Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
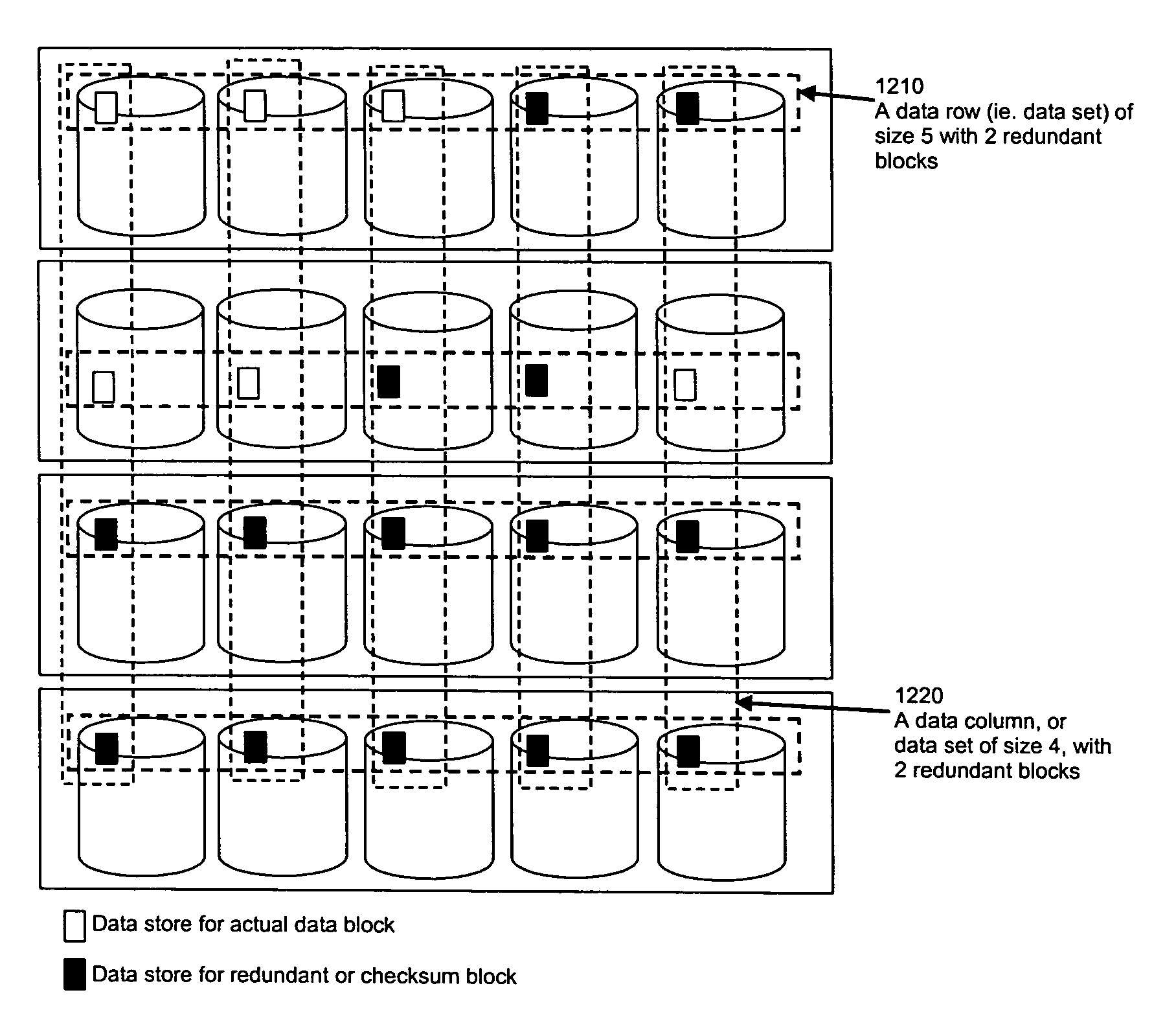
1608 results about "Checksum" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
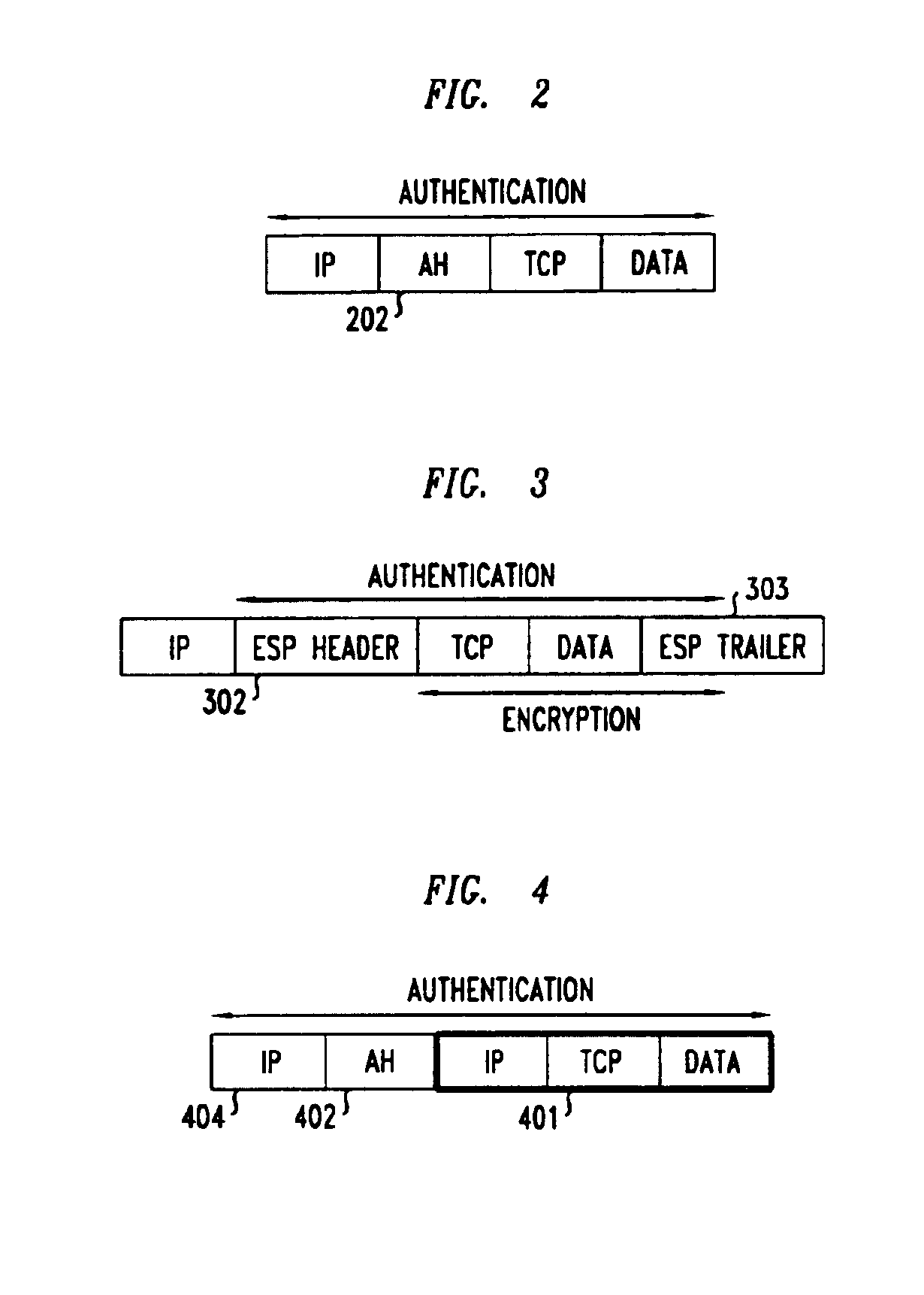
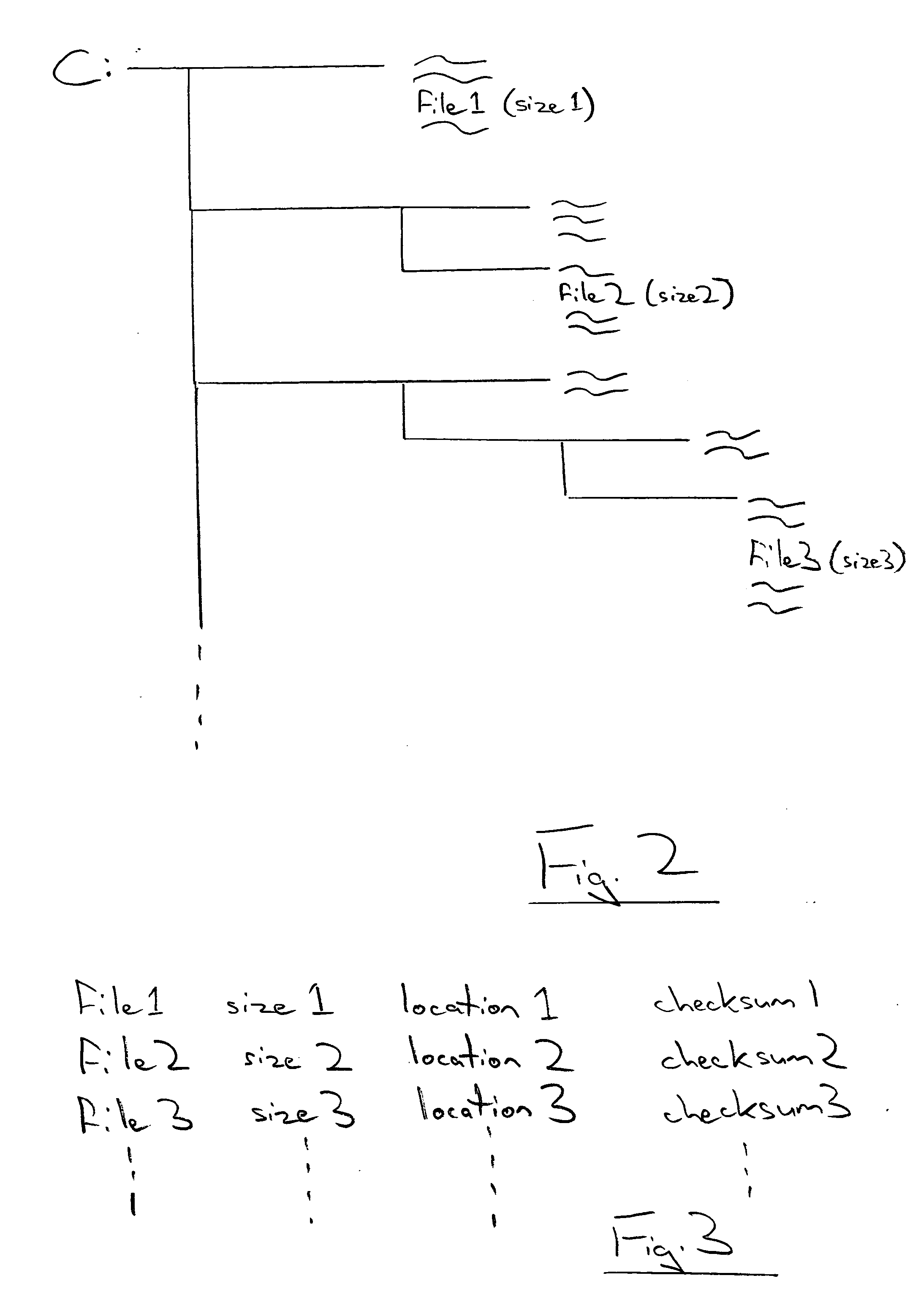
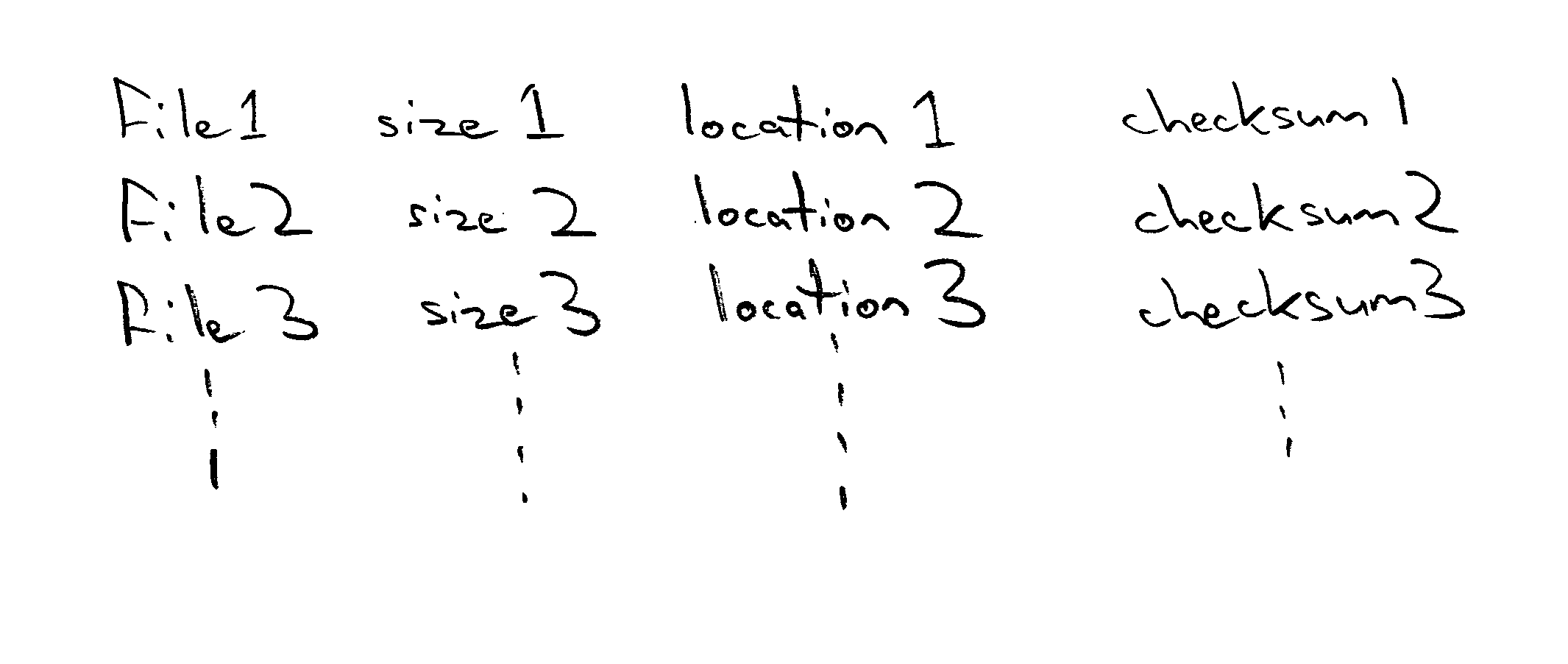
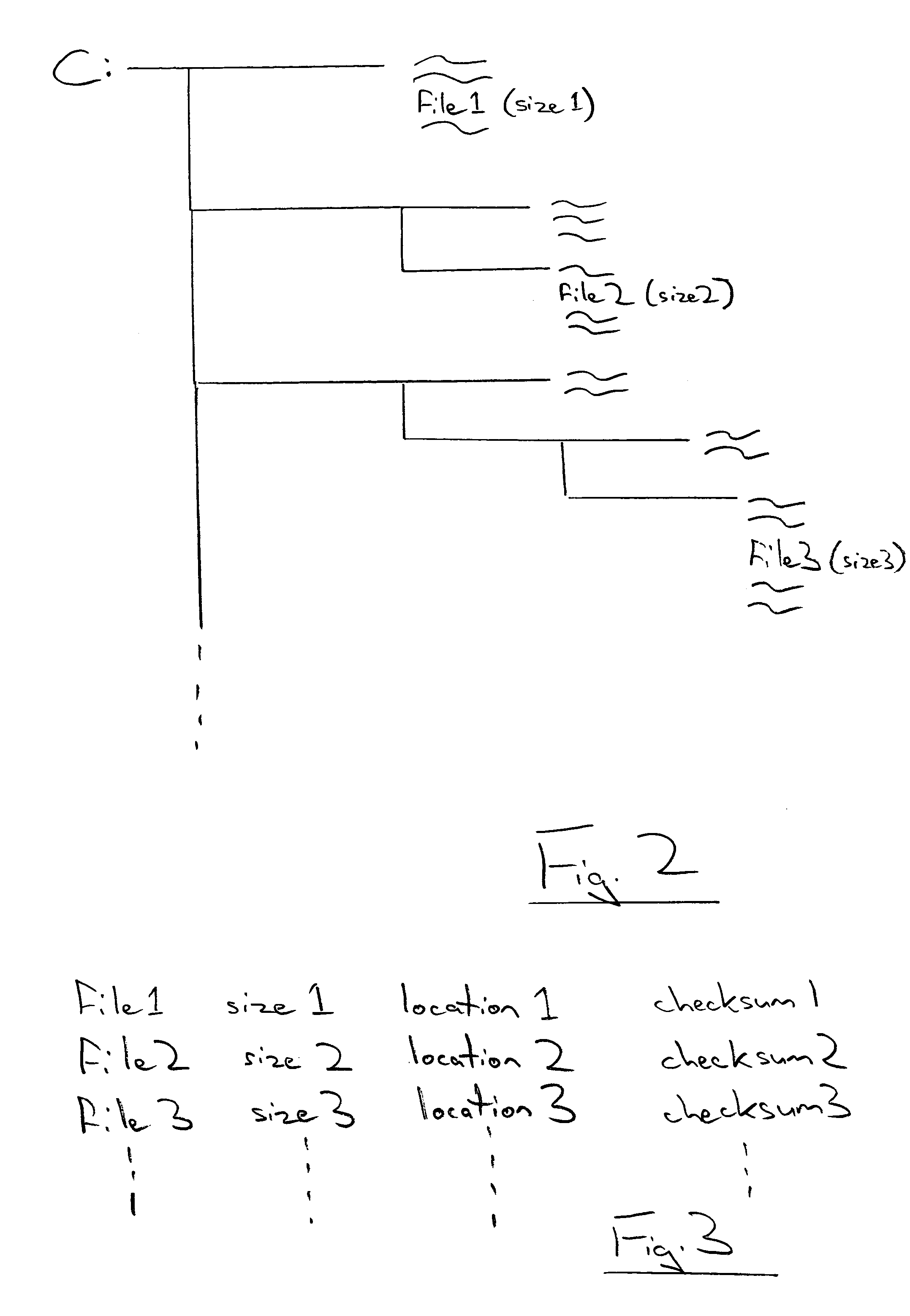
A checksum is a small-sized datum derived from a block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage. It is usually applied to an installation file after it is received from the download server. By themselves, checksums are often used to verify data integrity but are not relied upon to verify data authenticity.
Interference protection
InactiveUS7239657B1Memory record carrier reading problemsTransmissionInterference resistanceChecksum
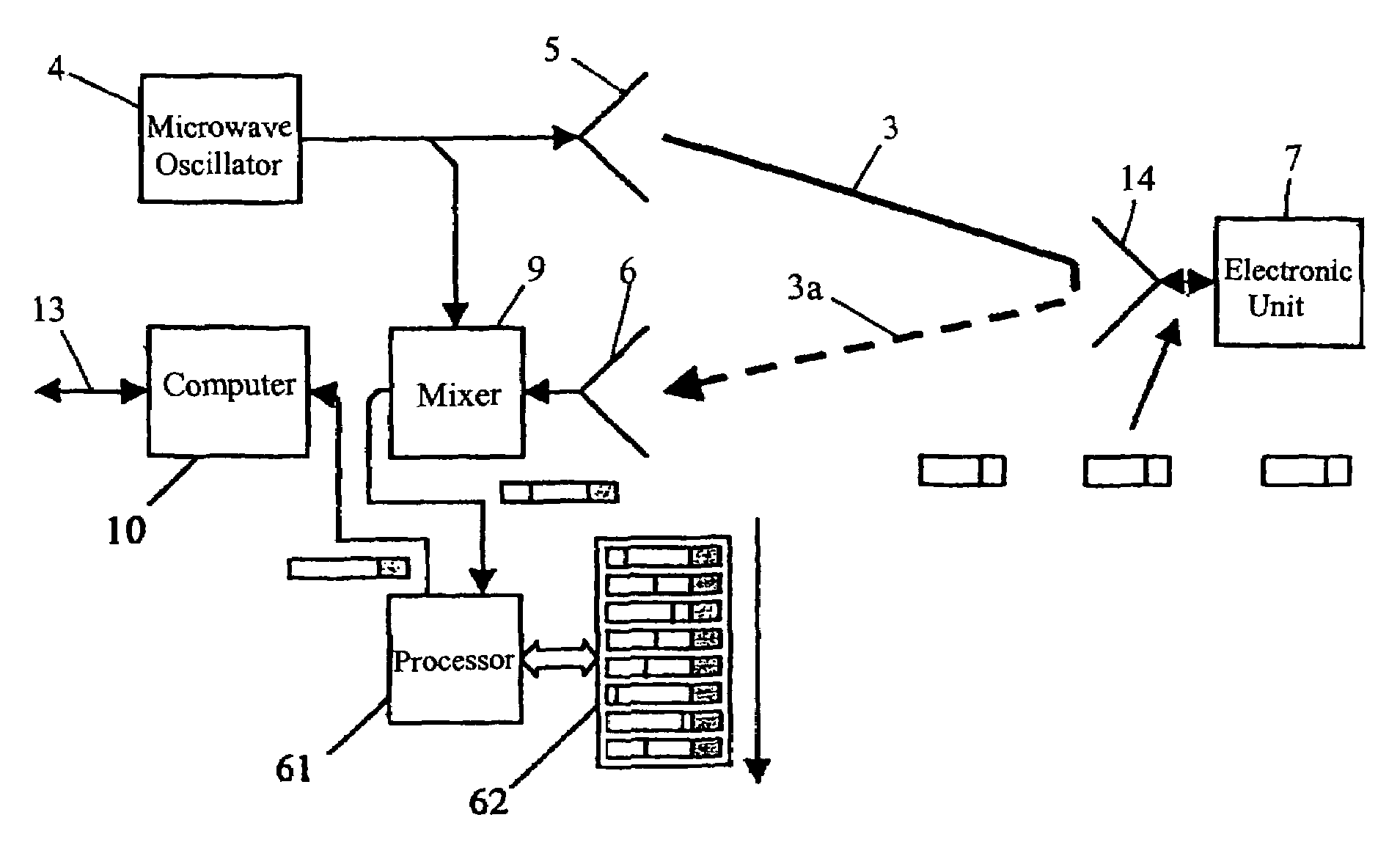
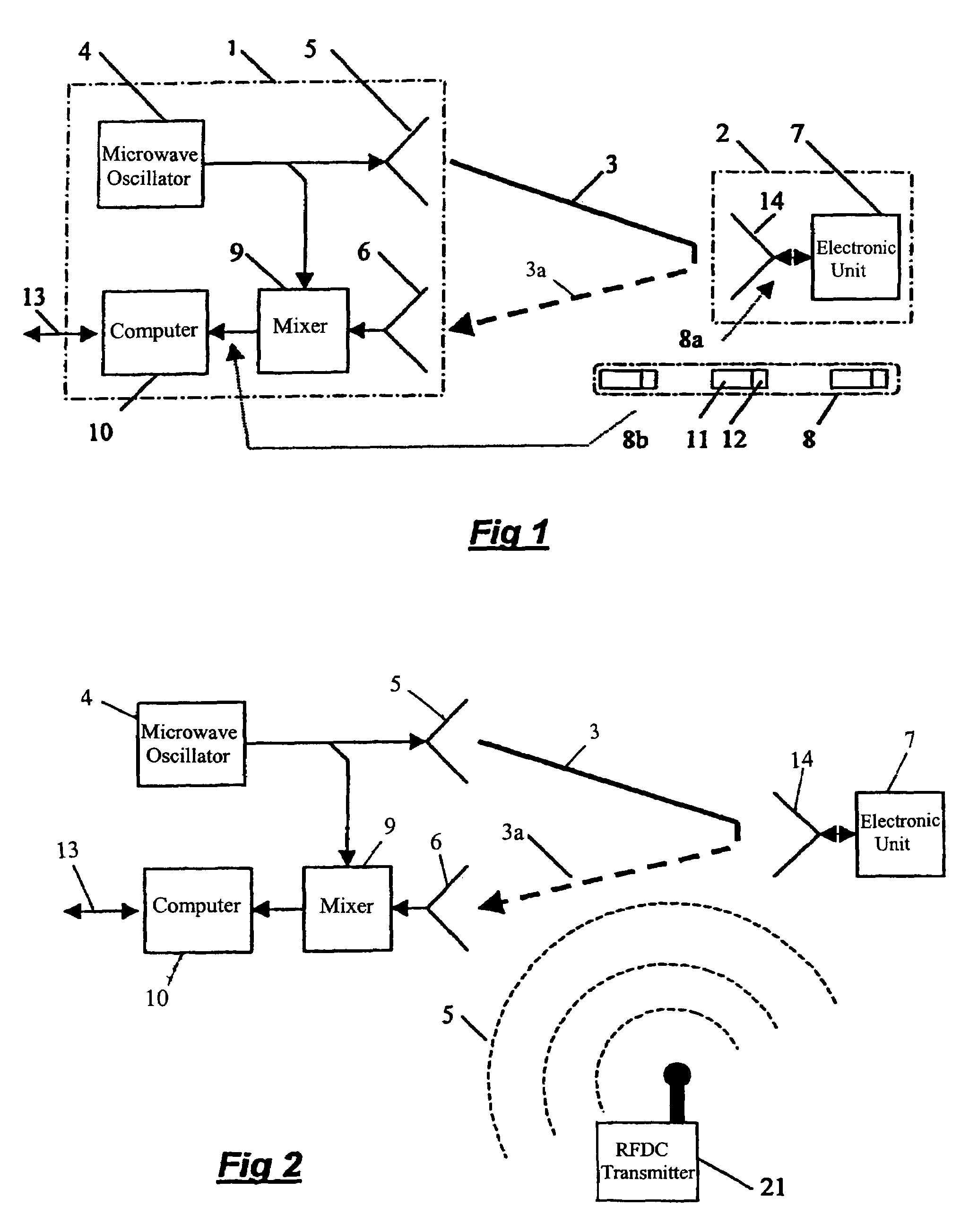
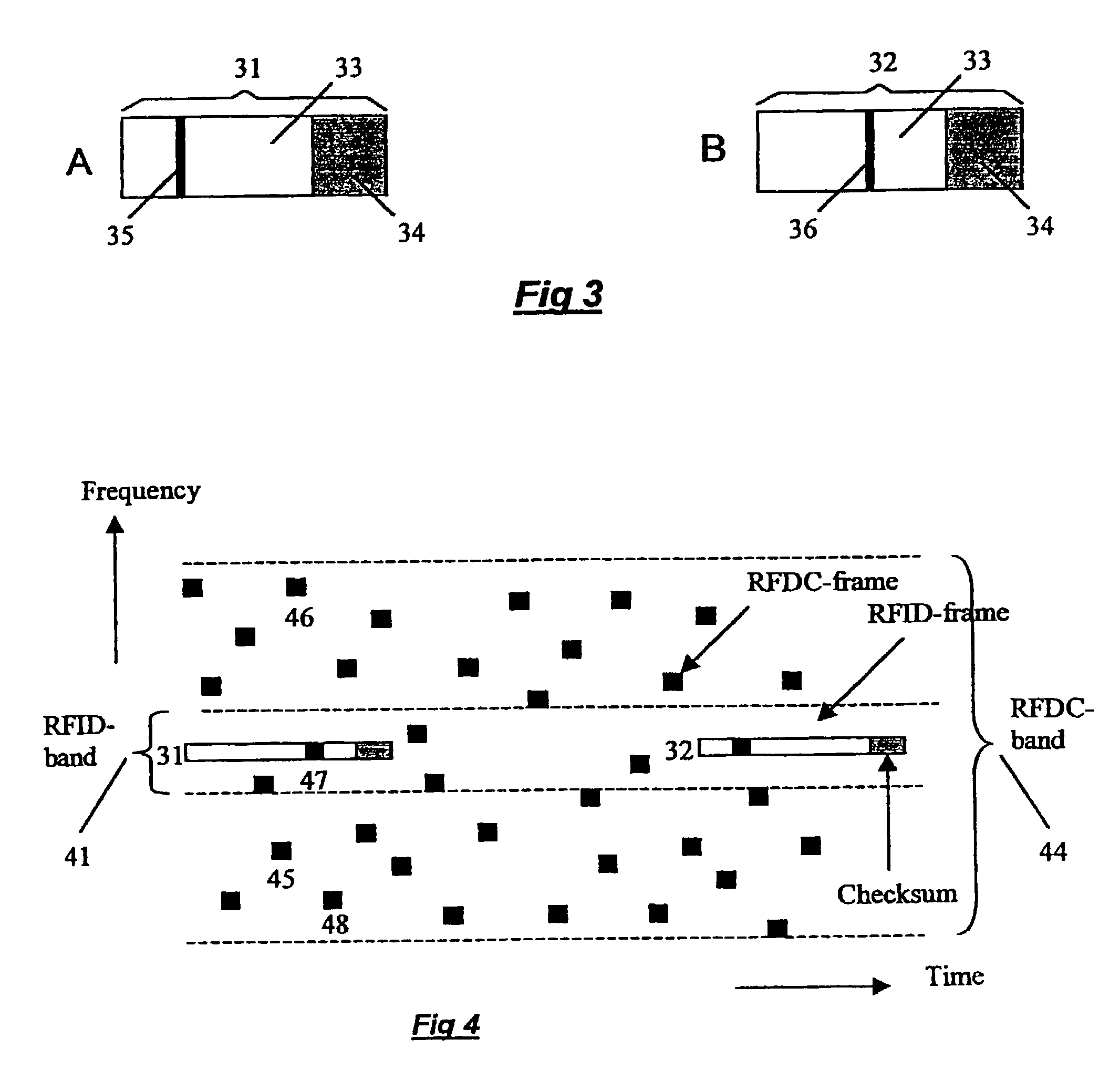
Apparatus and a method for enhancing the interference resistance of so-called RFID systems, wherein identification messages delivered from an identification device are longer than the time for which an anticipated interference or disturbance is calculated to continue, and wherein the messages contain redundancy, such as a checksum. The messages are delivered from the identification device repetitively, and are redundancy checked. In the event of any discrepancy in the redundancy check, such as when the checksum is checked against the data content of the message and is found in disagreement, successive messages are checked bit for bit against each other. Any deviations between otherwise previously rejected messages are assumed to be due to external interference and are thus successively substituted until the redundancy check gives an accepted result, such as through the medium of a checksum check according to the so-called CRC method.
