Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1282results about How to "Reduce system cost" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
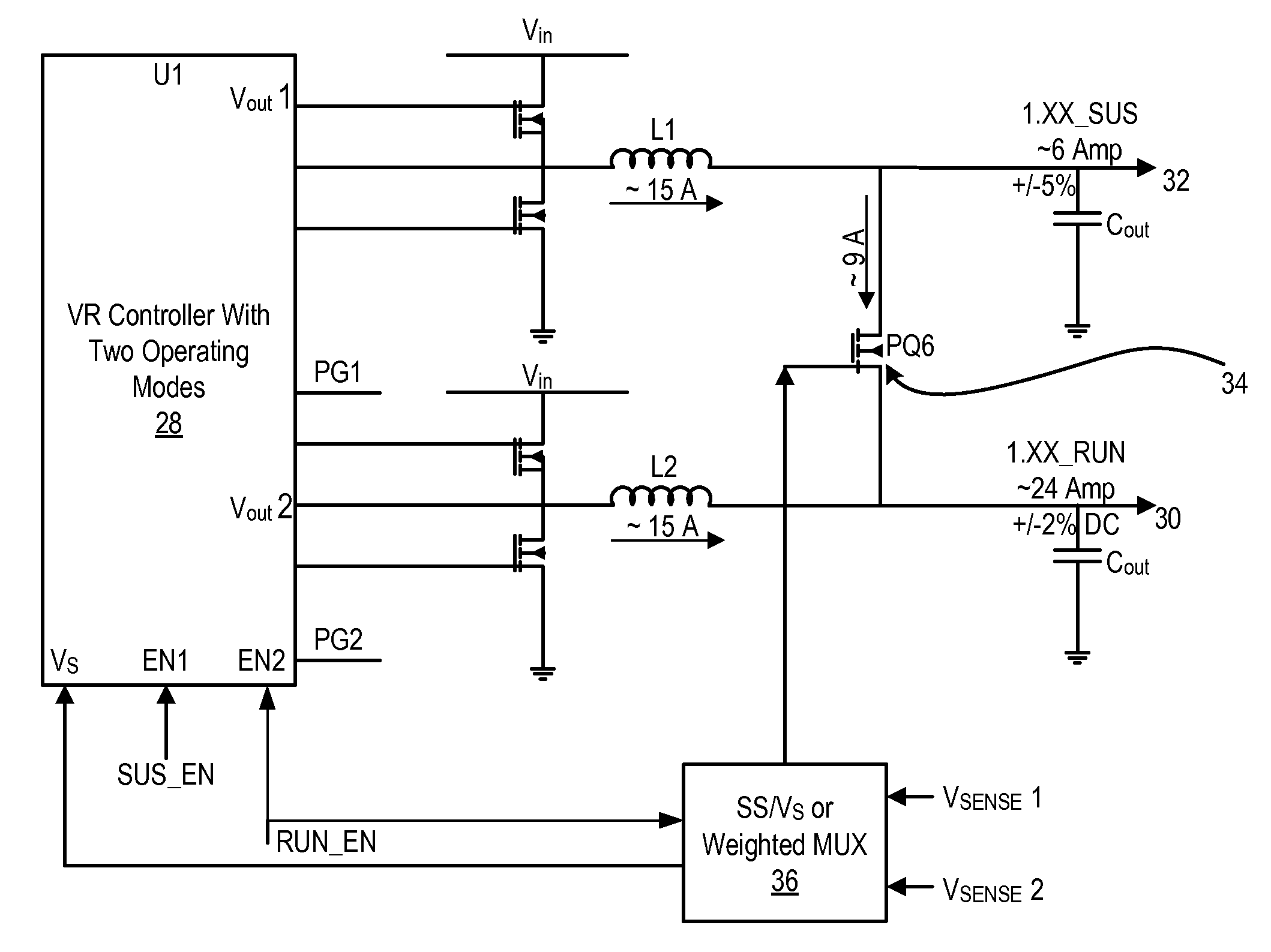
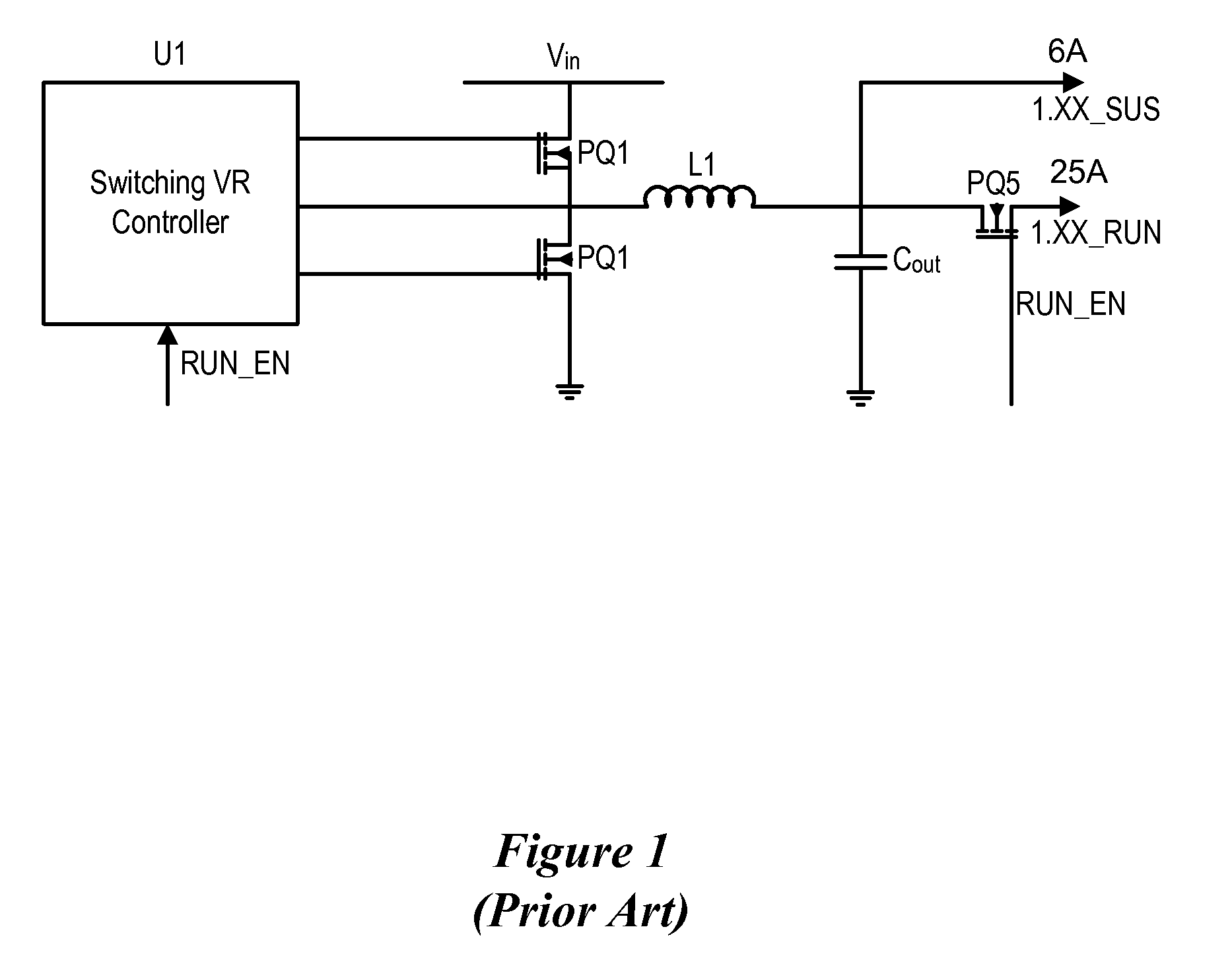
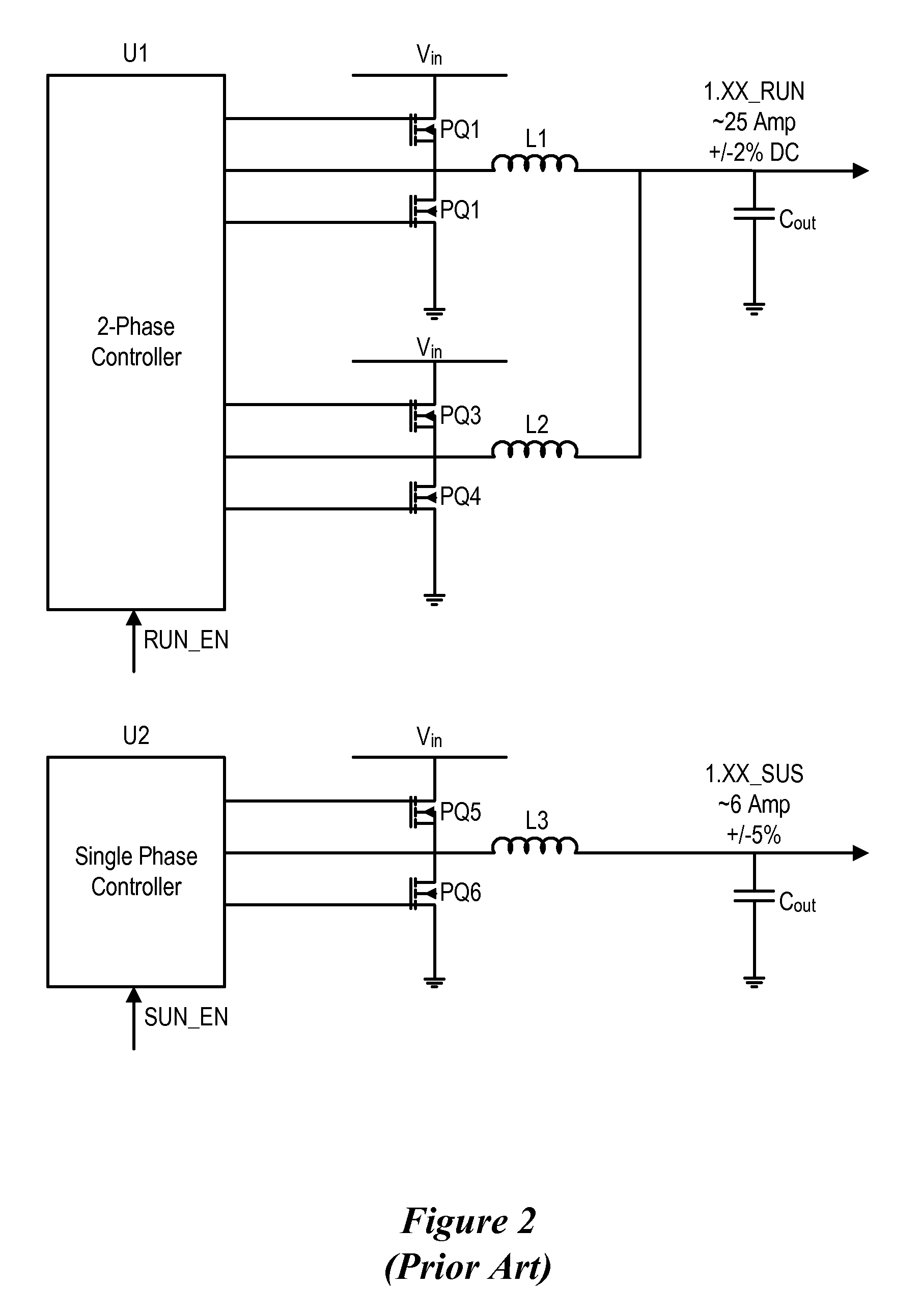
System and method for powering an information handling system in multiple power states
ActiveUS8063619B2Reduce disadvantagesReduce problemsElectric signal transmission systemsDc network circuit arrangementsMOSFETVoltage regulation
Power is supplied to an information handling system chipset with a single voltage regulator having dual phases. A first phase of the voltage regulator provides power to a low power state power rail in an independent mode to support a low power state, such as a suspend or hibernate state. A second phase of the voltage regulator provides power to a run power state power rail in combination with the first phase by activation of a switch, such as a MOSFET load switch, that connects the low power state power rail and the run power state power rail. Voltage sensed from both power rails is applied to control voltage output so that the run power state power rail is maintained within more precise constraints than the low power state power rail.
Owner:DELL PROD LP
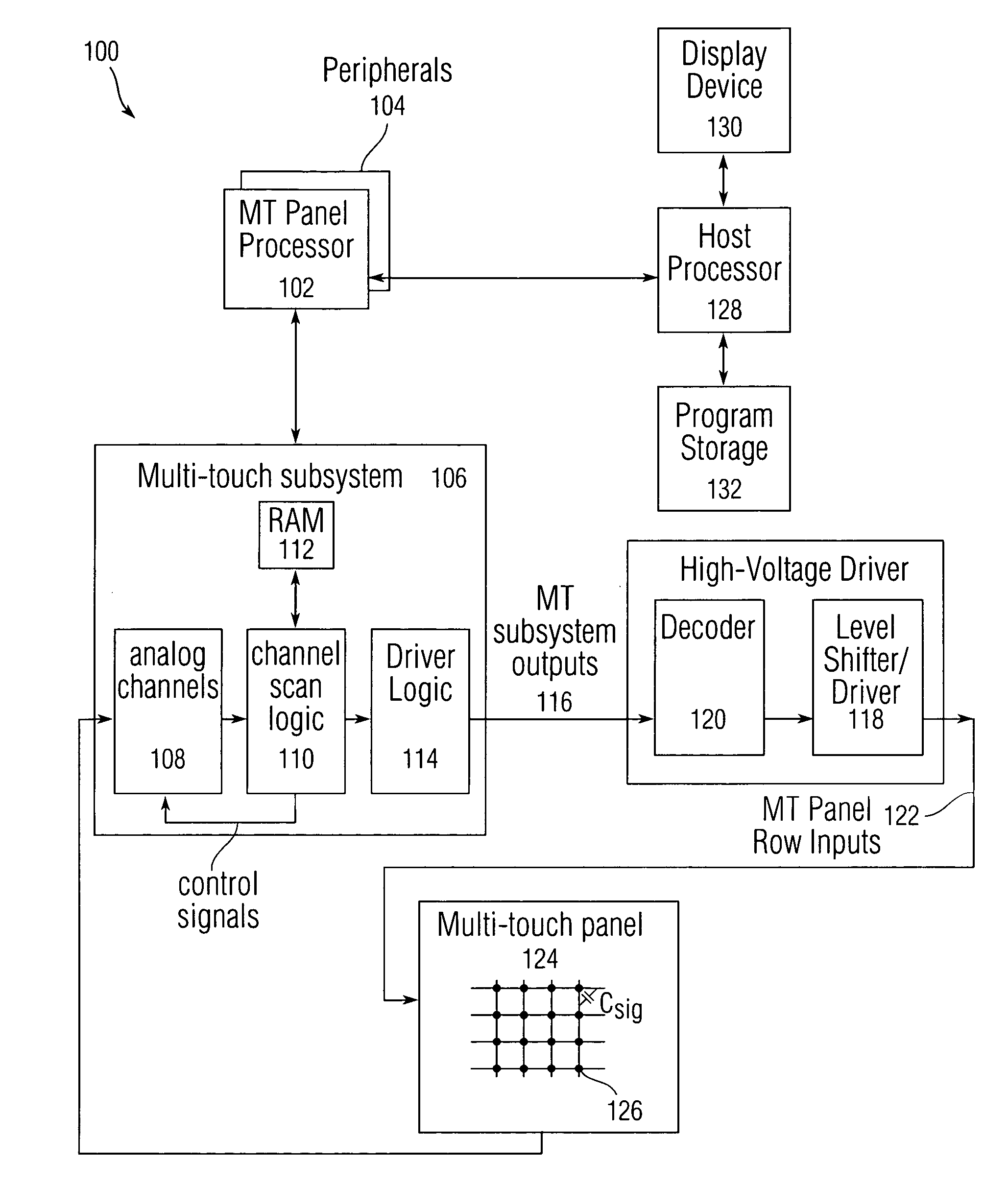
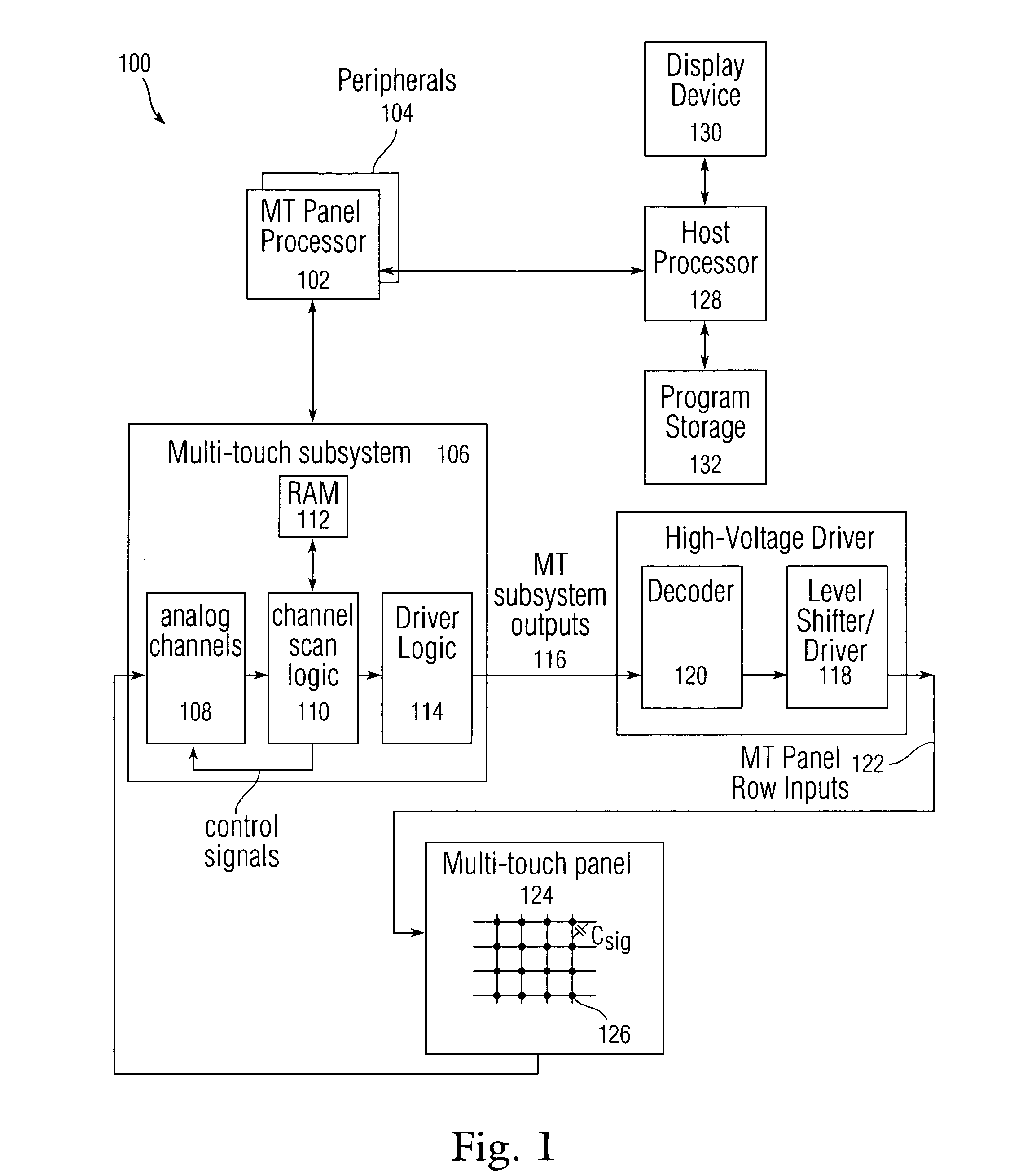
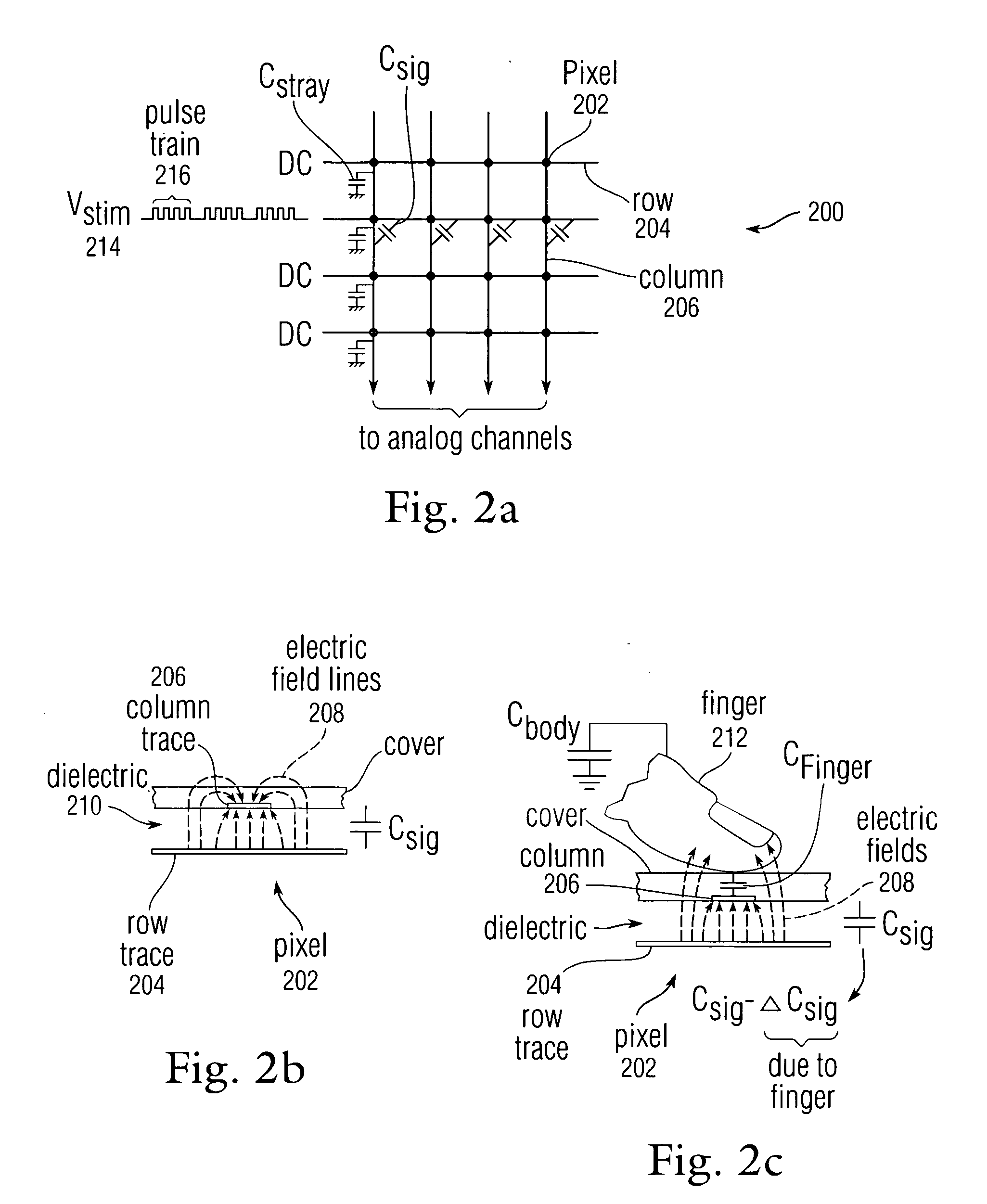
Proximity and multi-touch sensor detection and demodulation
ActiveUS20080158172A1Brightening displayDisplay delayEnergy efficient ICTPower network operation systems integrationProximity sensorEngineering
The use of one or more proximity sensors in combination with one or more touch sensors in a multi-touch panel to detect the presence of a finger, body part or other object and control or trigger one or more functions in accordance with an “image” of touch provided by the sensor outputs is disclosed. In some embodiments, one or more infrared (IR) proximity sensors can be driven with a specific stimulation frequency and emit IR light from one or more areas, which can in some embodiments correspond to one or more multi-touch sensor “pixel” locations. The reflected IR signal, if any, can be demodulated using synchronous demodulation. In some embodiments, both physical interfaces (touch and proximity sensors) can be connected to analog channels in the same electrical core.
Owner:APPLE INC
Multicarrier Sub-Layer for Direct Sequence Channel and Multiple-Access Coding
InactiveUS20070211786A1Low costImprove system performanceSecret communicationMultiplex code generationUltra-widebandTransmission protocol
