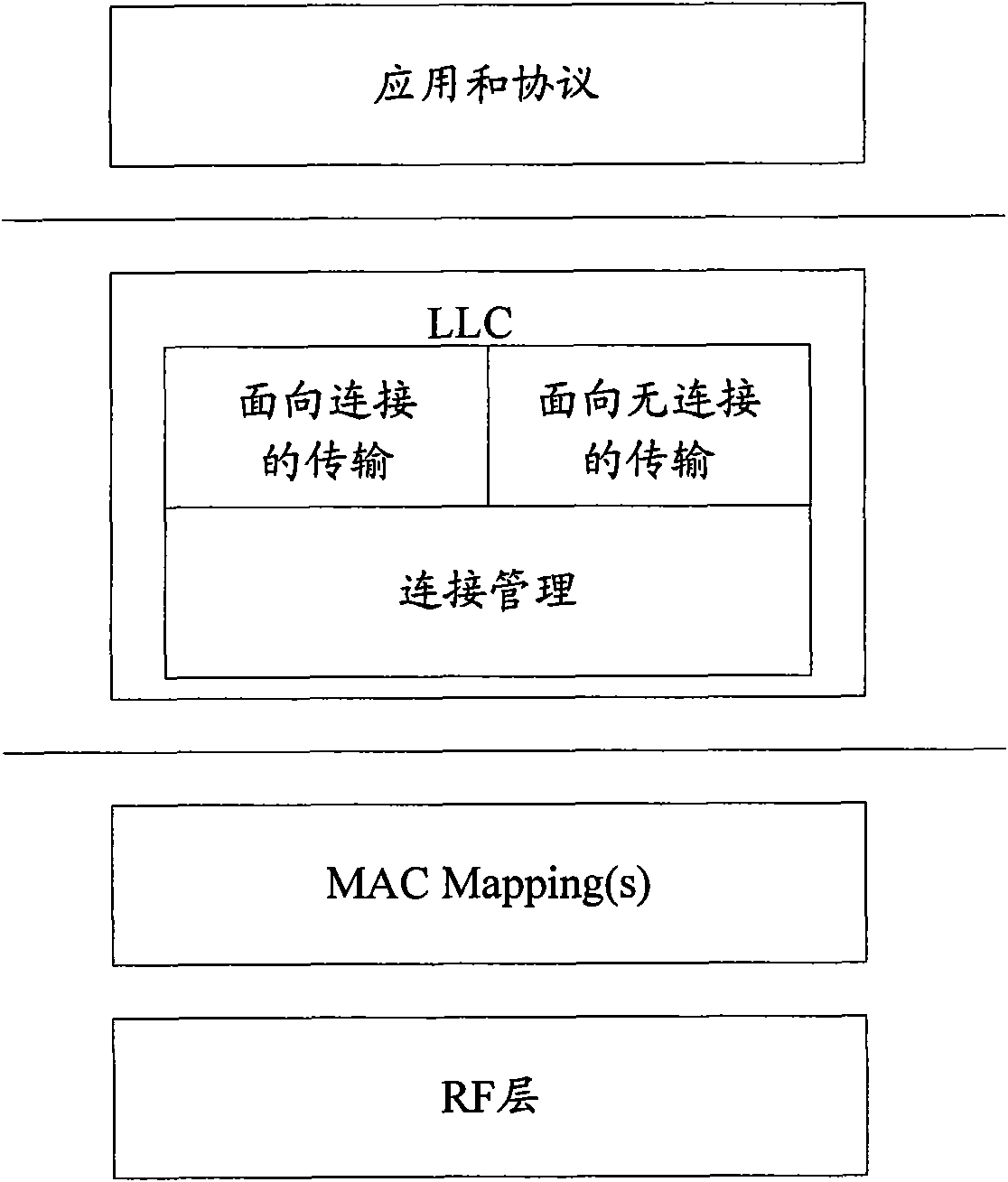
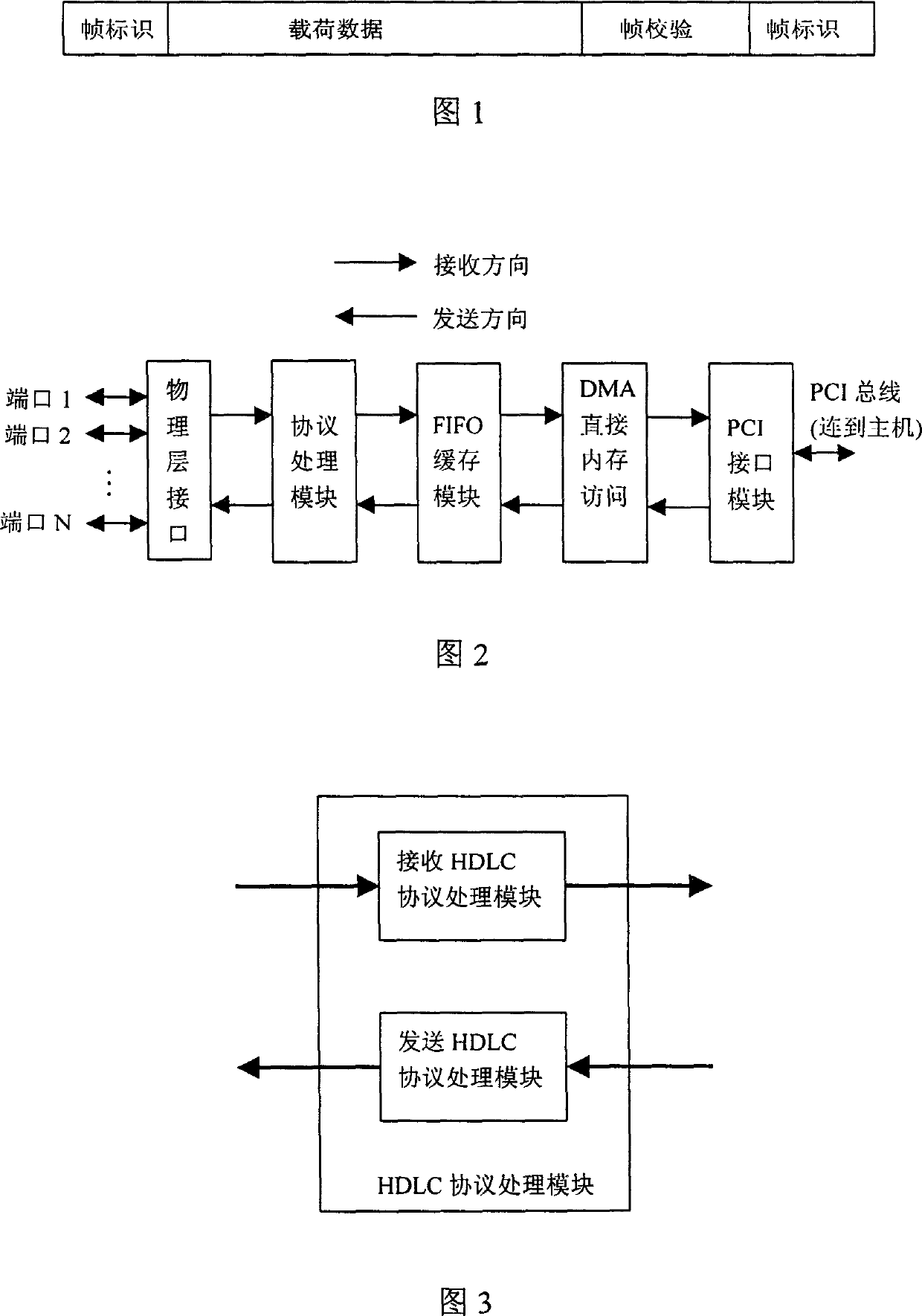
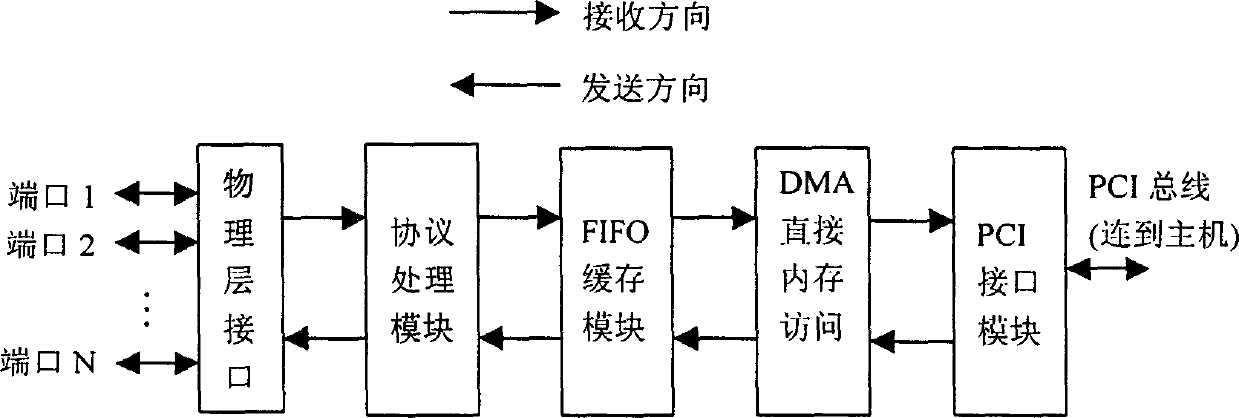
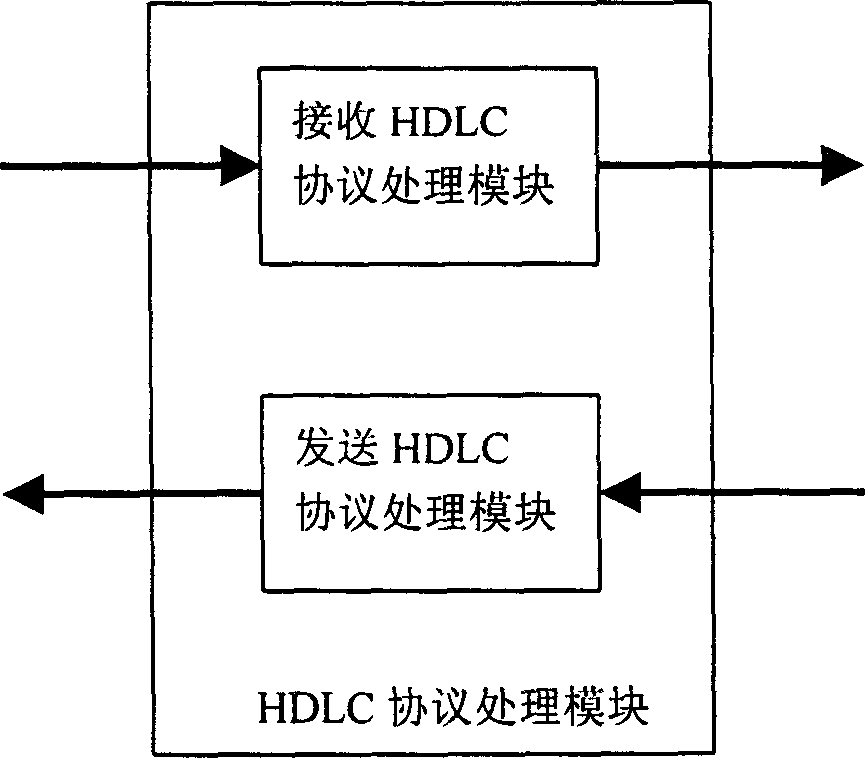
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
161 results about "Link Control Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
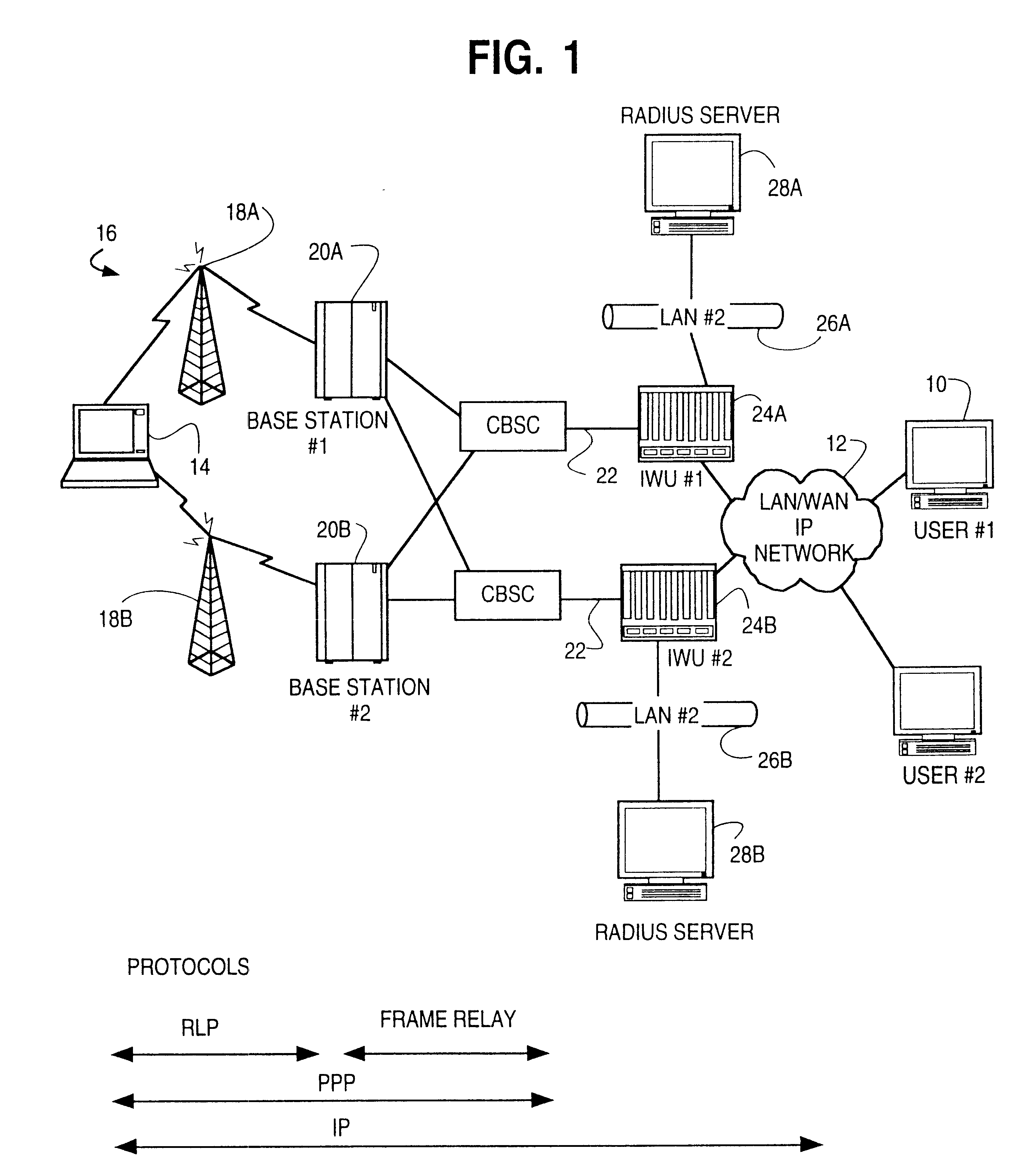
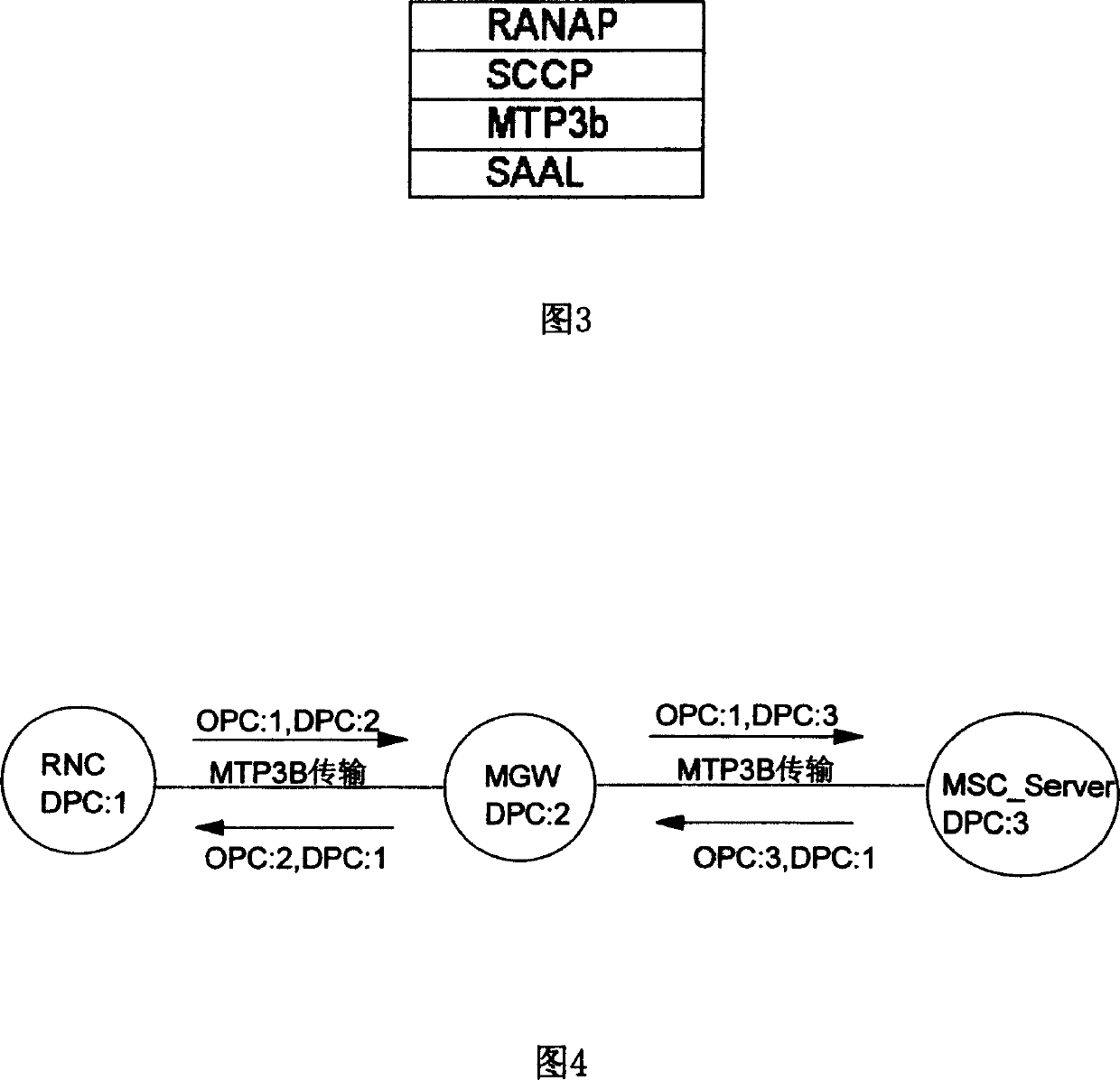
In computer networking, the Link Control Protocol (LCP) forms part of the Point-to-Point Protocol (PPP), within the family of Internet protocols. In setting up PPP communications, both the sending and receiving devices send out LCP packets to determine the standards of the ensuing data transmission.
Data link control proctocol for 3G wireless system
InactiveUS6542490B1Error prevention/detection by using return channelElectronic circuit testingTelecommunications linkDual mode
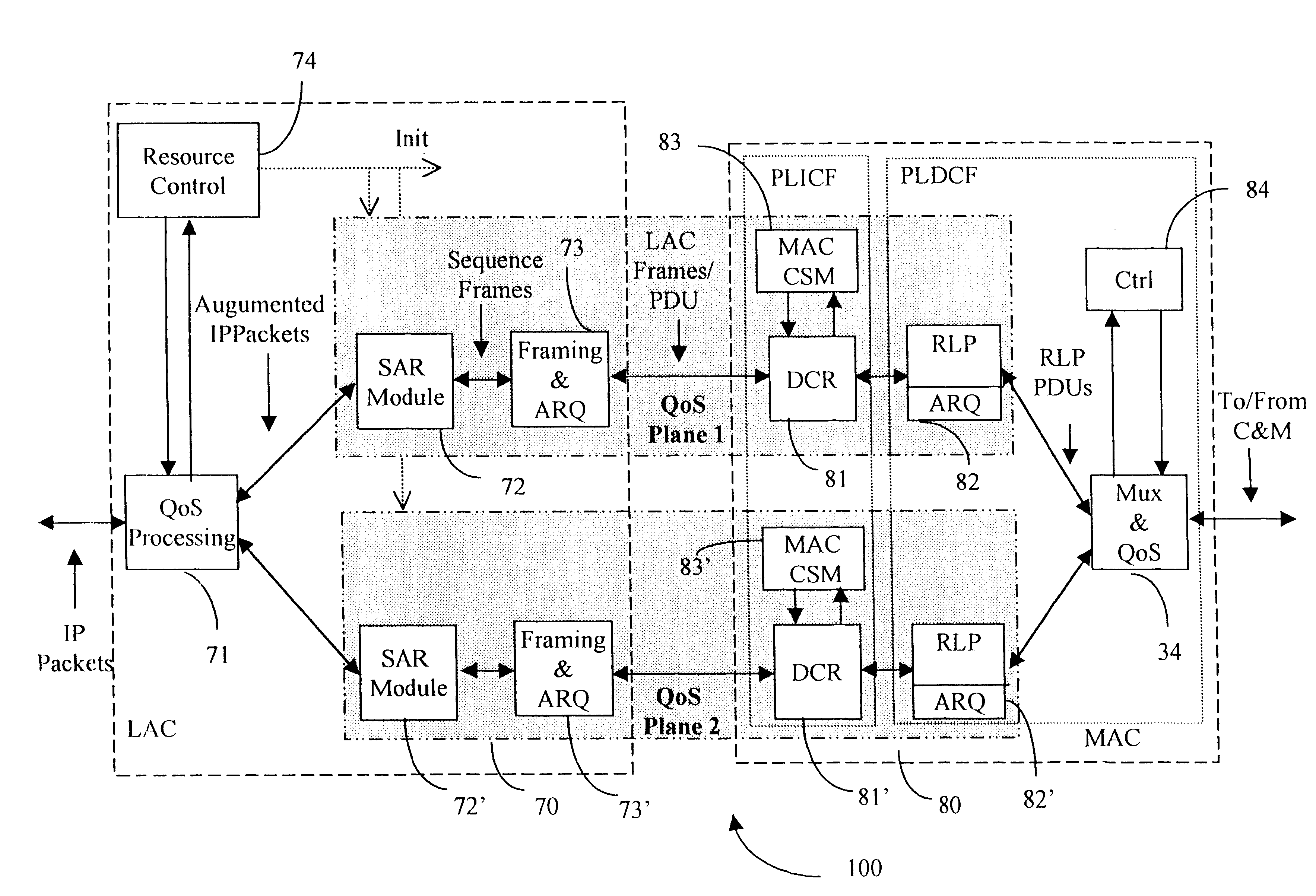
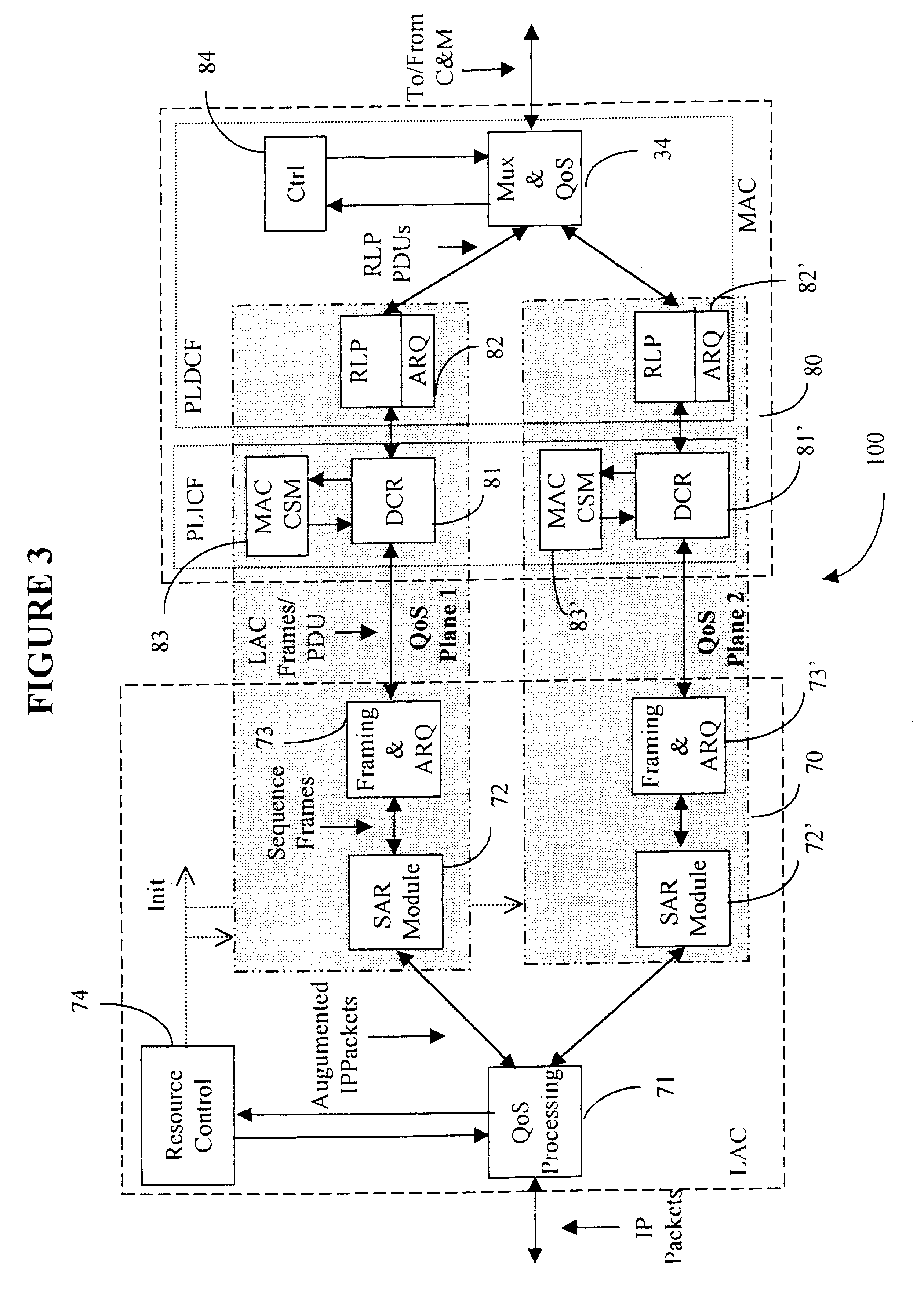
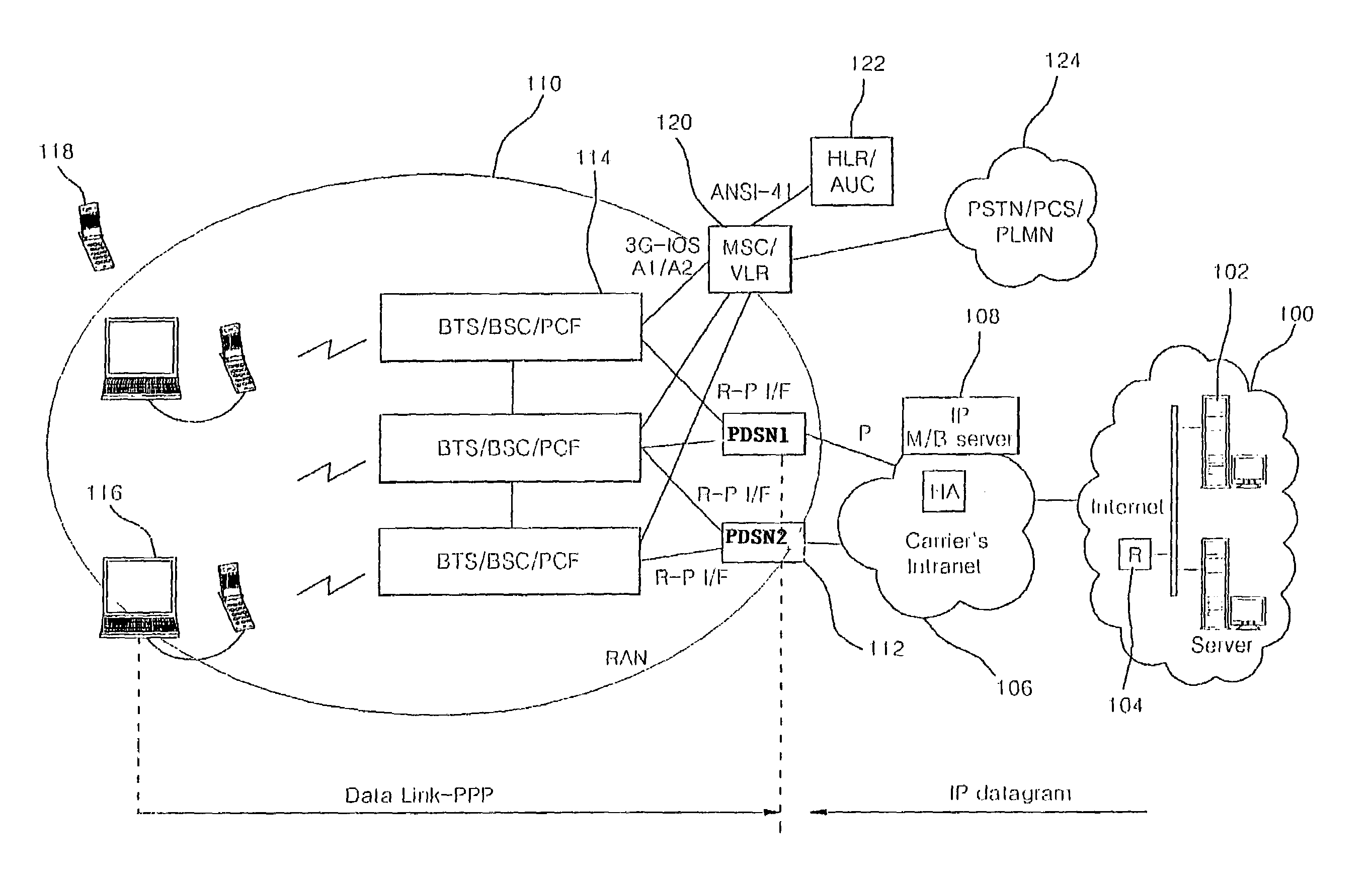
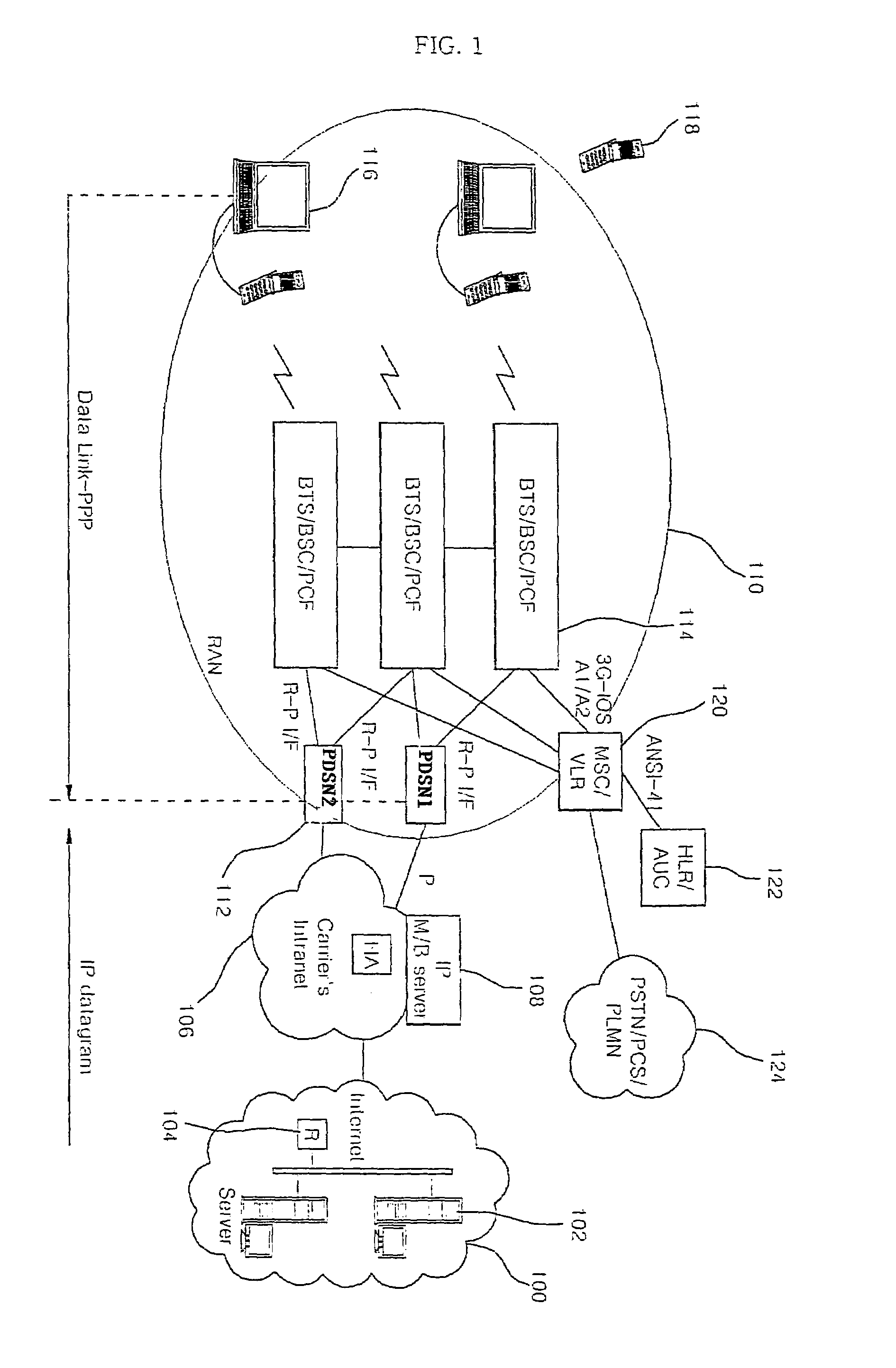
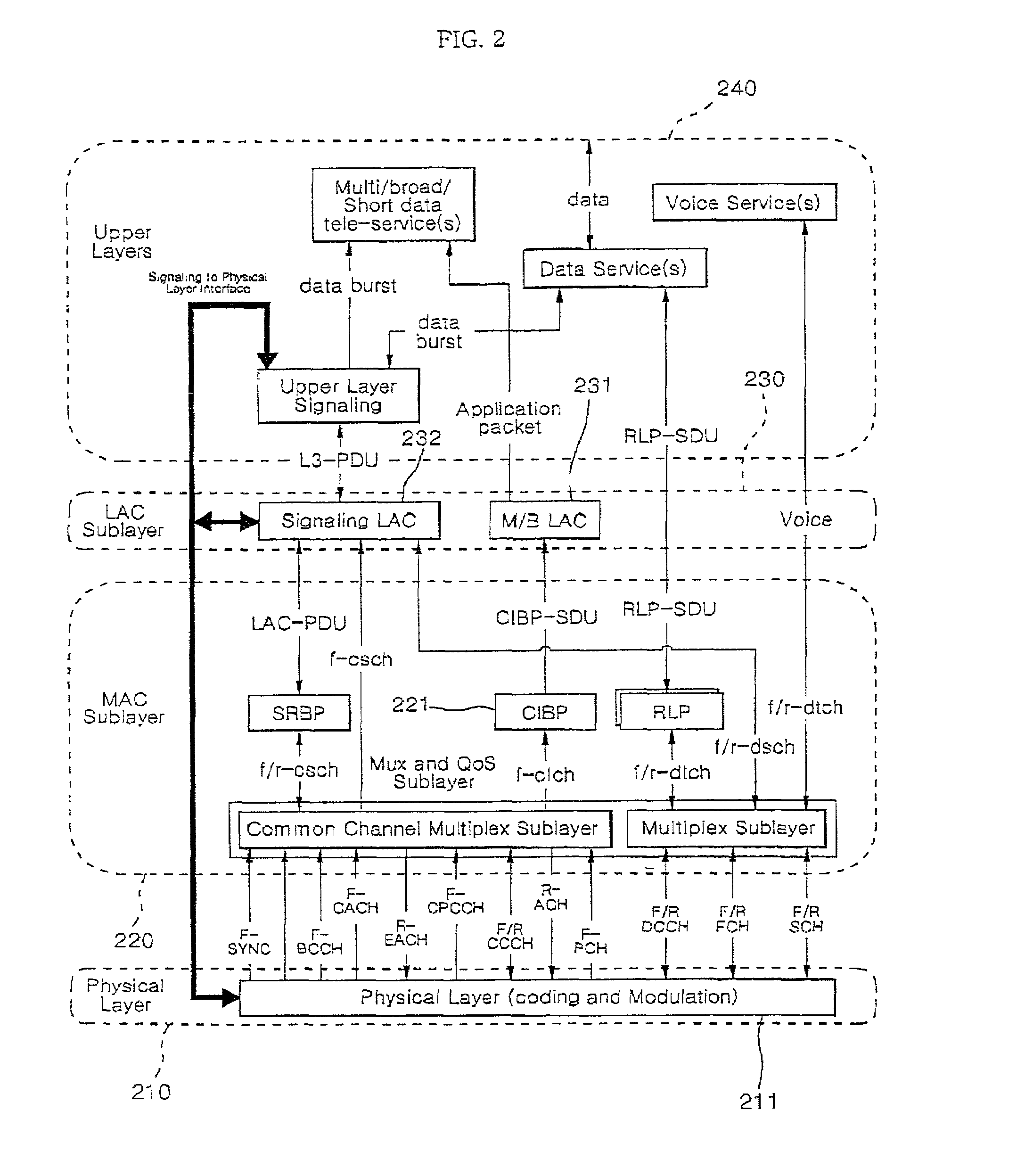
A Data Link Control protocol for 3G wireless communication system for direct support for network layer protocols, e.g. the Internet Protocol (IP), is provided. The Link Layer disclosed comprises a Link Access Control (LAC) sublayer and a Medium Access Control (MAC) sublayer. At a transmit end of the wireless system, a plurality of Quality of Service (QoS) data planes are created to directly support the IP QoS. Each QoS data plane is optimized to handle QoS requirements for a corresponding Class of Service (CoS). Data packets received at the LAC sublayer are directed to a QoS data plane according to the particular QoS information they contain and processed according to the particular QoS requirement to generate variable size LAC frames. The variable size LAC frames are transmitted to the MAC sublayer for generating radio link protocol data units (RLP PDUs) to be transmitted to a receiving end. A new level of error correction is provided at the LAC sublayer as the size of the LAC PDUs can be dynamically adjusted in response to the conditions of the communication link. A dual mode ARQ is provided at the MAC sublayer to improve the quality of the air transmission for bursty as well as non-bursty traffic conditions.
Owner:ALCATEL LUCENT SAS
Instant activation of point-to point protocol (PPP) connection using existing PPP state
InactiveUS6628671B1Time-division multiplexWide area networksNetwork access serverPoint-to-Point Protocol
