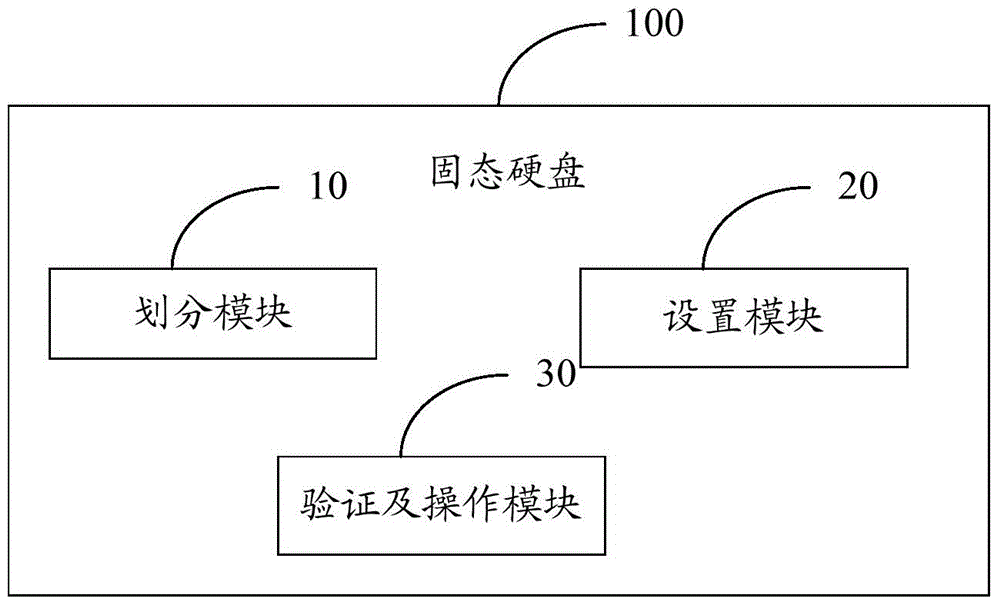
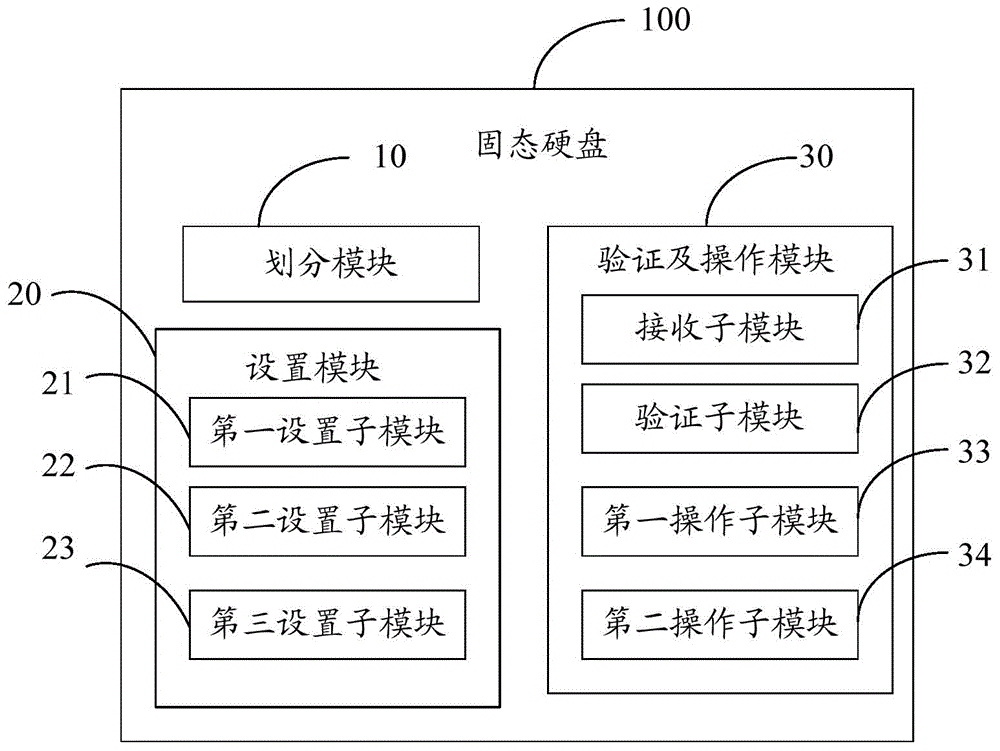
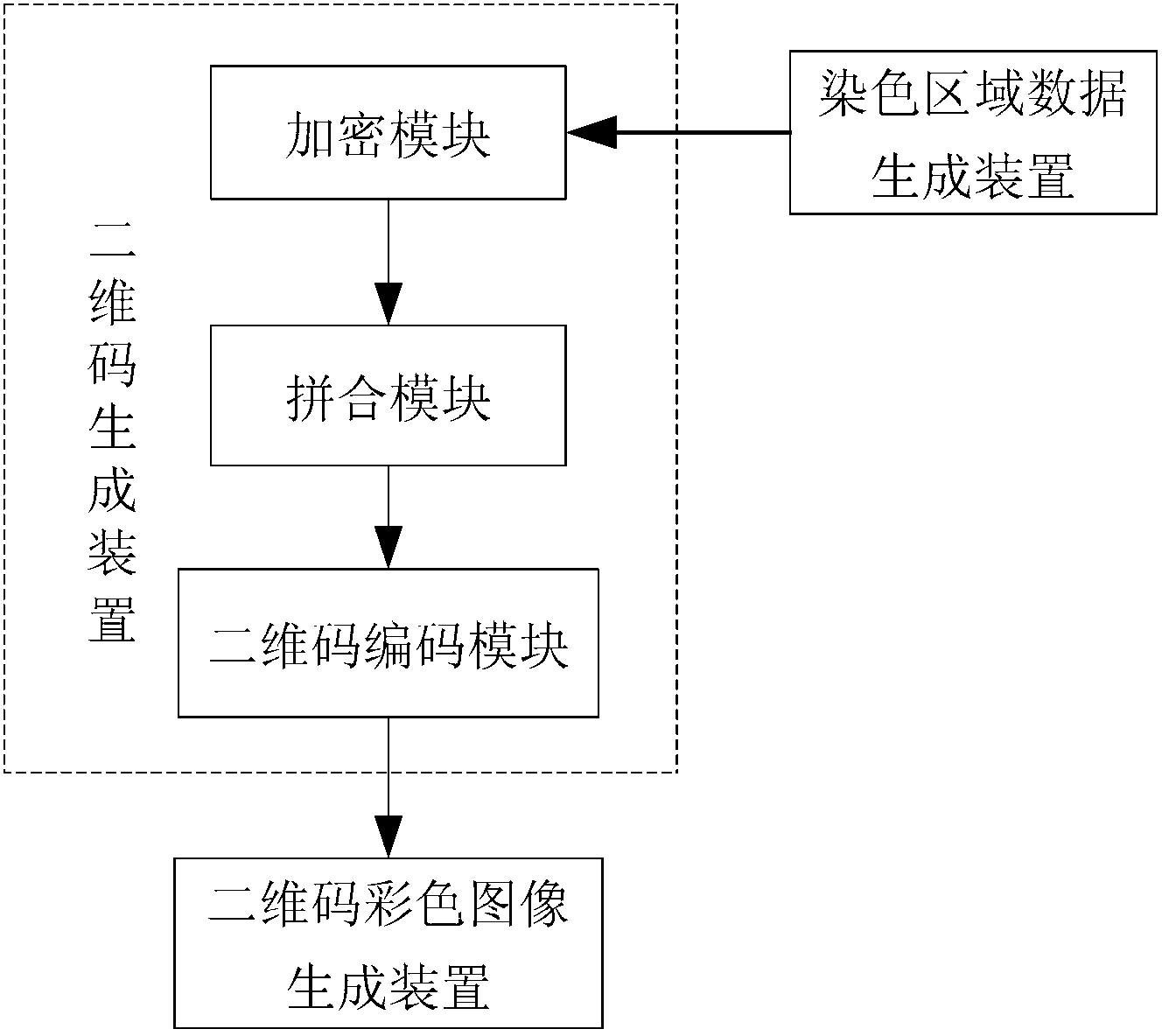
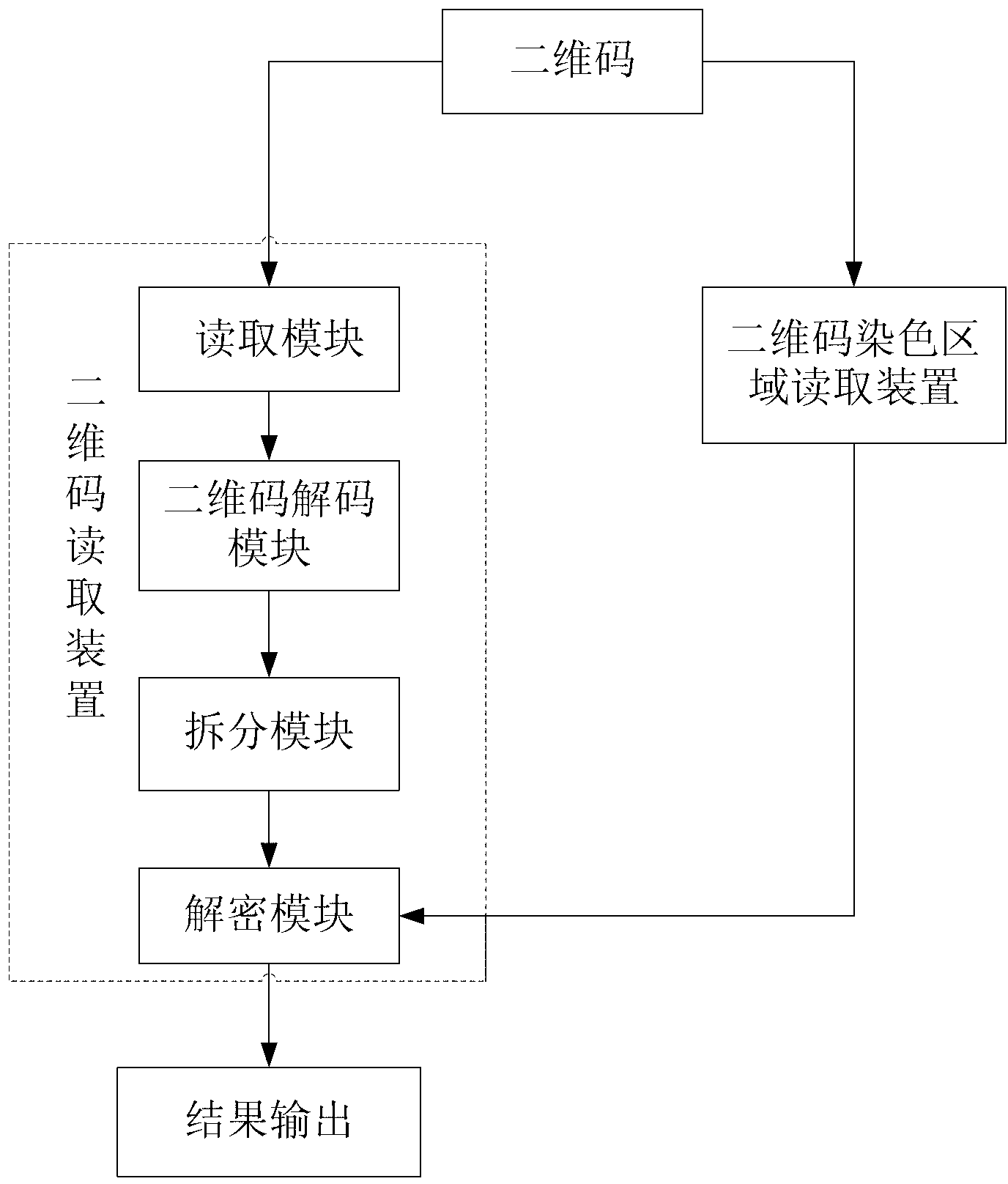
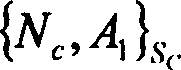Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1499results about How to "Guaranteed confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
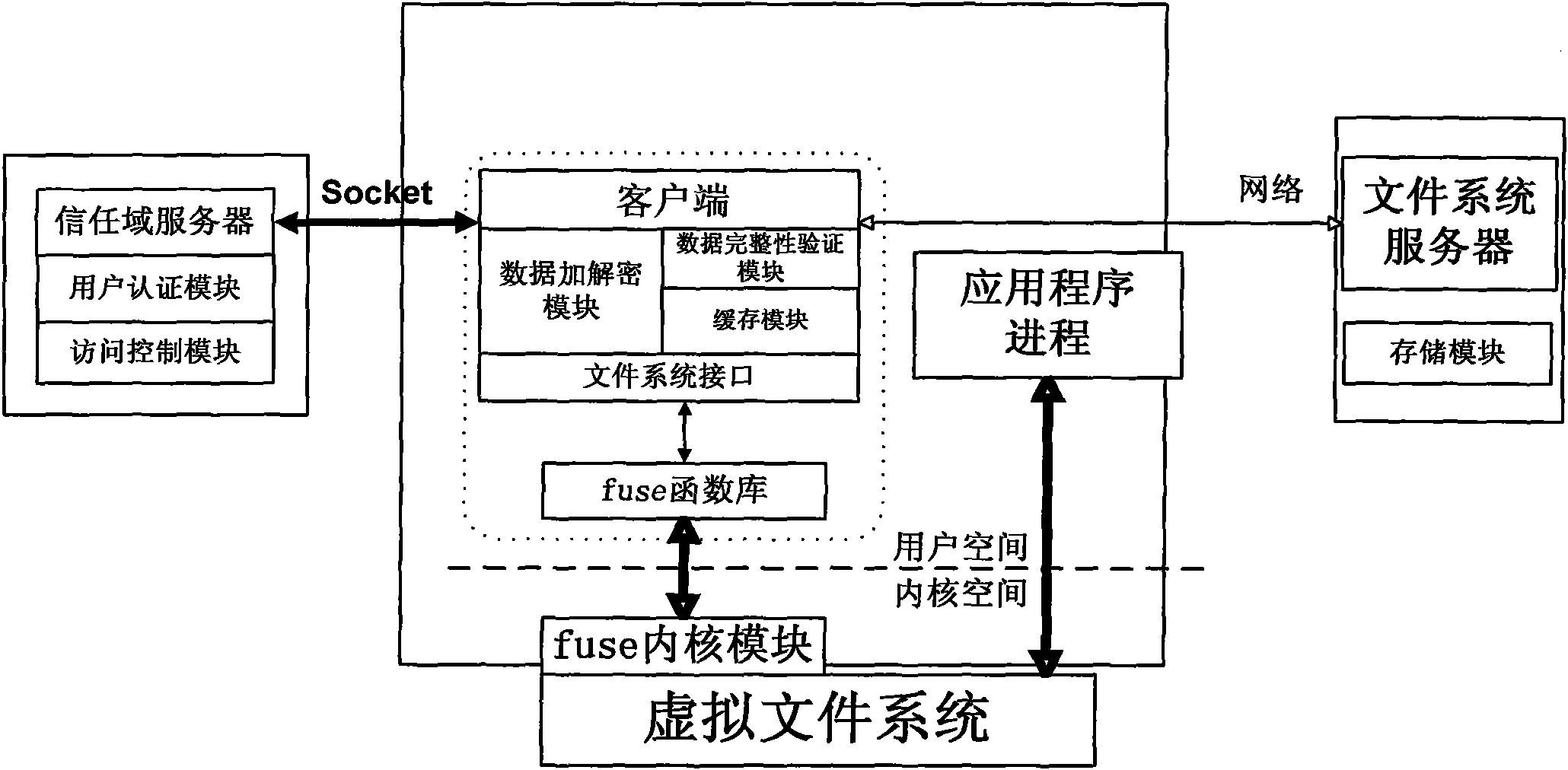
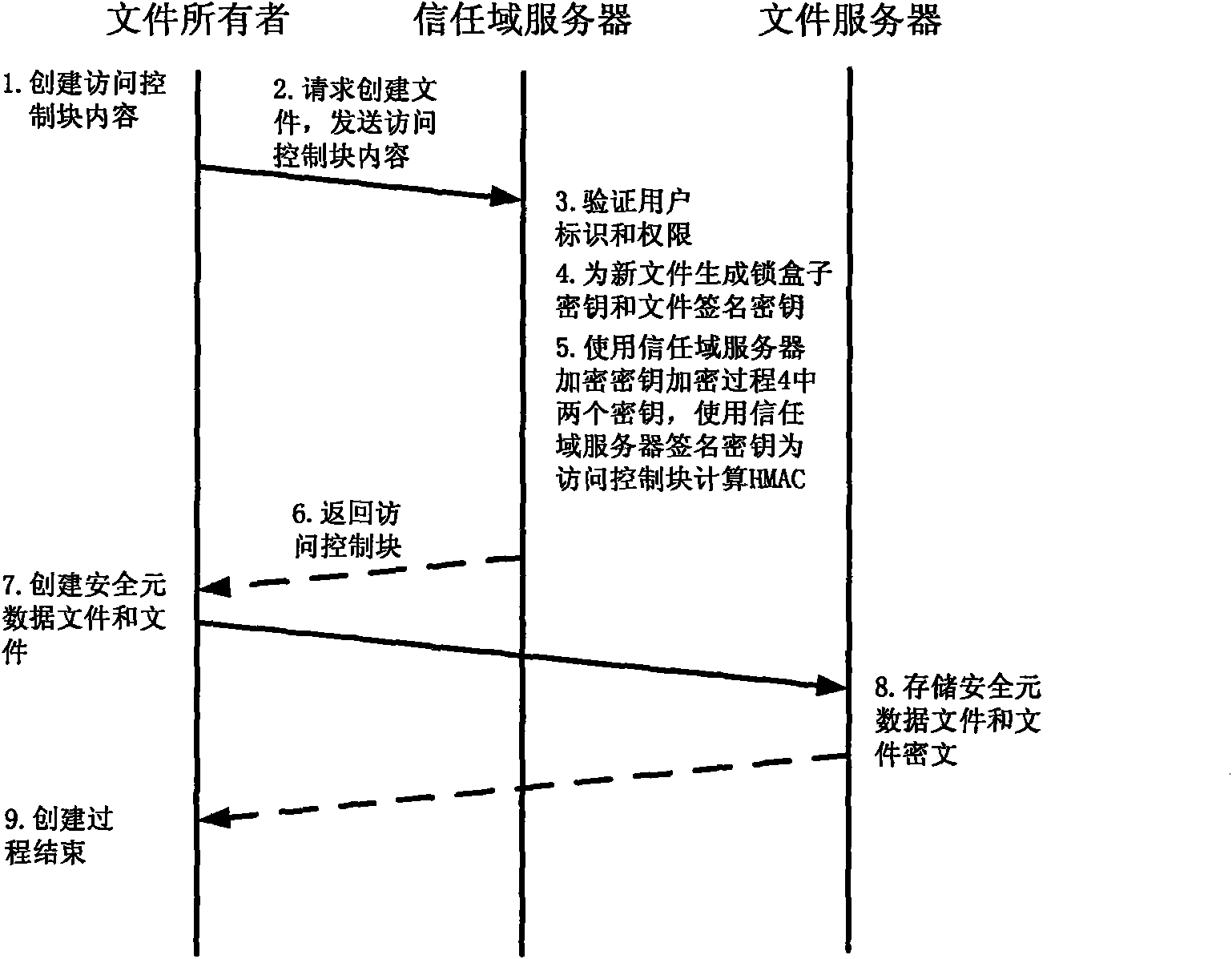
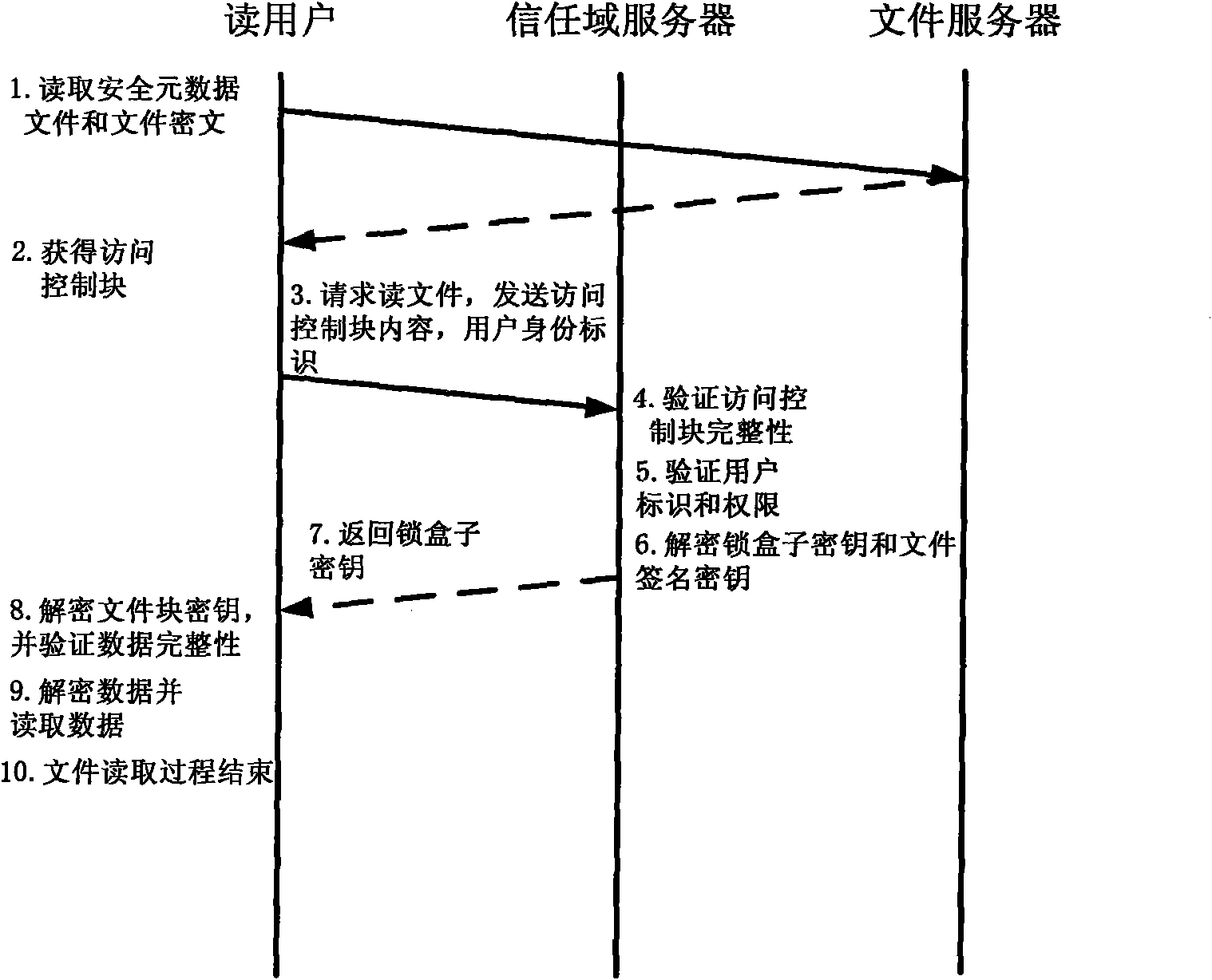
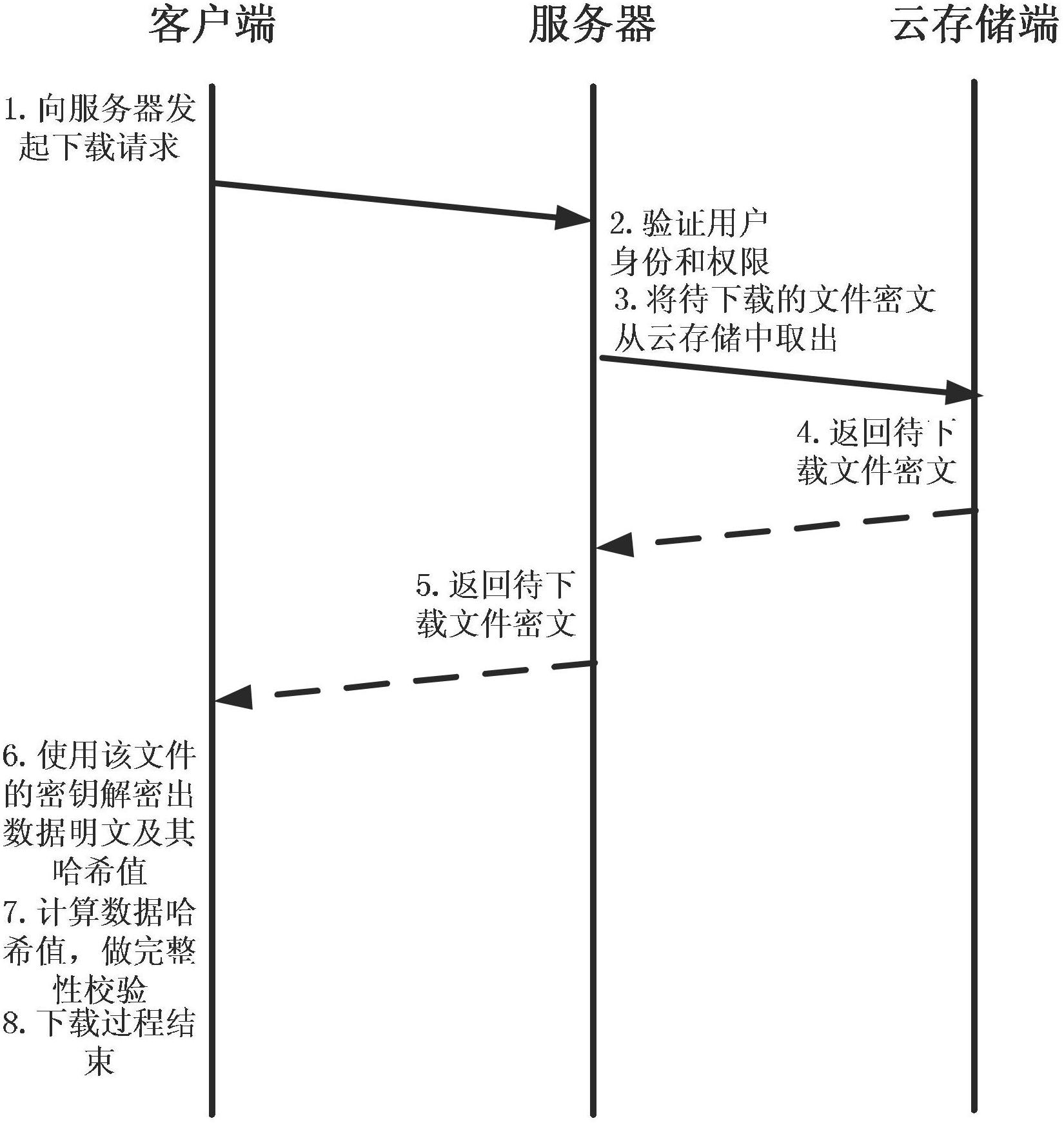
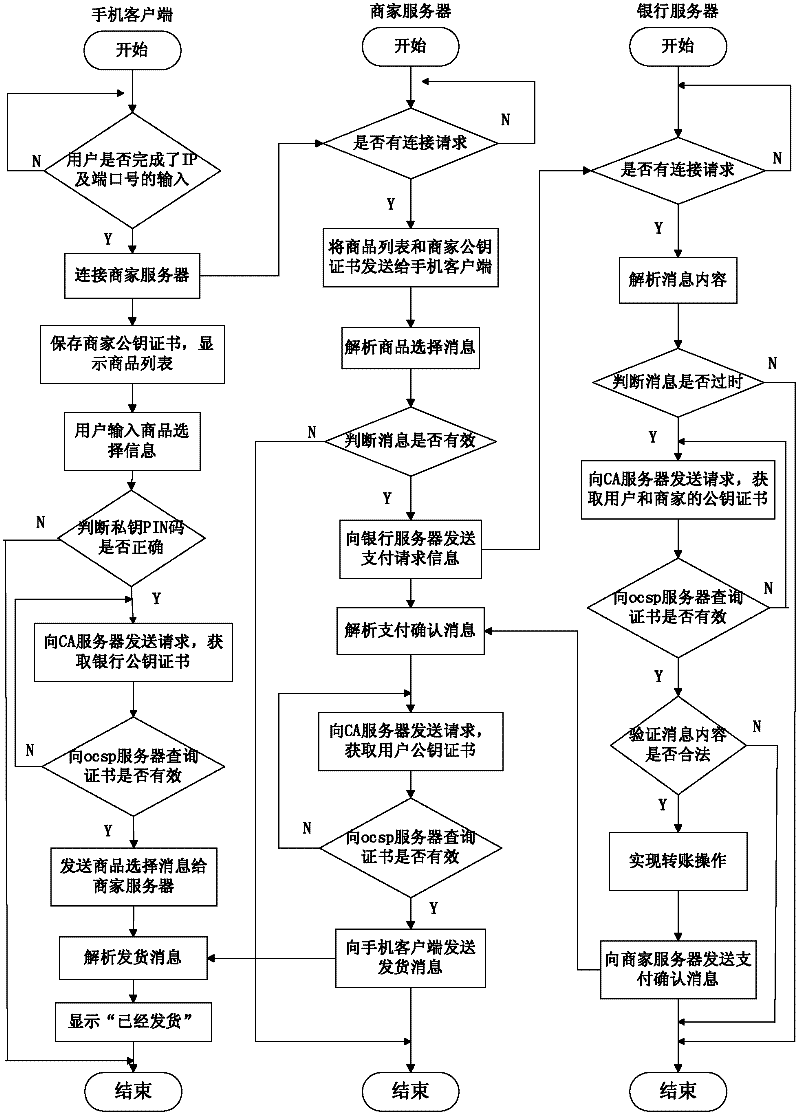
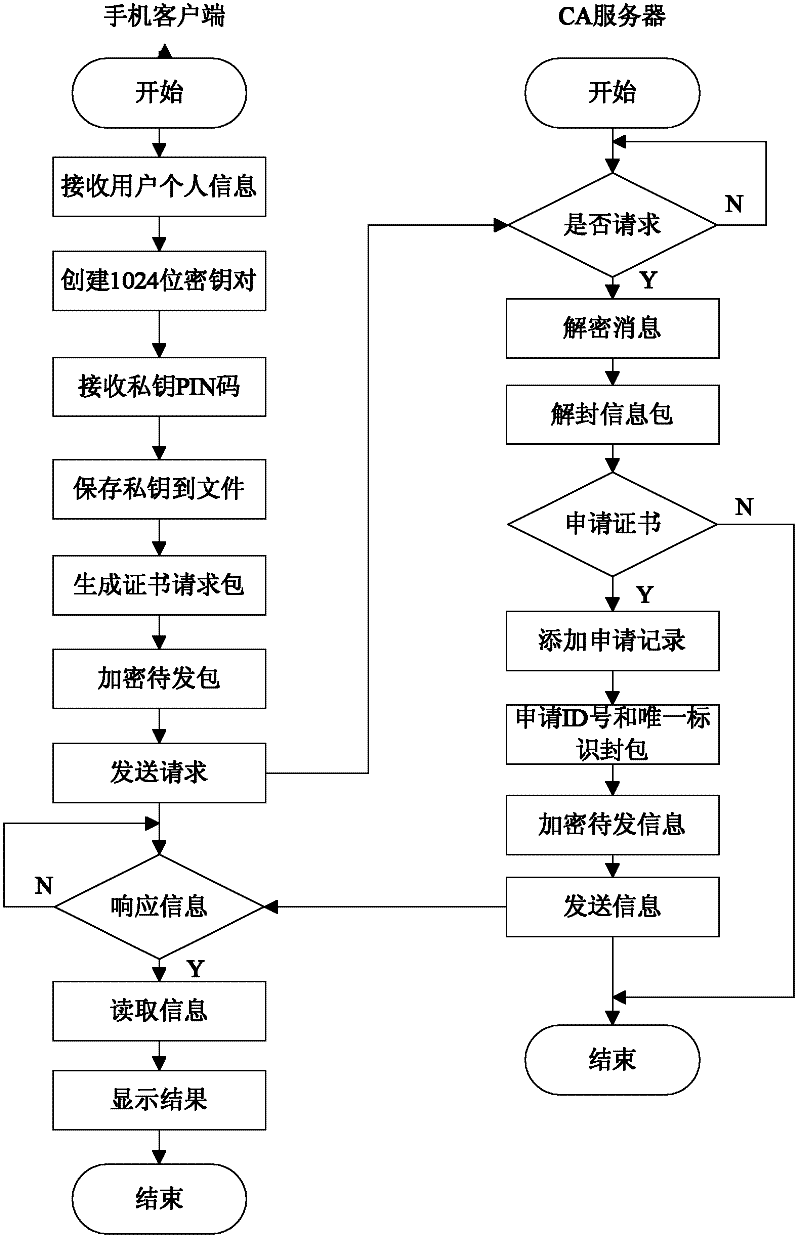
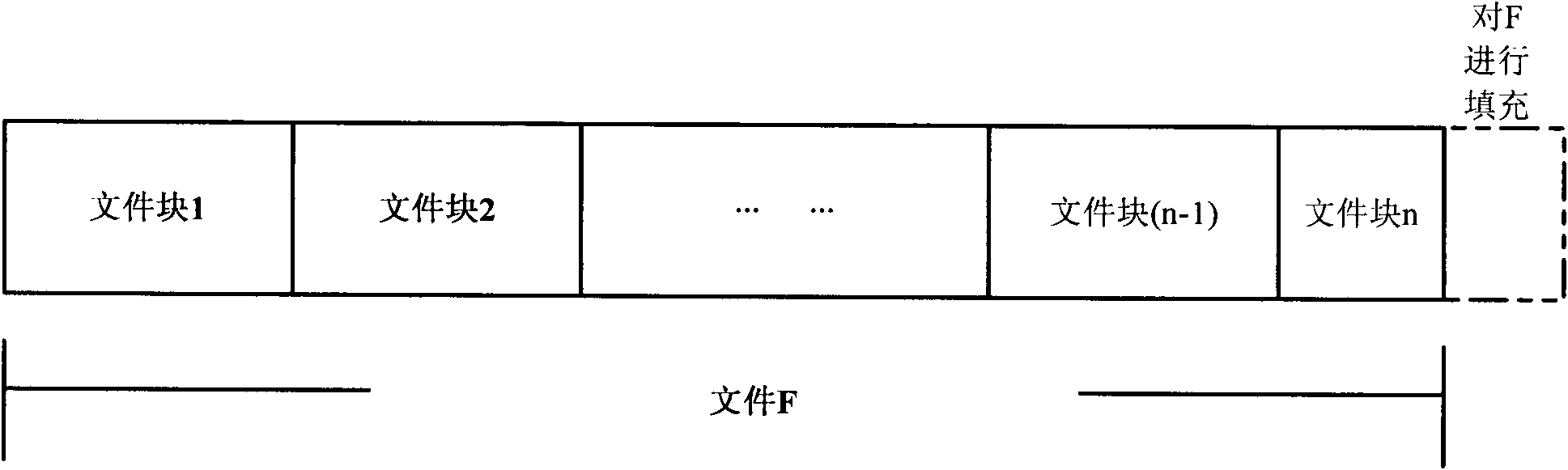
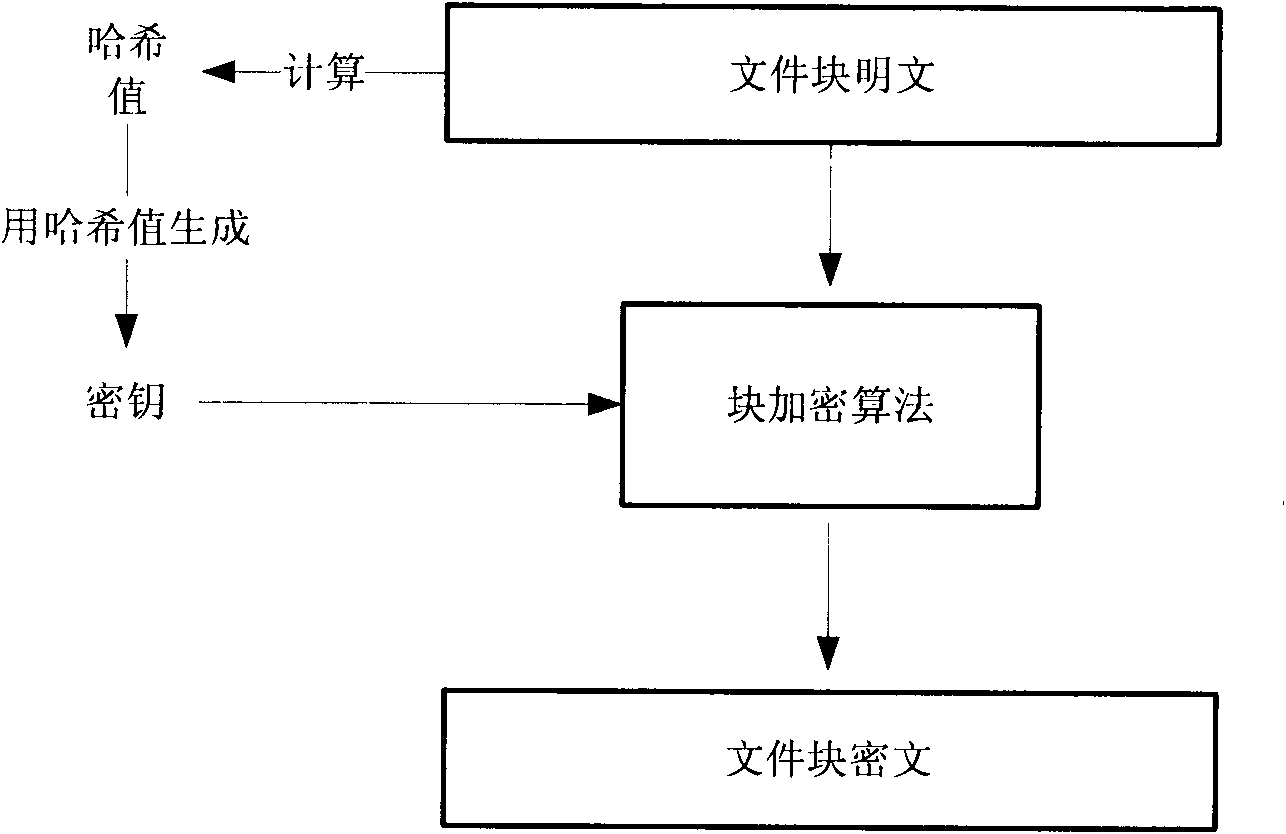
Method for implementing safe storage system in cloud storage environment
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
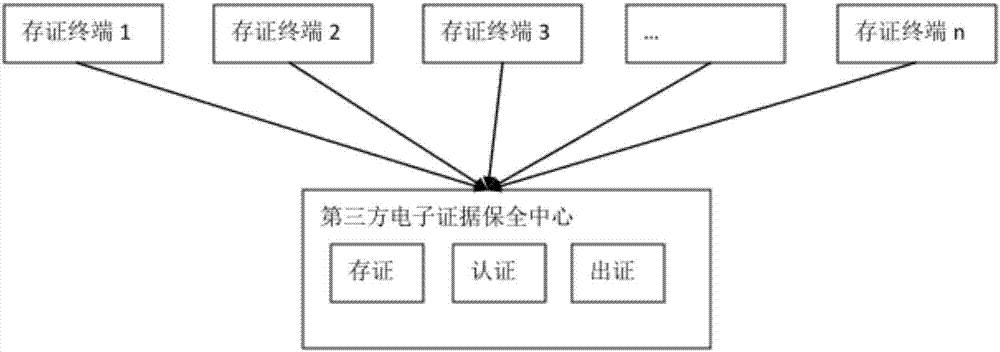
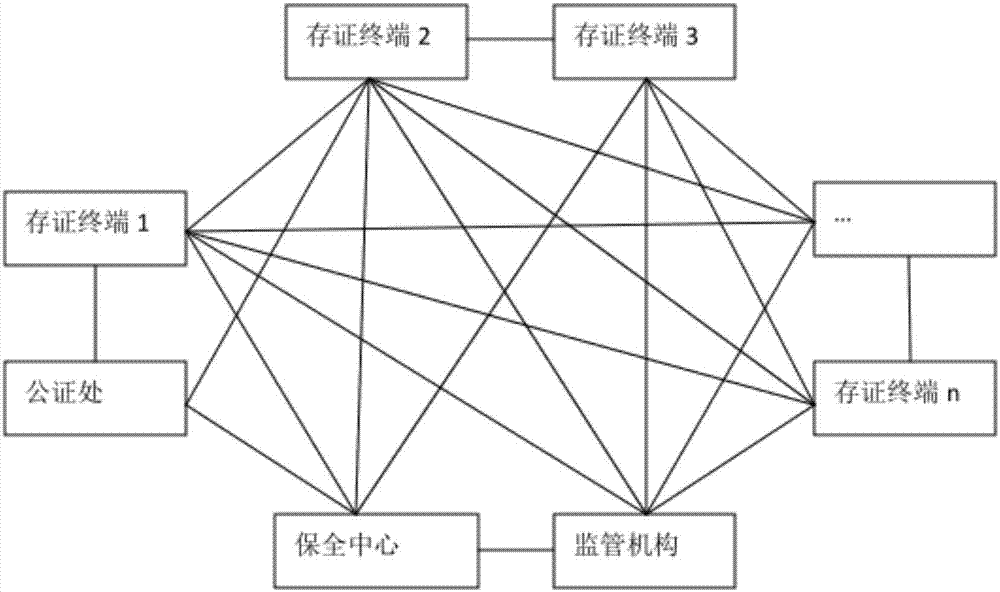
Electronic evidence preservation system and method based on block chain technology
InactiveCN107888375ASolve pain pointsFix bugsEncryption apparatus with shift registers/memoriesDigital data protectionOriginal dataComputer module
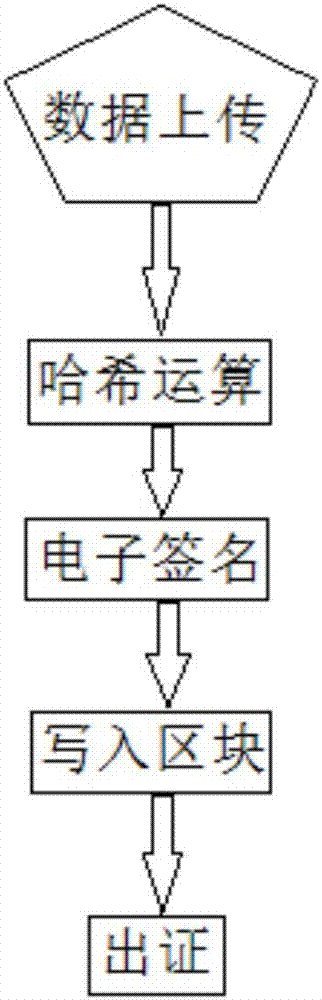
The invention discloses an electronic evidence preservation system and method based on the block chain technology. The preservation system comprises an evidence storage terminal and a block chain network. The evidence storage terminal comprises a hash operation module and an electronic signature module. The electronic data are uploaded to the evidence storage terminal, the evidence storage terminal performs hash operation on the uploaded electronic data to generate unique feature data of a fixed length of original data; then private key signature is performed on the generated data by using theasymmetric encryption technology, and the generated data are sent to the block chain network; and the block chain network performs primary consensus on the uploaded data and packs the uploaded data into blocks, and synchronously sends the blocks to nodes in the network for distributed storage. By establishing an evidence storage alliance by using the block chain technology, the electronic evidence preservation system has the characteristics of digitalized encryption, centralized grading, anti-tampering, data zero loss and so on. Each node in the block chain can preserve a complete block chaindata copy and witness the chain status of the blocks, so that the centralization risk can be effectively avoided.
Owner:SHENZHEN XIEWANG TECH CO LTD
Method for realizing secure network backup system under cloud storage environment
ActiveCN102685148AGuaranteed confidentialityIntegrity guaranteedTransmissionPublic key infrastructureRevision control