Carrier Interferometry (CI) provides wideband transmission protocols with frequency-band selectivity to improve interference rejection, reduce multipath fading, and enable operation across non-continuous frequency bands. Direct-sequence protocols, such as DS-CDMA, are provided with CI to greatly improve performance and reduce transceiver complexity. CI introduces families of orthogonal polyphase codes that can be used for channel coding, spreading, and / or multiple access. Unlike conventional DS-CDMA, CI coding is not necessary for energy spreading because a set of CI carriers has an inherently wide aggregate bandwidth. Instead, CI codes are used for channelization, energy smoothing in the frequency domain, and interference suppression. CI-based ultra-wideband protocols are implemented via frequency-domain processing to reduce synchronization problems, transceiver complexity, and poor multipath performance of conventional ultra-wideband systems. CI allows wideband protocols to be implemented with space-frequency processing and other array-processing techniques to provide either or both diversity combining and sub-space processing. CI also enables spatial processing without antenna arrays. Even the bandwidth efficiency of multicarrier protocols is greatly enhanced with CI. CI-based wavelets avoid time and frequency resolution trade-offs associated with conventional wavelet processing. CI-based Fourier transforms eliminate all multiplications, which greatly simplifies multi-frequency processing. The quantum-wave principles of CI improve all types of baseband and radio processing.
Owner:GENGHISCOMM HLDG
Forced-air zone climate control system for existing residential houses
ActiveUS6983889B2Improve comfortLow costLighting and heating apparatusTemperatue controlTemperature controlControl system
Owner:EMME E2MS
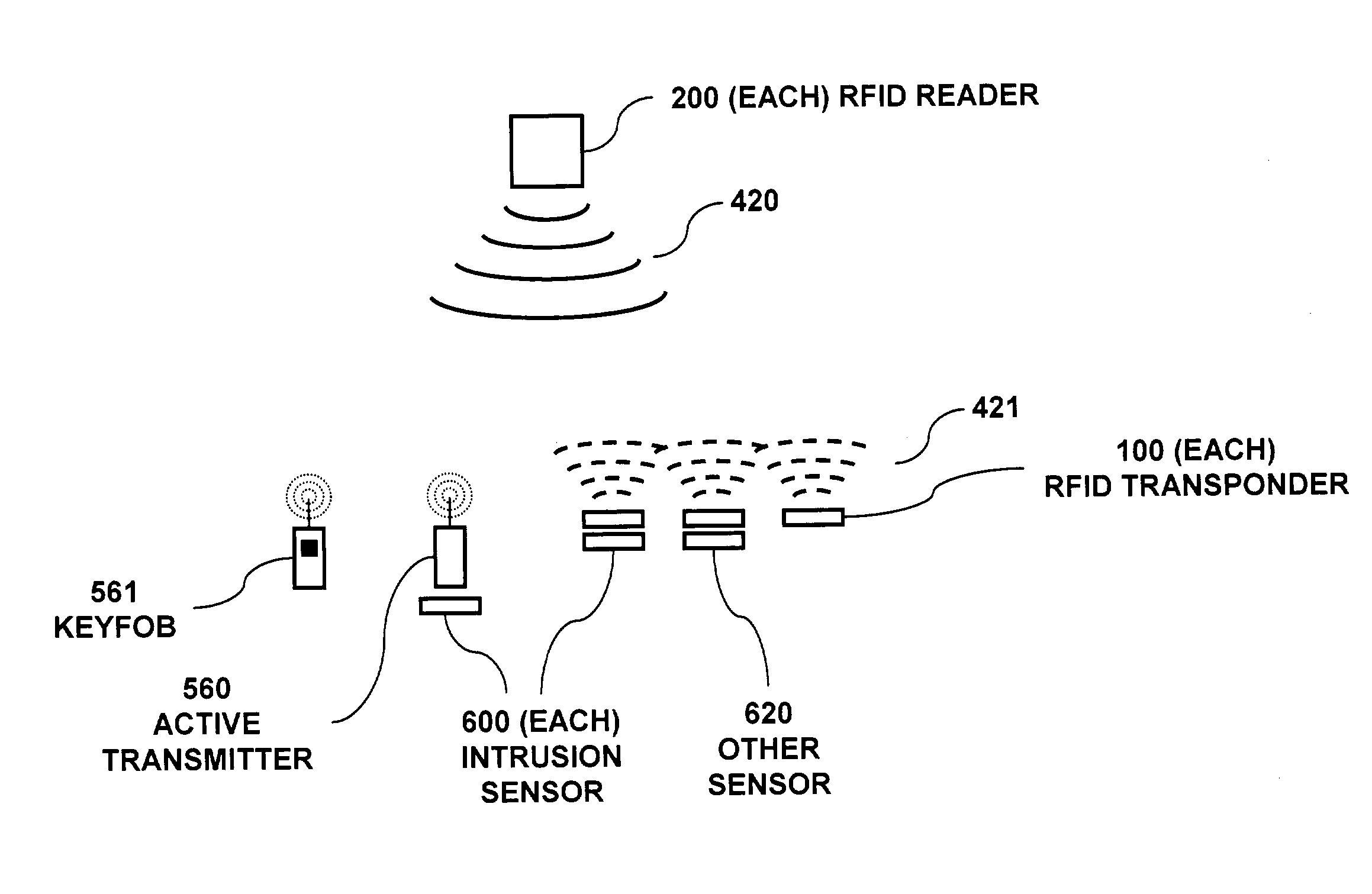
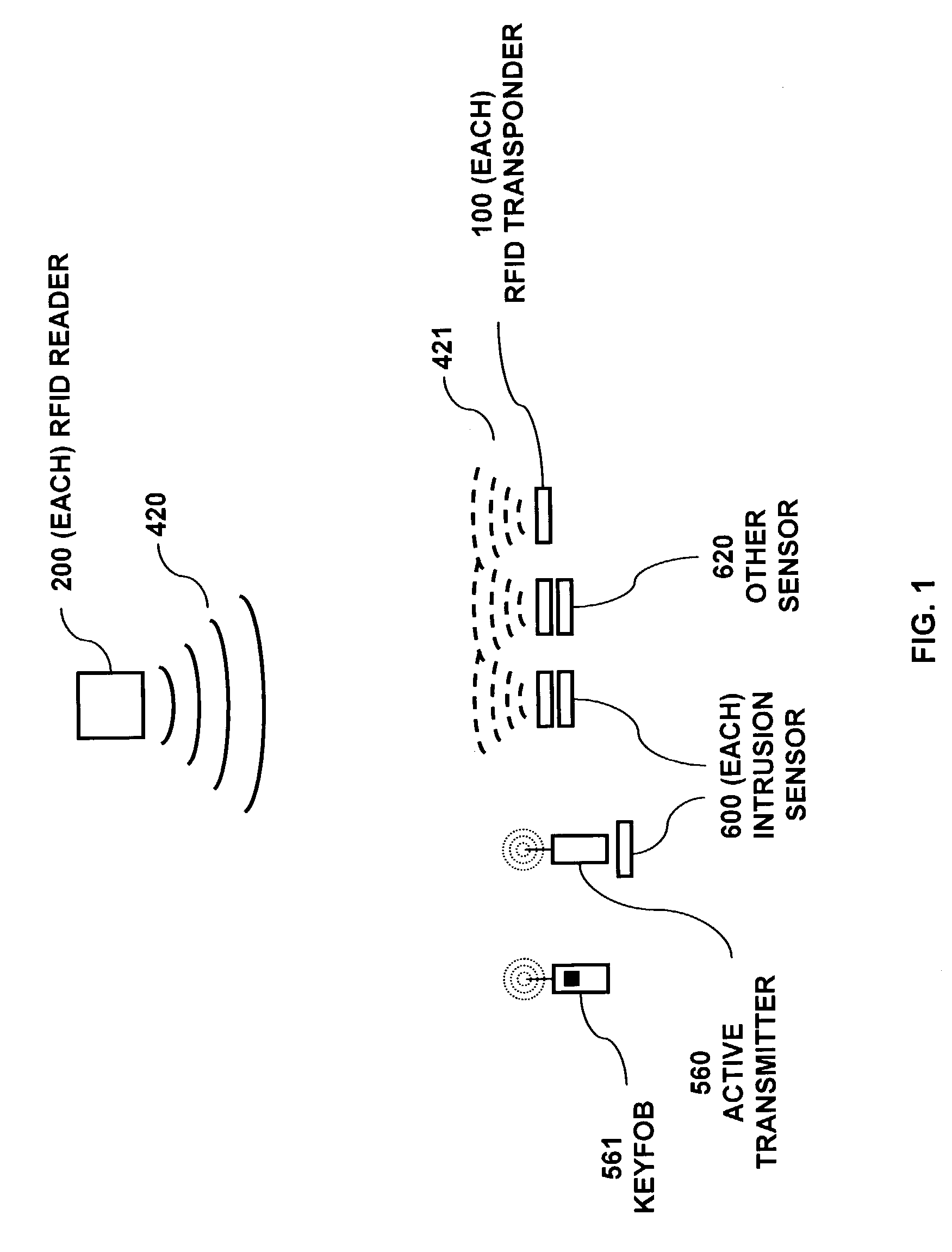
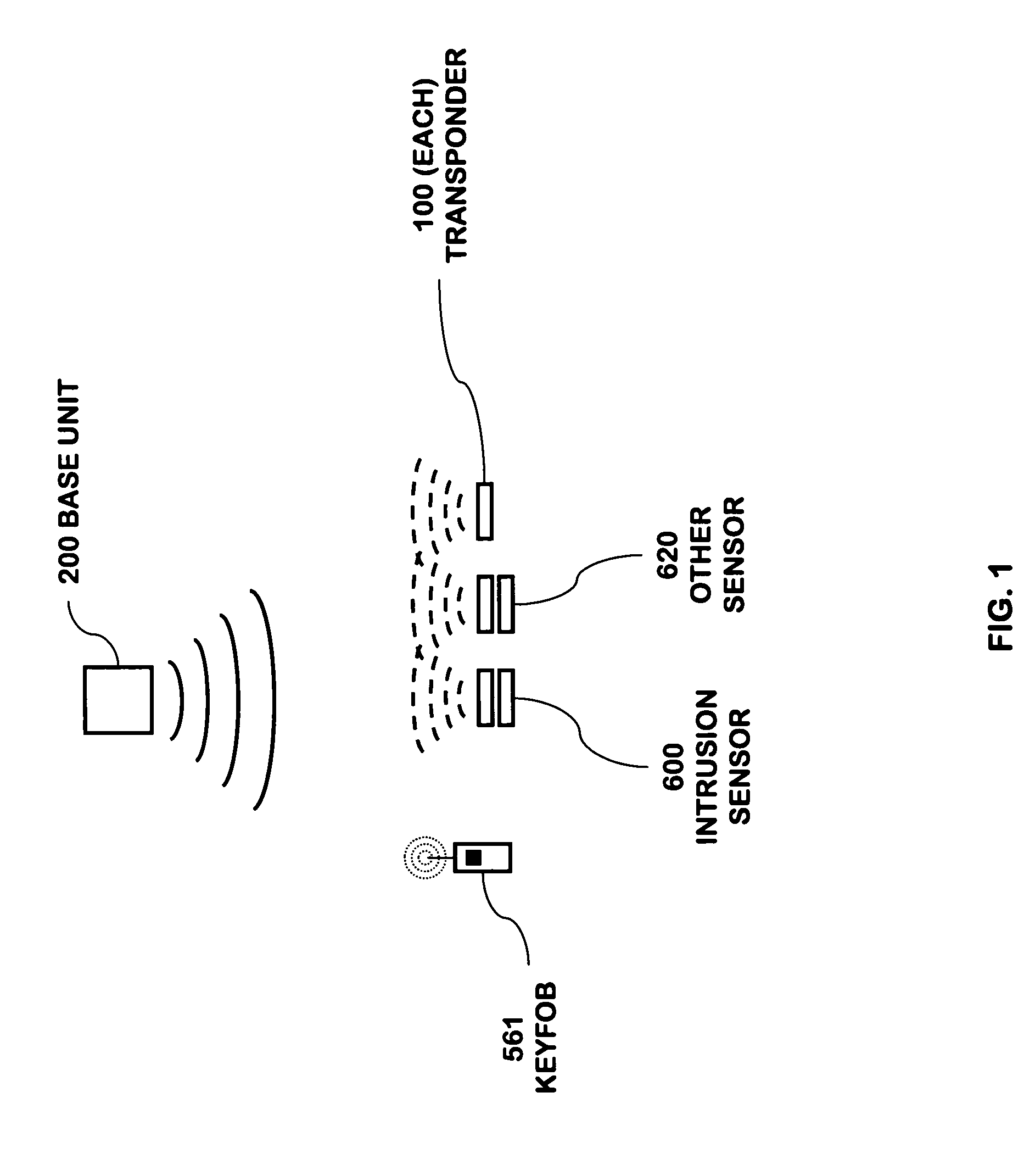
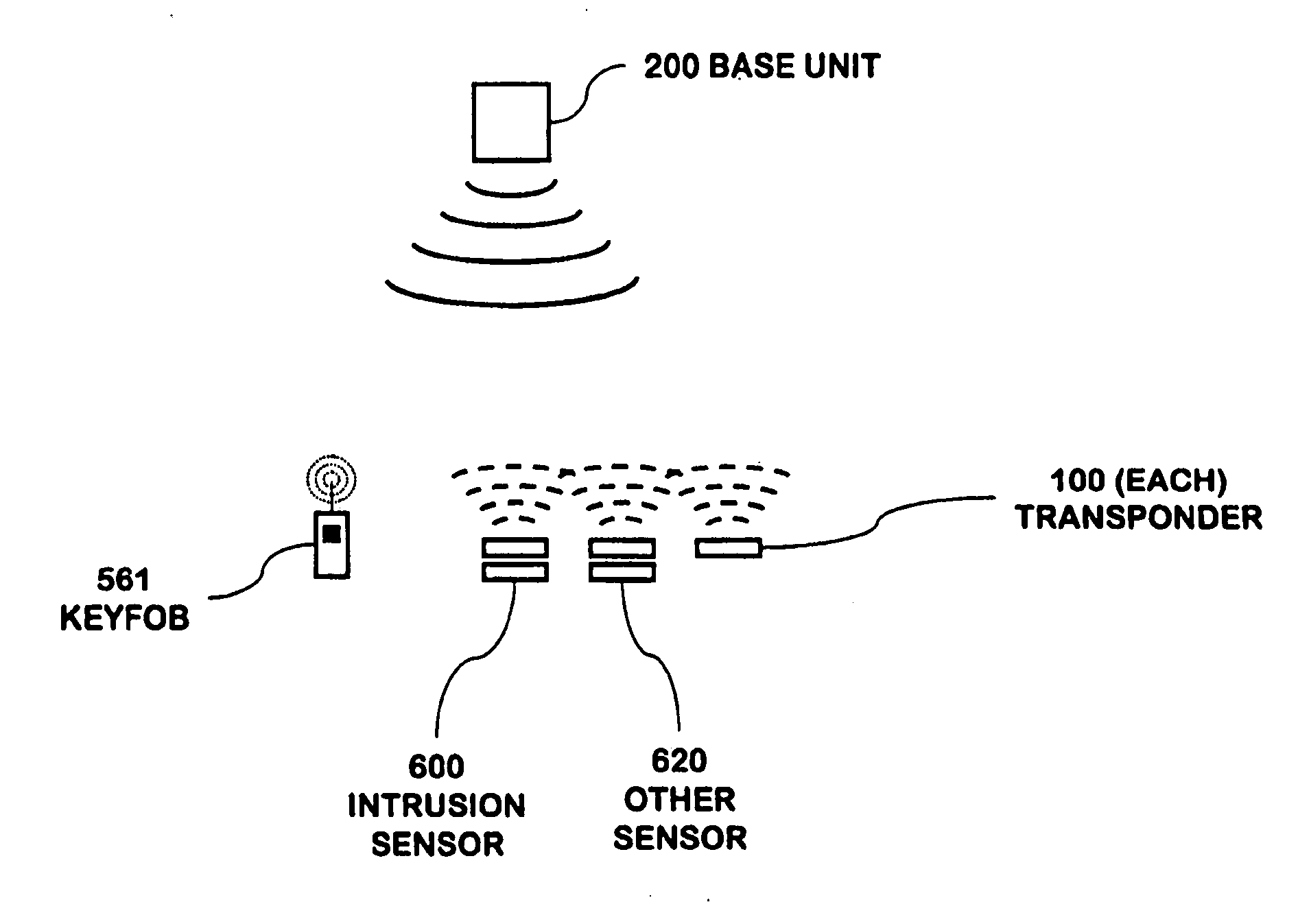
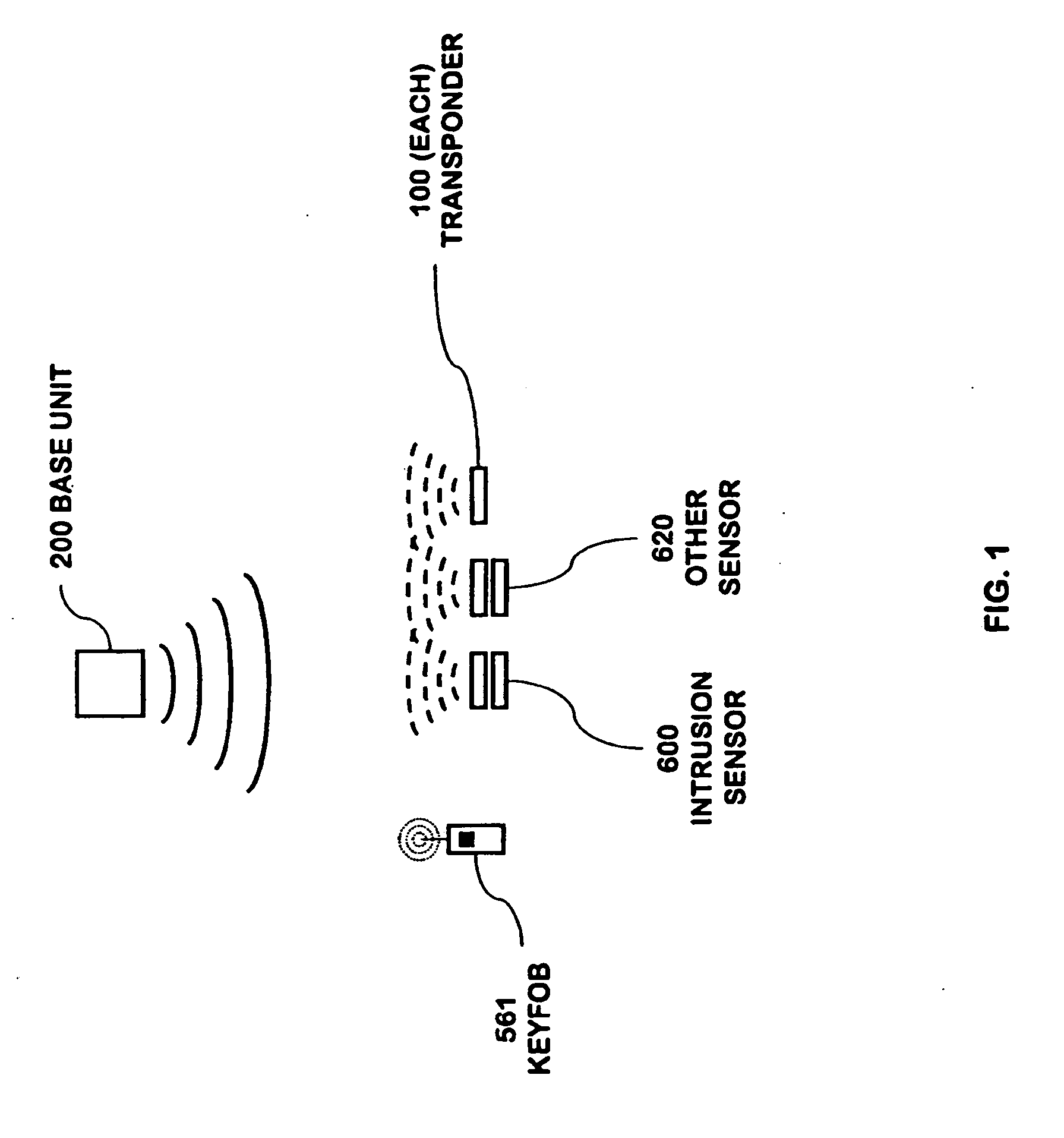
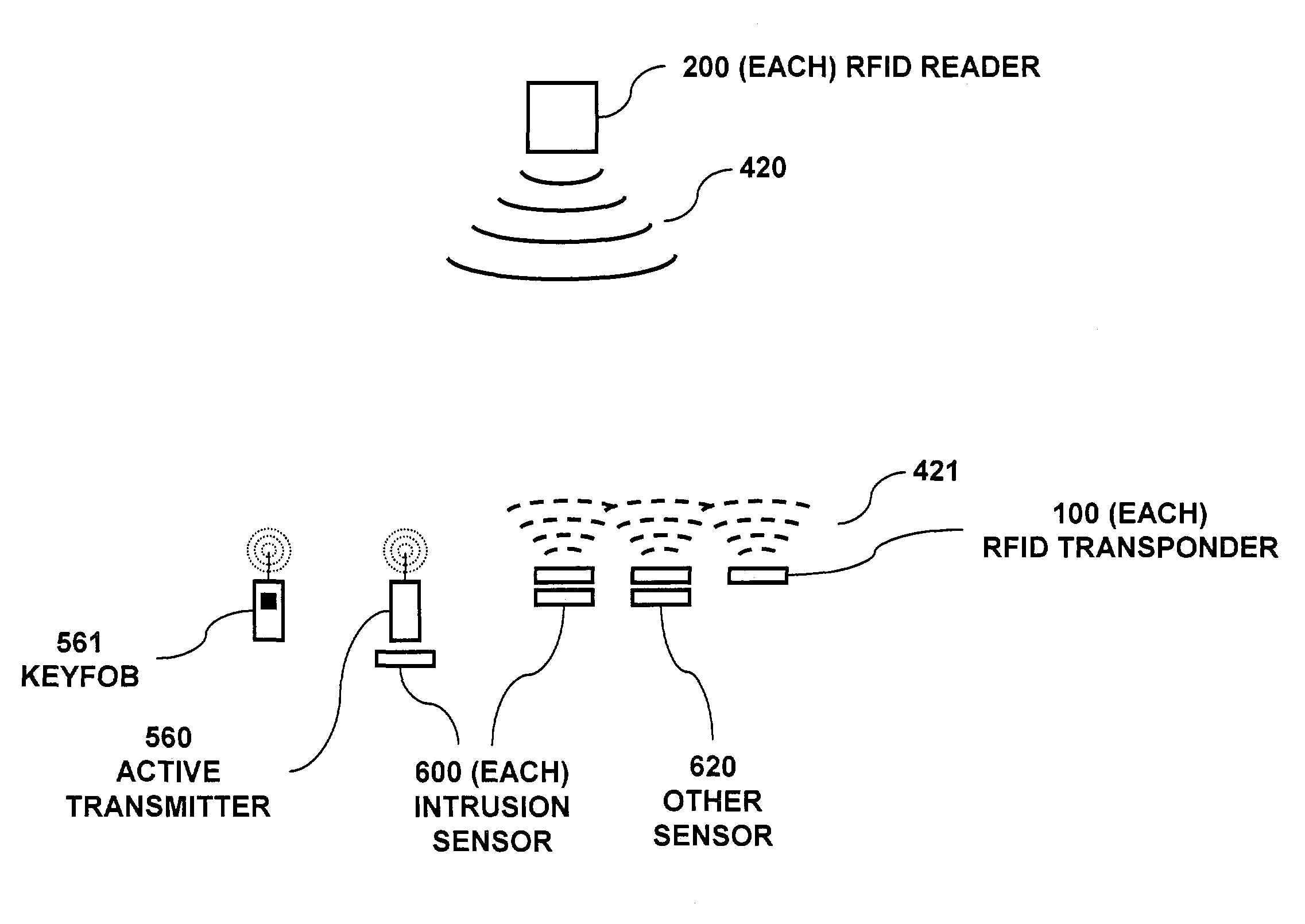
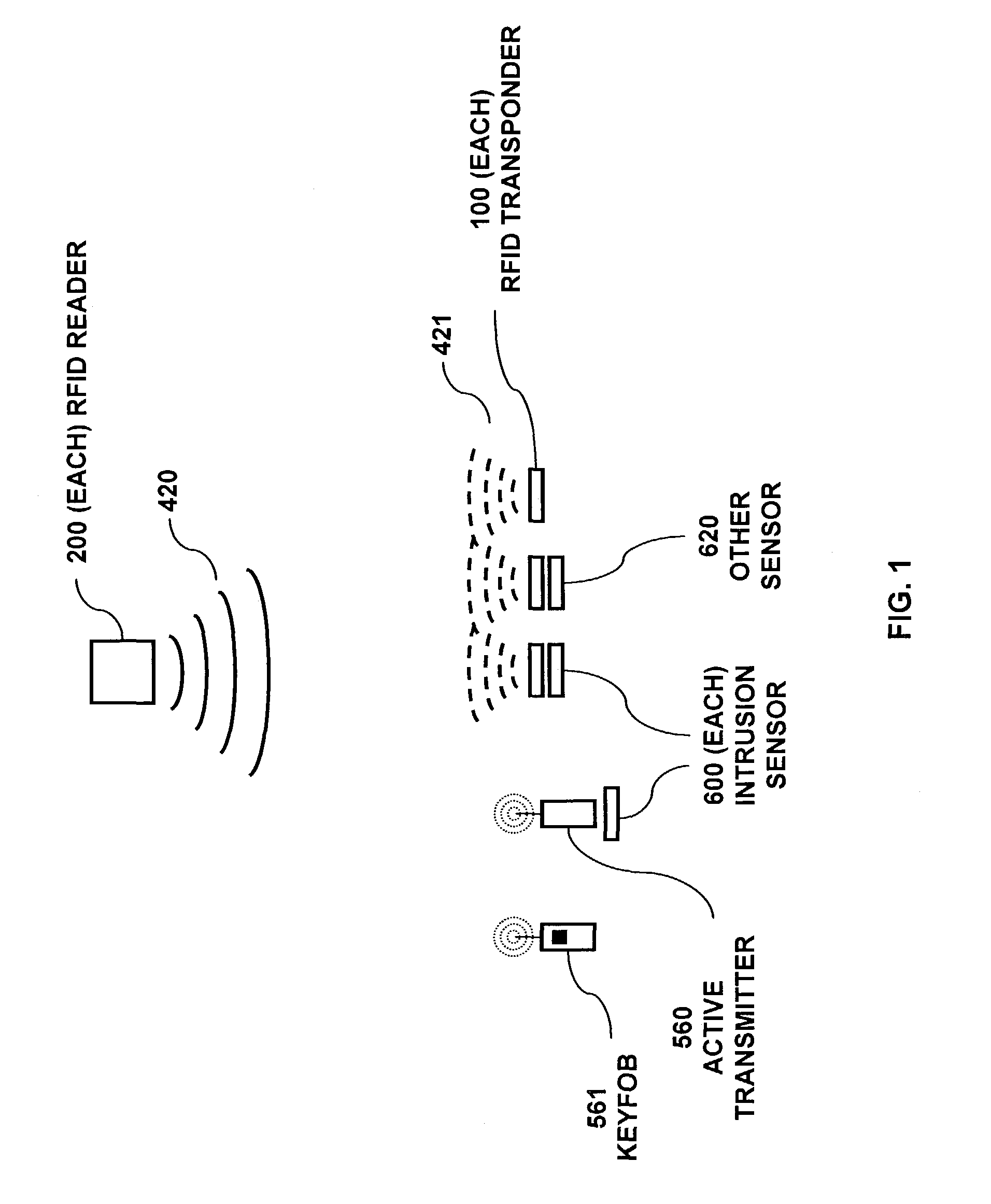
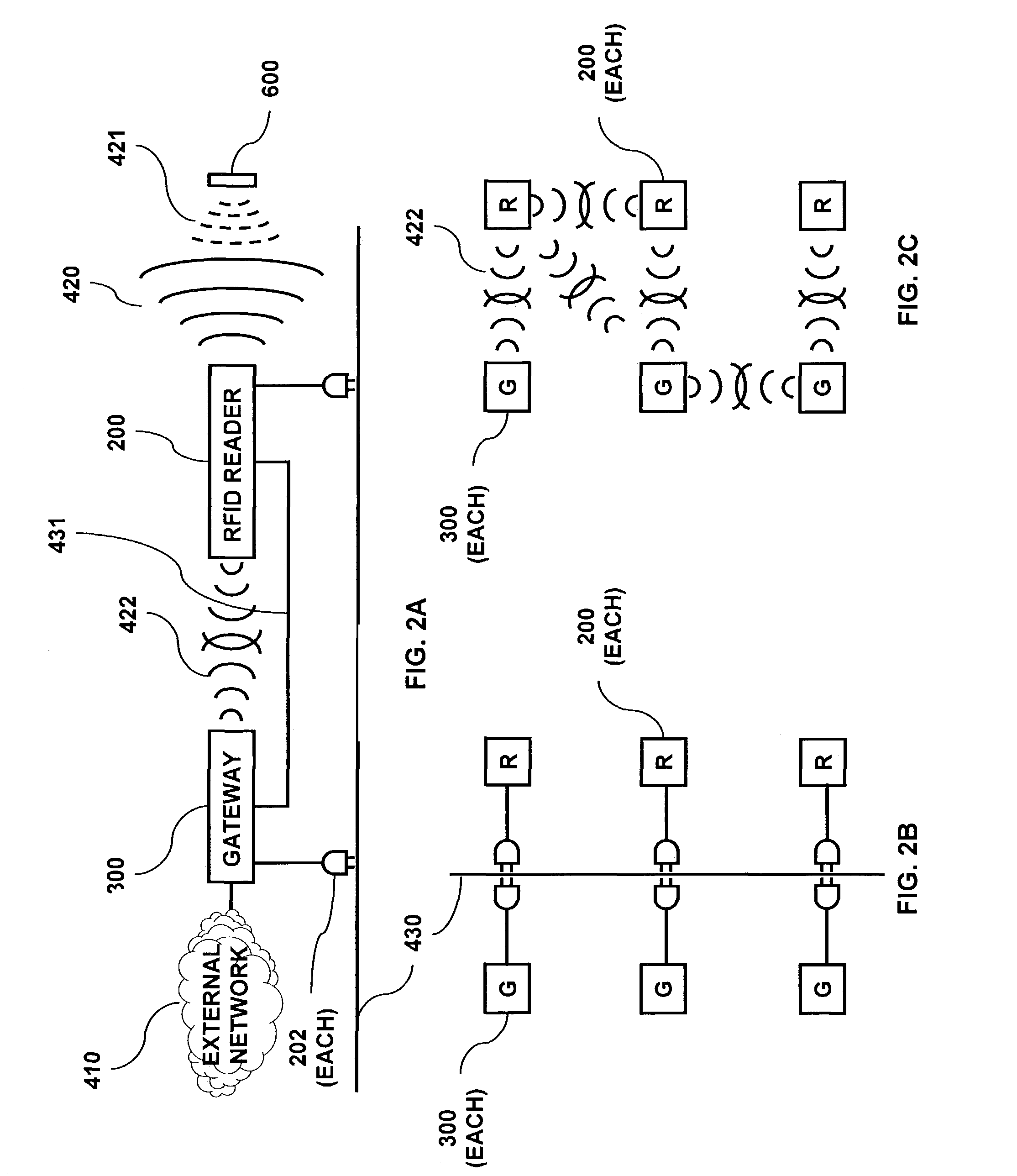
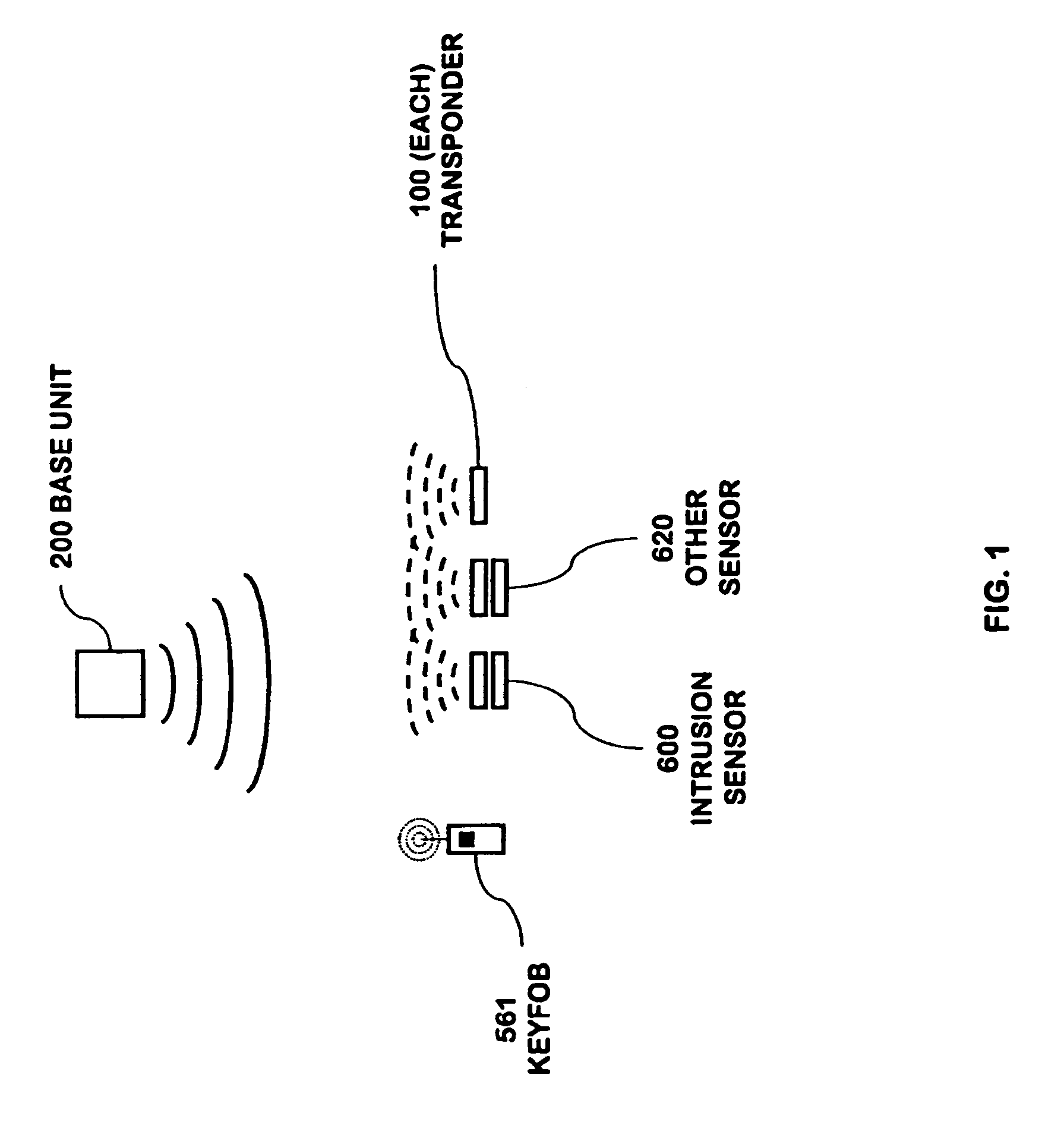
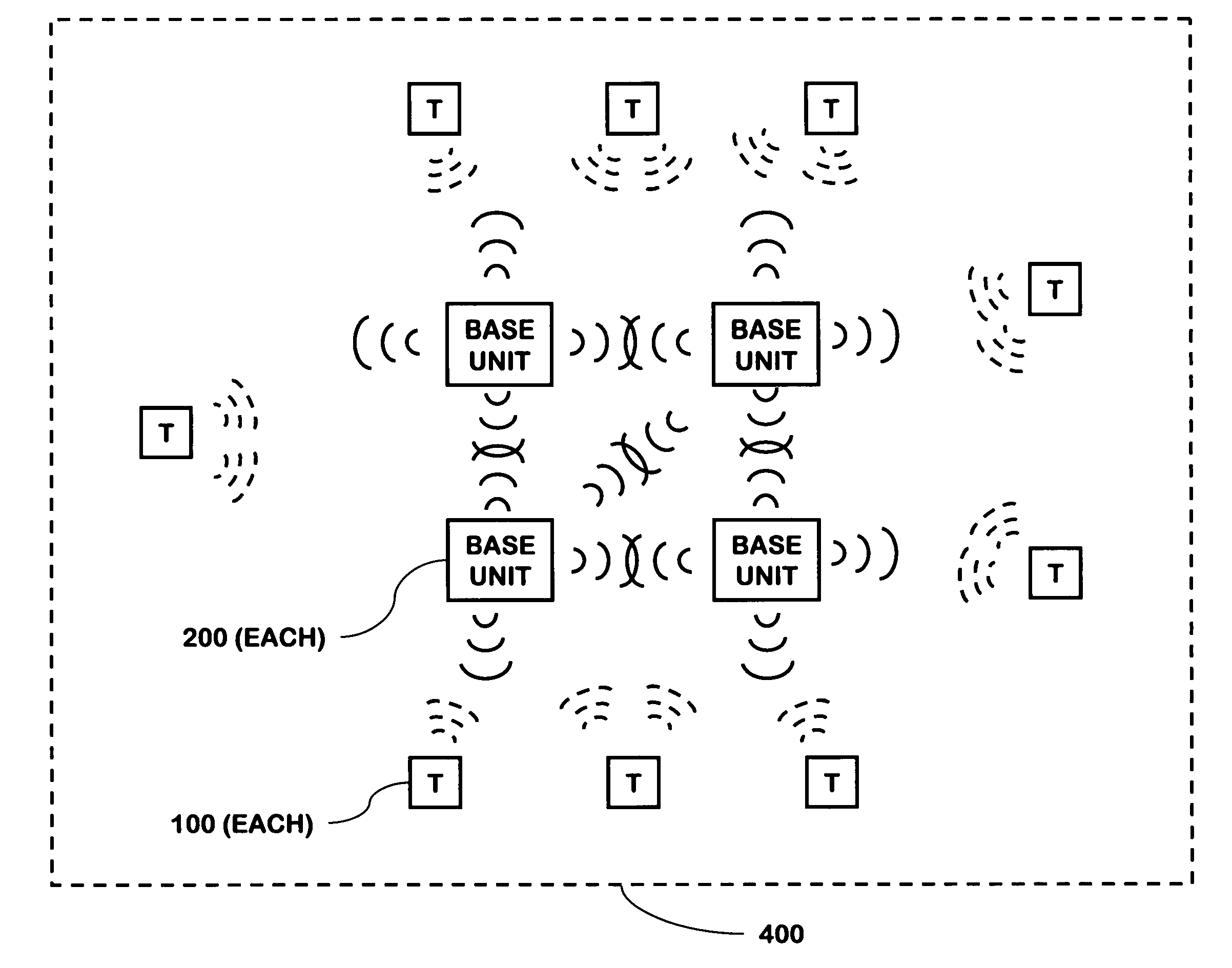
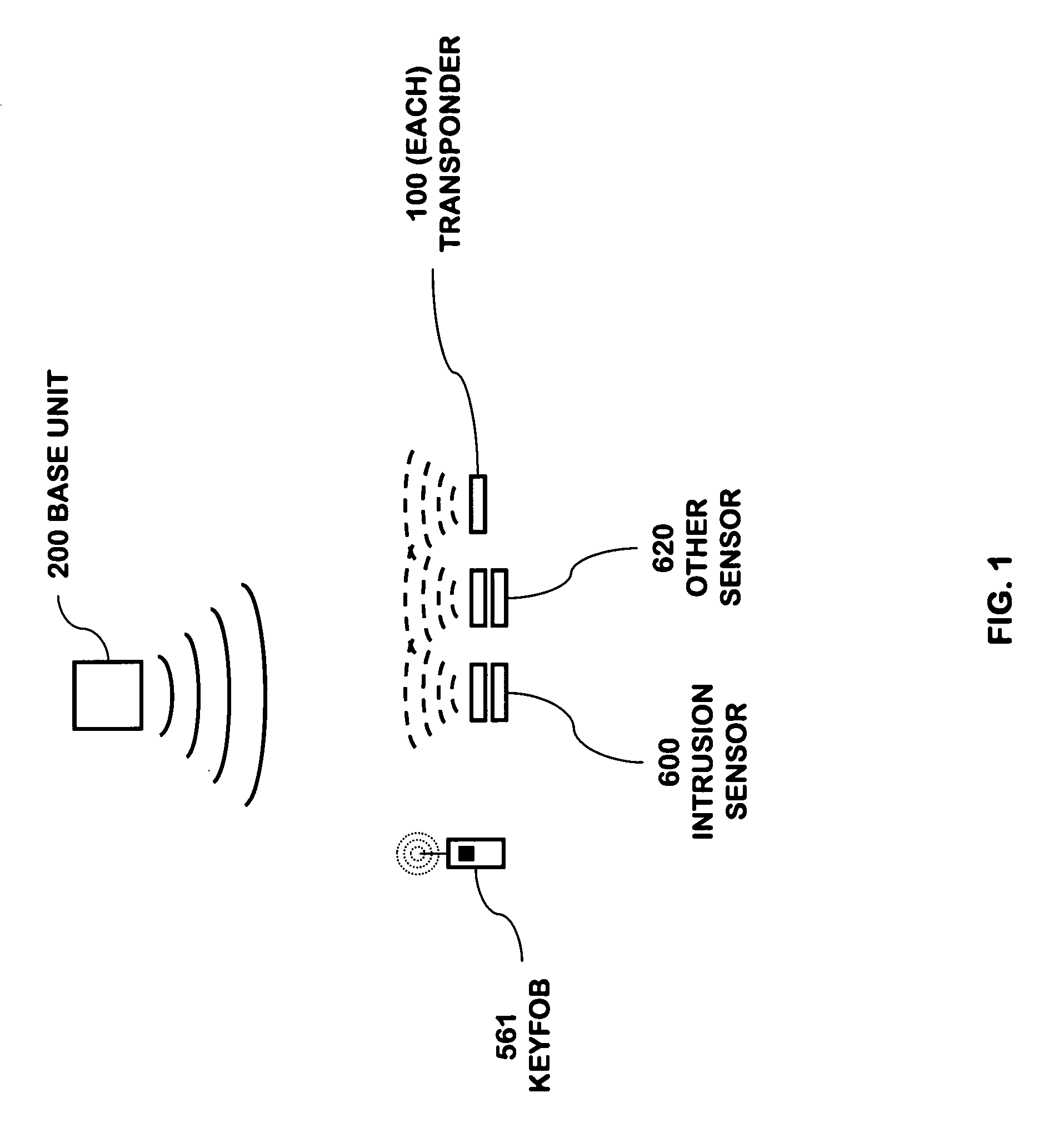
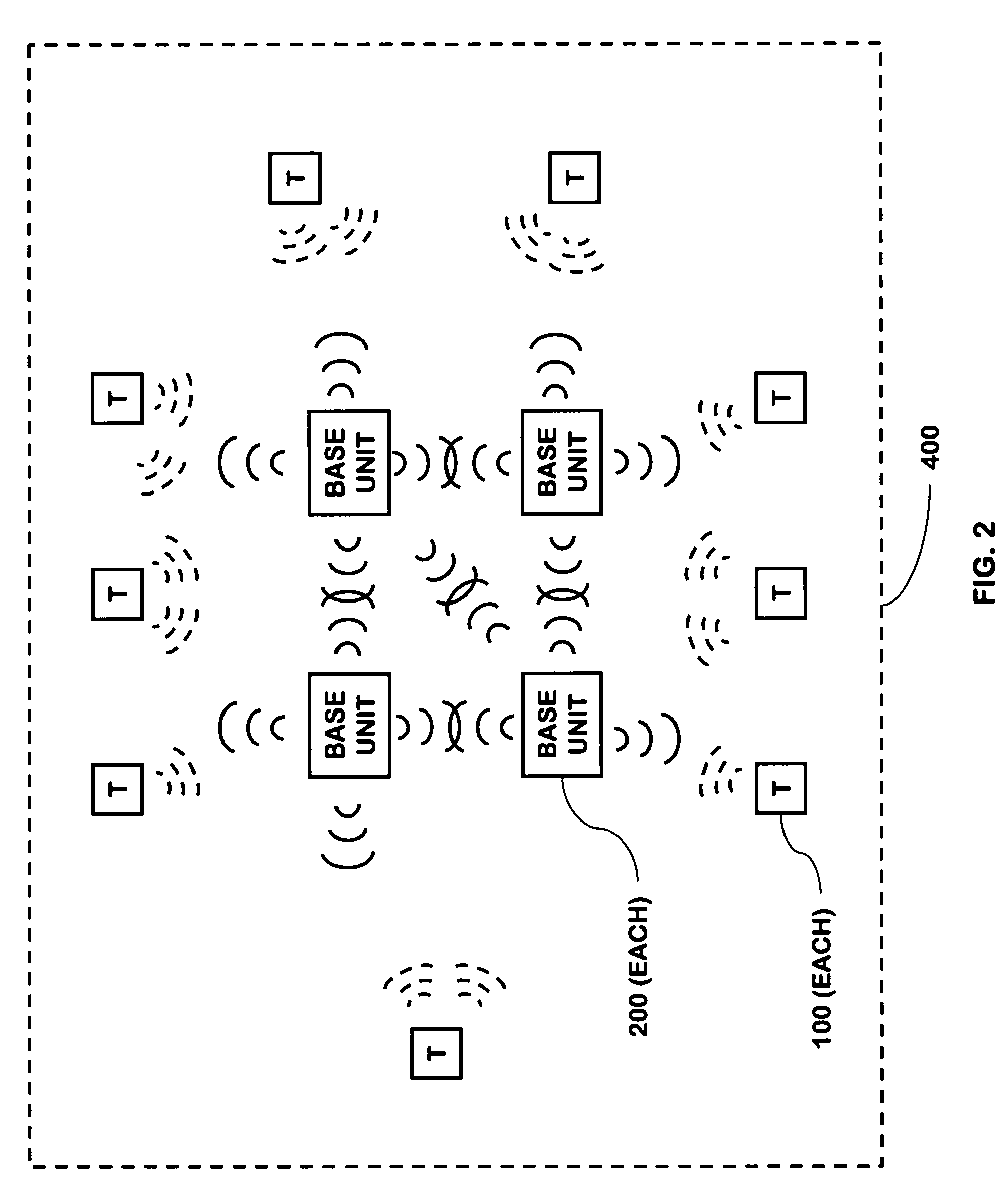
RFID based security network
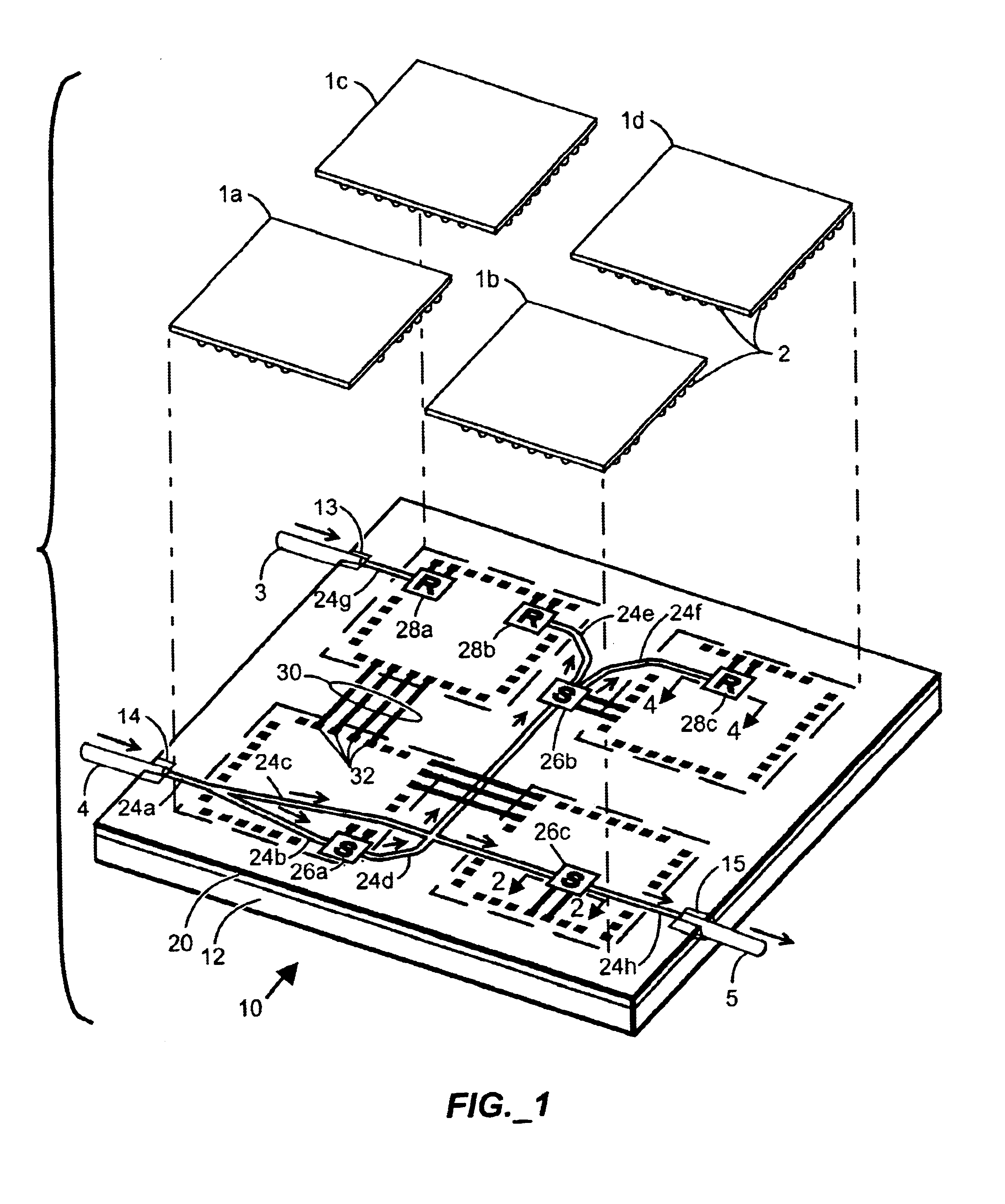
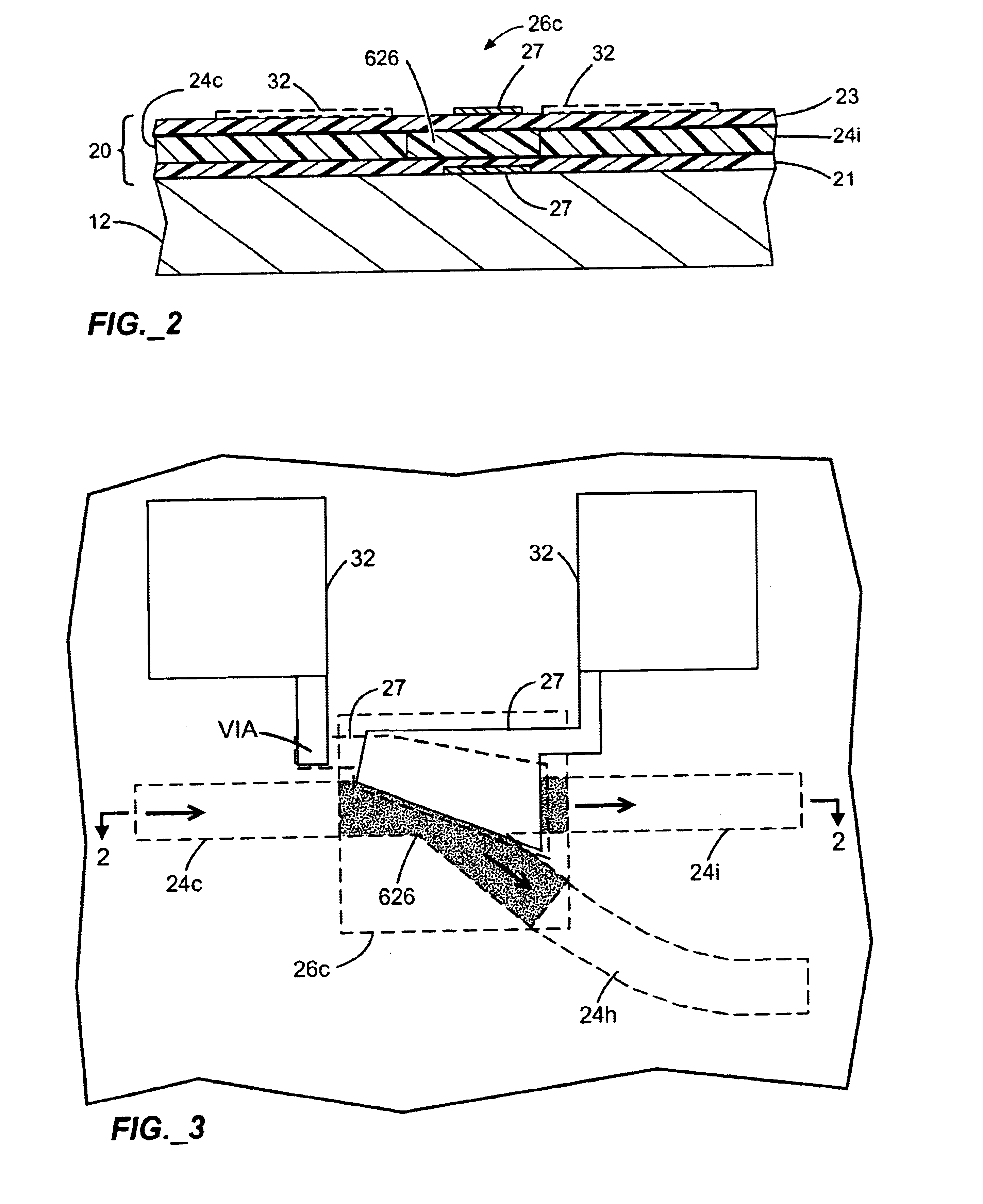
InactiveUS7019639B2Improve reliabilityLow costBurglar alarm by openingFrequency-division multiplex detailsNetwork Communication ProtocolsElectric power
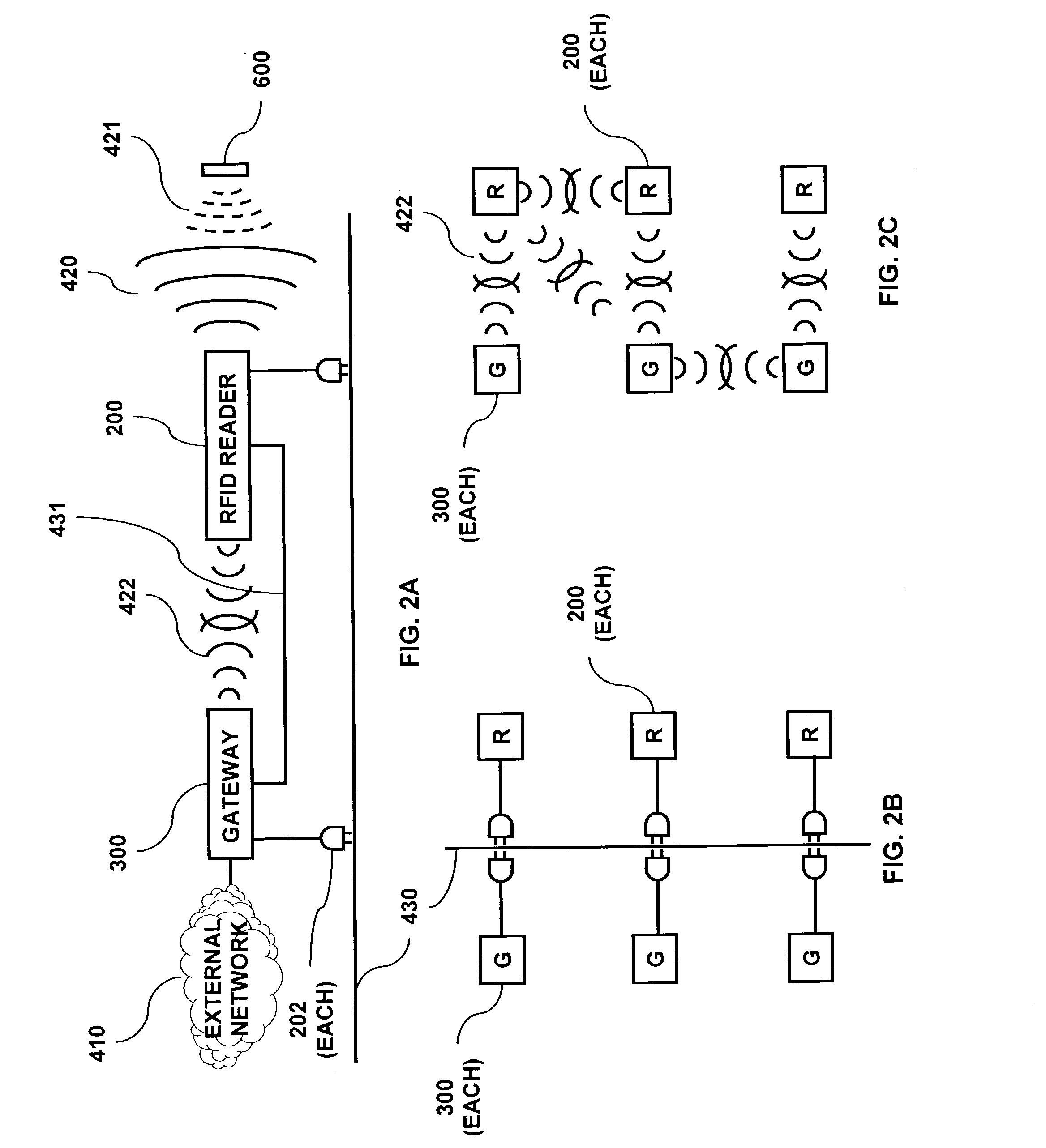
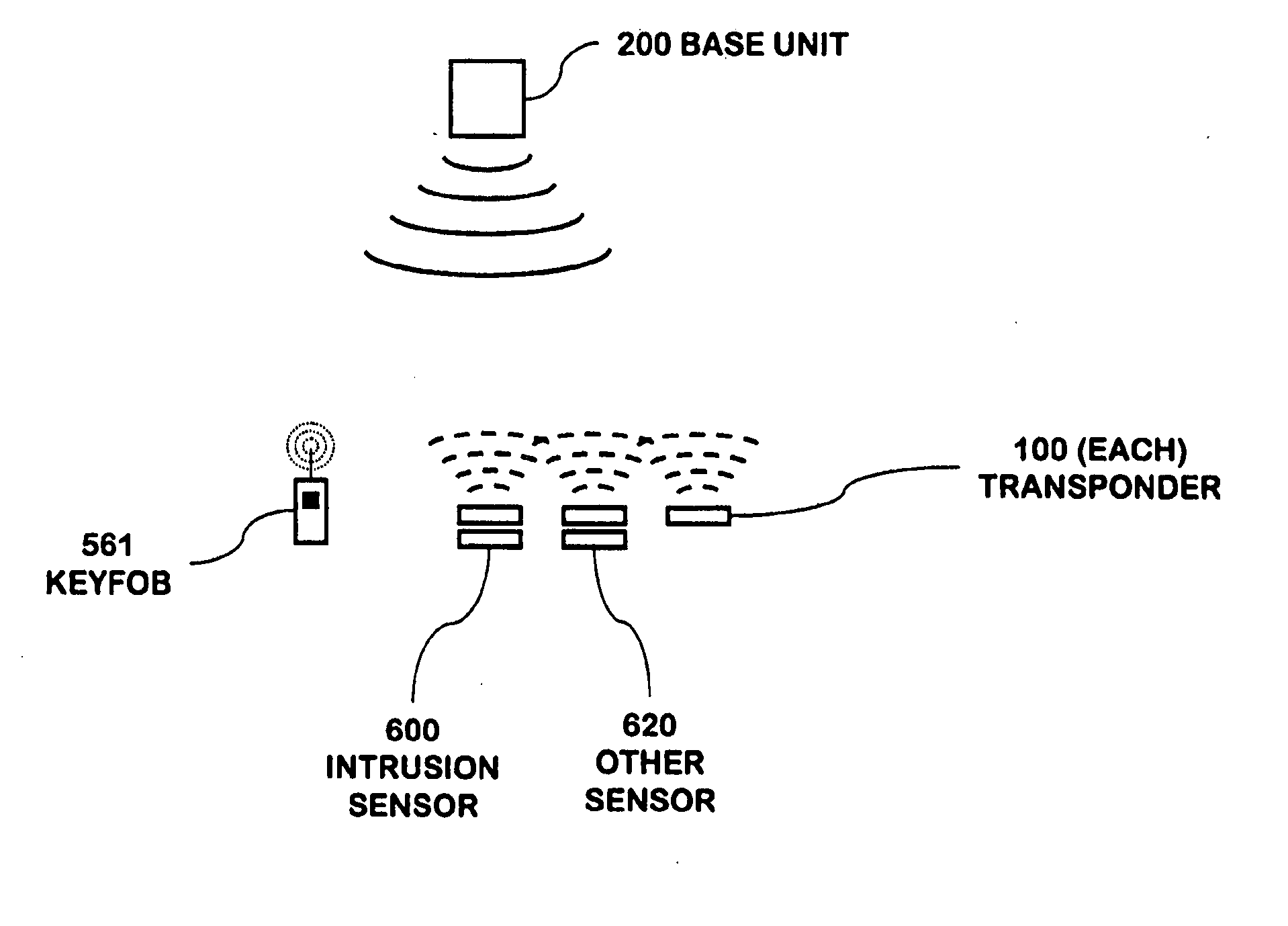
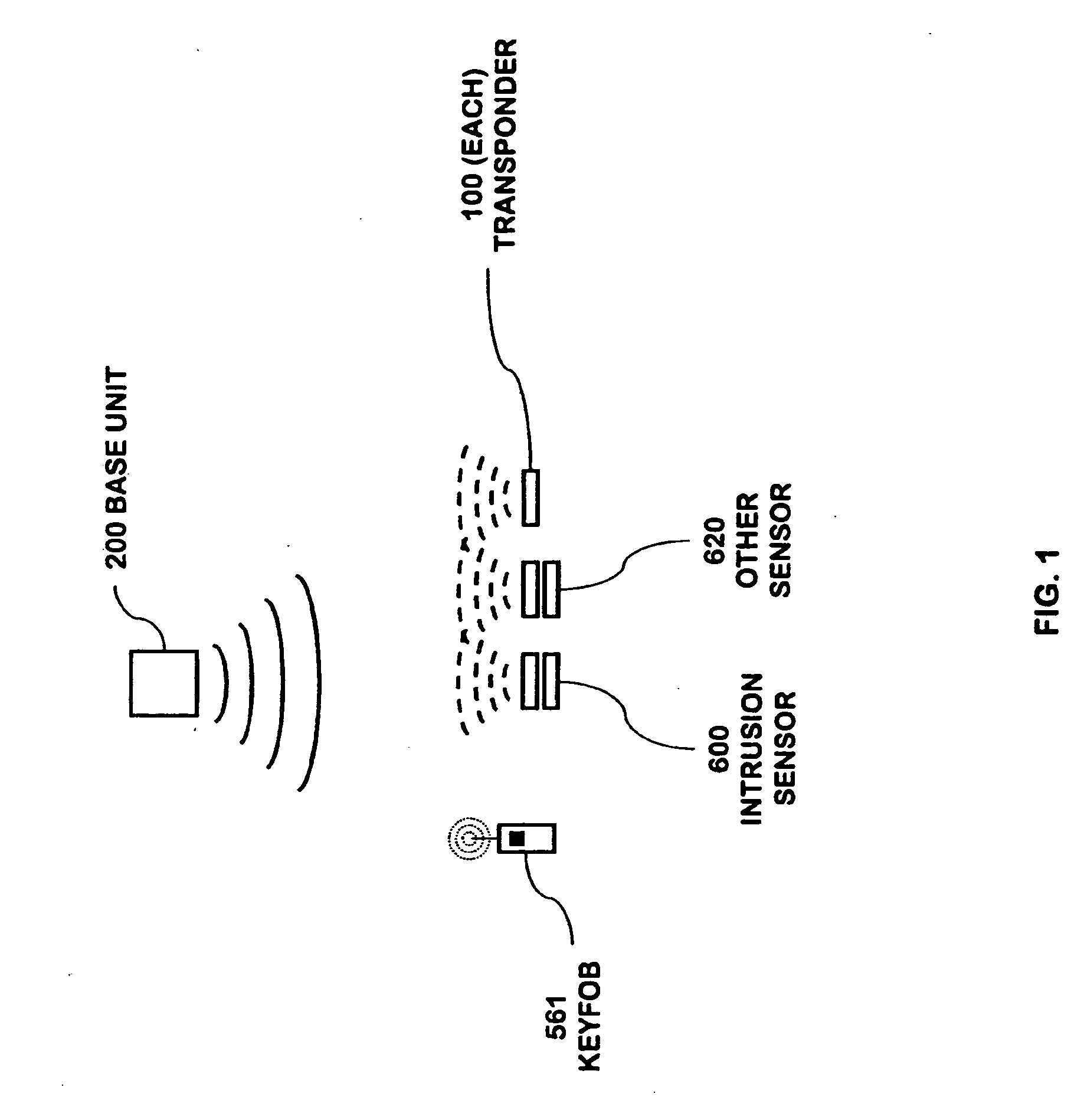
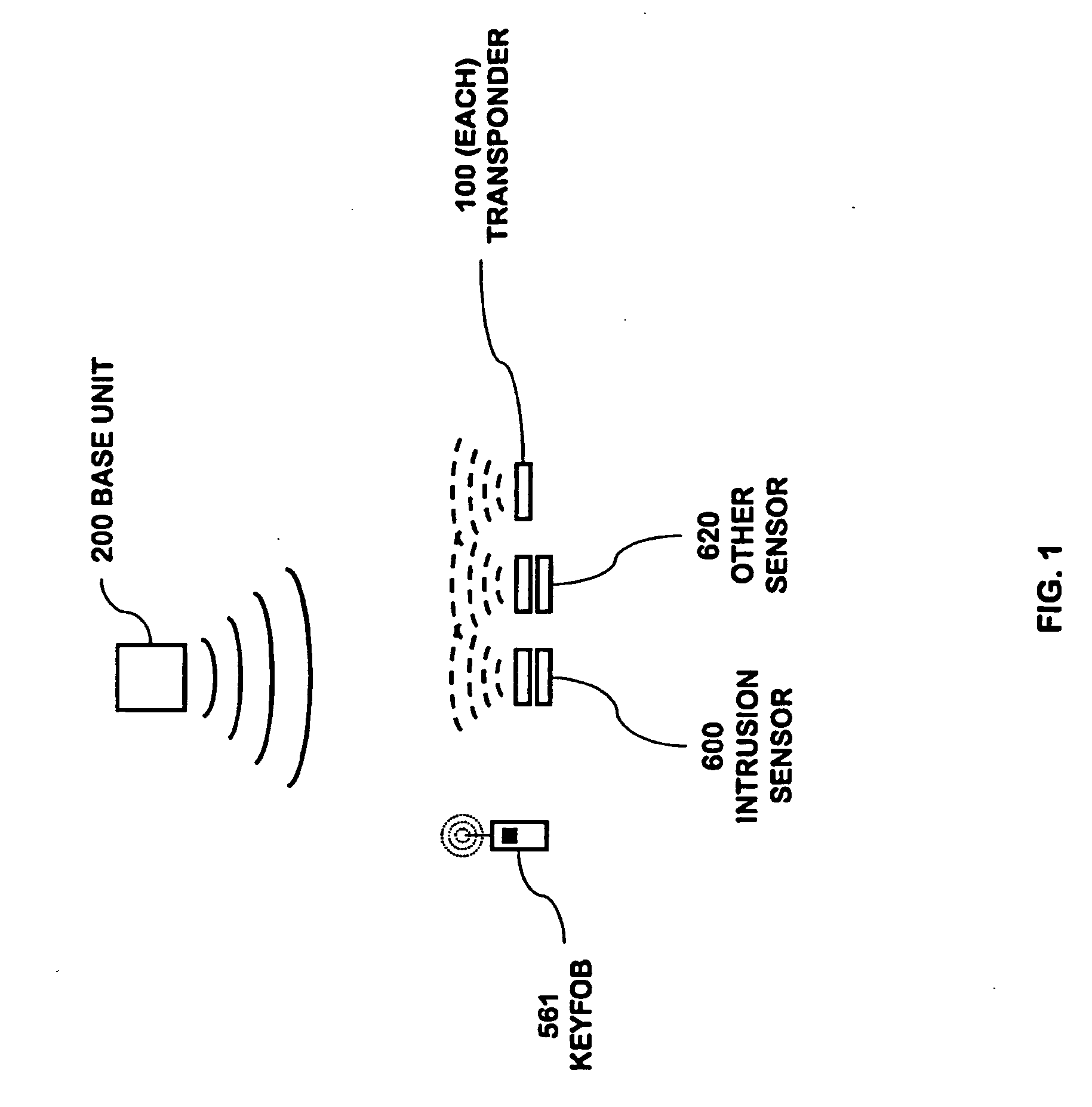
