Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2872 results about "Networking protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
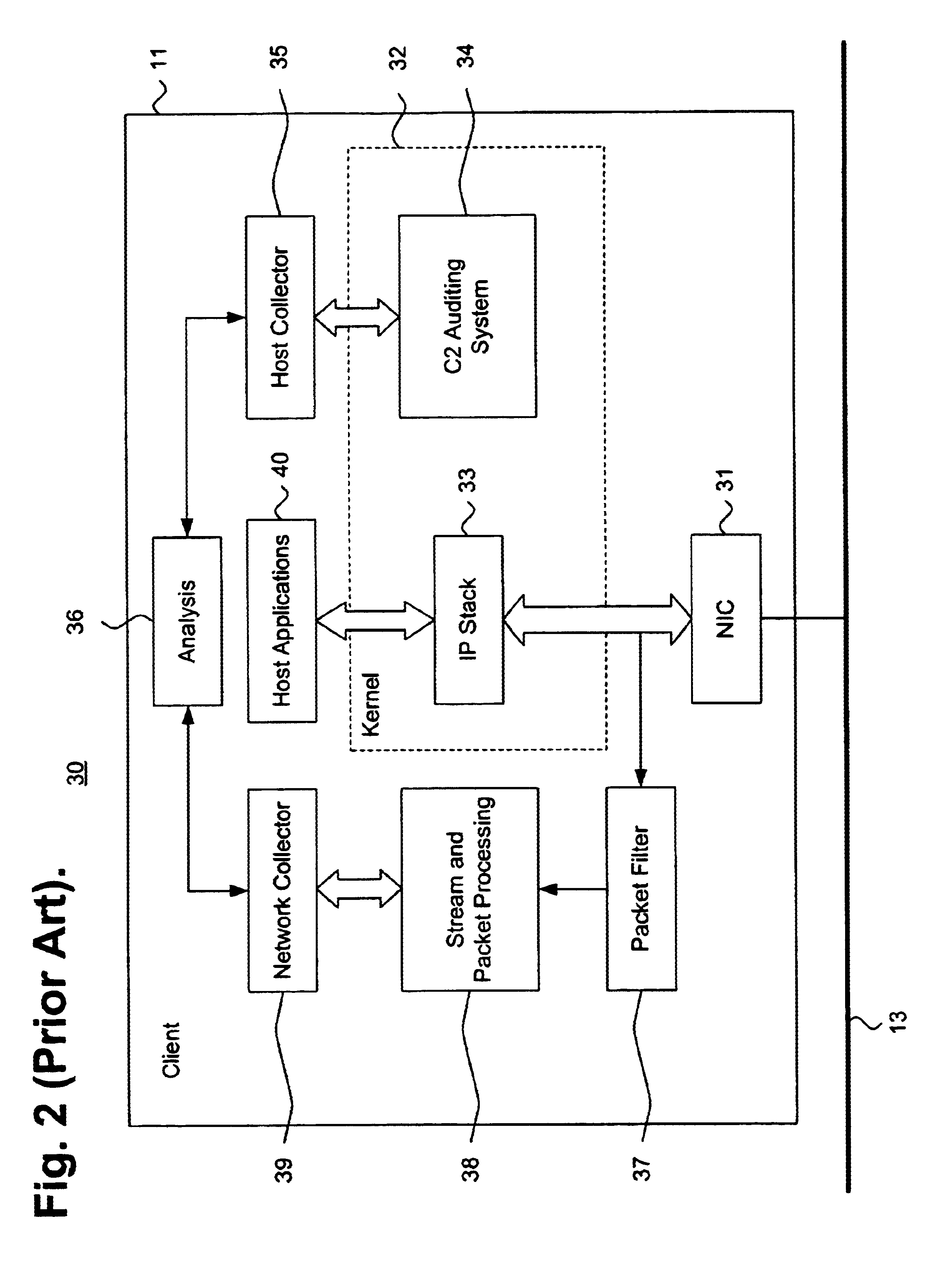
Network protocols are the language of rules and conventions used for handing communicated between network devices and ensuring the optimal operation of a network. Network protocols include key internet protocols such as IP and IPv6 as well as DNS and FTP, and it also includes more network-specific protocols like SNMP and NTP.
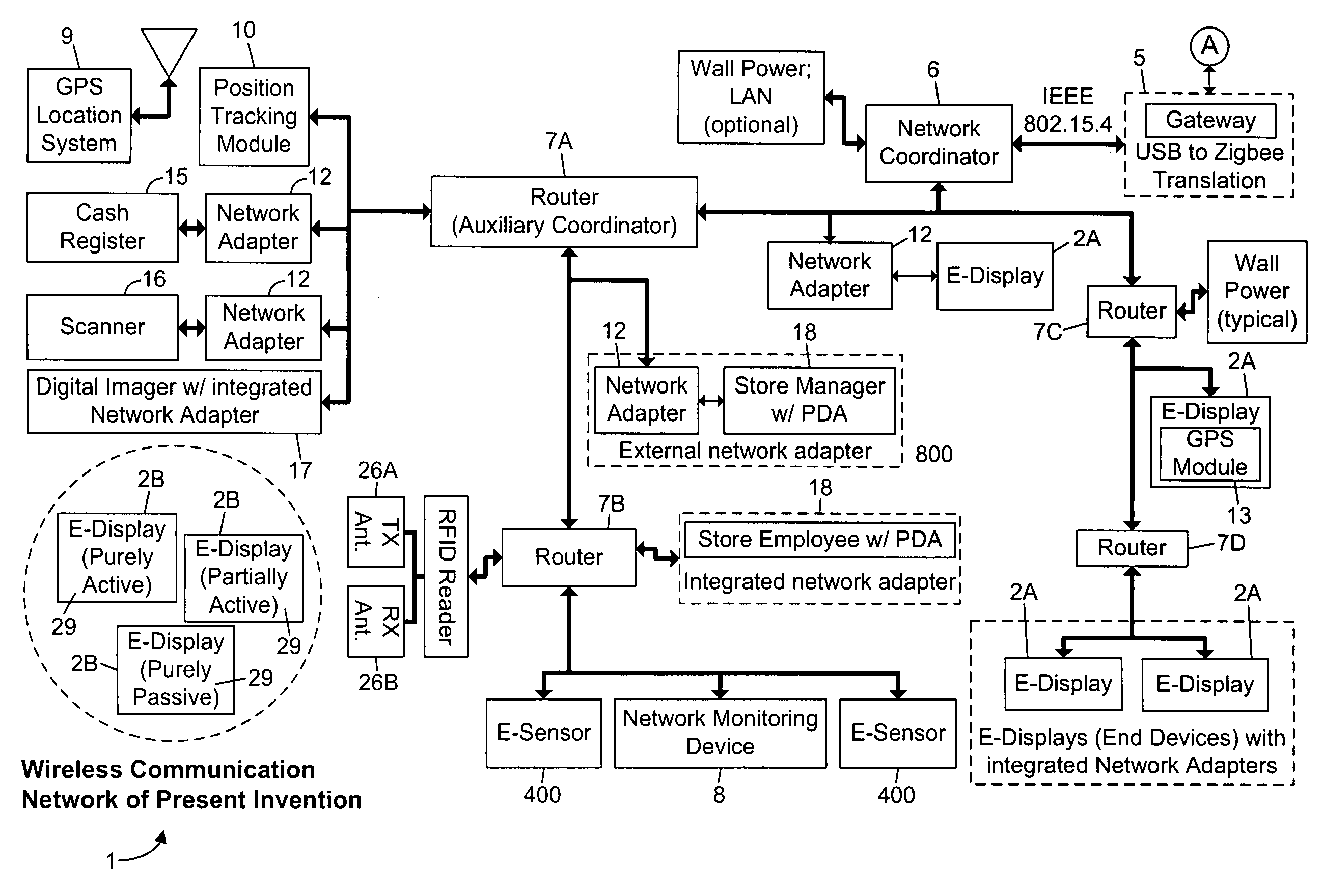
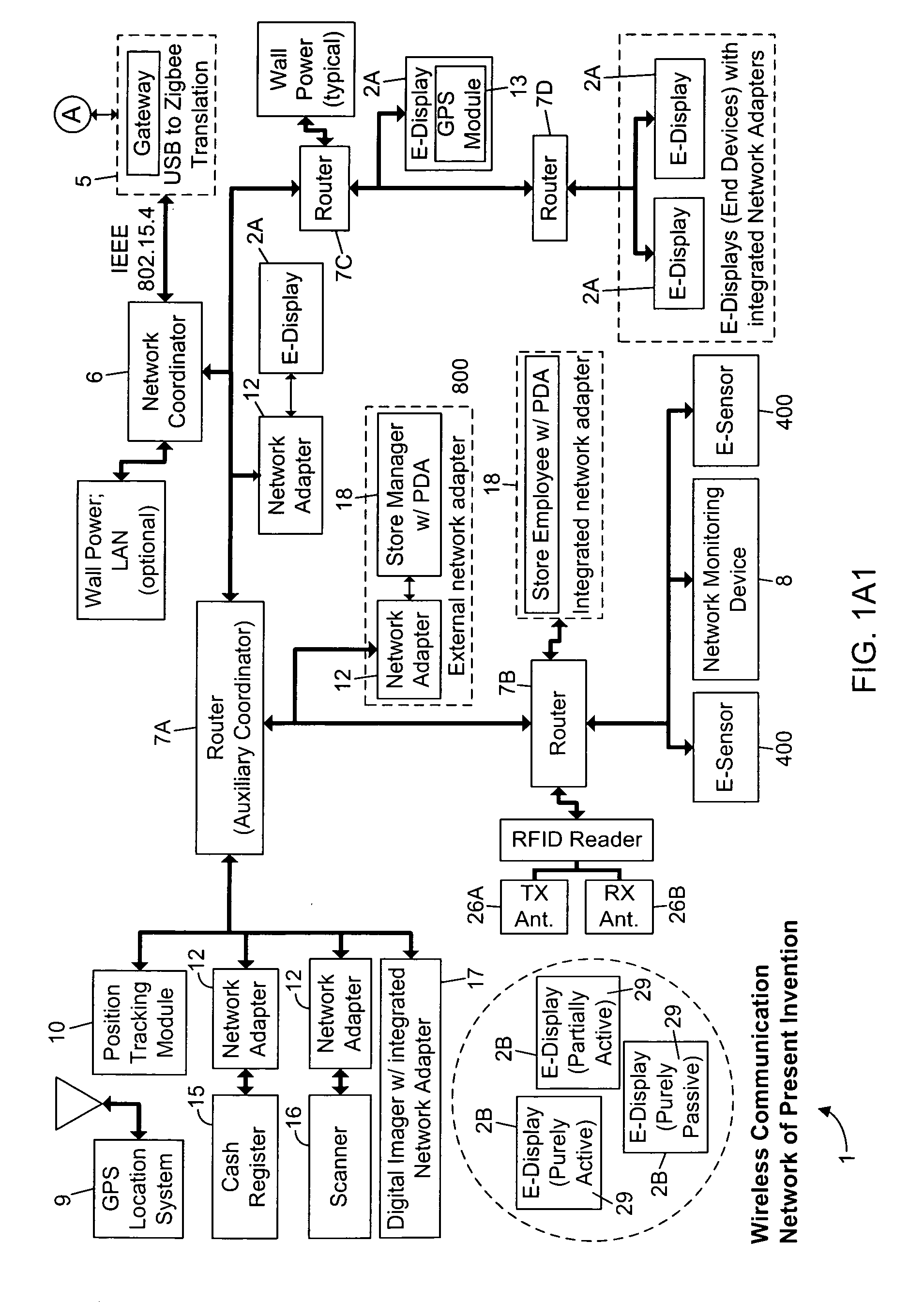
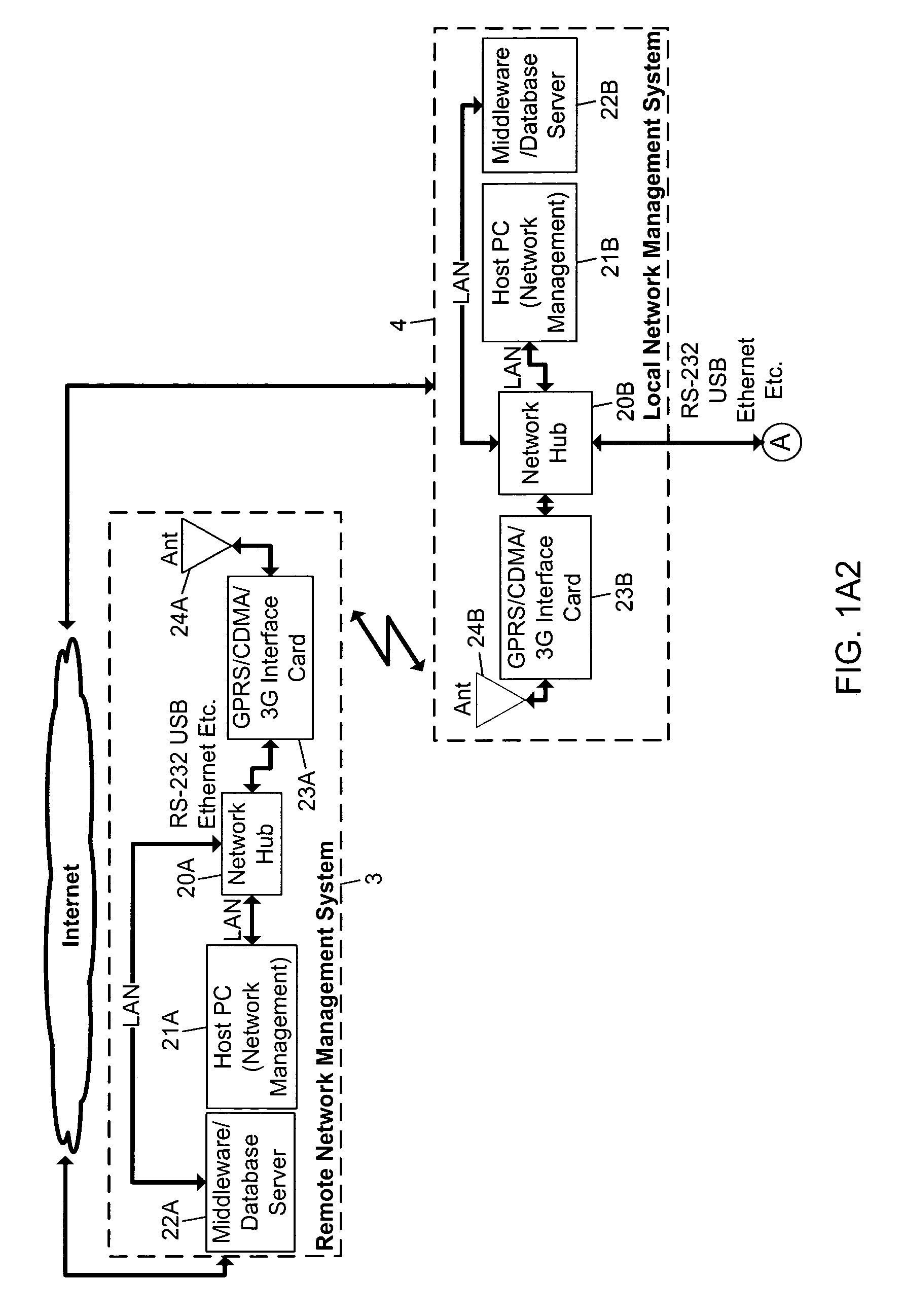
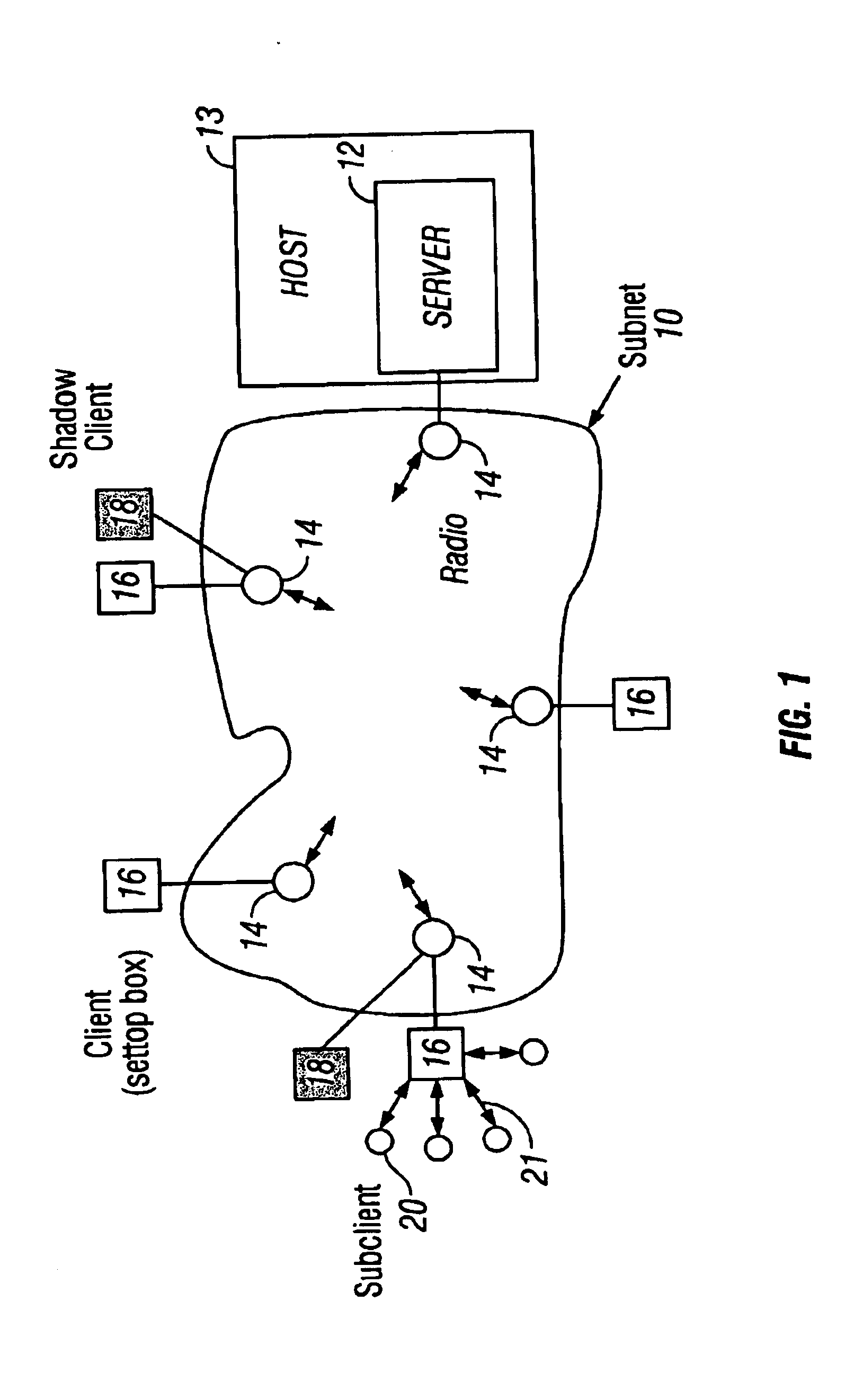
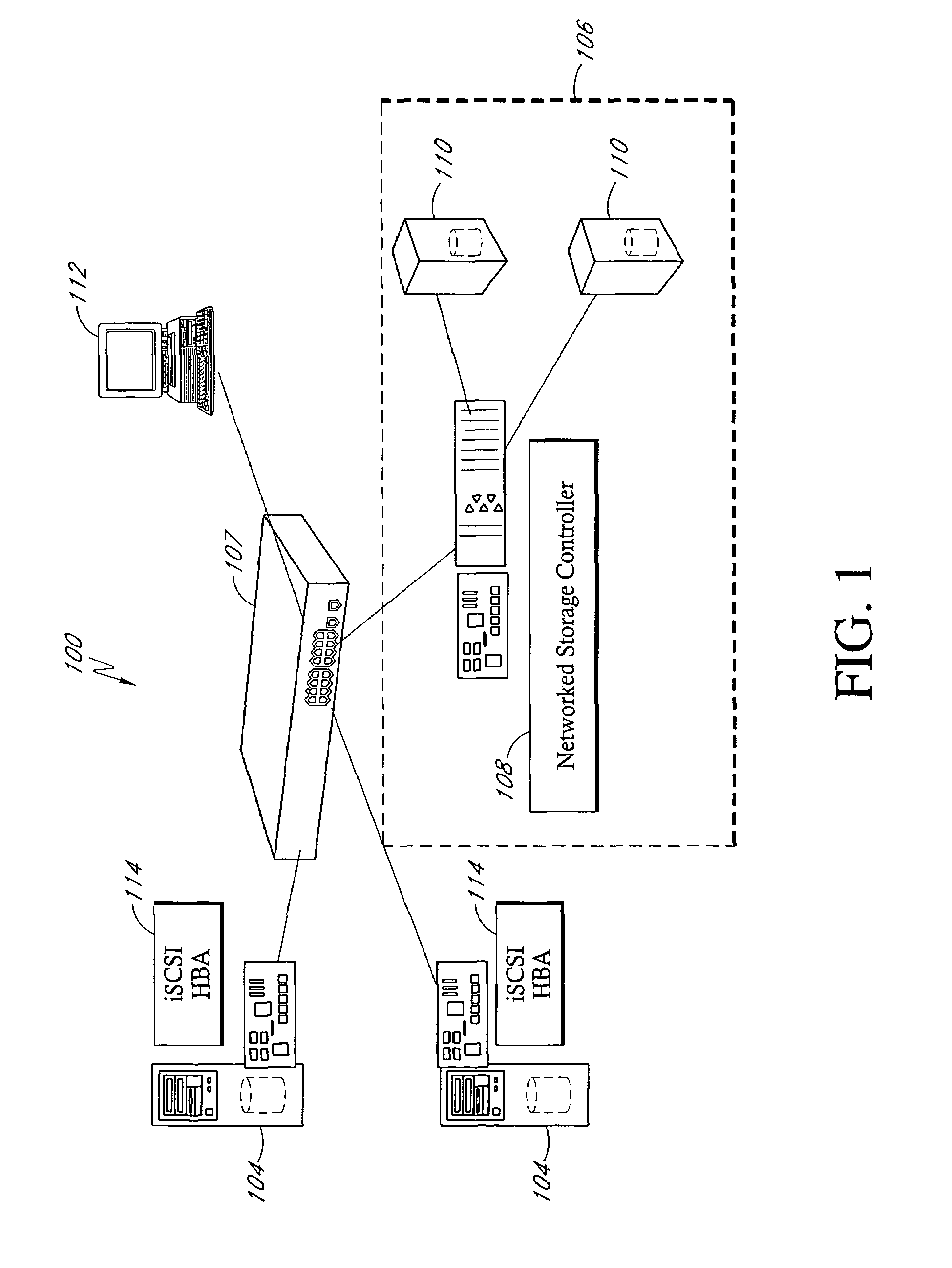
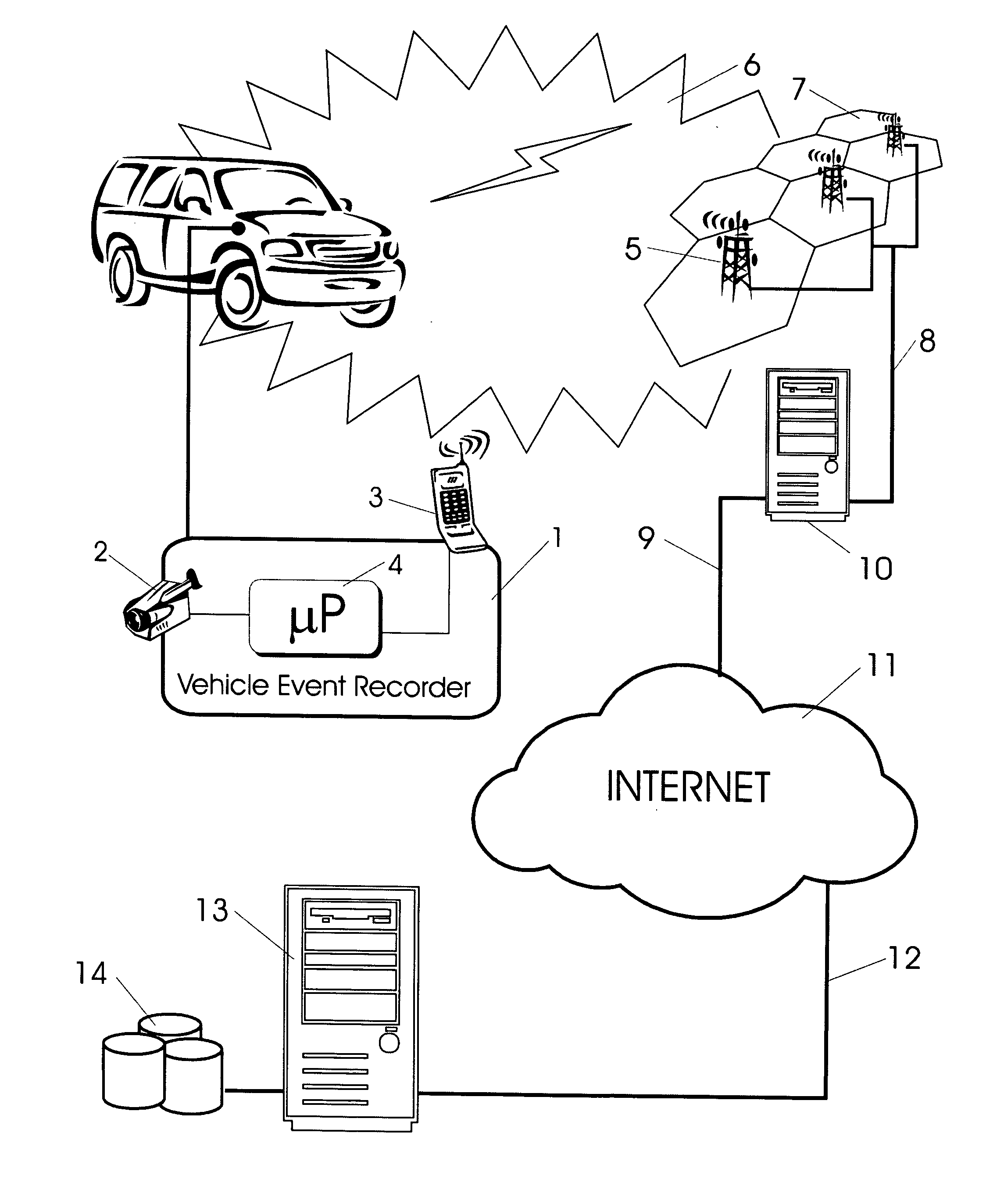
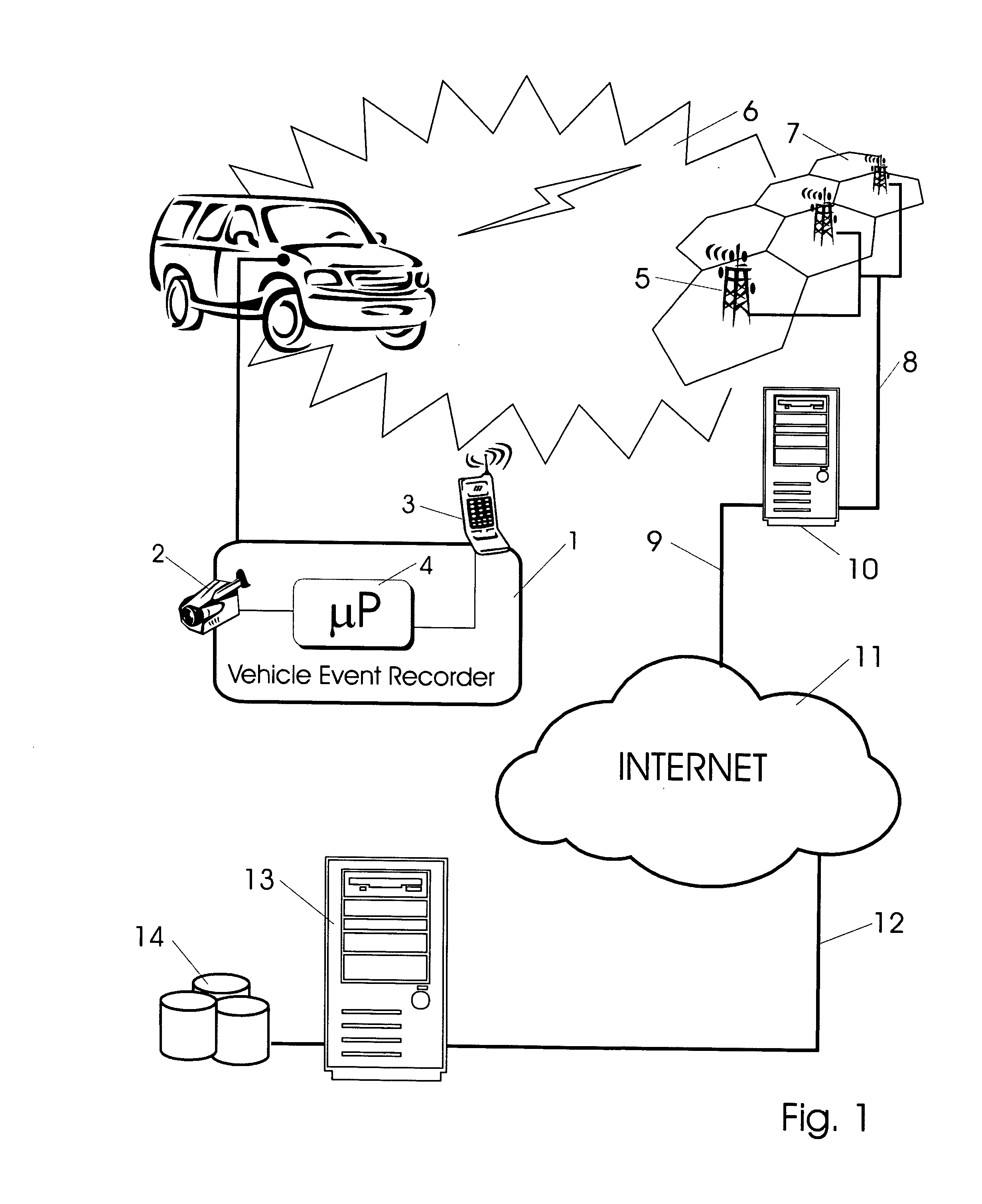
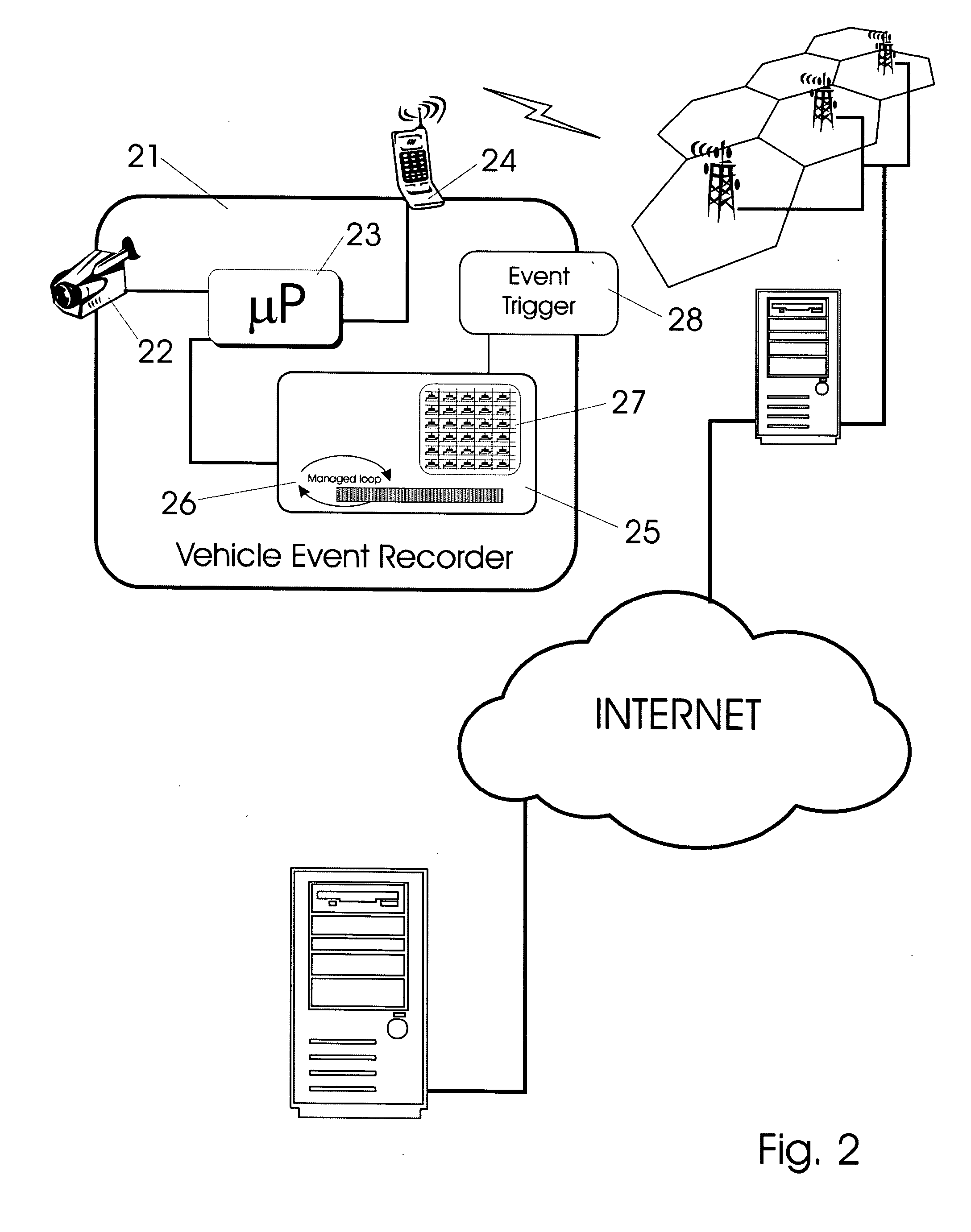
Methods of and apparatus for programming and managing diverse network components, including electronic-ink based display devices, in a mesh-type wireless communication network
InactiveUS20100177749A1Static indicating devicesDigital data processing detailsLogistics managementDisplay device
A wireless communication network for programming and monitoring a plurality of network-managed devices, including electronic-ink based display devices, comprising a network management computer system, a network gateway device, one or more wireless network routers, a plurality of network-managed devices, and a network coordinator. The wireless communication network of the present invention bridges the gap between wireless display networks, wireless sensor networks, and the worlds of passive, active and partially-active RFID and real-time locating systems. The wireless communication network of the present invention allows conventional communication network protocols to operate in more flexible ways in dynamic, diverse, and heterogeneous application environments, in fields including retail, healthcare, transport, logistics, manufacturing, education, etc. At the same time, the wireless communication network of the present invention is preferably based on the IEEE 802.15.4 network layer standard, which offers low-cost wireless network communication between a large number of wireless network end-devices.