The invention relates to a method for realizing a secure network backup system under a cloud storage environment, belonging to the technical field of storage security. The method is characterized in that a system architecture is invented in a trust network of a network backup system under the cloud storage environment, a trust domain is established in a server according to a user requirement, and then identity authentication is performed by using a public key infrastructure (PKI), so that the non-deceptiveness and non-repudiation of a user are guaranteed; a Hash algorithm is used to calculate a Hash value of a file, a key and an advanced encryption standard (AES) algorithm are used for data encryption, and then the ciphertext of the file is uploaded to a file server in a cloud storage area, so that the confidentiality and the completeness of data are guaranteed; a synchronization manner based on a directory tree is used to increase the synchronization efficiency and the confidentiality of the system; a hierarchical key management manner is used to reduce the management burden of the system while guaranteeing data security; a version control function is provided to guarantee the continuity of the version of the file; and encryption key selection manners of many levels of granularity are provided to increase the flexibility of the system.
Owner:TSINGHUA UNIV
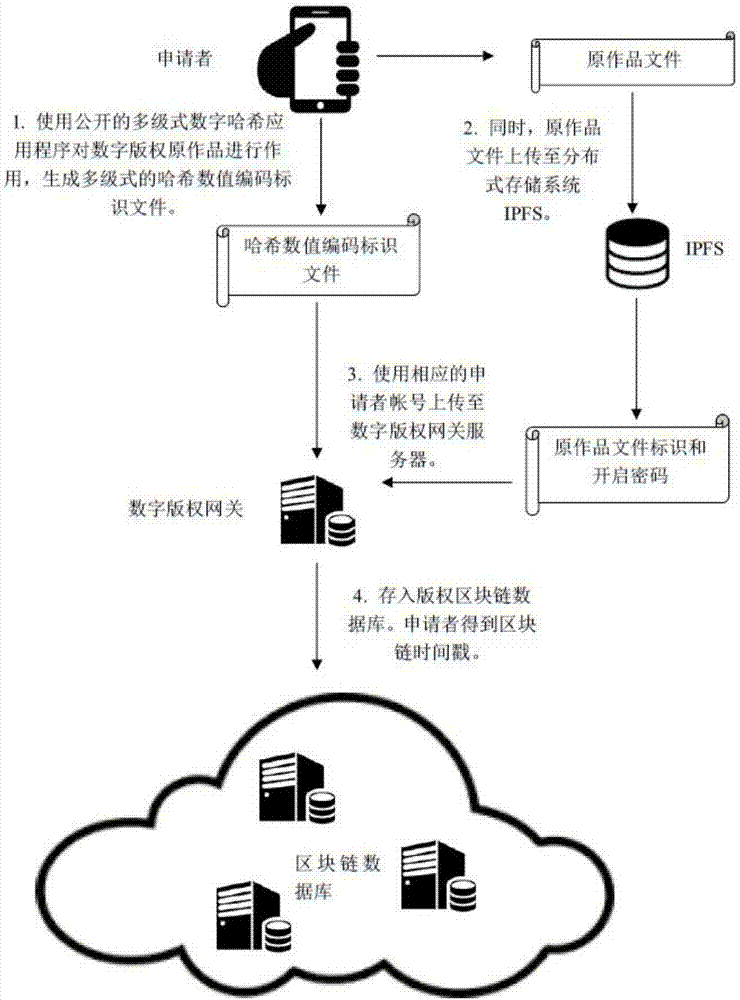
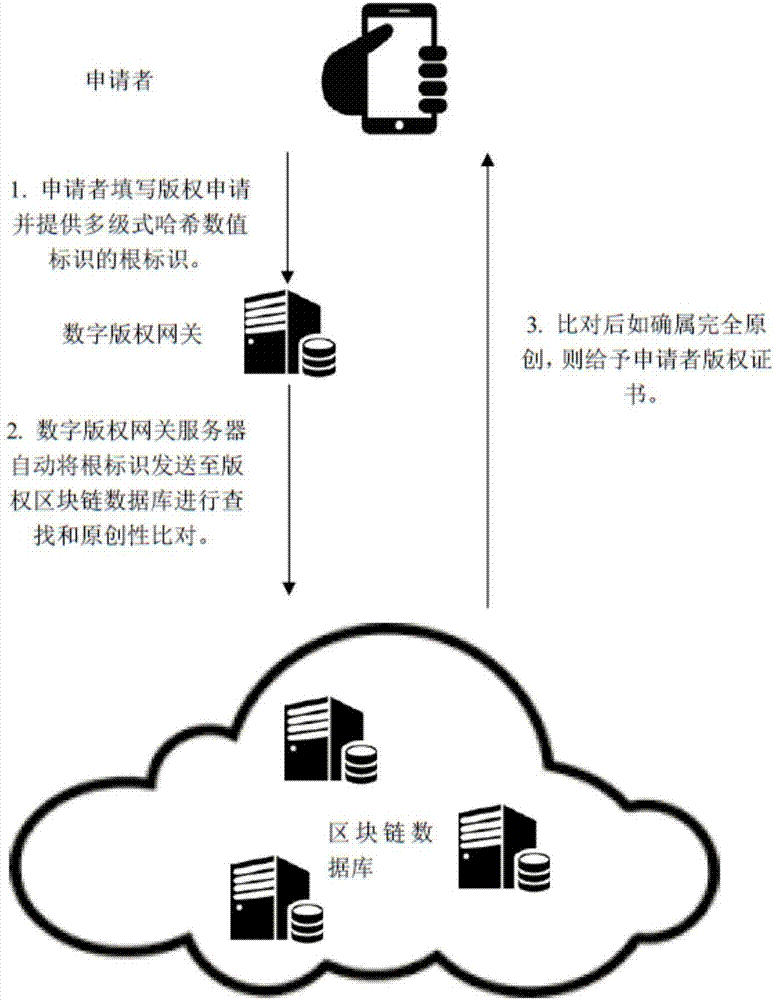
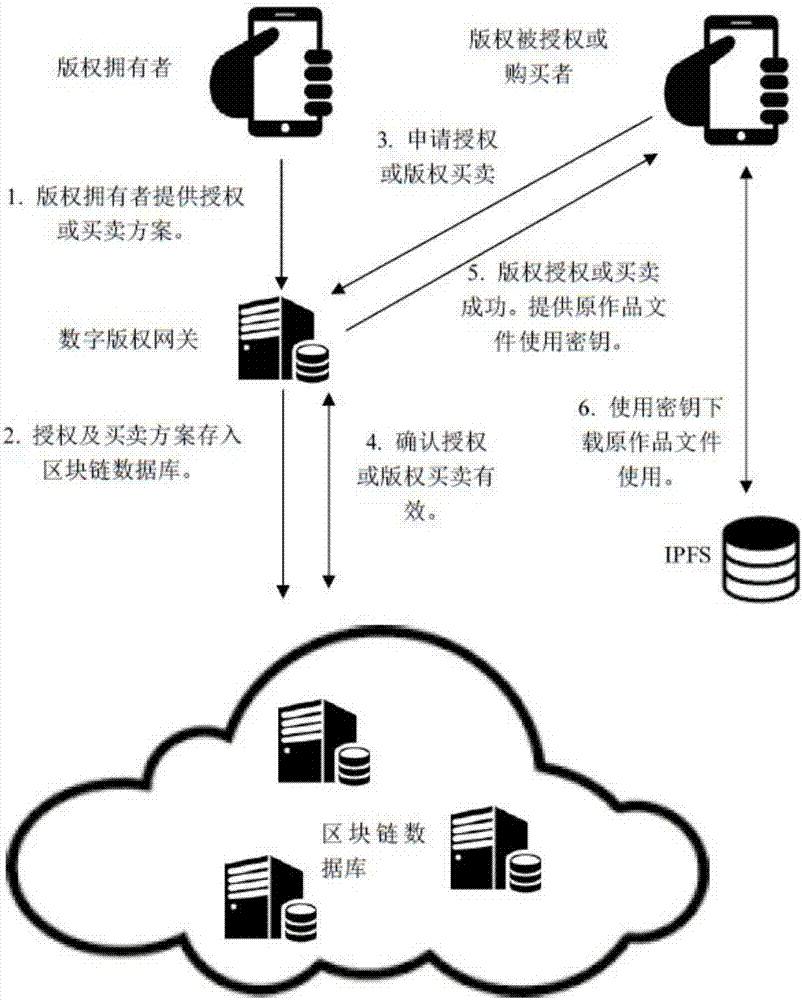
Copyright authorization method based on block chain
InactiveCN107086920AGuaranteed confidentialityShorten the overall cycleUser identity/authority verificationAuthorization certificateFinancial transaction
The invention discloses a copyright authorization method based on a block chain. The method comprises steps of: 1, uploading a work to a client so as to enable the work to become a multi-level hash value code identification document; 2, generating a self identity identifier in a copyright block chain database; 3, enabling a digital copyright gateway server to store the generated multi-level hash value code identification document uploaded by an applicant in self identity into a copyright block chain database; 4, enabling the applicant to fill in a copyright application agreement in detail through a digital copyright application website; 5, enabling the digital copyright application website system to search the duplicate records of various levels of digital identification codes in the block chain database, and to give a copyright authorization conclusion; 6, determining the ownership of copyright according to the copyright authorization conclusion, and sending to the applicant a copyright authorization certificate or an electronic copyright authorization certificate; and 7, enabling two copyright traders to apply for authorization and an authorization transaction at the digital copyright application website system. The method solves the shortcomings of conventional copyright authorization and ensures the high security and reliability of the copyright.
