Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3616 results about "Key management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Key management refers to management of cryptographic keys in a cryptosystem. This includes dealing with the generation, exchange, storage, use, crypto-shredding (destruction) and replacement of keys. It includes cryptographic protocol design, key servers, user procedures, and other relevant protocols.
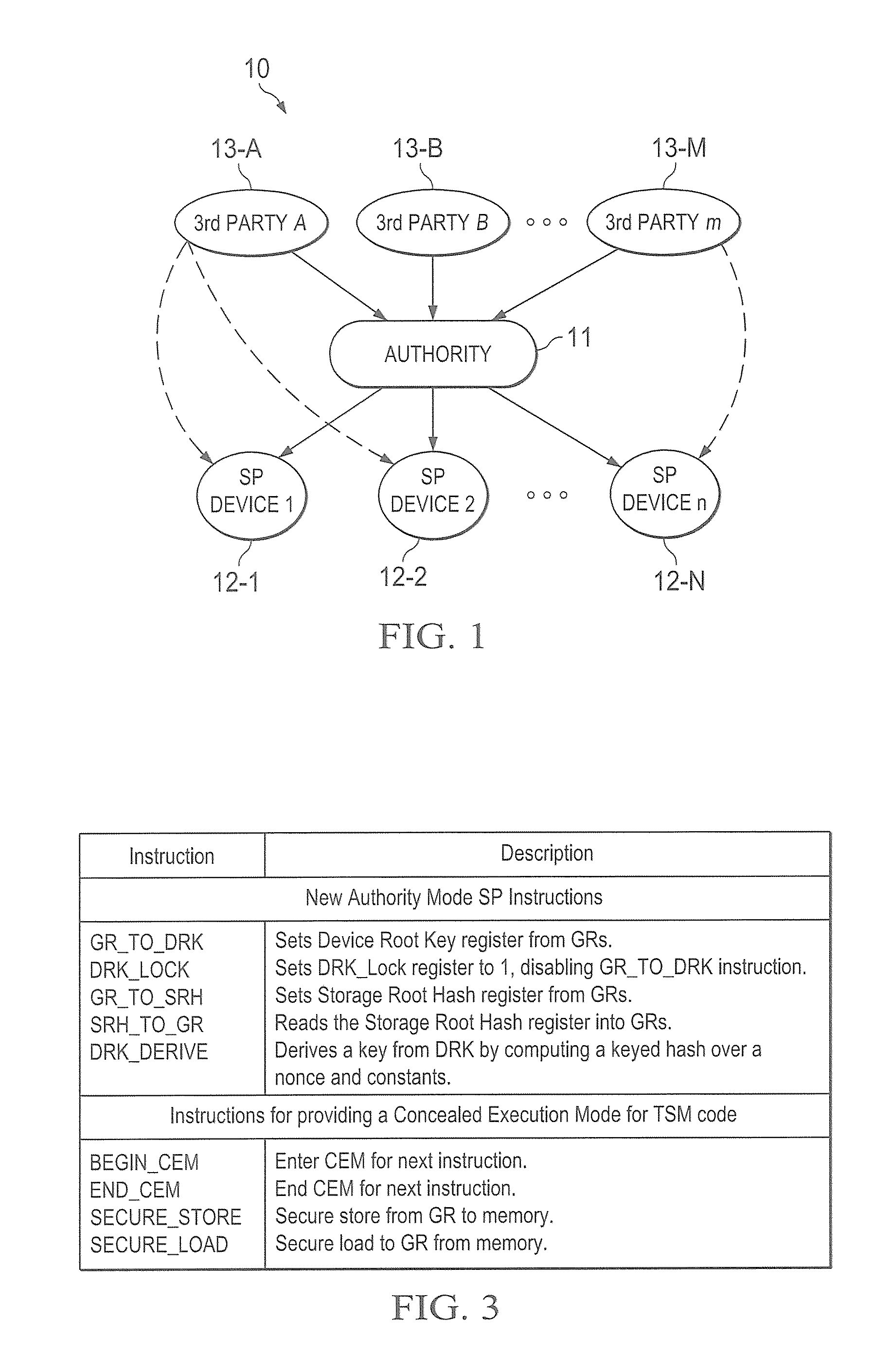
Method and apparatus for a web-based application service model for security management
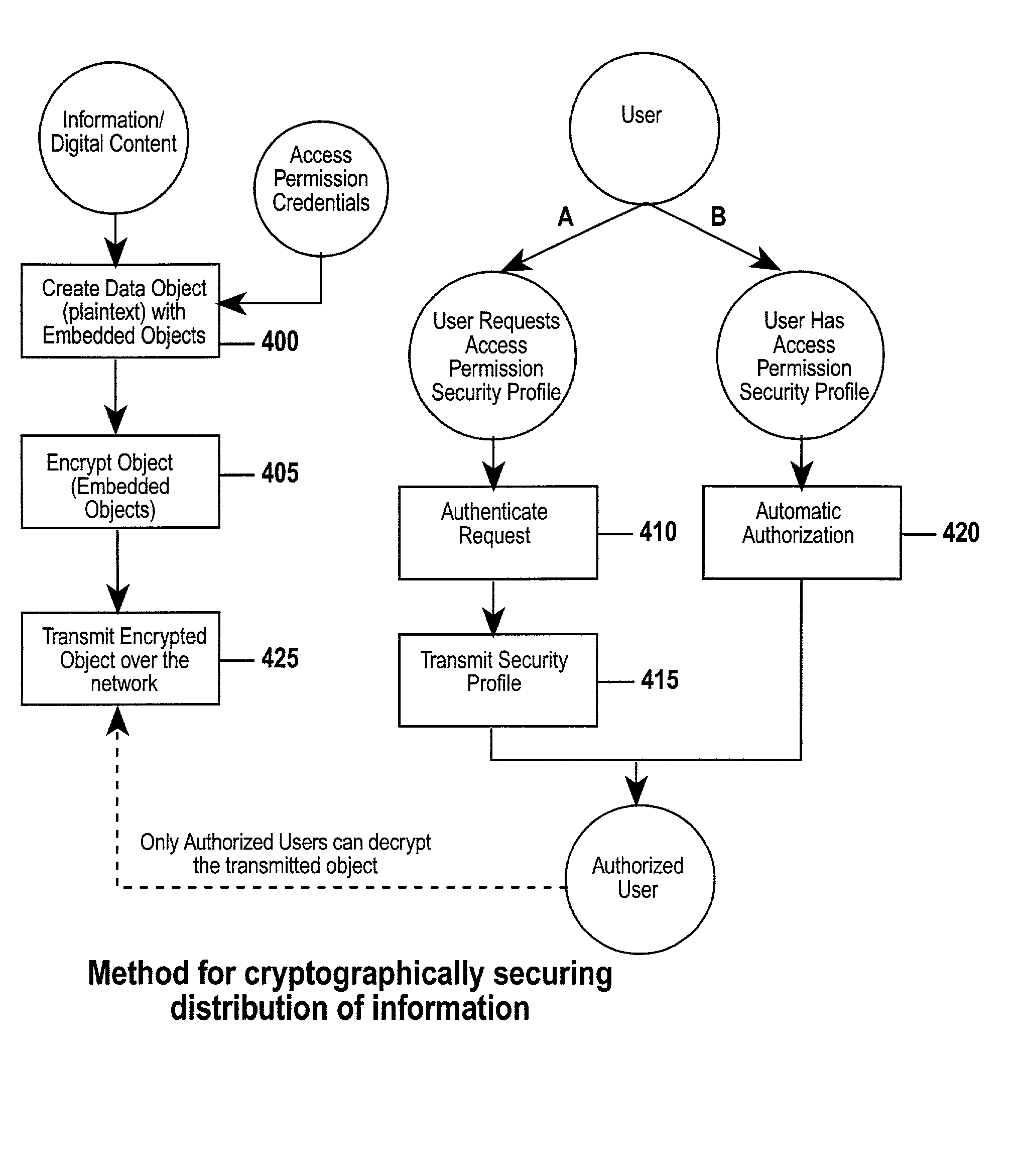
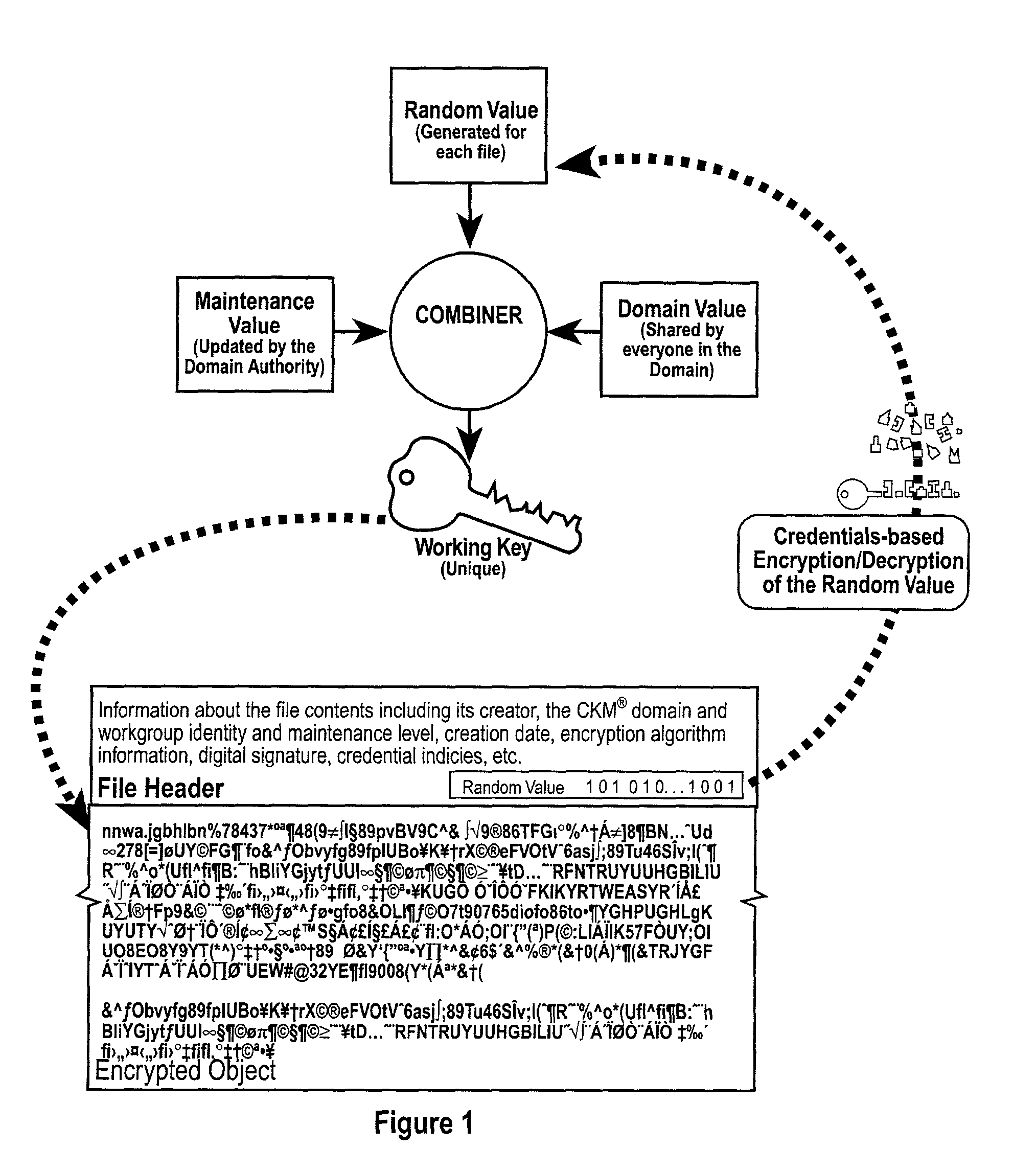
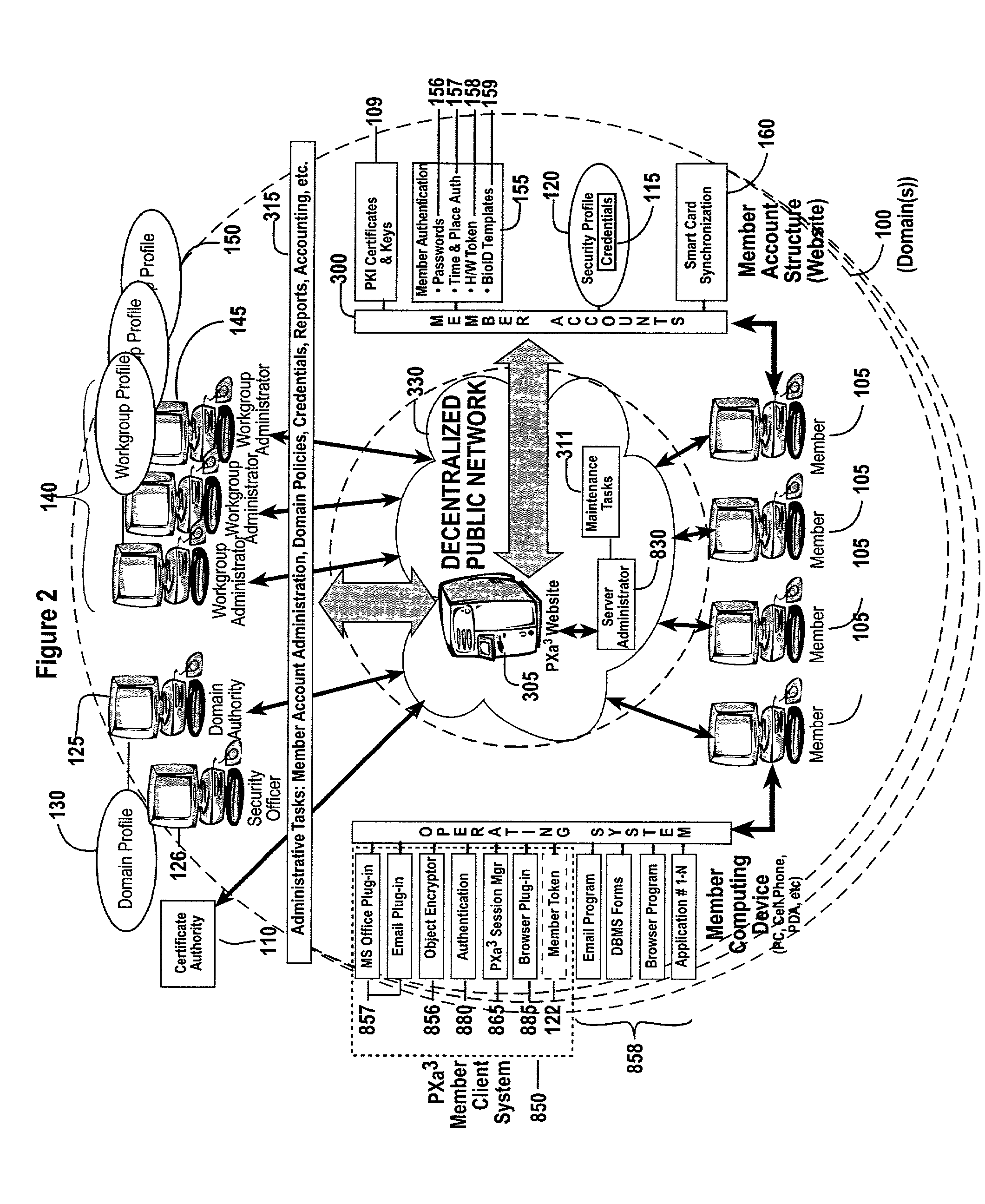
The invention combines cryptographic key management technology with various authentication options and the use of a companion PKI system in a web-centric cryptographic key management security method and apparatus called PXa3(TM) (Precise eXtensible Authentication, Authorization and Administration). The PXa3 model uses a security profile unique to a network user and the member domain(s) he / she belongs to. A PXa3 server holds all private keys and certificates, the user's security profile, including credentials and the optional authentication enrollment data. The server maintains a security profile for each user, and administrators simply transmitted credential updates and other periodic maintenance updates to users via their PXa3 server-based member accounts. Domain and workgroup administrators also perform administrative chores via a connection to the PXa3 web site, rather than on a local workstation. A member's security profile, containing algorithm access permissions, credentials, domain and maintenance values, a file header encrypting key, optional biometric templates, and domain-specific policies is contained in one of two places: either on a removable cryptographic token (e.g., a smart card), or on a central server-based profile maintained for each member and available as a downloadable "soft token" over any Internet connection.
Owner:SIVAULT INC
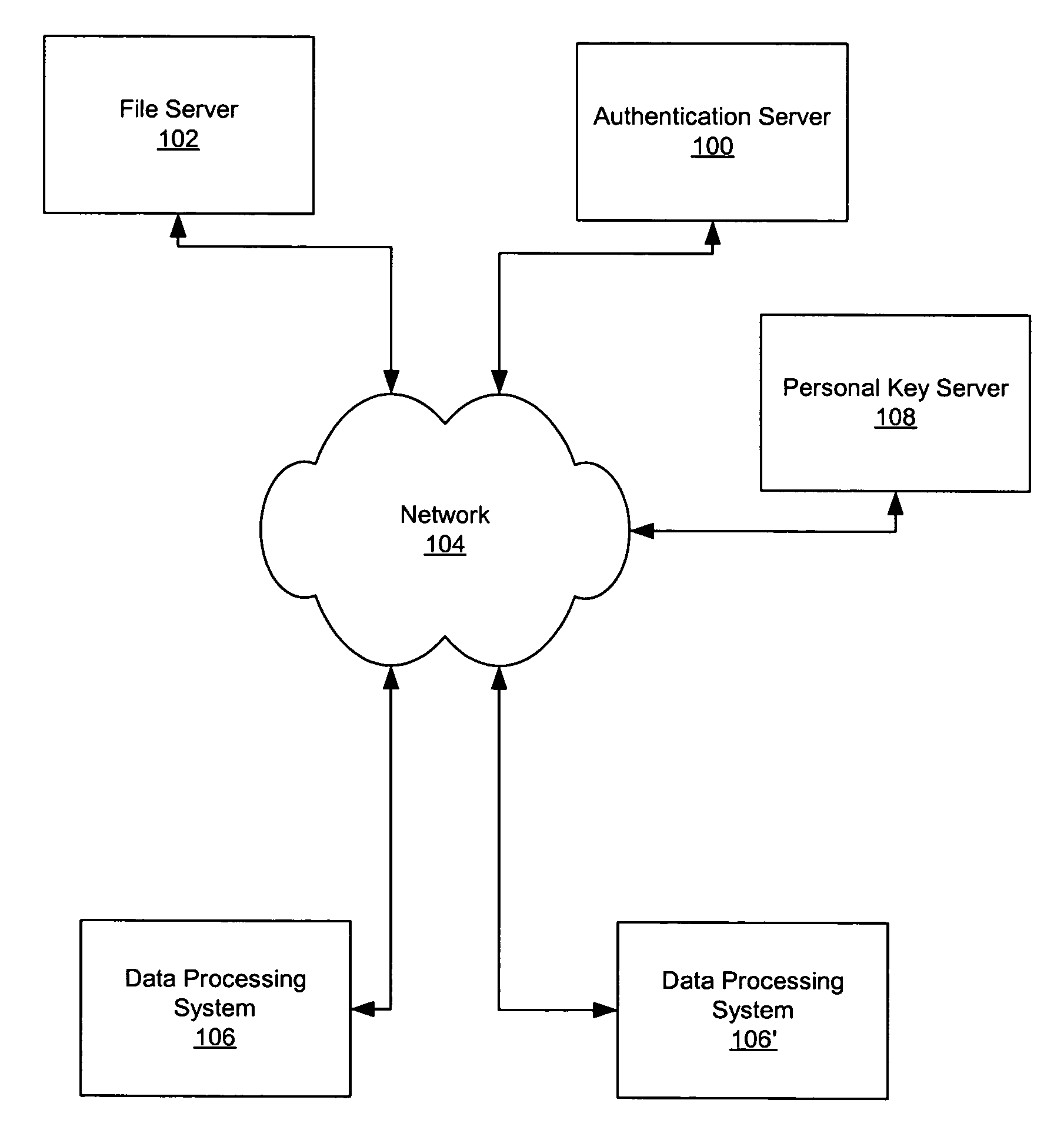
Secure data storage and retrieval with key management and user authentication
InactiveUS6947556B1Key distribution for secure communicationUser identity/authority verificationDigital dataPassphrase
Methods, systems and computer program products are provided which provide for controlling access to digital data in a file by encrypting the data with a first key, encrypting the first key with a second personal key generated from a password / passphrase associated with the file and further encrypting the encrypted first key with a control key which is managed by the system. In certain embodiments, user authentication may also be provided by issuing a ticket which is utilized to create, access and administer the files in the system.
Owner:IBM CORP
Secured transaction system and method
InactiveUS20130254117A1Reduce riskEasy to optimizePayment protocolsInternet privacyEncryption decryption
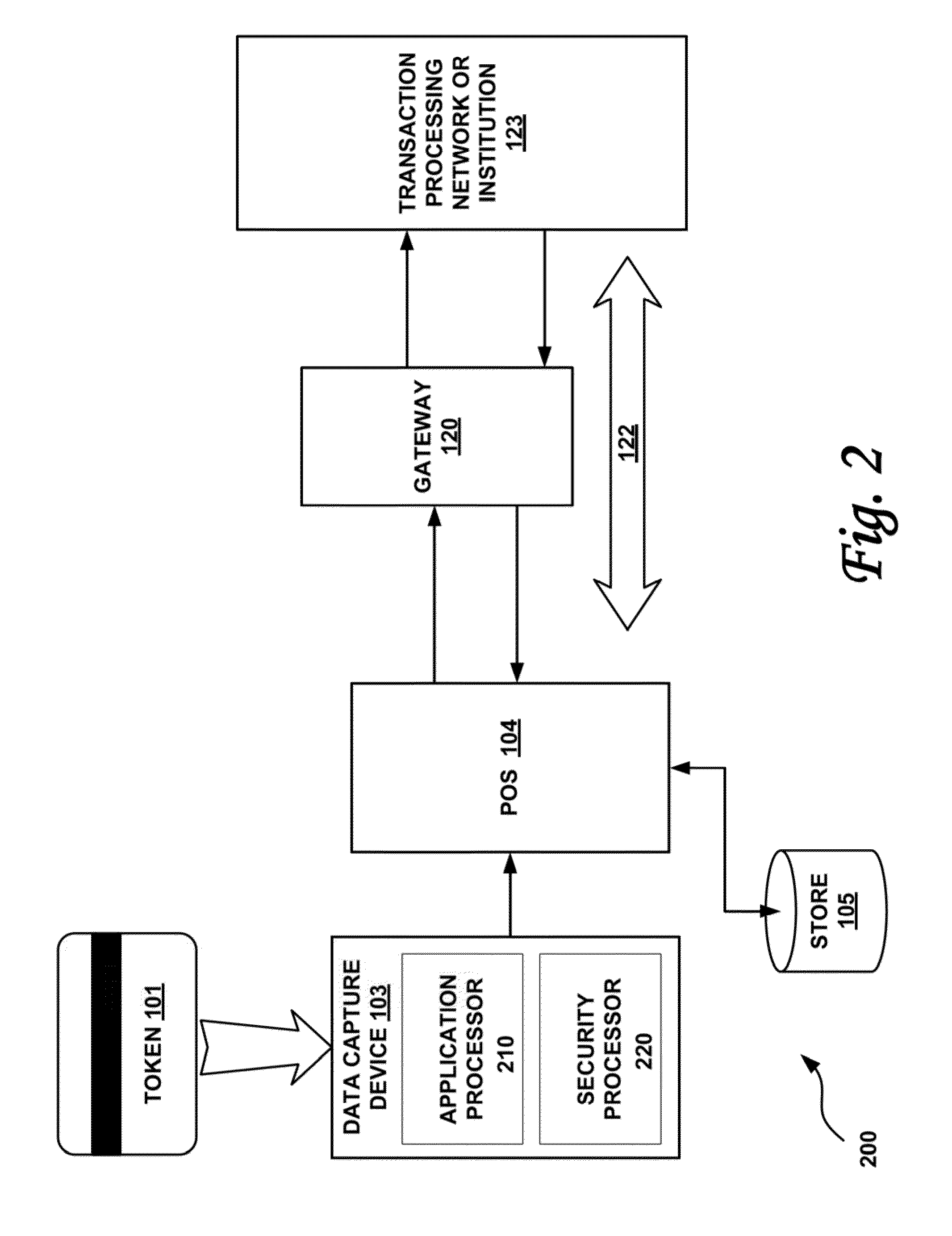
Systems and methods for performing financial transactions are provided. In one embodiment, the invention provides for method for bank card transactions, including: reading the token information at the point of swipe for traditional and non-traditional POS platforms; performing a low-security task on the token information using a first microprocessor, wherein the non-security task includes one or more tasks from the group of encryption determination, encryption-decryption request, key management, token information delivery, or transactional data delivery; and performing a security-related task on the token information using a second microprocessor based on a request from the first microprocessor, wherein the security-related task includes one or more tasks from the group of token information authentication, token information decryption, or token information encryption. Formatting the encrypted information such that it is compatible with the format of the current POS system.
Owner:VON MUELLER CLAY W +1
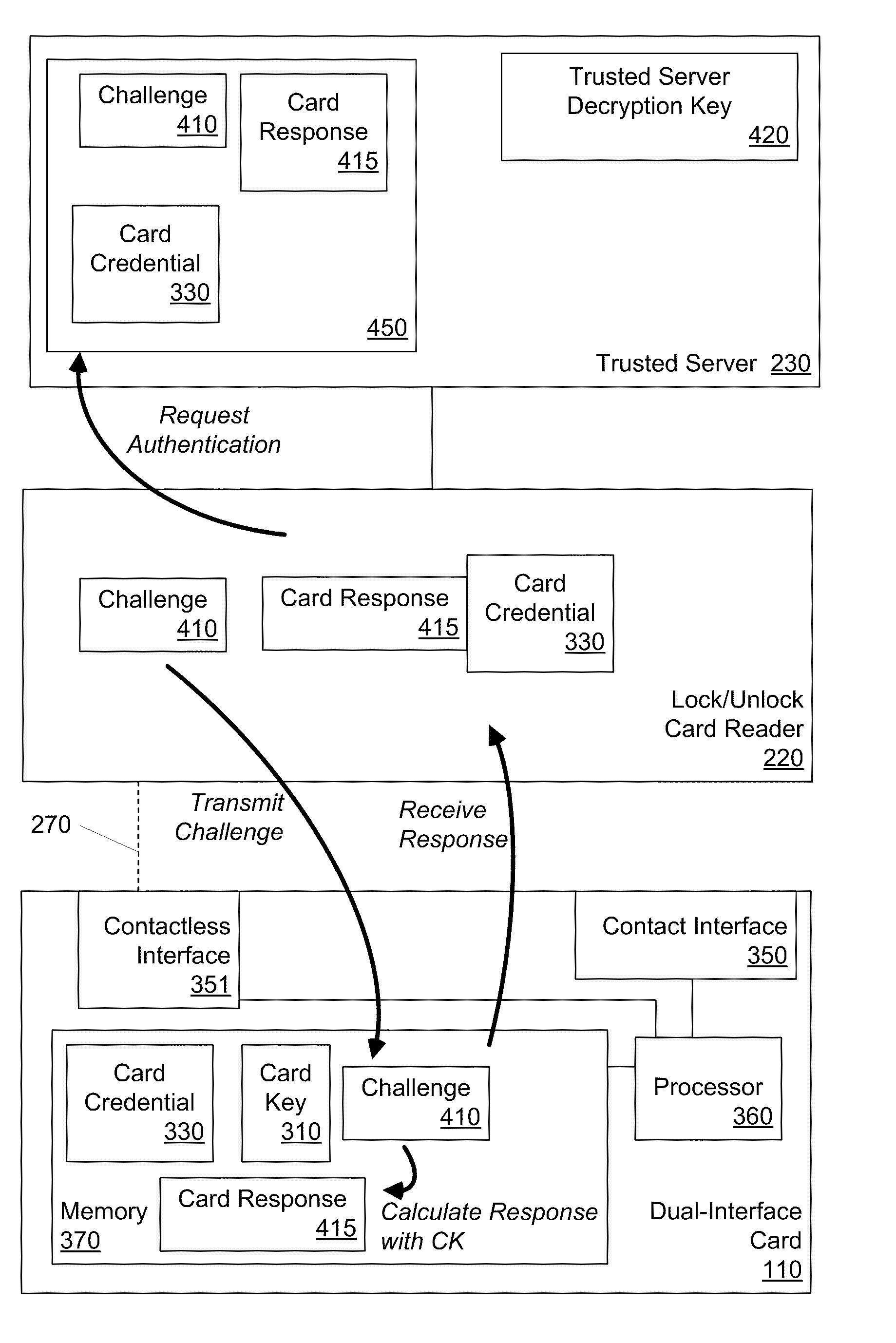
Dual-Interface Key Management
ActiveUS20110035604A1Lower security levelNear-field transmissionUnauthorized memory use protectionKey managementComputer security
In one embodiment, a device includes a first interface, a second interface, a memory, and a processor coupled to the first and second interfaces and to the memory. The processor is configured to receive key-management information via the second interface, and to store the key-management information in a protected portion of the memory as stored key-management information. The processor is also configured to perform a challenge-response authentication interaction via the first interface. The challenge-response authentication interaction is based at least in part on the stored key-management information. The device is configured to prevent data in the protected portion of the memory from being modified in response to information received via the first interface.
