Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2060results about "File system functions" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
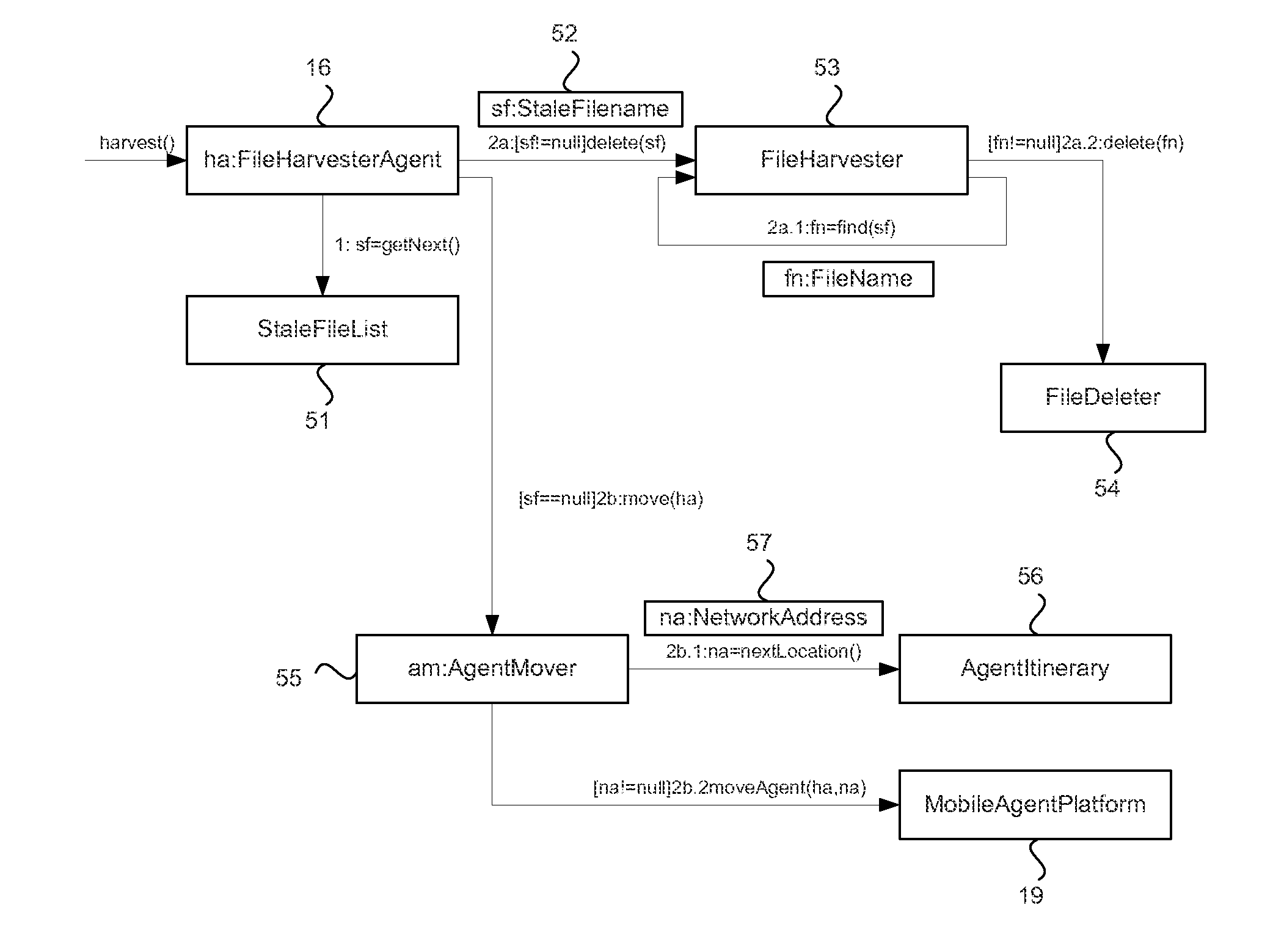
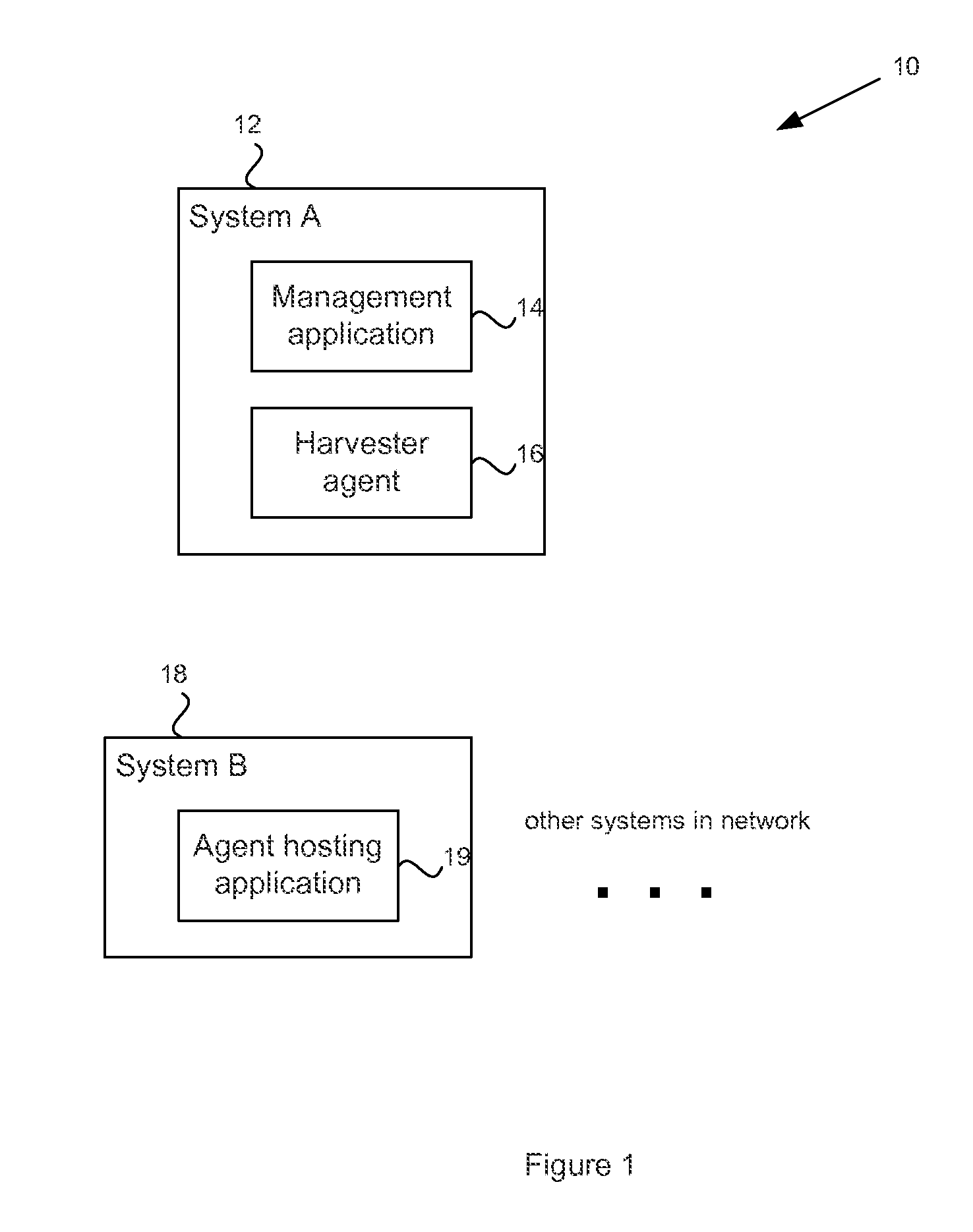
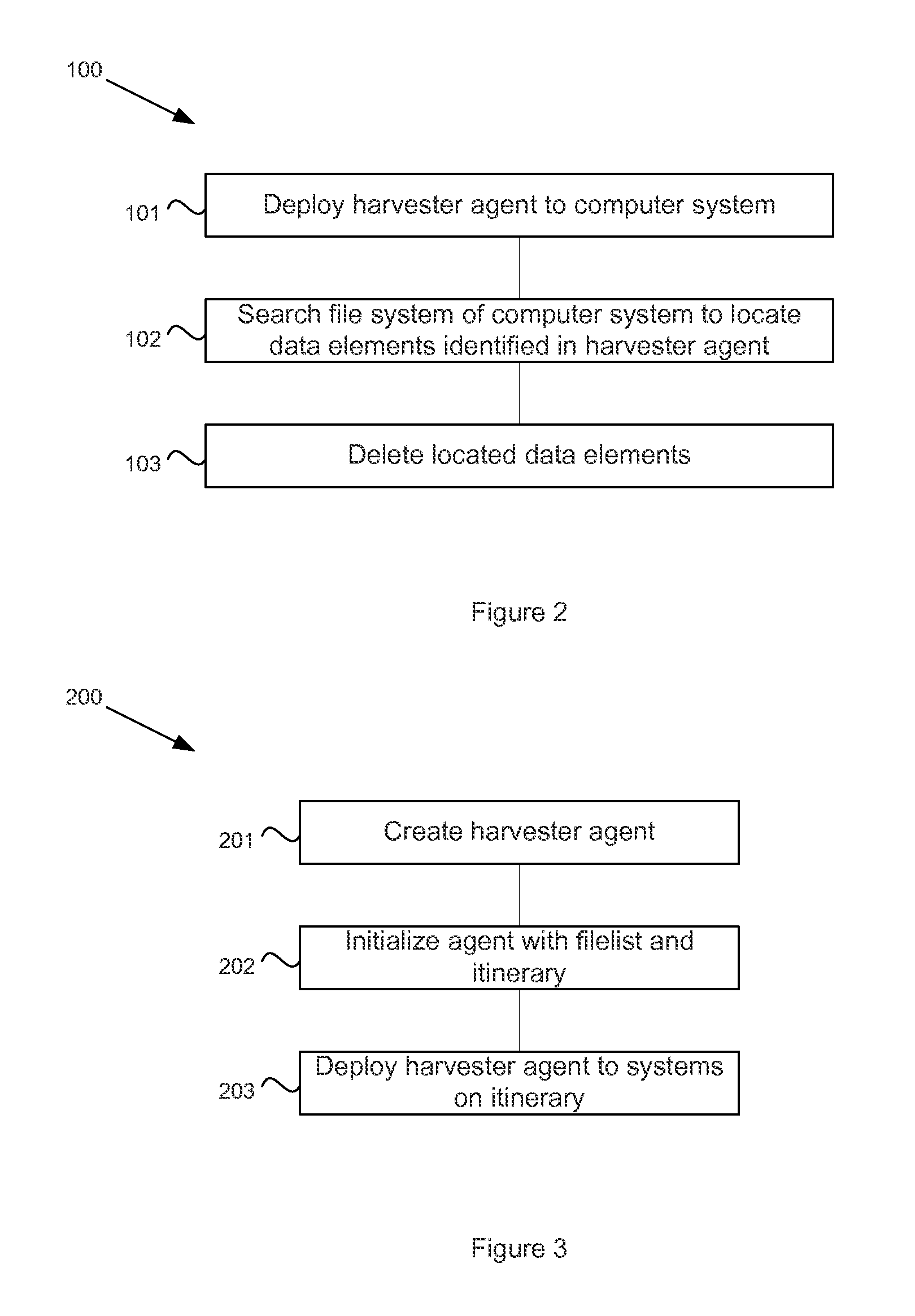
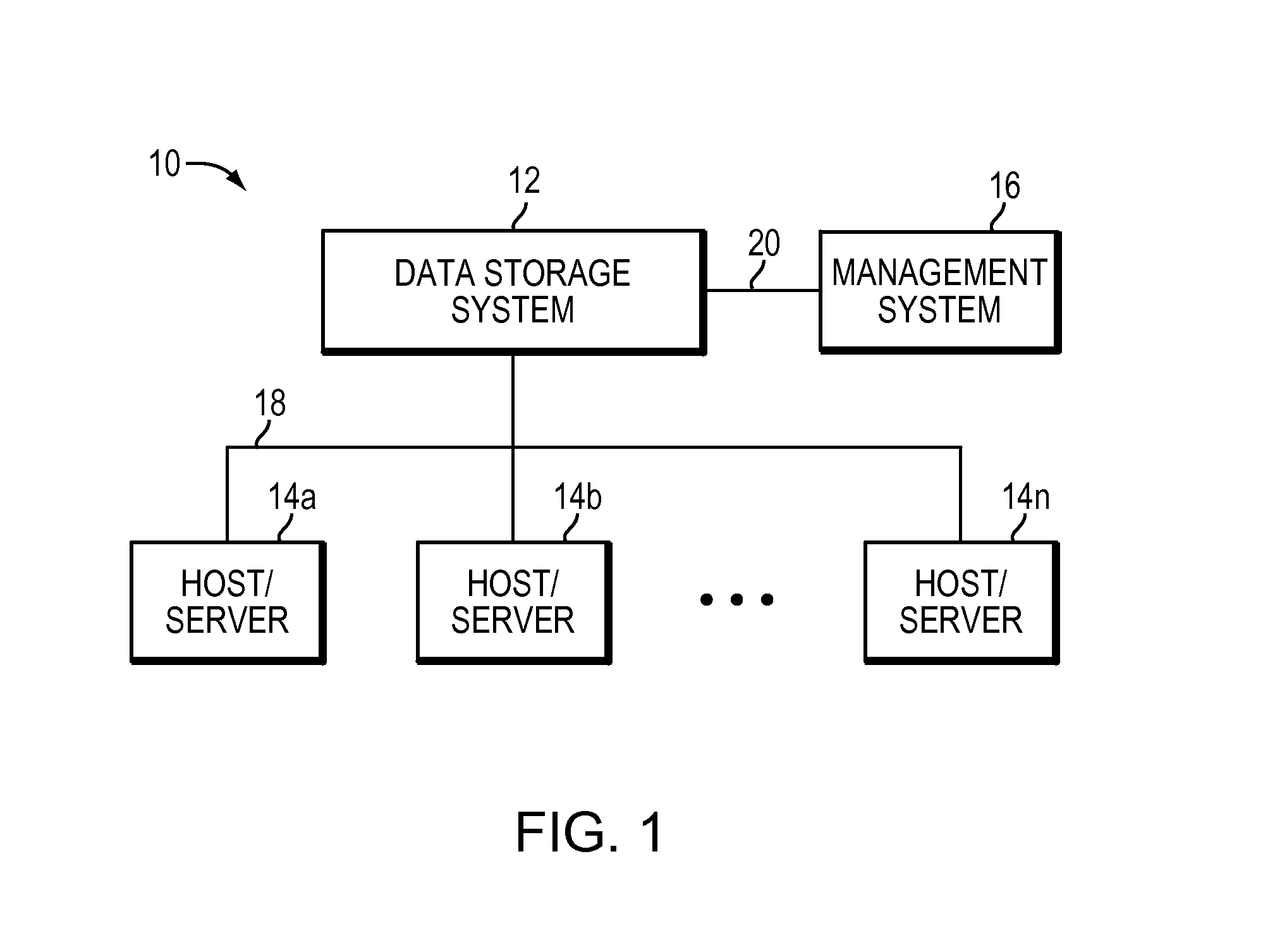
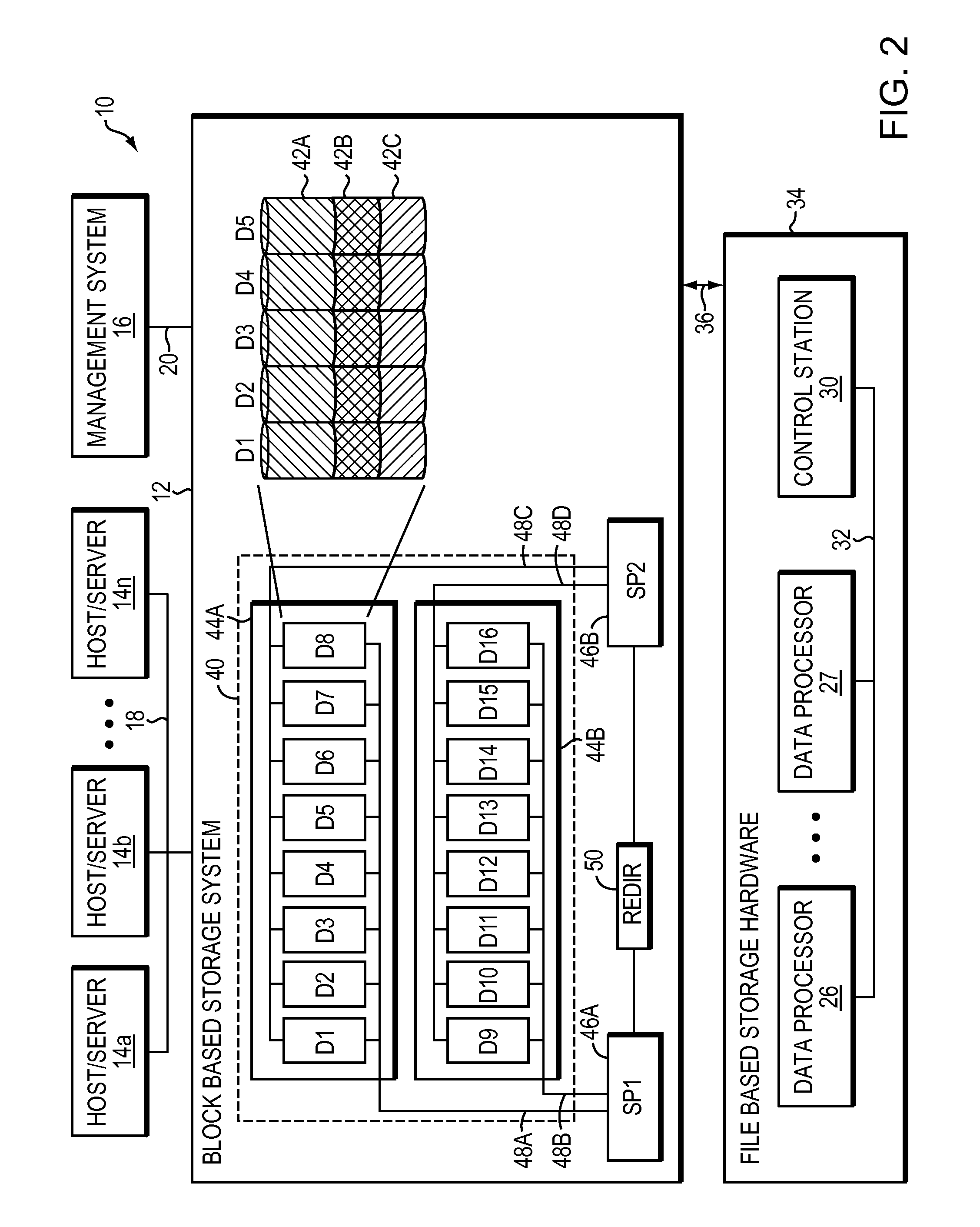
System and method for managing sensitive data using intelligent mobile agents on a network
ActiveUS20120254129A1Digital data processing detailsSpecial data processing applicationsFile systemData file
In order to manage stale data on a network of computer systems, a file harvester agent may be configured with a list of stale data files to be deleted. The file harvester agent may be deployed to the computer systems of a network. When executed in a computer system, the file harvester agent searches the file system of the computer system to locate any files or data indicated in the file list. Any located data files are deleted. Once the agent has finished processing the file list on a computer system, the agent can copy or replicate itself to other computer systems of the network in accordance with a pre-configured itinerary.
Owner:OPEN INVENTION NEWTORK LLC
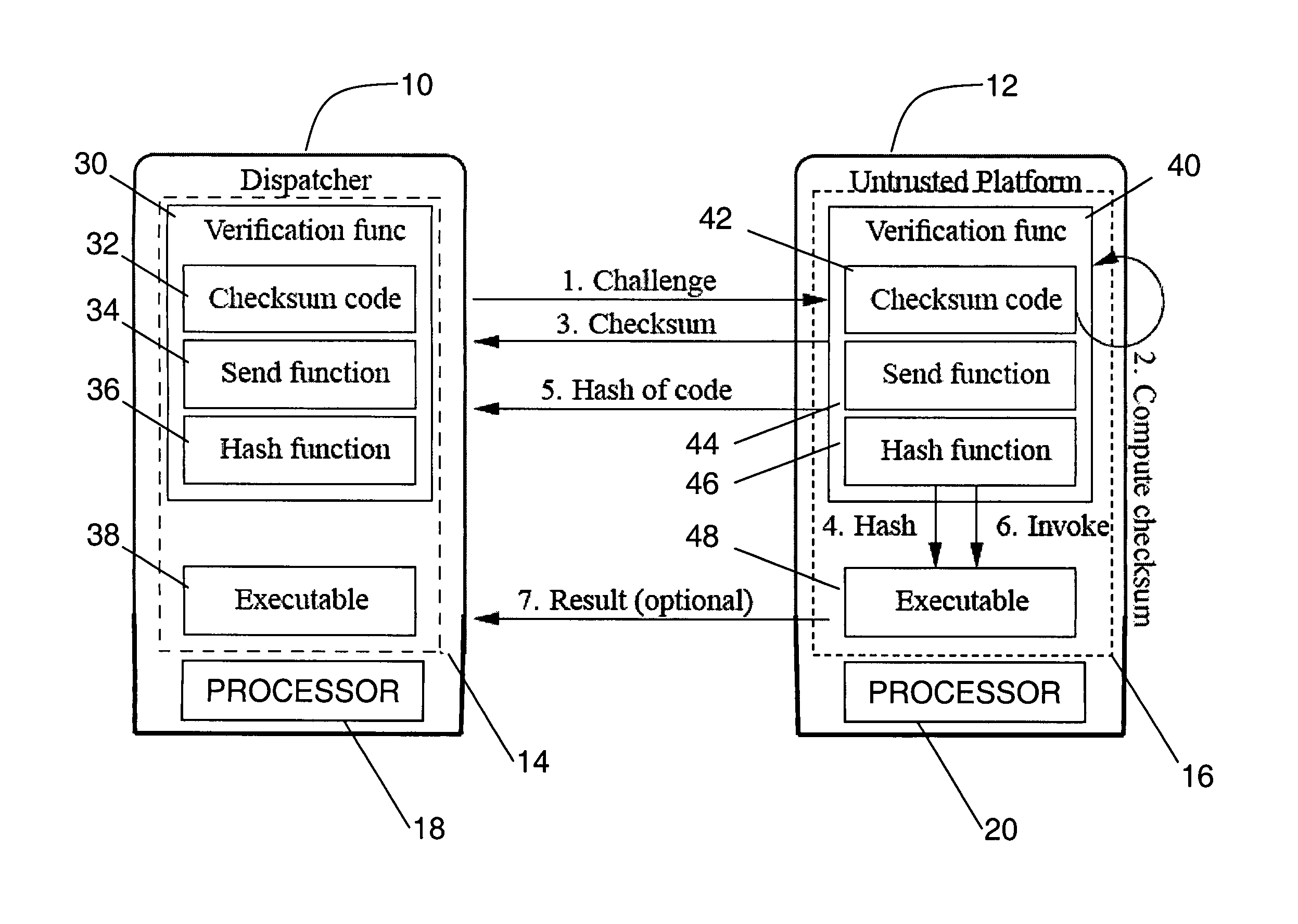
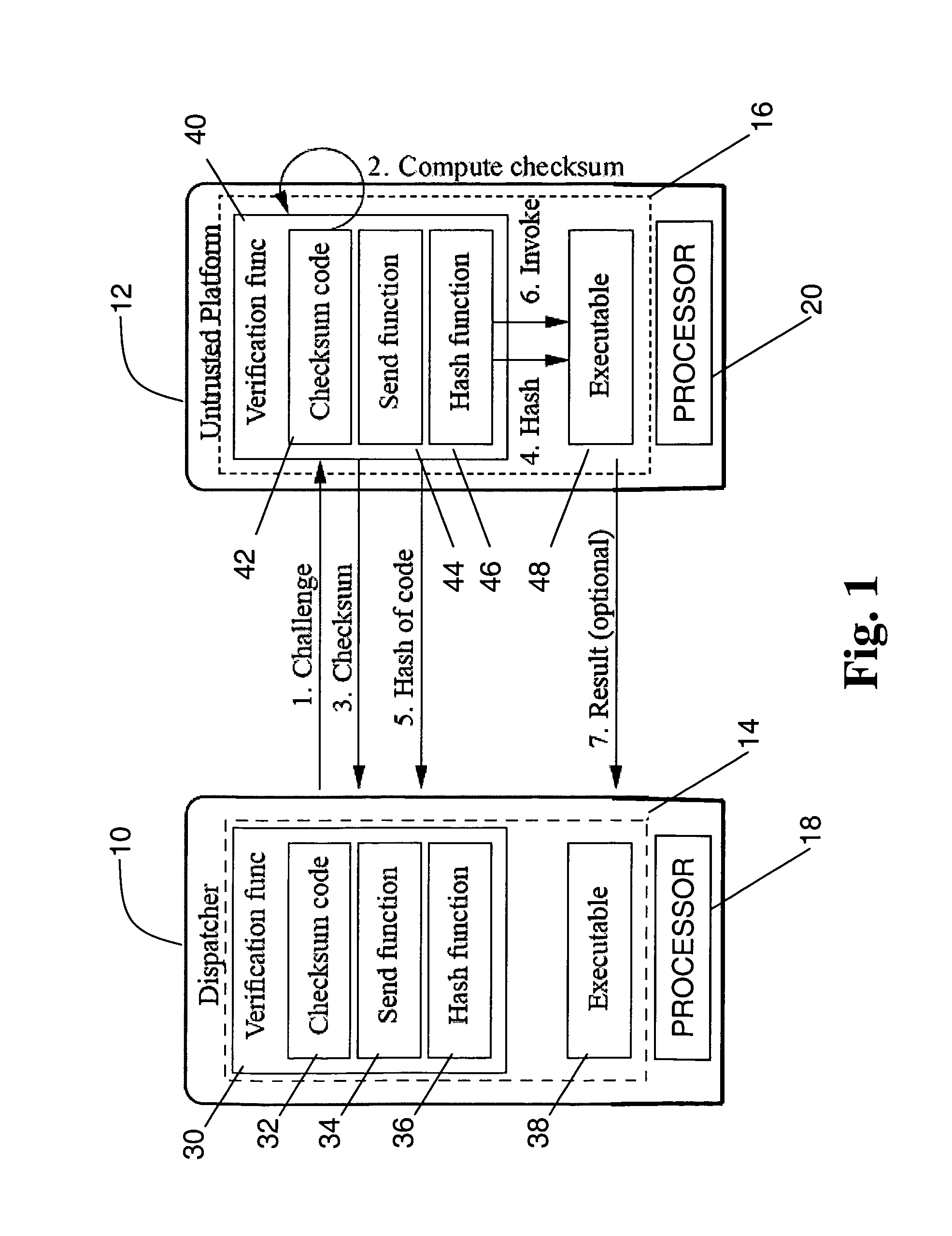
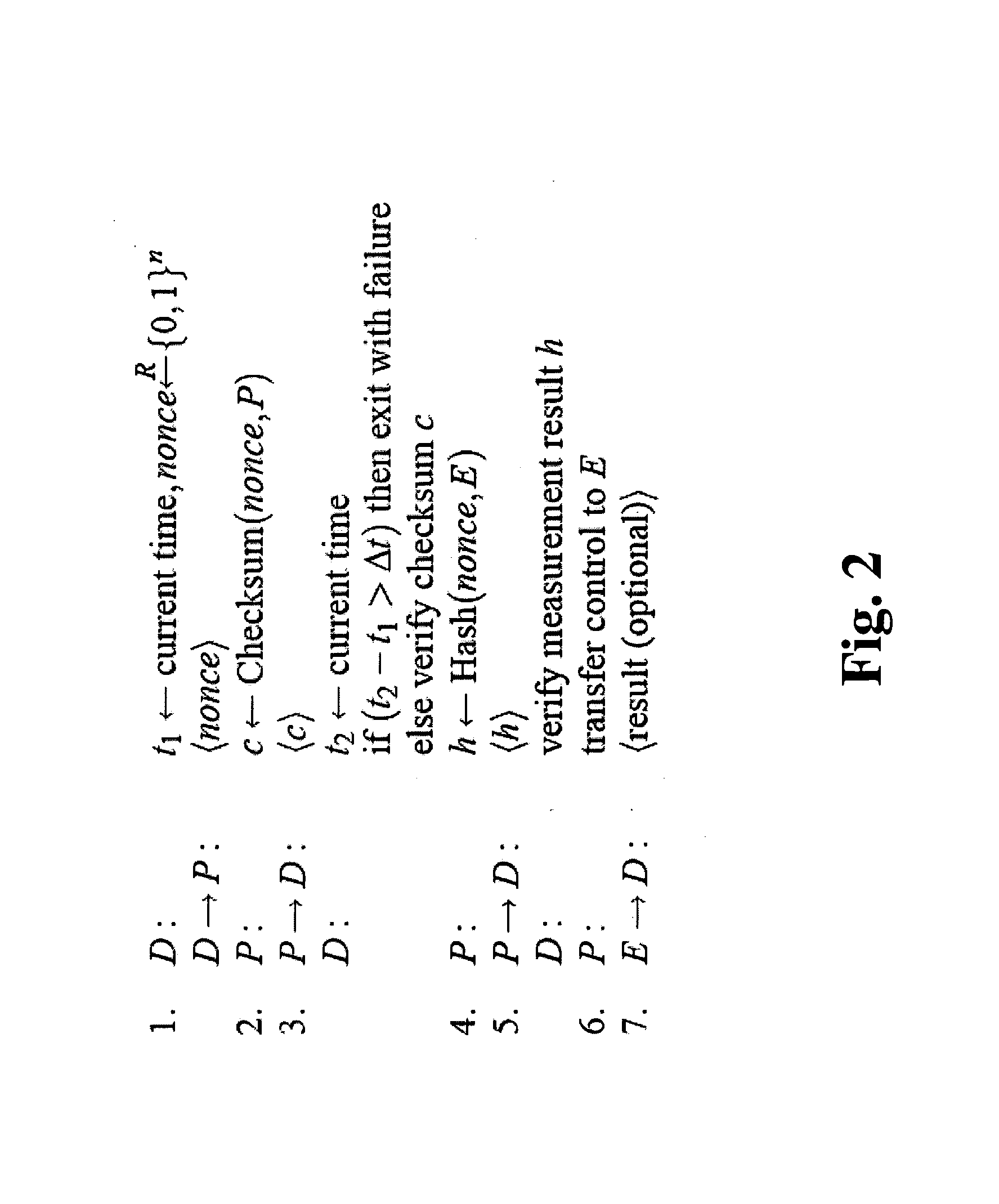
Verifying integrity and guaranteeing execution of code on untrusted computer platform
A method, system, and apparatus for verifying integrity and execution state of an untrusted computer. In one embodiment, the method includes placing a verification function in memory on the untrusted computer; invoking the verification function from a trusted computer; determining a checksum value over memory containing both the verification function and the execution state of a processor and hardware on the untrusted computer; sending the checksum value to the trusted computer; determining at the trusted computer whether the checksum value is correct; and determining at the trusted computer whether the checksum value is received within an expected time period.
