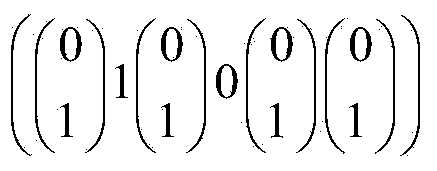Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
137 results about "Access control matrix" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
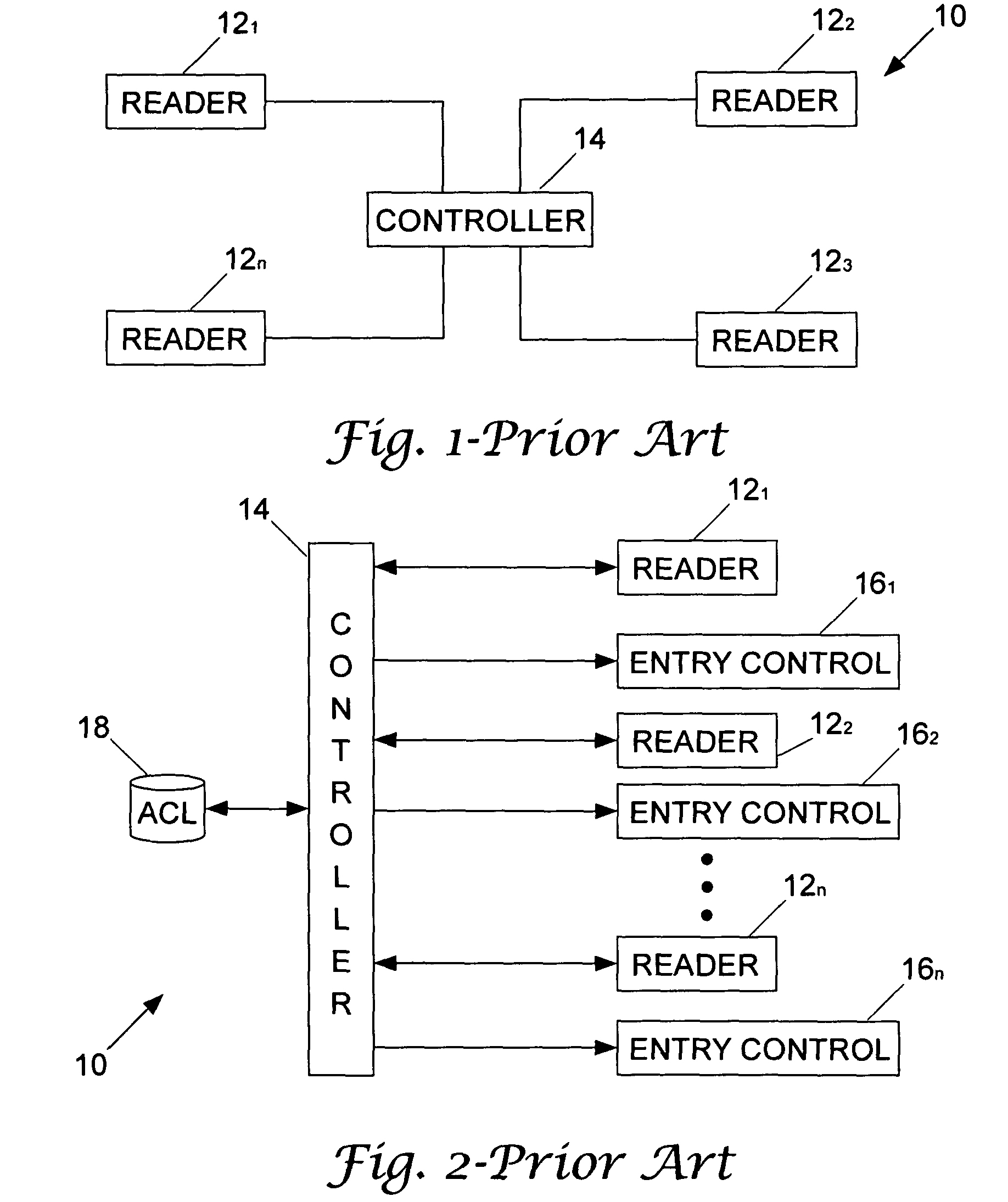
In computer science, an Access Control Matrix or Access Matrix is an abstract, formal security model of protection state in computer systems, that characterizes the rights of each subject with respect to every object in the system. It was first introduced by Butler W. Lampson in 1971.
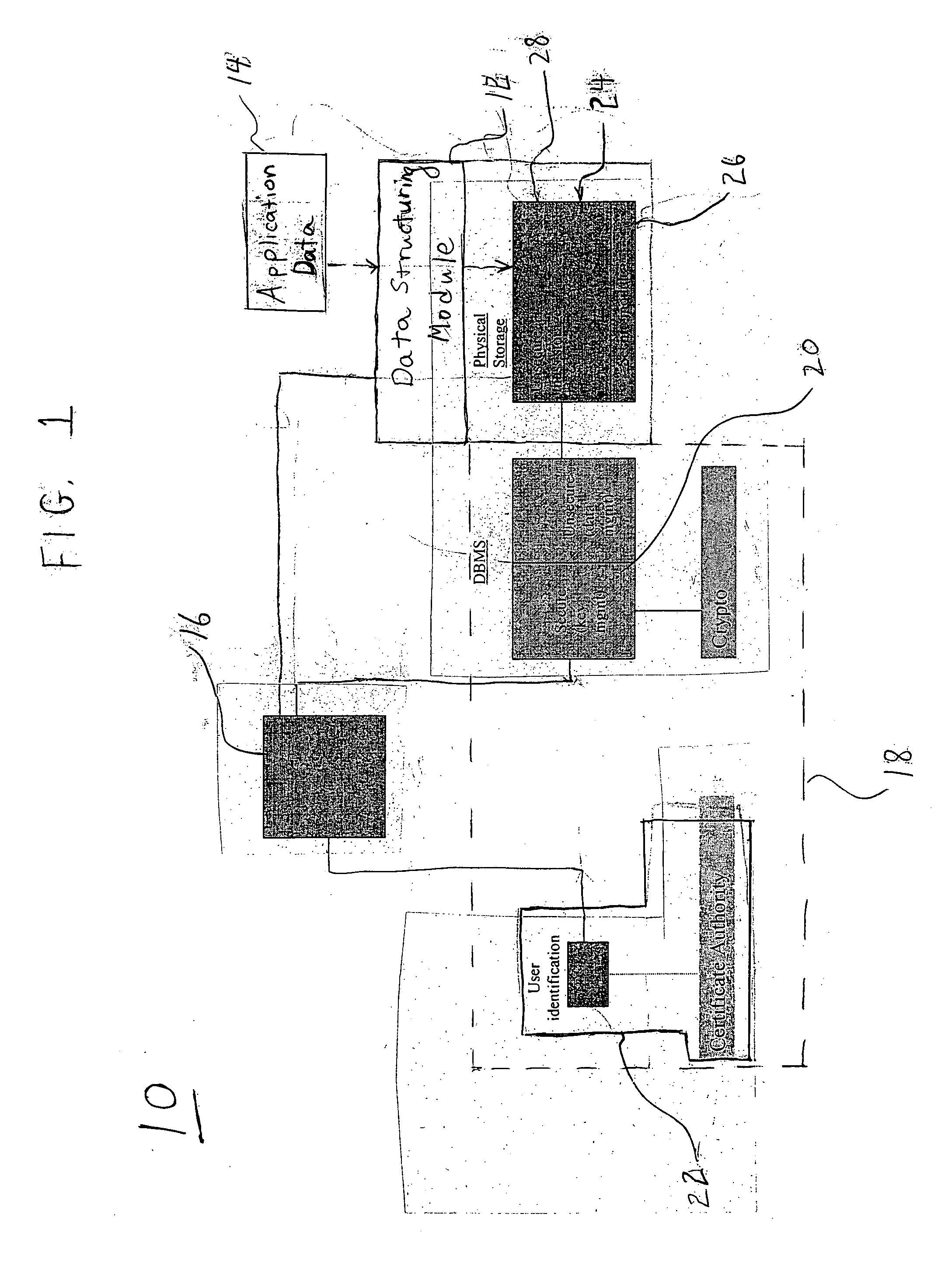
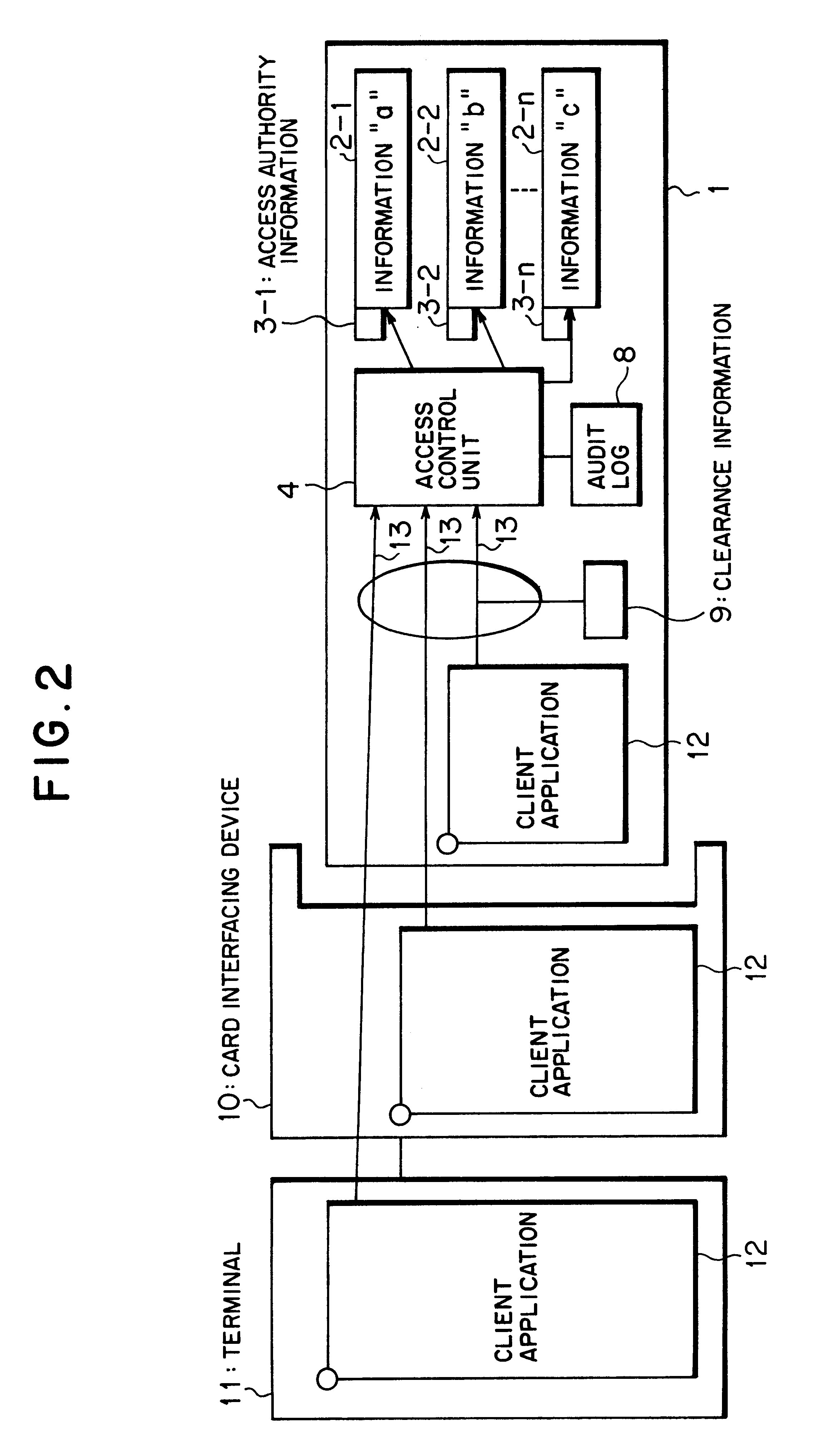
Method and system for providing a secure multi-user portable database
ActiveUS20070006322A1Easy to useLimited storage capabilityFinanceDigital data processing detailsMedical recordFile allocation
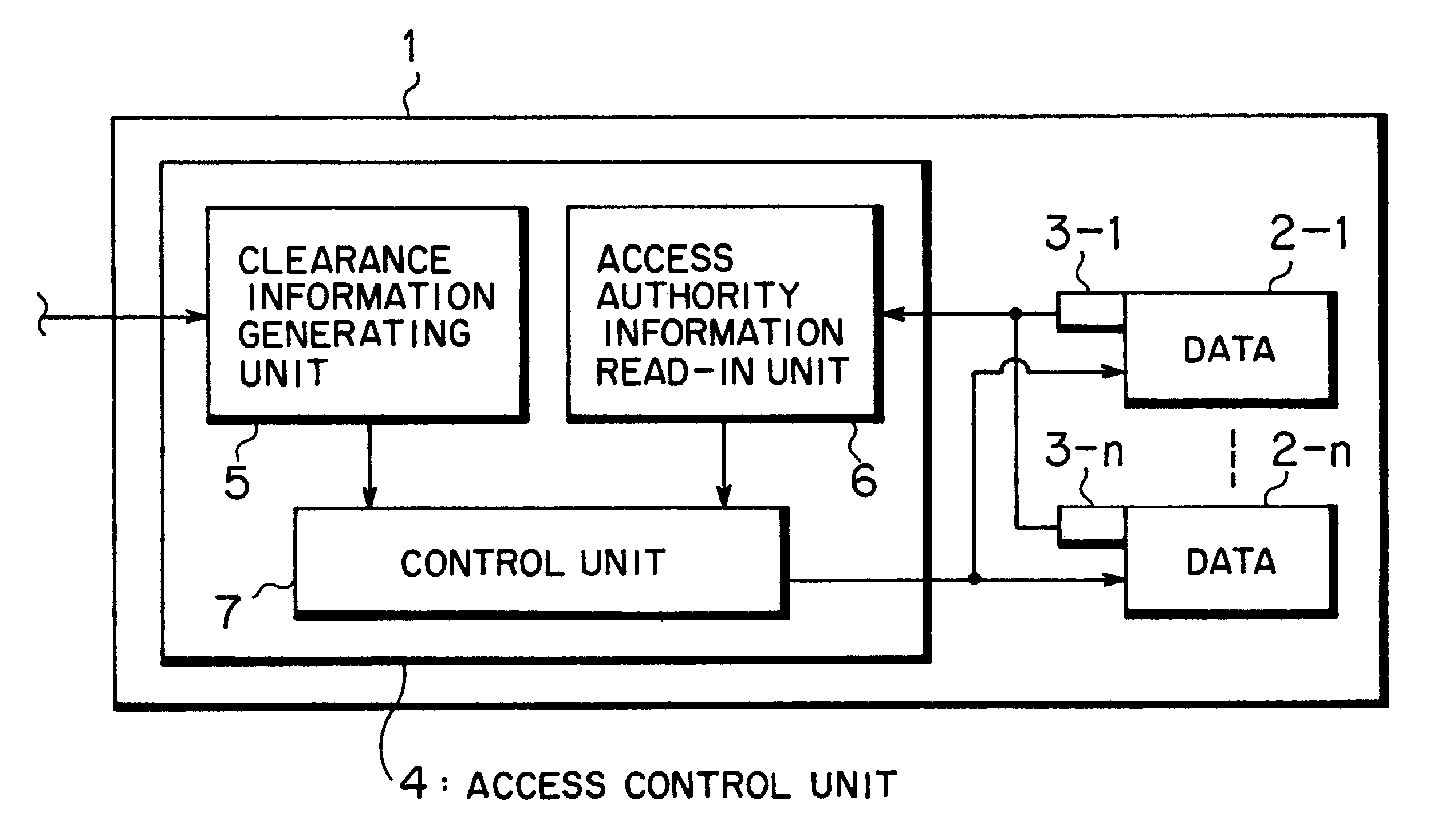
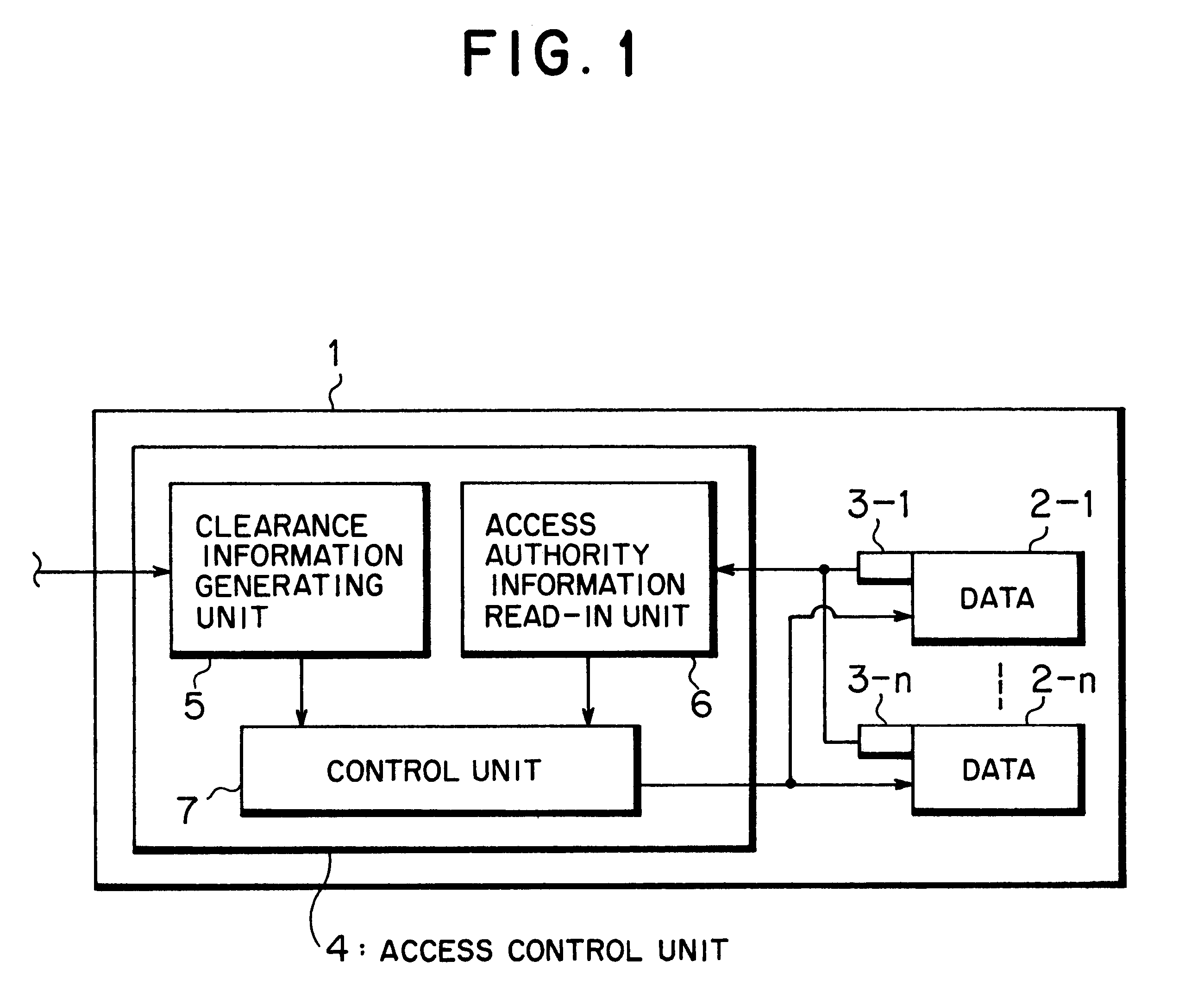
A system and method for providing, managing, and accessing a multi-user secure portable database using secure memory cards is provided. The database has a secure portion for storing security keys and a non-secure portion for encrypted data files. Access to the encrypted data files is controlled by assigning access rights through an access control matrix to each encrypted data file according to a hierarchical structure of users. A user requesting access is identified in the hierarchy, associated with a key for allowing the requested access, and the requested access allowed to a file in accordance with the rights allocated through the access control matrix. A patient can selectively grant access to encrypted medical records on his card to a physician. Authentication of the owner / patient is preferably required. Other records required by emergency medical personnel are readable from the same card without requiring permission from the patient.
