Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
9011 results about "Card reader" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
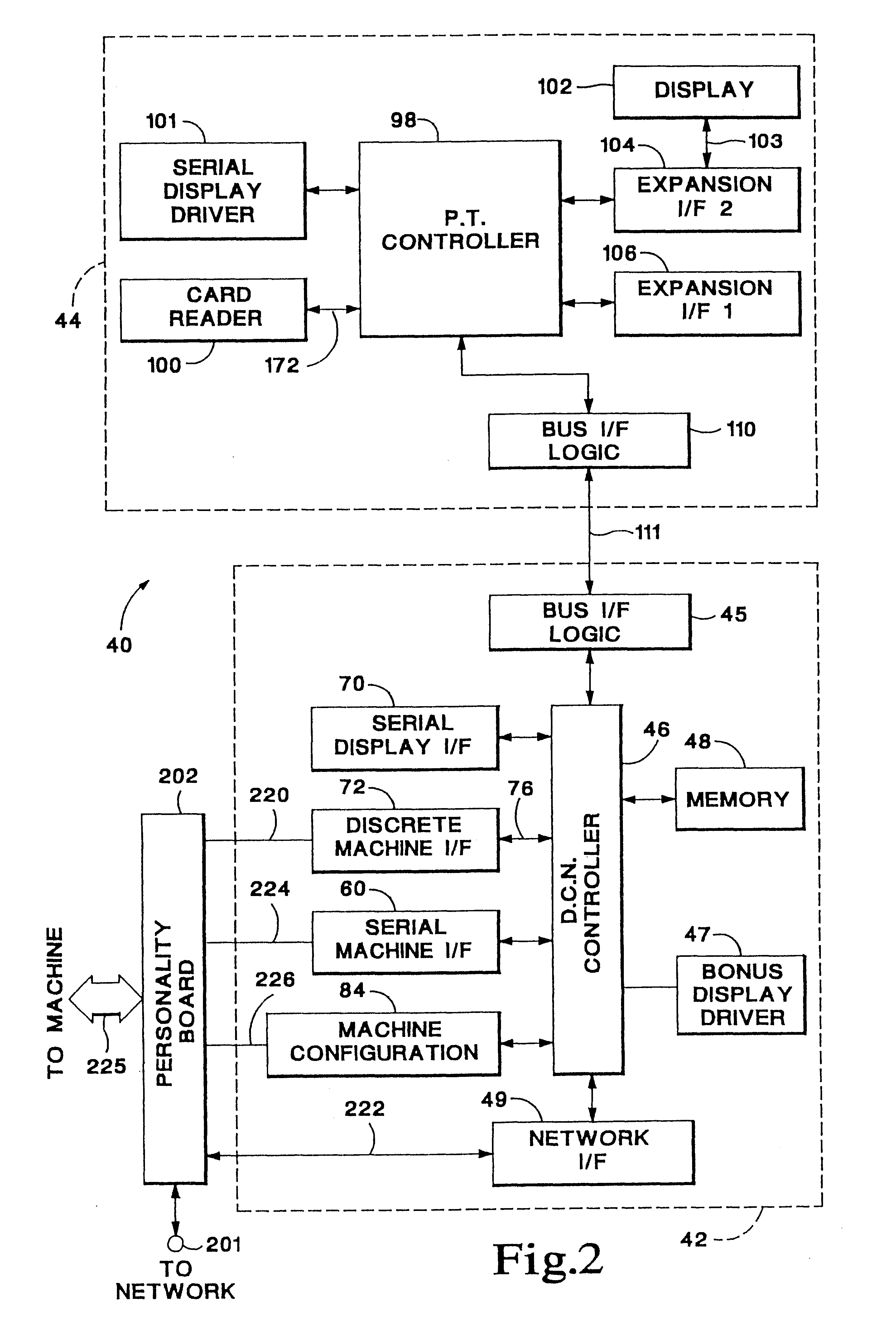
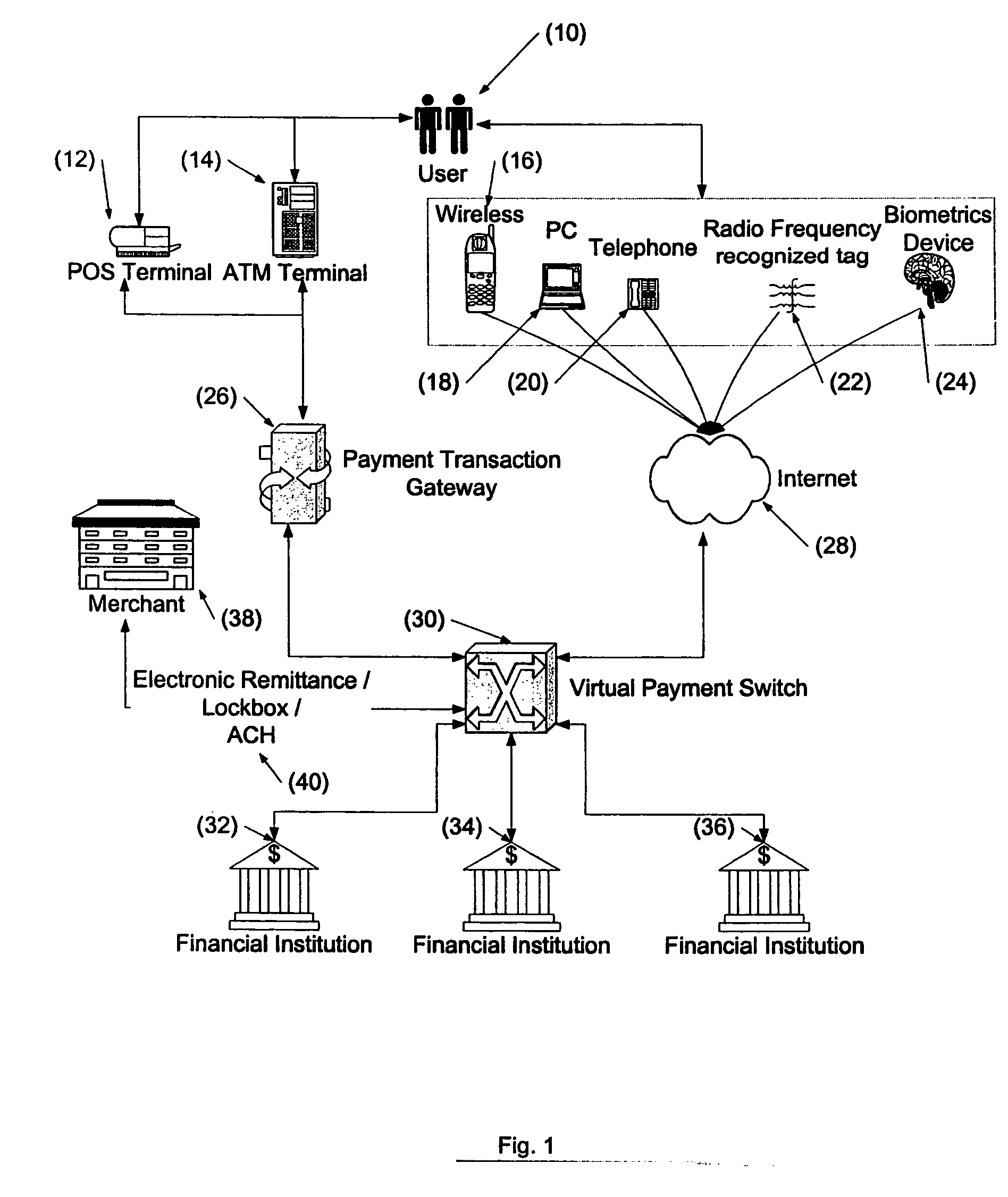
A card reader is a data input device that reads data from a card-shaped storage medium. The first were punched card readers, which read the paper or cardboard punched cards that were used during the first several decades of the computer industry to store information and programs for computer systems. Modern card readers are electronic devices that can read plastic cards embedded with either a barcode, magnetic strip, computer chip or another storage medium.
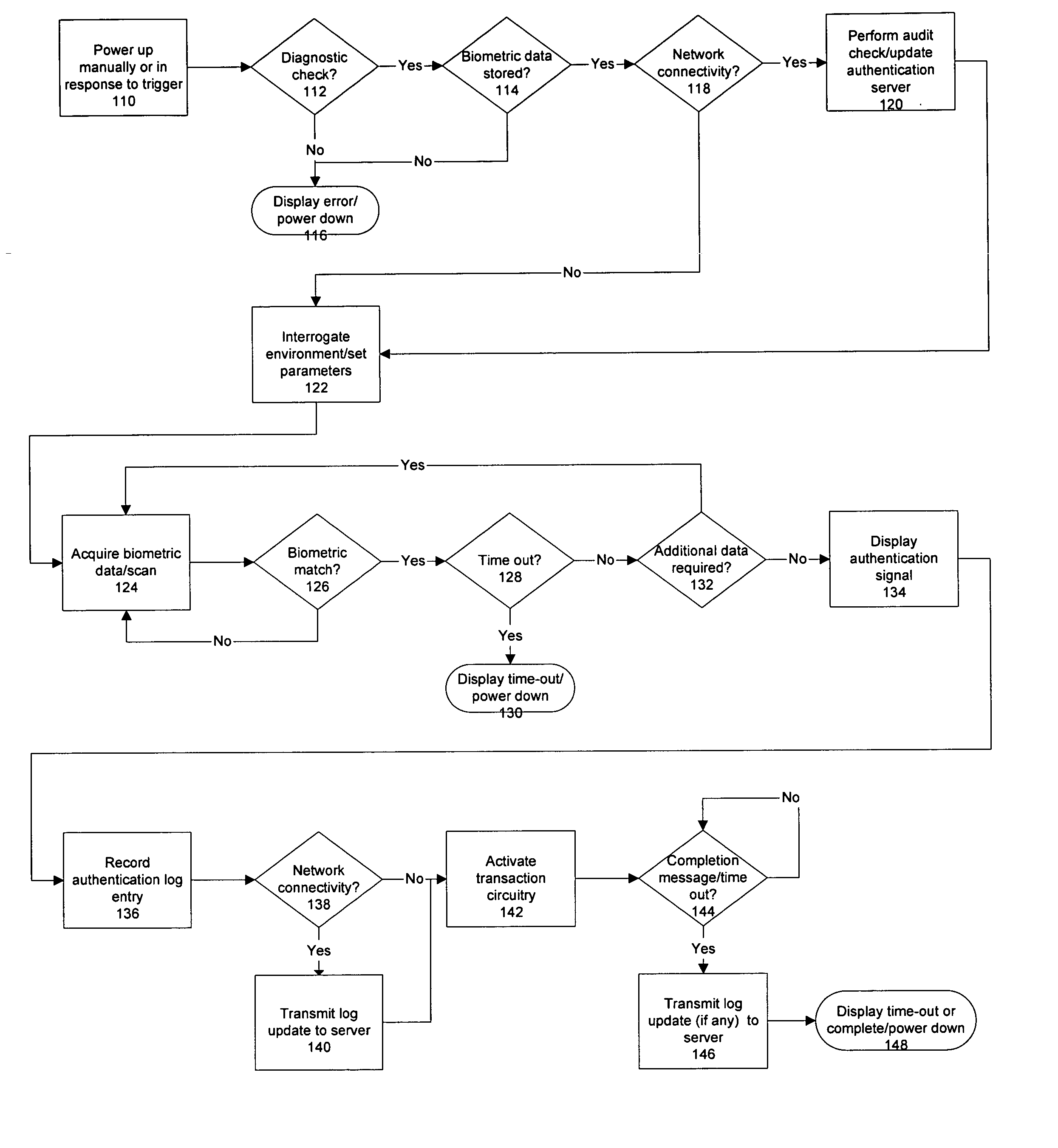
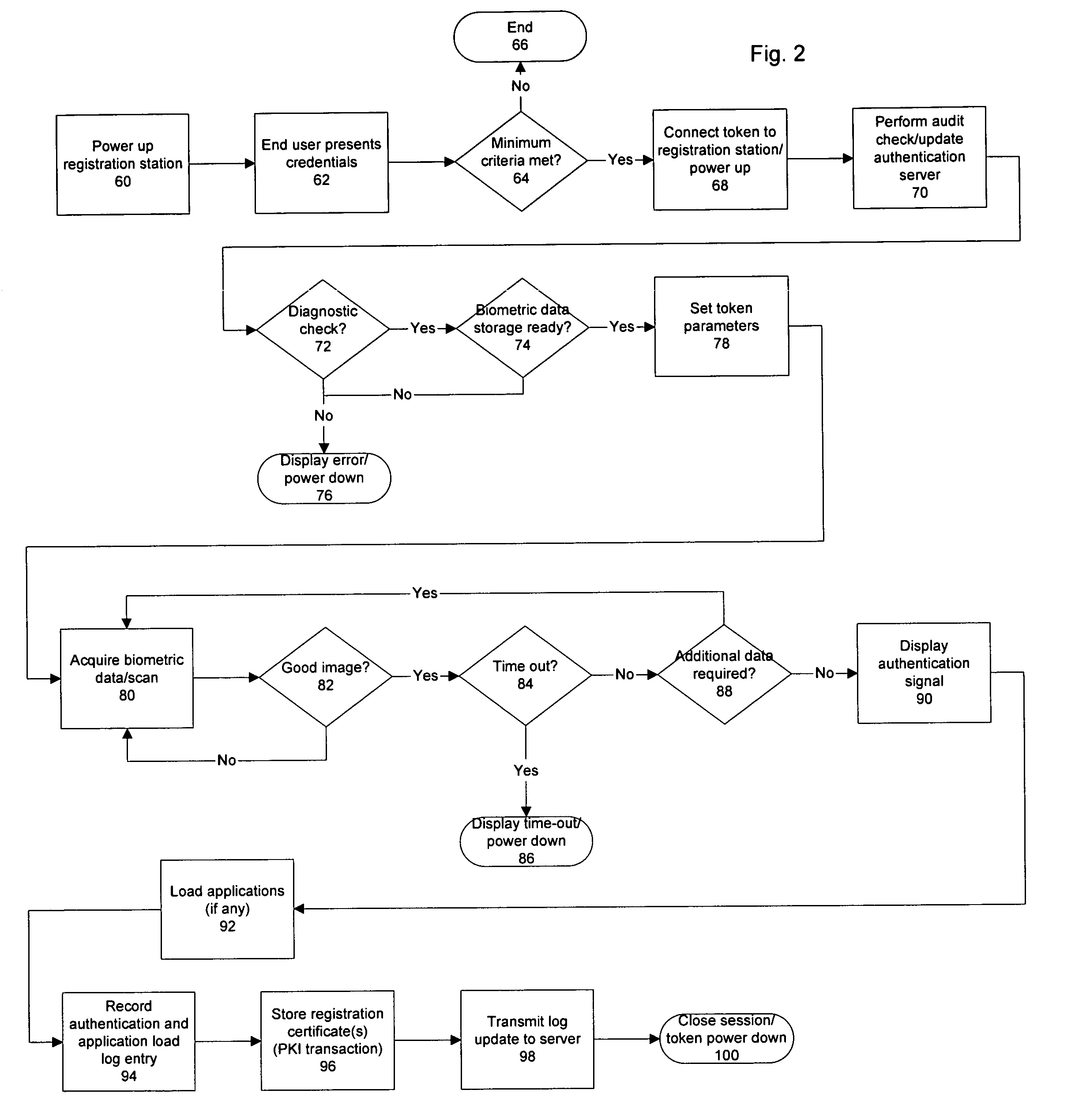
Physical presence digital authentication system
InactiveUS6607136B1Enhanced interactionMass scalableCredit registering devices actuationDiscounts/incentivesCrowdsAcoustic wave
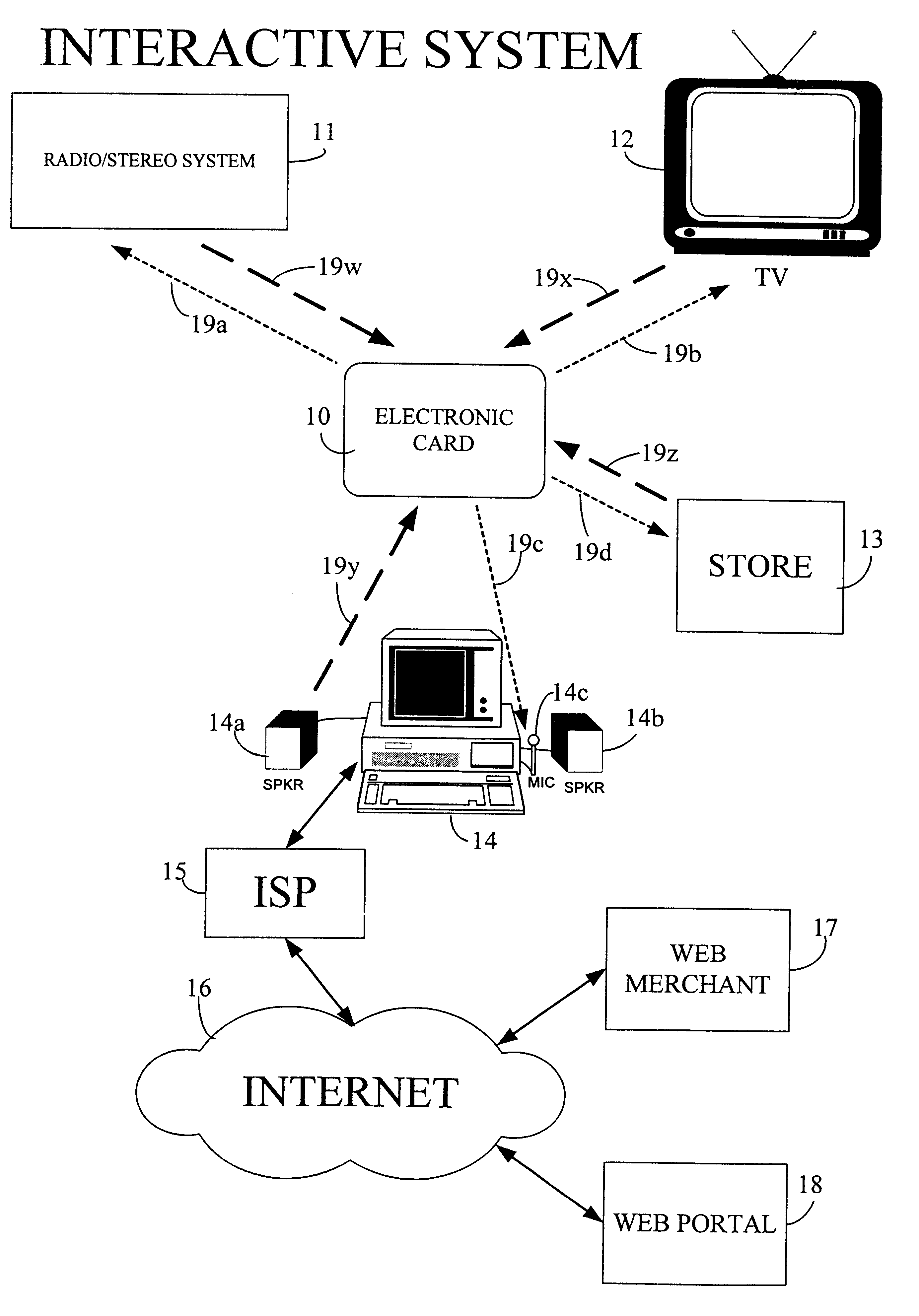
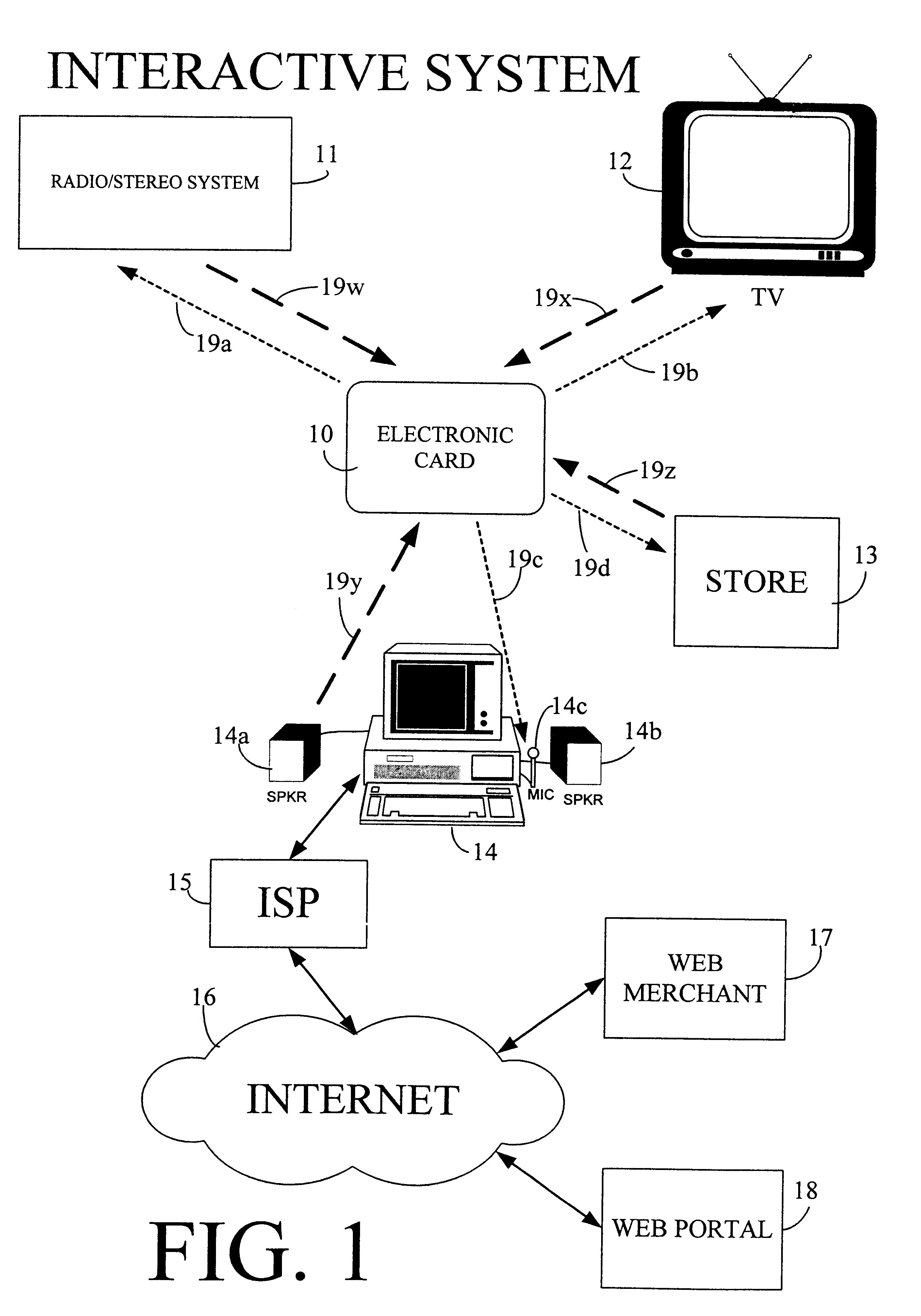
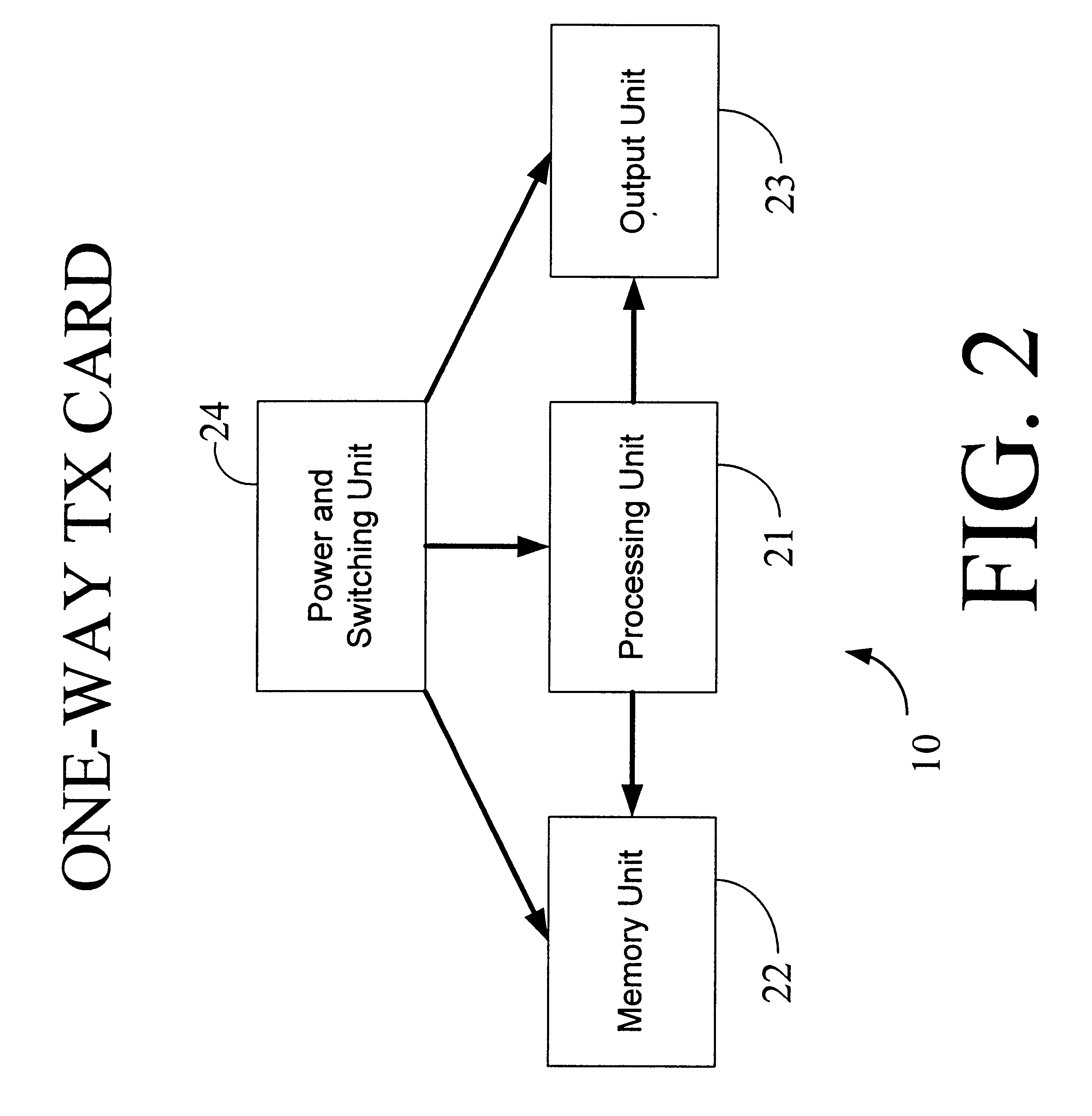
The interactive authentication system allows a consumer to interact with a base station, such as broadcast media (e.g., television and radio) or PC, to receive coupons, special sales offers, and other information with an electronic card. The electronic card can also be used to transmit a signal that can be received by the base station to perform a wide variety of tasks. These tasks can include launching an application, authenticating a user at a website, and completing a sales transaction