Owner:IBM CORP +1
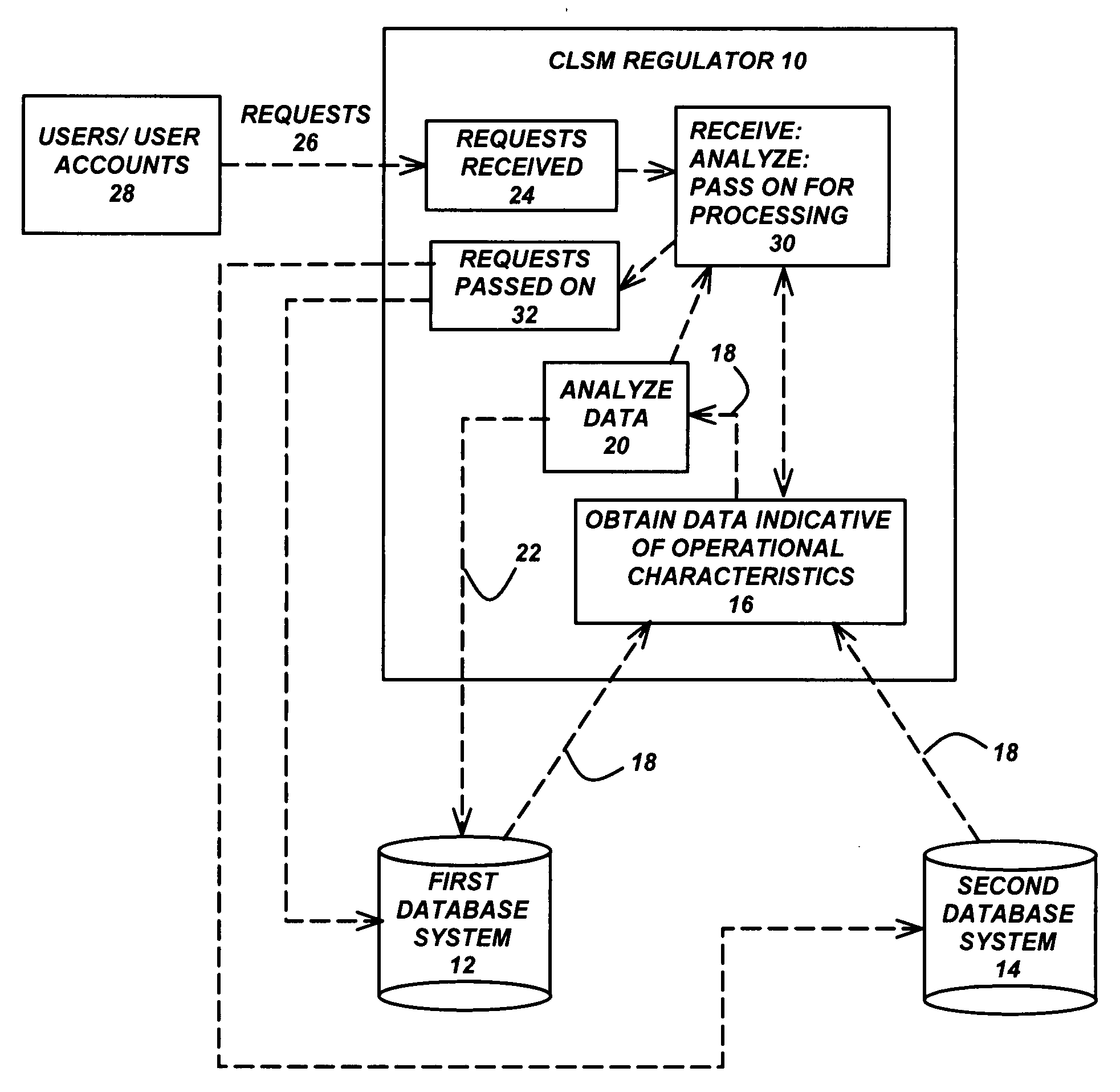
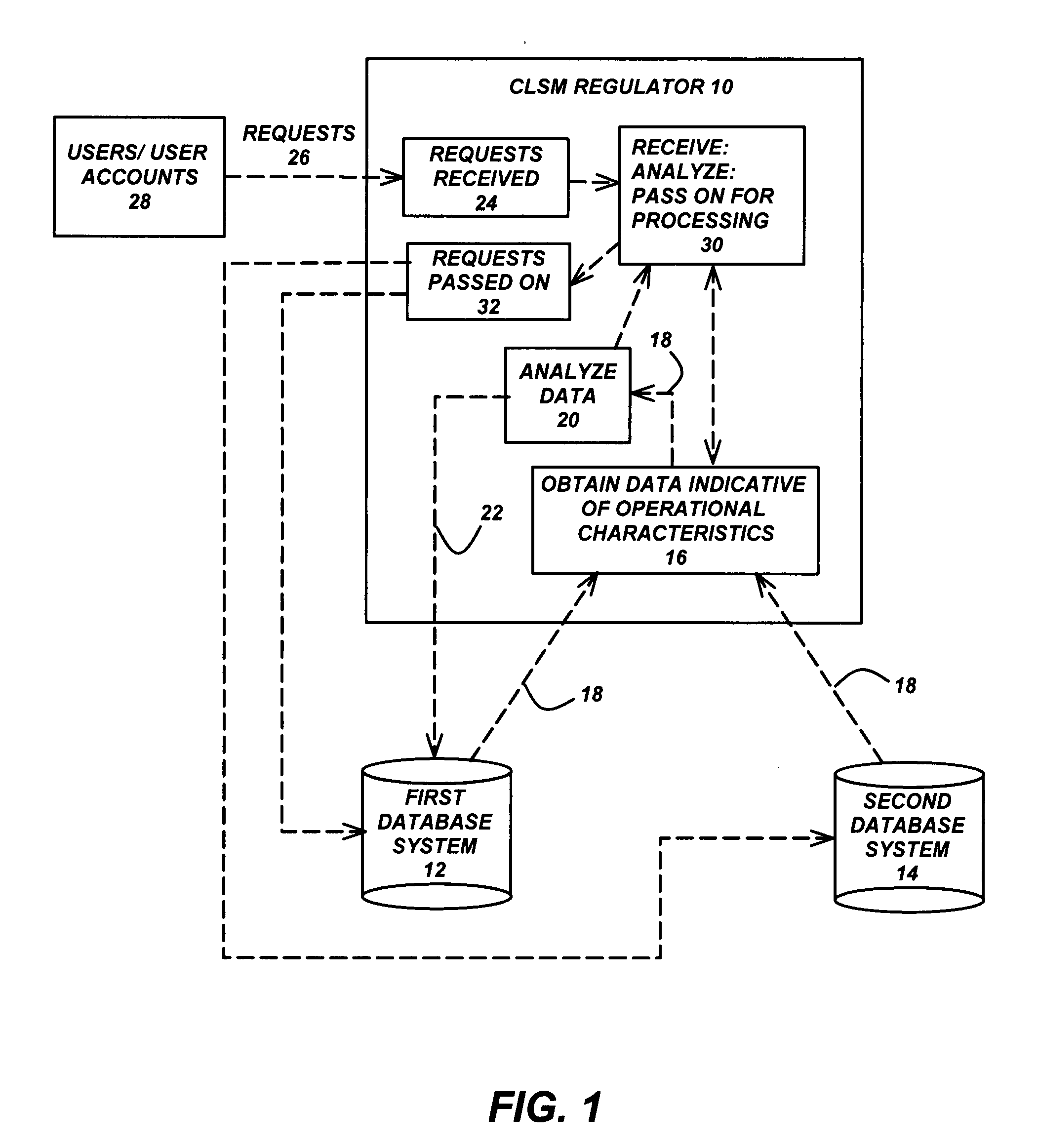
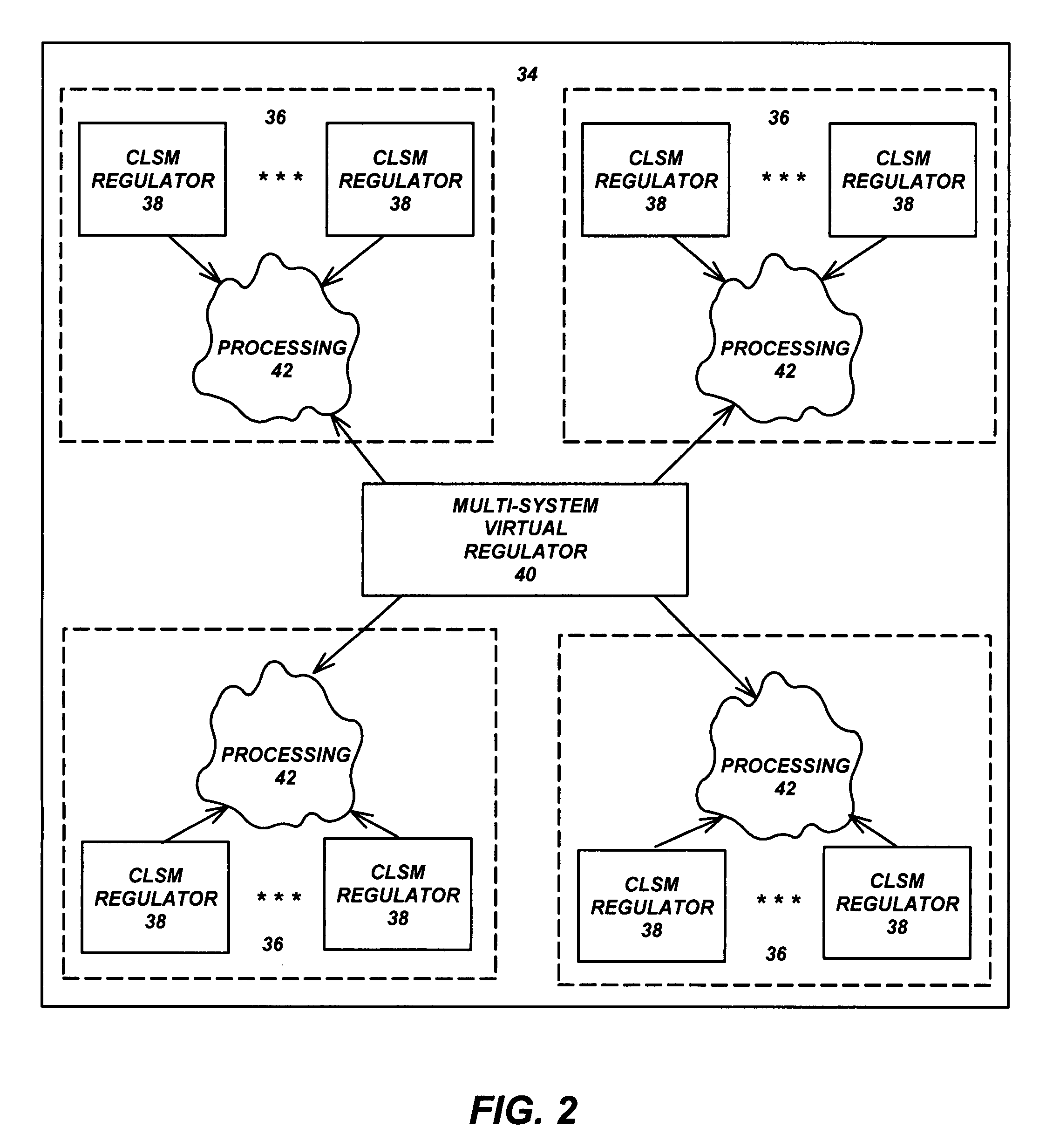
Virtual regulator for multi-databases systems
ActiveUS20080162583A1Data processing applicationsDigital data processing detailsSystems managementClosed loop
A system for managing a plurality of systems, includes a domain comprised of a plurality of systems, wherein the systems are managed by one or more closed-loop system management (CLSM) regulators. A virtual regulator manages operational characteristics of the domain and the plurality of systems, by communicating with the CLSM regulators to monitor the systems' states, events and conditions within the domain and to adjust the systems' operational characteristics in response to the systems' states, events and conditions.
Owner:TERADATA US
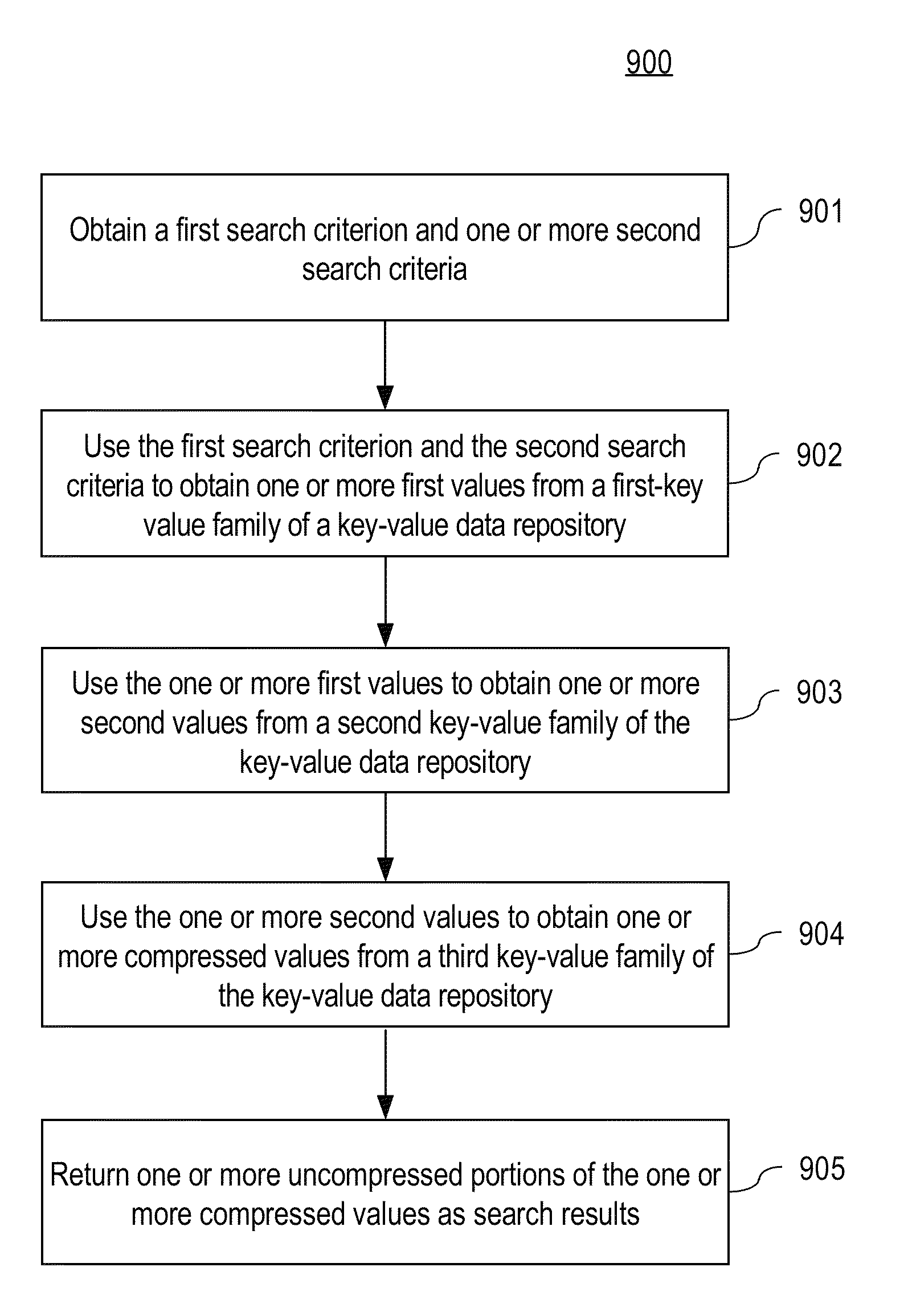
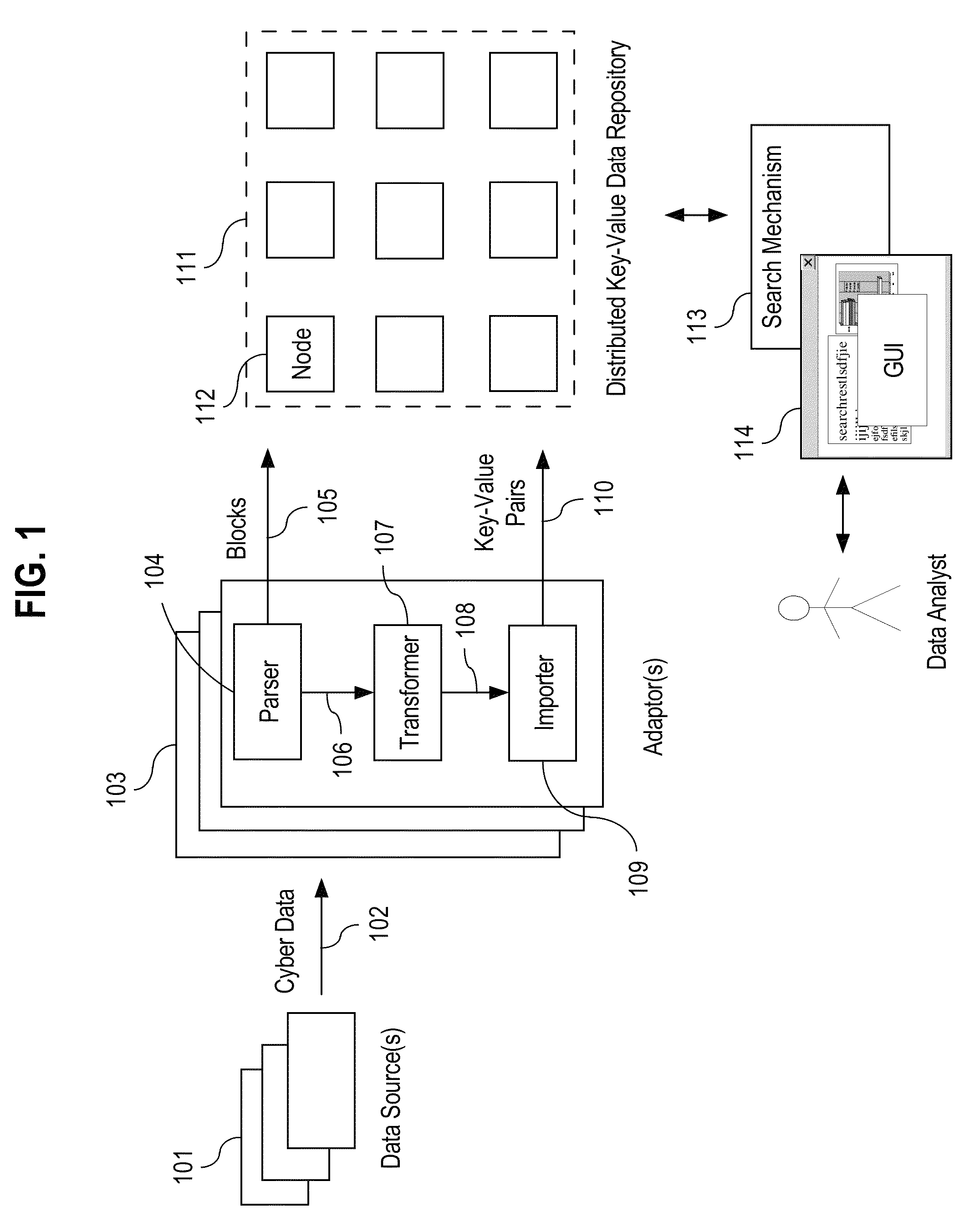
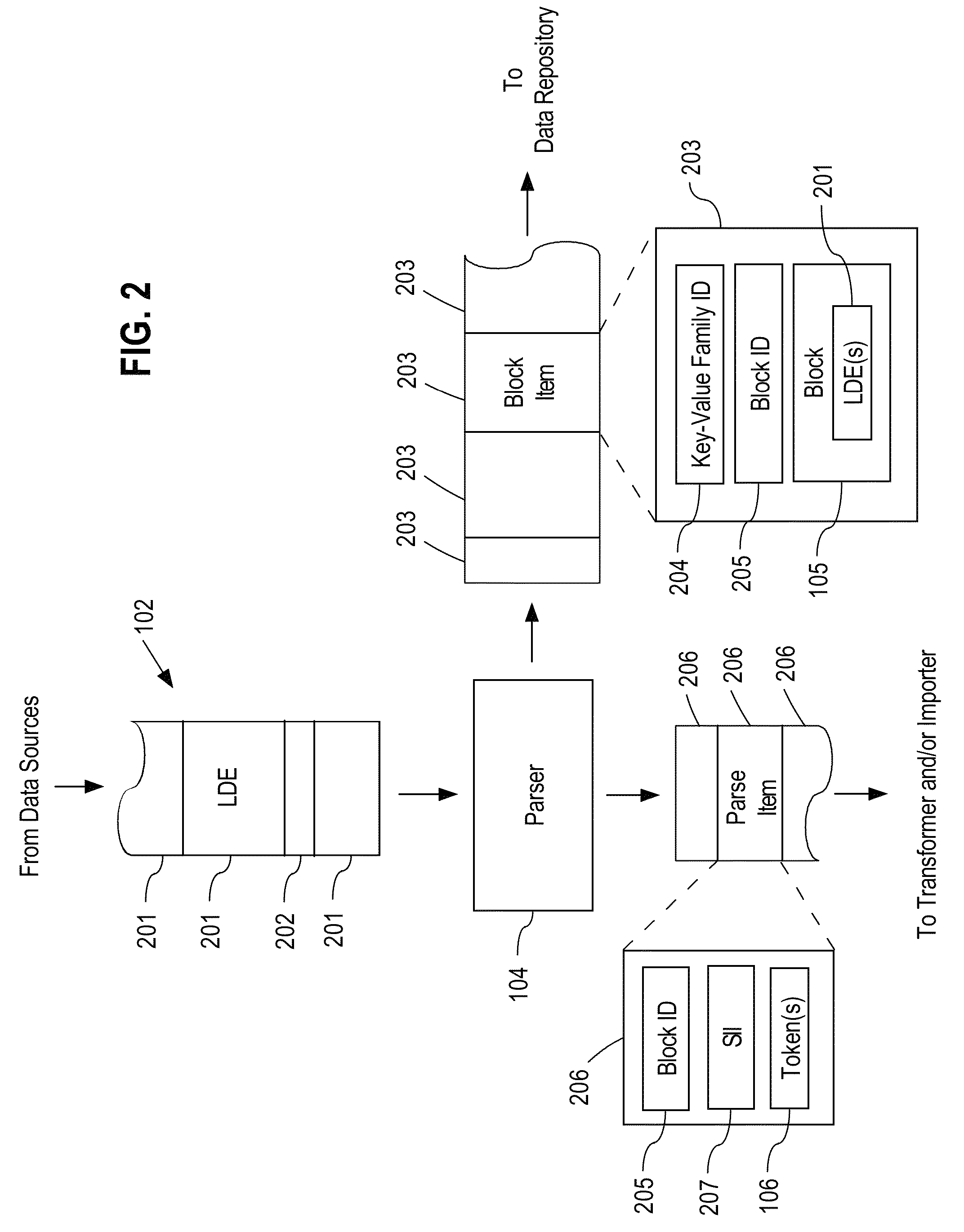
System and method for investigating large amounts of data
A data analysis system is proposed for providing fine-grained low latency access to high volume input data from possibly multiple heterogeneous input data sources. The input data is parsed, optionally transformed, indexed, and stored in a horizontally-scalable key-value data repository where it may be accessed using low latency searches. The input data may be compressed into blocks before being stored to minimize storage requirements. The results of searches present input data in its original form. The input data may include access logs, call data records (CDRs), e-mail messages, etc. The system allows a data analyst to efficiently identify information of interest in a very large dynamic data set up to multiple petabytes in size. Once information of interest has been identified, that subset of the large data set can be imported into a dedicated or specialized data analysis system for an additional in-depth investigation and contextual analysis.
