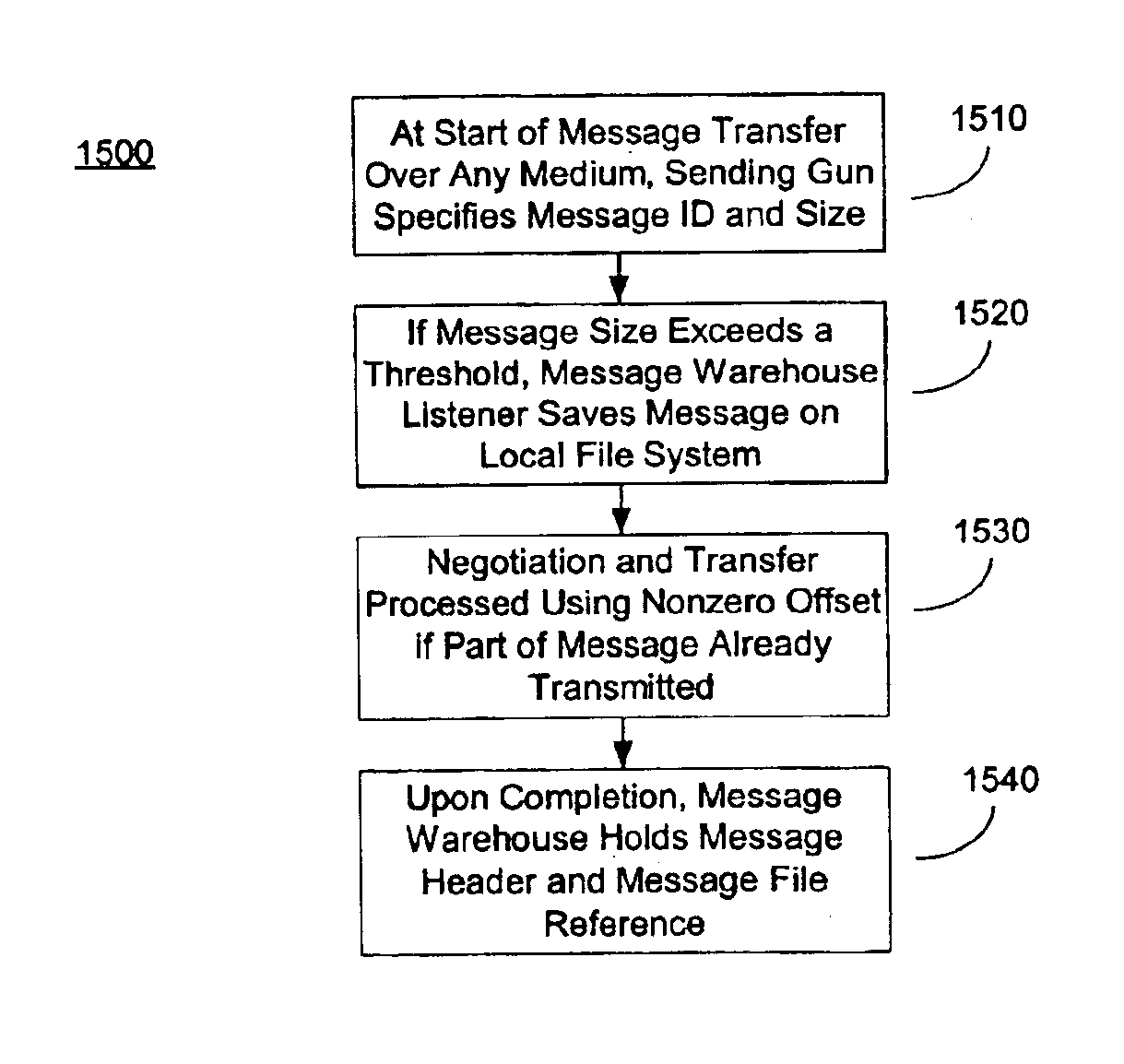
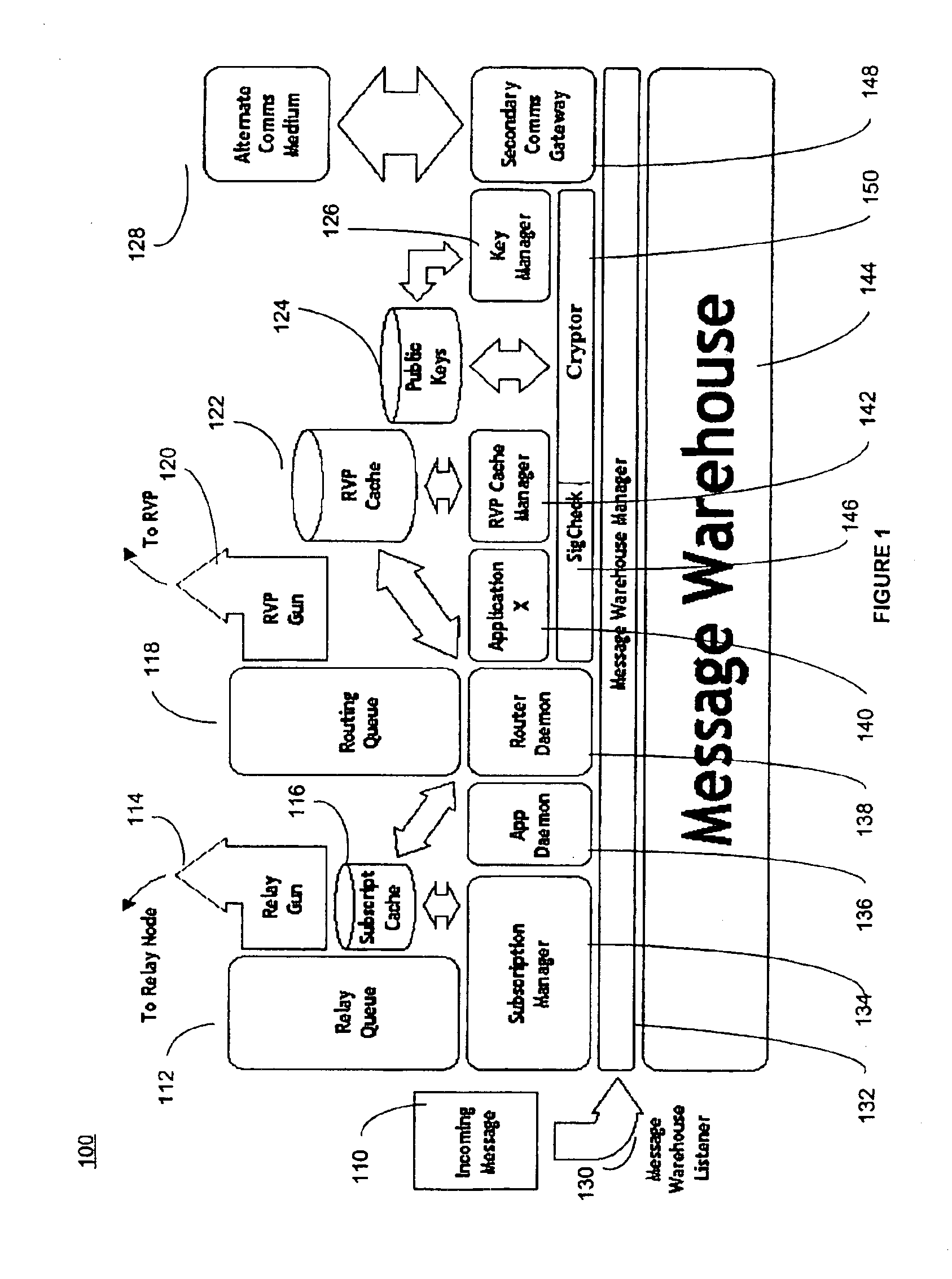
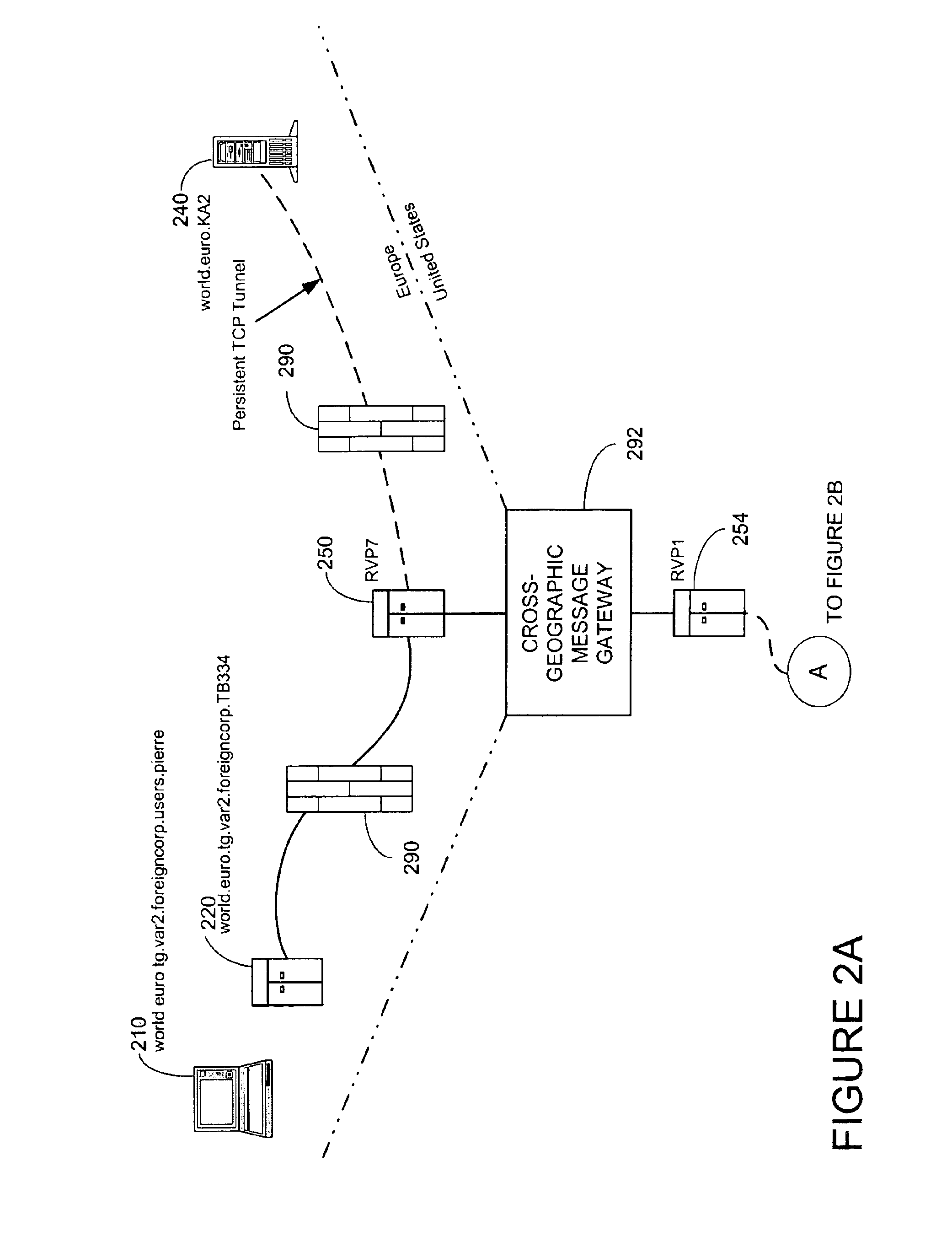
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
19524 results about "Network communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
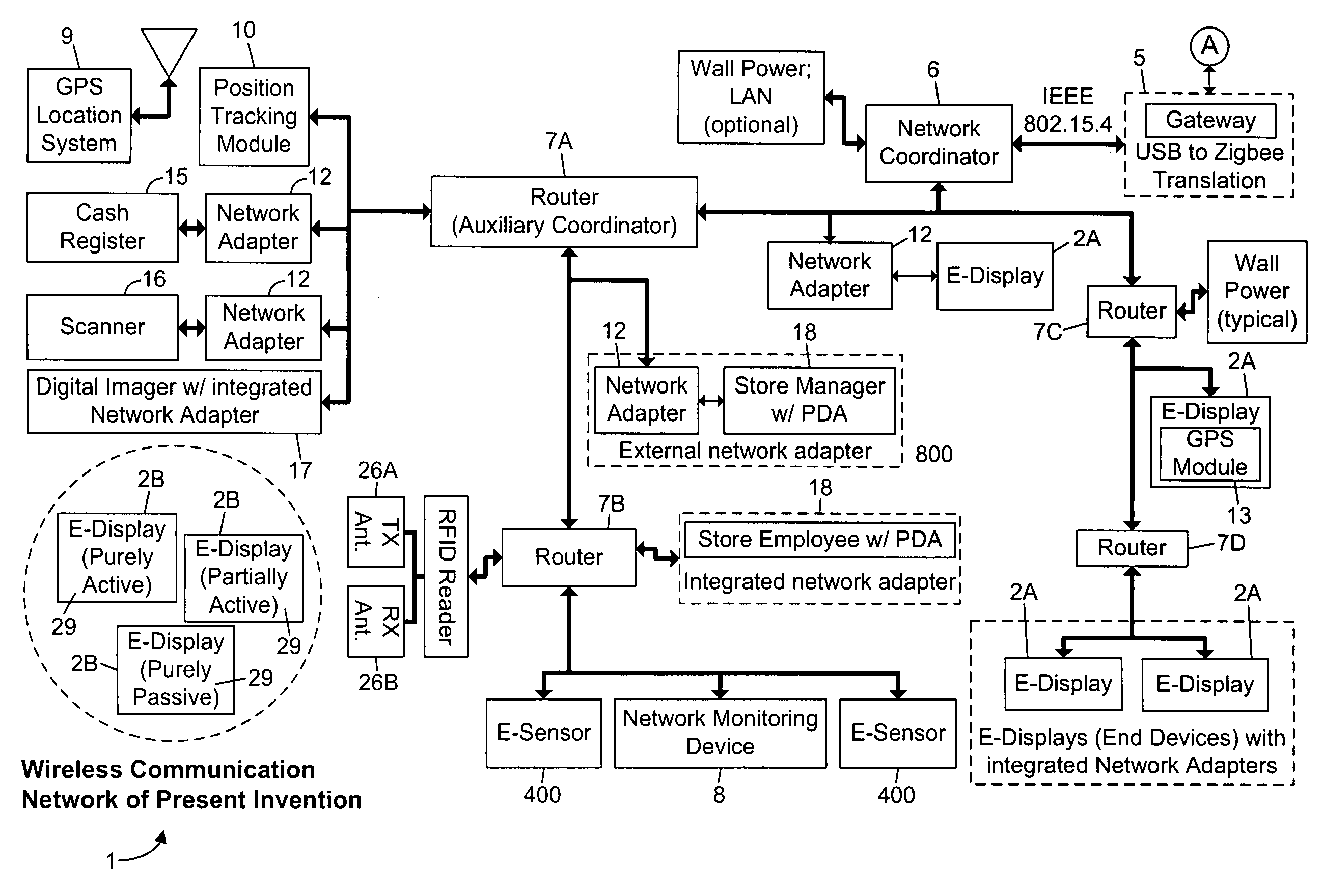
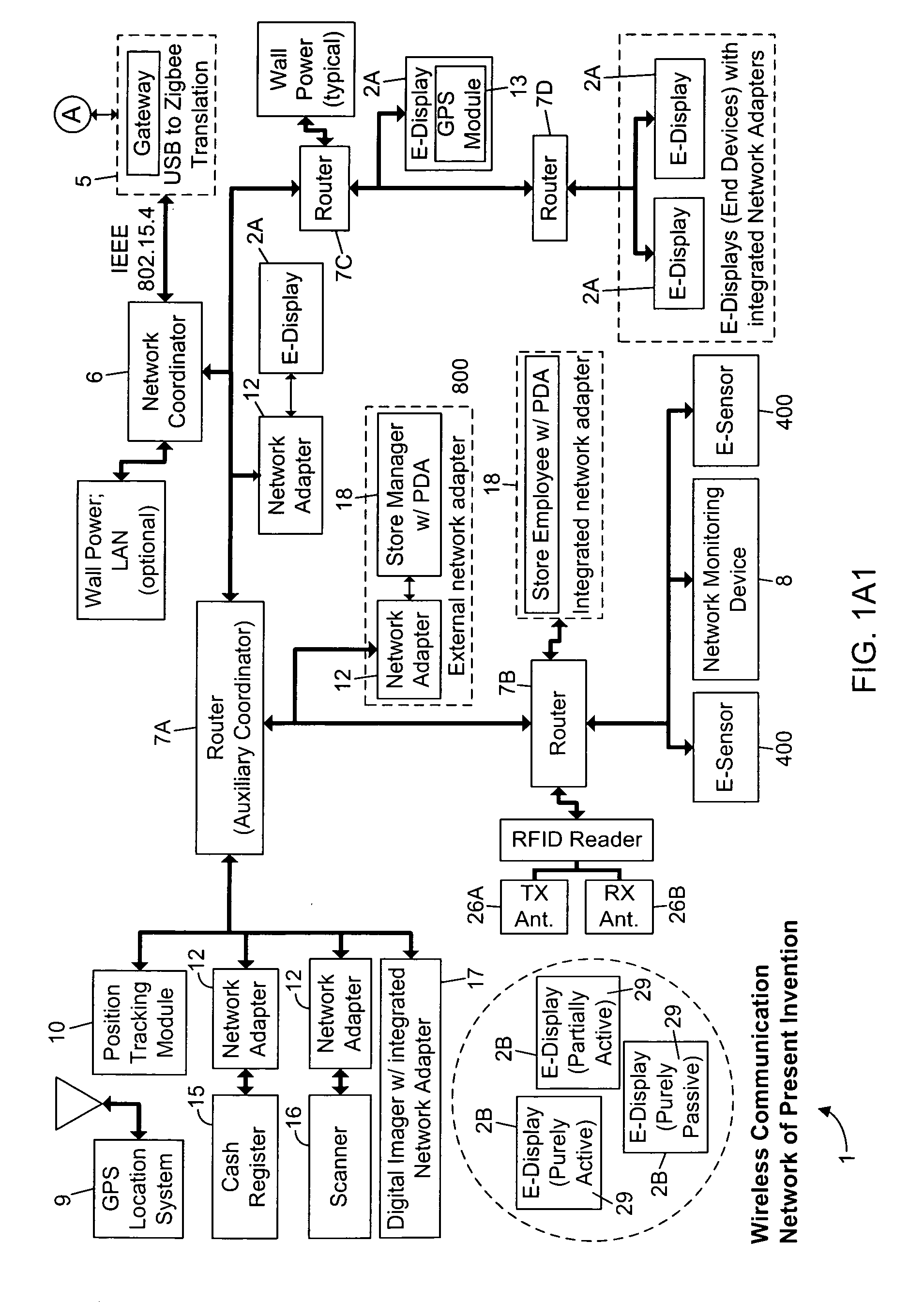
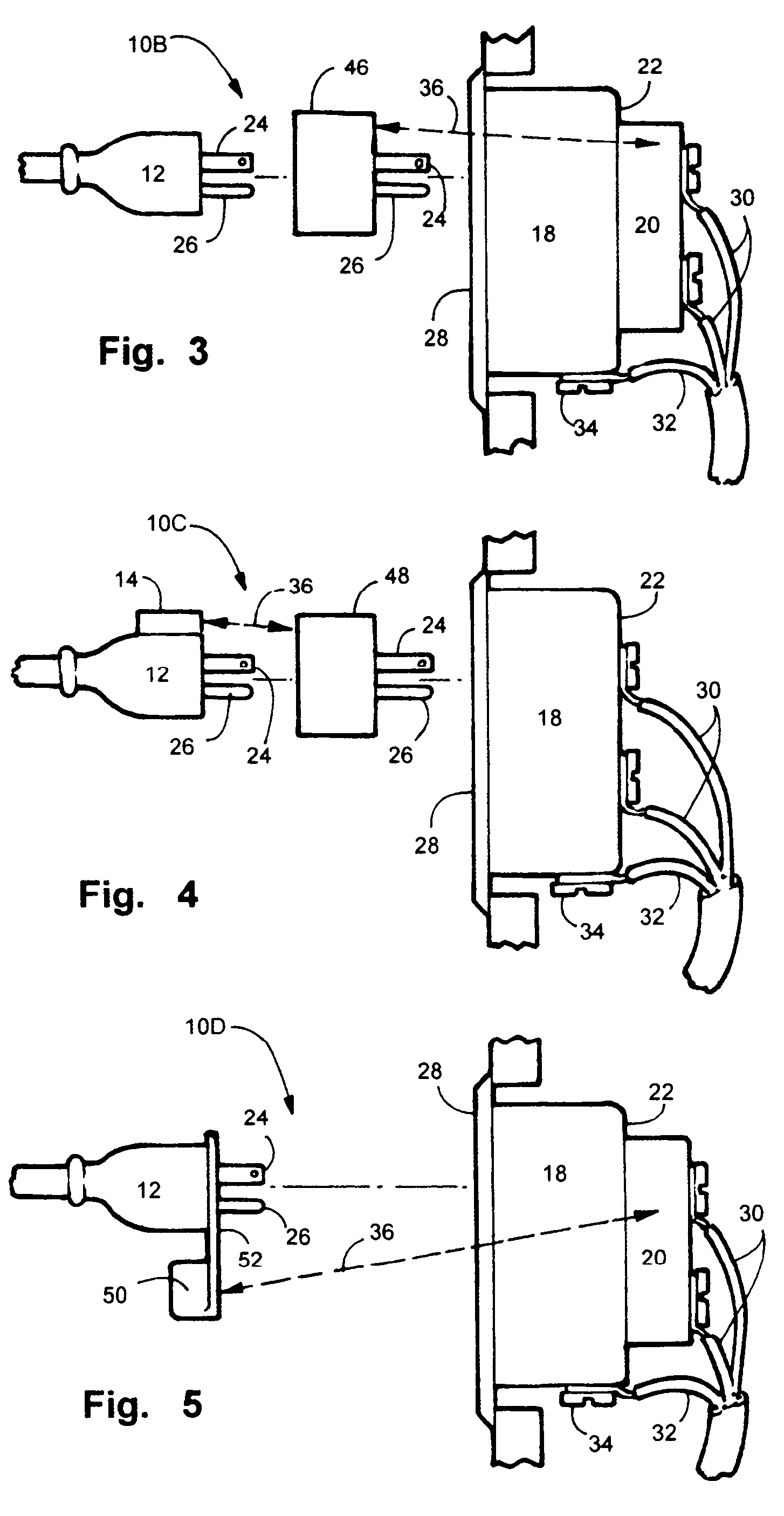
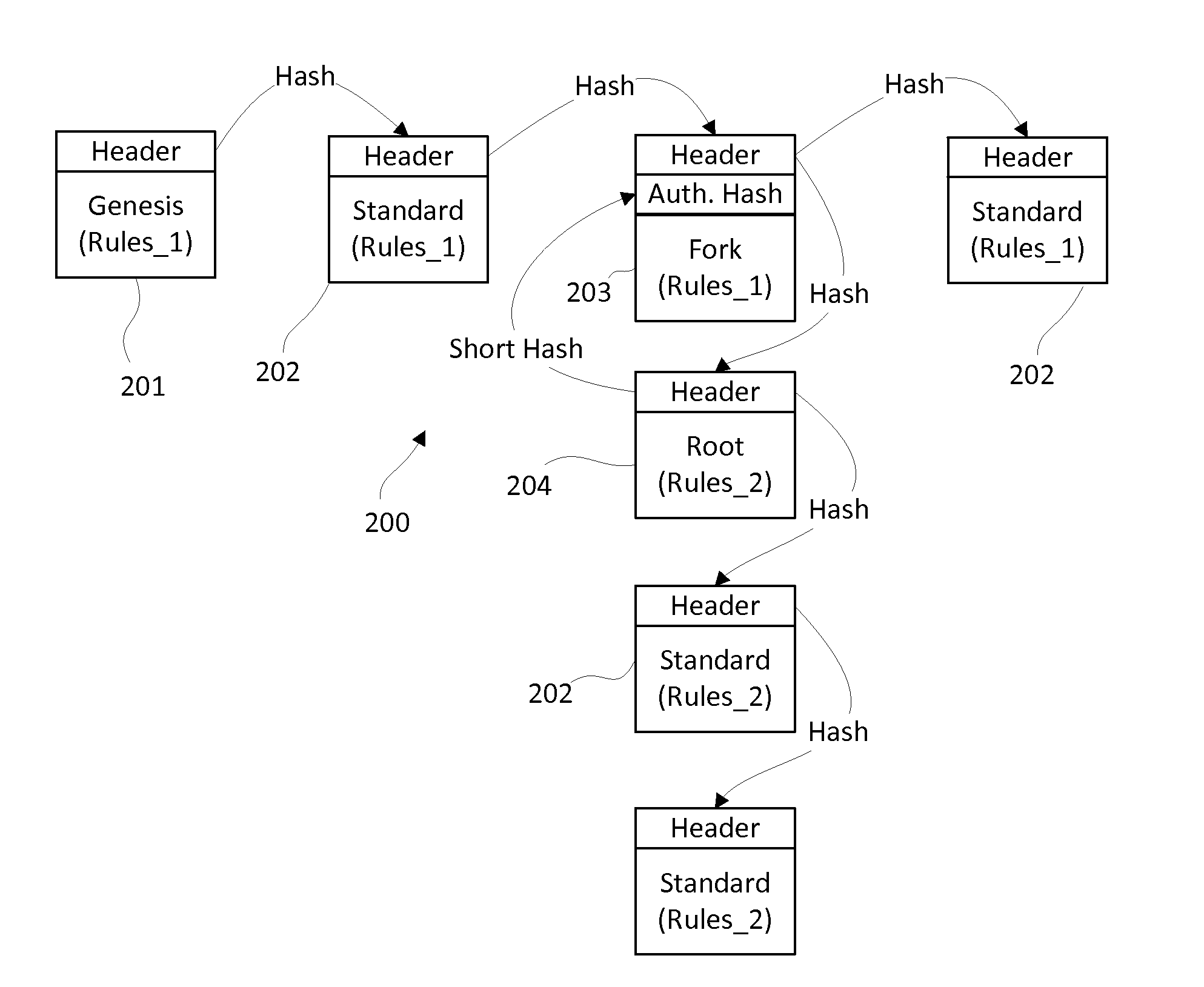
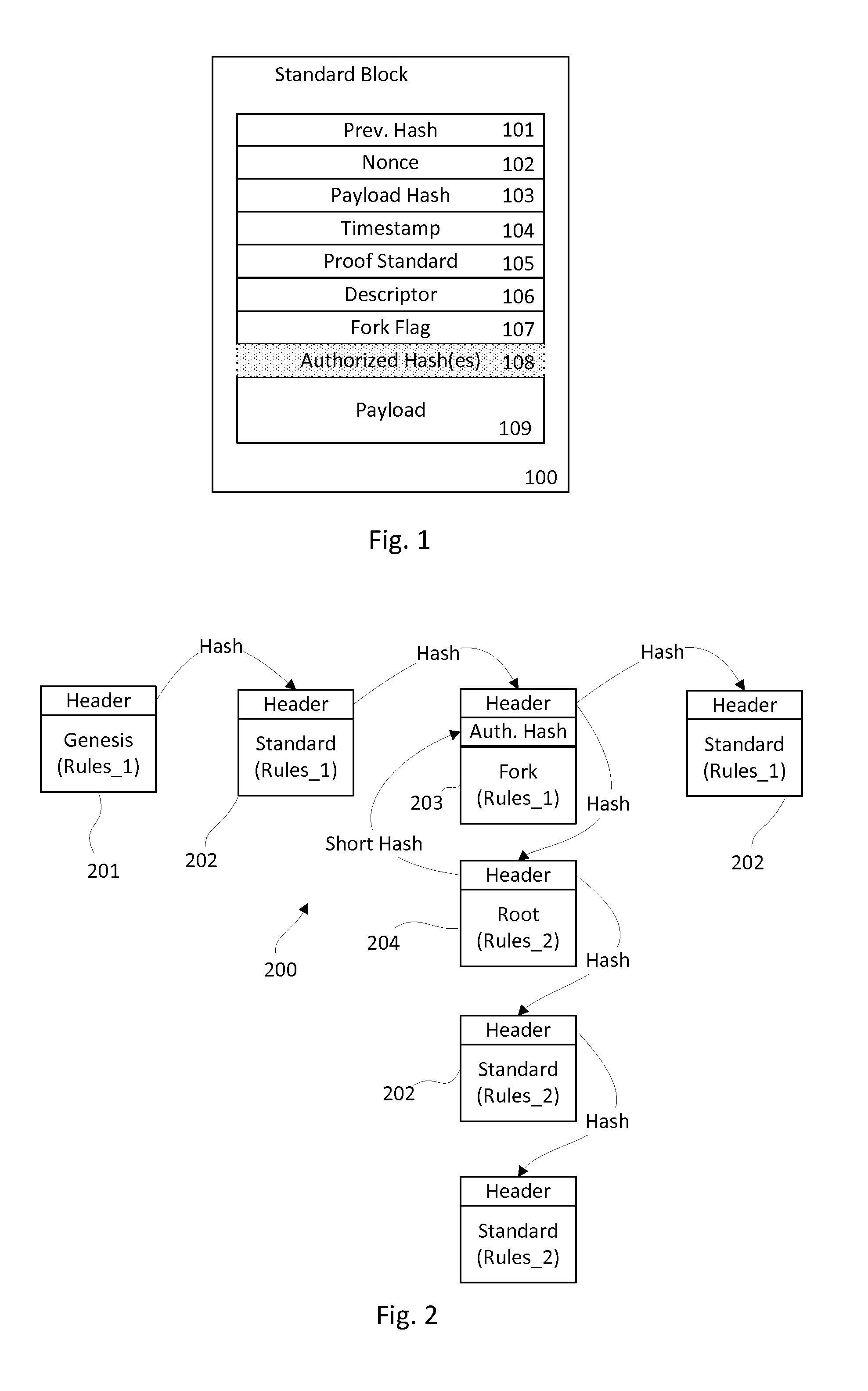
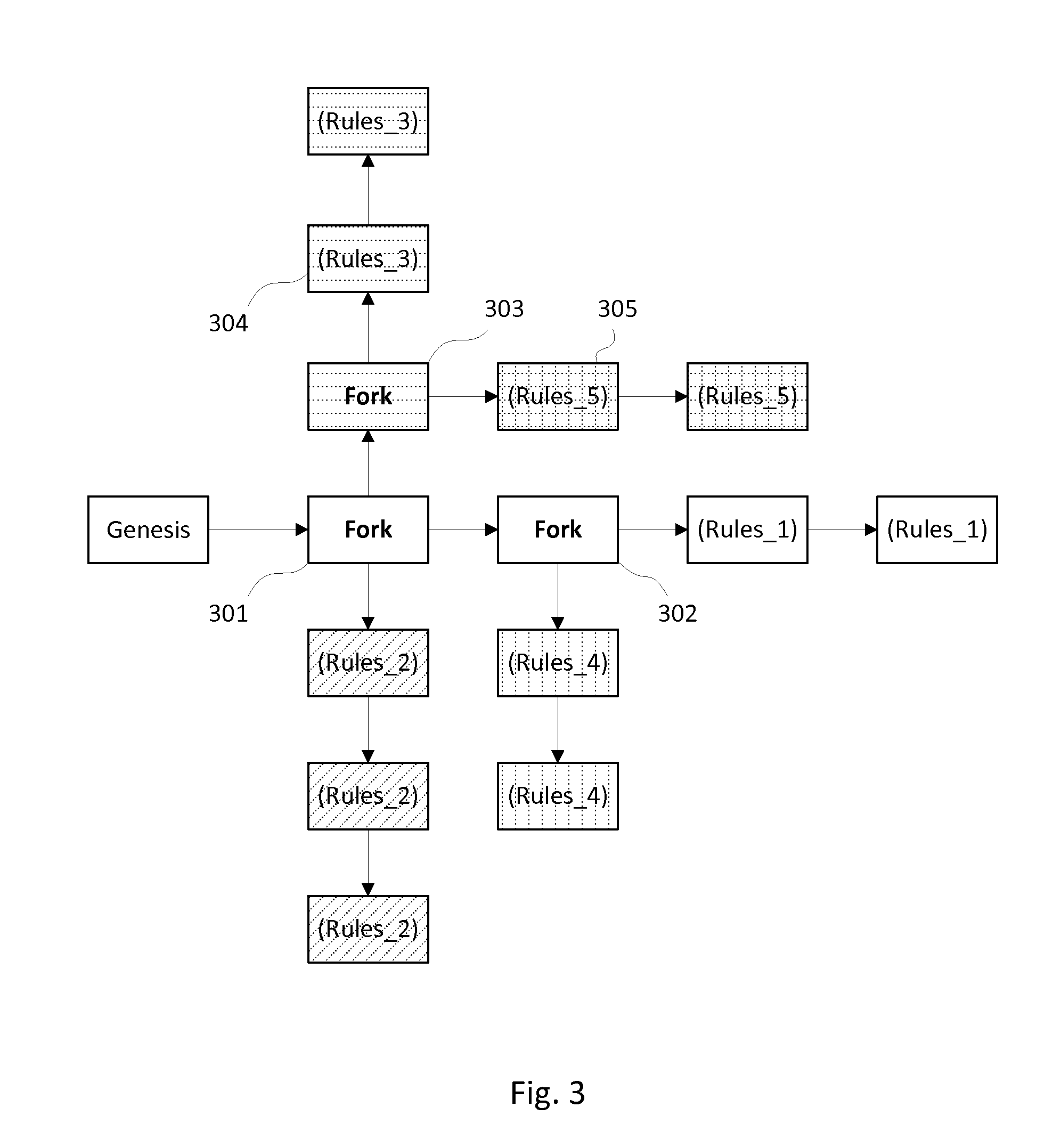
Methods of and apparatus for programming and managing diverse network components, including electronic-ink based display devices, in a mesh-type wireless communication network
InactiveUS20100177749A1Static indicating devicesDigital data processing detailsLogistics managementDisplay device
A wireless communication network for programming and monitoring a plurality of network-managed devices, including electronic-ink based display devices, comprising a network management computer system, a network gateway device, one or more wireless network routers, a plurality of network-managed devices, and a network coordinator. The wireless communication network of the present invention bridges the gap between wireless display networks, wireless sensor networks, and the worlds of passive, active and partially-active RFID and real-time locating systems. The wireless communication network of the present invention allows conventional communication network protocols to operate in more flexible ways in dynamic, diverse, and heterogeneous application environments, in fields including retail, healthcare, transport, logistics, manufacturing, education, etc. At the same time, the wireless communication network of the present invention is preferably based on the IEEE 802.15.4 network layer standard, which offers low-cost wireless network communication between a large number of wireless network end-devices.