Owner:PRIVAMED
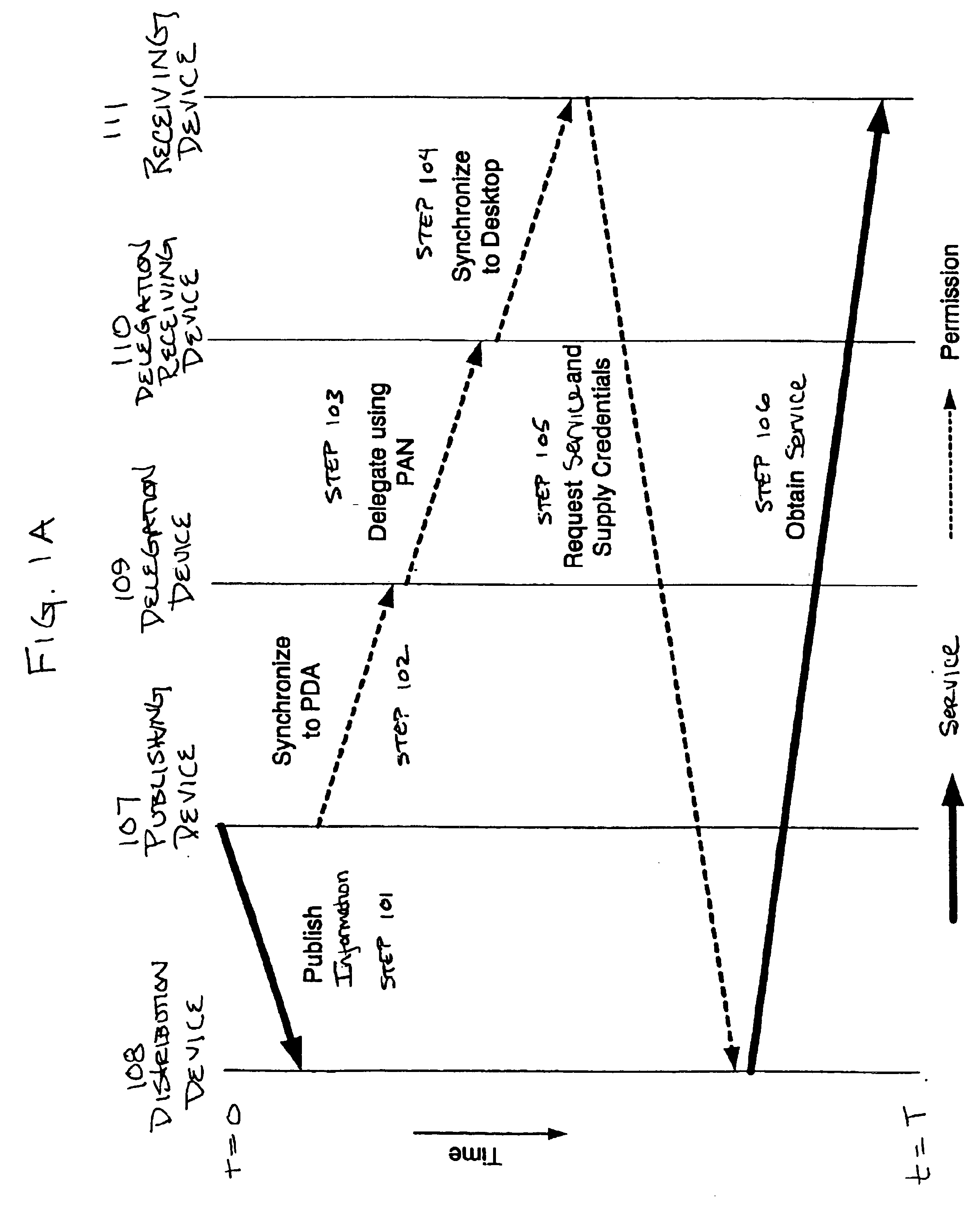
Method for automatically generating list of meeting participants and delegating permission
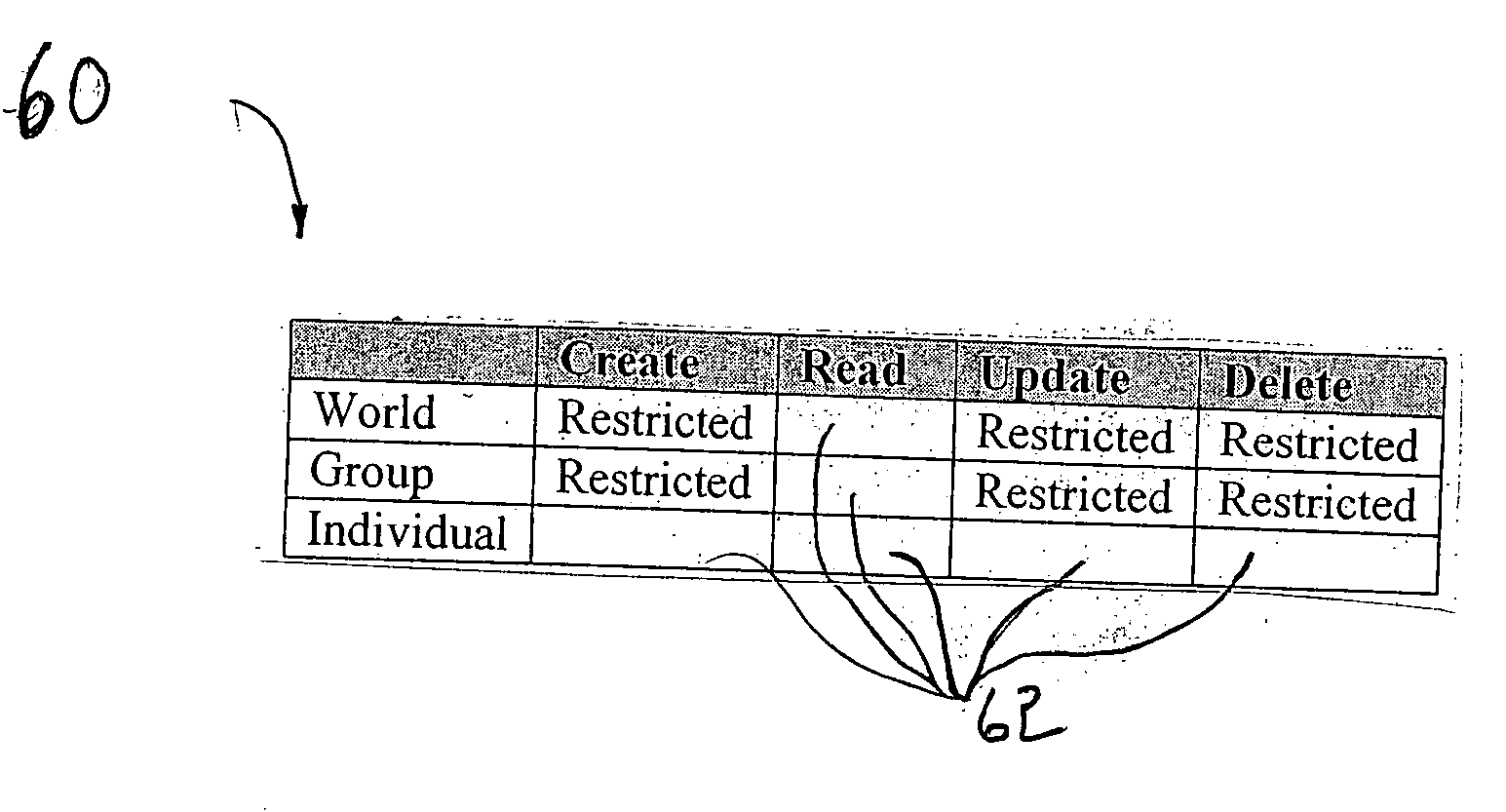
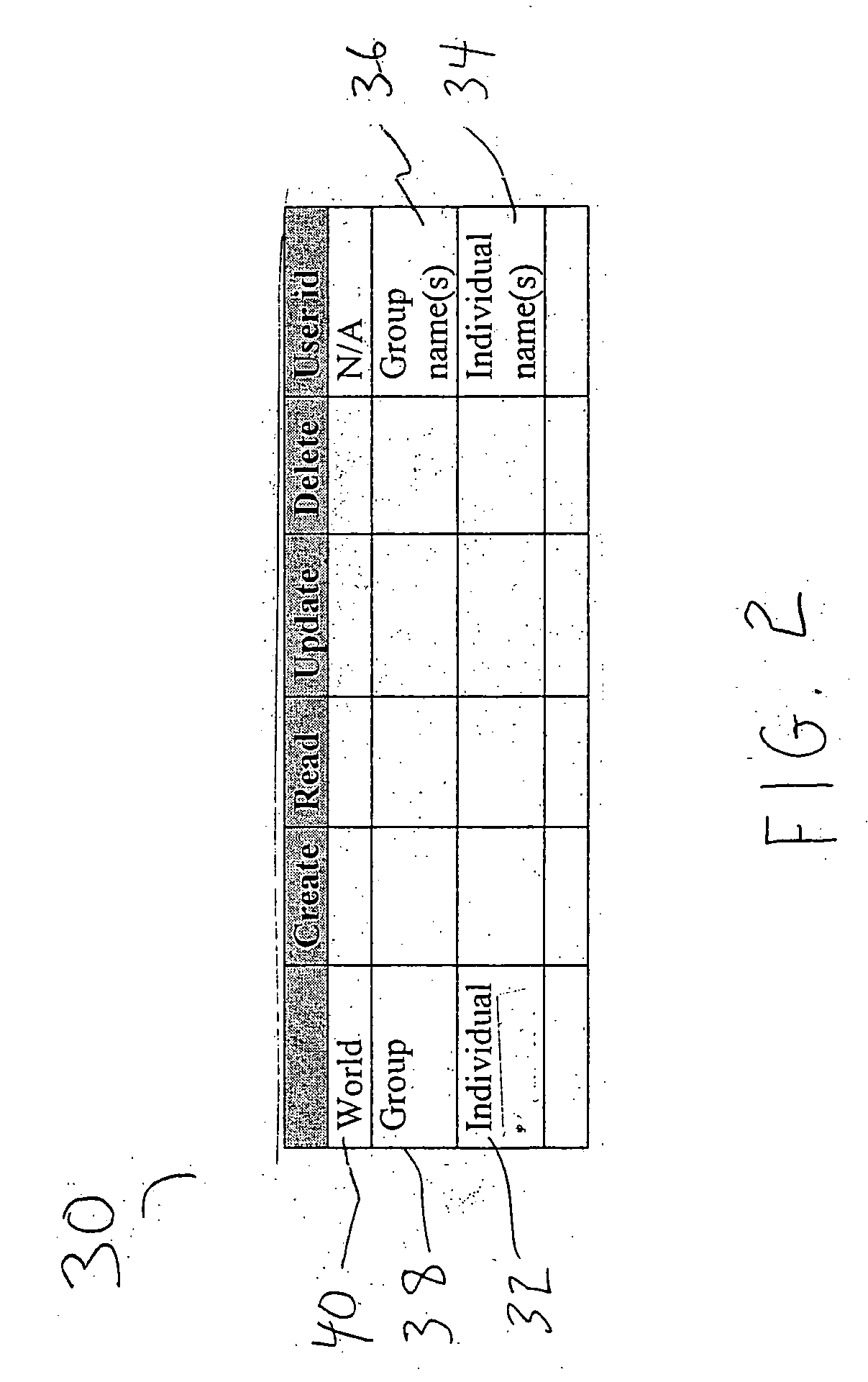
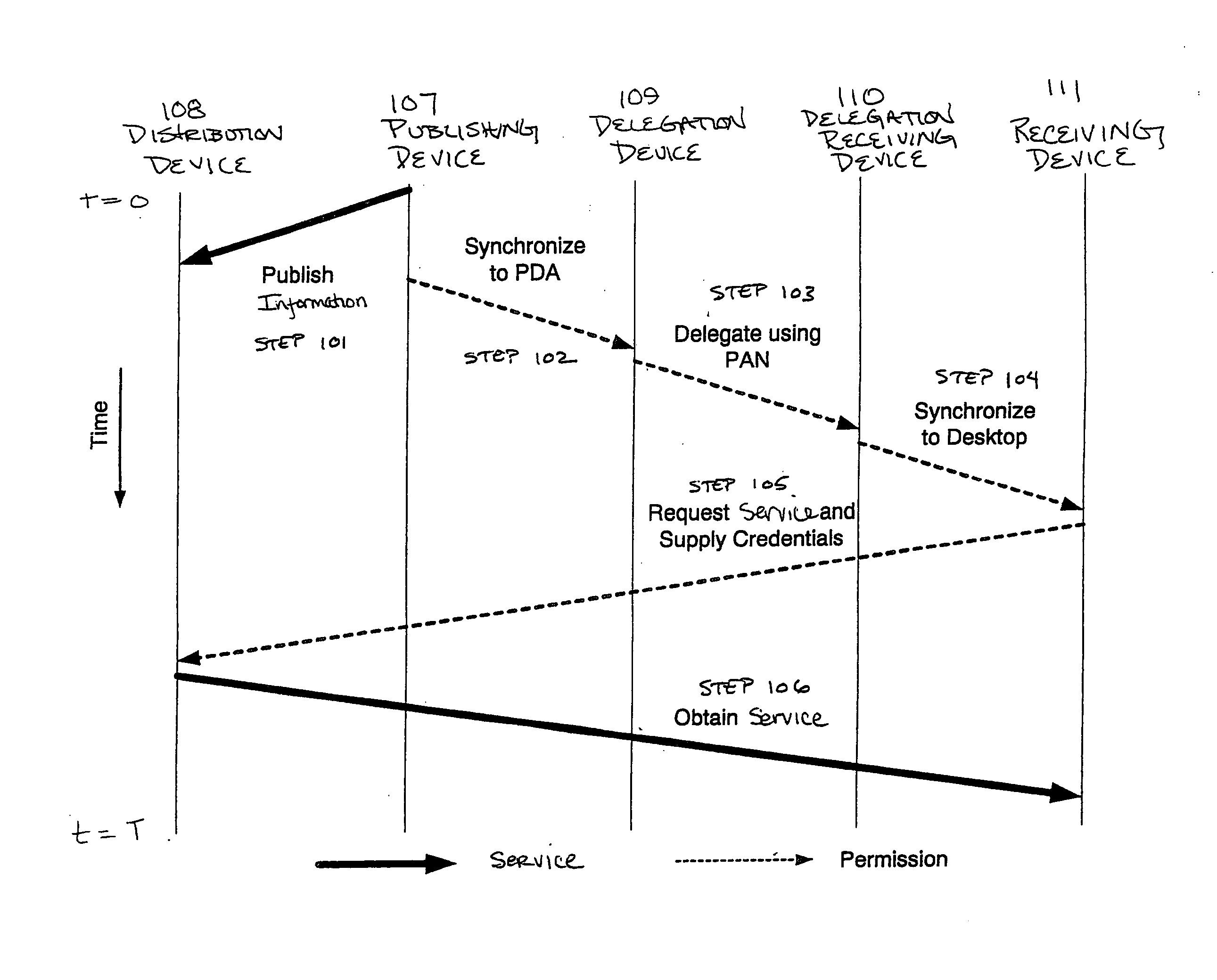
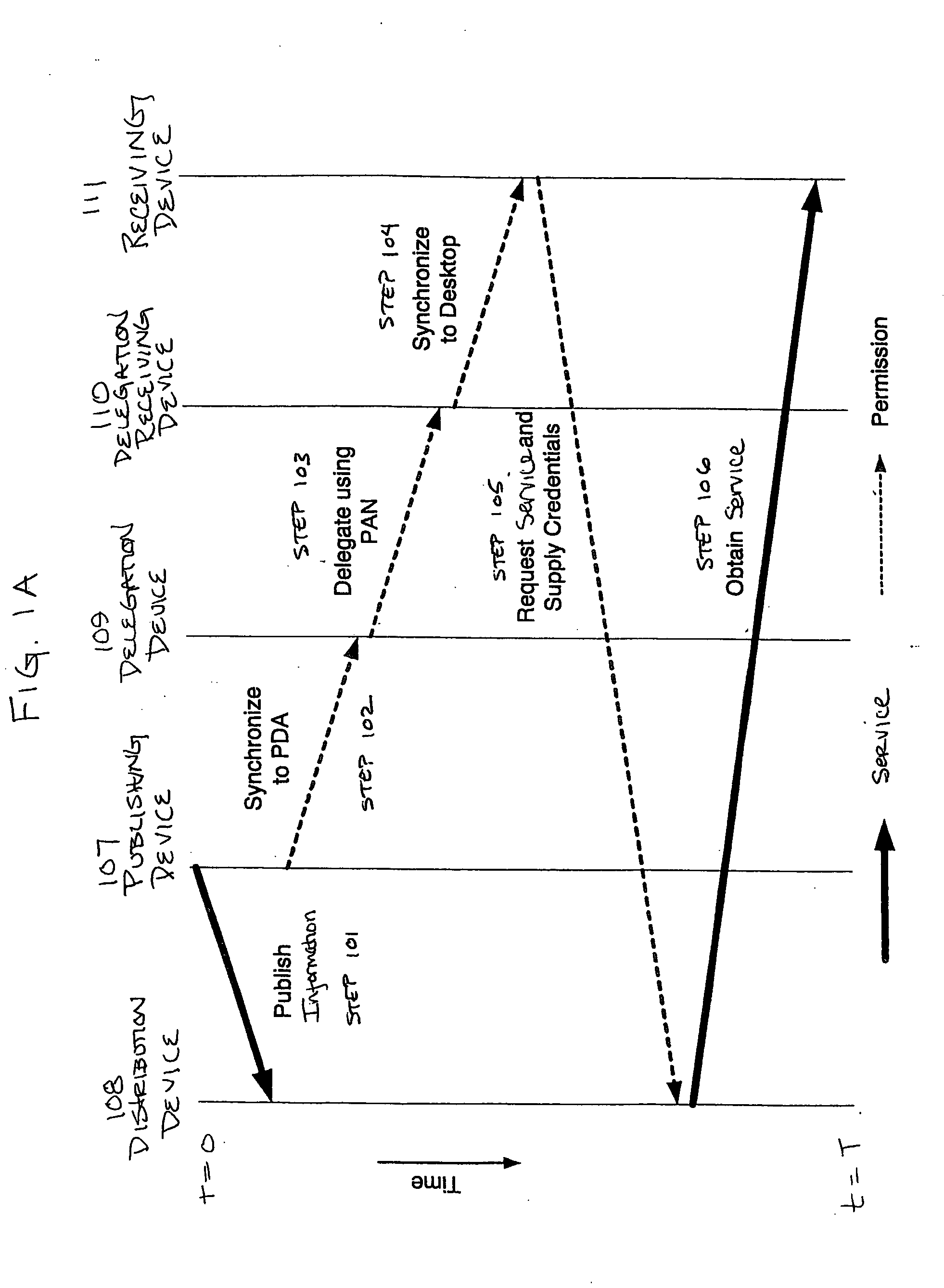
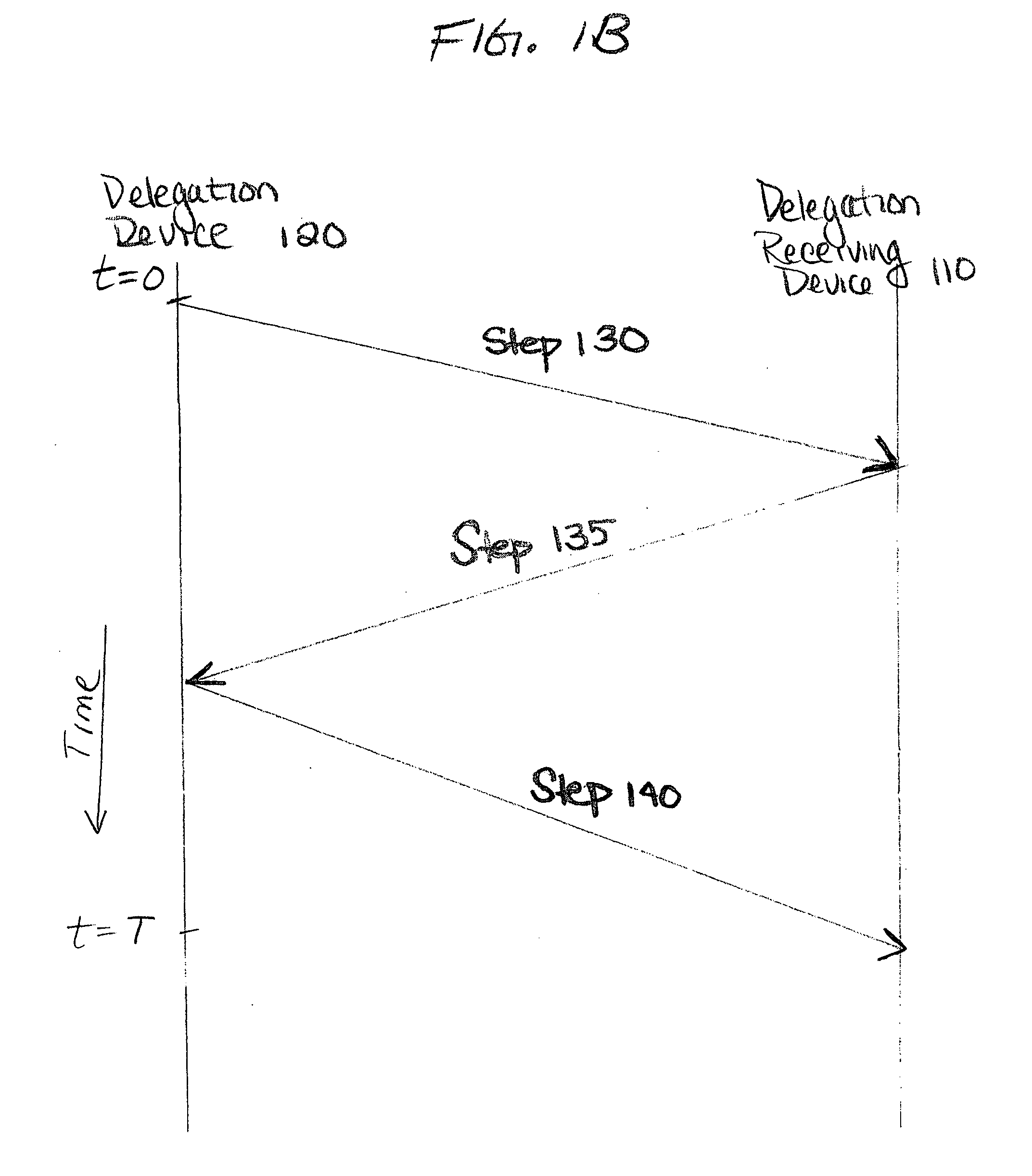
InactiveUS20050086540A1Improve securityModest management overheadDigital data processing detailsMultiple digital computer combinationsAccess control matrixWorld Wide Web
A method and system automatically generate a list of participants physically present at a meeting and distribute permission to the participants. Identity and key information is collected from the participants during the meeting using at least one personal area network. The identity and key information is stored on a delegation device. Permission to access the services is distributed to the participants over at least one personal area network using the delegation device. The delegation device may include an access control matrix or moveable icons for organizing and distributing participant and permission information.
Owner:PROBARIS TECH
Access control system, access control method, and access control program
ActiveUS7624424B2Efficient updateEffective controlDigital data processing detailsUser identity/authority verificationAccess control matrixData access control
Owner:NEC CORP
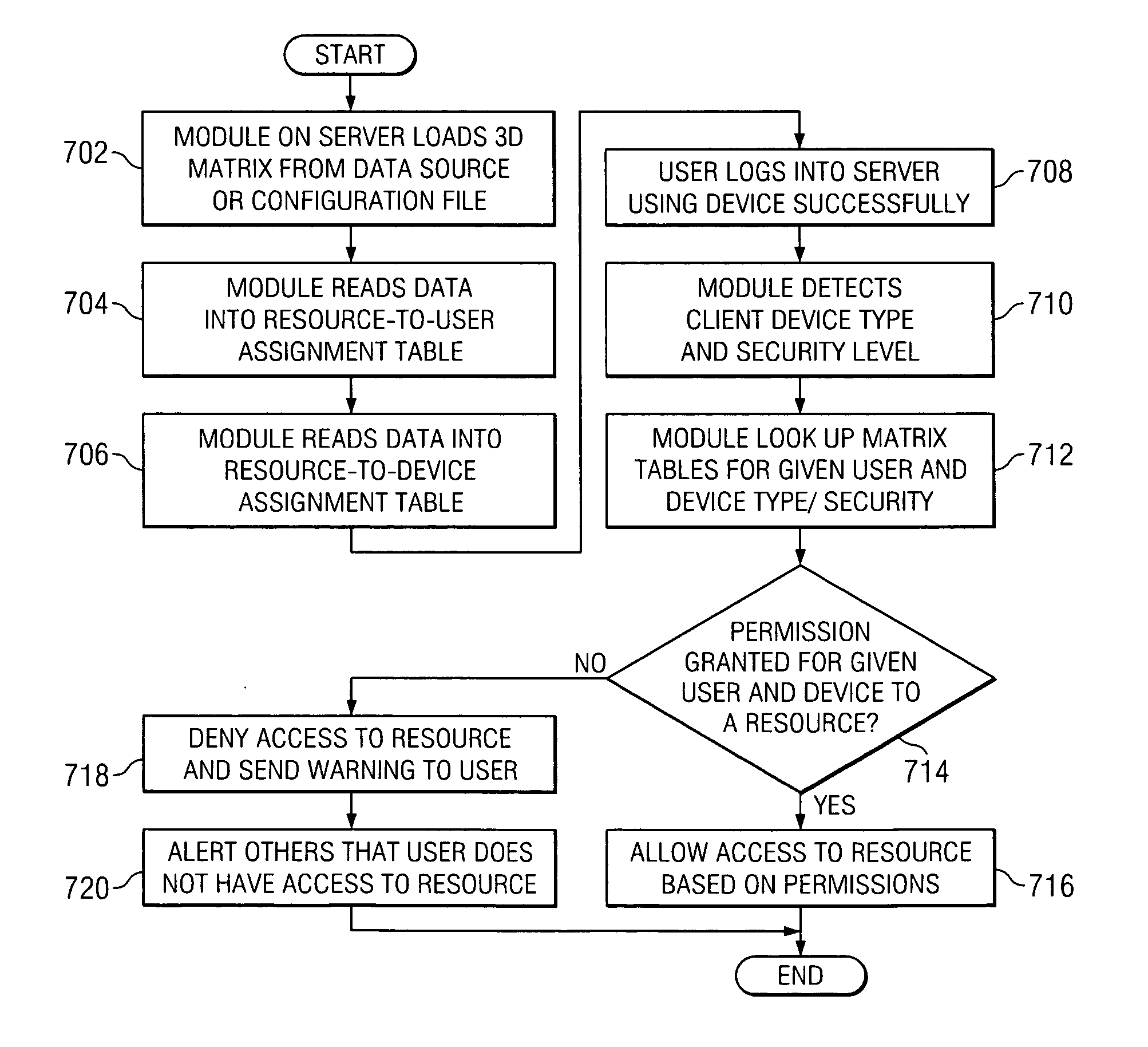
Method and apparatus for device dependent access control for device independent web content
InactiveUS20060236408A1Digital data processing detailsAnalogue secracy/subscription systemsWeb contentAccess control matrix
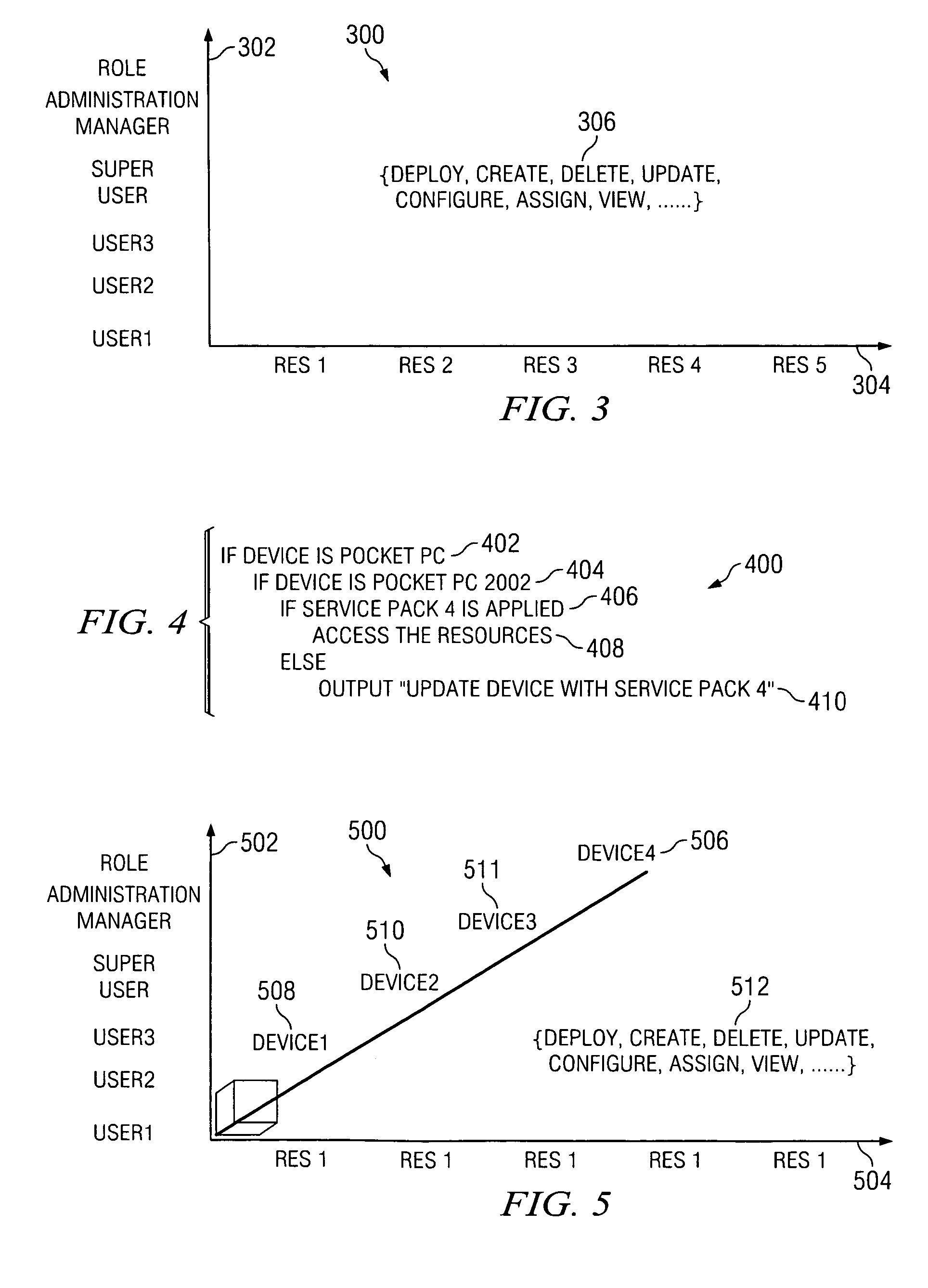
A method, an apparatus, and computer instructions are provided for device-dependent access control for device independent web content. In an illustrative embodiment, a module may be implemented in a computer program detects a client device and security level from a request for a resource by a client device. The module loads, from a data source or configuration file, a three-dimensional device dependent access control matrix, which includes a user role axis, a device axis, and a resource axis. Based on the security level of the device indicated by the device matrix, the module grants or denies access to the resource by the user device. The security levels may include security protocols implemented by different devices, encryption schemes implemented by different devices, and security patches applied by the same device.
