Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
549 results about "Network level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network Level Authentication (NLA) is a technology used in Remote Desktop Services (RDP Server) or Remote Desktop Connection (RDP Client) that requires the connecting user to authenticate themselves before a session is established with the server.. Originally, if a user opened an RDP (remote desktop) session to a server it would load the login screen from the server for the user.
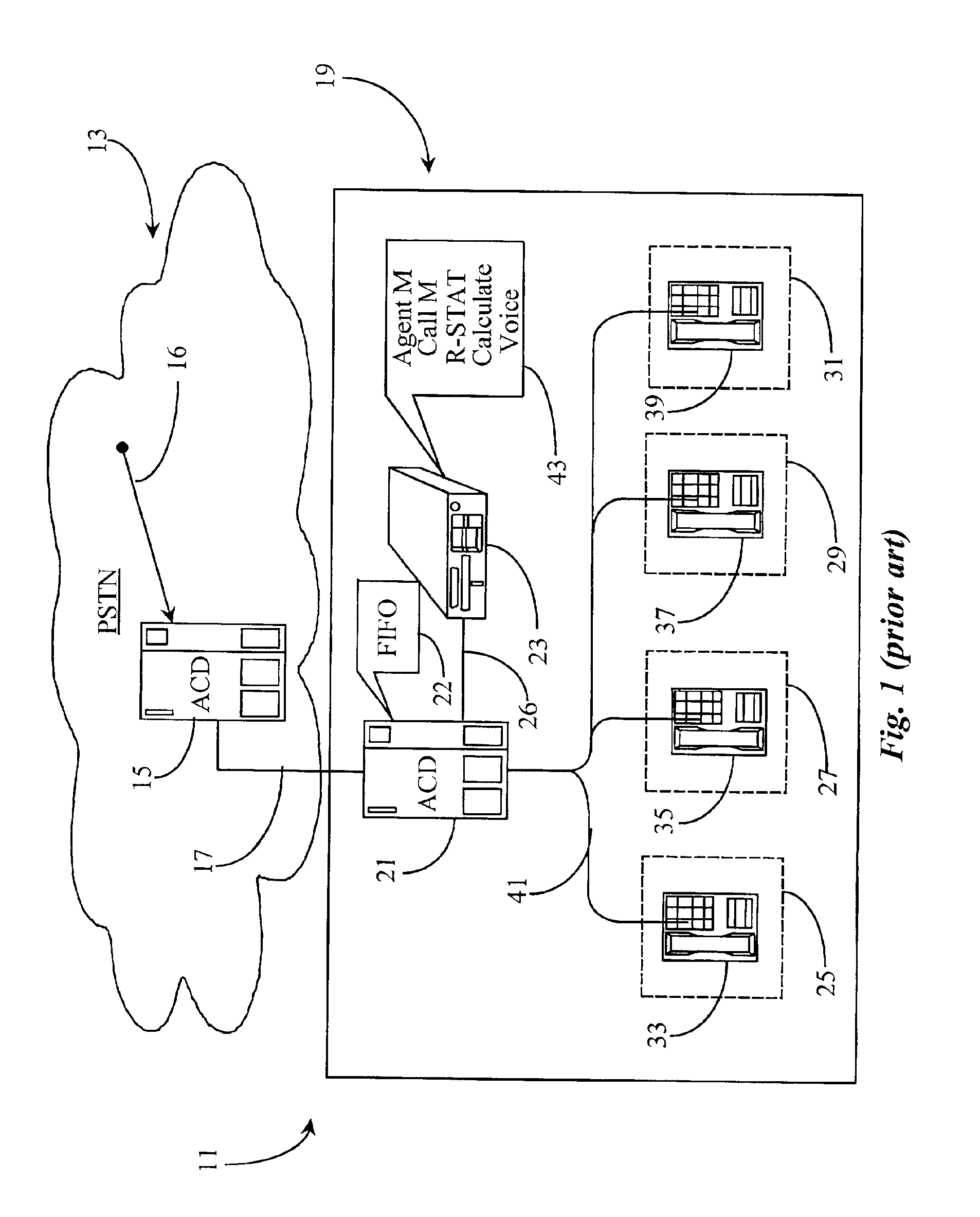
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS20070121596A1Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
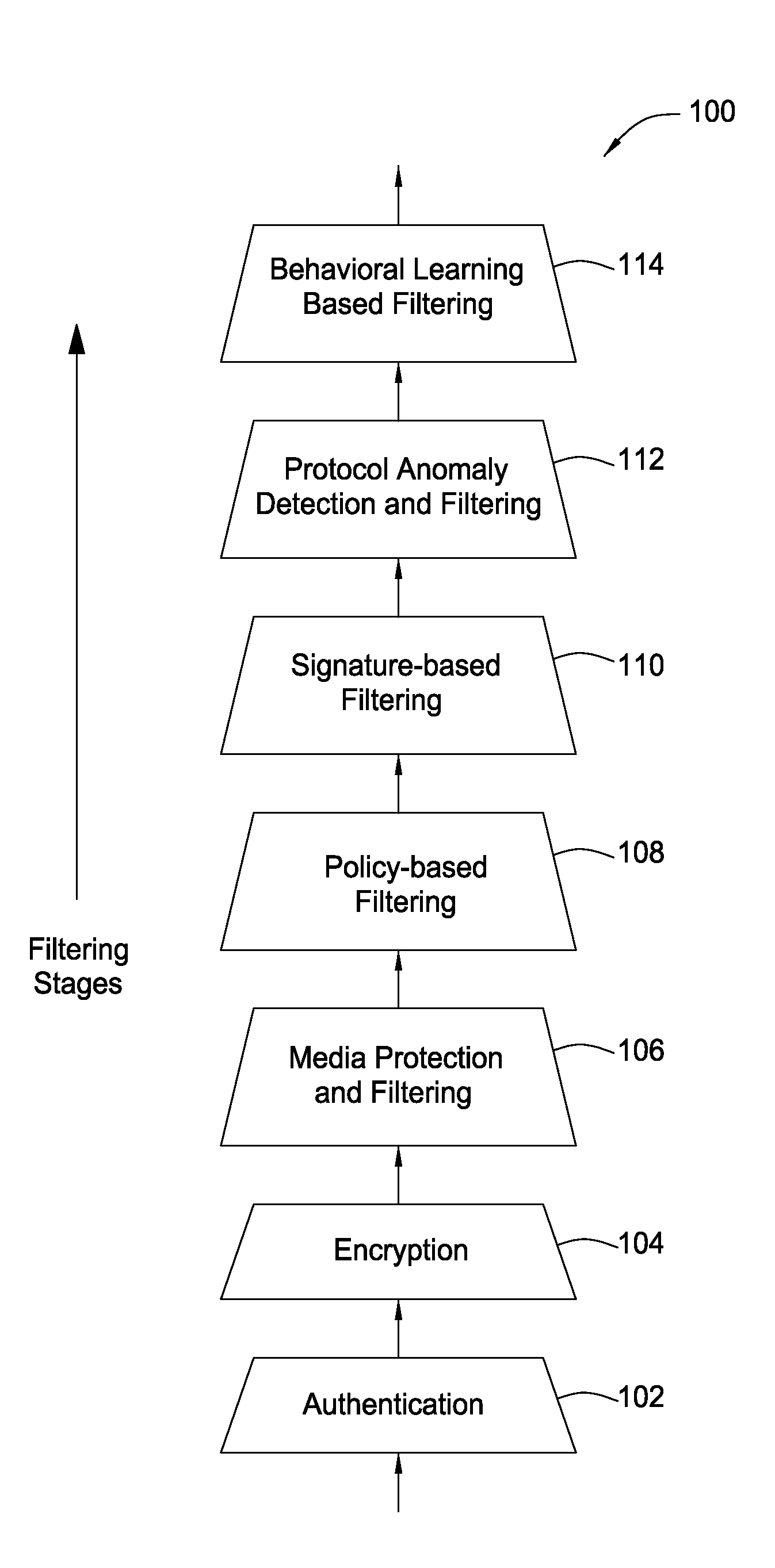
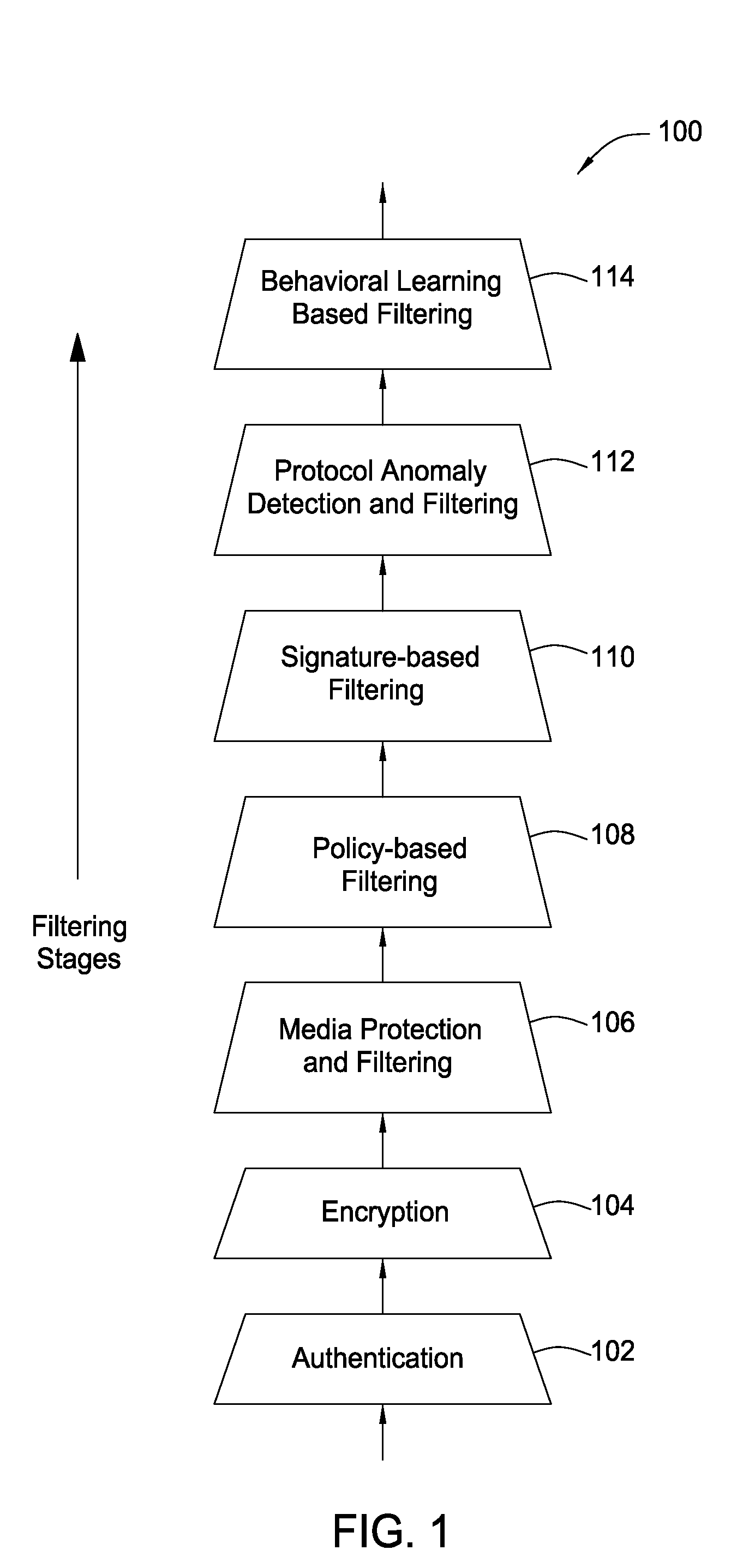
The present invention provides a system, method and apparatus for providing network level and nodal level vulnerability protection in VoIP networks by receiving a communication, filtering the received communication using three or more stages selected from the group comprising a media protection and filtering plane, a policy based filtering plane, a signature based filtering plane, a protocol anomaly detection and filtering plane and a behavioral learning based filtering plane, and either allowing or denying the received communication based the filtering step. The stages are applicable to one or more protocols including SIP, IMS, UMA, H.248, H.323, RTP, CSTA / XML or a combination thereof. In addition, the stages can be implemented within a single device or are distributed across a network (e.g., SIP network, a UMA network, an IMS network or a combination thereof).
Owner:AVAYA INC
Apparatus and method for analyzing and filtering email and for providing web related services
InactiveUS20060184632A1Eliminate the problemSoftware engineeringDigital data processing detailsService provisionSpamming
The inventive methodology provides an integrated plug and play solution designed to protect home networks against spam, phishing emails, viruses, spyware as well as other similar threats. The described content filtering appliance can be used for processing of web and email traffic implemented and can be deployed as a stand-alone appliance. In one implementation, the content processing appliance utilizes backend content filtering provided by a remote scanning service accessed via a network. The system employs network level analysis and translation of content and executes various procedures to handle the network traffic. In an embodiment of the invention, the appliance is provided with an automatic remote updating capability, wherein the software and data used by the appliance can be updated remotely via a network. Finally, the appliance may also implement parental controls.
Owner:MARINO JOSEPH P
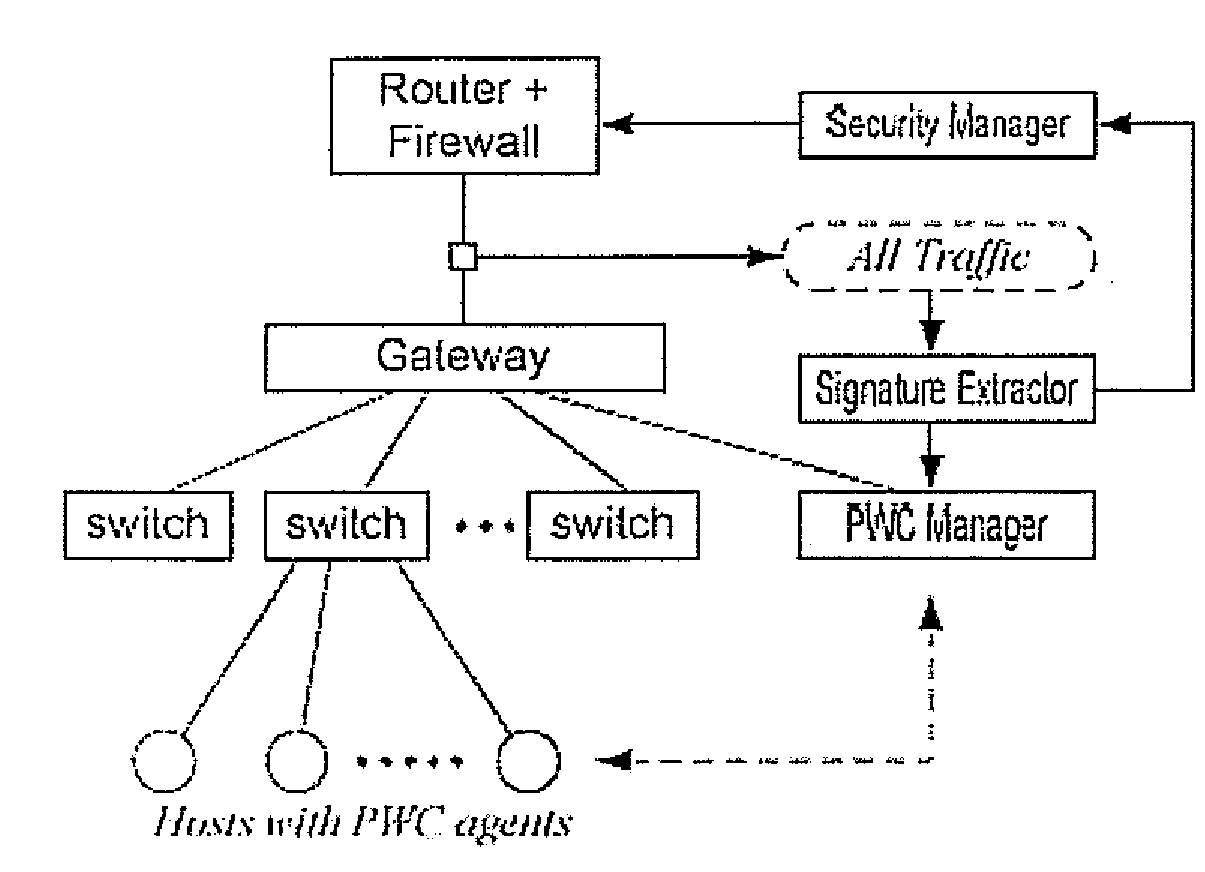
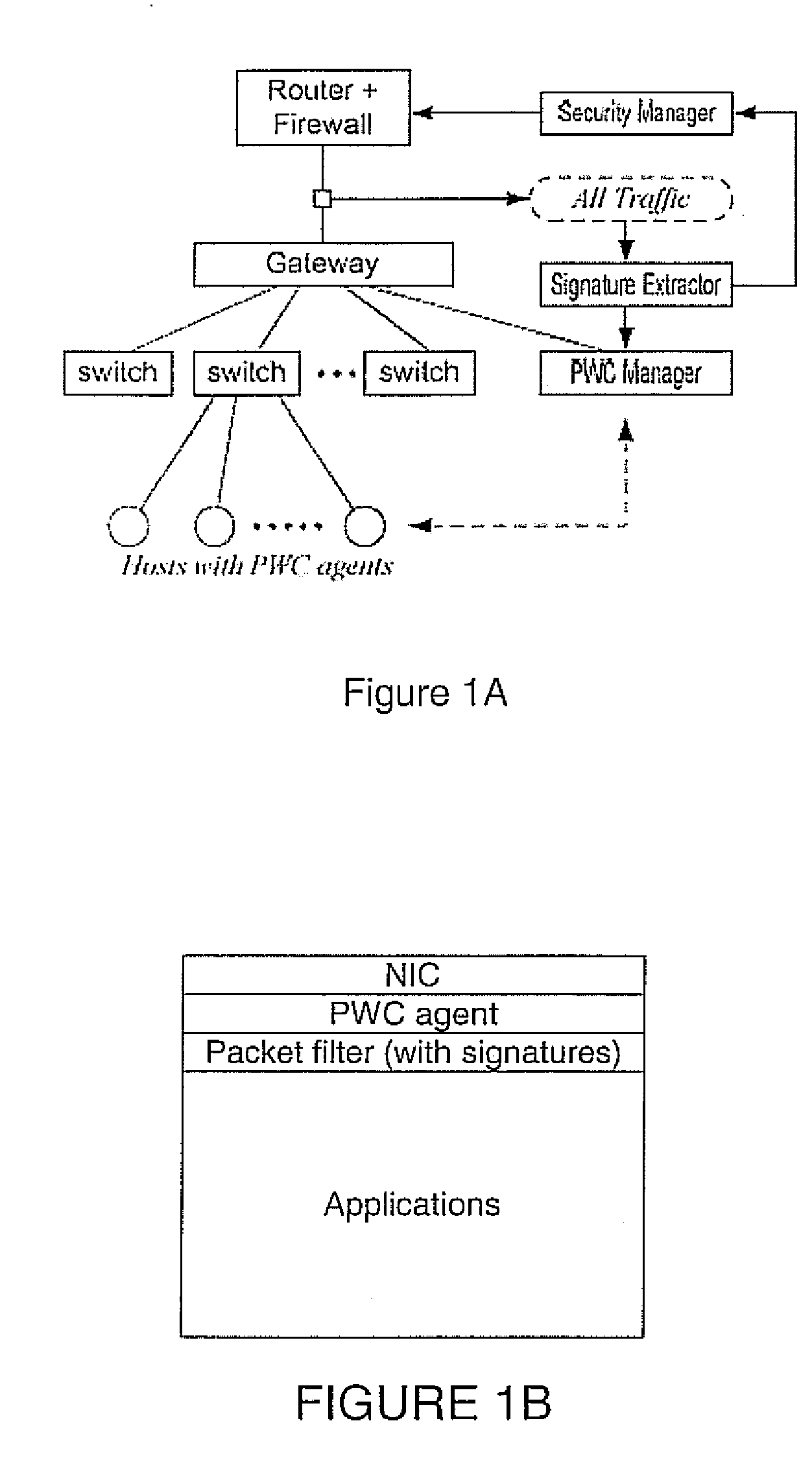
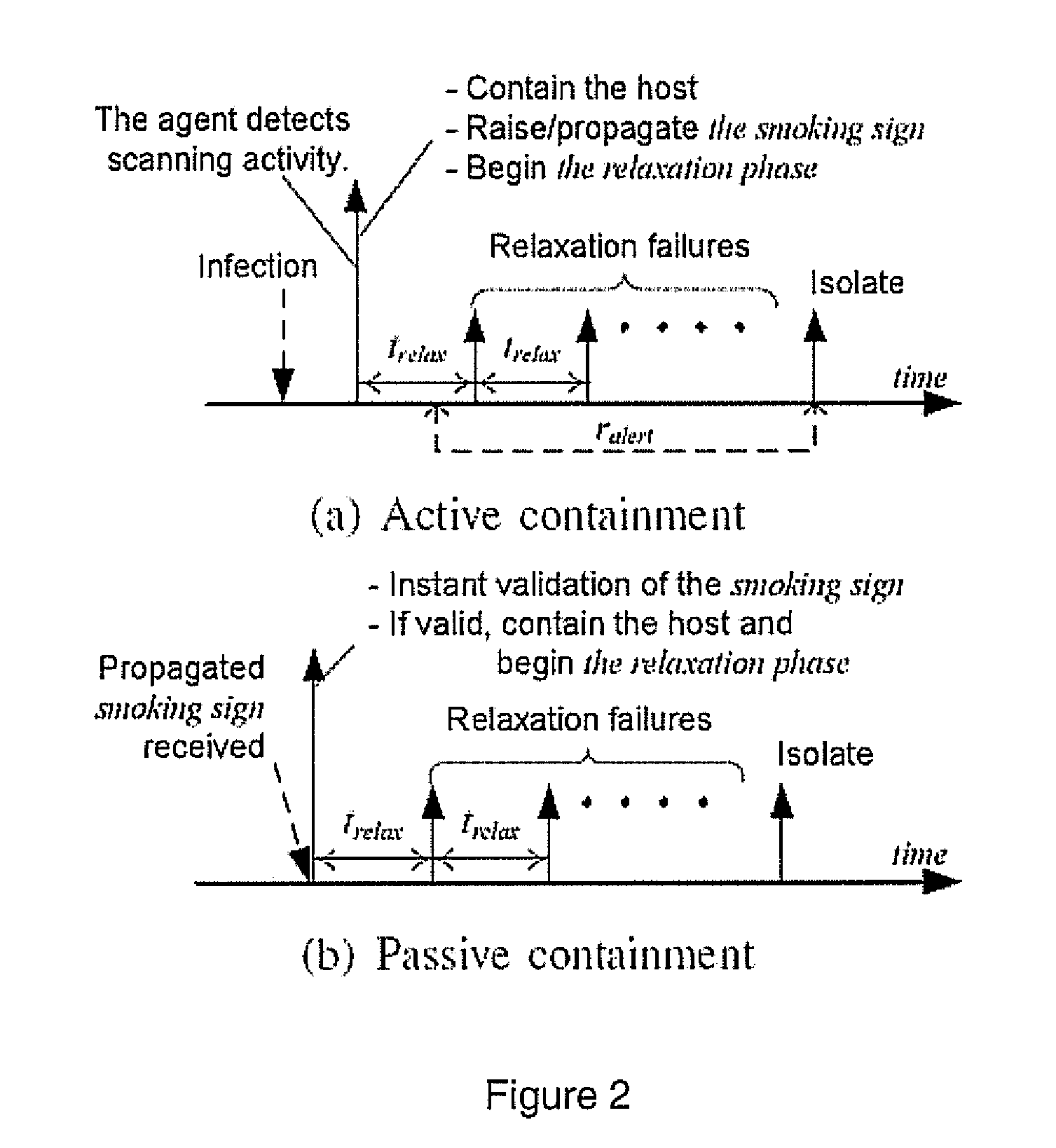
Proactive worm containment (PWC) for enterprise networks
ActiveUS20090031423A1Quick and proactive containmentAvoid false initial containmentMemory loss protectionError detection/correctionOperational systemNetwork level
A proactive worm containment (PWC) solution for enterprises uses a sustained faster-than-normal outgoing connection rate to determine if a host is infected. Two novel white detection techniques are used to reduce false positives, including a vulnerability time window lemma to avoid false initial containment, and a relaxation analysis to uncontain (or unblock) those mistakenly contained (or blocked) hosts, if there are any. The system integrates seamlessly with existing signature-based or filter-based worm scan filtering solutions. Nevertheless, the invention is signature free and does not rely on worm signatures. Nor is it protocol specific, as the approach performs containment consistently over a large range of worm scan rates. It is not sensitive to worm scan rate and, being a network-level approach deployed on a host, the system requires no changes to the host's OS, applications, or hardware.