Owner:METROLOGIC INSTR
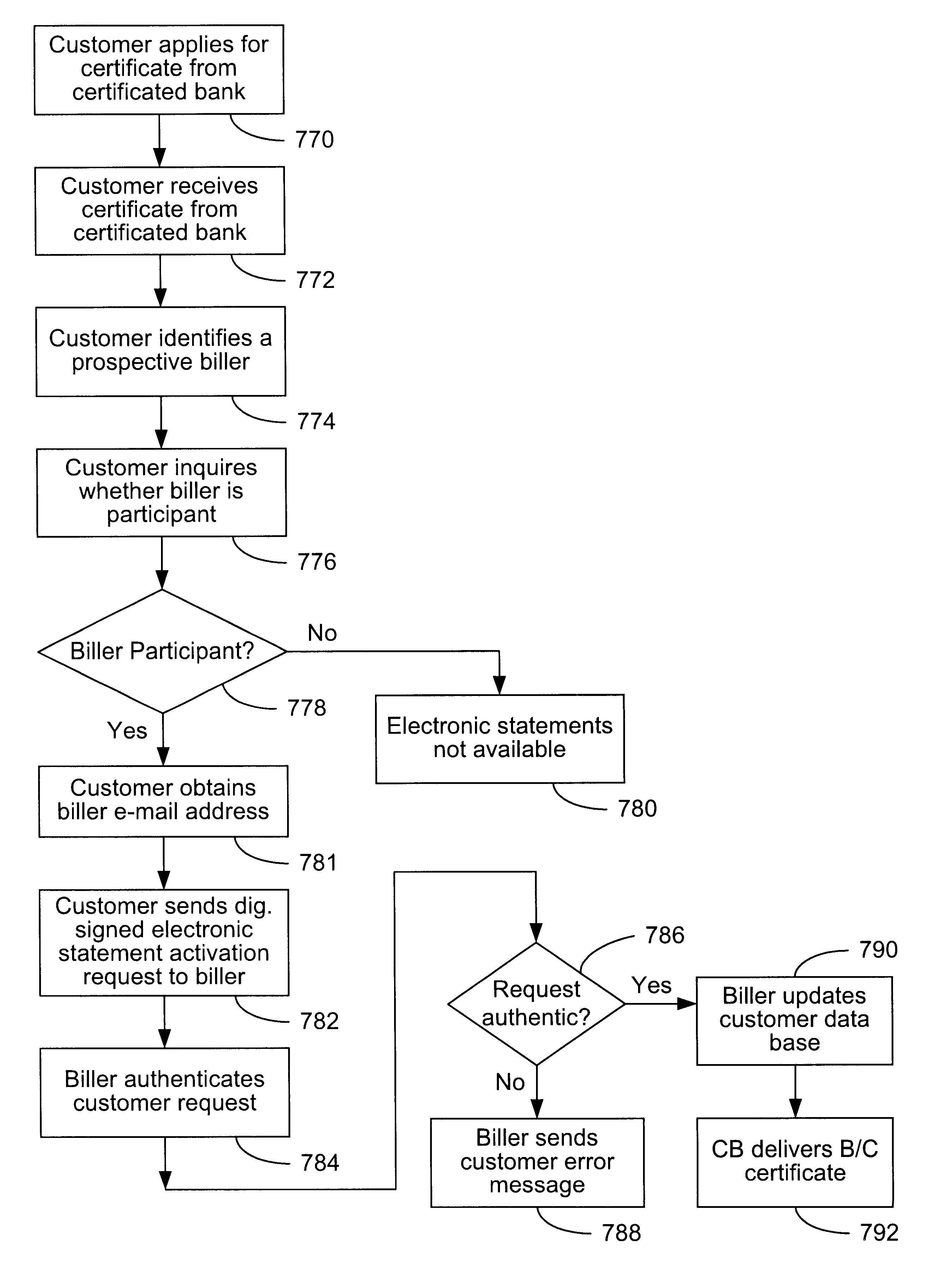
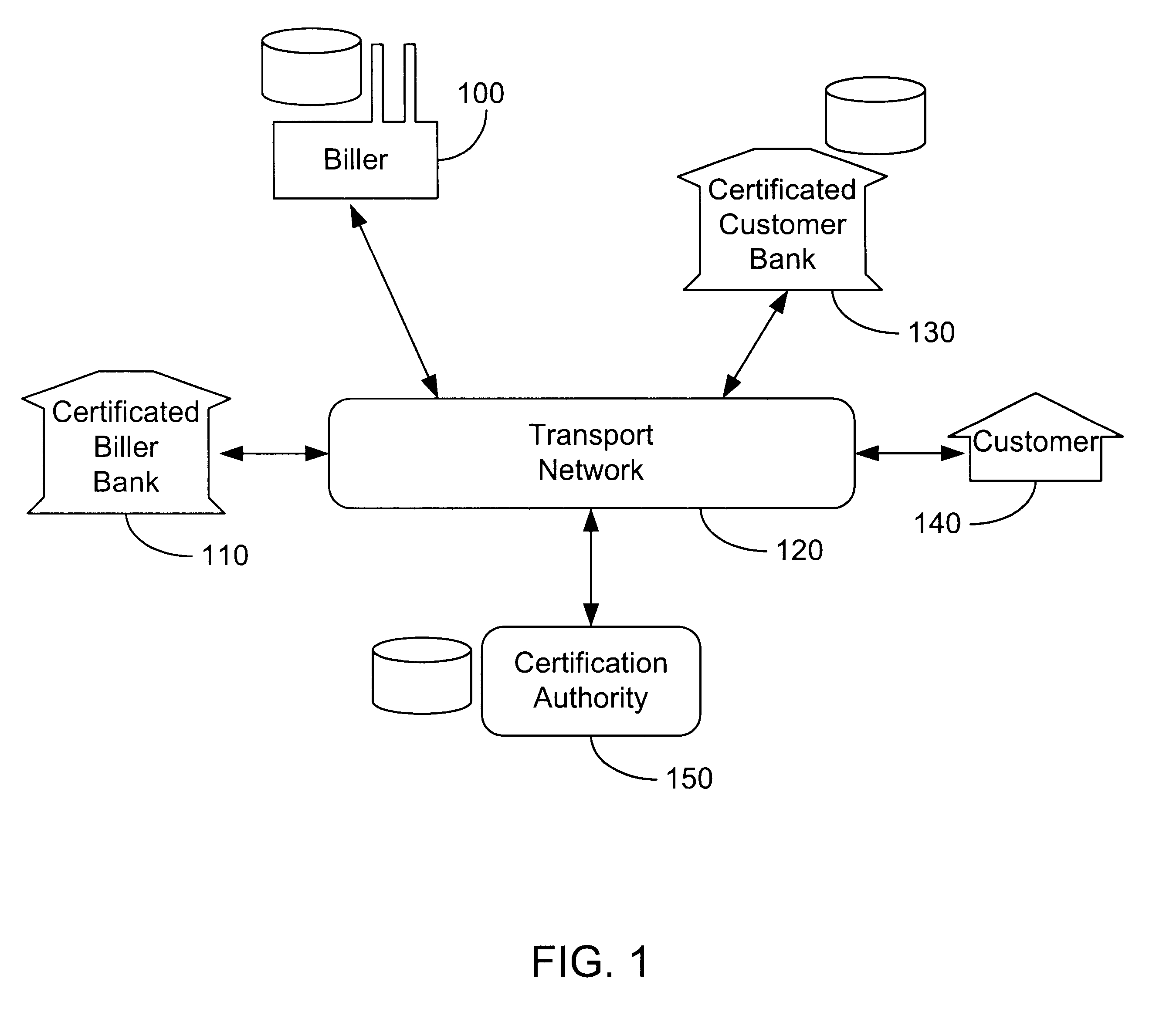
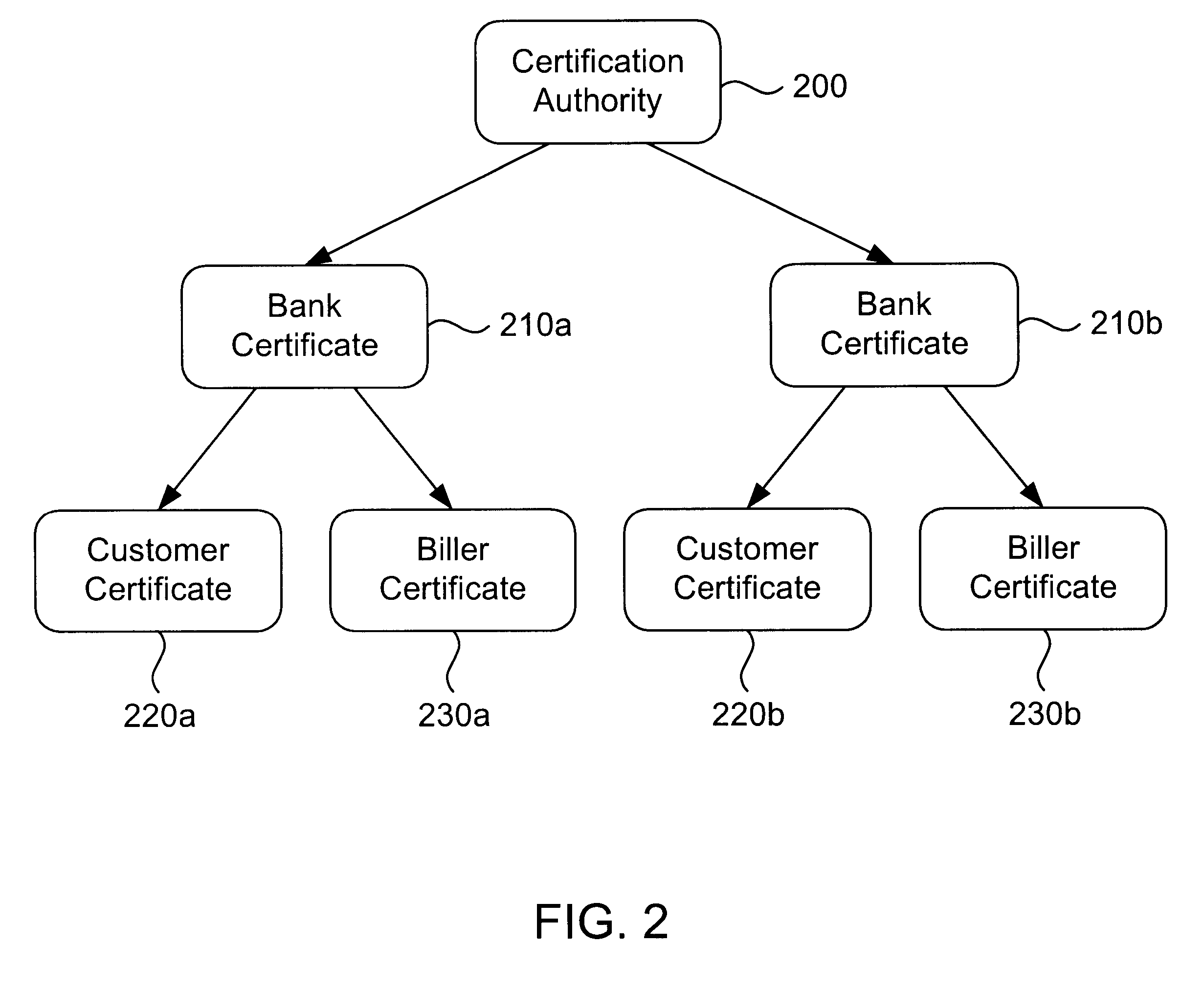
Secure interactive electronic account statement delivery system
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
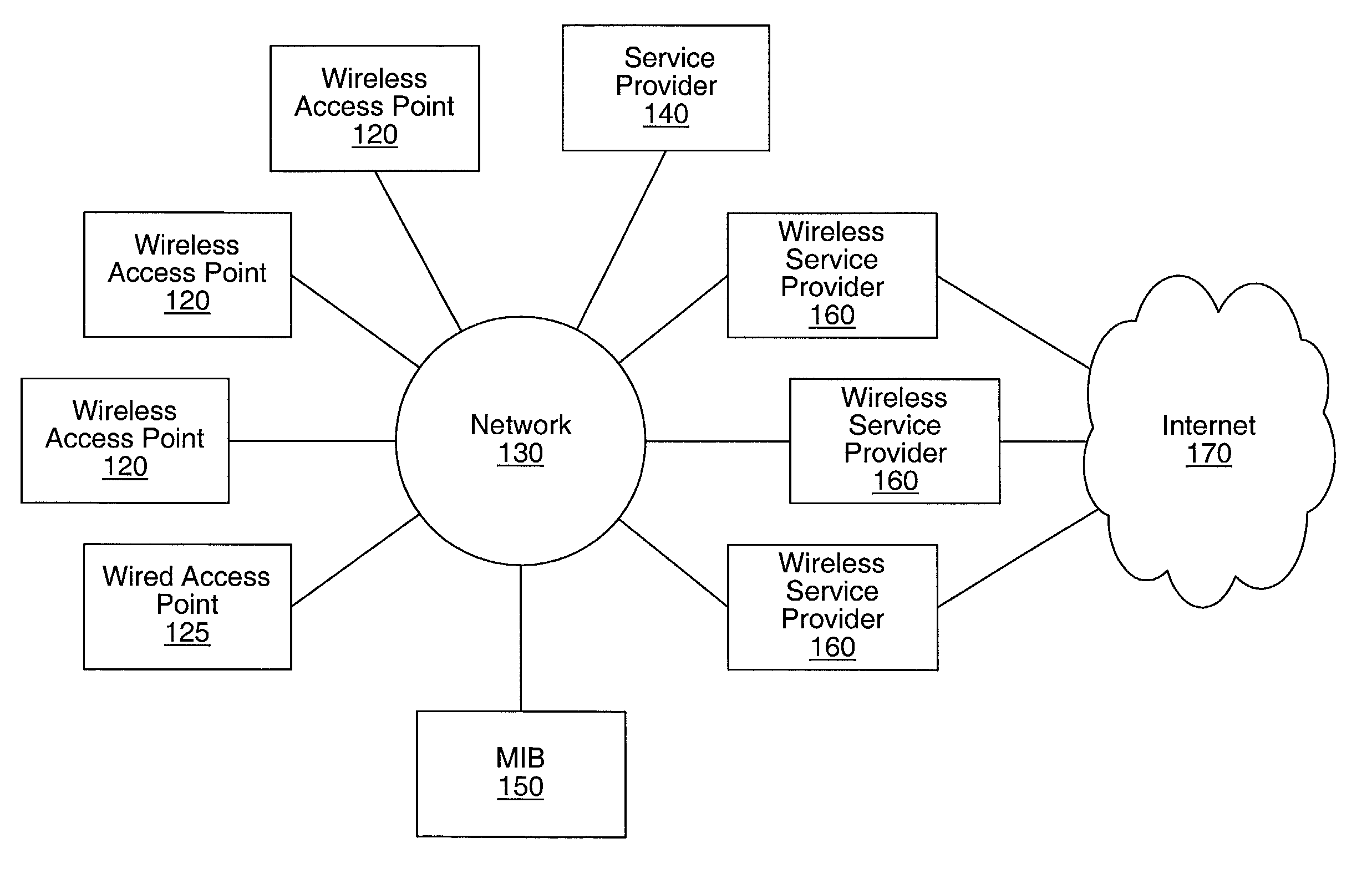
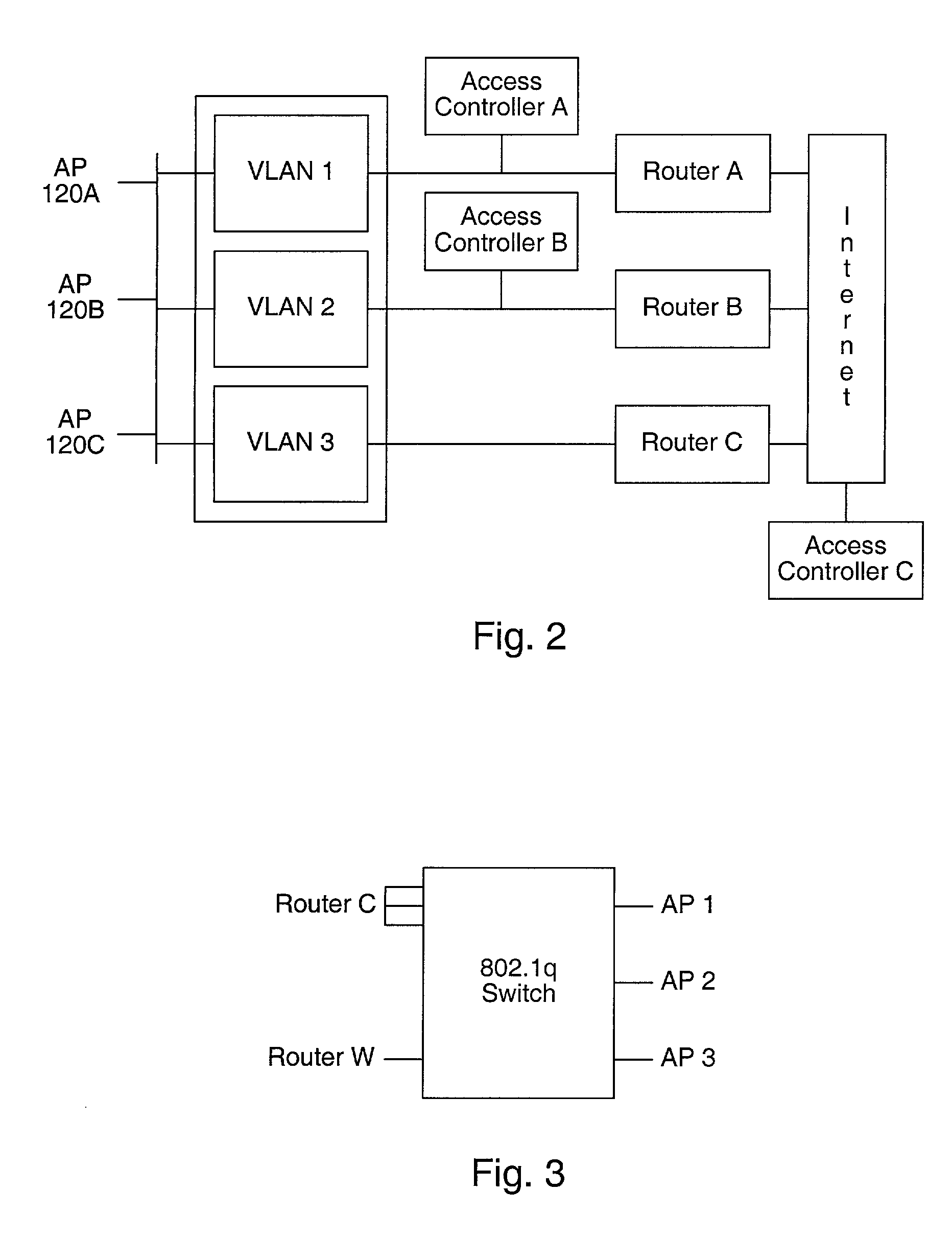
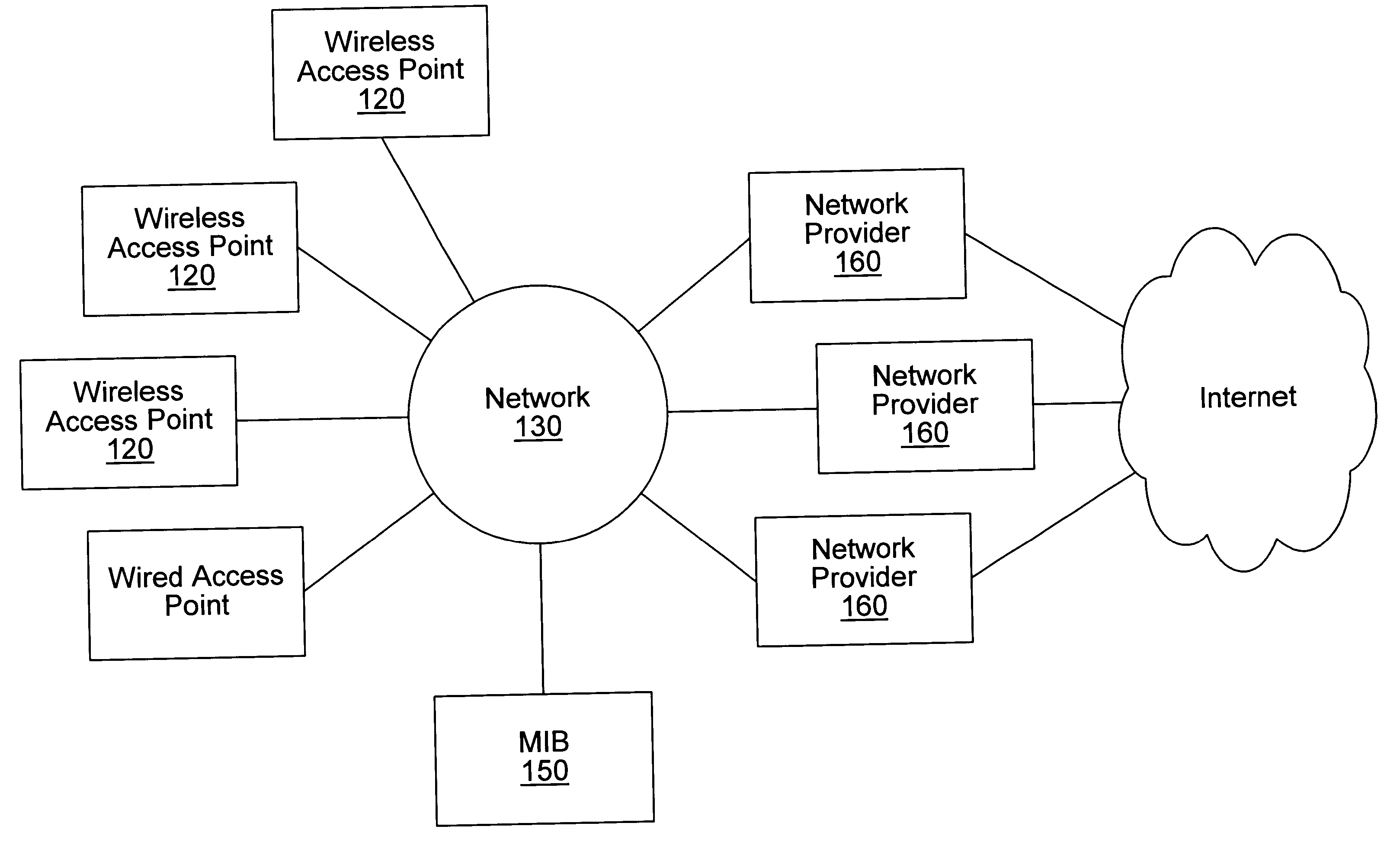
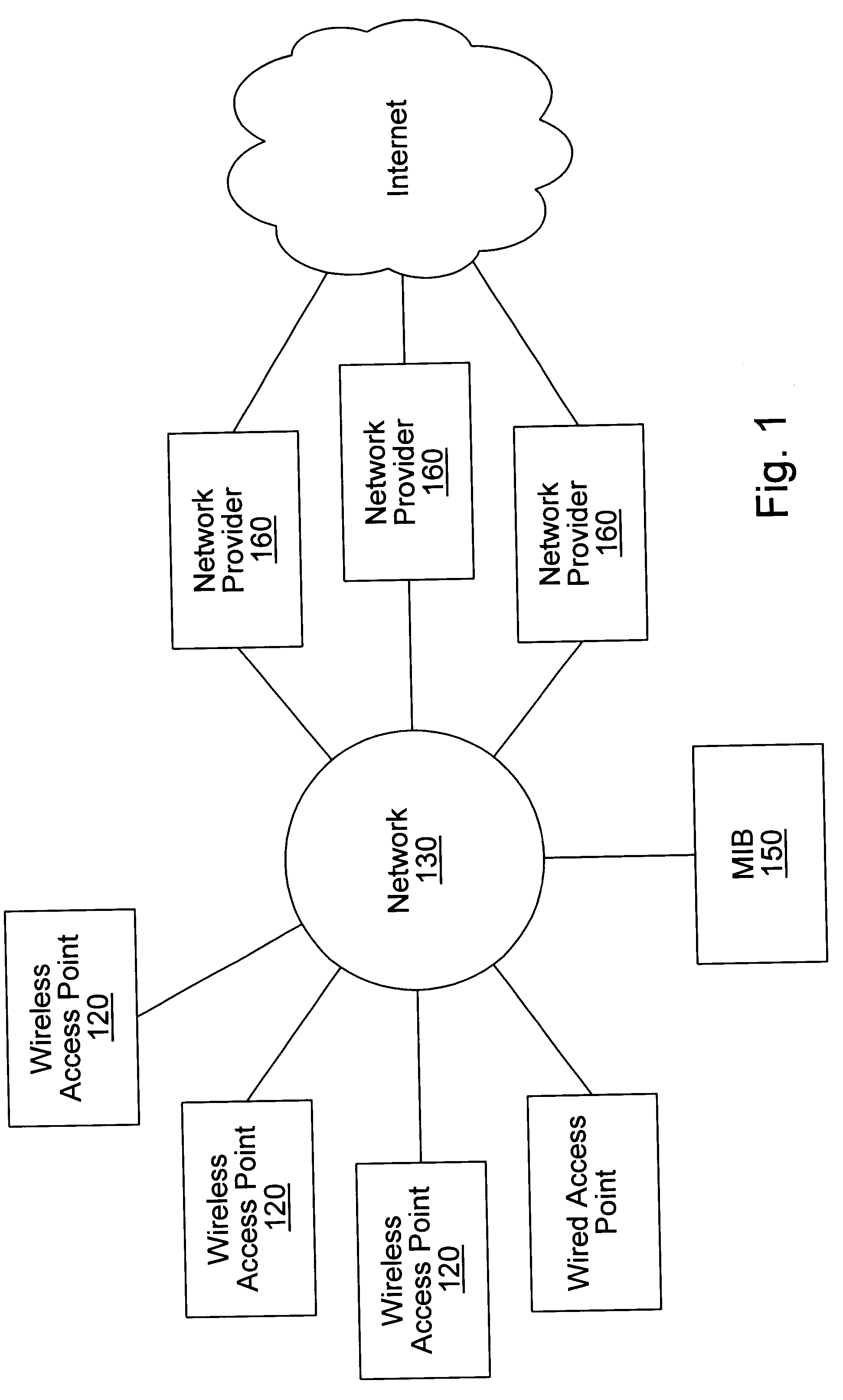
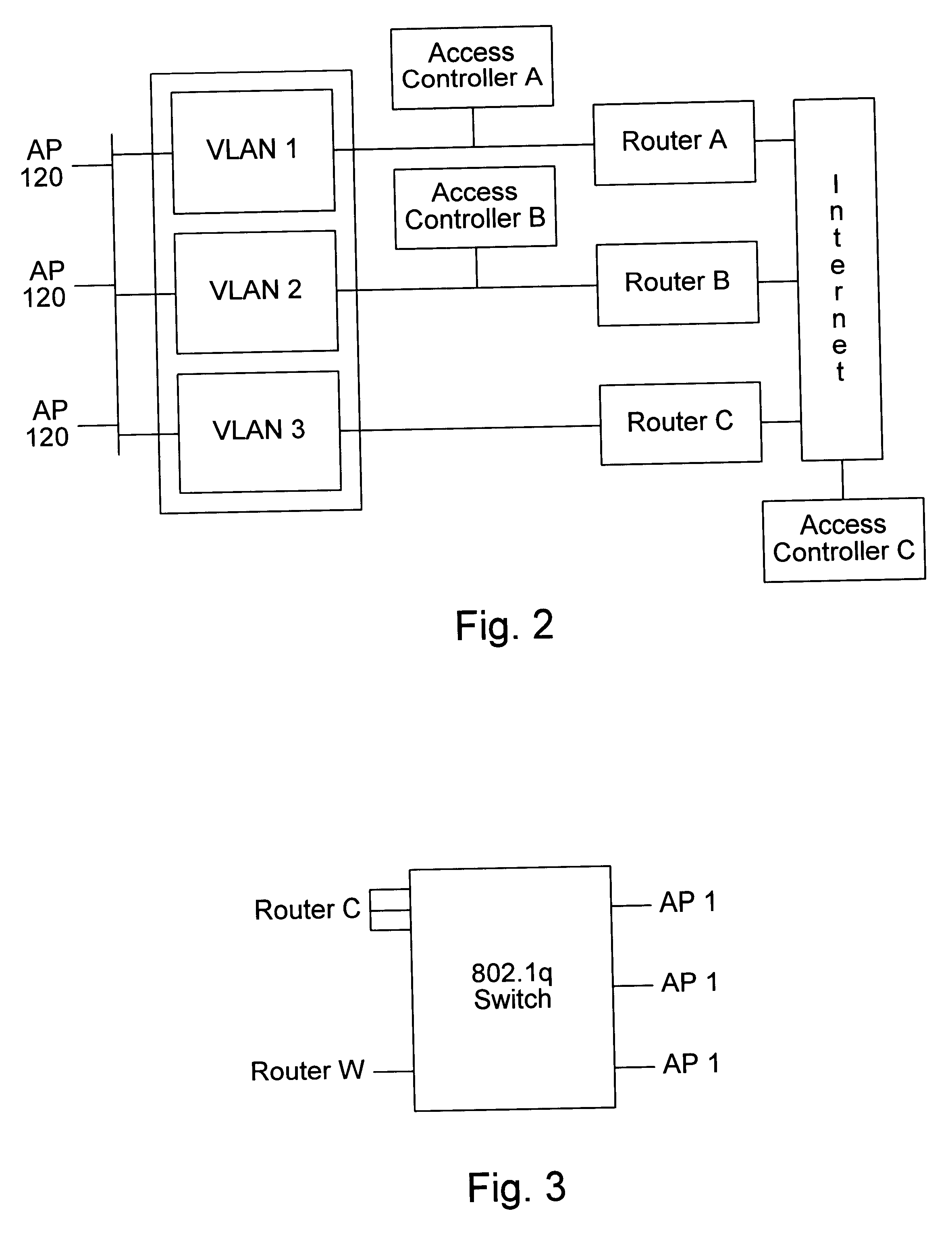
Distributed network communication system which allows multiple wireless service providers to share a common network infrastructure
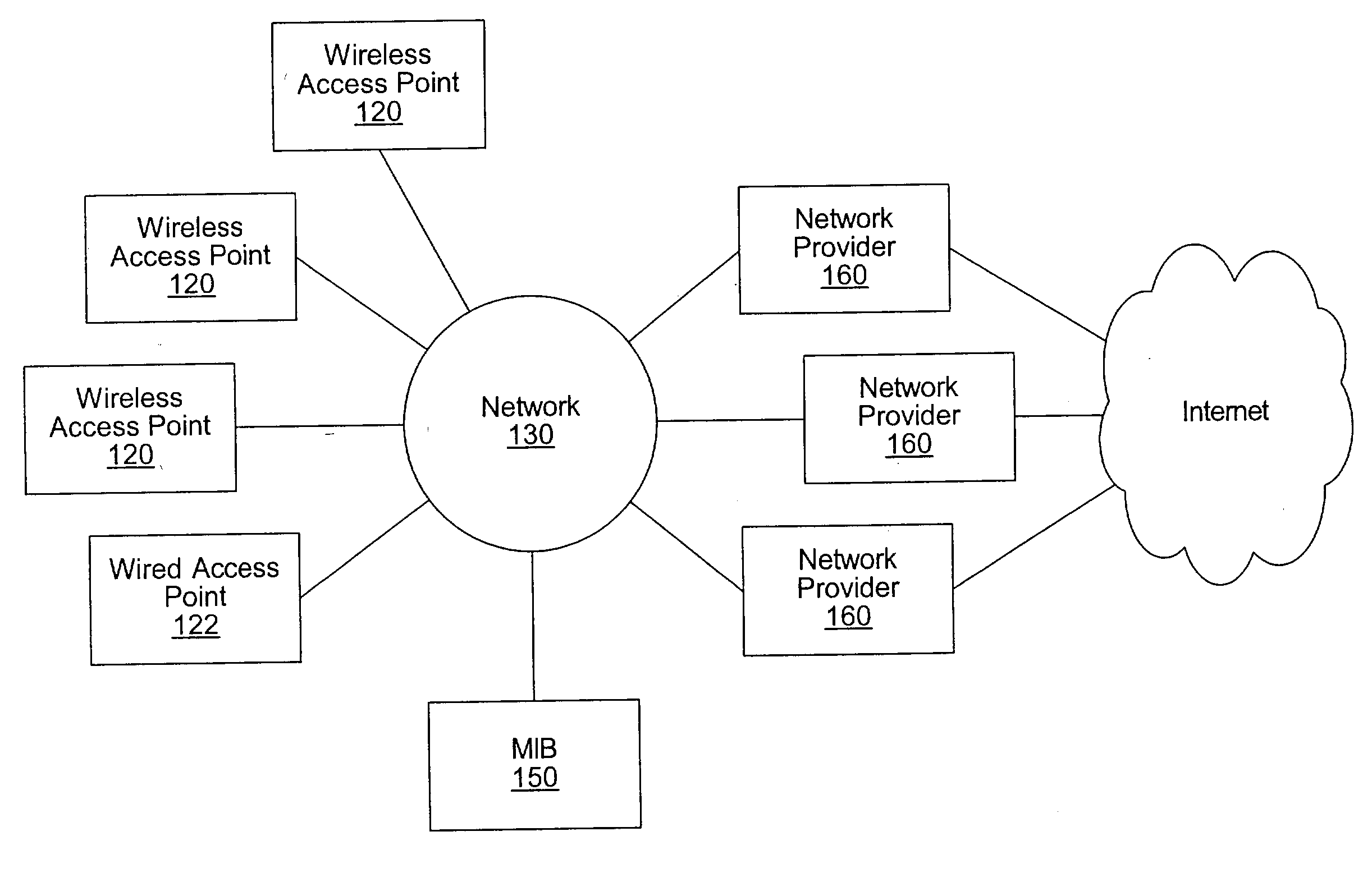
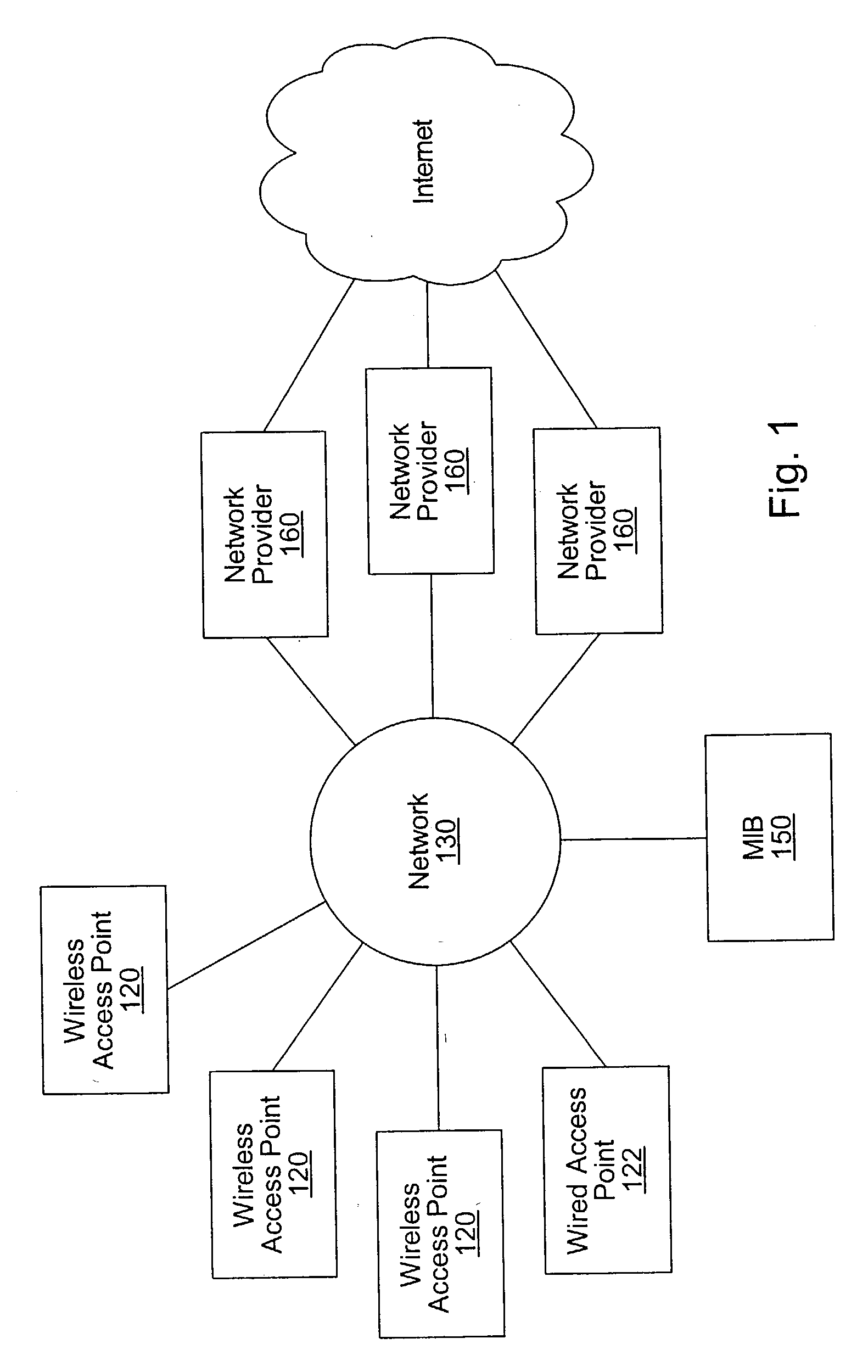
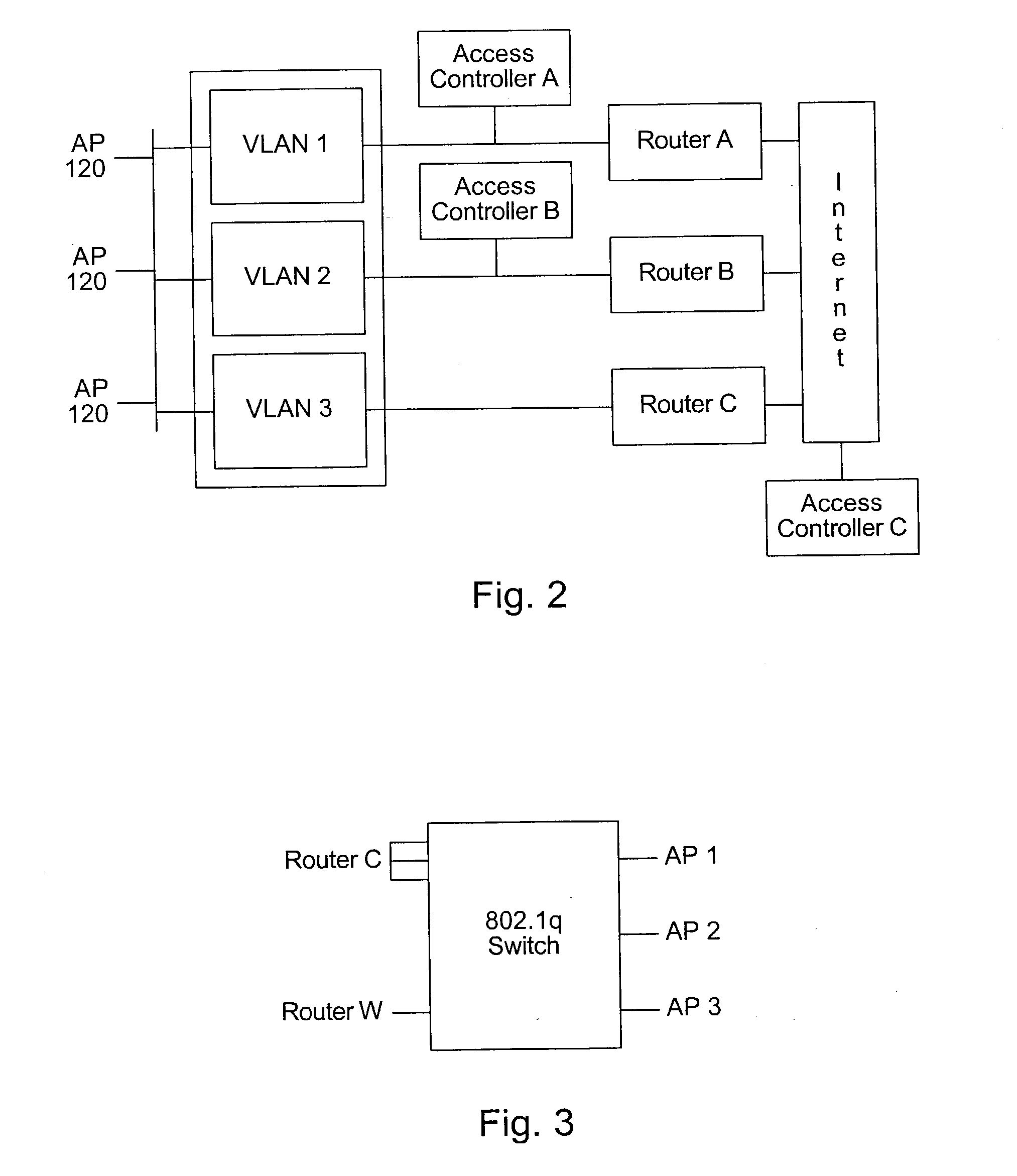
System and method for providing access to multiple wireless service providers (WSPs) on a shared network infrastructure. The system includes a plurality of access points (APs) coupled to a network which may be distributed in airports, mass-transit stations, businesses, etc. The network may couple to a wide area network, such as the Internet. Each AP may include a plurality of virtual APs (VAPs), each corresponding to a WSP. A portable computing device (PCD) of a user stores identification information indicating a WSP of a plurality of possible WSPs, and which may include an access level of the user. Each AP "listens for" or detects identification information associated with numerous WSPs. When the AP receives the identification information from the PCD, it determines the VAP / WSP for the PCD using the identification information. Network access is then provided to the PCD through the determined WSP at the determined access level.
