Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1034 results about "Data decryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
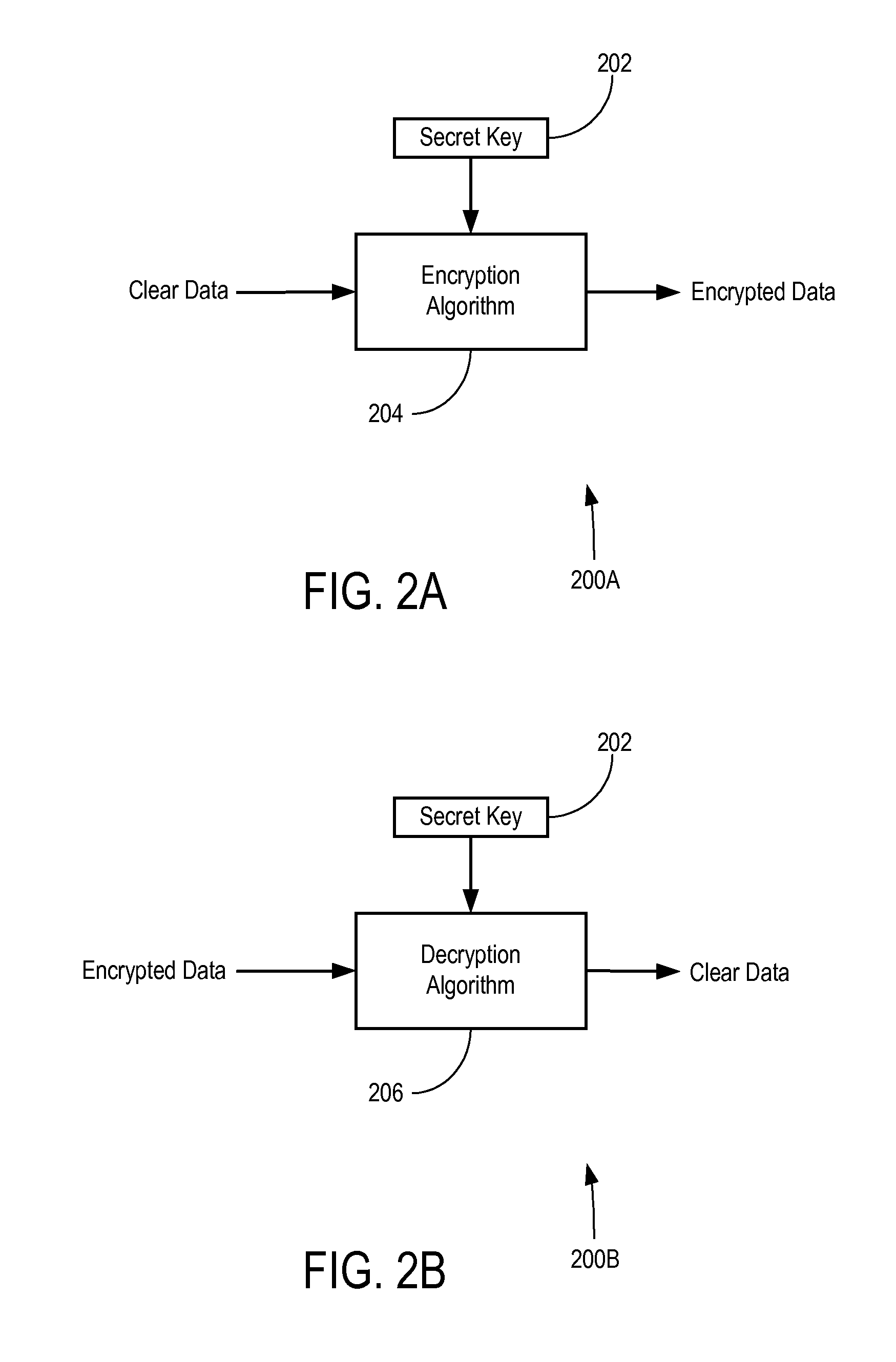
Decryption is the process of transforming data that has been rendered unreadable through encryption back to its unencrypted form. In decryption, the system extracts and converts the garbled data and transforms it to texts and images that are easily understandable not only by the reader but also by the system.
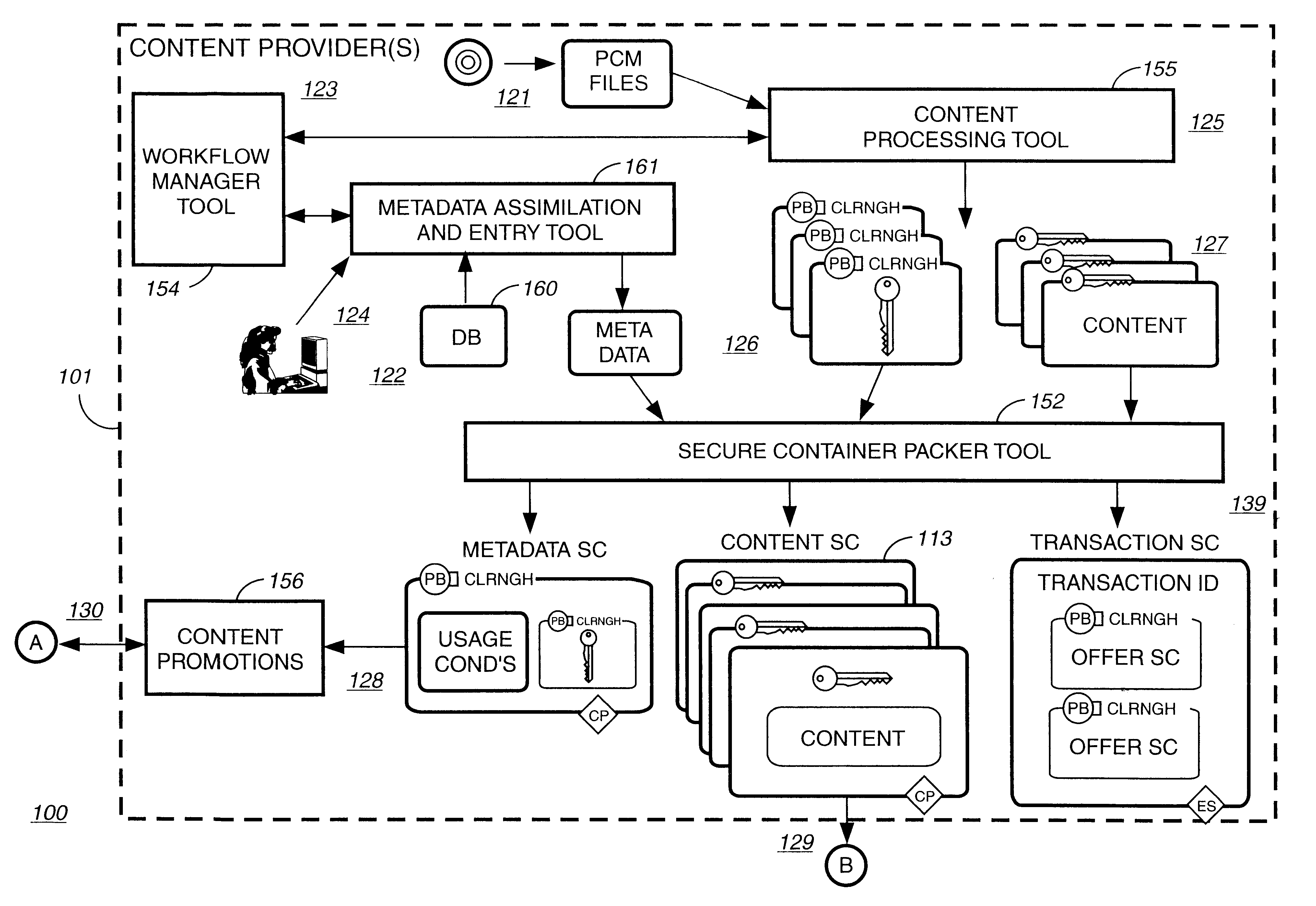
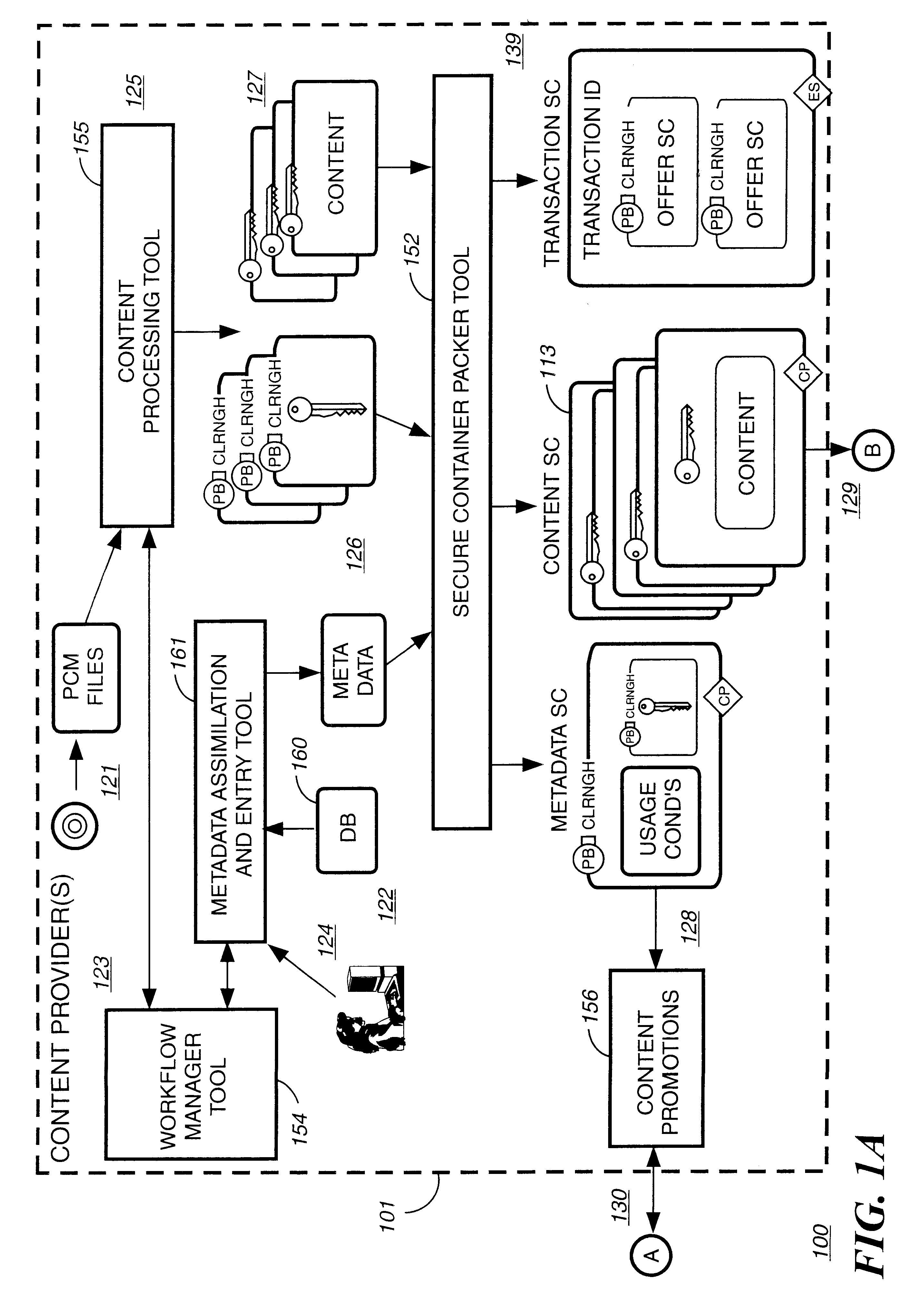
Electronic content delivery system
InactiveUS6226618B1Key distribution for secure communicationDigital data processing detailsDelivery systemSystem safety
Disclosed is a method and apparatus of securely providing data to a user's system. The data is encrypted so as to only be decryptable by a data decrypting key, the data decrypting key being encrypted using a first public key, and the encrypted data being accessible to the user's system, the method comprising the steps of: transferring the encrypted data decrypting key to a clearing house that possesses a first private key, which corresponds to the first public key; decrypting the data decrypting key using the first private key; re-encrypting the data decrypting key using a second public key; transferring the re-encrypted data decrypting key to the user's system, the user's system possessing a second private key, which corresponds to the second public key; and decrypting the re-encrypted data decrypting key using the second private key.
Owner:LEVEL 3 COMM LLC
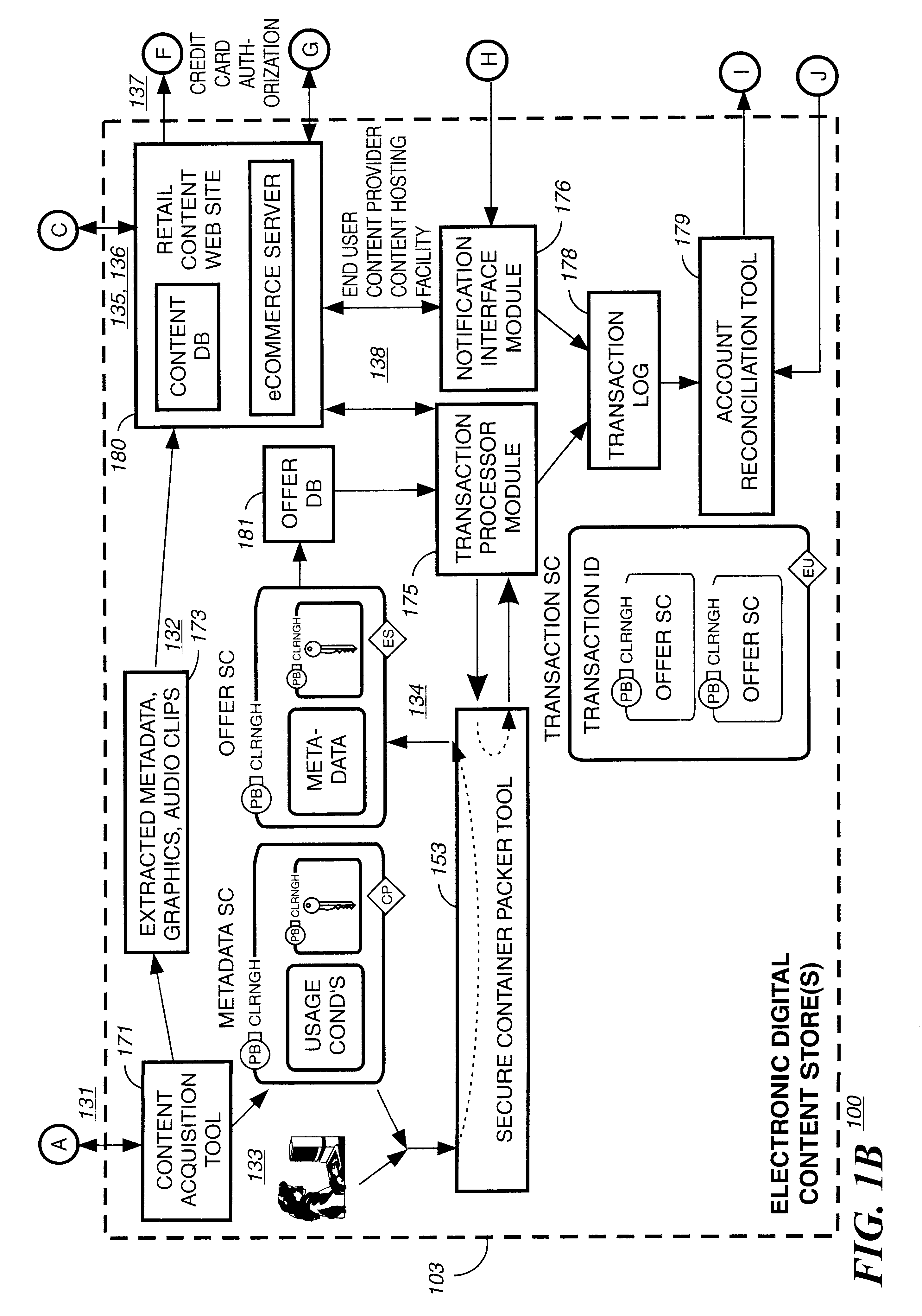
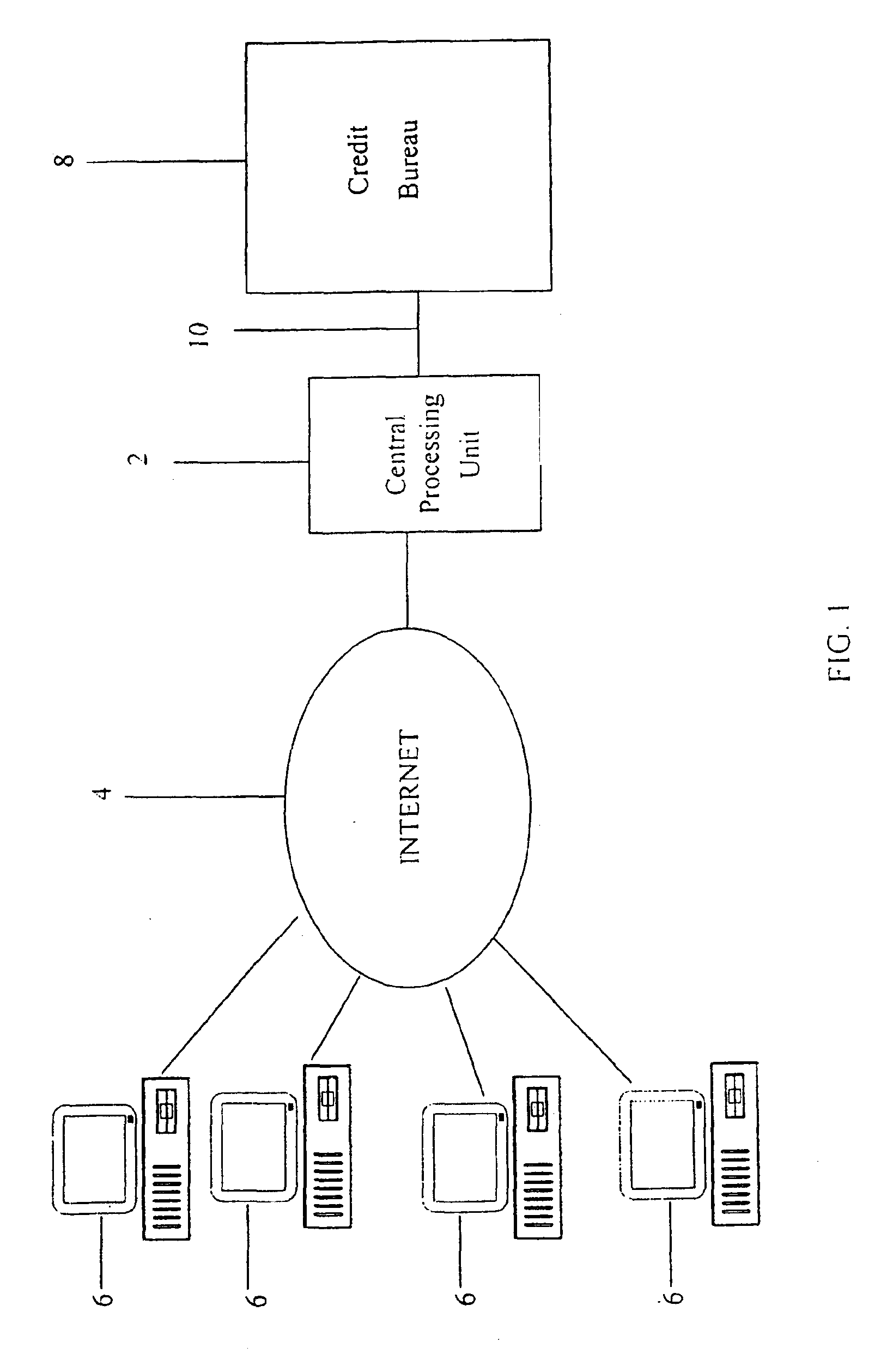
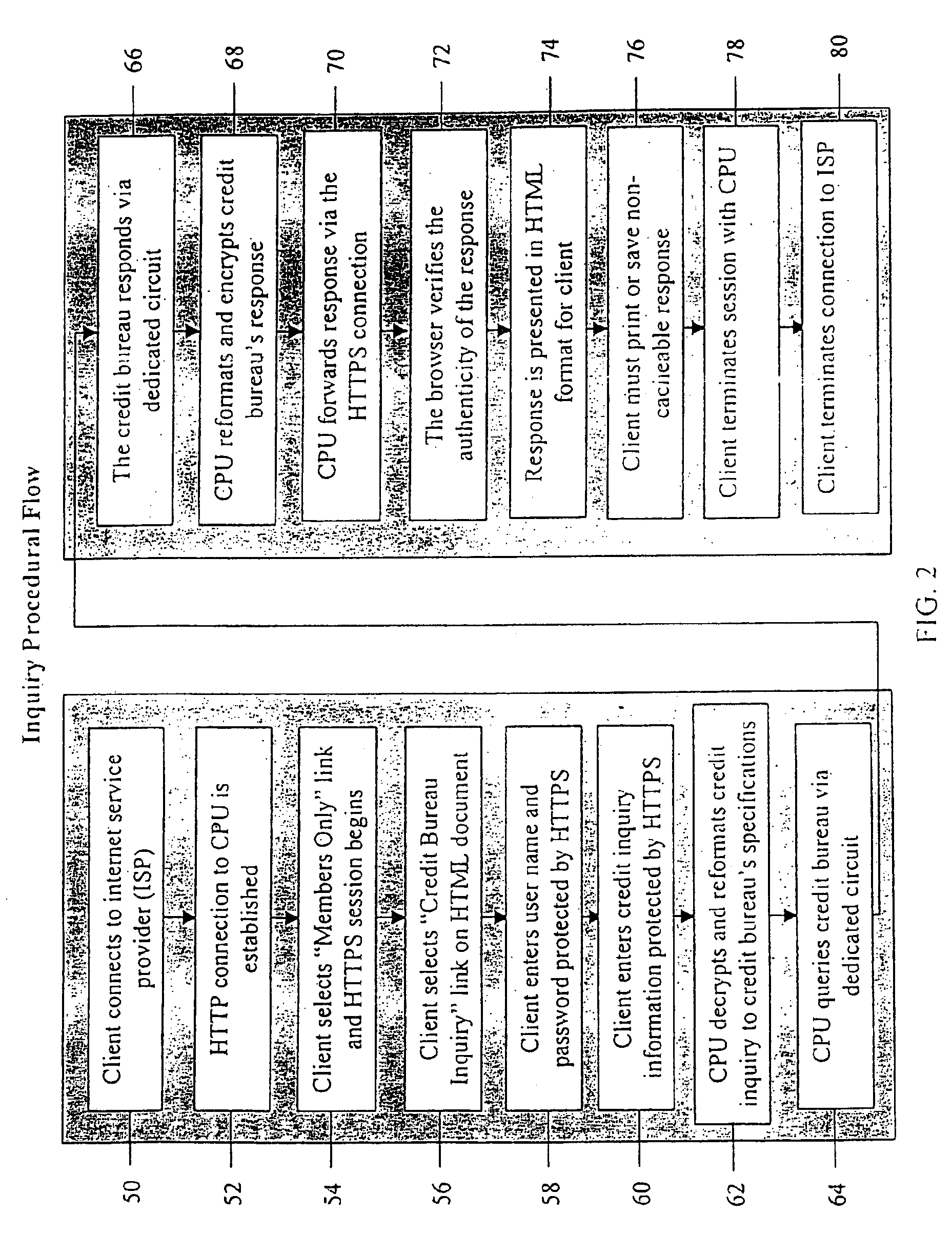
System and method for real-time electronic inquiry, delivery, and reporting of credit information
InactiveUS6988085B2More readable formatSecure transmissionComplete banking machinesFinanceWeb siteWeb browser
A system and method for providing electronic inquiry, delivery, and reporting of personal credit information to and from credit bureaus, preferably via the Internet. In the preferred embodiment, the system includes a web site that, by using a web browser, allows clients to request credit information from, or provide credit reports to, credit bureaus by entering certain data on pre-built forms in HTML format. The data is encrypted using means for secure transmission, such as a web browser with 128-bit secure socket layer (SSL) technology, then sent to a common gateway interface (CGI) application located on a web server. The CGI application decrypts and reformats the data to a standard format specified by the credit bureau. The CGI application initiates a query. Using a dedicated connection circuit to the credit bureau's computer, the CGI application reformats the response from the credit bureau to an HTML format and encrypts the data using the means for secure transmission. The HTML formatted data is then sent back to the client's computer over the Internet and displayed in the client's web browser in an easily read format.
