Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
857 results about "Computer platform" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A computing platform is the stage on which computer programs can run. A platform can be seen both as a constraint on the software development process, in that different platforms provide different functionality and restrictions; and as an assistance to the development process, in that they provide low-level functionality ready-made.
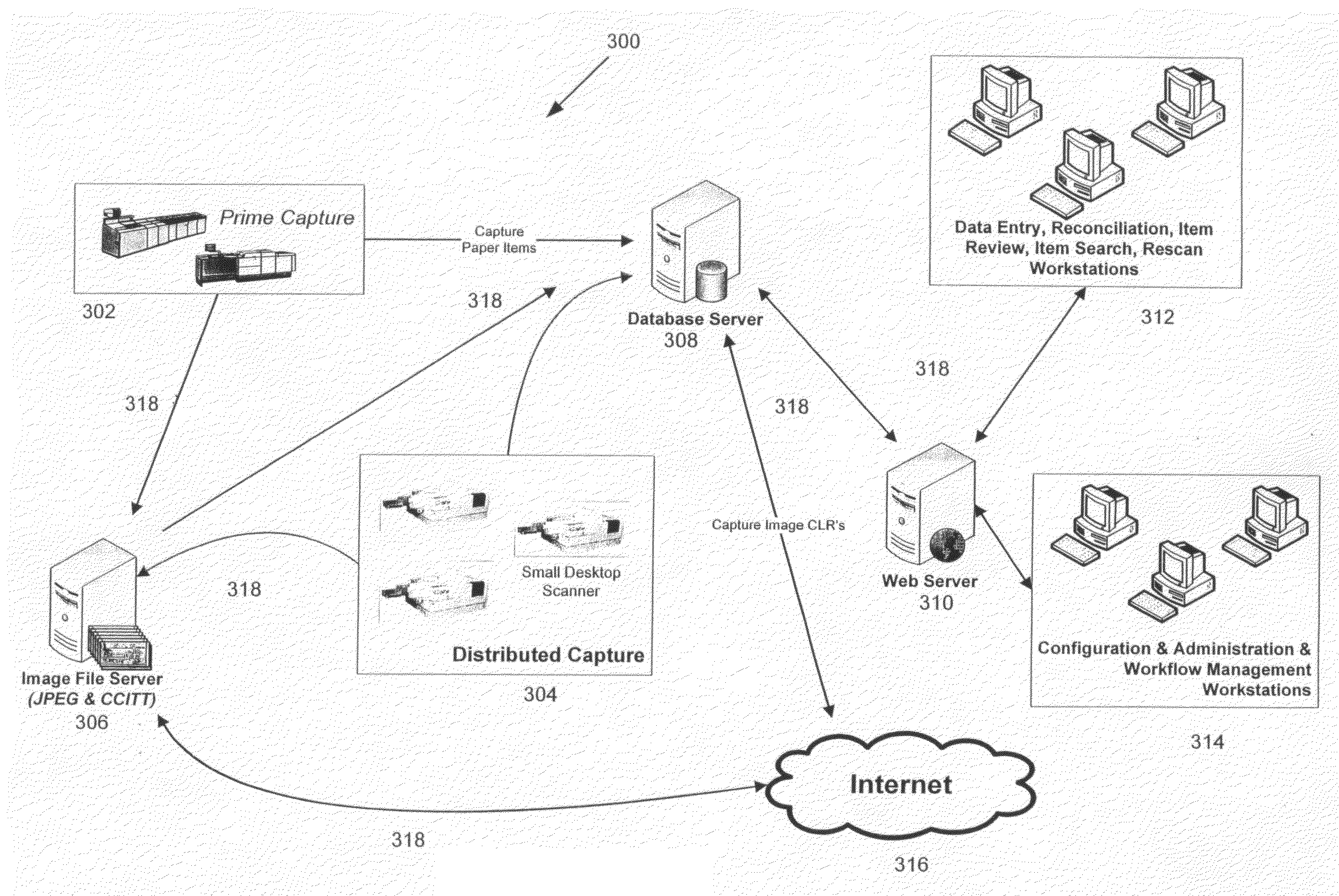
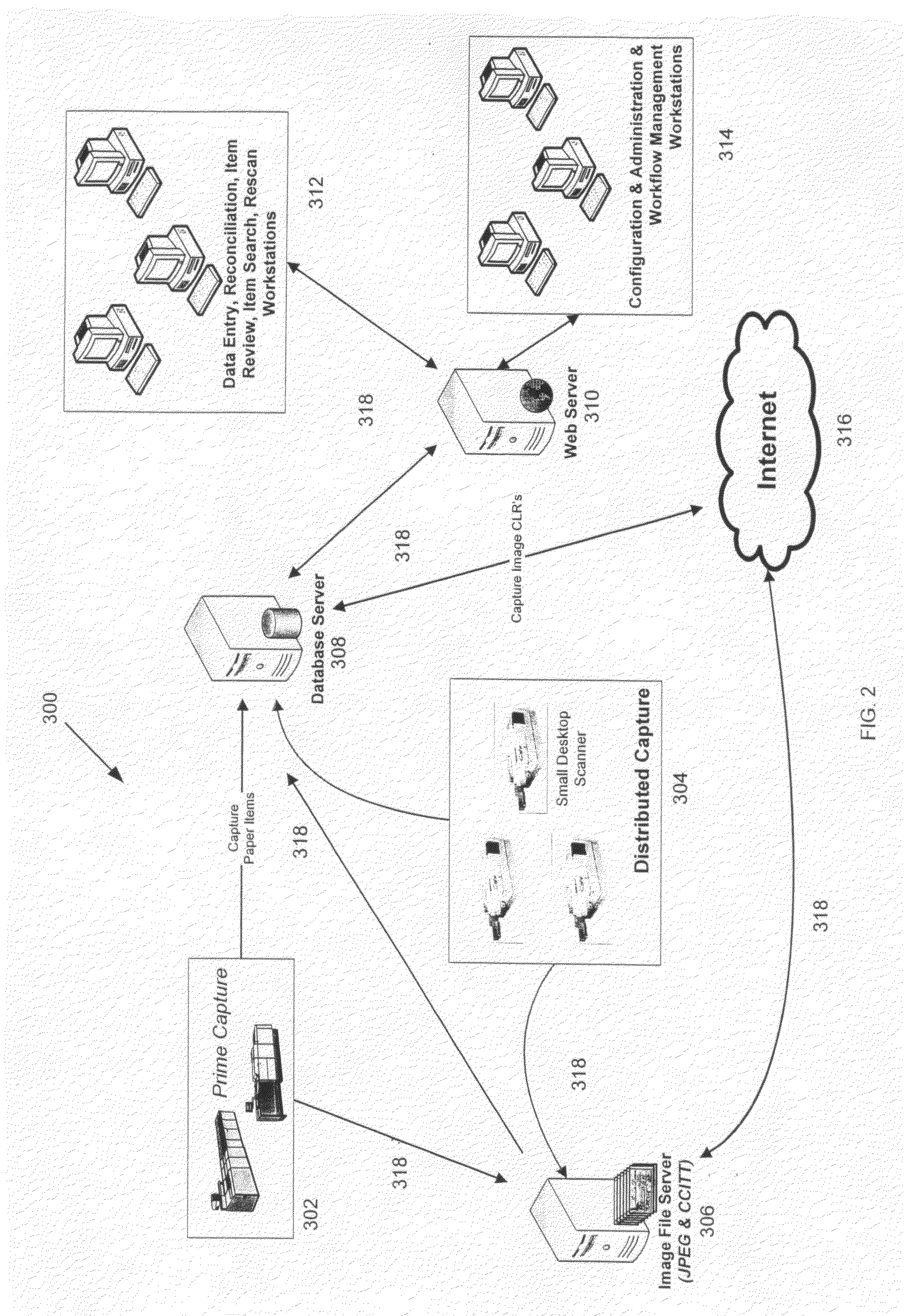
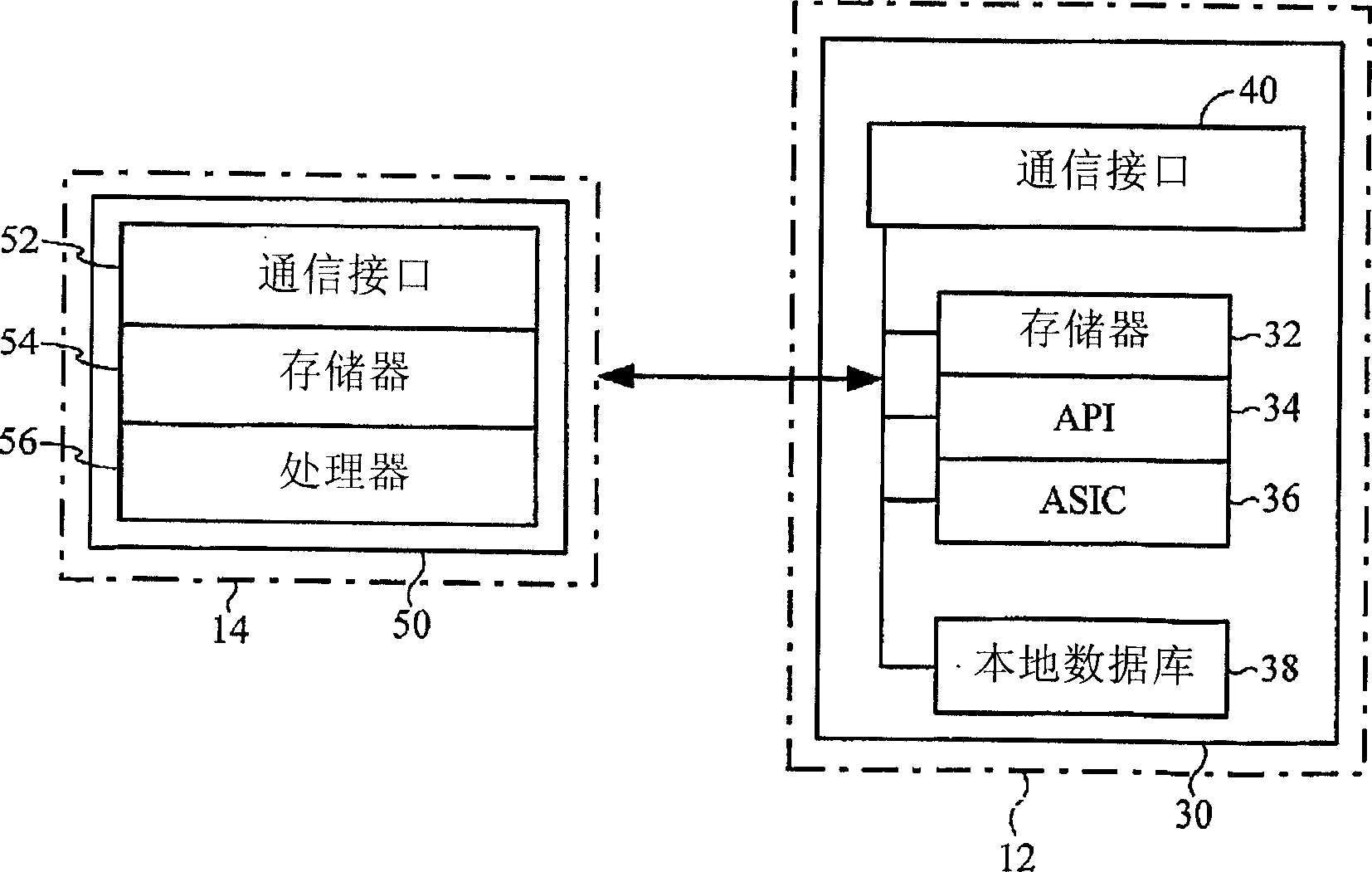
Check21 image based document and processing system
InactiveUS20070288382A1Easy to removeEasy to addFinanceCharacter and pattern recognitionSoftware systemModularity
A Check21 Act image based document and processing system, comprising a modular hardware and software image-based financial processing system with independent software modules supporting specific hardware and or processing applications; thereby, simplifying the process for the removal or addition of support for new computer platforms, components, features, peripherals, applications and / or interoperating with legacy hardware and software systems.
Owner:AVALON INT
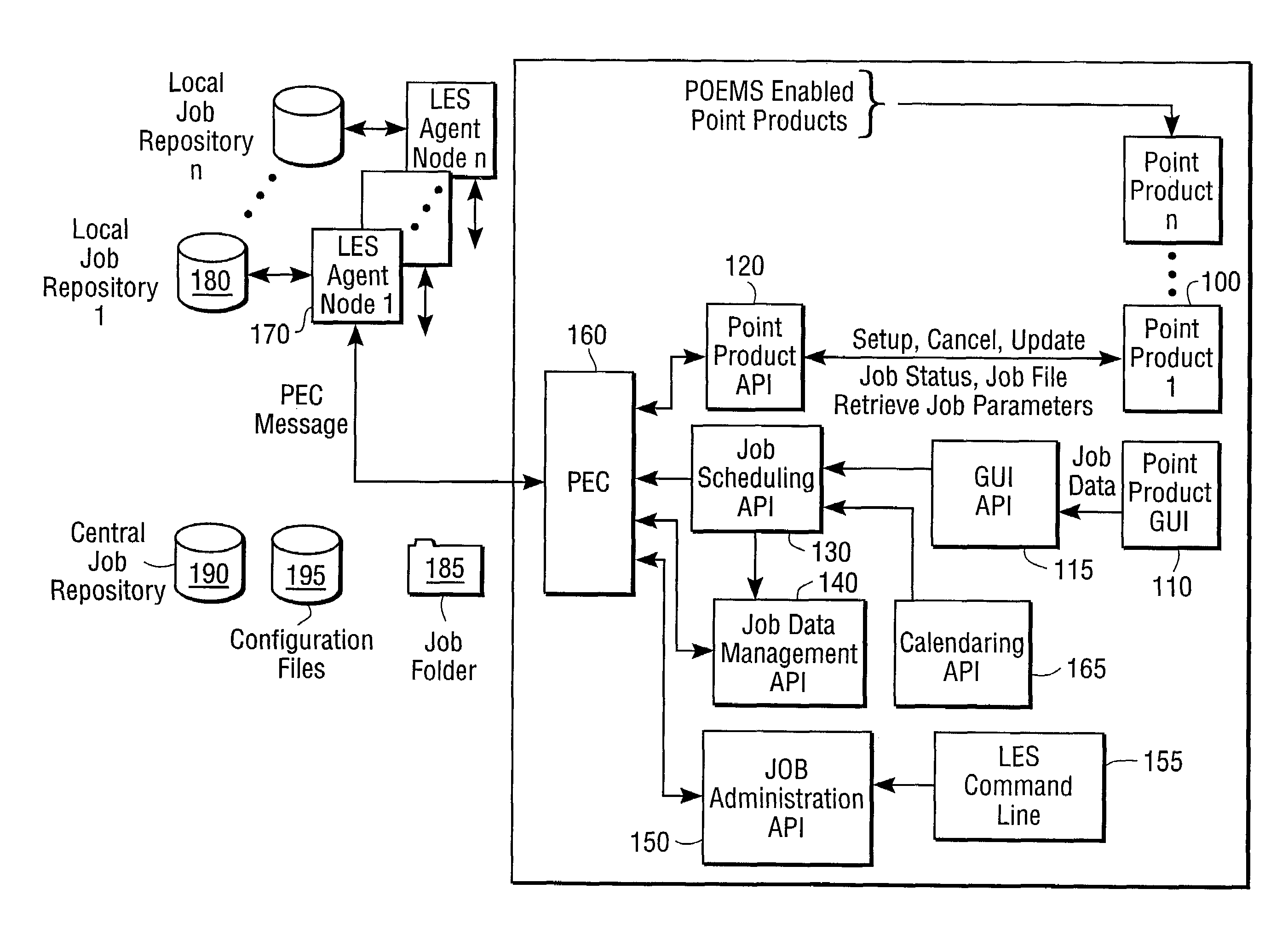
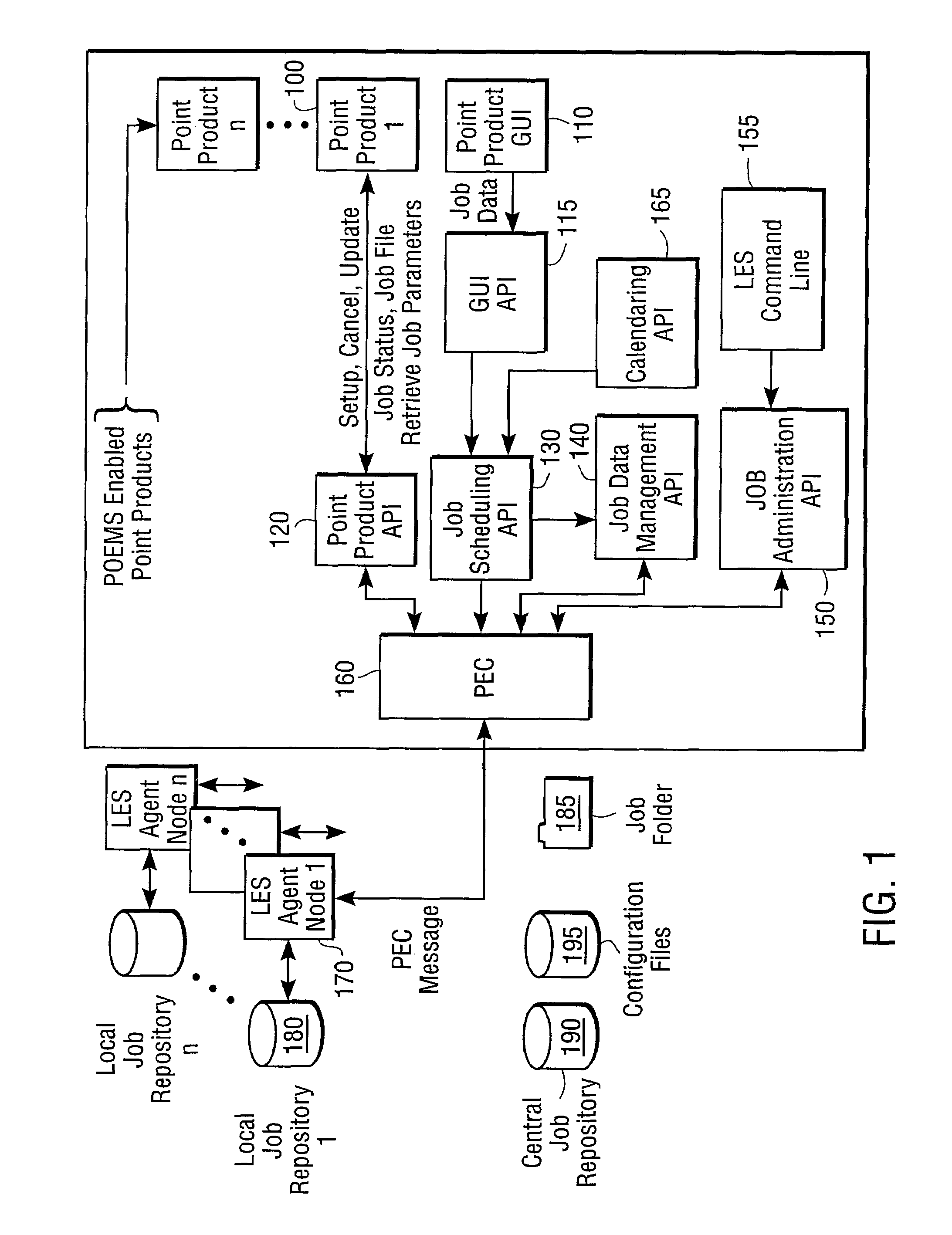
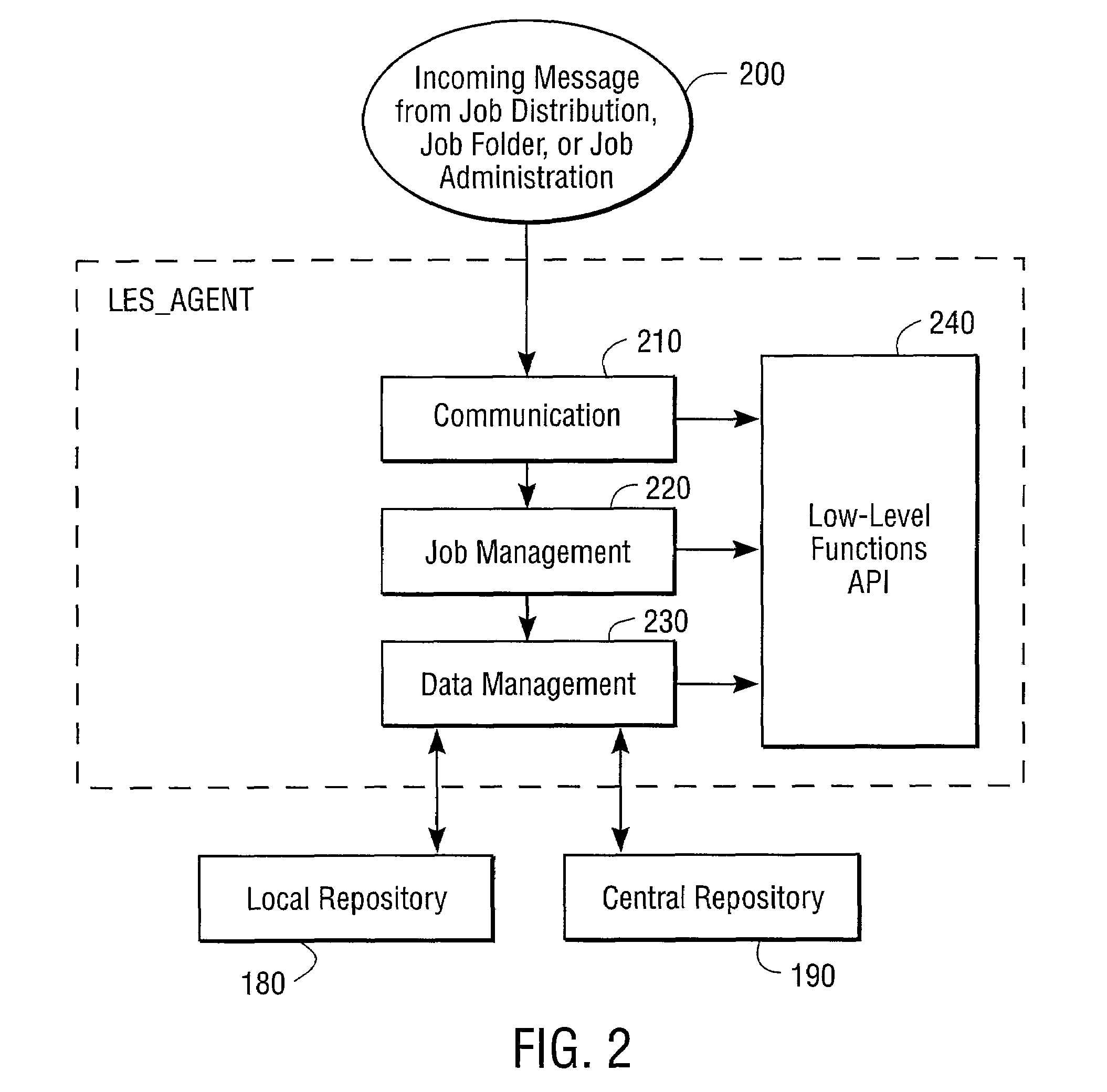
System for scheduling and monitoring computer processes
InactiveUS7386586B1Resource allocationMultiple digital computer combinationsApplication programming interfaceData management
A job scheduling device providing a consistent set of application programming interfaces (APIs) compiled and linked into an individual or suite of programs to provide scheduling services on a single computer or across multiple computing platforms, includes a GUI API for retrieving and validated job parameters, a job scheduling API for allocating jobs based on the job parameters, and an enterprise scheduling agent hosted on one or more nodes of the computer platforms. An enterprise communication agent sends messages containing jobs from a computer executing a program utilizing the job scheduling device to the enterprise scheduling agent on a selected node where the job is to execute. Then, the enterprise scheduling agent retrieves job parameters and launches the job on the selected node. The enterprise scheduling agent maintains a local job repository containing job information for each job run on its corresponding node and sends messages to a job data management API to maintain a central job repository containing information on jobs executed on all nodes.
Owner:COMP ASSOC THINK INC
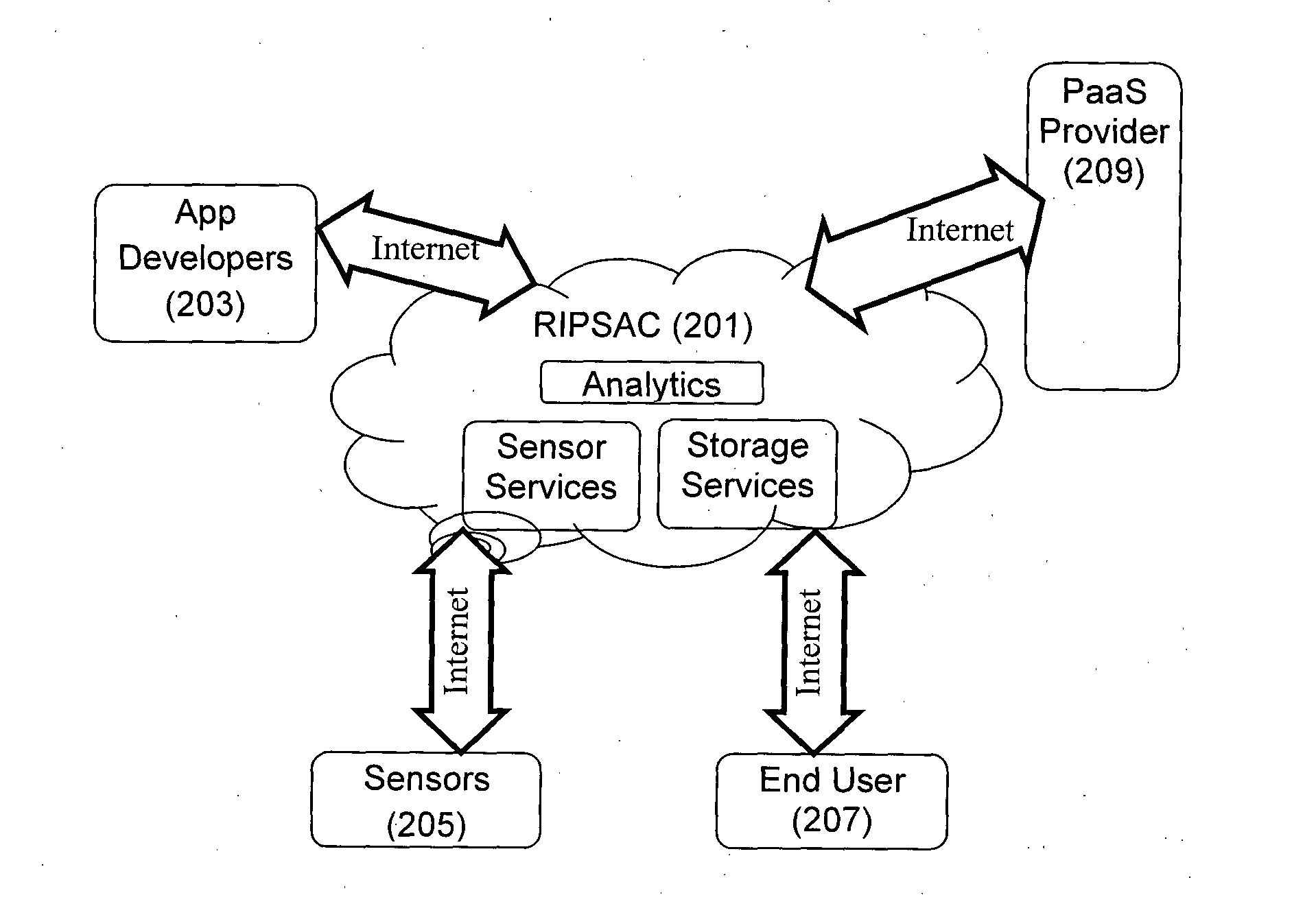
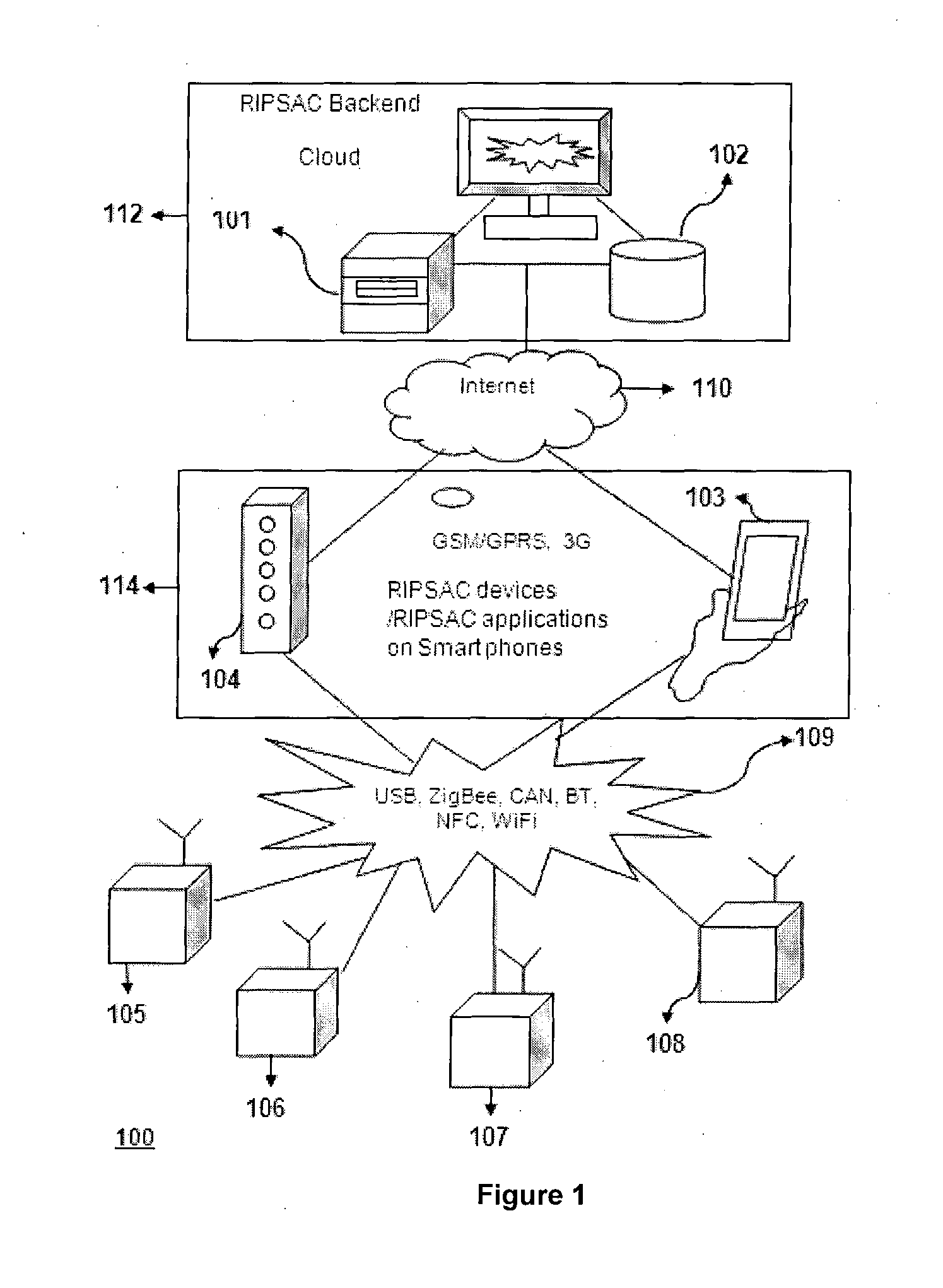
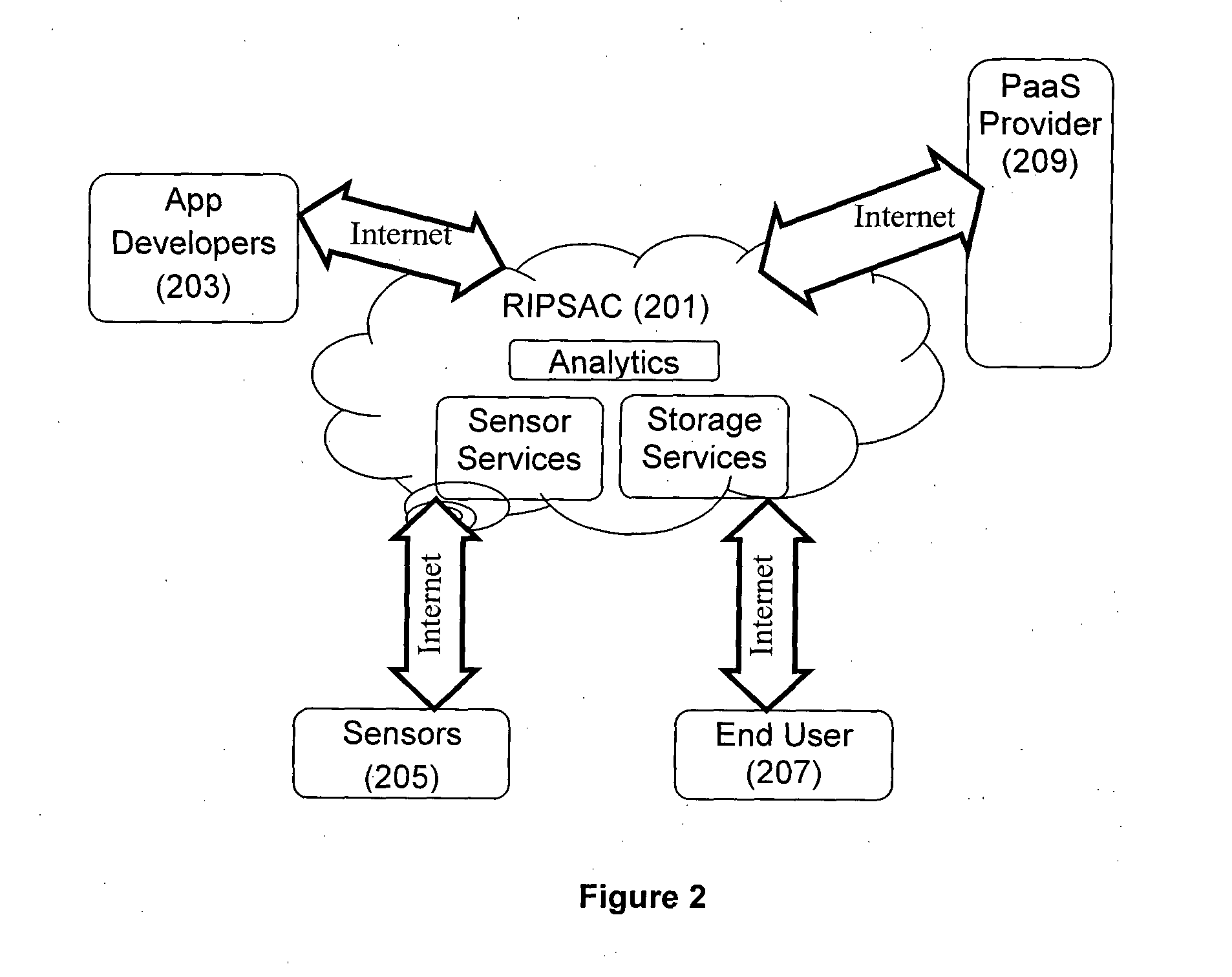
Computer Platform for Development and Deployment of Sensor Data Based Applications and Services
ActiveUS20140359552A1Facilitating crowd sourcing application developmentFacilitates and easy developmentError detection/correctionSoftware reuseReal time analysisCloud base
A method and system for real-time analytics of sensor-based data is disclosed. Also disclosed is a Cloud-based Paltform-as-a-Service (PaaS) offering for sensor driven applications with services and features for their complete life-cycle management including prompt development, testing, deployment and so forth. The method of the present disclosure enables real-time tracking of various physical parameters and attributes related to smart-spaces using sensor devices implemented in the premises of the smart-space environment and using crowd-sourced user input data. Further, the parameters obtained are sent to the cloud-computing server, wherein the analytics are performed in real-time based on the obtained parameters.