Owner:PENN STATE RES FOUND
Method and apparatus for providing fair access to agents in a communication center
InactiveUS7236584B2Long latencyShort incubation periodIntelligent networksSpecial service for subscribersLong latencyTimer
A system for granting access to agents at a communication center in response to requests for connection from network-level entities starts a fairness timer having a fairness time period when a first request is received for and agent, monitors any other requests for the same agent during the fairness time, and executes an algorithm at the end of the fairness time to select the network-level entity to which the request should be granted. In a preferred embodiment the fairness time is set to be equal to or greater than twice the difference between network round-trip latency for the longest latency and shortest latency routers requesting service from the communication center. In some embodiments an agent reservation timer is set at the same point as the fairness timer to prevent calls to the same agent, and has a period longer than the fairness timer by a time sufficient for a connection to be made to the agent station once access is granted, and for notification of the connection to be made to network-level entities.
Owner:GENESYS TELECOMM LAB INC AS GRANTOR +3
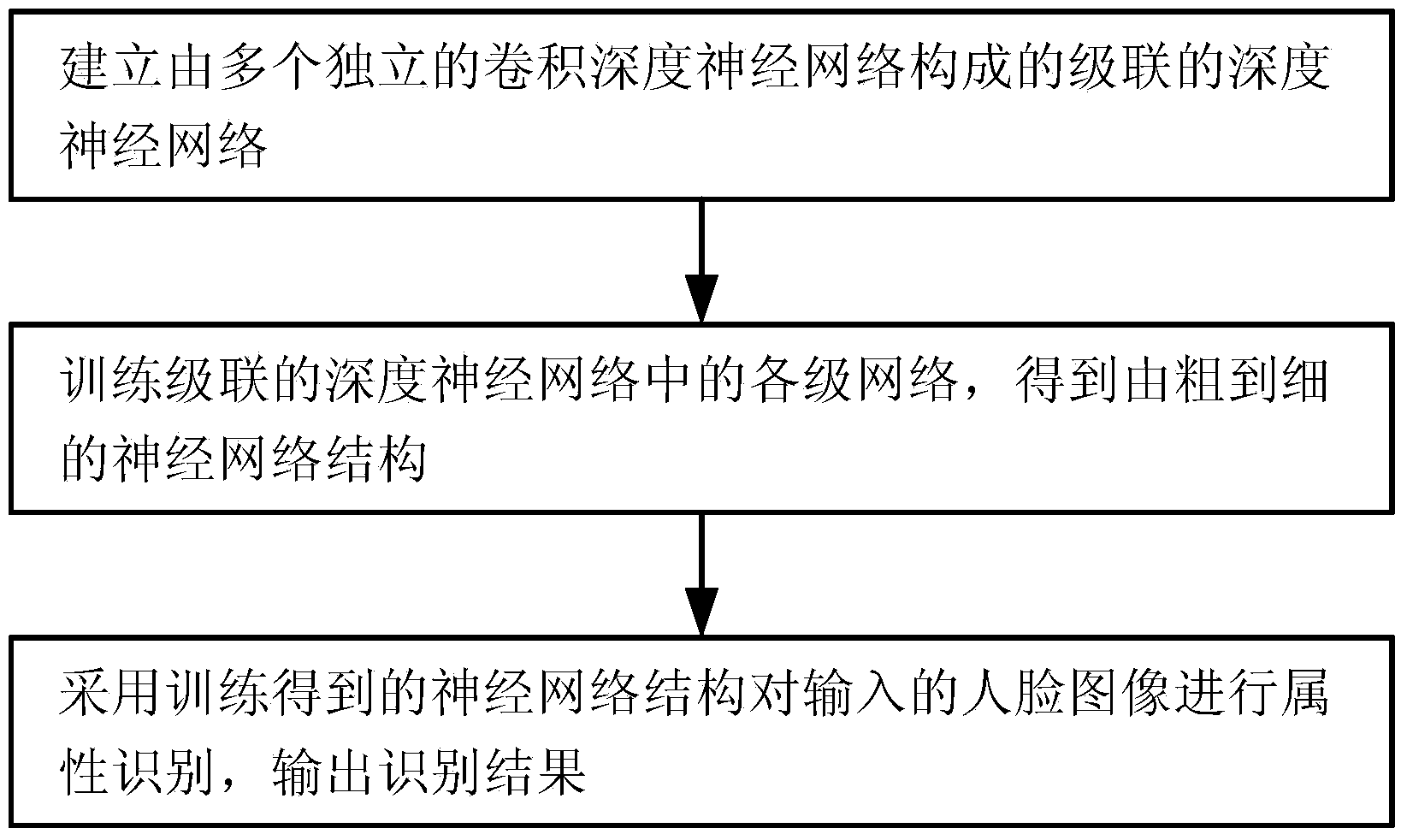
Cascaded depth neural network-based face attribute recognition method
ActiveCN103824054AHigh speedImprove accuracyCharacter and pattern recognitionNeural learning methodsPattern recognitionNetwork structure
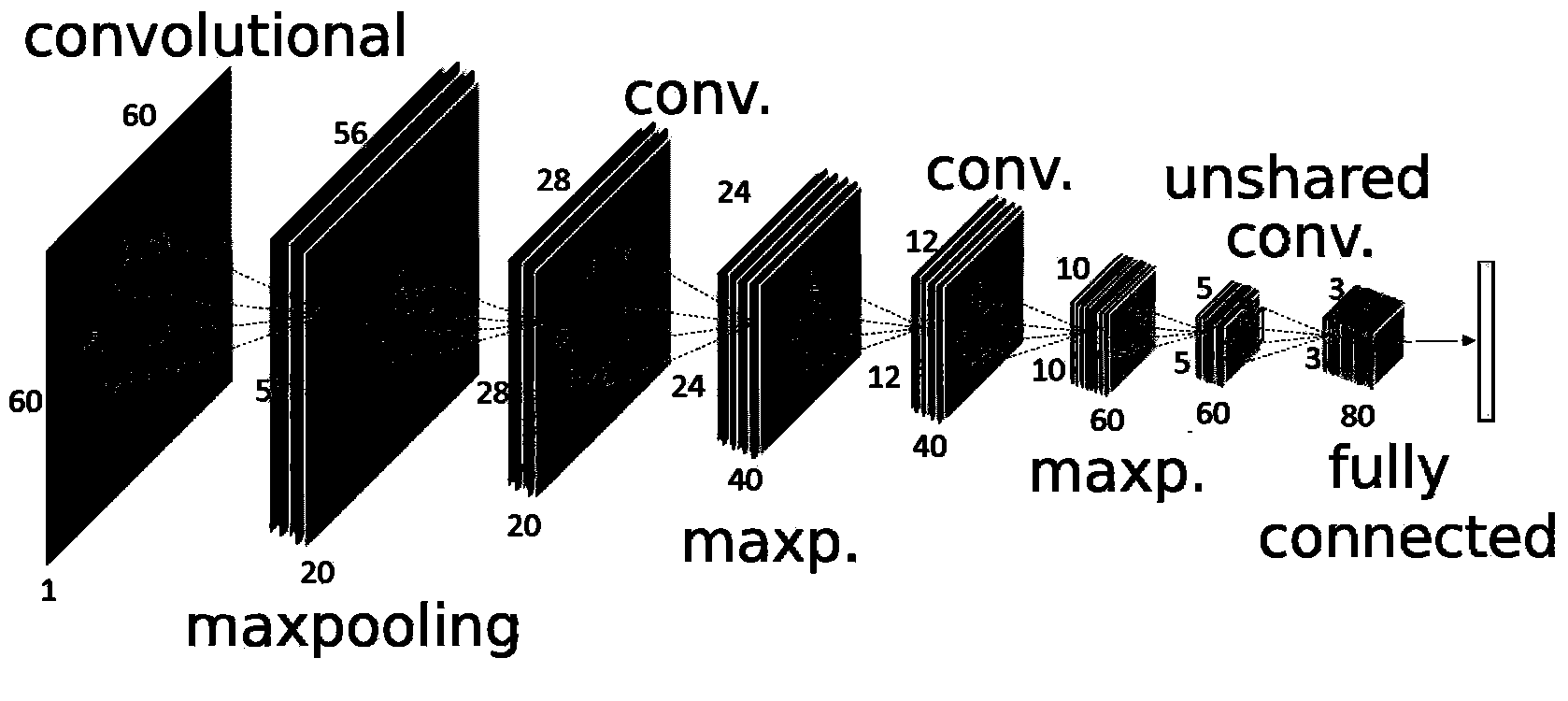
The invention relates to a cascaded depth neural network-based face attribute recognition method. The method includes the following steps that: 1) a cascaded depth neural network composed of a plurality of independent convolution depth neural networks is constructed; 2) a large number of face image data are adopted to train networks at all levels in the cascaded depth neural network level by level, and the output of networks of previous levels is adopted as the input of networks of posterior levels, such that a coarse-to-fine neural network structure can be obtained; and 3) the coarse-to-fine neural network structure is adopted to recognize the attributes of an inputted face image, and final recognition results can be outputted. According to the cascaded depth neural network-based face attribute recognition method of the invention, a cascade algorithm system is adopted based on depth learning, and therefore, training time can be accelerated; and a cascaded coarse-to-fine processing process is realized, and the performance of a final network can be improved by networks of each level through utilizing information of networks of upper levels, and therefore, the speed and the accuracy of face attribute recognition can be effectively improved.
Owner:BEIJING KUANGSHI TECH
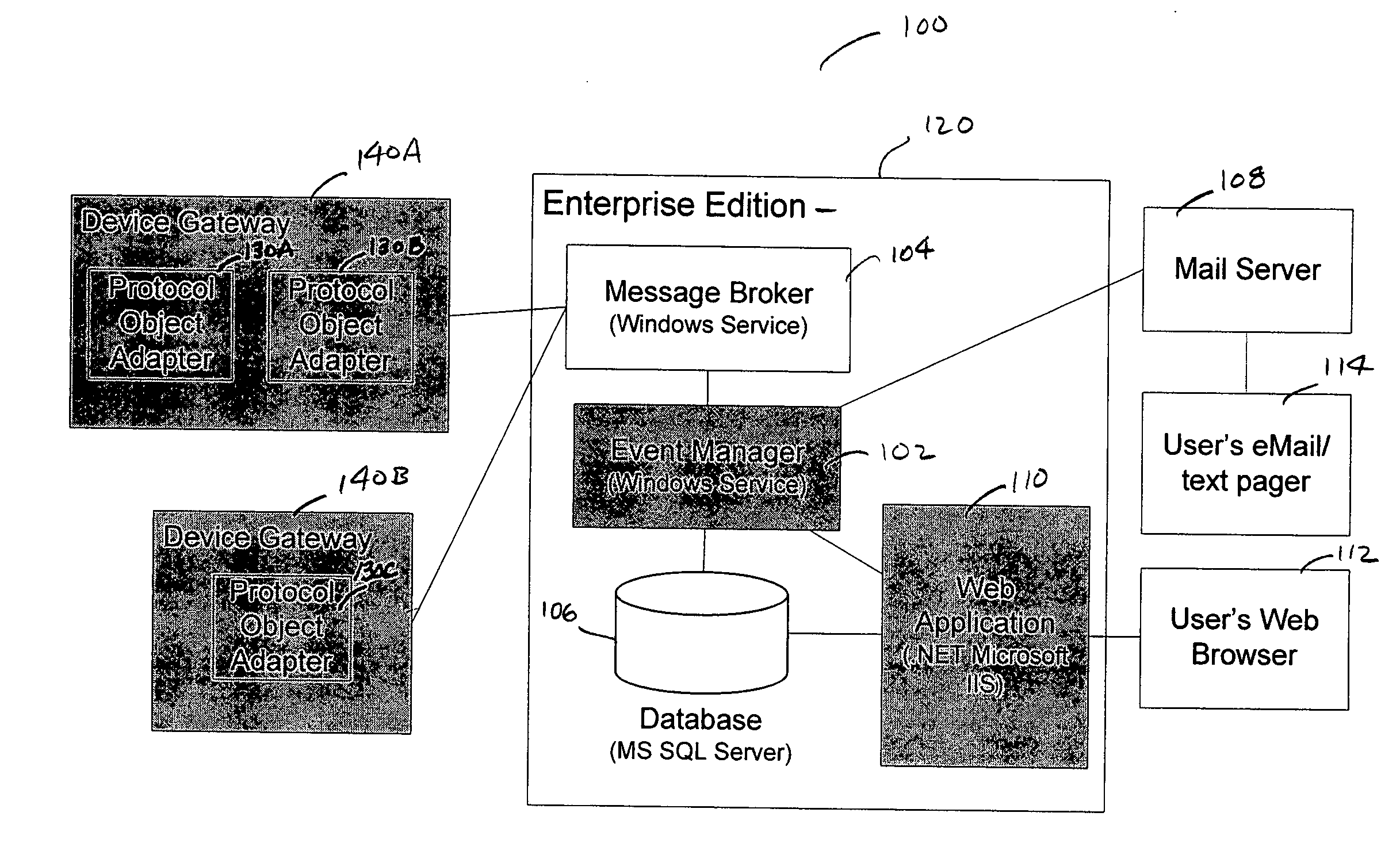
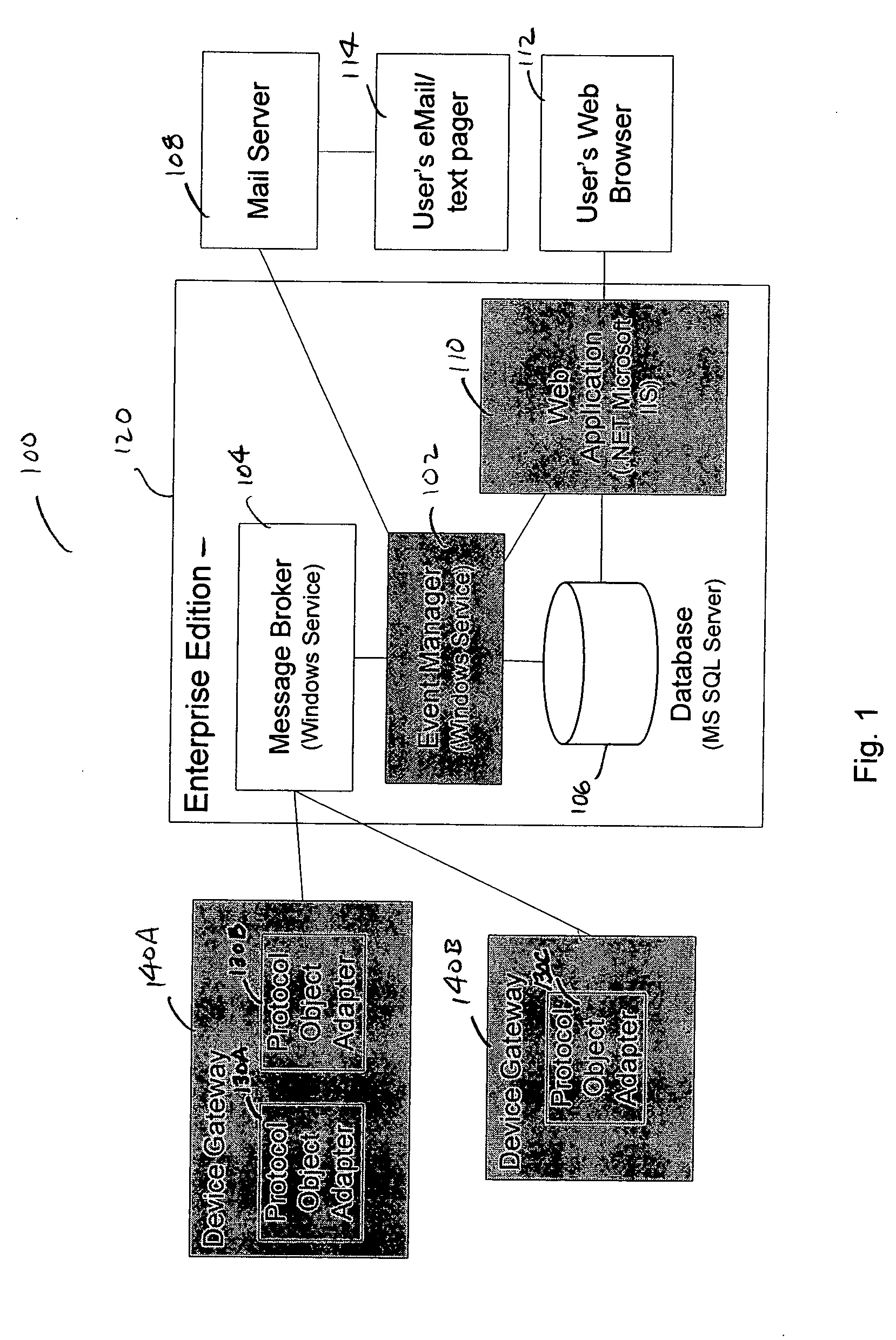
Event manager for use in a facilities monitoring system having network-level and protocol-neutral communication with a physical device
InactiveUS20060136558A1Multiple digital computer combinationsNetwork connectionsBuilding automationEvent management
A method and a system for the off site monitoring / diagnostics, command / control, alarm / event management, historical / trend analysis, and configuration / administration of building automation systems through an event manager for use in a facilities monitoring system having network-level and protocol-neutral communication with a physical device. The method includes managing a non internet protocol-based physical device, including coupling a device gateway with the physical device, wherein the device gateway is configured to expose the physical device as a networked device on a server. The method also includes receiving event information from the coupled physical device, wherein the event information includes an event and a device identifier; responsive to a determination that the event information includes an actionable event, processing the event, the device identifier, and the actionable event to determine a responsible process; and notifying the responsible process of the event.
Owner:MODIUS
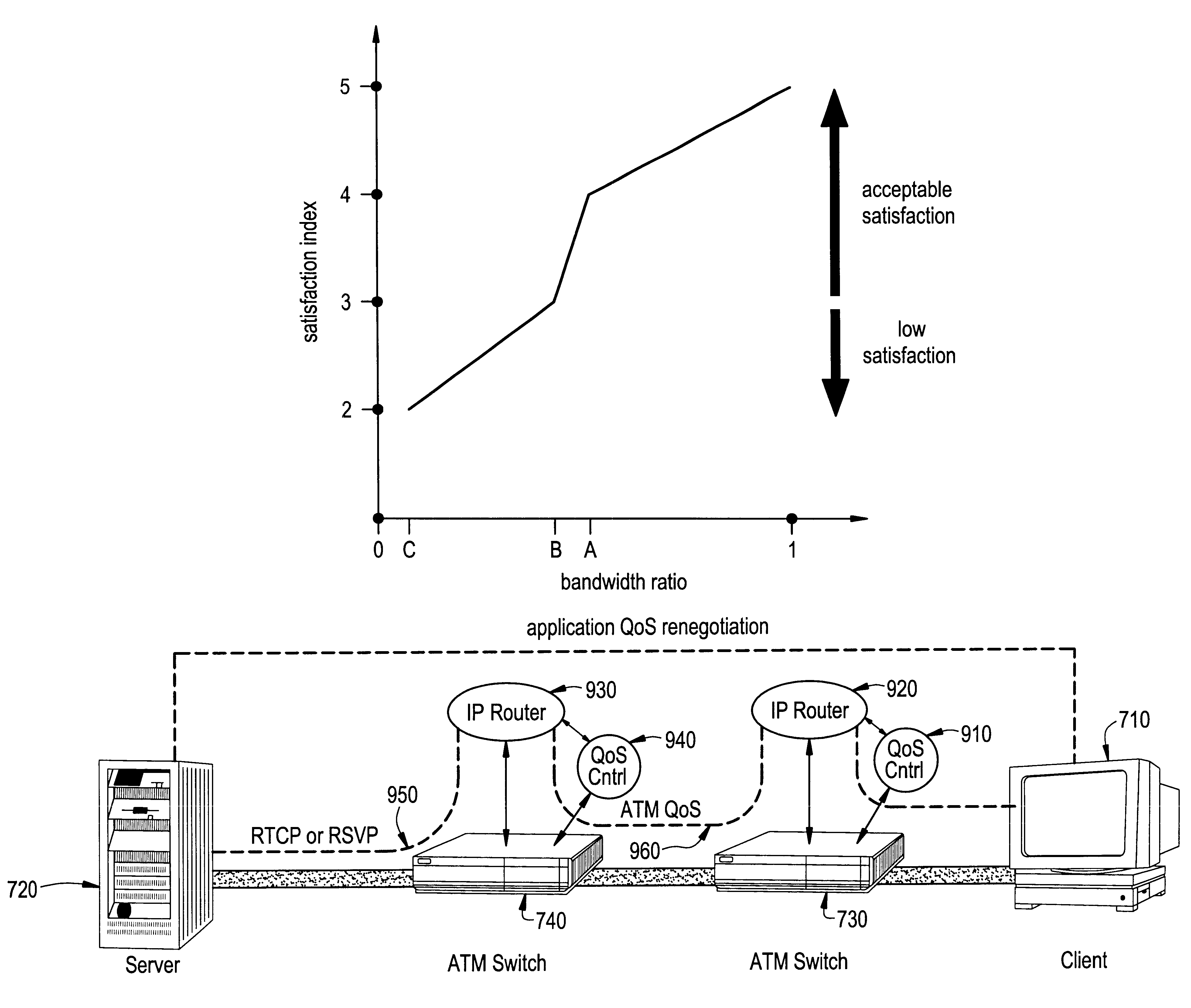
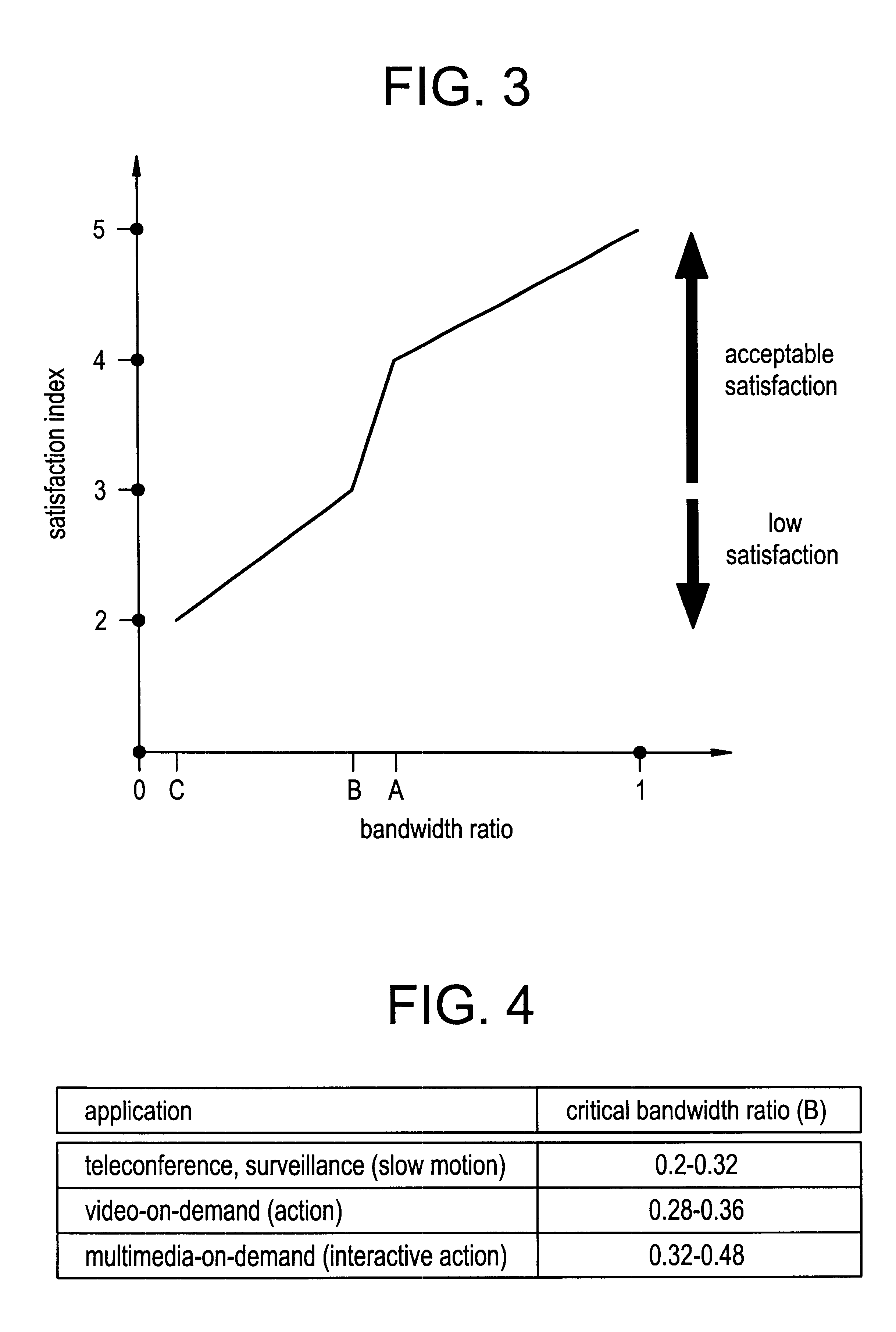
Dynamic network bandwidth allocation for multimedia applications with soft quality-of-service requirements
InactiveUS6404738B1Lower connection costsLow costError preventionFrequency-division multiplex detailsDynamic bandwidth allocationService level requirement
A new concept of soft quality-of-service (soft-QoS) is developed that bridges the gap between the efficient provision of network-level QoS and the requirements of multimedia applications. Soft-QoS is defined by a satisfaction index (a number that rates users' perceptual quality) and a softness profile (a function that captures the robustness of multimedia applications to network congestion). Another aspect of this invention is a bandwidth allocation scheme for multimedia applications with soft-QoS requirements is presented. The implementation of the bandwidth allocation scheme on a network element realizes a soft-QoS controller. The controller uses the connections' softness profiles to compute a bandwidth allocation that maximizes the minimum satisfaction index of active connections.