Owner:F POSZAT HU
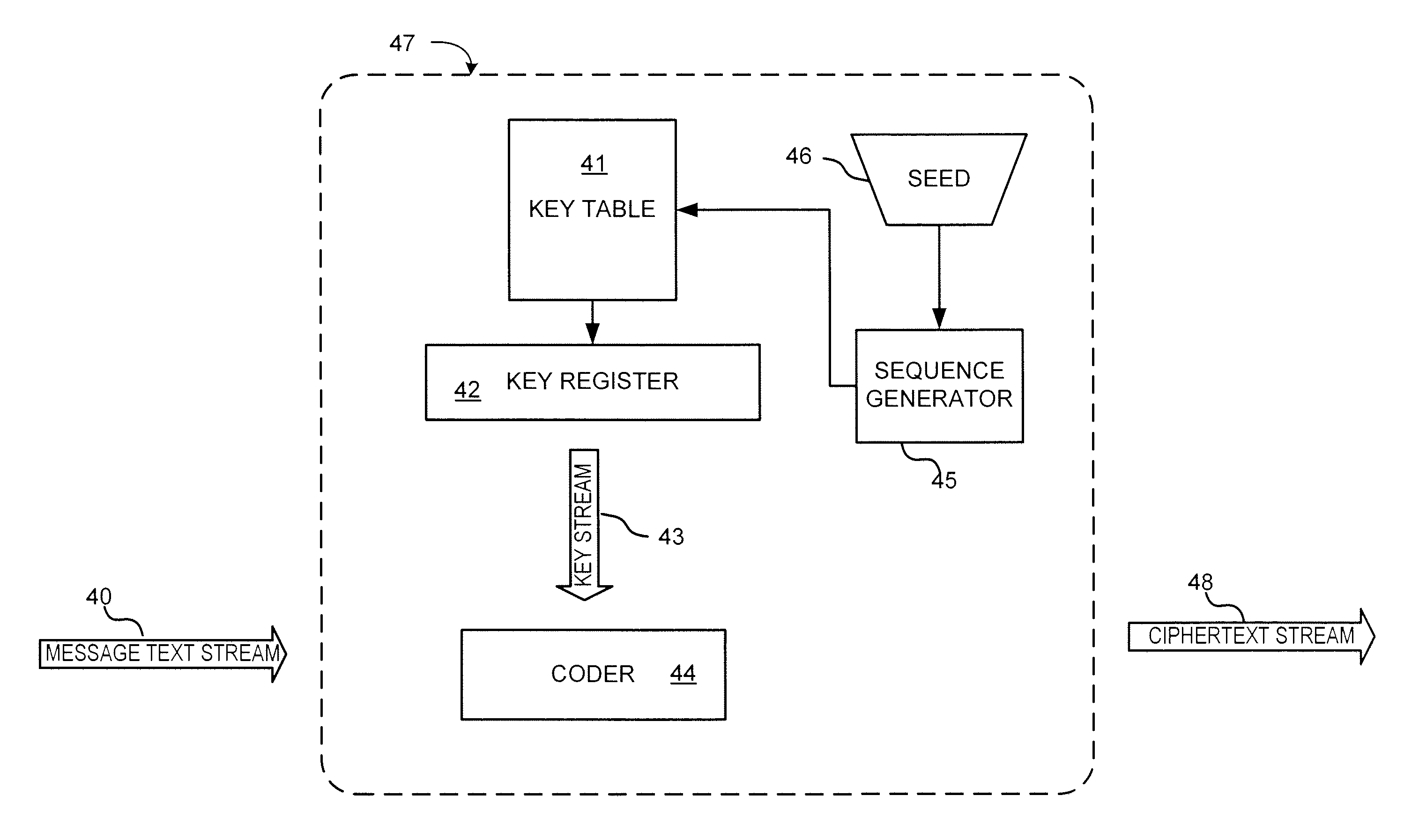
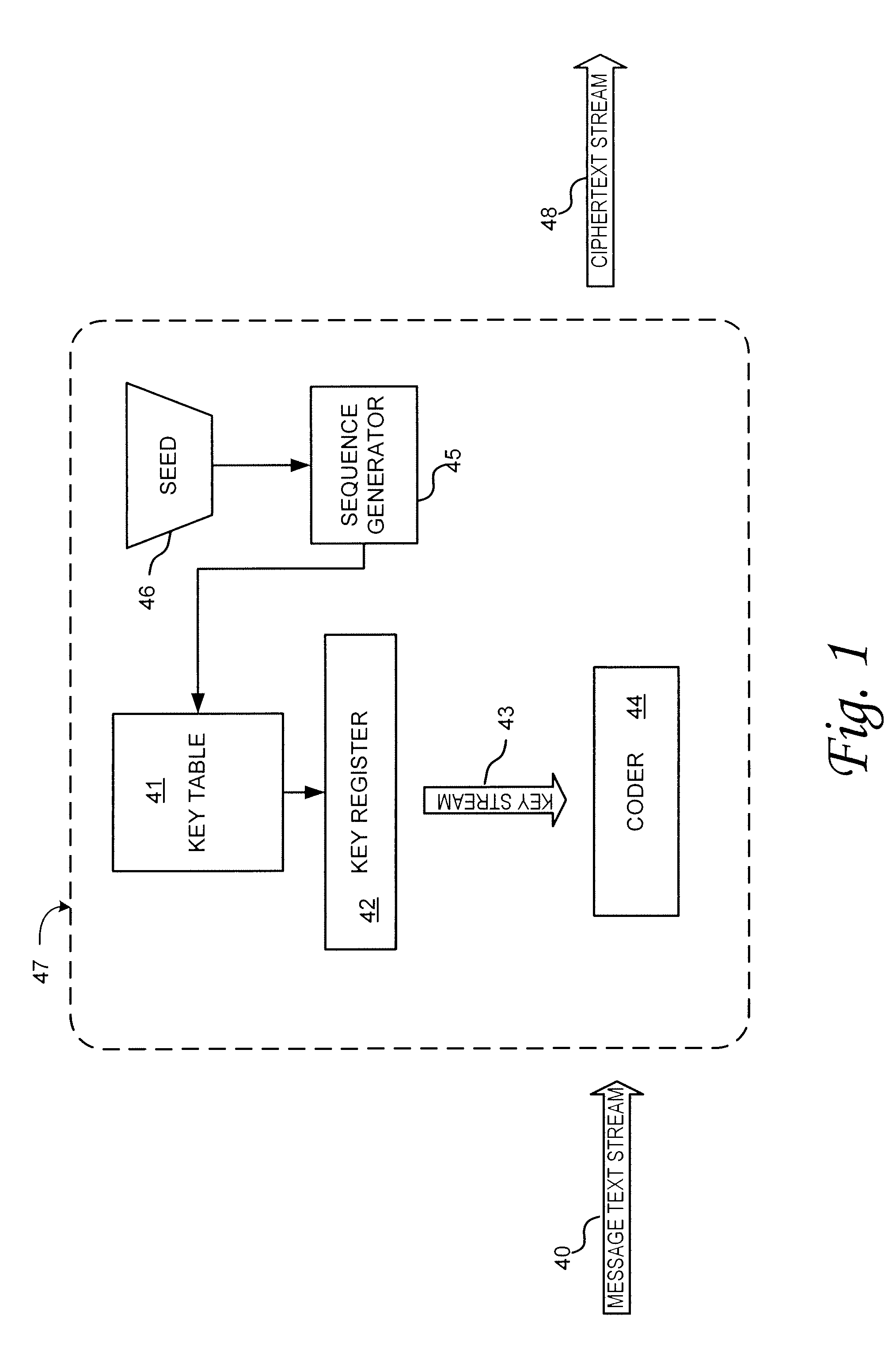
Chaotic cipher system and method for secure communication
ActiveUS20100211787A1Key distribution for secure communicationData stream serial/continuous modificationSecure communicationArray data structure
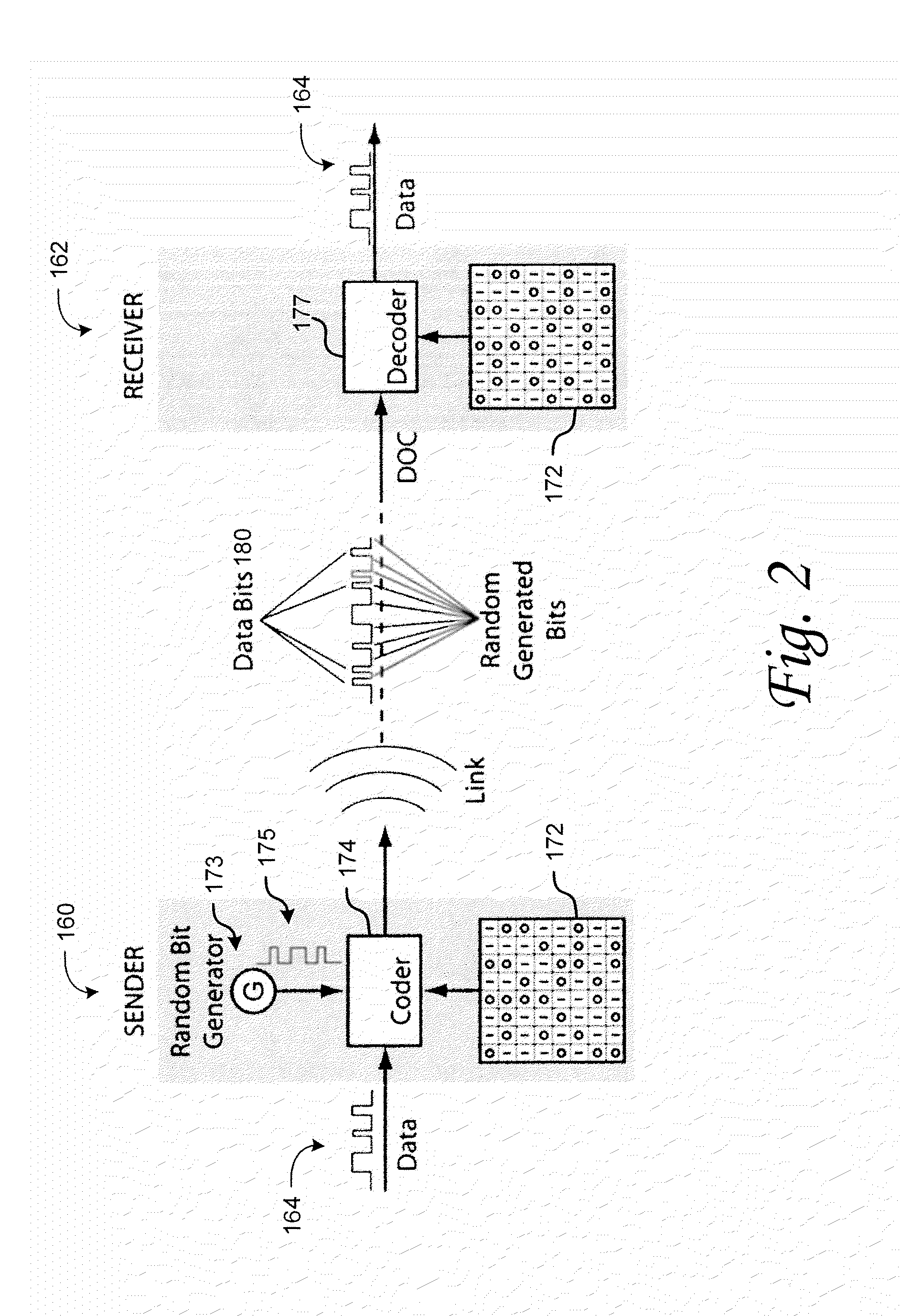
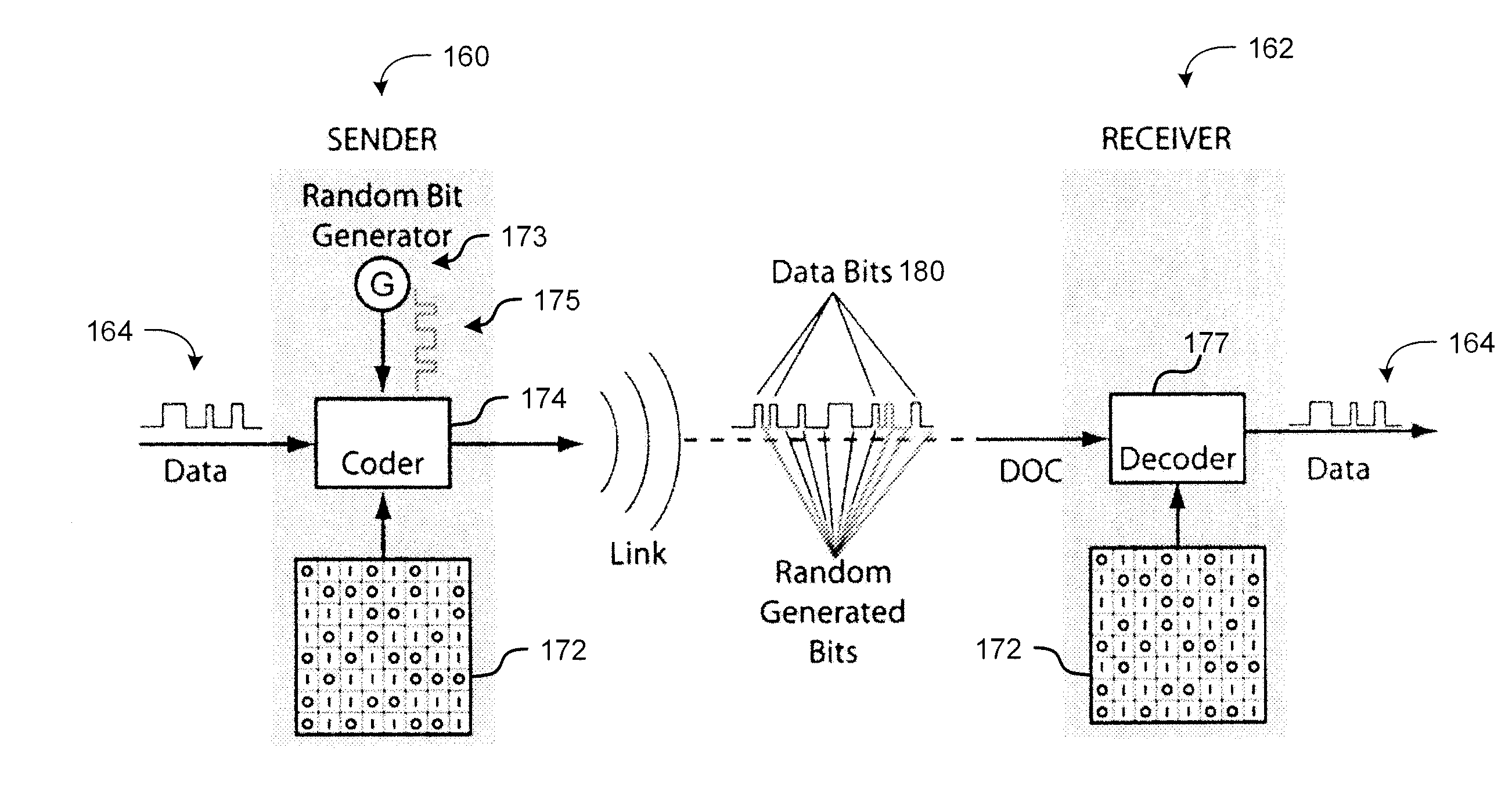
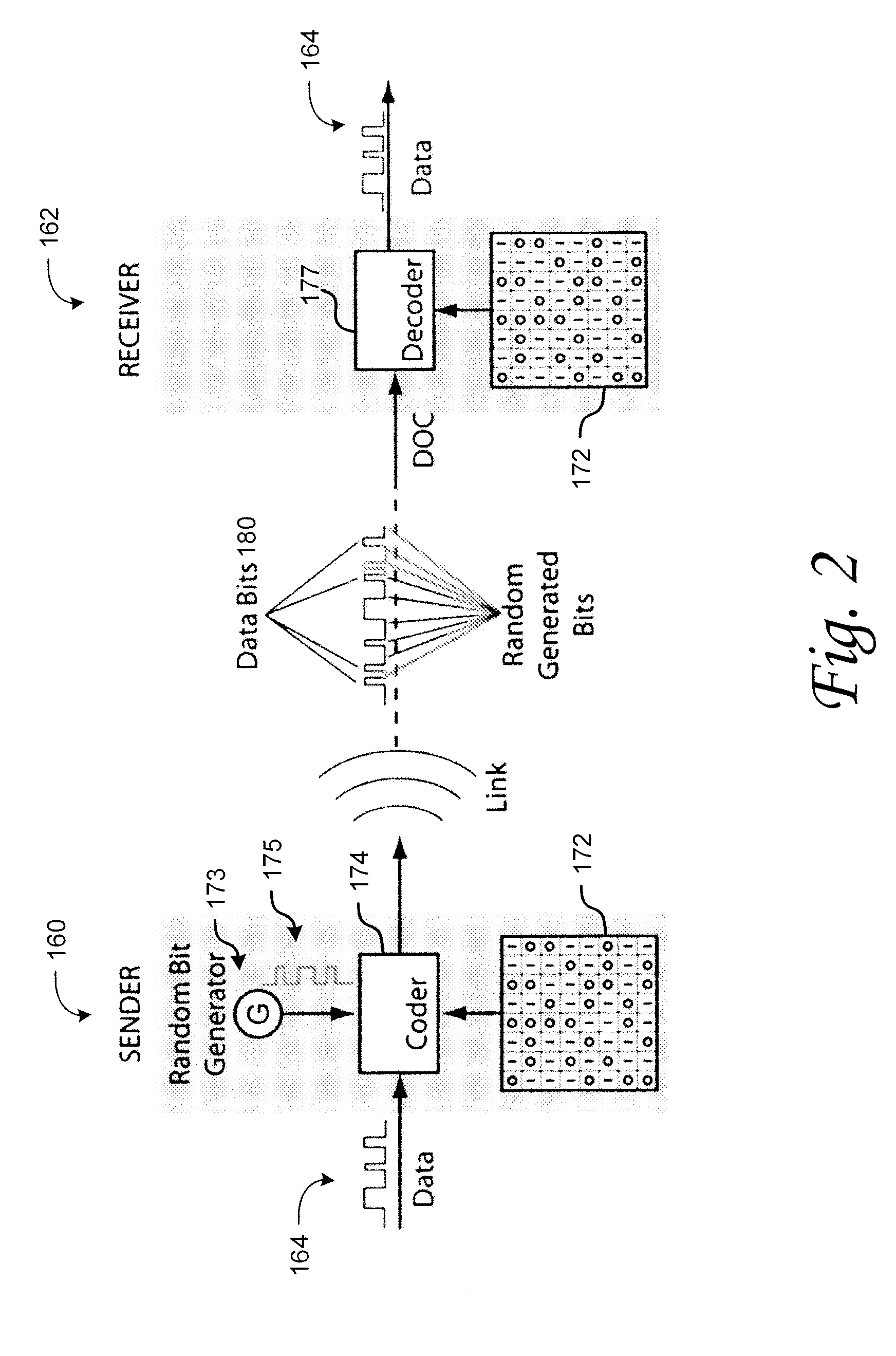
The present invention provides a method for a data encryption device to perform network communications, the method comprising obtaining an indexed array of encryption keys, wherein the indexed array of encryption keys is shared with a data decryption device; obtaining a message to be encrypted; using a first random or pseudorandom number to determine an index; obtaining a first key from the array of encryption keys, wherein the first key corresponds to the index; selecting a second key from the plurality of encryption keys; encrypting the message using the first key and a second random or pseudorandom number; encrypting the index using the second key and a third random or pseudorandom number; transmitting the encrypted message and the encrypted index to the data decryption device.
Owner:MERCURY MISSION SYST LLC
Chaotic cipher system and method for secure communication
ActiveUS20120250863A1Key distribution for secure communicationData stream serial/continuous modificationSecure communicationArray data structure
The present invention provides a method for a data encryption device to perform network communications, the method comprising obtaining an indexed array of encryption keys, wherein the indexed array of encryption keys is shared with a data decryption device; obtaining a message to be encrypted; using a first random or pseudorandom number to determine an index; obtaining a first key from the array of encryption keys, wherein the first key corresponds to the index; selecting a second key from the plurality of encryption keys; encrypting the message using the first key and a second random or pseudorandom number; encrypting the index using the second key and a third random or pseudorandom number; transmitting the encrypted message and the encrypted index to the data decryption device.
Owner:MERCURY MISSION SYST LLC
Method for realizing equipment authentication, data integrity and secrecy transmission for Internet of Things
ActiveCN101969438ALow costImprove operational efficiencyUser identity/authority verificationDigital data protectionWork statusAuthentication protocol
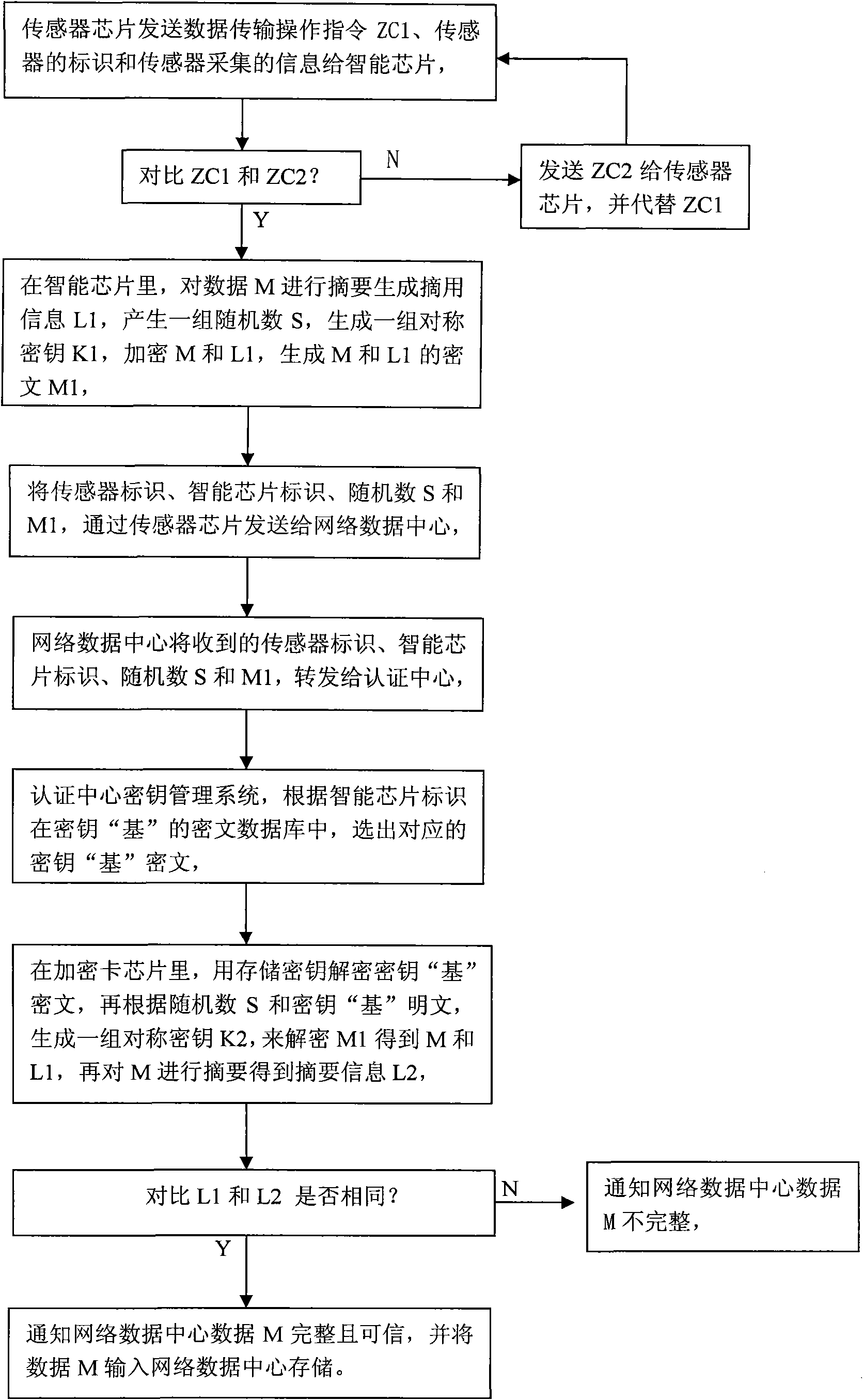
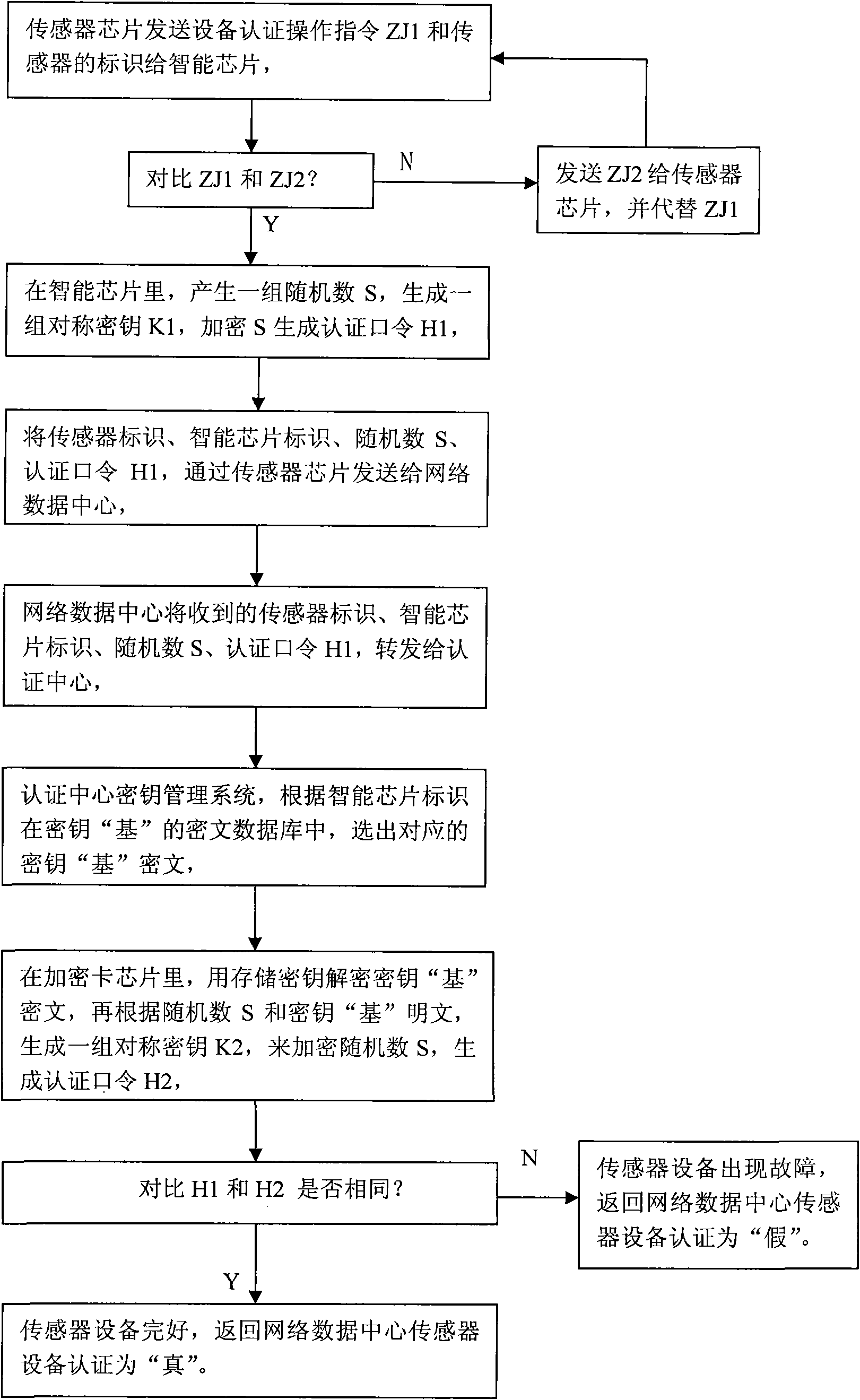
The invention relates to a method for realizing equipment authentication, data integrity and secrecy transmission for Internet of Things (IoT), which is characterized in that the information collected by a sensor is transmitted to a network data center after being subject to digital signature and encryption through an intelligent chip; the network date center obtains the complete and believable information collected by the sensor by utilizing an authentication center (AC) to carry out data deciphering and signature verification; the network data center transmits an operational order to a sensor terminal, the operational order is subject to the digital signature and the encryption by the AC and then transmits to the sensor; the sensor obtains a correct and complete operational order after operational order data obtained by the sensor is subject to the data deciphering and the signature verification through the intelligent chip; and an equipment authentication protocol of the AC to the sensor is used to determine whether the sensor equipment is confirmed to be in a normal operation state or not, thus an information safety system for the infrastructure authentication, the data integrity and the secrecy transmission of the IoT is established.