A network access server providing remote access to an IP network for a remote client initiates a PPP connection for a remote client quickly, and without requiring re-negotiation of Link Control Protocols and Network Control Protocols. The network access server has a PPP session with the remote client go dormant, for example when the user is a wireless user and goes out of range of a radio tower and associated base station. The network access server does not get rid of the PPP state for the dormant session, but rather switches that PPP state to a new session, such as when the client moves into range of a different radio tower and associated base station and initiates a new active session on the interface to the wireless network. The switching of PPP states may be within a single network access server, or from one network access server to another. This "context switching" of the active PPP session allows the mobile user to seamlessly move about the wireless network without having to re-negotiate Link Control Protocols and Network Control Protocols every time they move out of range of one radio tower and into range of another radio tower.
Owner:UTSTARCOM INC
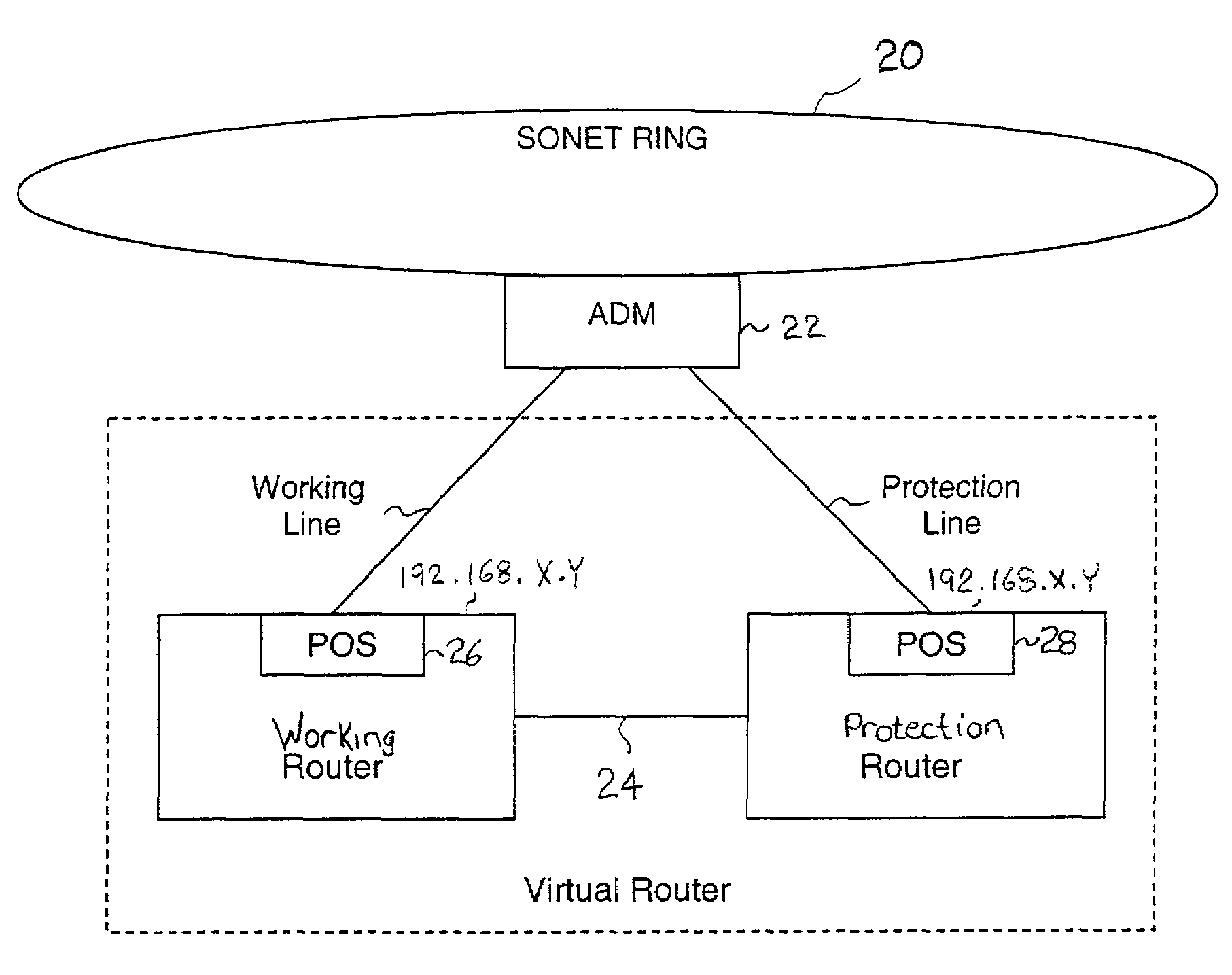
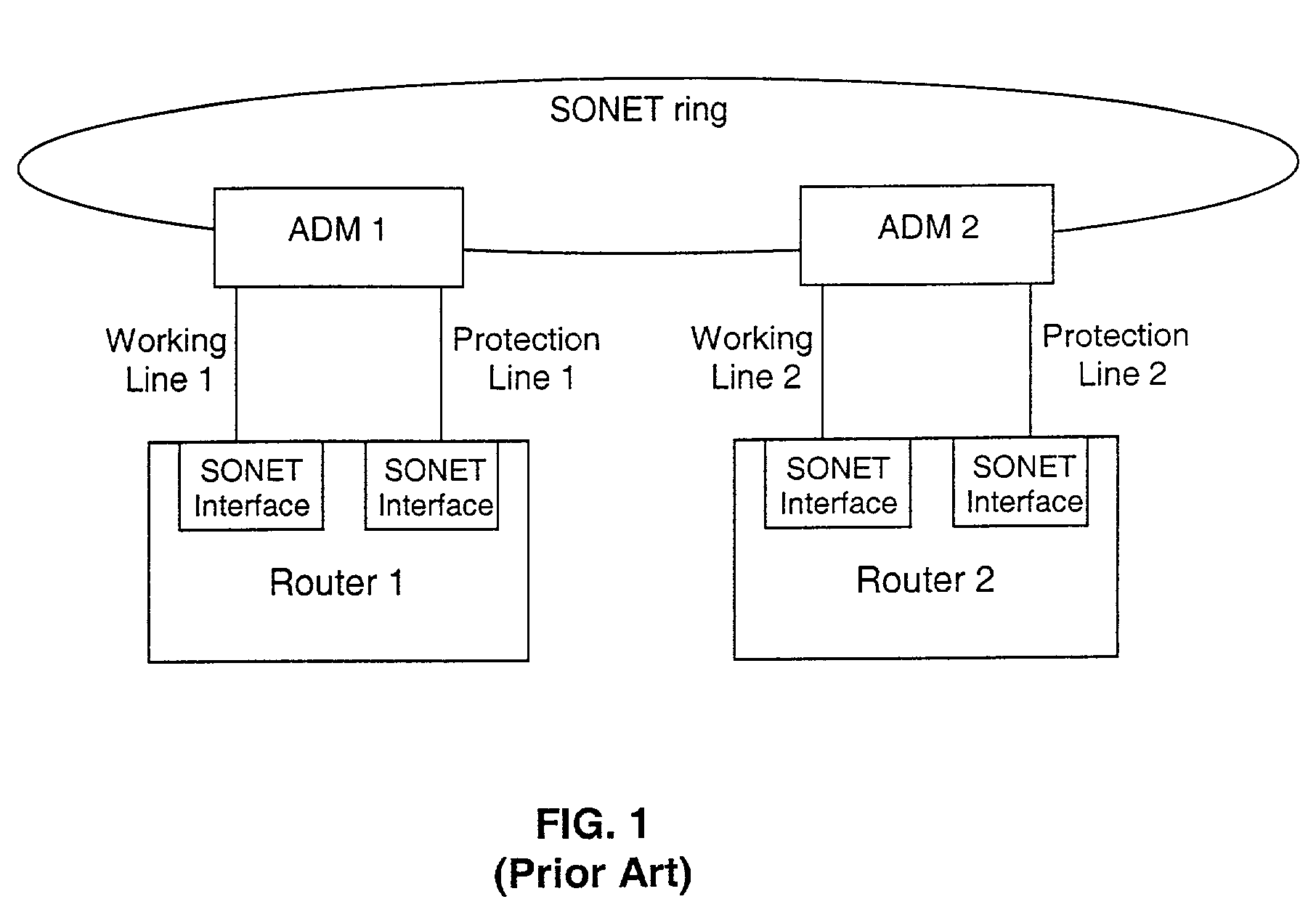
Fault tolerant automatic protection switching for distributed routers
InactiveUS6956816B1Providing fault toleranceError preventionTransmission systemsPoint-to-Point ProtocolAutomatic protection switching
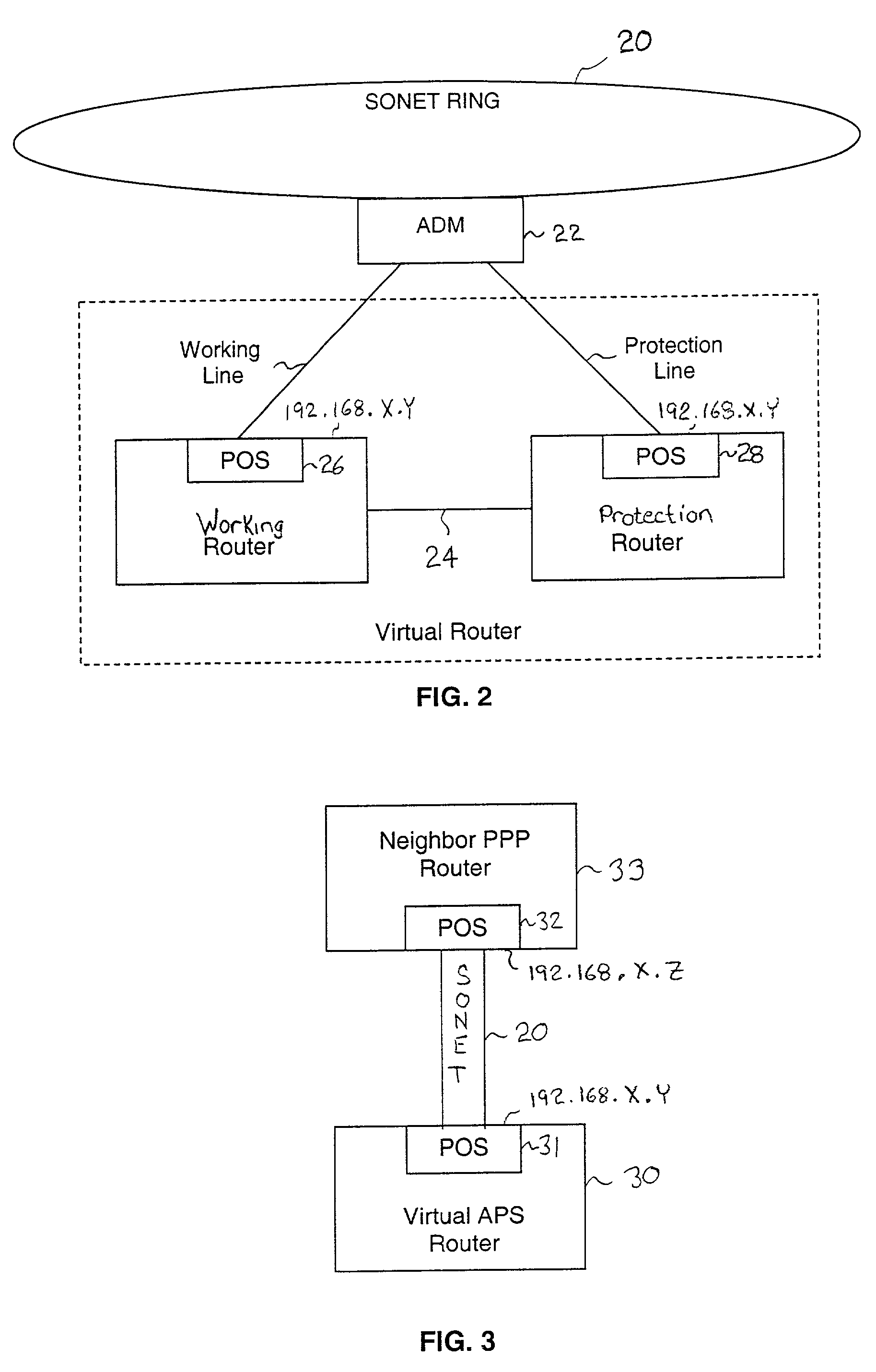
A working router is coupled to a SONET add-drop multiplexor (ADM) through a working line and a protection router is coupled to the ADM through a protection line. The routers are coupled to each other by a separate side-band connection and comprise a virtual router from the perspective of the neighboring router, which communicates with the virtual router over the SONET network using the Point-to-Point Protocol (PPP). The protection router transmits a heartbeat message to the working router over the side-band connection. If the protection router does not receive a response thereto, it initiates a line switch within the add-drop multiplexor. Once the line switch is complete, the protection router exchanges datagrams with the neighboring router, via the ADM and SONET ring to which the ADM is coupled. The protection router establishes a PPP connection between itself and the neighboring router device coupled to the SONET ring, utilizing the Link Control Protocol (LCP). The protection router includes a predetermined identifier value that identifies the originator of the request, in the LCP Identifier field of LCP request datagrams. The neighboring router includes the Identifier value received in a request datagram in the corresponding response datagram transmitted over the SONET ring to the ADM. Because datagrams received by the ADM from the SONET link are transmitted over both the working and the protect lines, the working router receives the same response as the protection router. Thus, by examining the identifier field, and recognizing the identifier value as that assigned to the protection router, the working router determines that the line switch to the protection router has occurred.