Owner:HABRAKEN G WOUTER
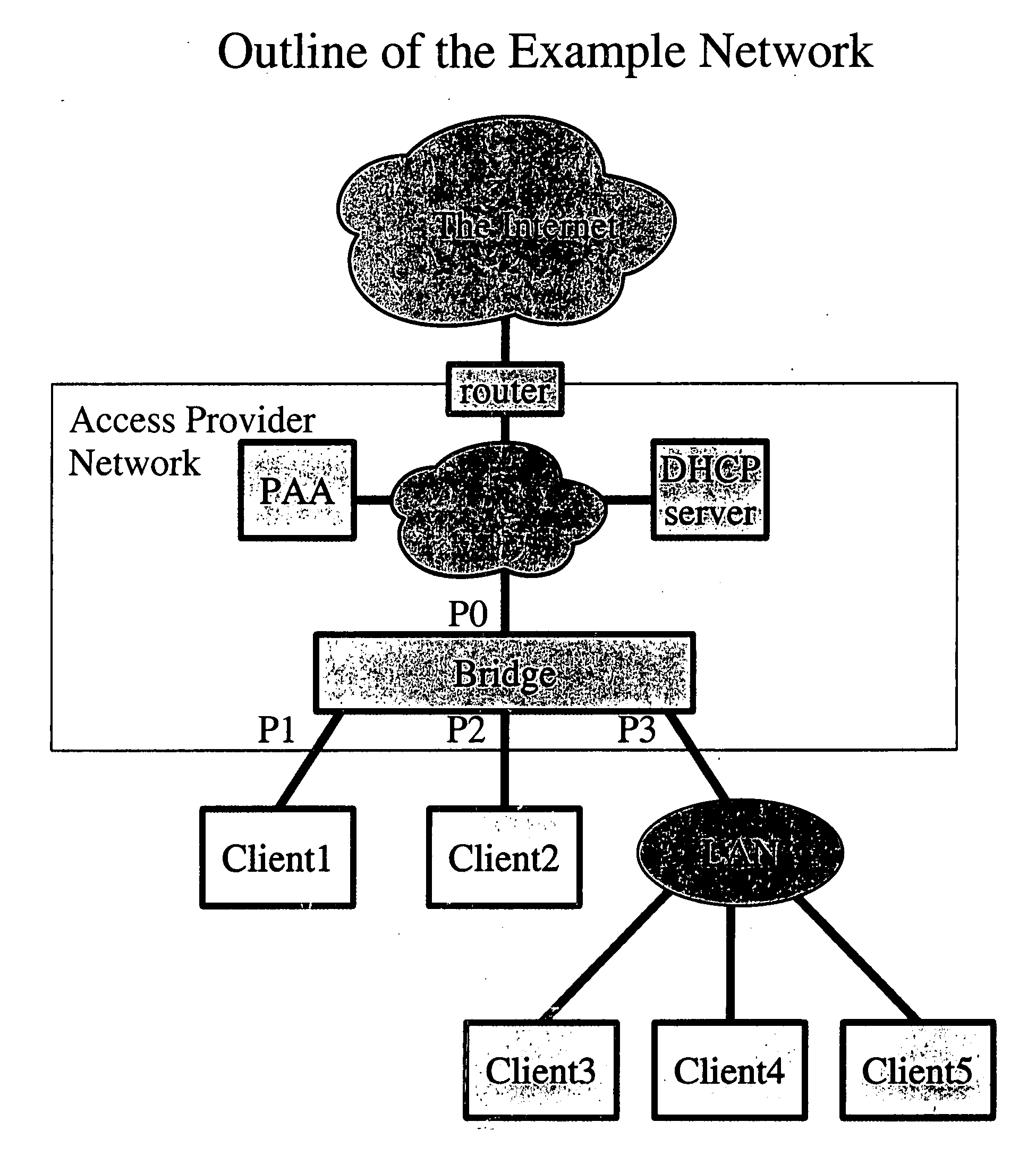
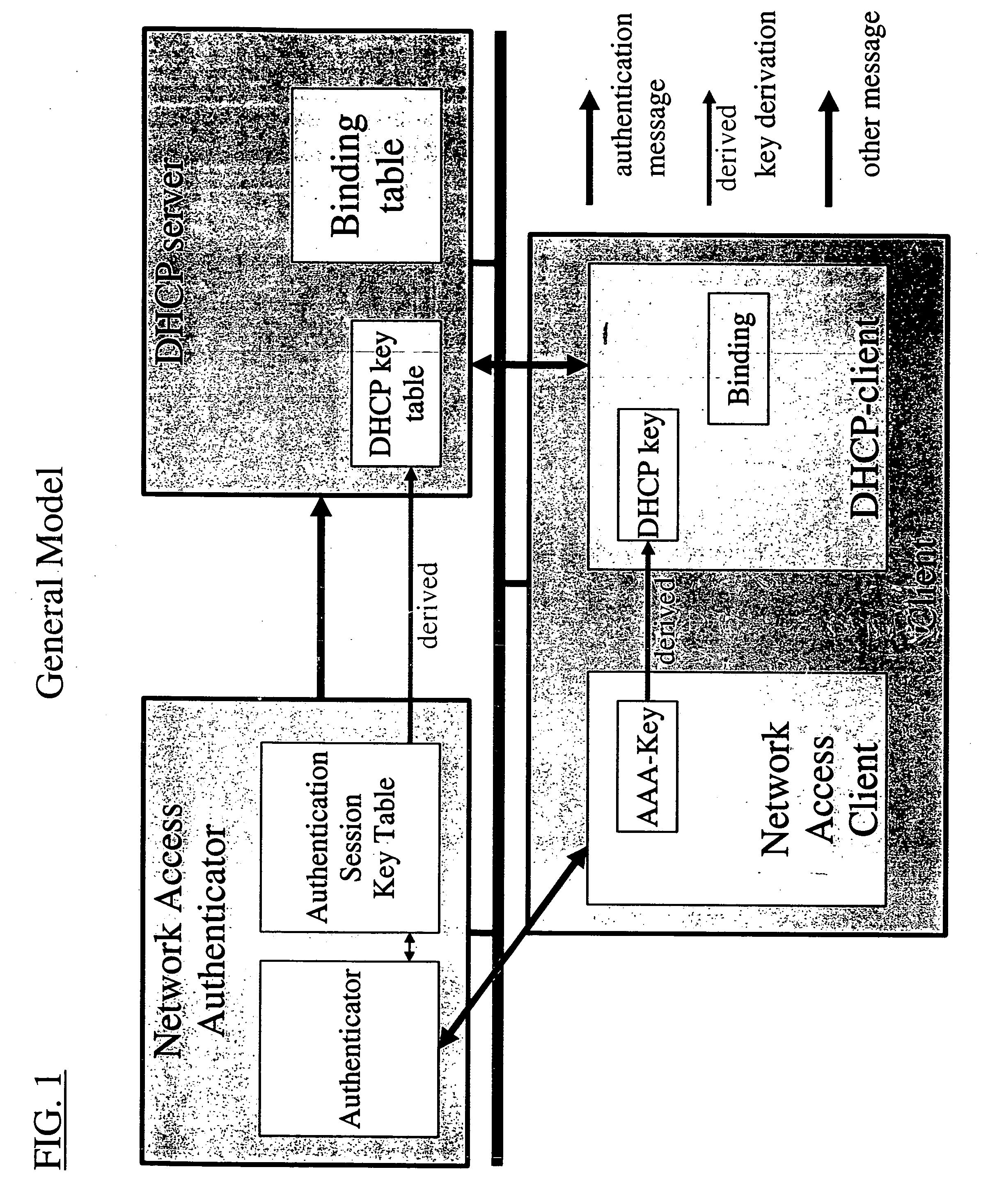
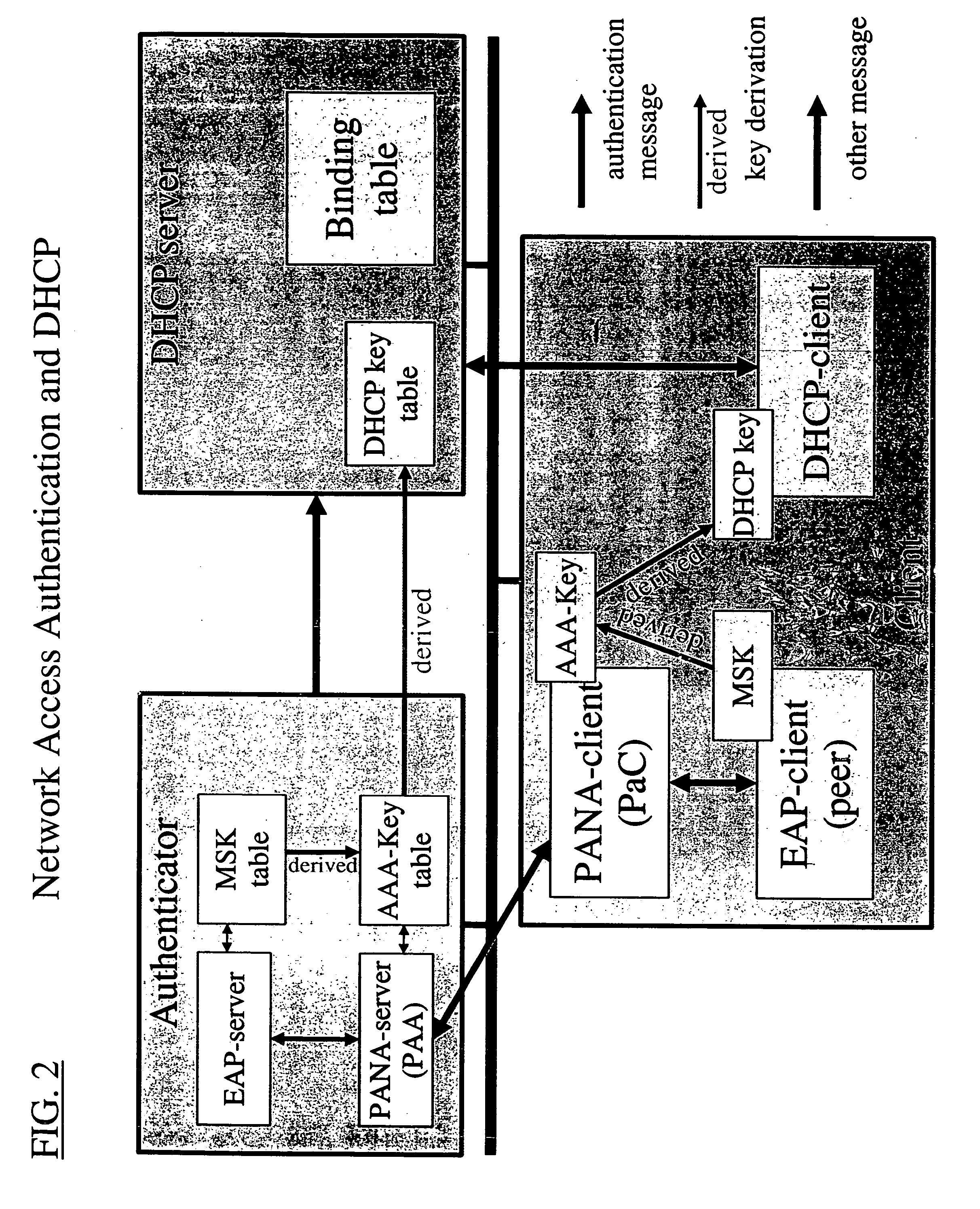
Dynamic host configuration and network access authentication
InactiveUS20060036733A1Digital computer detailsTransmissionIP multicastProtocol for Carrying Authentication for Network Access
Owner:FOUR BATONS WIRELESS LLC
Method and Apparatus for Hardware-Accelerated Encryption/Decryption
ActiveUS20090060197A1Avoid contactMaximize availabilityEncryption apparatus with shift registers/memoriesSecret communicationMultiple encryptionComputer hardware
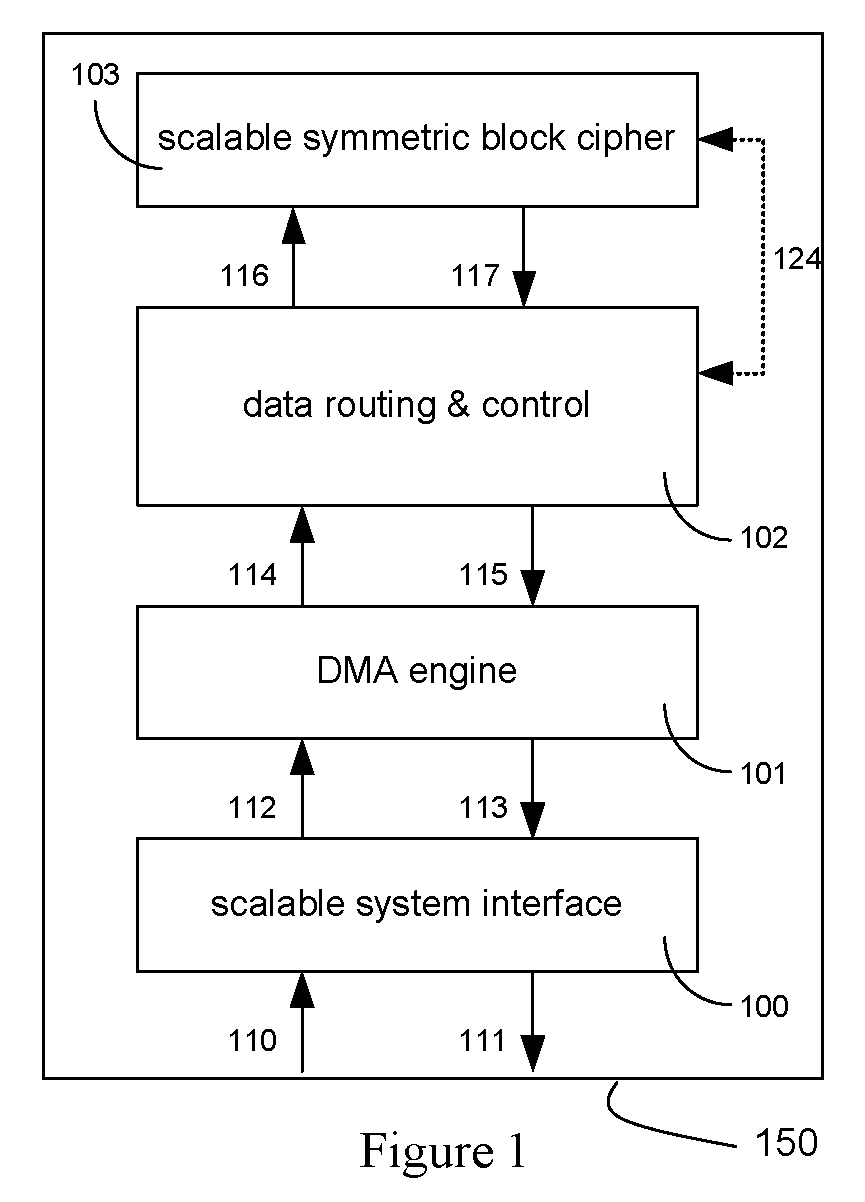
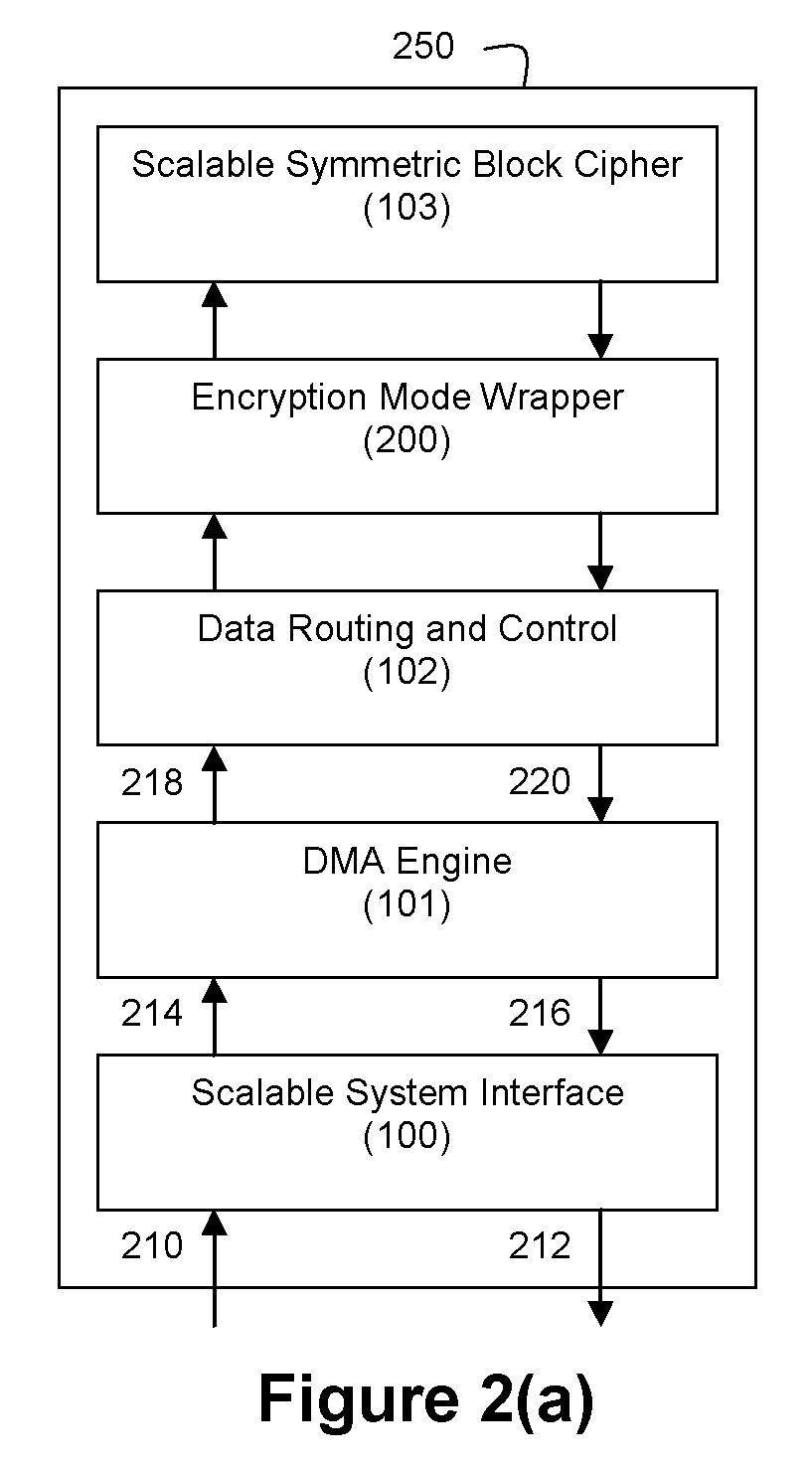
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
Method and system for managing programmed applications in an open api environment
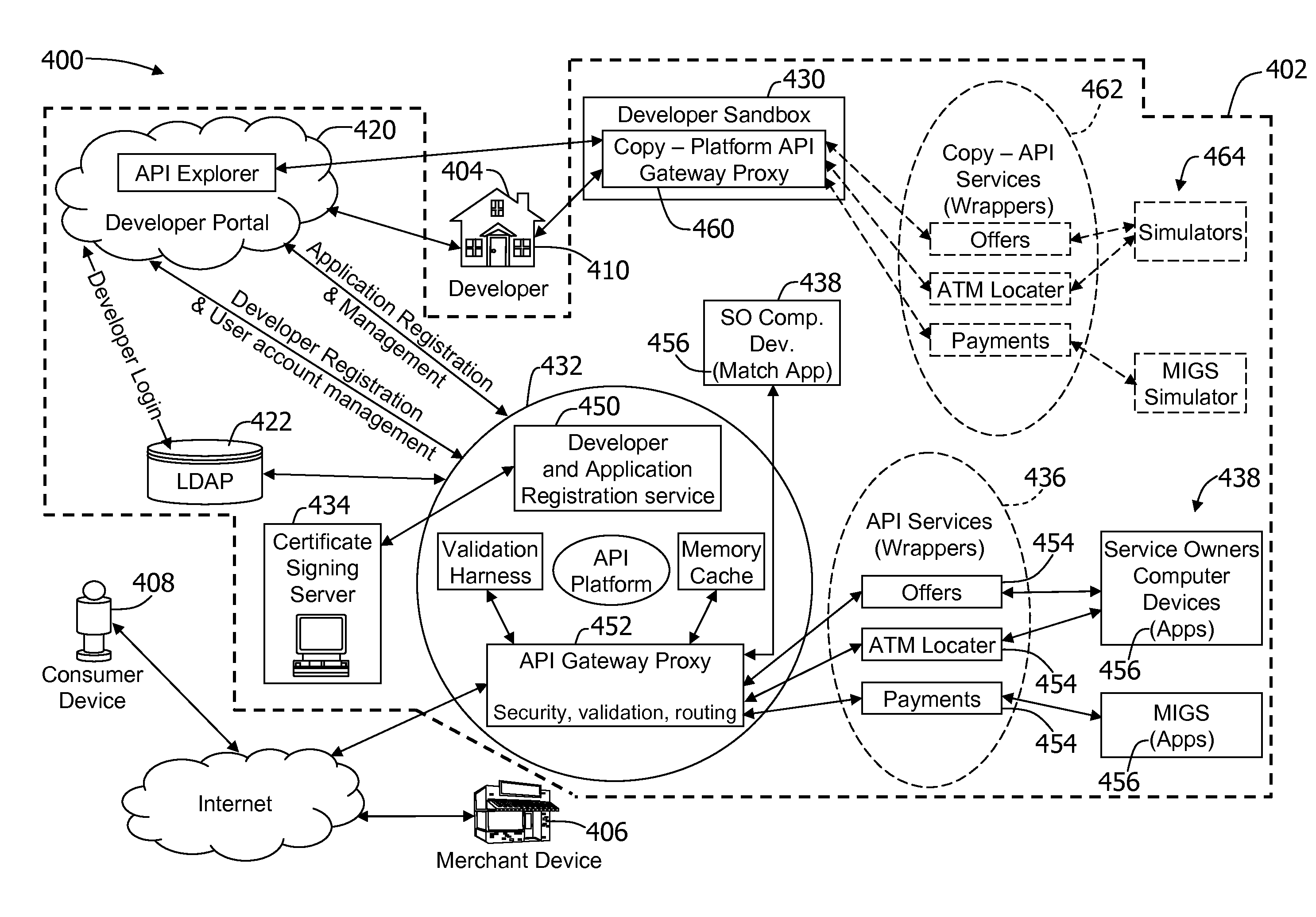
A method and system for an open API dashboard system for monitoring and managing one or more developer programmed applications configured to use one or more services provided by a service owner are provided. The system includes an application area associated with a corresponding programmed application, each application area including a call metrics group configured to display summarized metrics, a services used group configured to display a listing of each service called by the programmed application and metrics associated with each service, and a key management group configured to prompt a developer of the programmed application to request or revoke a key, wherein the key includes a developer identification, a programmed application identification, and signed certificates relating to services used by the programmed application. The system also includes a side bar area configured to prompt a developer to request information or help relating to the application area.
Owner:MASTERCARD INT INC
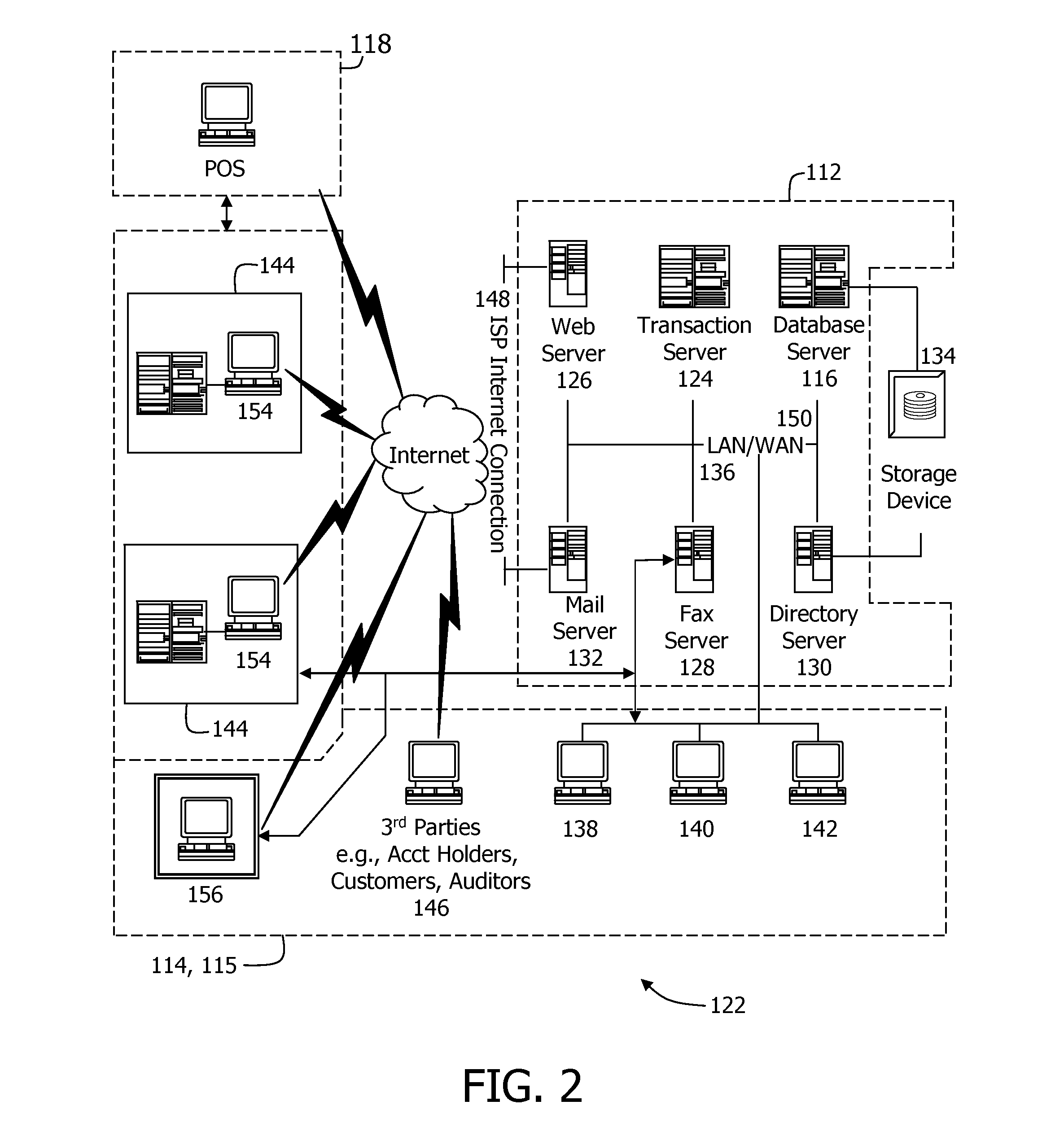
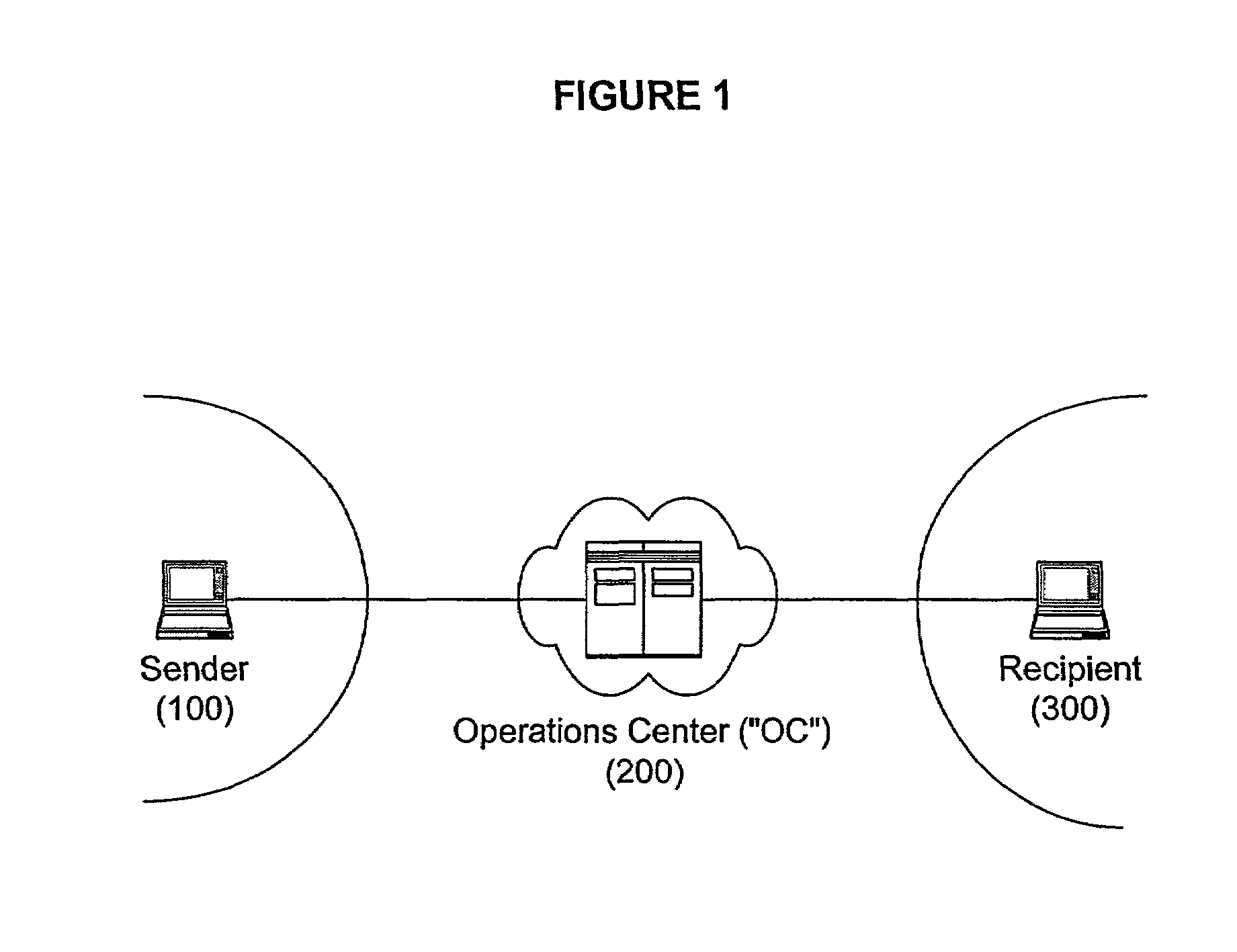
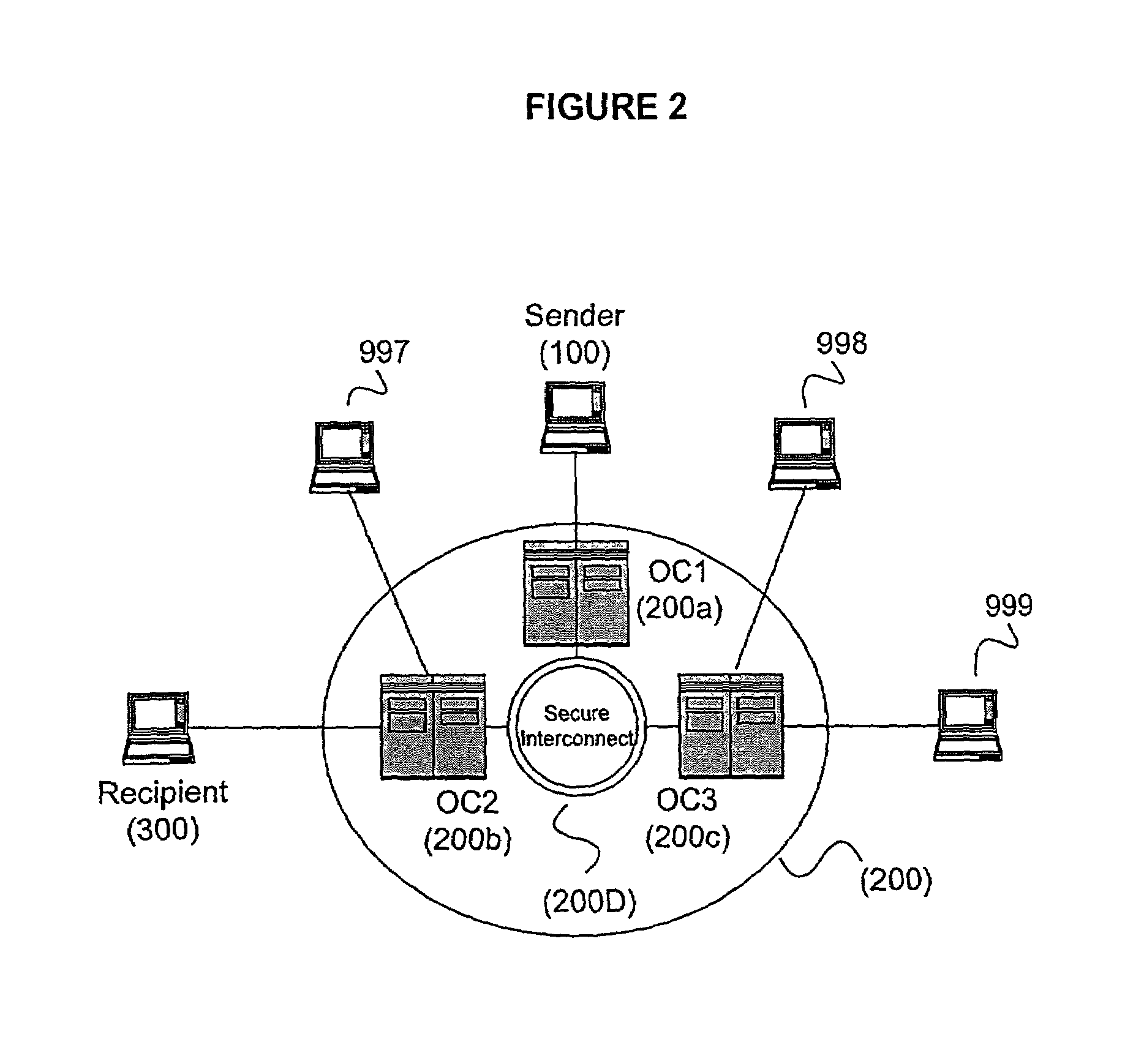
Secure and reliable document delivery
InactiveUS6988199B2Key distribution for secure communicationUser identity/authority verificationPrivate networkPaper document
An Operations Center (OC) (200) acts as a central key manager and intermediary in securely, reliably and non-repudiably delivering a document (3) from a sender (100) to a recipient (300). The OC (200) acts as a key manager to facilitate the process of strong authentication of the sender (100) and the recipient (300), encryption of the delivery (510), and setup of reliable connections (2A, 2B, 2C). In a preferred embodiment, the reliable connections (2A, 2B, 2C) are virtual private network connections.
