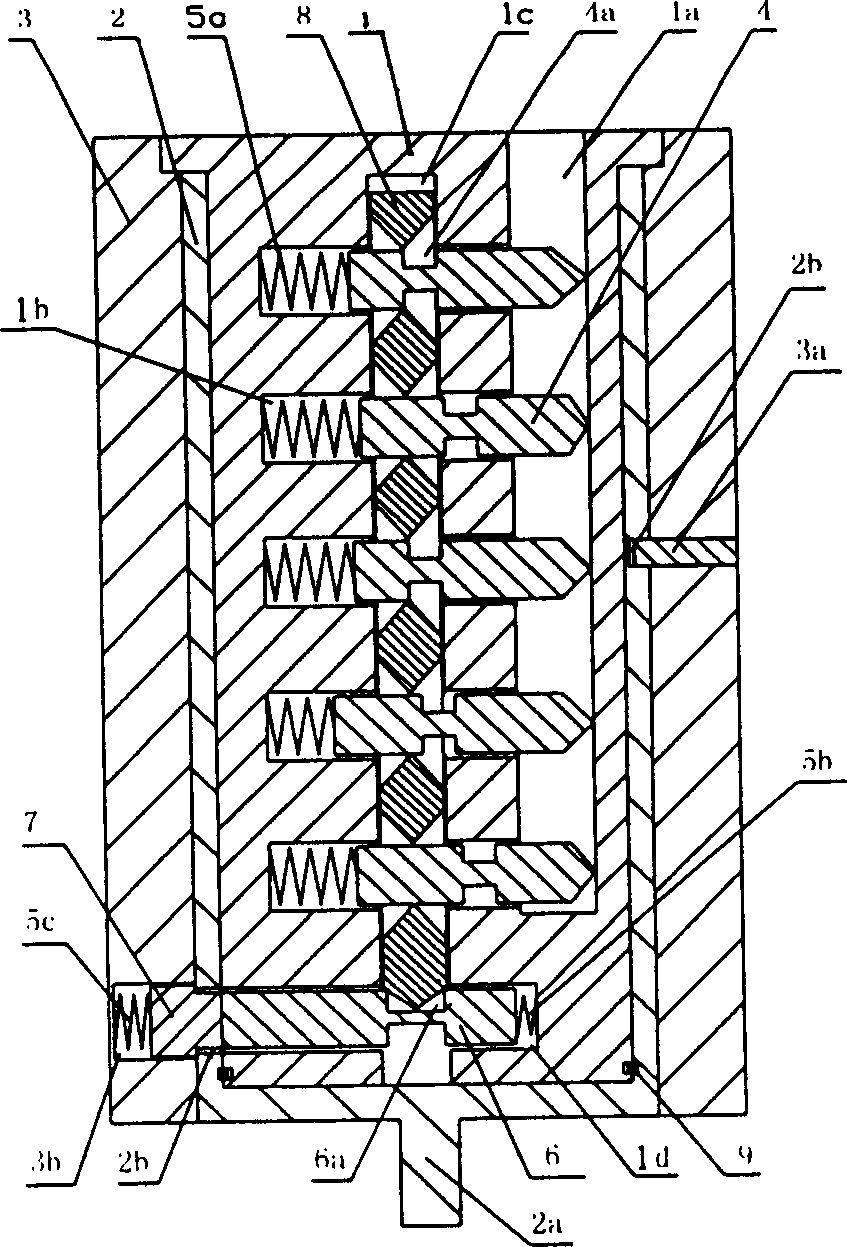
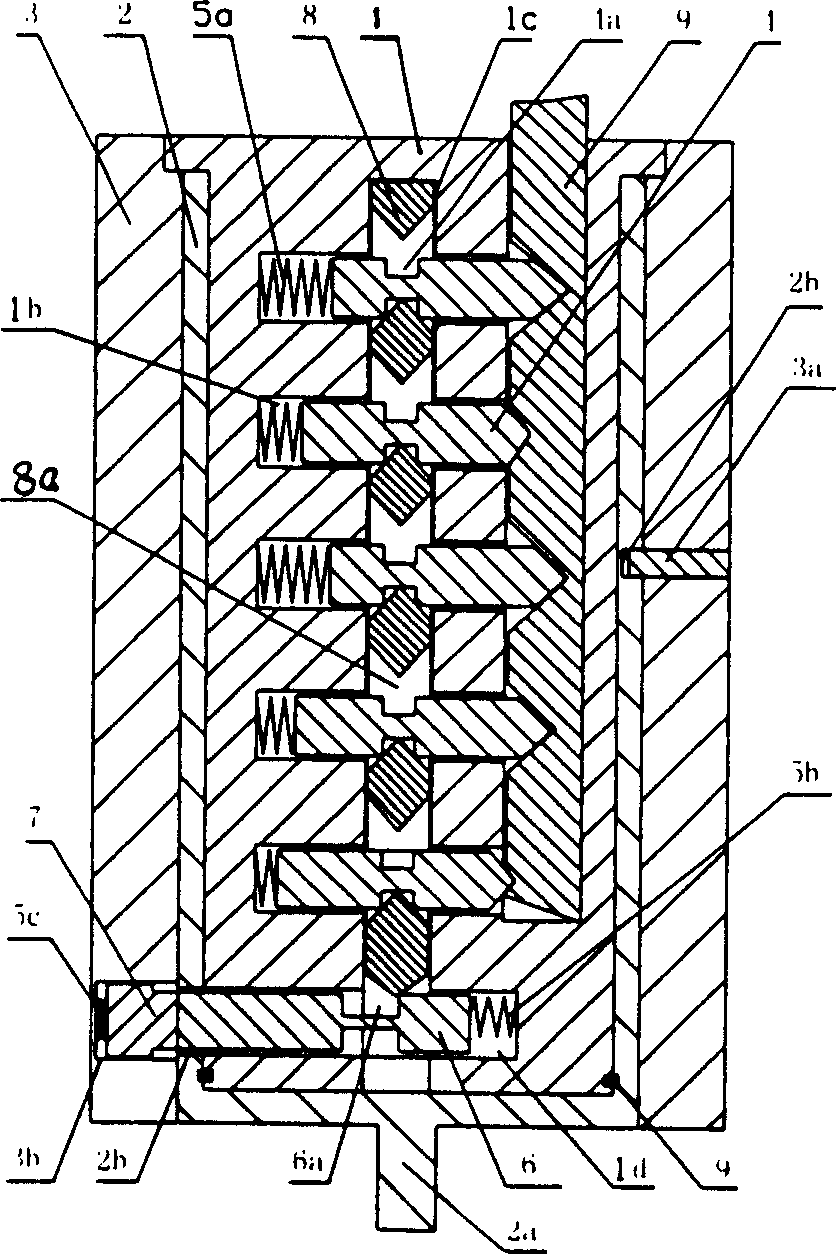
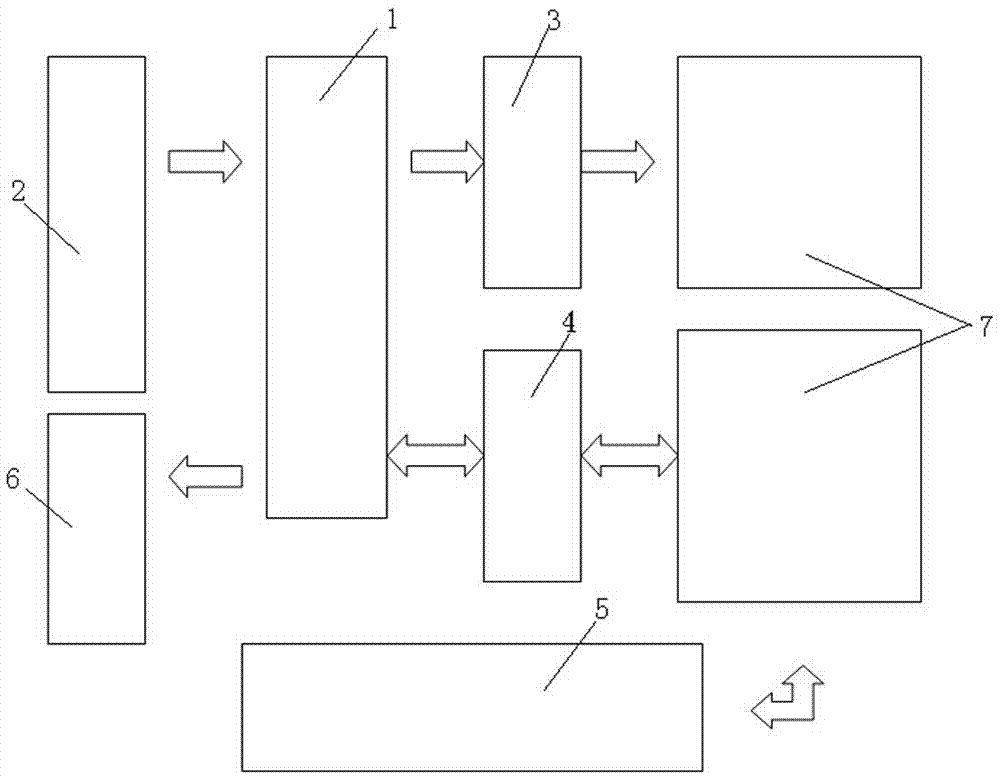
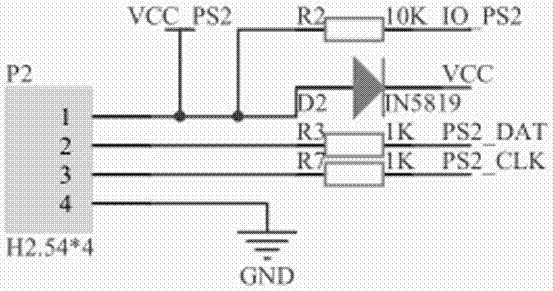
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
62 results about "Universal key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The universal key or universal scale is a concept employed in music theory in which specific notes or chord symbols in a key signature are replaced with numbers or Roman numerals, allowing for a discussion describing relationships between notes or chords that can be universally applied to all key signatures.
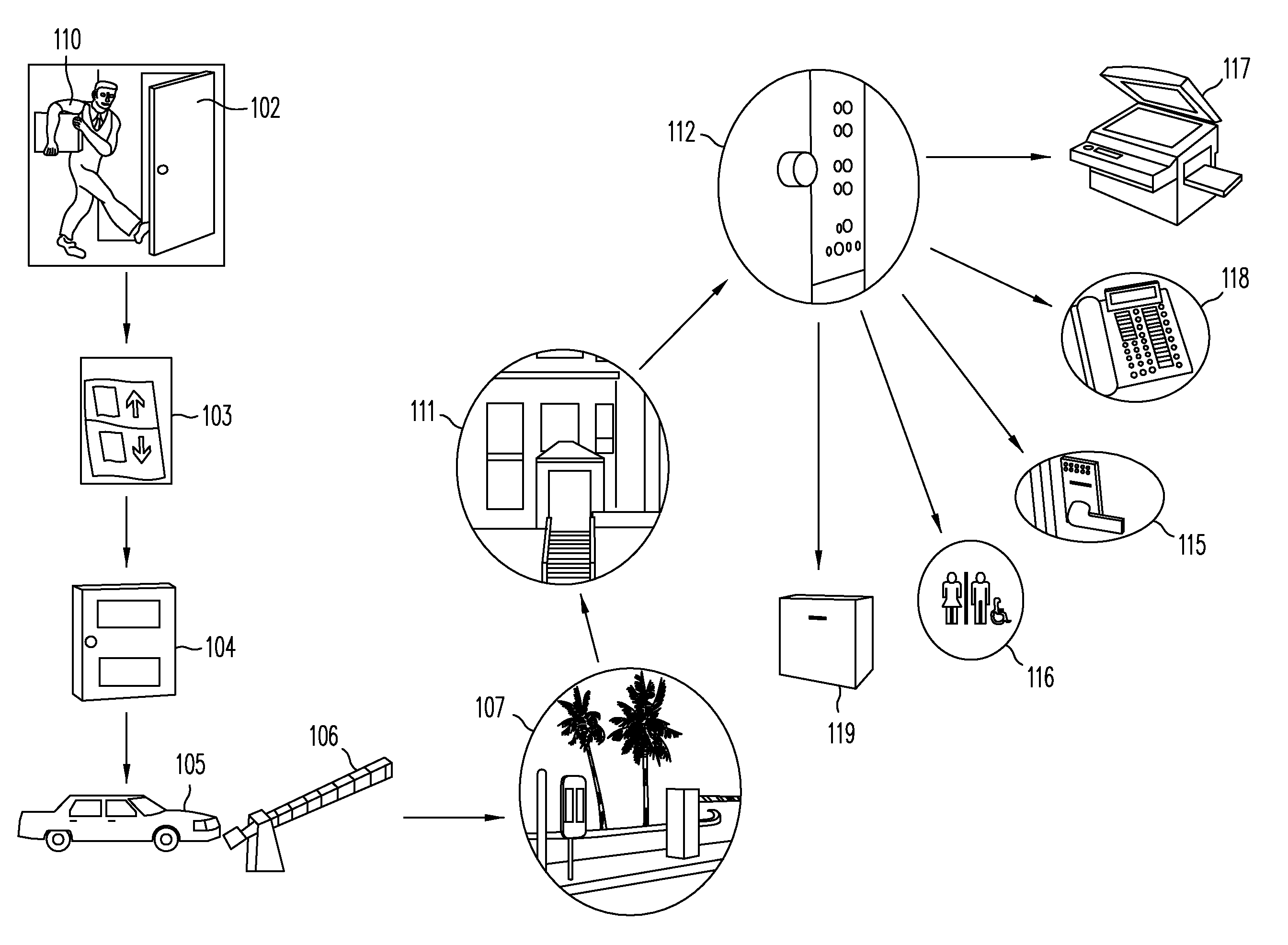
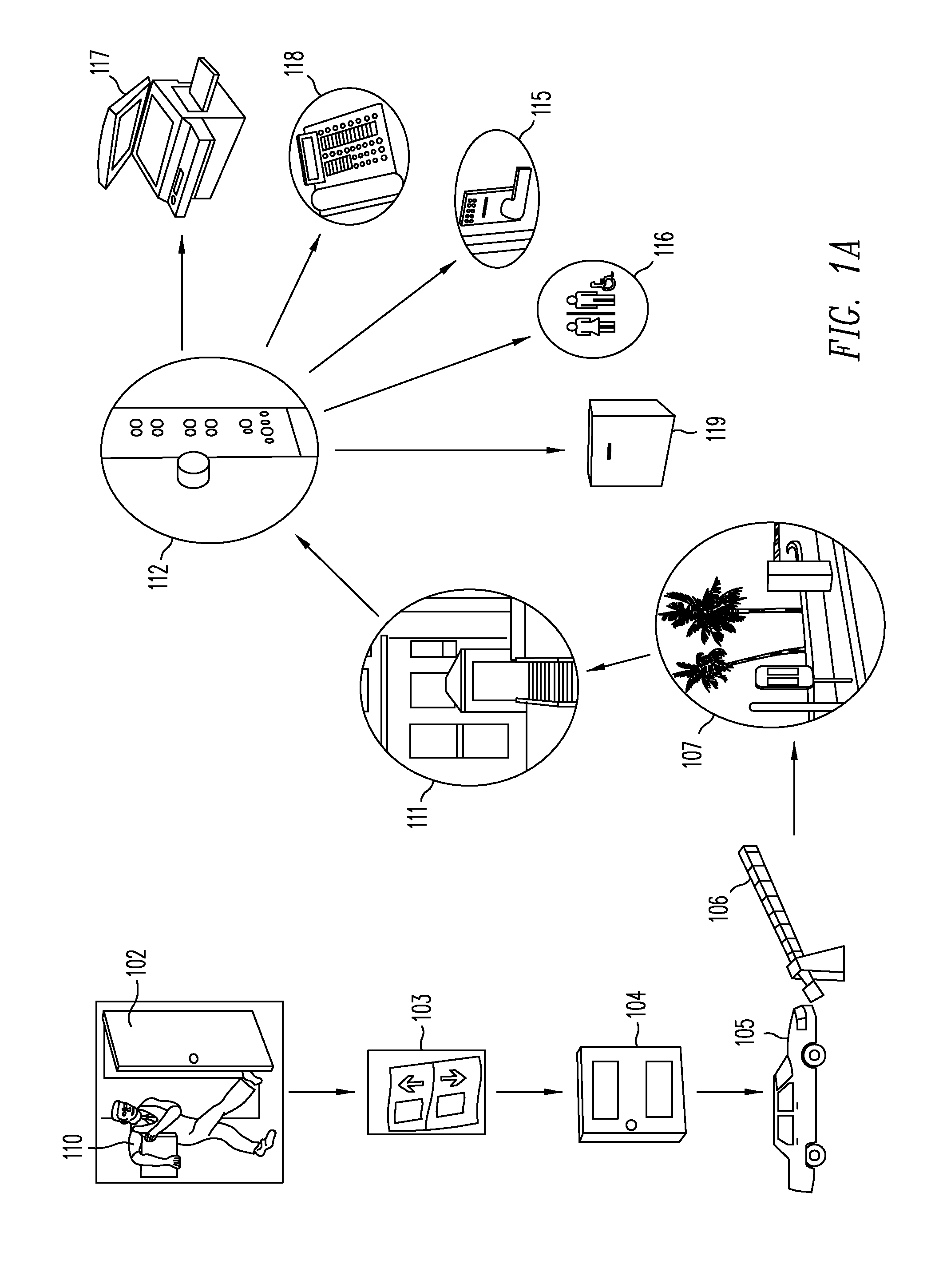
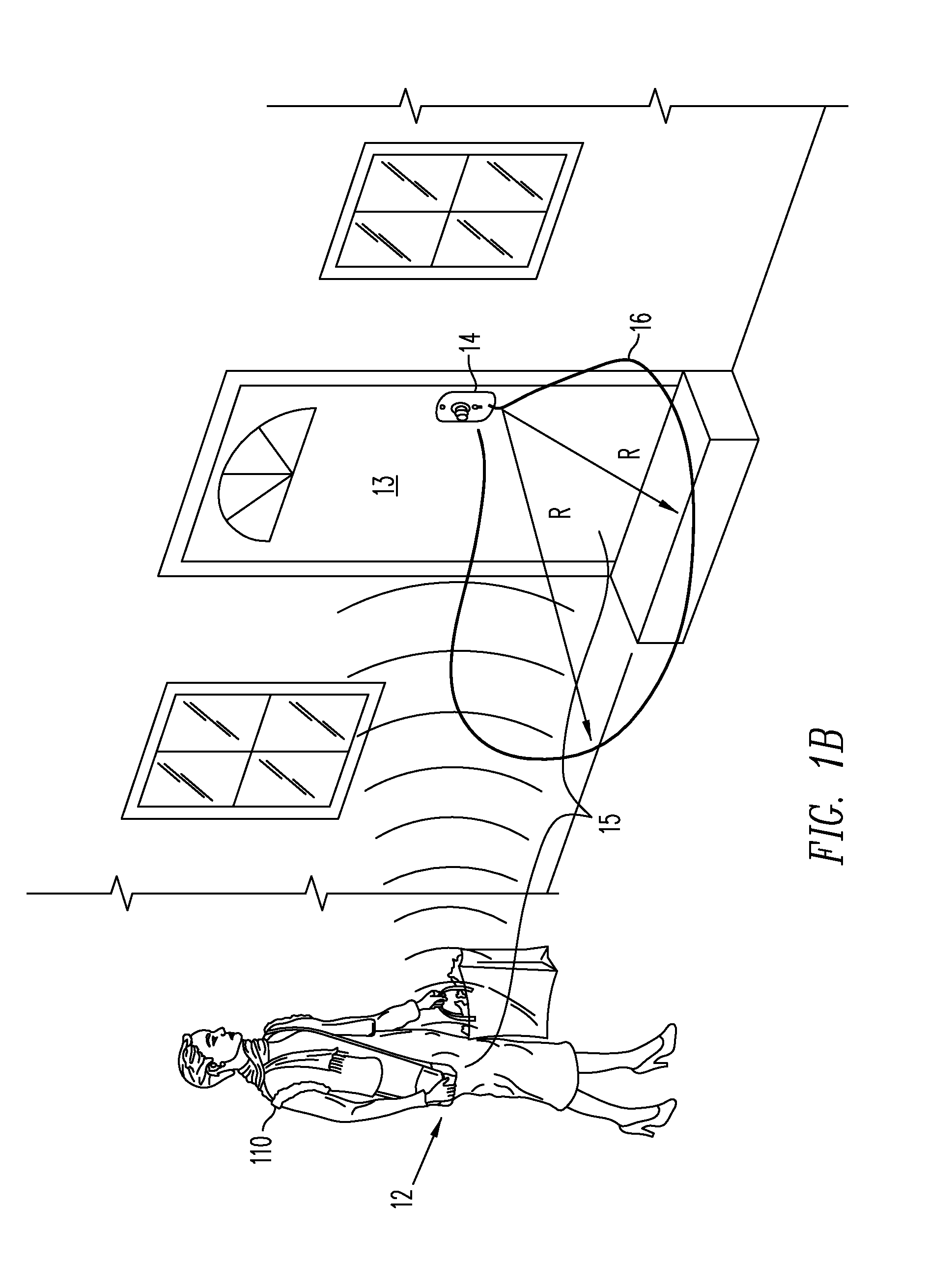
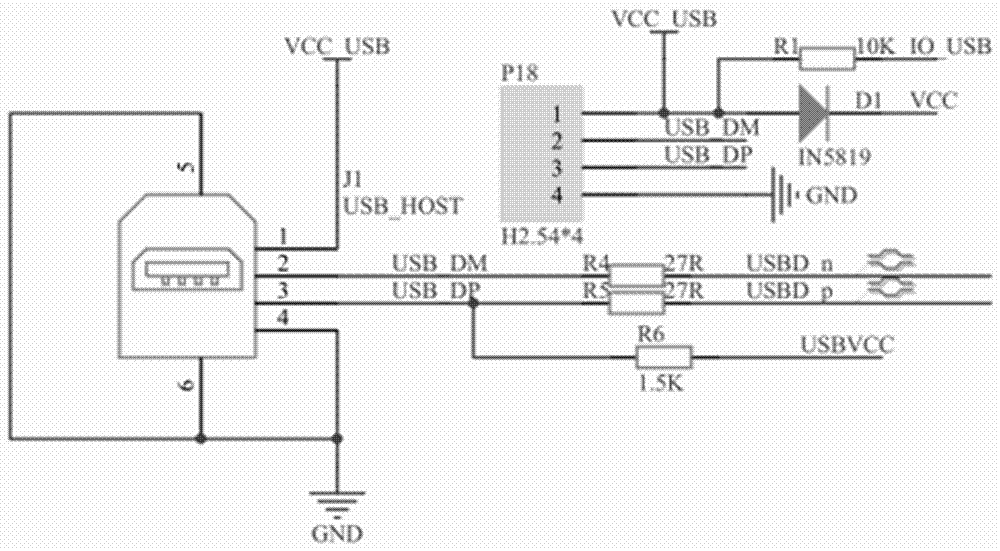
Universal hands free key and lock system
InactiveUS7446644B2Quickly and easily pass through otherwise locked doorEliminate needElectric signal transmission systemsDigital data processing detailsUser needsEngineering
Methods and systems are provided for a universal key that enables a user to have access to any type of secured portal, both physical and electronic, in a wireless, hands-free, distance-independent manner without requiring contact or line of sight access between the key and the secured portal. The universal key is not distance-dependent, and each secured portal can be provided with its own prescribed activation range, if desired. Some portals may be provided with long range activation, such as 50 feet, while other portals may be provided with short range activation of a few feet or less. The type of portal being secured and the range of activation may be selected by the user and is not limited by the universal key. In addition, the universal key will provide access to the secured portals in a hands-free fashion so that the user need not push any buttons or take any other action in order to obtain access to the portal. The user need only carry the universal key somewhere on their person in order to access the portal.