Owner:EXTREME NETWORKS INC
System and method for transmitting data between service gateway and relay terminals
InactiveCN102098725AReduce consumptionAvoid bringing inNetwork traffic/resource managementWireless network protocolsRadio Link ControlService gateway
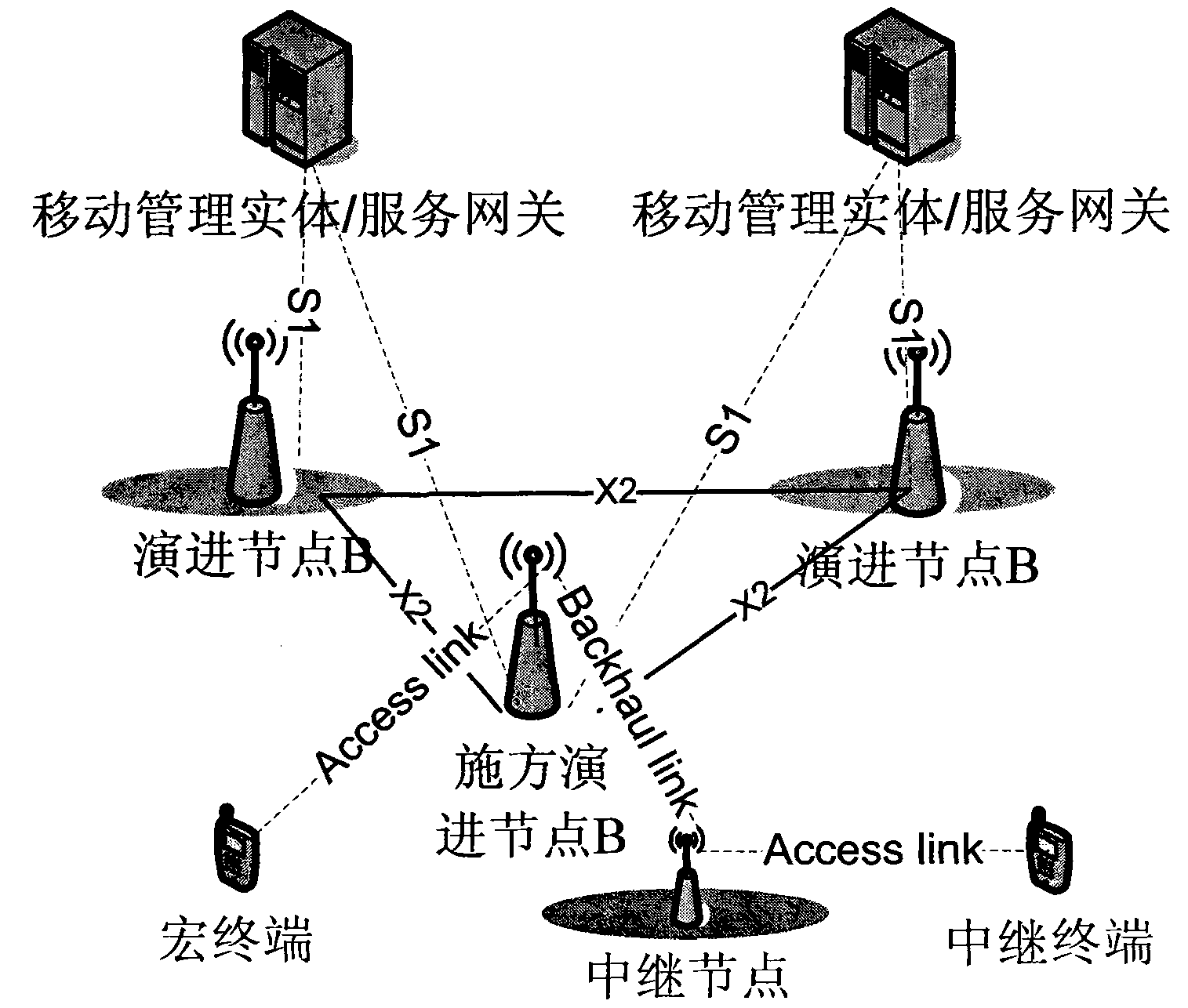
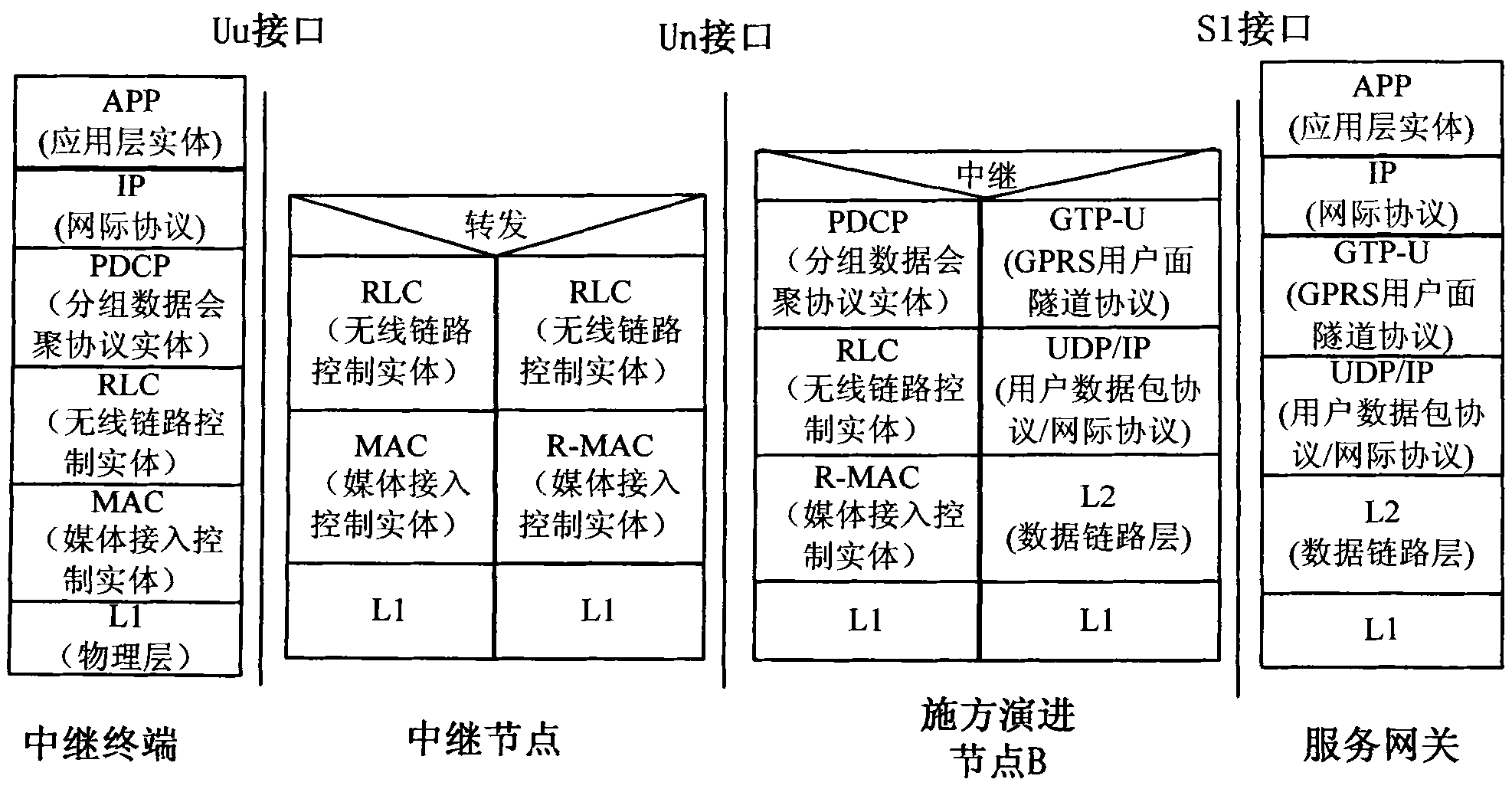
The invention provides a system and method for transmitting data between a service gateway and relay terminals. The method comprises the steps of: establishing evolution global terrestrial radio access bearer connection between the relay terminals and the service gateway; forming extracted packet data convergence protocol service data units (PDCP SDUs) into packet data convergence protocol protocol data units (PDCP PDUs) and multiplexing the PDCP PDUs to form radio link control protocol data units (RLC PDUs) after an evolution node B of an application side receives data sent by the service gateway; multiplexing the RLC PDU of each relay terminal to form a relay medium access control protocol data unit (R-MAC PDU) and then sending the R-MAC PDU to a relay node; extracting each RLC PDU from the R-MAC PDU by the relay node; and multiplexing all the RLC PDUs of the same relay terminal to form a media access control protocol data unit (MAC PDU) and then sending the MAC PDU to the corresponding relay terminal. By adopting the invention, the aims of introducing the relay node, reducing the cost and improving the efficiency are realized.
Owner:深圳市恒程汇文化科技有限公司
Management method for automatic retransmission request window
ActiveCN101478380AAvoid wastingAvoid injusticeError prevention/detection by using return channelAutomatic repeat requestLink Control Protocol
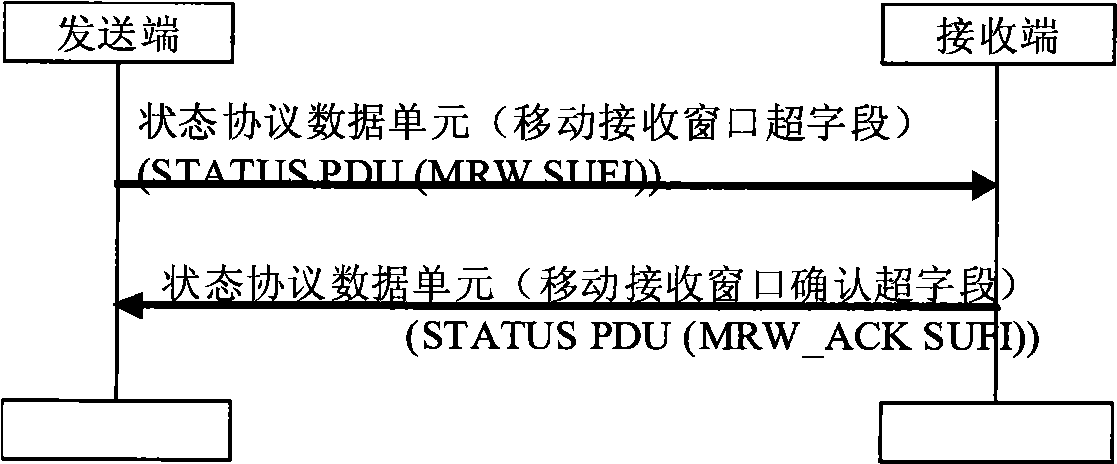
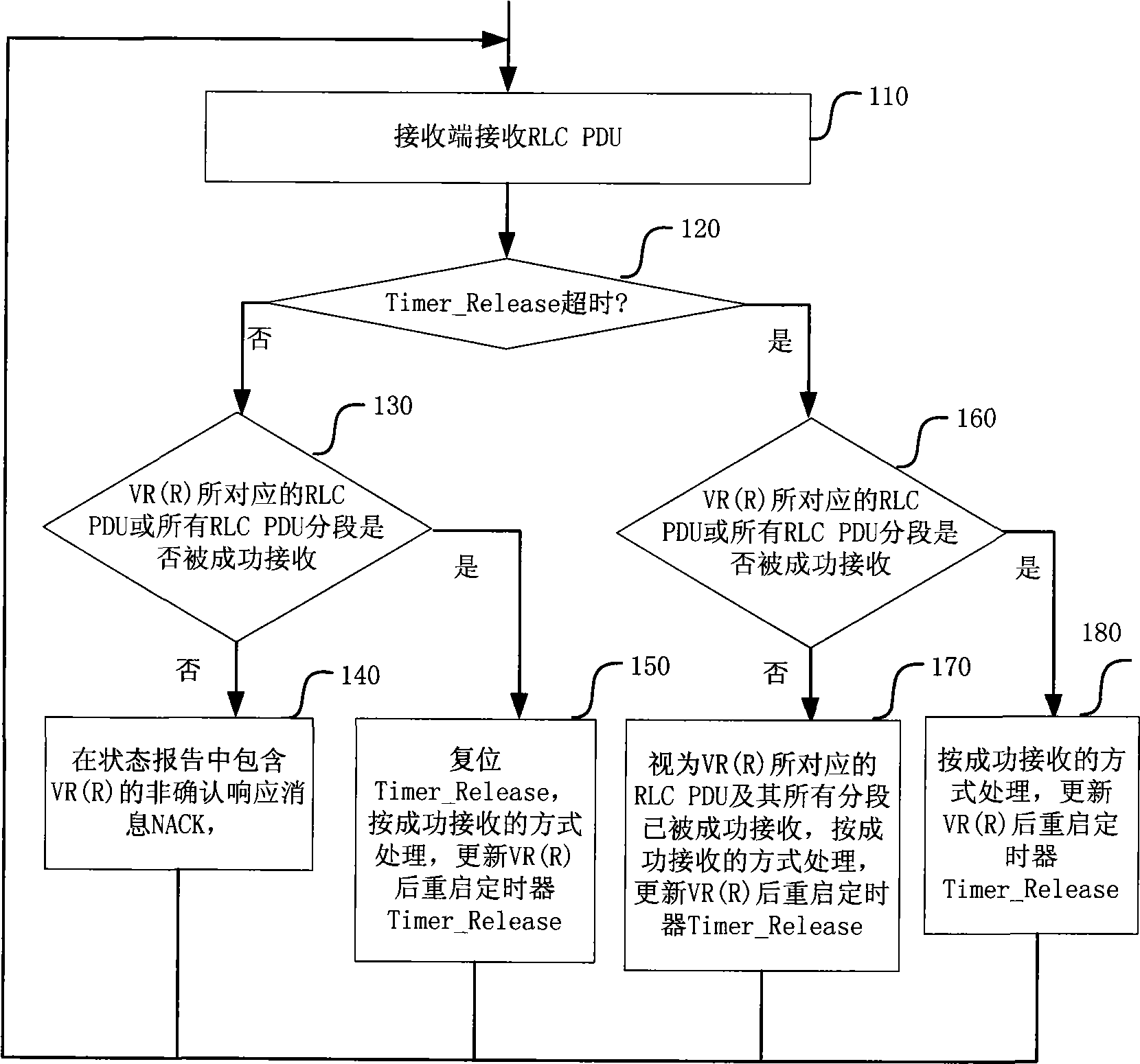
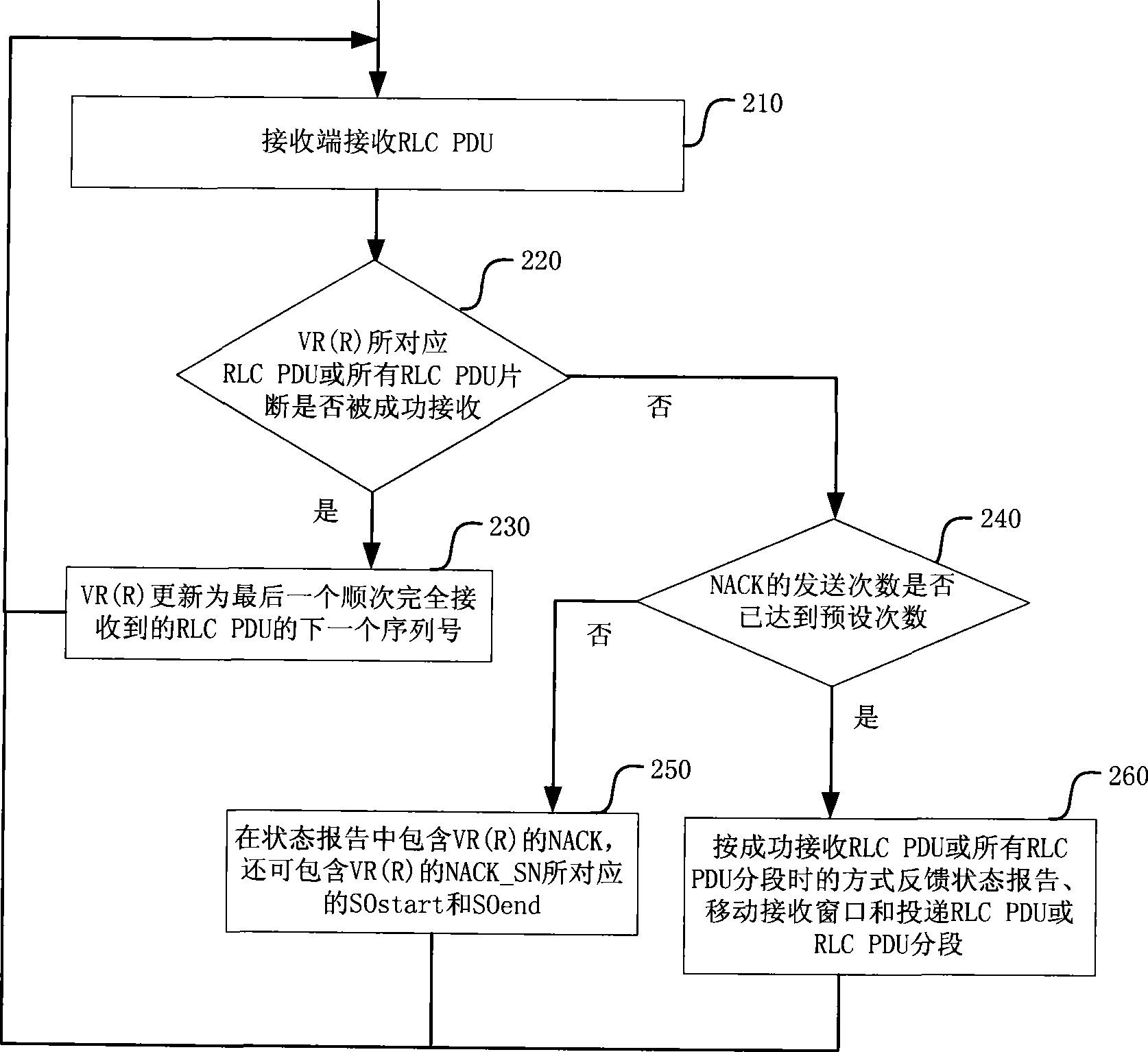
The invention discloses an automatic repeat request (ARQ) window management method which is characterized in that receiving terminals of layer entity are controlled by use of wireless links of confirmation mode; and when the sections of the wireless link control protocol data cell corresponding to the lower boundary of the currently-received window or all the wireless link control protocol data cells are not received successfully and the preset conditions are met, the receiving window are triggered to move continuously. The ARQ window management method overcomes the problems of wireless resource waste and unfairness when the service data unit (SDU) is discarded, and avoids the complexity of sending the move receiving window (Send MRW).
Owner:ZTE CORP
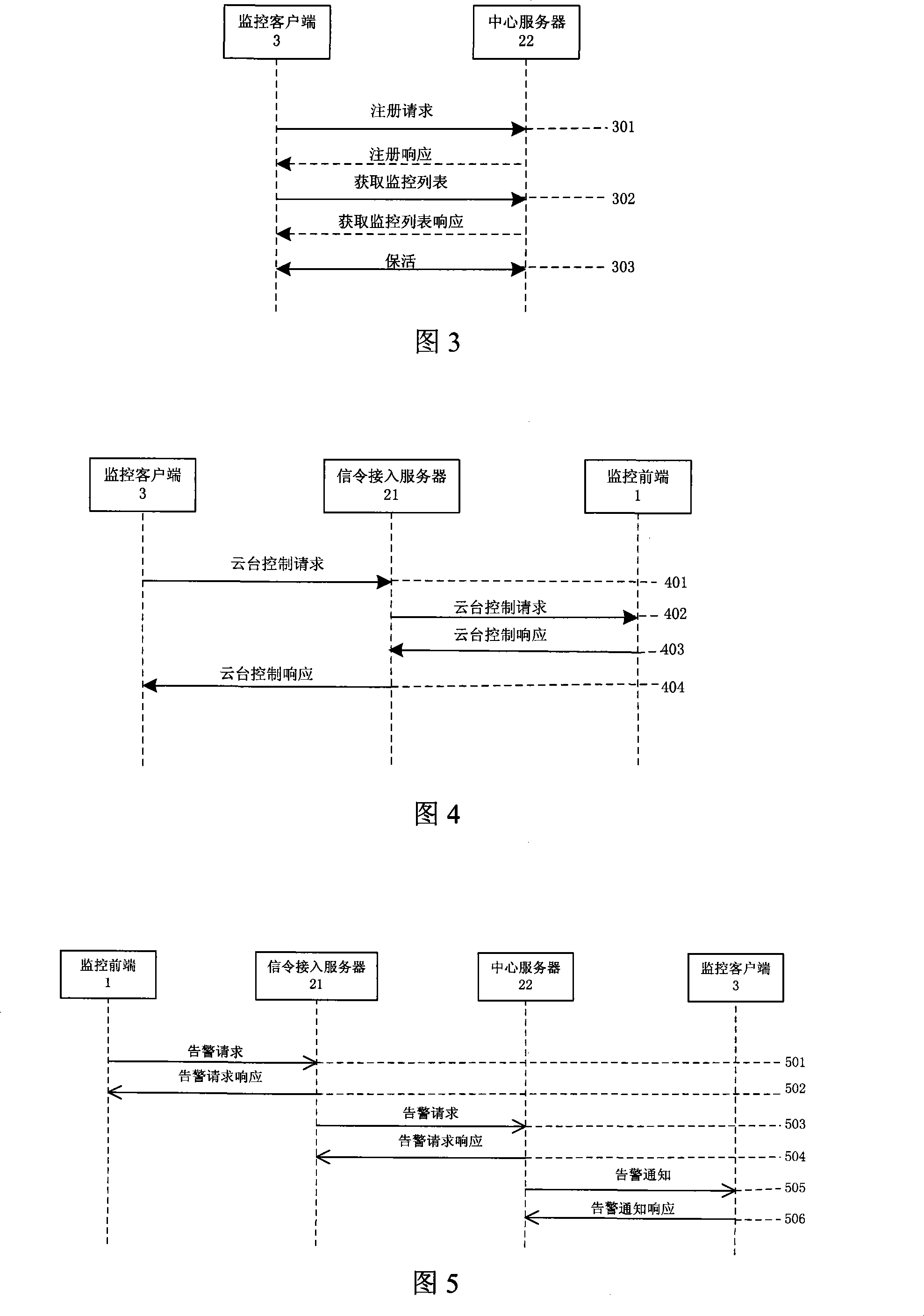
Control protocol and corresponding remote video supervisory control system
InactiveCN101207626AImprove scalabilityQuick responseClosed circuit television systemsData switching networksVideo monitoringInformation transmission
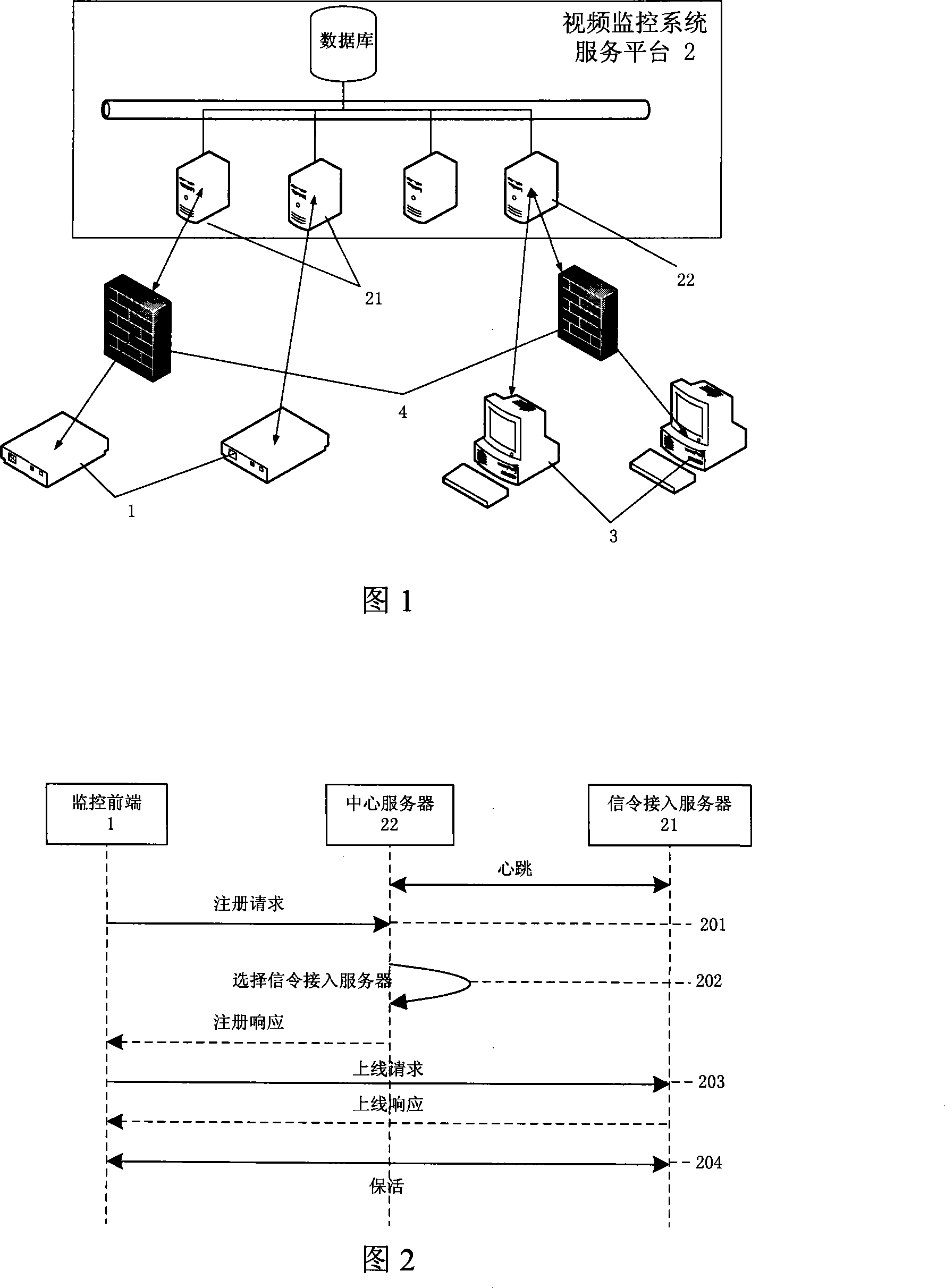
The invention relates to a control protocol and a corresponding remote video monitoring system, wherein, the control protocol uses a TCP way for transmission in an IP network, and controls the protocol content to adopt an XML pattern; the remote video monitoring system consists of a monitoring front-end (1), a signaling cut-in server(21), a central server (22), a medium cut-in server, a monitoring client end (3), and an IP network, and the control protocol is adopted in the monitoring of the front-end register and the information signaling transmission. The information transmission of the control protocol is instantaneous, and is realized simply and is convenient to be extended, the corresponding remote video monitoring system has the advantages that the signaling-control information response speed is rapid, at the same time, the networking is convenient, the extending is easy, and the load sharing is achieved, thereby increasing the system function.
Owner:ZTE CORP
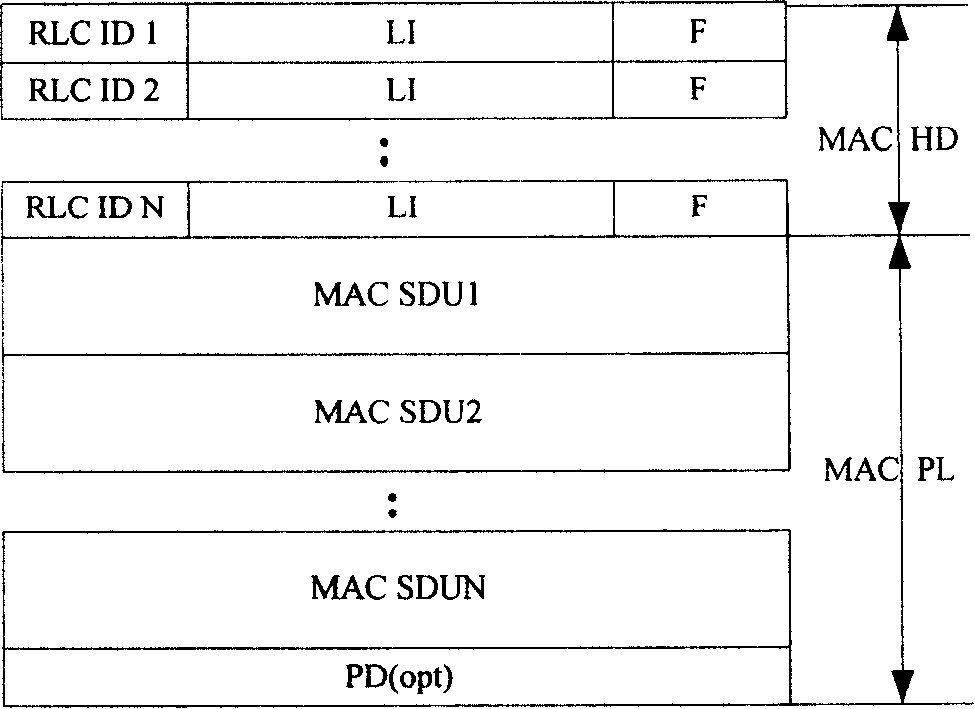
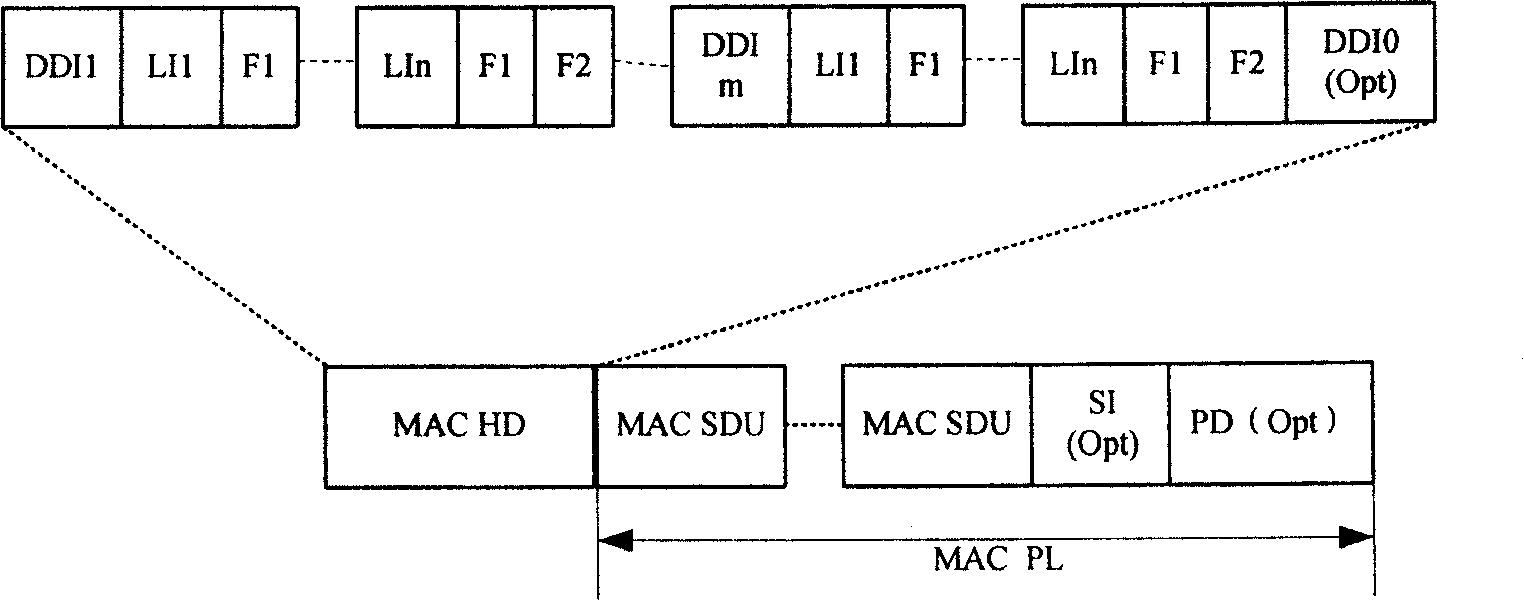
A transmission method and system for media access control protocol data unit
ActiveCN101166193AReduce overheadSave resourcesError prevention/detection by using return channelNetwork traffic/resource managementTransport systemMedia access control
The disclosed method is in use for solving issues existed in current technique that overhead of media access control protocol data unit (MAC PDU) in use for transmission is quite larger; and resource waste is caused by MAC PDU unable to carry wireless link control protocol data unit (RLC PDU) and MAC PDU at same time. Following format is accepted in the method: MAC PDU includes MAC head field and MAC load field are pointed to each logic channel of transmitting RLC PDU; the MAC head field includes a logic channel ID field (LCIDF) and information indication field (IIF); LCIDF saves ID information of the logic channel, and IIF saves information of all RLC PDU transferred by logic channel. The invention also discloses transmission system of MAC PDU. The invention saves overhead of head of MAC PDU, and reduces resource waste.