Owner:METROLOGIC INSTR
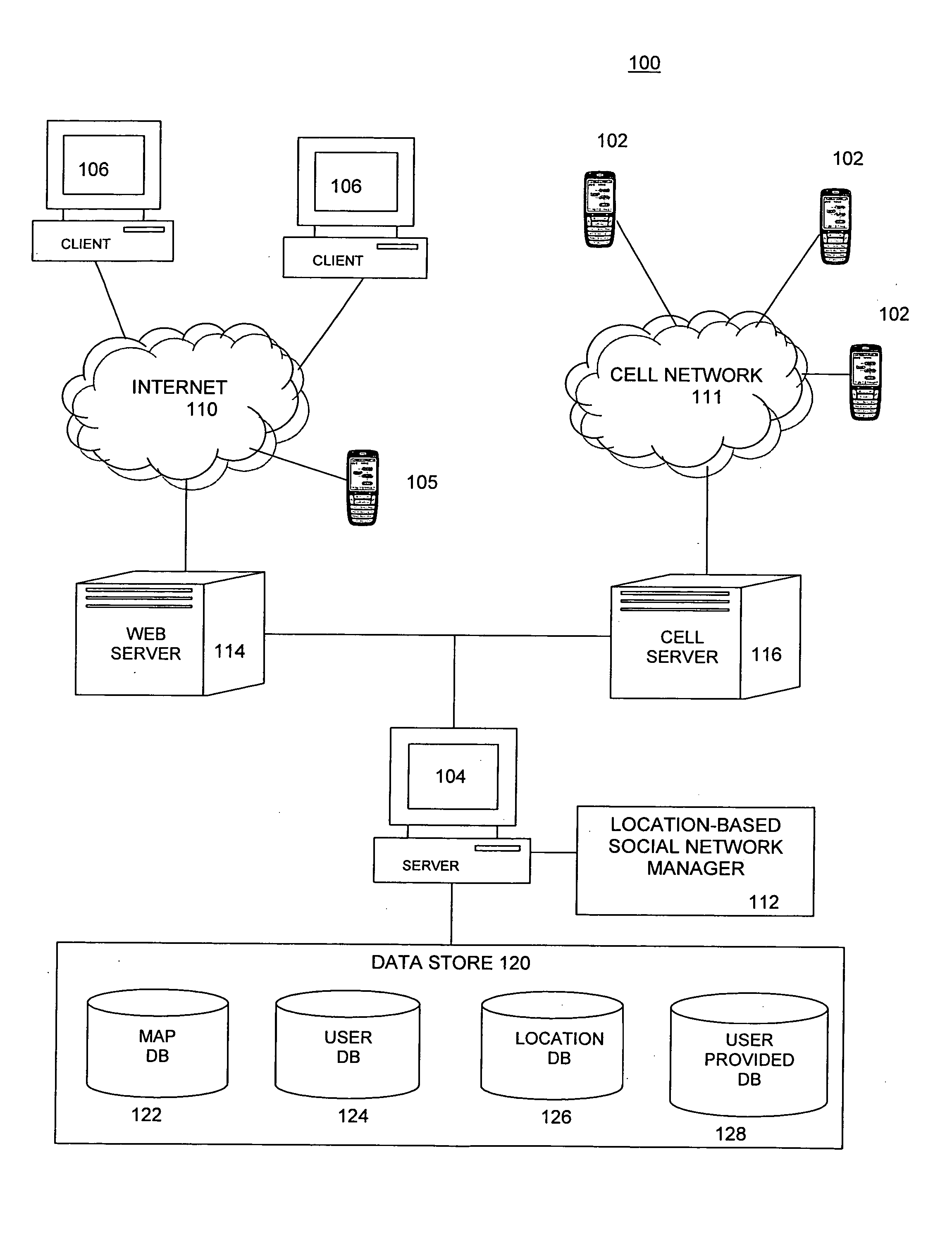
Displaying and tagging places of interest on location-aware mobile communication devices in a local area network
InactiveUS20070281690A1Facilitate information sharingInformation formatContent conversionInformation networksDisplay device
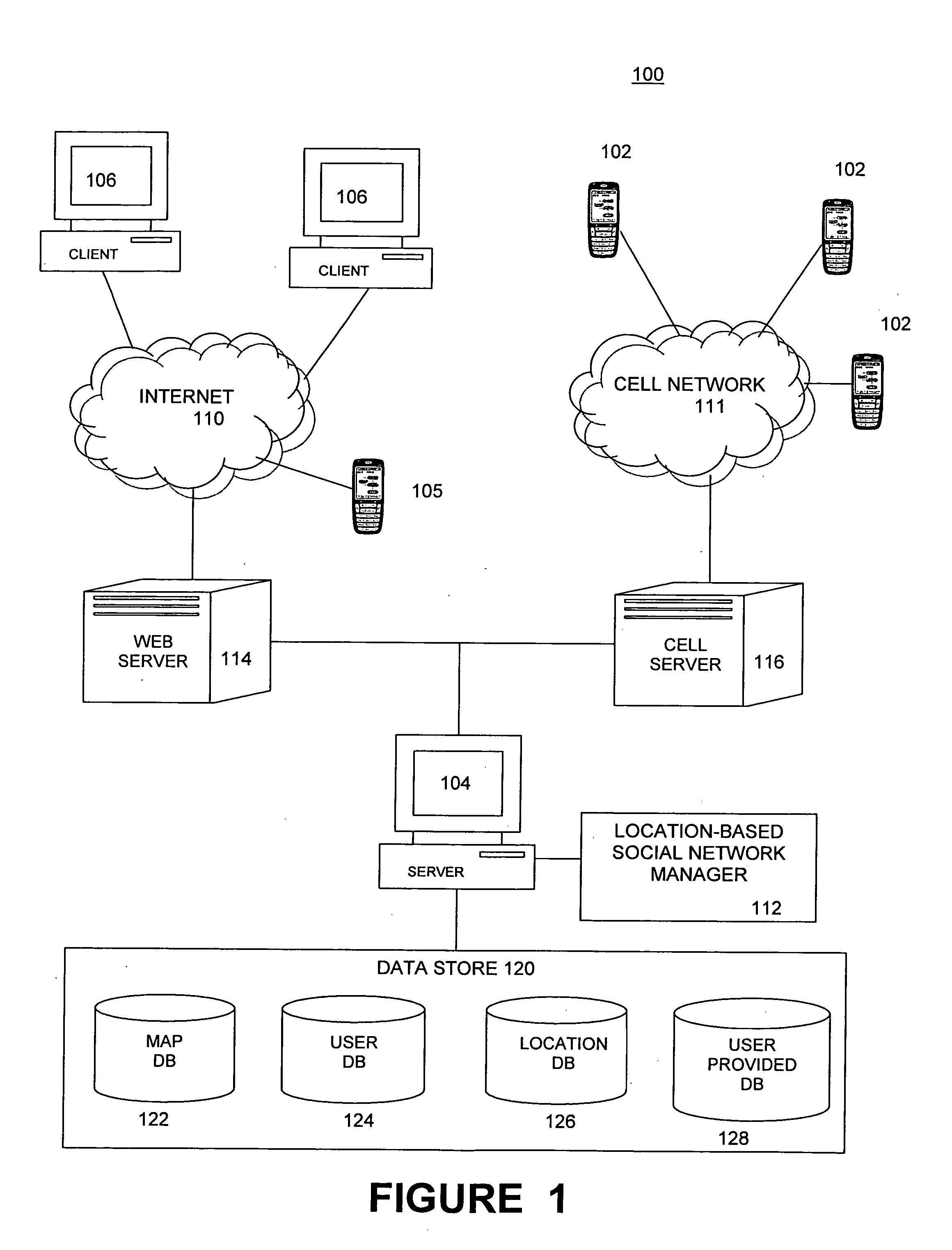
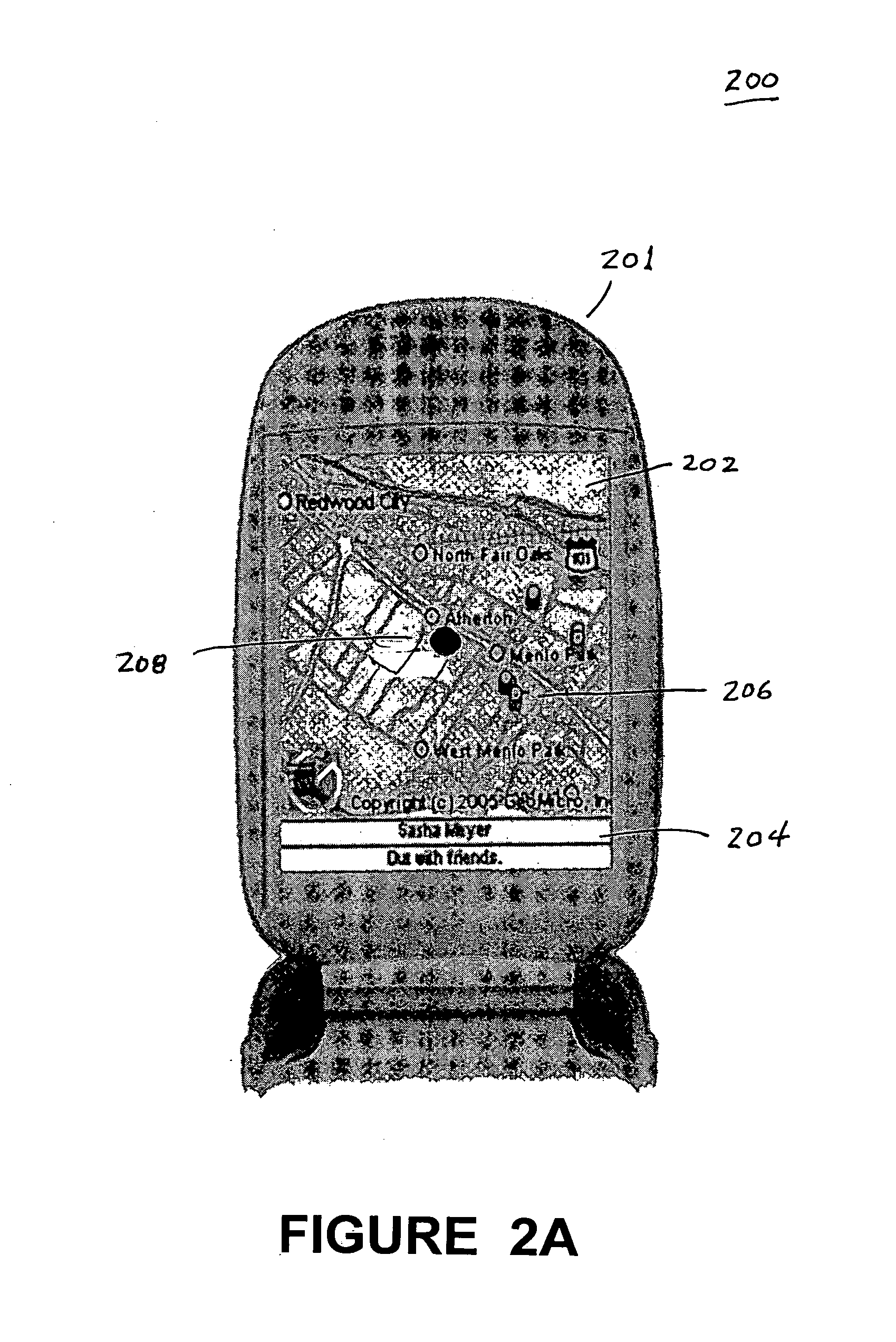
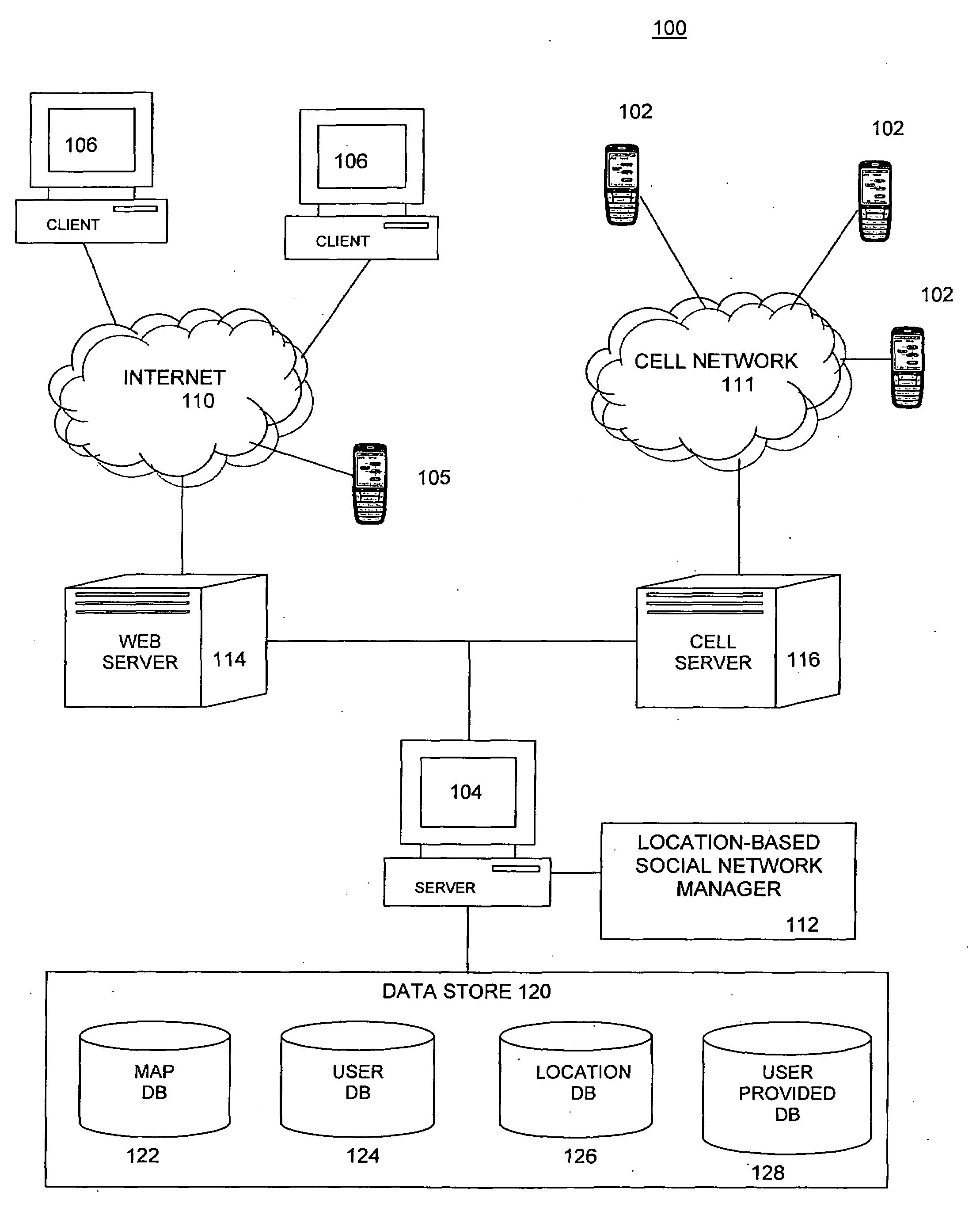
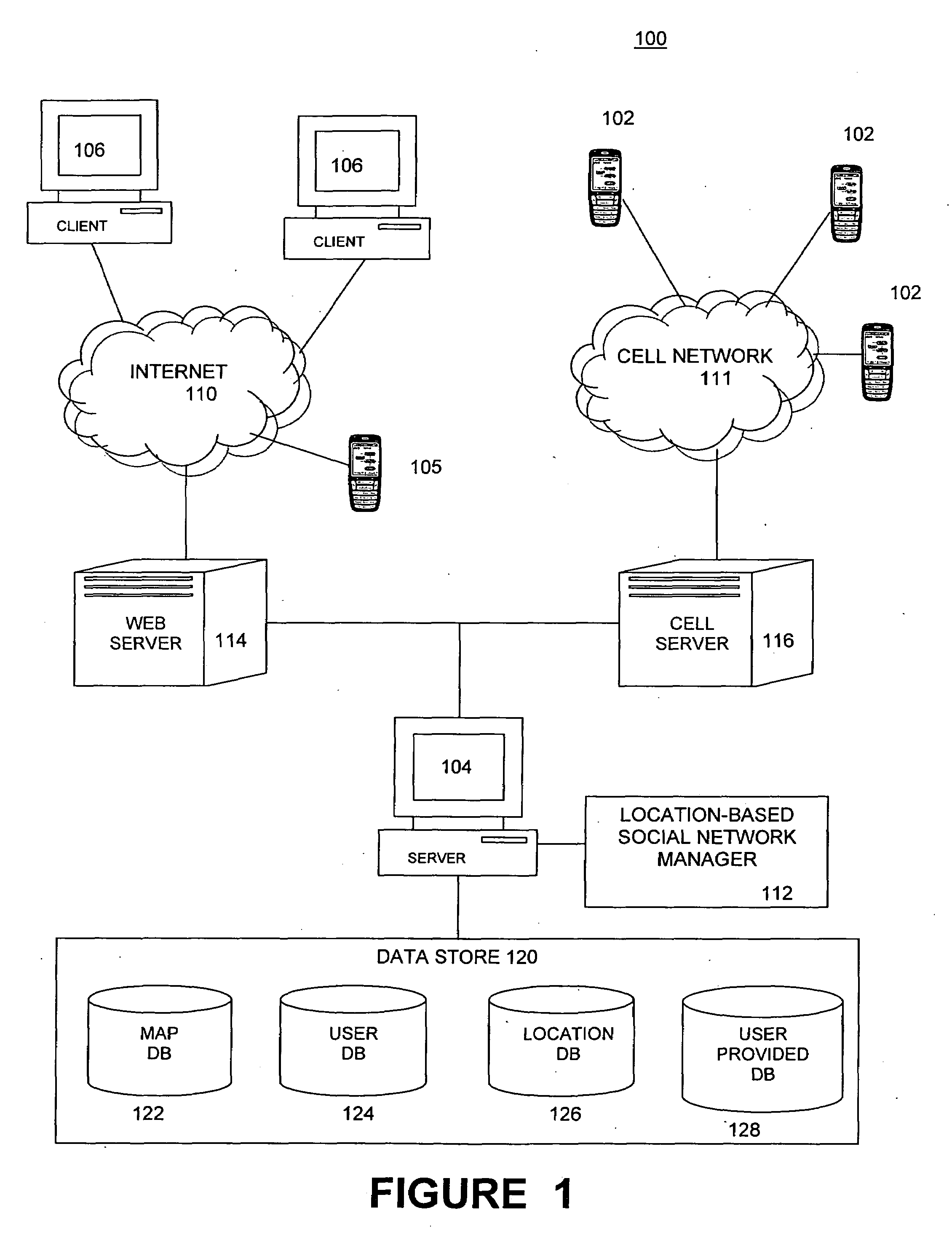
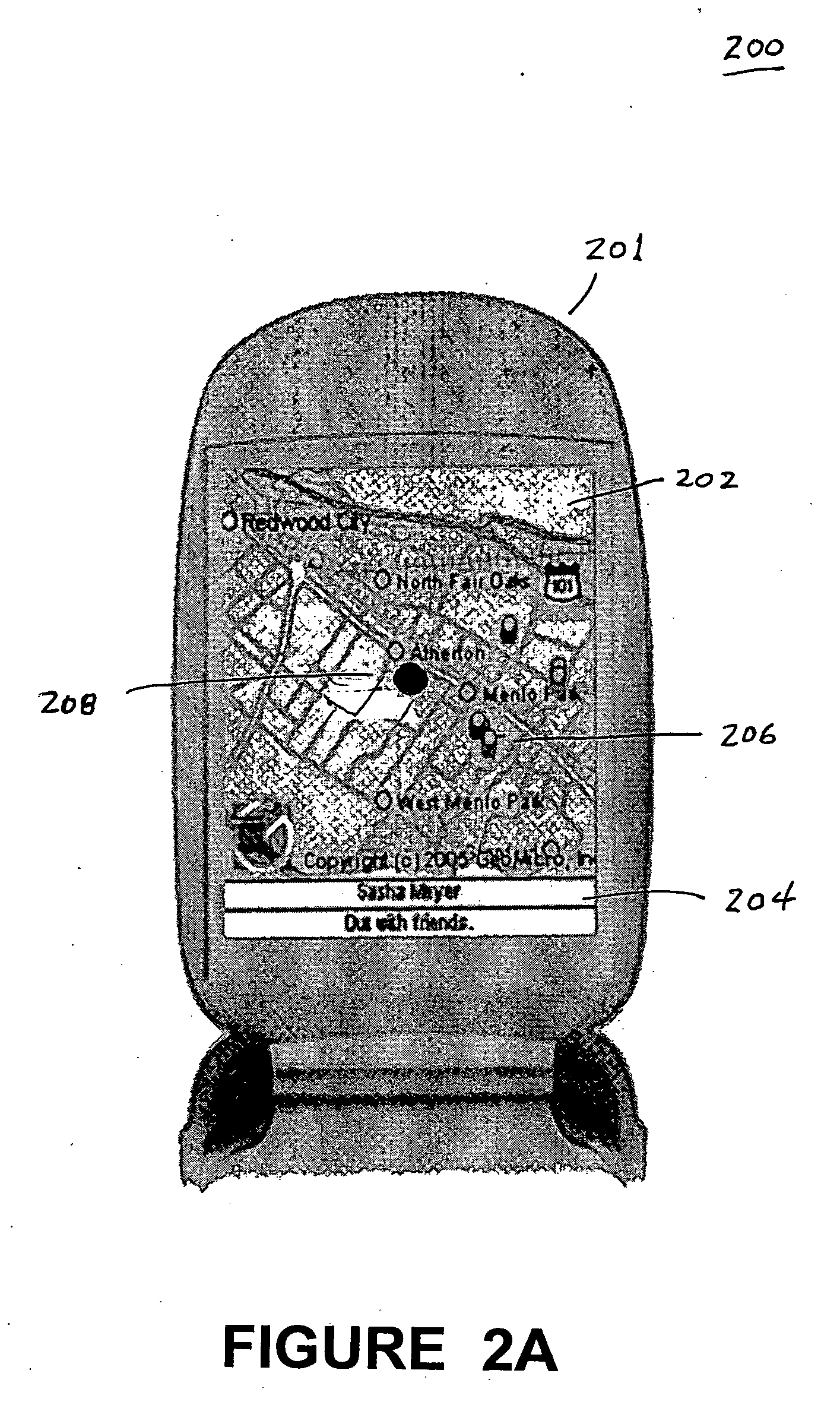
Embodiments of a location-based social network manager process are described. The process is executed on a server computer coupled to a plurality of location-aware mobile communication devices over a wireless network. The process determines the geographic location of a mobile communication device operated by a user within an area, displays a map representation of the area around the mobile communication device on a graphical user interface of the mobile communication device, and superimposes on the map the respective locations of one or more other users of mobile communication devices coupled to the mobile communication device over the network. The process establishes communication links between the user and the plurality of acquaintances through respective location aware mobile communication devices through a network protocol. The process facilitates the sharing information about places of interest among a plurality of users. The system stores location information for a place of interest in a region in a database along with information related to the place of interest. The location of the place of interest is displayed on each user's mobile communication device as an icon superimposed on the map shown on the display. The location of the users can be established with respect to their distance relative to a place of interest. Users can define their own places of interest as well as provide a quantitative or qualitative ranking for places of interest within a region. This information can then be shared with other users in the network.
Owner:LOOPT
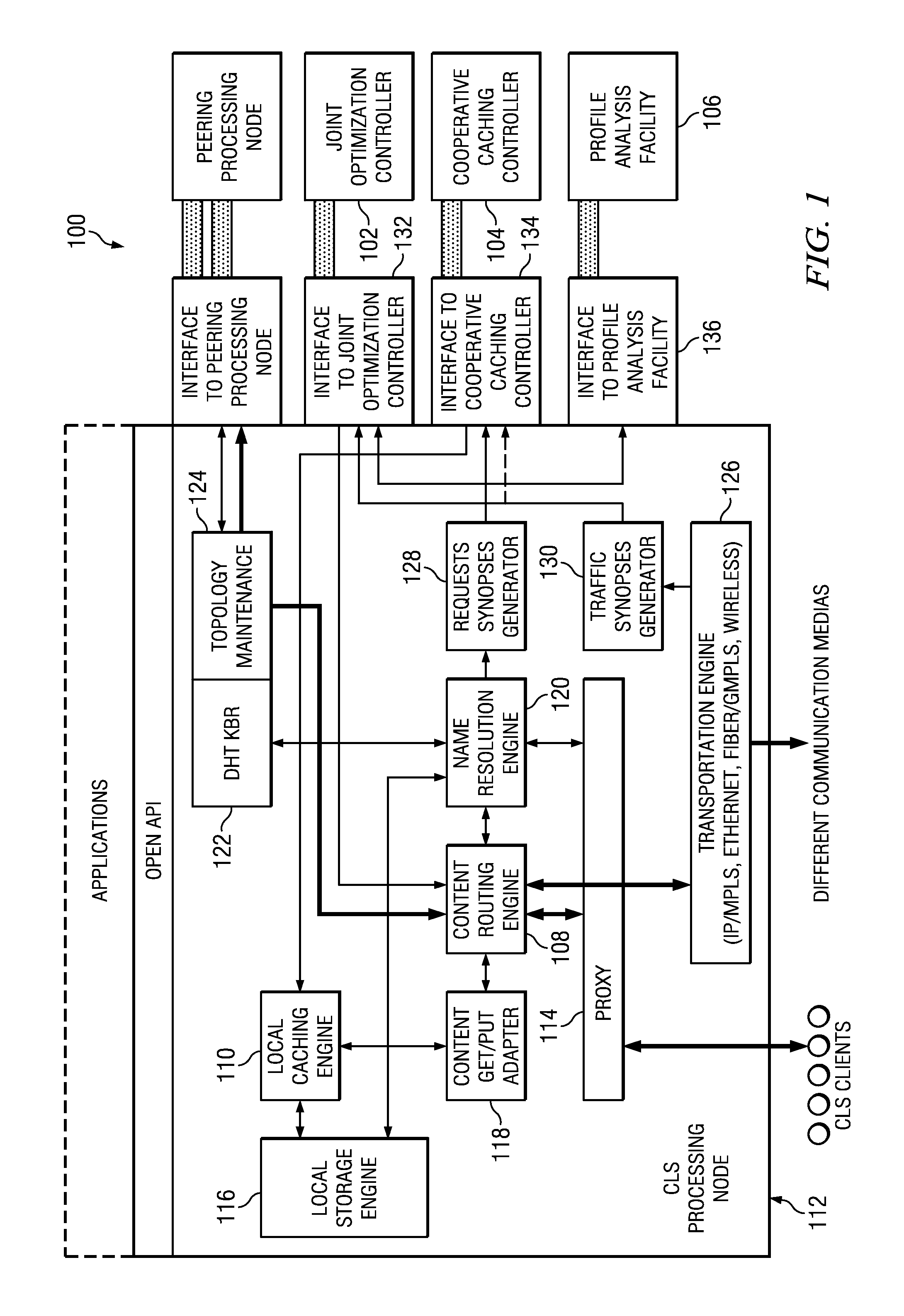
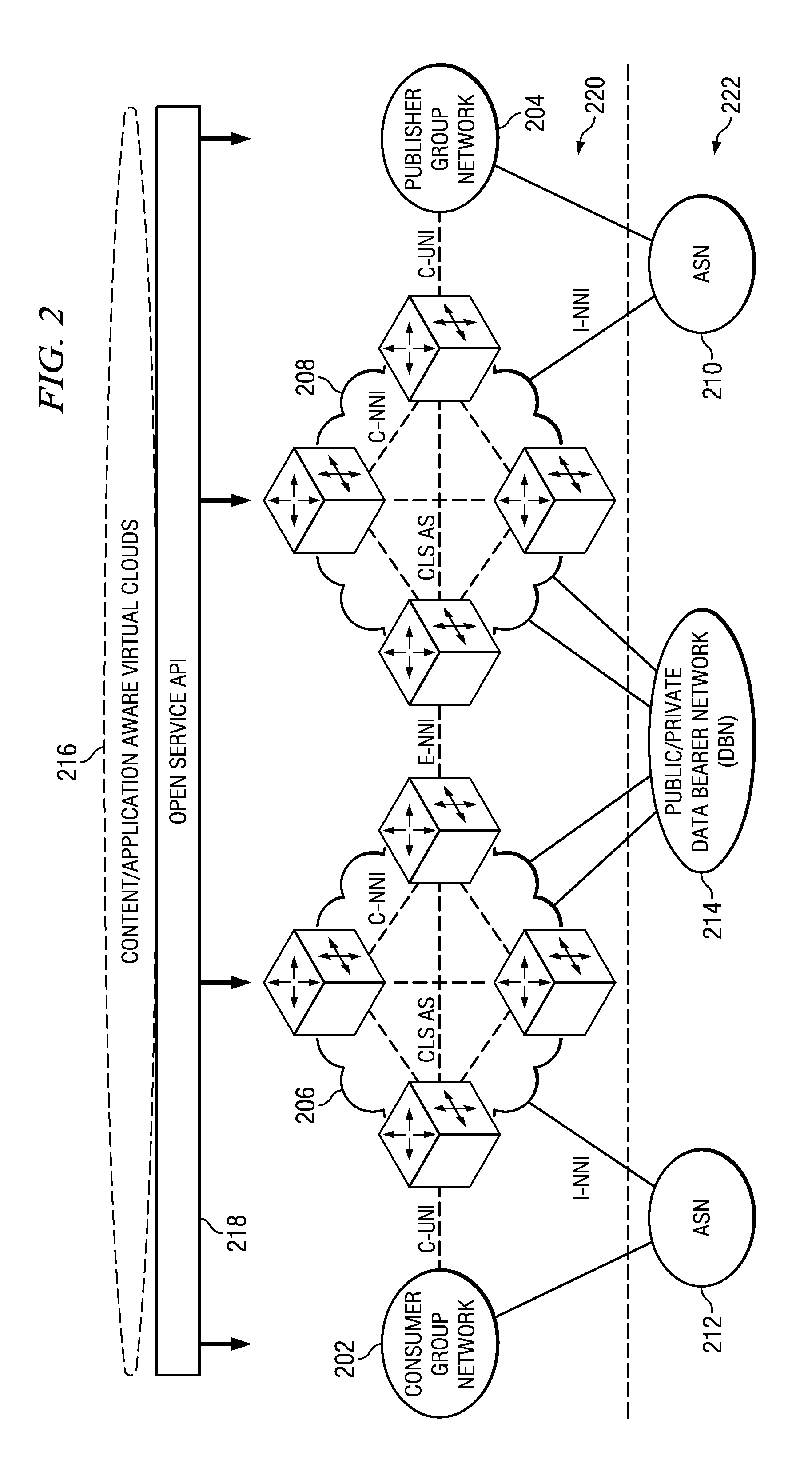
System and Method for a Context Layer Switch
ActiveUS20110271007A1Multiple digital computer combinationsTransmissionNetworking protocolWeb protocols
Owner:FUTUREWEI TECH INC
Multiple network protocol encoder/decoder and data processor
InactiveUS6034963AReduce system costLow costTime-division multiplexData switching by path configurationRaw socketByte
A multiple network protocol encoder / decoder comprising a network protocol layer, data handler, O.S. State machine, and memory manager state machines implemented at a hardware gate level. Network packets are received from a physical transport level mechanism by the network protocol layer state machine which decodes network protocols such as TCP, IP, User Datagram Protocol (UDP), PPP, and Raw Socket concurrently as each byte is received. Each protocol handler parses and strips header information immediately from the packet, requiring no intermediate memory. The resulting data are passed to the data handler which consists of data state machines that decode data formats such as email, graphics, Hypertext Transfer Protocol (HTTP), Java, and Hypertext Markup Language (HTML). Each data state machine reacts accordingly to the pertinent data, and any data that are required by more than one data state machine is provided to each state machine concurrently, and any data required more than once by a specific data state machine, are placed in a specific memory location with a pointer designating such data (thereby ensuring minimal memory usage). Resulting display data are immediately passed to a display controller. Any outgoing network packets are created by the data state machines and passed through the network protocol state machine which adds header information and forwards the resulting network packet via a transport level mechanism.
Owner:NVIDIA CORP
Headset-Based Telecommunications Platform
ActiveUS20100245585A1Extend battery lifeTelevision system detailsOptical rangefindersData streamPeer-to-peer
A hands-free wireless wearable GPS enabled video camera and audio-video communications headset, mobile phone and personal media player, capable of real-time two-way and multi-feed wireless voice, data and audio-video streaming, telecommunications, and teleconferencing, coordinated applications, and shared functionality between one or more wirelessly networked headsets or other paired or networked wired or wireless devices and optimized device and data management over multiple wired and wireless network connections. The headset can operate in concert with one or more wired or wireless devices as a paired accessory, as an autonomous hands-free wide area, metro or local area and personal area wireless audio-video communications and multimedia device and / or as a wearable docking station, hot spot and wireless router supporting direct connect multi-device ad-hoc virtual private networking (VPN). The headset has built-in intelligence to choose amongst available network protocols while supporting a variety of onboard, and remote operational controls including a retractable monocular viewfinder display for real time hands-free viewing of captured or received video feed and a duplex data-streaming platform supporting multi-channel communications and optimized data management within the device, within a managed or autonomous federation of devices or other peer-to-peer network configuration.