Owner:TAGMASTER AB
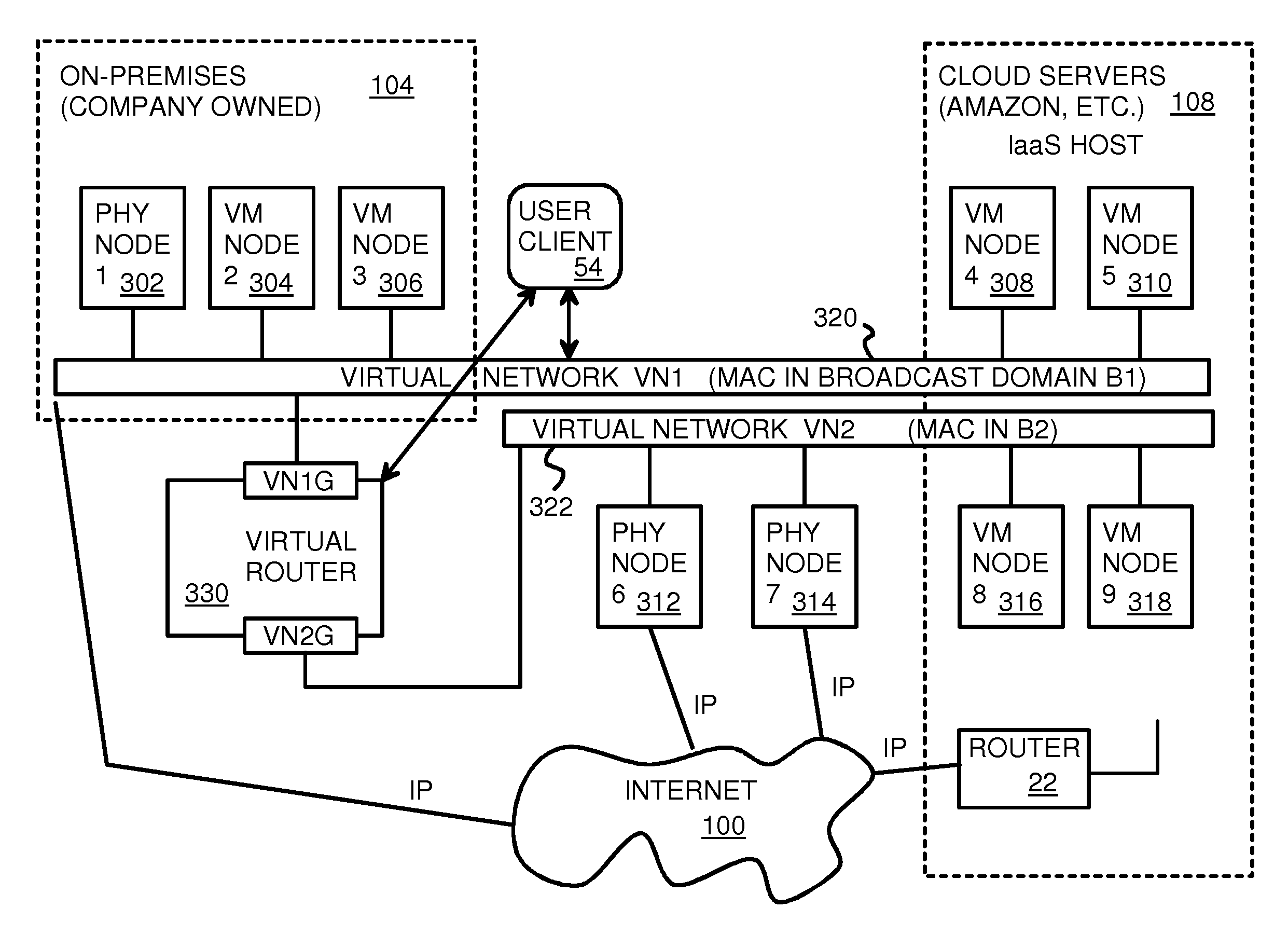
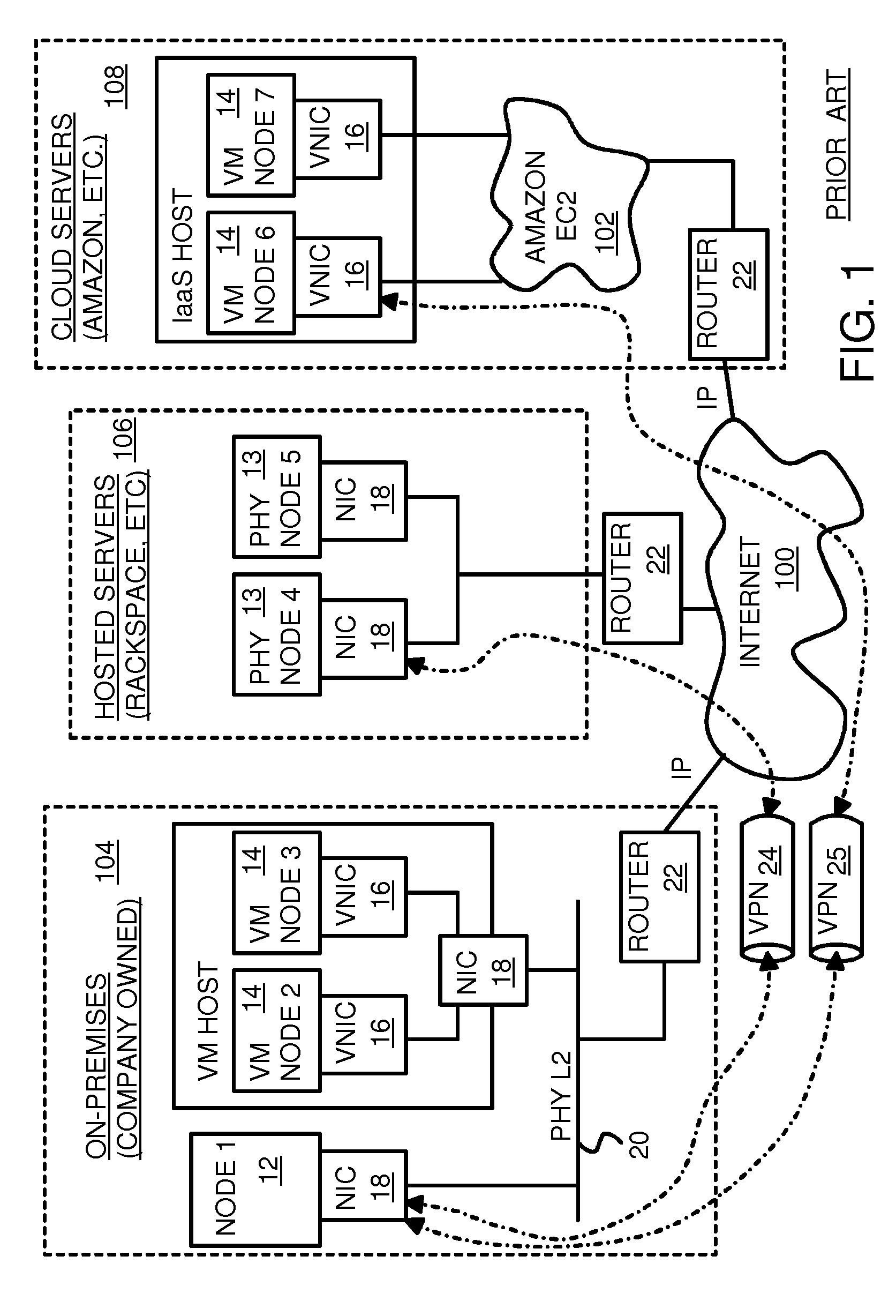
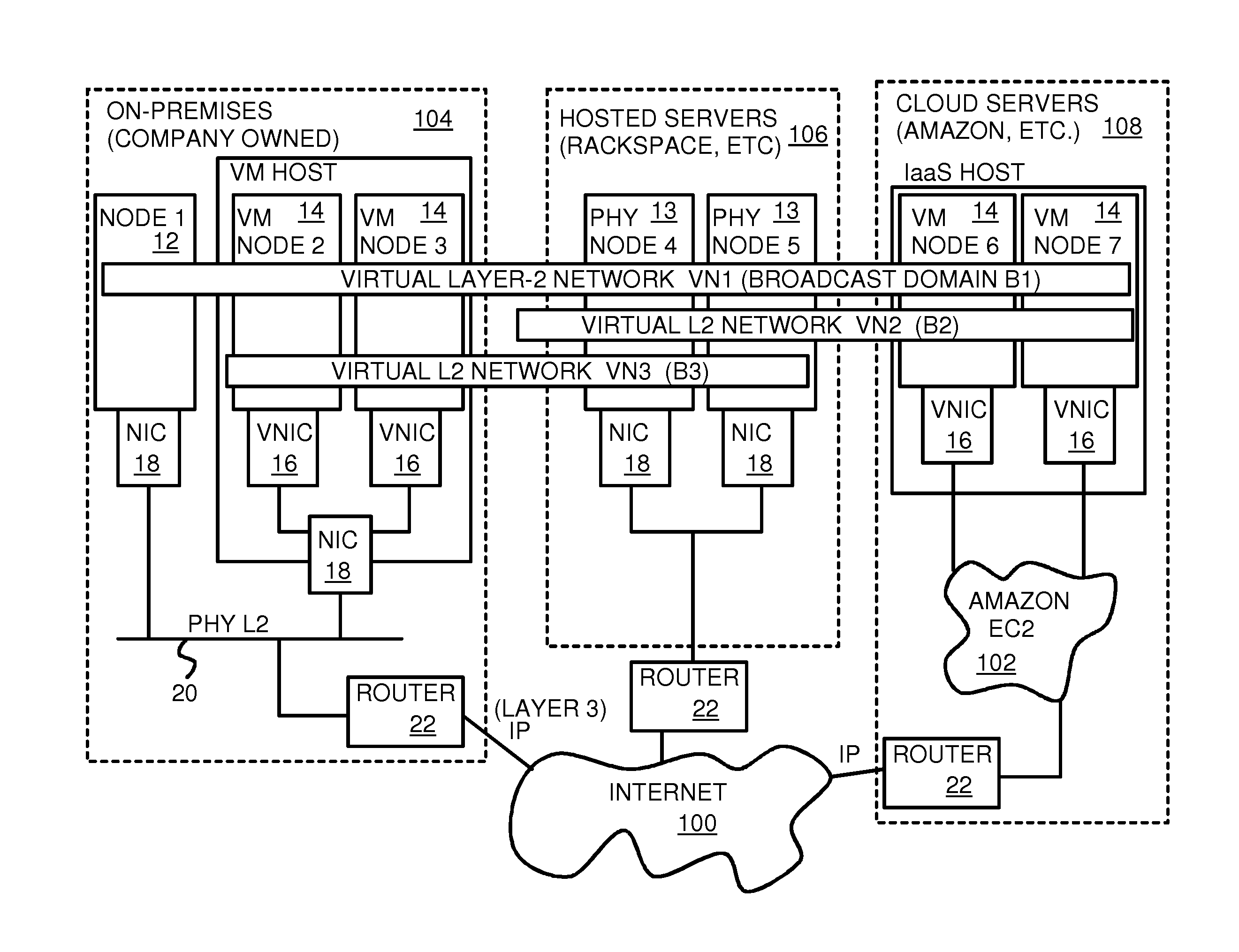
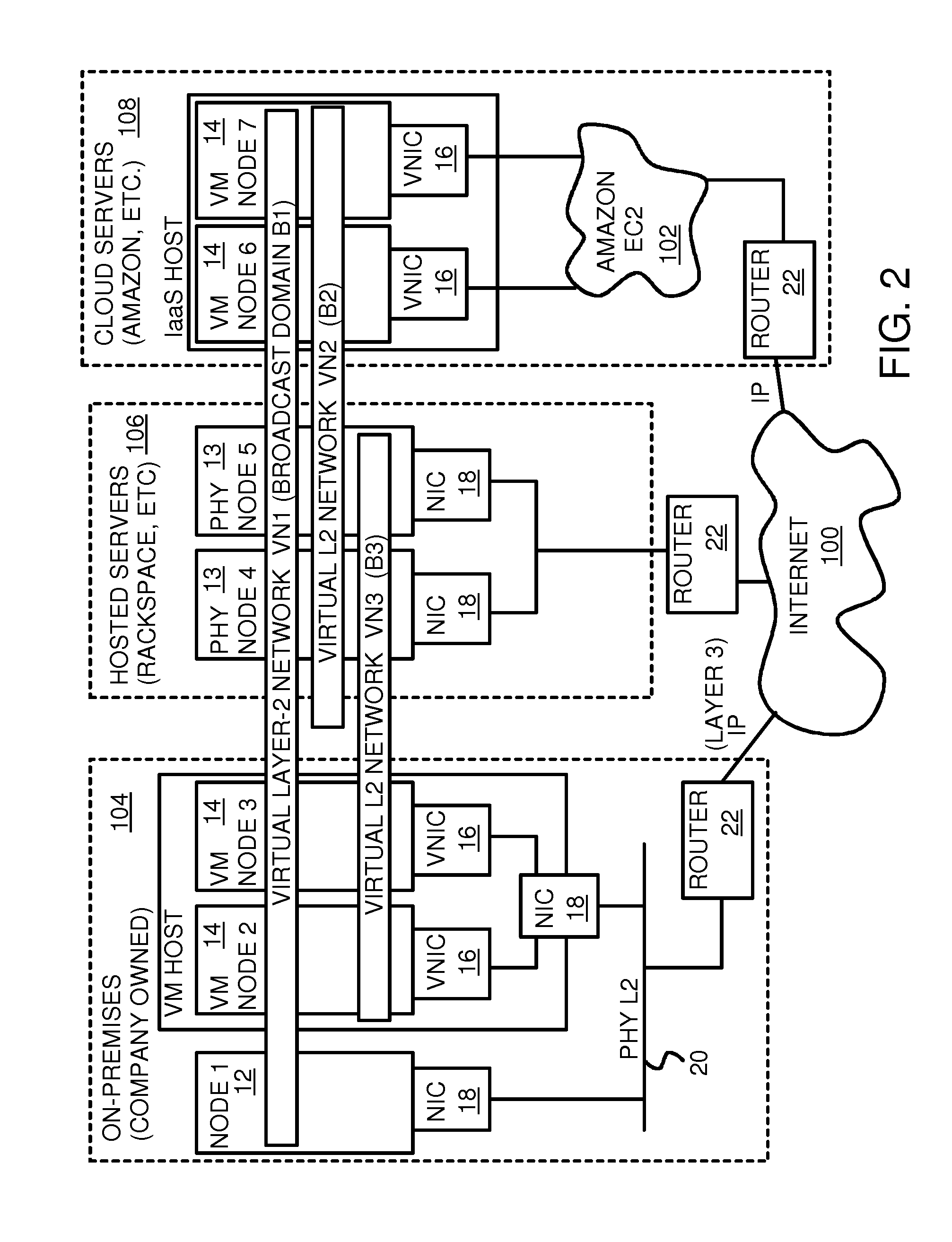
Fully distributed routing over a user-configured on-demand virtual network for infrastructure-as-a-service (IaaS) on hybrid cloud networks
A layer-3 virtual router connects two or more virtual networks. Virtual networks are overlaid upon physical networks. Each virtual network (VN) is a layer-2 network that appears to expand an organization's LAN using virtual MAC addresses. The network stack forms a virtual-network packet with a virtual gateway MAC address of the virtual router to reach a remote virtual network. A VN device driver shim intercepts packets and their virtual MAC and IP addresses and encapsulates them with physical packets sent over the Internet. A VN switch table is expanded to include entries for nodes on the remote virtual network so that all nodes on both virtual networks are accessible. A copy of the VN switch table is stored on each node by a virtual network management daemon on the node. A Time-To-Live field in the virtual-network packet is decremented for each virtual hop and a checksum recalculated.
Owner:CISCO TECH INC
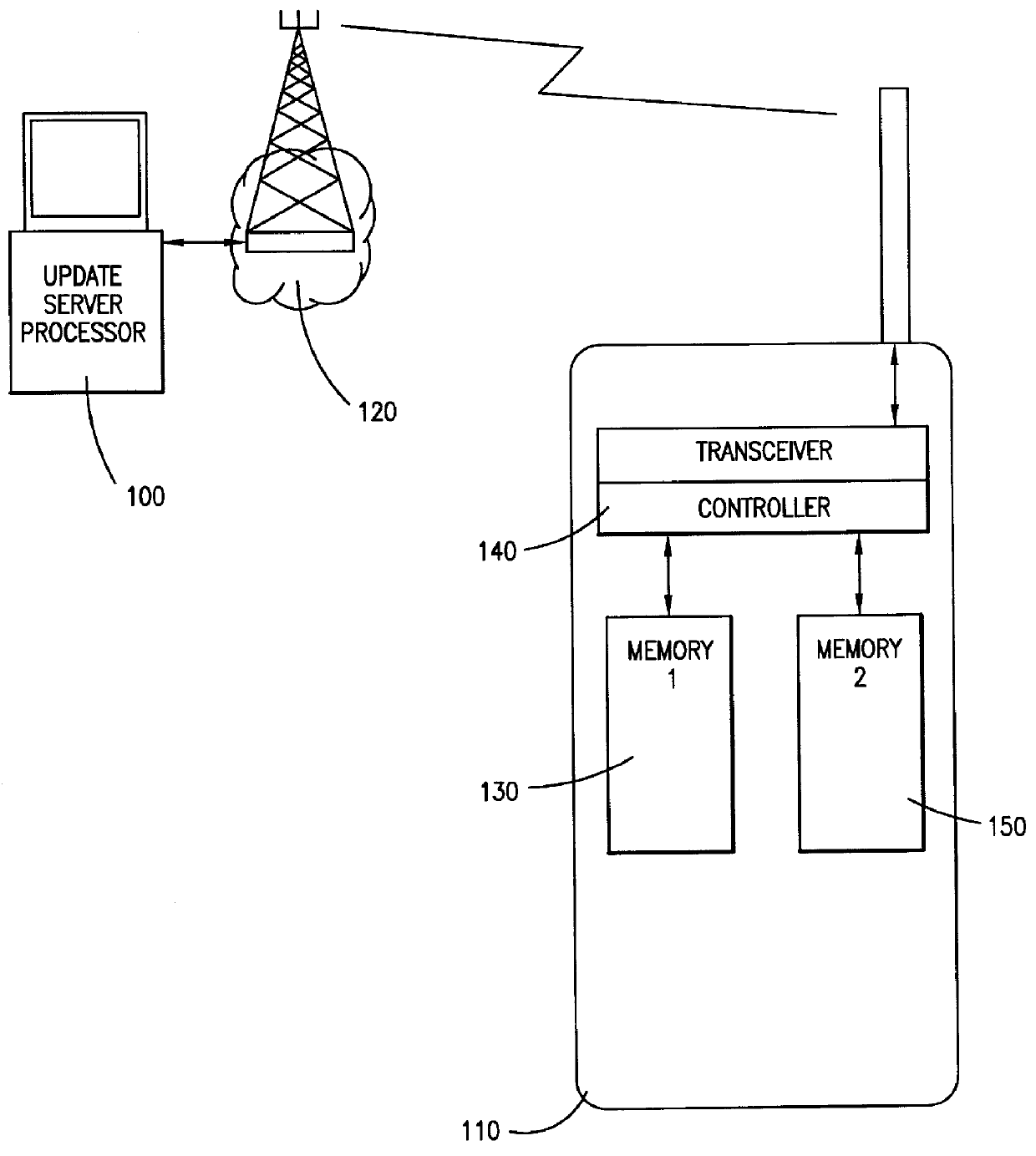
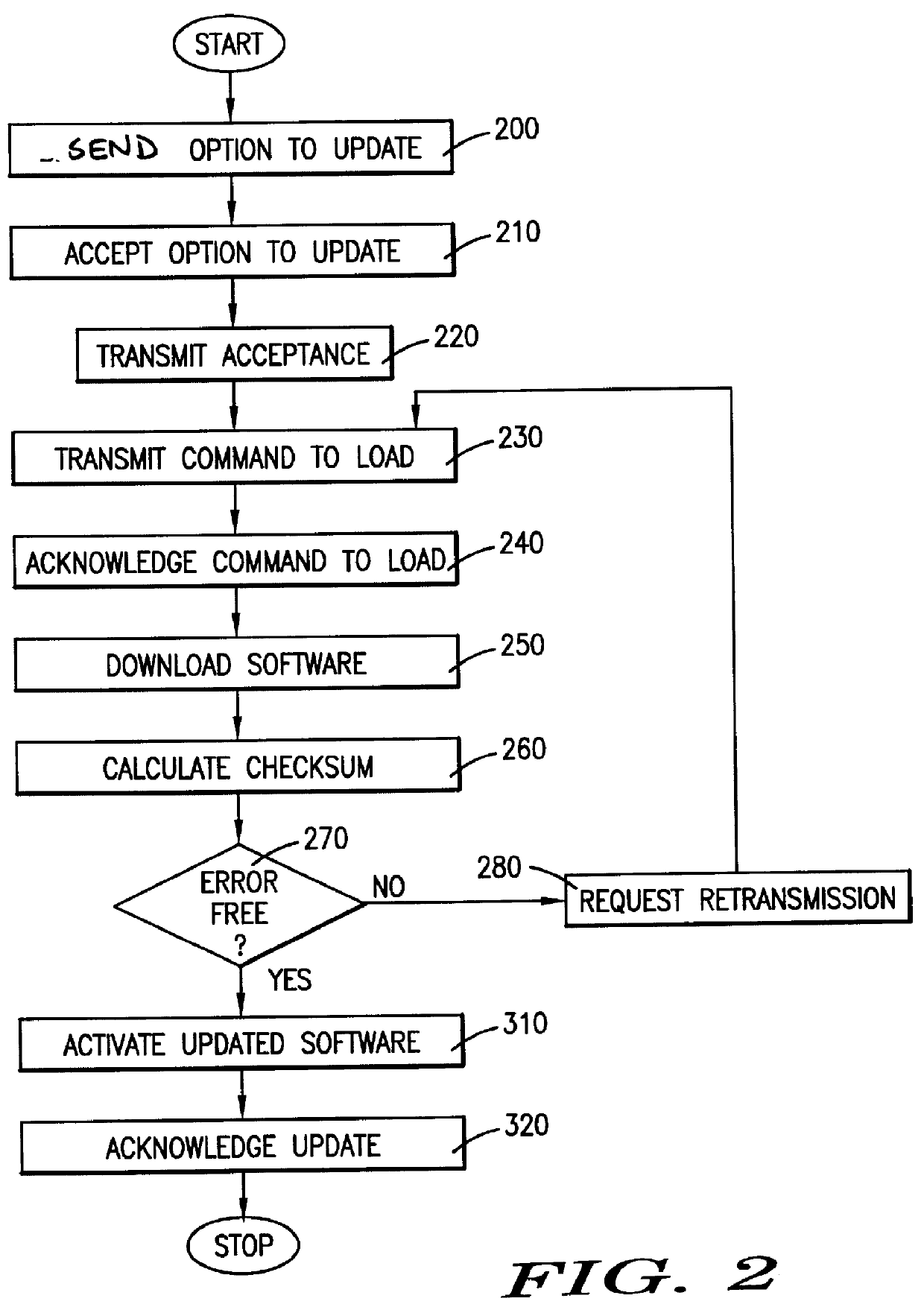
Method for downloading control software to a cellular telephone
InactiveUS6023620ACordless telephonesRadio/inductive link selection arrangementsChecksumControl software
The present invention comprises a method and apparatus for downloading software into a remotely located cellular telephone via wireless communication. The cellular telephone includes two memories for storing software with one memory storing the current software and the second memory available for downloading new software. The present invention further includes a processor in communication with the cellular telephone via cellular telephone network. The processor contains the new software and controls the downloading of the software from the processor into the cellular telephone memory. The cellular telephone includes a controller for loading the received software into the cellular telephone memory and for performing a checksum on the new software.
Owner:TELEFON AB LM ERICSSON (PUBL)
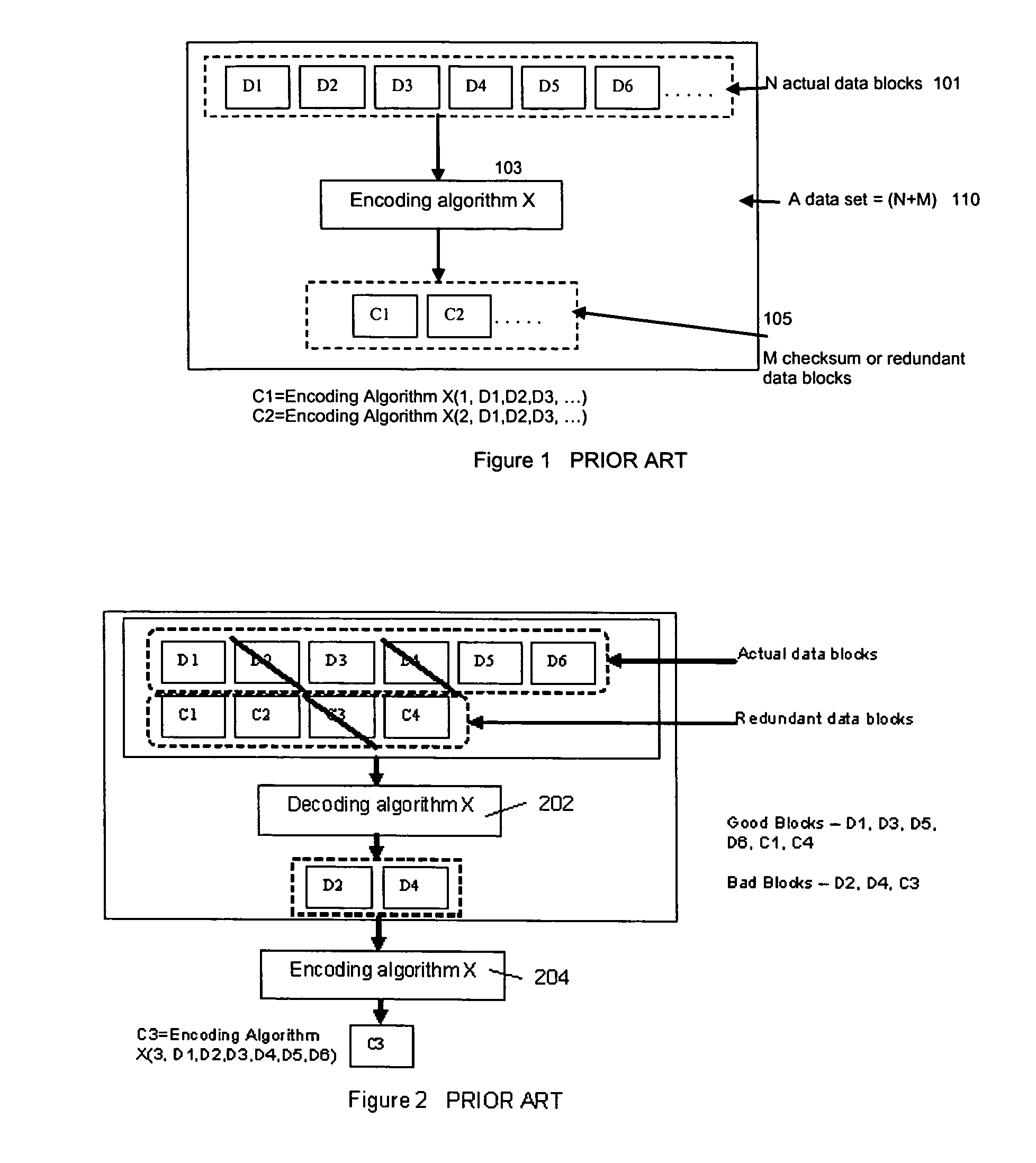
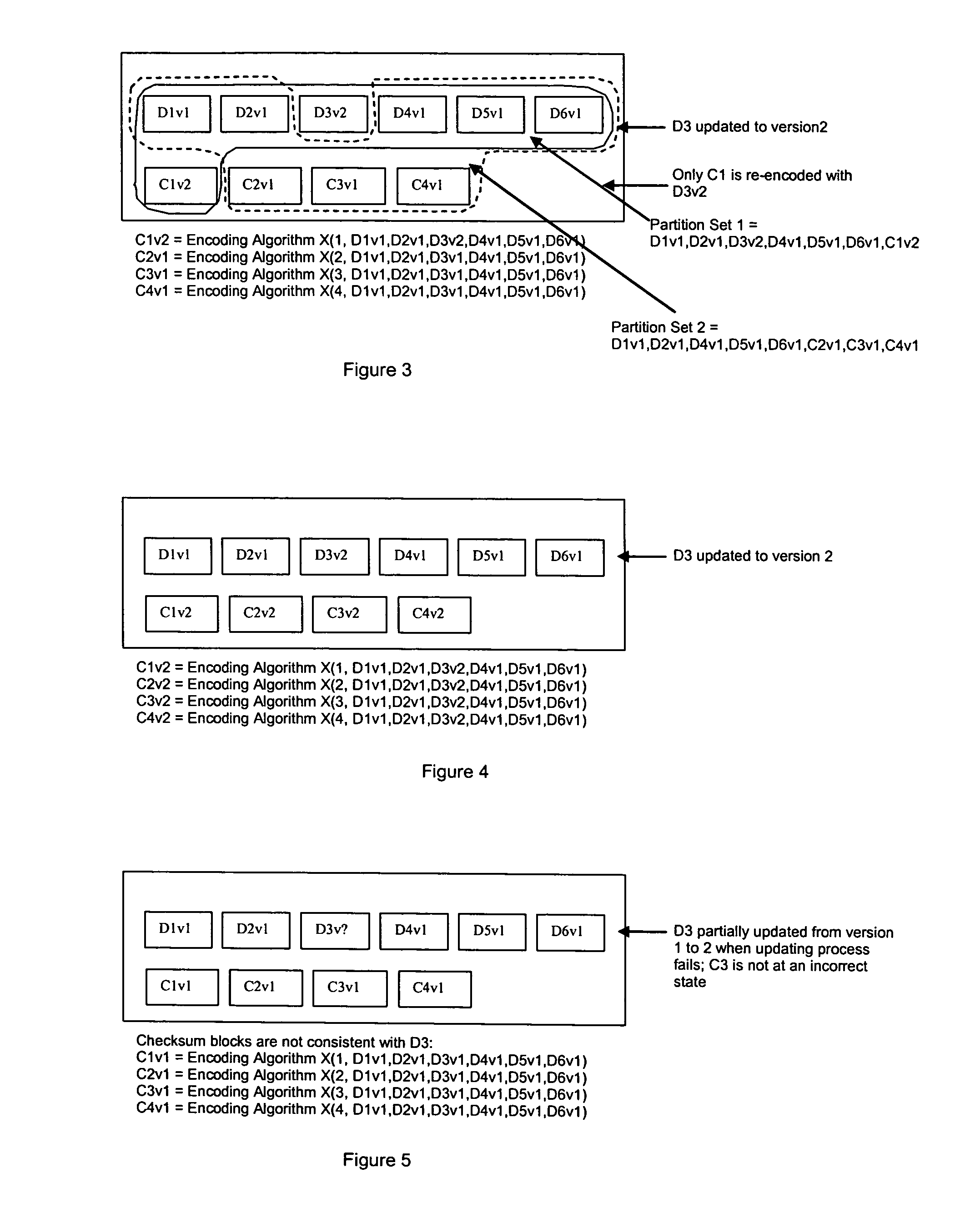
Method for erasure coding data across a plurality of data stores in a network
ActiveUS7681104B1Maintain data consistencyEffective applicationError preventionCode conversionData setTheoretical computer science
An efficient method to apply an erasure encoding and decoding scheme across dispersed data stores that receive constant updates. A data store is a persistent memory for storing a data block. Such data stores include, without limitation, a group of disks, a group of disk arrays, or the like. An encoding process applies a sequencing method to assign a sequence number to each data and checksum block as they are modified and updated onto their data stores. The method preferably uses the sequence number to identify data set consistency. The sequencing method allows for self-healing of each individual data store, and it maintains data consistency and correctness within a data block and among a group of data blocks. The inventive technique can be applied on many forms of distributed persistent data stores to provide failure resiliency and to maintain data consistency and correctness.
Owner:QUEST SOFTWARE INC
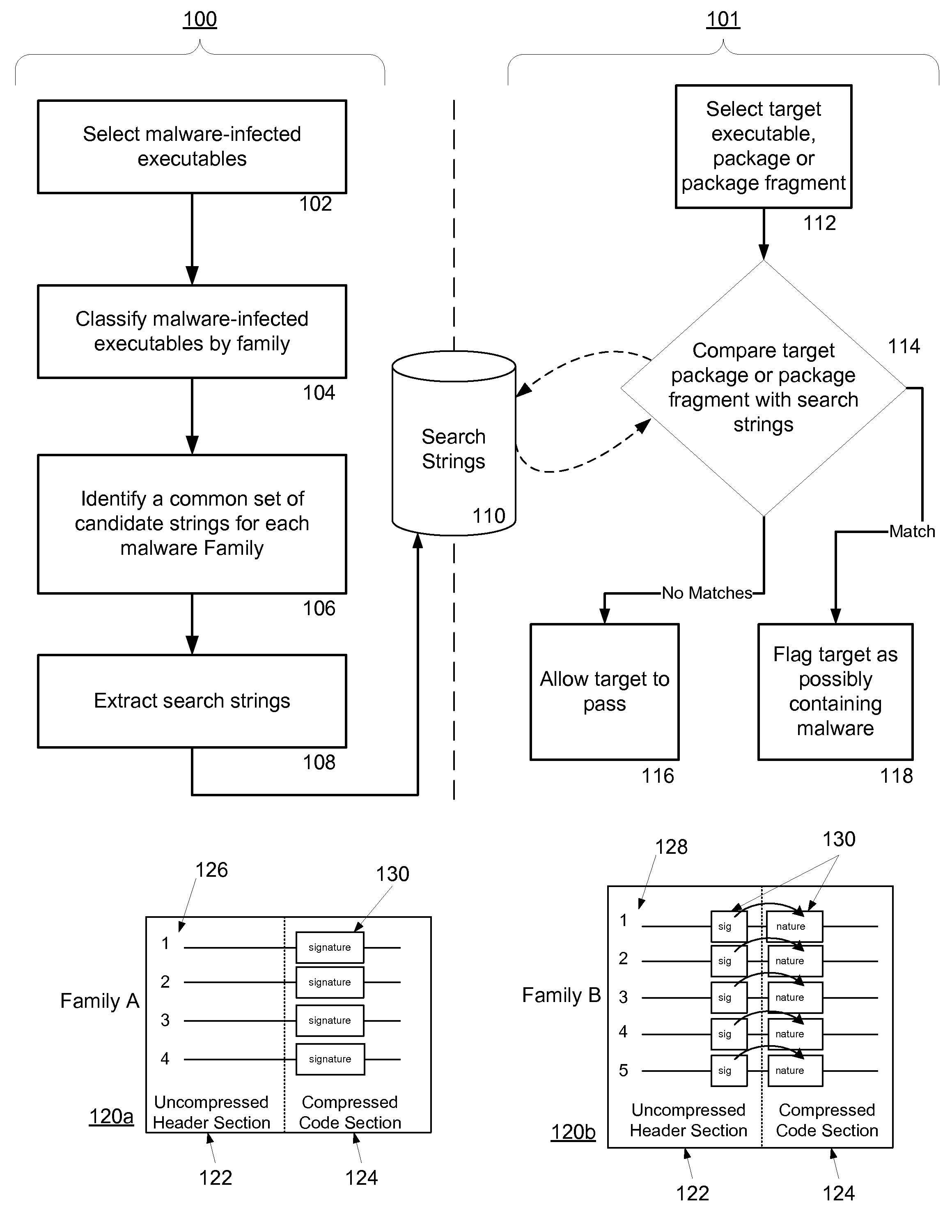
Non-Signature Malware Detection System and Method for Mobile Platforms
ActiveUS20070240221A1Suitable for useReliable detectionMemory loss protectionError detection/correctionEntry pointChecksum
A system and method for detecting malware on a mobile platform in a mobile network. The system and method verifies that an executable is malware-free by computing the checksum of the executable and comparing that checksum with a checksum obtained from a malware-free copy of the executable. The checksum is a sum of all 32-bit values in a code section and an import section of said executable, a byte sequence at an entry point in said executable, a size descriptor of an import table, a size descriptor of said import section, a cyclic redundancy check of said executable, or a combination thereof.