Owner:TATA CONSULTANCY SERVICES LTD
Computer Platform for Development and Deployment of Sensor-Driven Vehicle Telemetry Applications and Services
InactiveUS20140380264A1Promote application developmentFacilitates vehicle anomaly detectionSoftware testing/debuggingProgram loading/initiatingCloud baseEngineering
A computing platform for intelligent development, deployment and management of vehicle telemetry applications is disclosed herein. Further, the present disclosure provides a method and system that enables provision of Intelligent Transportation Service on the Cloud-based Platform that facilitates creation and deployment of vehicle telemetry applications configured for enabling traffic measurements, traffic shaping, vehicle surveillance and other vehicle related services.
Owner:TATA CONSULTANCY SERVICES LTD
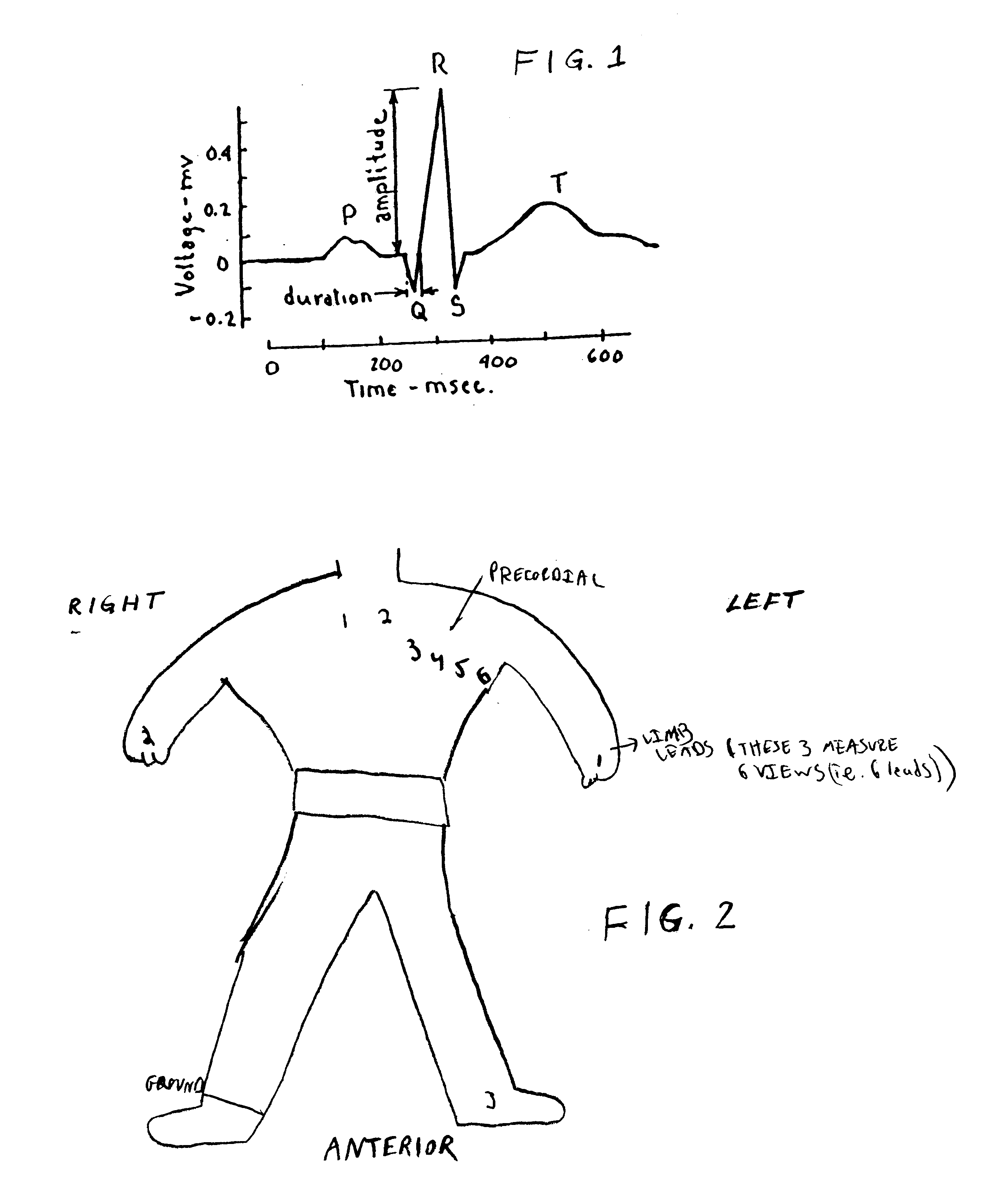
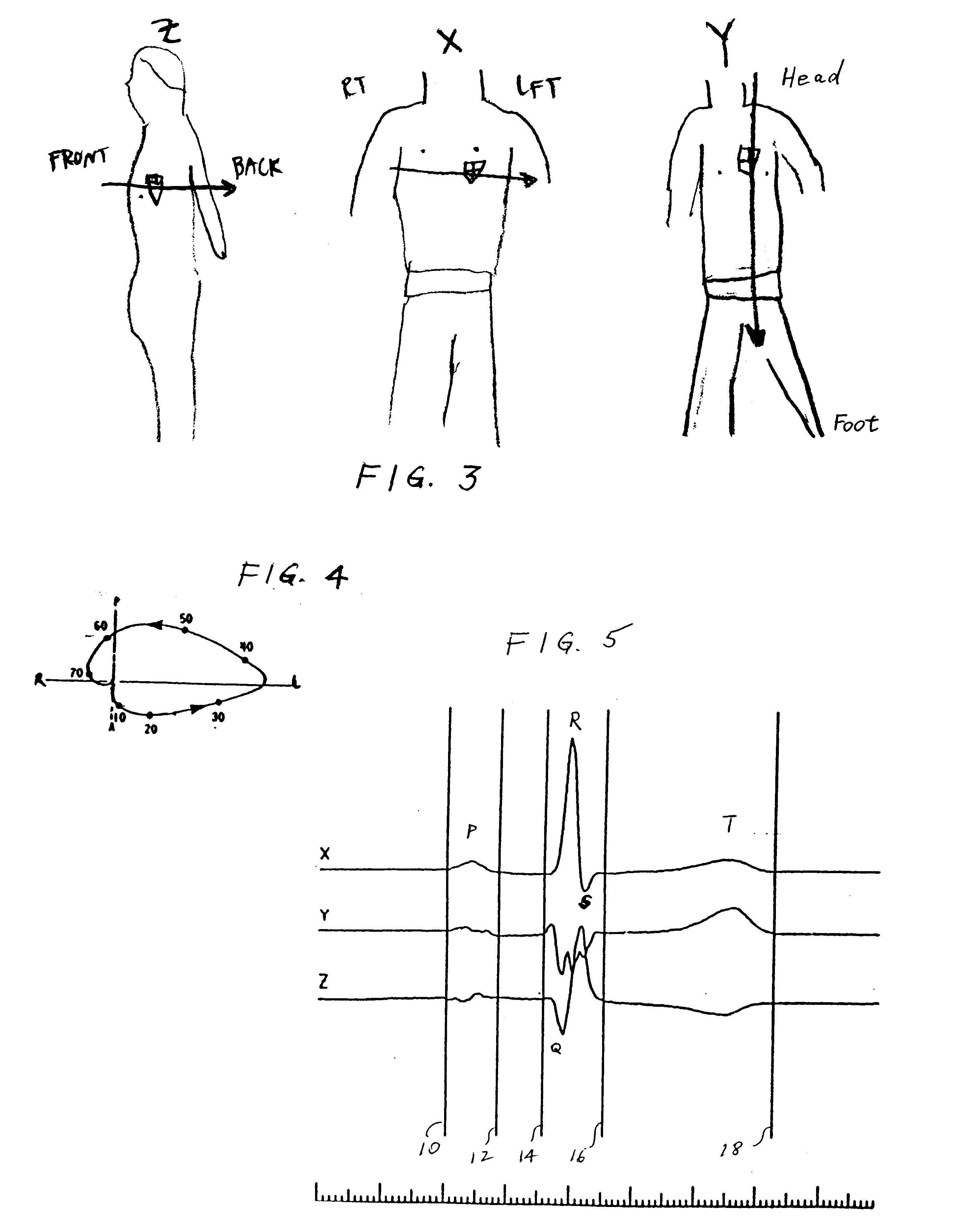
Method of analysis of the electrocardiogram
Owner:TOOLE J GERALD
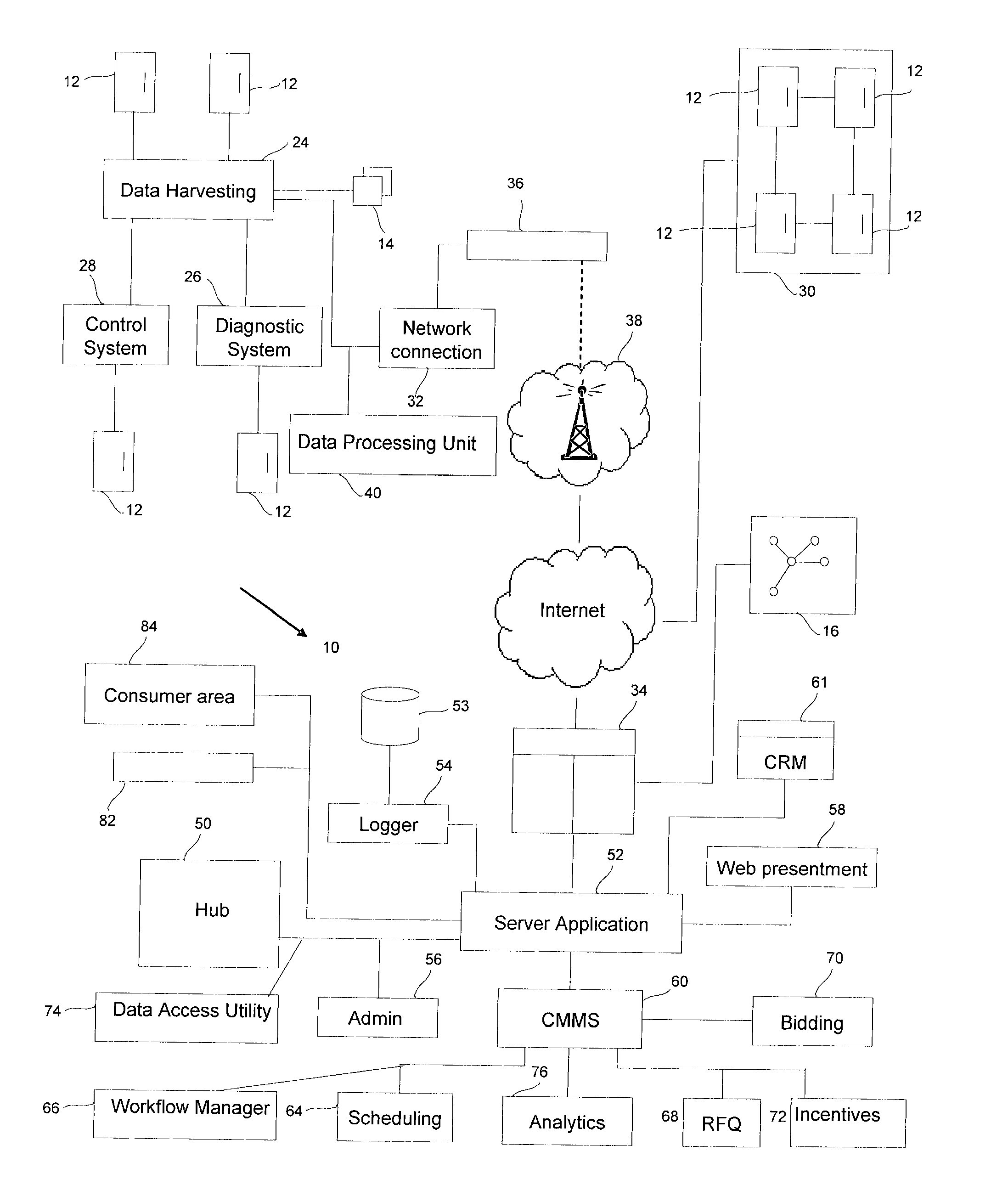
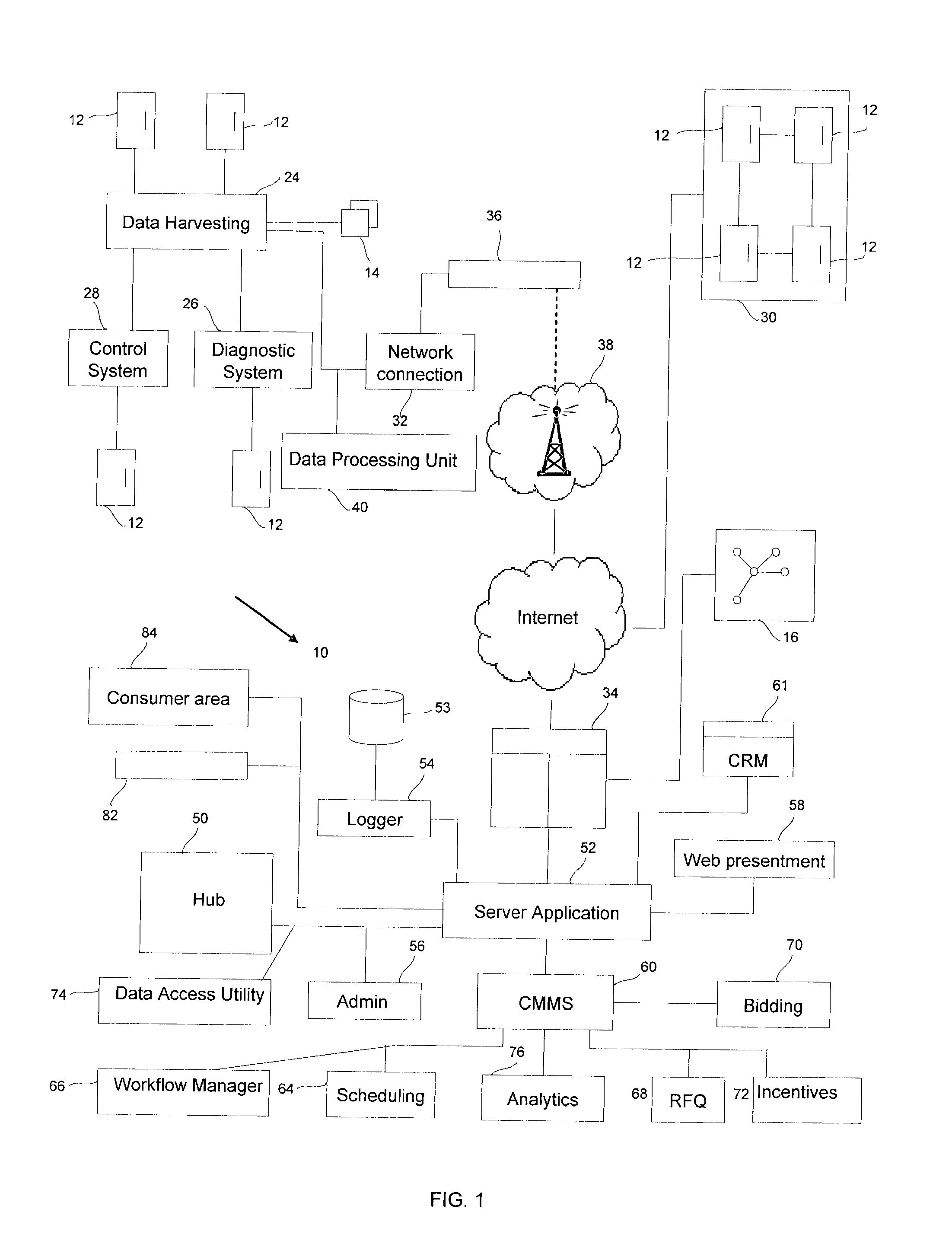
System and method for providing consumer side maintenance
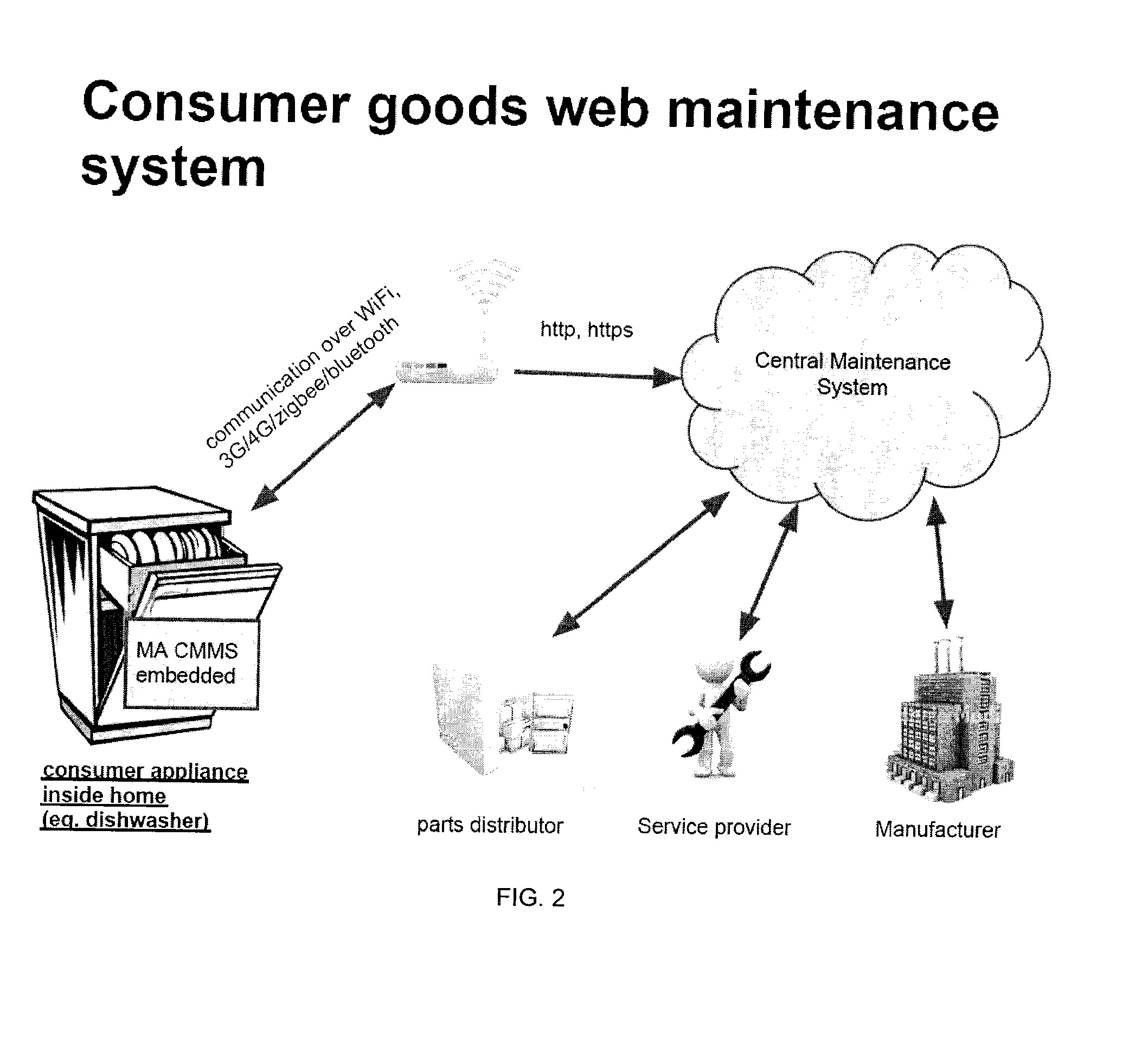
A computer system is provided that is connected to the Internet and enables a plurality of network connected devices to access a novel and innovative resource management platform. The computer system includes an Internet enabled computer platform that implements a multi-tenant architecture that enables multiple platform clients to populate the platform with various information regarding their maintenance service requirements. The computer system includes one or more tools that (i) track activities of consumers in connection with their appliances or other consumer resource, (ii) extracts insights from such activities, and / or (iii) enables service businesses or manufacturers to upload information or documents related to maintenance services, such tools enabling the automated suggestion of maintenance actions and / or product or service requirements of consumers. A range of different intelligent features are provided. The computer system may include a CMMS with intelligent features. A number of related computer implemented methods for managing maintenance in an intelligent way is also provided.
Owner:FIIX INC
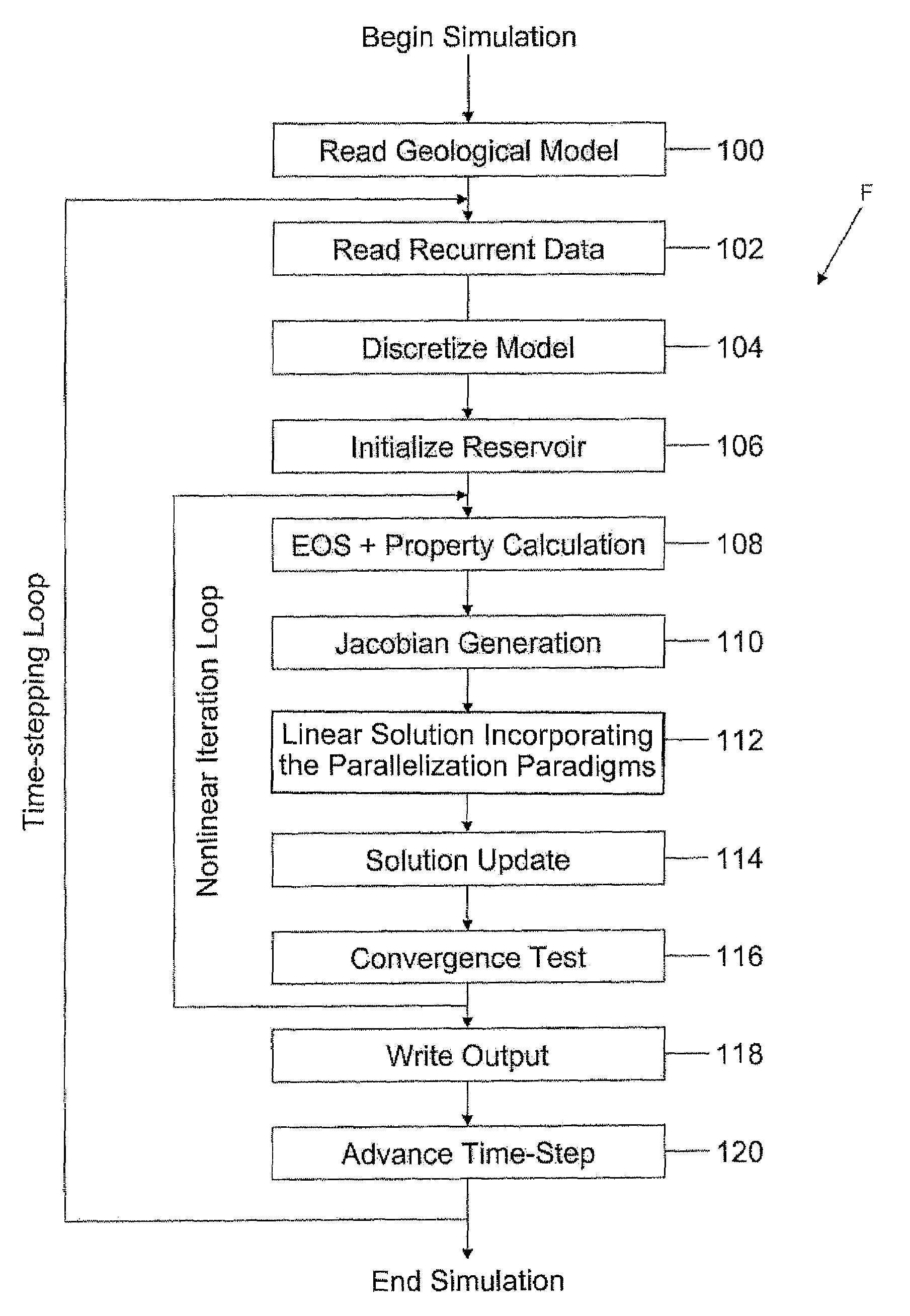
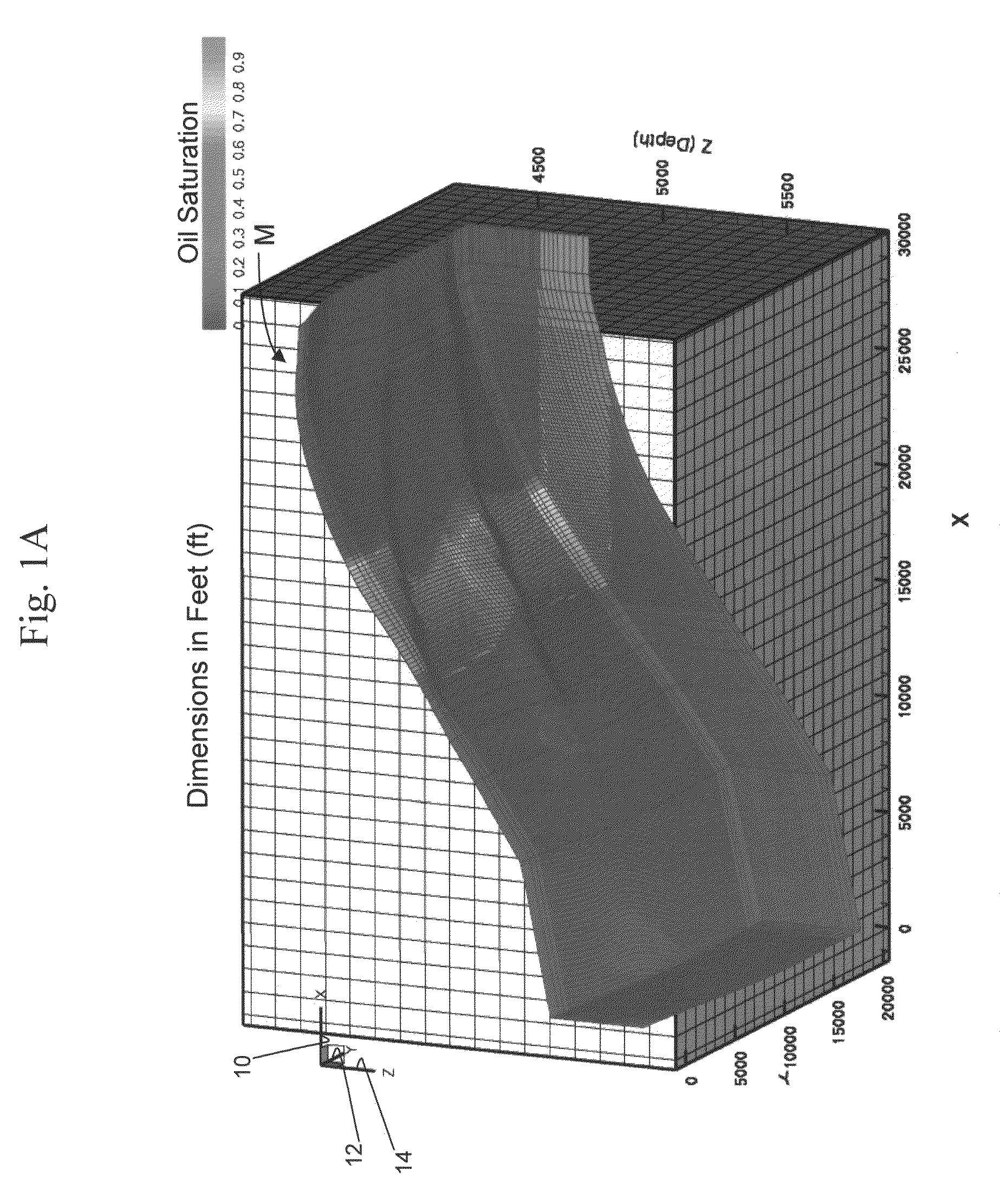
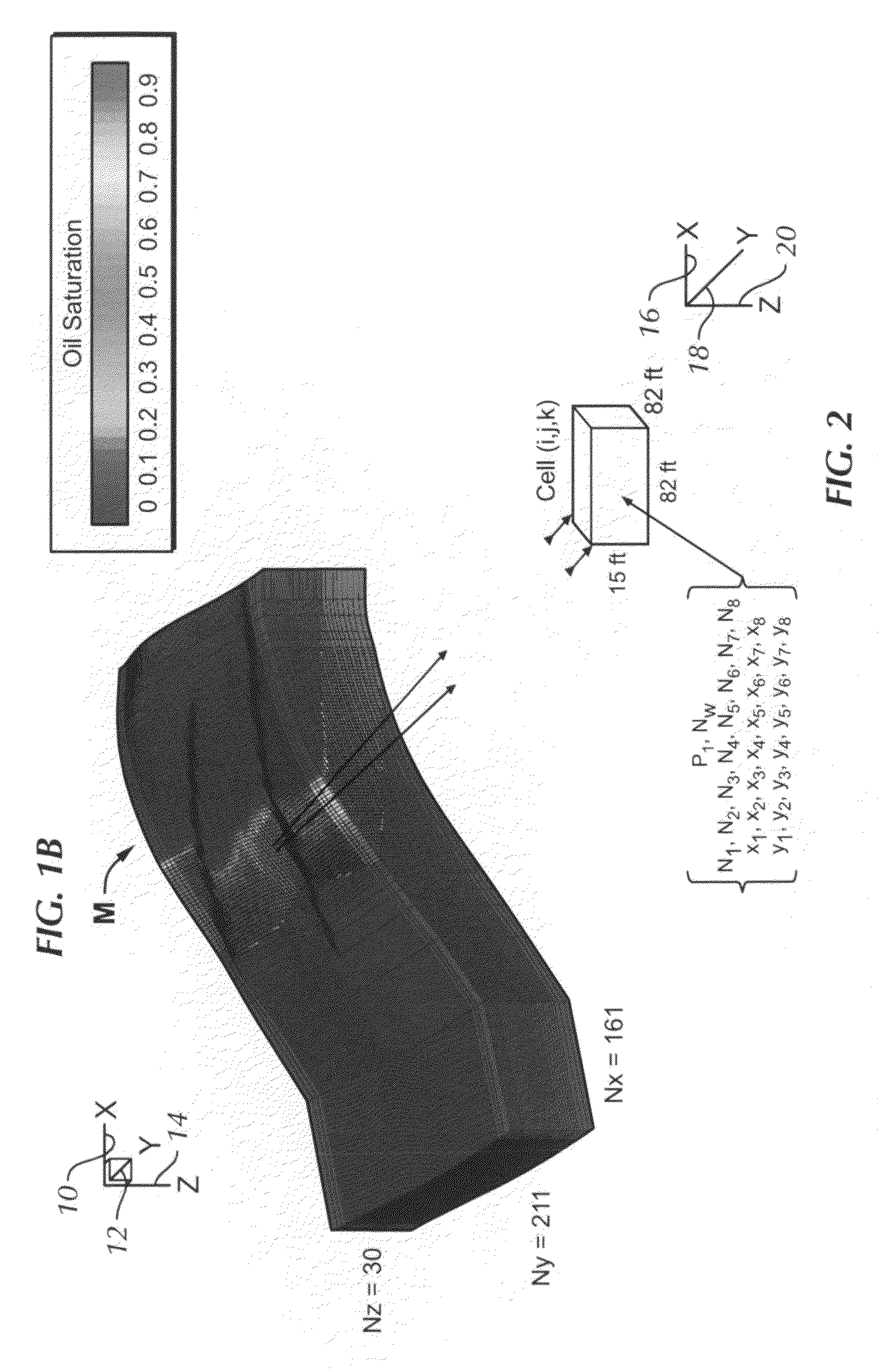
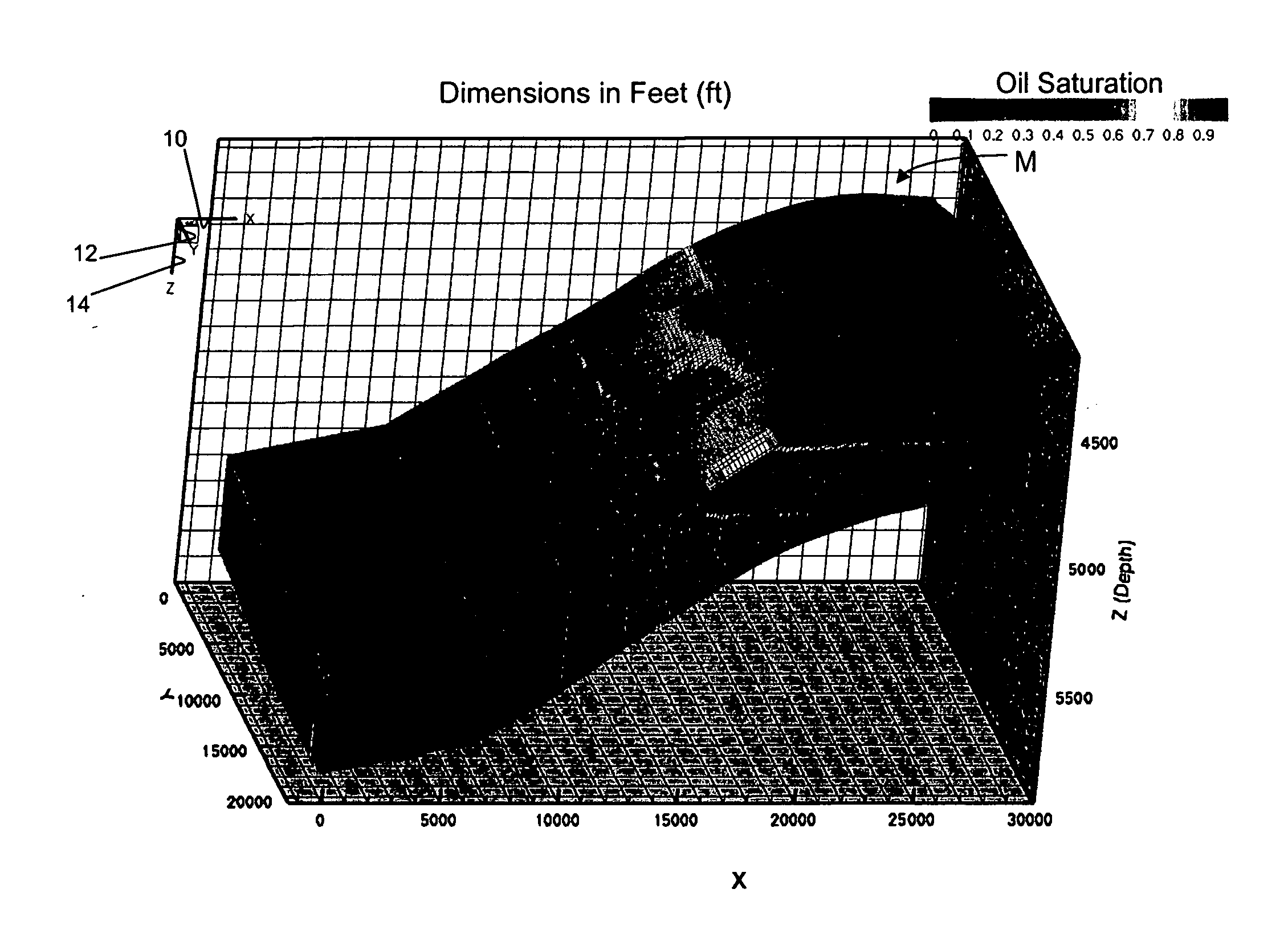
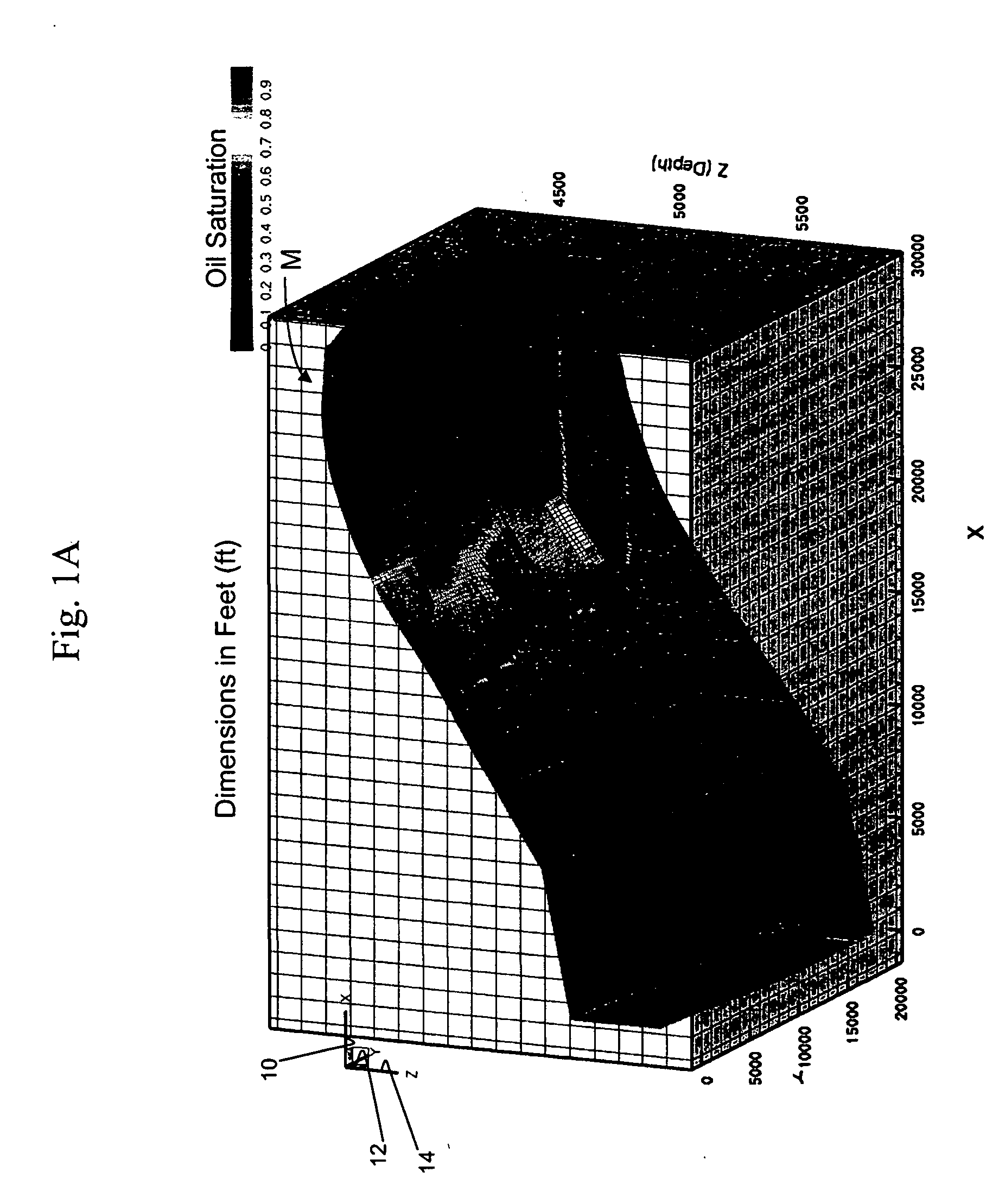
Highly-parallel, implicit compositional reservoir simulator for multi-million-cell models
ActiveUS7526418B2Reduce processing timeElectric/magnetic detection for well-loggingPermeability/surface area analysisSupercomputerDistributed memory
A fully-parallelized, highly-efficient compositional implicit hydrocarbon reservoir simulator is provided. The simulator is capable of solving giant reservoir models, of the type frequently encountered in the Middle East and elsewhere in the world, with fast turnaround time. The simulator may be implemented in a variety of computer platforms ranging from shared-memory and distributed-memory supercomputers to commercial and self-made clusters of personal computers. The performance capabilities enable analysis of reservoir models in full detail, using both fine geological characterization and detailed individual definition of the hydrocarbon components present in the reservoir fluids.