Owner:EYECAM INC
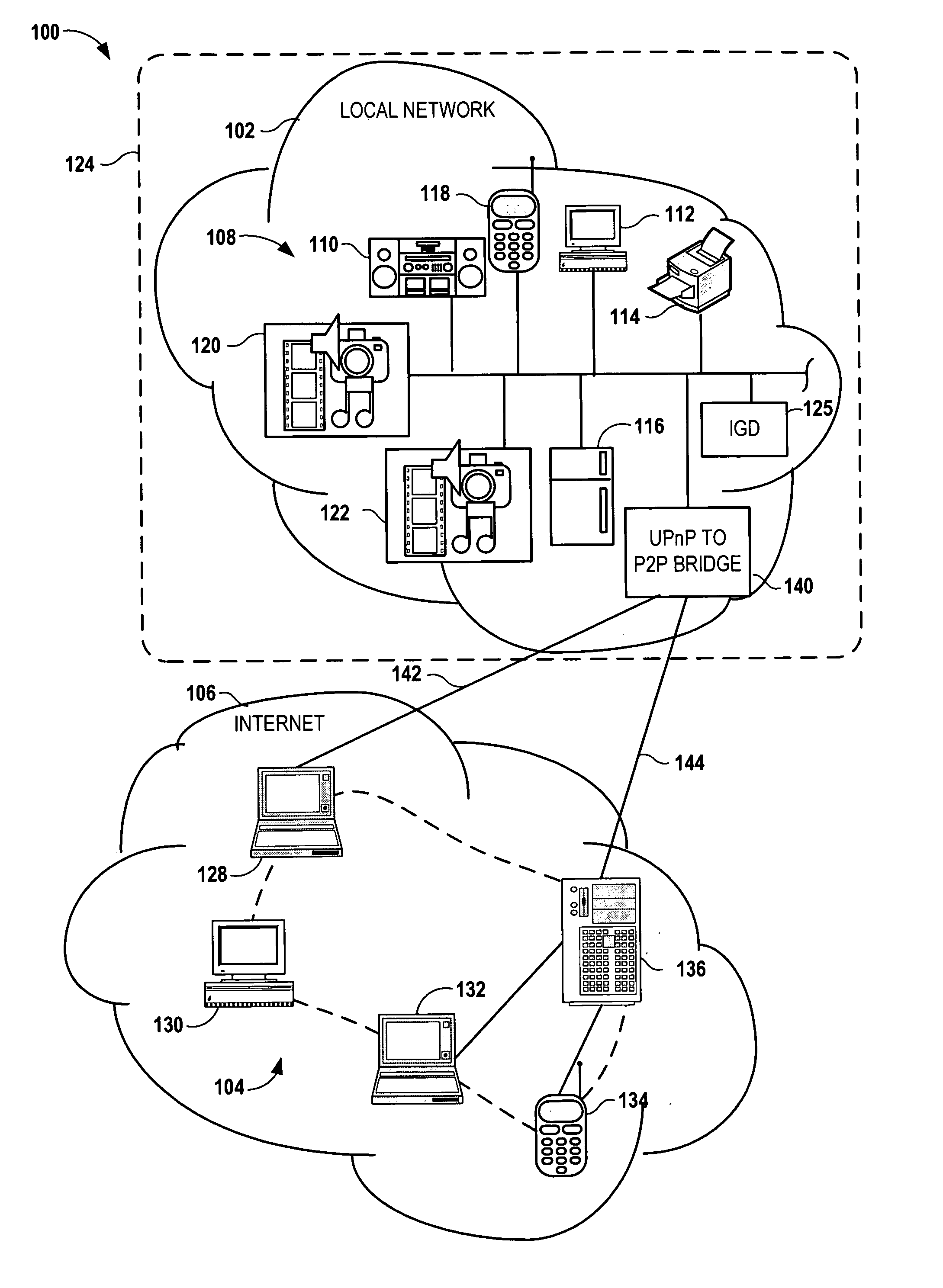
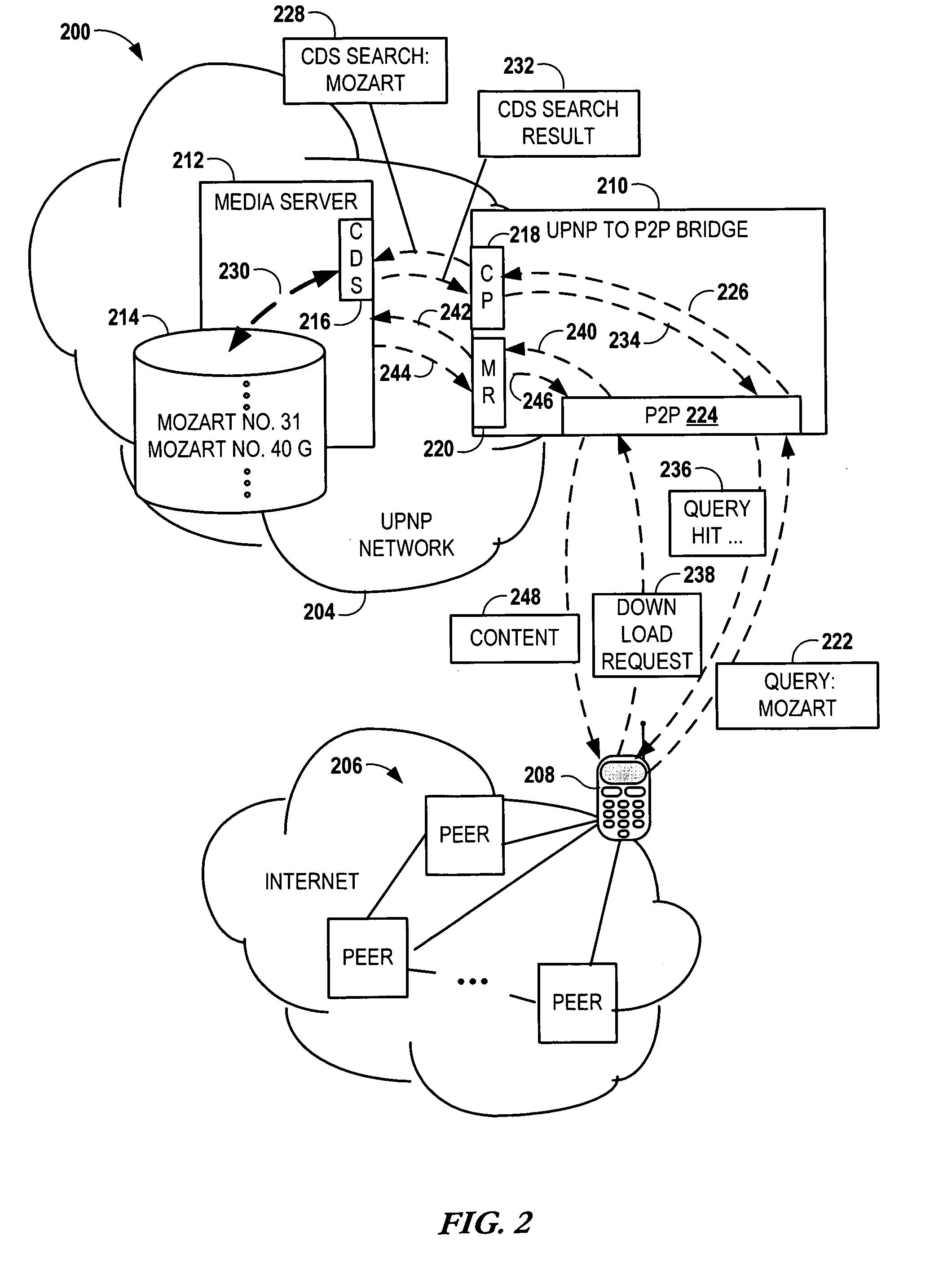
Bridging between AD HOC local networks and internet-based peer-to-peer networks
ActiveUS20070274327A1Easy to downloadFacilitate downloading the mediaData switching by path configurationMultiple digital computer combinationsNetworking protocolTTEthernet
Bridging between ad hoc local networks and Internet based peer-to-peer networks involves coupling a bridge device to a local network using an ad-hoc, peer-to-peer protocol used for exchanging data between consumer electronics devices. The bridge device is coupled to a public network using an Internet-based peer-to-peer networking protocol. In one arrangement, metadata related to media accessible from a media server of the local network is determined via the bridge device, and the metadata is transformed via the bridge device to enable peer-to-peer devices of the public network to discover the media via the bridge device using the Internet-based peer-to-peer networking protocol. In another arrangement, metadata related to media accessible from the public network is determined via the peer-to-peer networking protocol, and the metadata is transformed via the bridge device to enable a device of the local network to discover the media via the bridge device using the ad-hoc, peer-to-peer protocol.
Owner:CONVERSANT WIRELESS LICENSING LTD
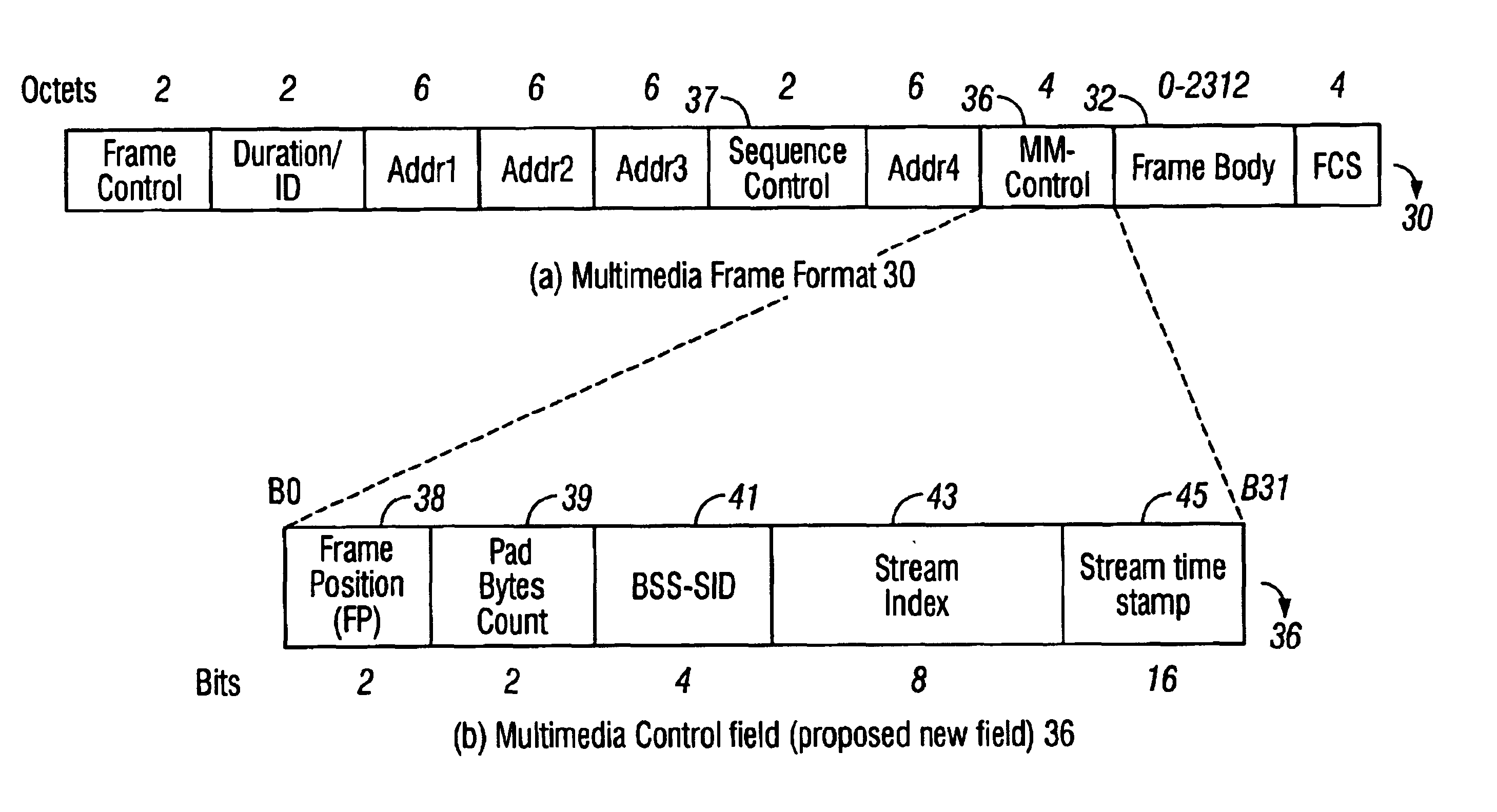
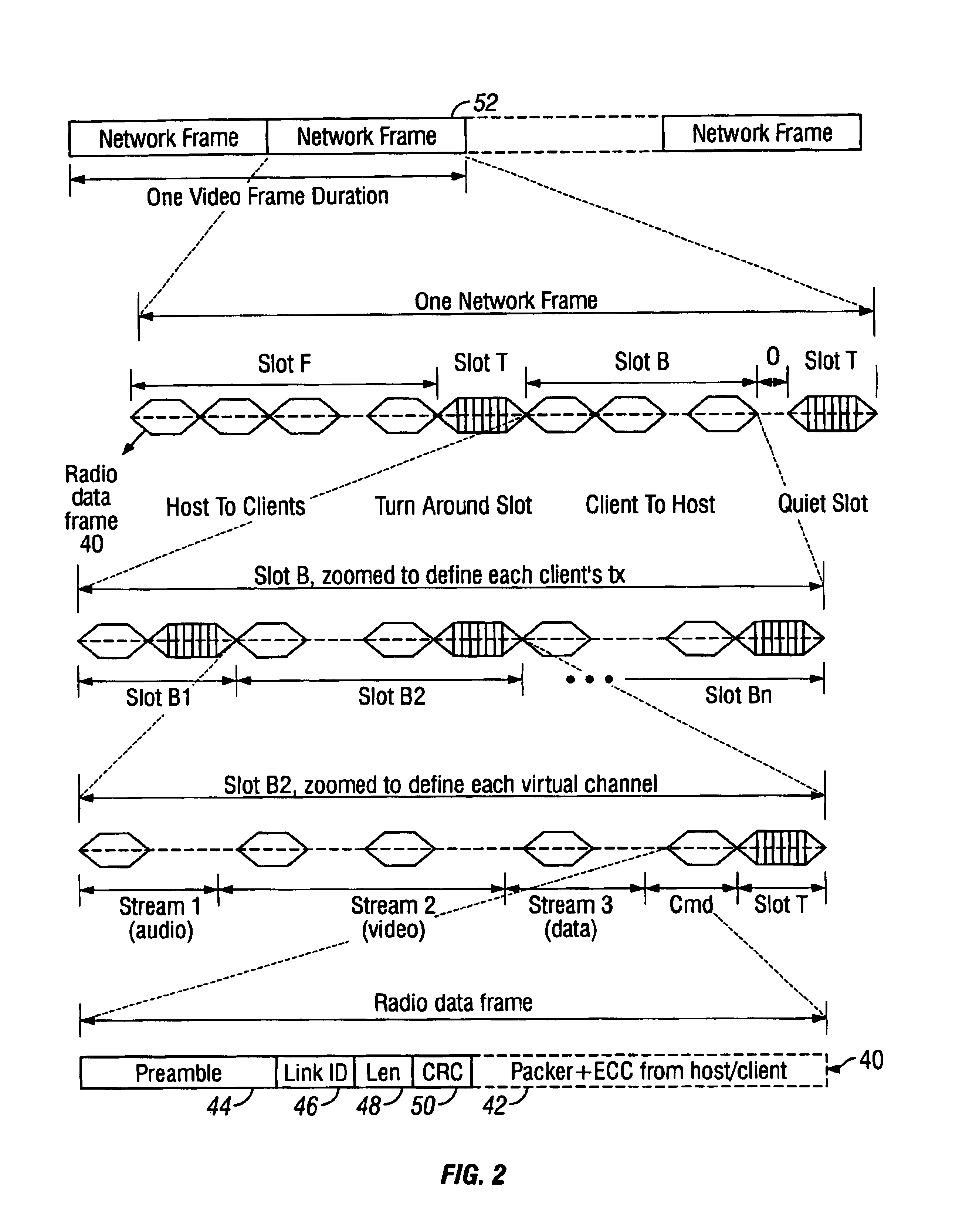
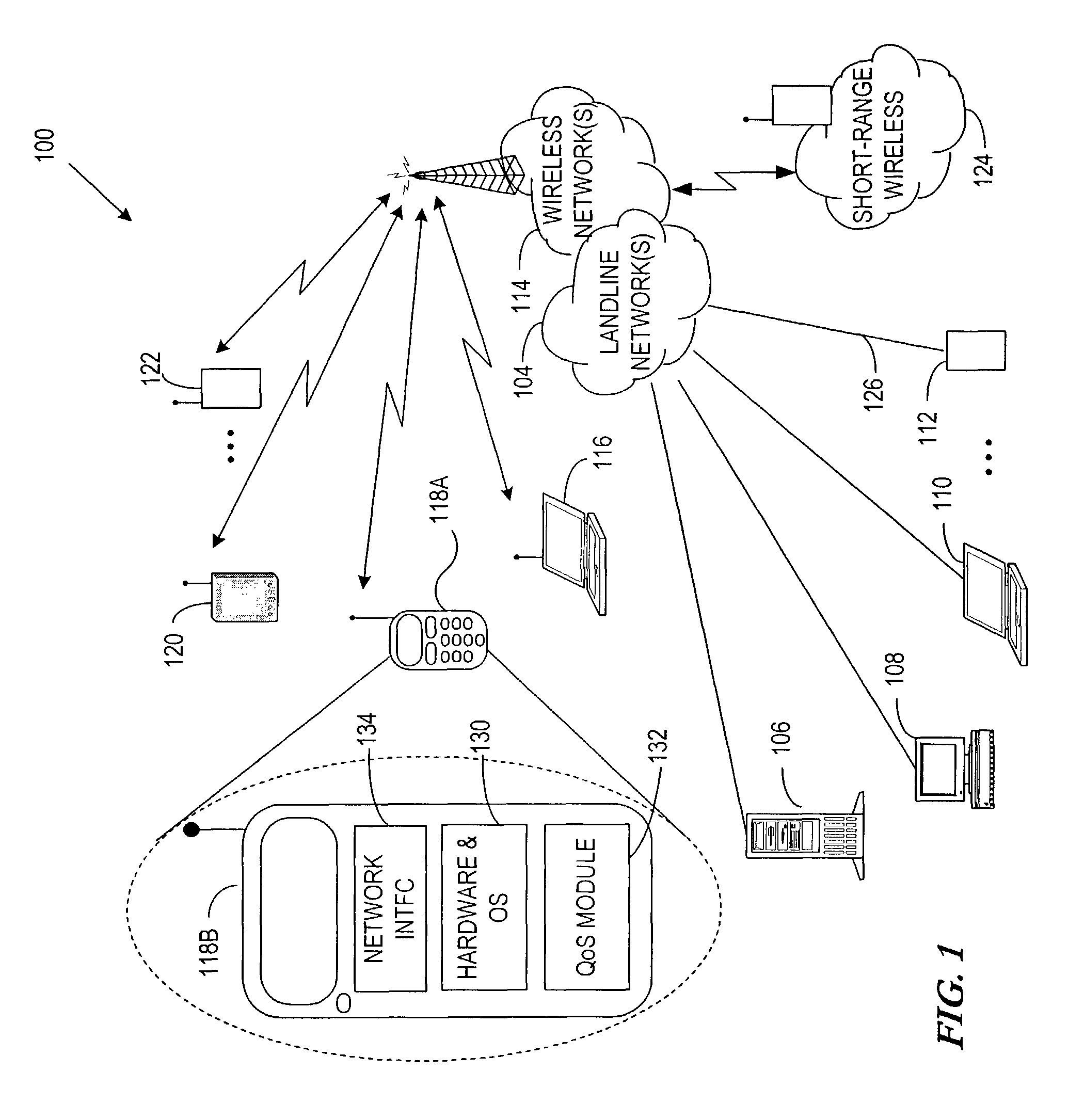
Quality of service extensions for multimedia applications in wireless computer networks
InactiveUS6934752B1Easy to operateBetter their inter-operationNetwork traffic/resource managementAssess restrictionQuality of serviceNetworking protocol
A networking protocol includes definitions of quality of service enhancements to provide reliable multimedia data stream connections in wireless computer networks. These enhancements may be implemented as extensions to packet headers, such as a multimedia control field made up of various sub fields.
Owner:CIRRUS LOGIC INC
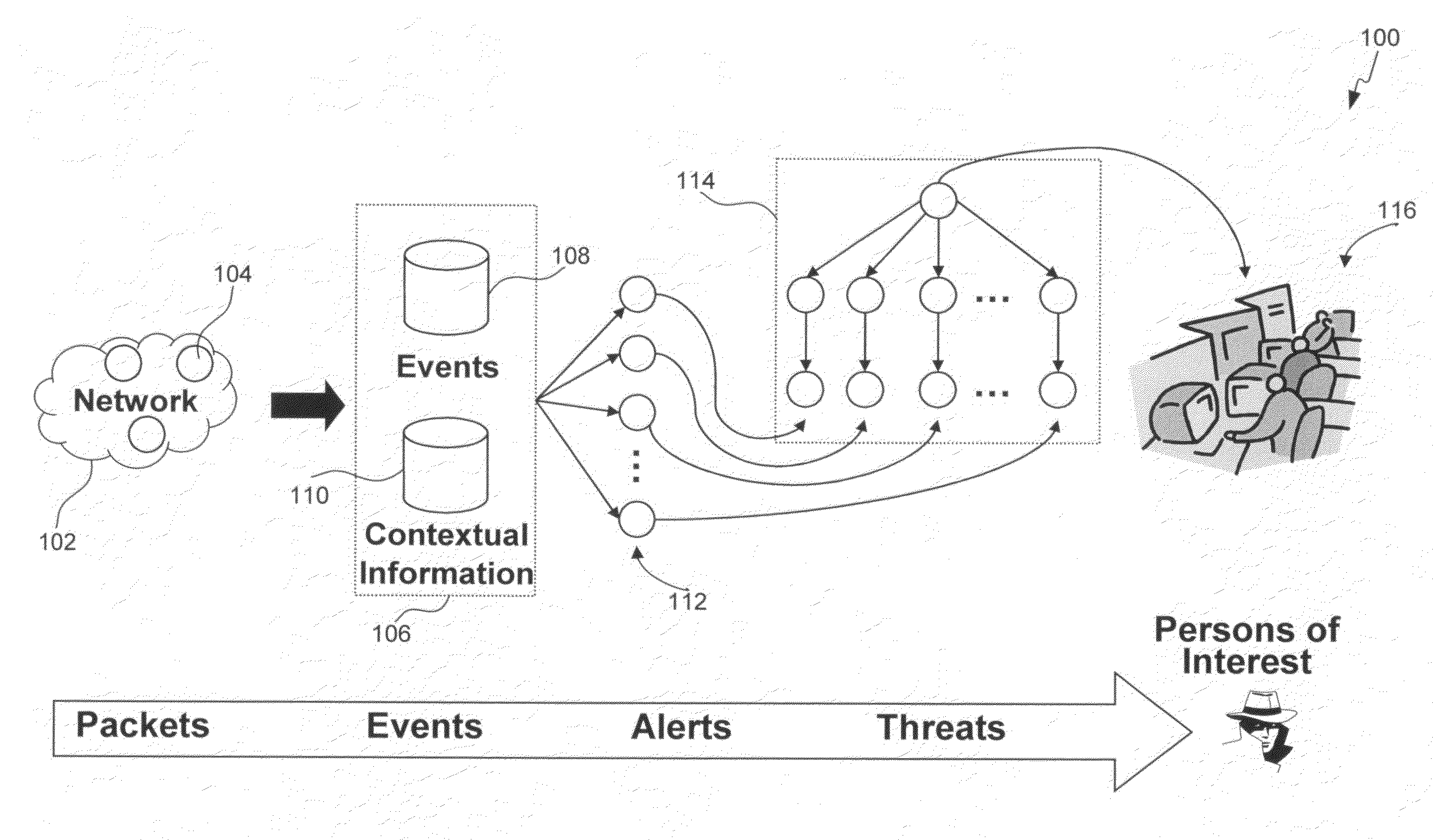
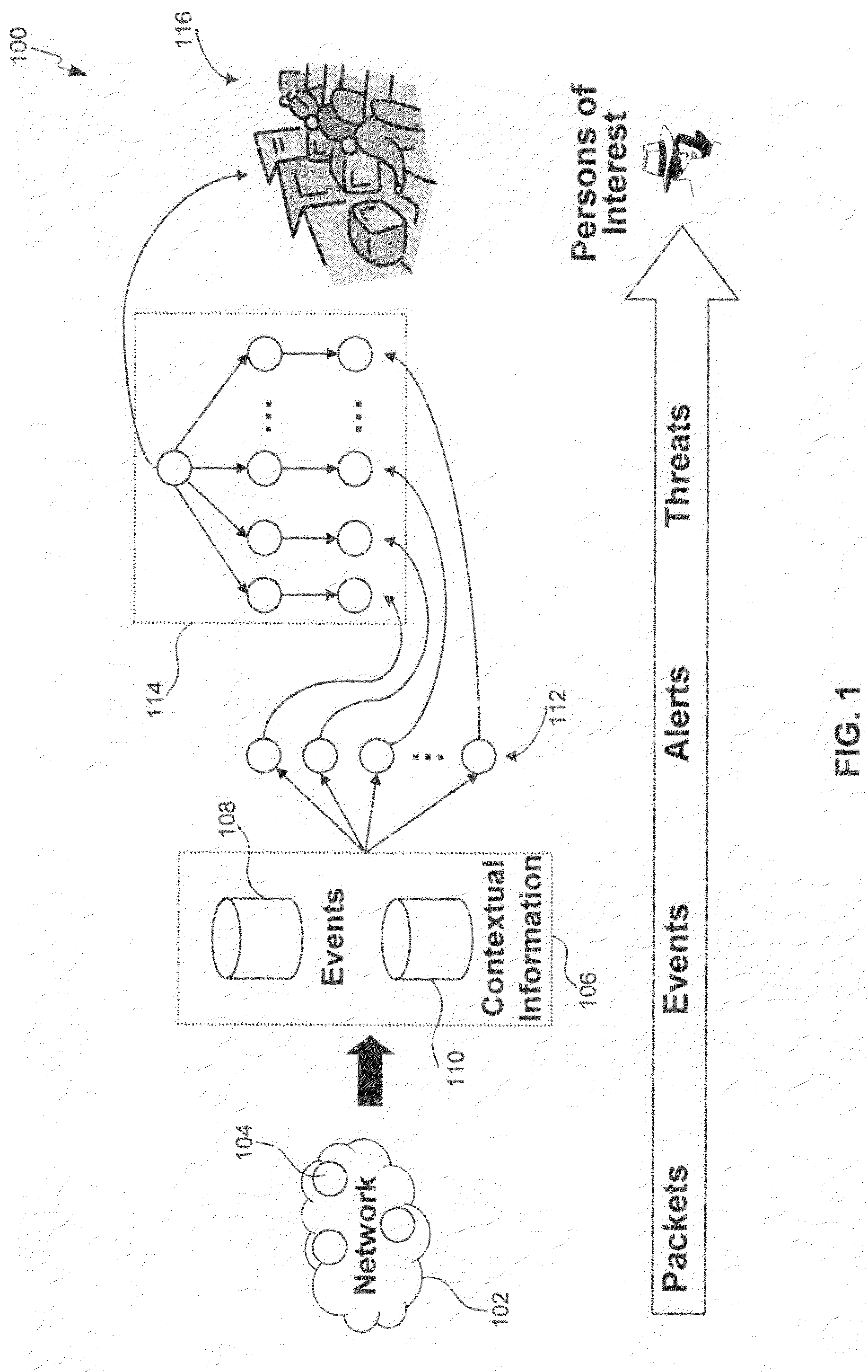
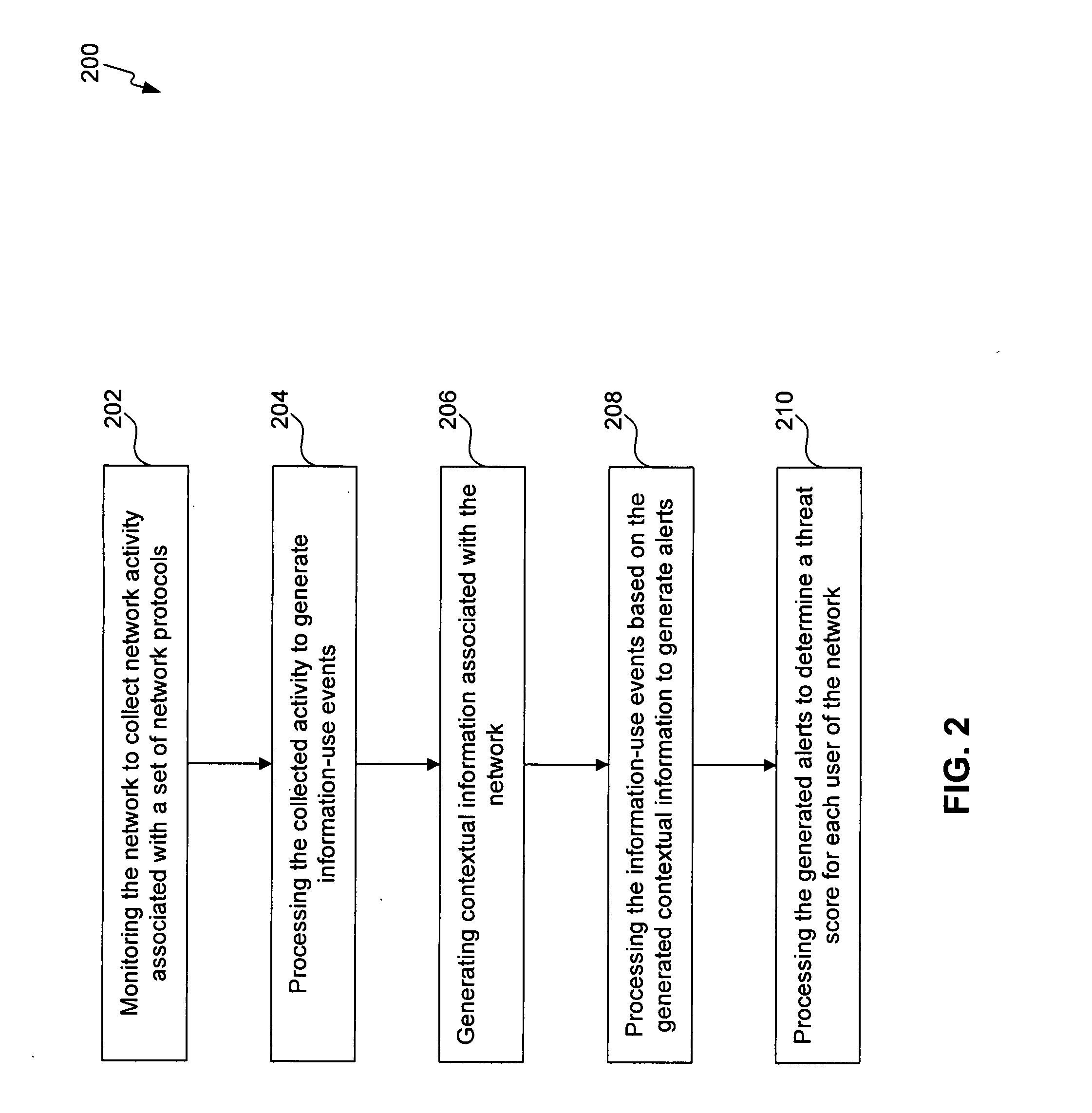
Insider threat detection
Methods, systems, and computer program products for insider threat detection are provided. Embodiments detect insiders who act on documents and / or files to which they have access but whose activity is inappropriate or uncharacteristic of them based on their identity, past activity, and / or organizational context. Embodiments work by monitoring the network to detect network activity associated with a set of network protocols; processing the detected activity to generate information-use events; generating contextual information associated with users of the network; and processing the information-use events based on the generated contextual information to generate alerts and threat scores for users of the network. Embodiments provide several information-misuse detectors that are used to examine generated information-use events in view of collected contextual information to detect volumetric anomalies, suspicious and / or evasive behavior. Embodiments provide a user threat ranking system and a user interface to examine user threat scores and analyze user activity.