Owner:CISCO TECH INC
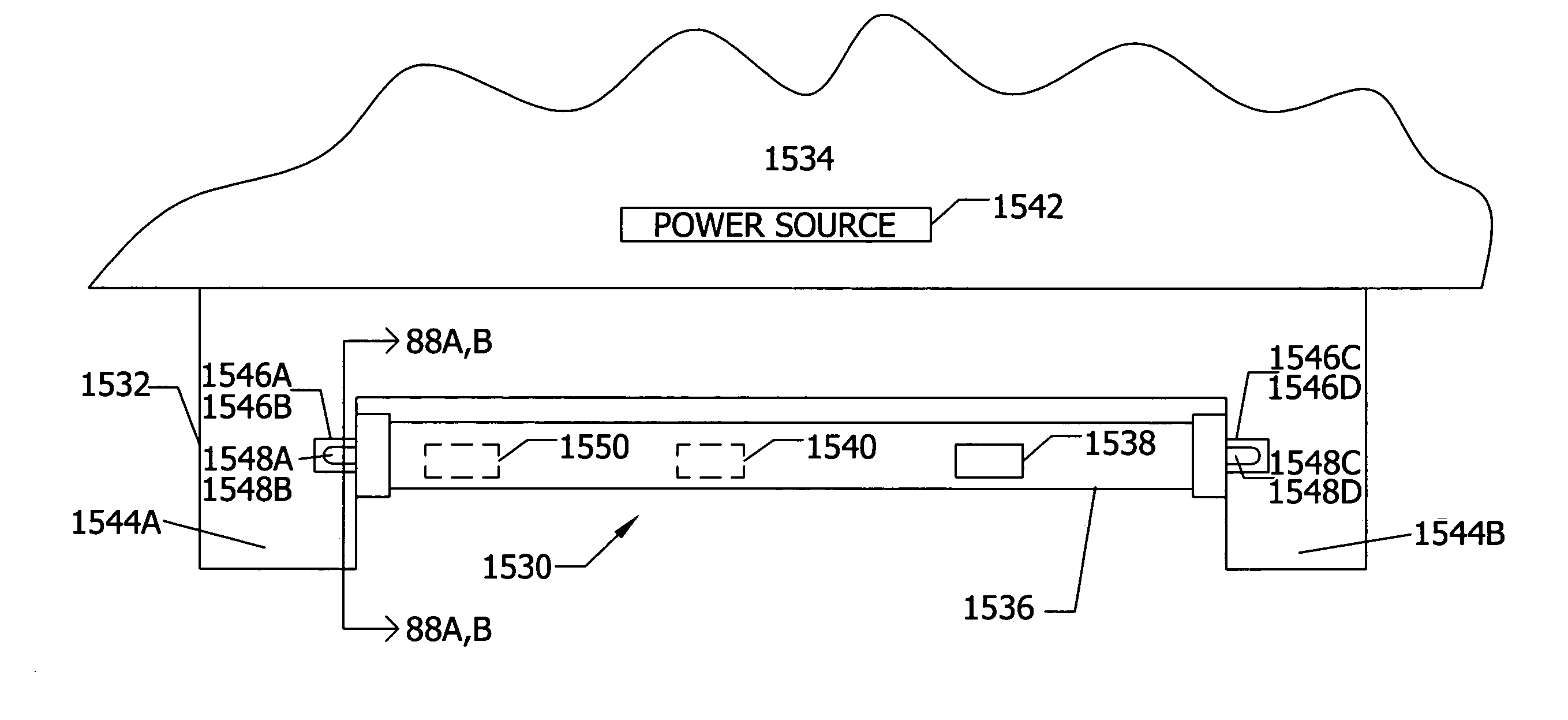
Retrofit LED lamp for fluorescent fixtures without ballast
ActiveUS20070228999A1Increase costLow costLighting support devicesPoint-like light sourceFluorescenceNetwork communication
An energy saving device for an LED lamp mounted to an existing fixture for a fluorescent lamp where the ballast is removed or bypassed. The LEDs are positioned within a tube and electrical power is delivered from a power source to the LEDs. The LED lamp includes means for controlling the delivery of the electrical power from the power source to the LEDs, wherein the use of electrical power can be reduced or eliminated automatically during periods of non-use. Such means for controlling includes means for detecting the level of daylight in the illumination area of said least one LED, in particular a light level photosensor, and means for transmitting to the means for controlling relating to the detected level of daylight from the photosensor. The photosensor can be used in operative association with an on-off switch in power connection to the LEDs, a timer, or with a computer or logic gate array in operative association with a switch, timer, or dimmer that regulates the power to the LEDs. An occupancy sensor that detects motion or a person in the illumination area of the LEDs can be also be used in association with the photosensor and the computer, switch, timer, or dimmer, or in solo operation by itself. Two or more such LED lamps with a computer or logic gate array used with at least one of the lamps can be in network communication with at least one photosensor and / or at least one occupancy sensor to control the power to all the LEDs.
Owner:SIGNIFY HLDG BV
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
InactiveUS6732176B1Metering/charging/biilling arrangementsMultiple digital computer combinationsCommunications systemNetworked system
A system and method for providing access and / or roaming features on a network system. The network system includes a plurality of wireless and / or wired access points coupled to a network. A portable computing device (PCD) of a user may store identification information which uniquely indicates a network provider of a plurality of possible network providers. The identification information may also or instead indicate an access or privilege level of the user. When the access point receives the identification information from a PCD of a user, the access point may determine the appropriate network provider for the portable computing device using the identification information. Network access may then be provided to the portable computing device through the determined network provider.
Owner:CISCO TECH INC
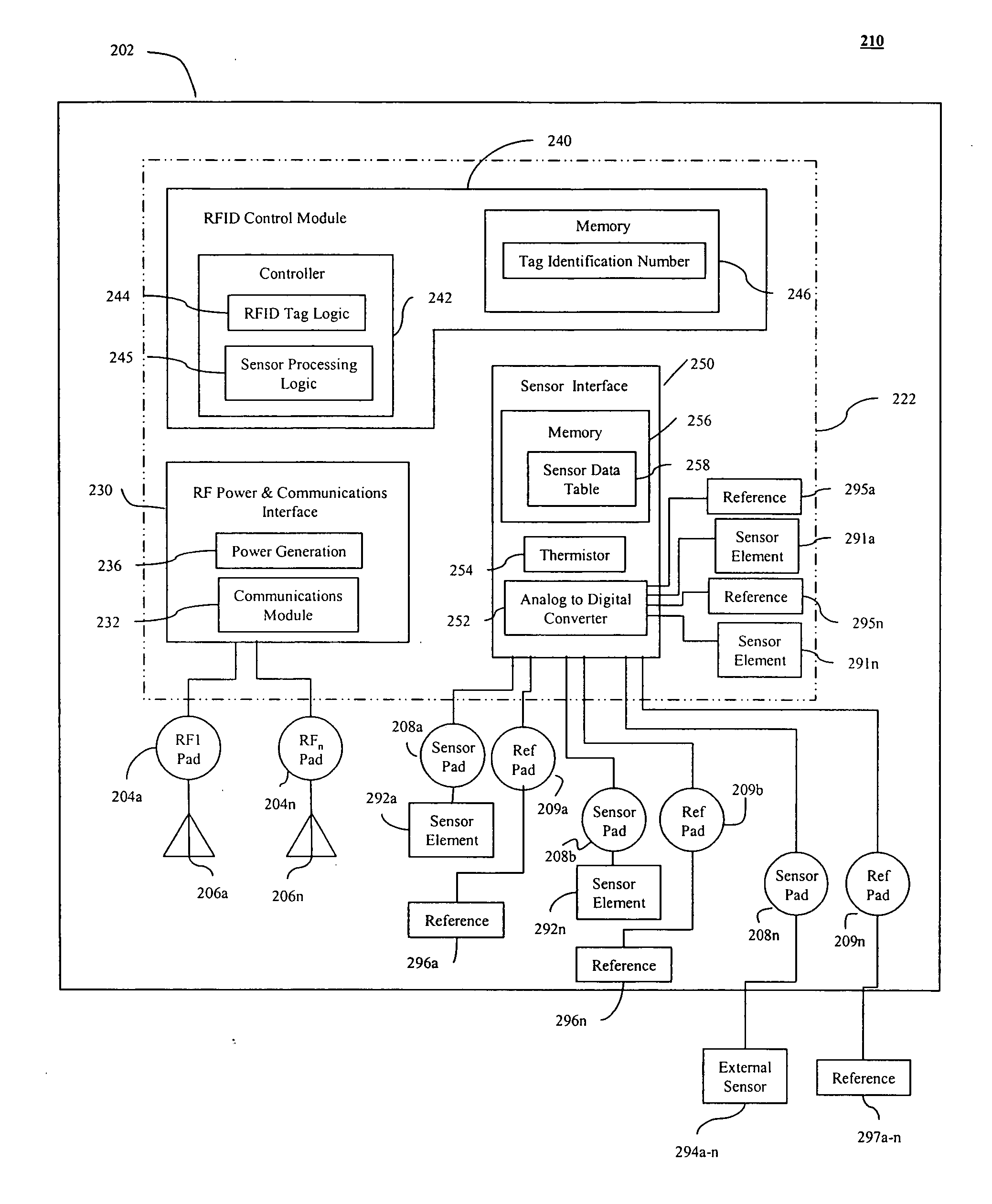
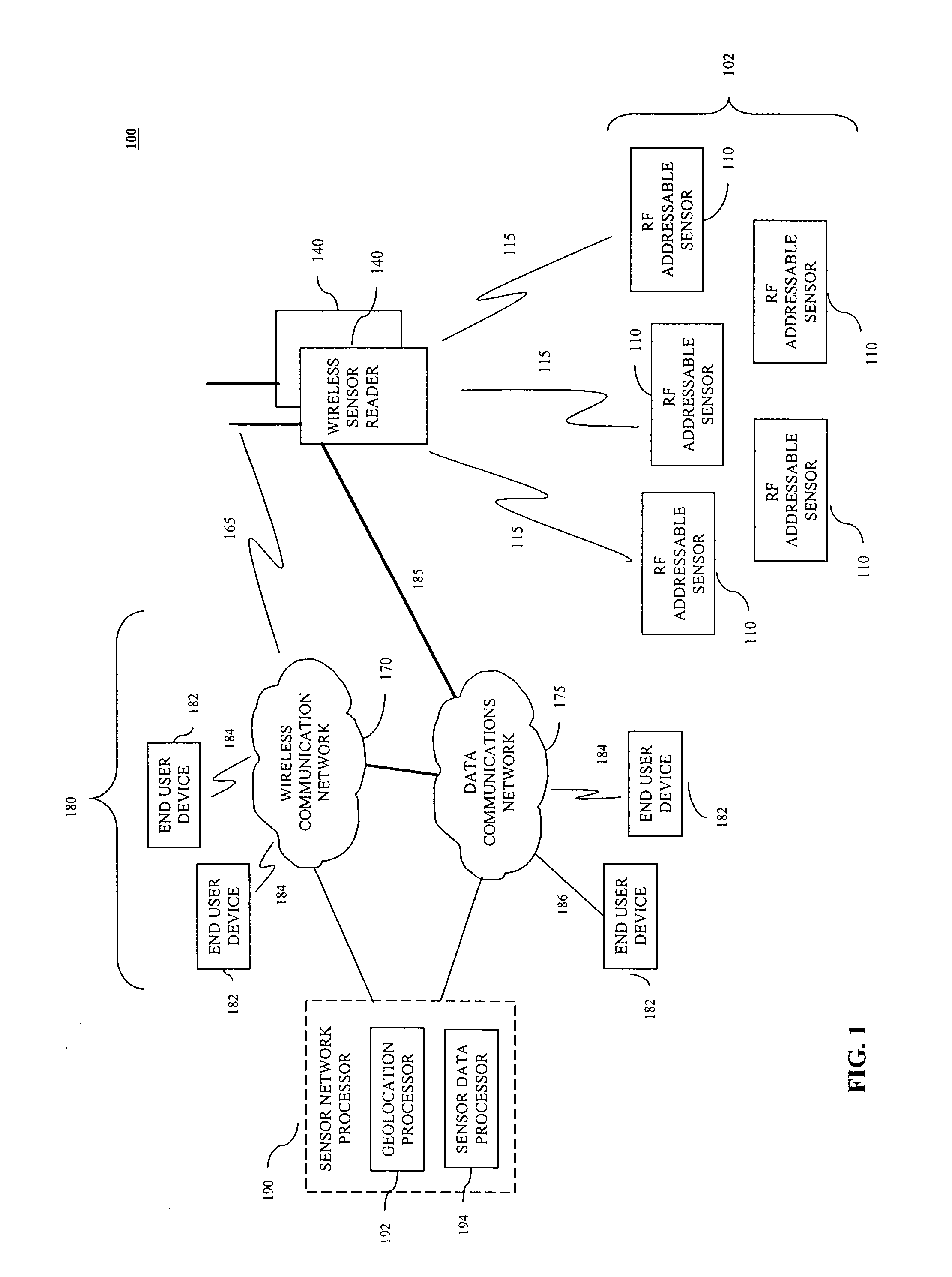
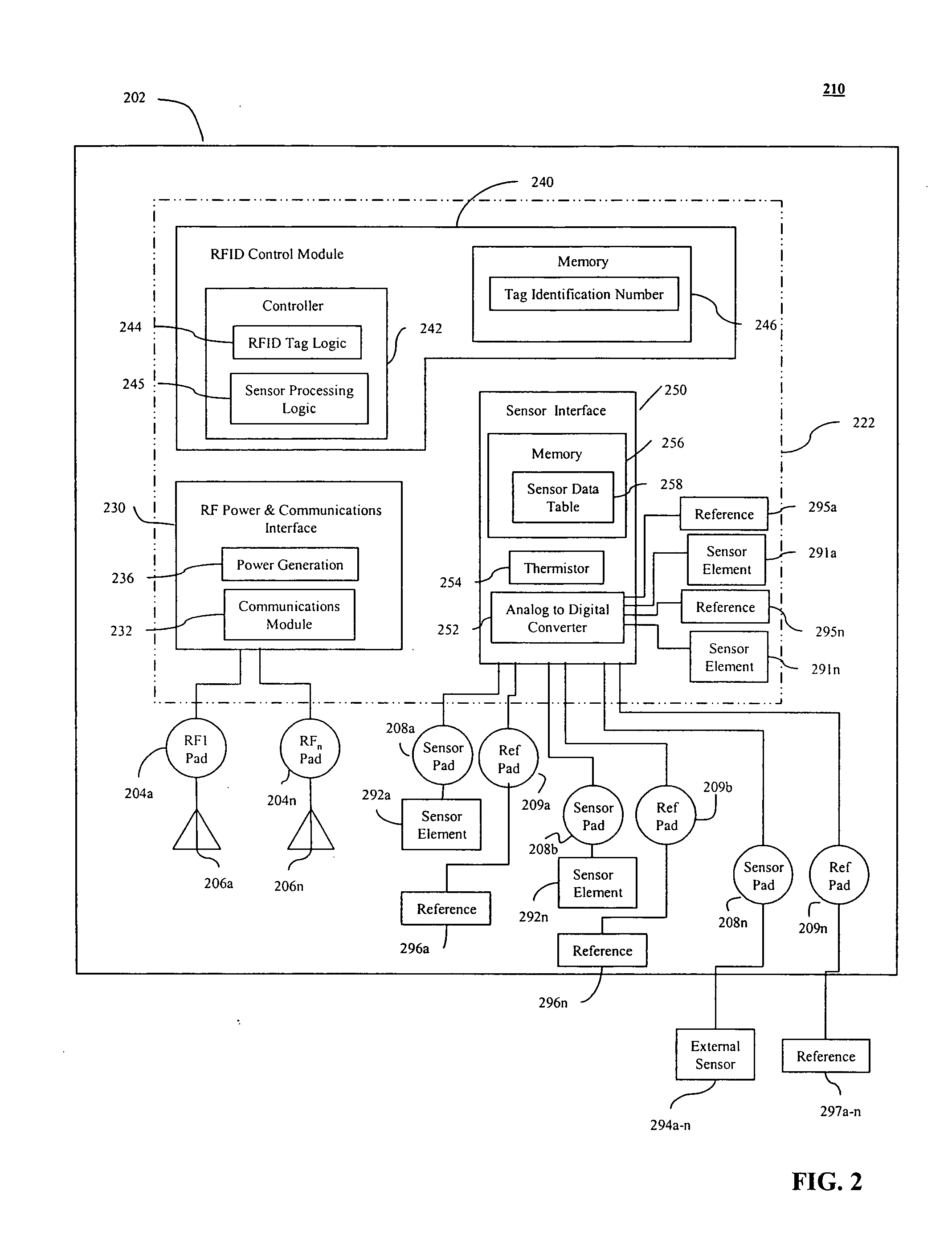
Radio frequency identification (RFID) based sensor networks
ActiveUS20050088299A1Low production costLow costElectric signal transmission systemsAlarmsCommunication interfaceNetwork architecture
An RF addressable sensor network architecture is provided. The RF addressable sensor network includes one or more RF addressable sensors, one or more wireless sensor readers coupled to a communications network, and one or more end user devices coupled to the communications network. The RF addressable sensor network may also include a sensor network processor. An RF addressable sensor includes one or more sensor elements, one or more antennas for communicating with the wireless sensor reader, an RF power and communications interface, and RFID control module, and a sensor interface. The wireless sensor reader includes one or more antennas, a user interface, a controller, a network communications module, and an RF addressable sensor logic module.
Owner:ALTIVERA +1
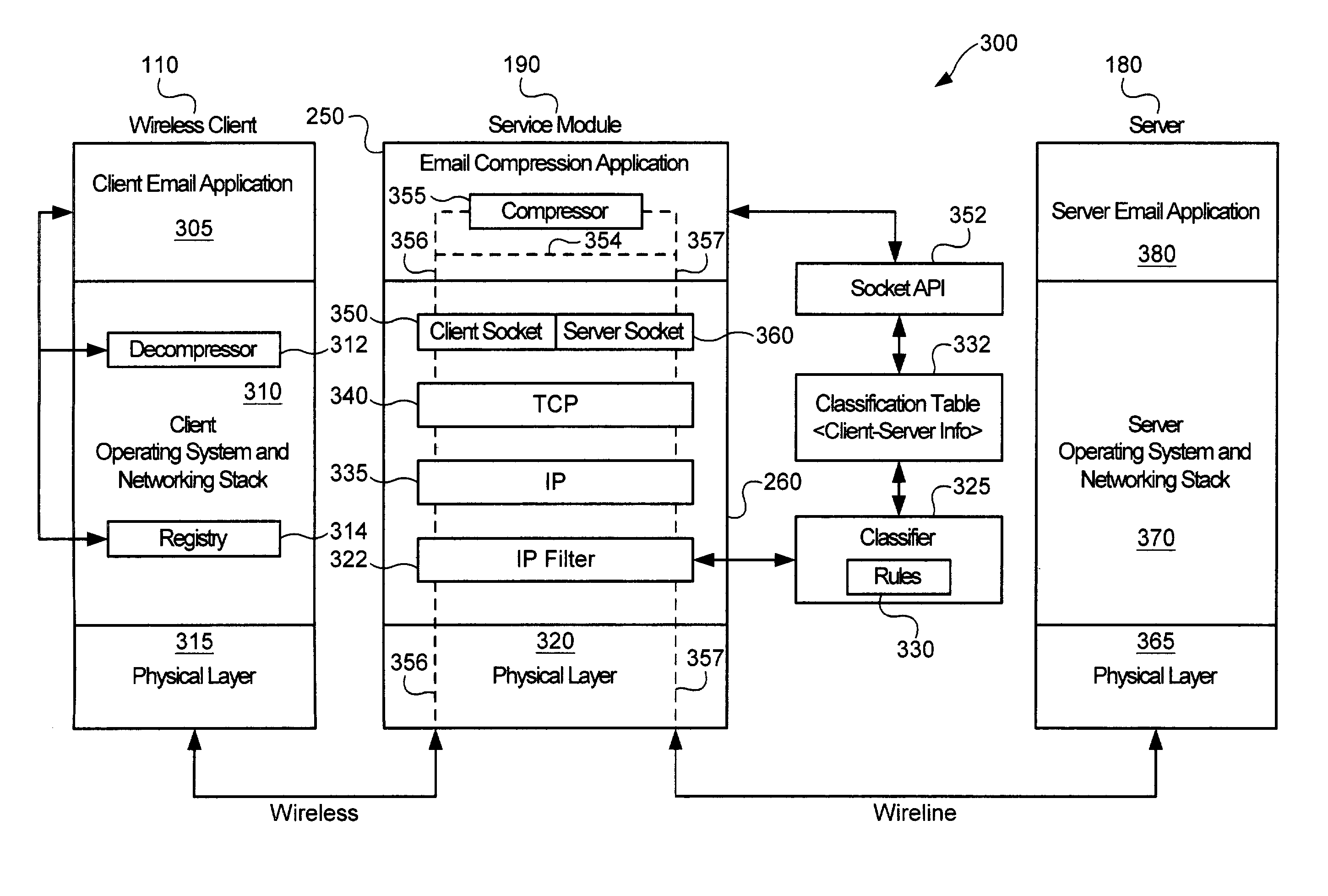
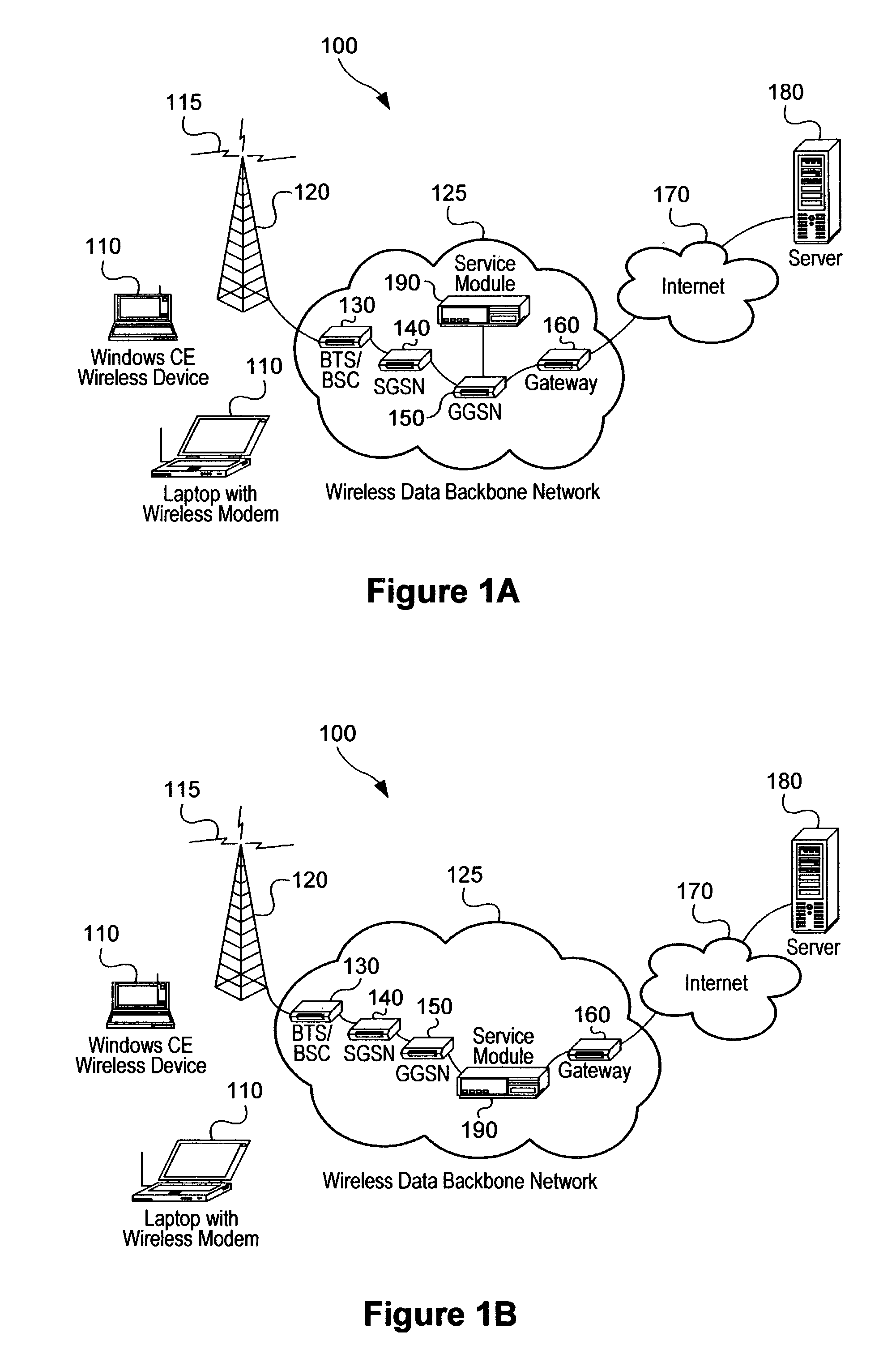
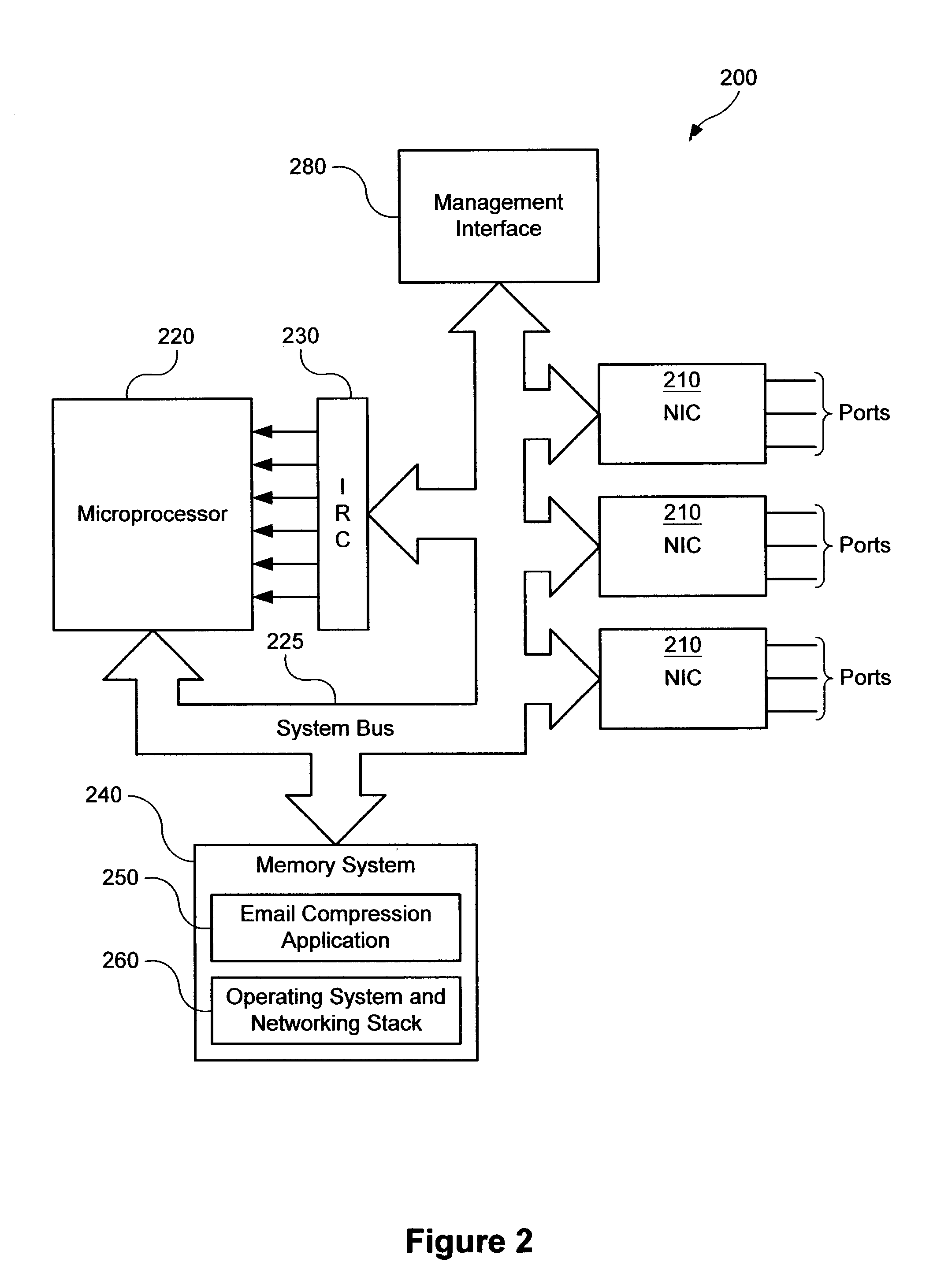
Service-based compression of content within a network communication system
ActiveUS7024460B2Easy to decompressMultiple digital computer combinationsData switching networksOperational systemData stream
A service module incorporated within the network infrastructure intercepts packets communicated between a client and a server to determine whether the connection corresponds to an email service. If so, the service module breaks the connection by terminating the connection with the client at the service module and opening a separate connection between the service module and the server. Packets communicated between the client and the server may then be redirected to an email compression application that monitors messages communicated between the client and the server and processes the messages in accordance with the state of the email session. For messages corresponding to connection establishment, user authentication and other protocol-specific messages, for example, the email compression application may be configured to forward the messages to the originally intended destination. Messages corresponding to an email message data, however, are buffered within the email compression application. Once the entire message has been received, the email compression application may strip the message headers and any protocol-specific data, compress the data and attach new message headers corresponding to the compressed email message. The compressed and reformatted email message is then reinserted into the data stream for transmission to the intended destination. Because compression may occur between the server and client, compression may be performed without requiring special processing by the server before email messages are sent. Furthermore, because the email messages may be compressed in a format that can be readily decompressed using decompression libraries incorporated within the operating system of client devices, such as the CAB format or GZIP format, the client may decompress received email messages utilizing software already incorporated within the operating system of the client device, without requiring download or installation of special decompression software and / or coordination of compression / decompression of email messages with the server or sending party.