Owner:IBM CORP
Fine-grained access control method for data in cloud storage
ActiveCN103179114AImplement access controlReduce overheadTransmissionUser PrivilegeAccess control matrix
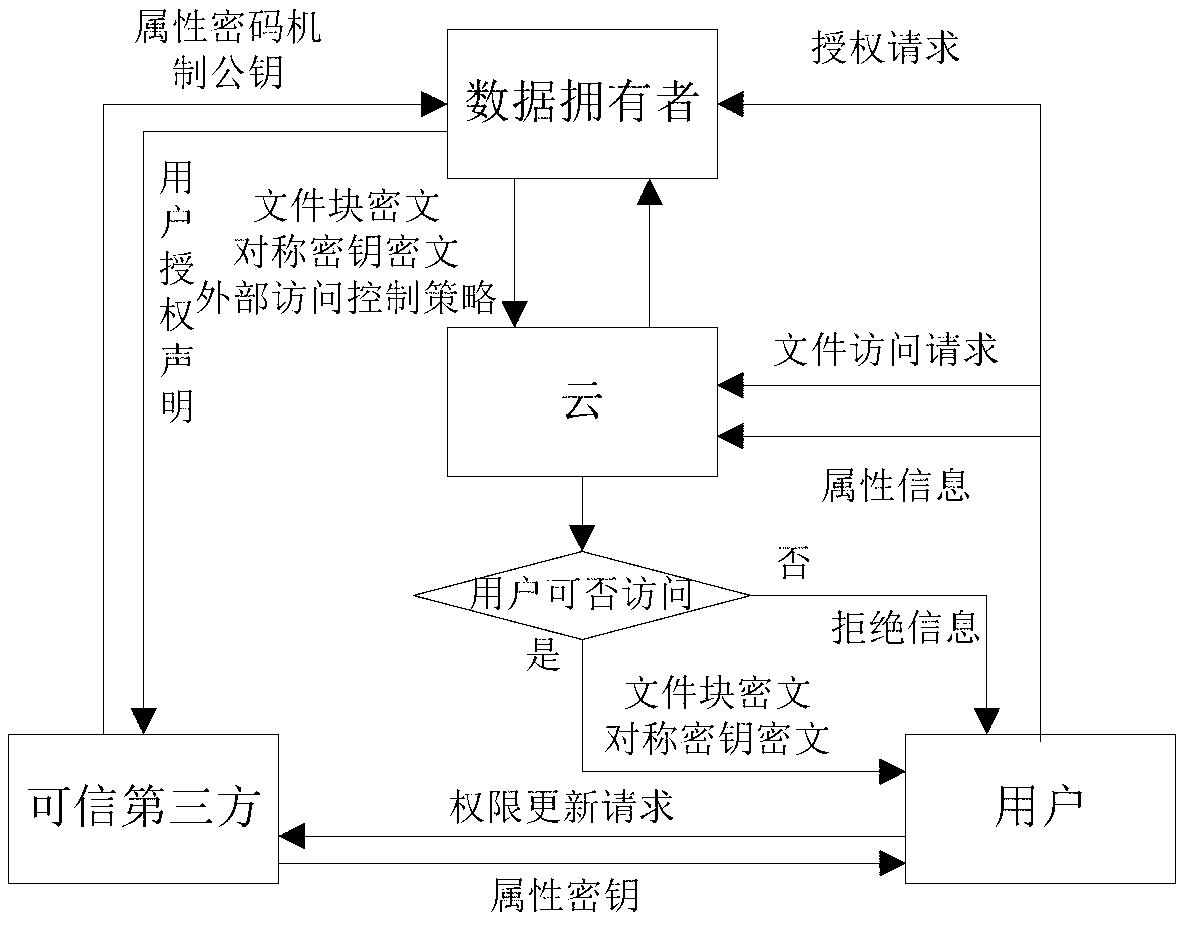
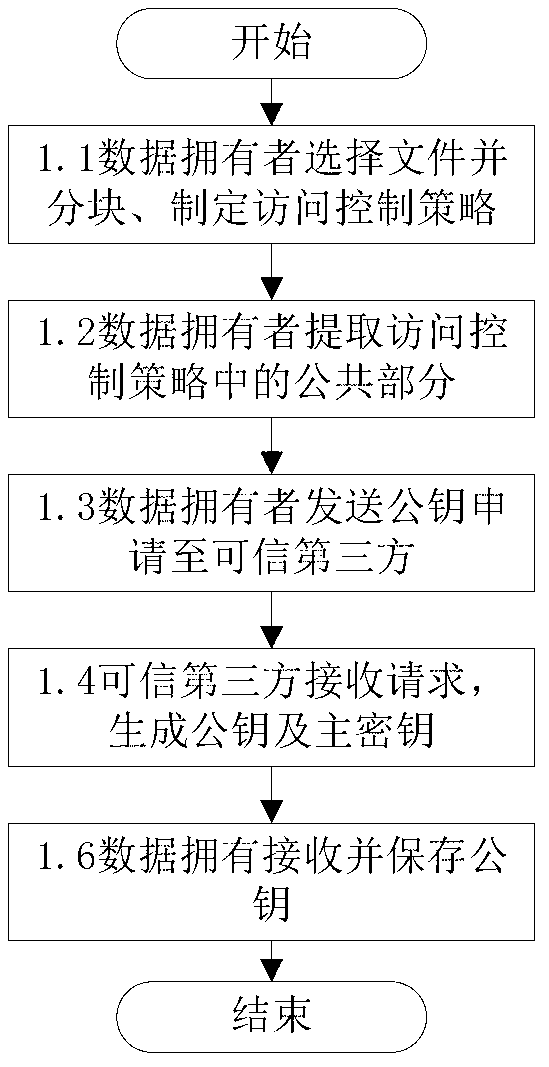
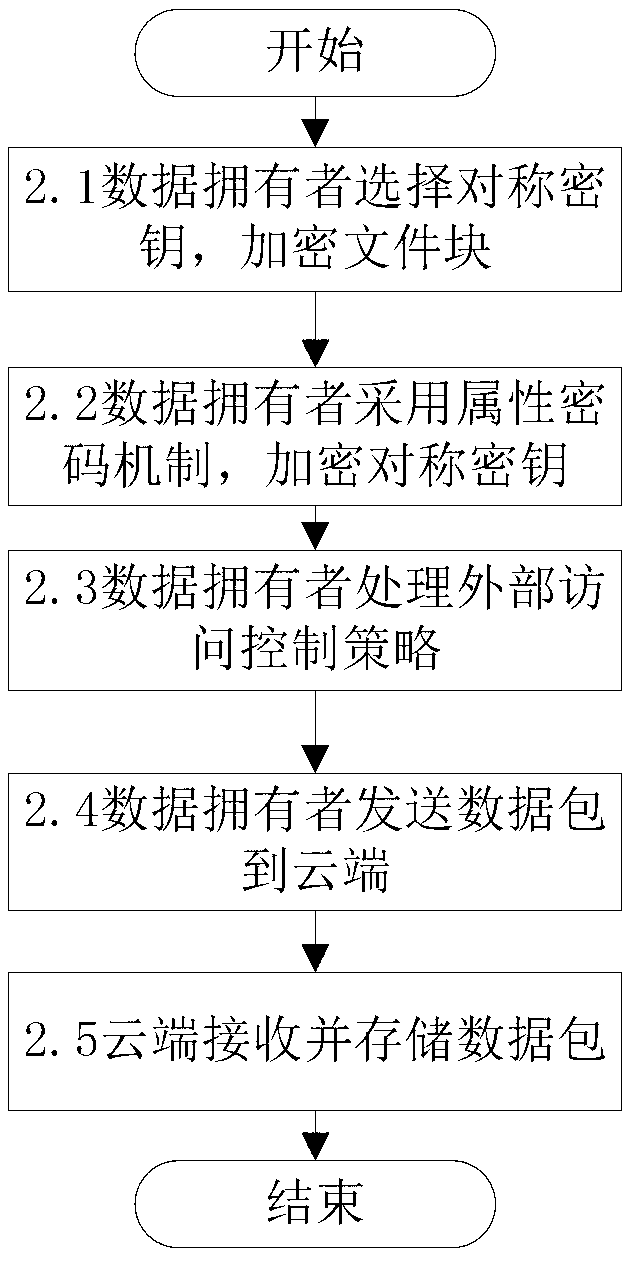
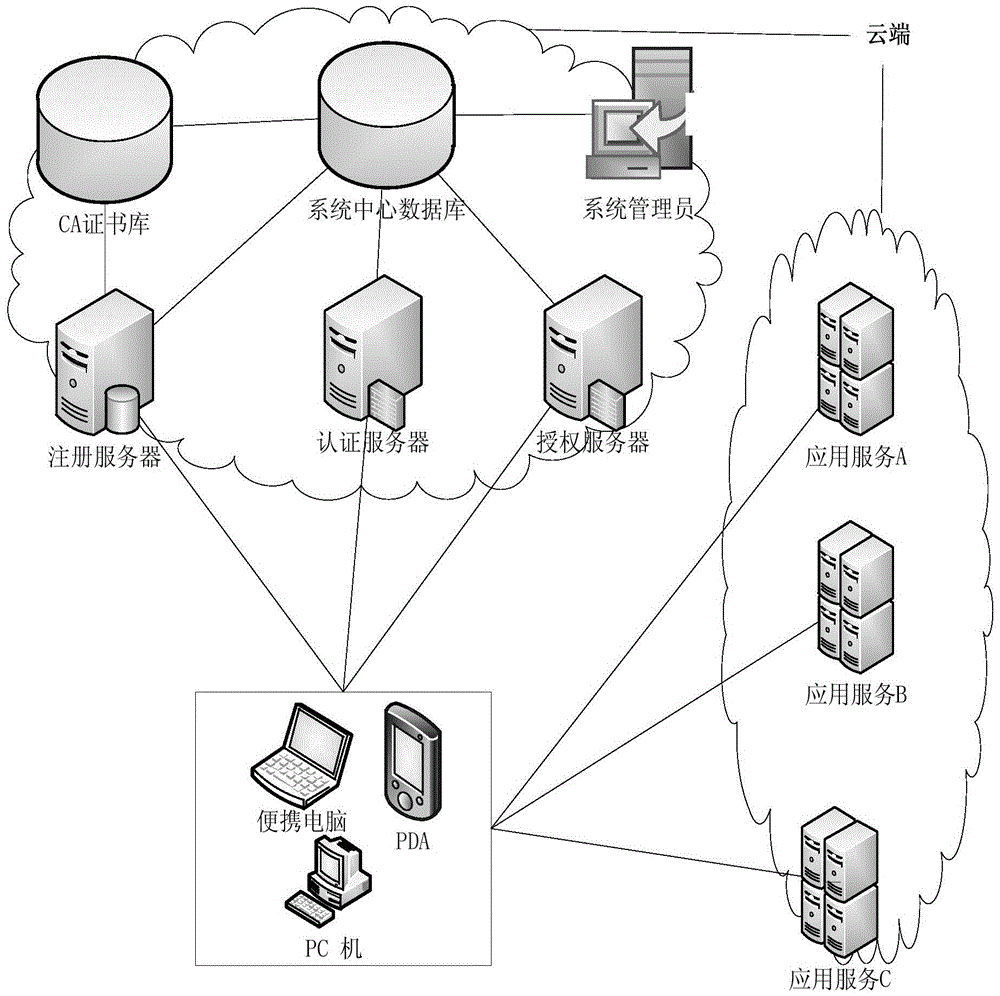
The invention discloses a fine-grained access control method for data in cloud storage. The method includes the steps: firstly, a data owner blocking files and formulating an external access strategy of file blocks and an internal access strategy of the file blocks according an access control policy, and a trusted third party generating a public key and a master key according to an attribute password mechanism; the data owner utilizing a symmetric password mechanism to encipher the file blocks, utilizing the attribute password mechanism to encipher a symmetric key, and sending a cypher text of the file blocks and a cypher text of a secret key to the cloud; the data owner and the trusted third party utilizing the attribute password mechanism to authorize a user, and generating an attribute key and an attribute processed by an attribute encryption function for each attribute of the user; the data owner sending an user permission change statement to the trusted third party; and the trusted third party judging whether adding or deleting the user permission or not for the user according to the user permission change statement. Compared with the prior art, the method for the fine-grained data access control in the cloud storage has the access control with more fine-grained data under the condition of not increasing additional costs.
Owner:HUAZHONG UNIV OF SCI & TECH
Identity and access control and management system and method in cloud environment
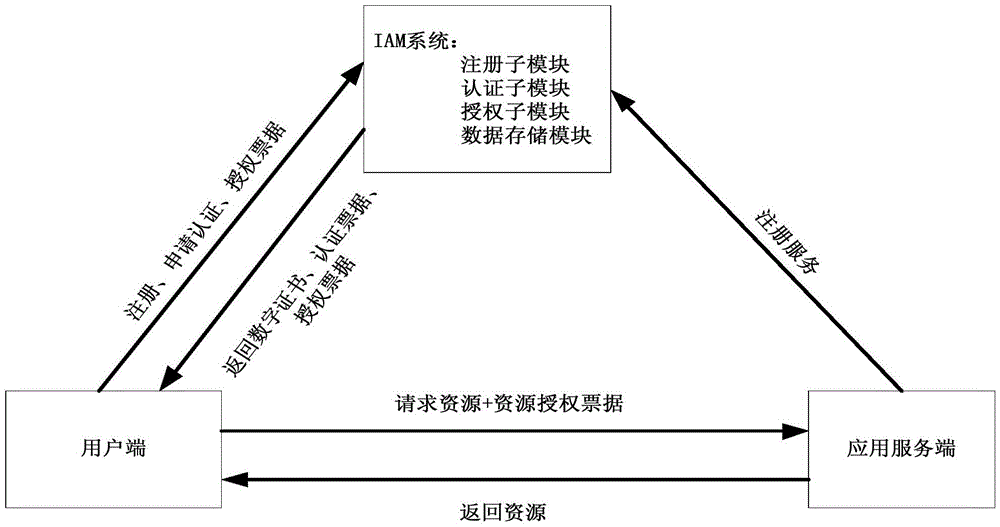
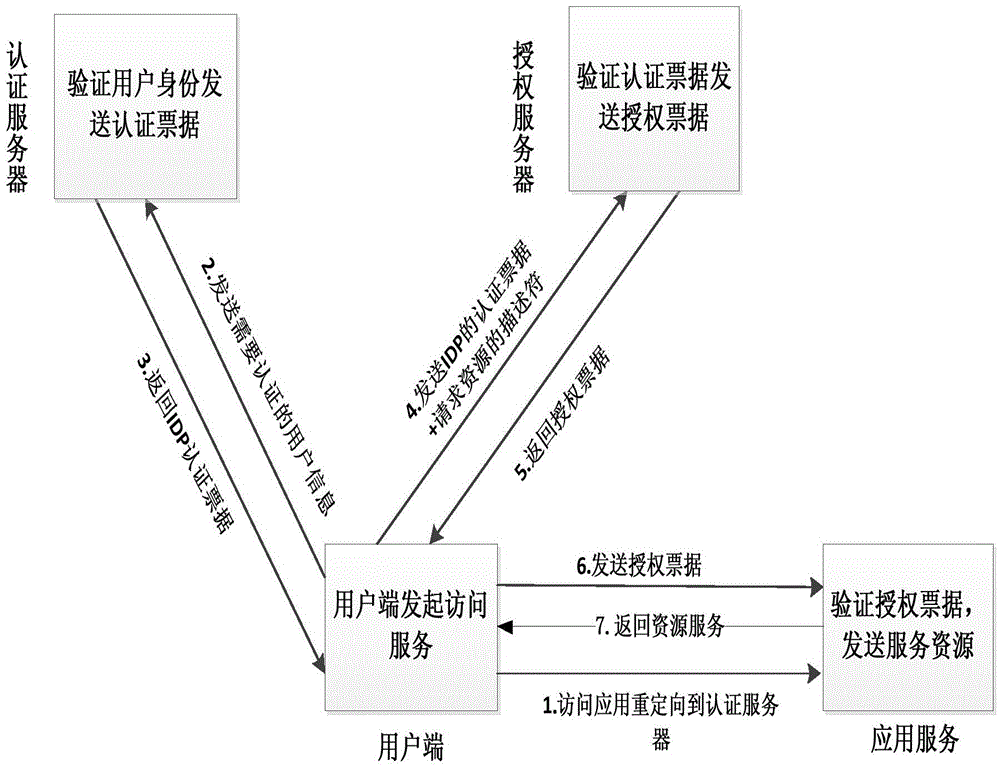
ActiveCN105577665ASafety managementEasy to manageTransmissionAccess control matrixApplication server
The invention discloses an identity and access control and management system and method in a cloud environment. The system comprises an identity and access control and management system (IAM), a user terminal and an application server. For different application services, integrated identity authentication and unified user management follow an identity authentication and access control separation principle, and user identity and access control management is realized. On the respect of user identity information management, from generation to cancellation of the user identity, a registration service provides self-help service for the user; on the respect of user authentication, a double-factor authentication technology is used for realizing the bidirectional authentication of the user and an authentication server and issuing an authentication bill to realize one-time authentication and multi-time use; and on the respect of access control and management, the access authority of the user is managed based on a role access control strategy of a user group, and the server is authorized to issue an authorized bill to the user. By adopting the identity and access control and management system and method disclosed by the invention, the user is convenient to manage the identity information, multi-time authentication is avoided, the authentication security is enhanced, and the illegal access of unauthorized users is prevented.
Owner:XIDIAN UNIV
Access control based on authentication
InactiveUS20160050209A1Digital data processing detailsMultiple digital computer combinationsUser deviceAccess control matrix
Systems and methods for granting access to different applications and / or functionalities on a user device based on at least a length of authentication provided by a user are described. A user preconfigures an authentication control program by establishing two or more authentications that are of different length or type from each other, and associates each authentication with a level of access. When the user provides a valid authentication for full access to unlock the user device, the user is granted access to all applications on the user device. When the user enters a valid authentication for partial access, the user is granted varying levels of access to applications on the user device depending on the length or type of the authentication.
Owner:PAYPAL INC
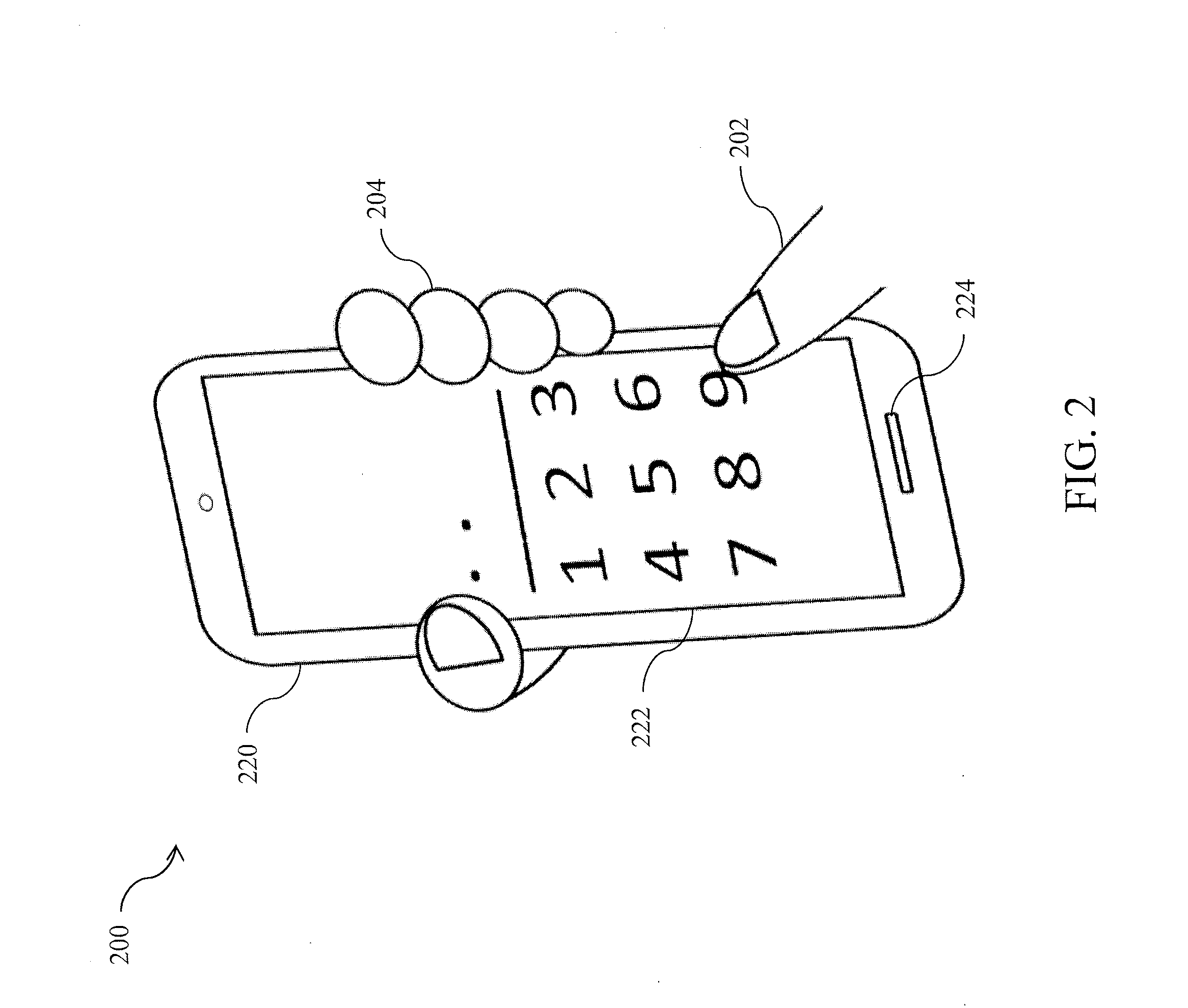
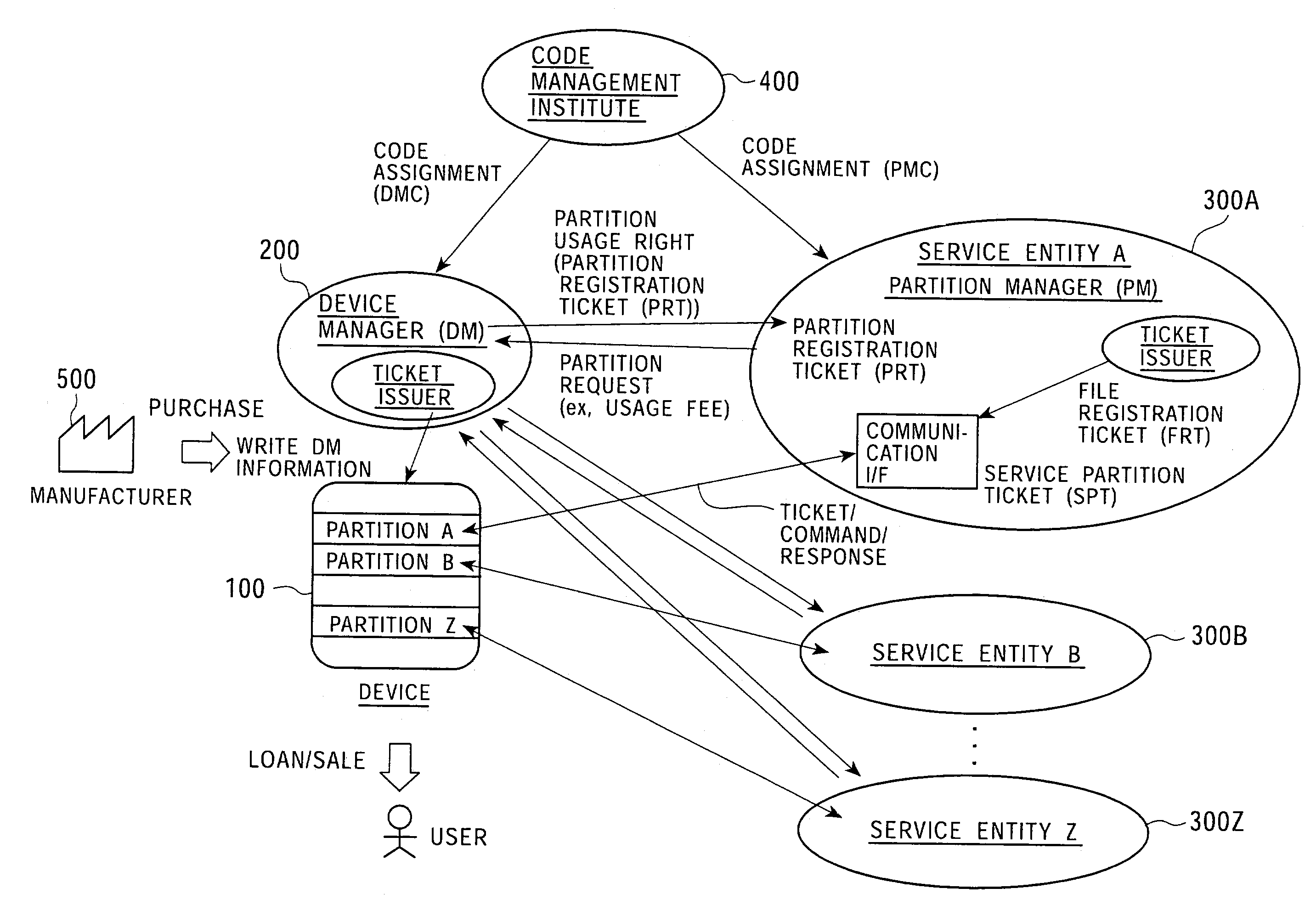
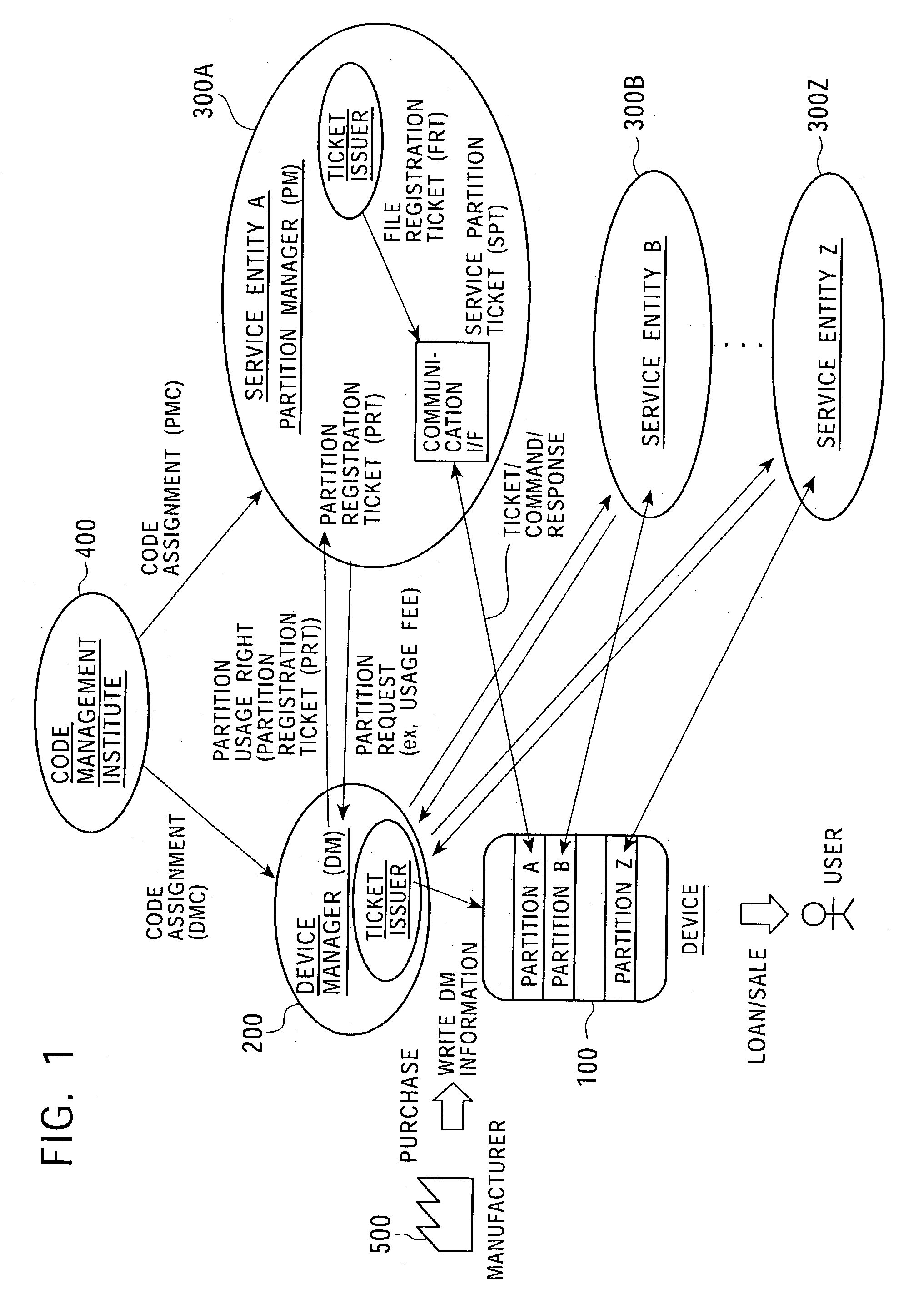
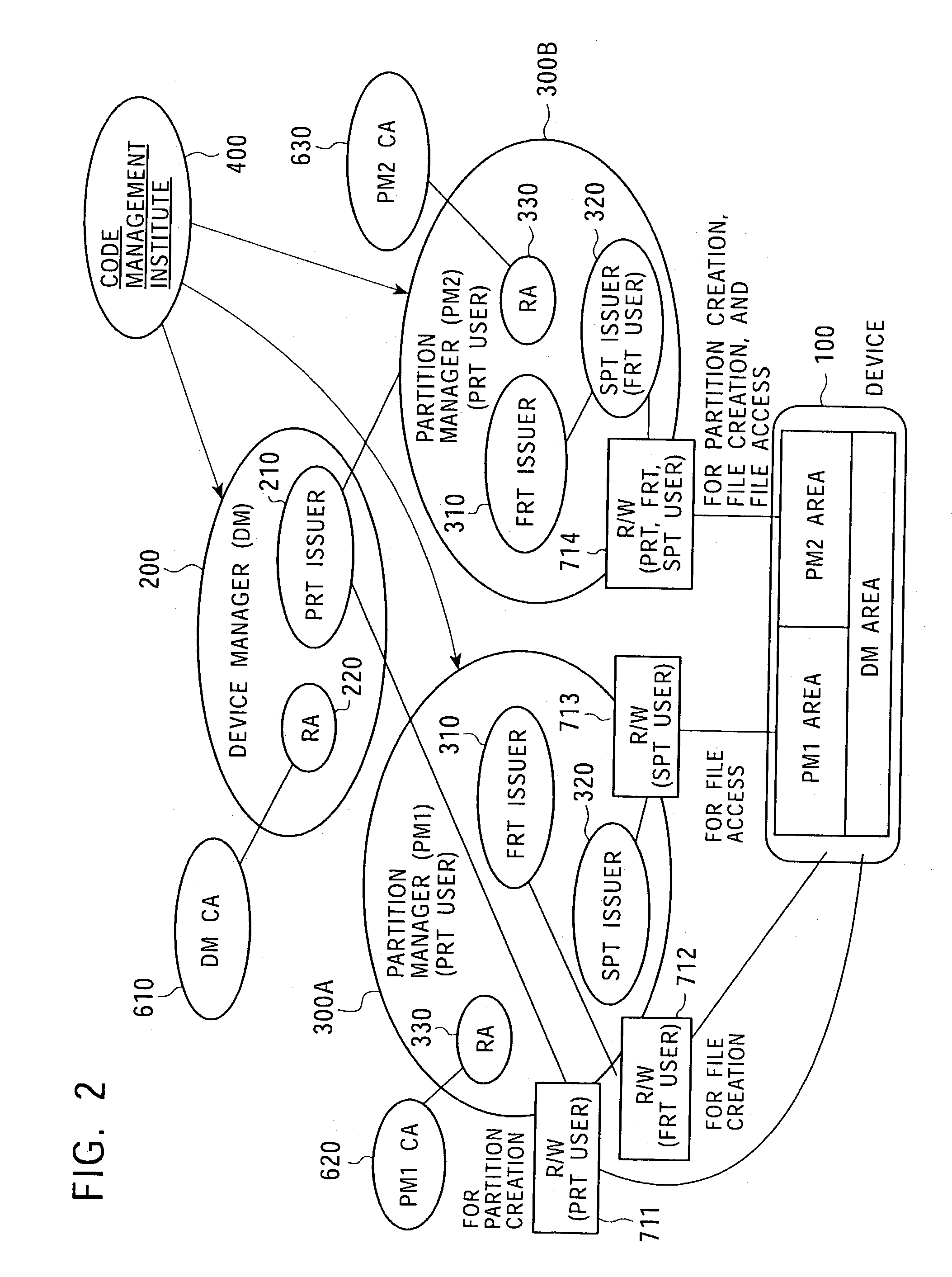
Memory access control system and management method using access control ticket
InactiveUS7225341B2Implement configurationUser identity/authority verificationUnauthorized memory use protectionComputer hardwareAccess control matrix
To provide a memory access control system in which partitions, which are divided memory areas generated in a device, can be independently managed. In response to access to the divided memory areas, which are a plurality of partitions, various types of access control tickets are issued under the management of each device or partition manager, and processing based on rules indicated in each ticket is performed in a memory-loaded device. A memory has a partition, which serves as a memory area managed by the partition manager, and a device manager management area managed by the device manager. Accordingly, partition authentication and device authentication can be executed according to either a public-key designation method or a common-key designation method.