Owner:BAE SYST APPLIED INTELLIGENCE US
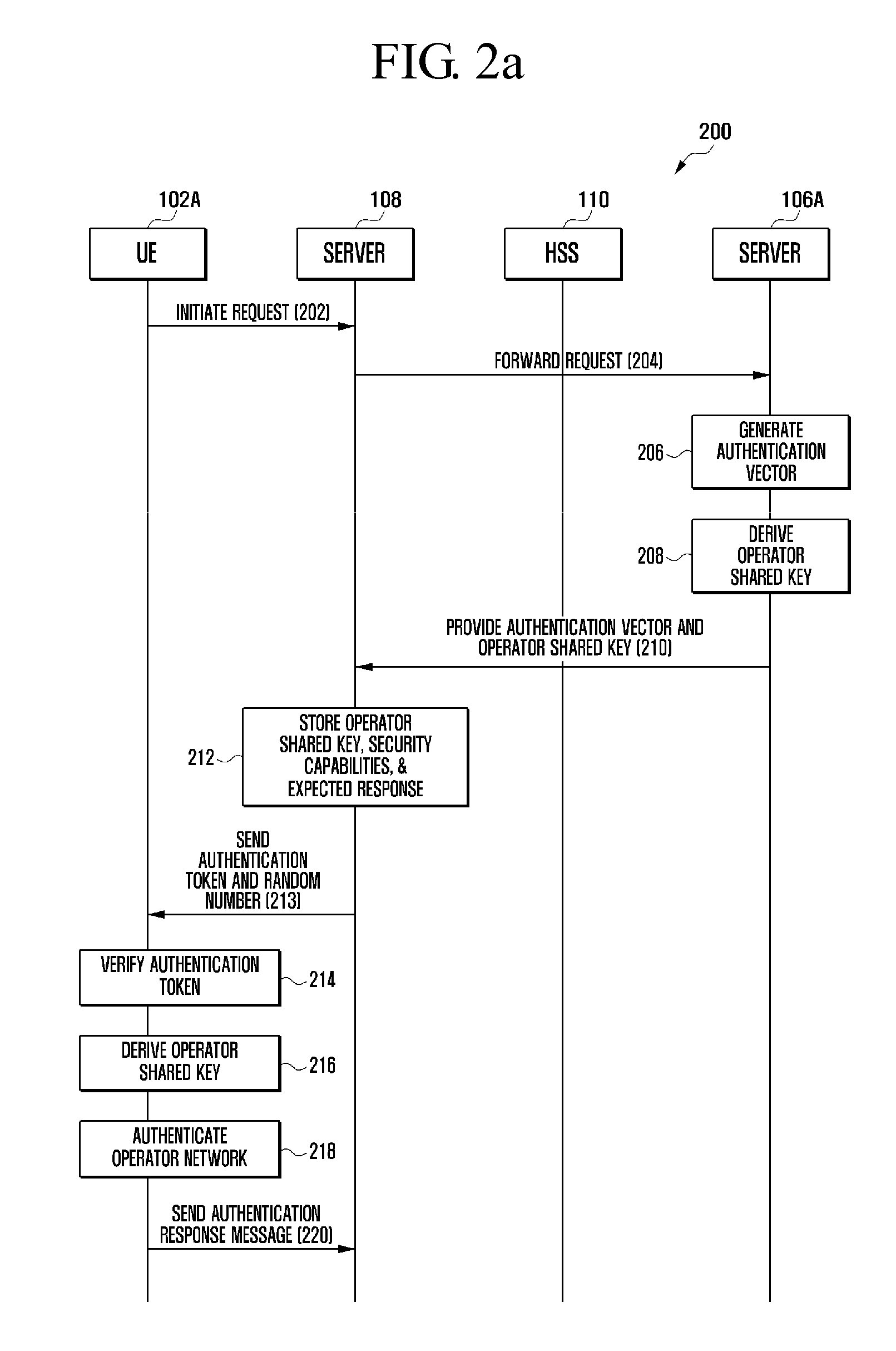
Method and system for secured remote provisioning of a universal integrated circuit card of a user equipment
ActiveUS20130012168A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwarePublic land mobile network
The present invention provides a method and system for secured remote provisioning of a universal integrated circuit card of a user equipment. A system includes a user equipment for initiating a request for remote provisioning of an universal integrated circuit card (UICC) in the user equipment, where the request for remote provisioning includes a machine identifier (MID) associated with the user equipment and a public land mobile network (PLMN) identifier (ID) associated with an network operator. The system also includes at least one shared key management server for dynamically generating security keys and an operator shared key using the security keys, the MID. Moreover, the system includes an operator network for generating a subscription key using the operator shared key and an international mobile subscriber identity (IMSI), and provisioning the IMSI in a secured manner to the UICC of the user equipment using the security keys.
Owner:SAMSUNG ELECTRONICS CO LTD
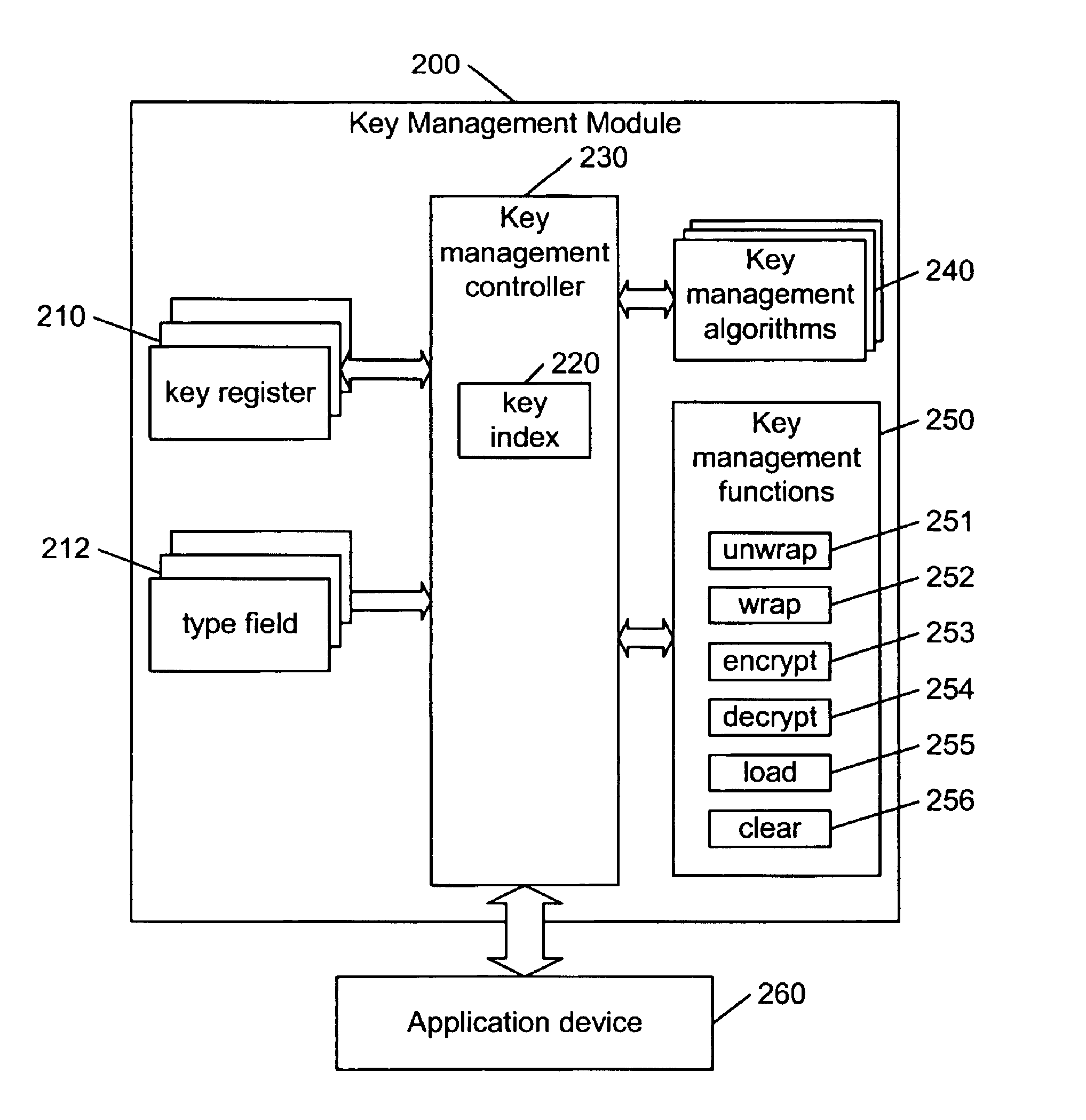
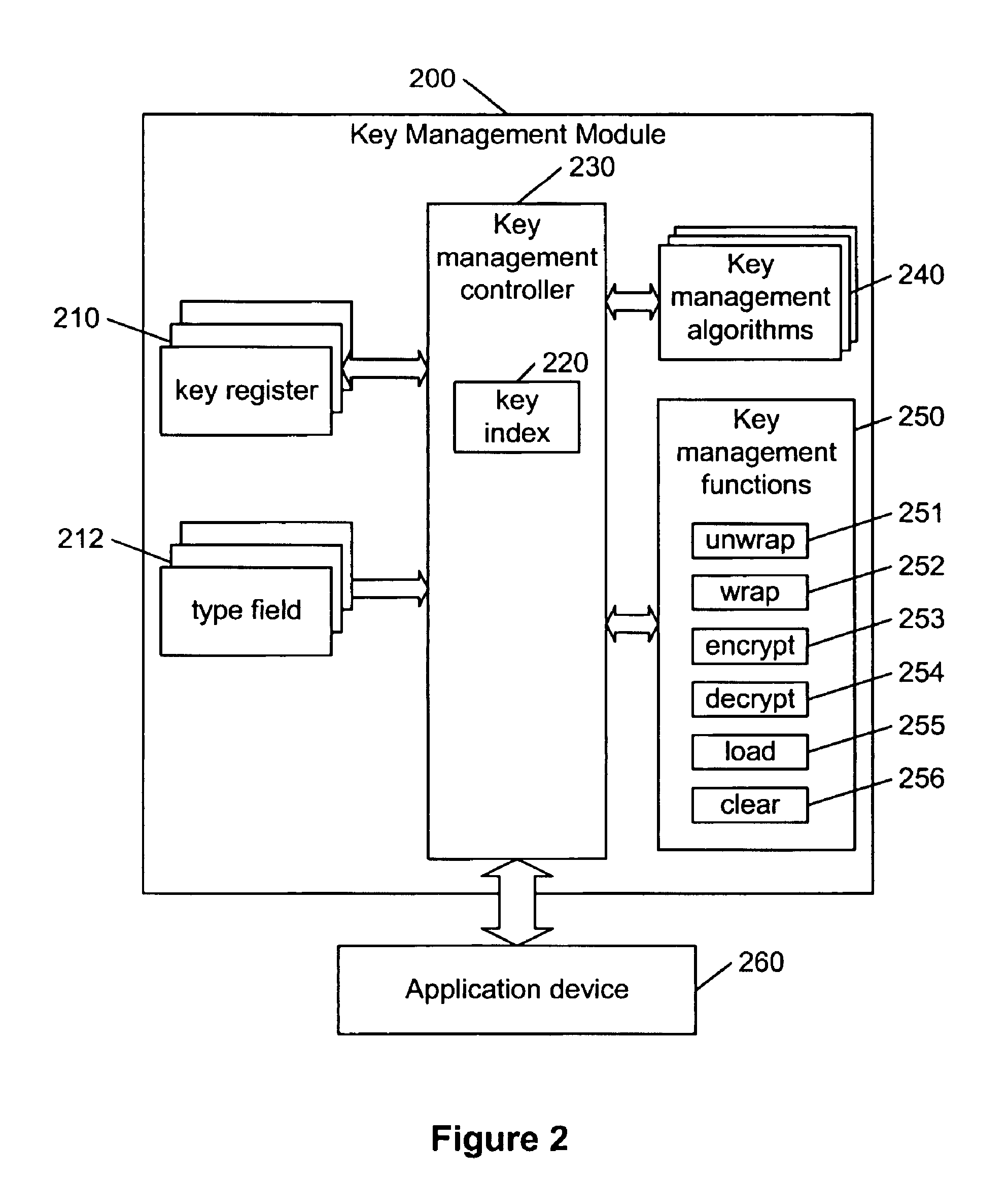
Hierarchical key management encoding and decoding
InactiveUS6907127B1Simple designSeparate applicationKey distribution for secure communicationDigital data processing detailsExclusive orInitialization vector
The present invention discloses a construction for key management module functionality which provides for secure encoding and decoding of messages which are up to two blocks long. A method for generating an encoded value having a first encoded value part and a second encoded value part from an unencoded value having a first unencoded value part and a second unencoded value part, comprising the steps of: obtaining an initialization vector; and generating the first and second encoded value parts. The first encoded value part is generated by: generating a first result by encrypting the first unencoded value part; generating a second result by performing an exclusive or operation on the first result and the second unencoded value part; generating a third result by performing an exclusive or operation on the second result and the initialization vector; generating a fourth result by encrypting the third result; generating a fifth result by performing an exclusive or operation on the fourth result and the first unencoded value part; and encrypting the fifth result. The second encoded value part is generated by encrypting the second result.
Owner:GOOGLE LLC
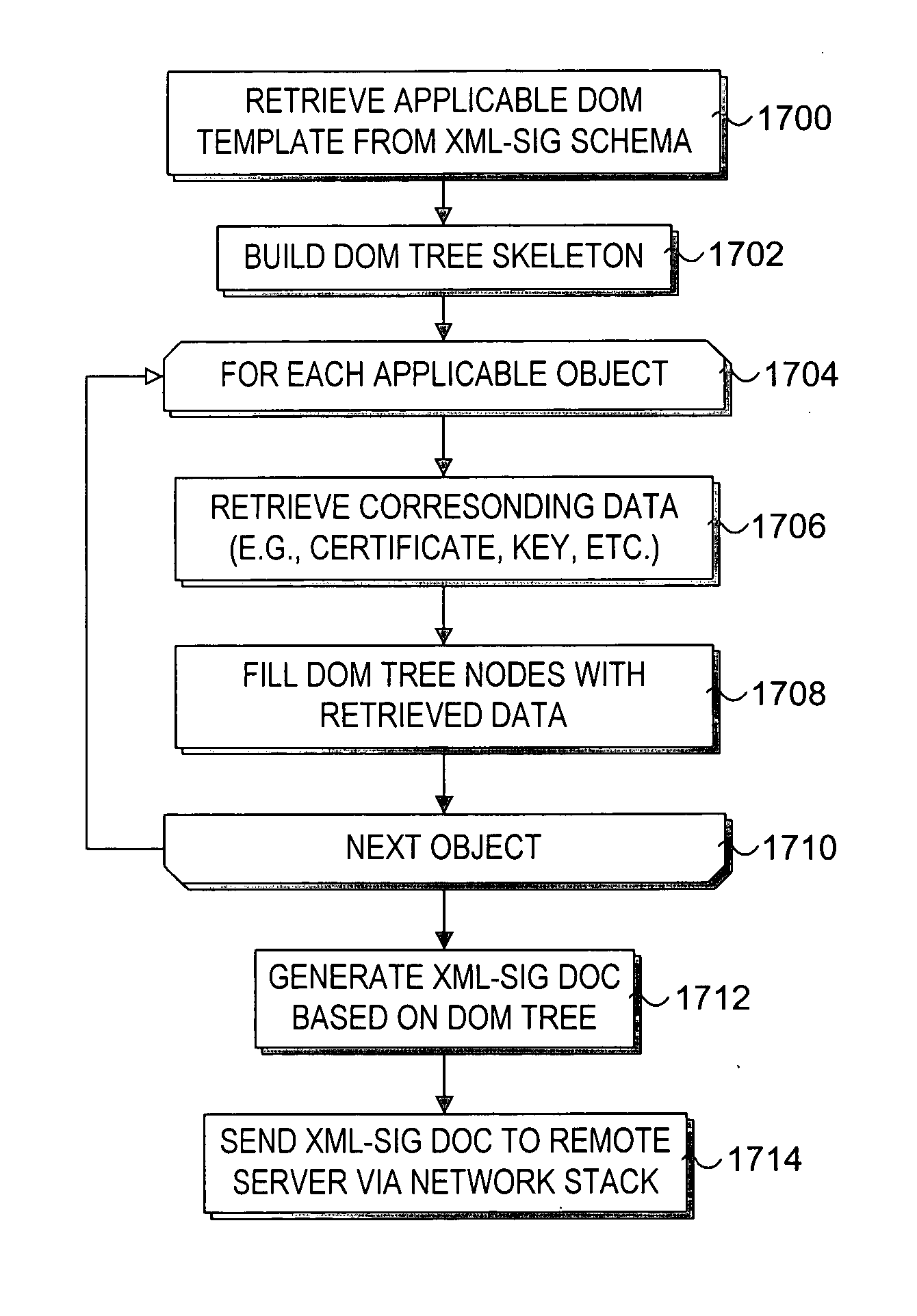
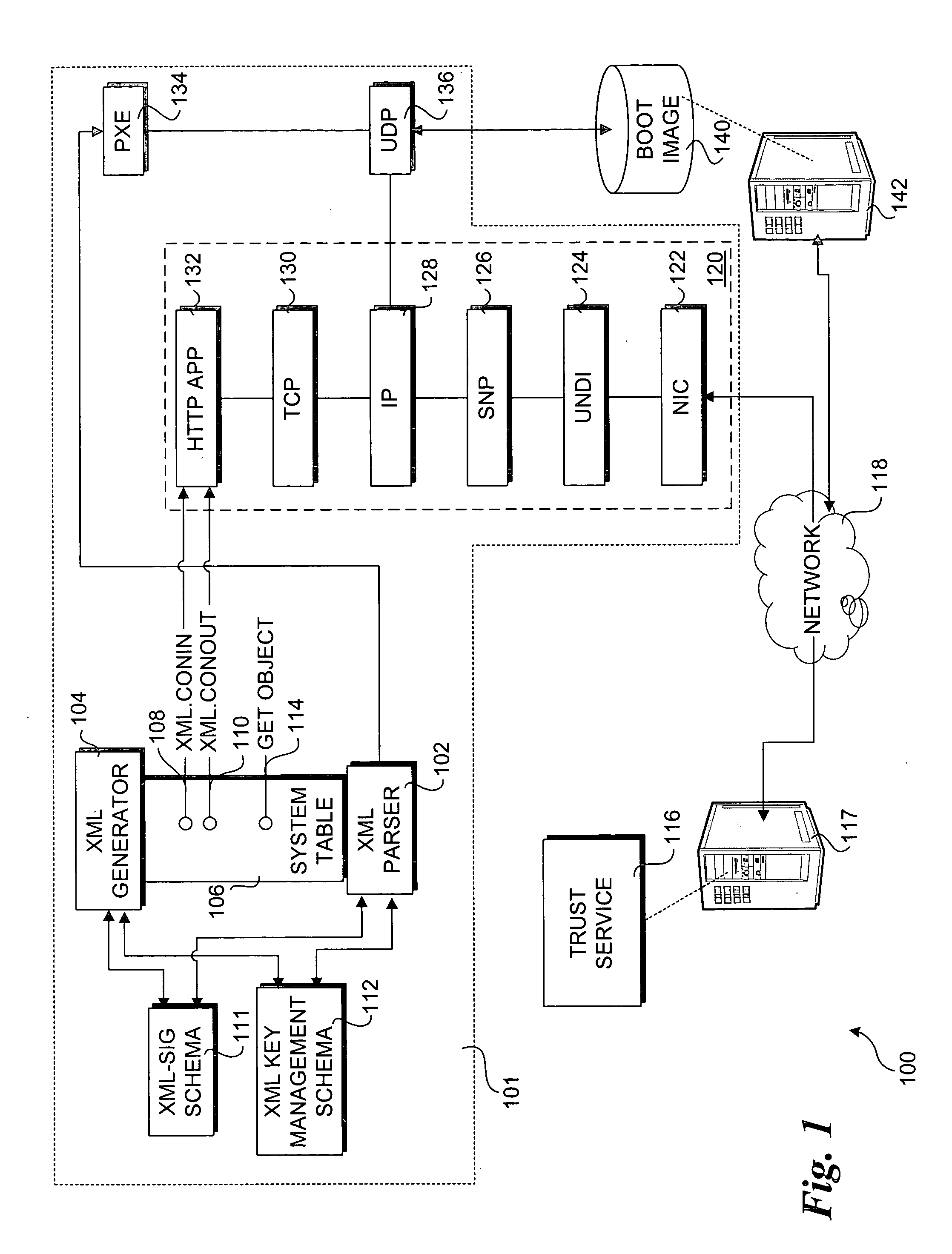
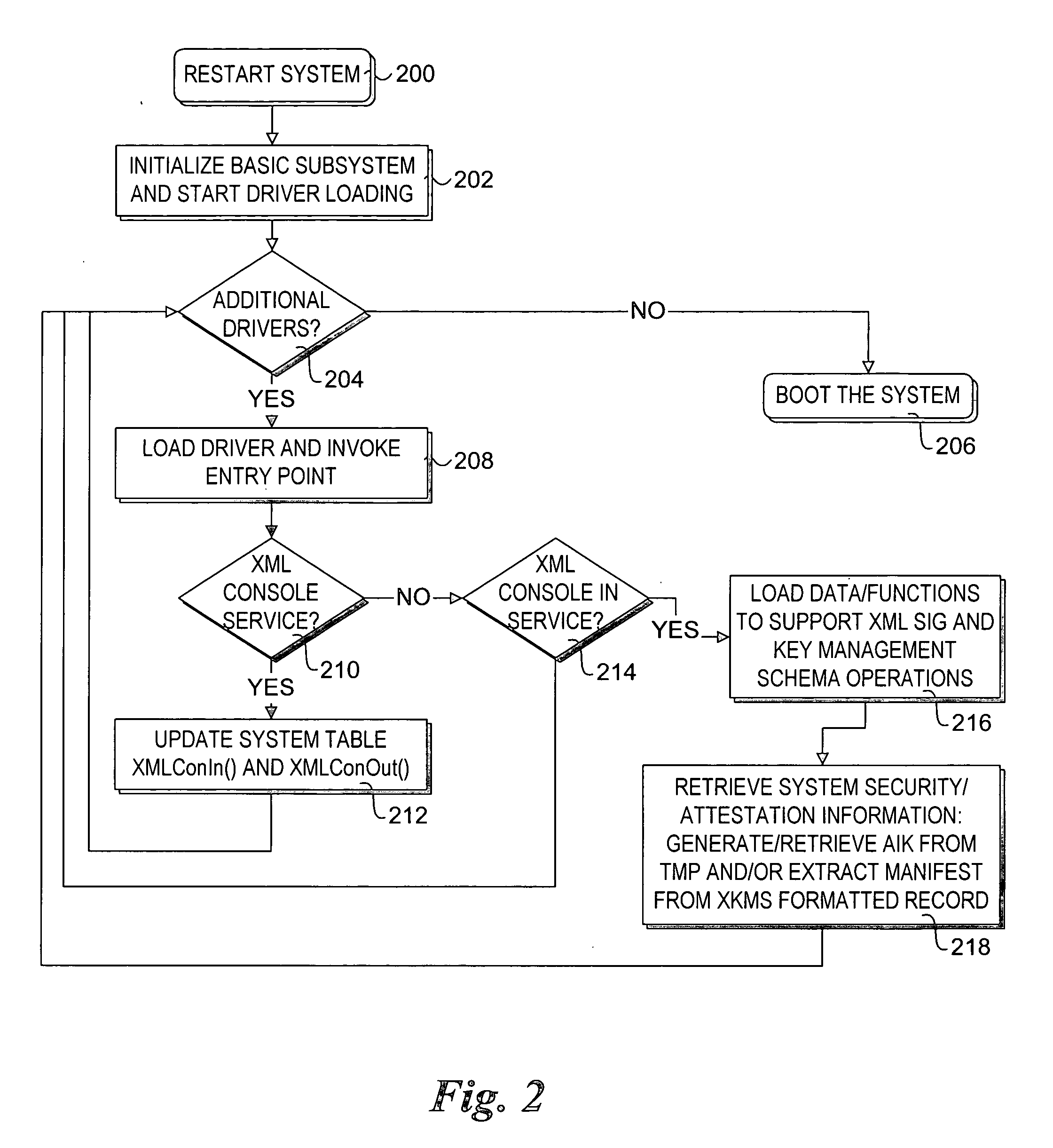
Method to support XML-based security and key management services in a pre-boot execution environment
InactiveUS20050149729A1Key distribution for secure communicationUser identity/authority verificationClient-sideXML Base
Methods and systems to support XML-based security and key management services in a pre-boot execution environment. During pre-boot, XML console in and console out interfaces are loaded, and corresponding API's are published to enable use of the interfaces by various firmware and software components. A network stack is set up to enable XML content received at the network interface to be forwarded to the XML console in interface and XML content provided at the XML content out interface to be sent out via the network interface. Security operations may then be performed to authenticate a client system hosting the XML interfaces, to authenticate remote servers to which the client system may communicate with, and to validate boot images provided to the computer system. Key management services are also supported.