Owner:JUMIPER NETWORKS INC
Unified routing scheme for ad-hoc internetworking
InactiveUS7159035B2Data switching by path configurationMultiple digital computer combinationsRouting tableShort path algorithm
Routing table update messages that include both network-level and link-level addresses of nodes of a computer network are exchanged among the nodes of the computer network. Further, a routing table maintained by a first one of the nodes of the computer network may be updated in response to receiving one or more of the update messages. The routing table is preferably updated by selecting a next node to a destination node of the computer network only if every intermediate node in a path from the next node to the destination node satisfies a set of nodal conditions required by the first node for its path to the destination node and the next node offers the shortest distance to the destination node and to every intermediate node along the path from the next node to the destination node. The shortest distance to the destination node may be determined according to one or more link-state and / or node-state metrics regarding communication links and nodes along the path to the destination node. Also, the nodal characteristics of the nodes of the computer system may be exchanged between neighbor nodes, prior to updating the routing table. Preferred paths to one or more destination nodes may be computed according to these nodal characteristics, for example using a Dijkstra shortest-path algorithm.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Graphical user interface for network management
InactiveUS20070208840A1Easy to navigateDigital computer detailsProgram controlData setNetwork management
A graphical user interface (GUI) provides a plurality of views of a network and its elements in the same viewing engine. A user can switch between the plurality of views in a context-sensitive manner, each view showing relationship or interconnection information. The GUI allows a user to view inter-related objects at the same level, and to view at a lower level sub-objects that make up each of those objects. Different functional views can be provided at the same hierarchical or logical level based on the stored relationship information. A user can navigate between a network level view, a site level view, a shelf level view, and a schematic level view, via element selection or by zooming. A network element data set provides context-sensitive data and images to each level and view for that network element and enables automatic generation of a network topology.
Owner:CIENA
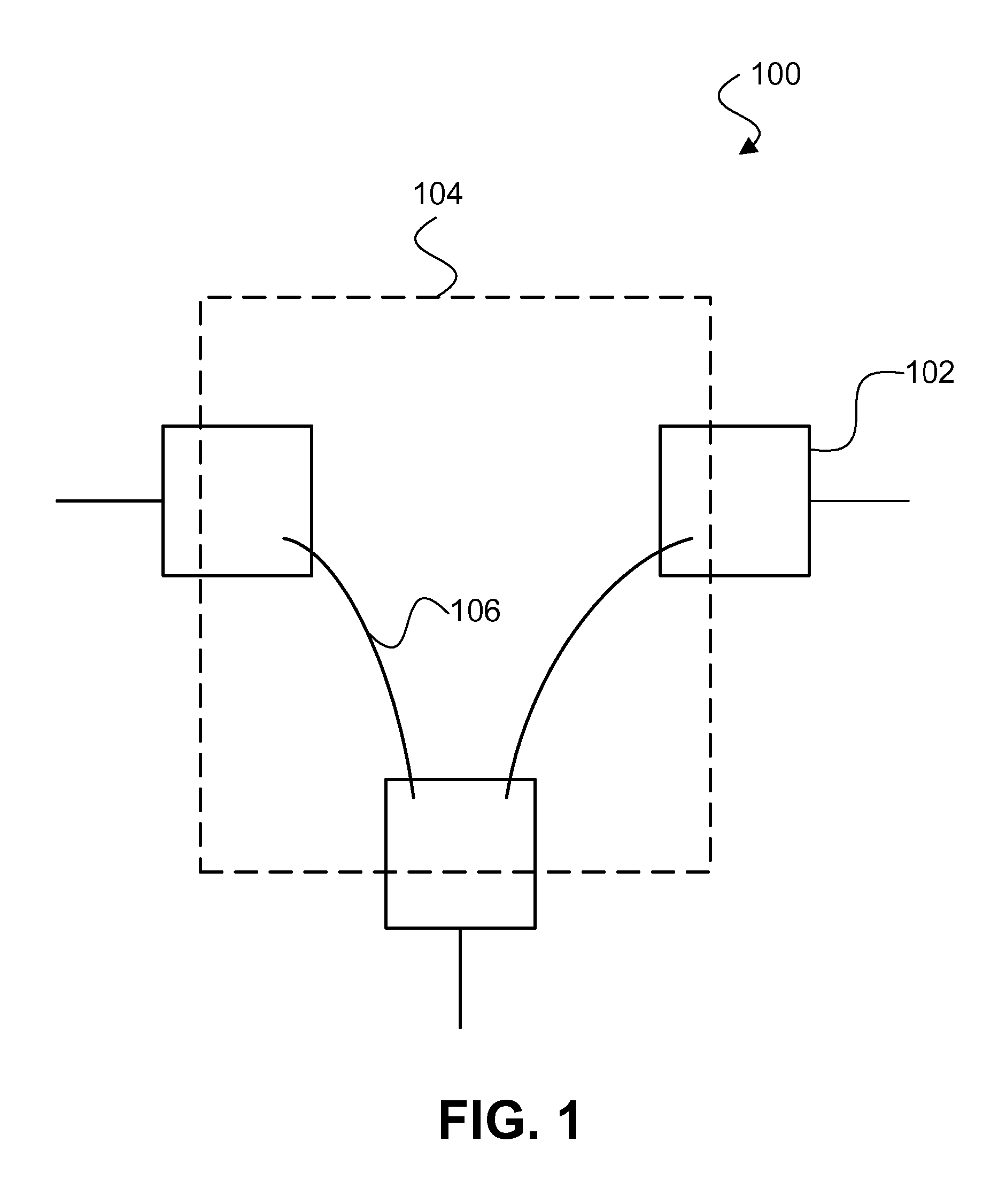
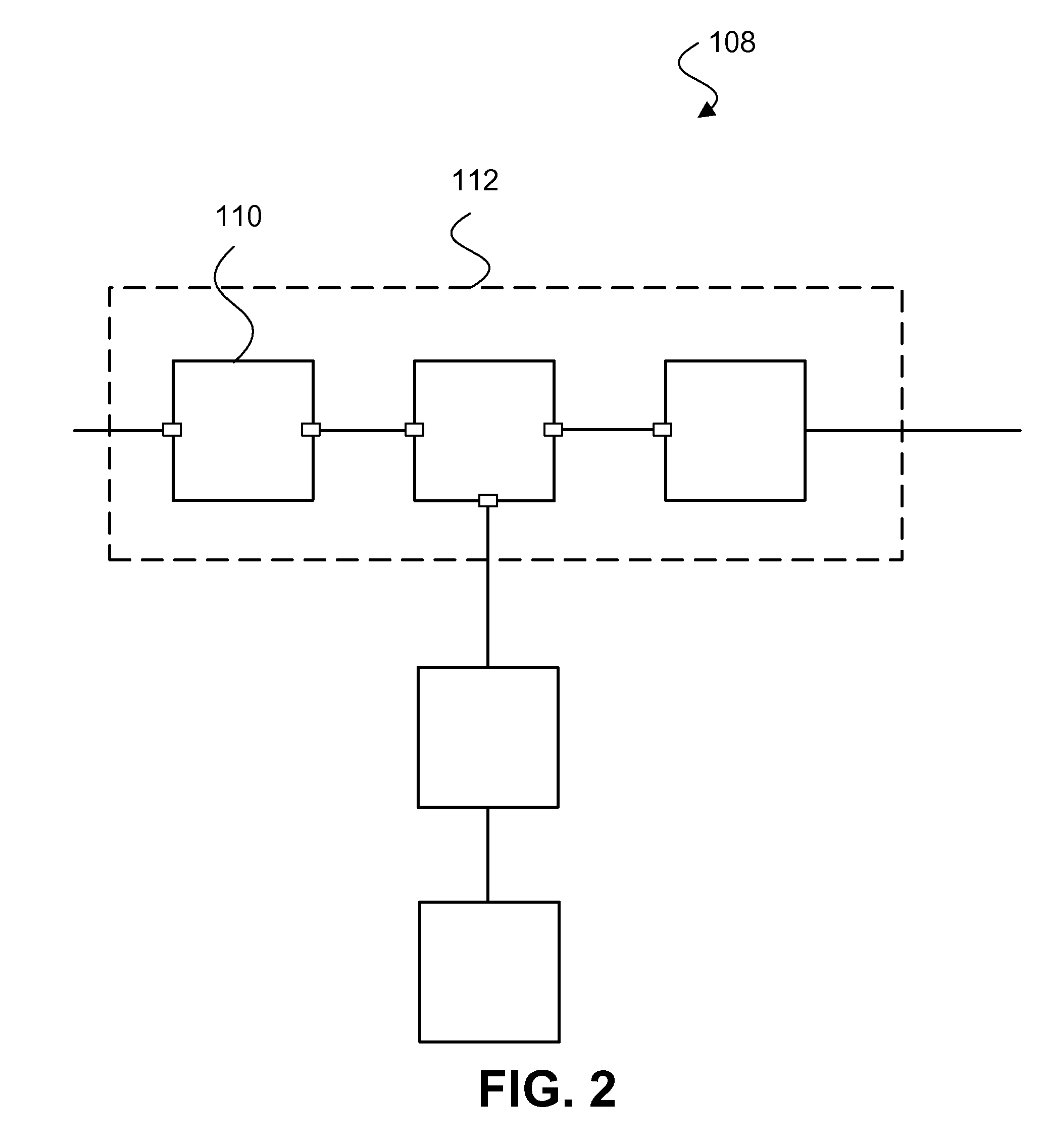
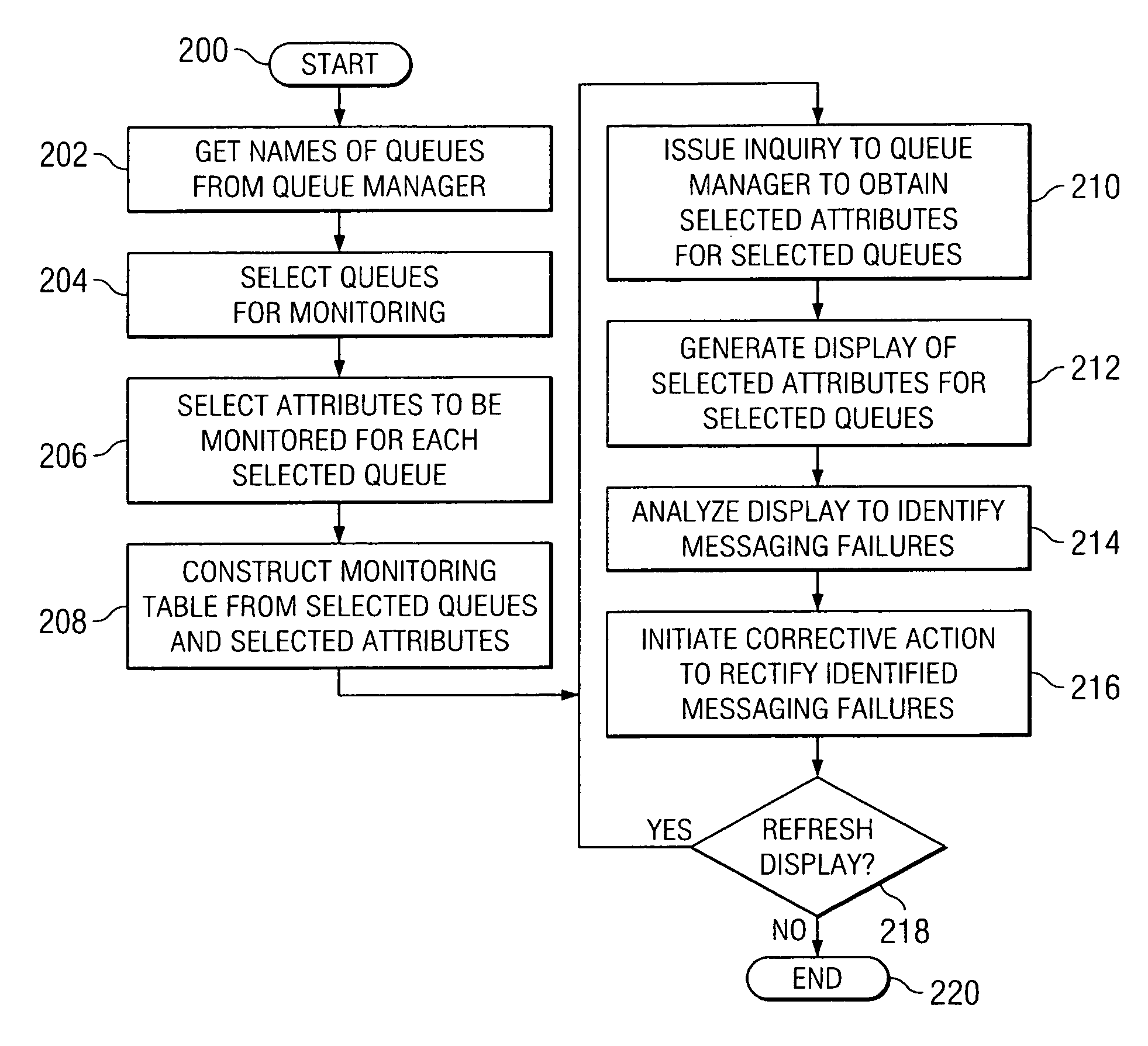
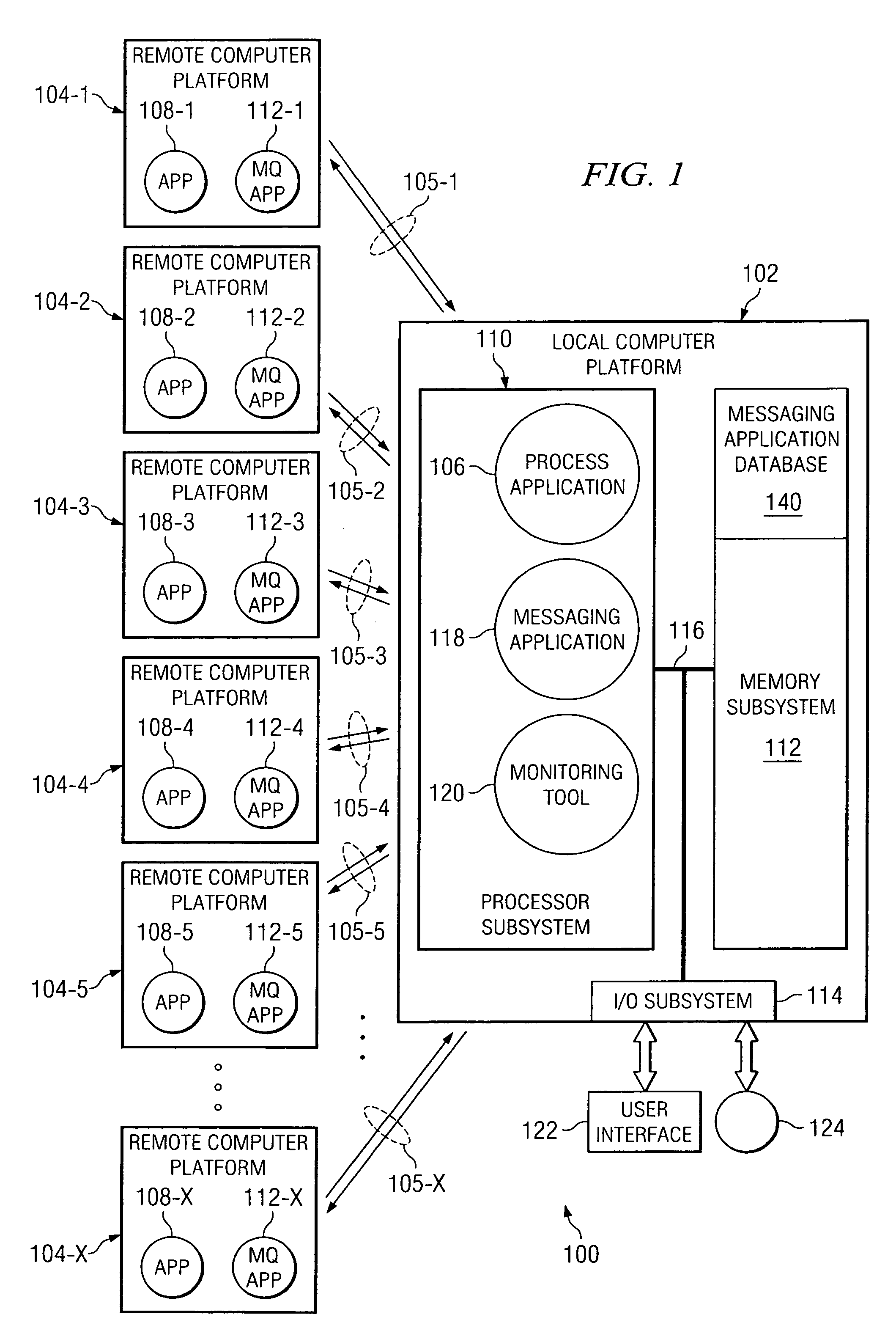
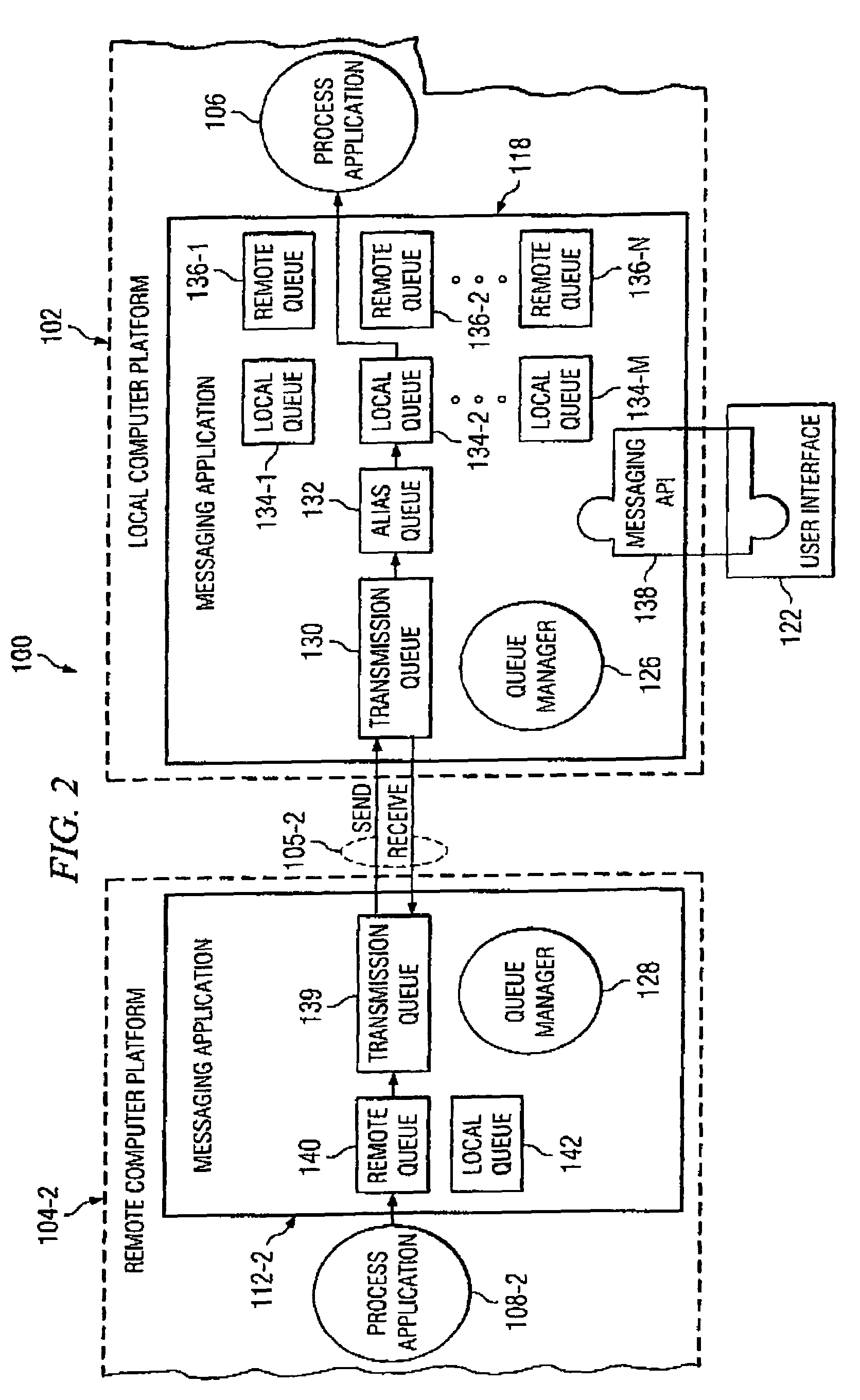
Method and apparatus for network-level monitoring of queue-based messaging systems
ActiveUS7127507B1Digital computer detailsTransmissionProgram managementDistributed Computing Environment
A distributed computing environment and associated method for monitoring a queue-based messaging system. The queue-based messaging system controls the exchange of messages between a server process and client process applications. A messaging application residing at the server computer platform and forming part of the queue-based messaging system manages a plurality of trigger-initiated local queues, each associated with one of the plurality of client process applications and having queue depth, trigger enable, get enable and put enable attributes. A monitoring tool residing on the server computer platform acquires a value for the queue depth, trigger enable, put enable and get enable attributes for a plurality of trigger-initiated local queues and generally simultaneously displays, on a user interface coupled to the server computer platform, the value for the queue depth, trigger enable, put enable and get enable attributes for each one of the plurality of trigger-initiated local queues.