Owner:SONY CORP
Access control method
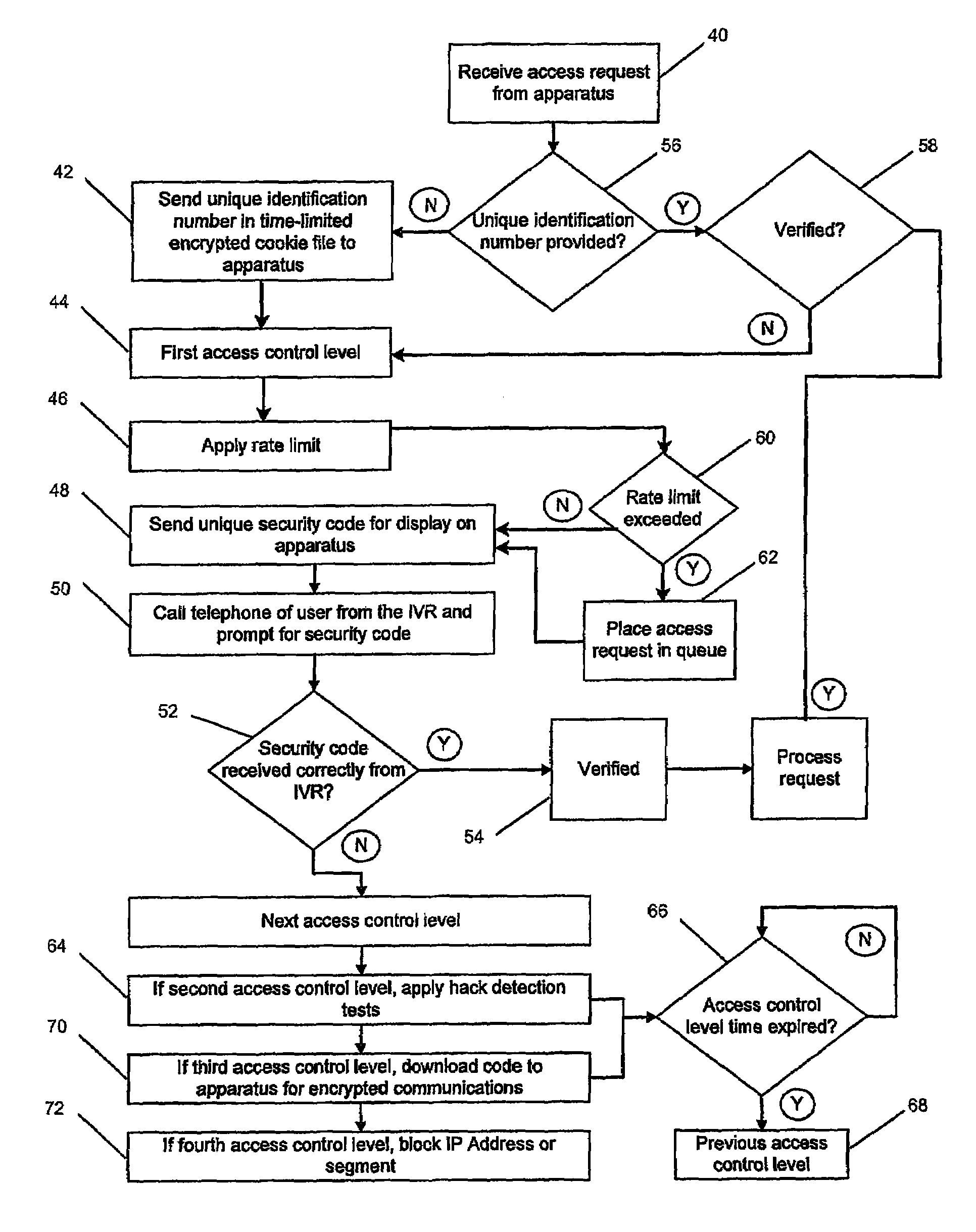
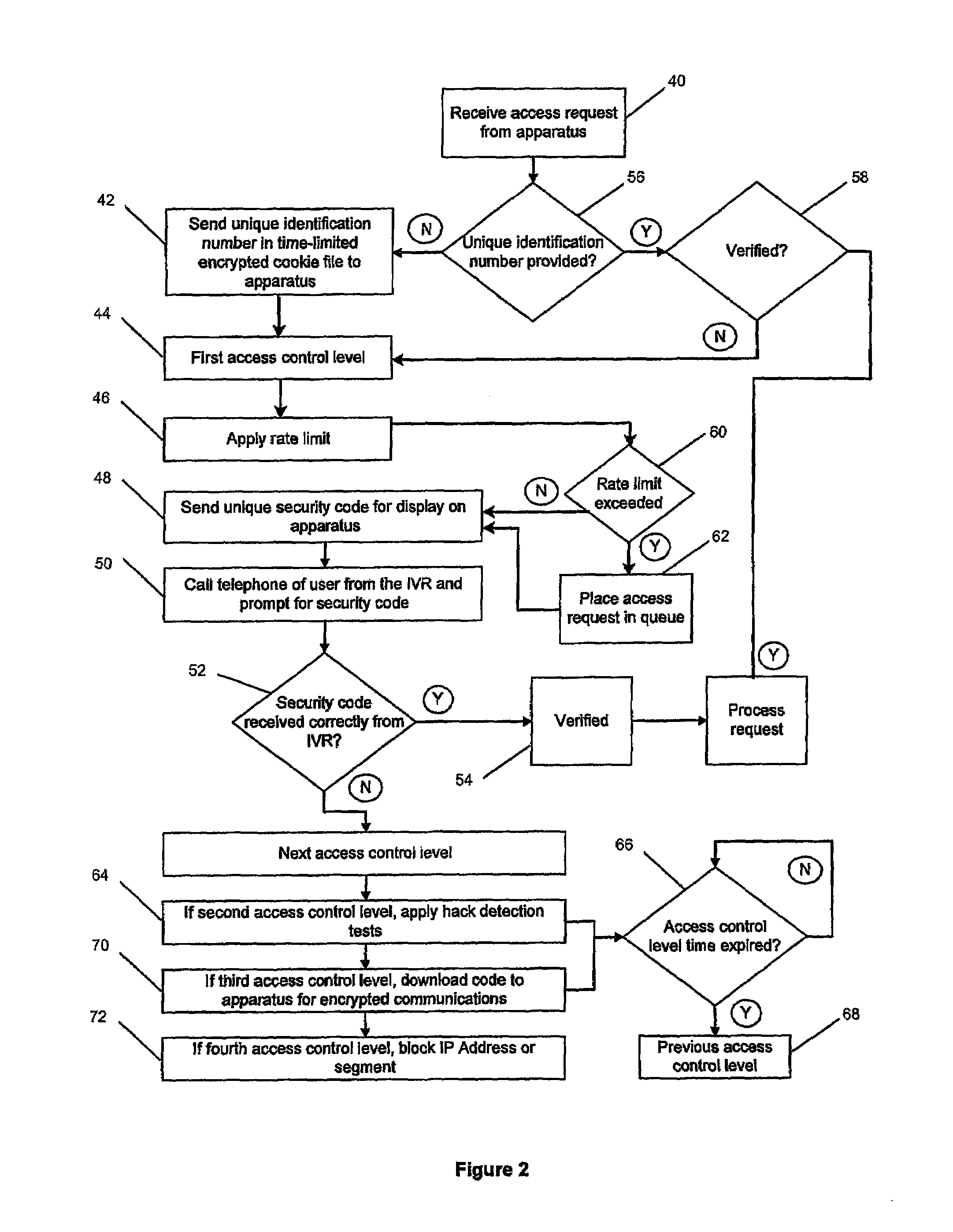
InactiveUS7454794B1Sensing by mechanical meansDigital data processing detailsRate limitingAccess control matrix
An access control method executed by a computer system, including applying an access rate limit until a user issuing access requests is verified, a first control level involving verifying the user, a second control level applying hack program detection tests to the access requests and verifying the user, a third control level requiring use of predetermined download software for transmitting the access requests and verifying the user, a fourth control level blocking access to the service on the basis of at least one communications address corresponding to the access requests, and invoking the control levels sequentially depending on a number of failed attempts to verify the user.
Owner:TELSTRA CORPORATION LIMITD
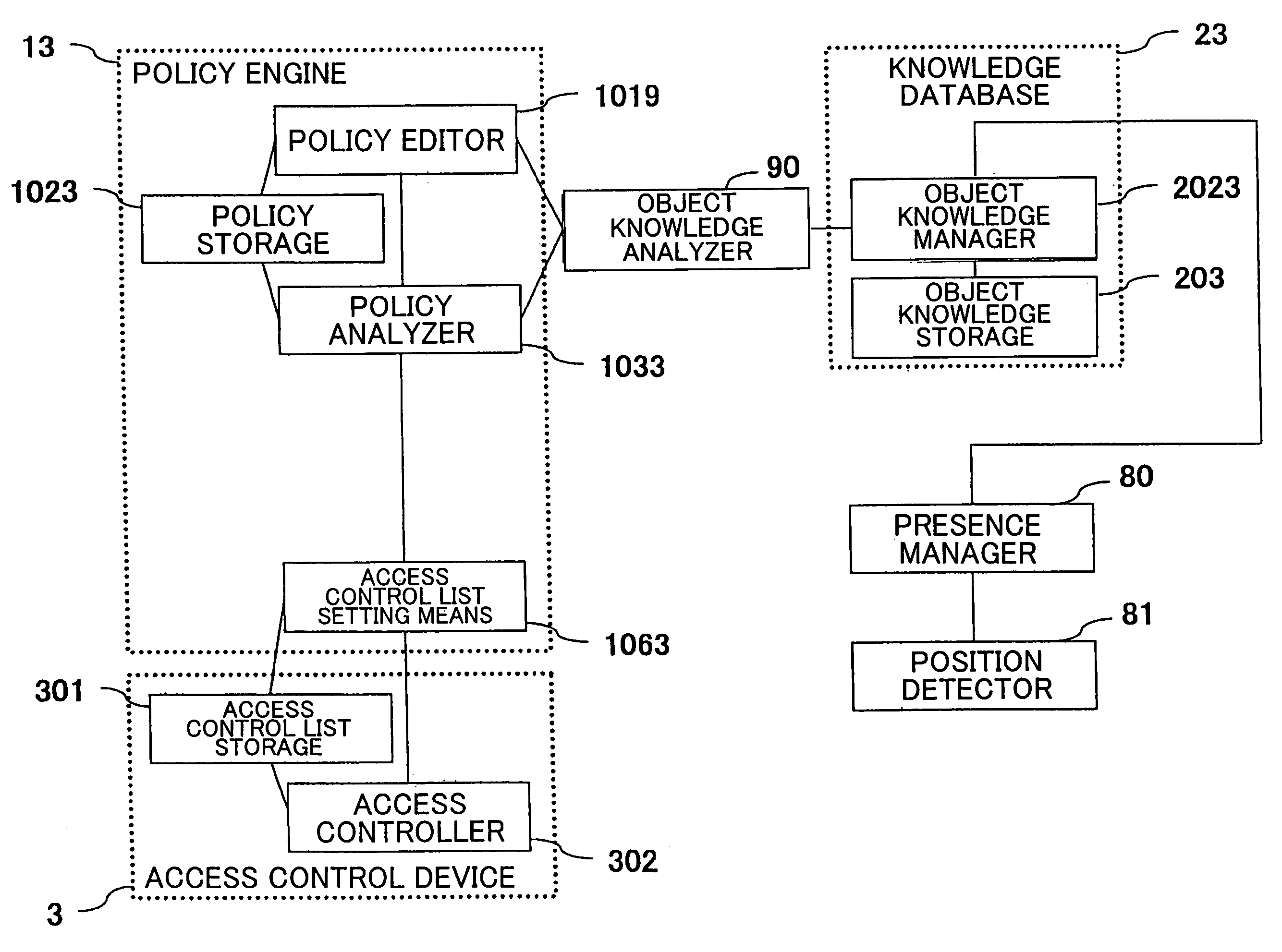
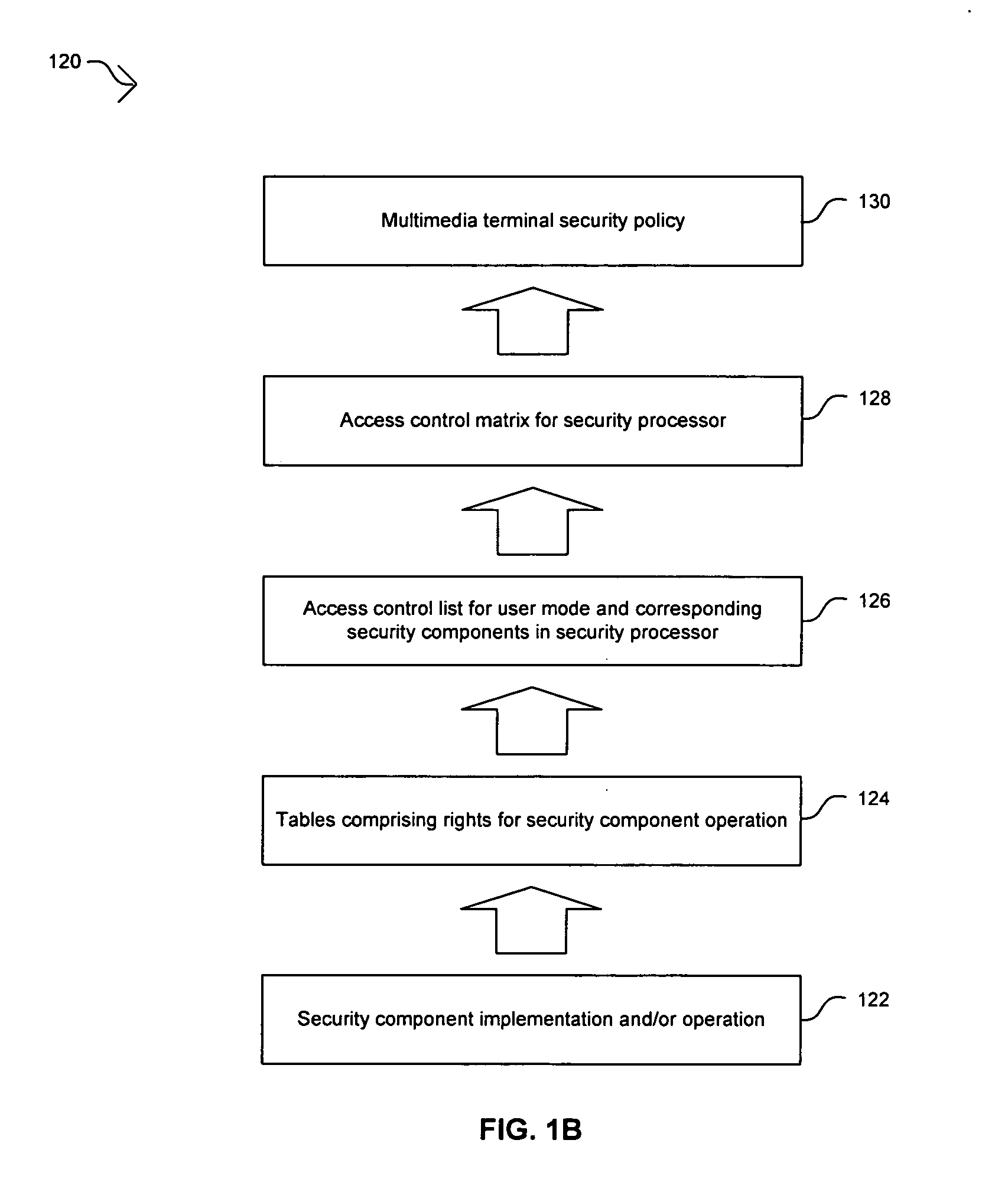
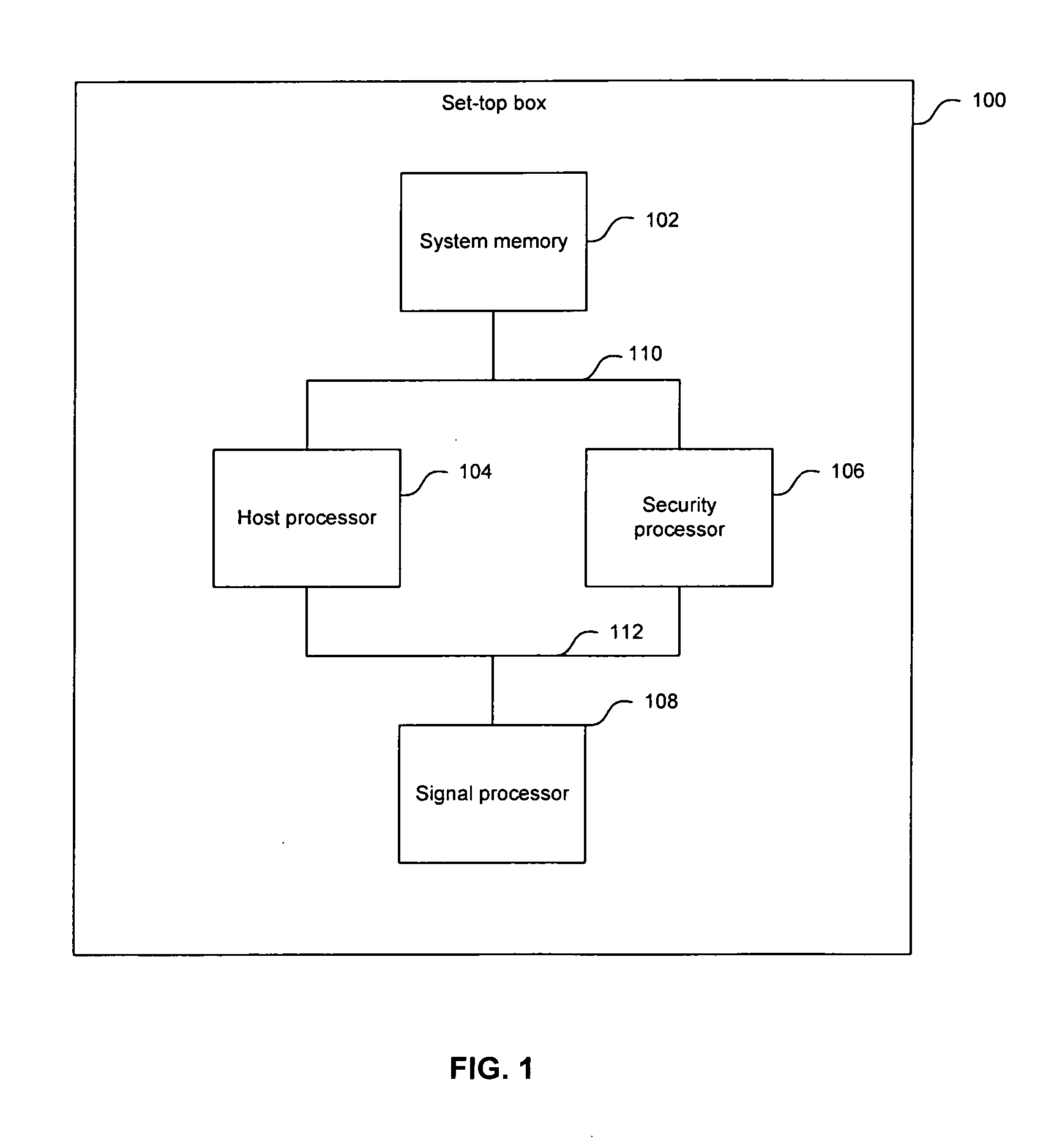
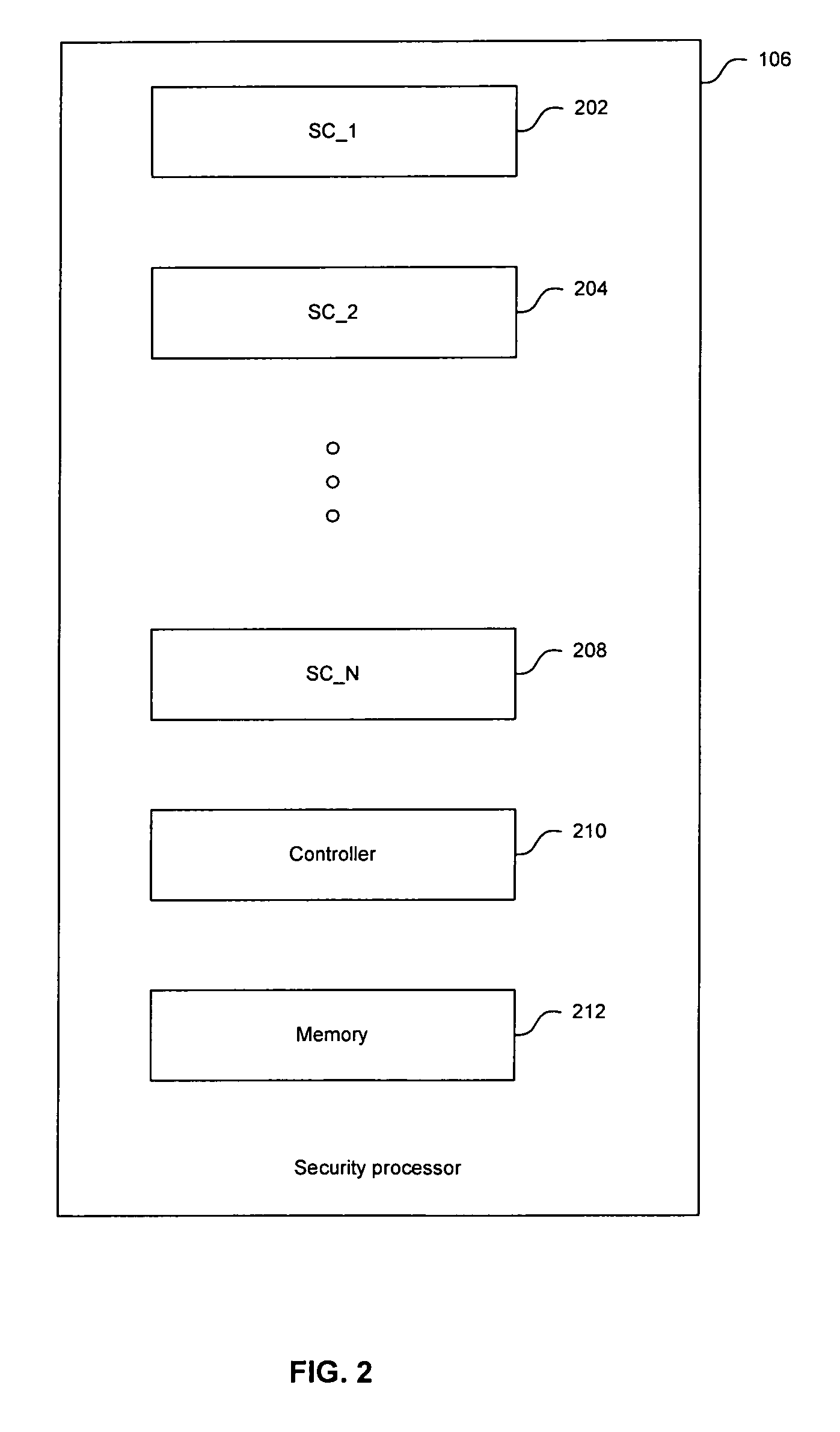
Method and apparatus for security policy and enforcing mechanism for a set-top box security processor
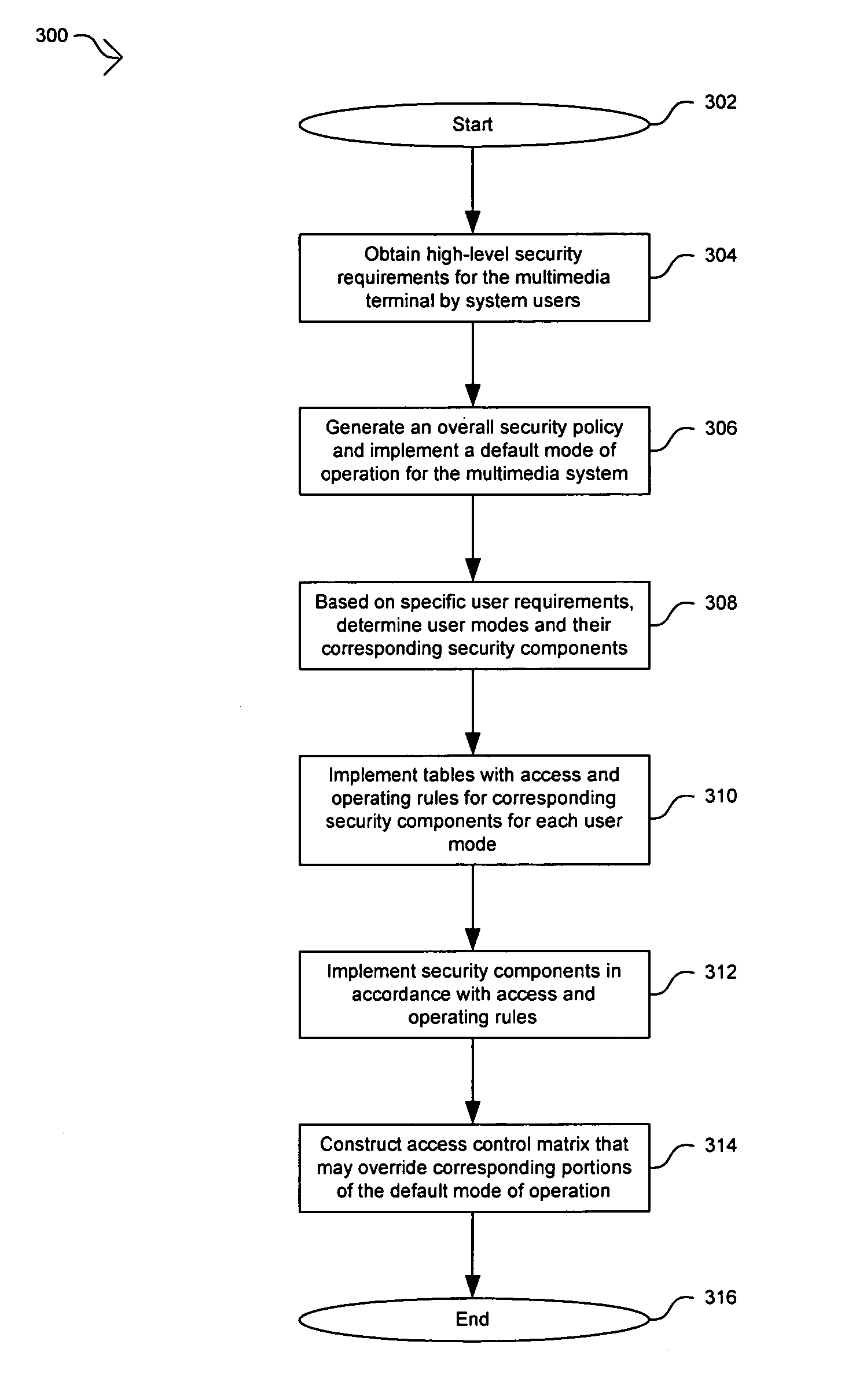
ActiveUS20060265733A1Digital data processing detailsAnalogue secracy/subscription systemsAccess control matrixOperation mode
In multimedia systems that implement secure access techniques, a method and apparatus for a security policy and enforcing mechanism for a set-top box security processor are provided. A security policy may be determined for a multimedia terminal based on high-level requirements by various system users. A default mode of operation may be generated based on the security policy and may be stored in a security policy memory. An access control matrix that indicates the operation of security components in a security processor for various user modes may be stored in the security policy memory. Control and / or access operations not supported by the access control matrix may be supported by the default mode of operation. The user modes in the access control matrix may include composition user modes. Accessing the information in the security policy memory may be utilized to enforce the security policy in the multimedia terminal.