Owner:DATANG MOBILE COMM EQUIP CO LTD
System and method for providing end to end authentication in a network environment
ActiveUS7024687B2Improve securityEffectively closedError preventionTransmission systemsGeneral Packet Radio ServiceNetwork service
A method for executing end to end authentication in a network environment is provided that includes initiating a communications tunnel with a layer two tunnel protocol (L2TP) network server (LNS) and communicating an activate context request that includes an authentication protocol in a protocol configuration option (PCO) field, the activate context request being received by a gateway general packet radio service (GPRS) support node (GGSN) that initiates a link control protocol (LCP) negotiation with the LNS, the GGSN being operable to communicate an activate context response that may be received by the mobile terminal. An authentication response may be calculated by using a secret value and a challenge value which is provided by the GGSN, the authentication response being used to establish a communication session associated with the mobile terminal.
Owner:CISCO TECH INC
Device and method for rebuilding connection in mobile communication system environment
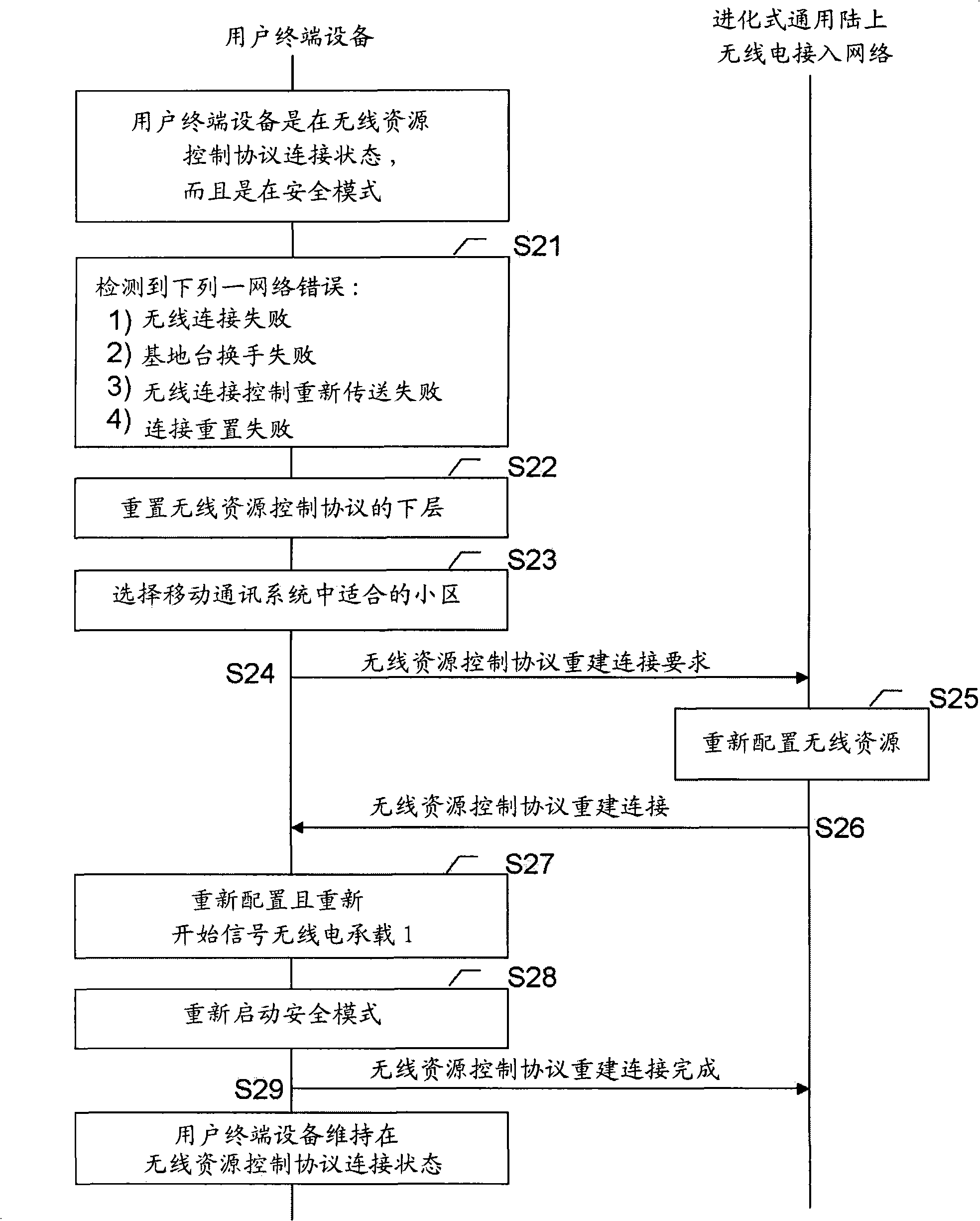
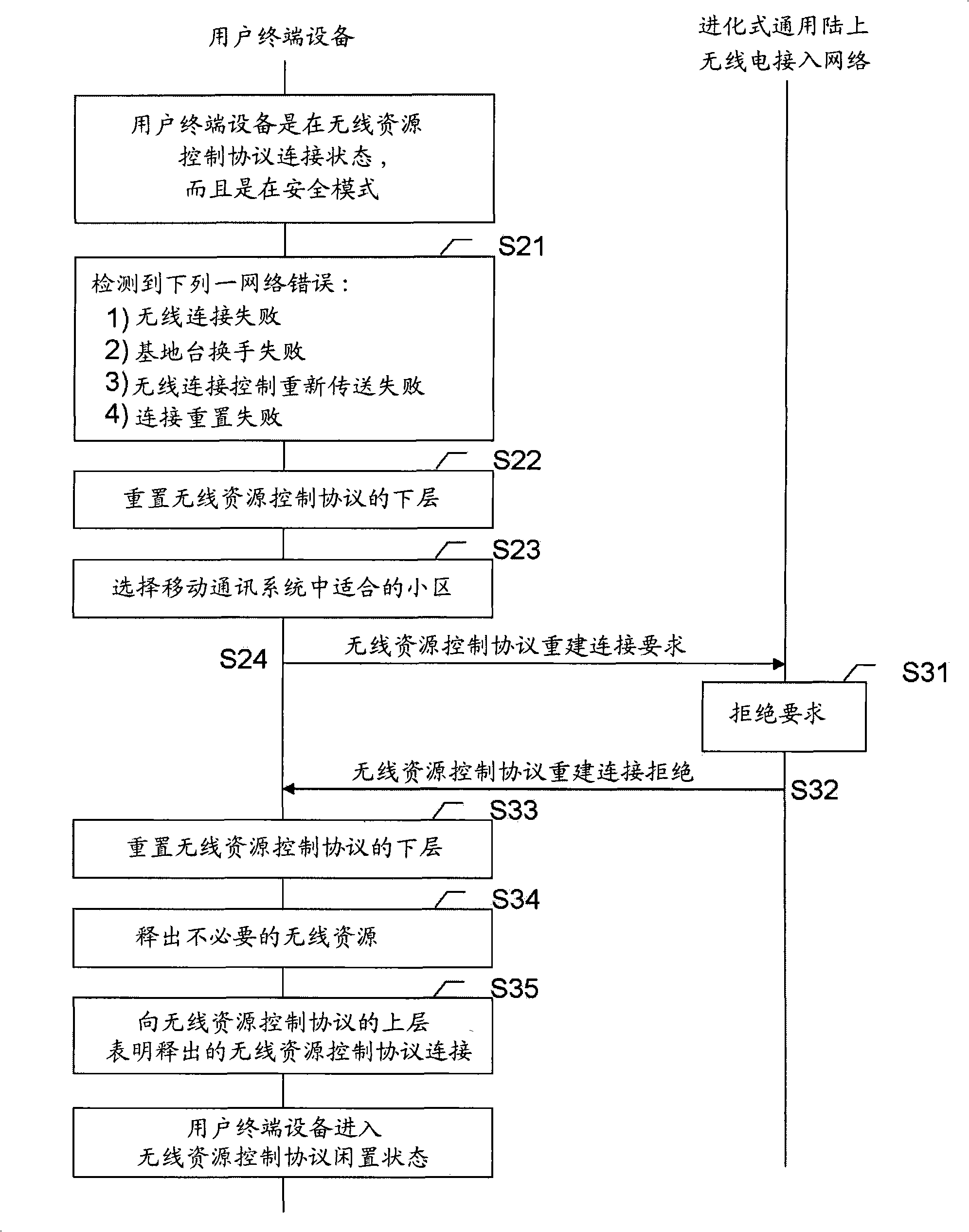
InactiveCN101409606ANetwork traffic/resource managementConnection managementCommunications systemTerminal equipment
The present invention provides a device and method using the radio resource control protocol (RRC protocol) in a mobile communication system environment the reconstruction of the connection. In an embodiment, a user terminal equipment (User Equipment) is provided, when the state of the user terminal equipment is a connection status connected to a mobile communications system, the reconstruction operation of the connection is performed. When problems occur in the network, a Security Mode is activated, and the user terminal equipment will start the reconstruction connection program of the RRC protocol. However, when the security mode is not activated and the RRC protocol represents that it has reached the maximum retransfer attempting number, the user terminal device will reset the lower layer of the radio resource control protocol, release unnecessary radio resource, and indicate the released RRC protocol connection to the upper layer of the RRC protocol; and then enters a radio resource control protocol idle status (RRC_IDLE State), and waits for the next trigger event.
Owner:VIA TELECOM INC
Method for encrypting data of an access virtual private network (VPN)
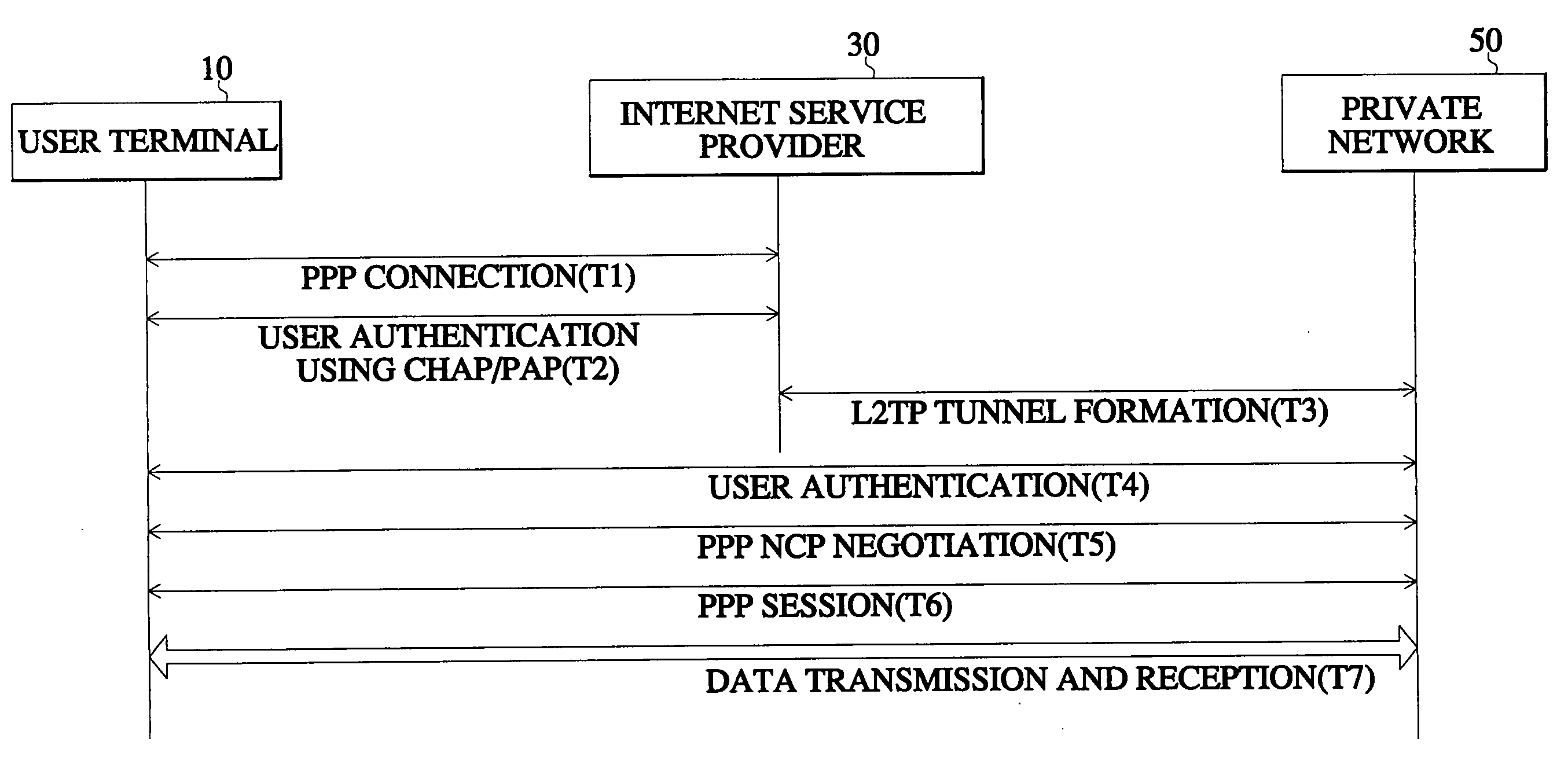
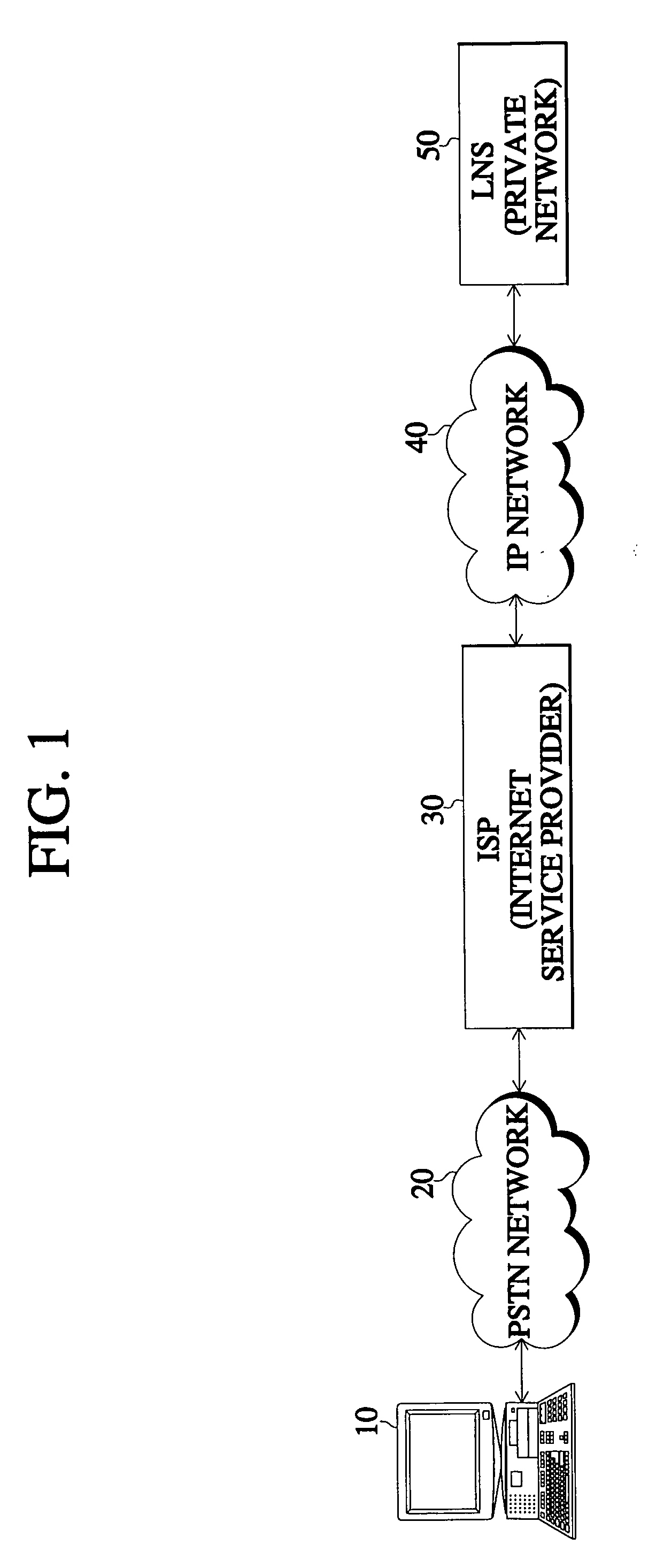
InactiveUS20040168049A1Safe receptionGuaranteed safe transmissionData taking preventionMultiple digital computer combinationsData compressionSecure communication
In a method for encrypting data in an access virtual private network (VPN), a subscriber performs a data encrypting step for data security upon accessing the private network of his company. In this method, access is set up in a dead step according to an access attempt signal by a user. A link control protocol (LCP) negotiation is performed with regard to a mutual authentication method, maximum number of reception bytes, and whether to perform data compression. When the LCP negotiation determines that mutual authentication and data encryption are necessary, the authenticating step is performed first, and mutual authentication is performed by use of a challenge handshake authentication protocol / password authentication protocol (CHAP / PAP). If the authentication is normally completed, the data encryption is performed. Therefore, data encryption is performed together with user authentication so that data is not easily exposed and communication with guaranteed security is performed.
Owner:SAMSUNG ELECTRONICS CO LTD
Point-to-point communication method based on near field communication and near field communication device
InactiveCN101656960AEnsure safetyImprove securityWireless network protocolsTransmissionComputer hardwareProtocol Application
The invention discloses a point-to-point communication method based on near field communication (NFC) and a near field communication (NFC) device, wherein the communication method comprises the following steps: a sender sets a safety module; the safety module is applied to a logic link control protocol (LLCP) layer and uses a first key to encrypt a second key and sends the encrypted second key toa receiver to notify the receiver that the second key is used when data are transmitted; the first key is a common key of the receiver and the second key is used for encrypting the transmitted data inthe communication between the sender and the receiver, and the safety module uses a first key to encrypt the data and sends the encrypted data to the receiver. Symmetrical keys are adopted with higher data decryption speed, thereby ensuring point-to-point data transmitting safety and enhancing efficiency. The safety module is applied to the logic link control protocol (LLCP) layer and is not arranged on an application layer for encryption, thereby achieving higher encryption safety.
Owner:ZTE CORP
Packet structure and packet transmission method of network control protocol
InactiveUS20090022151A1Effective controlData switching by path configurationPower line networkStructure of Management Information
A packet structure and a packet transmission method of a network control protocol. A user in the inside or outside of the house can effectively control various home appliances such as refrigerator or laundry machine or monitor operation state of the devices, over the living network such as RS-485 network, low-power RF network, and power line network so that the user can enjoy the remote control and the convenient monitoring. In addition, the packet structure for the inter-layer interface of the network control protocol can be managed. The packet structure at the application layer is generated by assigning one of an application layer protocol data unit header, a request message, a response message, and an event message, together with an application layer protocol data unit header The generated packet at the application layer is transmitted to thus interface layers of the network control protocol. Therefore, the packet structure at the application layer can be more efficiently managed and transmitted.
Owner:LG ELECTRONICS INC
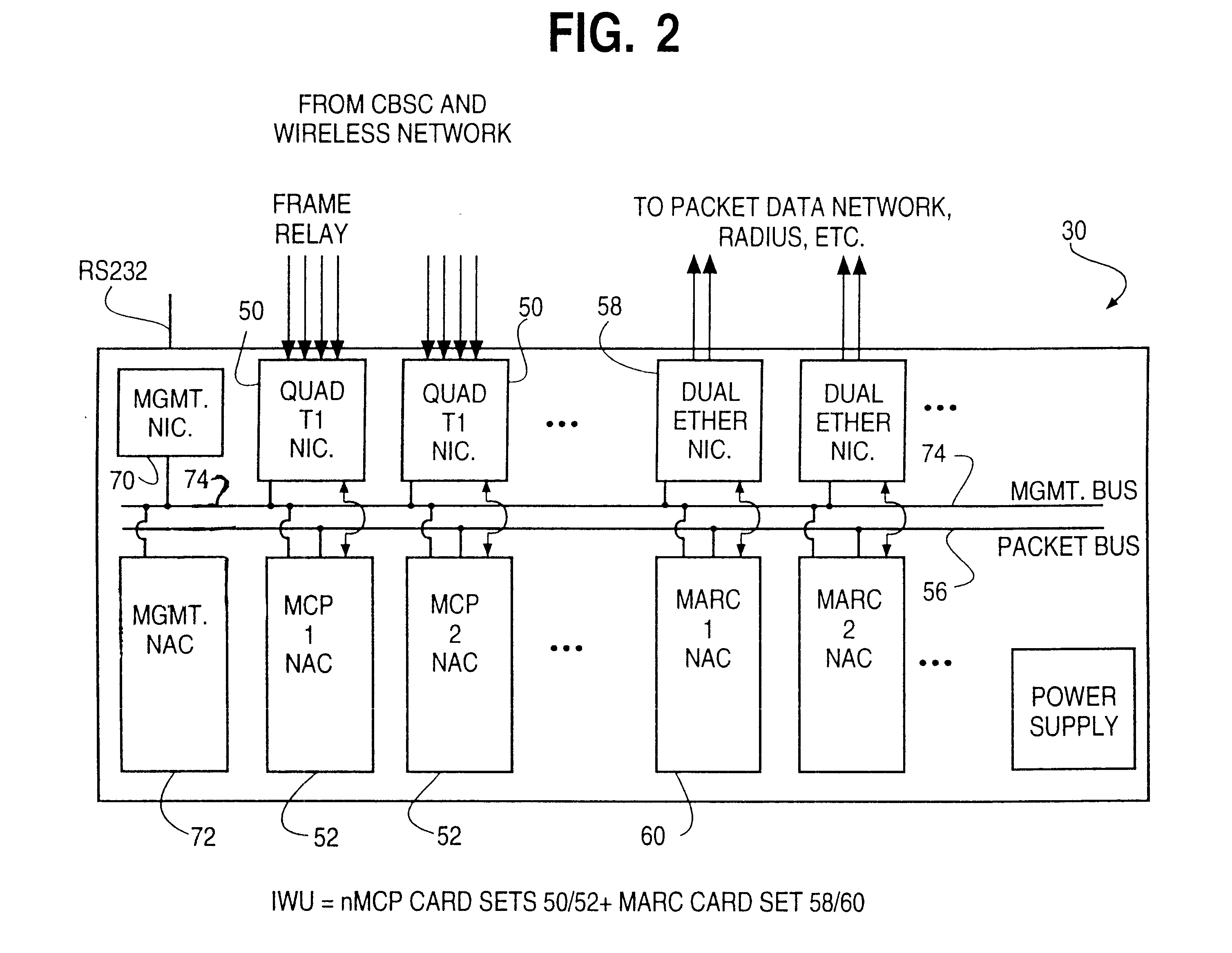
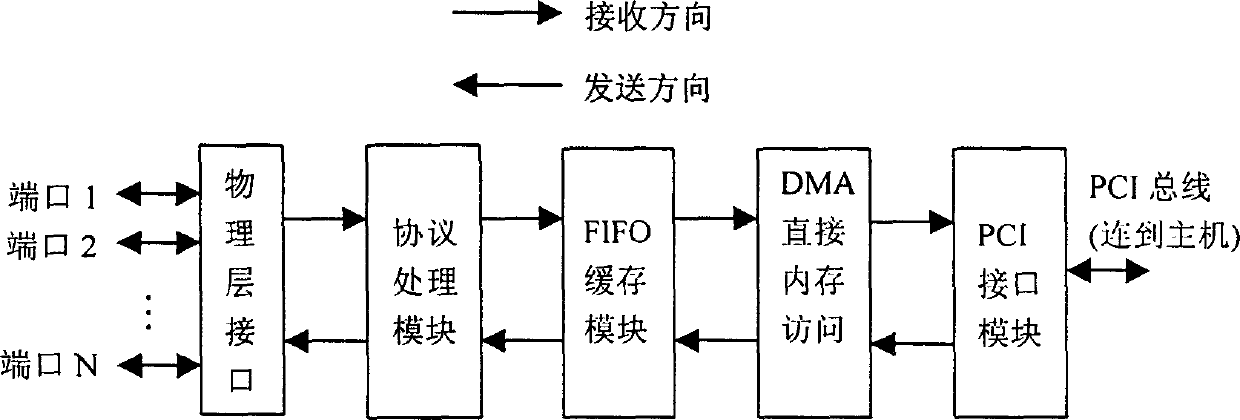
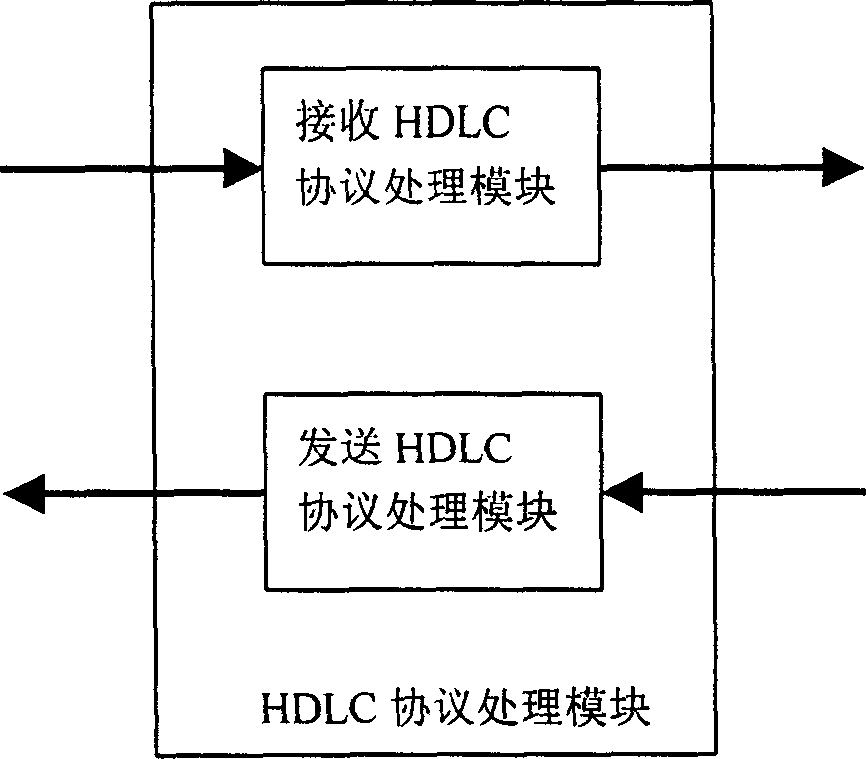
High speed link control protocol transmission processing/module and data processing/method
This invention relates to HDLC protocol transmission process module including a port arbitration module, a HDLC protocol transmission processor and a state memory module. The data process method is that the port arbitration module receives data request signals of N ports and transfers them to the HDLC protocol processor orderly according to the priorities and provides arbitration to the shared data process pipelines of N ports, the HDLC processor reads out unprocessed data from FIFO and reads out the state data of its belonged HDLC channel from the state memory module be processed wit hpipelines to be sent to related ports to write back to the state memory the new state data of HDLC channel.