Owner:SECUREALL CORP
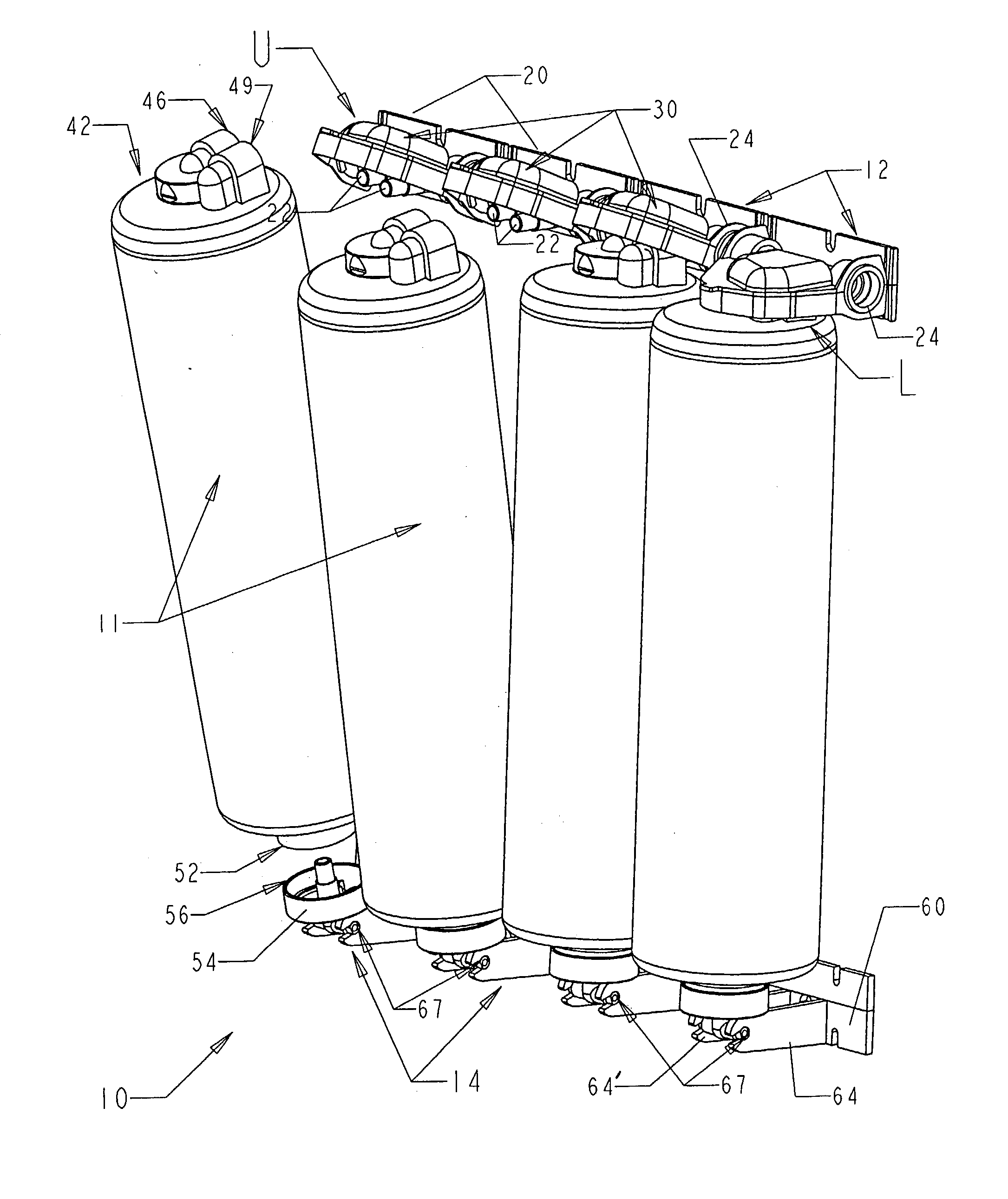
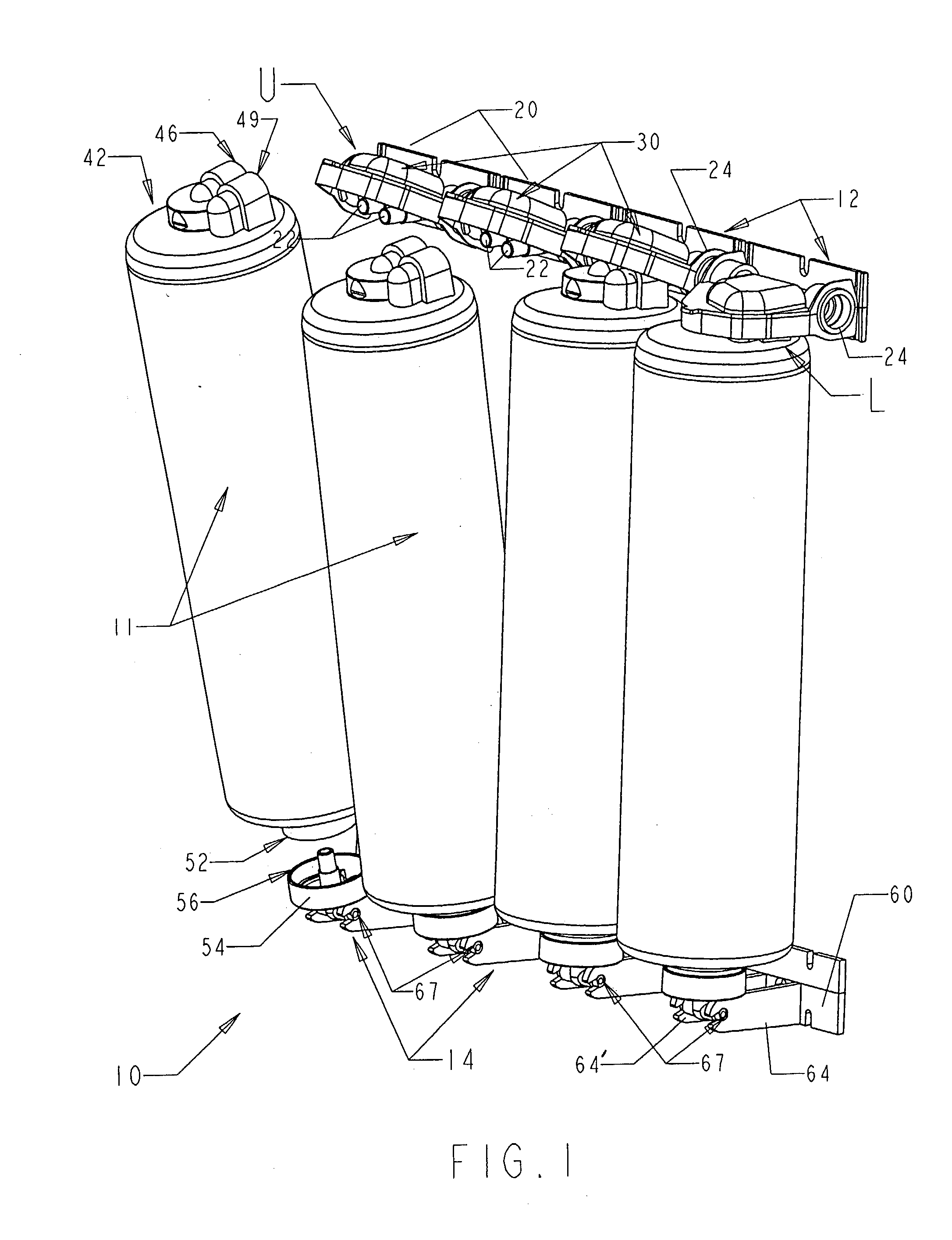
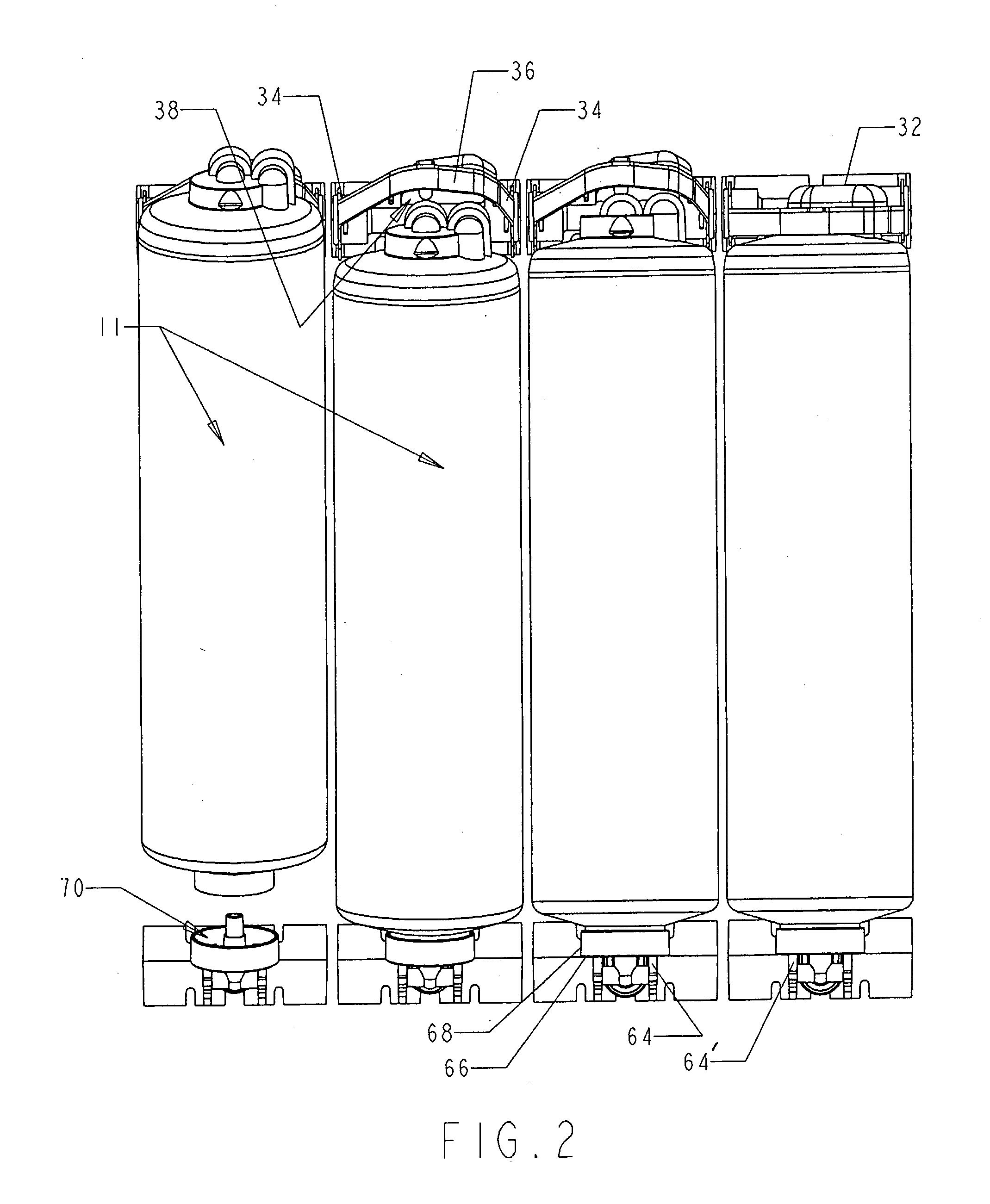
Quick change filter and bracket system with key system and universal key option
InactiveUS20030217958A1Carefully controlledIncentive to provide cheap, low quality copies will be minimizedPipe elementsLoose filtering material filtersFast releaseModularity
A bracket system holds a filter(s) in quick-attach and quick-release fashion. Brackets are combined in modular fashion, with conduit between the brackets, to create a "bank" of filters easily changed in number, arrangement, and flow scheme. Top brackets and bottom brackets capture / support the top end and bottom end of a filter, respectively, and filter inlet and outlet ports preferably slide onto and off of cooperating tubes / ports in the bracket modules without tools or threaded connections. A retainer may pivot on and off of its respective filter, holding the filter in place and releasing the filter, respectively. After pivoting the retainer up from the filter, the filter may be lifted up off of its respective bottom module, so that the filter is substantially vertically and pivotally removable from the bracket system. A keyed system may ensure that only the appropriate filter fits into the appropriate filter holder, wherein the keyed system includes key protrusions and cooperating key recesses on the mating surfaces that form a fluid connection between the filter and the filter holder. Sets of holders and filters may be provided wherein each set has key structure at different radial locations on the members, so that filters from a particular set cannot be used with any other set's holder. A universally-keyed filter may also be supplied that has key structure that fits with and cooperates with more than one of the differently-keyed filter holders so that the universally-keyed filter may be used with the various sets' holders.