at a website (e.g., by filling out a form automatically). The interaction between the base station and the electronic card is accomplished by using the conventional sound system in the base station so that a special reader hardware need not be installed to interact with the electronic card. The user is equipped with an electronic card that can receive and transmit data via sound waves. In the various embodiments, the sound waves can be audible or ultrasonic (which can be slightly audible to some groups of people).
Owner:SONIXIO INC
Method and system for biometric recognition based on electric and/or magnetic characteristics
InactiveUS6898299B1Electric signal transmission systemsDigital data processing detailsElectricityBiological body
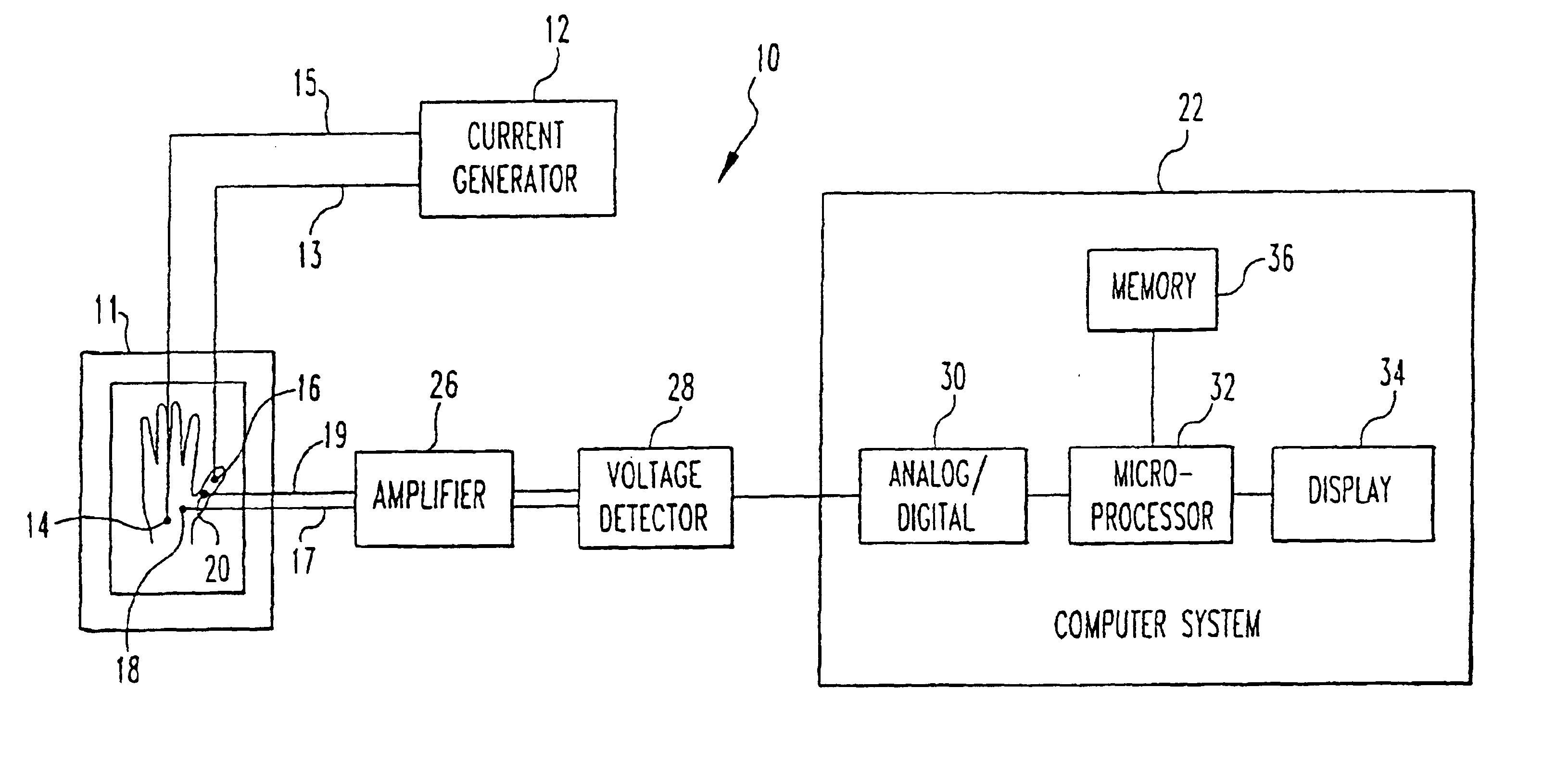
A method and apparatus for authenticating an individual living organism by recognizing a unique internal electric and / or magnetic and / or acoustic characteristic, which comprises a biometric signature, involve presenting a body part to a sensing device that senses the signature. The sensed presented biometric signature is compared to a known biometric signature to authenticate the individual. This authentication can then be used to authorize any of a wide variety of actions by the individual, such as accessing equipment or an area, or to perform actions, such as conducting financial transactions. A card having sensors is used to sense the biometric signature which is read by a card reader and sent to a local or remote reader for biometric signature comparison.