Owner:SAUDI ARABIAN OIL CO
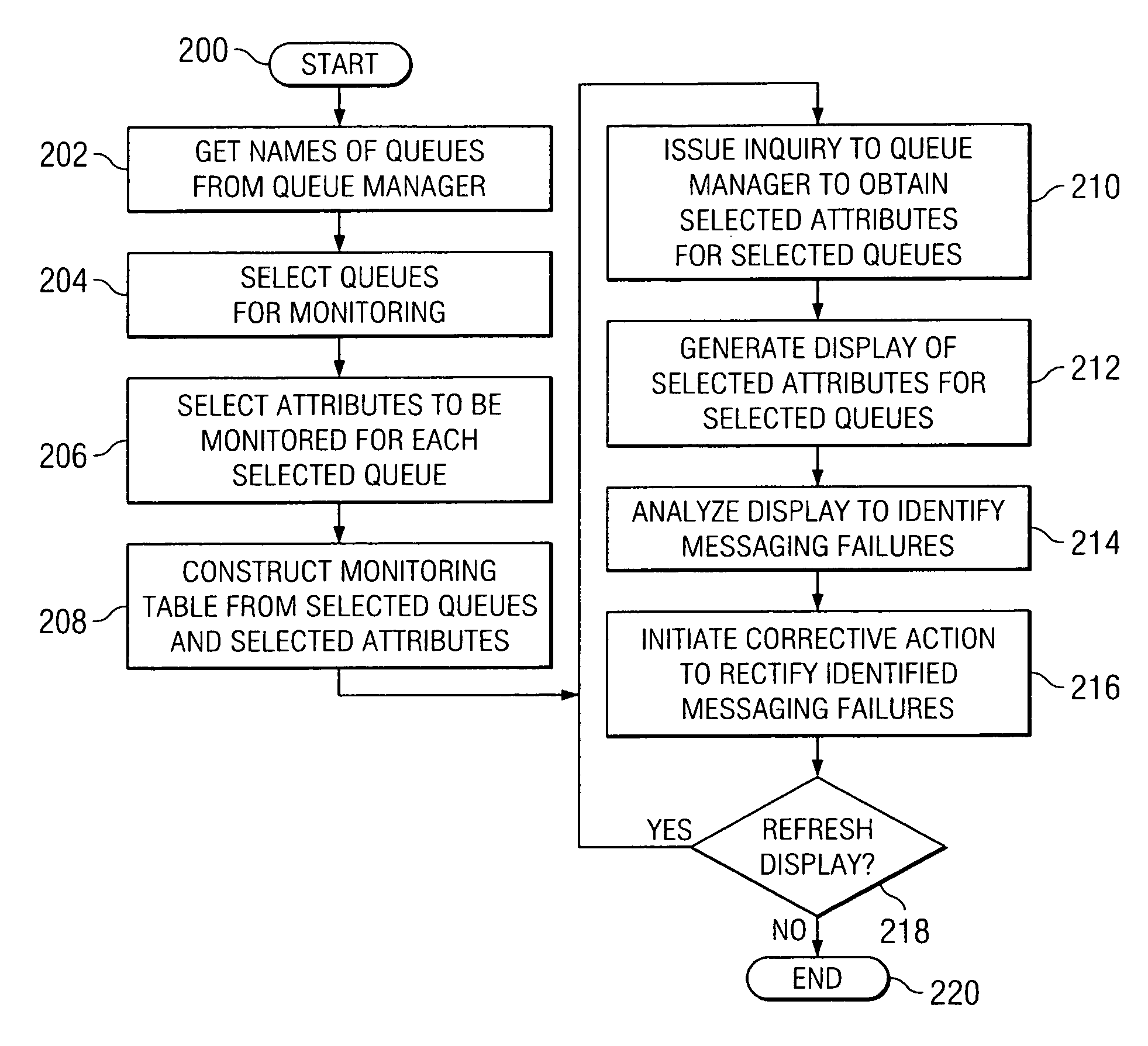
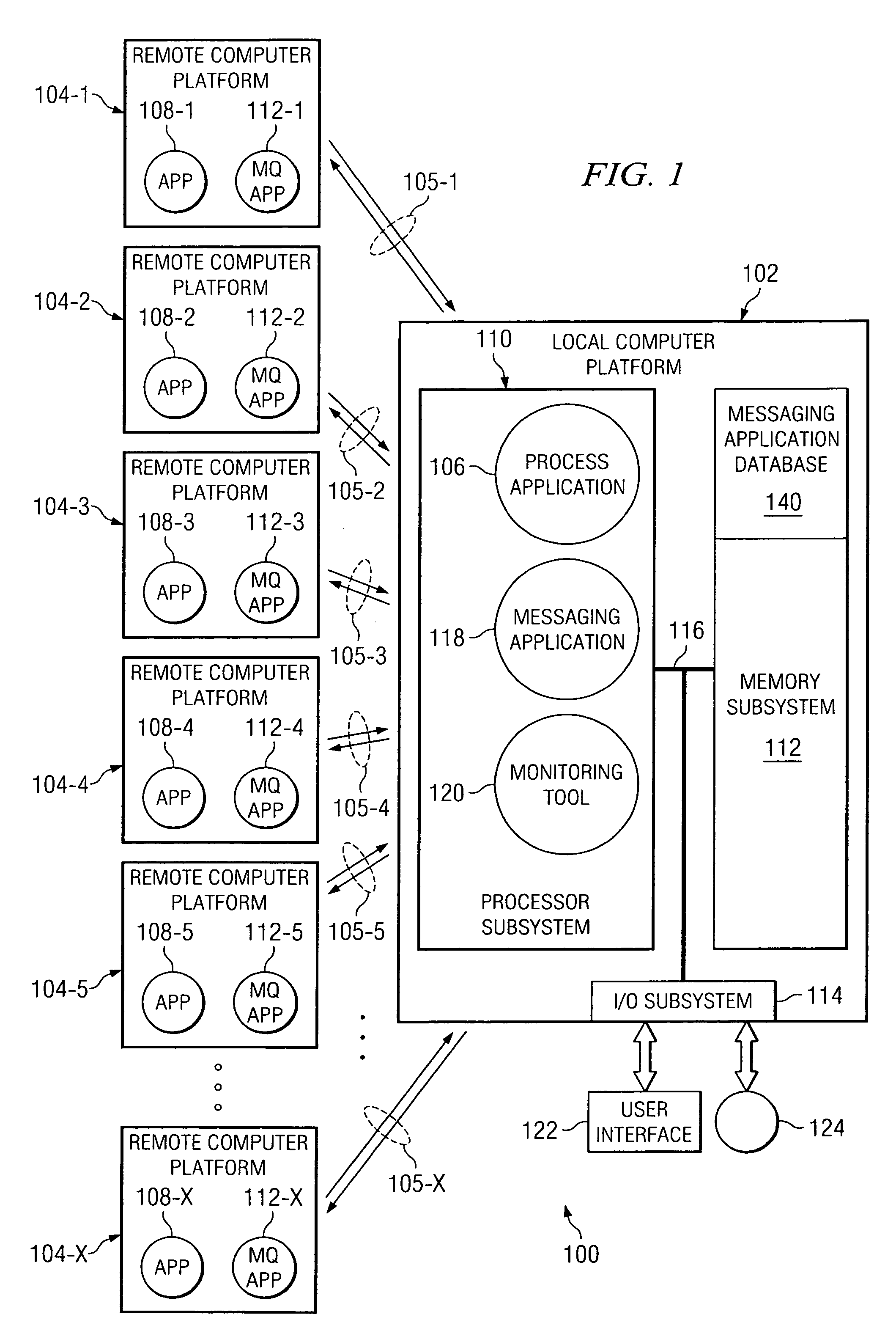
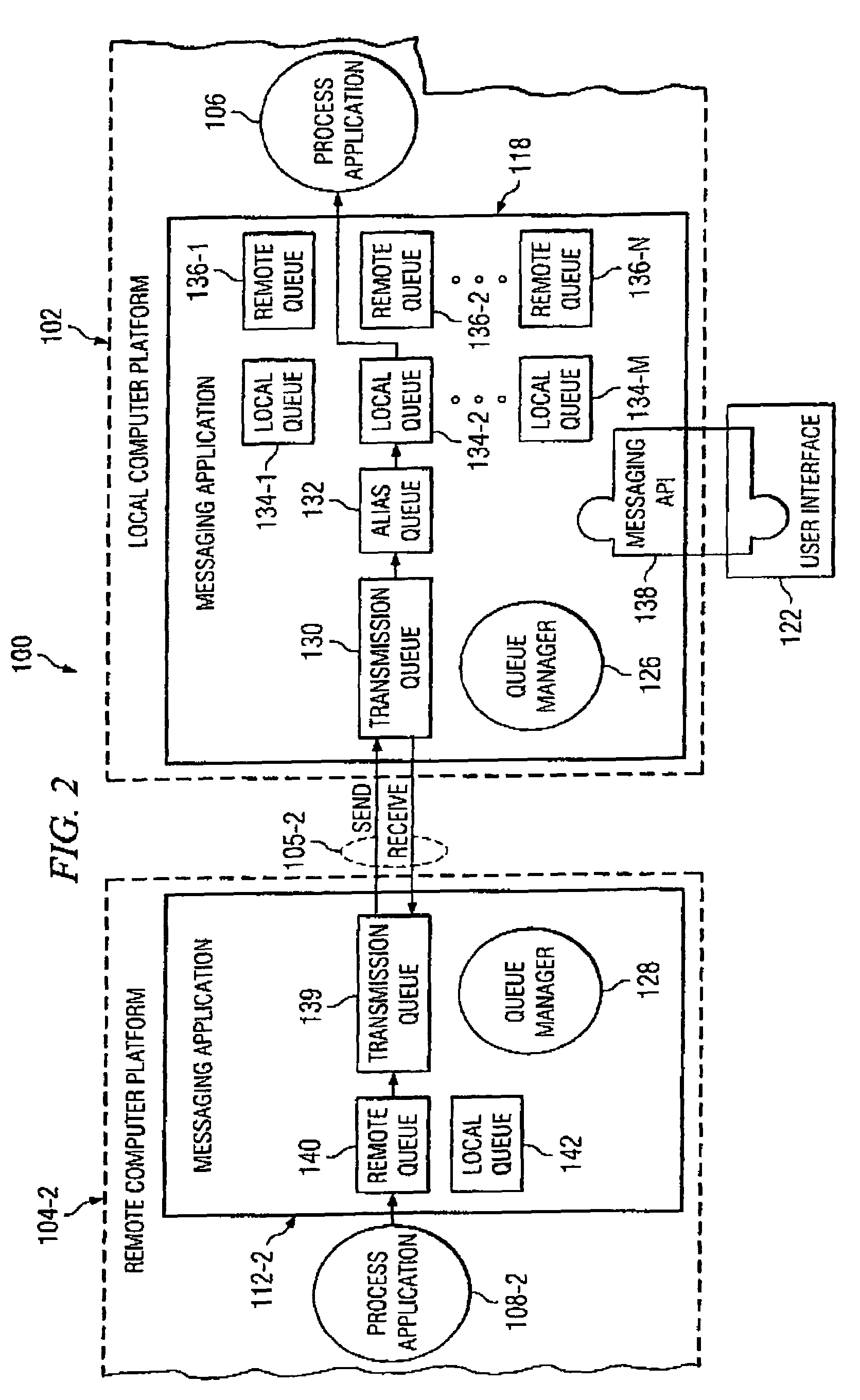
Method and apparatus for network-level monitoring of queue-based messaging systems
ActiveUS7127507B1Digital computer detailsTransmissionProgram managementDistributed Computing Environment
A distributed computing environment and associated method for monitoring a queue-based messaging system. The queue-based messaging system controls the exchange of messages between a server process and client process applications. A messaging application residing at the server computer platform and forming part of the queue-based messaging system manages a plurality of trigger-initiated local queues, each associated with one of the plurality of client process applications and having queue depth, trigger enable, get enable and put enable attributes. A monitoring tool residing on the server computer platform acquires a value for the queue depth, trigger enable, put enable and get enable attributes for a plurality of trigger-initiated local queues and generally simultaneously displays, on a user interface coupled to the server computer platform, the value for the queue depth, trigger enable, put enable and get enable attributes for each one of the plurality of trigger-initiated local queues.
Owner:T MOBILE INNOVATIONS LLC
System and method for establishing a communication between a peripheral device and a wireless device
InactiveUS20050097248A1Interprogram communicationData switching by path configurationOperational systemSystems approaches
A system, method and computer program for establishing communication between a peripheral device and programs resident on a wireless computer device. The device has a computer platform with a wireless communication portal and one or more resident programs, and the computer platform includes an operating system that manages wireless device resources and the interaction of the wireless device with other computer devices. When a peripheral device selectively communicates with the computer platform of the wireless device via a wired or wireless communication, the operating system of the wireless device identifies at least the type of peripheral device and links the peripheral device with one or more of the resident computer programs.
Owner:QUALCOMM INC
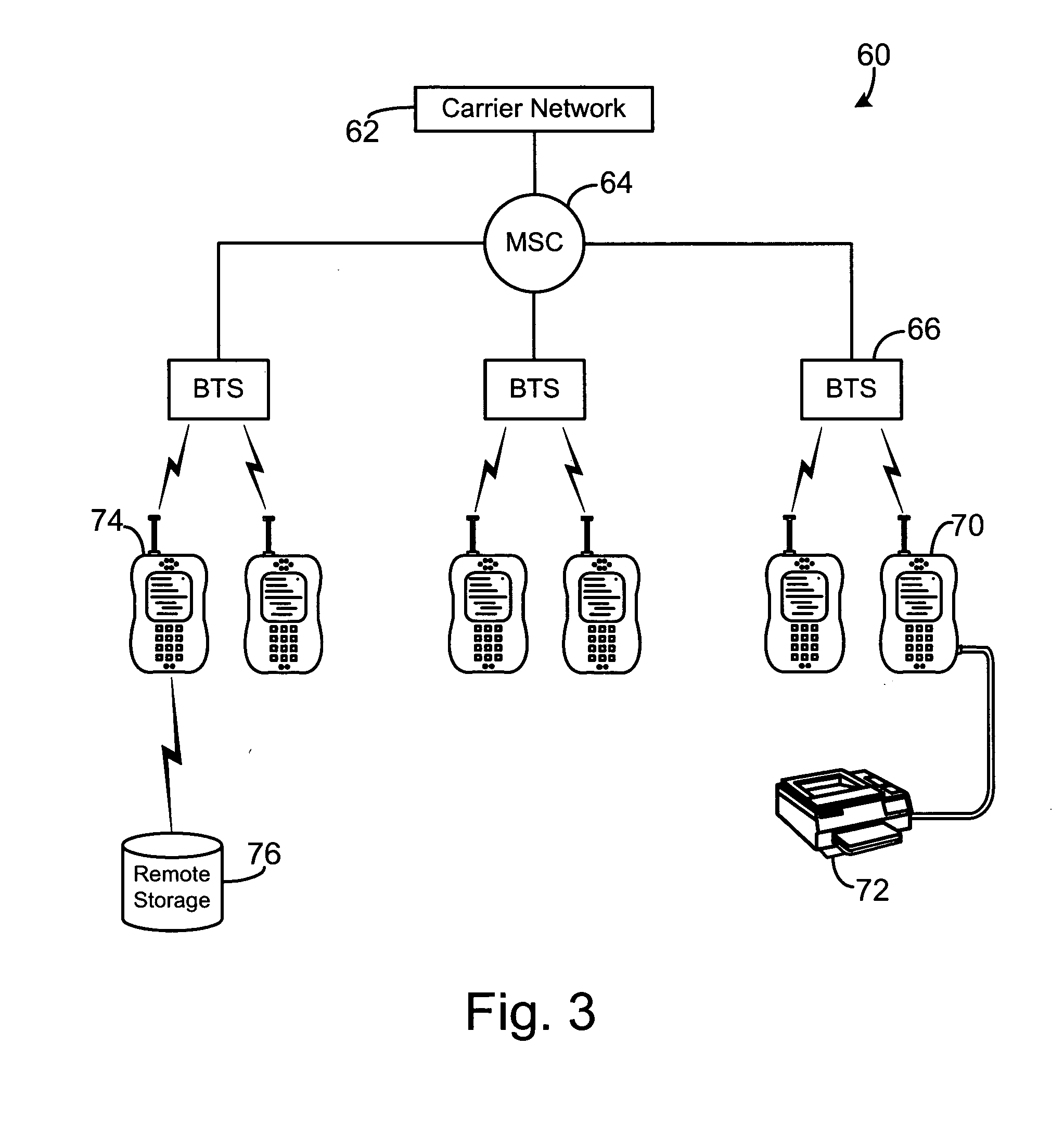
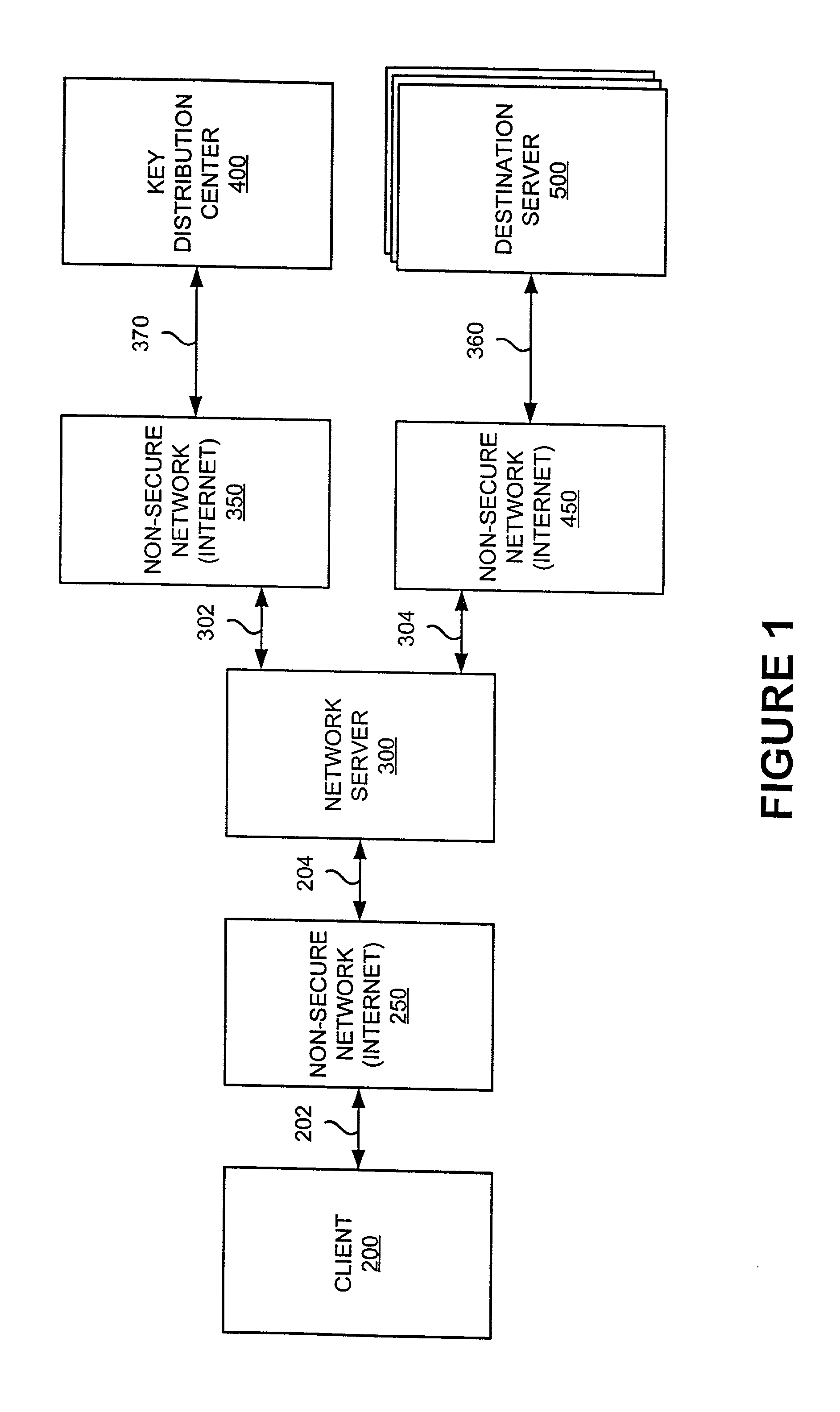
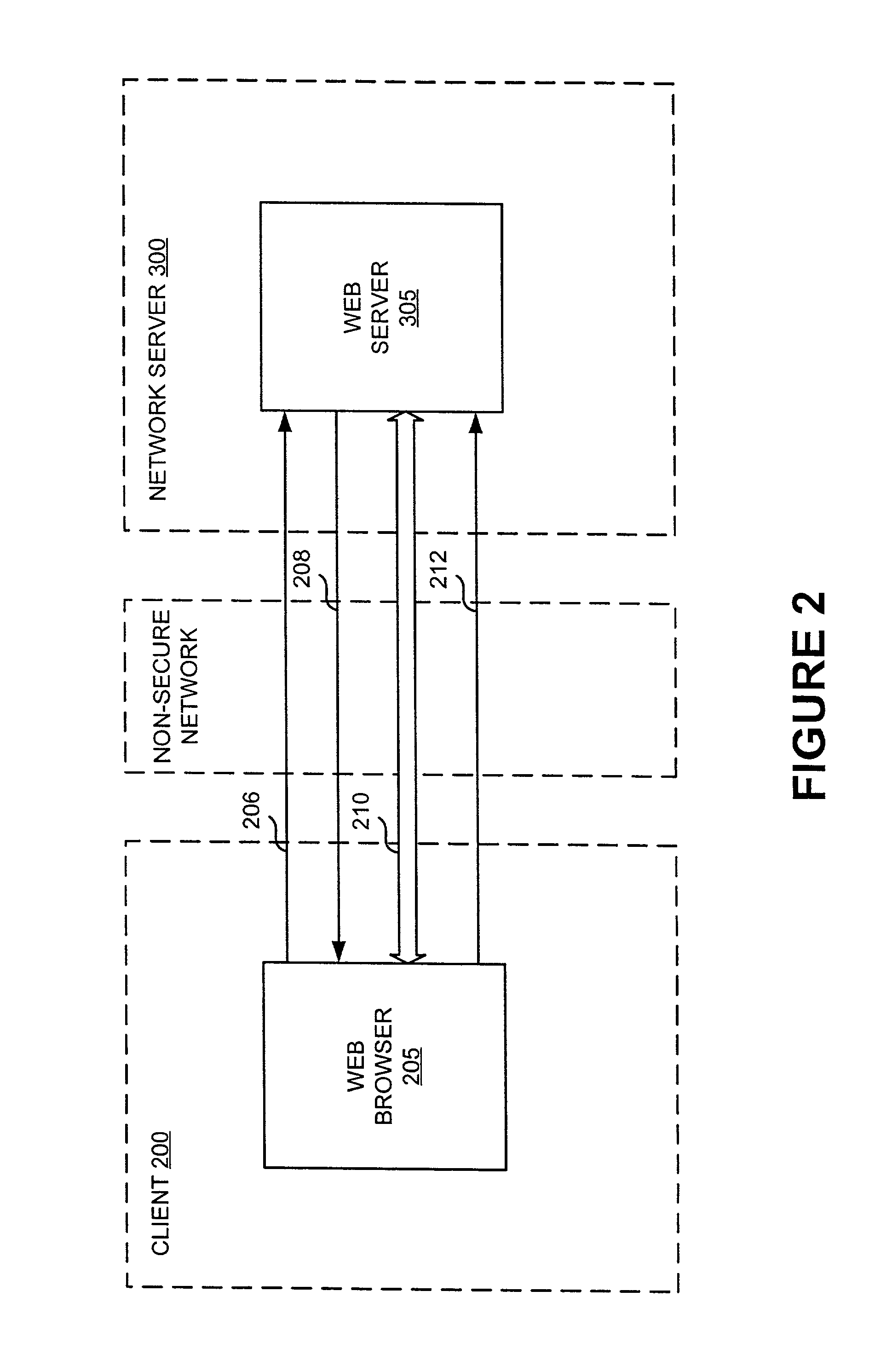
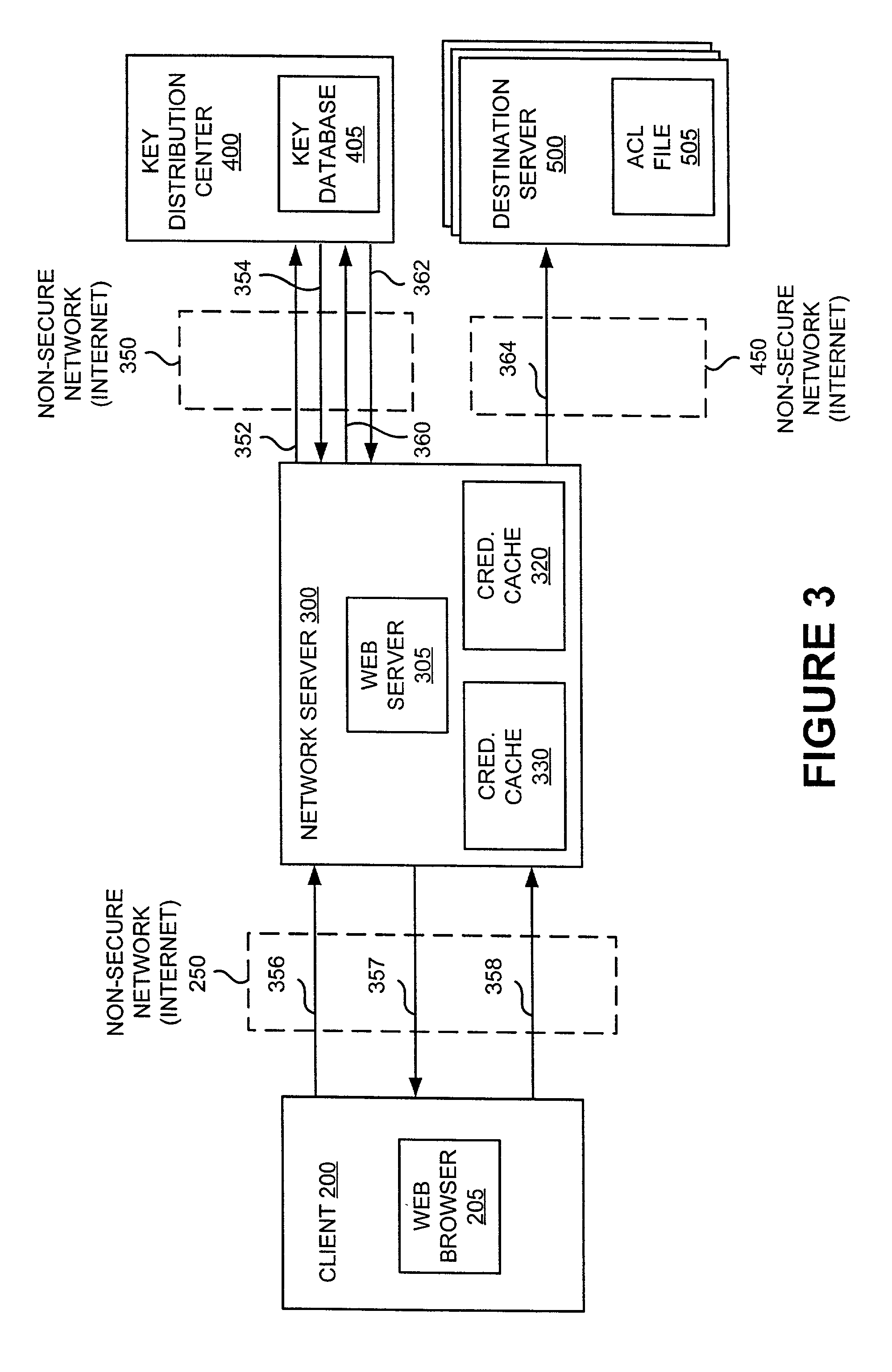
Platform-neutral system and method for providing secure remote operations over an insecure computer network
InactiveUS20010020274A1Improve securityImprove data securityKey distribution for secure communicationDigital data processing detailsClient-sideNetwork service
A method, system and computer program product are disclosed for enhancing the security of a message sent through a network server from a client computer to a destination server running any computer platform. Credentials for authorizing a principal are obtained by the client computer from a validation center. The principal-authentication information is transmitted to the network server. The network server may use the principal-authenticating information to obtain permission data from the validation center for use in accessing the destination server. Also described is a method of providing a remote interactive login connection using the same method.
