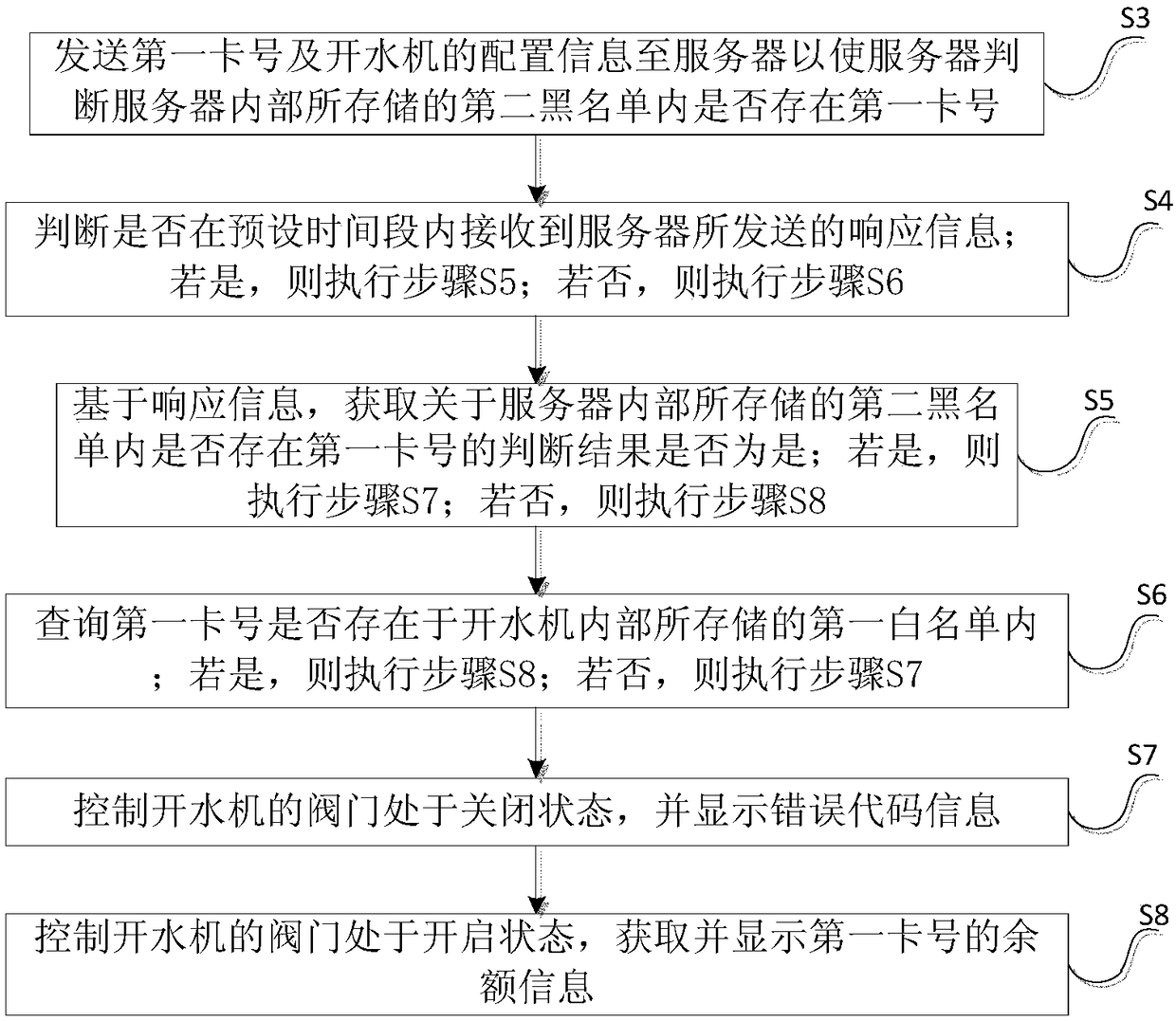
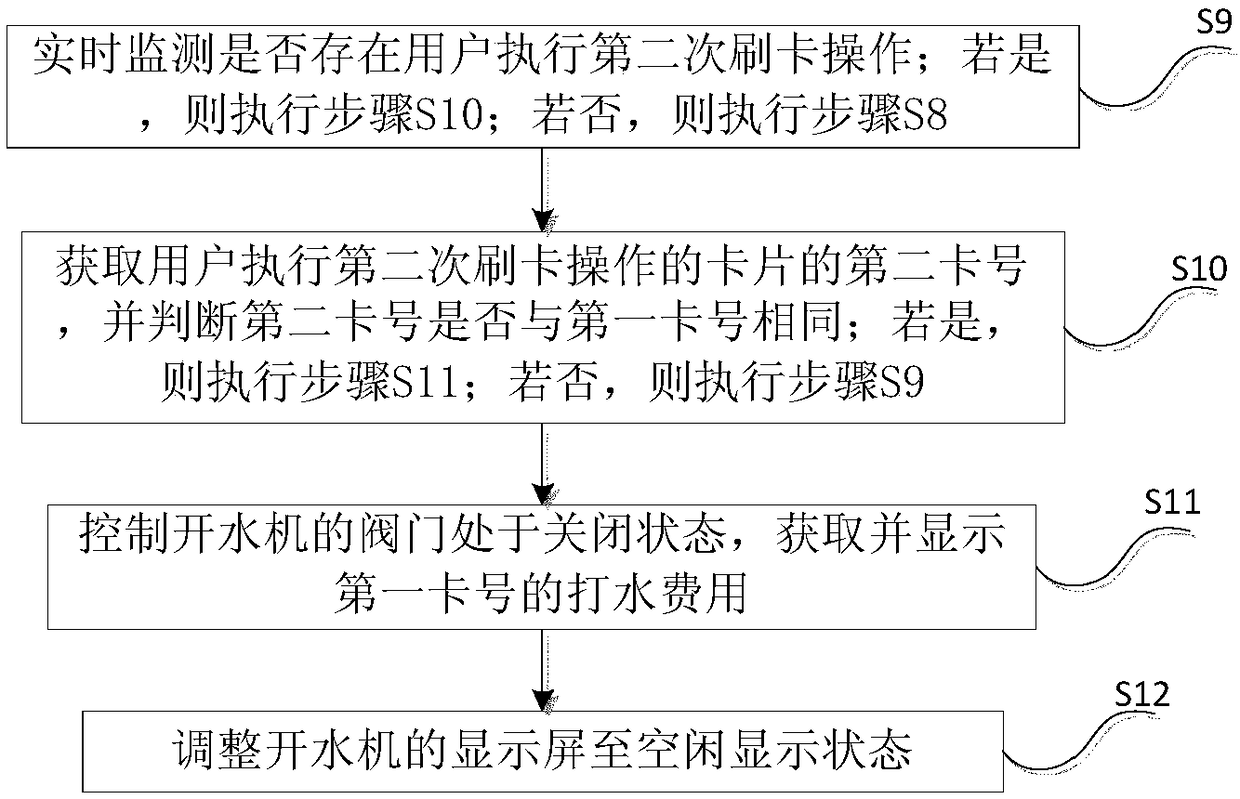
Authentication method and system based on internet of things intelligent water boiling machine
ActiveCN109326052AImprove experienceReduce loadApparatus for dispensing fluids/granular materialsProtocol authorisationComputer hardwareThe Internet
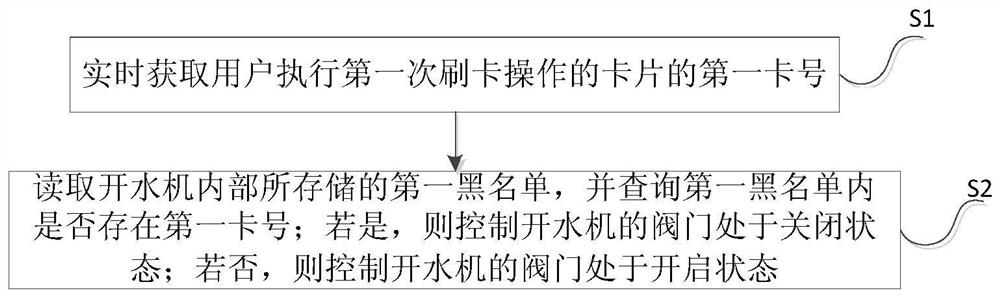
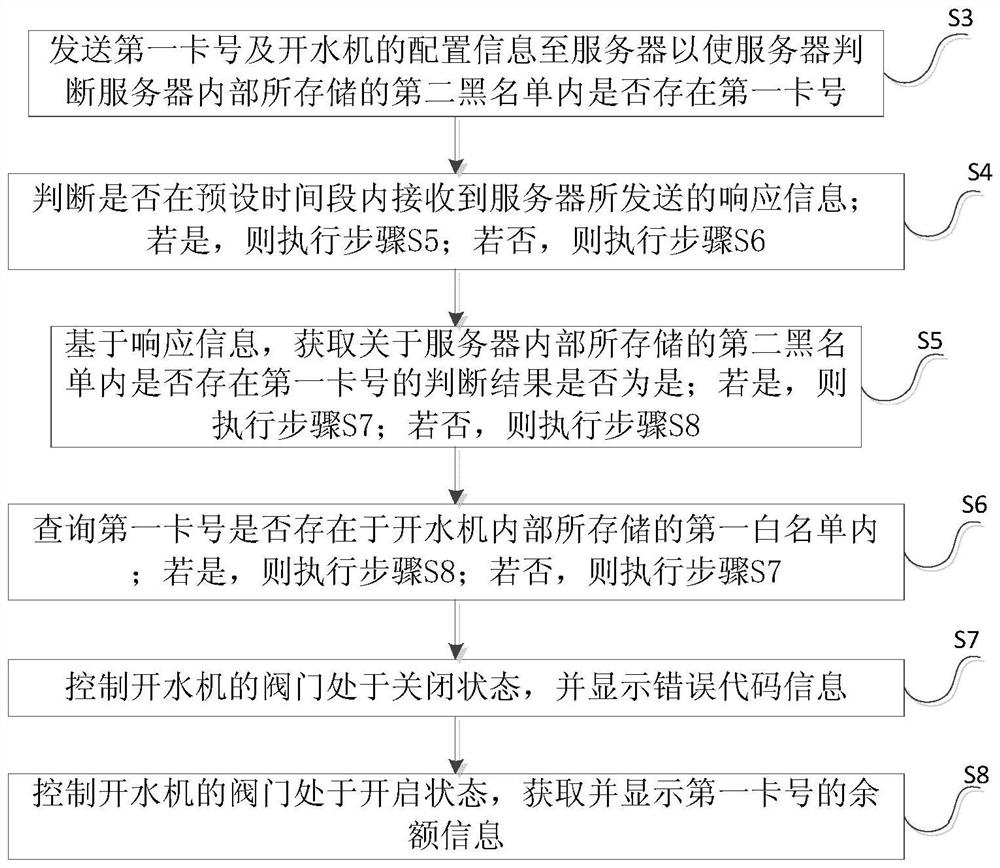
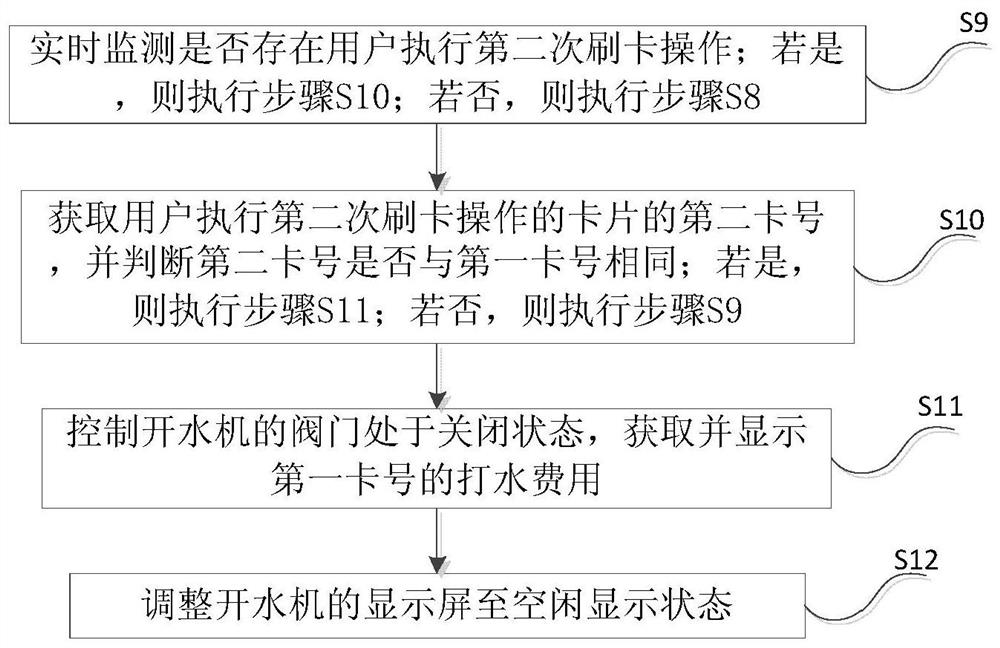
The invention discloses an authentication method and system based on an internet of things intelligent water boiling machine. The authentication method comprises the steps that S1, the first card number of a card for a user to perform the first card swiping operation is obtained in real time; S2, a first blacklist stored in the water boiling machine is read, and whether the first card number exists in the first blacklist or not is queried; if yes, a valve of the water boiling machine is controlled to be in a closed state; and if not, the valve of the water boiling machine is controlled to be in an open state. According to the technical scheme of the authentication method and system, the card number of the card used by the user to perform the card swipe operation is to authenticated based on the first black list stored in the internet of things intelligent water boiling machine, so that the problem of waste of resources caused by malicious card swiping by the user is solved, and the user experience is effectively improved.