Owner:AVAGO TECH INT SALES PTE LTD
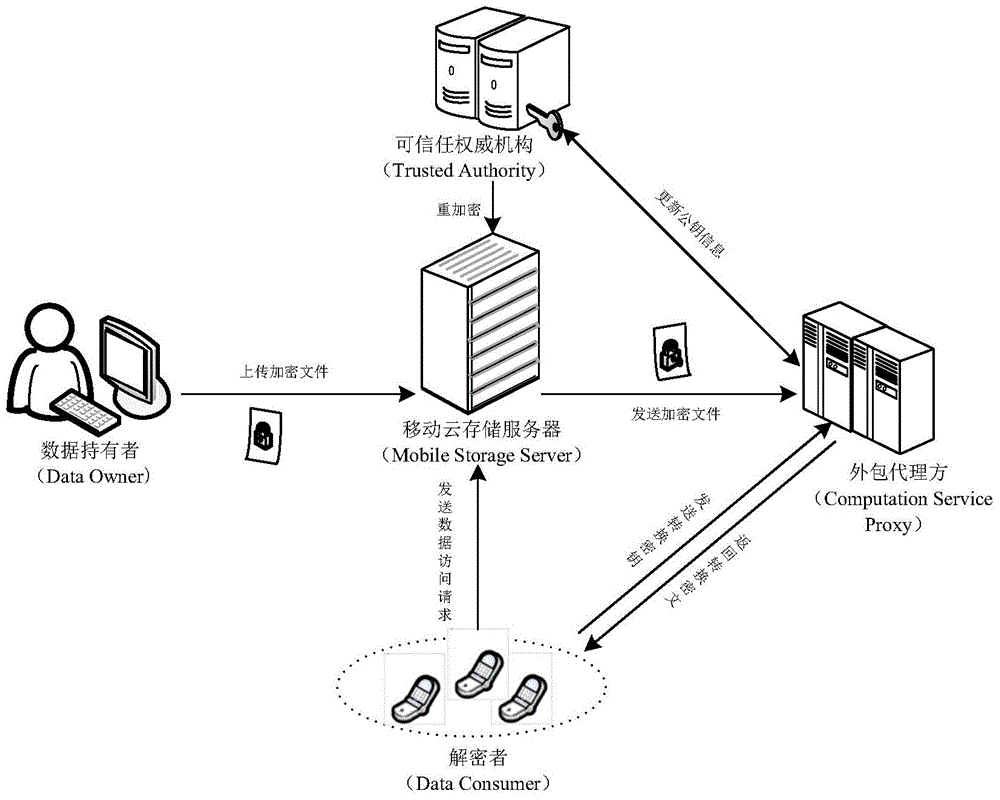
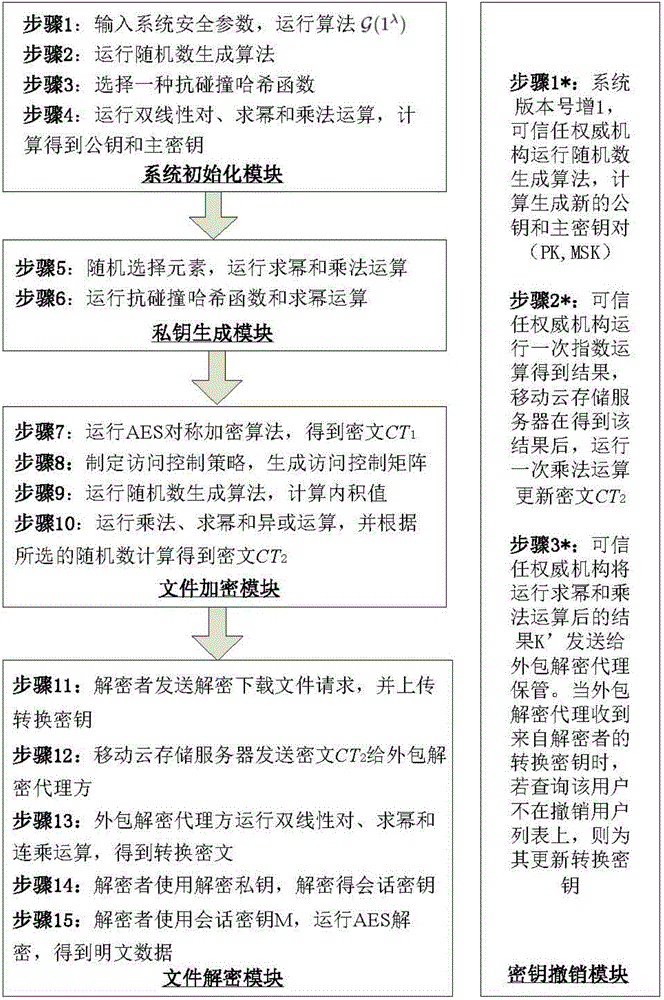
Revocable key external package decryption method based on content attributes
ActiveCN104486315APrevent unauthorized accessProtection securityUser identity/authority verificationComputer hardwareTrusted authority
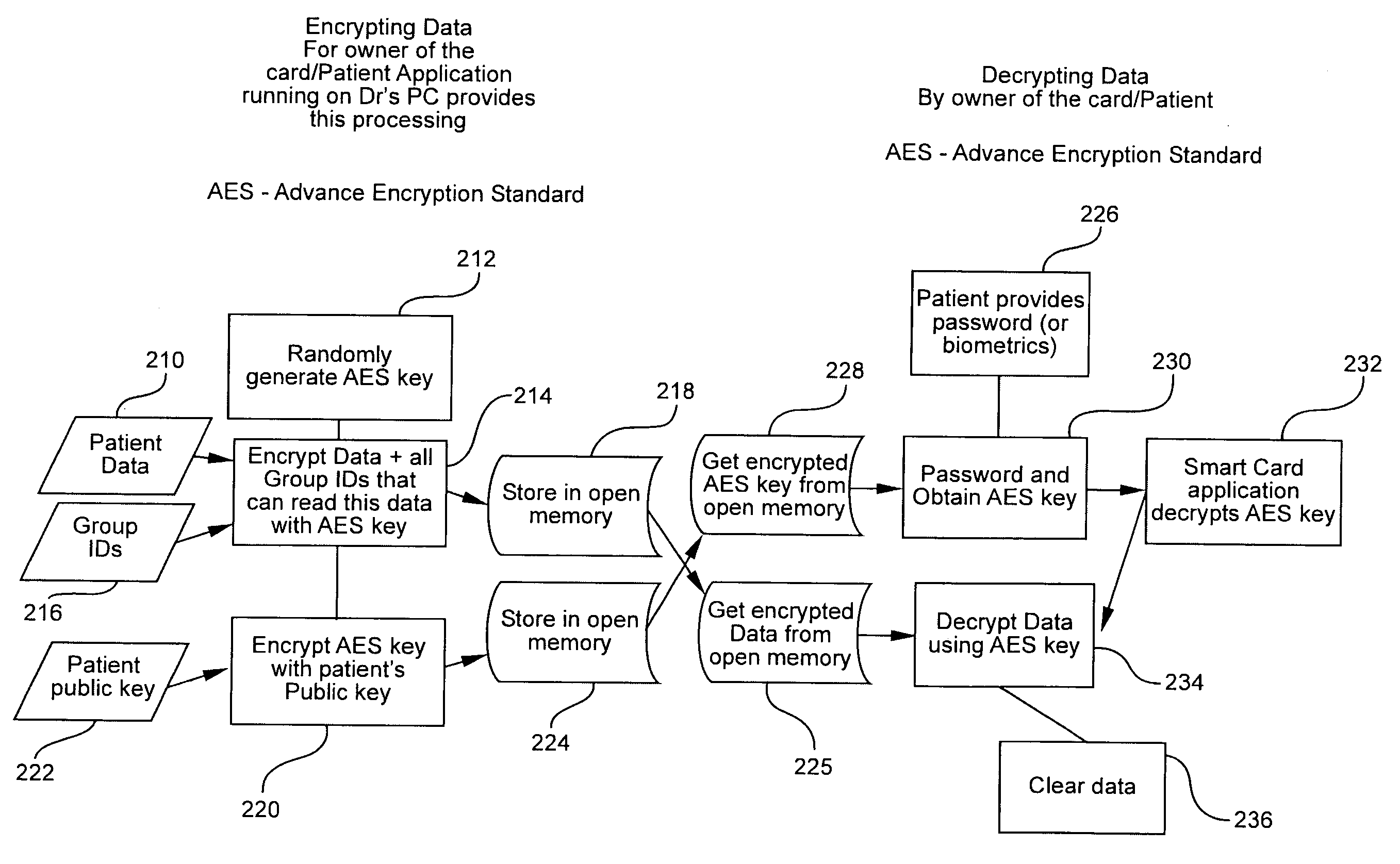
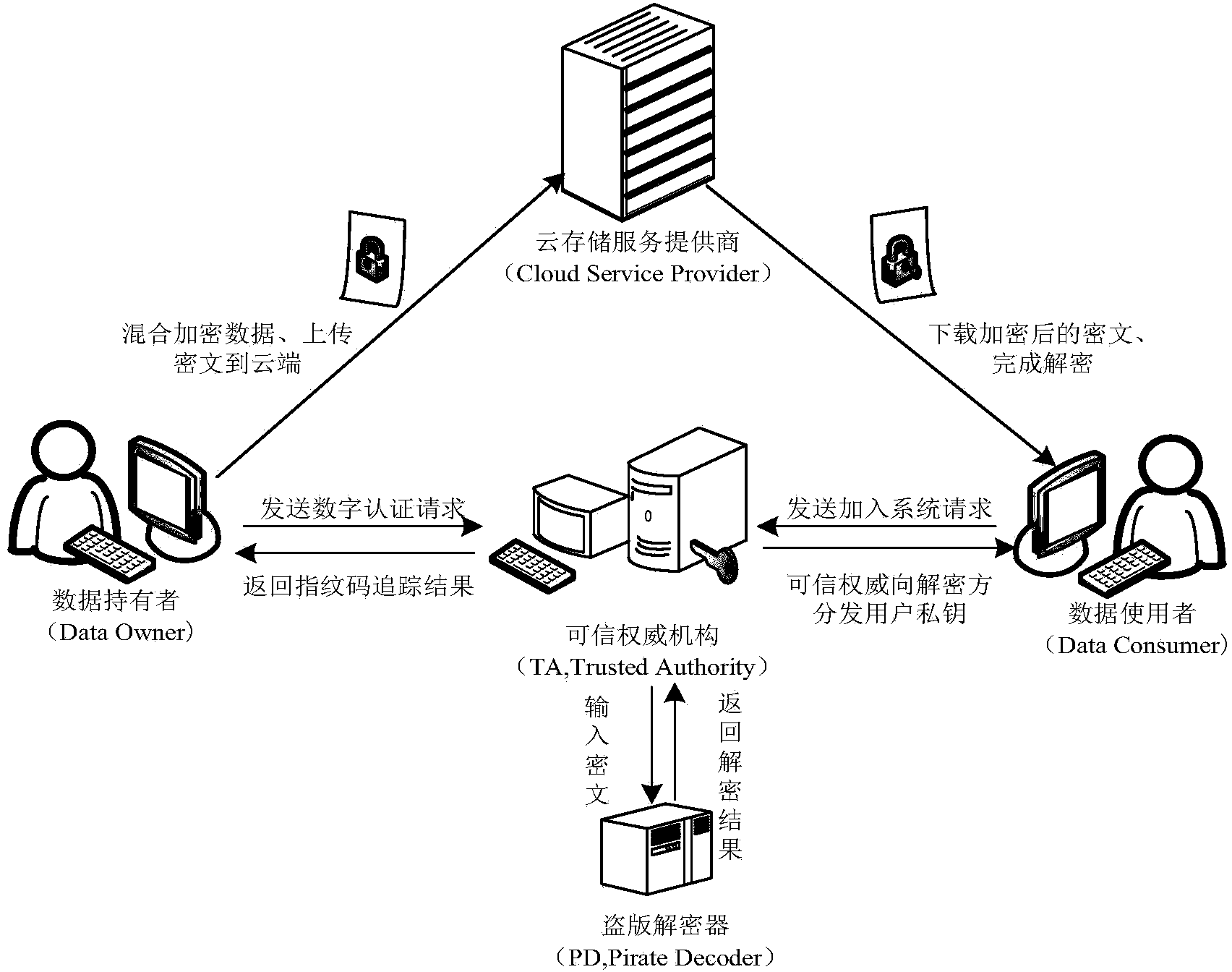
The invention relates to a revocable key external package decryption method based on content attributes. For a trusted authority, 1, initialization is carried out, and system parameters are output; 2, a random number generation algorithm operates; 3, a collision-resistant Hash function is selected, and the Hash value is calculated; 4, a public key and a main key are calculated; 5, the random number is selected, and exponentiation calculation and multiplication are carried out; 6, the collision-resistant Hash function operates, the exponentiation operation is carried out, and a decryption key is obtained. For a data holder, 7, AES data encryption is carried out; 8, an access control matrix is generated; 9, a random number is selected, and an inner product is calculated; 10, multiplication, exponentiation and exclusive-or operation is operated, and ciphertexts are obtained. For a decryption operator, 11, a decryption request and a transformation key are sent. For a mobile storage serve provider, 12, CT2 is sent to an external package decryption agency. For the external package decryption agency, 13, the transformation key is utilized, and the transformation ciphertext is calculated. For the decryption operator, 14, a conversation key is obtained through calculation; 15, AES data decryption is carried out.
Owner:HANGZHOU INNOVATION RES INST OF BEIJING UNIV OF AERONAUTICS & ASTRONAUTICS
System and method for access control
InactiveUS20030005333A1User identity/authority verificationUnauthorized memory use protectionData setAccess control matrix
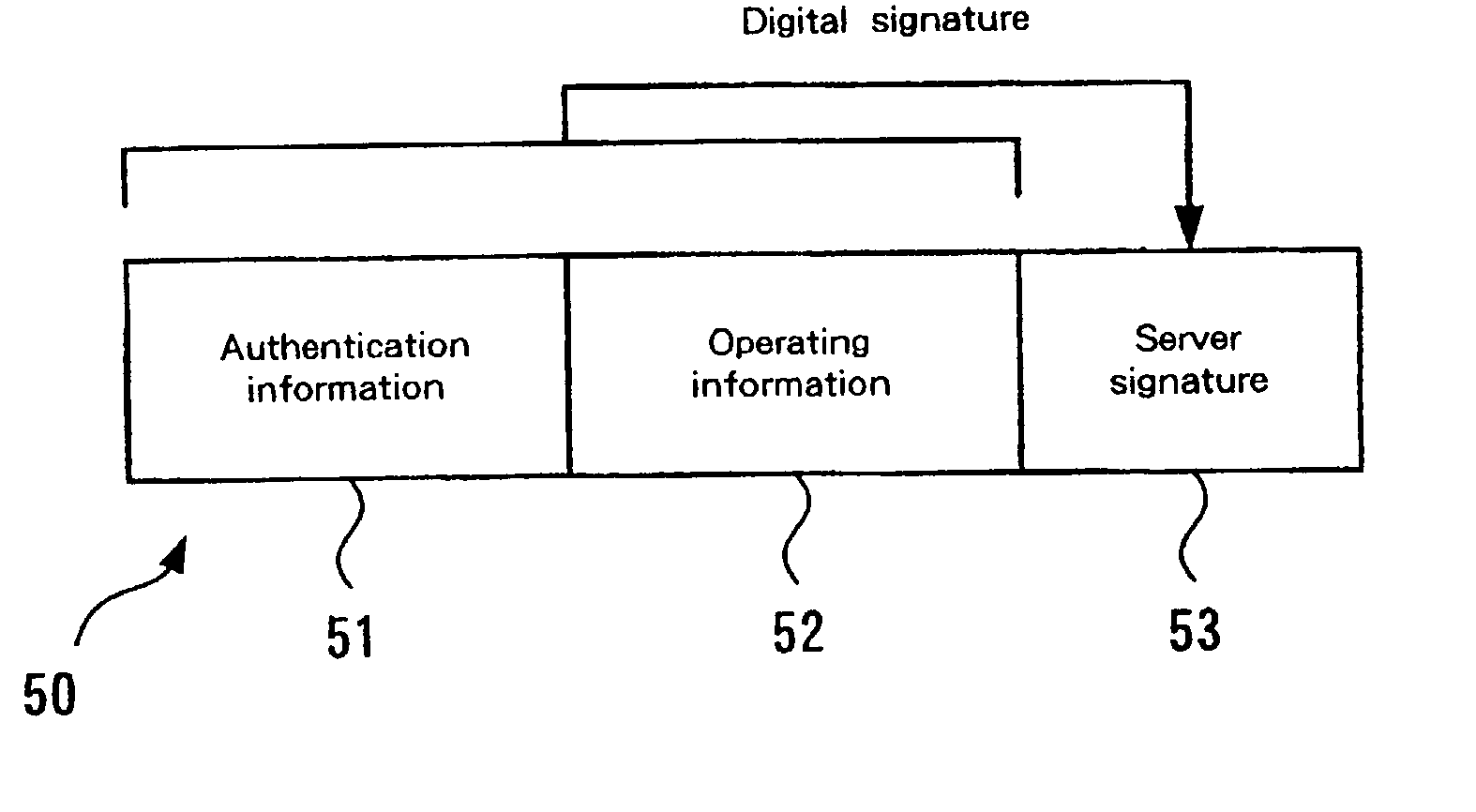
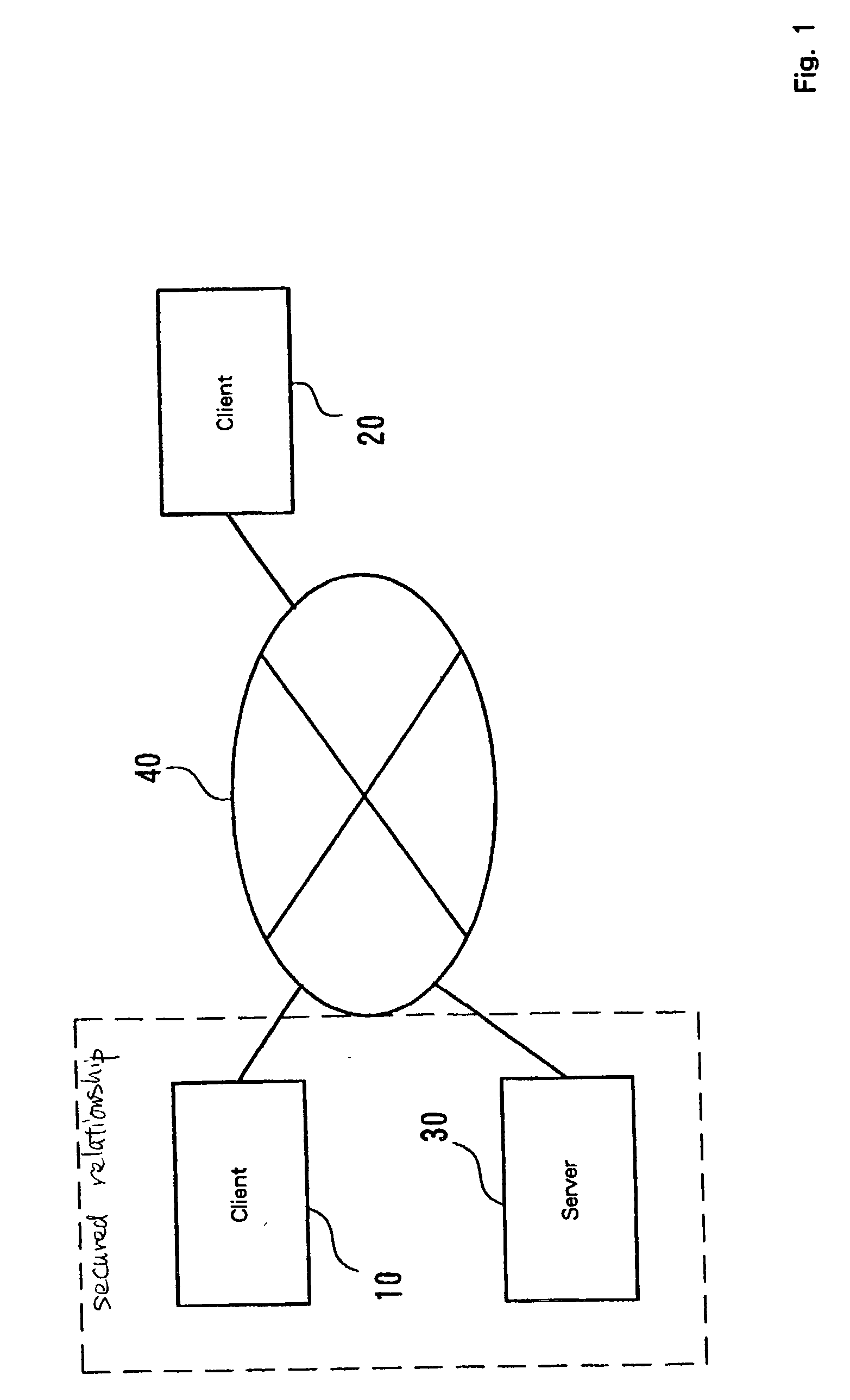
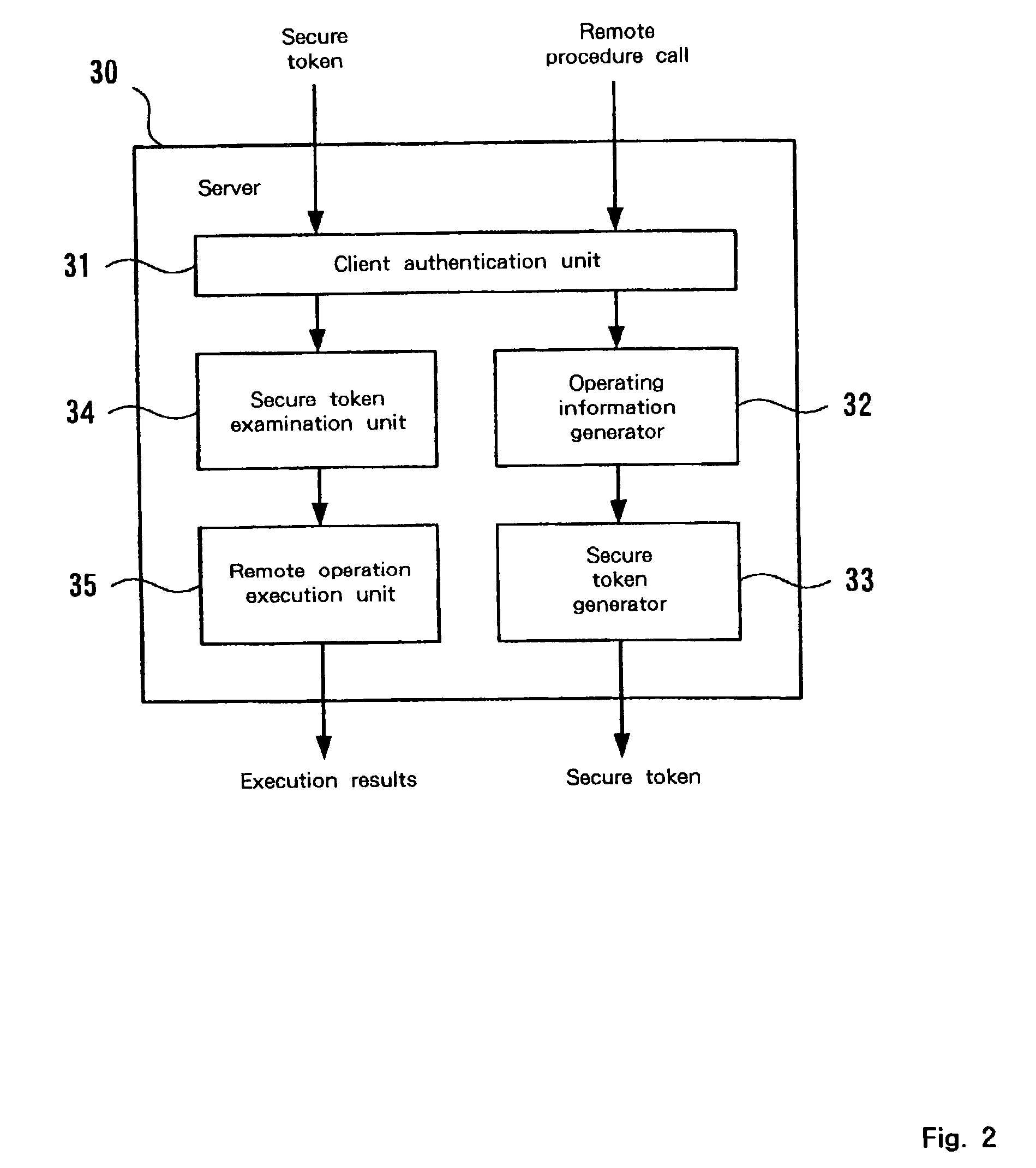
A mechanism for access control based on remote procedure calls is established whereby server management costs for the processing associated with the authentication of client access rights and the provision of requested resources can be reduced by distributing these costs among clients. A first client, which has an access right to a server via a network, can issue a remote procedure call to the server. The first client can also communicate with a second client, which doesn't have an access right to the server. The first client requests the server to issue a token, which is a data set for permitting the second client a limited access to the server, and subsequently the token prepared by the server is transmitted to the second client. The second client originally has no access rights relative to the server. However, if the second client transmits a remote procedure call using the received token, limited access is granted. The server performs a process designated by the remote procedure call from the second client. The token includes operating information for designating an operation to be performed based on the remote procedure call, and identification information for identifying the second client.