Owner:胡祥义
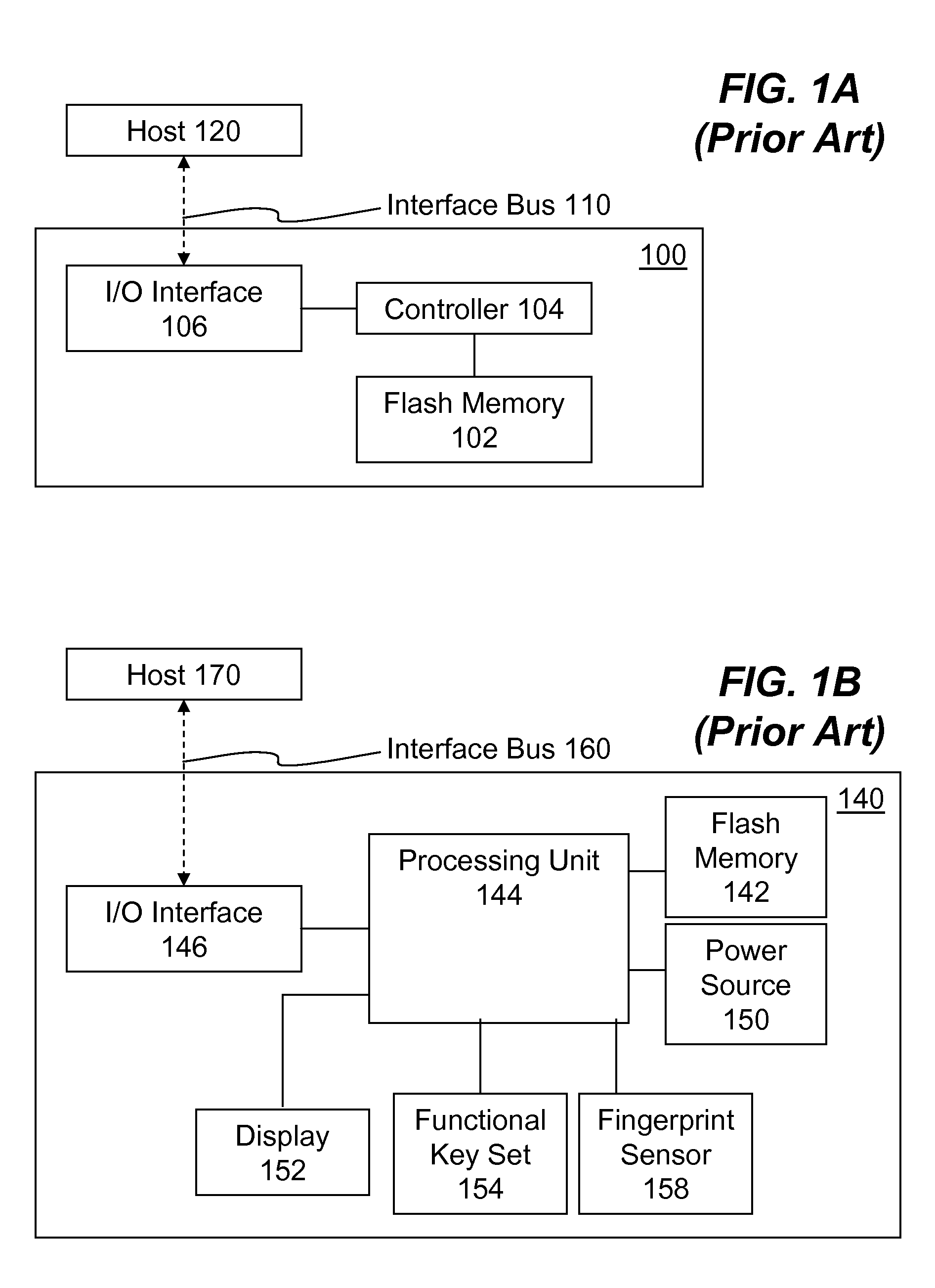
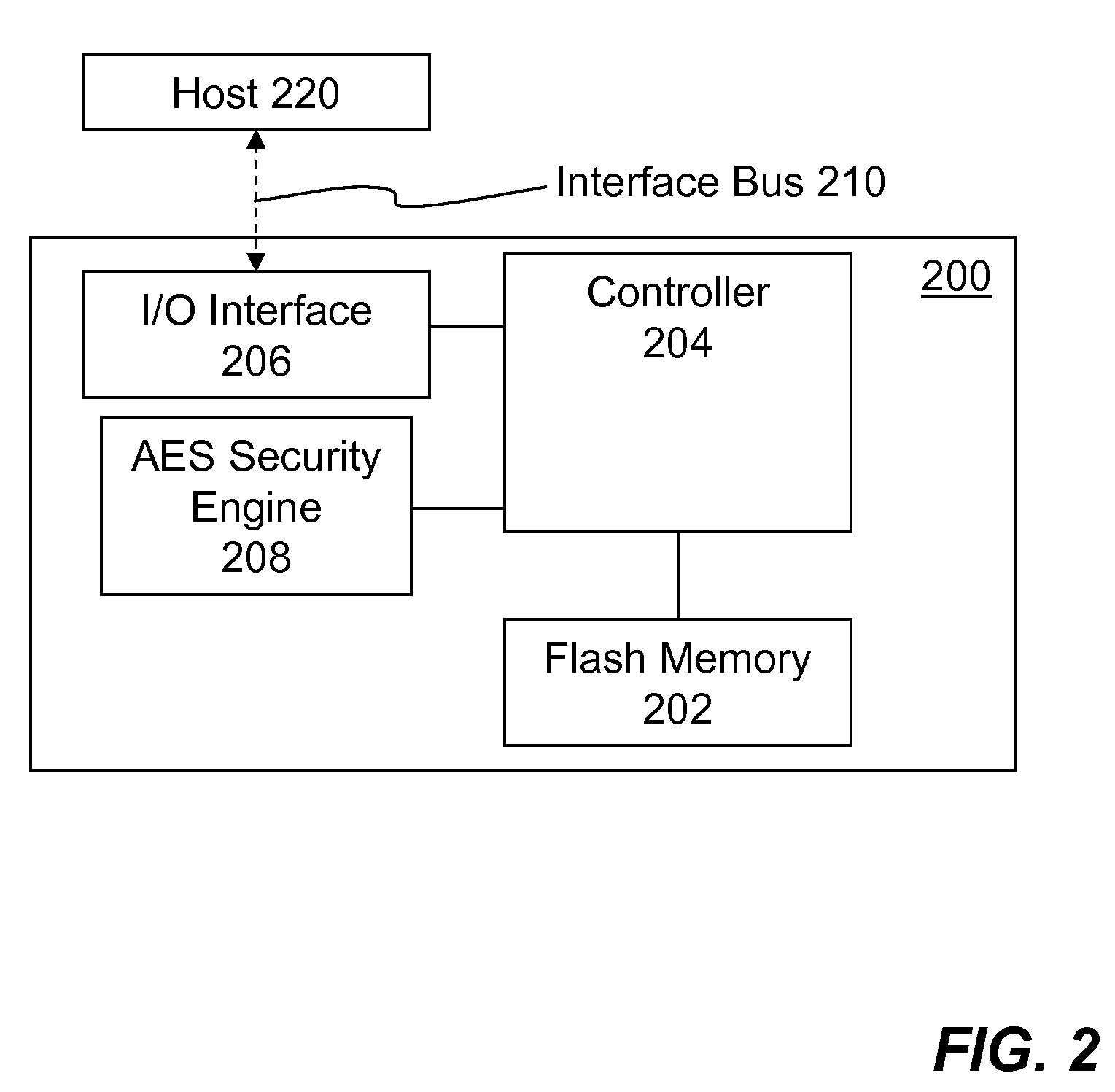
Portable Electronic Storage Devices with Hardware Security Based on Advanced Encryption Standard
InactiveUS20080192928A1Improve securityUnauthorized memory use protectionInternal/peripheral component protectionKey sizeAdvanced Encryption Standard
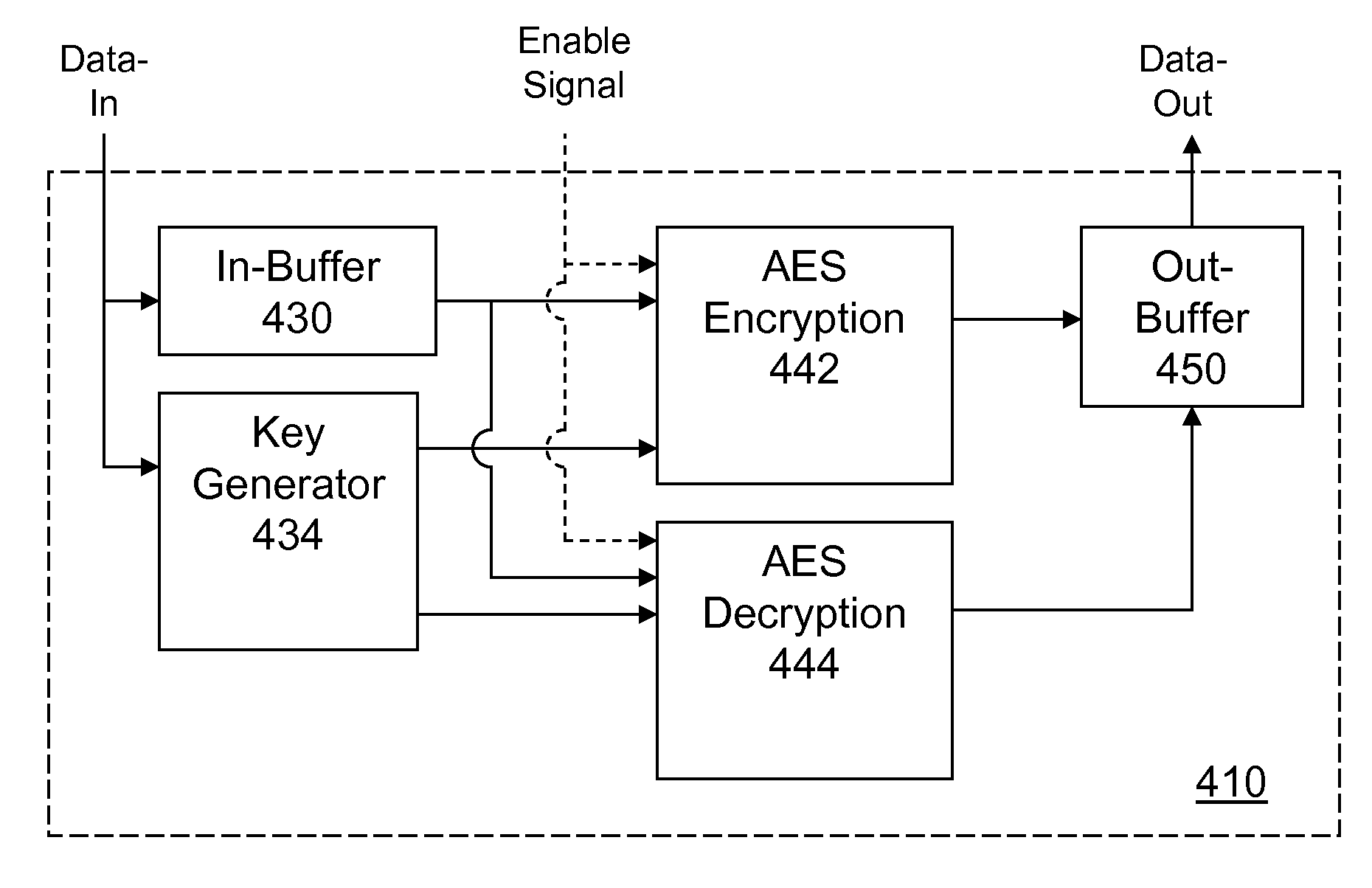
Portable electronic storage devices with hardware based security are described. According to one exemplary embodiment of the present invention, a portable electronic storage device (PESD) comprises a security engine integrated thereon. The security engine is configured to provide data encryption, data decryption, and encryption / decryption key (referred to as a key) generation according to a security standard (e.g., Advance Encryption Standard (AES)). AES is a symmetric encryption algorithm processing data in block of 128 bits. Under the influence of a key, a 128-bit data block is encrypted by transforming the data block in a unique way into a new data block of the same size. AES is symmetric sine the same key is used for encryption and the reverse transformation (i.e., decryption). The only secret necessary to keep for security is the key. AES may use different key-lengths (i.e., 128-bit, 192-bits and 256-bits).
Owner:SUPER TALENT ELECTRONICS
A model training method and a device based on shared data
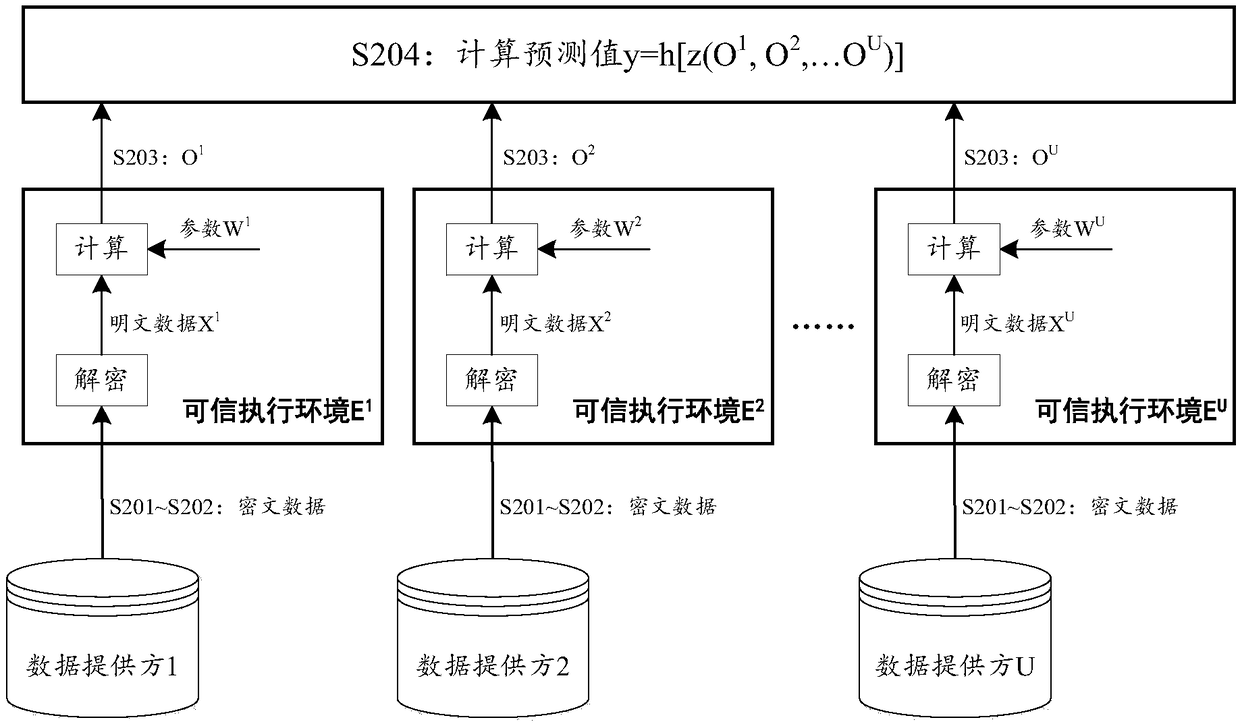
ActiveCN109308418AEnsure data securityExamples cannot be limitedCharacter and pattern recognitionDigital data protectionPlaintextData provider
Owner:ADVANCED NEW TECH CO LTD
Revocable key external package decryption method based on content attributes
ActiveCN104486315APrevent unauthorized accessProtection securityUser identity/authority verificationComputer hardwareTrusted authority
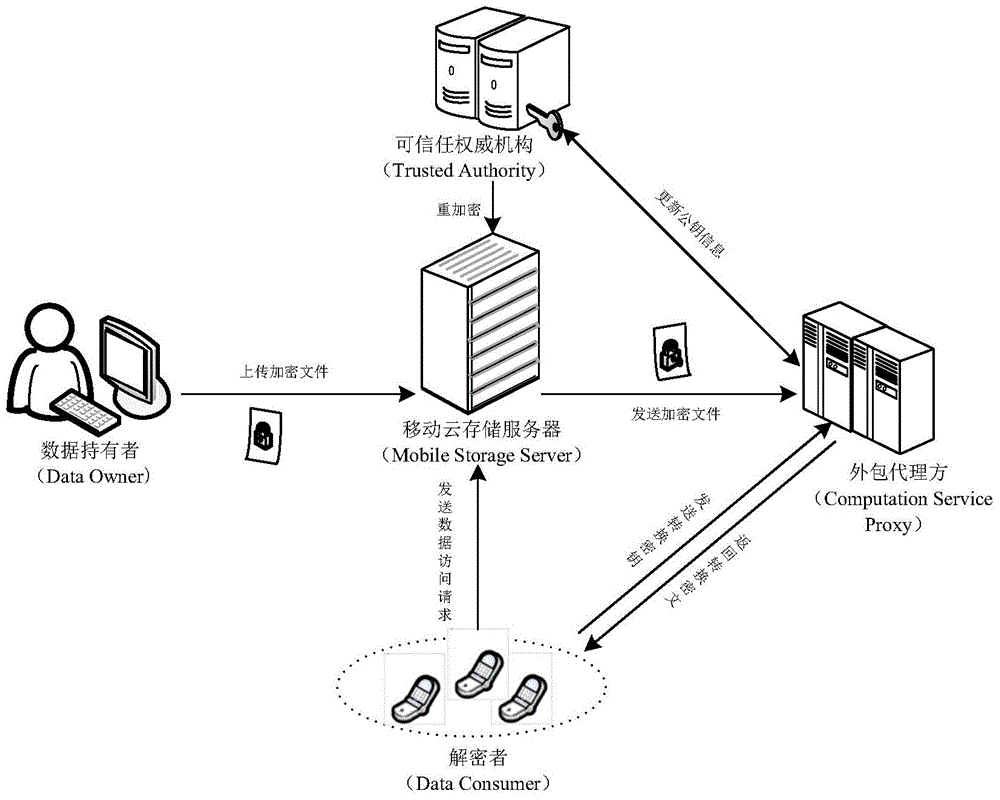
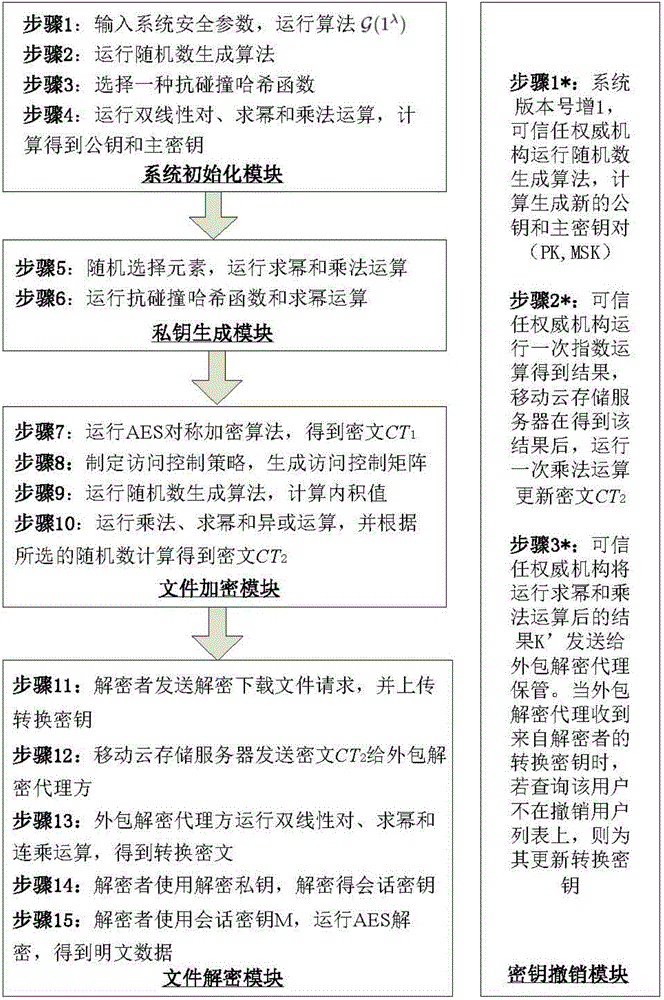
The invention relates to a revocable key external package decryption method based on content attributes. For a trusted authority, 1, initialization is carried out, and system parameters are output; 2, a random number generation algorithm operates; 3, a collision-resistant Hash function is selected, and the Hash value is calculated; 4, a public key and a main key are calculated; 5, the random number is selected, and exponentiation calculation and multiplication are carried out; 6, the collision-resistant Hash function operates, the exponentiation operation is carried out, and a decryption key is obtained. For a data holder, 7, AES data encryption is carried out; 8, an access control matrix is generated; 9, a random number is selected, and an inner product is calculated; 10, multiplication, exponentiation and exclusive-or operation is operated, and ciphertexts are obtained. For a decryption operator, 11, a decryption request and a transformation key are sent. For a mobile storage serve provider, 12, CT2 is sent to an external package decryption agency. For the external package decryption agency, 13, the transformation key is utilized, and the transformation ciphertext is calculated. For the decryption operator, 14, a conversation key is obtained through calculation; 15, AES data decryption is carried out.
Owner:HANGZHOU INNOVATION RES INST OF BEIJING UNIV OF AERONAUTICS & ASTRONAUTICS
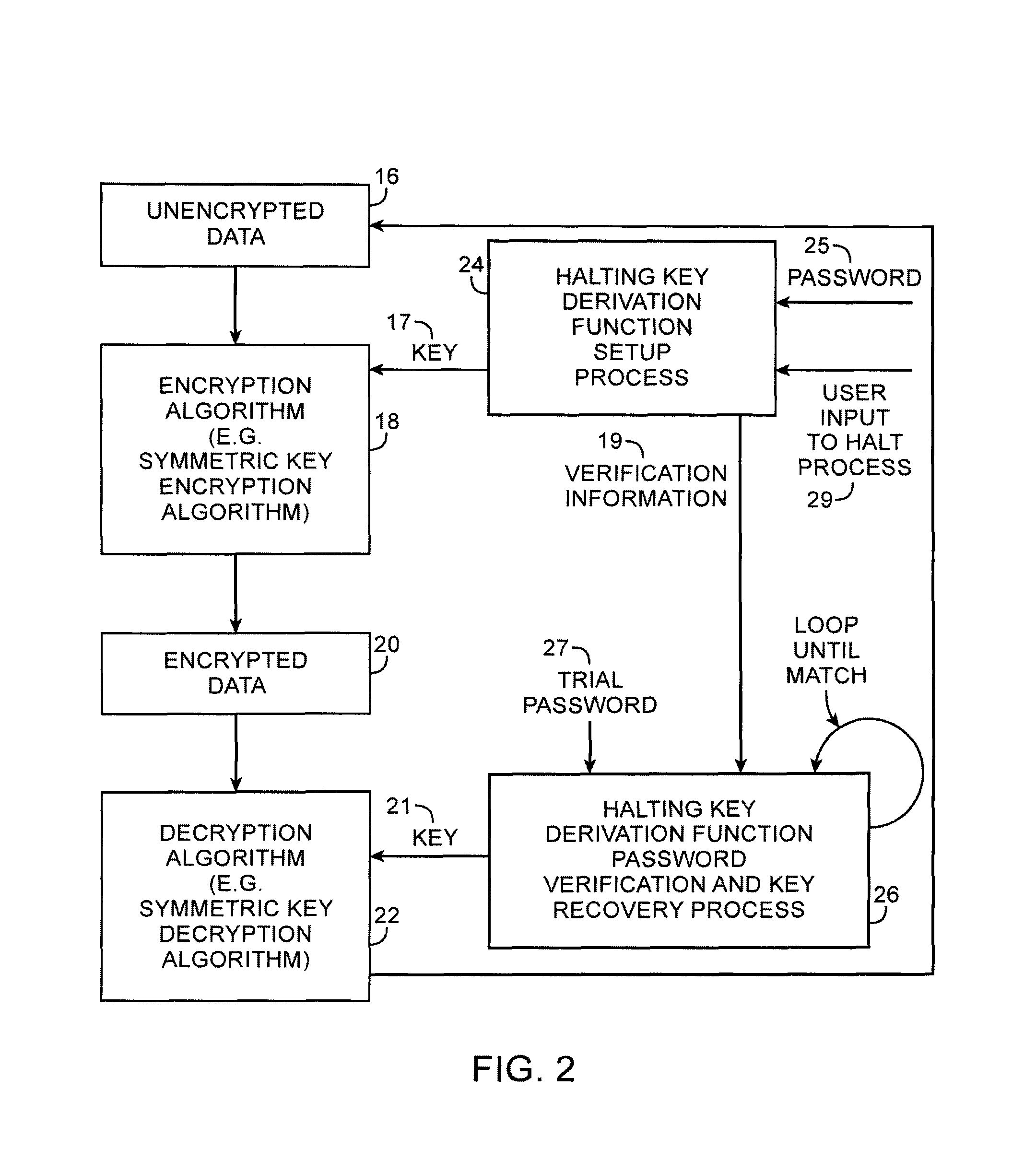
Cryptographic system with halting key derivation function capabilities
ActiveUS8254571B1Key distribution for secure communicationDigital data processing detailsUser inputPassword
A halting key derivation function is provided. A setup process scrambles a user-supplied password and a random string in a loop. When the loop is halted by user input, the setup process may generate verification information and a cryptographic key. The key may be used to encrypt data. During a subsequent password verification and key recovery process, the verification information is retrieved, a user-supplied trial password obtained, and both are used together to recover the key using a loop computation. During the loop, the verification process repeatedly tests the results produced by the looping scrambling function against the verification information. In case of match, the trial password is correct and a cryptographic key matching the key produced by the setup process may be generated and used for data decryption. As long as there is no match, the loop may continue indefinitely until interrupted exogenously, such as by user input.