Owner:REID ROGER P
Mobile application for extracting geometric elements and mapping to a master key-code database
InactiveUS20140064597A1Character and pattern recognitionUsing optical meansComputer hardwareImaging processing
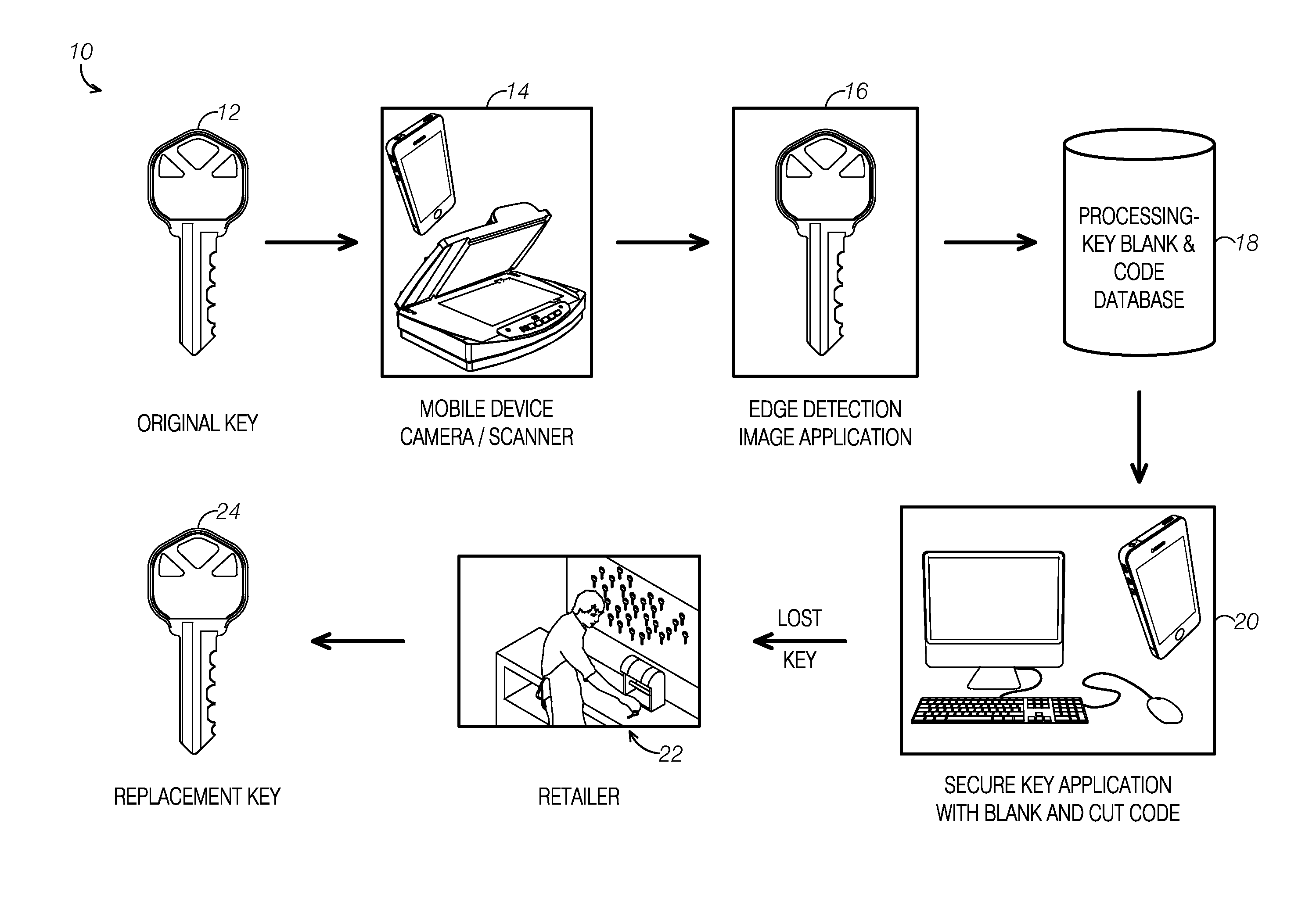
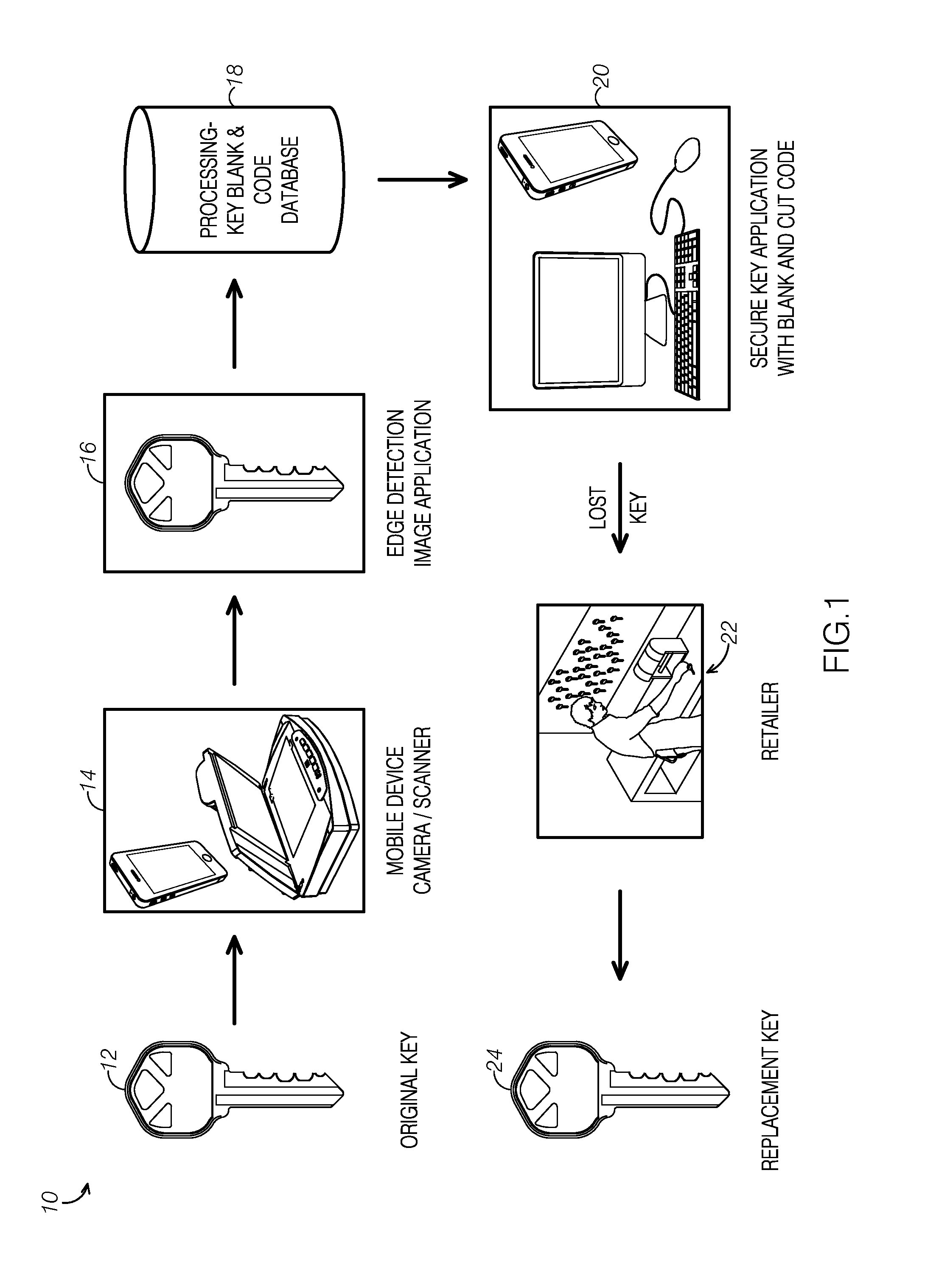
A method and application provide a universal key code for use when a key is lost. The code can be taken to a locksmith or retailer for duplication. The user can take a picture of their key and a software application can extract unique key geometries from the key, via, for example, edge detection technology and / or other mathematical methods, digital image processing methods and standard image processing methods. A key code can be determined from this extracted information and mapped to a known key code database. The software application can output, from a picture of an original key, the key blank and key cut code to allow a consumer to simply and conveniently obtain a duplicate key.
Owner:FAGAN ADAM PHILIP +1
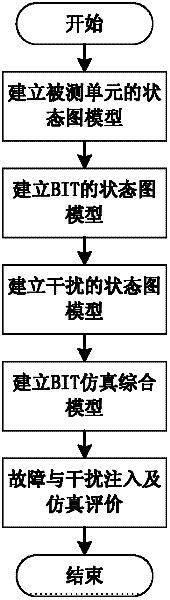
A Modeling and Simulation Method of In-machine Testing Based on State Diagram
InactiveCN102270253AShortcut decompositionSpecial data processing applicationsDecompositionState diagram
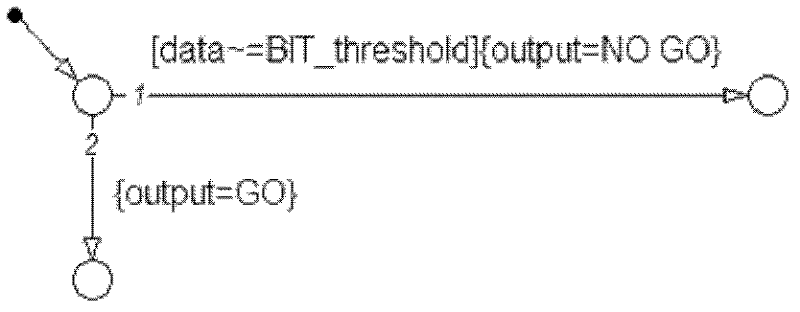
The invention discloses a built-in test (BIT) modeling simulation method based on a state diagram, belonging to the technical field of test of electronic information. The method comprises the following steps of: step 1, establishing a state diagram model of a tested unit; step 2, establishing a state diagram model of the BIT; step 3, establishing a state diagram model of interference; step 4, establishing a BIT simulation comprehensive model; step 5, performing fault and interference injection and simulation evaluation. The method provides a universal key element template of the BIT based on design characteristics of the BIT, and BIT key element decomposition can be quickly performed according to the template; and the method provides basic modes for state diagram modeling of each element in the BIT, and can perform modeling on common analogue BIT, digital BIT and software BIT. The invention provides a simulative injection method for the fault and the interference, and fault detection and false alarm suppression capability of the BIT can be analyzed through state simulation.
Owner:北京恒兴易康科技有限公司
Unmanned substation universal unlocking key fingerprint network authorization system and method
InactiveCN101710431AImprove securityAvoid misuseIndividual entry/exit registersInformation processingElectricity
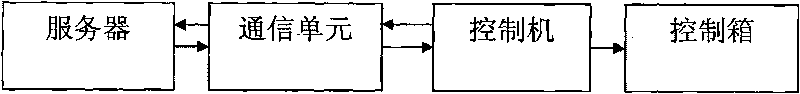
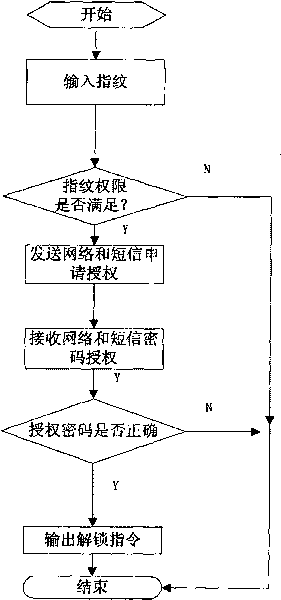
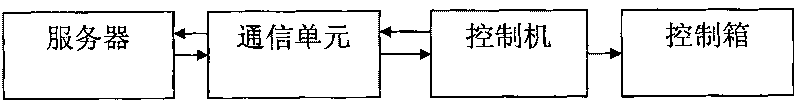
The invention relates to an unmanned substation universal unlocking key fingerprint network authorization system which is characterized in that: the system comprises a server, a communication unit, a controlling machine and a control box; wherein an electric lock is arranged on the control box, the controlling machine comprises a fingerprint acquisition unit and a fingerprint information processing unit, the signal output end of the fingerprint acquisition unit is connected with the signal input end of the fingerprint information processing unit, the control signal output end of the fingerprint information processing unit is connected with the control end of the electric lock on the control box, and the server is communicated with the controlling machine by the communication unit; the invention further provides an unmanned substation universal unlocking key fingerprint network authorization method, after the fingerprint is verified to be matched, and then a server application authorization code way is used, so as to greatly improve the safety of key management and eliminate miss operation owning to privately using the universal key.
Owner:王柳 +1
Semantics vein document searching method
InactiveCN101751420AImprove precisionReduce readSpecial data processing applicationsMatching testTest document
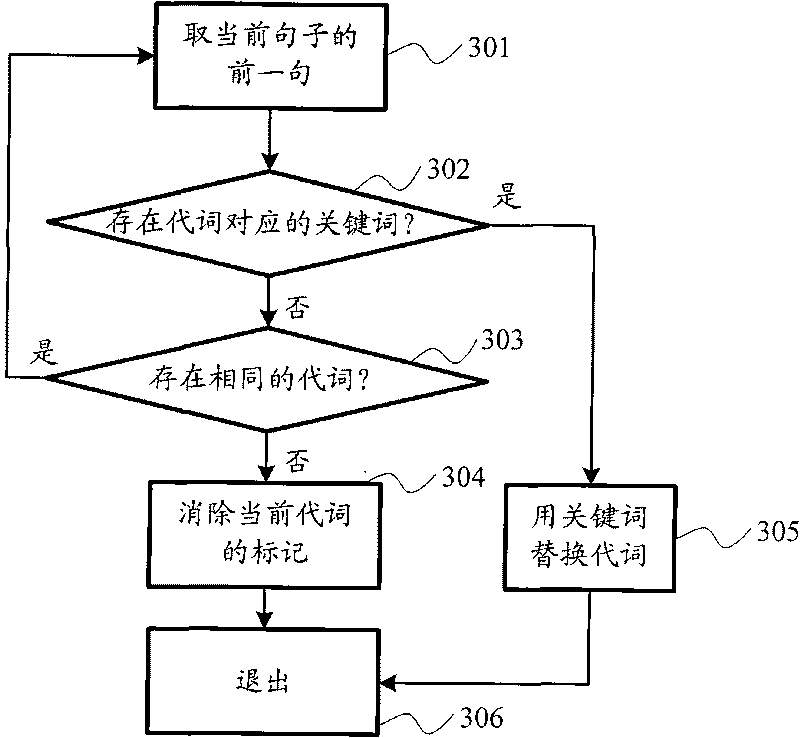
The invention discloses a discloses a document searching method based on semantics, which is applied to document searching, in particular to network document searching. The method includes the steps of converting the searching requirements inputted by a user into searching semantics veins, which represents to discompose the inputted searching sentences into different key words and structure relationship; then marking the searched documents according to key wards, sentences separators and pronouns, and replacing the key wards, sentences separators and pronouns into corresponding key words according to a pronoun reference relationship; finally implementing matching test on each sentence of searched semantics veins and tested documents according to the setting of the user on the key words and structure relationship; as only as one sentence matched with the searched semantics veins exists in the tested document, then the document is the document needed by the user. The method does not need to implement complex semantic analysis on the document, has a low development difficulty, and is consistent with the currently universal key word searching using method.
Owner:HUAZHONG UNIV OF SCI & TECH
Set-top box program recording and playback method and system
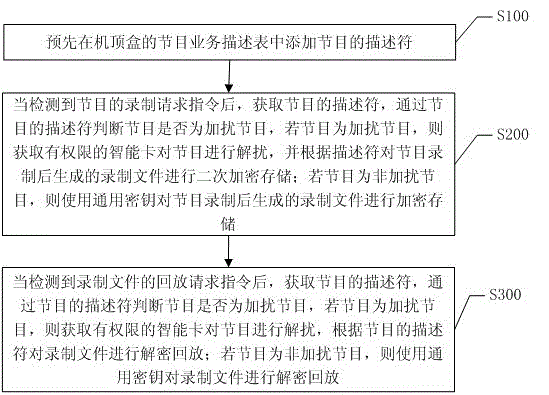
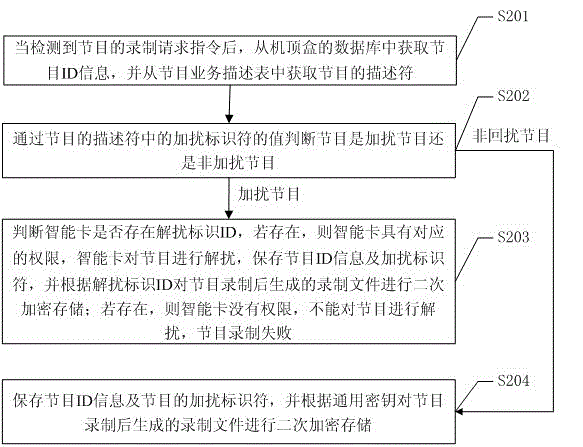
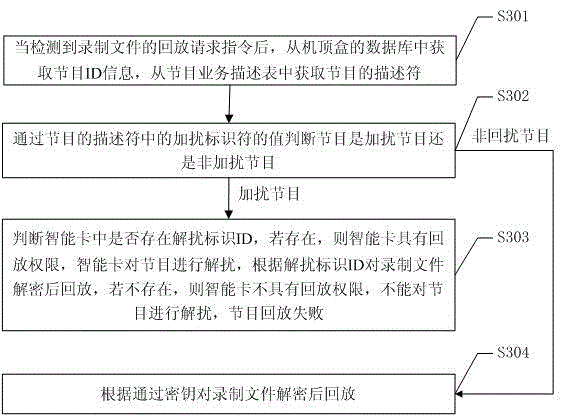
The invention discloses a set-top box based program recording and playback method and system. The set-top box based program recording and playback method comprises the steps of judging whether a program is a scrambled program when a program recording request is detected; if the program is the scrambled program, obtaining an intelligent card with permission to descramble the program and carrying out secondary encrypted storage for a recorded file based on a descriptor; if the program is not the scrambled program, carrying out encrypted storage for the recorded file by using a universal key; after a playback request instruction of the recorded file is detected, judging whether the program is the scrambled program; if the program is the scrambled program, obtaining the intelligent card with permission to descramble the program and carrying out decrypted playback for the recorded file based on the descriptor of the program; and if the program is not the scrambled program, carrying out decrypted playback for the record file by using the universal key. According to the set-top box based program recording and playback method, the recorded file can be subjected to secondary encryption, other set-top boxes having permission of the program also can play back the recorded file while the safety of the recorded file is guaranteed, and convenience is brought to program recording and playback of the user.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD +1
Remote control door bolt
InactiveCN101078316ADon't worry about being stolenStrengthen and optimize the locking structureNon-mechanical controlsElectricityRemote control
The invention relates to a remote control bolt. On the box (3) set on a door a bolt (6) with the same direction of lock tongue of lock tongue is set. At the inner end of bolt (6) a rack (4) is set and at one side of rack (1) a micro-motor (7) is set. A bolt (6) of gear transmission of gear (5) and rack (4) is connected with the shaft of micro-motor (7). A power supply (2) and a signal receiver (1) matched with remote controller (8) are set on the box (3). The signal receiver (1) is connected with the micro-motor (7) in current. The invention can realize automatic open and close of indoor bolt by remote controller out of door. Even if thief uses universal key to open the door lock he still can not enter room when there is no remote controller to relieve the bolt switch. So when building host goes to work out of door, goes on business or the family tour there is no need to worry about being stolen.