Owner:T MOBILE INNOVATIONS LLC
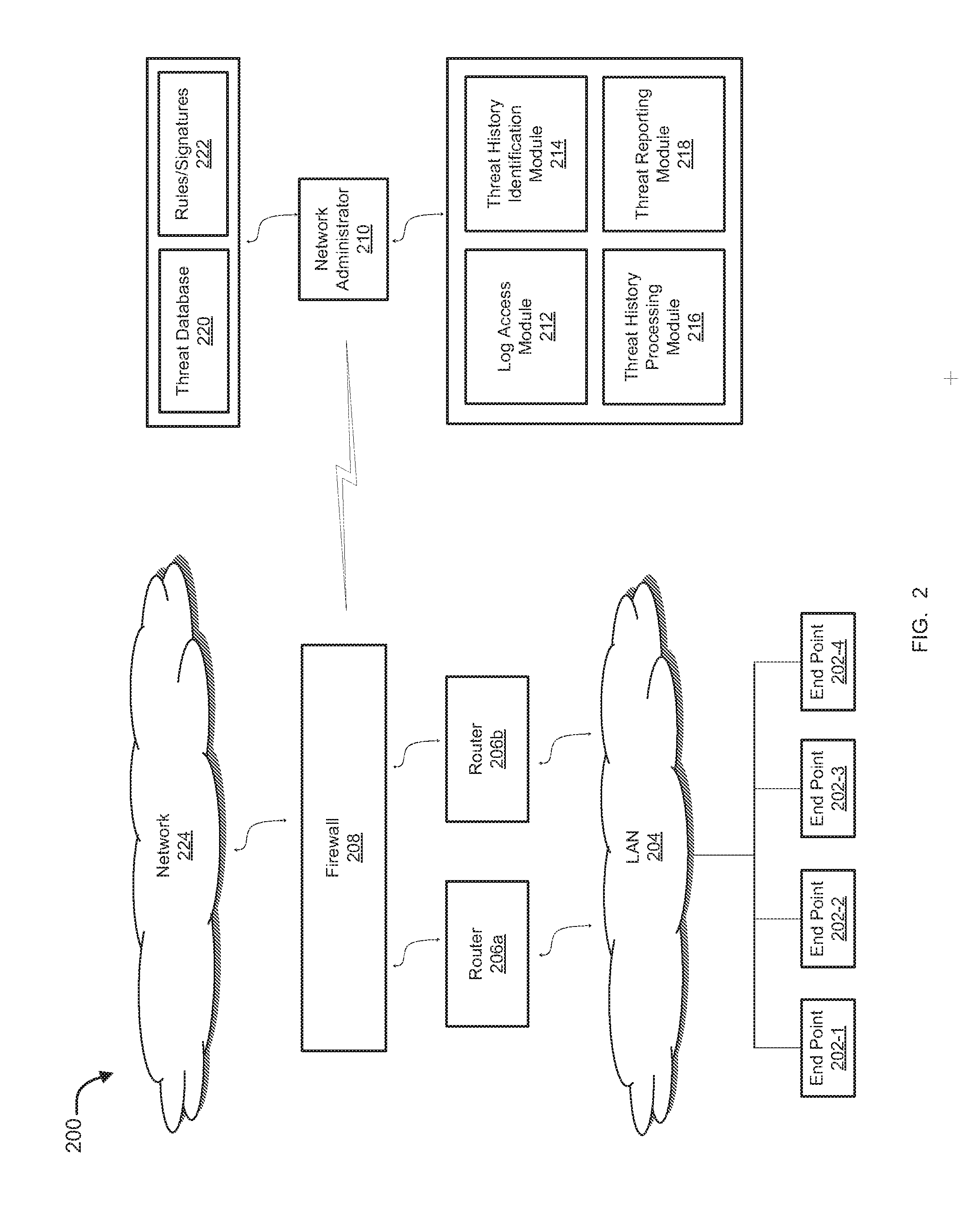
Presentation of threat history associated with network activity
ActiveUS20160173446A1Multiple digital computer combinationsProgram controlNetwork activityInternet privacy
Methods and systems for extracting, processing, displaying, and analyzing events that are associated with one or more threats are provided. According to one embodiment, threat information, including information from one or more of firewall logs and historical threat logs, is maintained in a database. Information regarding threat filtering parameters, including one or more of types of threats to be extracted from the database, parameters of the threats, network-level details of the threats, a time interval of detection of the threats and source-destination details of the threats, is received. Information regarding threats matching the threat filtering parameters are extracted from the database and is presented in a form of an interactive historical graph. Responsive to receiving from a user an indication regarding a selected subset of time in which to zoom into for further details, a list of threats within the selected subset is presented in tabular form.
Owner:FORTINET
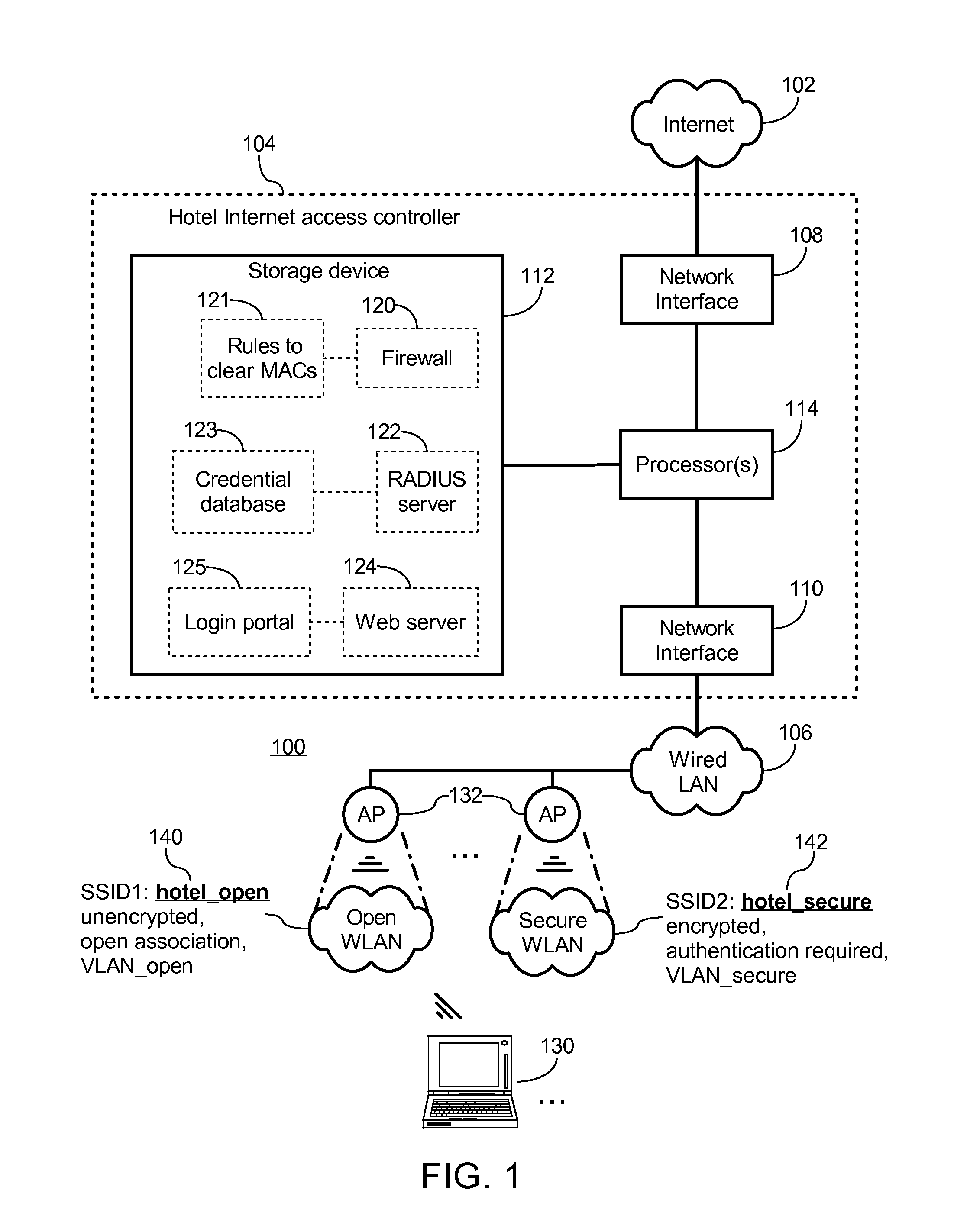
Authorizing secured wireless access at hotspot having open wireless network and secure wireless network
ActiveUS20130347073A1Cryptography processingDigital data processing detailsClient-sideComputer science
A hotspot provides an open wireless network and a secure wireless network. The open wireless network has no network-level encryption and allows open association therewith. The secure wireless network employs network-level encryption and requires authentication of a received access credential from a client device before allowing association therewith. A system for authorizing the client device for secured access at the hotspot includes an access controller configured to establish an encrypted connection between the client device and a login portal of the hotspot over the open wireless network, and to store a user-specific access credential transmitted via the encrypted connection as a valid access credential in a credential database. The credential database is accessed by wireless access points of the hotspot to authenticate the received access credential from the client device in response to a request from the client device to associate with the secure wireless network.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
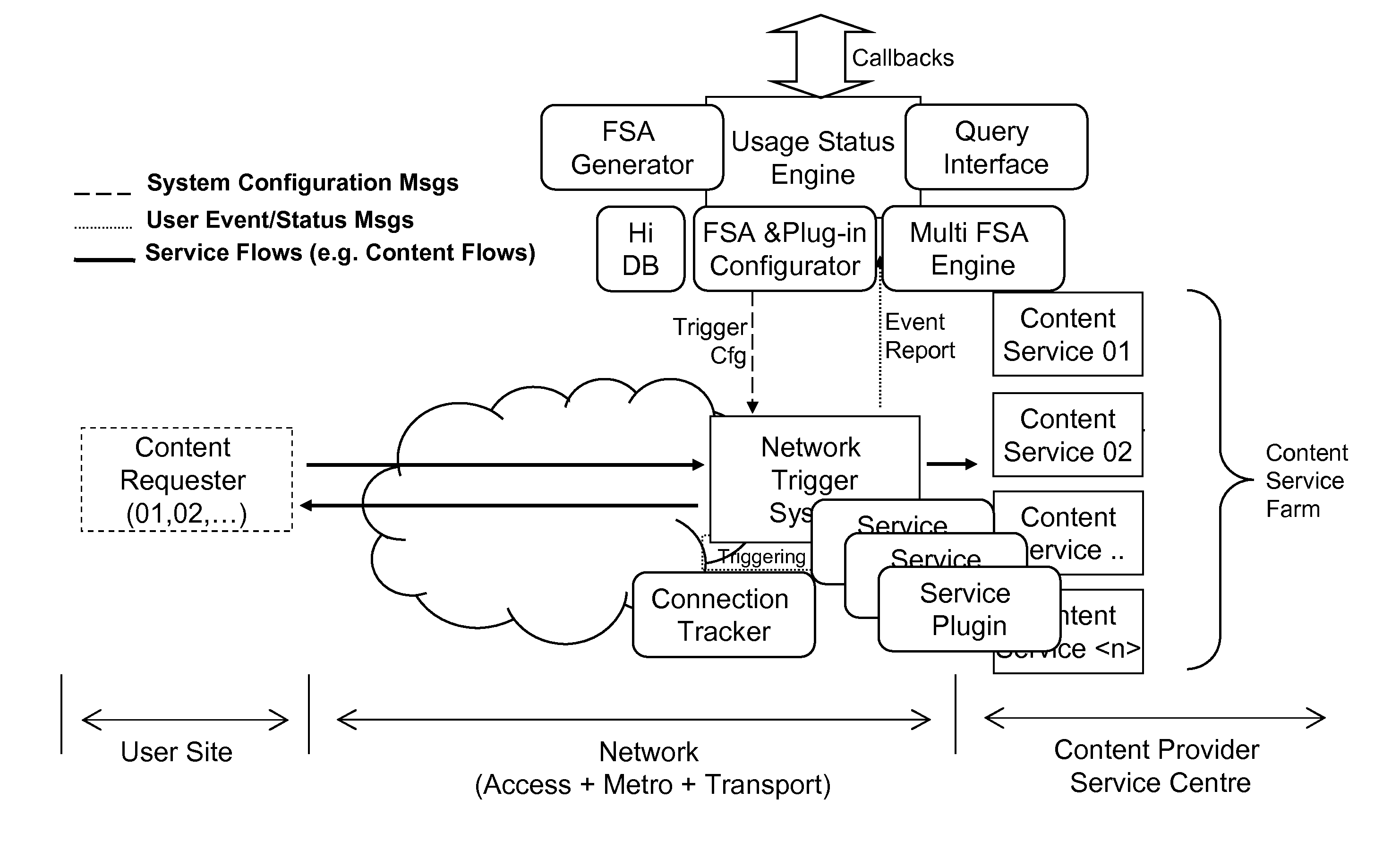
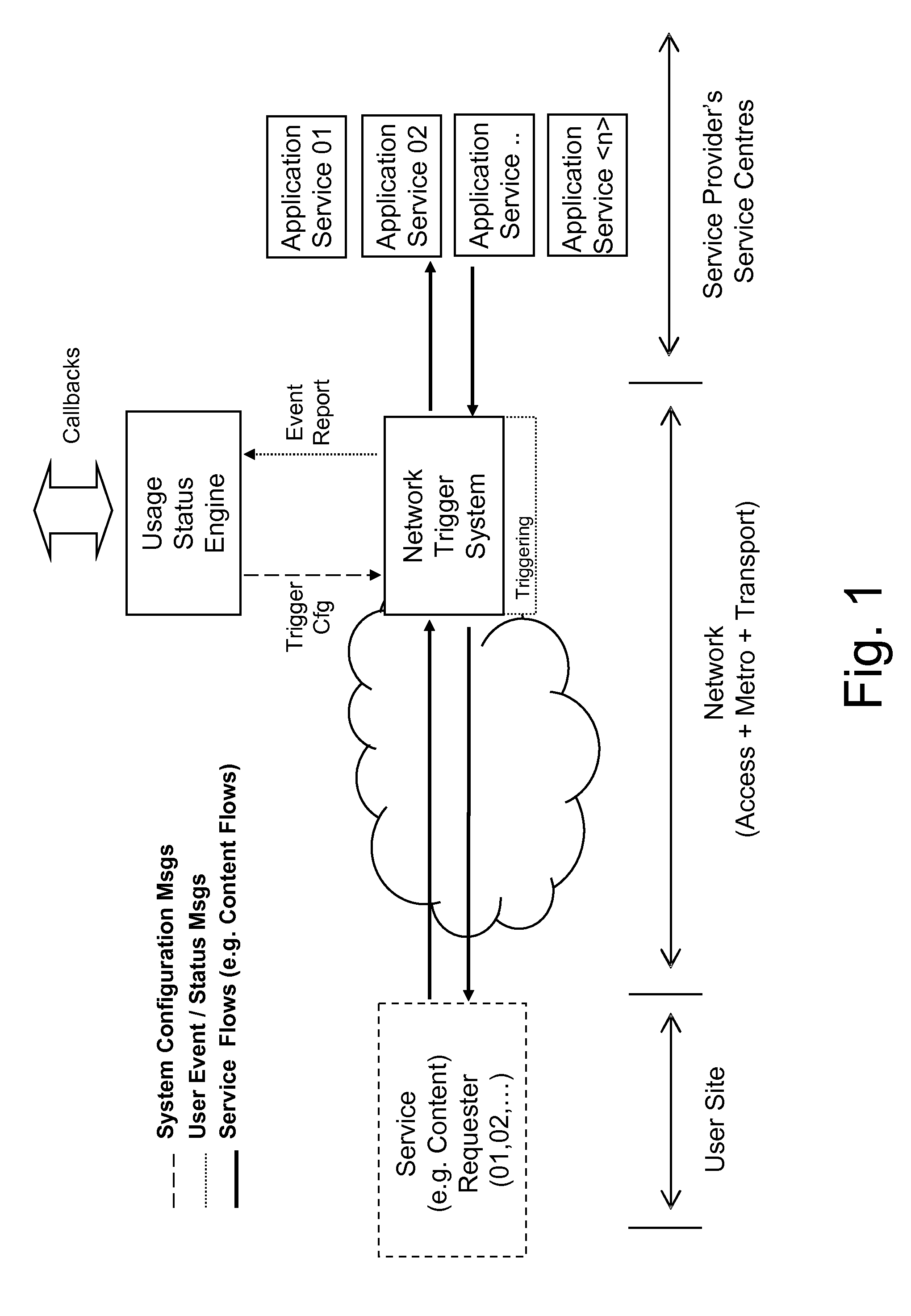
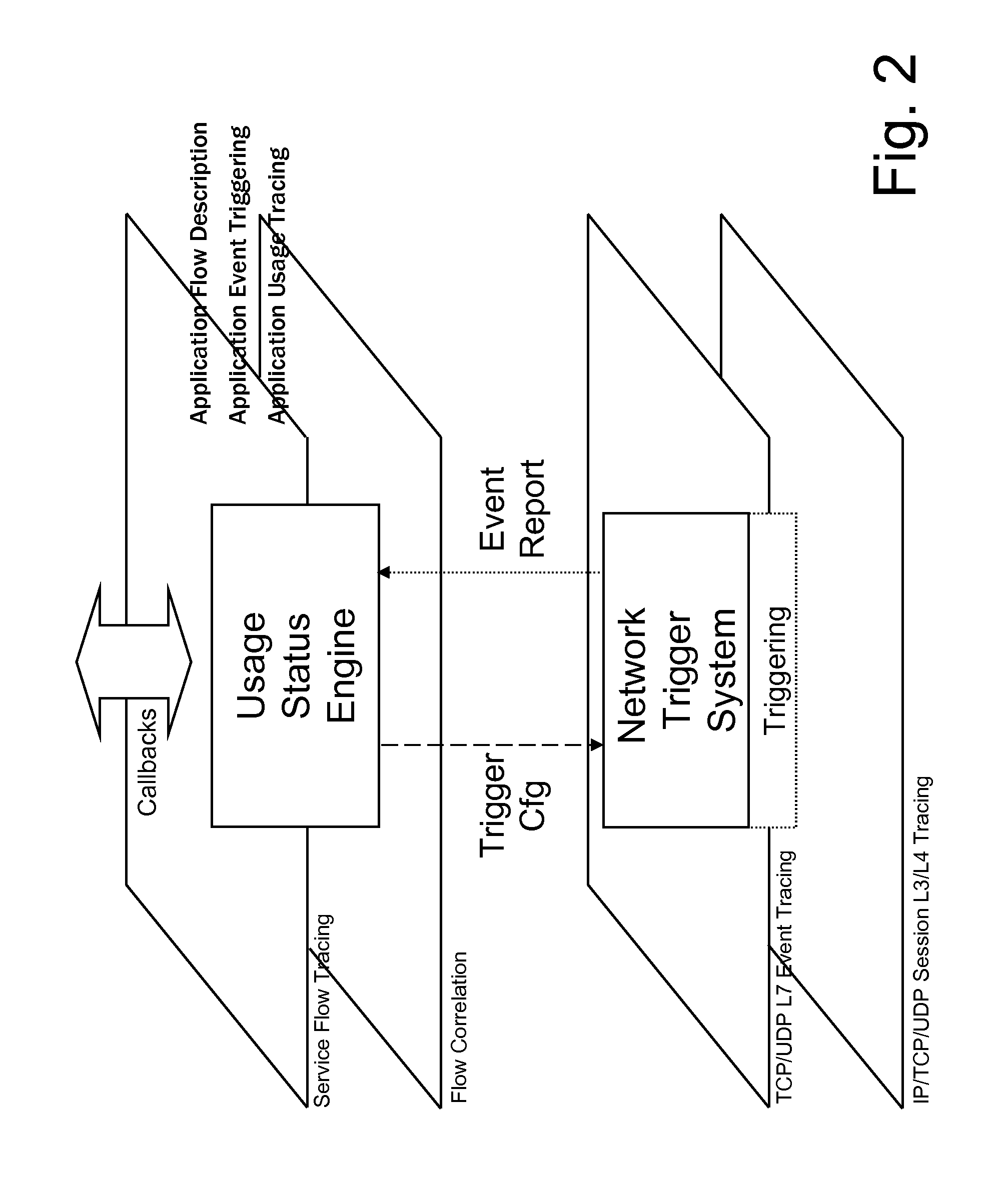
Application data flow management in an IP network
ActiveUS8504687B2Overcomes drawbackReduce complexityDigital computer detailsData switching by path configurationData streamApplication software
Disclosed herein is a two-level, network-based application control (NBAC) architecture for monitoring services provided via a packet-based network. The NBAC architecture includes a Network Trigger System provided at a network level to analyze data flows relating to services to be monitored to detect occurrence of configurable events, and to generate and send event reports; and a Usage Status Engine provided at a control level to configure the Network Trigger System to detect occurrence of events of interest, and to receive and process the event reports from the Network Trigger System to monitor the services.