Owner:ZHEJIANG UNIVERSITY OF SCIENCE AND TECHNOLOGY +1
Bill swiping recognition method and bill swiping recognition device
ActiveCN109285009BImprove recognition efficiencyEfficient identificationCommerceEngineeringIdentification device
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
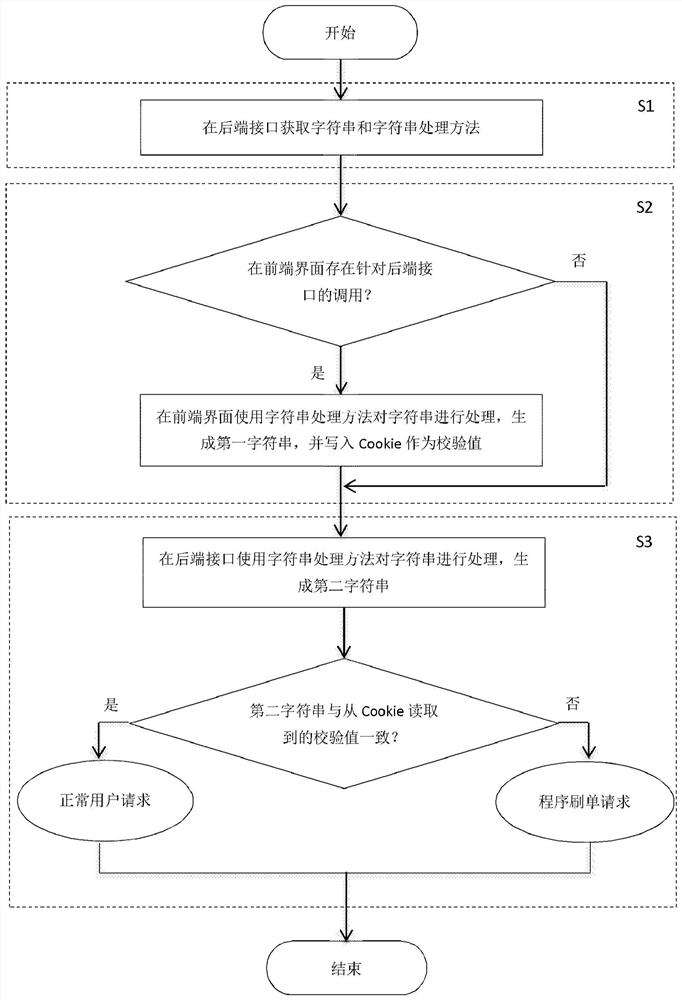
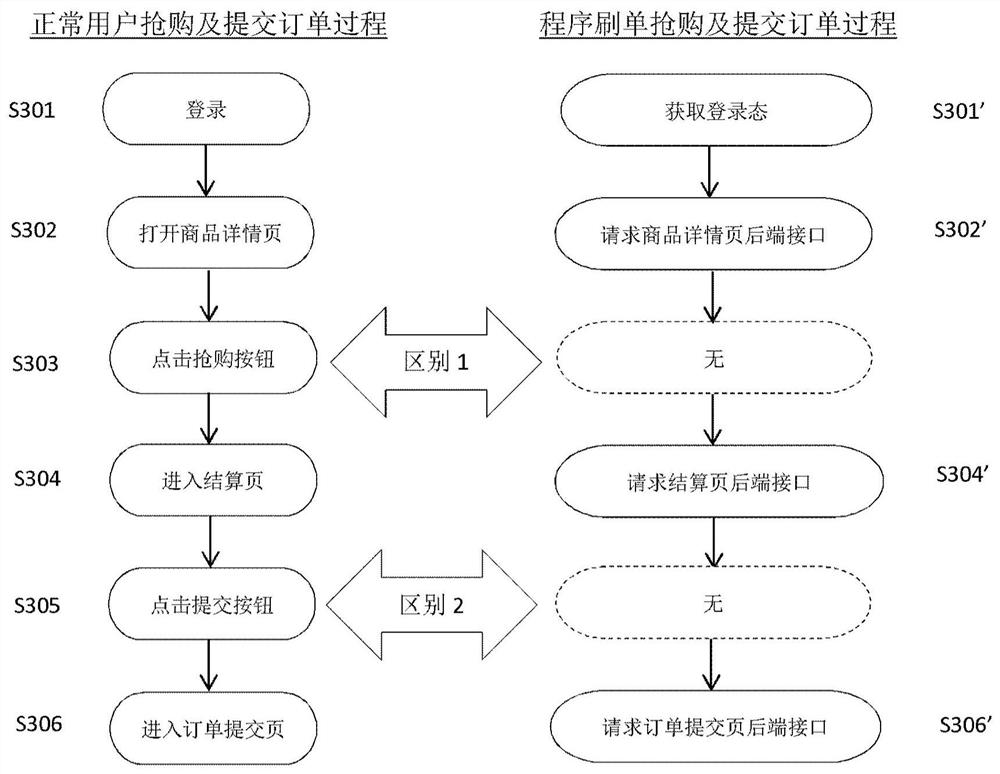
Method and device for program brushing identification
ActiveCN108305078BImprove experienceSimple algorithmCommerceProgramming languageSoftware engineering
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Quick service terminal for identifying customers using legacy customer identification instruments
Apparatus for providing a QST are disclosed herein. The QST may identify a customer in response to a swipe of a customer identifying instrument. The QST may include a reading head, a processor, a keypad, and a communications medium. The reading head may detect identification information in response to the swipe of the instrument. The identification information may be associated with a personal identification instrument. The processor may bypass a PIN acceptance state and perform a search for at least one banking record corresponding to the personal identification instrument. The processor may terminate the identification session in response to failure to obtain a record corresponding to the identification instrument. In response, at least in part, to identification of at least one record that corresponds to the personal identification instrument, the communications medium may receive a session-auth instruction from a remote location. The session-auth instruction may initiate a banking session.
Owner:BANK OF AMERICA CORP
Anti-tailgating linkage interlock safety door entry and exit app record query system
ActiveCN111275865BEfficiencyConvenient and fast record queryIndividual entry/exit registersEngineeringRecords management
The invention discloses an anti-tailgating linkage interlocking safety door entry and exit APP record query system, including the first card swiping block controlling the opening and closing of the first baffle and the second baffle through the server, and the second card swiping block controlling the third baffle and the second baffle through the server The opening and closing of the fourth baffle, the transmitter and the receiver are used to receive and count the number of people standing after the user swipes the card on the first card swiping block. Through the record of the user swiping the card for access control, the administrator can conveniently and quickly query the records through the APP. And the access control exception information that can be pushed by the server can record the problem in time, which solves the problems of inconvenient query and record through the PC terminal and untimely problem record in the prior art; through the first card swiping block, the second card swiping block, the transmitter and With the combined use of the device, even if people follow into the channel after swiping the card through the first card swiping block, they cannot leave the channel normally through the second card swiping block, which solves the problem that people often follow through the access control in the existing access control.
Owner:安徽扬子安防股份有限公司
An authentication method and system for an intelligent water boiler based on the Internet of Things
ActiveCN109326052BImprove experienceReduce loadApparatus for dispensing fluids/granular materialsProtocol authorisationThe InternetEngineering
The invention discloses an authentication method and system based on an internet of things intelligent water boiling machine. The authentication method comprises the steps that S1, the first card number of a card for a user to perform the first card swiping operation is obtained in real time; S2, a first blacklist stored in the water boiling machine is read, and whether the first card number exists in the first blacklist or not is queried; if yes, a valve of the water boiling machine is controlled to be in a closed state; and if not, the valve of the water boiling machine is controlled to be in an open state. According to the technical scheme of the authentication method and system, the card number of the card used by the user to perform the card swipe operation is to authenticated based on the first black list stored in the internet of things intelligent water boiling machine, so that the problem of waste of resources caused by malicious card swiping by the user is solved, and the user experience is effectively improved.