Owner:GR INTELLECTUAL RESERVE LLC
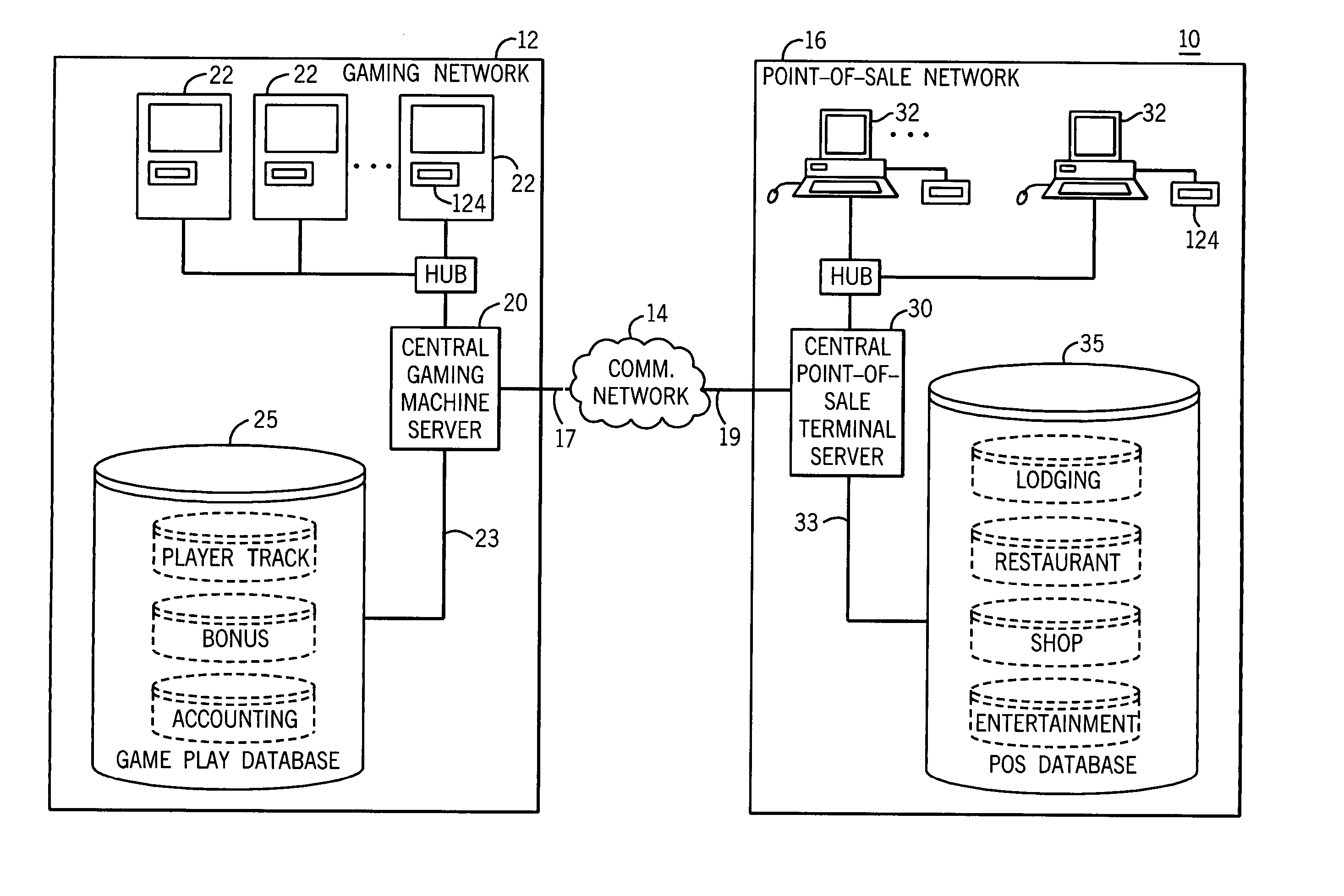
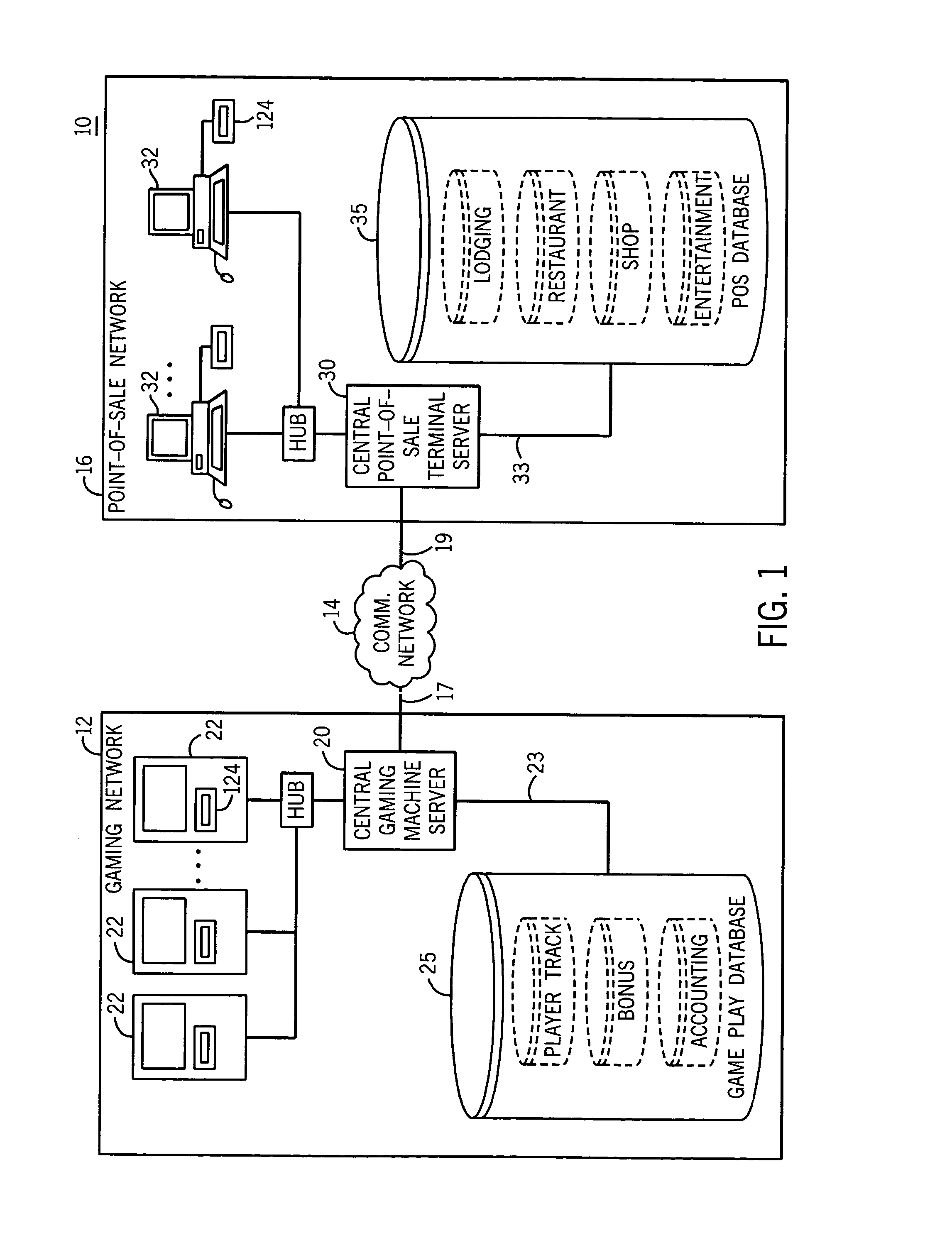
Method and apparatus for operating networked gaming devices
InactiveUSRE37885E1Coin countersApparatus for meter-controlled dispensingComputer moduleComputer terminal
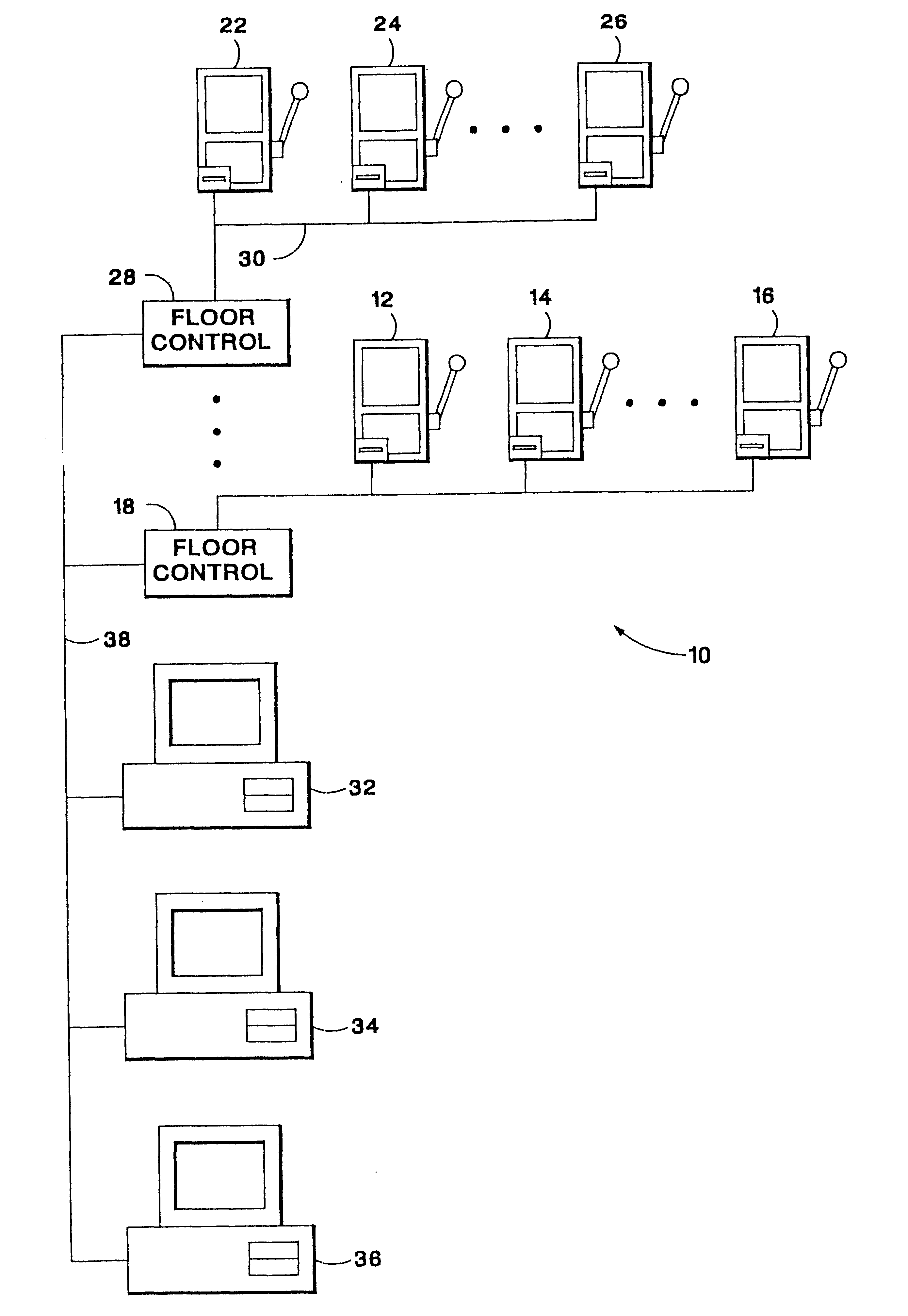
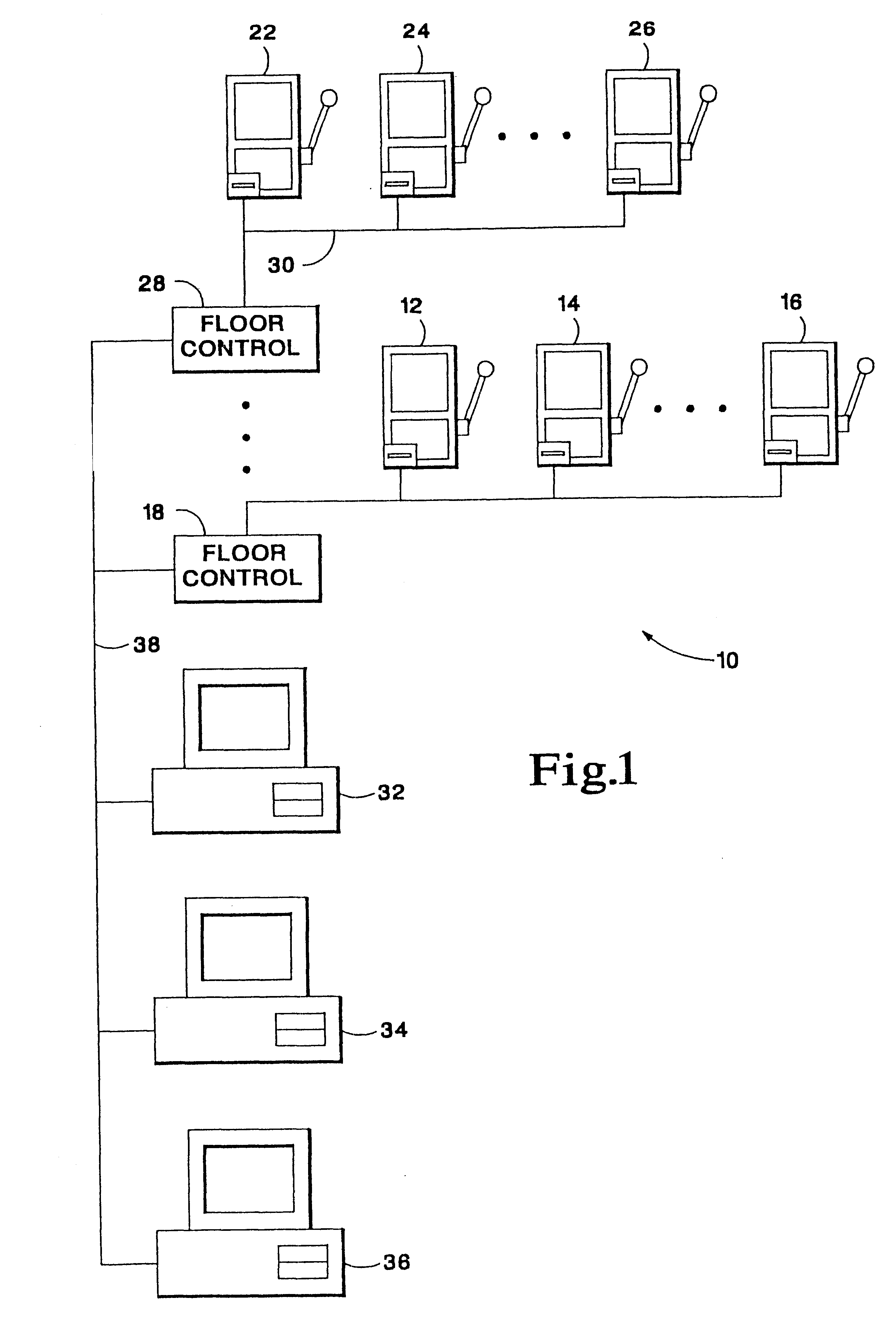
A system for monitoring and configuring gaming devices interconnected over a high-speed network is disclosed. The system can support a file server, one or more floor controllers, one or more pit terminals, and other terminals all interconnected over the network. Each gaming device includes an electronic module which allows the gaming device to communicate with a floor controller over a current loop network. The electronic module includes a player tracking module and a data communication node. The player tracking module includes a card reader for detecting a player tracking card inserted therein which identifies the player. The data communication node communicates with both the floor controller and the gaming device. The data communication node communicates with the gaming device over a serial interface through which the data communication node transmits reconfiguration commands. The gaming device reconfigures its payout schedule responsive to the reconfiguration commands to provide a variety of promotional bonuses such as multiple jackpot bonuses, mystery jackpot bonuses, progressive jackpot bonuses, or player specific bonuses.