Owner:PALANTIR TECHNOLOGIES
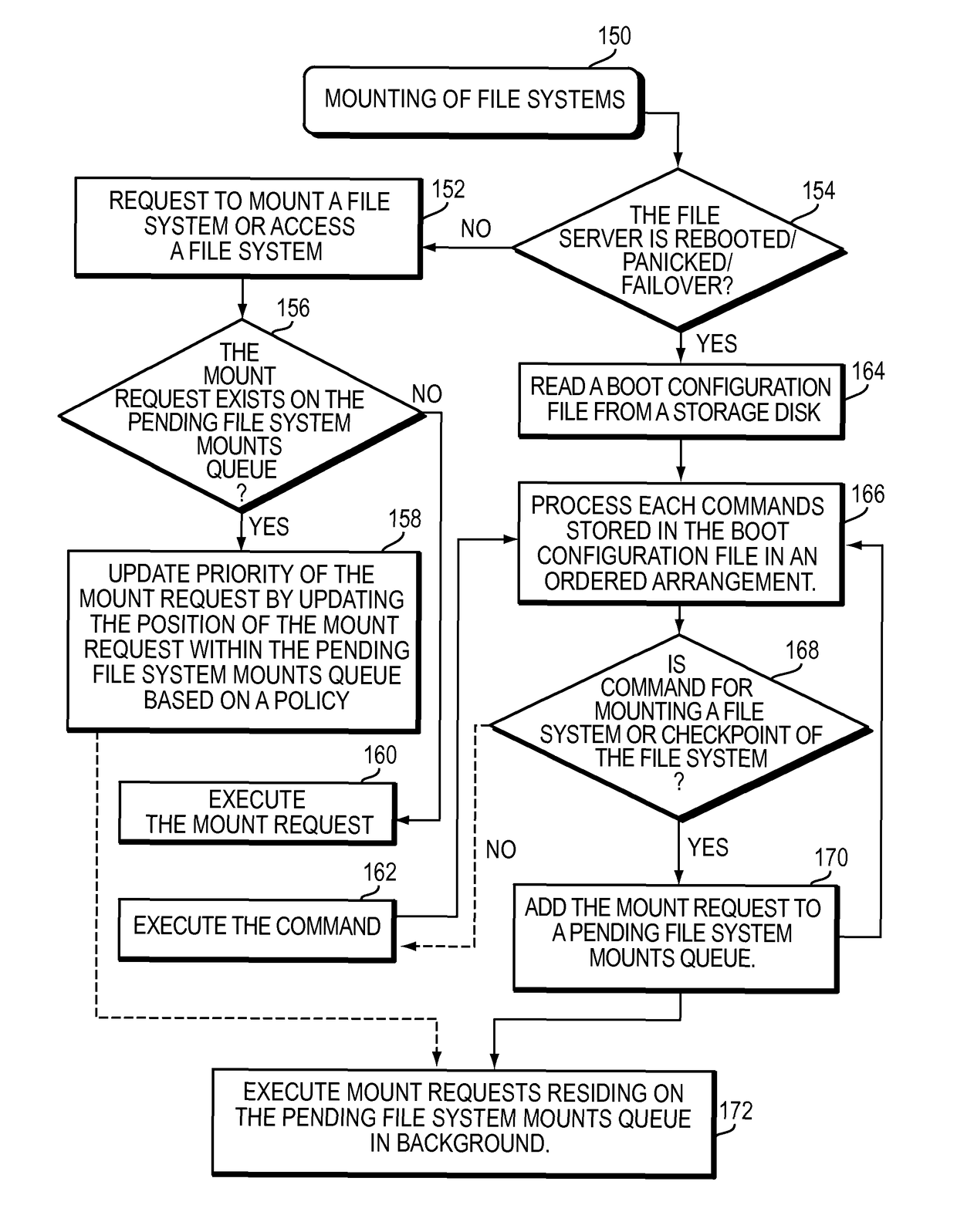
Managing mounting of file systems
A method is used in managing mounting of file systems. A request is received to mount a file system. The request to mount the file system is added in a pending file system mounts queue based on a policy. The file system is mounted in background. Access to the file system is provided before mounting the file system.
Owner:EMC IP HLDG CO LLC
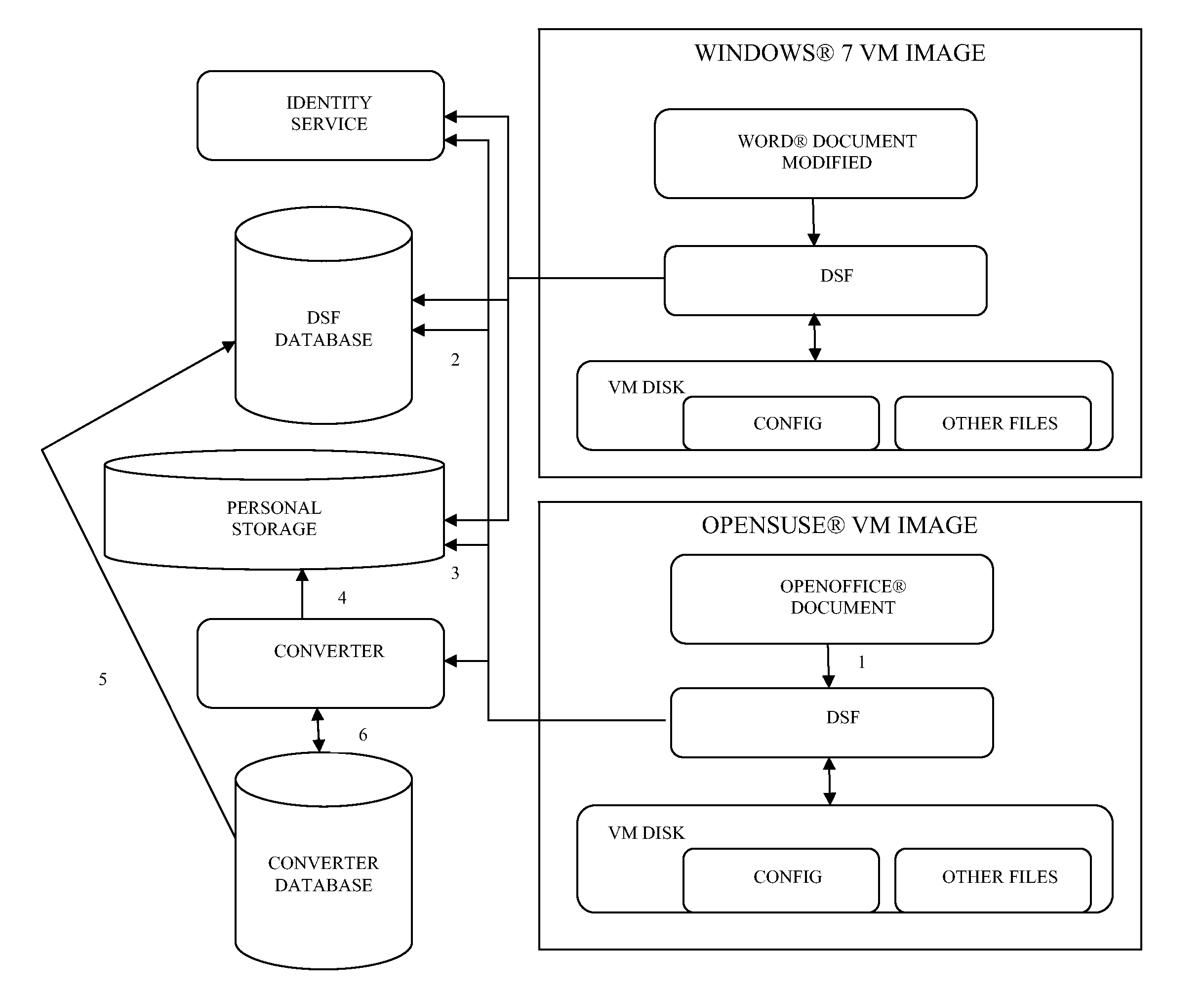
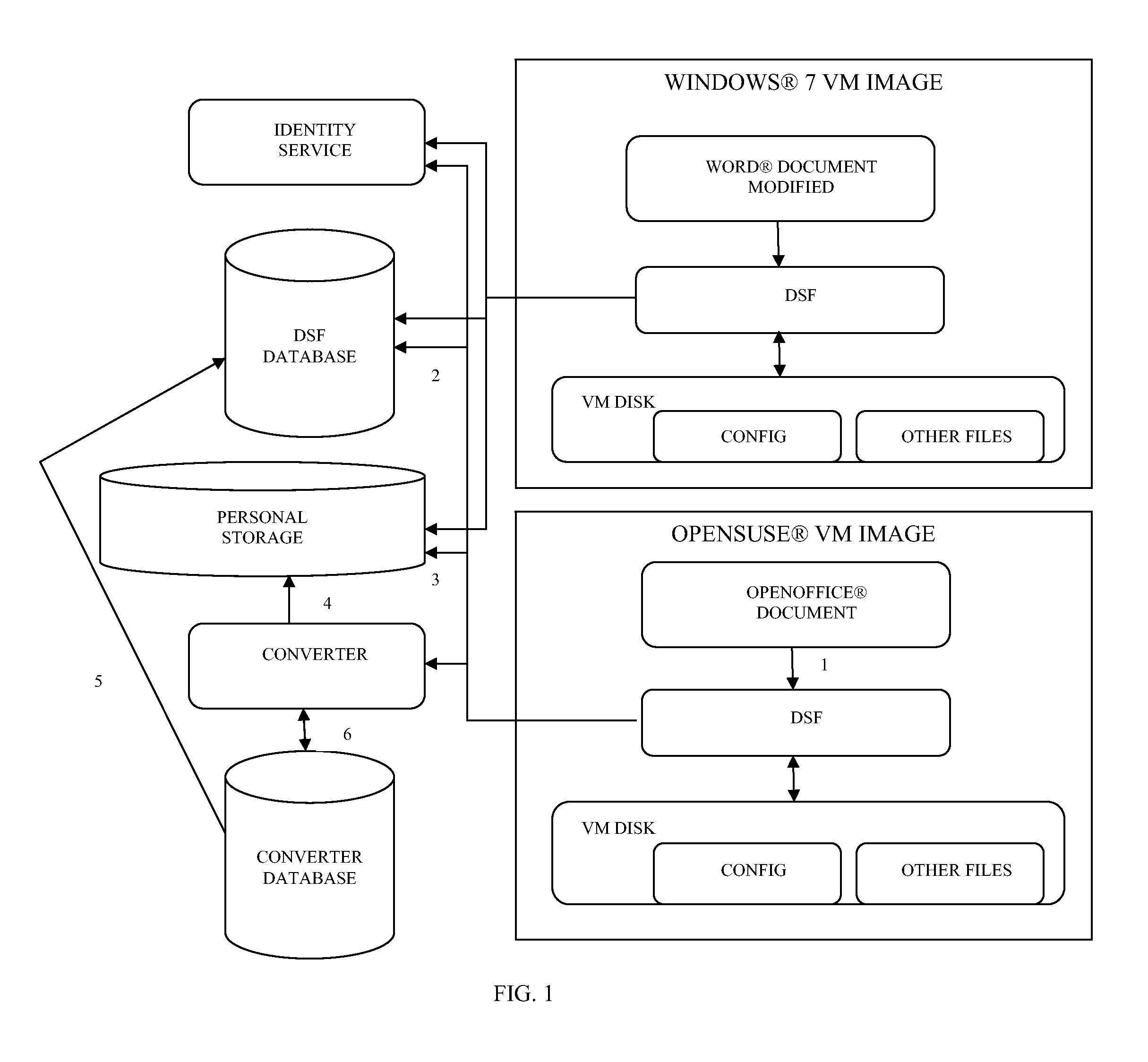
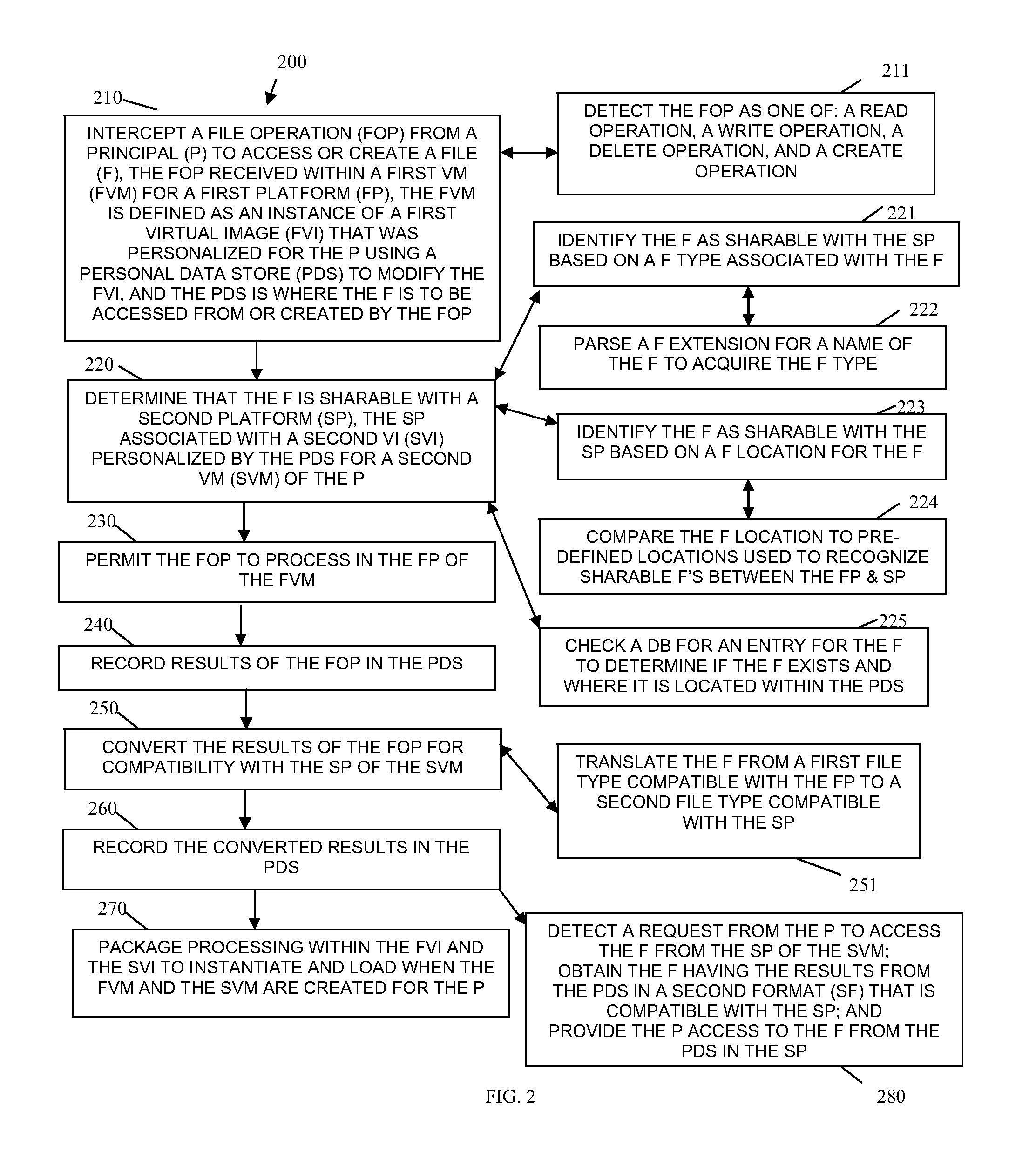
File mapping and converting for dynamic disk personalization for multiple platforms
ActiveUS20110313982A1Digital data processing detailsSoftware simulation/interpretation/emulationPersonalizationMultiple platform
File mapping and converting for dynamic disk personalization for multiple platforms are provided. A volatile file operation is detected in a first platform. The file supported by the first platform. A determination is made that the file is sharable with a second platform. The volatile operation is performed on the file in the first platform and the modified file is converted to a second file supported by the second platform. The modified file and second file are stored in a personalized disk for a user. The personalized disk is used to modify base images for VMs of the user when the user accesses the first platform or second platform. The modified file is available within the first platform and the second file is available within the second platform.
Owner:MICRO FOCUS SOFTWARE INC
File merging method and device
ActiveCN103593436ASmall granularityImprove read performanceSpecial data processing applicationsFile system functionsCluster systemsDatabase
The embodiment of the invention provides a file merging method and device. The file merging method comprises the steps of carrying out partitioning on sections in the charge of nodes in a cluster system according to key value information of user data, determining that each node meets a first triggering condition, reading at least two first files from disks of the nodes to caches corresponding to the nodes, respectively determining the target partition which each key value belongs to according to the key values of the data, corresponding to users, stored in the first files, merging the data with the same key value, and storing the merged data corresponding to the key values into the corresponding target partitions. Partitioning is carried out on the sections in the nodes, the data are merged once, and the data with the same key value are stored in the same partition. In the inquiry process, the partitions where the data are located are determined according to the key values, and then the files in the partitions are scanned. As the number of the files in each partition is small, data screening only needs to be carried out on fewer files, and therefore the read performance is improved.
Owner:HUAWEI TECH CO LTD
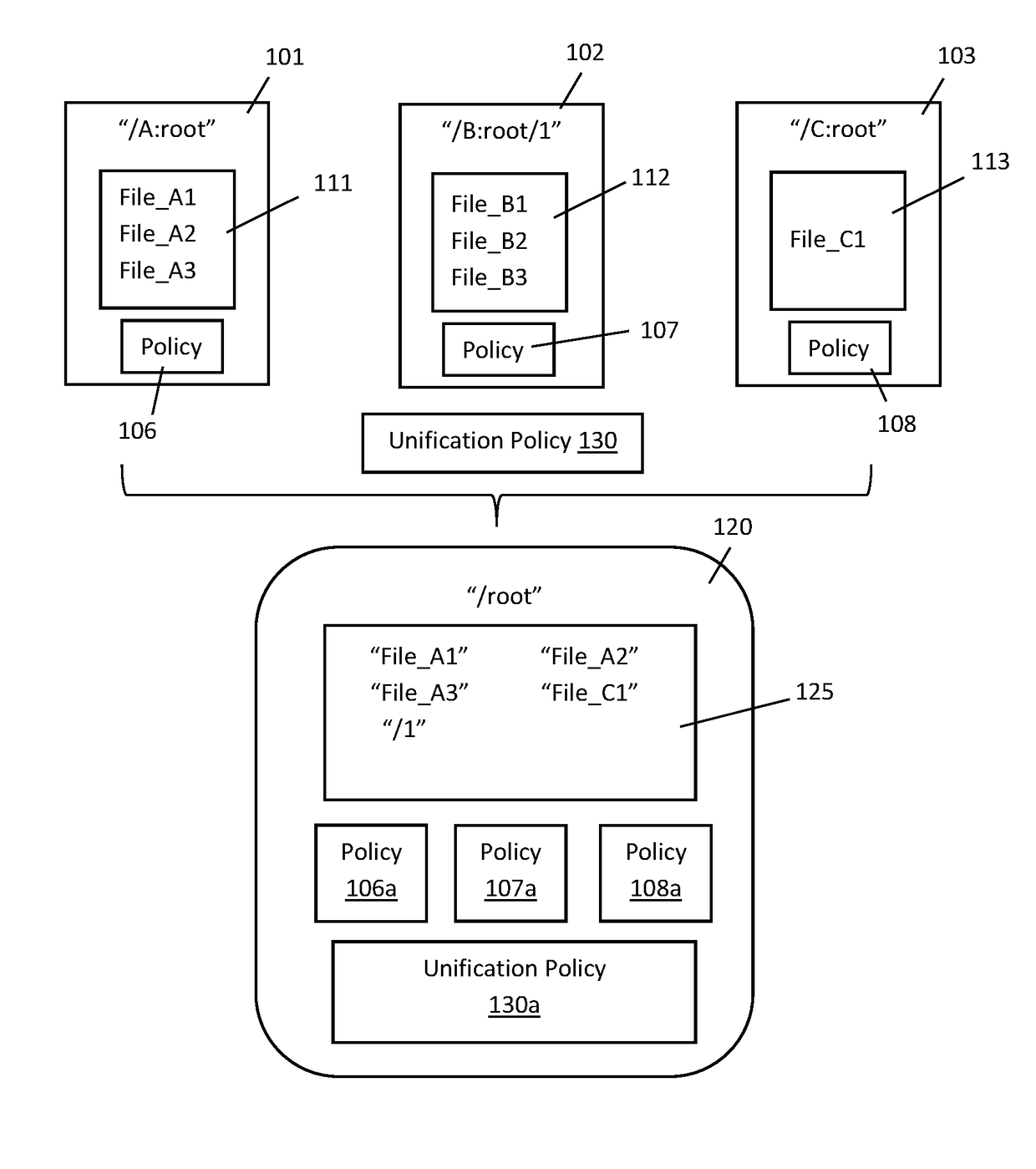
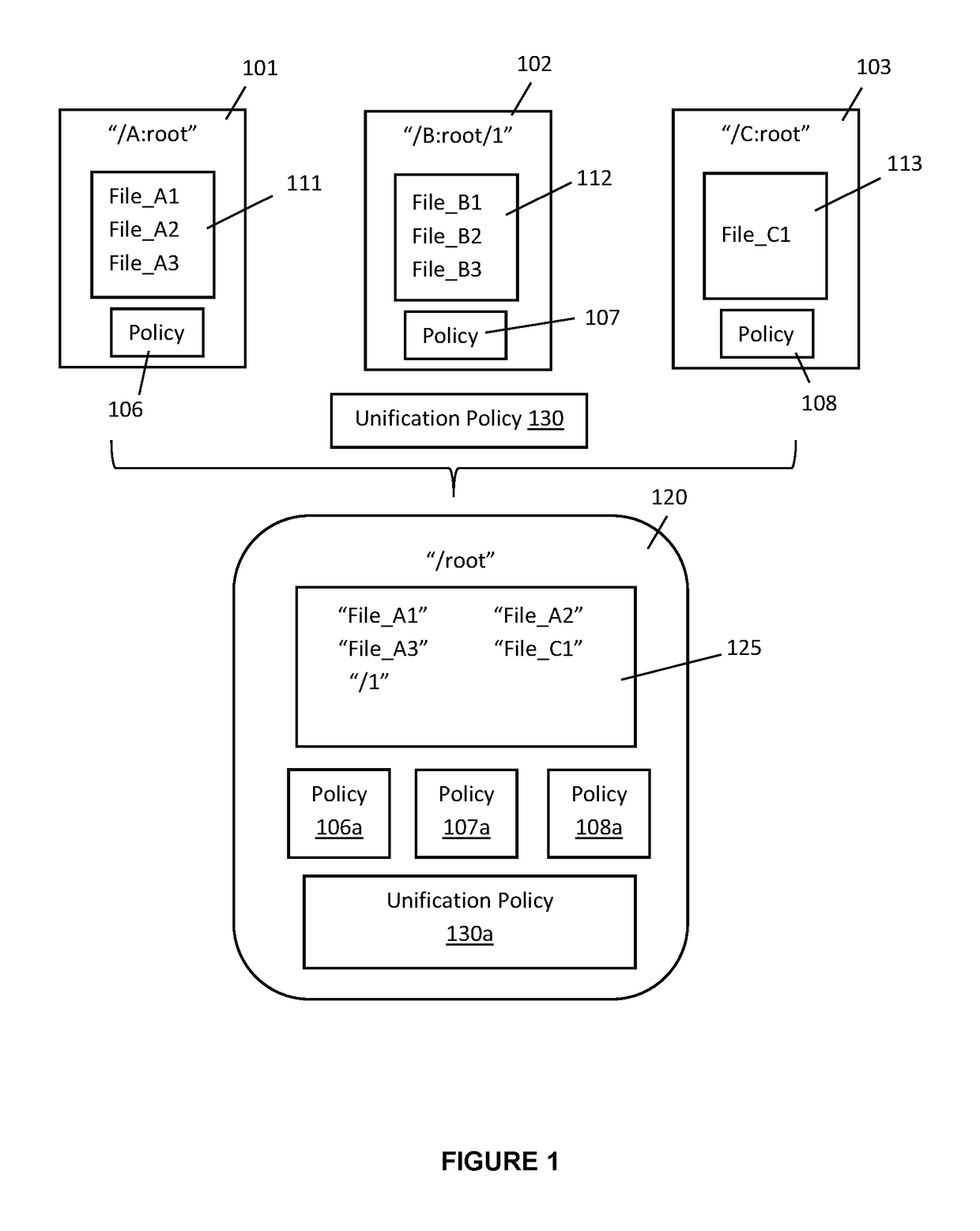
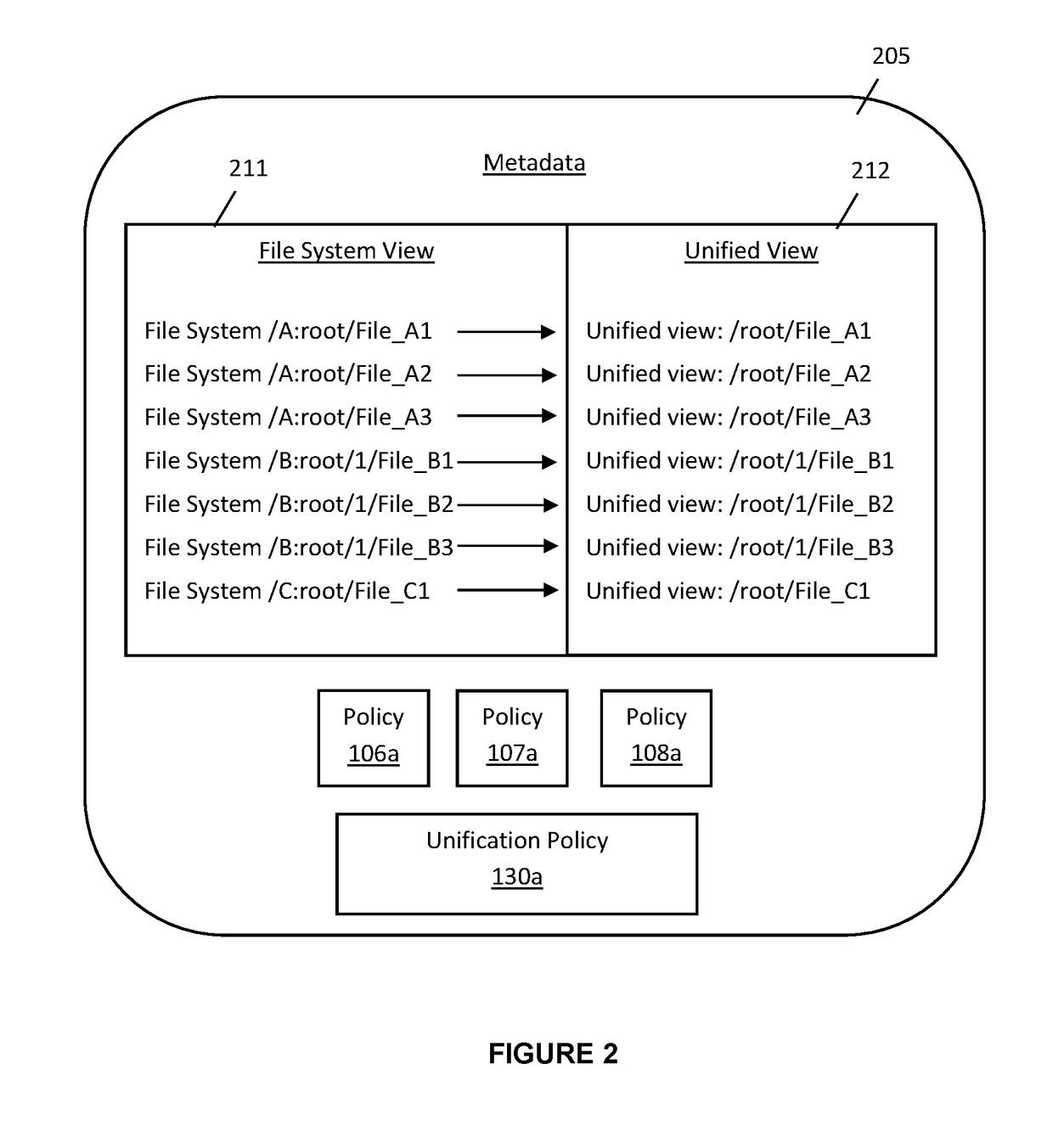
Policy aware unified file system
ActiveUS20180150640A1Improve securityDigital data protectionSpecial data processing applicationsFile systemRunning time
A system and method for operating a policy aware unification file system within a computer system that takes into account the security requirements of each file system as each file system is unified into the unified file system. As the application is compatible with existing run time policies of files and directories within each file system that is to be unified, the application supports the enforcement of security policies or requirements of each file and / or directory that has been unified into the unified file system.
