Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4312 results about "Fault tolerance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Fault tolerance is the property that enables a system to continue operating properly in the event of the failure of (or one or more faults within) some of its components. If its operating quality decreases at all, the decrease is proportional to the severity of the failure, as compared to a naively designed system, in which even a small failure can cause total breakdown. Fault tolerance is particularly sought after in high-availability or life-critical systems. The ability of maintaining functionality when portions of a system break down is referred to as graceful degradation.
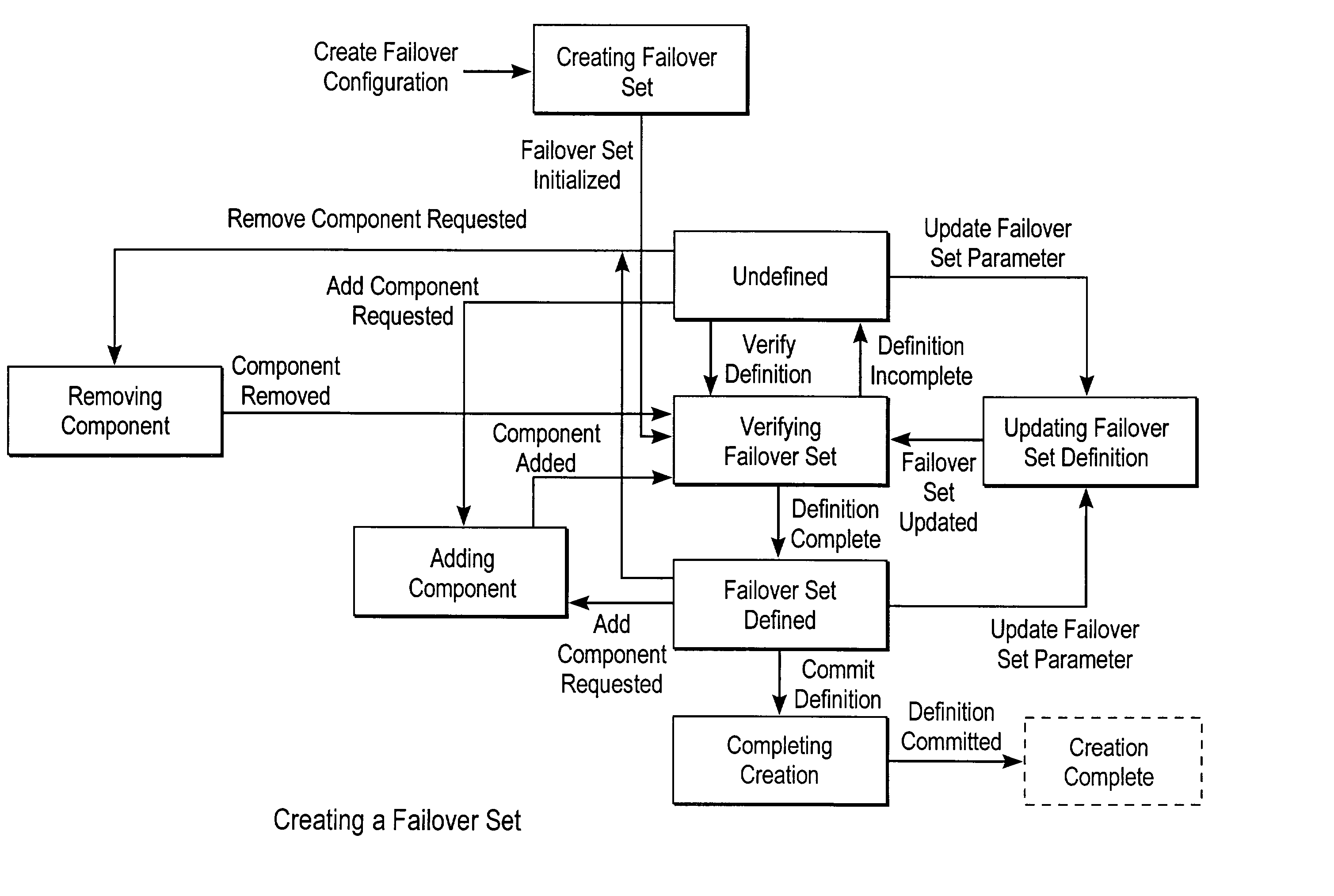
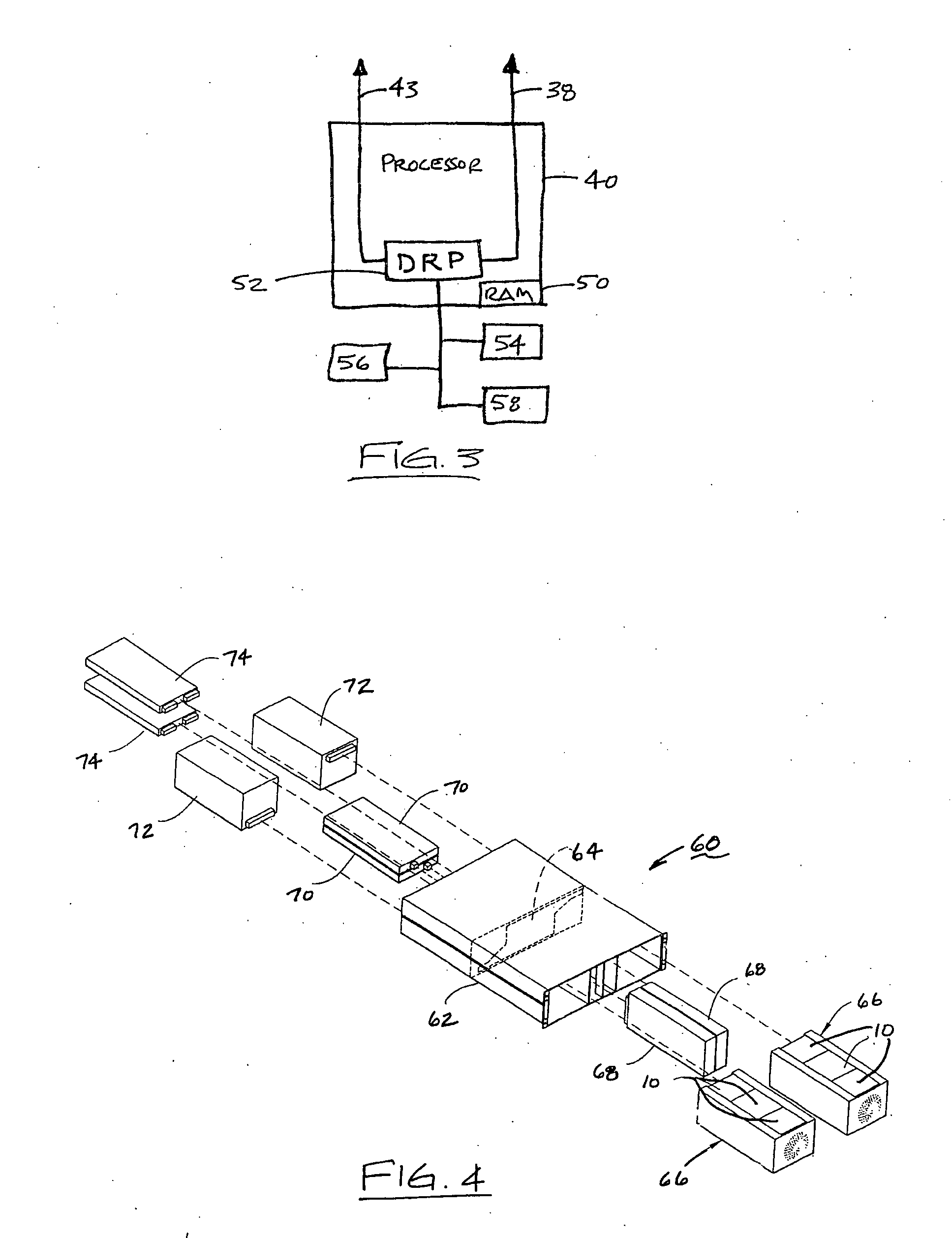
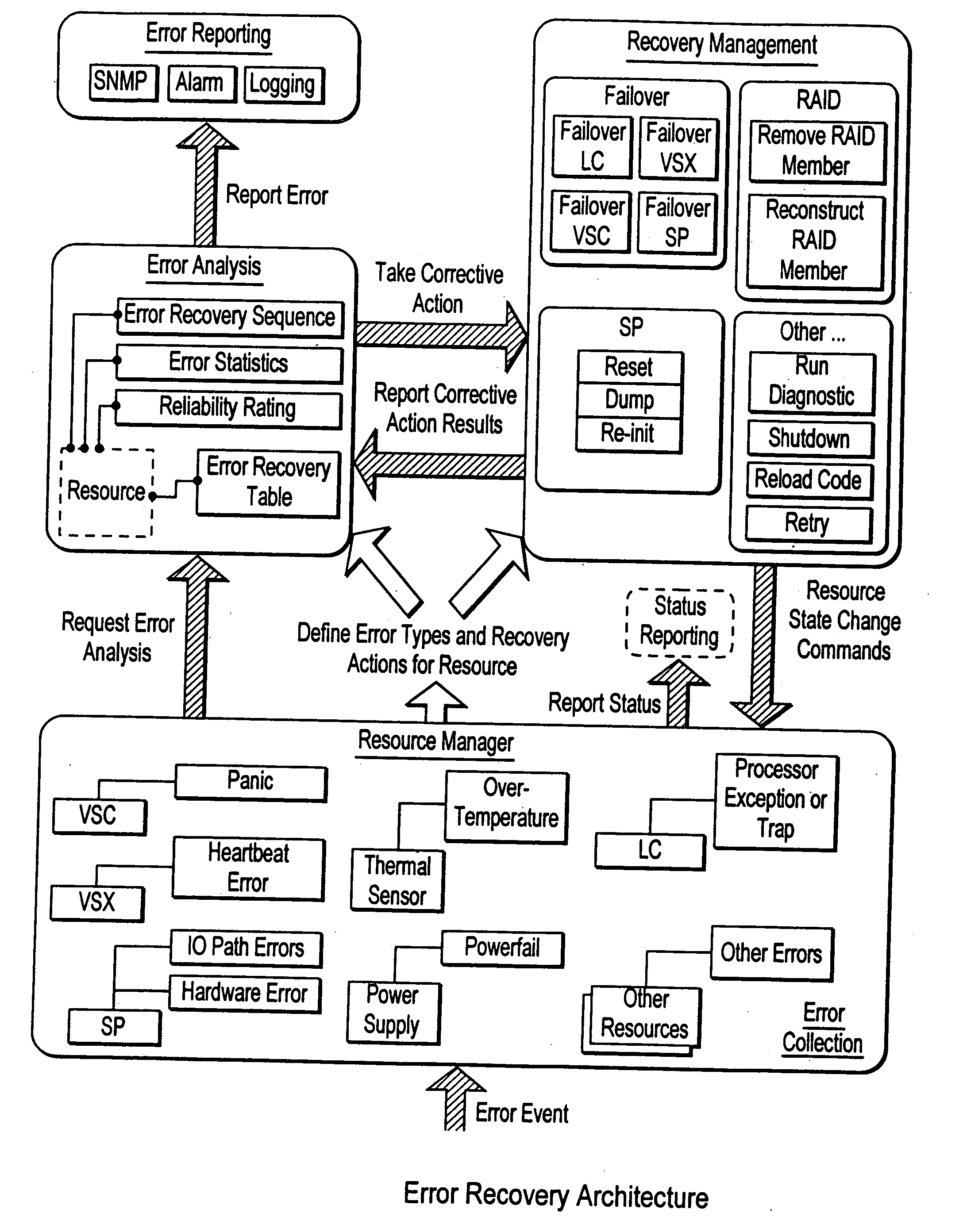
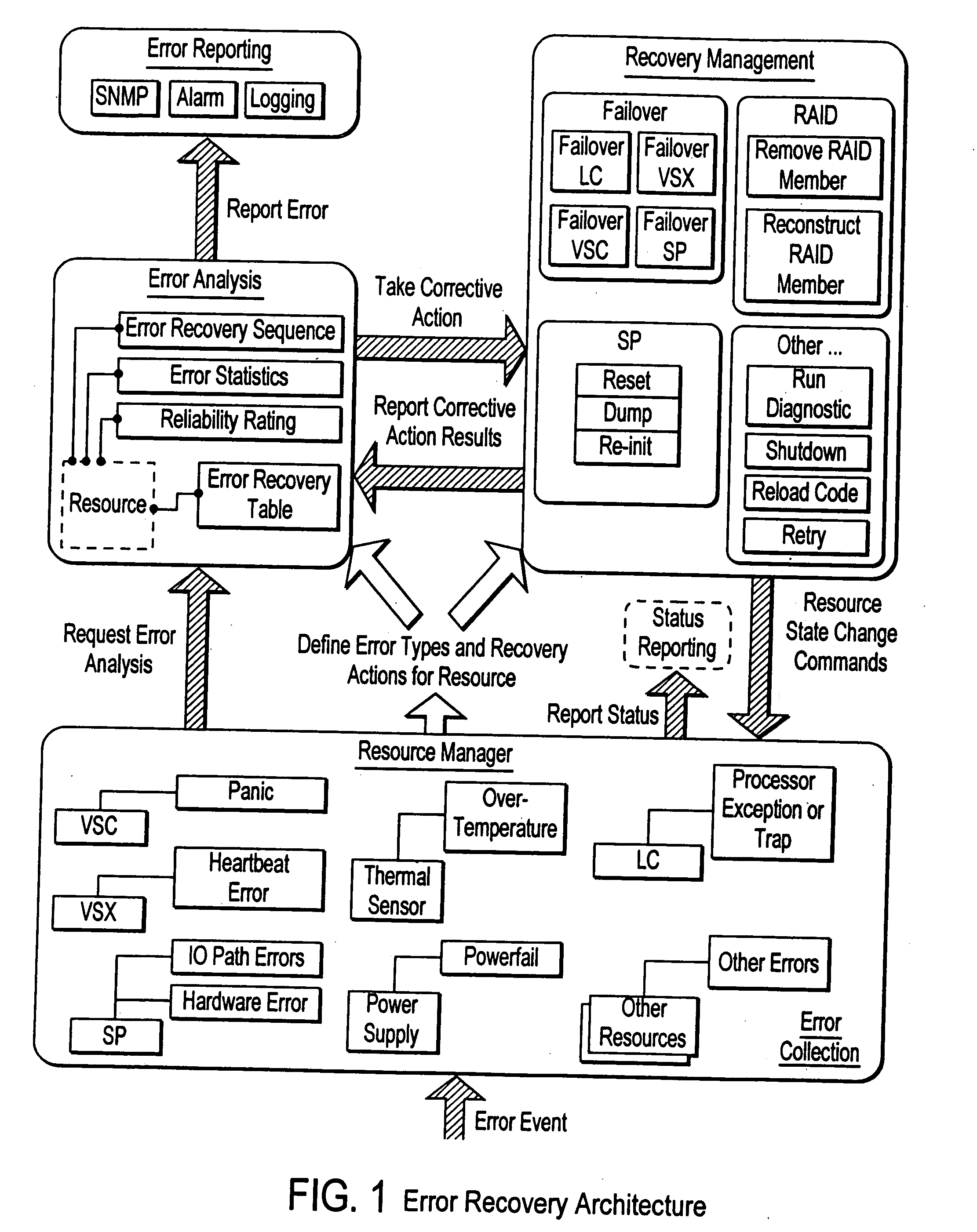
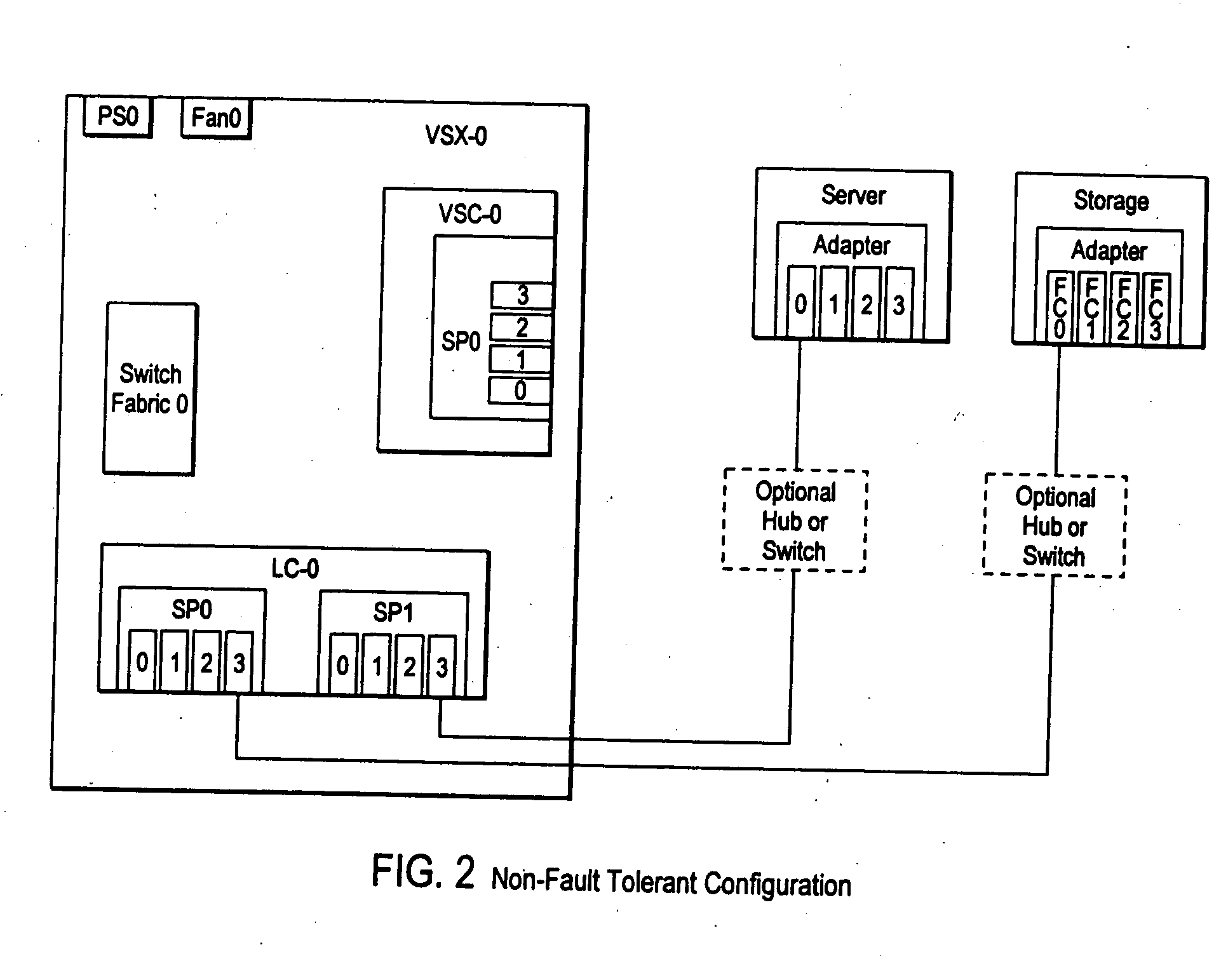
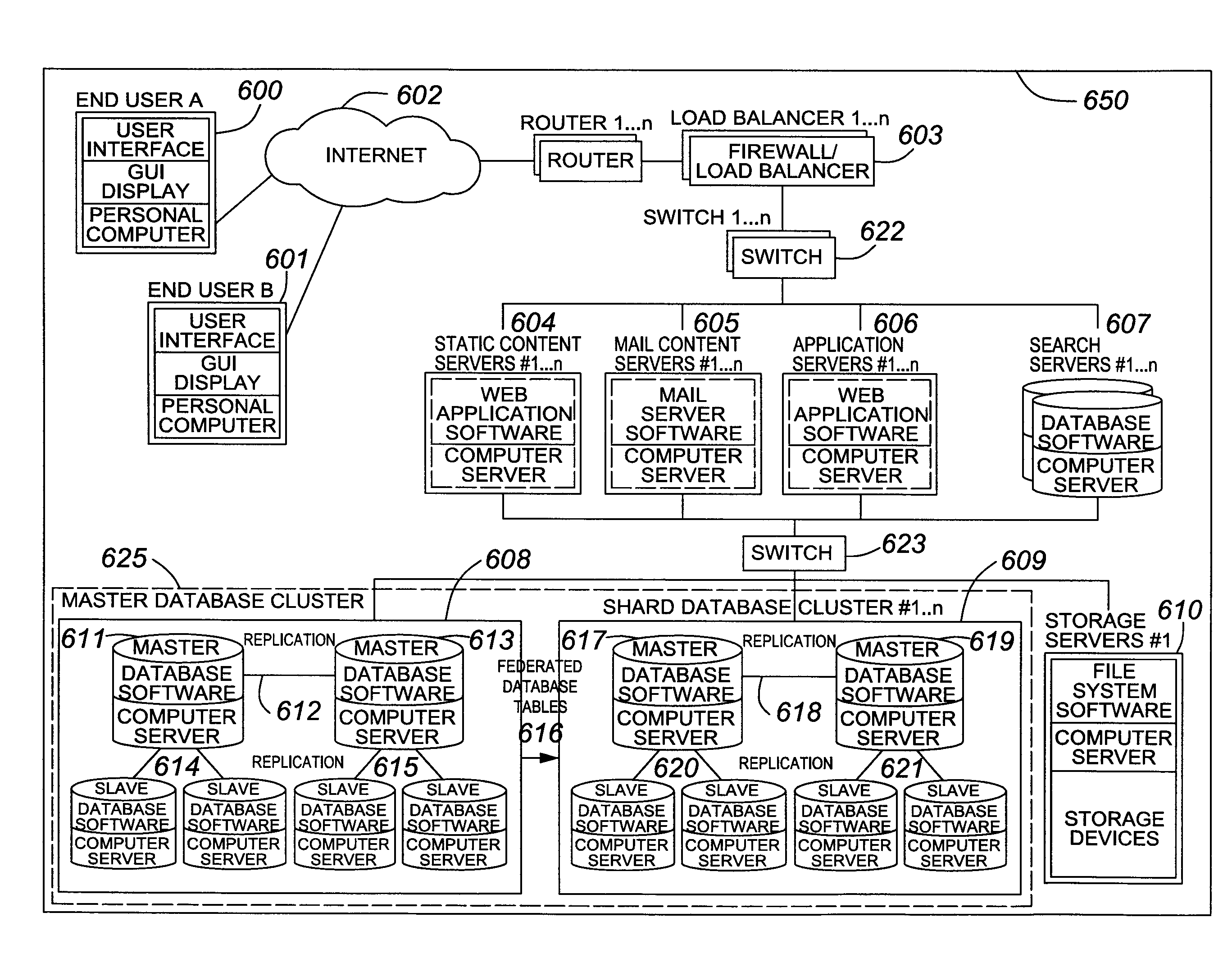
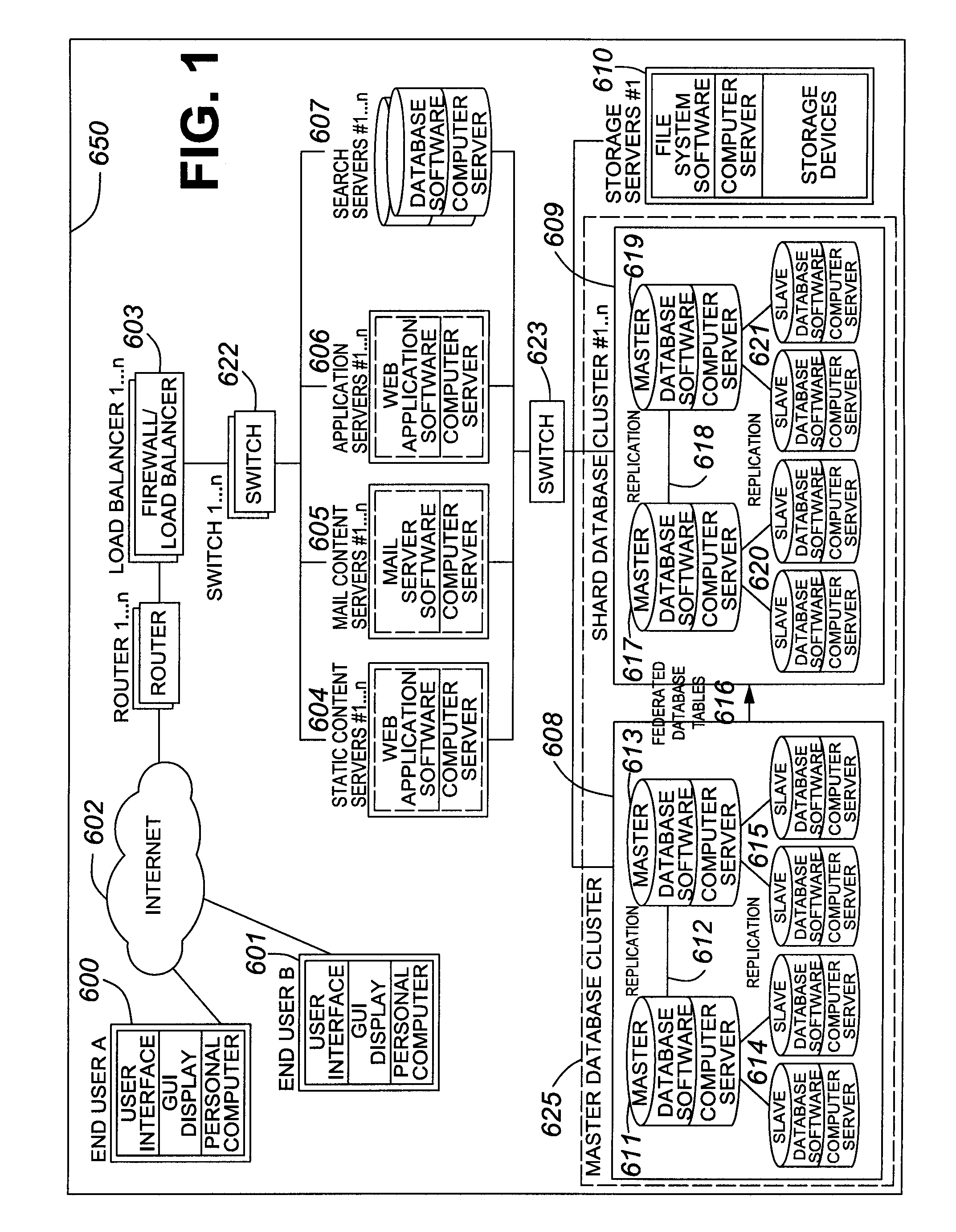
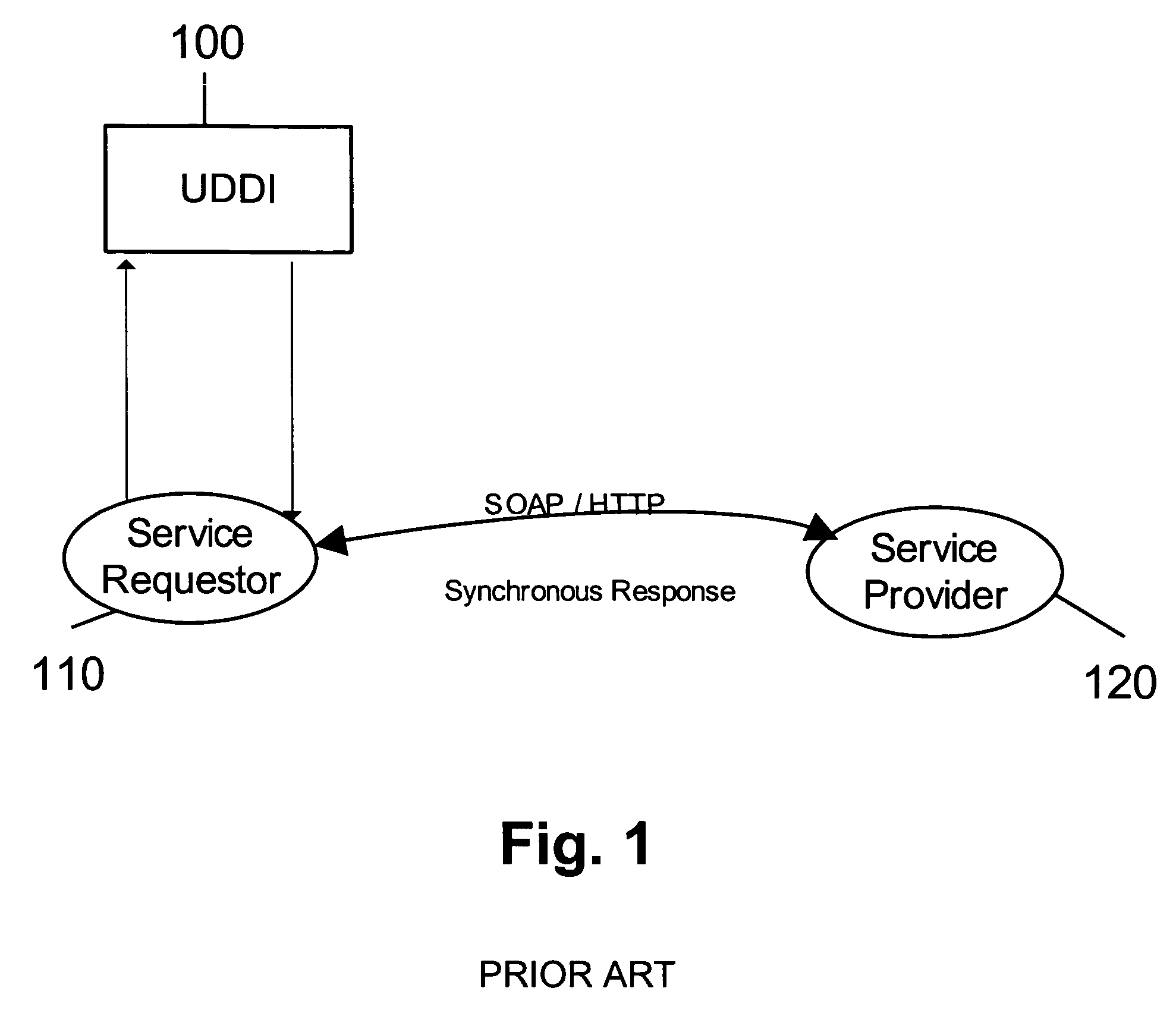
Failover processing in a storage system
InactiveUS7039827B2Improve usabilityInput/output to record carriersDigital data processing detailsFault toleranceFailover
Failover processing in storage server system utilizes policies for managing fault tolerance (FT) and high availability (HA) configurations. The approach encapsulates the knowledge of failover recovery between components within a storage server and between storage server systems. This knowledge includes information about what components are participating in a Failover Set, how they are configured for failover, what is the Fail-Stop policy, and what are the steps to perform when “failing-over” a component.