Owner:HUAWEI TECH CO LTD
Apparatus and method of realizing link access control protocol for IP multicasting packet transmission in a mobile communication network
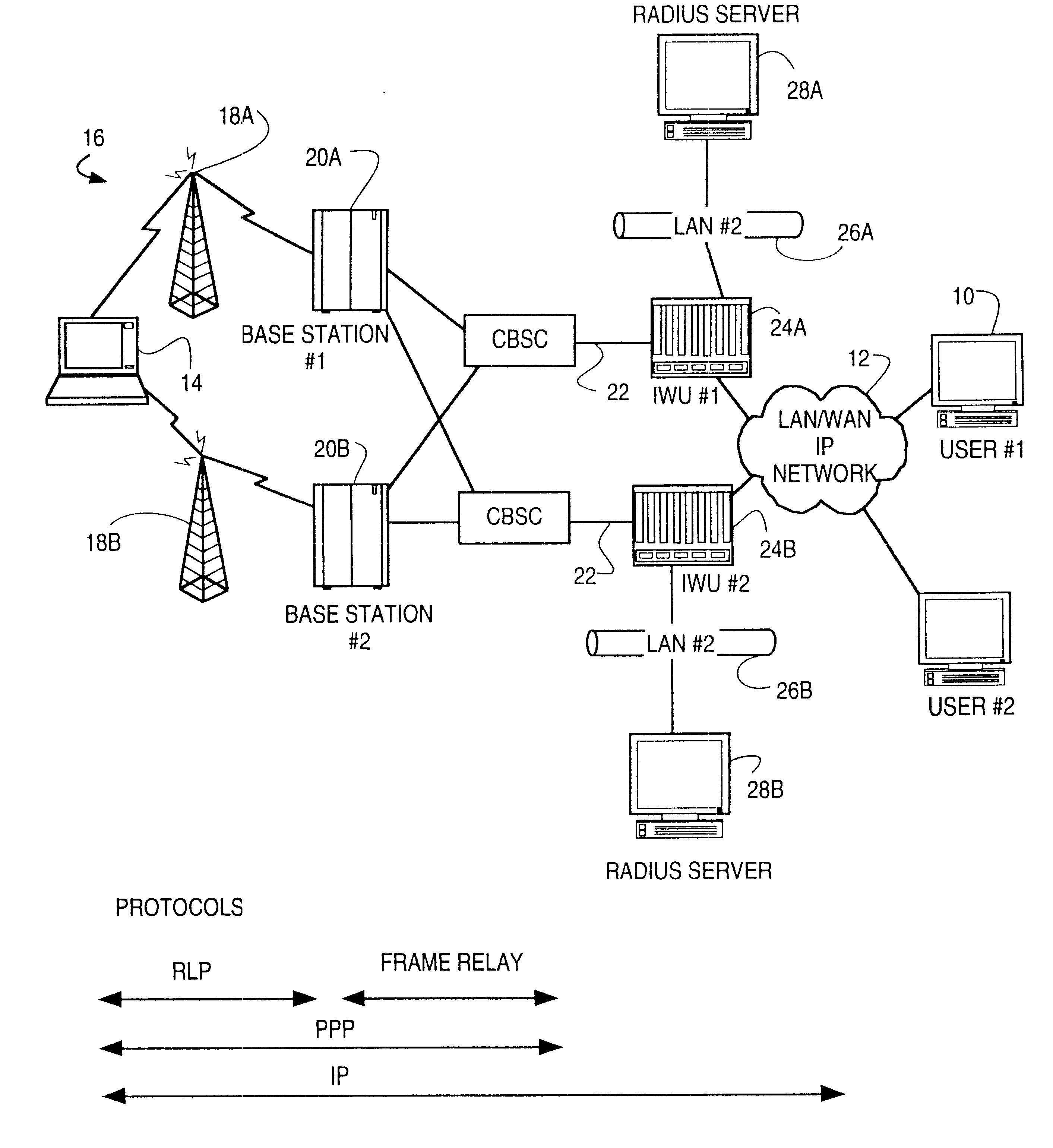
InactiveUS7190680B2Easy transferSpecial service provision for substationError prevention/detection by using return channelIP multicastThe Internet
Disclosed is a method of realizing a link access control protocol for IP M / B packet transmission in a mobile communication network. The method of the invention comprises the steps of: receiving by an LAC of a BTS / BSC an Internet IP M / B packet transferred via a BSC / PCF from an Internet host and a multicasting server, storing the Internet IP M / B packet into an internal buffer, and segmenting the Internet IP M / B packet into a radio packet frame size; adding sequence numbers to the segmented radio packet frames and transmitting a CIBP SDU into a mobile terminal; and assembling, in the mobile terminal, the CIBP SDU for the received radio packet frames and forming the IP M / B packet, and transferring the formed IP M / B packet into an upper layer.
Owner:LG ELECTRONICS INC
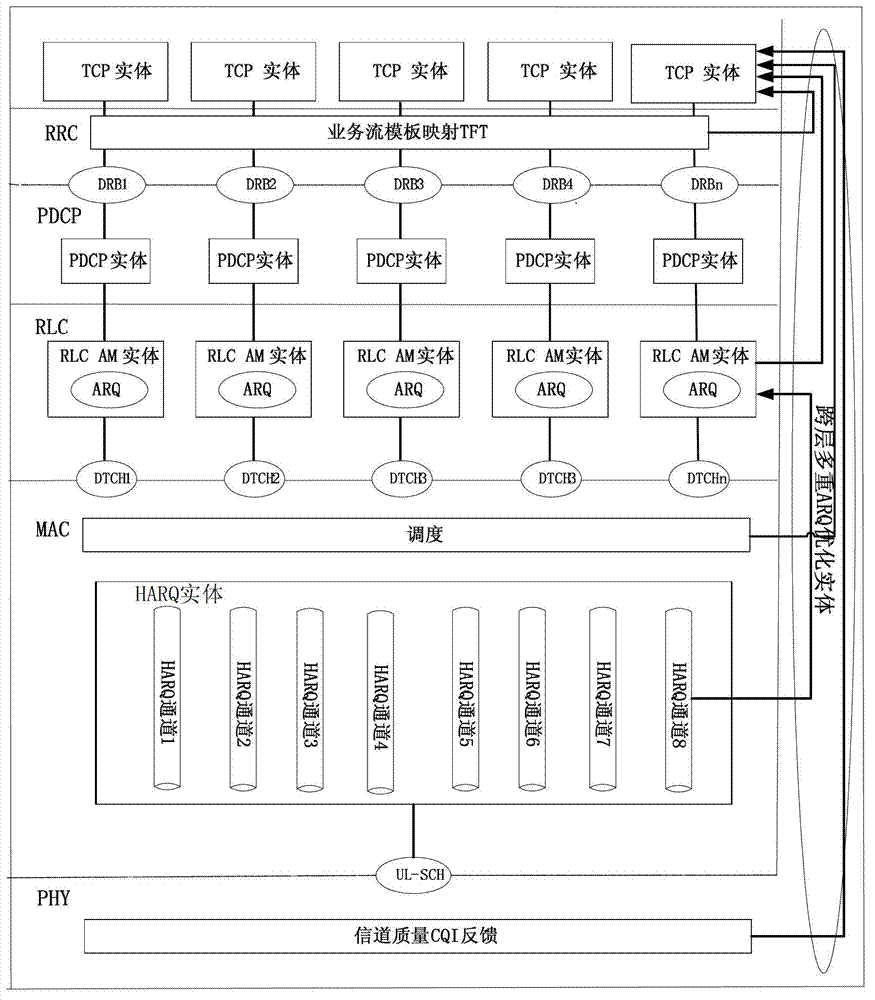
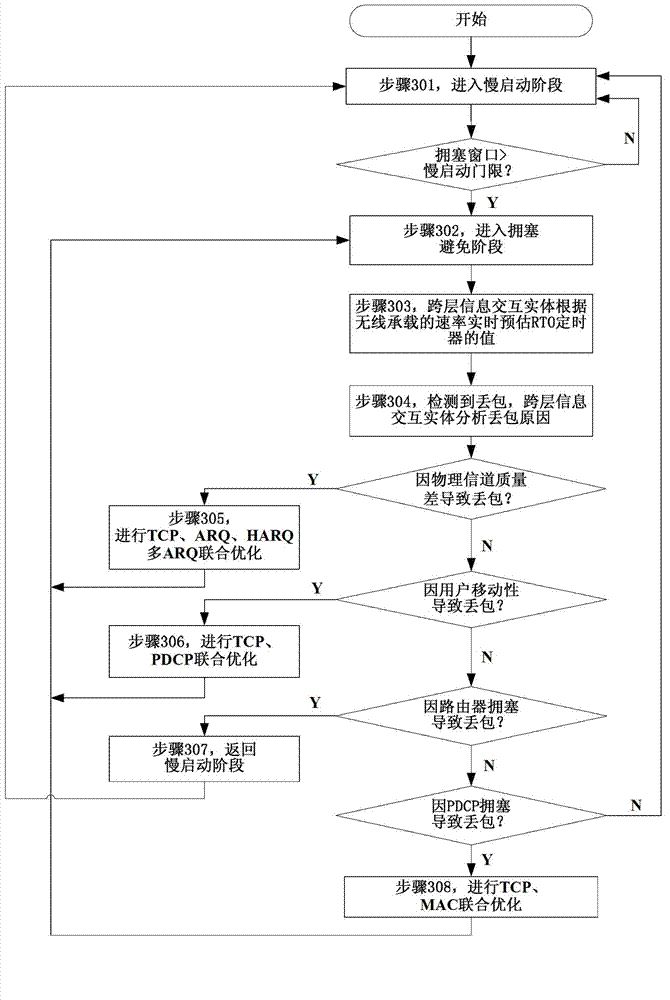
Method for optimizing terminal control protocol (TCP) under wireless environment
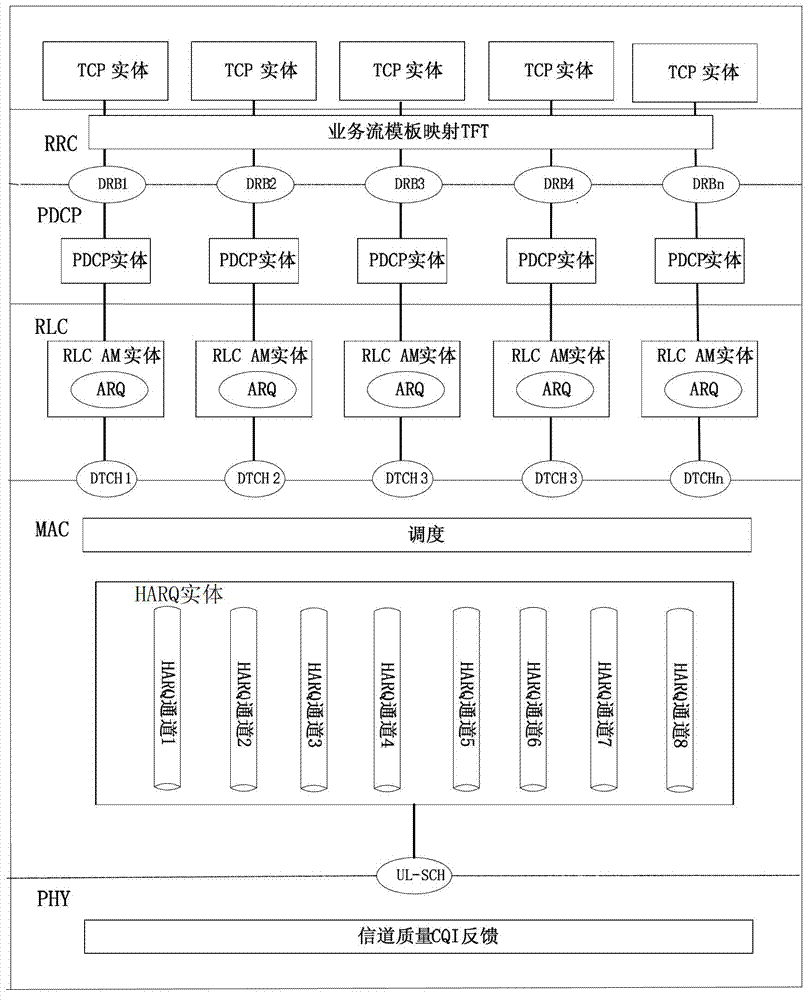
InactiveCN102833783APreserve functional independenceImprove performanceNetwork traffic/resource managementWireless network protocolsPDCPRTP Control Protocol
The invention relates to the technical field of wireless communication. The invention discloses a method for optimizing a terminal control protocol (TCP) under a wireless environment. The invention comprises the following steps of: comprehensively analyzing physical layer (PHY) channel condition information and hybrid automatic requestor (HARQ) information, multi-access computer (MAC) layer scheduling information, radio link control (RLC) layer automatic repeat quest (ARQ) information, and packet data convergence protocol PDCP switching information through the cross-layer information, judging whether loss of a TCP layer message is caused by router congestion at a core network side or the loss of a data message of a wireless chain side, therefore, misleading of starting congestion of a TCP layer is avoided, user sending speed influenced by an algorithm is avoided, retransmission competition between the TCP and an ARQ / HARQ caused by misleading the TCP to start a quick retransmission algorithm is avoided simultaneously, and a performance of the TCP protocol under the wireless environment is optimized. A layer-cross structure provided by the invention keeps an interface and a port between middle layers of a long term evolution (LTE) layering protocol framework unchanged; furthermore, running efficiency of the TCP protocol under the wireless environment is improved on the basis of keeping interconnection and intercommunication with an original network.
Owner:BEIJING UNIV OF POSTS & TELECOMM
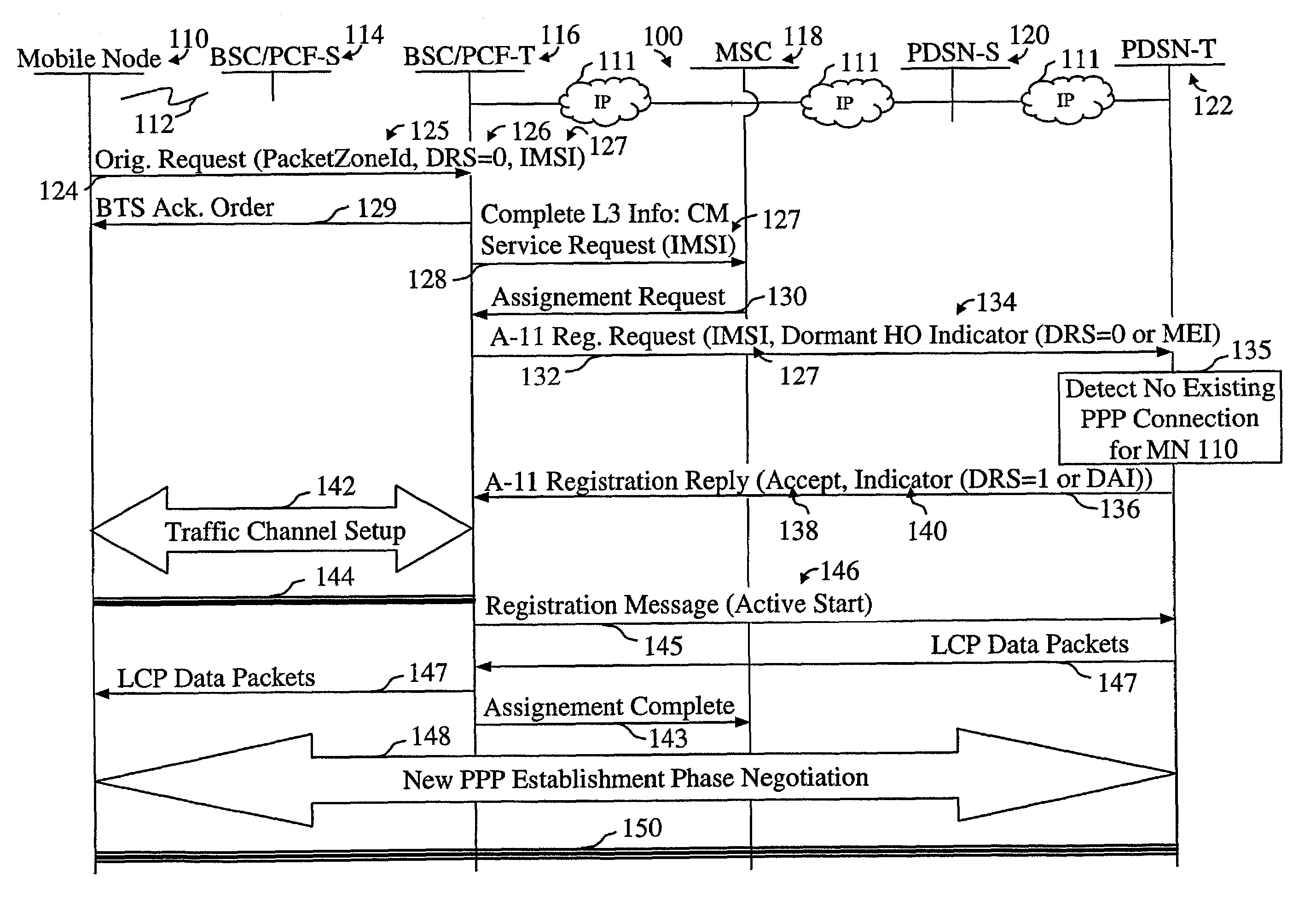
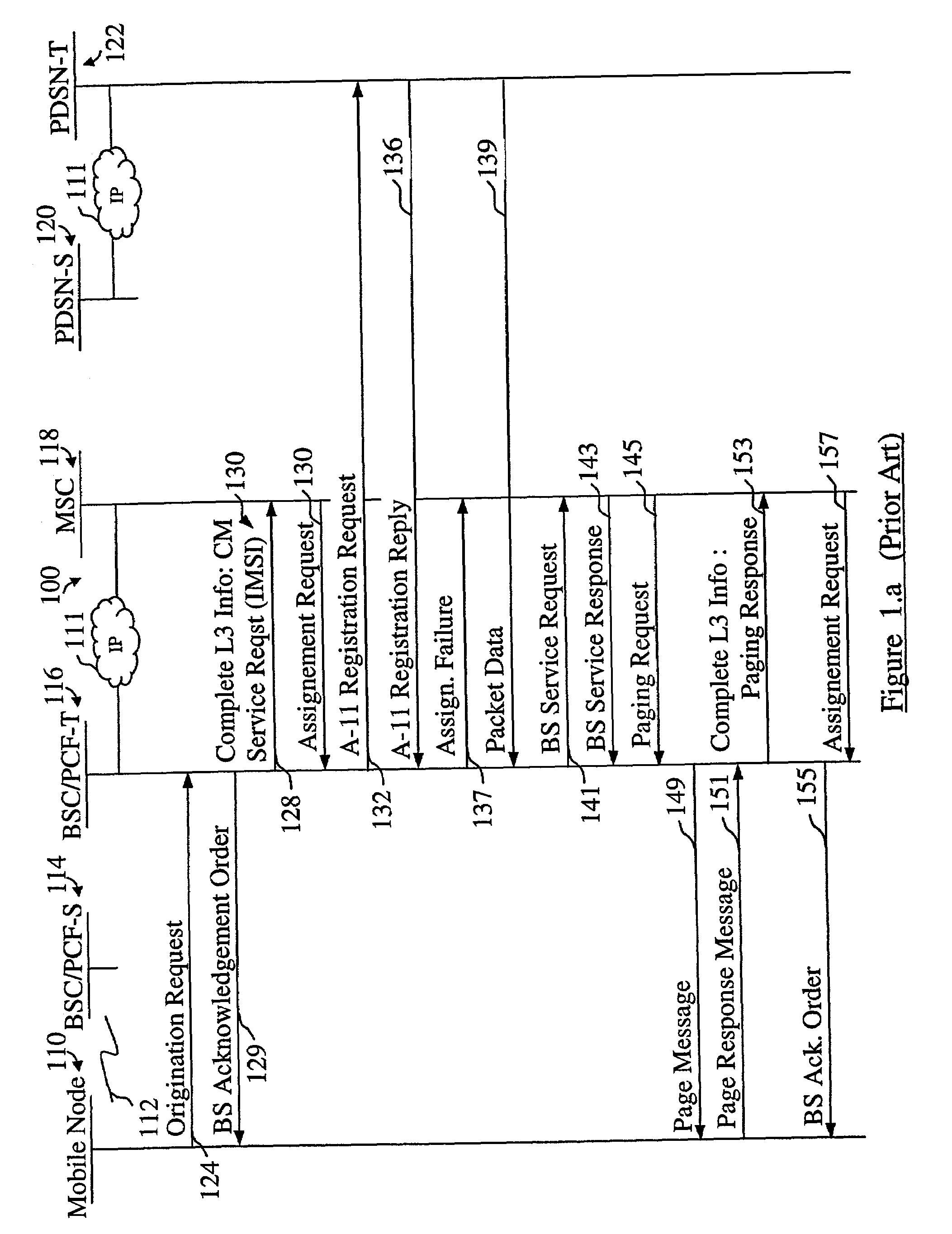
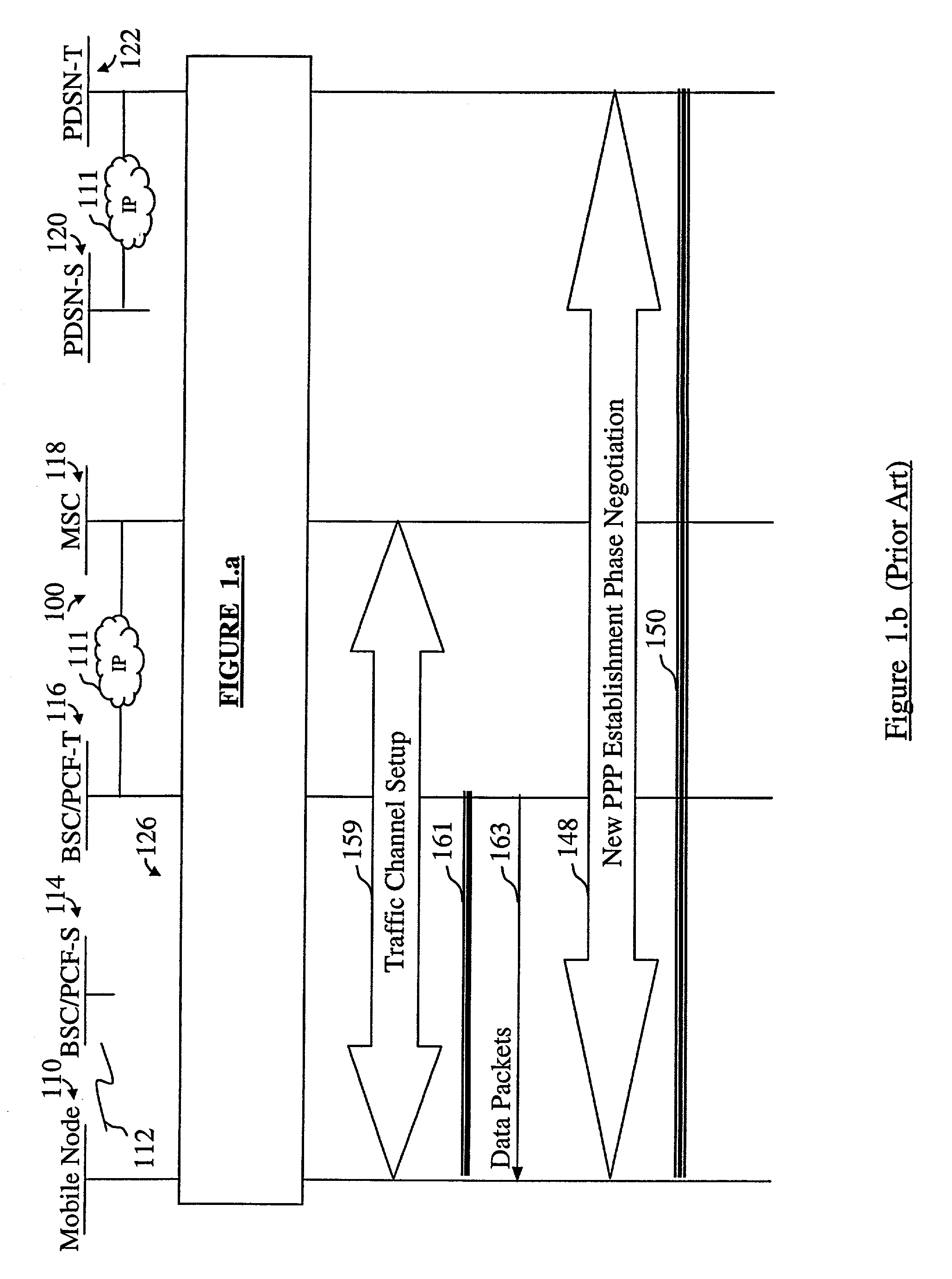
Mobile IP mobility management at dormant hand-over in CDMA IP-based cellular packet-data network
InactiveUS7065062B2Network traffic/resource managementTime-division multiplexPacket data serving nodeBase code
In an IP-based Code Division Multiple Access (CDMA) 2000 packet-data cellular telecommunications network, a method and system for handing over a dormant Mobile Node (MN) to a target packet zone. According to the invention, first the dormant MN sends an origination request message to the target Base Station Controller and Packet Control Function (BSC / PCF), which further sends a registration request comprising an indication that the MN is dormant to a Packet Data Service Node (PDSN). The PDSN replies to the BSC / PCF with a registration reply message for requesting the establishment of a traffic channel for the MN, and for indicating that it has data packets ready to be sent to the MN, such as for example Link Control Protocol (LCP) data packets for use in the negotiation of a new Point-to-Point Protocol (PPP) connection. The registration reply message comprises an indication such as for example a Data ready to Sent (DRS) parameter set to 1. The BSC / PCF establishes the traffic channel and forwards the data packets to the MN. Following the receipt of the registration reply in the BSC / PCF, the paging of the MN is avoided.