Owner:HUAWEI INT +1
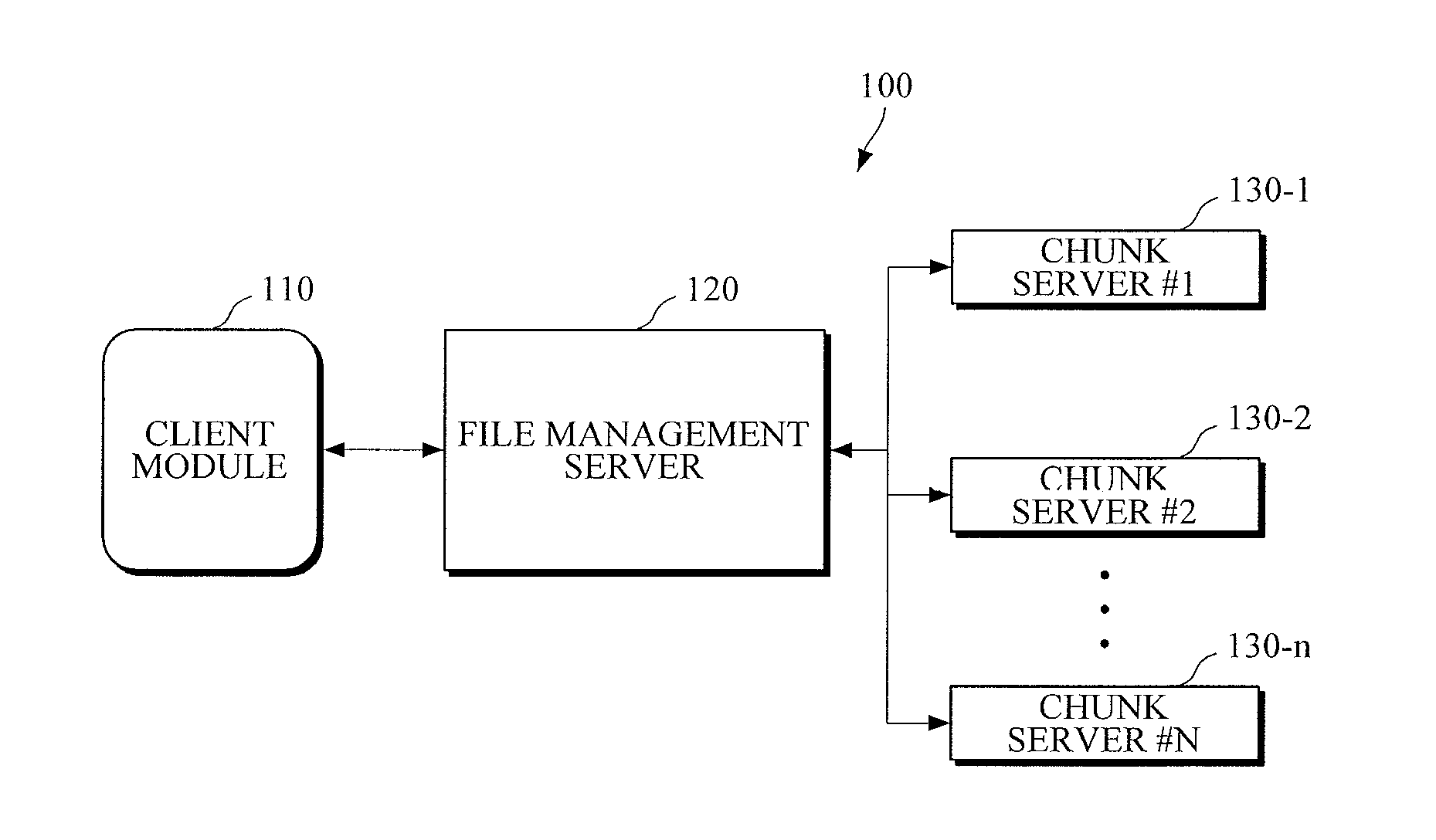
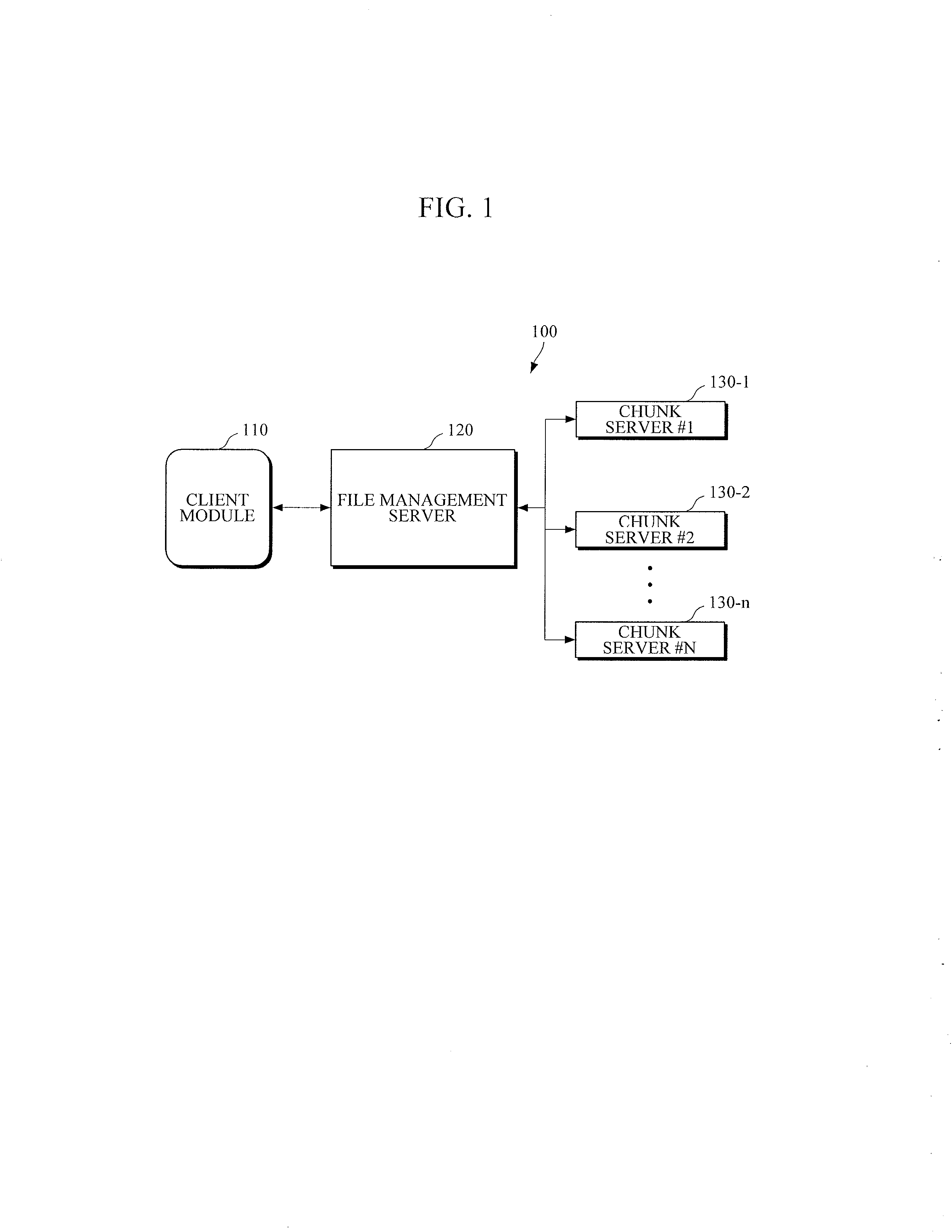
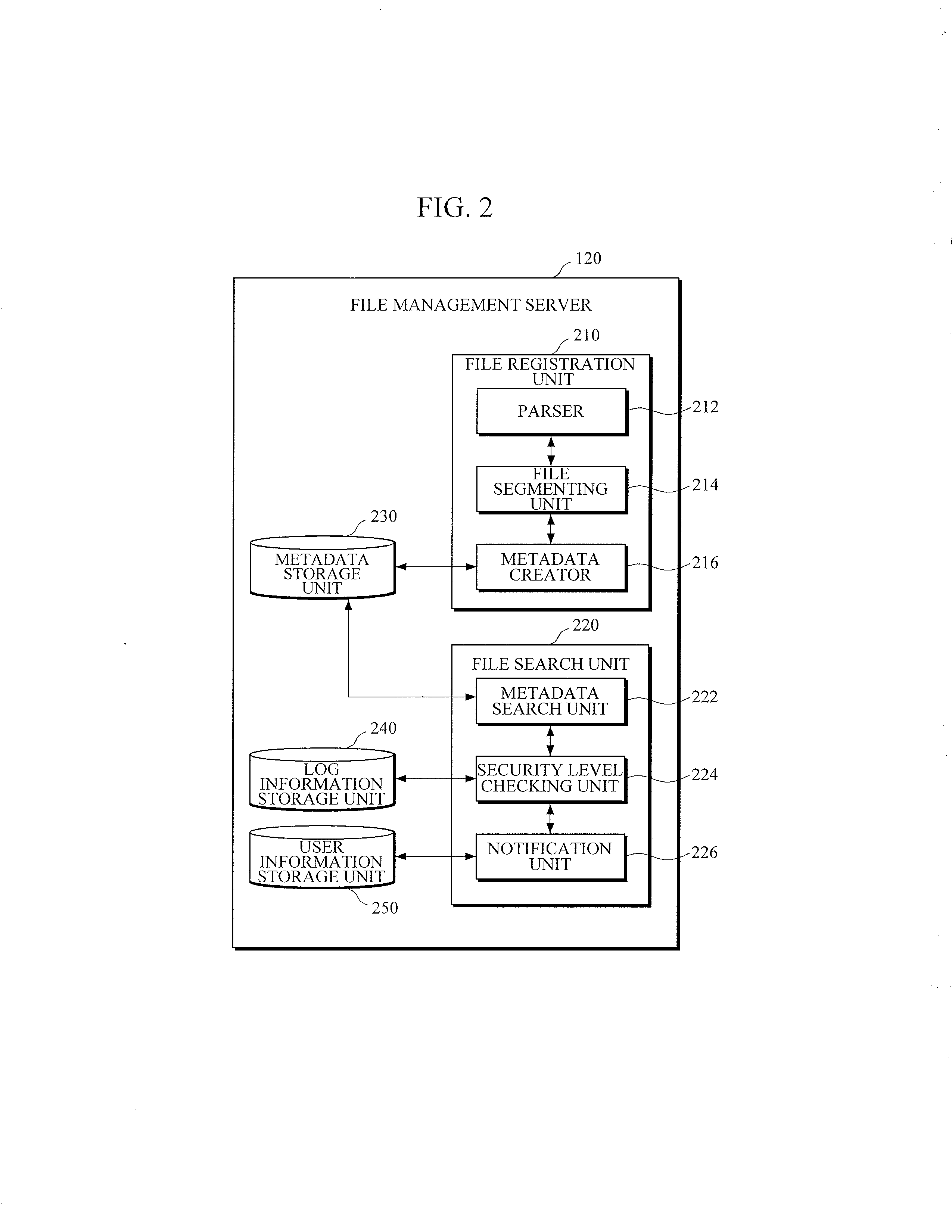
System and method for alerting leakage of personal information in cloud computing environment
InactiveUS20130179495A1Improve reliabilityMultiple digital computer combinationsDigital data authenticationClient-sideSecurity level
There are provided a file management server for ensuring security in a cloud computing environment, and a file management method thereof. The file management server includes: a file registration unit configured to store a file in a plurality of chunk servers, and to manage a security level of the file; and a file search unit configured to receive a file access request from a client module, to check a security level of a file corresponding to the file access request, to notify, if the security level of the file is equal to or higher than a predetermined security level, the file's owner that a request for accessing the file has been made.
Owner:ELECTRONICS & TELECOMM RES INST
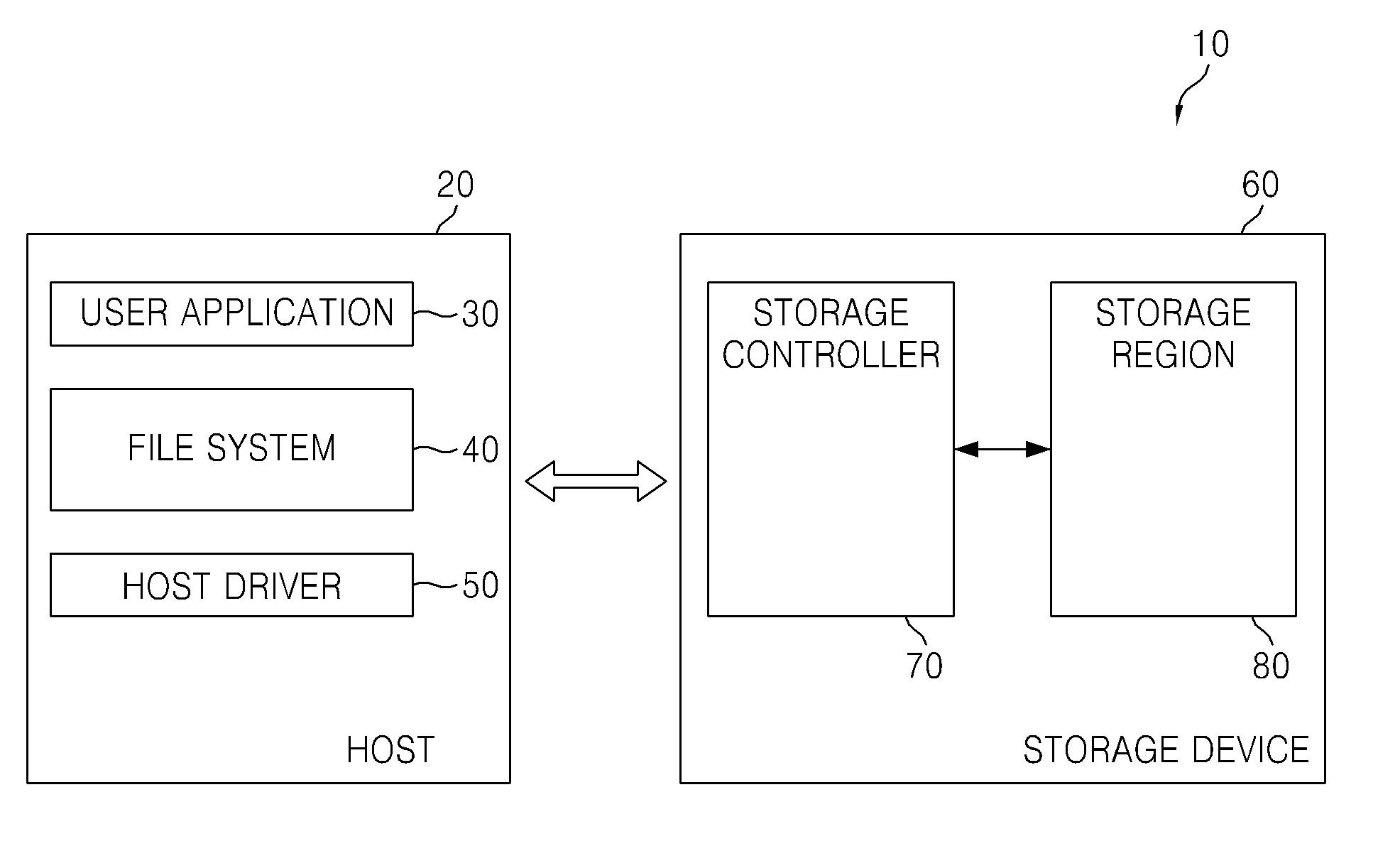
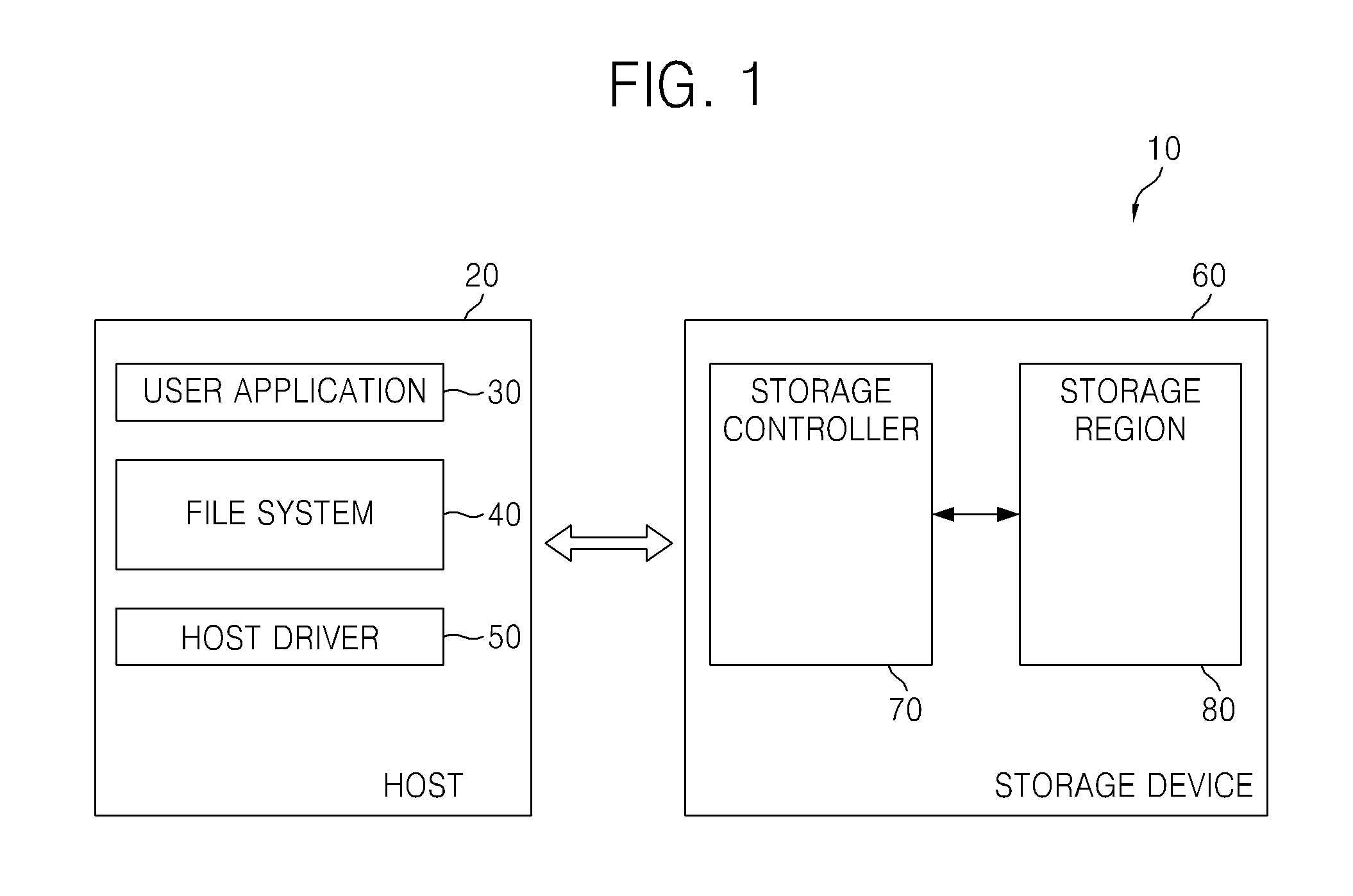
File system operating method and devices using the same
ActiveUS20120209893A1Special data processing applicationsFile system functionsFile systemData storing
A method of operating a file system in a host configured to store write data in a data storage device including a first region and a second region is disclosed, and includes; receiving a write data request for write data associated with a file, classifying the write data as hot data or cold data using file meta data for the file, and if the write data is classified as hot data, storing the write data in the first region, and otherwise if the write data is classified as cold data storing the write data in the second region.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and device for identifying and saving file to be downloaded and quickly searching for downloaded file through mobile terminal
ActiveCN104199897AImprove experienceImprove download efficiencyExecution for user interfacesFile system functionsDocument IdentifierDocument handling
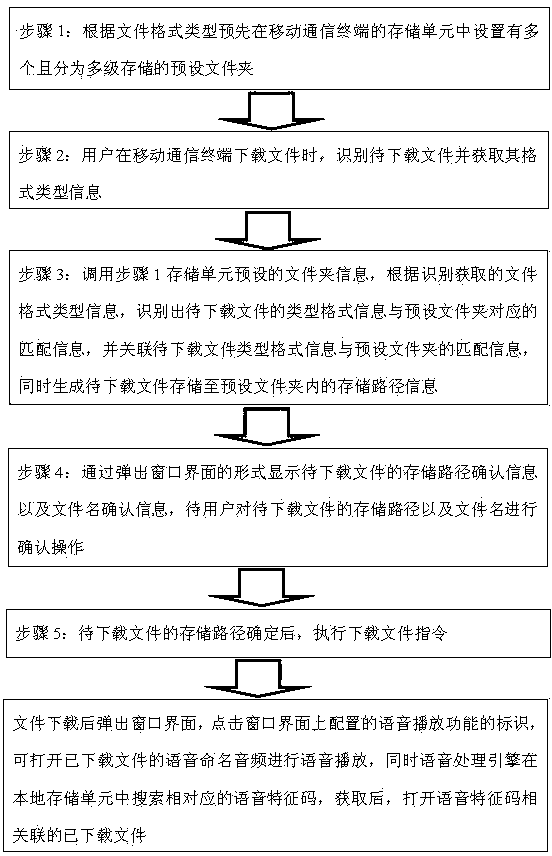
The invention discloses a method for identifying and saving a file to be downloaded and quickly searching for the downloaded file through a mobile terminal. The method comprises the steps that a preset folder is set in advance; in the downloading process of the file, the file to be downloaded is identified, and format type information of the file to be downloaded is obtained; the format type information of the file to be downloaded and matching information corresponding to the preset folder are judged and correlated to generate storage path information; storage path confirmation information and file name confirmation information are displayed, and a file downloading instruction is executed after the storage path confirmation information and the file name confirmation information are confirmed by a user; after the file is downloaded, a window interface is popped up, and then voice named audio of the downloaded file and the downloaded file can be opened. A device for identifying and saving the file to be downloaded and quickly searching for the downloaded file through the mobile terminal comprises a storage unit, a file identifying unit, a file judgment unit, a file processing unit, a path display unit, a path providing unit, a voice analysis engine and a voice processing engine. The method and device can facilitate downloading of the file and search for the downloaded file by the user.