Owner:谢奇
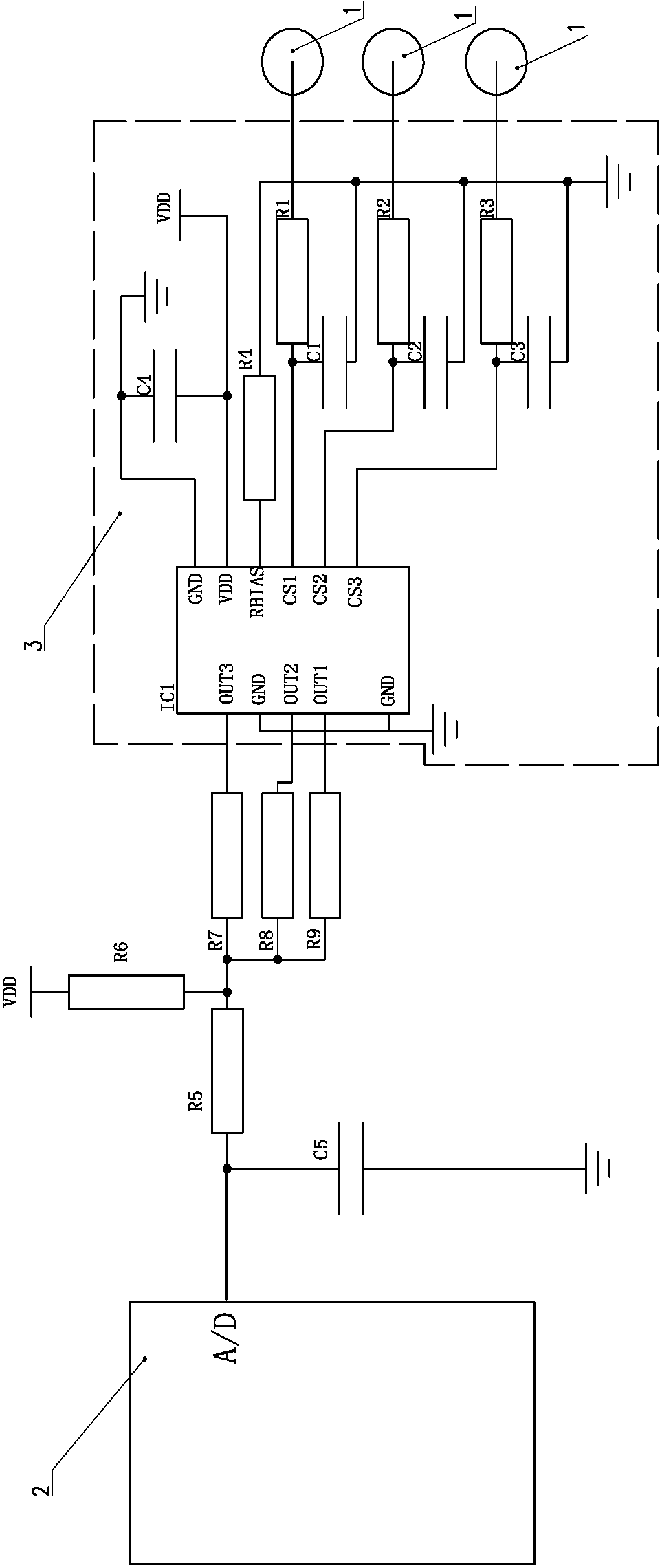
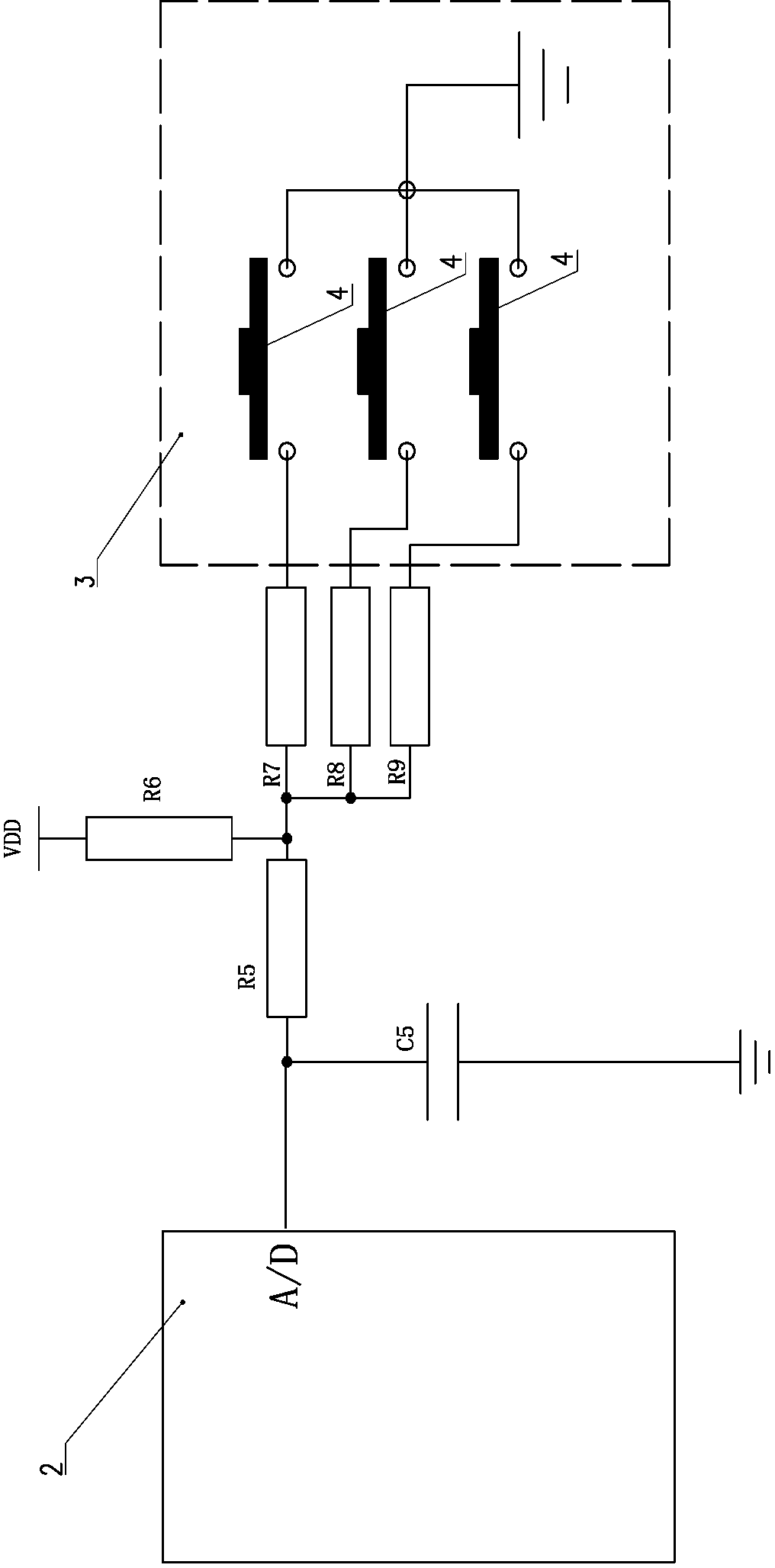
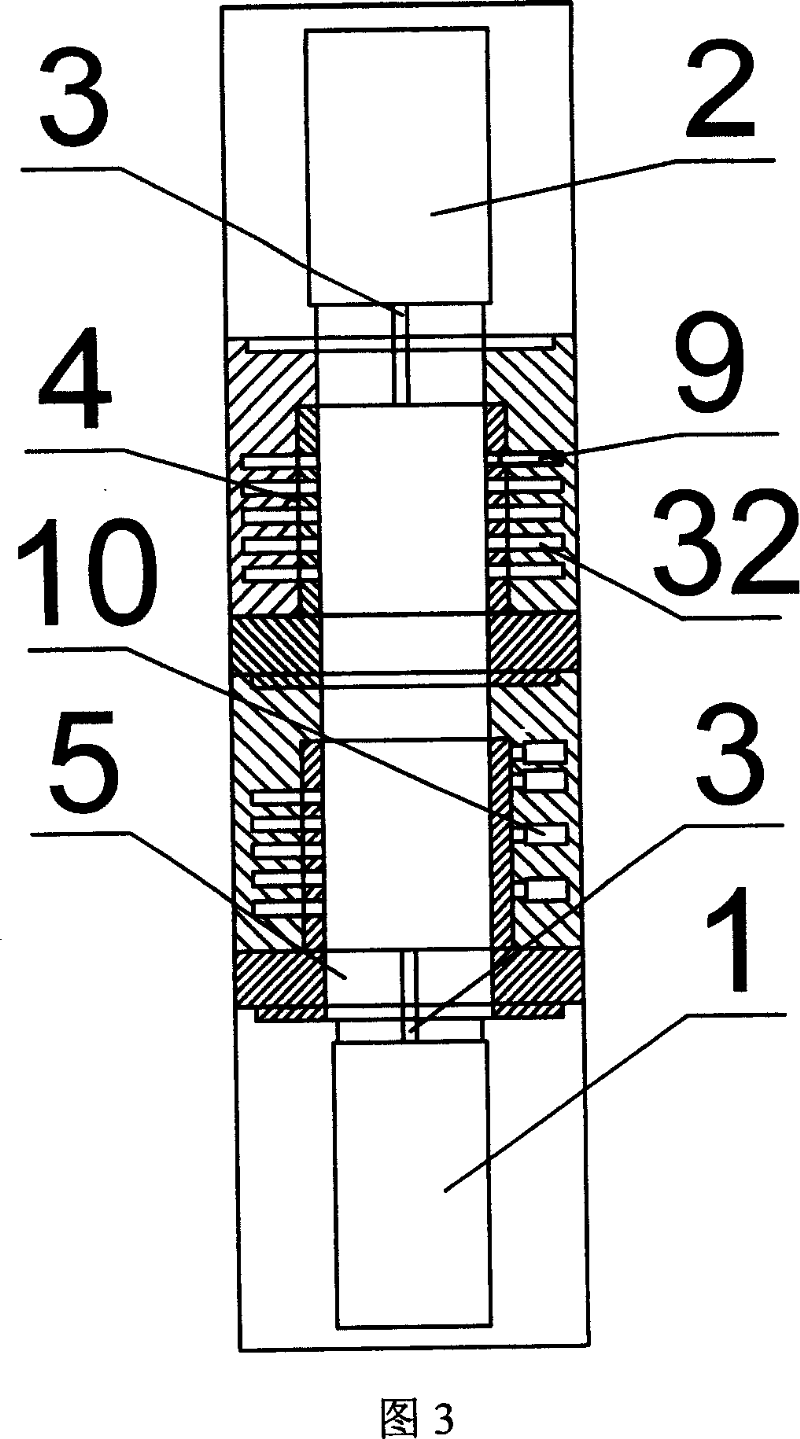
Portability key circuit
ActiveCN102868392AReduce development costsNo wiring changes requiredElectronic switchingElectrical resistance and conductanceElectricity
The invention discloses a portability key circuit which comprises a central control chip, a power supply, a pull-up resistor and a plurality of divider resistors with different resistances, wherein the plurality of divider resistors are connected with each other in parallel; parallel-connected ends of the plurality of divider resistors are electrically connected with the pull-up resistor and an AD (analog-to-digital) port of the central control chip; the portability key circuit is characterized by further comprising a universal key access unit, wherein the universal key access unit is electrically connected with the other ends of the plurality of divider resistors. The universal key access unit is used for acquiring information of touch keys or key switches; and the portability key circuit has the characteristics of good portability and circuit cost saving.
Owner:GUANGDONG VANWARD NEW ELECTRIC CO LTD
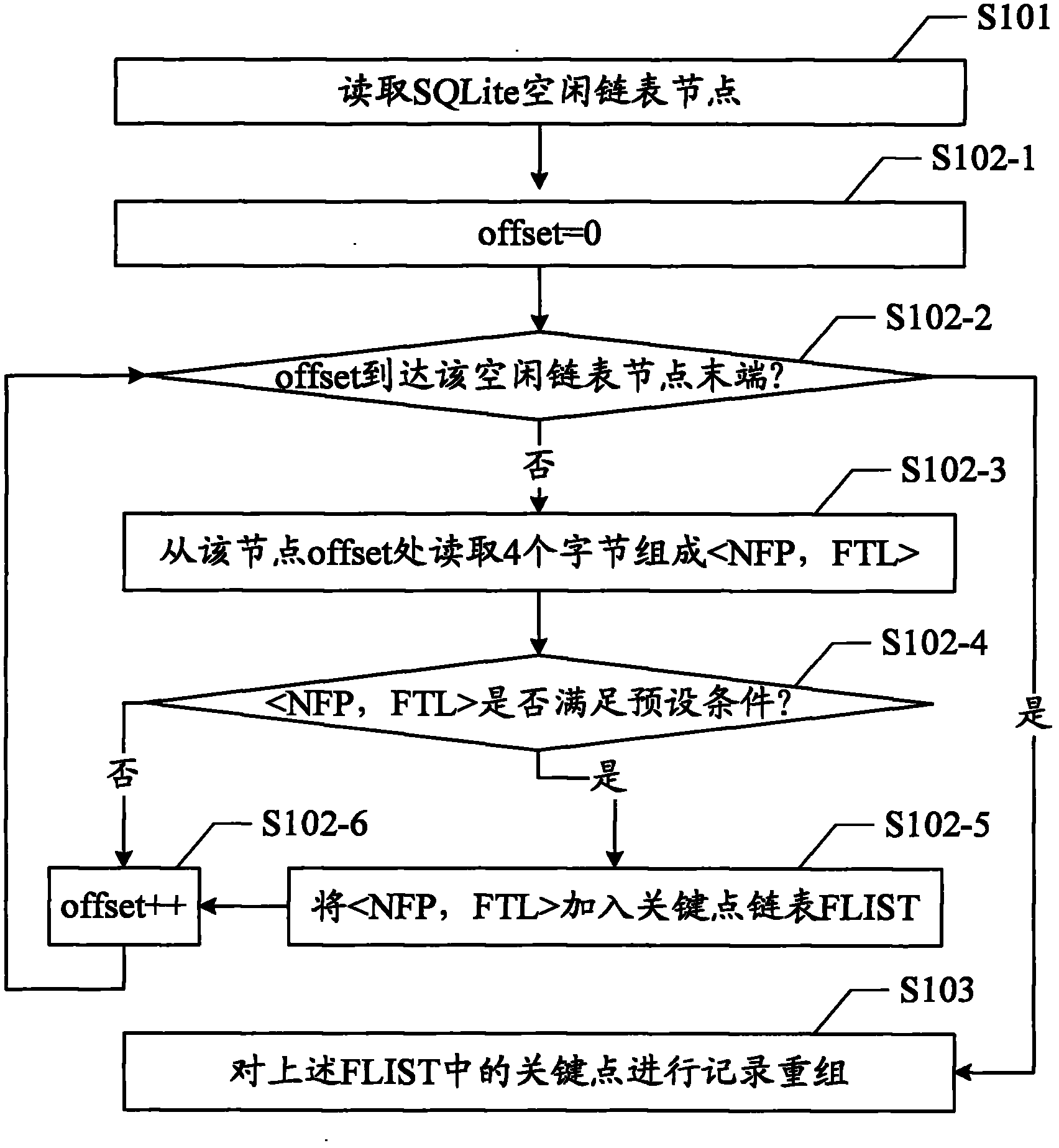
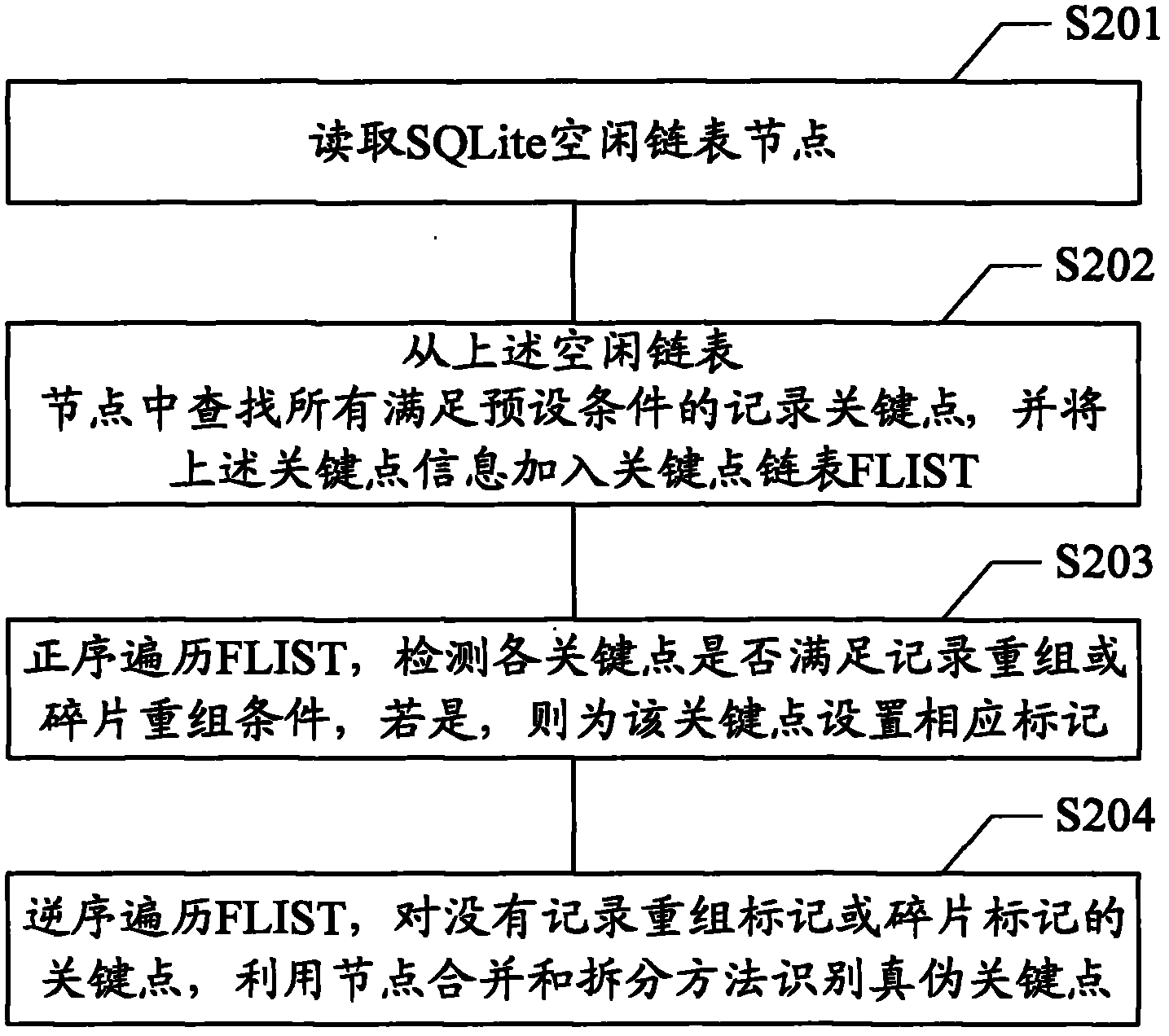
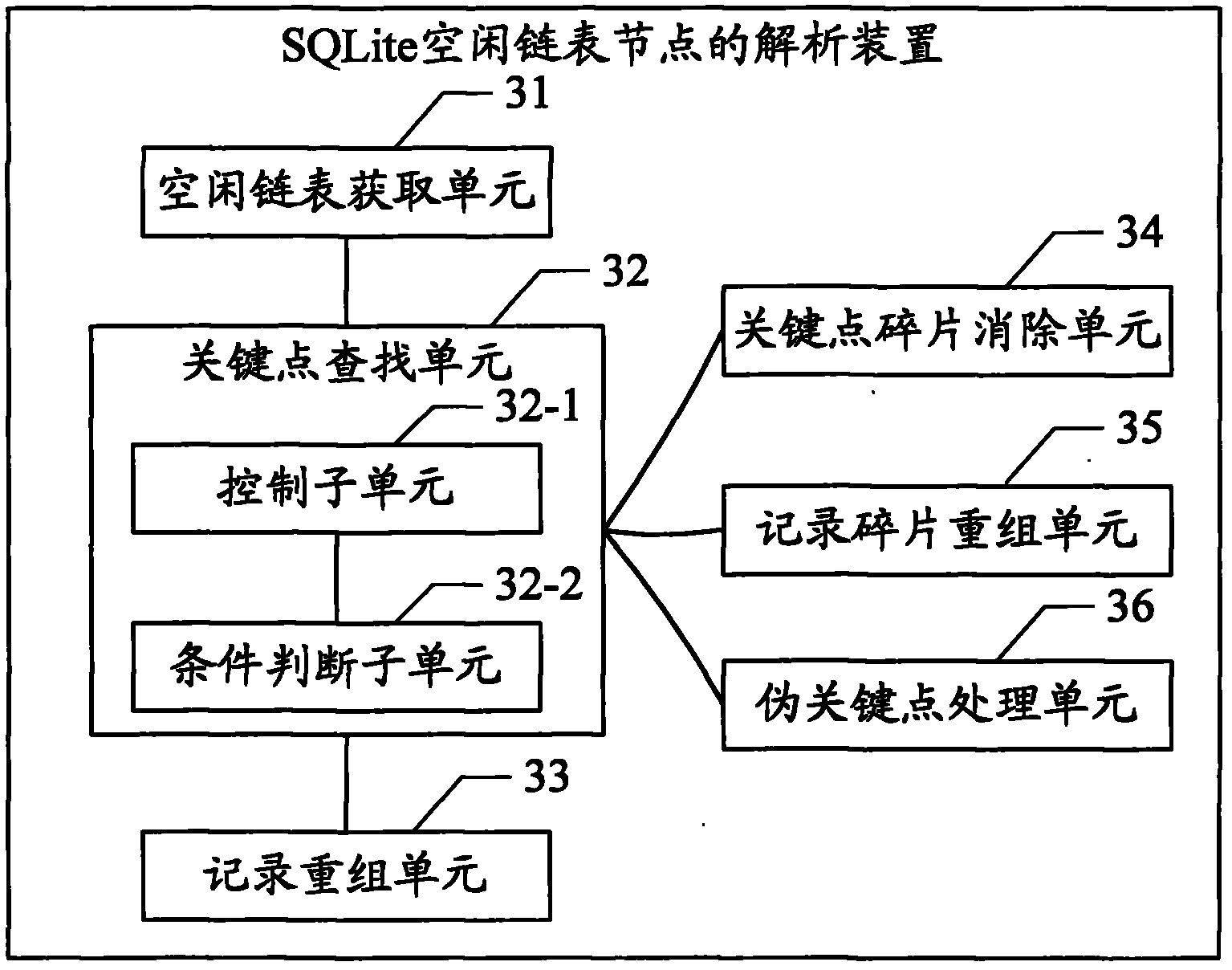
Analysis method and analysis device for SQLite idle struct nodes
ActiveCN102591941AParsing fastAccurate analysisSpecial data processing applicationsNODALDatabase file
The invention provides an analysis method and an analysis device for SQLite idle struct nodes. The method includes the steps: reading the SQLite idle struct nodes; searching all recording key points meeting preset conditions from the idle struct nodes; and recording and recombining the key points. Each recording key point refers to a two-tuple (NFP, FTL) consisting of four bytes, and the preset conditions refer to value (NFP) > addr(NFP) and value (FTL)<[0,PSZ-addr(NFP)]. Based on SQLite database file formats and deletion and insertion rules for records, key point information is recognized by deleting universal key point features for recording two-tuple information, and all data records in the key points are recombined, so that multiple recording tuples of the SQLite idle struct nodes are quickly and accurately analyzed.