A security network for a building using at least one RFID reader to communicate with at least one RFID transponder to provide the radio link between each of a number of openings and a control function capable of causing an alert in the event of an intrusion. A gateway provides an interface between the security network and various external networks. The control function can be located in either or both of the RFID reader and the gateway. The RFID transponder is connected to an intrusion sensor. The gateway can communicate with the RFID reader using active RF communications, power-line communications protocol, or hardwire connection. The RFID transponder can contain an energy store. The RFID reader contains means for transferring power to an RFID transponder for the purpose of charging any energy store. The security network can contain more than one RFID reader.
Owner:ADT US HLDG INC
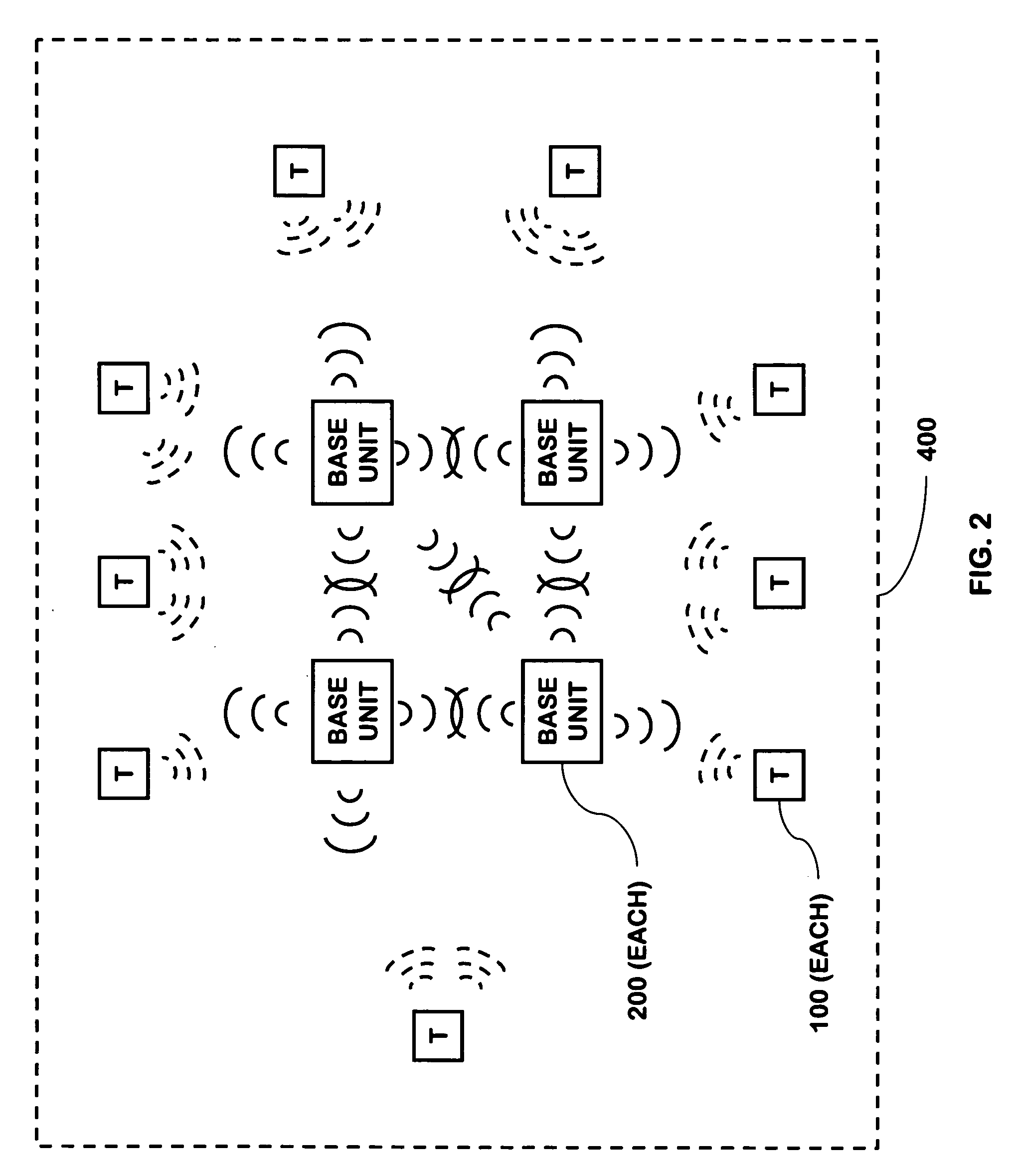
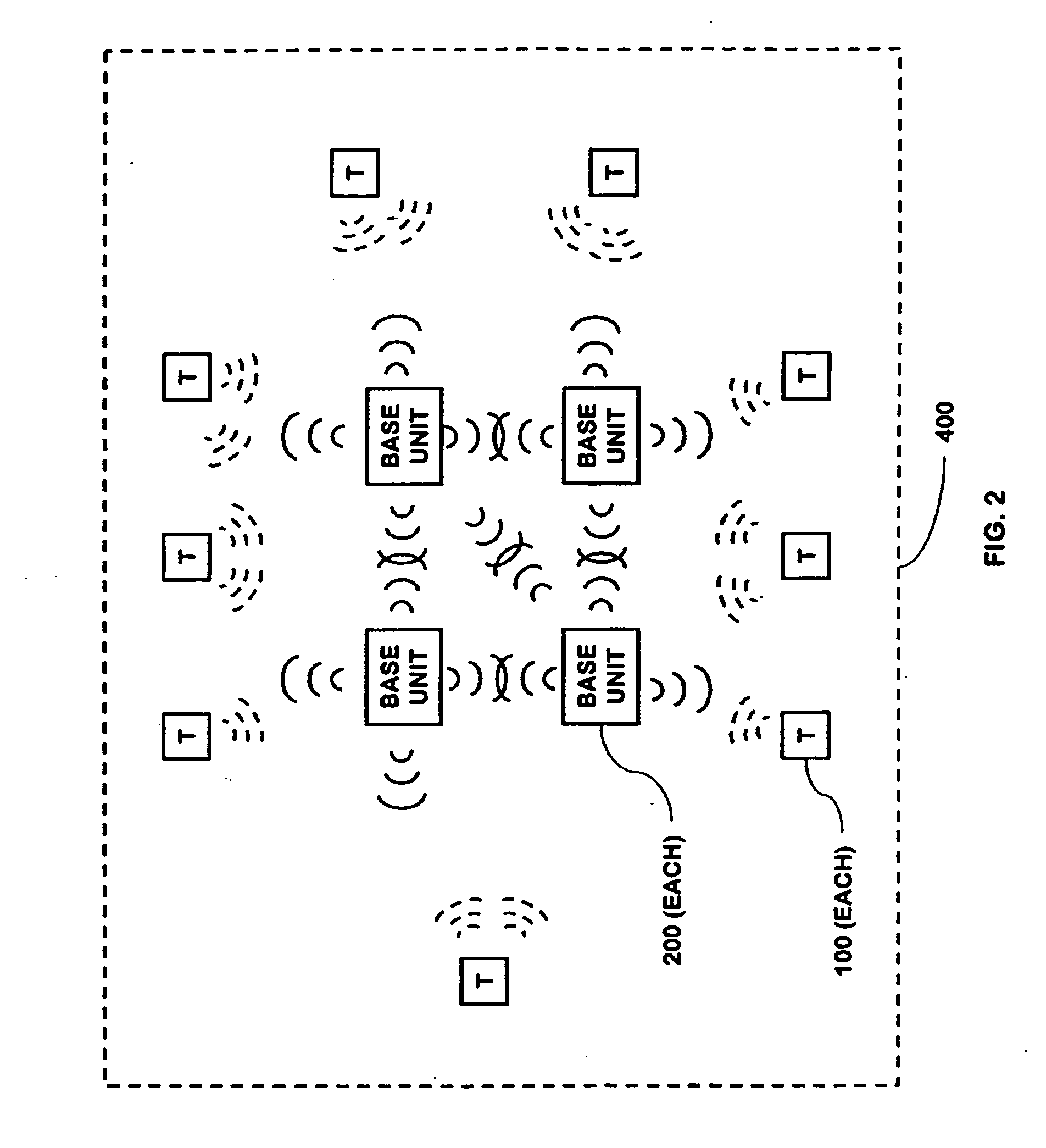
Multi-controller security network
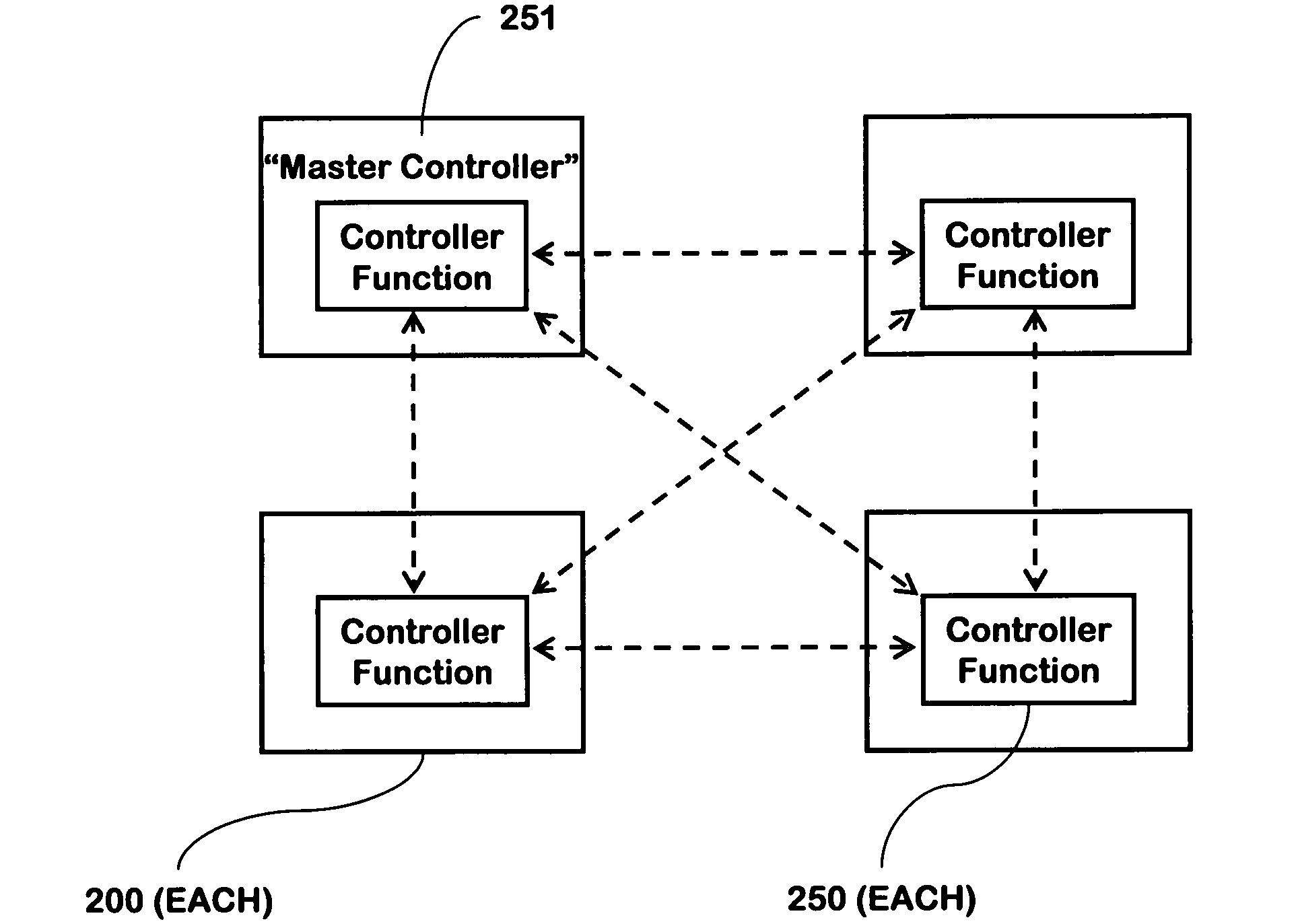
InactiveUS7079020B2Improve reliabilityLow costMemory record carrier reading problemsElectric signalling detailsOperating energyMaster controller
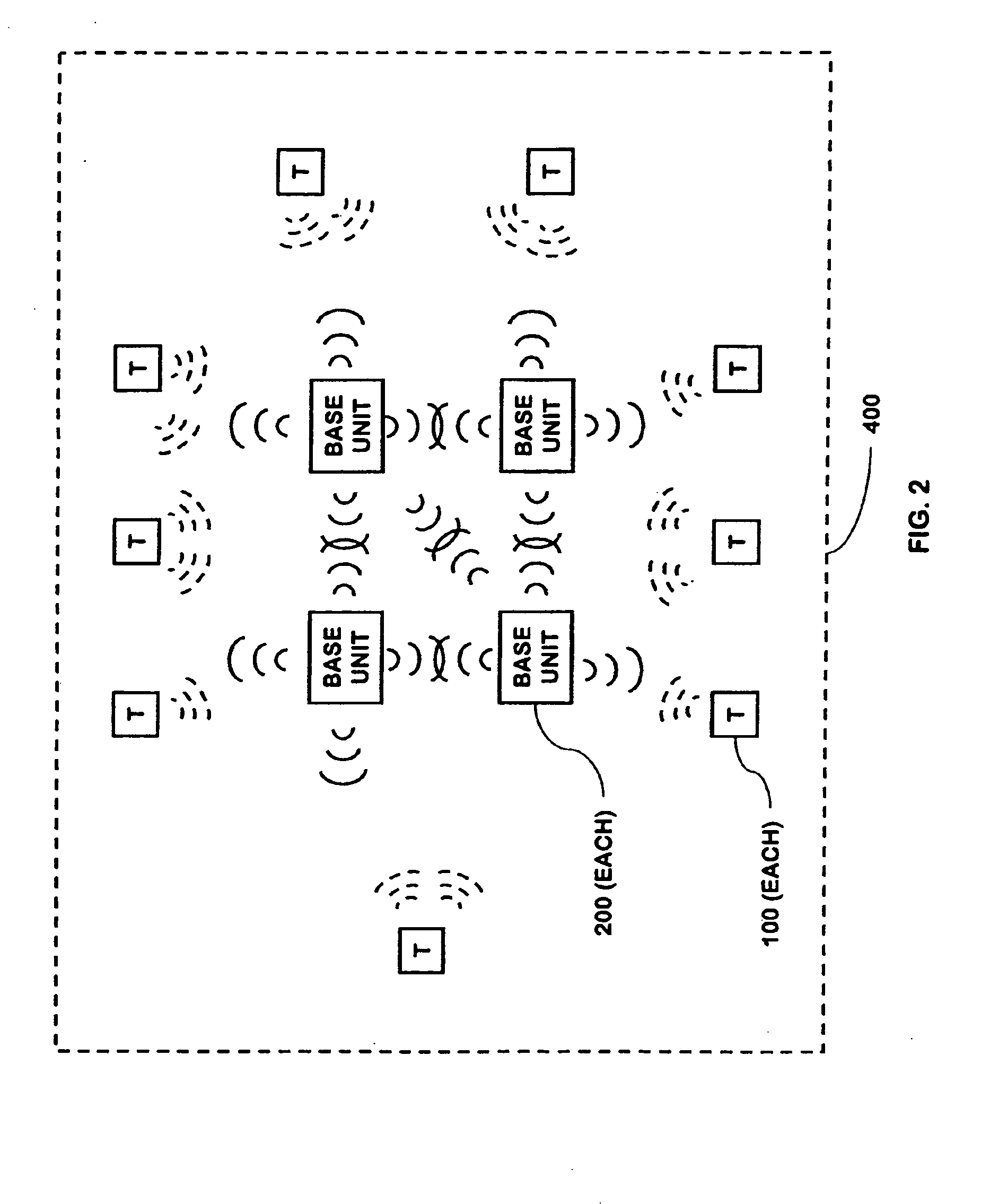
A security network containing multiple controller functions that communicate using wireless communications. The controller functions are contained within base units. One controller function may be the master controller. Other controller functions may receive a copy of the configuration data contained within the master controller. If the master controller fails, another controller function may become the master controller. The controller functions may use encryption keys to encrypt and / or authenticate communications. Some base units may contain a telecommunications interface. Controller units may relay communications between themselves to reach a telecommunications interface. Controller functions located in different buildings may communicate. Controller functions may each receive wireless communications from a transponder and combine the received communications to reduce errors.
Owner:ADT US HLDG INC
Analyte concentration information collection and communication system
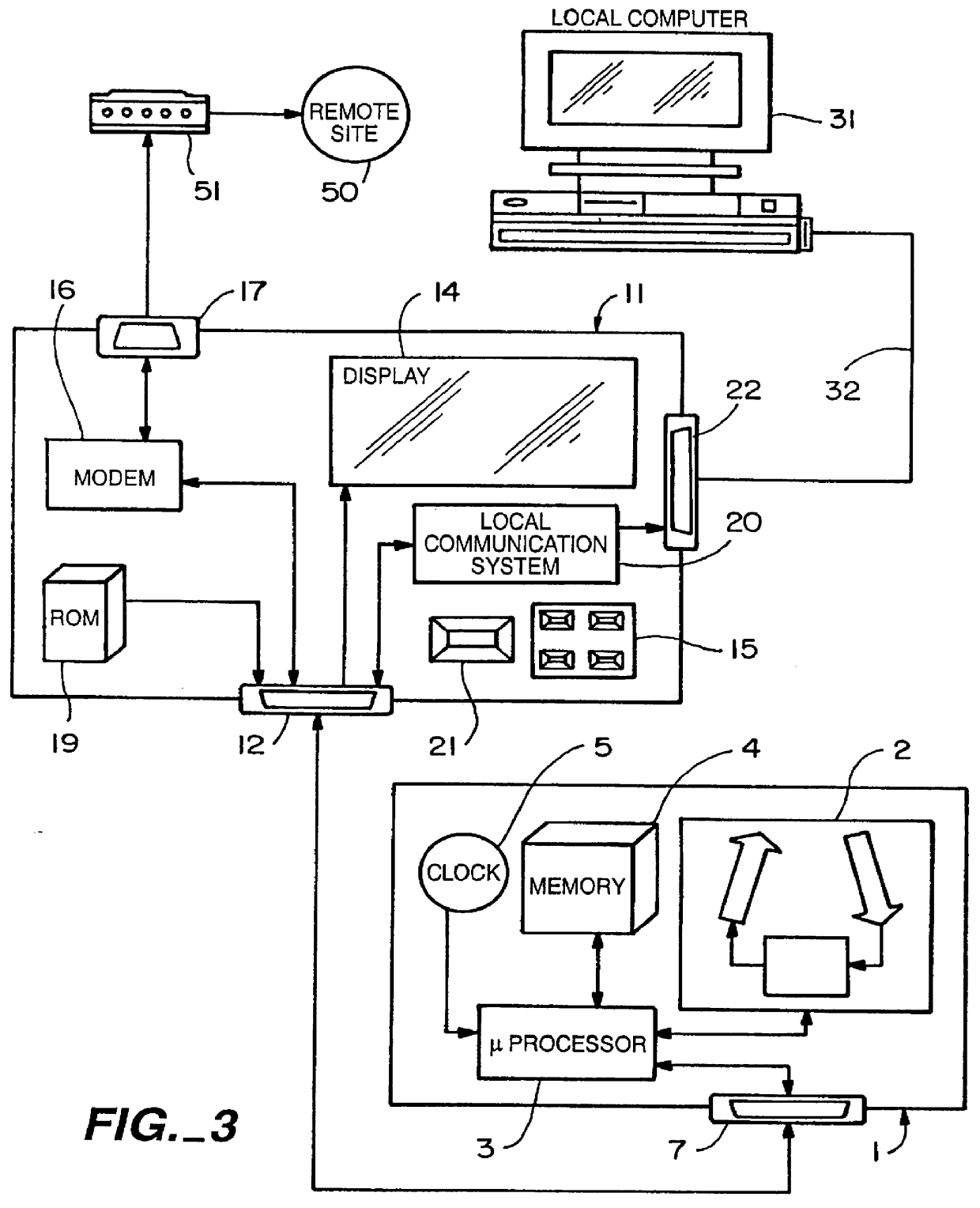
InactiveUS6134504AReduce system costIncrease transfer speedData processing applicationsLocal control/monitoringModem deviceExercise time
A monitoring system which collects patient physiological date is designed specifically for communication with a communication module which facilitates data transfer from the monitoring system to a remote site. The communication module has data input mechanisms to facilitate setting parameters of the monitoring system and / or the communication module. The communication module is provided with a modem member which is used to communicate with the remote site and an optional data exchange module which is designed to communicate the same information with a local computer system. The remote site may be a bulletin board system or internet site where the monitoring information can be stored by the patient using the monitoring system by patient identification or name and include monitoring readings, time and date stamp, conditions such as meal times, exercise times and therapy amounts and their associated date and time.