Owner:宁波高智创新科技开发有限公司
Event identification
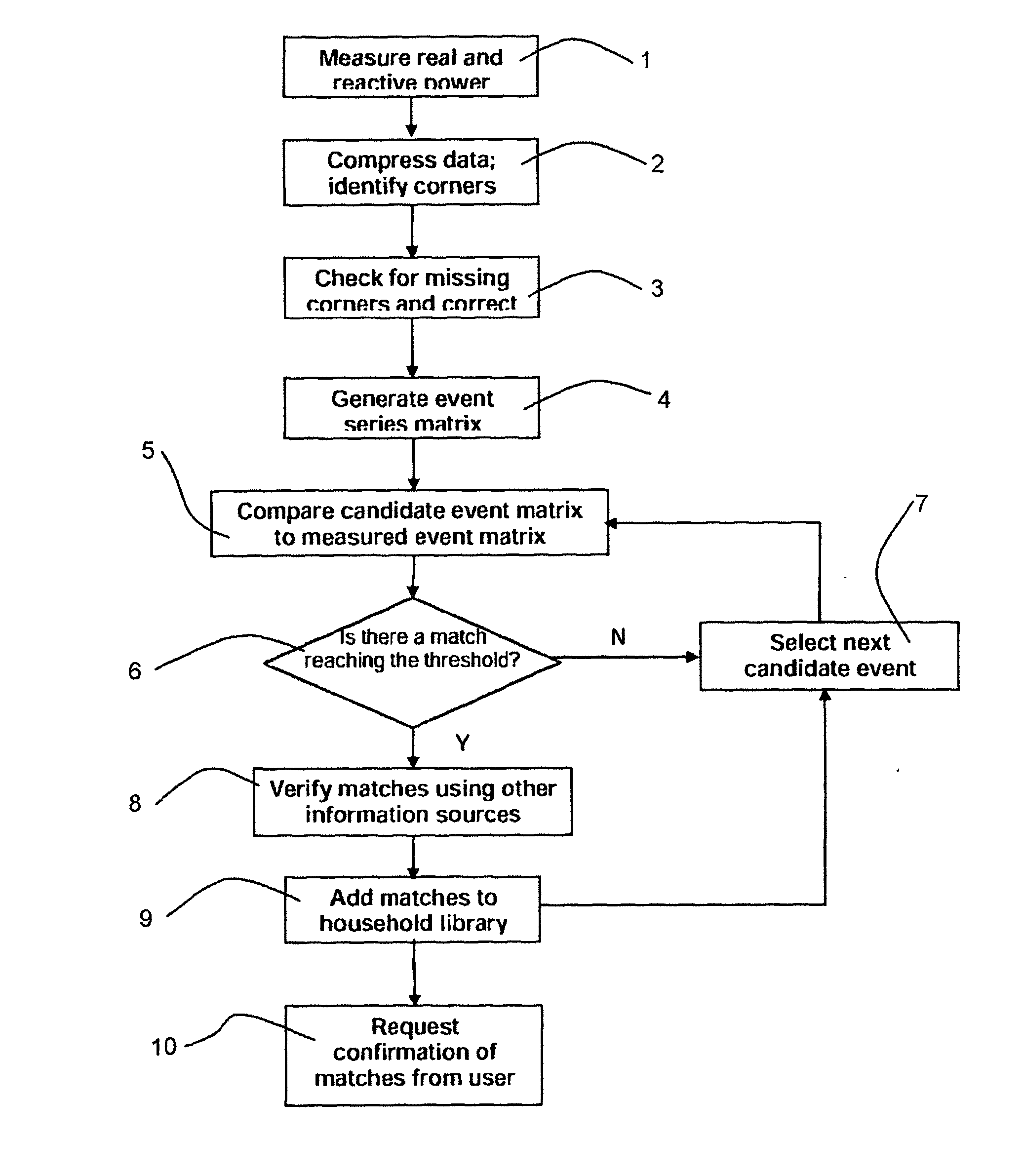
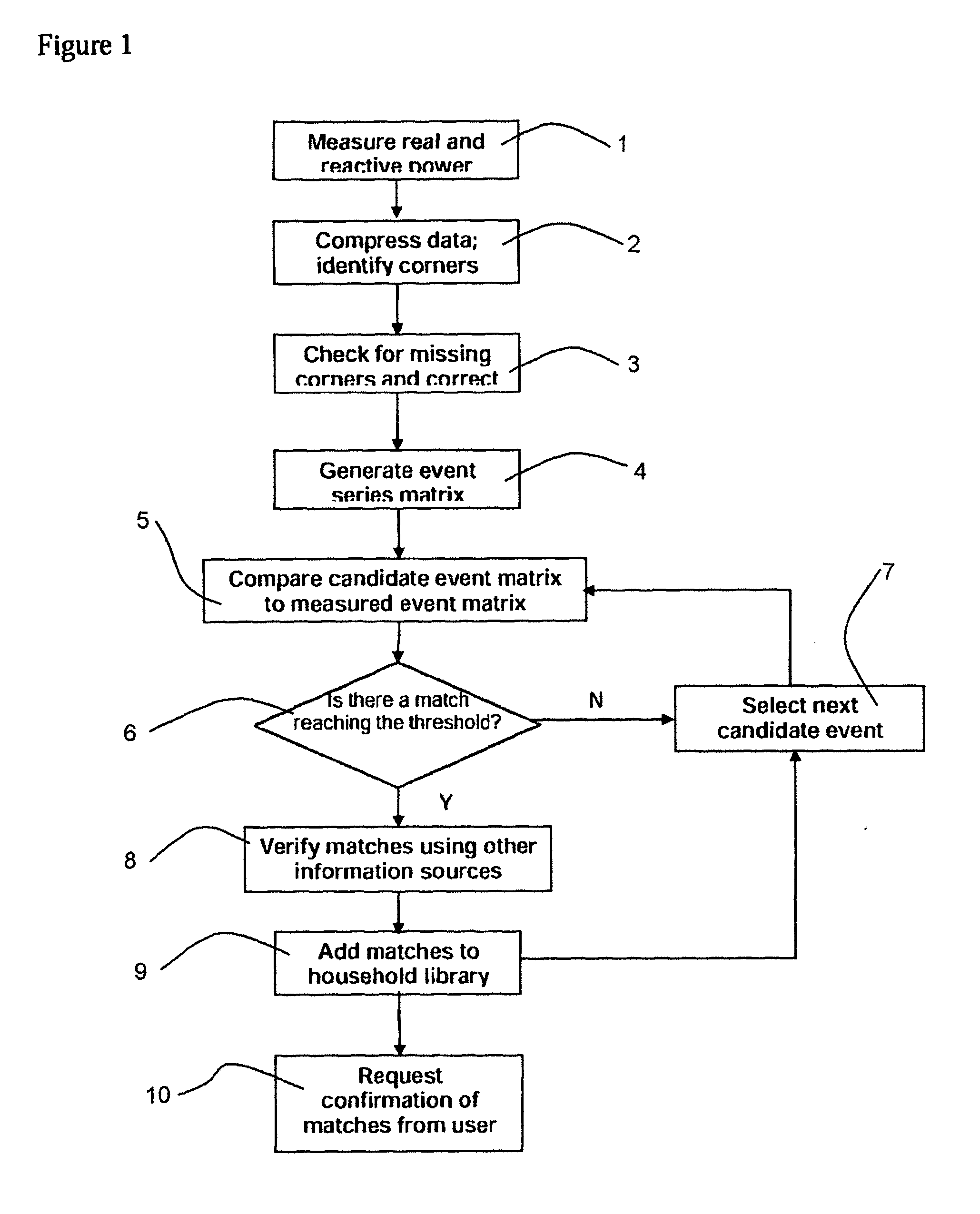
InactiveUS20130103656A1Digital data processing detailsRelational databasesContinuous measurementMeasurement point
A method of identifying an event associated with consumption of a utility comprising the steps of: generating a utility consumption profile from utility consumption data, the utility consumption data comprising a plurality of utility consumption values measured at a corresponding plurality of measurement points; wherein generating the utility consumption profile comprises the step of determining a gradient of rate of change of utility consumption between consecutive measurement points; identifying measurement points at which a change in gradient exceeds a predetermined threshold; and storing in the utility consumption profile the utility consumption value at measurement points where the threshold is exceeded; and identifying an event within the utility consumption profile that matches the profile of an event stored in a database of utility consumption profiles.
Owner:ONZO
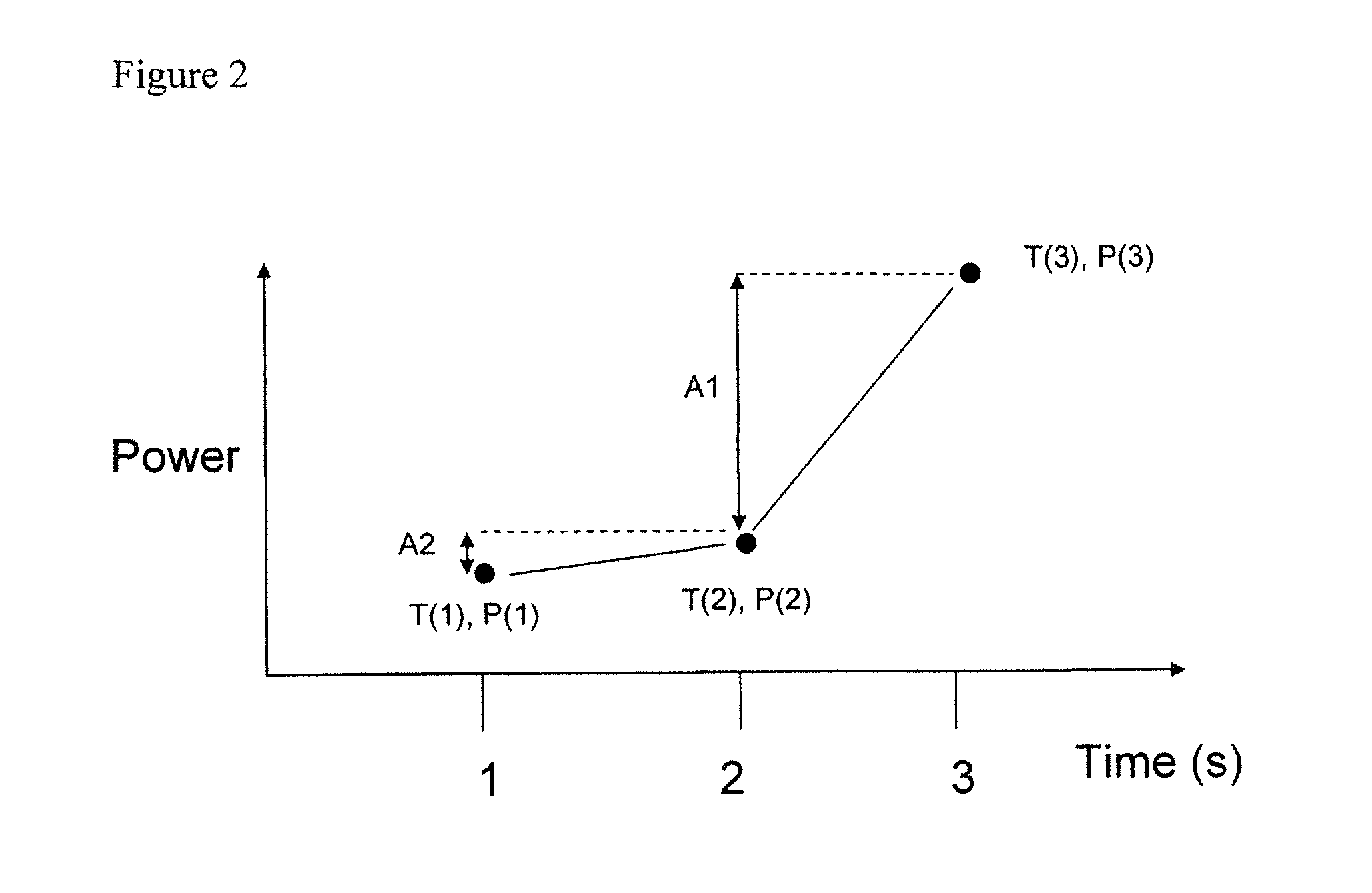
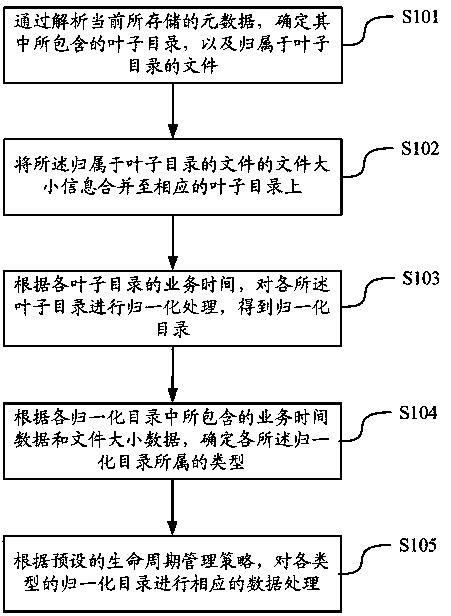
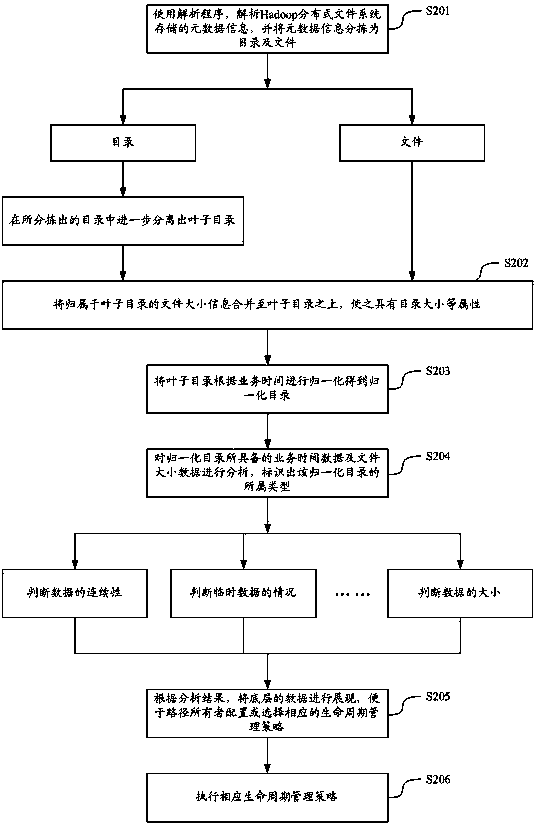
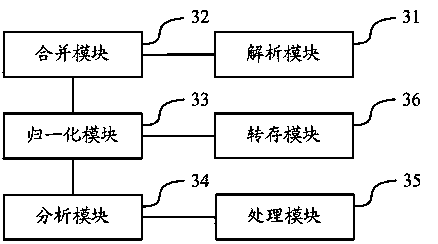
Life cycle management method and equipment for data file of Hadoop distributed file system
ActiveCN103778148AImprove processing efficiencySpecial data processing applicationsFile system functionsData fileFile size
The invention discloses a life cycle management method and life cycle management equipment for data files of a Hadoop distributed file system. The life cycle management method includes: separating leaf directories from the current metadata, giving the file size attributes of the corresponding files to the leaf directories, normalizing according to the service time of each leaf directory to obtain a normalized directory, determining the type of each normalized directory according to the service time data and the file size data in each normalized directory, and correspondingly processing the data of each type of normalized directory according to preset life cycle management strategies so as to lead the service time concept of the data to a data storage and management process. The life cycle management method and the life cycle management equipment solve the problem of big data processing load due to the fact that the existing life cycle management needs to mark data in large scale in terms of different types and levels of data, effectively use the time attributes of the data files to improve the data processing efficiency, and finally realize to mark the attributes of the data files of the distributed file system and manage the life cycles of the data files of the distributed file system.
Owner:TAOBAO CHINA SOFTWARE
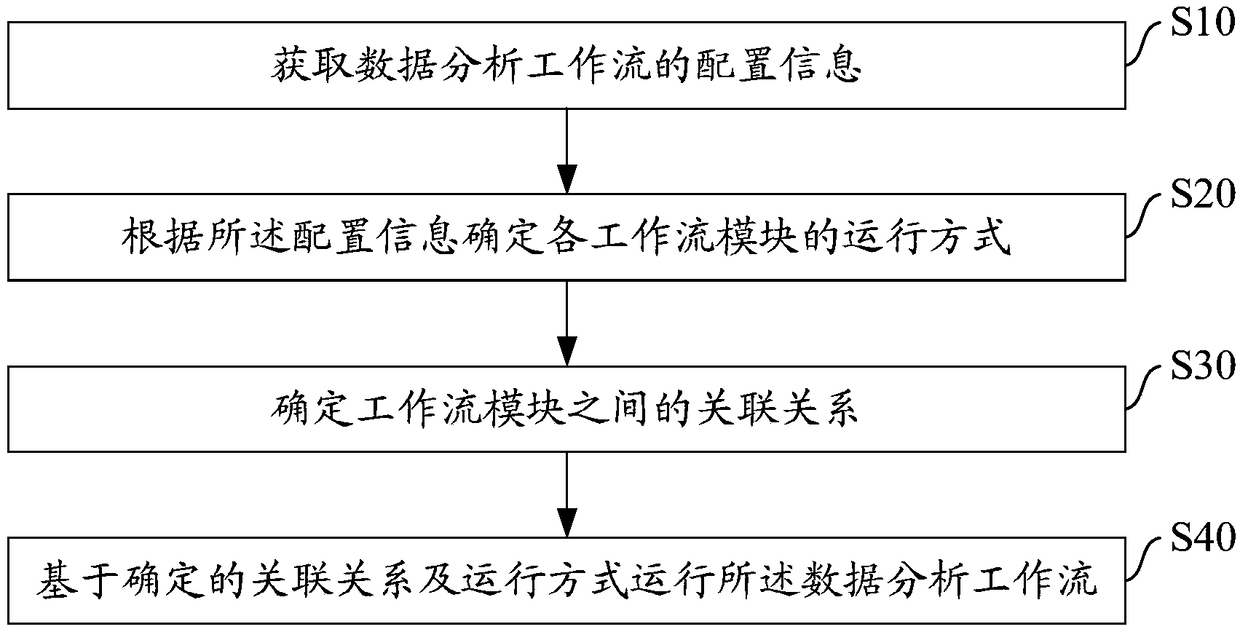
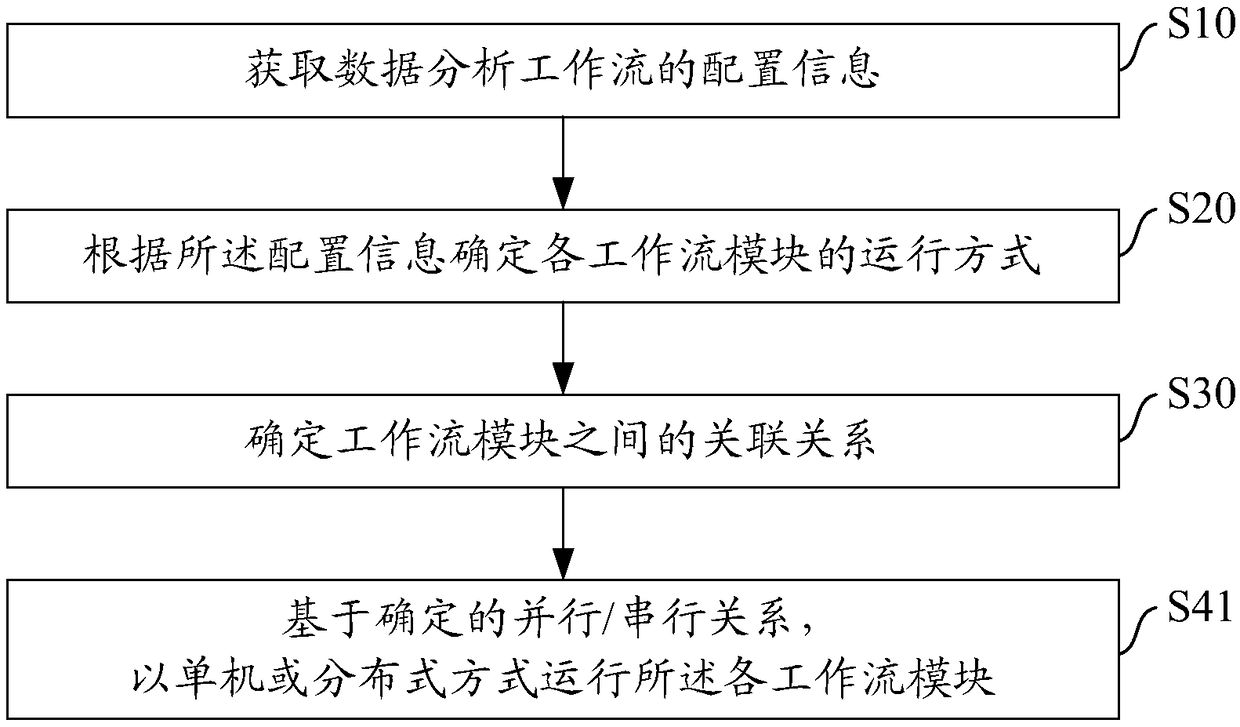
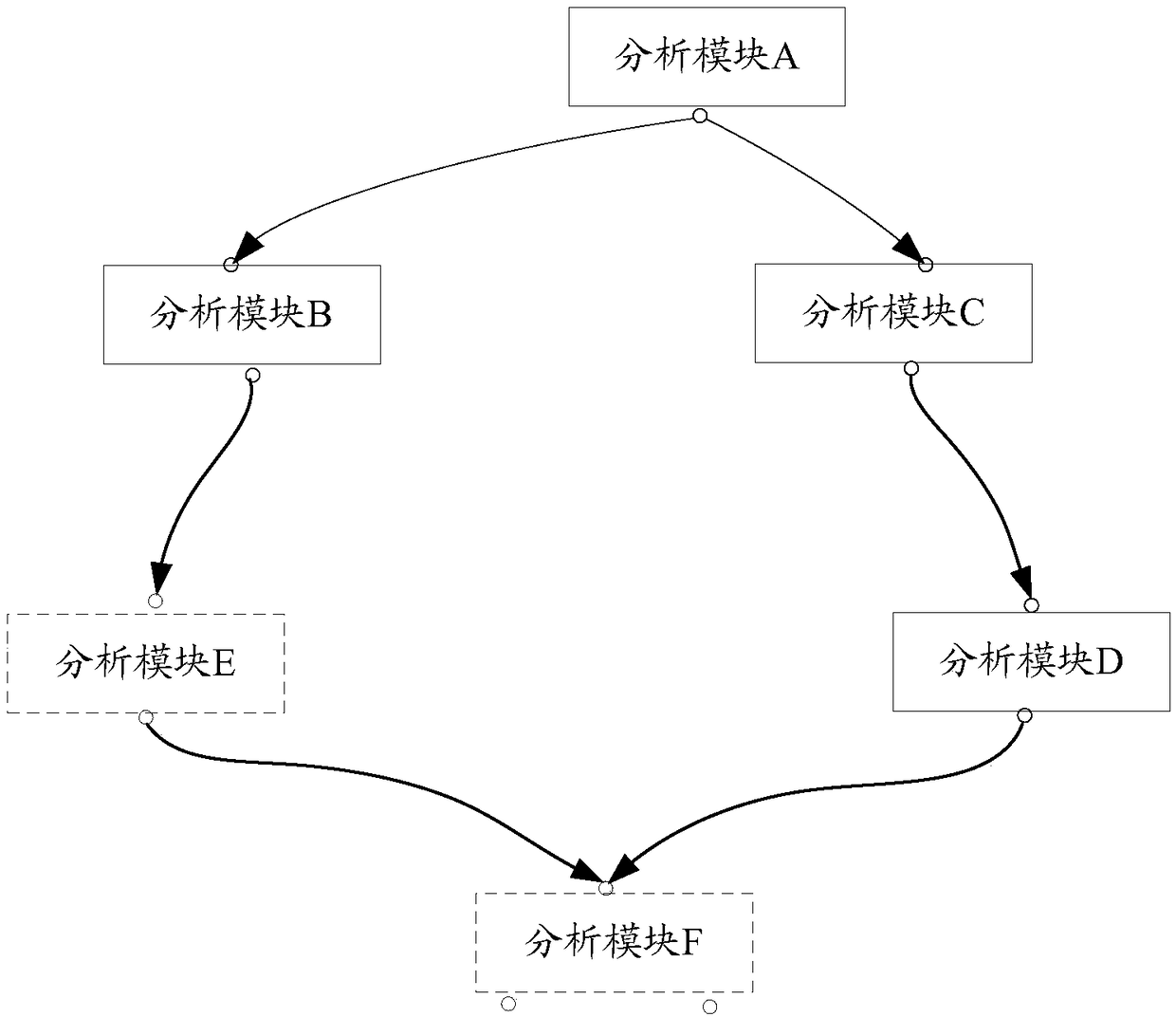
Running method of data analysis workflow, data analysis system and storage medium
ActiveCN109189750AImprove efficiencyFlexible configurationFile system administrationSpecial data processing applicationsResource consumptionOperation mode
The invention provides a running method of a data analysis workflow. According to the obtained configuration information of the data analysis workflow, the running mode of each workflow module of thedata analysis workflow is determined, and the association relationship among the workflow modules is determined. Finally, the data analysis workflow is run based on the determined association relationship and the running mode. The invention also provides a data analysis system and a storage medium. By determining the operation mode of each workflow module and the correlation relationship between the workflow modules, The data analysis workflow can be run in a single computer and / or distributed mode flexibly, and the fine balance between resource consumption and data analysis can be flexibly configured when the big data analysis system is used to process the big data service, so that the efficiency of the big data analysis system can be improved.