Owner:IGT
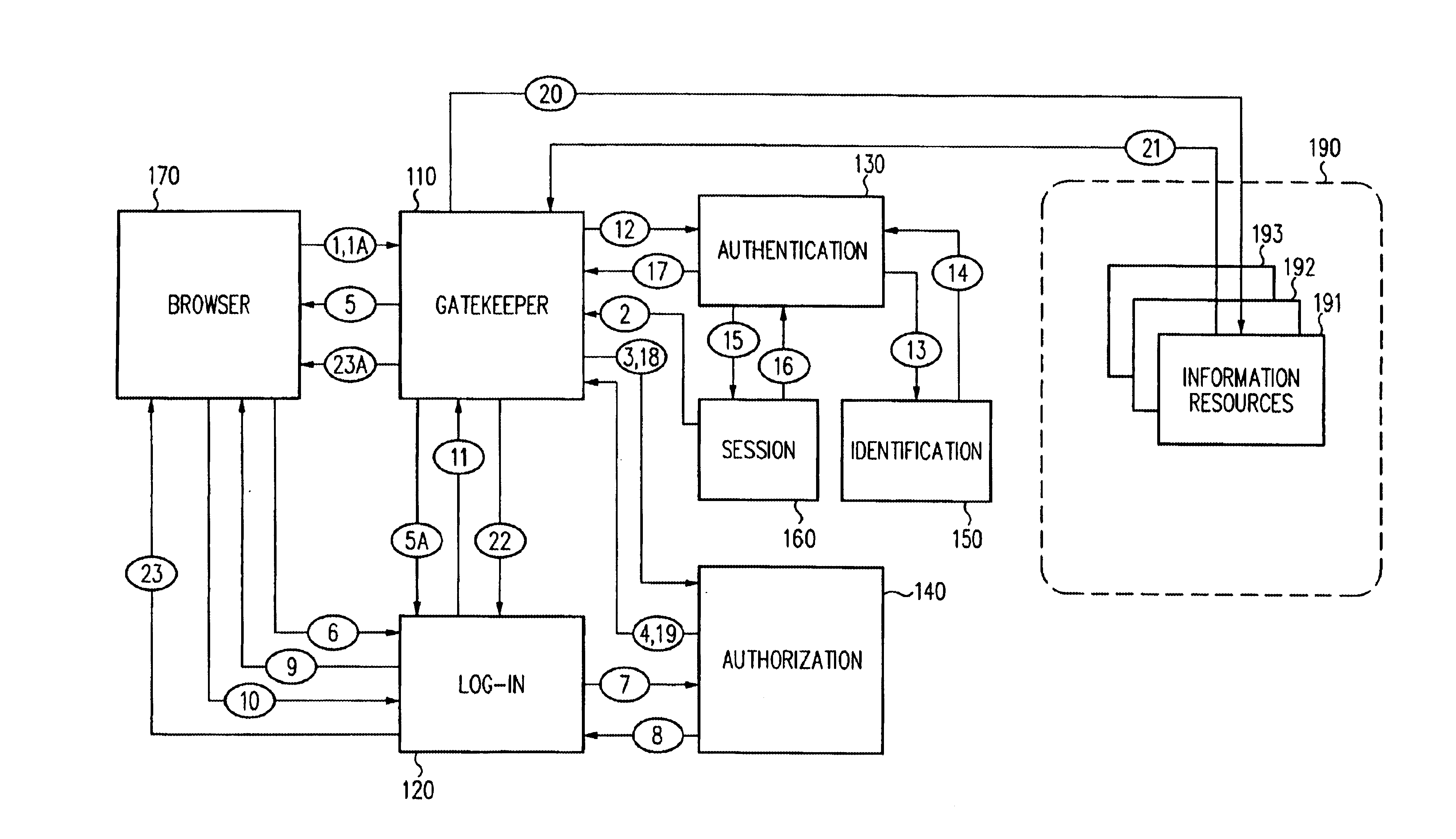
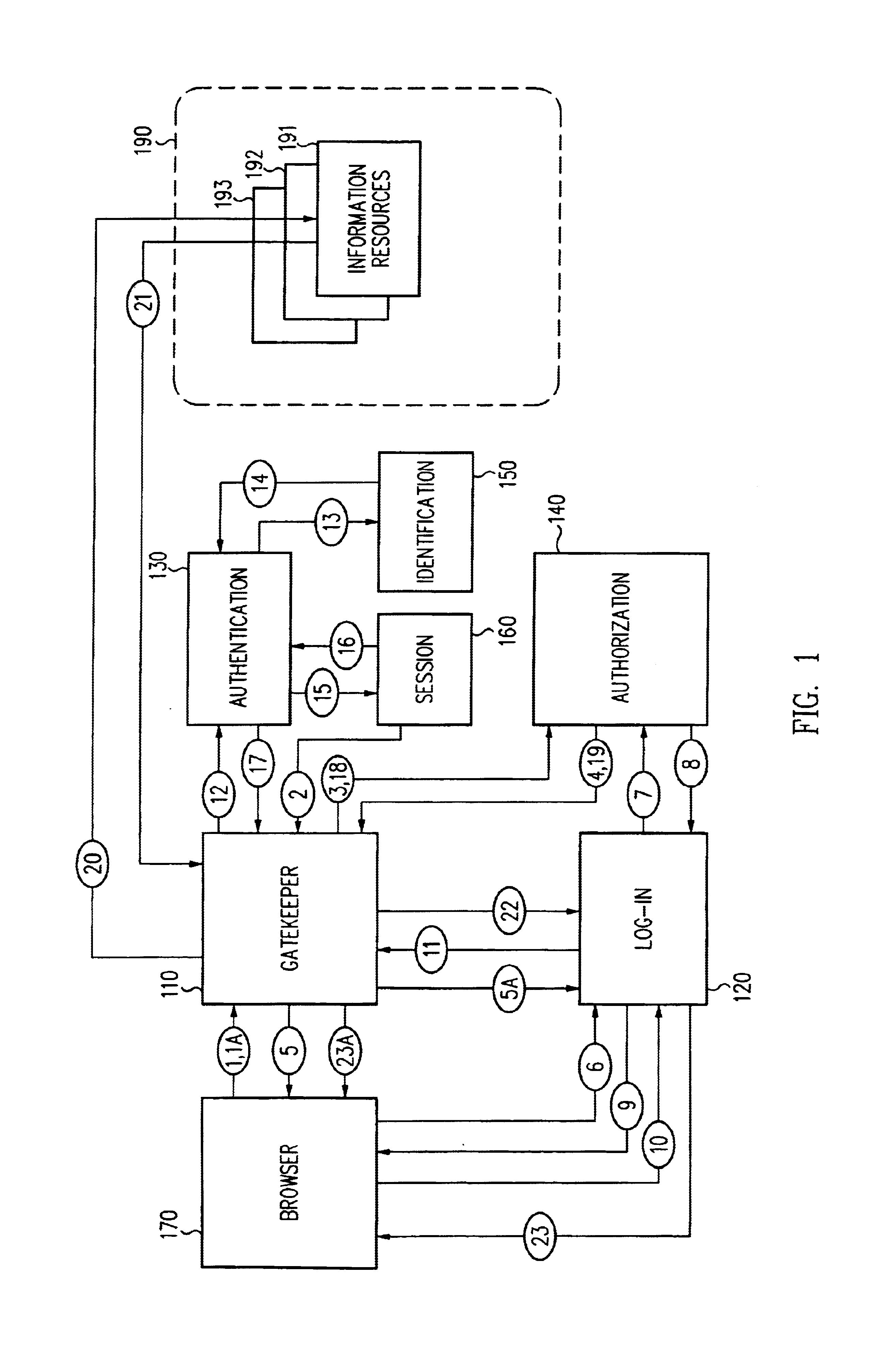
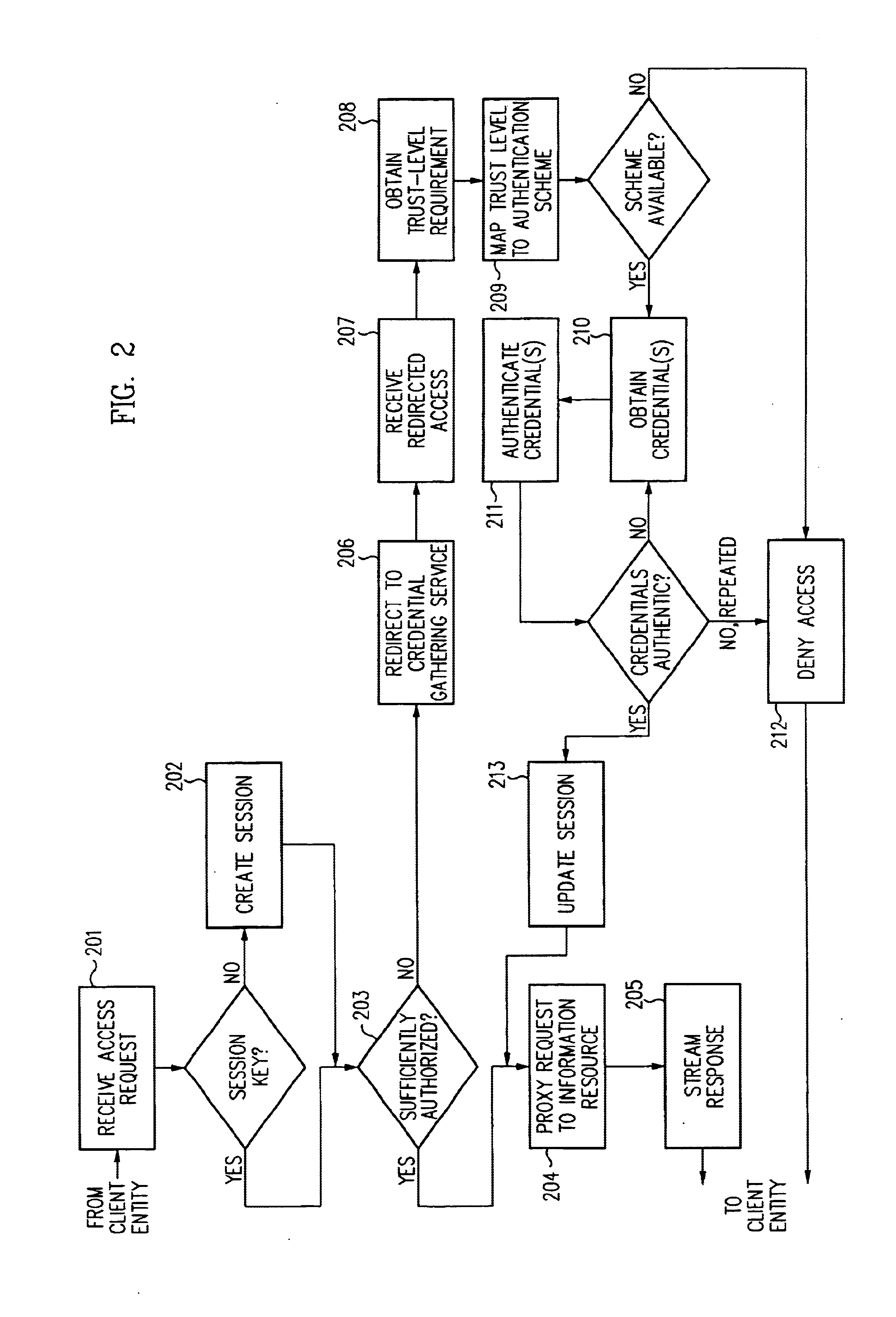
Security architecture with environment sensitive credential sufficiency evaluation
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
Universal personal identifier for accessing patron information at a gaming venue
InactiveUS20050054438A1Easy to rememberApparatus for meter-controlled dispensingVideo gamesCard readerBluetooth
A method and apparatus for associating a patron with wagering game play at a gaming machine in a server-based gaming network is disclosed. The method includes associating a unique patron identification with the patron, establishing a patron account for the patron where the patron account is identified by the unique patron identification, associating the gaming machine with a universal personal identifier device for receiving a universal personal identifier having a patron identification where the universal personal identifier device is capable of detecting and transmitting the patron identification, receiving the patron identification, comparing the patron identification to the unique patron identification, and enabling collection of patron accounting data resulting from wagering game play if the patron identification matches the unique patron identification. The universal personal identifier device may be a card reader, a touch screen, a biometric device, a Bluetooth™ module device, a microchip scanner, or a combination thereof.