Owner:NETWORK APPLIANCE INC
Apparatus and method for providing secure network communication
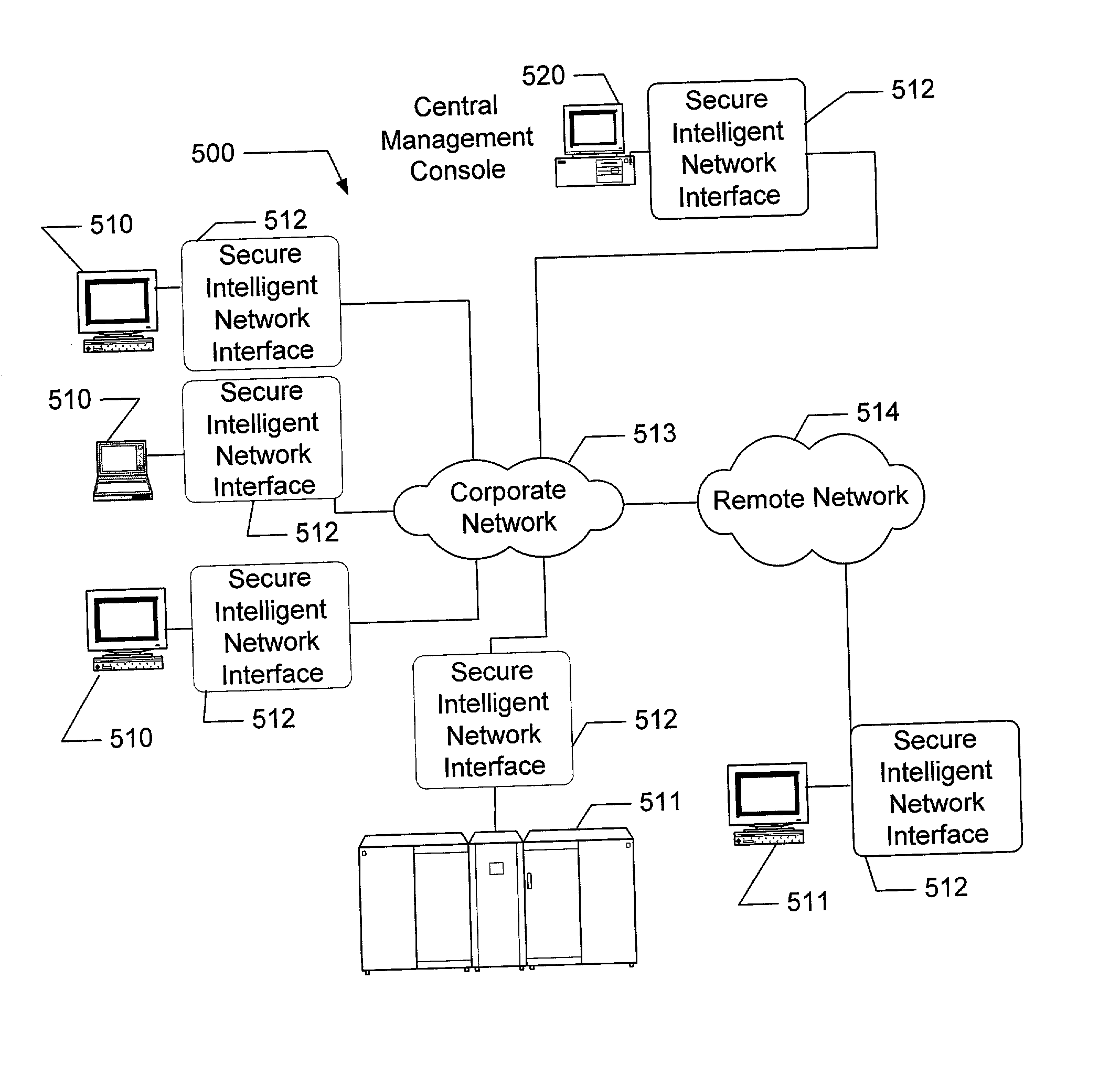
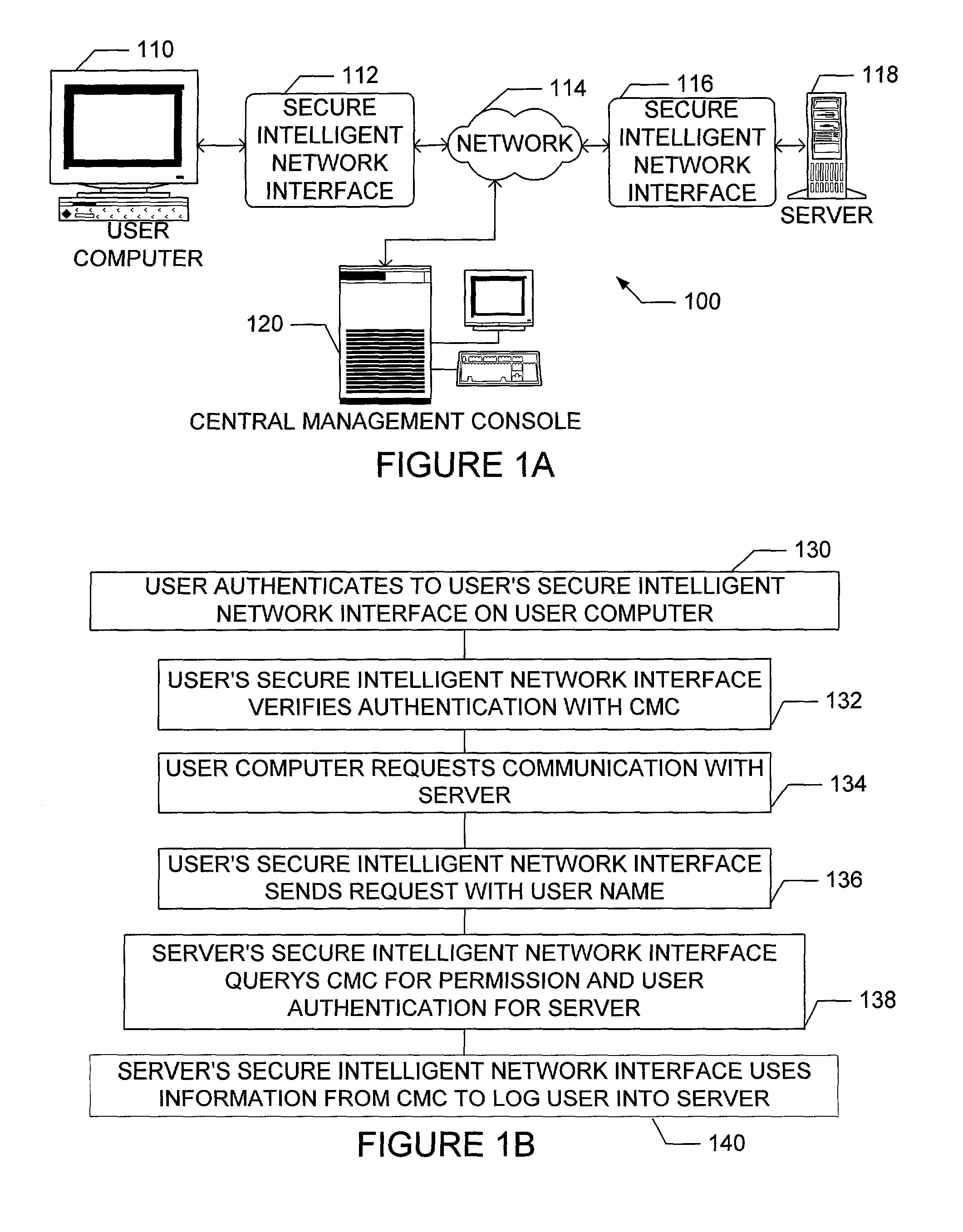
InactiveUS20020162026A1Eliminate attackEliminate needData taking preventionDigital data processing detailsFault toleranceIntelligent Network
The present invention is drawn to an apparatus and method for providing secure network communication. Each node or computer on the network has a secure, intelligent network interface with a coprocessor that handles all network communication. The intelligent network interface can be built into a network interface card (NIC) or be a separate box between each machine and the network. The intelligent network interface encrypts outgoing packets and decrypts incoming packets from the network based on a key and algorithm managed by a centralized management console (CMC) on the network. The intelligent network interface can also be configured by the CMC with dynamically distributed code to perform authentication functions, protocol translations, single sign-on functions, multi-level firewall functions, distinguished-name based firewall functions, centralized user management functions, machine diagnostics, proxy functions, fault tolerance functions, centralized patching functions, Web-filtering functions, virus-scanning functions, auditing functions, and gateway intrusion detection functions.
Owner:NEUMAN MICHAEL +1
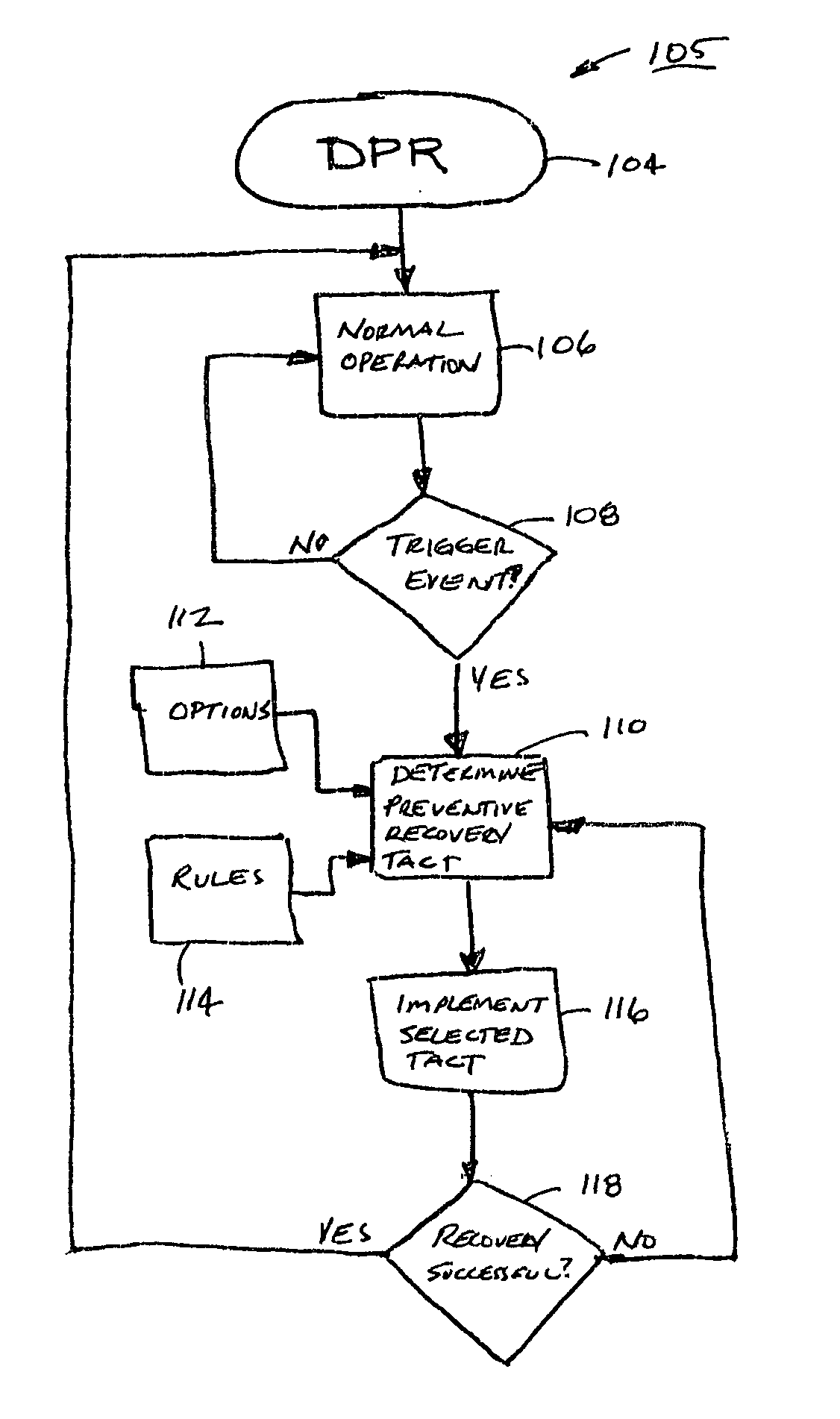
Deterministic preventive recovery from a predicted failure in a distributed storage system
A data storage subsystem in a distributed storage system having a plurality of predictive failure analyzing data storage devices. The subsystem furthermore has a circuit that is responsive to a predicted failure indication by a data storage device in relation to predetermined rules stored in memory for deterministically initiating a preventive recovery either by a data recovery procedure in the data storage device or by a fault tolerance storage arrangement in the subsystem.
Owner:SEAGATE TECH LLC
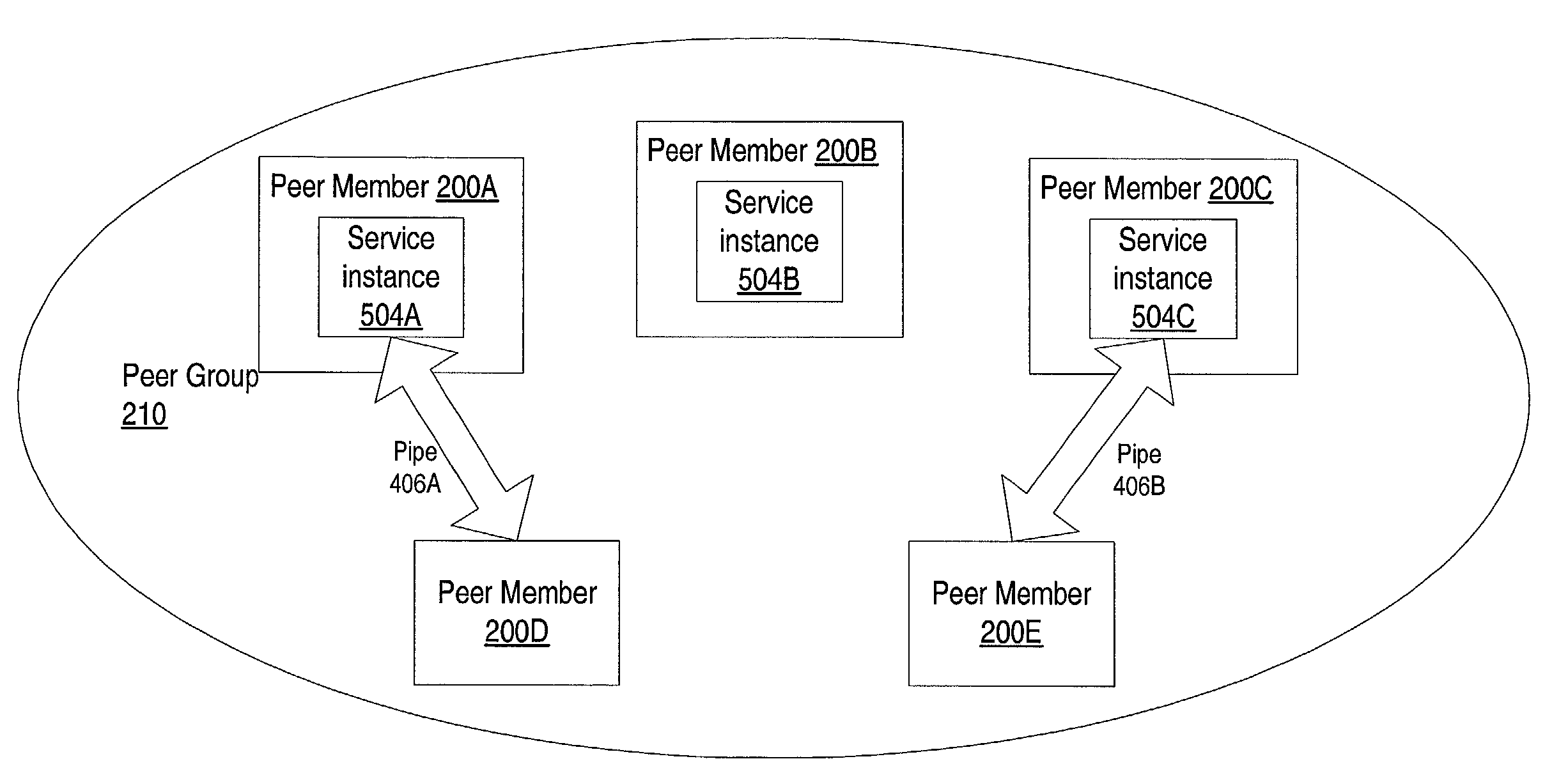
System and method for dynamic, transparent migration of services
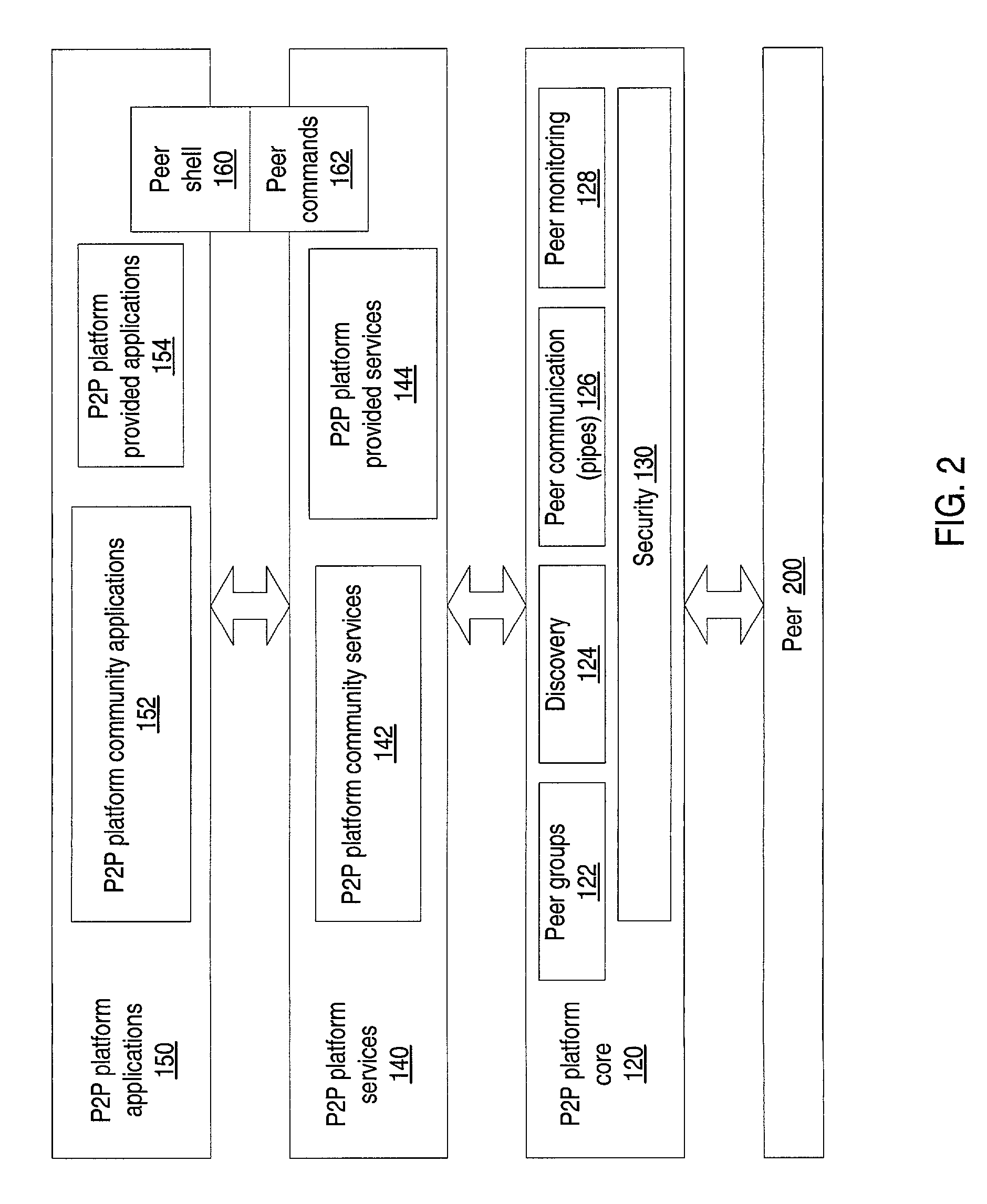
ActiveUS7165107B2Reduce chanceImprove usabilityMultiprogramming arrangementsMultiple digital computer combinationsFailoverFault tolerance
System and method for the dynamic and transparent migration of services in a peer-to-peer networking environment. Member peers in a peer group using a peer-to-peer platform may cooperate to provide redundant instances of services to member peers. Dynamic migration of a service may be performed by unbinding one or more peer-to-peer platform pipes from a peer hosting an instance of the service and binding the pipes to another peer hosting a different instance of the service. Using pipes, services may transparently failover from one physical peer endpoint to another in order to mask a service or peer failure, or to access a newly published instance of a service. Thus, a collection of peers may provide a high level of fault tolerance, where, for example, a new peer at a different location may replace a crashed peer, with the new peer taking over the existing pipe to keep the communication going.
Owner:ORACLE INT CORP
Failover processing in a storage system
InactiveUS20060117212A1Improve usabilityInput/output to record carriersDigital data processing detailsFault toleranceFailover
Failover processing in storage server system utilizes policies for managing fault tolerance (FT) and high availability (HA) configurations. The approach encapsulates the knowledge of failover recovery between components within a storage server and between storage server systems. This knowledge includes information about what components are participating in a Failover Set, how they are configured for failover, what is the Fail-Stop policy, and what are the steps to perform when “failing-over” a component.
Owner:NETWORK APPLIANCE INC
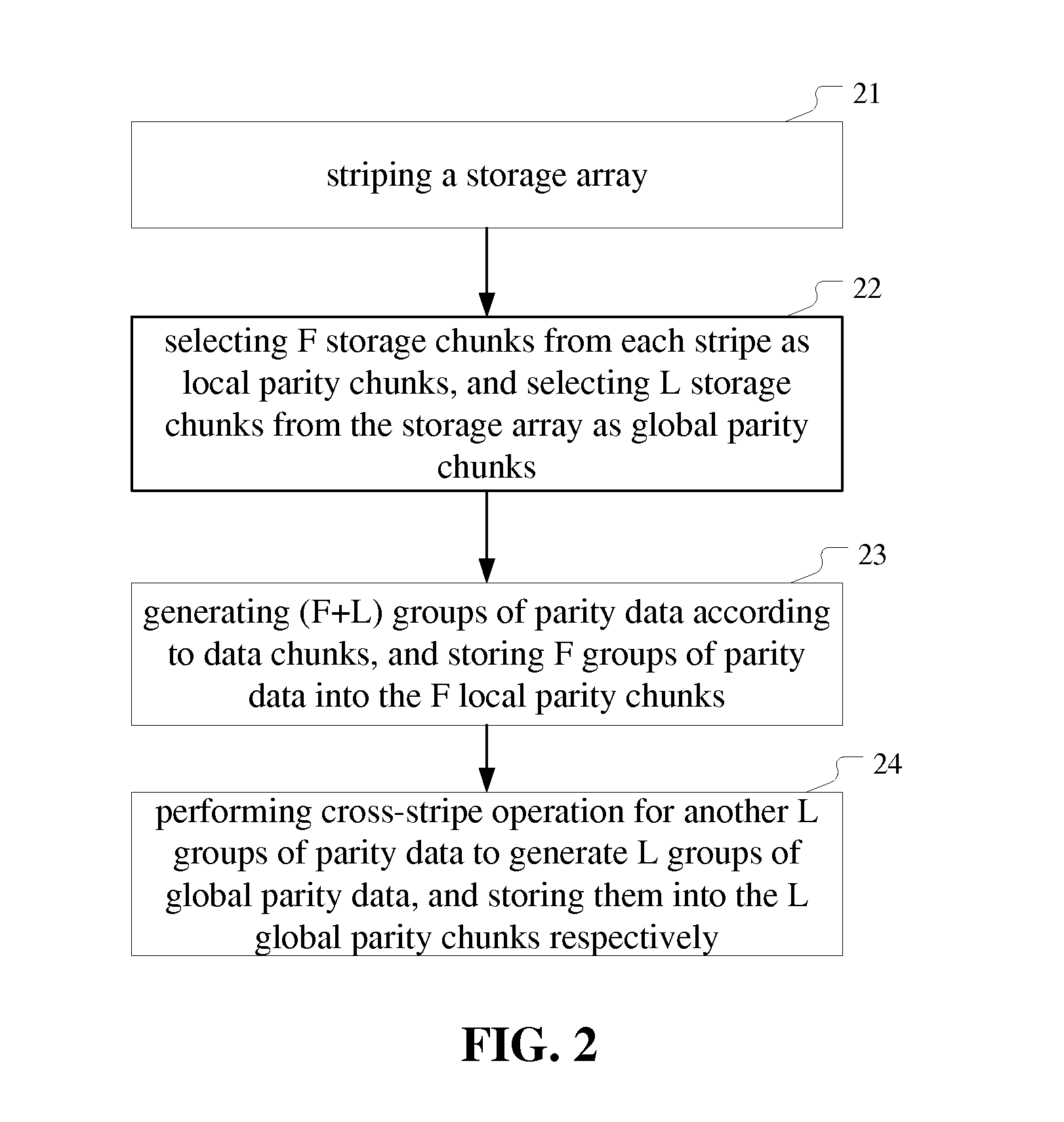
Managing a storage array
ActiveUS20140040702A1Easy to manageError capabilityCode conversionError correction/detection using interleaving techniquesFault toleranceErasure code
The present invention provides a method and apparatus of managing a storage array. The method comprises: striping the storage array to form a plurality of stripes; selecting F storage chunks from each stripe as local parity chunks, and selecting another L storage chunks from the storage array as global parity chunks; performing (F+L) fault tolerant erasure coding on all data chunks in a stripe to generate (F+L) groups of parity data, and storing F groups of parity data therein into the F local parity chunks; performing cross-stripe operation on another L groups of parity data to generate L groups of global parity data, and storing them into the L global parity chunks, respectively. The apparatus corresponds to the method. With the invention, a plurality of errors in the storage array can be detected and / or recovered to improve fault tolerance and space utilization of the storage array.
Owner:IBM CORP
System and method for dynamic, transparent migration of services
System and method for the dynamic and transparent migration of services in a peer-to-peer networking environment. Member peers in a peer group using a peer-to-peer platform may cooperate to provide redundant instances of services to member peers. Dynamic migration of a service may be performed by unbinding one or more peer-to-peer platform pipes from a peer hosting an instance of the service and binding the pipes to another peer hosting a different instance of the service. Using pipes, services may transparently failover from one physical peer endpoint to another in order to mask a service or peer failure, or to access a newly published instance of a service. Thus, a collection of peers may provide a high level of fault tolerance, where, for example, a new peer at a different location may replace a crashed peer, with the new peer taking over the existing pipe to keep the communication going.