Owner:DATACANVAS LTD
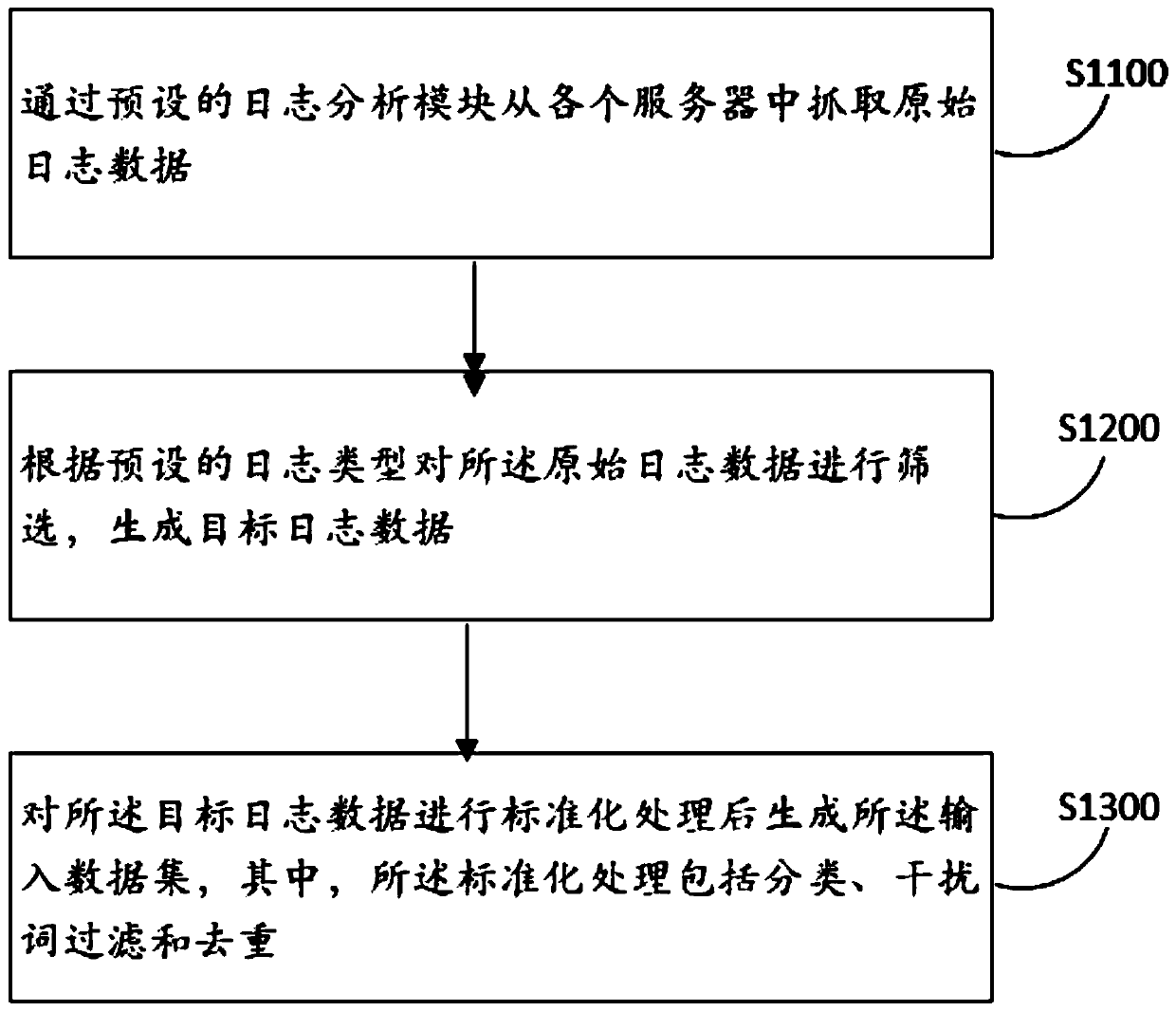
Log analysis method and device, computer equipment and storage medium
PendingCN111177095AImplement auto-scalingImprove adaptabilityHardware monitoringNeural learning methodsAnalytic modelData set
The invention discloses a log analysis method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining an input data set which is data with a unified data structure after the standardization of the obtained original log data; inputting the input data set into a preset exception analysis model to generate exception data, the exception analysis model being arecurrent neural network model which is trained to a convergence state in advance and is used for extracting the exception data in the log data; and performing association processing on the abnormaldata based on a preset abnormal historical database. According to the method, the original log data from different servers can be quickly acquired; the log data is subjected to standardization processing to have the same data structure, and then the log data is subjected to anomaly identification by adopting the recurrent neural network model, so that even if the data volume is huge, the log datacan be rapidly identified, and the abnormal data is subjected to correlation processing to accelerate the abnormal data processing speed and improve the abnormal data processing accuracy.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
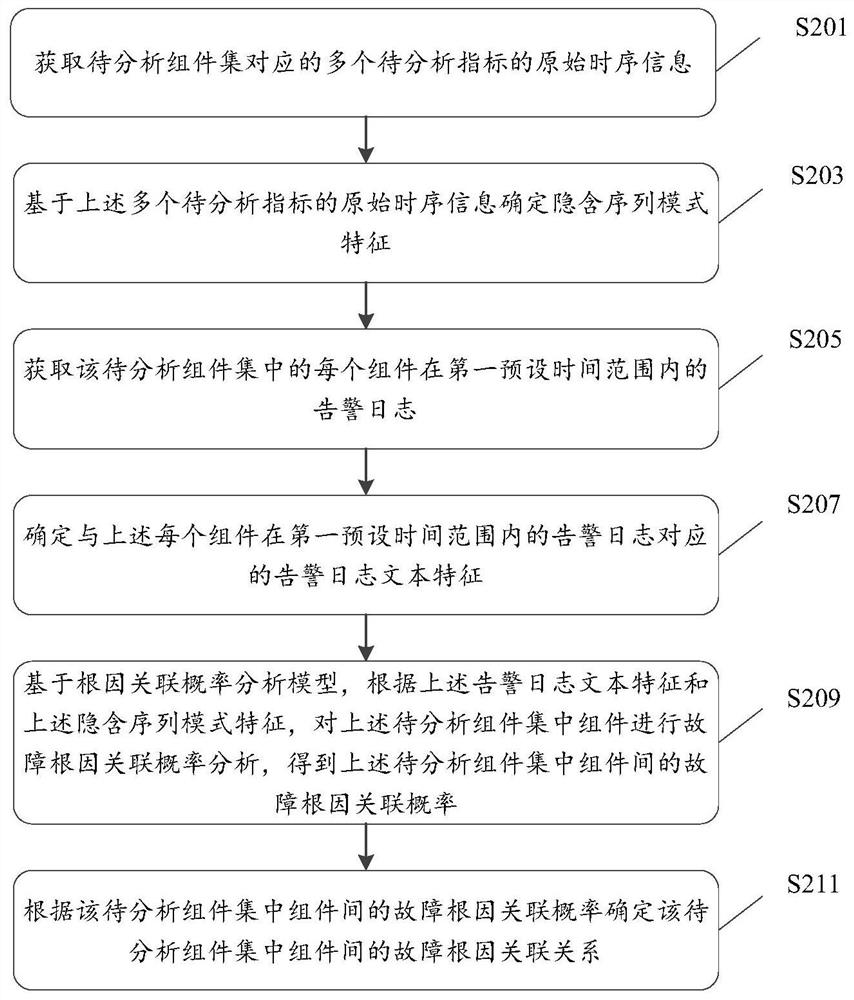
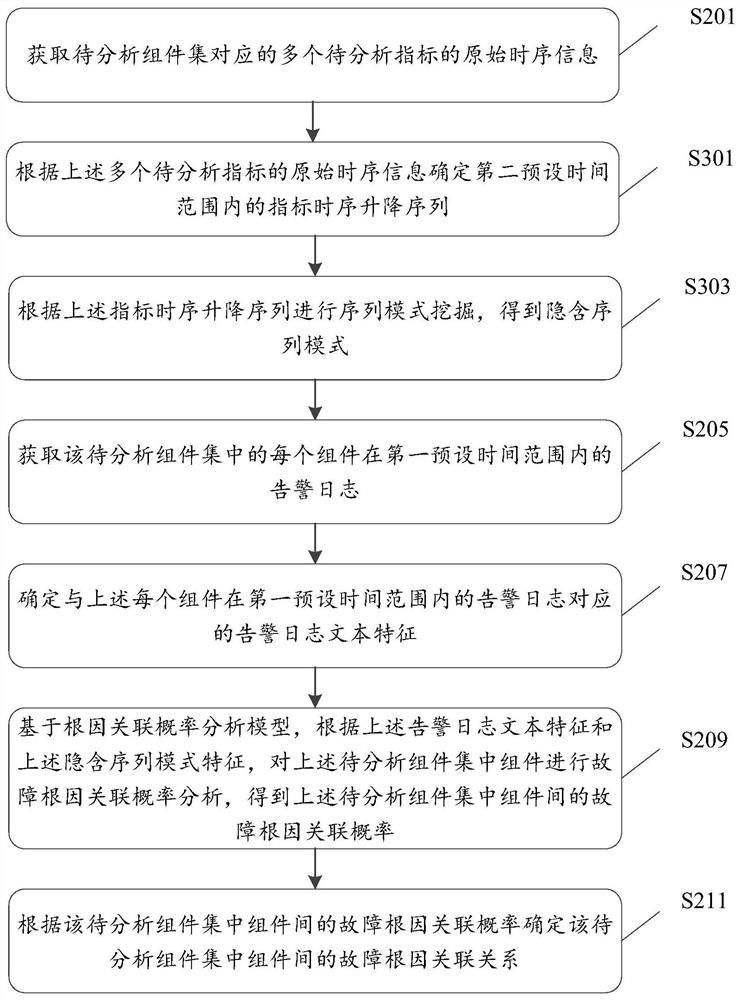
Fault root cause analysis method, device and equipment and storage medium
ActiveCN112052151AAccurately determineImprove reliabilityVisual data miningStructured data browsingTime rangeRoot cause
The invention discloses a fault root cause analysis method, device and equipment, and a storage medium. The method comprises the steps of obtaining original time sequence information of multiple to-be-analyzed indexes corresponding to a to-be-analyzed component set; determining implicit sequence mode features based on the original time sequence information; obtaining an alarm log of each componentin the to-be-analyzed component set in a first preset time range; determining an alarm log text feature corresponding to the alarm log of each component in the first preset time range; based on a root cause association probability analysis model, according to the alarm log text features and the implicit sequence mode features, carrying out fault root cause association probability analysis on thecomponents in the to-be-analyzed component set to obtain fault root cause association probabilities among the components in the to-be-analyzed component set; and determining a fault root cause association relationship between the components according to the fault root cause association probability. By utilizing the technical scheme provided by the invention, the fault root cause association relationship between the components can be efficiently and accurately determined in fault detection, and the reliability of fault root cause analysis is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Electric power network security monitoring method and system based on ELK log collection and analysis
InactiveCN109376532AImprove the level of safety monitoringMeeting Compliance Audit NeedsPlatform integrity maintainanceFile system functionsLog managementPower grid
The present application provides a power network security monitoring method and system based on ELK log collection and analysis. The method comprises the following steps: adopting a centralized log management method to collect a network security equipment log of a power monitoring system; Filtering, normalizing and storing the collected network security equipment logs of the power monitoring system; Using the distributed log retrieval method, the stored logs are retrieved and counted; displaying the log data in a summarized manner. The electric power network security monitoring method and system based on ELK log collection and analysis provided by the application adopts a cluster mode, data storage, query is efficient and fast, realizes real-time log monitoring and storage, and meets log storage requirements; and through the visualization mode for log display, friendly interface, simple and easy to use, log analysis rules can be customized to facilitate staff real-time monitoring of network security events, improve the network security monitoring level of power monitoring system.
Owner:YUNNAN POWER GRID
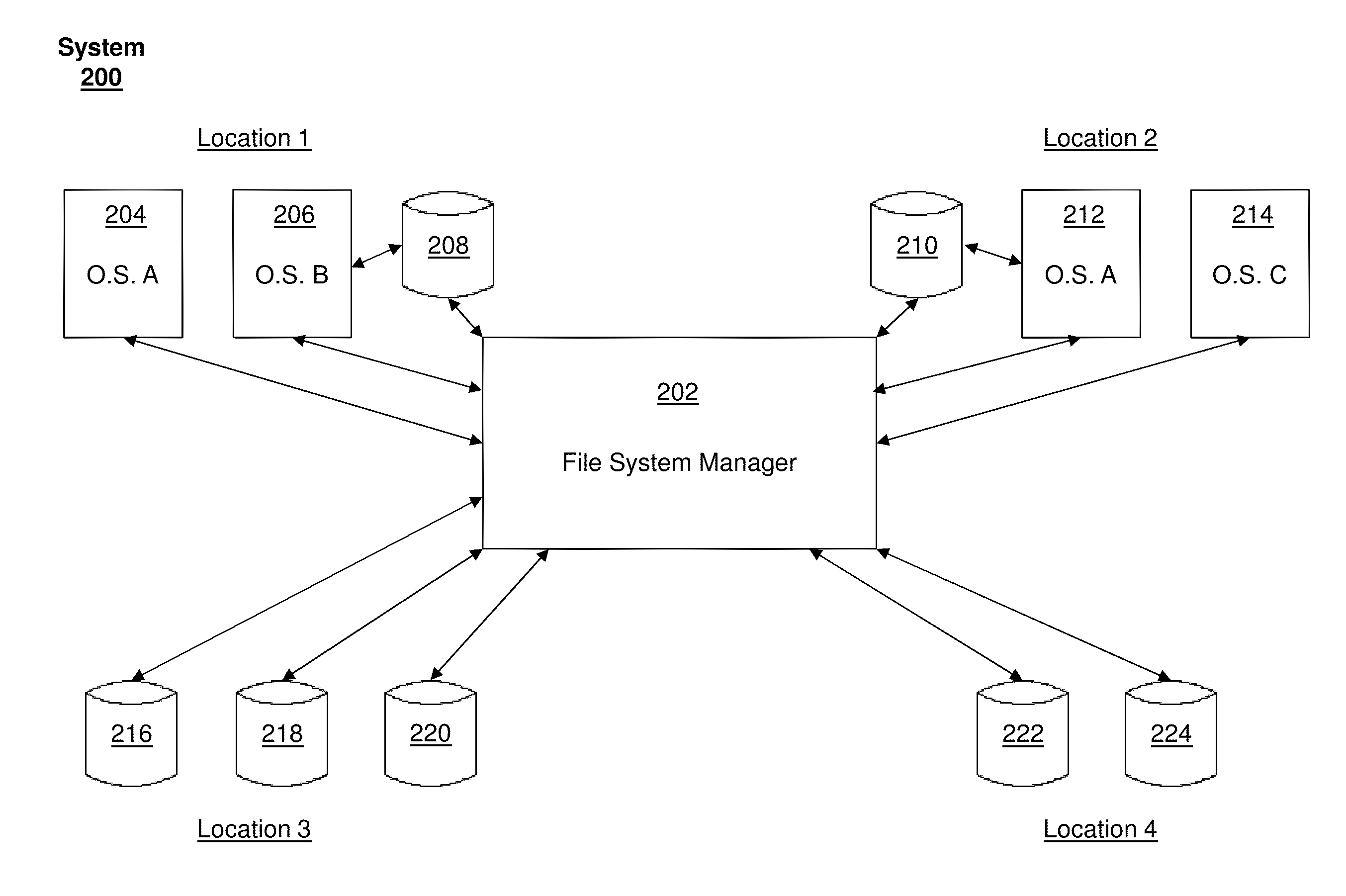
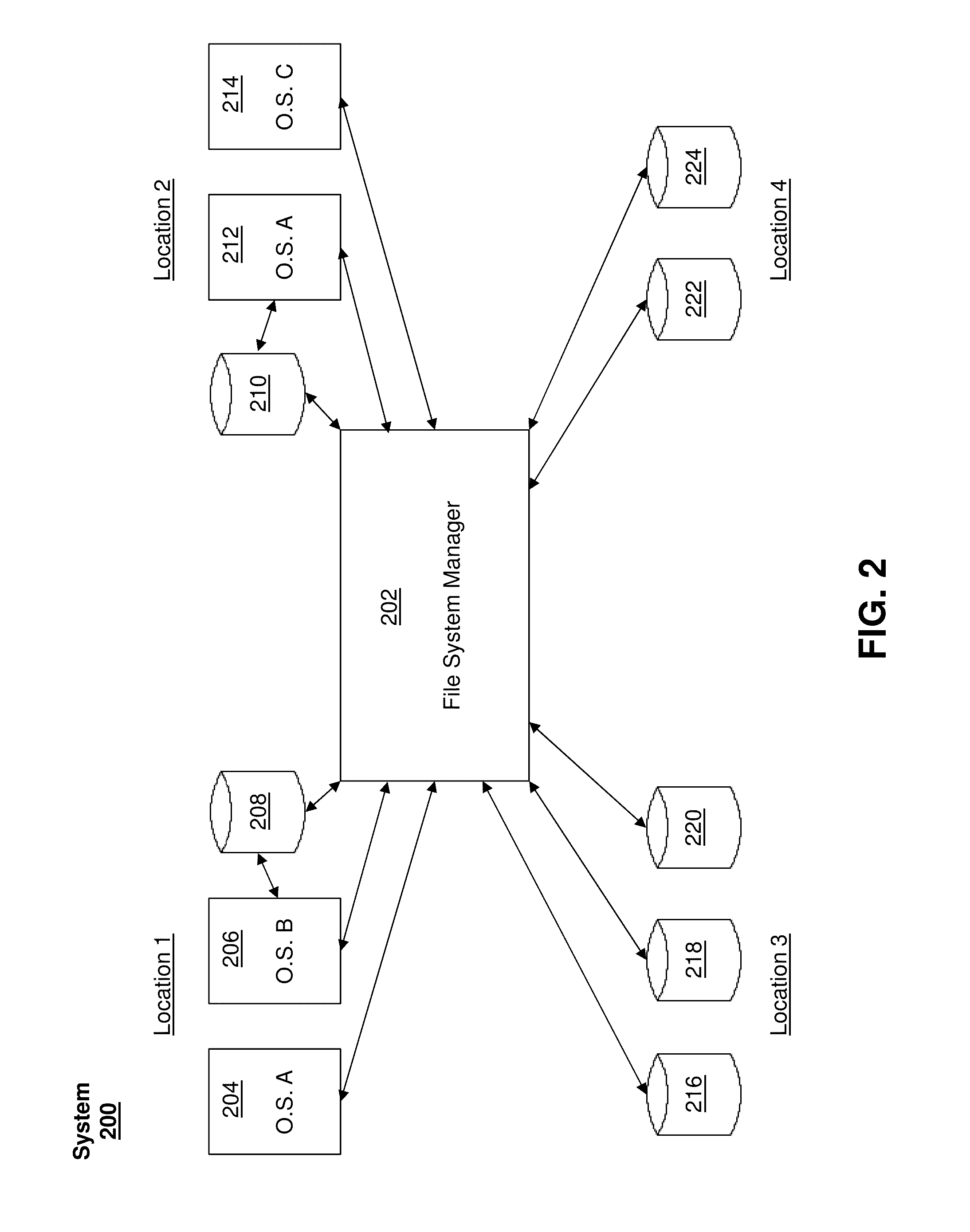
File system manager for customized resource allocation
Systems and processes provide network clients on various platforms a customized file system experience on demand while managing files (e.g., computer animation files) across a variety of storage devices spread across a network of arbitrary size (local area networks, wide area networks, worldwide networks, the world wide web, etc.). Clients may specify a set of requirements for an instantiation of a file system interface or object for a given application. Such requirements may include storage location, file quality, capacity, scale, permanence, speed, and the like. The system may then provide to the client a customized file system interface with particular hardware resources allocated to satisfy the designated file system requirements. The file system interface may coordinate file delivery, allocation, tracking, transportation, caching, deletion, and the like. The system may manage and allocate hardware resources ranging from a local client computer to distant hard drive banks across the world.
Owner:DREAMWORKS ANIMATION LLC
A financial robot system
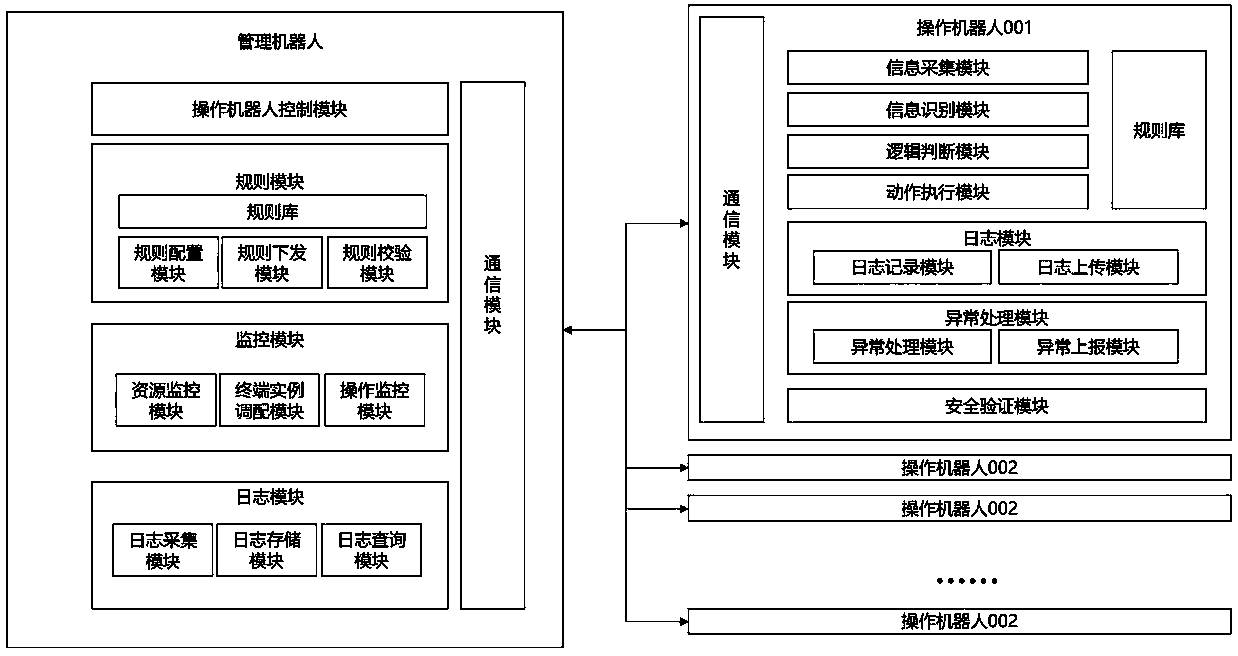
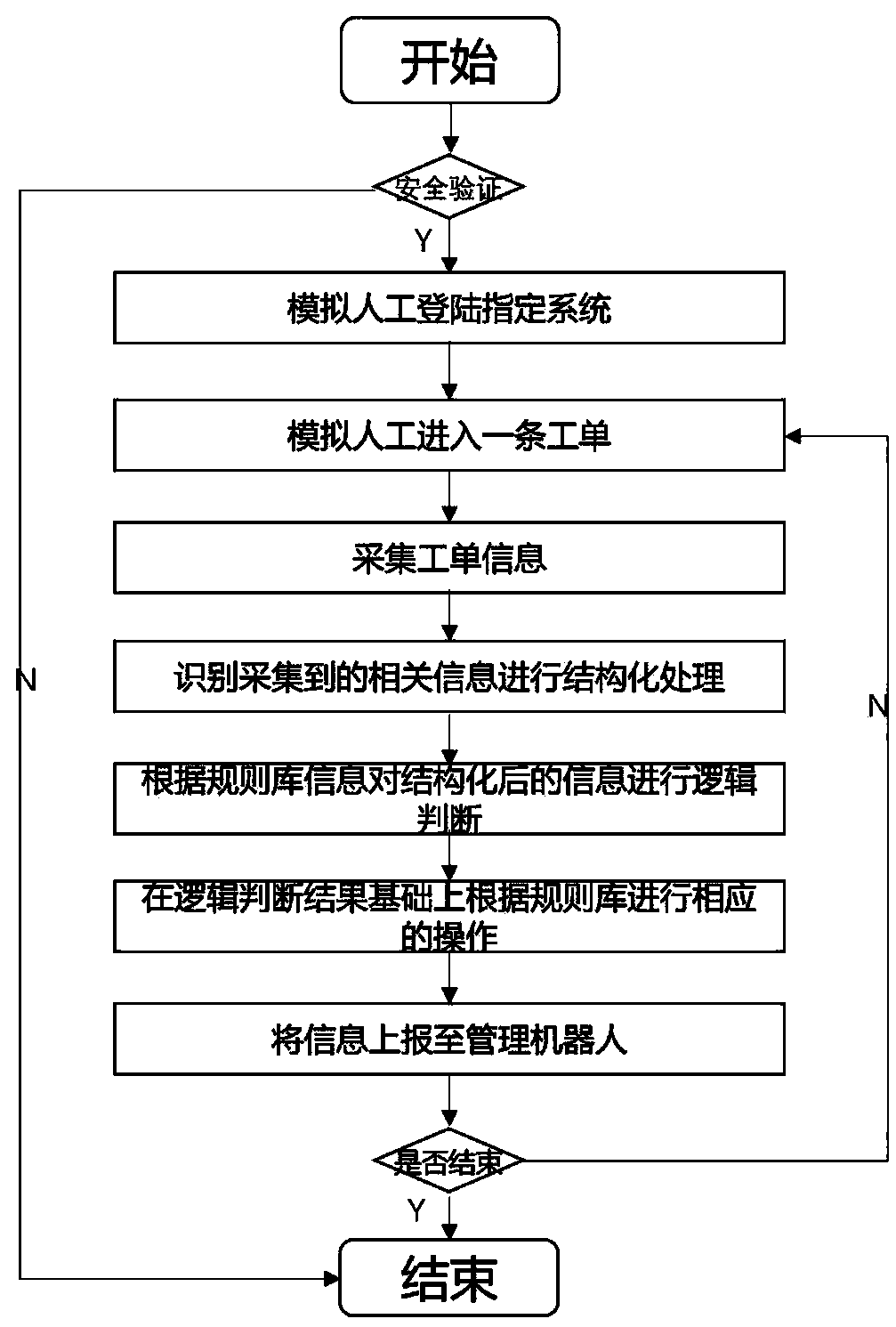
InactiveCN109325734ALow costImprove the quality of workFinanceDigital data protectionRobotic systemsRobot control
A disclosed financial robot system is characterized by comprising a management robot and a plurality of manipulating robots, wherein the management robot comprises an operation robot control module, arule module, a monitoring module, a log module and a communication module, and the operation robot comprises a communication module, an information collection module, an information recognition module, a logic judgment module, an action execution module, a rule base, a log module, an exception handling module and a safety handling module. The financial robot system of the invention realizes the automation of the financial process through the intelligent robot, improves the working quality, improves the service supporting capacity and saves the personnel cost.
Owner:JIANGSU HONGXIN SYST INTEGRATION
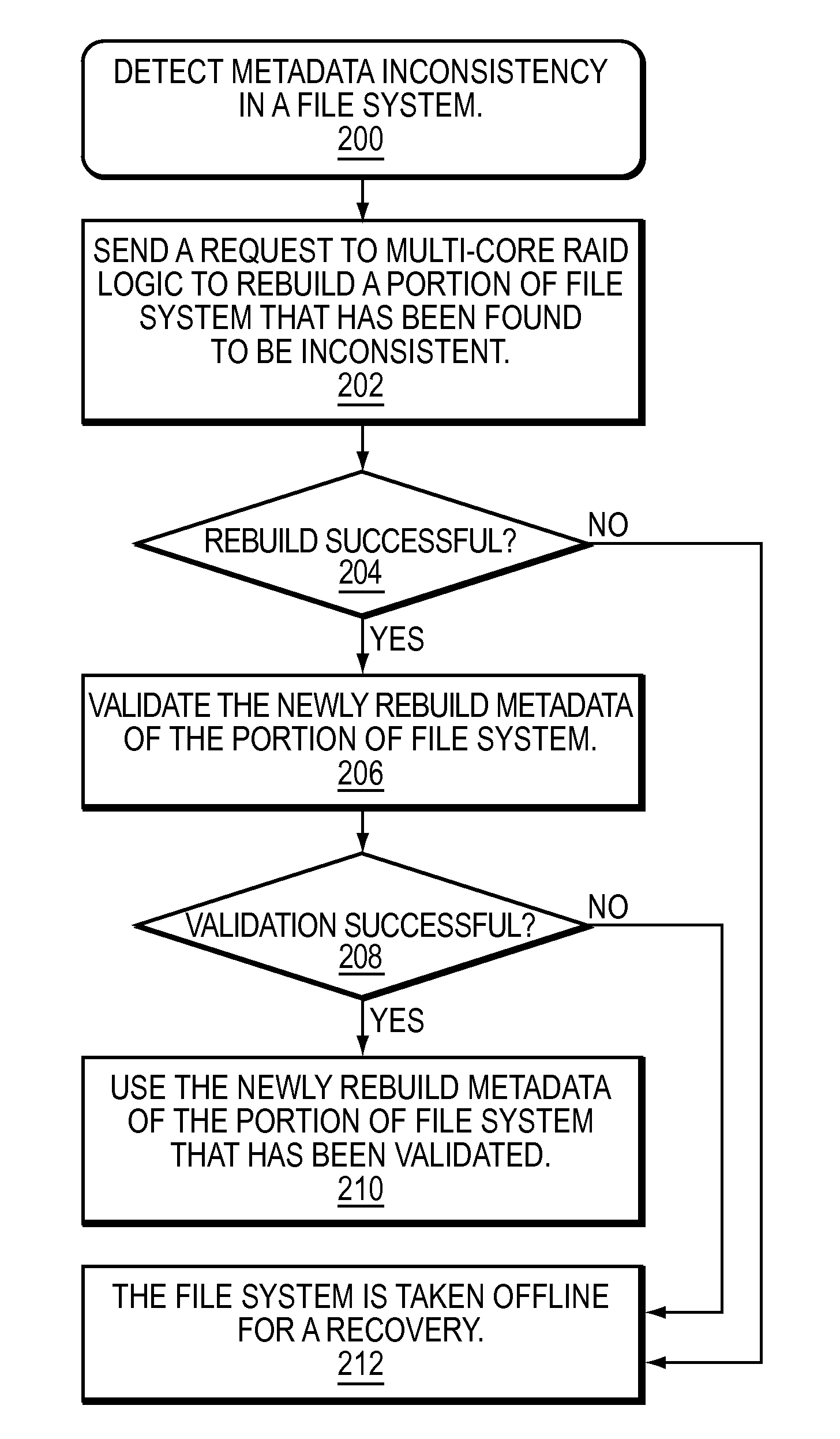
Recovering from metadata inconsistencies in storage systems
ActiveUS9558068B1Input/output to record carriersSpecial data processing applicationsFile systemDatabase
A method is used in recovering from metadata inconsistencies in storage systems. A metadata inconsistency is detected in a portion of a file system. The file system is managed by upper-layer component. The portion of the file system is recovered. Lower-layer component recovers the portion of the file system. The portion of the file system is validated. The upper-layer component validates the portion of the file system.