Owner:无锡井通网络科技有限公司
File safe protection system and method thereof
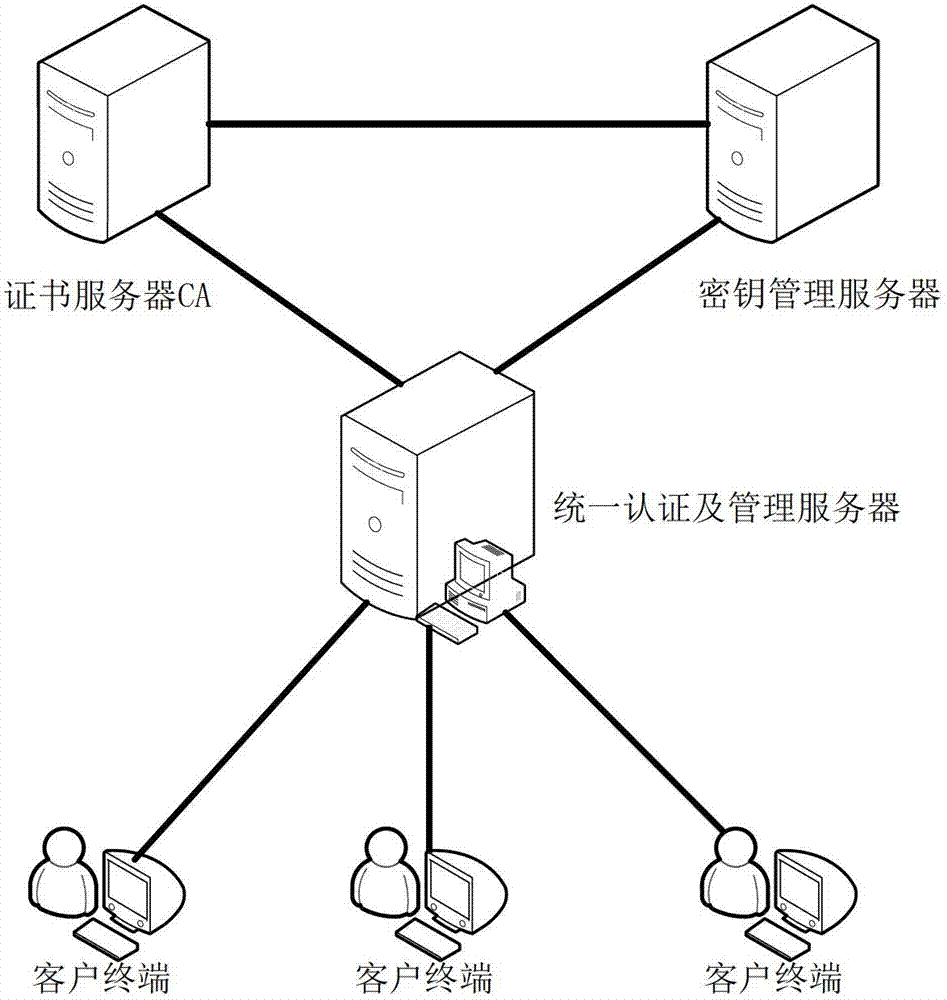
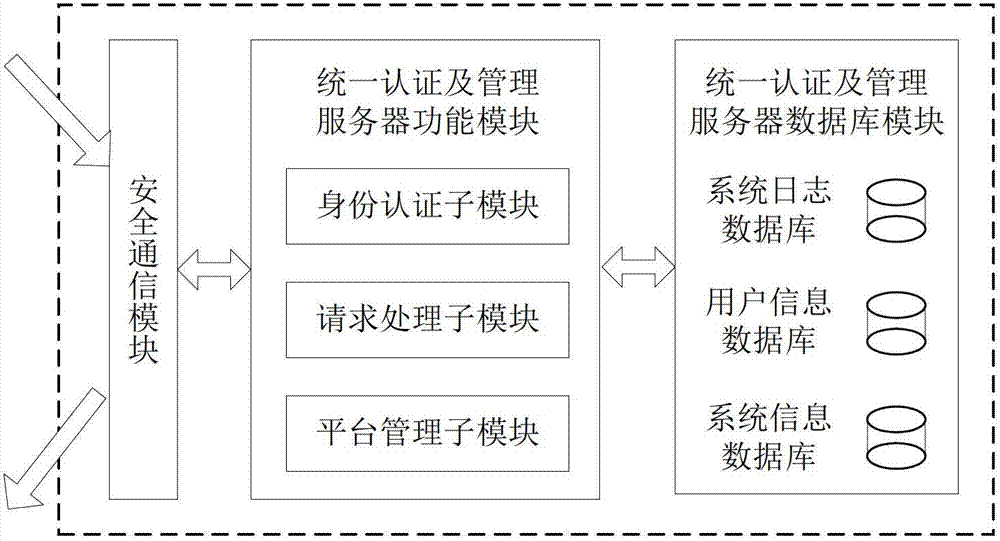
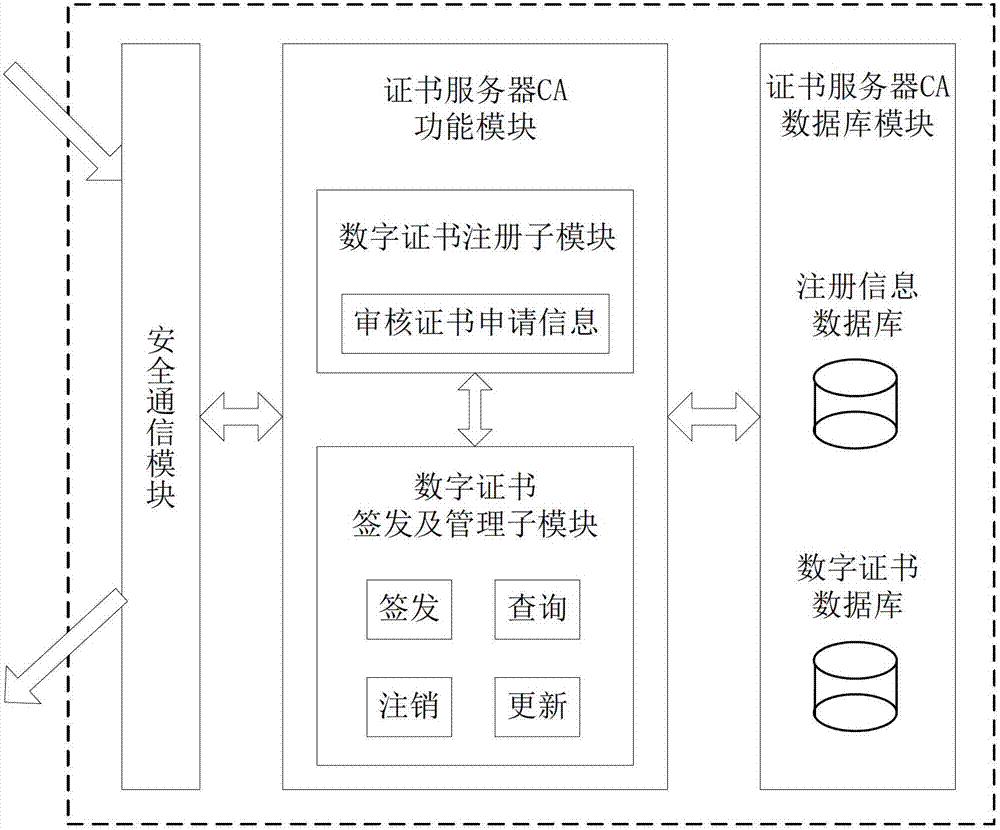
ActiveCN102970299ASimple structureEasy to buildKey distribution for secure communicationUser identity/authority verificationConfidentialityComputer terminal
The invention discloses a file safe protection system and a method, which mainly solves the problems of network illegal invasion, information stealing and tamping, impersonation and weak deny resistance in the conventional information system. The file safe protection system consists of a unified authentication and management server, a certificate server CA, a secret key management server and a client terminal; the unified authentication and management server is used as a middle node and is used for processing or transmitting a service request sent by the client terminal; the certificate server CA processes a certificate service request of the client terminal and provides basic support for identification; and the secret key management server processes the secrete key service requests of the client terminal and the certificate server CA, and is used for encrypting and decrypting a file for the client terminal and providing parameter support for a digital certificate signed by the certificate server CA. With the adoption of the file safe protection system and method provided by the invention, identification, confidentiality, integration and non-repudiation services can be provided; and the file can be safely protected in transmission, storage, sharing and access processes.
Owner:XIDIAN UNIV
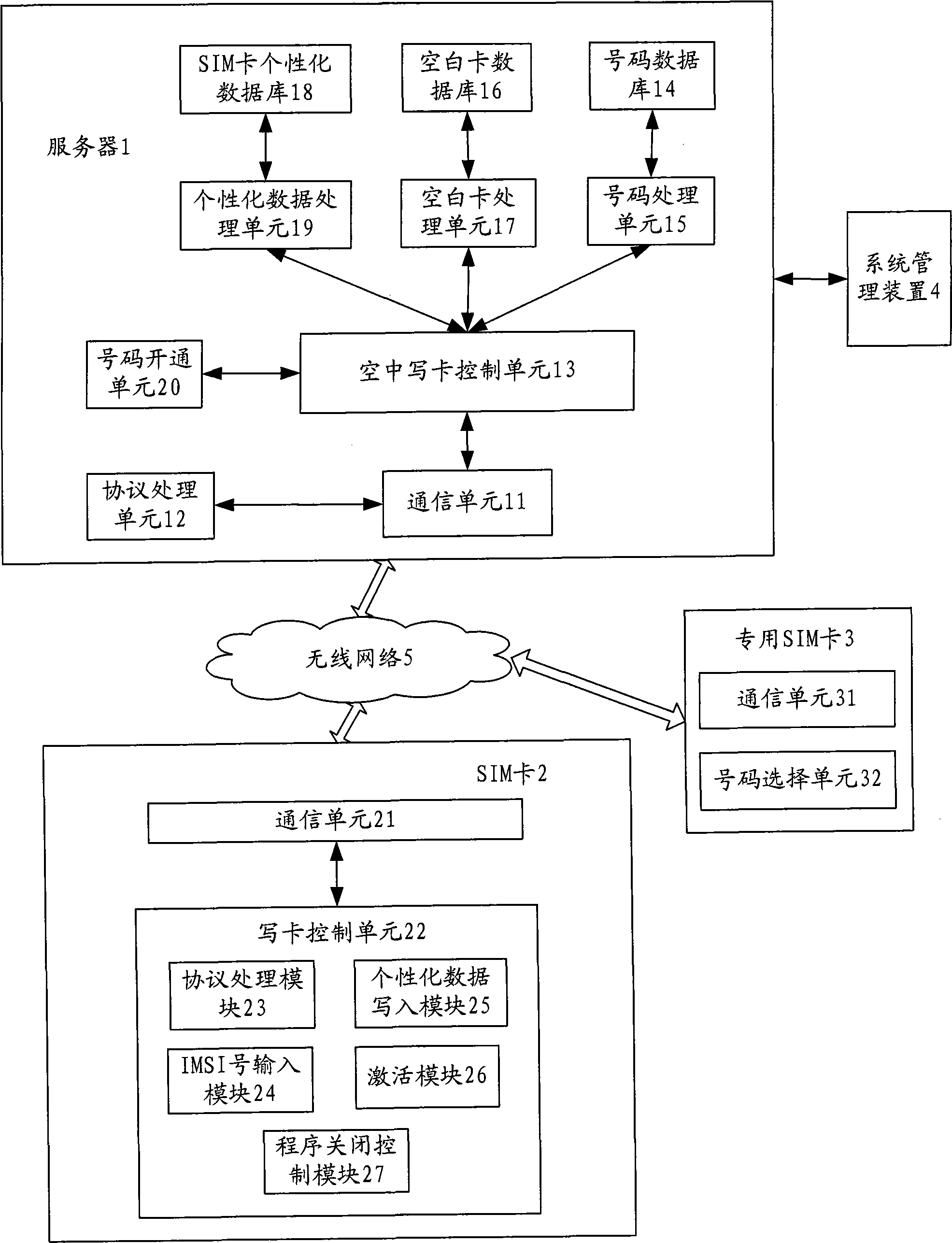
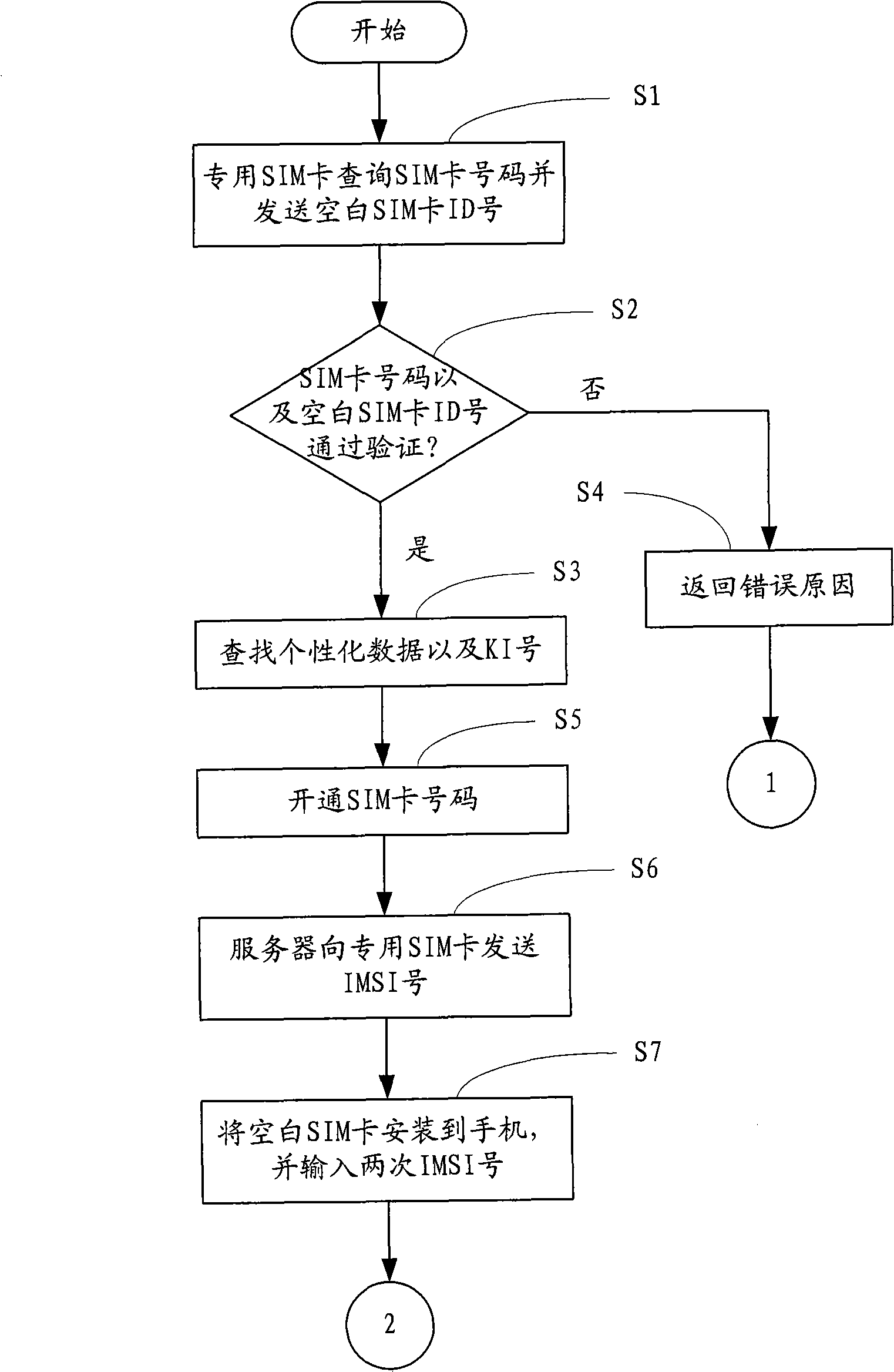
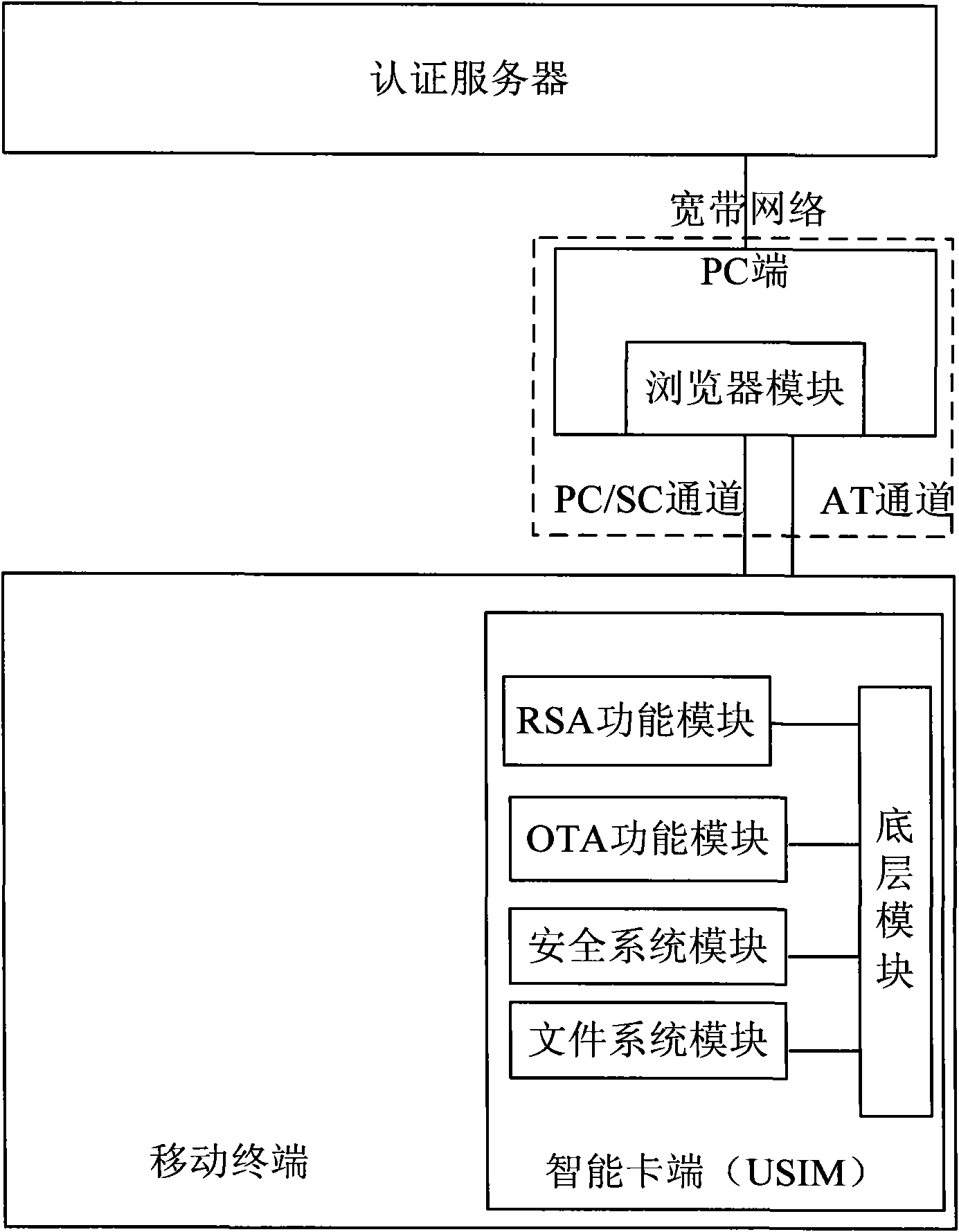
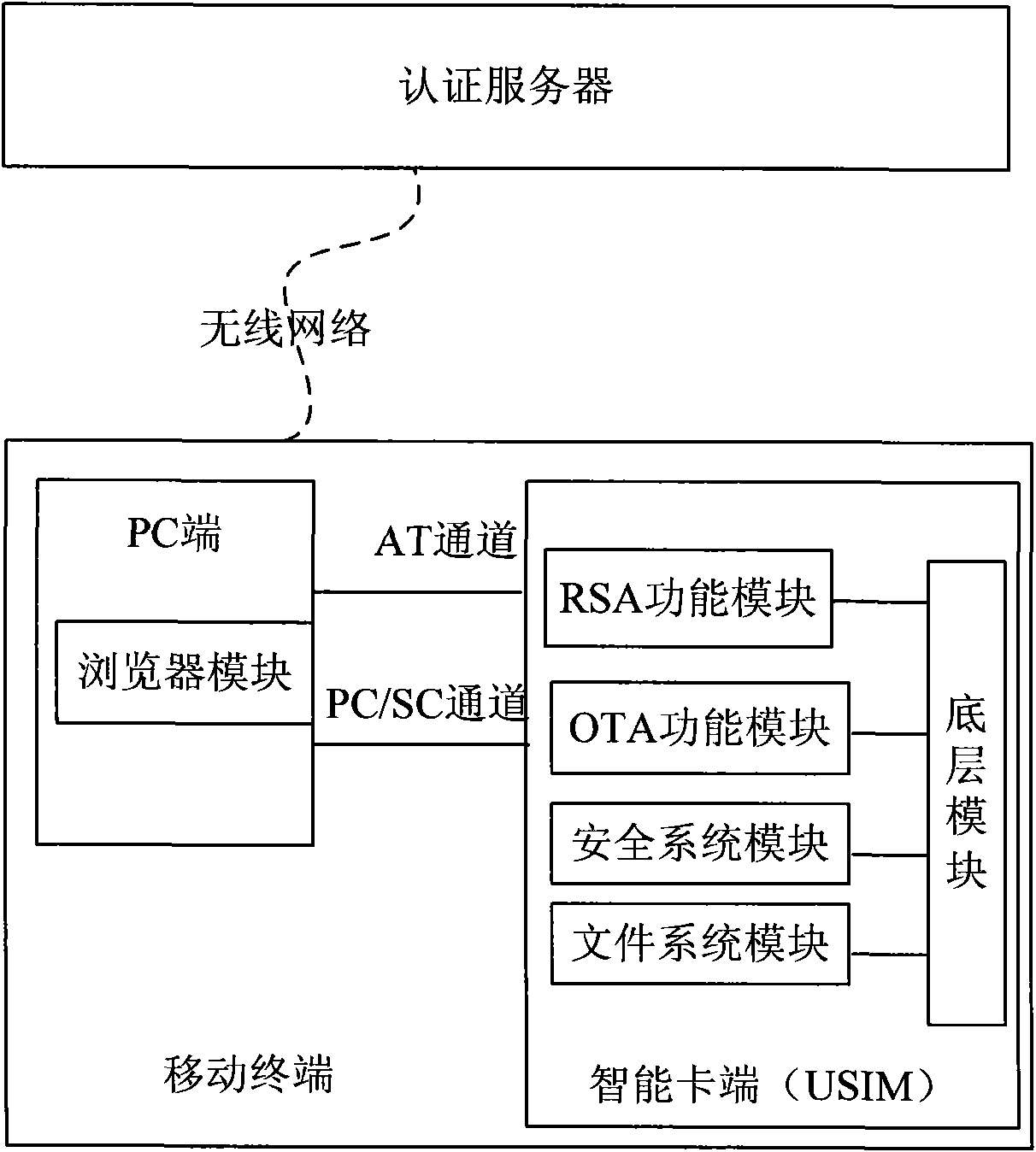
A telecom intelligent card, an air card writing system and an air card writing method
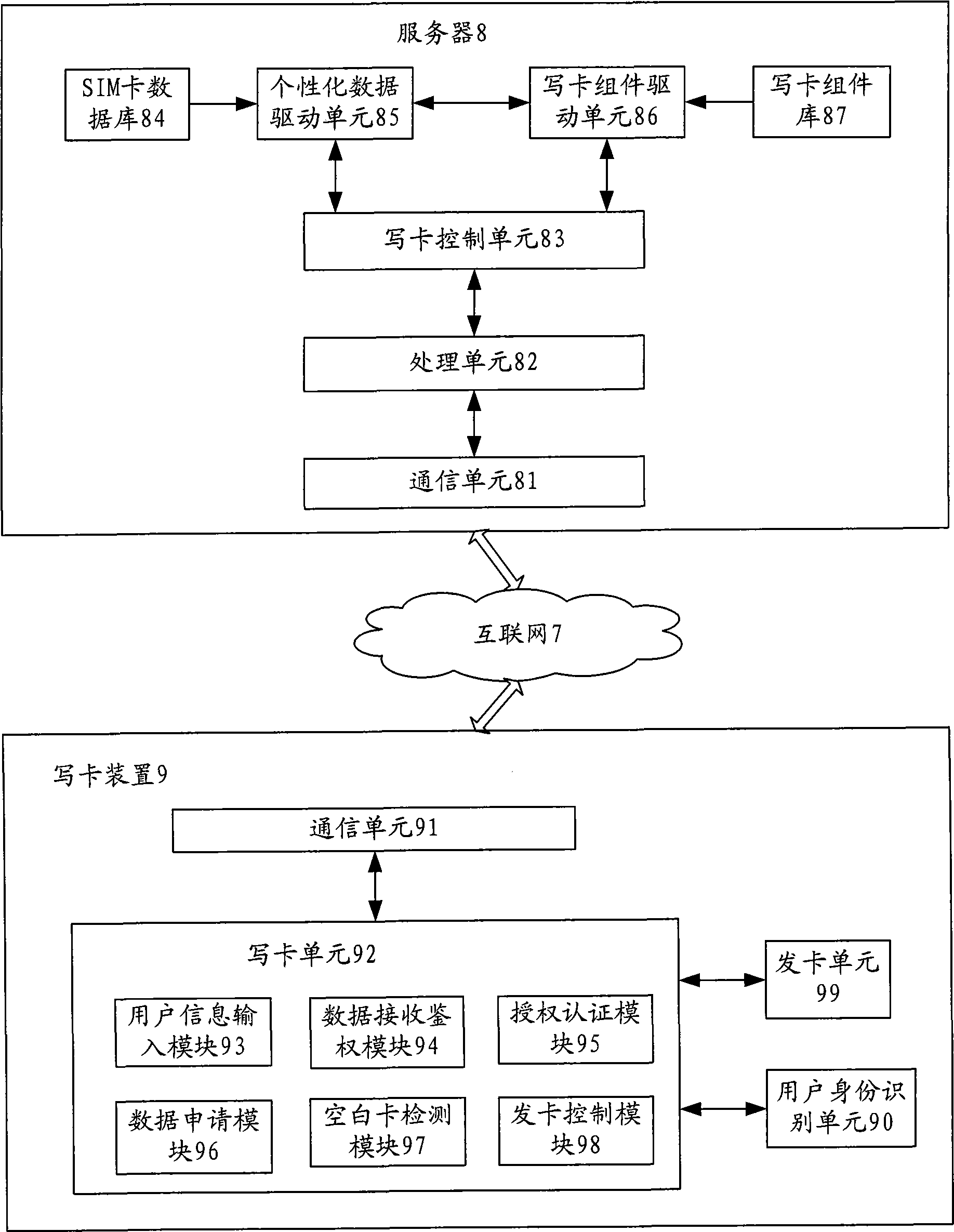
ActiveCN101547437ARealize write card operationGuaranteed confidentialityTransmissionSecurity arrangementPersonalizationSmart card
The invention provides a telecom intelligent card, an air card writing system and an air card writing method. The telecom intelligent card pre-writes KI numbers and is provided with an IMSI number input module which is used for inputting IMSI numbers of the intelligent card, and also an individualized data writing module which receives and writes individualized data of the intelligent card. The card writing method includes the following steps: users send numbers needed to be opened and ID numbers of blank telecom intelligent cards to a server through a client service; the server obtains individualized data with IMSI numbers after testing the numbers to pre-open numbers and send the IMSI numbers to the client device; users install the blank telecom intelligent card to a mobile phone and input the IMSI numbers; the sever sends the individualized data to the blank telecom intelligent card which writes the individualized data. The card, card writing system and method can realize the air card writing in remote areas; the running and maintenance cost of the card writing system is lower, thus being good for the popularization and application of the air card writing system.