Owner:TAHOE RES LTD
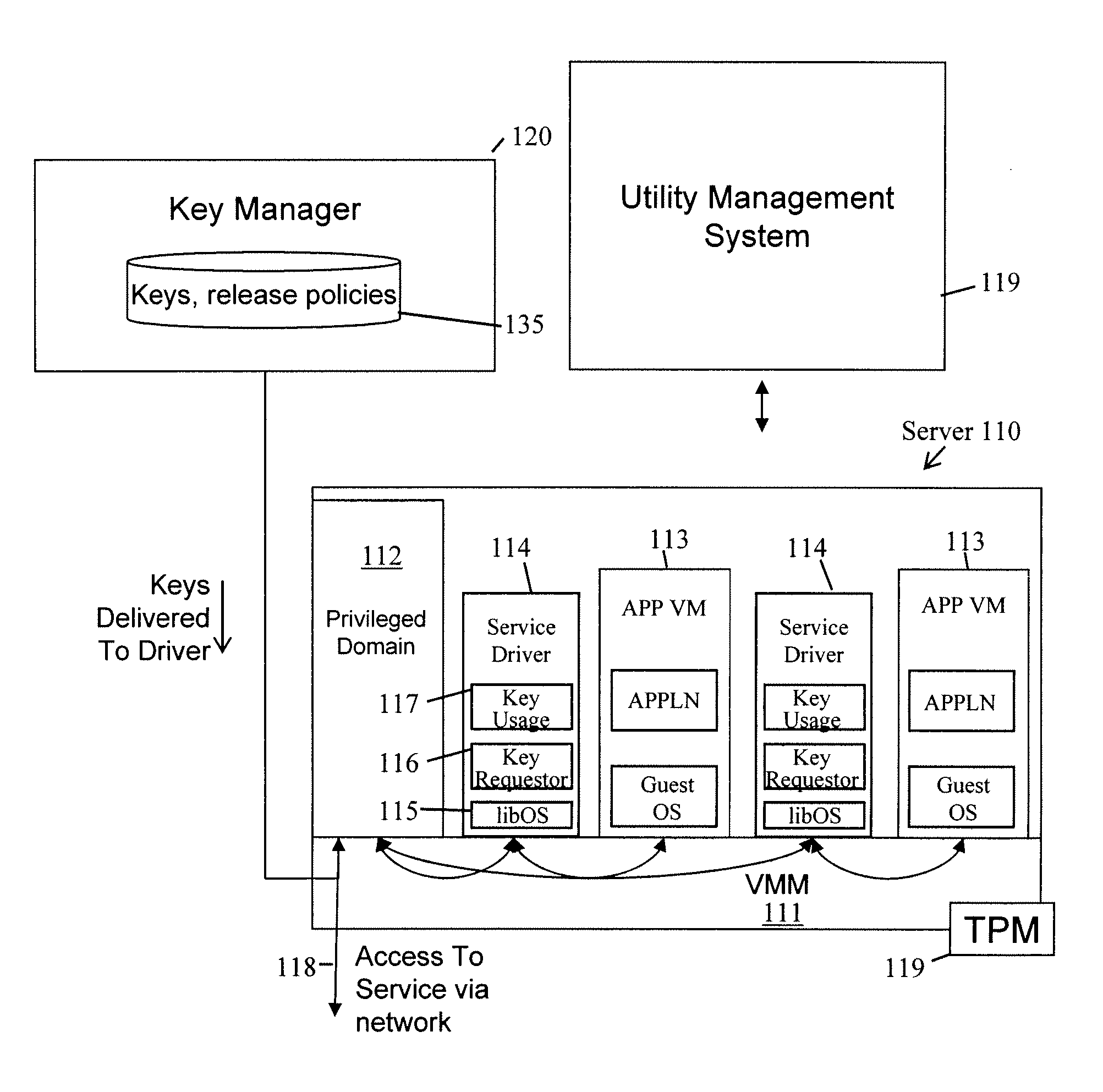
Trusted key management for virtualized platforms
ActiveUS20100082991A1Key distribution for secure communicationUser identity/authority verificationVirtualizationVirtual machine
To provide a secure service to an application virtual machine running in a first domain of a virtualized computing platform, a second domain is arranged to run a corresponding service driver exclusively for the application virtual machine. As part of the secure service, the service driver effects a key-based cryptographic operation; to do so, the service driver has to obtain the appropriate key from a key manager. The key manager is arranged to store the key and to release it to the service driver only upon receiving evidence of its identity and being satisfied of compliance with release policies associated with the key. These policies include receipt of valid integrity metrics, signed by trusted-device functionality of the virtualized computing platform, for the service driver and the code on which it depends.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and system for managing cryptographic keys
InactiveUS7920706B2Reduce overheadImprove securityKey distribution for secure communicationDigital data processing detailsNetwork packetData library
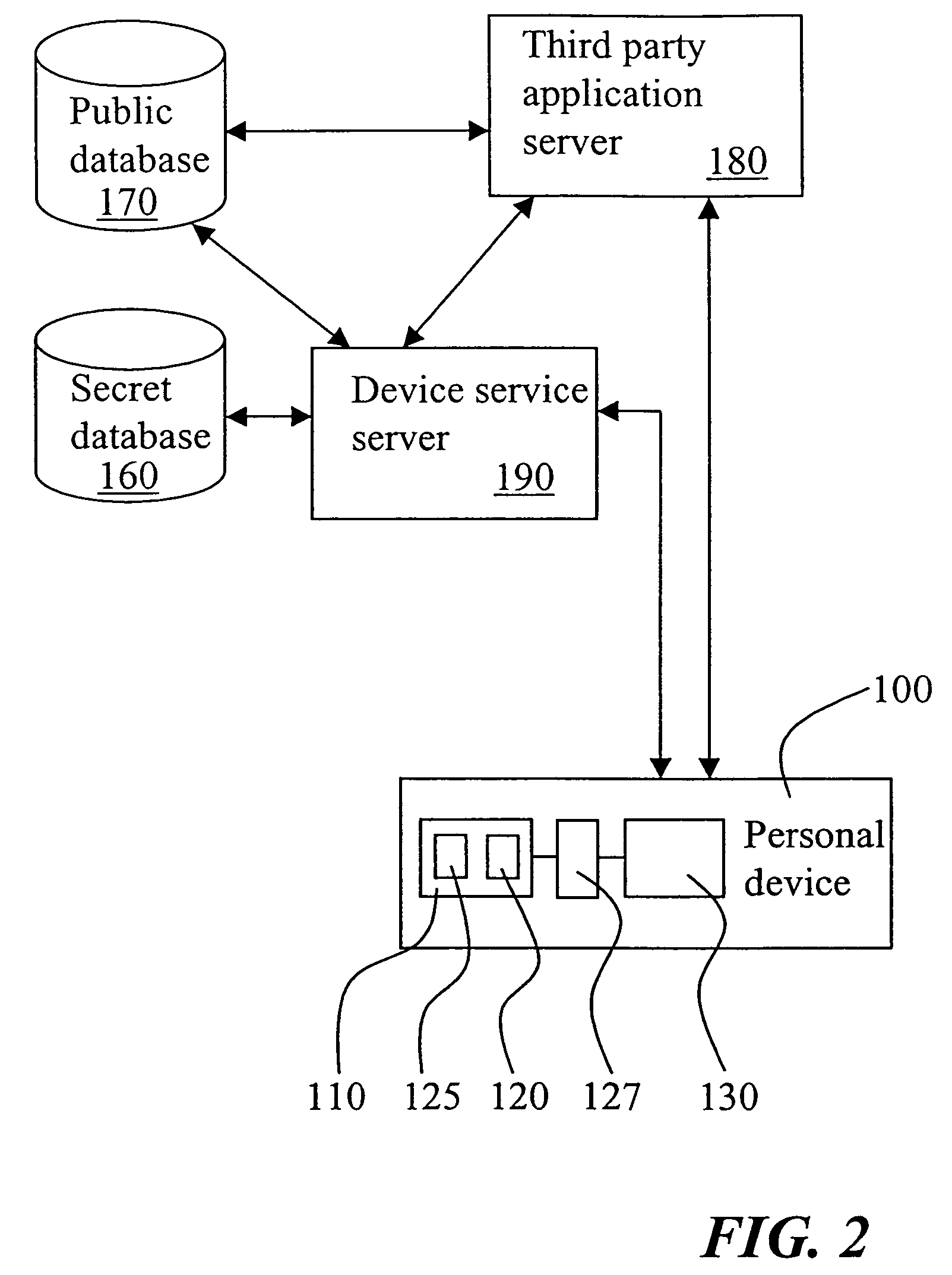
A key management of cryptographic keys has a data package including one or more cryptographic keys that are transferred to a personal device 100 from a secure processing point 150 of a device assembly line in order to store device specific cryptographic keys in the personal device 100. In response to the transferred data package, a backup data package is received by the secure processing point 150 from the personal device 100, which backup data package is the data package encrypted with a unique secret chip key stored in a tamper-resistant secret storage 125 of a chip 110 included in the personal device 100. The secure processing point 150 is arranged to store the backup data package, together with an associated unique chip identifier read from the personal device 100, in a permanent, public database 170.
Owner:NOKIA TECHNOLOGLES OY
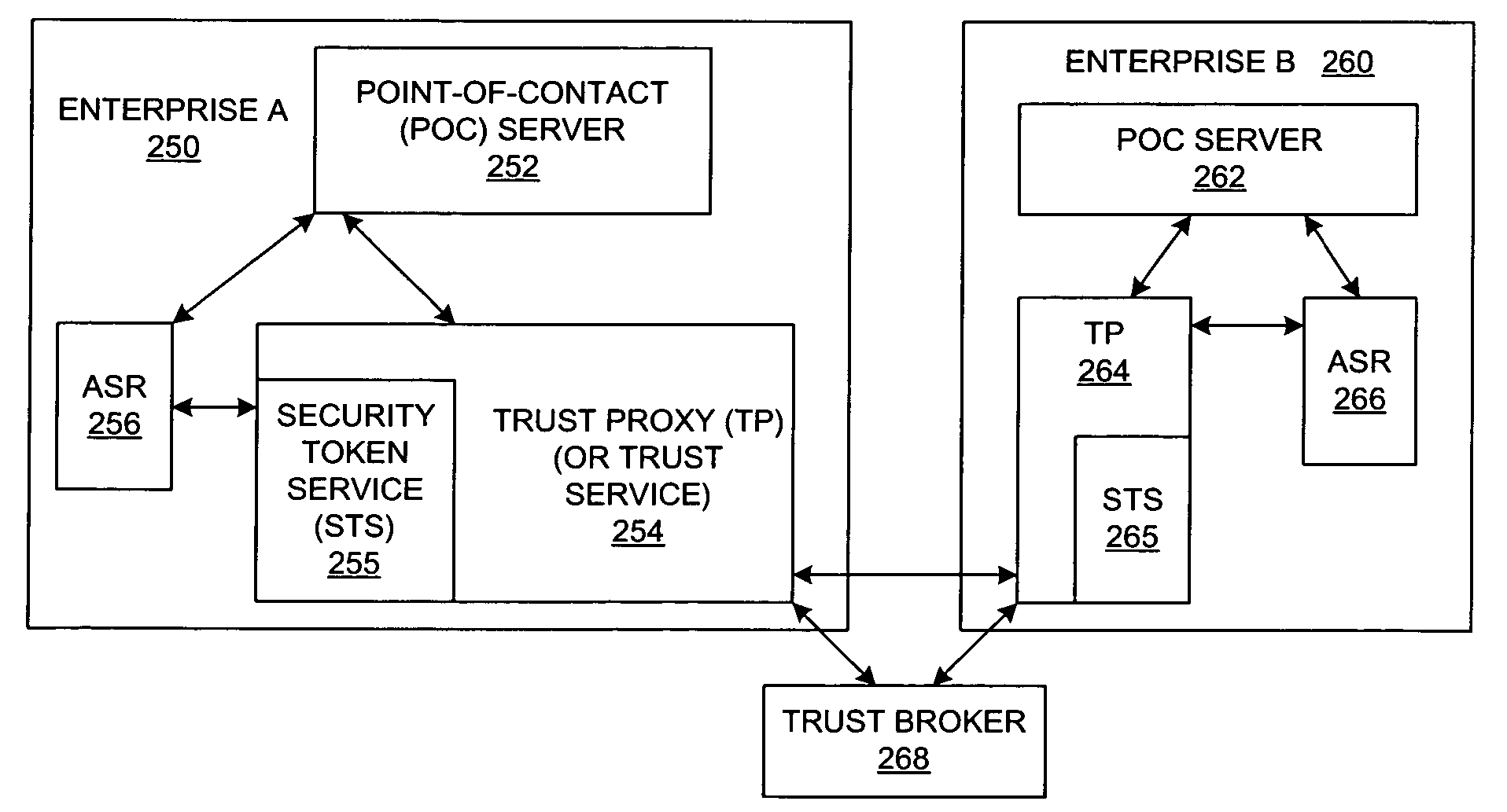
Method and system for enabling trust infrastructure support for federated user lifecycle management
InactiveUS20060021018A1Digital data processing detailsUser identity/authority verificationTrust relationshipKey management
A method and a system are presented in which computing environments of different enterprises interact within a federated computing environment. Federated operations can be initiated at the computing environments of federation partners on behalf of a user at a different federated computing environment. A point-of-contact service relies upon a trust service to manage trust relationships between a computing environment and computing environments of federation partners. The trust service employs a key management service, an identity / attribute service, and a security token service. A federated user lifecycle management service implements federated user lifecycle functions and interacts with the point-of-contact service and the trust service.
Owner:IBM CORP
Automated key management system
ActiveUS20060291664A1Suitable for useKey distribution for secure communicationUnauthorized memory use protectionControl systemKey management
A system for automated cryptographic key management comprises a key control system, a key management agent system, and a key system application program interface. A method for automated cryptographic key management is also disclosed. The method comprises the automatic generation of cryptographic keys by the key control system and distribution of such keys by the key control system to the key management agent system.
Owner:WELLS FARGO BANK NA
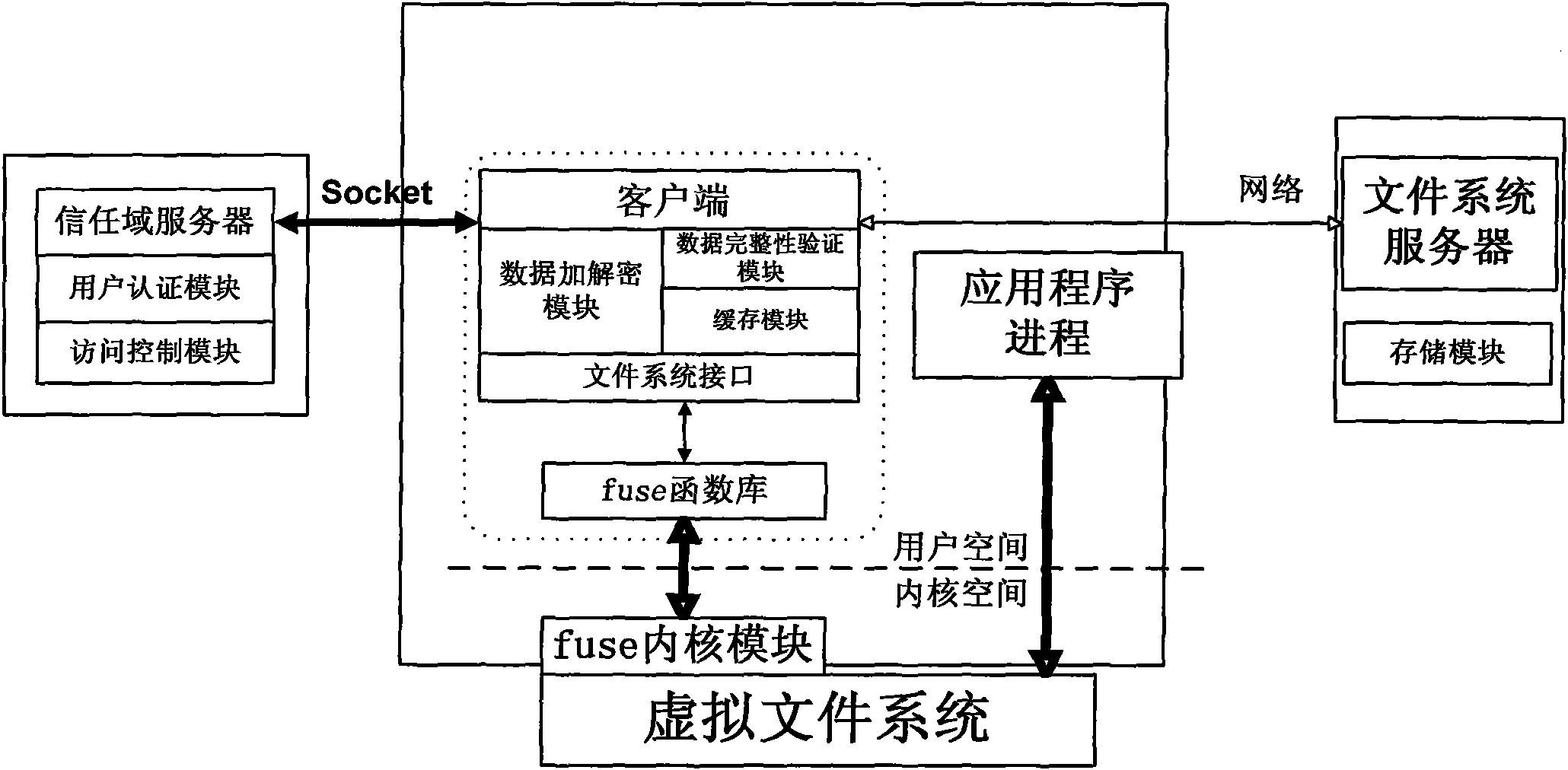