Owner:TELECOM ITALIA SPA
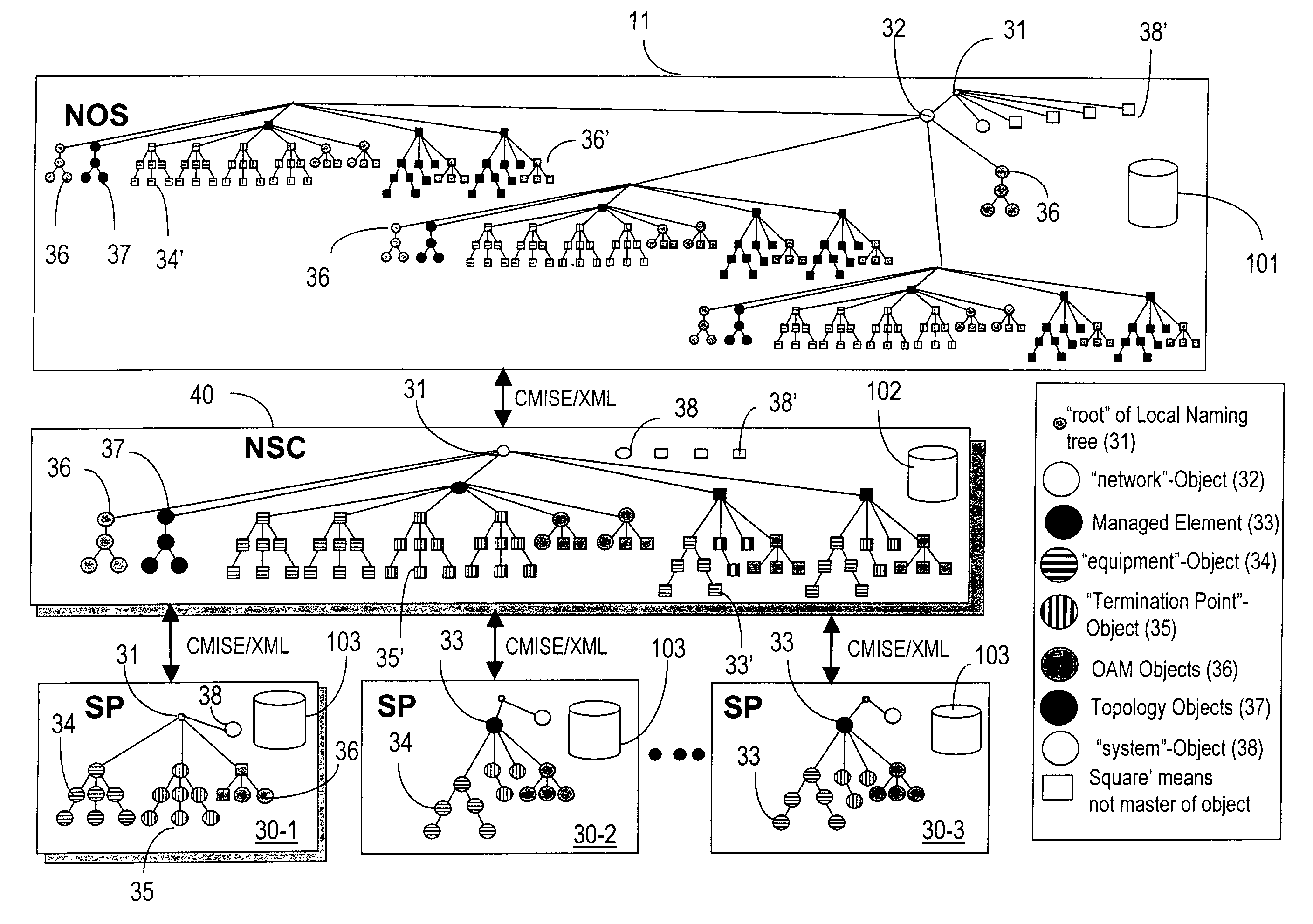
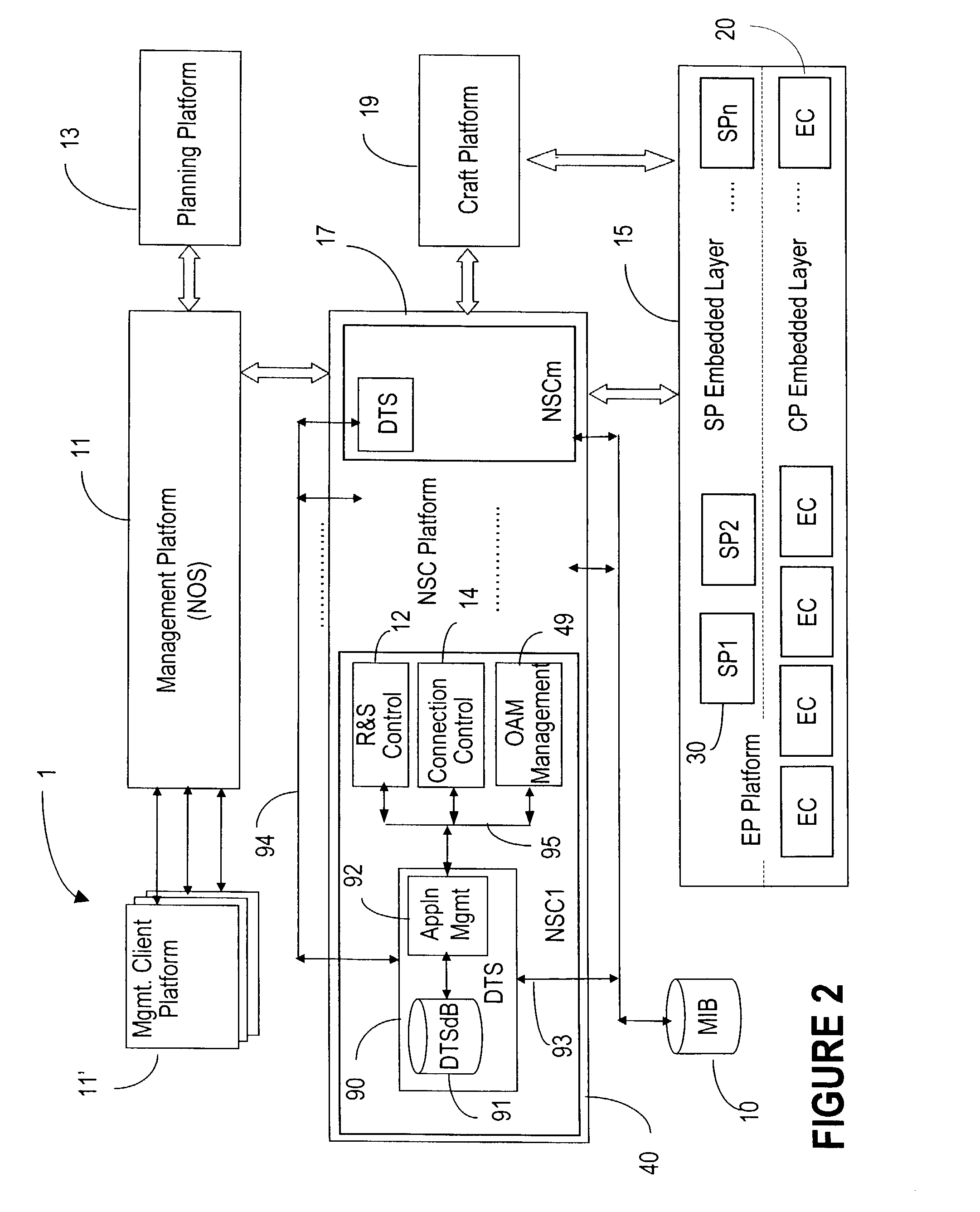
Network operating system with distributed data architecture
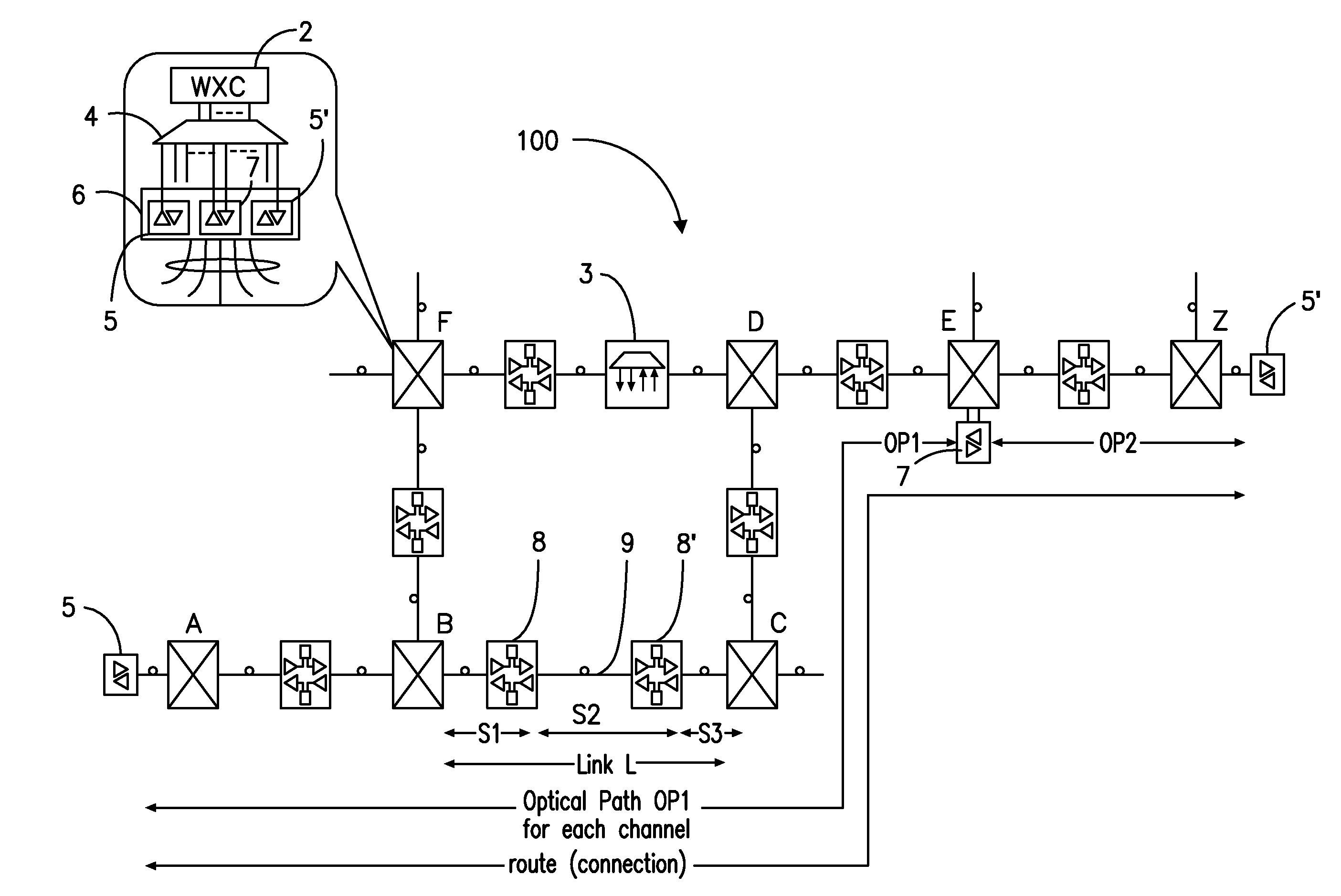
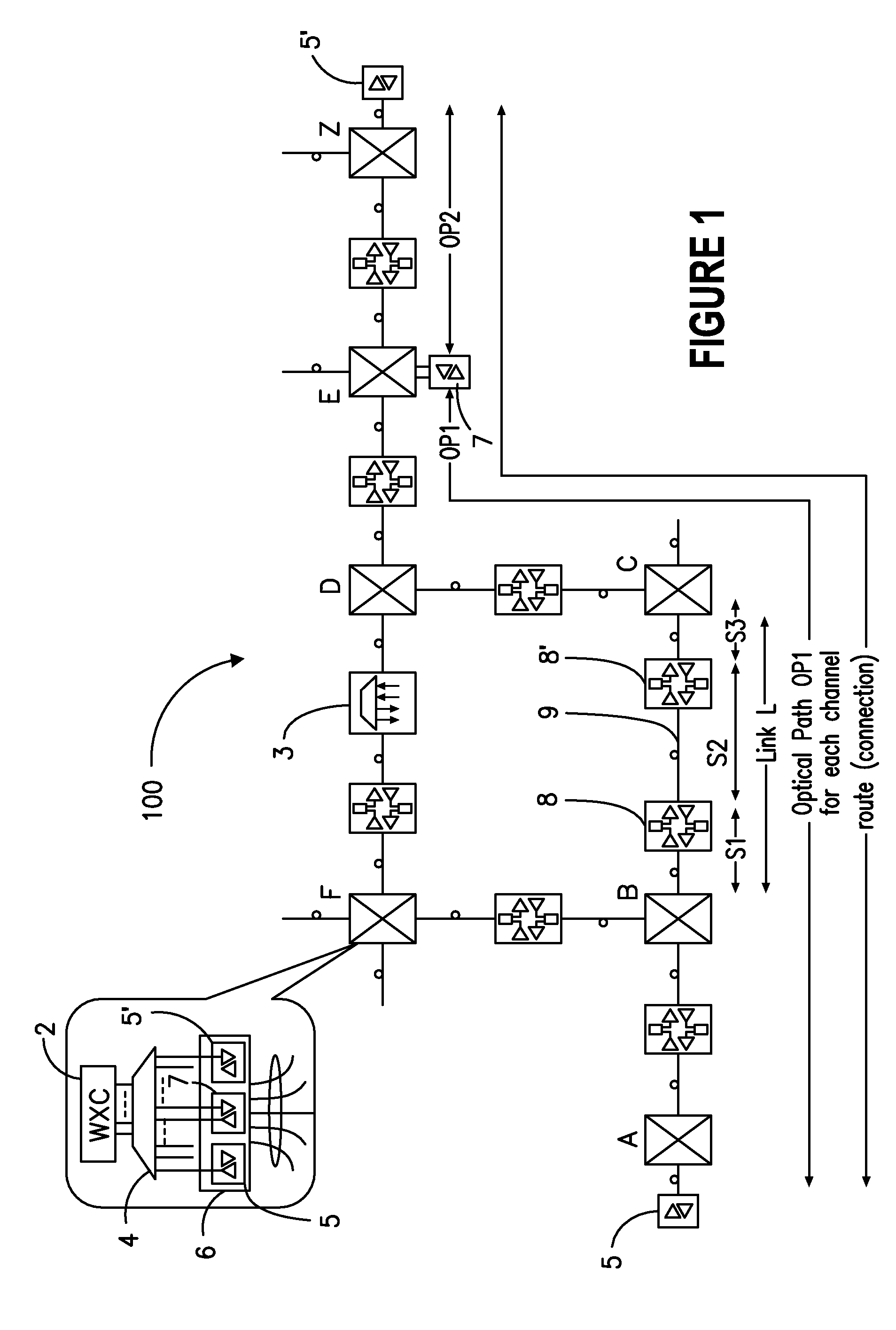
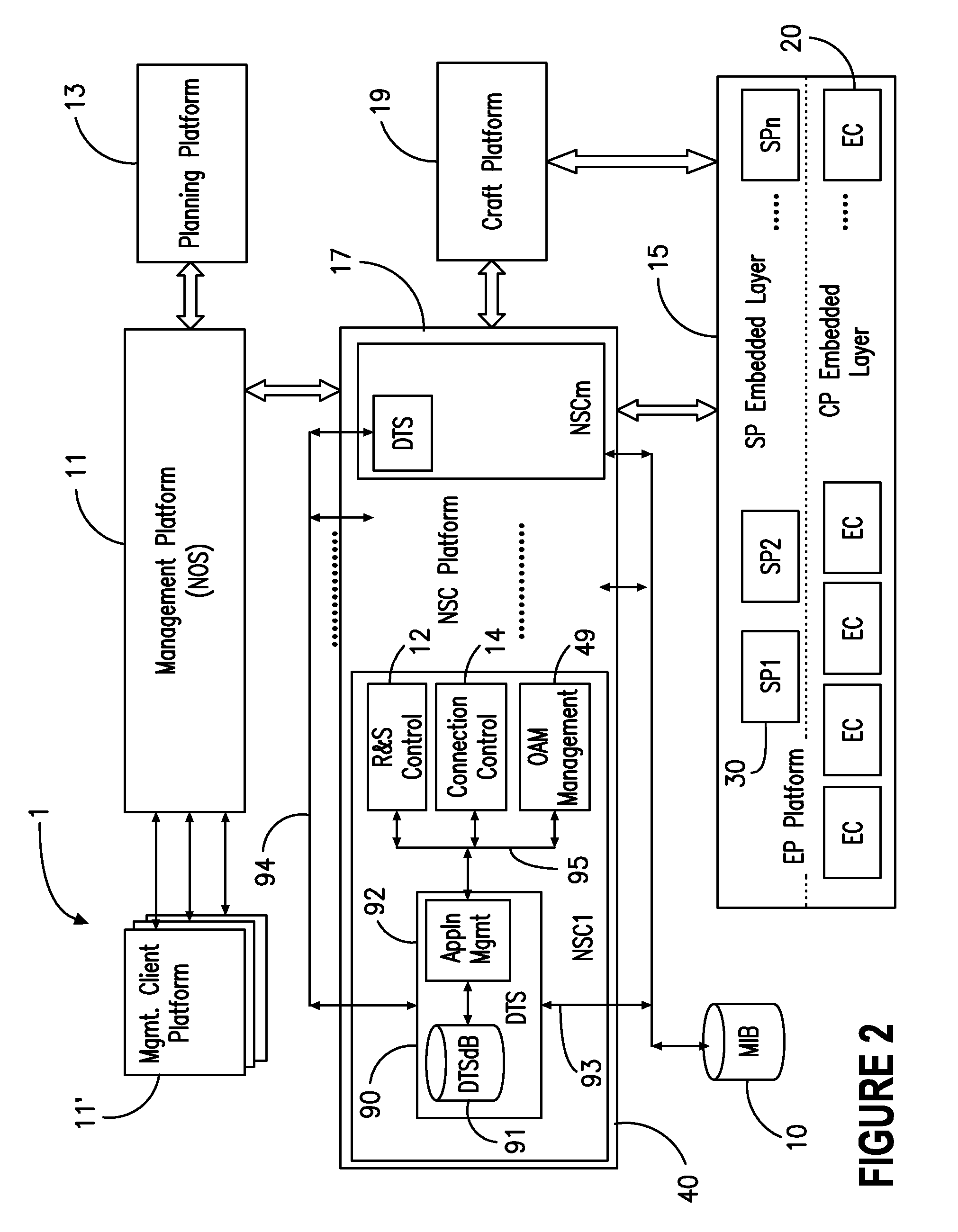
ActiveUS7263290B2Dynamic reconfiguration of network connectivity, flexibility and scalabilityDynamic reconfiguration of network connectionsMultiplex system selection arrangementsOptical multiplexInformation repositoryNetwork operating system
A network operating system NOS for an agile optical network with a plurality of mesh interconnected switching nodes, manages the network using an object-oriented network information model. The model is common to all applications requiring the data stored in the network managed information base. The core model can be expanded for serving specific application areas. The NOS is organized in layers, at the optical module level, connection level and network level. A distributed topology server DTS organizes the physical, logical and topological data defining all network entities as managed objects MO and topology objects TO for constructing a complete network view. The network information model associates a network element NE information model, specified by managed objects MO and a topological information model, specified by topology objects TO. The MOs are abstract specific NE data that define network implementation details and do not include any topological data, while the TOs abstract specific topological data for defining a trail established within the network, and do not include any NE data. The models are associated in a minimal number of points to construct the model of a trial in response to a connection request.
Owner:WSOU INVESTMENTS LLC
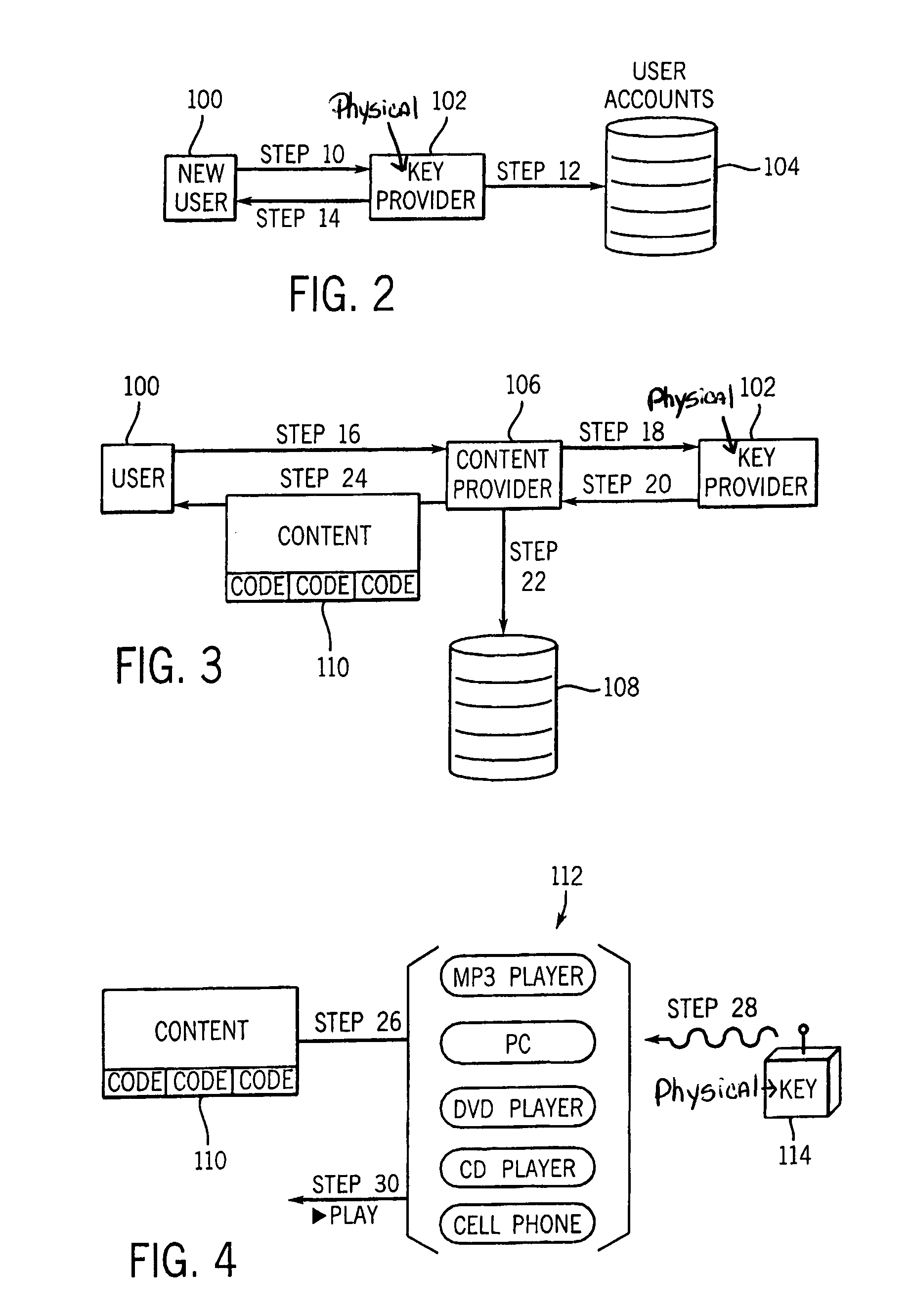
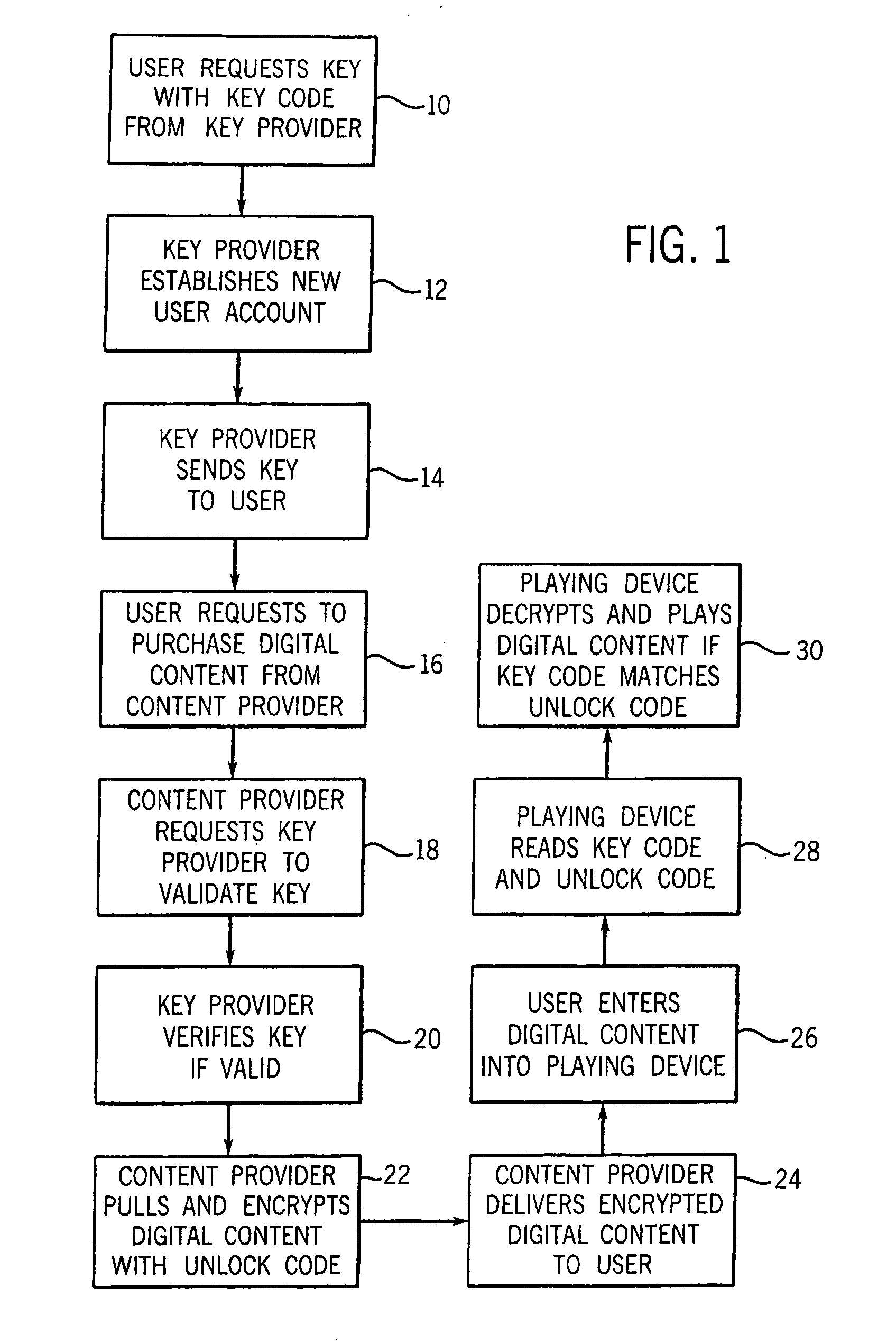
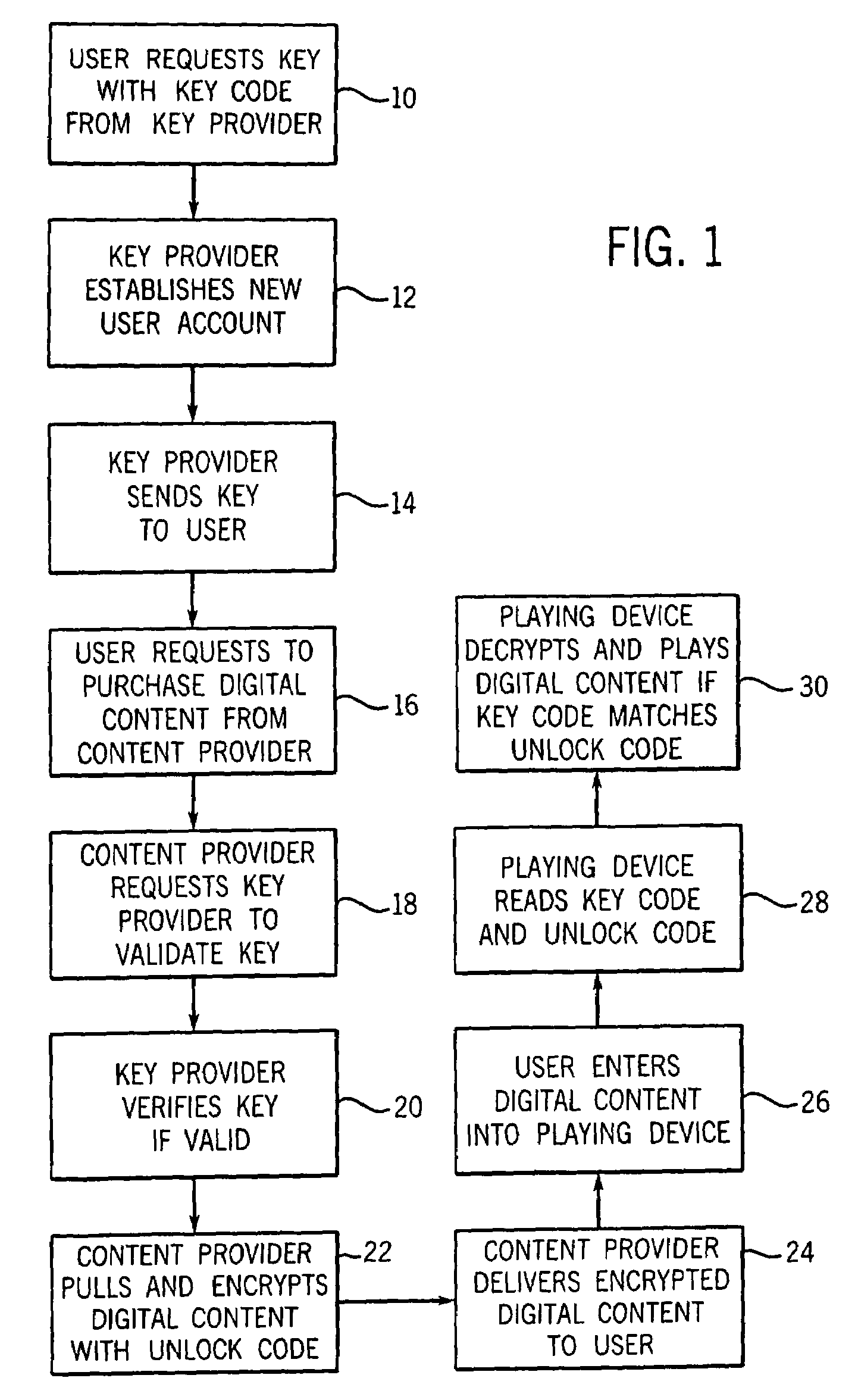
Digital content security system
InactiveUS6973576B2Provide protectionDigital data processing detailsUser identity/authority verificationHard disc driveOperational system
A Personal Digital Key Digital Content Security System (PDK-DCSS) is used to protect computers from unauthorized use and protect the digital content stored on computers from being wrongfully accessed, copied, and / or distributed. The basic components of the PDK-DCSS are (1) a standard hard drive device, with the addition of a PDK Receiver / Decoder Circuit (PDK-RDC) optionally integrated into the hard drive's controller, and (2) a PDK-Key associated with the PDK-RDC. The PDK-Key and RDC technology is utilized to provide two categories of protection: (1) hard drive access control for providing Drive-Level and Sector-Level protection and (2) operating system-level independent file protection for providing File-Level and Network-Level protection.