Owner:ZHEJIANG UNIVERSITY OF SCIENCE AND TECHNOLOGY +1
Swipe card system with data protection
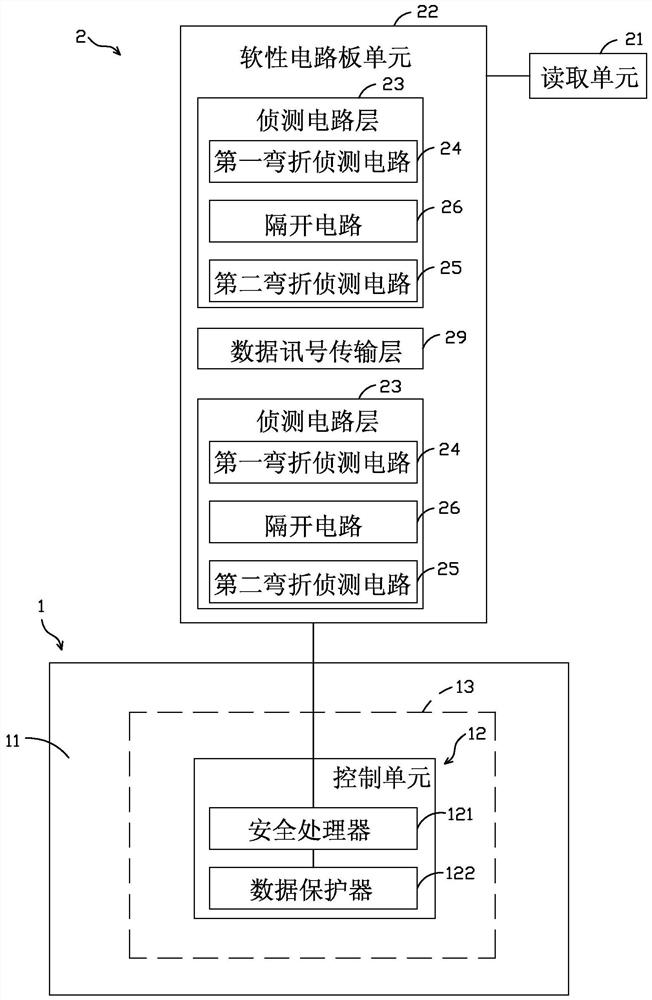
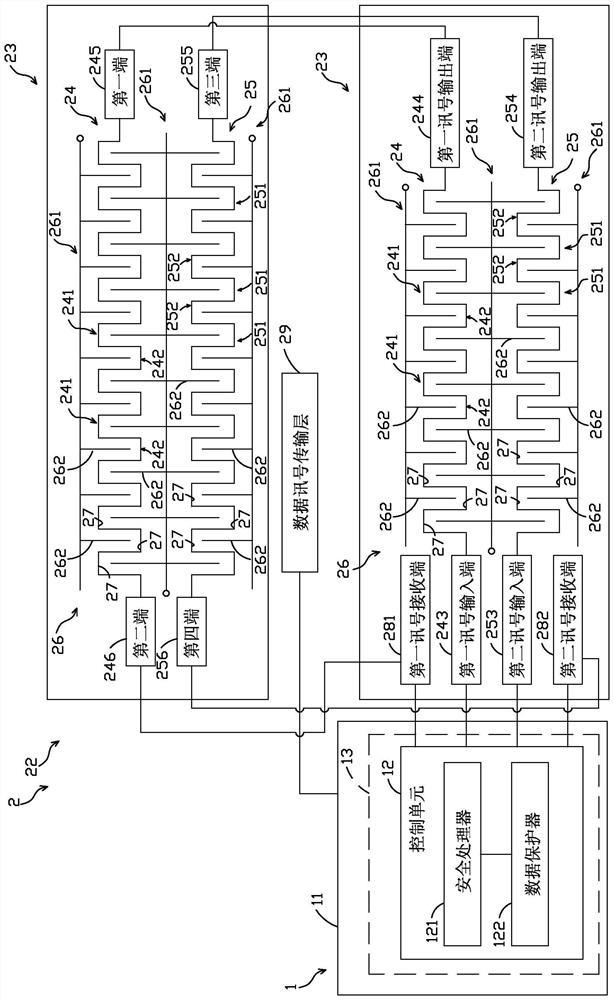
ActiveCN109215214BImprove data protectionImprove the implementation of this data protection modeCash registersCoded identity card or credit card actuationComputer hardwareFlexible circuits
A card swiping system with data protection function comprises a safety processing device and a reading device linked to the safety processing device. The security processing device includes a control unit. The reading device includes a flexible circuit board unit connected with the control unit. The flexible circuit board unit has two detection circuit layers. Each detection circuit layer has a first bend detection circuit for a first signal transmission, a second bend detection circuit for a second signal transmission, and a partition for a third signal transmission circuit. The first bend detection circuit and the second bend detection circuit respectively form a plurality of bend intervals. The isolated circuit has a plurality of branch line parts stretched in the corresponding bending intervals. In this way, the branch line effectively separates the two adjacent bends that are spaced apart from each other in the first and second bend detection circuits, so that the bends cannot be easily connected by an external bridge, effectively Improve data protection.
Owner:MITAC COMP (SHUN DE) LTD +1
ECU flash fault processing method and device, electronic equipment and storage medium
PendingCN114265382AImprove work efficiencyLow costElectric testing/monitoringEngineeringEmbedded system
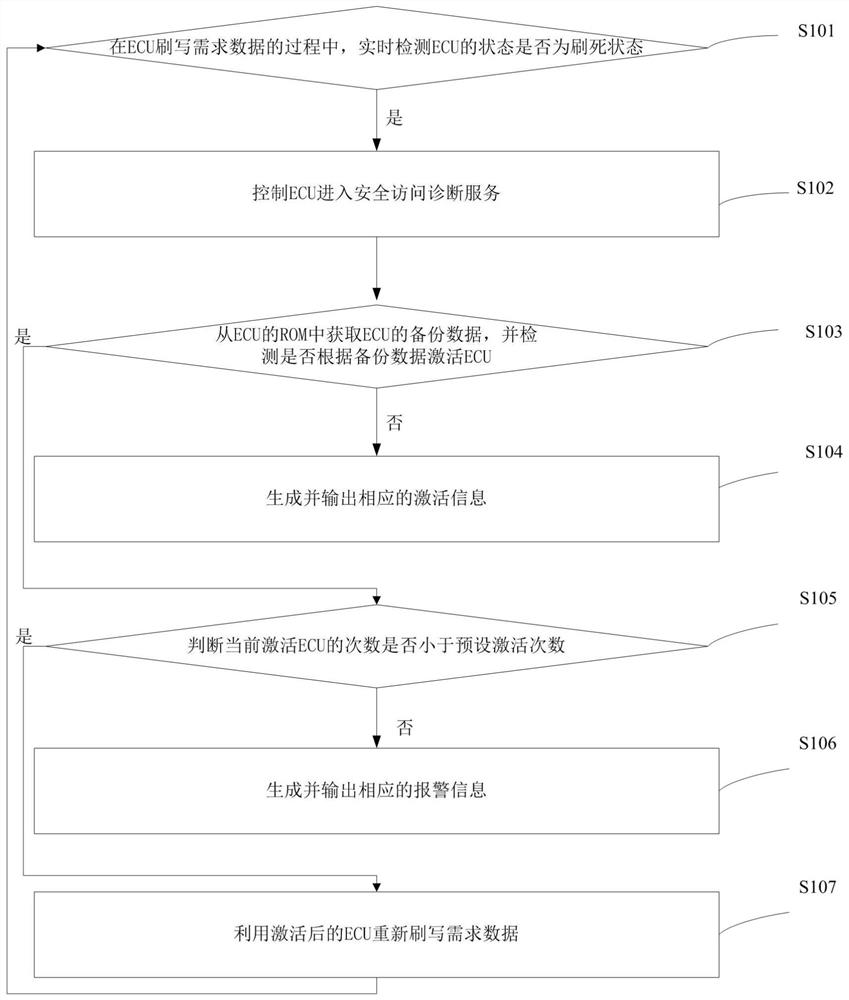
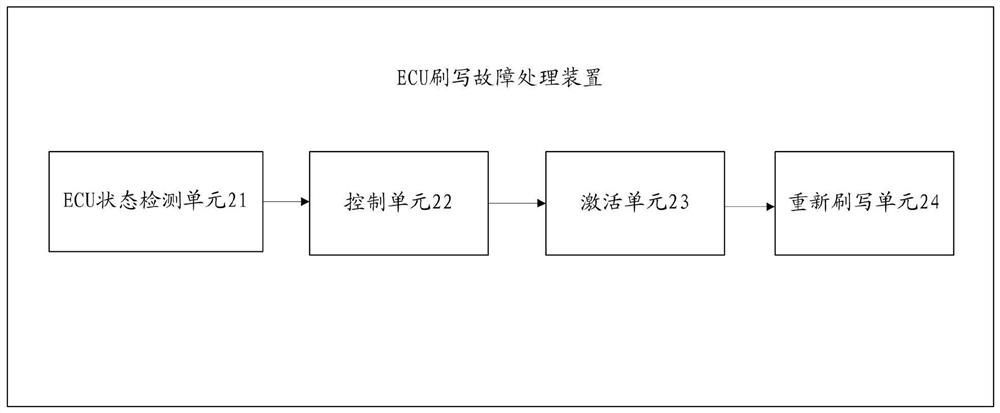
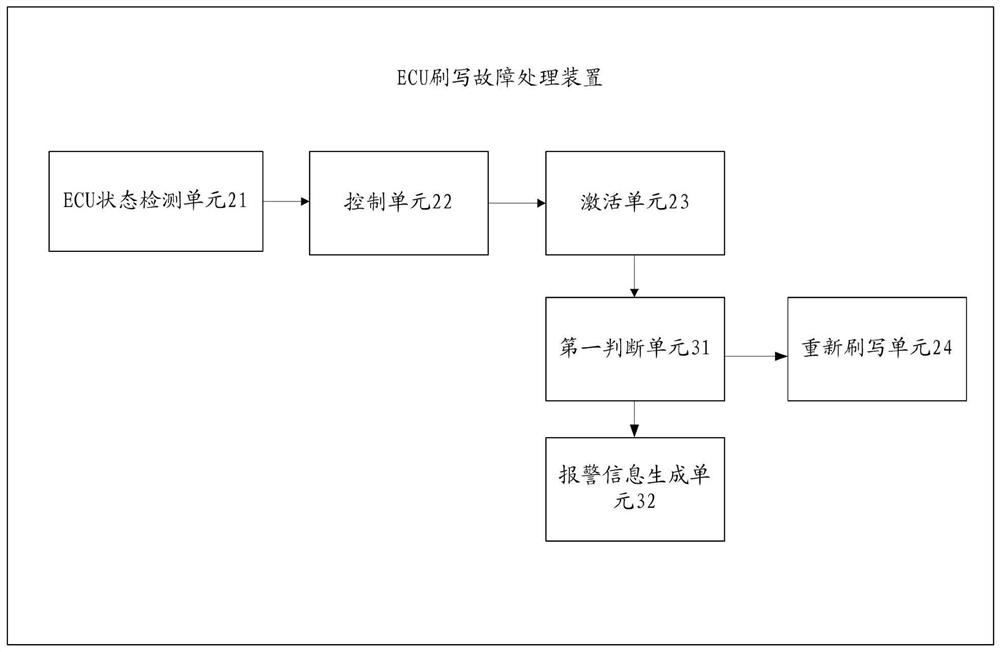
The invention provides an ECU flashing fault processing method and device, electronic equipment and a storage medium, and the method comprises the steps: detecting whether the state of an ECU is a dead flashing state or not in real time in a process that the ECU flashes required data; if it is detected that the state of the ECU is a swipe-dead state, the ECU is controlled to enter a security access diagnosis service; acquiring backup data of the ECU from an ROM (Read Only Memory) of the ECU, and detecting whether the ECU is activated or not according to the backup data; and if the ECU is successfully activated, re-writing the required data by using the activated ECU. Based on the method and the device, the cost can be reduced, and the ECU flashing efficiency can be improved.