Owner:ORACLE INT CORP
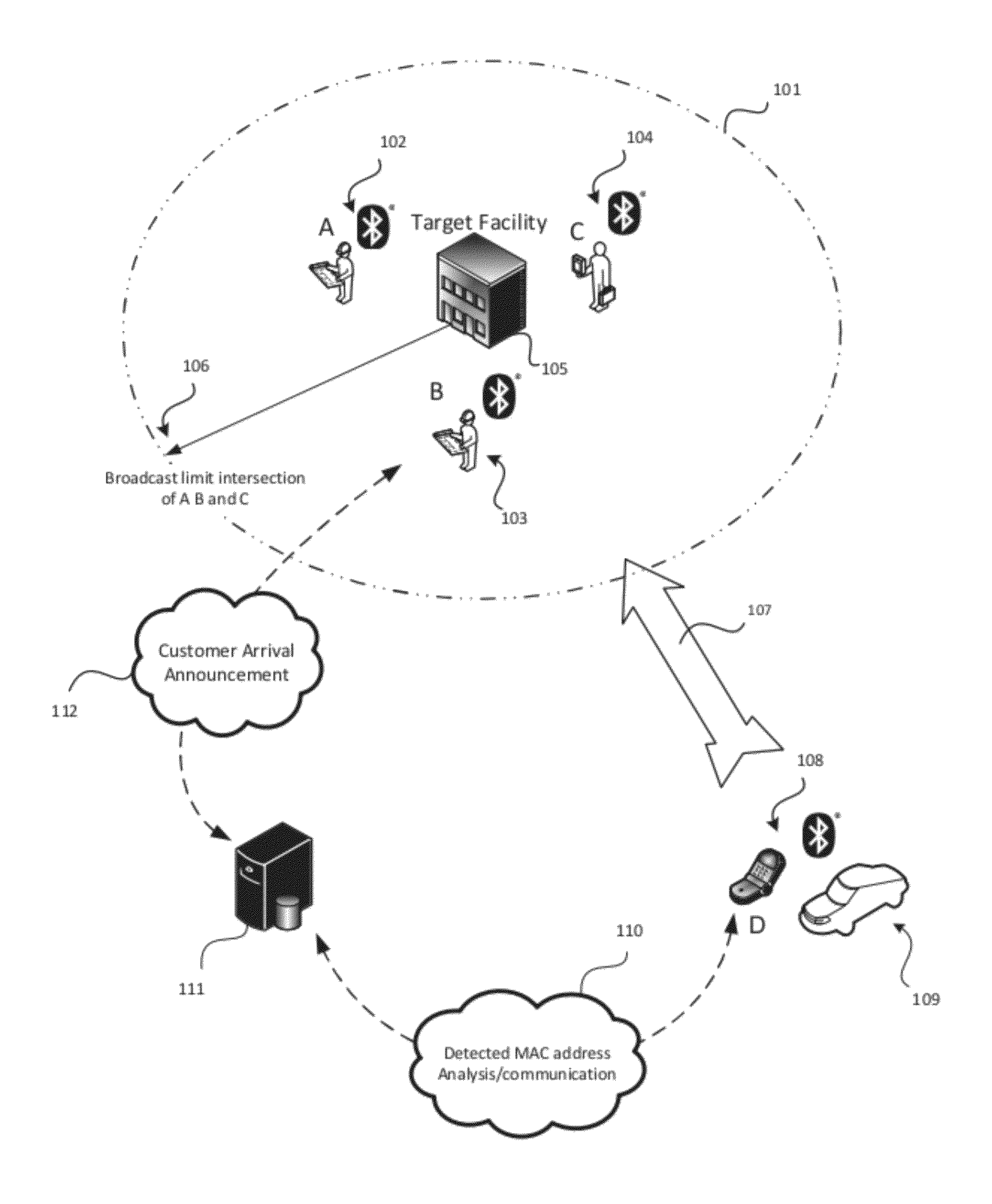
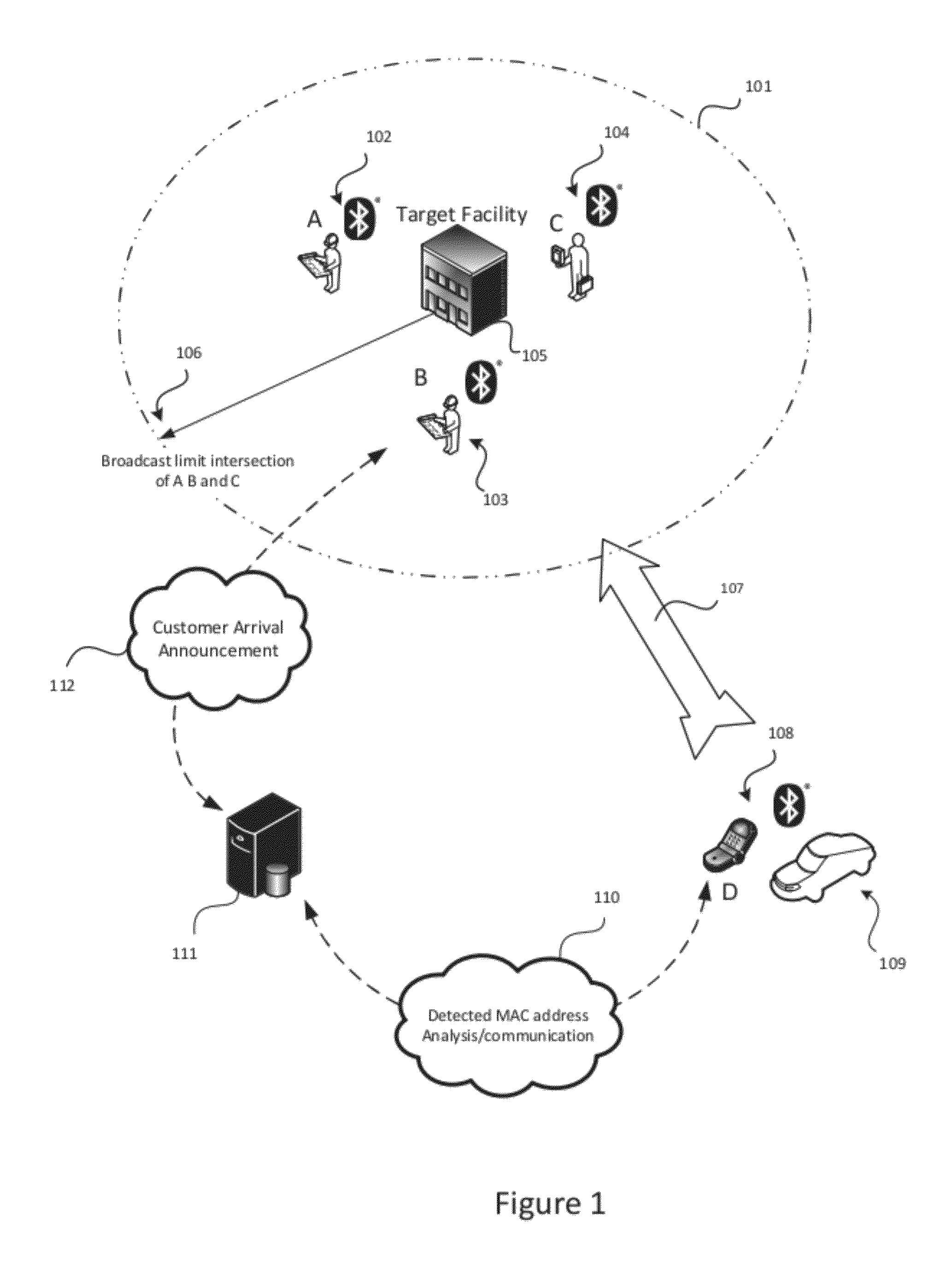
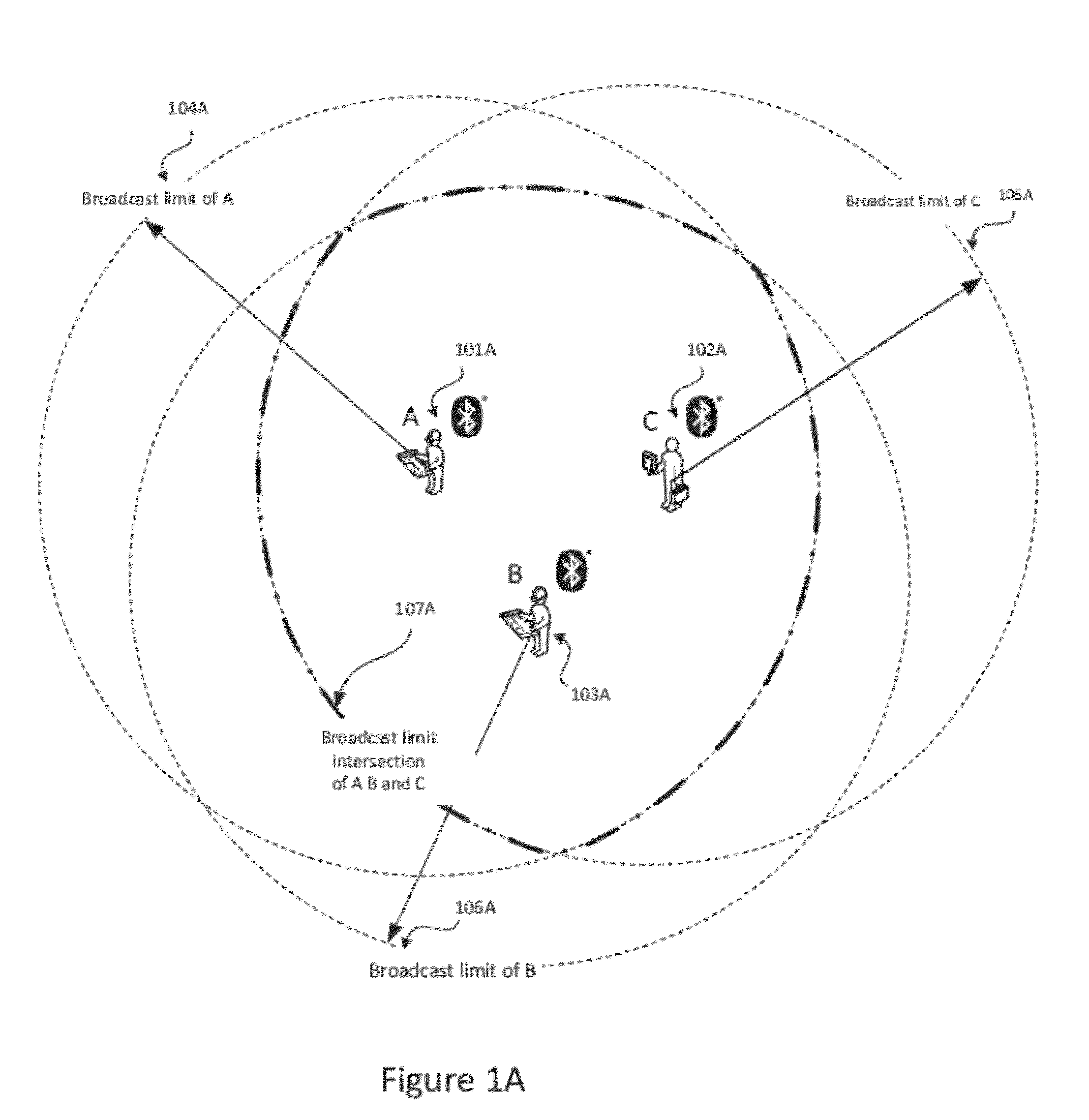
System and Method for Proximity Detection
InactiveUS20120235865A1Improving the accuracy of the confidence computationImprove accuracyDirection finders using radio wavesSpecial service for subscribersFault toleranceConfidence interval
The present invention is for a system and method for determining the proximity of a mobile device to a location without the use of a satellite based or other location awareness system, nor a stationary beacon of any kind Instead, the mobile device monitors radio frequency broadcast identification codes from nearby mobile devices, and determines if the set of detected identification codes is sufficiently similar to a weighted set of identification codes attributed to specified location. If the calculation of similarity meets the confidence conditions of the system, notification is made that the customer or visitor has arrived. The invention utilizes a combination of confidence interval computation, machine learning, and fault tolerance mechanisms to optimize the success of correctly detecting that the device is near the relevant location.
Owner:KAARYA
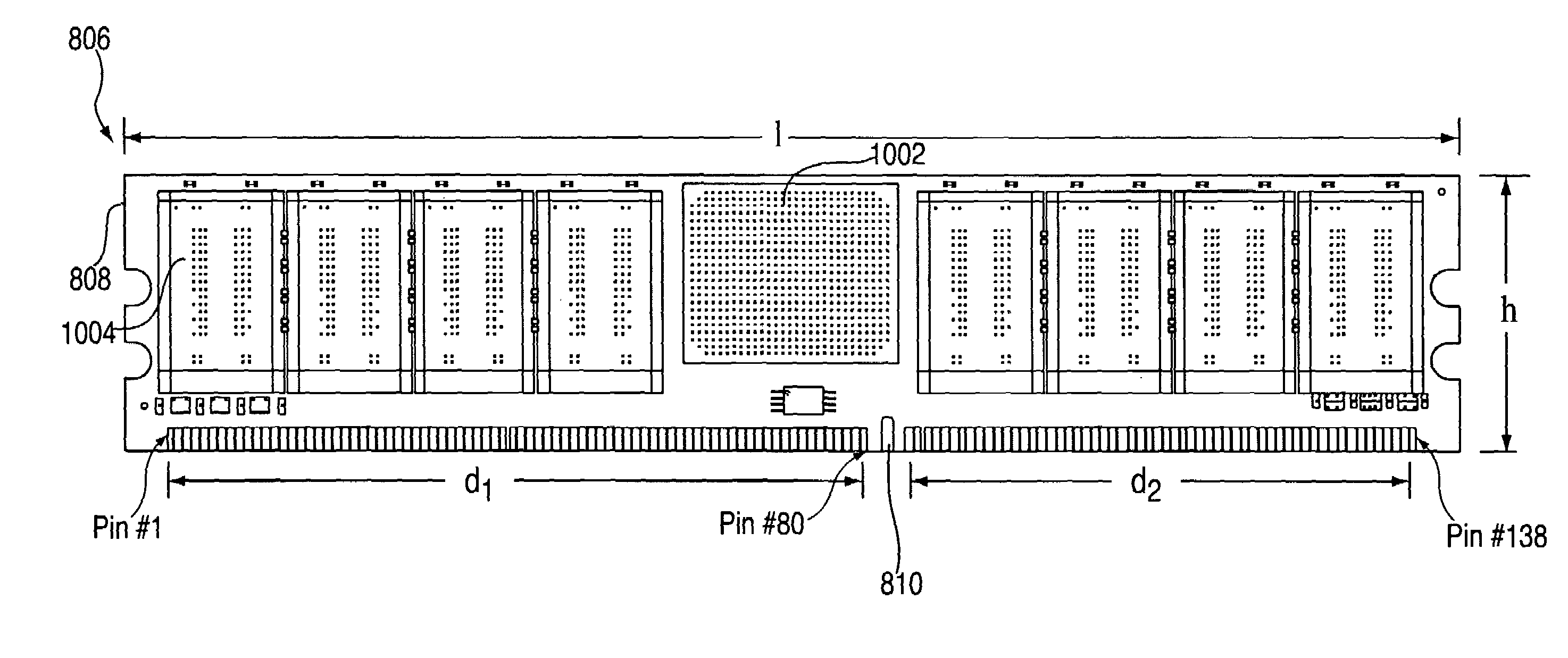
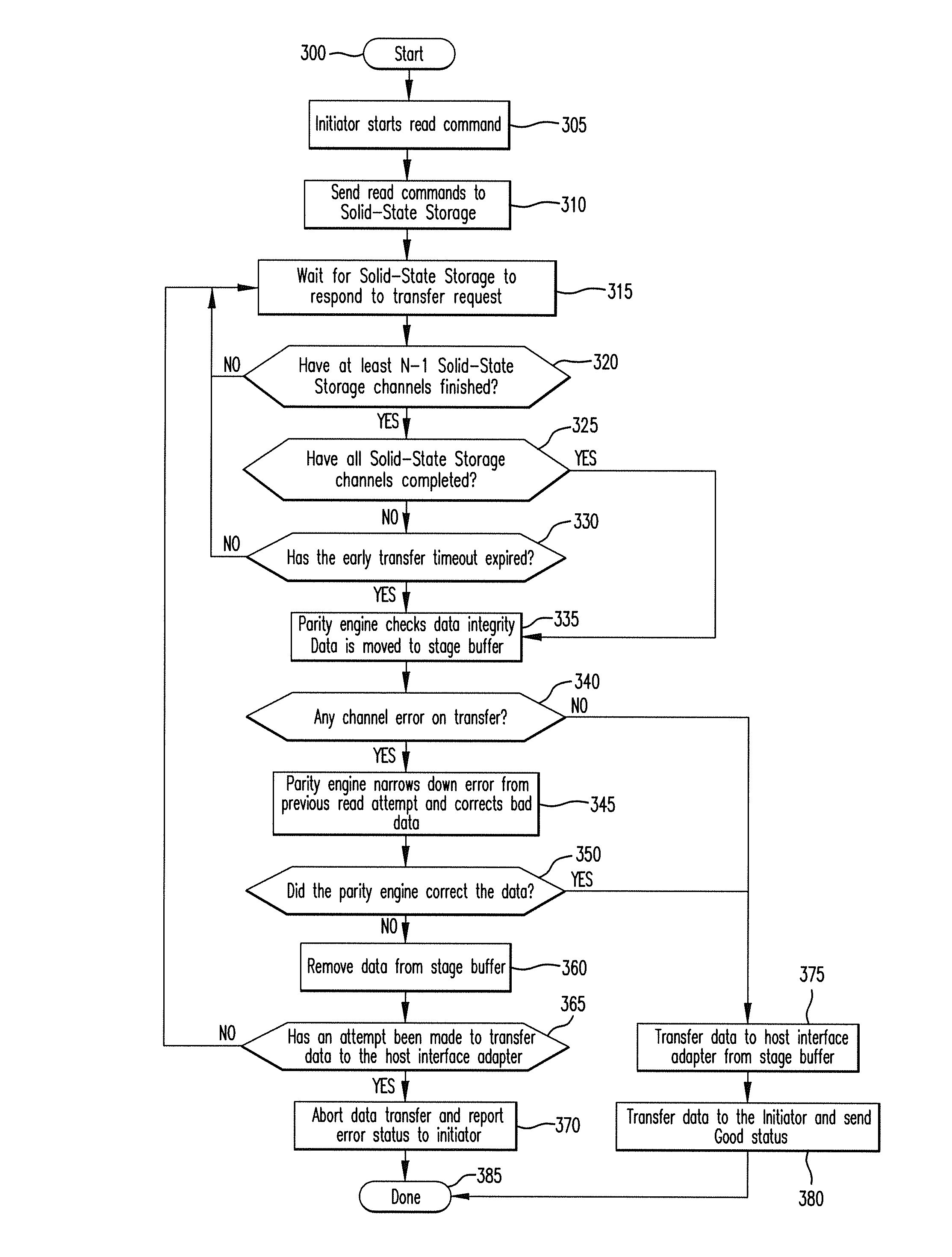
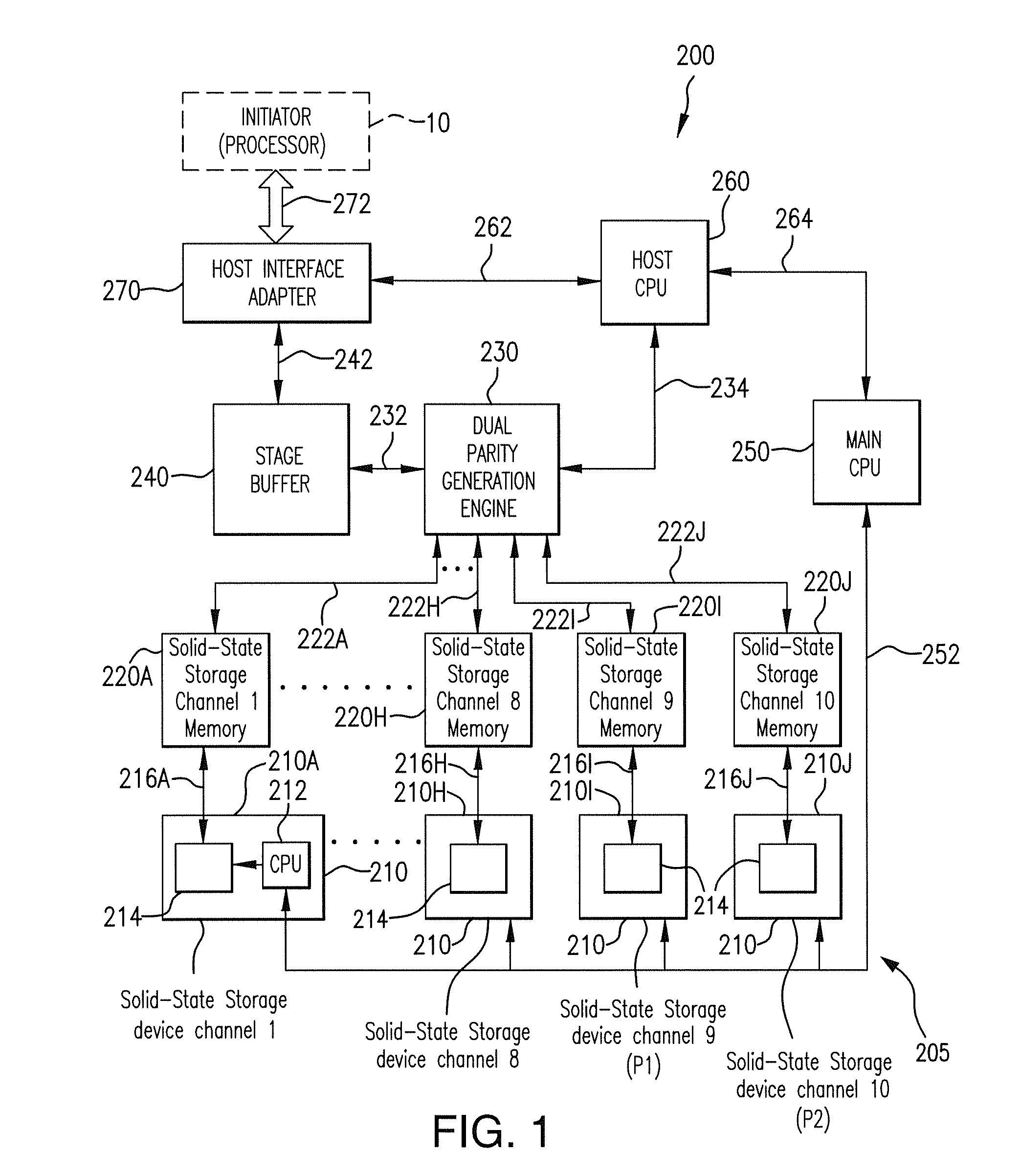
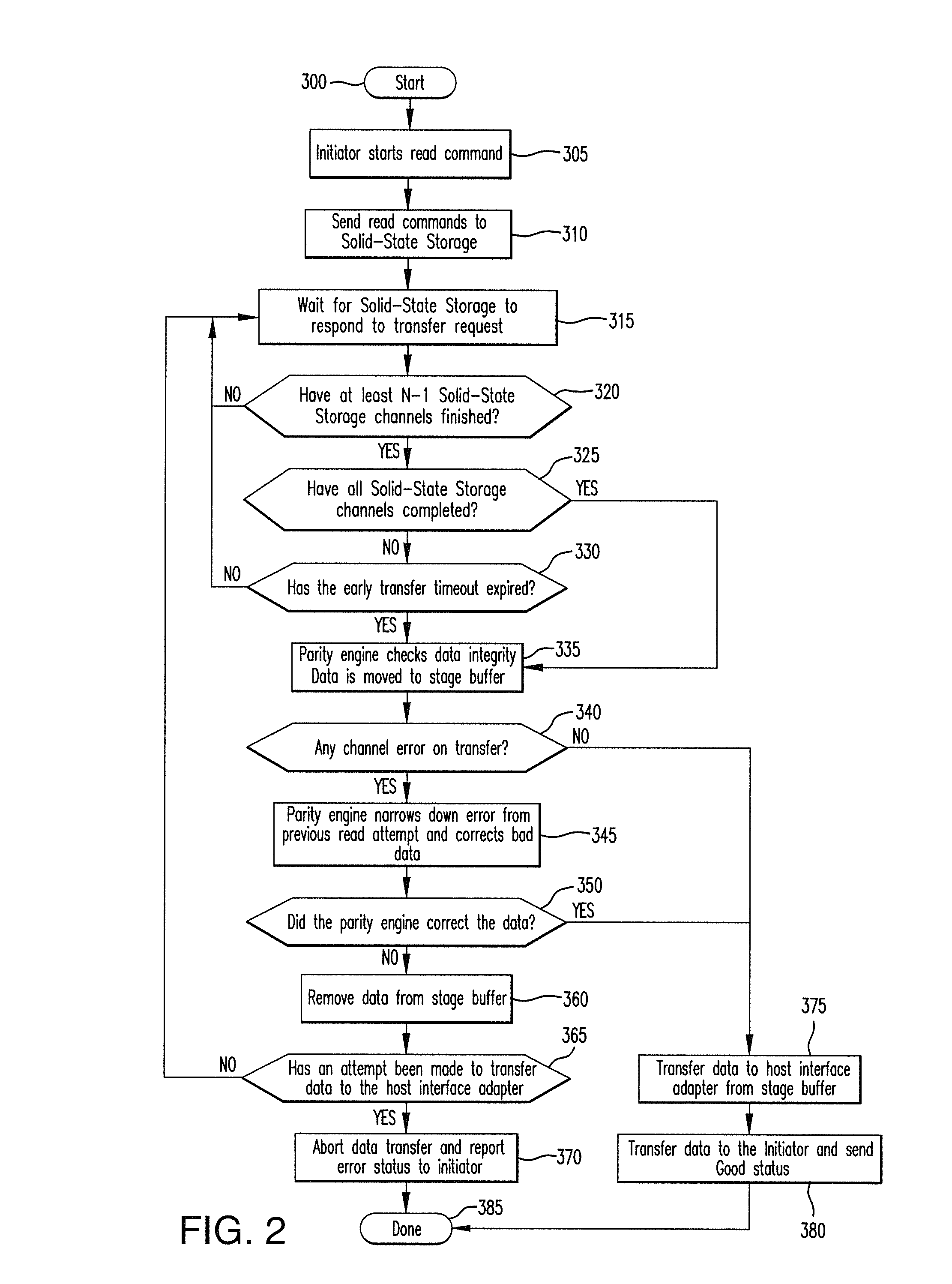
Method for reducing latency in a solid-state memory system while maintaining data integrity
ActiveUS8661218B1Easy accessReduce energy consumptionError prevention/detection by using return channelTransmission systemsSolid-state storageFault tolerance
A latency reduction method for read operations of an array of N solid-state storage devices having n solid-state storage devices for data storage and p solid-state storage devices for storing parity data is provided. Utilizing the parity generation engine fault tolerance for a loss of valid data from at least two of the N solid-state storage devices, the integrity of the data is determined when N−1 of the solid-state storage devices have completed executing a read command. If the data is determined to be valid, the missing data of the Nth solid-state storage device is reconstructed and the data transmitted to the requesting processor. By that arrangement the time necessary for the Nth solid-state storage device to complete execution of the read command is saved, thereby improving the performance of the solid-state memory system.