Owner:PULSE SECURE
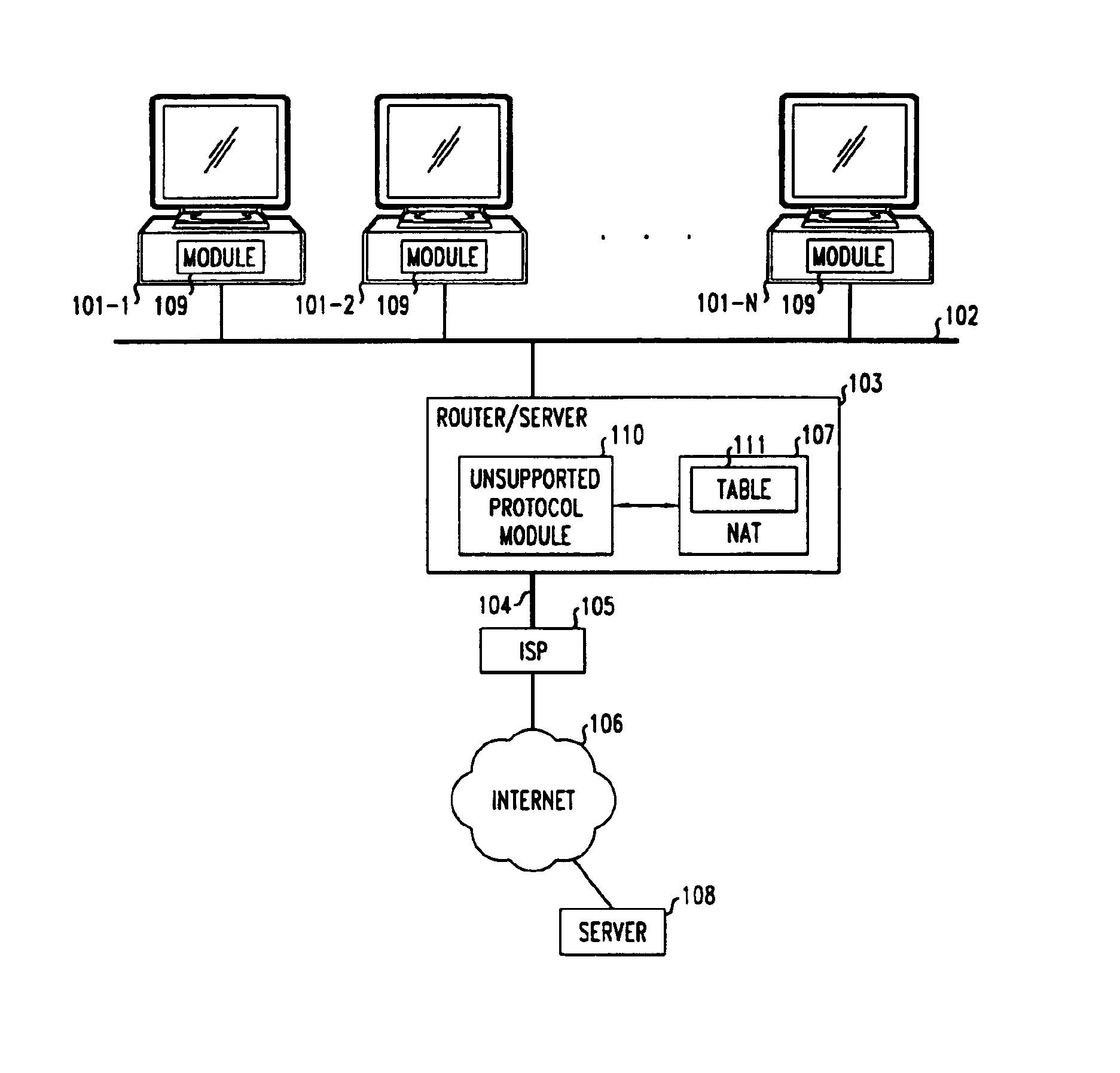
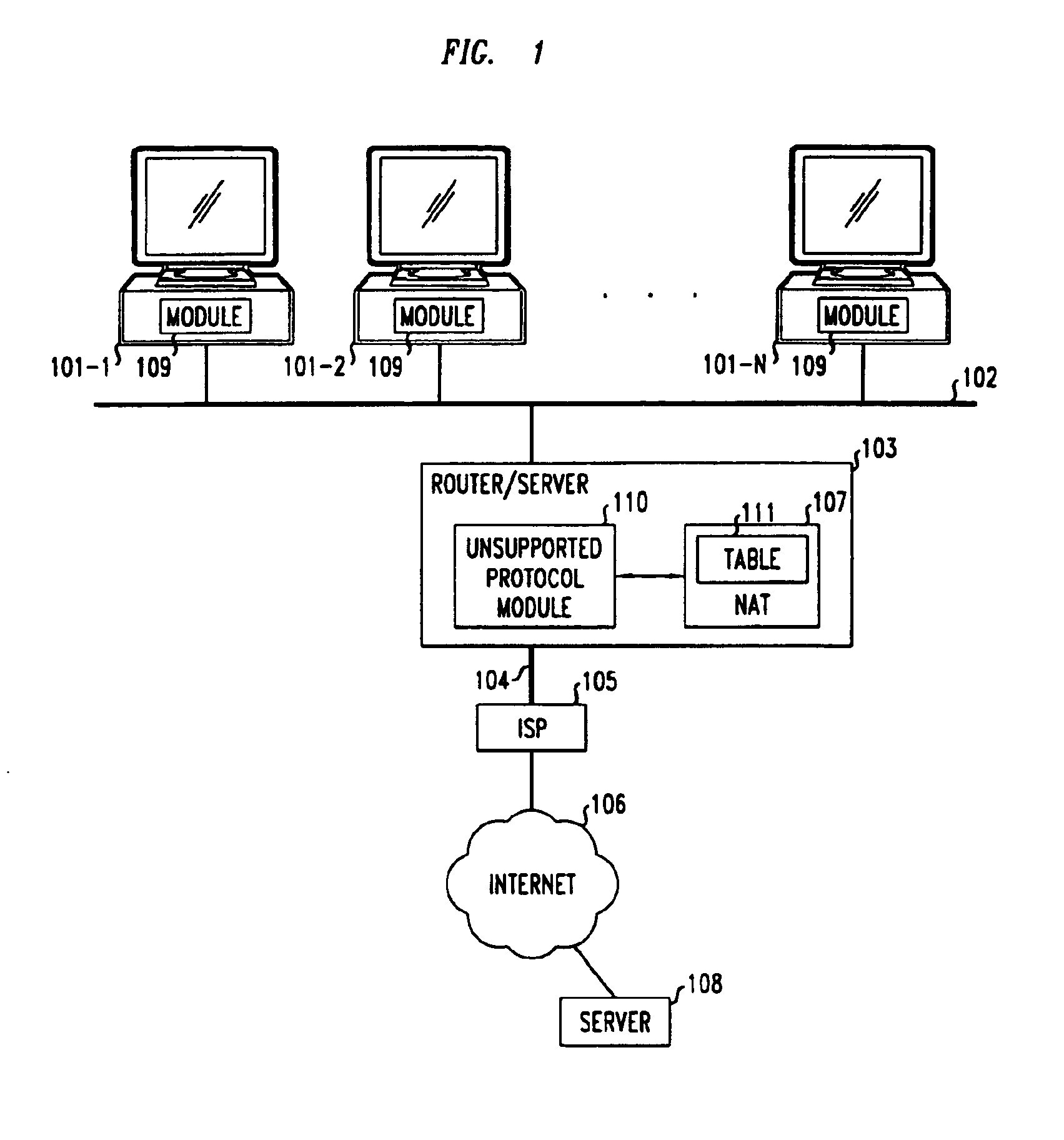
Method and apparatus for extending network address translation for unsupported protocols
InactiveUS6886103B1Ensure safetyMultiple digital computer combinationsProgram controlExpiration TimeIp address
Clients that are connected on a private network and which are assigned a private IP address that is not routable on the Internet can connect to the Internet through a router / server that includes a network address translator (NAT). For outgoing packets, the NAT translates the client's private source IP address and generalized port number (GPN) to the NAT's global IP address and GPN. For incoming packets sent to the NAT's global IP address and GPN, the NAT translates the global destination IP address and GPN to the client's private IP address and GPN. For protocols which cannot be directly supported by the NAT, such as those in the IPSec security protocol suite, the NAT is extended by creating in the NAT's translation table an entry that associates, for a specific unsupported protocol, a client's private IP address and GPN, the NAT's global IP address and GPN, and a foreign address on the Internet, that is valid until a specified or default expiration time. Outgoing packets from the client to that foreign address and incoming packets from that foreign address to the NAT's global IP address and GPN are translated according to the entry until the entry expires. In associations with these translations to outgoing and incoming packets, the client implements any Application Layer Gateway (ALG) that would otherwise be implemented at the NAT. Further, at the client, outgoing packets are modified before being transmitted so as to pre-compensate for the effects of the translations. Incoming packets at the client from the NAT are similarly modified so as to post-compensate for the effects of the translations. For the IPSec protocol, these modification include adjusting the checksum in the TCP or UDP header to account for IP address and TCP or UDP port number translations.
Owner:ALCATEL-LUCENT USA INC
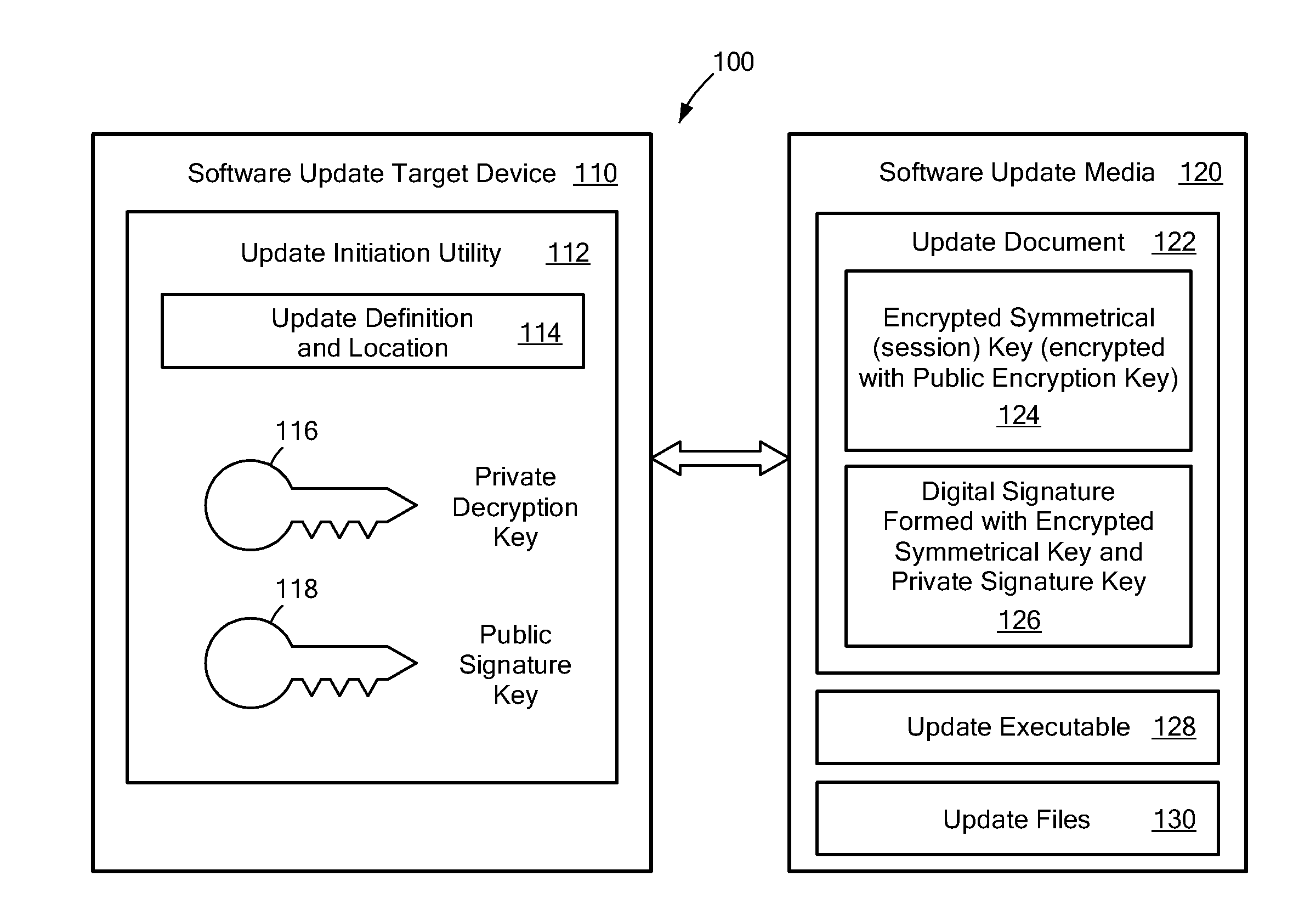
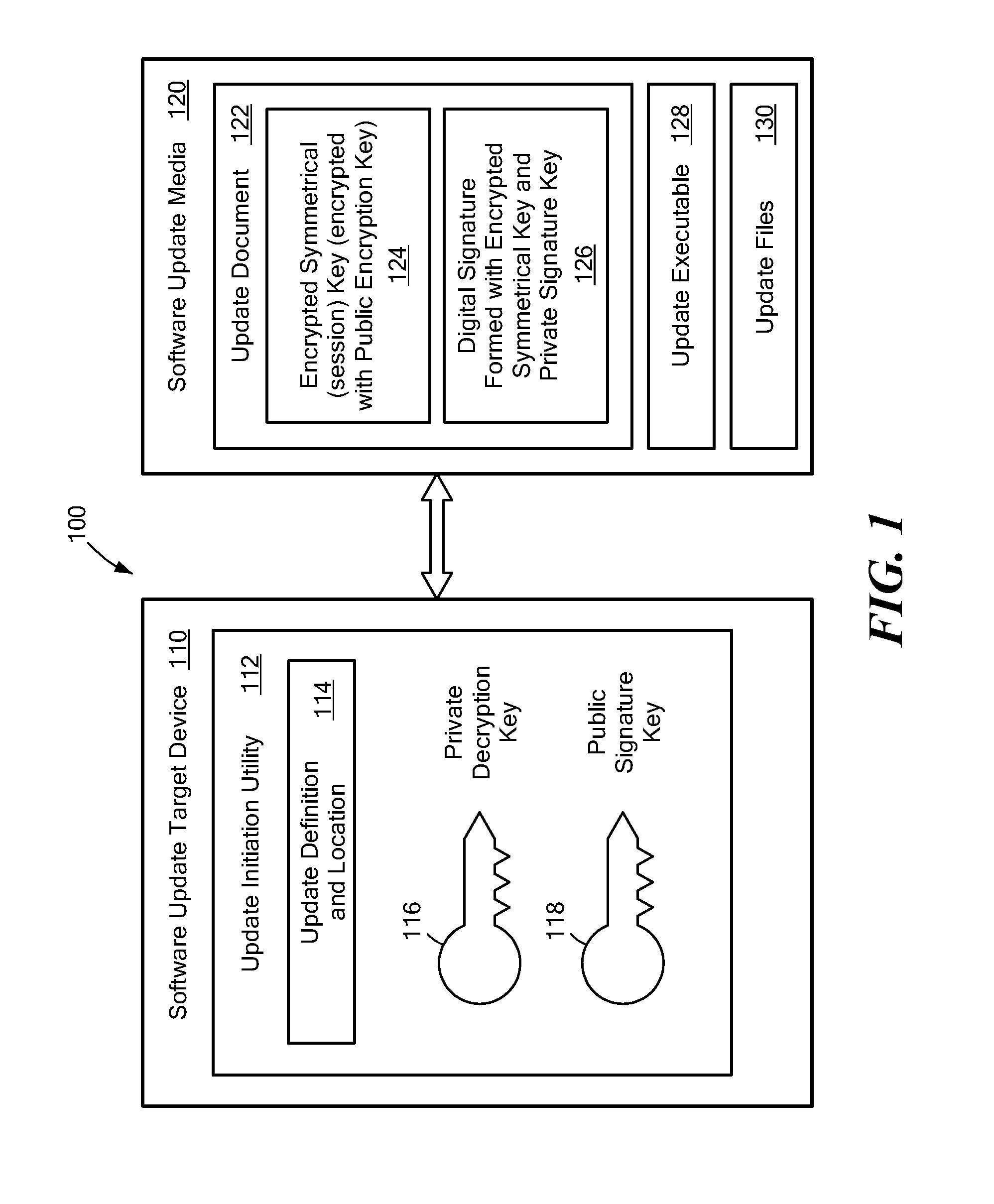
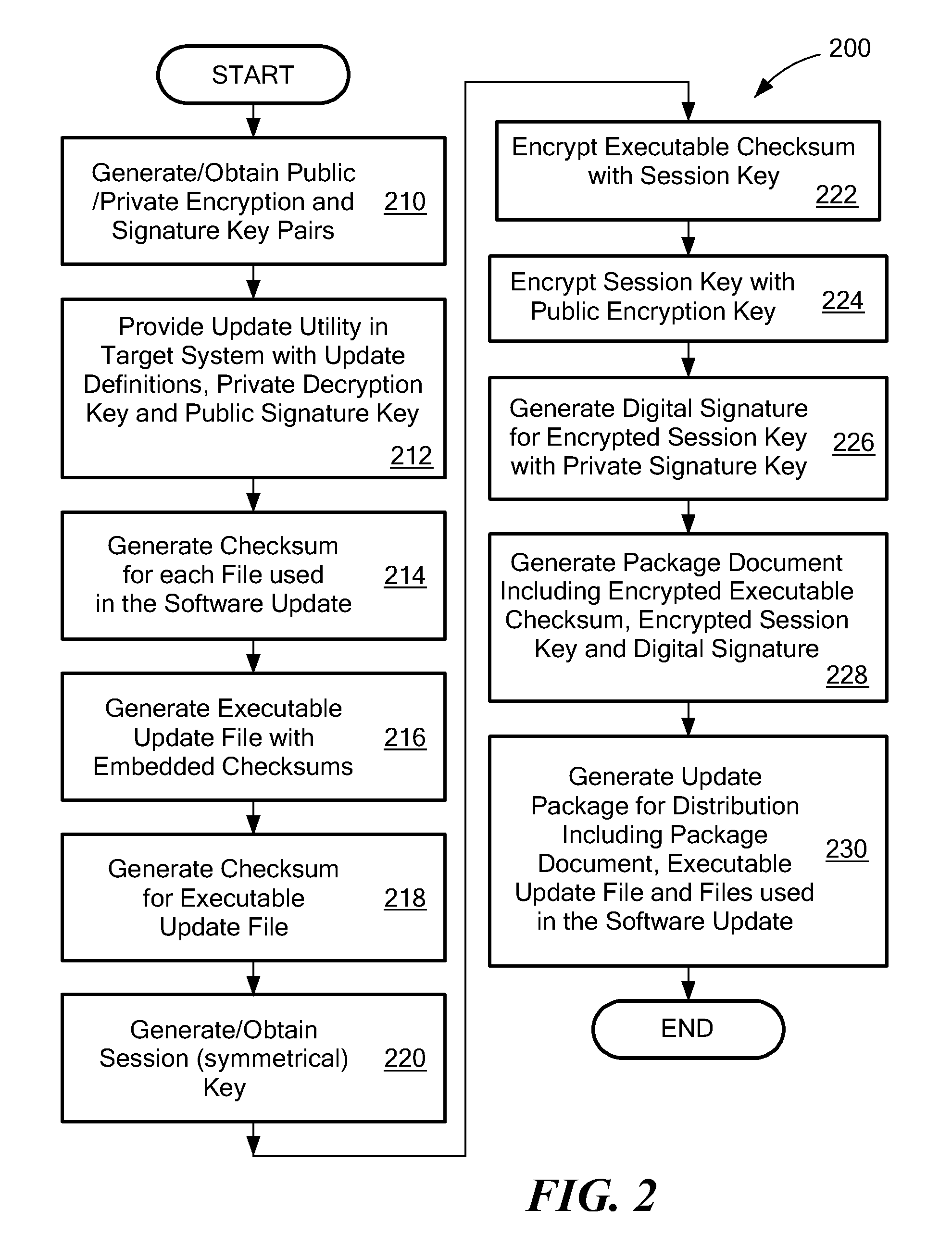
System and Method for Secure Software Update
ActiveUS20130318357A1User identity/authority verificationDigital data protectionThird partySecurity software
A secure software update provides an update utility with an update definition, a private encryption key and a public signature key to a target device. A software update package is prepared on portable media that includes an executable update program, a checksum for the program that is encrypted with a symmetrical key, an encrypted symmetrical key that is encrypted with a public encryption key and a digital signature prepared with a private signature key. The update process authenticates the digital signature, decrypts the symmetrical key using the private encryption key, and decrypts the checksum using the symmetrical key. A new checksum is generated for the executable update program and compared to the decrypted checksum. If inconsistencies are detected during the update process, the process is terminated. Otherwise, the software update can be installed with a relatively high degree of assurance against corruption, viruses and third party interference.
Owner:SIEMENS HEALTHCARE DIAGNOSTICS INC
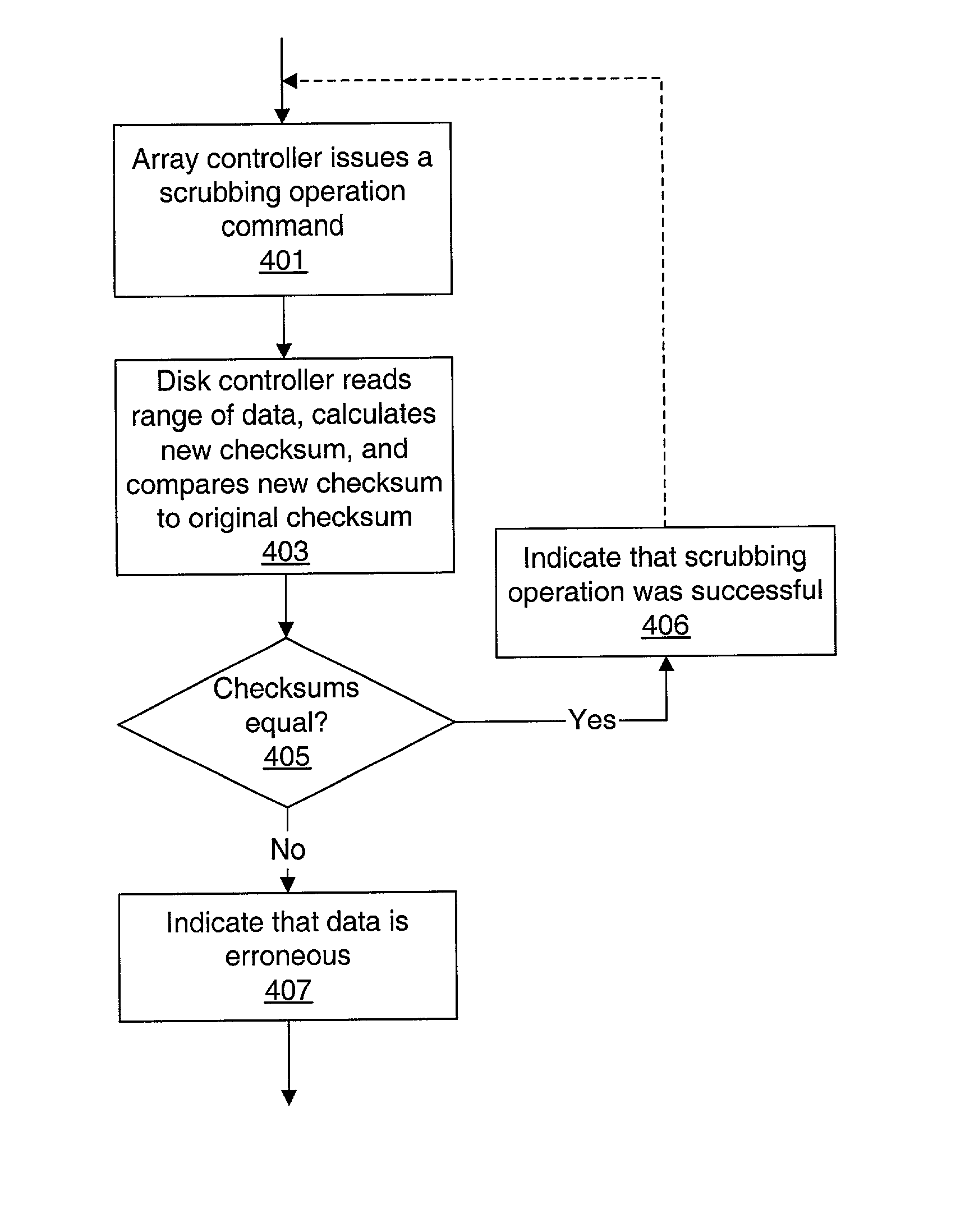
Storage array employing scrubbing operations at the disk-controller level
A storage system comprises a storage array controller and a storage array, which includes multiple disk drives and disk drive controllers. The storage array controller issues scrubbing operation commands to one or more of the disk drive controllers. In response, each disk drive controller that receives a scrubbing operation command reads data from within a data range from at least one of the disk drives, calculates a new checksum for the data, and compares the new checksum to a preexisting checksum for the data. If the new checksum doesn't equal the preexisting checksum, the data within the data range is determined to be erroneous.
Owner:ORACLE INT CORP
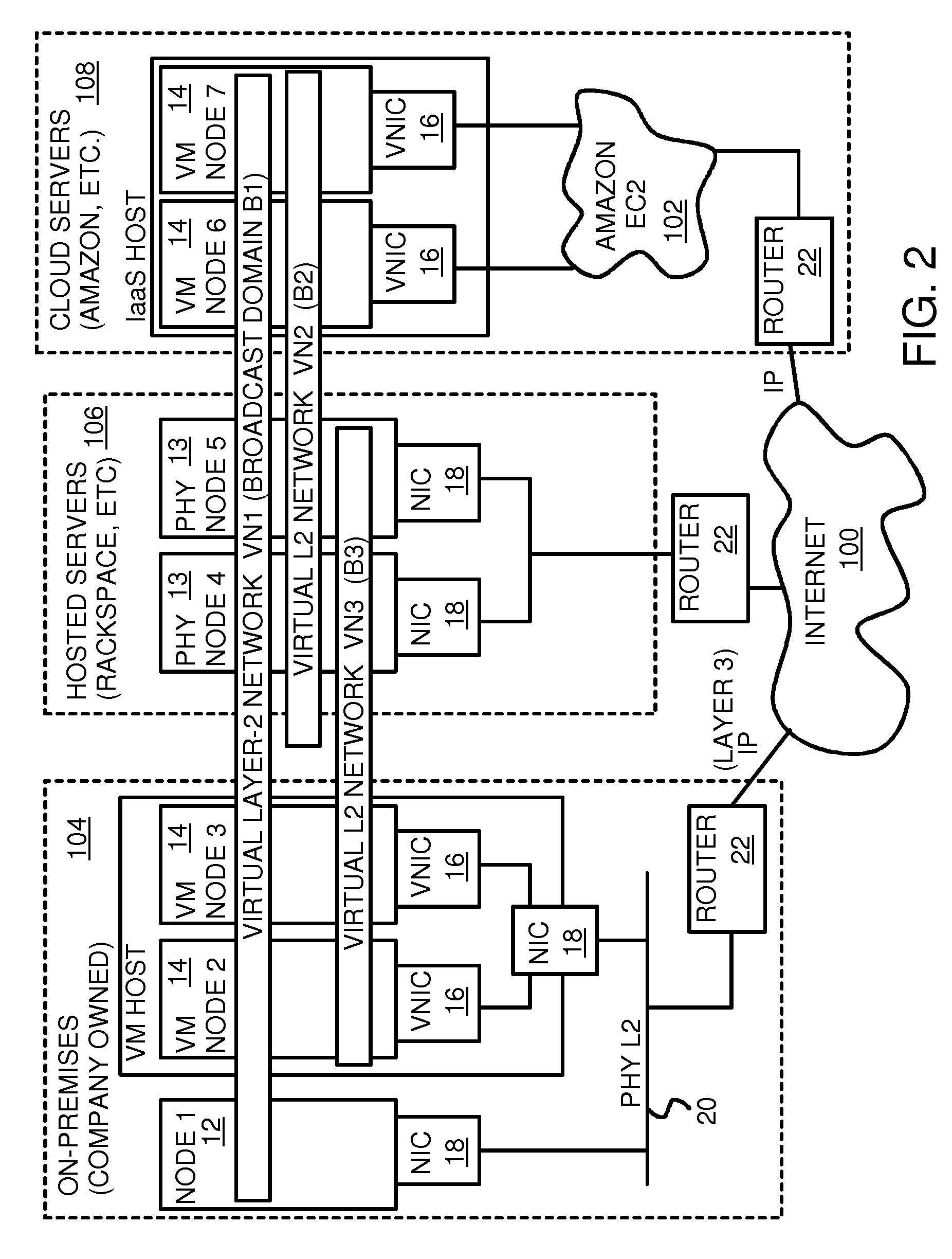
Fully Distributed Routing over a User-Configured On-Demand Virtual Network for Infrastructure-as-a-Service (IaaS) on Hybrid Cloud Networks
A layer-3 virtual router connects two or more virtual networks. Virtual networks are overlaid upon physical networks. Each virtual network (VN) is a layer-2 network that appears to expand an organization's LAN using virtual MAC addresses. The network stack forms a virtual-network packet with a virtual gateway MAC address of the virtual router to reach a remote virtual network. A VN device driver shim intercepts packets and their virtual MAC and IP addresses and encapsulates them with physical packets sent over the Internet. A VN switch table is expanded to include entries for nodes on the remote virtual network so that all nodes on both virtual networks are accessible. A copy of the VN switch table is stored on each node by a virtual network management daemon on the node. A Time-To-Live field in the virtual-network packet is decremented for each virtual hop and a checksum recalculated.
Owner:CISCO TECH INC
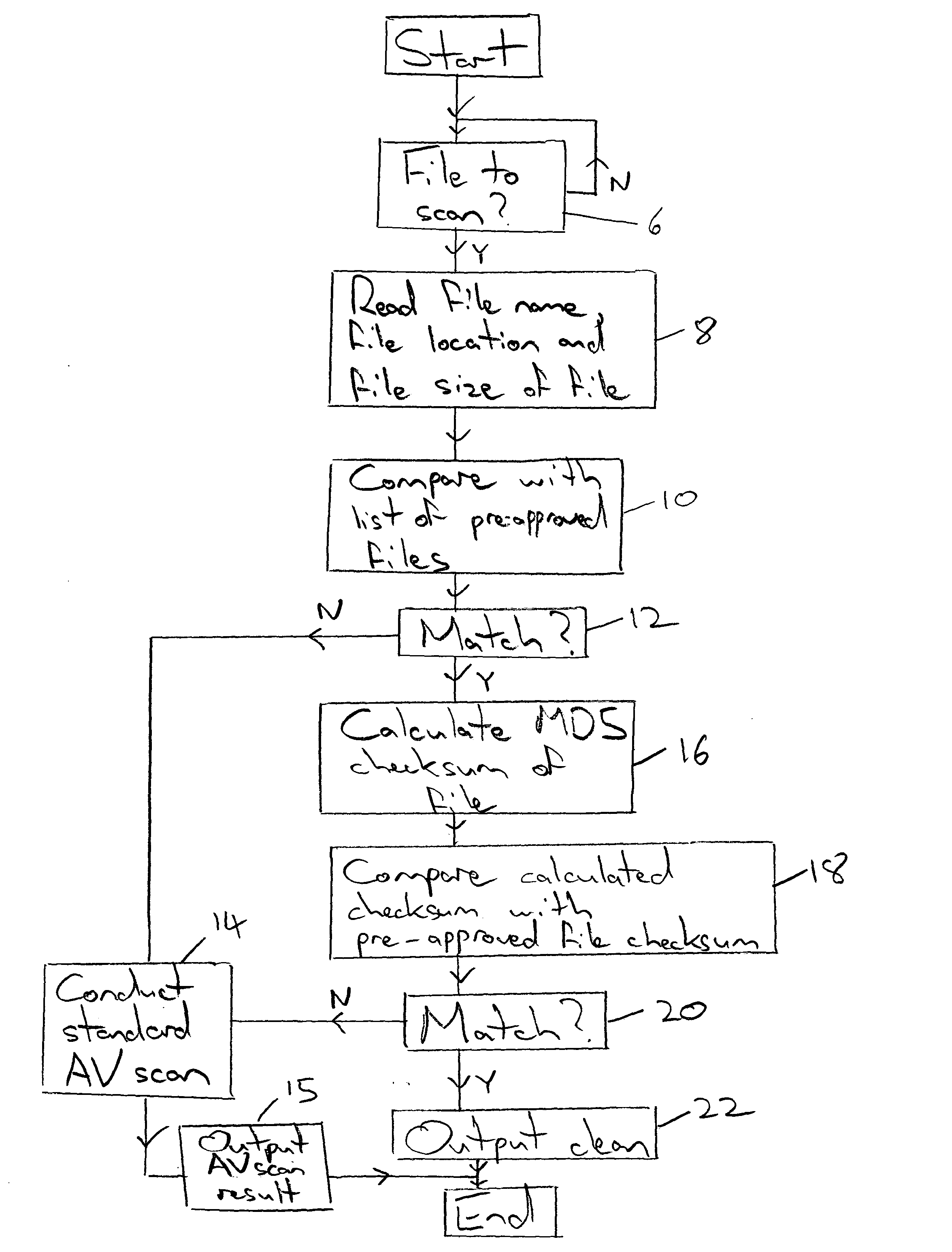
Pre-approval of computer files during a malware detection
InactiveUS20050021994A1Addressing slow performanceEffectively ensureMemory loss protectionDigital data processing detailsChecksumFile size
A malware detection system seeking to identify computer viruses, worms, Trojans, banned files and the like acts to determine from the file name, file size and storage location of a computer file being tested, whether that computer file potentially matches a specific known malware free computer file stored within a list of such specific known malware free computer files. If a match occurs indicating that the candidate computer file is potentially the specific known malware free computer file, then this is confirmed by calculating a checksum of the candidate computer file and comparing this against a stored corresponding checksum of the specific known malware free computer file. If these checksums match, then the candidate computer file can be passed as clean without requiring further time consuming malware detection scanning.