Owner:WEICHAI POWER CO LTD +1
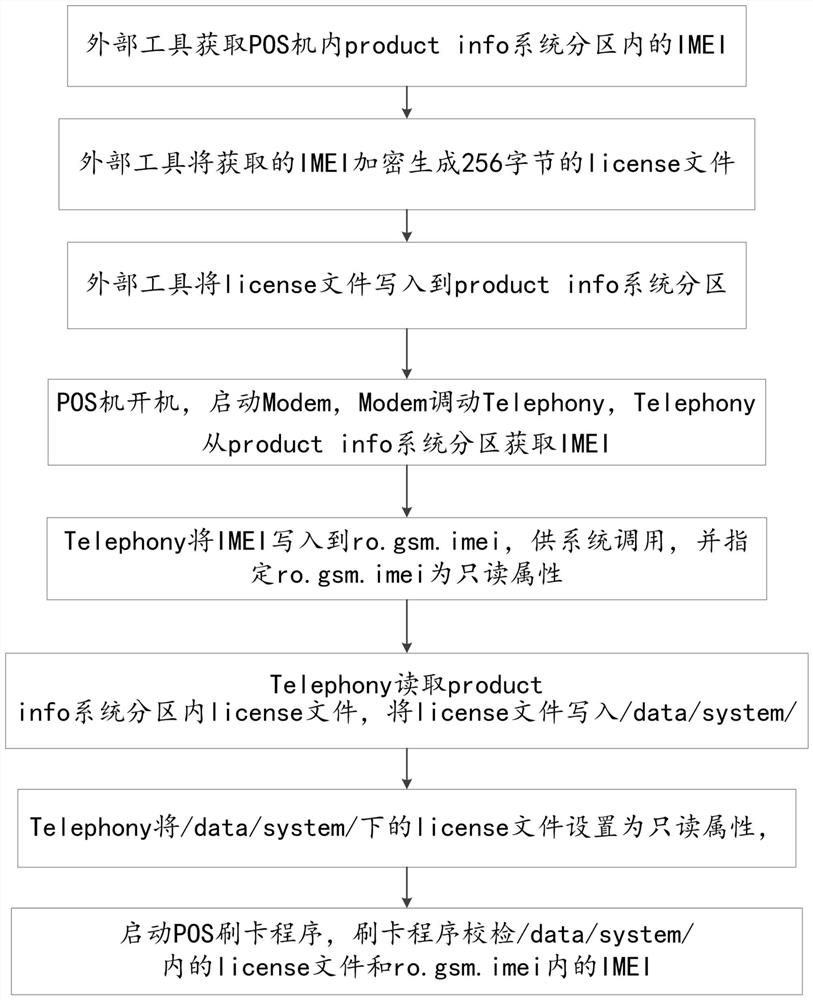
A POS machine terminal decoding library authorization code verification method
ActiveCN108595962BAvoid lossPrevent malicious tamperingDigital data protectionCash registersSoftware engineeringDirectory
Owner:SHENZHEN TOPWISE COMM CO LTD
A kind of anti-duplication and anti-tampering method of IC card
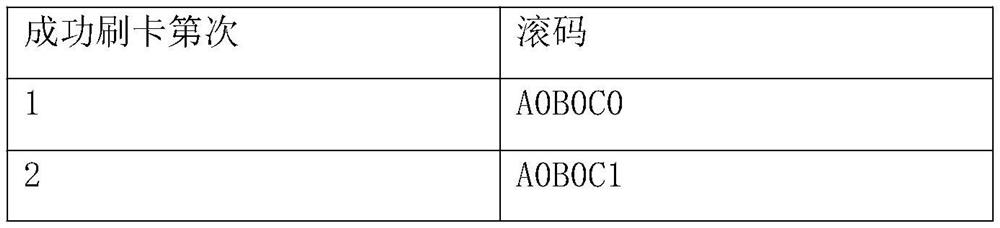
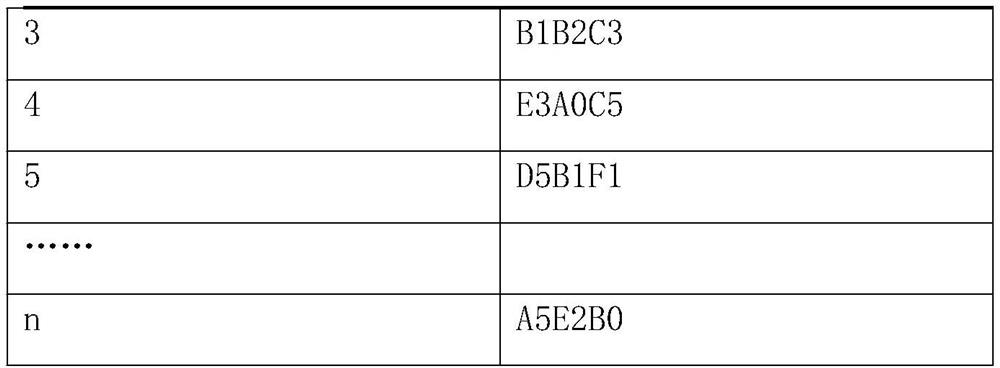
InactiveCN109753837BAvoid coexistenceEnhanced tamper resistance levelSensing by electromagnetic radiationTamper resistanceCode book
The invention provides a method for realizing anti-duplication and anti-tampering of IC cards at the reader-writer level. The first codebook and the second codebook are added to the reader-writer, and these two codebooks are only known by the manufacturer and are kept secret from the outside world, and the reader-writer will write the rolling code and the rolling code of the first codebook to the IC card. The encryption code of the second codebook is used as the authentication element for the next swiping of the IC card, which can ensure that the actual capacity of the business system will not increase due to a certain card being copied, or the actual capacity of the business system will not be increased due to a certain card being copied and the data has been tampered with. Management has lost. The present invention has the following advantages: 1) It can prevent the coexistence of the original card and the copy card in the business system; 2) The anti-tampering level of the data in the card is greatly improved; 3) There is no need to change the hardware structure of the reader-writer; 4) When authenticating There is no need for networking between different readers.
Owner:FOSHAN WABON ELECTRONICS TECH
Dual-slot, quick service terminal for identifying customers using legacy customer identification instruments