Owner:EMC IP HLDG CO LLC
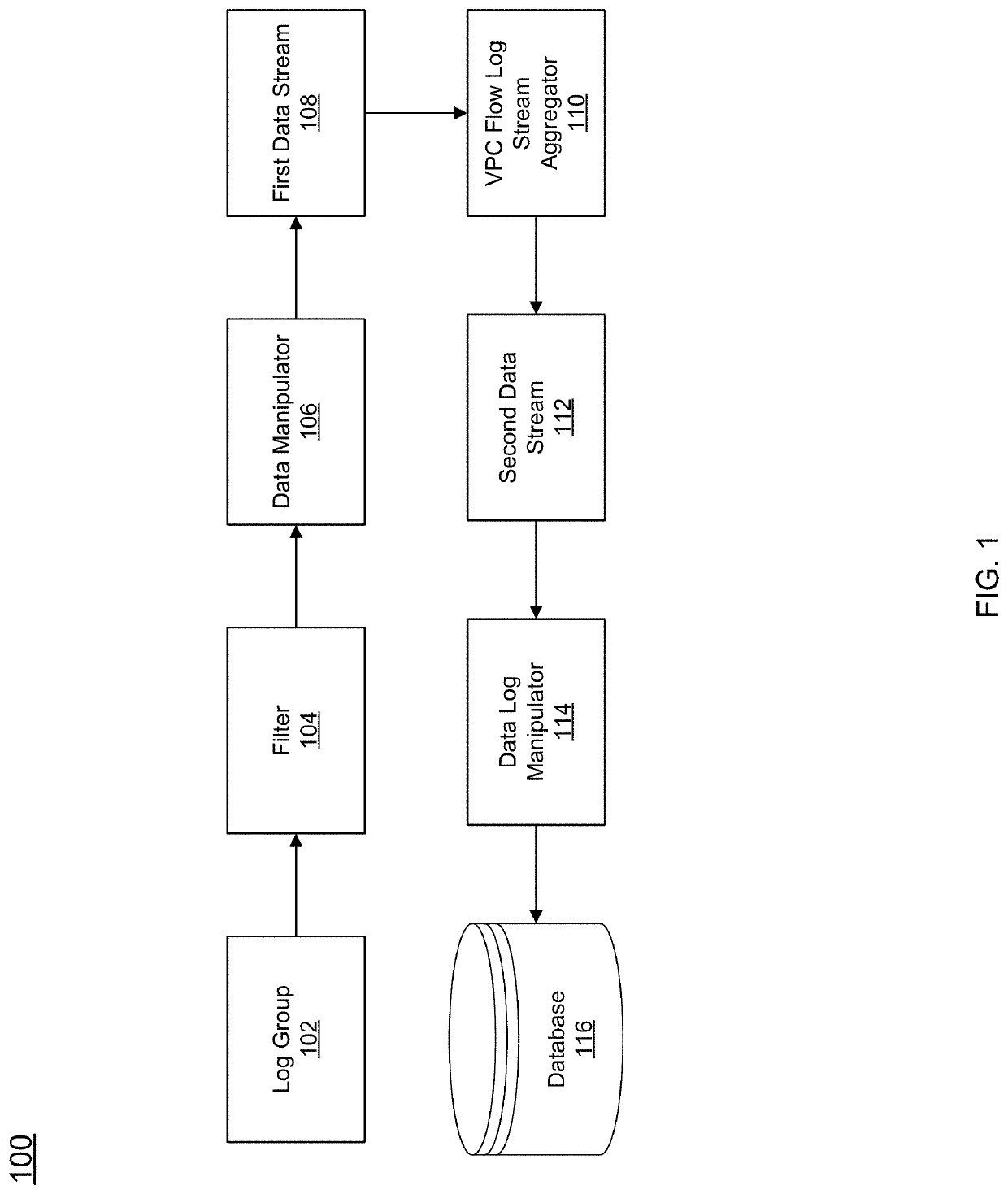
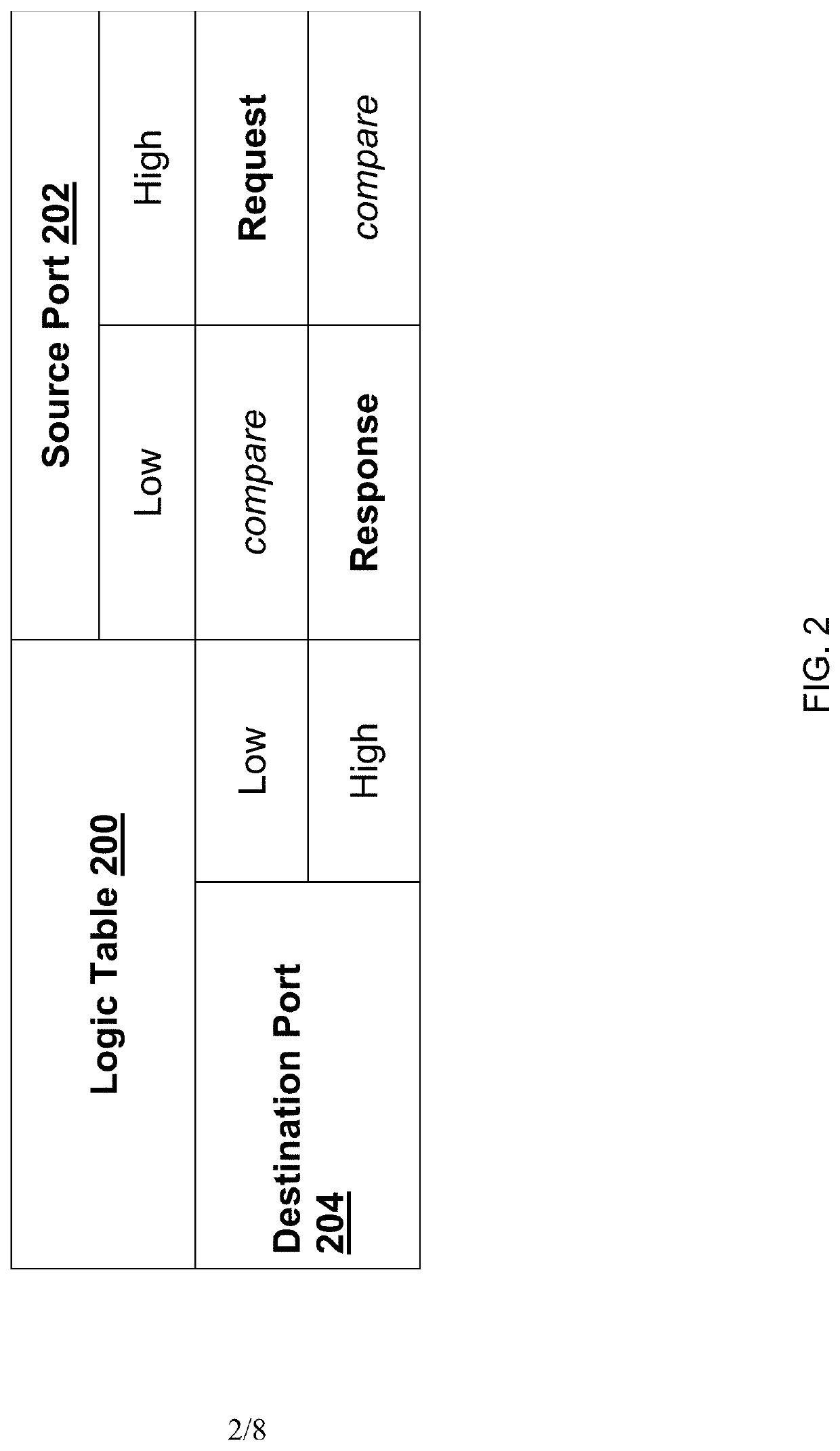
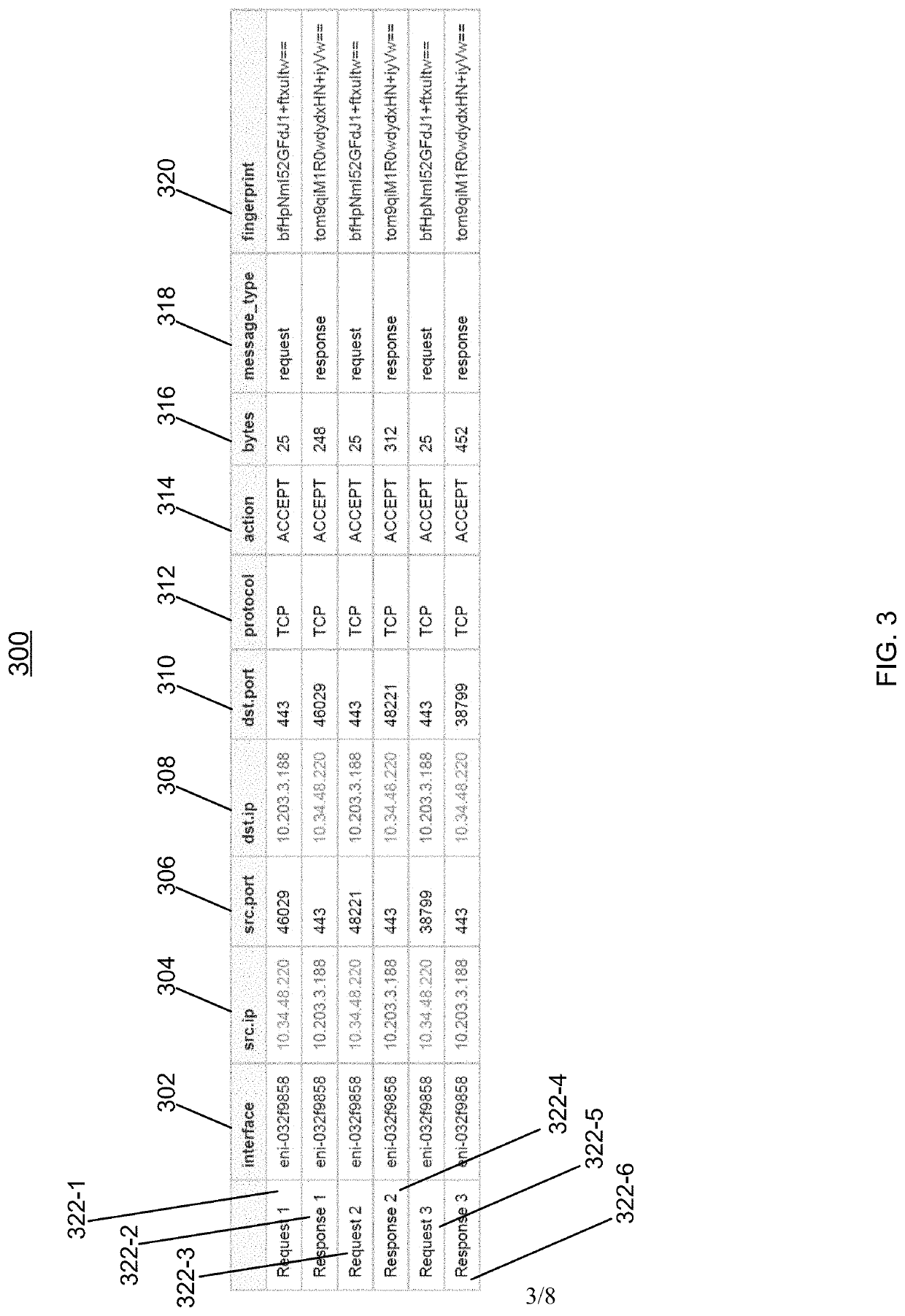
Virtual private cloud flow log event fingerprinting and aggregation
Techniques for fingerprinting and aggregating a virtual private cloud (VPC) flow log stream are provided. Each VPC flow log event in the VPC flow log is first determined to be a request event or a response event. A fingerprint is then generated for each VPC flow log event. The fingerprint for a VPC flow log event is generated based on the determination whether the VPC flow log event is a request event or a response event and by concatenating and encoding data contained in a set of data fields corresponding to the VPC flow log event. Based on the fingerprint generated for each VPC flow log event, related events can be detected and aggregated to form an aggregated event. Information stored with each aggregated event can then be used to better monitor the VPC.
Owner:CAPITAL ONE SERVICES
Scalable file management for a shared file system
ActiveUS8341130B2Digital data processing detailsFile system administrationFile systemDirectory traversal attack
Managing a shared file system comprising a directory and files stored on a multiple storage devices shared by plural processing nodes, is provided. A plurality of parallel directory traversal records are partitioned into a plurality of ranges to allow for the records in each range to be written independently in parallel by plural processing nodes during parallel directory traversal. Parallel operations are performed comprising parallel directory traversal of all directory paths and files in the shared file system.
Owner:INT BUSINESS MASCH CORP
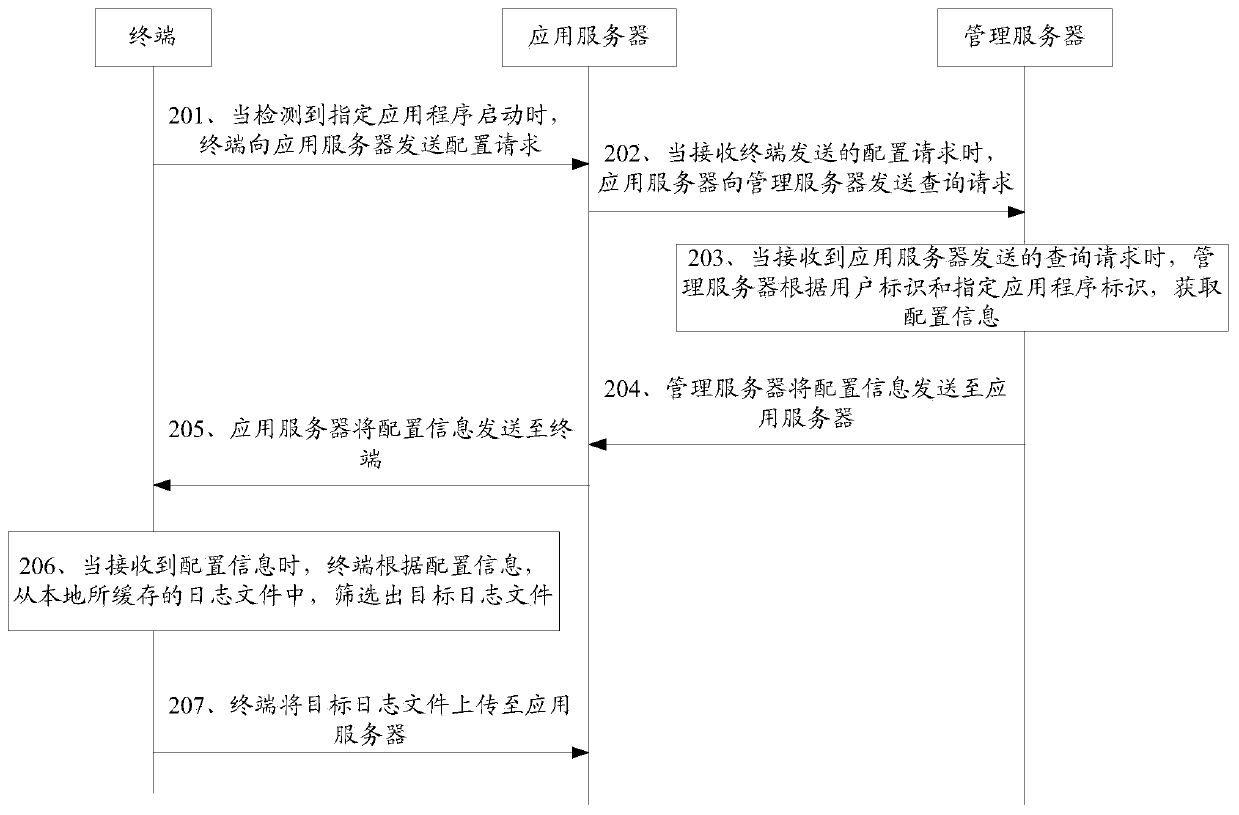
Log file obtaining method and device and storage medium
ActiveCN110232048ASave storage spaceReduce file sizeFile metadata searchingEnergy efficient computingApplication serverFile size
The invention discloses a log file obtaining method and device and a storage medium, and belongs to the technical field of computers. The method comprises the steps that when detecting that an appointed application program is started, sending a configuration request to an application server, and using the configuration request for the application server to obtain configuration information and return the configuration information; when configuration information is received, screening out a target log file from locally cached log files according to the configuration information; and uploading the target log file to an application server. The configuration request is sent to the application server, the configuration information is obtained, the target log file is screened out according to theconfiguration information, and then the target log file is uploaded to the application server. Due to the fact that the cached log files are not completely uploaded to the application server, the screened target log files are uploaded, the file size of the uploaded log files is reduced, the storage space of the server is saved, and the positioning efficiency is improved.
Owner:TENCENT TECH CHENGDU
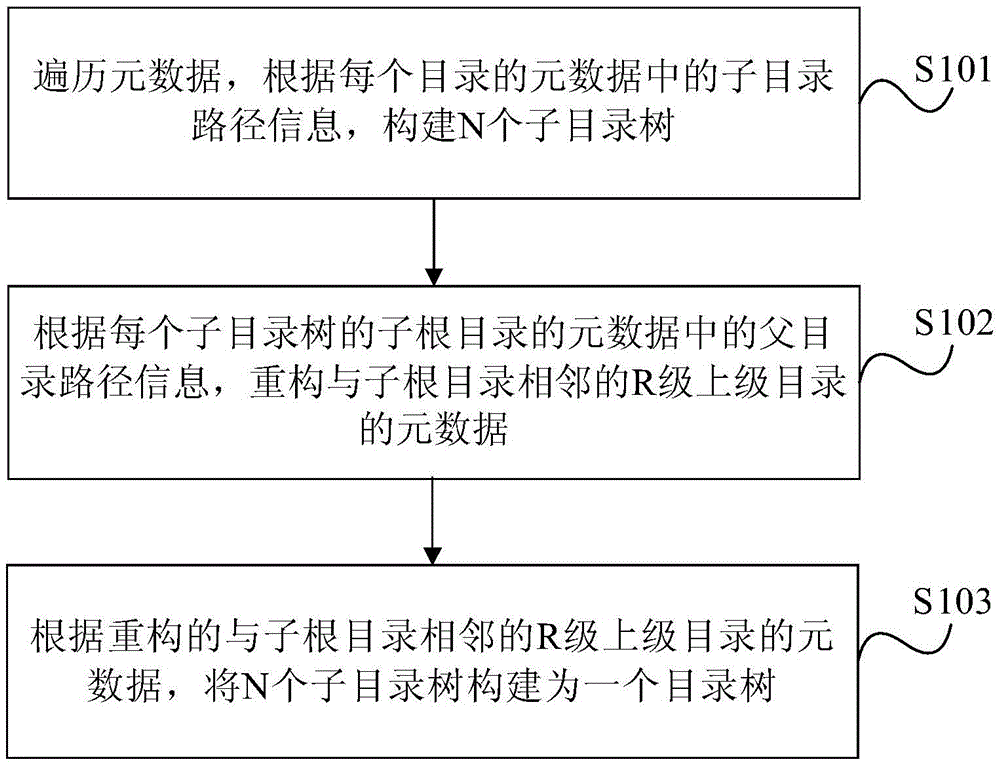
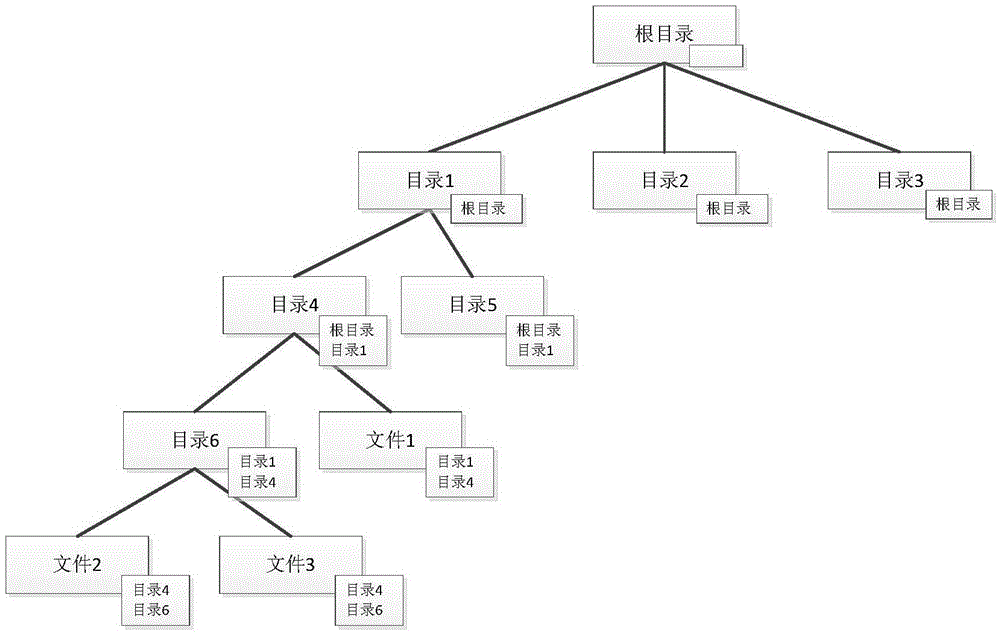
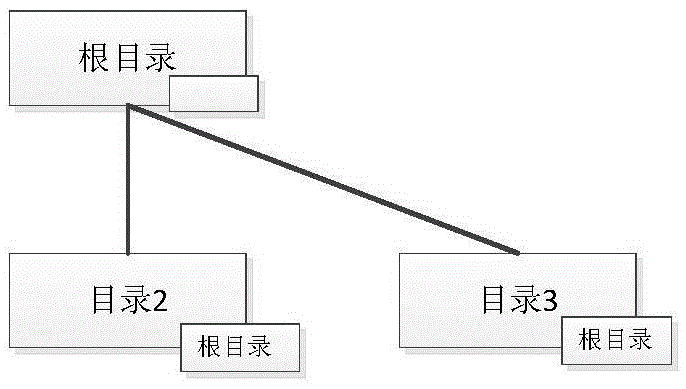
Repairing method and device of file system directory tree
The invention provides a repairing method and device of a file system directory tree. Parent directory path information is added into the metadata of each directory; when metadata in the directory tree is damaged, the metadata is traversed, N sub-directory trees are constructed according to sub-directory path information in the metadata of each directory; then, according to the parent directory path information of a sub root directory of a sub directory tree, the damaged directory is determined; according to the parent directory path information of the sub root directory of the sub directory tree, the metadata of an R-level upper directory adjacent to the sub root directory is reconstructed, i.e., the metadata of the damaged directory is reconstructed; and according to the reconstructed metadata of the R-level upper directory adjacent to the sub root directory, the N sub directory trees are constructed into one directory tree. Therefore, an original file system directory tree is reduced, and influence caused by the damage of the file system directory tree is reduced.
Owner:CHENGDU HUAWEI TECH
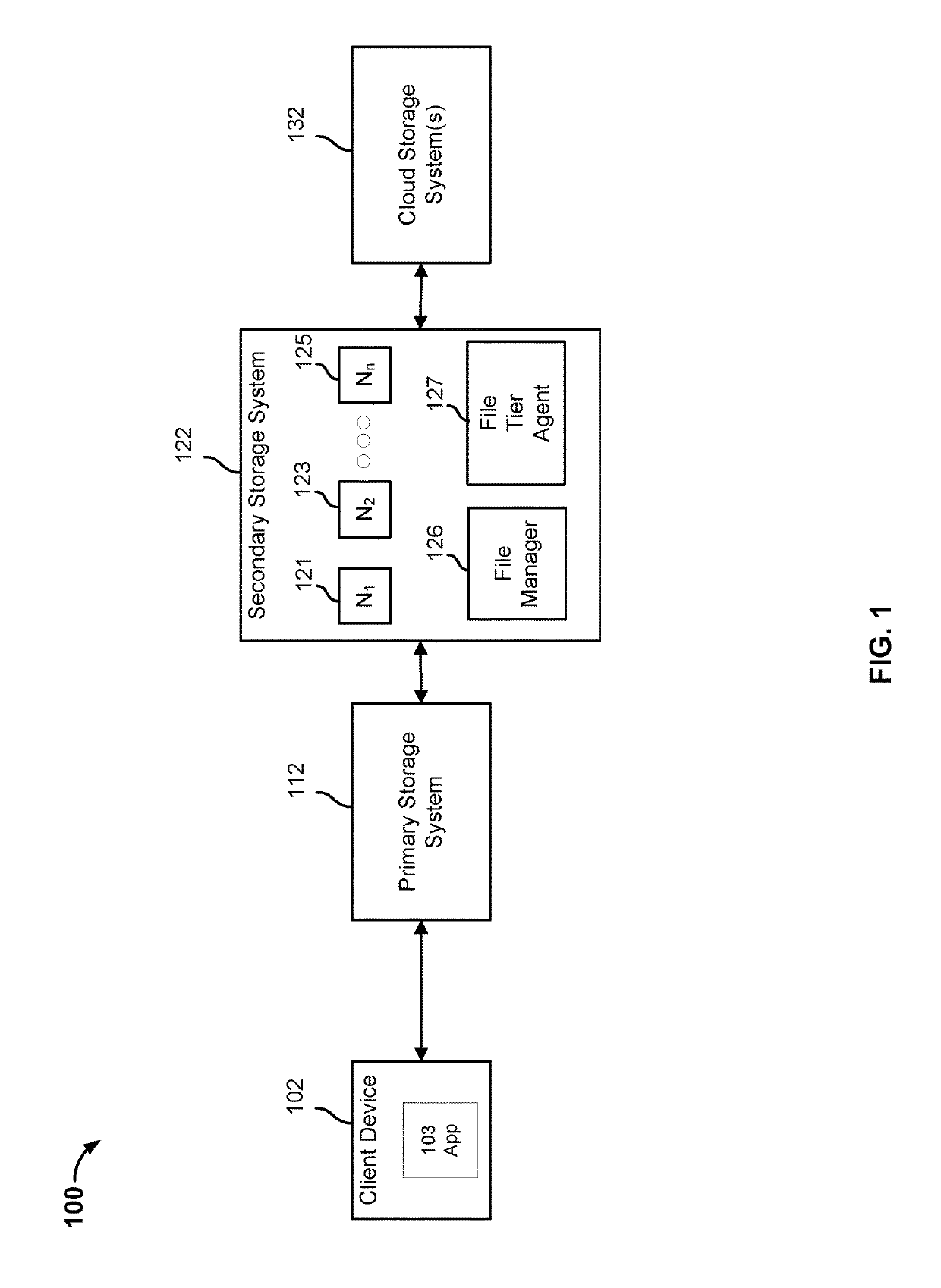
Integrated hierarchical storage movement
File access statistics associated with a content file are maintained by a file tier agent of a secondary storage system. The content file is accessible via a primary storage system. A target storage tier corresponding to the file access statistics associated with the content file is determined according to one or more policies. At least a portion of data of the content file is migrated to the determined storage tier while accessibility of the content file via the primary storage system is maintained.