Method for implementing safe storage system in cloud storage environment
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
Hidden link dynamic key manager for use in computer systems with database structure for storage of encrypted data and method for storage and retrieval of encrypted data
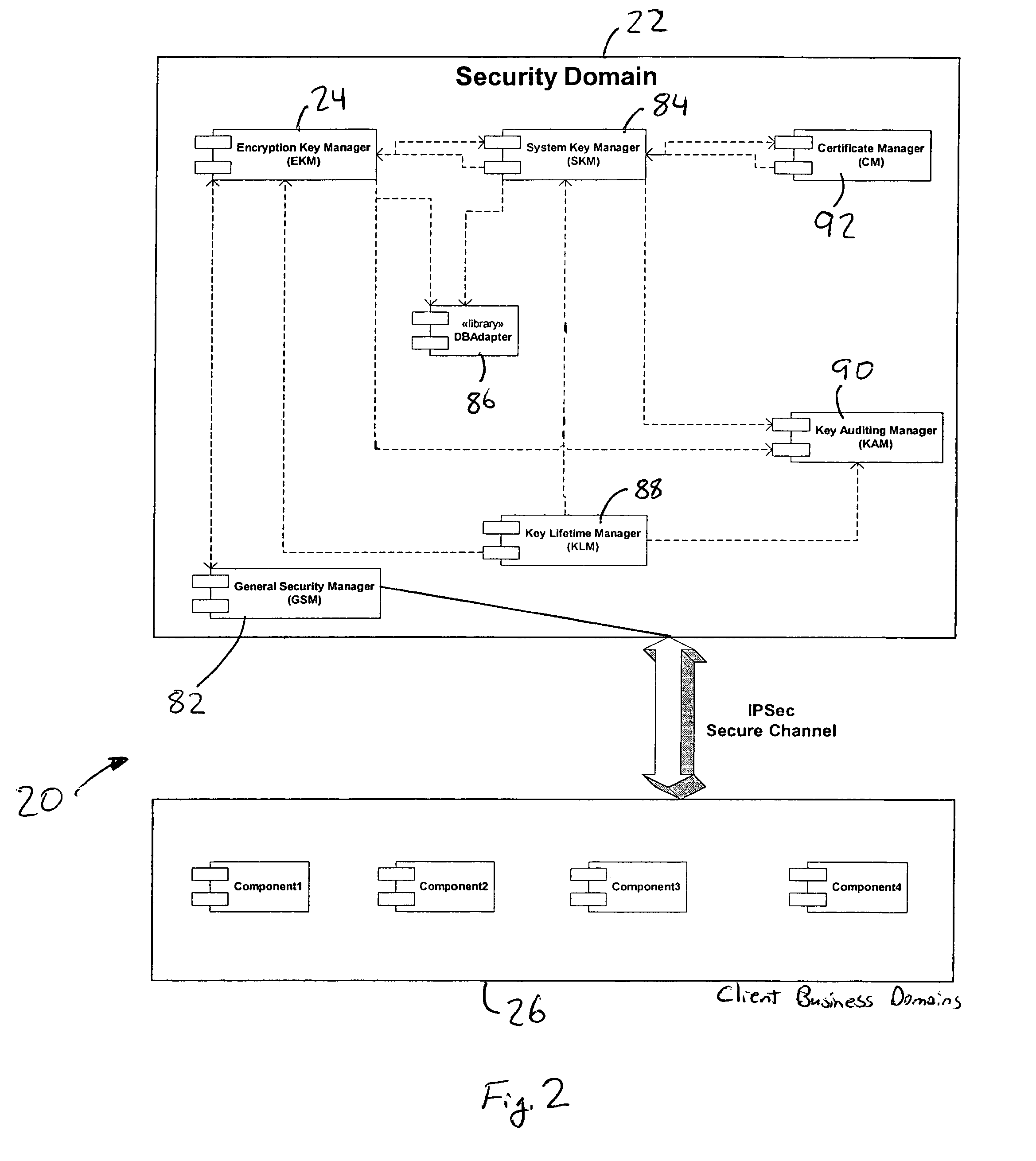
InactiveUS7362868B2Improve securityOpportunities decreaseMultiple keys/algorithms usageComputer security arrangementsCommon nameSecurity domain
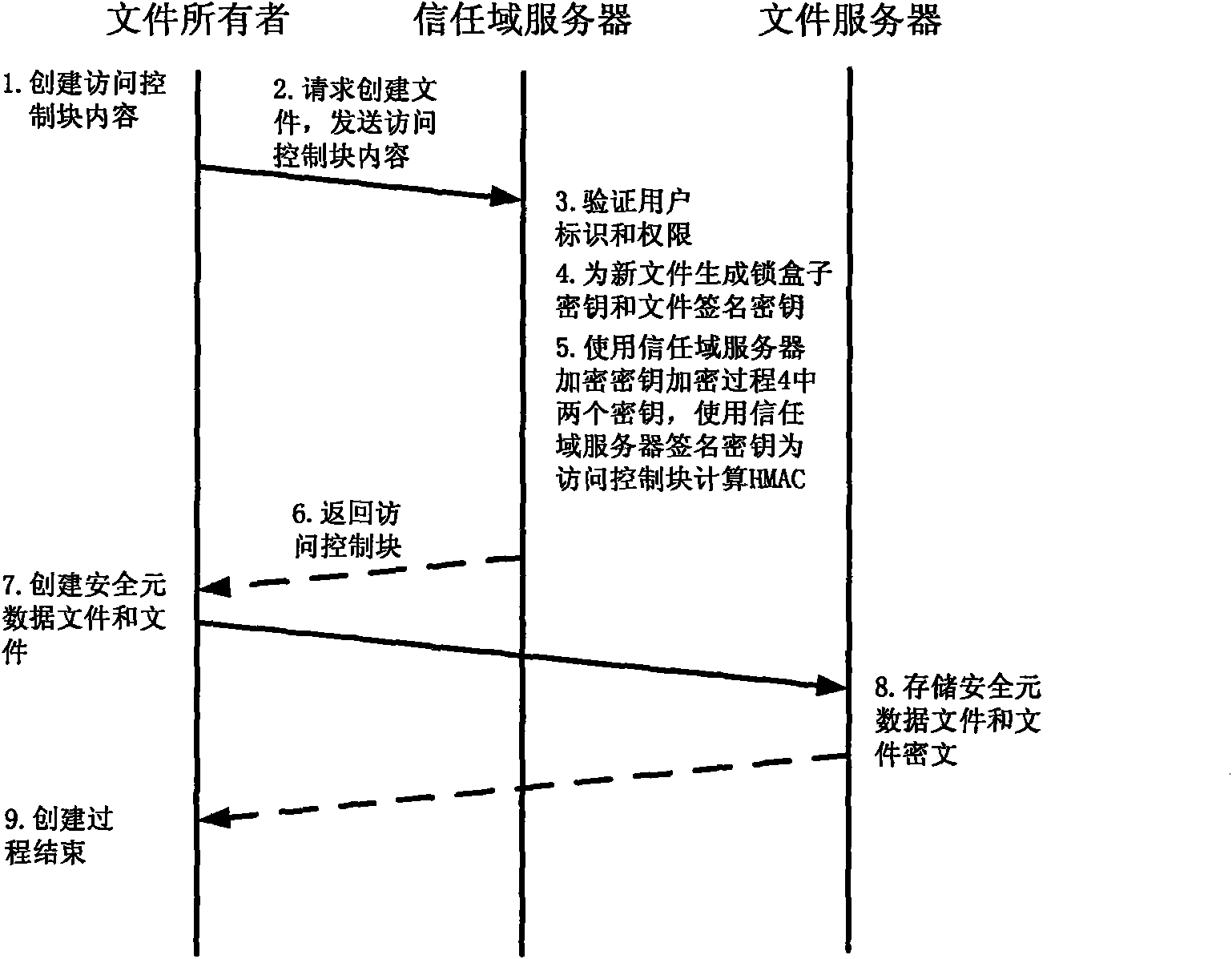
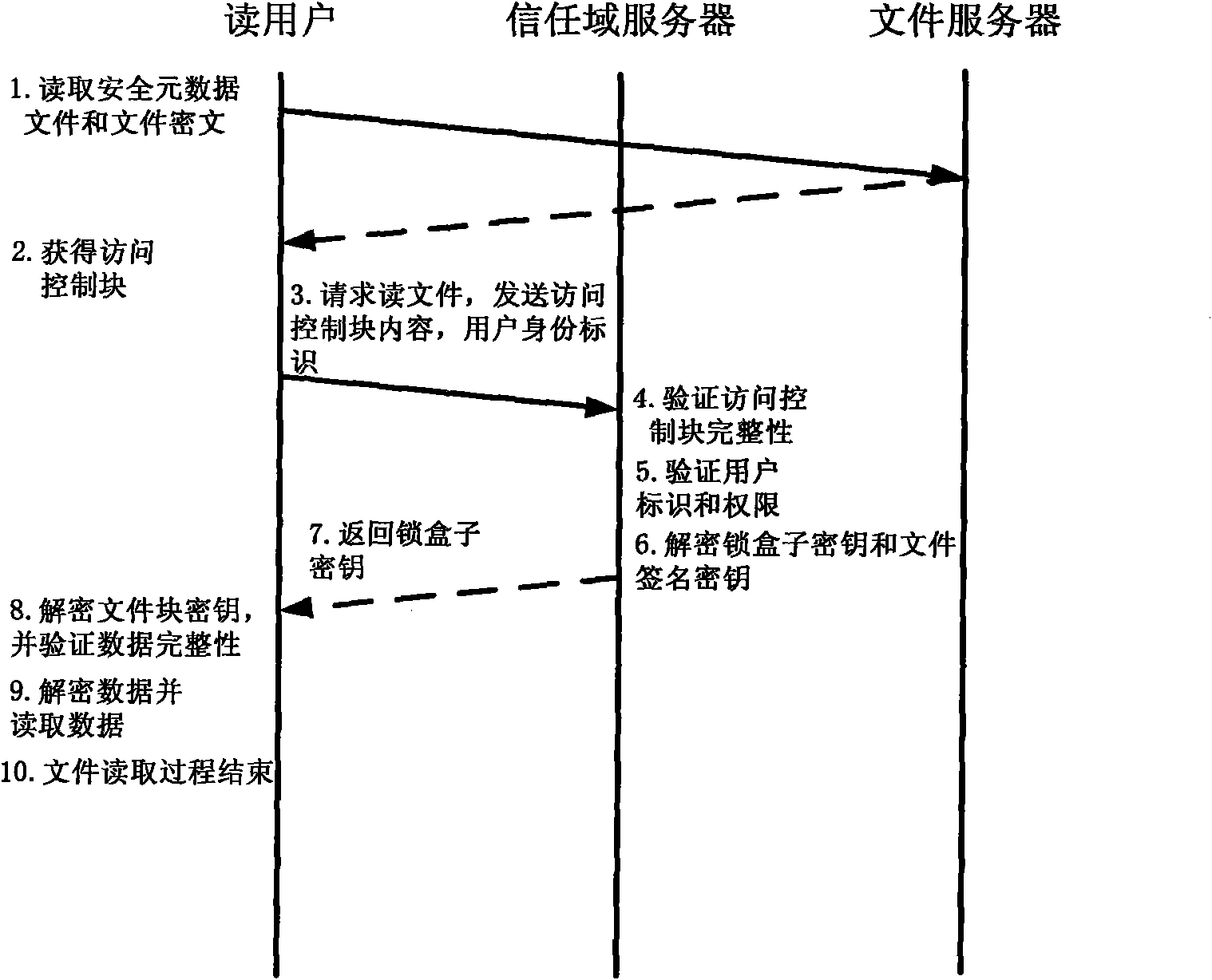
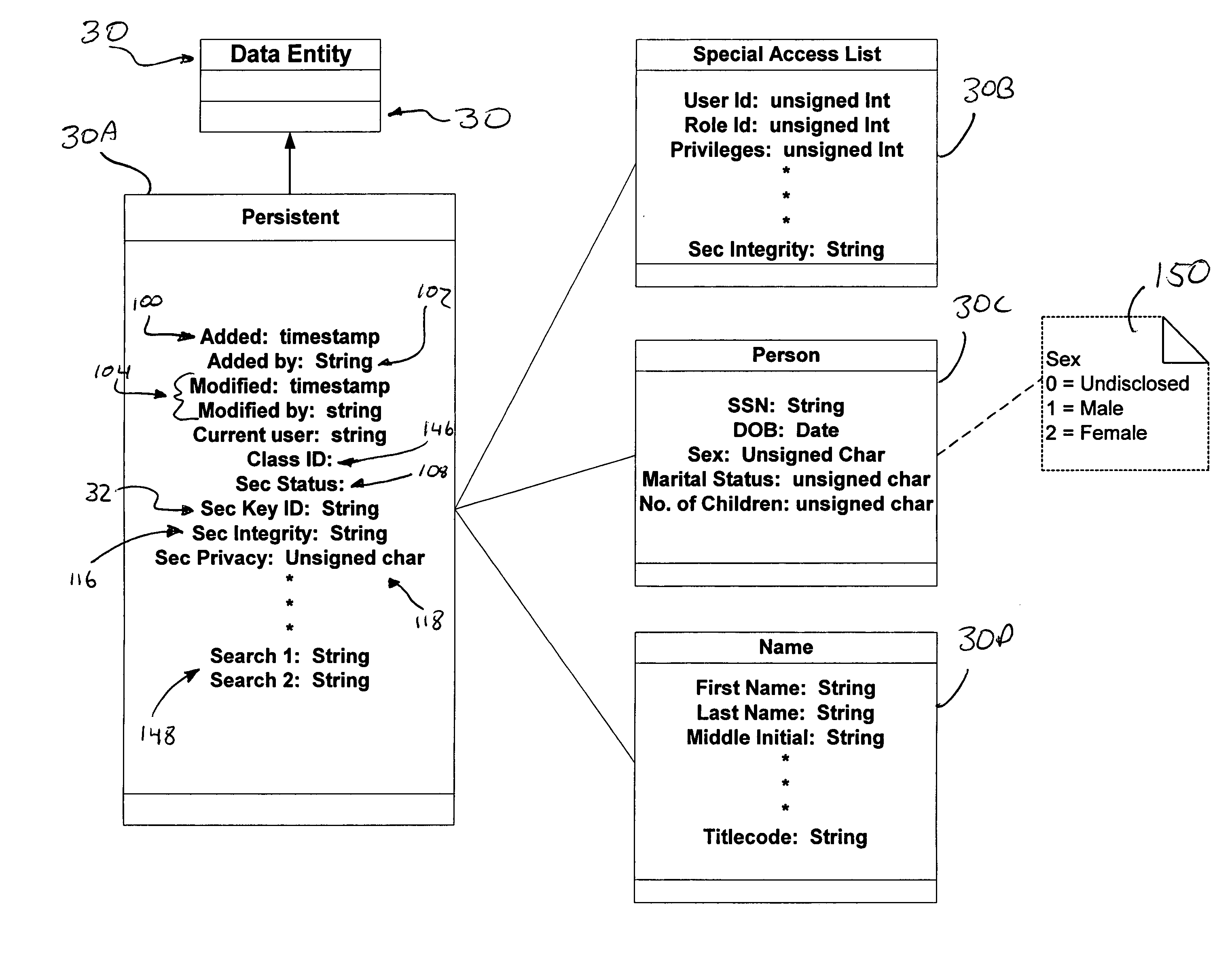
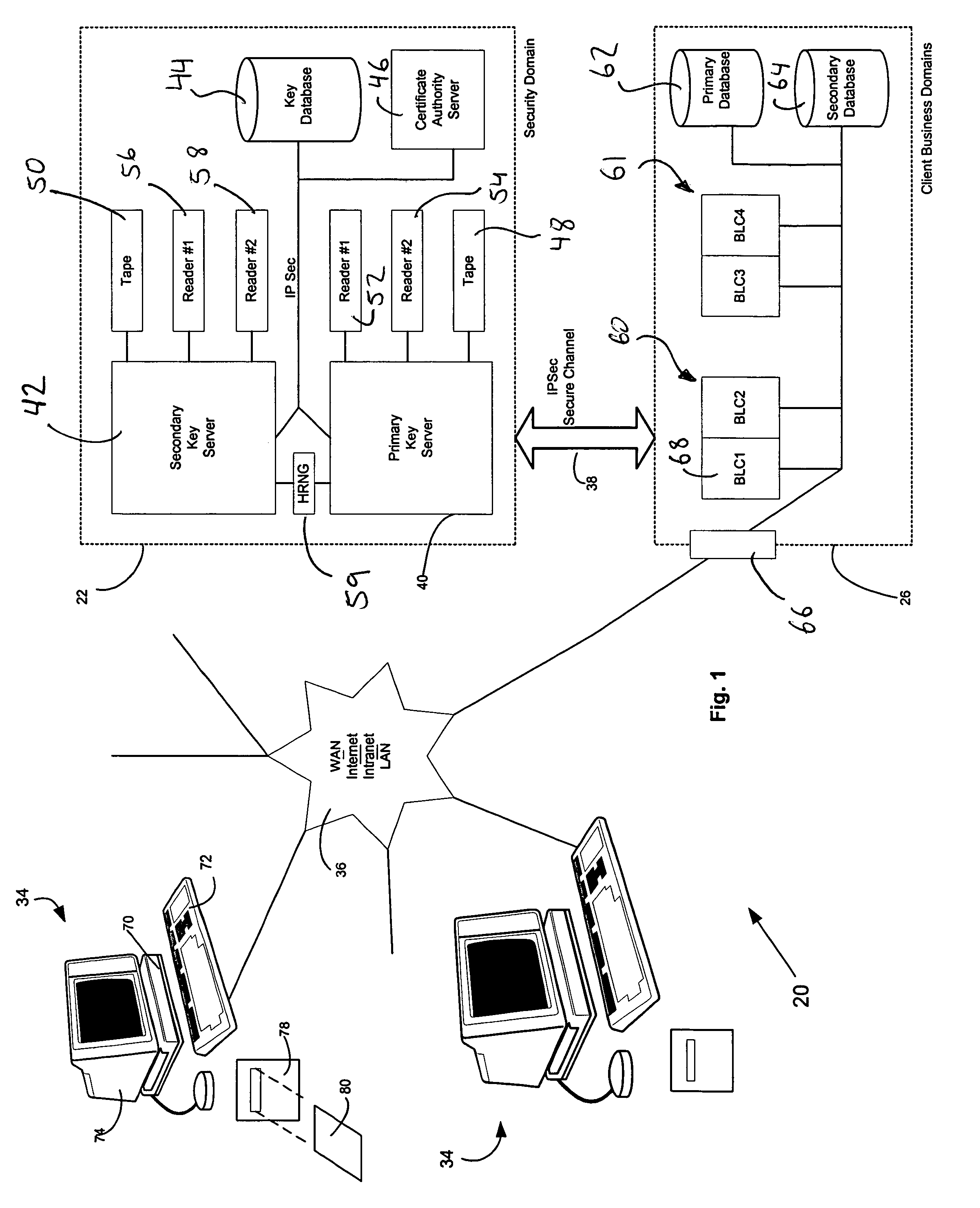
A computer system (20) having a security domain (22), at least one client business domain (26), and a plurality of client terminals (34) utilizes a hidden link dynamic key manager (24, 84) and a database structure that includes encrypted data entities (30C, 30D) and a security identification attribute (32) for storage of encrypted data. Methods for encrypting data and for storing, decrypting, and retrieving encrypted data operate on the computer system (20), which also includes an information database (62) and a key database (44). The key database (44) is isolated from the information database (62). The hidden link key manager is stored in the security domain (22) and includes a system key manager (84) operable to generate system keys with system key common names and an encryption key manager (24) operable to generate encryption keys having encryption key identifications. The key managers (24, 84) operate on a key server (40), which is mirrored by a secondary key server (42). A general security manager (82) also operates on the key server (40) to control access to the security domain (22). The security information attribute (32) is stored with a persistent data entity (30A) that is associated with the other encrypted data entities (30C, 30D) by a database schema. The encryption key identification (112) for the encryption key used to encrypt the data entities (30C, 30D) is encrypted by a system key and then stored as part of the security information attribute (32). The system key common name hash value (114) is also stored in the security information attribute (32). The information data entities (30) are stored on the information database (62), but the encryption key identification (153), encryption key (154), system key common name hash value (156, 157), and system key common name (158) are stored in the key database (44) inside the security domain (22). The system key itself is stored on a Smart Card reader (56) inside the security domain.
Owner:FARRUKH ABDALLAH DR +1
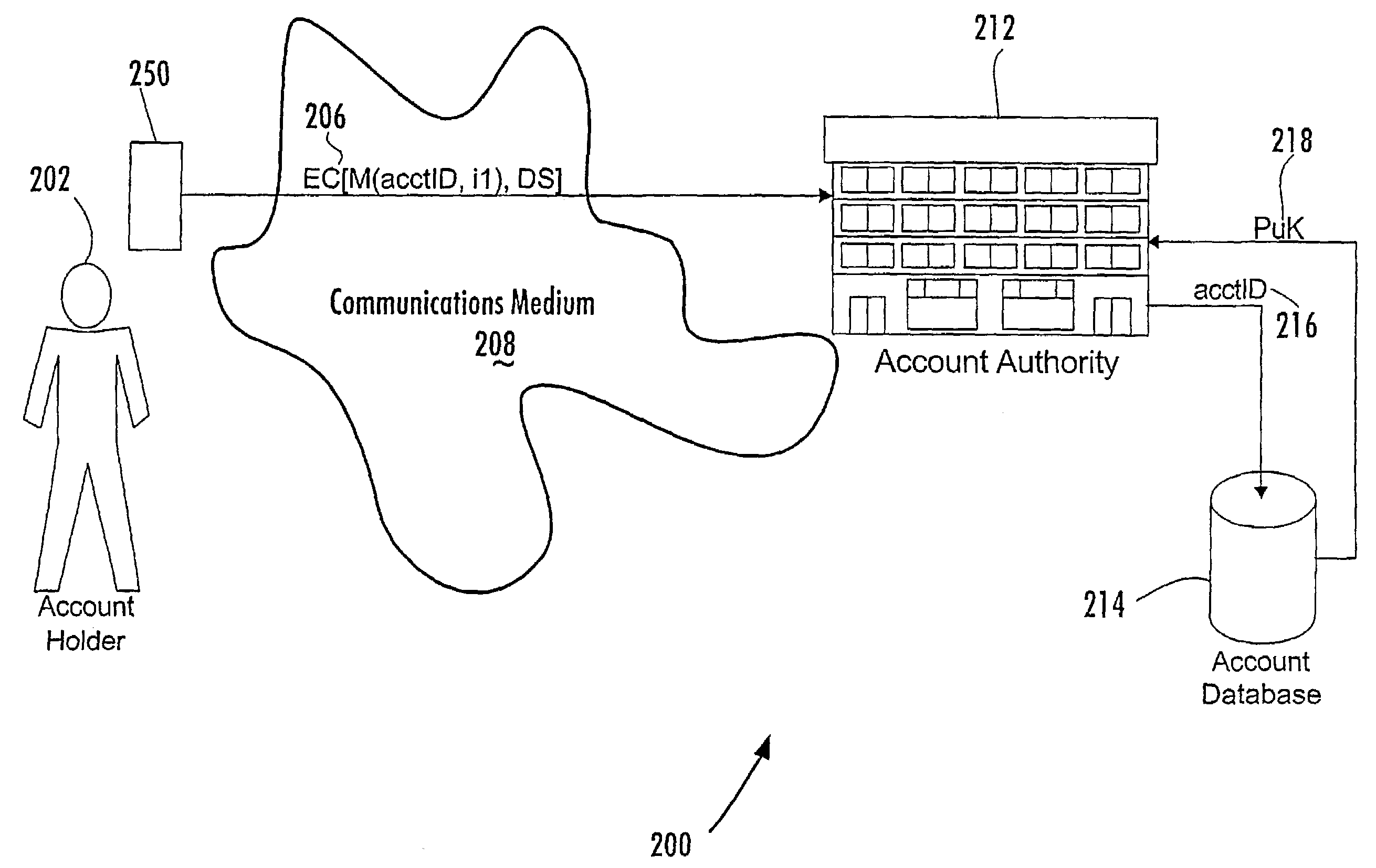
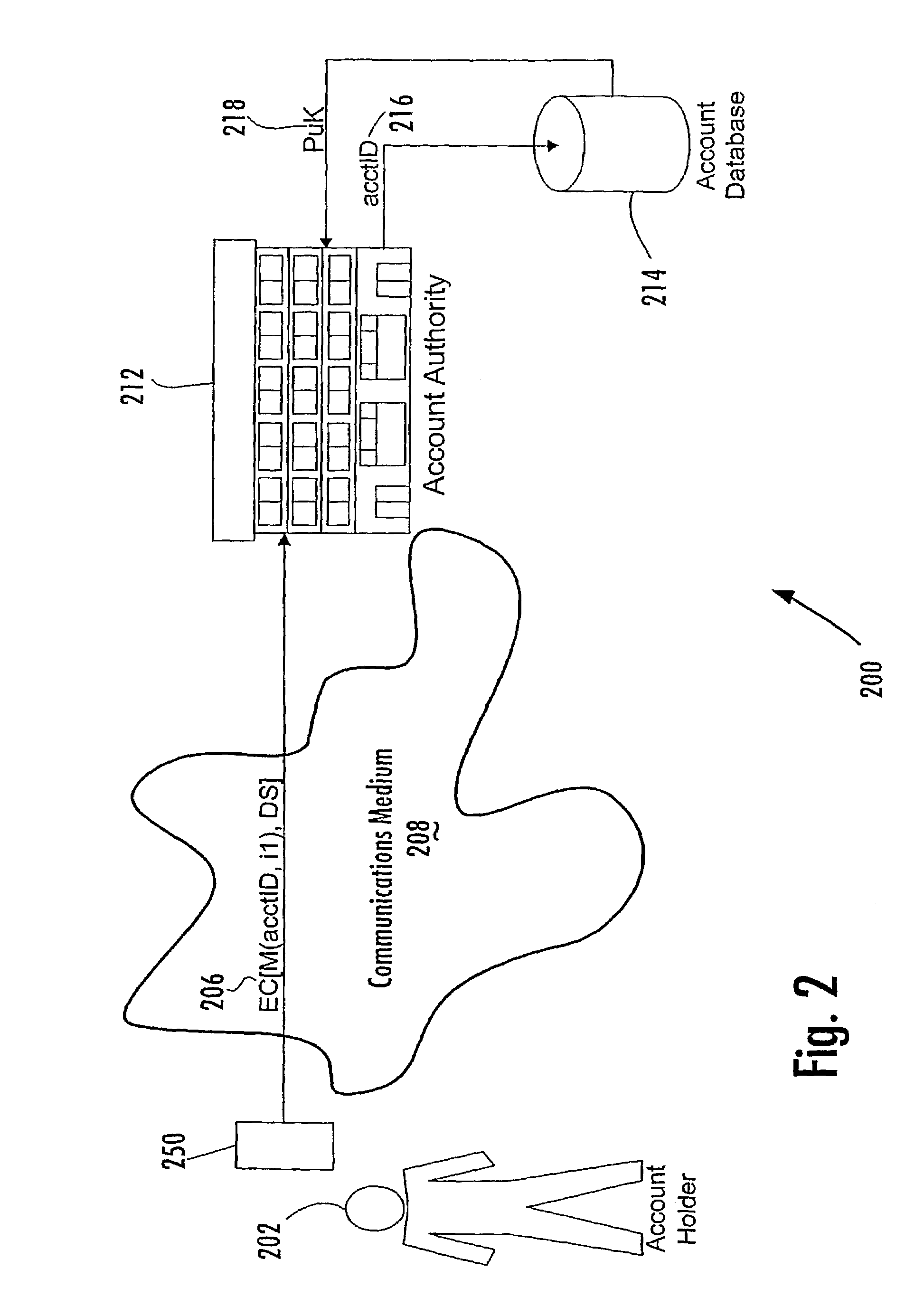
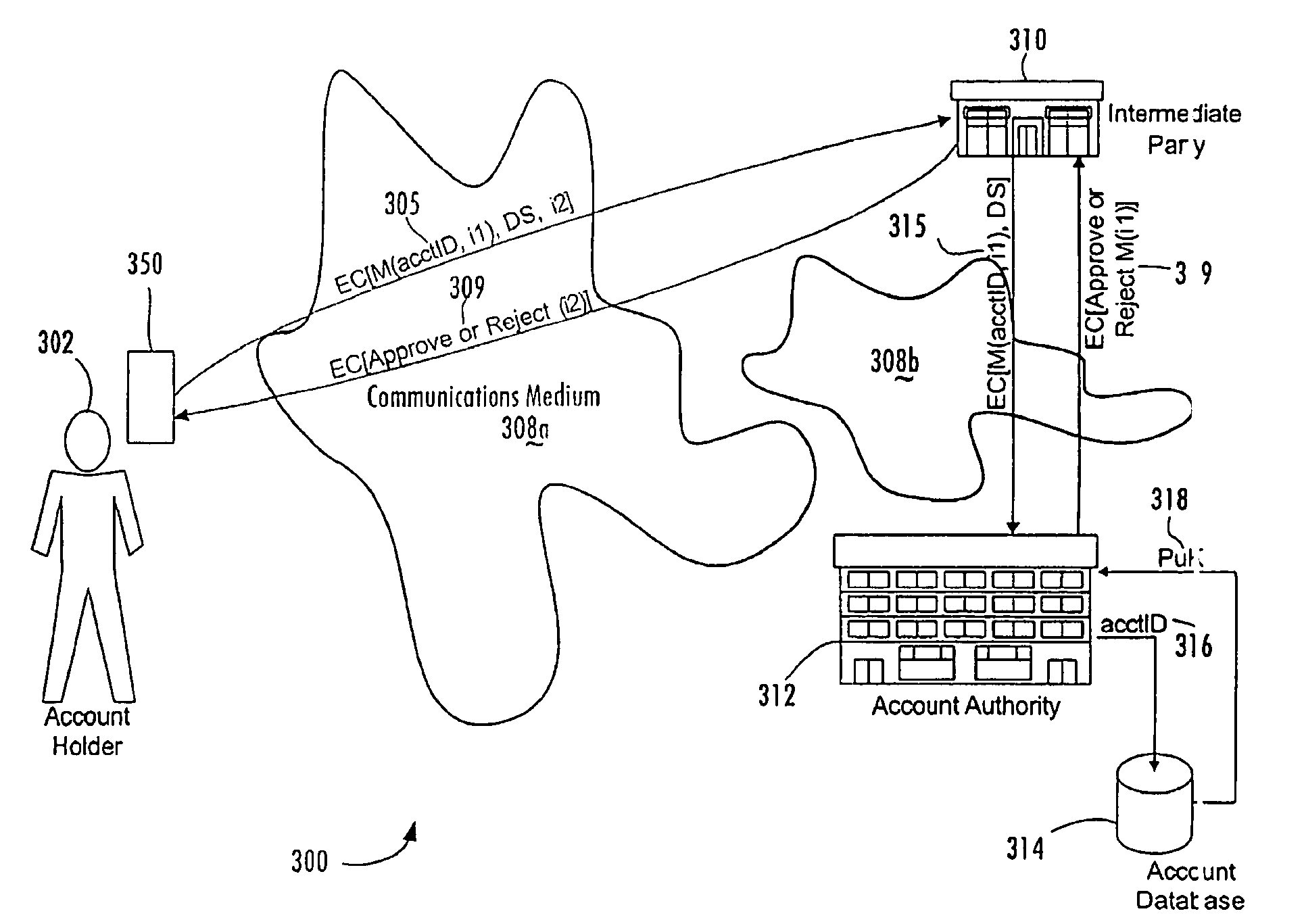
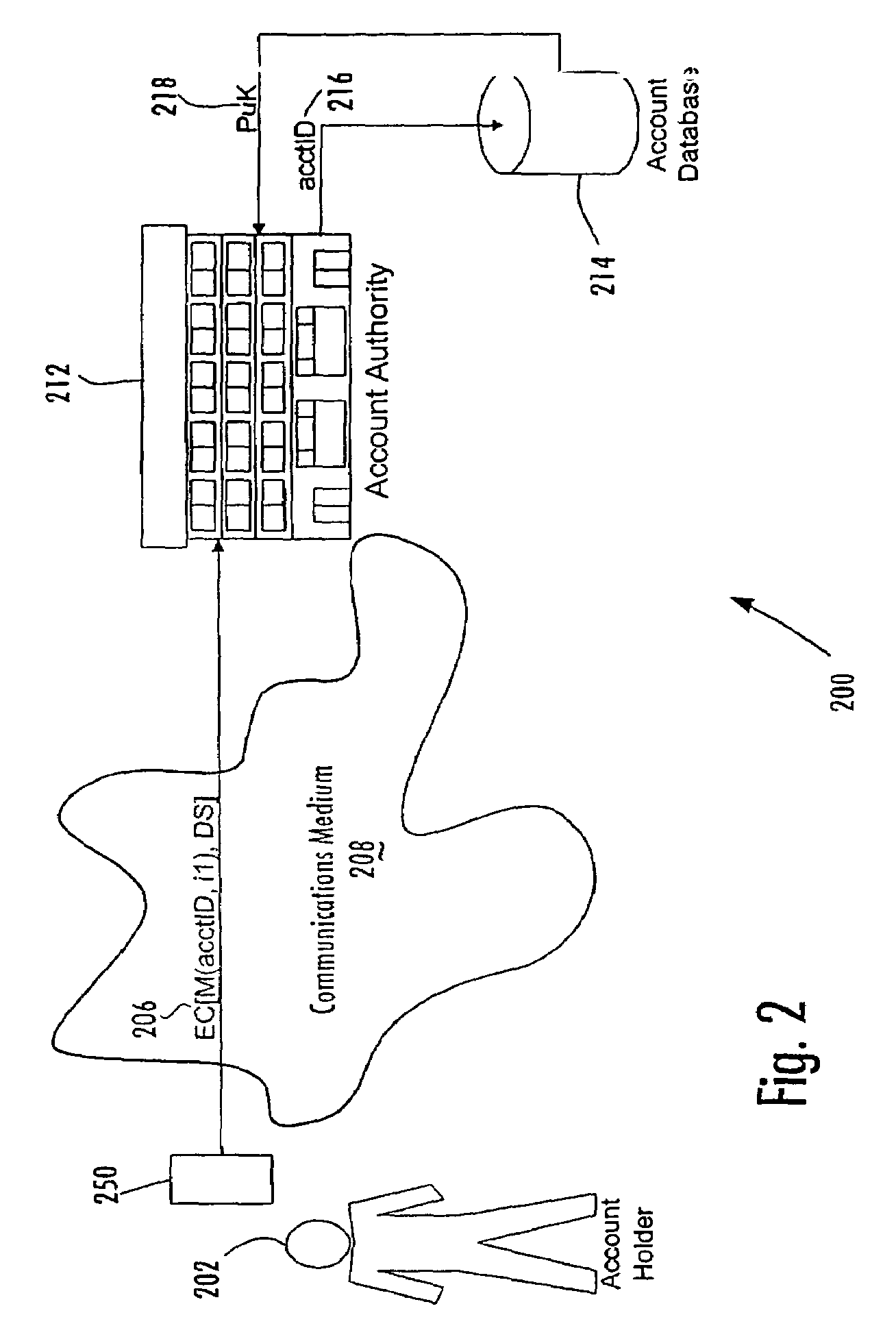
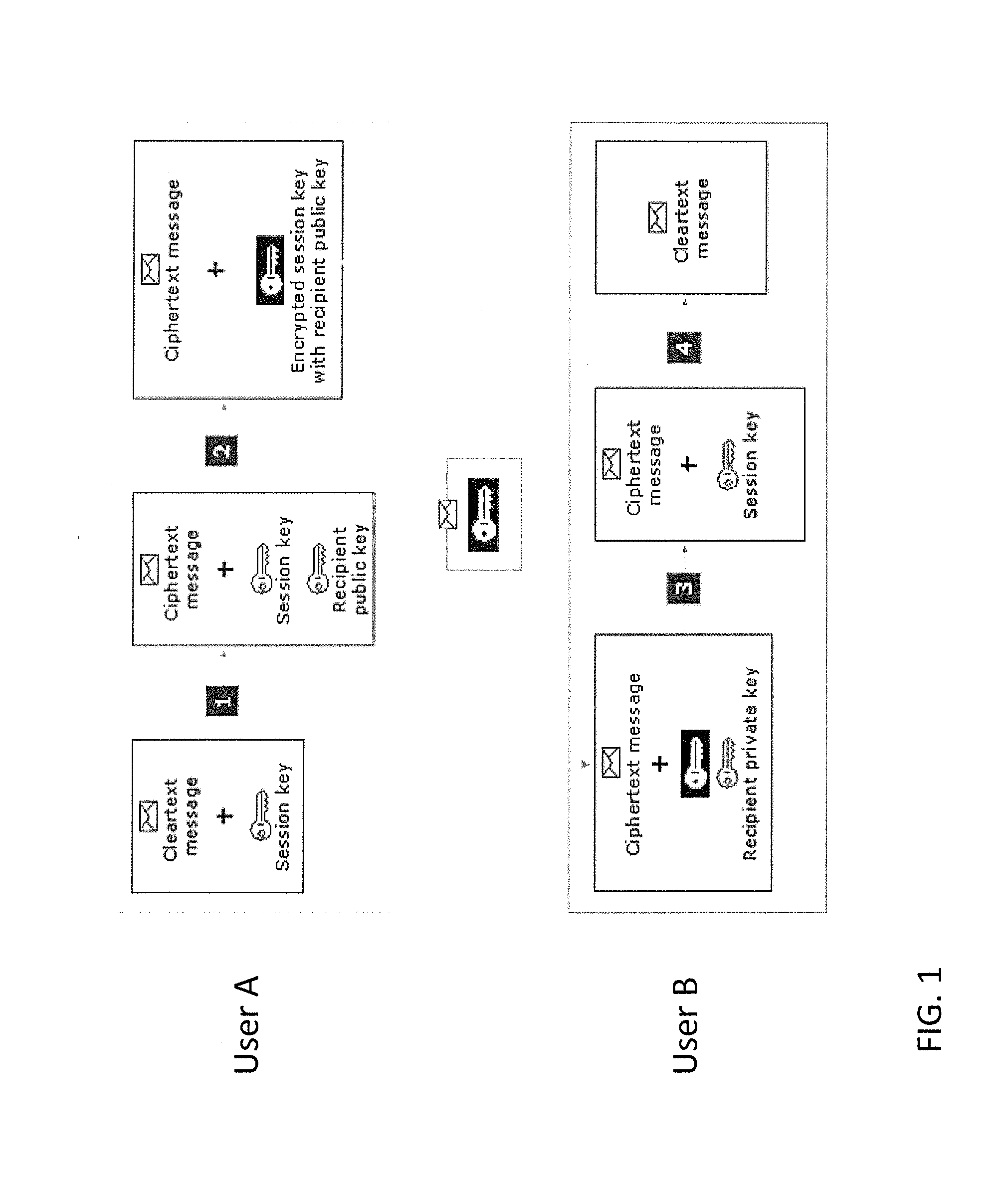
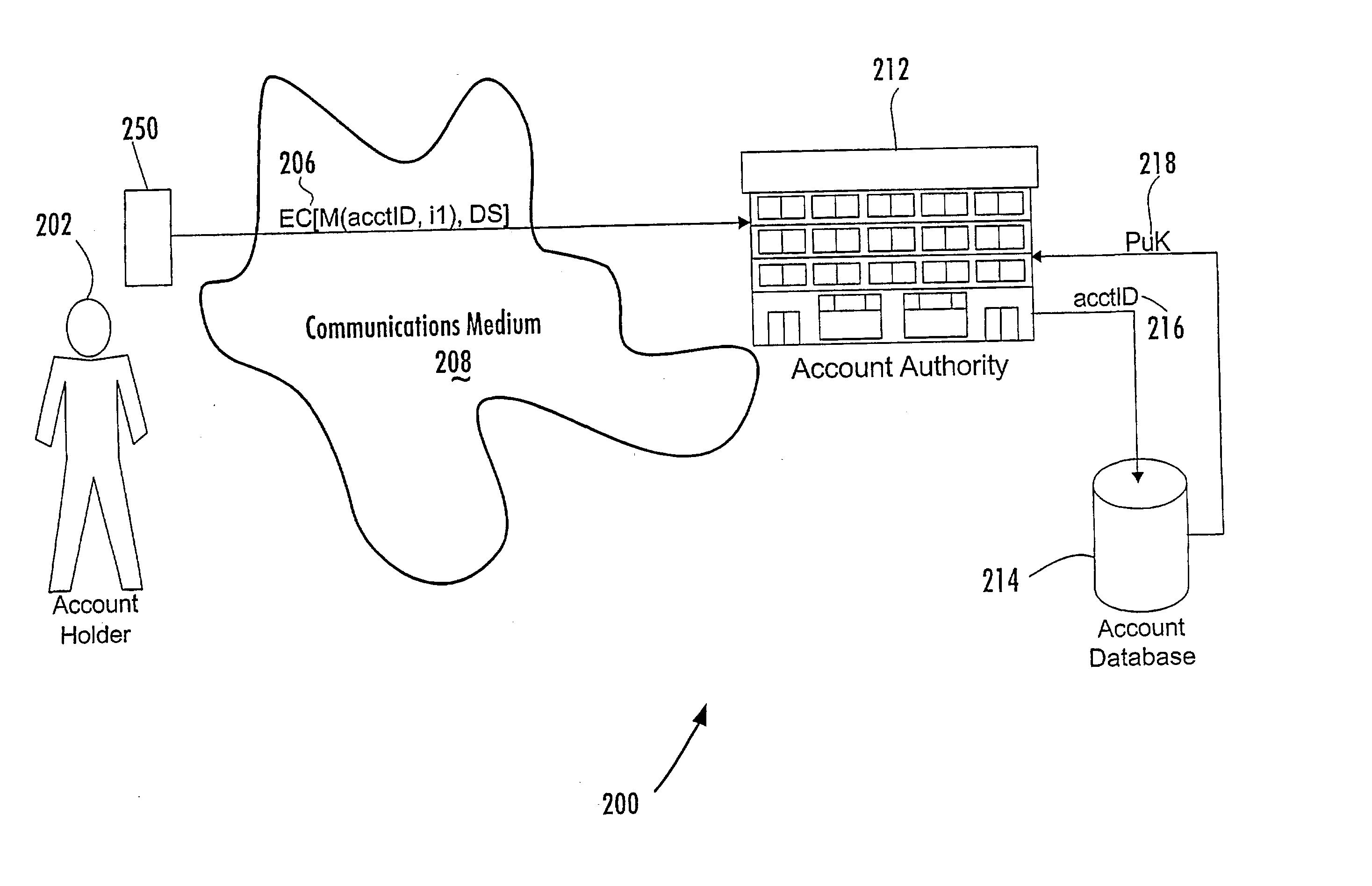
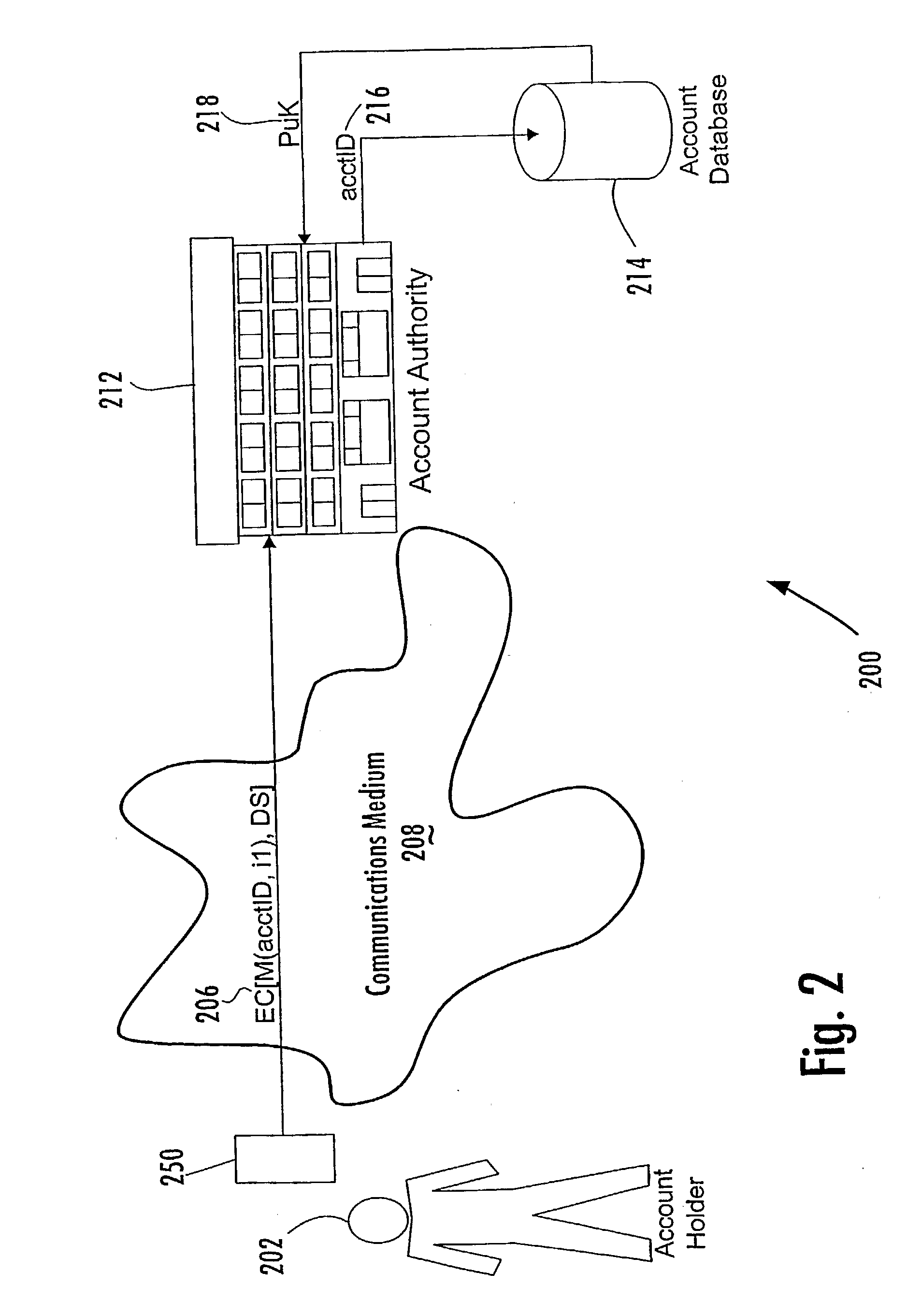
Person-centric account-based digital signature system
In a method of managing a database of existing accounts (214) for account holders (202), each account holder (202) has multiple accounts with one or more account authorities (212) for use of a single device with multiple accounts, with each account of each account holder being associated with a public key of a public-private key pair of that account holder. A record of information pertaining to all accounts of a particular account holder is maintained in a central location by a central key authority. The information for that account includes the public keys of that account holder. The central key authority transfers information from the record for an account holder to a new account authority for which that account holder desires to establish a new account; the central key authority also receives information from account authorities for inclusion in the record centrally maintained for that account holder.