Owner:MCAFEE INC
Ensuring data integrity on a dispersed storage grid
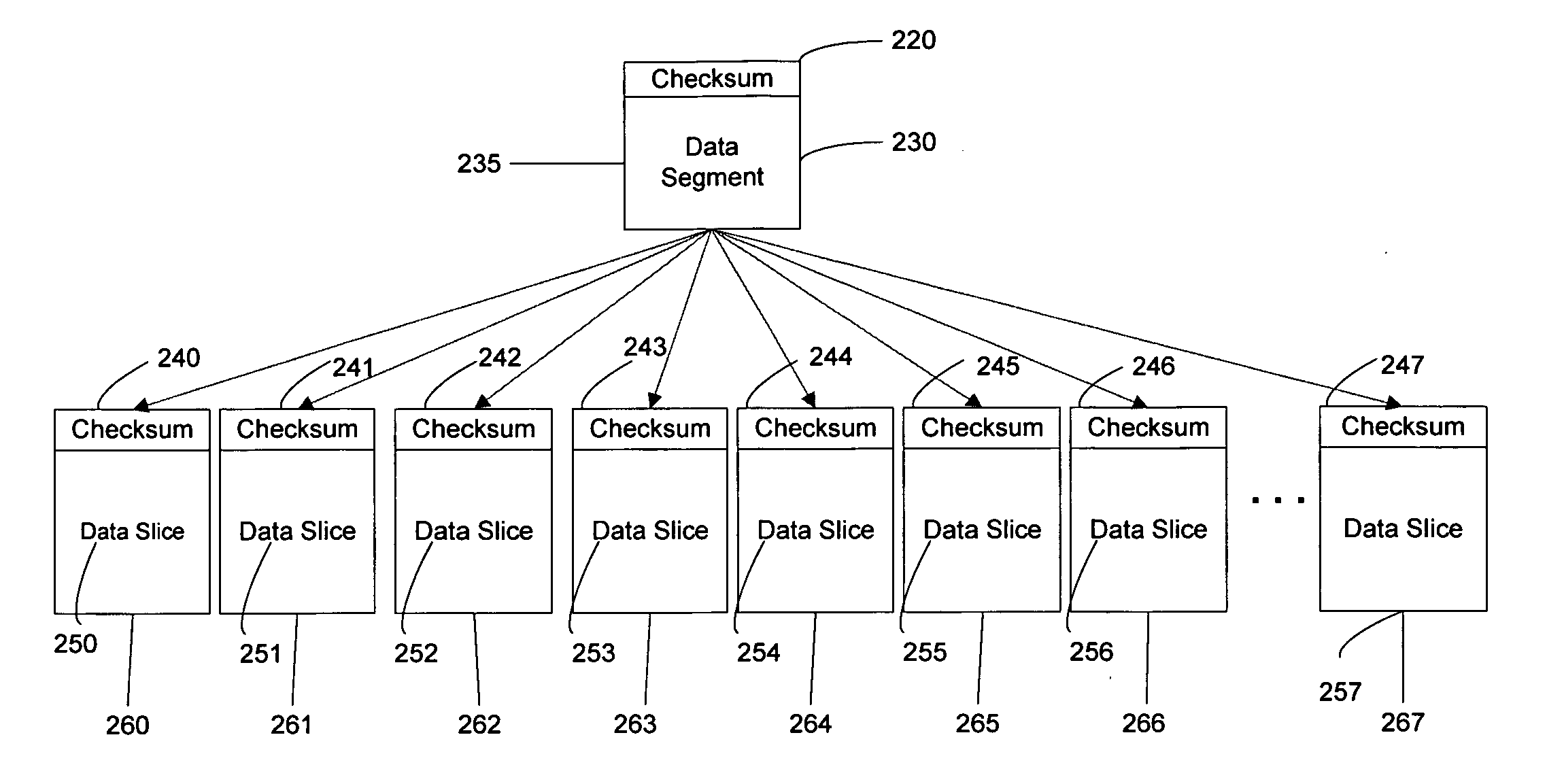
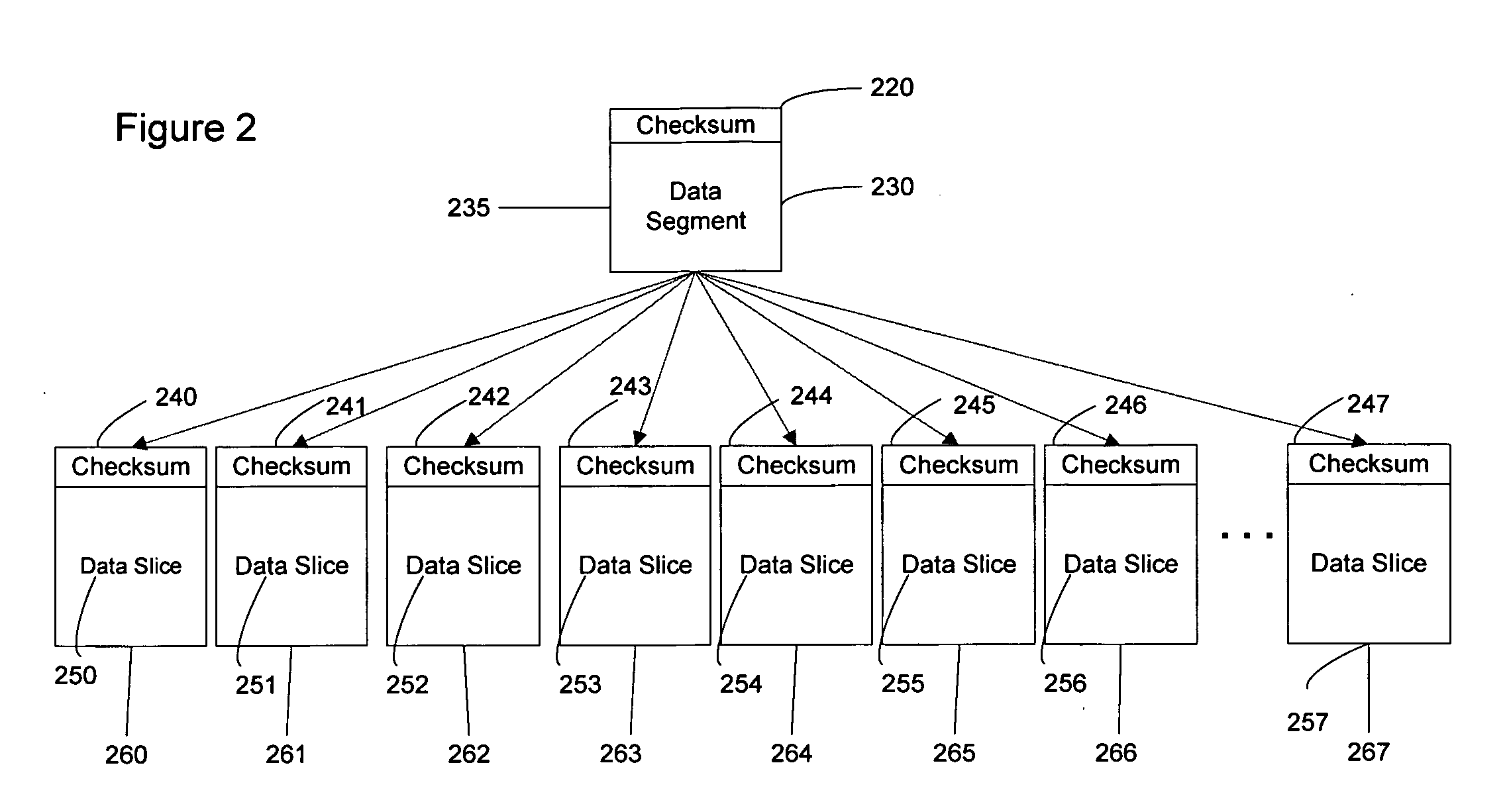
ActiveUS20090094250A1Error detection/correctionSpecial data processing applicationsData integrityData segment
An improved system is disclosed for ensuring the integrity of data stored on a dispersed data storage network. Checksums are used to ensure integrity of both data segments and data slices. Checksums appended to data slices are checked by receiving slice servers to ensure that no errors occurred during transmission. Slice servers also periodically recalculate checksums for stored data slices to ensure that data slices have not been corrupted during storage. Checksums appended to data segments are checked when data segments are read from the storage network.
Owner:PURE STORAGE
Storing and retrieving computer data files using an encrypted network drive file system
ActiveUS20060206547A1Easy to storeEasy retrievalData processing applicationsError detection/correctionHard disc driveData file
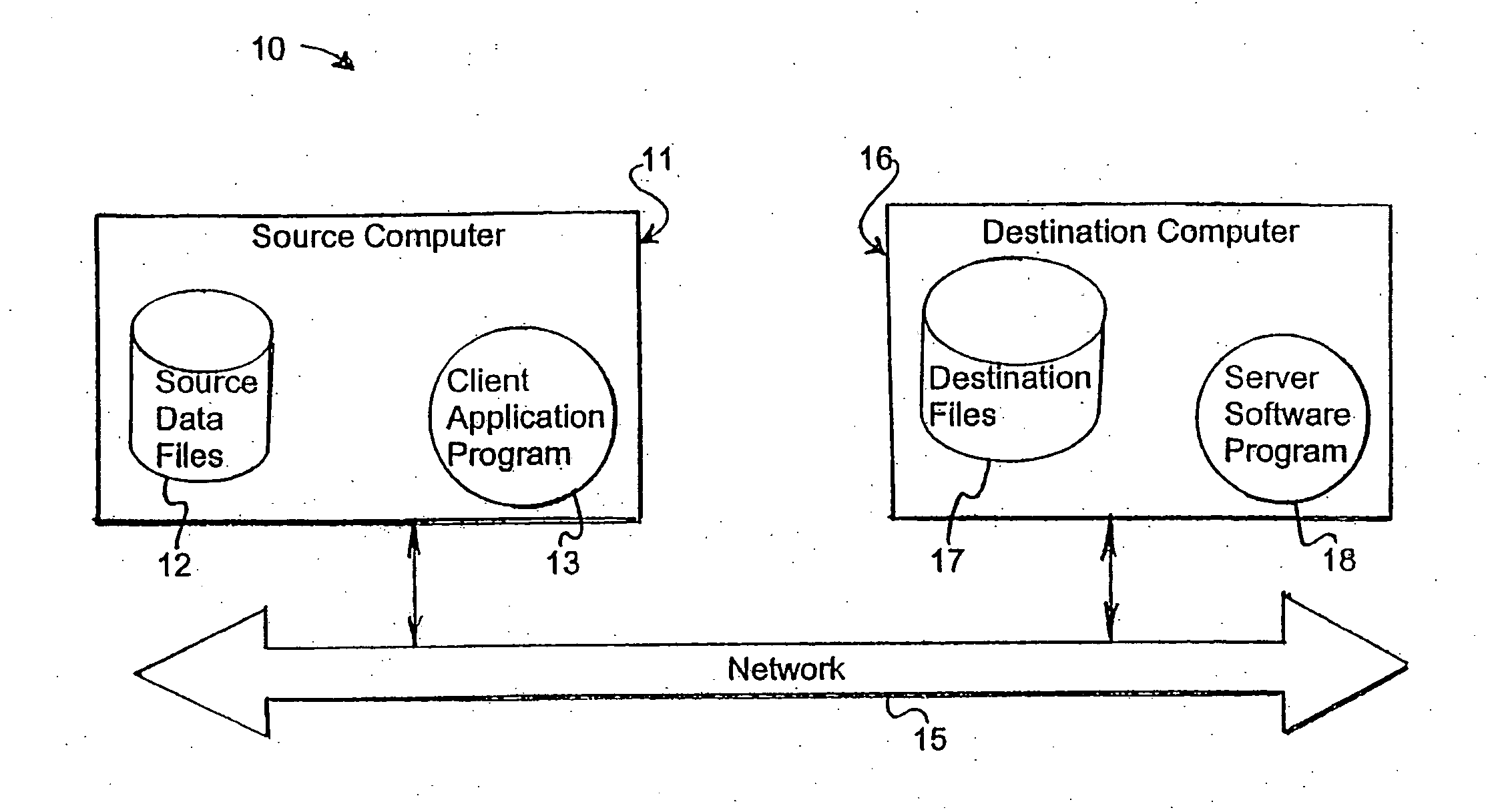
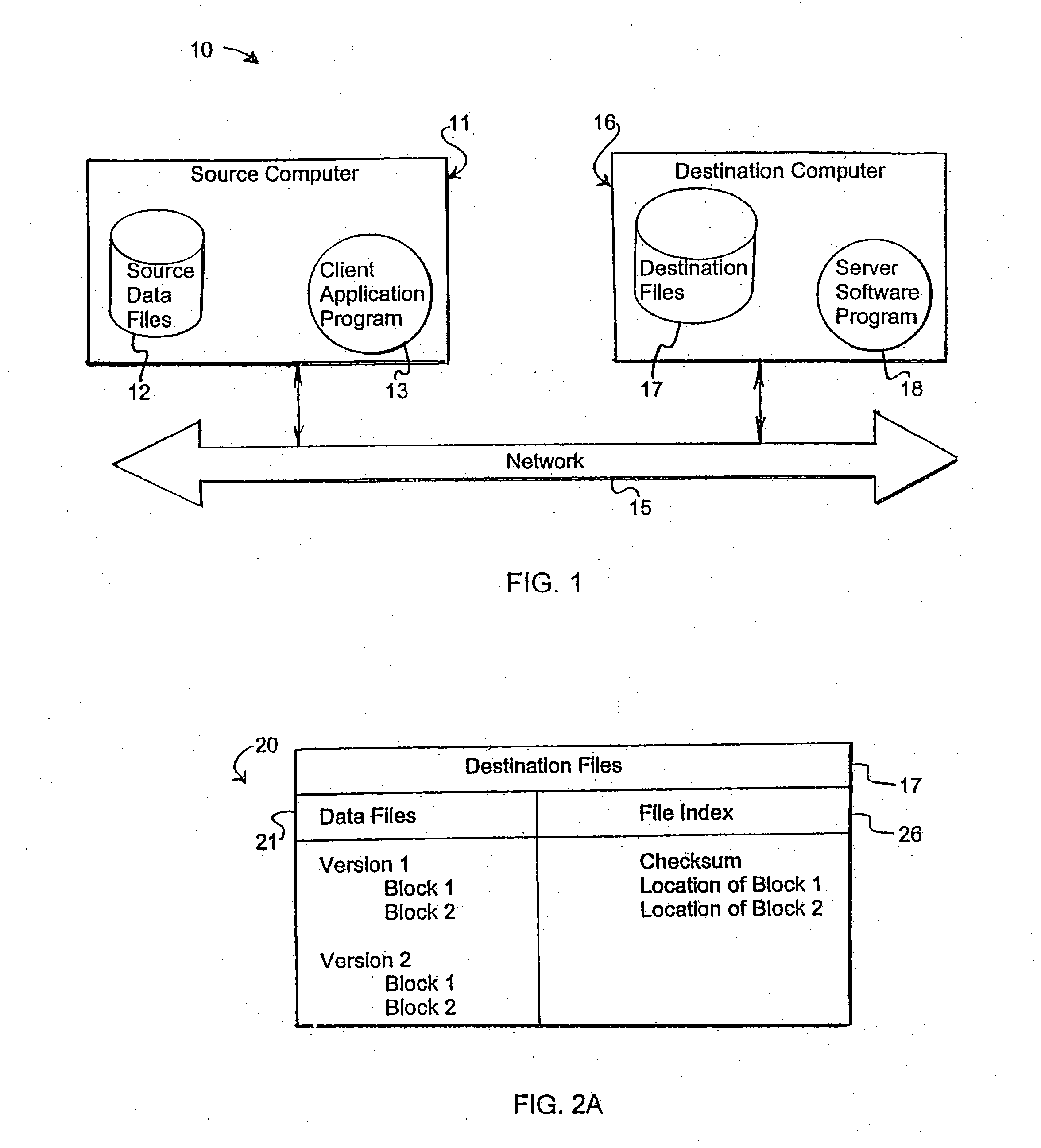
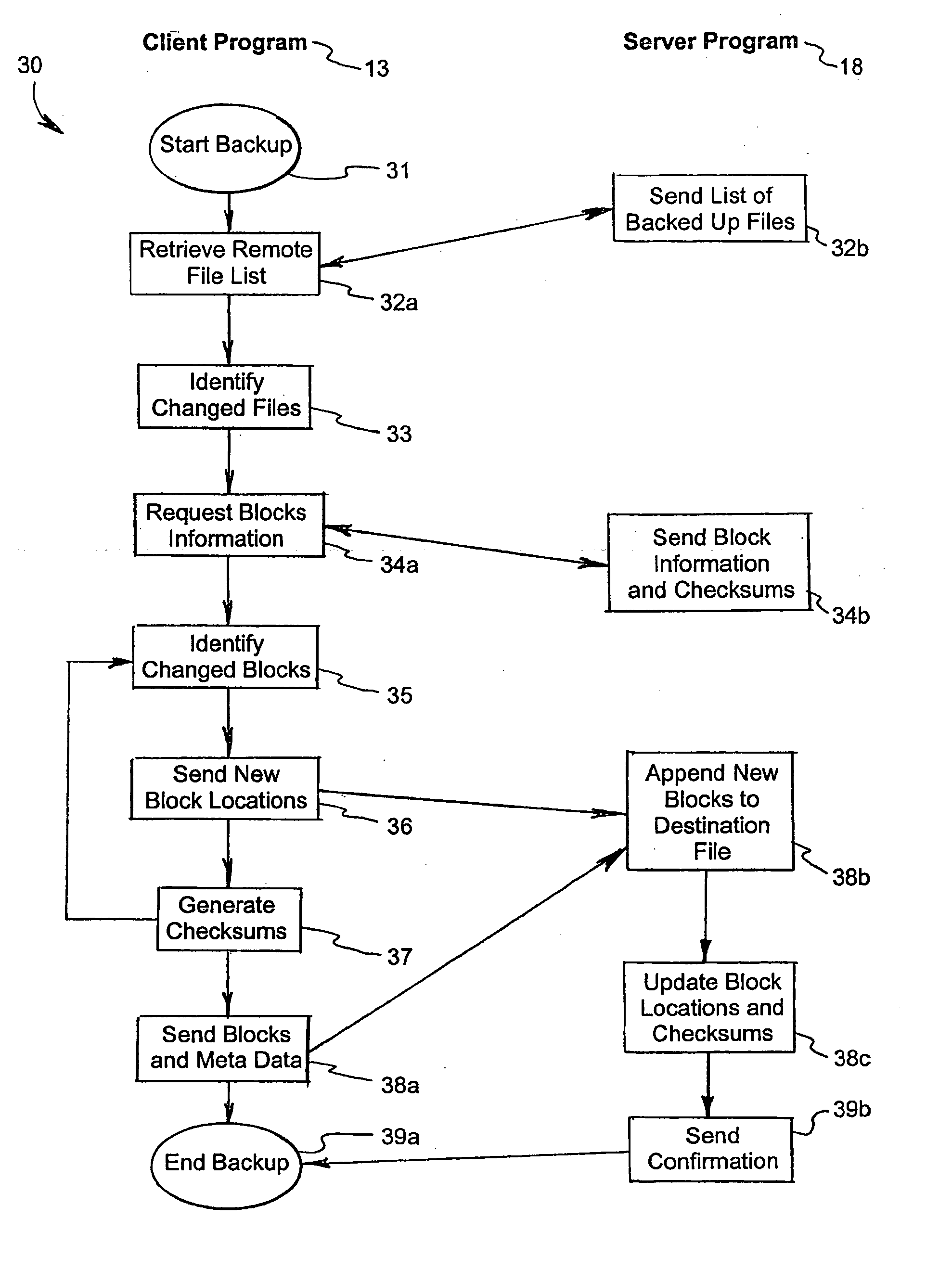
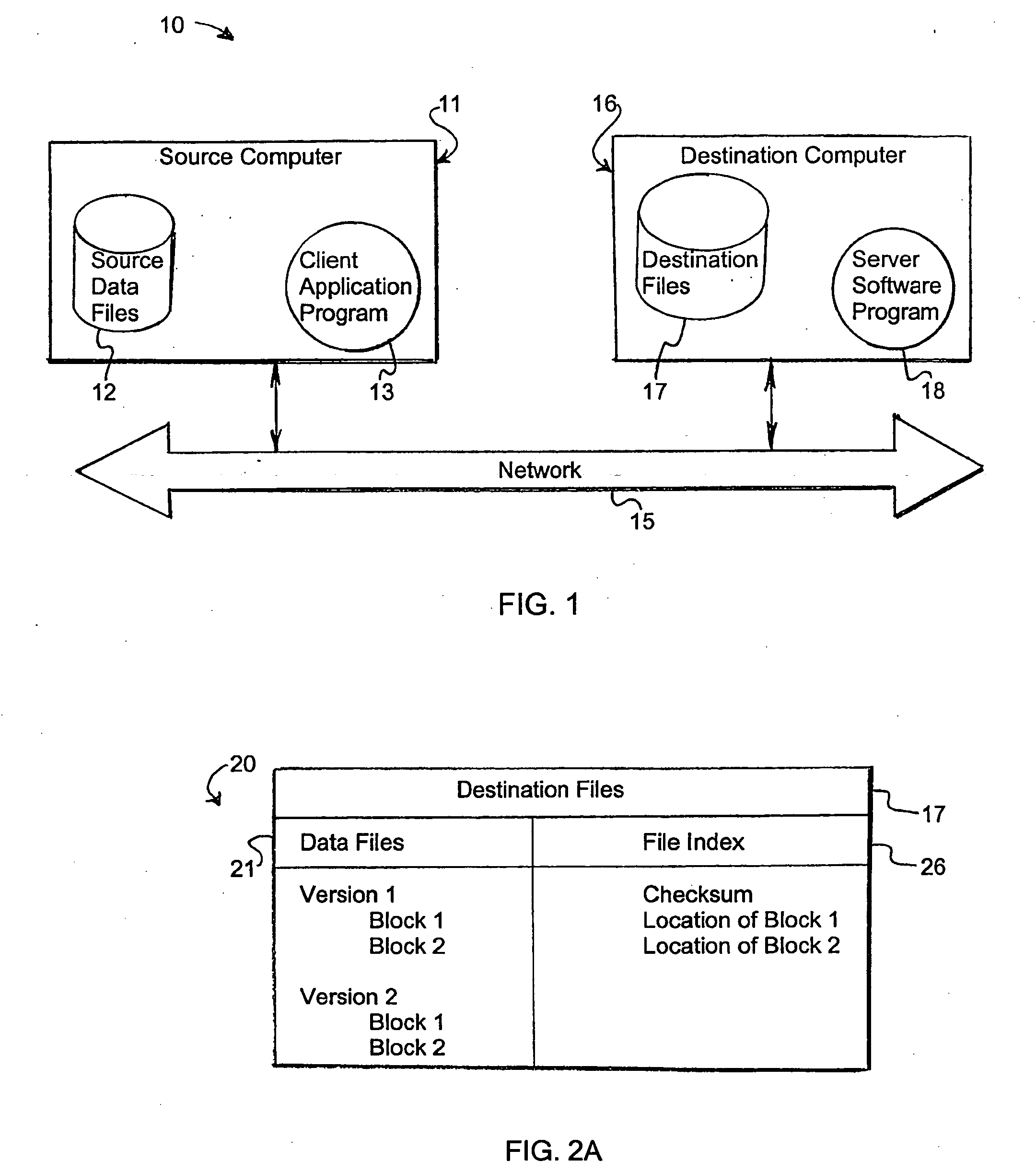
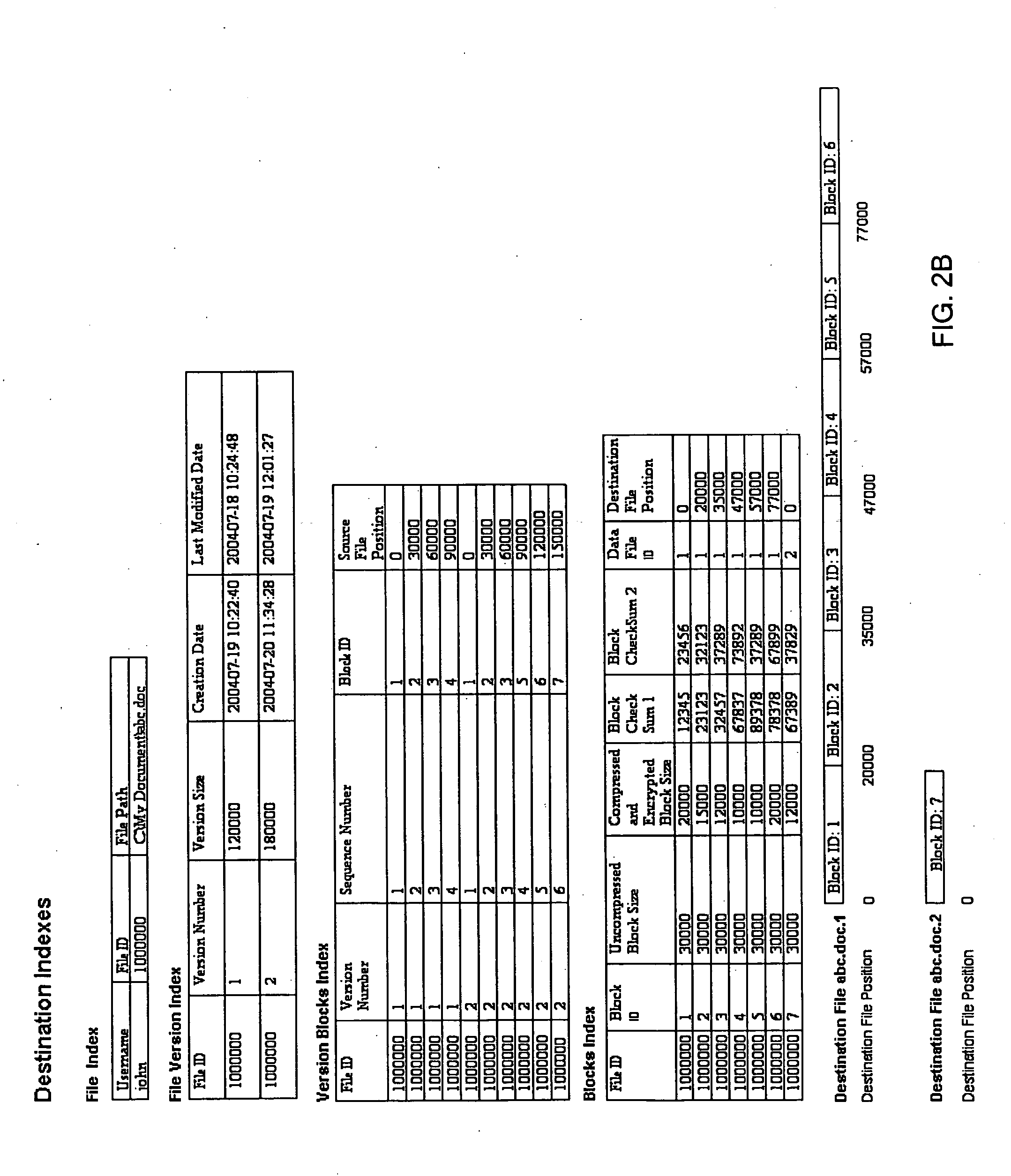
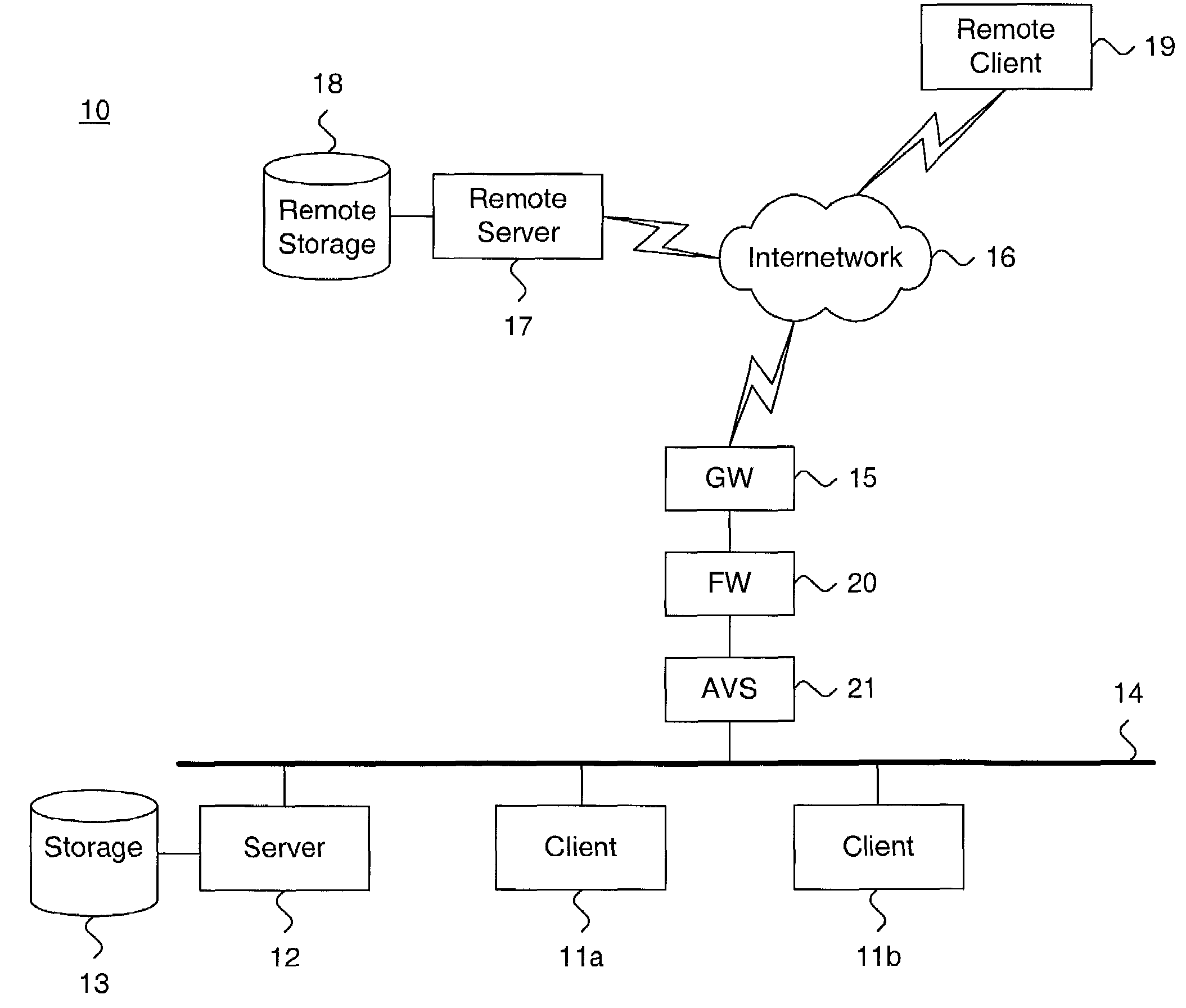
A system and method for storing computer files in a destination file is described, which may be an incremental backup system. File headers related to the files may be stored in a file index separate from a data file, or subsequent versions may be stored in the same data file while maintaining earlier versions. File headers may include locations of files, checksums, metadata about individual blocks corresponding to the data files. A system may include a client application program stored on a client computer, a network, and a server software program on a destination computer. Embodiments may include compression, encryption, or both, performed by the client application program. Files may be divided into blocks, and metadata may include locations of blocks. Files may be restored from the destination computer to the source computer. Files storage locations on the destination computer may be mapped to the client computer to appear as a virtual hard drive for convenient access by a user.
Owner:IDRIVE INC
Method and apparatus for harvesting file system metadata
InactiveUS20100088317A1Efficient storageEfficient accessDigital data processing detailsMultiple digital computer combinationsFile systemBusiness enterprise
A harvester is disclosed for harvesting metadata of managed objects (files and directories) across file systems which are generally not interoperable in an enterprise environment. Harvested metadata may include 1) file system attributes such as size, owner, recency; 2) content-specific attributes such as the presence or absence of various keywords (or combinations of keywords) within documents as well as concepts comprised of natural language entities; 3) synthetic attributes such as mathematical checksums or hashes of file contents; and 4) high-level semantic attributes that serve to classify and categorize files and documents. The classification itself can trigger an action in compliance with a policy rule. Harvested metadata are stored in a metadata repository to facilitate the automated or semi-automated application of policies.