Owner:BALLY GAMING INC
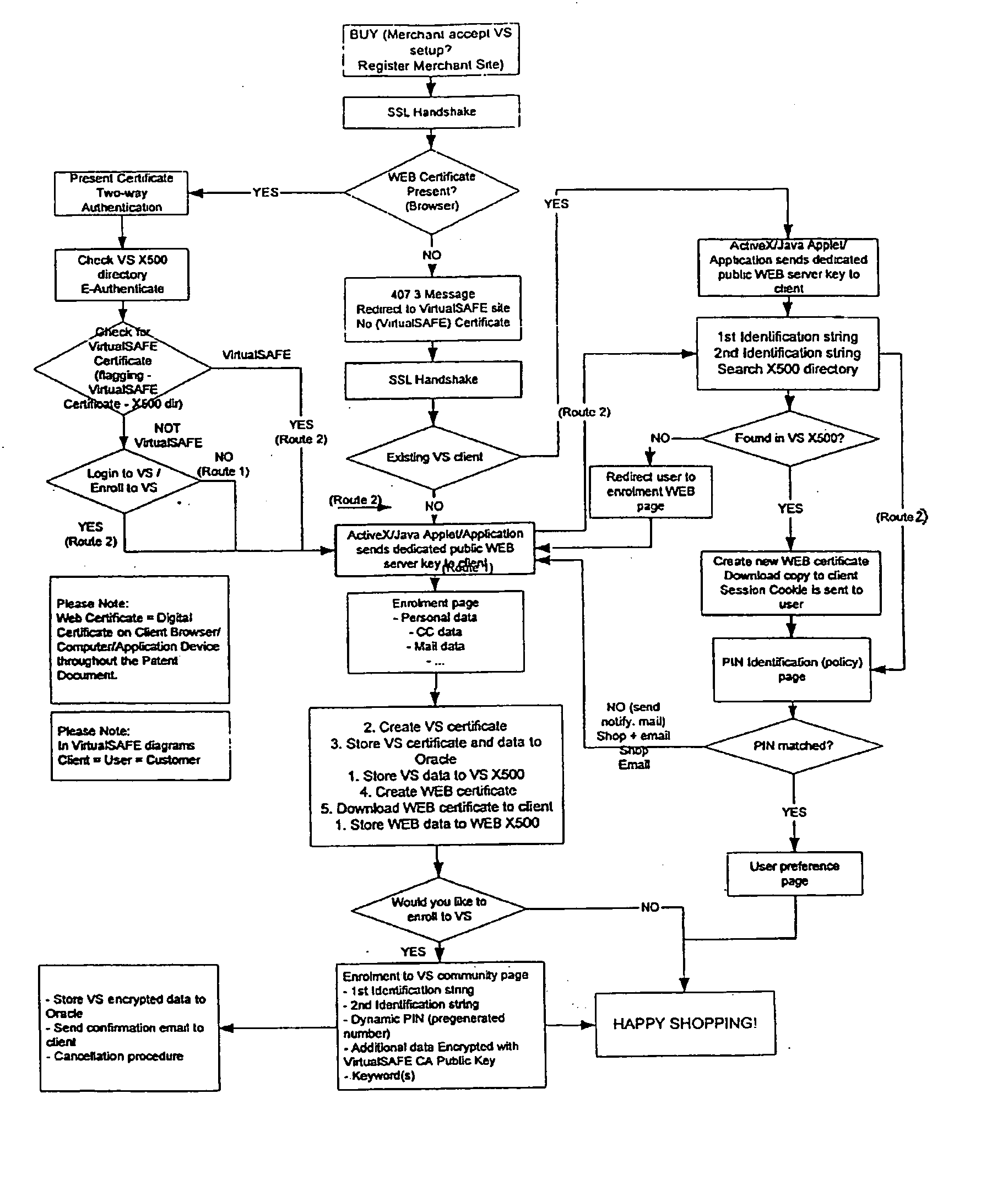
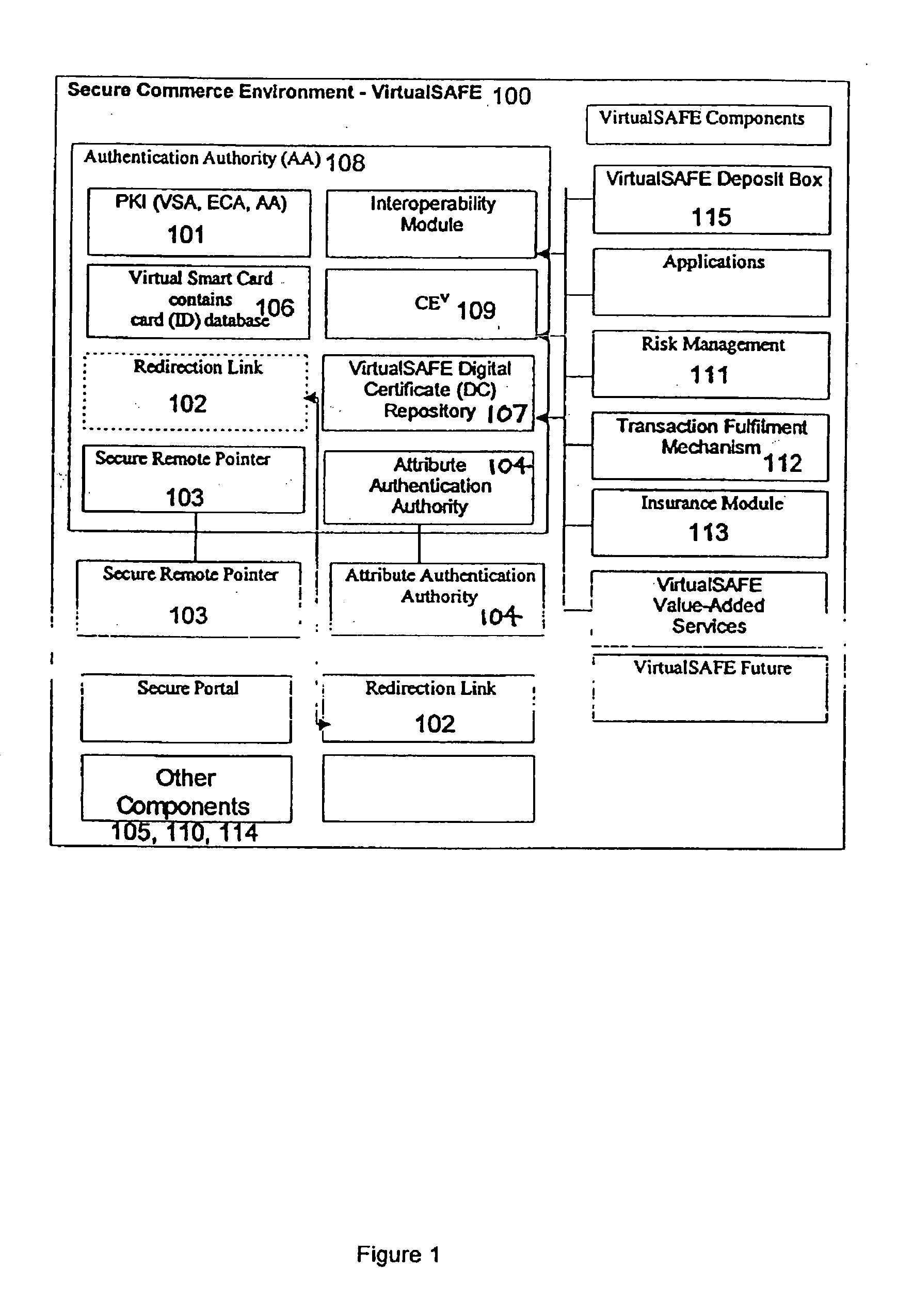
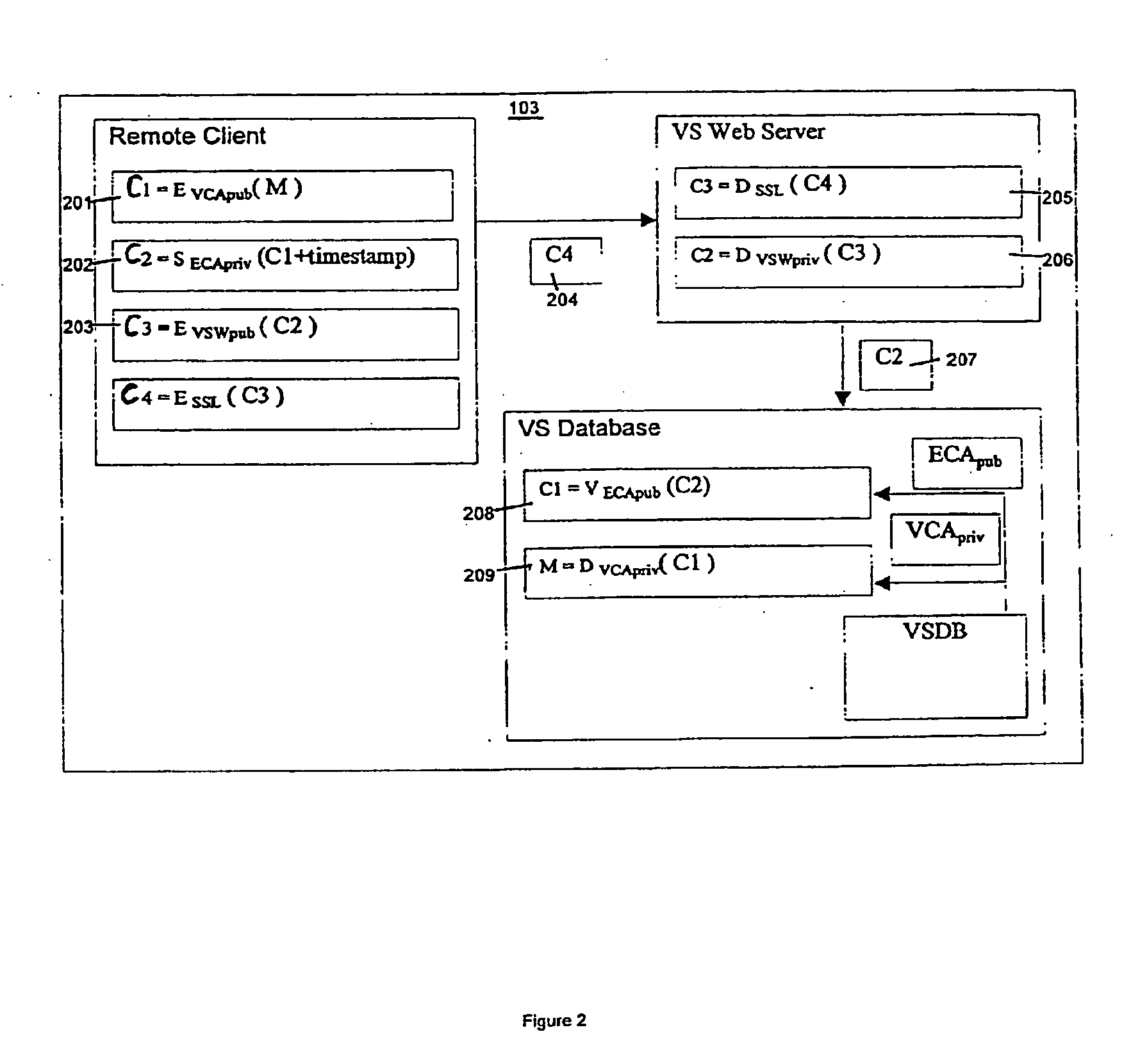
Method and system for a virtual safe
Owner:SARCANIN BRANKO
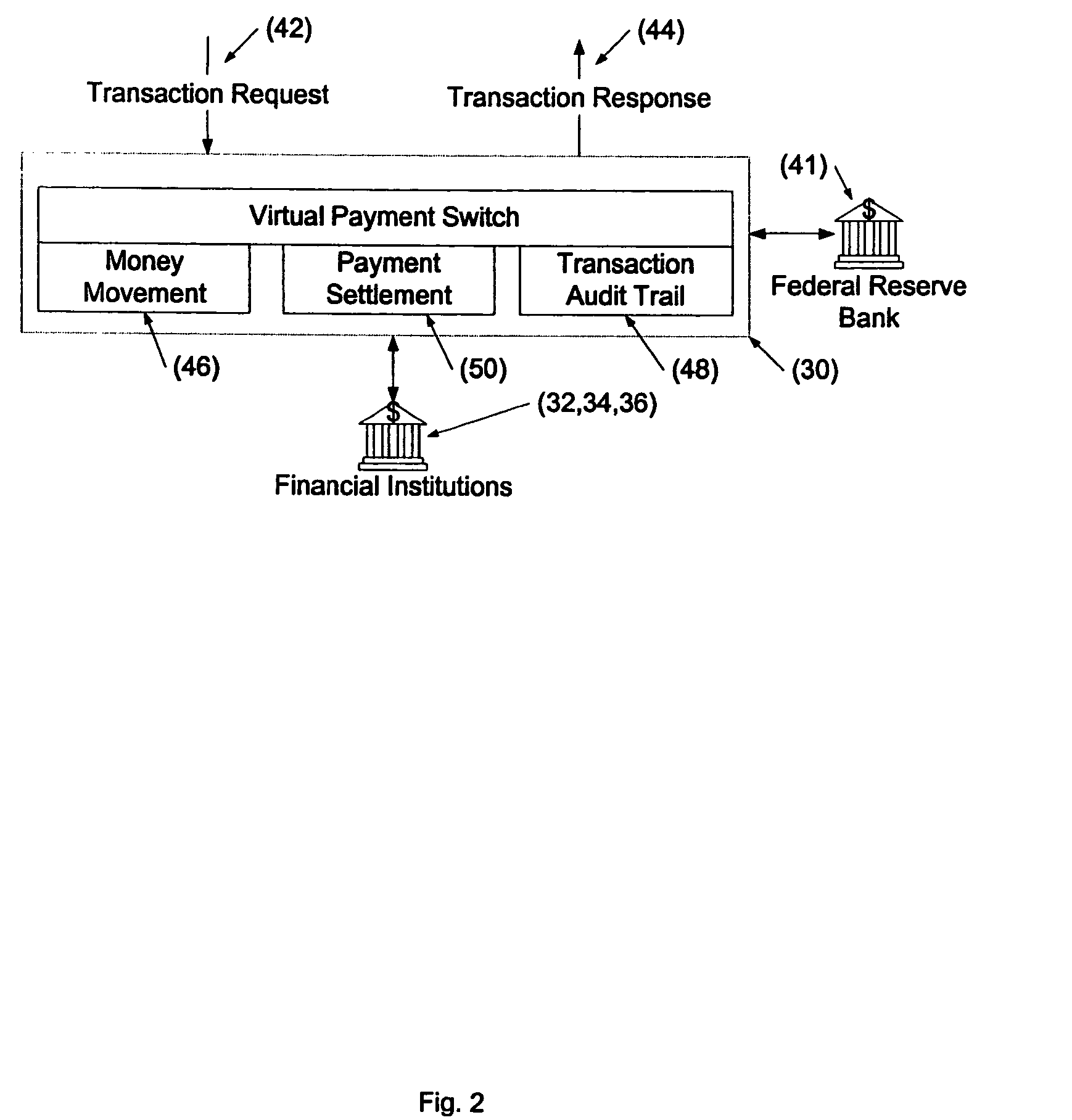
Internet payment, authentication and loading system using virtual smart card
InactiveUS7908216B1Advantageous for small dollar amount transactionMinimal timeFinancePayment circuitsMerchant servicesPayment
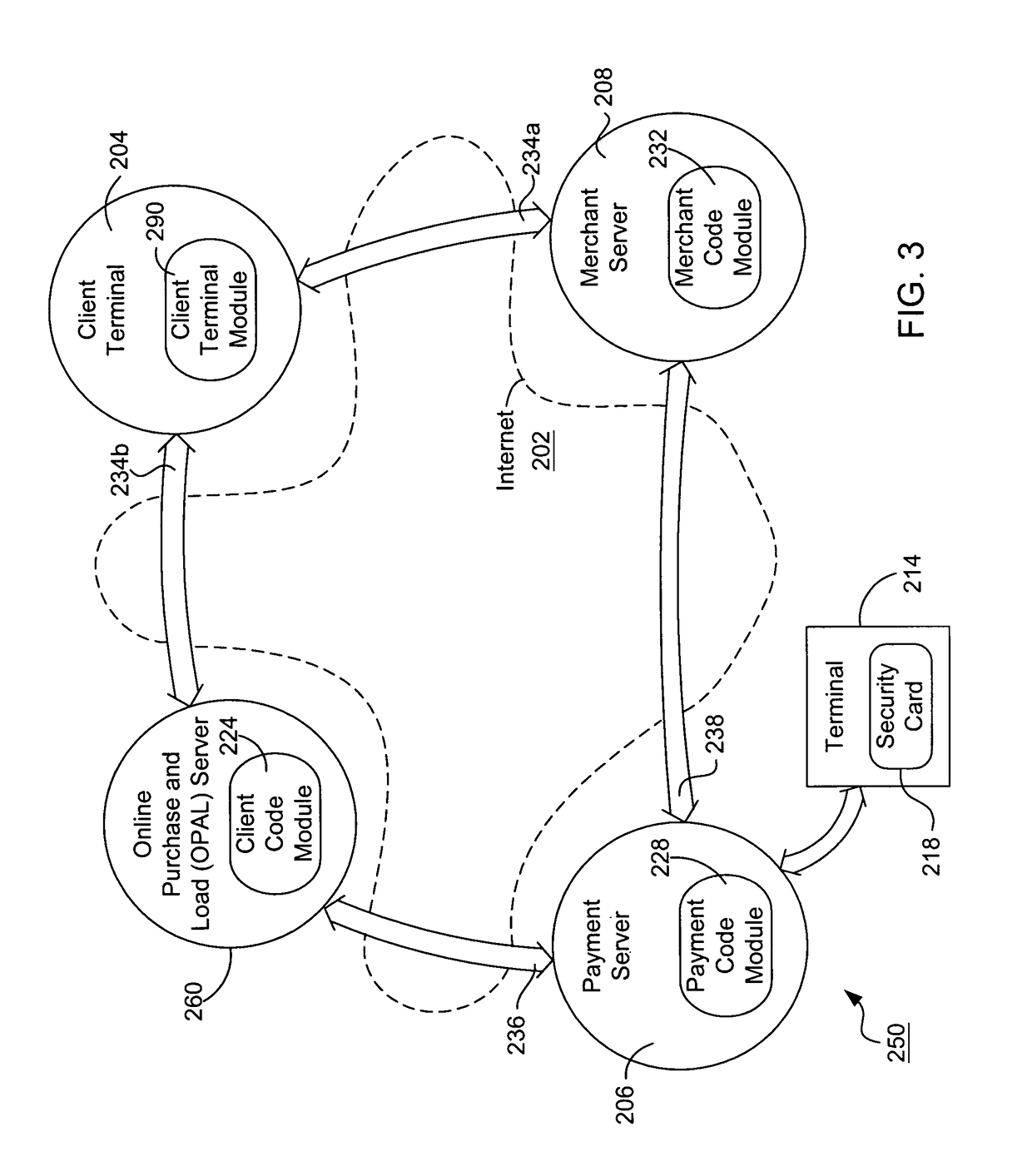
A system loads, authenticates and uses a virtual smart card for payment of goods and / or services purchased on-line over the Internet. An online purchase and load (OPAL) server includes a virtual smart card data base that has a record of information for each smart card that it represents for a user at the behest of an issuer. The server includes a smart card emulator that emulates a smart card by using the card data base and a hardware security module. The emulator interacts with a pseudo card reader module in the server that imitates a physical card reader. The server also includes a client code module that interacts with the pseudo card reader and a remote payment or load server. A pass-through client terminal presents a user interface and passes information between the OPAL server and a merchant server, and between the OPAL server and a bank server. The Internet provides the routing functionality between the client terminal and the various servers. A merchant advertises goods on a web site. A user uses the client terminal to purchase goods and / or services from the remote merchant server. The payment server processes, confirms and replies to the merchant server. The payment server is also used to authenticate the holder of a virtual card who wishes to redeem loyalty points from a merchant. To load value, the client terminal requests a load from a user account at the bank server. The load server processes, confirms and replies to the bank server.