Owner:DATADIRECT NETWORKS
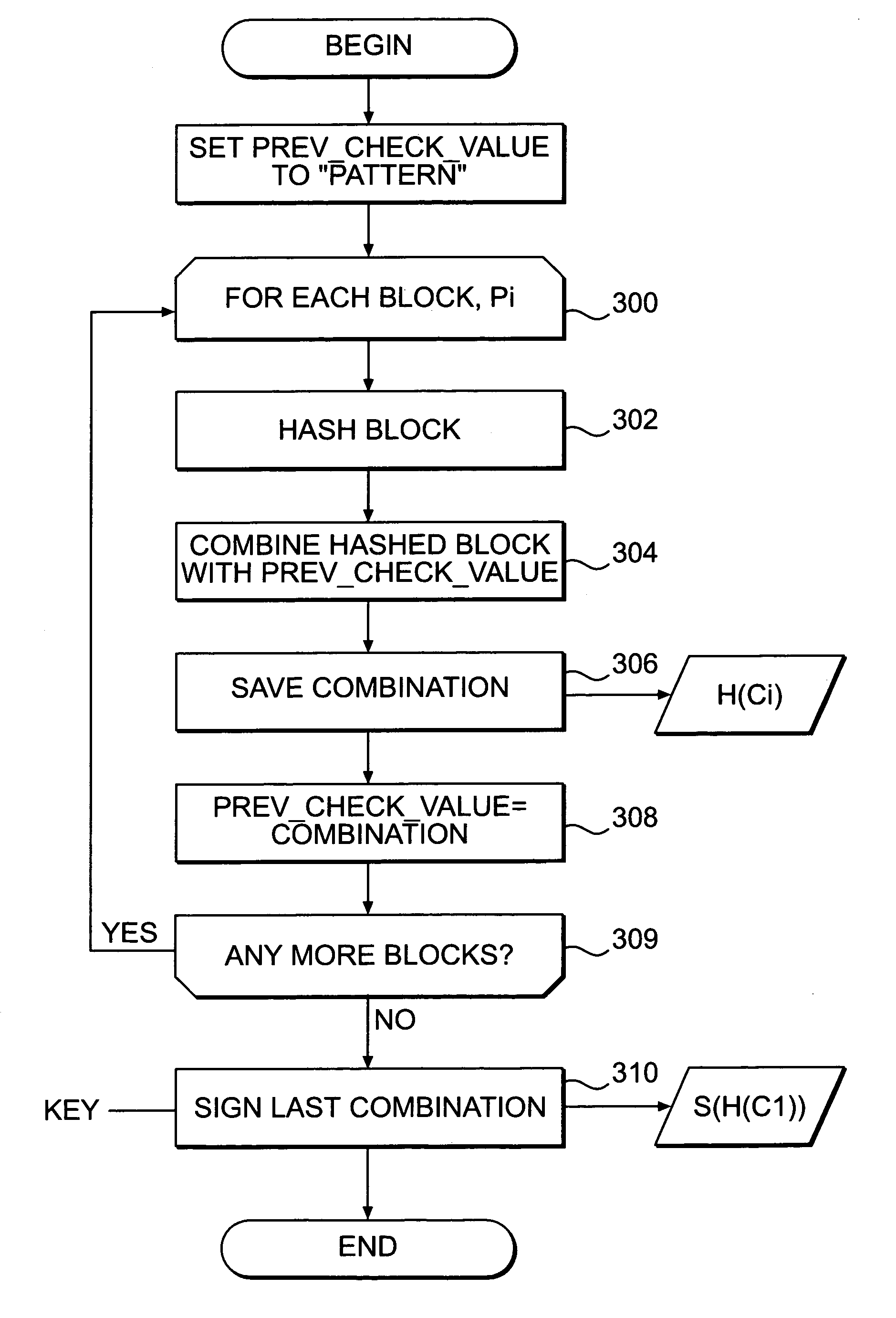
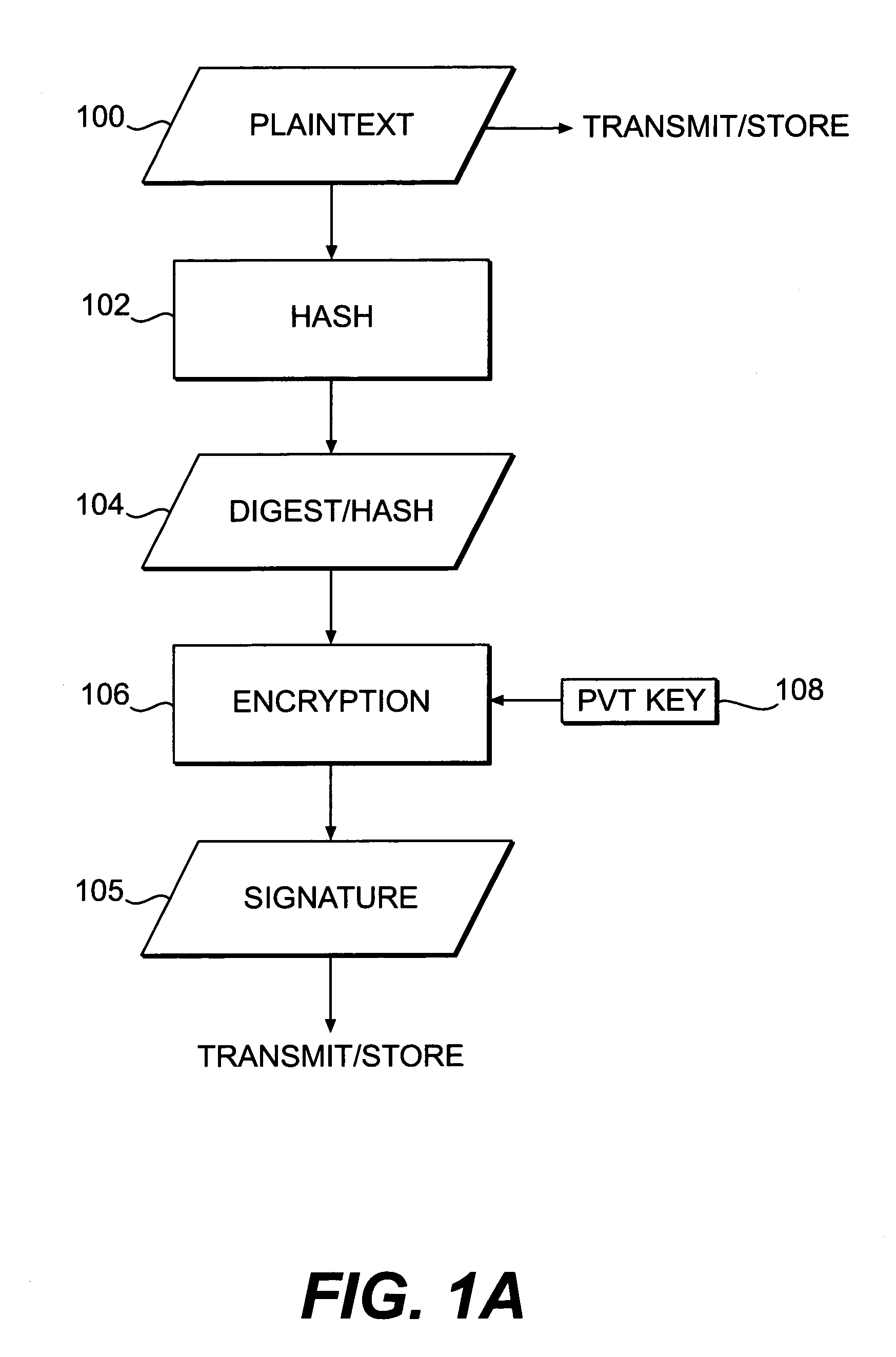
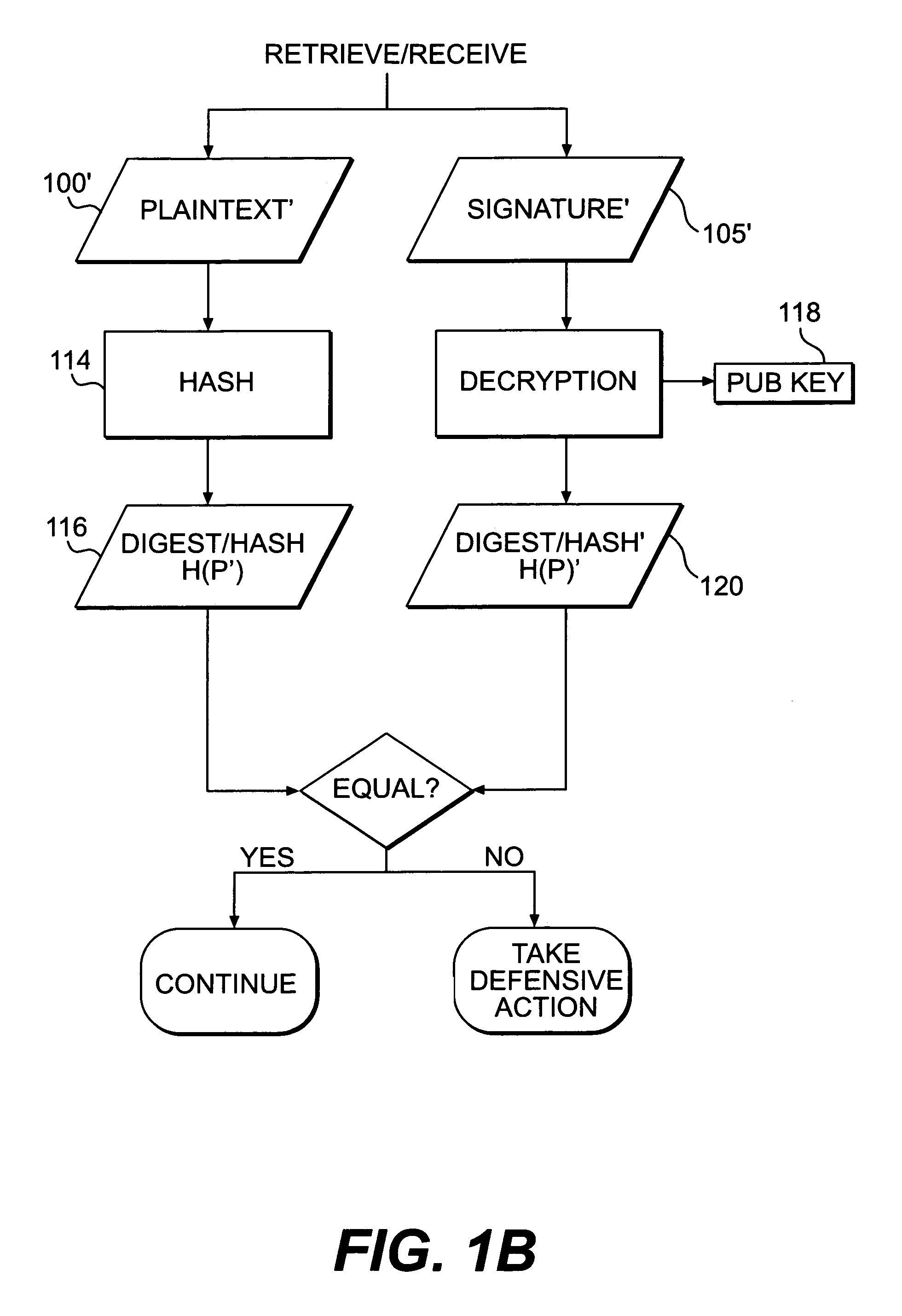
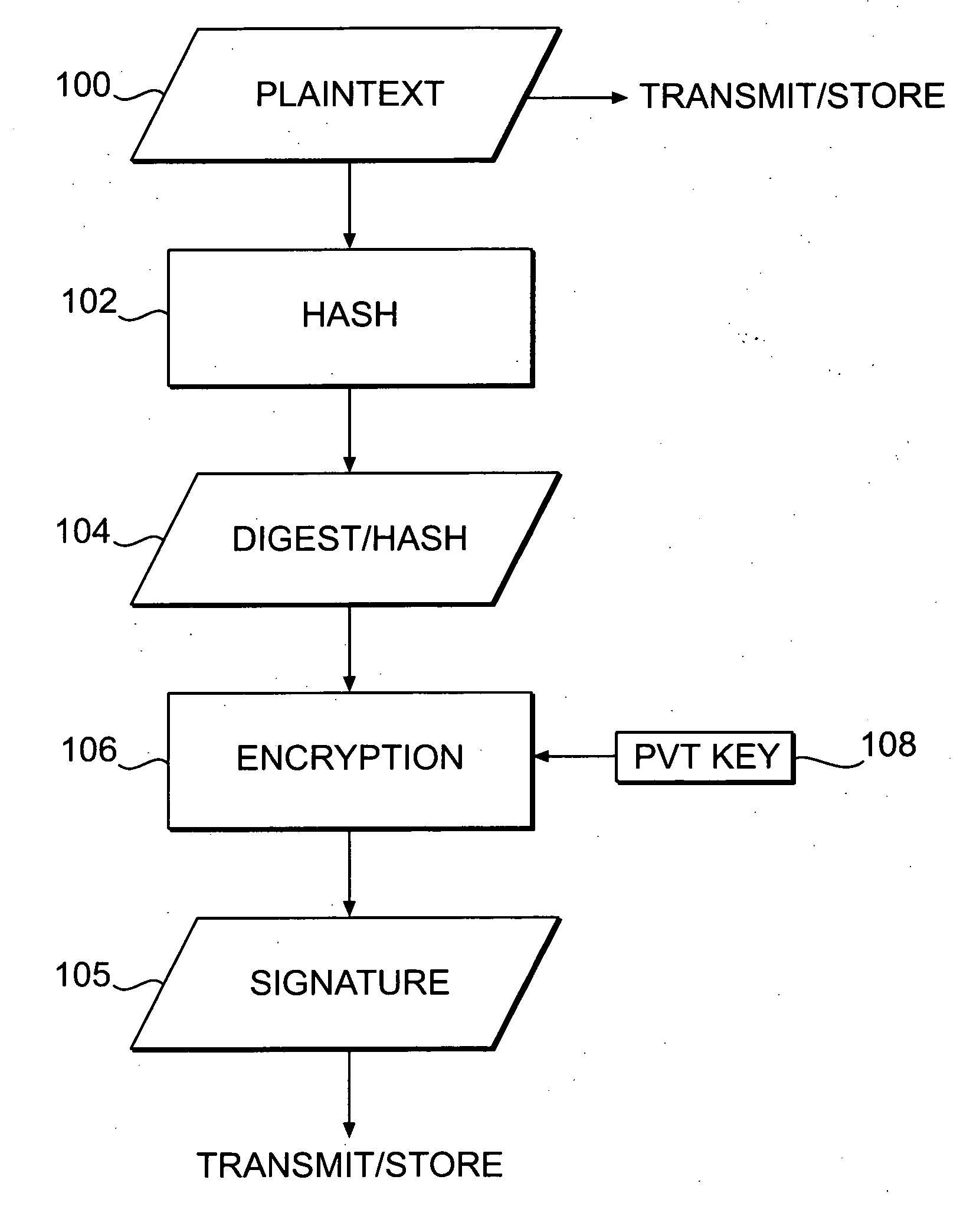
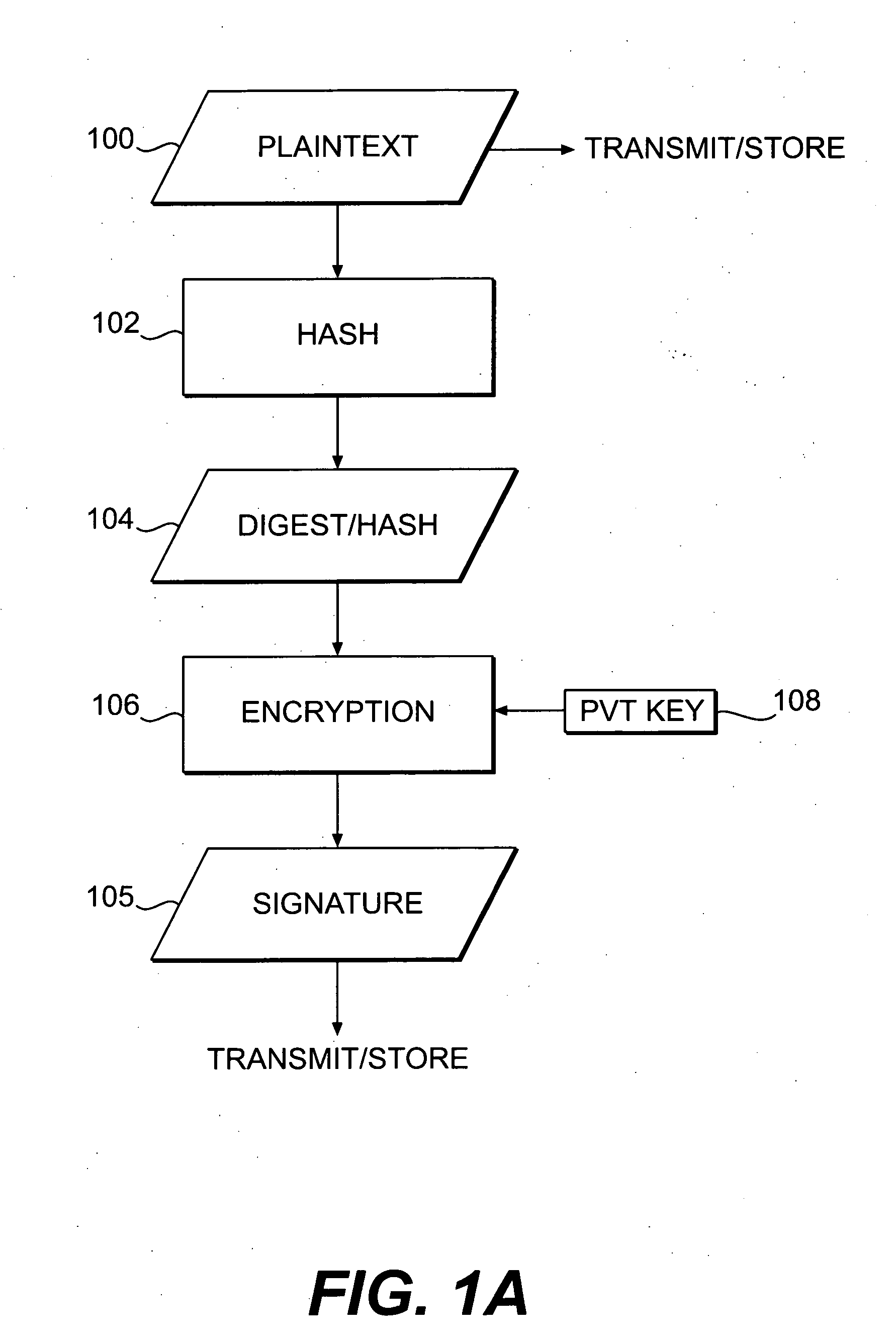
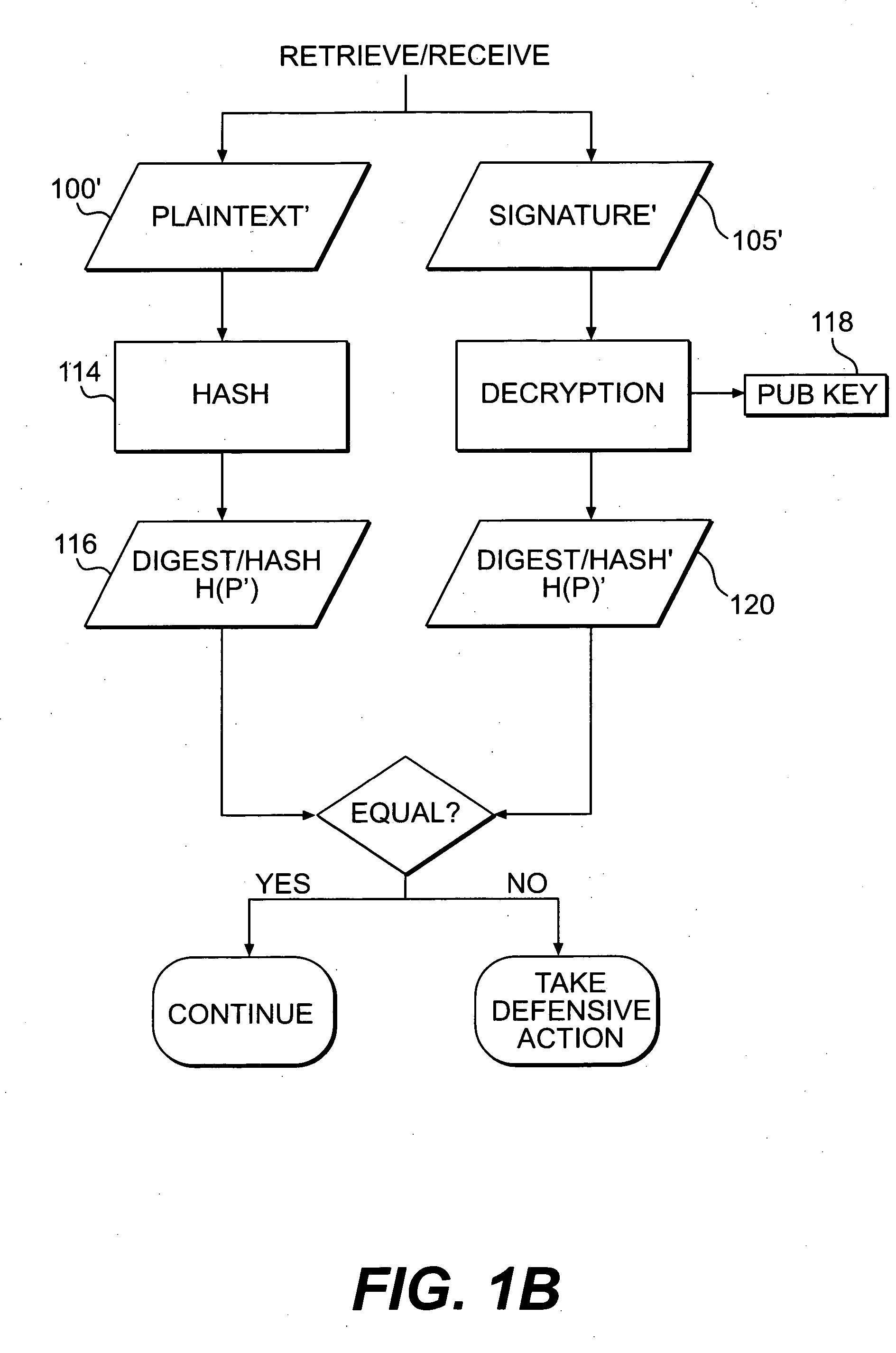
Systems and methods for authenticating and protecting the integrity of data streams and other data
InactiveUS6959384B1Authentication is convenientDetecting errorUser identity/authority verificationDigital data protectionError checkFault tolerance
Systems and methods are disclosed for enabling a recipient of a cryptographically-signed electronic communication to verify the authenticity of the communication on-the-fly using a signed chain of check values, the chain being constructed from the original content of the communication, and each check value in the chain being at least partially dependent on the signed root of the chain and a portion of the communication. Fault tolerance can be provided by including error-check values in the communication that enable a decoding device to maintain the chain's security in the face of communication errors. In one embodiment, systems and methods are provided for enabling secure quasi-random access to a content file by constructing a hierarchy of hash values from the file, the hierarchy deriving its security in a manner similar to that used by the above-described chain. The hierarchy culminates with a signed hash that can be used to verify the integrity of other hash values in the hierarchy, and these other hash values can, in turn, be used to efficiently verify the authenticity of arbitrary portions of the content file.
Owner:INTERTRUST TECH CORP
Systems and methods for authenticating and protecting the integrity of data streams and other data
InactiveUS20050235154A1Authentication is convenientDetecting errorUser identity/authority verificationDigital data protectionError checkFault tolerance
Systems and methods are disclosed for enabling a recipient of a cryptographically-signed electronic communication to verify the authenticity of the communication on-the-fly using a signed chain of check values, the chain being constructed from the original content of the communication, and each check value in the chain being at least partially dependent on the signed root of the chain and a portion of the communication. Fault tolerance can be provided by including error-check values in the communication that enable a decoding device to maintain the chain's security in the face of communication errors. In one embodiment, systems and methods are provided for enabling secure quasi-random access to a content file by constructing a hierarchy of hash values from the file, the hierarchy deriving its security in a manner similar to that used by the above-described chain. The hierarchy culminates with a signed hash that can be used to verify the integrity of other hash values in the hierarchy, and these other hash values can, in turn, be used to efficiently verify the authenticity of arbitrary portions of the content file.
Owner:INTERTRUST TECH CORP
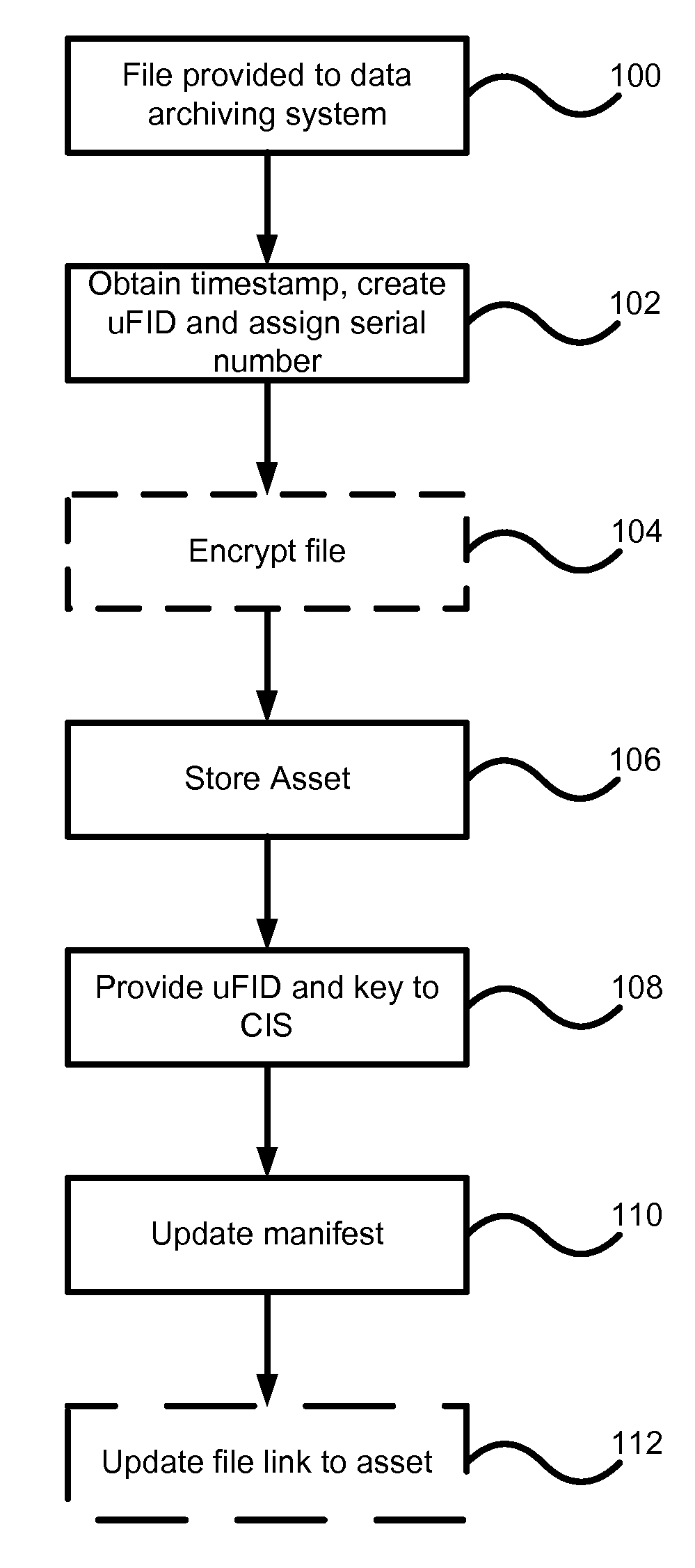
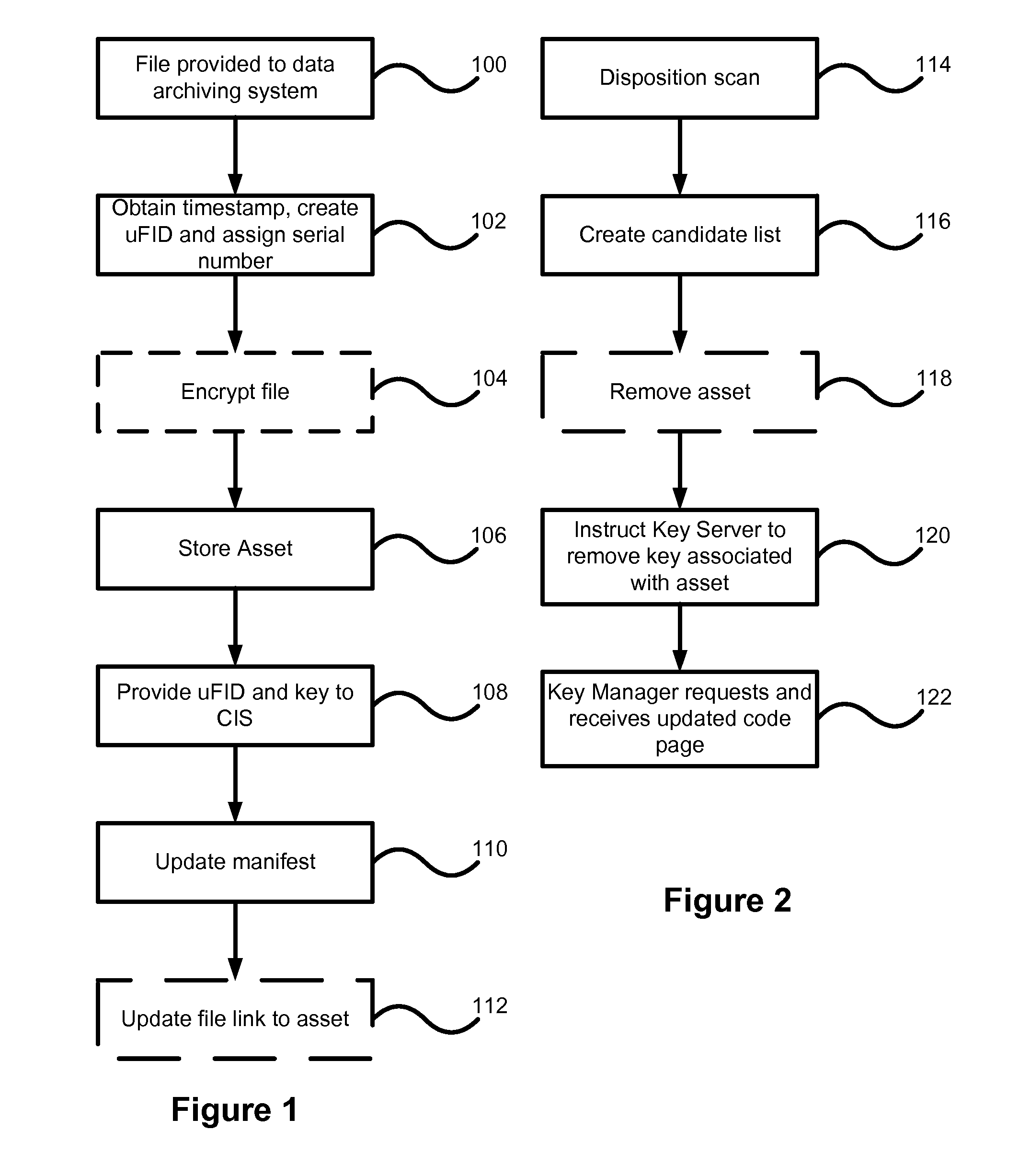
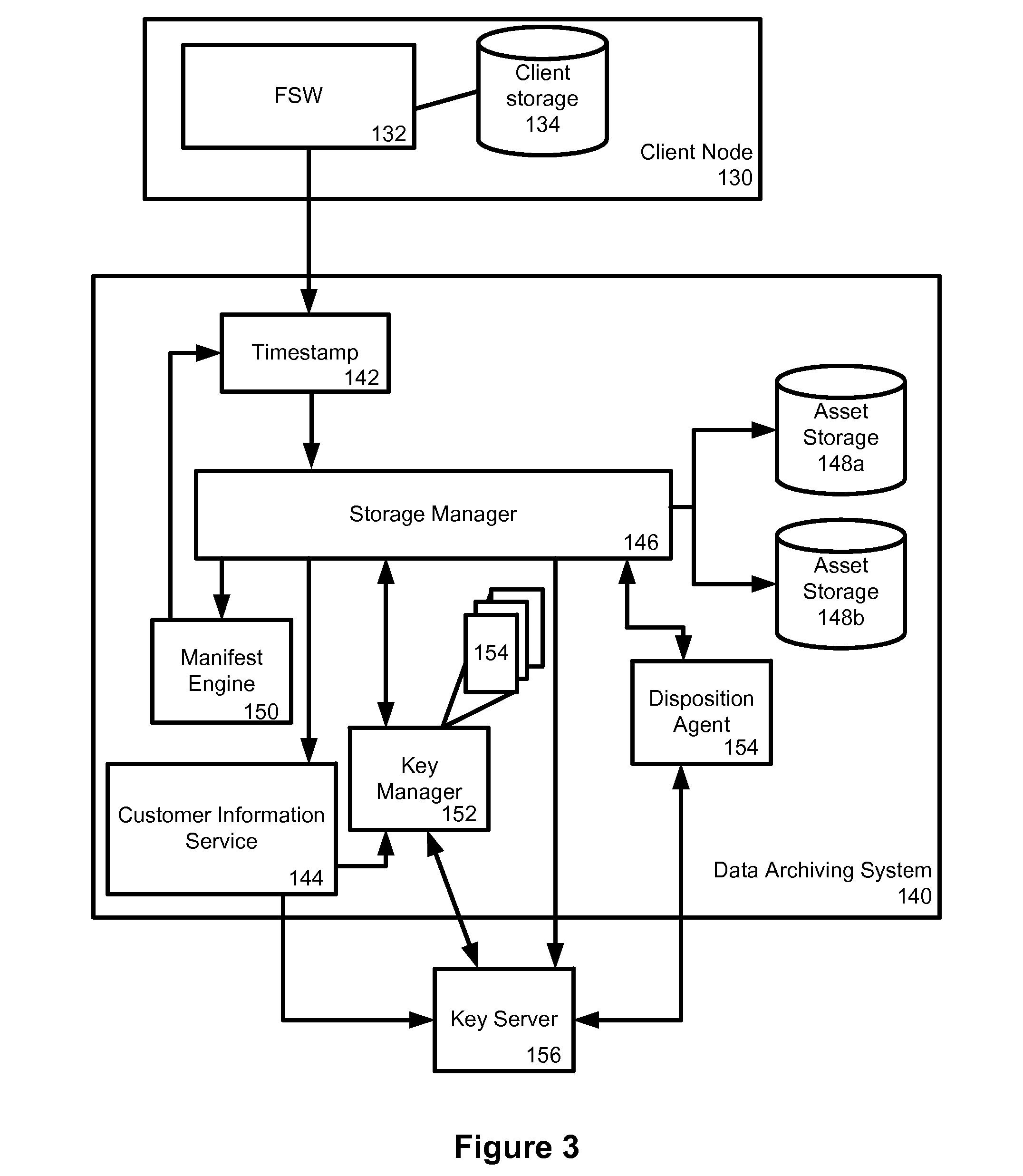
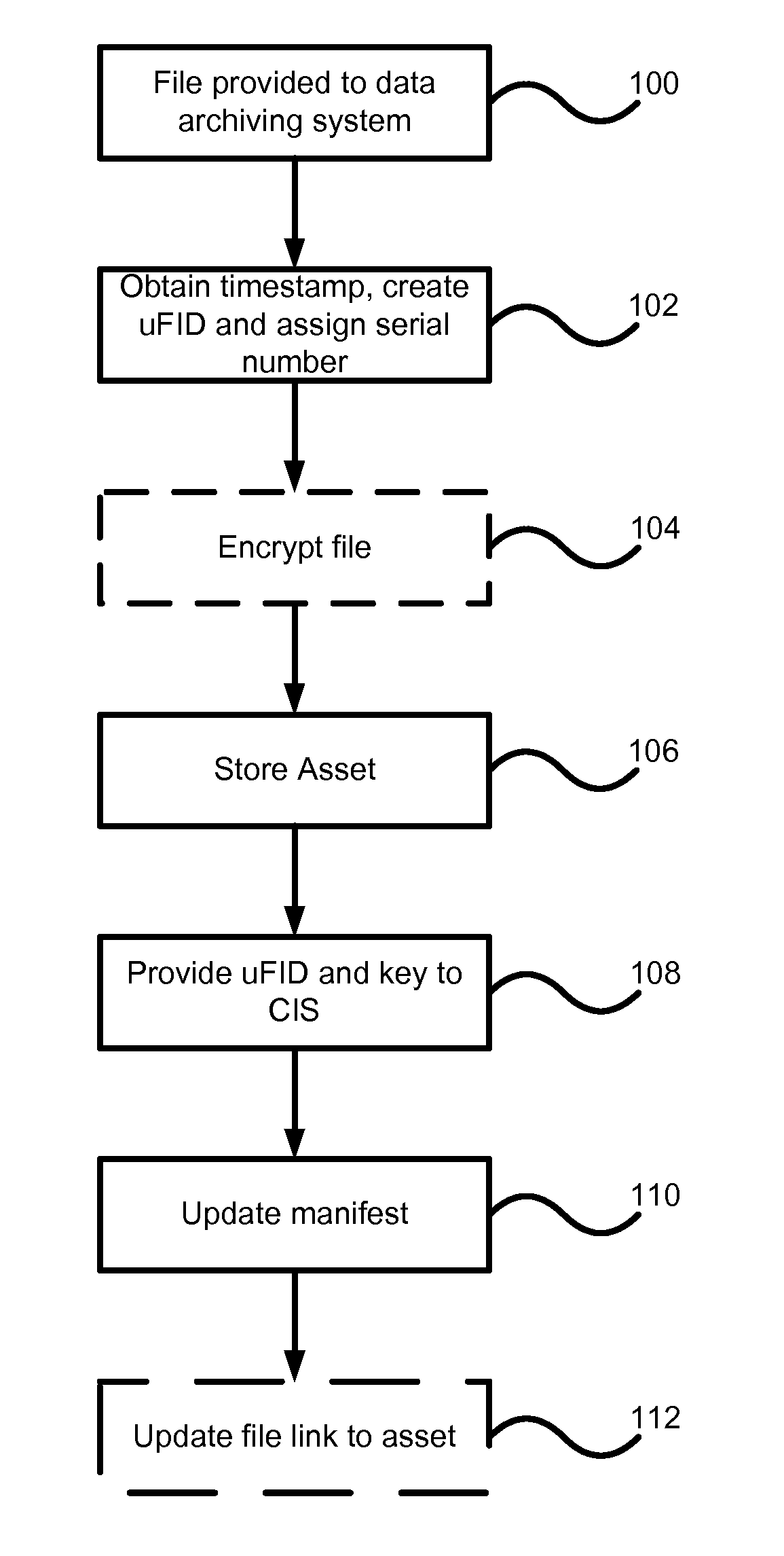
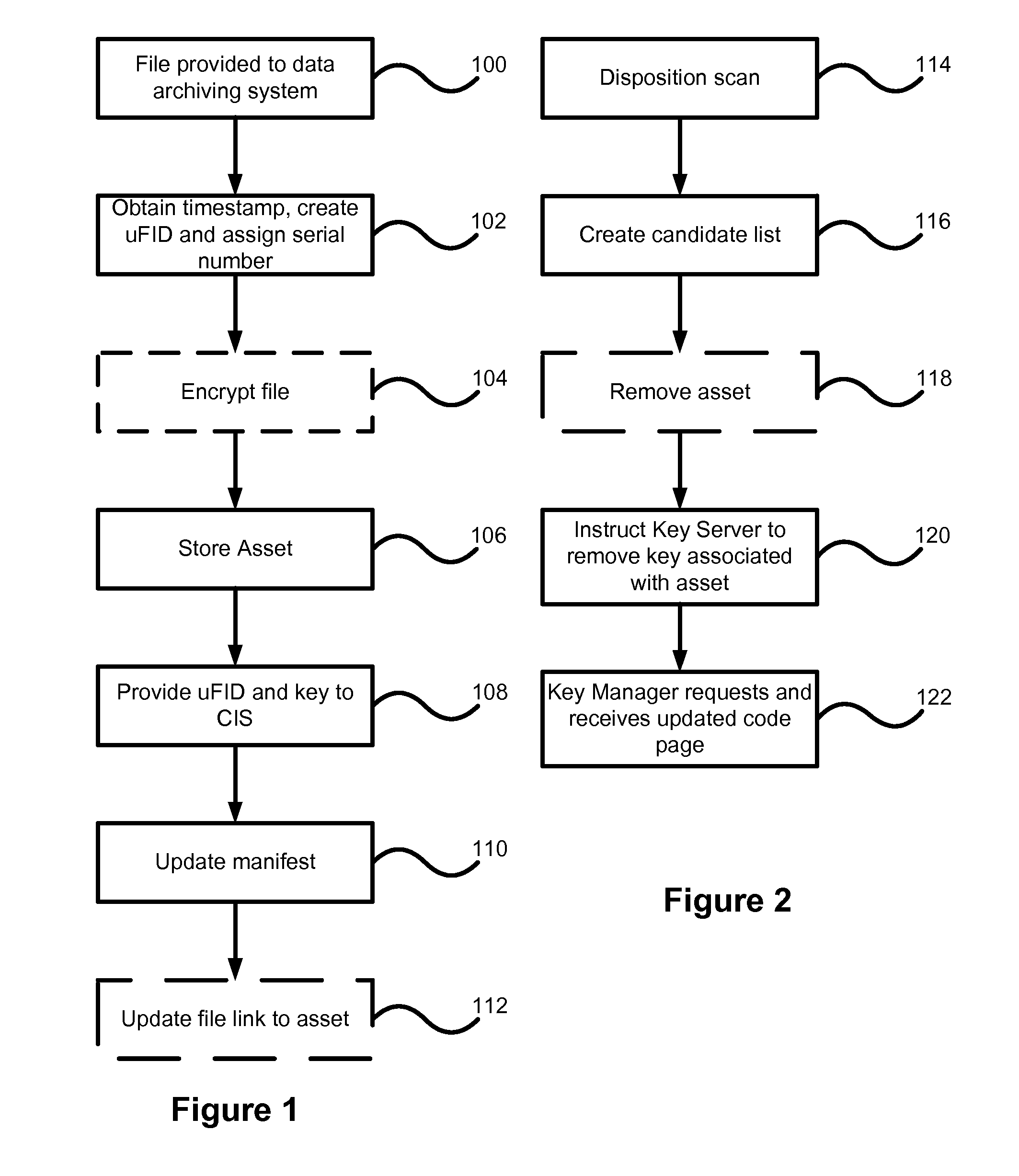
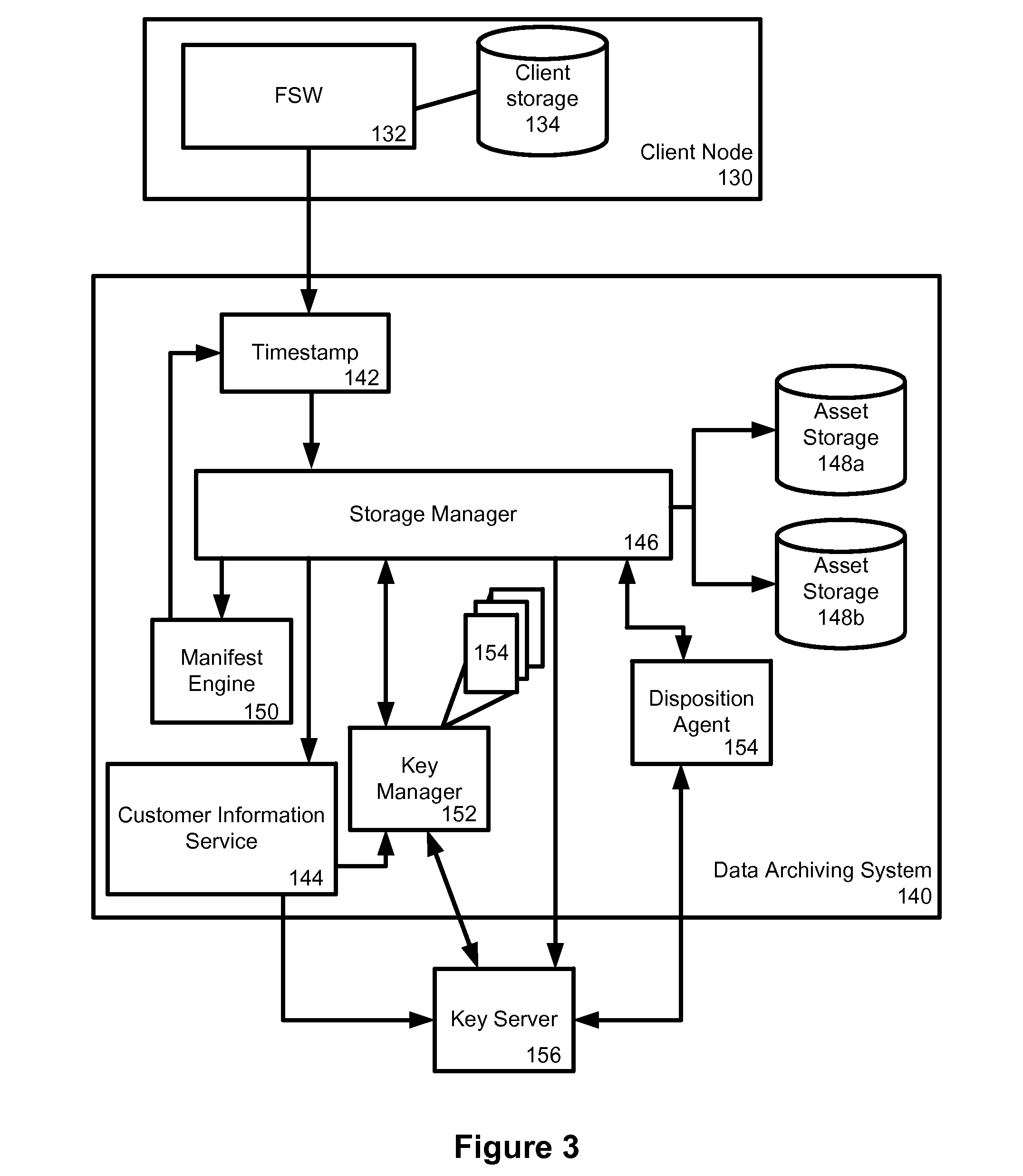
Data archiving system
ActiveUS7801871B2Digital data processing detailsComputer security arrangementsFault toleranceApplication server
An encrypted file storage solution consists of a cluster of processing nodes, external data storage, and a software agent (the “File System Watcher”), which is installed on the application servers. Cluster sizes of one node up to many hundreds of nodes are possible. There are also remote “Key Servers” which provide various services to one or more clusters. The preceding describes a preferred embodiment, though in some cases it may be desirable to “collapse” some of the functionality into a smaller number of hardware devices, typically trading off cost versus security and fault-tolerance.