Owner:IBM CORP
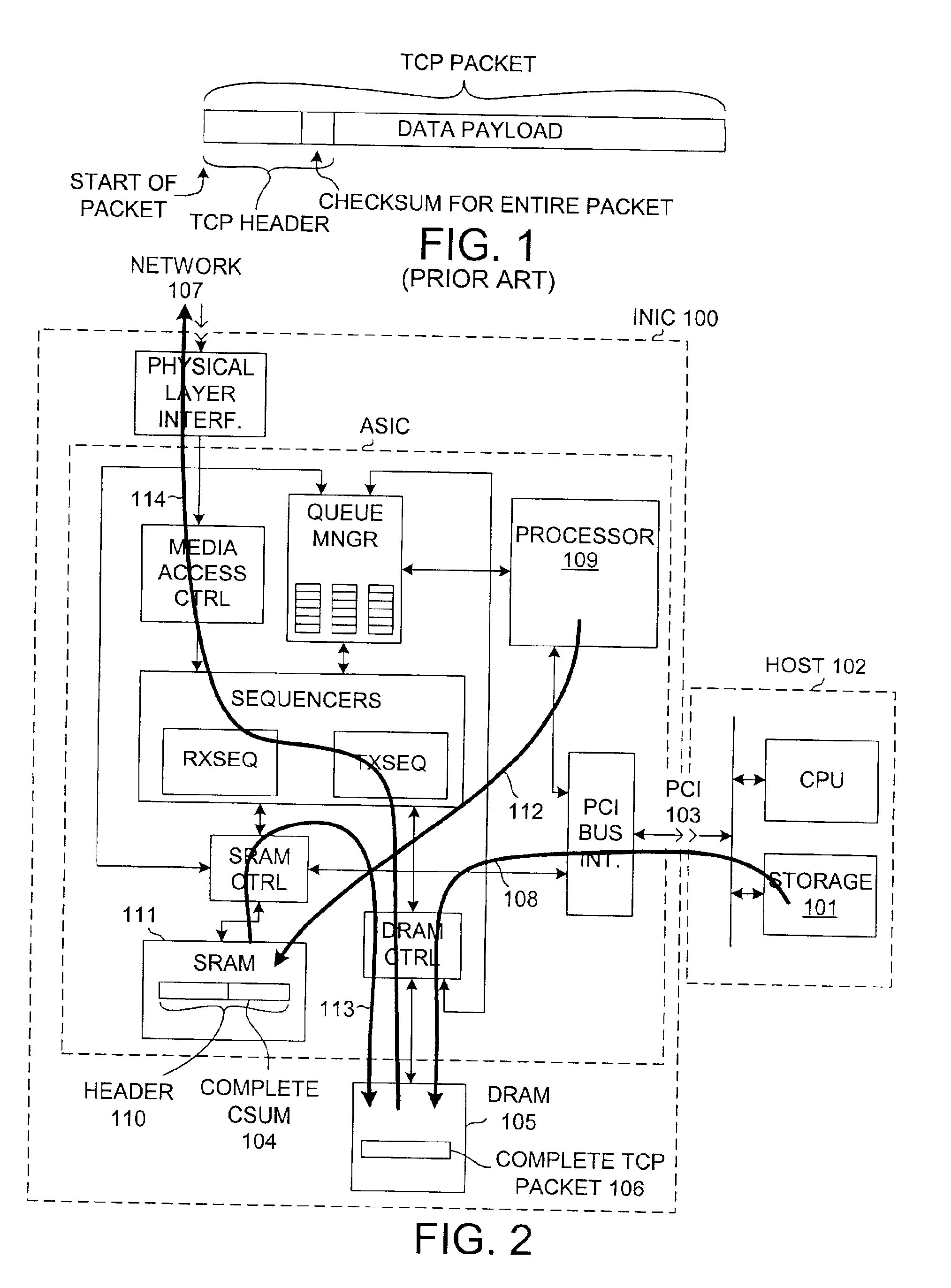
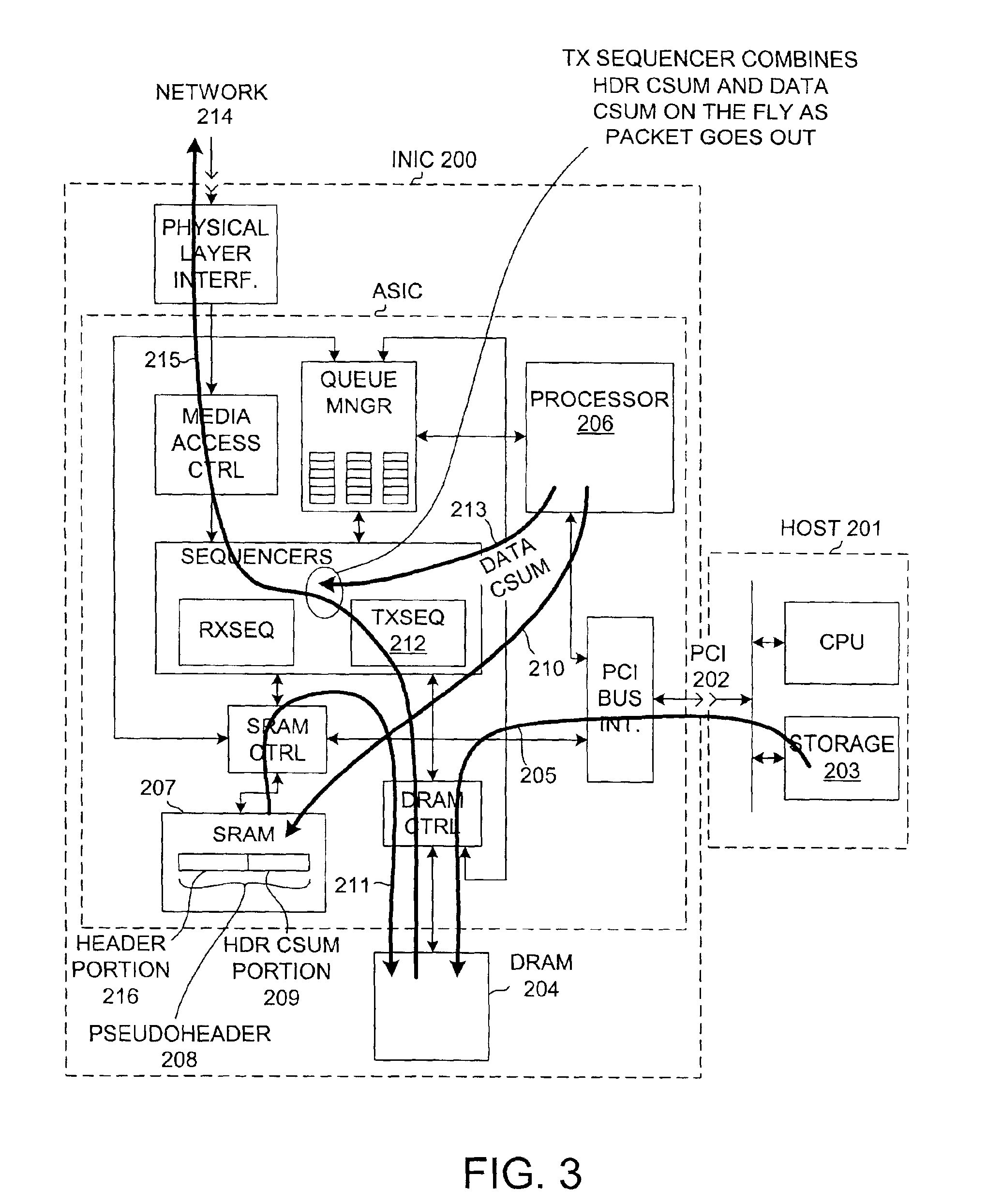
Reducing delays associated with inserting a checksum into a network message
A first partial checksum for the header portion of a TCP header is generated on an intelligent network interface card (INIC) before all the data of the data payload of the TCP message has been transferred to the INIC. A pseudopacket with the first partial checksum and the data is assembled in DRAM on the INIC as the data arrives onto the INIC. When the last portion of the data of the data payload is received onto the INIC, a second partial checksum for the data payload is generated. The pseudopacket is read out of DRAM for transfer to a network. While the pseudopacket is being transferred, the second partial header is combined with the first partial header and the resulting final checksum is inserted into the pseudopacket so that a complete TCP packet with a correct checksum is output from the INIC to the network.
Owner:ALACRITECH
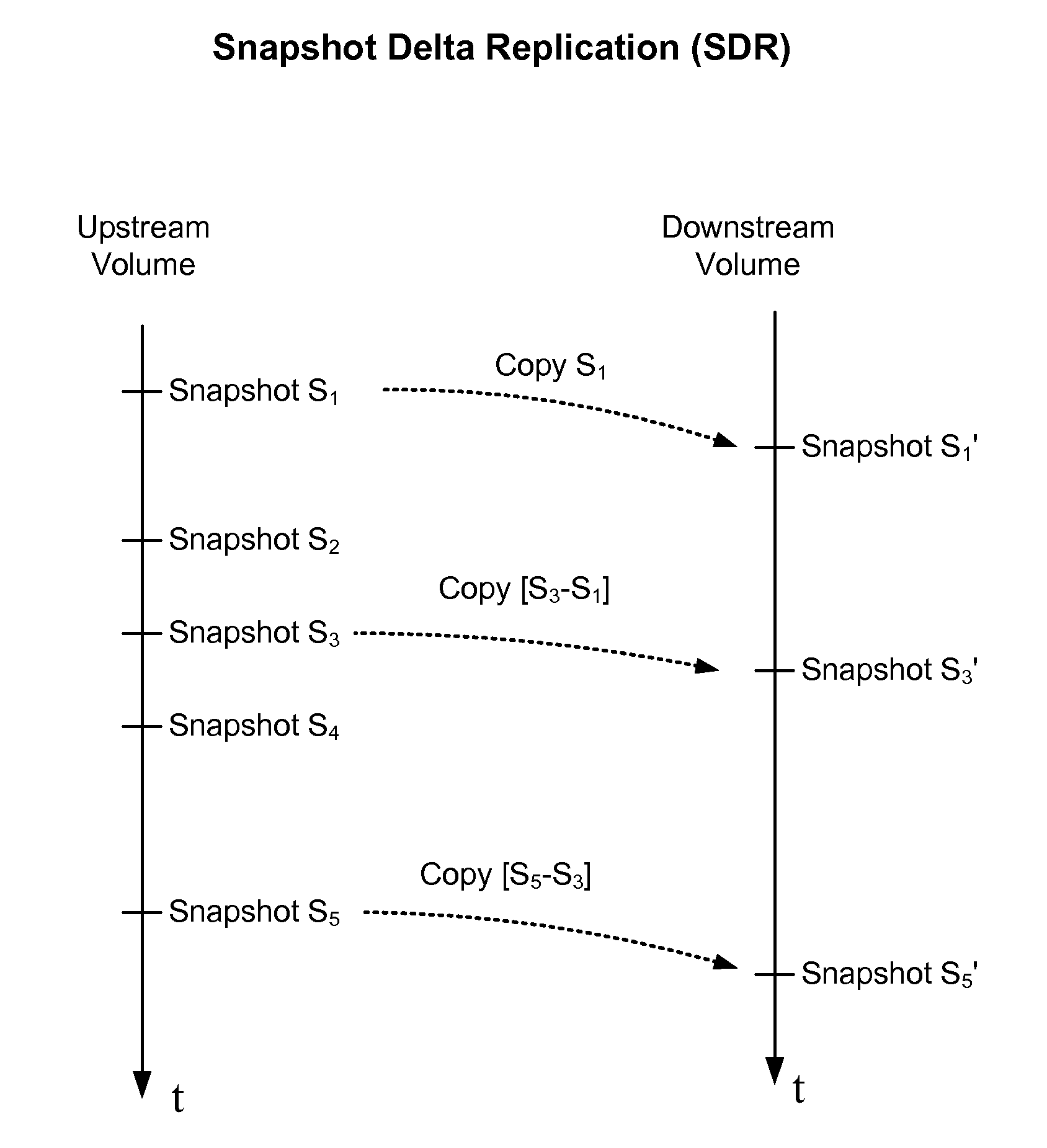
Content-based replication of data between storage units
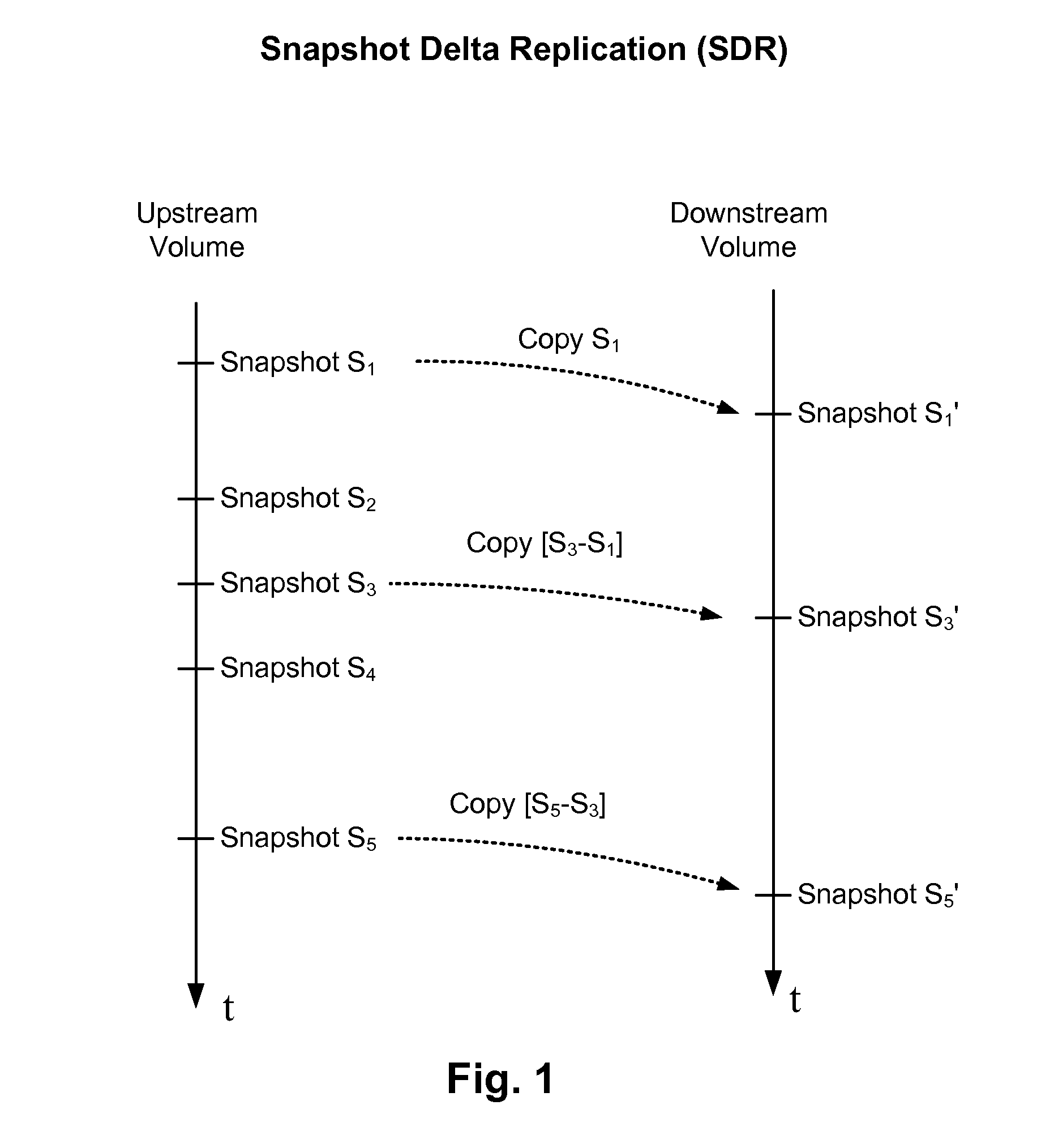
InactiveUS20160150012A1Input/output to record carriersDatabase distribution/replicationParallel computingChecksum
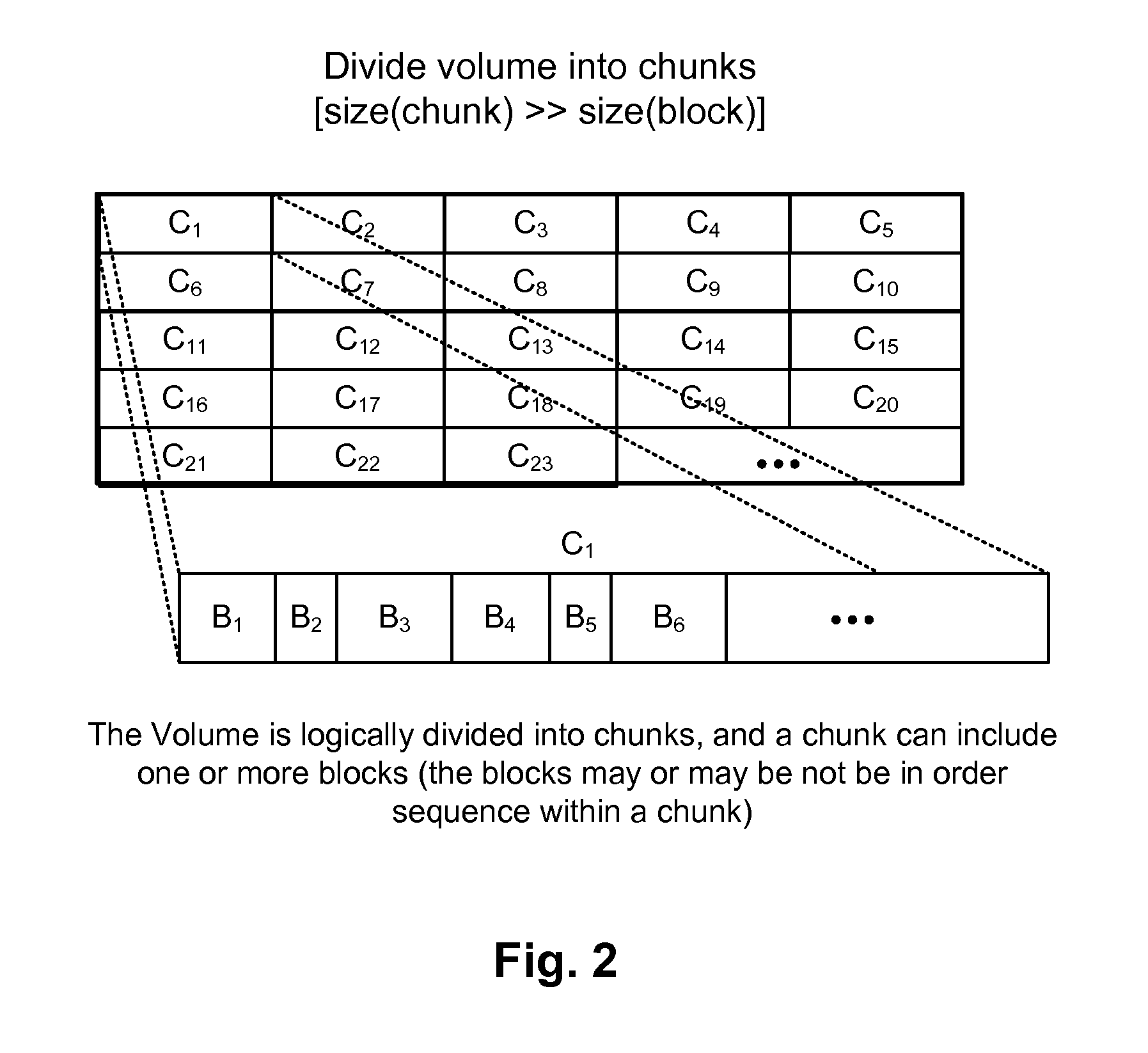
Methods, systems, and computer programs are presented for replicating data across storage systems. One method includes an operation for transferring a snapshot of a volume from an upstream array to a downstream array. The method further includes an operation for comparing an upstream snapshot checksum of the snapshot in the upstream array with a downstream snapshot checksum of the snapshot in the downstream array. When the upstream snapshot checksum is different from the downstream snapshot checksum, a plurality of chunks in the snapshot are defined. Further, for each chunk in the snapshot, a comparison is made of an upstream chunk checksum calculated by the upstream array with a downstream chunk checksum calculated by the downstream array. When the upstream chunk checksum is different from the downstream chunk checksum then the data of the chunk is sent from the upstream array to the downstream array.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
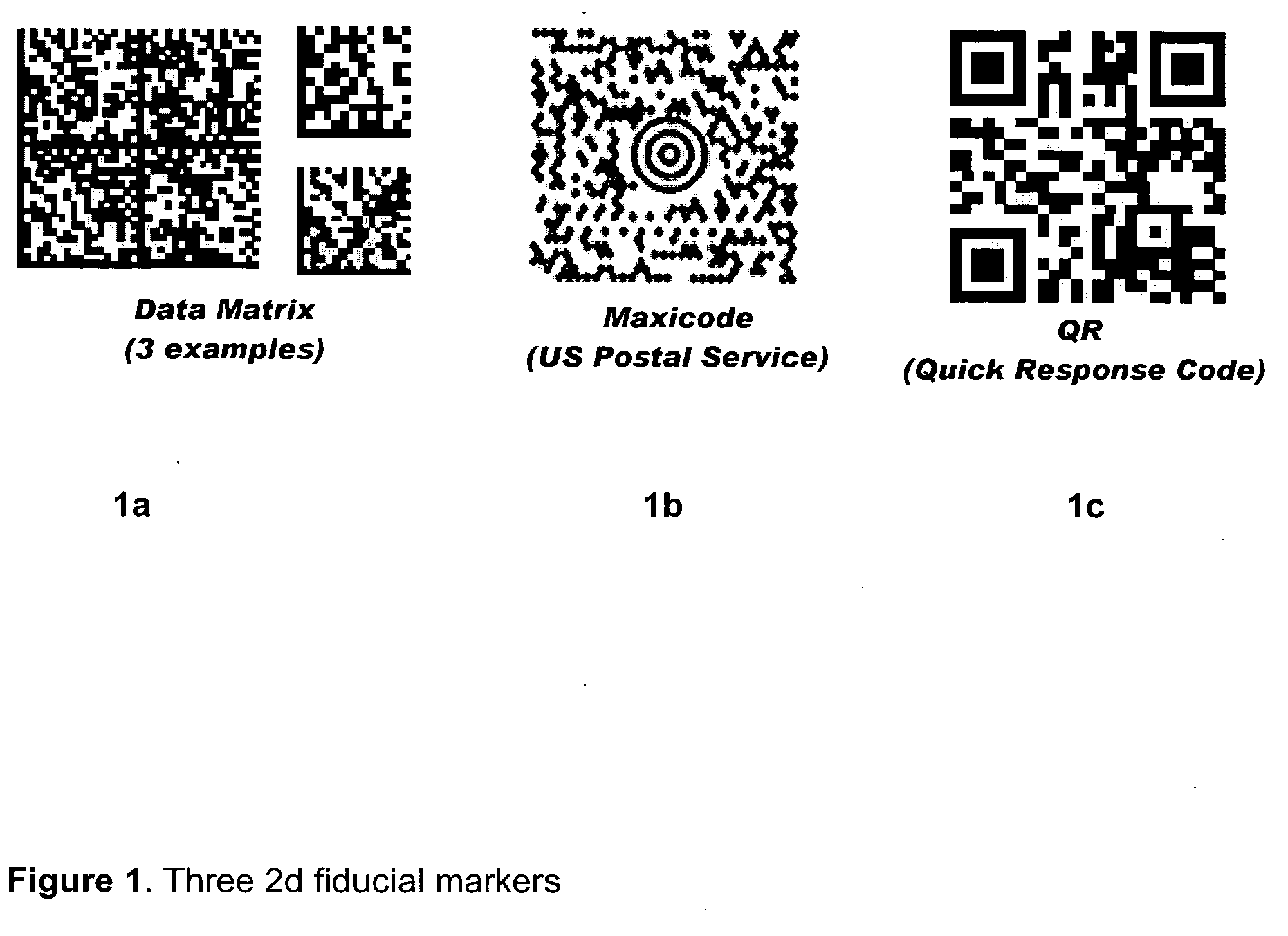
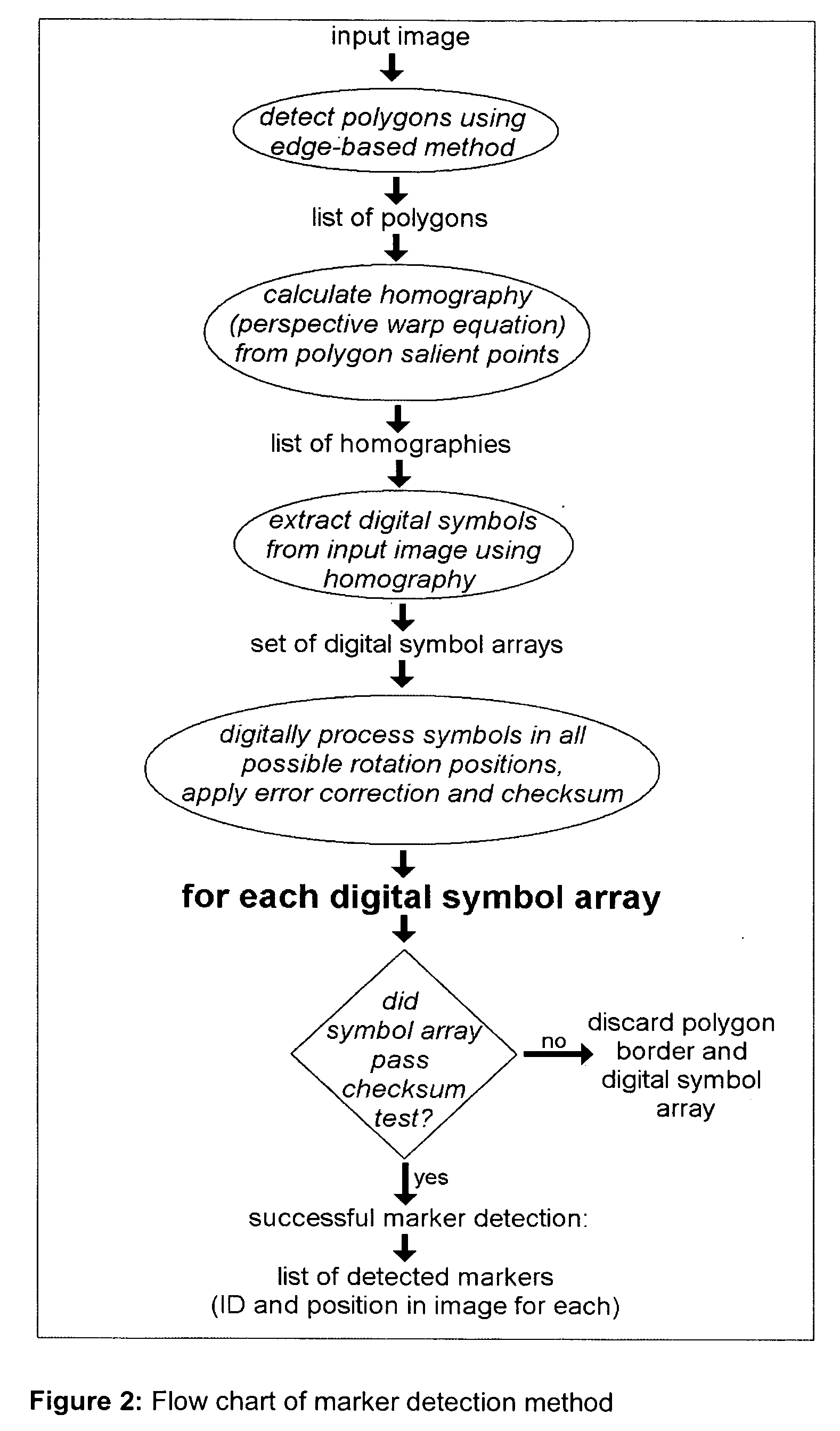
Marker and method for detecting said marker
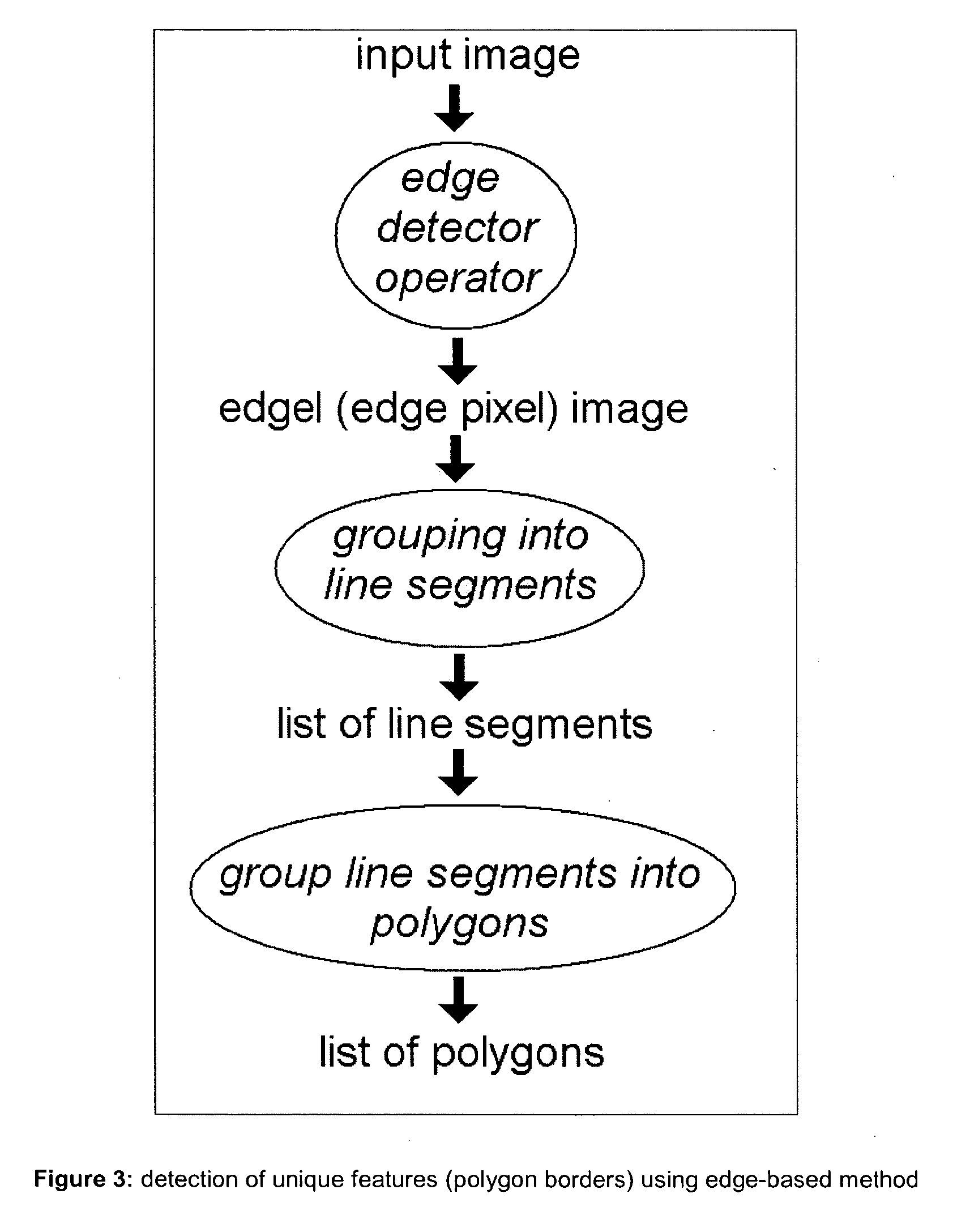
This invention discloses marker detectable by visual means comprising; a polygonal border having of at least four non collinear salient points. The marker has on it a pattern in binary digital code. The binary code data contains information data, checksum and error correction. The binary code data is on two levels; a first level of binary code readable at a first given distance, a second level of binary code readable at a second given distance, where the second given distance is less than the first given distance and the second level binary code is smaller in size than the first level binary code. The second level of binary code does not interfere with the reading of the first level binary code. It also discloses a method for detecting a marker comprising the steps of detecting an image, using an edge detector to detect an edge in said image, grouping more than one edge into a polygon having salient points, calculating homography from polygon salient points, generating a list of homographies, extracting binary data from input image having homographies, identifying and verifying binary data.
Owner:MILLENNIUM THREE TECH
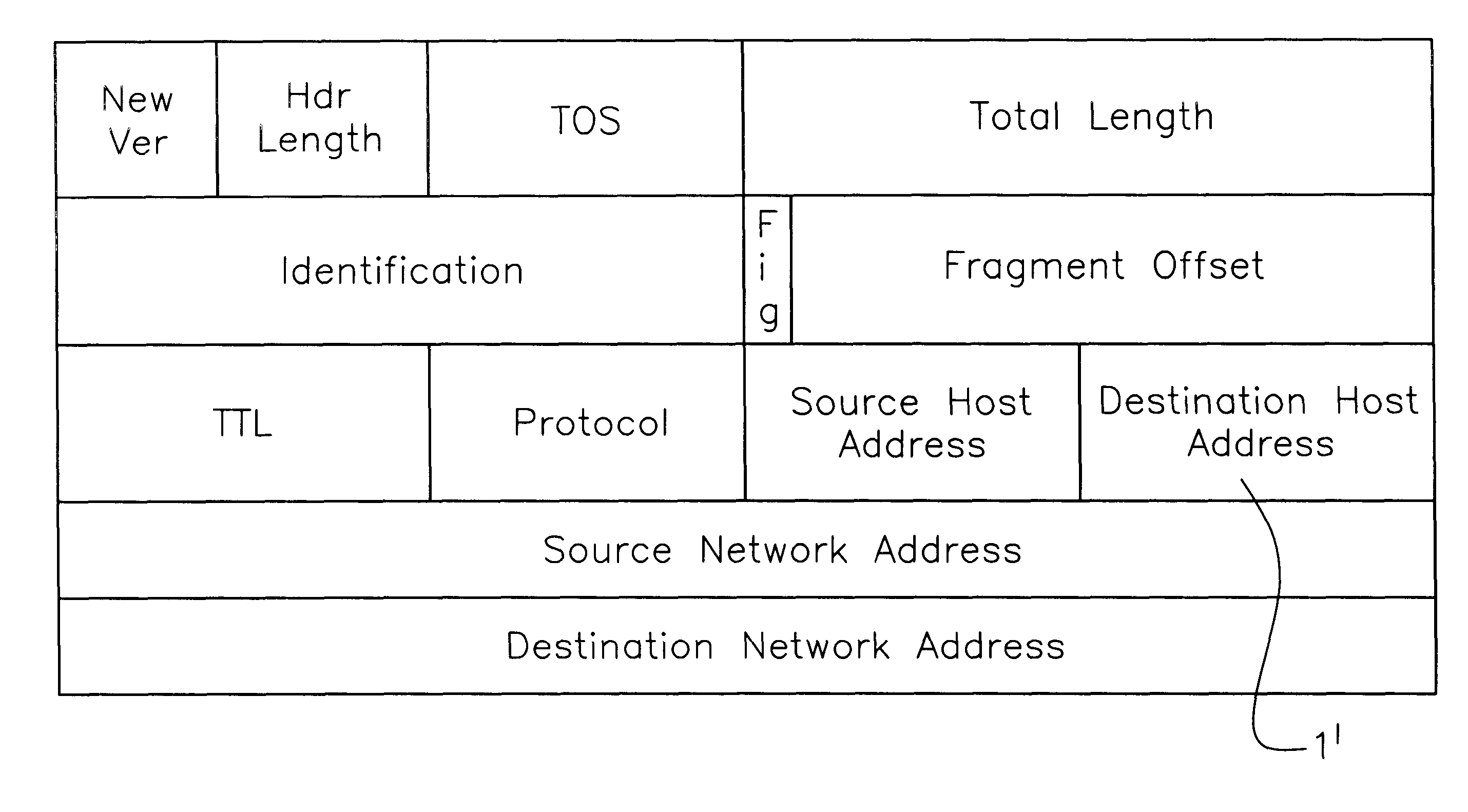
Internet and related networks, a method of and system for substitute use of checksum field space in information processing datagram headers for obviating processing speed and addressing space limitations and providing other features
InactiveUS6330614B1Add featureIncrease internet speedElectric signal transmission systemsTime-division multiplexInformation processingPrivate network
In Internet and related networks, a method of and system for substitute use of the normal checksum field space in information processing (IP) datagram headers for obviating current processing time and addressing space limitations, involving replacing the current checksum usage in the checksum field with its attendant processing time with further source host and destination host addresses of lesser processing time, thereby increasing the address space for the network and decreasing the require header processing time, and / or providing space for autonomous system numbers, a higher layer protocol-based routing information (including of the MPLS type) or for Virtual Private Networks Indentifiers in the header.
Owner:NEXABIT NETWORKS
Pre-approval of computer files during a malware detection
InactiveUS7257842B2Abundant resourcesImpact speedMemory loss protectionDigital data processing detailsChecksumMalware
A malware detection system seeking to identify computer viruses, worms, Trojans, banned files and the like acts to determine from the file name, file size and storage location of a computer file being tested, whether that computer file potentially matches a specific known malware free computer file stored within a list of such specific known malware free computer files. If a match occurs indicating that the candidate computer file is potentially the specific known malware free computer file, then this is confirmed by calculating a checksum of the candidate computer file and comparing this against a stored corresponding checksum of the specific known malware free computer file. If these checksums match, then the candidate computer file can be passed as clean without requiring further time consuming malware detection scanning.