Owner:MITRE SPORTS INT LTD
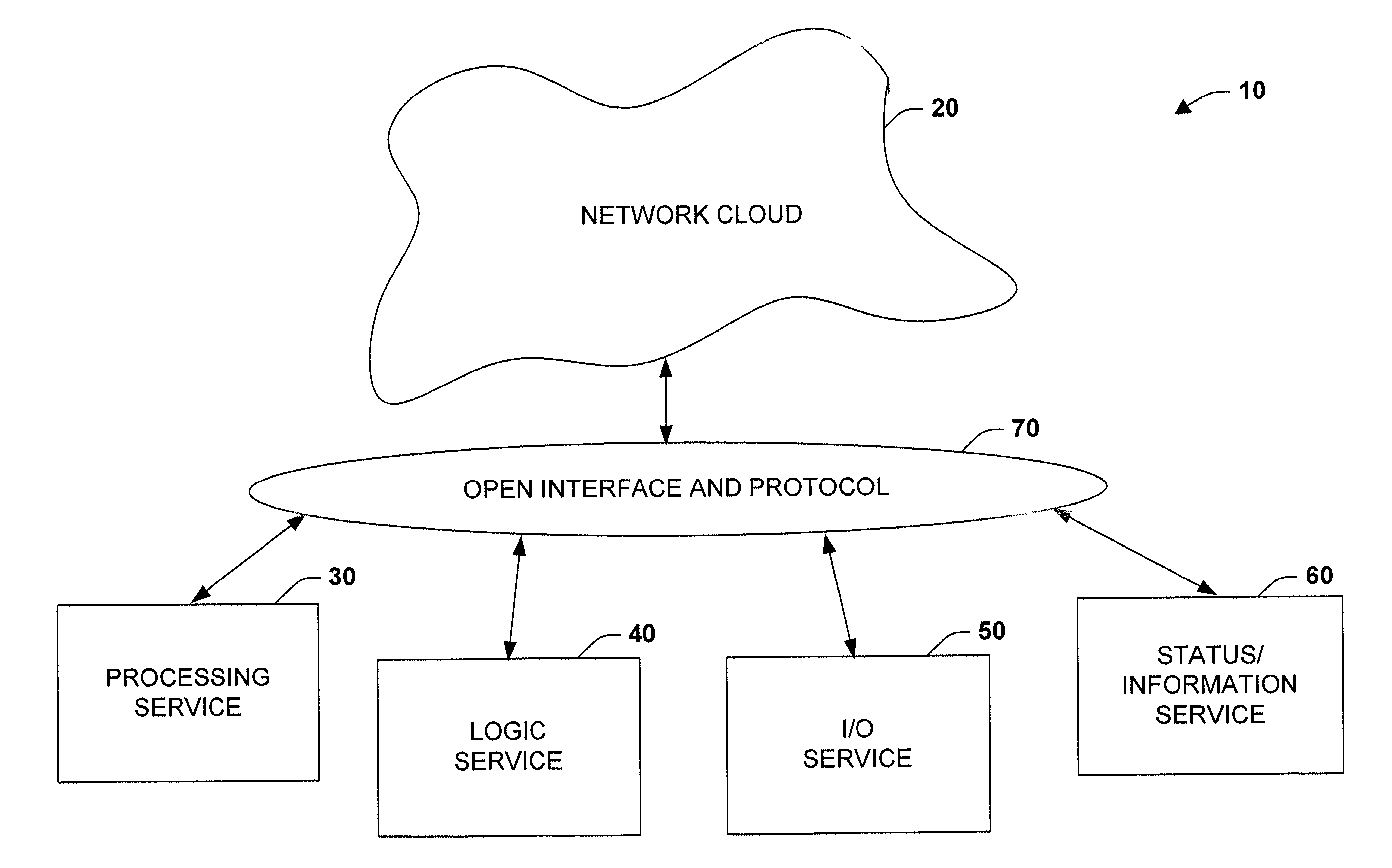
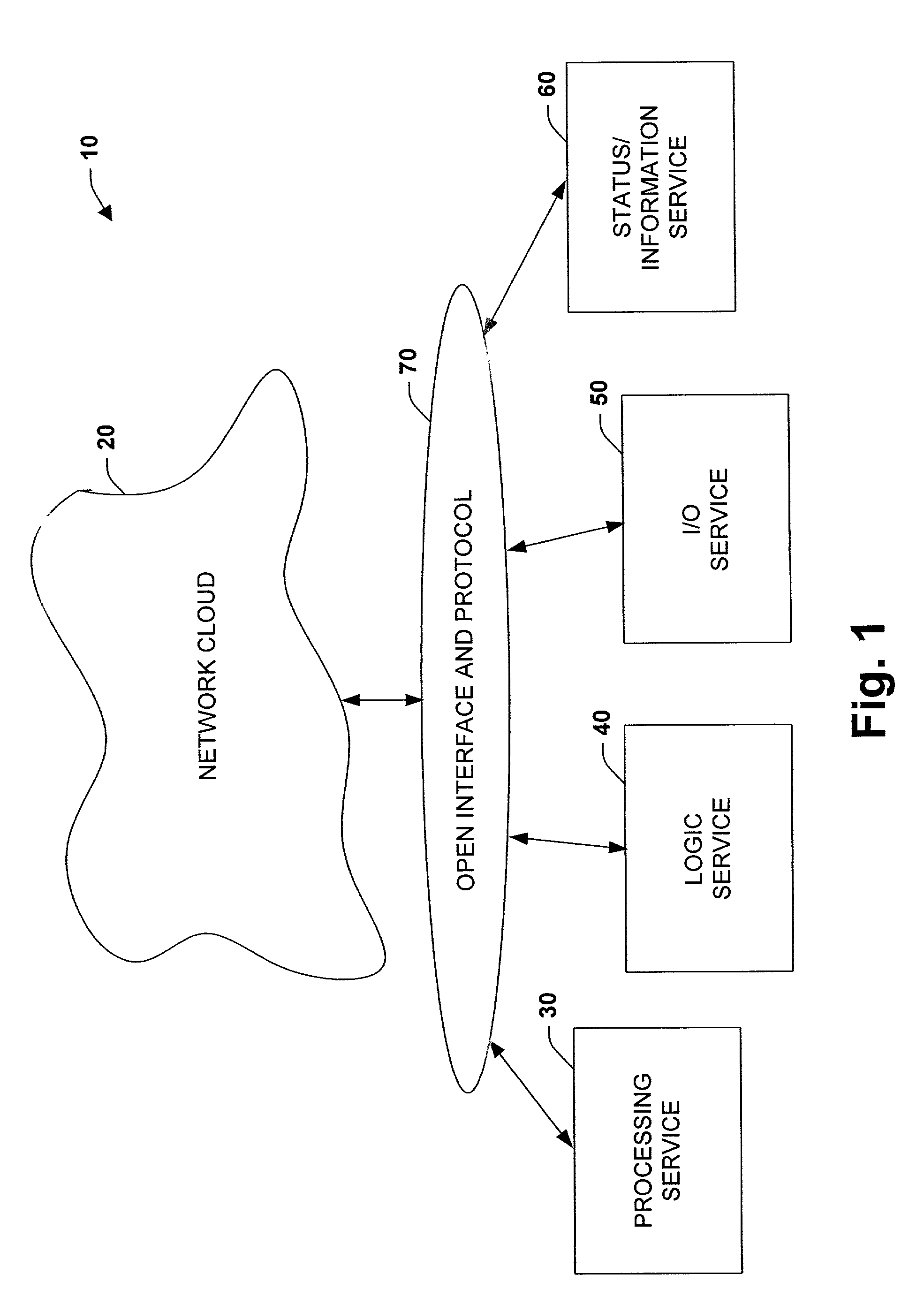
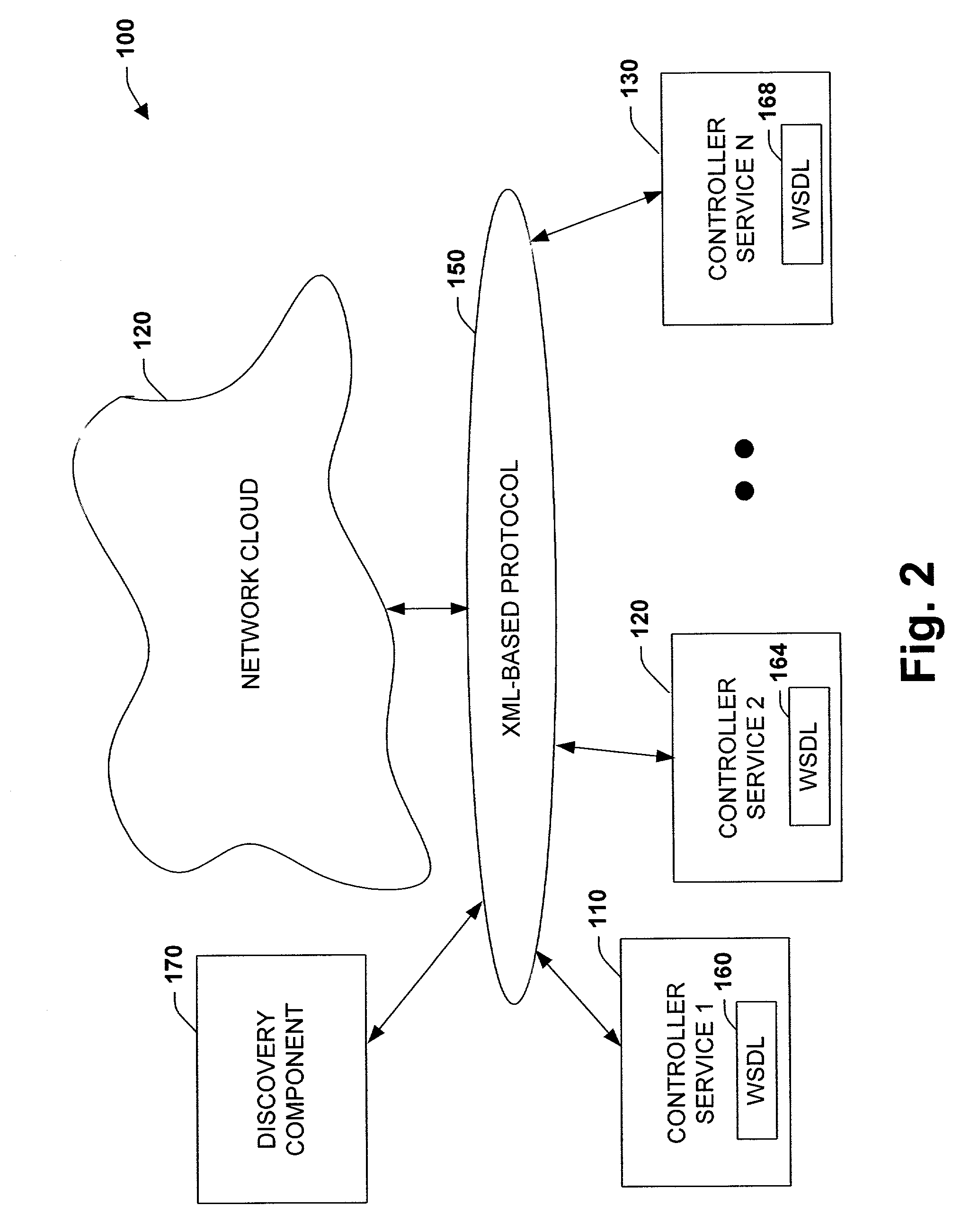
System and methodology providing open interface and distributed processing in an industrial controller environment
ActiveUS7151966B1Facilitate communicationPromote collaborationProgramme controlElectric controllersNetworking protocolApplication software
The present invention relates to a system and methodology providing virtual and remote component interactions in a networked industrial control environment. One or more components of an industrial control system are defined as a web service, wherein the components cooperate to support distributed controller functionality in all or portions of a virtual operating framework. For example, the components can include processing, logic, I / O and status components of an industrial control system. Standard and commonly available interfaces describe controller functionality in terms of the services, whereby controller applications are constructed via the components and associated interfaces. This can include discovery of other related services and employment of common web protocols to communicate between the services.
Owner:ROCKWELL AUTOMATION TECH
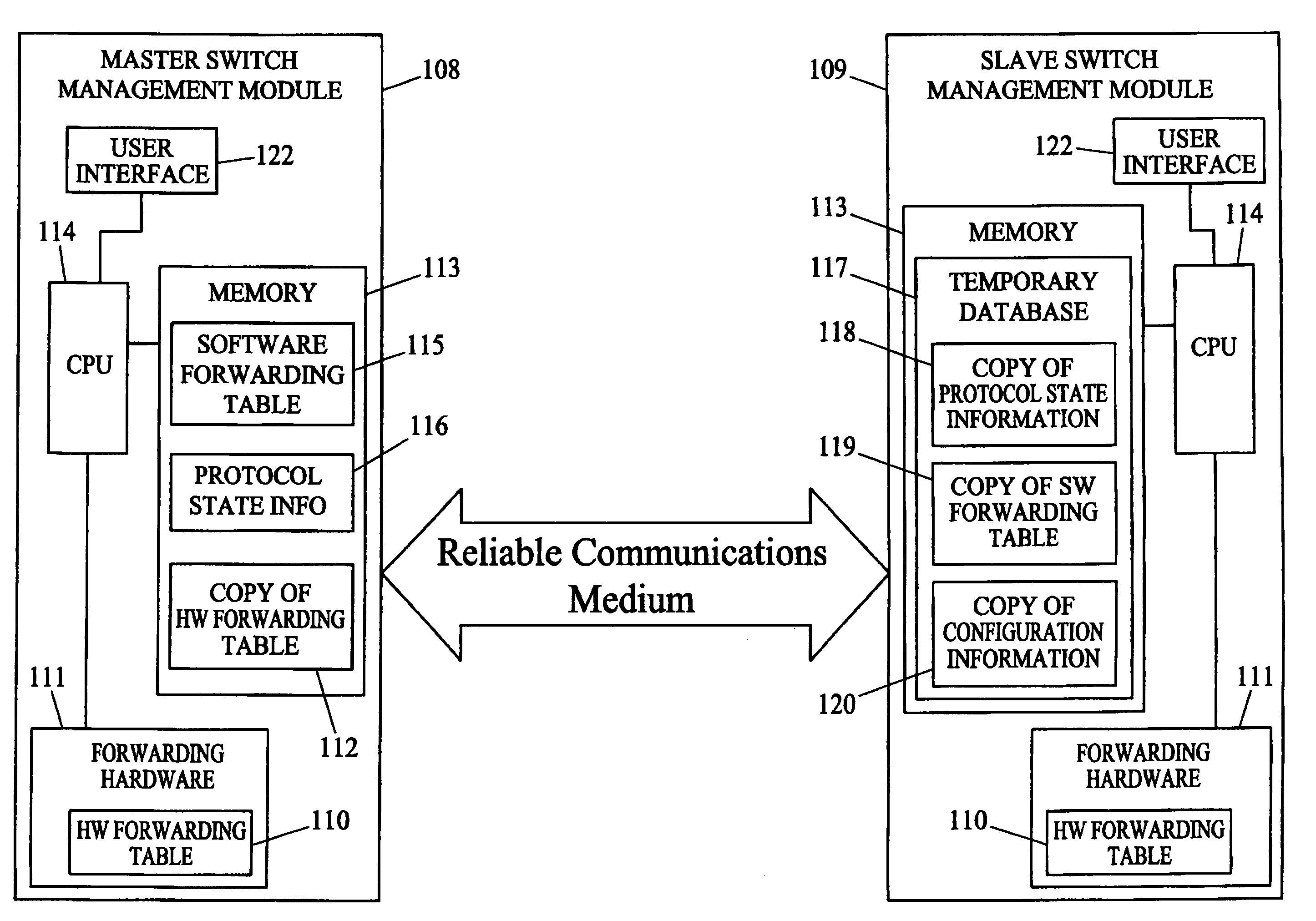
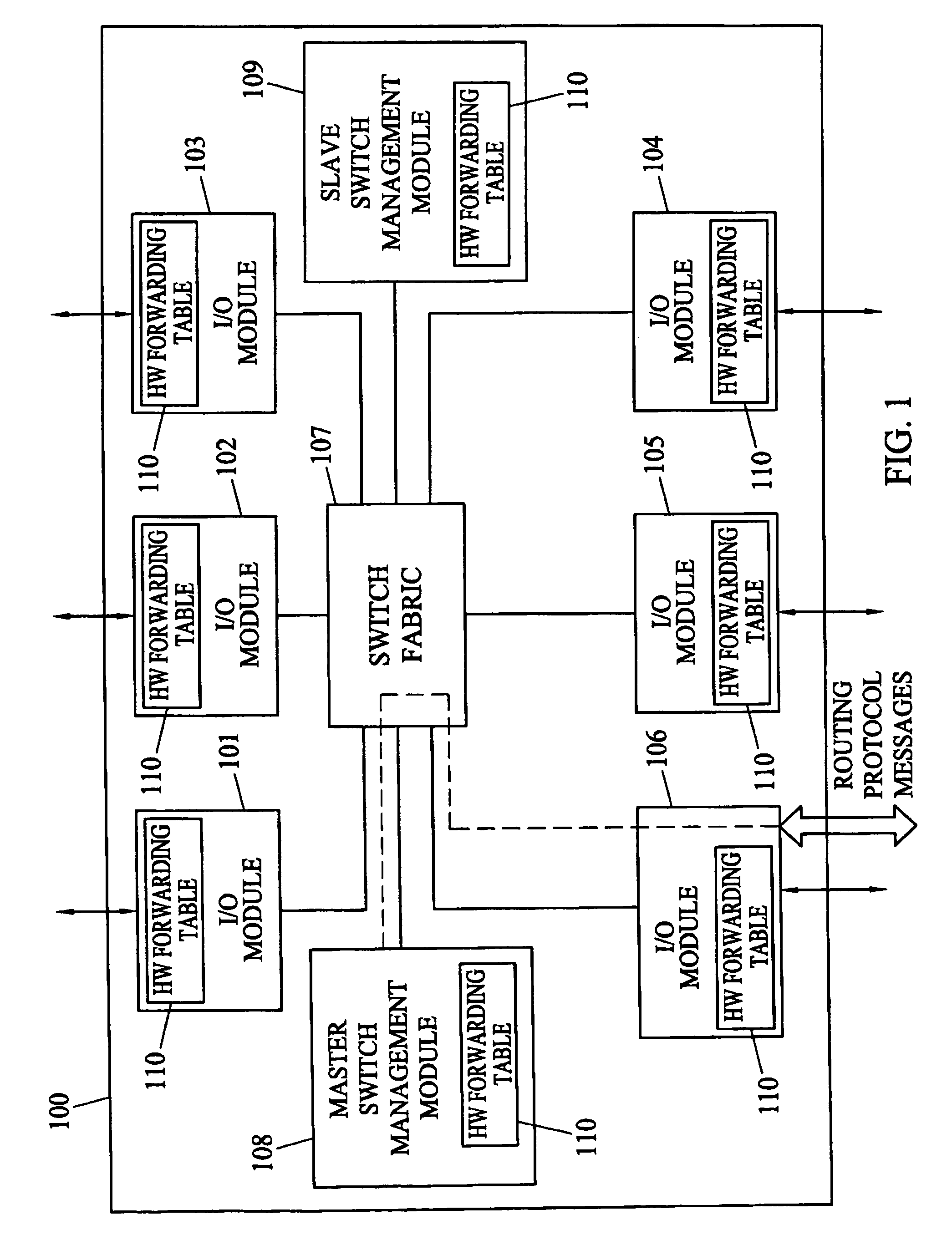
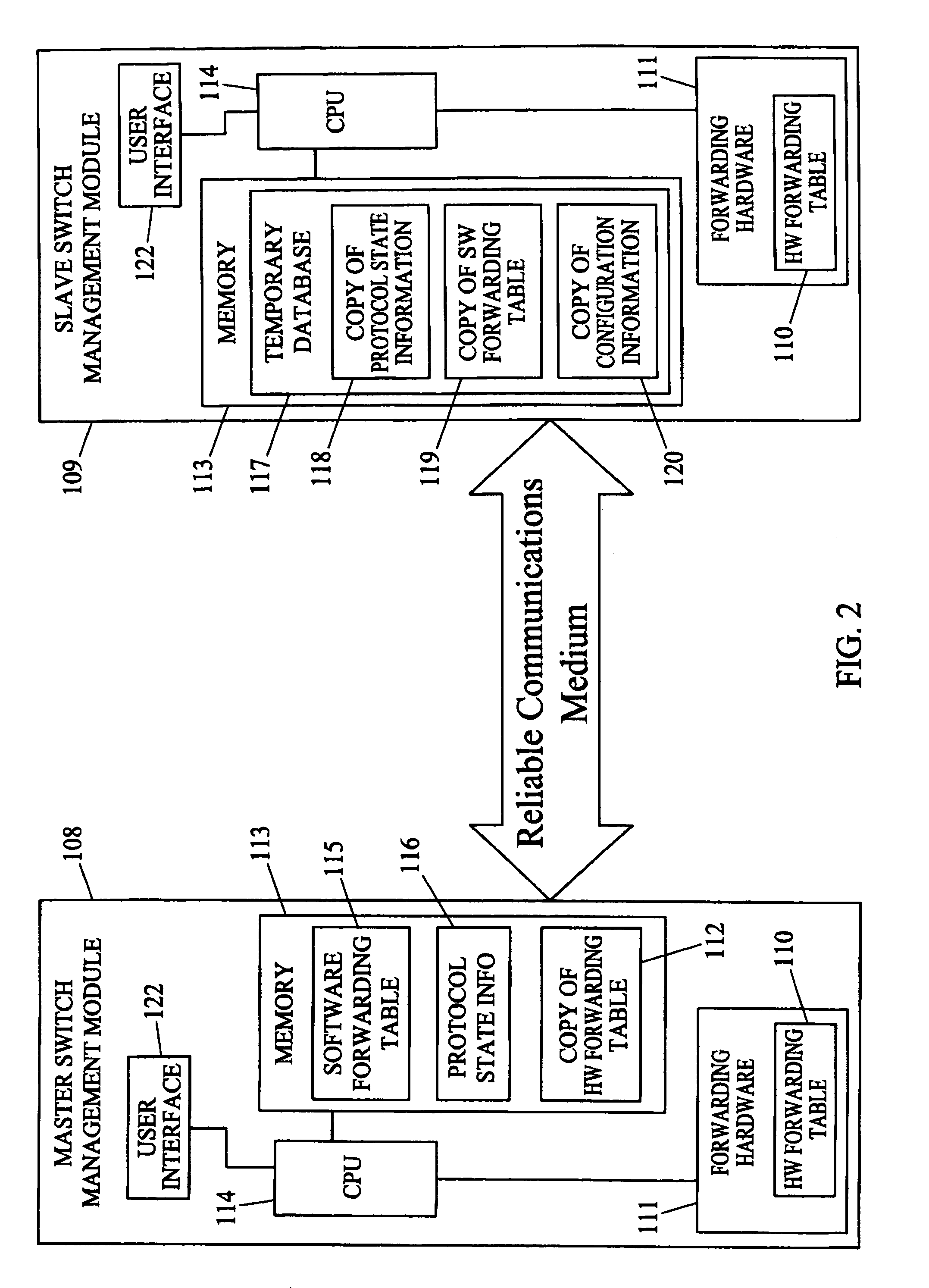
Methods and systems for hitless switch management module failover and upgrade
Methods and systems for hitless switch management module failover and upgrade are disclosed. According to one method, a master switch management module participates in network protocols and performs packet forwarding operations. The master switch management module distributes protocol state and packet forwarding information to the slave switch management module. The slave switch management module continuously monitors the operational state of the master switch management module. In response to detecting failure of the master switch management module or a forced failover initiated by the user interface on the master switch management module, the slave switch management module begins network protocol operation in the master mode in a state where the master switch management module last operated correctly.
Owner:EXTREME NETWORKS INC
System and method for a context layer switch
Owner:FUTUREWEI TECH INC
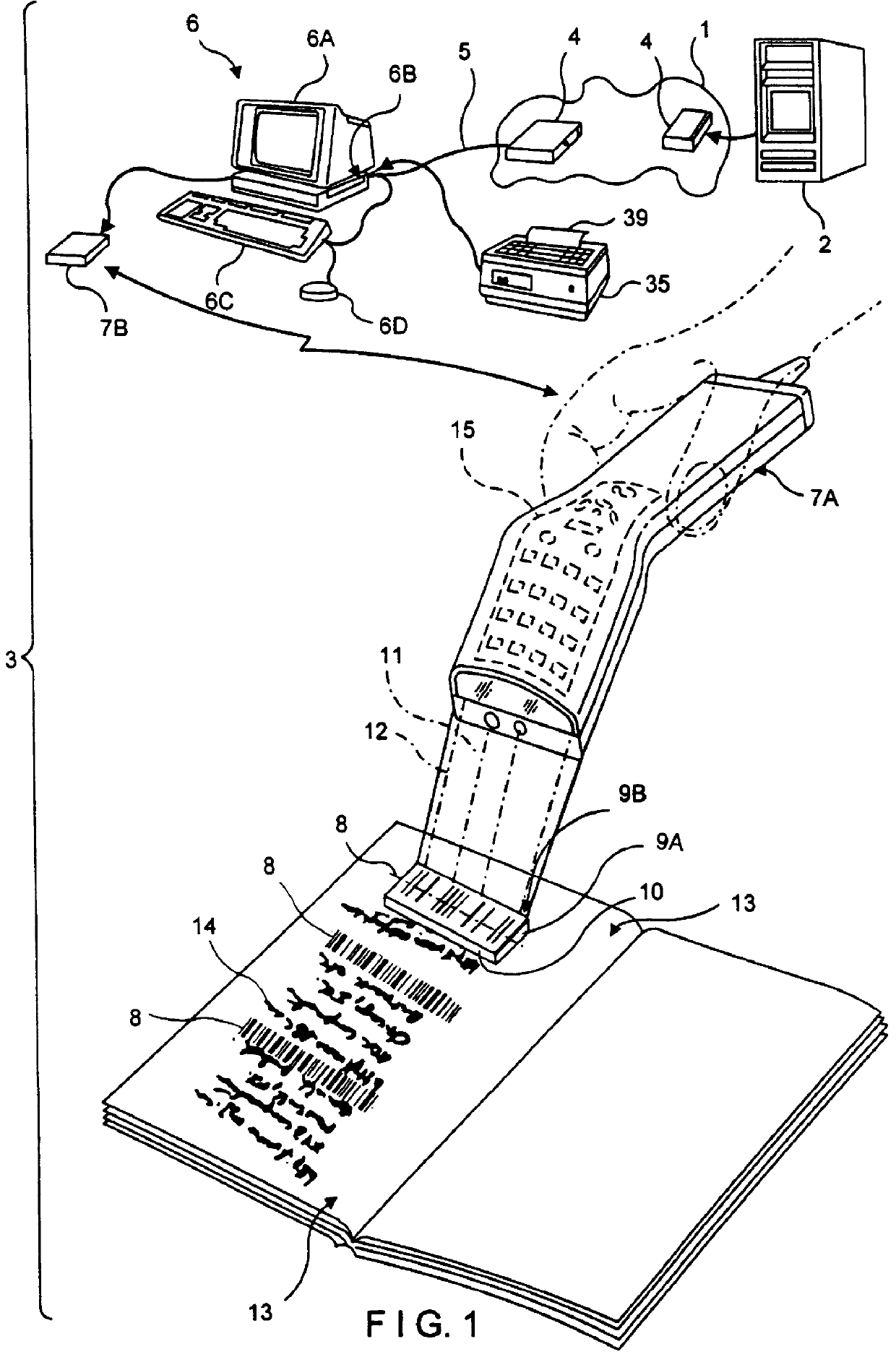
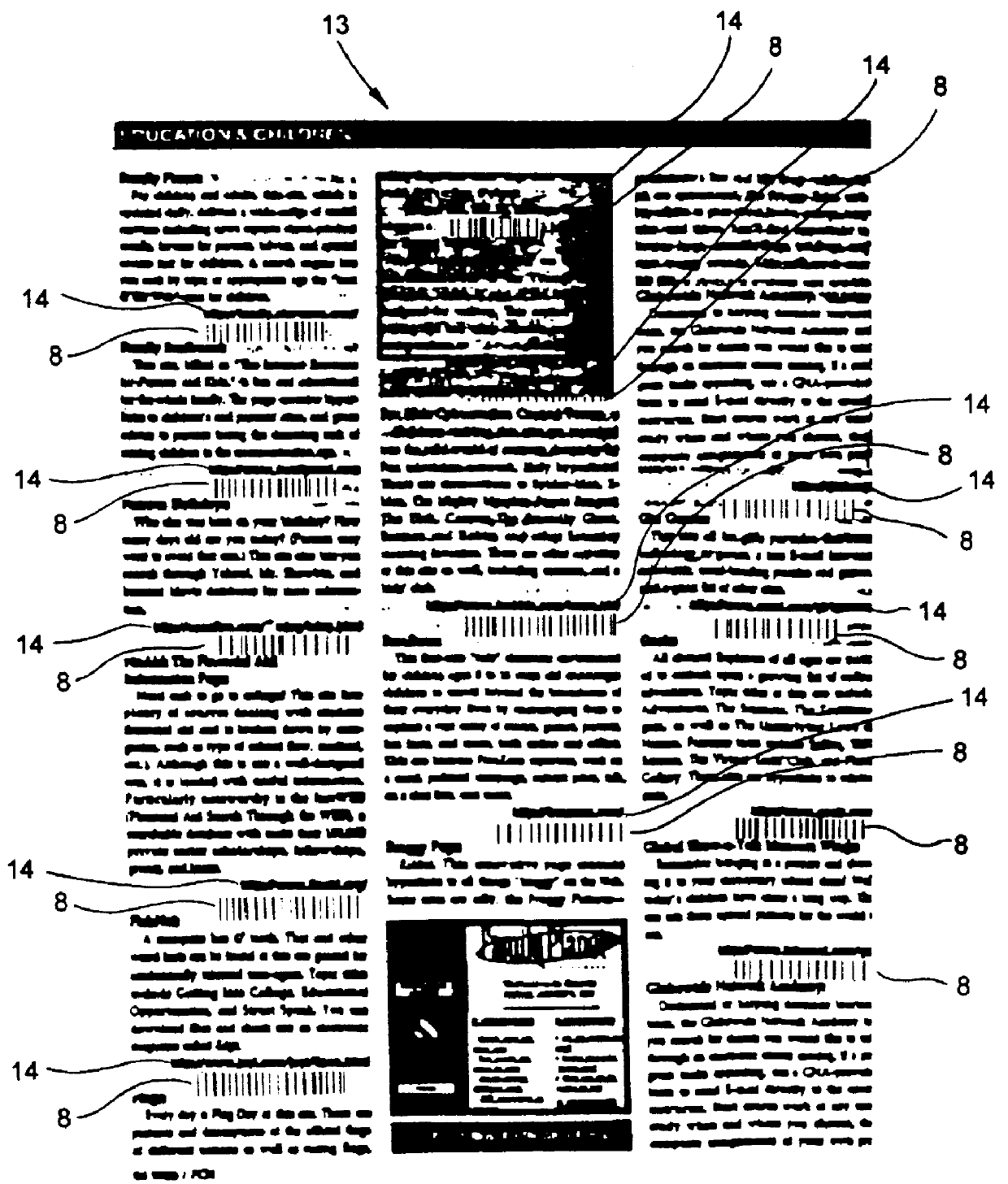
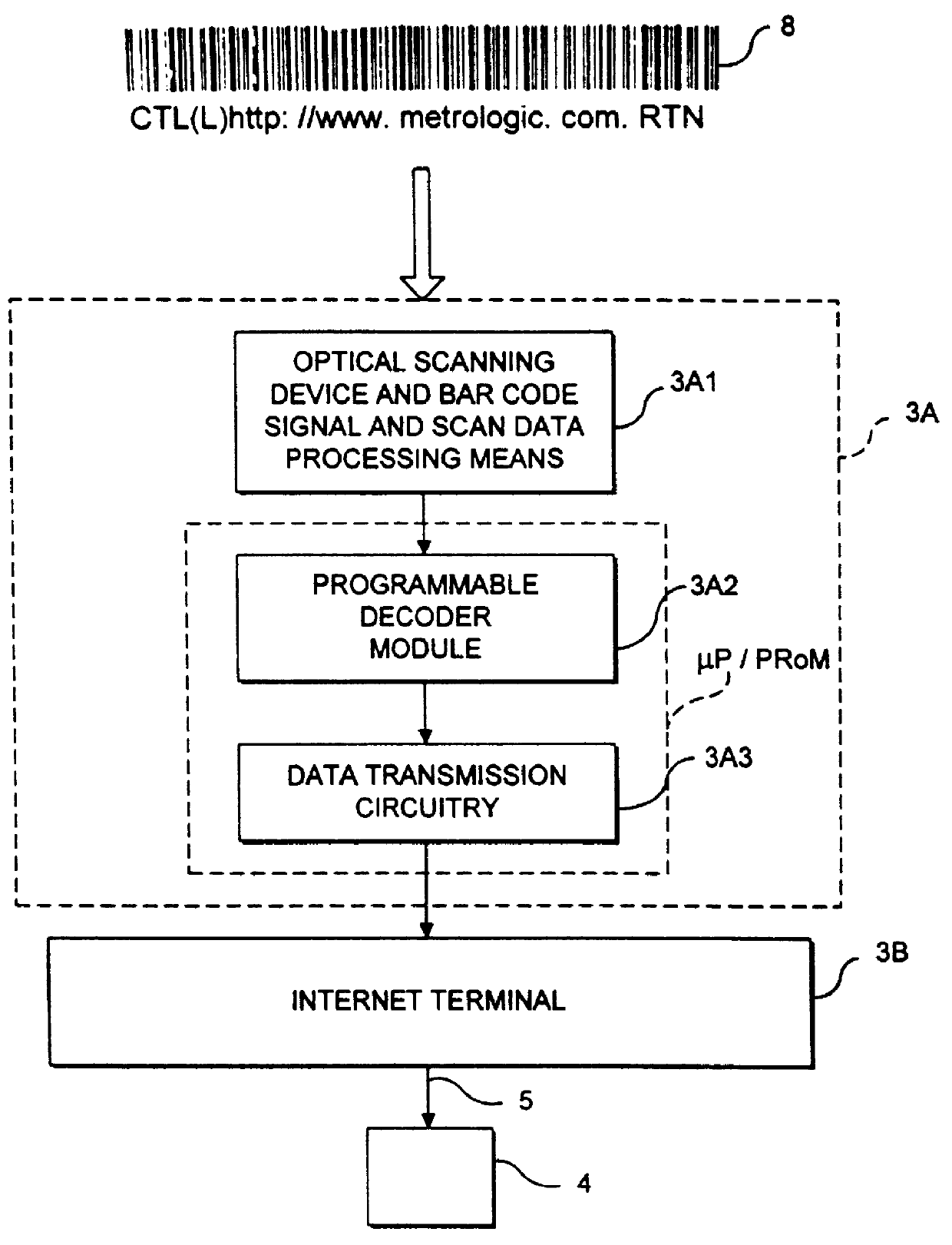
Web-based system and method for enabling a viewer to access and display HTML-encoded documents located on the world wide web (WWW) by reading URL-encoded bar code symbols printed on a web-based information resource guide
InactiveUS6076733AEasy accessDigital data information retrievalCharacter and pattern recognitionNetworking protocolInformation resource
A Web-based system and method for enabling an operator to access and display HTML-encoded documents located on the WWW. The system comprises one or more Internet information servers, an Internet access terminal, and an audio-visual monitor. The Internet information servers store a plurality of HTML-encoded documents at a plurality of storage locations specified by a plurality of Uniform Resource Locators (URLs). The Internet access terminal is operably connected to the infrastructure of the Internet and embodies a GUI-based Internet browser program, supporting the TCP / IP networking protocol. The Internet access terminal includes a bar code symbol reader for reading bar code symbols. The bar code symbol reader is programmed for reading bar code symbols encoded with URLs specifying the location of HTML-encoded documents on the WWW, and producing data representative of each encoded URL. In response to reading a URL-encoded bar code symbol on the pages of a printed WWW-site guide, the bar code symbol reader produces data representative of the URL, and the produced data is transmitted to the Internet access terminal. Thereupon, the GUI-based Internet browser program automatically accesses the HTML-encoded document specified by the URLusing the TCP / IP networking protocol, and the Internet access terminal automatically displays the accessed HTML-encoded document on the audio-visual monitor for viewing.