Owner:STORCENTRIC DIP LENDER LLC +1
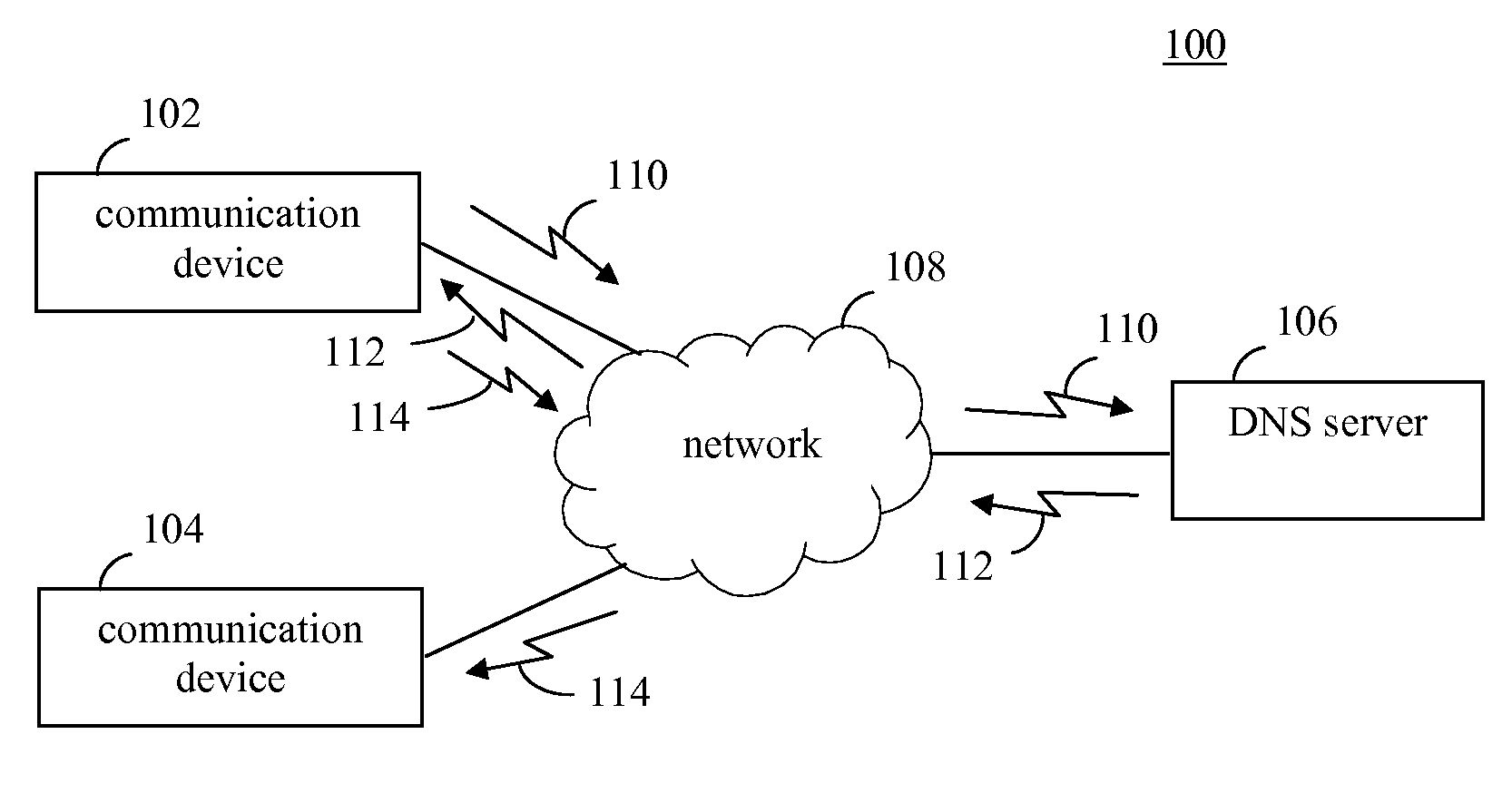
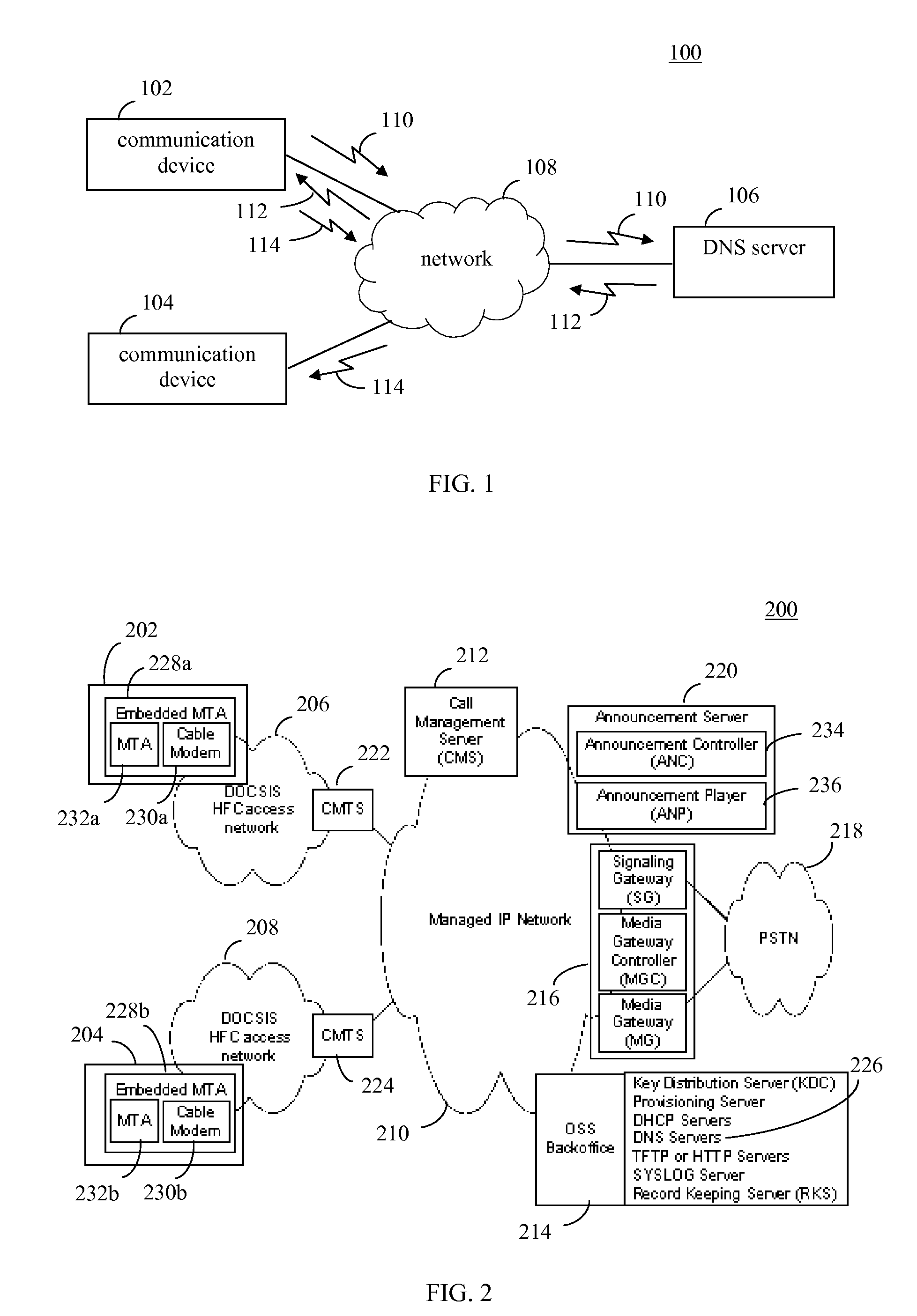
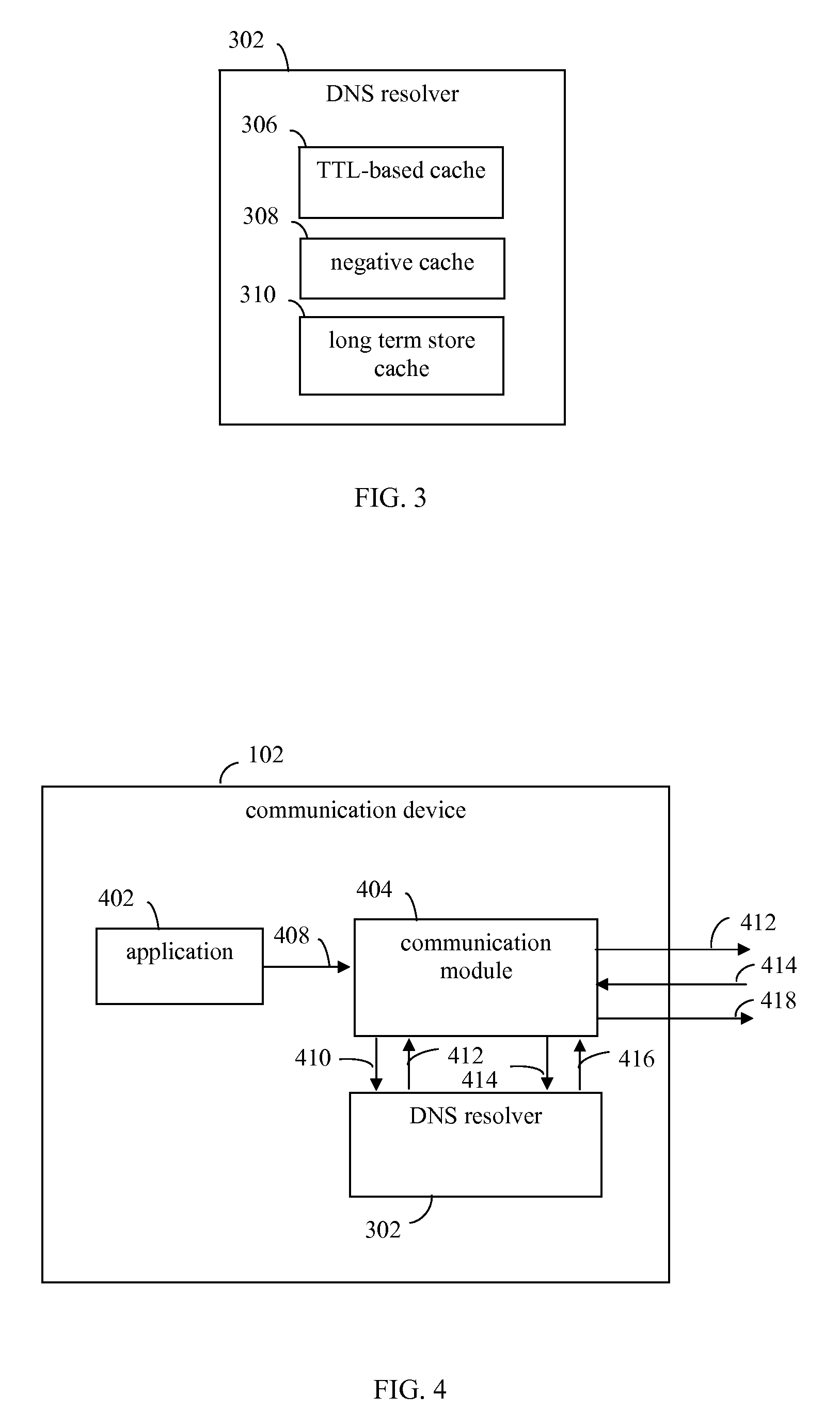
Fault tolerance approaches for DNS server failures
ActiveUS20100332680A1Multiple digital computer combinationsData switching networksDomain nameIndefinite time
Techniques are provided for handling failures of DNS (domain name system) servers to respond to DNS queries. A DNS resolver is configured to resolve domain names, and includes a time-to-live (TTL)-based cache, a negative cache, and a long term store cache. The TTL-based cache is configured to temporarily store domain names with resolved IP addresses. The negative cache is configured to store negative entries that include information indicating domain names that were failed to be resolved. The long term store cache is configured to store domain names with resolved IP address for an indefinite time period. The caches are accessed in a manner that enables fewer DNS query retries to be performed when a DNS server is non-responsive, to reduce delays and network traffic. Furthermore, the DNS resolver may reduce a number of DNS queries performed the longer the DNS server stays non-responsive.
Owner:AVAGO TECH INT SALES PTE LTD
Data archiving system
ActiveUS20070038857A1Digital data processing detailsComputer security arrangementsFault toleranceExternal storage
An encrypted file storage solution consists of a cluster of processing nodes, external data storage, and a software agent (the “File System Watcher”), which is installed on the application servers. Cluster sizes of one node up to many hundreds of nodes are possible. There are also remote “Key Servers” which provide various services to one or more clusters. The preceding describes a preferred embodiment, though in some cases it may be desirable to “collapse” some of the functionality into a smaller number of hardware devices, typically trading off cost versus security and fault-tolerance.
Owner:STORCENTRIC DIP LENDER LLC +1
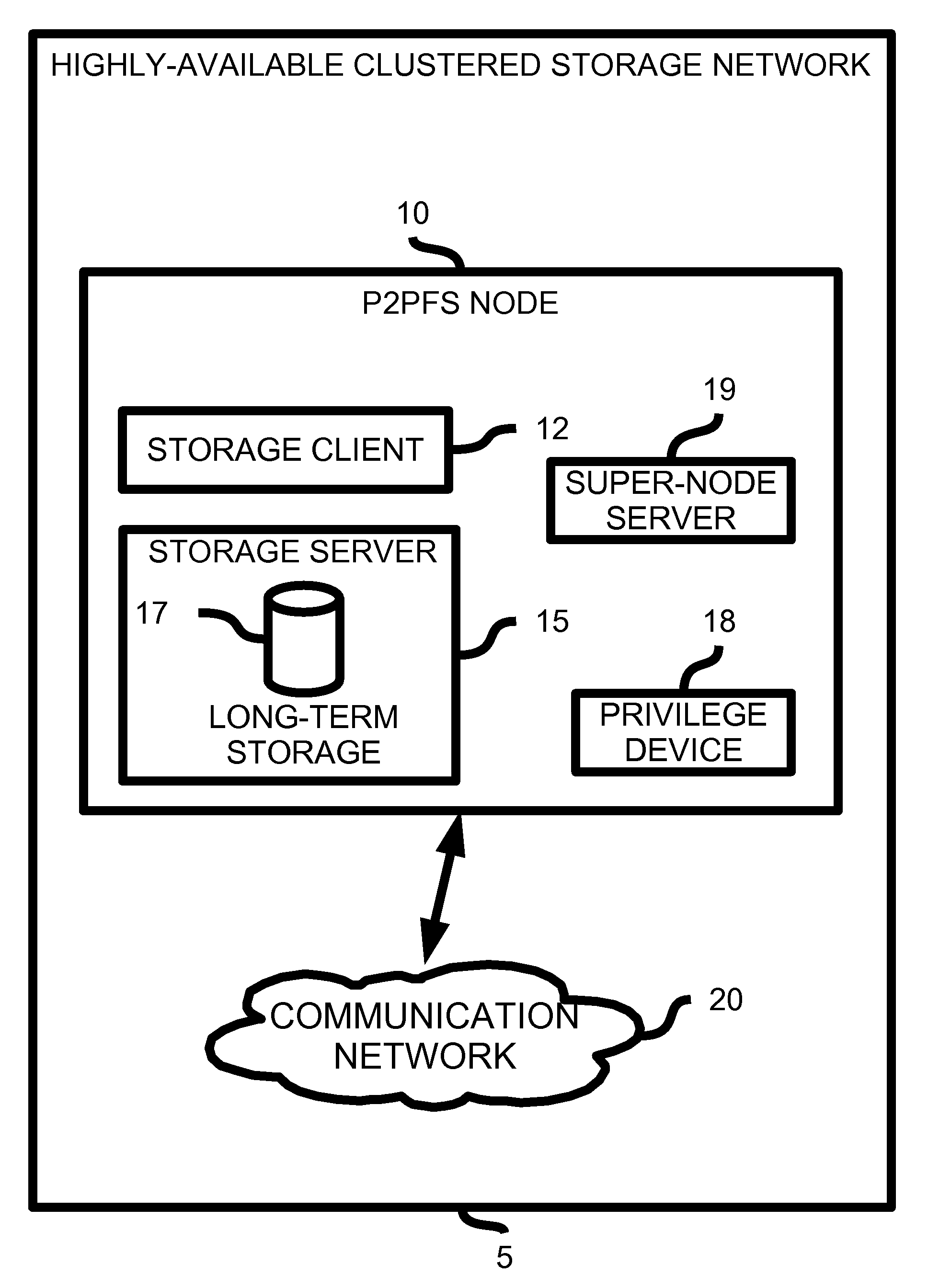
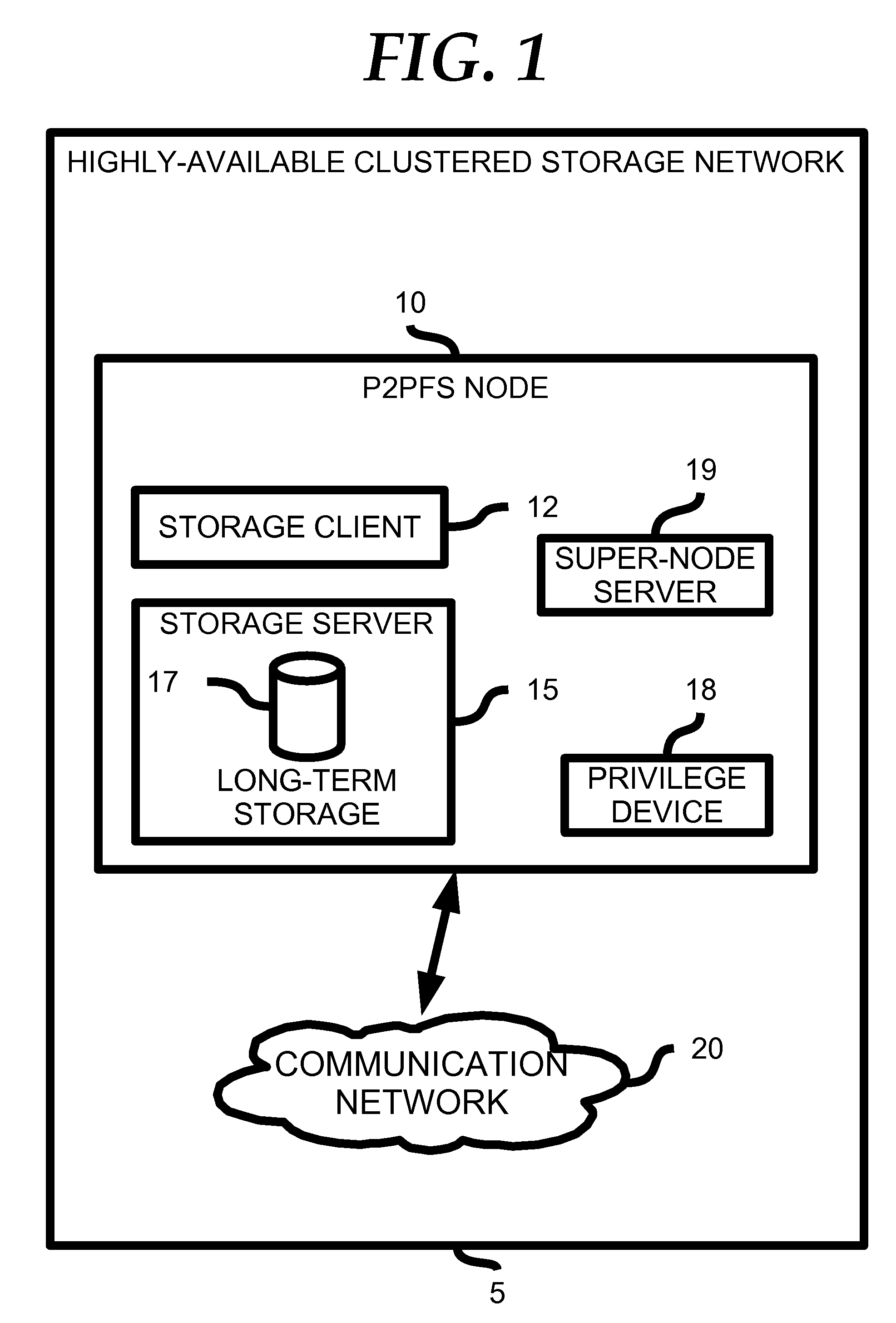
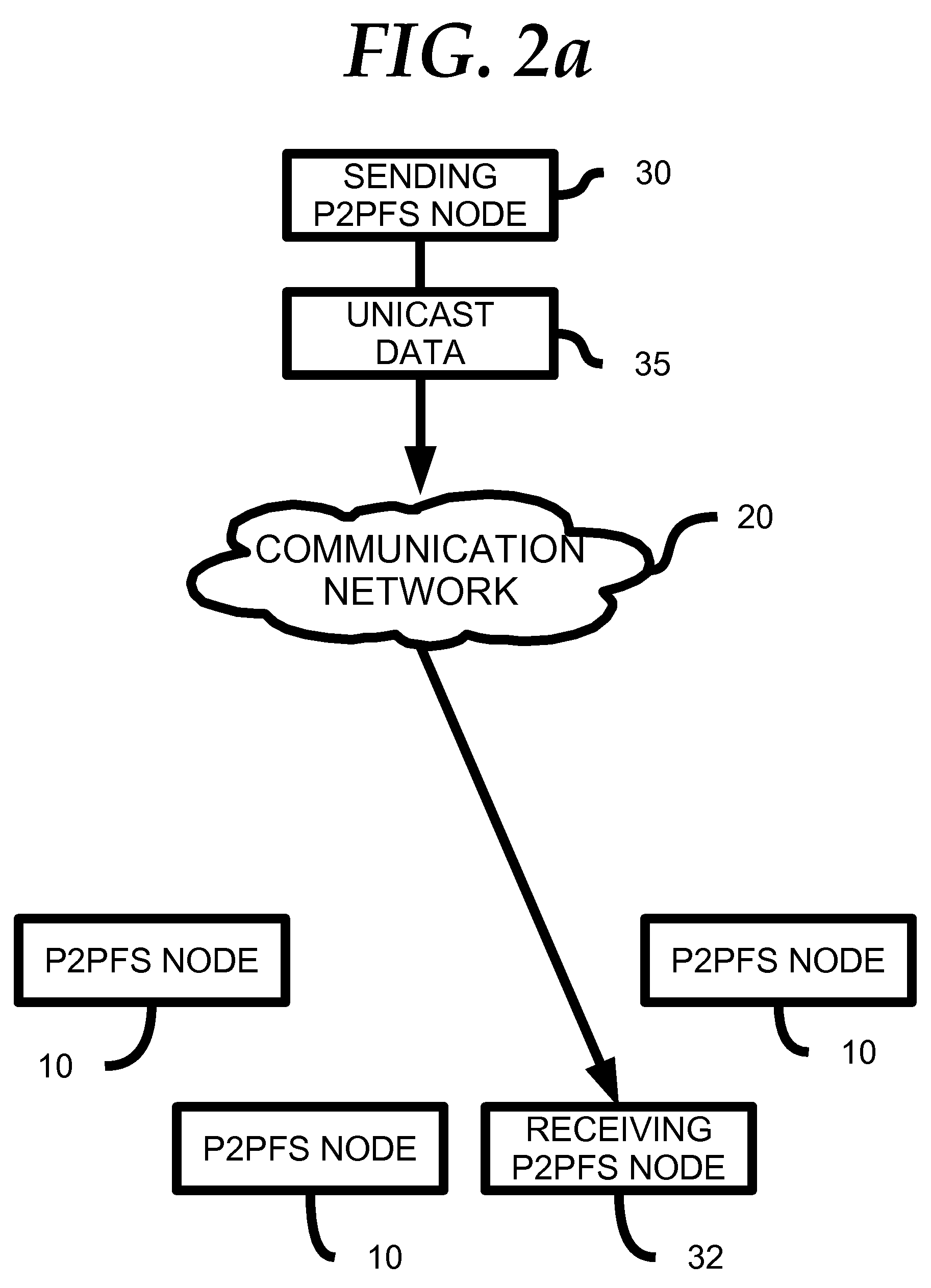
Highly Available Clustered Storage Network
InactiveUS20080077635A1Highly auto-configuringImprove scalabilityDigital data information retrievalSpecial data processing applicationsFault toleranceClustered file system
A computing method and system is presented that allows multiple heterogeneous computing systems containing file storage mechanisms to work together in a peer-to-peer fashion to provide a fault-tolerant decentralized highly available clustered file system. The file system can be used by multiple heterogeneous systems to store and retrieve files. The system automatically ensures fault tolerance by storing files in multiple locations and requires hardly any configuration for a computing device to join the clustered file system. Most importantly, there is no central authority regarding meta-data storage, ensuring no single point of failure.