Owner:XIAMEN MEIYA PICO INFORMATION
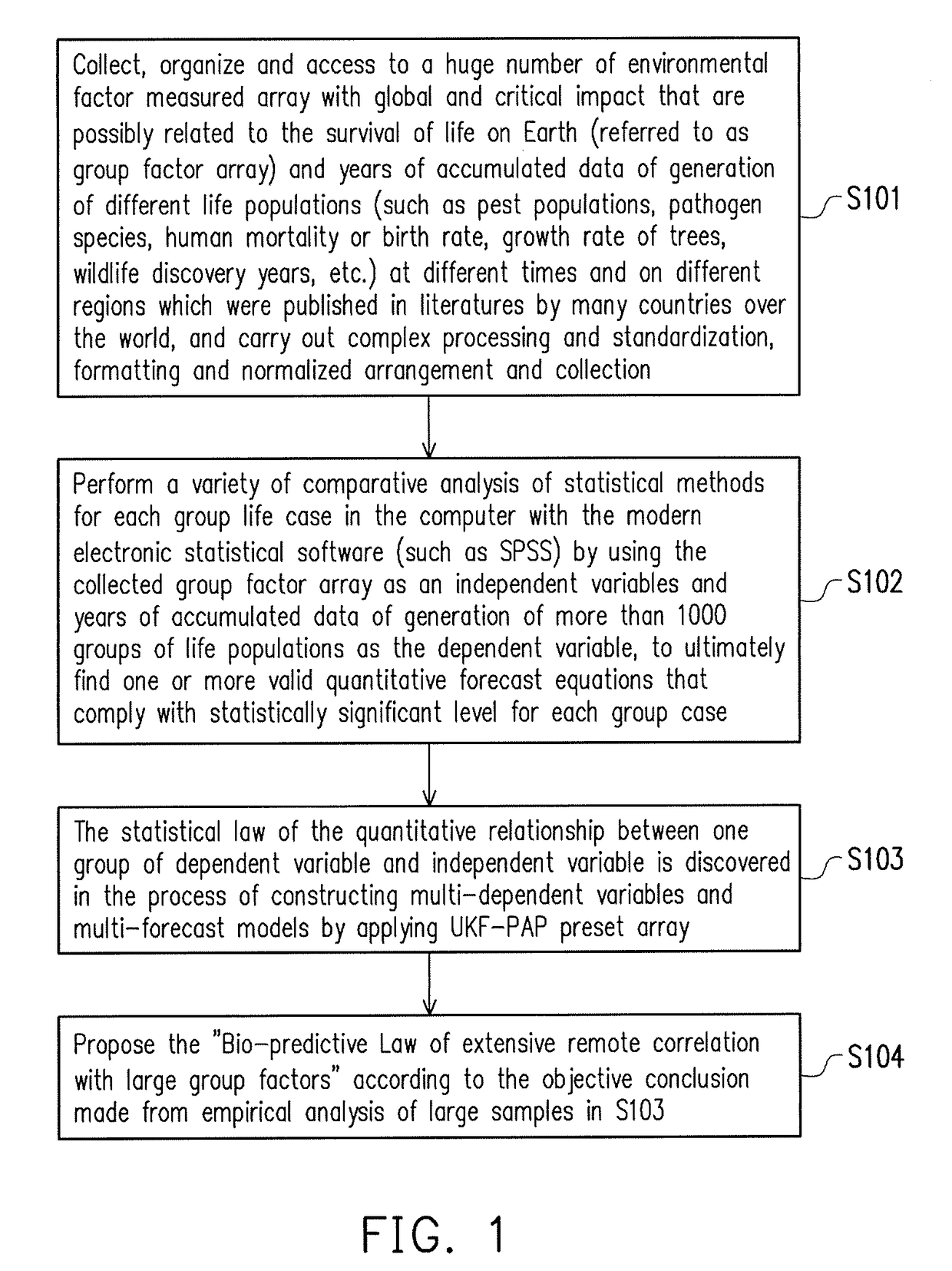
Globally universal key factor preset array platform for dynamic forecast analysis of biological populations
InactiveUS20170255722A1Reduce riskImprove accuracyMedical simulationDesign optimisation/simulationInternet usersBusiness forecasting
The present invention discloses a globally universal key factor preset array platform for dynamic forecast analysis of biological populations, which can be used to preset massive arrays of standard environmental factors; and through the Internet user's registration system, global users for biological population dynamic forecast can instantly select the contents suitable for their own country or local region to construct an accurate statistically forecast model for specific area and specific biological population dynamics, so as to make an accurate quantitative forecast of biological population dynamics in the future. Each preset data is co-located by a row variable coordinate and a column variable coordinate. Each located individual data can not be interchanged up and down or to and fro, the row variable coordinate is time coordinate and the column variable coordinate is space coordinate. This invention effectively resolves the existing problems in the current life population forecasting such as incapability to construct an effective forecast models or poor forecast effect or narrow application scope of the constructed model for many important biotic populations due to it is difficulty to timely access to adequate and effective environmental information amount for users.
Owner:HUNAN AGRICULTURAL UNIV
Mobile and desktop application for extracting geometric elements and mapping to a master key-code database
InactiveUS20140064598A1Image analysisCharacter and pattern recognitionComputer hardwareImaging processing
A method and application provide a universal key code for use when a key is lost. The code can be taken to a locksmith or retailer for duplication. The user can obtain a digital image of their key and a software application can extract unique key geometries from the key, via, for example, edge detection technology and / or other mathematical methods, digital image processing methods and standard image processing methods. A key code can be determined from this extracted information and mapped to a known key code database. The software application can output, from a digital image of an original key, the key blank and key cut code to allow a consumer to simply and conveniently obtain a duplicate key.
Owner:FAGAN ADAM P +1
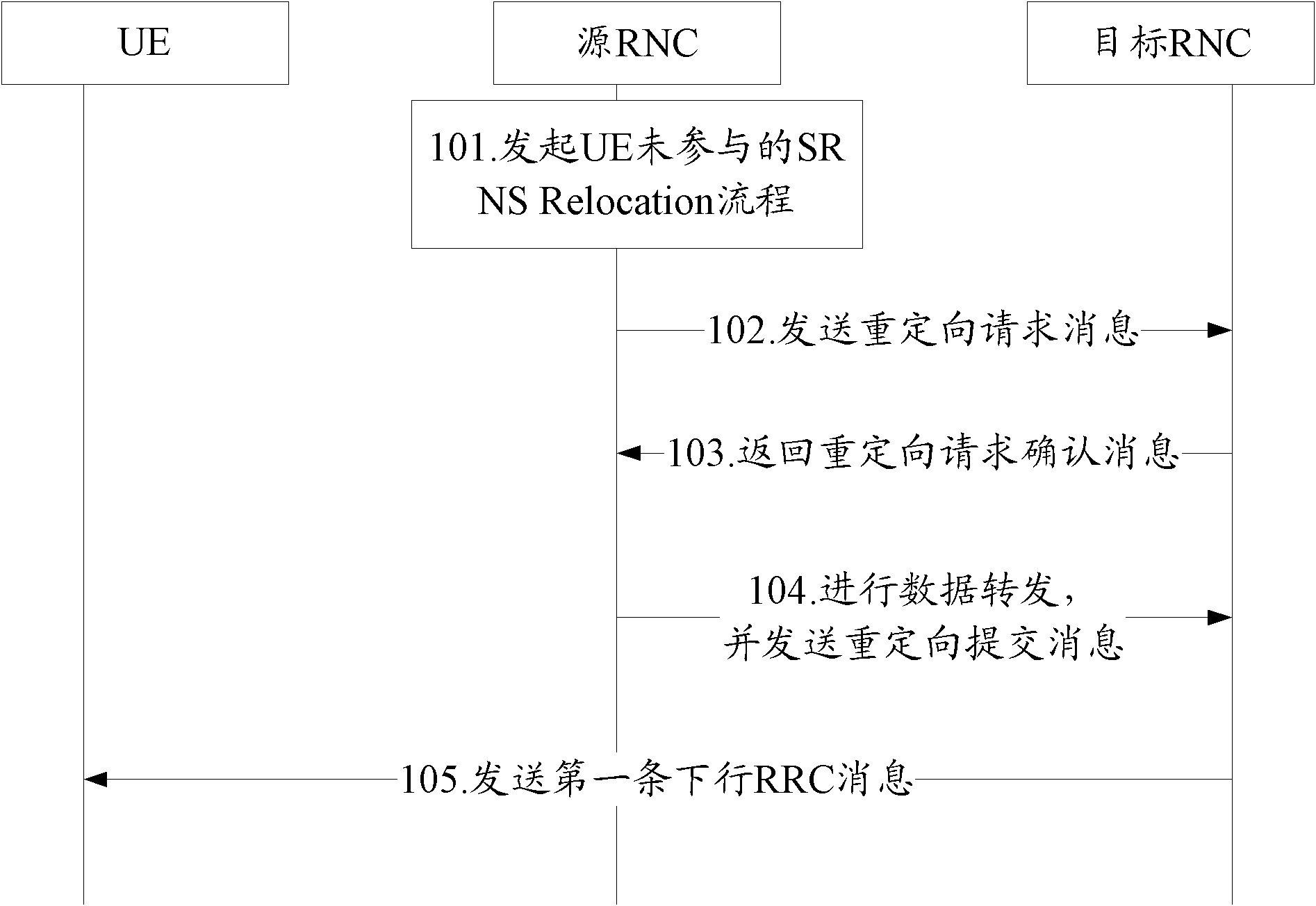
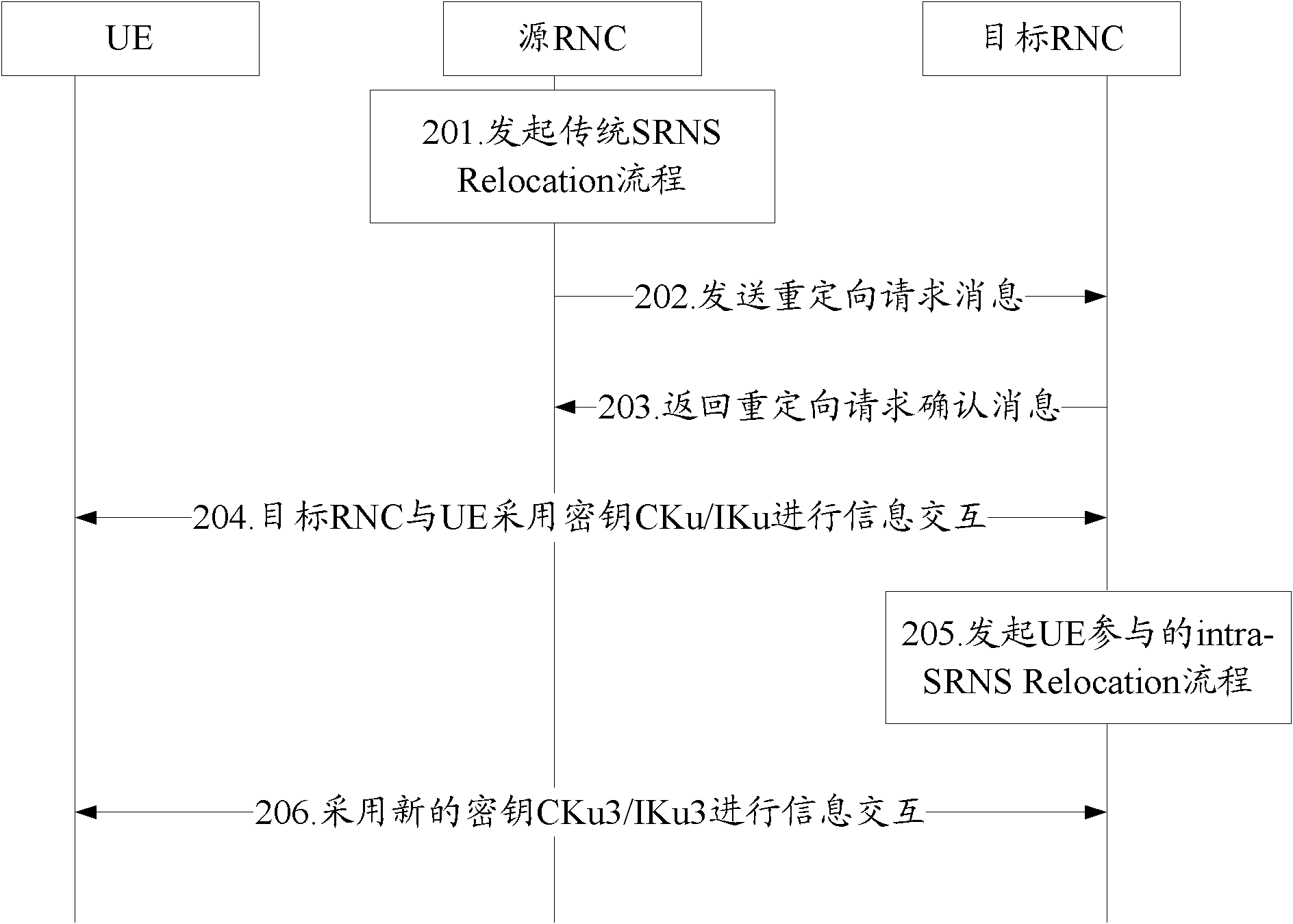
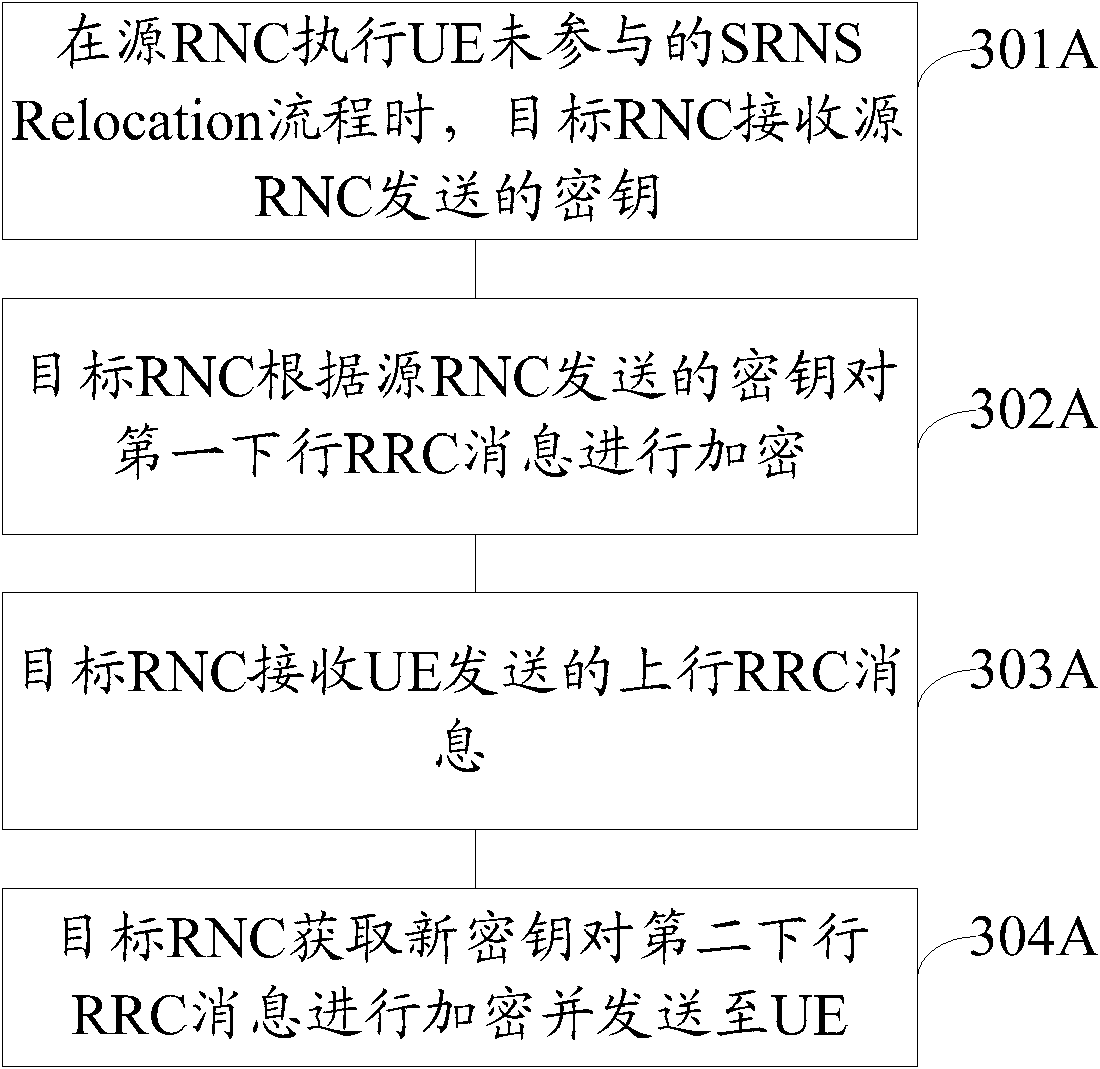
Key setting method in radio network controller (RNC) and wireless network controller as well as terminal
InactiveCN102469454AAchieve isolationRealize information interactionSecurity arrangementRadio networksTelecommunications
The embodiment of the invention provides a key setting method in a radio network controller (RNC) and a wireless network controller as well as a terminal. When a source RNC executes a serving radio network subsystem (SRNS) relocation flow which is not anticipated by a user equipment (UE), the method comprises the following steps that: a target RNC receives a key transmitted by the source RNC, and the key is obtained by deriving a key utilized by the source RNC; the target RNC encrypts a first downlink radio resource control (RRC) message according to the key transmitted by the source RNC and transmits the encrypted first downlink RRC message to the UE, and the encrypted first downlink RRC message includes information that the target RNC supports a universal key holder (UKH); the target RNC receives an uplink RRC message transmitted by the UE, and the uplink RRC message includes the information that the UE supports the UKH; and the target RNC acquires a new key to encrypt a second downlink RRC message and transmits the second downlink RRC message to the UE. The embodiment realizes the information interaction between the target RNC and the UE and the isolation of the key.
Owner:HUAWEI TECH CO LTD
Character input method and character input device based on one-key click or multi-key simultaneous click
InactiveCN102929402AReduce the number of keysReduce volumeInput/output processes for data processingKey pressingTyping
The invention relates to a character input method and an input device for implementing the method. The input device using the input method provided by the invention is provided with five or more than five keys; a character is input in the mode of independently clicking one key or clicking a plurality of keys at the same time; and when a plurality of keys are clicked at the same time, the input of different characters is realized by the combination of different keys. By the input method and the input device, the number of the keys required for inputting the characters can be greatly reduced; the size or the area of the input device is reduced; particularly all visible characters of a current universal keyboard can be input by one hand easily and conveniently, so that a one-hand keyboard in a true sense is realized; and all universal keyboard characters can be input by one-hand touch-typing by a user with a little practice. The input method can be widely used in input devices such as the keyboard, an input board and a touch screen.