Owner:AMIRA MEDICAL +1
Multi-level meshed security network
InactiveUS20060145842A1Improve reliabilityLow costSafety arrangmentsComputer controlEngineeringSecondary layer
Owner:ADT US HLDG INC
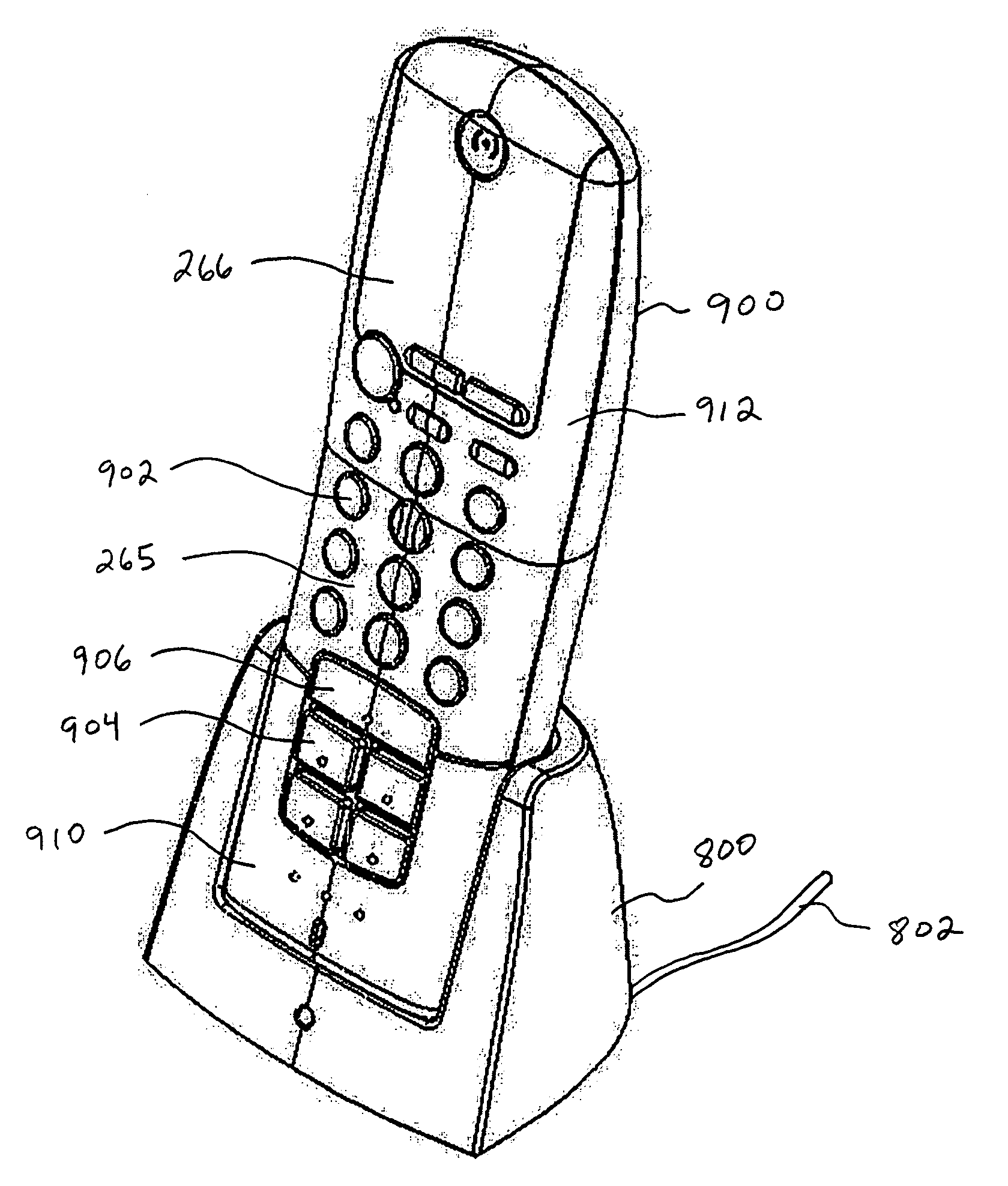
Portable telephone in a security network
InactiveUS20080001734A1Improve reliabilityLow costSafety arrangmentsComputer controlKey pressingNetwork communication
A security network for use in a building with an opening to be monitored for possible intrusion. The network includes an intrusion sensor monitoring the opening; an RFID transponder associated with the sensor; an RFID reader in wireless communication with the transponder; and a portable telephone handset having first keys activating conventional telephone capability and second keys activating interaction with the other security network components. The handset wirelessly communicates with the reader. The reader may take the form of a security cradle for the handset. Alternatively, the reader may take the form of a telephone console. The console has keys enabling a user to dial remote telephone numbers; circuitry adapted to receive wireless communications from the transponder; circuitry in wireless communication with the handset; circuitry in communication with an external network; and a processor executing program code enabling the handset to communicate with the external network via the telephone console.
Owner:ADT US HLDG INC
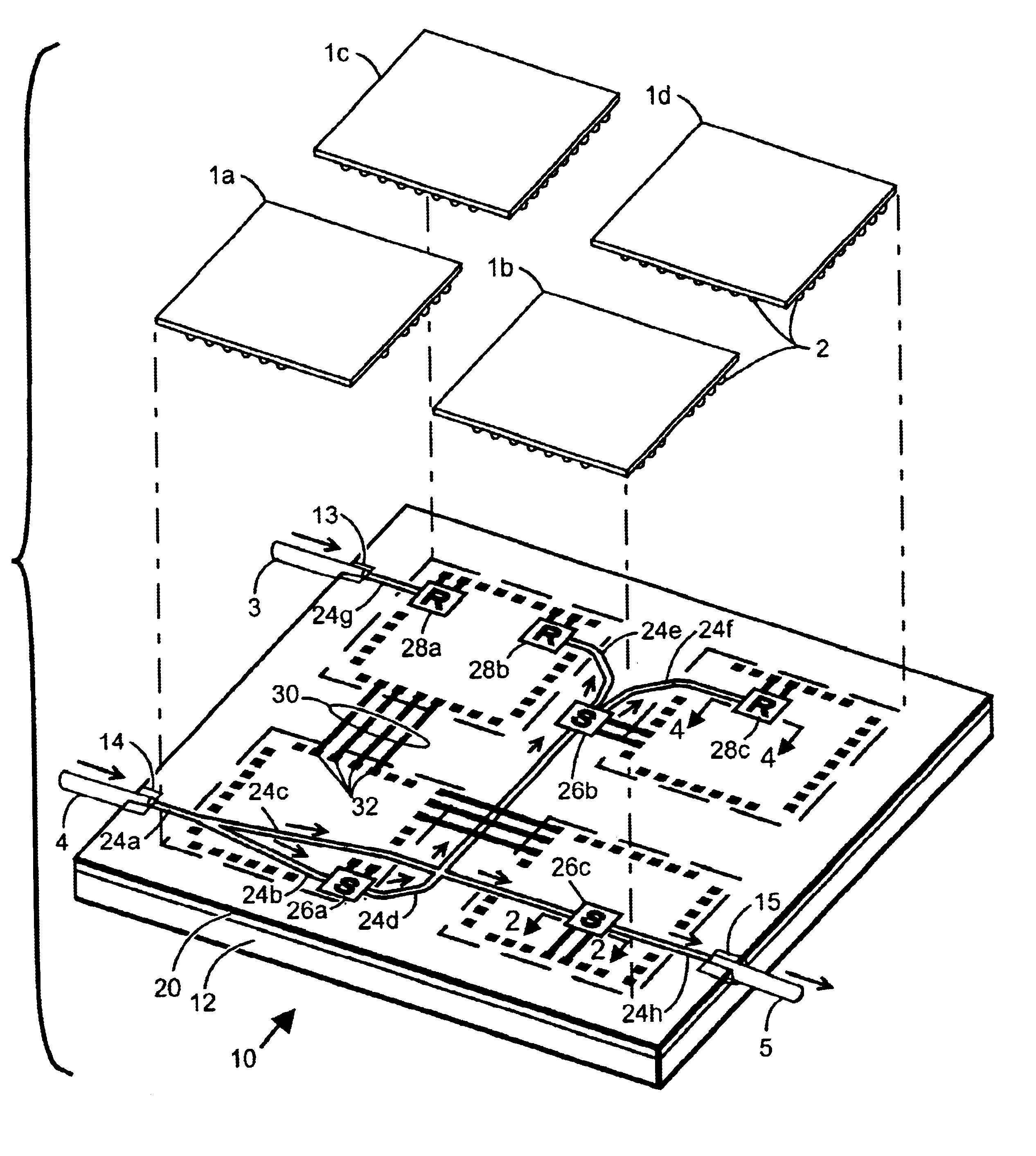
Multi-layer opto-electronic substrates with electrical and optical interconnections and methods for making
InactiveUS6845184B1Reduce area requirementsOptical coupling efficiency improvementSemiconductor/solid-state device detailsSolid-state devicesElectricityThin layer
Opto-electrical systems having electrical and optical interconnections formed in thin layers are disclosed. In one set of preferred embodiments, optical signals are conveyed between layers by respective vertical optical couplers disposed on the layers. In other preferred embodiments, optical signals are conveyed by stack optical waveguide coupling means. Yet other preferred embodiments have electrical via means formed in one or more layers to covey electrical signals between two or more layers.
Owner:FUJITSU LTD
Power management of transponders and sensors in an RFID security network
InactiveUS20060132302A1Improve reliabilityLow costElectric signal transmission systemsSafety arrangmentsAudio power amplifierOn-off keying
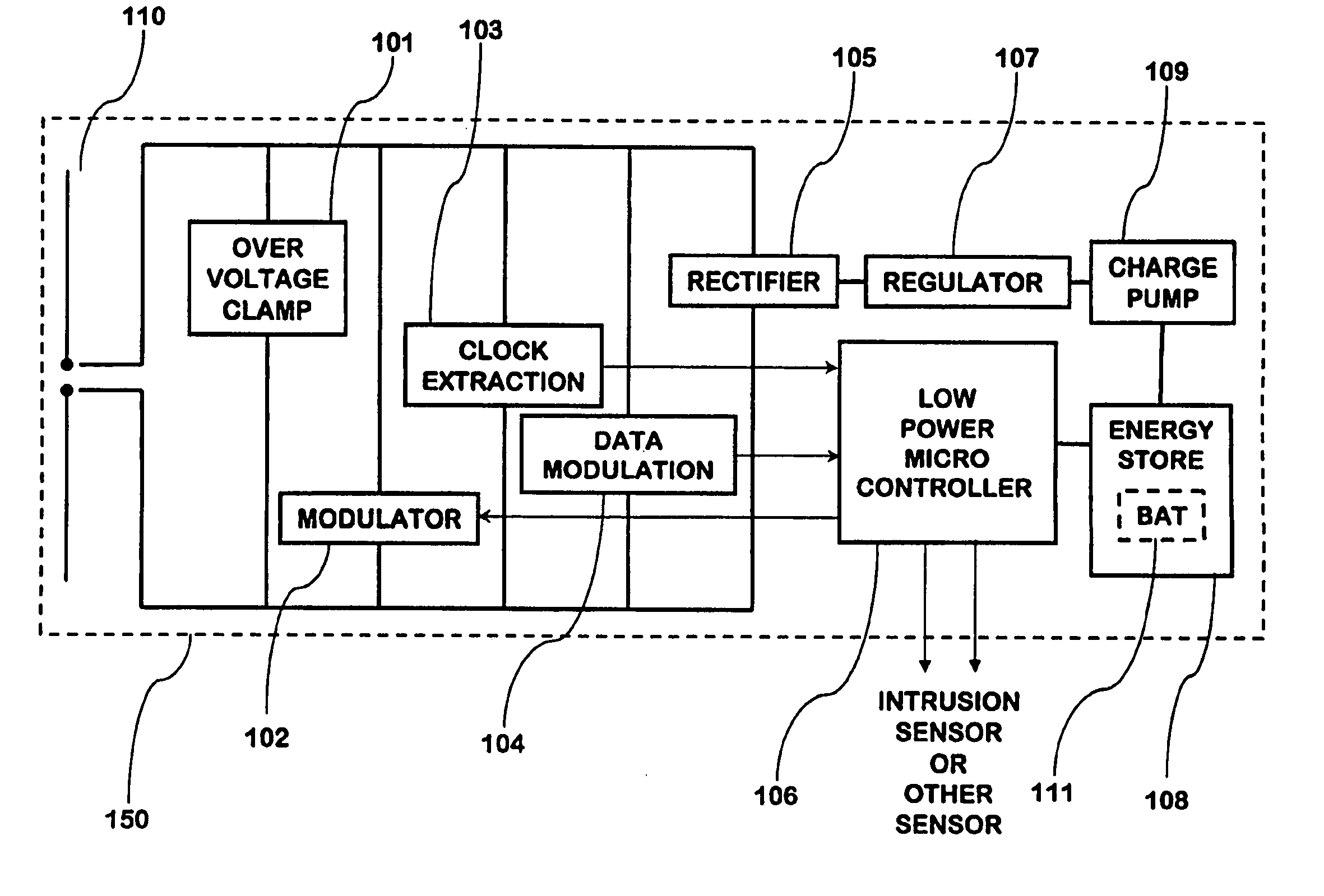
An RFID transponder with an associated sensor used in a security network including at least one RFID reader that transmits signals at a first frequency. The transponder has a processor controlling its other components. Transmitter circuitry coupled to a transmit antenna transmits signals to the reader at a second frequency. A receive antenna receives signals in a frequency band that includes the first frequency. One or more RF diodes obtain the signal from the receive antenna and output a power envelope signal representing the power level of the signal obtained from the receive antenna. An amplifier coupled to the output of the RF diode amplifies the power envelope signal received from the RF diode. The processor receives the amplified power envelope signal and decodes any data that have been encoded using an on-off keyed modulation scheme applied to the signal obtained from the receive antenna.
Owner:INGRID
TCP/IP offload device with reduced sequential processing
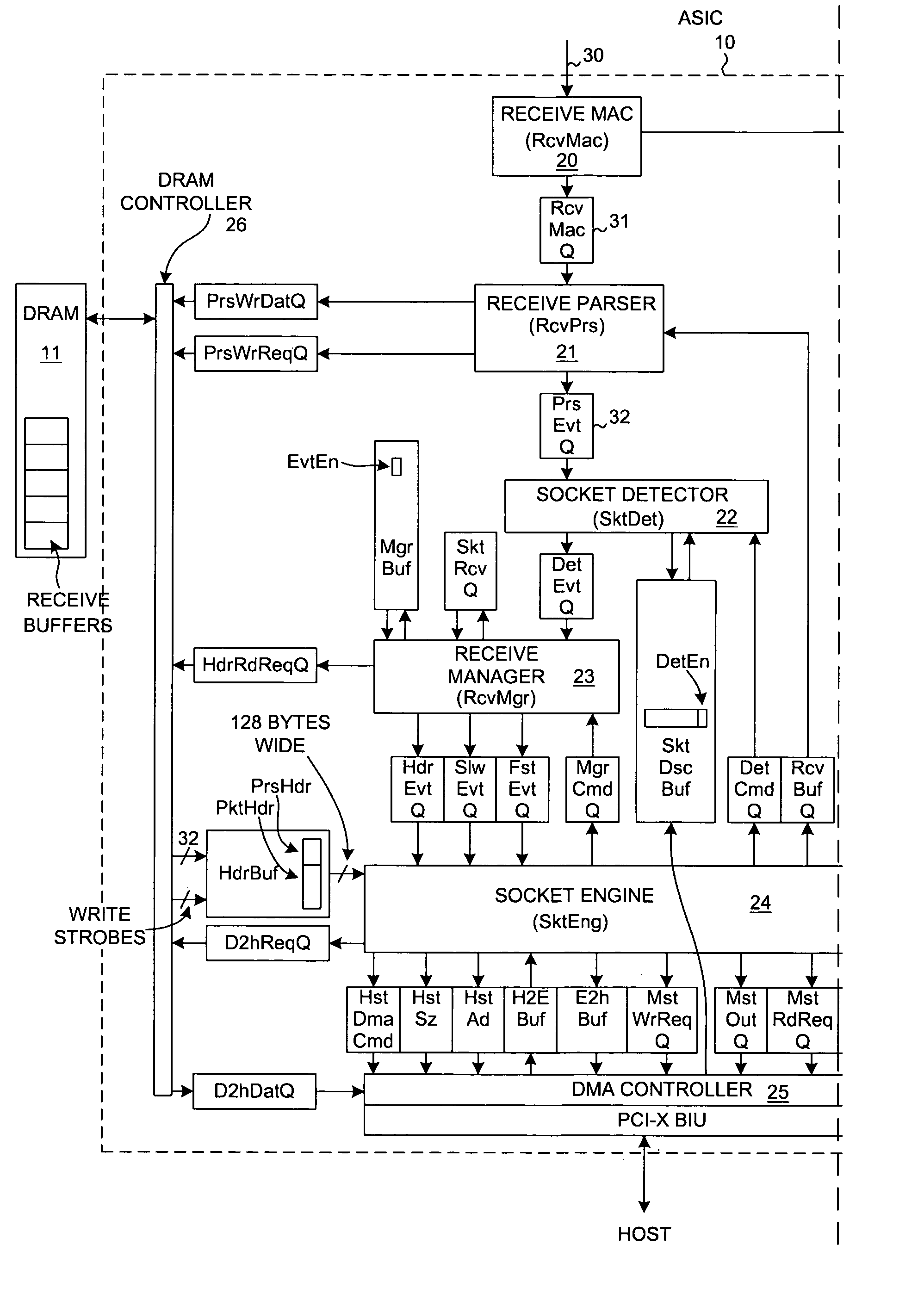
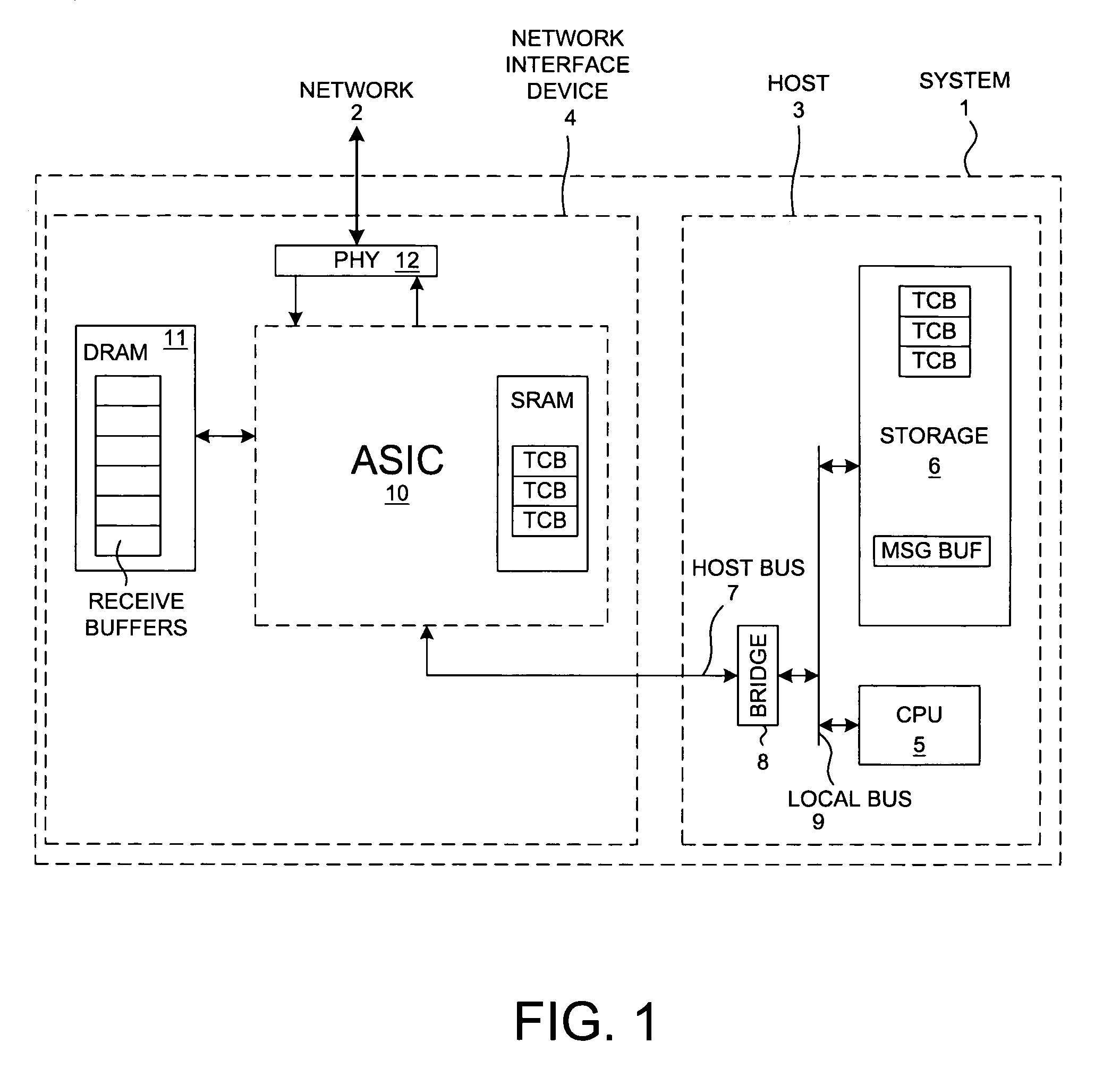
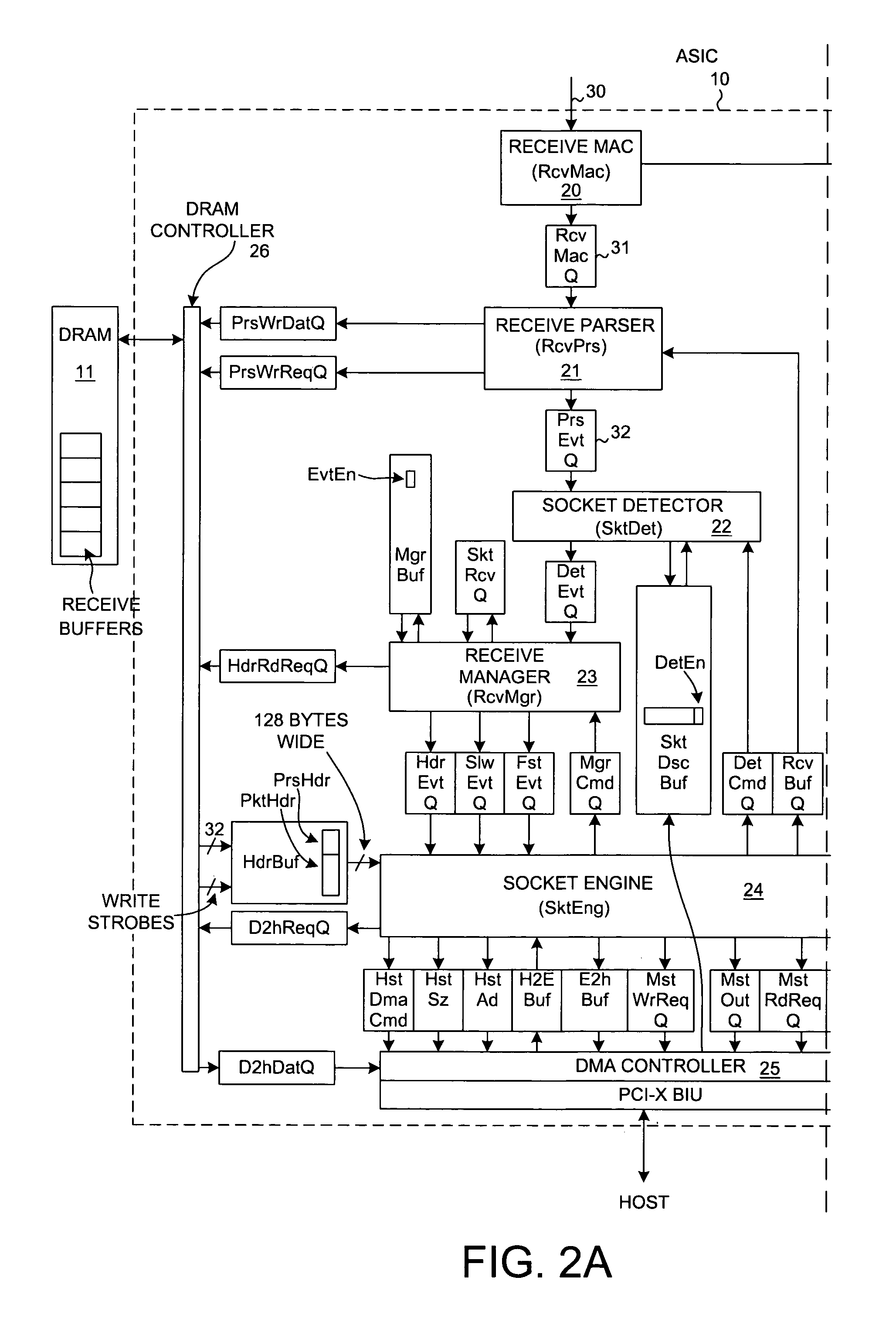
ActiveUS6996070B2Block valueNarrow structureError preventionTransmission systemsProtocol processingState variable
A TCP Offload Engine (TOE) device includes a state machine that performs TCP / IP protocol processing operations in parallel. In a first aspect, the state machine includes a first memory, a second memory, and combinatorial logic. The first memory stores and simultaneously outputs multiple TCP state variables. The second memory stores and simultaneously outputs multiple header values. In contrast to a sequential processor technique, the combinatorial logic generates a flush detect signal from the TCP state variables and header values without performing sequential processor instructions or sequential memory accesses. In a second aspect, a TOE includes a state machine that performs an update of multiple TCP state variables in a TCB buffer all simultaneously, thereby avoiding multiple sequential writes to the TCB buffer memory. In a third aspect, a TOE involves a state machine that sets up a DMA move in a single state machine clock cycle.
Owner:ALACRITECH
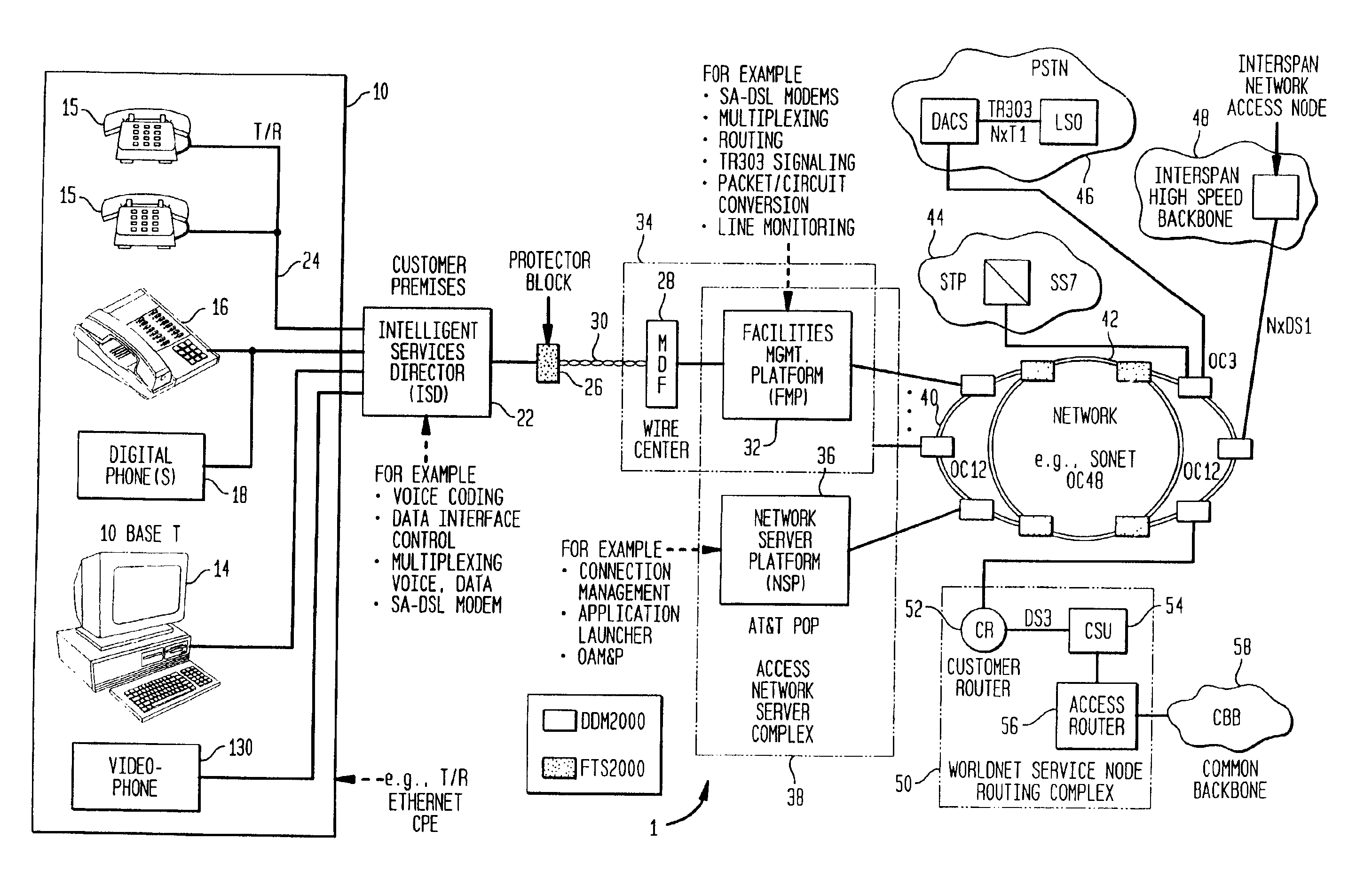
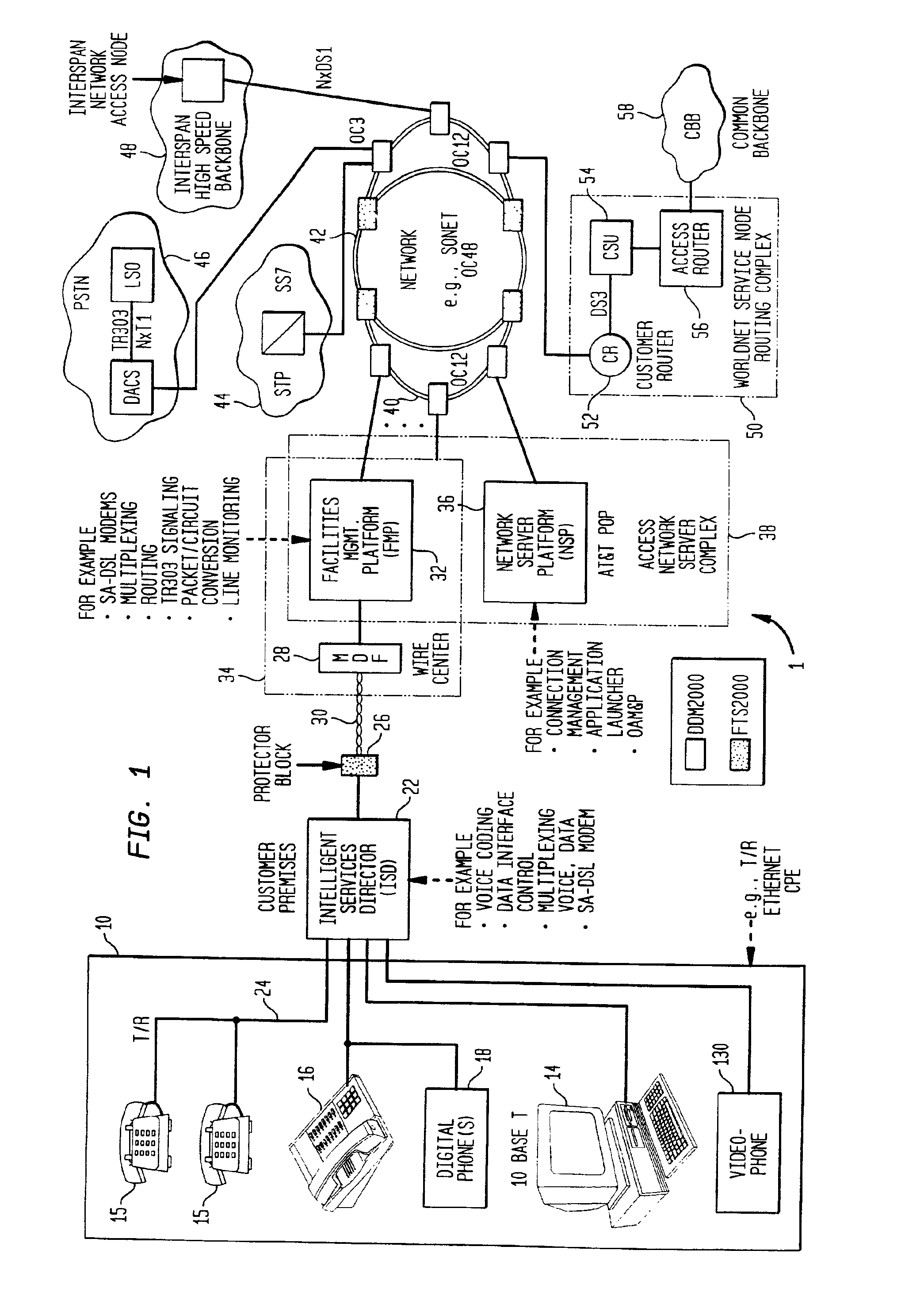
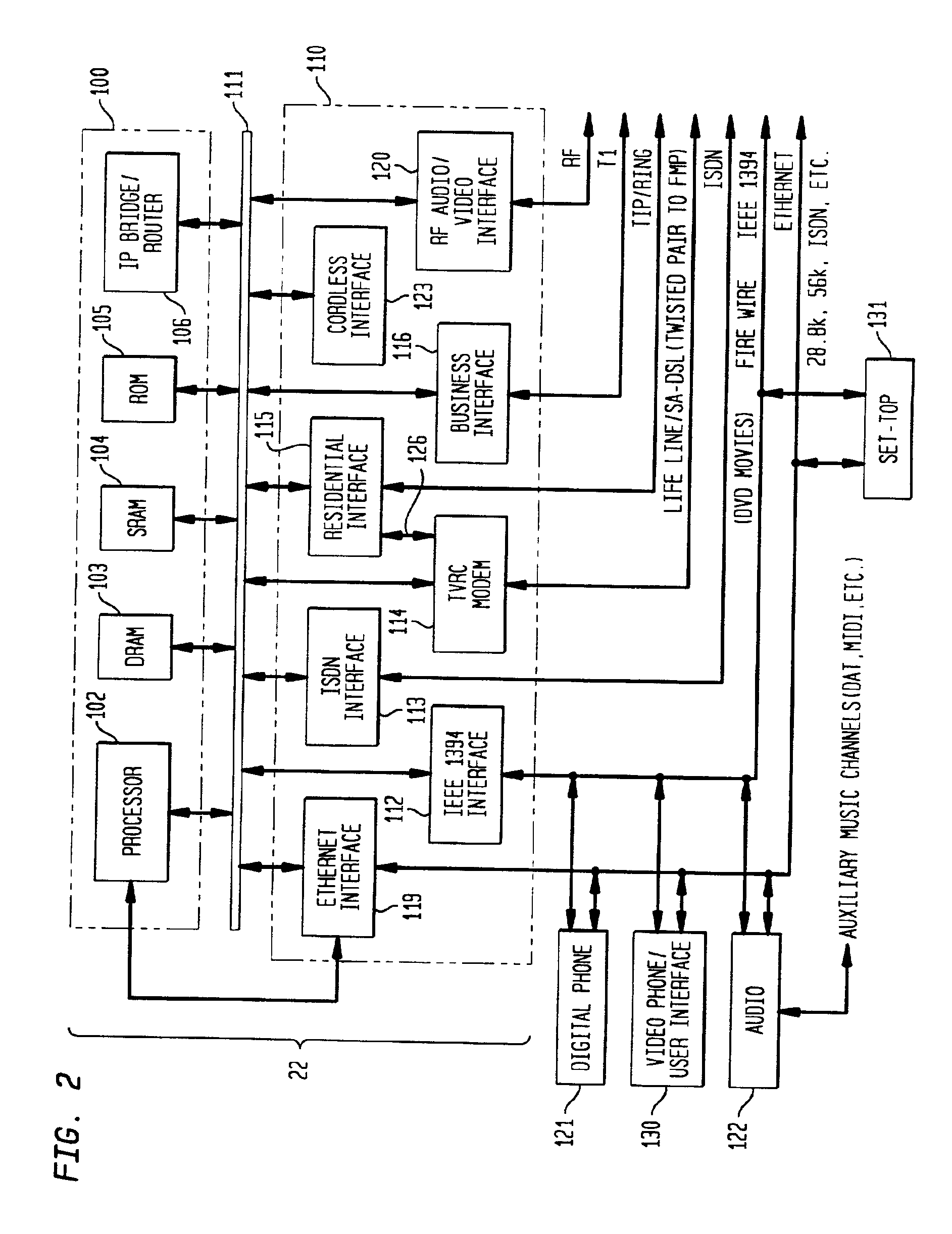
Multifunction interface facility connecting wideband multiple access subscriber loops with various networks
InactiveUS6937595B2Lower system costHigh bandwidthTelephonic communicationTime-division multiplexData conversionBroadband
An device, called a facilities management platform (FMP) connects current digital and analog carrier networks and packet switched networks of interexchange carriers with high speed multiple access subscriber links implemented over twisted pair lines. The subscriber line is terminated by an access module containing one or more modems. In preferred embodiments, the modems are high-speed digital tethered vial radio channel or xDSL modems. The FMP interface applies and receives signaling and voice through a digital loop carrier (DLC) via a multiplexer connected directly to the DLC backplane. The multiplexer is controlled by a controller of an access module. It translates data from the subscriber link to the form compatible with the digital backplane to create the appearance of one or more line cards. The FMP also may contain a sound generator to allow it to handle calls through an analog carrier network. The FMP, through the same access module transmits data to and from the modems directly through connected digital networks, such as ATM or SONET, of an interexchange carrier. Through this interface, different network companies can offer competing products through different networks all seamlessly connected through a high speed subscriber line.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
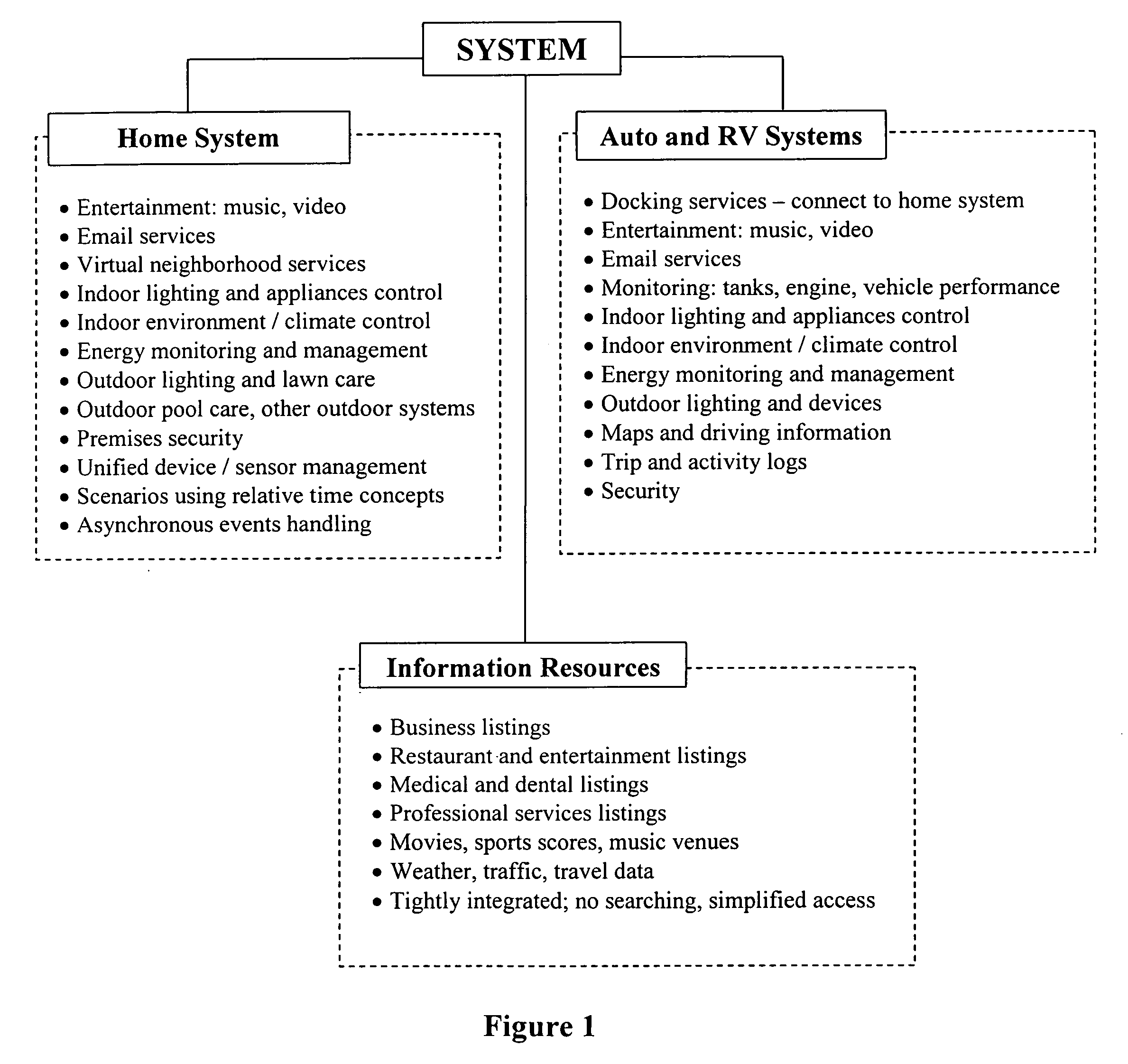
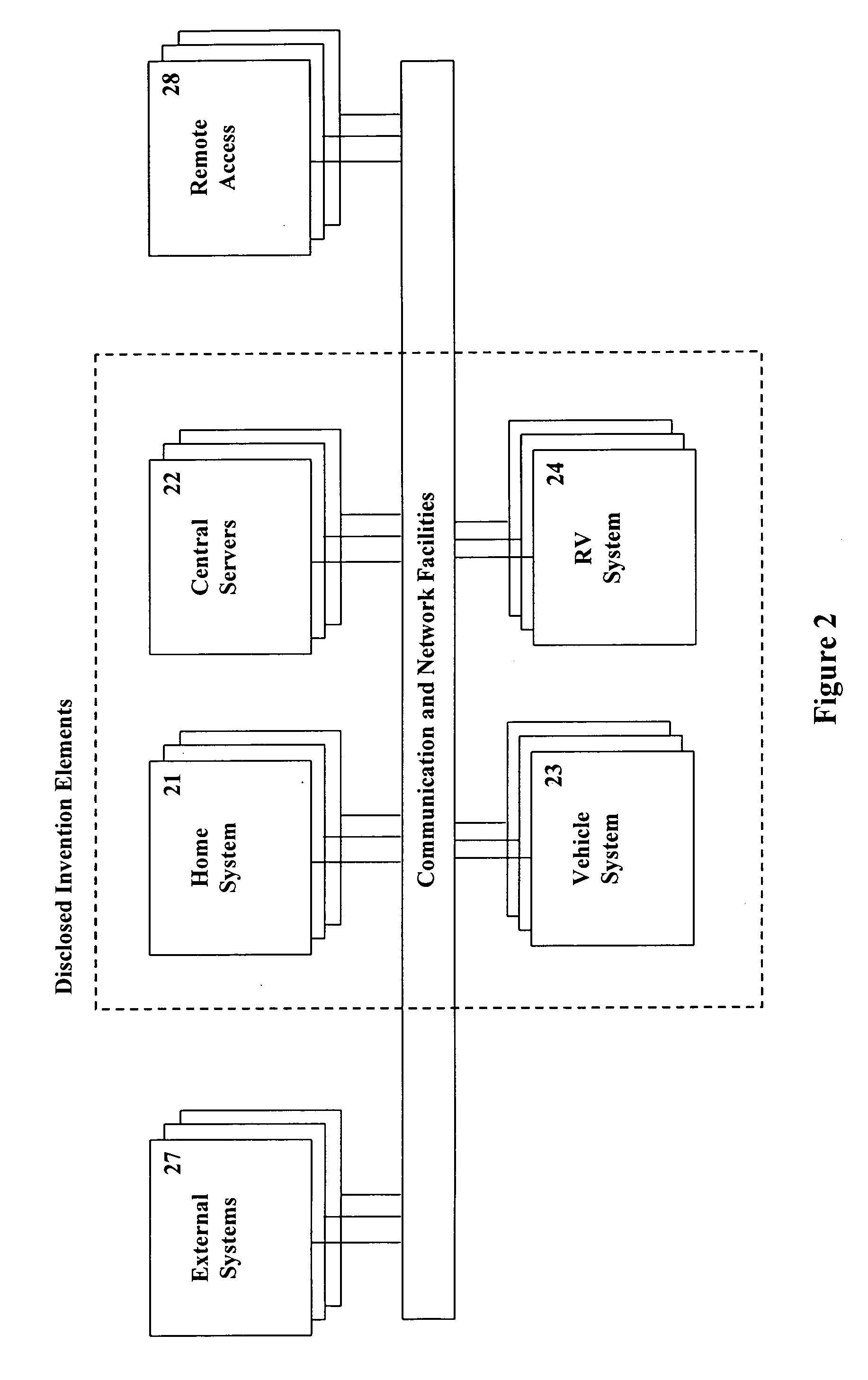
Methods and systems for automating the control of objects within a defined human environment
InactiveUS20060218244A1Reduce system costSimple systemMultiple digital computer combinationsTransmissionAutomatic controlAction function
Methods and systems are described for the automation of a human living environment such as a home, an apartment, a workplace, or a vehicle. The methods and systems are directed to the control of various groups of objects within the human living environments according to defined criteria and defined object groupings, in a manner that establishes operational themes and scenarios within the environment. The methods and systems utilize devices for characterizing the environment (sensors), making decisions about actions appropriate in the environment (processors), and effecting actions and activities within the environment (switches, controls and actuators). The automation operates on multiple levels including; responsive safety functionality, one time action functionality, sporadically initiated timed action functionality, and periodically scheduled action functionality. The systems integrate with off-site information and action routing services that increase the decision making ability of the individuals within the environment.