Owner:DIGITAL BAZAR
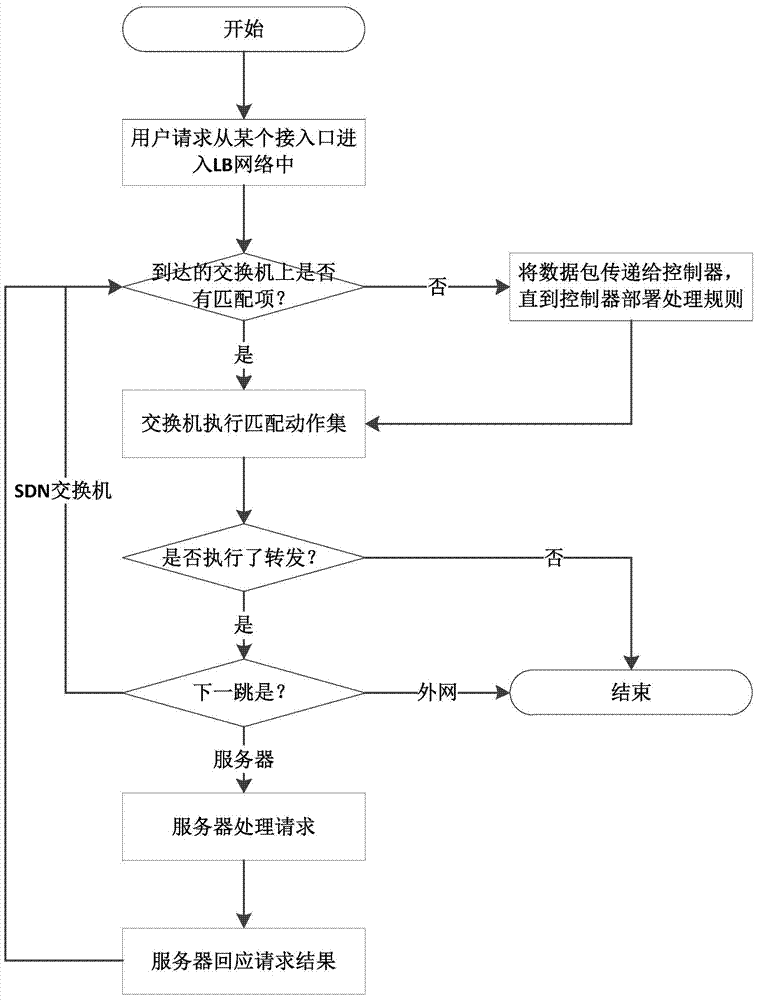
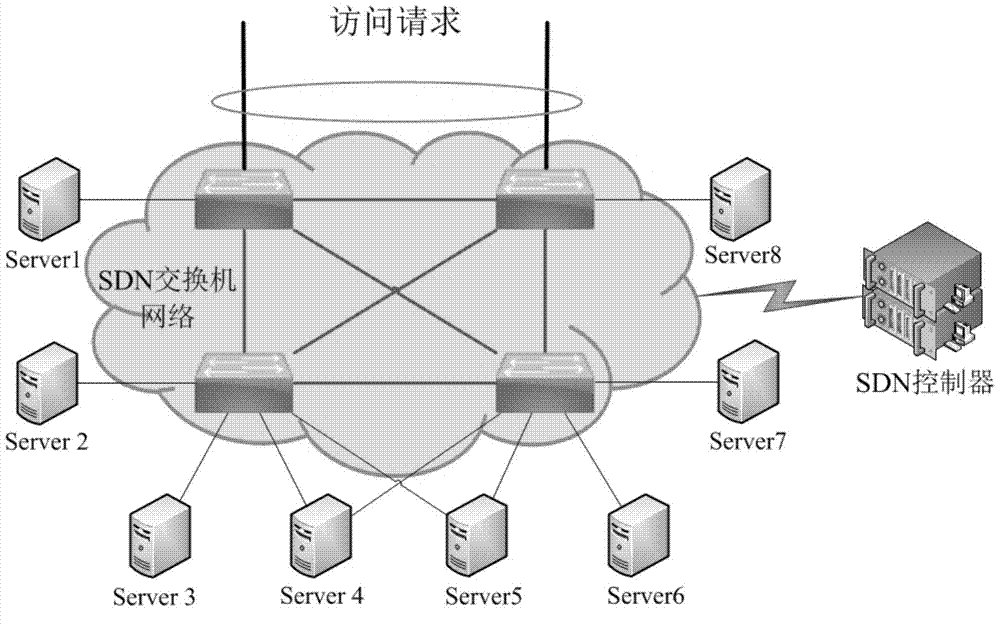
Distributed server load balancing method based on SDN
InactiveCN103795805AReal-time collectionDoes not affect normal workTransmissionFault toleranceDistributed servers
The invention discloses a distributed server load balancing method based on the SDN. Through the advantage of the SDN structure where a control face and a forwarding face are separated, a user access request arrives at a certain device on the SDN, then, an SDN controller dynamically dispatches the user access request to an appropriate server according to the network running state, and therefore server load balancing is achieved. By means of the distributed server load balancing method, comprehensive fault tolerance can be achieved from the access process and the forwarding process to the service process, the total load bearing capacity of a server cluster is brought into full play, and running expandability and running reliability of the whole system are improved.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
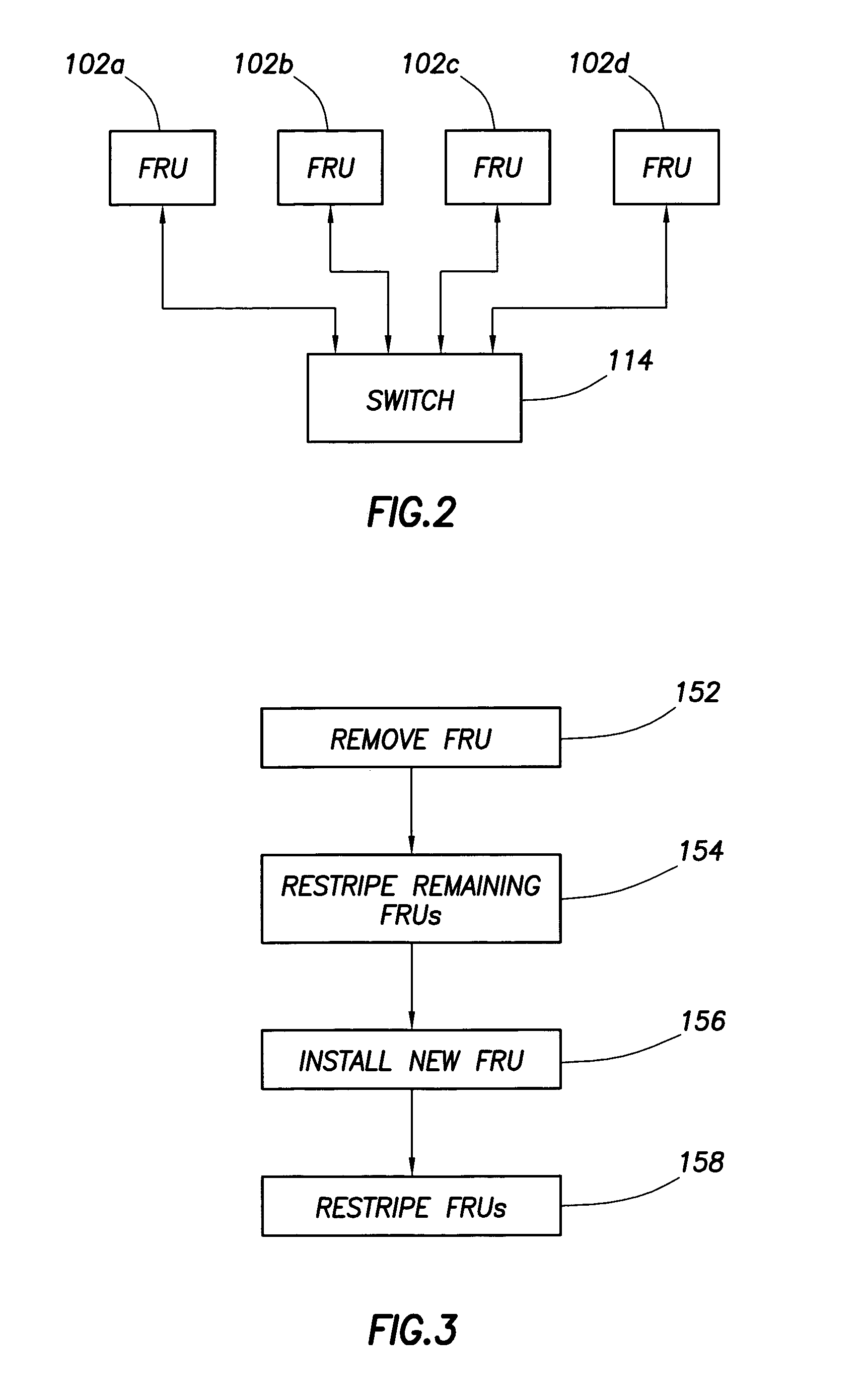
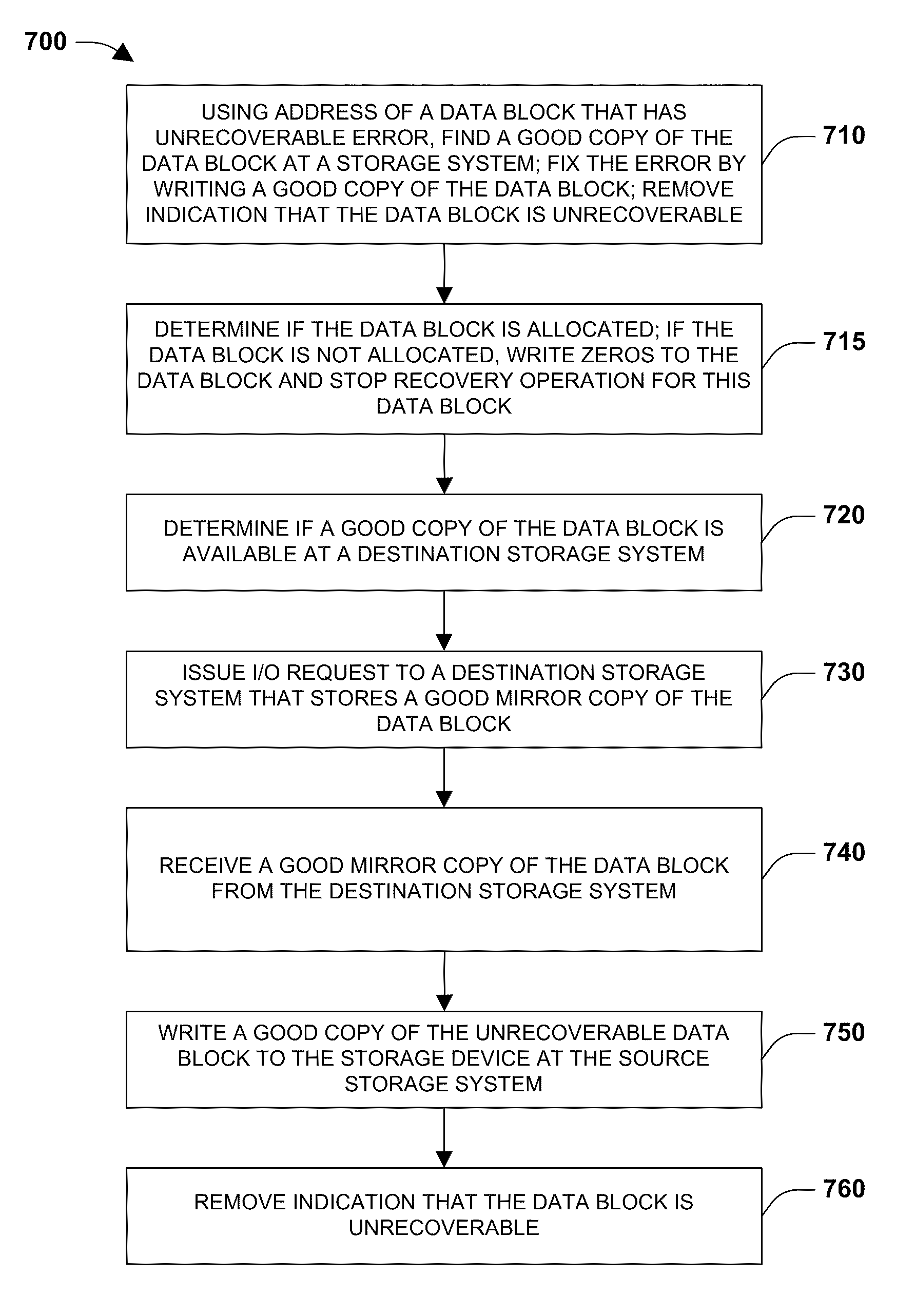
Mechanism for correcting errors beyond the fault tolerant level of a raid array in a storage system
ActiveUS8417987B1Increase resiliencyImprove availabilityRedundant hardware error correctionRAIDFault tolerance
Embodiments of the present invention provide novel, reliable and efficient technique for tracking, tolerating and correcting unrecoverable errors (i.e., errors that cannot be recovered by the existing RAID protection schemes) in a RAID array by reducing the need to perform drastic recovery actions, such as a file system consistency check, which typically disrupts client access to the storage system. Advantageously, ability to tolerate and correct errors in the RAID array beyond the fault tolerance level of the underlying RAID technique increases resiliency and availability of the storage system.
Owner:NETWORK APPLIANCE INC
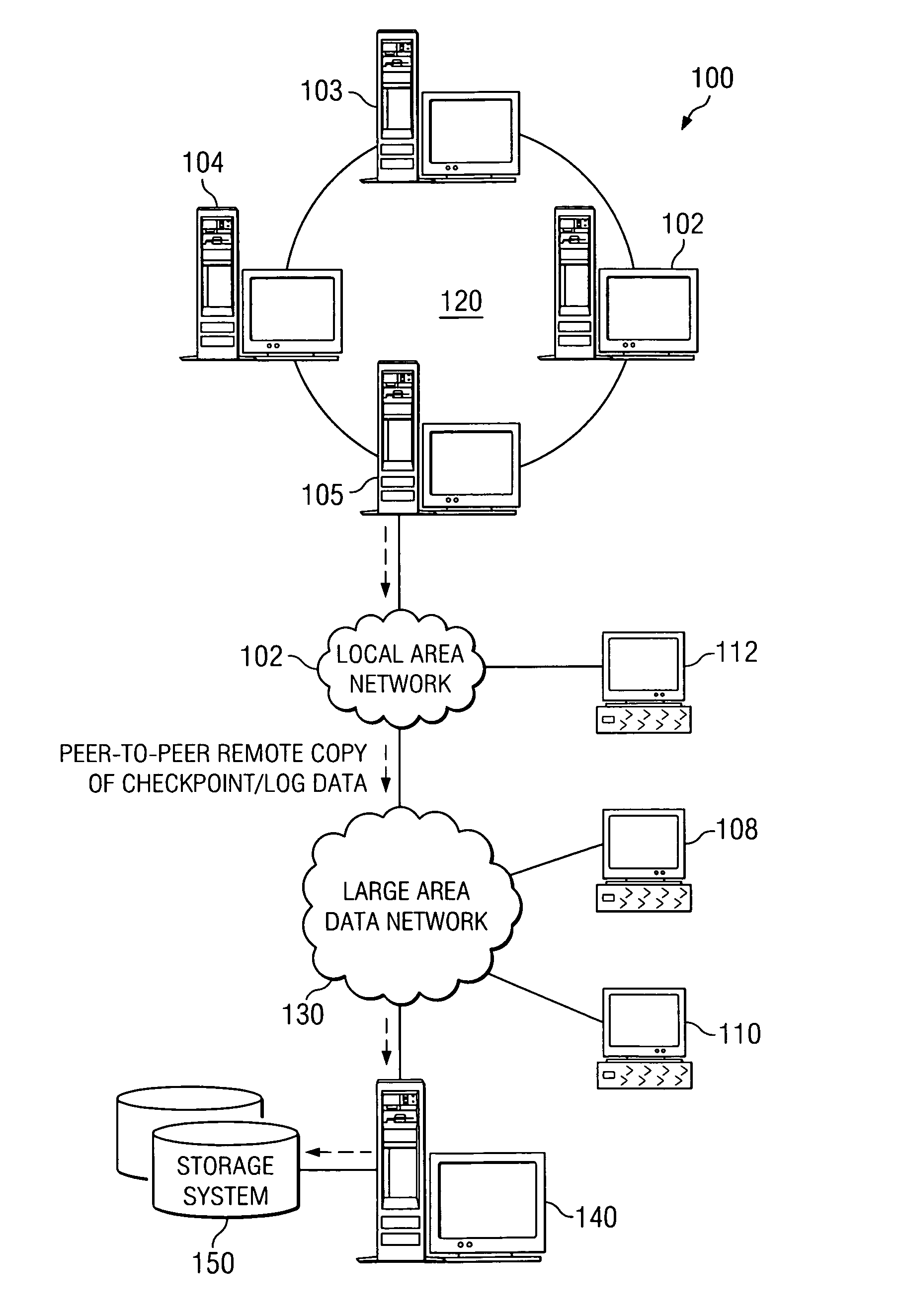
System and method for application fault tolerance and recovery using topologically remotely located computing devices
InactiveUS20070244937A1Error detection/correctionSpecial data processing applicationsFault tolerancePeer-to-peer
A system and method for application fault tolerance and recover using topologically remotely located computing devices are provided. A primary computing device runs one instance of an application (i.e. the primary application instance) at a production site and an active standby computing device runs a second instance of the application (i.e. the shadow application instance) at a recovery site which may be topologically remotely located from the production site. The two instances of the application are brought into a consistent state by running an initial application “checkpoint” on the primary computing device followed by an application “restart” on the active standby computing device. Events occurring in the primary application instance may be automatically and continuously recorded in a log and transferred to the recovery site using a peer-to-peer remote copy operation so as to maintain the states of the application instances consistent.
Owner:IBM CORP
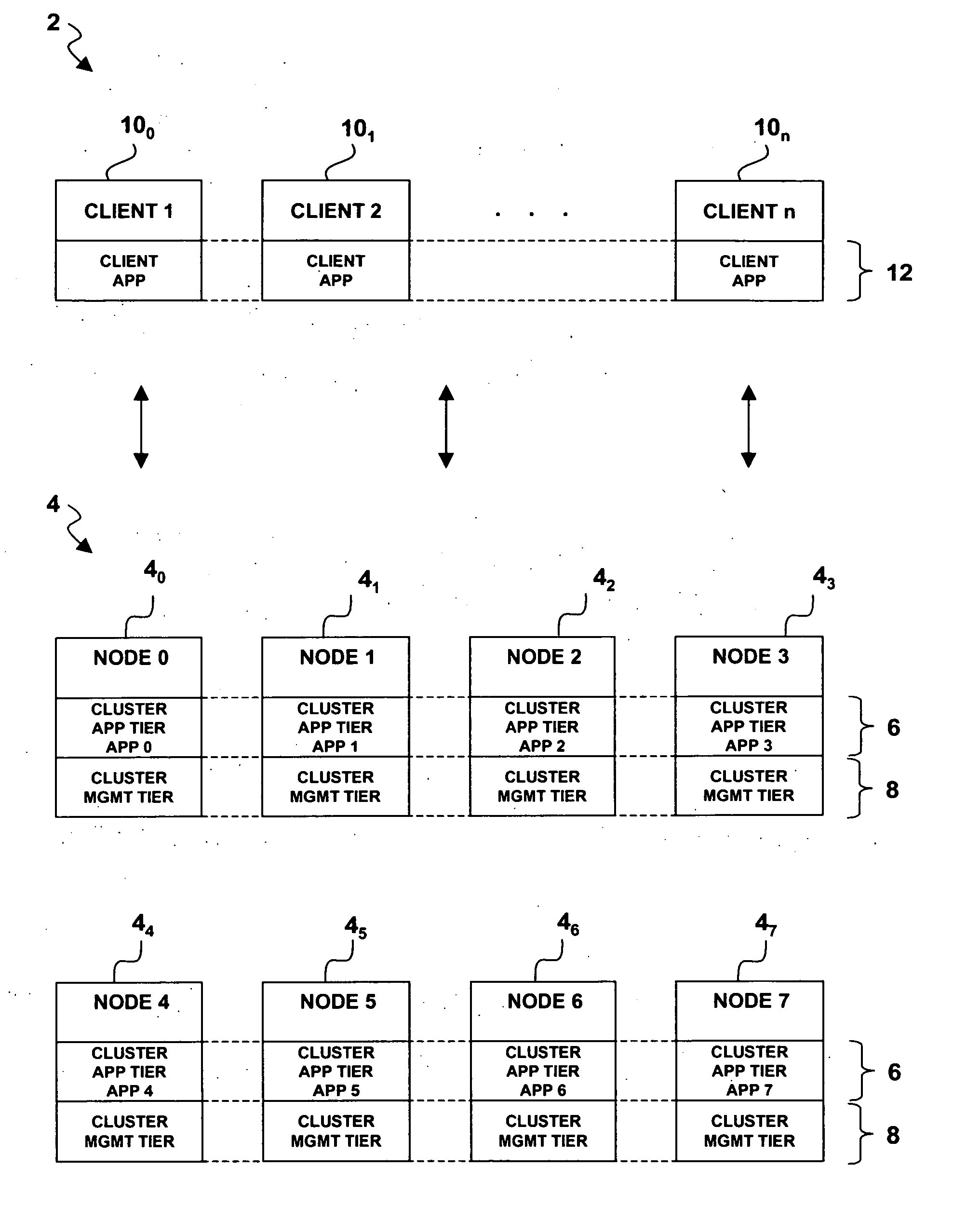
Fault-tolerance and fault-containment models for zoning clustered application silos into continuous availability and high availability zones in clustered systems during recovery and maintenance
InactiveUS20070006015A1No impact on transaction processingSmall sizeError detection/correctionTransmissionFault toleranceIslanding
A cluster recovery and maintenance system, method and computer program product for use in a server cluster having plural nodes implementing a server tier in a client-server computing architecture. A first group of N active nodes each run a software stack comprising a cluster management tier and a cluster application tier that actively provides services on behalf of one or more client applications running in a client application tier on the clients. A second group of M spare nodes each run a software stack comprising a cluster management tier and a cluster application tier that does not actively provide services on behalf of client applications. First and second zones in the cluster are determined in response to an active node membership change involving one or more active nodes departing from or being added to the first group as a result of an active node failing or becoming unreachable or as a result of a maintenance operation involving an active node. The first zone is a fault tolerant zone comprising all active nodes that remain operational. The second zone is a fault containment zone comprising all active nodes participating in the membership change and at least a corresponding number of spare nodes to the extent that the membership change involves a node departure. During recovery and maintenance, fast recovery / maintenance and high application availability are implemented in the fault containment zone, while continuous application availability is maintained in the fault tolerant zone.
Owner:IBM CORP
Communication system with distributed intelligence
InactiveUS20050232252A1Easily be added to existing networkFault toleranceAutomatic exchangesNetwork connectionsFault toleranceDistributed intelligence
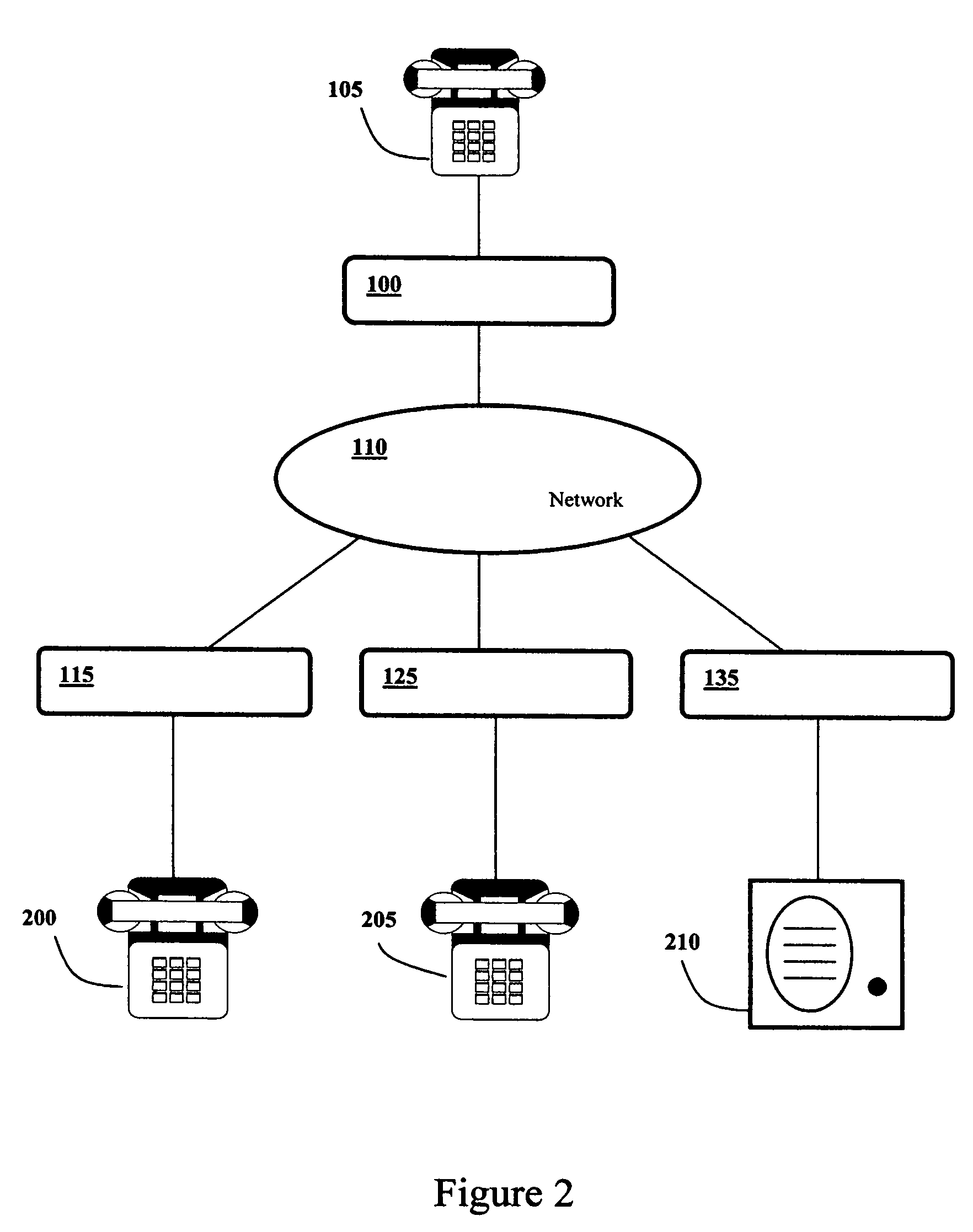
A communications system with distributed intelligence thereby allowing easy expansion of the system while also providing a high degree of fault tolerance. The communications system allows for conversion, transmission and restoration of the human voice over a digital network. A telephone can be used as the input device for receiving the analog signal, or human voice. The telephone is also used to select a destination for the analog signal. The information is transmitted over the digital network and may also traverse through a private branch exchange and a wireless network before it arrives at its destination. At the destination the transmitted information is restored to an analog signal and played over one or more speakers. The present system is especially suited for use with an existing network.