Owner:EASTCOMPEACE TECH
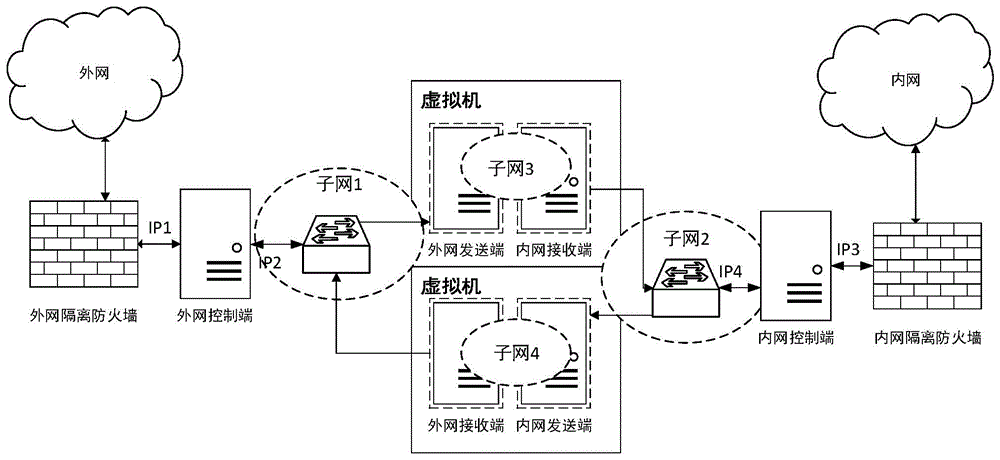
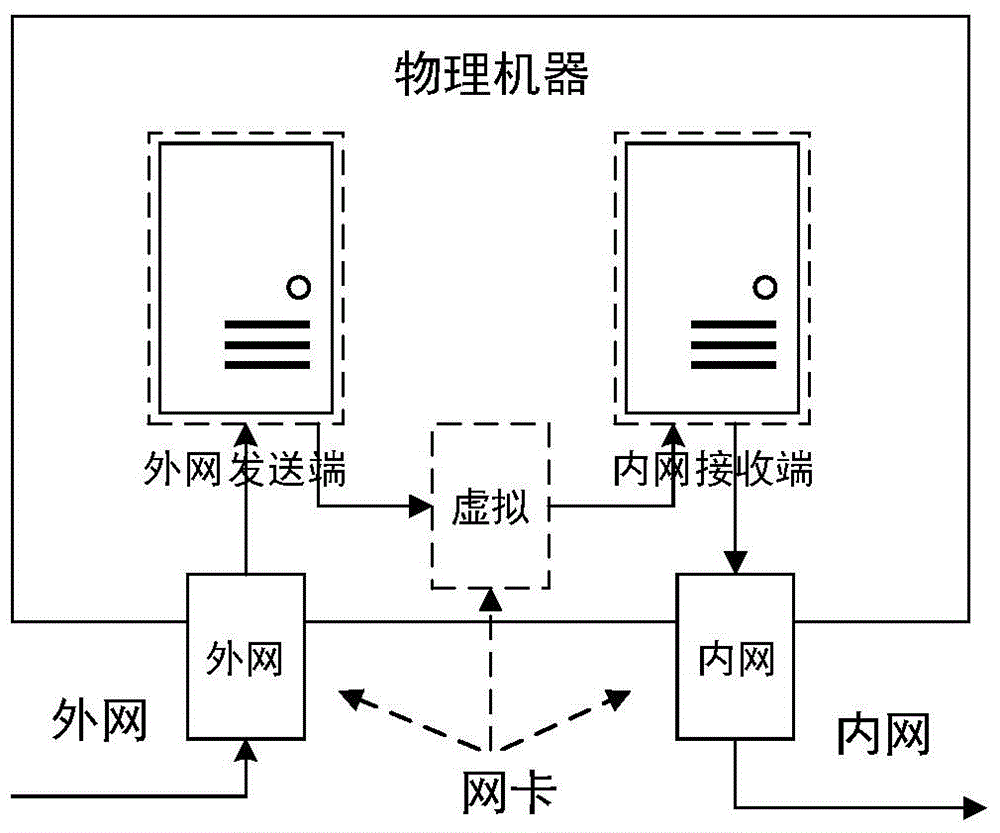
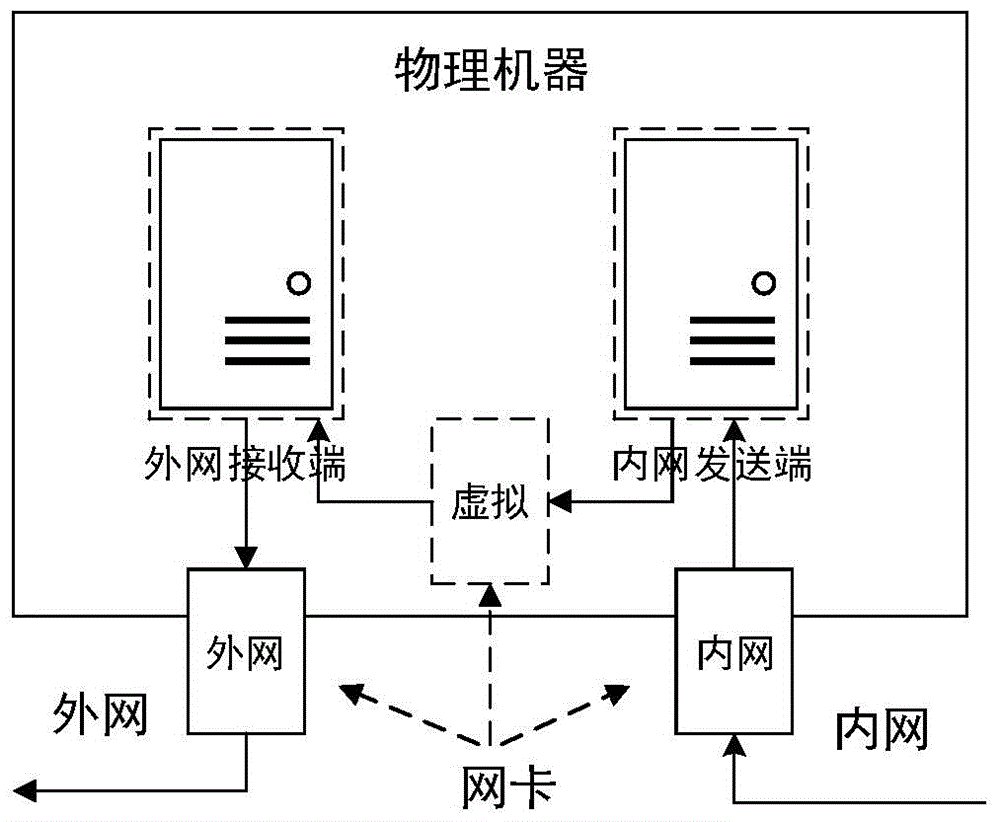
Network safety isolation file transmission control method
InactiveCN104363221AEnsure safetyKeep Content SafeSecuring communicationComputer hardwareConfidentiality
The invention relates to a safety isolation file transmission control method, in particular to a file transmission control method between taxation network safety isolation systems. A transmission control system comprises an external network isolation firewall, an external network control end, an external network transmitting end, an external network receiving end, an internal network transmitting end, an internal network receiving end, an internal network control end and an internal network isolation firewall. A computer system, a virtual machine system and the isolation firewalls are combined to achieved a relatively universal safety data transmission manner, safe and reliable bidirectional data transmission is achieved by the control method with a special safety protocol, confidentiality, completeness and non-repudiation during information transmission are achieved by safety techniques such as data encryption, digital signatures and information authentication codes, data exchanging performance is increased while safety of internal and external network systems is guaranteed, and the whole system can work reliably and stably.
Owner:QINGDAO WEIZHIHUI INFORMATION
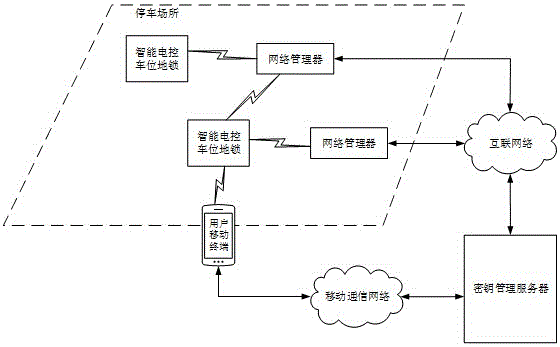
Appointment service system for shared parking stalls
ActiveCN105931485AReduce deliveryGood exclusive securityIndication of parksing free spacesIndividual entry/exit registersComputer terminalShared parking
The invention provides an appointment service system for shared parking stalls. A mobile terminal of a user applies for an electronic key for an intelligent electric-control parking stall ground lock of certain shared parking stall; a secret key management server establishes an unlocking pairing relation between user identification information of the user mobile terminal and parking stall identification information of the corresponding intelligent electric-control parking stall ground lock; according to the unlocking pairing relation, the electronic key of the corresponding intelligent electric-control parking stall ground lock is generated and returned to the user mobile terminal; and the electronic key is used to unlock the intelligent electric-control parking stall ground lock. Namely, the right of using the shared parking stall is handed over remotely, the electronic key is used for unlocking to identify and verify individual difference among users, remote handover of the right of using the shared parking stall is highly exclusive safe, the shared parking stalls can be used temporarily and rapidly, and the technical problem in applying and popularizing vacant parking stall resource can be solved.
Owner:CHONGQING JINOU SCI & TECH DEV
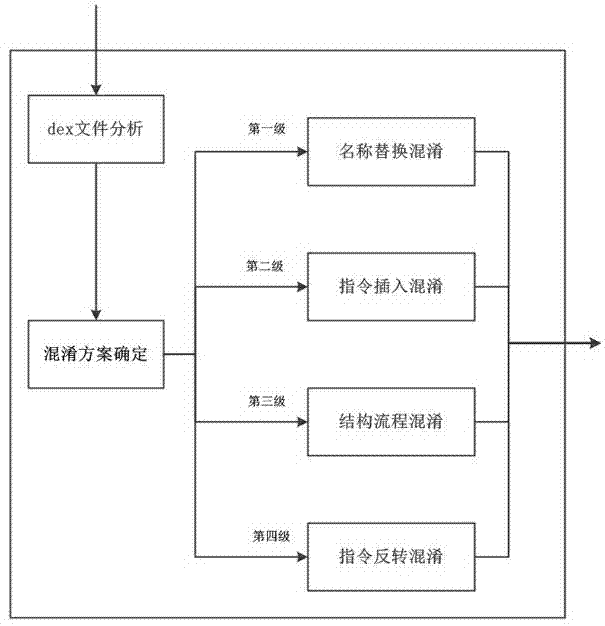
Deep code obfuscation method for Android system applications
ActiveCN103544414AImprove securityGuaranteed confidentialityProgram/content distribution protectionBase codeObfuscation
The invention discloses a deep code obfuscation method for Android system applications. The method uses graded code obfuscation. The graded code obfuscation includes first-grade name replacement obfuscation, second-grade command insertion obfuscation, third-grade structure process obfuscation, and fourth-grade command inversion obfuscation. For an application installation package developed and to be released, the method includes: extracting a DEX file, analyzing the file structure, a Dalvik instruction set and a program running process, determining an obfuscation scheme of corresponding grade or multiple combined grades to perform deep code obfuscation on the DEX file, generating a new DEX file, and re-packaging the file. The deep code obfuscation method according to the technical scheme has the advantages that the limitations of the traditional source-code-based code obfuscation scheme can be broken through, the DEX executable files are directly obfuscated in terms of element name, instruction and process structure, applications can be effectively protected from illegal cracking or inversion, safety of applications in the Android system is improved, and confidentiality of business software is guaranteed.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
Remote mobile payment system based on digital certificate and payment method
InactiveCN102609841AGuaranteed confidentialityProtect transaction detailsProtocol authorisationConfidentialityDigital signature
The invention relates to a remote mobile payment system based on a digital certificate and a payment method and belongs to the technical field of mobile payment. According to the invention, the digital certificate is used for binding an identity of a user with a public key of the user and the problem of difficulty in managing a secret key during a transaction process is solved. All communication information is encrypted by using the secret key, so that the confidentiality of the transaction information is ensured, the transaction details of the user are protected and the privacy is prevented from being revealed. Meanwhile, each piece of transaction information is digitally signed by using a private key of a sender; as long as a receiver successfully verifies the signature by using the public key of the sender, the sender cannot deny the performed operation of sending the information, so that the undeniable property of information is achieved; an abstract value of the information is calculated for each piece of transaction information; and the receiver firstly compares the abstract value of the information with the received information, so as to judge if the information is distorted and ensure the completeness of the information.
Owner:何文秀
Safety metadata management method based on integrality checking
InactiveCN101976322AGuaranteed confidentialityWarranty requirementsDigital data protectionSpecial data processing applicationsMetadata managementData management
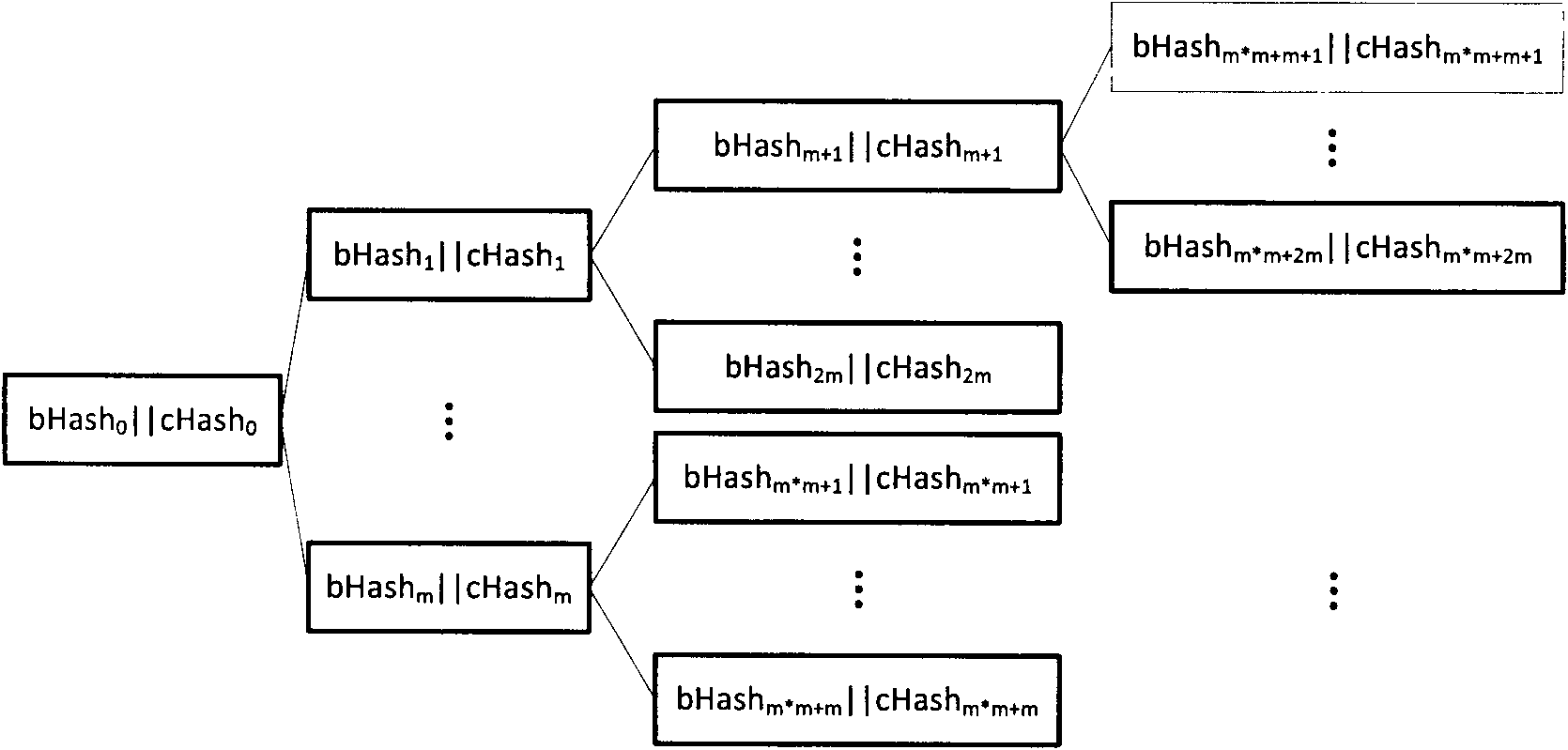
The invention relates to a safety metadata management method based on integrality checking, belonging to the field of storage safety. The method is characterized in that a self encryption technology for file data is used at a client to encrypt the file data, thereby improving the storage efficiency; a 64-heap hash tree is used at a safety metadata management server end to maintain the hash value of a file block, thereby providing integrality protection on the hash value of the file data block and realizing the high-efficiency verification on the user's access to file and the high-efficiency data updating; and simultaneously a root hash virtual linked list technology is used, thereby ensuring the integrality of root hash values of multiple 64-heap hash trees belonging to one file and supporting the user's concurrent access to the file to a certain extent.