Owner:MICRO FOCUS LLC
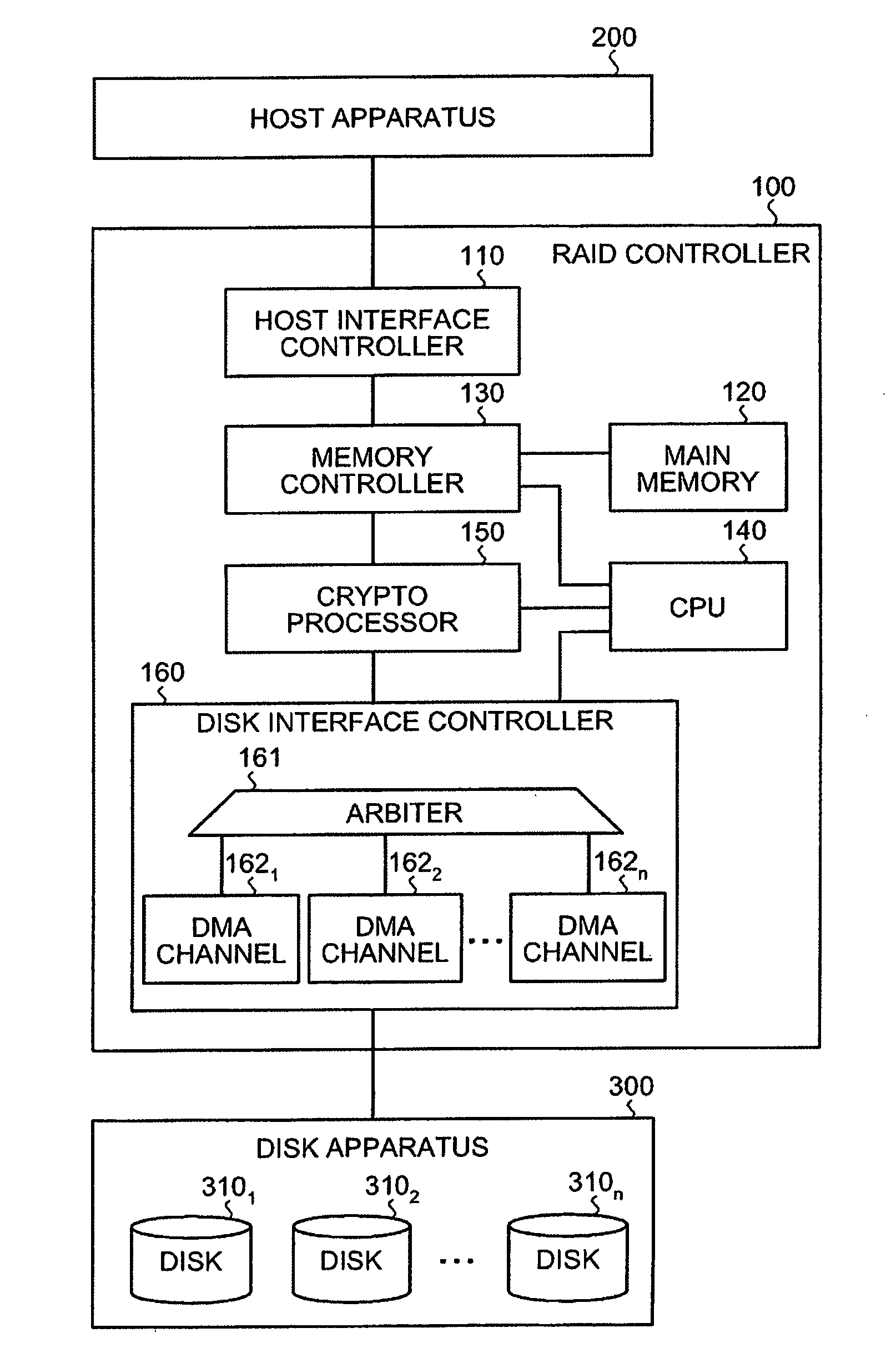
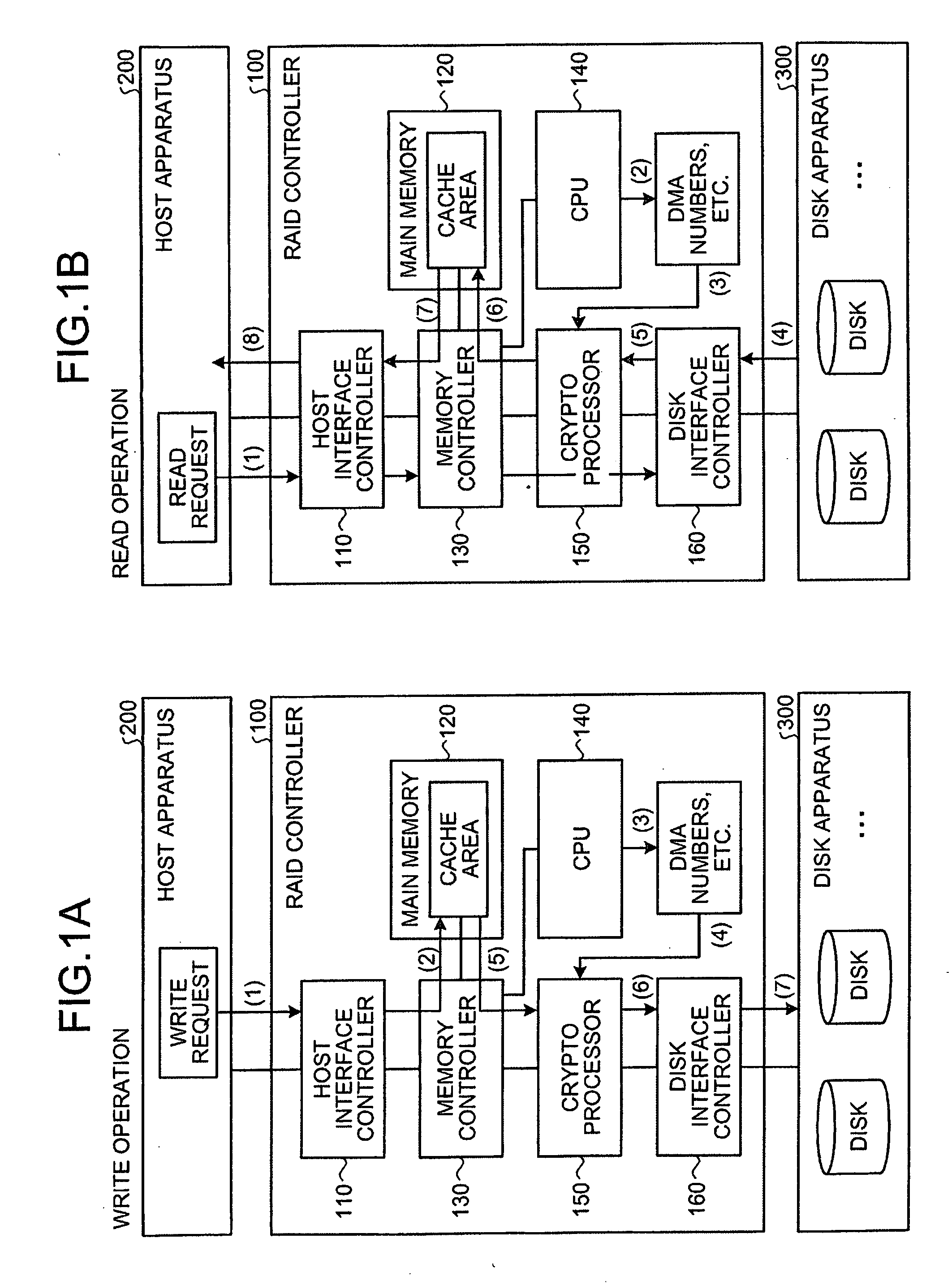
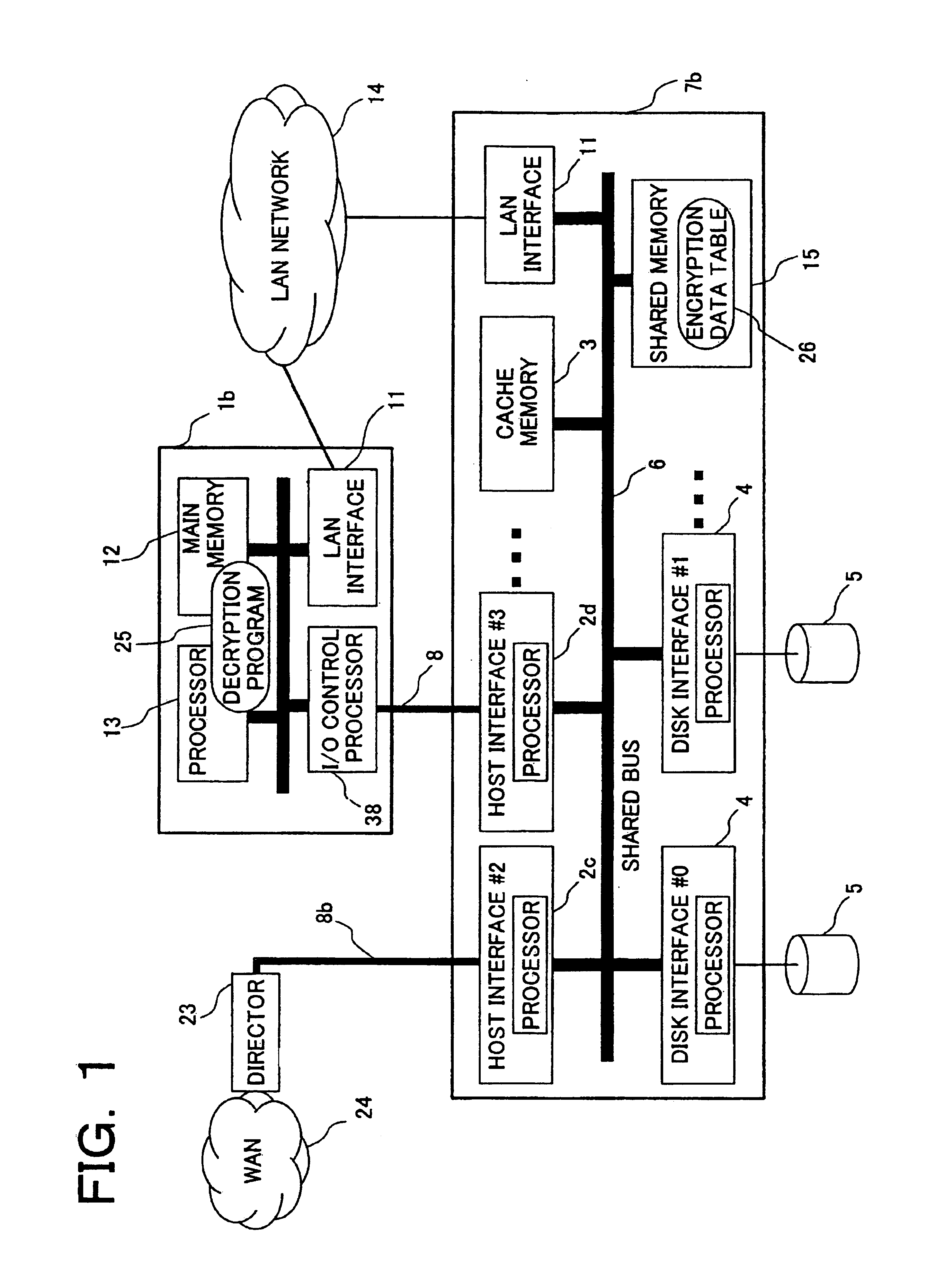
Data encryption apparatus, data decryption apparatus, data encryption method, data decryption method, and data transfer controlling apparatus
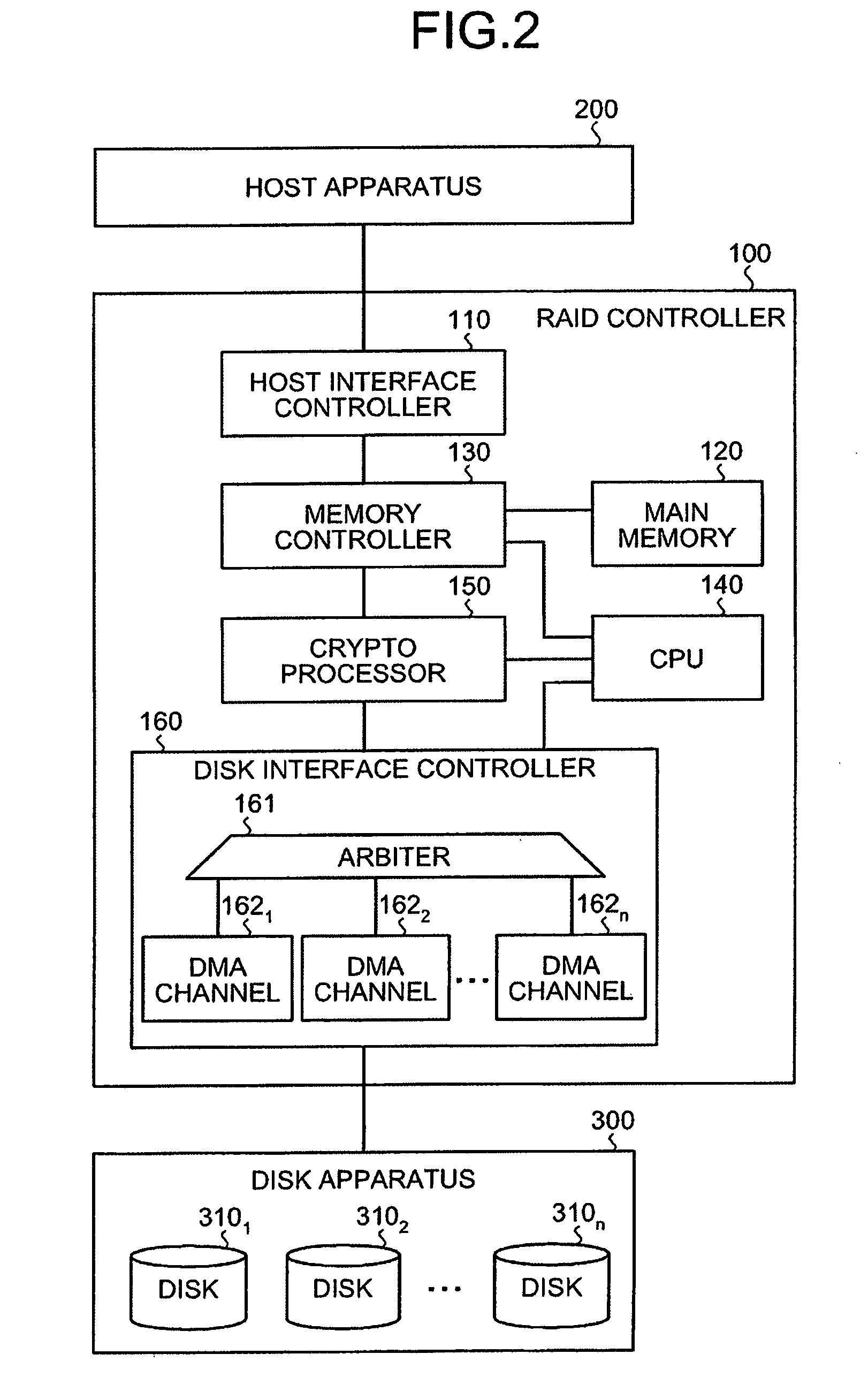
InactiveUS20080209203A1Input/output to record carriersUnauthorized memory use protectionComputer hardwareDirect memory access
A crypt processor is connected to a host computer and a storage apparatus. Data from the host computer is transferred to the crypt processor via DMA (Direct Memory Access) to be encrypted and then stored in the storage apparatus. The crypto processor acquires a descriptor defining a DMA number for identifying a DMA channel used to DMA-transfer the data. The crypto processor stores therein, based on the DMA number included in the acquired descriptor, the data transferred using the same DMA channel in units of a data size specified in a data bus. The crypto processor then encrypts the stored data in units of data size specified in a crypt system, and transfers the encrypted data to the storage apparatus.
Owner:FUJITSU LTD
System and method for file encryption and decryption
InactiveUS20080104417A1Public key for secure communicationUser identity/authority verificationData decryptionDisk encryption
There is disclosed a system and method for file encryption and decryption. In an embodiment, a method of encrypting a file on backup media involves encrypting clear data using a data encryption key applied to a data encryption algorithm and outputting encrypted data; storing the encrypted data on the backup media; encrypting the data encryption key using a reference cryptographic key applied to a key encryption algorithm and outputting an encrypted data encryption key; and storing the encrypted data encryption key and reconstitution data in a header of the backup media. The encrypted data may be subsequently decrypted by identifying the reference cryptographic key using the reference cryptographic key name; applying the reference cryptographic key to a key decryption algorithm to decrypt the encrypted data encryption key; and applying the decrypted data encryption key to a data decryption algorithm to decrypt the encrypted data.
Owner:IBM CORP
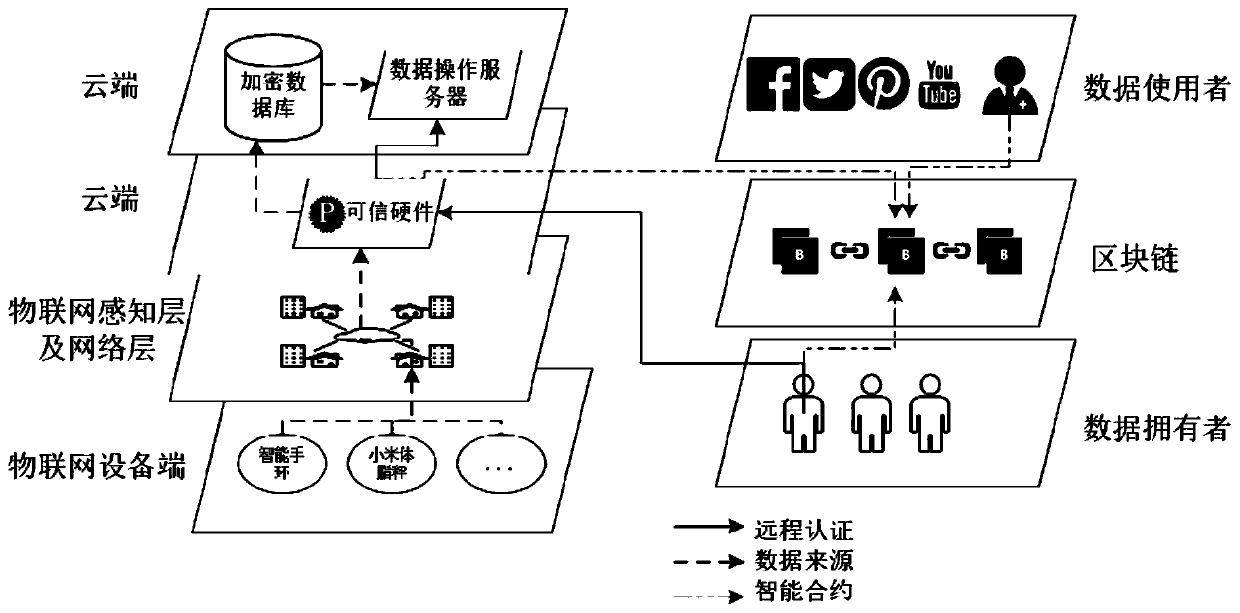
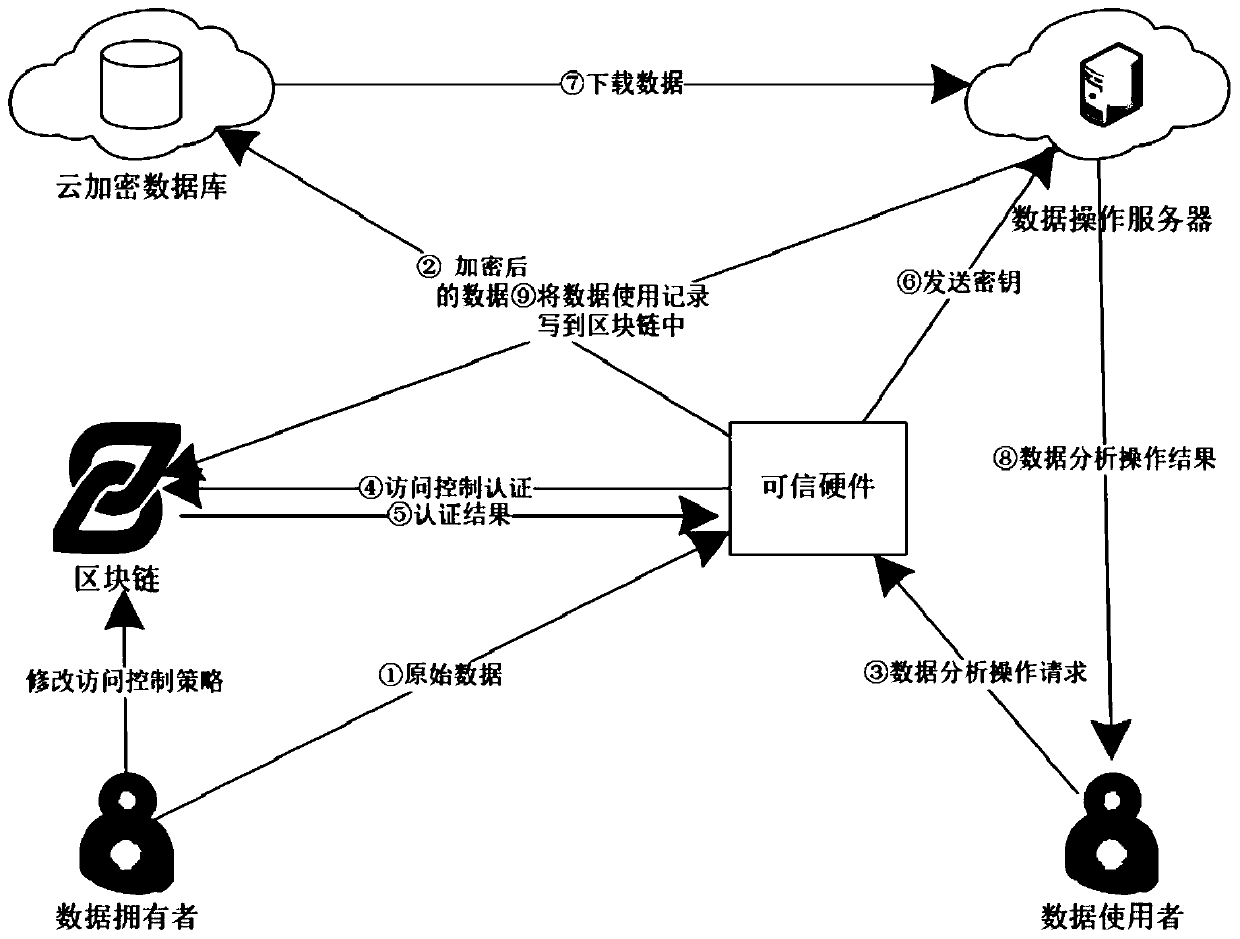
Internet of Things data privacy protection method based on block chain and trusted hardware
ActiveCN110086804AEnsure safetyGuaranteed reliabilityUser identity/authority verificationDigital data protectionData privacy protectionTrusted hardware
The invention relates to an Internet of Things data privacy protection method based on a block chain and the trusted hardware. The method comprises three stages of secret key management and data generation, data access control strategy definition and intelligent contract deployment and data access and intelligent contract execution, and Internet of Things data is encrypted by a hardware trusted entity IDA and uploaded to a cloud for storage; when there is an operation request, the trusted entity calls an access control authentication interface of the smart contract to carry out authority authentication; after the authority authentication passes, the trusted entity carries out security authentication on the operation execution server and sends the secret key to the data operation executionserver through a security channel; and the server downloads the data from the cloud, then decrypts the data and executes the operation, and writes the data use record into the block chain after the data analysis operation is completed. According to the scheme, the block chain is combined with the trusted entity, the data is effectively operated under the condition that the original data privacy isnot leaked, and the integrity and the safety of the data use records are guaranteed.
Owner:GUANGZHOU UNIVERSITY
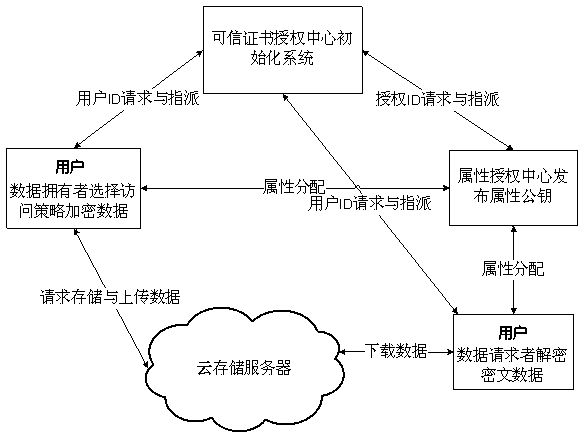
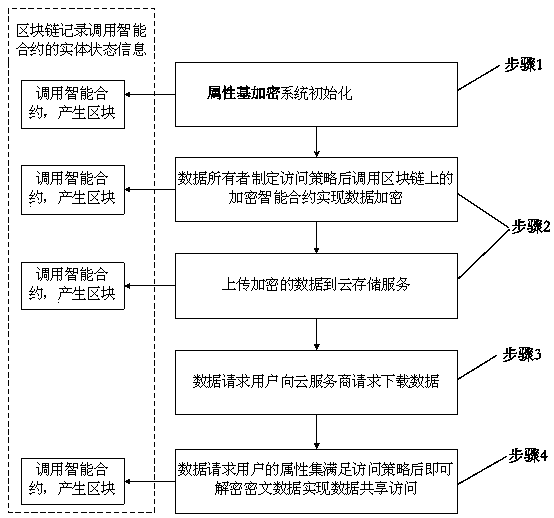
A cloud data security sharing method based on a block chain
Owner:CHONGQING UNIV
Regular data backup and recovery method based on cloud storage
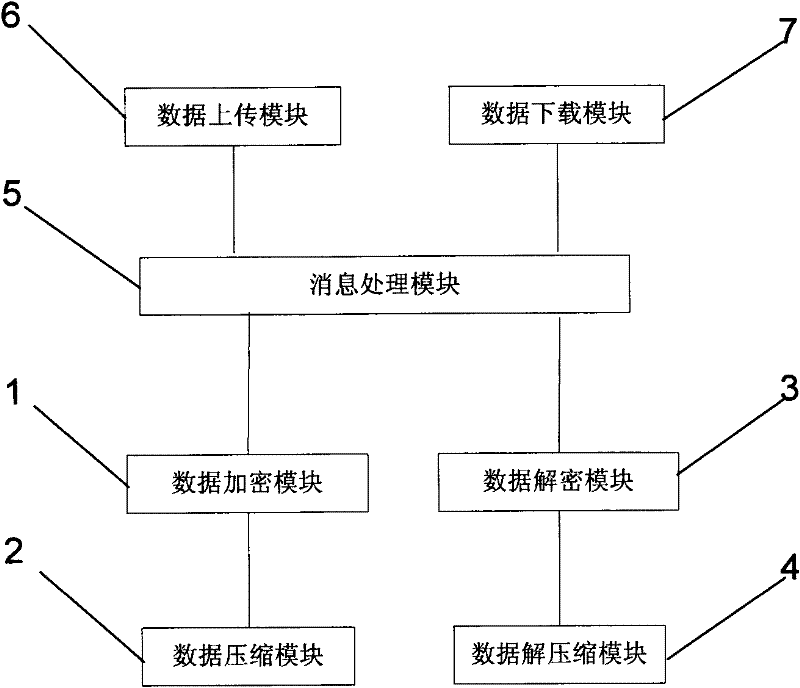
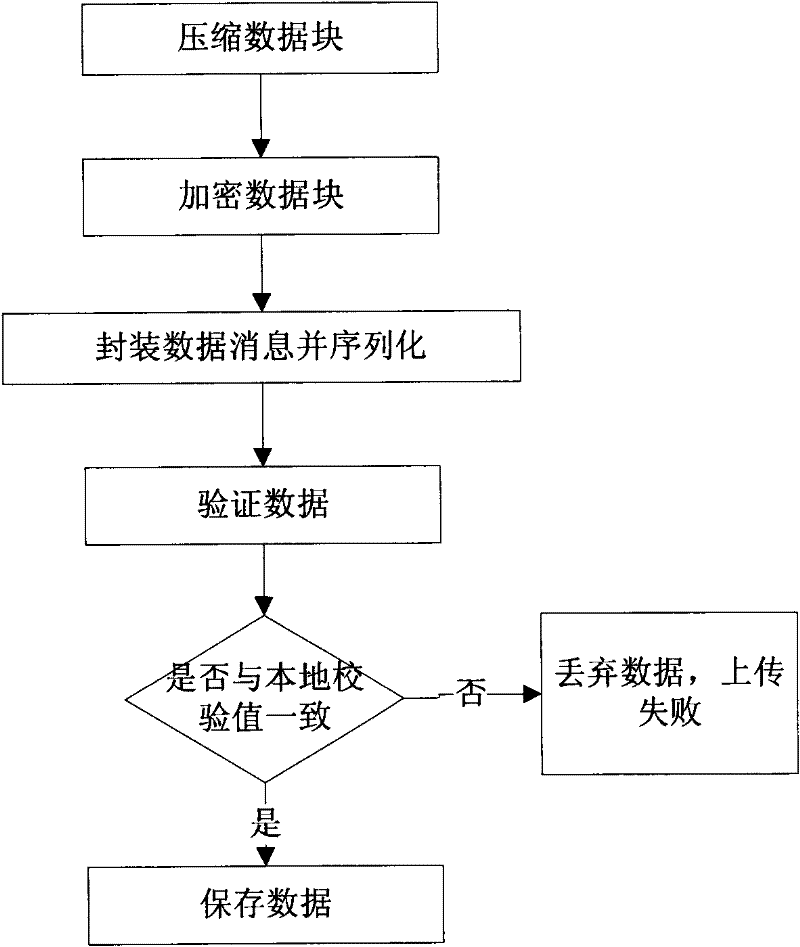
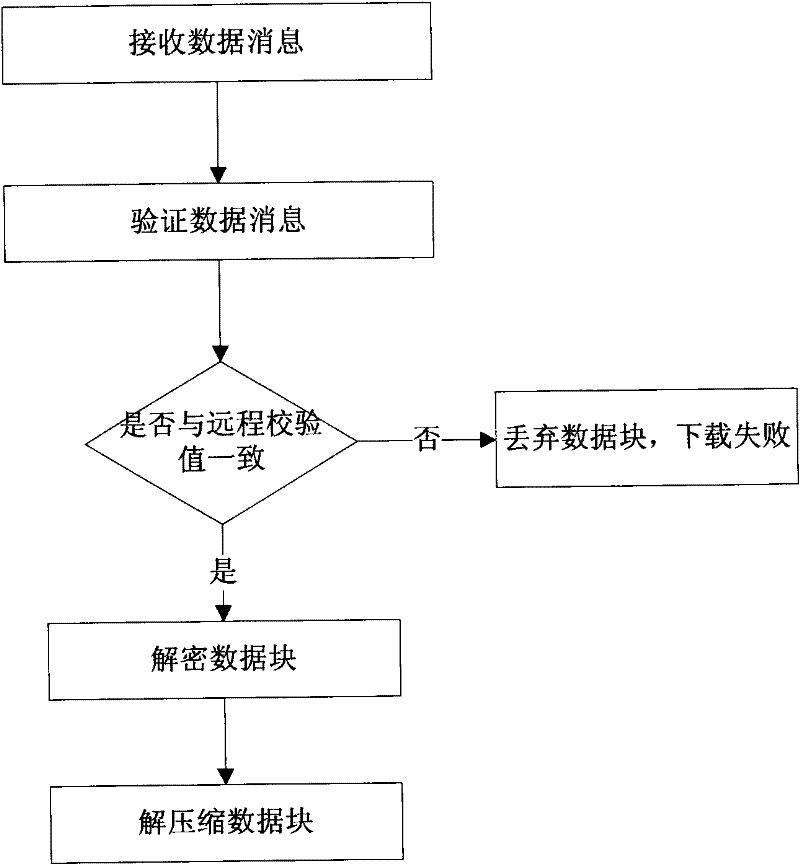
ActiveCN102306114AImprove data backupSpeed up recoveryTransmissionRedundant operation error correctionData compressionRecovery method
The invention relates to the technical field of cloud computing, in particular to a regular data backup and recovery method based on cloud storage. In the regular data backup and recovery method, a data compression module, a data decompression module, a data encryption module, a data decryption module, a message encapsulation module, a data uploading module and a data downloading module are involved; the method comprises the following steps of: performing operation such as encryption, compression, message processing, uploading, checking and the like on data during data backup; and performing operation such as downloading, message processing, checking, decompression, decryption and the like on the data during data recovery. By the method, the data backup and recovery speed of a cloud storage system can be increased, the data backup and recovery efficiency can be improved, and the data transmission security can be enhanced; and the method can be applied to data backup and recovery of the cloud storage system.