Owner:HOOVER THOMAS R
Distributed control system
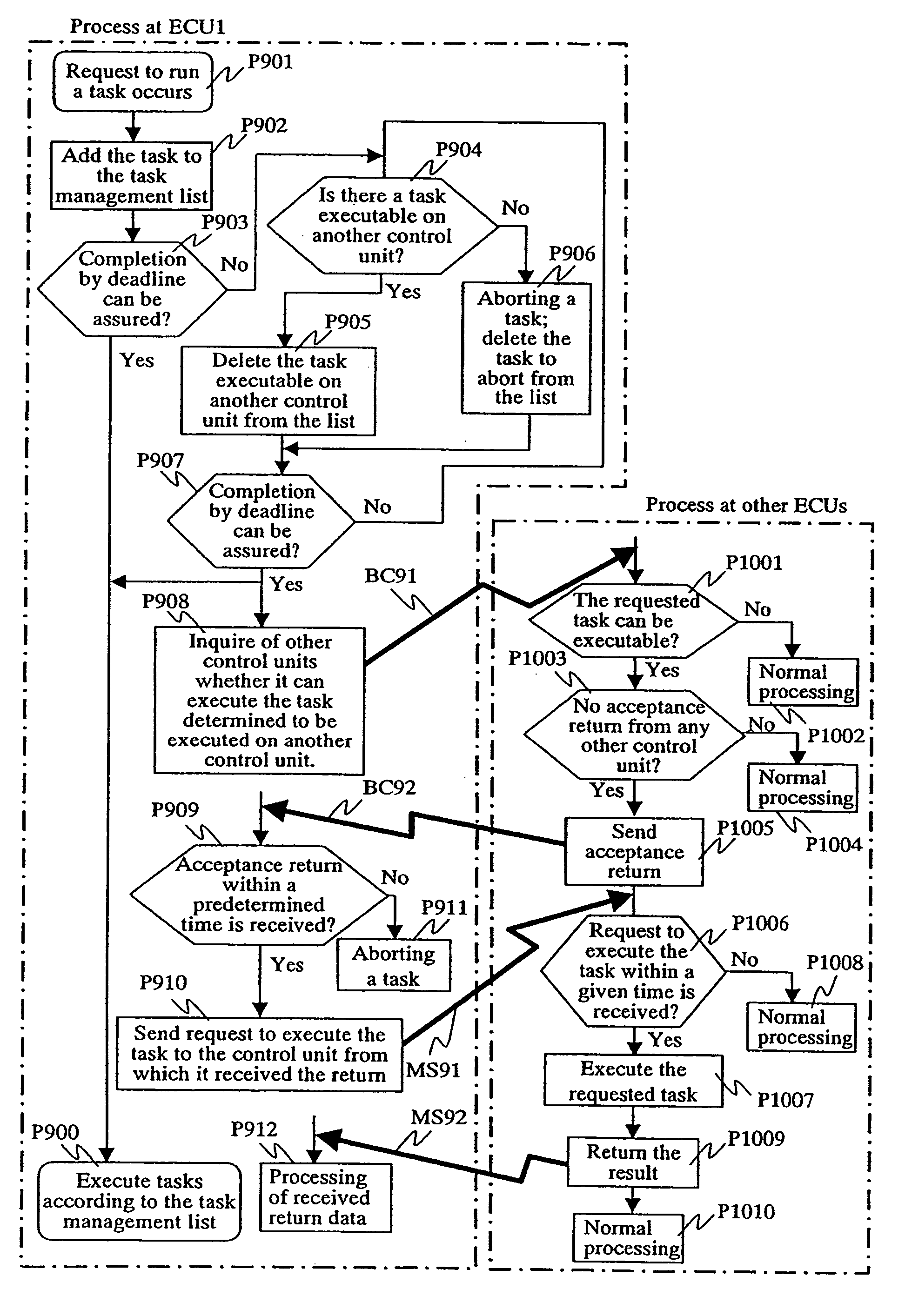
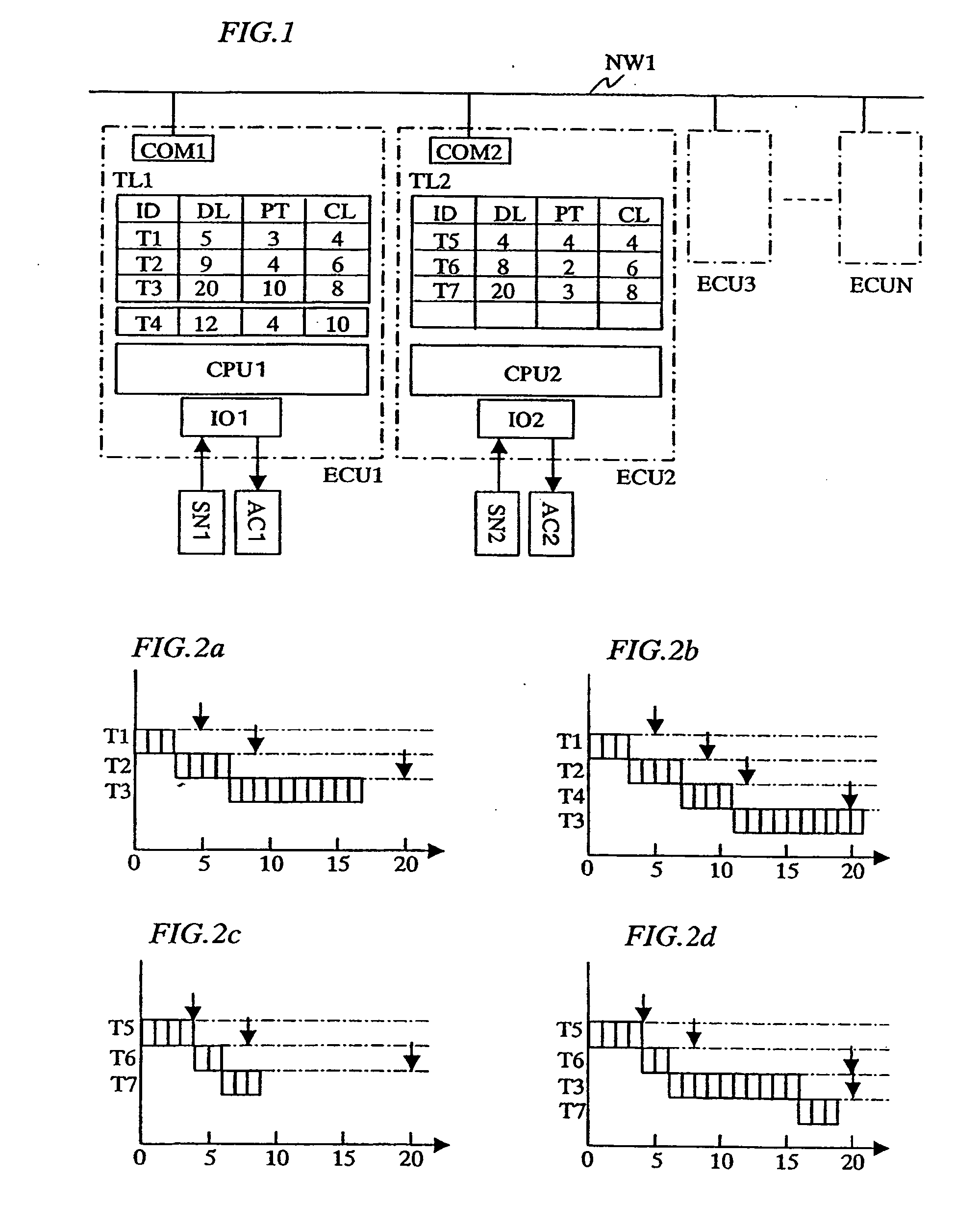
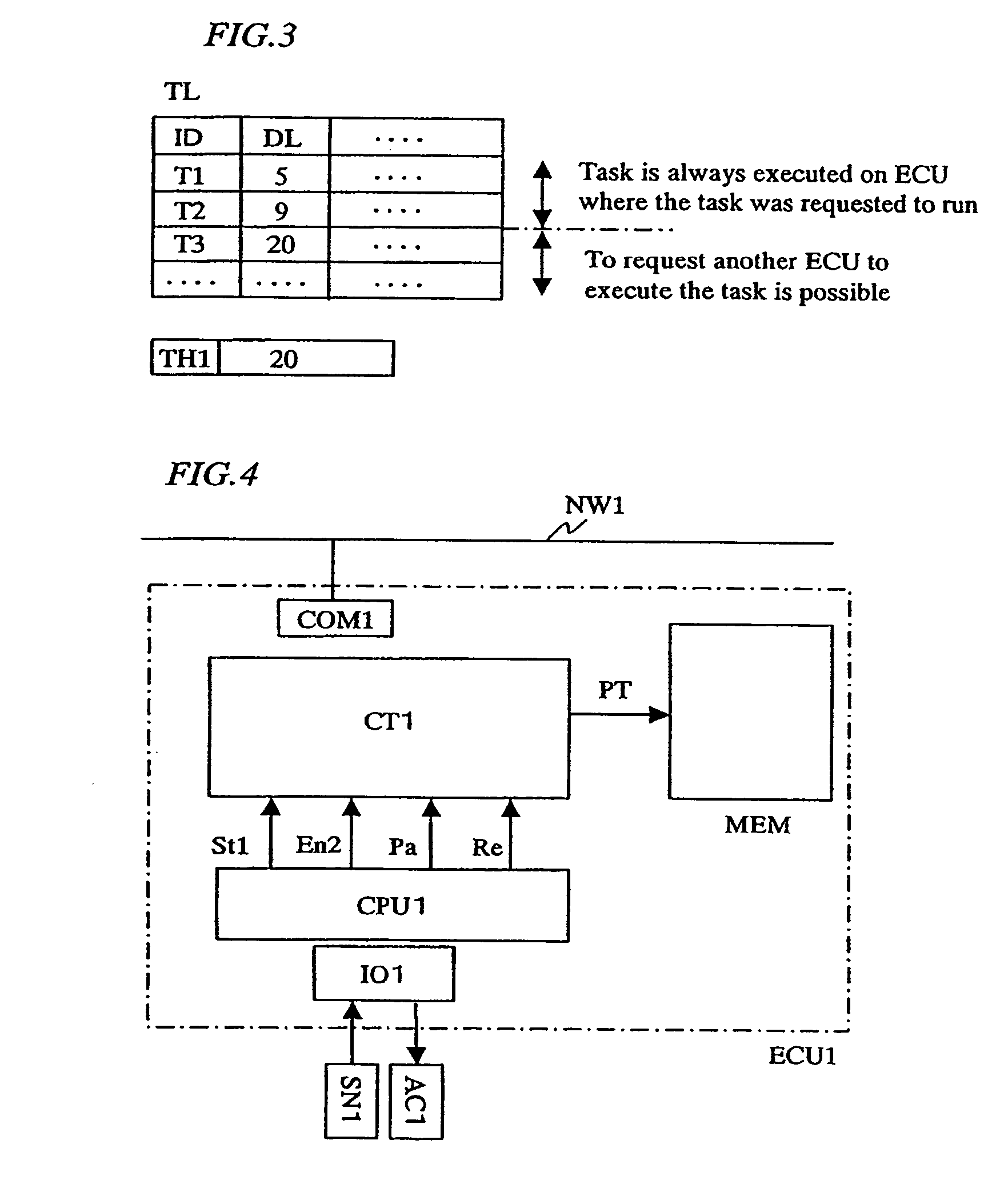
InactiveUS20060101465A1Easy to operateEnsure performanceProgramme controlMultiprogramming arrangementsFault toleranceTask completion
In a distributed control system where a plurality of control units are connected via a network, the invention allows for efficient operation of each control unit, while ensuring real-time processing. To provide a distributed control system in which ensured real-time processing and enhanced fault tolerance are achieved, information of a deadline or task run cycle period as time required until task completion is given for each task and a control unit on which a task will be executed is selected according to the deadline or task cycle period. A first control circuit and related sensors and actuators are connected by a dedicated path on which fast response time is easy to ensure and another control circuit and related sensors and actuators are connected via a network. When the first control circuit operates normally with sufficient throughput, the first control circuit is used for control; in case the first control circuit fails or if its throughput is insufficient, another control circuit is used.
Owner:HITACHI LTD
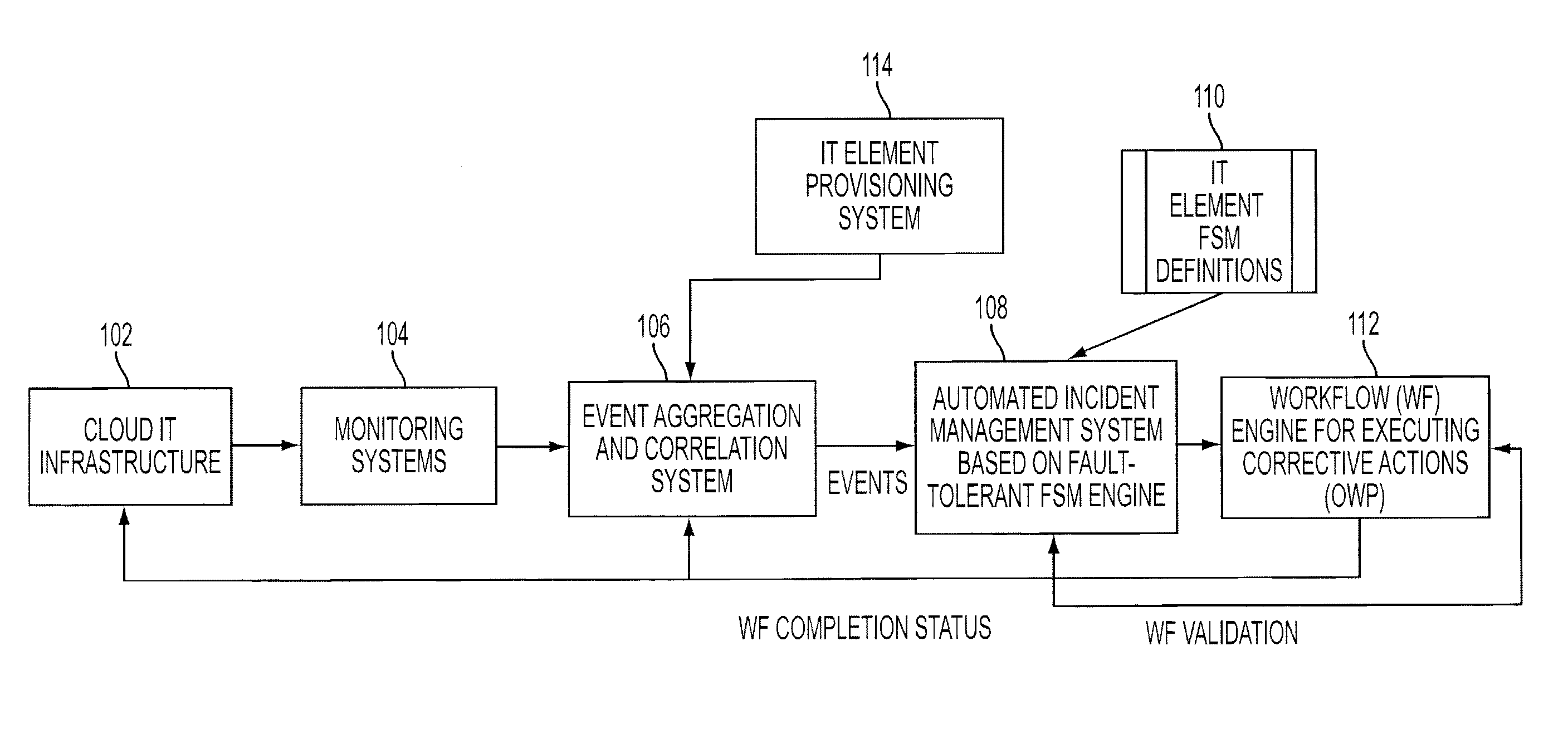
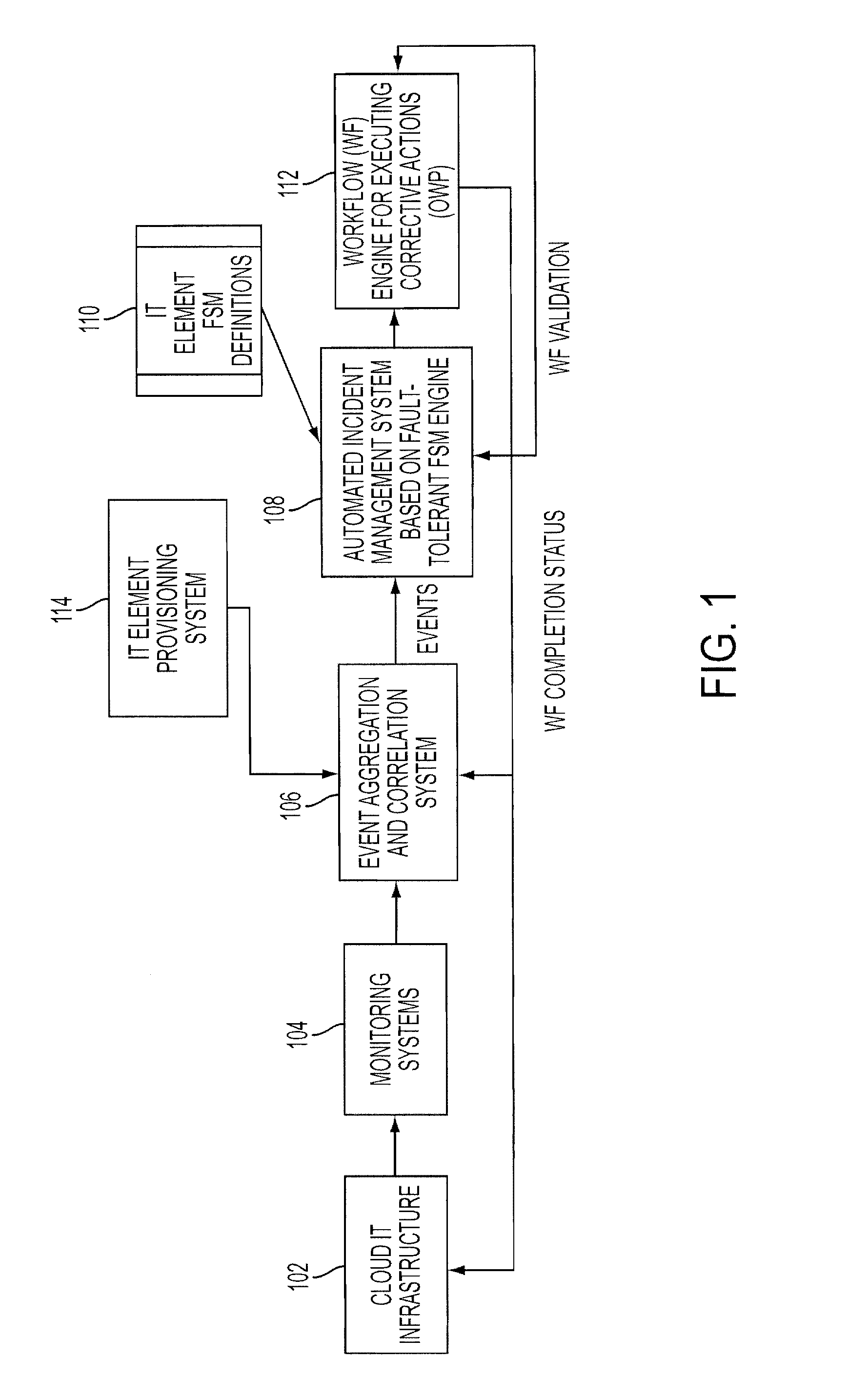
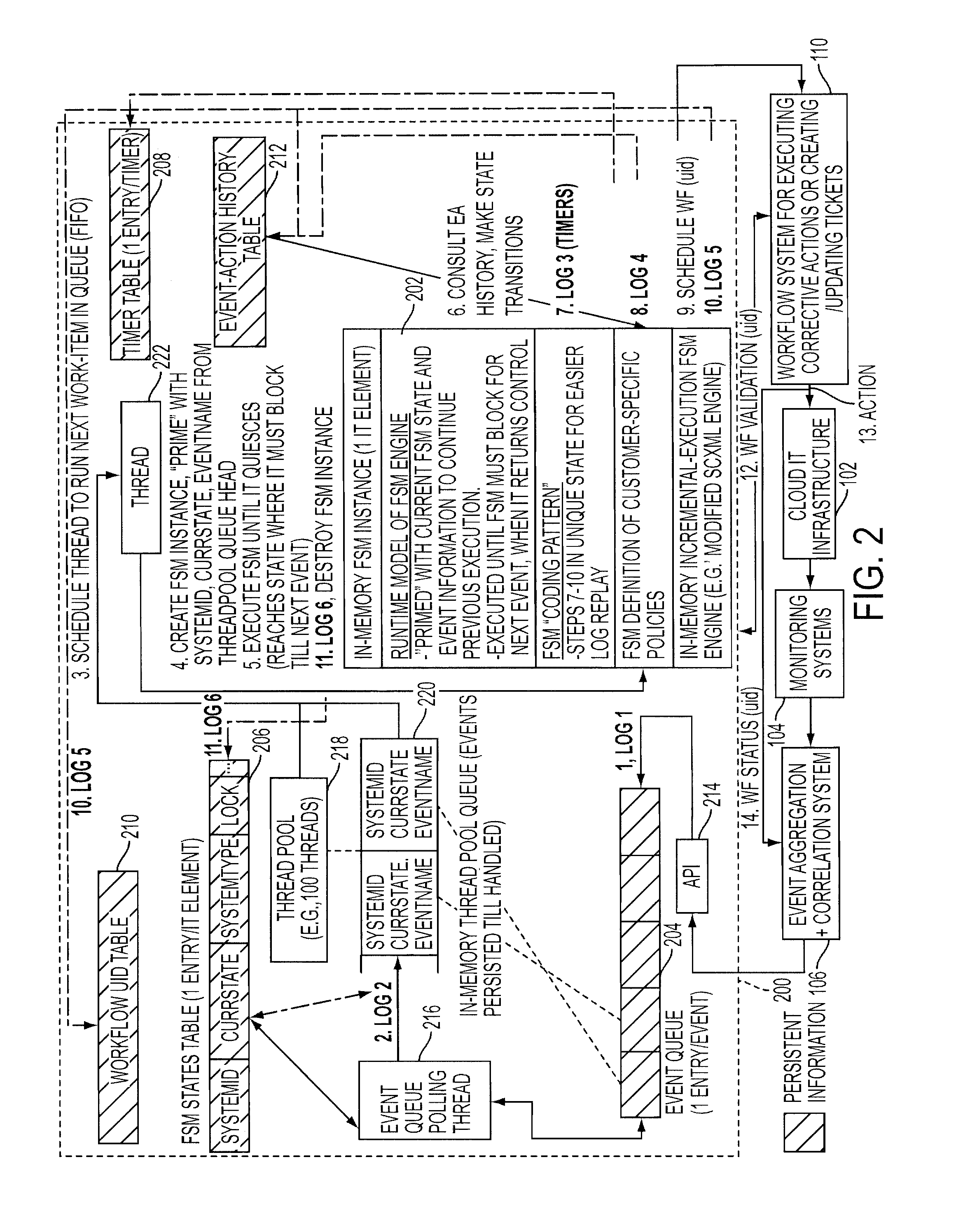
Adding scalability and fault tolerance to generic finite state machine frameworks for use in automated incident management of cloud computing infrastructures
InactiveUS20120151272A1Program controlRedundant operation error correctionFault toleranceExtensibility
A scalable and fault tolerant finite state machine engine, for example, for use in an automated incident management system, logs or records data in persistent storage at different points or levels during various internal processing of an event associated with an information technology element, and action taken associated with the event, by executing a finite state machine instance that encodes policies for handling incidents on such types of information technology elements. In the event that the finite state machine engine is shutdown during processing, the finite state machine engine is able to pick up from where it left off when it was shutdown, for each abnormally terminated finite state machine instance, by using the data logged in the persistent storage and determining a point of processing from where it should continue its execution.
Owner:GLOBALFOUNDRIES US INC
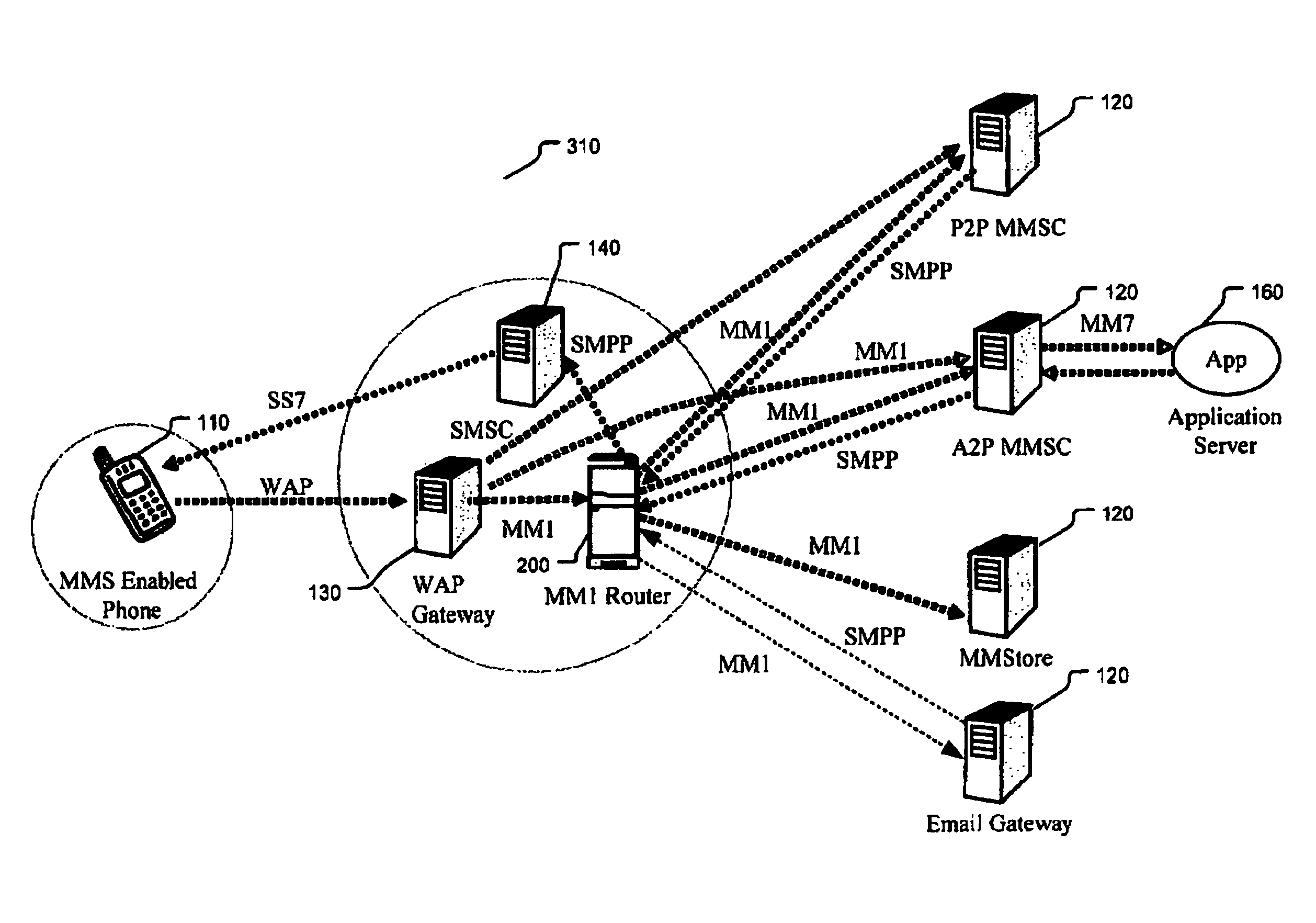
Apparatus and method for routing multimedia messages between a user agent and multiple multimedia message service centers
ActiveUS20050141522A1Special service provision for substationNetwork traffic/resource managementFault toleranceComputer science
An apparatus and a method for routing a multimedia message sent by a user agent to one of a plurality of multimedia message service centers, the user agent applying a pre-determined determined destination address to the multimedia message. The multimedia message is received at the pre-determined destination address, a target multimedia message service center is selected and the multimedia message is forwarded to the target multimedia message service center. Routing is based on address information contained in the multimedia message, session identification information associated with the multimedia message, load-balancing and fault-tolerance information associated with each one of the plurality of multimedia message service centers, service identifying information contained in the multimedia message and combinations thereof.
Owner:MAVENIR SYSTEMS
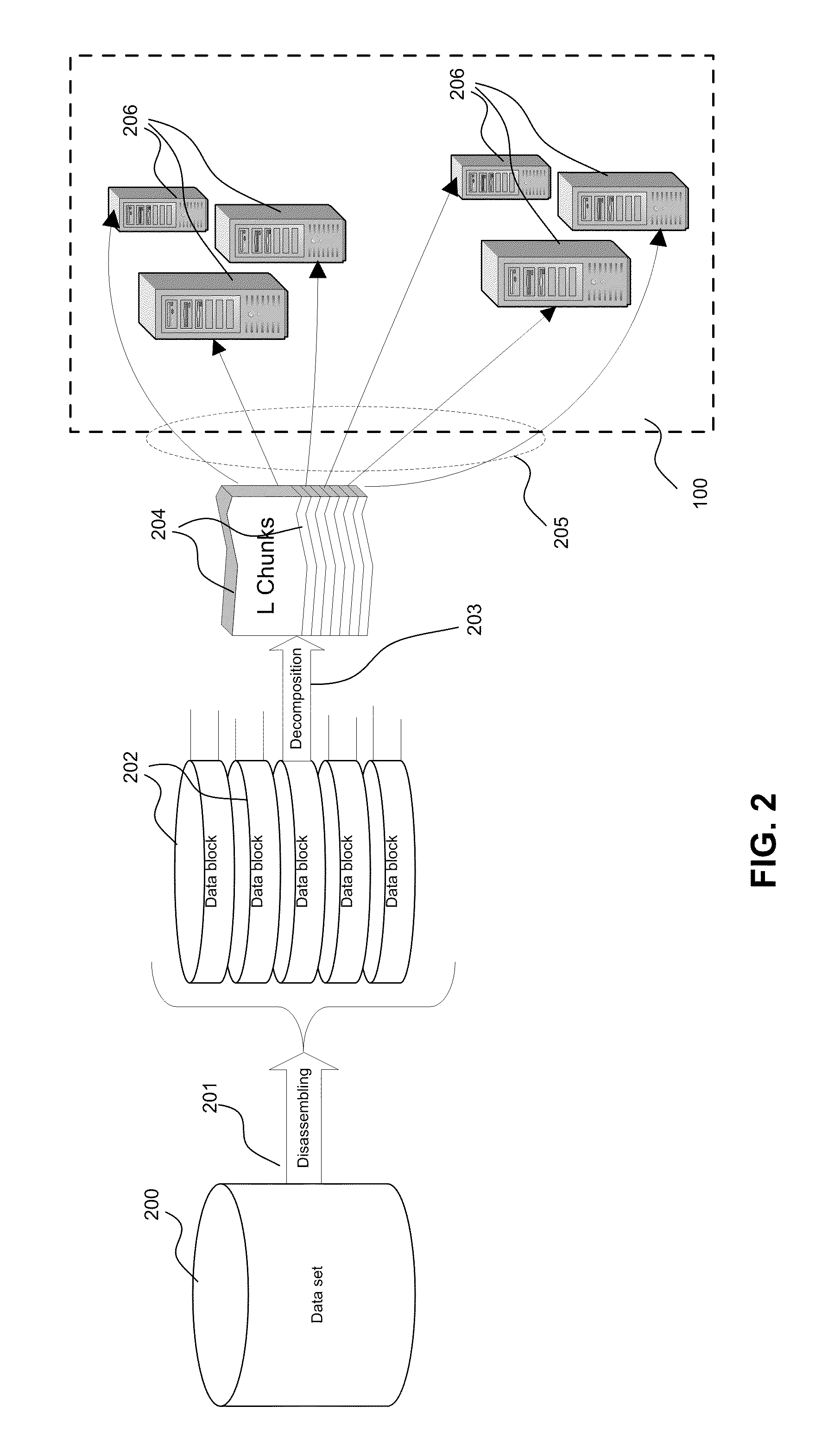
Fault tolerant distributed storage for cloud computing
Data sets and blocks are stored in a set of independent, functionally equivalent chunks. These chunks are placed on different elements of a distributed network to achieve pre-defined level of fault tolerance. Terms of fault tolerance are defined in terms of amount of unavailable sites in the network allowing receipt and access to the data block. Maximal and minimal number of chunks available are variable method parameters. The minimal amount of data chunks K needed to restore a data block is defined. The size of each chunk is approximately 1 / K of the original block size. The maximal amounts of chunks are defined during distribution operation and depend upon a requested fault tolerance level. Redundancy in data storage is minimized and varies dynamically by changing the total amount of chunks available. Significant increase in data transfer rate is possible because all block chunks could be transferred in parallel and independently.