Owner:METROLOGIC INSTR INC
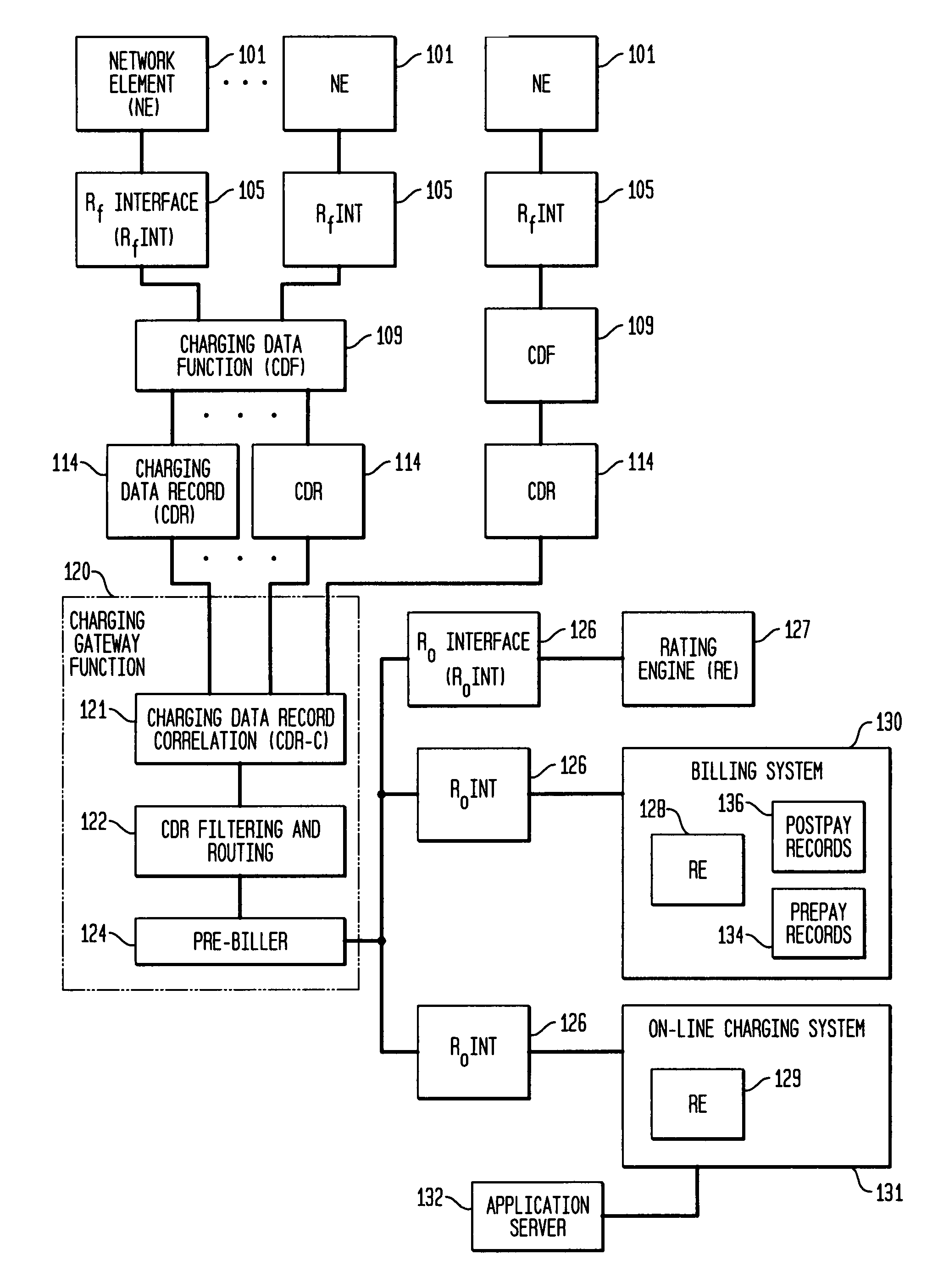
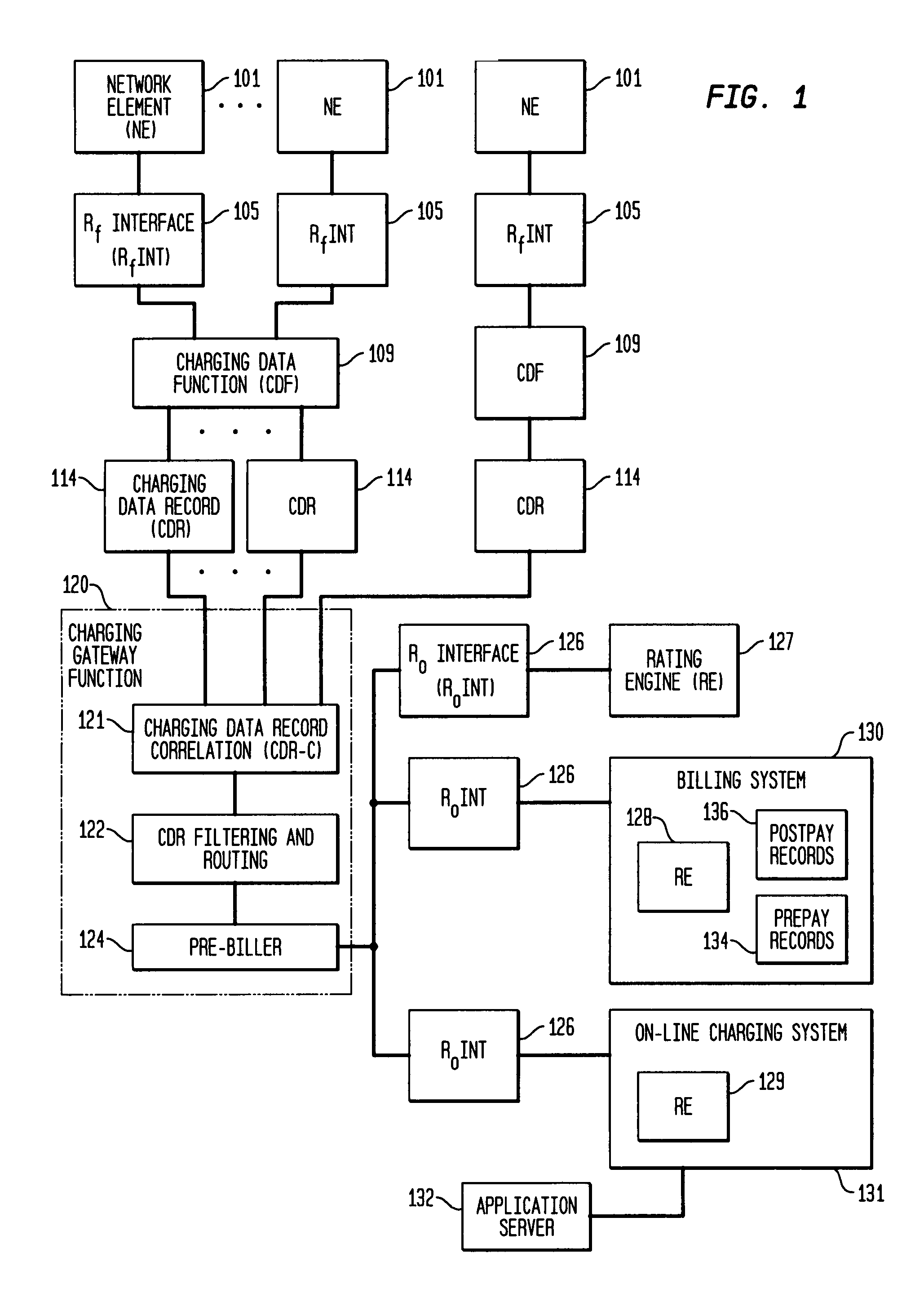
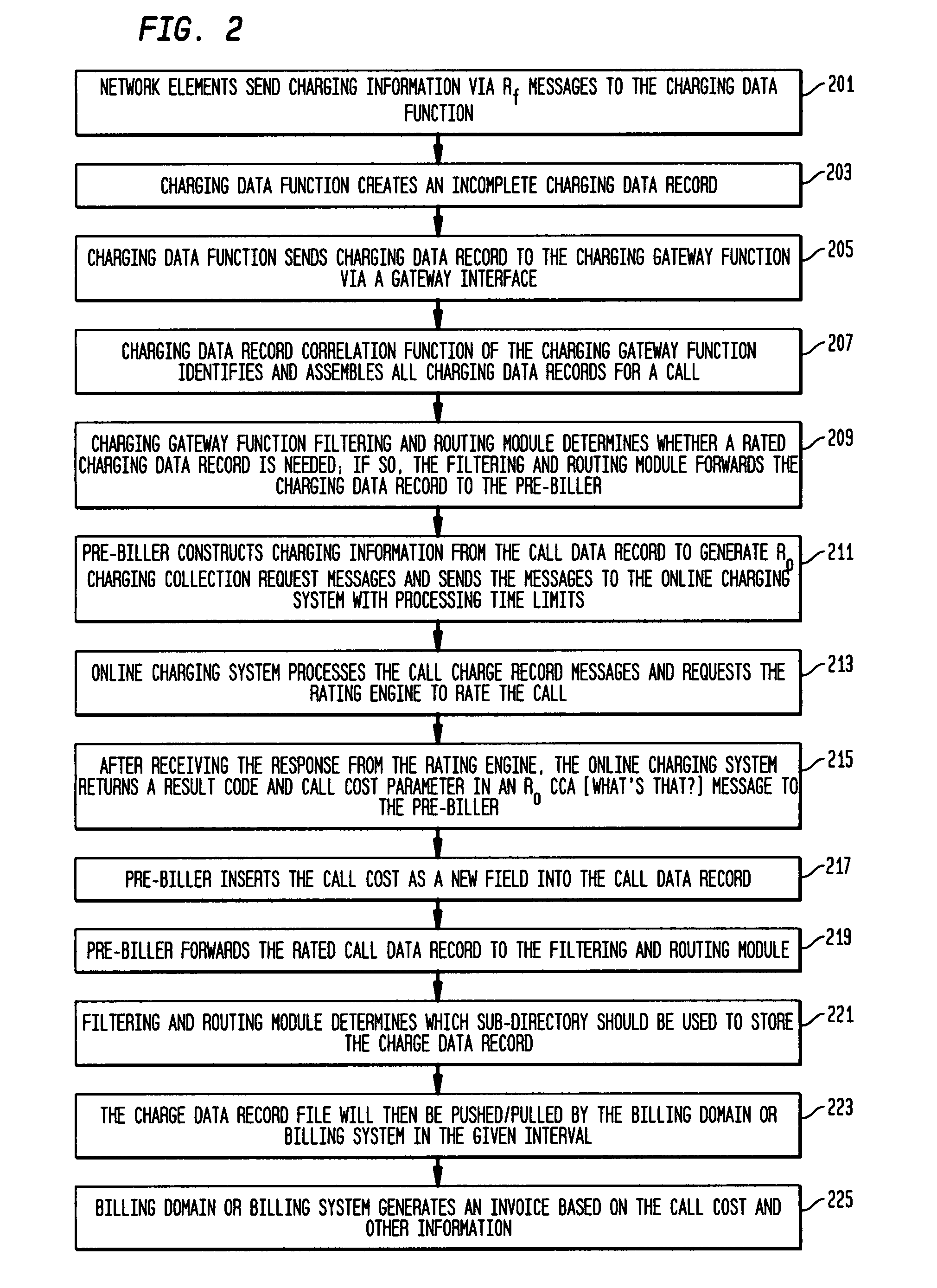
Pre-biller in internet protocol multimedia subsystem (IMS) charging gateway function (CGF)
InactiveUS8126123B2Metering/charging/biilling arrangementsAccounting/billing servicesNetworking protocolCAC protocol
This invention relates to apparatus and a method for assembling and coordinating call data records from a plurality of network elements of an Internet Protocol Multimedia System call to generate charging information. A pre-biller stores an integrated charging record and accesses a rating engine to obtain the charging information to complete a charging data record. Advantageously, the information from a plurality of network elements is integrated into a combined charging data record.
Owner:WSOU INVESTMENTS LLC
Message transmission system for users of location-aware mobile communication devices in a local area network
InactiveUS20070281716A1Promote disseminationServices signallingConnection managementTelecommunications linkTransport system
Embodiments of a location-based social network manager process are described. The process is executed on a server computer coupled to a plurality of mobile communication devices over a wireless network. Each mobile device is a location-aware mobile communication device. The process determines the geographic location of a mobile communication device operated by a user within an area, displays a map representation of the area around the mobile communication device on a graphical user interface of the mobile communication device, and superimposes on the map the respective locations of one or more other users of mobile communication devices coupled to the mobile communication device over the network. The process establishes communication links between the user and the plurality of acquaintances through respective location aware mobile communication devices through a network protocol. The user can create one or more groups of acquaintances based on one or more characteristics common to members of each group. The process facilitates the transmission of a user specified message or a pre-defined message to one or more acquaintances of the groups of acquaintances within a pre-defined distance to the user. The contents of the user specified message and pre-defined message is based on the characteristics of the group and the relative distance of the members to the user. The process can also be configured to automatically transmit a message to a user who is within a pre-defined distance to a point of interest within the displayed area.
Owner:LOOPT
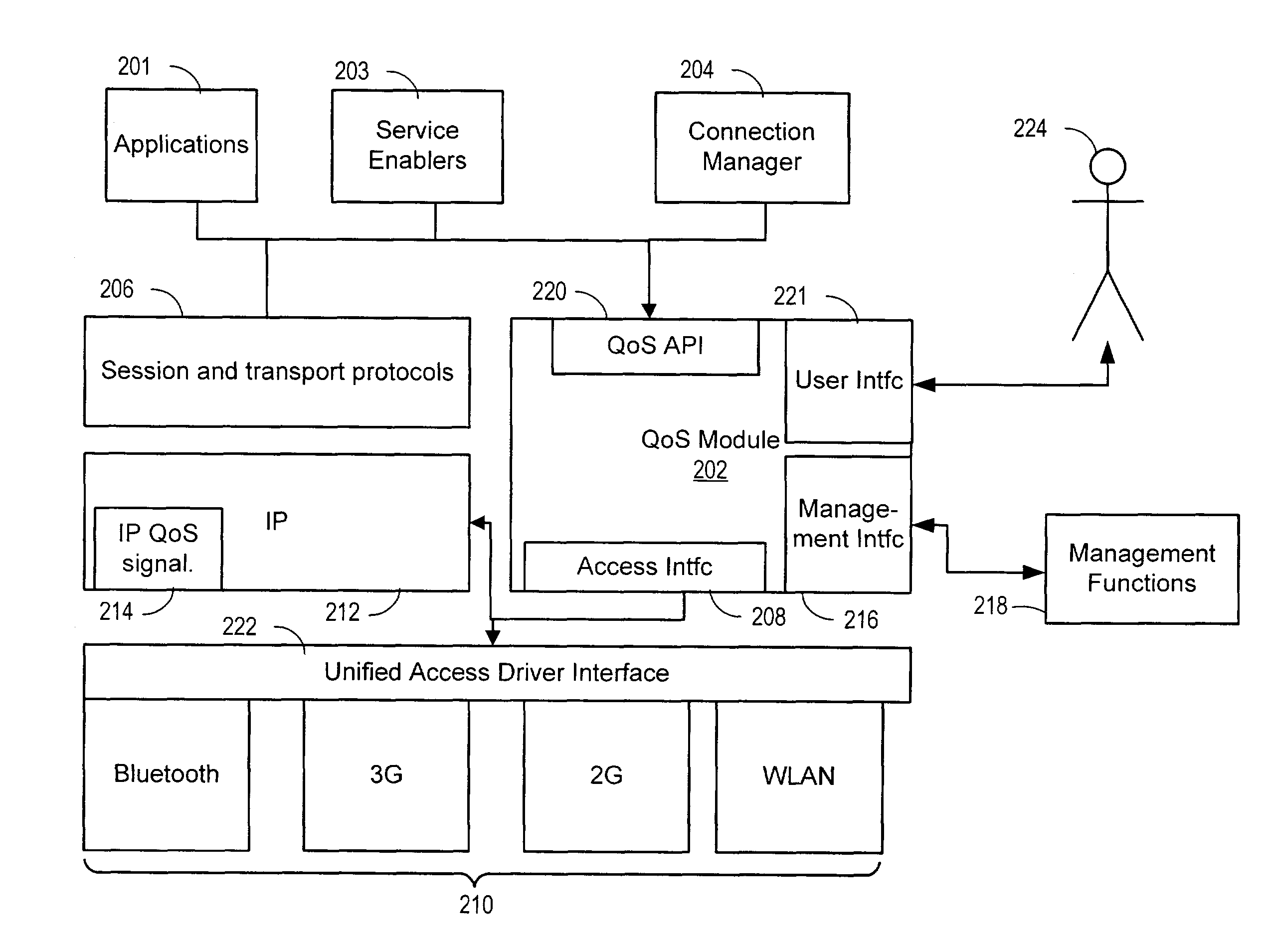
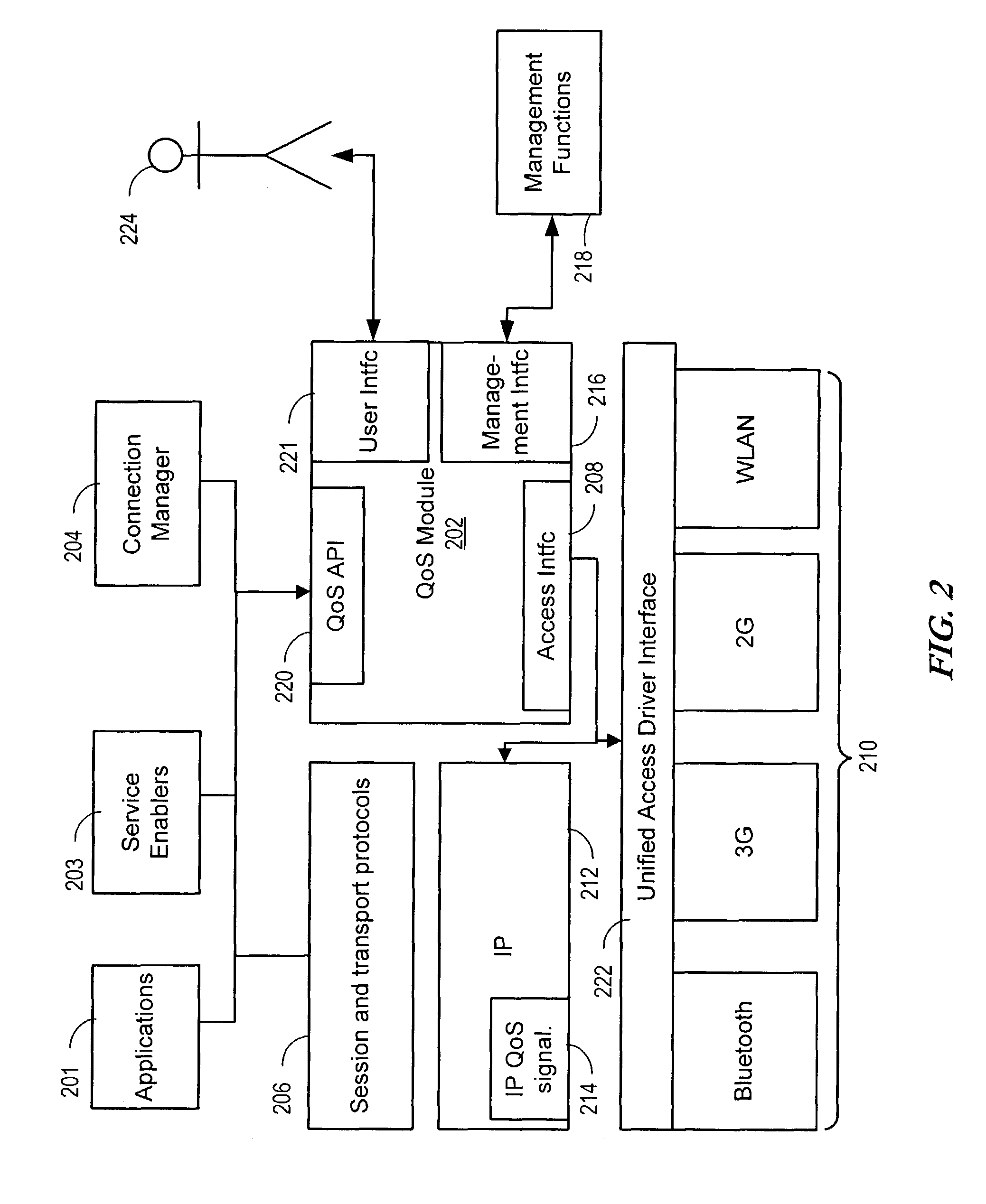
Apparatus and method for providing quality of service for a network data connection
ActiveUS8108520B2Providing serviceNetwork traffic/resource managementData switching by path configurationQuality of serviceData connection
A system, apparatus, and method are disclosed for providing quality of service (QoS) for a network data connection. The network data connection uses a network protocol selectable from a plurality of network protocols. A QoS module can receive a request for a generic QoS and apply this to the network protocol using a specific QoS associated with the protocol. The QoS module may include features for automatic management of QoS and a user interface for changing data connection parameters.
Owner:WSOU INVESTMENTS LLC
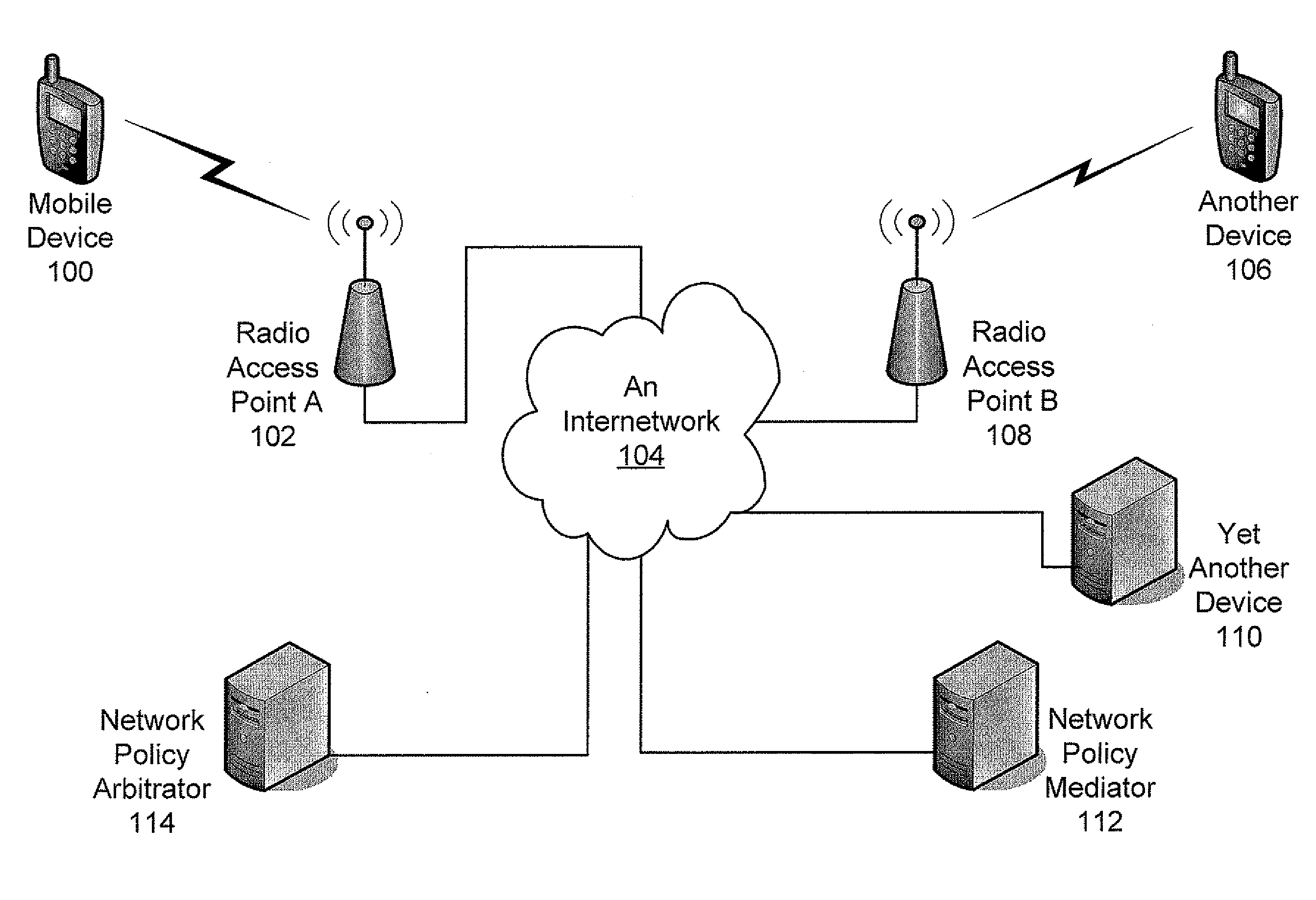
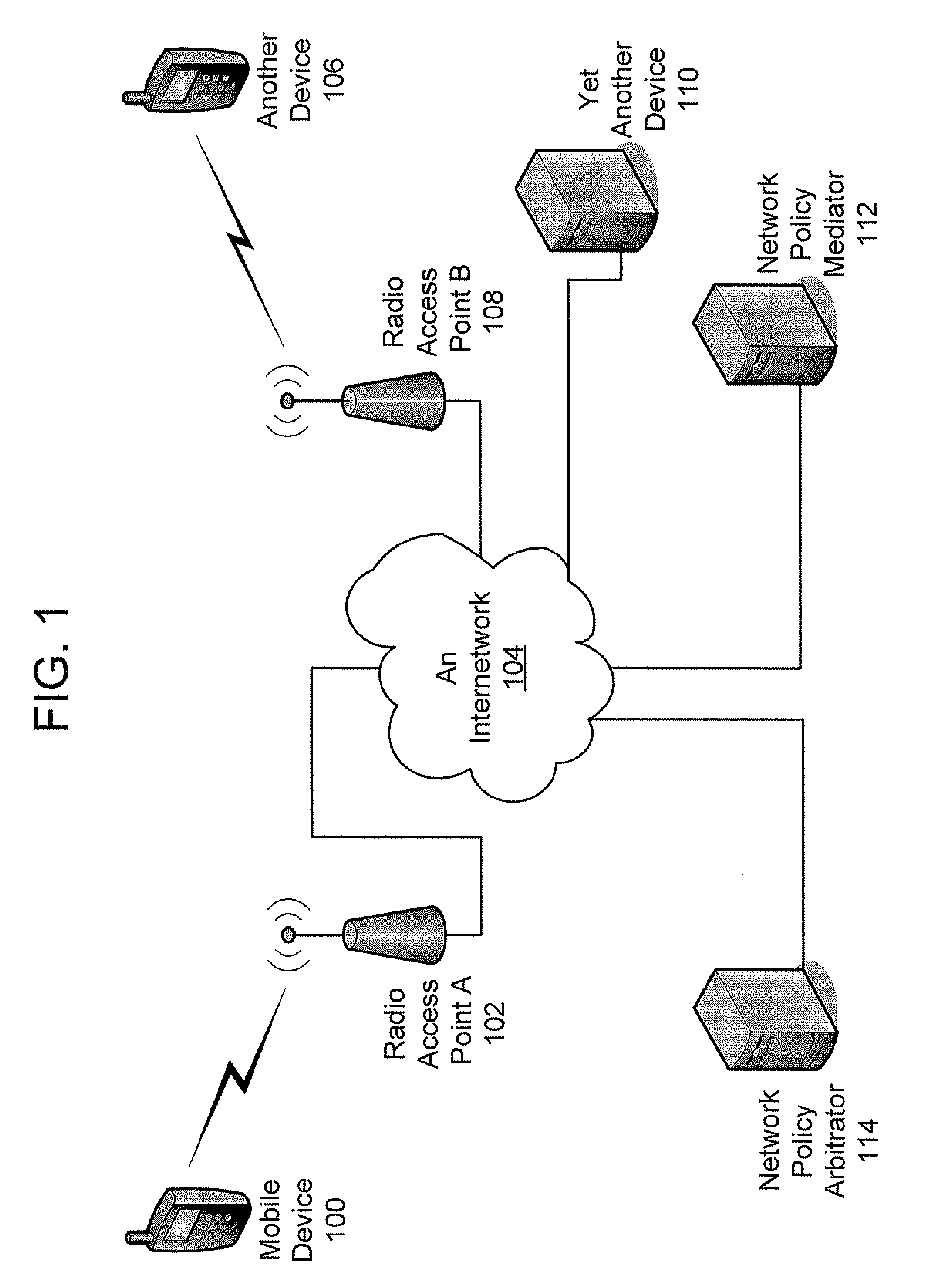
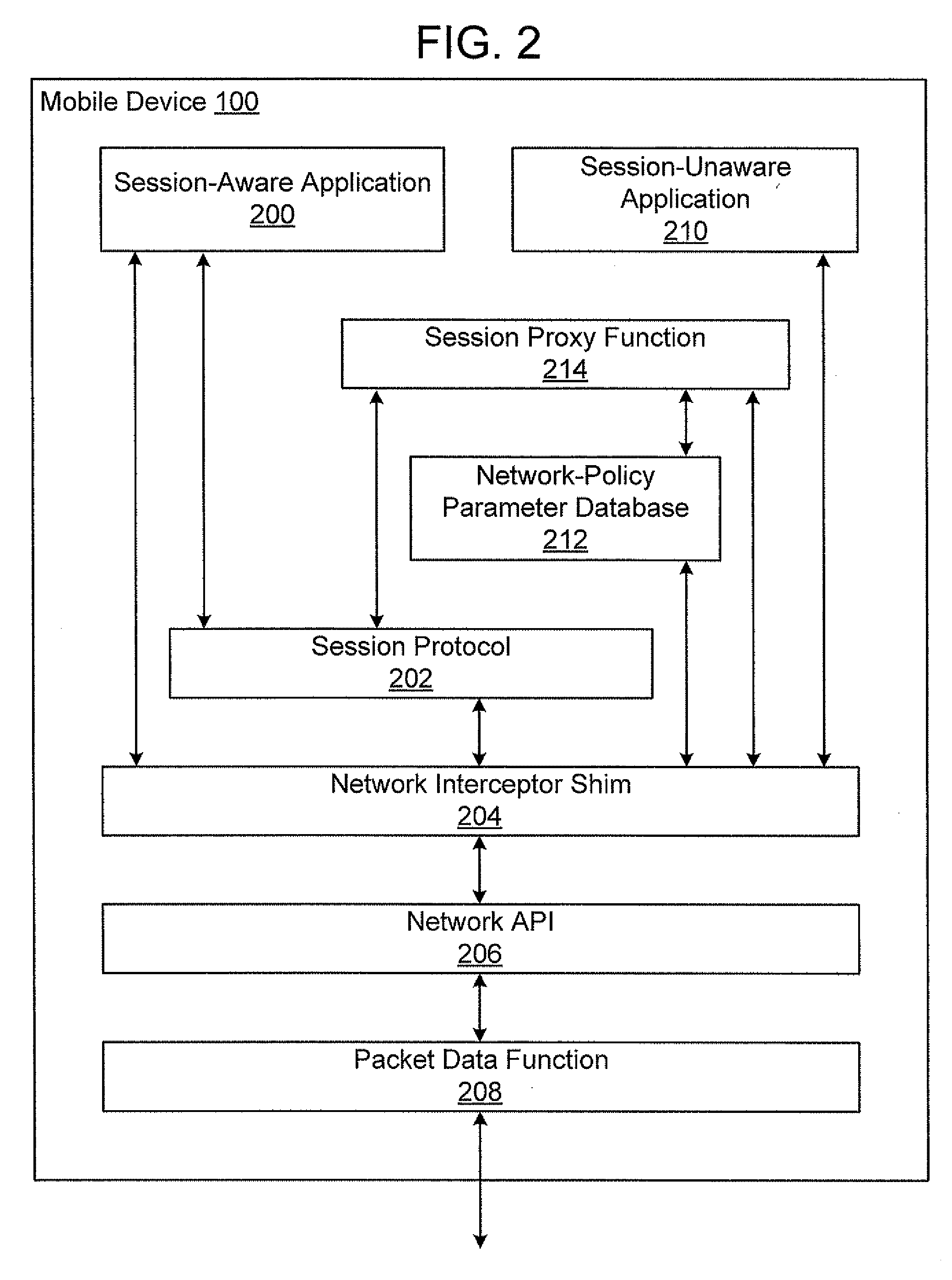
Establishing Network Policy For Session-Unaware Mobile-Device Applications
ActiveUS20080162704A1Network traffic/resource managementAssess restrictionNetworking protocolApplication software
The present invention provides the benefits of negotiated network resources to session-unaware applications. When a session-unaware application runs on a mobile device, the device, knowing that the application is session-unaware, negotiates appropriate network-policy parameters for the application. The application remains unaware, but it receives the benefits of the network-policy parameter negotiation. The network-policy parameter negotiation is carried on between the mobile device and a “network policy mediator” in the network. Together, they reserve the appropriate network resources and secure the appropriate guarantees. In some embodiments, a software “shim” runs in the network-protocol stack on the mobile device. By intercepting network-access attempts sent by the session-unaware application, the shim knows to begin the network-policy parameter negotiation. In some embodiments, the mobile device downloads information about session-unaware applications from the network. This information includes a list of which network-policy parameter guarantees would be most beneficial to each application.