Owner:FIRST DATA
Central key authority database in an ABDS system
Managing a database of a central key authority for a plurality of account holders, each account holder having at least one account associated with a public key of a public-private key pair of that account holder, includes maintaining for each account holder a record of information pertaining to the accounts of that account holder associated with the public keys of the account holder. The information pertaining to the accounts of an account holder includes (a) a public key of a user device that generates digital signatures, and (b) third-party account identifiers each of which identifies to a third-party an account of the user that is maintained with the third-party and that has been associated with the user's public key by the third-party.
Owner:FIRST DATA
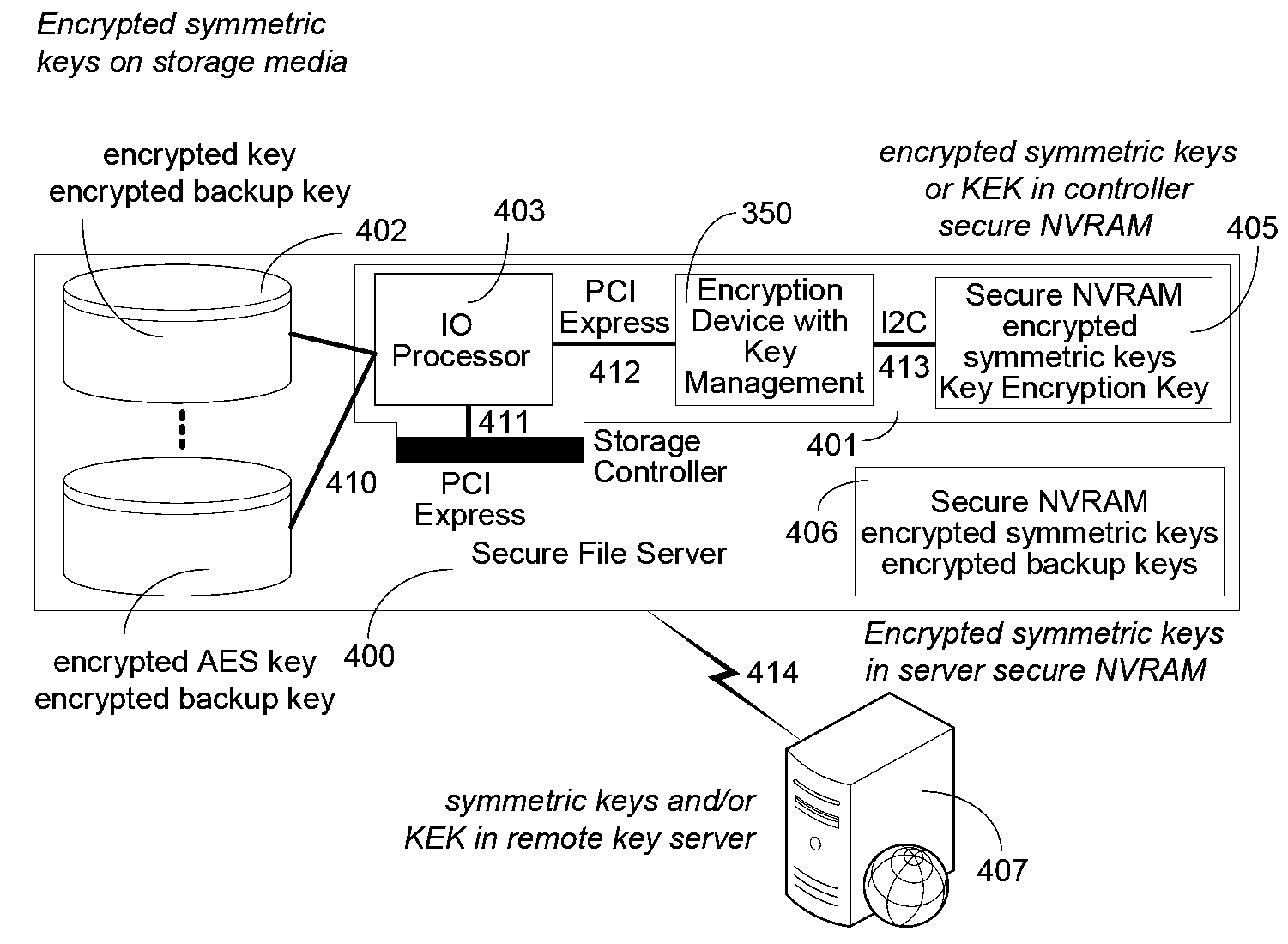
Cryptographic key management for stored data
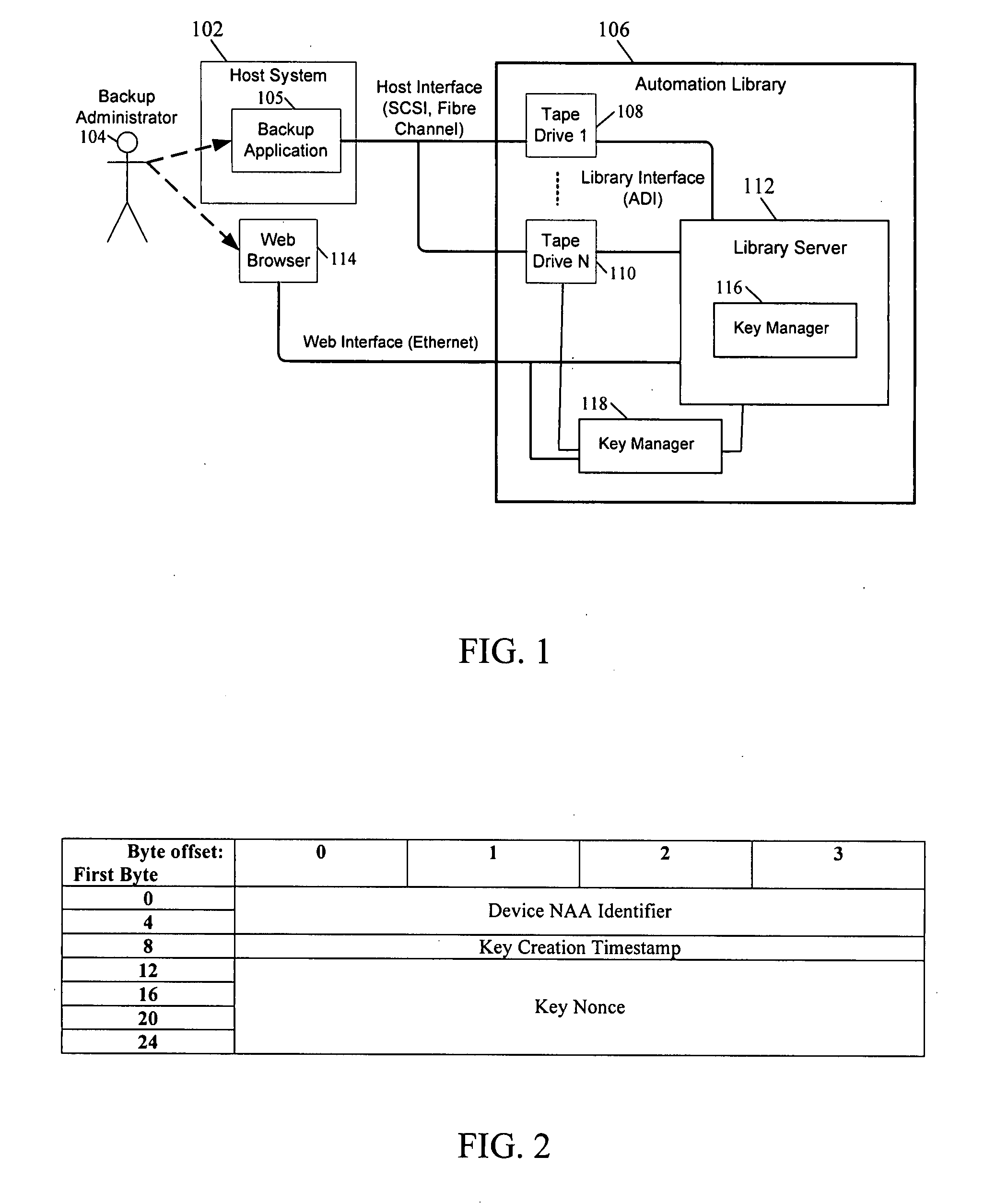
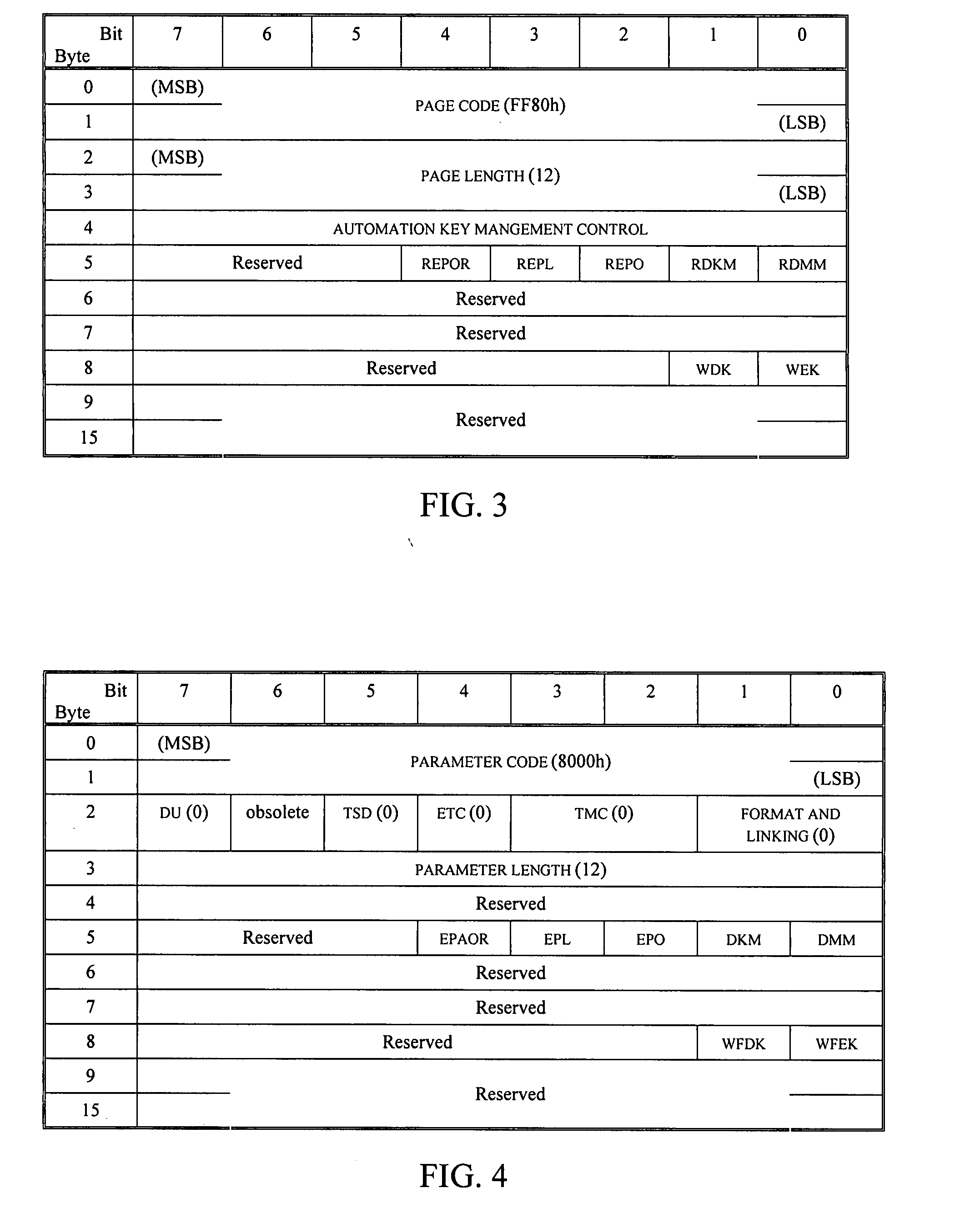
InactiveUS20080219449A1Digital data protectionInternal/peripheral component protectionMagnetic tapeRemovable media
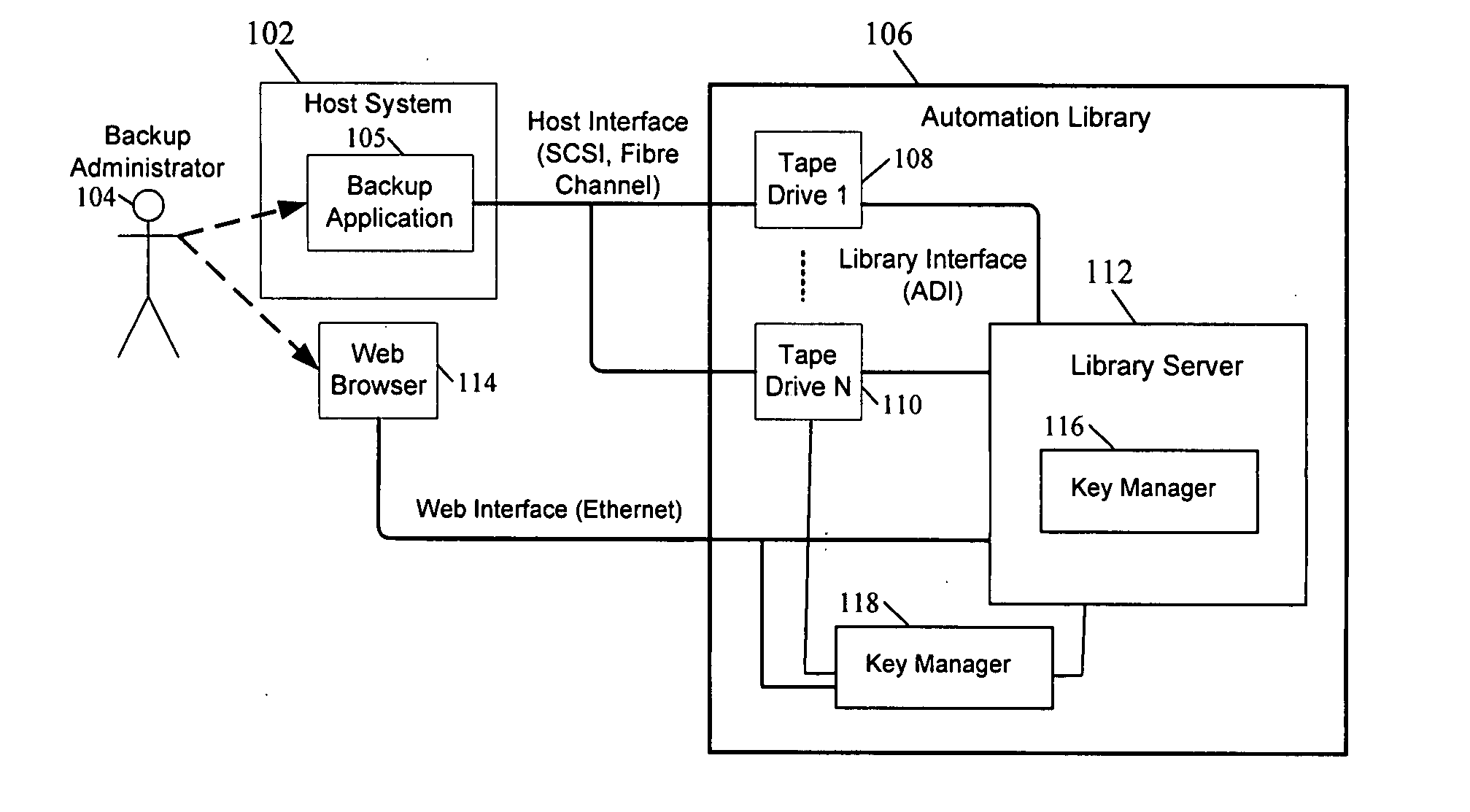
A method is provided for performing application-transparent key management in a storage library associated with an encrypting removable storage device. Encryption and decryption is performed by a key manager and the removable storage device, and is transparent to the application. Data is encrypted using keys that are managed by the storage key manager. An administrative interface allows an administrator to specify and manage encryption keys. A key identifier is associated with each key, and the key identifier is written to the tape along with the encrypted data. When reading encrypted data, the removable storage device reads the key identifier from the tape and requests the corresponding encryption key from the key manager. The removable storage device then provides the decrypted data to the application. The encryption key may be exported from the key manager or library in an encrypted XML format. Encrypted tapes can therefore be decrypted in different libraries by exporting the keys from one library to another.
Owner:QUANTUM CORP
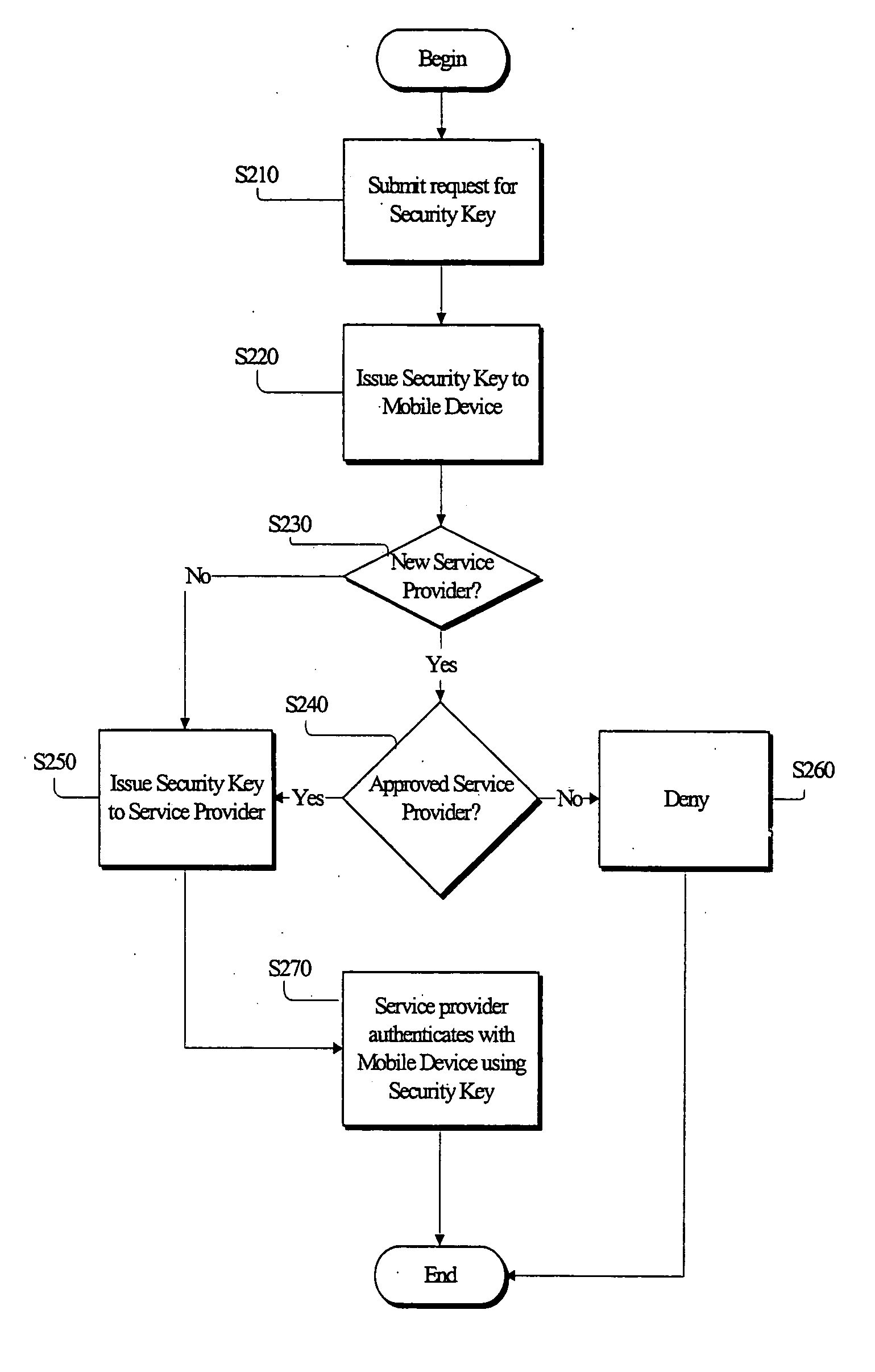
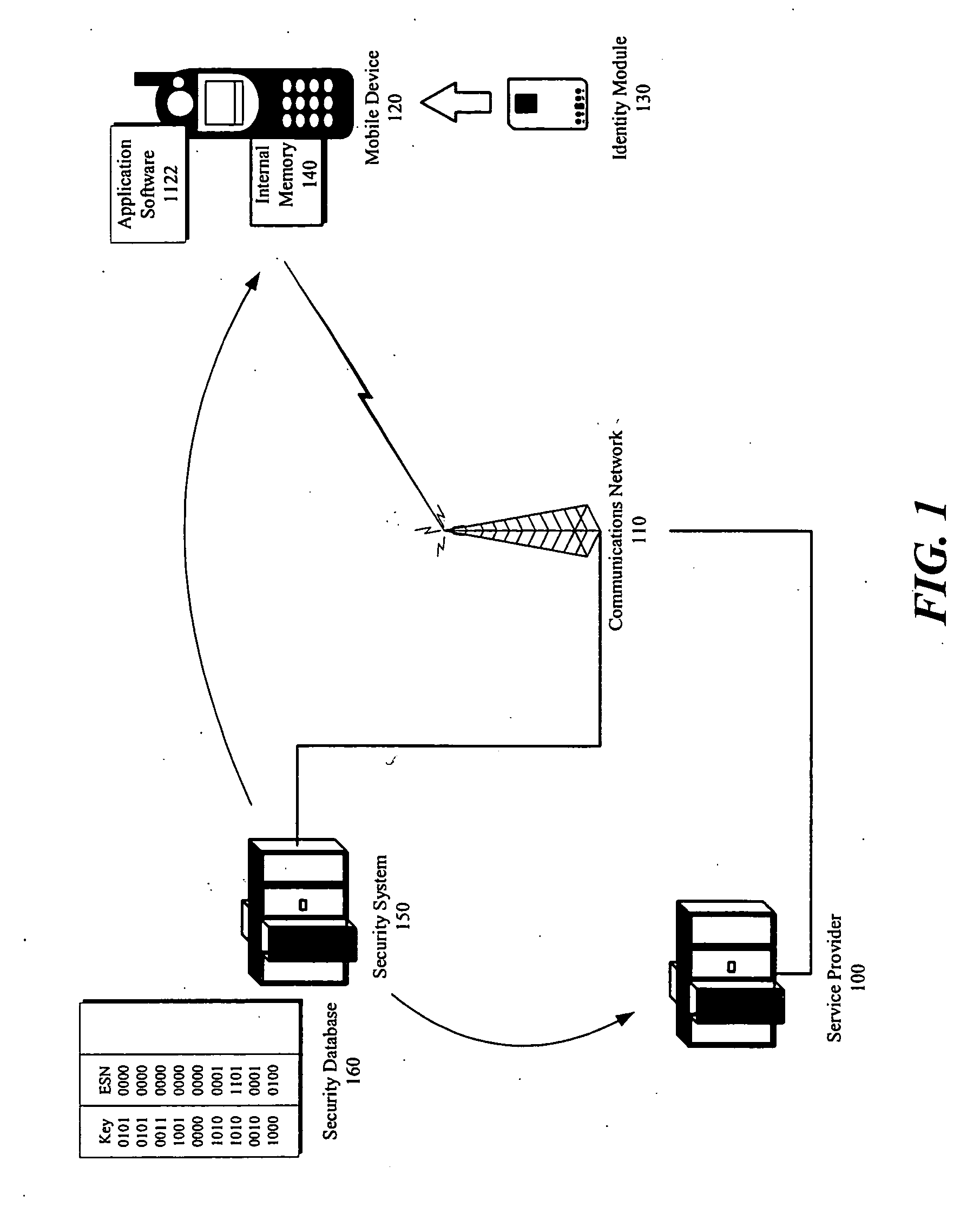
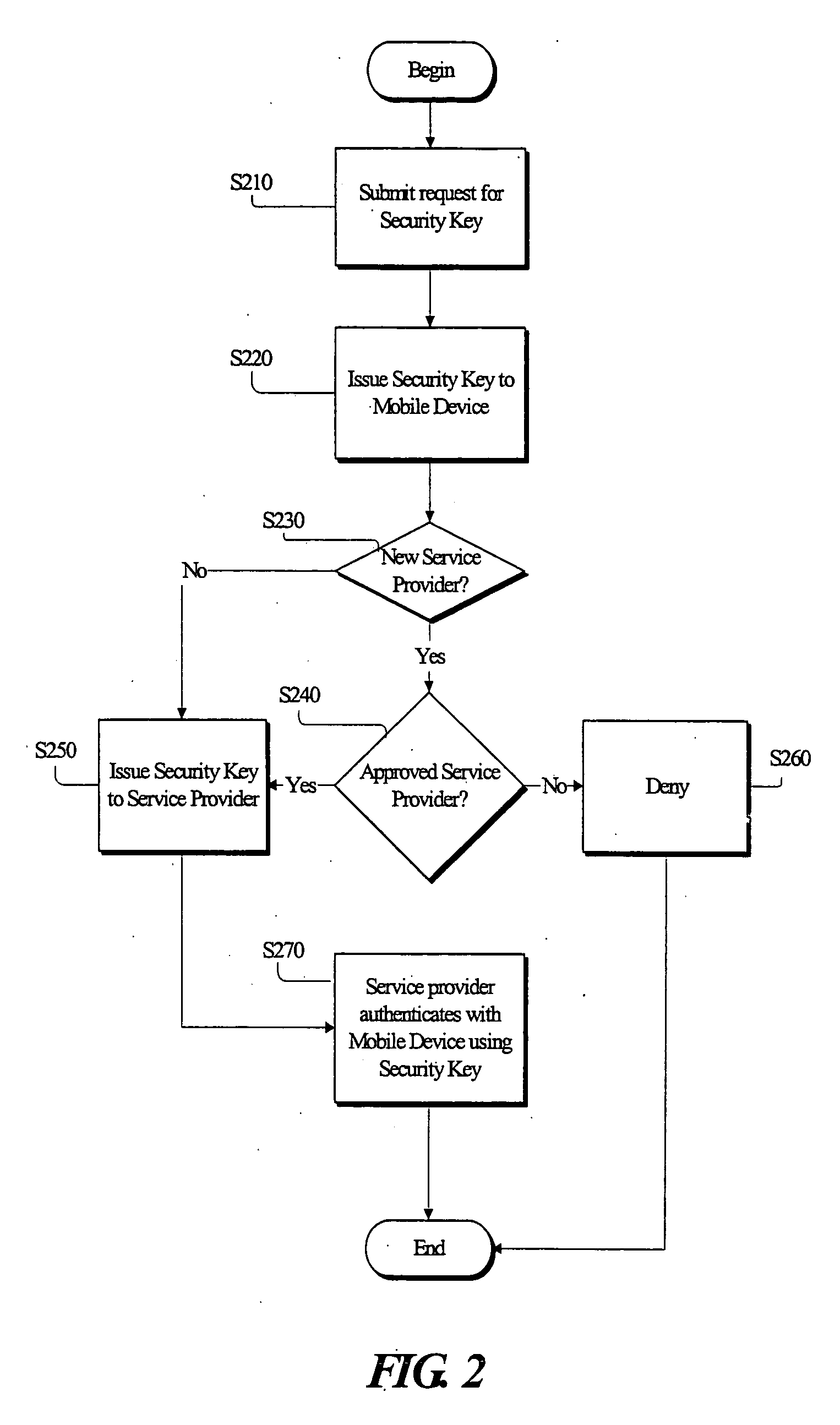
Security key management system and method in a mobile communication network
InactiveUS20050227669A1Request can be deniedUnauthorised/fraudulent call preventionEavesdropping prevention circuitsService provisionKey assignment
A security system for managing security key assignment in a mobile communications terminal, the security system comprising a key generating mechanism for generating a unique security key for a mobile device, in response to a request received by the security system from the mobile device; a transmission mechanism for transmitting the unique security key to the mobile device; and a data storage mechanism for storing the unique security key for the mobile device in association with an identifier identifying the mobile device, wherein the unique security key is transmitted to a service provider, in response to a request submitted by the service provider to the security system.