Apparatus for providing a QST are disclosed herein. The QST may identify a customer in response to a swipe of a customer identifying instrument. The QST may include a reading head, a processor, a keypad, and a communications medium. The reading head may detect identification information in response to the swipe of the instrument. The identification information may be associated with a personal identification instrument. The processor may bypass a PIN acceptance state and perform a search for at least one banking record corresponding to the personal identification instrument. The processor may terminate the identification session in response to failure to obtain a record corresponding to the identification instrument. In response, at least in part, to identification of at least one record that corresponds to the personal identification instrument, the communications medium may receive a session-auth instruction from a remote location. The session-auth instruction may initiate a banking session.
Owner:BANK OF AMERICA CORP
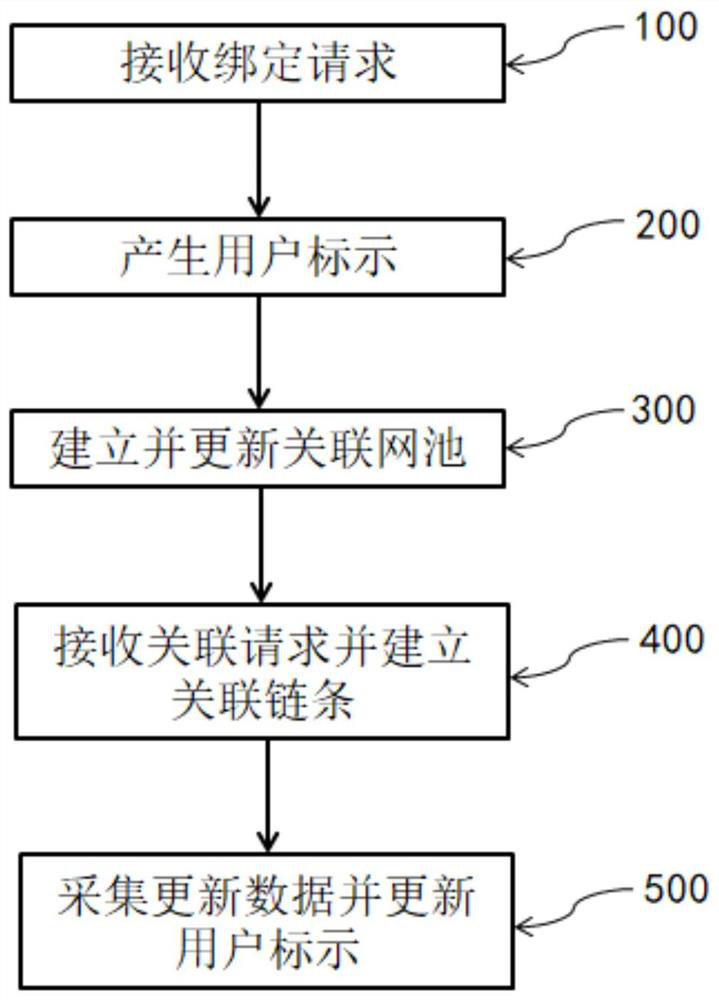
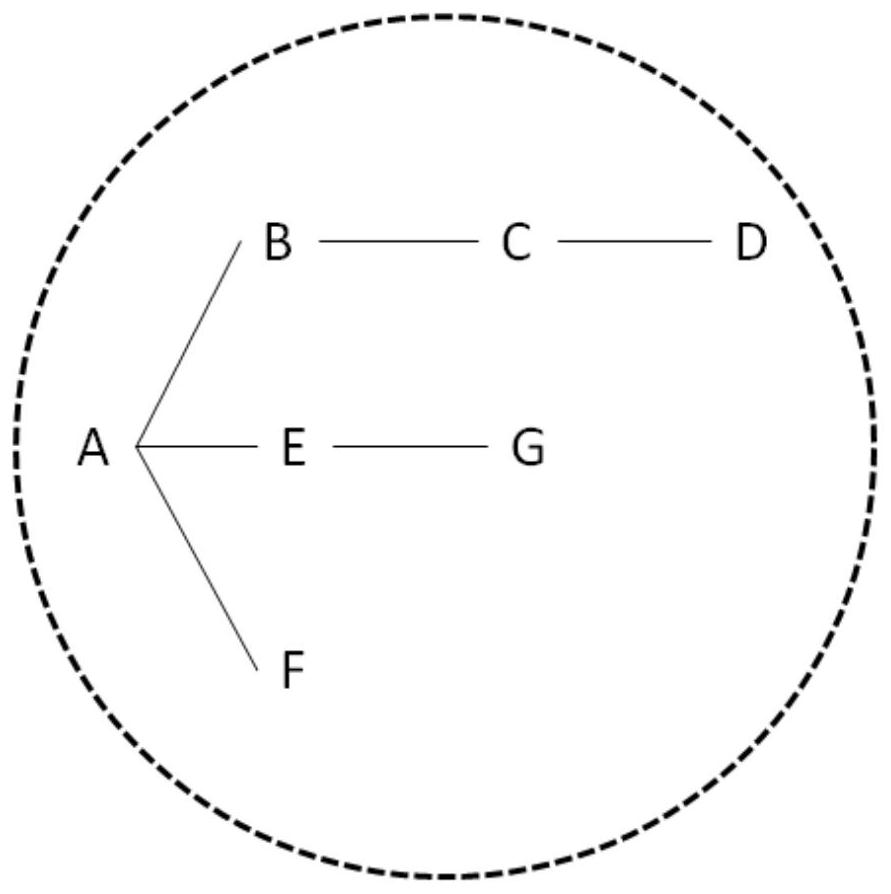
Population flow monitoring method
ActiveCN113241191AImprove securityFast monitoring responseData processing applicationsEpidemiological alert systemsEngineeringUser identifier
The invention discloses a population flow monitoring method. The method comprises the following steps: receiving a binding request; generating a user identifier according to the binding request, wherein the user identifier comprises an eID, a type tag and a state tag; establishing and updating an associated network pool according to the user identifier; receiving an association request, querying two user identifiers in an association network pool according to the association request, and establishing an association chain between the two user identifiers; and acquiring update data and updating the state label marked by the user in the association network pool according to the update data. According to the ivnention, contact between people is converted into data point-to-point network chain connection through code scanning, card swiping or face recognition. The method has the beneficial effects that firstly, one point is tracked through a network chain, so that the monitoring response speed is increased; secondly, identity information and place and place records are not included, so that the data security is improved; 3, the data volume only comprises an association chain and time, so that data volume is small, the monitoring response speed is further improved, and cyclic updating is facilitated.
Owner:上海璟勰信息技术有限公司
Card skimmer detection