Owner:RASMUSSEN JUNG A +1
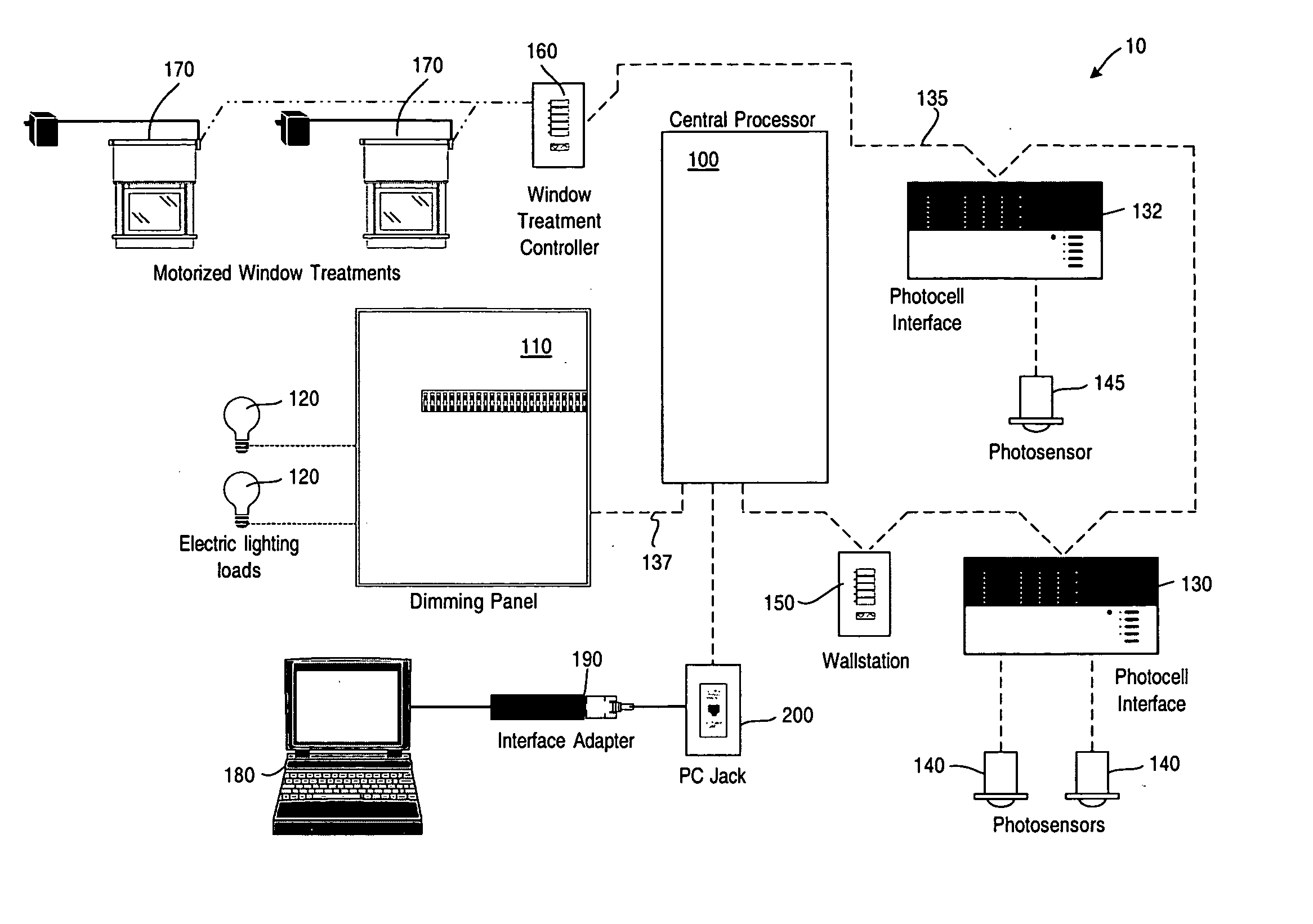
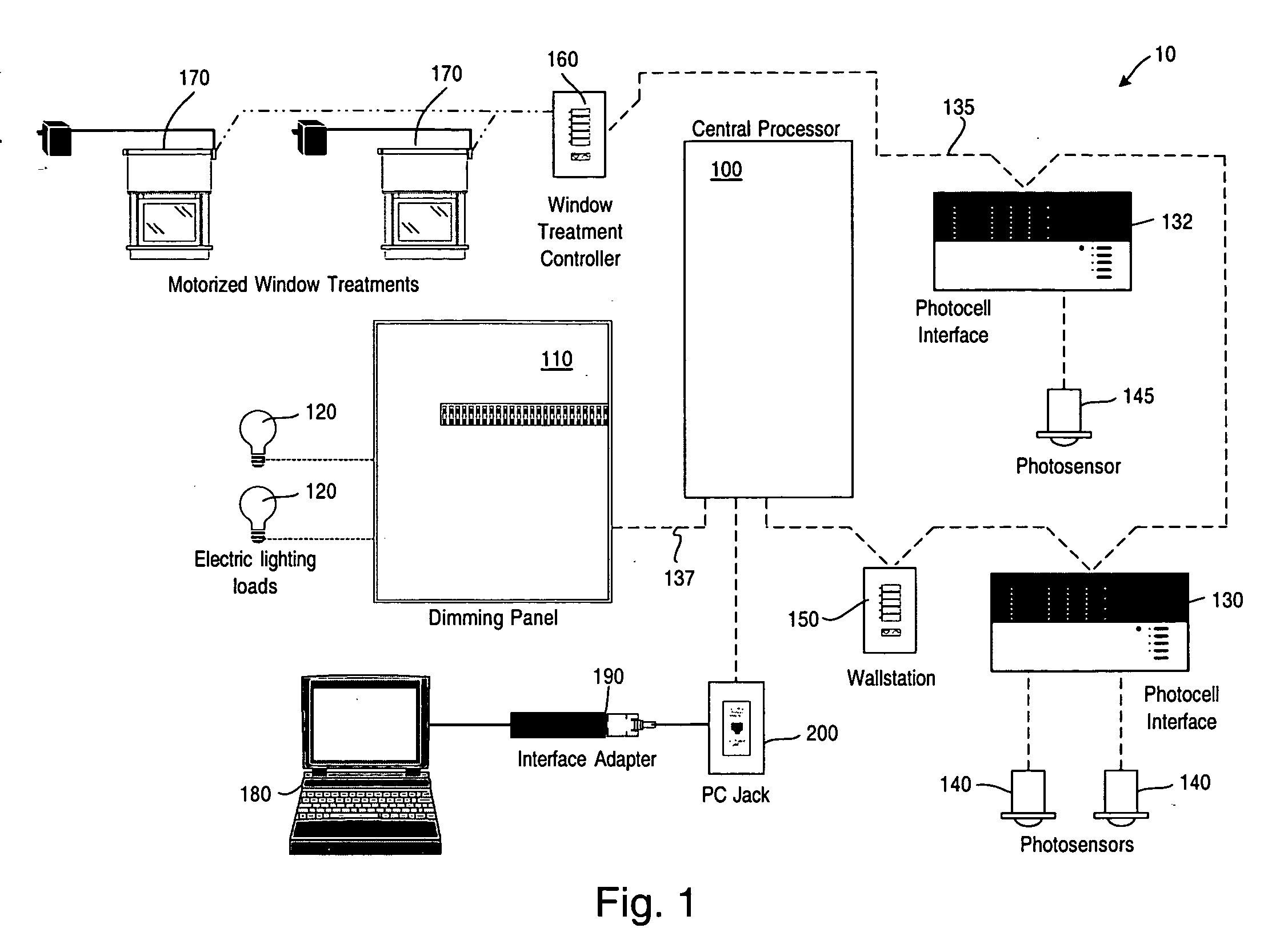
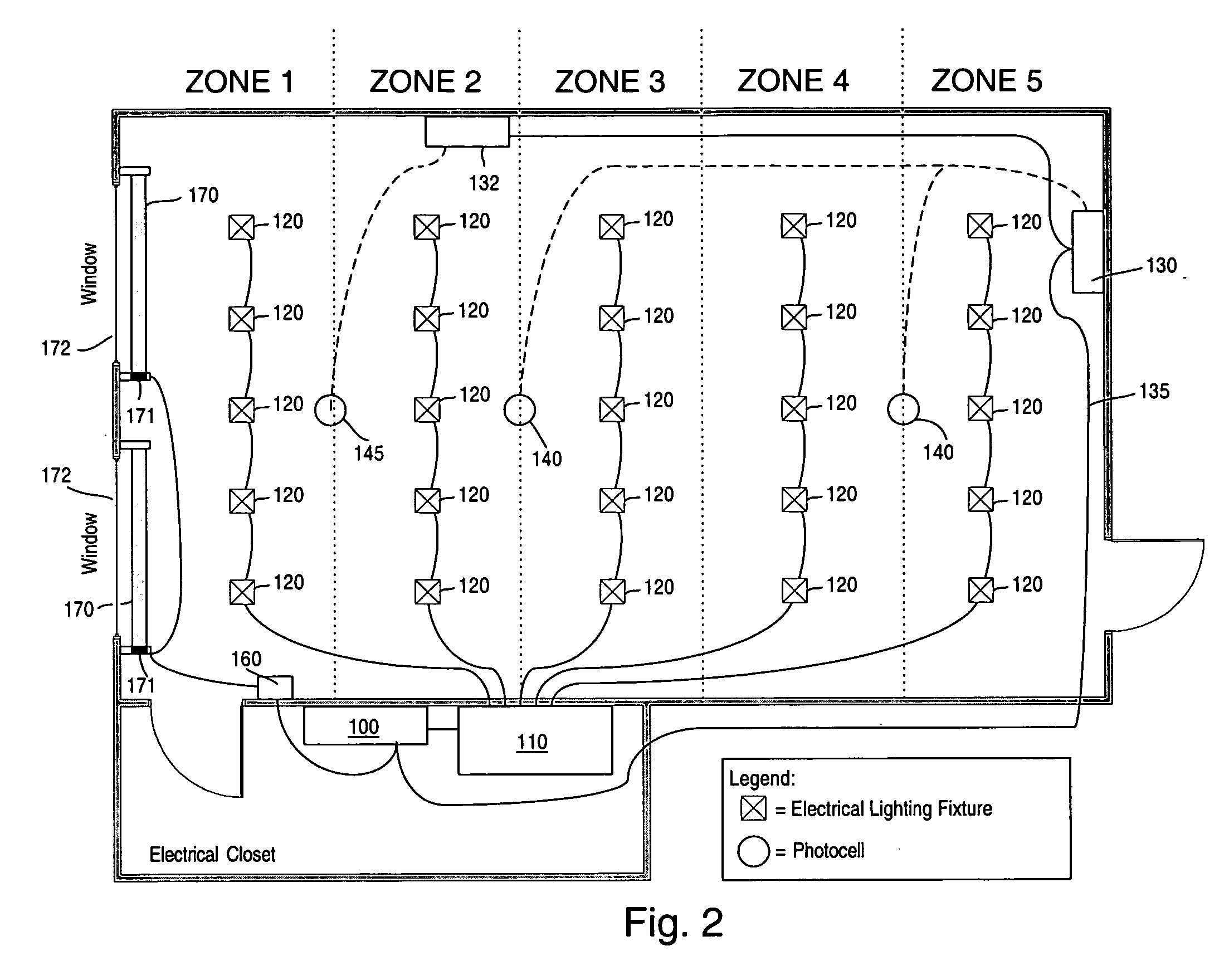
System to control daylight and artificial illumination and sun glare in a space
ActiveUS20050110416A1Reduce system costEliminate needLight dependant control systemsElectrical apparatusControl systemElectric light
An illumination maintenance system for maintaining a desired illumination profile in a space throughout at least a portion of a day where the illumination sources include daylight and artificial light, the system comprising a first sensor for sensing an illumination level in at least a portion of the space, at least one window treatment for at least one opening for allowing daylight into the space, the window treatment selectively altering the amount of daylight entering the space, a plurality of electric lamps providing artificial light to supplement the daylight illumination of the space; the electric lamps being dimmable, a control system controlling the at least one window treatment and the plurality of electric lamps to maintain the desired illumination profile in the space, the control system controlling the plurality of electric lamps so that the dimming level of each lamp is adjusted to achieve the desired lighting profile and compensate for the daylight illumination in the space throughout at least the portion of the day; and the control system further operating to adjust the window treatment in the event of sun glare through the opening to reduce the sun glare and such that when the desired illumination profile within a defined tolerance is achieved, the control system stops varying the dimming levels of the lamps and the adjustment of the at least one window treatment.
Owner:LUTRON TECH CO LLC
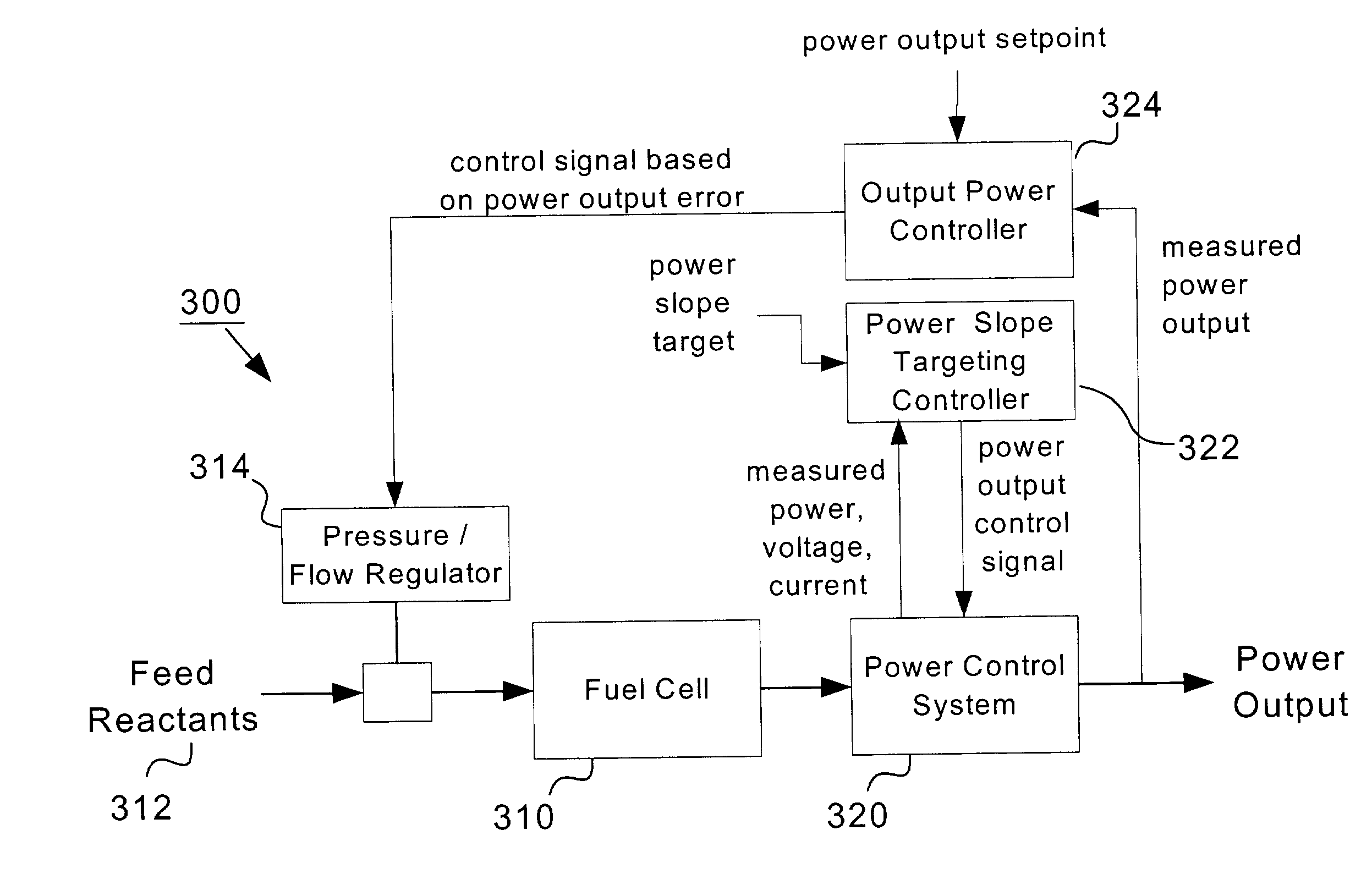
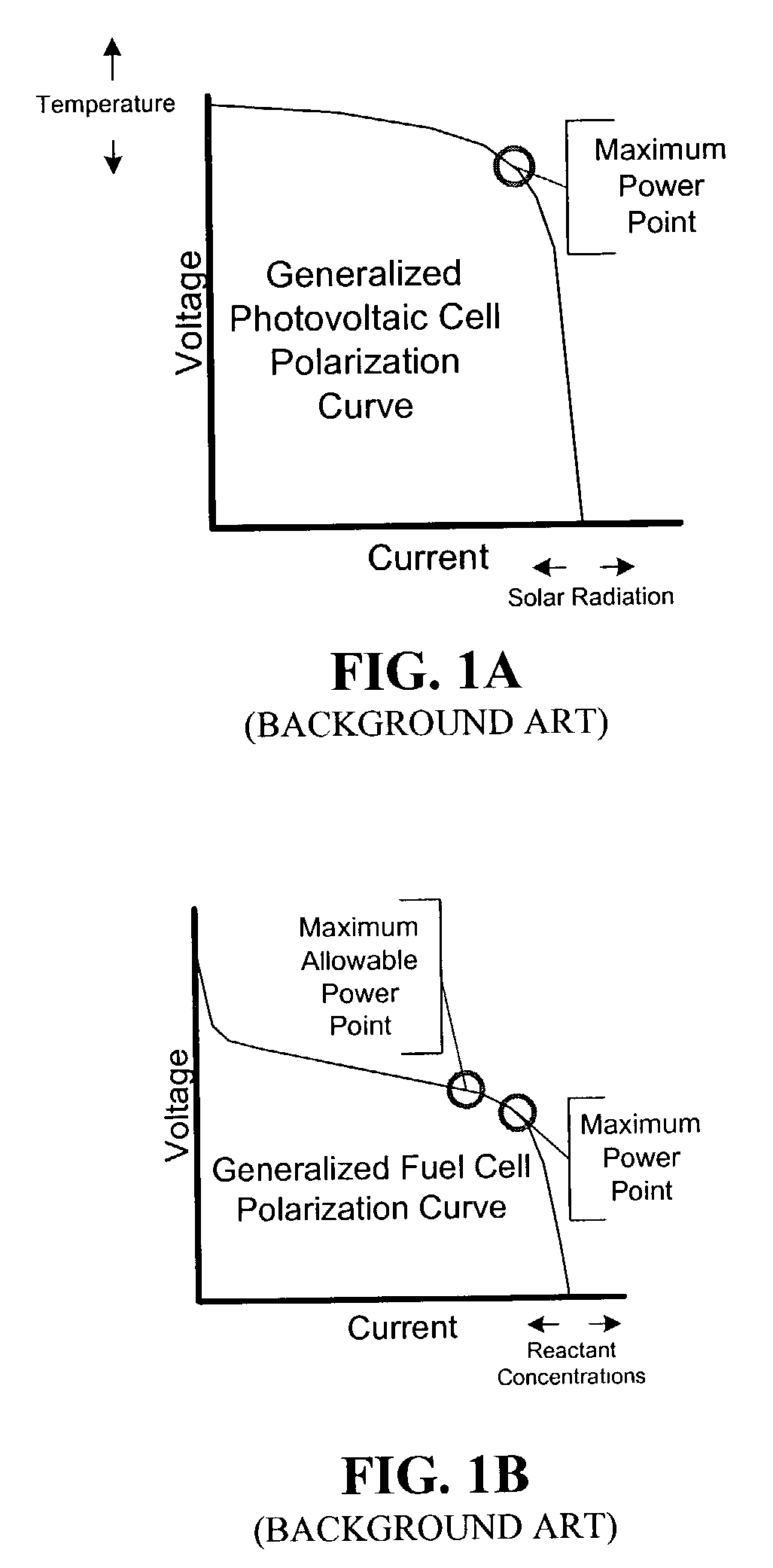
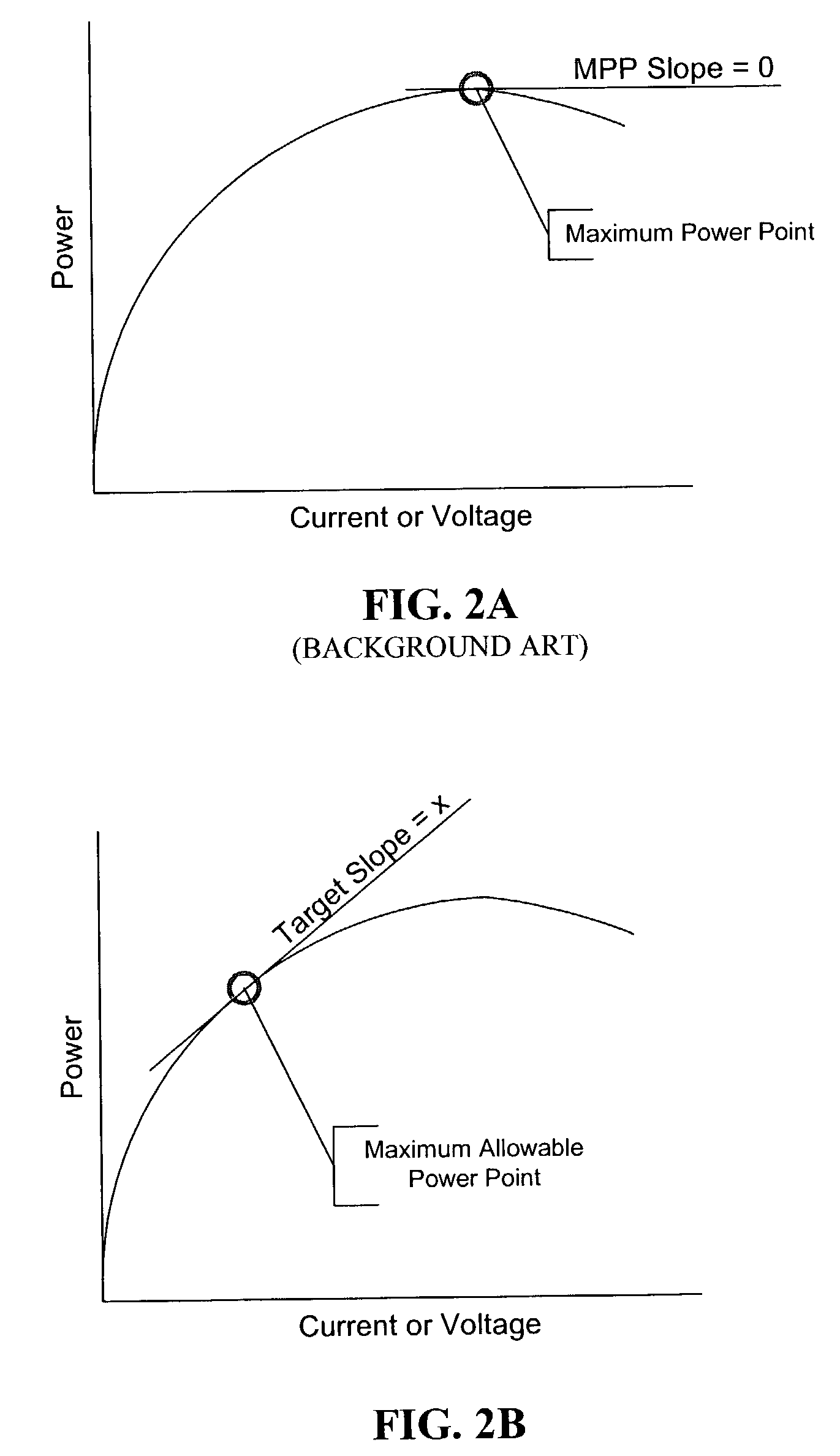
Power slope targeting for DC generators
InactiveUS7087332B2Increase and decrease power outputEfficient operation of powerBatteries circuit arrangementsFuel cell auxillariesElectric generatorMaximum power point tracking controller
A simple feedback control loop, in conjunction with an improved maximum power point tracking intermediate controller, can be used ensure efficient operation of a power generator. The improved maximum power point tracking controller operates the generator at its maximum allowable power point. A power output of the generator is measured and compared to a power output setpoint. Operating characteristics of the generator are then adjusted to cause the maximum allowable power point and measured power output to approximate the power output setpoint. Although applicable to all types of generators, this is particularly beneficial in fuel cell generator systems and other systems where damage to generator components can occur if operated above a maximum allowable power output level. In other systems, the maximum allowable power output may approach or equal a maximum power point (or maximum possible power point).
Owner:SUSTAINABLE ENERGY SYST
RFID reader for a security network
InactiveUS7023341B2Improve reliabilityLow costBurglar alarm by openingFrequency-division multiplex detailsComputer hardwareTransducer
An RFID reader for use in a security network based upon RFID techniques. The RFID reader can use wireless communications to communicate with RFID transponders and other devices in the security network. The RFID reader of the security network can be provided with multiple modulation techniques, multiple antennas, and the capability to vary its power level and carrier frequency. The RFID reader can transmit RF energy useful for detecting motion or for charging the batteries in RFID transponders. The RFID reader can contain an audio transducer, a camera, or various environmental sensors to detect parameters such as smoke, temperature, and water, among others. The program code of the RFID reader can be updated. A master controller within the security network can control operations within the RFID reader.
Owner:ADT US HLDG INC
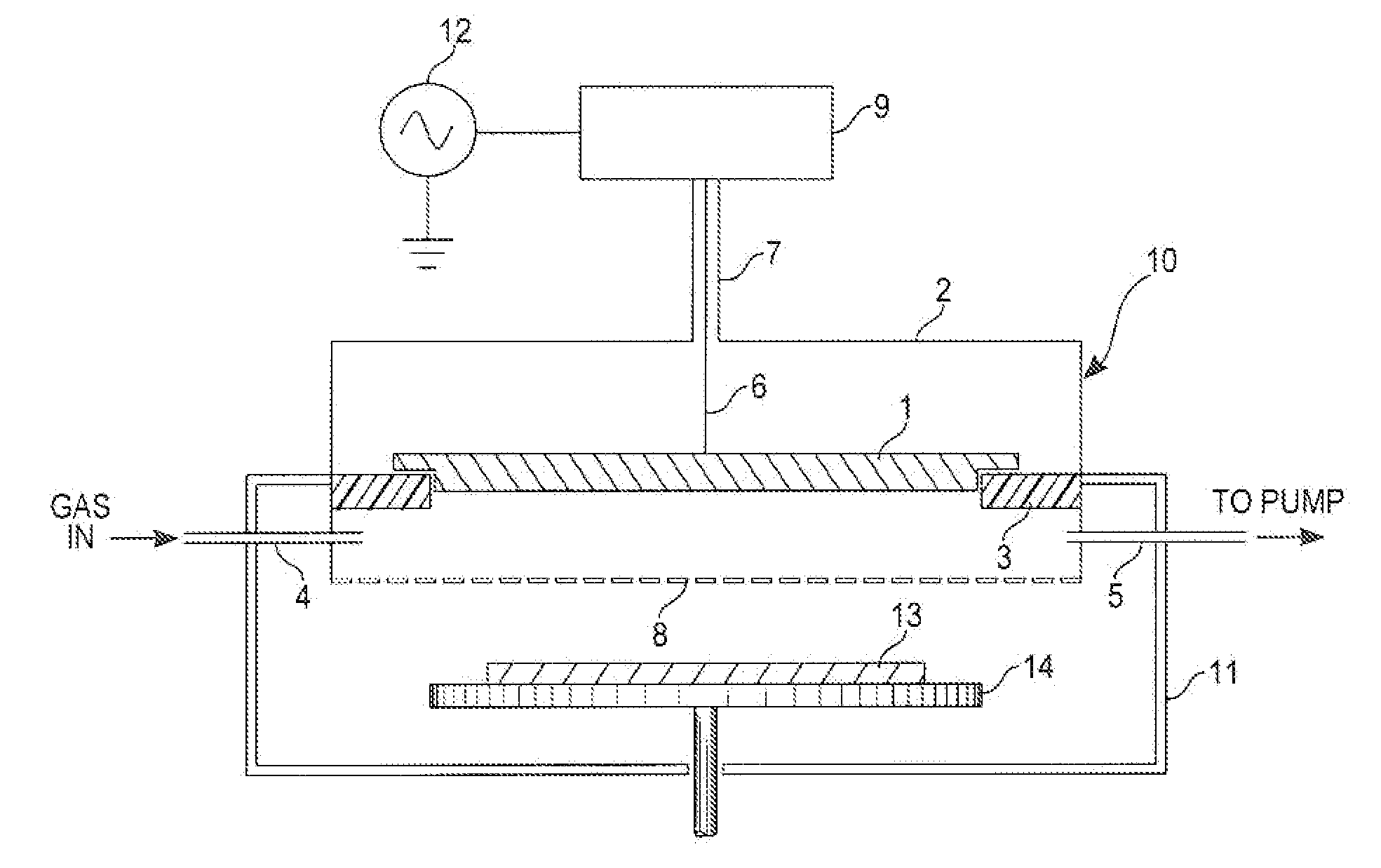
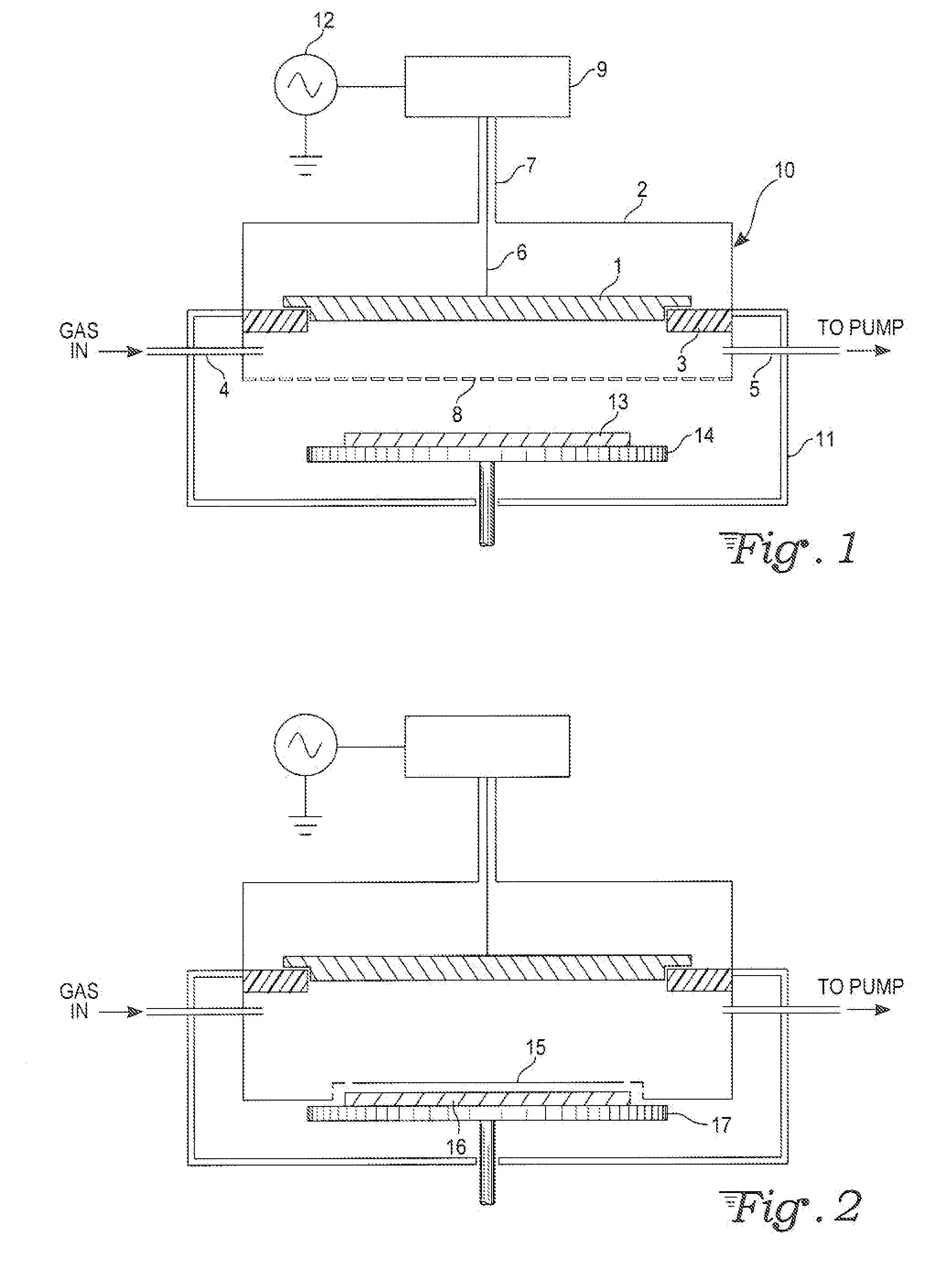
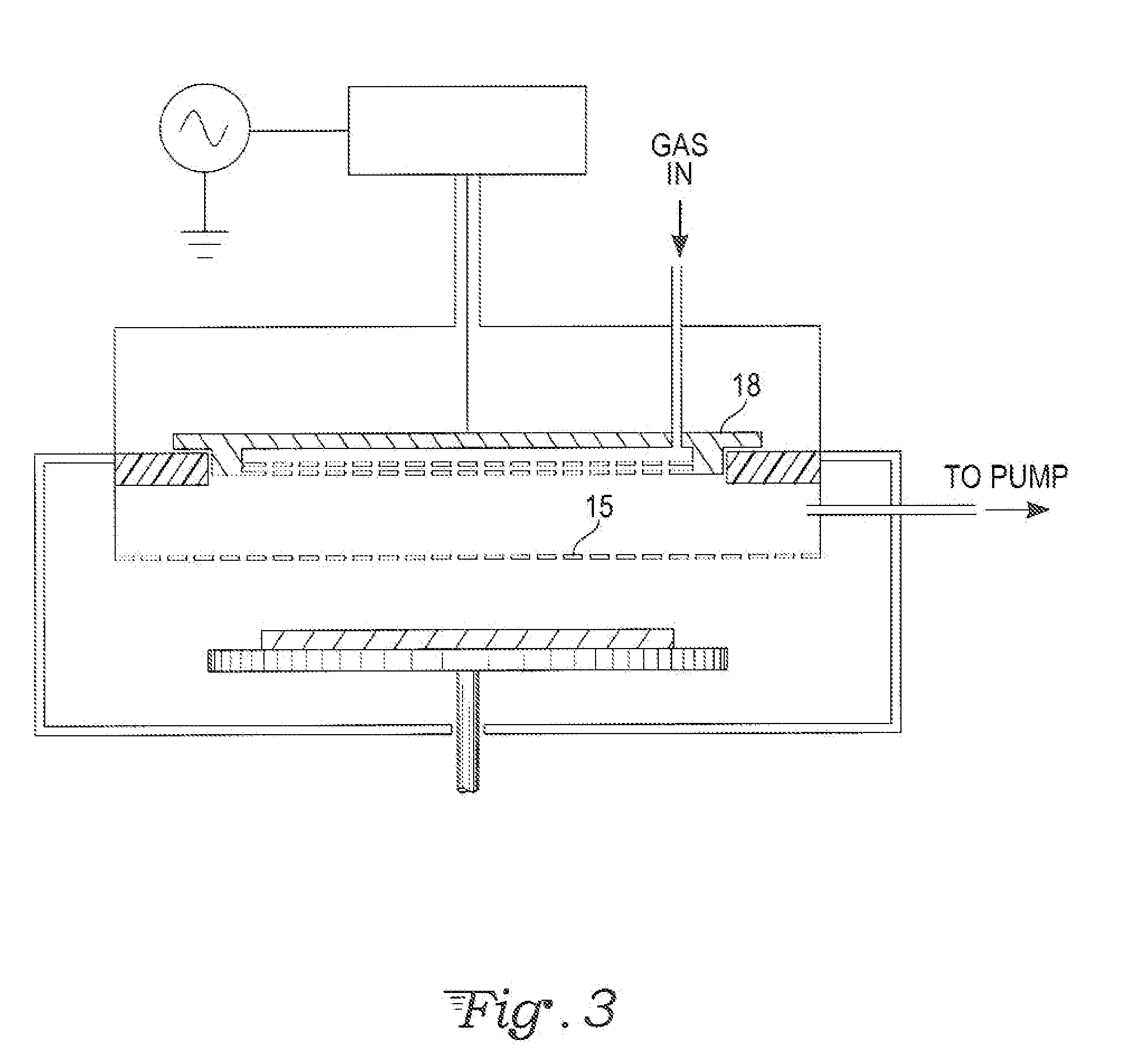
Capacitively coupled remote plasma source with large operating pressure range
InactiveUS20100101727A1System costExtension of timeElectric discharge tubesSemiconductor/solid-state device manufacturingCapacitanceRadio frequency
A radio frequency (RF) coaxial resonator feeding a saltshaker-like gas distributing electrode assembly forms a capacitively coupled plasma source. This apparatus can generate plasma of high density over a wide pressure range and large process window. The system may be used as a remote radical-rich plasma source for materials surface processing.