Owner:IBM CORP
Decentralized access control framework
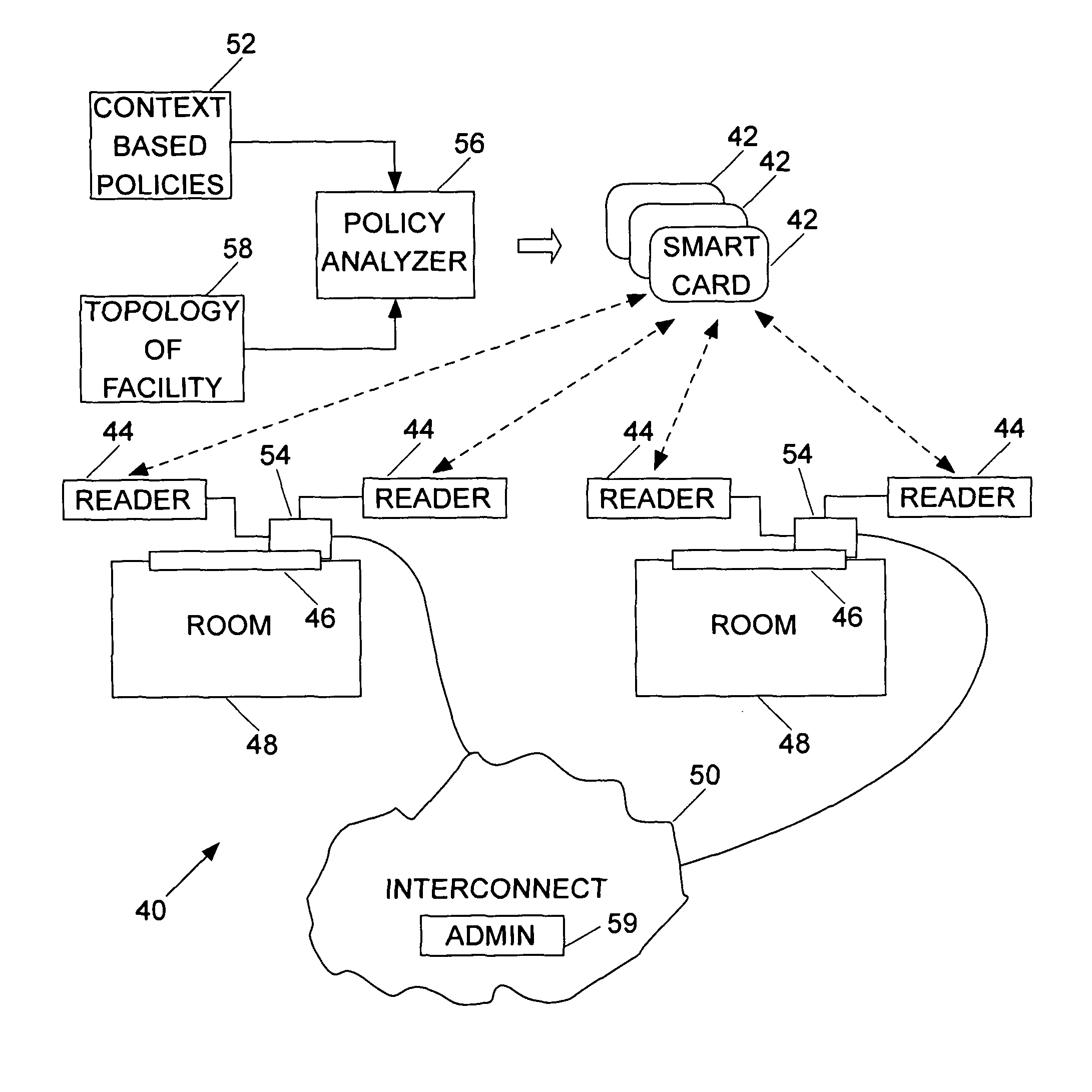
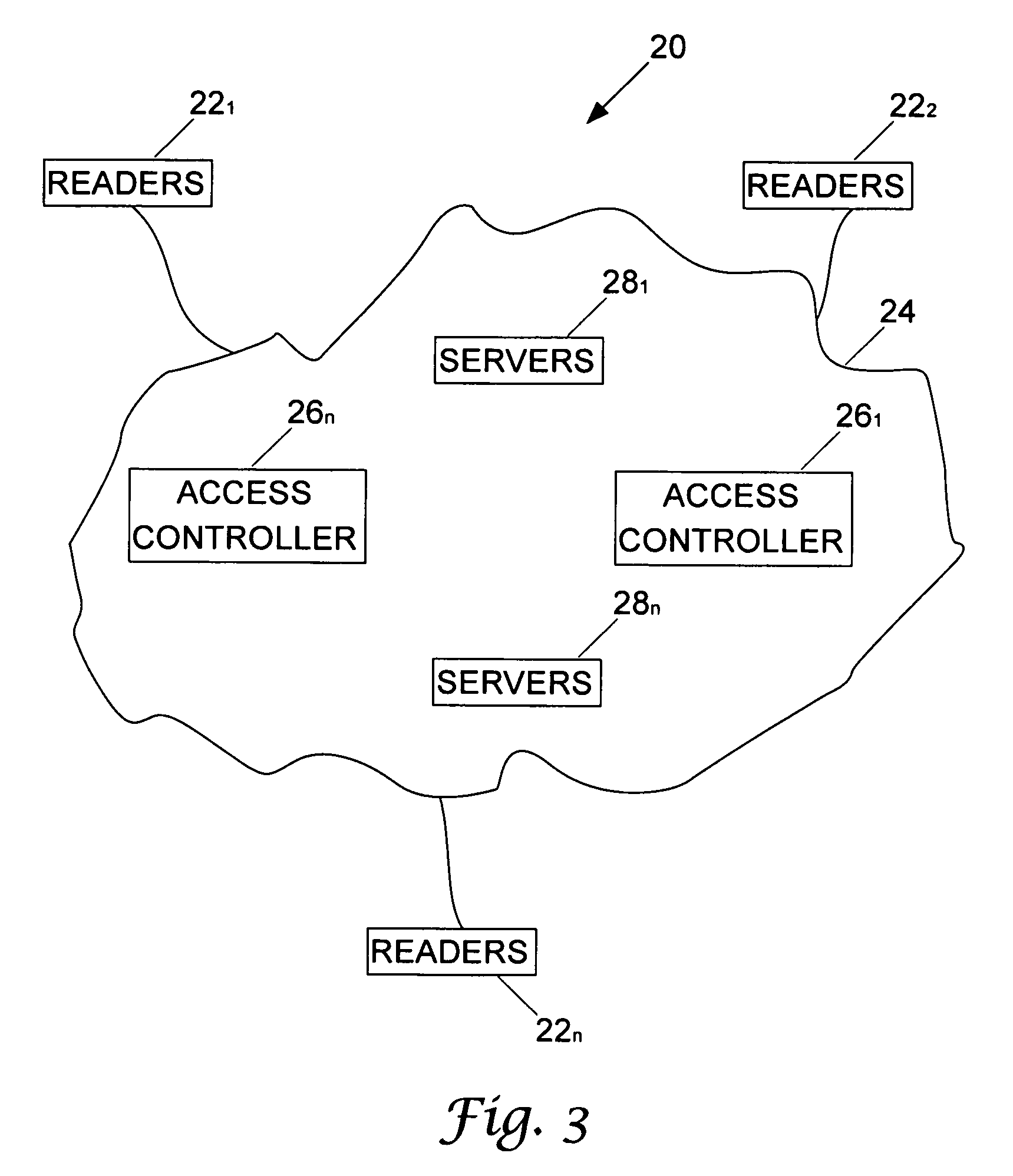
ActiveUS8166532B2Electric signal transmission systemsDigital data processing detailsAccess control matrixControl system
A functional architecture is provided for decentralizing the authorization function of an access control system that incorporates user carried access devices, such as smart cards, and door controllers that interact so as to make access decisions. Access to individual rooms is guarded by parameters partially carried by the user carried access devices and partially included in the door controllers.
Owner:HONEYWELL INT INC
Card type recording medium and access control method for card type recording medium and computer-readable recording medium having access control program for card type recording medium recorded
InactiveUS6371377B2Simplify workGuaranteed uptimeOther printing matterUnauthorized memory use protectionComputer hardwareAccess control matrix
Owner:FUJITSU LTD
Method and system for providing a secure multi-user portable database
A system and method for providing, managing, and accessing a multi-user secure portable database using secure memory cards is provided. The database has a secure portion for storing security keys and a non-secure portion for encrypted data files. Access to the encrypted data files is controlled by assigning access rights through an access control matrix to each encrypted data file according to a hierarchical structure of users. A user requesting access is identified in the hierarchy, associated with a key for allowing the requested access, and the requested access allowed to a file in accordance with the rights allocated through the access control matrix. A patient can selectively grant access to encrypted medical records on his card to a physician. Authentication of the owner / patient is preferably required. Other records required by emergency medical personnel are readable from the same card without requiring permission from the patient.
Owner:PRIVAMED
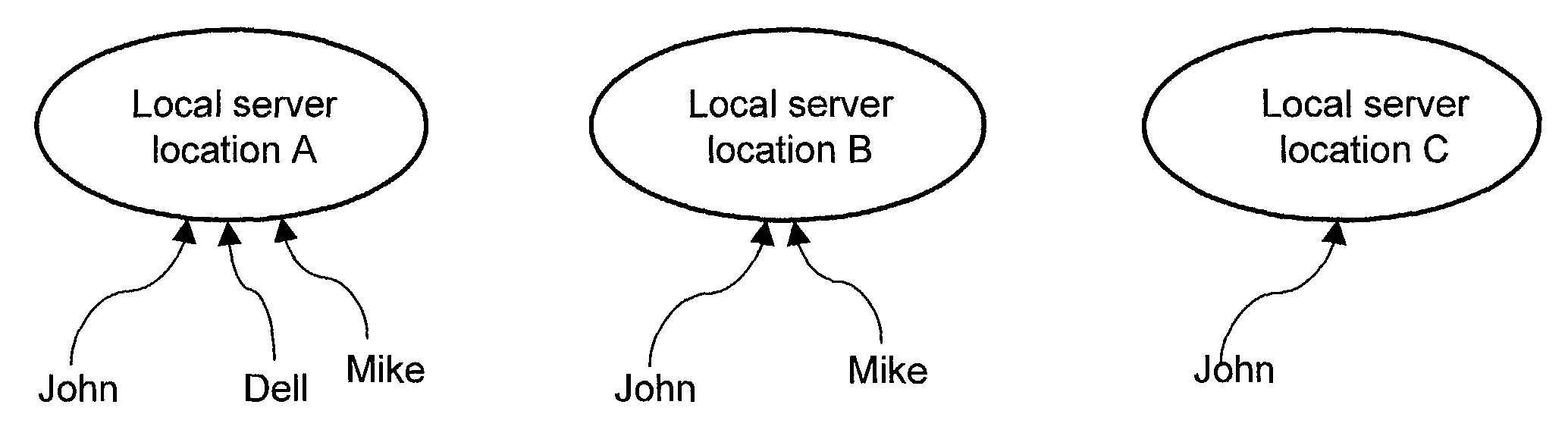
System and method for providing distributed access control to secured documents
ActiveUS7783765B2Ensures dependability and reliability and scalabilityEfficient executionDigital data processing detailsAnalogue secracy/subscription systemsAccess control matrixControl system
A system and method for providing distributed access control are disclosed. A number of local servers are employed to operate largely on behalf of a central server responsible for centralized access control management. Such a distributed fashion ensures the dependability, reliability and scalability of the access control management undertaking by the central server. According to one embodiment, a distributed access control system that restricts access to secured items can include at least a central server having a server module that provides overall access control, and a plurality of local servers. Each of the local servers can include a local module that provides local access control. The access control, performed by the central server or the local servers, operates to permit or deny access requests to the secured items by requestors.
Owner:INTELLECTUAL VENTURES I LLC
Method for performing access control in next-generation mobile communication network, and user equipment
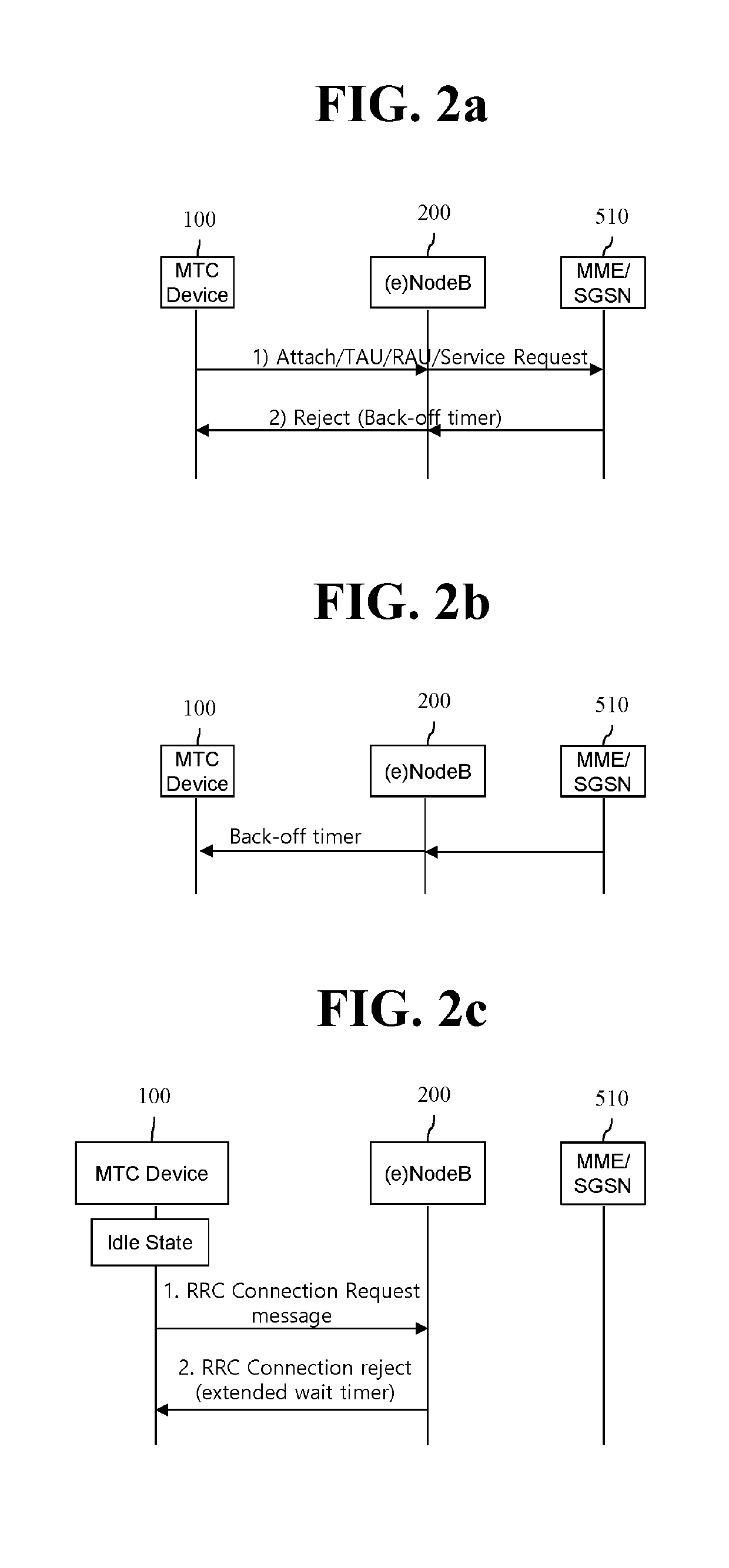
ActiveUS20190313473A1Solve the real problemAssess restrictionConnection managementAccess control matrixTelecommunications
Disclosed in the present specification is a method by which a user equipment (UE) performs access control. The method comprises the steps of: allowing a non-access-stratum (NAS) layer of the UE to transfer information on an important service and a NAS signaling request to a radio resource control (RRC) layer, when the important service is required even if access to a cell is currently interrupted or a back-off timer is operated; and allowing the RRC layer to skip or override an inspection for access control on the basis of the information on the important service, wherein, the information on the important service can be set in advance.
Owner:LG ELECTRONICS INC
Method for automatically generating list of meeting participants and delegation permission
InactiveUS6885388B2Secure and convenient distributionImprove securityCathode-ray tube indicatorsMultiple digital computer combinationsAccess control matrixWorld Wide Web
A method and system automatically generate a list of participants physically present at a meeting and distribute permission to the participants. Identity and key information is collected from the participants during the meeting using at least one personal area network. The identity and key information is stored on a delegation device. Permission to access the services is distributed to the participants over at least one personal area network using the delegation device. The delegation device may include an access control matrix or moveable icons for organizing and distributing participant and permission information.
Owner:WIDEPOINT CYBERSECURITY SOLUTIONS CORP
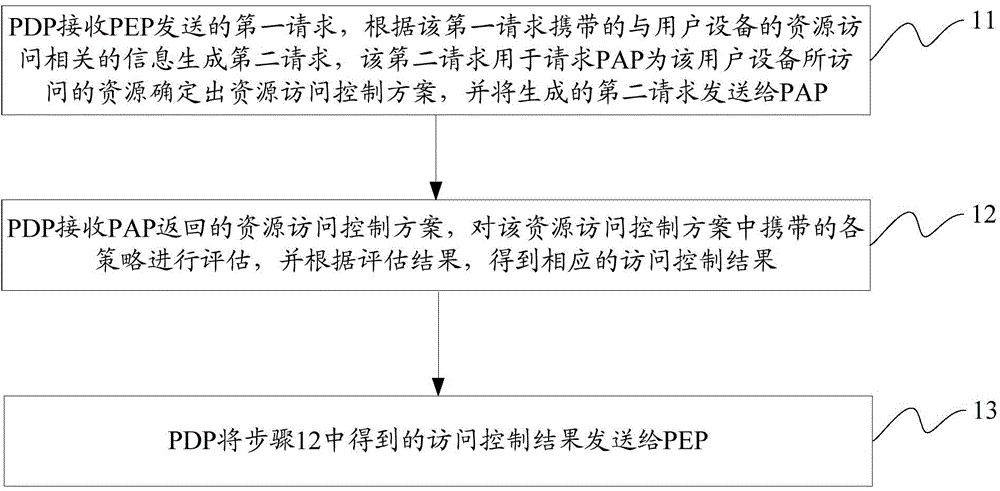
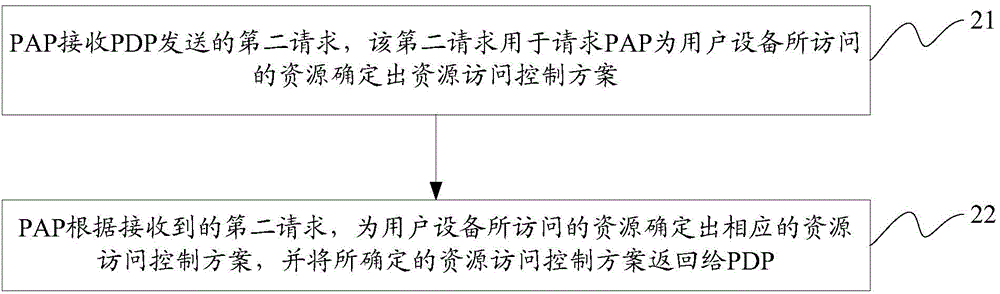
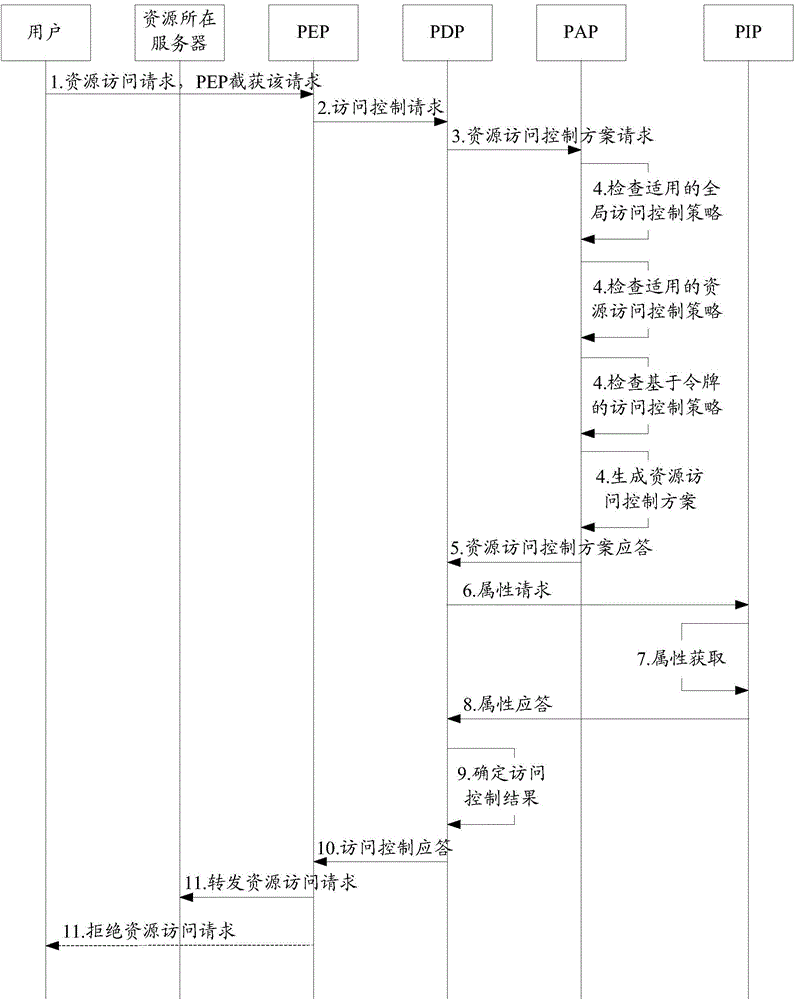
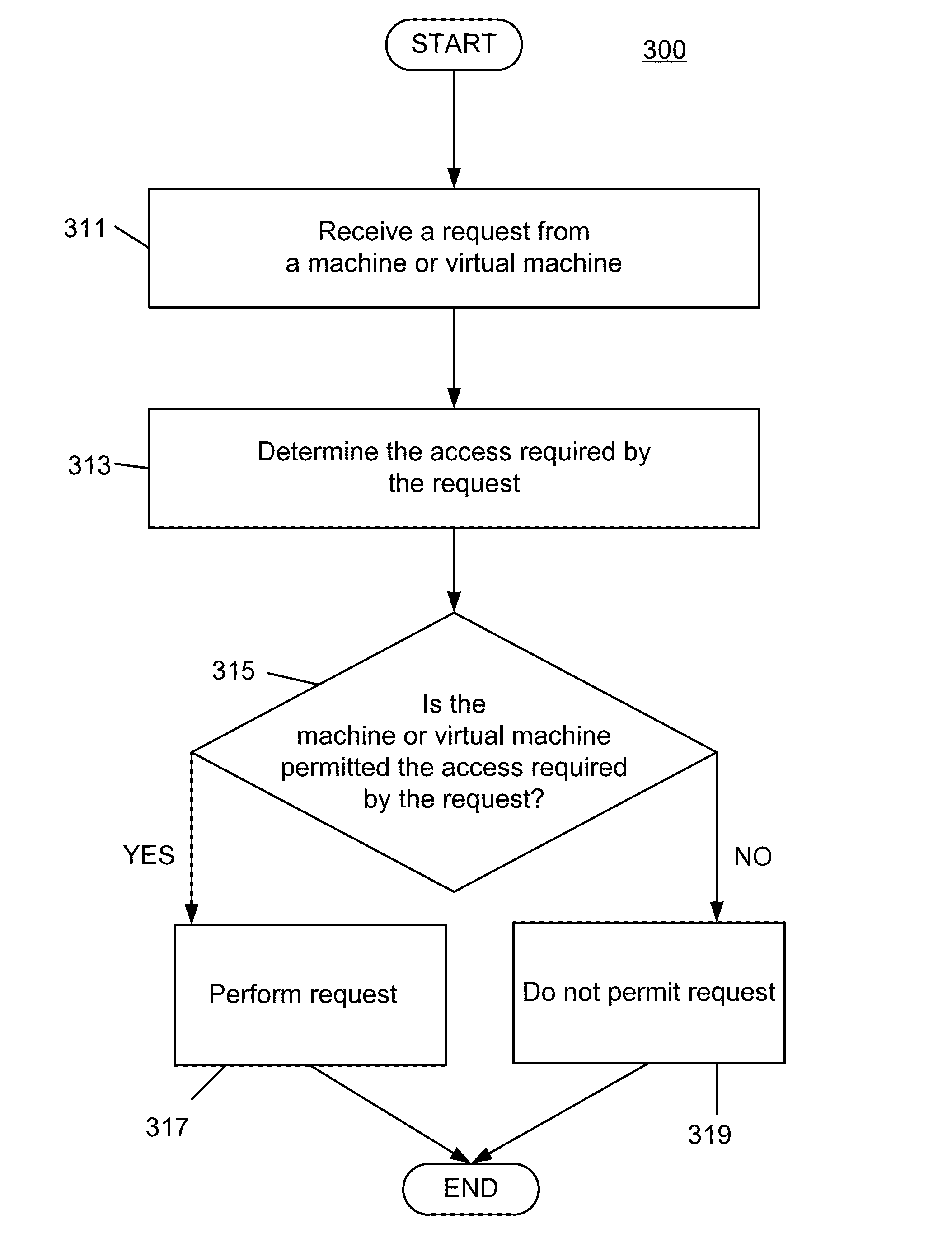
Decision method for access control and equipment
The invention discloses a decision method for access control and equipment. The objective of the invention is to satisfy requirements for access control in one machine-to-machine (M2M) system. The methods includes the following steps that: a policy decision point (PDP) receives a first request transmitted by a policy execution point (PEP), and generates a second request according to information which is carried by the for the first request and is relates to resource access of user equipment, and transmits the second request to a policy access point (PAP), wherein the second request is used for requesting the policy access point (PAP) to determine a resource access control scheme for resources accessed by the user equipment; and the policy decision point (PDP) receives the resource access control scheme returned by the policy access point (PAP) and assess the first request according to policies carried by the resource access control scheme; and the policy decision point (PDP) performs computation an obtained assessment result according to a logical computation relationship carried by the resource access control scheme, so as to generate an access control result and transmits the access control result to the policy execution point (PEP).
Owner:CHINA ACAD OF TELECOMM TECH
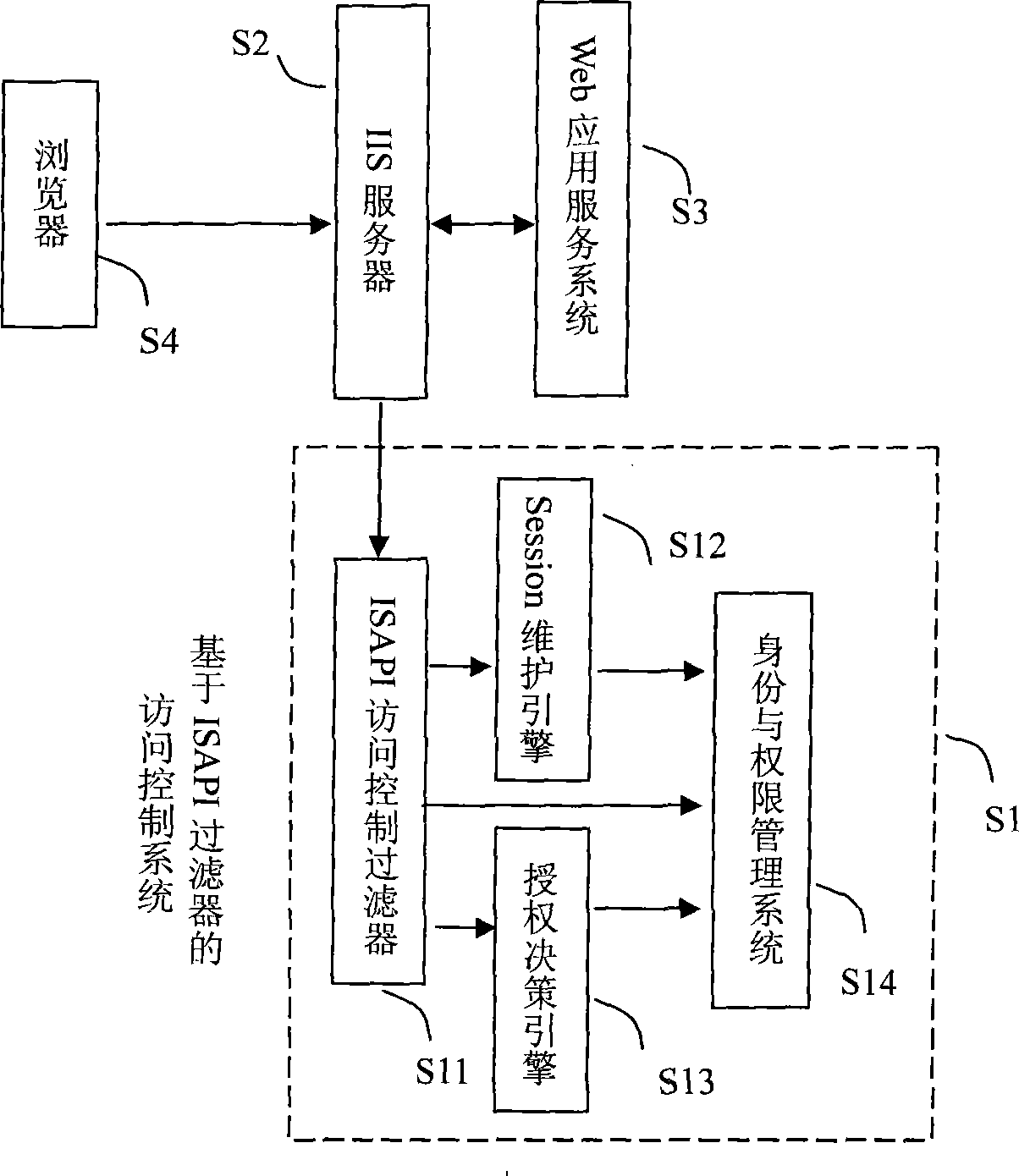
ISAPI access control system for Session ID fully transparent transmission
InactiveCN101247395ACorrectly modify the transmission data length indicationService outage brieflyTransmissionUniform resource locatorSession ID
The present invention relates to ISAPI access control system with Session full transparent transfer, which can realize user Session maintenance and SessionID transfer without involving, modifying and using Cookie in Web system, and provides user identity identification and visiting control function for Web application on IIS server. It includes four components: ISAPI accessing control filter, Session maintenance engines, authorization decision engines, and identity and authority management system. The present invention resolves referred key technology problem about ISAPI visiting URL chaining adding SessionID information in control filter rewrite respond message successfully, such as transfering related information between filter call-back function, correctly modifying length indication in respond message data block, etc.