Owner:VIRTUOZZO INT GMBH
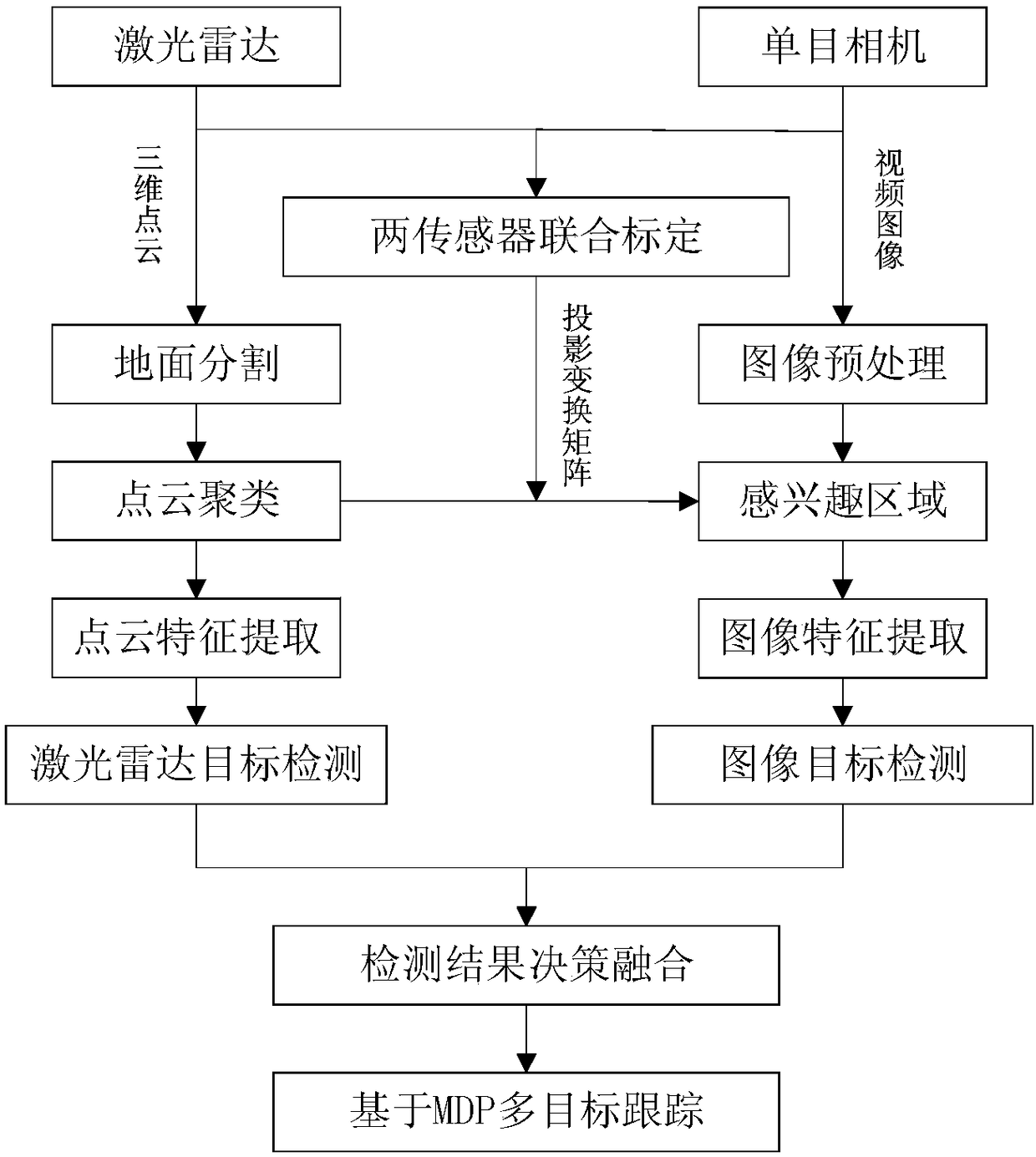
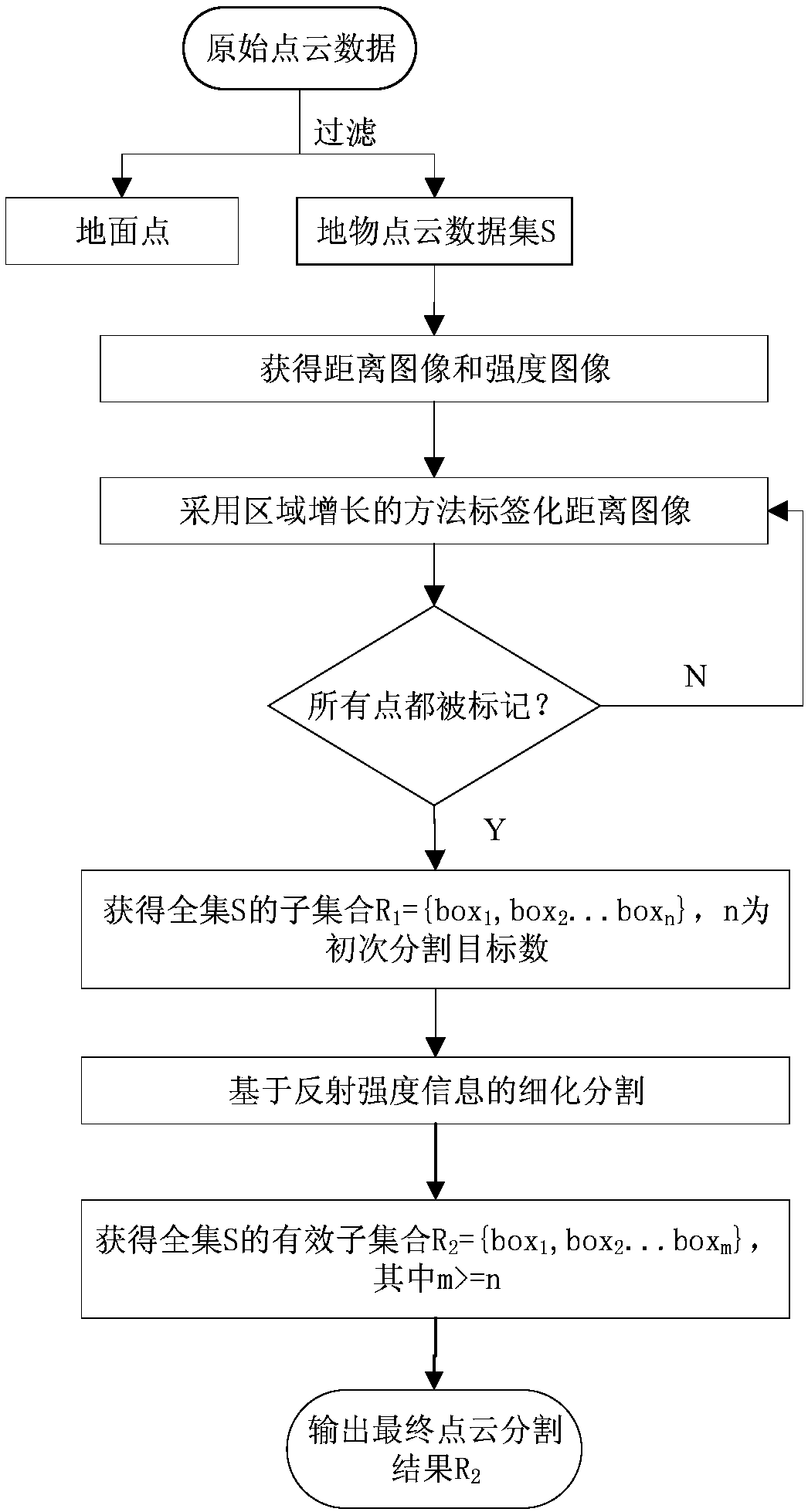
Object detection and tracking method of fusing laser point clouds and images
ActiveCN108509918AImprove detection efficiencyHigh precisionScene recognitionBiometric pattern recognitionFault tolerancePoint cloud
The invention discloses an object detection and tracking method of fusing laser point clouds and images. The method comprises the steps of: S1, respectively collecting laser point cloud data and imagedata of an object, carrying out first object detection according to the collected point cloud data to obtain a first object detection result, and carrying out second object detection according to thecollected image data to obtain a second object detection result; S2, carrying out fusion judgment on the first object detection result and the second object detection result on the basis of Bayesiandecision to obtain final object detection result output; and S3, carrying out object tracking according to a final object detection result. The method has the advantages of a simple and highly-efficient realization method, high object detection and tracking accuracy, high environment adaptability and fault tolerance, stability, reliability and the like.
Owner:NAT UNIV OF DEFENSE TECH
Social networking site and system
InactiveUS20100269158A1Digital data information retrievalDigital data processing detailsFault toleranceData loss
Various methods and systems are described for use in operating and maintaining a user subscribed system, such as a website or network. For example, a social networking site or network is contemplated with a member account having one or more member profiles associated with his or her member account. In accordance with one embodiment of the invention, the described systems and methods may provide a user selective access to member-related information, such as topic-based electronic content associated with the member, member-related or identifying information, and other such information, in accordance with member selected categorization and / or organisation. Users may be categorized hierarchically into contact groups, such that access to member-related information by user in a given contact group depends on the permission rights granted to that contact group. The methods and systems described provide a scalable infrastructure to support large volumes of users and requests in a network while ensuring a high degree of fault tolerance, so as to minimize service interruptions and unexpected data loss, for example.
Owner:RAMIUS CORP
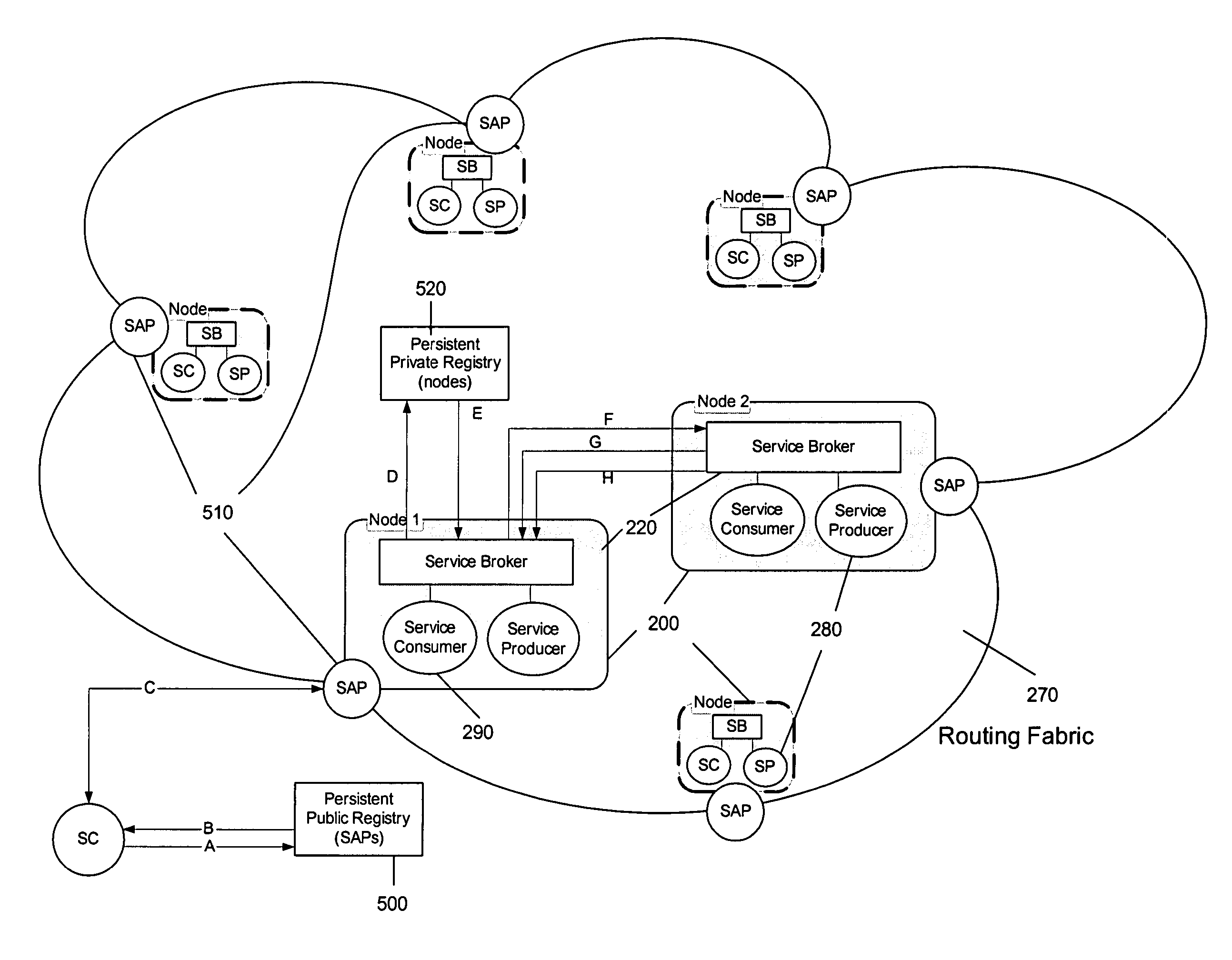
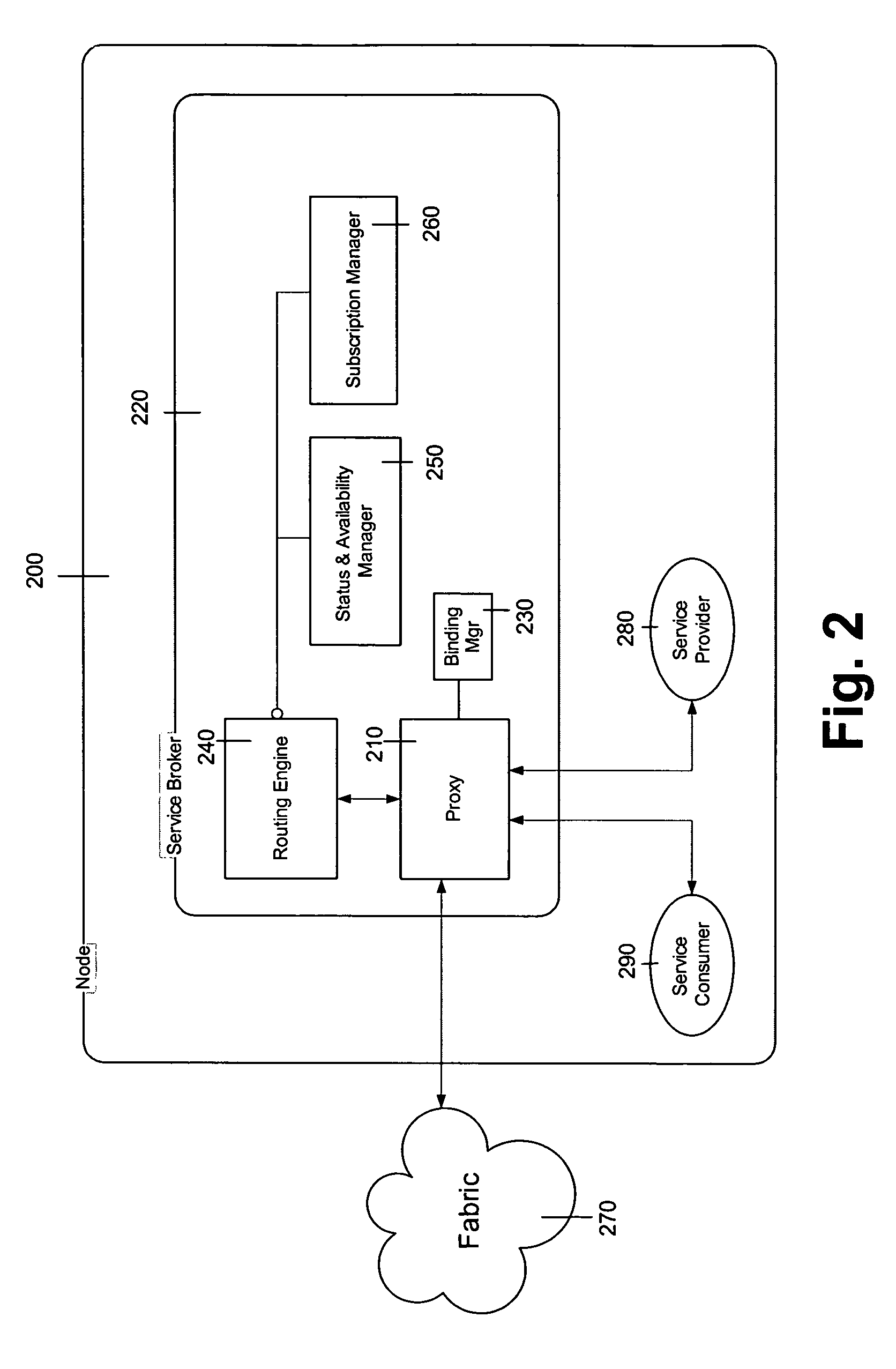
Method and apparatus to accomplish peer-to-peer application data routing between service consumers and service providers within a service oriented architecture
ActiveUS8868779B2Multiple digital computer combinationsData switching networksFault toleranceLoad Shedding
A Peer-to-Peer Application Data Routing Fabric is described. The Fabric provides routing between endpoints resident in peer nodes of a Service Oriented Architecture where the routing is based on endpoint presence, availability, status, and location to satisfy the requirements of fault tolerance and load balancing among homogenous endpoints; or routing by address among instances of differing type. In the preferred embodiment of the Fabric, the Session Initiation Protocol components, interactions and transport mechanisms are leveraged and extended.
Owner:ACCENTURE GLOBAL SERVICES LTD
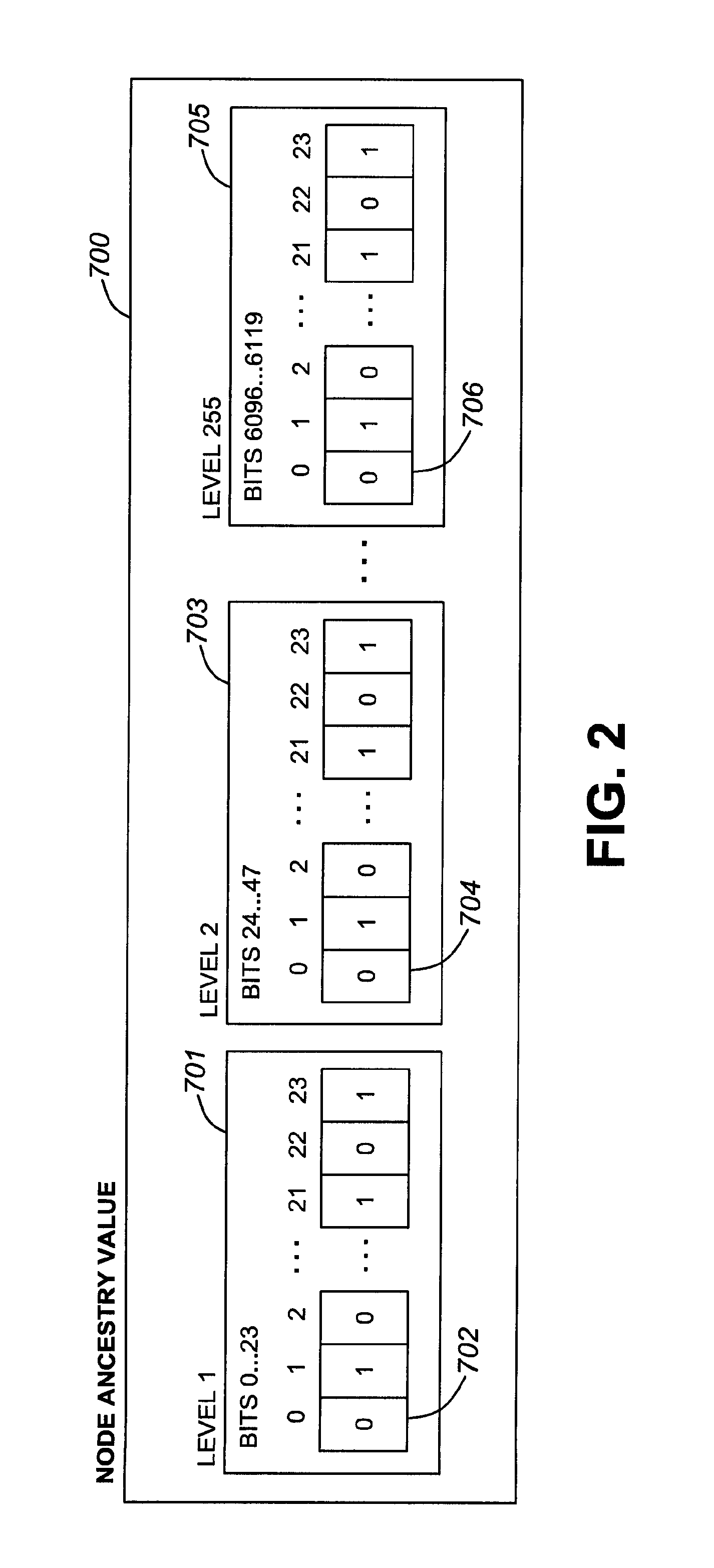
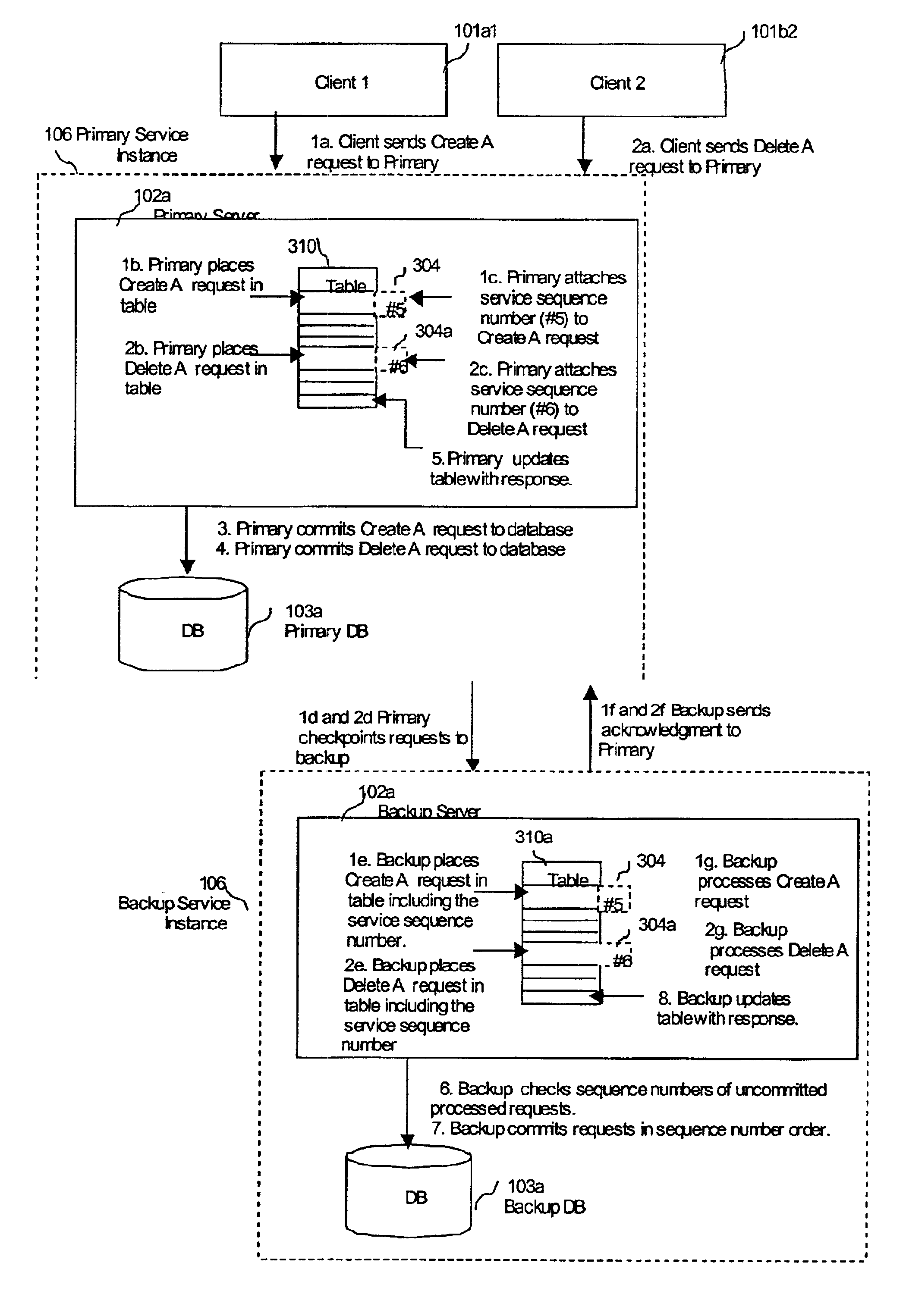
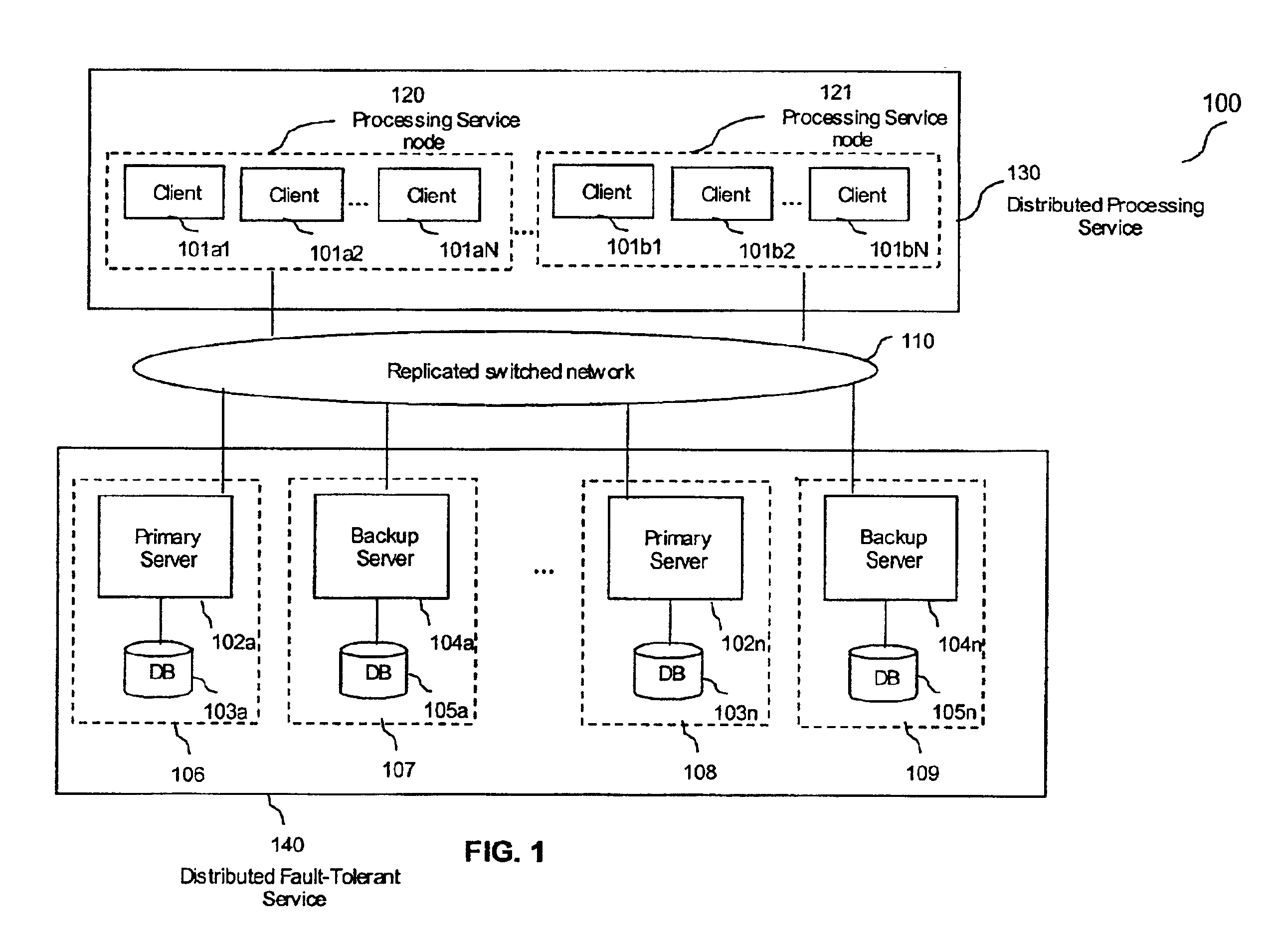
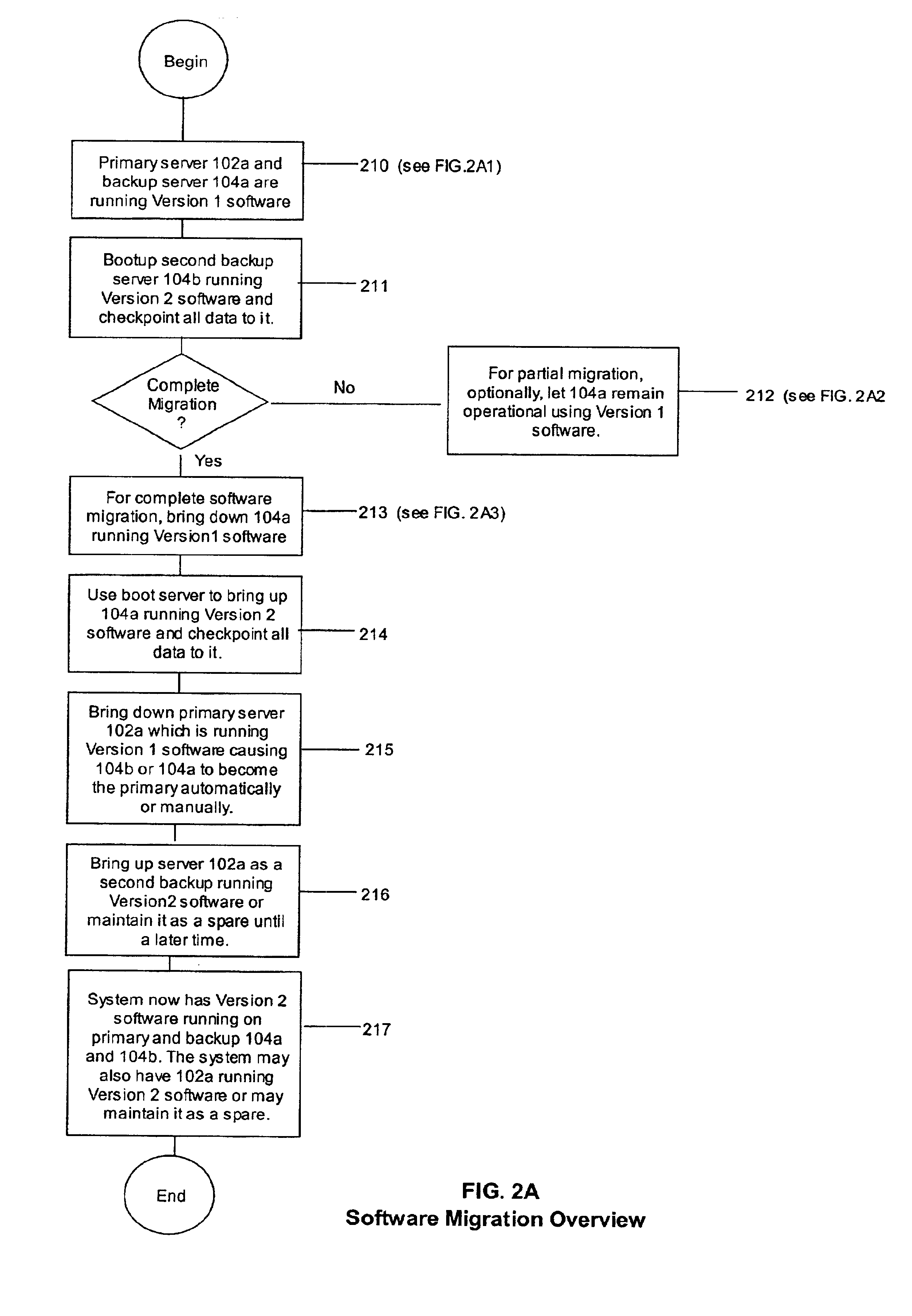
Fault tolerance using logical checkpointing in computing systems
InactiveUS6954877B2Checkpointing is lightweight and greatly simplifiedInput/output to record carriersRedundant operation error correctionFault toleranceNetworking protocol
A system and method for checkpointing a primary computer process to a backup computer process such that if there is a failure of a primary process, the backup process can takeover without interruption. In addition, upgrades to different version of software or equipment can take place without interruption. The invention provides a lightweight checkpointing method that allows checkpointing of only external requests or messages that change the state of the service instance, thereby reducing the overhead and performance penalties. In addition, the present invention checkpoints data for primary and backups that do not share resources but are logically equivalent. All communication between the primary and backup takes places using network protocols.
Owner:ZAMBEEL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com