Owner:COHESITY
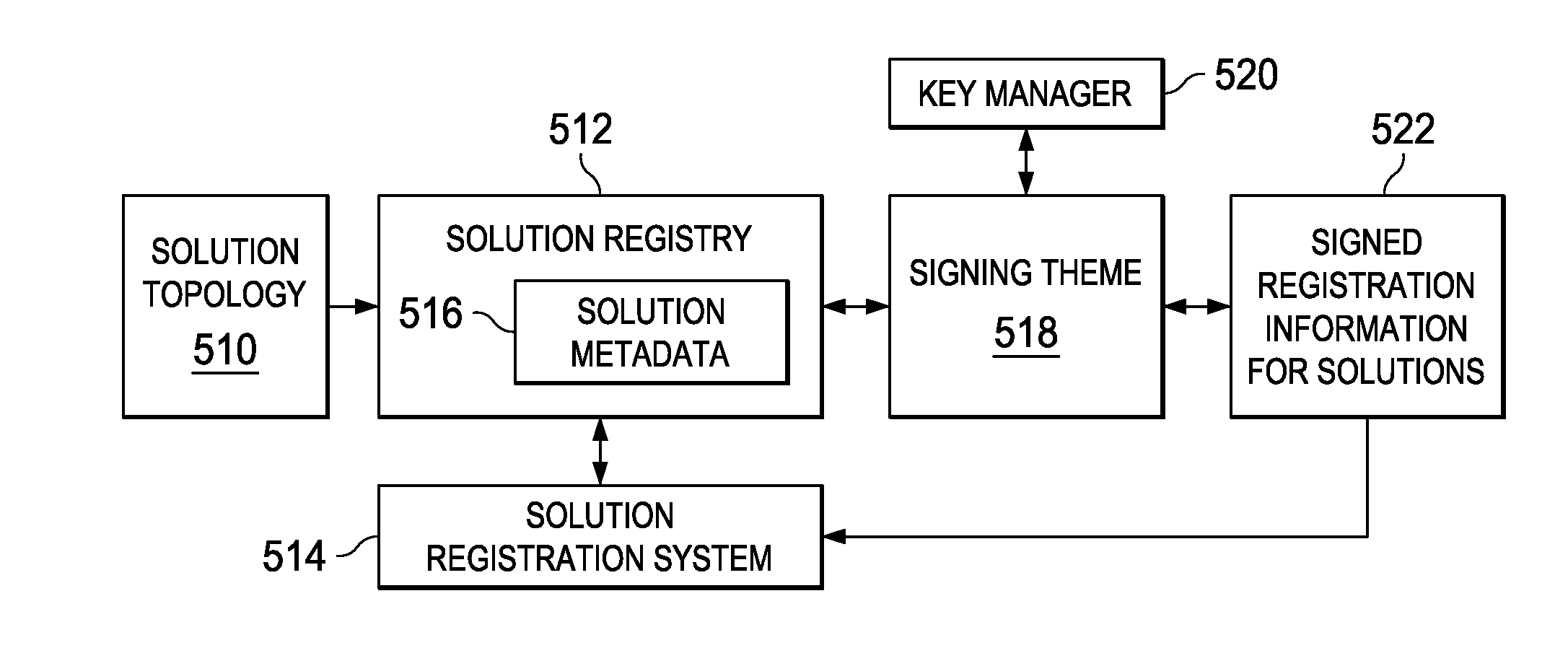
Method and apparatus for authentication of solution topology
InactiveUS20140181984A1Digital data processing detailsAnalogue secracy/subscription systemsAuthenticationVirtual machine
A computer implemented method is provided to verify an integrity of a solution. The computer implemented method comprises hashing, by a computer, a set of virtual machine instances in a solution topology of the solution. The computer hashes a set of connections in the solution topology. The set of connections comprising a connection between ones of the set of virtual machine instances, a connection between a first component of a first one of the set of virtual machine instances and a second component of a second one of the set of virtual machine instances, and combinations thereof. The computer hashes a set of solution-specific information, and then signs the hashes to create a first signed topology.
Owner:IBM CORP
Data storage method and device
ActiveCN103678293AImprove storage efficiencyImprove query efficiencySpecial data processing applicationsFile system functionsEncoding algorithmData file
The invention discloses a data storage method and device. The data storage method includes the steps that an encoding algorithm is selected in advance, and value taking intervals of codes are segmented; identification information of target data files are encoded by means of the encoding algorithm; according to the encoding result, multiple data files in the same segmentation of encoded values are integrated and stored. By the adoption of the technical scheme, a proper encoding mode is selected in advance, the encoded value taking intervals are segmented, and then the data files in the same segmentation are integrated and stored according to the encoding result through identification of the data files. Compared with the prior art, file fragmentations are reduced because of integration and storage of the data files, and storage efficiency and query efficiency can be obviously improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
A method and apparatus for cleaning log file cache
ActiveCN109271355AEasy to cleanEase occupancyFile/folder operationsFile system functionsService moduleRecovery cycle
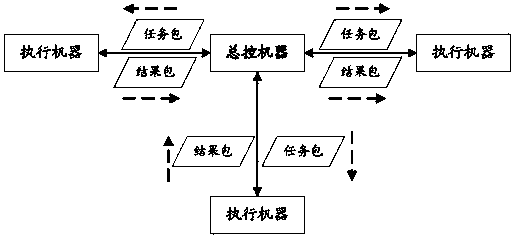
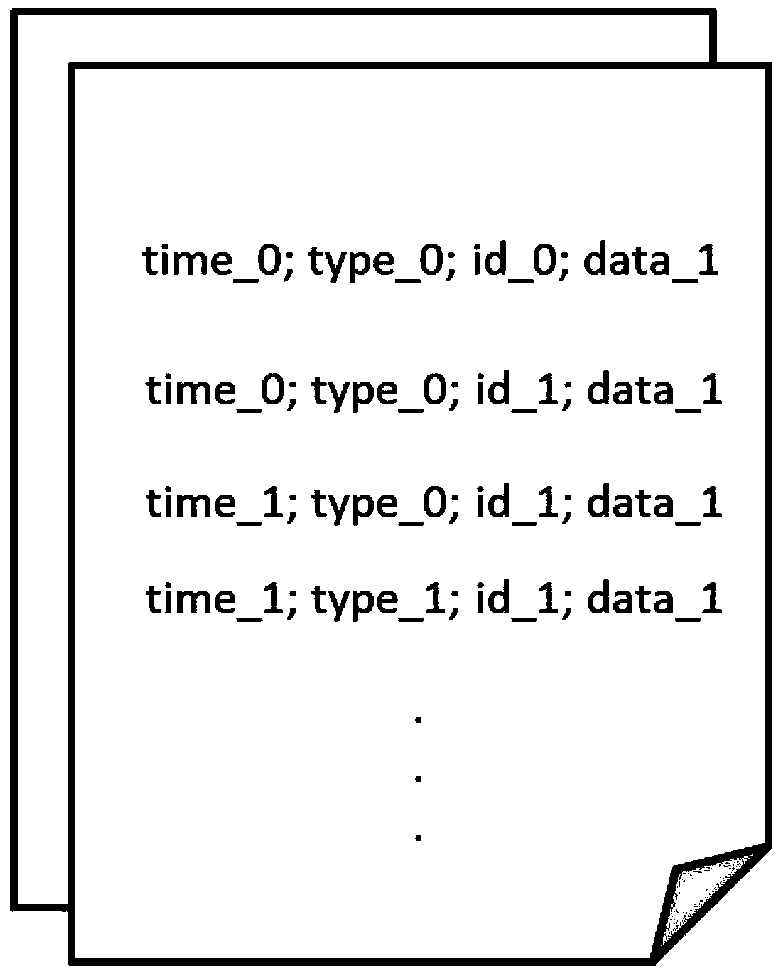
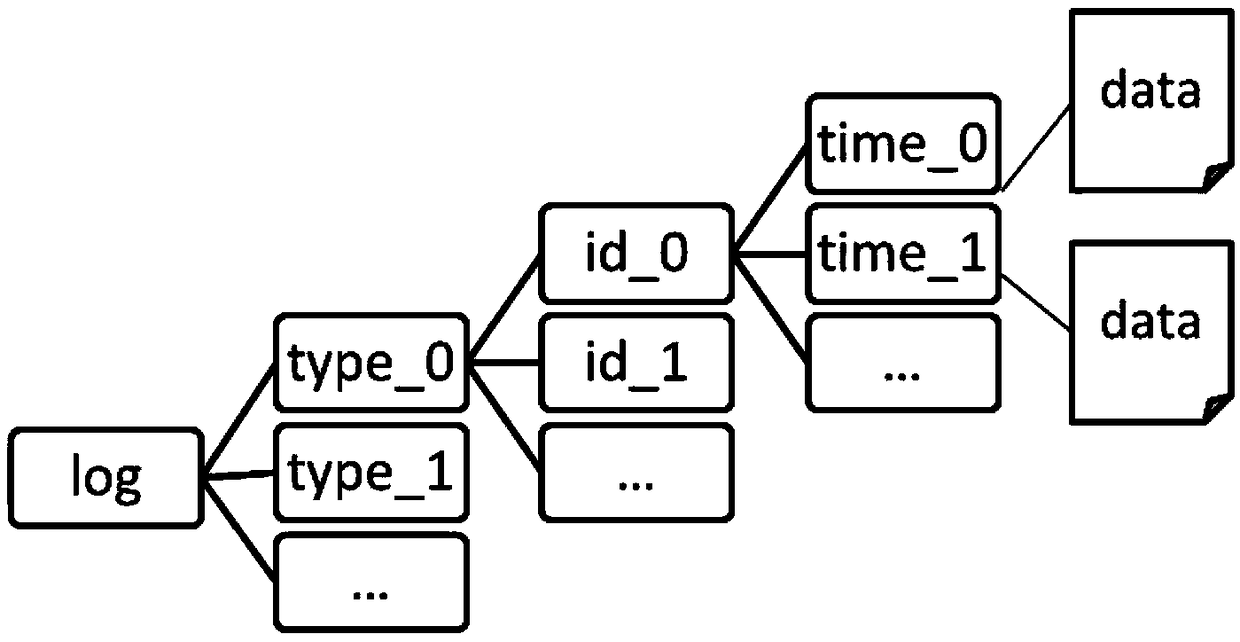
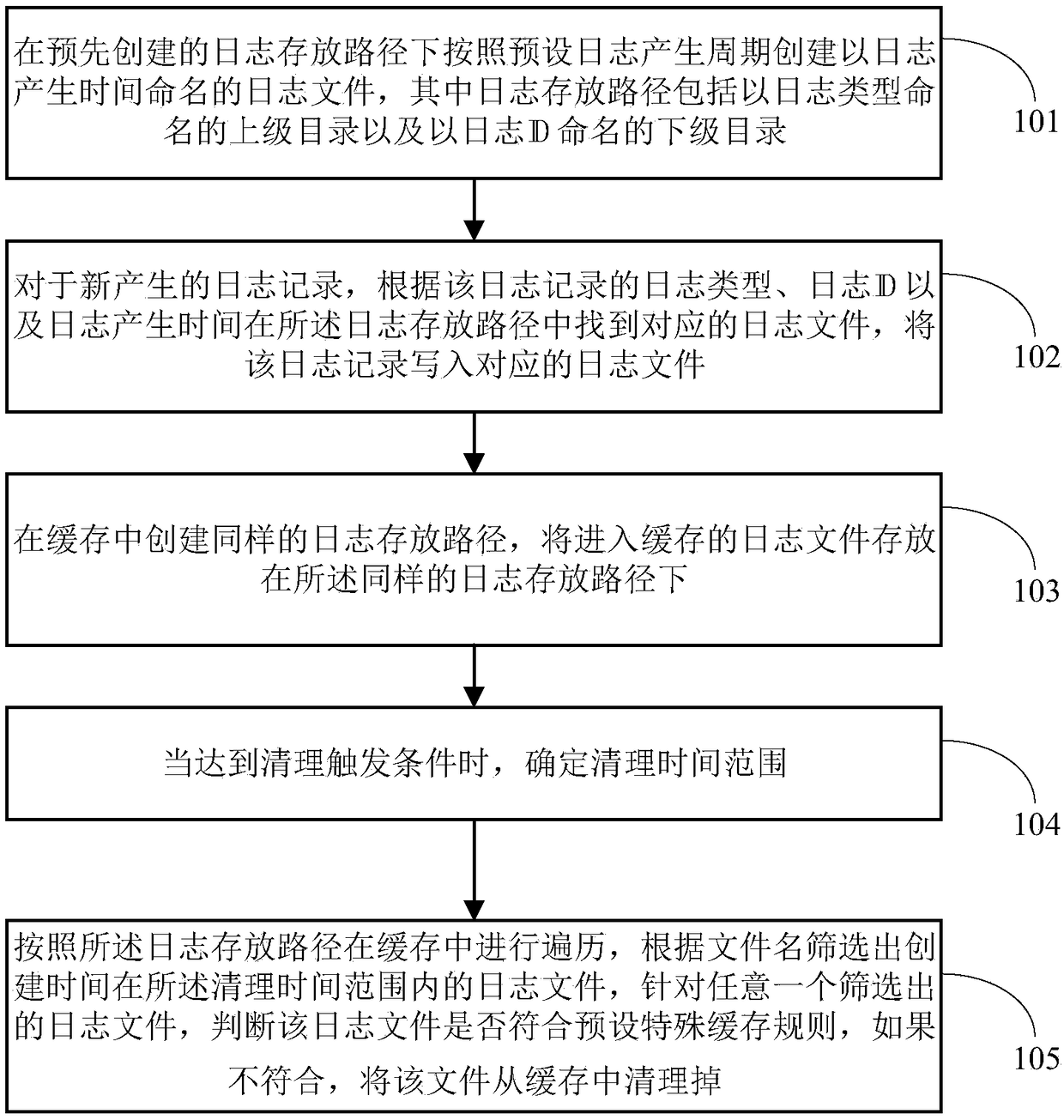
The present application provides a method and apparatus for cleaning a log file cache. According to the specific path to build log file storage mode, the log record cache arranged in chronological order is stored according to log type and the log ID classification, so that the number of log caches traversed and cleaned up by the system is greatly reduced, and the system cleanup process delay is reduced. In addition, the method of setting a fixed time to clean the cache file in the prior art cannot be combined with the actual system memory usage, so that the resource is often wasted in actual use. The application triggers the cache cleaning by setting a dynamic recovery cycle, and dynamically adjusts the frequency of the cache cleaning according to the memory usage status and the latest cleaning time cycle in real time, so as to ensure the normal operation of the service module.
Owner:杭州迪普信息技术有限公司
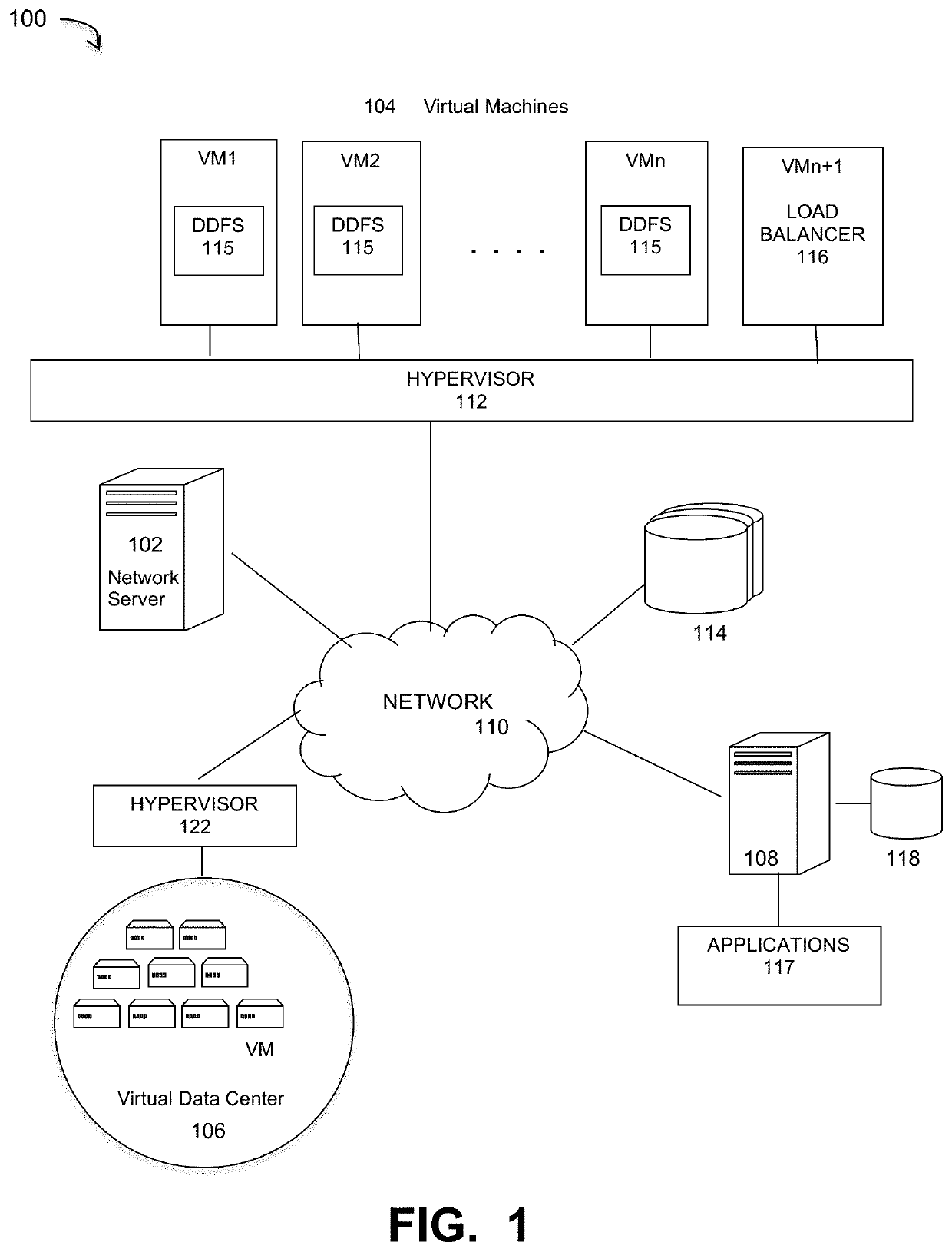
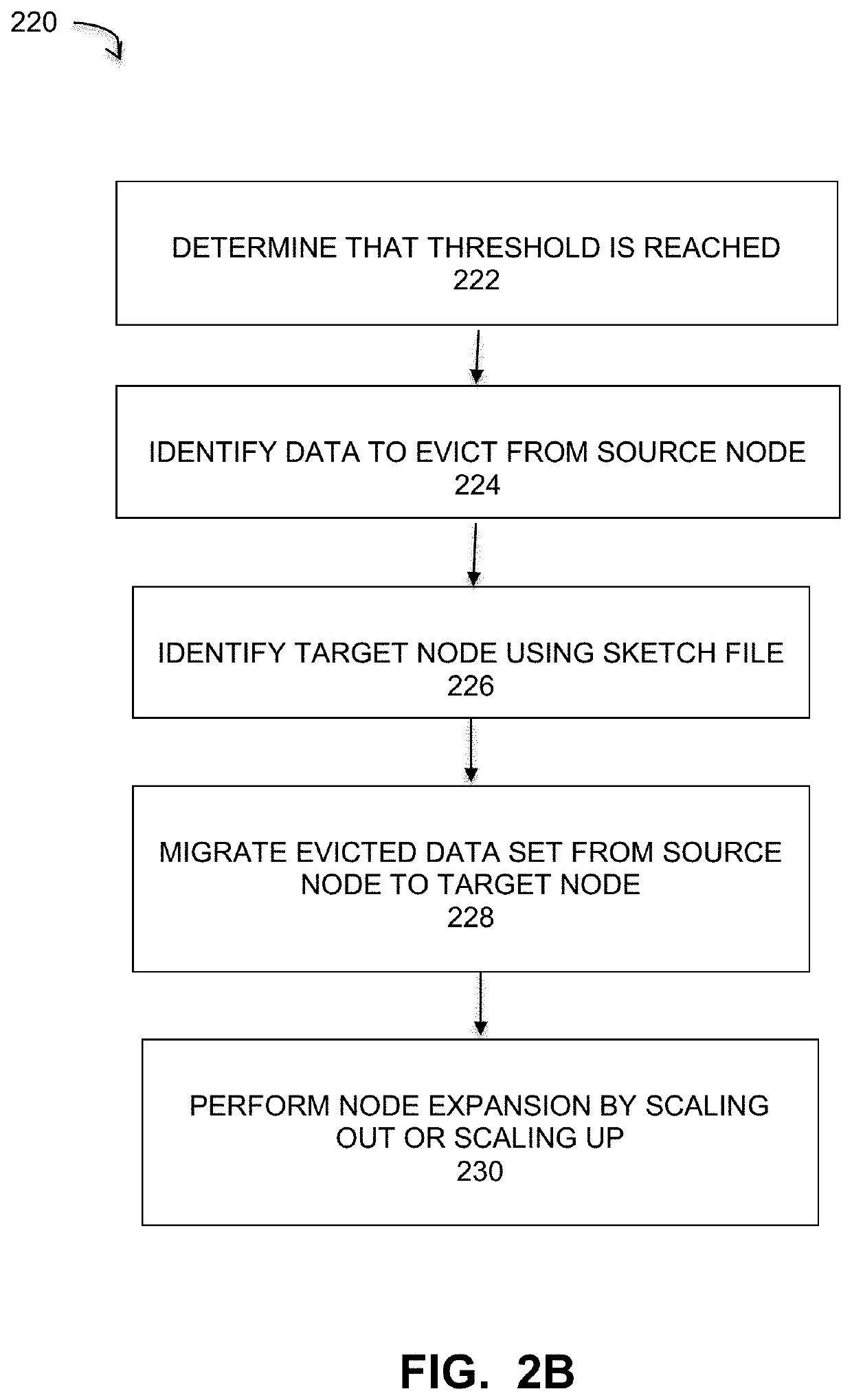
Scale out capacity load-balancing for backup appliances
Embodiments are directed to a load balancer process for use in a deduplication backup process implemented in a cluster system that provides ideal placement of the Mtrees on the expanded capacity by monitoring the available capacity and providing recommendations on the best node to place newly created Mtrees. Continuous monitoring of the capacity and activity level of the nodes helps identify the appropriate node to place a new Mtree. The monitoring of existing node in the cluster and balancing capacity by recommending migration of files from heavily-utilized nodes to under-utilized nodes produces an overall increase in cluster performance.
Owner:EMC IP HLDG CO LLC
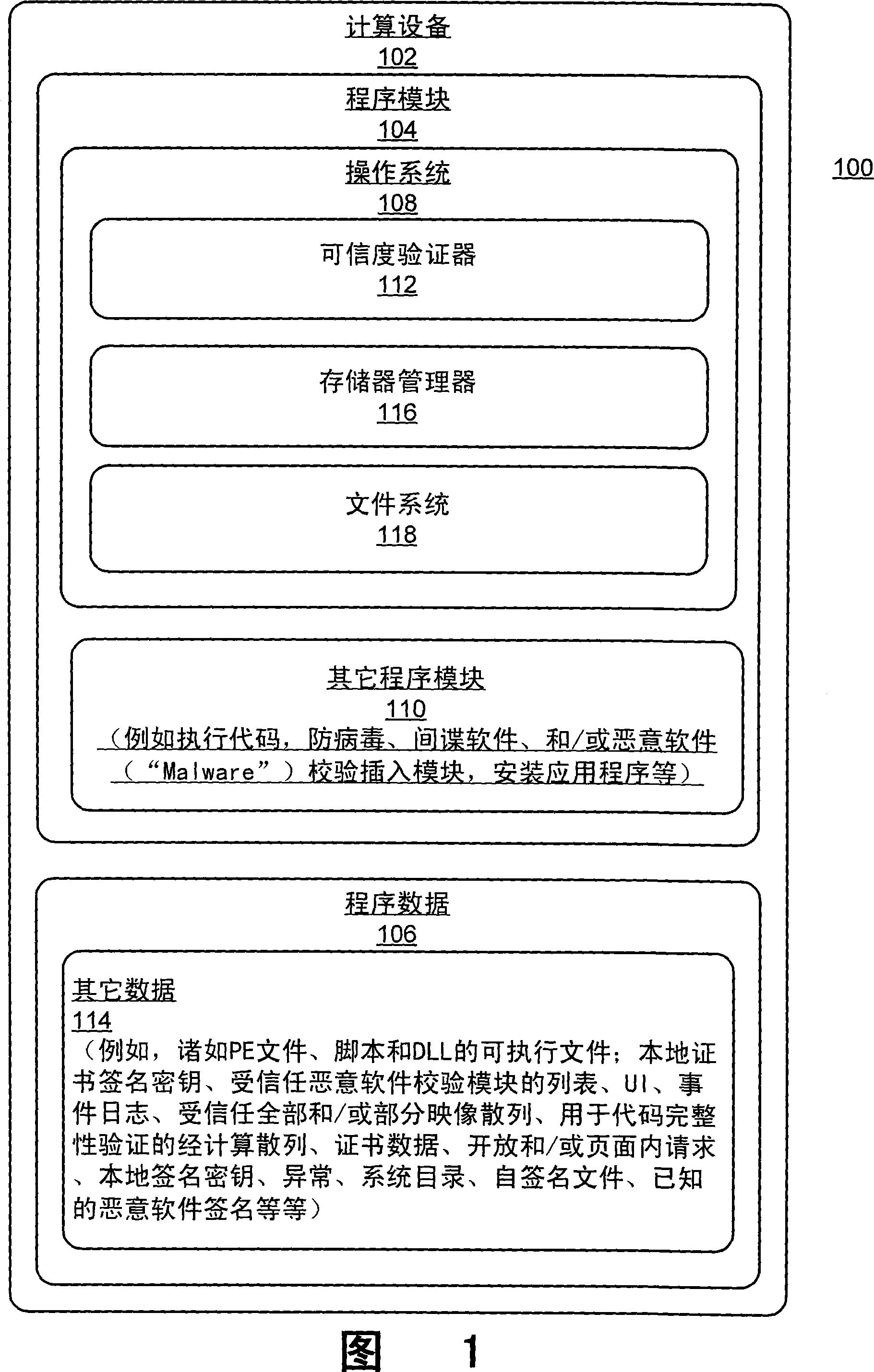
Systems and methods for verifying trust of executable files
Systems and methods for validating integrity of an executable file are described. In one aspect, the systems and methods determine that an executable file is being introduced into a path of execution. The executable file is then automatically evaluated in view of multiple malware checks to detect if the executable file represents a type of malware. If the executable file represents a type of malware, a protection path is implemented.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com