Owner:JI HELIN
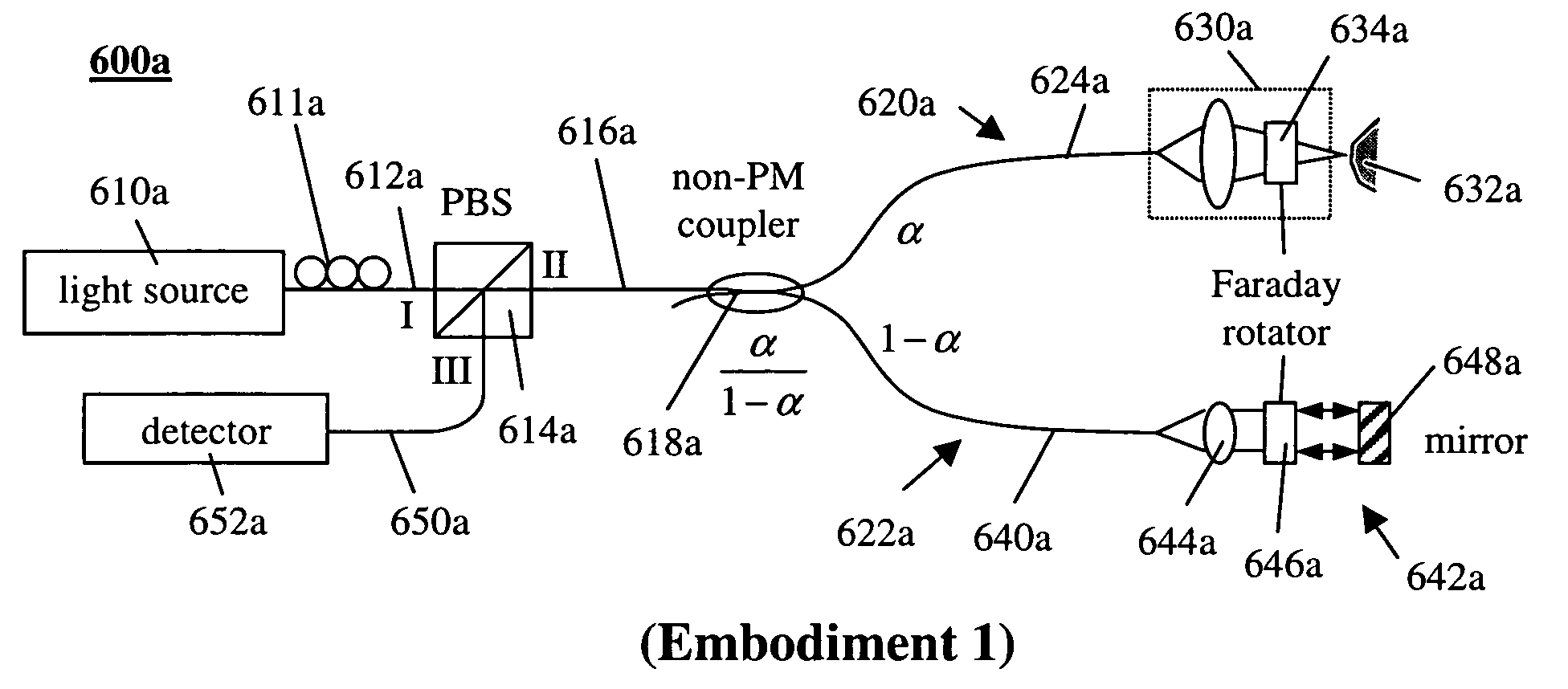
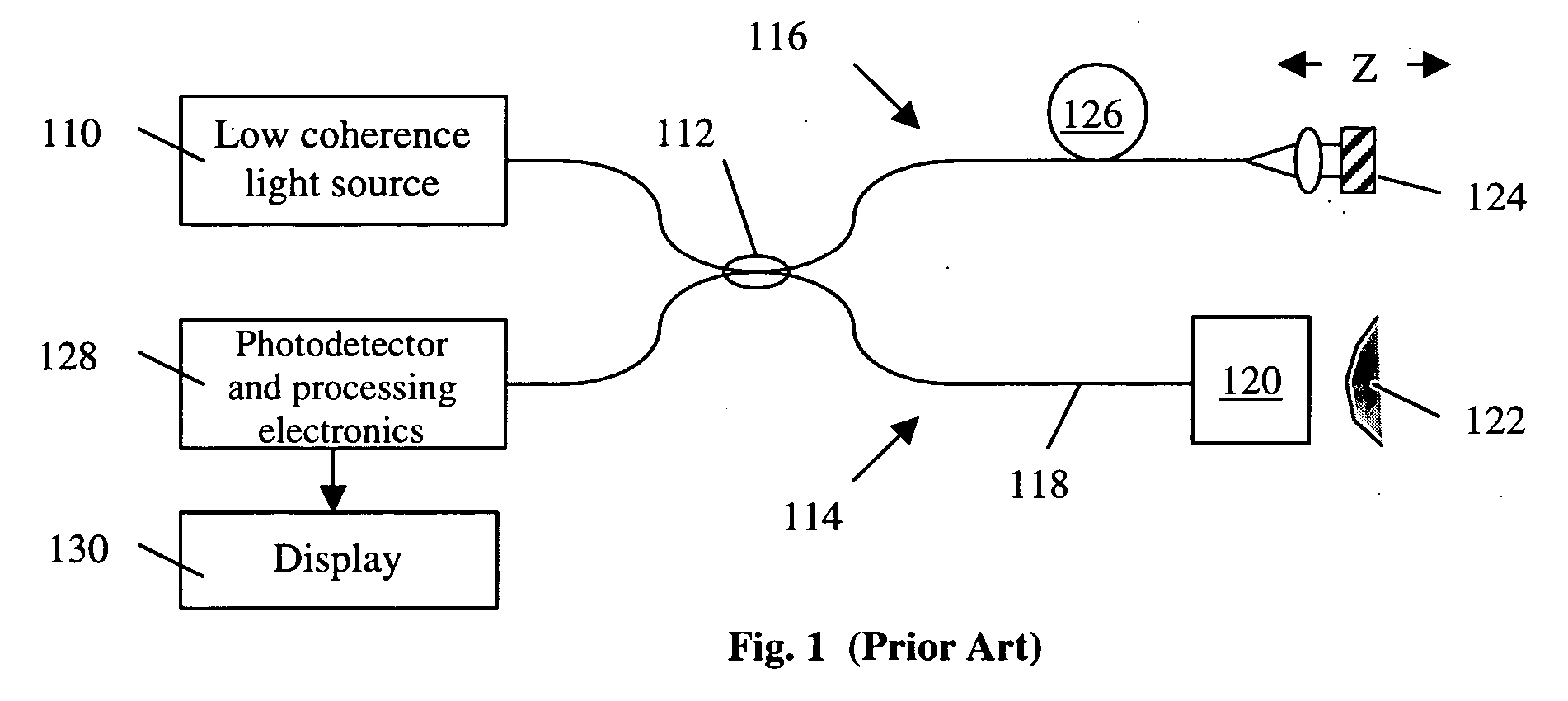
Simple high efficiency optical coherence domain reflectometer design
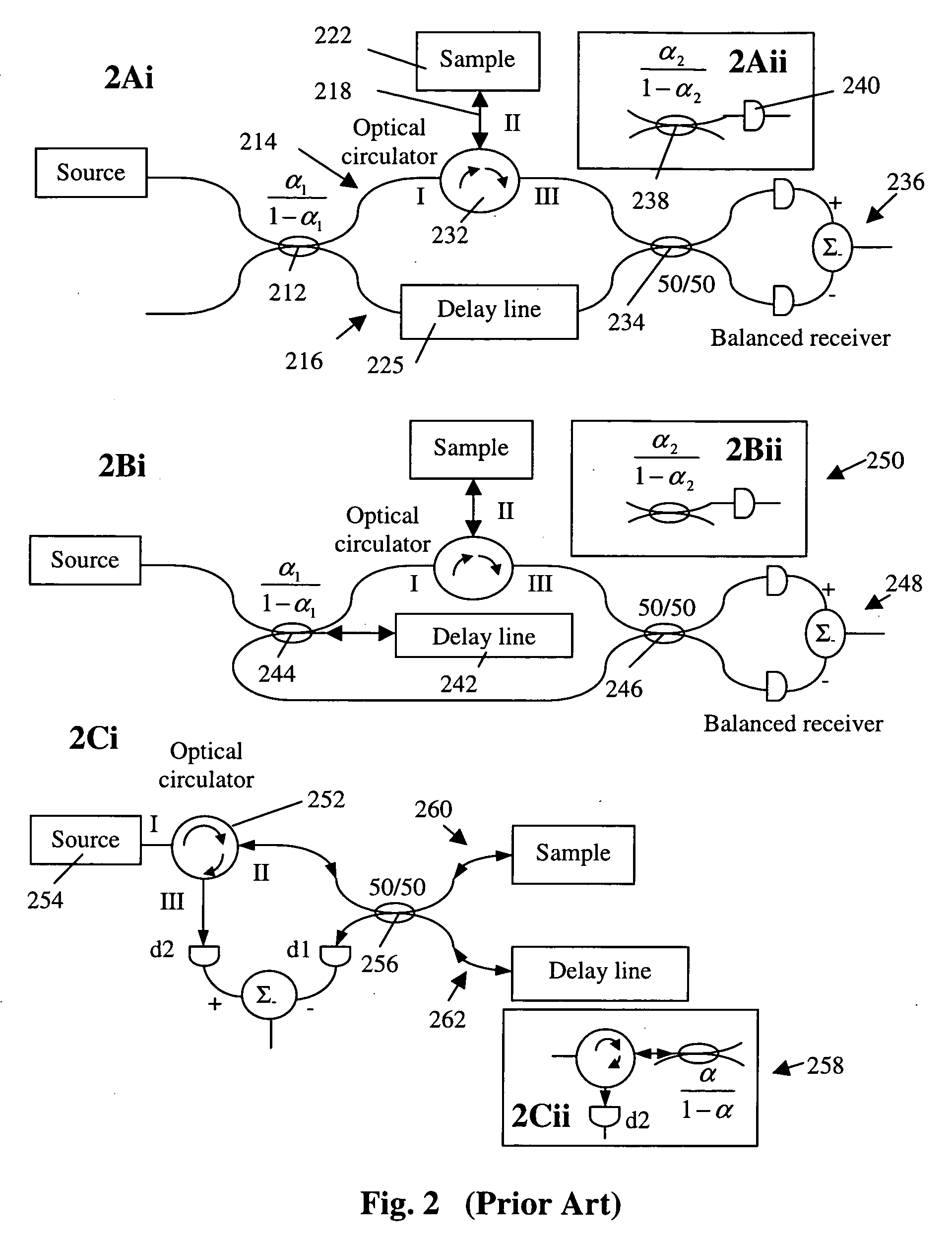
ActiveUS20050213103A1Reduce system costLow costReflectometers dealing with polarizationInterferometersBeam splitterDetector array
The present invention discloses simple and yet highly efficient configurations of optical coherence domain reflectometry systems. The combined use of a polarizing beam splitter with one or two polarization manipulator(s) that rotate the returned light wave polarization to an orthogonal direction, enables one to achieve high optical power delivery efficiency as well as fixed or predetermined output polarization state of the interfering light waves reaching a detector or detector array, which is especially beneficial for spectral domain optical coherence tomography. In addition, the system can be made insensitive to polarization fading resulting from the birefringence change in the sample and reference arms. Dispersion matching can also be easily achieved between the sample and the reference arm for high resolution longitudinal scanning.
Owner:CARL ZEISS MEDITEC INC
Cellular communications system featuring a central radio pool/traffic router
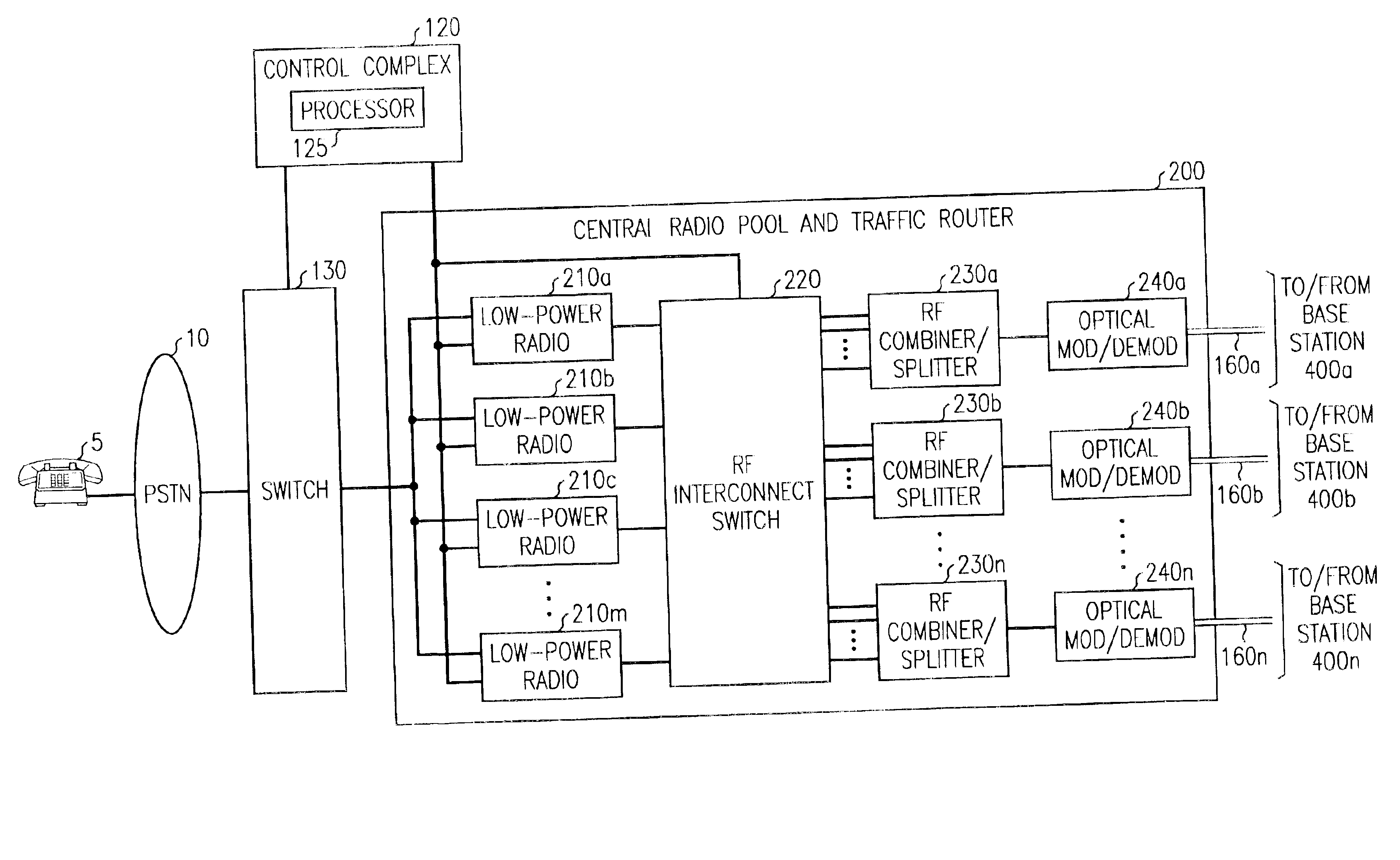
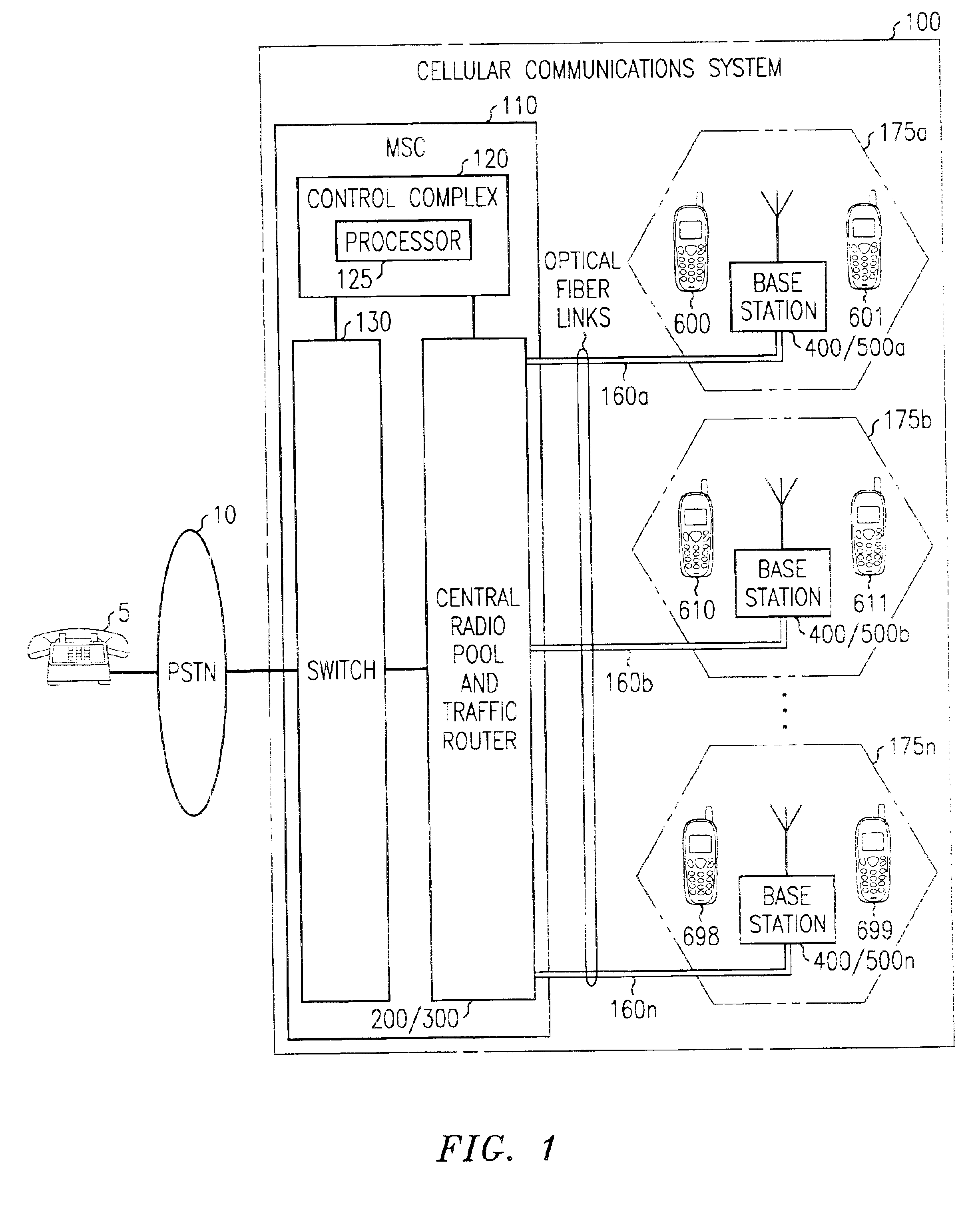
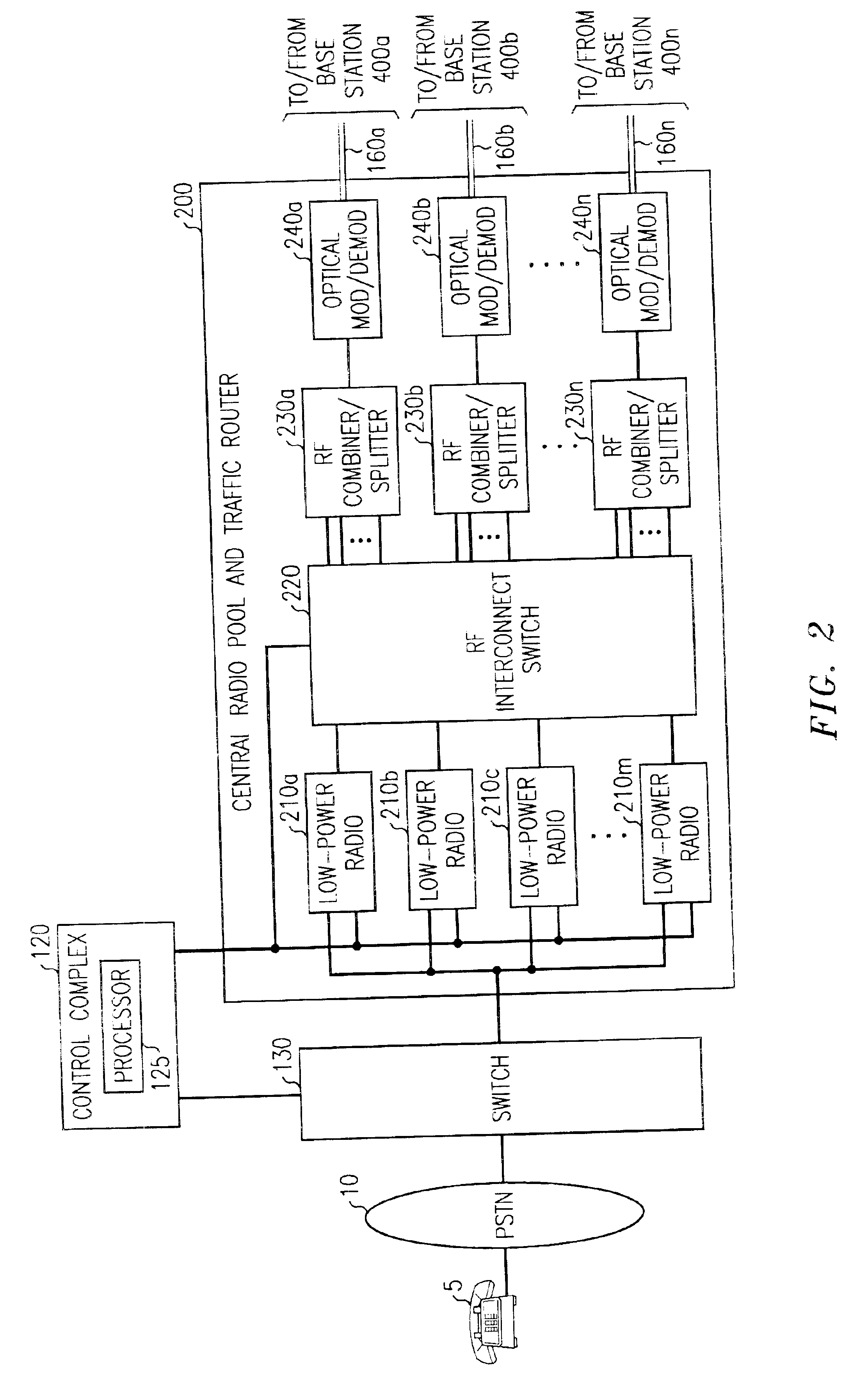
InactiveUS6865390B2Easy to useEasy maintenanceSubstation equipmentRadio/inductive link selection arrangementsFiberRadio equipment
The present invention provides a cellular communication system that includes a central radio pool / traffic router (CRP / TR) that sends control and traffic signals over fiber optic transmission links that connect the CRP / TR with base stations of the cellular communication system. The high bandwidth capacity of each fiber link allows a large band of radio frequencies representing many radio channels to pass between the CRP / TR and individual base stations. Radio resources can be shared by all base stations in the cellular communication system, dynamically, when and where needed, to meet access demands throughout the system. The CRP / TR includes low-powered digital and / or analog radios and also switching and modulation means used to convey signals between the radios and various base stations within the system.
Owner:LUCENT TECH INC
System and technique for retrieving depth information about a surface by projecting a composite image of modulated light patterns
InactiveUS7440590B1More detailed and large depth mappingLimited bandwidthProjectorsCathode-ray tube indicatorsInteraction interfaceTelecollaboration
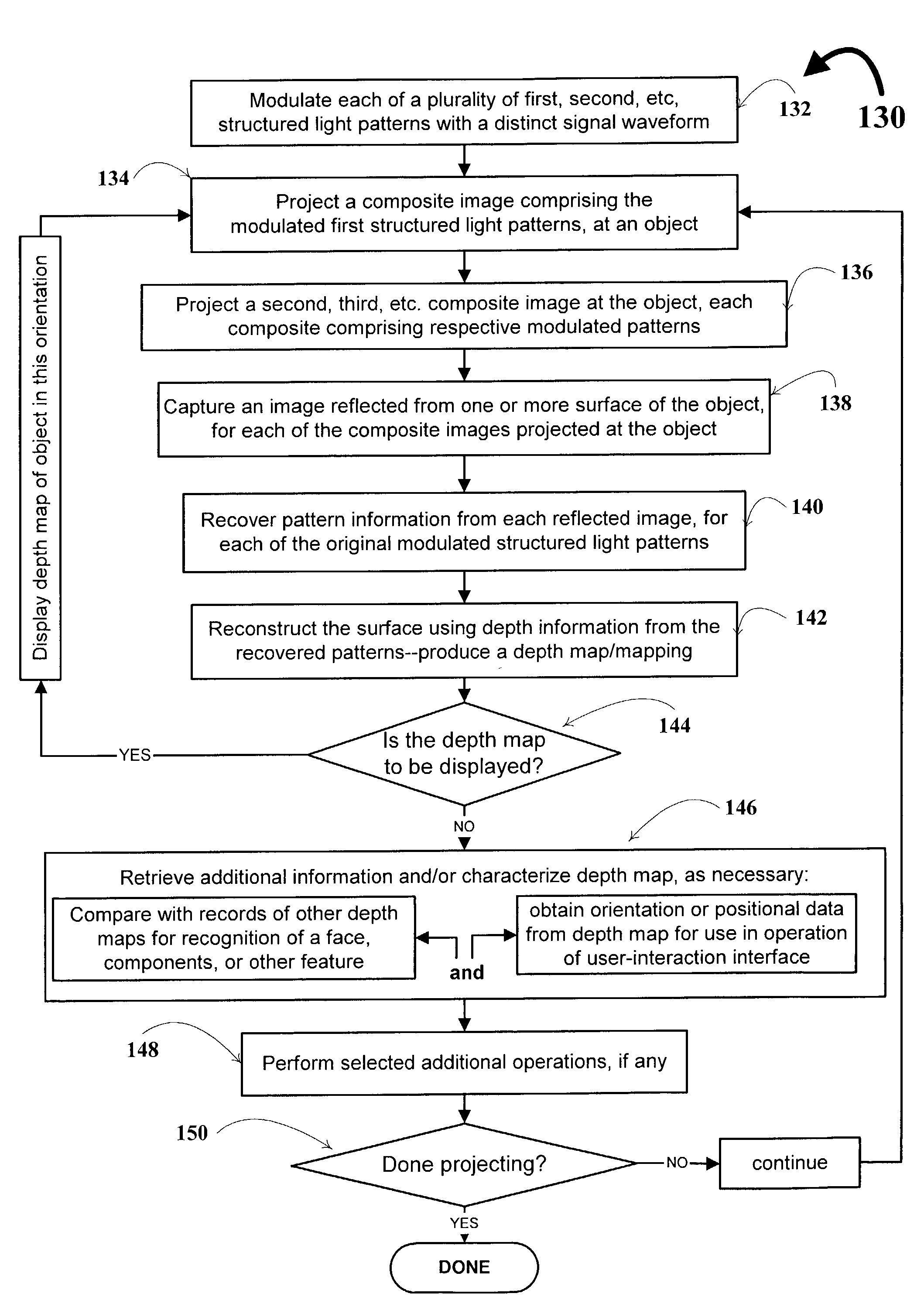
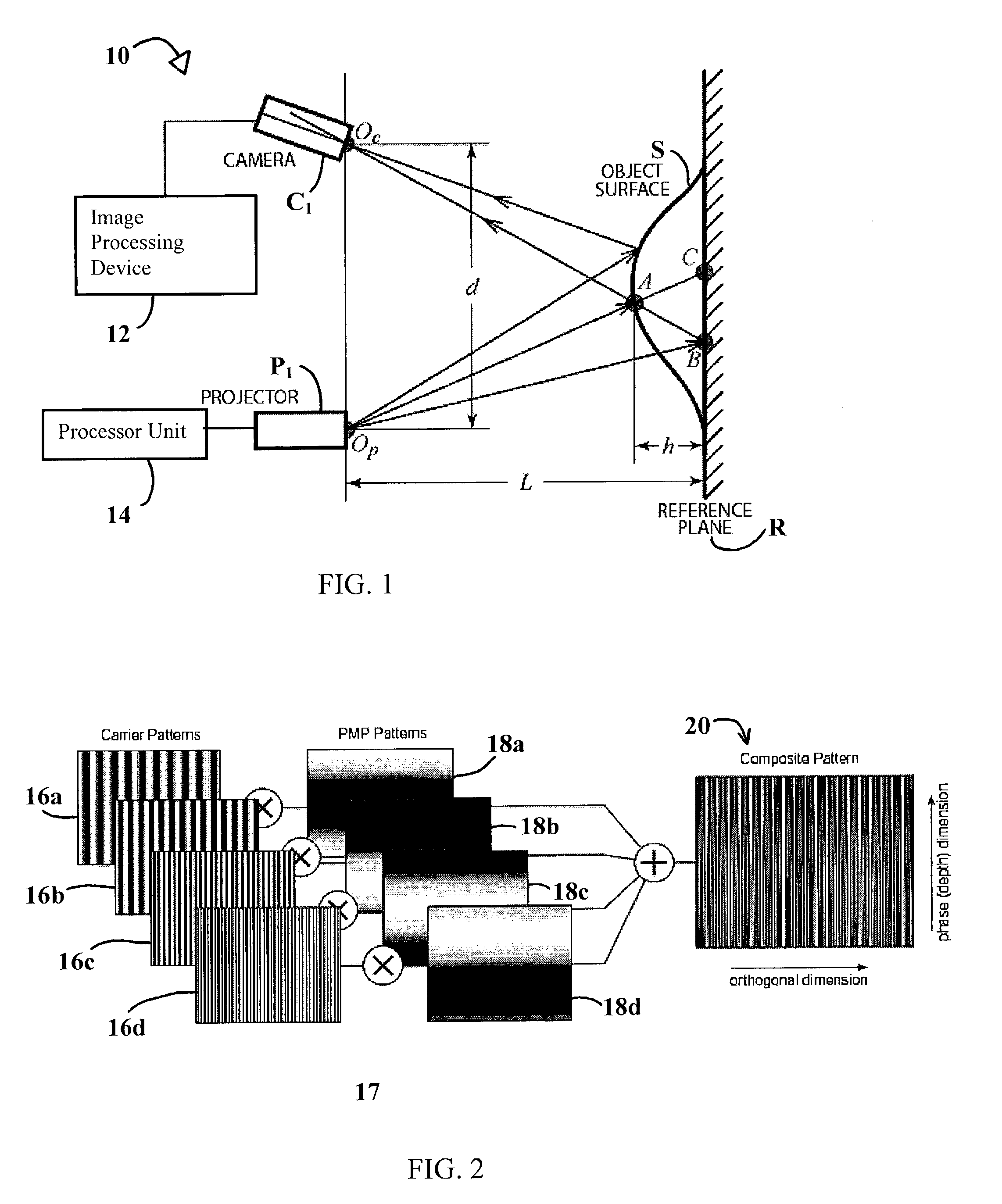
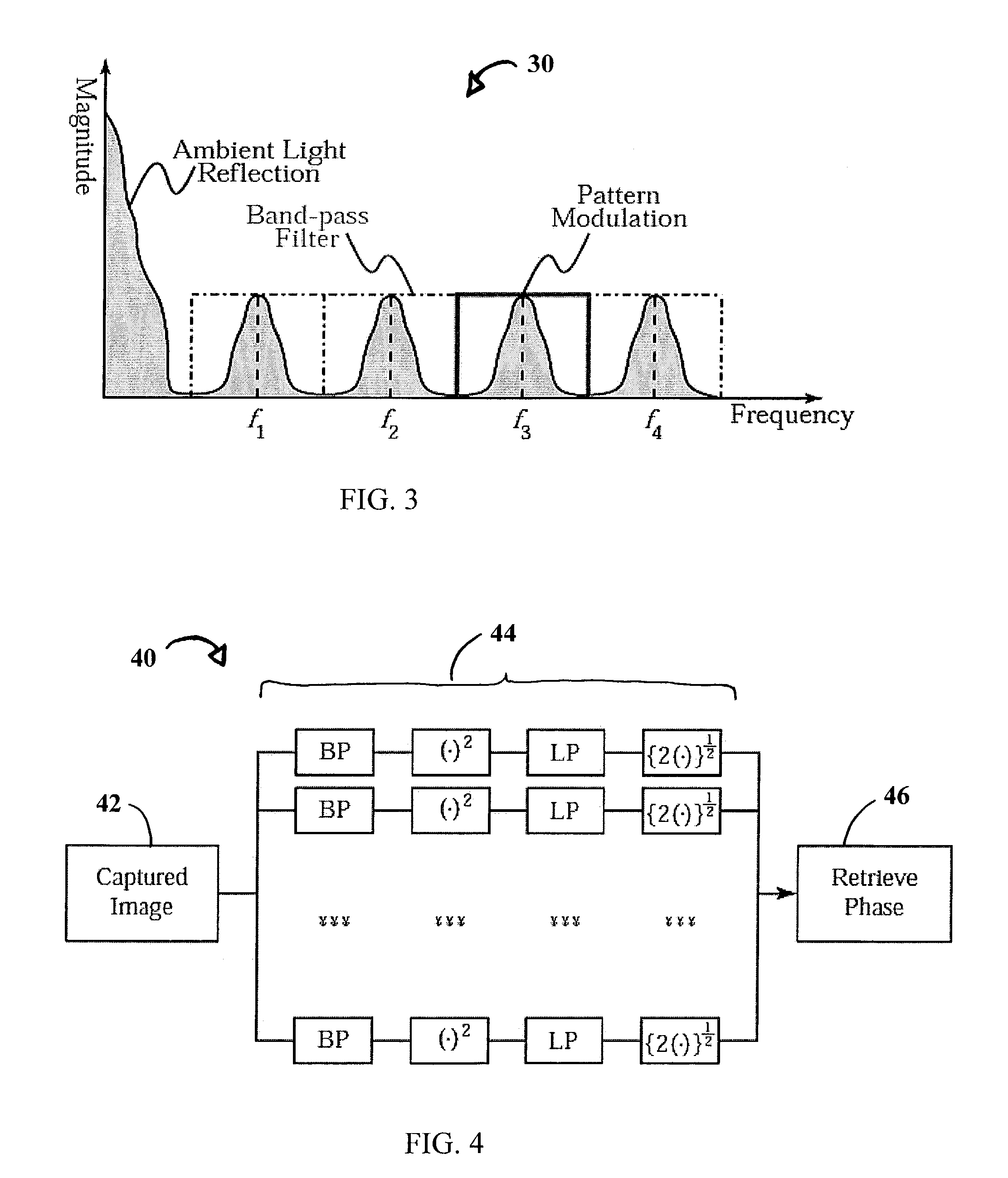
A technique, associated system and program code, for retrieving depth information about at least one surface of an object. Core features include: projecting a composite image comprising a plurality of modulated structured light patterns, at the object; capturing an image reflected from the surface; and recovering pattern information from the reflected image, for each of the modulated structured light patterns. Pattern information is preferably recovered for each modulated structured light pattern used to create the composite, by performing a demodulation of the reflected image. Reconstruction of the surface can be accomplished by using depth information from the recovered patterns to produce a depth map / mapping thereof. Each signal waveform used for the modulation of a respective structured light pattern, is distinct from each of the other signal waveforms used for the modulation of other structured light patterns of a composite image; these signal waveforms may be selected from suitable types in any combination of distinct signal waveforms, provided the waveforms used are uncorrelated with respect to each other. The depth map / mapping to be utilized in a host of applications, for example: displaying a 3-D view of the object; virtual reality user-interaction interface with a computerized device; face—or other animal feature or inanimate object—recognition and comparison techniques for security or identification purposes; and 3-D video teleconferencing / telecollaboration.