Owner:TSINGHUA UNIV
Network authentication and key allocation method across secure domains
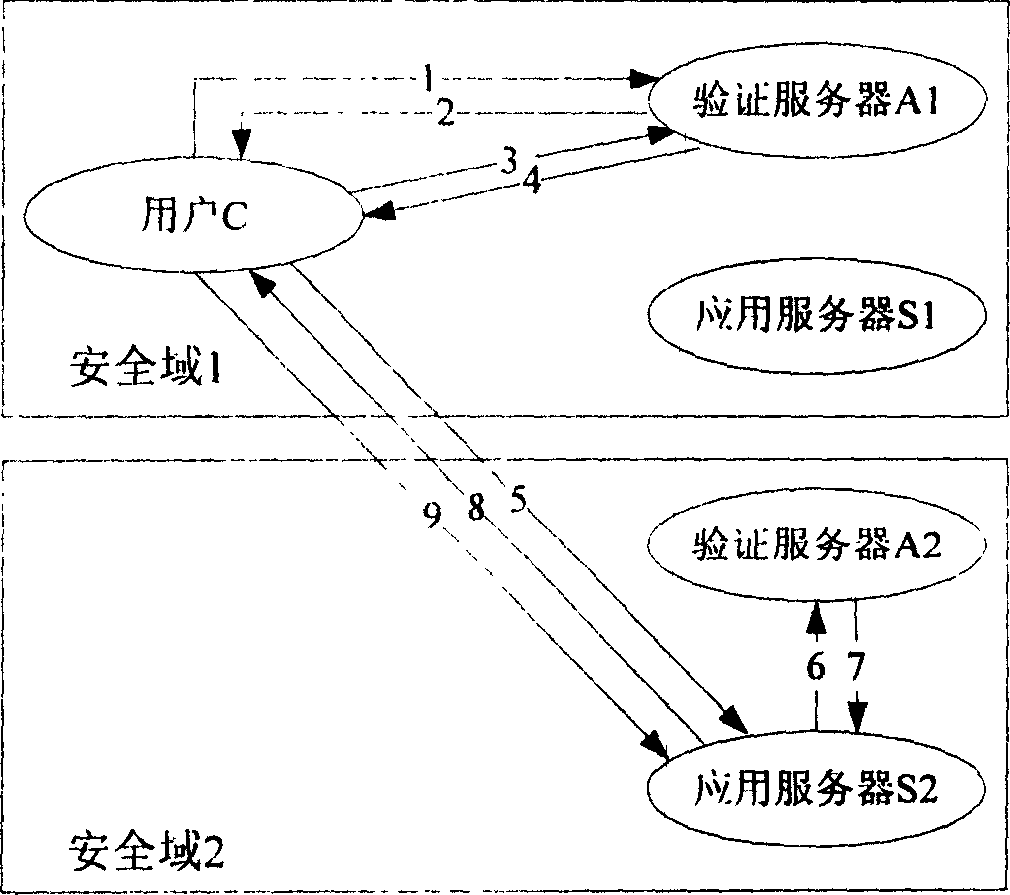
InactiveCN1805341AOvercoming the shortcomings of decentralized authenticationEnsure safetyKey distribution for secure communicationUser identity/authority verificationApplication serverWeb authentication
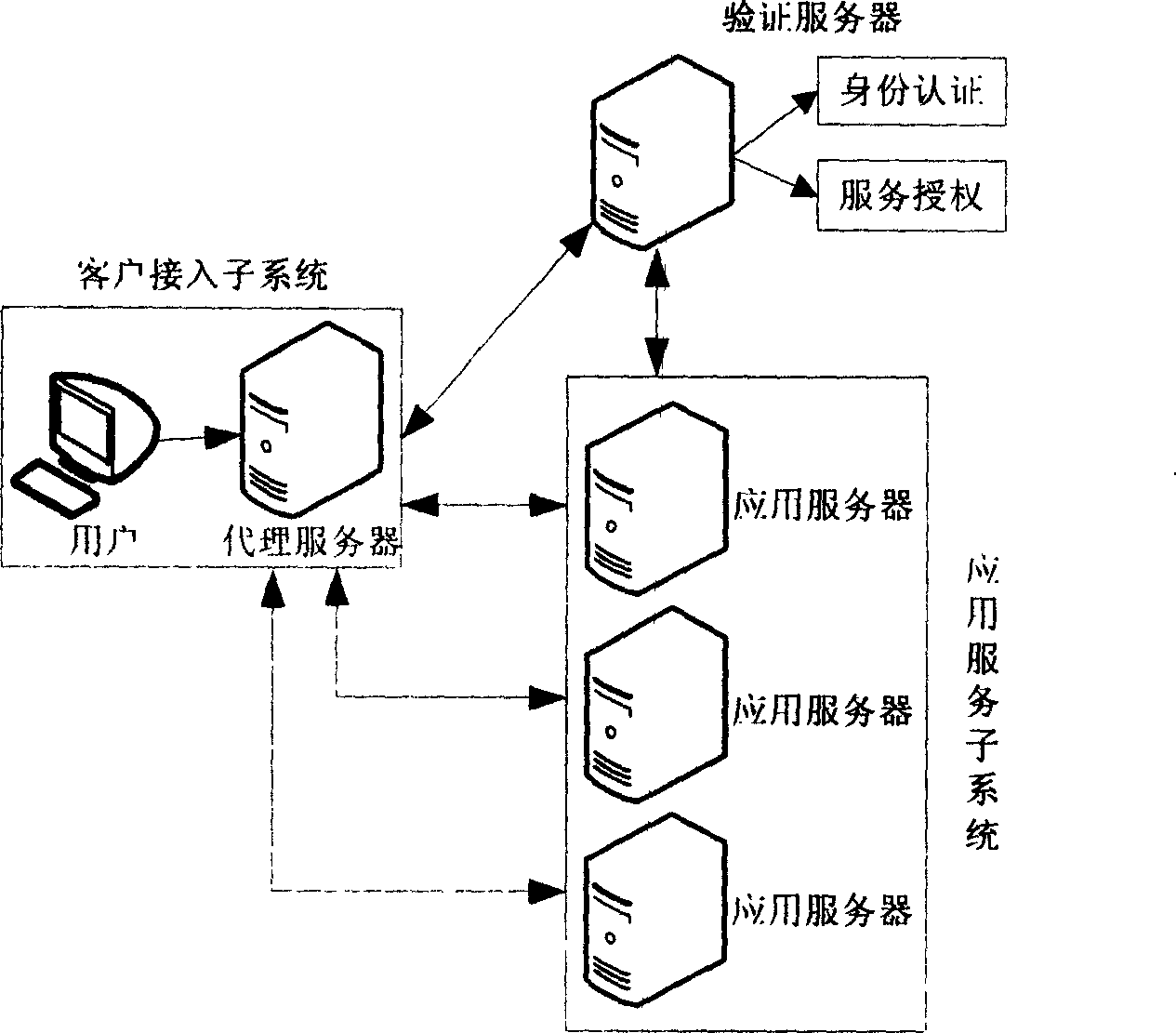
The invention relates to a network authentication and key distribution method. based on the single point log-in, connecting one authentication server and several application servers into each safety field; distributing the authentication and keys according to the demand of application server when the user accesses into different safety fields. First, user processes the identification authentication in said safety field to attain a server card communicating with the application server in another safety field; then the user at the accessed safety field validates the card to attain the service connecting with the application server; at last, the user processes the identification authentication on said application server. The inventive system comprises a client access subsystem, an application service subsystem and a validate server which can complete the user identification authentication and the service authorization. The invention has simple process, with high safety and effect.
Owner:XIDIAN UNIV
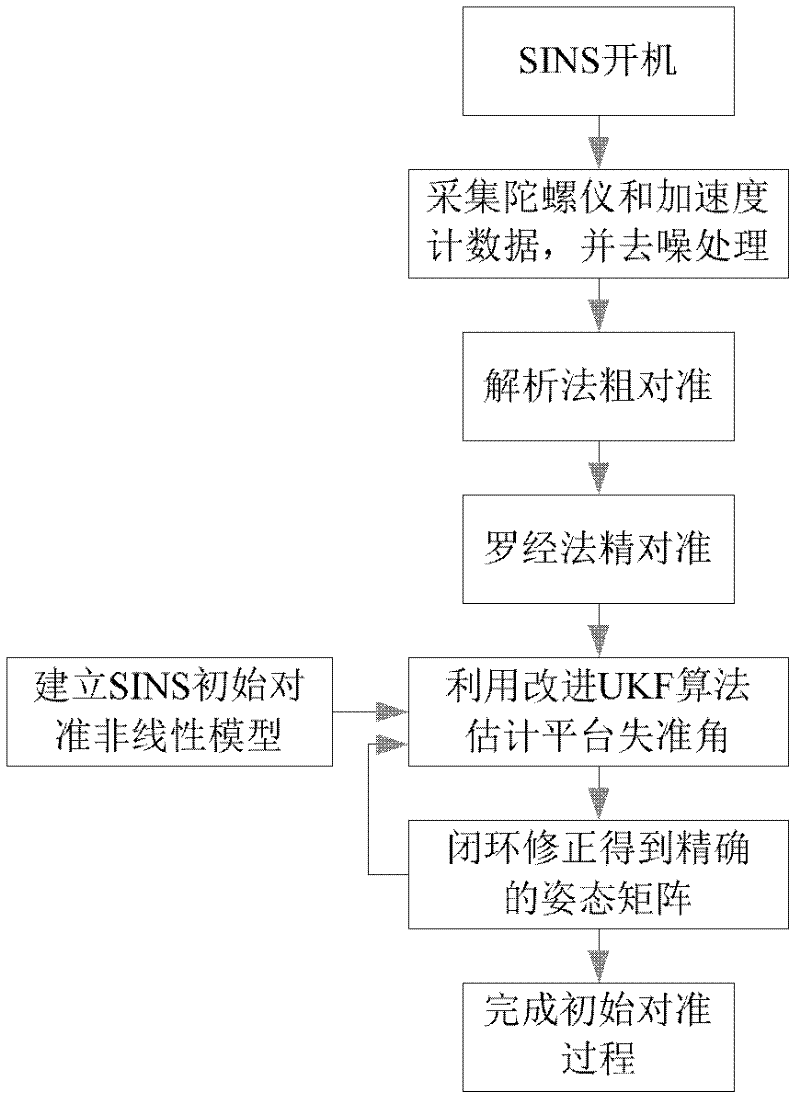
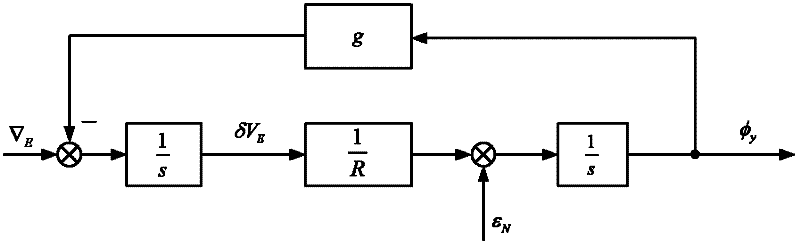
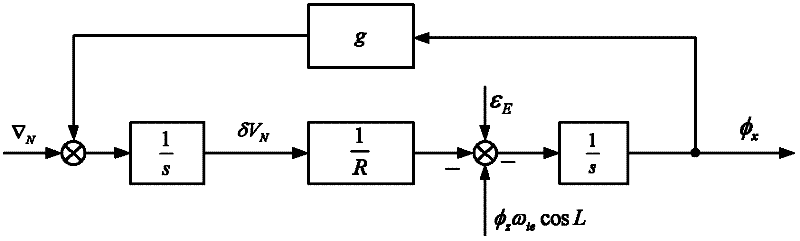
Non-linear alignment method of strapdown inertial navigation system
ActiveCN102519460AEnsure safetyGuaranteed confidentialityNavigational calculation instrumentsNavigation by speed/acceleration measurementsAccelerometerComputation complexity
A non-linear alignment method of a strapdown inertial navigation system comprises the following steps of: acquiring data of an accelerometer and a fiber gyroscope of the fiber strapdown inertial navigation system and carrying out denoise processing, realizing coarse alignment and fine alignment processes by the utilization of an analysis method and a compass method, establishing a quaternion-based strapdown inertial navigation system non-linear error model under the condition that attitude angle and azimuth angle are both large misalignment angles, establishing an observation model with speed as observed quantity, carrying out iterative and filter estimation by the use of an improved UKF algorithm on the basis of the model so as to obtain the misaligned angle of the platform, continuously carrying out closed-loop feedback and correcting attitude matrix of the strapdown inertia system in the previous period, so as to accurately complete the initial alignment process. The method can be used to guarantee safety and confidentiality of the initial alignment without the utilization of other sensor information. By the introduction of the quaternion error based non-linear system error model, linearization is not required to guarantee the precision of the model. Computational complexity is reduced, and filtering is carried out on the established non-linear system so as to complete fine alignment.
Owner:SOUTHEAST UNIV
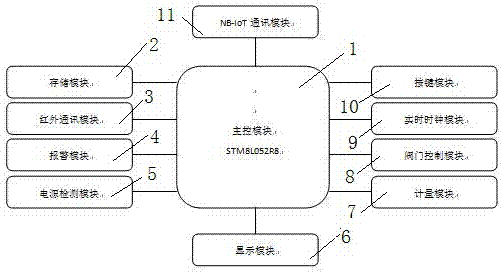
Internet of things gas meter communication system based on NB-IoT communication technology and internet of things gas meter communication method thereof
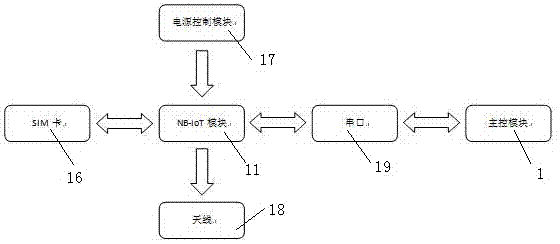
ActiveCN107390569ARealize remote monitoringWith external network access abilityProgramme controlTransmission systemsKey pressingReal-time clock
The invention discloses an internet of things gas meter communication system based on the NB-IoT communication technology and an internet of things gas meter communication method thereof. The system comprises a master control module, a storage module, an infrared communication module, an alarm module, a power supply detection module, a display module, a metering module, a valve control module, a real-time clock module, a key module and an NB-IoT module. The master control module is simultaneously connected with all other modules. Wireless network data transmission is realized by using the NB-IoT module, the system has the extranet access capacity, remote monitoring of the gas meter metering, valve and meter state data can be realized and the objectives of remote meter reading, tiered gas price real-time adjustment, remote valve control and big data collection and analysis can be realized without manual visiting for meter reading.
Owner:GOLDCARD HIGH TECH
Consumable chip and a communication method thereof, and system and method for communication between consumable chip and imaging device
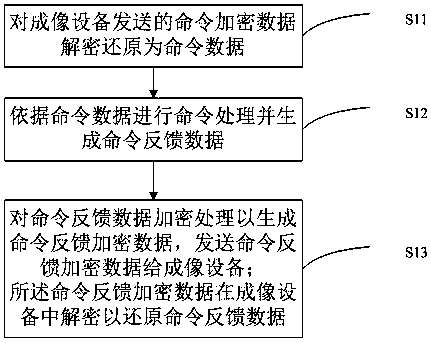
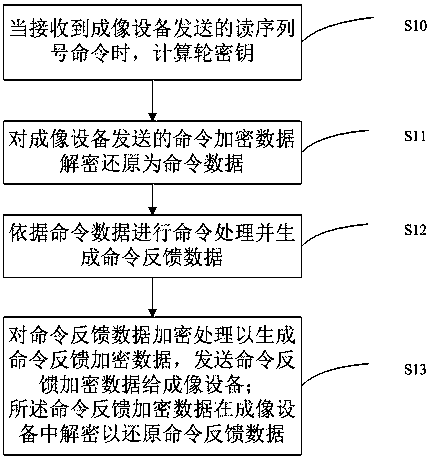
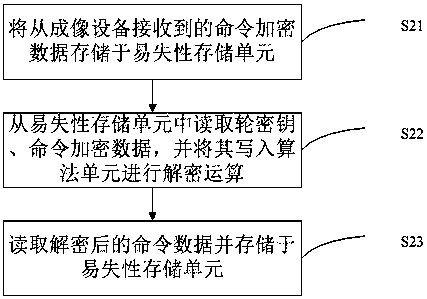
ActiveCN108819486AAvoid crackingImprove safety and reliabilityDigital data protectionInternal/peripheral component protectionComputer hardwareReverse analysis
The invention, which belongs to the technical field of printer consumables, provides a consumable chip and a communication method thereof, and a system and method for communication between a consumable chip and an imaging device. The communication method comprises: command encrypted data sent by an imaging device are decrypted and restored into command data; command processing is carried out basedon the command data and command feedback data are generated; and the command feedback data are encrypted to generate command feedback encrypted data and the command feedback encrypted data are sent to the imaging device, wherein the command feedback encrypted data are decrypted in the imaging device to restore the command feedback data. The consumable chip comprises a decryption unit for carryingout decryption and restoration on command encrypted data sent by an imaging device, an execution chip for carrying out command processing based on the command data and generating command feedback data, and an encryption unit for encrypting the command feedback data, generating command feedback encrypted data, and sending the command feedback encrypted data to the imaging device. The encrypted communication is simple; and a phenomenon of cracking the communication data by reverse analysis of the communication waveform is avoided.
Owner:HANGZHOU CHIPJET TECH
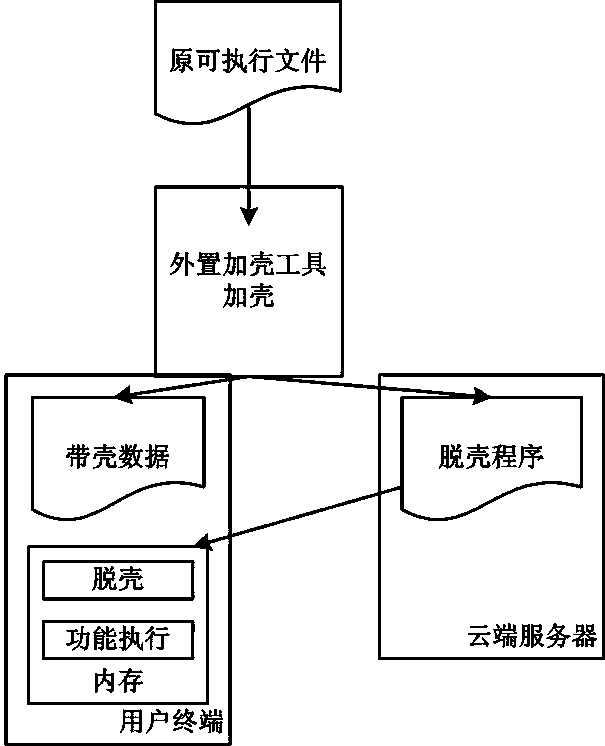
Shell adding and removing method for Android platform application program protection
InactiveCN103530535AProtect confidentialityProtection securityProgram/content distribution protectionApplication softwareCommercial software
The invention discloses a shell adding and removing method for Android platform application program protection. The method includes the shell adding step and the shell removing step for an original executive file of an Android platform application program. The shell adding step refers to the step that the file format structure of the original executive file is analyzed through an externally-arranged shell adding tool, and a source program is encrypted to form data with a shell. The shell removing step refers to the step that before the application program operates, a shell removing program is preferentially loaded and operates in a memory of a mobile terminal, source program decrypting is carried out on the data with the shell, and then the original executive file is loaded to the memory and normally operates. Due to the adoption of the technical scheme of shell adding and removing, innovative thinking and feasible technical solving ways are provided for application shell adding and removing under an Android platform, and the shell adding and removing method can be used for protecting the executive file of the mobile platform, prevent the program from being attacked by hacker means like decompilation, guarantee confidentiality of commercial software and protect user application safety.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