Owner:U S CELLULAR
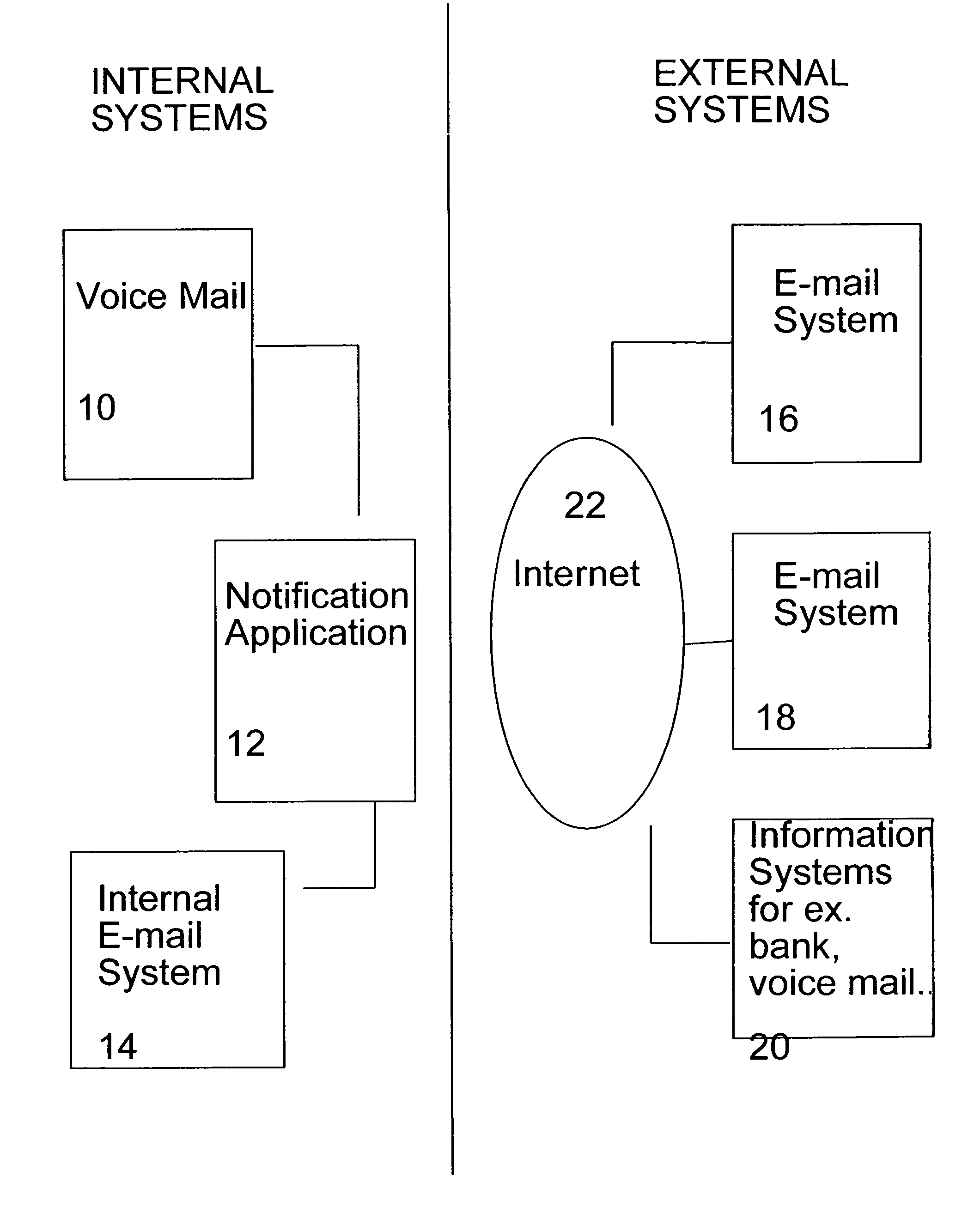
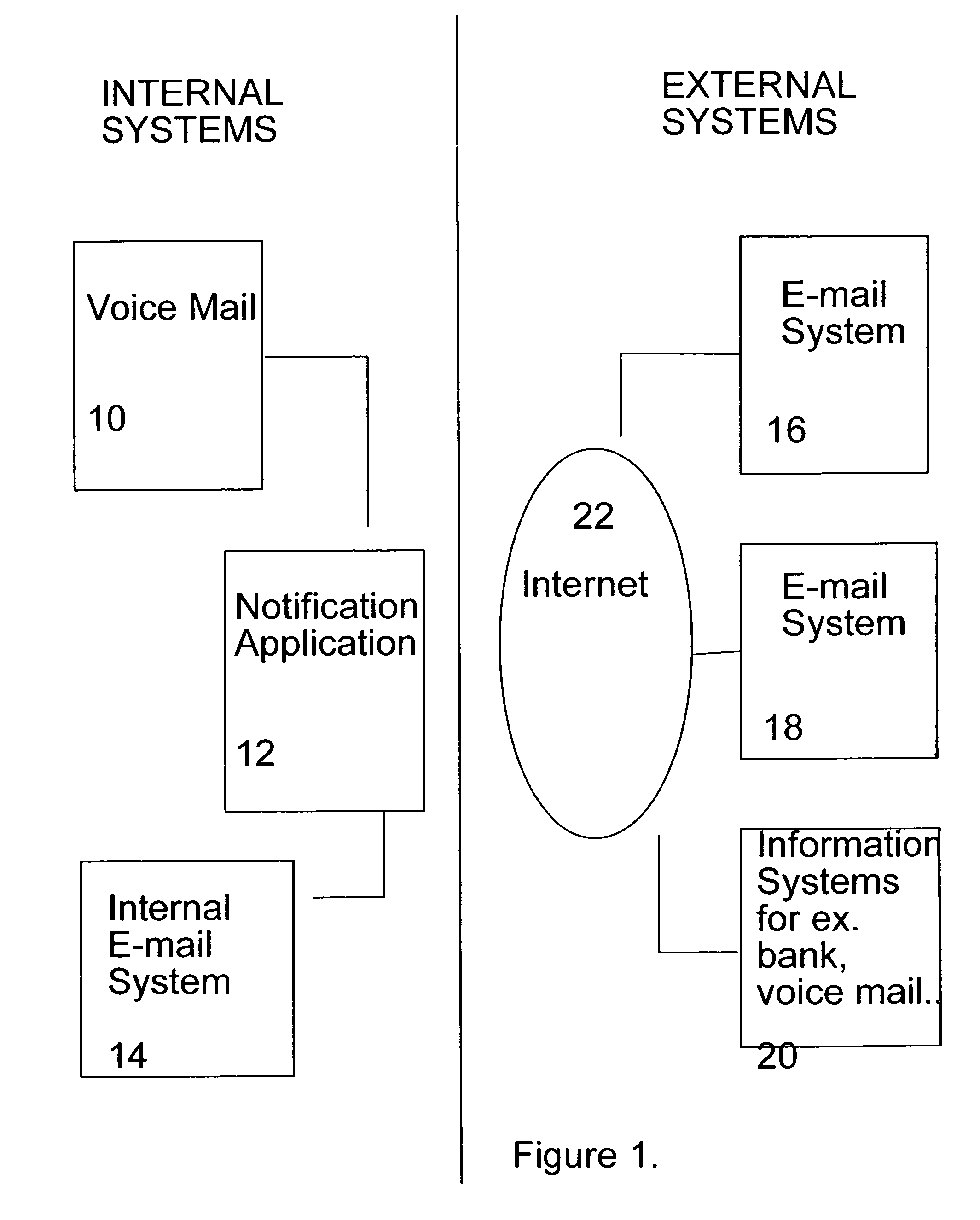
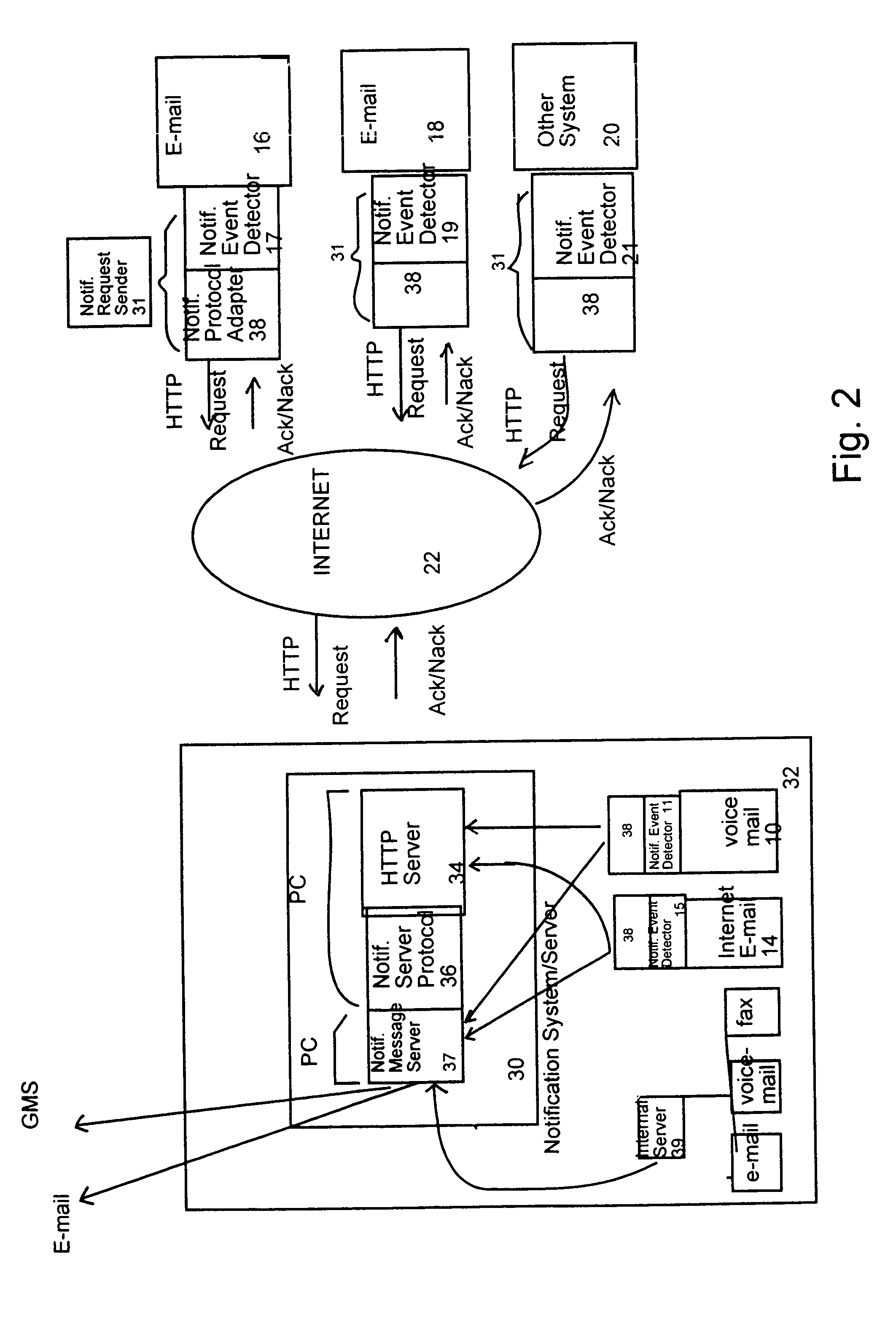
System and method for notification of an event
InactiveUS6965917B1Multiple digital computer combinationsData switching networksMessage passingCellular telephone
A method and a system for notifying a subscriber of the occurrence of an event, which may be a messaging event, in which a message is received by a messaging service associated with the particular subscriber; or a non-messaging event, such as the occurrence of a particular stock price. For example, an e-mail message is optionally received by the mailbox of the subscriber, which is detected by the notification request sender according to the present invention. The notification request sender then prepares a notification request according to a standard network protocol, such as HTTP for example, for transmission to a notification server for the subscriber. This server parses the notification request, and notifies the subscriber with a message according to a particular messaging service, such as an SMS (short message system) message sent to a cellular telephone of the subscriber, for example. Optionally and preferably, if a plurality of such messaging systems for notifying the subscriber is available, then the notification server determines the best messaging system or systems for notifying the subscriber, for example according to the preference of the subscriber.
Owner:COMVERSE
Web-based television system and method for enabling a viewer to access and display HTML-encoded documents located on the World Wide Web (WWW) by reading bar code symbols printed in a WWW-site guide using a wireless bar-code driven remote control device
InactiveUS6321991B1Digital data information retrievalTransmission systemsTelecommunications linkInternet information services
A Web-based television system for enabling an operator to access and display HTML-encoded documents located on the WWW. The system comprises one or more Internet information servers, an Internet terminal unit, and television set having a wireless remote control device and an audio-visual monitor. The Internet information servers store a plurality of HTML-encoded documents at a plurality of storage locations specified by a plurality of Uniform Resource Locators (URLs). The Internet terminal unit is operably connected to the infrastructure of the Internet and embodies a GUI-based Internet browser program, supporting the TCP / IP networking protocol. The television set is operably connected to the Internet terminal unit. The wireless remote control device includes a bar code symbol reader for reading bar code symbols, and an IR-based communication circuit for establishing a wireless communication link with the Internet terminal unit. A WWW-site guide is provided to television viewers. On the guide, a plurality of bar code symbols are preprinted along with a plurality of Web-site descriptions. Each preprinted bar code symbol is encoded with information related to one of the plurality of URLs. The bar code symbol reader is programmed for reading the bar code symbols in the WWW-site guide. In response to reading each bar code symbol, the bar code symbol reader produces information related to one of the URLs, and this information is transmitted, over the wireless information communication link, to the Internet terminal unit. Thereupon, the GUI-based Internet browser uses the TCP / IP networking standard and the produced information to automatically access the HTML-encoded document specified by the related URL, and automatically display the accessed HTML-encoded document on the audio-visual monitor of the television set, for viewing purposes.
Owner:METROLOGIC INSTR
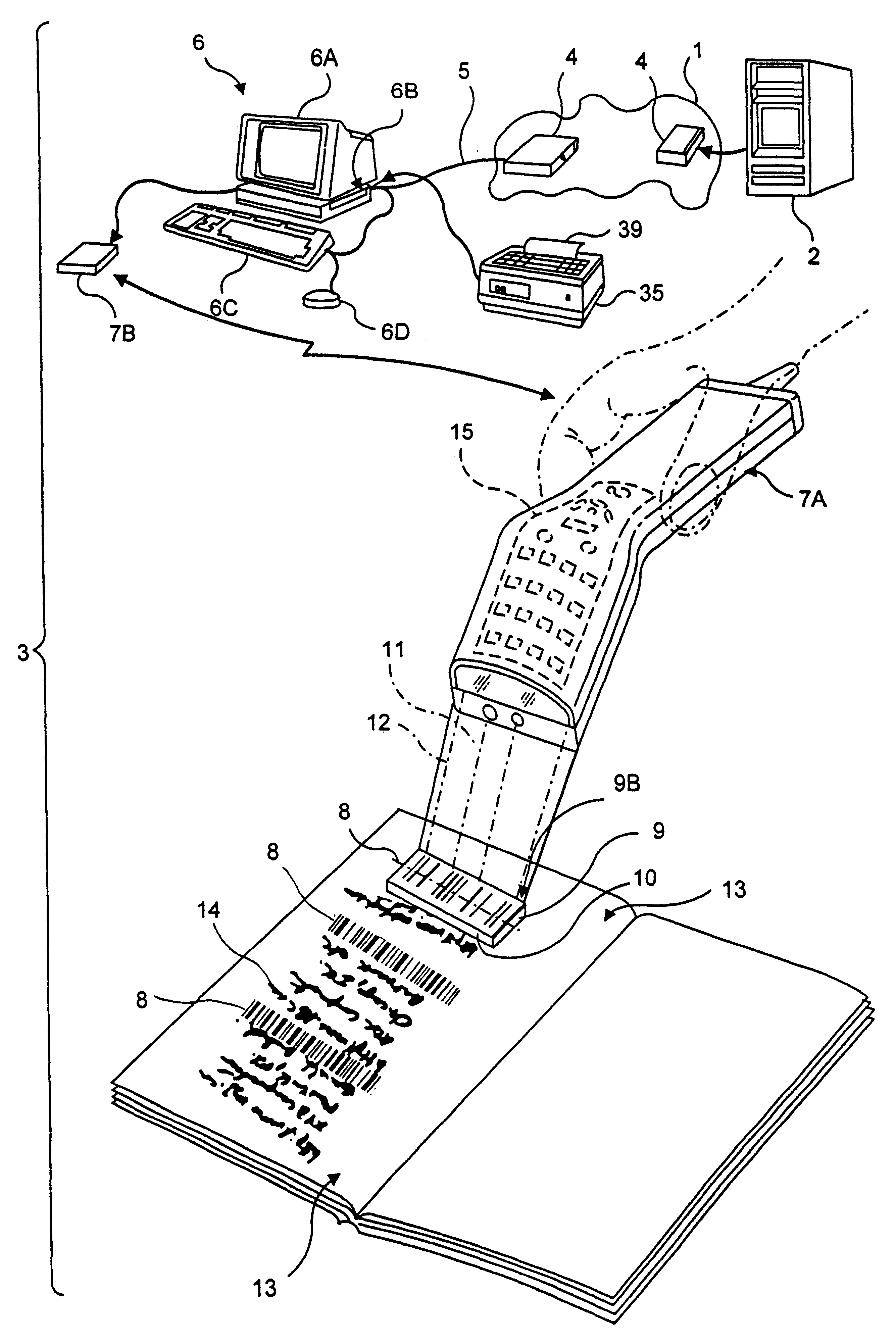
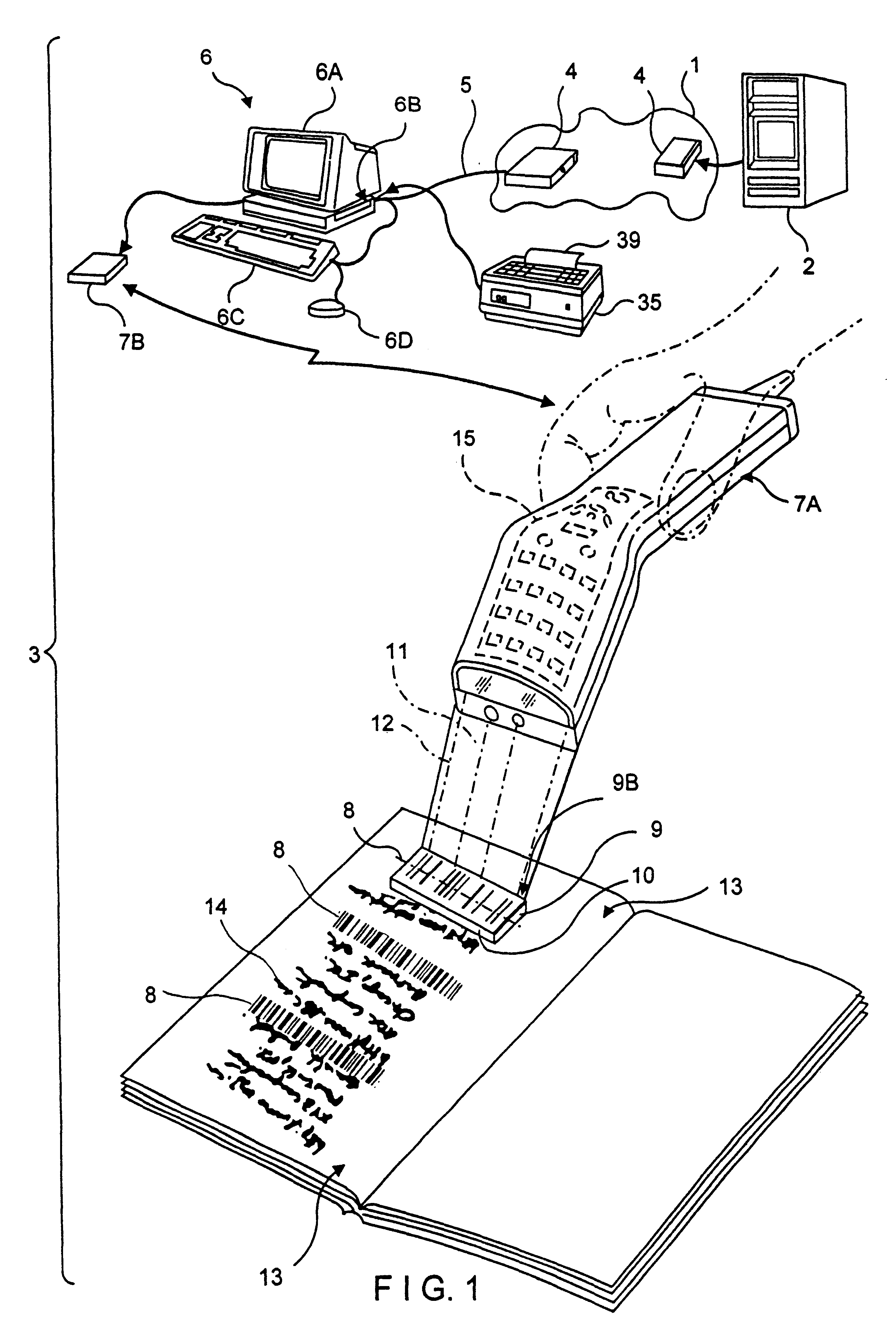
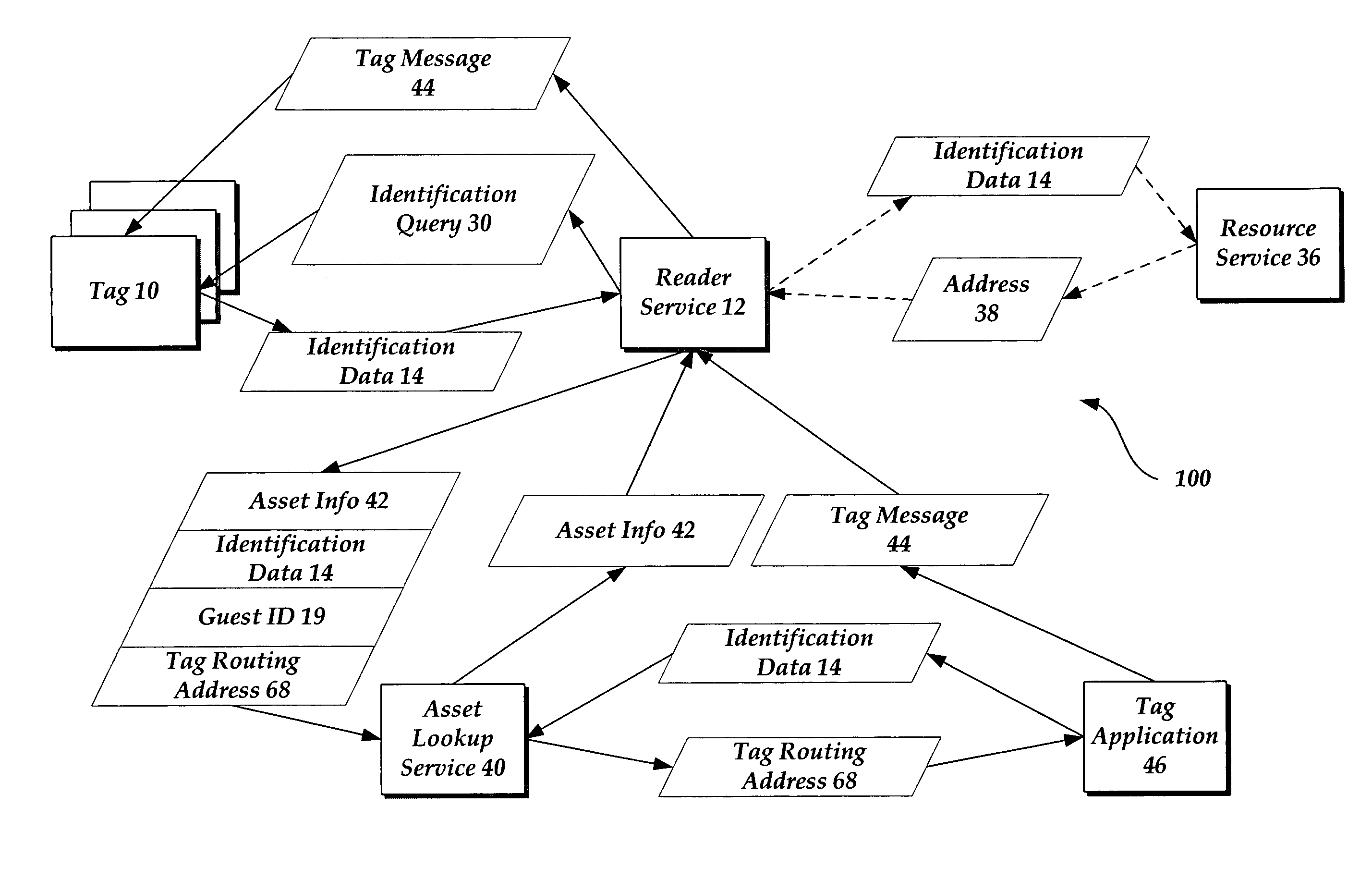
Method and system for communicating with identification tags
ActiveUS20050199716A1Electric signal transmission systemsDigital data processing detailsNetworking protocolWorld Wide Web
A method, identification tag reader and computer program product for communication with an identification tag are disclosed. To communicate with the tag, identification data may be retrieved from an identification tag. A guest identification, compliant with at least a portion of a standard network protocol address, may be assigned to the identification tag. A message addressed to a tag routing address of the tag may be received, and a response to the message may be sent.
Owner:MICROSOFT TECH LICENSING LLC
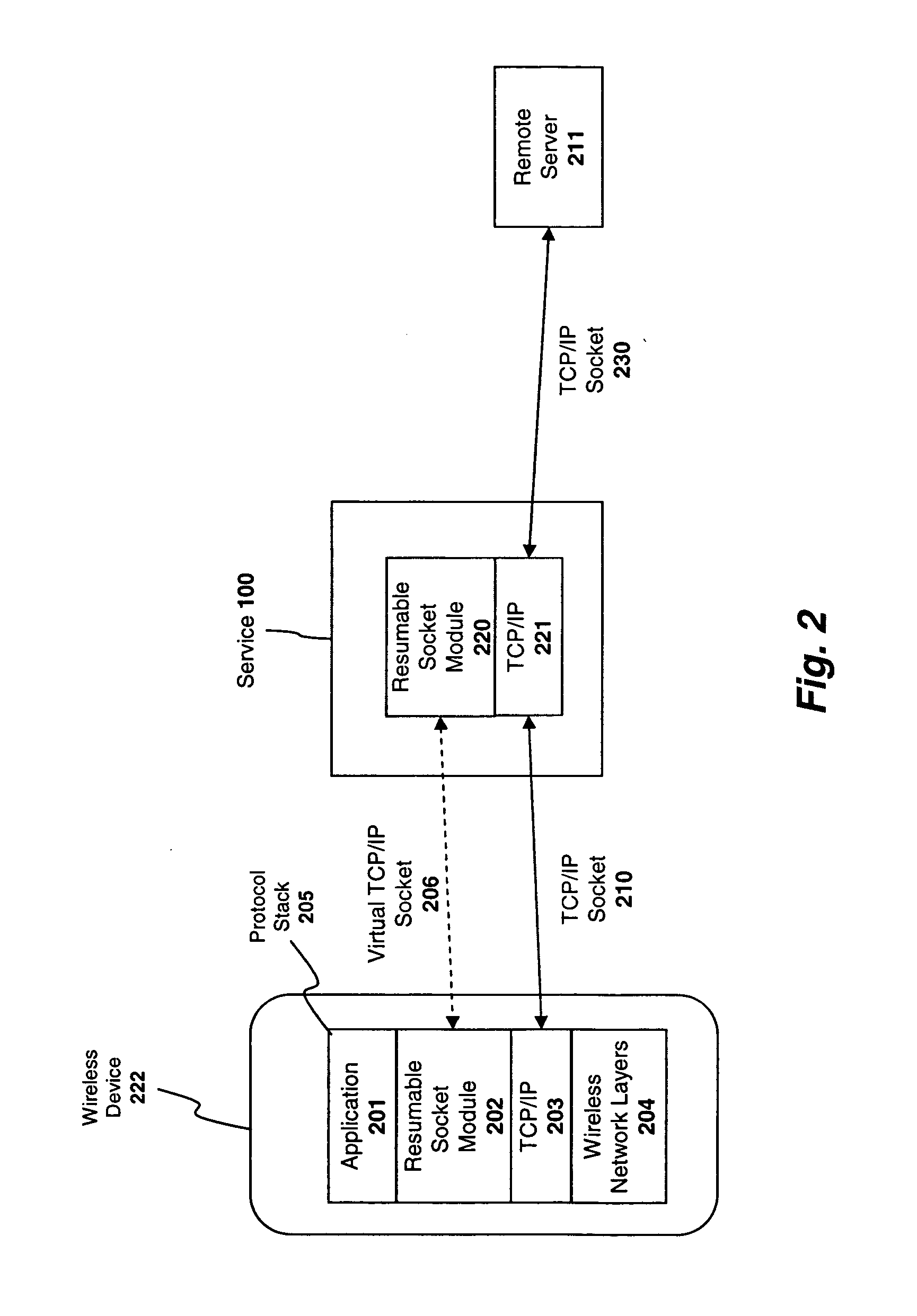
System and method for preserving socket connections over a wireless network
InactiveUS20090103515A1Time-division multiplexWireless commuication servicesNetworking protocolService provision
A system, apparatus, and method for maintaining a socket connection over a wireless network. For example, one embodiment of the invention is a wireless data processing device for emulating a socket connection comprising: a wireless radio for establishing a wireless communication channel with a wireless service provider over a wireless network; a network protocol stack including at least one layer configured to establish a socket connection with a remote server over the wireless network, the network protocol stack further including an application layer for executing applications capable of transmitting and receiving data over the socket connection; and a resumable socket module configured to emulate an open socket connection transparently to applications within the application layer, even when the wireless communication channel is temporarily lost, the resumable socket module counting a number of bytes transmitted or to be transmitted to the remote server and maintaining a buffer containing the bytes transmitted or to be transmitted.
Owner:MICROSOFT TECH LICENSING LLC
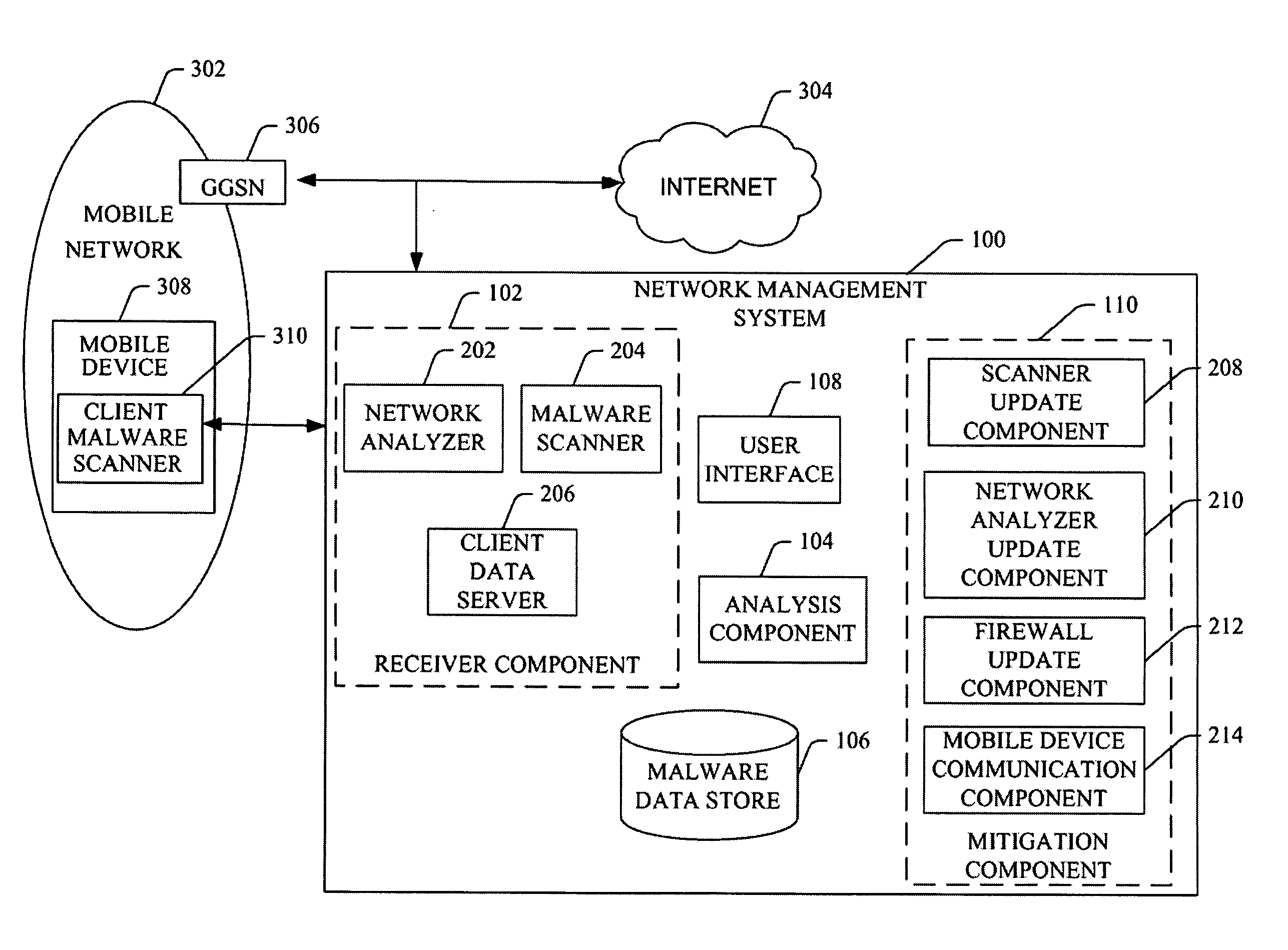
System and method of malware sample collection on mobile networks
ActiveUS20080086776A1Raise the possibilityMemory loss protectionError detection/correctionNetworking protocolProxify
A collection agent monitors a mobile network for data samples containing executable code. The collection agent accepts executables and forwards them to a sample collection center for further analysis, reporting, or in some instances initiating one or more mitigating actions. Depending on the network protocol being monitored, the collection agent responds to connection attempts from nearby mobile devices.
Owner:PULSE SECURE
System for home automation
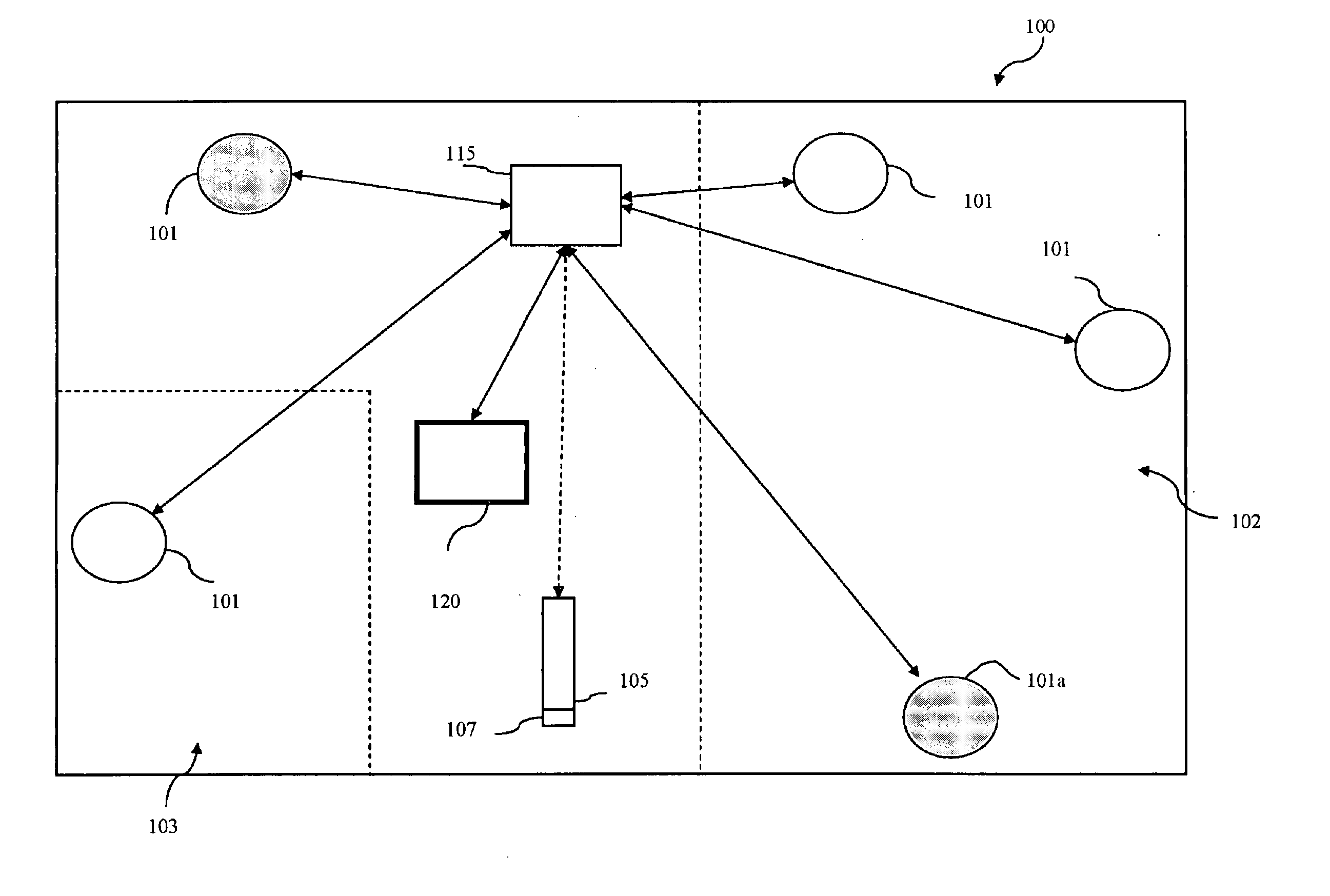
A home automation protocol system provides a network consisting of a number of node devices, controllers, and servers for storing information about node device settings and scene settings in a home environment is provided. The node devices are controlled by the controllers, in that the node devices are set to create scenes, which are stored in a scene server, while the operational states of the node devices are stored in a status server. The status server and scene server may be provided as separate units. The home automation protocol network is controlled by sending commands to the devices and servers, and new devices and controllers are added or updated, and new scenes are programmed. The network protocol allows devices running different protocols to be incorporated into the network.