Owner:HANGER SOLUTIONS LLC
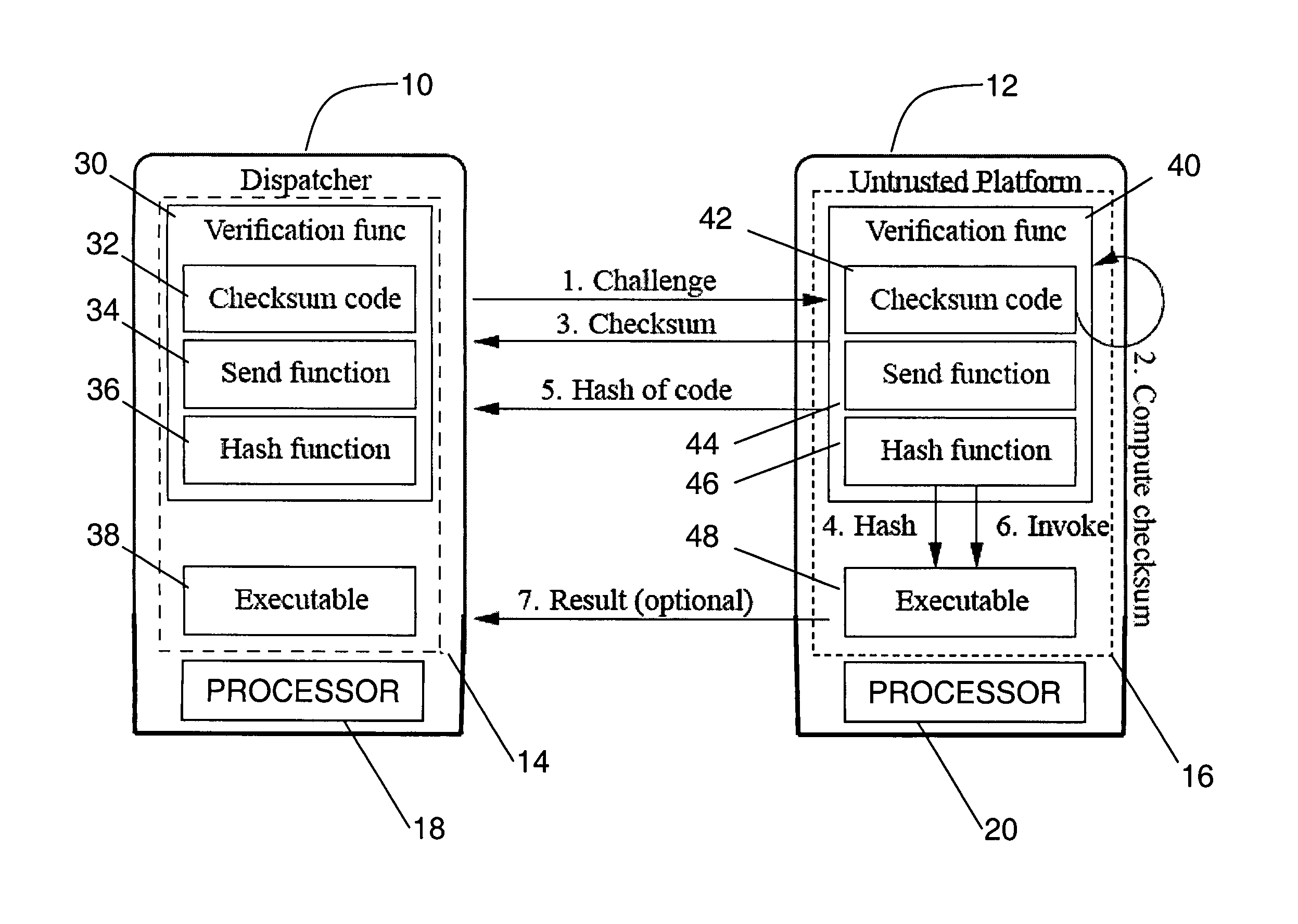
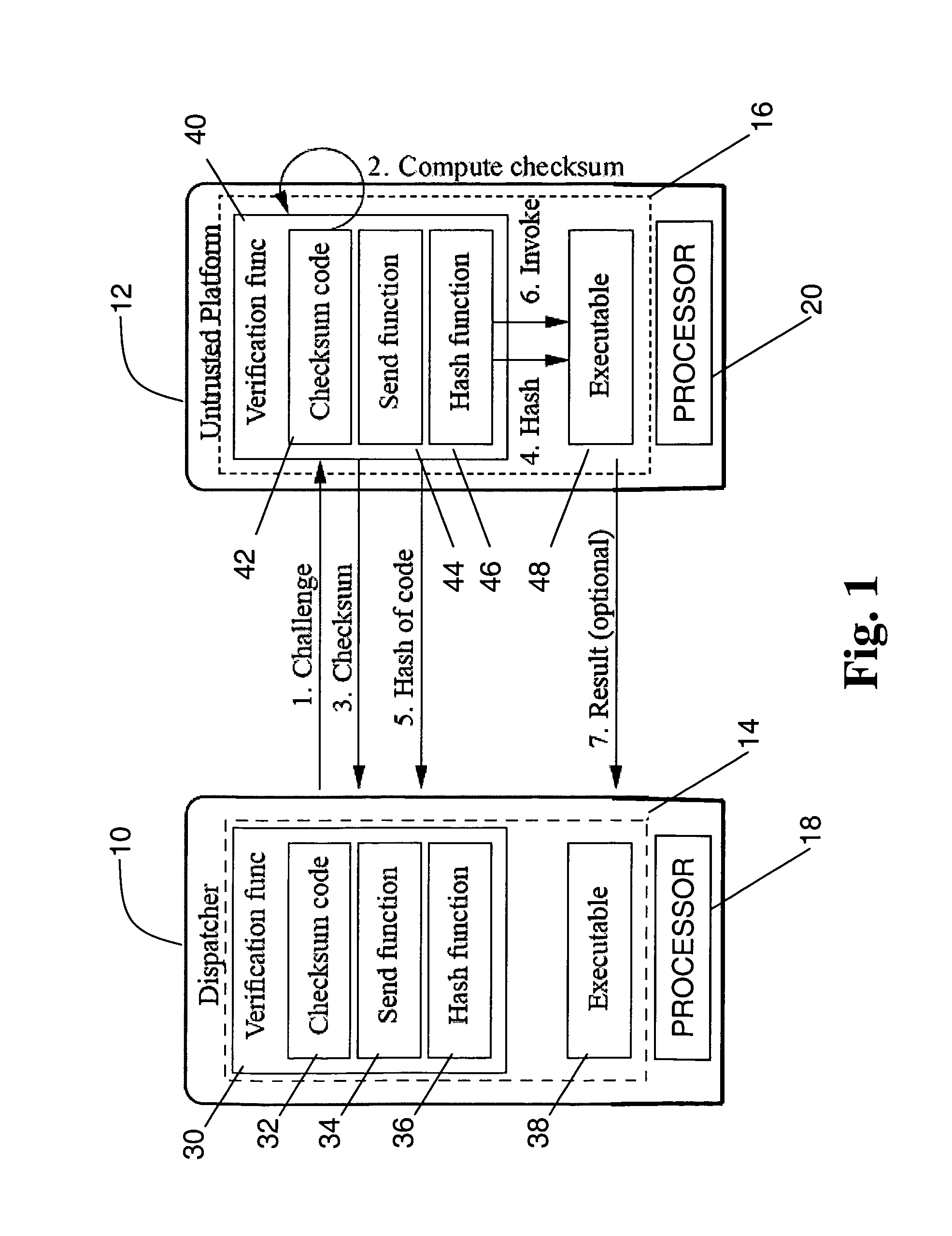
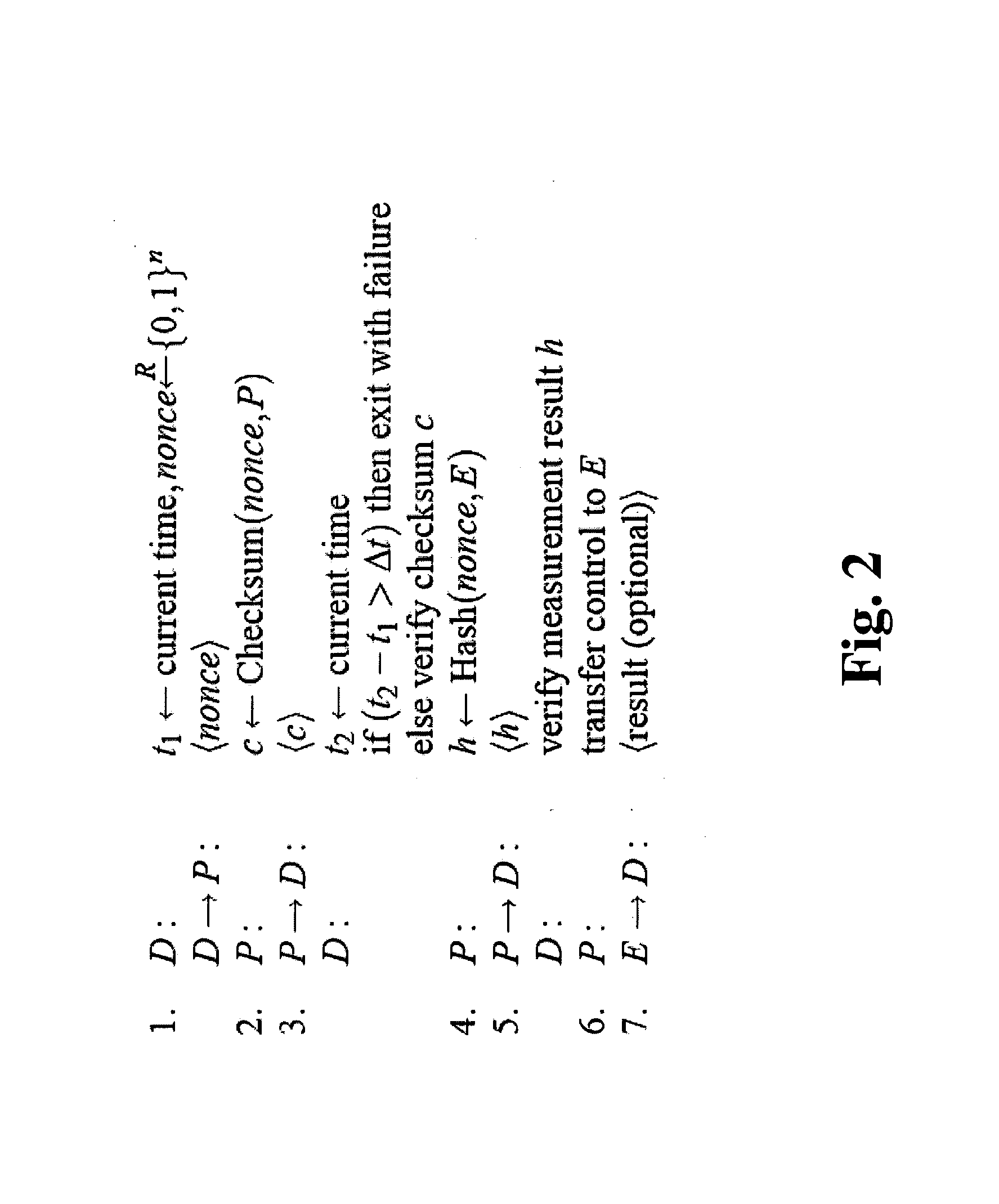
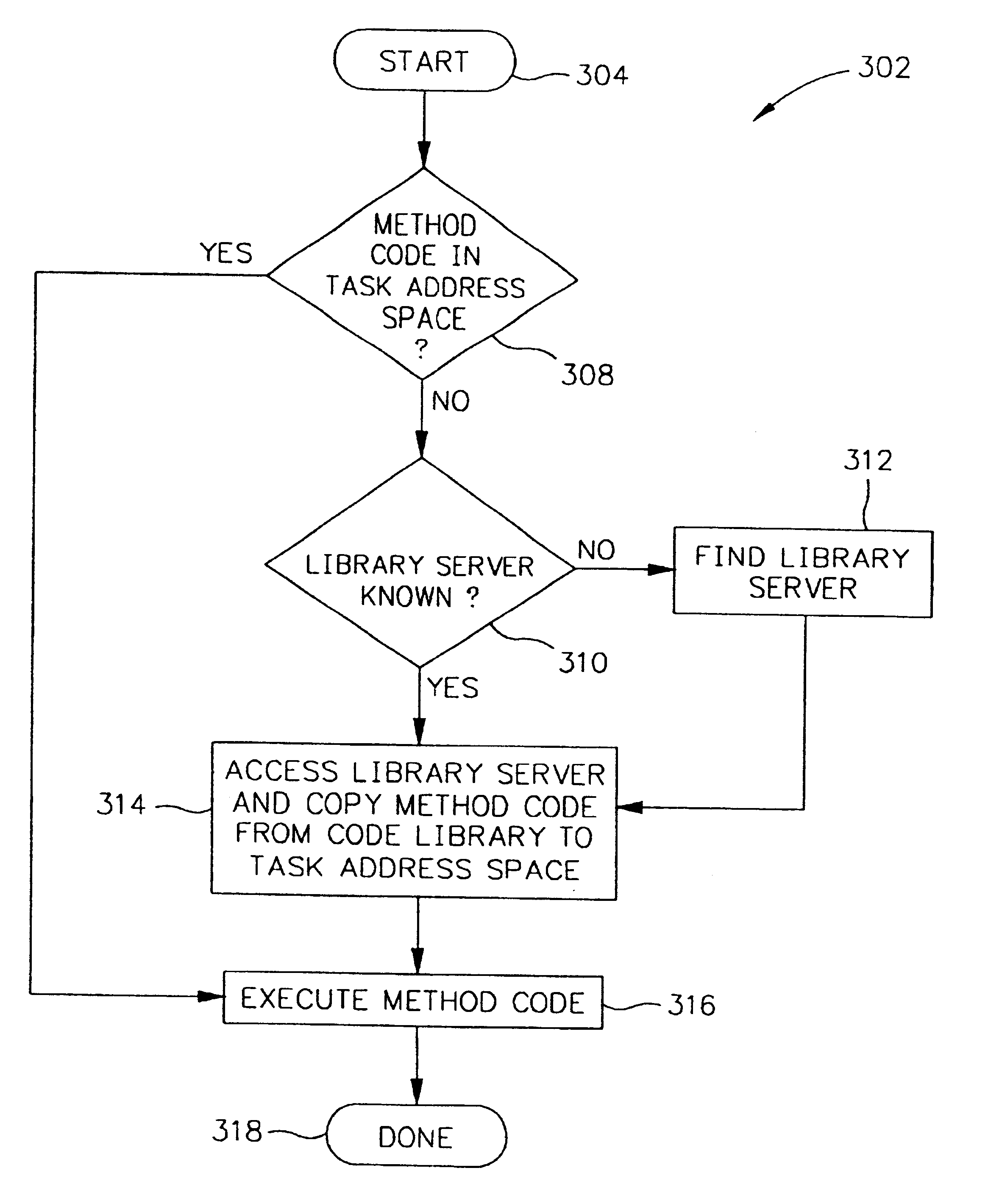
Verifying integrity and guaranteeing execution of code on untrusted computer platform
A method, system, and apparatus for verifying integrity and execution state of an untrusted computer. In one embodiment, the method includes placing a verification function in memory on the untrusted computer; invoking the verification function from a trusted computer; determining a checksum value over memory containing both the verification function and the execution state of a processor and hardware on the untrusted computer; sending the checksum value to the trusted computer; determining at the trusted computer whether the checksum value is correct; and determining at the trusted computer whether the checksum value is received within an expected time period.
Owner:IBM CORP +1
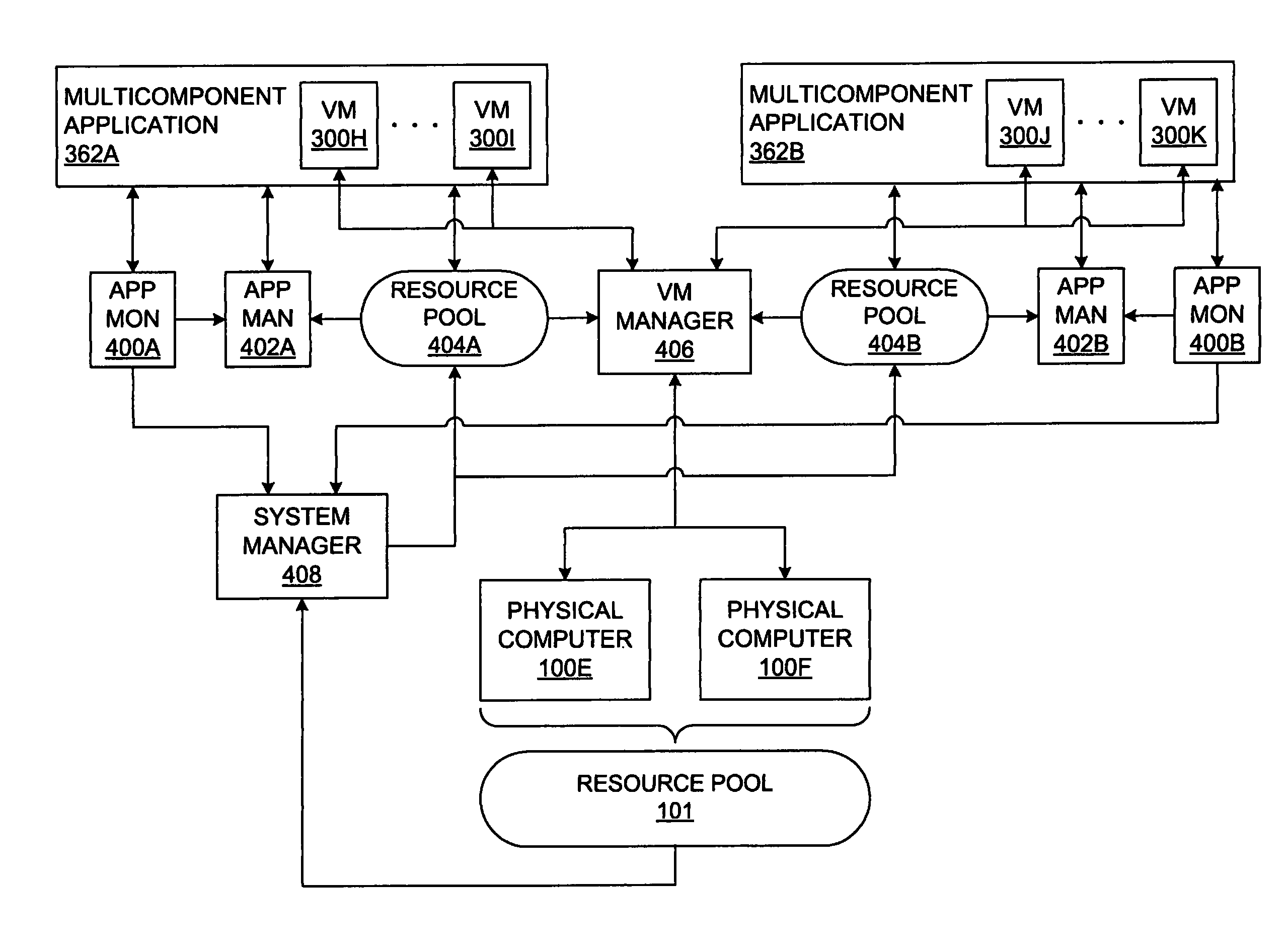
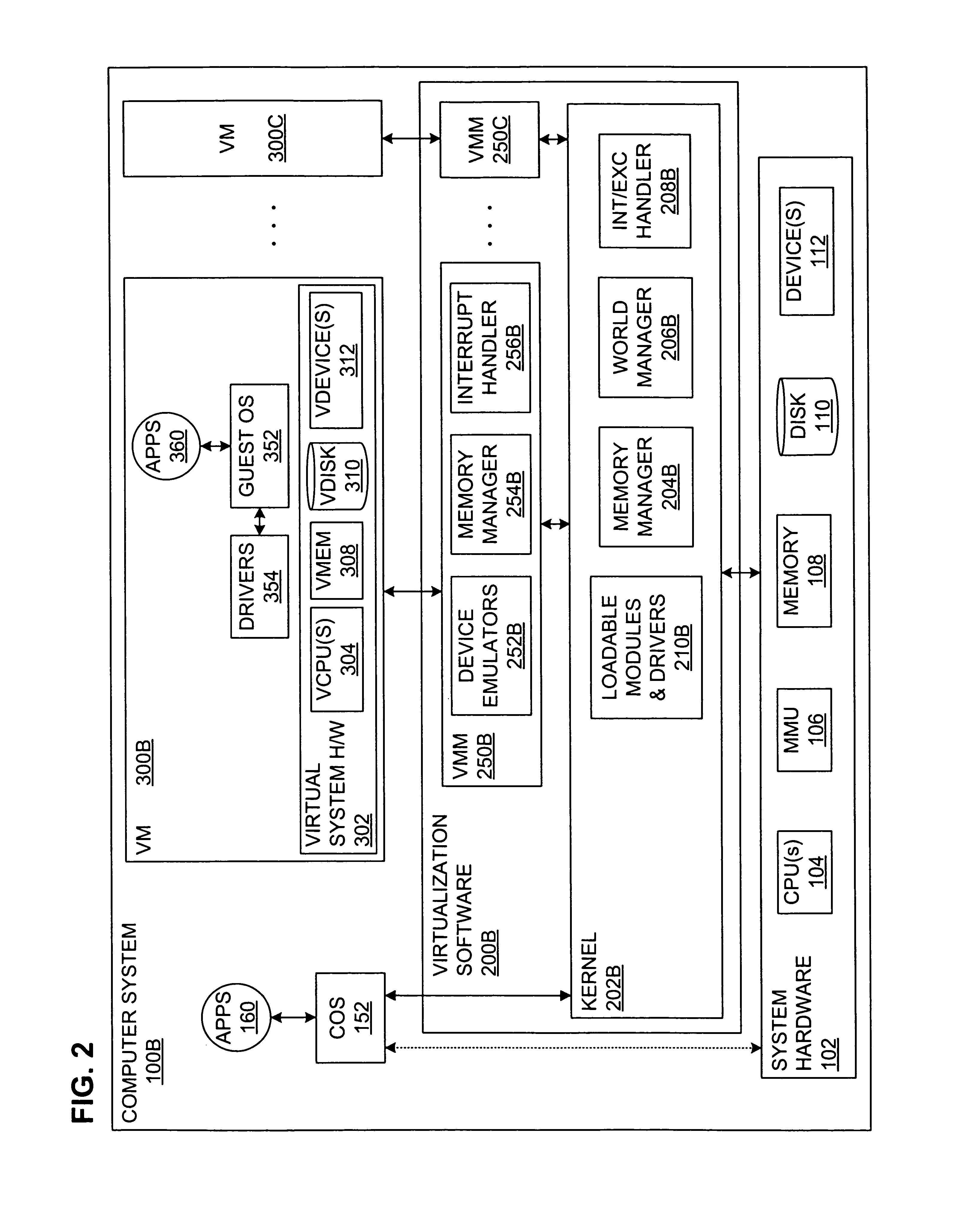
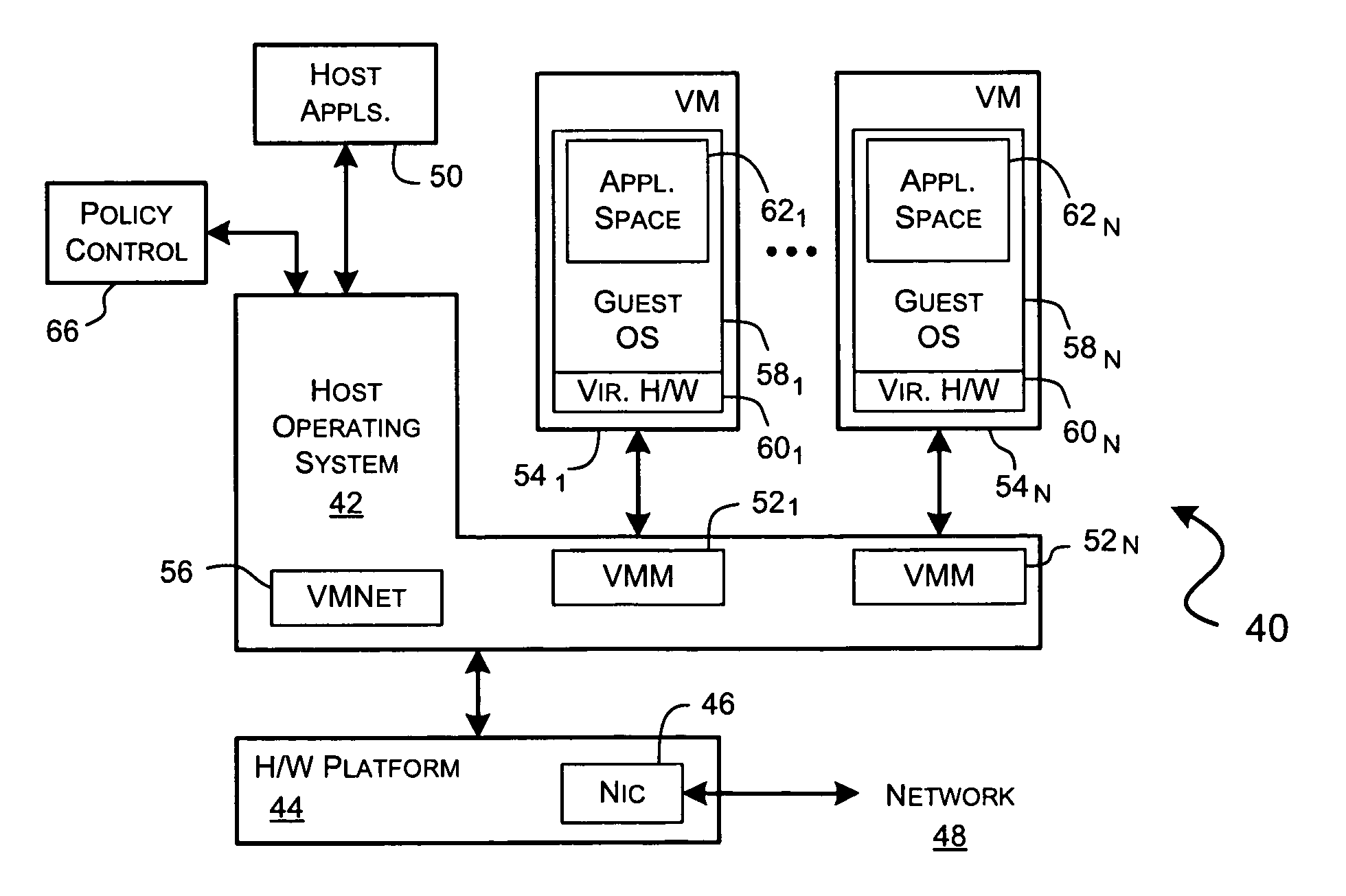
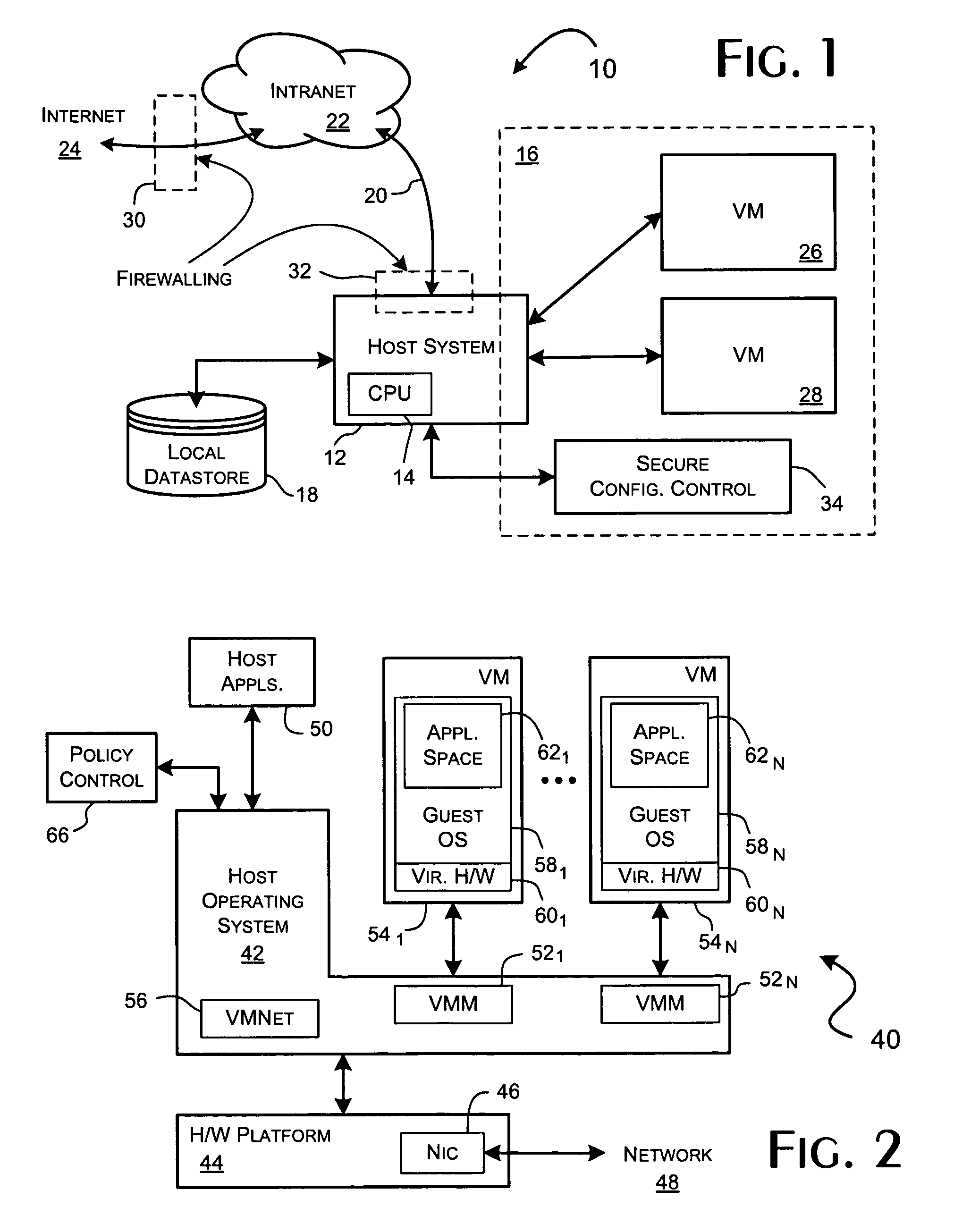
Executing a multicomponent software application on a virtualized computer platform
ActiveUS8286174B1Digital computer detailsMultiprogramming arrangementsVirtualizationHigh availability
A virtualized computer platform is established and maintained by virtualization software on one or more physical computers. A multicomponent software application may execute on the virtualized computer platform, with different components of the application executing in different virtual machines, which are supported by the virtualization software. The virtualization software may also provide, and / or facilitate the provision of, one or more services that may be beneficial to the operation of the multicomponent software application, such as automated provisioning, resource allocation, VM distribution, performance monitoring, resource management, high availability, backup, disaster recovery, alarms, security, etc. In some embodiments of the invention, some of these services are provided through coordinated efforts of a system resource manager, a VM manager, an application monitor and an application resource manager. In some of these embodiments, an application monitor and an application manager may be included with a multicomponent software application in a single installation package.