Electronic voting method and system and recording medium having recorded thereon a program for implementing the method
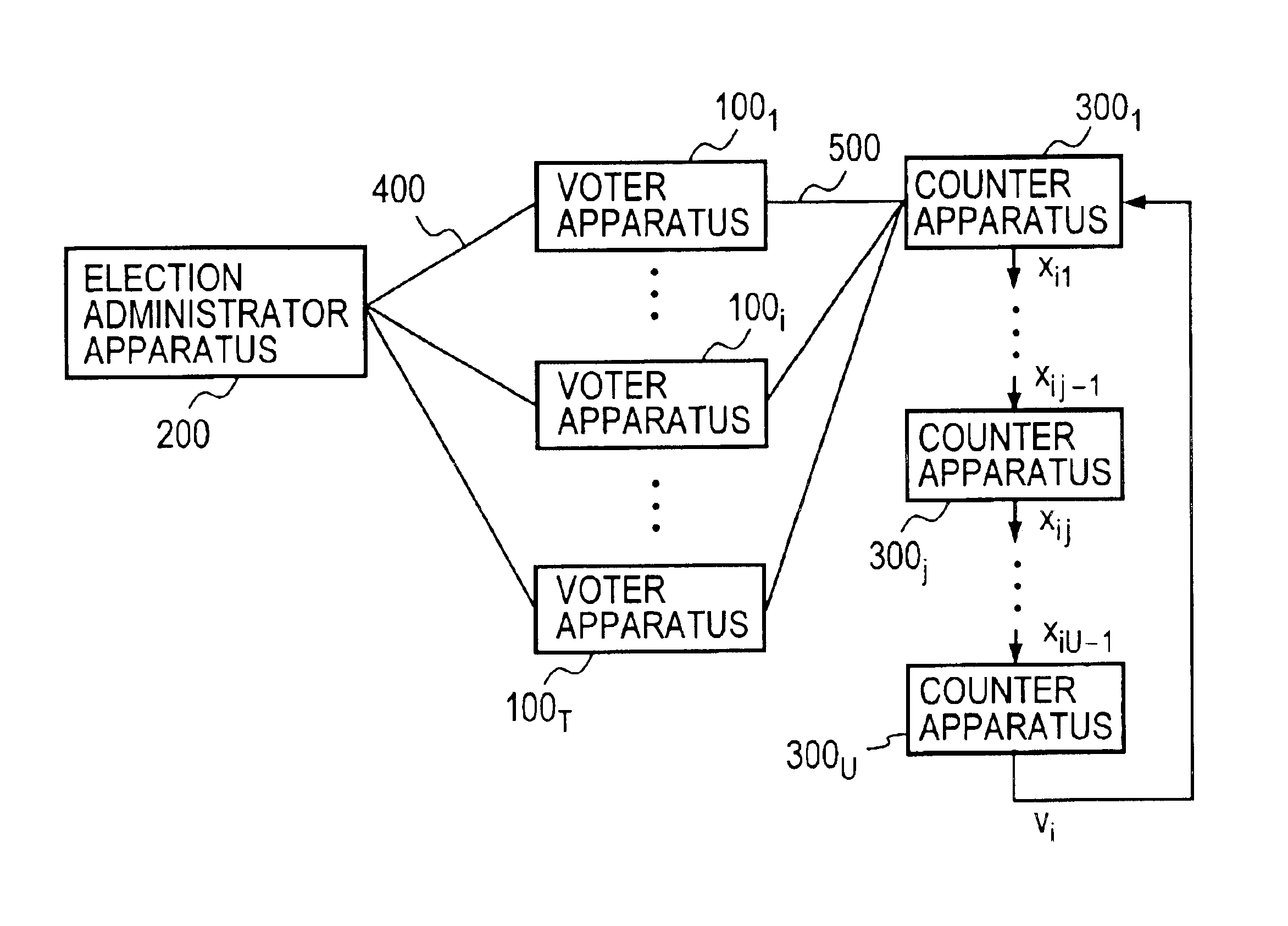
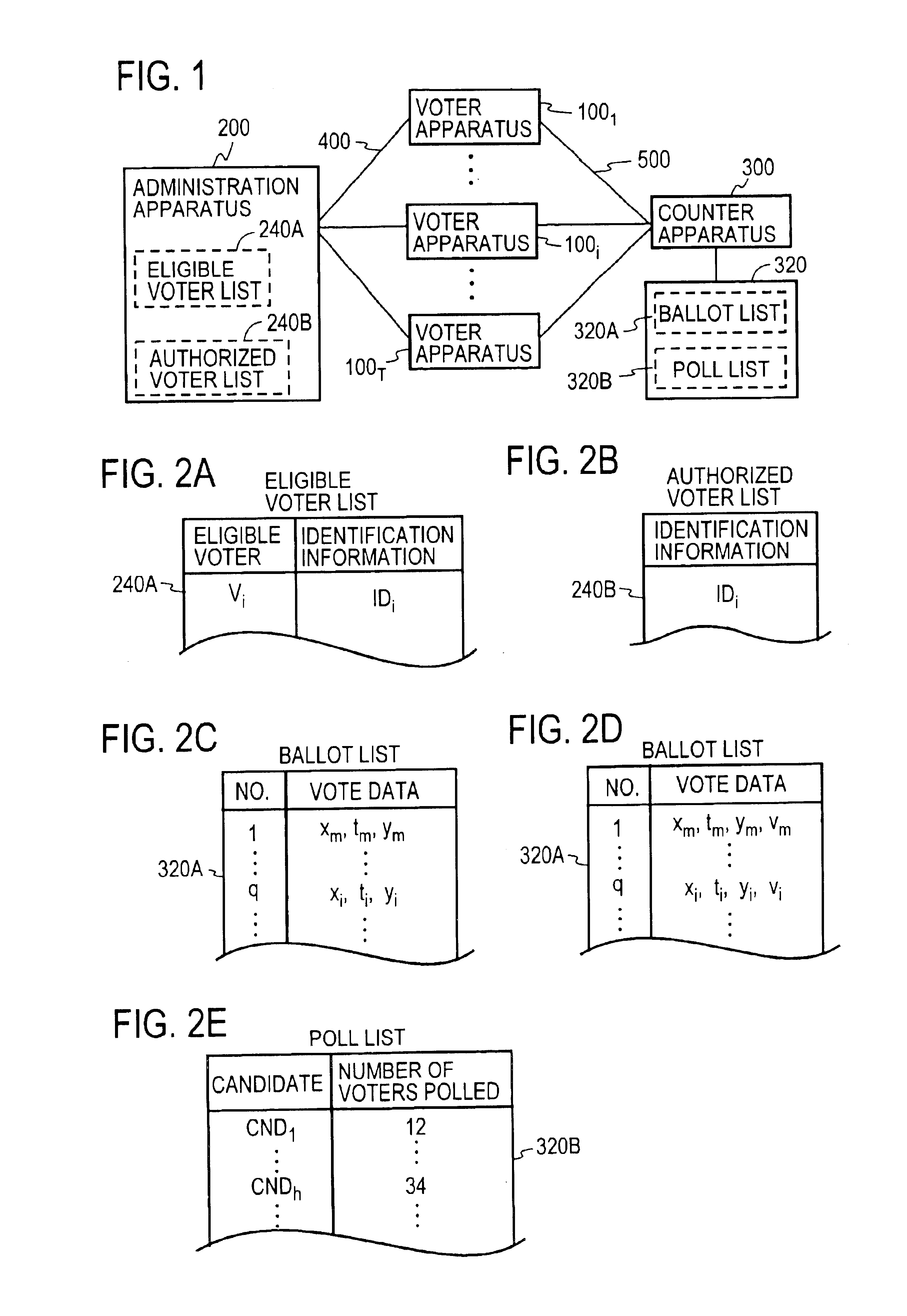
InactiveUS6845447B1Ensuring privacyEasy to optimizeVoting apparatusError detection/correctionBlind signatureRecording media
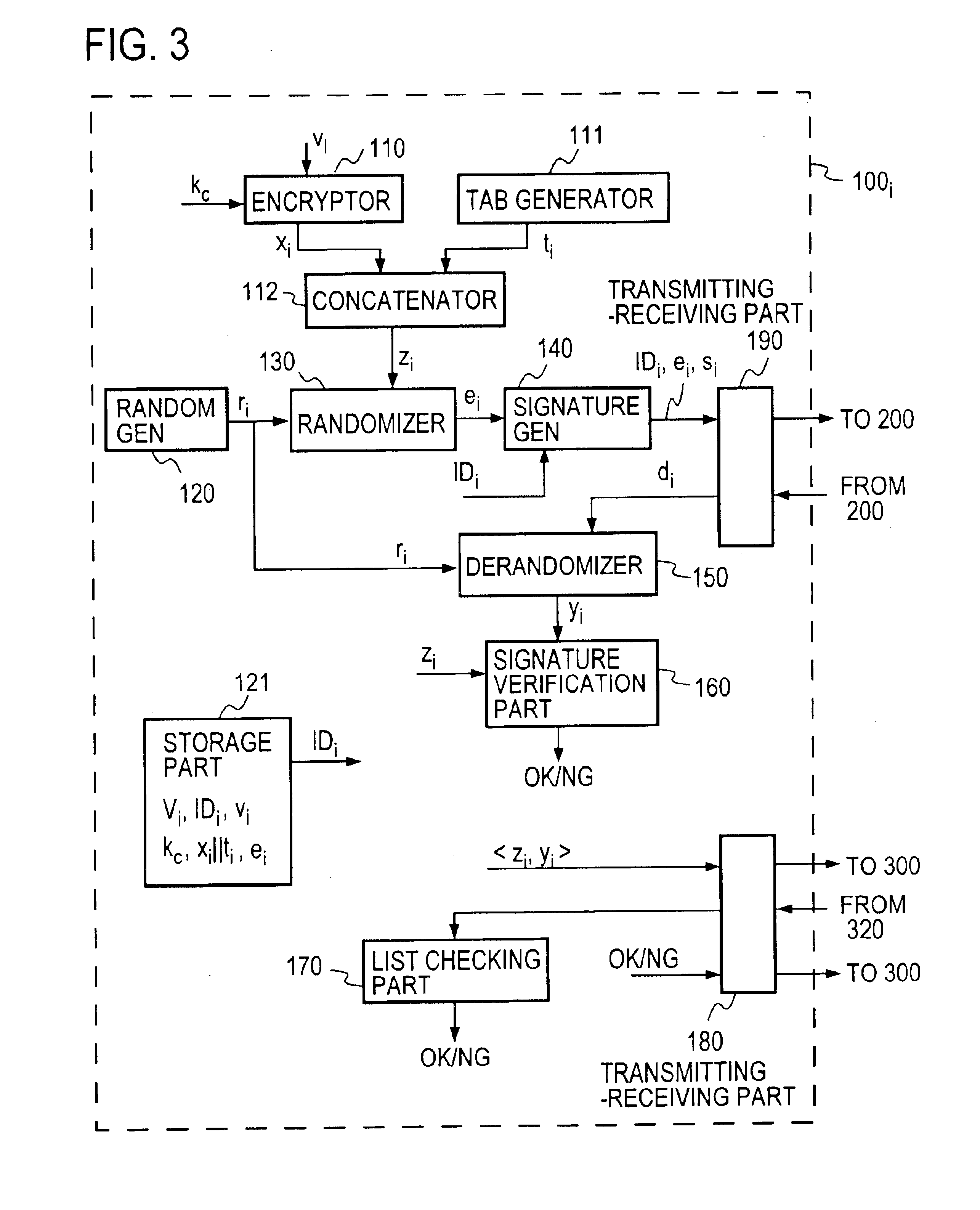
A voter Vi encrypts his vote content vi with a public key kPC of a counter C, then concatenates the encrypted vote content xi with a tag ti to obtain a ballot zi, then randomizes it with a random number ri to create a preprocessed text ei, and sends it and a signature si therefor to an election administrator A. The administrator A generates a blind signature di for the preprocessed text ei and sends it back to the voter Vi. The voter Vi excludes the influence of the random number ri from the blind signature di to obtain administrator signature yi, and sends vote data <zi, yi> to a counter C. The counter C verifies the validity of the administrator signature yi and, if valid, generates and publishes a vote list containing the data <zi, yi> to the voter Vi. The voter Vi checks the vote list to make sure that it contains the data <zi, yi> with his tag ti held in the ballot zi. The counter C decrypts the encrypted vote content xi in the ballot zi to obtain the vote content vi, and counts the number of votes polled for each candidate.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Mixed encoding and decoding method and device of barcode and two-dimensional code
InactiveCN102270294AIntegrity guaranteedEnsure safetySensing by electromagnetic radiationDecoding methodsConfidentiality
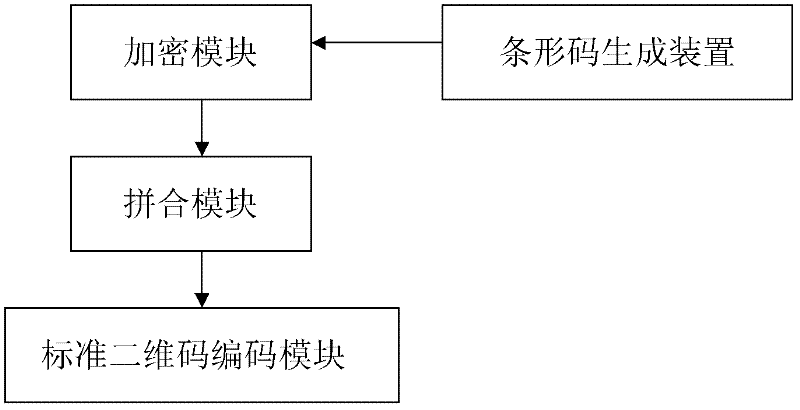
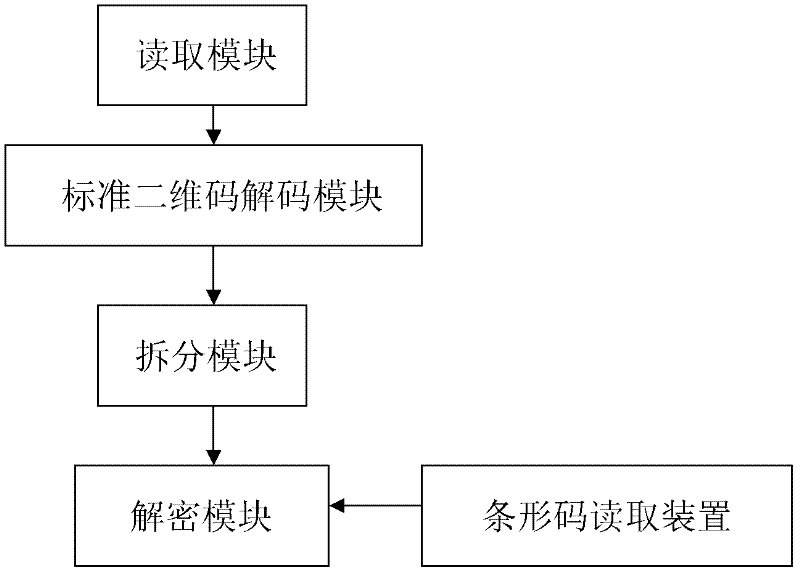
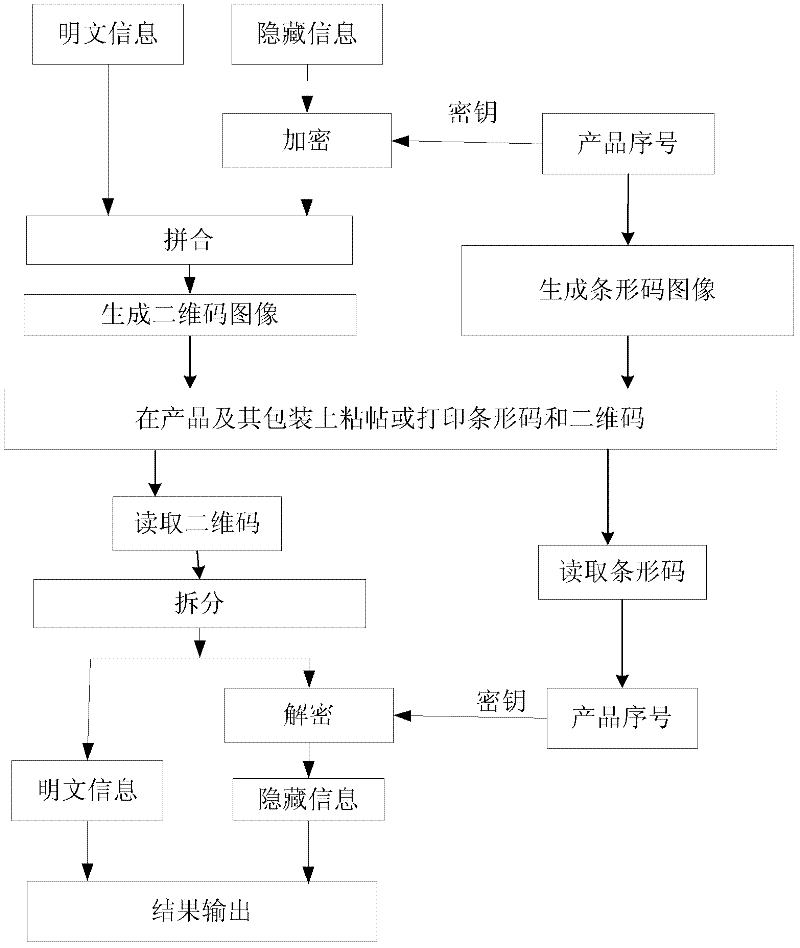
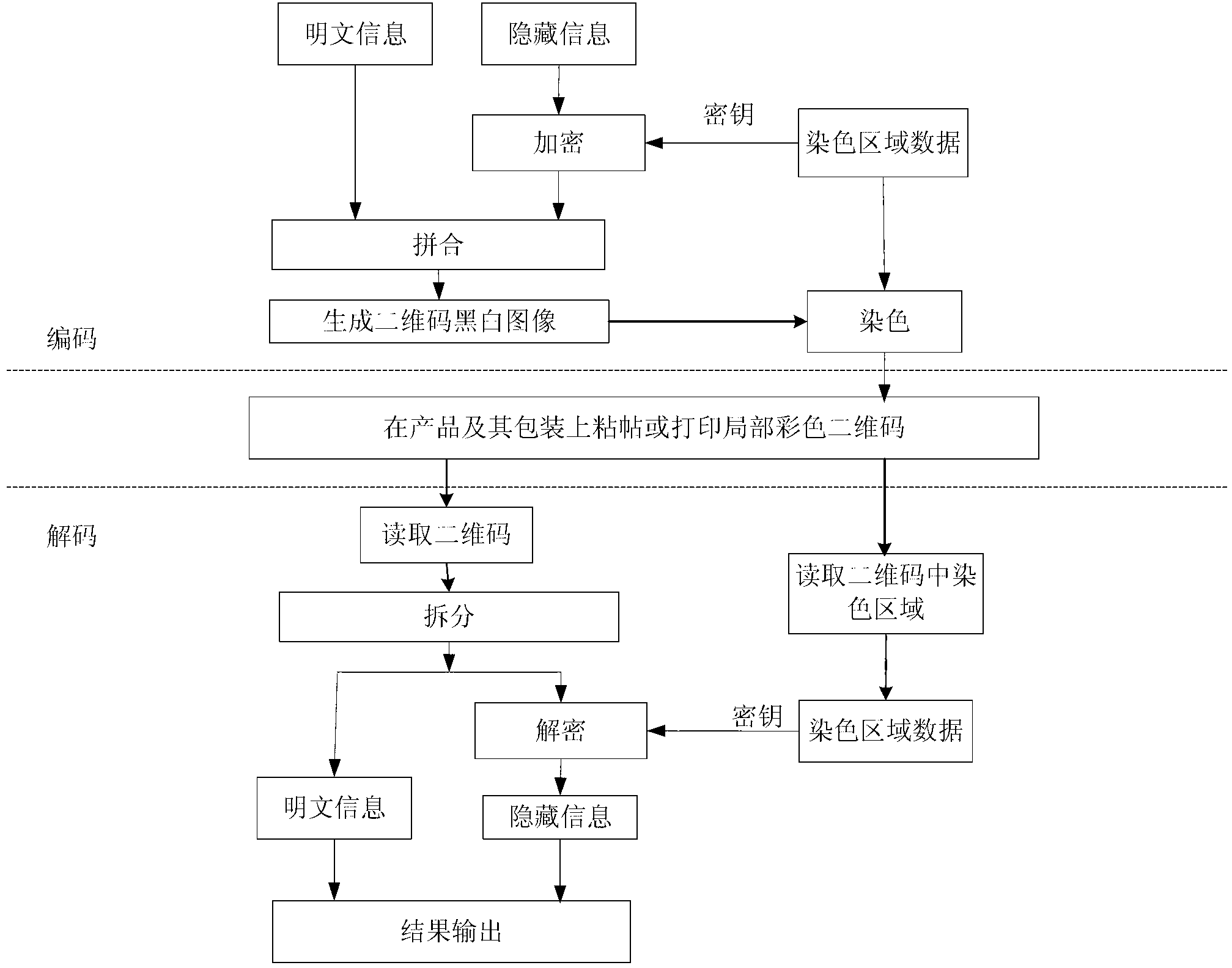
The invention discloses a coding method for mixing barcodes and two-dimensional codes, which comprises the following steps: (1) generating barcode images through barcode algorithms through barcode data; Encrypting as a key to obtain two-dimensional code generation information; (3) generating a two-dimensional code image by using the two-dimensional code generation information obtained in step (2) through a two-dimensional code generation algorithm. The invention also discloses a decoding method and an encoding and decoding device of the encoding method. On the one hand, the present invention can use naked eyes to identify products, certificates or bills through the barcode, and on the other hand, the two-dimensional code reading device of the present invention can be used to read the information hidden in the two-dimensional code, ensuring the integrity of the two-dimensional code Safety, security and confidentiality, and enable the two-dimensional code to carry hidden information, strengthen the anti-counterfeiting and uniqueness of the two-dimensional code, and open up a new application field of the two-dimensional code as a data label.
Owner:SOUTH CHINA AGRI UNIV
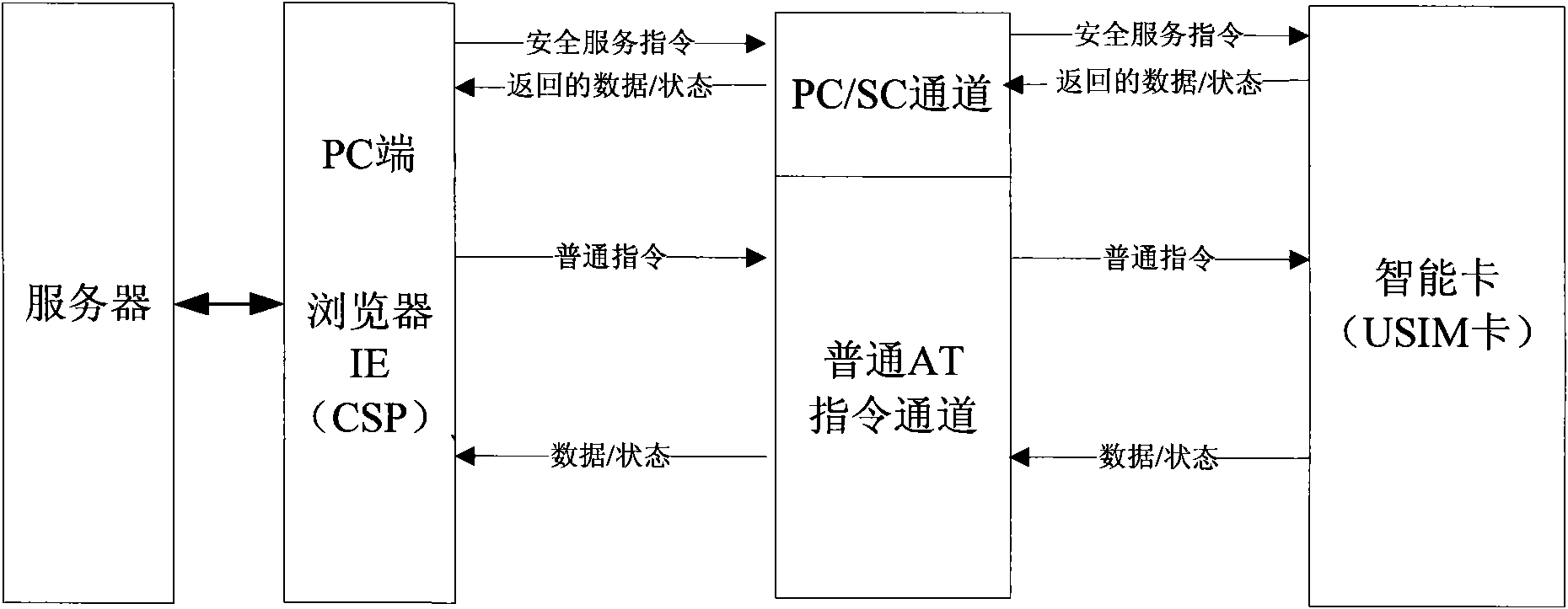
Mobile terminal signature-based remote payment system and method
InactiveCN101938520AImprove securityImprove portabilityPayment protocolsTransmissionSmart cardAuthentication server
The invention discloses a mobile terminal signature-based remote payment system and a mobile terminal signature-based remote payment method, and a mobile terminal and an intelligent card of the mobile terminal in the system. The intelligent card (such as a USIM card) of the mobile terminal is improved, and a PC / SC channel interacted with the PC side is provided; a digital certificate is stored on the intelligent card, and during authentication, after being exported by the intelligent card, the stored digital certificate is sent by the mobile terminal to an authentication server for certificate register; and the authentication server transmits a signature instruction to the mobile terminal, the mobile terminal sends a private key signature instruction to the built-in intelligent card, and a signature result is sent by the intelligent card and is reported to the authentication server by the mobile terminal, wherein the digital certificate can be acquired by interacting the intelligent card with the authentication server on line. The remote payment system has high safety and portability, is convenient for users to use during remote payment, and is favorable for protecting personal privacy information of the users and guaranteeing the safety of the remote payment.
Owner:ZTE CORP
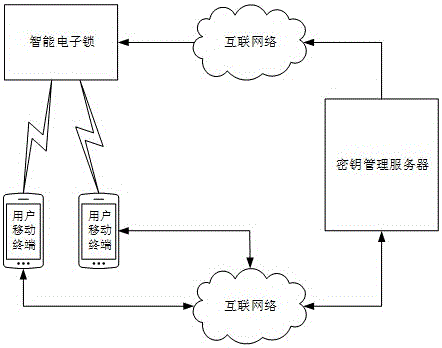
Electronic key sharing service system for house renting
ActiveCN105915344AMeet the needs of useRealize identification verificationKey distribution for secure communicationPublic key for secure communicationUser - individualKey sharing
The invention provides an electronic key sharing service system for house renting. Asymmetric encryption operation is carried out by using user identification information to generate a uniquely corresponding public renting key and a uniquely corresponding private renting key, wherein the private renting key is used for generating an electronic private key with an established unique corresponding relationship between an individual user and an intelligent electronic lock in an encrypted mode and the public renting key is used for executing delocking identification verification with user individual variation for decryption of the electronic key by the smart electronic lock. The private renting key is kept by a private key management server to guarantee security of the distribution and delocking process of the electronic key. Possible different using requirements for randomness, individual variation, and security in house renting sharing can be met well; convenience of the system in house renting sharing application is improved; the convenience degree of housing renting is enhanced; and development of the intelligent door lock industry can be promoted. Therefore, the system has the broad market promotion and application prospects.
Owner:CHONGQING JINOU SCI & TECH DEV
Method for encrypting solid state disk partitions and solid state disk
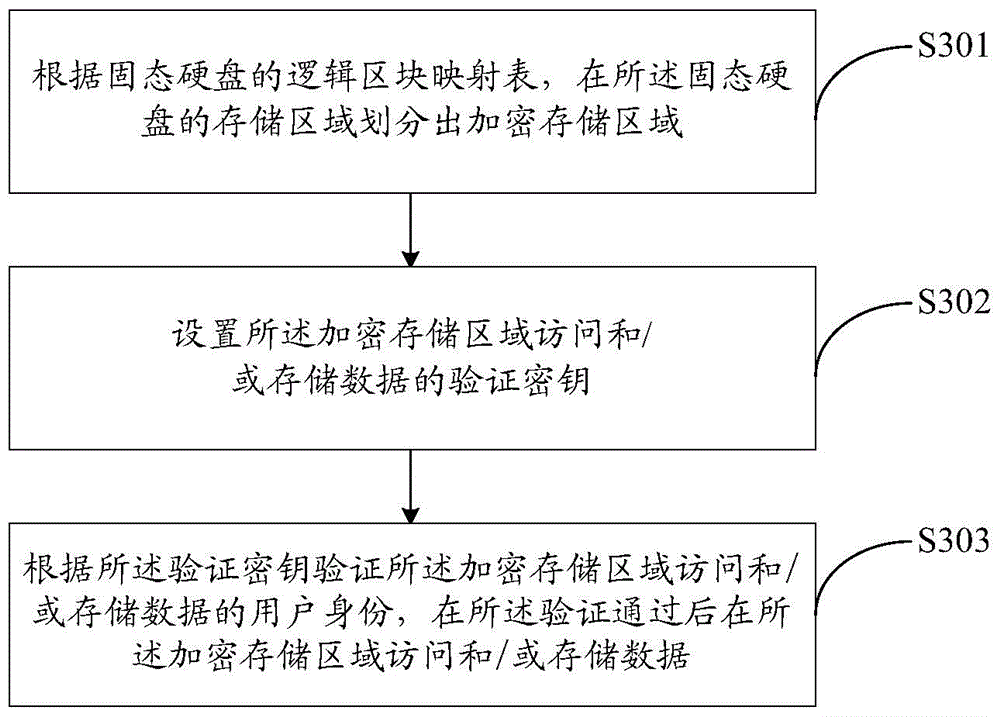
InactiveCN103558994AImplement encrypted storageGuaranteed confidentialityInput/output to record carriersConfidentialitySolid-state drive
The invention relates to the technical field of communication and provides a method for encrypting solid state disk partitions and a solid state disk. The method includes the steps of A, dividing an encrypted storage area in the storage area of the solid state disk according to the logic block mapping table of the solid state disk; B, setting a verification key for accessing and / or data storage of the encrypted storage area; C, verifying the identity of a user requiring accessing and / or data storage of the encrypted storage area according to the verification key, and accessing and / or data storage can only be performed when the verification is passed. By the method, confidentiality of the solid state disk is increased.