Owner:GUANGDONG ELECTRONICS IND INST
Data encryption method, decryption method and decryption device
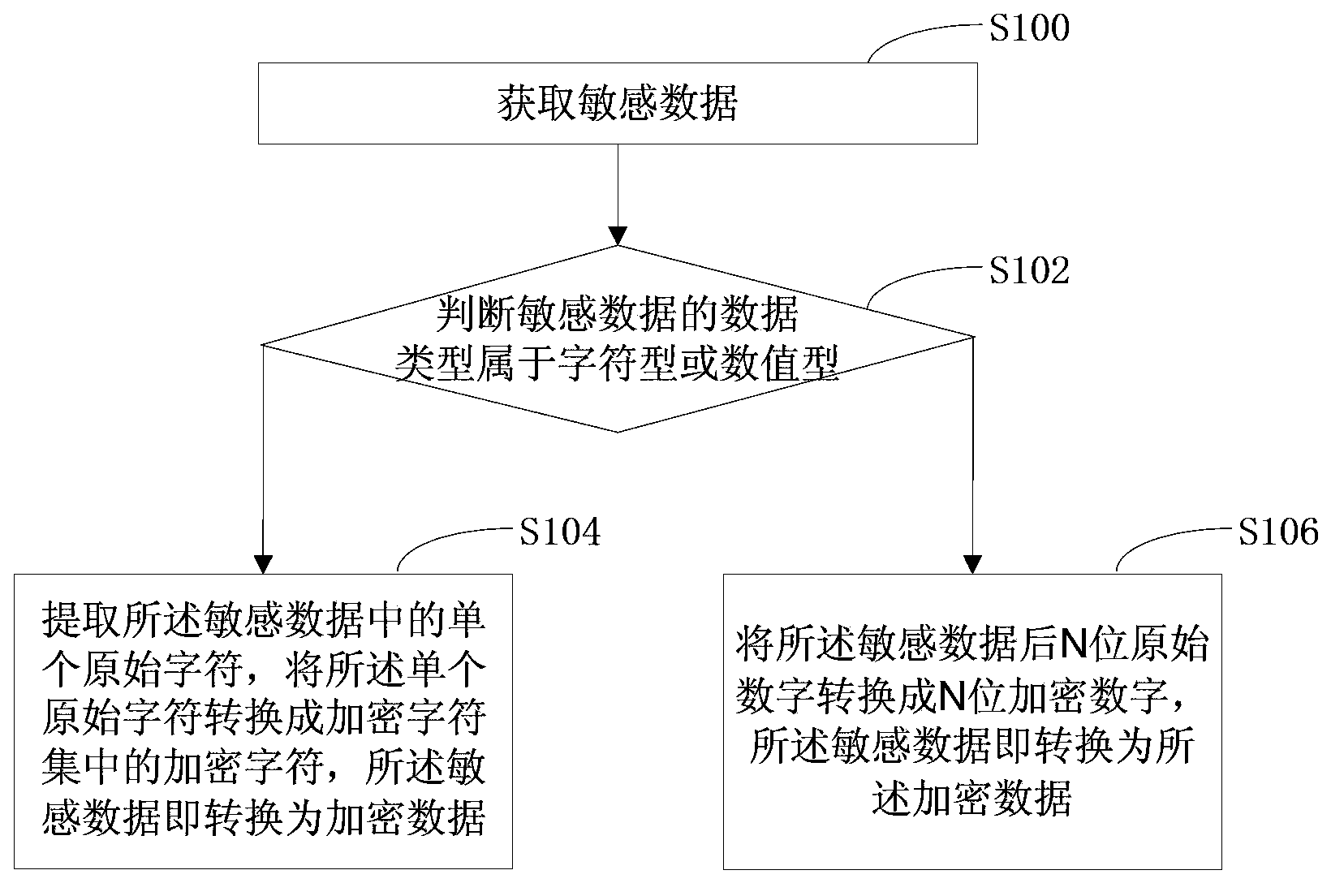
ActiveCN103853985AThe encryption method is reversibleReduce system overheadDigital data protectionSpecial data processing applicationsComputer hardwareOriginal data
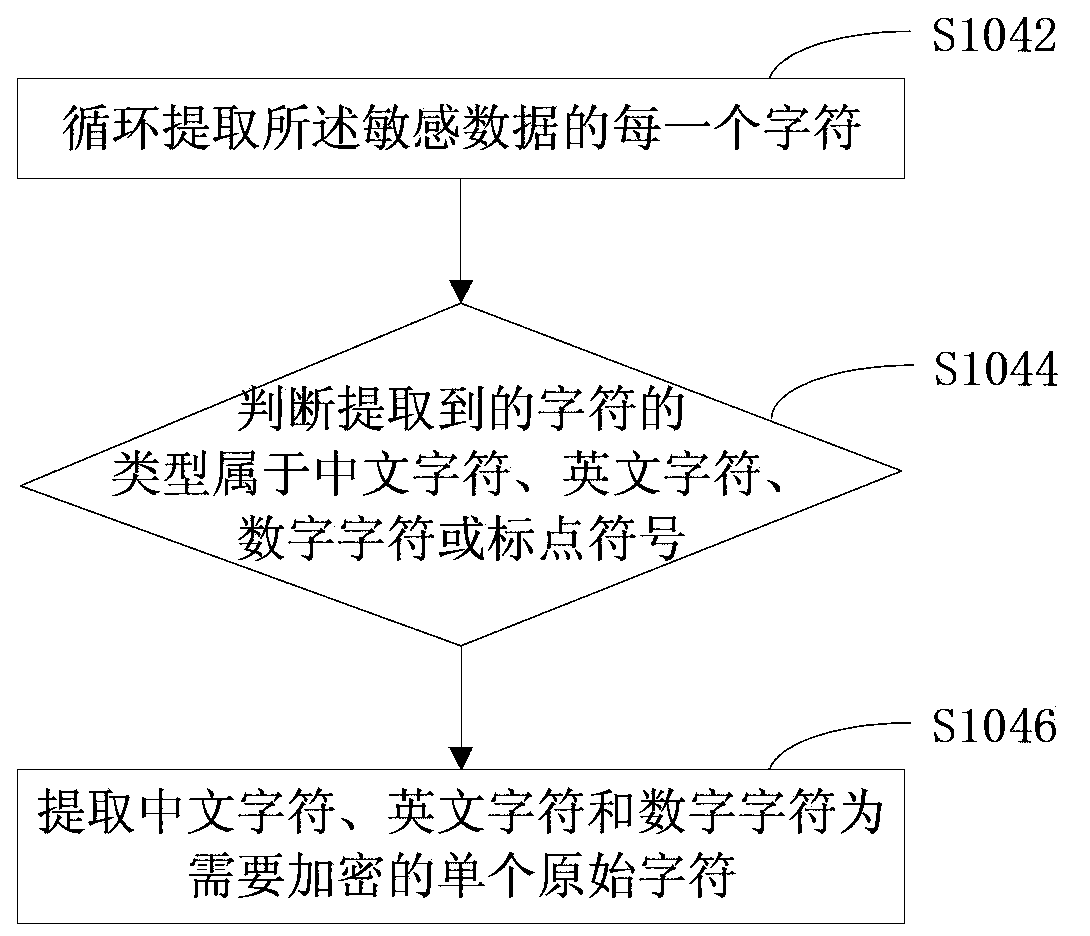
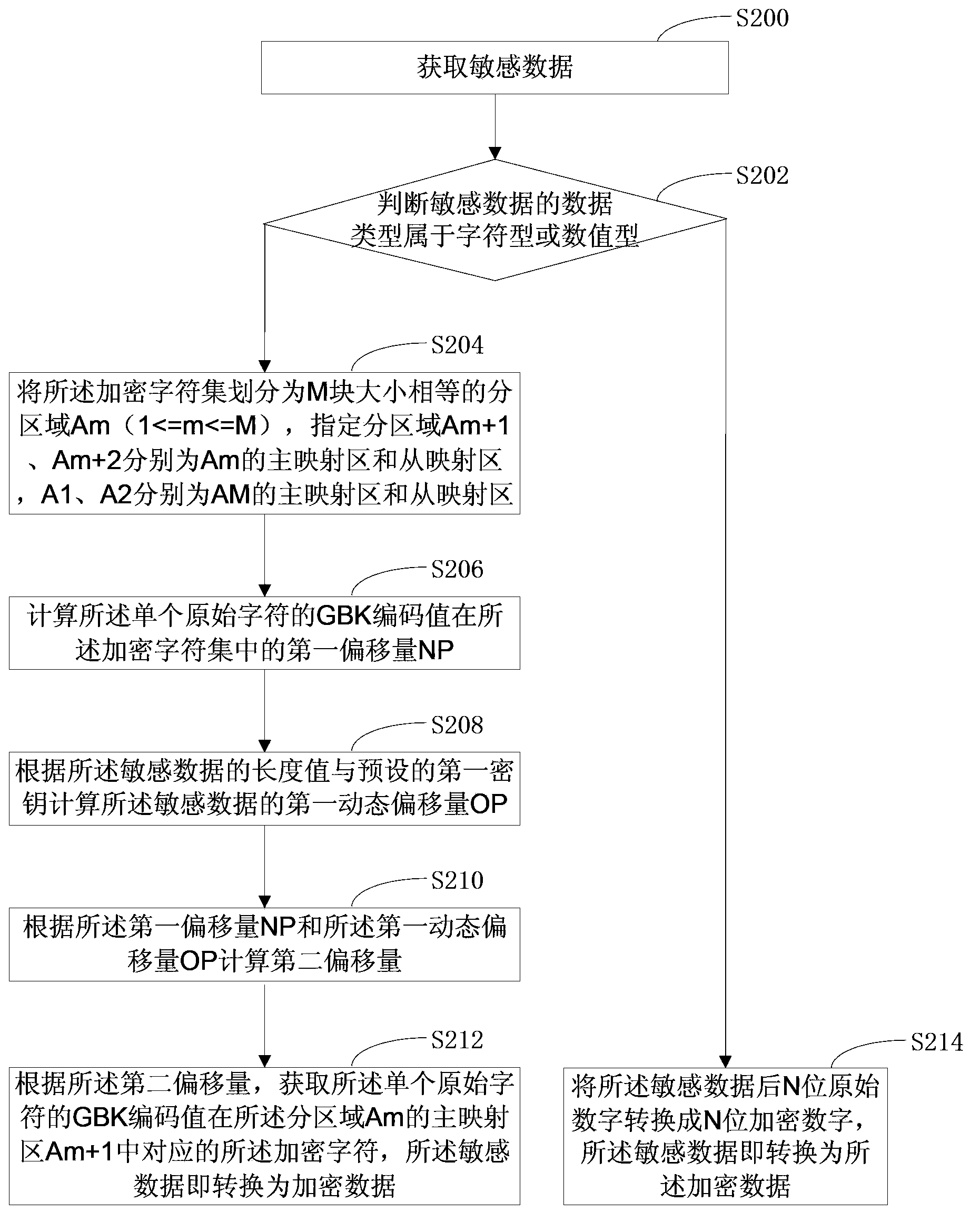
The invention discloses a data encryption method, a data encryption device, a data decryption method and a data decryption device. The method comprises the following steps: obtaining sensitive data, and judging that the data type of the sensitive data belongs to a character type or a numeric type; if the data type of the sensitive data belongs to the character type, extracting single original characters in the sensitive data, and converting the single original characters into encryption characters in an encryption character set so that the sensitive data are converted into encryption data; if the data type of the sensitive data belongs to the numeric type, converting later N original numbers in the sensitive data into N encryption numbers so that the sensitive data are converted into the encryption data. The data are encrypted by retaining the manner of original data, so that the required storage space of the encryption data in a data storage system is not changed, and the system overhead and communication overhead of a traditional encryption algorithm are reduced.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
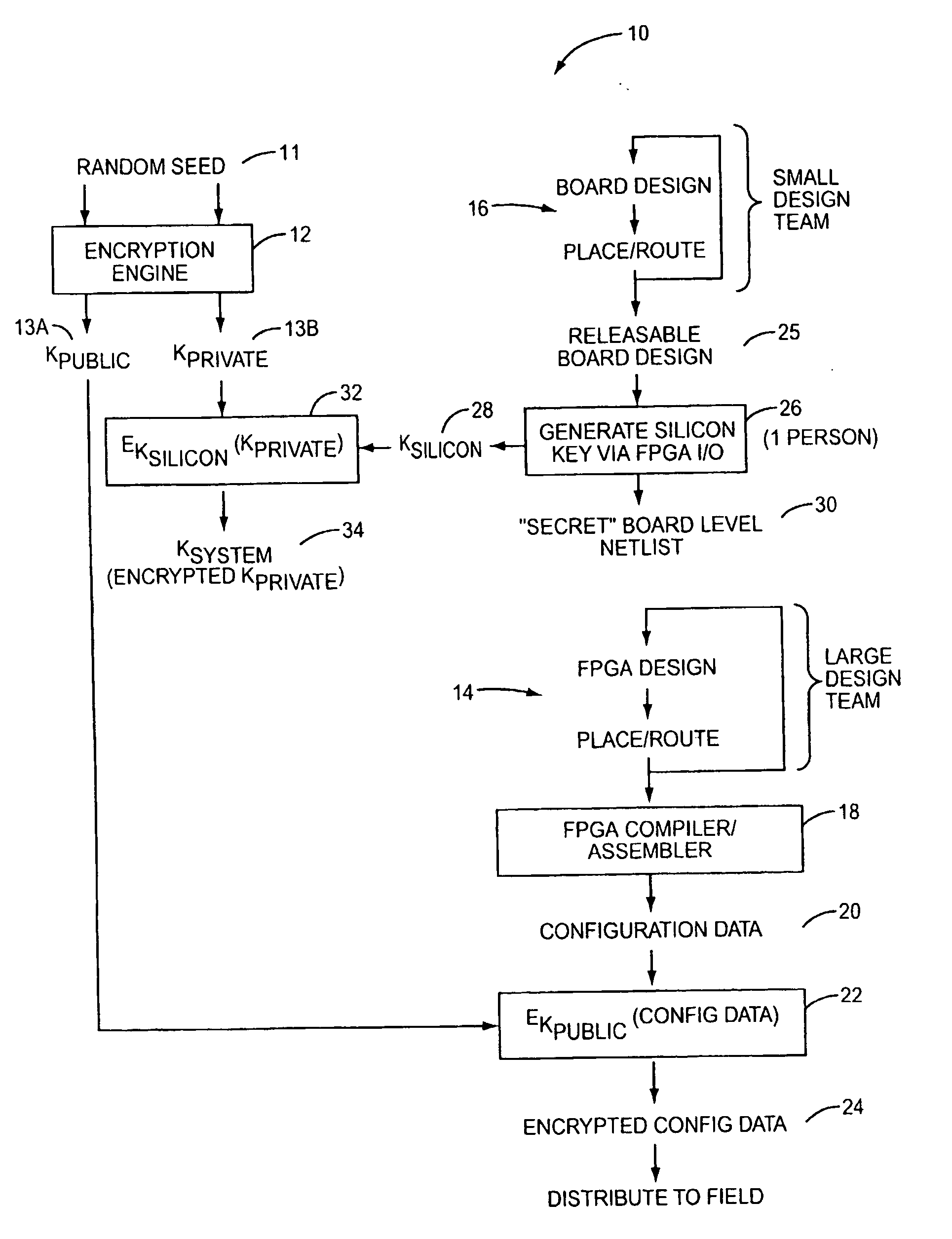
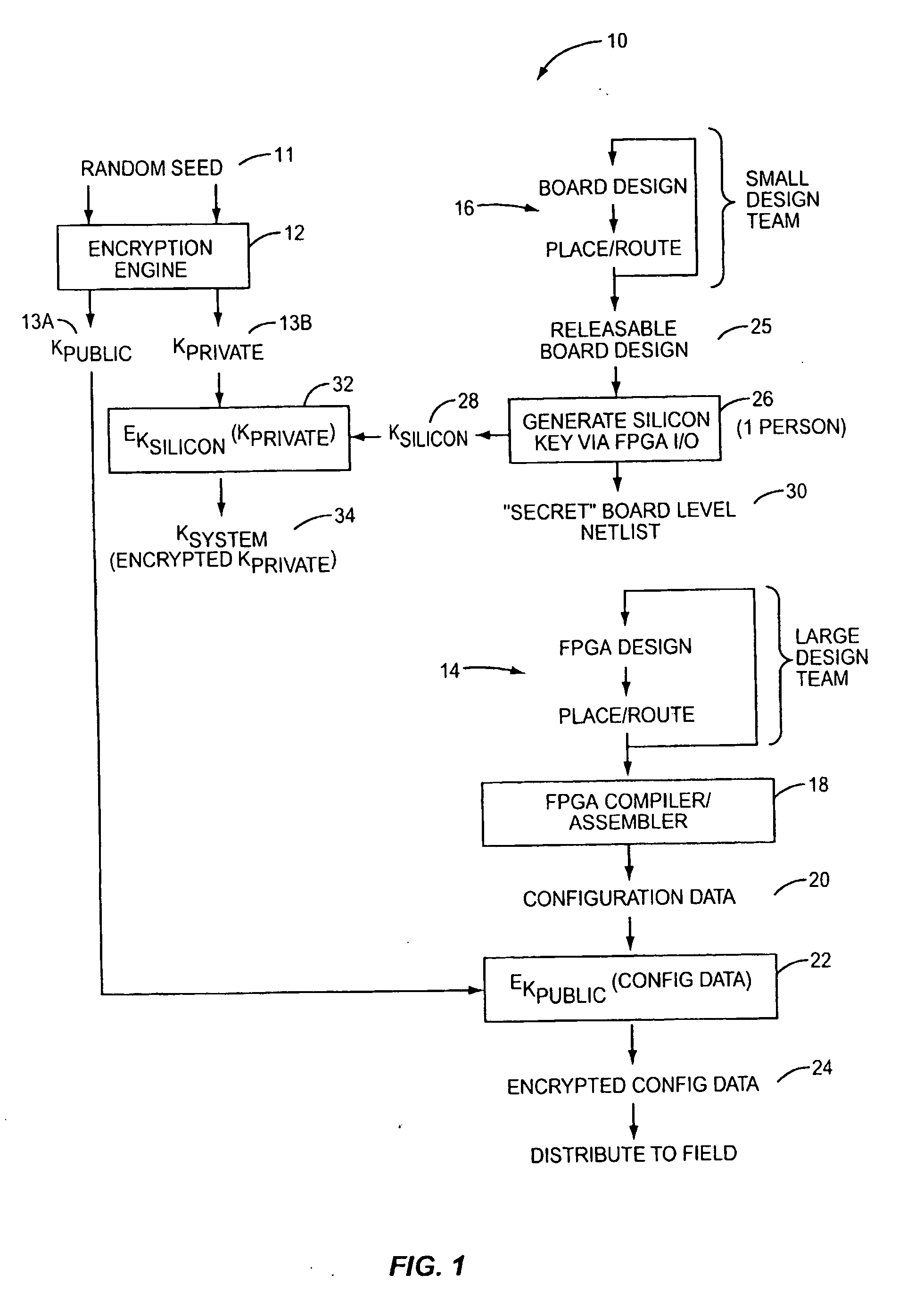
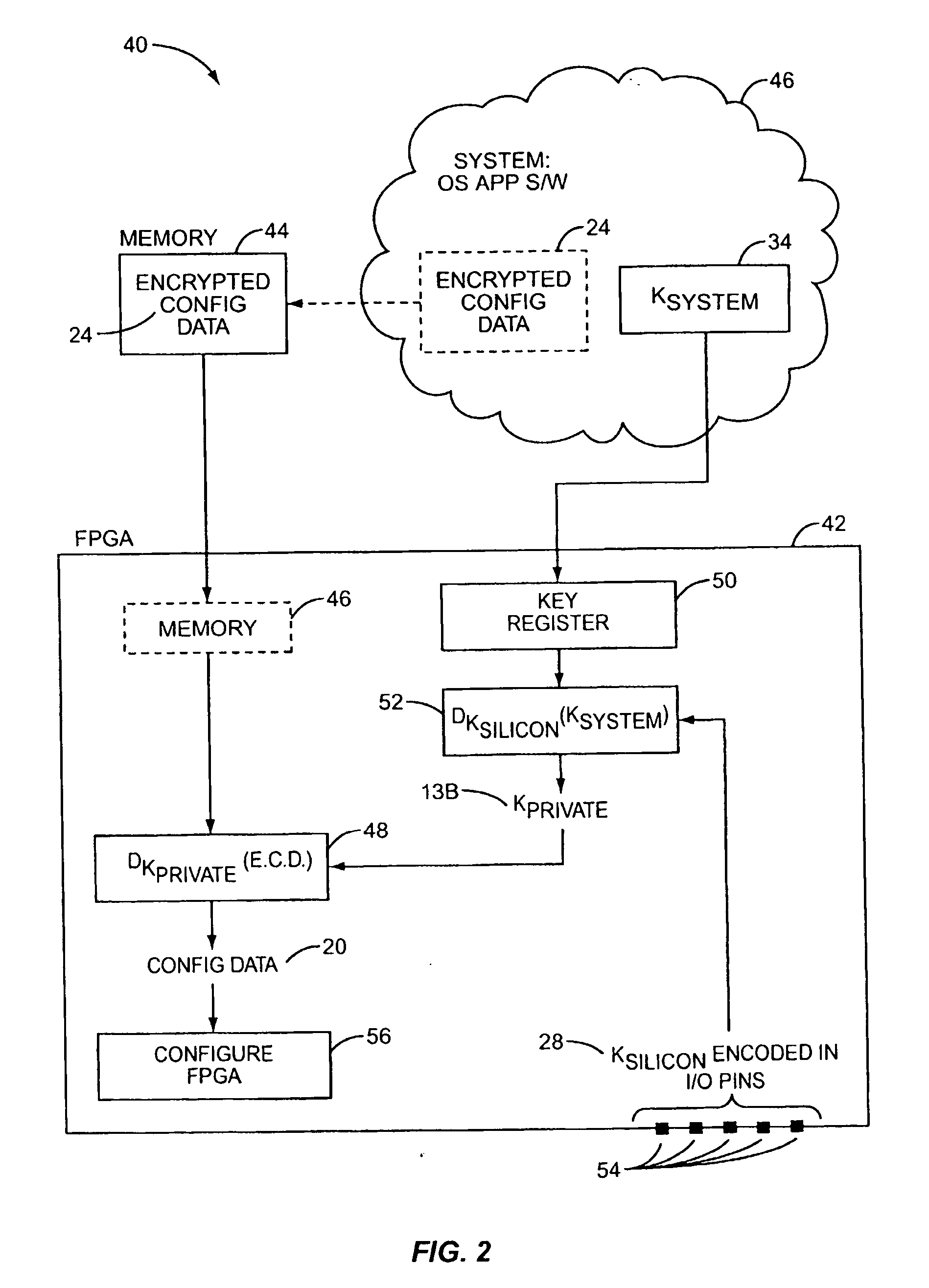
Method of securing programmable logic configuration data
InactiveUS20070074045A1Unauthorized memory use protectionHardware monitoringProgrammable logic deviceHigh voltage
Owner:CARNEGIE MELLON UNIV
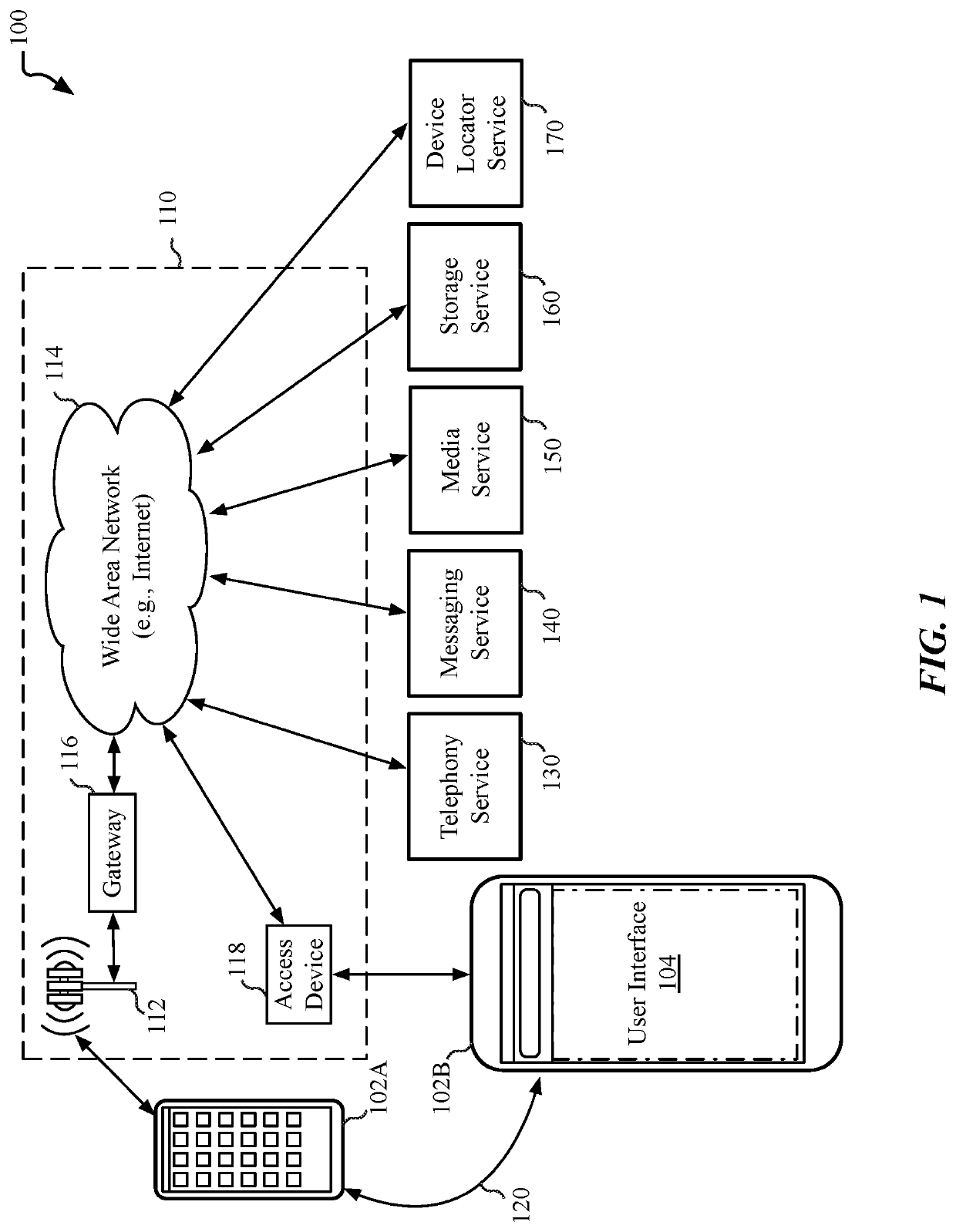
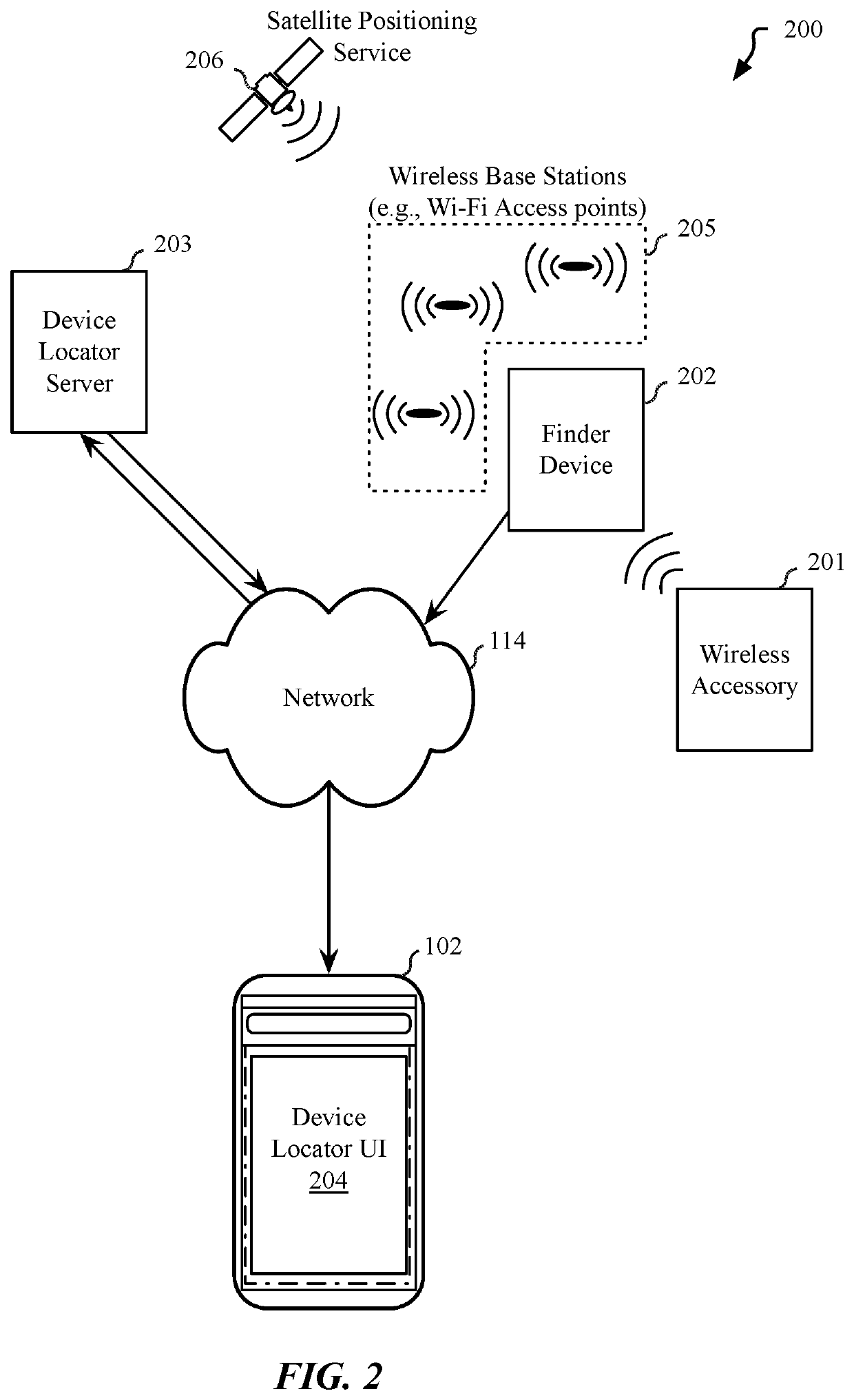
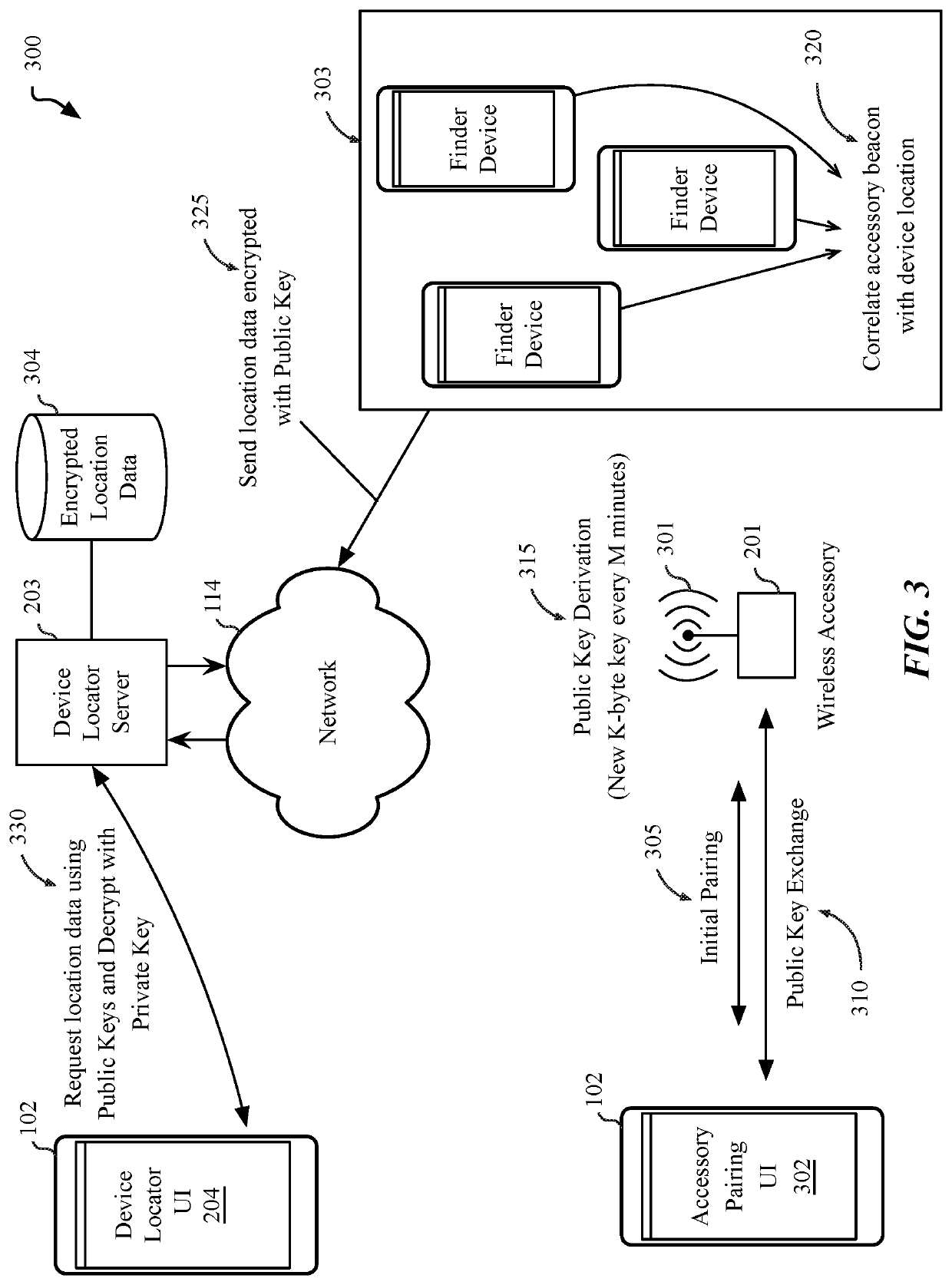
System and method for locating wireless accessories
Embodiments described herein provide for system and methods to crowdsource the location of wireless devices and accessories that lack a connection to a wide area network. One embodiment provides for a data processing system configured to perform operations comprising loading a user interface on an electronic device, the user interface to enable the determination of a location of a wireless accessory that is associated with the electronic device, generating a set of public keys included within a signal broadcast by the wireless accessory, the signal broadcast during a first period, sending the set of public keys to a server with a request to return data that corresponds with a public key in the set of public keys, decrypting the location data using a private key associated with the public key, and processing the location data to determine a probable location for the wireless accessory.