Owner:OPTIMORPHIX INC
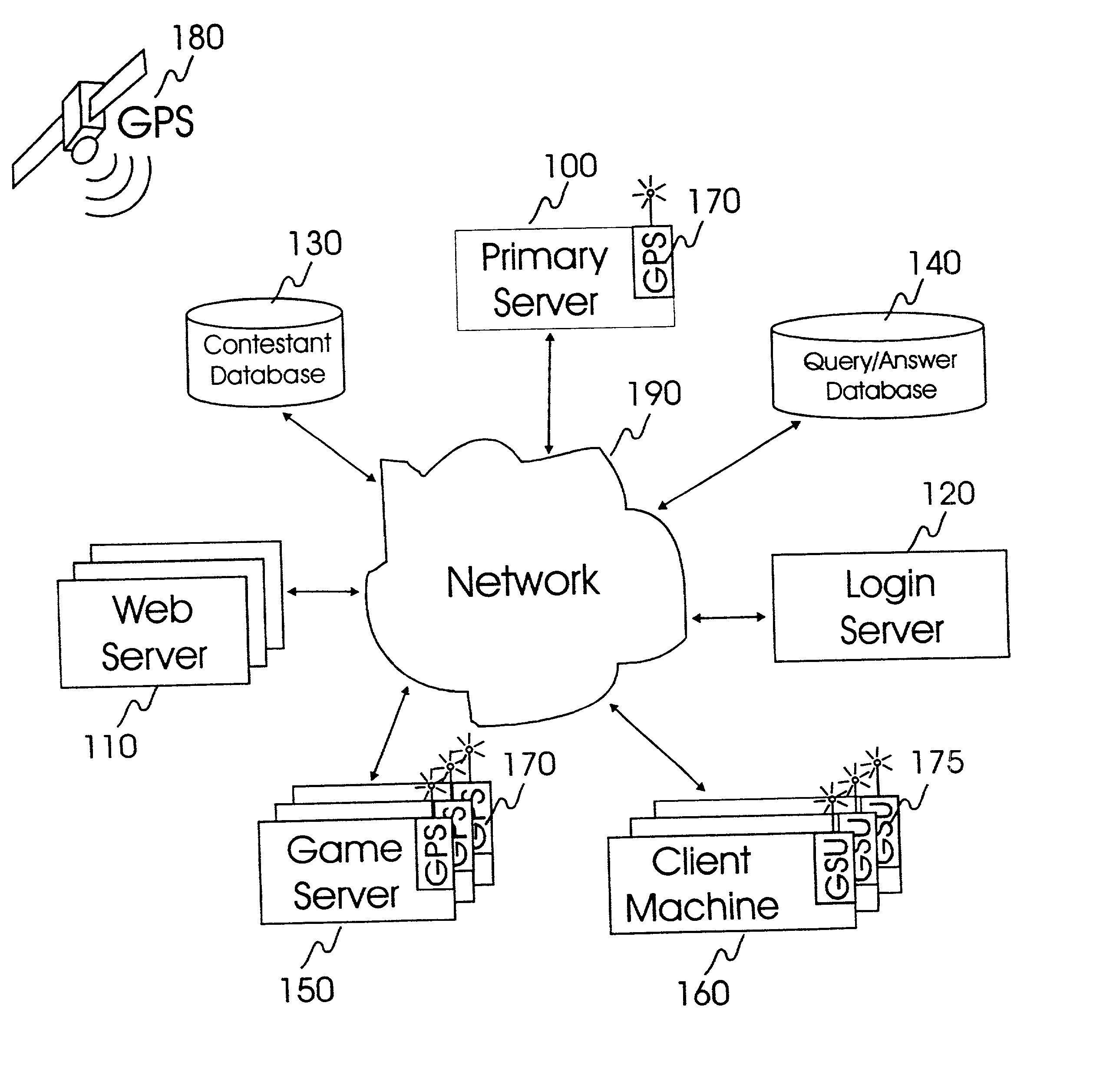
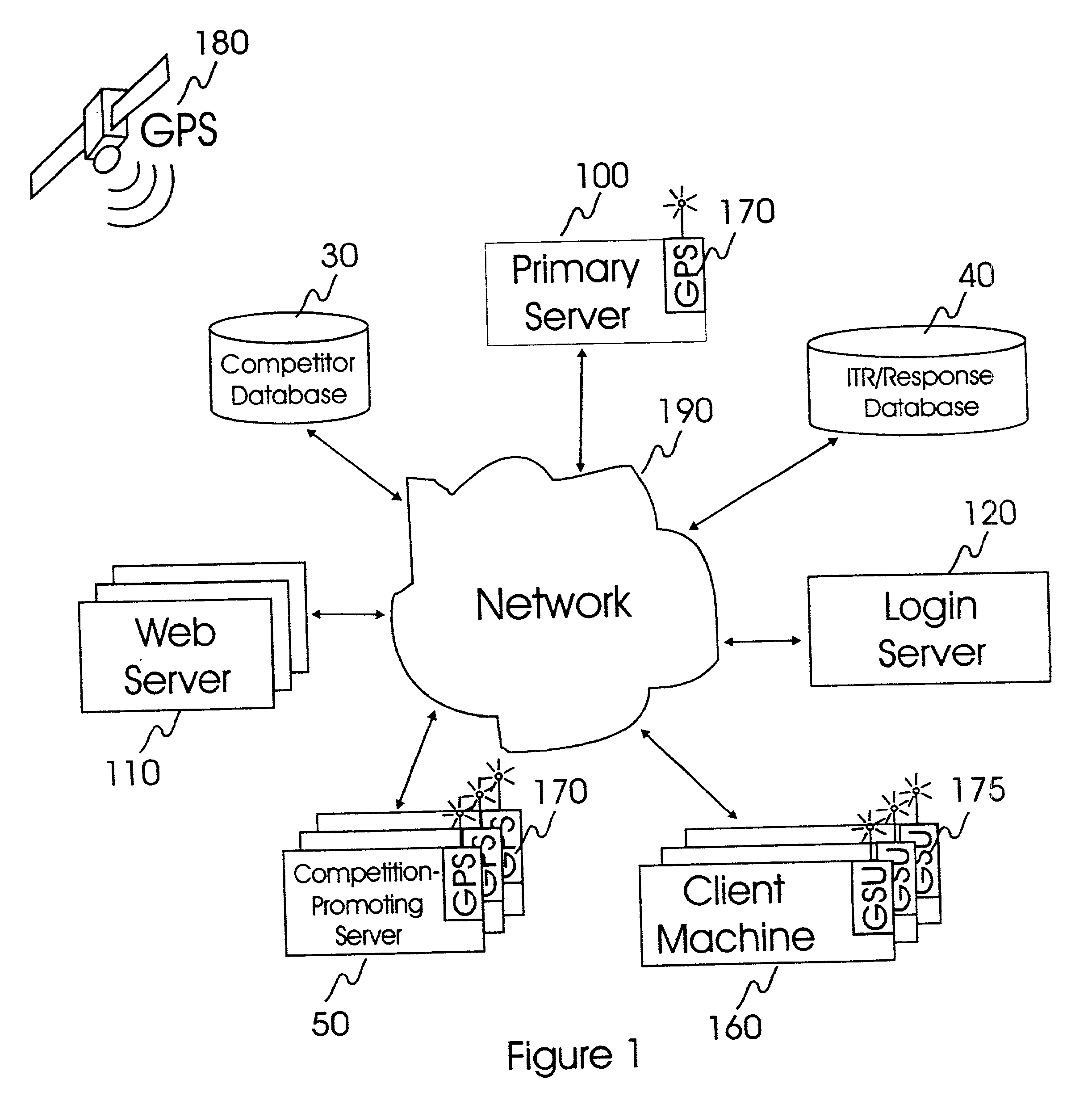
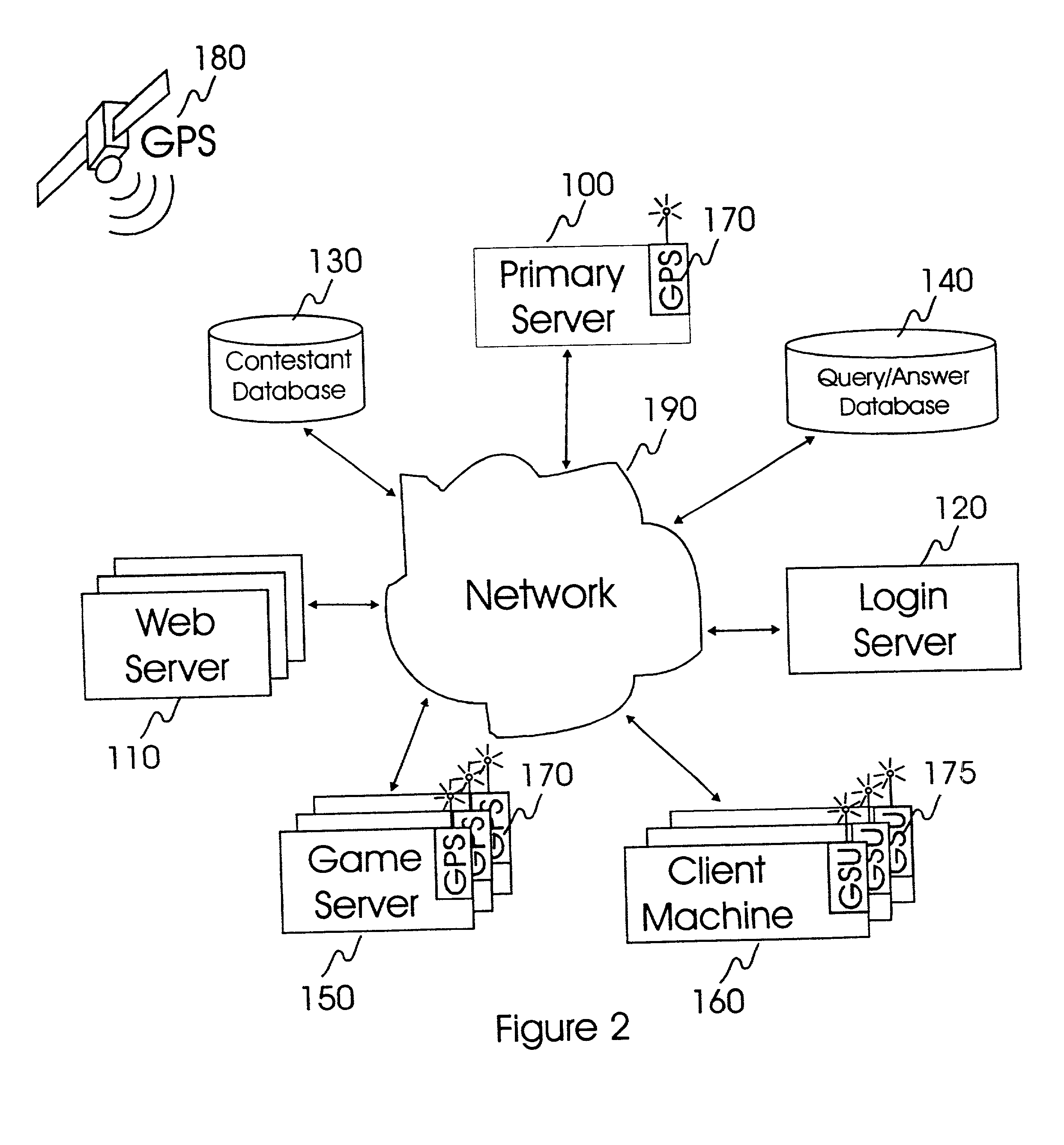
Internet-based system and method for fairly and securely enabling timed-constrained competition using globally time-sychronized client subsystems and information servers having microsecond client-event resolution
InactiveUS20020026321A1Avoiding shortcoming and drawbackBetterment of human societyBuying/selling/leasing transactionsVideo gamesTime responseTTEthernet
An improved system and method of fairly and securely enabling timed-constrained competitions over the Internet among millions of competitors while compensating for the variable network communication latencies experienced by client machines used by the competitors. The system employs globally time-synchronized Internet information servers and client machines in order to synchronize the initial display of each invitation to respond (e.g. stock price to buy or sell, query to answer, or problem to solve) on a client machine so each competitor can respond to the invitation at substantially the same time, regardless of his or her location on the planet, or the type of Internet-connection used by his or her client machine. Also, by using globally time-synchronized client machines, each competitor's response is securely time and space stamped at the client machine to ensure that competitor responses are resolved within microsecond accuracy.
Owner:REVEO
System and method for user access to a distributed network communication system using persistent identification of subscribers
InactiveUS20030233332A1Market predictionsMetering/charging/biilling arrangementsDevice registerCommunications system
A system and method for providing network access are disclosed. After connecting to a network at an access point, a user of a computing device registers for network access with a network provider. In response to the registration, the network provider sends a completion page to the computing device. The completion page includes a link to an embedded file such as a small, transparent GIF image. When the computing device retrieves the embedded file, the embedded file is associated with a header than includes an instruction to generate a network system identifier (e.g., a cookie). The network system identifier may be stored by the computing device and later used to identify the computing device as a registrant for network access with the network provider. The embedded file may also be sent at other times, such as after authentication of the user for network access.
Owner:WAYPORT
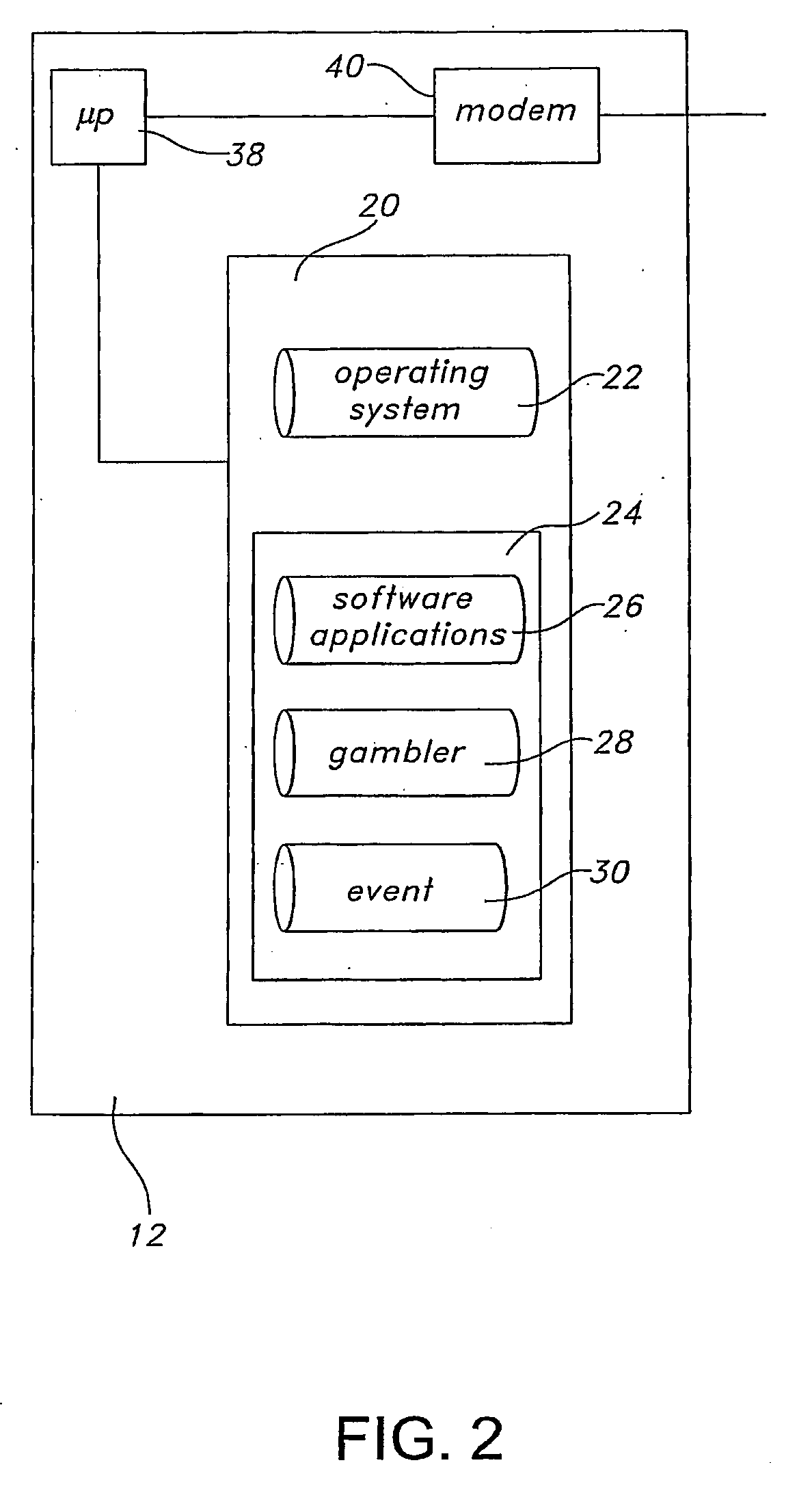
Methods and systems for betting with pari-mutuel payouts
InactiveUS20080113816A1Improved initial payoutQuick buildCard gamesApparatus for meter-controlled dispensingOperational systemEvent data
A server for facilitating real-time betting, wherein the server communicates with clients via a distributed computing network. The server includes a memory storing an operating system, an instruction set, event data related to a sporting event, gambler data related to gamblers participating in a competition based upon the sporting event and site data related to electronic pages associated with the real-time para-mutuel betting. A processor runs the instruction set and communicates with the memory and the distributed computing network. The processor is operative to enroll the gamblers by presenting betting rules associated with the sporting event, collect wagering from the gamblers, accept predictions for discrete events within the sporting event from each gambler and determine a first winner of the competition based upon the predictions. Applications include lotteries with entries received from mobile devices.
Owner:HF SCI INC
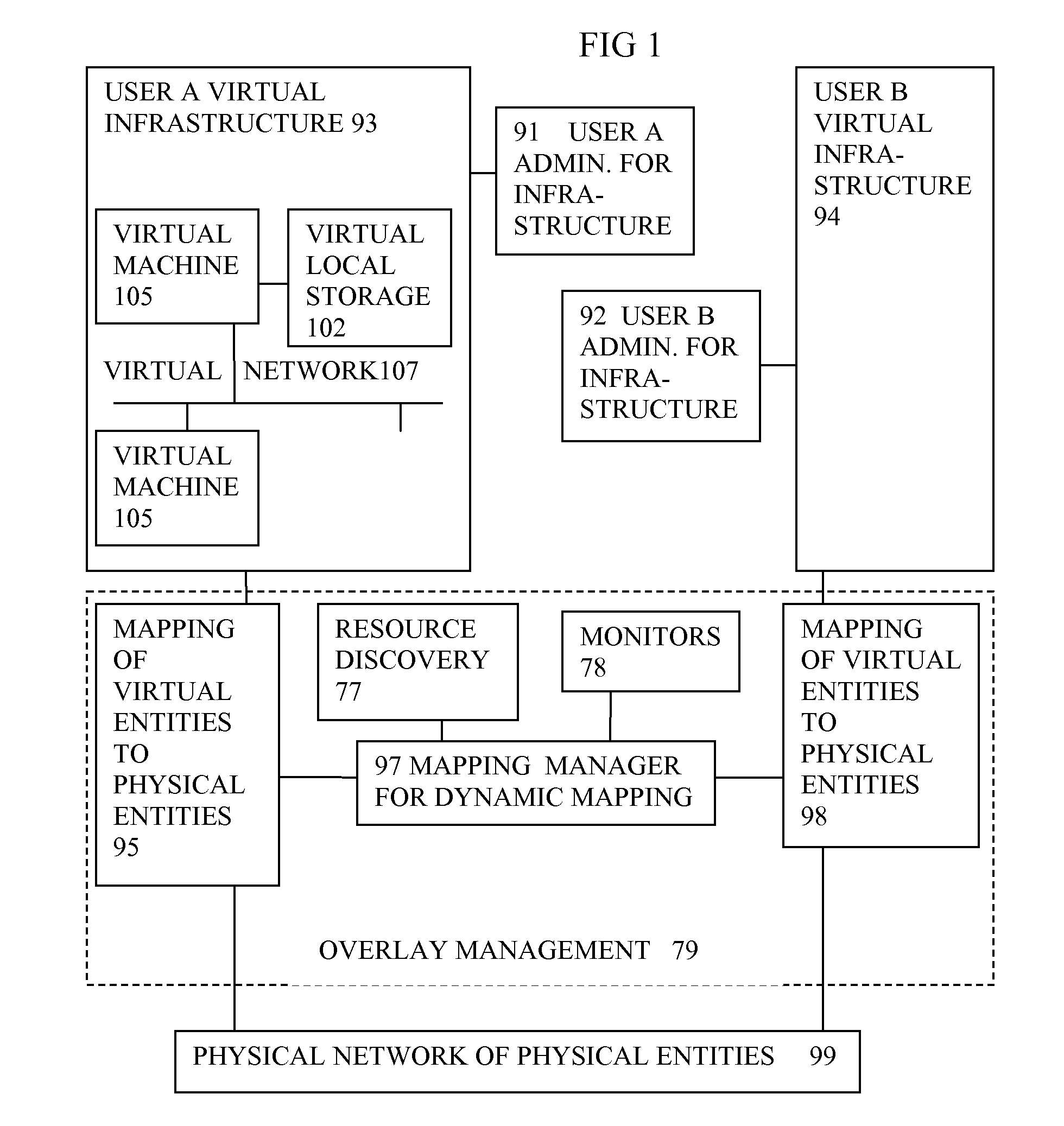
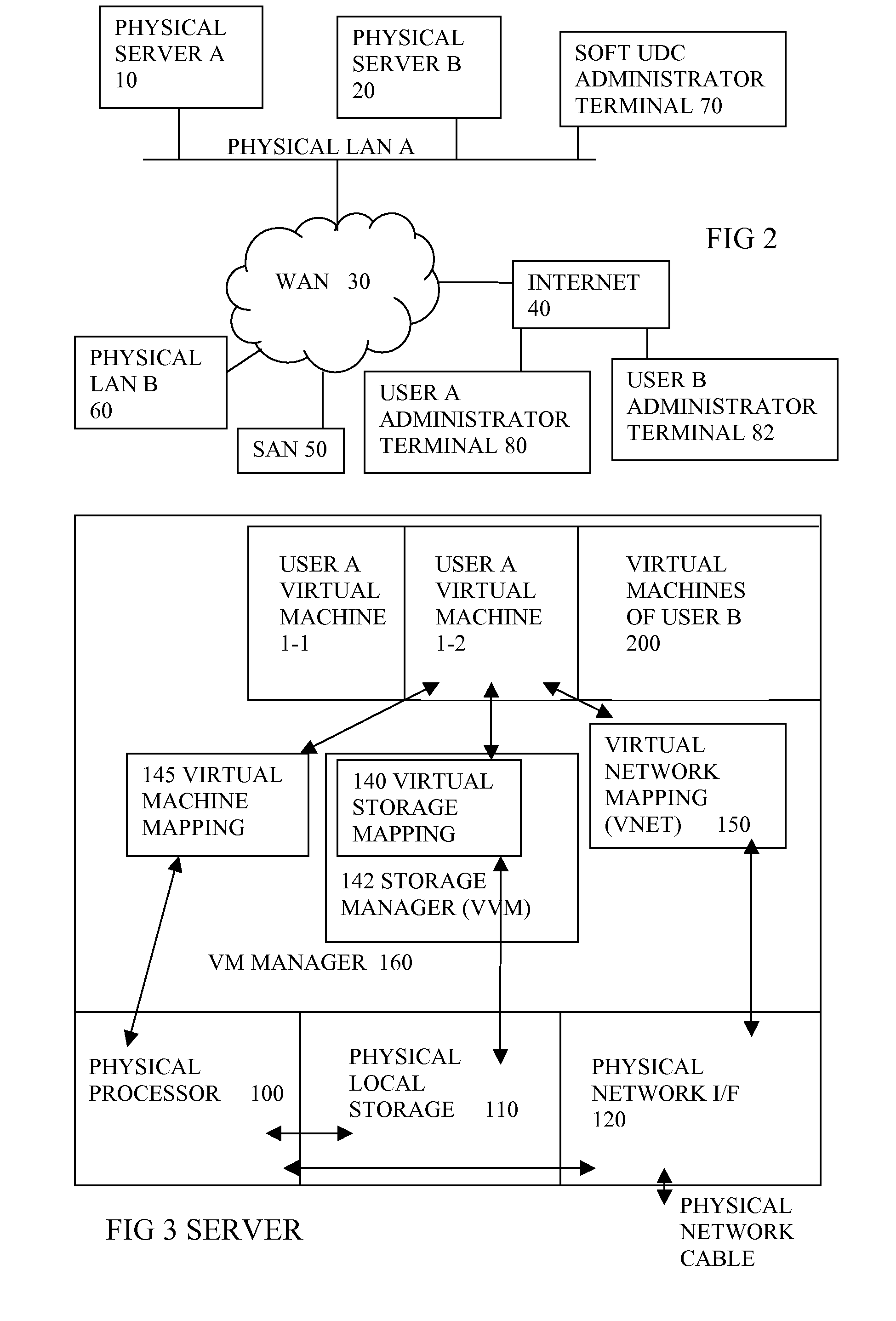
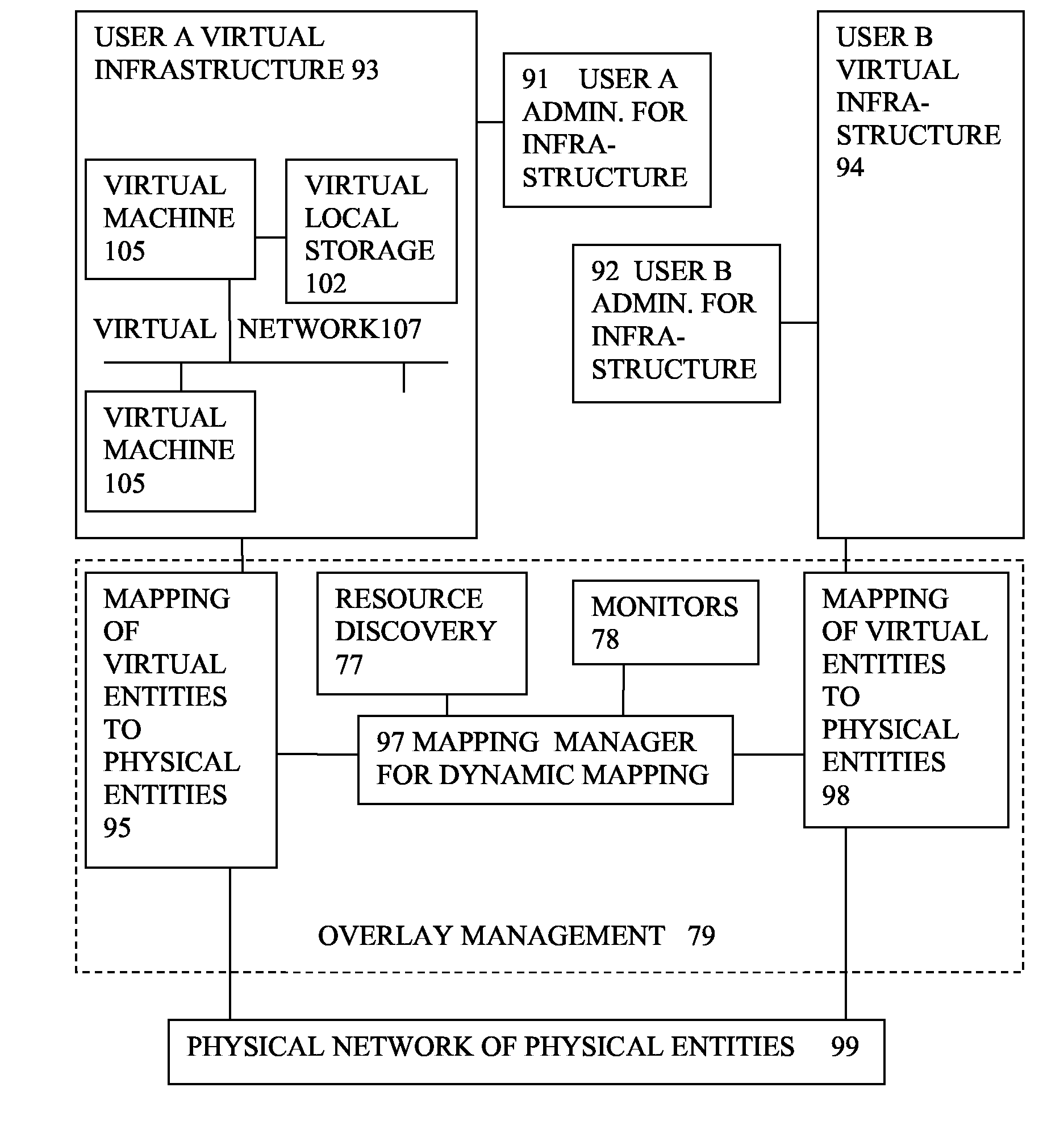
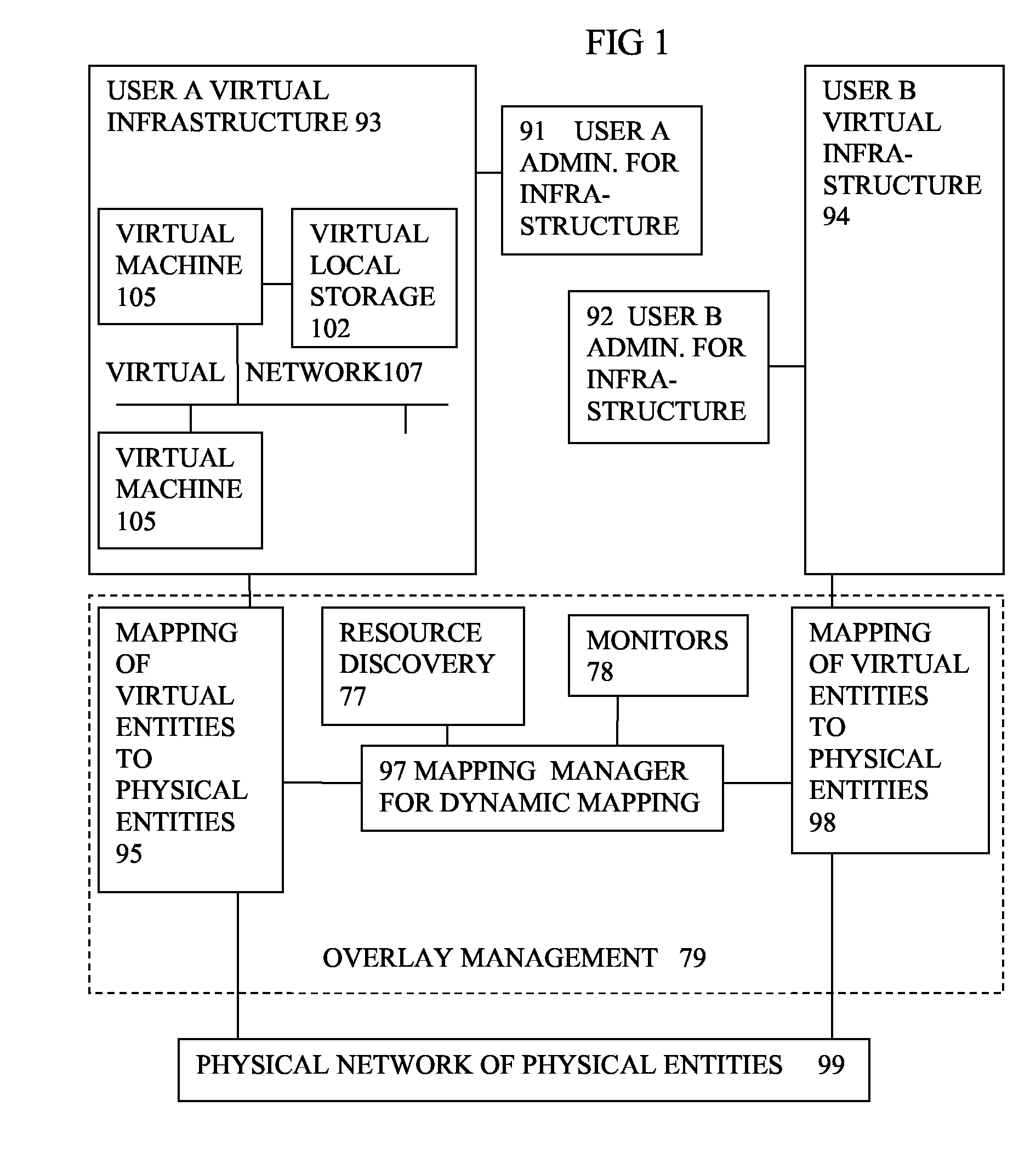
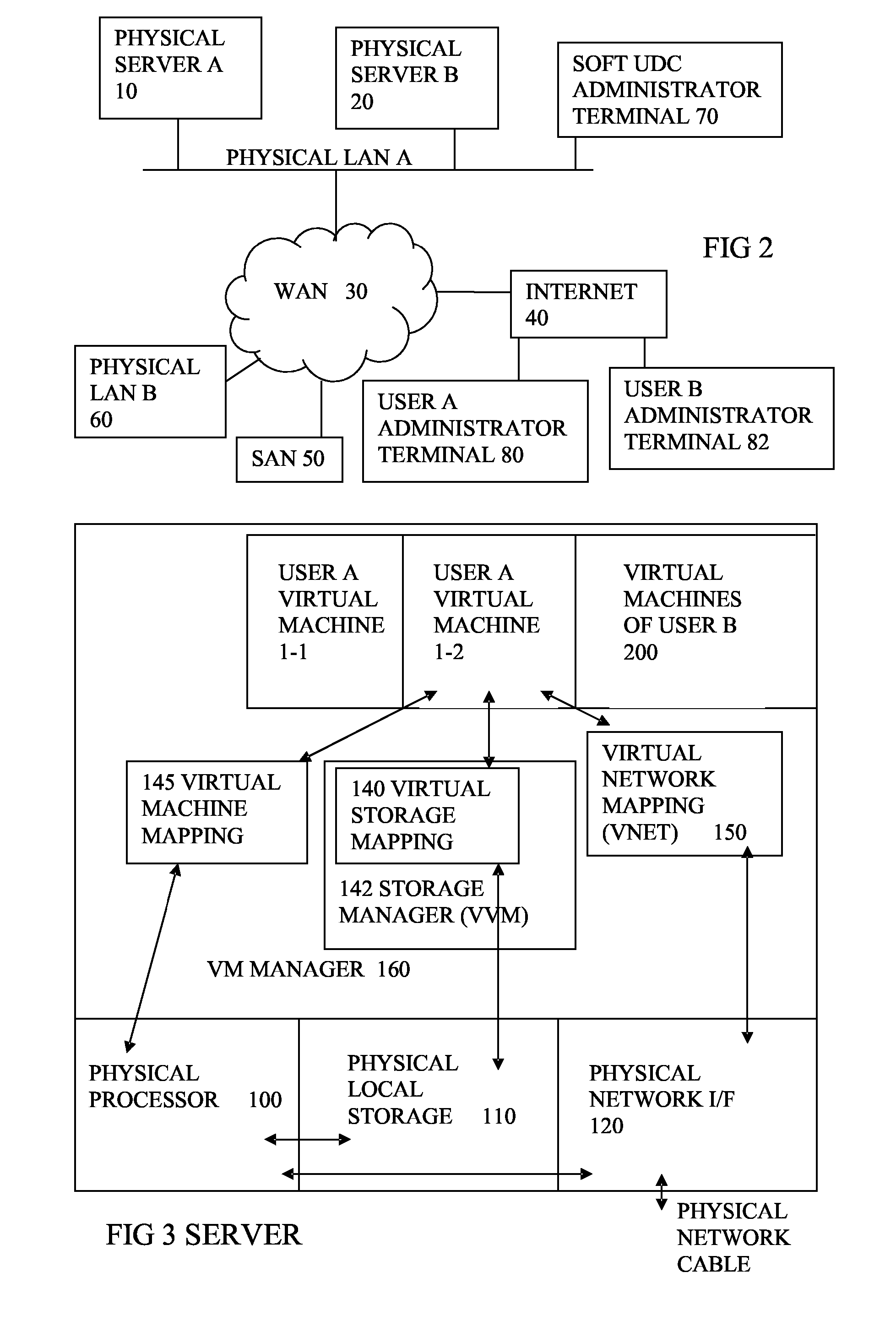
Virtual computing infrastructure
InactiveUS20090199177A1Overcome disadvantagesCritical applicationResource allocationTransmissionVirtualizationNetwork communication
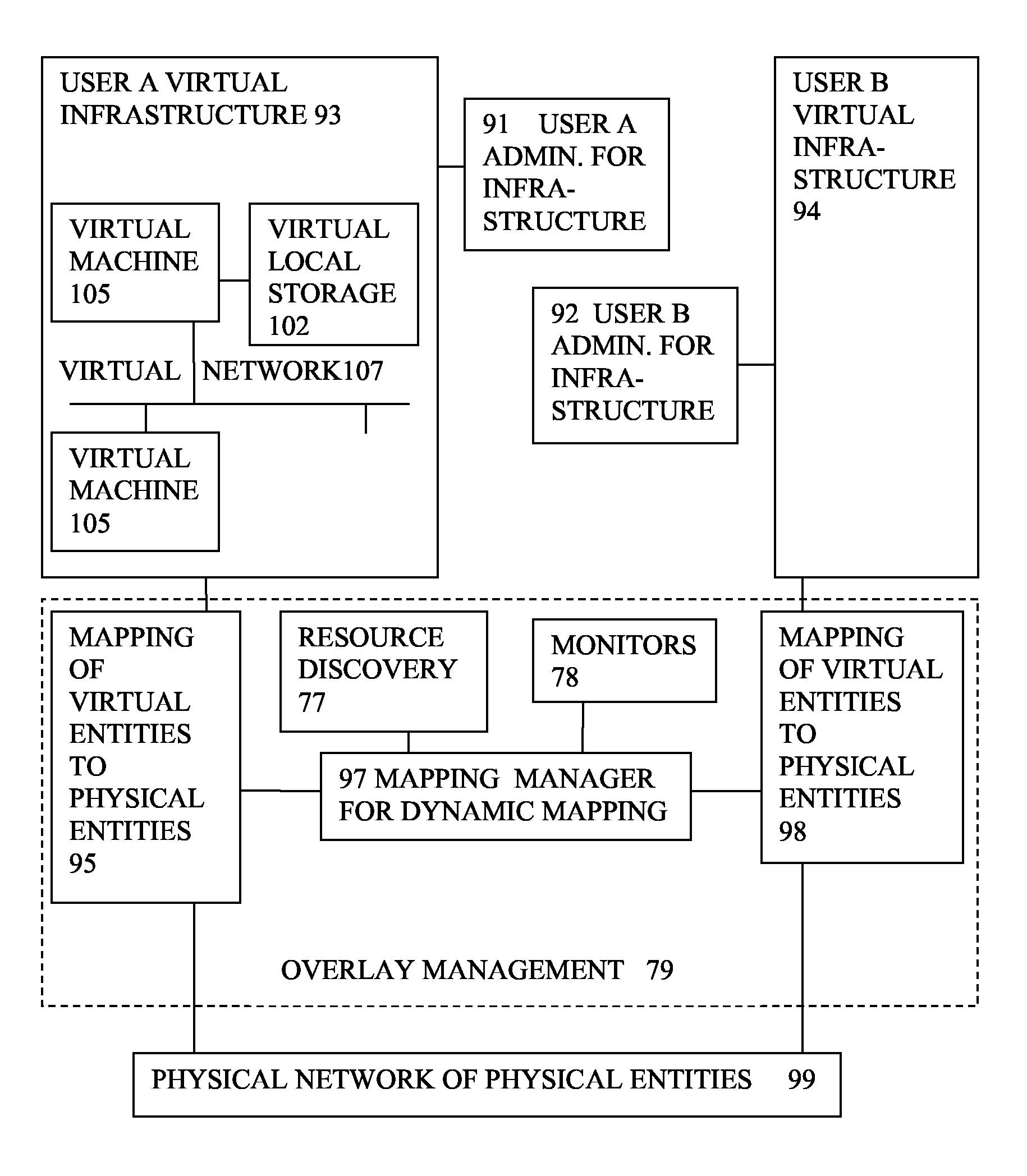
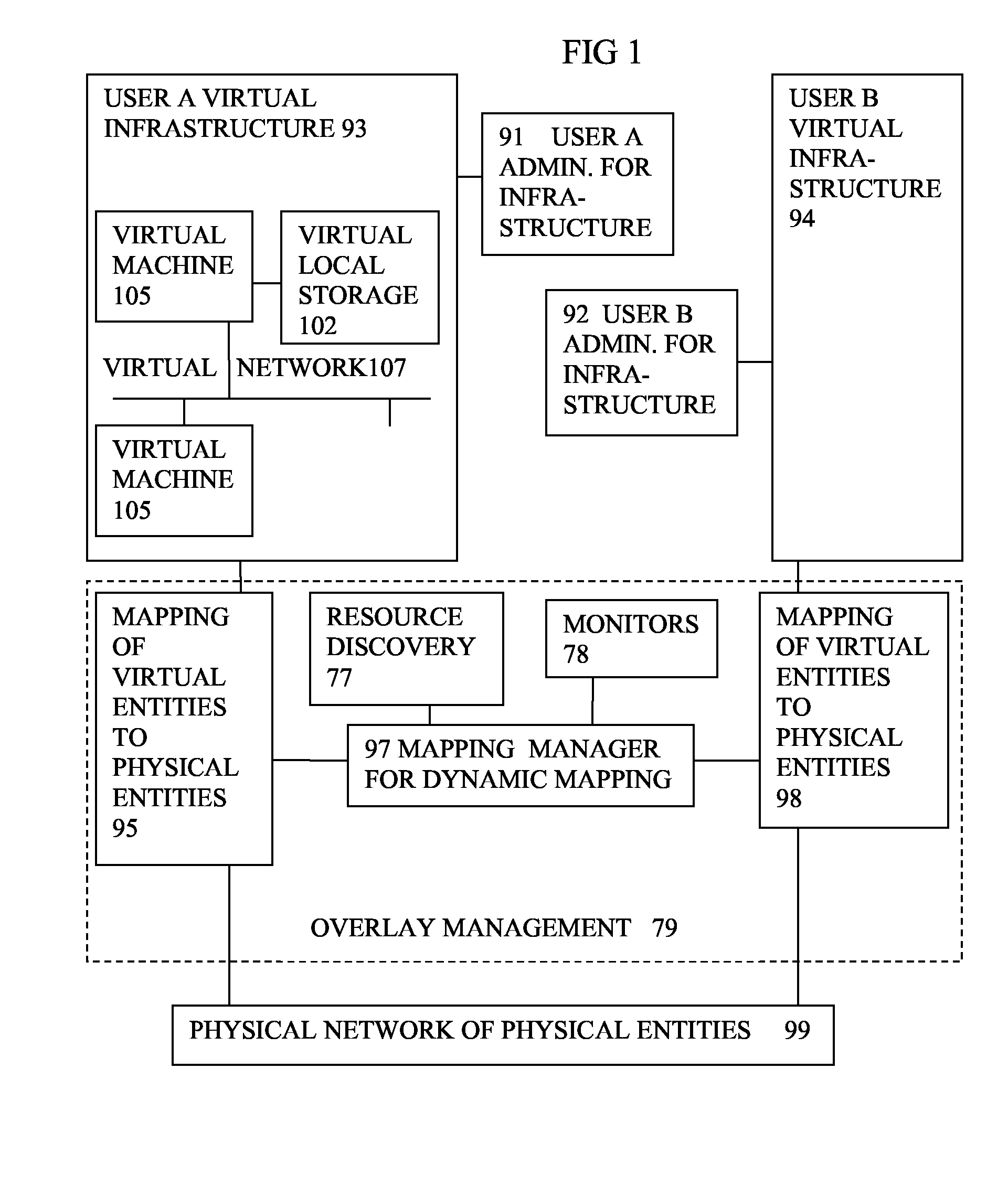
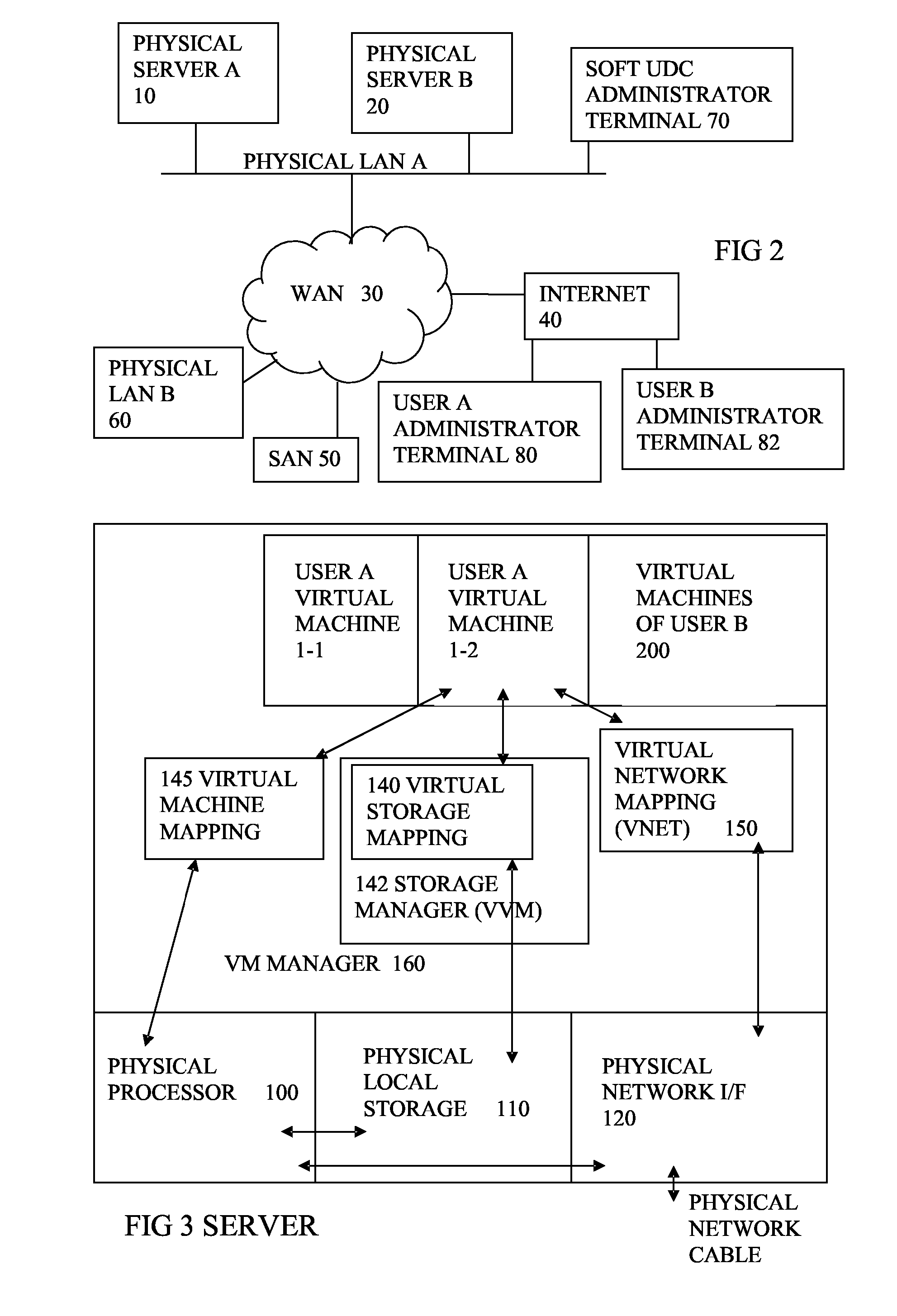
A system has a virtual overlay infrastructure mapped onto physical resources for processing, storage and network communications, the virtual infrastructure having virtual entities for processing, storage and network communications. The system has a mapping manager to dynamically alter the mapping for balancing, performance, and redundancy. There can be more independence from the underlying physical configuration, compared to known methods of virtualizing only some of the entities. The mapping manager can be distributed across a number of entities on different physical servers arranged to cooperate with each other.
Owner:HEWLETT PACKARD DEV CO LP
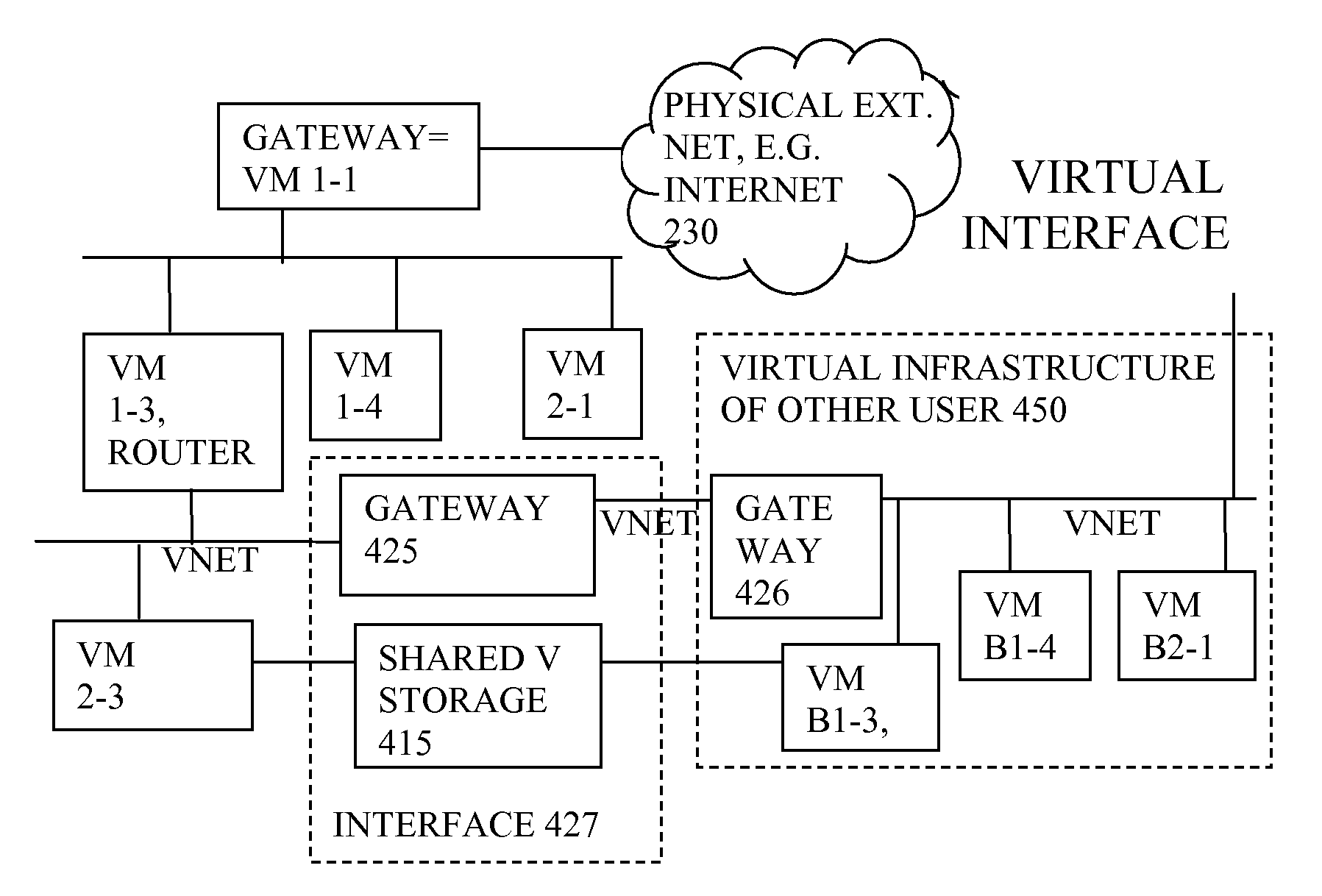
Virtual computing infrastructure
ActiveUS20110119748A1More separatedReduce hardware costsResource allocationComputer security arrangementsNetwork communicationApplication software