Owner:RAMAXEL TECH SHENZHEN
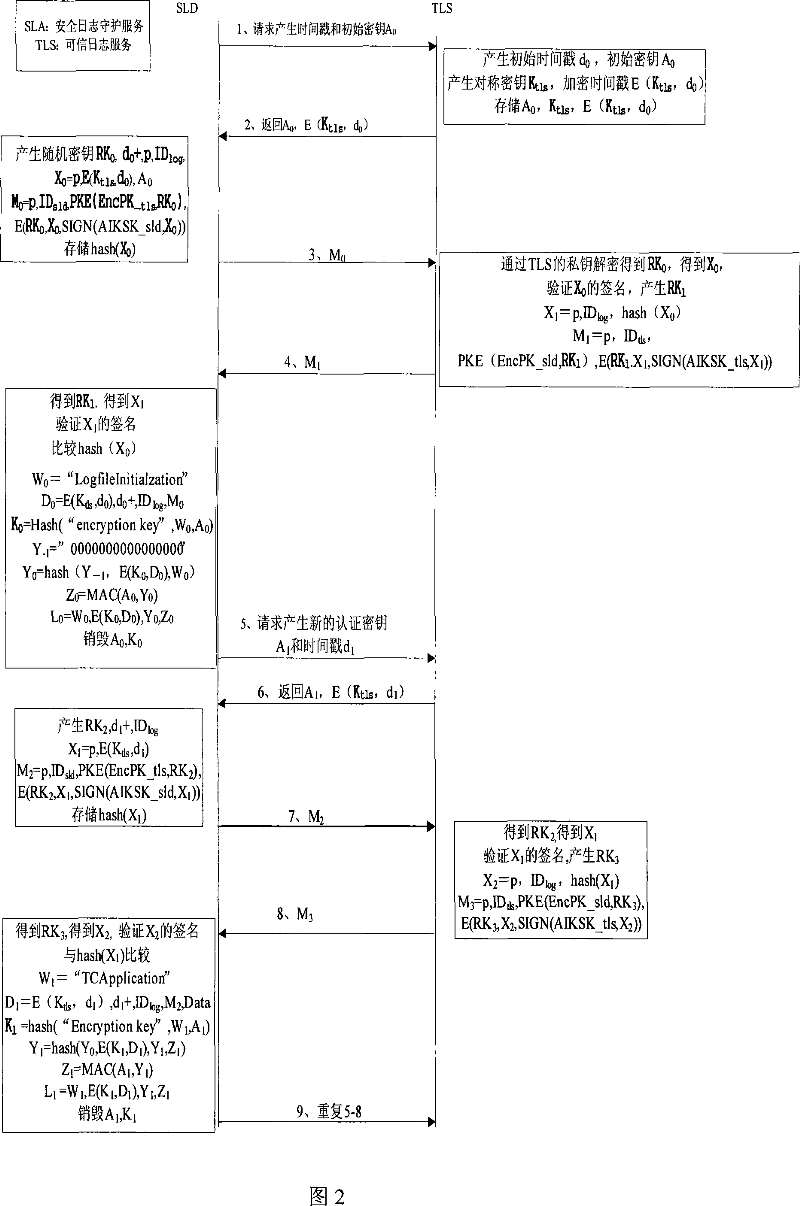
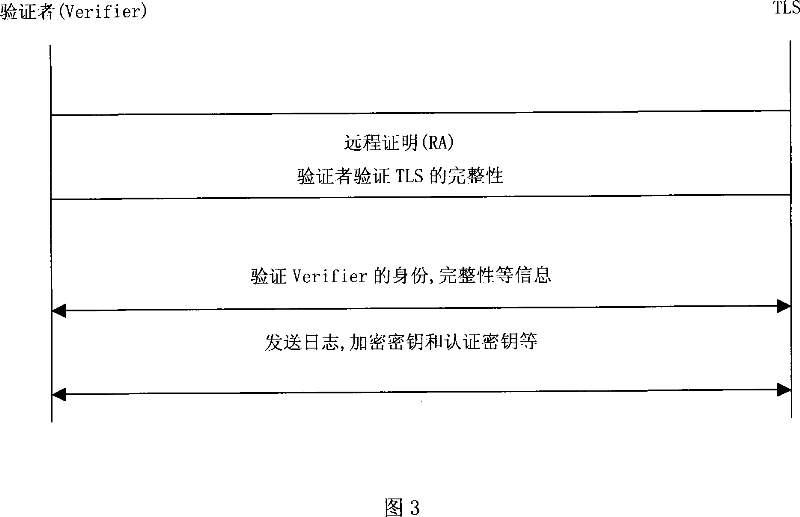
Method for auditing safely system log
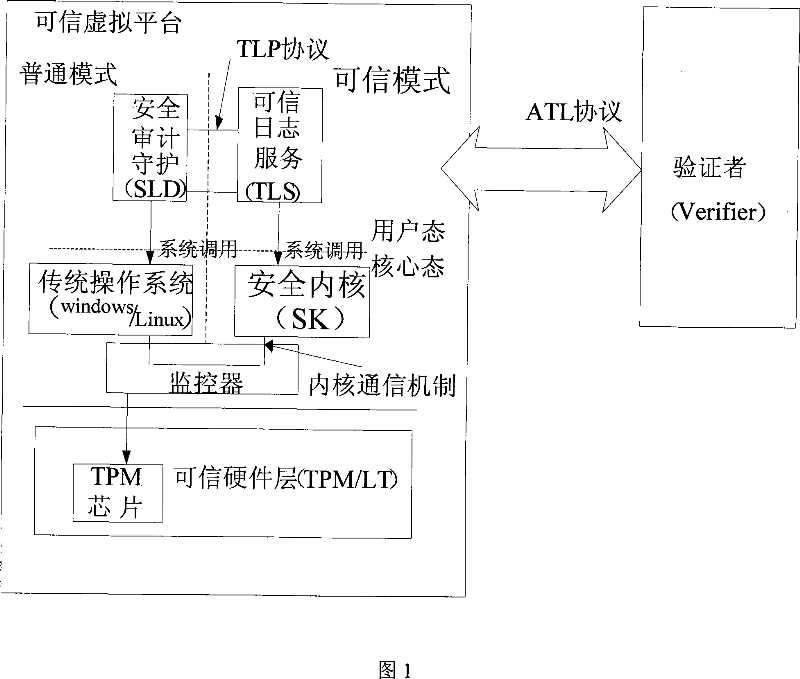
InactiveCN101039186AEliminate dependenciesGuaranteed confidentialityUser identity/authority verificationData switching networksThird partyTrusted Platform Module
The present invention belonging to computer technology field relates to a security auditing method of system log, which is created and accessed on the virtual platform based on trusted computing. With the help of the trusted platform module, which is a hardware trust root, the system log is created locally and credibly. The trust to server can be transferred to the trusted platform, and the credibility of the trusted platform log storage can be improved by the remote proof and packaging storage property which is provided by the trusted platform. Without relying on a credible third party server, the machine platform can complete high credible security audit. The invention can be widely used in the security audit of computer system.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
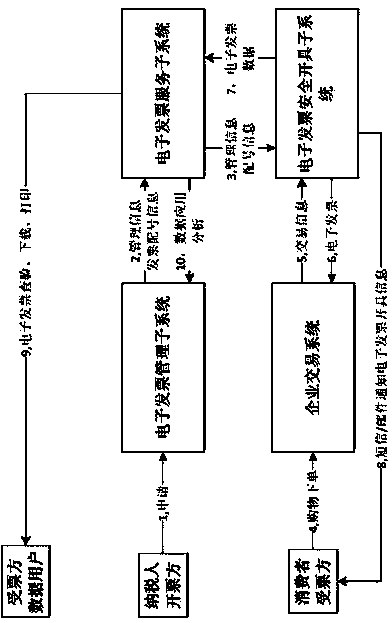
Electronic invoice security management service system based on cloud computing and cryptography
InactiveCN103870983AReduce application couplingIsolate dependenciesDigital data protectionBilling/invoicingInformatizationInvoice
The invention relates to the technical field of electronic invoice service management, in particular to an electronic invoice security management service system based on cloud computing and cryptography. The electronic invoice security management service system based on the cloud computing and the cryptography adopts technologies of the cloud computing, big data, anti-fake encryption, internet and mobile internet to ensure the correct generation, reliable storage, safety and uniqueness of electronic invoices, and provides convenient query authentication and other electronic invoice data services. The system can ensure the correct generation, reliable storage, query authentication, safety and uniqueness of electronic invoice information, realizes paperless, electronic, networked and automatic management of invoices, reduces the invoice cost and improves the informatization management level.
Owner:INSPUR QILU SOFTWARE IND
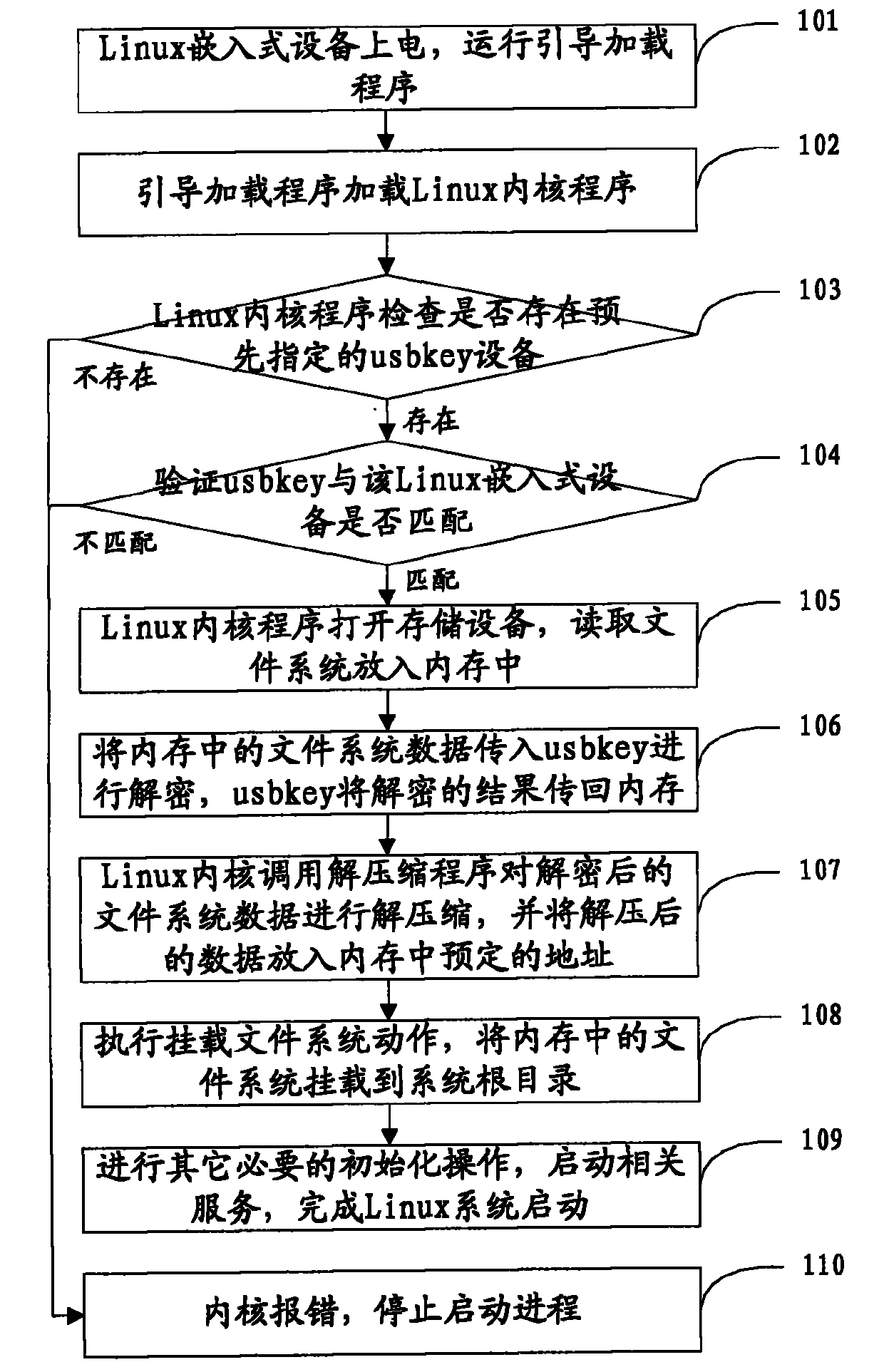
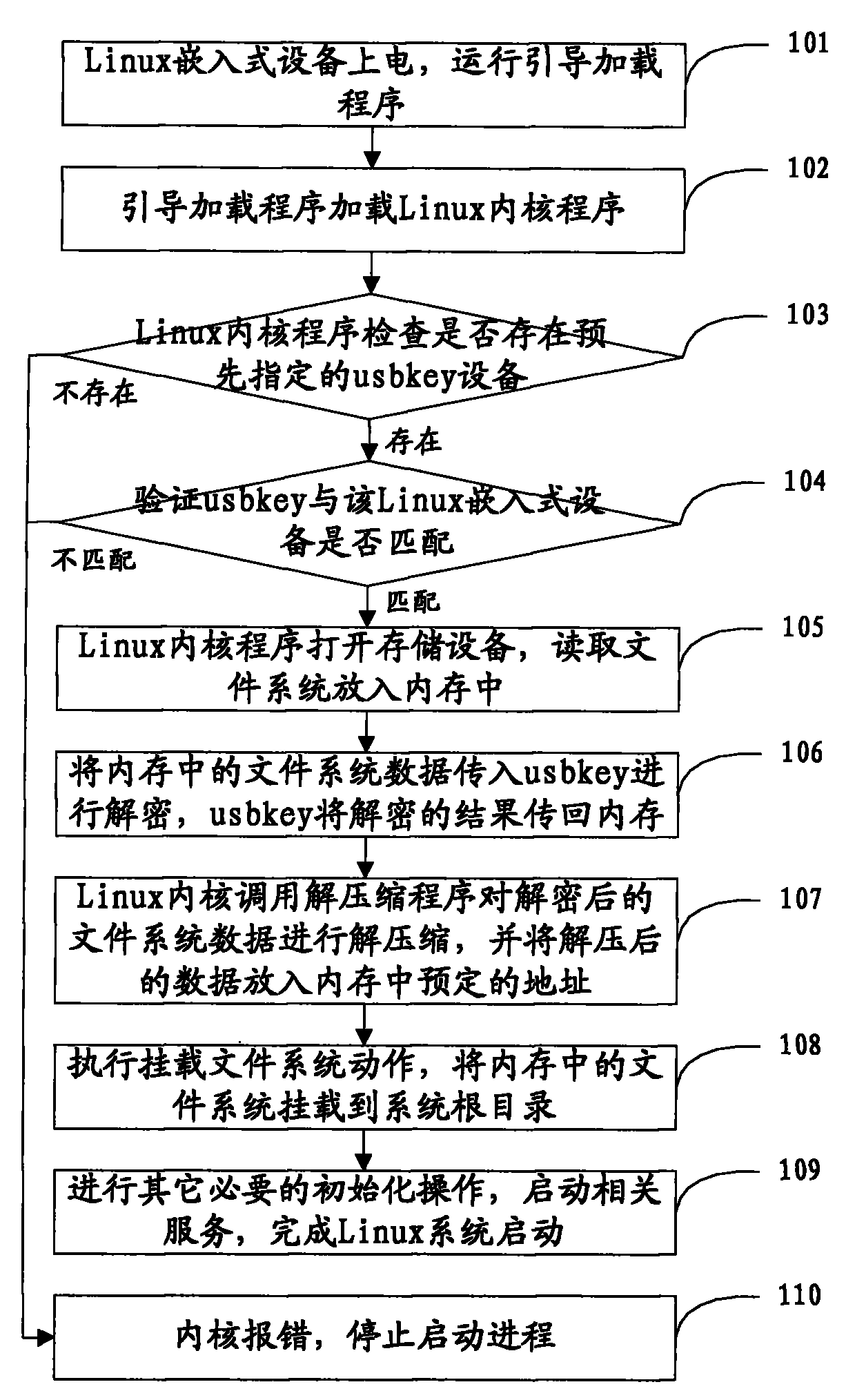
Safe startup method for Linux embedded system
ActiveCN101770386AImprove securityGuaranteed confidentialityProgram loading/initiatingPlaintextInternal memory
The invention discloses a safe startup method for a Linux embedded system and belongs to the field of information safety. The safe startup method for the Linux embedded system comprises that: a bootstrap loader is operated in a Linux embedded device to load Linux kernel; the Linux kernel checks whether predetermined encryption / decryption equipment is connected to the Linux embedded device; if thepredetermined encryption / decryption equipment is connected to the Linux embedded device, a cipher text of the Linux file system data is transmitted to the encryption / decryption equipment for decryption, the decrypted clear text of the Linux file system data is transmitted to an internal memory, a system root directory is mounted, and other operations for starting up the Linux embedded system are continuously executed; and if the predetermined encryption / decryption equipment is not connected to the Linux embedded device, the operation for starting up the Linux embedded system is stopped so as to guarantee the information safety of the Linux file system data.
Owner:北京坚石诚信科技有限公司
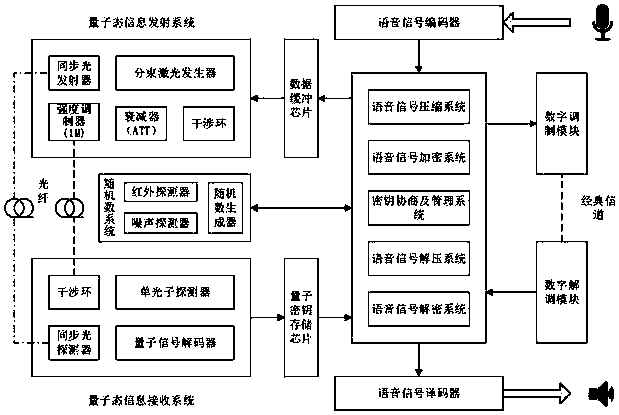
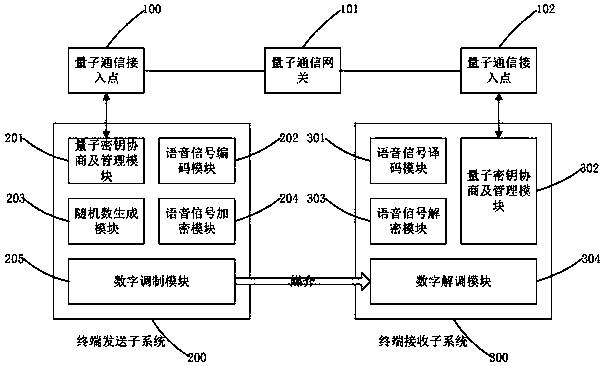
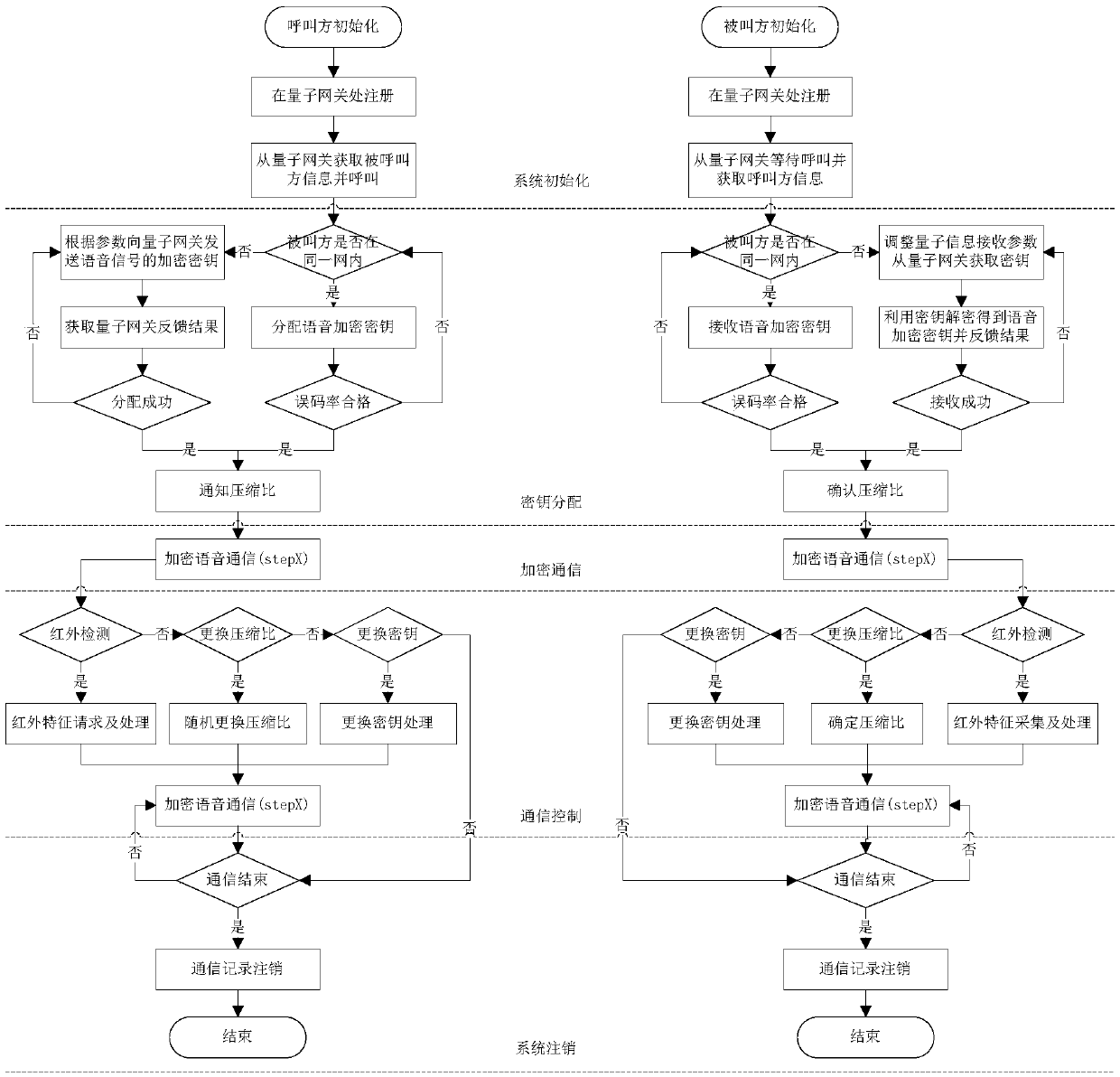
Voice signal quantum encryption communication system based on random number
ActiveCN108768542ARandomUnpredictableKey distribution for secure communicationSpeech analysisSignal encodingSignal decoding
The invention relates to a voice signal quantum encryption communication system based on a random number, which comprises terminal equipment, a quantum communication access point, a quantum communication gateway and a quantum communication access point, wherein the terminal equipment consists of a terminal sending subsystem and a terminal receiving subsystem; the terminal sending subsystem comprises a quantum key agreement and management module, a voice signal encoding module, a random number generation module, a voice encryption module and a digital modulation module; and the terminal receiving subsystem comprises a voice signal decoding module, a quantum key agreement and management module, a voice decryption module and a digital demodulation module. One piece of terminal equipment simultaneously comprises the terminal sending subsystem and the terminal receiving subsystem. According to the invention, the terminal sending subsystem is applied to send a voice signal with good encryption performance and high anti-interference performance and meanwhile, the terminal receiving subsystem is utilized to receive and reduce the voice signal, so that safety and integrity in the communication process are ensured.
Owner:CHINA THREE GORGES UNIV
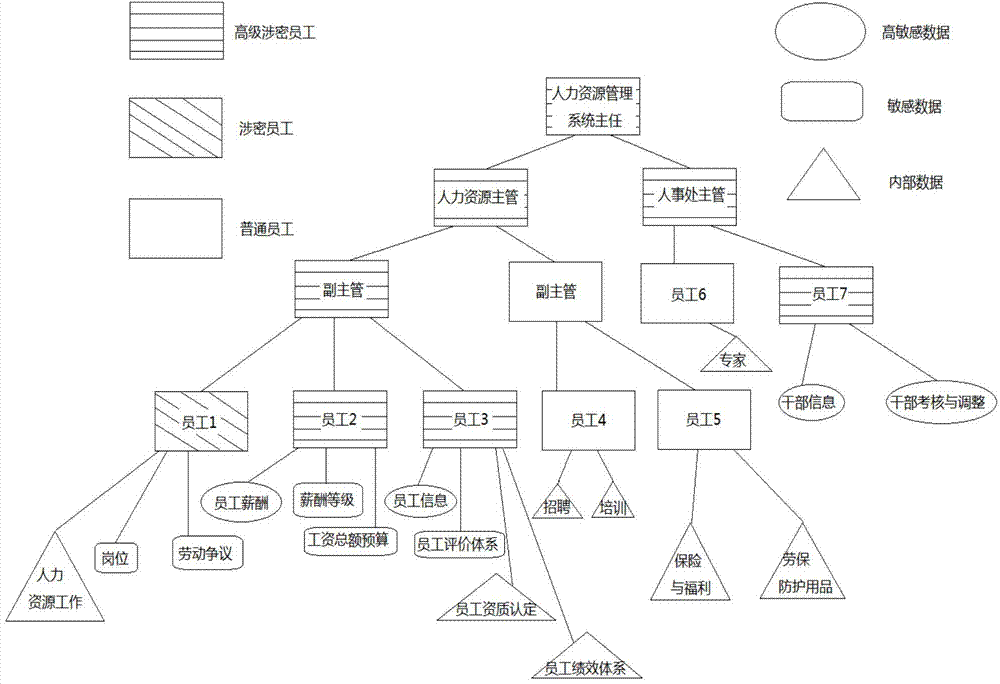
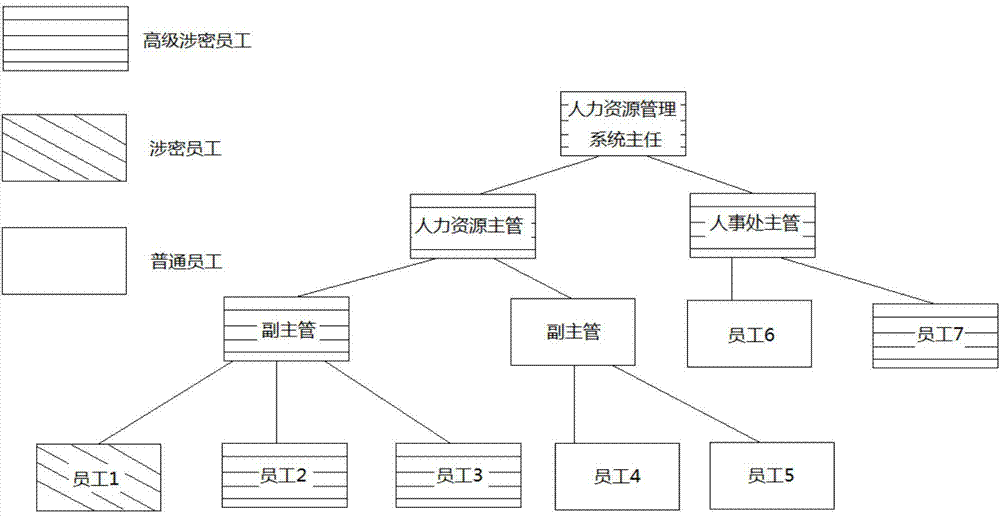
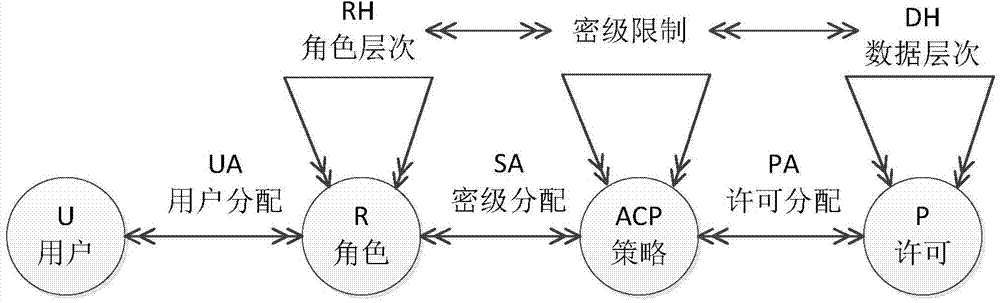
Hierarchical classification access authorization management method based on roles
ActiveCN104780175APrivacy protectionPrevent leakageUser identity/authority verificationInformation resourceAuthorization
The invention discloses a hierarchical classification access authorization management method based on roles. The hierarchical classification access authorization management method includes the following steps: S1, initialization is carried out, wherein it is assumed that n+1 data classes and m users exist in an assumed information system, an encryption key hierarchical tree is built, and calculation indexing is carried out on a main encryption key Kj and a class encryption key Kx; S2, data encryption is carried out; S3, user registration is carried out; S4, access requesting is proposed; S5, decryption is carried out. According to the hierarchical classification access authorization management method, a hierarchical classification authorization module based on the roles is built, a hierarchical encryption key management scheme based on the roles is used in the model, and permissions of the users for accessing specific data are given according to the roles and the grades of the users, so that the aim of more-fine-grained access control is achieved, the problem of unauthorized accesses caused by weak identity authentication is effectively solved, and meanwhile, the privacy of information resource in the system is effectively protected; in addition, the invention further provides an intermediate node for hiding hierarchical data structures in the system through access paths invisible to the users, and the leakage of sensitive information in the system is further prevented.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
Two-dimension code coding and decoding method and device based on local color verification
ActiveCN102916804ARealize monitoringRealize regulationEncryption apparatus with shift registers/memoriesRecord carriers used with machinesPattern recognitionCode space
The invention discloses a two-dimension code coding and decoding method and devices based on local color verification. The coding method comprises the following steps of: generating coloring region data randomly according to a predefined coloring region coding and decoding table, and taking the generated coloring region data as a secret key to perform encryption so as to obtain two-dimension code generation information; generating two-dimension code black-and-white images by a two-dimension code generation algorithm; and finally coloring the generated two-dimension code black-and-white images according to the coloring region data to obtain local colored two-dimension code images. The decoding method comprises the following steps of: reading the coloring region data on the two-dimension code images, and using a standard two-dimension code decoding algorithm to decode; and performing decryption on the decoded information by taking the coloring region data as the secret key via a decipherment algorithm to obtain original information of the two-dimension cod images. By using the invention based on original black and white colors, the coloring region information is increased, coding space of two-dimension codes can be expanded, and counterfeited difficulty is increased.