Owner:VMWARE INC
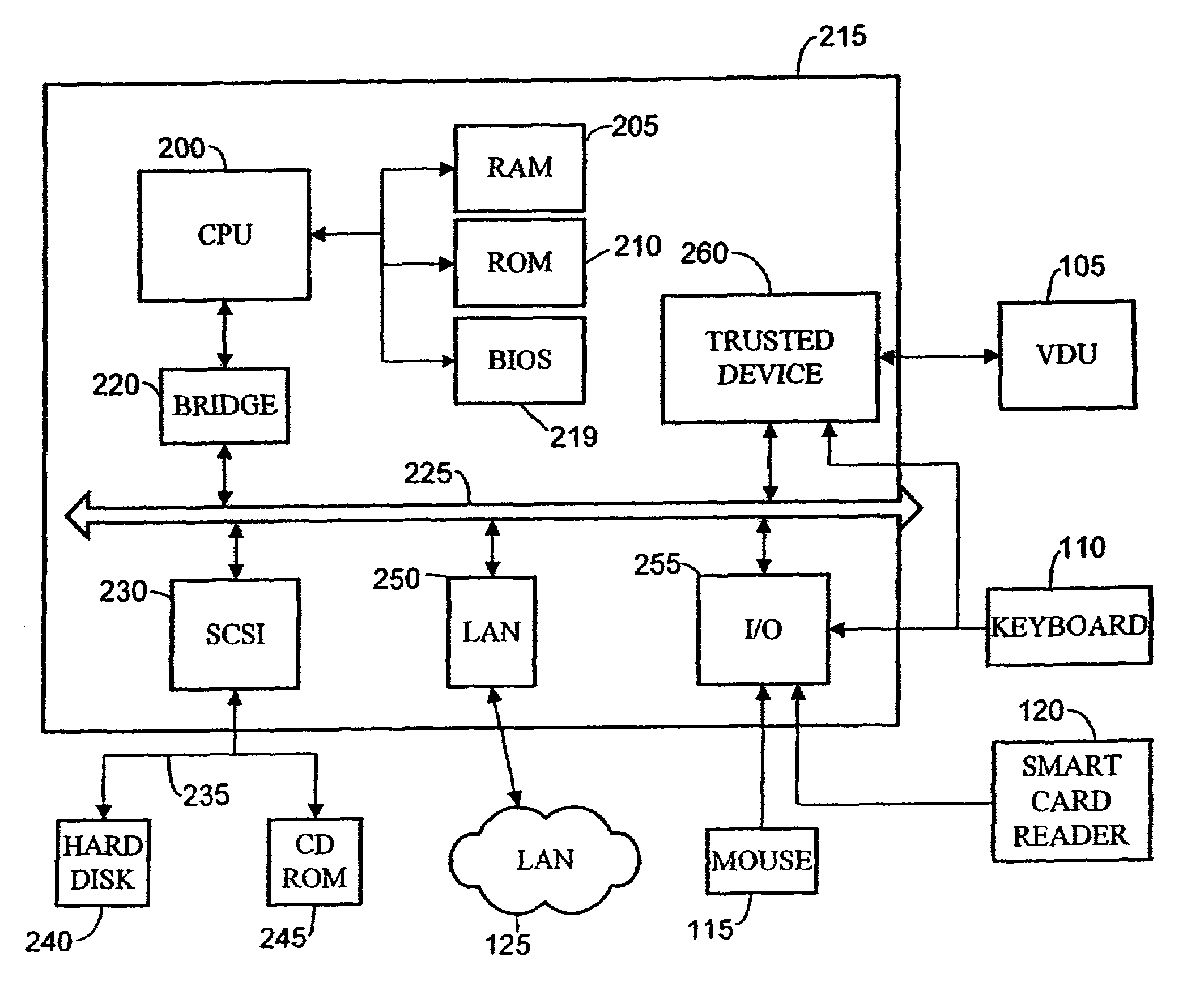
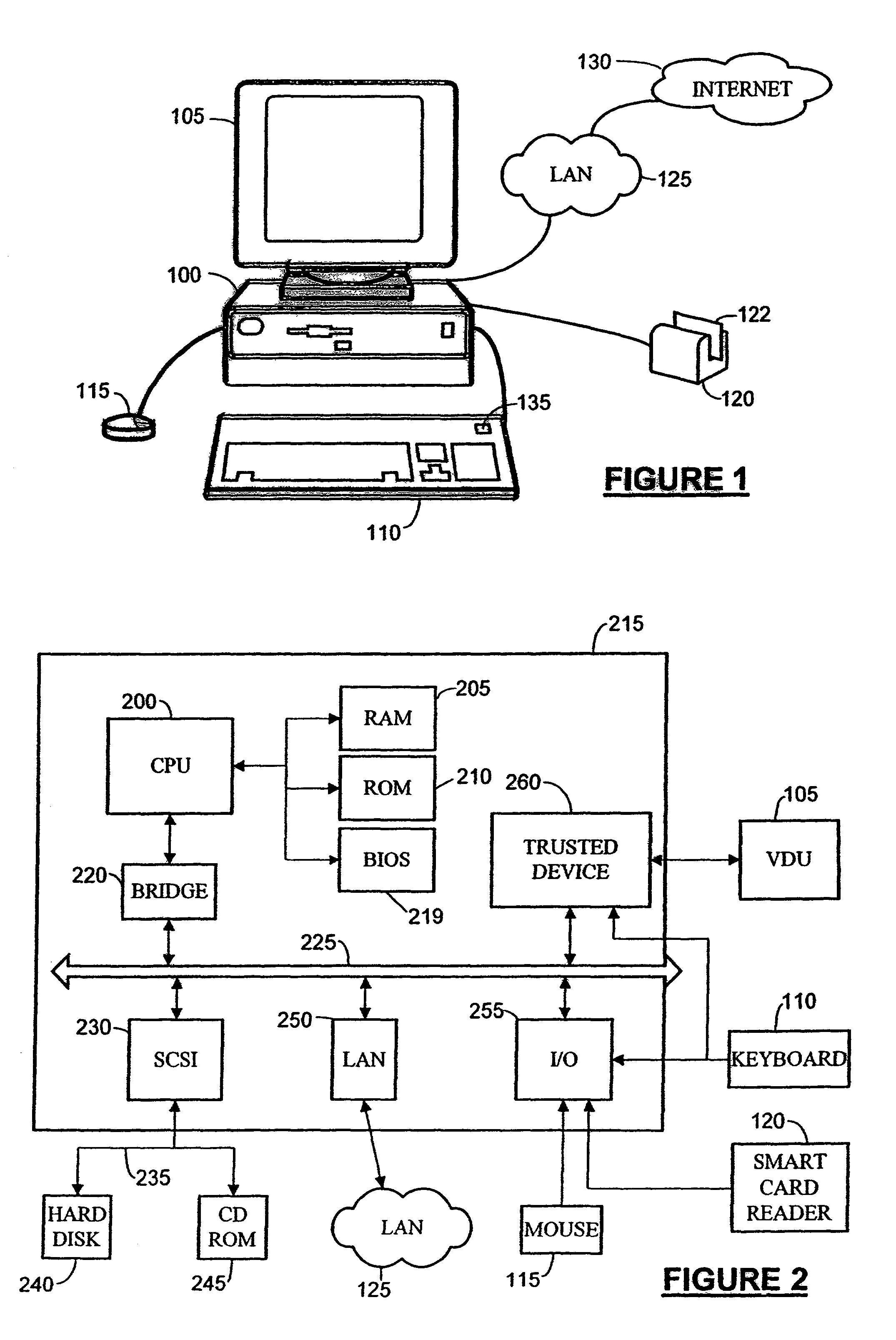
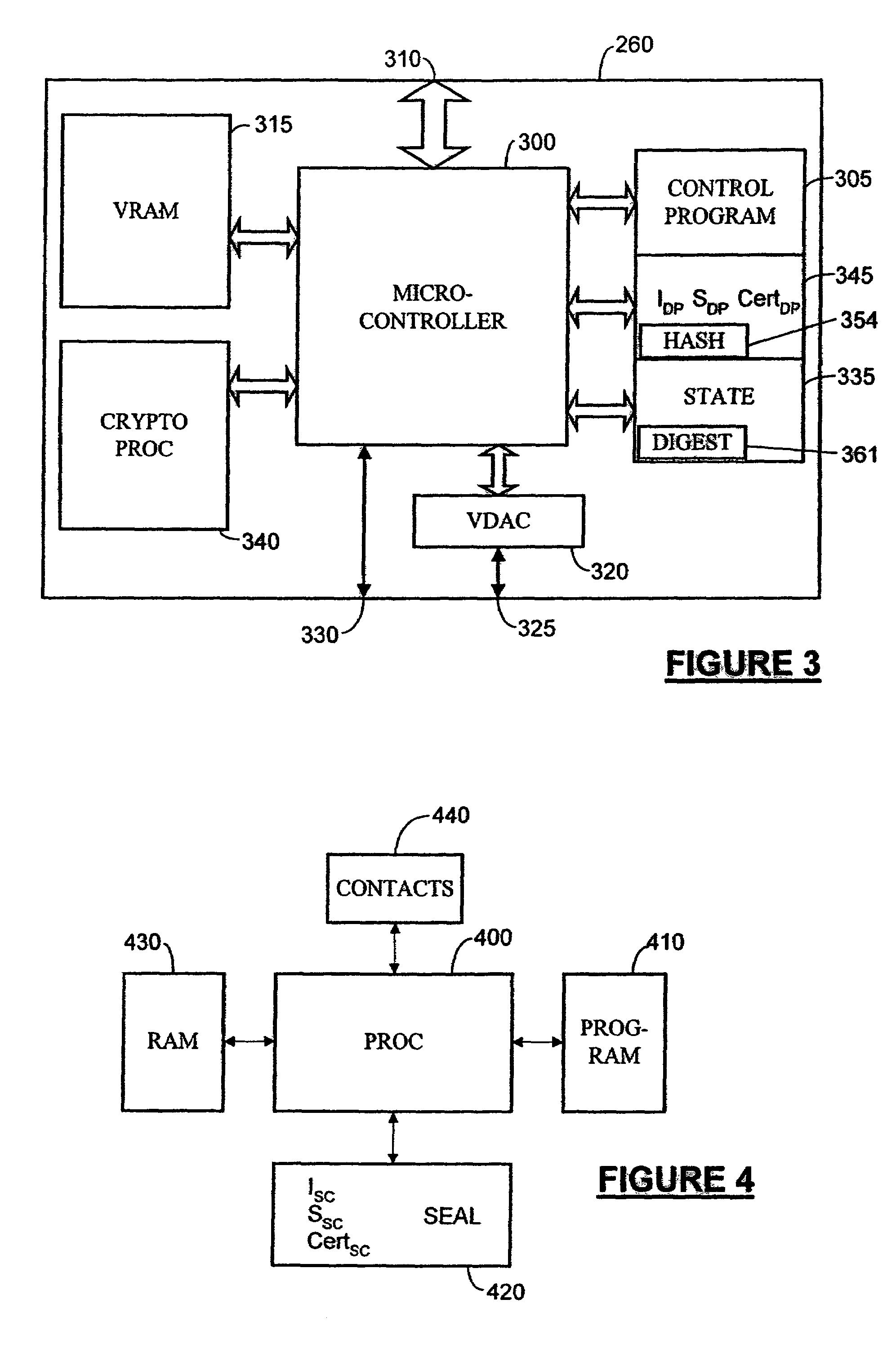
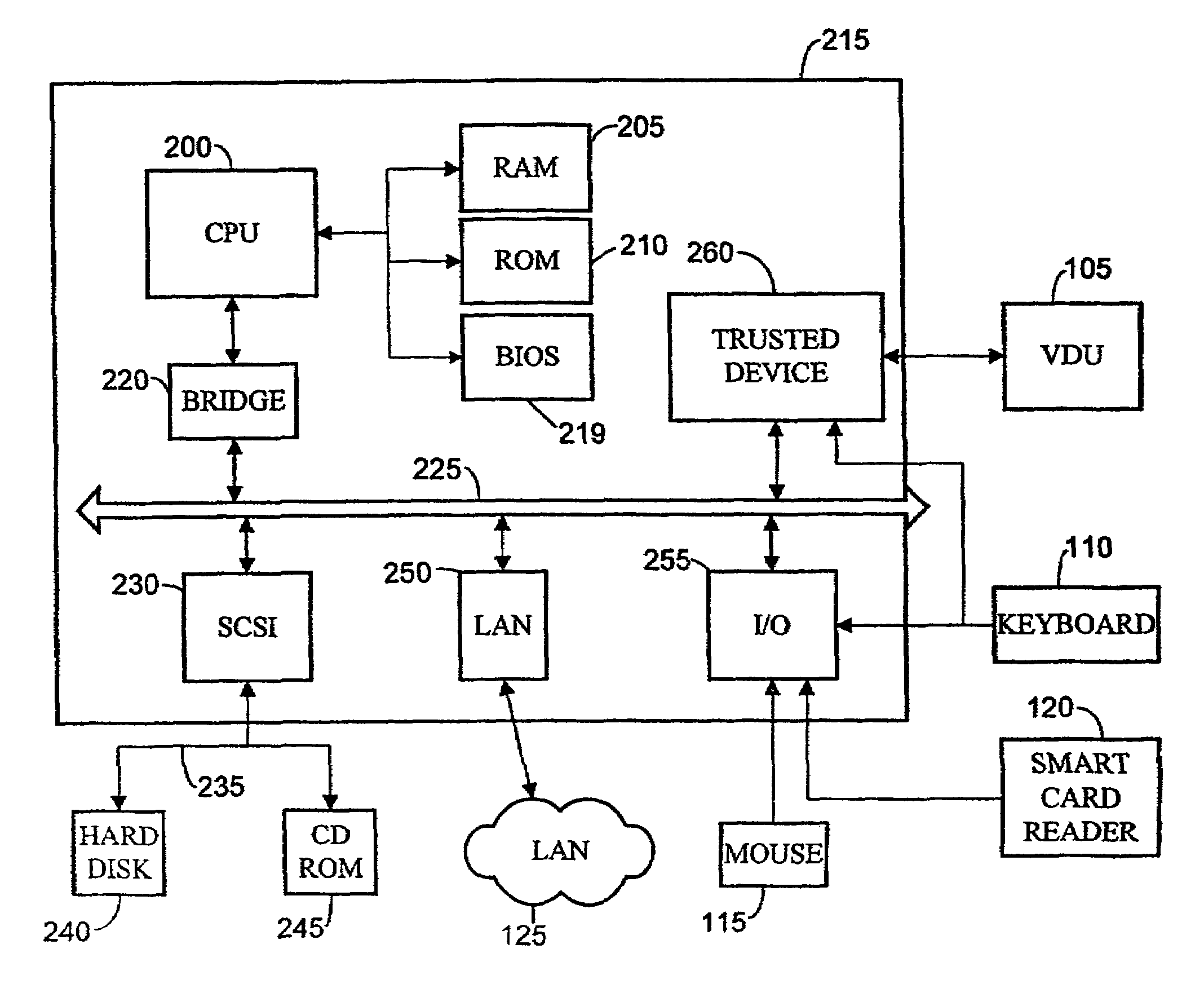
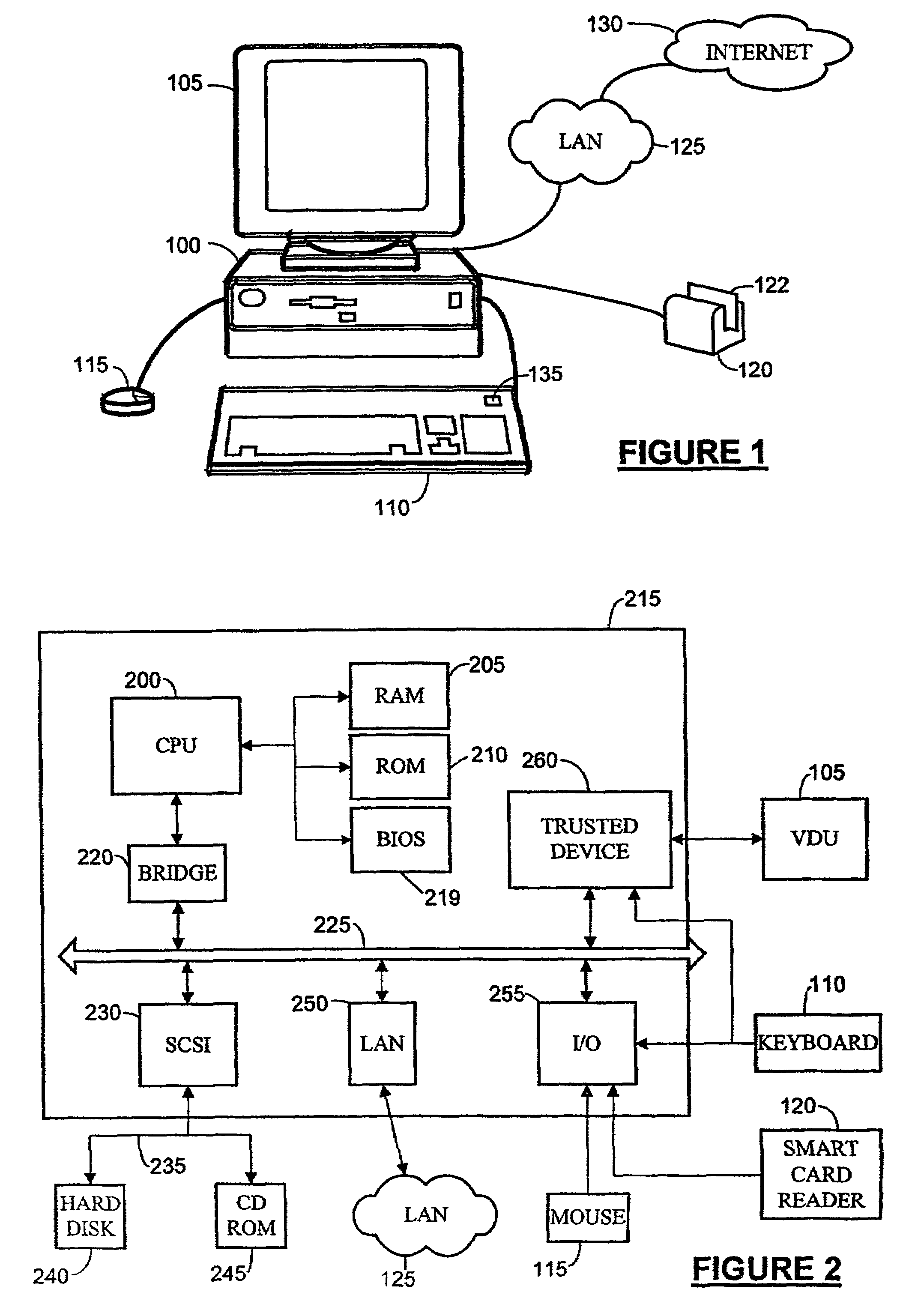
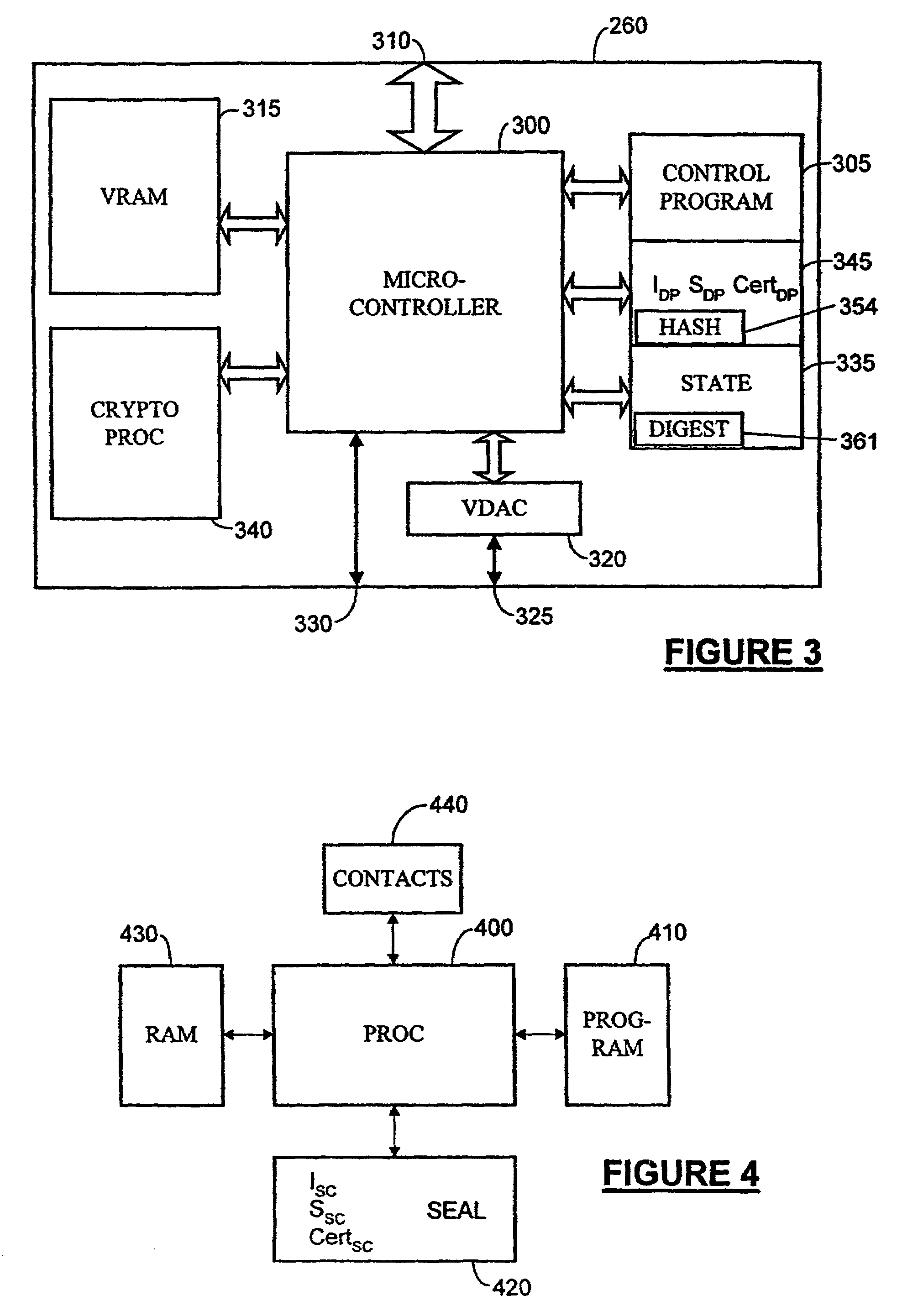
Operation of trusted state in computing platform
ActiveUS7302698B1Improve trustSimple taskDigital data processing detailsUser identity/authority verificationOperational systemModem device
A computing entity comprises a trusted monitoring component having a first processing means and a first memory means, the trusted monitoring component being a self-contained autonomous data processing unit, and a computer platform having a main processing means and a main memory area, along with a plurality of associated physical and logical resources such as peripheral devices including printers, modems, application programs, operating systems and the like. The computer platform is capable of entering a plurality of different states of operation, each state of operation having a different level of security and trustworthiness. Selected ones of the states comprise trusted states in which a user can enter sensitive confidential information with a high degree of certainty that the computer platform has not been compromised by external influences such as viruses, hackers or hostile attacks. To enter a trusted state, references made automatically to the trusted component, and to exit a trusted state reference must be made to the trusted component. On exiting the trusted state, all references to the trusted state are deleted from the computer platform. On entering the trusted state, the state is entered in a reproducible and known manner, having a reproducible and known configuration which is confirmed by the trusted component.
Owner:META PLATFORMS INC
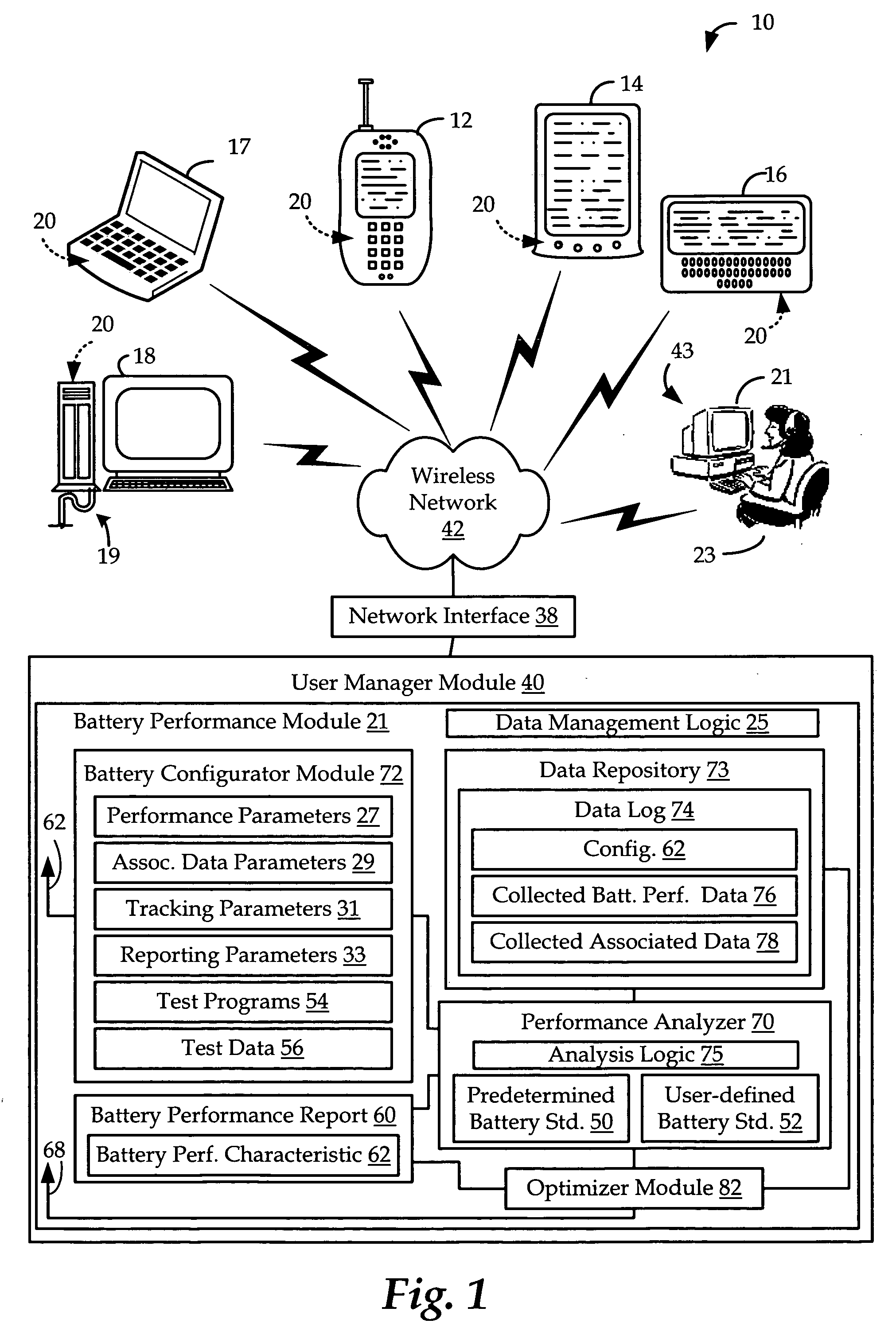
Apparatus and methods for managing battery performance of a wireless device
ActiveUS20060217152A1Circuit monitoring/indicationDifferent batteries chargingEmbedded systemNew device
Apparatus, methods, and programs that determine and manage battery performance characteristics of a wireless device. Embodiments include a wireless device having a computer platform with a processing engine operable to generate a plurality of battery performance data associated with activities on the wireless device. The wireless device further includes a battery performance module operable, based on a received battery performance configuration, to collect selected ones of the plurality of battery performance data. The embodiments may also include an apparatus operable to generate the battery performance configuration, and operable to receive the collected battery performance data and to generate a performance report characterizing the battery performance of the wireless device. Further, embodiments of the apparatus may also generate and transmit to the wireless device a new device operational configuration, based on the collected battery performance data, effective to change the battery performance of the wireless device.
Owner:QUALCOMM INC
Data event logging in computing platform
InactiveUS7194623B1None of methods is secureDigital data processing detailsUser identity/authority verificationTrusted componentsData file
There is disclosed a computer entity having a trusted component which compiles an event log for events occurring on a computer platform. The event log contains event data of types which are pre-specified by a user by inputting details through a dialogue display generated by the trusted component. Items which can be monitored include data files, applications drivers and the like. The trusted component operates through a monitoring agent which may be launched onto the computer platform. The monitoring agent may be periodically interrogated to make sure that it is operating correctly and responding to interrogations by the trusted component.