Owner:MCAFEE INC
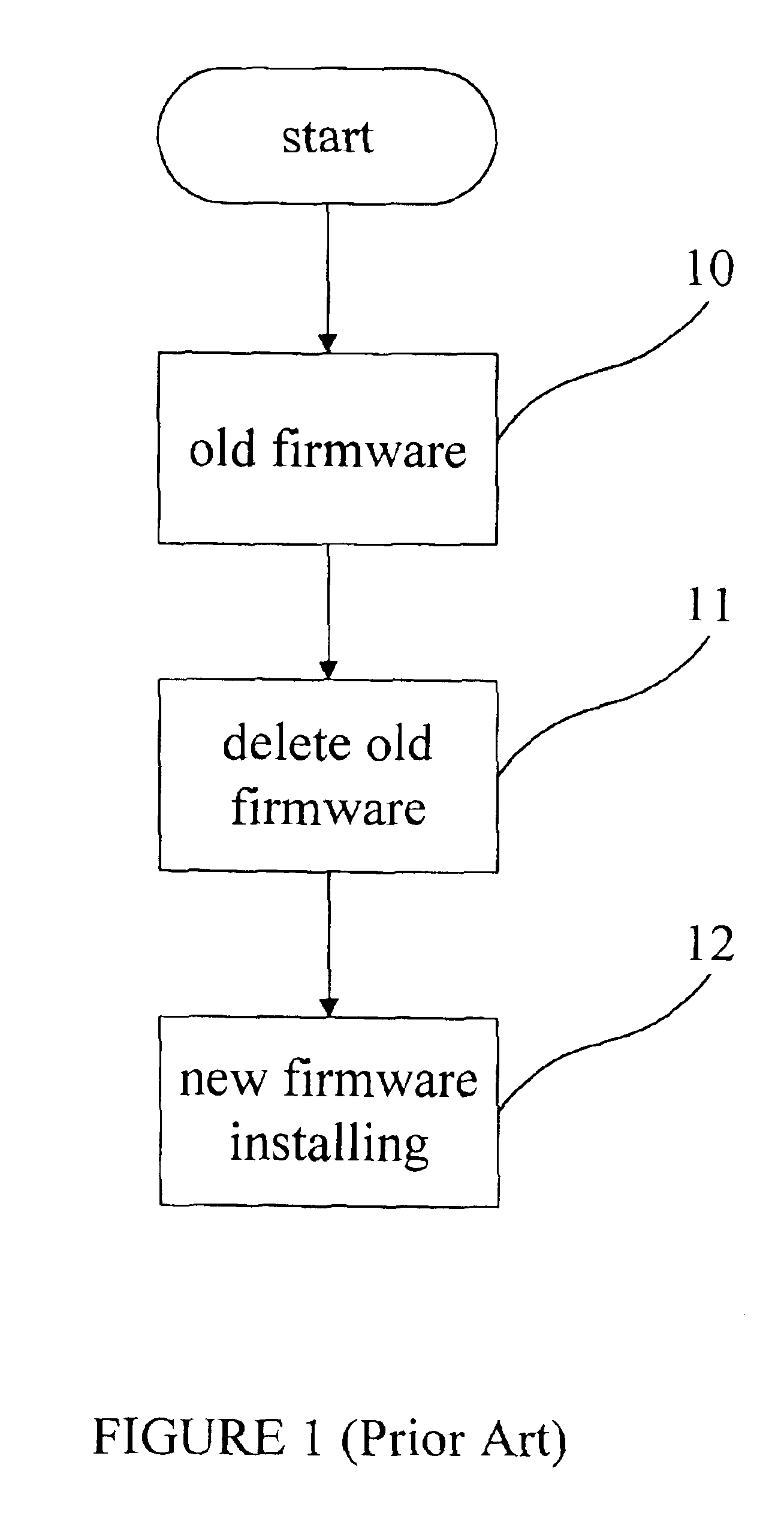
Method for updating firmware of computer device
A method for updating firmware includes dividing a memory of a computer device into five portions, wherein an initial program, an old program, an old backup firmware, the checksum of the old firmware, and the checksum of the old backup firmware are saved, respectively, in the first portion, the second portion, the third portion, the fourth portion and the fifth portion; executing the initial program in the first portion; writing a new firmware into the second portion from an external device for replacing the old firmware; writing the checksum of the new firmware into the fourth portion; writing the new firmware into the third portion for replacing the old backup firmware; writing the checksum of the new firmware into the fifth portion; and executing the new firmware in the second portion for operating the computer device.
Owner:CEDAR LANE TECH INC
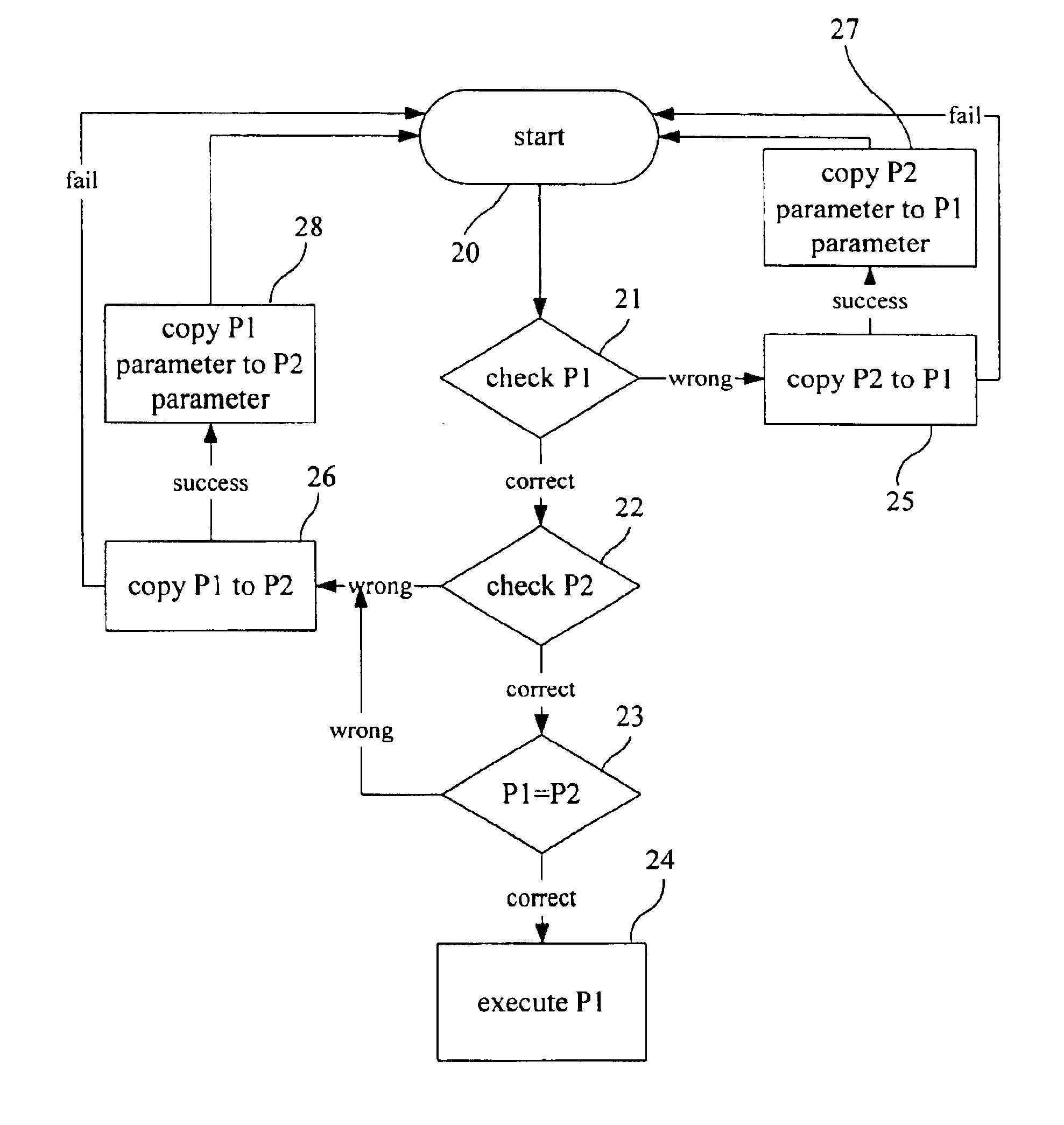
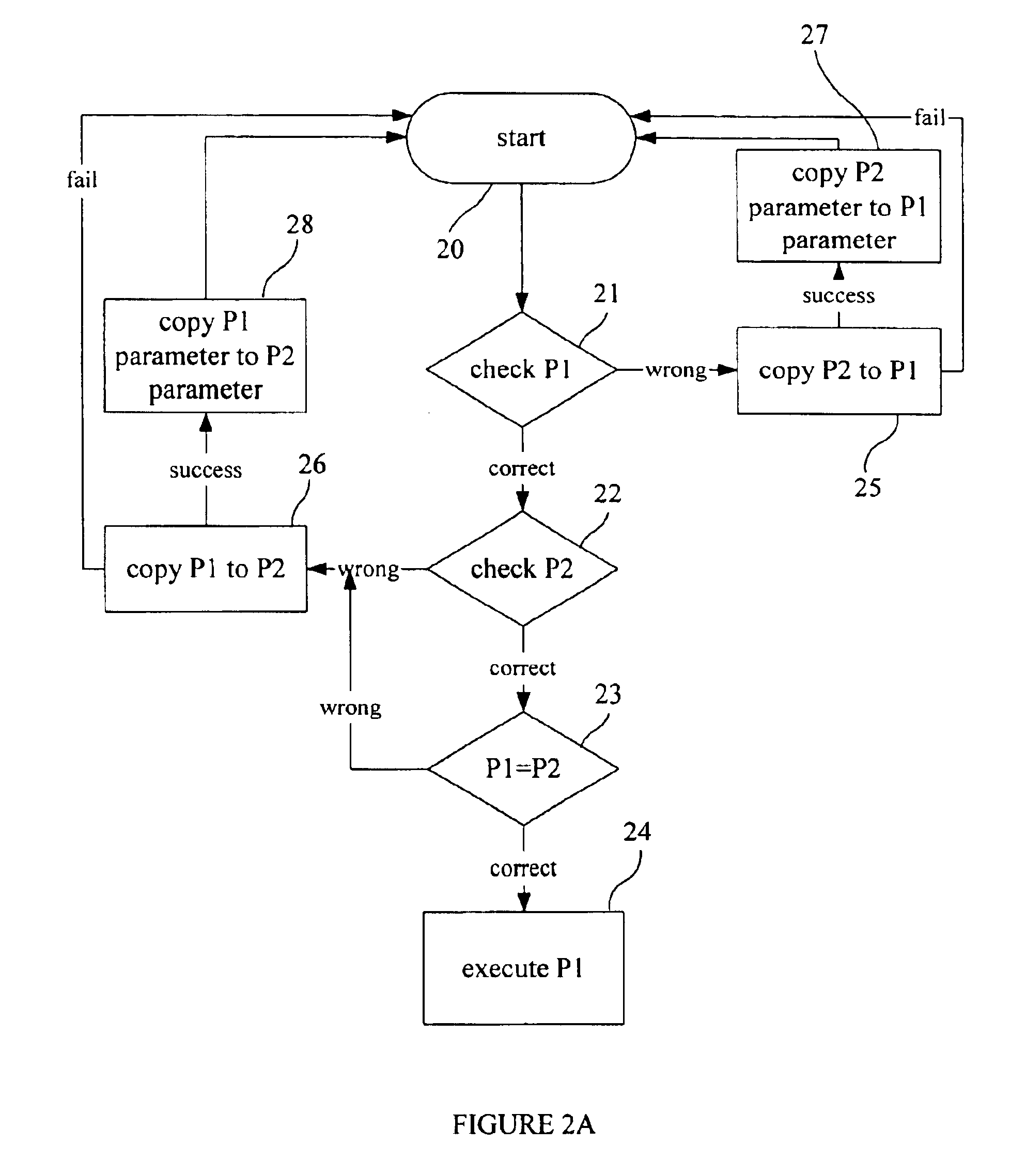
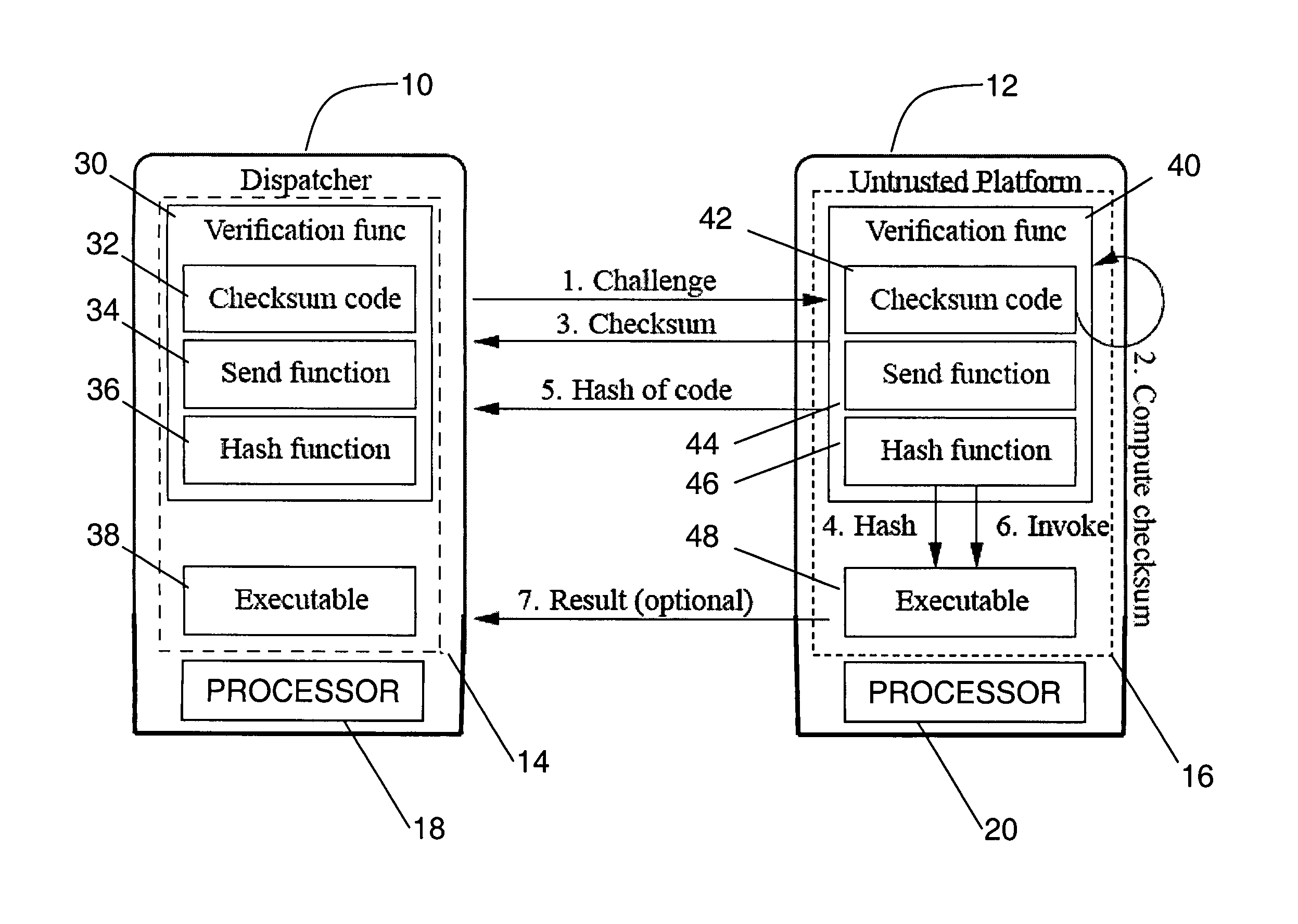
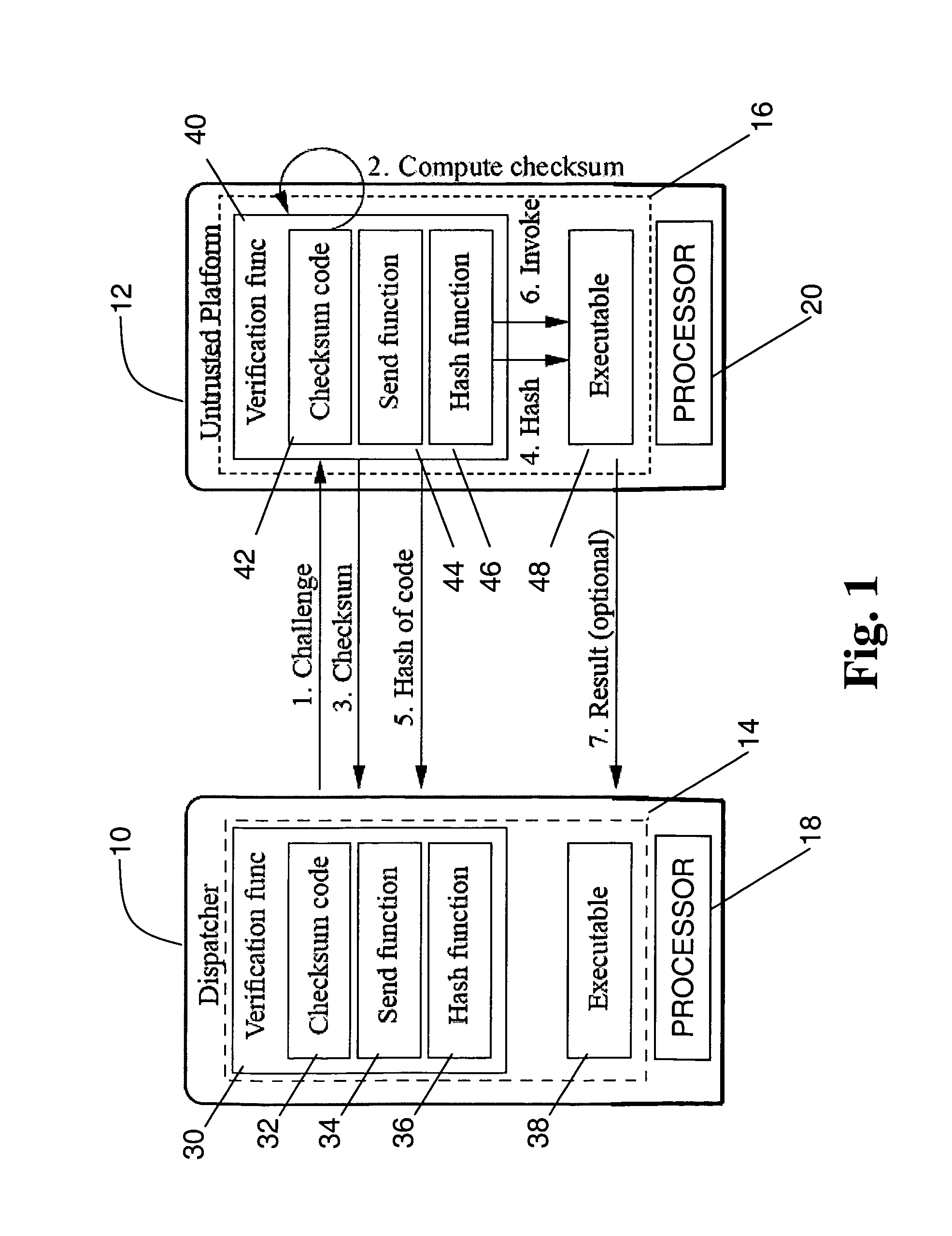
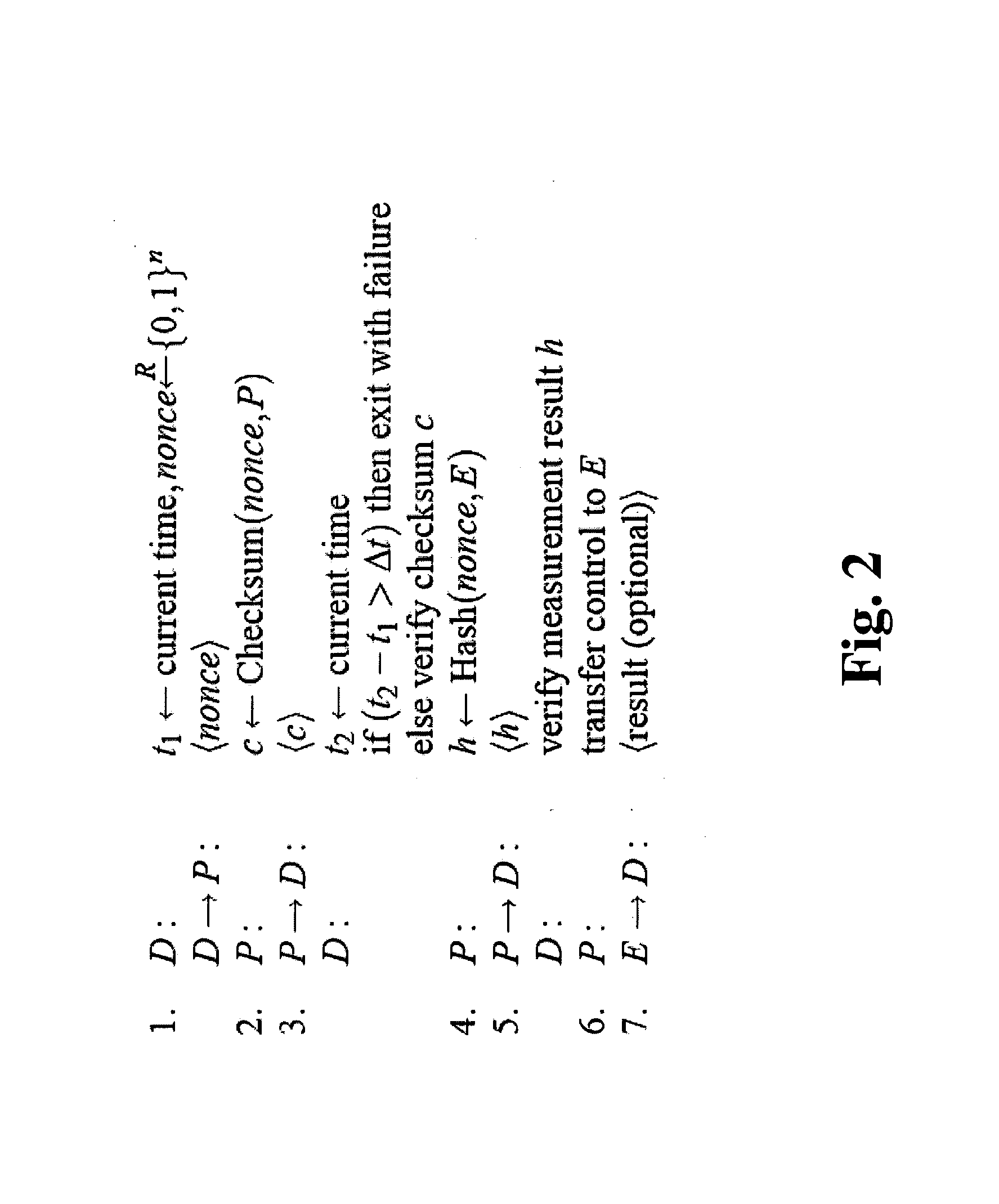
Verifying integrity and guaranteeing execution of code on untrusted computer platform
A method, system, and apparatus for verifying integrity and execution state of an untrusted computer. In one embodiment, the method includes placing a verification function in memory on the untrusted computer; invoking the verification function from a trusted computer; determining a checksum value over memory containing both the verification function and the execution state of a processor and hardware on the untrusted computer; sending the checksum value to the trusted computer; determining at the trusted computer whether the checksum value is correct; and determining at the trusted computer whether the checksum value is received within an expected time period.
Owner:IBM CORP +1
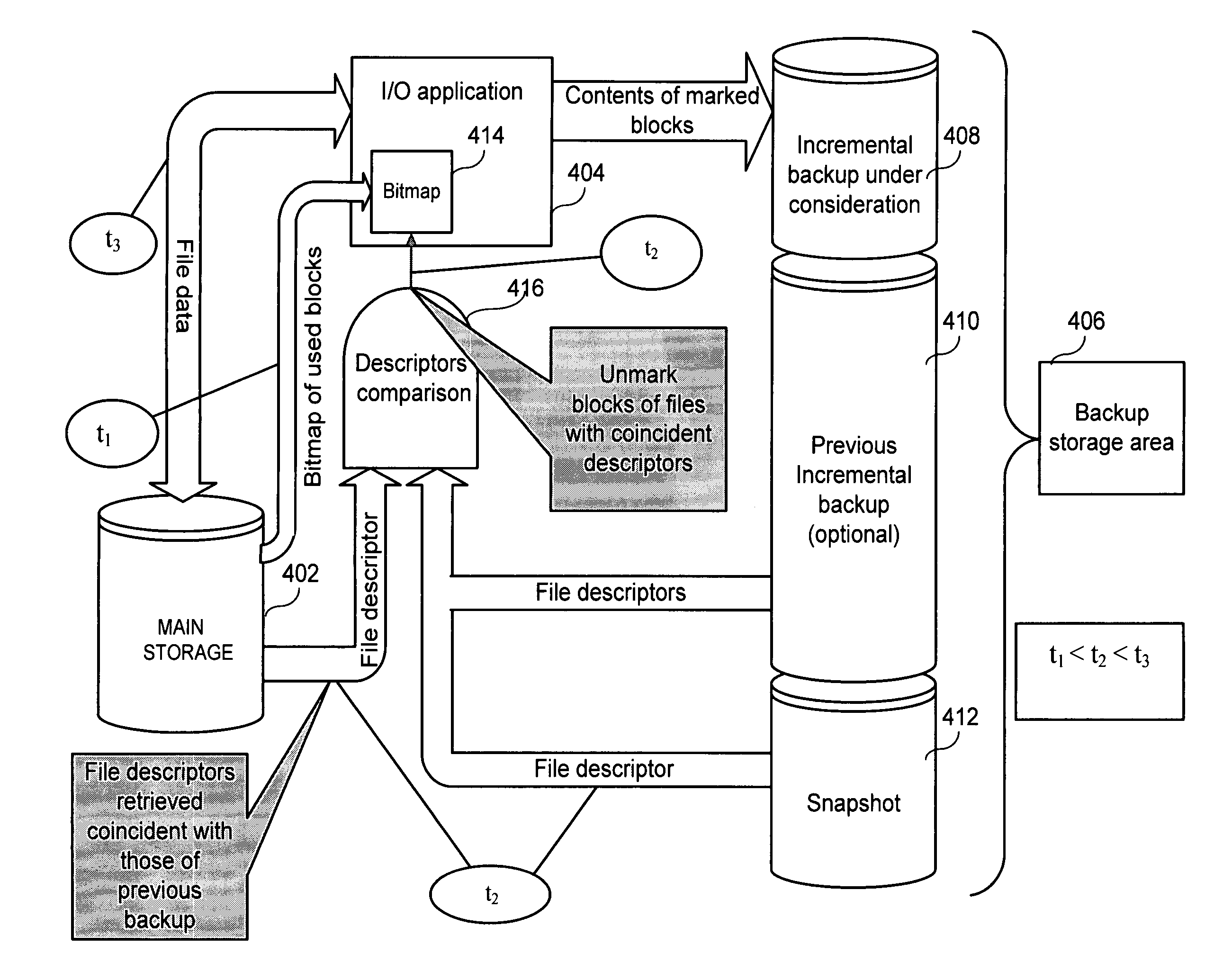
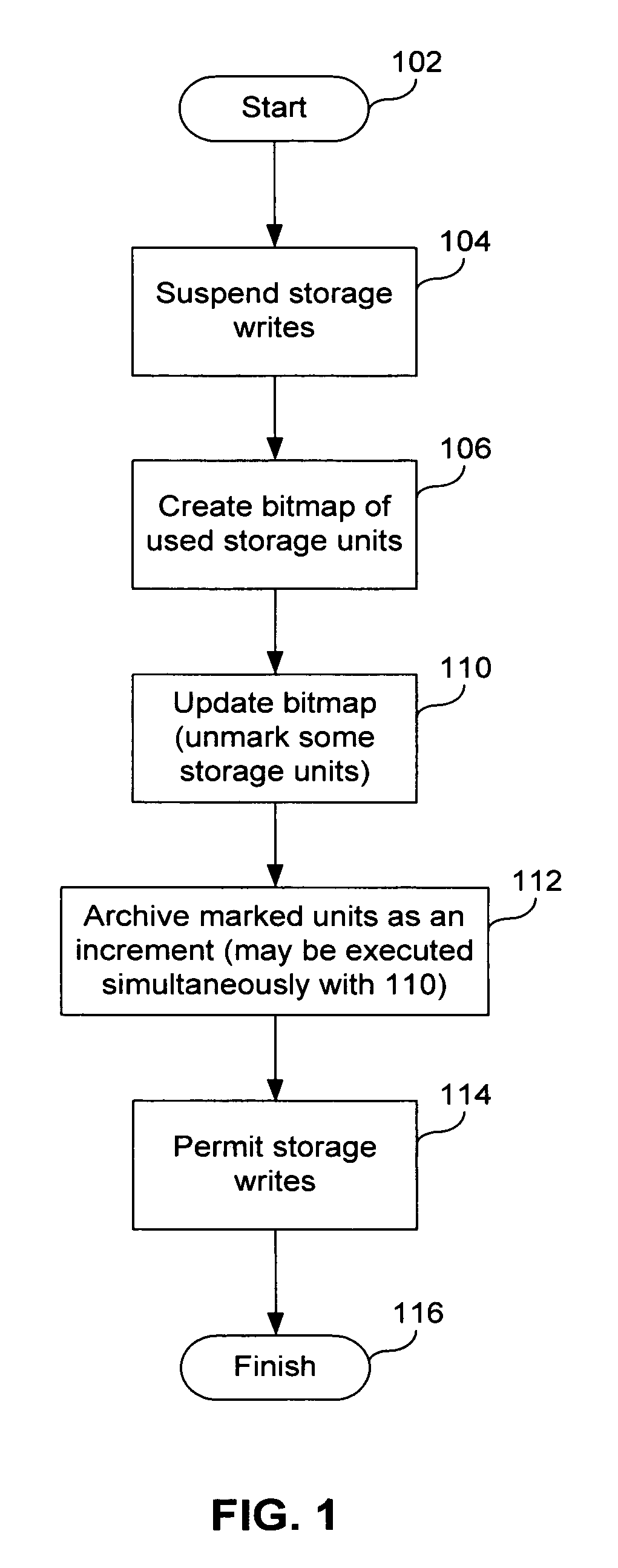
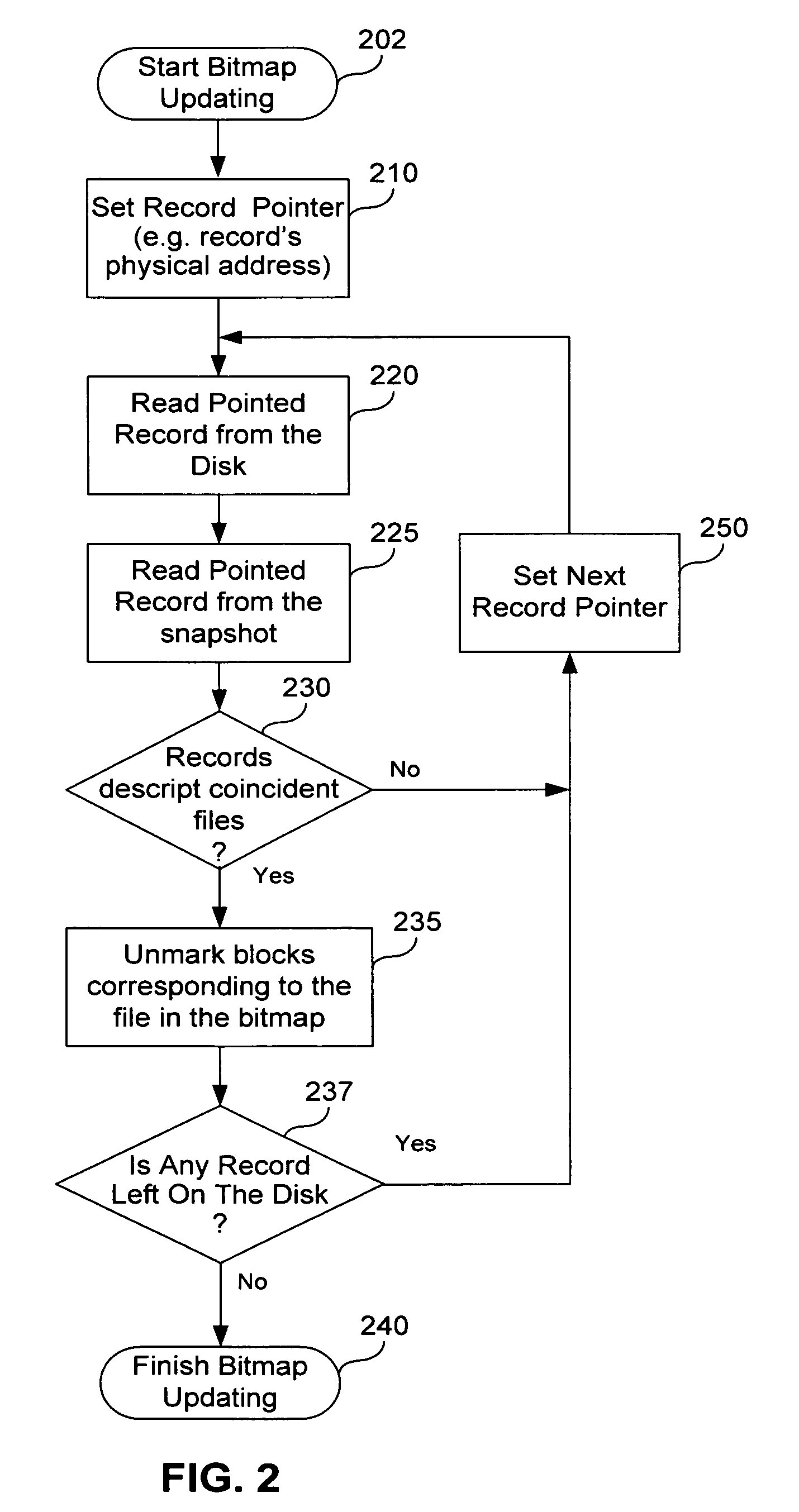
Fast incremental backup method and system
A method of incremental backup of a storage device includes reading descriptors of logical storage units of the storage device; comparing the descriptors of the logical storage units of the storage device with descriptors of archived logical storage units; for logical storage units of the storage device whose descriptors are not identical to the descriptors of the archived logical storage units, backing up contents of physical storage units that correspond to those logical storage units of the storage device; and, for logical storage units of the storage device whose descriptors are identical, performing a comparison step to check if these logical storage units need to be backed up. The logical storage units can be files. The comparison step can be, e.g., (1) bit-wise comparison of the logical blocks, (2) comparing control sums of the logical blocks, and (3) comparing log files relating to the logical storage units The physical storage units can be blocks. The descriptors can be, e.g., MFT entries, hash function values, timestamps, checksums, and file metadata. The descriptors can be compared on a physical storage unit basis. The method further can optionally include generating a bitmap of the physical storage units of the storage device; marking, in the bitmap, those physical storage units that correspond to logical storage units with different descriptors; and archiving content of the physical storage units marked in the bitmap. The method can further optionally include archiving logical storage units of the storage device having the same name as corresponding archived logical storage units of the storage device, but different time stamps.