Owner:APPLE INC
Privacy preserving computation protocol for data analytics
PendingUS20180373882A1Efficient privacy-preservingEfficient privacy-preserving protocolKey distribution for secure communicationMultiple keys/algorithms usagePlaintextEncrypted function
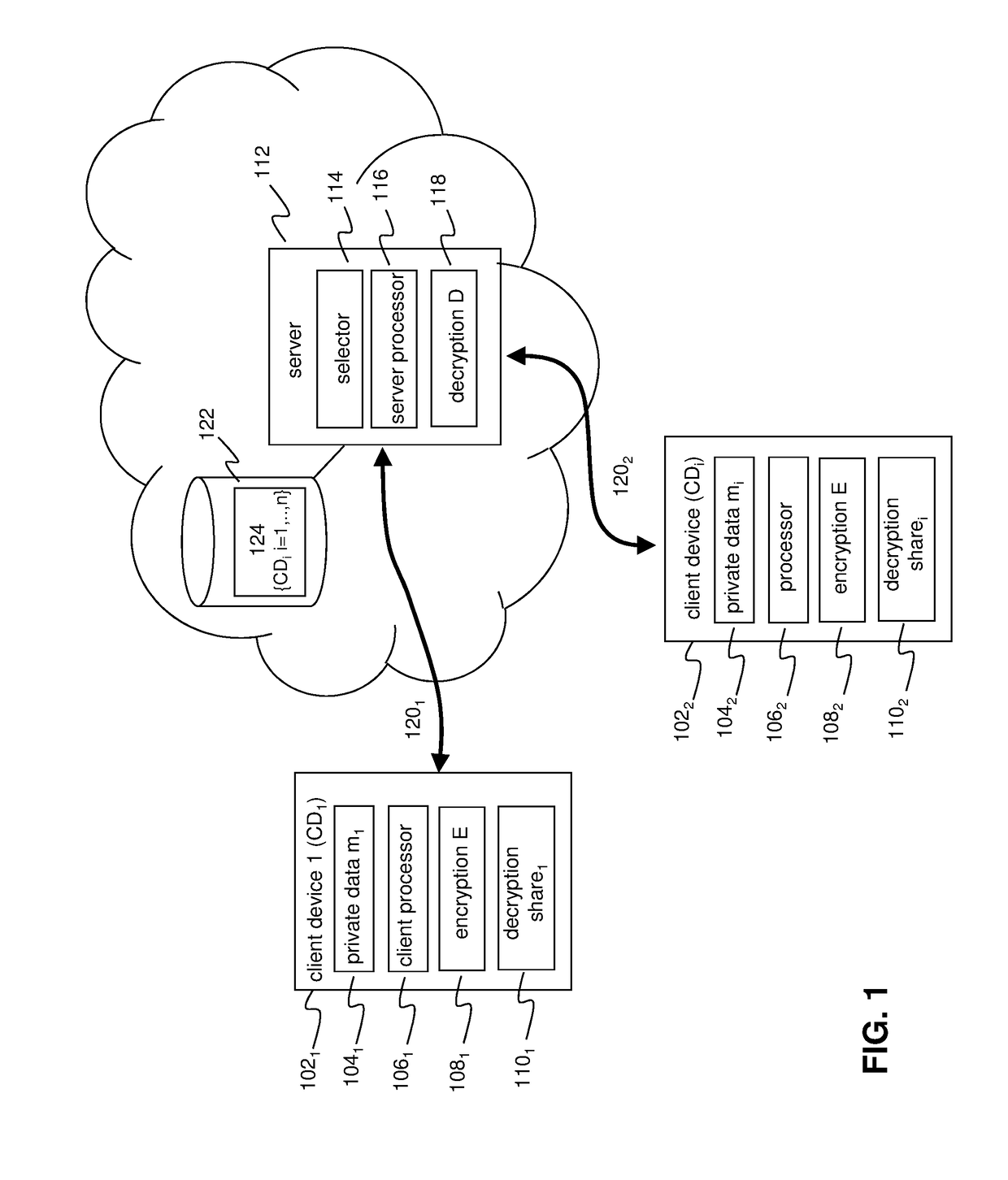
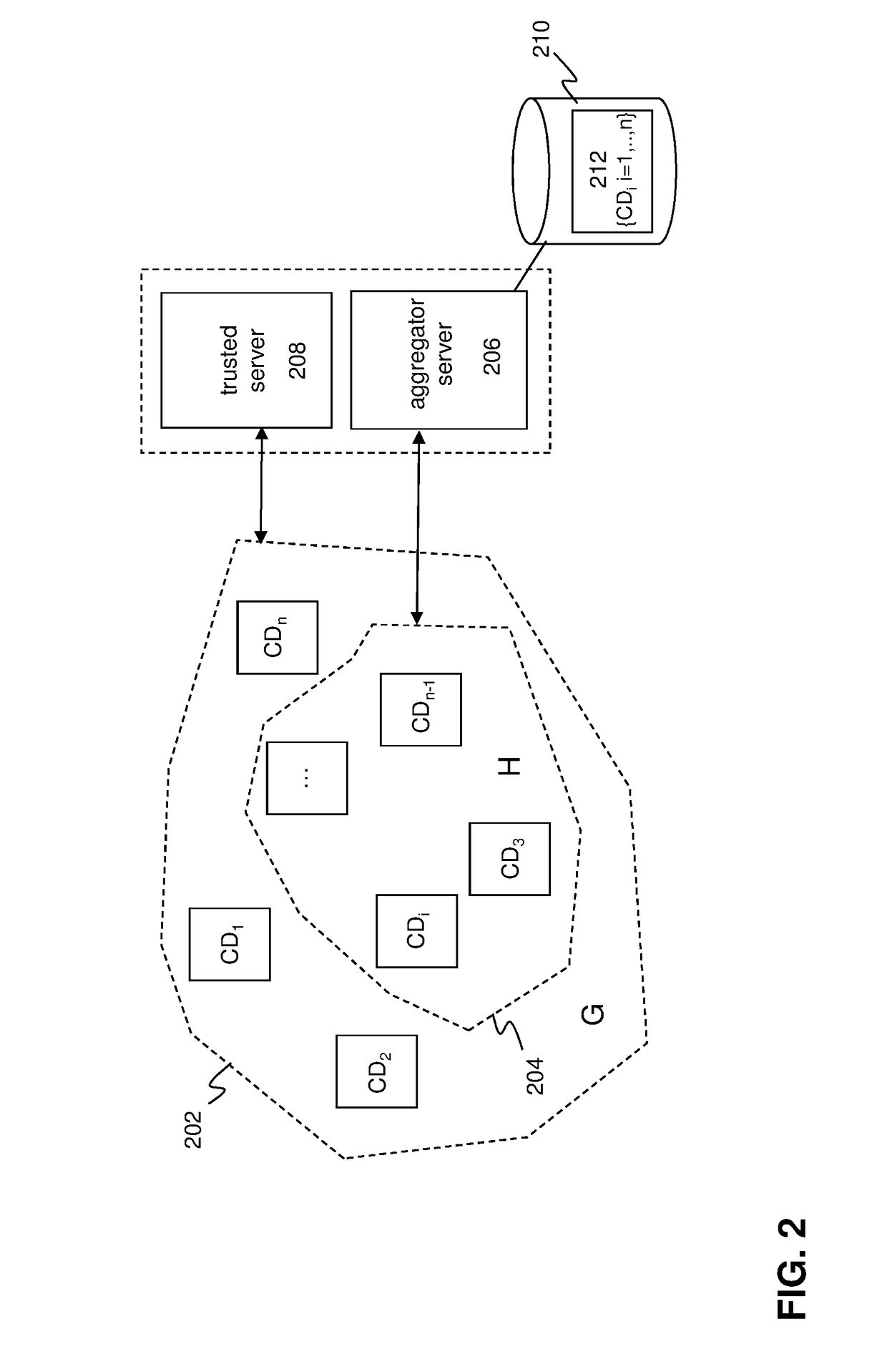
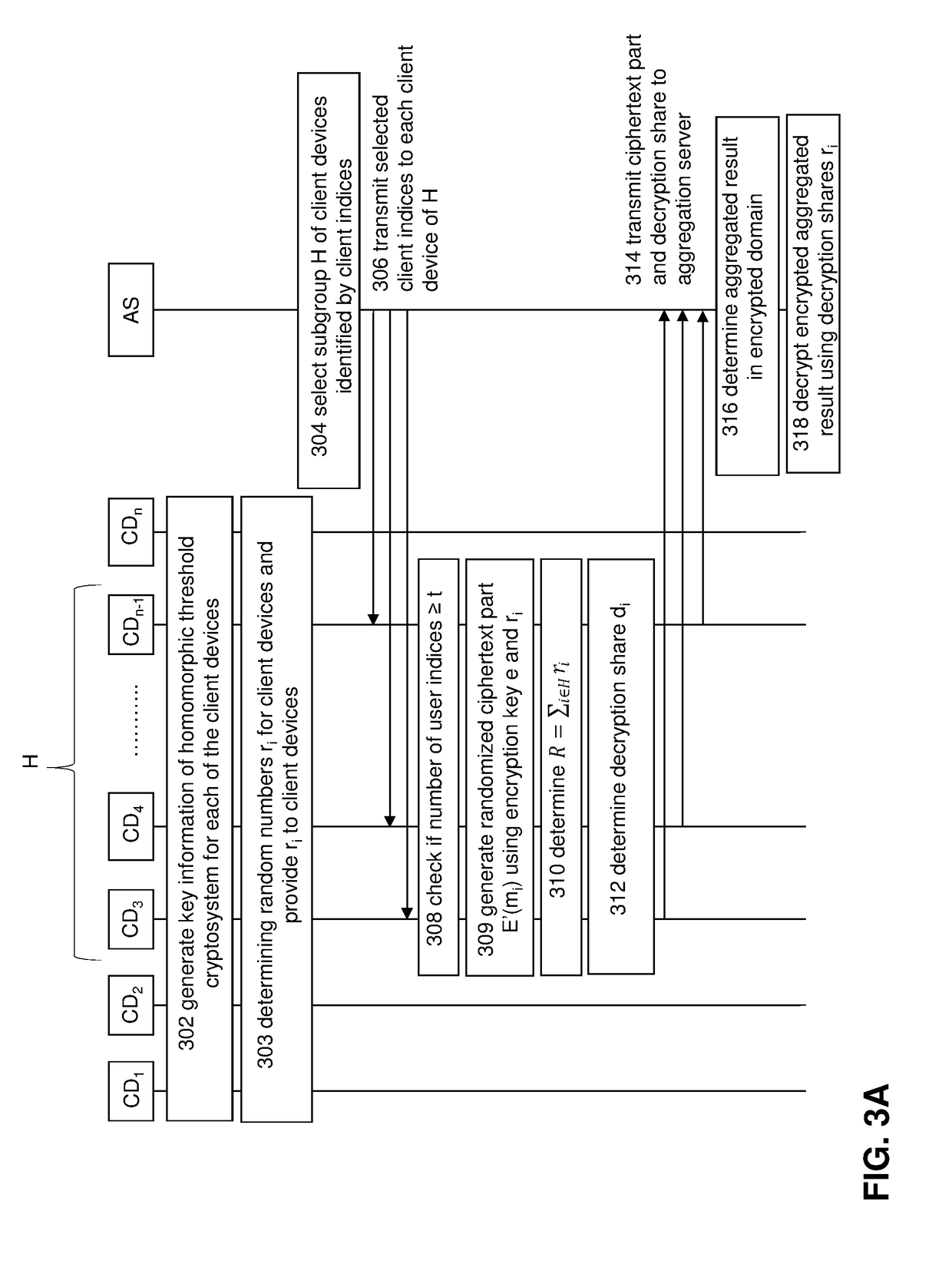
A privacy preserving computation protocol for data analytics is described. The protocol includes a method for privacy-preserving computation of aggregated private data of a group of client devices wherein the method comprises: a server selecting at least t client devices from the group of client devices, each client device in the group: being identifiable by client index i; comprising an encryption function; being provided with key information including an encryption key e and a decryption key of a homomorphic threshold cryptosystem; generating or being provided with an random value ri and having access to or being provided with the random values of the other client devices in the group; the server transmitting client information to each selected client device, the client information including client indices identifying the selected client devices, the client information signalling a client device that the server would like aggregate encrypted private data of each of the selected client devices; the server receiving randomized encrypted private data and an associated decryption share from each selected client device, the decryption shares being configured such that decryption key d can be reconstructed on the basis of t decryption shares; and, the server aggregating, preferably summing or adding, the received randomized encrypted private data of the selected client devices using the homomorphic properties of the cryptosystem and using the decryption shares for decrypting the aggregated randomized encrypted private data into cleartext.
Owner:FLYTXT MOBILE SOLUTIONS
Trusted network architecture based on identity
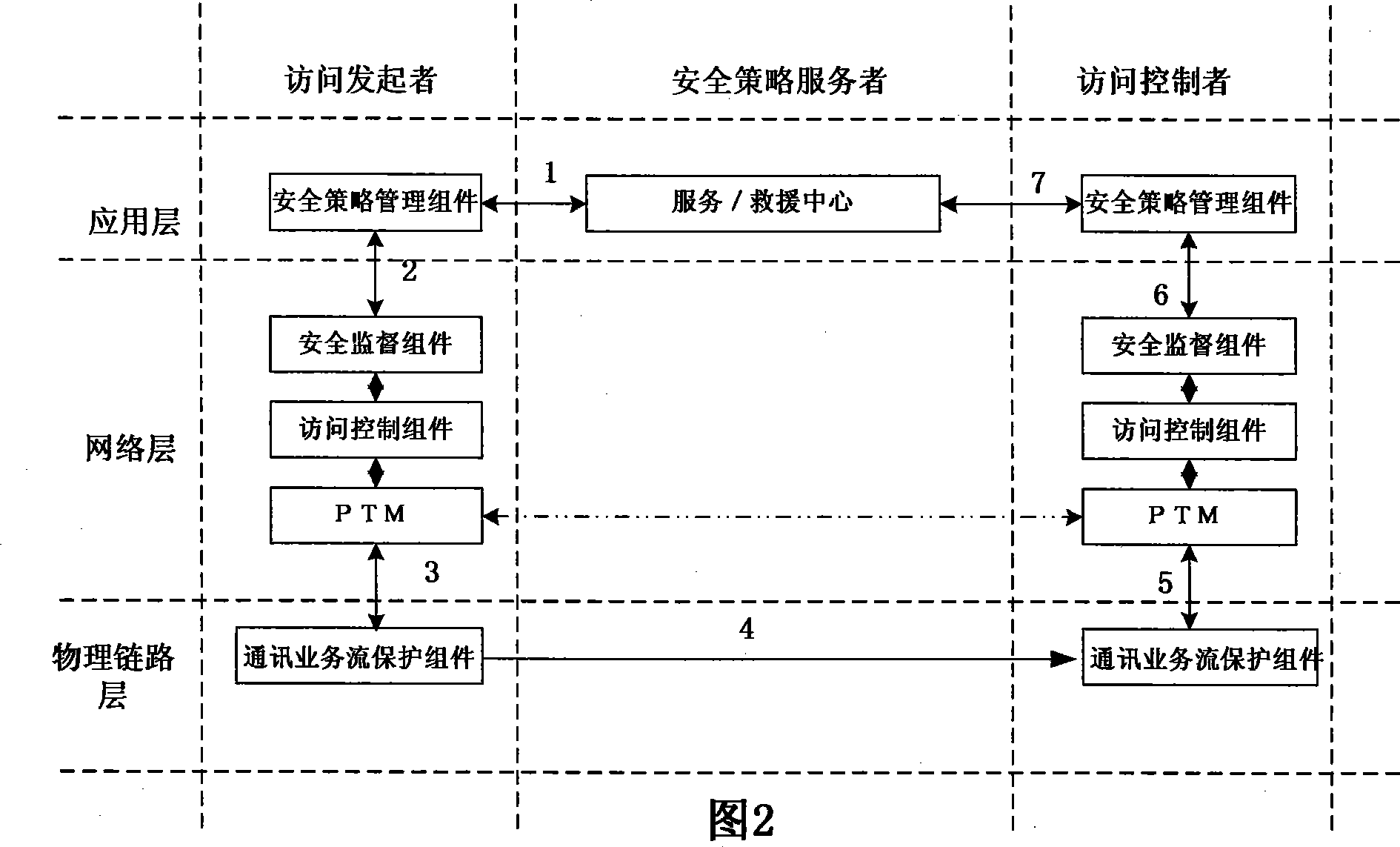
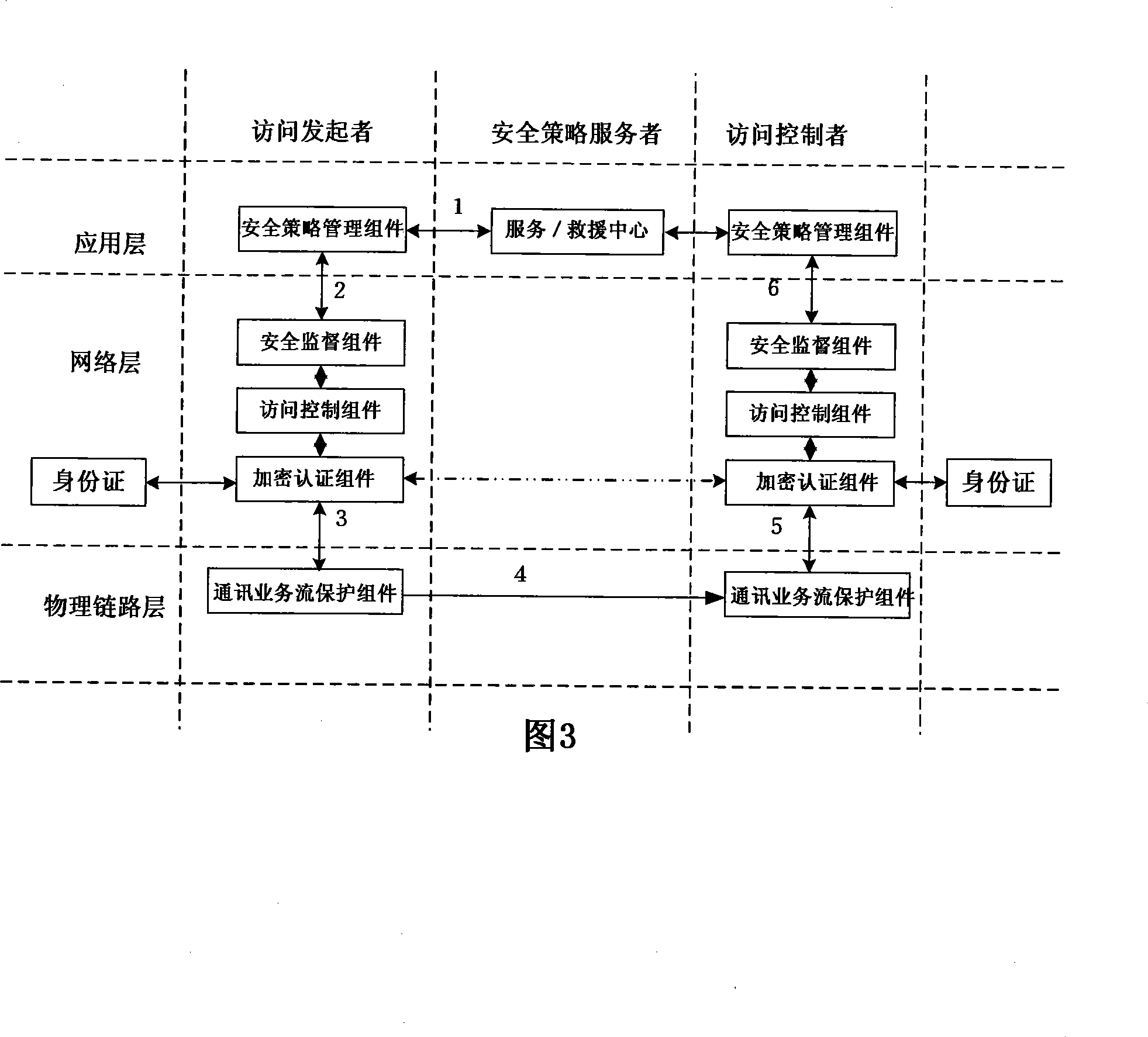
InactiveCN101425903ASimple technical implementationSimple and efficient structureUser identity/authority verificationData switching networksData streamNetwork architecture
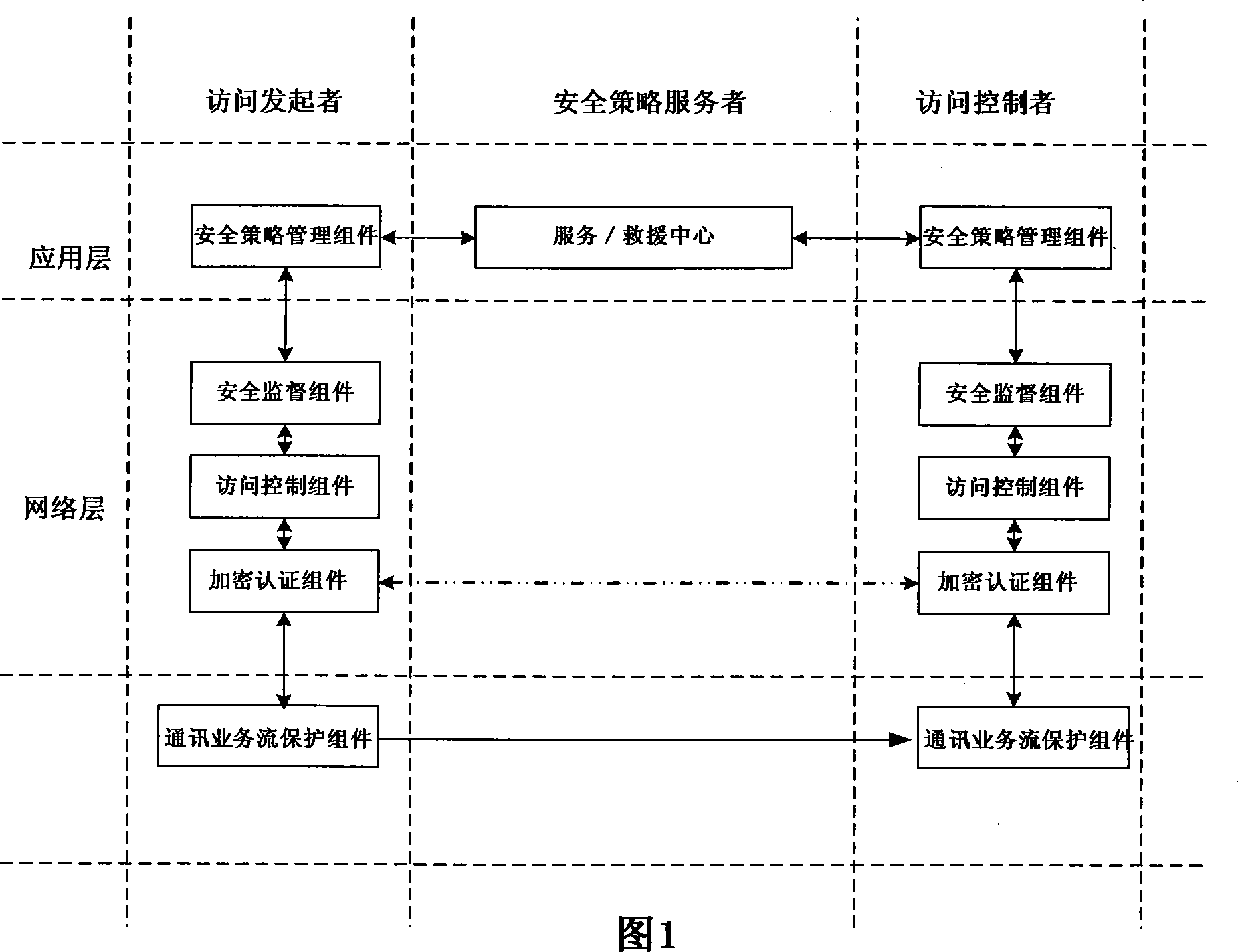
A credibility network framework based on identities belongs to the technical field of information security, which comprises three layers and three entities, wherein the three layers are a physical transmission layer, a network layer and an application program layer; and the three entities are a network access sponsor, a network access controller and a safety tactics server. The credibility network framework adopts a vector quantity encryption authentication mechanism based on the identifies of accessors, and guarantees that the requirements of all network accessors are the encryption data streams bound with accessor entities, as long as access controllers use personal identify labels and identify information of access requesting labels to obtain accurate proof test value through decrypting requesting data, bidirectional equipotent identify authentication is realized, then authority and content are evaluated and detected by access control assemblies and safety monitoring assemblies so as to guarantee that all access requirements are safe, and unsafe access requirements are refused, thereby the credibility network framework is realized.
Owner:冯振周
Encrypting operating system
InactiveUS7810133B2Effective meanEncryption apparatus with shift registers/memoriesDigital data processing detailsOperational systemFile system
A method of and system for encrypting and decrypting data on a computer system is disclosed. In one embodiment, the system comprises an encrypting operating system (EOS), which is a modified UNIX operating system. The EOS is configured to use a symmetric encryption algorithm and an encryption key to encrypt data transferred from physical memory to secondary devices, such as disks, swap devices, network file systems, network buffers, pseudo file systems, or any other structures external to the physical memory and on which can data can be stored. The EOS further uses the symmetric encryption algorithm and the encryption key to decrypt data transferred from the secondary devices back to physical memory. In other embodiments, the EOS adds an extra layer of security by also encrypting the directory structure used to locate the encrypted data. In a further embodiment a user or process is authenticated and its credentials checked before a file can be accessed, using a key management facility that controls access to one or more keys for encrypting and decrypting data.