Owner:HEWLETT PACKARD DEV CO LP
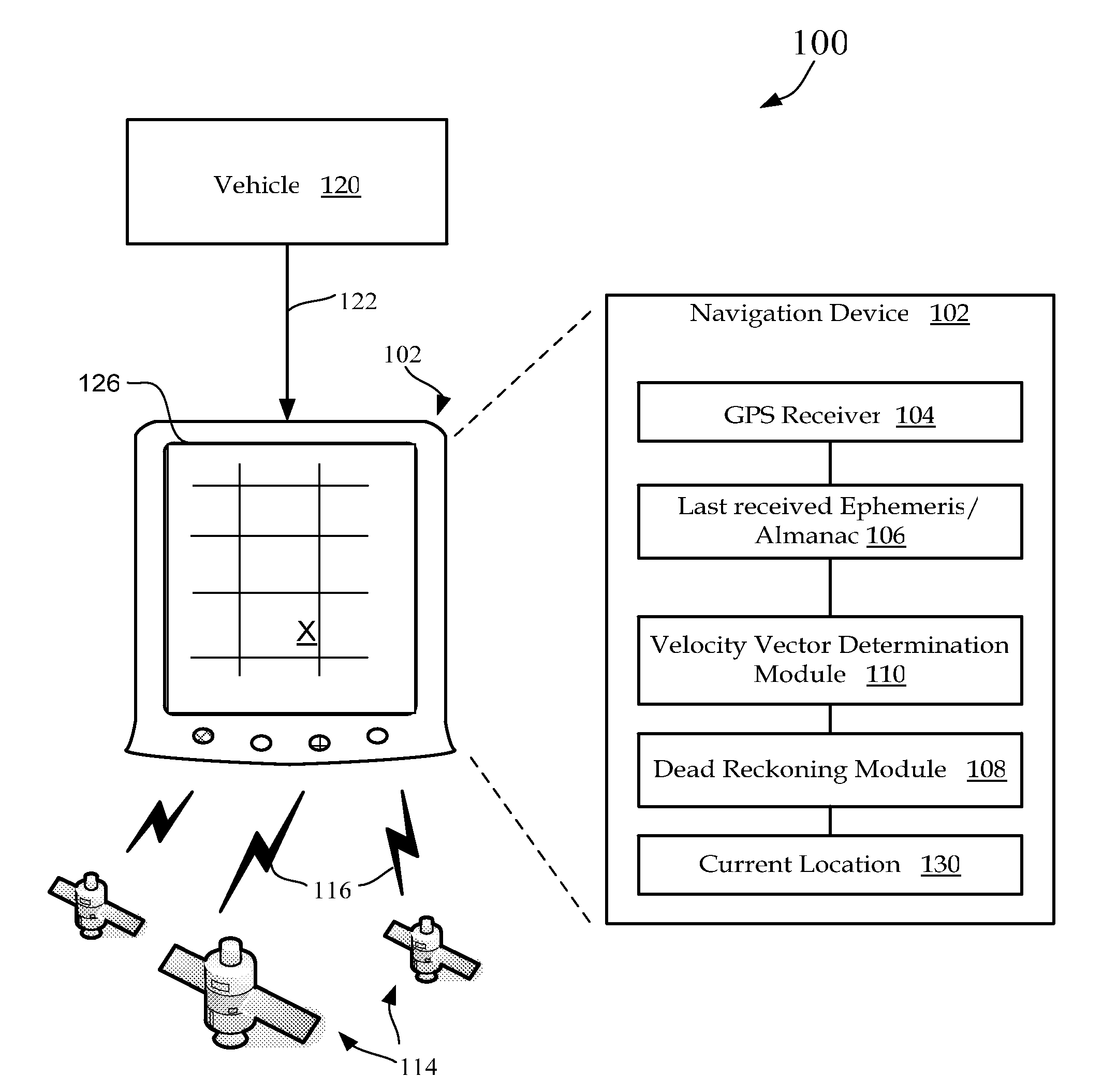
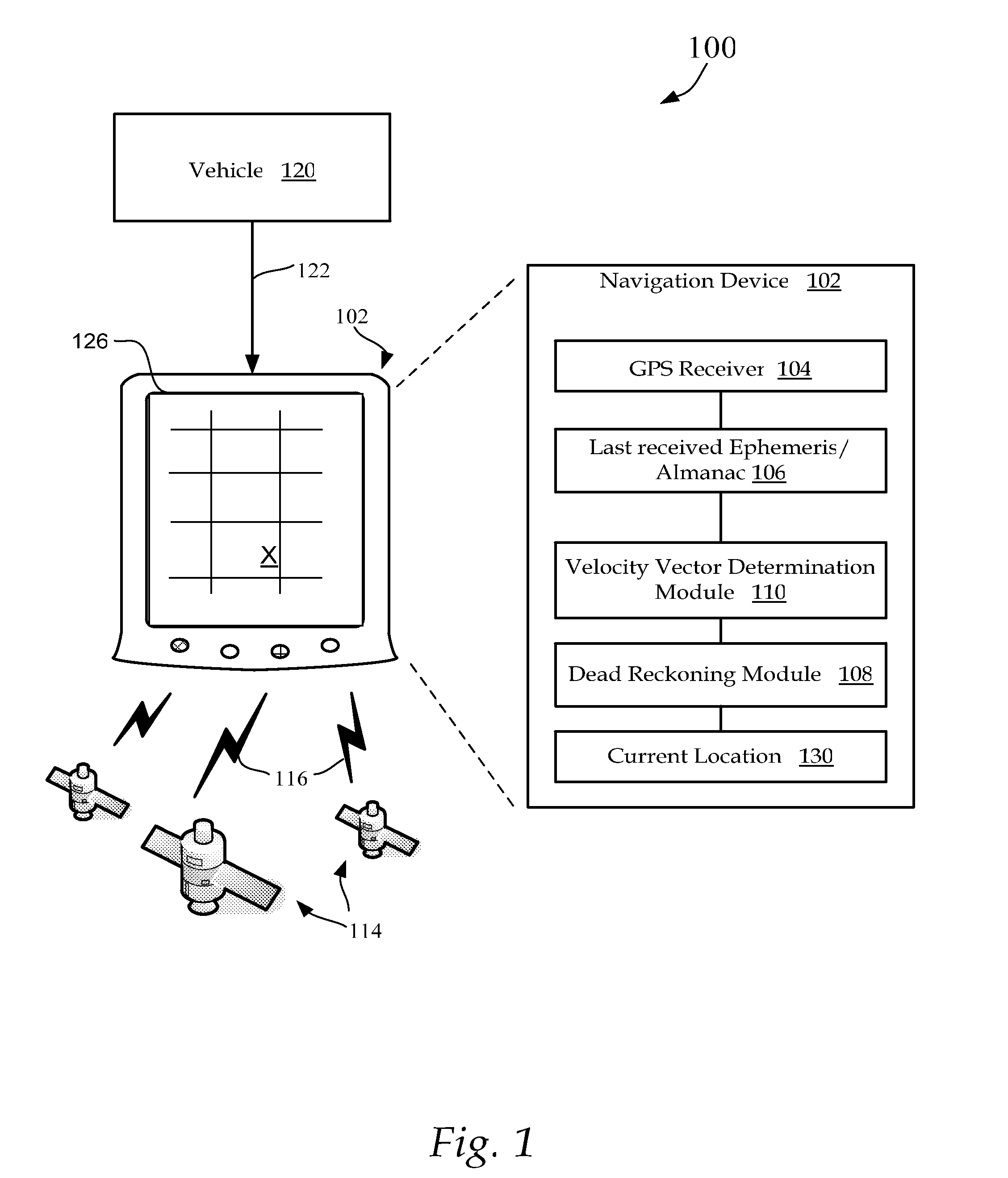
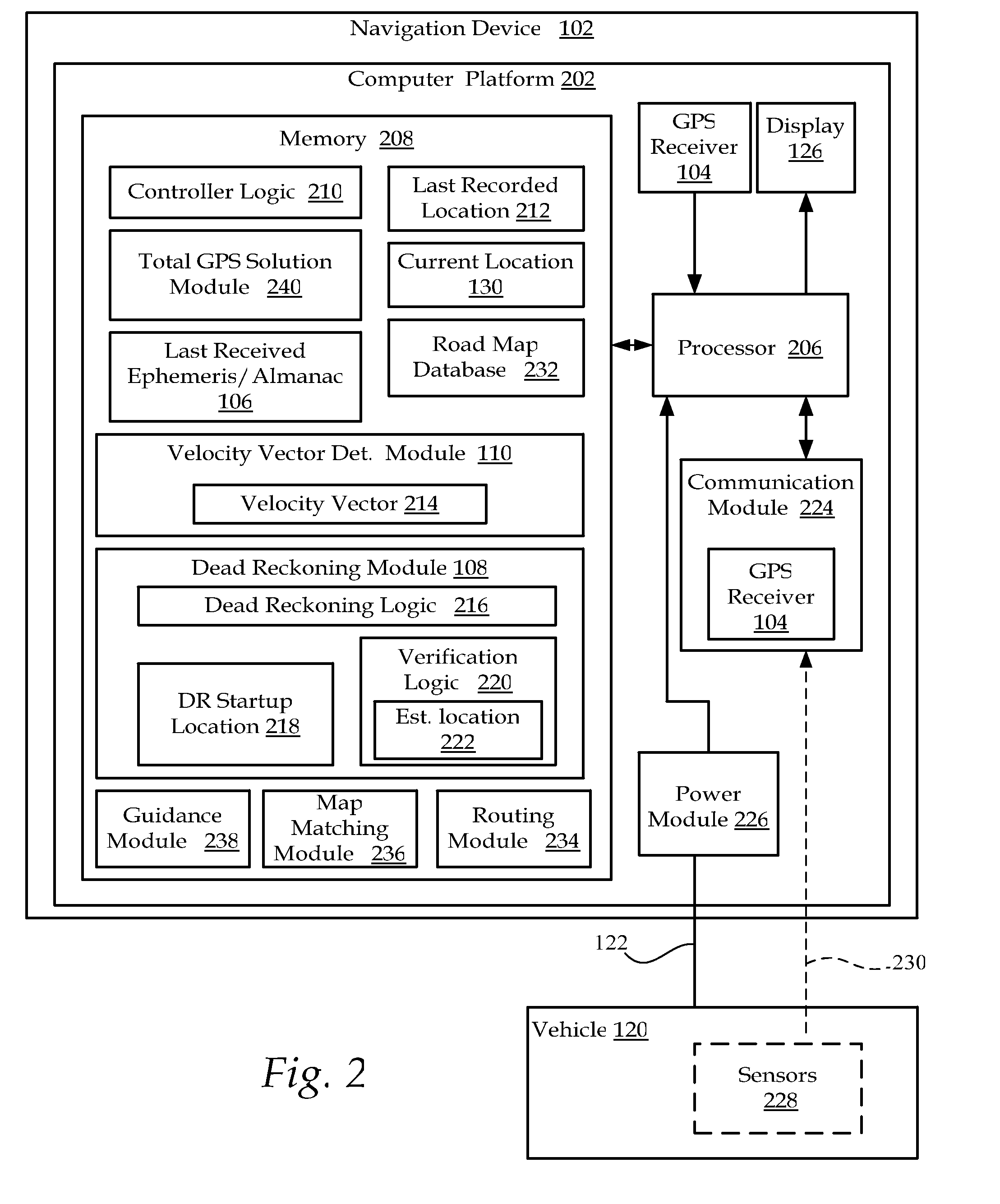
Method and system for navigation using GPS velocity vector
ActiveUS20080262728A1Accurate calculationPosition fixationNavigation instrumentsCurrent velocityEphemeris
A navigation device includes a computer platform that includes a global positioning system (GPS) receiver operable to acquire and track a GPS signal, a processor assembly, and a memory. The memory includes at least one of last recorded Ephemeris and Almanac information, and a GPS velocity vector determination module operable to generate a velocity vector output in the absence of current Ephemeris based upon the tracked GPS signal and the last recorded GPS information. A method of vehicle navigation in the absence of current Ephemeris includes acquiring and tracking a GPS signal, retrieving from a memory a last recorded location of a vehicle, setting a dead reckoning startup location equal to the last recorded location, retrieving from a memory at least one of a last recorded Ephemeris and Almanac, determining a current velocity vector and determining a current location based upon the velocity vector and the dead reckoning startup location.
Owner:MITAC INT CORP
Highly-parallel, implicit compositional reservoir simulator for multi-million-cell models
ActiveUS20060036418A1Reducing computer processing timeReduce processing timeElectric/magnetic detection for well-loggingPermeability/surface area analysisSupercomputerDistributed memory
A fully-parallelized, highly-efficient compositional implicit hydrocarbon reservoir simulator is provided. The simulator is capable of solving giant reservoir models, of the type frequently encountered in the Middle East and elsewhere in the world, with fast turnaround time. The simulator may be implemented in a variety of computer platforms ranging from shared-memory and distributed-memory supercomputers to commercial and self-made clusters of personal computers. The performance capabilities enable analysis of reservoir models in full detail, using both fine geological characterization and detailed individual definition of the hydrocarbon components present in the reservoir fluids.
Owner:SAUDI ARABIAN OIL CO
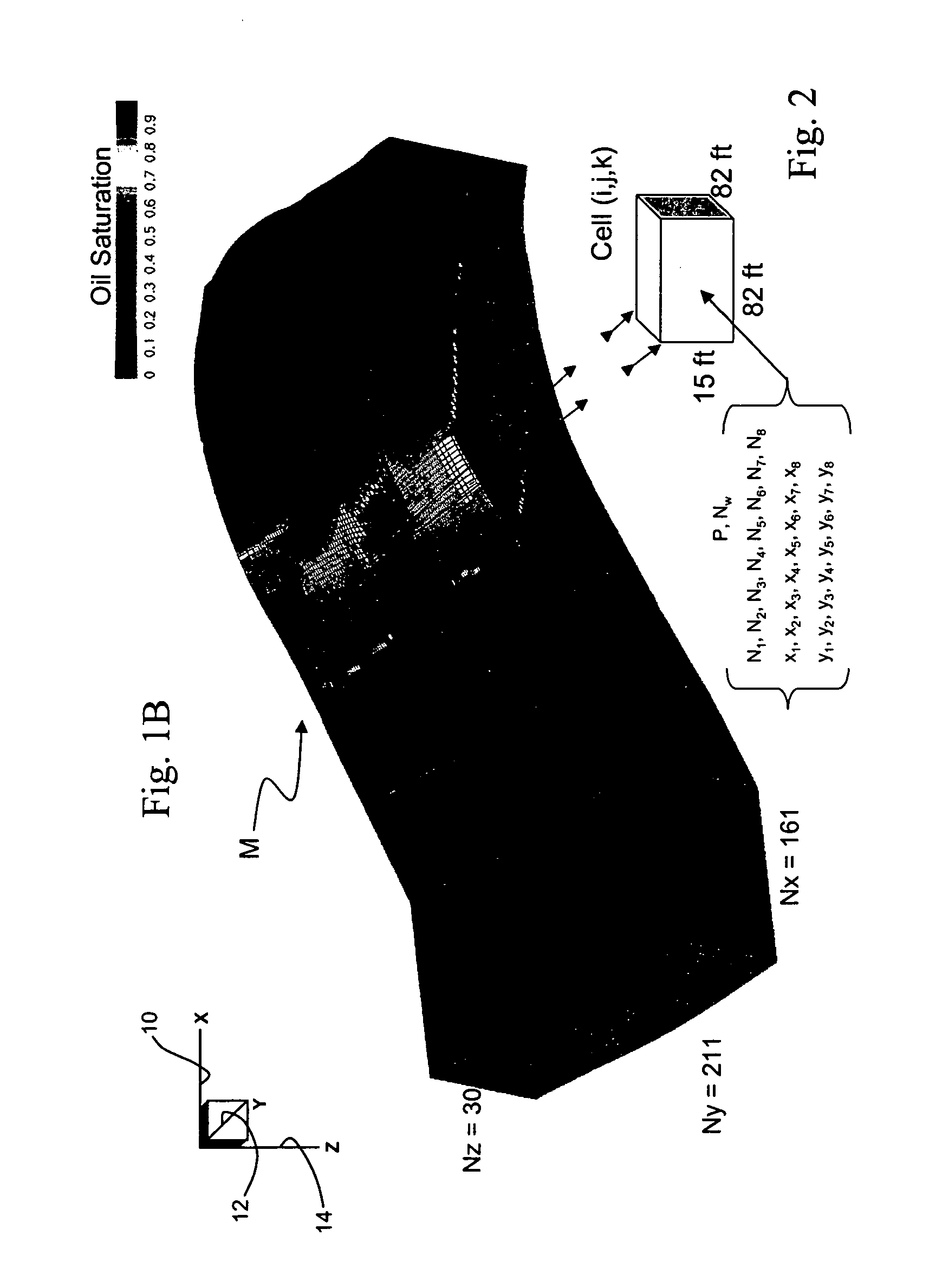
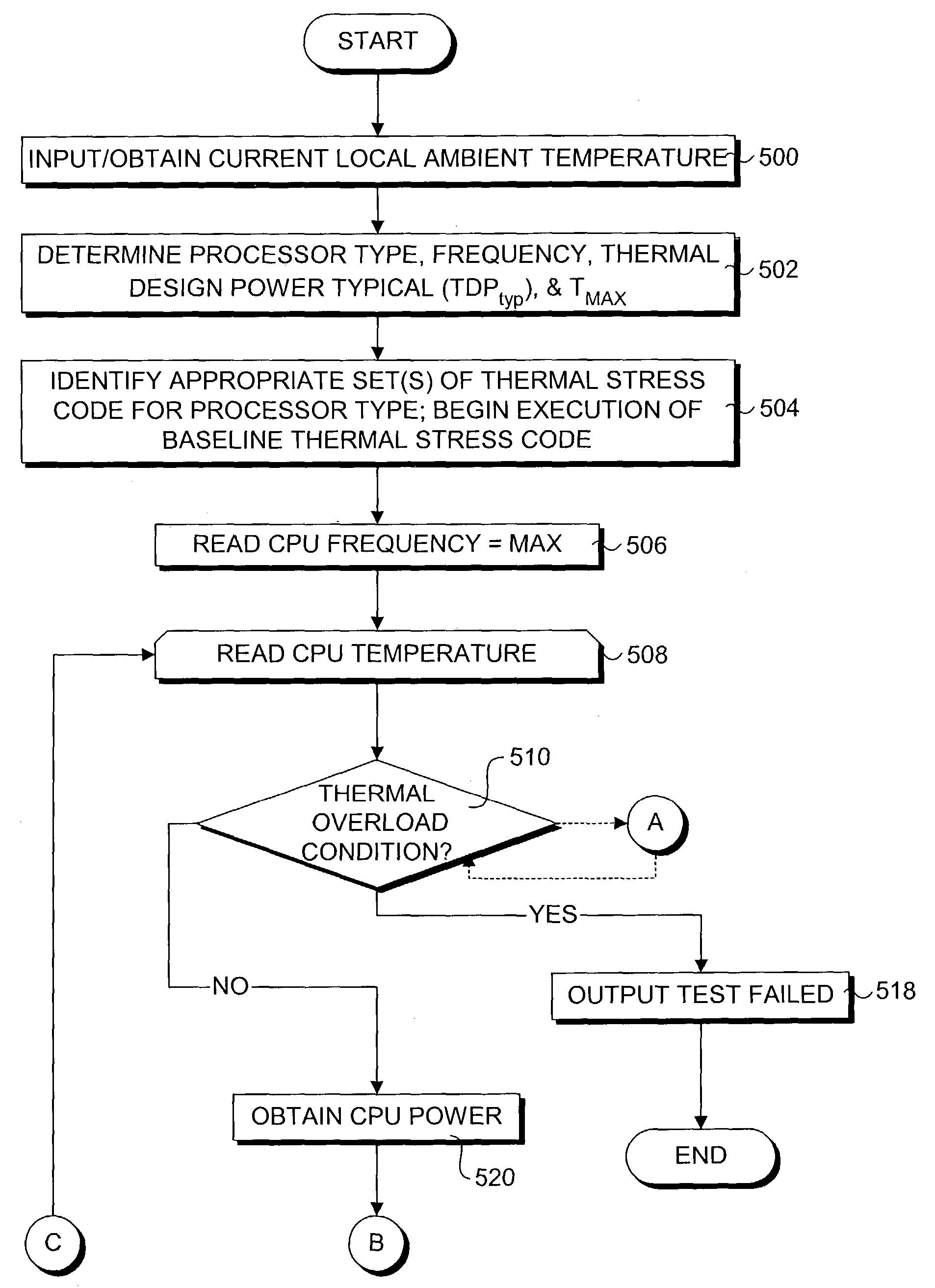
Automated method and apparatus for processor thermal validation
InactiveUS20040128101A1Thermometer detailsDigital data processing detailsThermal solutionAutomated method
A method and corresponding software for automatically validating a computer platform thermal solution. An application program is employed to selectively execute thermal stress code to cause the platform's processor to dissipate an amount of power corresponding to a predetermined value, such as a thermal design power dissipation value specified by the processor's manufacturer. In one embodiment, tests are performed while operating at this power dissipation level to determine if a thermal overload condition exists, which may be determined by the processor's temperature, an indication that the processor is throttled, or a signal provided by the processor indicating the processor has detected a thermal overload condition. In another embodiment, a thermal resistance value is calculated based on the processor power dissipation, the temperature of the processor, and the ambient temperature of the test environment. In one embodiment the entire validation process is automatically performed by the application program without requiring any extraneous test equipment or temperature probes.
Owner:INTEL CORP
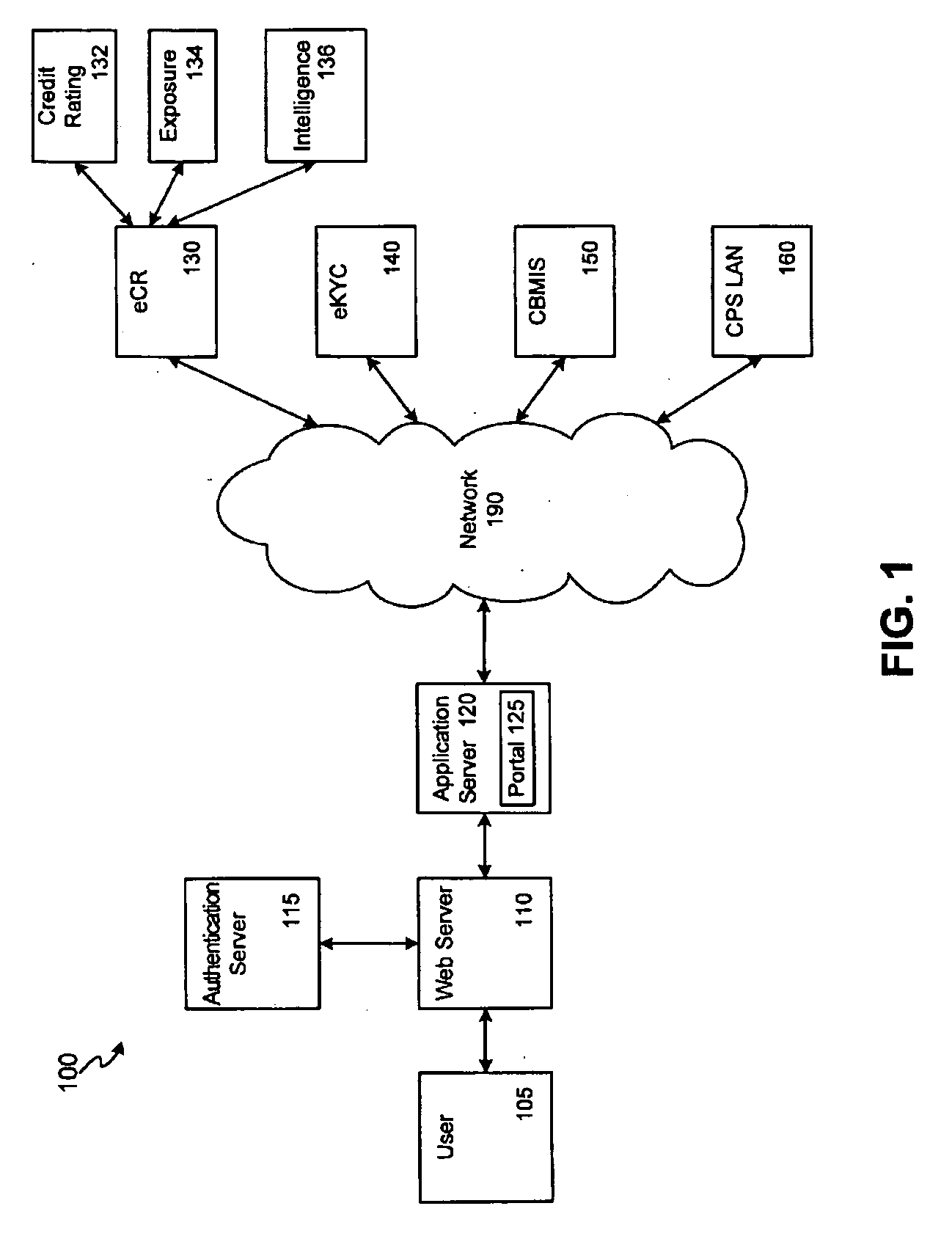
Financial institution portal system and method
Systems and methods utilizing a portal on a single computer platform for improving risk assessment and business reporting are disclosed. The portal integrates at least two financial information resources such as, for example, an electronic credit report (eCR) database, an electronic know your customer (eKYC) database, a client business management information system, and a customer profitability system large area network. The eCR database includes a link to an exposure database, a credit rating database, and / or an intelligence database. The eKYC database includes an anti-money laundering scoring module, and / or a standard KYC form or an enhanced KYC form.
Owner:STANDARD CHARTERED UK HLDG
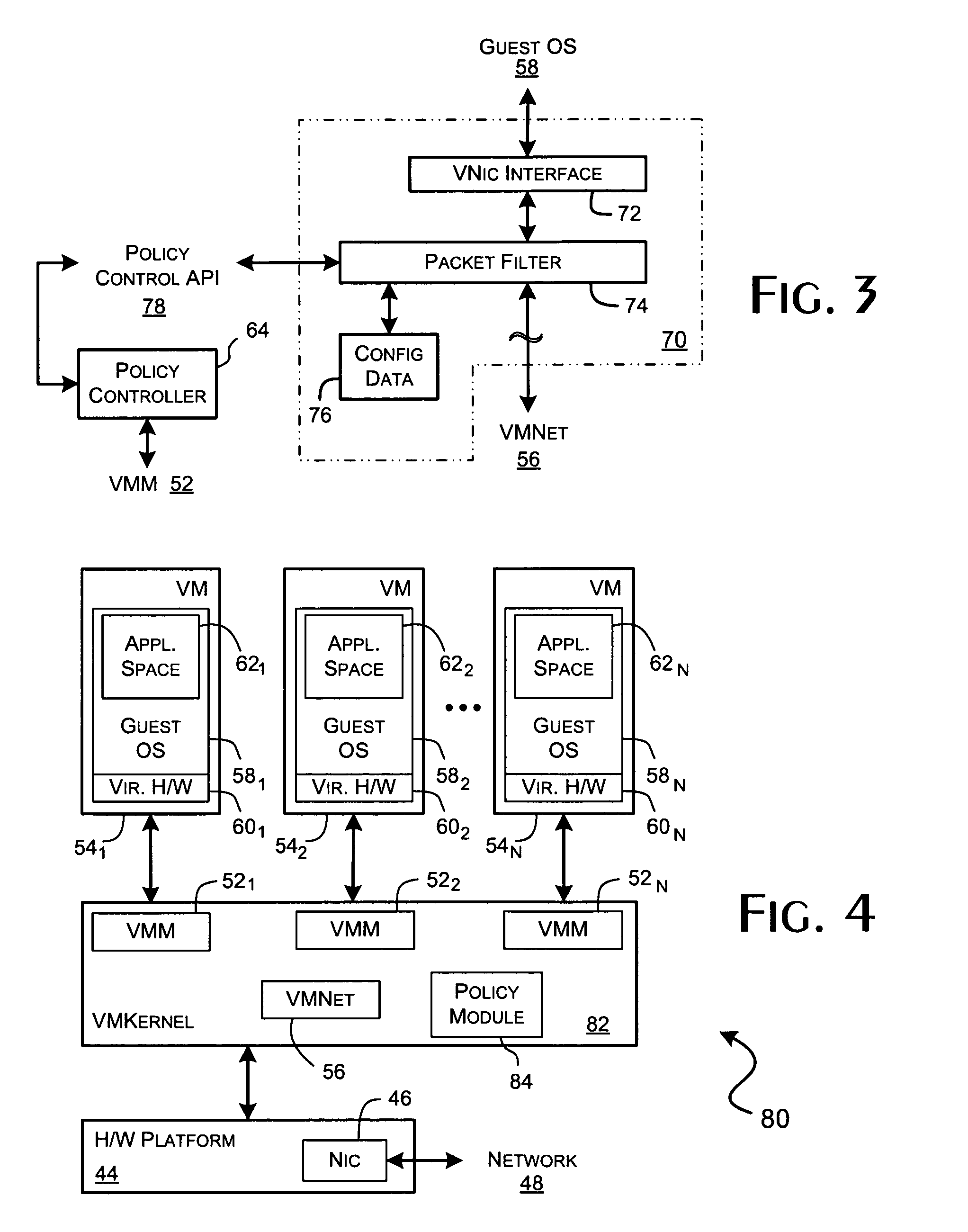
System and methods for implementing network traffic management for virtual and physical machines
ActiveUS8166474B1Ensure safetyEasy to useDigital computer detailsSoftware simulation/interpretation/emulationVirtualizationTraffic capacity
A virtualization framework provides security between multiple virtual machines with respect to network communications between the virtual machines and between the virtual machines and a physical network coupled to the underlying physical computer platform. The virtualization framework includes a network interface controller driver that provides an interface to the platform network interface controller and supports execution of a plurality of virtual machines. Each virtual machine includes a virtual network interface controller that provides a network communications path between the virtual machines and to the network interface controller driver. Each virtual network interface controller further contains a programmable network packet filter that controls the selective transfer of network packets with respect to a corresponding virtual machine.