Owner:MIDCAP FINANCIAL TRUST
Systems and methods for storing, backing up and recovering computer data files
ActiveUS20060179083A1Promote recoveryFaster and efficient incremental backupData processing applicationsError detection/correctionData fileChecksum
Owner:IDRIVE INC
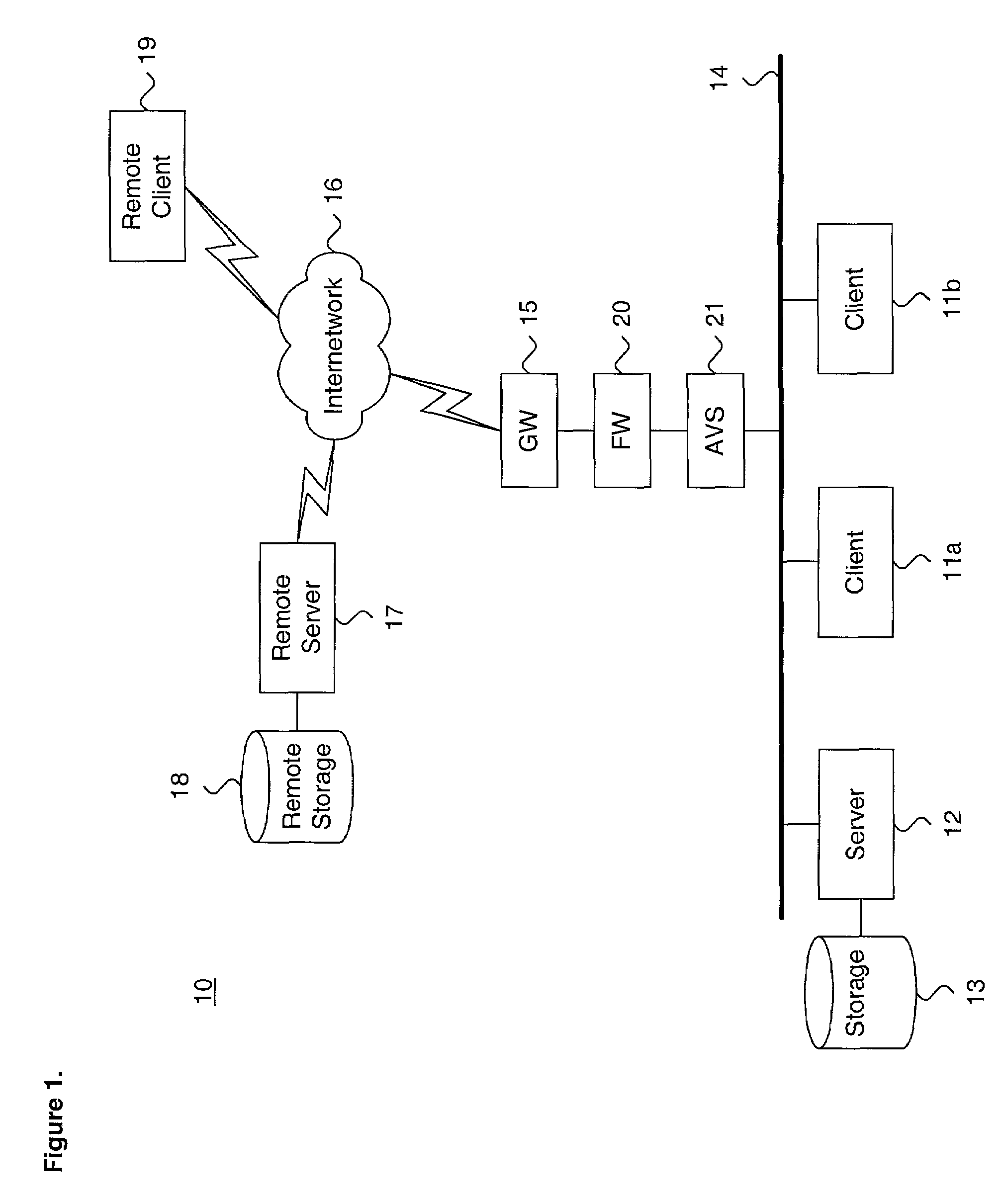
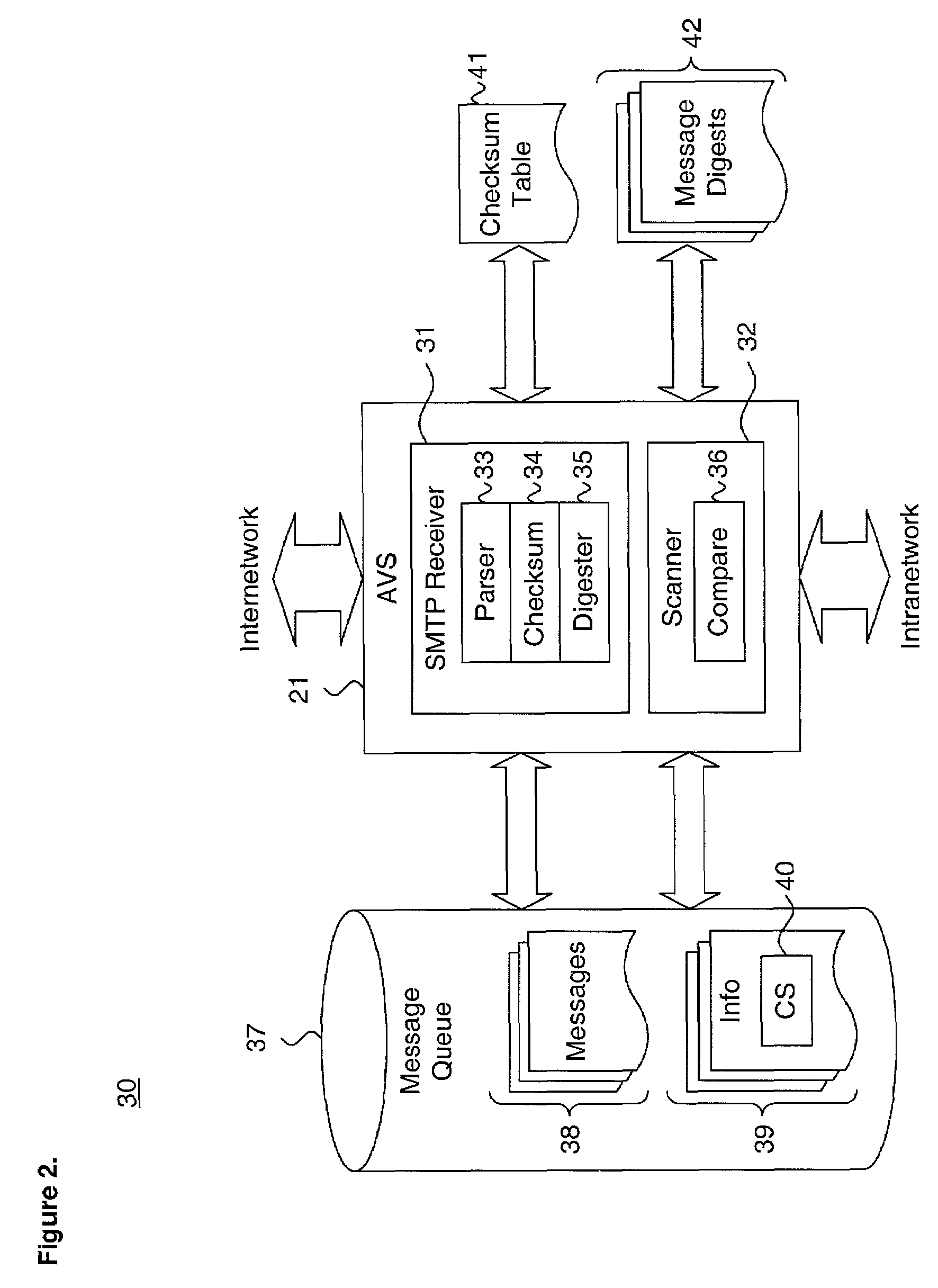
System and method for performing efficient computer virus scanning of transient messages using checksums in a distributed computing environment
ActiveUS6993660B1Efficient detectionMemory loss protectionUser identity/authority verificationDistributed Computing EnvironmentChecksum
A system and method for performing efficient computer virus scanning of transient messages using checksums in a distributed computing environment is described. An incoming message is intercepted at a network domain boundary. The incoming message includes a body storing message content. The message content is parsed from the body and a checksum is calculated over the parsed message content. The checksum is stored in an information file associated with the incoming message in a transient message store. The incoming message is scanned for a presence of at least one of a computer virus and malware to identify infected message contents. The checksum corresponding to each infected message content and an infection indicator is recorded.
Owner:MCAFEE LLC
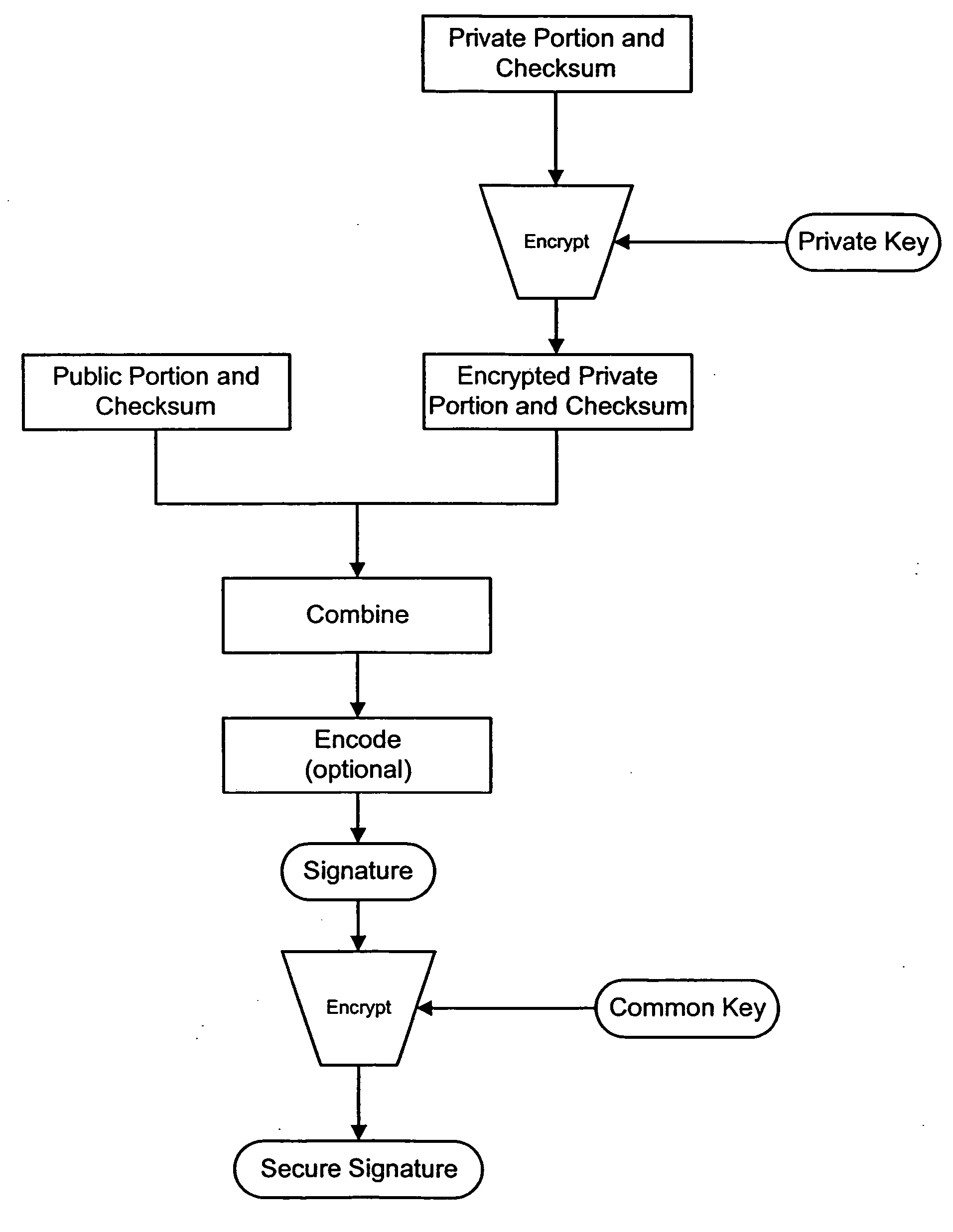
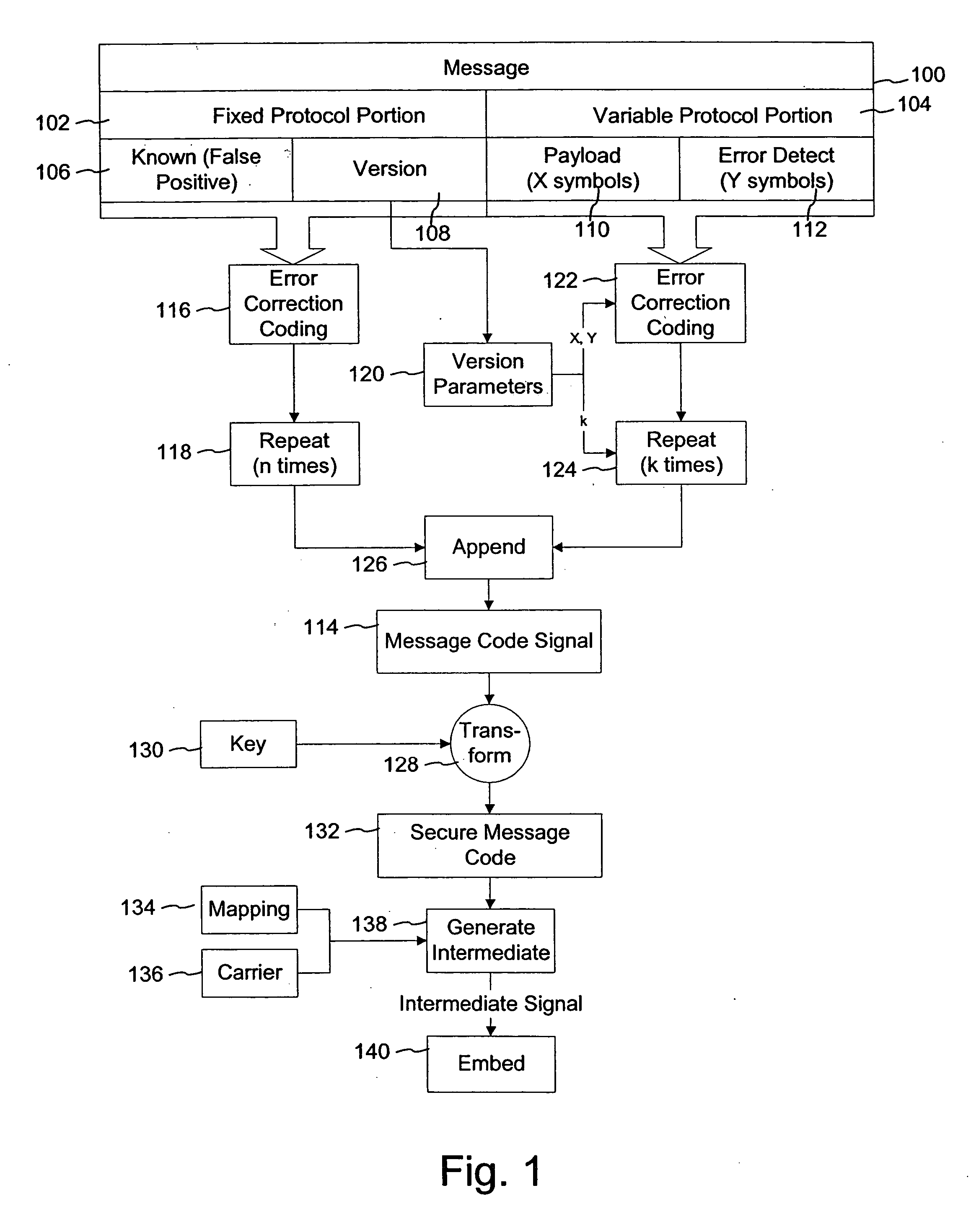
Watermark payload encryption methods and systems
InactiveUS20050271246A1User identity/authority verificationCharacter and pattern recognitionInternet privacyChecksum
The present invention provides a method of securing messages steganographically embedded in media (e.g., printed or electronic objects, audio and video). In one implementation, a message includes a first portion and a second portion. The first portion includes a first message and a first checksum, which are encrypted with a private key. The encrypted first portion is combined with the second portion. The second portion includes a second message and as second checksum. The combined encrypted first portion and the second portion form a signature. The signature is encrypted with a common or universal key, perhaps after error correction coding. The private key is uniquely associated with an entity such as a document issuing jurisdiction. In another implementation, a method appends information to a watermark message received from a remote device. The information preferably corresponds to the remote device or to a user of the remote device. In yet another implementation, a method provides standardized watermark payloads from various input data, regardless of the size of the input data.
Owner:DIGIMARC CORP
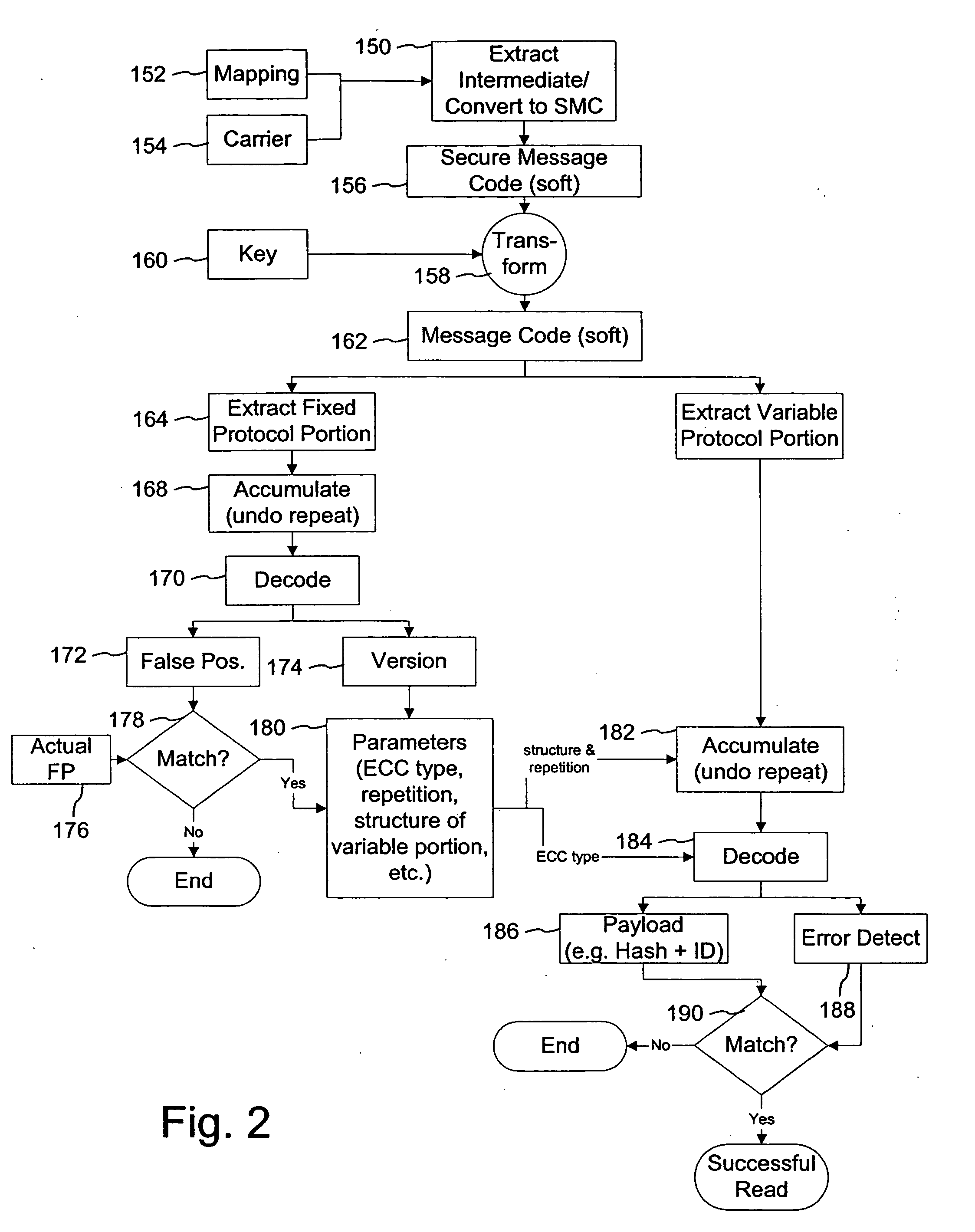
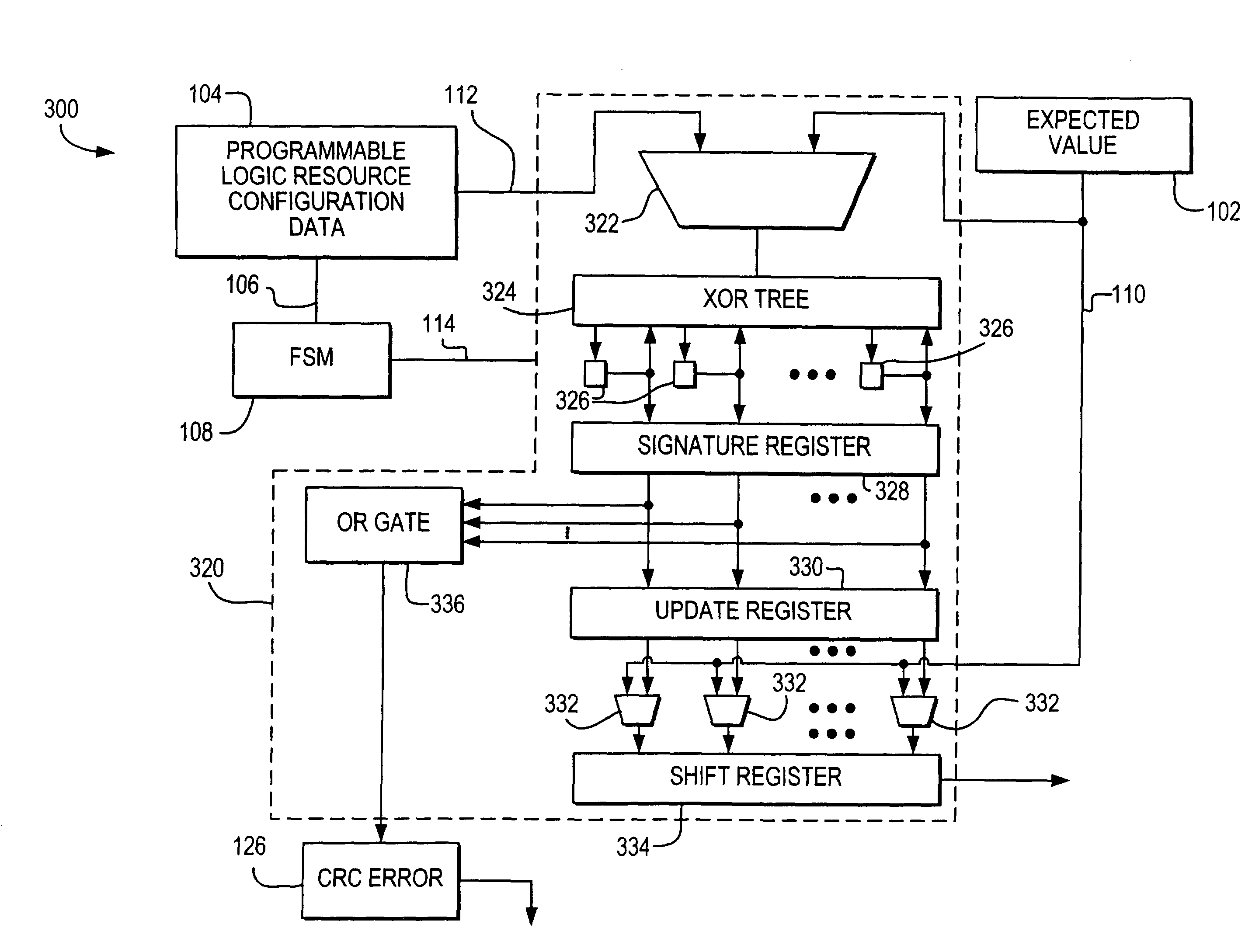
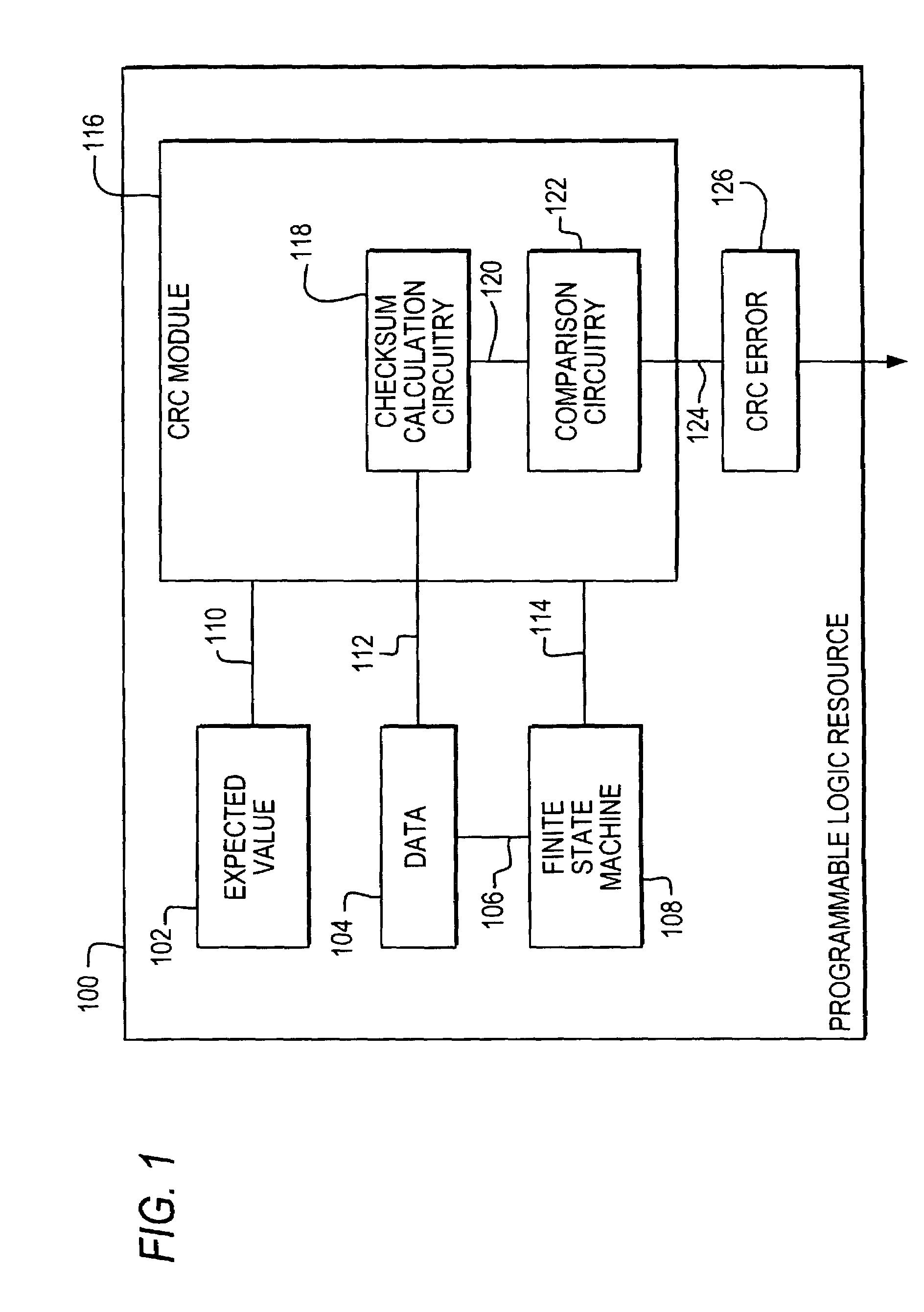
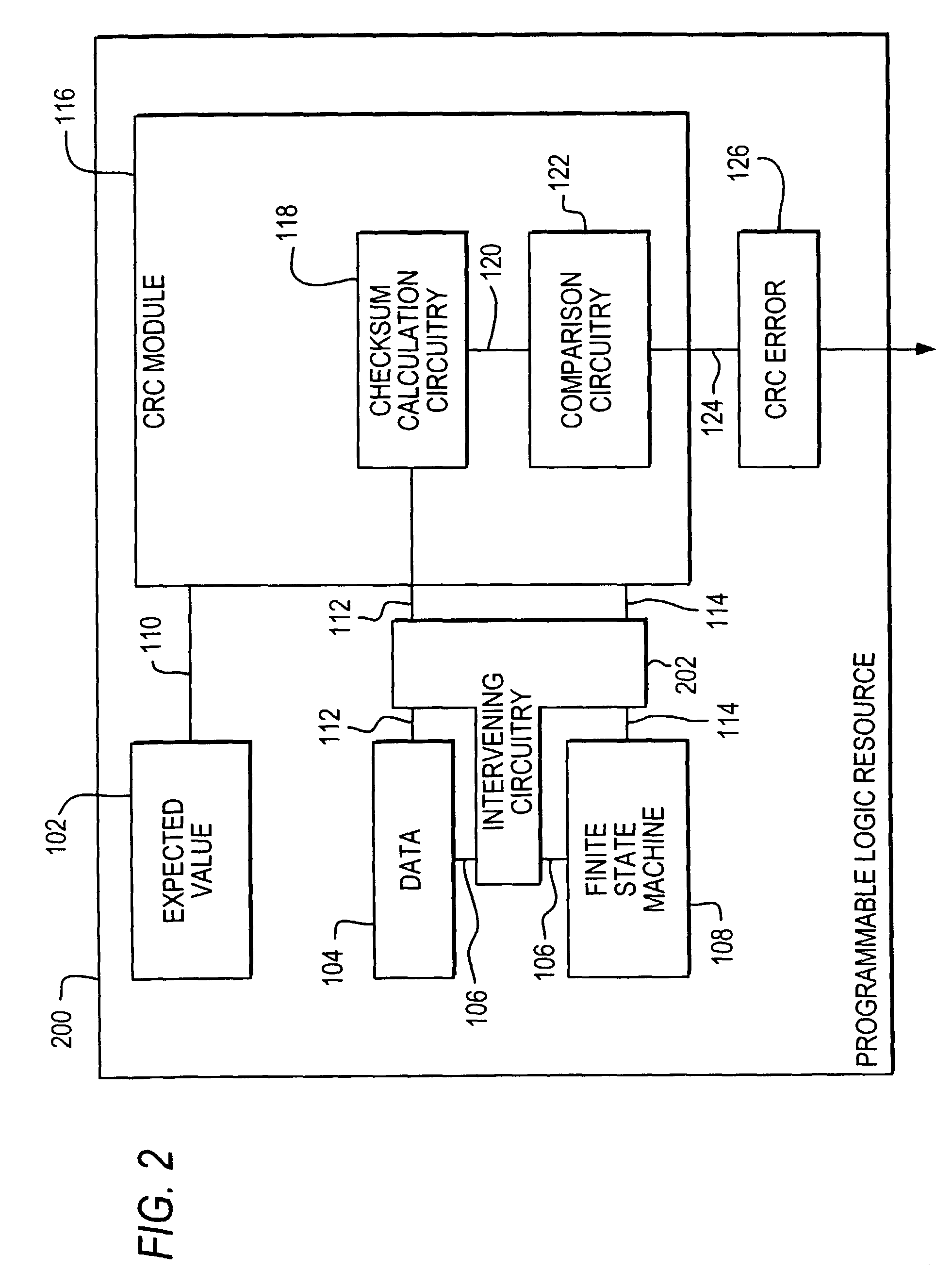
Error detection on programmable logic resources
InactiveUS7310757B2Electronic circuit testingDetecting faulty computer hardwareProgrammable logic deviceChecksum
Error detection circuitry is provided on a programmable logic resource. Programmable logic resource configuration data is loaded into a cyclic redundancy check (CRC) module where a checksum calculation may be performed. In one embodiment, the checksum may be compared to an expected value, which is a precomputed checksum on data prior to being programmed into or while data is being programmed into a programmable logic resource. In another embodiment, the expected value may be included in the checksum calculation. An output indicating whether an error is detected may be generated depending on the relationship between the checksum and the expected value, or on the value of the checksum. This output may be sent to an output pin that is accessible by user logic.