A system has a virtual overlay infrastructure mapped onto physical resources for processing, storage and network communications, the virtual infrastructure having virtual entities for processing, storage and network communications. Virtual infrastructures of different users share physical resources but are isolated and have their own management entities. An interface between infrastructures allows controlled relaxation of the isolation, using a gateway between virtual nets, or shared virtual storage devices. This can allow businesses to share data or applications, while maintaining control of security.
Owner:RED HAT +1
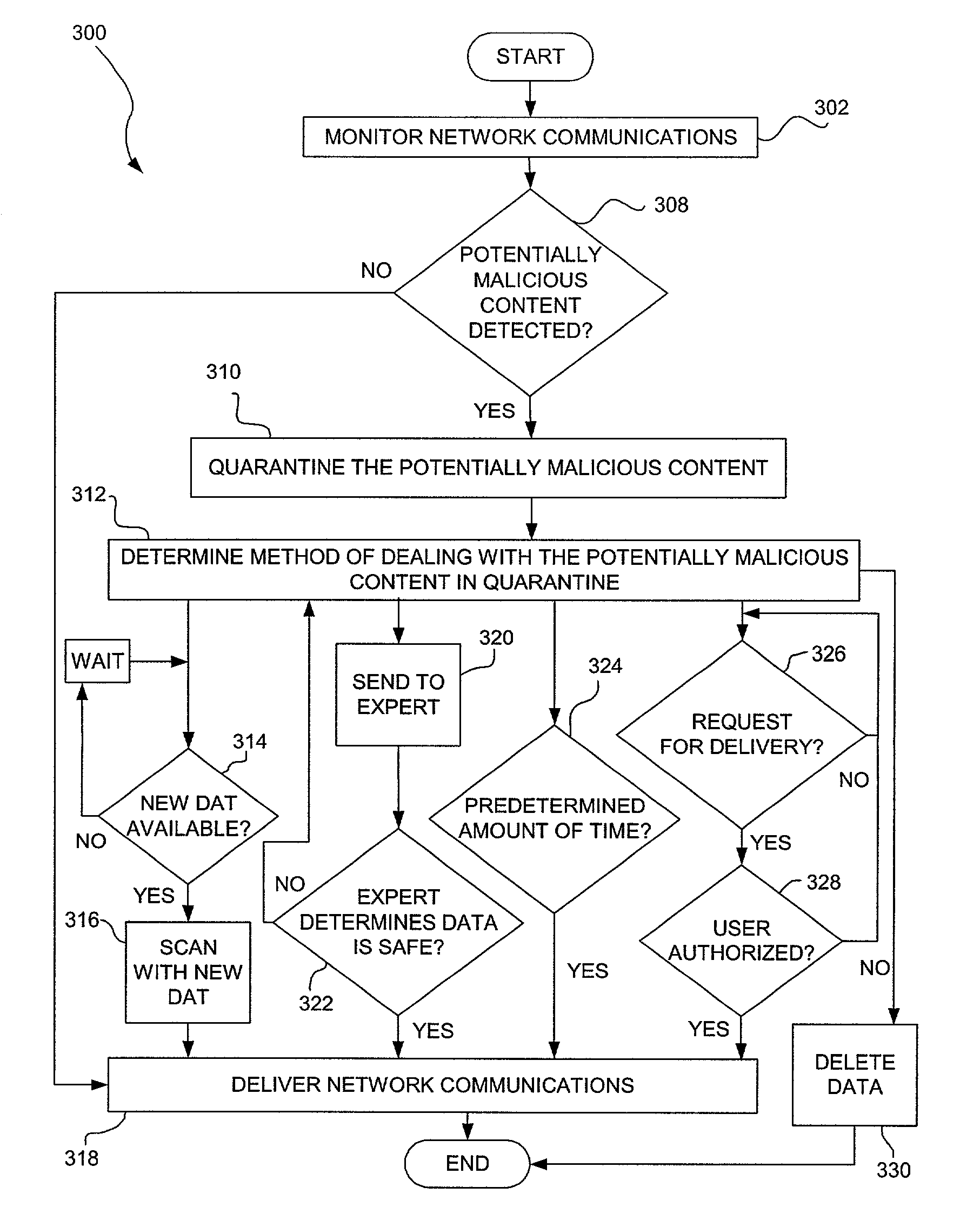
Delayed-delivery quarantining of network communications having suspicious contents
ActiveUS7080408B1Avoid spreadingAvoid damageMemory loss protectionError detection/correctionNetwork communicationQuarantine
A system, method and computer program product are provided for network-based scanning for potentially malicious content. Incoming and / or outgoing network communications traveling over a network are monitored, preferably at a gateway. Potentially malicious content in the network communications is identified. The identified potentially malicious content of the network communications is quarantined to help prevent damage that could be caused if the content is indeed malicious. In one embodiment, a pattern for testing the potentially malicious content network communications for malicious code can be executed. The network communications are conditionally delivered over the network based on the testing. In other embodiments, the network communications are delivered over the network after a predetermined delay and / or upon receiving a user request to release the suspect content from quarantine.
Owner:MCAFEE LLC
Retrofit LED lamp for fluorescent fixtures without ballast
ActiveUS7507001B2Reduce flickerReduce usageLighting support devicesPoint-like light sourceFluorescenceNetwork communication
An energy saving device for an LED lamp mounted to an existing fixture for a fluorescent lamp where the ballast is removed or bypassed. The LEDs are positioned within a tube and electrical power is delivered from a power source to the LEDs. The LED lamp includes means for controlling the delivery of the electrical power from the power source to the LEDs, wherein the use of electrical power can be reduced or eliminated automatically during periods of non-use. Such means for controlling includes means for detecting the level of daylight in the illumination area of said least one LED, in particular a light level photosensor, and means for transmitting to the means for controlling relating to the detected level of daylight from the photosensor. The photosensor can be used in operative association with an on-off switch in power connection to the LEDs, a timer, or with a computer or logic gate array in operative association with a switch, timer, or dimmer that regulates the power to the LEDs. An occupancy sensor that detects motion or a person in the illumination area of the LEDs can be also be used in association with the photosensor and the computer, switch, timer, or dimmer, or in solo operation by itself. Two or more such LED lamps with a computer or logic gate array used with at least one of the lamps can be in network communication with at least one photosensor and / or at least one occupancy sensor to control the power to all the LEDs.
Owner:SIGNIFY HLDG BV
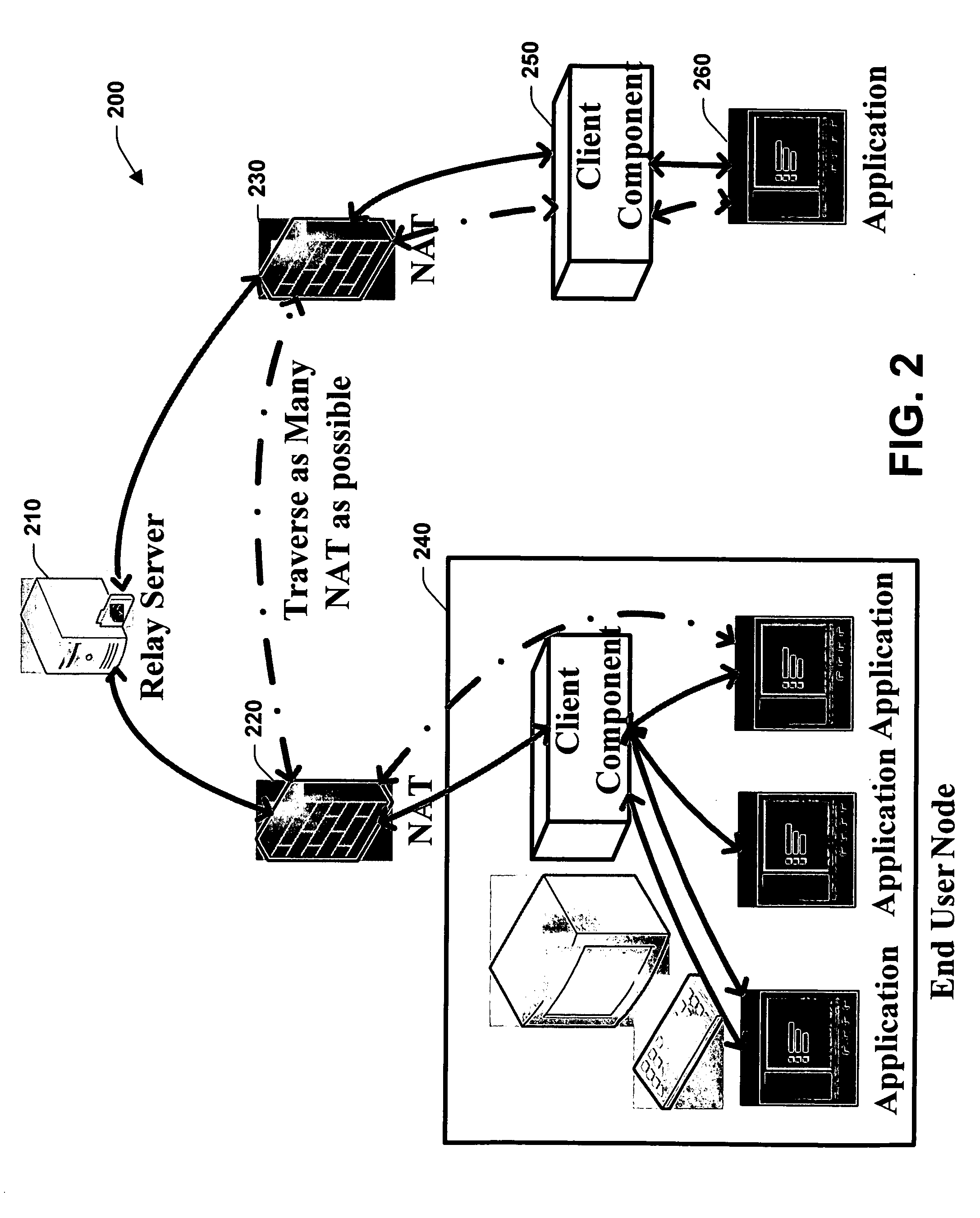
Automated NAT traversal for peer-to-peer networks
InactiveUS20060182100A1Facilitate communicationReduce administrative burdenData switching by path configurationMultiple digital computer combinationsCommunications systemNAT traversal
The subject invention relates to systems and methods that facilitate direct network communications between peers that operate behind Network Address Translators. In one aspect, a network communications system is provided. The system includes one or more Network Address Translators (NAT) to communicate data across a network between peers. A protocol selection component that automatically selects among a plurality of protocols according to one or more NAT types in order to determine a subset of the protocols that facilitate communications between the peers.
Owner:MICROSOFT TECH LICENSING LLC
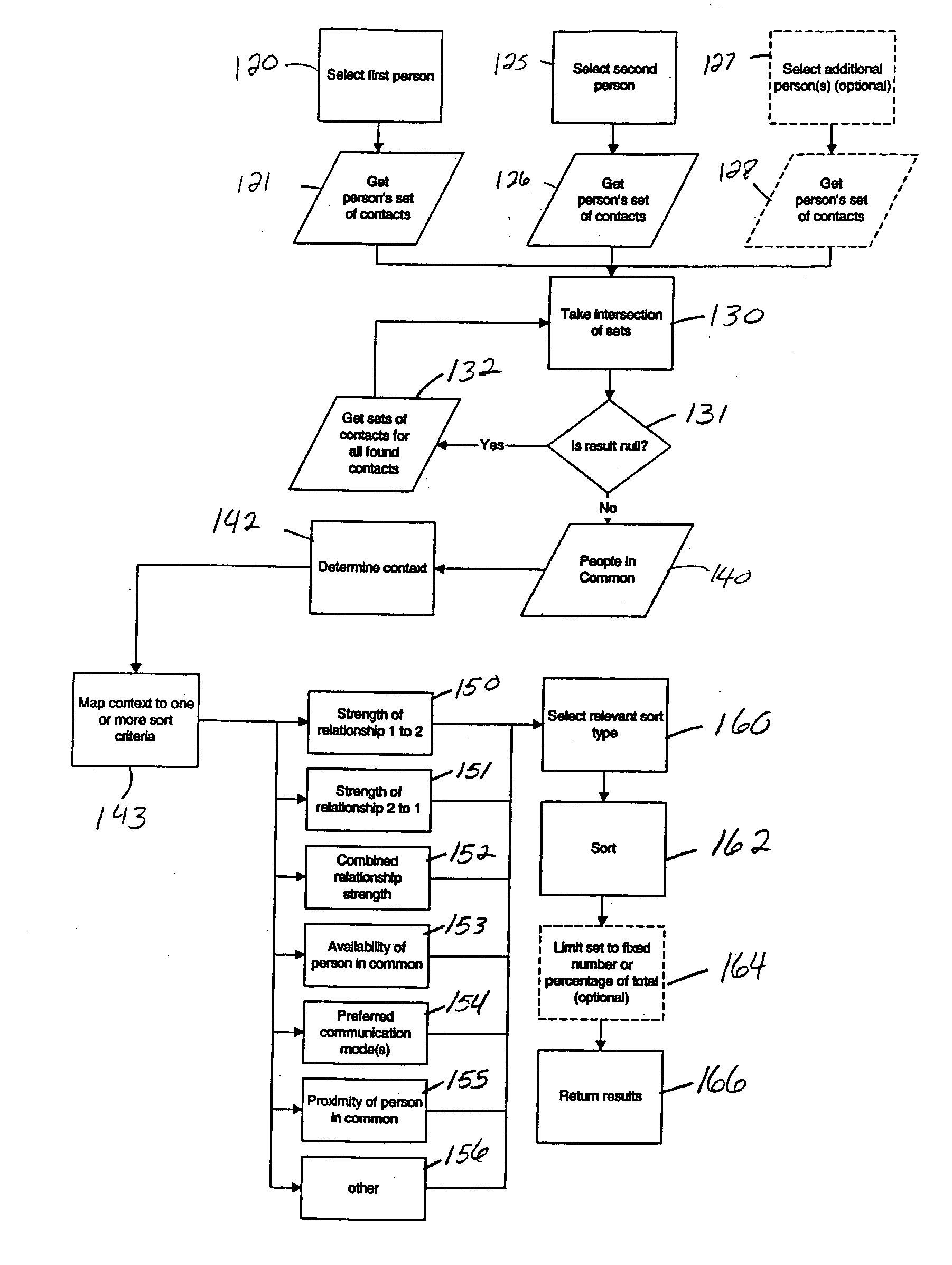
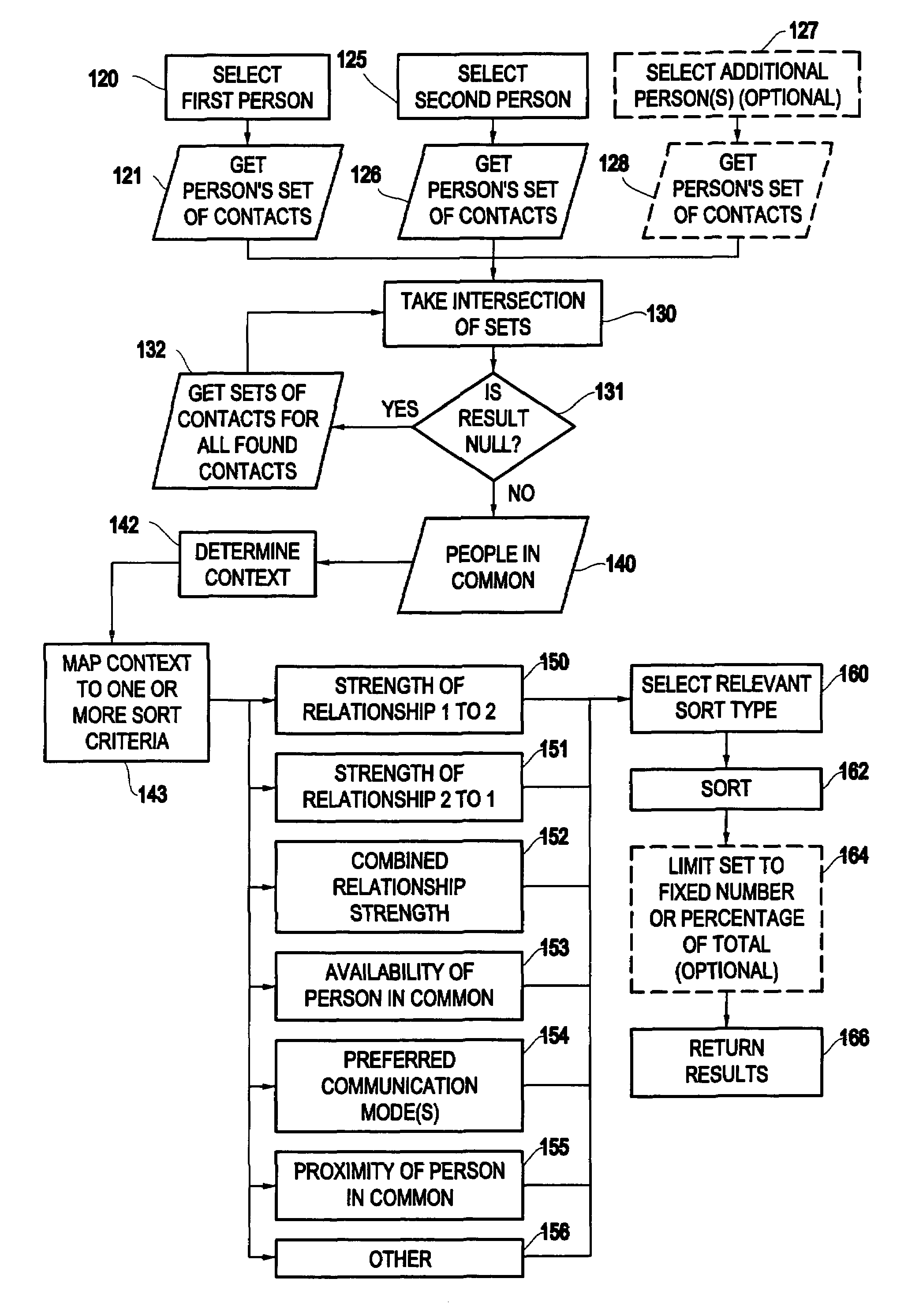
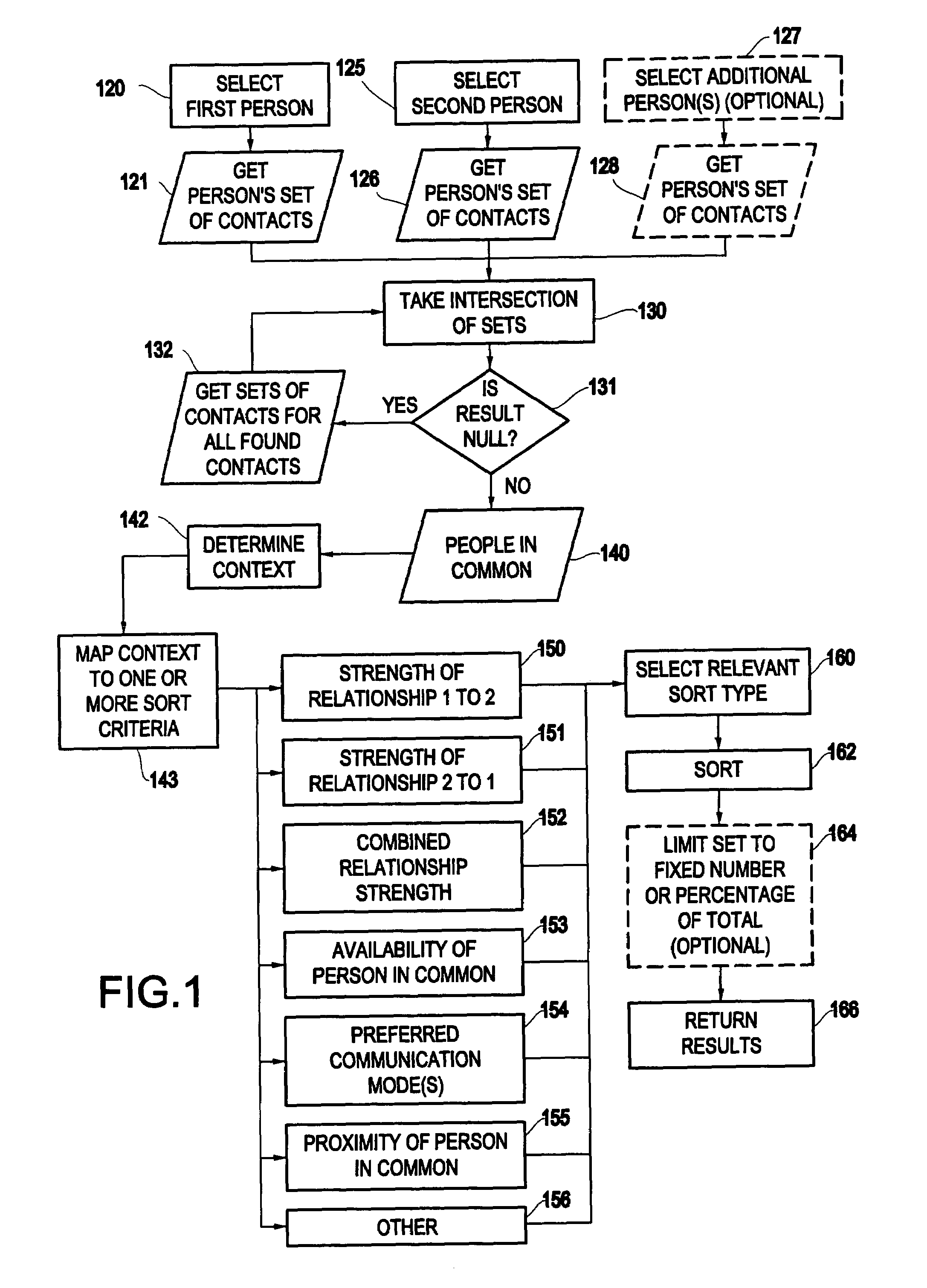
Method of creating and displaying relationship chains between users of a computerized network
ActiveUS20040122855A1Digital data processing detailsMultiple digital computer combinationsNetwork communicationComputer science
A method and structure for identifying potential relationships between users of a computer network is disclosed. The invention extracts relationship information from databases in the computer network in order to establish multiple relationship chains of the users from the relationship information. More specifically, the invention evaluates network information and network communications between the users to produce metrics and processes the metrics to produce contact information. The contact information indicates whether a personal relationship exists between two users. In addition, the invention can produce relationship values representing strengths of social relationships between users of the computer network based on such relationship information.