Owner:TELEFON AB LM ERICSSON (PUBL)
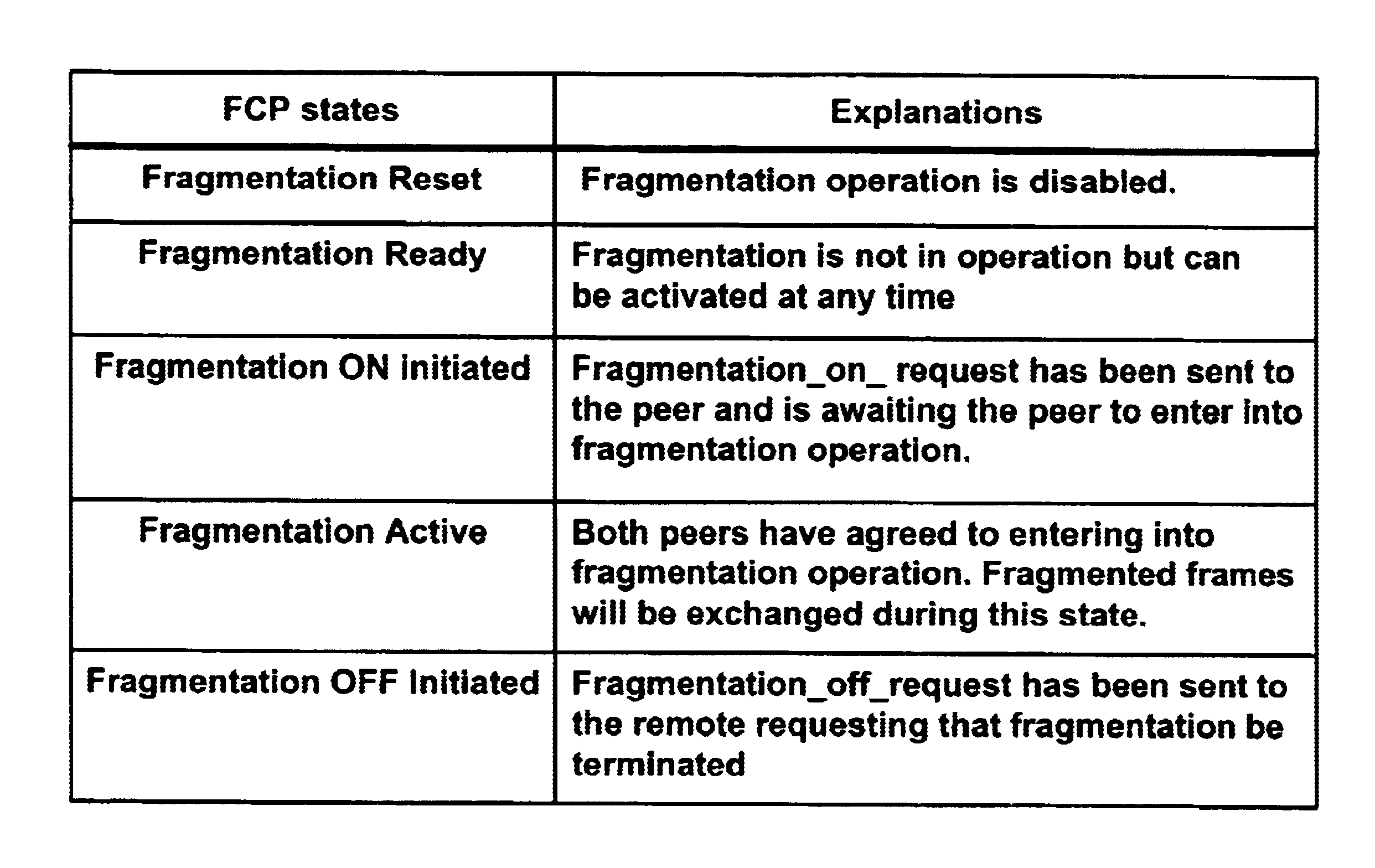
Dynamic control protocol for frame relay fragmentation in support of real-time applications such as VOIP and VOFR
Frame Relay (FR) fragmentation control protocol for enabling FR access device and switches to support real-time traffic, such as VoIP and VOFR, enables communicating peers to negotiate dynamically for fragmentation operation and configuration parameters, as well as to terminate such an operation. Procedure is applicable to FR UNI or NNI fragmentation and end-to-end fragmentation, as well as to PPP fragmentation. Effectively, fragmentation is deployable on demand, and configuration negotiation is supportable across the network. Preferably, such control protocol allows systems with fragmentation to interoperate with older systems that do not support fragmentation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
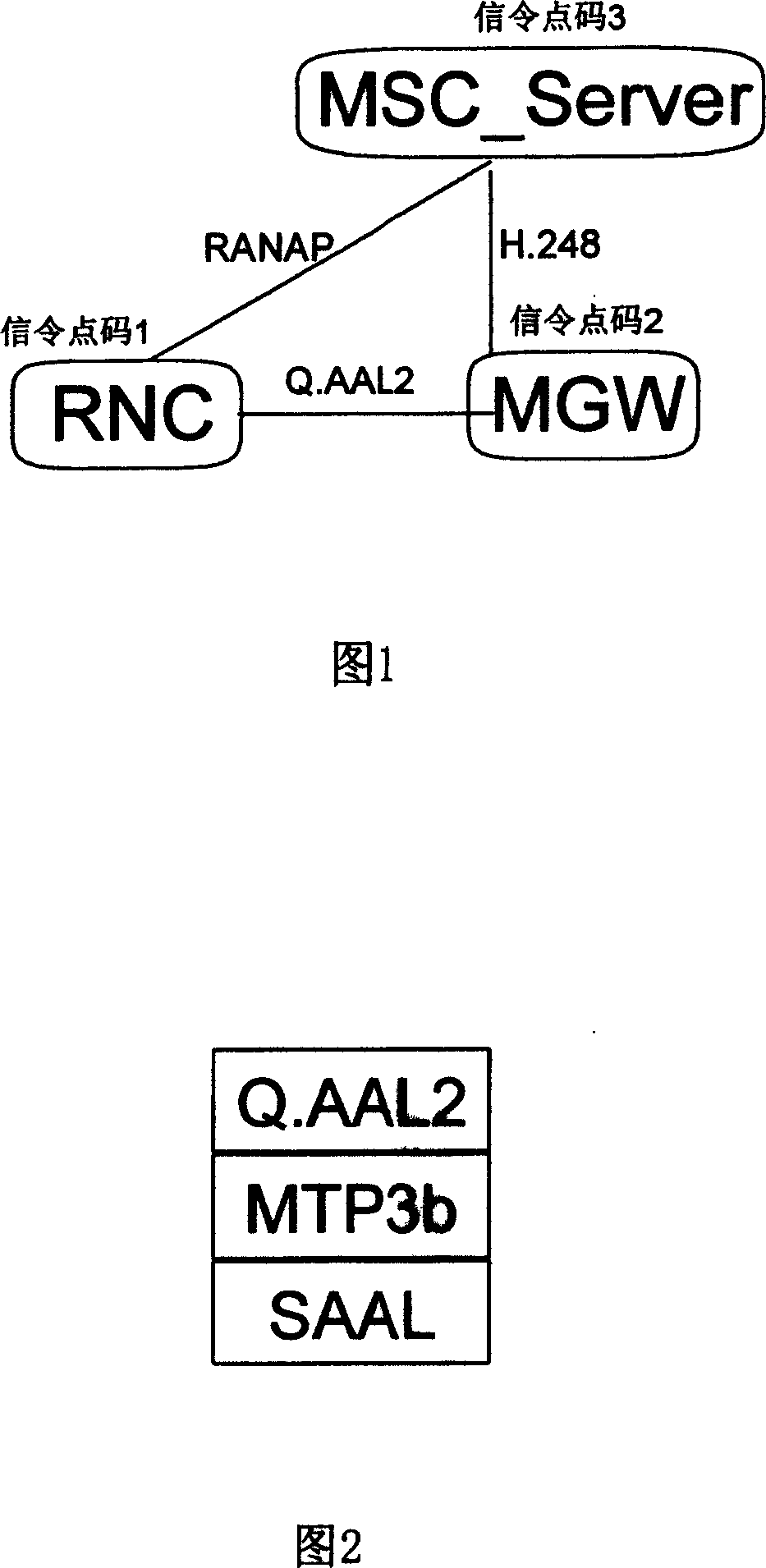
Method for accessing wireless network controller in broadband CDMA mobile network
InactiveCN1508992ASmooth and seamless accessTake advantage ofAssess restrictionCommmunication supplementary servicesMobile businessRTP Control Protocol
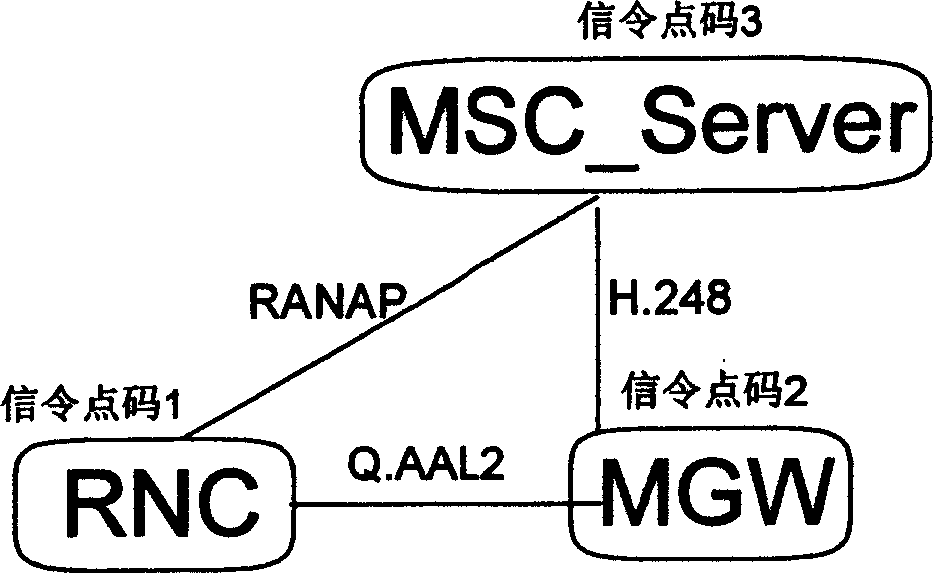
In the invention, radio network controller (RNC) sends message of load control protocol and message of call control protocol to media gateway (MGW). MGW own processes the message of load control protocol, and MGW transmits the received message of call control protocol to a mobile switching center server (MSC) to process. MSC_Server configures MGW as a signaling transit point (STP) to reach RNC. Thus, message of call control protocol is sent to MGW first, and then is transmitted to RNC. The invention provides a method for RNC of R99 to switch in WCDMA R4 network seamless so as to utilize current network equipment fully. The invention makes current network equipment upgrade to R4 network smoothly so as to save investment.
Owner:HUAWEI TECH CO LTD
Fast network access method upon restart of IP STB
InactiveCN101035192AImprove performanceHigh speedTelevision system detailsColor television detailsAccess methodIp address
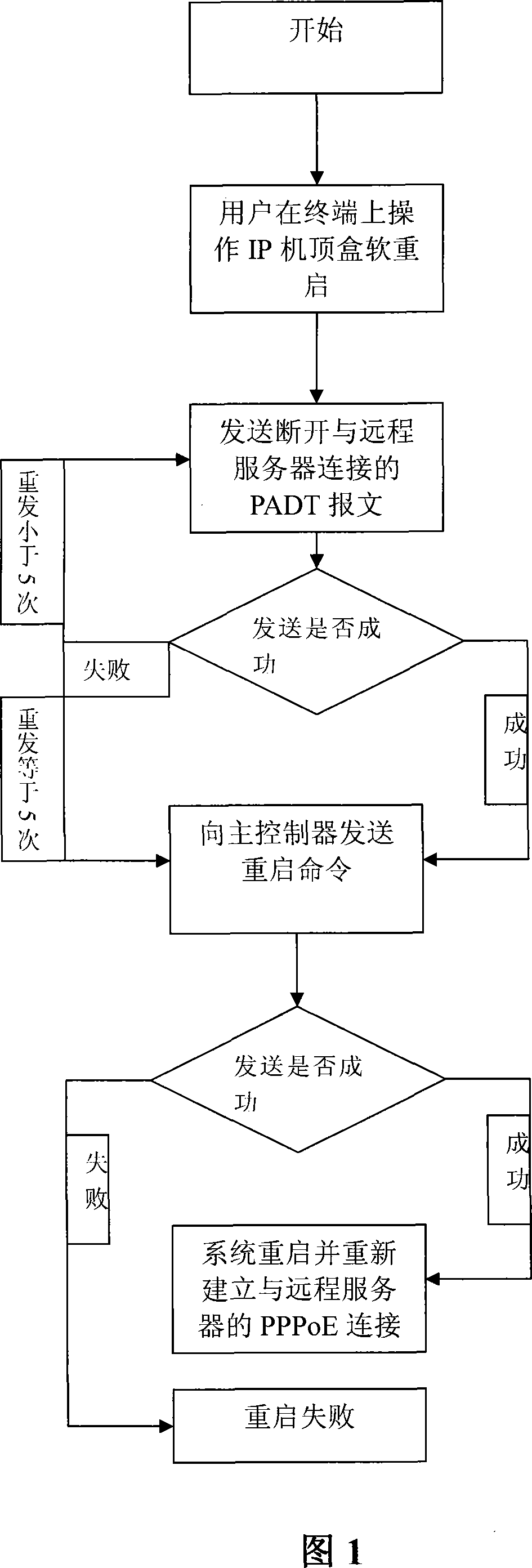
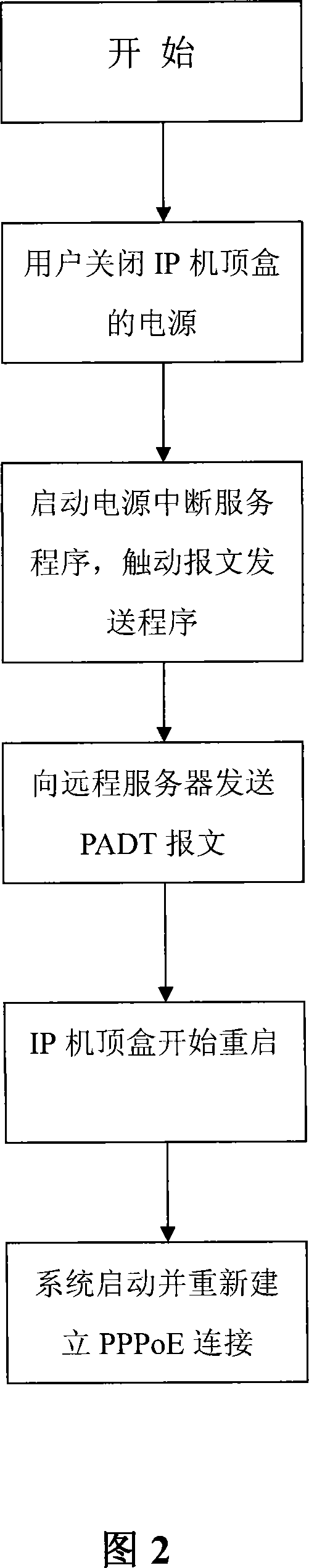
The invention relates to an IP set-top box(STB) opens again when fast turns on the network the method, its characteristic lies in by the customer end IP set-top box (STB) terminated PPPoE before heavy start pass machine-hour to the long-distance server transmission the connection the PADT text of a telegram, after the long-distance server receives the PADT text of a telegram first to release and the customer end network level connection, takes back originally assigns for the customer end IP address, then the link controlling agreement release data link layer connection, finally releases the physical connection, after the IP set-top box(STB) starts again, again between fast establishment customer end and long-distance server connection. This invention, an IP set-top box (STB), opens again when fast turns on the network the method, after the massive experiments proved this method has the feasibility and the stability, the connection long-distance server speed obvious improvement, greatly saved the user to connect the server the time and has promoted the IP set-top box (STB) performance in the certain degree.
Owner:深圳智衡技术有限公司
Data transmission in packet-switched radio system implementing user equipment location service
ActiveUS7068634B2Efficient implementationChange is minimalUnauthorised/fraudulent call preventionEavesdropping prevention circuitsRadio networksData transmission
The invention relates to method and system for transmitting data between user equipment and serving mobile location center in packet-switched-radio system implementing user equipment location service. The method comprises: (302) data to be transmitted is placed in a message of a third-layer radio resource protocol; (304) the radio resource protocol message is transmitted to the radio network using a logical link control protocol set on the second layer of the packet protocol stack; (306) a logical link control protocol relay set on the second layer of the packet protocol stack in the radio network directs the logical link protocol message to a second party; (308) the second-layer logical link control protocol residing in the second party transmits the radio resource protocol message to the radio resource protocol set on the third layer; (310) the second party disassembles the transmitted data from the radio resource protocol message.
Owner:NOKIA TECHNOLOGLES OY
Method for implementing control protocol of random and periodical media access of radio network
InactiveCN101631325AMulti-channel hidden node problem solvingImprove spectrum utilizationNetwork traffic/resource managementWireless network protocolsWork periodRadio networks
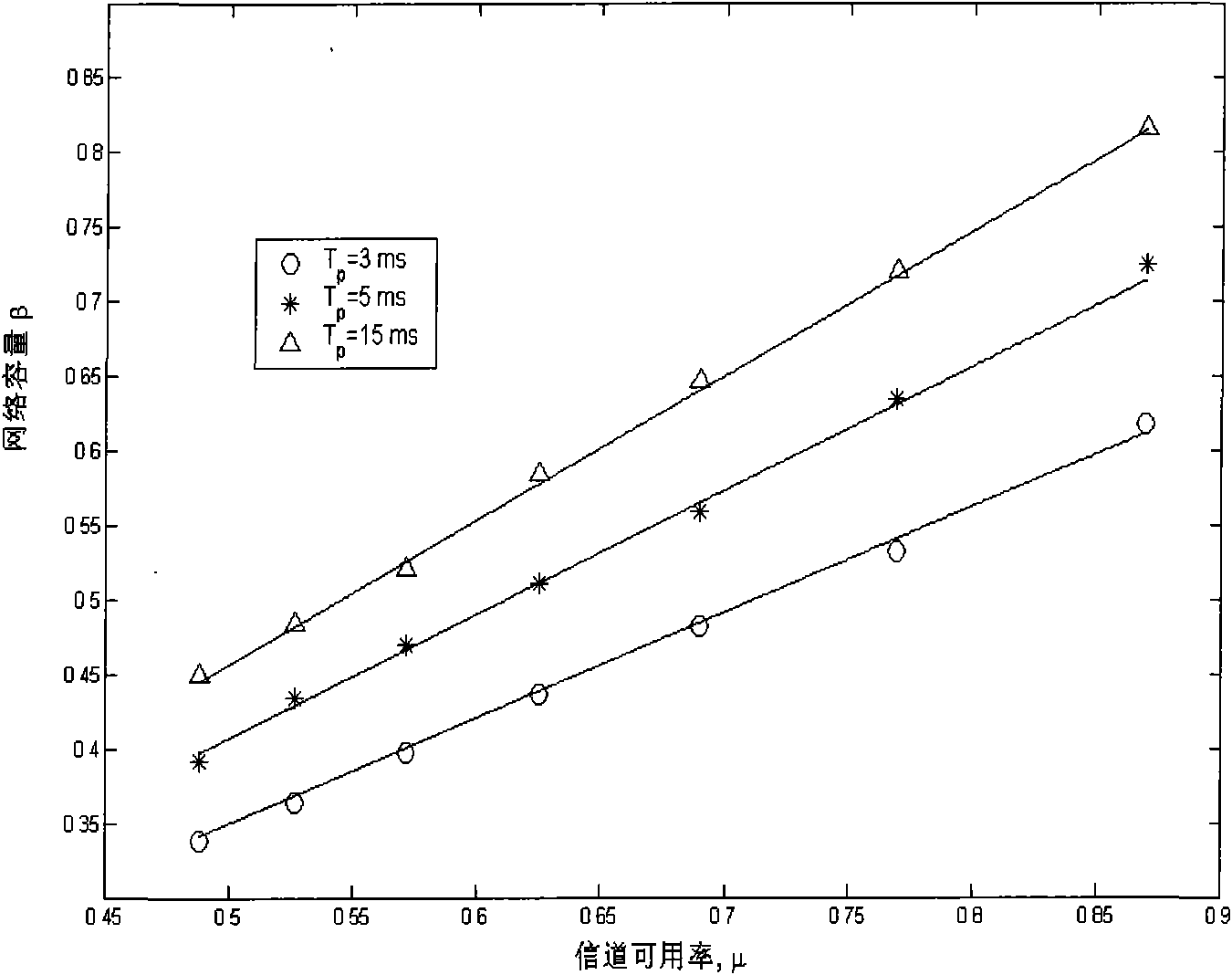
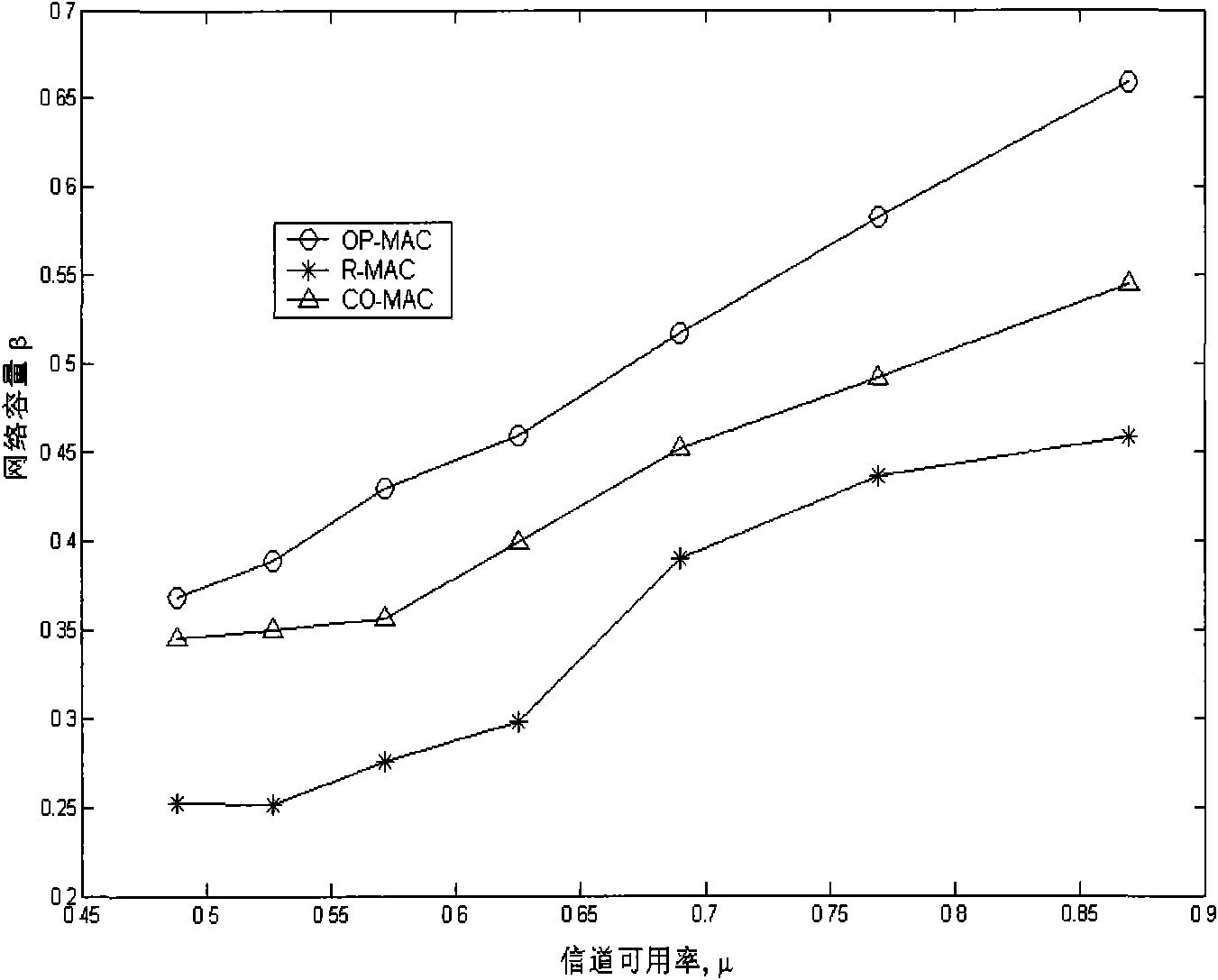
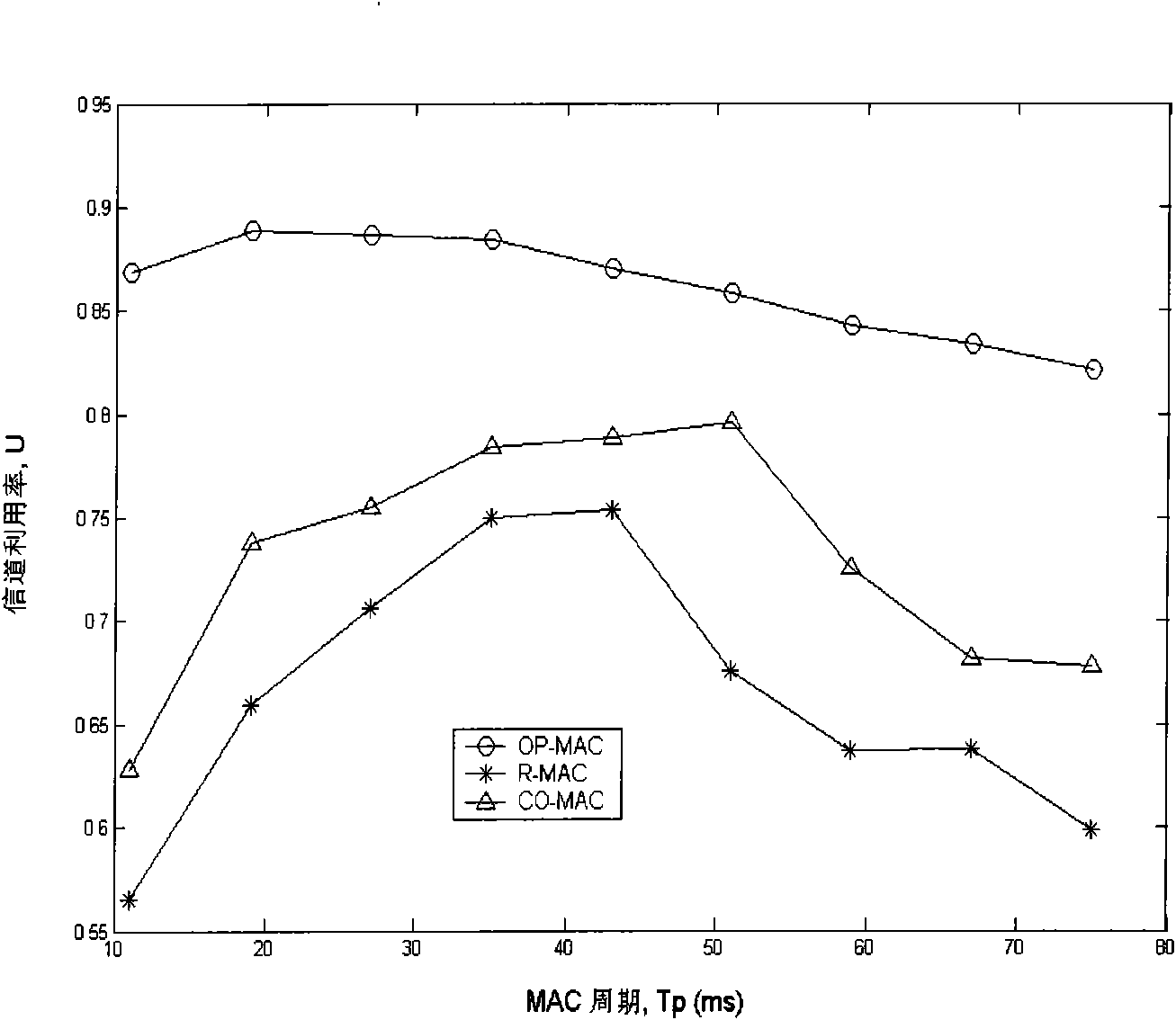
The invention relates to a method for implementing the control protocol of the random and periodical media access of a radio network, comprising the following steps: step 1, after network initialization, each SU synchronously and periodically repeats one work period Tpointed by OP-MAC; step 2, in the OP-MAC work period, each SU monitors signal paths in the network firstly; step 3, each SU respectively reports the results of the monitored signal channels so that all SU in the network can share the monitored information of idle signal channels; step 4, SU competition is carried out, and available idle signal channels are reserved; and step 5, each SU which succeeds in the competition in the transmission reservation stage transmits data. The network capability of the OP-MAC protocol of the invention in the cognitive radio network is obviously superior to CO-MAC and R-MAC.