Owner:VISA INT SERVICE ASSOC
Computer Apparatus with added functionality
InactiveUS20060007151A1Add to and enhance functionLow costCathode-ray tube indicatorsInput/output processes for data processingHard disc driveWi-Fi
A computer apparatus such as a mouse, keyboard, or PC headset with additional devices disposed within the apparatus enclosure, which can enhance the functionality of such computer apparatus. In the preferred embodiment, the additional devices are disposed within or along the length of a mouse apparatus. The additional devices typically function independently of the mouse apparatus. However, the additional components may share one or more wired or wireless paths to a host PC and to other devices, or to a network. The additional devices either integrated within the mouse enclosure or removable from the mouse enclosure, include a wireless adapter (Wi-Fi, Bluetooth, 3G, GSM, etc. . . . ), RAM, ROM, a mini hard drive, a GPS receiver module, a flash memory, flash memory drive reader, a USB Hub, a Trackpoint™ device, a keyboard or keypad, a fingerprint reader, or a SIM card reader. Also disclosed, are software controls for mapping the mouse velocity to a cursor velocity and for controlling the function and settings of the Trackpoint device. Further disclosed is a method for assigning the mouse's data output to a variety of devices connected to a wired or wireless network.
Owner:RAM PRANIL
Charging apparatus and charging system
ActiveUS20070069687A1Avoid power supplyAccurate detectionCircuit authenticationElectromagnetic wave systemCard readerElectric power
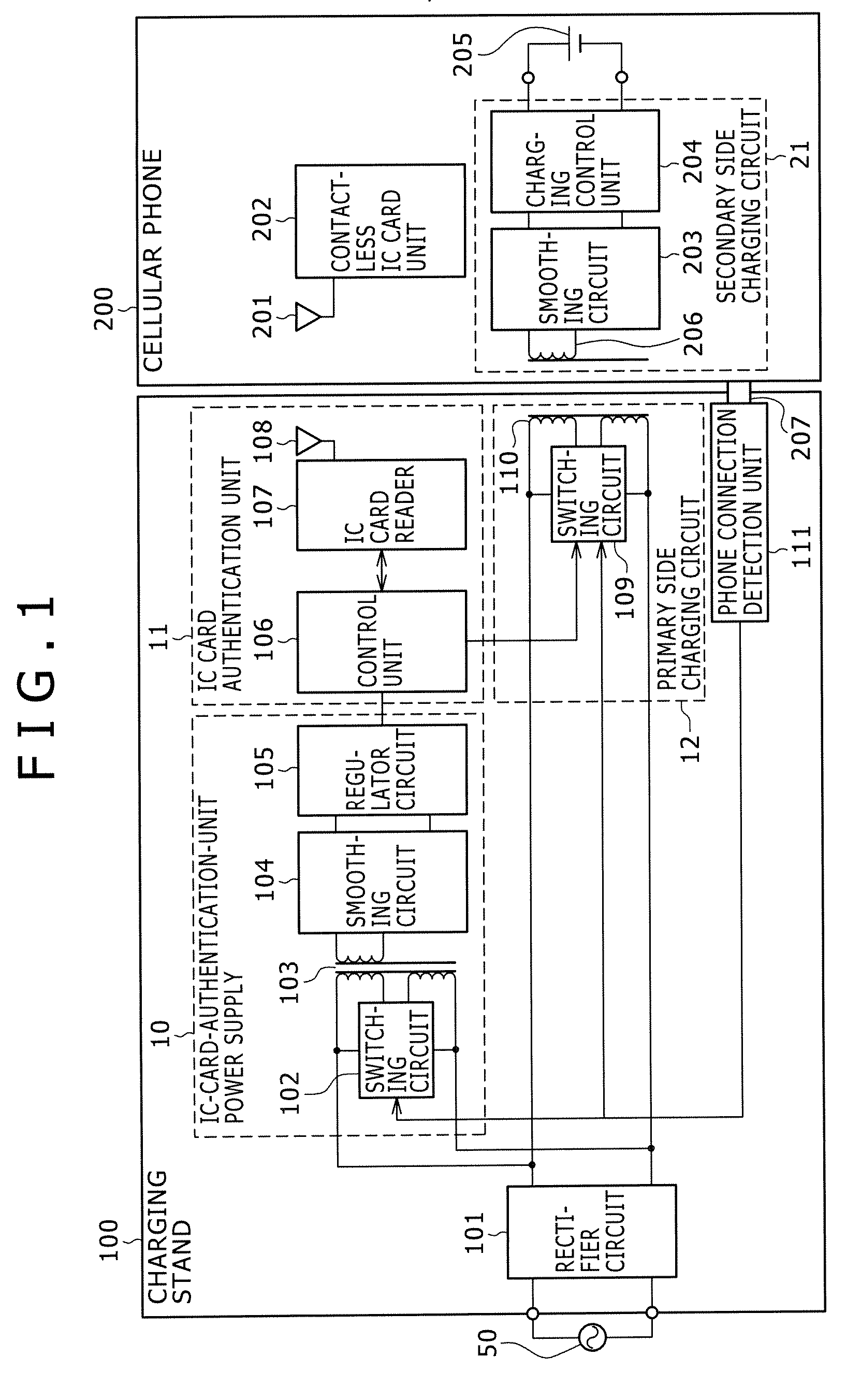
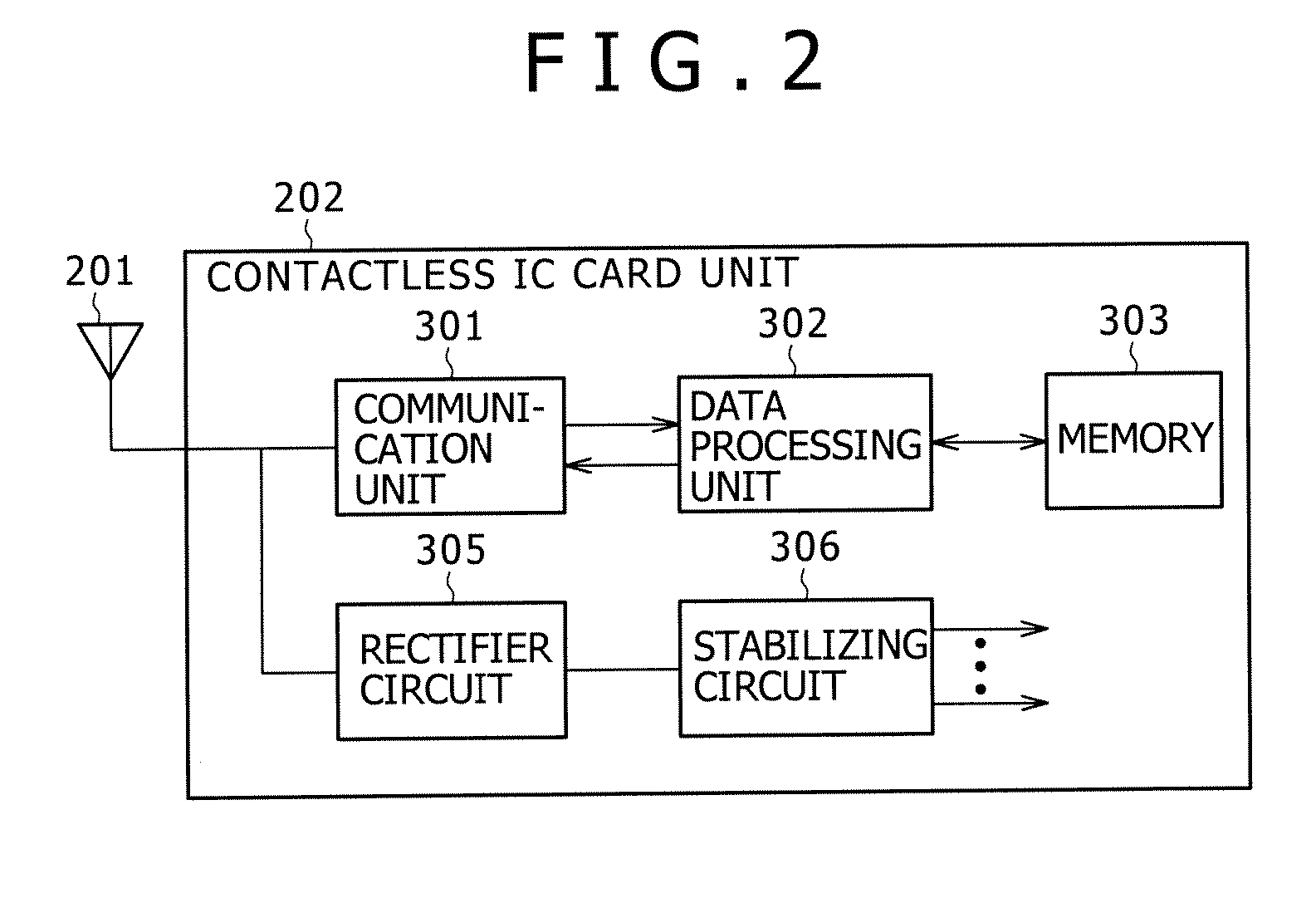
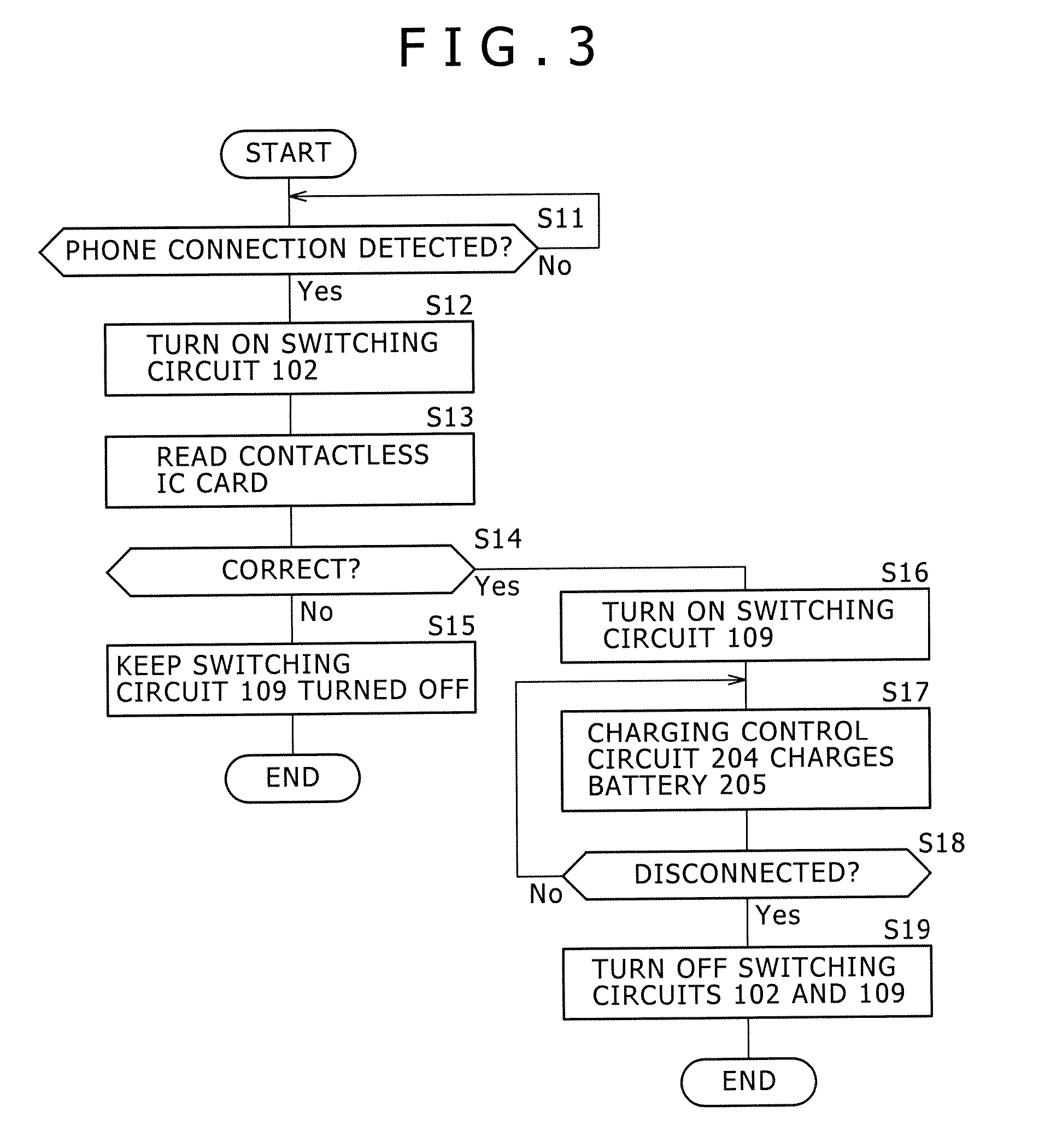
Disclosed is a charging apparatus for charging a secondary battery incorporated in a portable electronic device. The charging apparatus includes a contactless IC card reader configured to supply operating power to a contactless IC card unit incorporated in the portable electronic device and have an authentication function of authenticating that an object to be authenticated is a correct one, a charging circuit configured to perform contactless charging of the secondary battery, and a control unit configured to activate the charging circuit if an authentication result is OK after the contactless IC card reader authenticates an object to be authenticated when the object to be authenticated is placed.