Owner:GLOBALFOUNDRIES US INC
System and method for secure message-oriented network communications
InactiveUS6959393B2Minimize threatFacilitate and control accessKey distribution for secure communicationDigital data processing detailsSecurity MeasureNetwork communication
The present invention provides a message-oriented middleware solution for securely transmitting messages and files across public networks unencumbered by intervening network barriers implemented as security measures. It also provides a dynamic, dedicated, application level VPN solution that is facilitated by the message-oriented middleware. Standard encryption algorithms are used to minimize the threat of eavesdropping and an Open-Pull Protocol (OPP) that allows target nodes to pull and verify the credentials of requestors prior to the passing of any data. Messaging can be segregated into multiple and distinct missions that all share the same nodes. The security network's architecture is built to resist and automatically recover from poor, slow, and degrading communications channels. Peers are identifiable by hardware appliance, software agent, and personally identifiable sessions. The security network provides a dynamic, private transport for sensitive data over existing non-secure networks without the overhead and limited security associated with traditional VPN solutions.
Owner:THREATGUARD
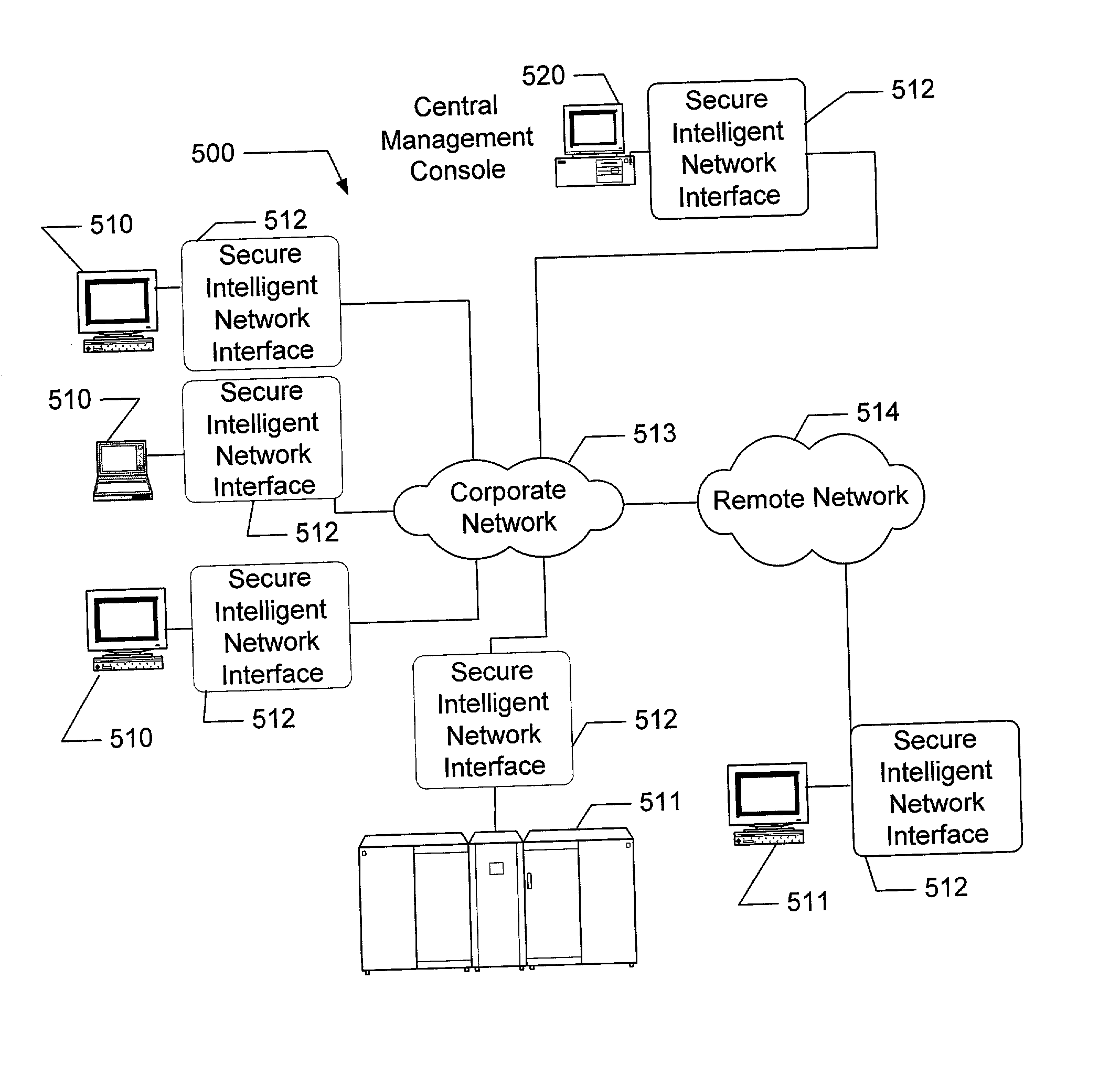
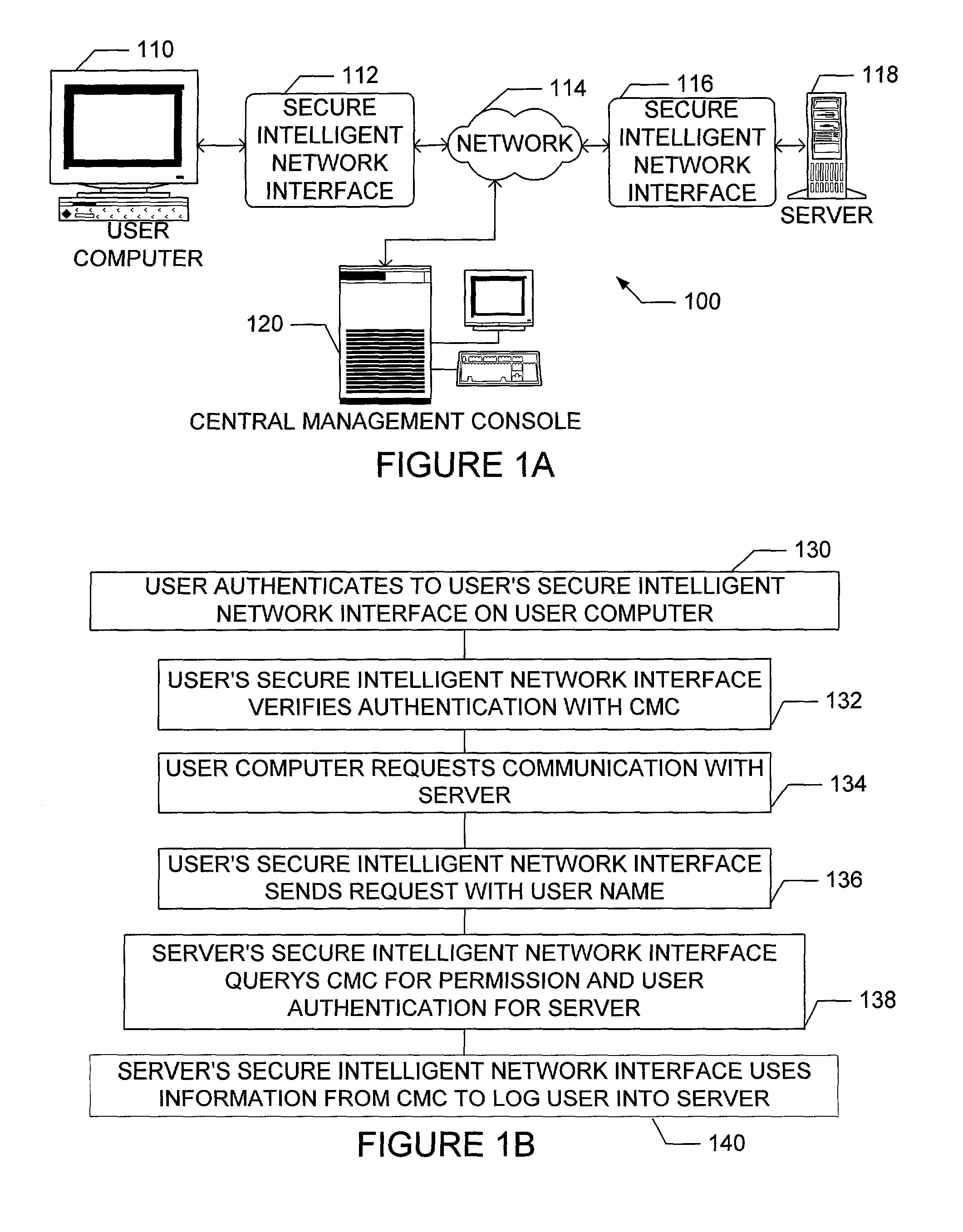
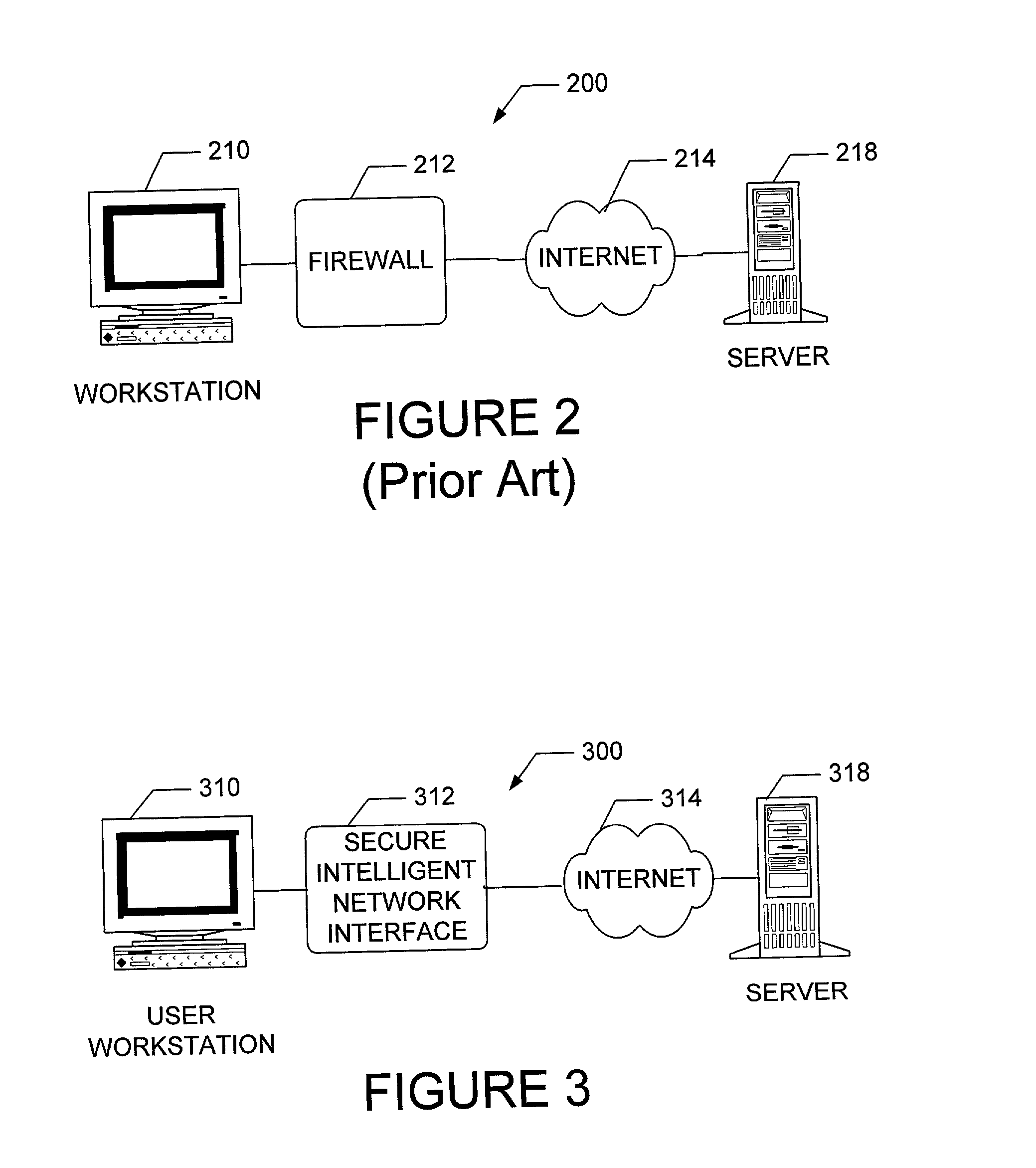
Apparatus and method for providing secure network communication
InactiveUS20020162026A1Eliminate attackEliminate needData taking preventionDigital data processing detailsFault toleranceIntelligent Network
The present invention is drawn to an apparatus and method for providing secure network communication. Each node or computer on the network has a secure, intelligent network interface with a coprocessor that handles all network communication. The intelligent network interface can be built into a network interface card (NIC) or be a separate box between each machine and the network. The intelligent network interface encrypts outgoing packets and decrypts incoming packets from the network based on a key and algorithm managed by a centralized management console (CMC) on the network. The intelligent network interface can also be configured by the CMC with dynamically distributed code to perform authentication functions, protocol translations, single sign-on functions, multi-level firewall functions, distinguished-name based firewall functions, centralized user management functions, machine diagnostics, proxy functions, fault tolerance functions, centralized patching functions, Web-filtering functions, virus-scanning functions, auditing functions, and gateway intrusion detection functions.
Owner:NEUMAN MICHAEL +1
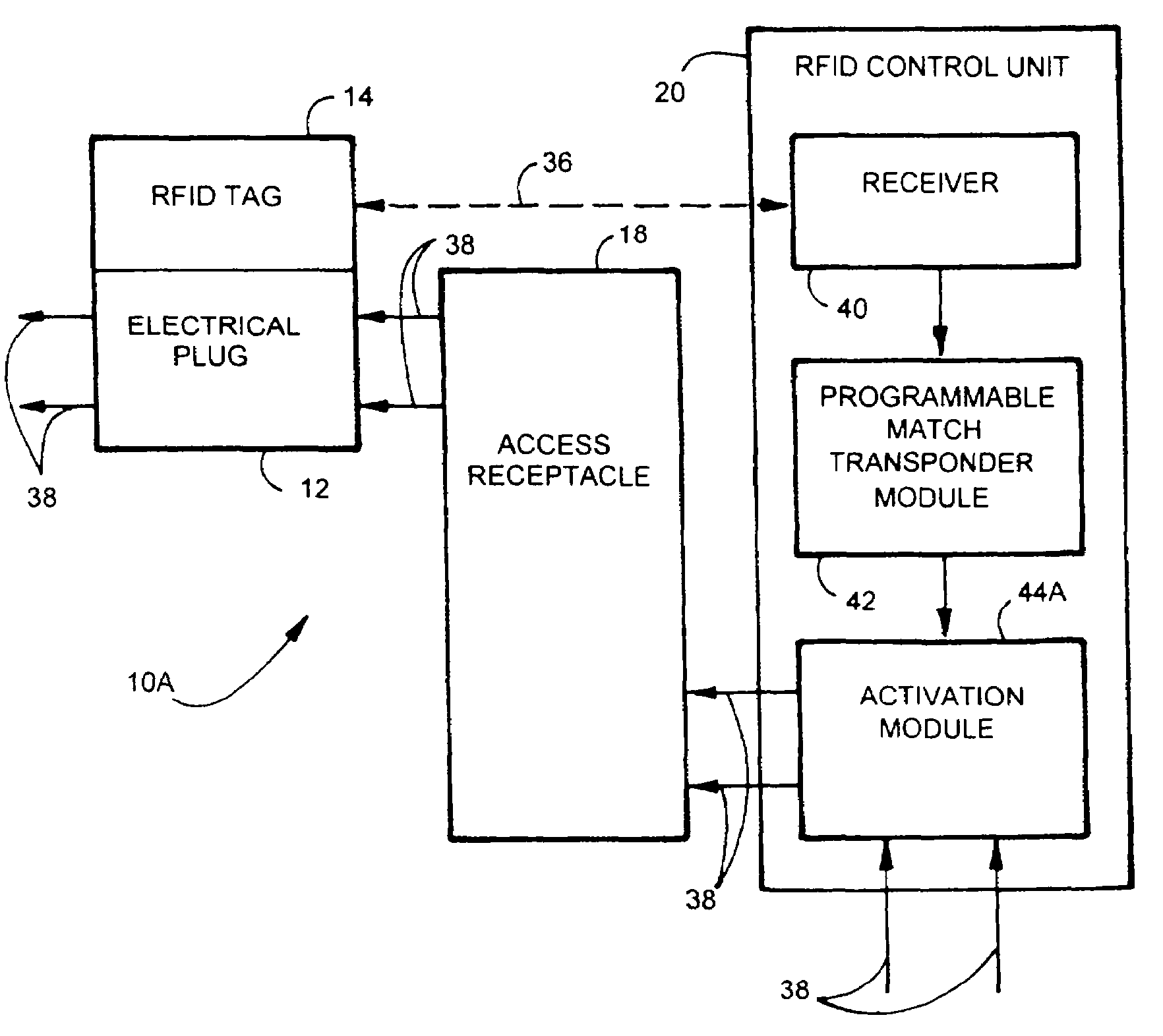
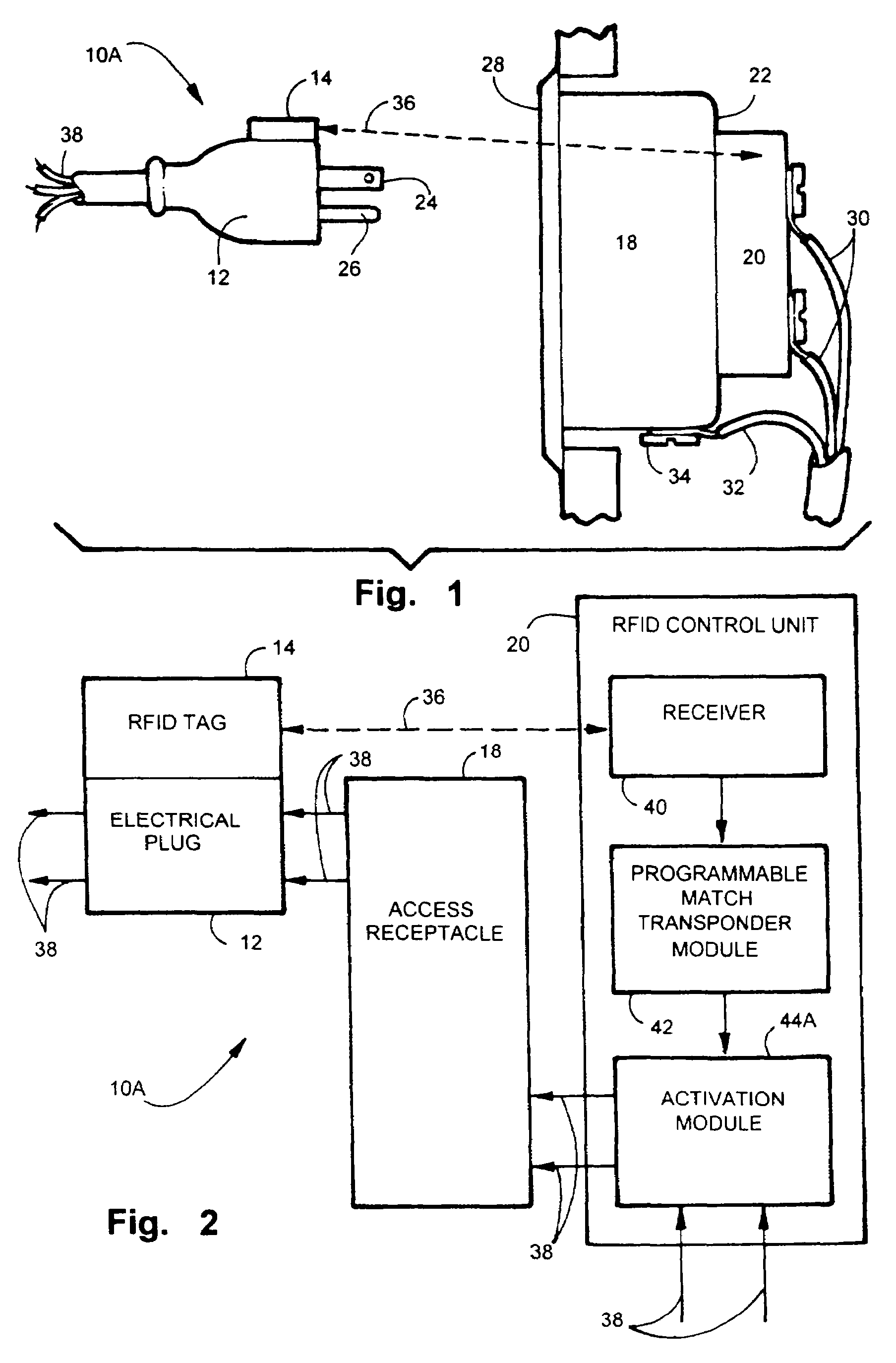
Electric, telephone or network access control system and method
InactiveUS7167078B2EasilyEasy to installElectric signal transmission systemsMultiple keys/algorithms usageElectricityControl system
An apparatus and method for controlling user access to electrical receptacles and telephone and network communications receptacles. The device features a short range radio receiver and one or a plurality of RF energized radio identification tags with transmittable identification transponder codes. The receptacle contains circuitry that detects the immediate presence of energized transponders with proper identification codes and only enables the electric, telephone or network access from the receptacle to become active if the correct matching transponder identification code is present. The tag is a small flexible device having one side that may be attached to the plug or the receptacle or interfaced therebetween. Access to the power or network is allowed for a defined duration of time or only so long as the transponder remains energized and transmits the identification code.
Owner:POURCHOT SHAWN C
System and method for securely receiving and counting votes in an election
ActiveUS20160027229A1Improve securityPrevent fraudVoting arrangementKey distribution for secure communicationBarcodeNetwork communication
The present invention generally relates to blockchain technology. Specifically, this invention relates to adapting blockchain technology for the storage of voting data in an electronic voting system. The system includes a distributed network of voting machines in communication with each other. Each voting machine has a barcode scanner, a network communications device and a computer system running a voting client. Votes are received through the barcode scanner or a voter interface system and stored securely on a blockchain. The tally for various candidates in the election is updated and stored as each vote is received and counted. This creates an auditable trail of votes and the tally which can be used to detect, correct, and prevent fraud and error in the vote counting process.
Owner:BLOCKTECH LLC
Determining client latencies over a network
InactiveUS7676570B2Multiple digital computer combinationsTransmissionTime informationNetwork communication
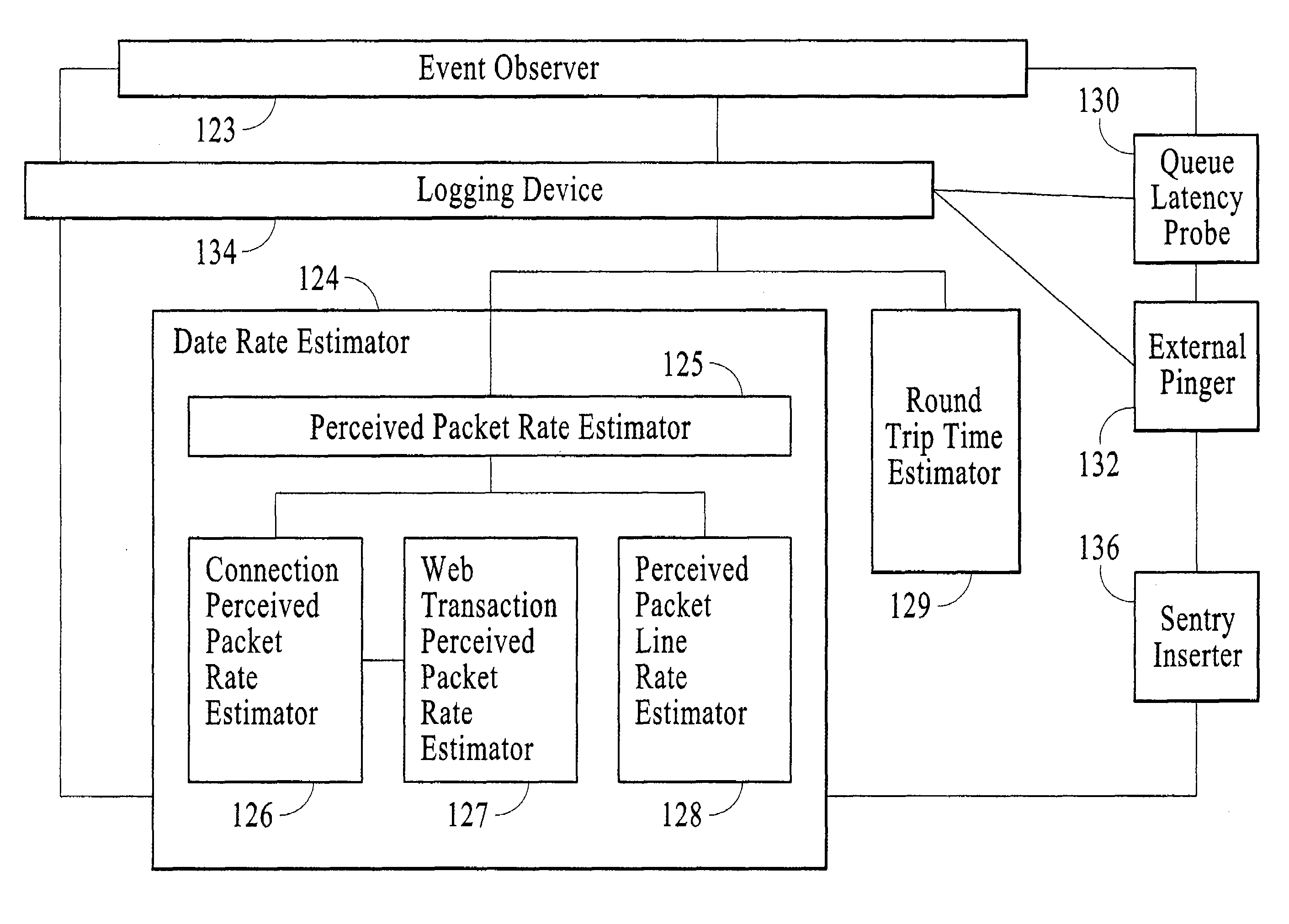
A network latency estimation apparatus for estimating latency in network communications between a server and a client. The apparatus comprises an event observer for observing occurrences of pre-selected events. The events associated with the communication occurring at the server. A logging device associated with the event observer for logging into a data store the occurrence of the events together with respective time information. A latency estimator associated with the logging device for using the logged occurrences with the respective time information to arrive at an estimation of a client's latency for the communication.
Owner:ZARBANA DIGITAL FUND
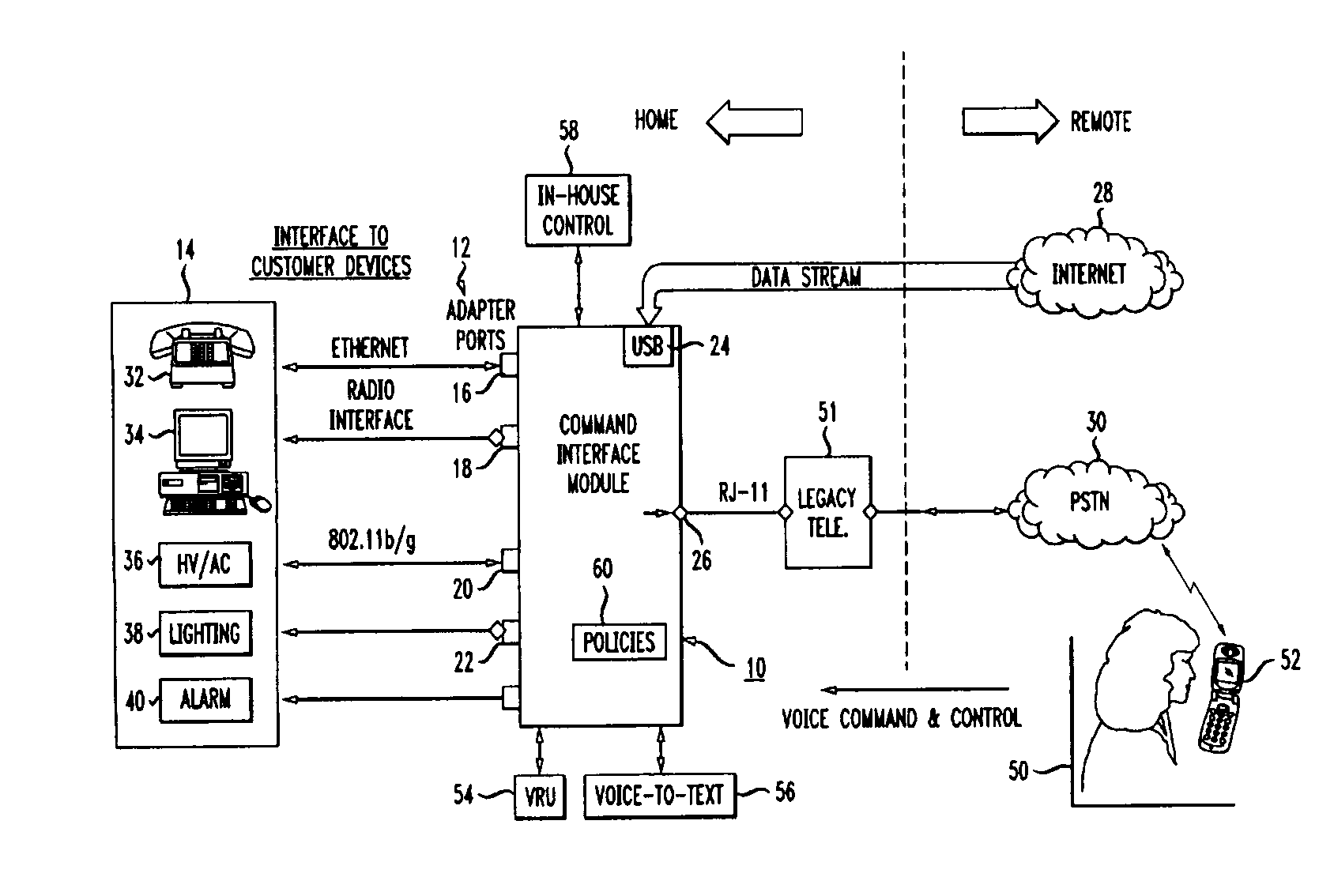
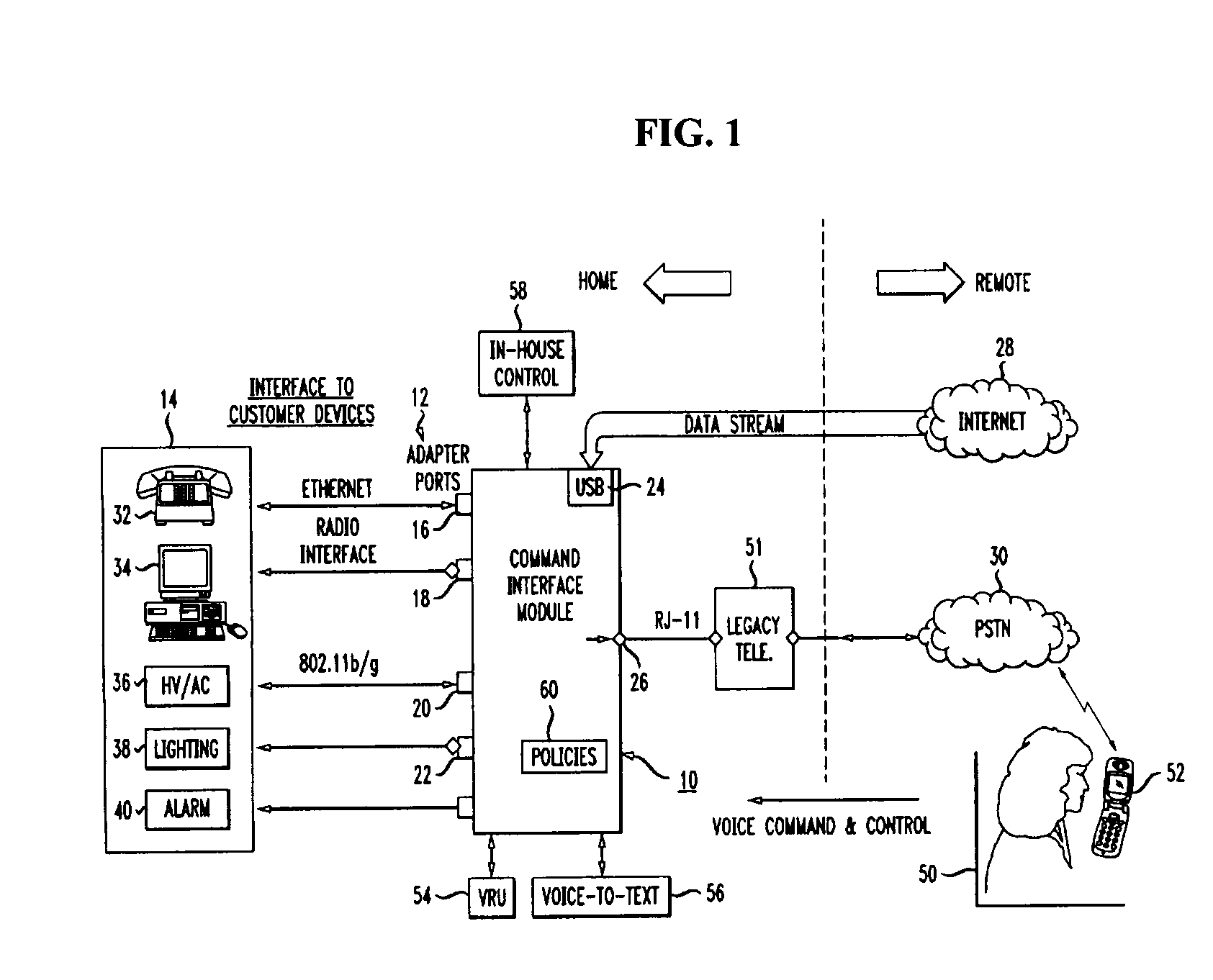
Home control, monitoring and communication system using remote voice commands
ActiveUS8654936B1Devices with voice recognitionAutomatic call-answering/message-recording/conversation-recordingCommunication interfaceCommunications system
A voice-activated command interface module for interacting with a plurality of home-based electronic devices so as to allow for a remotely-located home owner to communicate with, command and control various ones of the electronic devices. The module includes a plurality of communication ports, each communication port associated with a different type of communication interface for providing communications to and from the plurality of electronic devices. The module also includes a voice network communication port for receiving the voice commands from the home owner and a data network communication port for transmitting monitoring and control information between the plurality of electronic devices and the home owner. In operation, the command interface module is responsive to voice commands received from a remote user via an incoming telephone line (either data or voice). A voice recognition unit within the command interface module is utilized to translate the received voice signal into an “action / control” signal and then perform the desired activity.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Method of creating and displaying relationship chains between users of a computerized network
ActiveUS7177880B2Easy to understandMaximize easeDigital data processing detailsMultiple digital computer combinationsNetwork communicationData science
A method and structure for identifying potential relationships between users of a computer network is disclosed. The invention extracts relationship information from databases in the computer network in order to establish multiple relationship chains of the users from the relationship information. More specifically, the invention evaluates network information and network communications between the users to produce metrics and processes the metrics to produce contact information. The contact information indicates whether a personal relationship exists between two users. In addition, the invention can produce relationship values representing strengths of social relationships between users of the computer network based on such relationship information.