Owner:UNIV OF KENTUCKY RES FOUND
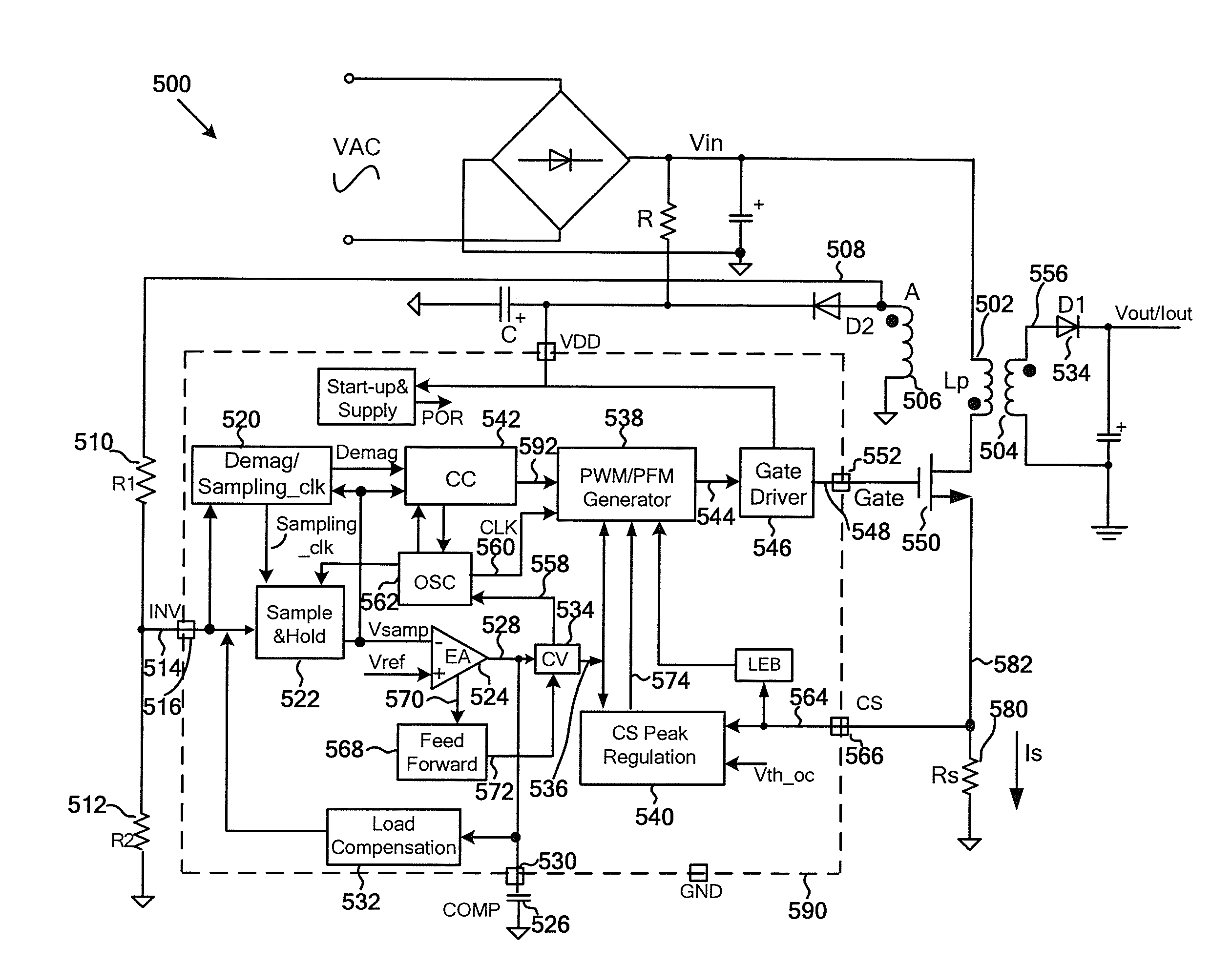
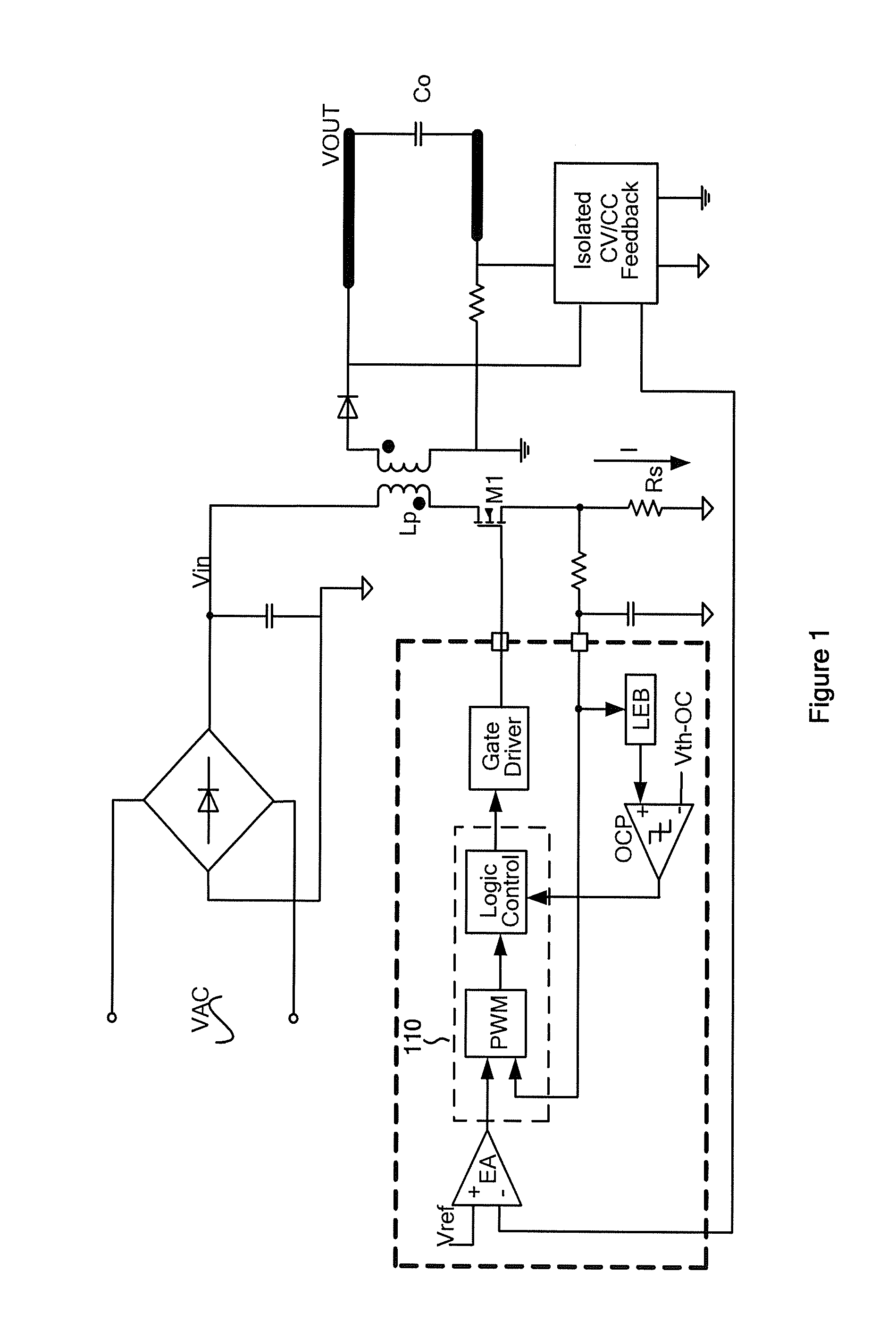
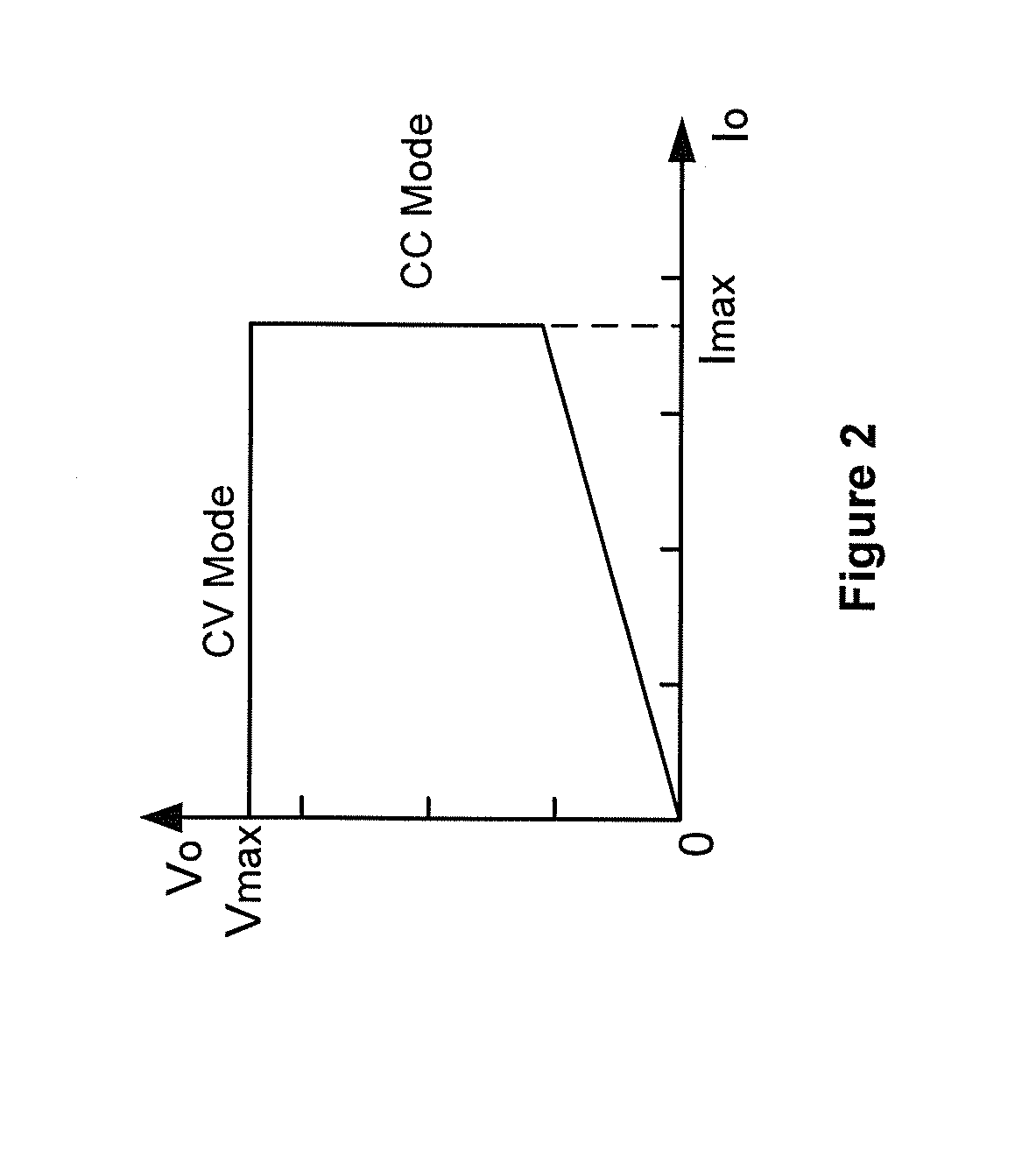
Systems and methods for constant voltage mode and constant current mode in flyback power converters with primary-side sensing and regulation
ActiveUS20120075891A1Simple circuit designShorten the counting processElectroluminescent light sourcesDc-dc conversionSignal generatorConductor Coil
System and method for regulating a power converter. The system includes a first signal generator configured to receive a first sensed signal and generate an output signal associated with demagnetization. The first sensed signal is related to a first winding coupled to a secondary winding for a power converter, and the secondary winding is associated with at least an output current for the power converter. Additionally, the system includes a ramping signal generator configured to receive the output signal and generate a ramping signal, and a first comparator configured to receive the ramping signal and a first threshold signal and generate a first comparison signal based on at least information associated with the ramping signal and the first threshold signal. Moreover, the system includes a second comparator configured to receive a second sensed signal and a second threshold signal and generate a second comparison signal.
Owner:ON BRIGHT ELECTRONICS SHANGHAI
Portable telephone in a security network
InactiveUS7511614B2Improve reliabilityLow costSafety arrangmentsComputer controlCard readerProgram code
A security network for use in a building with an opening to be monitored for possible intrusion. The network includes an intrusion sensor monitoring the opening; an RFID transponder associated with the sensor; an RFID reader in wireless communication with the transponder; and a portable telephone handset having first keys activating conventional telephone capability and second keys activating interaction with the other security network components. The handset wirelessly communicates with the reader. The reader may take the form of a security cradle for the handset. Alternatively, the reader may take the form of a telephone console. The console has keys enabling a user to dial remote telephone numbers; circuitry adapted to receive wireless communications from the transponder; circuitry in wireless communication with the handset; circuitry in communication with an external network; and a processor executing program code enabling the handset to communicate with the external network via the telephone console.
Owner:ADT US HLDG INC
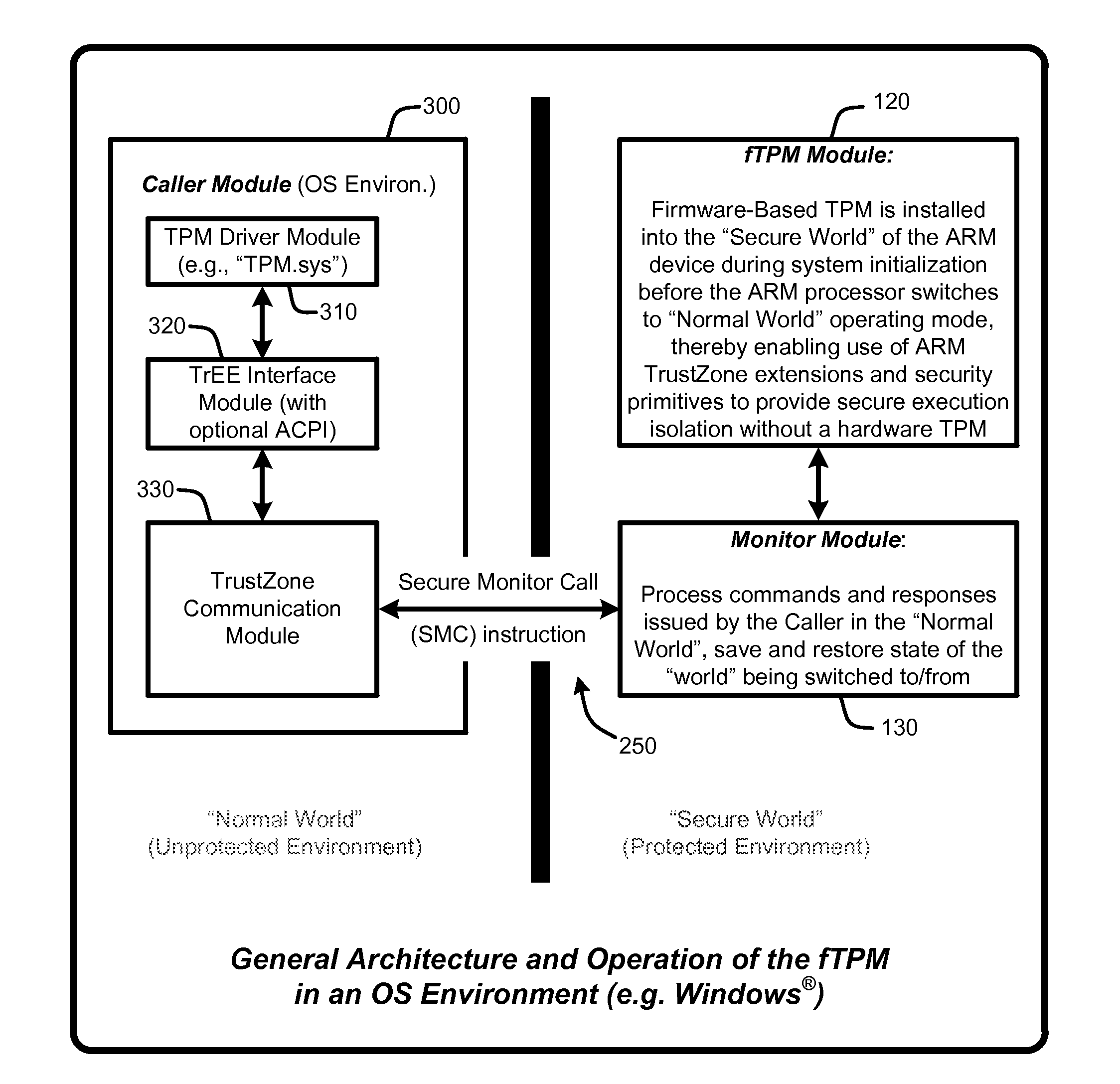
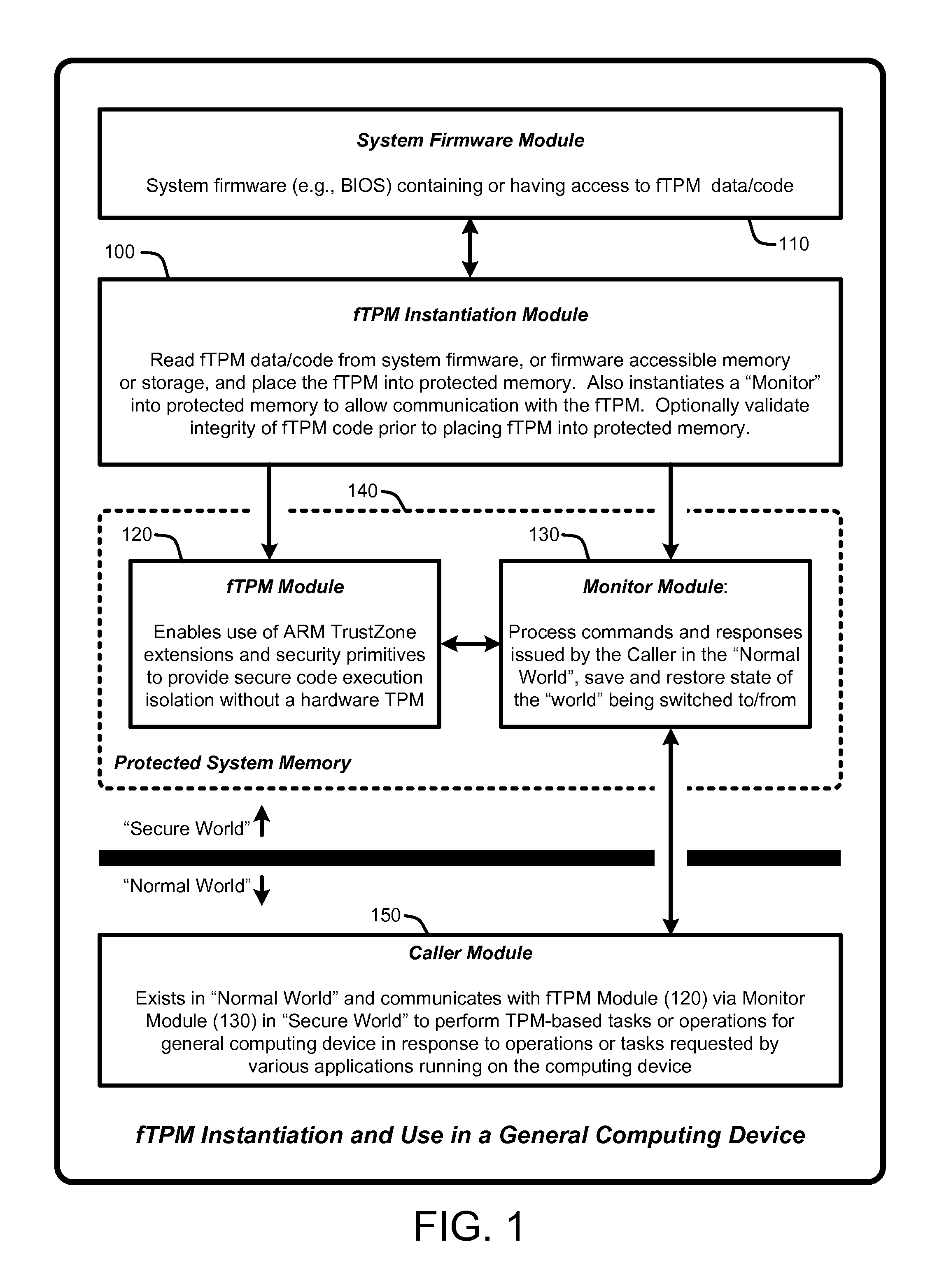
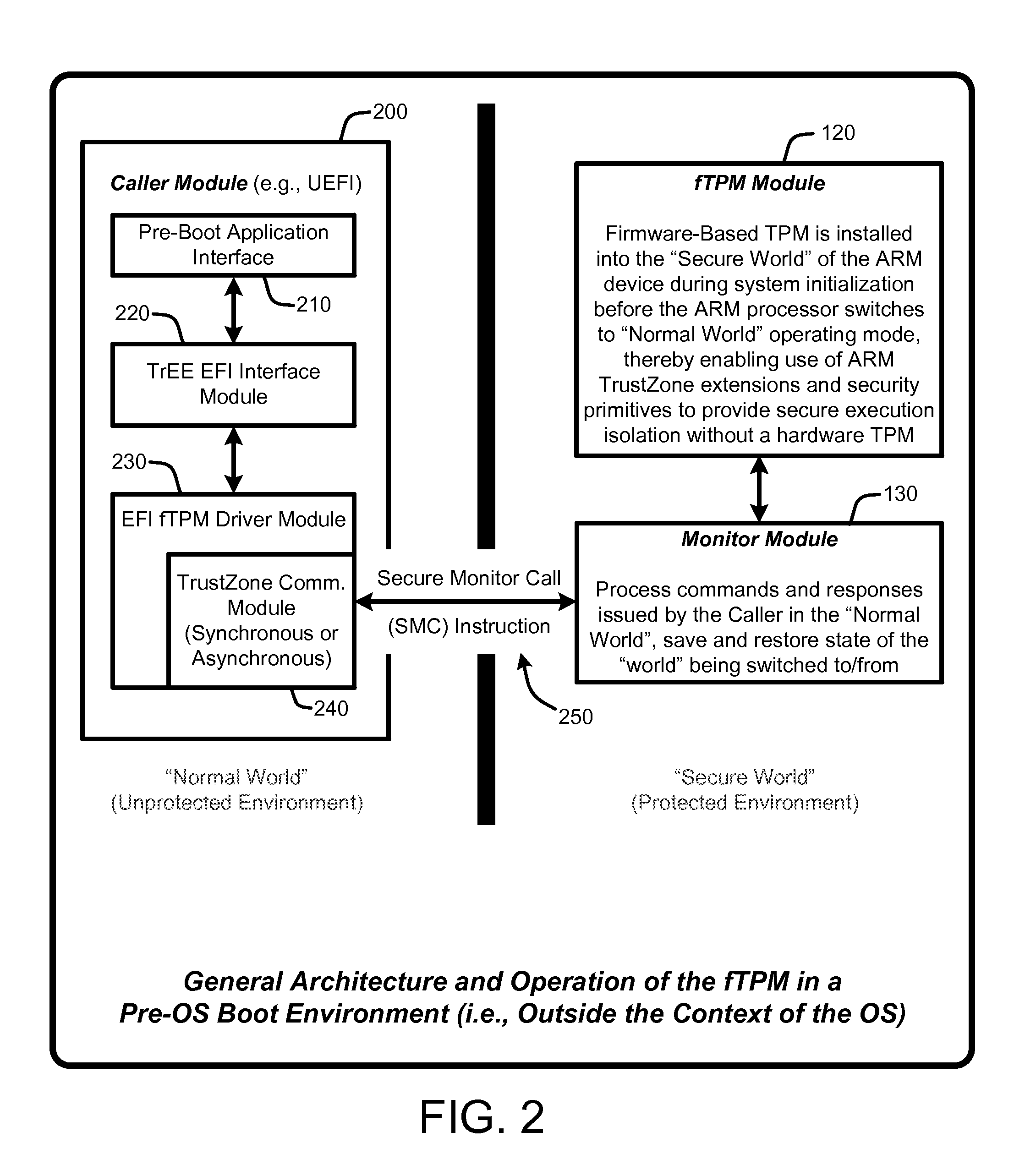
Firmware-based trusted platform module for arm processor architectures and trustzone security extensions
ActiveUS20130031374A1Increase costReduce system costDigital data processing detailsUnauthorized memory use protectionTrusted Platform ModuleSafe handling
A “Firmware-Based TPM” or “fTPM” ensures that secure code execution is isolated to prevent a wide variety of potential security breaches. Unlike a conventional hardware based Trusted Platform Module (TPM), isolation is achieved without the use of dedicated security processor hardware or silicon. In general, the fTPM is first instantiated in a pre-OS boot environment by reading the fTPM from system firmware or firmware accessible memory or storage and placed into read-only protected memory of the device. Once instantiated, the fTPM enables execution isolation for ensuring secure code execution. More specifically, the fTPM is placed into protected read-only memory to enable the device to use hardware such as the ARM® architecture's TrustZone™ extensions and security primitives (or similar processor architectures), and thus the devices based on such architectures, to provide secure execution isolation within a “firmware-based TPM” without requiring hardware modifications to existing devices.
Owner:MICROSOFT TECH LICENSING LLC
Infusion device with optical sensor
InactiveUS6110153APrecise positioningReduce system costInvestigating moving fluids/granular solidsSurgeryTotal internal reflectionEngineering
An infusion device with a disposable administration set which is inexpensive to manufacture. In the preferred embodiment of the present invention the disposable administration set has a plurality of elongated cam followers connected to a plate assembly, wherein the cam followers are displace in a predetermined sequence and forced against a delivery tube by cam means driven by rotary drive means. The device also includes an optical occlusion sensor which is synchronized to operate in phase with the movement of the cam followers to measure pressure within the delivery tube at one pump phase, thereby sensing downstream occlusions, and to measure vacuum within the delivery tube at a second pump phase, thereby sensing upstream occlusions. The occlusion sensor is optical, and measures the degree of total internal reflection at the interface of the tube and the plate assembly, occlusion in the tubing.
Owner:CAREFUSION 303 INC
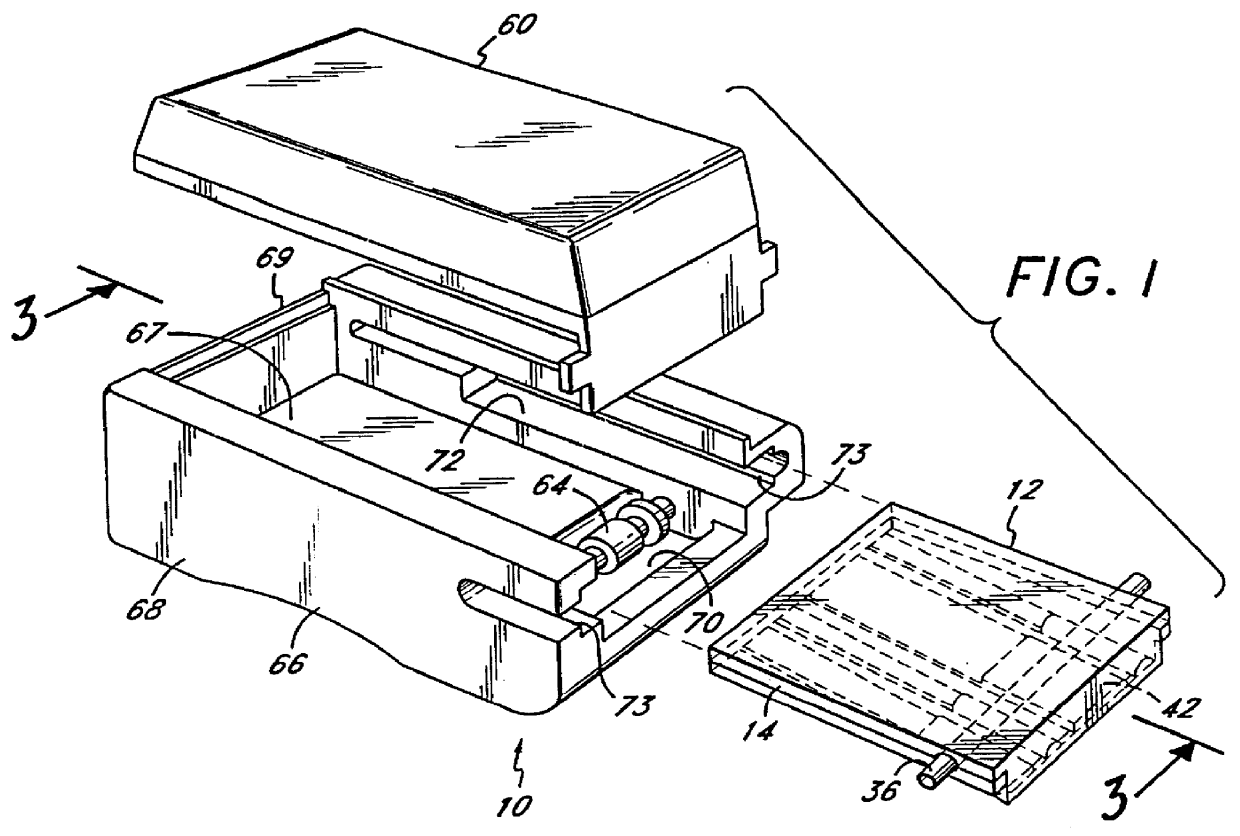
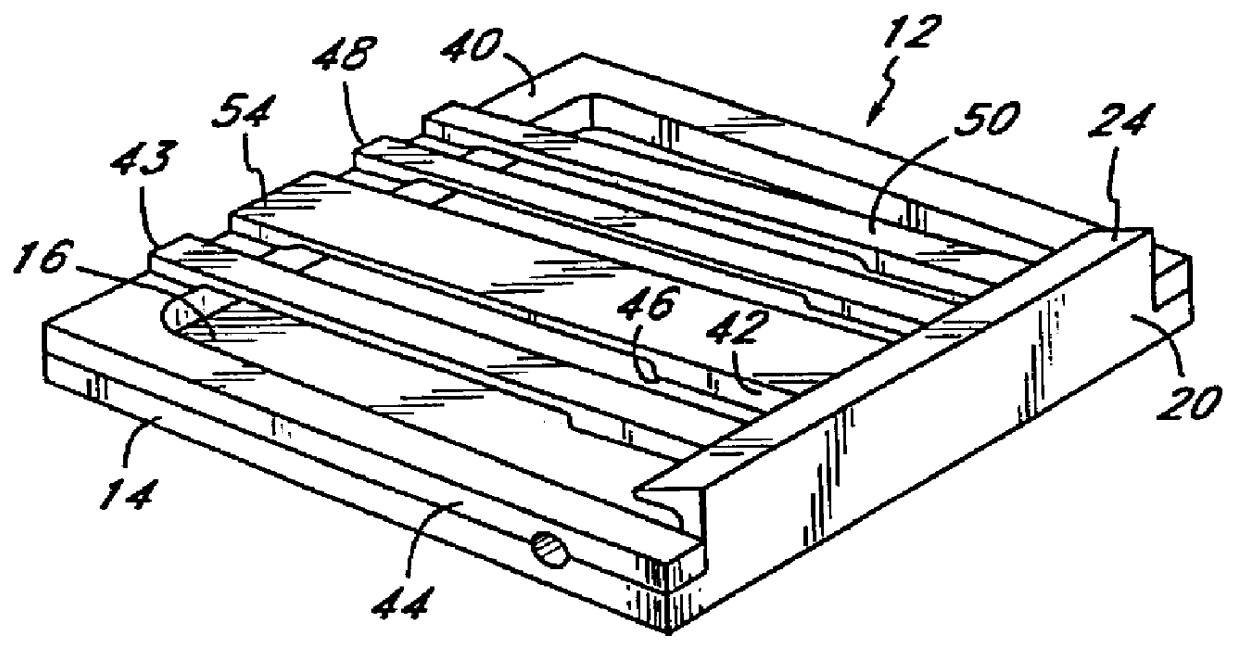
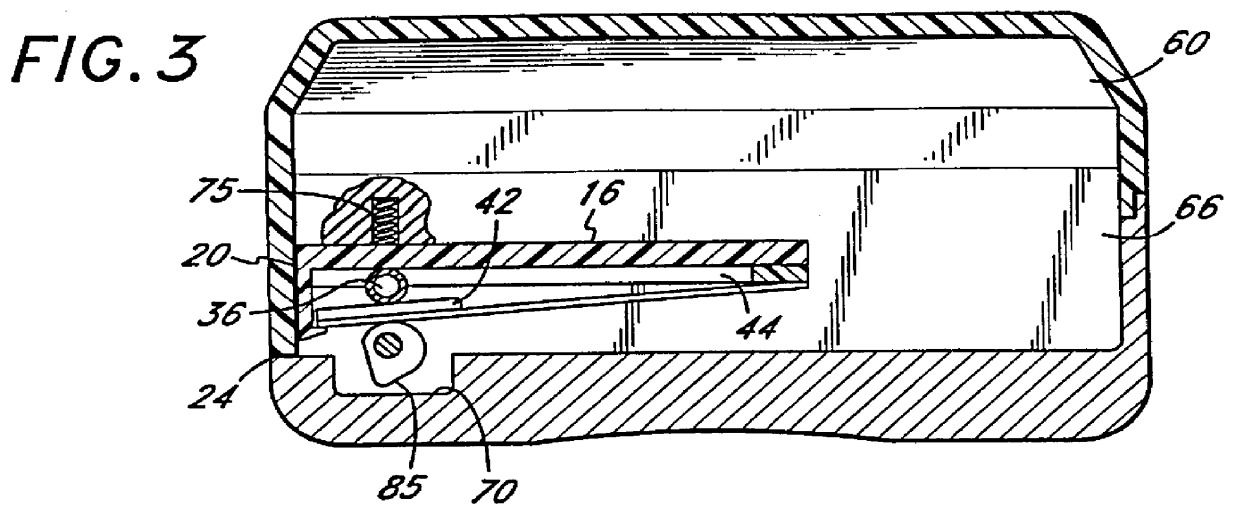
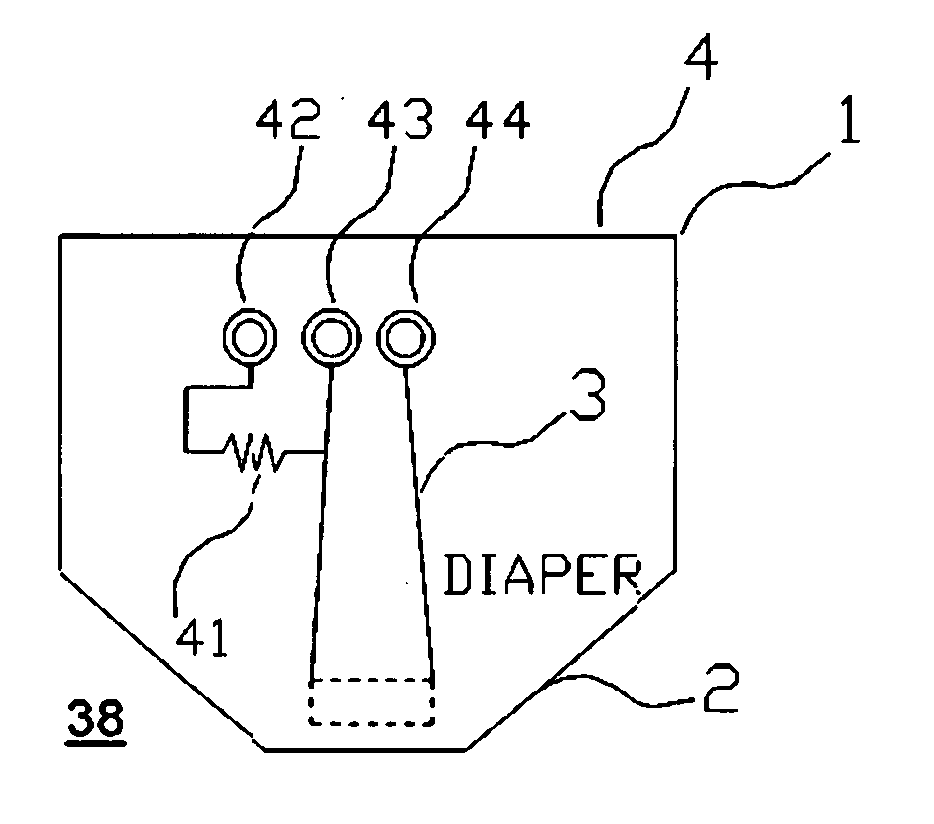
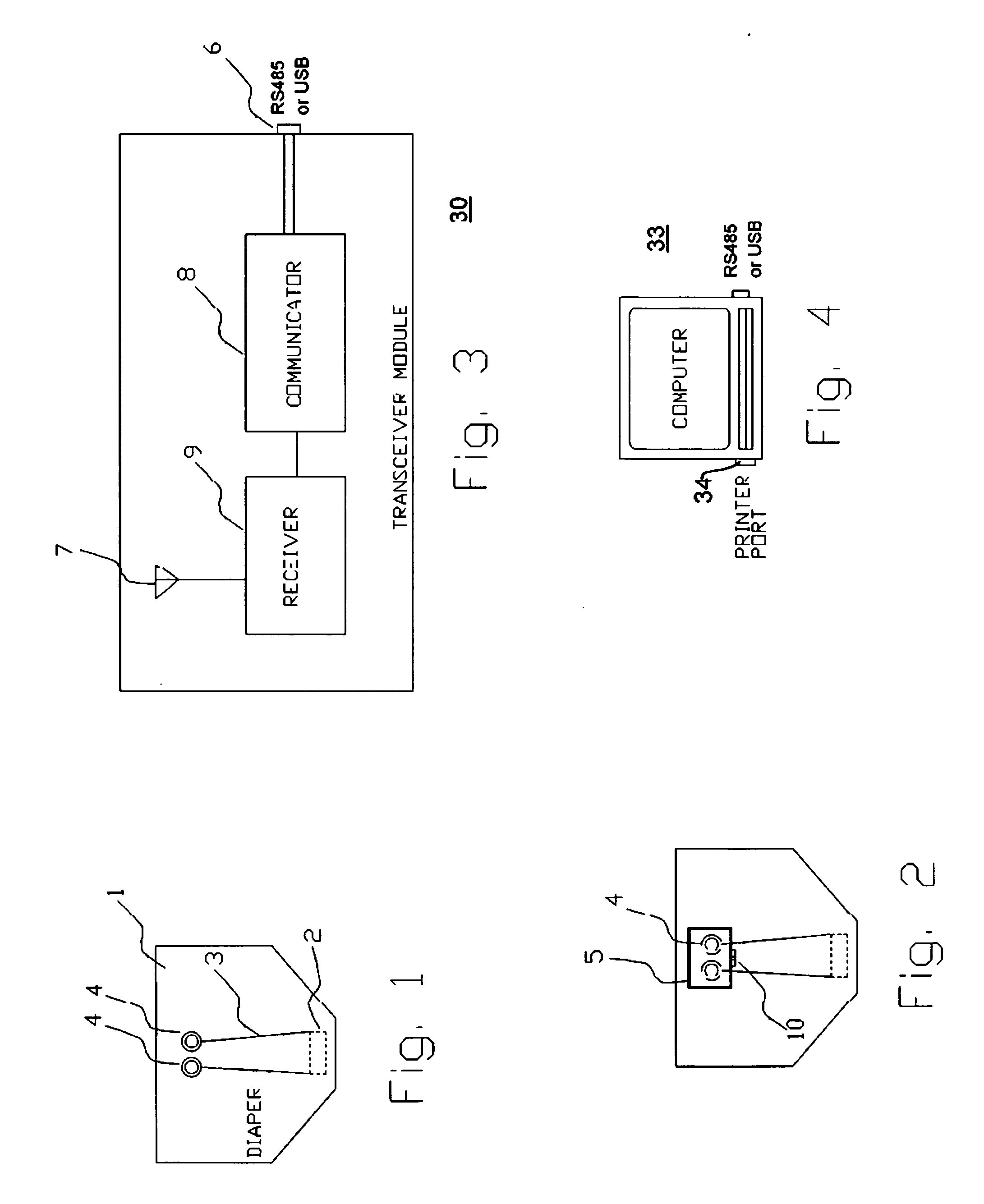
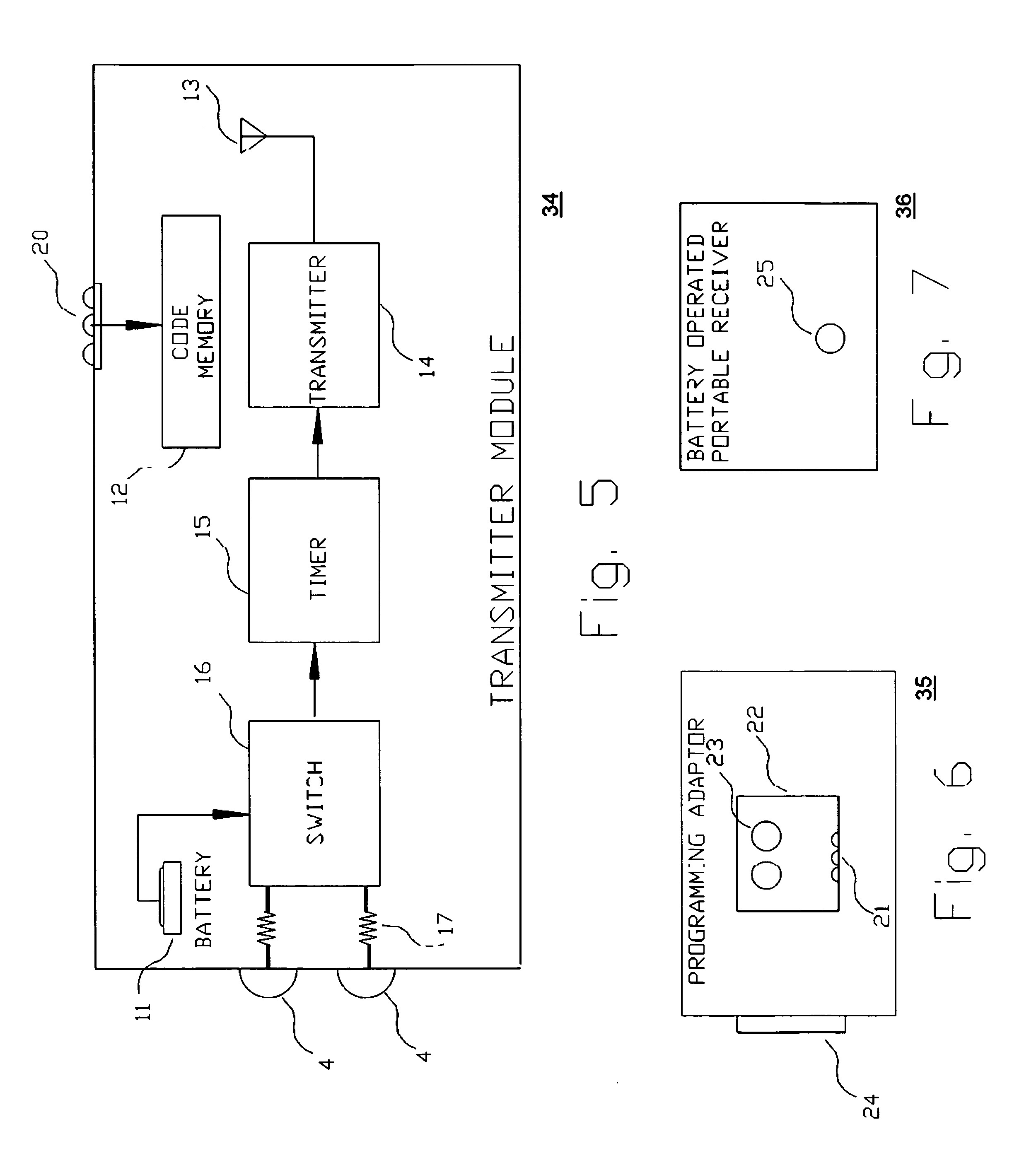
Diaper wetness annunciator system
InactiveUS20050156744A1Easily be washed and disinfectedReduce system costAbsorbent padsAlarmsWireless transmissionMonitoring system
A monitoring system identifies a wet diaper by embedding an inexpensive disposable passive humidity sensor, which may be formed of conductive ink, and attaching to the outside of the diaper a detachable transmitting module that is triggered into transmission by the humidity sensor. The transmitting module is sealed and transferable from the wet diaper to a dry one. Uniquely coded data is wirelessly transmitted to a remote receiver. The receiver may be a battery powered portable unit carried by the baby's guardian. In a day care center a multiple function receiver can identify any of several diapers. In hospitals, several strategically located receivers are each capable of recognizing and reporting any wet diaper within its range to a central computer. Low cost and long range are achieved by using a detachable and transportable active transmitter that is not discarded with the wet diaper and therefore can be re-used. False transmissions are prevented by a confirmatory resistance.