Owner:SONY CORP
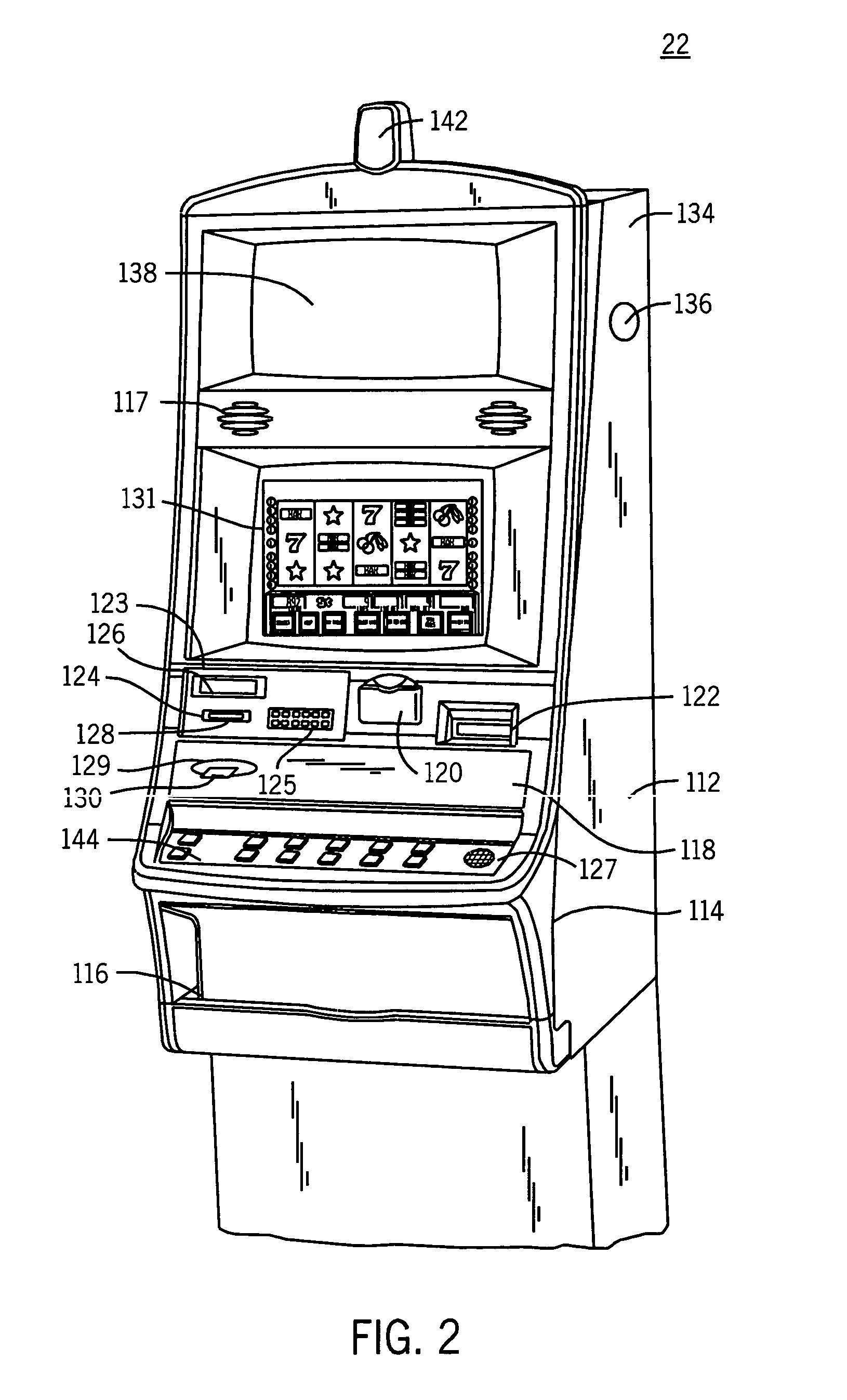
Lighted keypad assembly and method for a player tracking system
InactiveUS6409595B1Improve system efficiencyComplete banking machinesElectric/electromagnetic visible signallingCard readerTracking system
A keypad assembly and method for use with a card reader adapted to receive and read a player identification card therein. The keypad assembly includes a keypad mechanism having a plurality of keys to input data, and a feedback mechanism coupled to the keypad. A validation device is provided which is adapted to determine the validation of information relating to the identification card upon reading thereof in the card reader. The validation device is further operably coupled to the feedback mechanism to visually inform the Player that the information relating to identification card has been validated.
Owner:IGT
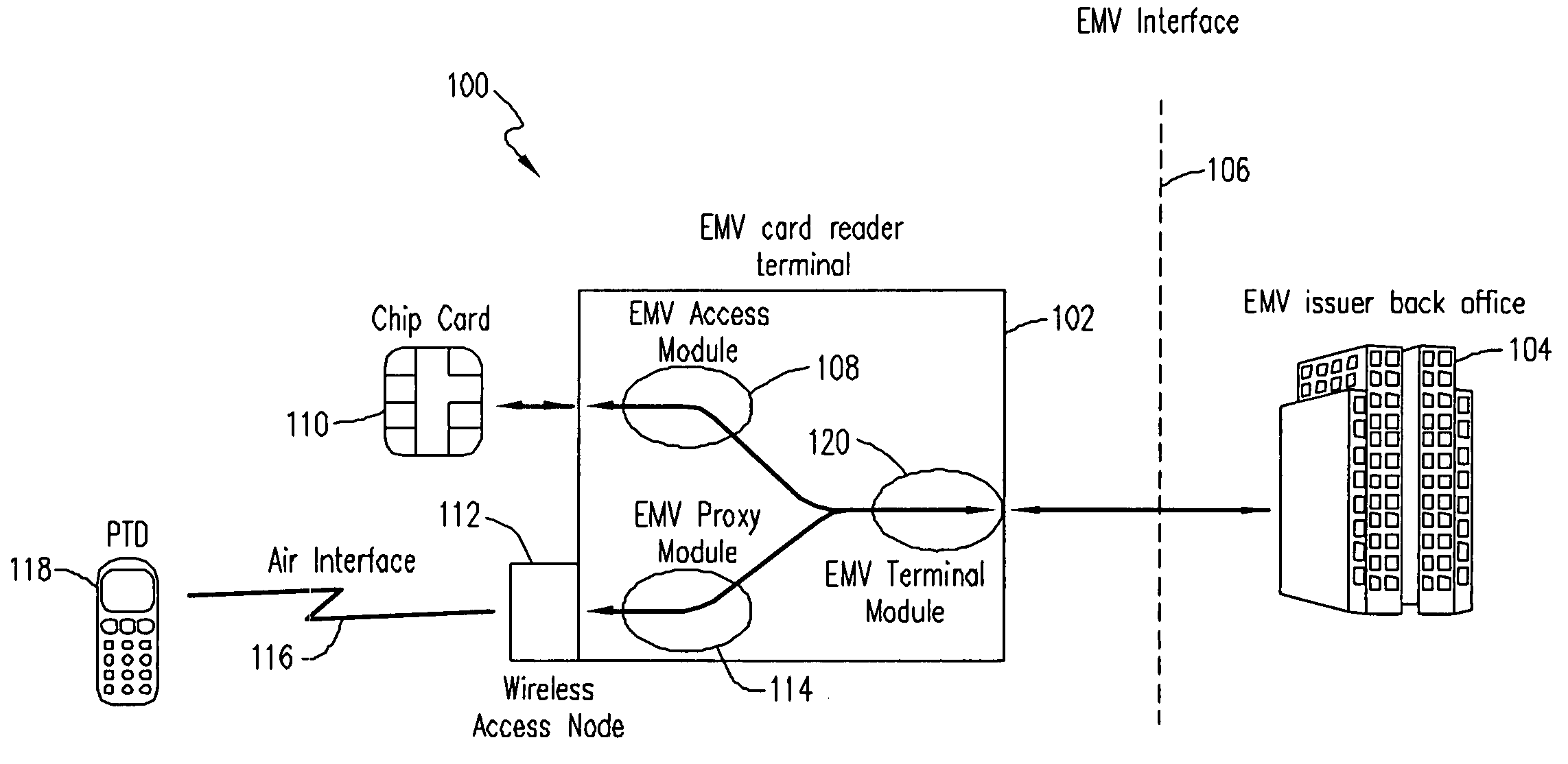
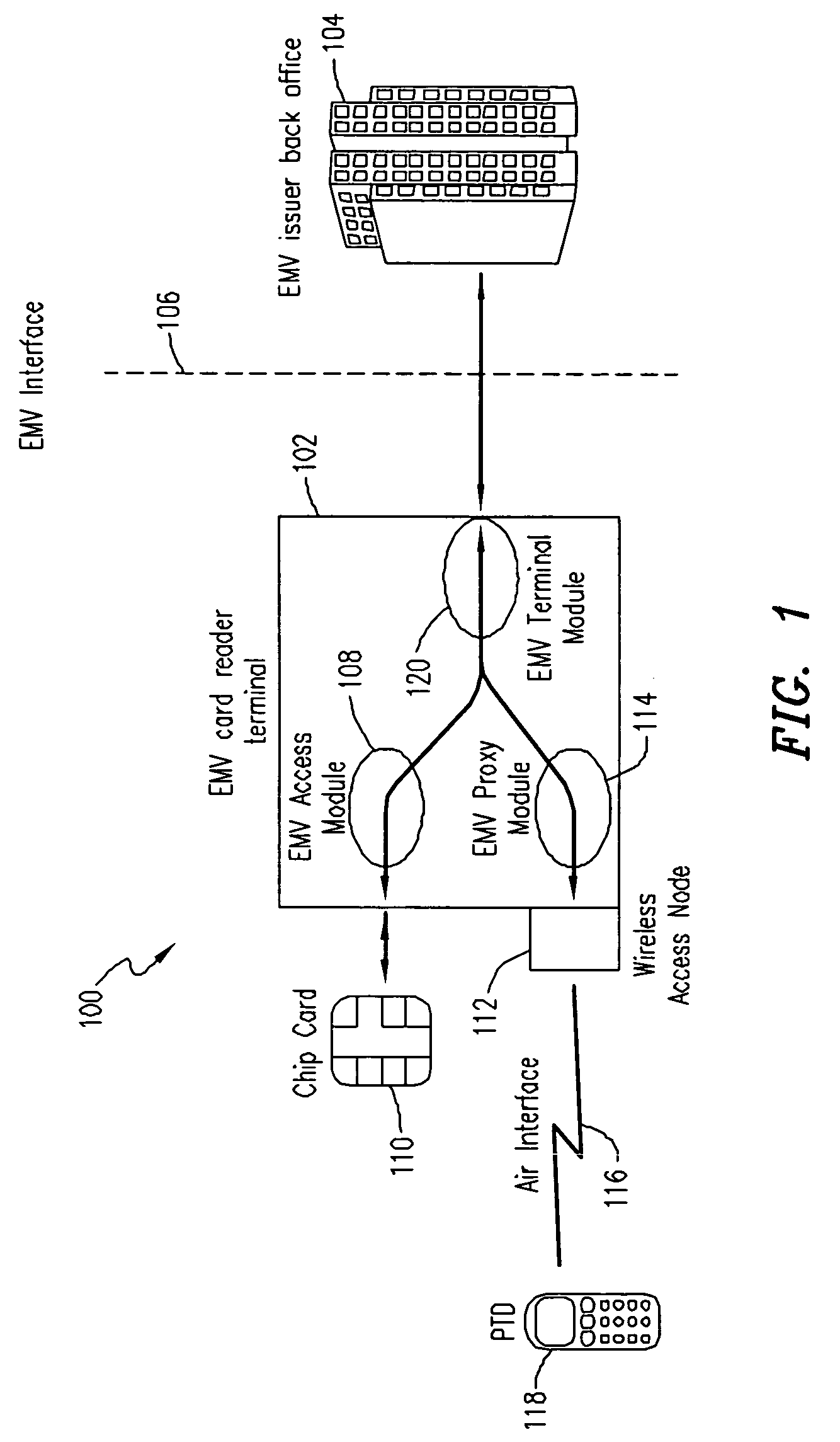
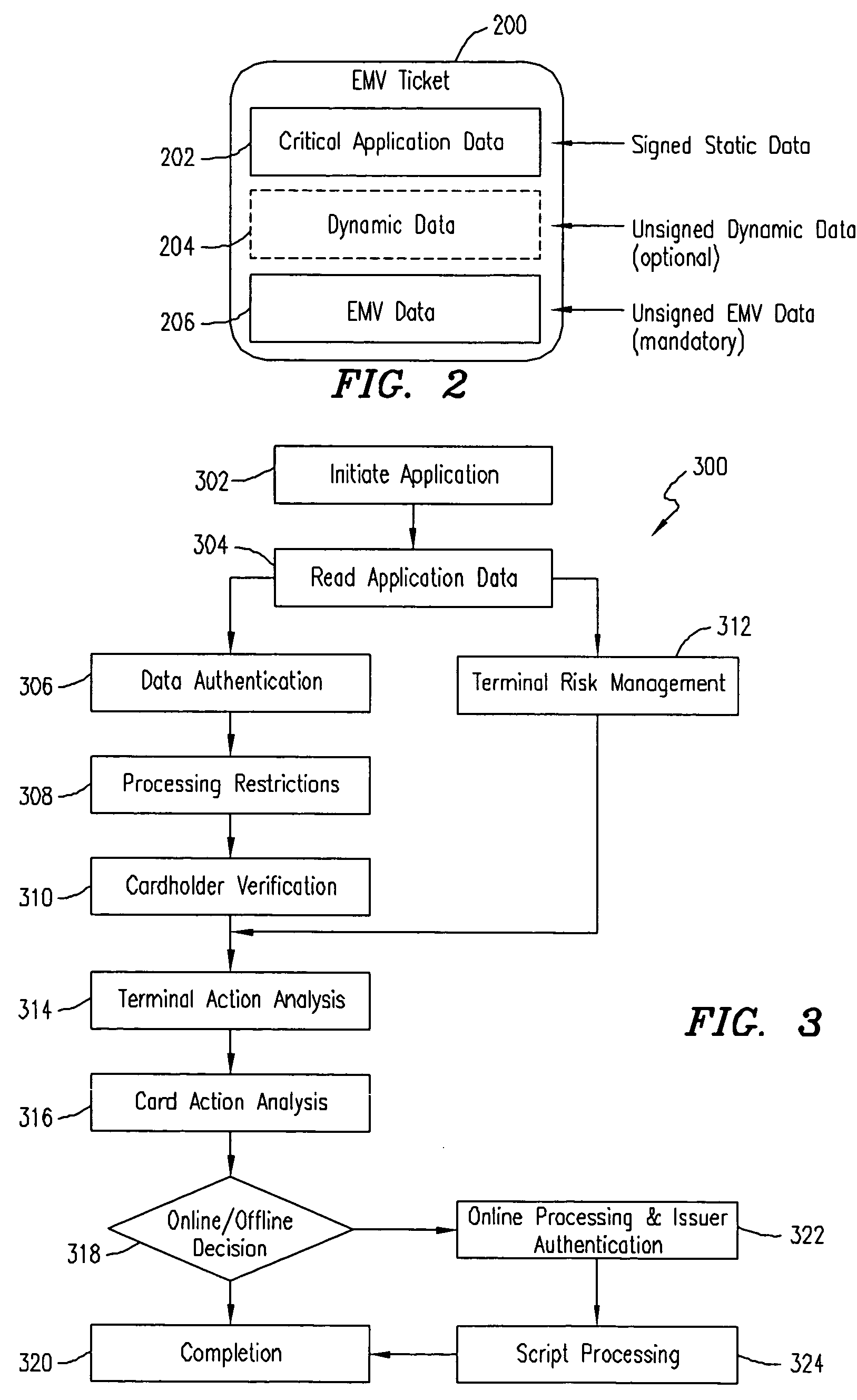
EMV transactions in mobile terminals
ActiveUS20050156026A1Facilitate communicationComplete banking machinesFinanceCard readerDynamic data
A mobile terminal is enabled to conduct an EMV transaction. A wireless access node in the EMV card-reader terminal is provided for connecting a mobile terminal to the card-reader terminal. An EMV-proxy module executing in the card-reader terminal facilitates communication between the mobile terminal and the card-reader terminal. The EMV-proxy module lets the mobile terminal function in essentially the same way as a regular EMV chip card with respect to