Owner:GLOBALFOUNDRIES U S INC
Virtual computing infrastructure
ActiveUS20090300605A1More separatedReduce hardware costsResource allocationSoftware simulation/interpretation/emulationOperational systemNetwork communication
A system has a virtual overlay infrastructure mapped onto physical resources for processing, storage and network communications, the virtual infrastructure having virtual entities for processing, storage and network communications. Each virtual infrastructure can be passivated by suspending applications, stopping operating systems, and storing state, to enable later reactivation. This is simpler for a complete virtual infrastructure than for groups of virtual entities and physical entities. It enables cloned virtual infrastructure to be created for testing, upgrading or sharing without risk to the parent. On failure, reversion to a previous working clone is feasible.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
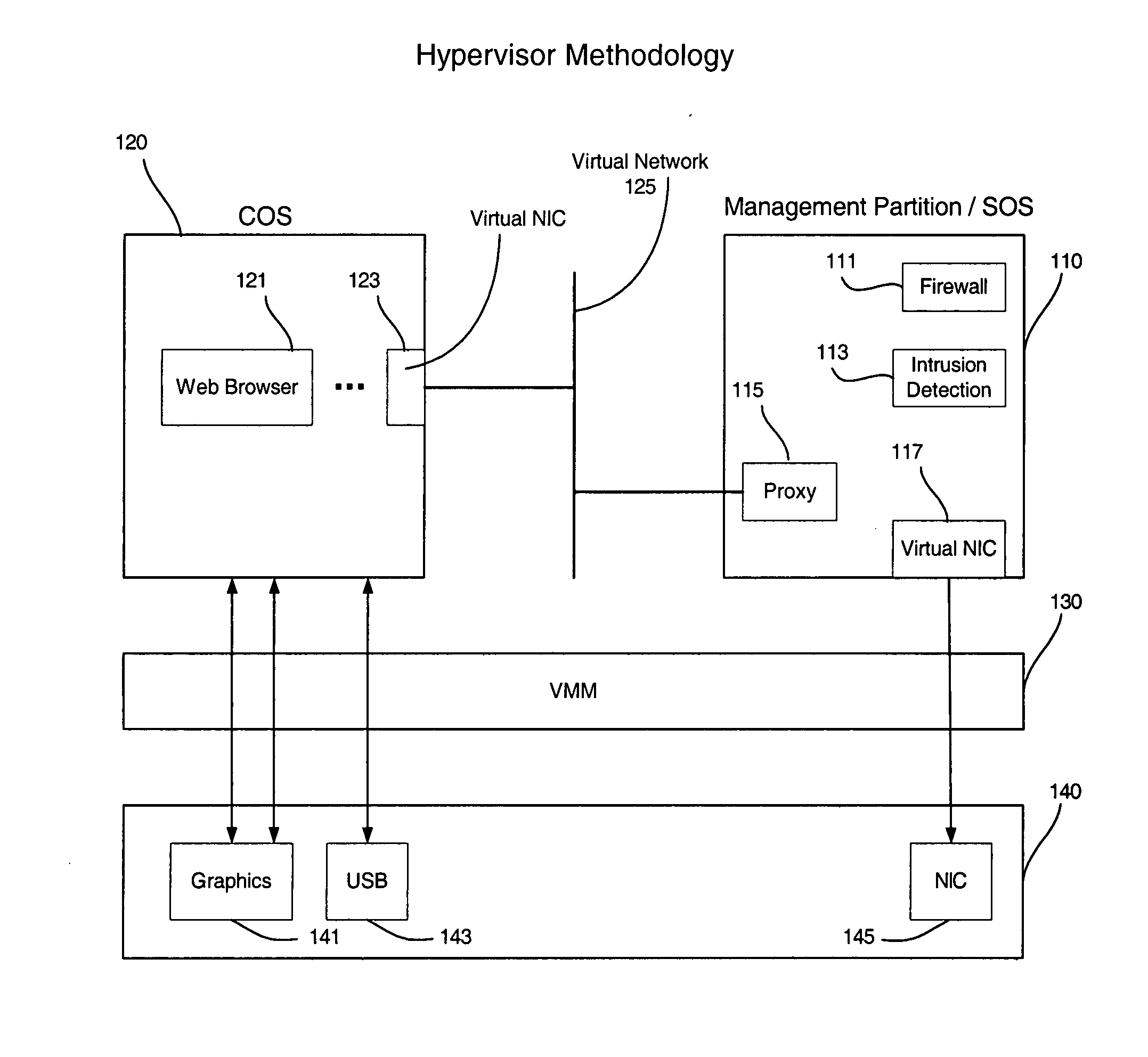
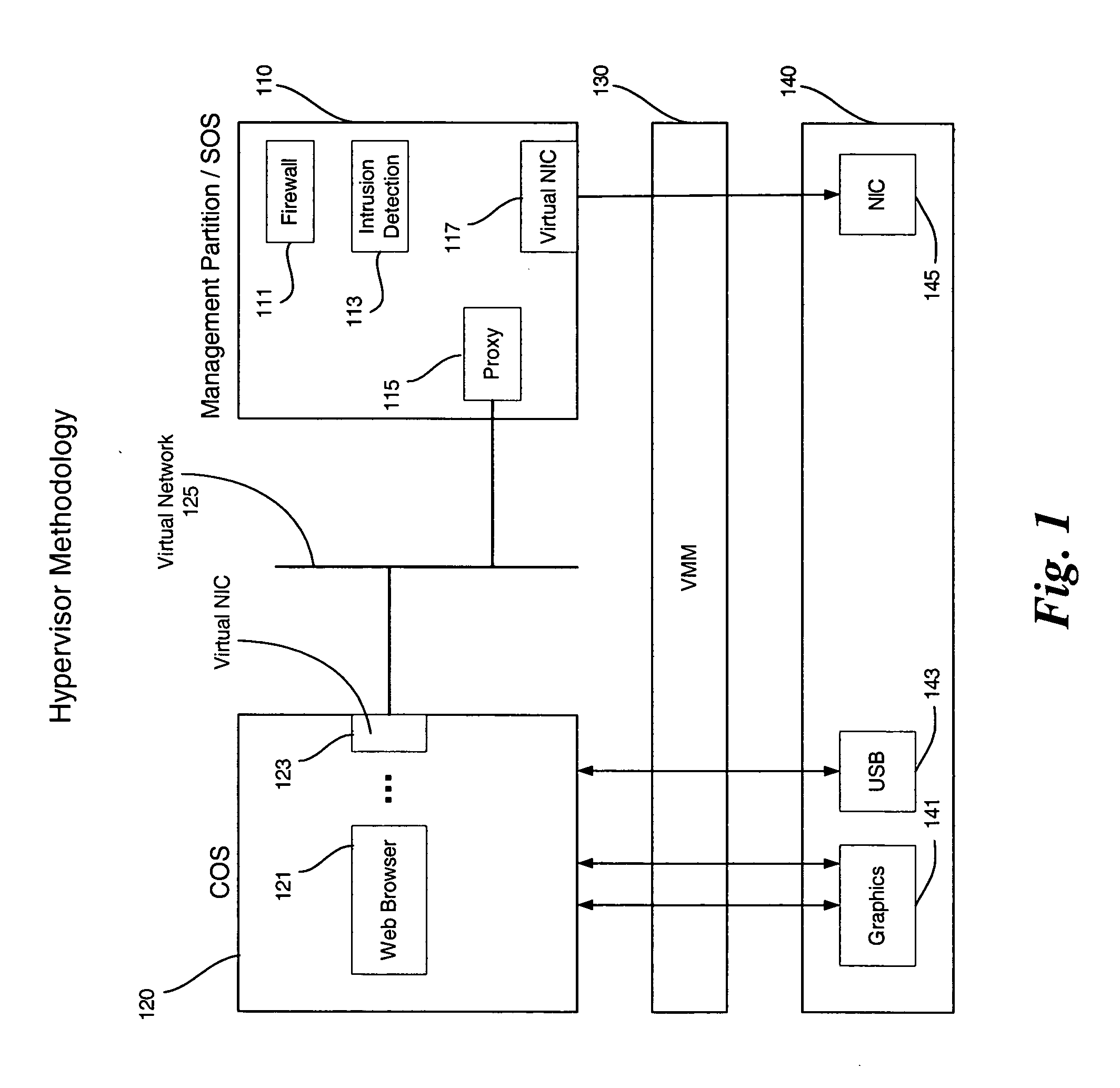
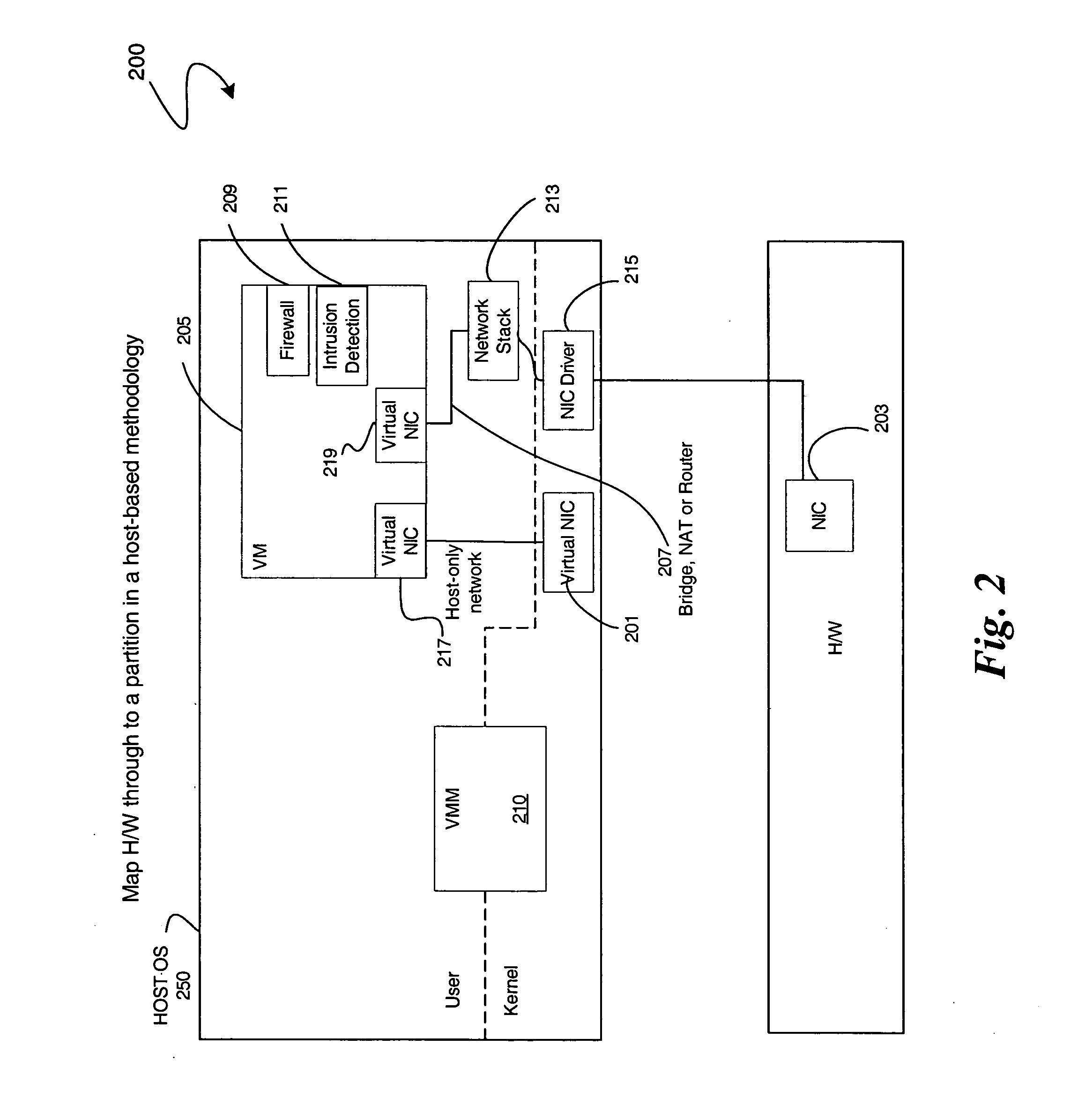
Enabling platform network stack control in a virtualization platform
InactiveUS20060070066A1TransmissionSoftware simulation/interpretation/emulationVirtualizationData pack
In some embodiments, the invention involves protecting network communications in a virtualized platform. An embodiment of the present invention is a system and method relating to protecting network communication flow using packet encoding / certification and the network stack. One embodiment uses a specialized engine or driver in the network stack to encode packets before being sent to physical network controller. The network controller may use a specialized driver to decode the packets, or have a hardware implementation of a decoder. If the decoded packet is certified, the packet is transmitted. Otherwise, the packet is dropped. An embodiment of the present invention utilizes virtualization architecture to implement the network communication paths. Other embodiments are described and claimed.
Owner:INTEL CORP
Medium access control (MAC) protocol for wireless ATM
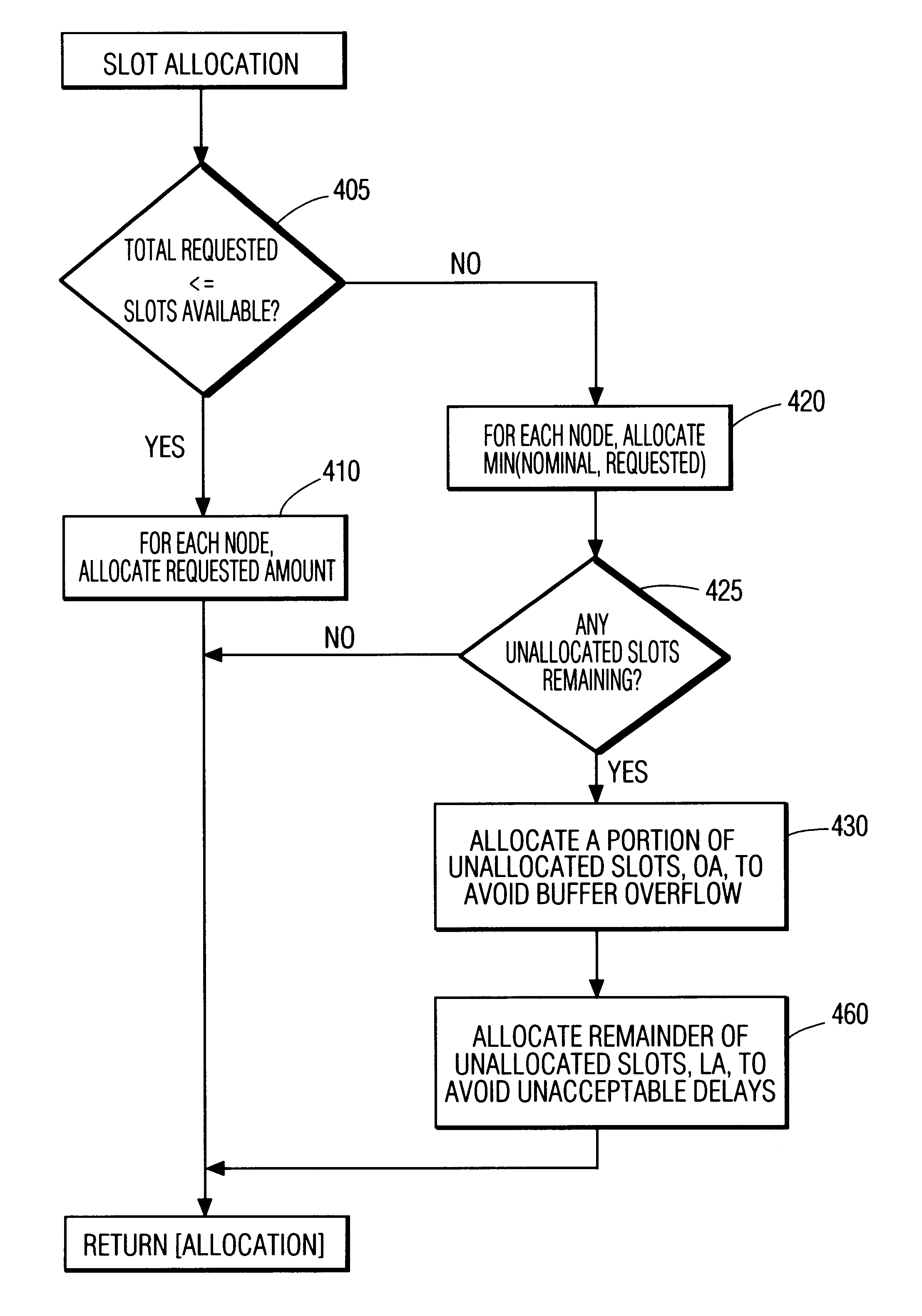
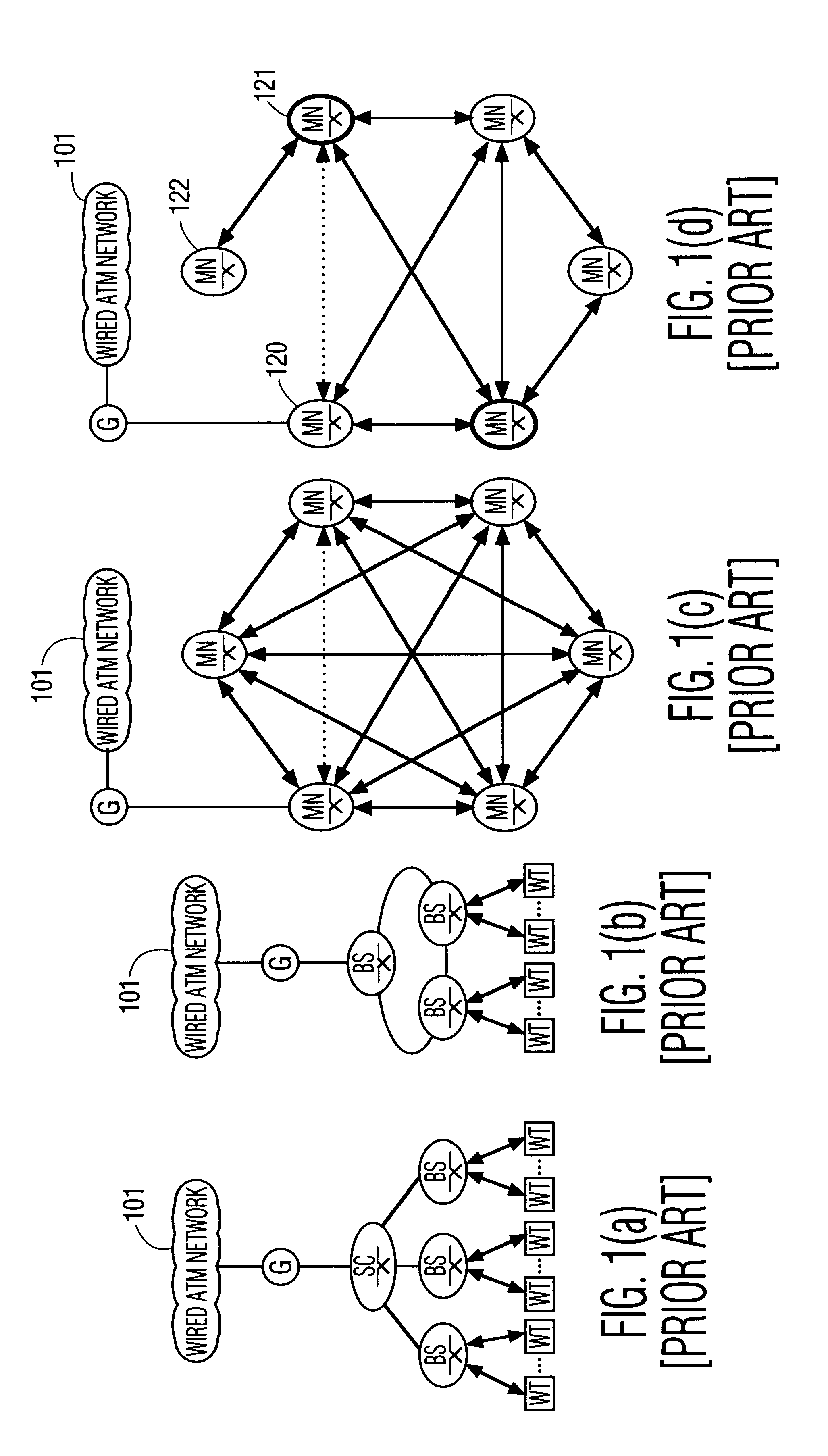
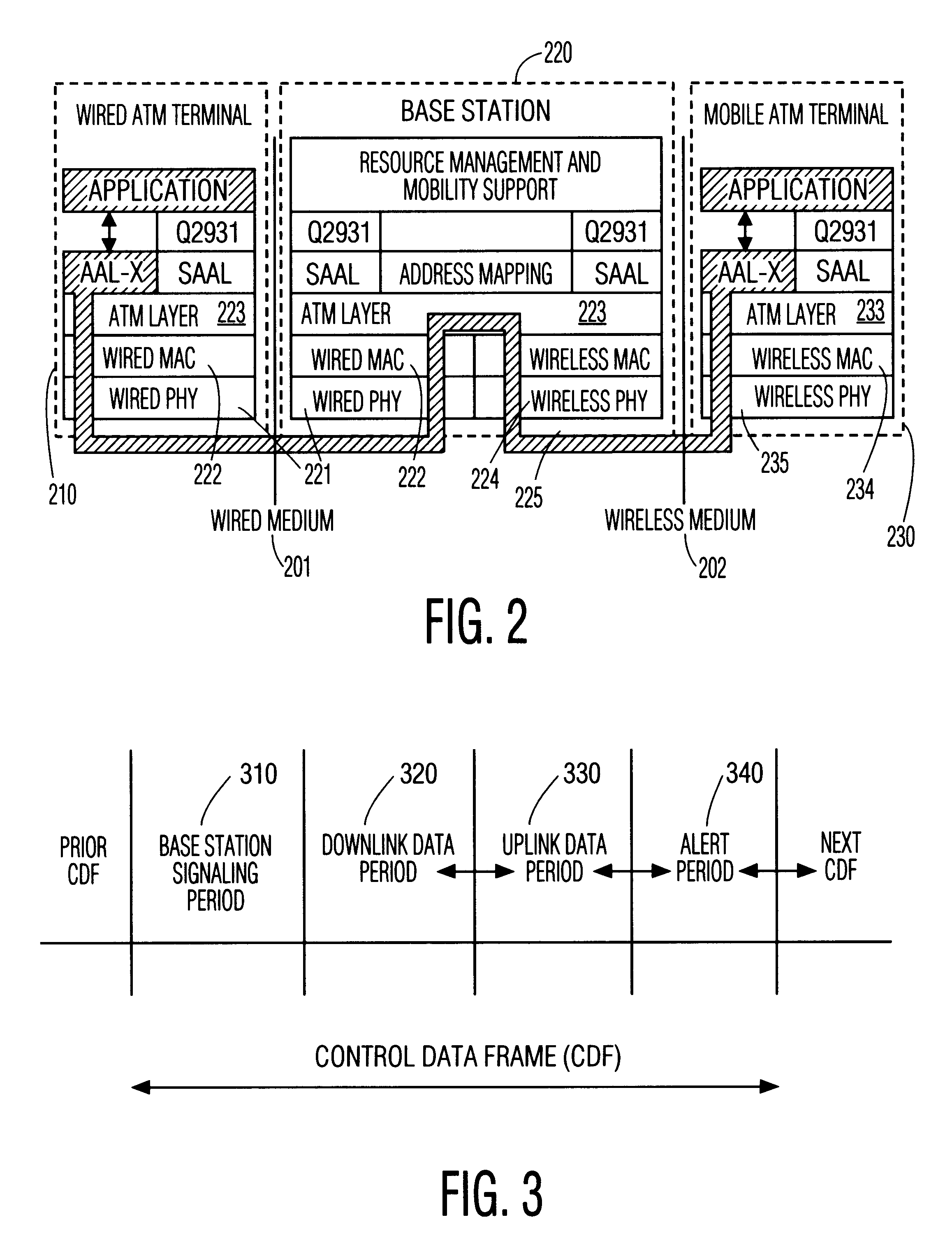
InactiveUS6198728B1Structure is limitedMinimize timePower managementNetwork traffic/resource managementNetwork communicationMedia access control
A protocol, method, and apparatus for managing network communications which are particularly well suited for ATM communications across a wireless medium. Contiguous time slots within a frame are allocated to each node having traffic to send. Each node is assured a nominal bandwidth, and excess bandwidth is distributed by demand. The allocation of excess bandwidth can be dependent upon the size of the buffer at each node, as well as the time-criticality of each message. Nodes communicate their requests for allocation by appending such control information to the first of their transmitted packets. The allocation, of each node's transmit and receive time slots, is transmitted to all the nodes at the beginning of each frame. Thereafter, each node need not participate on the network until their allocated time periods, thereby allowing portable devices to enter inactive states to conserve power. The network is operated in a connection mode; connections are established in a relatively non-interfering manner by the use of periodically occurring beacons. Inactive, unconnected, nodes need only monitor the network during these beacon periods, further allowing for power conservation.
Owner:UNILOC 2017 LLC
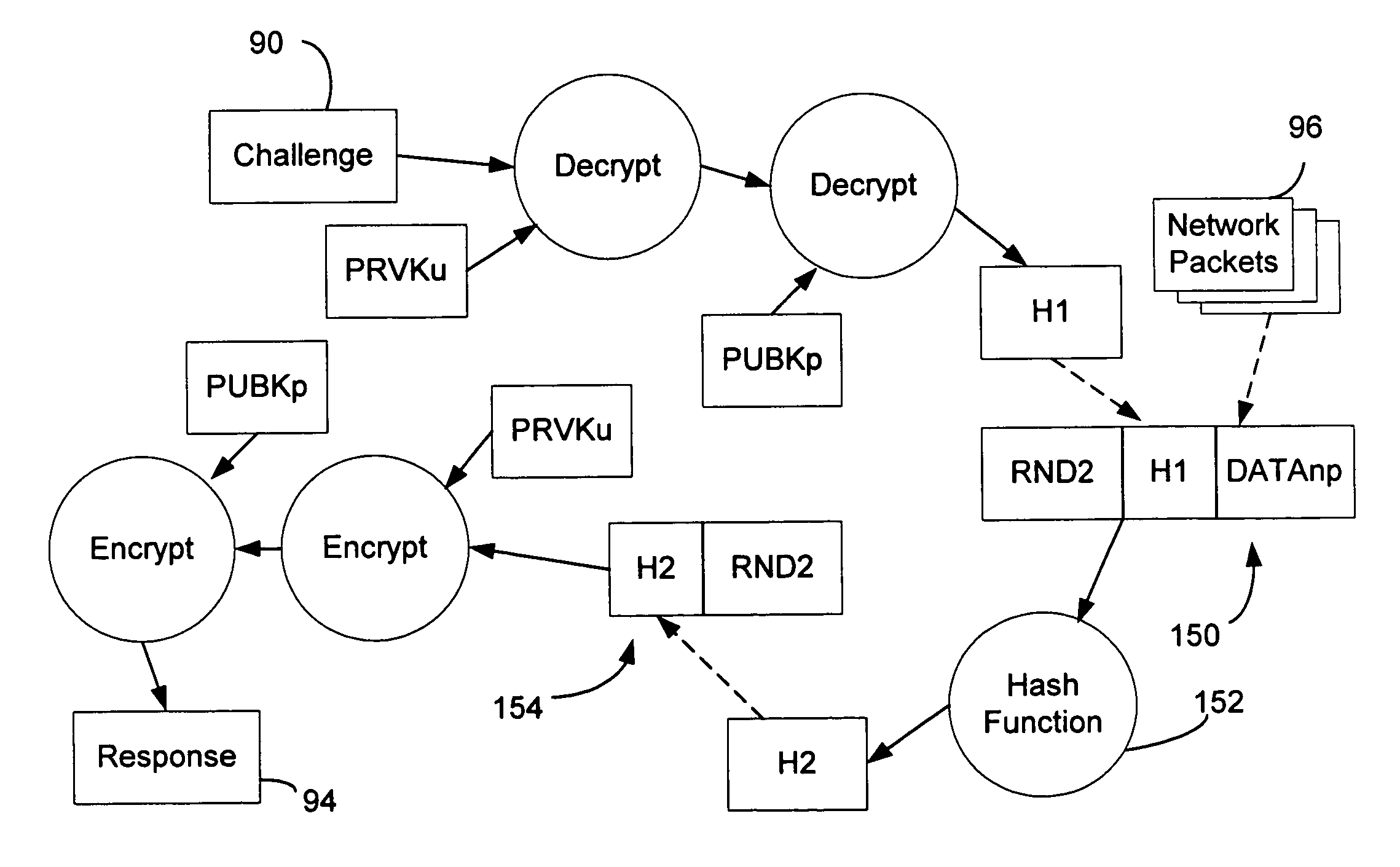
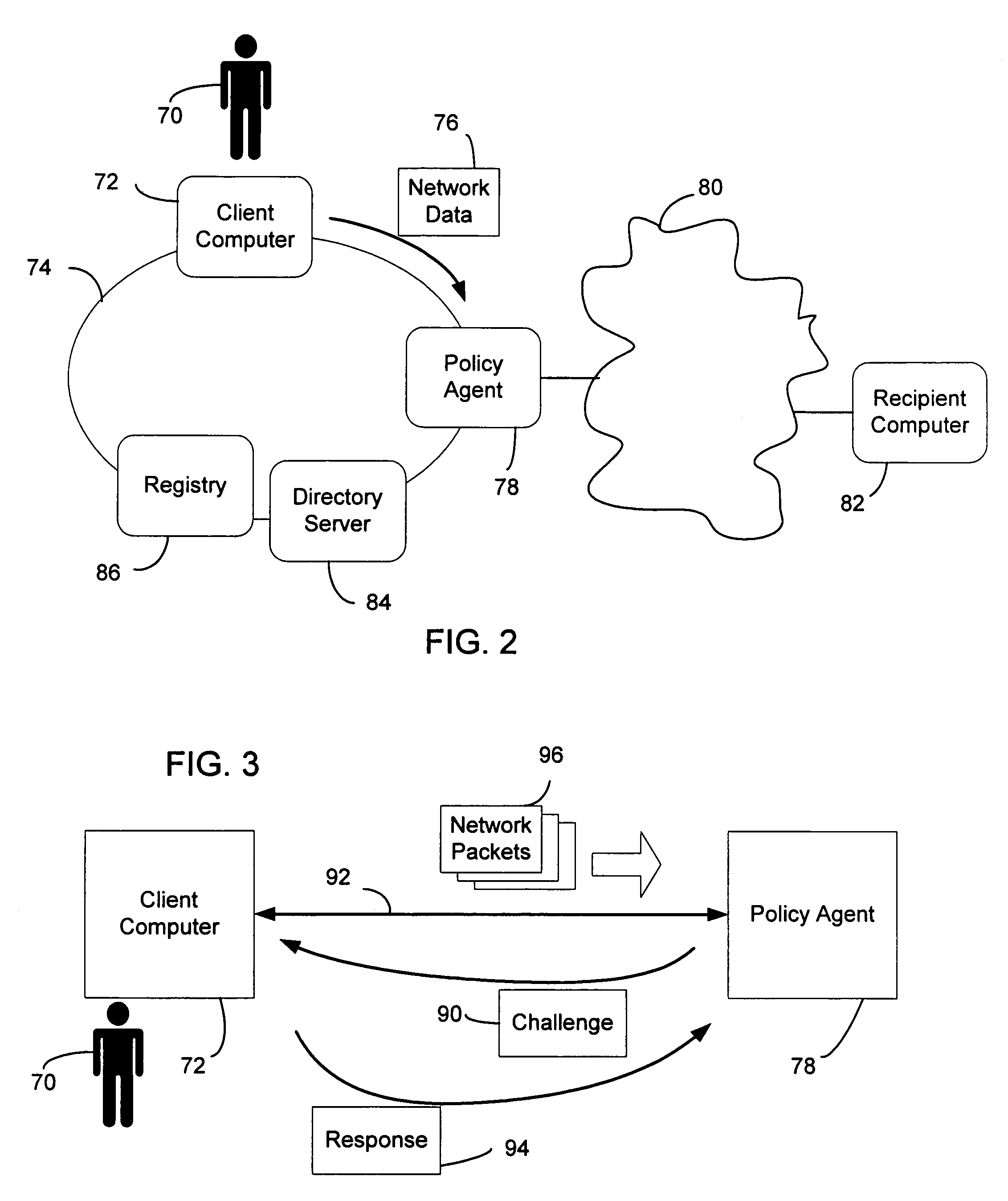
System and method of user authentication for network communication through a policy agent
InactiveUS7039713B1Digital data processing detailsComputer security arrangementsData connectionUser authentication
A policy agent of a network performs an out-of-band user authentication process to verify the identity of a user of a client computer and associates the network data received from the client computer with the user. When the client computer initiates a network data connection to or through the policy agent, the policy agent sends an encrypted challenge to the client computer. The challenge is encrypted with a private key of the policy agent. When the client computer receives the challenge, it decrypts the challenge and prepares a message digest value based on the challenge and the network data sent by the user. The message digest value is then encrypted with the private key of the user to form a response, and the response is sent to the policy agent. The policy agent decrypts the response with the public key of the user to obtain the message digest value and calculates a digest value based on the challenge and the received network data. The policy agent then compares the calculated digest value with the decrypted digest value. A match between the two digest values indicates that the user is successfully authenticated and that the received network data are associated with the user. The policy agent may then apply network policies based on the credentials of the authenticated user.