Owner:SHANGHAI JIAO TONG UNIV
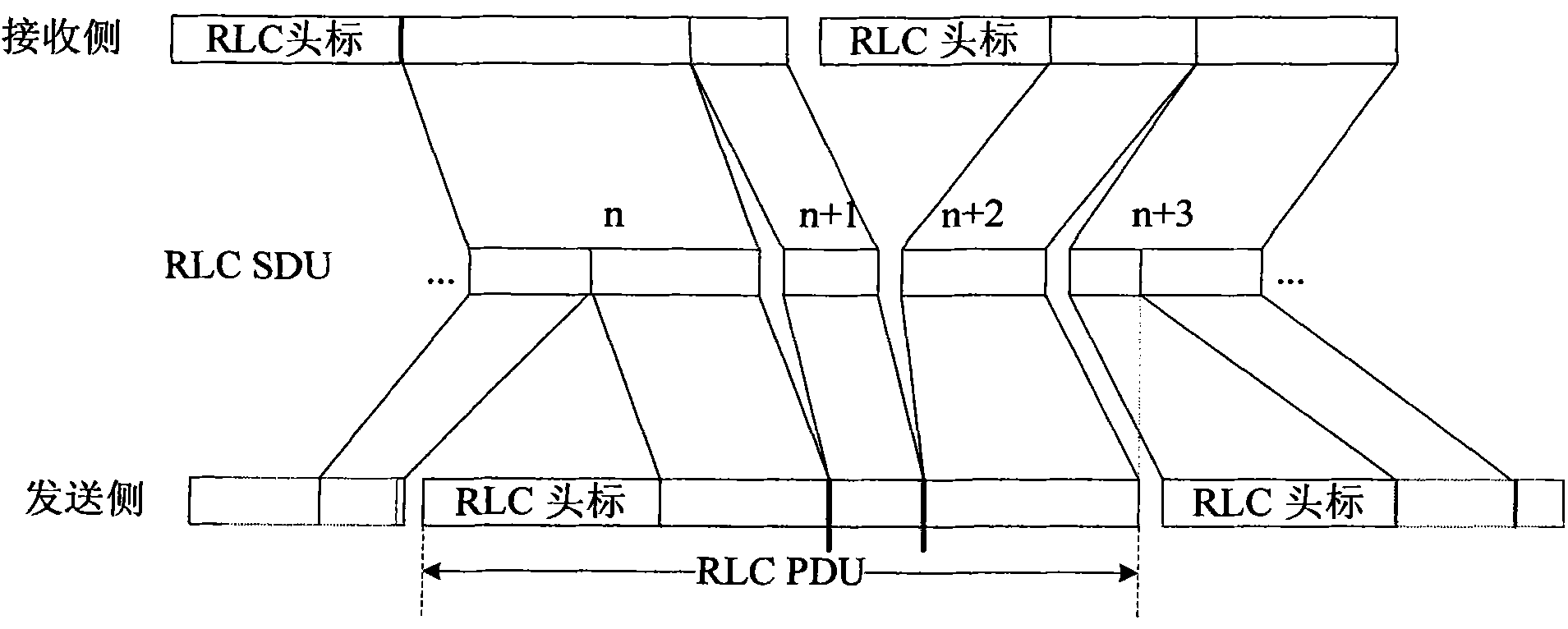
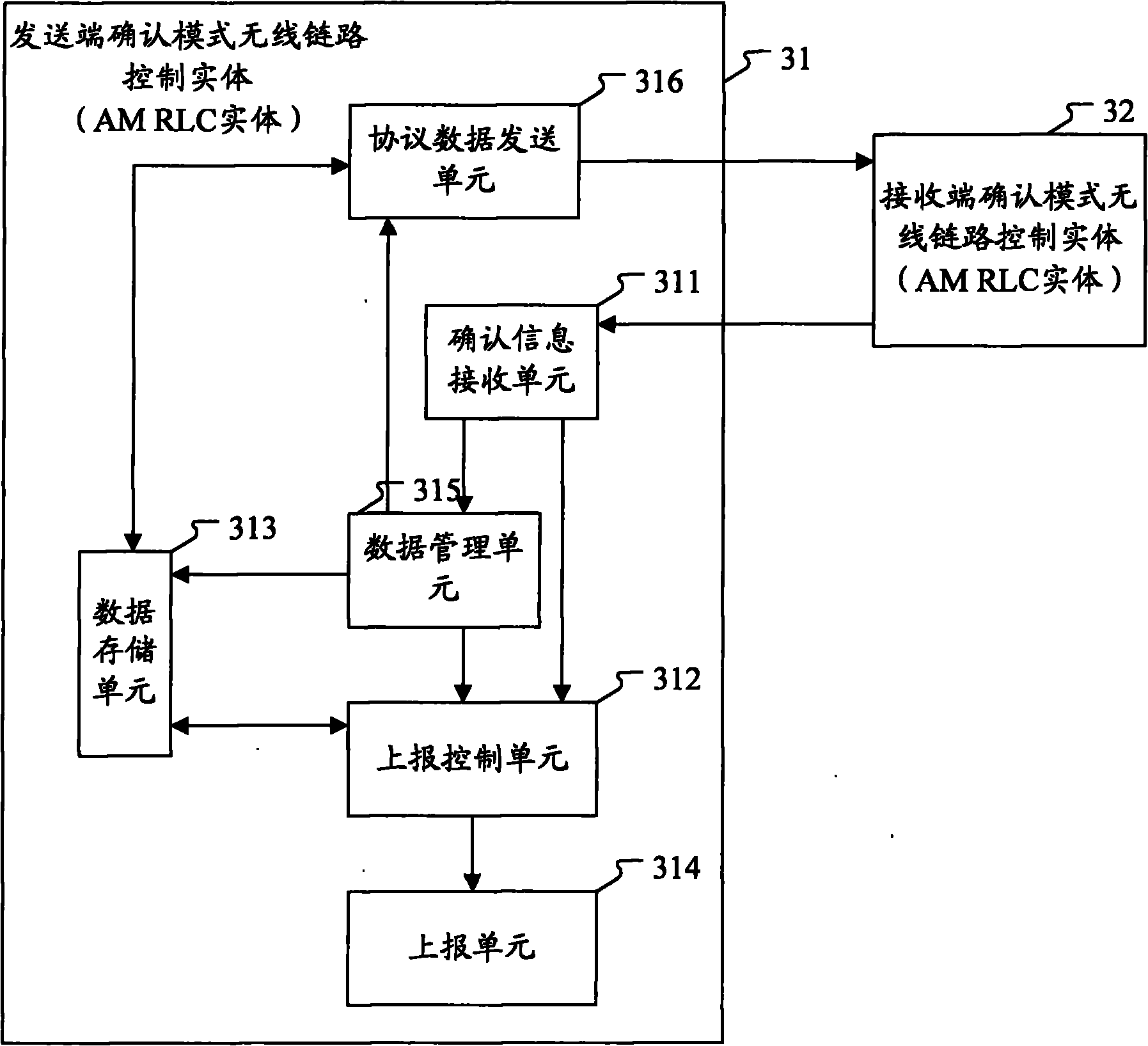
Method and system for processing acknowledgment information in acknowledgement mode based on RLC protocol
InactiveCN101925195AAvoid retransmissionSave storage resourcesError preventionWireless network protocolsQuality of serviceRadio Link Control
The invention discloses a method for processing acknowledgement information in an acknowledgement mode based on an RLC (Radio Link Control) protocol, which comprises the following steps of: receiving the acknowledgement information by an acknowledgement mode radio link control (AM RLC) entity of a sending end; and judging whether a radio link control protocol service data unit (RLC SDU) is transmitted successfully or not according to the received acknowledgment information, if so, reporting the transmission success message of the successfully transmitted RLC SDU to an upper layer, otherwise, not reporting. The invention further discloses a corresponding processing system. In the invention, as the transmission success message about the successfully transmitted RLC SDU is always reported to the upper layer no mater whether the transmission success acknowledgement of an AMD PDU corresponding to the lower boundary of a sending window is received or not, the transmission success message can be reported in time. Therefore, the storage resources and the transmission resources are saved, and the quality of service is improved.
Owner:ZTE CORP
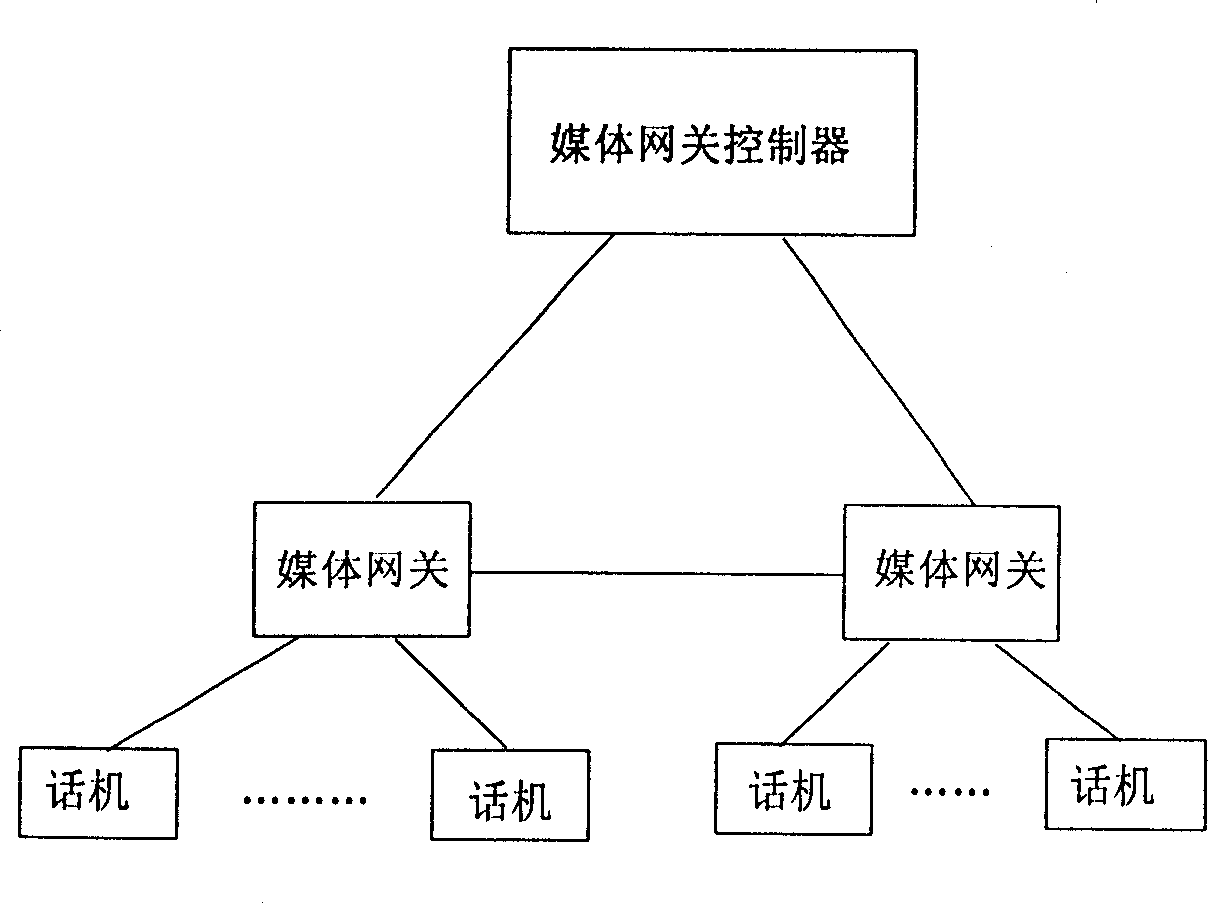
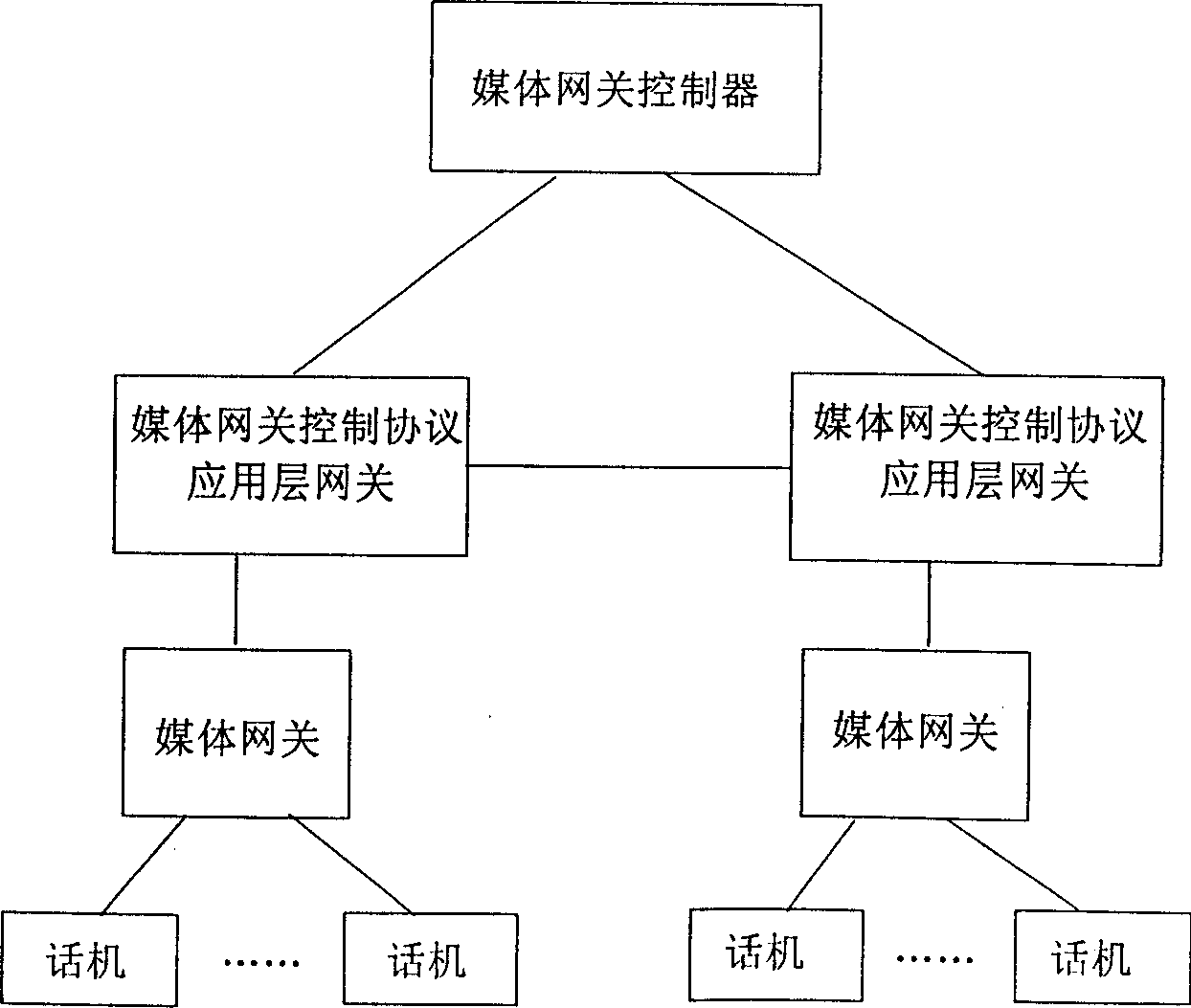
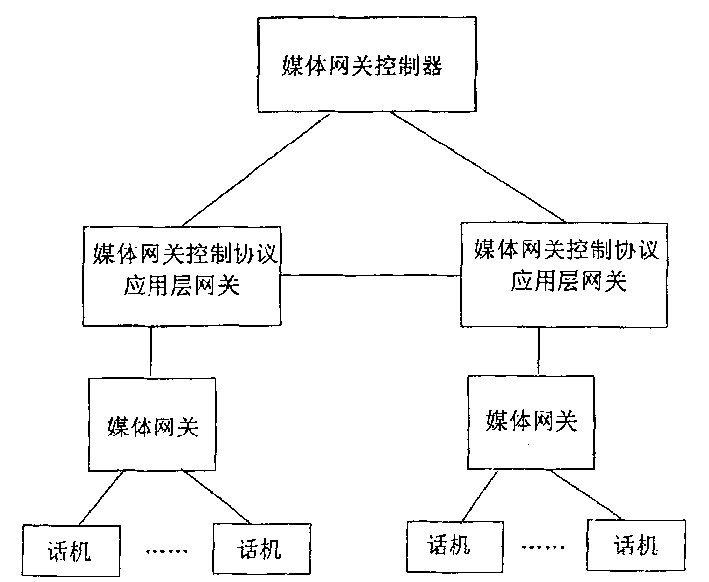
Network system and method for processing VOIP business based on media net-link control protocol
InactiveCN1489355AAvoid attackSolve the problem of excessive consumption of public network IP addressesTelephonic communicationTransmissionIp addressPrivate network
The system comprises following pats. (1) Through Internet connected media gateway controller (MGC) and media gateway (MG). (2) Customer station set connected to media gateway. (3) Located between MGC and MG, media gateway control protocol application layer gateway (MGCP ALG) capable of carrying conversion of network address based on MGCP protocol. (4) Signaling interaction between MGC and MG is carried out through MGCP protocol; data exchange of voice media flow between MGs is carried out through RTP / RTCP protocol; MG connected to MGCP ALG is utilized to collocate IP address of private network. The scheme solves issue that current network consumes too many IP addresses of public network. Meanwhile, effect of MGCP ALG firewall avoids MG suffering attack from Internet directly.
Owner:HUAWEI TECH CO LTD
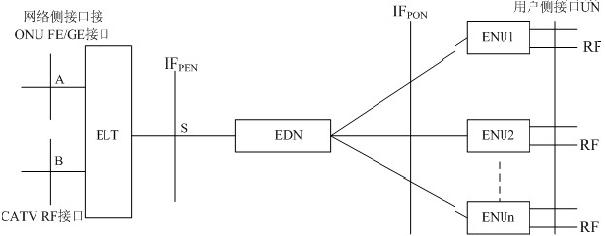
Ethernet passive electric network
InactiveCN101808344AAvoid collisionReduce electromagnetic interferenceWireless communicationElectronic networkTechnical standard
The invention relates to the technical field of optical fiber-coaxial cable hybrid network access. Aiming at the limitations of the existing EoC technology application and combining with EPON technology application, the invention provides a multi-point control protocol based Ethernet passive electrical network (Ethernet Passive Electronic Network-EPEN), which comprises head end equipment connected with the FTTx optical node of an Ethernet passive optical network, terminal equipment (ENU) connected with user units and a passive electric distribution network (EDN), wherein the EDN consists of coaxial cables and one or more passive power splitters and provides electric channel connection between the ELT and the ENU, and a physical layer adopts the orthogonal frequency division multiplexing technology (OFDM); and a data link layer adopts the multi-point control protocol (MPCP), so that the two-way Ethernet data services carry in a point-to-multi-point coaxial access network. The invention can effectively realize the two-way transformation of an HFC network to which the EPON and the EPEN access in a compositing way, and has improved technology advancement, user access bandwidth and supported maximum number of users compared with other EoC technical standards.
Owner:HUAZHONG UNIV OF SCI & TECH
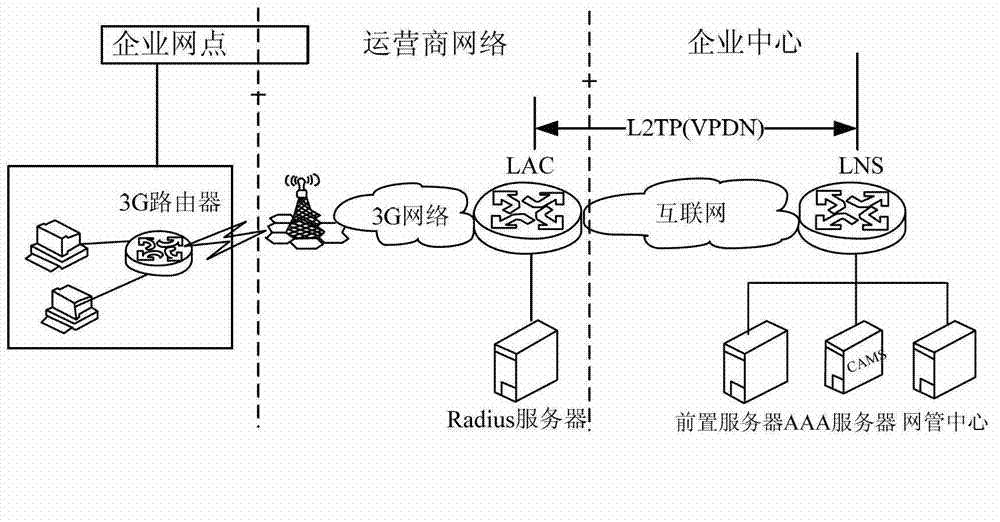
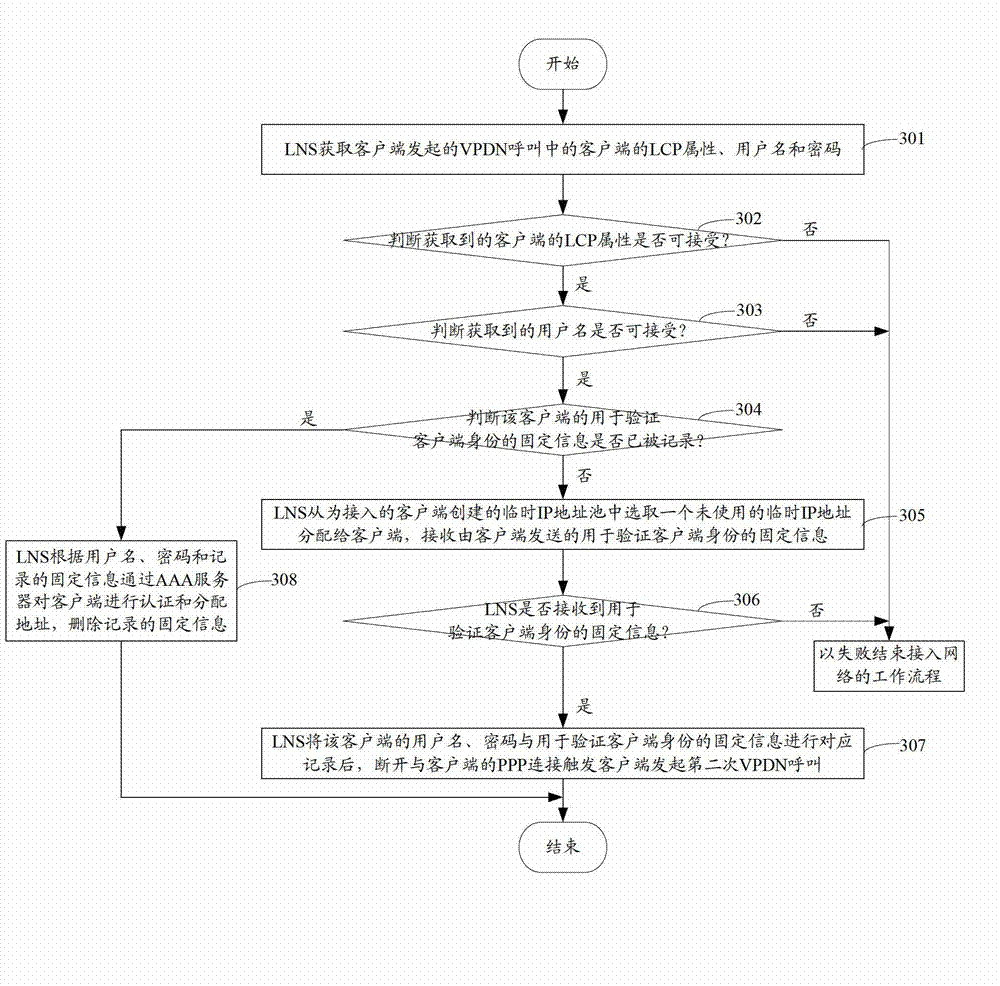
Method and device for enabling third generation (3G) user to safely access to network
The invention discloses a method and a device for enabling a third generation (3G) user to safely access to network. When a link control protocol (LCP) attribute and a user name of a client, which are acquired by layer 2 tunneling protocol network server (LNS), are acceptable, an temporary internet protocol (IP) address is selected from an established temporary IP address pool and distributed to the client, fixed information which is sent by the client and can verify the client identity is received, when the fixed information is received, the fixed information is correspondingly recorded with the user name and a password, the point-to-point protocol (PPP) connection with the client is disconnected to trigger the client to initiate a second time virtual private dial-up network (VPDN) call, the client is informed of the specified IP address which is distributed by authentication, authorization and accounting (AAA) server to the client according to the recorded fixed information, the user name and the password, or when the fixed information is received, the fixed information, the user name and the password are directly sent to the AAA server to verify the client, and after the client passes the authentication, the client is informed of the specified IP address which is distributed by the AAA server to the client. By means of the method and the device, the client can access to network only when the client is subjected to safety authentication by the LNS, and the safety of network access is improved.
Owner:NEW H3C TECH CO LTD
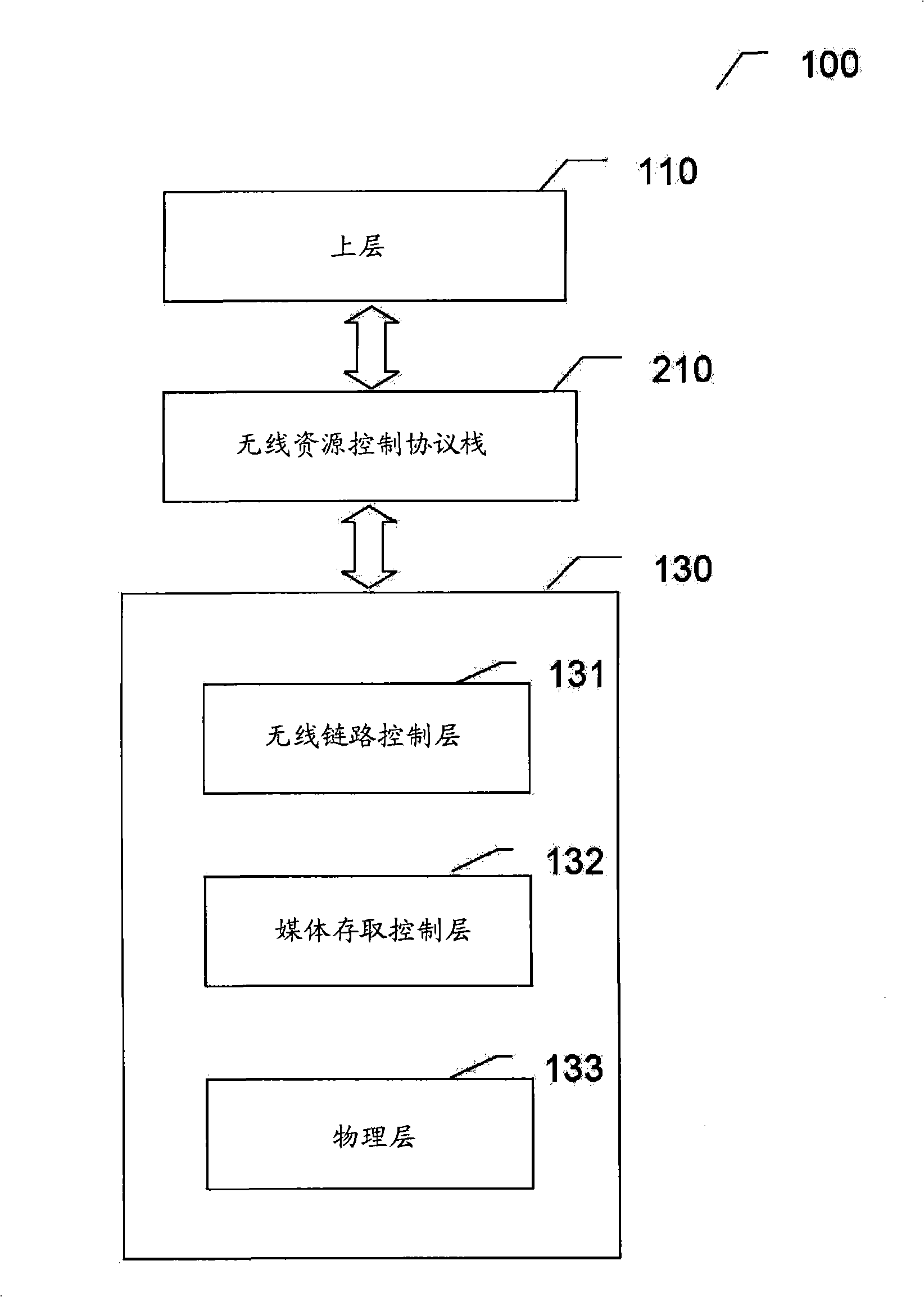
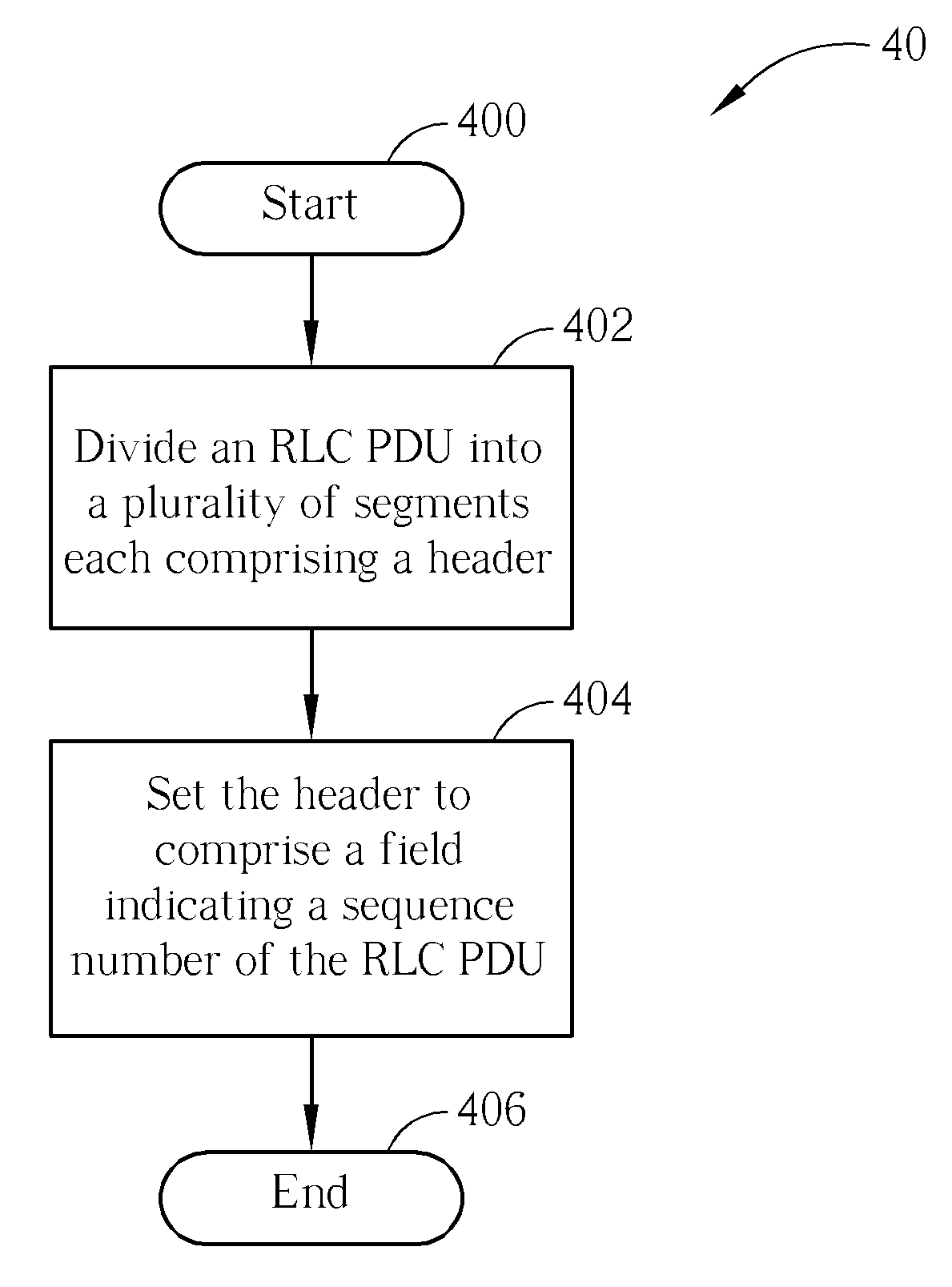
Method and Apparatus for Setting Headers in a Wireless Communications System
InactiveUS20090046608A1Accurate settingNetwork traffic/resource managementRadio/inductive link selection arrangementsCommunications systemRadio Link Control
A method for setting headers in a transmitter of a wireless communications system includes dividing a Radio Link Control Protocol Data Unit into a plurality of segments each including a header, and setting the header to include a field indicating a sequence number of the Radio Link Control Protocol Data Unit.