Owner:PROXENSE
Method and system for reducing power consumption in wireless sensor networks
InactiveUS20090147714A1Reduce power consumptionEnergy efficient ICTPower managementMobile wireless sensor networkWireless mesh network
The present invention provides a method and system for reducing power consumption in a Wireless Sensor Network. The Wireless Sensor Network includes a plurality of nodes forming a tree structure. The nodes send data towards a root node via parent nodes. The nodes adaptively control the wake-up schedules of radio transceivers based on the network level information of the nodes, thereby reducing the active wake-up interval of the radio transceivers and in turn decreasing the overall power consumption of the Wireless Sensor Network.
Owner:VIRTUALWIRE TECH PRIVATE
System for configuring network devices
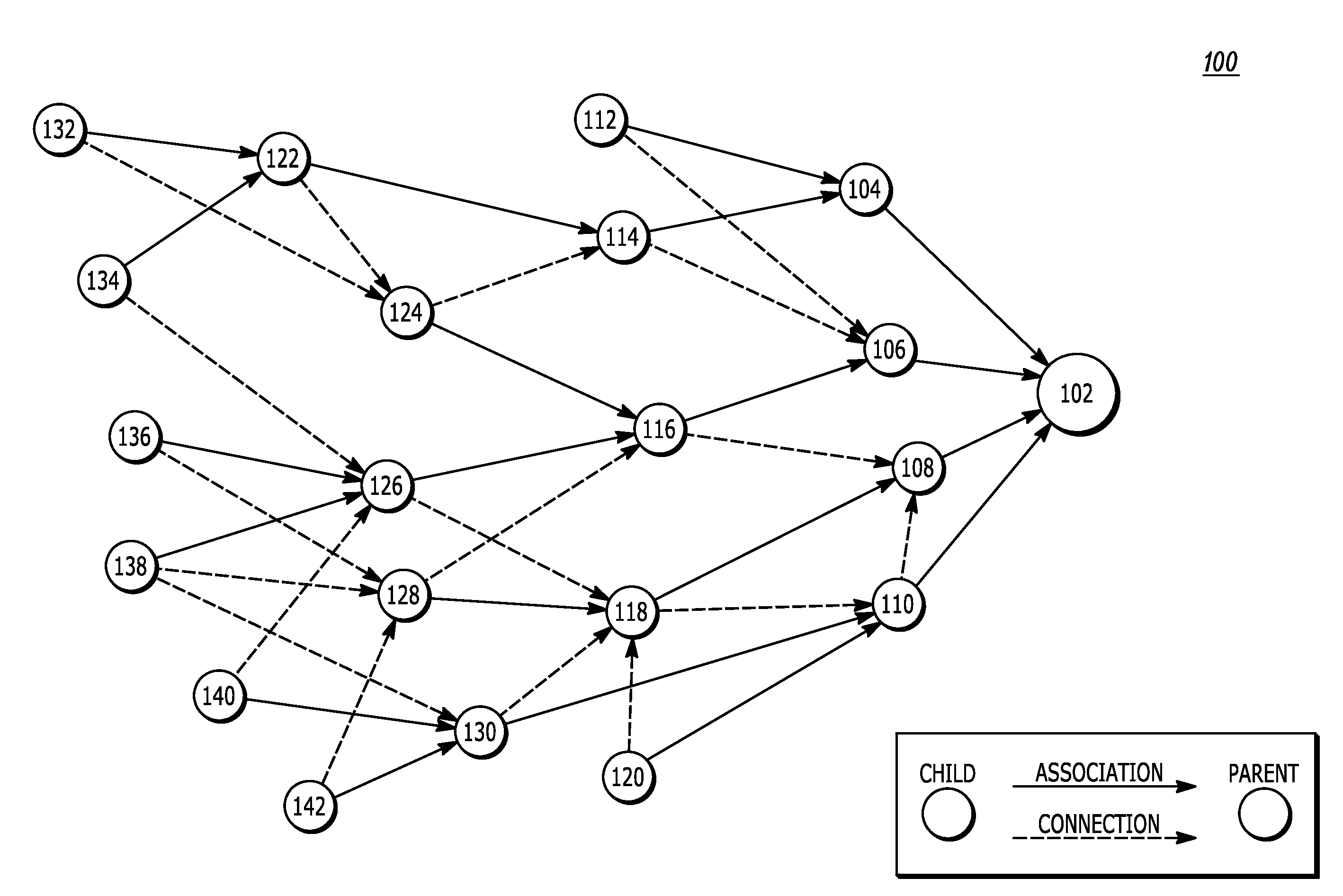
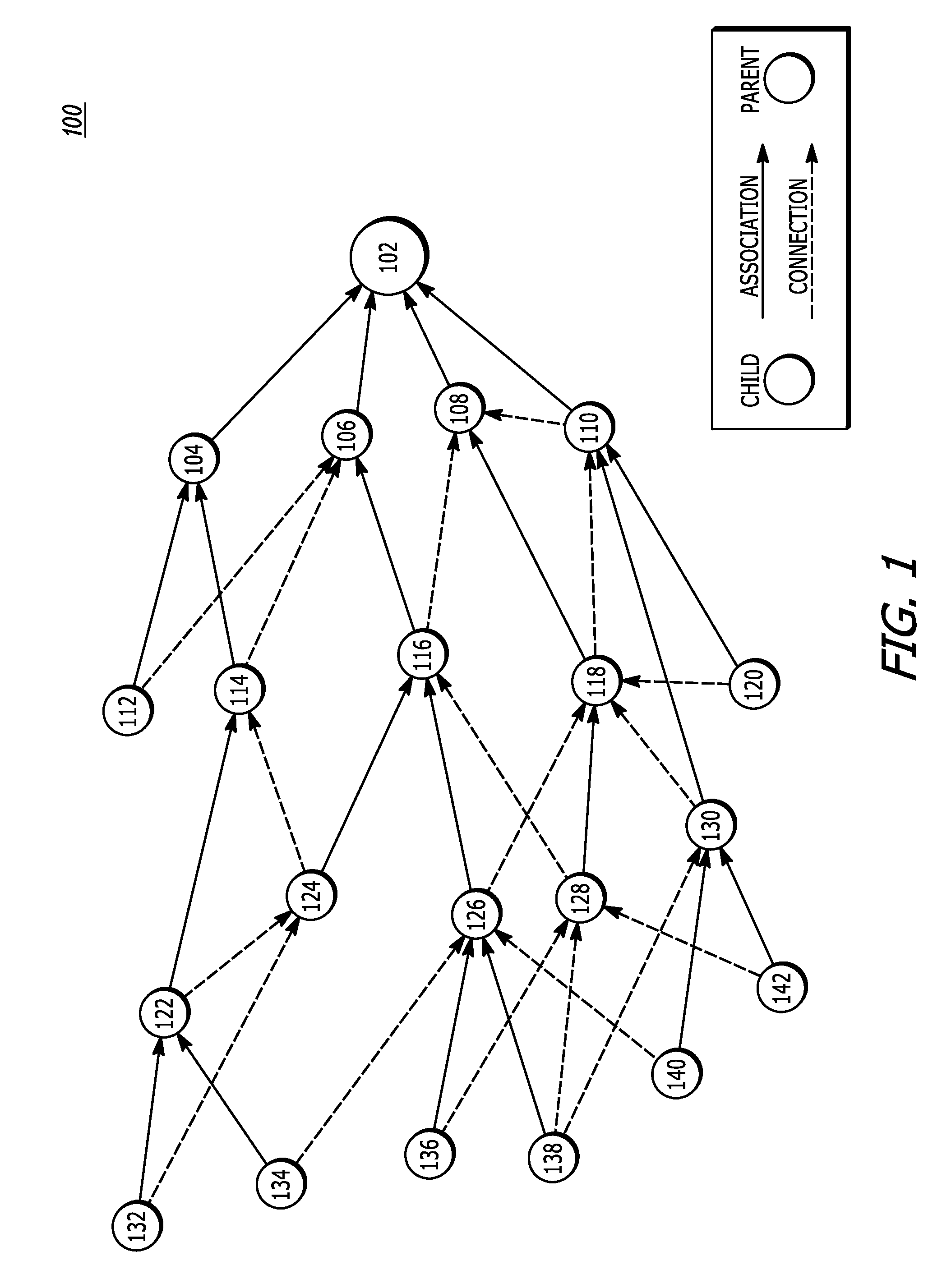
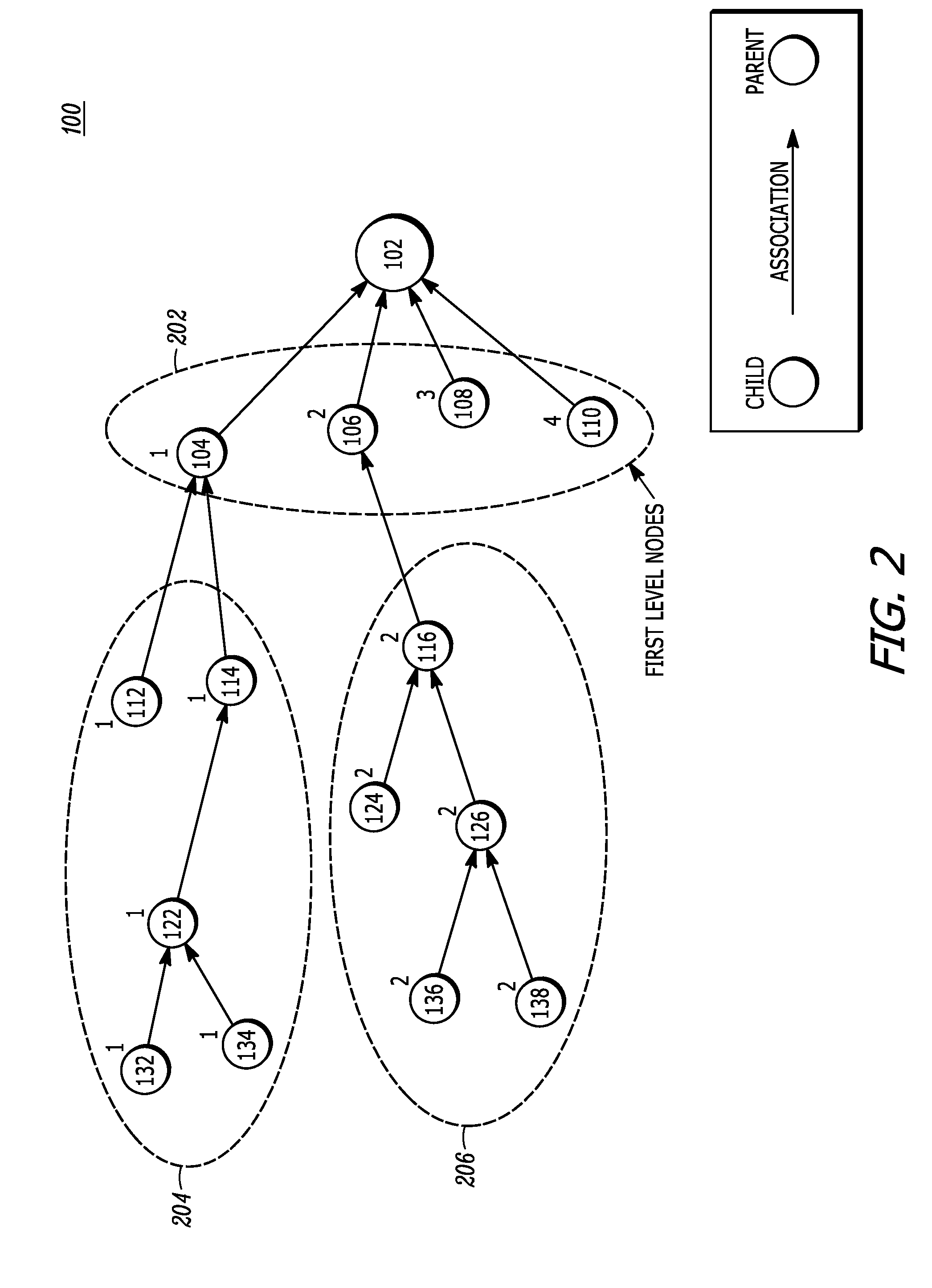
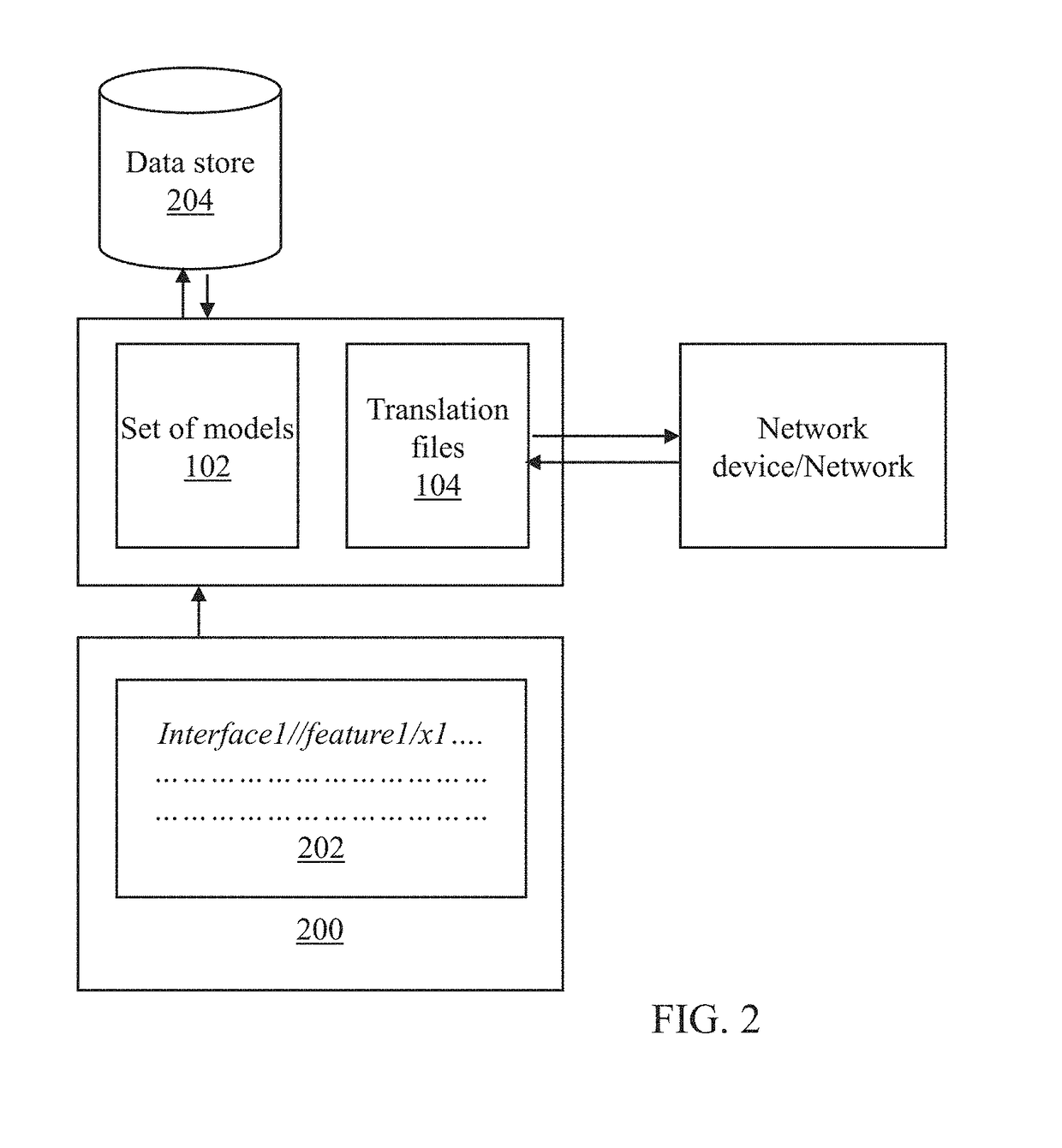
An embodiment provides a system for configuring network devices. The system includes a database, wherein the database further includes a set of models and a plurality of translator files. The system further includes one or more processors. The set of models represent / define plurality of network level or device level features as per YANG models, wherein one model corresponds to one device or network level feature in a way agnostic to device manufacturer or device families. A translator file among the plurality of translator files is executed by the processor to convert an instruction, as represented by the set of models, into network or device specific instructions in a second format.