Owner:MICROSOFT TECH LICENSING LLC
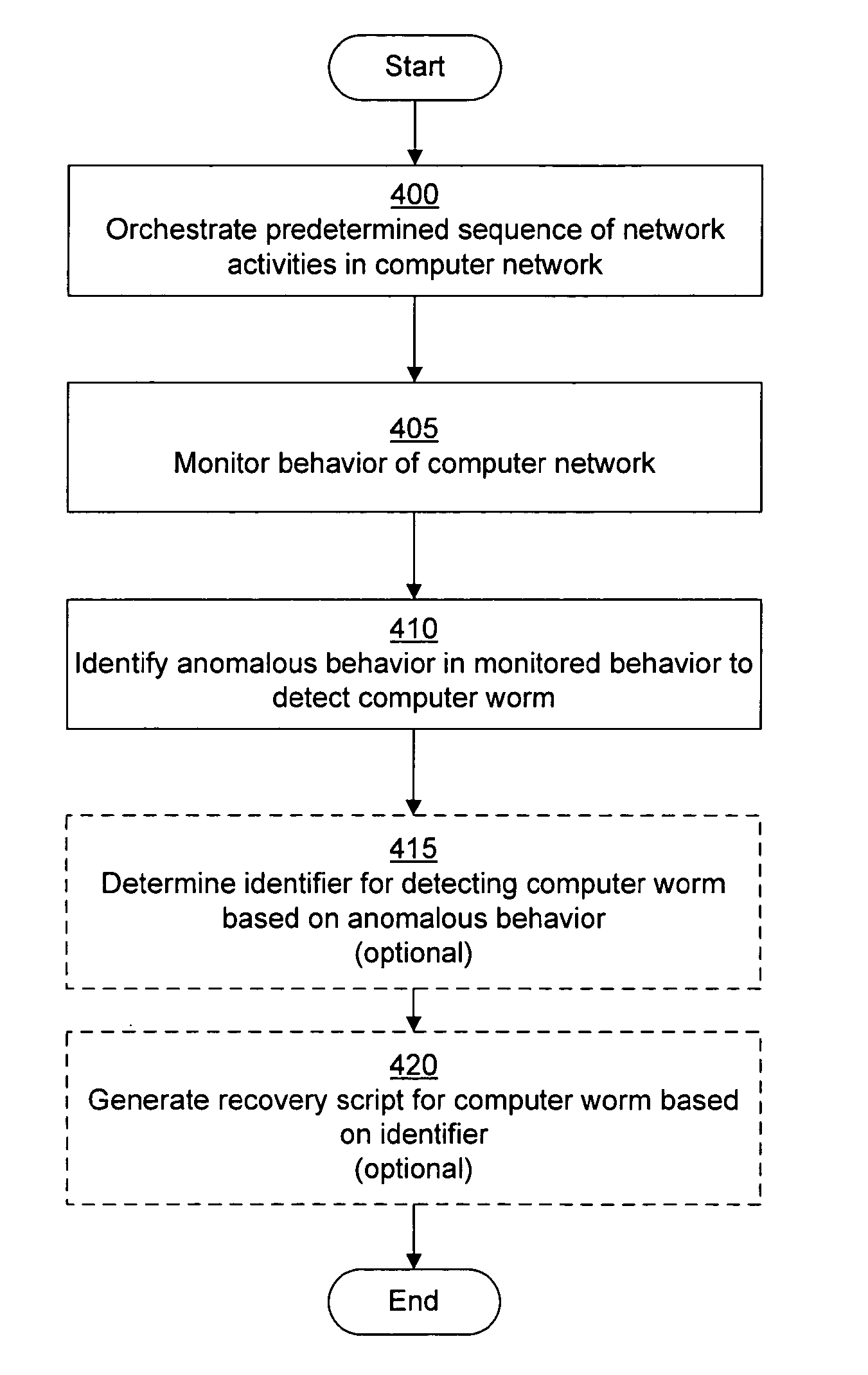
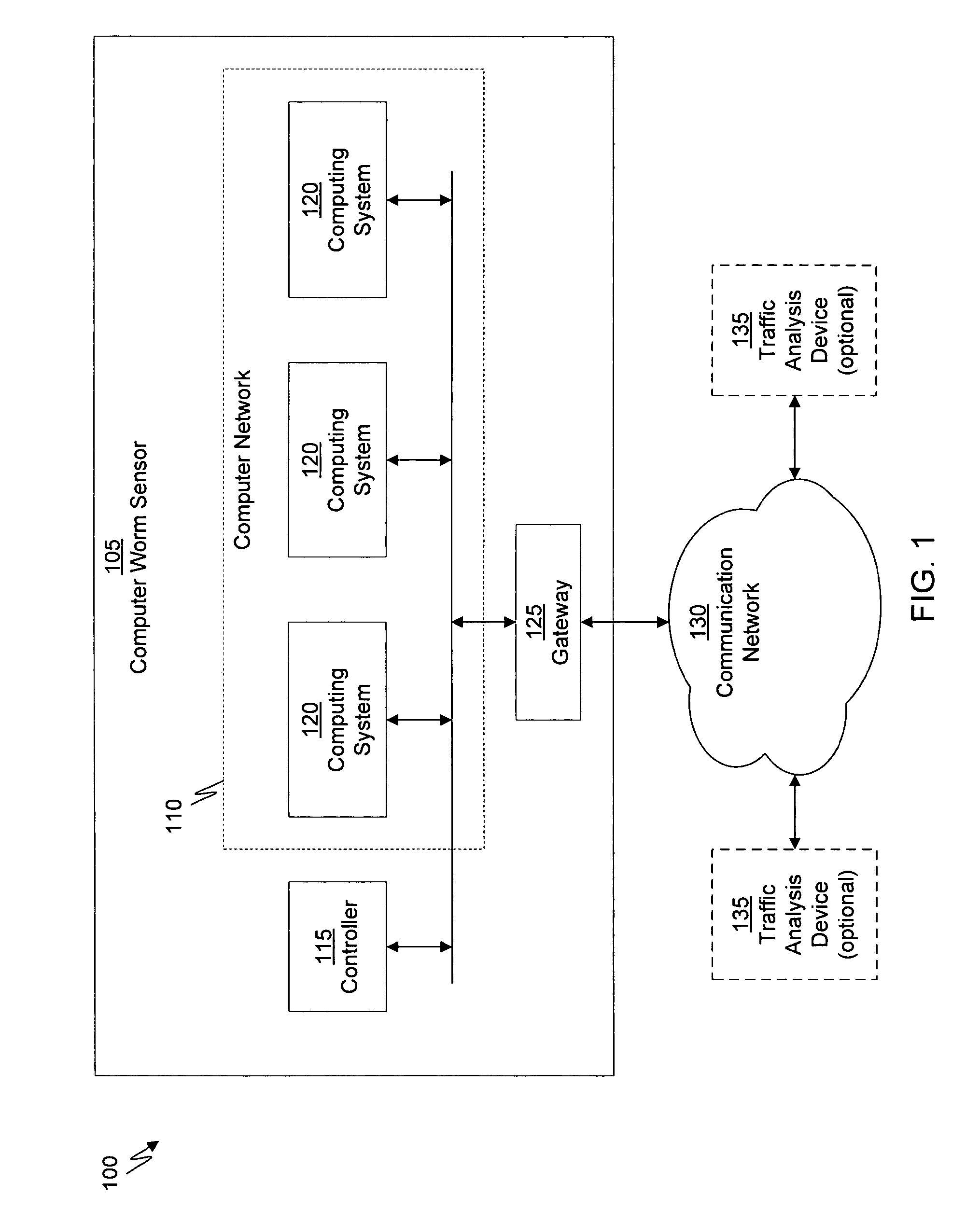
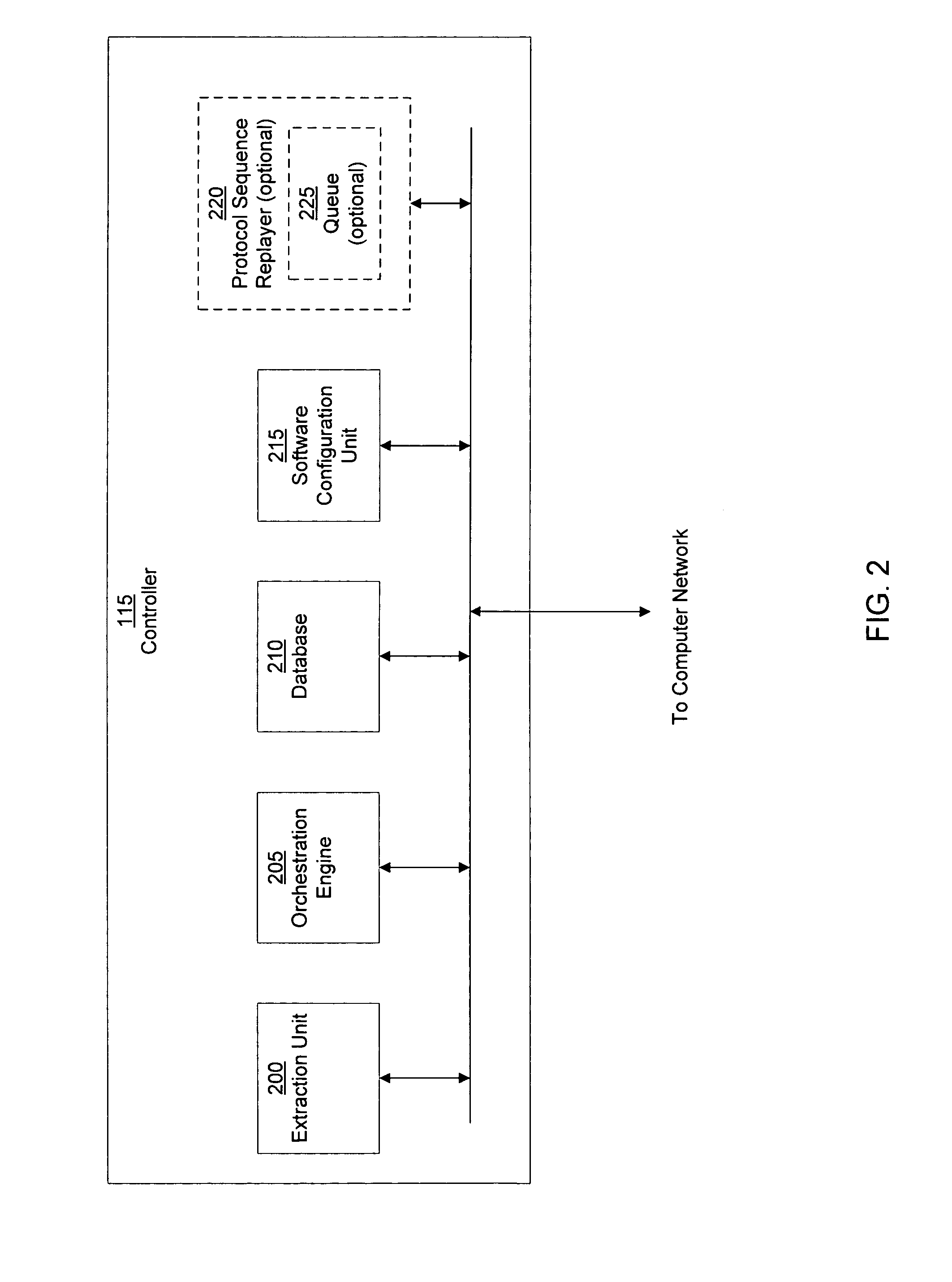
System and method of detecting time-delayed malicious traffic
A system for detecting a computer worm comprises a traffic analysis device in communication with a network device. The traffic analysis device can analyze network traffic received over a communication network and duplicate at least select network communications within the network traffic having characteristics associated with one or more computer worms. The network device comprises a controller in communication with one or more virtual machines that are configured to receive the duplicated network communications from the traffic analysis device. The network device may (i) monitor a behavior of a first virtual machine of the one or more virtual machines in response to processing of the duplicated network communications within the first virtual machine, (ii) identify an anomalous behavior as an unexpected occurrence in the monitored behavior, and (iii) determine, based on the identified anomalous behavior, the presence of the one or more computer worms in the duplicated network communications.
Owner:FIREEYE SECURITY HLDG US LLC
Conditional requirements for remote medical device programming
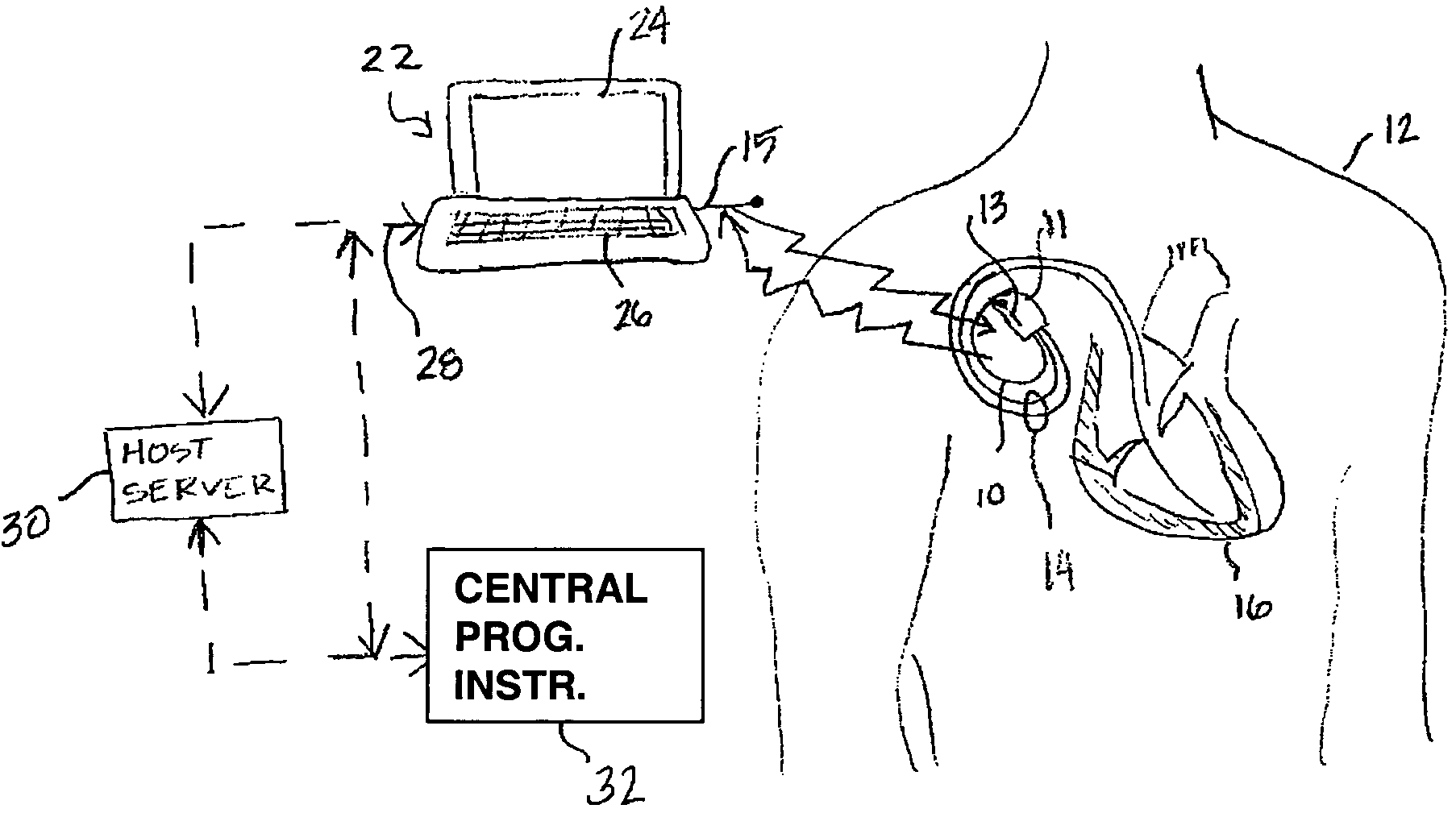
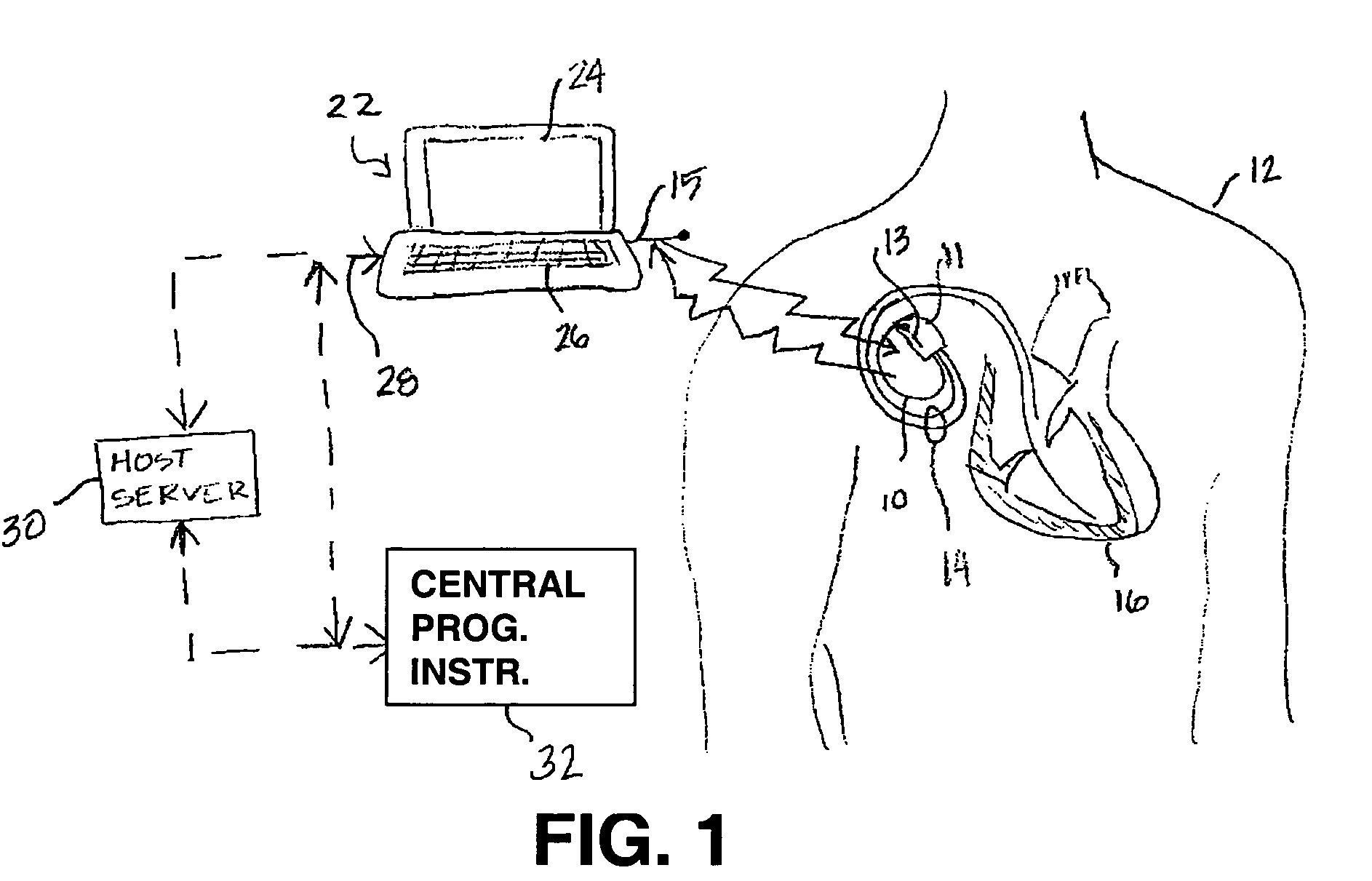
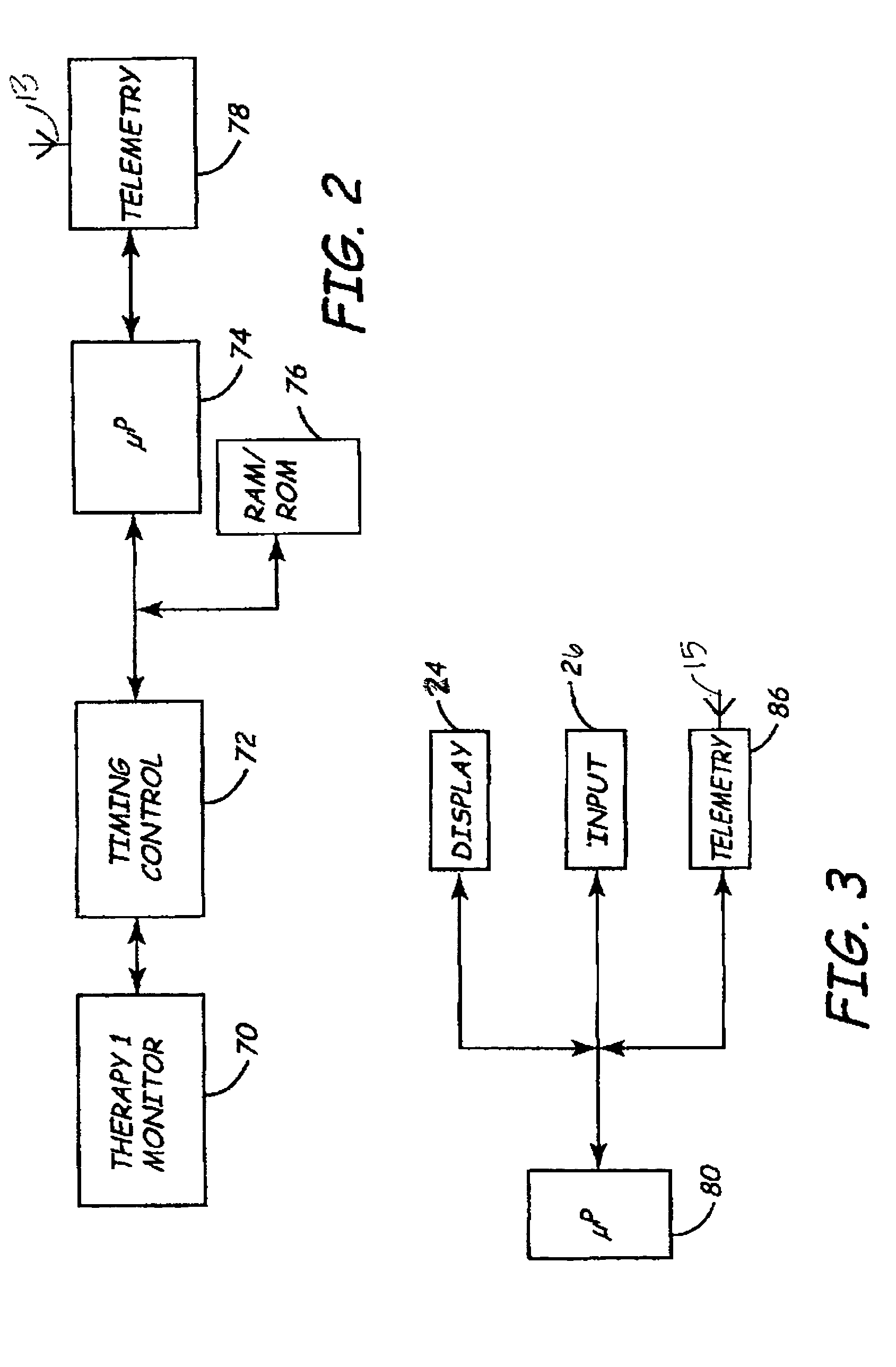
InactiveUS7565197B2Promote safe and secure remote programmingReduce the possibilityElectrotherapyTelemedicineThird partyNetwork communication
Owner:MEDTRONIC INC
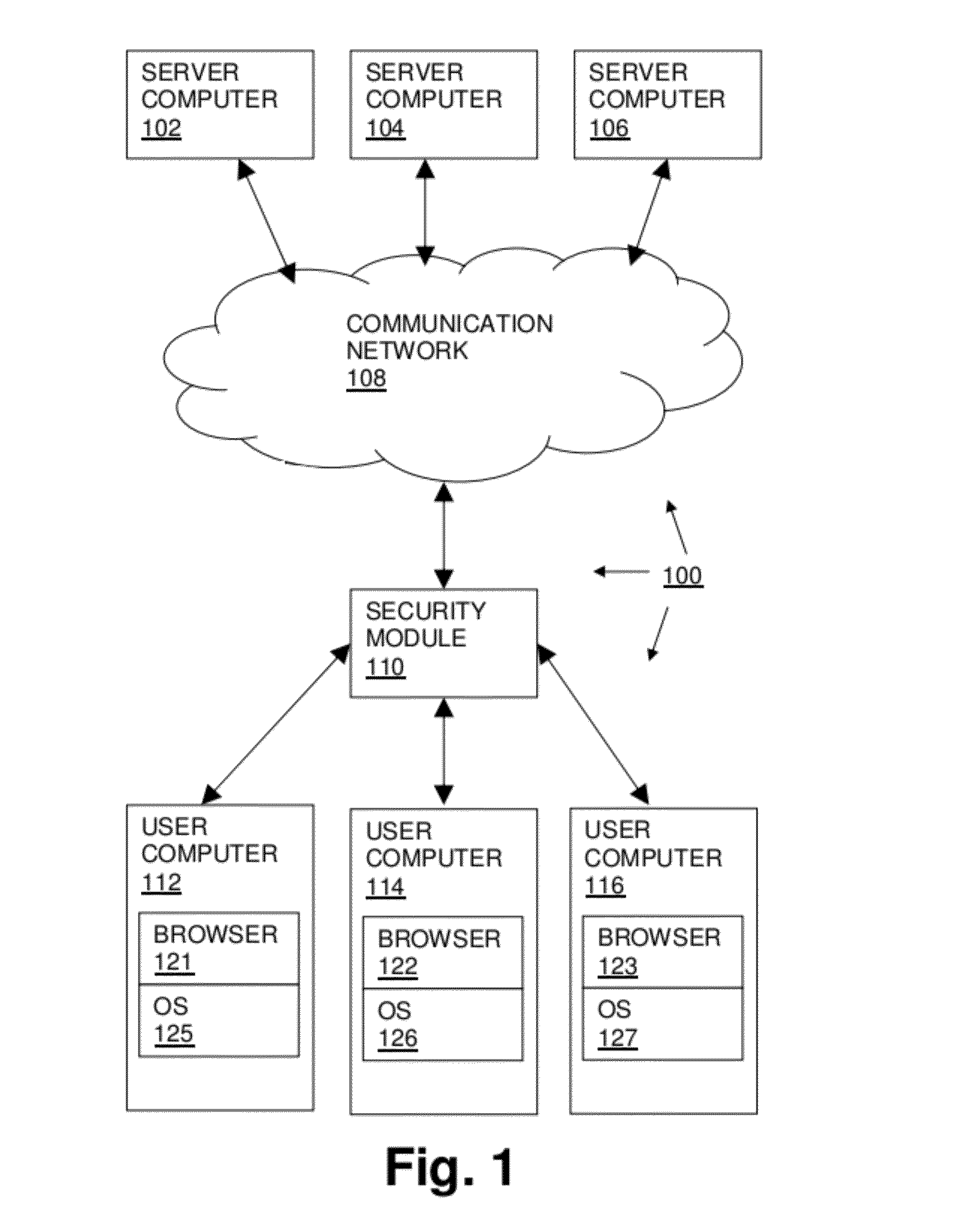
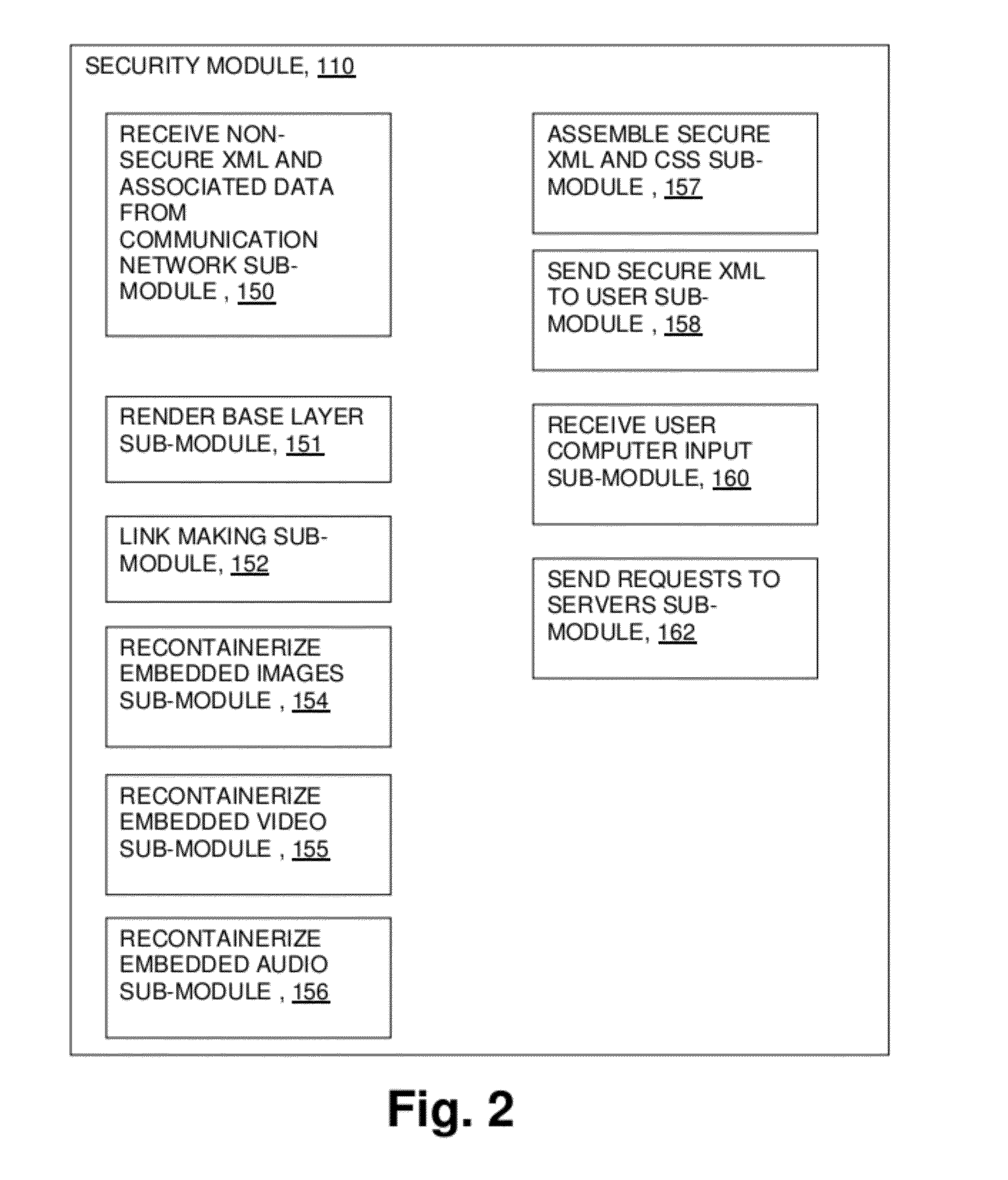
Network Communication System With Improved Security
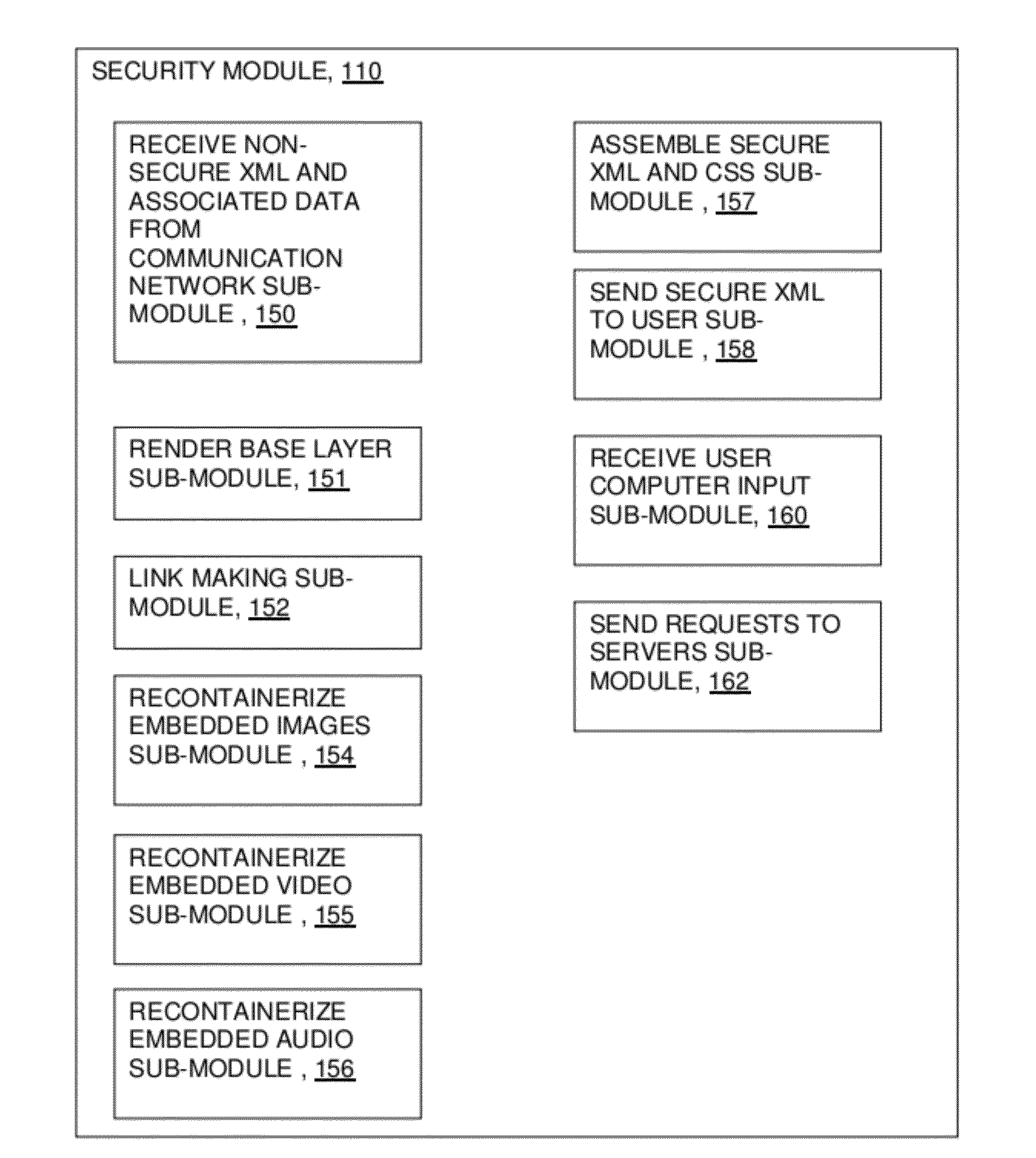
ActiveUS20120174218A1Effectively shut downEffectively shut down the targets internet connection capabilityMemory loss protectionError detection/correctionPathPingSoftware engineering
A computer network communication method and system wherein software rendering software is interposed in the data communication path between a browser running on a user computer and the internet data sources (for example, internet-accessible server computers) that the user browser wants to receive information from. The software rendering application gets data from internet data sources, but this data may contain malware. To provide enhanced security, the software rendering application renders this data to form a new browser readable code set (for example, an xml page with CSS layers), and this new and safe browser readable code set is sent along to the browser on the user computer for appropriate presentation to the user. As part of the rendering process, dedicated and distinct virtual machines may be used to render certain portion of the data, such as executable code. These virtual machines may be watched, and quickly destroyed if it is detected that they have encountered some type of malware.
Owner:TOUCHPOINT PROJECTION SOLUTIONS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com