Owner:INNOVATIVE SONIC
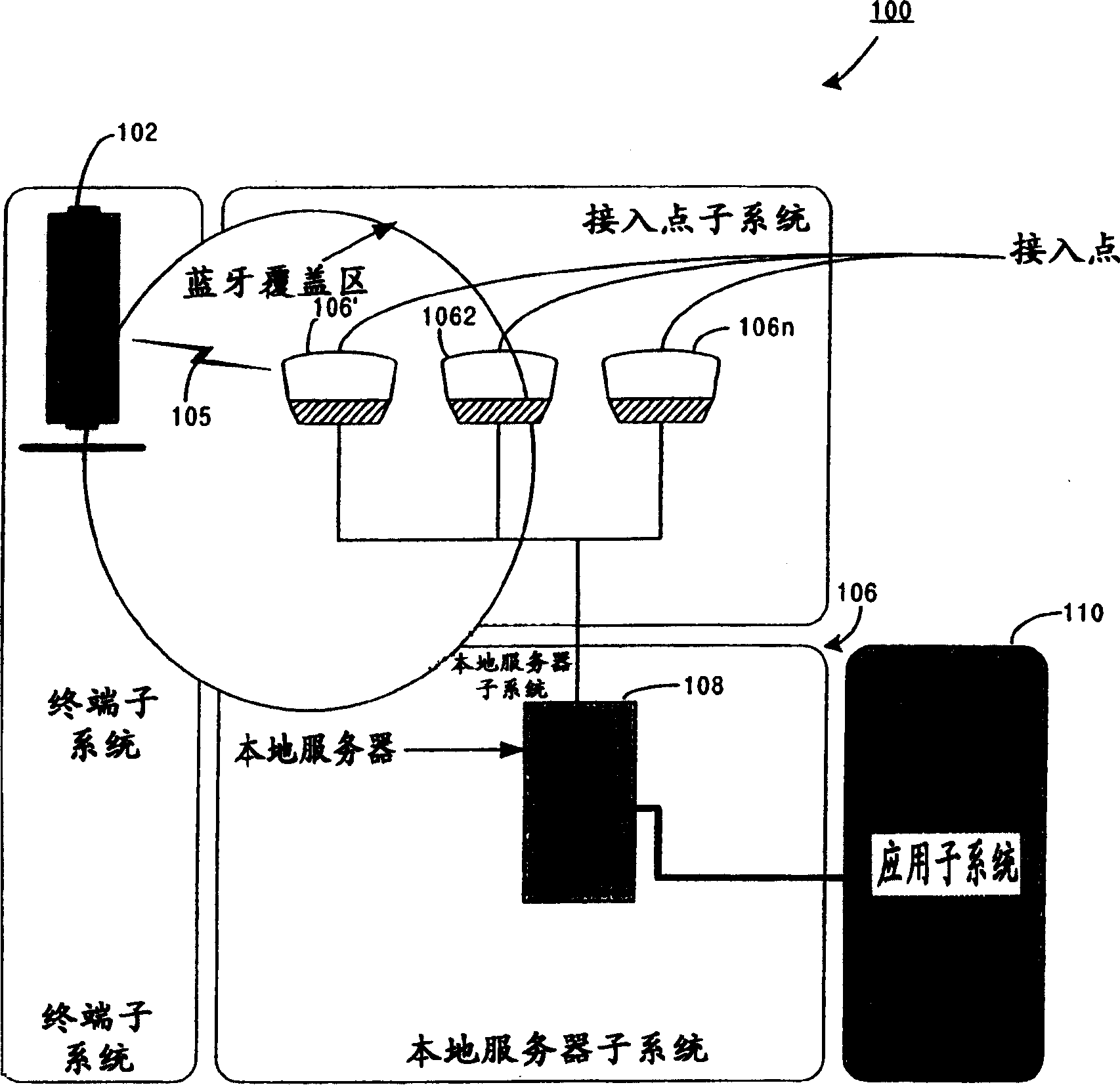
Short-range radio terminal adapted for data streaming and real time services
InactiveCN1538633ASend appropriateData switching by path configurationNear-field systems using receiversStreaming dataReal time services
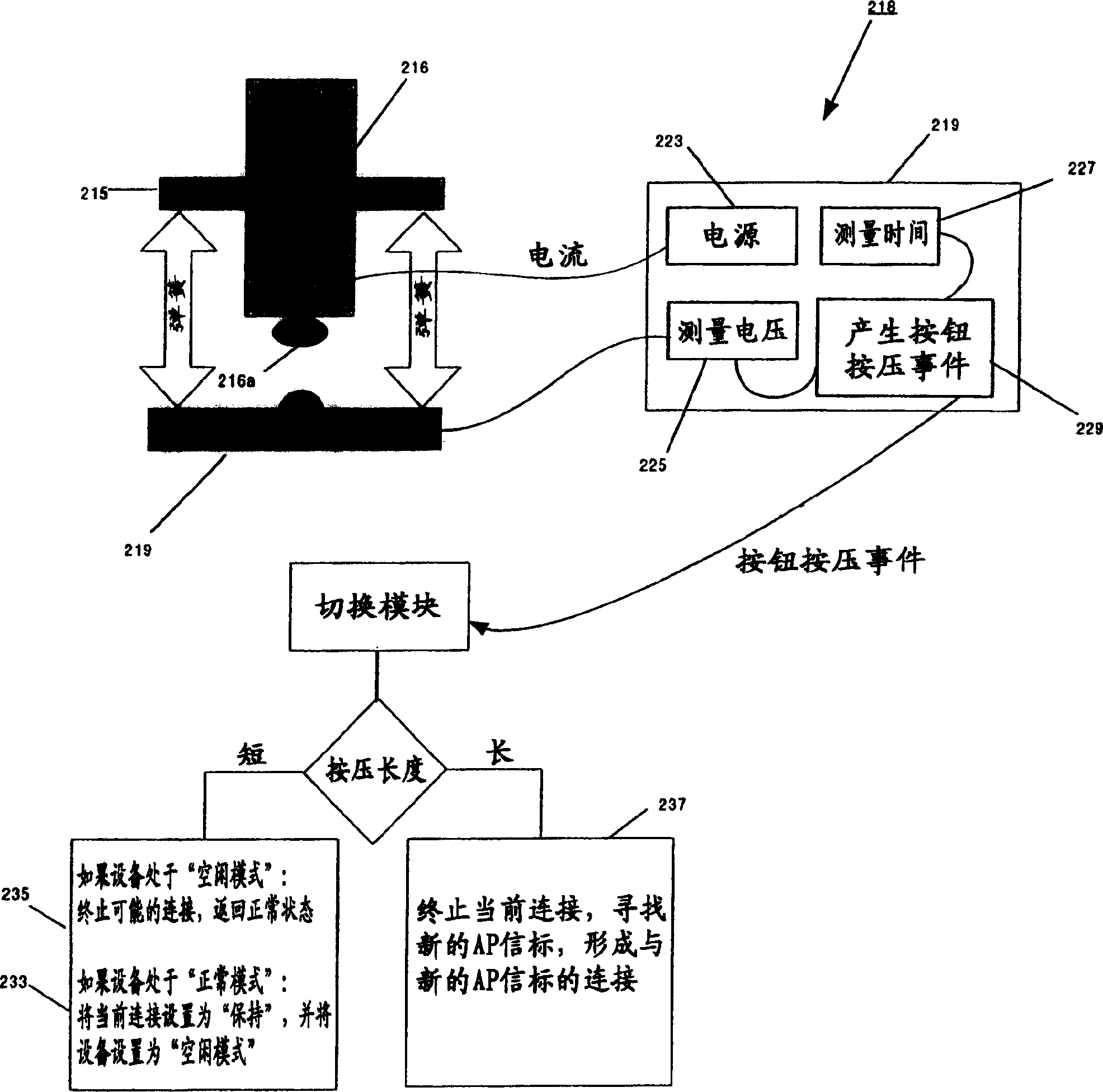
A local services platform including a server subsystem is connected to one or more APs; an application subsystem and provides headset / terminals (HS) with real-time services. A streaming interface is installed between the server and the application. The HS is capable of being activated and paired with a host device, typically a telephone under standard Link Control Protocol. The HS includes an extra button, when operated, causes the host to place the HS in an 'idle' mode. During the 'idle' mode, the HS listens to AP inquiries or carries out inquiries. When an AP beacon is detected, the HS requests a HOLD state from the paired telephone and receives streaming data after completing a connection to the AP beacon. When the streaming data is in channels, the HS can switch among the channels or end the transmission by operating the idle button.
Owner:NOKIA TECHNOLOGLES OY
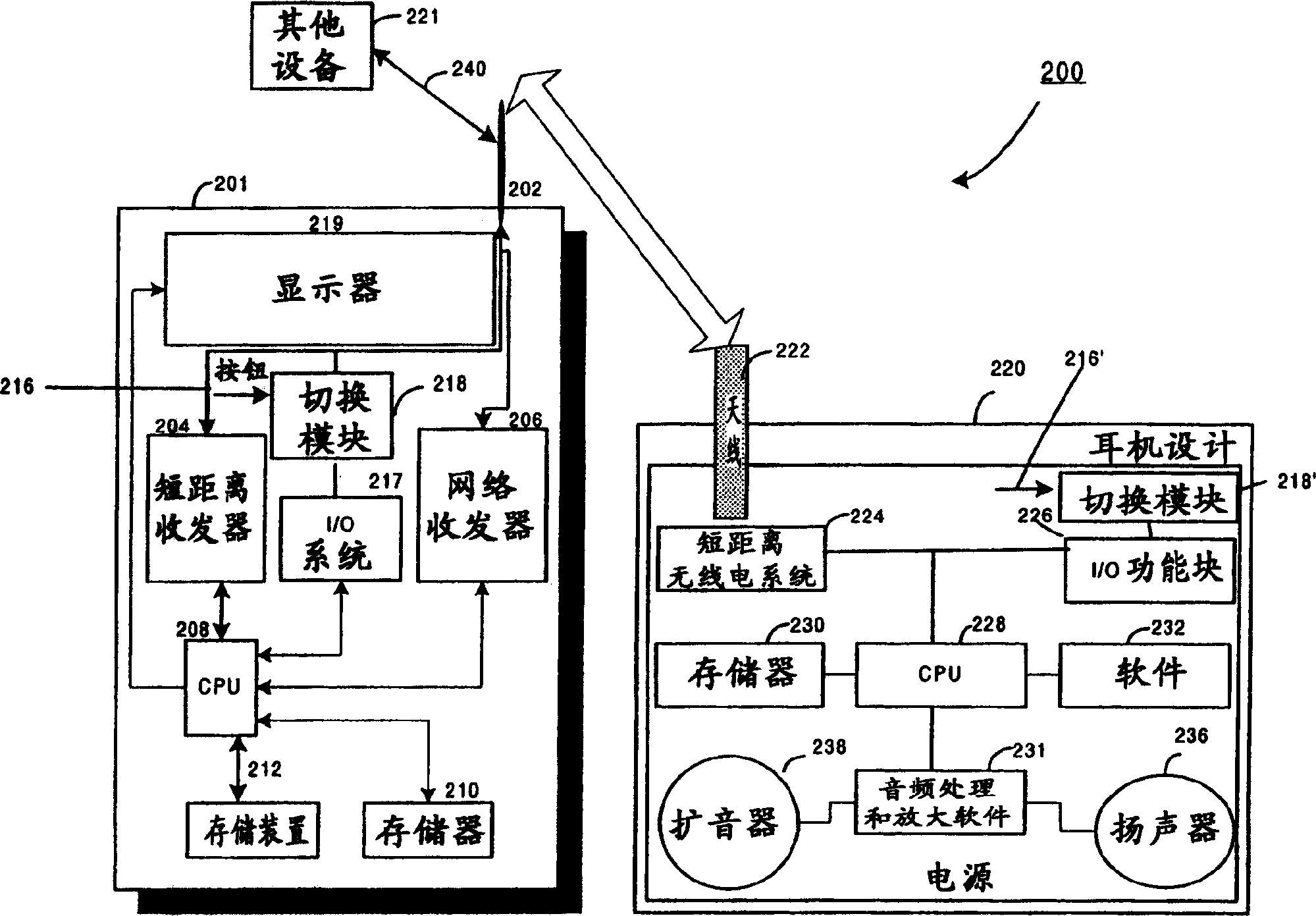
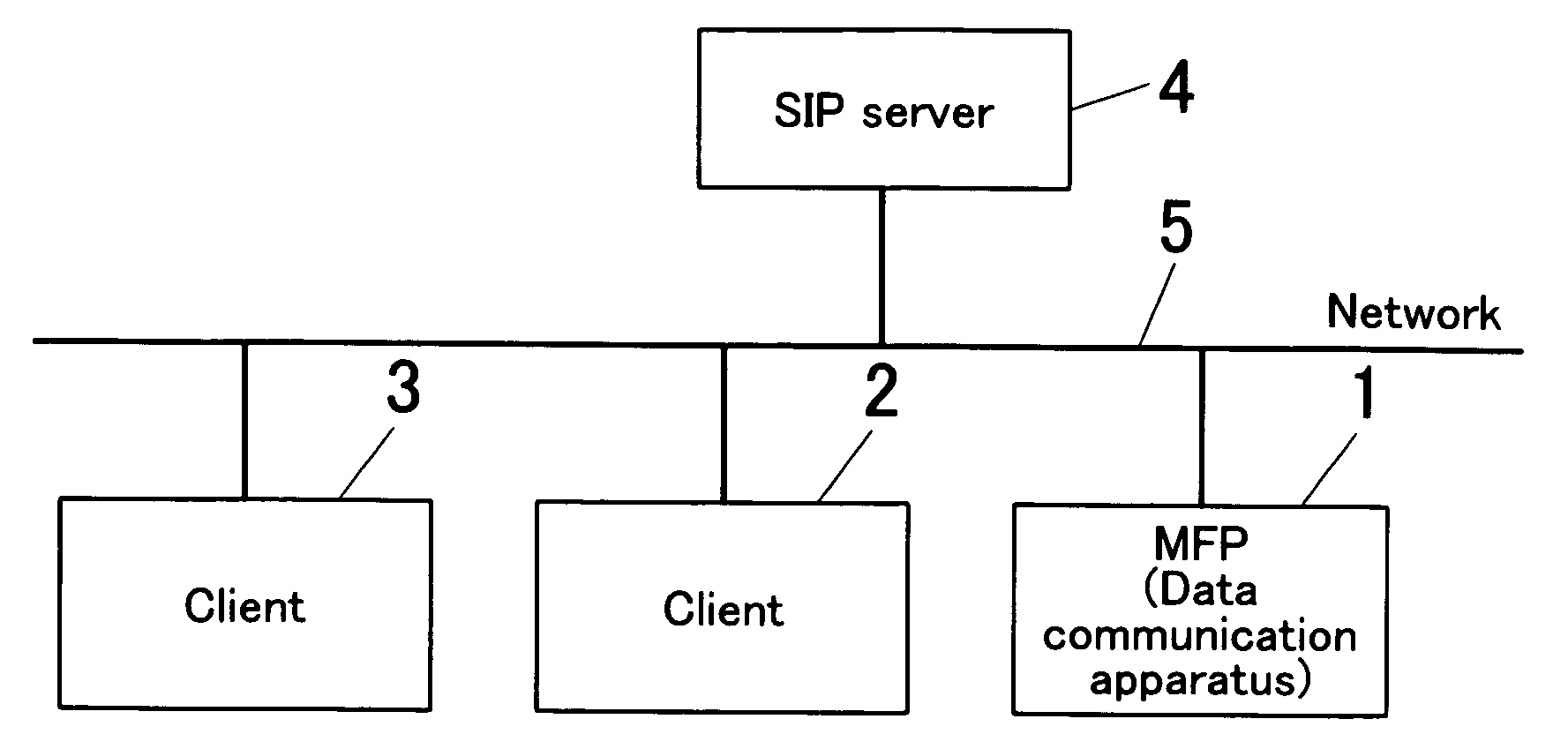
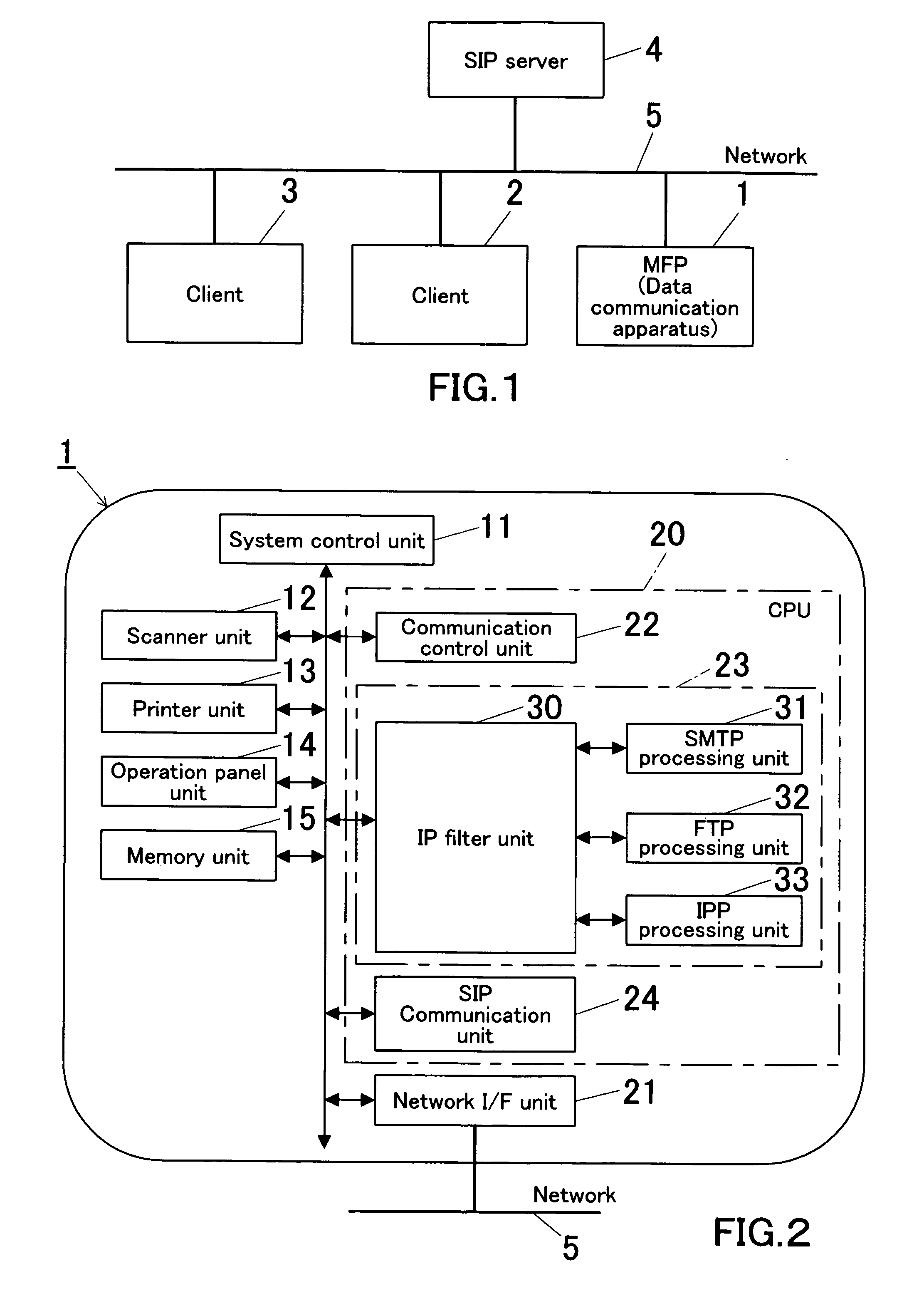
Data communication apparatus, data communication method and data communication processing program
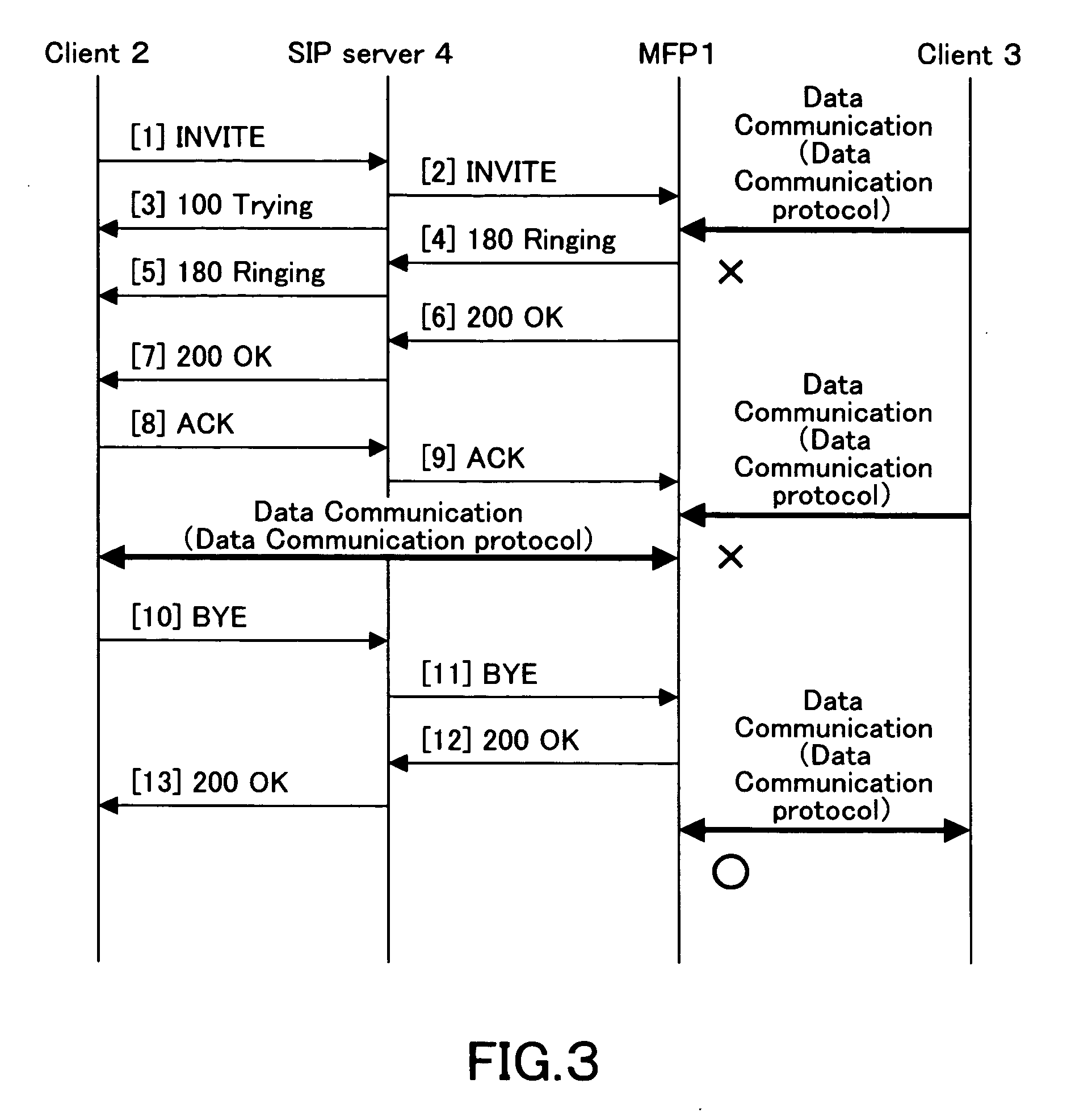
ActiveUS20070171821A1Efficient receptionError preventionTransmission systemsIp addressNetwork Communication Protocols
A data communication apparatus, comprising: a first control unit for controlling a client trying to access in order to establish a session by a call control protocol, for data communication by a data communication protocol that is other than said call control protocol; an IP address acquiring unit for acquiring an IP address of said client from the data of said call control protocol; and a second control unit for rejecting data communication from a client, which IP address is other than said acquired IP address, while and after said session is established.
Owner:KONICA MINOLTA BUSINESS TECH INC
Method for transmitting data packets by utilizing real-time transmission protocol and its control protocol
A method of transmitting data packets, in particular a real-time or near-real-time data over an internet protocol (IP) network using a real-time protocol (RTP) for media data packets and a real-time control protocol (RTCP) for control data packets. Each protocol is allocated a fraction of the available transmission bandwidth. The method comprises the steps of determining the needed RTCP bandwidth based on known link parameters for an individual media session, transmitting control data packets using the needed RTCP bandwidth and transmitting media data packets using the remainder of the available bandwidth.
Owner:PANASONIC CORP
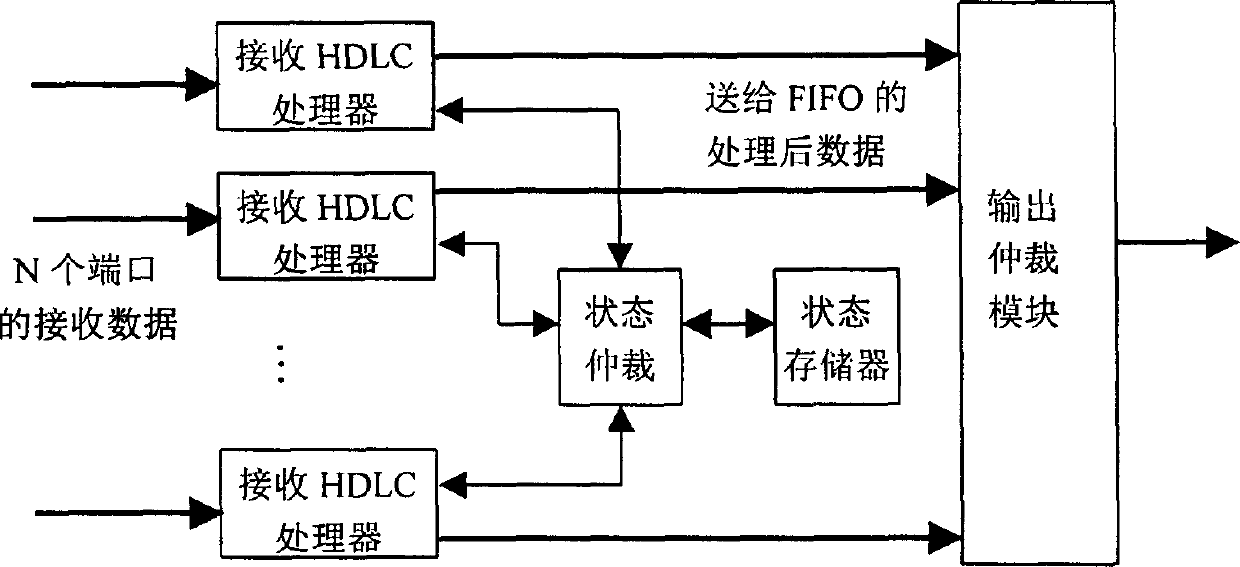
High speed data link control protocol receiving processing module and data processing/method
This invention relates to a HDLC protocol receiving process module and its data process method, in which, the module is composed of a port arbitration module, a receiving HDLC protocol processor and a module of state memory. The data process method is that N-port shared data process pipelines provide arbitration to the port arbitration module and send data to be processed to the receiving HDLC protocol processor orderly according to priorities which reads out the state data of its belonged HDLC channel from the state memory module to be processed in pipeline and write back the new state data to the memory. Using one parallel HDLC protocol receiving processor to process all port data streams.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com