Owner:WUHAN UNIV OF TECH +1
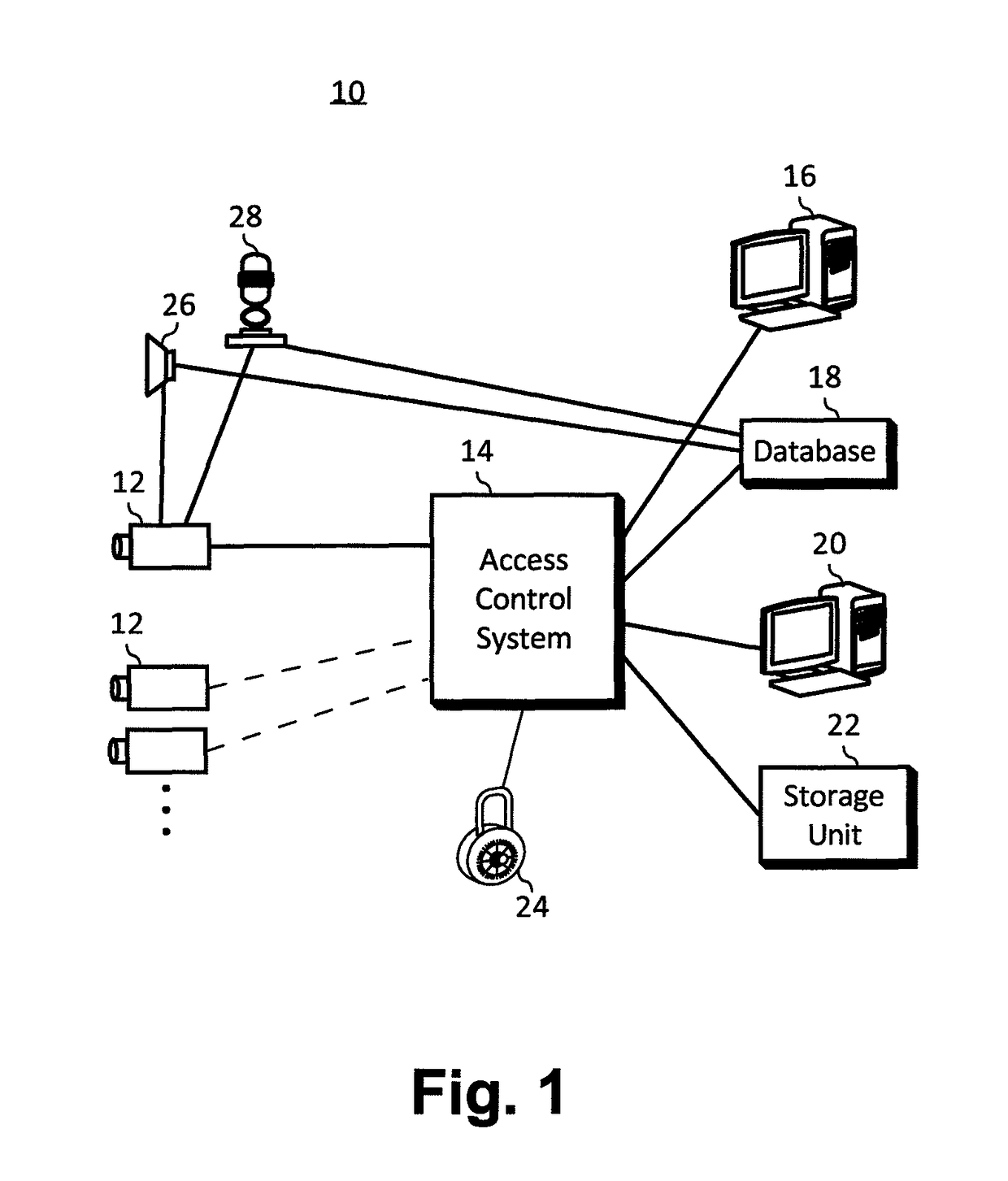
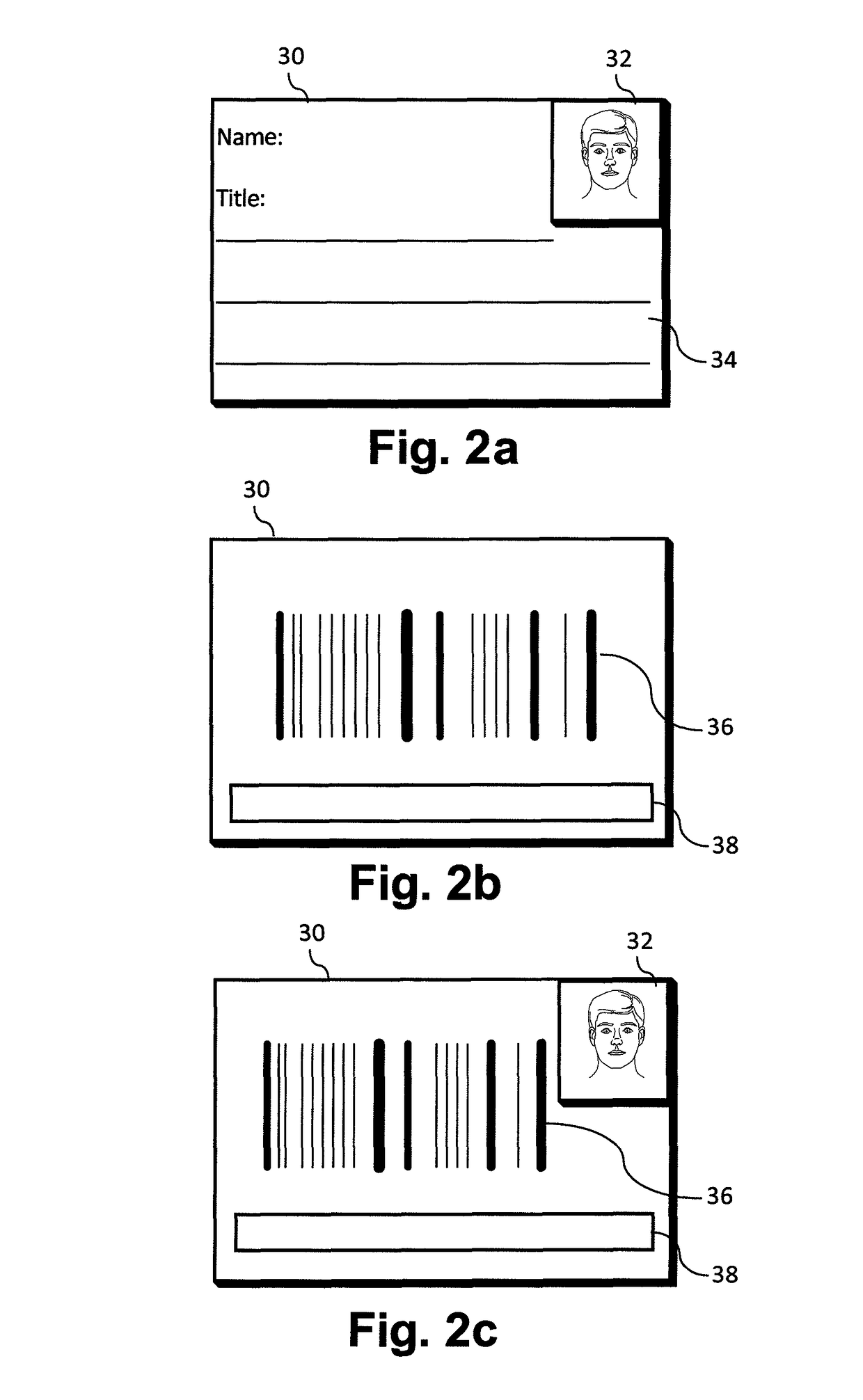
Access control system with symbol recognition
InactiveUS7907753B2Eliminate needCharacter and pattern recognitionColor television detailsAccess control matrixInternet privacy
A video camera is located at a secure access point and is connected to a computer network. The camera is used as a conventional security camera and also provides automated assistance with access control. When an identity badge is presented to the camera by a person requesting access to the facility, a computer that is monitoring the camera recognizes a bar code or other symbols on the badge and accesses a database to locate information associated with that identity badge. This information is then used to determine if the person should be granted access.
Owner:HONEYWELL SILENT WITNESS
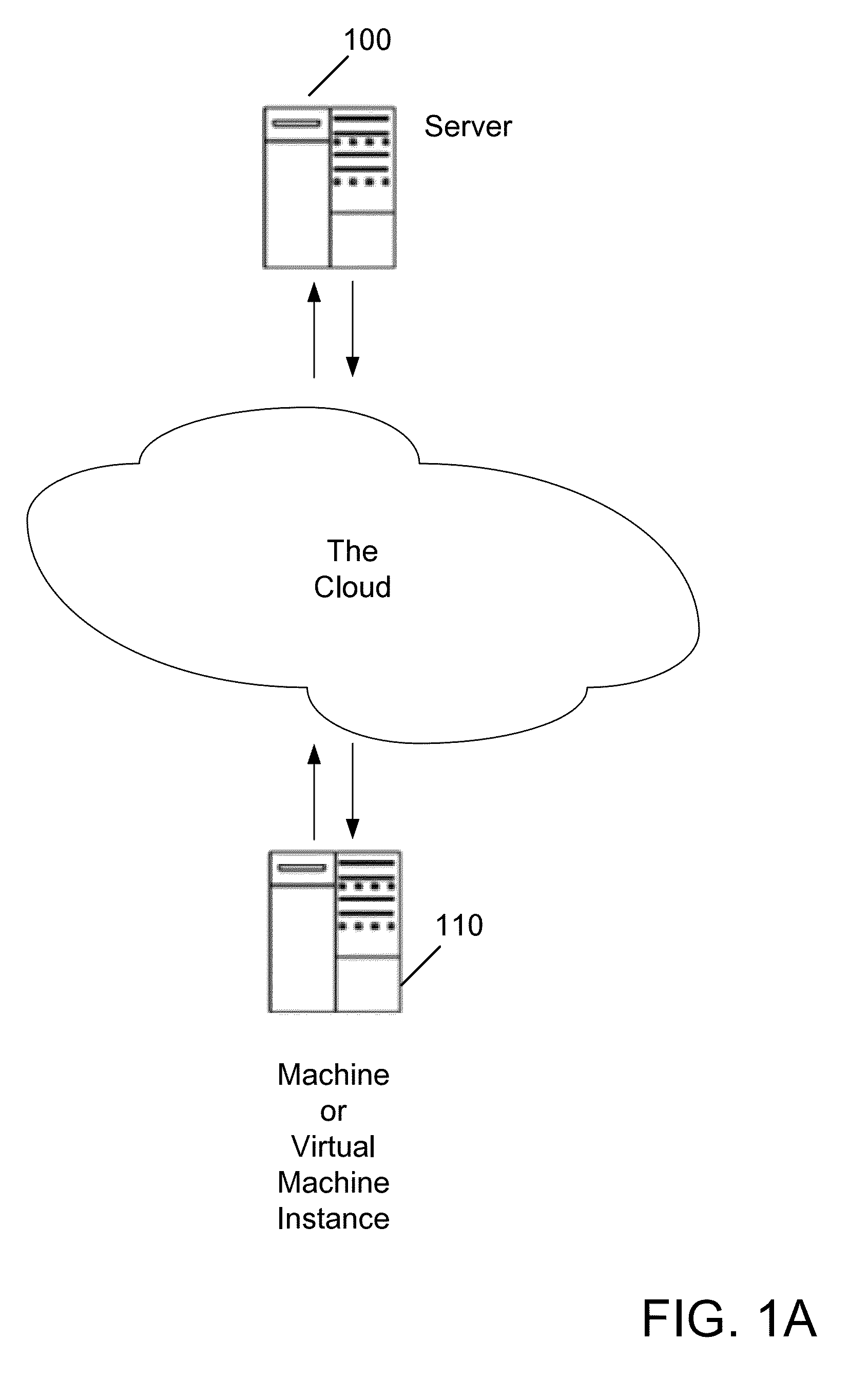
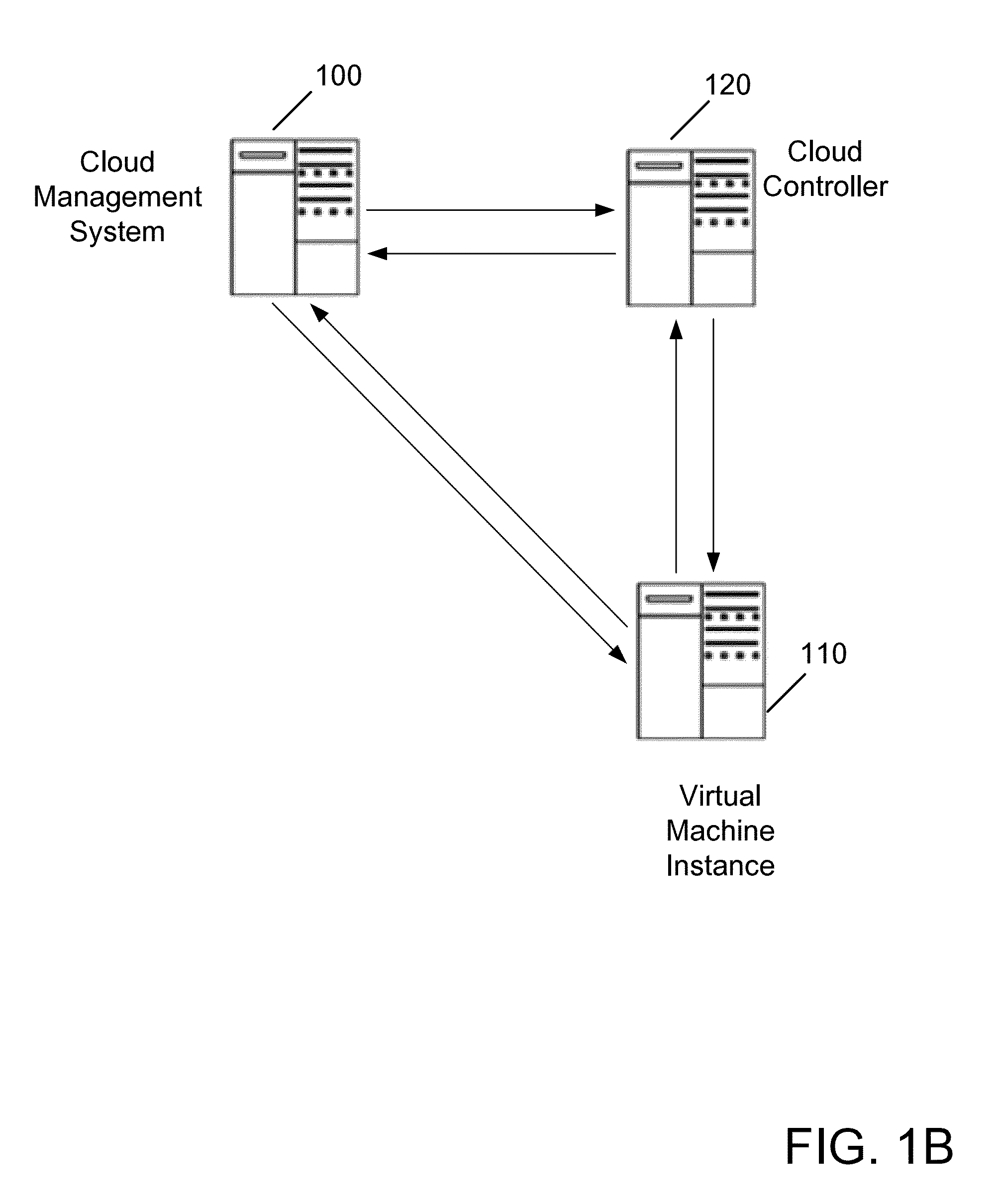
Systems and methods for associating a virtual machine with an access control right
ActiveUS20140082699A1Digital data processing detailsMultiple digital computer combinationsAccess control matrixCloud base
The present invention is related to associating a machine or virtual machine instance with an access control right in a cloud-based computing environment. In one aspect, the present invention relates to an apparatus for or a method of associating a machine or virtual machine instance with an access control right in a cloud-based computing environment. In various embodiments, the apparatus is capable of, and the method includes, the following: receiving, in a cloud-based computing environment, a request to perform an action; using an identifier for the machine or virtual machine instance to determine that the received request was sent by, or on behalf of, the machine or virtual machine instance; and identifying an access control right associated with the machine or virtual machine instance making the request, to determine whether to perform the action on behalf of, or grant access by, the machine or virtual machine instance.
Owner:BRIGHTSCALE INC
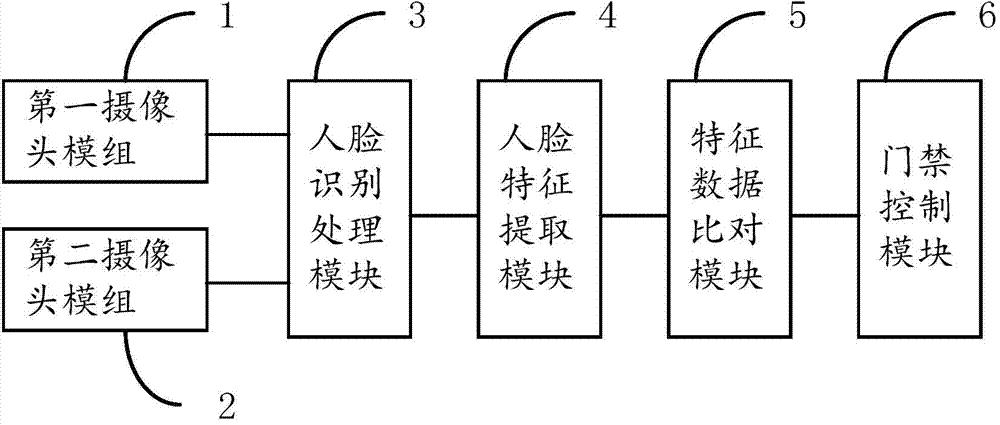
Face recognition-based attendance access control system
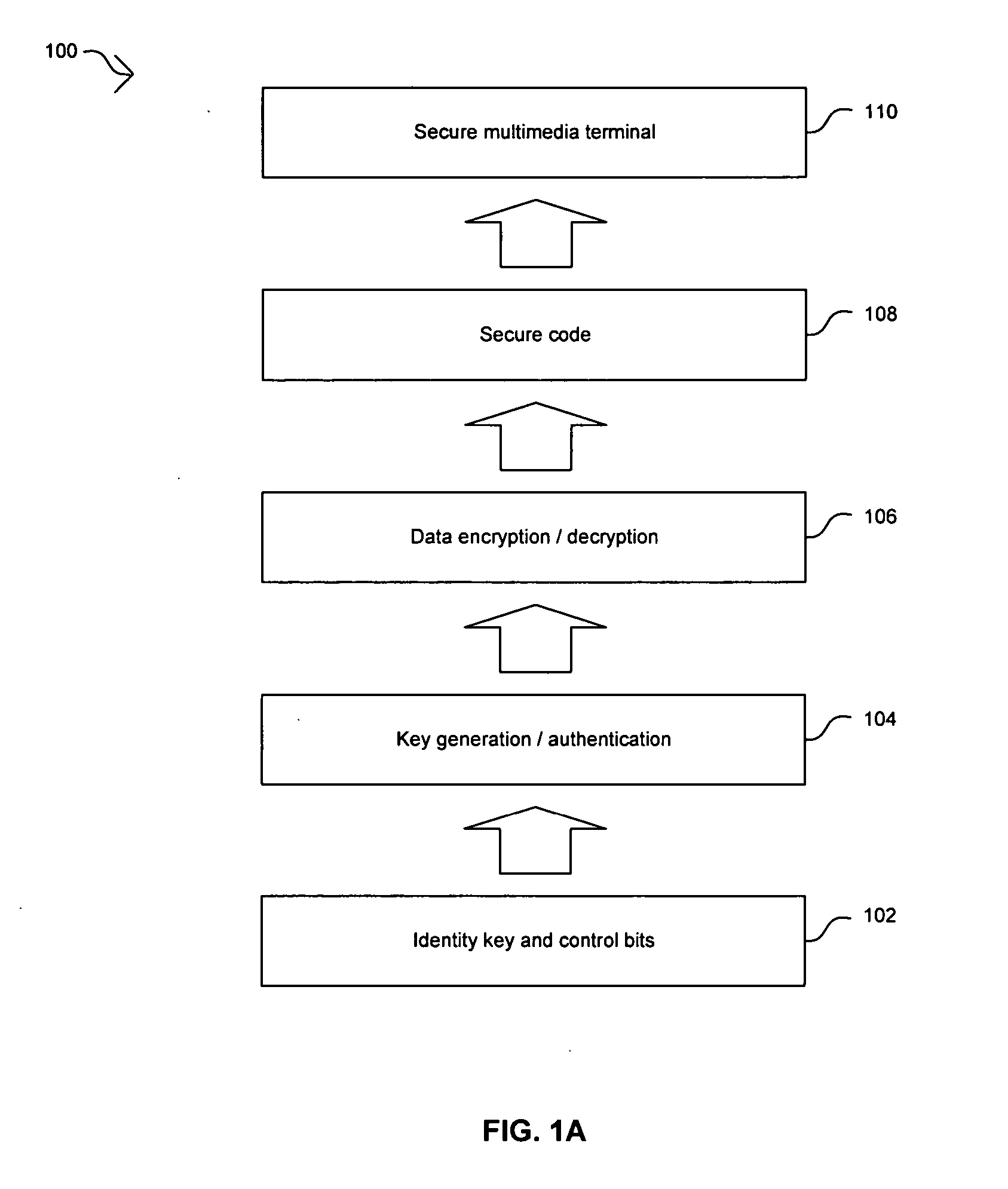
InactiveCN104851140ARealize functionSave human resourcesRegistering/indicating time of eventsCharacter and pattern recognitionFeature extractionAccess control matrix
The present invention provides a face recognition-based attendance access control system, which comprises a first camera module used for acquiring a first image information in a first preset to-be-monitored space, a second camera module used for acquiring a second image information in a second preset to-be-monitored space, a face recognition and processing module used for conducting the gray processing and the illumination compensation processing on the acquired first and second image information so as to obtain an grayscale image, and extracting the feature information of face components from the grayscale image, a feature data comparison module used for conducting the similarity comparison on the feature information of face components and the pre-stored face data information, and generating an access control switch control signal when the similarity achieves a similar threshold, and an access control module used for receiving the access control switch control signal to open or close a door. According to the invention, the cross monitoring function on the image information in different to-be-monitored spaces can be realized by the first camera module and the second camera module. Therefore, the recognition accuracy is improved.
Owner:CHONGQING KAIZE TECH
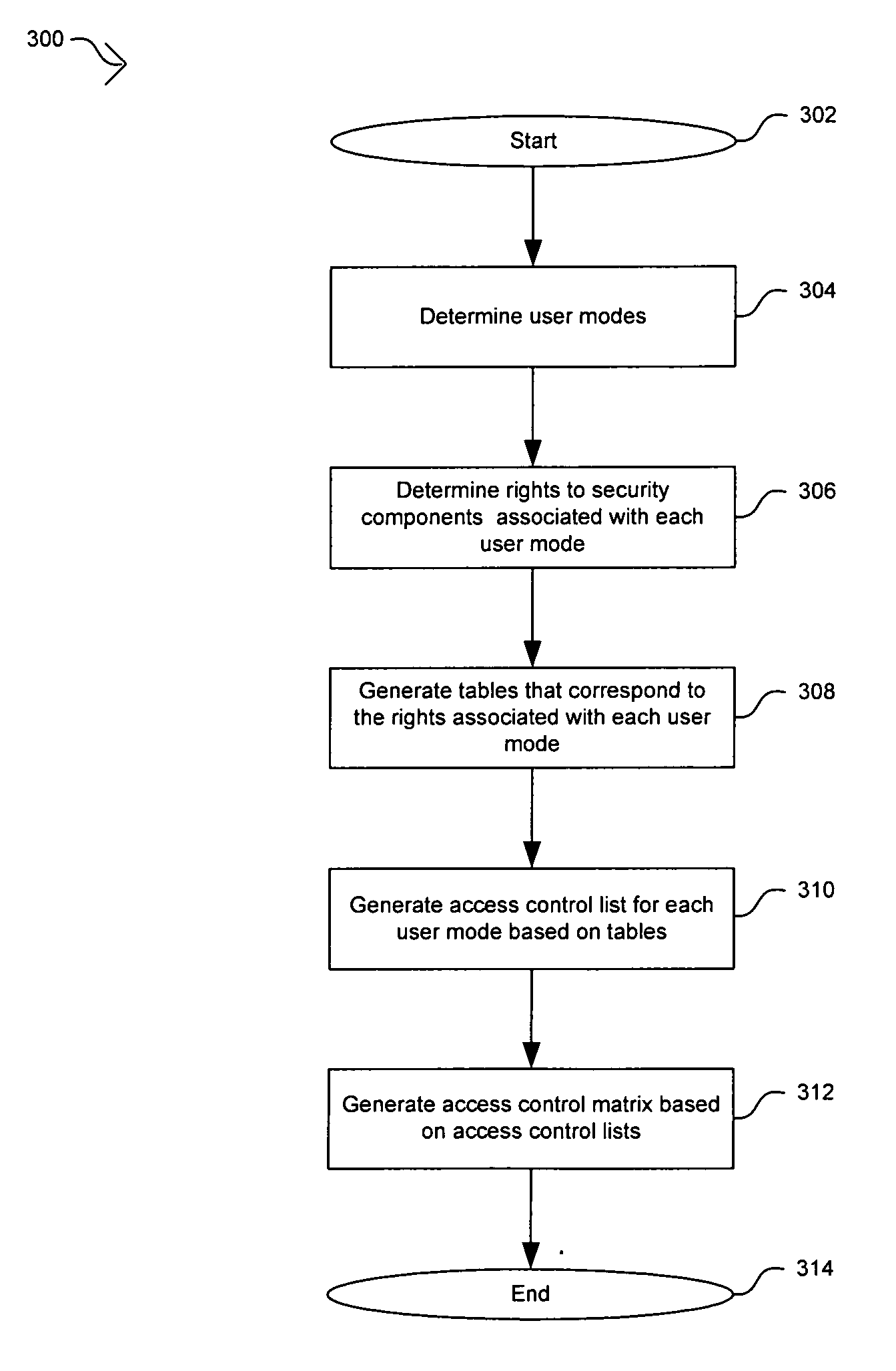
Method and apparatus for constructing an access control matrix for a set-top box security processor
ActiveUS20060265734A1Digital data processing detailsUser identity/authority verificationAccess control matrixMultimedia system
In multimedia systems requiring secure access, a method and apparatus for constructing an access control matrix for a set-top box security processor are provided. A security processor may comprise multiple security components and may support multiple user modes. For each user mode supported, at least one access rule table may be generated to indicate access rules to a security component in the security processor. An access control list comprises information regarding the access rules for a particular user mode to the security components in the security processor. An access control matrix may be generated based on the access control lists for the user modes supported by the security component. The access control matrix may be implemented and / or stored in the security processor for verifying access rights of a user mode.
Owner:AVAGO TECH INT SALES PTE LTD
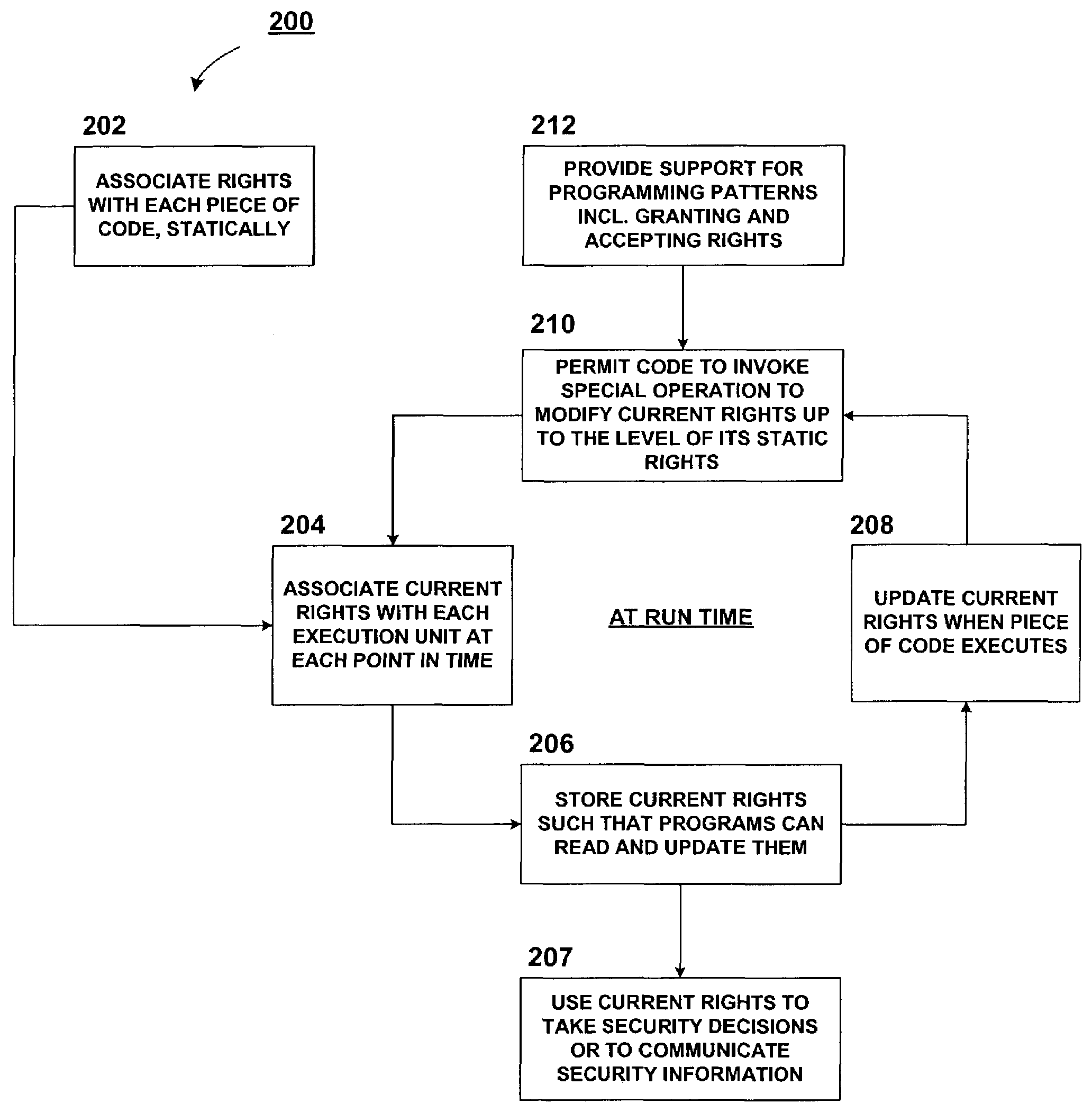
History based rights computation for managed code
InactiveUS7203833B1Memory loss protectionError detection/correctionAccess control matrixManaged code
In the access control model of security, an access control matrix associates rights for operations on objects with subjects. An approach for assigning rights to code at run-time involves determining the run-time rights of a piece of code by examining the attributes of the pieces of code that have run (including their origins) and any explicit requests to augment rights. Thus, this approach relies on the execution history for security. This history based approach reduces the difficulties and the error-proneness of securing extensible software systems.