Owner:IXI MOBILE R&D
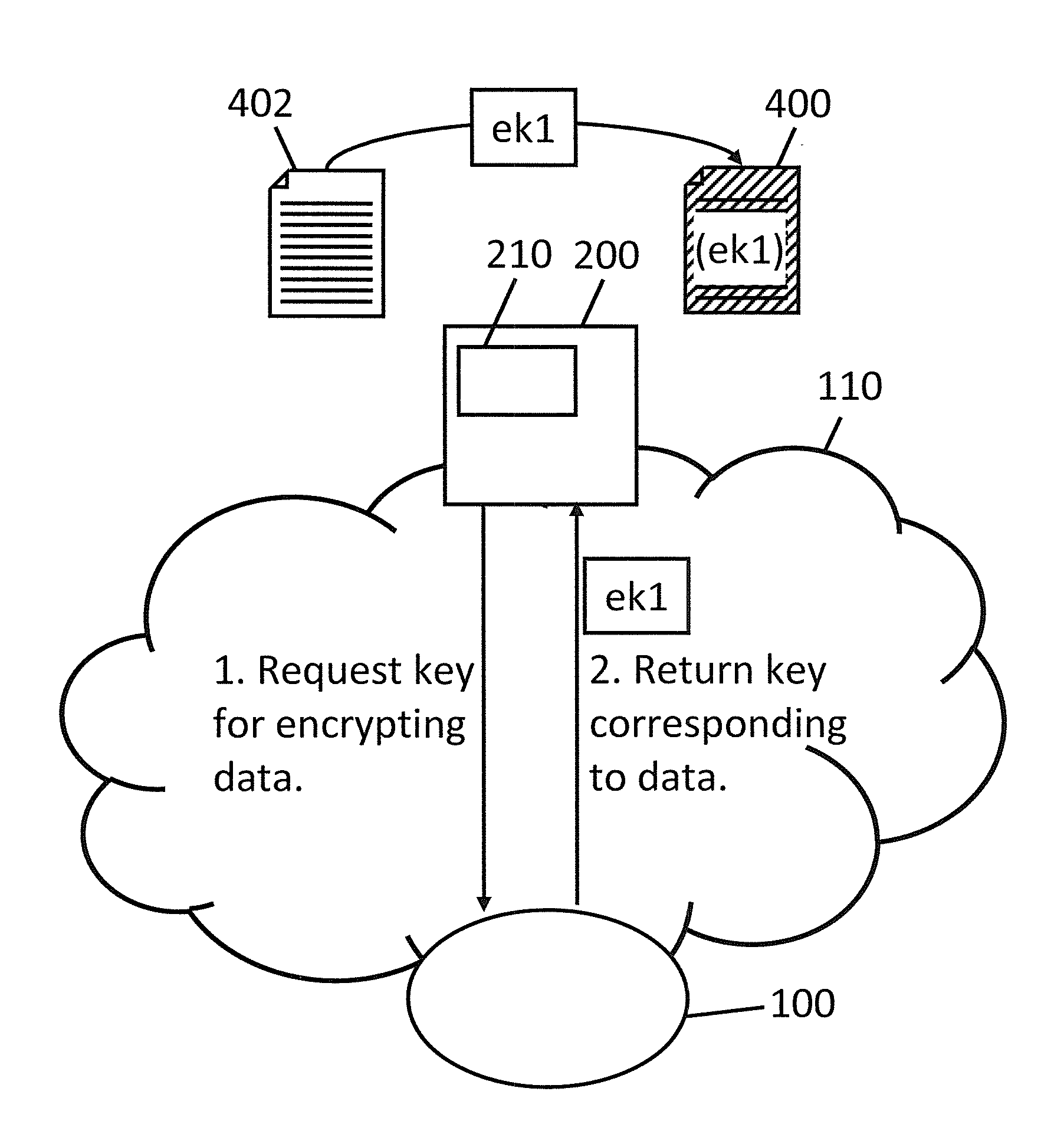
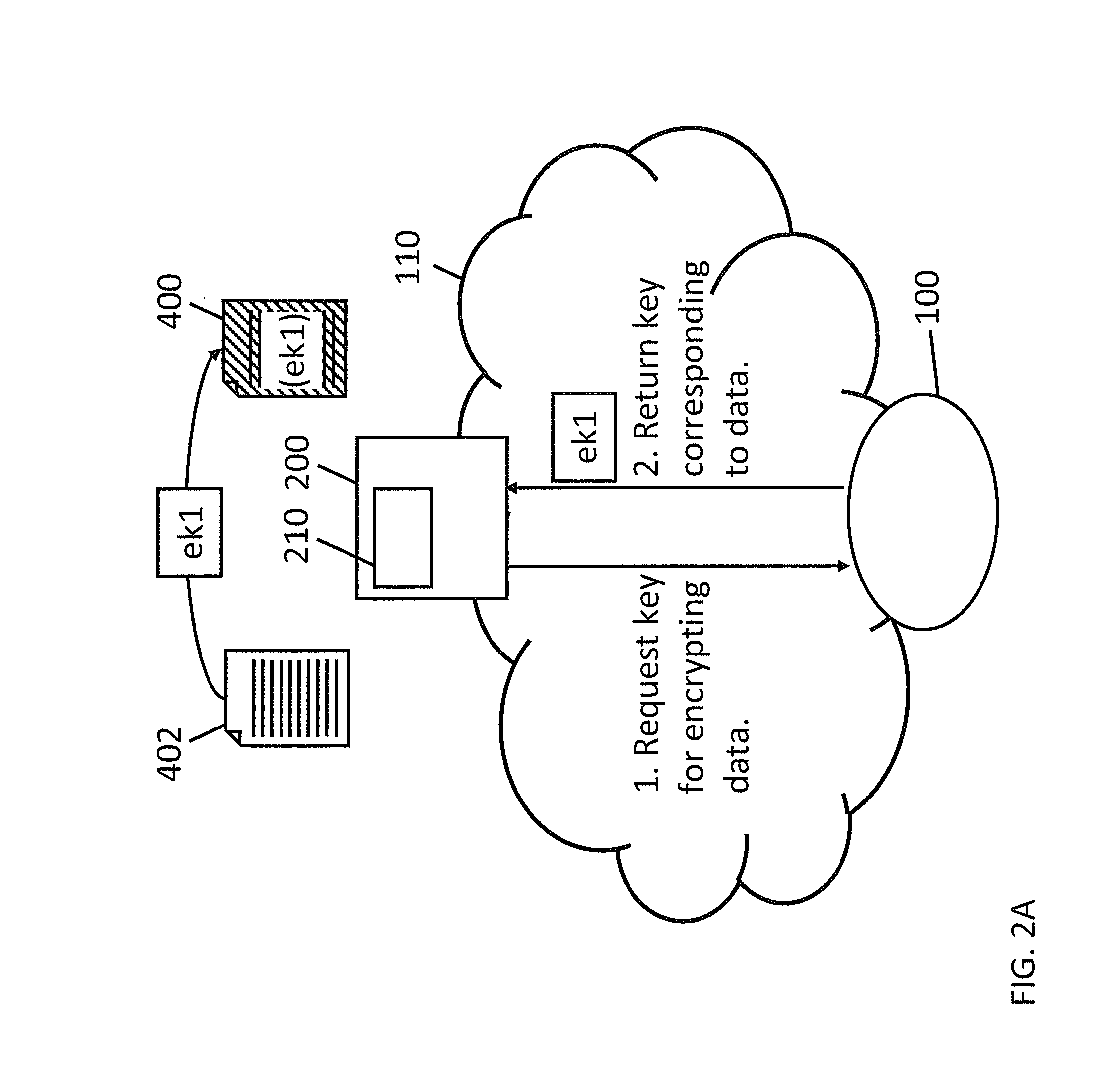
Cloud key management
InactiveUS20140019753A1Maintain the secrecy of the encryption keysAvoid less flexibilityKey distribution for secure communicationClient-sideA domain
A system for managing encryption keys within a domain includes: a client computer coupled to a cloud key management server over a network, the client computer being configured to supply a request for an encryption key, the request including an object identifier associated with the encryption key; and a cloud key management service comprising the cloud key management server, the cloud key management service being configured to: store a plurality of encryption keys in association with a plurality of object identifiers; receive the request from the client computer; identify an encryption key of the stored encryption keys associated with the object identifier of the request; and send the identified encryption key to the client computer in response to the request.
Owner:RAYTHEON BBN TECH CORP
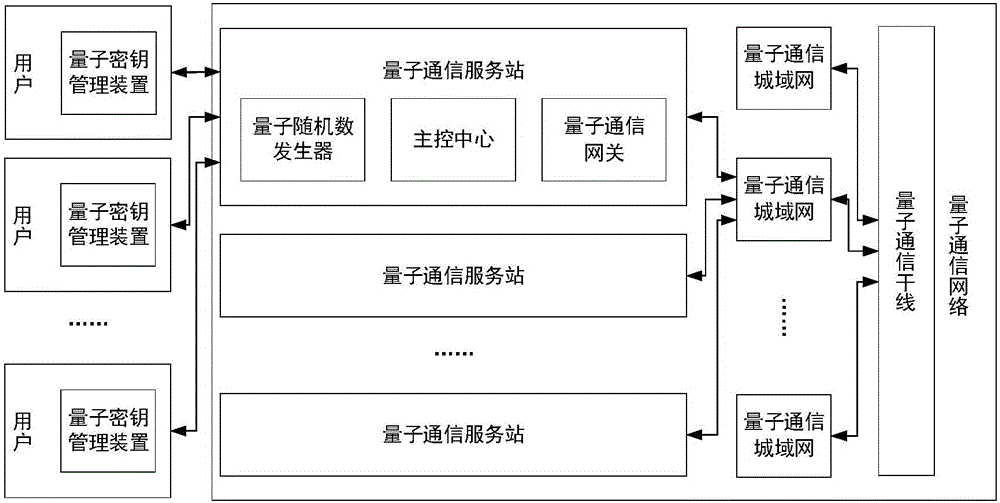
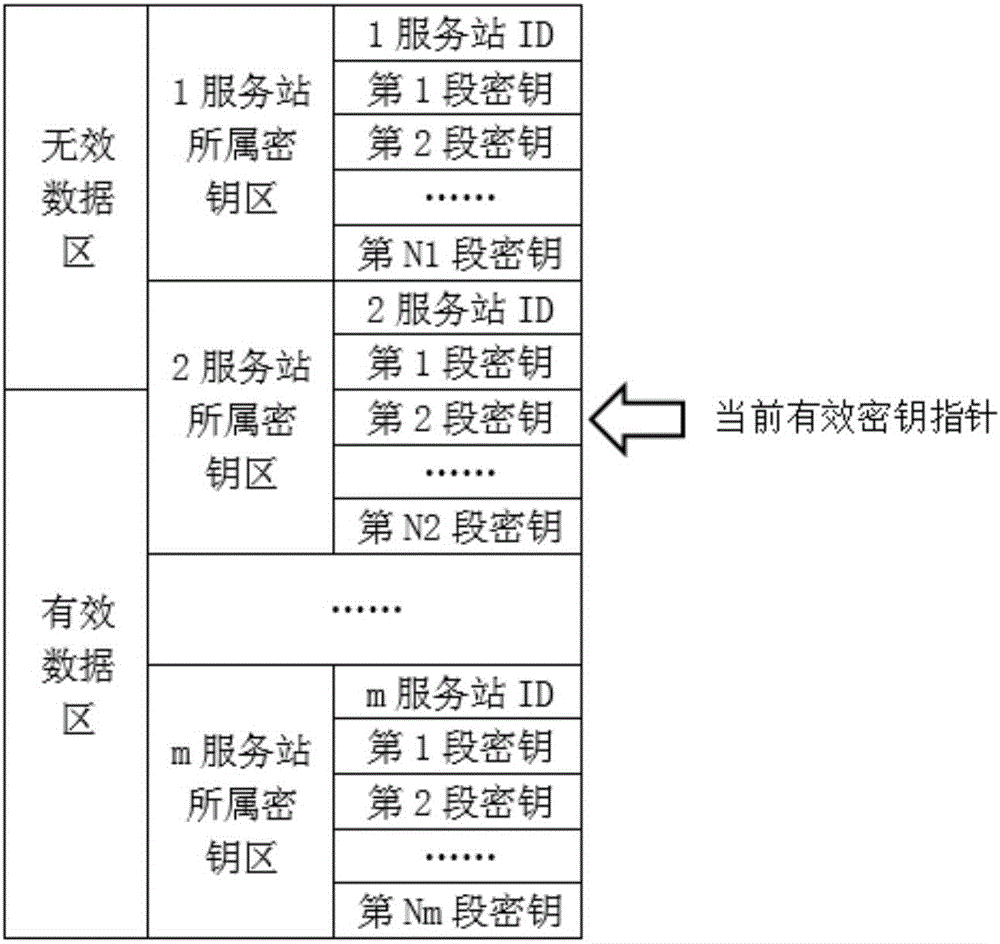
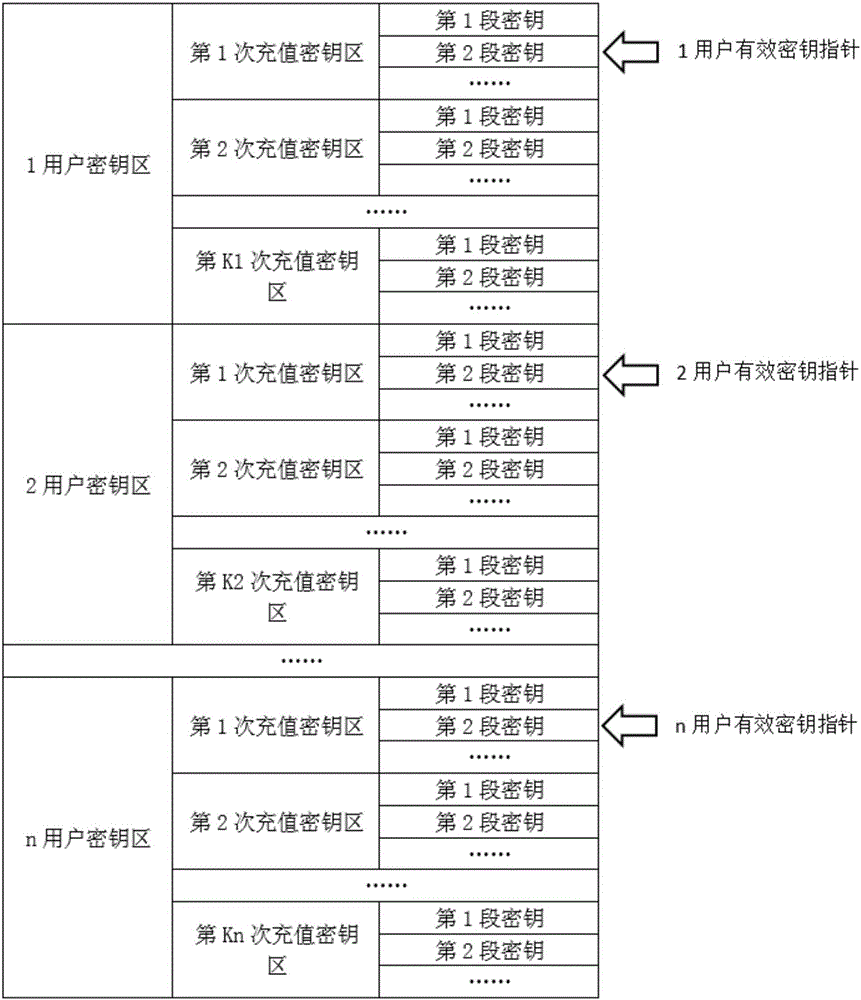
Quantum communication service station, quantum key management device, key configuration network, and key configuration method
ActiveCN106452740AAddress access security issuesAchieve coverageKey distribution for secure communicationSecurity questionKey distribution
The invention discloses a quantum communication service station, a quantum key management device, a key configuration network, and a key configuration method. The key configuration method comprises the following steps: responding to a key distribution request; authenticating a user of the key distribution request; writing a key generated with a true random number into a quantum key management device of the authenticated user. The key configuration method is different from the existing quantum key distribution QKD method in that key distribution of ultra high security is realized by pairing quantum key management devices and service stations at the end of a quantum communication network, the problem about access security at the end of a quantum communication network is solved, and terminal access is not a weak link of a quantum communication scheme. The quantum communication network can completely cover and replace the classic communication network in service.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
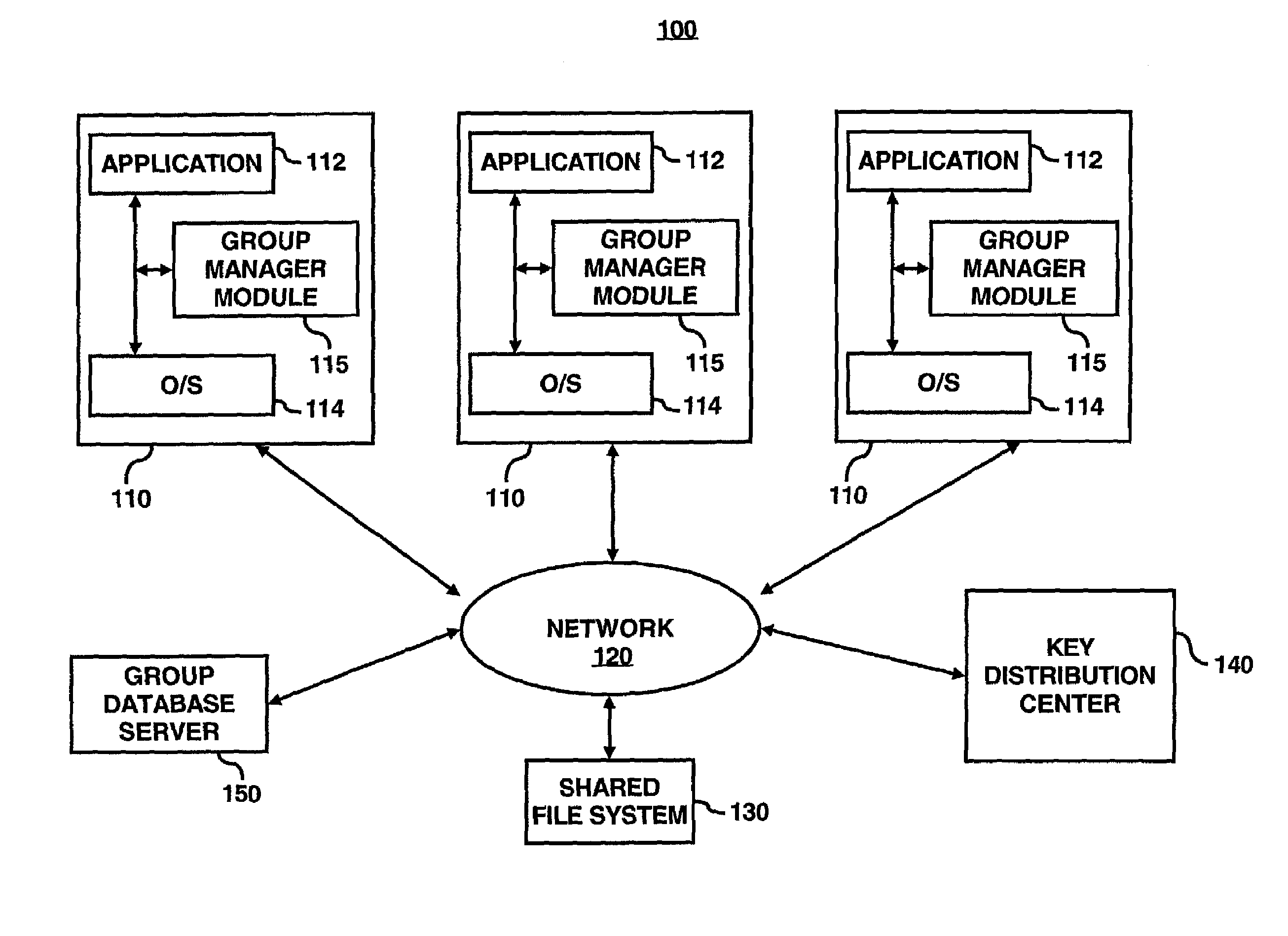
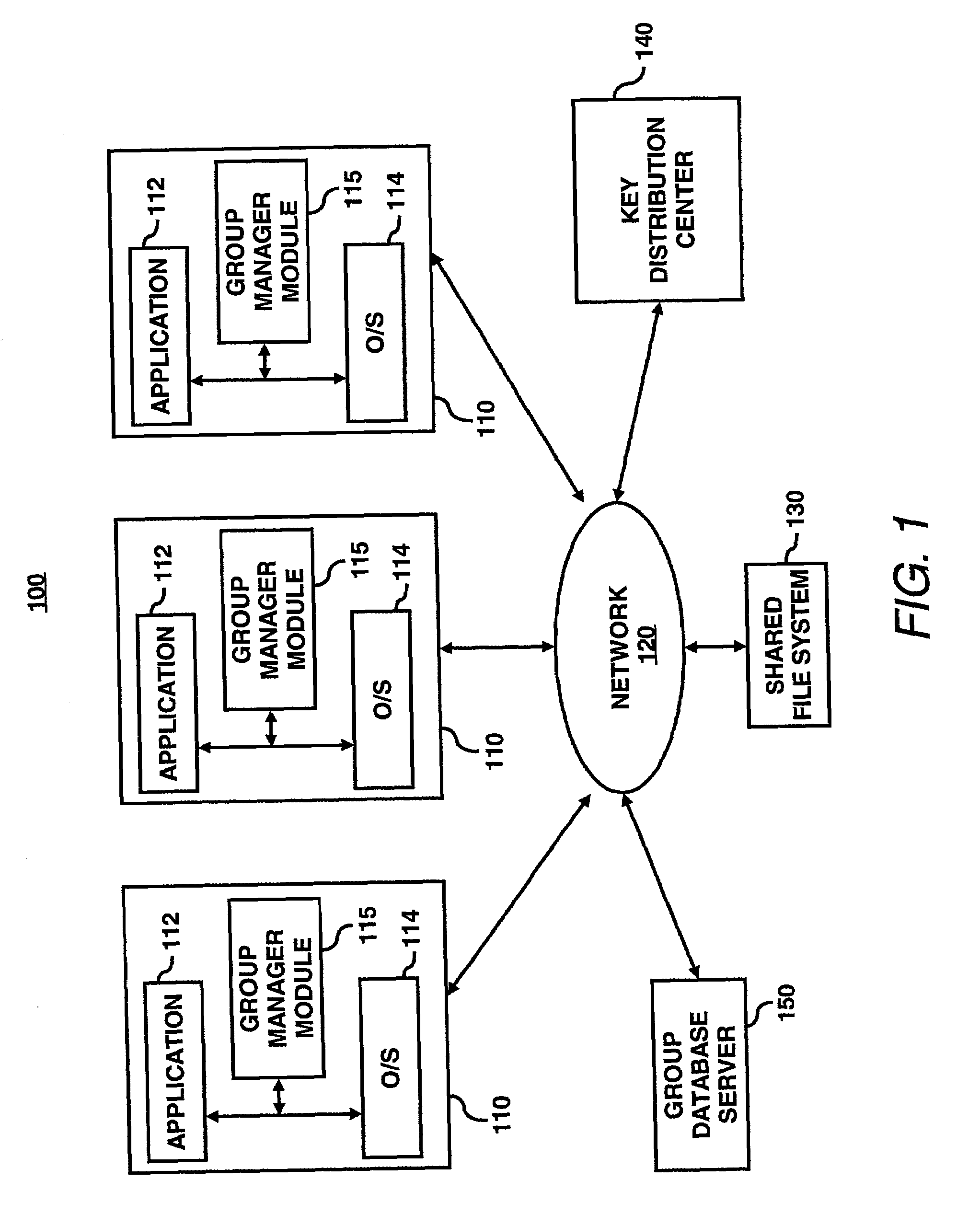
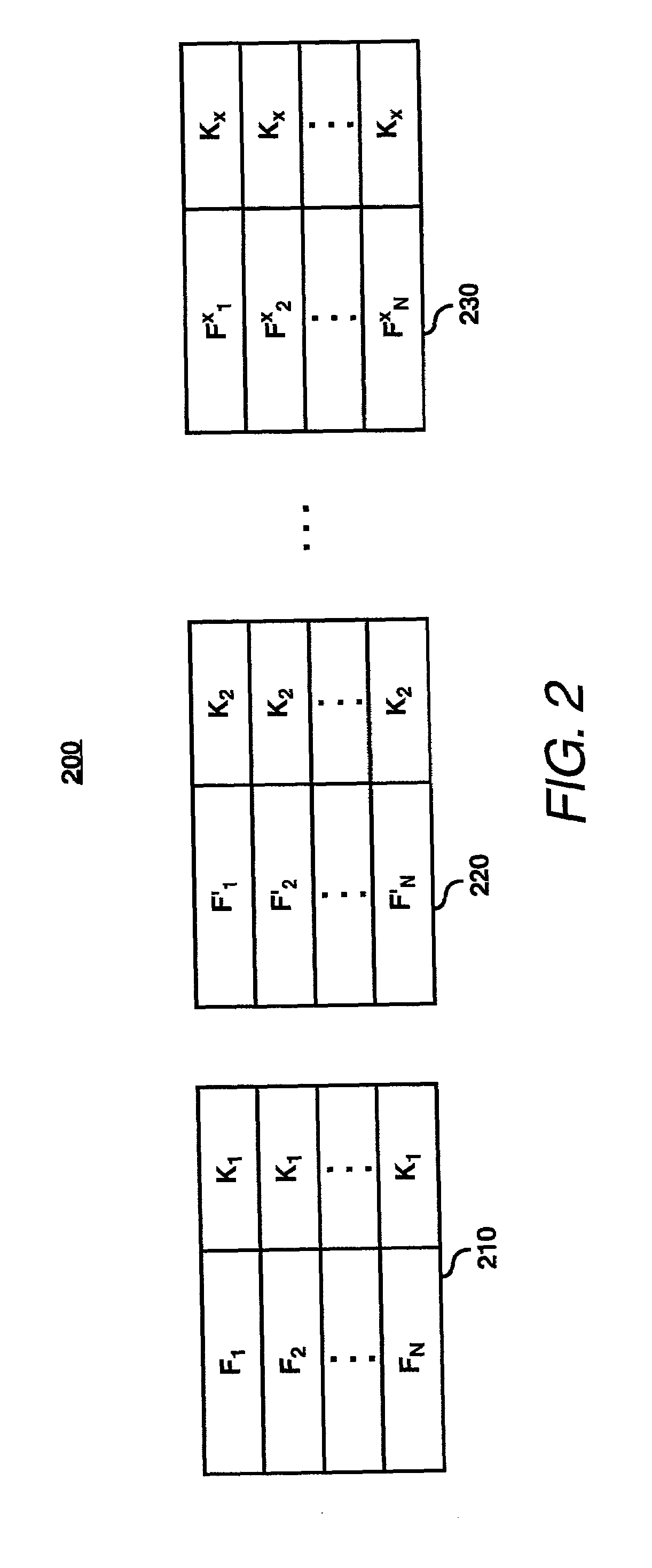
System for optimized key management with file groups
A group manager module may provide the capability to segregate or associate files into file encryption groups. A file may be placed into a file encryption group based on the attributes of the file. The attributes may be characteristics / parameters that describe who has access to a file such as UNIX permission / mode bits (group-read / write / executable bit, owner-read / write / executable bits, users-read / write / executable bits) or other system for access control lists (ACLs). Once associated with a file encryption group, the file may be encrypted with the encryption (or write) key of the selected file encryption group, and thus, decrypted with the decryption (or read) key of the file encryption group. A user may have membership into multiple file encryption groups as long as the user possesses the appropriate read / write key pairs. Membership of a file in a file encryption group is determined automatically by the system based on the permission attributes assigned by the system—groups are not explicitly created by administrators or other centralized authority. It is not users that belong to groups based on their access rights, but files which belong to groups based on their permission attributes.