Owner:ALTERA CORP
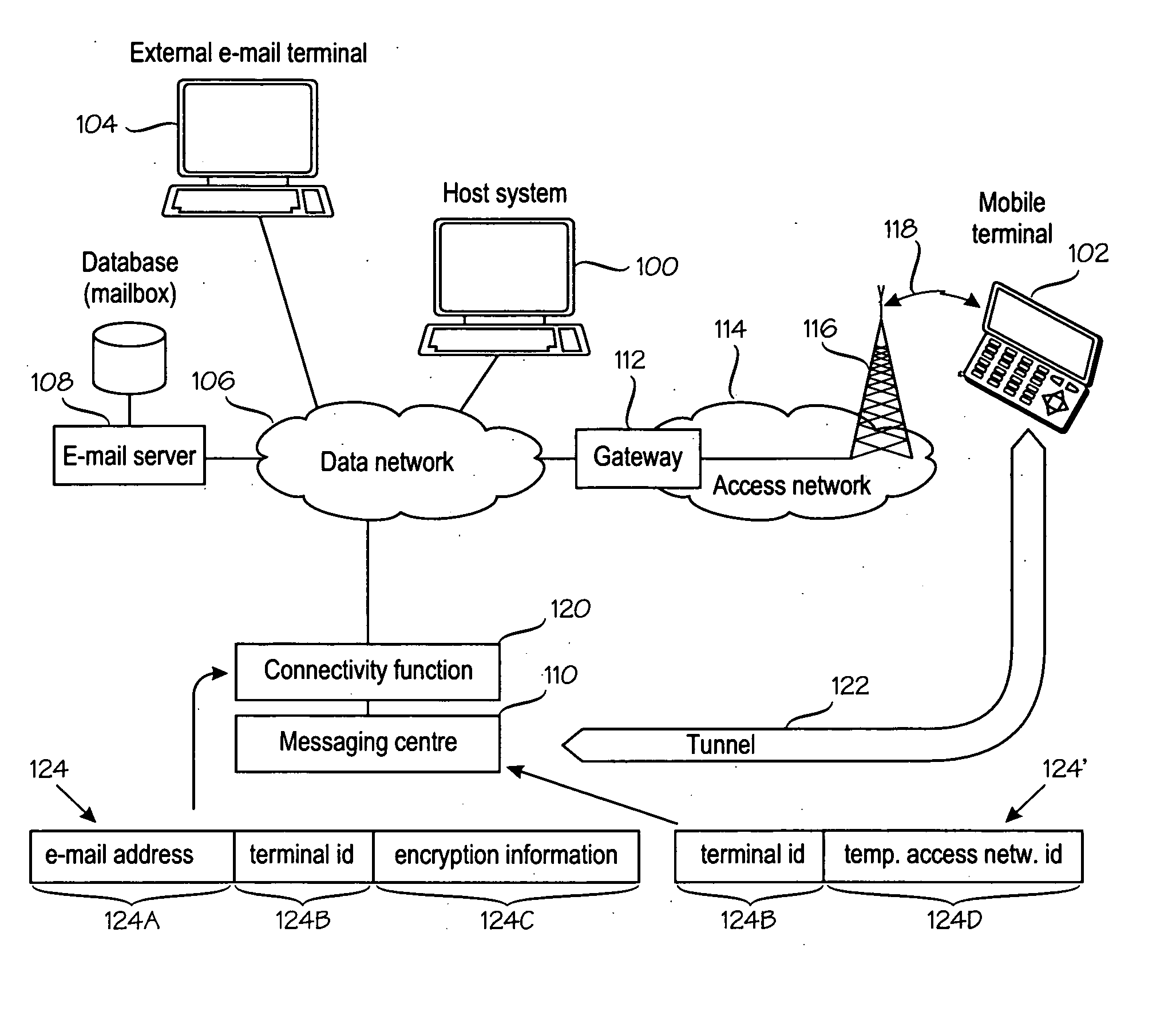
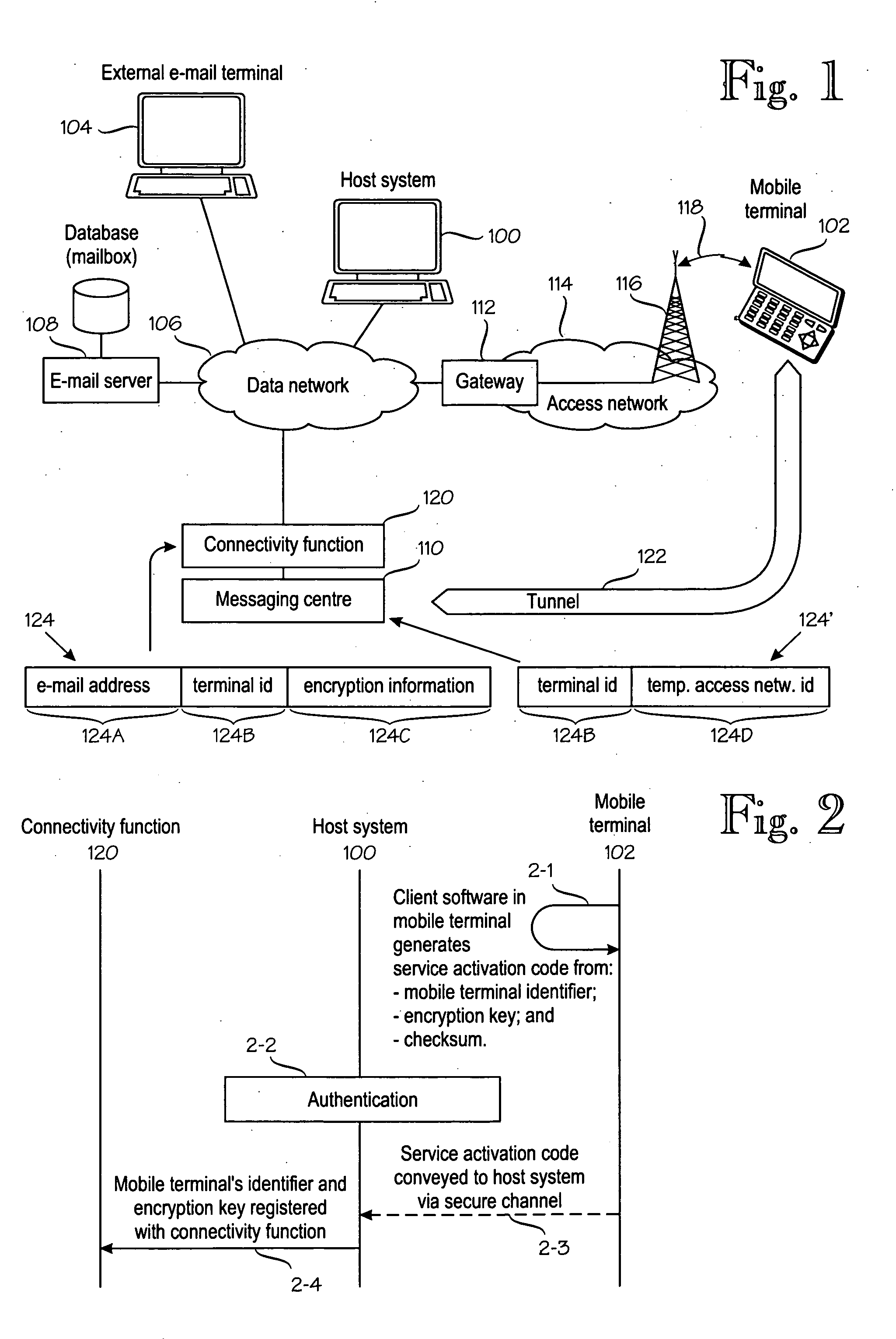
Data security in a mobile e-mail service
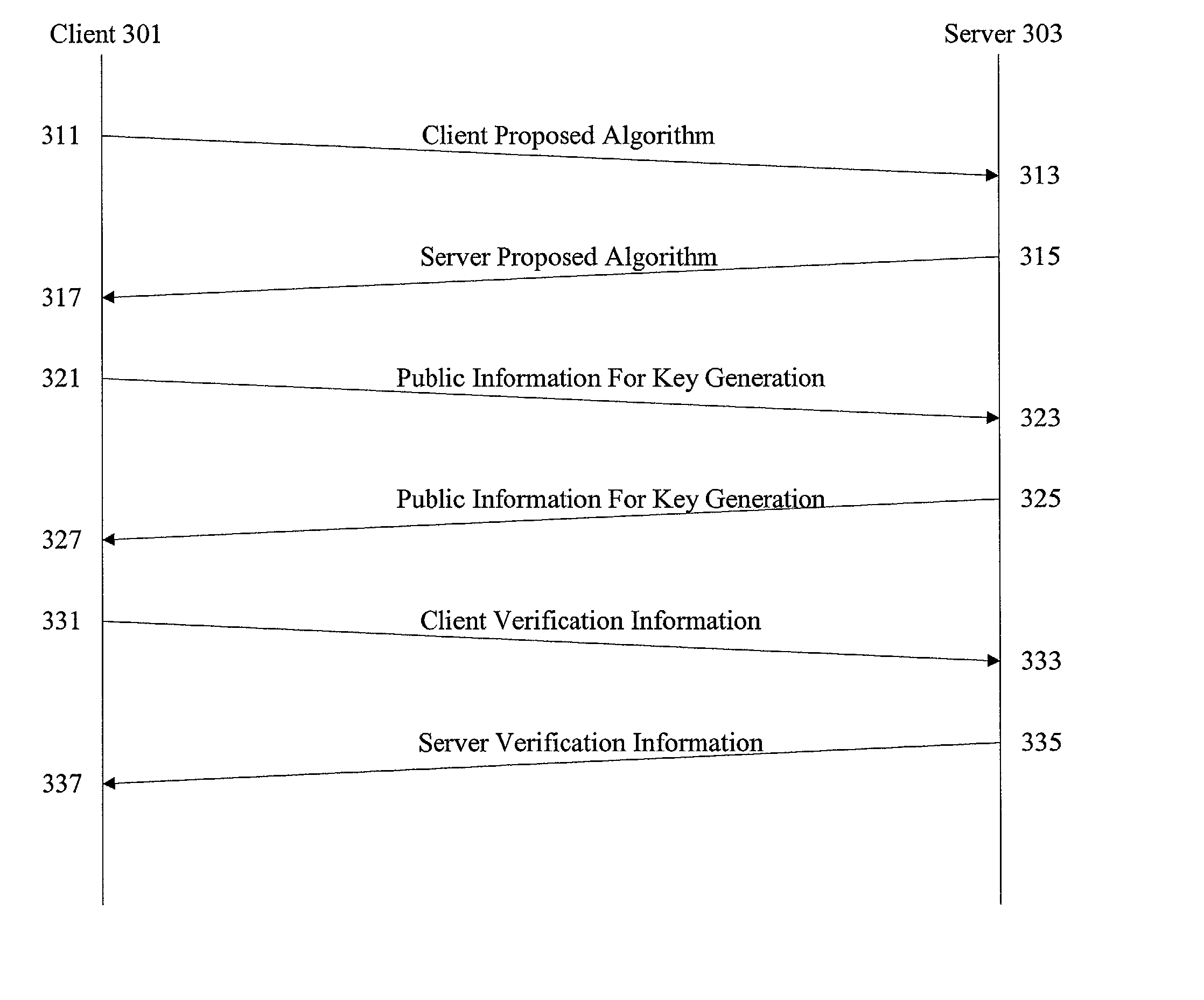
A method for conveying e-mail traffic between an e-mail server (108) and a mobile terminal (102) which has an e-mail address (122A) under the e-mail server and permanent terminal identity (122B) and a temporary identity (122D) in an access network (114). A connectivity function (600) is operationally coupled to the e-mail server (108) and the access network (114). The connectivity function (120) encrypts e-mail traffic to the mobile terminal and decrypt e-mail traffic from the mobile terminal, by using encryption information (122C). The mobile terminal generates (2-1) a service activation code which comprises an identifier (124D) of the mobile terminal, encryption information (122C) and checksum information. The service activation code is conveyed (2-3, 2-4) via a secure channel (2-3) to an authenticating terminal (100), from which the identifier (124D) of the mobile terminal and the encryption information (122C) are conveyed to the connectivity function (600).
Owner:SEVEN NETWORKS INC
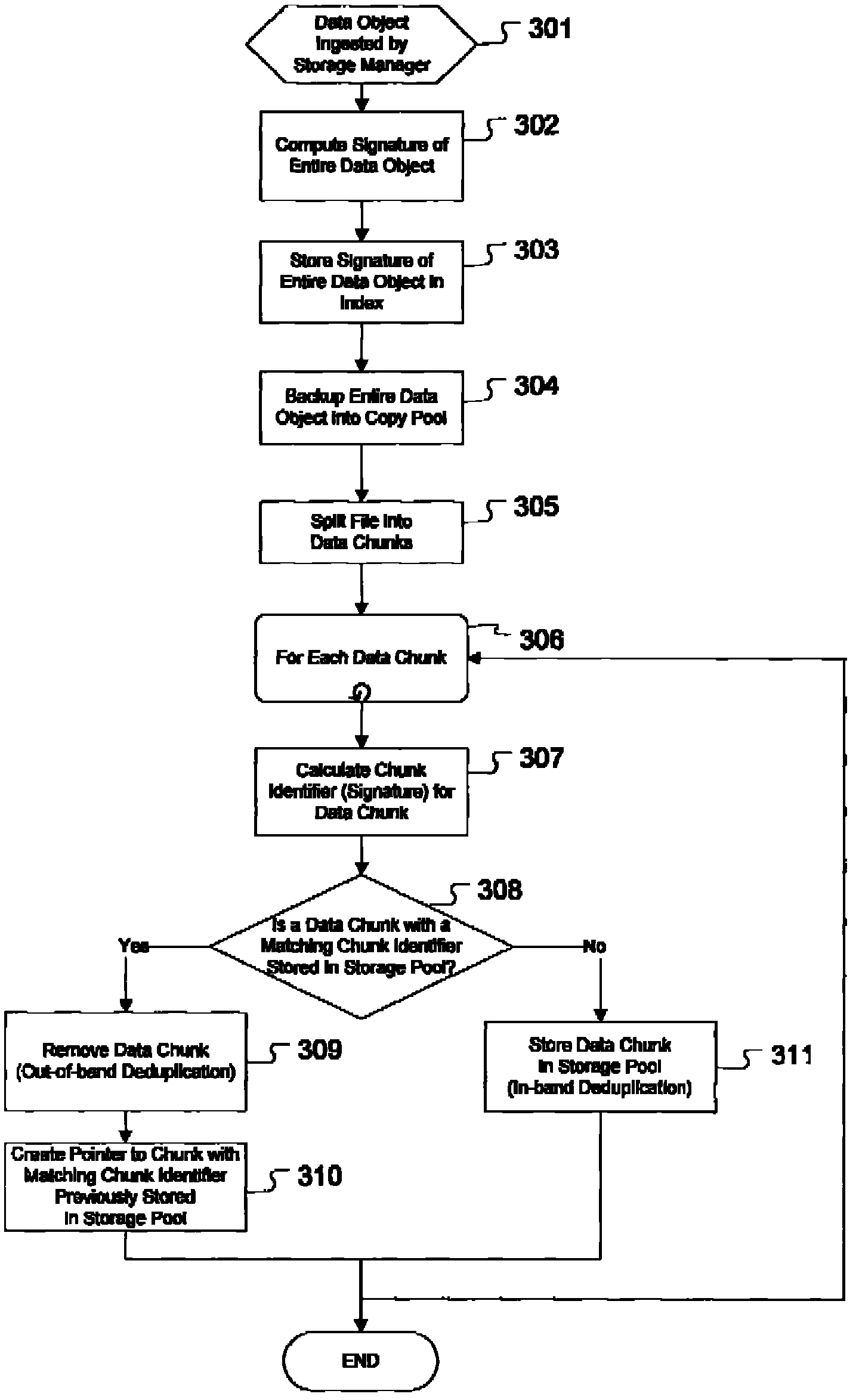
Method and system for assuring integrity of deduplicated data
InactiveUS20090234892A1Digital data information retrievalError detection/correctionDigital signatureChecksum
The present invention provides for a system and method for assuring integrity of deduplicated data objects stored within a storage system. A data object is copied to secondary storage media, and a digital signature such as a checksum is generated of the data object. Then, deduplication is performed upon the data object and the data object is split into chunks. The chunks are combined when the data object is subsequently accessed, and a signature is generated for the reassembled data object. The reassembled data object is provided if the newly generated signature is identical to the originally generated signature, and otherwise a backup copy of the data object is provided from secondary storage media.
Owner:IBM CORP
Programming content distribution
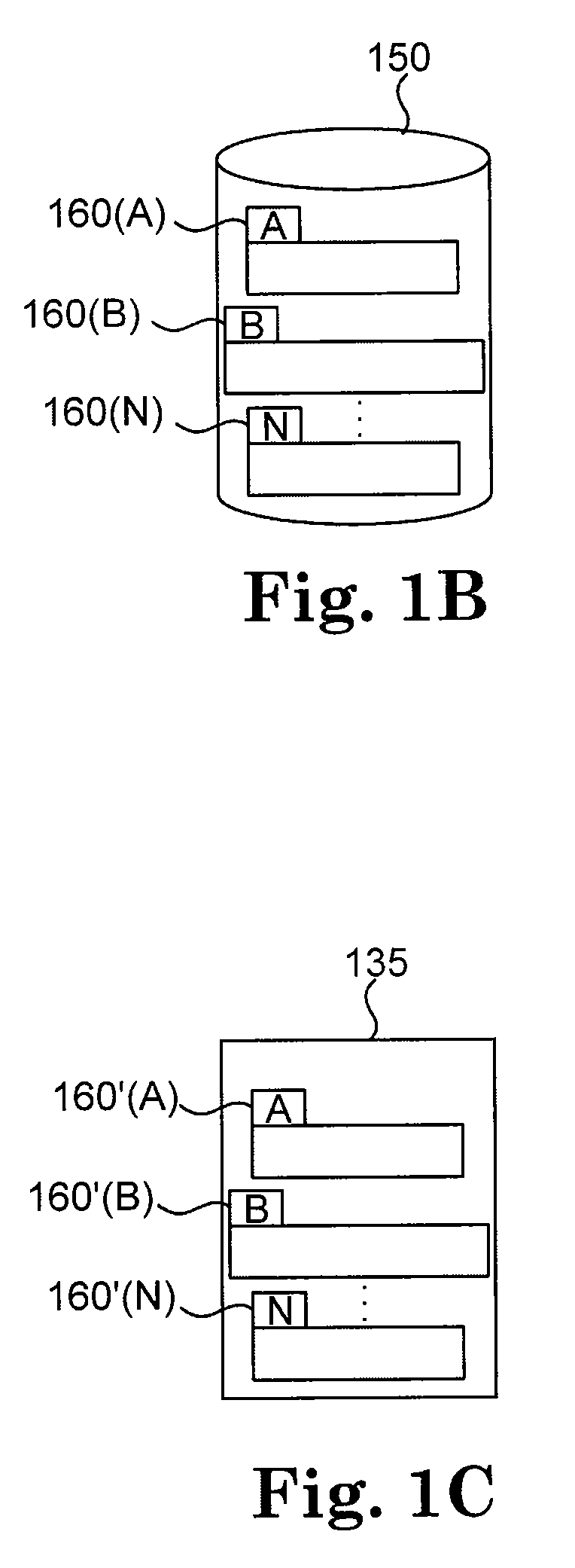
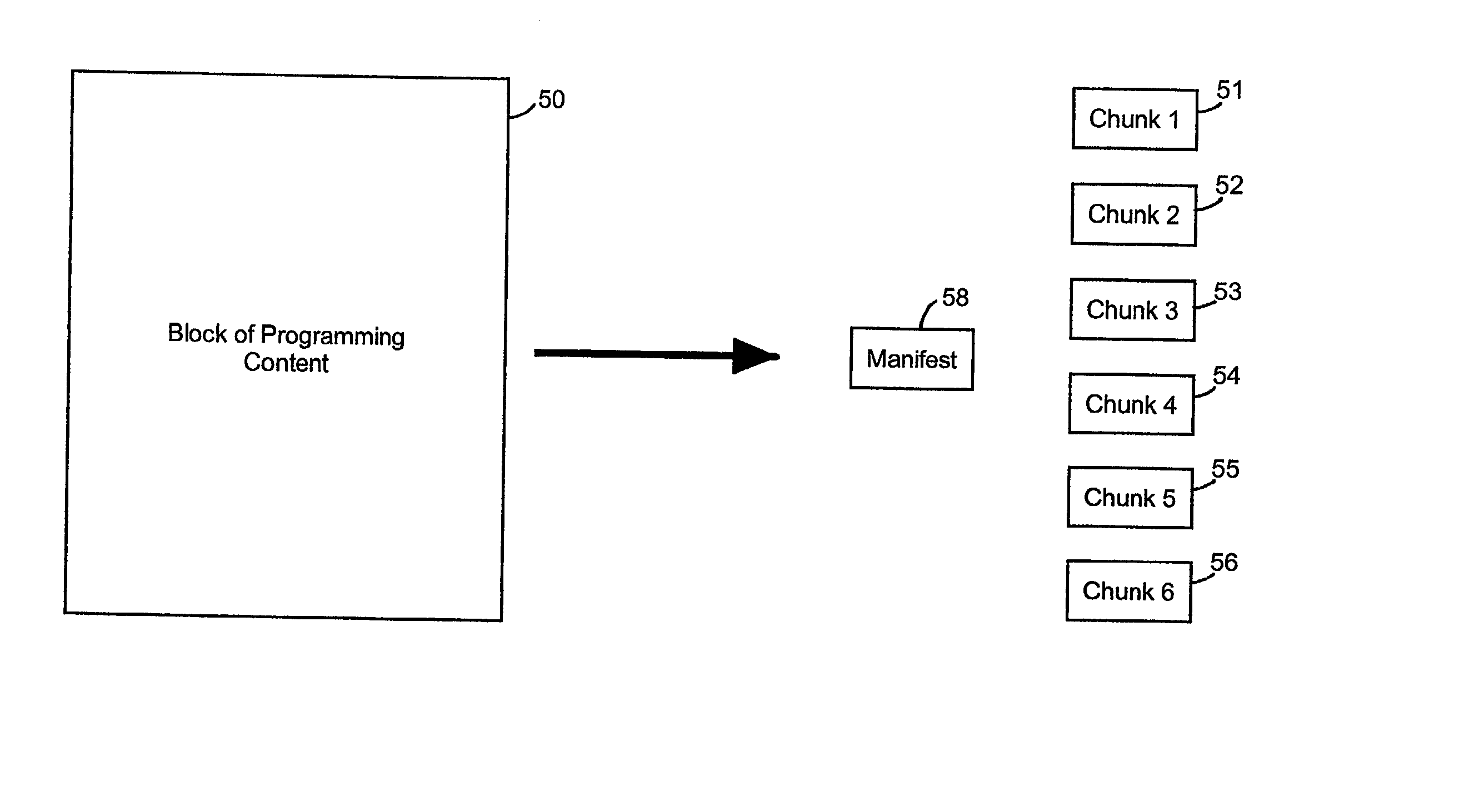
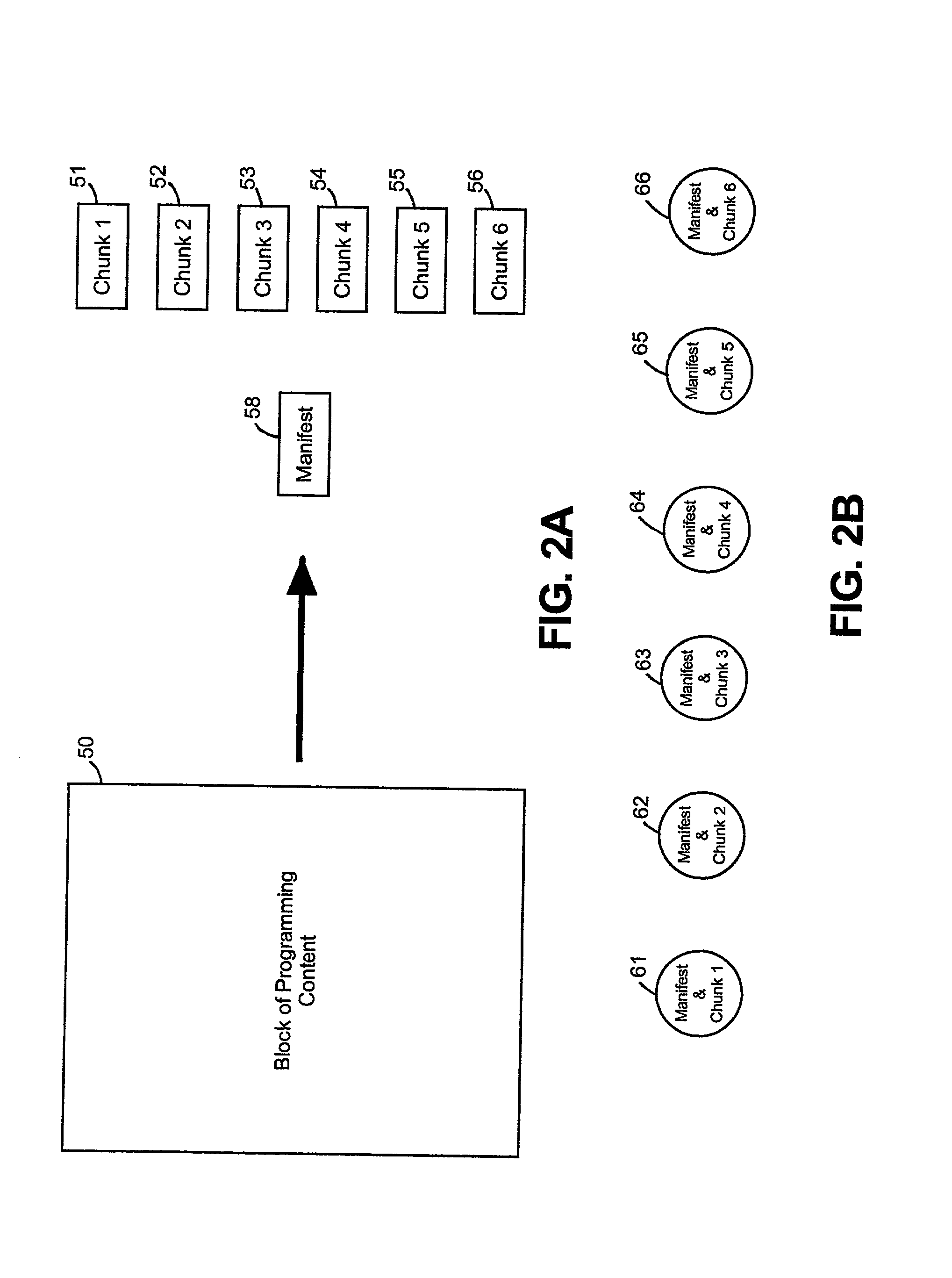
InactiveUS20020156912A1Multiple digital computer combinationsElectric digital data processingManifest fileContent distribution
Programming content, such as a digital motion picture, is delivered by dividing the programming content into smaller chunks of data and creating a chunk file for each chunk of data. The chunk file includes the chunk of data and a message digest (e.g., a checksum or CRC code) for verifying integrity of the chunk of data. A manifest file that includes information describing how to assemble the chunks of data also is generated. At the receiving end, multiple chunk files and a manifest file are received. The chunk files include chunks of data that together make up programming content, and each chunk file also includes a message digest for verifying integrity of the chunk of data within the chunk file. The manifest file includes information describing how to assemble the chunks of data. The chunks of data are stored, and assembled and played according to the information in the manifest file.
Owner:AVICA TECH CORP
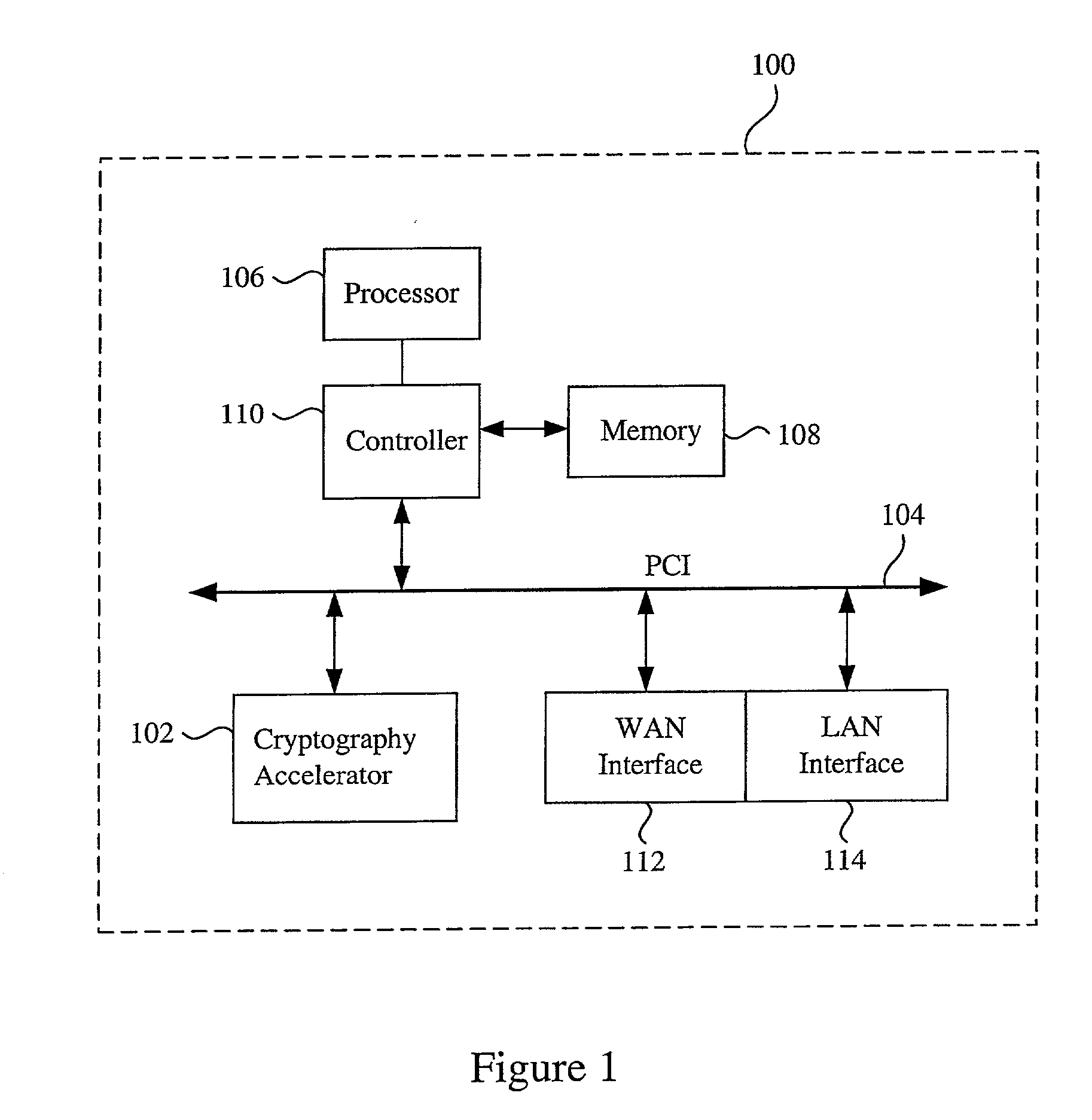
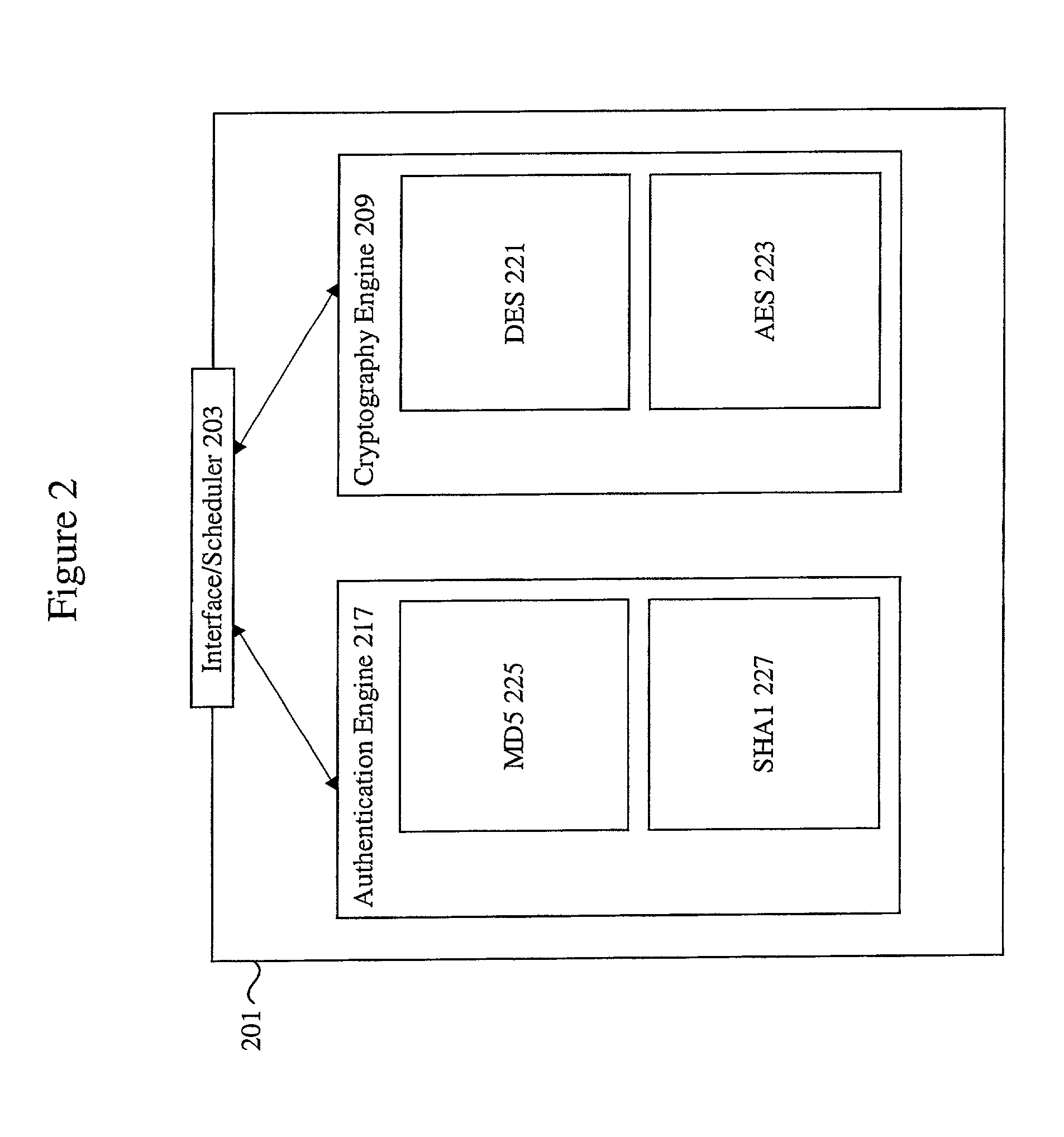
Data transfer efficiency in a cryptography accelerator system
InactiveUS20030226018A1User identity/authority verificationInternal/peripheral component protectionCryptographic acceleratorChecksum
Methods and apparatus are provided for performing authentication and decryption operations in a cryptography accelerator system. Input data passed to a cryptography accelerator from a host such a CPU includes information for a cryptography accelerator to determine where to write the processed data. In one example, processed data is formatted as packet payloads in a network buffer. Checksum information is precalculated and an offset for a header is maintained.
Owner:AVAGO TECH INT SALES PTE LTD
Method and system for assuring integrity of deduplicated data
InactiveUS7814074B2Digital data information retrievalDigital data processing detailsDigital signatureChecksum
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com