Owner:MICROSOFT TECH LICENSING LLC
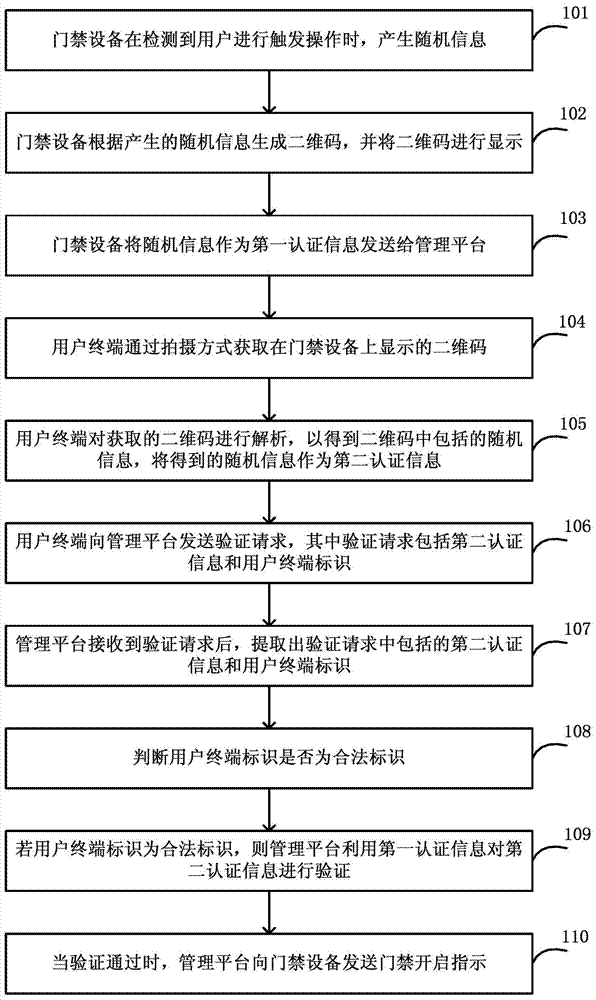
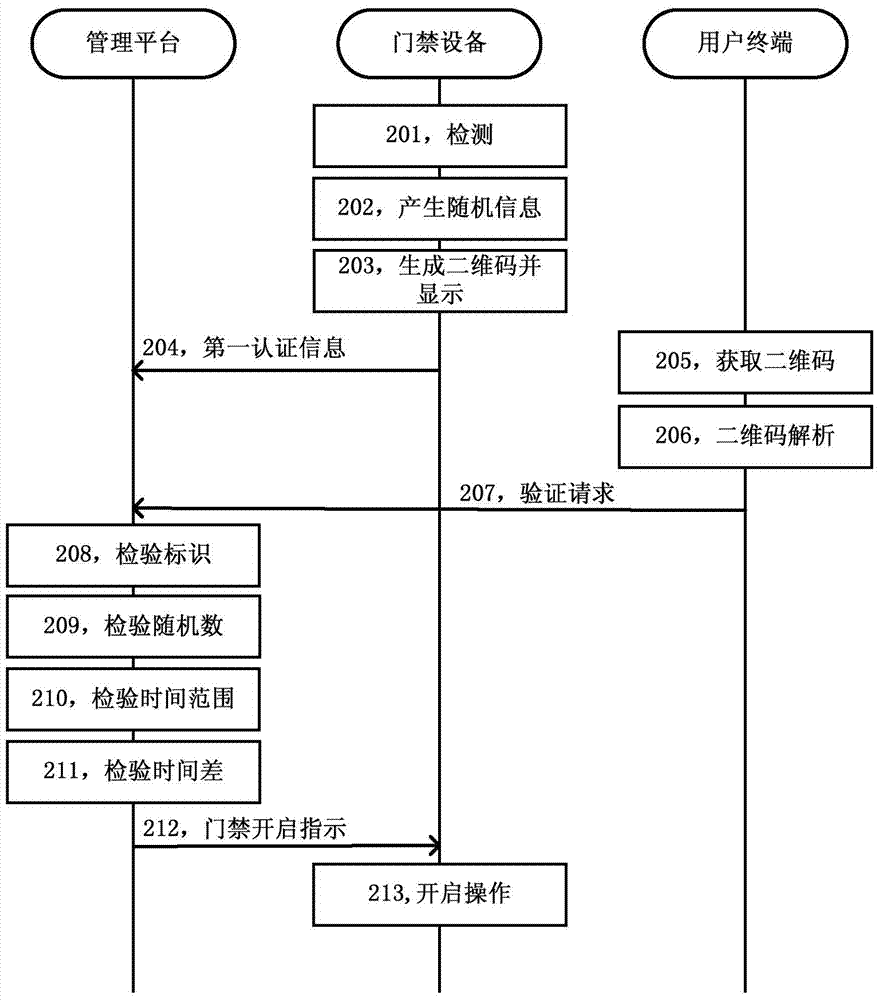
Access control method and system based on two-dimension code
ActiveCN104780043AImprove safety and reliabilityUser identity/authority verificationIndividual entry/exit registersAccess control matrixComputer terminal
The invention discloses an access control method and an access control system based on a two-dimension code, wherein the method comprises the steps as follows: access control equipment generating random information when detecting an operation triggered by a user, generating the two-dimension code according to the generated random information, displaying the two-dimension code, transmitting to a management platform via using the random information as first authentication information; a user terminal obtaining the two-dimension code displayed on the access control equipment via shooting, analyzing the two-dimension code to obtain the random information; using the obtained random information as second authentication information, transmitting a verification request to the management platform, wherein the verification request comprises the second authentication information and a user terminal identification; the management platform using the first authentication information to verify the second authentication information when judging that the user terminal identification is a legal identification, the management platform transmitting an access control opening instruction to the access control equipment when the verification is passed. The method of the invention improves the safe reliability of authentication because the management platform performs dual authentication to information of the two-dimension code and identity of the user.
Owner:CHINA TELECOM CORP LTD
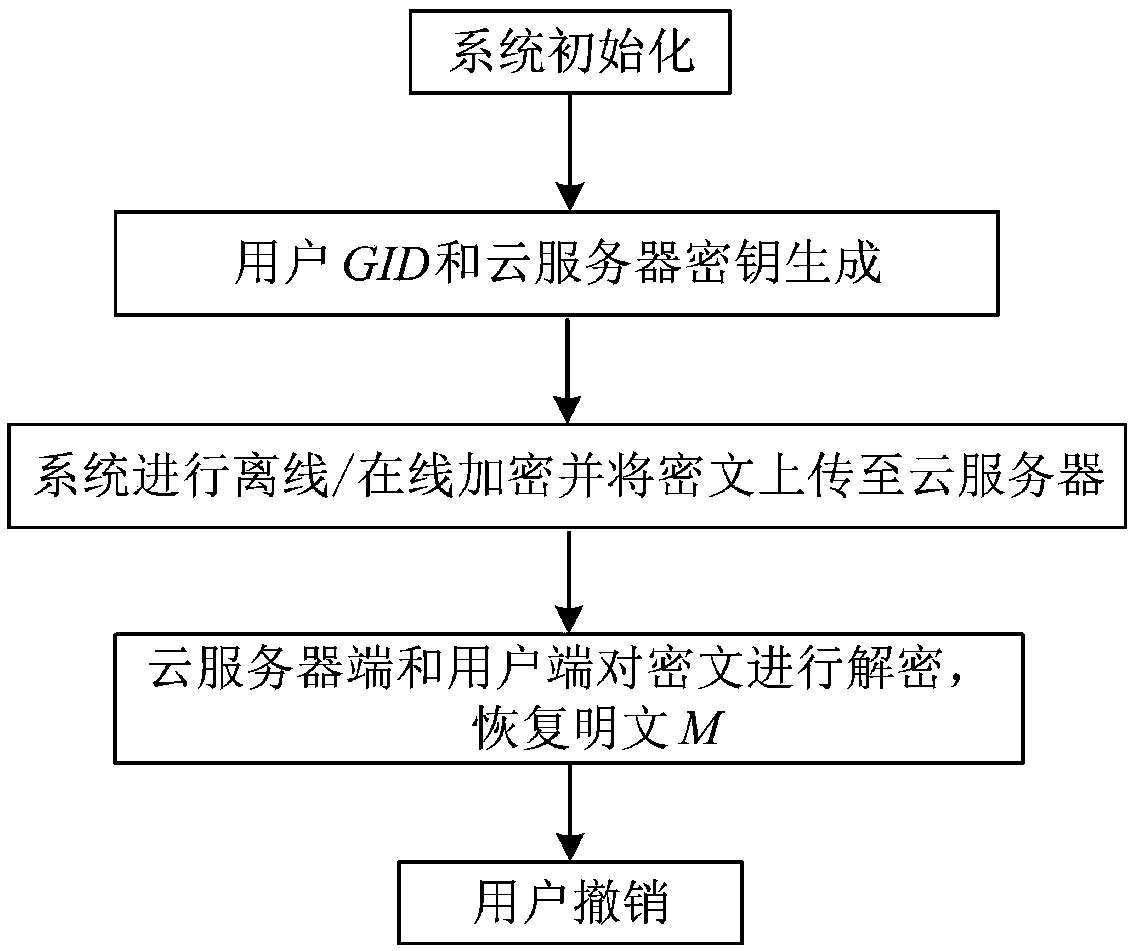
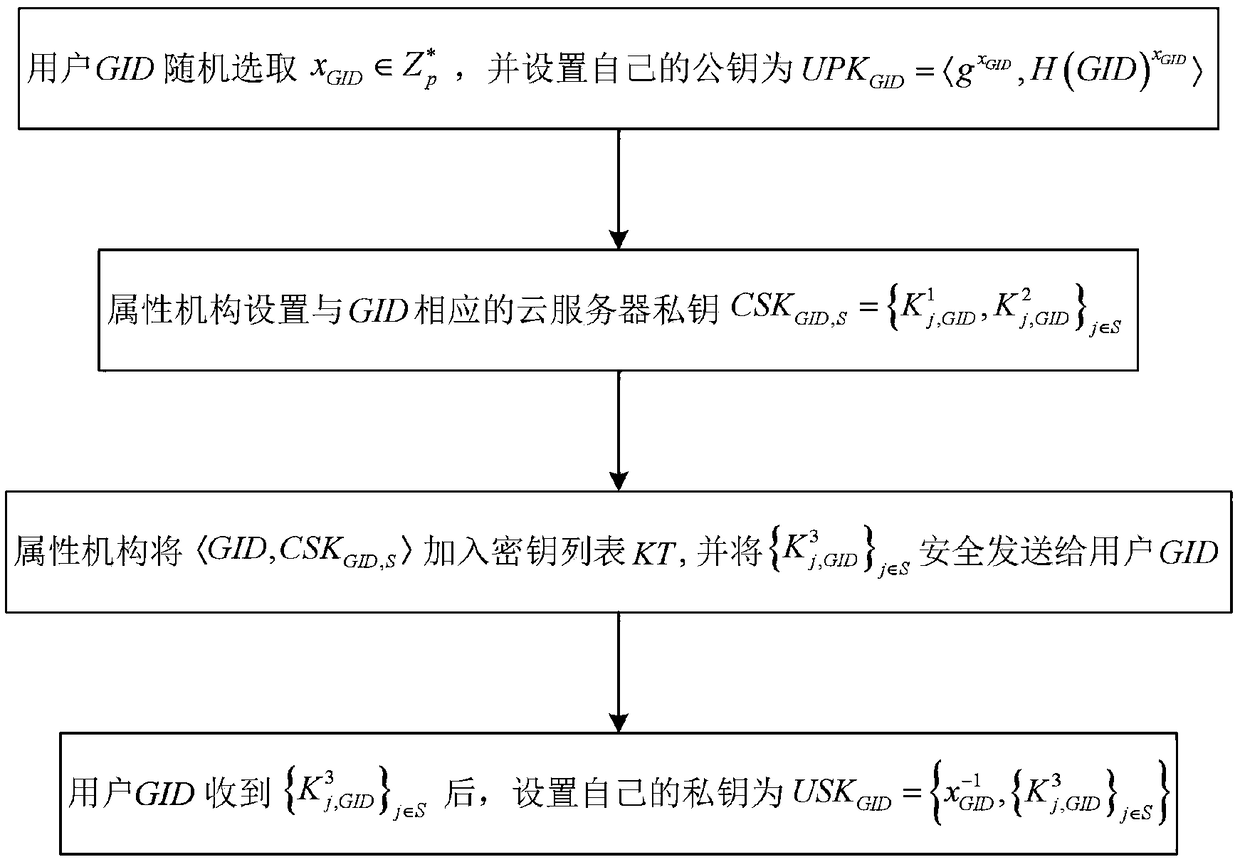
Multifunctional fine-grained access control method for cloud storage
The invention discloses a multifunctional fine-grained access control method for cloud storage, and solves the problem of fine-grained access control of data in cloud storage. The implementation stepsof the method are as follows: performing global initialization and attribute organization initialization; generating the public and private keys of a user and a private key of a cloud server; enabling a system to perform offline / online encryption, wherein the system is provided with a strategy hiding mechanism; uploading a final ciphertext to the cloud server; enabling the cloud server and a userterminal to decrypt and verify the correctness of the keys; enabling the cloud server to delete the corresponding entry from a key list for user revocation. The invention proposes a multi-system CP-ABE scheme with multiple characteristics, and the offline / online encryption mechanism is constructed in detail, which greatly reduces the computational cost of the user. The method has the functions ofattribute revocation, keyless collocation problem, the offline / online encryption mechanism, the strategy hiding and verifiability, and can be applied to fine-grained access control of data in cloud environments such as education, business and medical fields.
Owner:陕西链诚致远科技有限公司
Access control method based on attribute-based access control policy
The invention discloses an access control method based on an attribute-based access control policy. The method is characterized by 1) extracting attribute information of a user-role table and a role-authority table in a database and generating a user-role-authority access control relation Hash table; 2) generating an access control policy according to the access control relation Hash table: carrying out iteration traversal on the access control relation Hash table to obtain key value pairs, that is, an attribute set of each user and authority thereof, and then, generating an access control policy rule of the user according to the authority attribute of the user; and 3) for each received access request, an internet-of-thing search engine judging the access request according to the access control policy rule to determine whether access is allowed. The method can give a quick response to the search request, thereby greatly improving efficiency of the internet-of-thing search engine.
Owner:INST OF INFORMATION ENG CAS
Attribute-based hybrid encryption method capable of tracing leaked secret key
ActiveCN104168108AEnsure safetyAvoid destructionEncryption apparatus with shift registers/memoriesUser identity/authority verificationTrusted authorityHash function
Disclosed is an attribute-based hybrid encryption method capable of tracing a leaked secret key. The method comprises the following steps: a trusted authority: 1, inputting a coefficient lambda, and outputting a system parameter; 2, running a randomized number generation algorithm; 3, selecting one anti-bump Hash function, and calculating a Hash value; 4, running a fingerprint code generation algorithm GenFC; 5, calculating a bilinear pair exponentiation operation; 6, distributing a fingerprint code to a user, and specifying an attribute set S; 7, running the randomized number generation algorithm, multiplication and exponentiation operation; and 8, embedding the fingerprint code in a user private key; a data holder: 9, carrying out AES data encryption; 10, generating an access control matrix; 11, running an attribute-based hybrid encryption algorithm Encapsulate, and encrypting an AES session secret key; and 12, running a bilinear pair and multiplication and division operation to obtain a session secret key; a data user: 13, running an AES data decryption algorithm; and the trusted authority: 1*, searching for an adaptability code word; 2*, calculating pj and Z; and 3, calculating a weight sum, and outputting a set C.
Owner:BEIHANG UNIV
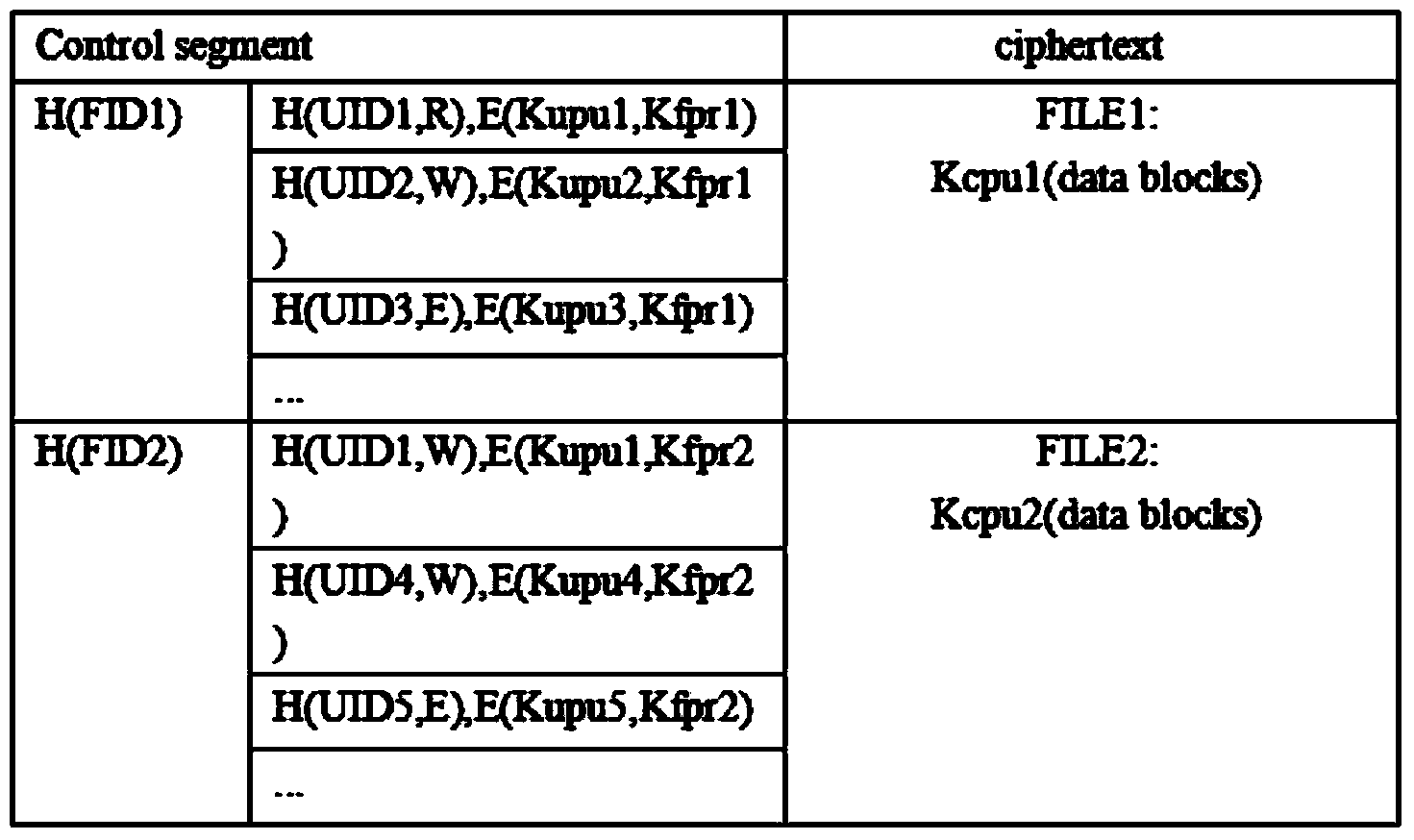
Fine-grained cloud platform security access control method based on user identity capacity
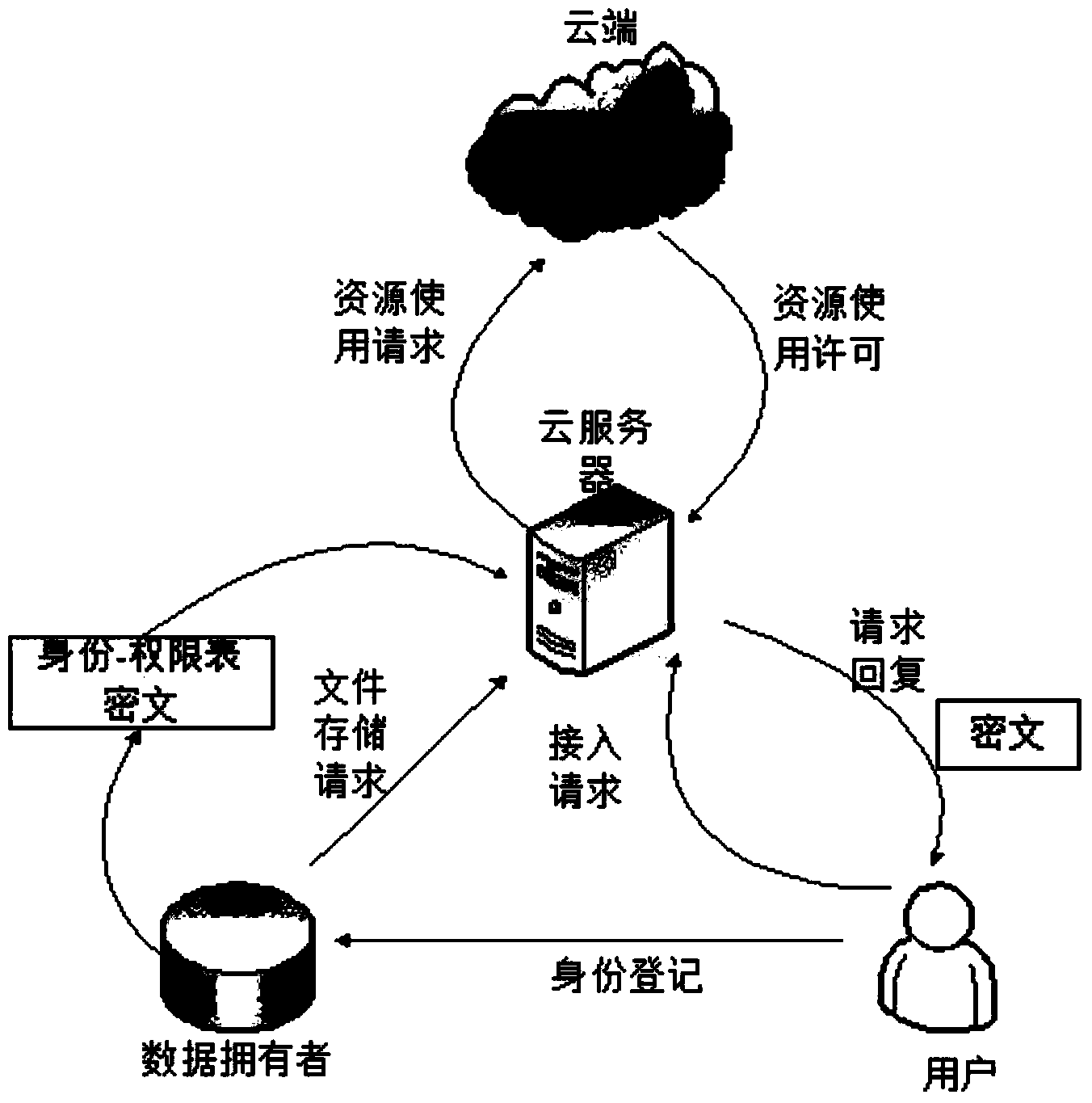
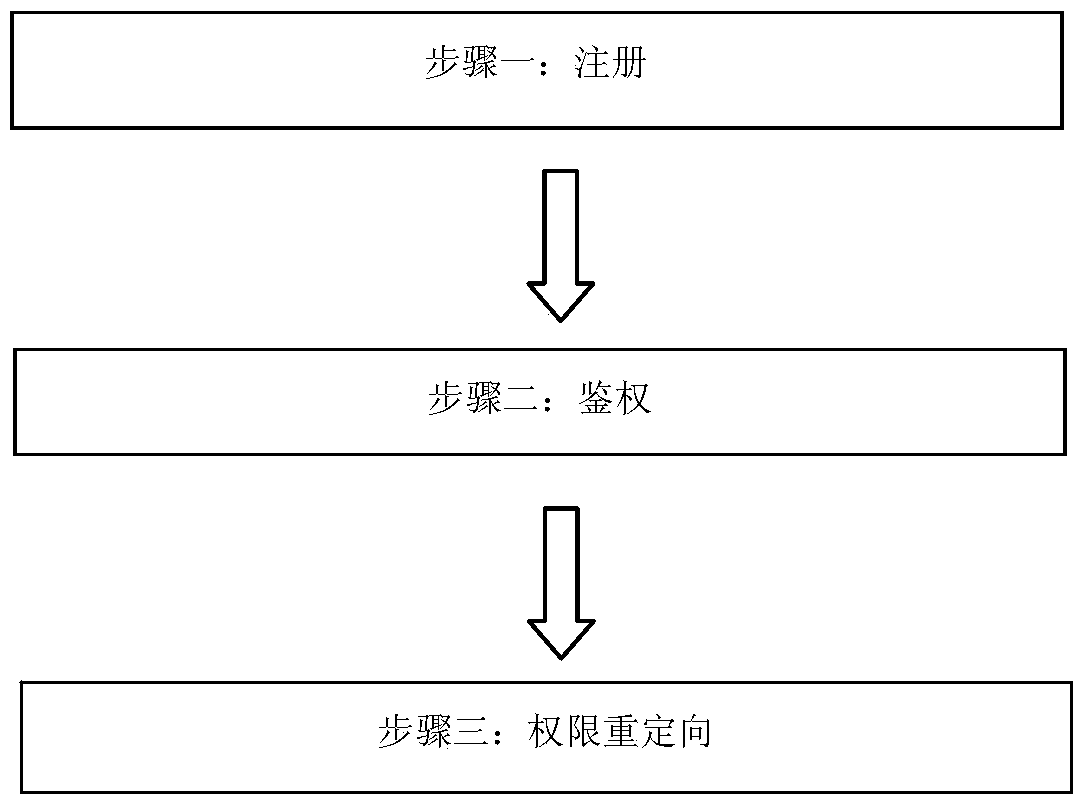
The invention relates to a fine-grained cloud platform security access control method based on user identity capacity, and belongs to the technical field of resource access. According to the method, a file uploaded by a data owner is divided into control fields and ciphertext fields, the ciphertext fields are stored in cloud physical nodes, the control fields are stored by a cloud server, a cloud server agent conducts intervention control, network resources are distributed reasonably, burden of the data owner is relieved, a control list needs to be partially updated in the access permission redirection process, each globally unique document number identifier is associated with a globally unique user identity identifier, operation permissions of users are bounded so as to achieve fine-grained access control, an uploaded identity-permission-ciphertext list is encrypted, the confidentiality and the integrity of user information and file information are guaranteed, and information leakage risks are reduced at a third-party cloud platform.
Owner:蜻蜓数字乡村研究院(苏州)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com