Owner:李新宇
Encryption and decryption method, equipment and computer storage medium
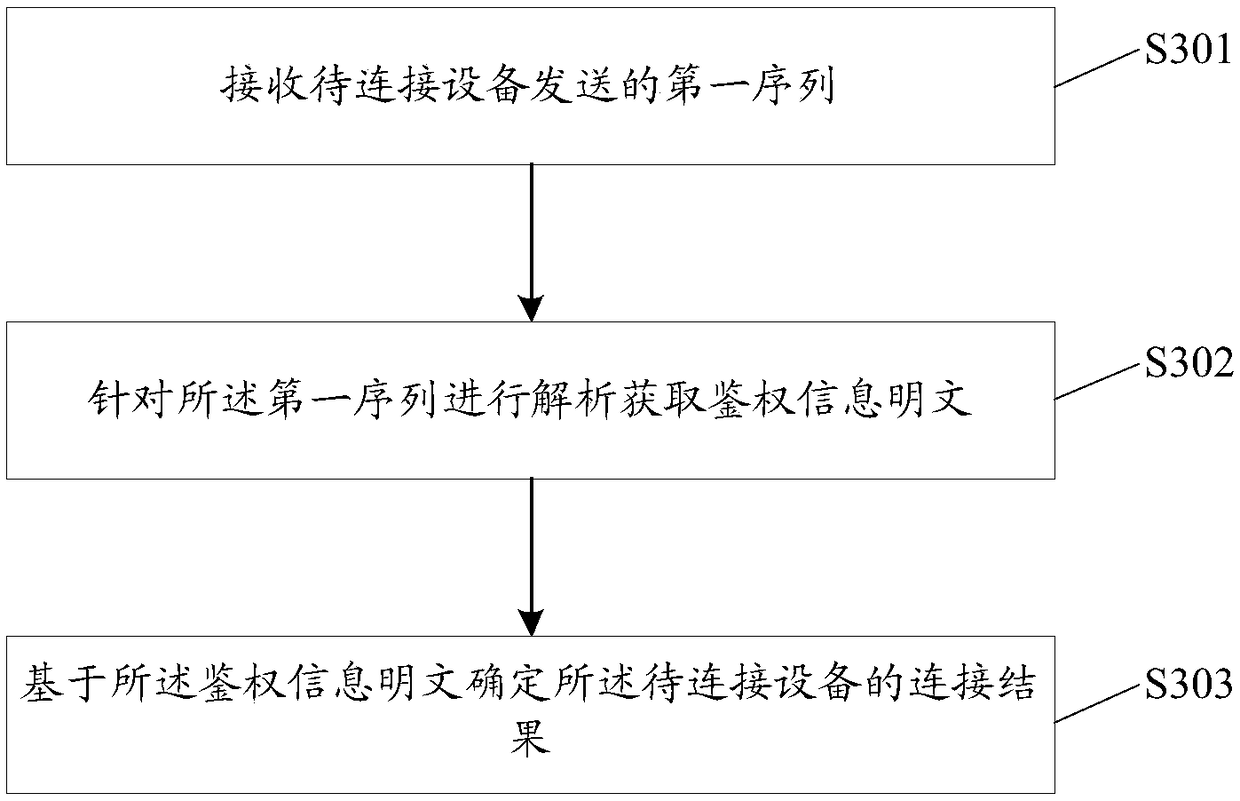
ActiveCN108616878AAvoid abnormal access phenomenonImprove securityConnection managementSecurity arrangementPlaintextWifi network
The embodiment of the invention discloses an encryption and decryption method, equipment and a computer storage medium. The encryption and decryption method comprises the steps of receiving a first sequence sent by equipment to be connected, wherein the first sequence includes an authentication information plaintext and parameter information of the equipment to be connected; parsing the first sequence to obtain the authentication information plaintext; and determining a connection result of the equipment to be connected based on the authentication information plaintext. According to the method, the authentication information plaintext is obtained through parsing the first sequence including the authentication information plaintext and the parameter information of the equipment to be connected so as to determine the connection result of the equipment to be connected, thereby avoiding a phenomenon that cracking tools such as universal key software can access to a wifi network through directly reading a password plaintext, and achieving an effect of improving the security of the wifi network.
Owner:NUBIA TECHNOLOGY CO LTD
Electrically adjusted self-compensating plug valve
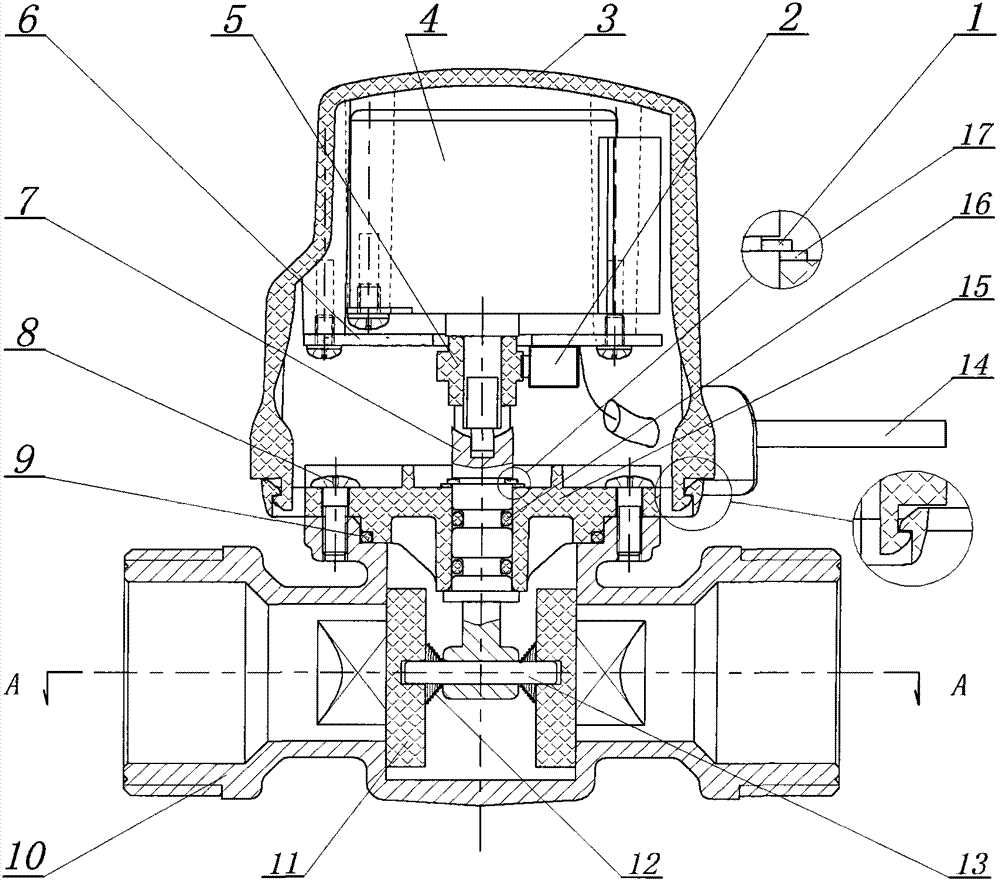
InactiveCN102829207AImprove sealingSimple structurePlug valvesOperating means/releasing devices for valvesAxial forceEngineering
The invention relates to an electrically adjusted self-compensating plug valve which comprises a check ring, a micro-switch, an upper driver shell, a motor, a cam, a circuit board, a valve rod, a bolt, a big sealing ring, a valve body, a valve chip, a spring, a cylinder pin, a power line, a lower driver shell, a small sealing ring and a gasket. A floating type valve core structure is adopted by the electrically adjusted self-compensating plug valve; the valve chip is made of a nylon plastic soft substrate material; a fluid backpressure is utilized as a locking force for sealing the valve; the traditional method for increasing the locking force for sealing a conical surface by increasing an axial force of the valve core is replaced; the universal key technologies of the valve, such as, the sealing property of the plug valve, the self-compensating value after the sealing surface is abraded, the switching torsion moment, and the like, are greatly increased; the structure of a sealing part of the valve core is simplified; the manufacturing and assembling technologies are simple; and the production cost is lowered.
Owner:ZHEJIANG HENGSEN IND GROUP
Paged universal key remote controller
InactiveCN104574886ASolve the inconvenienceSolve the problem of one machine with one remote controlNon-electrical signal transmission systemsKey pressingRemote control
The invention discloses a paged universal key remote controller. The paged universal key remote controller comprises a control page and identification module, a key code inputting and mapping module, a remote control signal output module, and a remote control code database storage module. A user can select different control pages, and control multiple electronic products according to operation tips displayed on the corresponding pages. The paged universal key remote controller is simple to operate and convenient to use, and solves the problems that a large number of remote controllers are required, and a universal remote controller is complicated to operate and is high in cost. Therefore, resources are saved and environmental protection is achieved.
Owner:余江
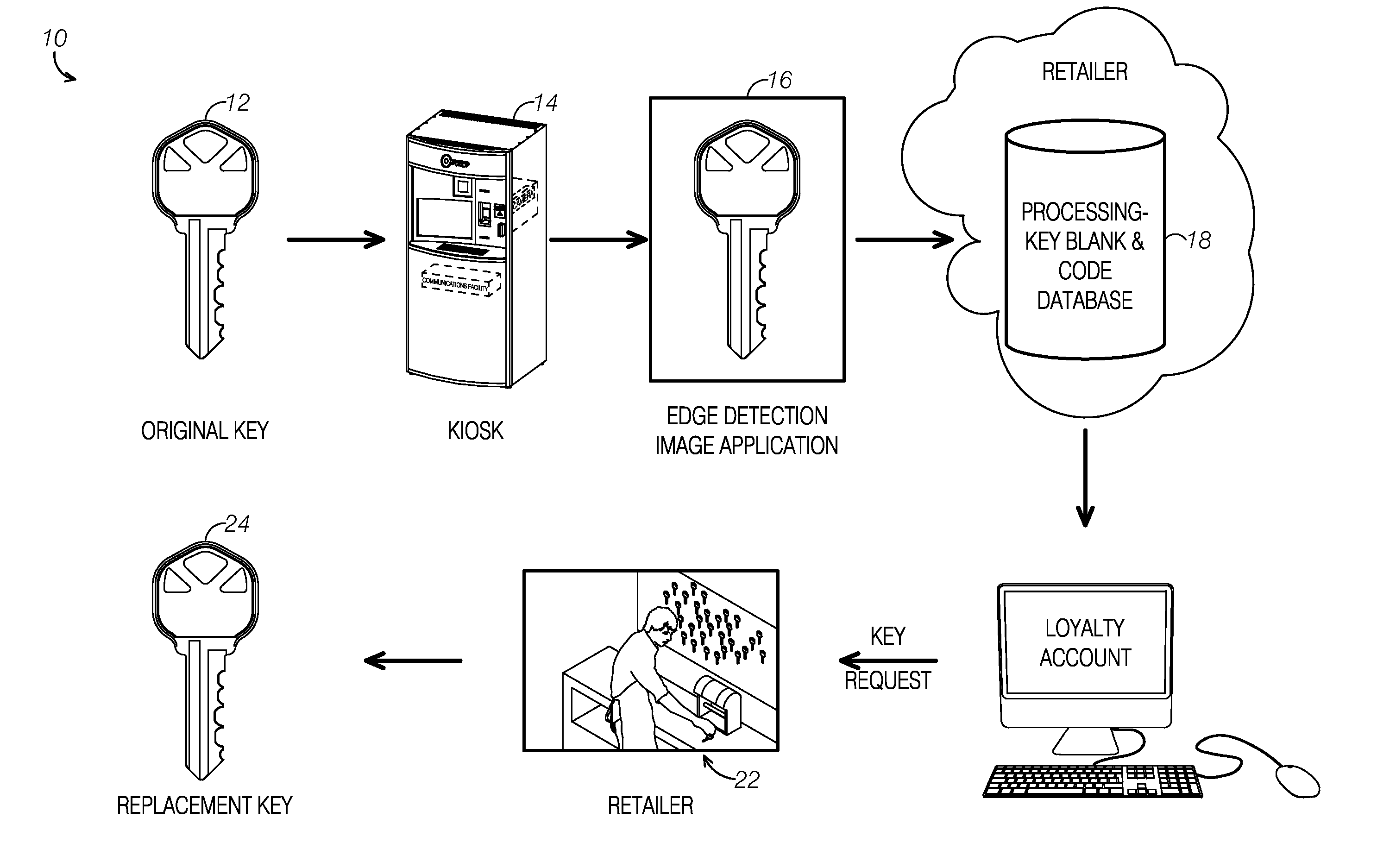
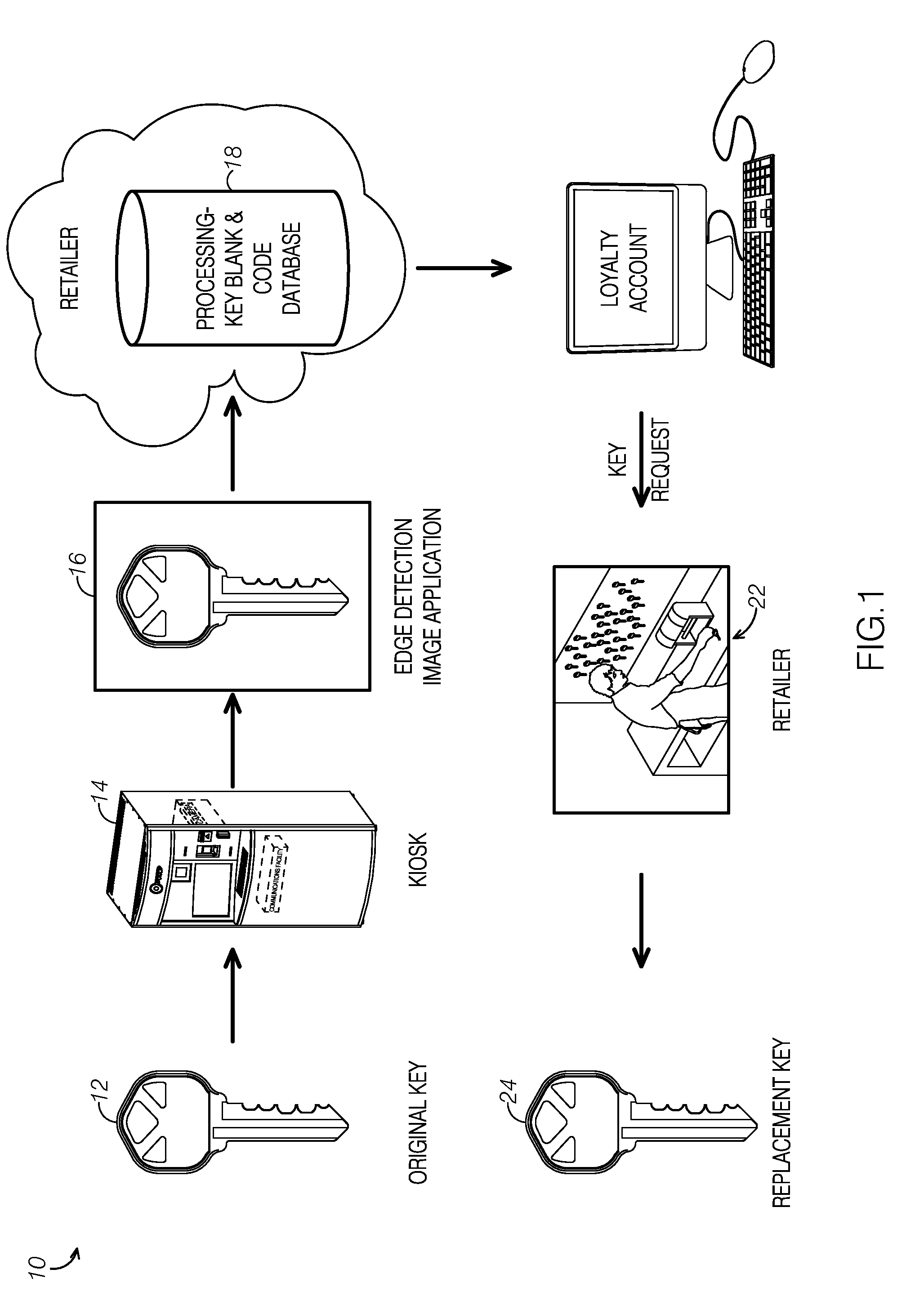
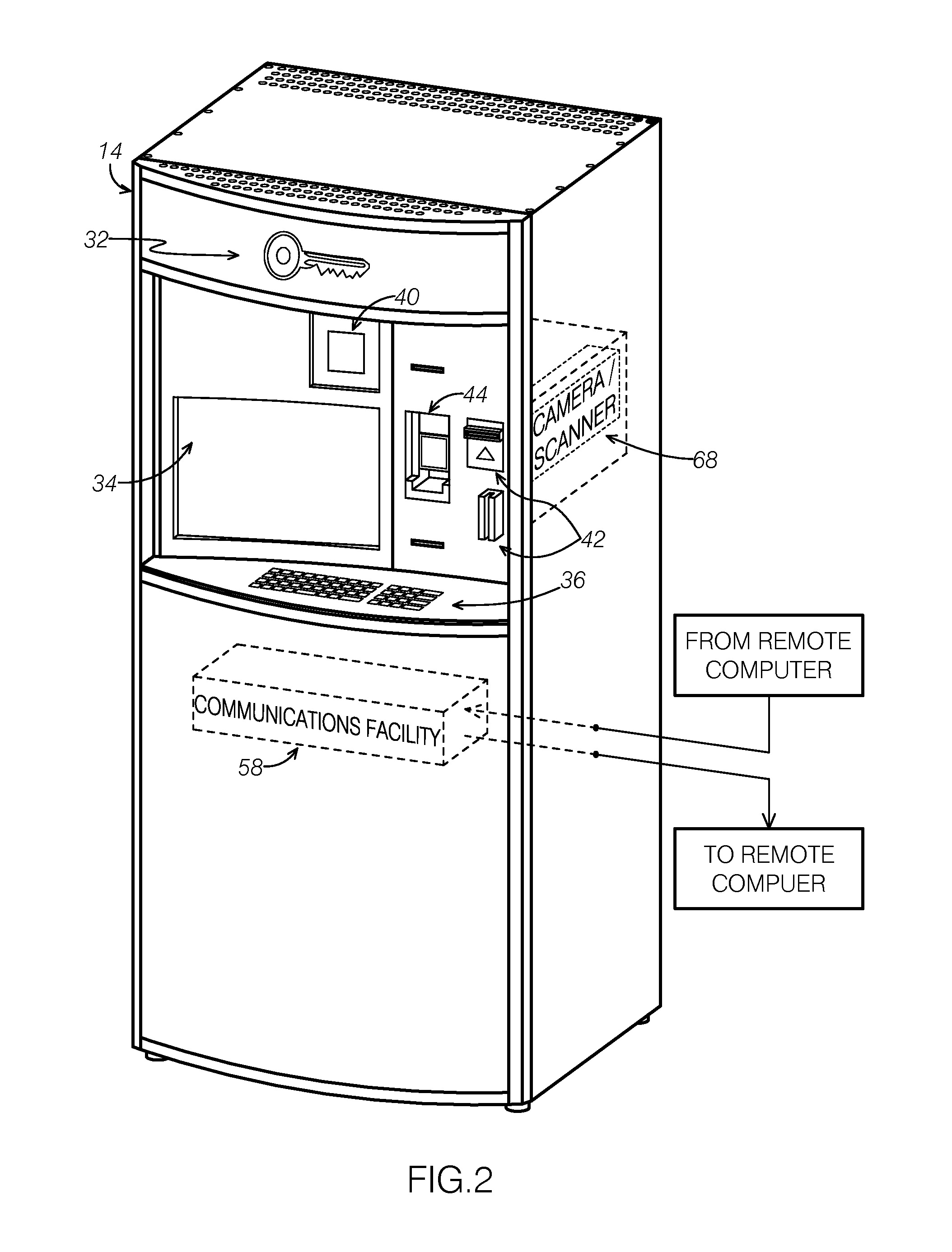
Kiosk for extracting geometric elements of a key, mapping to a master key-code database, and saving data into a customer's loyalty account
A method and application provides a universal key code for use when a key is lost. The code can be taken to a locksmith or retailer for duplication. The user can take their key to a kiosk located, for example, at a merchant's location. The kiosk can have the ability to extract a digital image of their key and a software application can extract unique key geometries from the key, via, for example, edge detection technology and / or other mathematical methods, digital image processing methods and standard image processing methods. A key code can be determined from this extracted information and mapped to a known key code database. The software application can output the key blank and key cut code to allow a consumer to simply and conveniently obtain a duplicate key. This information can be saved into a customer's loyalty account with a particular merchant for later retrieval as needed.