Owner:EXIT CUBE HONG KONG
Hybrid encrypted network data security method and system
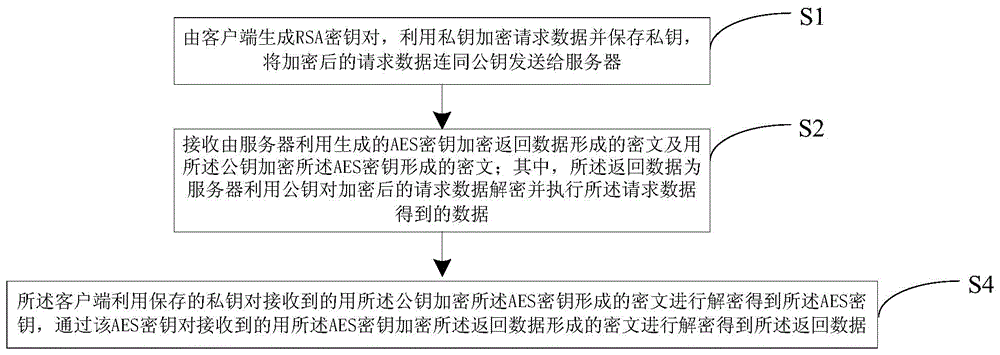
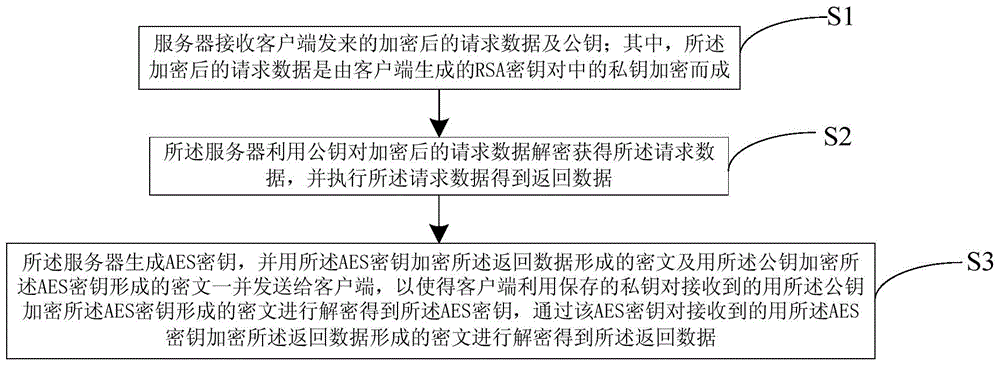
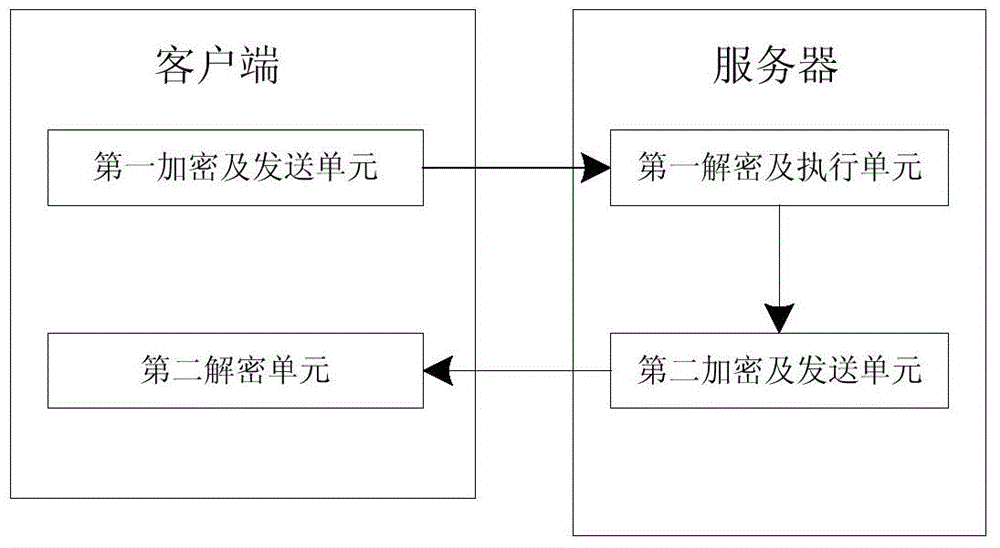
InactiveCN104821944APrevent leakageEncryption increaseTransmissionNetworked Transport of RTCM via Internet ProtocolCiphertext
The invention relates to a hybrid encrypted network data security method and system. The method comprises the steps that an RSA secret key pair is generated by a client terminal, request data are encrypted by utilizing a private key and the private key is stored, and the encrypted request data together with a public key are transmitted to a server; a cryptograph formed by the server via utilizing the generated AES secret key to encrypt returning data and a cryptograph formed via utilizing the public key to encrypt the AES secret key are received; the returning data are data obtained by the server via utilizing the public key to decrypt and perform the encrypted request data; and the client terminal utilizes the stored private key to decrypt the received cryptograph formed by encrypting the AES secret key via the public key so as to obtain the AES secret key, and the received cryptograph formed by encrypting the returning data via the AES secret key is decrypted by the AES secret key so that the returning data are obtained. A hybrid encryption mode of symmetric encryption and asymmetric encryption is adopted so that secret key leakage or decryption can be prevented, and network transmission data encryption can be increased. The client terminal controls the asymmetric secret key so that the number of requests can be reduced and efficiency can be enhanced.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
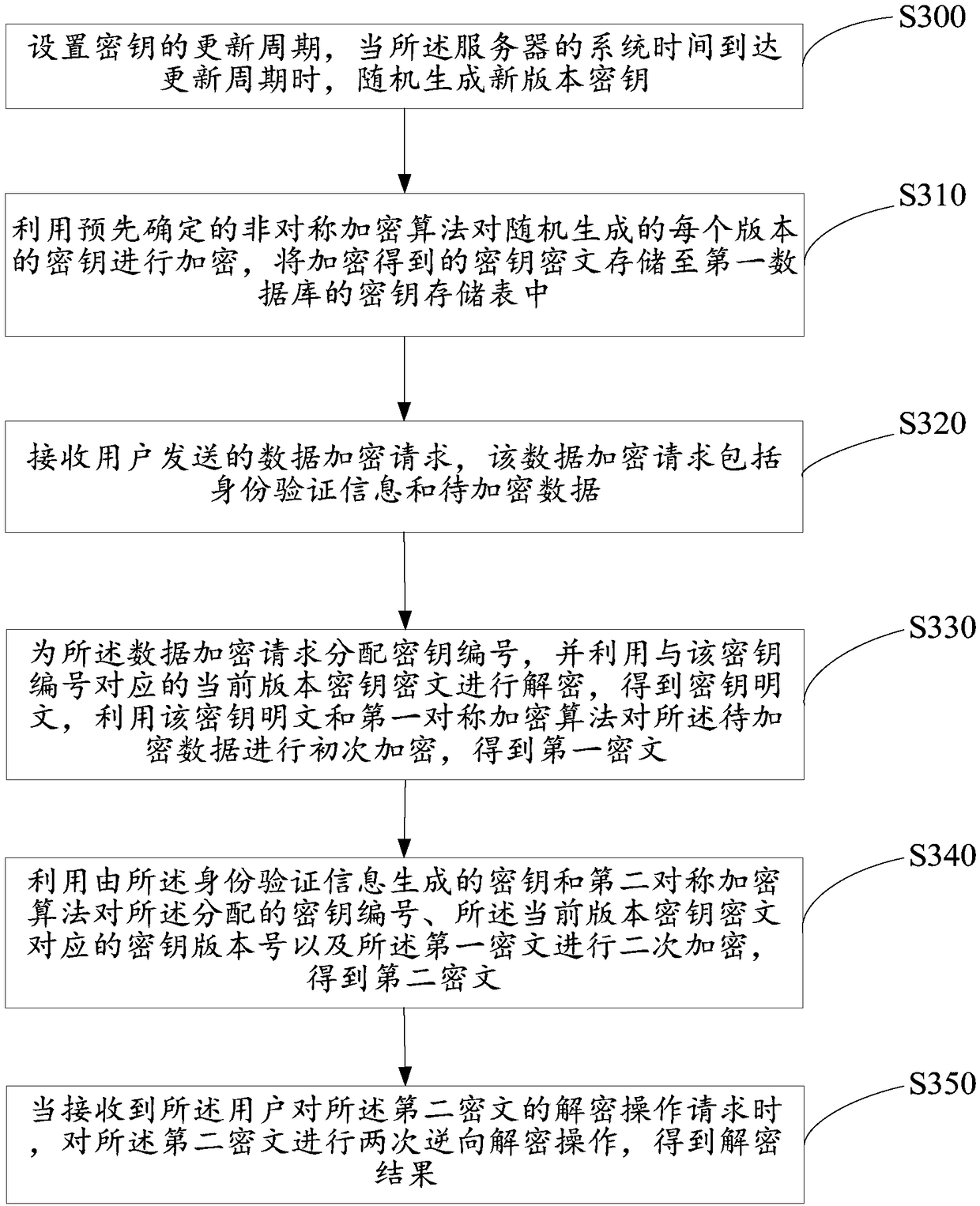
Data encryption and decryption method, server and storage medium
ActiveCN109474423AImprove securityEnsure data securityKey distribution for secure communicationCiphertextPassword
The invention relates to a password technology, and provides a data encryption and decryption method, a server and a storage medium. The method comprises the steps of setting an update period of a key, and generating and storing multi-version keys; receiving a data encryption request, including identity authentication information and data to be encrypted, sent by the user; distributing a key number for the data encryption request, and primarily symmetrically encrypting the data to be encrypted by using a current-version key corresponding to the key number, to acquire a first ciphertext; secondarily symmetrically encrypting the key number, the key version number of the current-version key and the first ciphertext by using the identity authentication information, to acquire a second ciphertext; and receiving a data decryption request sent by the user, and performing an inverse decryption operation on the second ciphertext, to acquire a decryption result. By using the method, server and medium provided by the invention, the key can be periodically updated, and the key security is enhanced.
Owner:PING AN TECH (SHENZHEN) CO LTD
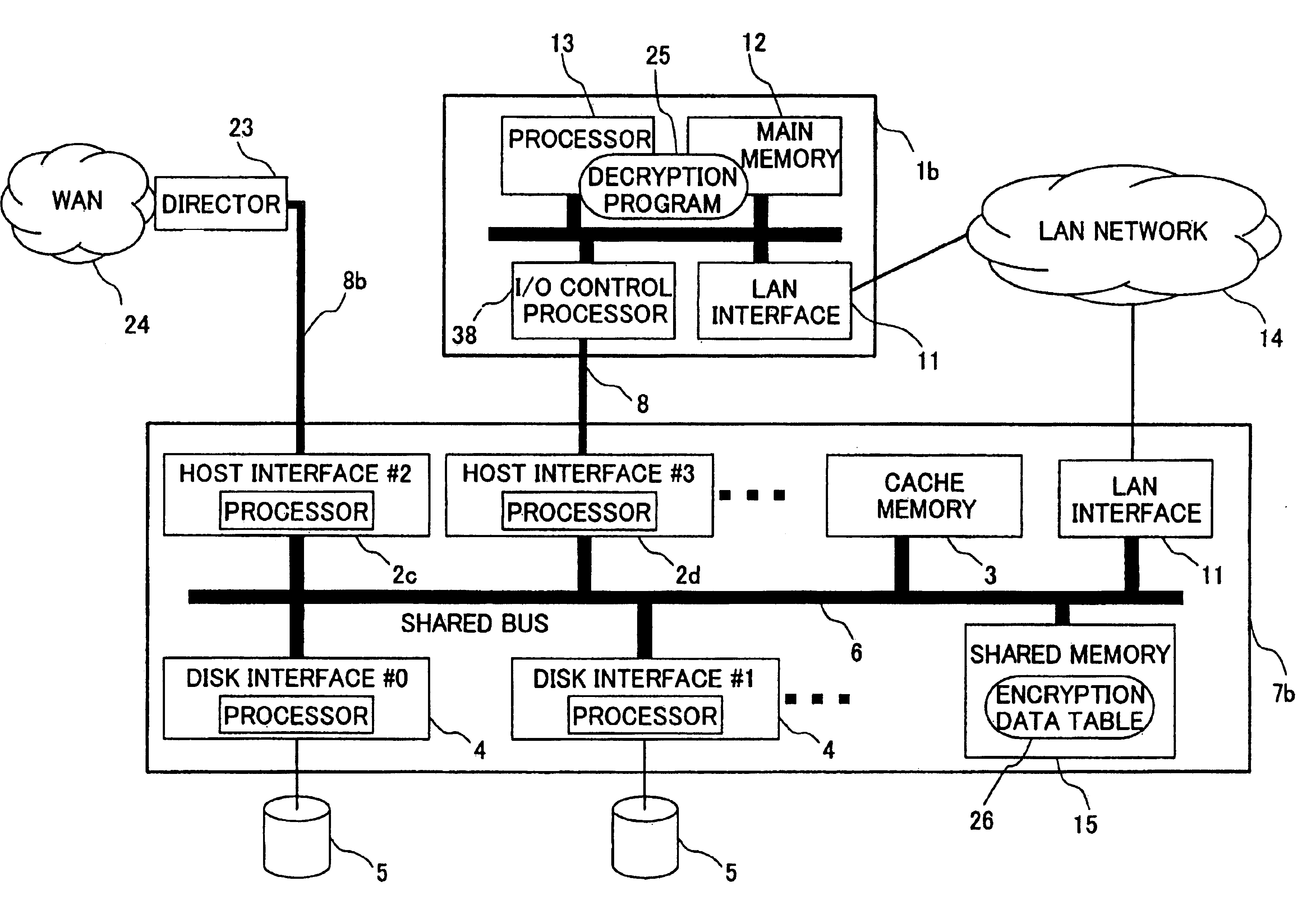
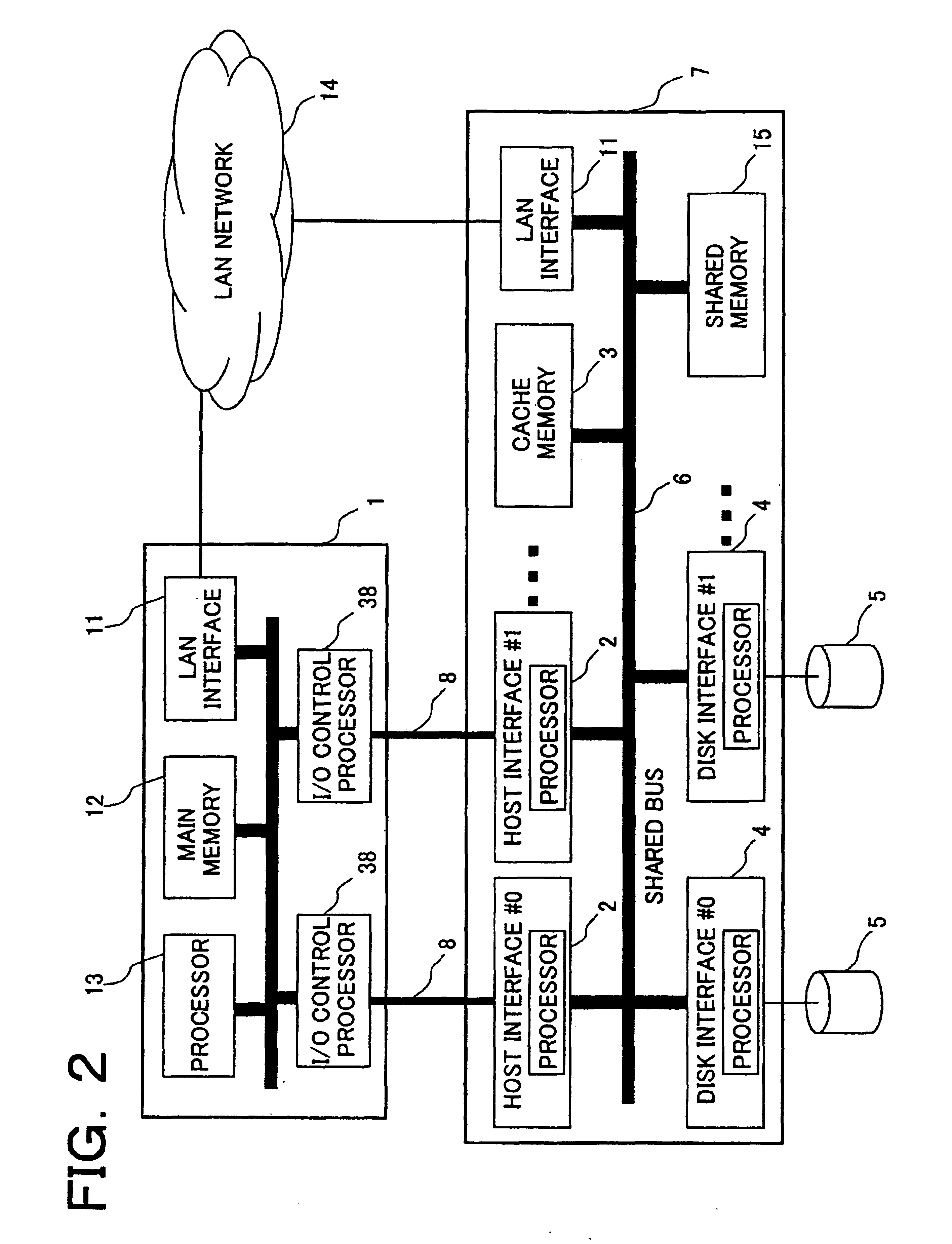
Computing system and data decryption method and computer system with remote copy facility
InactiveUS6966001B2High cryptographic strengthImprove data transfer performanceDigital data processing detailsUnauthorized memory use protectionComputer hardwareCiphertext
A computing system and encryption / decryption method realizes assurance of security and improvement of throughput in a remote system. For this purpose, encrypted data is written to a storage system, it is determined whether data in the storage system is ciphertext or plaintext, and encrypted data is read, decrypted and re-written in storage asyncronously with writing encrypted data to storage.
Owner:GOOGLE LLC
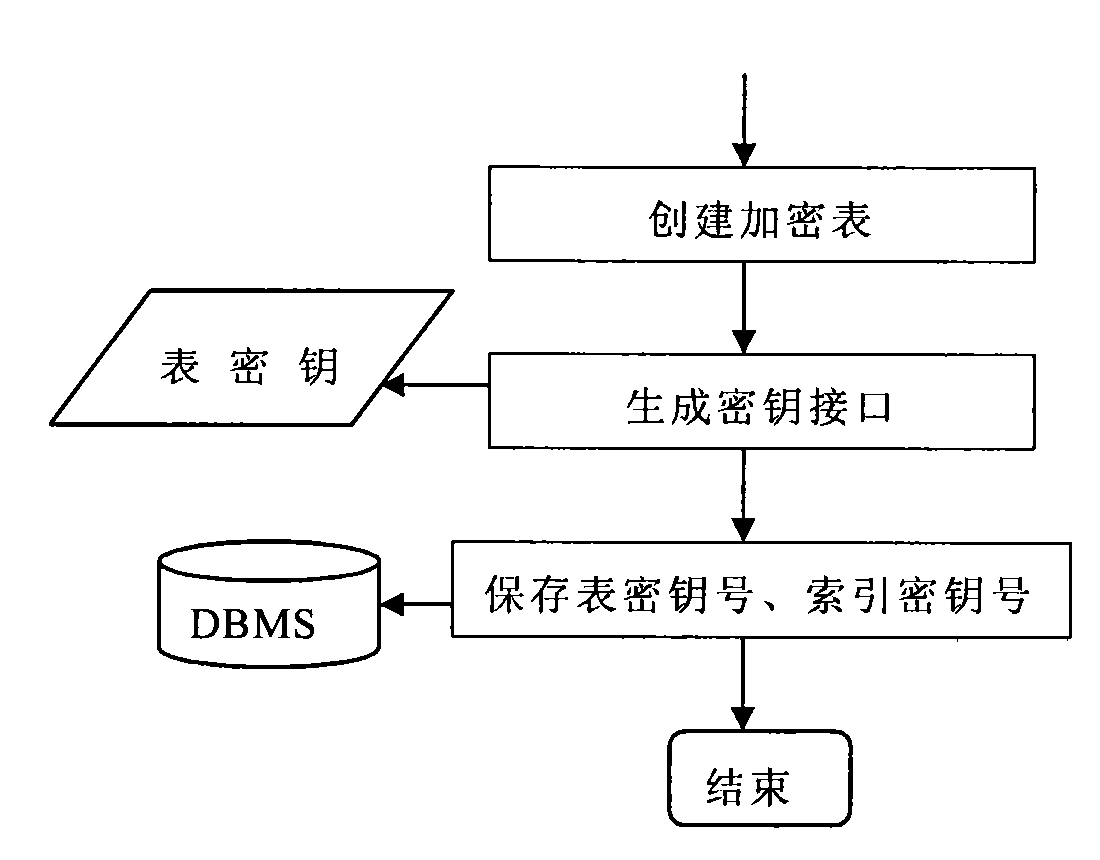
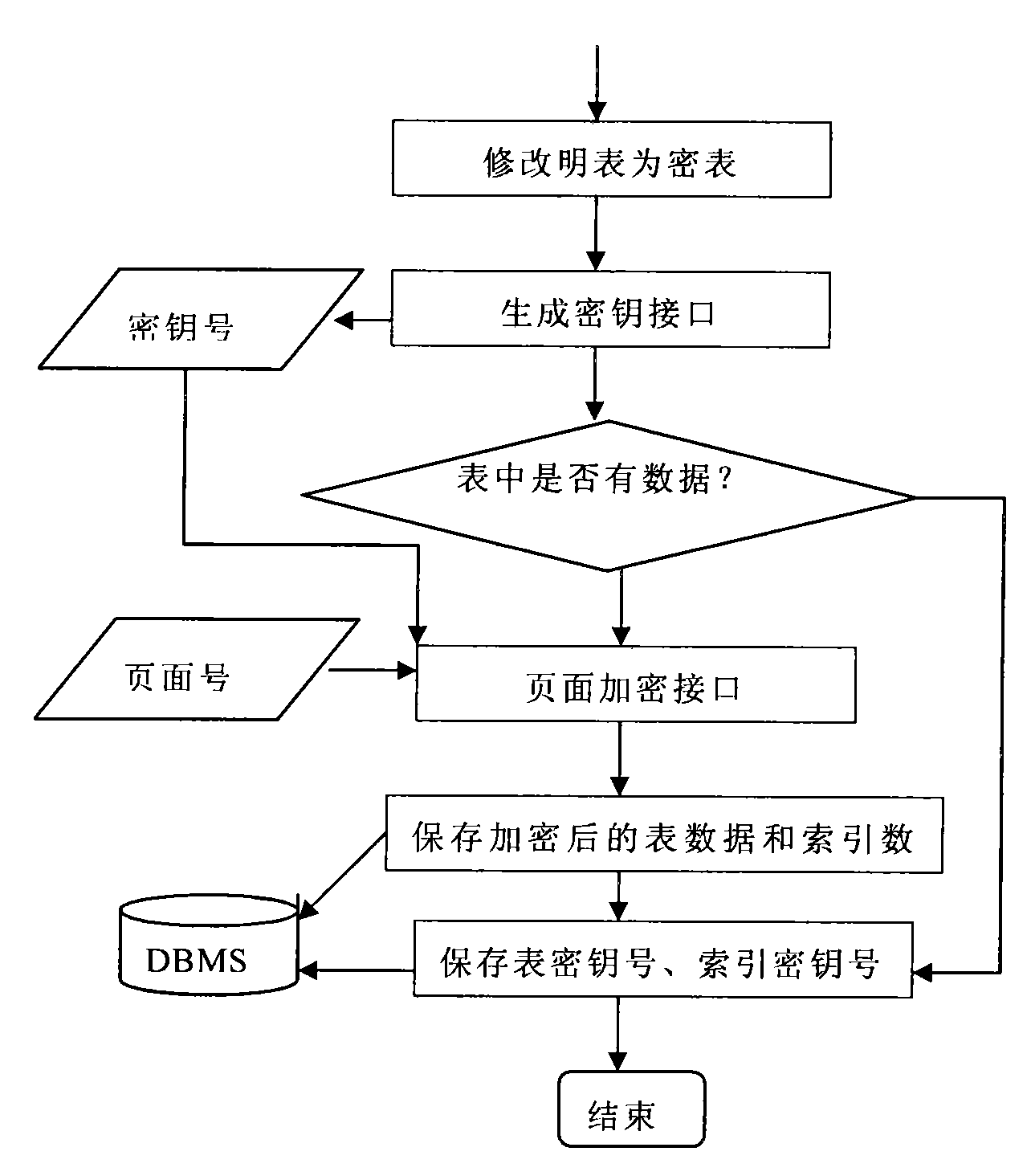
Database management system kernel oriented data encryption/decryption system and method thereof
InactiveCN101587479AReduce the burden onNot easy to be stolenSpecial data processing applicationsData operationsClient-side
The invention discloses a database management system kernel oriented data encryption / decryption system and a concrete method for performing encryption / decryption processing on data in a database by utilizing the same. The data encryption / decryption system comprises user request interface units which are distributed at clients and an encryption definition unit, an inquiry processing units, a data operation unit, a key management unit, a data decryption unit, a data encryption unit and a key database which are distributed at a server end. The system and the method realize the storage and the encryption of data in a database management system kernel. When the retrieval with a key is performed on the data in the database, the prior optimization strategy of the database can still be used, so the high-performance retrieval with the key can be provided.
Owner:北京人大金仓信息技术股份有限公司
Data encrypting method and device and data decrypting method and device
ActiveCN105760765ARealize multi-dimensional encryptionAvoid crackingEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareOriginal data
The invention relates to the field of data encrypting and decrypting, in particular to a data encrypting method and device and a data decrypting method and device.The data encrypting method comprises the steps that at first, an encryption key and original data are obtained; then, an encryption rule is selected from a preset encryption rule base; the encryption key is adopted for encrypting the original data according to the encryption rule to obtain intermediate data; then, identification information corresponding to the encryption rule is obtained; finally, the intermediate data and the identification information are packaged to generate encrypted data.Compared with the prior art, encryption information does not only depend on the carrier key, the encryption rule is selectively used, and the encryption rule is encrypted; meanwhile, in the file transmitting process, only the identification information of the encryption rule exists in the transmission information, and the specific content of the encryption rule does not exist, so that multi-dimensional encryption is achieved, the encryption means is more complex, the key can not be decrypted easily, and encryption safety is higher.