A brush fraud detection device (402) is selectively interfaced to part of a chip card reader (401) integrated in a terminal. The swiping detection means is configured to detect when a swiping device is inserted into the chip card reader during a card transaction at the terminal, and to take automatic action in response thereto.
Owner:NCR CORP
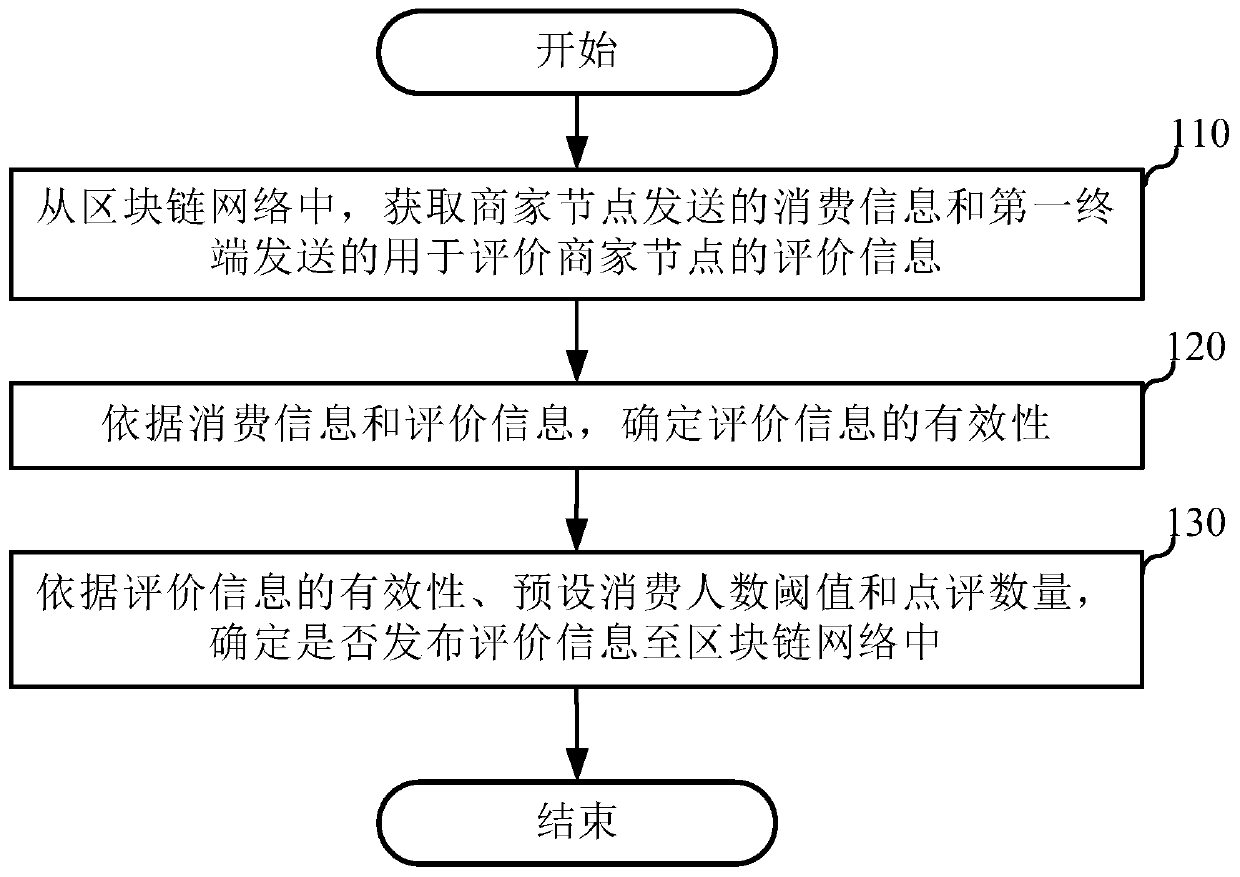
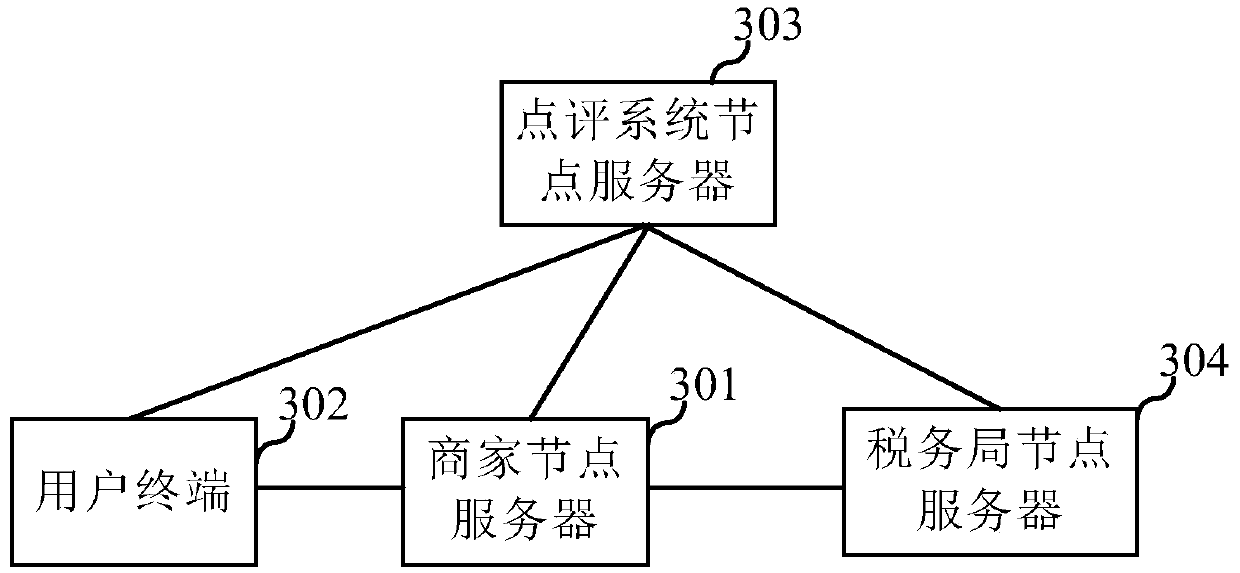
Commenting method and device
ActiveCN111415230AAvoid brushingIncrease authenticityPayment protocolsBuying/selling/leasing transactionsChain networkData mining
The invention discloses a commenting method and device, and the method comprises the steps: obtaining the consumption information transmitted by a merchant node and the evaluation information which istransmitted by a first terminal and is used for evaluating the merchant node from a block chain network, and enabling the consumption information to comprise the commenting number; determining the validity of the evaluation information according to the consumption information and the evaluation information; and determining whether to publish the evaluation information to the block chain network according to the validity of the evaluation information, a preset consumer number threshold and the comment number. By determining the validity of the evaluation information, invalid evaluation information is prevented from being published to a network, and the validity of the evaluation information is ensured; and by obtaining a preset consumer number threshold value and a commenting quantity included in consumption information, whether the evaluation information is published or not is determined, so that the comment quantity can be controlled within the range of the preset consumer number threshold, the situation that merchants swipe orders is avoided, the authenticity of the comment information is improved, the rights and interests of consumers are guaranteed, and the user experience isimproved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Water supply tank device for smart home plant wall
ActiveCN109315180BReduce power consumptionEasy to controlSelf-acting watering devicesCultivating equipmentsNetwork connectionControl signal