Owner:VMWARE INC
Data integrity monitoring in trusted computing entity
InactiveUS7457951B1Digital data processing detailsUnauthorized memory use protectionData integrityTrusted components
A method of security monitoring of data files in a computer platform is carried out by a trusted component having a processor and trusted memory area. The method comprises creating one or a plurality of data files in an untrusted memory area of said computing platform, for each created data file, periodically generating a digest data by applying a hash function to each data file, storing the digest data in a trusted memory area and for each file periodically comparing a current digest data of the file with a previously generated digest data of the file. Any differences between a previous and a current digest data indicate that a file in the untrusted memory area has been corrupted.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
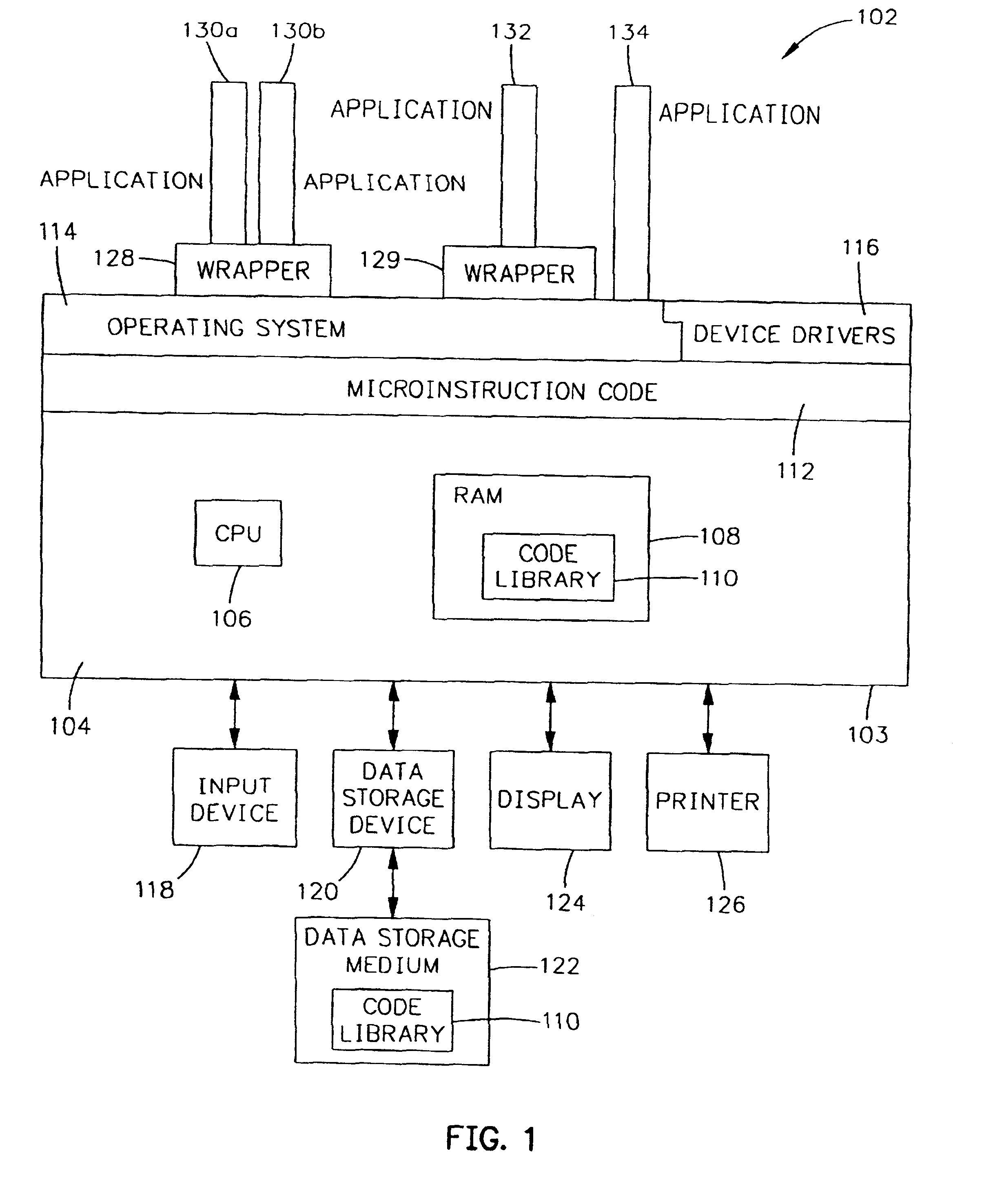
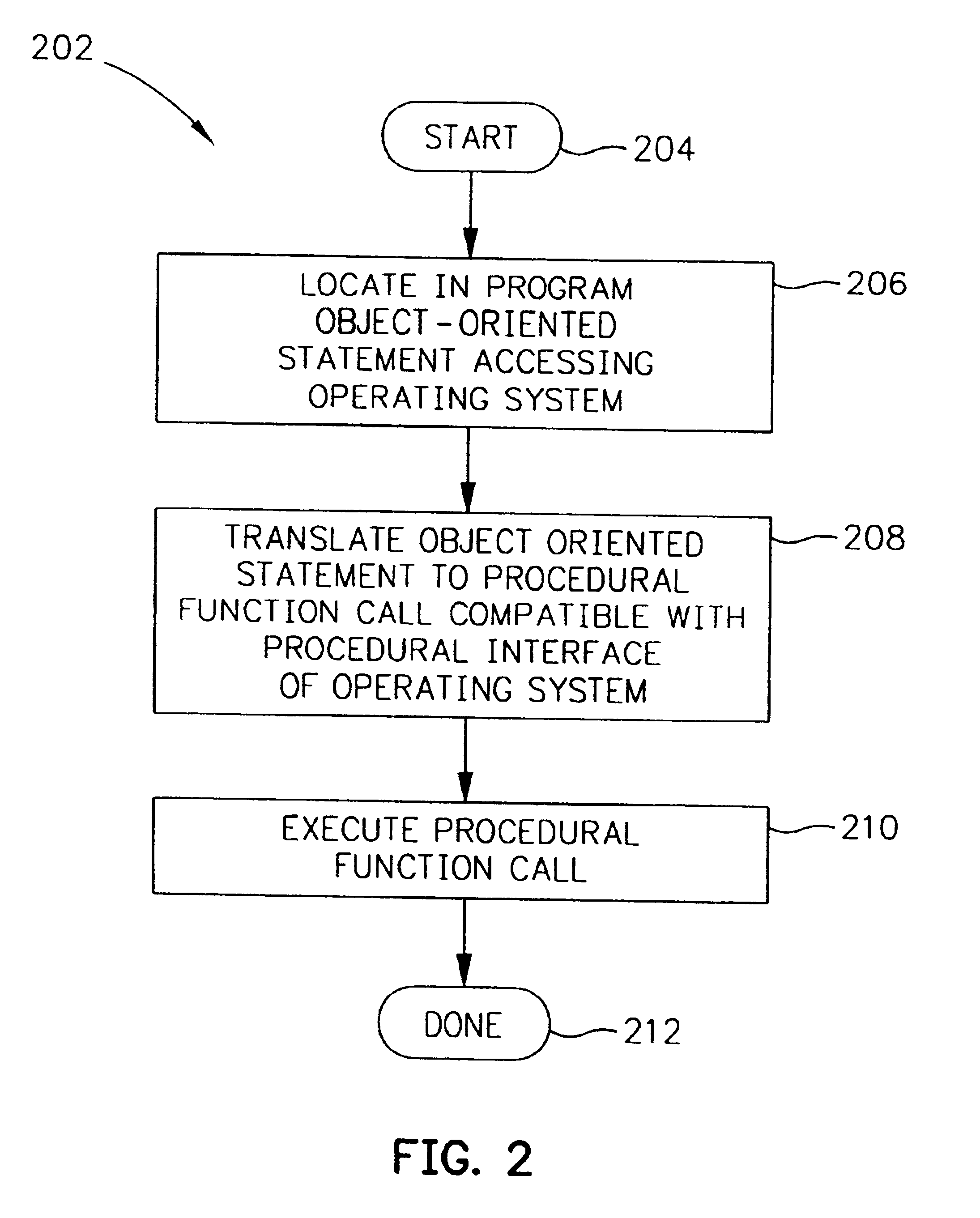
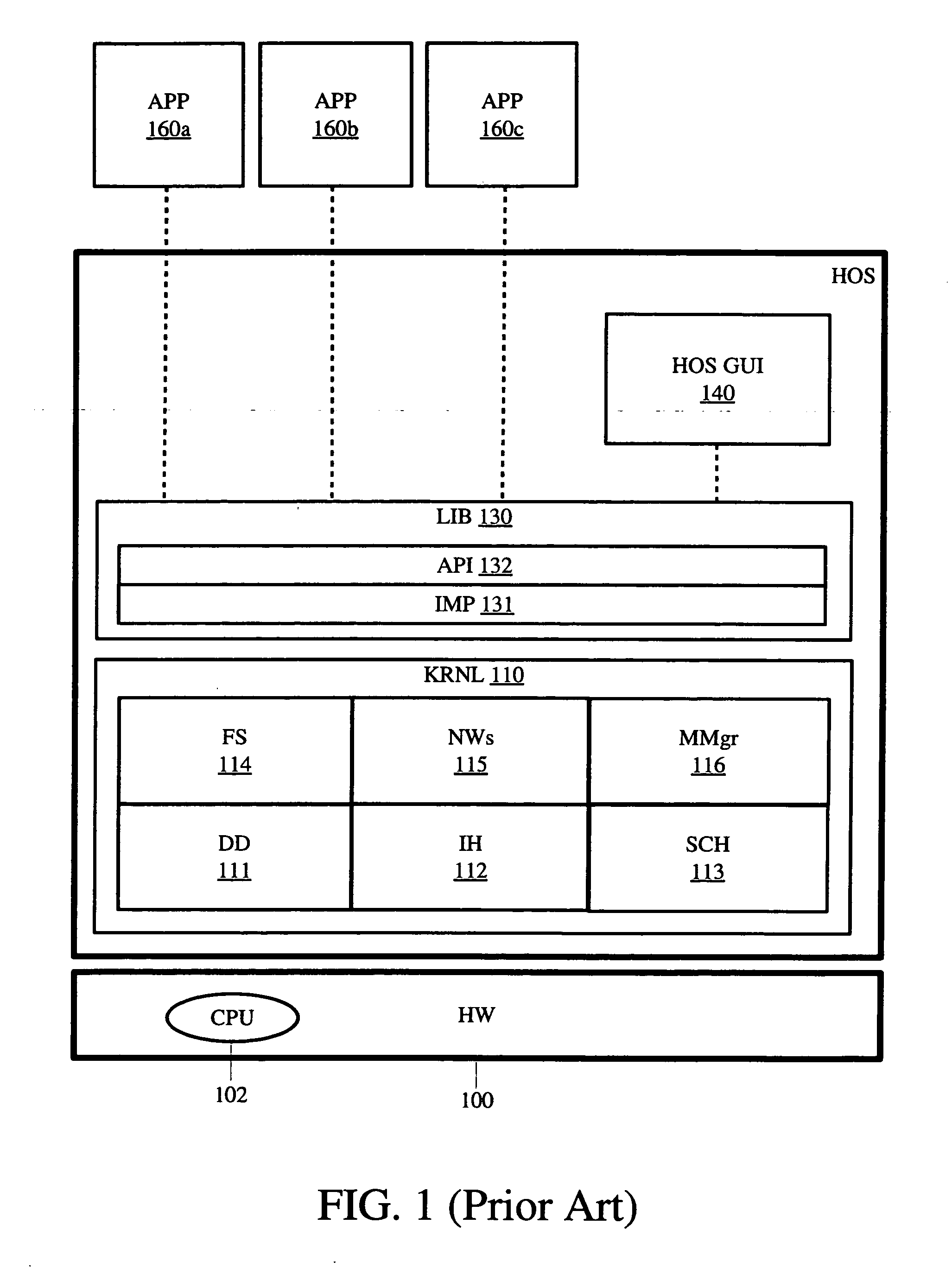
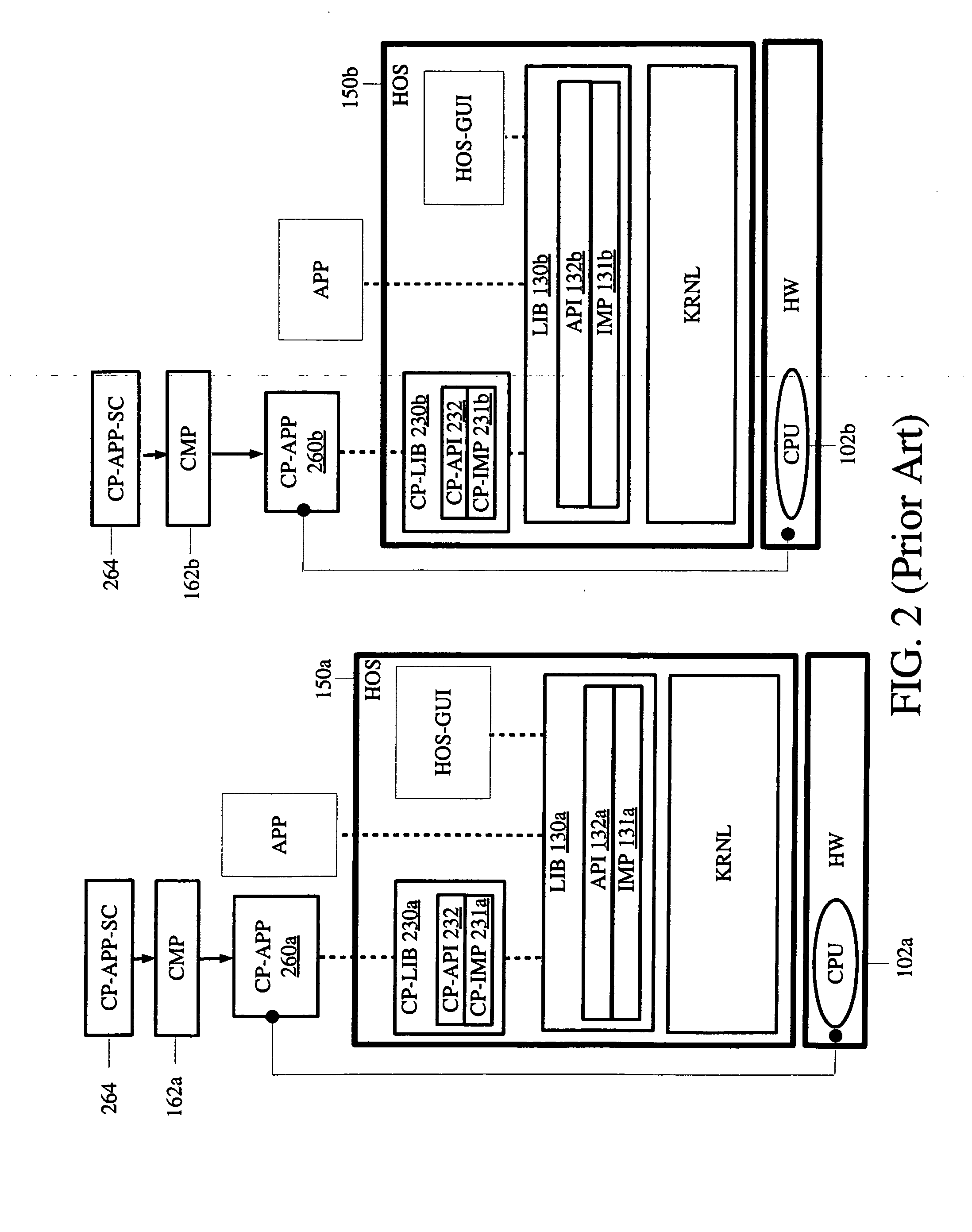
Object-oriented interface for portability to diverse operating systems or hardware platforms
InactiveUS6606742B1Program control using stored programsMultiprogramming arrangementsOperational systemComputerized system
An object-oriented interface is disclosed for conferring portability for object-oriented programming to diverse operating systems on diverse hardware platforms in a computer system. The object-oriented interface is executable on a plurality of different computer platforms and includes classes of object-oriented methods. The interface is responsive to the object-oriented programming which instantiates its objects from its own classes and invokes the object oriented methods of the interface. Operating system specific, procedural program logic is compiled for use on a given computer platform that includes given computer hardware and a given procedural operating system which is executable on the hardware. A determination is made if the object-oriented methods of the interface to be invoked during runtime execution are present in the program memory of the computer hardware. A runtime loader selectively loads into the program memory any required object-oriented methods of the interface during runtime before their invocation by the object-oriented programming. The object-oriented interface thereby provides native system services to the object-oriented programming from the given computer hardware and procedural operating system.
Owner:APPLE INC
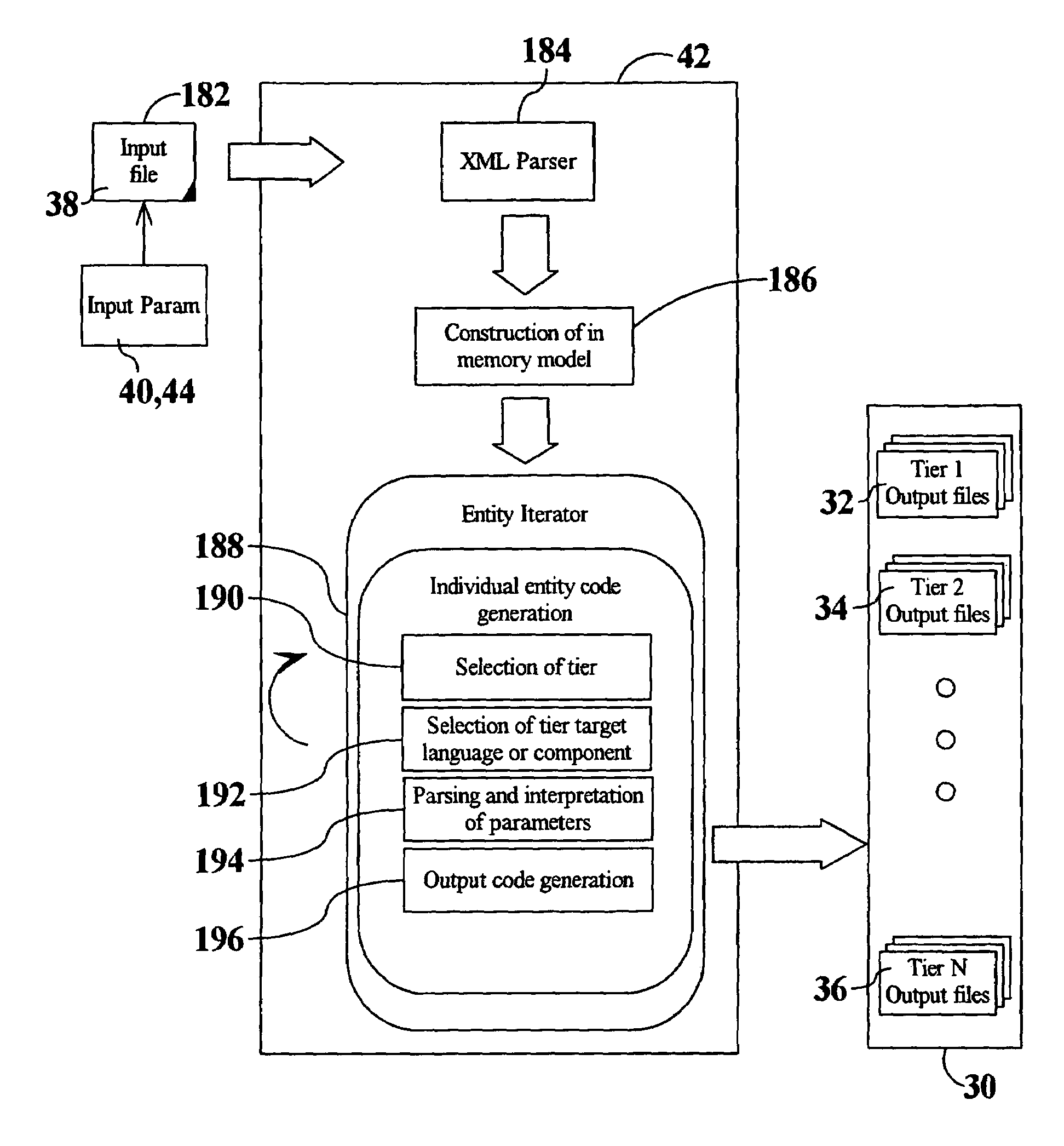
System and method for multiple level architecture by use of abstract application notation
InactiveUS7043716B2Special data processing applicationsSpecific program execution arrangementsAs DirectedApplication software
A system and method of translating an abstract notation of an application to a series of sub-applications representing a central application. Also described is a multi-tier application system for generating the central application for deployment on a predetermined combination of selected components. The system comprises an abstract notation description file to contain data for the central application. The system also has an application editor for entering a selected set of input parameters to provide the data, and an application generator for transforming the data from the abstract notation to a selected platform notation corresponding to the selected components. The selected notation is contained in the central application, wherein the deployment of the central application monitors the communication of component data between the selected components. The sub-application can be generated for a variety of computer platforms or languages for deployment on an n-tier system, as directed by the intended components. The central application can be applied to distributed web data-centric application.
Owner:DOXIM SOLUTIONS ULC
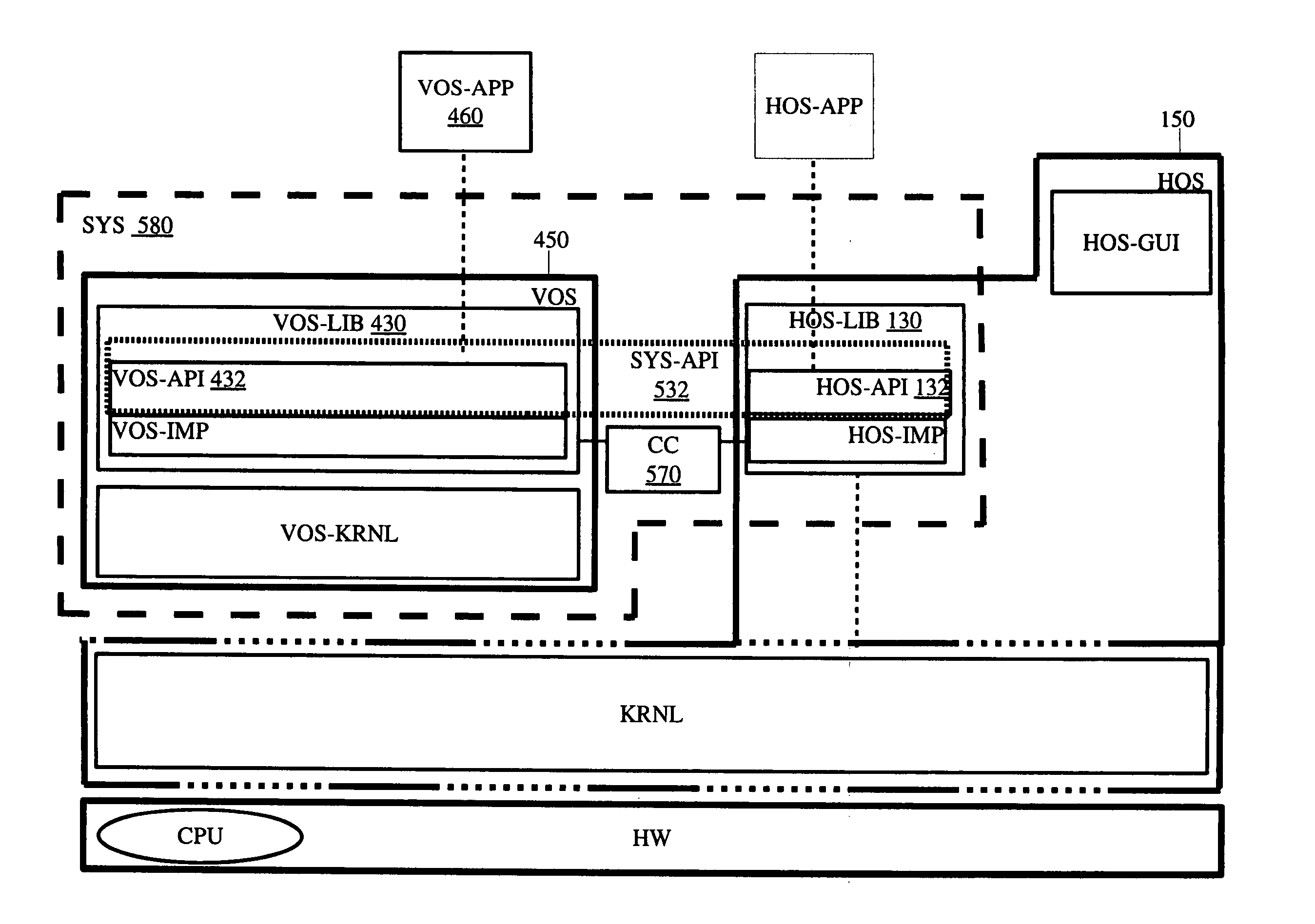
Method and apparatus for providing cross-platform hardware support for computer platforms
InactiveUS20070067769A1Software simulation/interpretation/emulationMemory systemsDevice typeOperational system
A method and apparatus for providing cross-platform hardware support for a computing platform are described herein. In one embodiment, an example of a computing system includes, but is not limited to, at least one physical hardware device, a host operating system (HOS), a virtual platform running on the HOS including a virtual operating system (VOS) and at least one virtual hardware device associated with a device type of the physical hardware device, a virtual device driver included in the VOS to control the at least one virtual hardware device, and a mechanism to synchronize the at least one virtual hardware device with the at least one physical hardware device through a direct use of at least one device driver library on the HOS. Other methods and apparatuses are also described.
Owner:DLOO
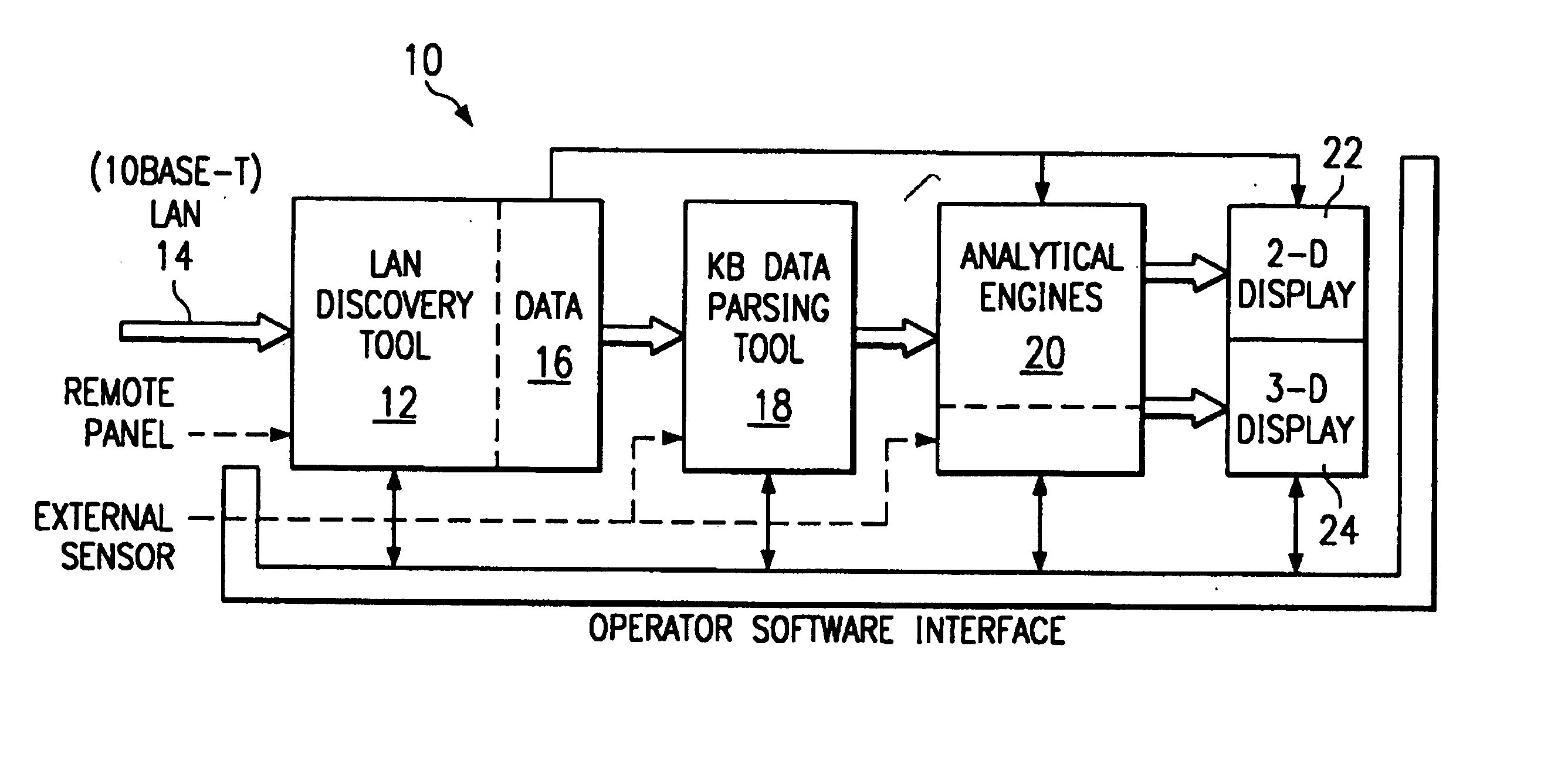
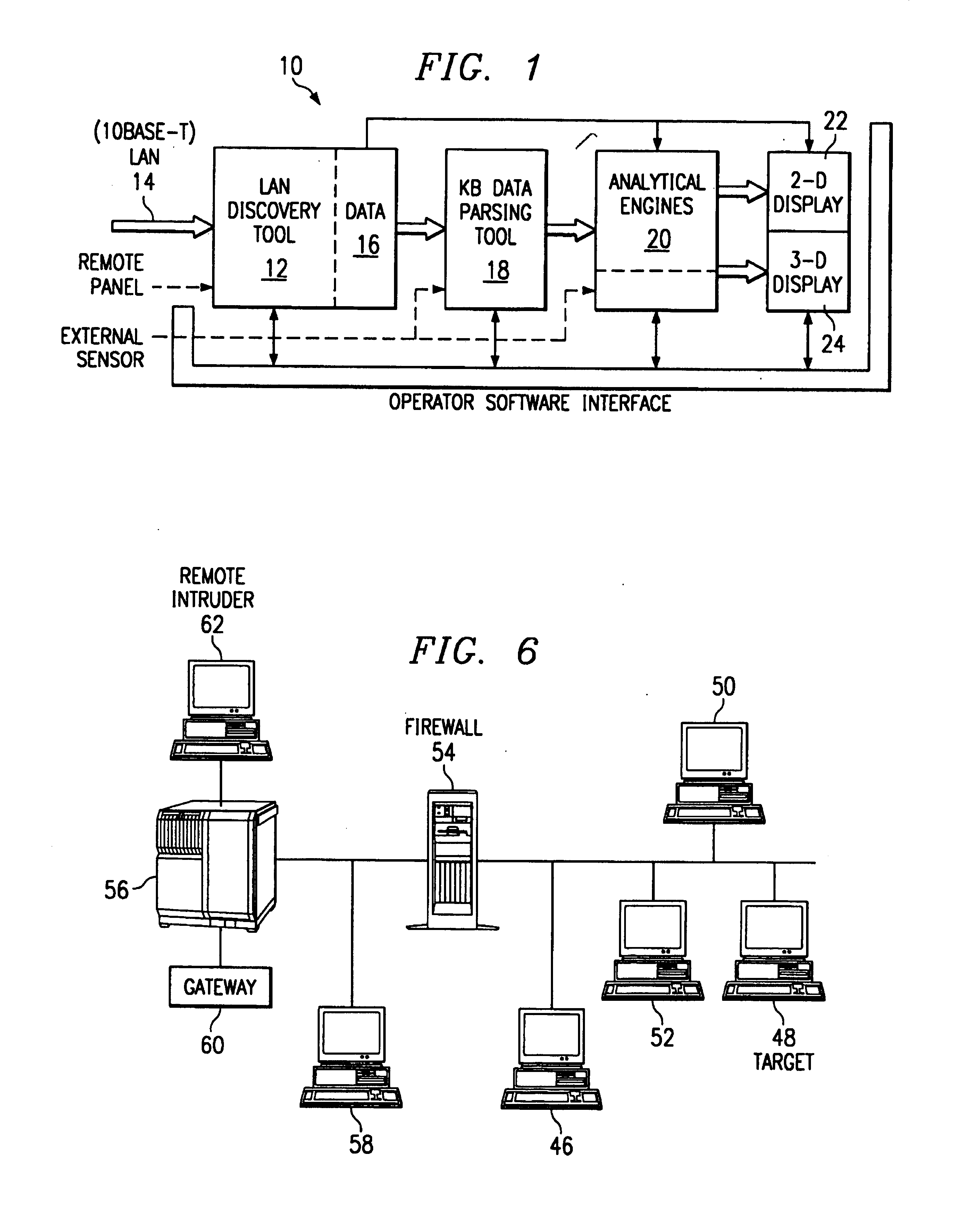
Information security analysis system
InactiveUS7047423B1Reduce bandwidth usageTraffic bottleneckDigital data processing detailsDigital computer detailsDigital dataOperational system
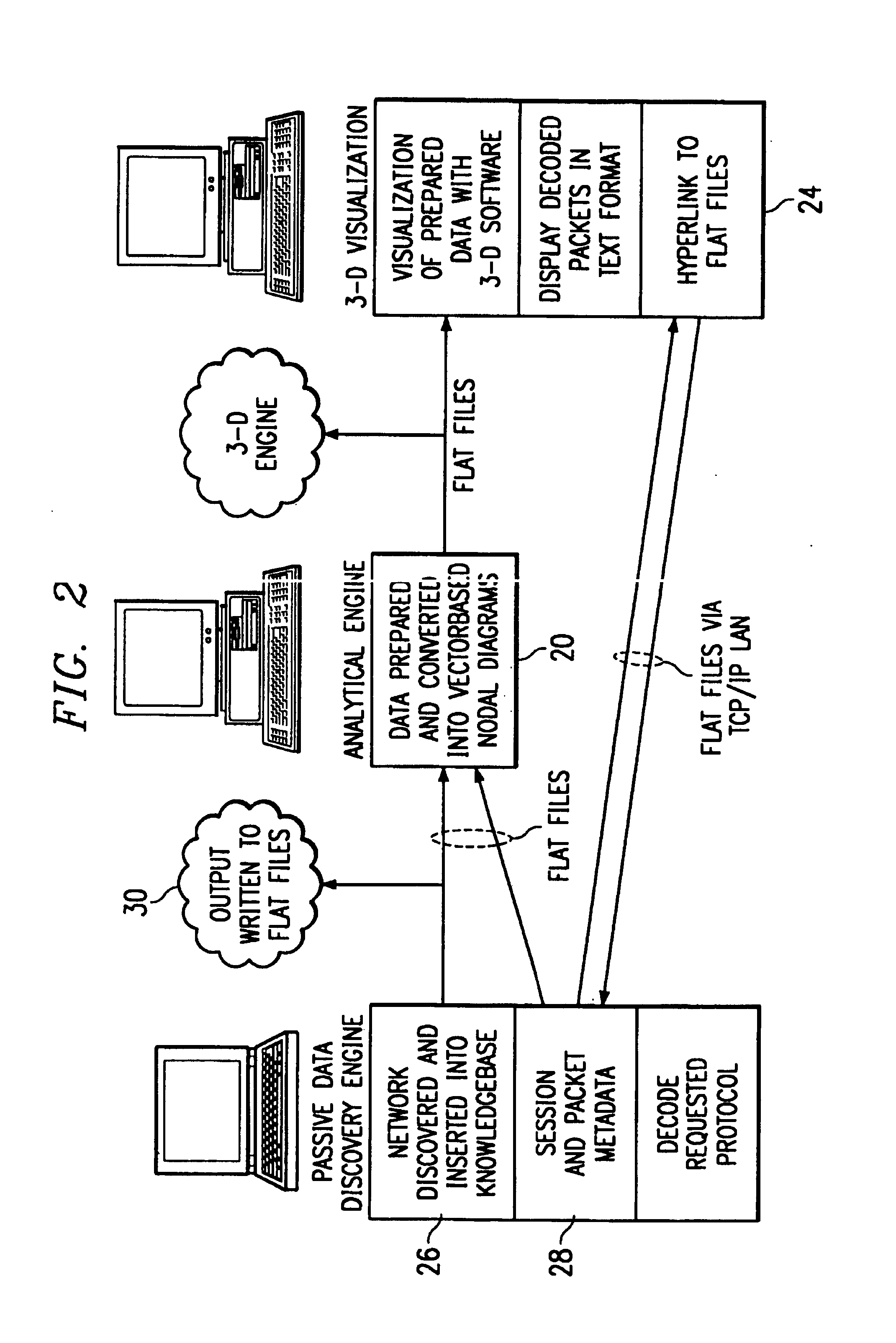
The analysis system is a collection, configuration and integration of software programs that reside on multiple interconnected computer platforms. The software, less computer operating systems, is a combination of sensor, analysis, data conversion, and visualization programs. The hardware platforms consist of several different types of interconnected computers, which share the software programs, data files, and visualization programs via a Local Area Network (LAN). This collection and integration of software and the migration to a single computer platform results in an approach to LAN / WAN monitoring in either a passive and / or active mode. The architecture permits digital data input from external sensors for analysis, display and correlation with data and displays derived from four major software concept groups. These are: Virus Computer Code Detection; Analysis of Computer Source and Executable Code; Dynamic Monitoring of Data Communication Networks; 3-D Visualization and Animation of Data.