Owner:BEIJING SEEYON INTERNET SOFTWARE CORP
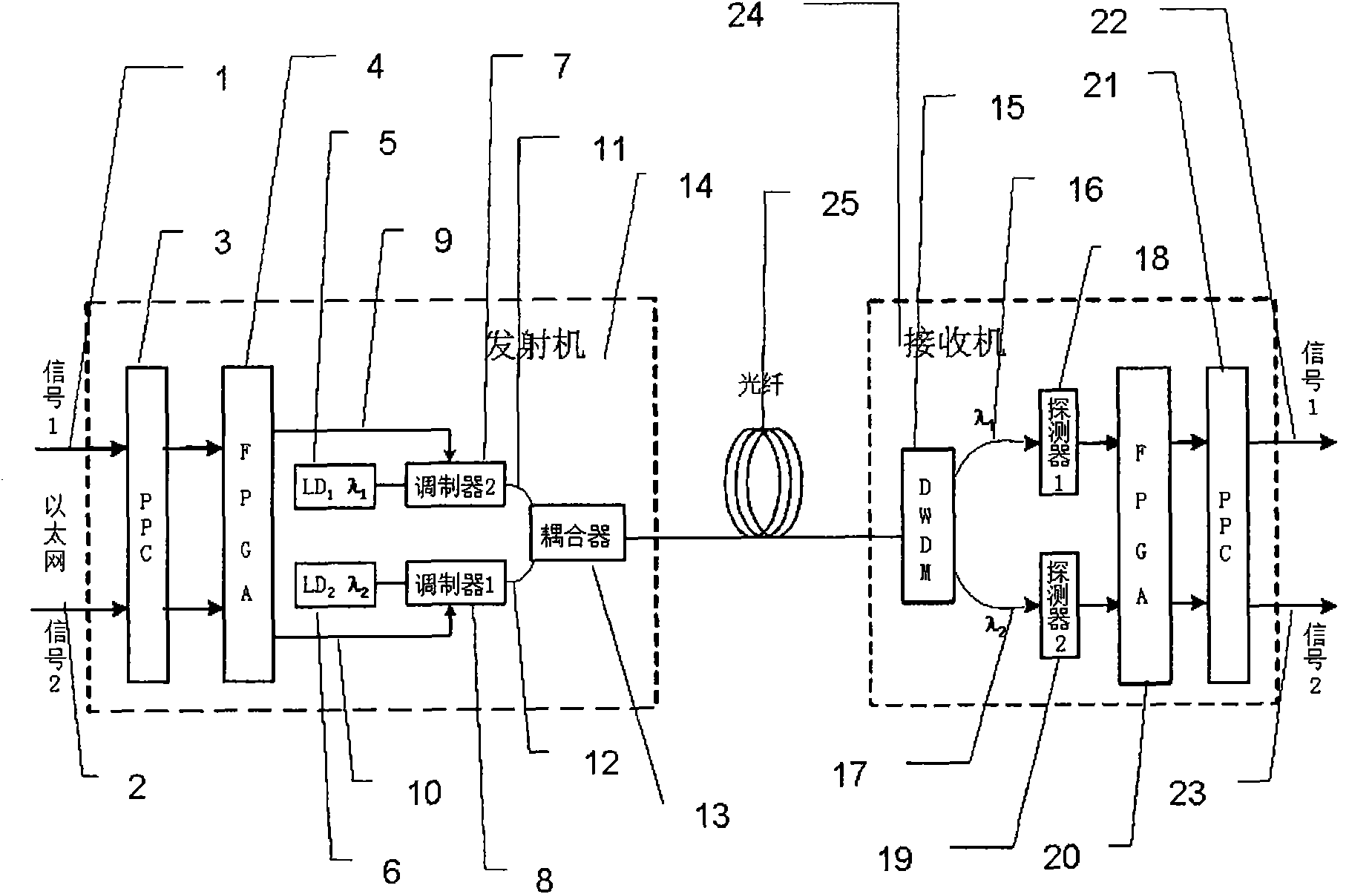
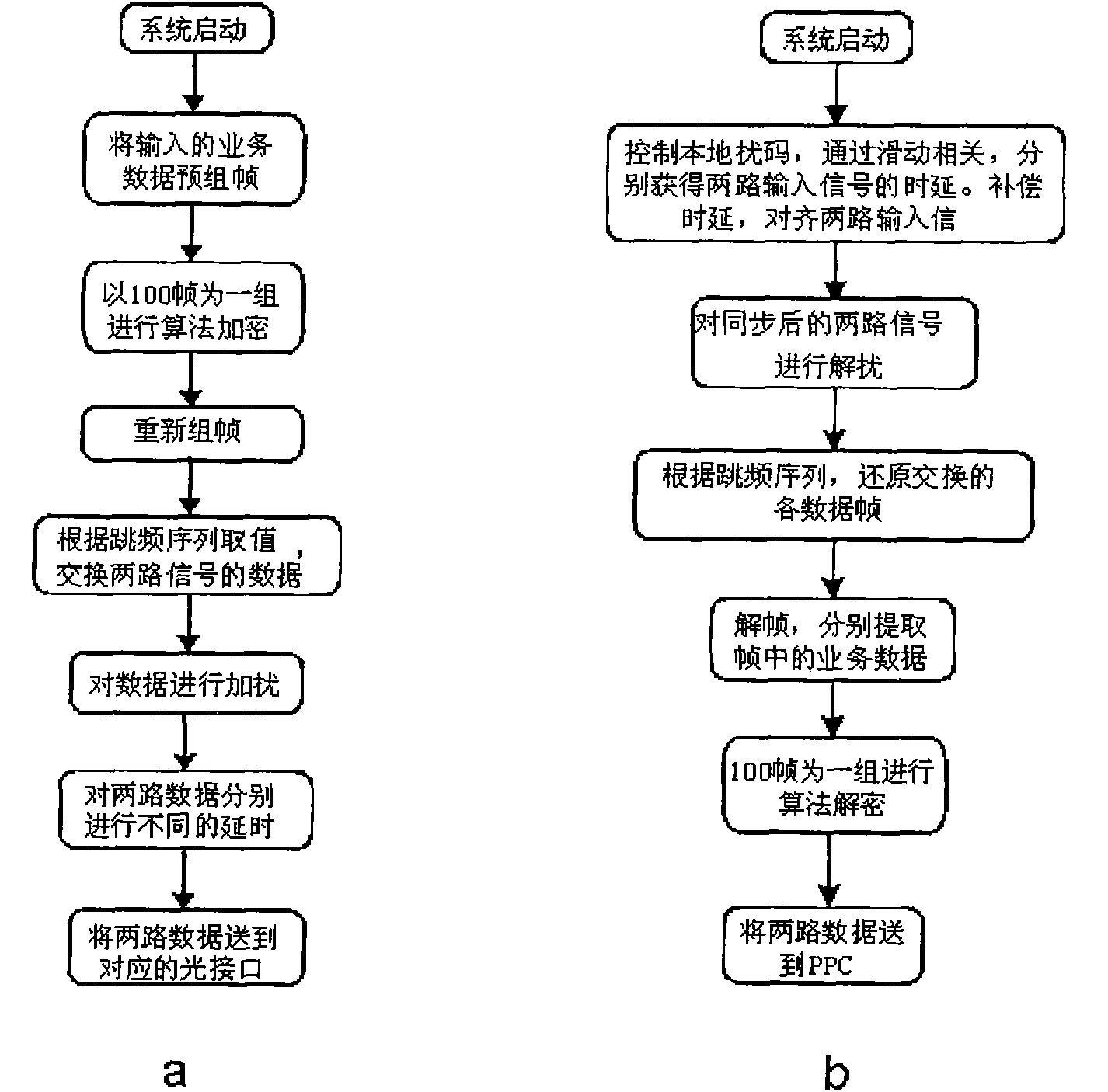
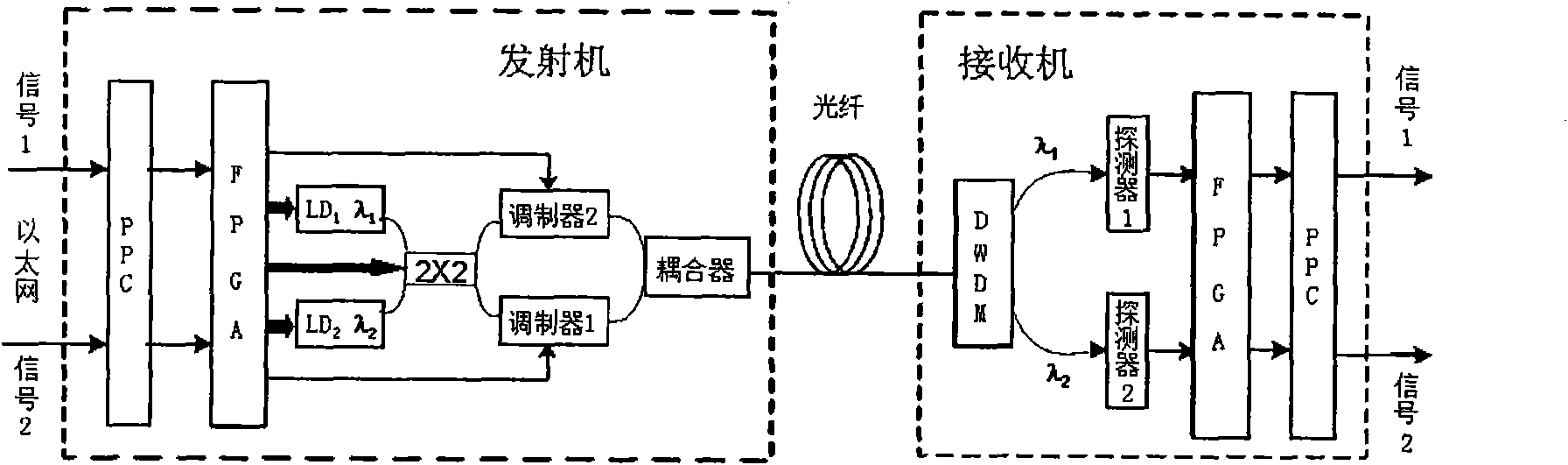
Optical-fiber secret communication device and data encryption method thereof
ActiveCN102055584AContinuous reductionIncrease the difficulty of crackingEncryption apparatus with shift registers/memoriesElectromagnetic transmission optical aspectsOptical fiber couplerField-programmable gate array
The invention discloses an optical-fiber secret communication device and a data encryption method thereof. The device is formed by connecting a transmitter and a receiver through an optical fiber. The transmitter comprises a PPC power PC) processor unit, a field-programmable gate array testing plate, a light-transmitting module, an optical-fiber coupler and a connecting optical fiber; and the receiver comprises a wavelength division multiplexer, a connecting optical fiber, a light detector, a field-programmable gate array testing plate, a PPC processor unit and a signal output interface. At atransmitting end, two paths or multiple paths of input data are retransmitted through a PPC and then sent to the light-transmitting module with two or multiple wavelengths after the encryption processing by an FPGA (Field-Programmable Gate Array) to convert electrical signals into light signals. At a receiving end, two- or multi-wavelength signals respectively enter the light detector to be converted into electrical signals and then retransmitted and output after the encryption by the FPGA by the PPC. By utilizing the invention, the secrecy of transmitted data is improved, and the data decryption difficulty is improved.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
Point-to-point communication method based on near field communication and near field communication device
InactiveCN101656960AEnsure safetyImprove securityWireless network protocolsTransmissionComputer hardwareProtocol Application
The invention discloses a point-to-point communication method based on near field communication (NFC) and a near field communication (NFC) device, wherein the communication method comprises the following steps: a sender sets a safety module; the safety module is applied to a logic link control protocol (LLCP) layer and uses a first key to encrypt a second key and sends the encrypted second key toa receiver to notify the receiver that the second key is used when data are transmitted; the first key is a common key of the receiver and the second key is used for encrypting the transmitted data inthe communication between the sender and the receiver, and the safety module uses a first key to encrypt the data and sends the encrypted data to the receiver. Symmetrical keys are adopted with higher data decryption speed, thereby ensuring point-to-point data transmitting safety and enhancing efficiency. The safety module is applied to the logic link control protocol (LLCP) layer and is not arranged on an application layer for encryption, thereby achieving higher encryption safety.
Owner:ZTE CORP
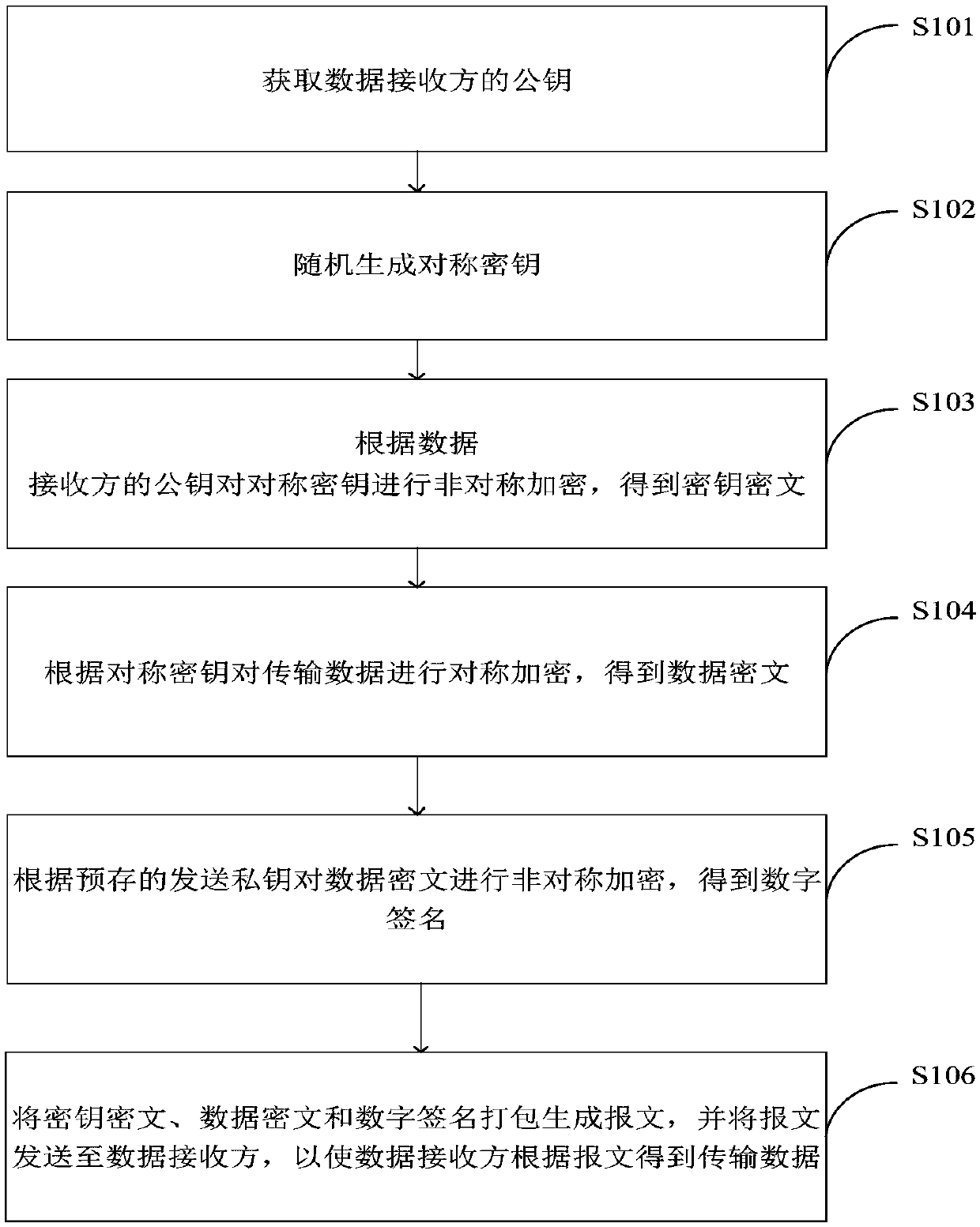
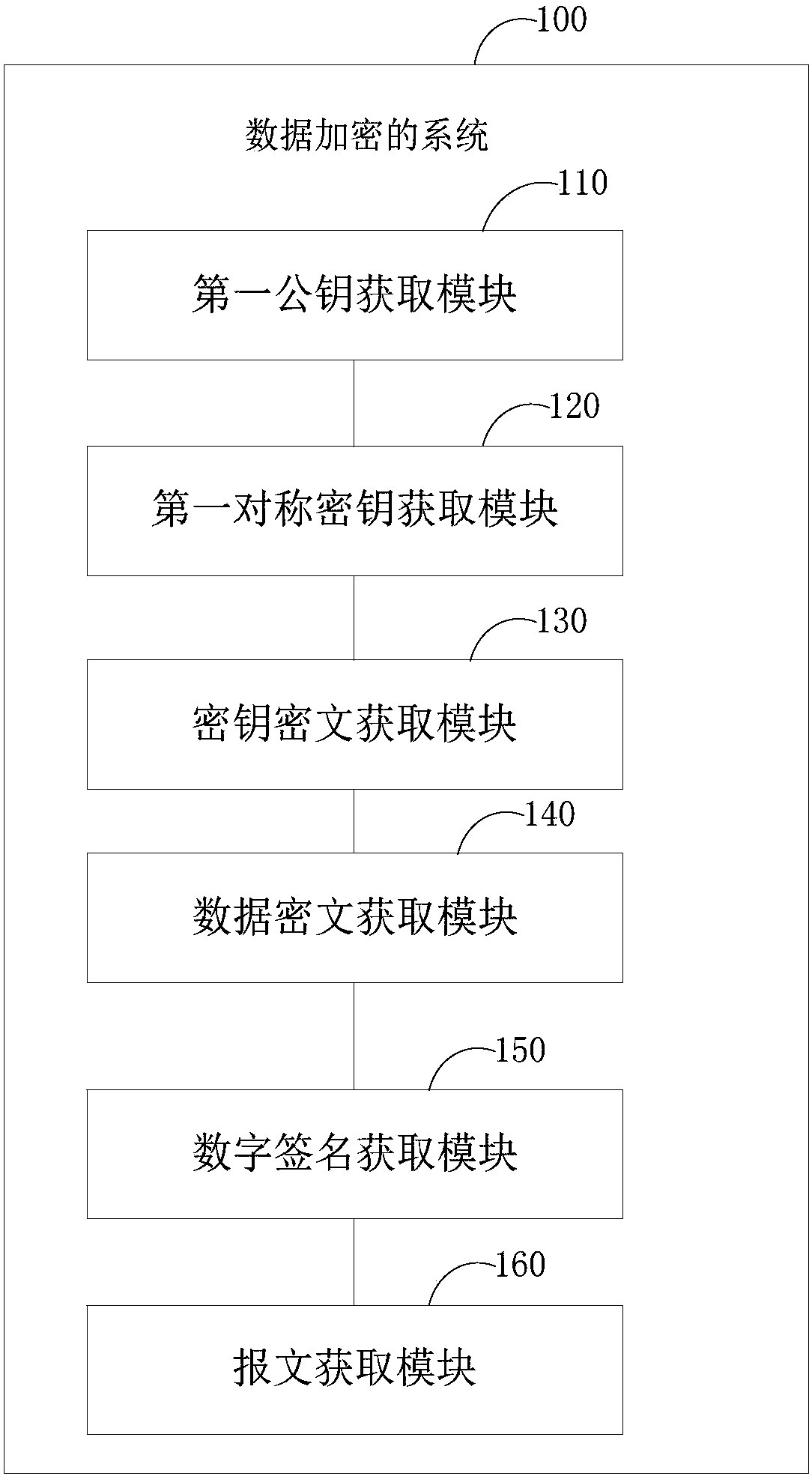
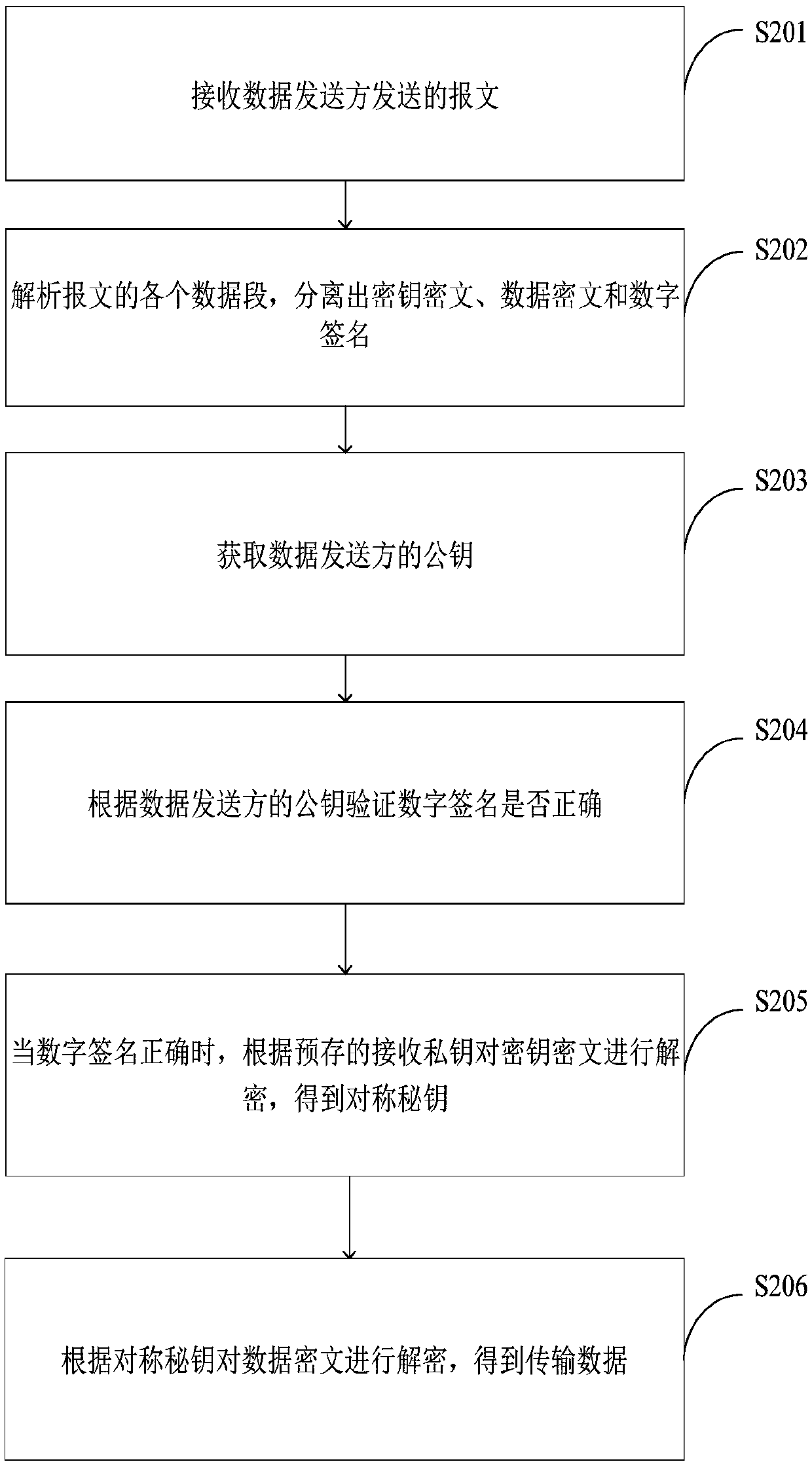
Data encryption method and system, data decryption method and system and terminal equipment
InactiveCN109802825AImprove securityGuaranteed reliabilityKey distribution for secure communicationPublic key for secure communicationCiphertextDigital signature
The method is suitable for the technical field of data encryption. The invention provides a data encryption method and system, data decryption method and system and terminal equipment. During data encryption, the data receiver obtains a public key of the data receiver to achieve RANDOM GENERATION OF SYMMETRIC KEYS, the symmetric key is encrypted according to the public key of the data receiver sothat Key ciphertext is acquired. the transmission data is encrypted according to the symmetric key to obtain a data ciphertext, the data ciphertext is encrypted according to a pre-stored sending private key to obtain a digital signature, the key ciphertext is packaged the data ciphertext and the digital signature to generate a message, the message is snet to a data receiver, and when the data is decrypted, the transmission data is acquired by the data receiver according to the message. Therefore, the problem that when the encrypted data sent by the data sender is maliciously attacked by the man-in-the-middle, the sender and the receiver of the data cannot know whether the encrypted data is attacked or not, so that the security of data transmission is low is effectively solved.
Owner:金证财富南京科技有限公司
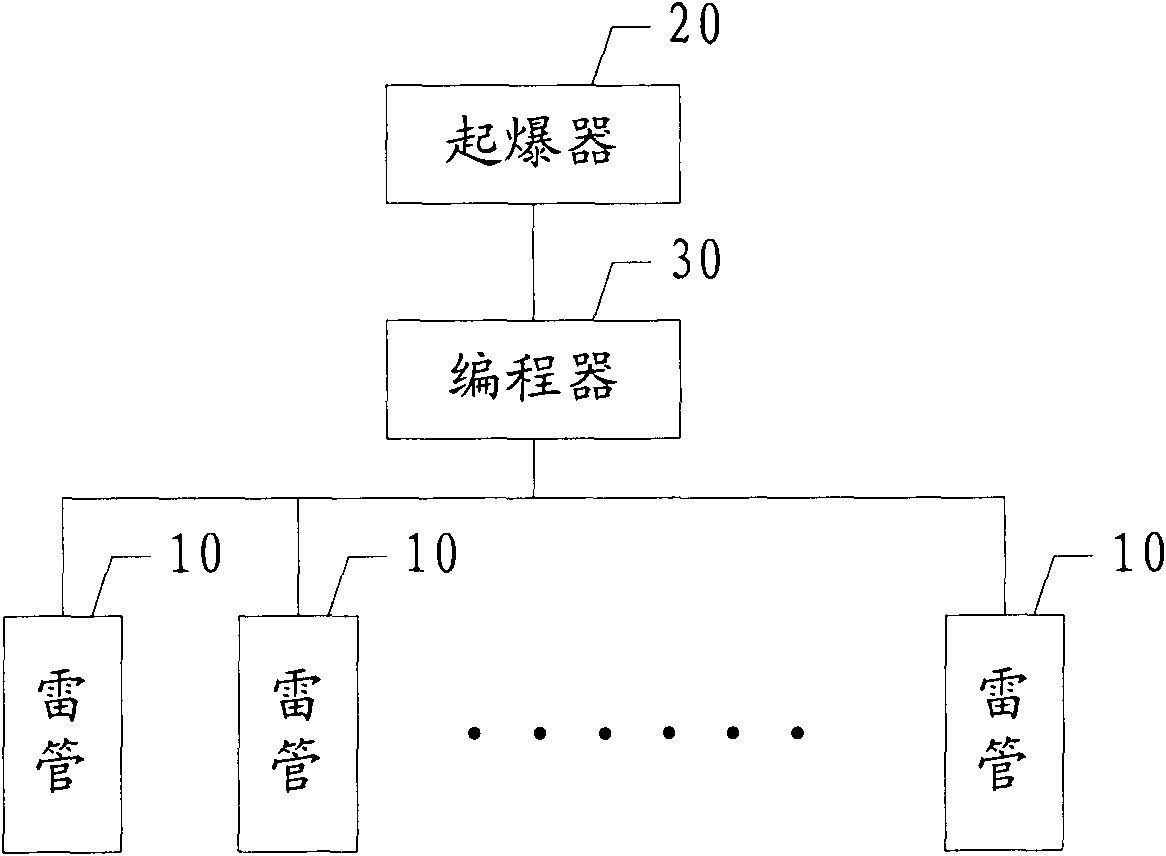
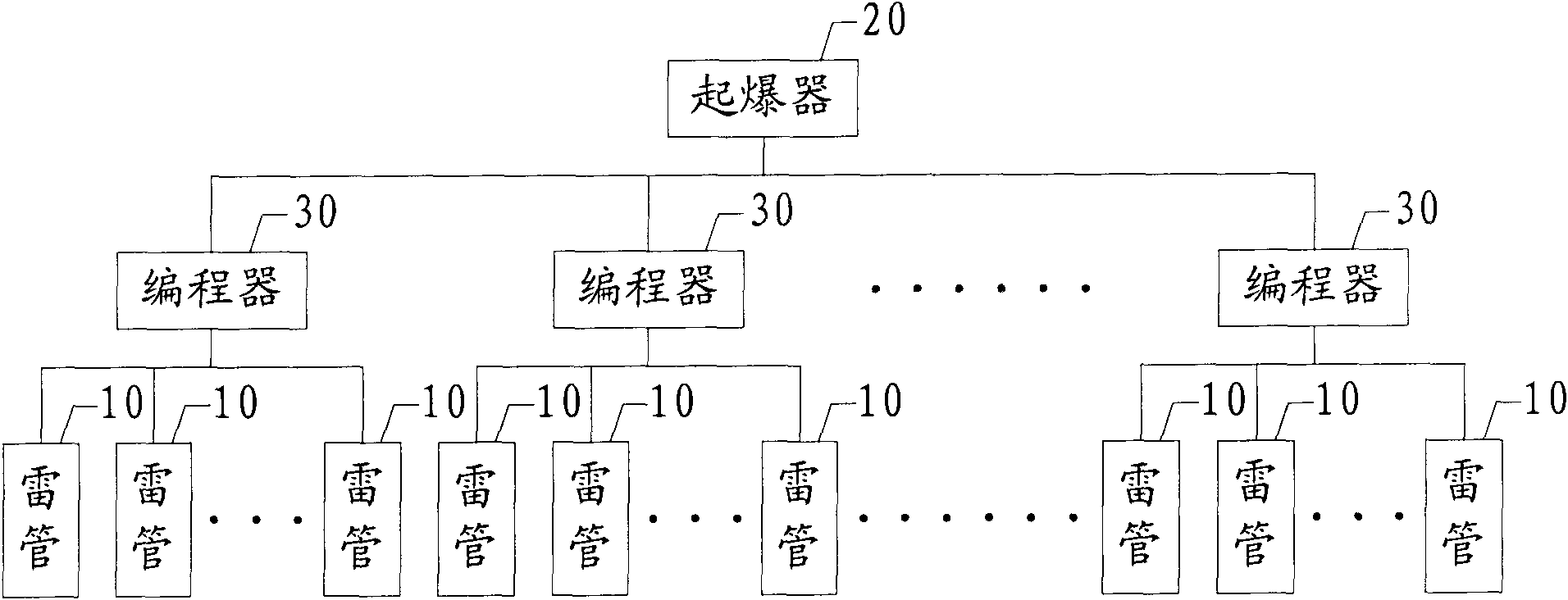
Digital electronic detonator blasting system and control method thereof
ActiveCN101666598AVerification GuaranteePrevent disturbance of social orderBlastingAmmunition fuzesDetonatorSystem testing
The invention provides a digital electronic detonator blasting system and a control method thereof; the digital electronic detonator blasting system comprises an initiator, one or a plurality of programming units, and one or a plurality of digital electronic detonators; the initiator, the programming units and the digital electronic detonators are connected in a double bus way. The control methodof the digital electronic detonator blasting system comprises the following steps: self-detection of the initiator, authentication of operating personnel of the initiator, blasting design, authentication of the initiator, obtaining license information o f the initiator, data decryption of initiation, validity authentication of time and position information, self-detection of the programming unit,authentication of operating personnel of the programming unit, blasting design task decomposition, detonator charging, detection of working state of the detonator, programming, system test, initiatingcommand authentication, synchronous test, initiating authorization verification, broadcasting initiating command and data backup.
Owner:RONGGUI SICHUANG BEIJING TECH
Data encryption method and device, data decryption method and device and solid state disk
InactiveCN101582109AImprove securityDigital data protectionDigital storageConfidentialitySolid-state drive
The embodiment of the invention provides a data encryption method and a device thereof, a data decryption method and a device thereof, and a solid state disk, wherein the data encryption method comprises the steps of: receiving data to be encrypted and obtaining the position information of the data to be encrypted; receiving an encryption key decrypted by a controller and obtaining a session key used for encrypting the data to be encrypted according to the encryption key after decryption and the position information; and encrypting the data to be encrypted according to the session key. By carrying out predetermined operation on the KEY and the position information of data storage in the encryption process to generate the corresponding session key, the aim of using the corresponding session key to encrypt the data entering and going out of the address can be realized; as each data storage position corresponds to a unique session key, the attacker cannot reversely reckon the KEY even obtaining a certain session key through decryption, thus guaranteeing the confidentiality of data in SSD and improving the data safety.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com