The invention discloses a water supply tank device for a plant wall in a smart home. Strip water diversion cotton is placed in a flower pot. The system is connected to the network by setting a LoRa node module. The module receives the signal and transmits it to the control circuit. The control circuit controls the solenoid valve to open and supplies water to the water supply tank. The water level is monitored by the water level monitoring device A on the water supply tank. After reaching the preset value, it is fed back to the control circuit. The control circuit sends an order to close the solenoid valve. Complete a plant water replenishment; easy to control; LoRa node module has low power consumption, self-organizing network, transmission advantages that can coexist with the existing network, and can be controlled through the Internet through mobile phones, solving the problem that there is no plant wall based on smart home systems at present From the remote control of water supply, it is inconvenient for people who are away from home for a long time to water the plant wall.
Owner:绵阳鹏志远科技有限公司
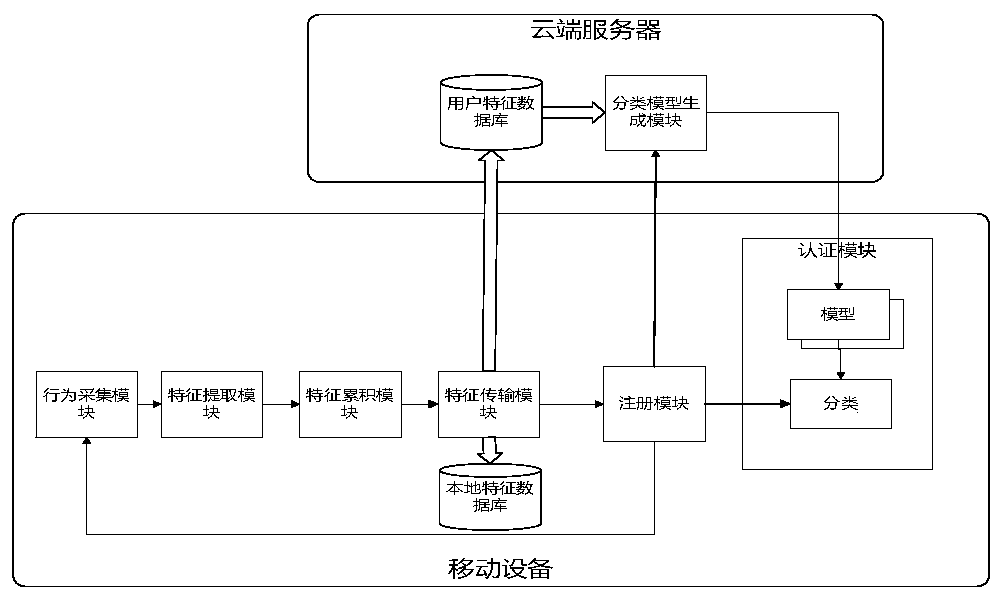
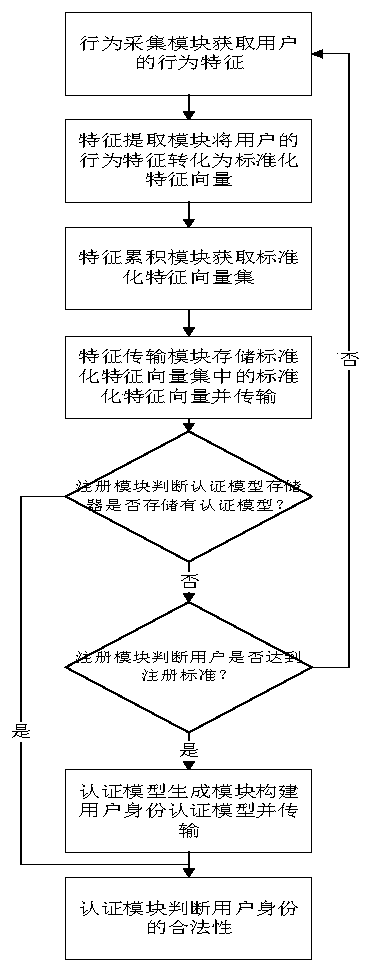
Identity authentication method based on user sliding and clicking behavior
ActiveCN108549806BEasy to chooseImprove accuracyDigital data authenticationFeature extractionInternet privacy
The invention provides a user sliding and clicking behavior-based identity authentication method, which is used for solving the problem of relatively low user identity authentication accuracy in an implicit authentication process. The method comprises the implementation steps that a behavior collection module obtains behavior features of a user; a feature extraction module converts the behavior features of the user into standardized eigenvectors; a feature accumulation module obtains a standardized eigenvector set; a feature transmission module stores and transmits the standardized eigenvectors in the standardized eigenvector set; a registration module judges whether an authentication model memory stores an authentication model or not; the registration module judges whether the user reaches registration standards or not; an authentication model generation module builds and transmits a user identity authentication model; and an authentication module judges the legality of a user identity. According to the method, sliding and clicking behaviors of the user are accumulated together for performing identity authentication on the user, so that the user identity authentication accuracy isimproved.
Owner:XIDIAN UNIV
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com