Owner:COMP ASSOC THINK INC
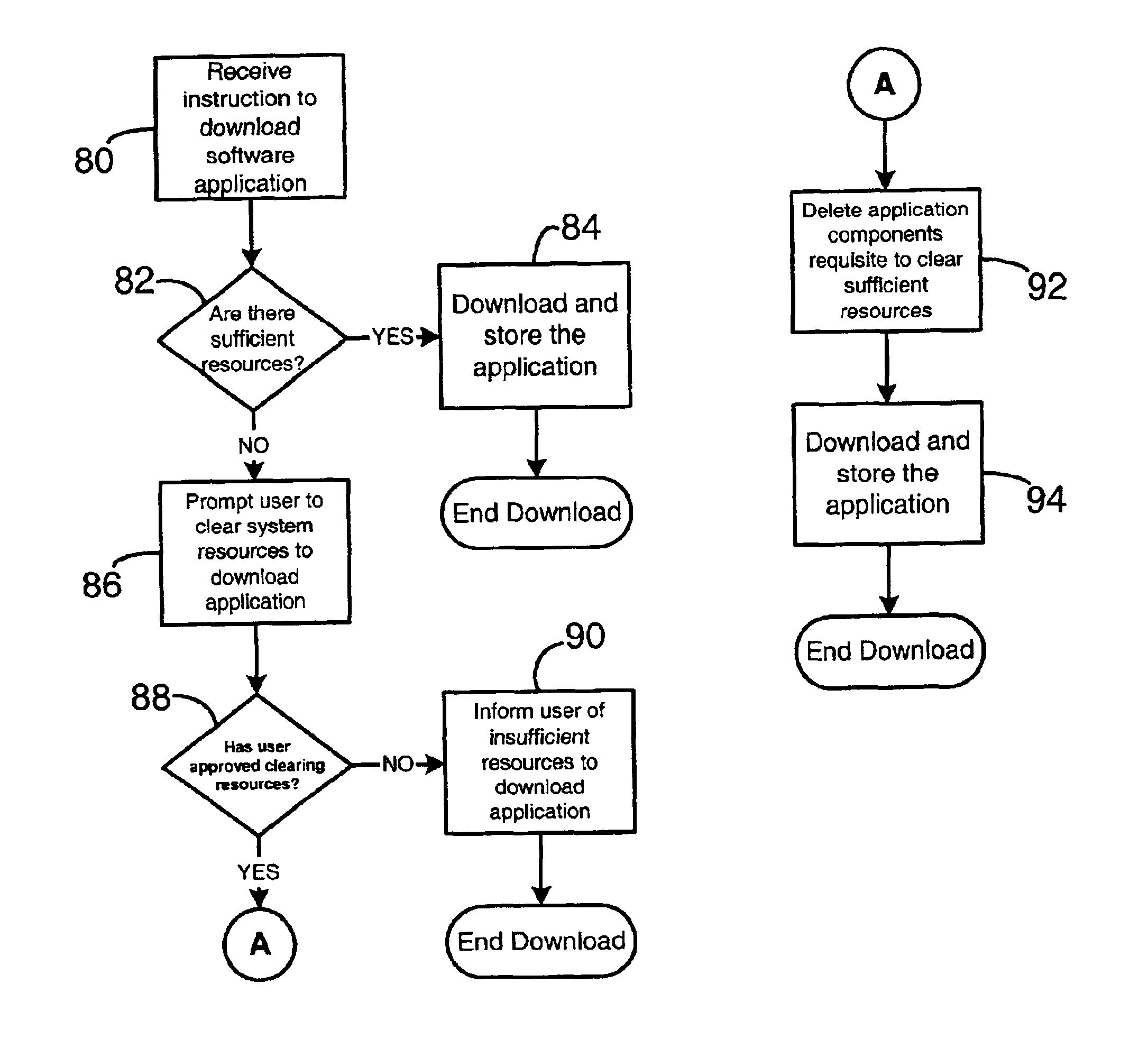
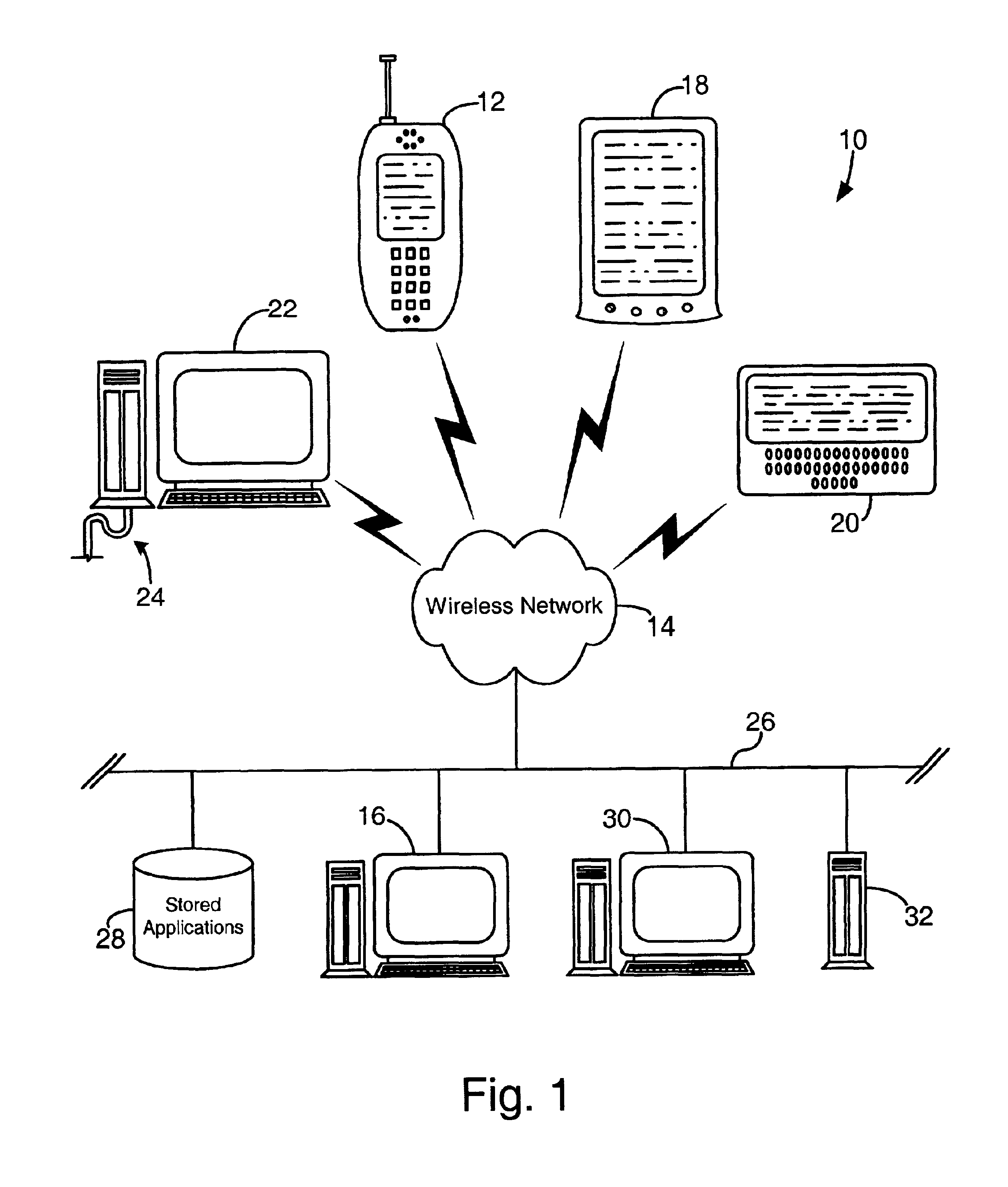
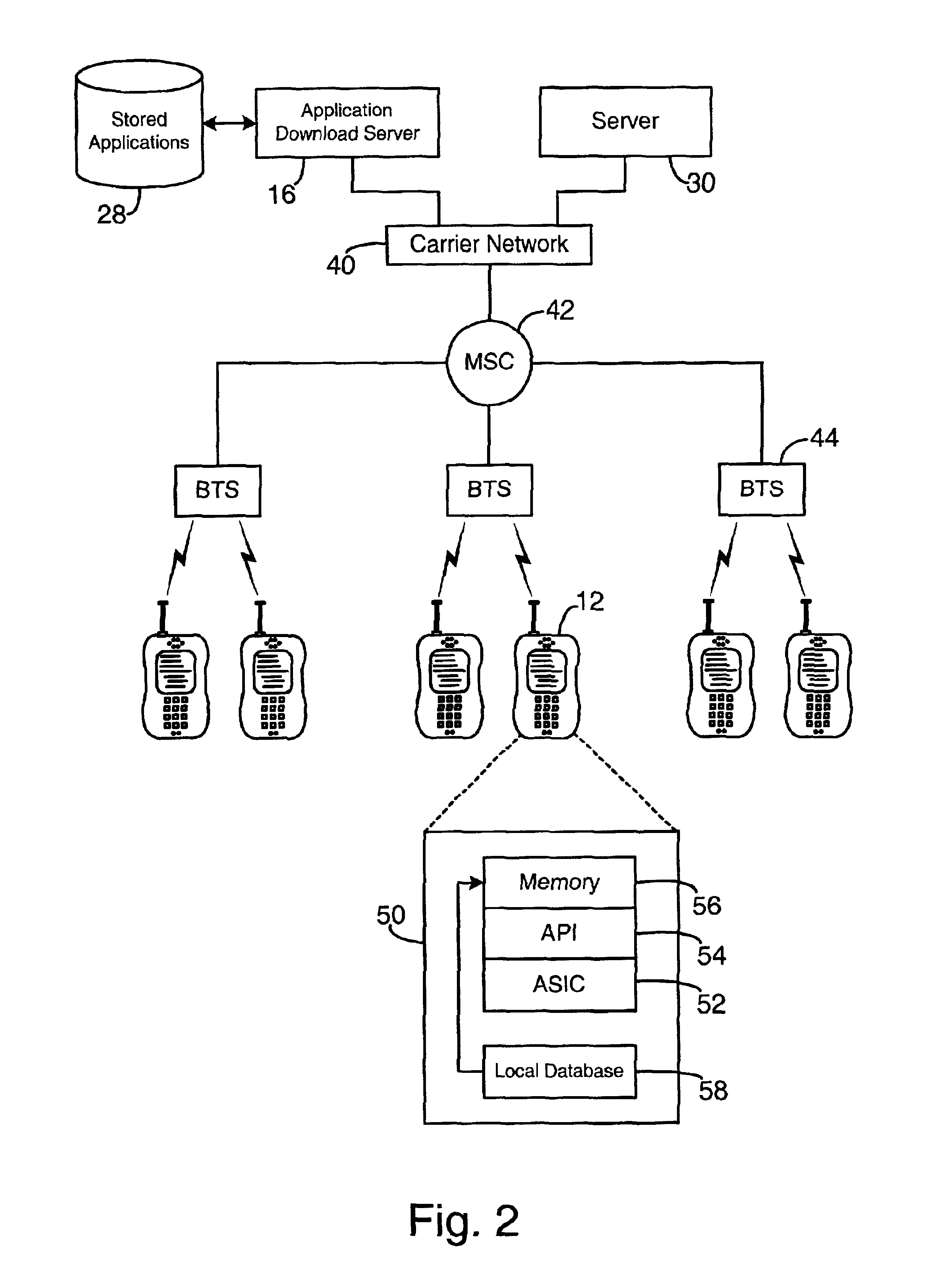
System and method for temporary application component deletion and reload on a wireless device
InactiveUS6941135B2Maximize utilizationEasy to useSpecial service for subscribersDigital computer detailsSoftware licensePager
A system and method for managing the deleting and reloading of software application components on a wireless device, such as a cellular telephone, personal digital assistant, pager, or other computer platform. The wireless device has one or more resident executable software applications wherein each application has one or more application components and application-associated data, such as software licenses and user-specific data. The wireless device selectively deletes one or more application components of the resident software applications without loss of the application-associated data to clear resources on the wireless device, and selectively prompts an application download server across a wireless network to transmit deleted application components needed to be reinstalled on the wireless device to execute the application.
Owner:QUALCOMM INC
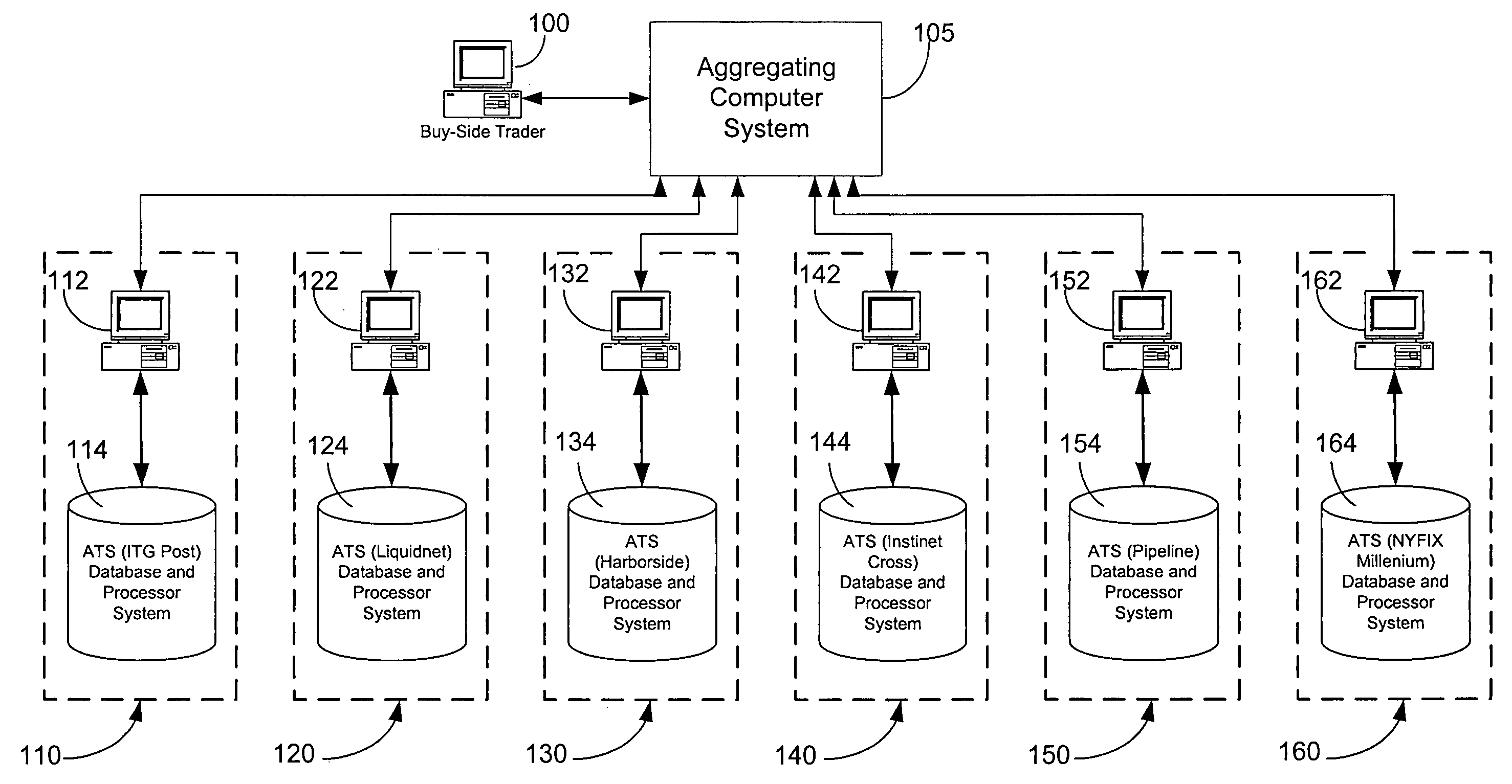
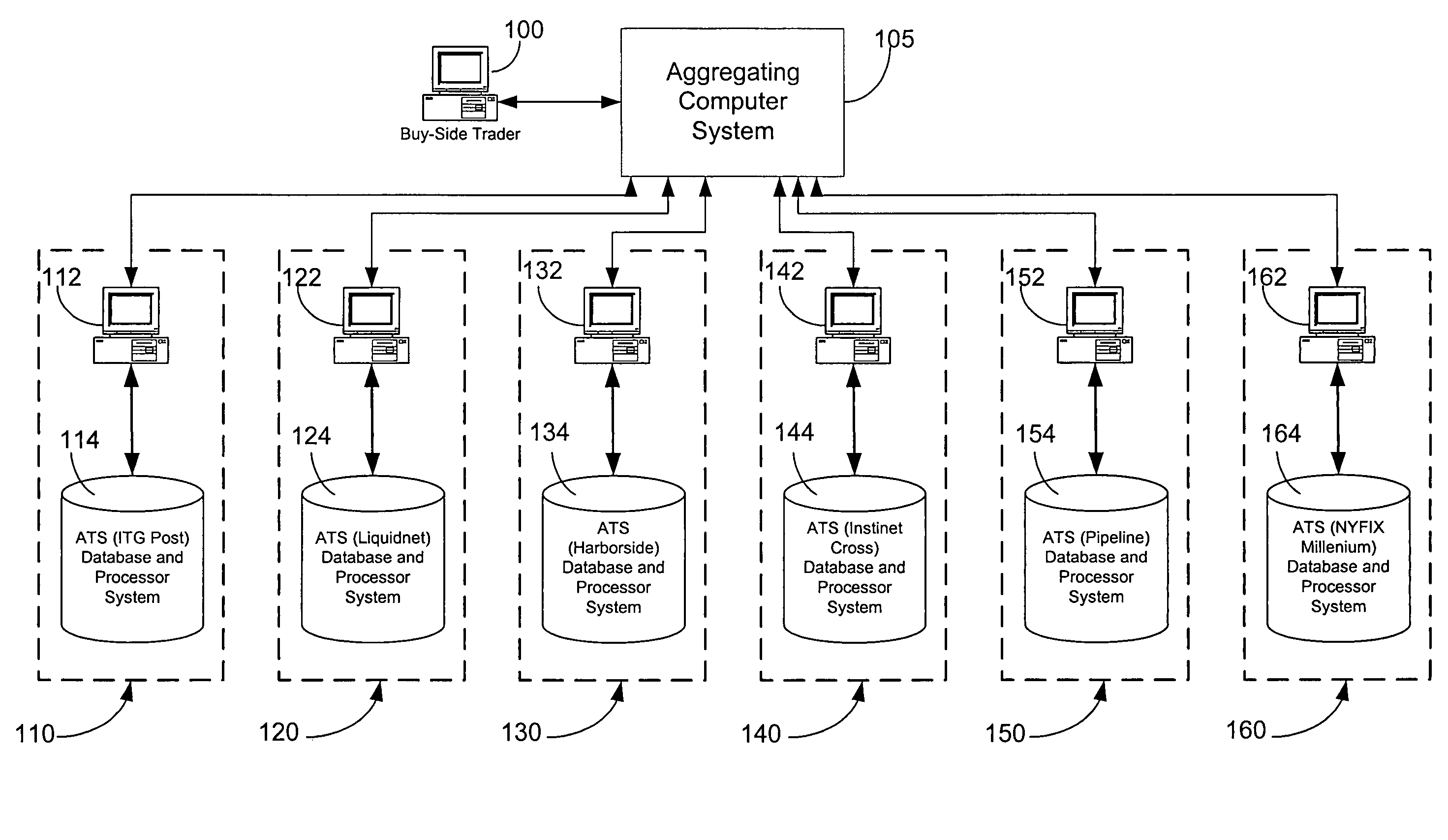
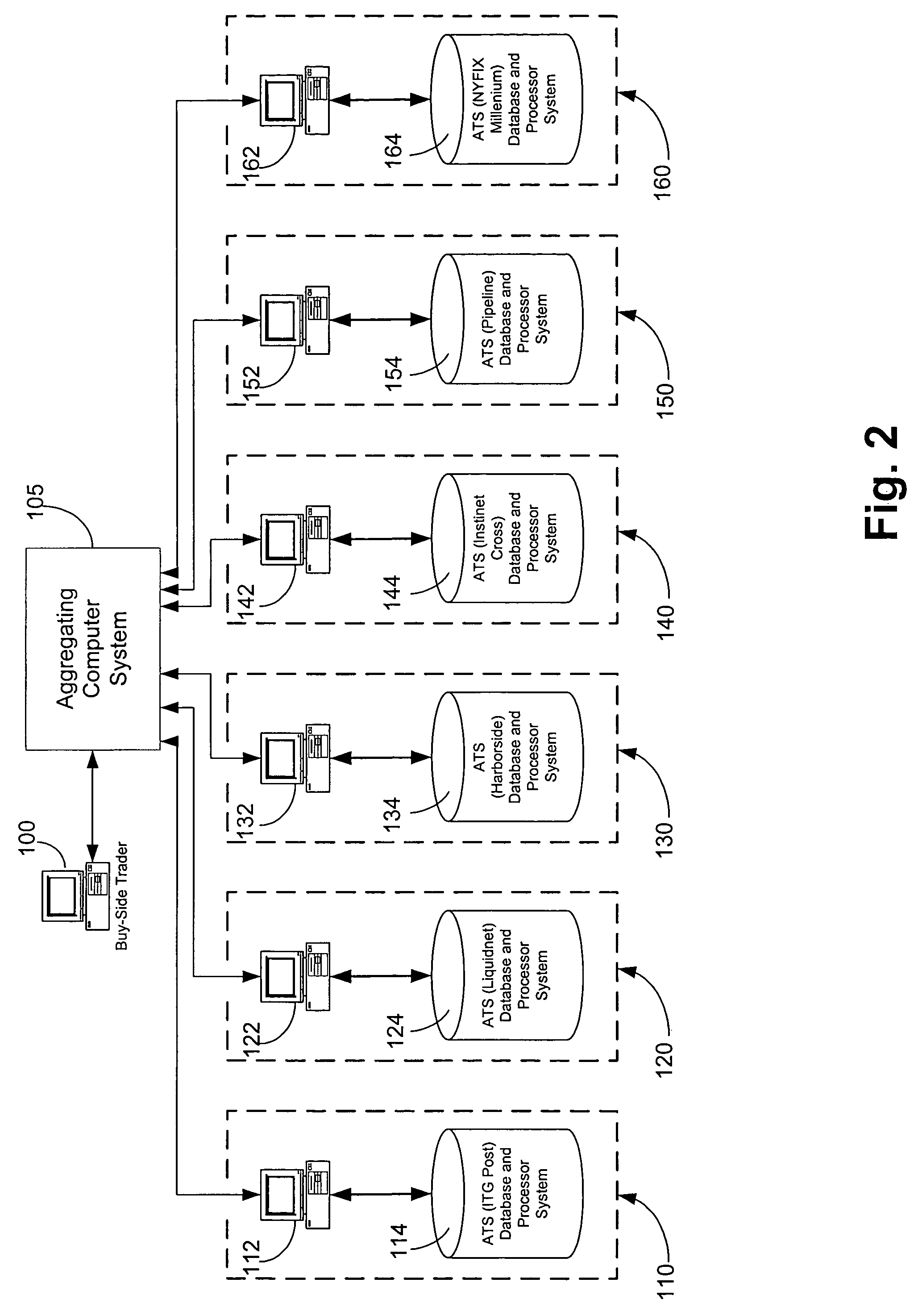
Method for providing aggregation of trading on multiple alternative trading systems
A method for performing financial trading amongst a plurality of alternative trading systems using a common financial computer platform. The method including the steps of receiving at the common financial computer platform a buy-order for a prescribed number shares at a prescribed price. Electronic communication is then established between the common financial computer platform and each of the plurality of alternative trading systems. At least a portion of the buy-order is then submitted from the common financial computer platform to each of the plurality of alternative trading systems. The common financial common platform then monitors each of the plurality of alternative trading systems to determine if at least a portion of the buy-order was executed by one of the plurality of alternative trading systems. And if yes, then that indicated execution for one of the plurality of alternative trading systems is automatically accepted and automatically canceled are the remaining buy orders that were submitted to the other alternative trading system which were not yet executed.
Owner:ITG SOFTWARE SOLUTIONS INC
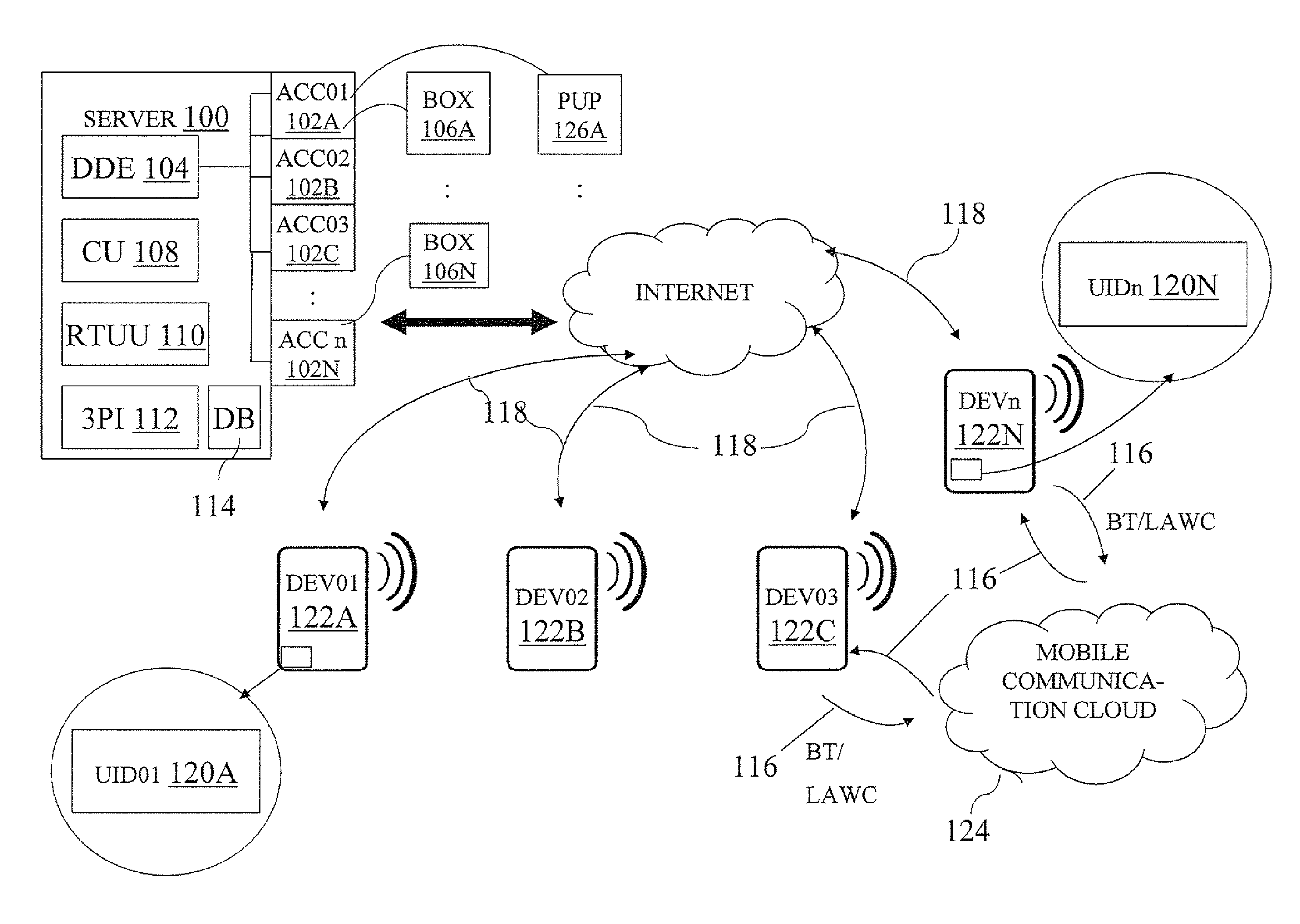
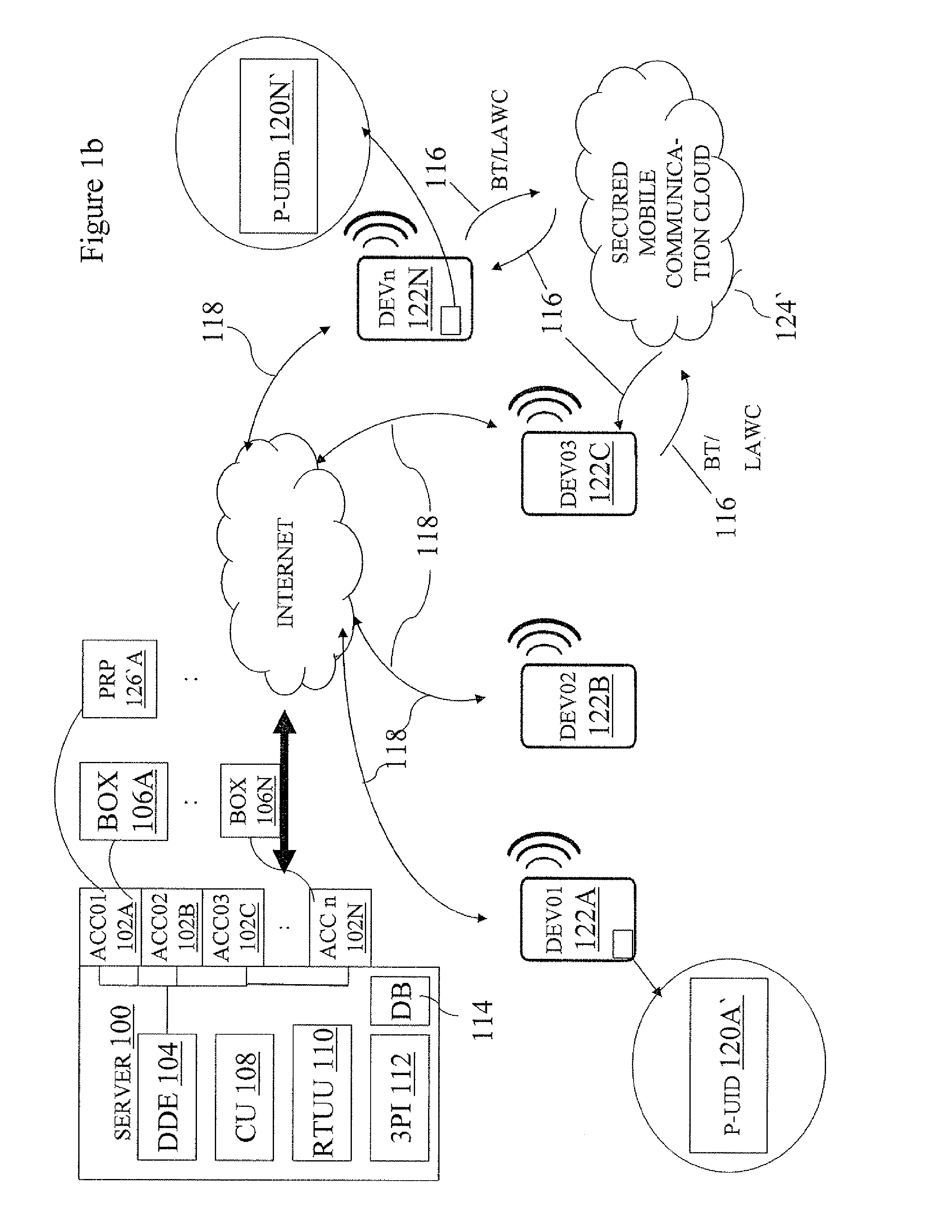
Location-aware Mobile Connectivity and Information Exchange System
ActiveUS20130103946A1Enhanced interactionKey distribution for secure communicationUser identity/authority verificationUser deviceLocation aware
A computer platform and method for managing secure data transactions between user accounts on a server, based on the respective locations of mobile user devices related to the user accounts, where the user devices create a secured mobile communication cloud between themselves to ensure secure data communications.
Owner:BINENSTOCK ISHAI
System and method for establishing a communication between a peripheral device and a wireless device
InactiveCN1902609AInterprogram communicationData switching by path configurationComputer networkOperational system
Owner:QUALCOMM INC
Method for providing aggregation of trading on multiple alternative trading systems
A method for performing financial trading amongst a plurality of alternative trading systems using a common financial computer platform. The method including the steps of receiving at the common financial computer platform a buy-order for a prescribed number shares at a prescribed price. Electronic communication is then established between the common financial computer platform and each of the plurality of alternative trading systems. At least a portion of the buy-order is then submitted from the common financial computer platform to each of the plurality of alternative trading systems. The common financial common platform then monitors each of the plurality of alternative trading systems to determine if at least a portion of the buy-order was executed by one of the plurality of alternative trading systems. And if yes, then that indicated execution for one of the plurality of alternative trading systems is automatically accepted and automatically canceled are the remaining buy orders that were submitted to the other alternative trading system which were not yet executed.
Owner:ITG SOFTWARE SOLUTIONS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com