Owner:INTERMATIC
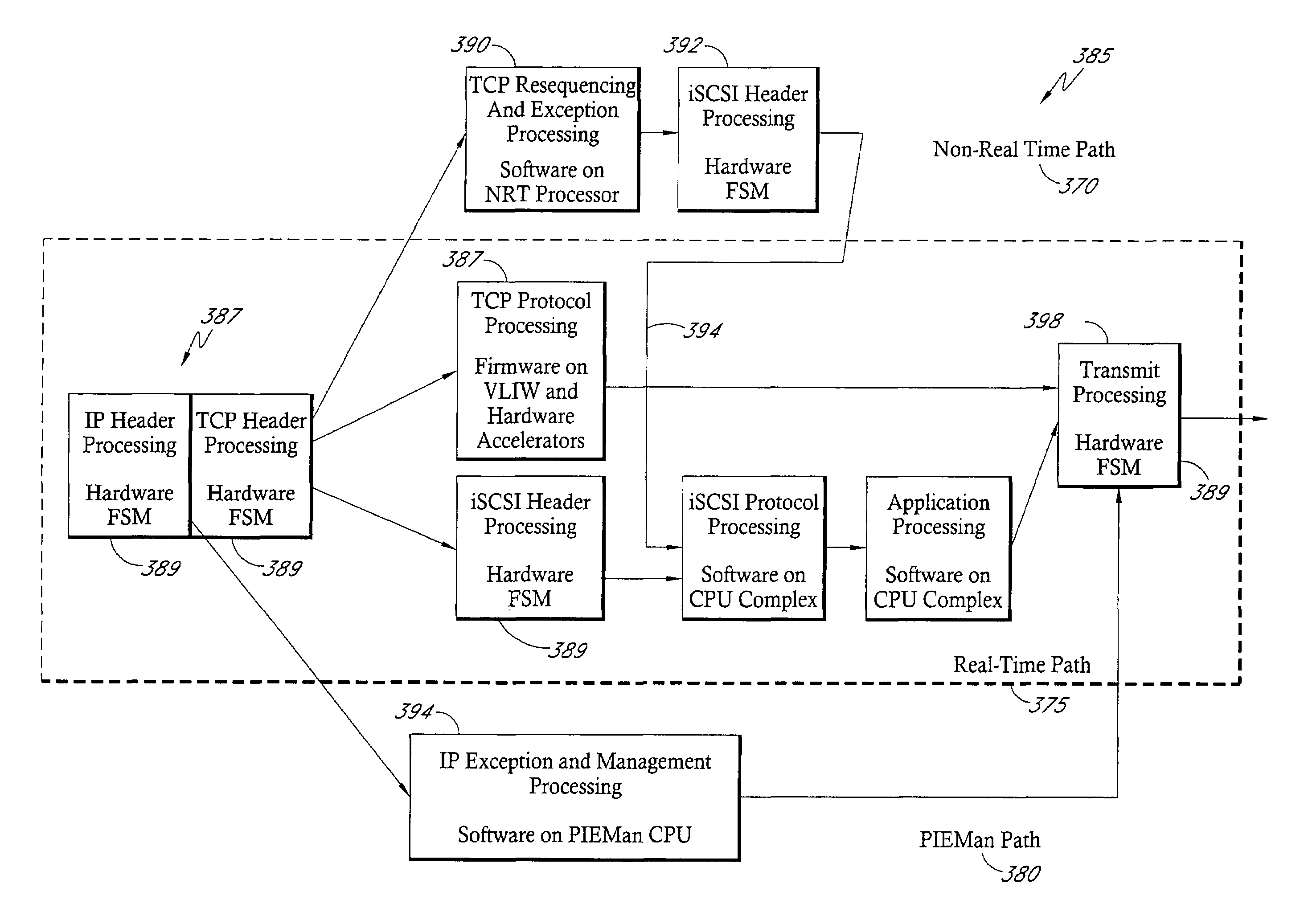
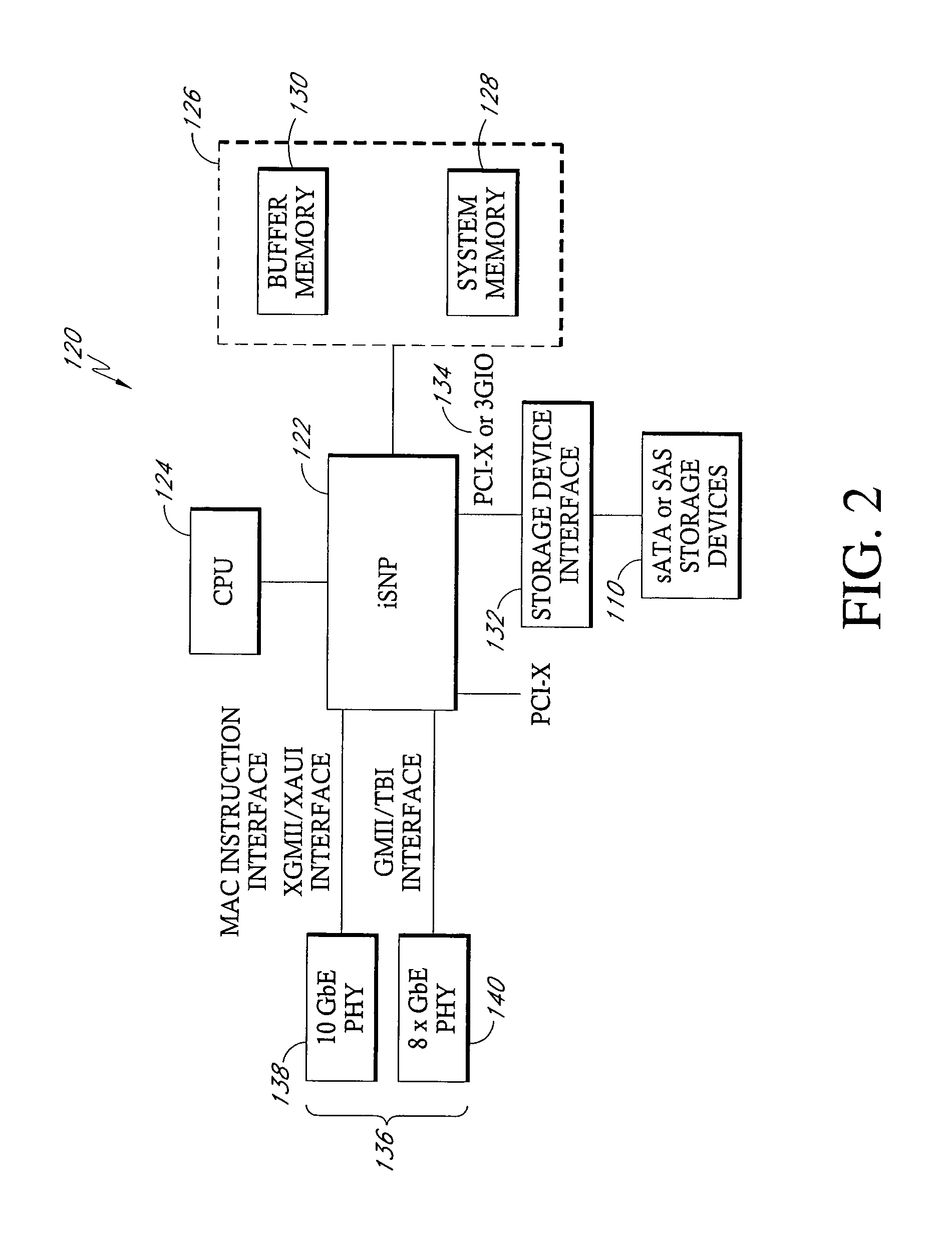
System and methods for high rate hardware-accelerated network protocol processing
InactiveUS7389462B1Improve network performanceImprove storage performanceError prevention/detection by using return channelTransmission systemsTraffic capacityHigh rate
Disclosed is a system and methods for accelerating network protocol processing for devices configured to process network traffic at relatively high data rates. The system incorporates a hardware-accelerated protocol processing module that handles steady state network traffic and a software-based processing module that handles infrequent and exception cases in network traffic processing.
Owner:PROMISE TECHNOLOGY
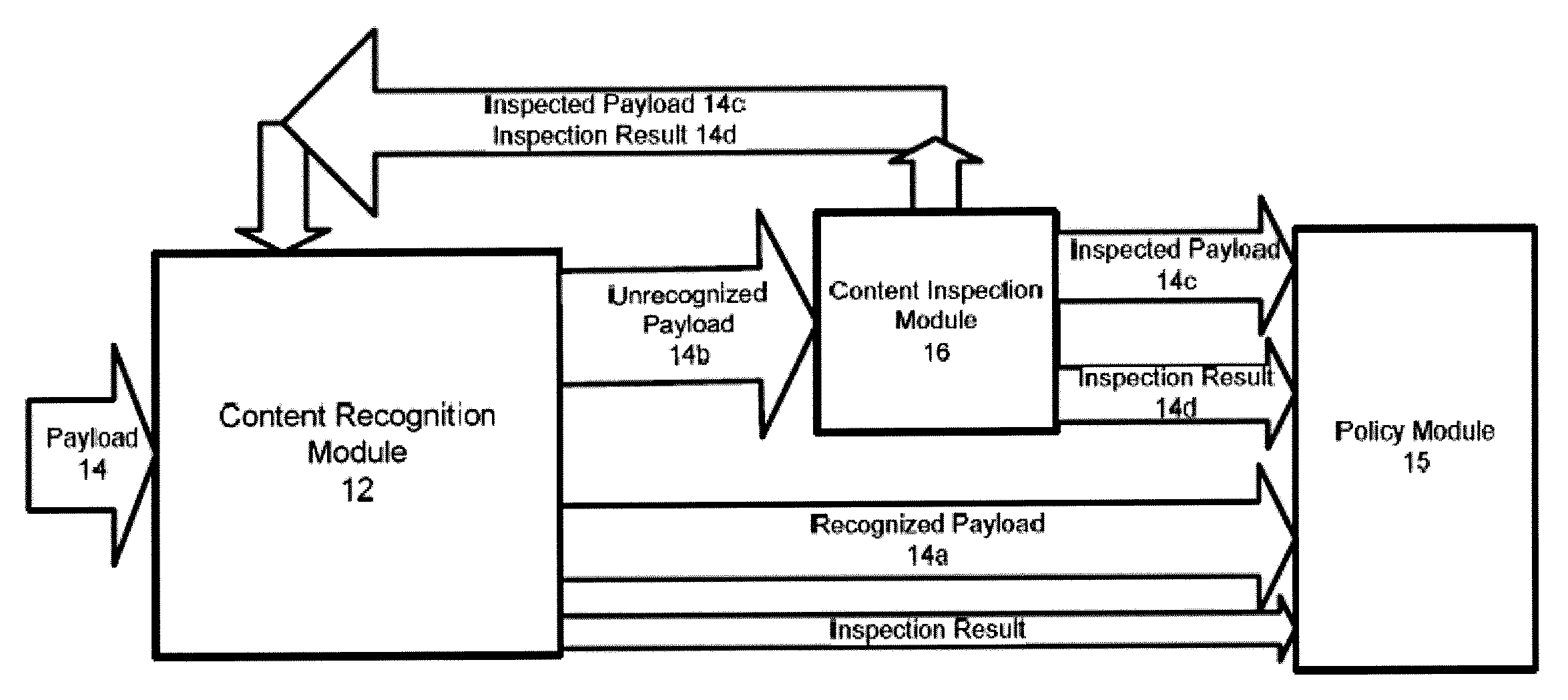
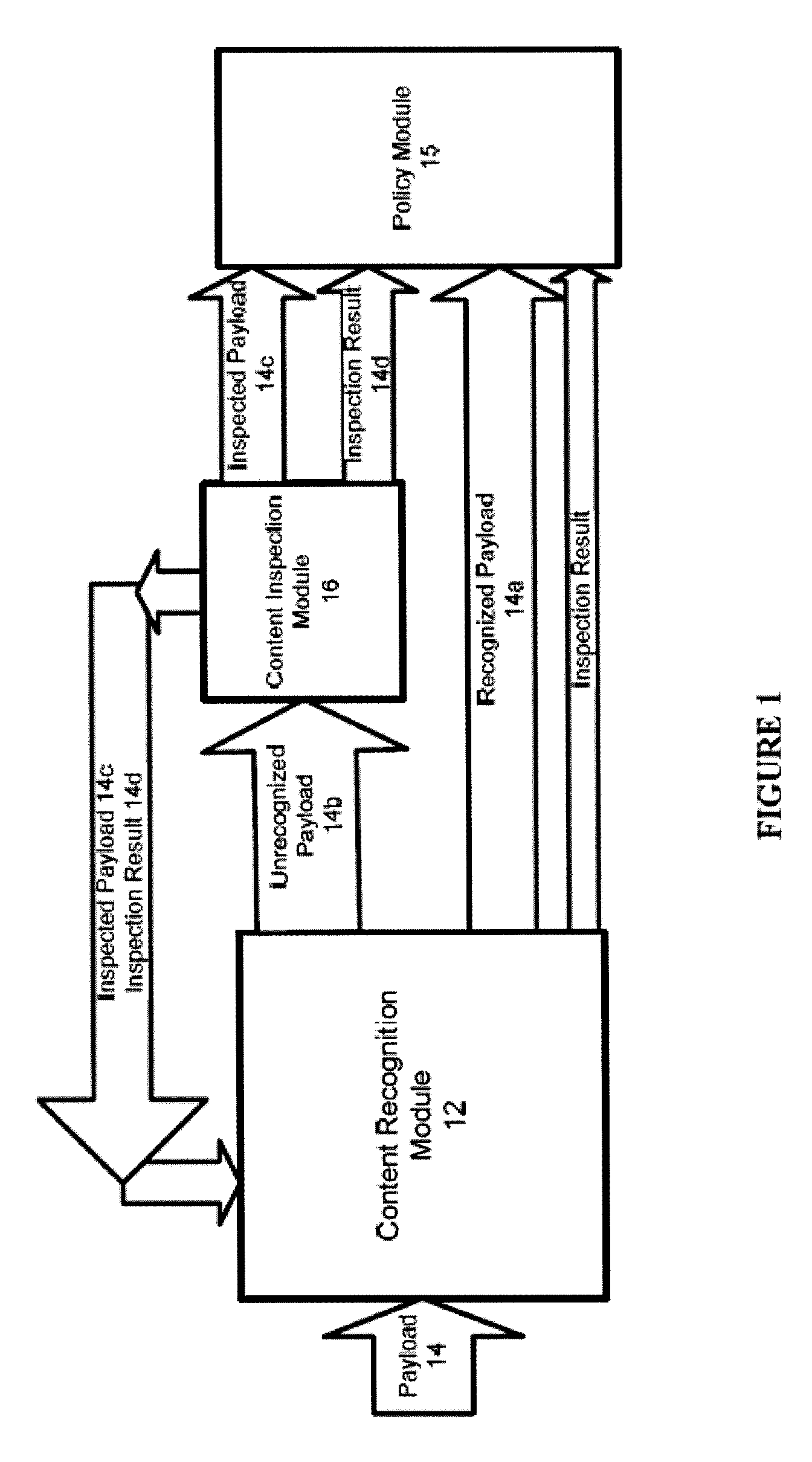
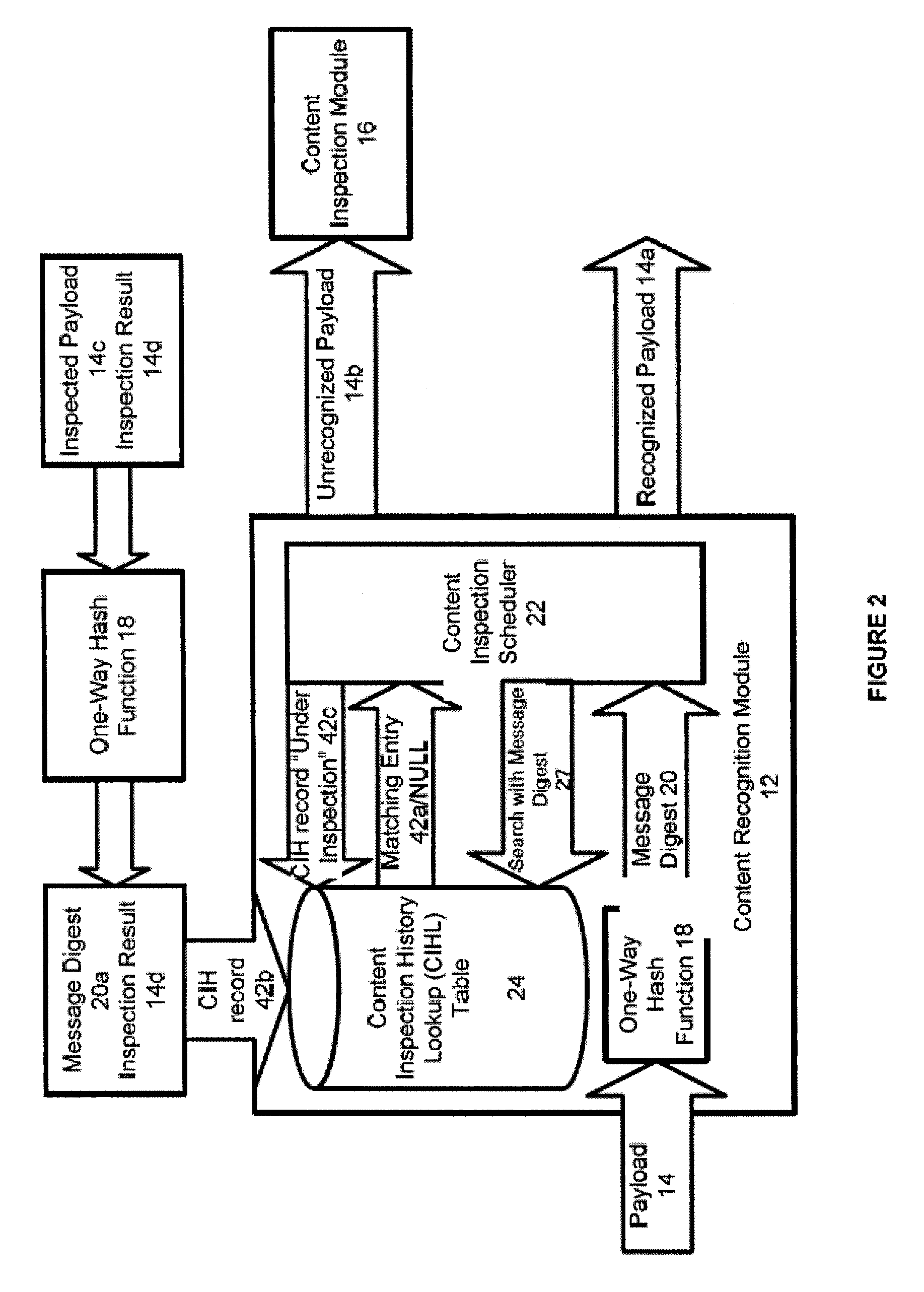
Systems And Methods For Improved Network Based Content Inspection
ActiveUS20070160062A1Efficient and effective inspectionRisk minimizationData switching by path configurationPlatform integrity maintainanceNetworking protocolKnowledge gain
The invention relates to network based content inspection (NBCI). More specifically, the invention provides systems and methods for improved NBCI in complex networks that are typical for enterprises and service providers. These networks are shared by large numbers of concurrent users who send and retrieve application content of various sizes via a variety of communication protocols. This invention improves the efficiency of the NBCI of an individual communication session by learning from the processing results of other communication sessions which may be carried via different network protocols. In addition, the invention provides methods that do not weaken the overall security for the network and that improve the stability of NBCI systems by minimizing the risk of system resource exhaustion if subjected to a burst of large payloads. The invention also improves perceived network stability by preventing the system resources from being “live-locked” by a few large content inspection tasks. Further still, the invention improves the cost-effectiveness of NBCI by allowing the optimization knowledge gained by one NBCI node be shared with other nodes.
Owner:WEDGE NETWORKS
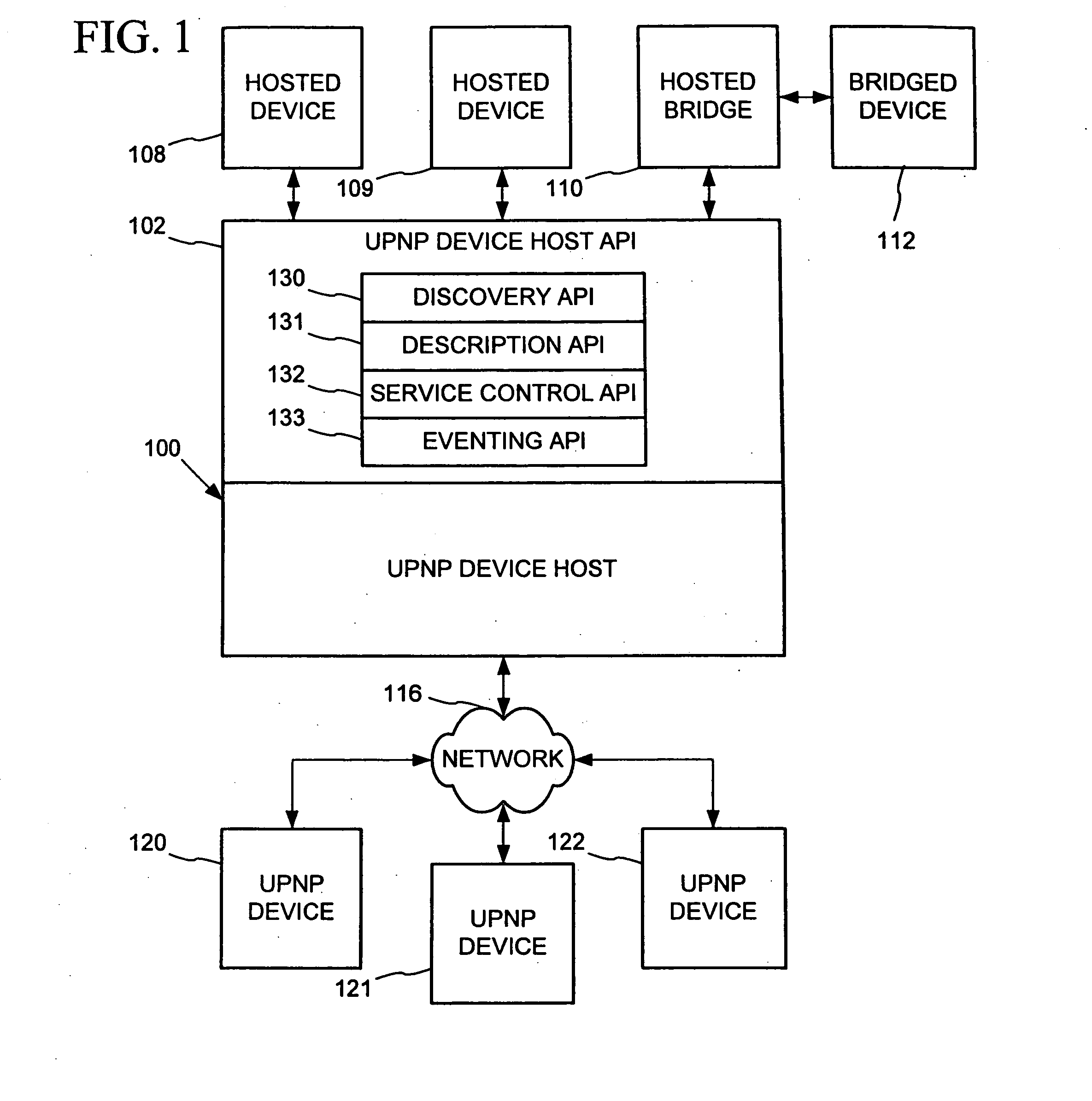
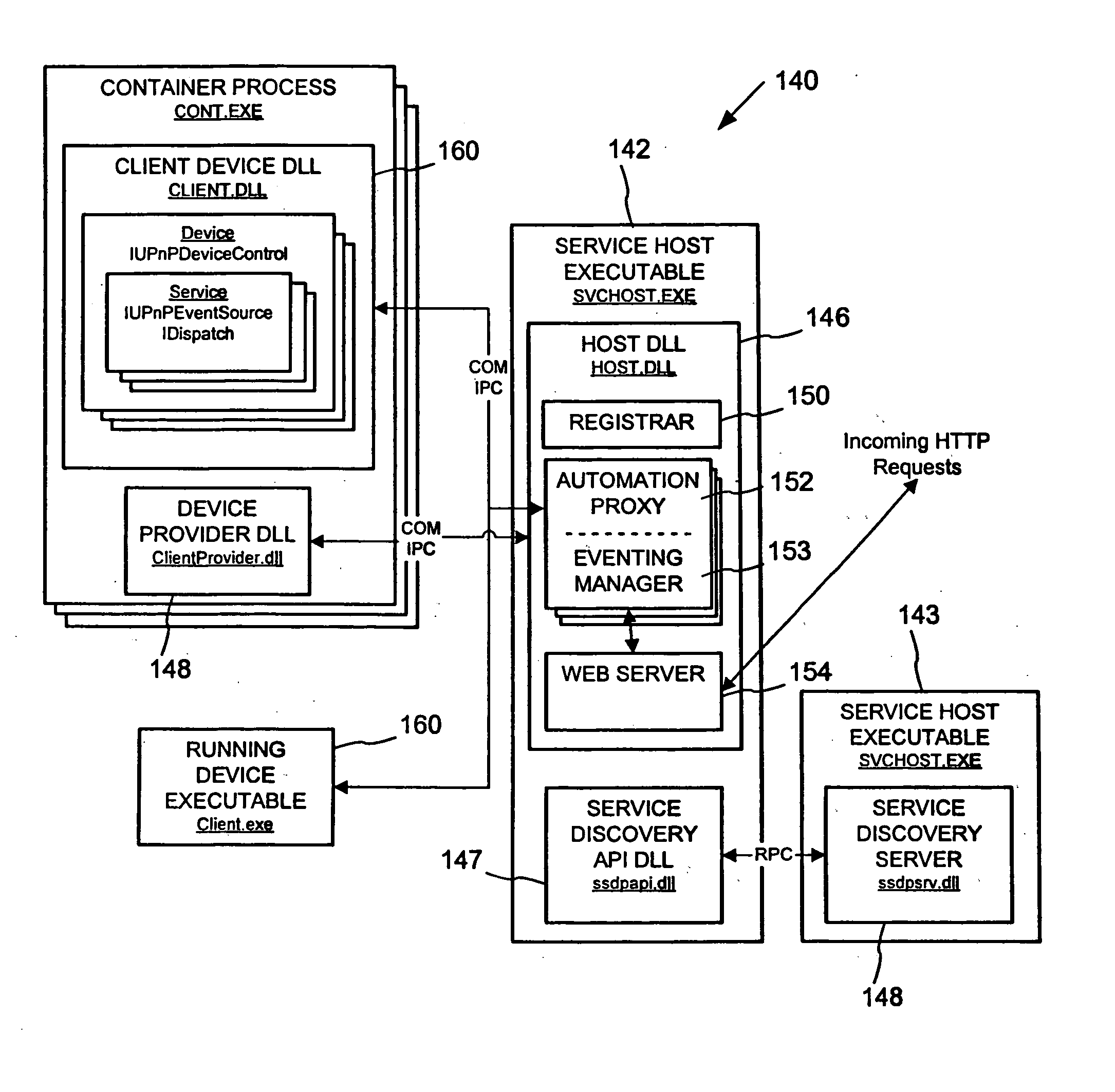
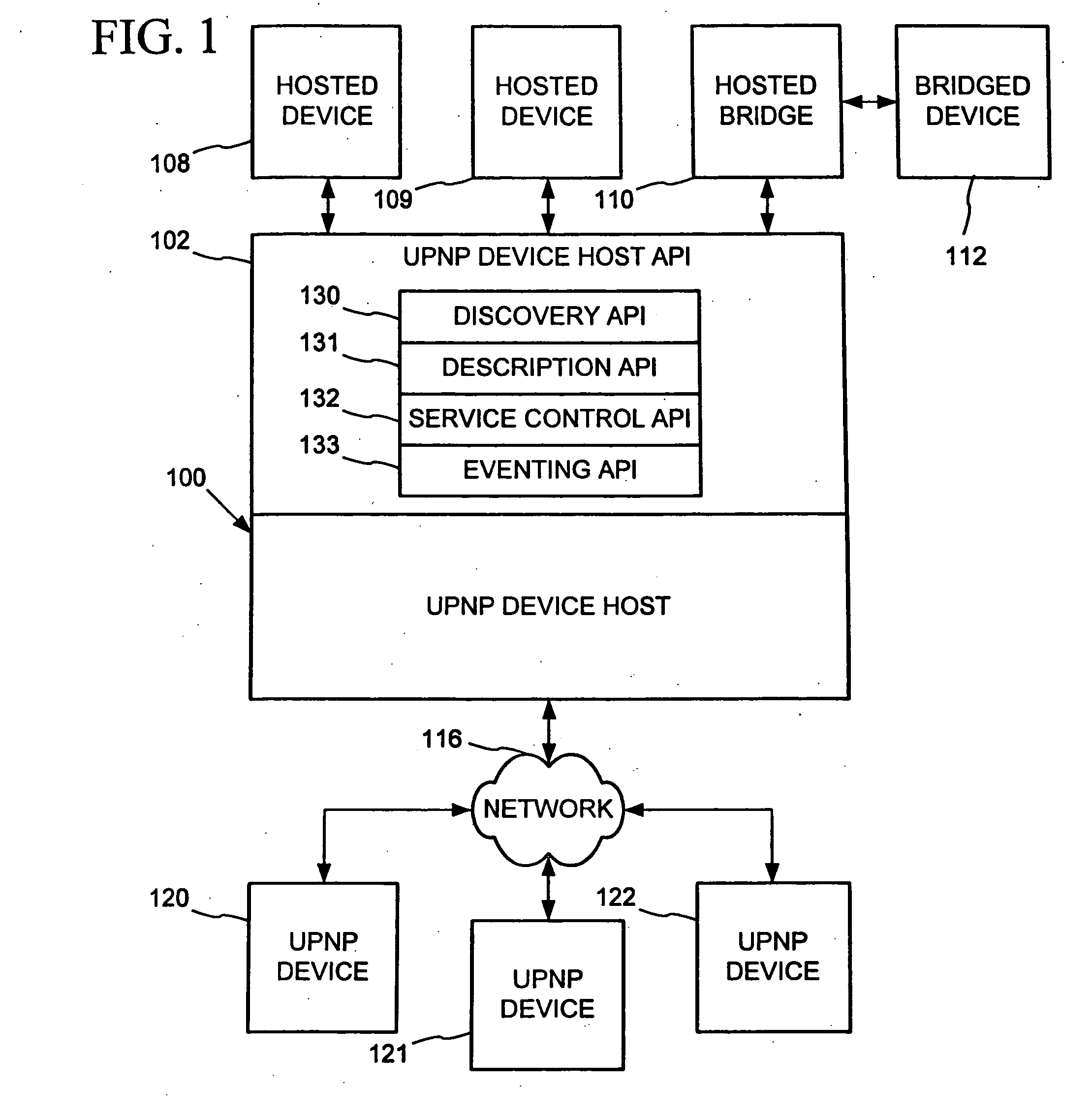
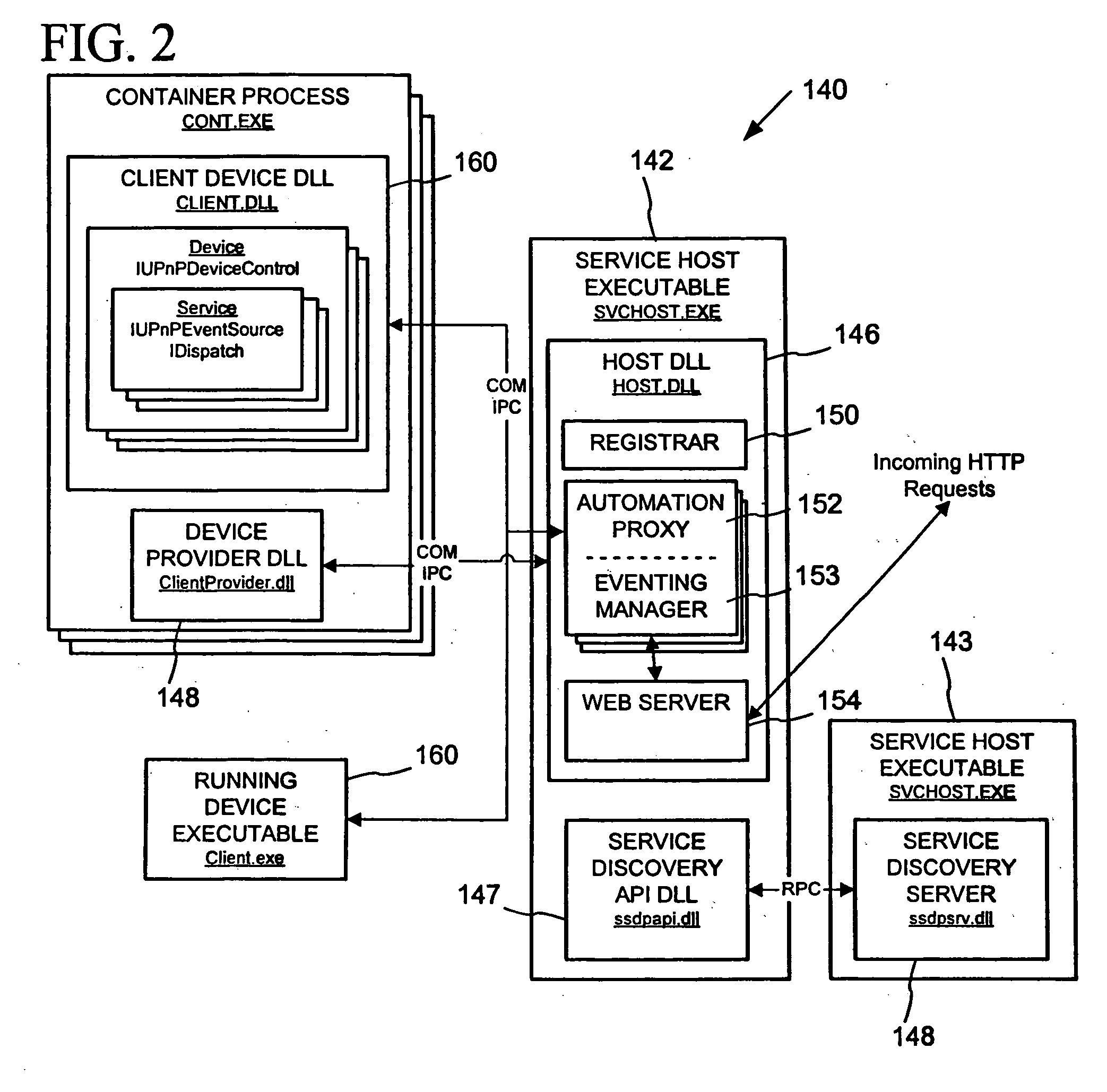
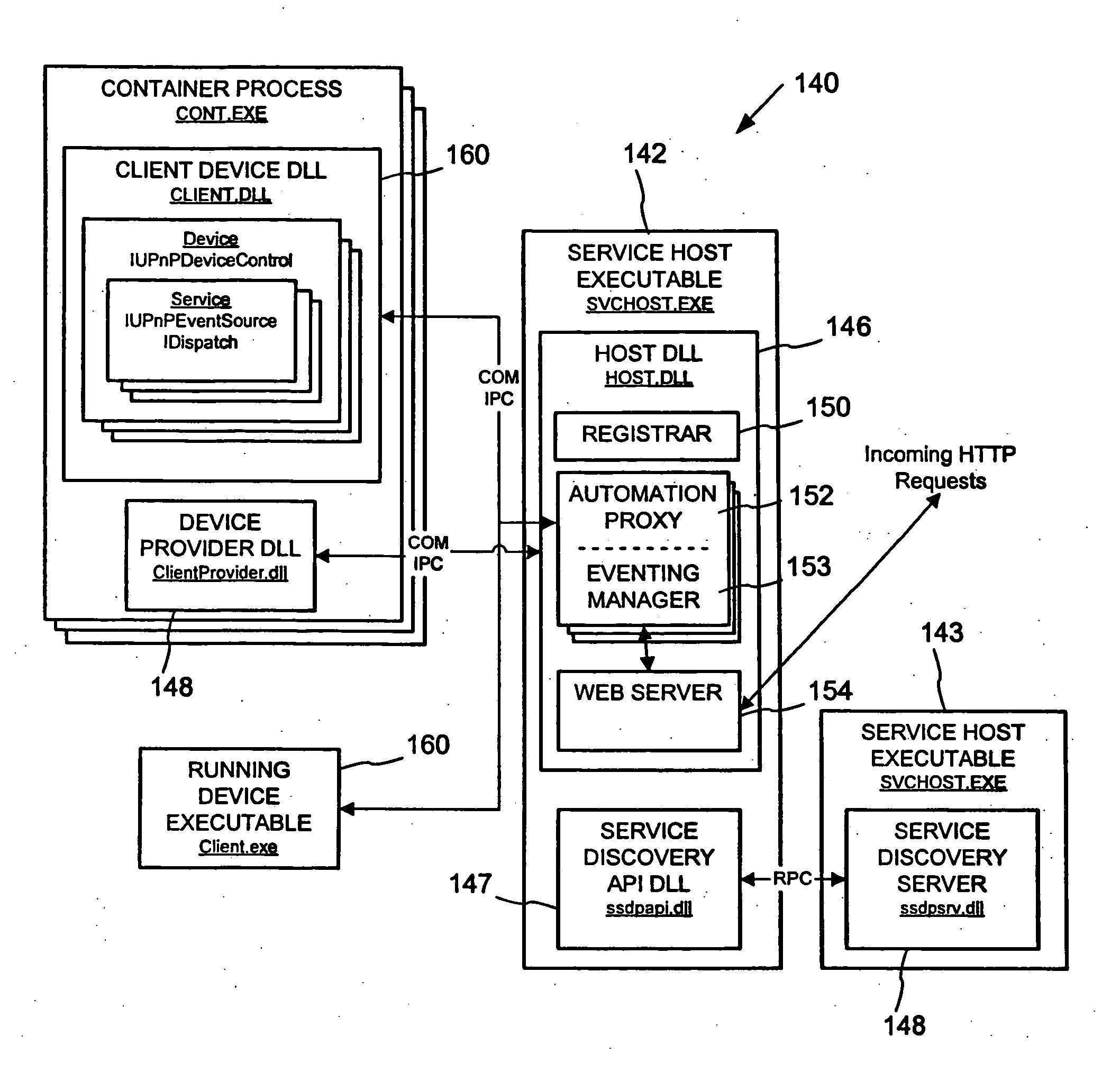
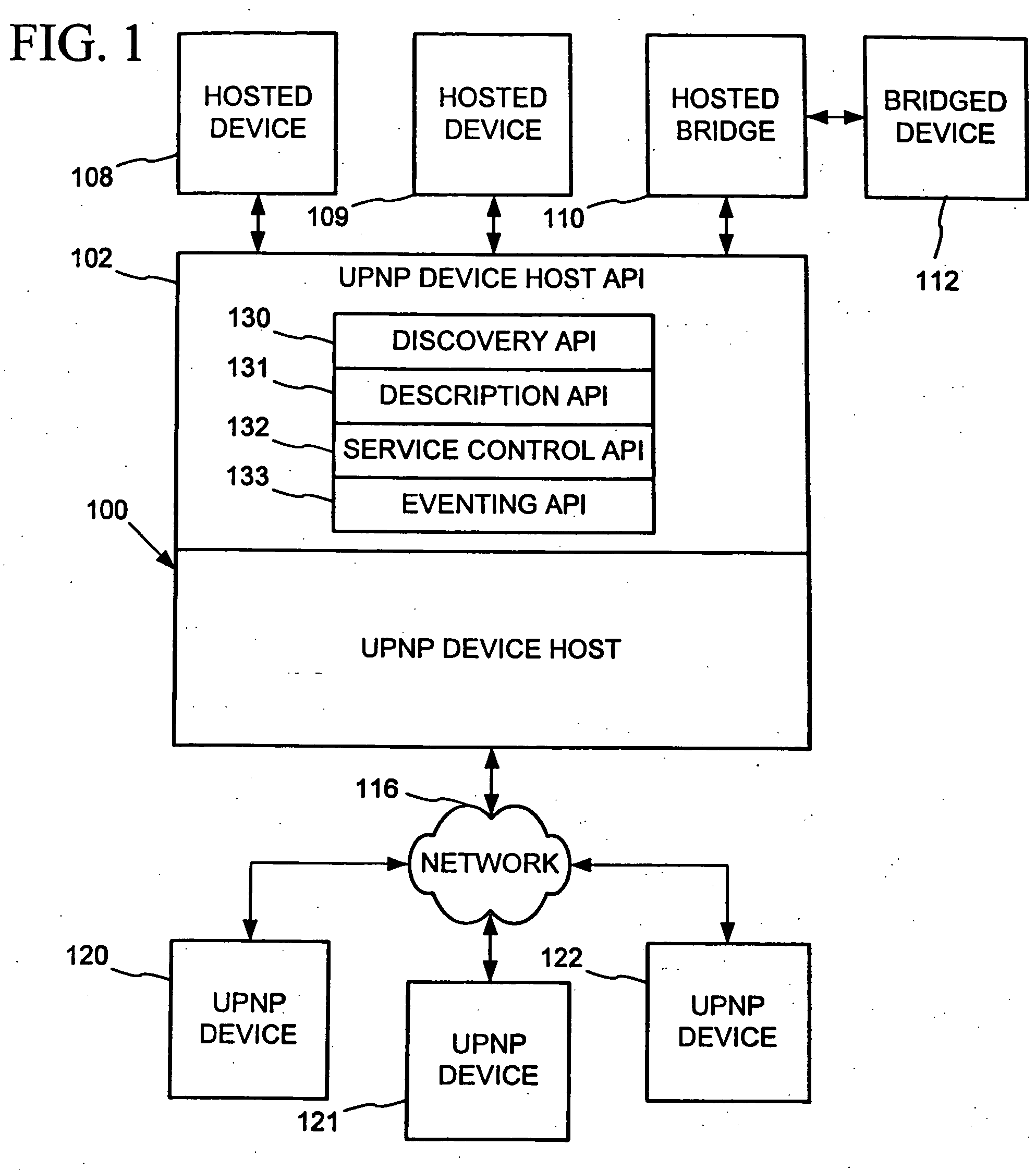
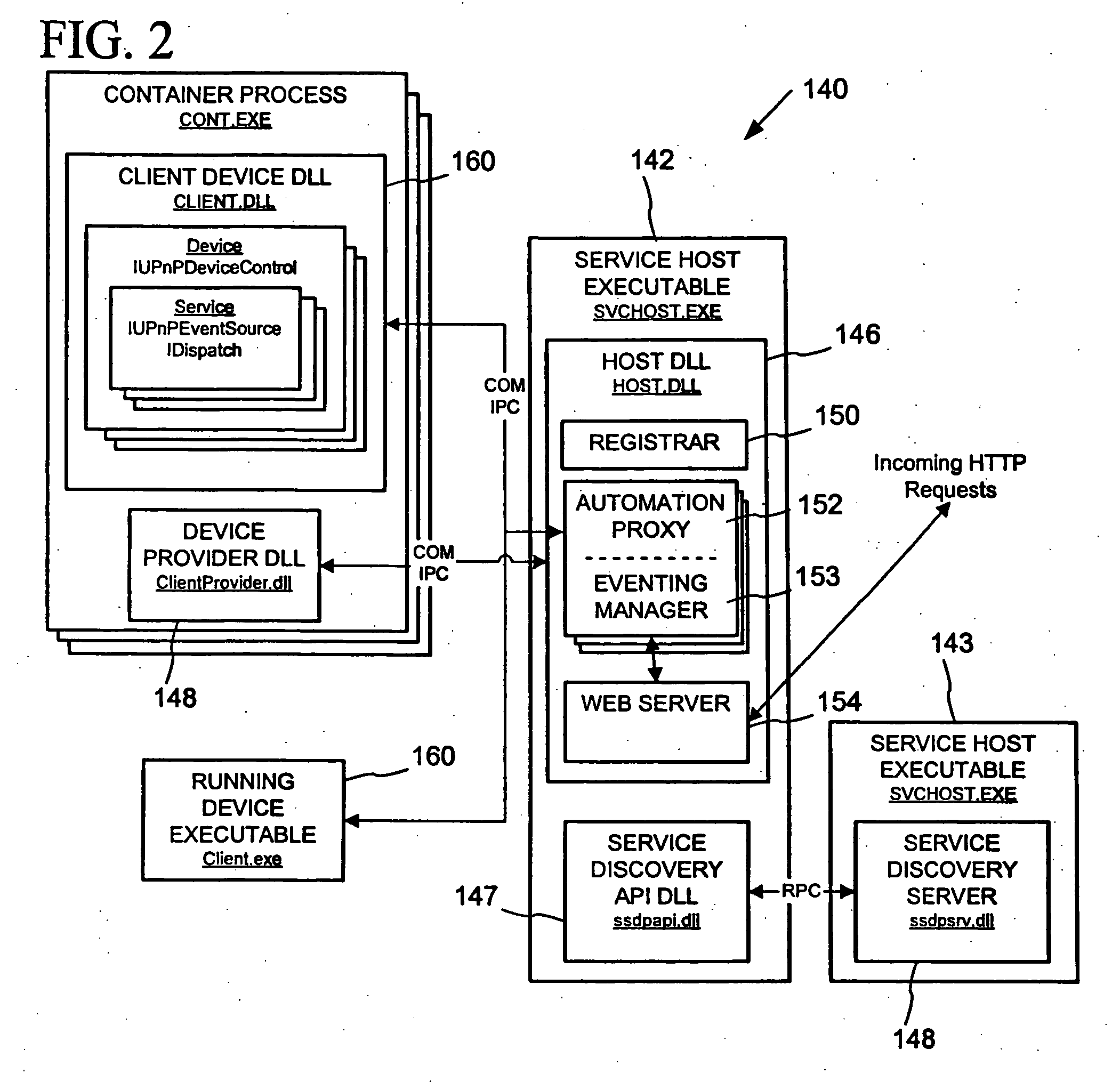
Peer networking host framework and hosting API
InactiveUS20060168159A1Eliminating implementationEliminate separationDigital computer detailsProgram loading/initiatingNetworking protocolDistributed computing
A device hosting framework provides hosting for software-implemented logical devices (including peripheral devices bridges) on a computer to expose their services as controlled devices per a peer networking protocol. The device hosting framework encapsulates discovery, description and control protocol operations of the peer networking protocol, which frees the developers of the hosted devices from having to individually implement the peer networking protocol in the hosted devices' software and need implement only the core functionality of the hosted device. The device hosting framework operates as a host supporting device interoperability via the peer networking protocol for multiple hosted devices.
Owner:MICROSOFT TECH LICENSING LLC
Peer networking host framework and hosting API
InactiveUS20060123125A1Eliminate separationEliminating duplicative implementationMultiple digital computer combinationsProgram loading/initiatingNetworking protocolDistributed computing
A device hosting framework provides hosting for software-implemented logical devices (including peripheral devices bridges) on a computer to expose their services as controlled devices per a peer networking protocol. The device hosting framework encapsulates discovery, description and control protocol operations of the peer networking protocol, which frees the developers of the hosted devices from having to individually implement the peer networking protocol in the hosted devices' software and need implement only the core functionality of the hosted device. The device hosting framework operates as a host supporting device interoperability via the peer networking protocol for multiple hosted devices.