Owner:SOUTH CHINA AGRI UNIV
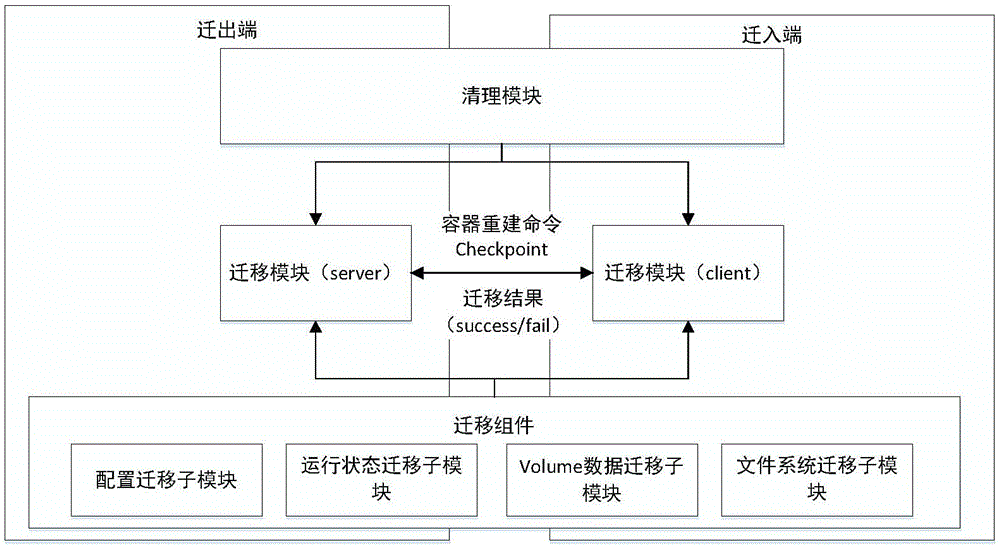
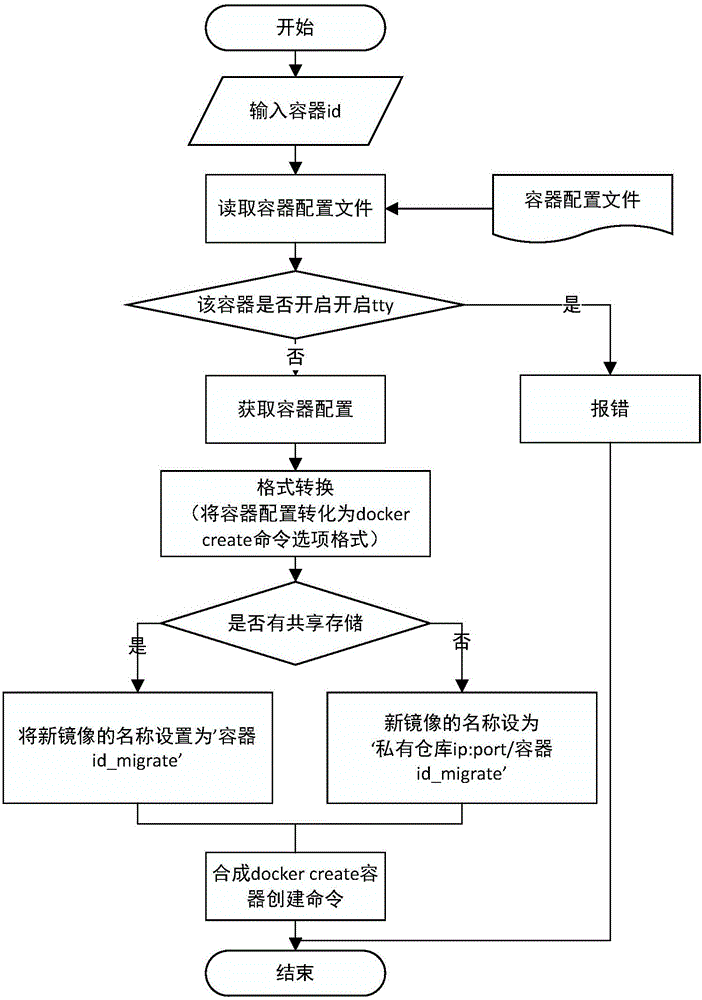
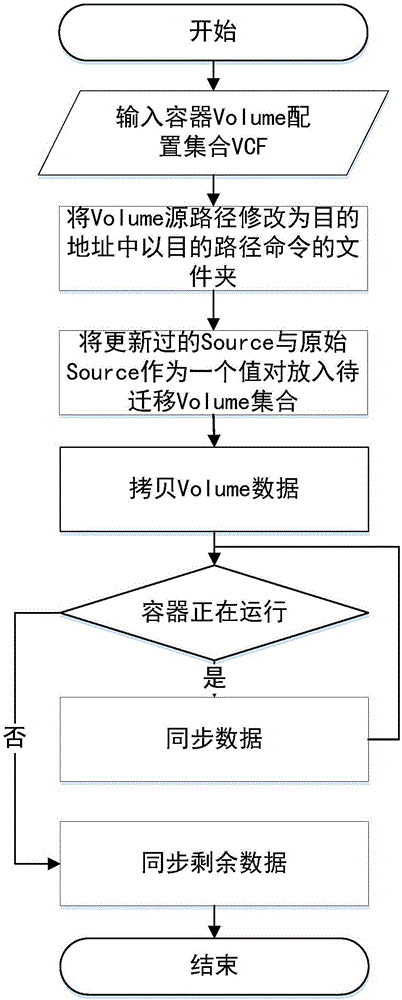
CRIU-based Docker container heat migration method and system
ActiveCN107526626AEasy to migrateGuaranteed confidentialityProgram initiation/switchingTransmissionFile systemConfidentiality
The invention discloses a CRIU-based Docker container heat migration method and system. According to the scheme, a container creation instruction is reestablished based on configuration information of a Docker container, so that configuration migration of the Docker container is realized; and in combination with characteristics of shared storage and non shared storage, file system migration of the Docker container is realized by adopting different Docker mirror image distribution methods, thereby avoiding the problem of Docker daemon restarting caused by direct migration of disk files of the container in an existing scheme. By performing normalization processing on volume sources, and based on this, proposing a volume heat migration algorithm, volume migration of the Docker container is simplified. By introducing a Docker warehouse security mechanism and an Rsync+SSH network communication mechanism, the scheme can ensure the confidentiality and integrity of migrated data during the migration process in a non shared storage environment.
Owner:WUHAN UNIV
Encryption device, system and method for encryption, identification using the encryption device
ActiveCN101183456AImprove securityDealing with transaction hijackingFinanceTransmissionDisk encryptionWork status
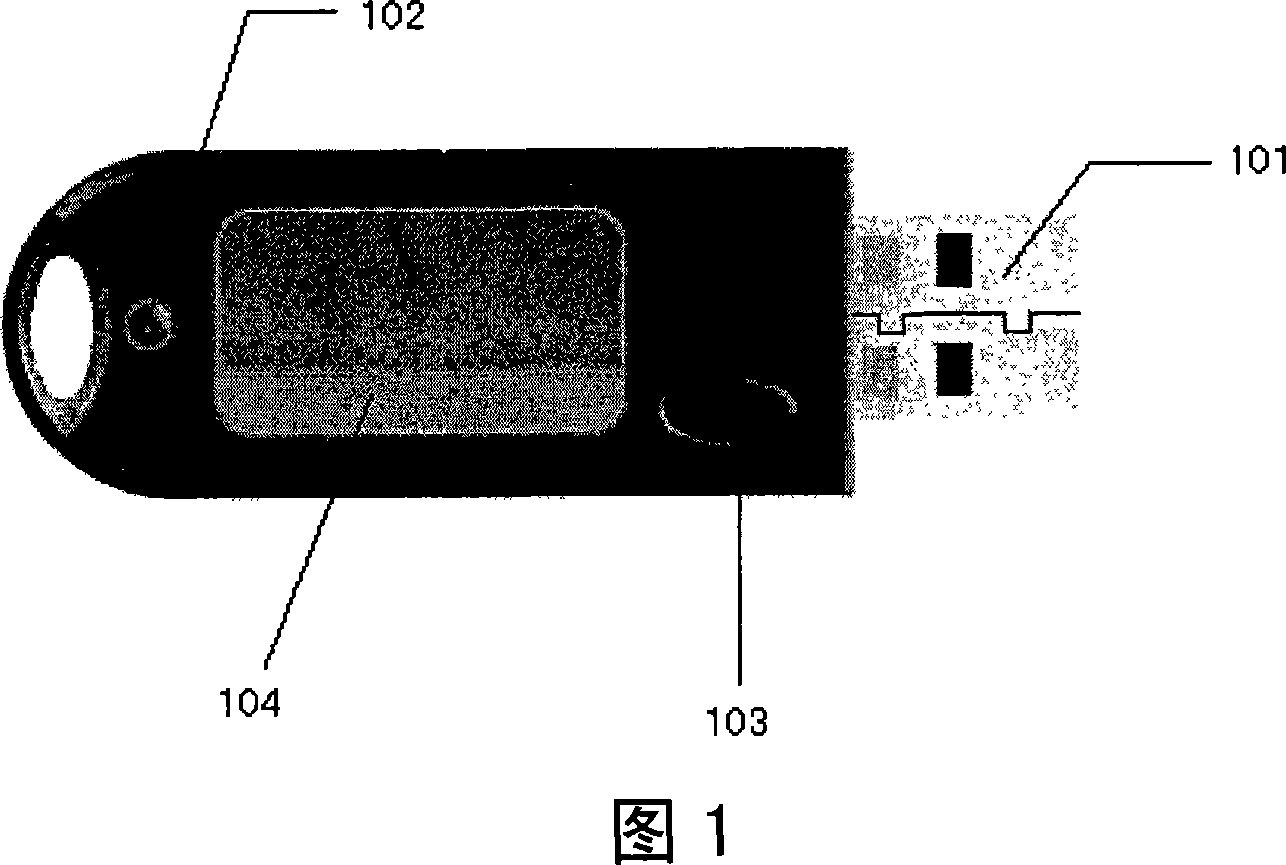
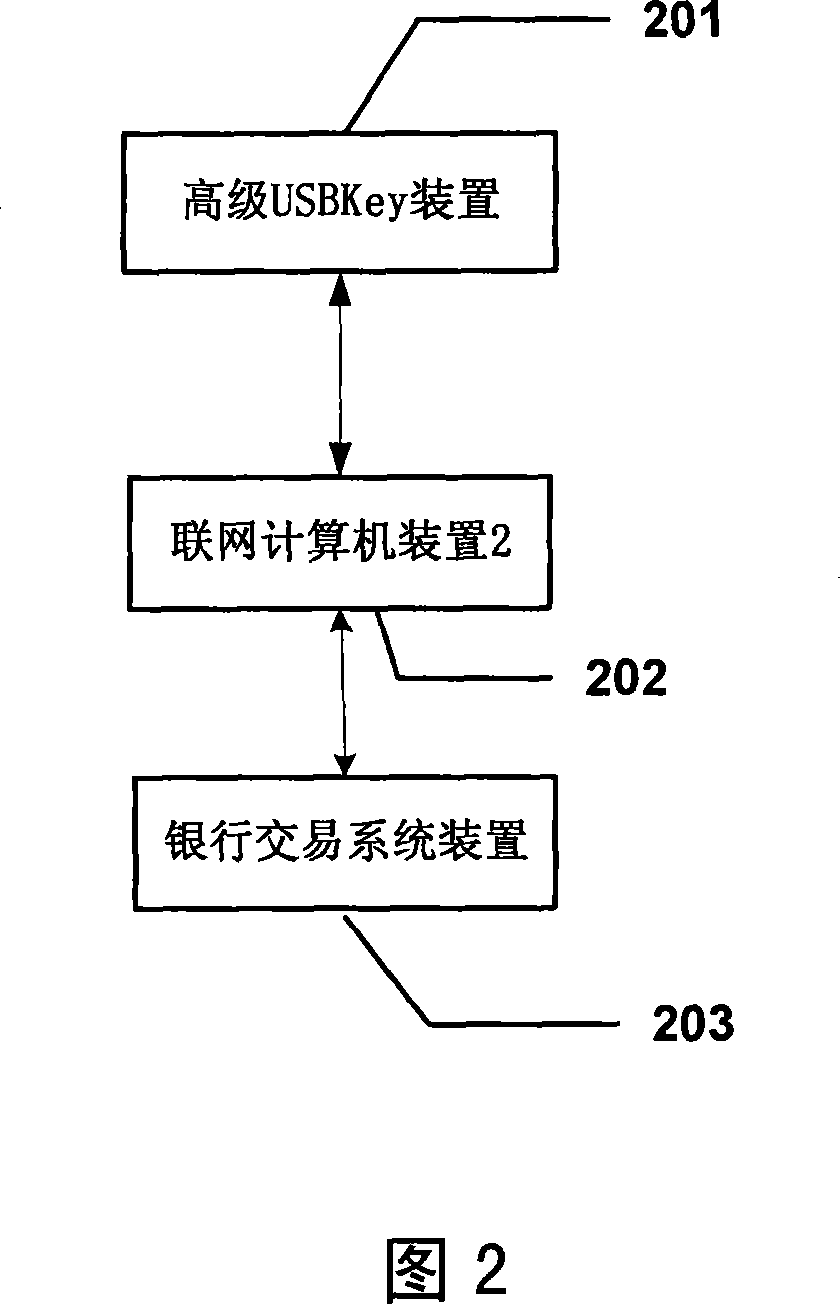
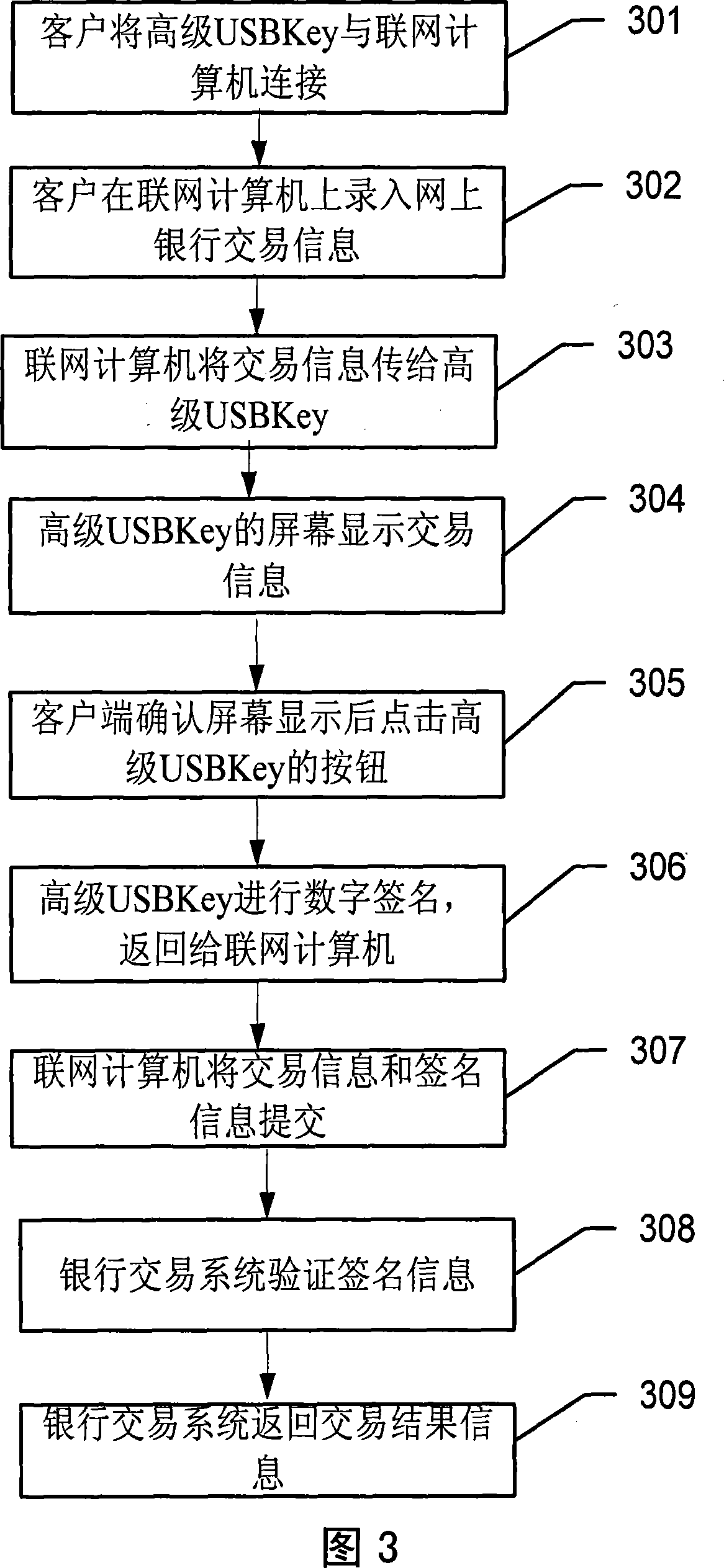
The invention provides a USBKey encryption device, a system and a method using the USBKey encryption device for encryption and identification; wherein, the USBKey device comprises: a USB interface used for connection between an USB socket and a computer, an indicator used for indicting work status of the USBKey device and a built-in chip storing unique serial number of the USBKey device when leaving the factory and storing digital certificate and private key used for identifying identification of clients; the private key cannot be imported from the USBKey device. The invention is characterized in that: the USBKey device also comprises a visual screen used for displaying information under signing when digital signature is made for the USBKey device; the USBKey device also comprises one or a plurality of buttons for operations such as confirming or cancelling the information under signing; the visual screen can also be a touch panel.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
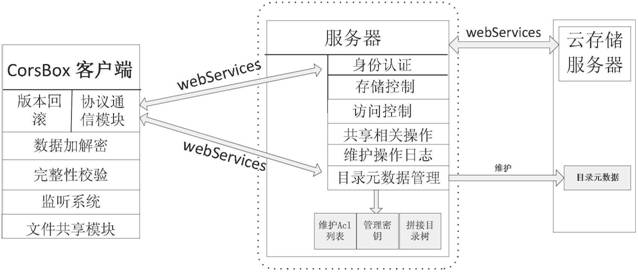
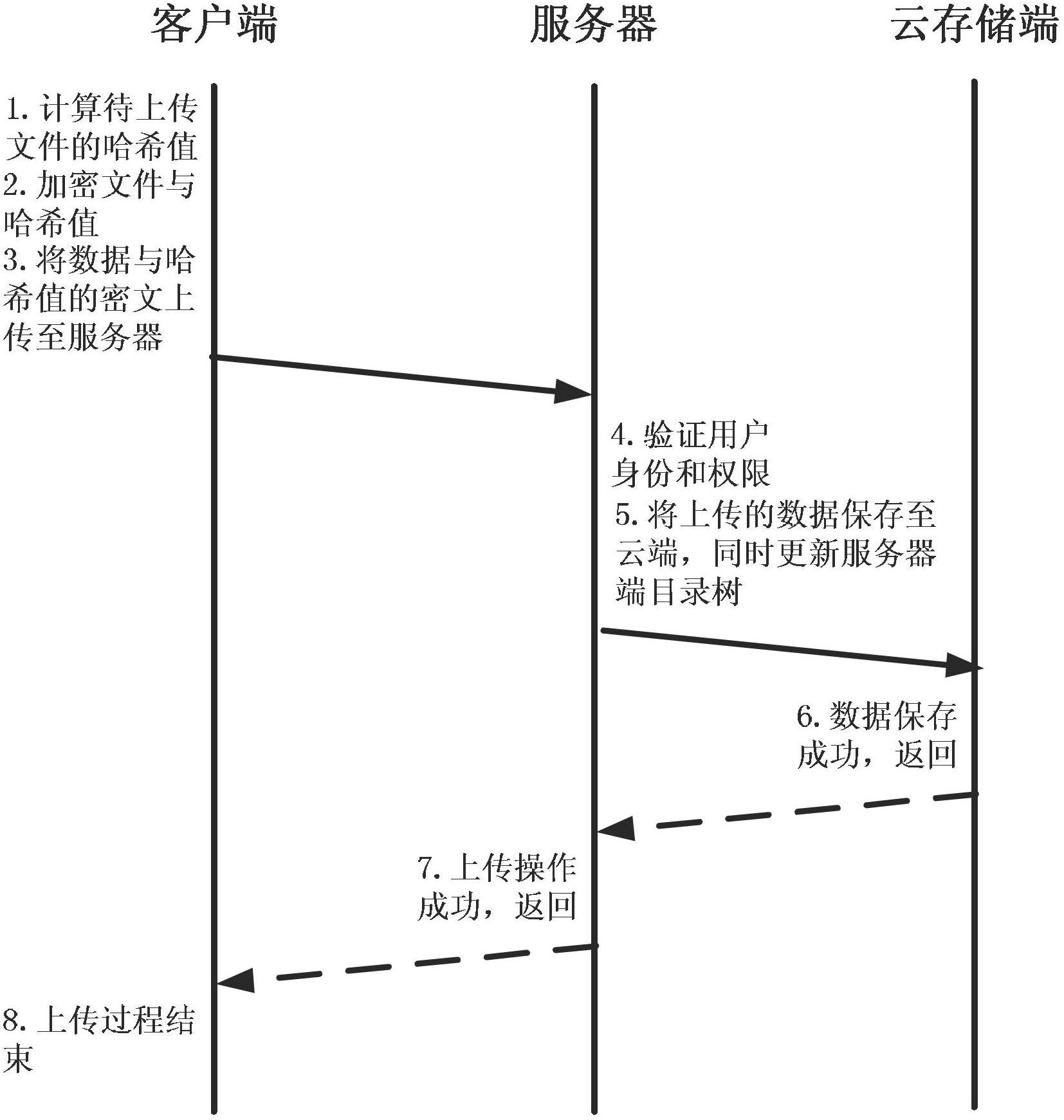
Data access control method and system in cloud storage environment
ActiveCN104980477AGuaranteed confidentialityIntegrity guaranteedTransmissionSpecial data processing applicationsConfidentialityData access control
Embodiments of the invention provide a data access control method and system in a cloud storage environment. The method mainly comprises the steps that a user registers personal information to a cloud server through a client side; when a data owner determines that the data to be transmitted to the cloud server is shared data, the client side of the data owner uses a symmetric key to encrypt the data, and sends the encrypted data, the symmetrical key, a hash operation result of the data and a shared attribute of the data to the cloud server; when the data is not the shared data, the client side of the data owner uses its own public key to encrypt the data, and sends the encrypted data, the hash operation result of the data and the shared attribute of the data to the cloud server. Through adoption of the method and system, confidentiality and integrity of the user data are guaranteed, and confidentiality of the user files is classified, so that authority control under data sharing is better realized, and security improvement of data access control under cloud storage is effectively provided.
Owner:黑龙江航天信息有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com