Owner:NUVISO NETWORKS INC
Method and apparatus for network immunization
InactiveUS20060123481A1Avoid dataAvoid spreadingMemory loss protectionError detection/correctionSecurity softwareFiltering rules
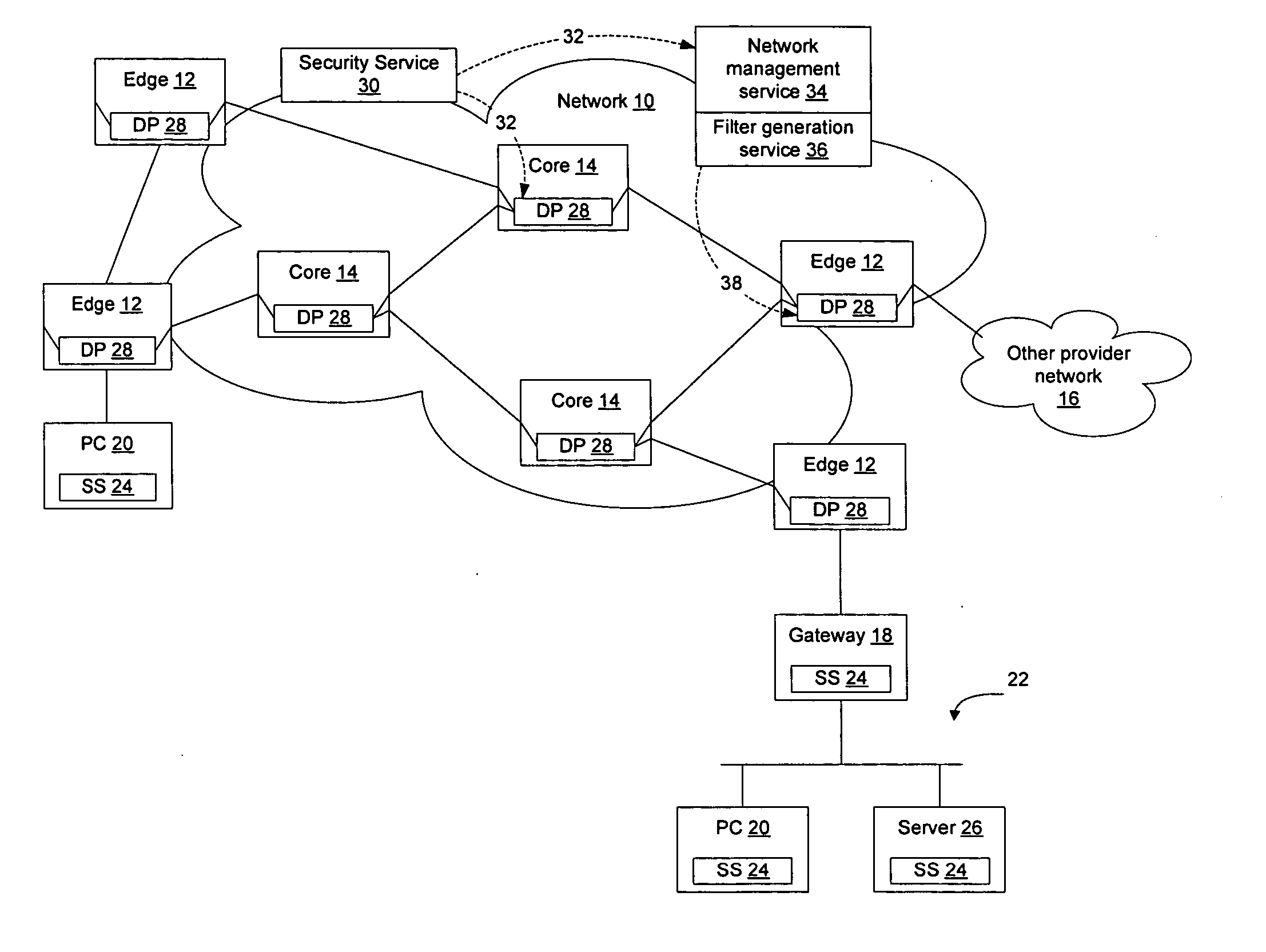
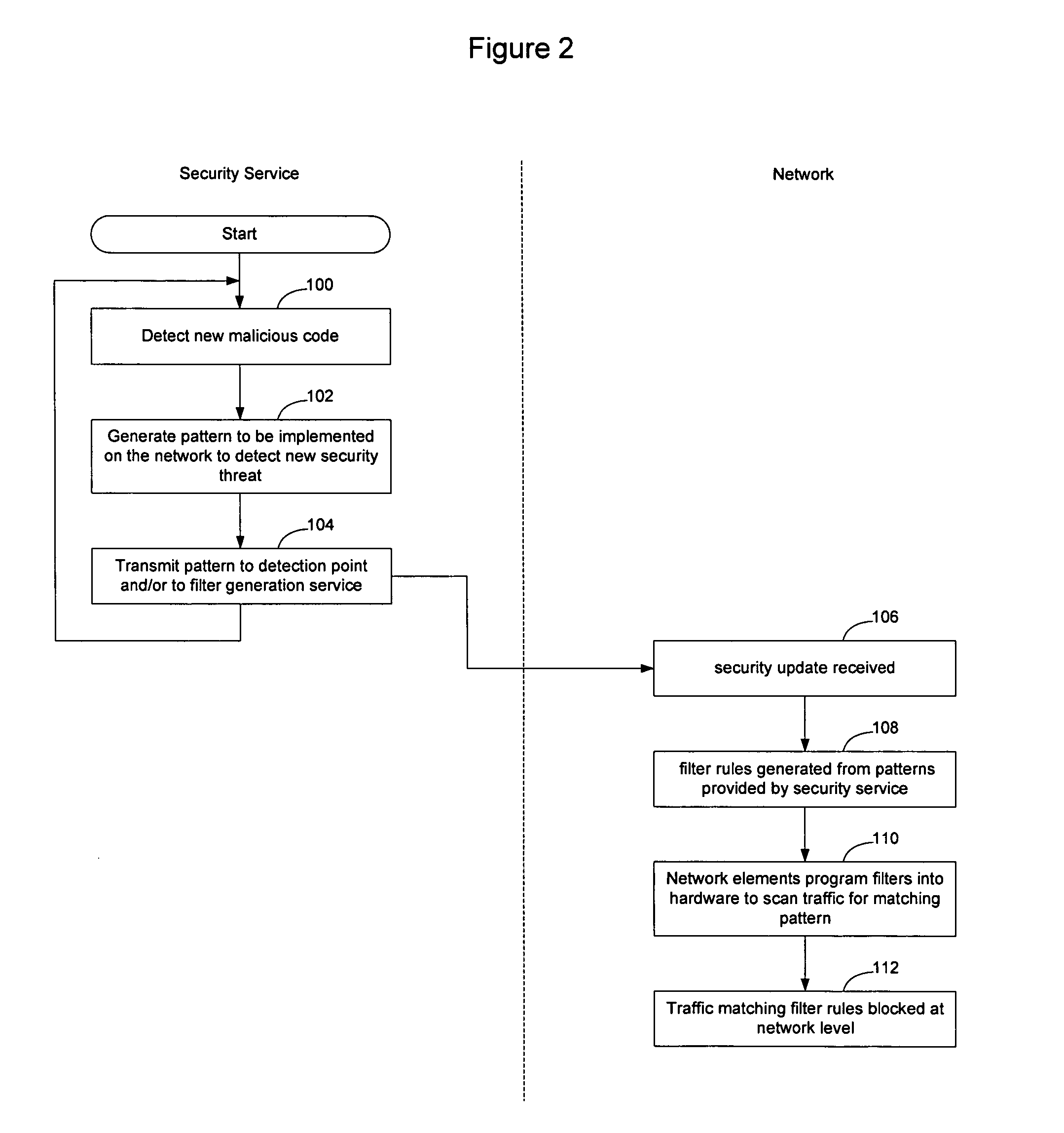
Network elements that are configured to perform deep packet inspection may be dynamically updated with patterns associated with malicious code, so that malicious code may be detected and blocked at the network level. As new threats are identified by a security service, new patterns may be created for those threats, and the new patterns may then be passed out onto the network in real time. The real time availability of patterns enables filter rules derived from the patterns to be applied by the network elements so that malicious code may be filtered on the network before it reaches the end users. The filter rules may be derived by security software resident in the network elements or may be generated by a filter generation service configured to generate network element specific filter rules for those network elements that are to be implemented as detection points on the network.
Owner:AVAYA INC
Acorn: providing network-level security in P2P overlay architectures
InactiveUS20070149279A1Broadcast specific applicationsDigital computer detailsObfuscationComputer science
To address the problem of providing network-based security to mitigate and detect cheating in peer-to-peer (P2P) gaming architecture, an architecture suite called architectures with coordinator obfuscation for resilient P2P gaming networks (ACORN) is presented that uses a combination of low overhead, per-packet access authentication, moving-coordinator and cheat detection mechanisms to effectively mitigate security threats.
Owner:RPX CORP
Computer program product configured to control modular transmission system components
A computer program product is configured to control a modular transmission system having a control processor and at least N power amplifier modules, each having a controller submodule, wherein the system receives an input signal which may be a single carrier or multiple carriers. The signal is passed to a one-by-N divider which divides the signal N ways. Each of the N divided signals are independently amplified by the power amplifier (PA) modules "slices" (i.e., PA modules) that includes an RF amplifier module, a microcontroller module, and a power supply module, all of which are tightly coupled via a plurality of signal, power, control, and status connections. Each the PA slices amplifies its respective input signal and outputs a respective radio frequency output signal at a predetermined power level as controlled by the microcontrol module, the driver, and the system controller, or a network manager via a system input / output interface. The output coupler provides power coupling and status monitoring via feedback lines to support control at a module-level, a system-level, and a network-level.
Owner:THALES BROADCAST & MULTIMEDIA
Enhanced Features for Direction of Communication Traffic
InactiveUS20080201413A1Avoid problemsMultiple digital computer combinationsAutomatic exchangesTraffic capacityWeb browser
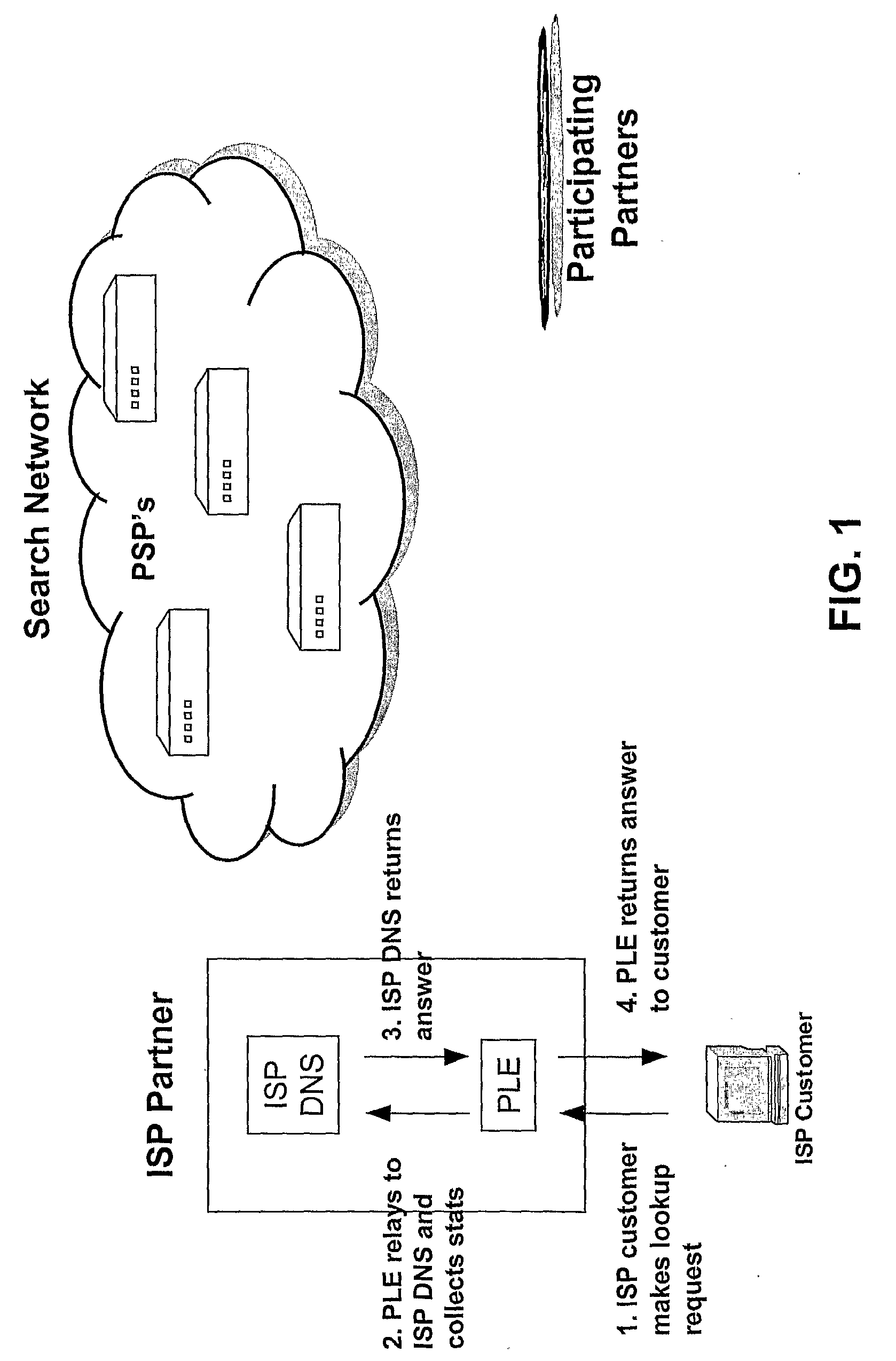
An internet traffic redirection architecture is disclosed that allows for directing of various traffic to specified sites. The system and method allow a controller, such as an ISP, to benefit from unresolved IP Address requests and keyword and hotword queries by capturing this traffic and directing it to participating partners who provide content relevant and / or geographically relevant results. The system and method can decrease lost traffic, irrelevant redirection by web browsers resident on user's personal computers. The technique further provides enhanced features at the ISP network level which are conventionally only available at the personal user level.
Owner:PAXFIRE
Network operating system with distributed data architecture
ActiveUS20080212963A1Dynamic reconfiguration of network connectivity, flexibility and scalabilityDynamic reconfiguration of network connectionsMultiplex system selection arrangementsOptical multiplexInformation repositoryNetwork operating system
A network operating system NOS for an agile optical network with a plurality of mesh interconnected switching nodes, manages the network using an object-oriented network information model. The model is common to all applications requiring the data stored in the network managed information base. The core model can be expanded for serving specific application areas. The NOS is organized in layers, at the optical module level, connection level and network level. A distributed topology server DTS organizes the physical, logical and topological data defining all network entities as managed objects MO and topology objects TO for constructing a complete network view. The network information model associates a network element NE information model, specified by managed objects MO and a topological information model, specified by topology objects TO. The MOs are abstract specific NE data that define network implementation details and do not include any topological data, while the TOs abstract specific topological data for defining a trail established within the network, and do not include any NE data. The models are associated in a minimal number of points to construct the model of a trial in response to a connection request.
Owner:WSOU INVESTMENTS LLC
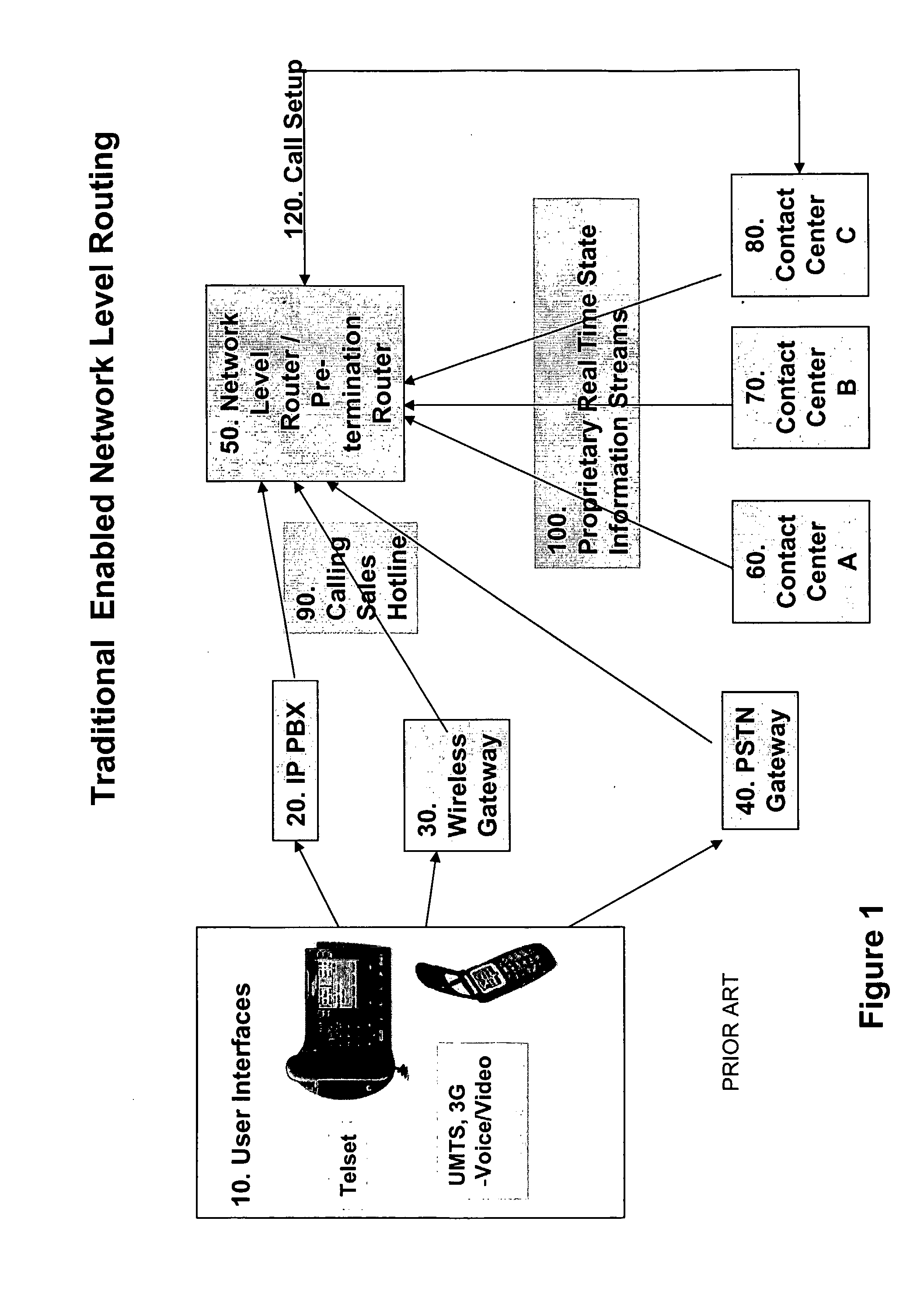
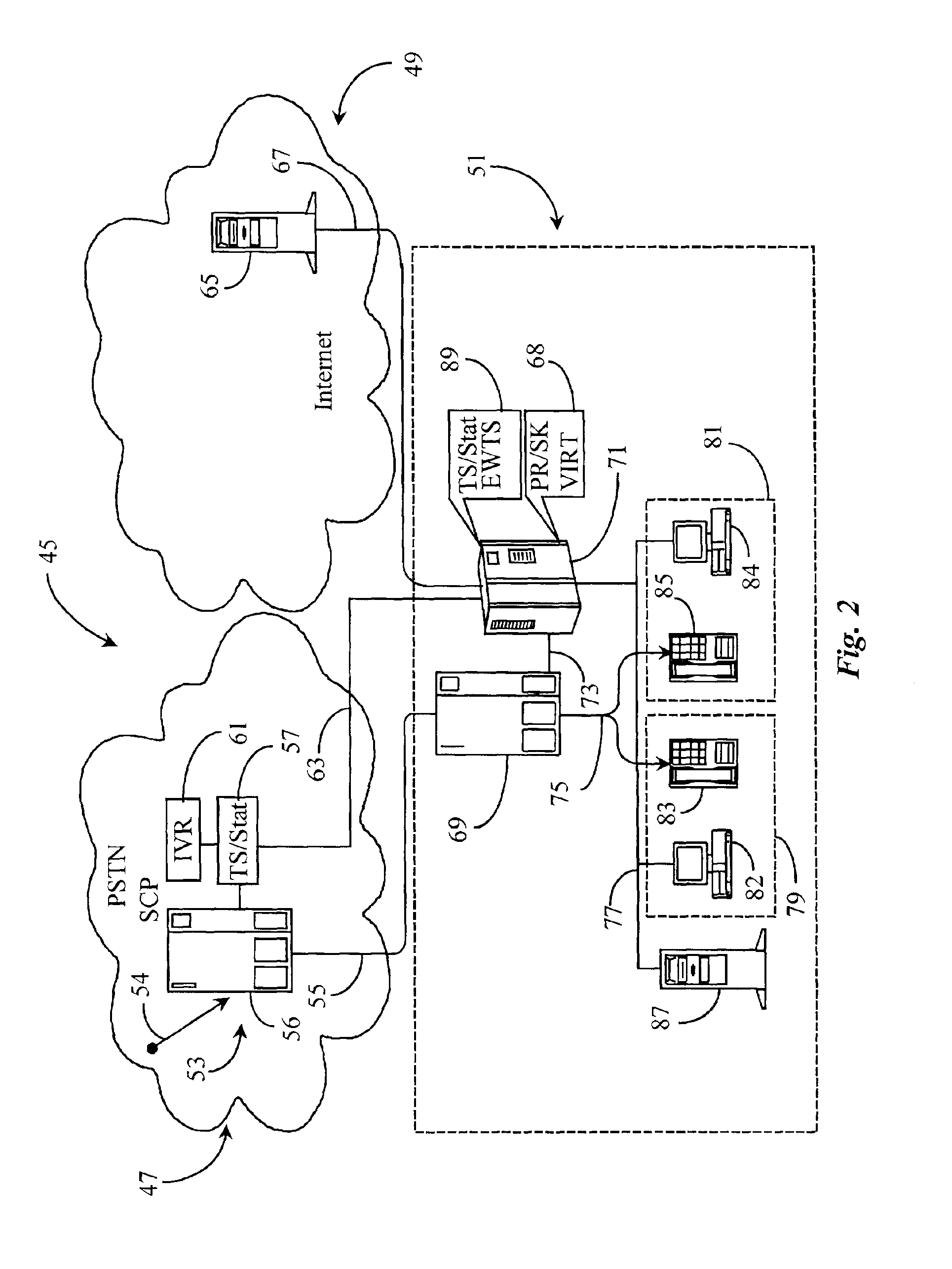
Method of Operating A Contact Center
ActiveUS20100077082A1Facilitate decision-makingFunction increaseTelephone data network interconnectionsSpecial service for subscribersProtocol for Carrying Authentication for Network AccessNetwork level
Some known Contact Centers rely on a Network Level Router to determine which of a number of available Contact Centers should deal with a given contact. This decision is made by the NLR based on real time information provided by the Contact Centers. However, the format of such information is proprietary which means that the NLR must translate and collate this information. This invention seeks to use session initiation protocol (SIP) Presence for such information transfer which enables improved decision making and further enables additional functionality to be added to the Contact Center system. The invention provides a SIP enabled Contact Center (180, 190, 200) comprising a Contact Center server arranged to send SIP messages to one or more other SIP enabled nodes in a SIP communications network, said SIP messages comprising SIP presence information about the current state of the Contact Center.