Owner:MICROSOFT TECH LICENSING LLC
Peer networking host framework and hosting API
InactiveUS20060123124A1Eliminate separationEliminating duplicative implementationMultiple digital computer combinationsProgram loading/initiatingNetworking protocolDistributed computing
A device hosting framework provides hosting for software-implemented logical devices (including peripheral devices bridges) on a computer to expose their services as controlled devices per a peer networking protocol. The device hosting framework encapsulates discovery, description and control protocol operations of the peer networking protocol, which frees the developers of the hosted devices from having to individually implement the peer networking protocol in the hosted devices' software and need implement only the core functionality of the hosted device. The device hosting framework operates as a host supporting device interoperability via the peer networking protocol for multiple hosted devices.
Owner:MICROSOFT TECH LICENSING LLC
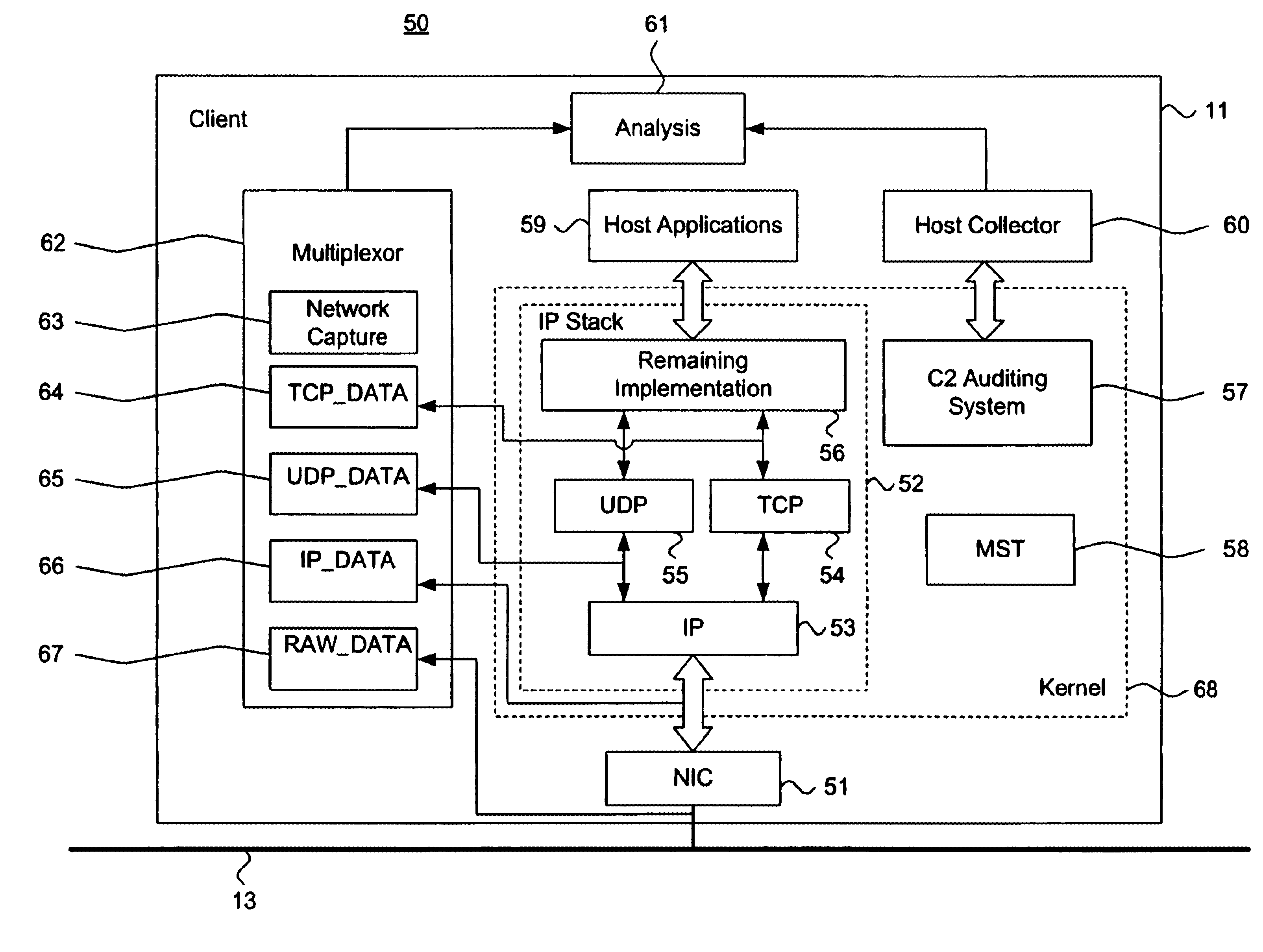
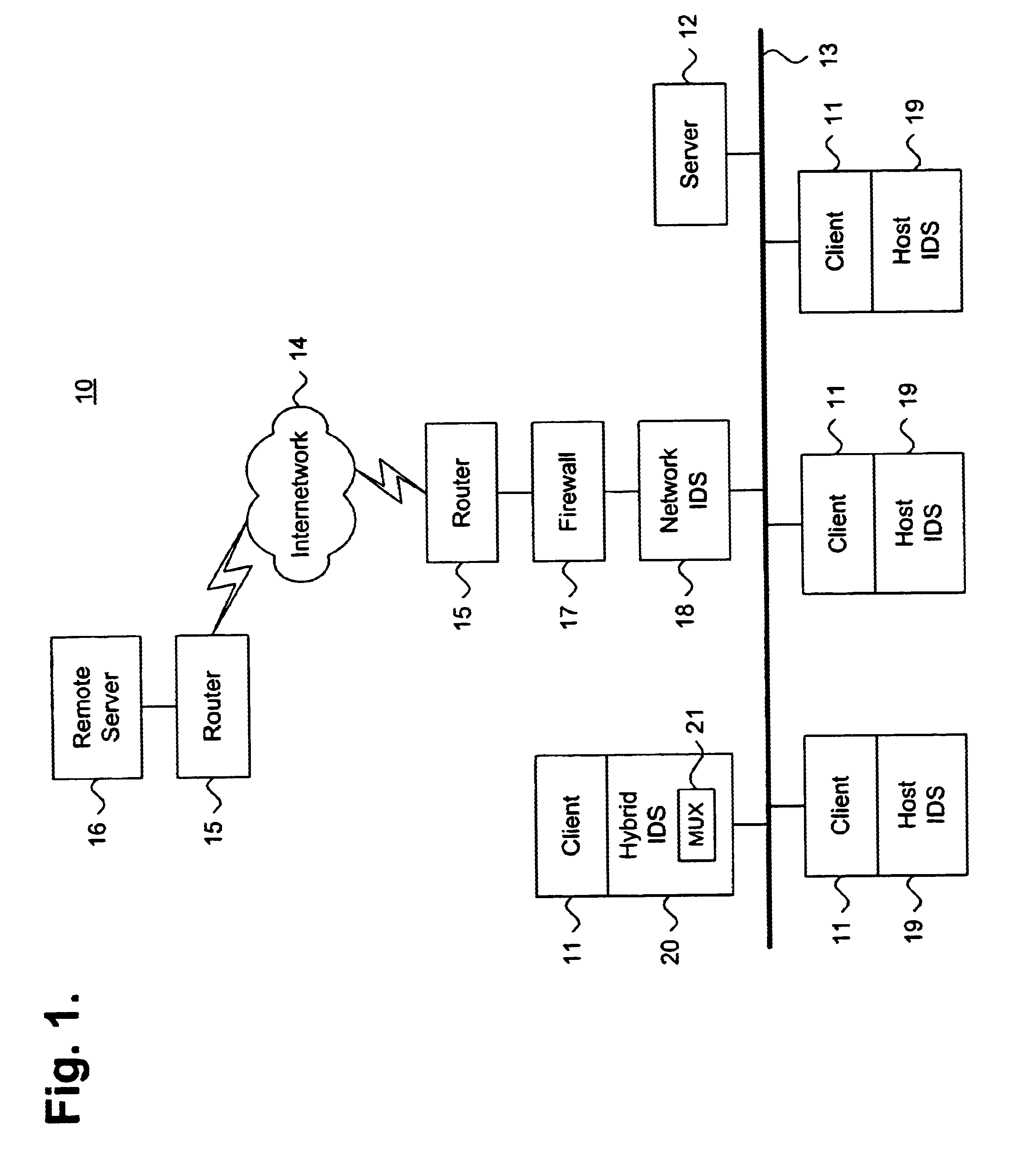
System and method for intrusion detection data collection using a network protocol stack multiplexor
InactiveUS6851061B1Memory loss protectionDigital computer detailsProtocol processingNetworking protocol
A system and method for detecting network intrusions using a protocol stack multiplexor is described. A network protocol stack includes a plurality of hierarchically structured protocol layers. Each such protocol layer includes a read queue and a write queue for staging transitory data packets and a set of procedures for processing the transitory data packets in accordance with the associated protocol. A protocol stack multiplexor is interfaced directly to at least one such protocol layer through a set of redirected pointers to the processing procedures of the interfaced protocol layer. A data packet collector references at least one of the read queue and the write queue for the associated protocol layer. A data packet exchanger communicates a memory reference to each transitory data packet from the referenced at least one of the read queue and the write queue for the associated protocol layer. An analysis module receives the communicated memory reference and performs intrusion detection based thereon.
Owner:MCAFEE LLC
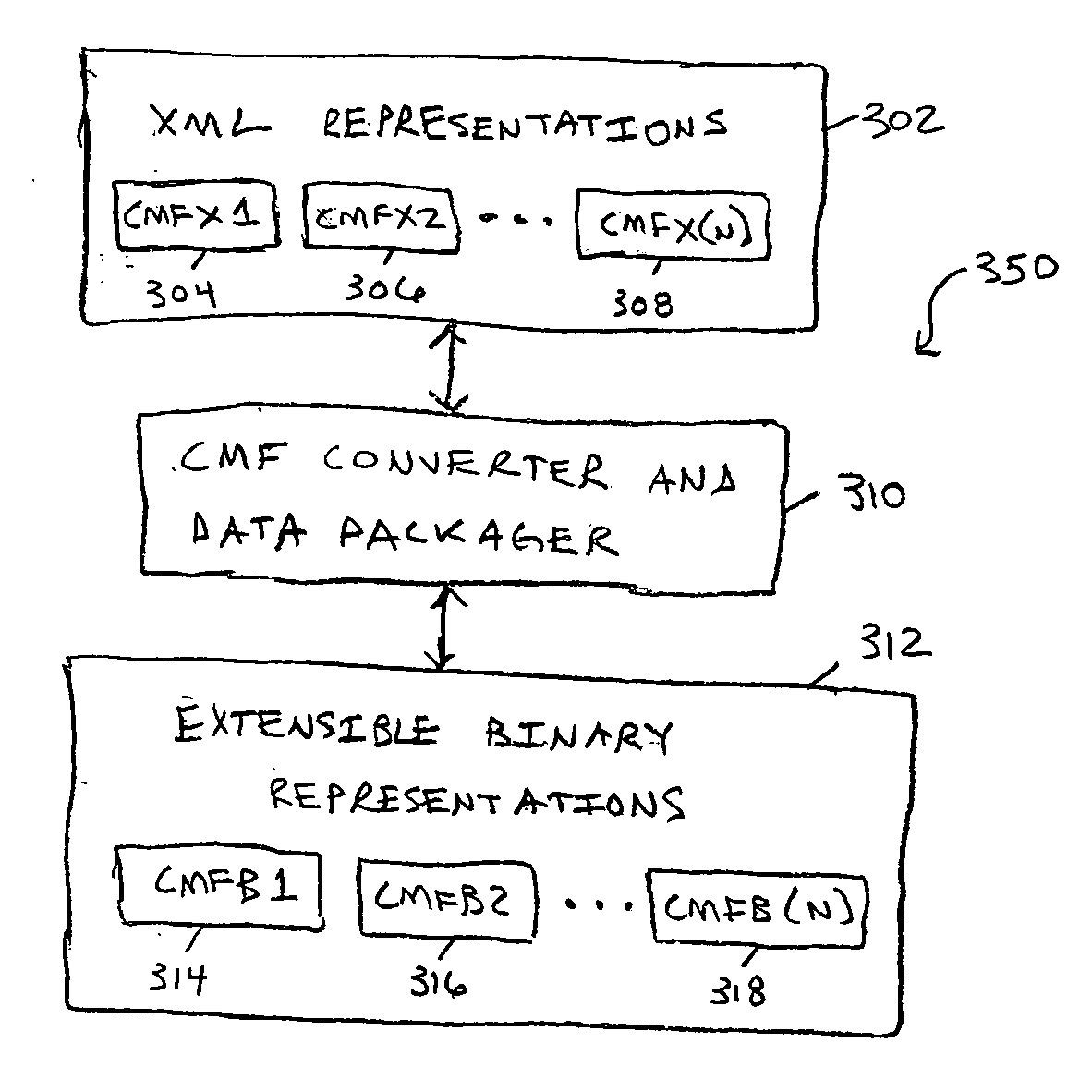
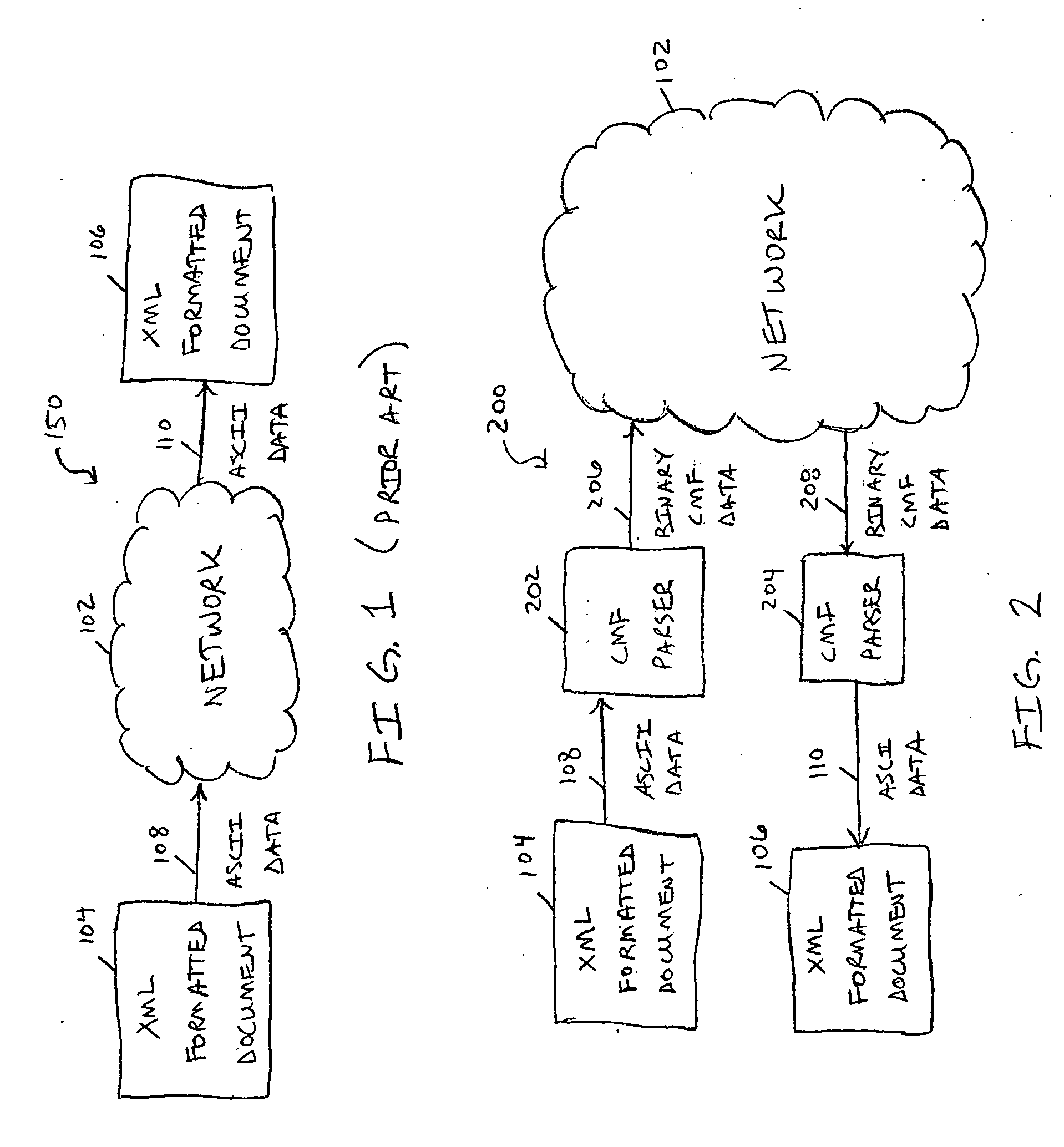
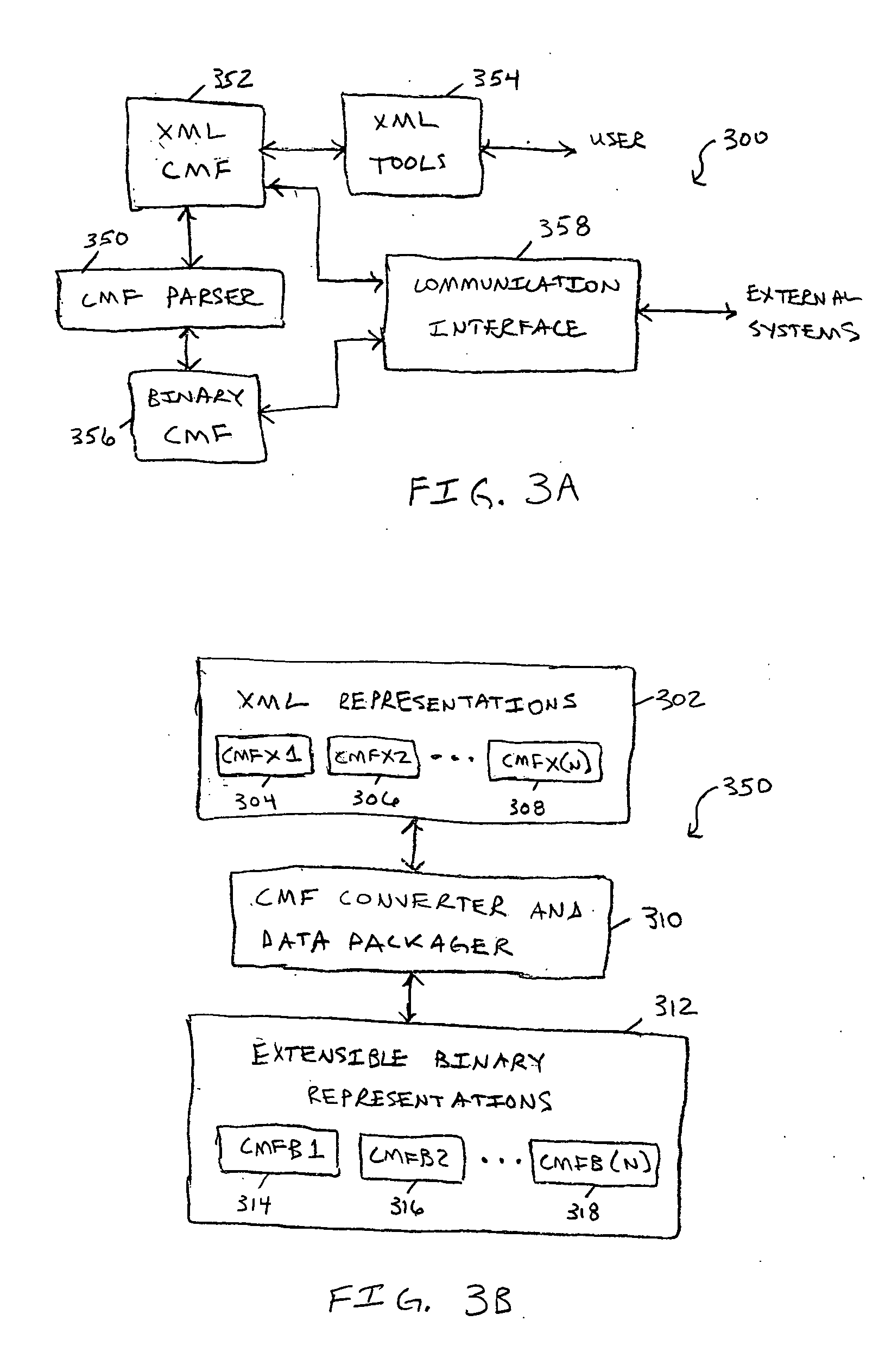
Extensible binary mark-up language for efficient XML-based data communications and related systems and methods
InactiveUS20050278616A1Improve efficiencyEfficient transportNatural language data processingMultiple digital computer combinationsExtensible markupCommunications media
An extensible binary mark-up language is disclosed that is compatible with existing XML standards yet provides significantly improved efficiencies for XML-based data storage and communications, particularly for narrow and low bandwidth communication media. A corresponding extensible non-binary mark-up language is also disclosed that is compatible with the XML standard. This dual-representation common message format (CMF) allows standard XML tools to be utilized in viewing and editing XML-based data and allows a CMF parser to be utilized to convert the XML formatted information into an extensible binary representation for actual communication through a medium or storage on a wide range of media. Advantages include a very compact, yet flexible and extensible binary data representation (CMF-B) for a corresponding extensible mark-up language (CMF-X), a data packaging scheme that allows for the effective transport of XML-based data over existing data channels, including narrow-bandwidth channels that utilize existing network protocols, and a CMF parser that allows for seamless conversion between CMF-B and CMF-X.
Owner:L 3 INTEGRATED SYST +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com