Owner:FAGAN ADAM PHILIP +1
Refueling reactor core safety evaluation method
ActiveCN109492910AEliminate RestrictionsIncrease flexibilityResourcesNuclear engineeringSelection criterion
The invention discloses a refueling reactor core safety evaluation method. The safety evaluation method comprises the following steps: 1) obtaining universal key safety parameters; 2) obtaining special key safety parameters for a specific accident; 3) comparing the obtained general key safety parameters, the obtained special key safety parameters for the specific accident and input parameters usedfor reference safety analysis; and 4) performing fuel assembly performance verification. According to the method, on the basis of a traditional refueling reactor core safety evaluation method, the definition, selection criteria and range of key safety parameters are expanded, analysis modules specifically constructed in safety evaluation are reasonably designed, the limitation requirement for refueling reactor core power distribution is eliminated, and the application range of reference safety analysis is effectively expanded. The conclusion that the refueling reactor core meets the final safety analysis report can be proved from the perspective of reactor physics and thermotechnical hydraulics only through normal refueling reactor core safety evaluation work.
Owner:NUCLEAR POWER INSTITUTE OF CHINA
Intelligent electric lock
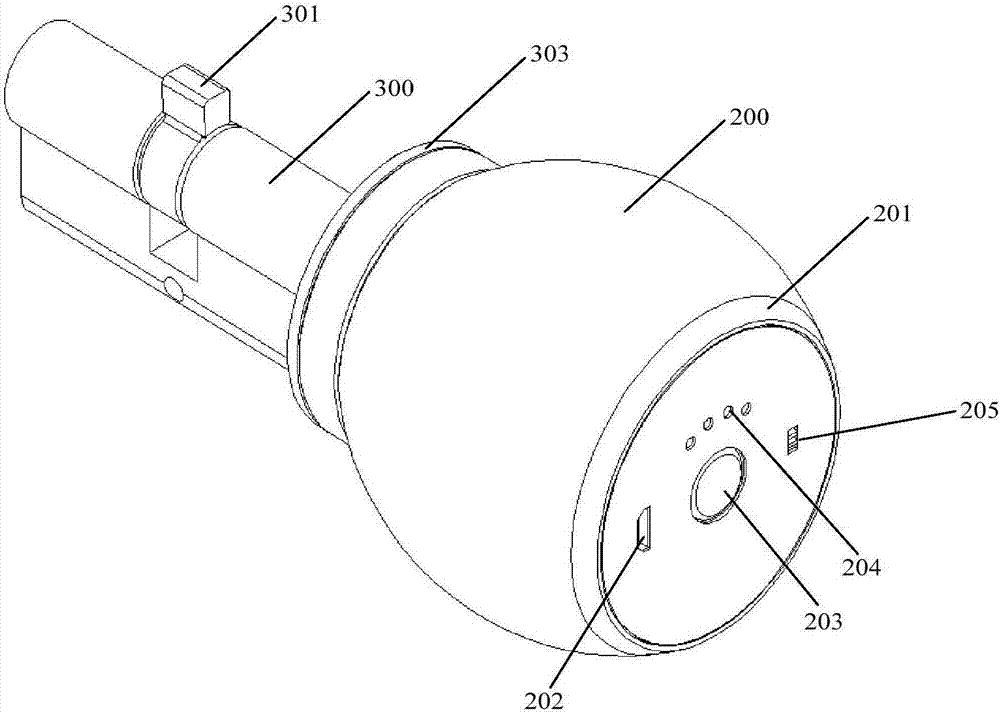
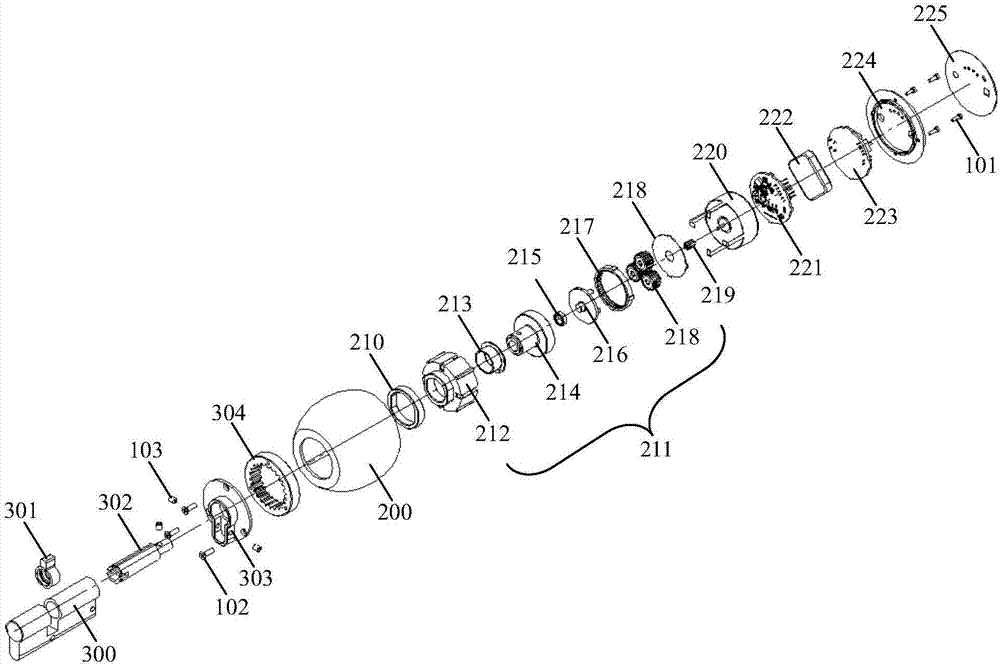
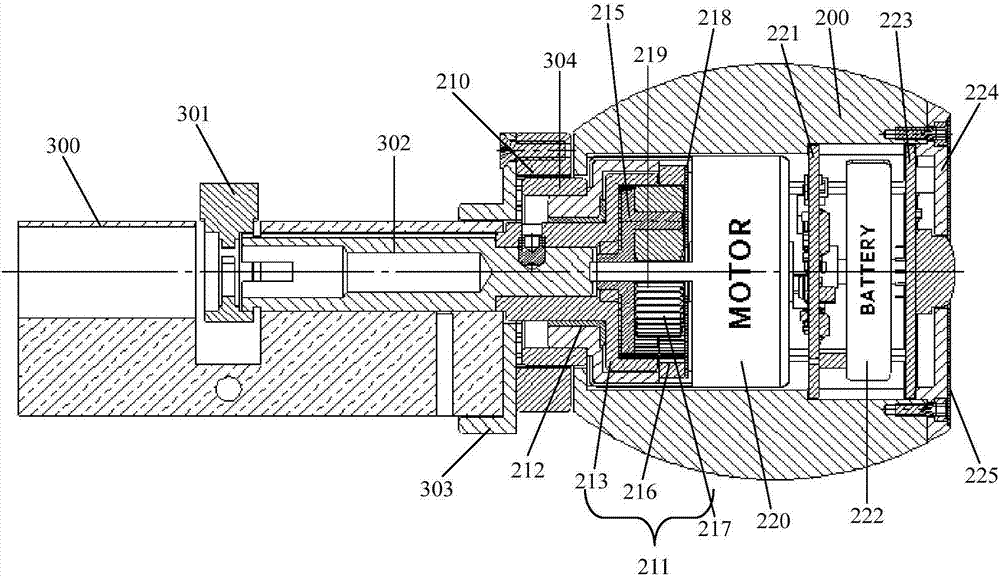
InactiveCN106968522AHighly integratedEasy to beautify the designNon-mechanical controlsElectric permutation locksElectric machineryIntegrated design
The present invention is applicable to the field of electric locks, and provides an intelligent electric lock, which includes a general outdoor key handle, an indoor electric handle and a lock core, a lock tongue, a lock core shaft, a lock core support plate and an end cover, and a lock core There is a magnetic ring on the support plate, and the indoor electric handle includes a coaxial multi-layer integrated structure in sequence along the central axis from the direction of the lock cylinder support plate to the direction of the end cover: permanent magnet ring, gear box, sliding bearing , output internal gear, rolling bearing, planetary wheel turret, fixed internal gear, planetary wheel, gasket, motor pinion, motor, motor drive board, battery and control board; charging interface and quick release button are set on the end cover; lock cylinder It has a general installation structure size. In the present invention, the motor, gear box, motor drive board, battery, and control board are designed in a coaxial multi-layer integration, which improves the overall integration of the lock and reduces the size of the lock; and the installation structure size of the lock cylinder is different from that of the traditional lock. Universal, easy to replace the lock cylinder.
Owner:SHENZHEN GENIUSMART TECH CO LTD
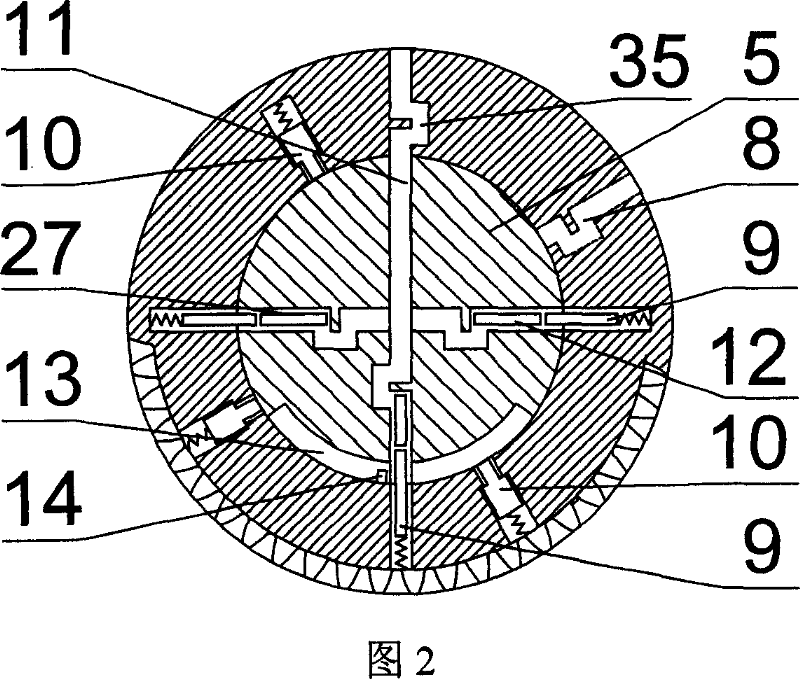
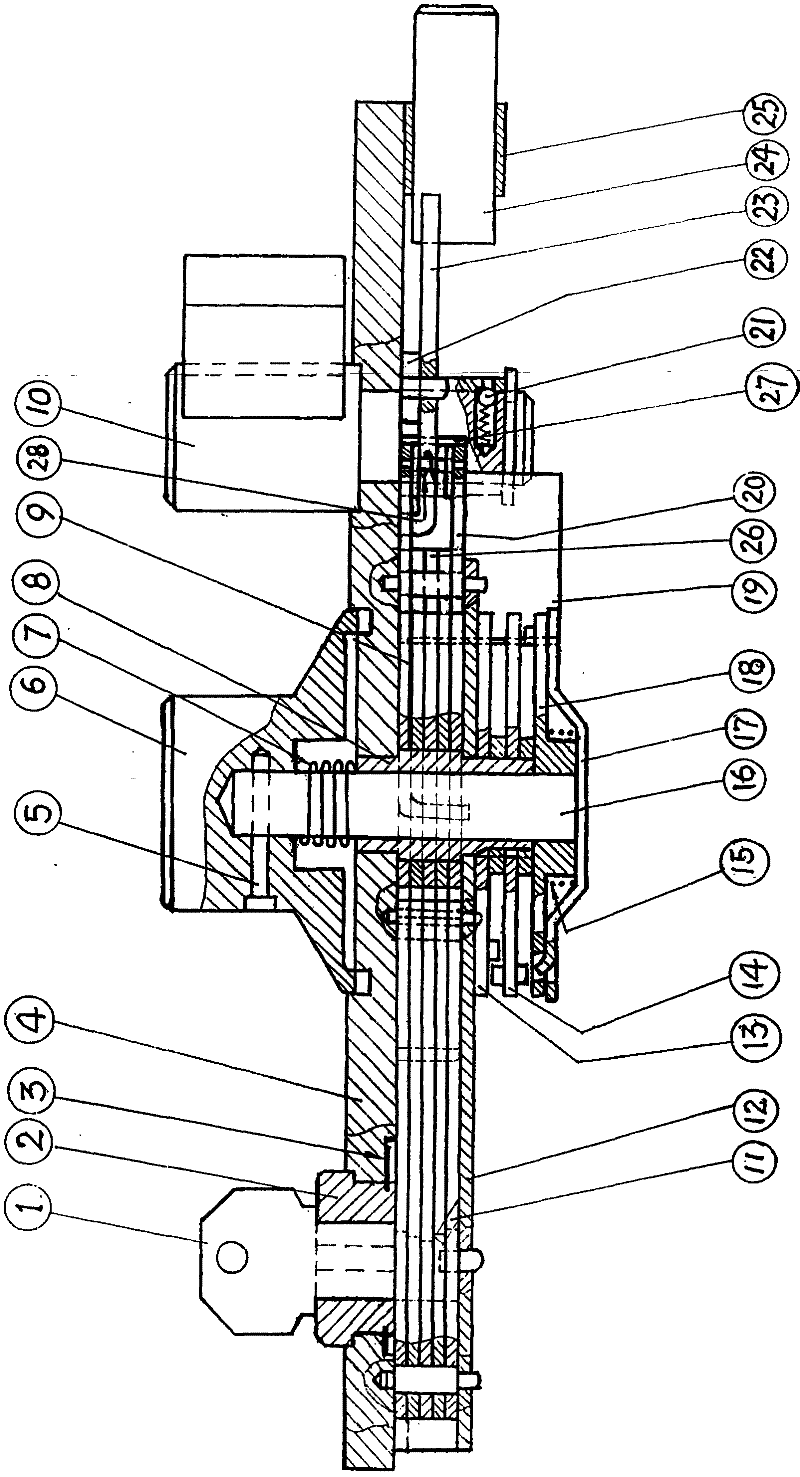
Lock core device for anti-pry and anti-universal key
The lock core device capable of preventing pick and resisting universal key includes an inner lock core, an outer lock core and a lock core fixing seat connected successively. The outer lock core is provided with lock bolt to shift the lock tongue in the bottom. The inner lock core is provided with balls or blades and movable pins, the balls or blades are provided with code aligning part in the specific position, the movable pins are provided with corresponding joint part, and the code aligning part and the joint part are cooperated to locate the movable pins axially and locate the normal contact surface between the driving pins and the locking pins radially. Before the correct key is inserted, the inner lock core may be rotated freely, and this can avoid the test with universal key and the pick with some tool, such as a screw driver.
Owner:吴建金
Programmable controller for game peripheral
InactiveCN106955490AExperienceResponse speedVideo gamesProgrammable logic controllerInterface protocol
The invention discloses a programmable controller for a game peripheral. The programmable controller is characterized by comprising a micro-processor, a key input interface, a PS2 keyboard interface and a USB keyboard interface, wherein the PS2 keyboard interface and the USB keyboard interface are connected with a PC (personal computer) through an interface protocol, and the micro-processor only recognizes one keyboard interface during working; the key input interface comprises two setting keys, four direction keys, two auxiliary keys, multiple attack keys and one reset key, and the keys except the setting keys and the reset key all correspond to a key value of a universal key of the PC; multiple conventional game key layouts are stored in the micro-processor, and factory default key value parameters are restored by pressing the reset key for a long time. The programmable controller has the advantages that the programmable controller is no longer limited to several unchanged arcade games supported by gamepads and can be widely applied to various online games and single games. The games can be configured in the micro-processor before delivery and can also be automatically downloaded through software configured on the PC.
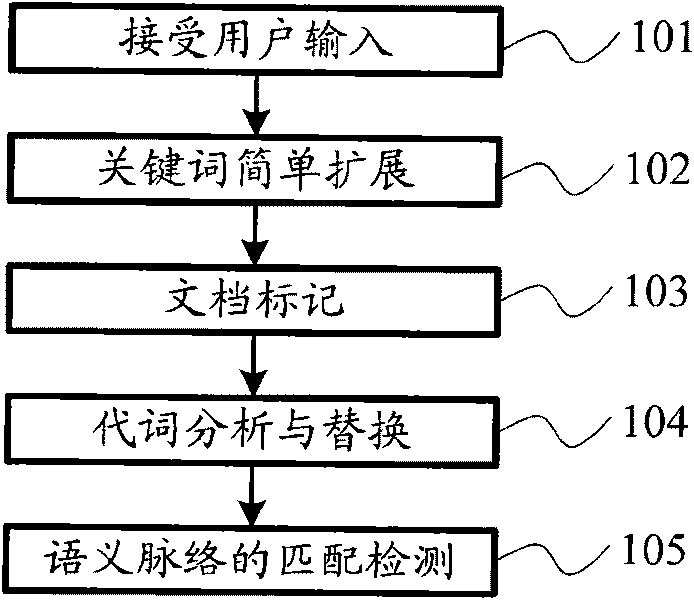
Owner:张志刚
Universal key bracelet for different vehicles and universal control method
InactiveCN107274524AImprove experienceSolve the inconvenience of carryingIndividual entry/exit registersTransceiverRadio frequency
The invention discloses a universal key bracelet for different vehicles and a universal control method. The bracket comprises a bracket main body, a master control chip card slot arranged in the bracket main body, a radio frequency transceiver and an MCU, wherein the master control chip card slot and the radio frequency transceiver are connected with the MCU separately; the master control chip card slot is arranged to bear two or more than three master control chips; the radio frequency transceiver is arranged to build communication connection of the MCU and one or more than two BCMs within a communication range; and the MCU is arranged to obtain an ID of a vehicle through the BCMs in communication connection, to transmit the obtained ID to the born master control chips and to transmit a specified operation signal to the BCMs in communication connection after receiving a matching signal of the obtained ID and a statically stored ID from the master control chips. The universal key bracelet is simple and convenient in operation, the problems that a plurality of keys are inconvenient to carry, easy to drop and disordered in application are solved and the user experience is improved.