Owner:HEWLETT PACKARD DEV CO LP
Method and system for enterprise network access control and management for government and corporate entities
InactiveUS20090254392A1Data processing applicationsComputer security arrangementsNetwork Access ControlIdentity management
A method, system, computer program product, and devices for enterprise network access control and management for Government and Corporate entities, including interagency identity management; connectors and controls; an interagency directory services transformation service; a user / duty position resolving service; role-based encryption key management; role-based business process modeling; and proximity-based access control enabled by user-role-track association.
Owner:ZANDER VAN S
Remote Pre-Boot Authentication
InactiveUS20120179904A1Key distribution for secure communicationDigital data protectionPre-boot authenticationVirtual machine
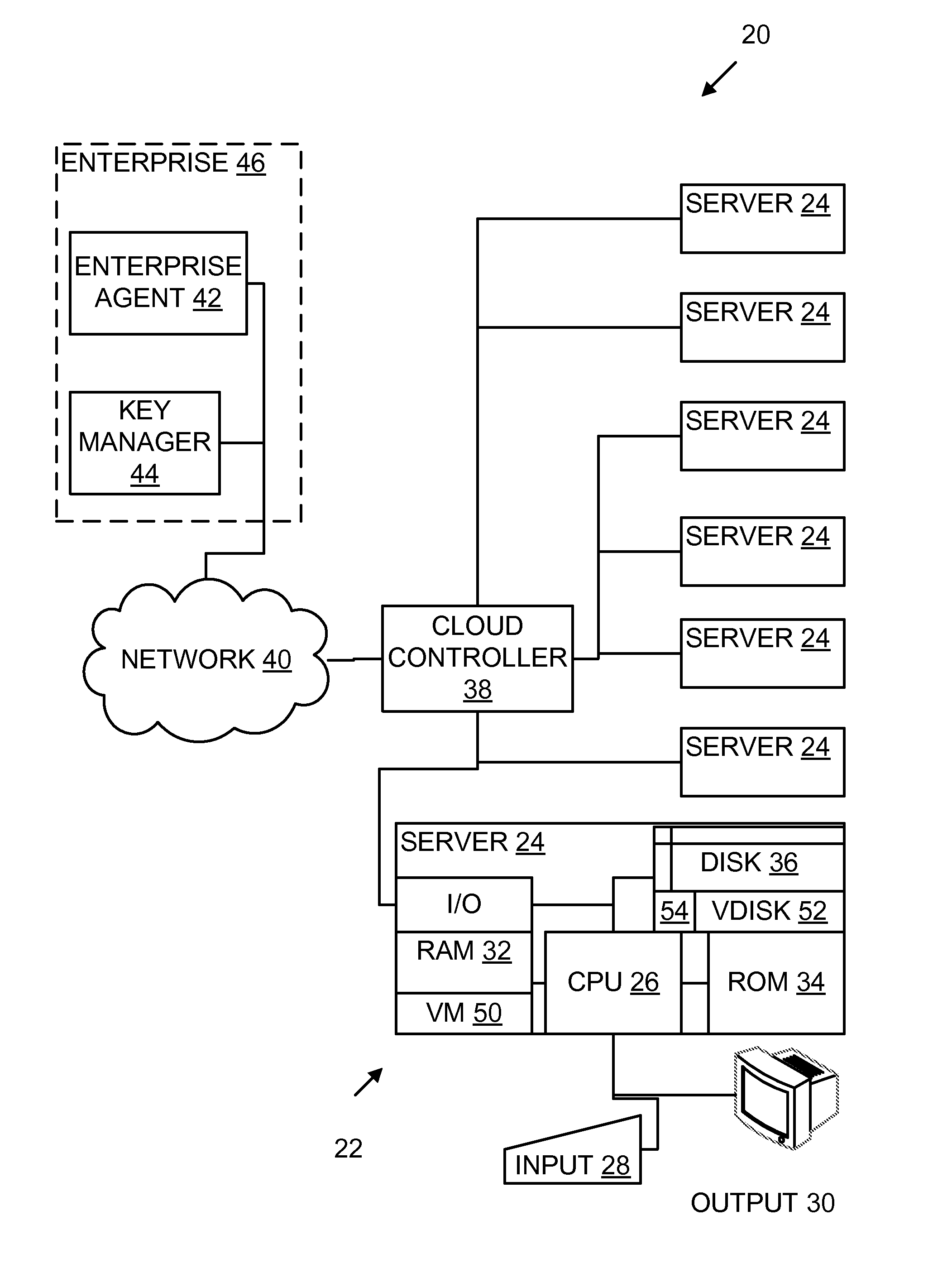
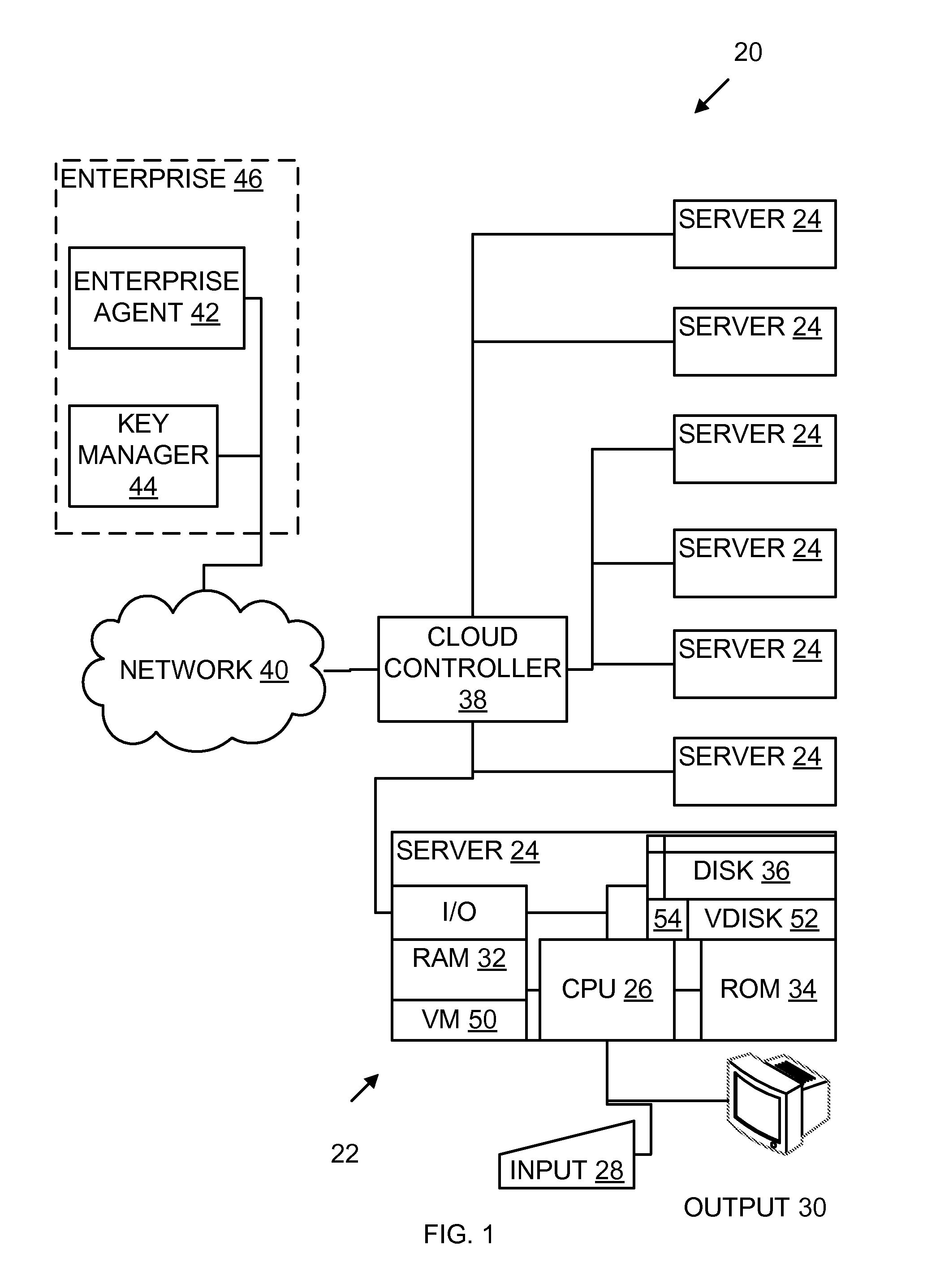
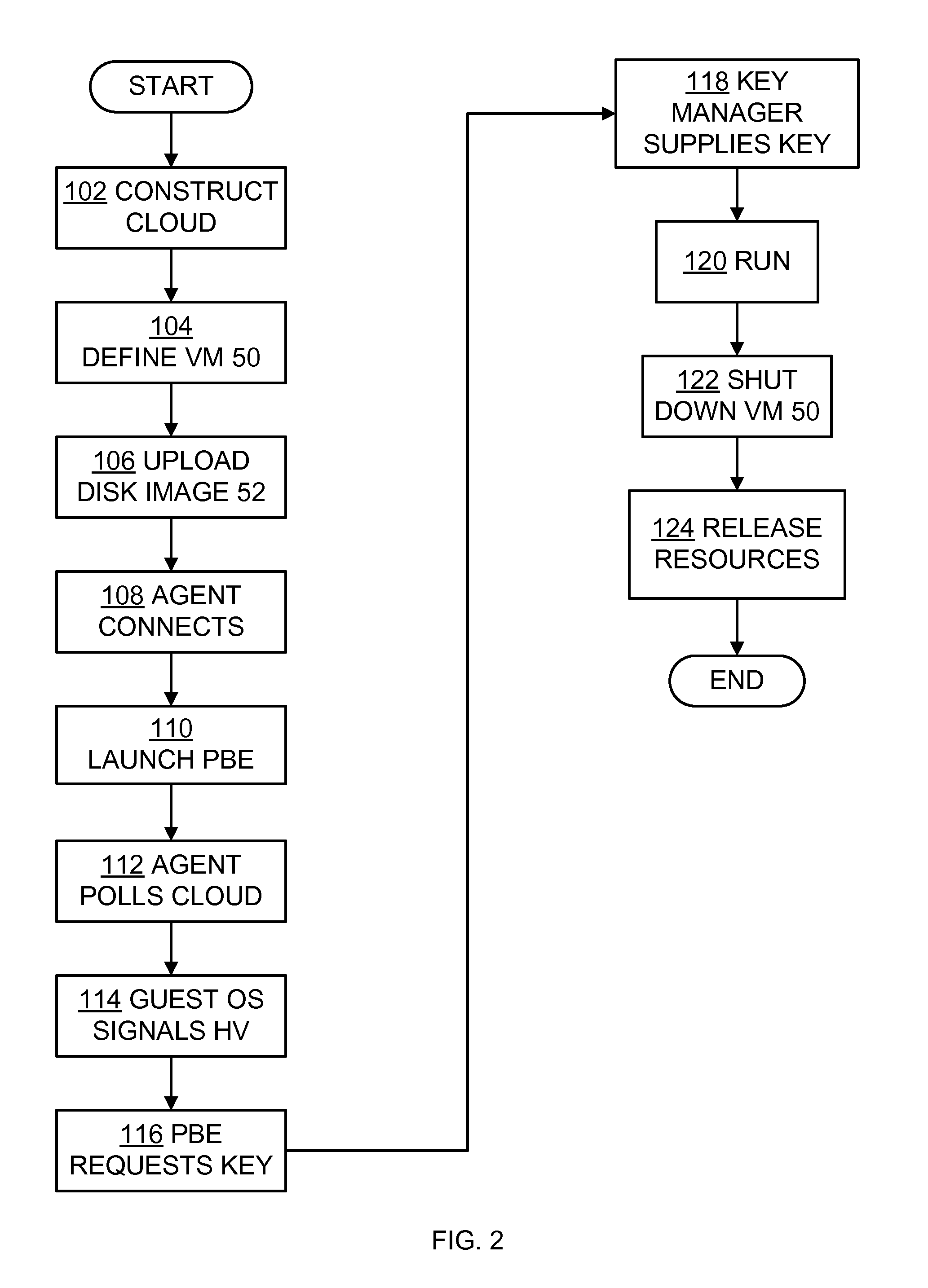
A host computer cloud has a processor and supports a virtual machine. An agent under control of a user is in communication with the cloud over a network. A key management server is in communication with the cloud over a network. The cloud stores the virtual machine in the form of a virtual encrypted disk on a non-volatile storage medium. When commanded by the agent, the cloud requests a disk-wrapping key from the key management server and decrypts the encrypted disk using the disk-wrapping key.
Owner:SAFENET
Hardware trust anchors in sp-enabled processors
ActiveUS20100042824A1User identity/authority verificationDigital computer detailsOperational systemConfidentiality
A trust system and method is disclosed for use in computing devices, particularly portable devices, in which a central Authority shares secrets and sensitive data with users of the respective devices. The central Authority maintains control over how and when shared secrets and data are used. In one embodiment, the secrets and data are protected by hardware-rooted encryption and cryptographic hashing, and can be stored securely in untrusted storage. The problem of transient trust and revocation of data is reduced to that of secure key management and keeping a runtime check of the integrity of the secure storage areas containing these keys (and other secrets). These hardware-protected keys and other secrets can further protect the confidentiality and / or integrity of any amount of other information of arbitrary size (e.g., files, programs, data) by the use of strong encryption and / or keyed-hashing, respectively. In addition to secrets the Authority owns, the system provides access to third party secrets from the computing devices. In one embodiment, the hardware-rooted encryption and hashing each use a single hardware register fabricated as part of the computing device's processor or System-on-Chip (SoC) and protected from external probing. The secret data is protected while in the device even during operating system malfunctions and becomes non-accessible from storage according to various rules, one of the rules being the passage of a certain time period. The use of the keys (or other secrets) can be bound to security policies that cannot be separated from the keys (or other secrets). The Authority is also able to establish remote trust and secure communications to the devices after deployment in the field using a special tamper-resistant hardware register in the device, to enable, disable or update the keys or secrets stored securely by the device.
Owner:THE TRUSTEES FOR PRINCETON UNIV +1
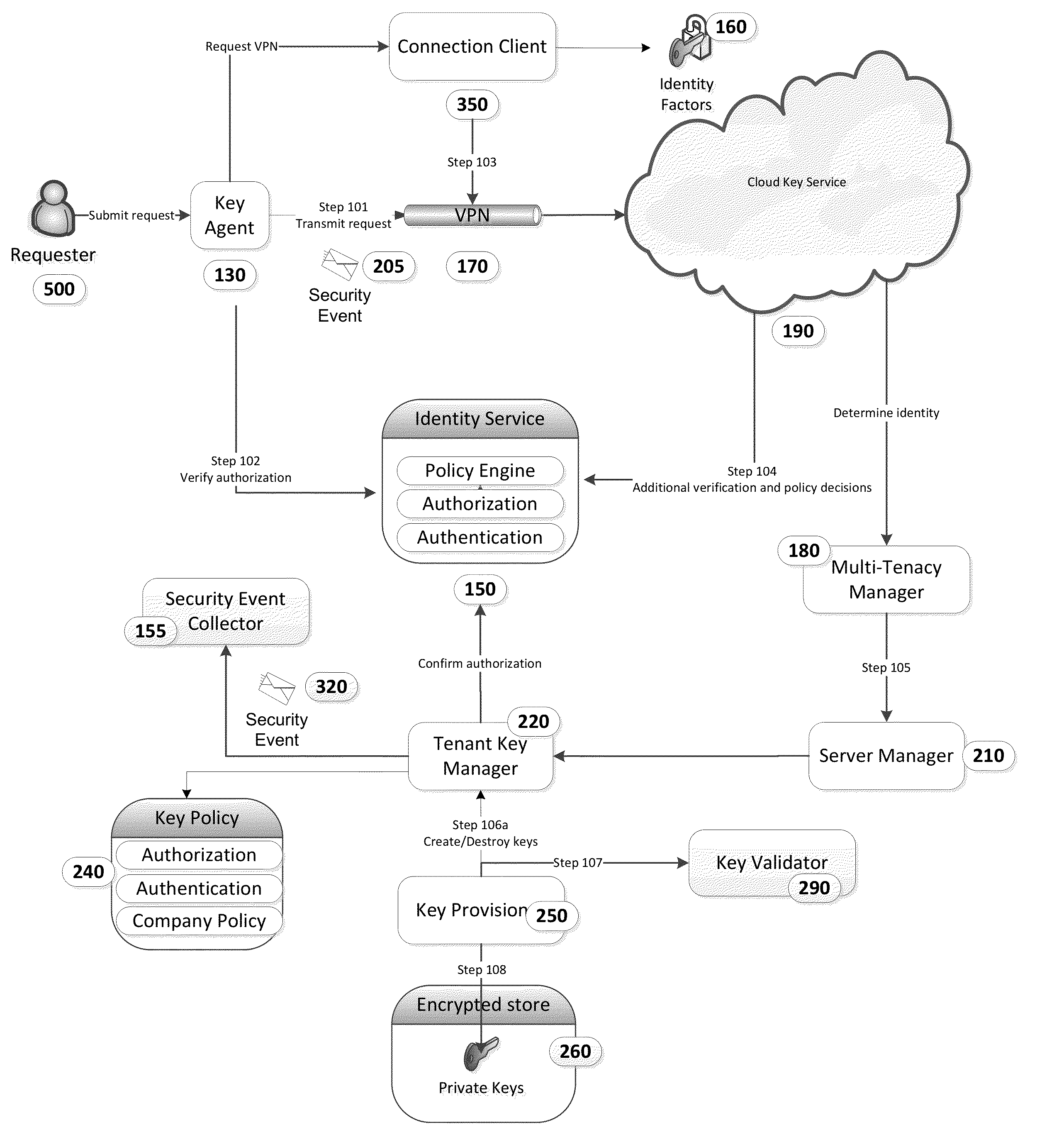
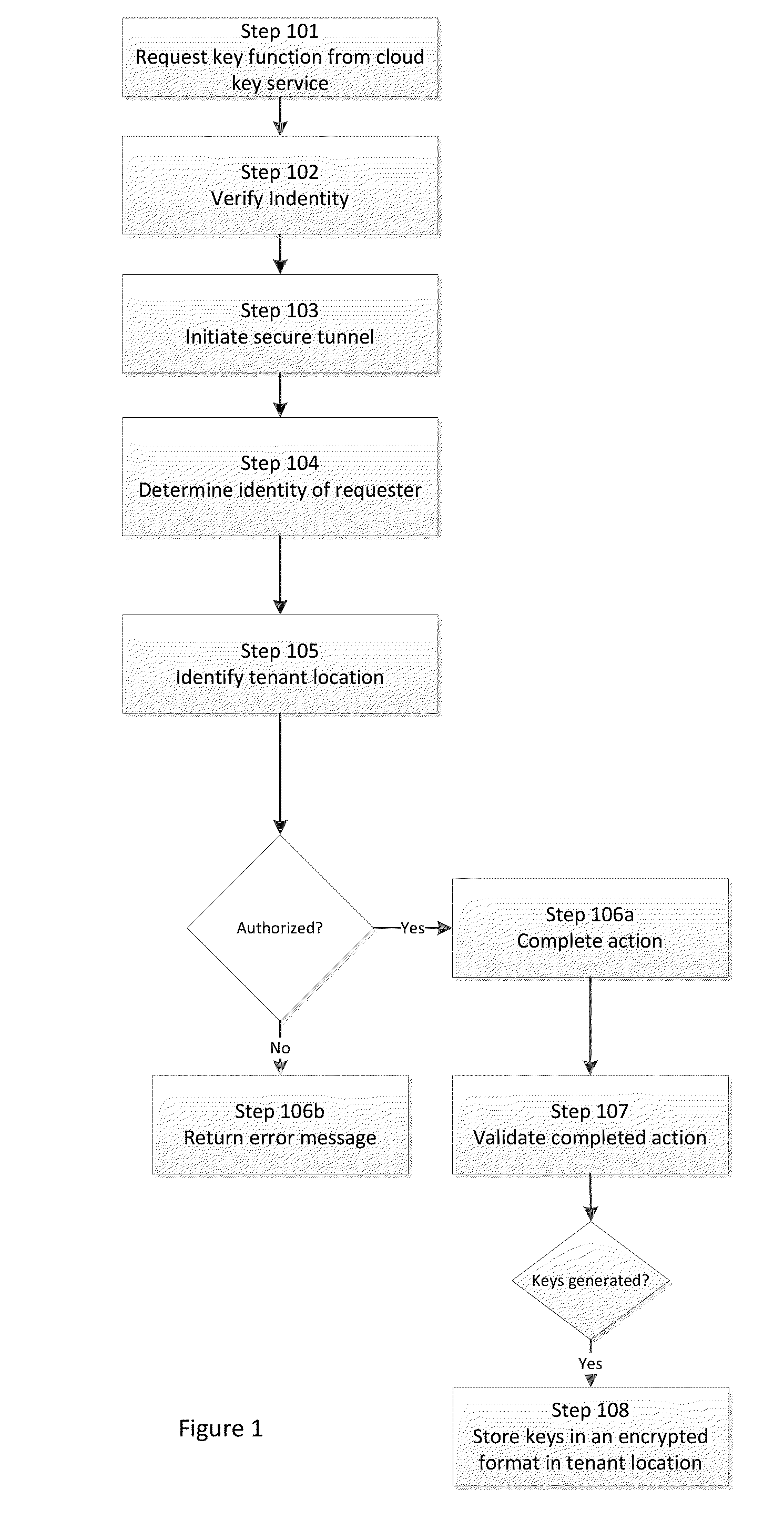
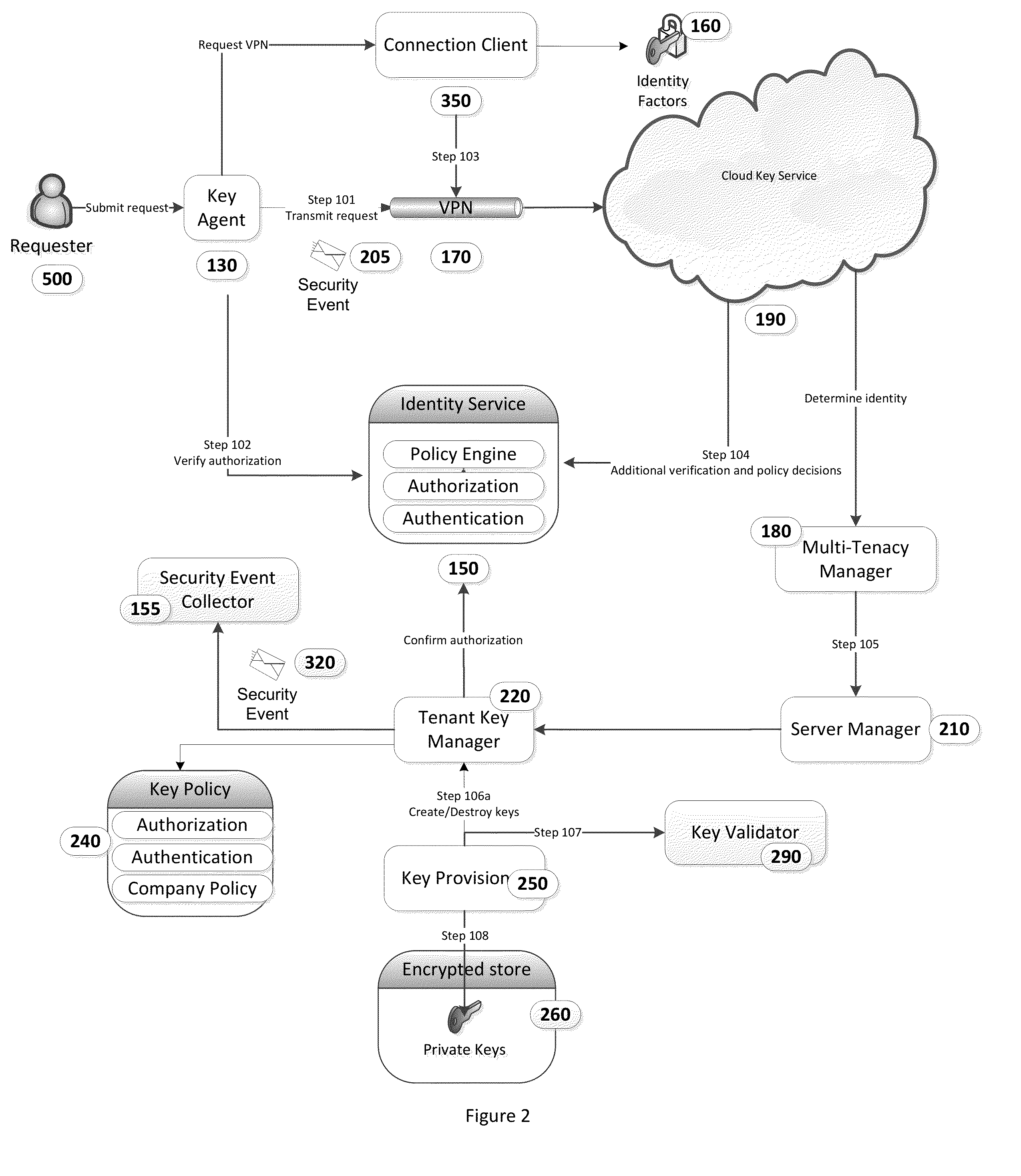
Cloud Key Management System
ActiveUS20140050317A1Avoid confusionImprove securityKey distribution for secure communicationCloud baseManagement system
This invention uses a cloud-based key management system to store, retrieve, generate, and perform other key operations. The cloud-based system ensures security of the keys while preventing their loss or destruction. Using this invention, a company can now manage, audit, and maintain control and security around their keys. Security event auditing permits evaluation of the operations to ensure that each step is completely securely.
Owner:DIGICERT +1
Person-centric account-based digital signature system
In a method of managing a database of existing accounts (214) for account holders (202), each account holder (202) has multiple accounts with one or more account authorities (212) for use of a single device with multiple accounts, with each account of each account holder being associated with a public key of a public-private key pair of that accuont holder. A record of information pertaining to all accounts of a particular account holder is maintained in a central location by a central key authority. The information for that account includes the public keys of that account holder. The central key authority transfers information from the record for an account holder to a new account authority for which that account holder desires to establish a new account; the central key authority also receives information from account authorities for inclusion in the record centrally maintained for that account holder.
Owner:FIRST DATA
Apparatus for encryption key management
ActiveUS7200868B2Key distribution for secure communicationDigital data processing detailsBroadband communicationKey management
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com