Owner:AVAYA INC
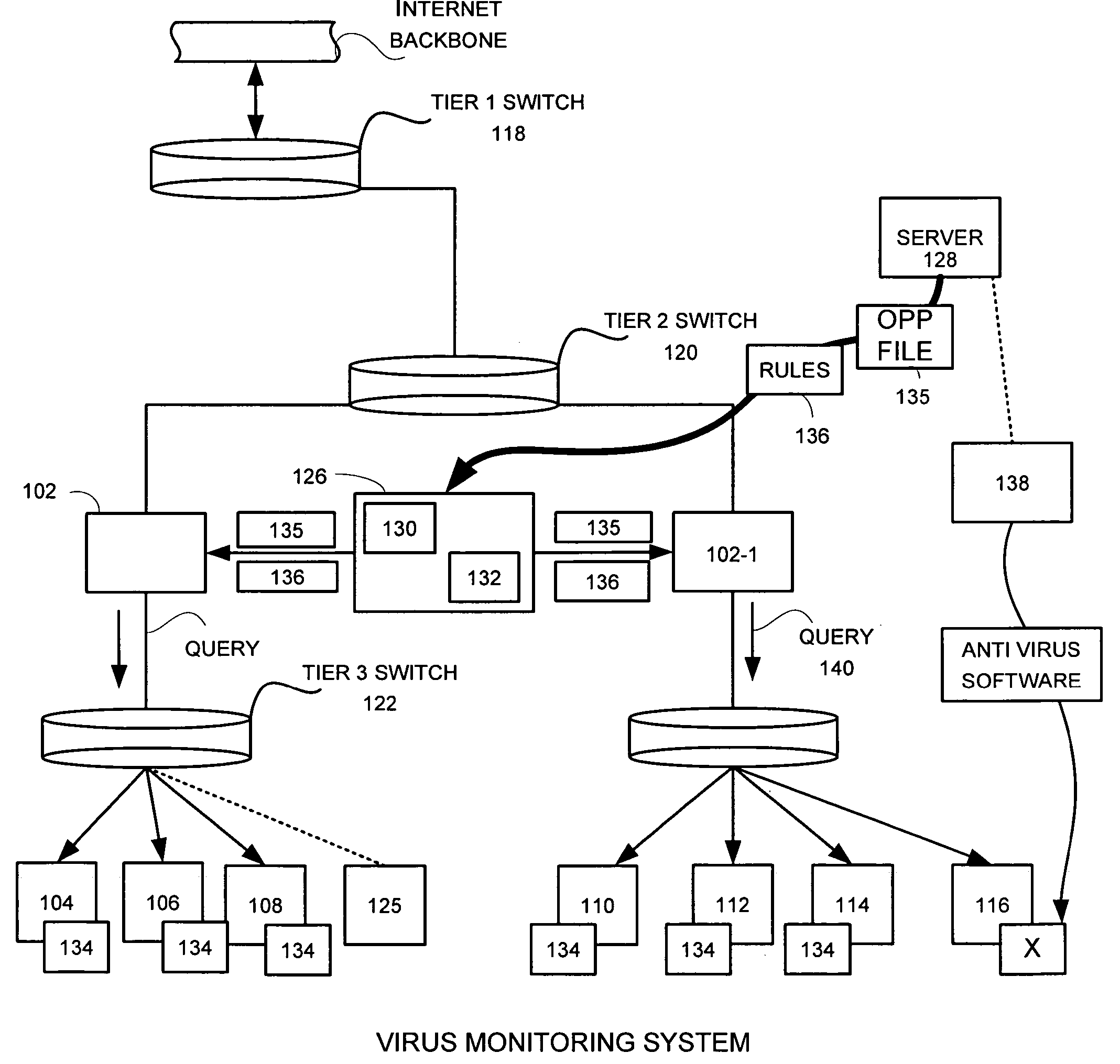
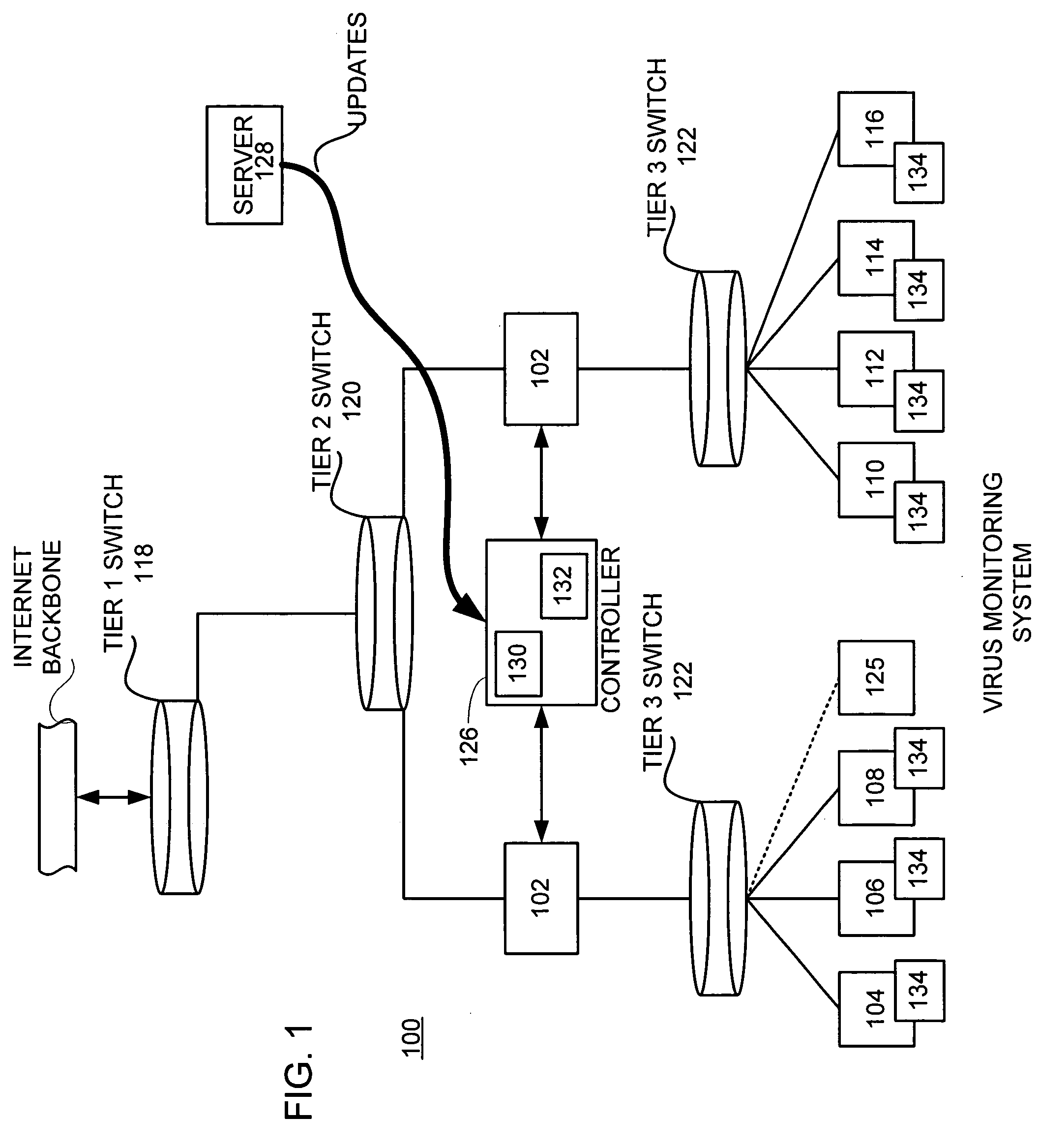
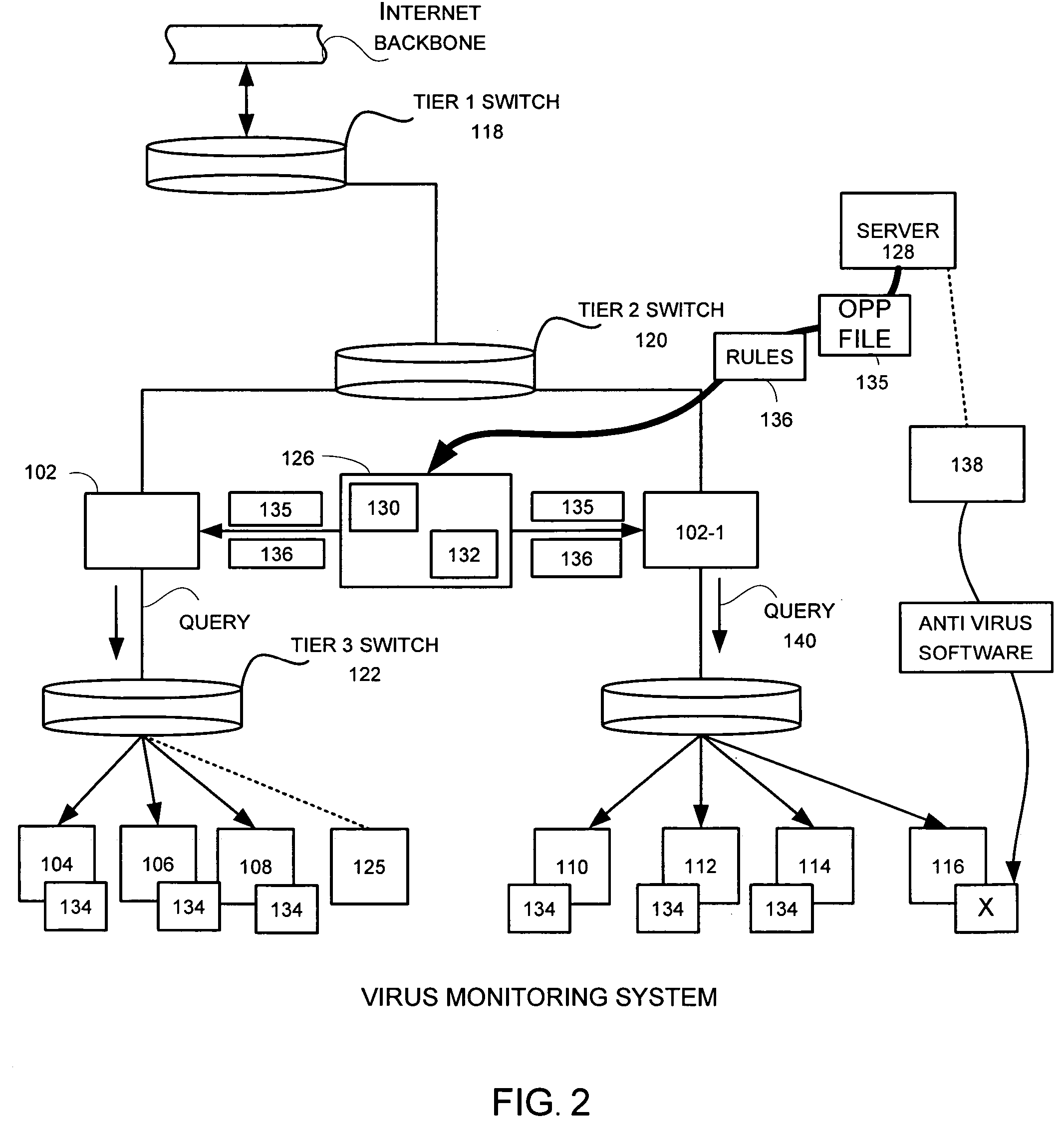
Virus monitor and methods of use thereof
A network level virus monitoring system capable of monitoring a flow of network traffic in any of a number of inspection modes depending upon the particular needs of a system administrator. The monitoring provides an early warning of a virus attack thereby facilitating quarantine procedures directed at containing a virus outbreak. By providing such an early warning, the network virus monitor reduces the number of computers ultimately affected by the virus attack resulting in a concomitant reduction in both the cost of repair to the system and the amount of downtime. In this way, the inventive network virus monitor provides a great improvement in system uptime and reduction in system losses.
Owner:TREND MICRO INC
Digital content security system
InactiveUS20060064605A1Digital data processing detailsUser identity/authority verificationHard disc driveOperational system
Owner:PROXENSE
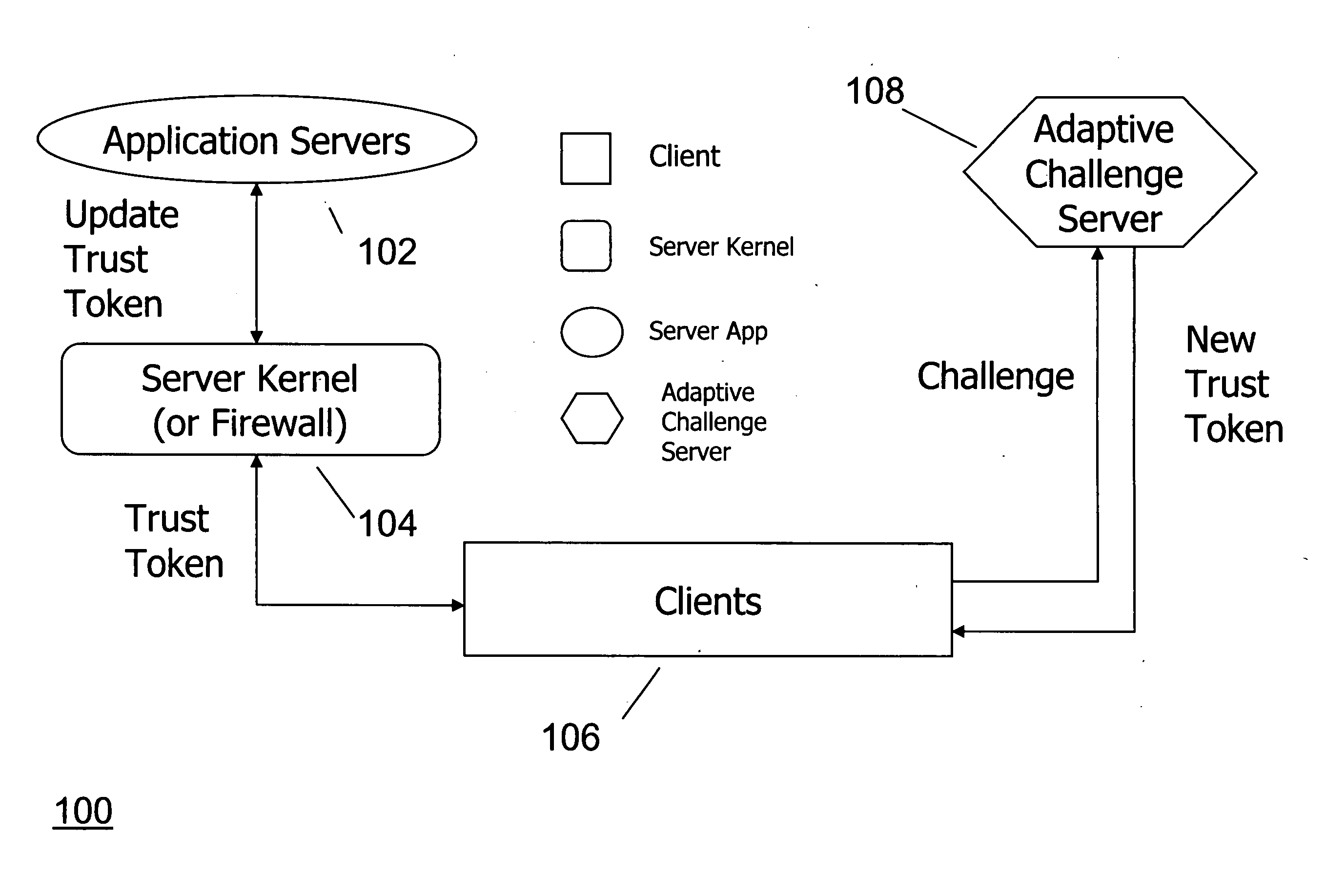
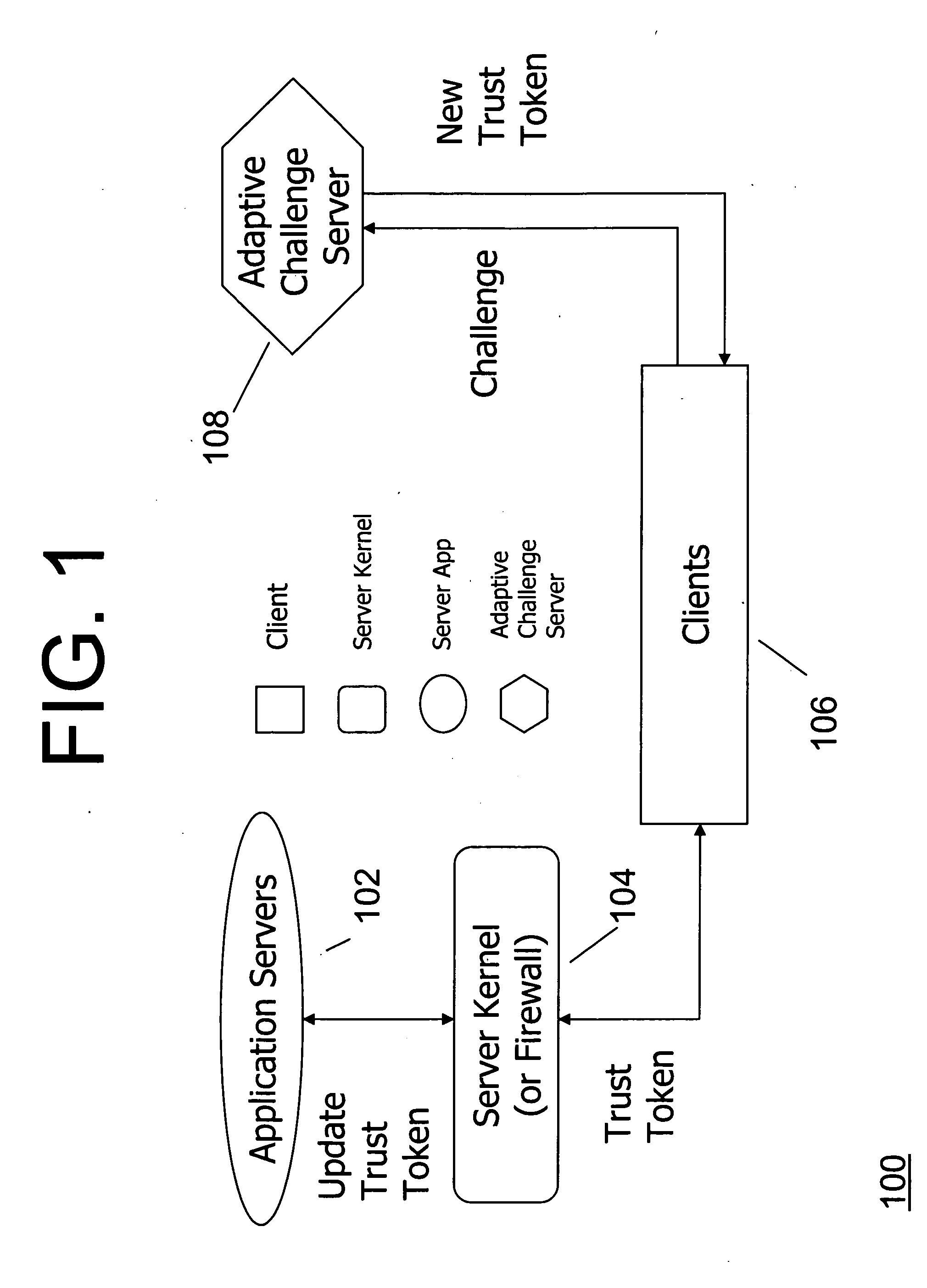
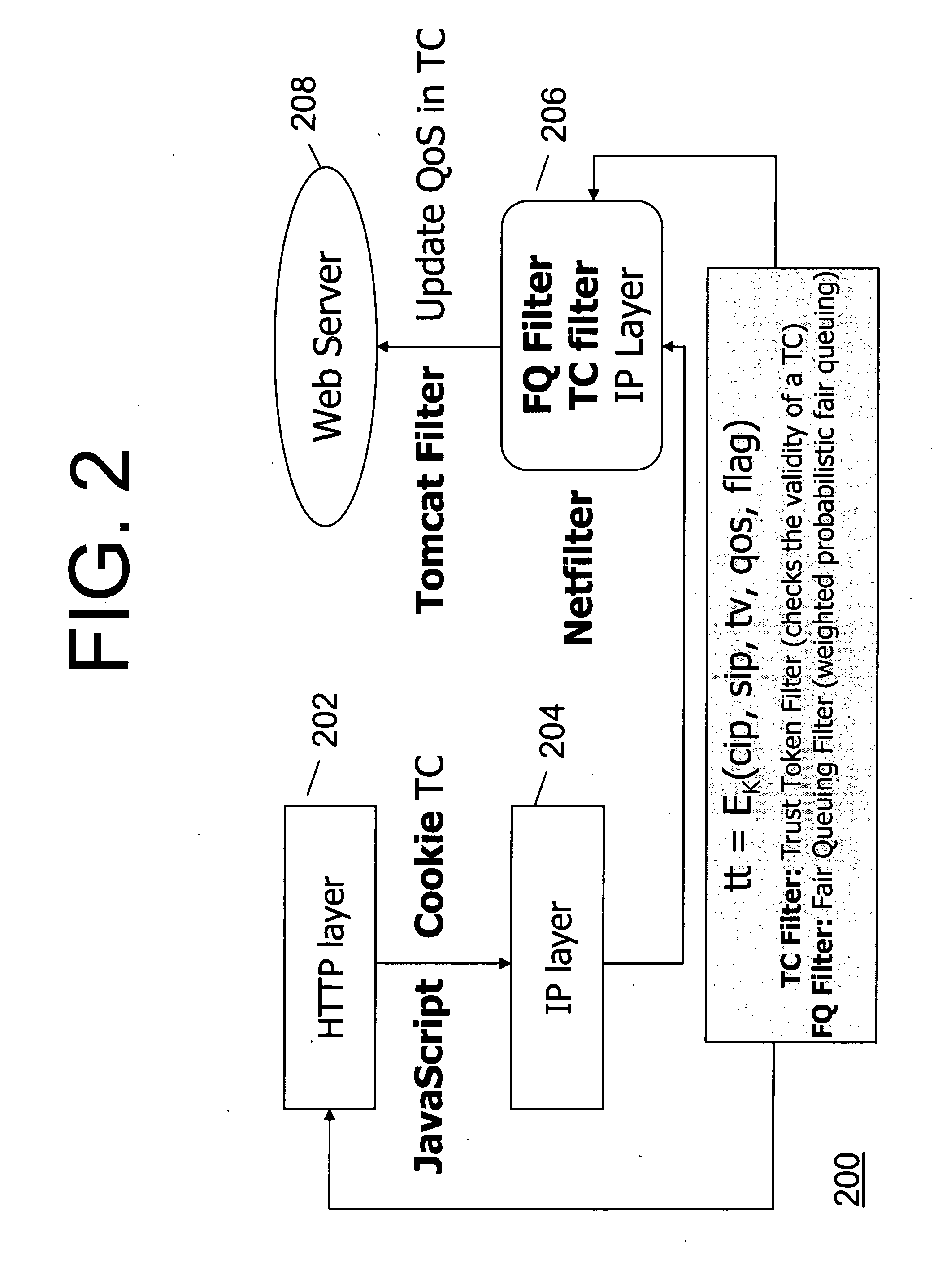
Method and system for protecting against denial of service attacks using trust, quality of service, personalization, and hide port messages
InactiveUS20070266426A1Random number generatorsUser identity/authority verificationPersonalizationQuality of service
According to an embodiment of the invention, a method for processing a plurality of service requests in a client-server system includes server steps of receiving at least one request for service from a client and providing a level of service based on a trust level provided in the at least one request. According to another embodiment, a method of authenticating messages includes steps of: embedding authentication information into a message at the application level; downloading a script from a computer for sending the message; running said script to send said message to a server; and checking said message by said server at the network level.
Owner:IBM CORP
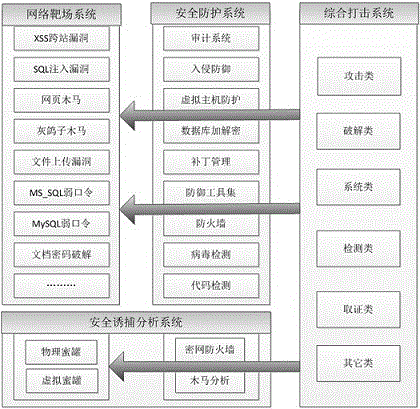
Information safety attack and defense system structure of cloud platform
ActiveCN104410617AReduce security risksLow implementation costTransmissionVirtualizationOperational system
The invention provides an information safety attack and defense system structure of a cloud platform. The system structure comprises a network target range system, a security defending system, a comprehensive striking environment and a safety trap analysis system; the network target range system comprises a plurality of information security hole environments capable of simulating the security holes of an operating system level, an application level and a network level; the security defending system comprises a plurality of information safety protection tools which have monitoring, defending and audit capacities; the comprehensive striking system comprises a plurality of osmosis attacking tools with the comprehensive and multidirectional attacking capacity; the trap analysis system comprises diversified trap environments which can attract and trap hostile attack behaviors, and provide the analysis capacity on the attack behaviors to obtain the attacking features. The information safety attack and defense system structure provided by the invention is applicable to an information security attack and defense and verification system of the cloud platform; furthermore, by the combination of a virtualized service-oriented application technology, the problem of information security risk that the security system of the cloud platform is difficult to verify can be solved.
Owner:XIAN UNIV OF POSTS & TELECOMM +1
Automatically discovering management information about services in a communication network
An automatic service discovery approach allows a network management system to discover service managed objects from the network, eliminating the need for a user or other management application to provide such information. As a result, a network management system can automatically perform network-level or services level discovery of objects and services for which network components have no understanding. Embodiments are applicable, for example, in the context of management of packet voice (VoIP, VoATM) and metro Ethernet (TLS service) domains, as well as other domains.
Owner:CISCO TECH INC
Method for estimating telephony system-queue waiting time in an agent level routing environment
InactiveUS6898190B2Special service provision for substationError preventionComputer telephony integrationNetwork level
A system for estimating call waiting time for a call in a queue takes into account multiple queues wherein agents are shared between queues, abandoned call history, and virtual and priority queues. The system in a preferred embodiment is a computer-telephony integration (CTI) software application adapted to execute on a CTI processor, which may be coupled to switching equipment at network level in a connection-oriented, switched telephony (COST) network or to a switch at call-center level, or both.
Owner:GENESYS TELECOMM LAB INC AS GRANTOR +3
Digital content security system
InactiveUS7305560B2Digital data processing detailsUnauthorized memory use protectionHard disc driveOperational system
A Personal Digital Key Digital Content Security System (PDK-DCSS) is used to protect computers from unauthorized use and protect the digital content stored on computers from being wrongfully accessed, copied, and / or distributed. The basic components of the PDK-DCSS are (1) a standard hard drive device, with the addition of a PDK Receiver / Decoder Circuit (PDK-RDC) optionally integrated into the hard drive's controller, and (2) a PDK-Key associated with the PDK-RDC. The PDK-Key and RDC technology is utilized to provide two categories of protection: (1) hard drive access control for providing Drive-Level and Sector-Level protection and (2) operating system-level independent file protection for providing File-Level and Network-Level protection.
Owner:PROXENSE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com