Owner:PIRES HAROLD GEORGE
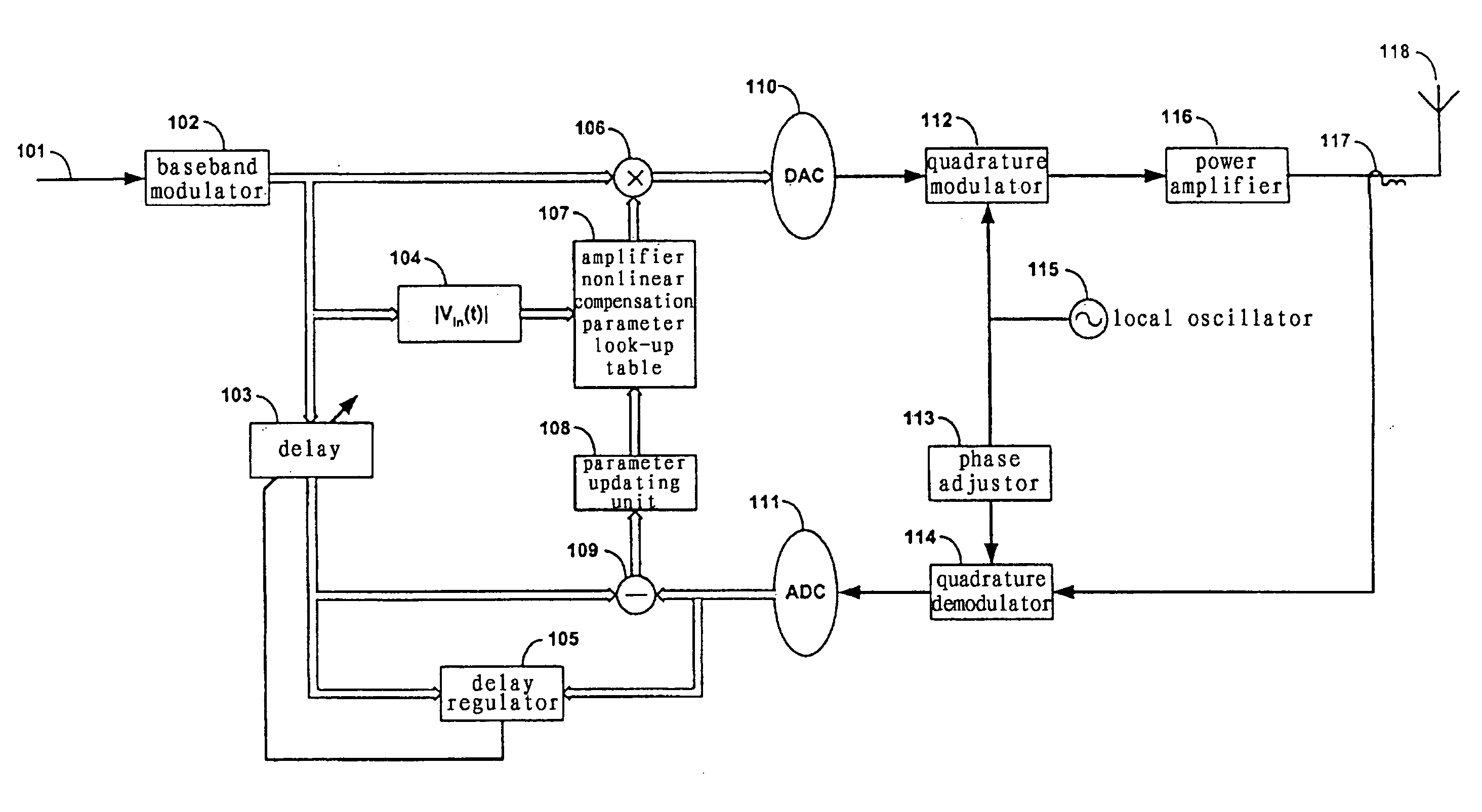
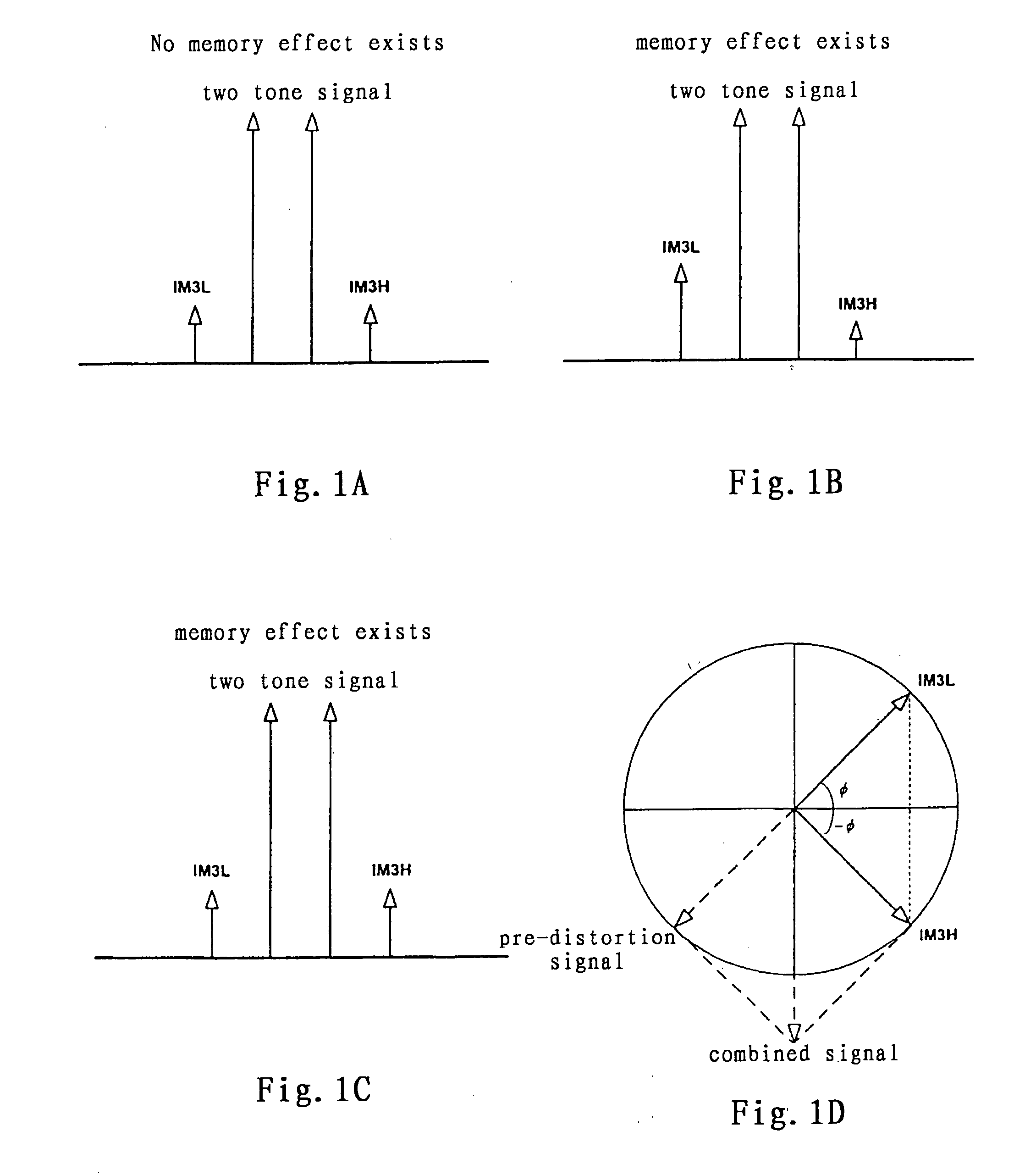
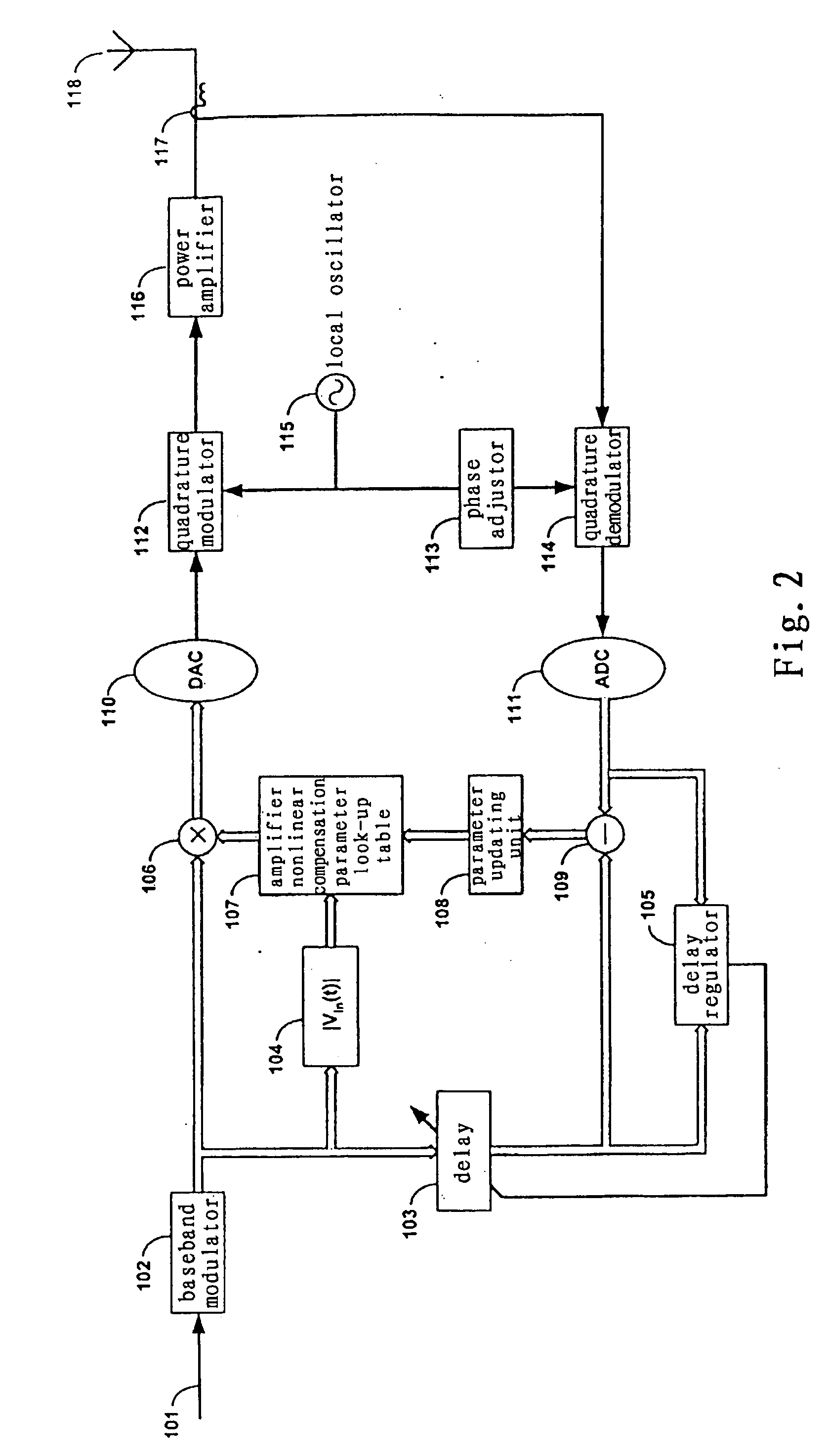
Method and system for broadband predistortion linearization
InactiveUS20060240786A1Improve linearization performanceExtends linearization bandwidthAmplifier modifications to reduce non-linear distortionAmplifiers with memory effect compensationTime domainRadio frequency
The invention relates to a method and system for wideband digital pre-distortion linearization, which is used to overcome the influence of memory effect in radio frequency power amplifier, to expand digital pre-distortion linearization bandwidth, and to improve digital pre-distortion linearization performance. The method and system can get an in-band pre-distortion signal and an out-of-band pre-distortion signal according to the characteristic parameter of the amplifier; the in-band pre-distortion signal is up-converted and the up-converted signal is added to the out-of-band pre-distortion signal, which is not up-converted, then the combined signal is inputted to the power amplifier as an input signal; a part of the output signal from the power amplifier, serving as a feedback signal, can be compared with the original input signal, and the characteristic parameter of the amplifier for generating the in-band pre-distortion signal and the out-of-band pre-distortion signal is adaptively regulated according to the comparison result, so that the waveform of time domain or the frequency domain of the feedback signal can be close to that of the original input signal as much as possible.
Owner:ZTE CORP
Communications architecture for a security network
InactiveUS7084756B2Improve reliabilityLow costMemory record carrier reading problemsTelephonic communicationTransmitted powerSI base unit
A communications architecture for a security network using low power and high power wireless communications. The low power and high power wireless communications will typically be operating in different frequency bands and at different transmit power levels. The security network contains base units and transponders. Base units may be in the form of cordless phone handsets or cordless phone base stations. Transmissions from a transponder may be received at more than one base unit. A base unit may forward communications from a transponder to another base unit. Transponder communications may contain identifying information and may further encrypt information sent in the communications. Base units may contain data used in determining whether to route communications to another base unit.
Owner:LIFESHIELD LLC
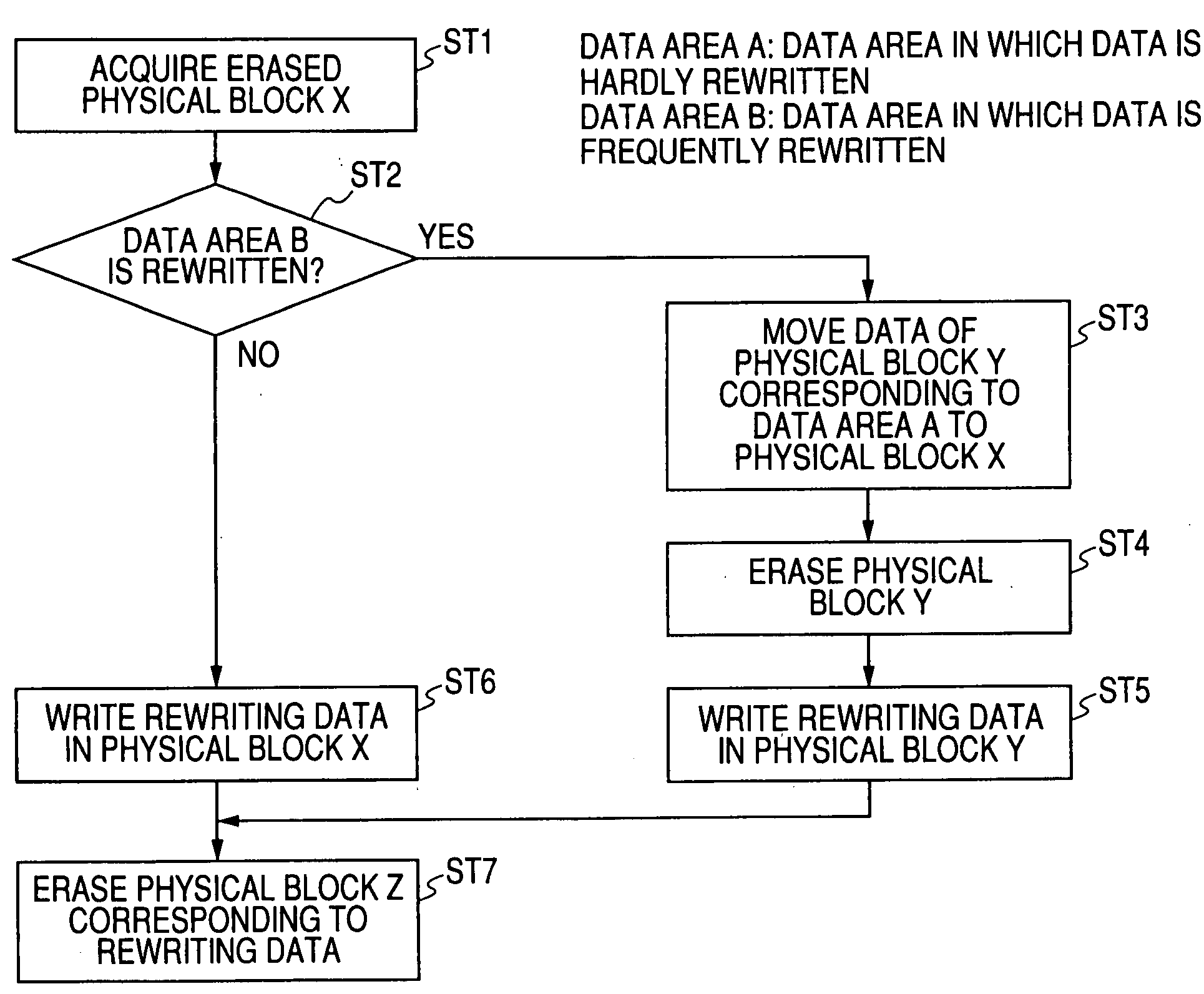
Memory system
ActiveUS20070103992A1Extend effective lifeEasy to controlMemory architecture accessing/allocationRead-only memoriesLogical block addressingSemiconductor storage devices
A memory system including a nonvolatile semiconductor storage device includes: a nonvolatile memory unit that includes a first data area in which data is frequently rewritten and a second data area in which data is hardly rewritten; and a control unit. The control unit sequentially selects logical block addresses in the second data area in which data is hardly rewritten and updates physical block addresses at new rewriting destinations in the first data area in which data is frequently rewritten to physical block addresses corresponding to the logical block addresses selected.
Owner:SONY CORP
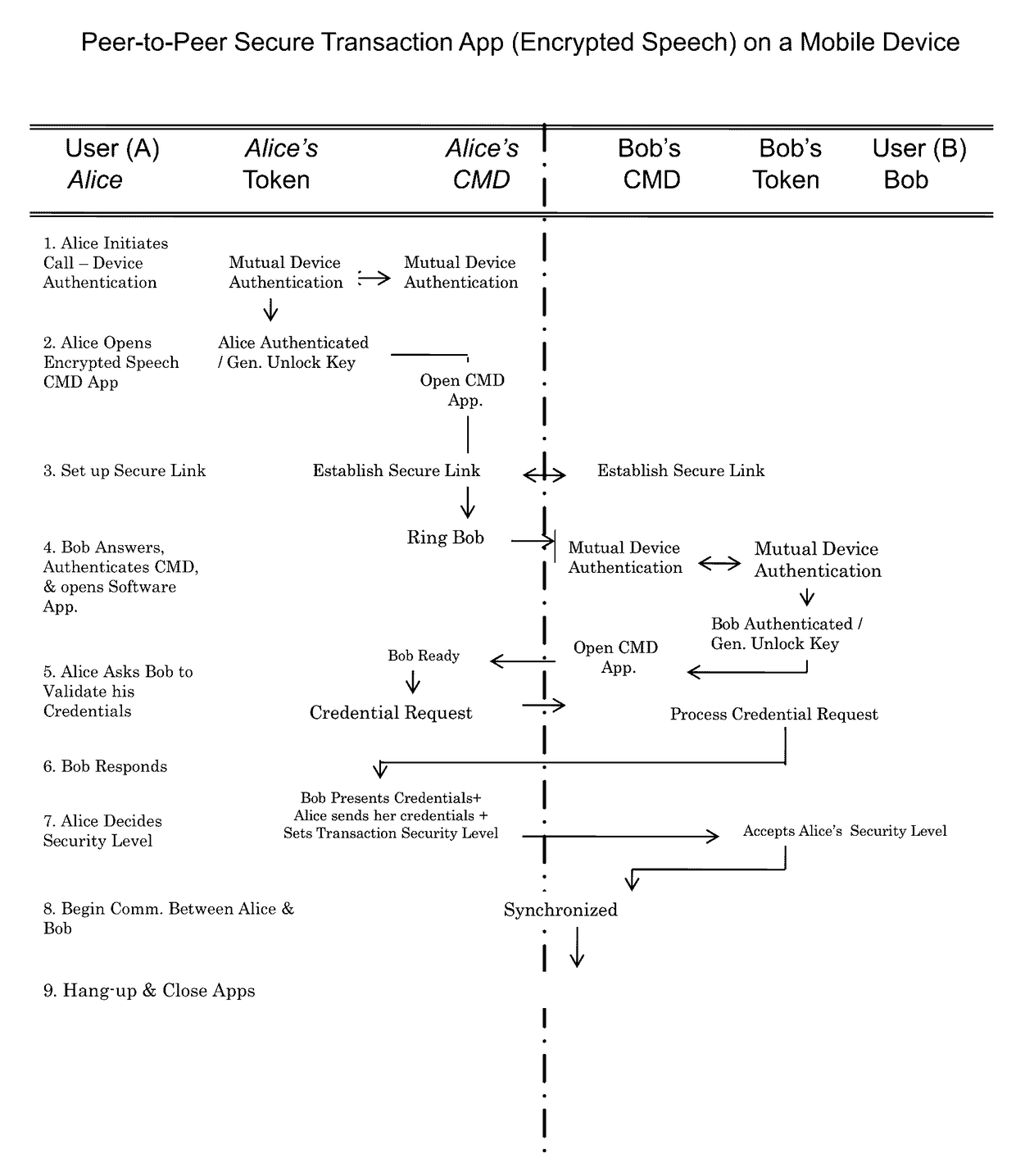
Method and system for secure peer-to-peer mobile communications
ActiveUS9674705B2Big advantageSecure and scalableUser identity/authority verificationNear-field for read/write/interrrogation/identification systemsComputer hardwareCryptosystem
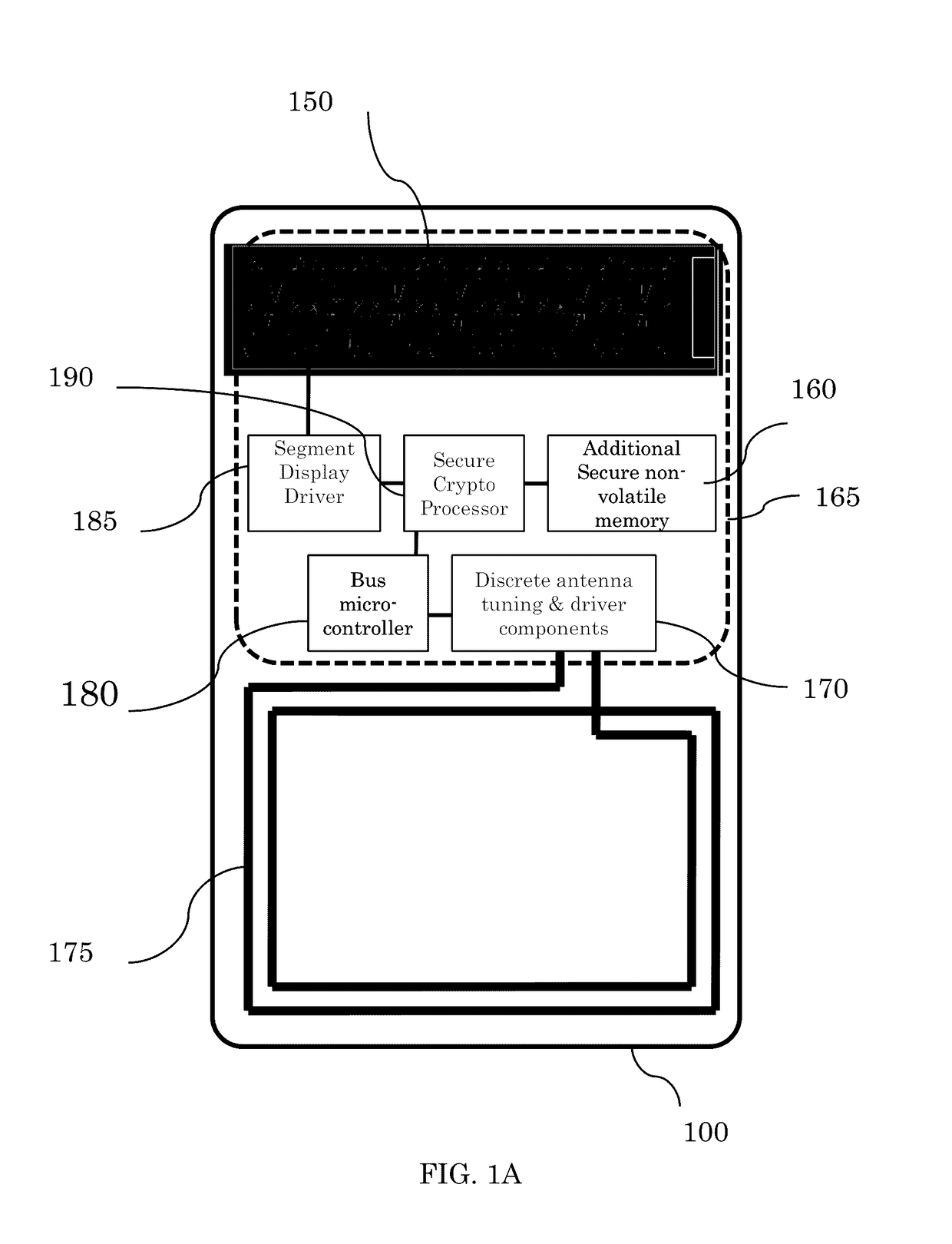
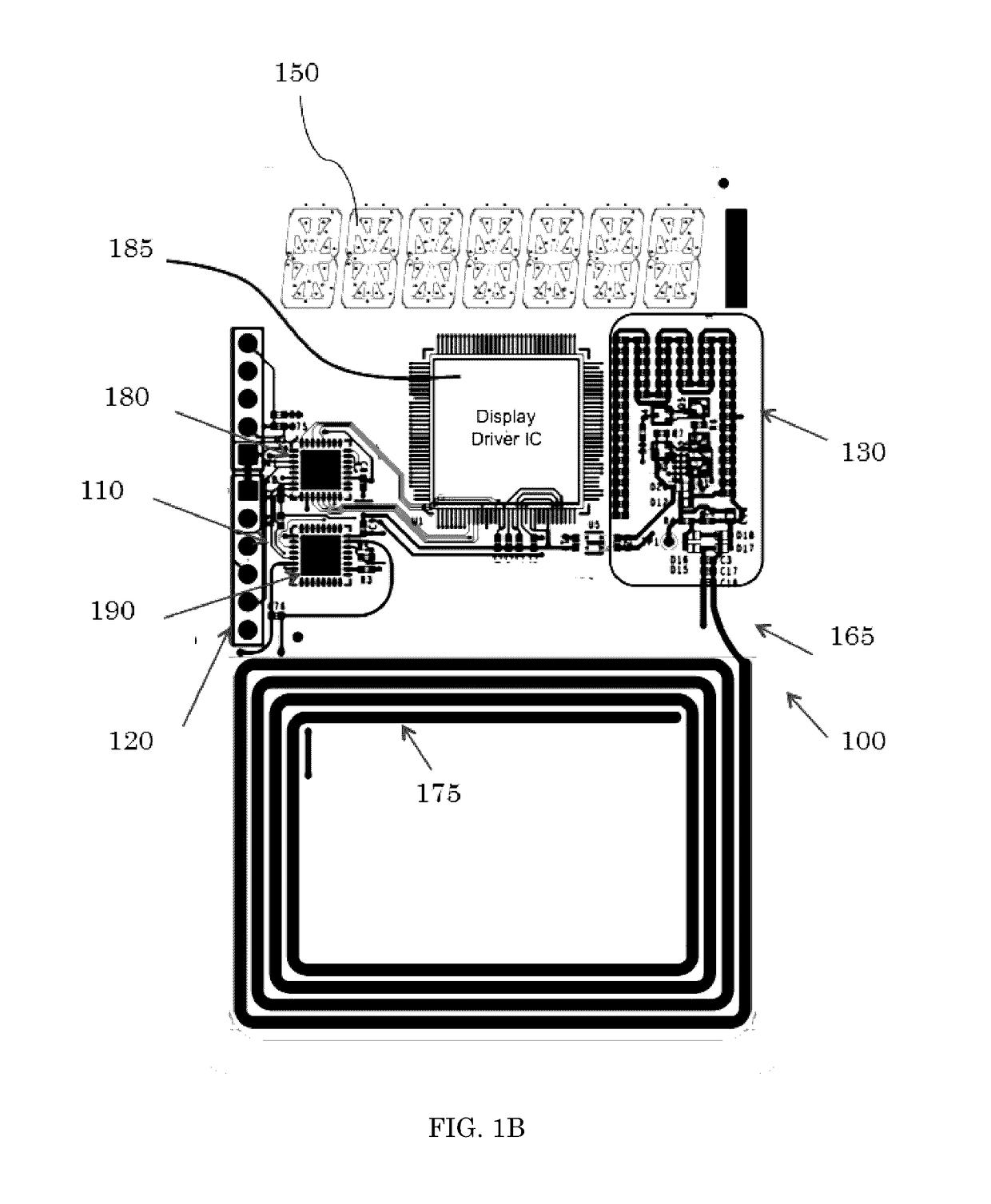
A system and method for secure peer-to-peer mobile communications using cryptographic mobile unlock tokens (“CK tokens”) in conjunction with mobile devices. Each CK token integrates an entire cryptosystem. Executing these cryptographic based functions entirely in the token have significant operational advantages over the typically memory-only tokens. A more secure, scalable, and lower overall system cost are just a few advantages of the CK token over executing these functions within the smartphone. Of the many uses discussed for the CK token, mobile phone enabling, stored value and medical applications, most have centered on the use of the card in conjunction with a smartphone as the touch point in the transaction.
Owner:TOCREO LABS L L C
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com