Owner:YANNAN GUOCHUANG TECH BEIJING CO LTD
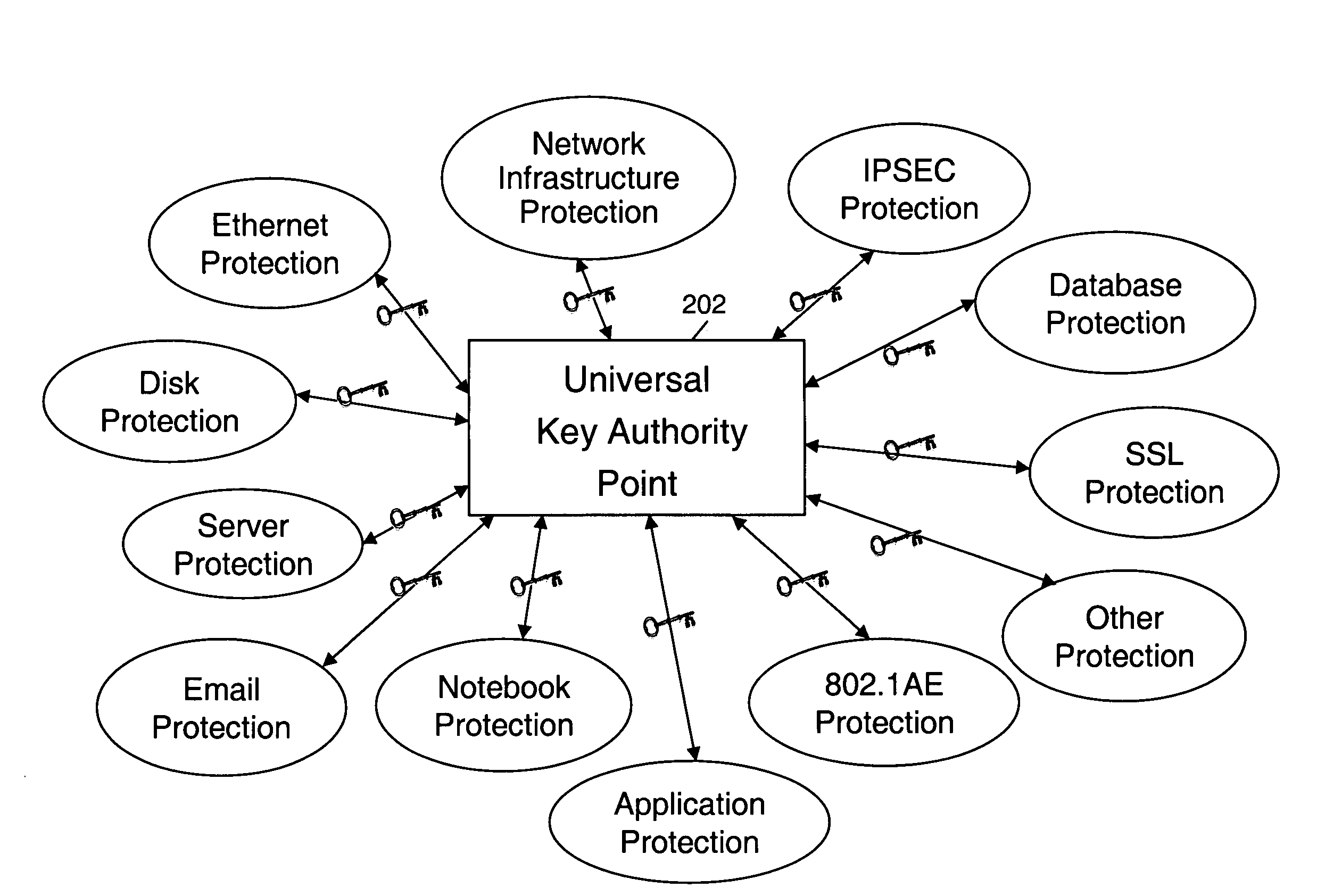
Universal key authority point with key distribution/generation capability to any form of encryption
System and methods for simplified management of secured data and communications networks with a universal key authority point for the generation and distribution of keys and management of same within the network.
Owner:CIPHEROPTICS
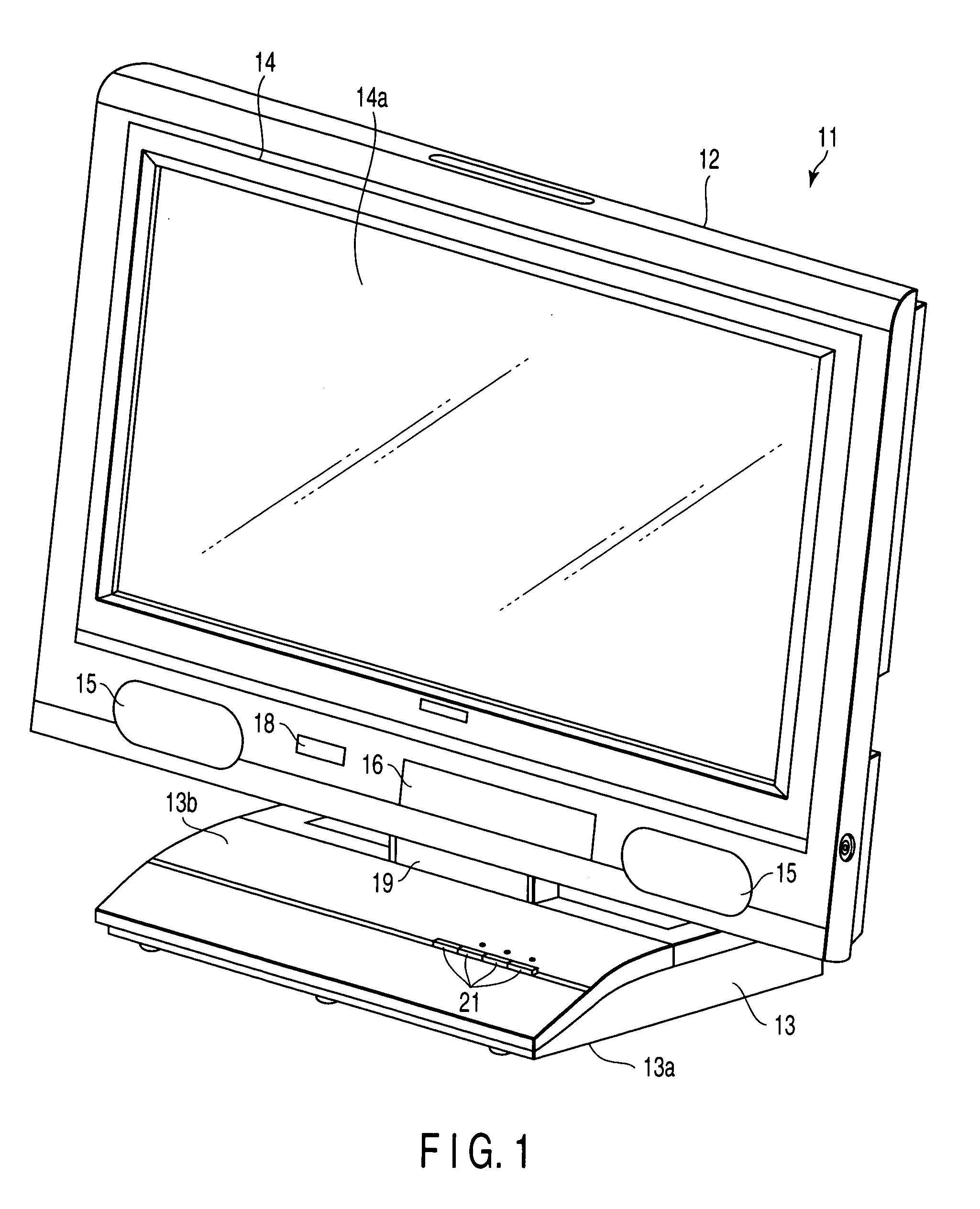
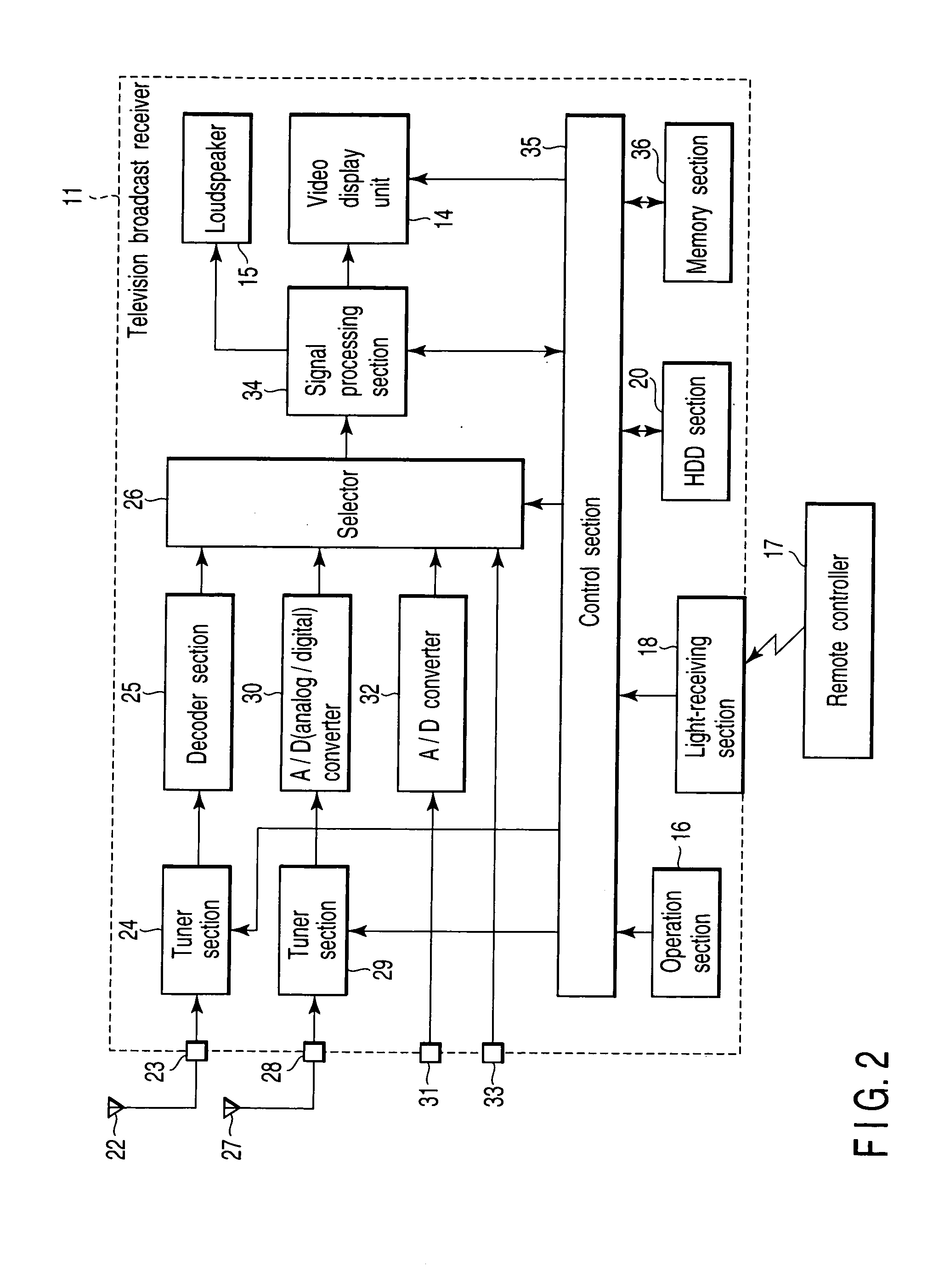
Video display device and video display method
InactiveUS20070002184A1Television system detailsTelemetry/telecontrol selection arrangementsComputer hardwareSpecific function
According to one embodiment, a key code of a key selected from a plurality of universal keys and information representing a function selected from a plurality of functions held by a main device are stored in a storage section in association with each other. When a key code transmitted from a remote controller is of a key corresponding to a specific function, a function corresponding to the key code is executed on the basis of a stored content of the storage section.
Owner:KK TOSHIBA
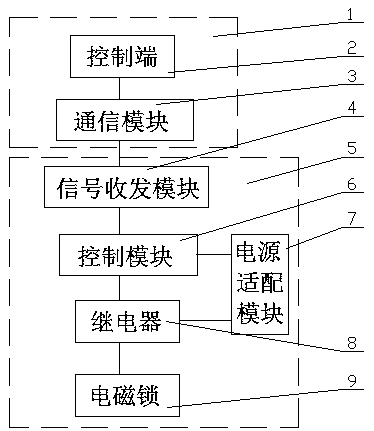
Intelligent five-prevention operation universal key management device
InactiveCN110164011APrevent fallingGood orientationTransmission systemsIndividual entry/exit registersElectromagnetic lockHuman power
The invention provides an intelligent five-prevention operation universal key management device. The device comprises a master control module, and a site module, wherein the master control module comprises a control end issuing a command, and a communication module used to communicate with the site module; and the site module comprises a box body where a universal key is placed, an electromagneticlock arranged on the box body, a power adaptation module used to supply power to the electromagnetic lock, a control module controlling the electromagnetic lock, and a signal transceiving module receiving the control command. The device provided by the invention has the advantages that the operation is convenient and rapid, the safety of operators and equipment is protected, the operation time isshortened, and the manual cost is reduced, so that resource allocation is greatly optimized, the operation efficiency is improved, and high system safety and high power supply reliability are ensured.
Owner:STATE GRID HENAN ELECTRIC ZHOUKOU POWER SUPPLY +1
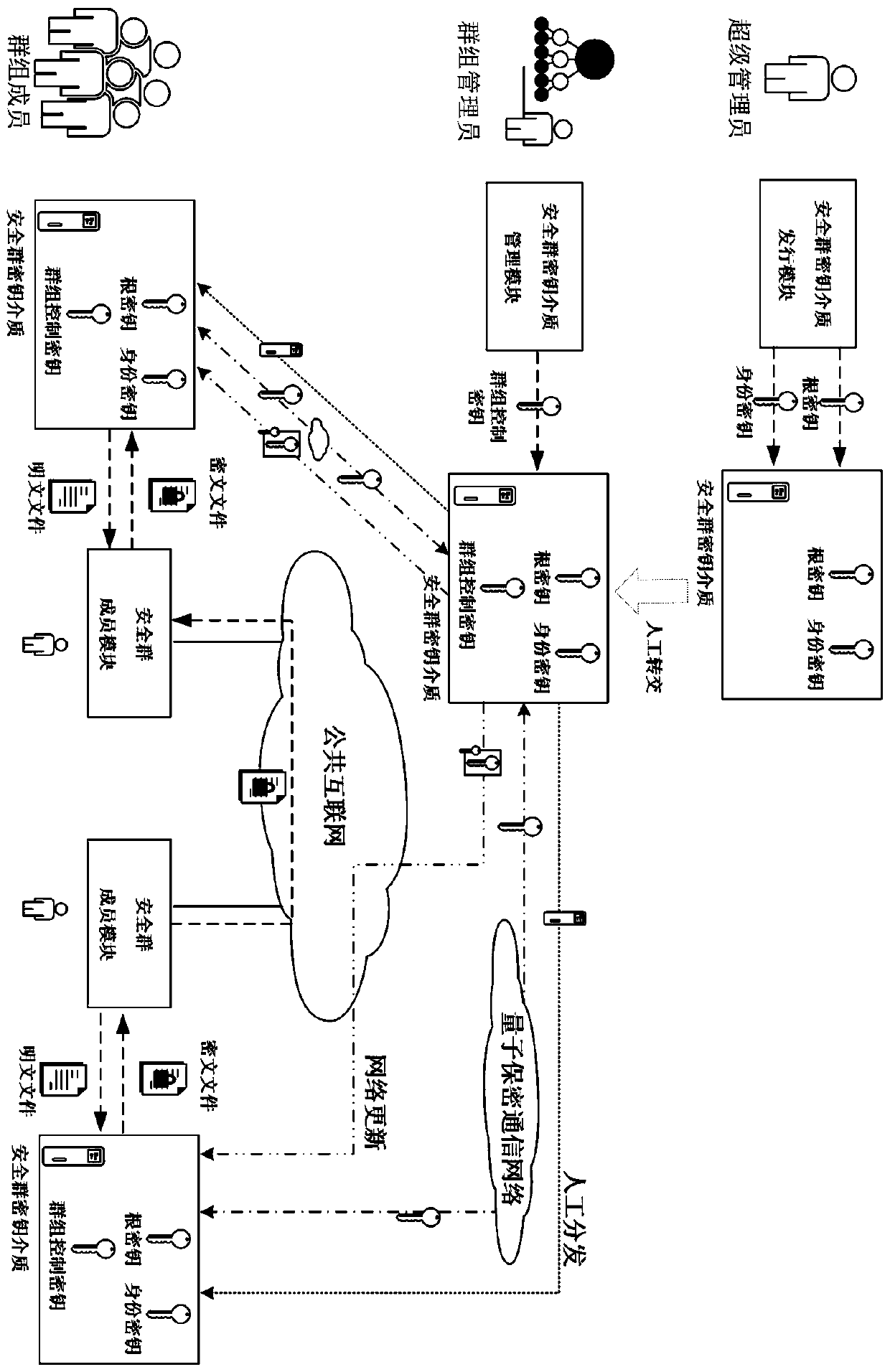
Information security transmission system and method with group decryption authority control
InactiveCN110474768AImprove anti-quantum computing abilityImprove computing powerKey distribution for secure communicationInteraction controlPassword
The invention discloses an information security transmission system and method with group decryption authority control. The information security transmission system comprises a security group key medium issuing module, a security group key medium management module, a security group key medium and a security group member module, wherein the security group key medium issuing module is a super administrator and is used for completing initial configuration of a root key and an identity key on a universal key medium conforming to GM / T 0016 intelligent password key password application interface specifications to generate a security group key medium; and the security group key medium management module is used for generating a group control key by a group administrator according to a group memberinformation interaction control requirement, injecting the group control key into a security group key medium, and distributing the security group key medium subjected to group management configuration to corresponding group users. According to the invention, the requirement of group users for realizing information encryption transmission across the public Internet can be met, and the group management mode is flexible and diverse, and the encryption strength is high, and the information security transmission system is safer and more reliable.
Owner:上海安密信科技有限公司
Combined lockset capable of preventing unlocked by universal key
The invention discloses a combined lock capable of preventing skeleton key from unlocking, characterized in that key inlet and outlet of the lock are provided on both ends, One or one more locking pieces are provided between key inlet and the outlet, the locking piece is provided with bullet hole, spring and bullet for opening-closing the locking piece, and bullet hole, spring and bullet for forward sliding of the key; There is provided with an angle between lock slot on sides of the up-down locking pieces to enclosing the keyhole. The lock of the invention is formed by combination of a plurality of locking pieces. An angle is provided between key shank grooves of each locking piece, when the lock pin is rotating during unlocking process, the keyhole is synchronously enclosed by using angle difference between key inlet and key shank grooves of each locking piece, thereby preventing skeleton key from unlocking. The key can be kept in the lock by utilization of reverse preventing pin between locking pieces and interior back locking structure, thus, the lost or formulated key can be found, which is safer.
Owner:李向阳
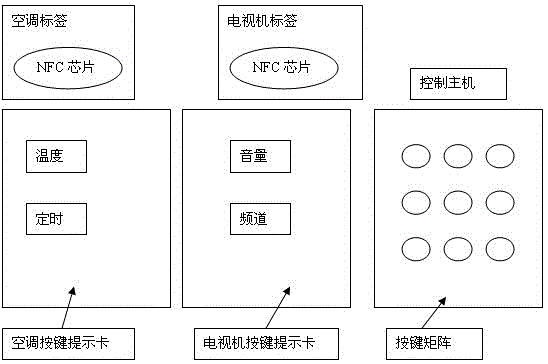
Electronic tag-type universal key remote controller
InactiveCN105989701ASolve the inconvenienceSolve the problem of one machine with one remote controlNon-electrical signal transmission systemsRemote controlEngineering
The invention discloses an electronic tag-type universal key remote controller. The remote controller is composed of an electronic tag having remote control codes, a key function prompt card, and a control host. The user uses the control host for scanning the electronic tag to obtain a remote control signal code and a key scanning code, and then the key can be pressed to control the corresponding electronic products. The electronic tag-type universal key remote controller is simple to operate and convenient to use, and solves the problems that a large number of remote controllers are required, and a universal remote controller is complicated to operate and is high in cost. Therefore, resources are saved and environmental protection is achieved.
Owner:牟梦雅
Key code fused A1 type safe lock for eliminating 12 hidden dangers by multiple protections
InactiveCN102191883AEliminate interoperability hazardsEliminate reopening hazardsPuzzle locksPermutation locksConfidentialityDynamic balance
The invention discloses a key code fused A1 type safe lock for eliminating 12 hidden dangers by multiple protections, and relates to a mechanical coded lock and a key lock for a safe. The double locks are fused and controlled mutually, a knob is in engaged and disengaged fit with the coded lock, and a counterweight unlocking plate linkage body is linked with an elastic buffer body; dynamic balance adjustment is performed on the coded lock, so that 10 hidden dangers comprising frictional opening, percussive opening, tested dynamic balance opening and coded full-test opening of the coded lock and frictional opening, percussive opening, code variable full-test opening, universal key type opening, oscillator type opening and integral locking full-test opening of the key lock are eliminated; meanwhile, inherent mutual opening hidden danger and reopening hidden danger of the key lock are simultaneously eliminated; according to 13.6 million times of code variables, the lock becomes a general mechanical safe lock with strongest confidentiality in the ancient and modern in China and abroad, and is to become an upgraded product in the industry; and the lock has simple structure, and is suitable for safes used in national defense, scientific research, public security, financial institutions and households.
Owner:石淳民
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com