the card-reader terminal. The card-reader terminal may then conduct EMV transactions on behalf of the mobile terminal without requiring new software and / or hardware at the EMV issuer. EMV data is stored in the mobile terminal in the form of secure dynamic data objects. This Abstract is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:TELEFON AB LM ERICSSON (PUBL)
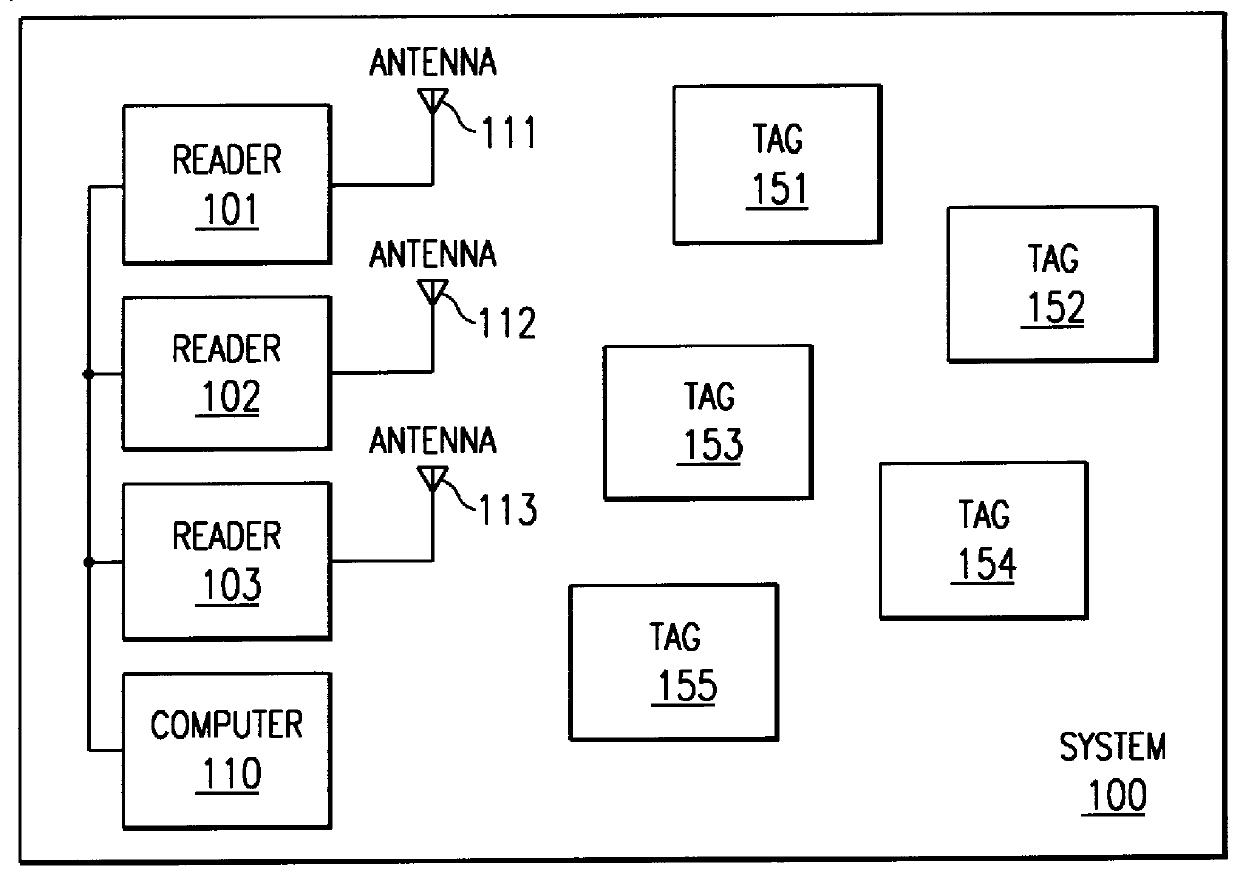
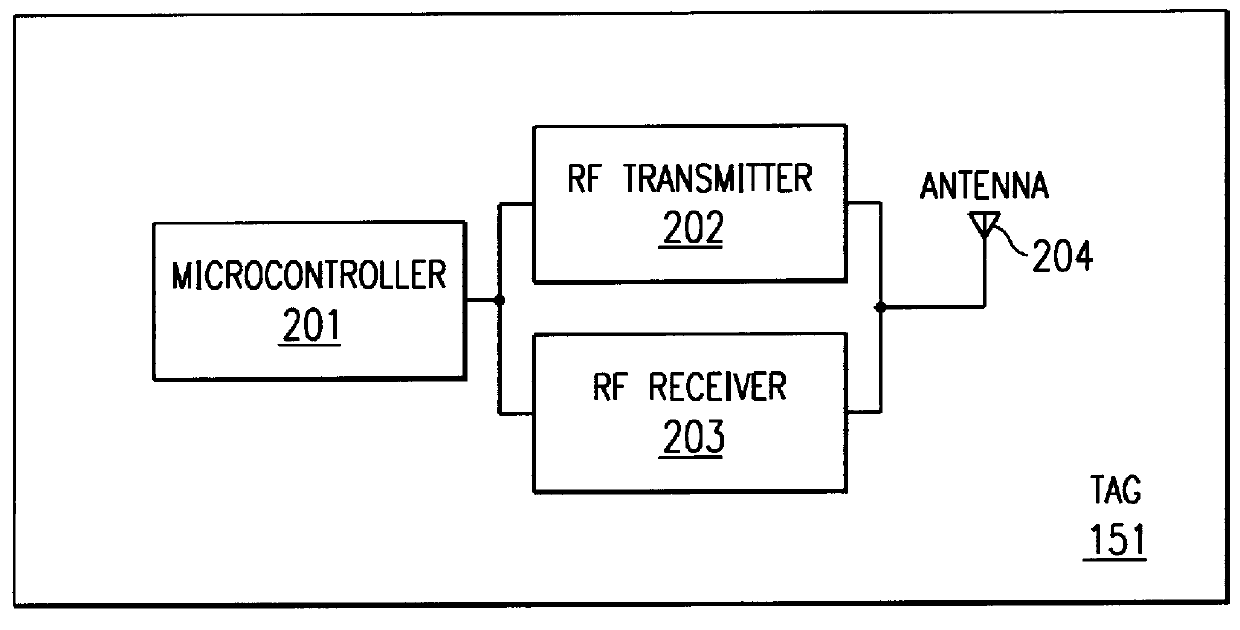
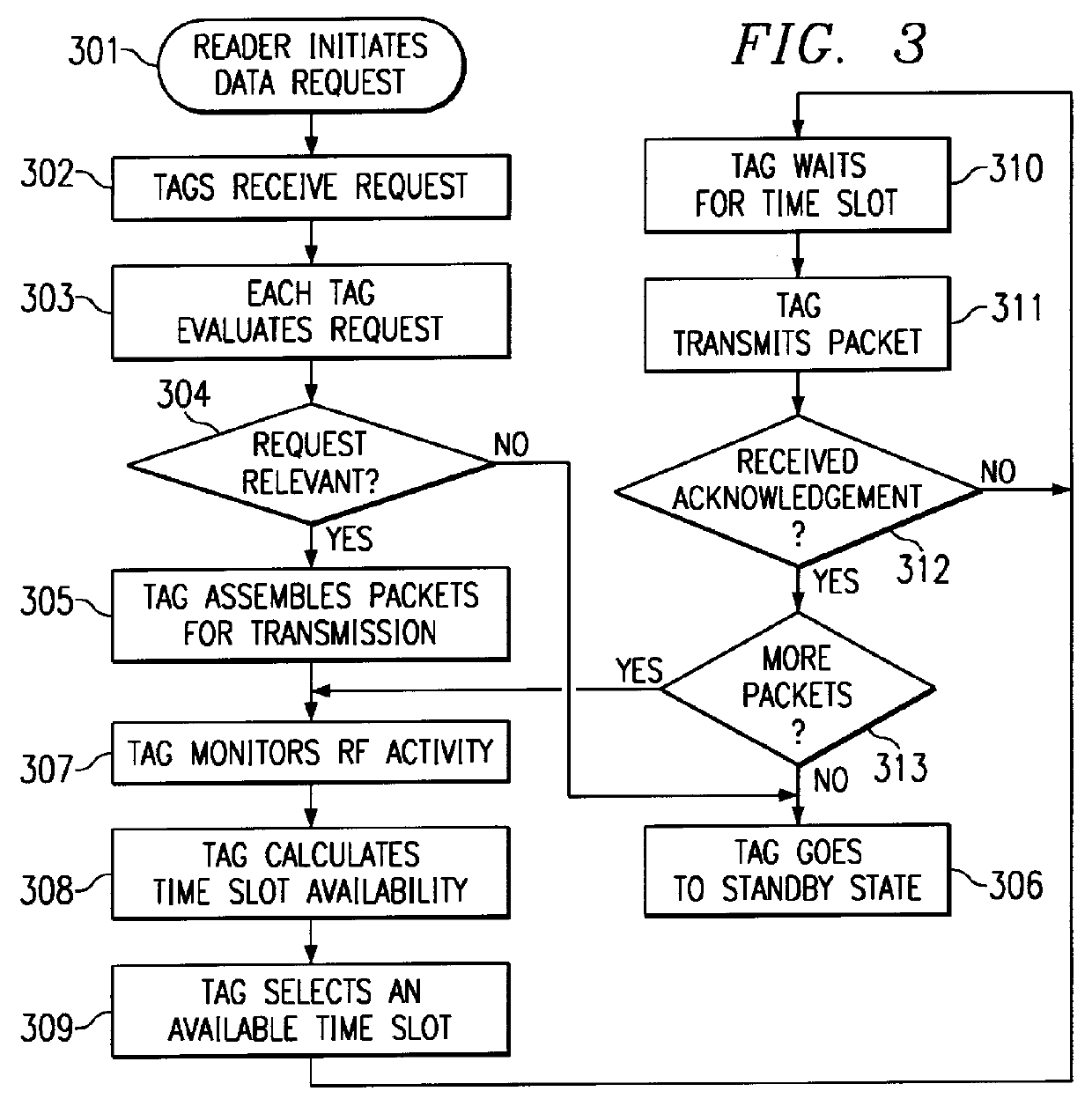
Radio tag system and method with improved tag interference avoidance
InactiveUS6034603ASolution to short lifeLow costTicket-issuing apparatusRoad vehicles traffic controlTransceiverModularity
A data transmission system includes a reader transceiver and one or more tag transceivers. The reader transmits an activation signal to a tag. The tag selectively transmits a response signal to the reader at a specific time determined by a detected level of communications channel activity. The detector operates in a low-power standby state until the time it receives the activation signal, and then operates in an active state. The invention further incorporates a technique to maintain an extremely low power state to the tag during quiescent mode while retaining full sensitivity to reader activation signals. The reader transceivers are of a modular architecture with each module operating independently, yet in concert with the others. The modules are interconnected in a media independent method and can interact remotely with other modules.
Owner:AXCESS INT INC
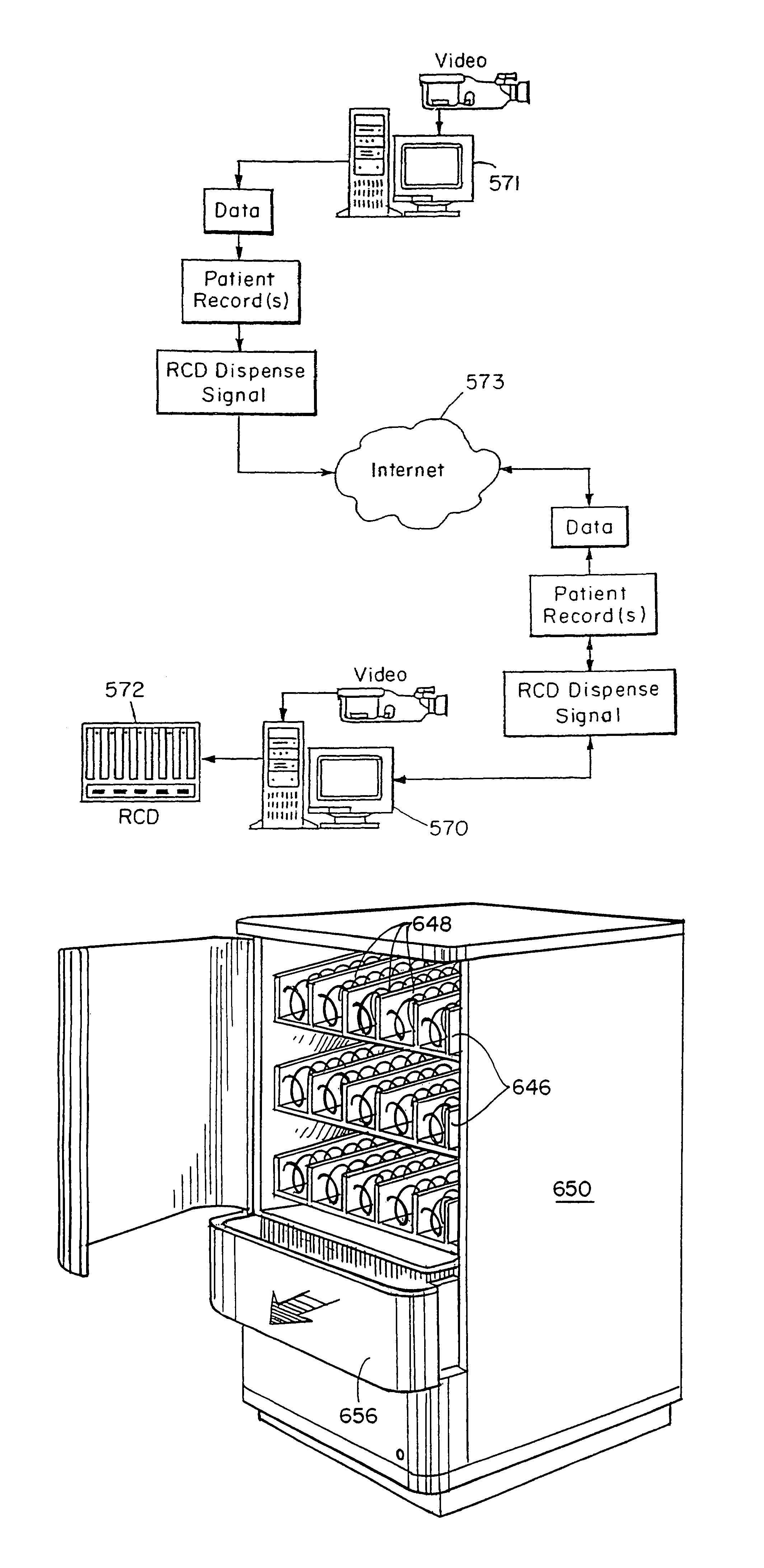
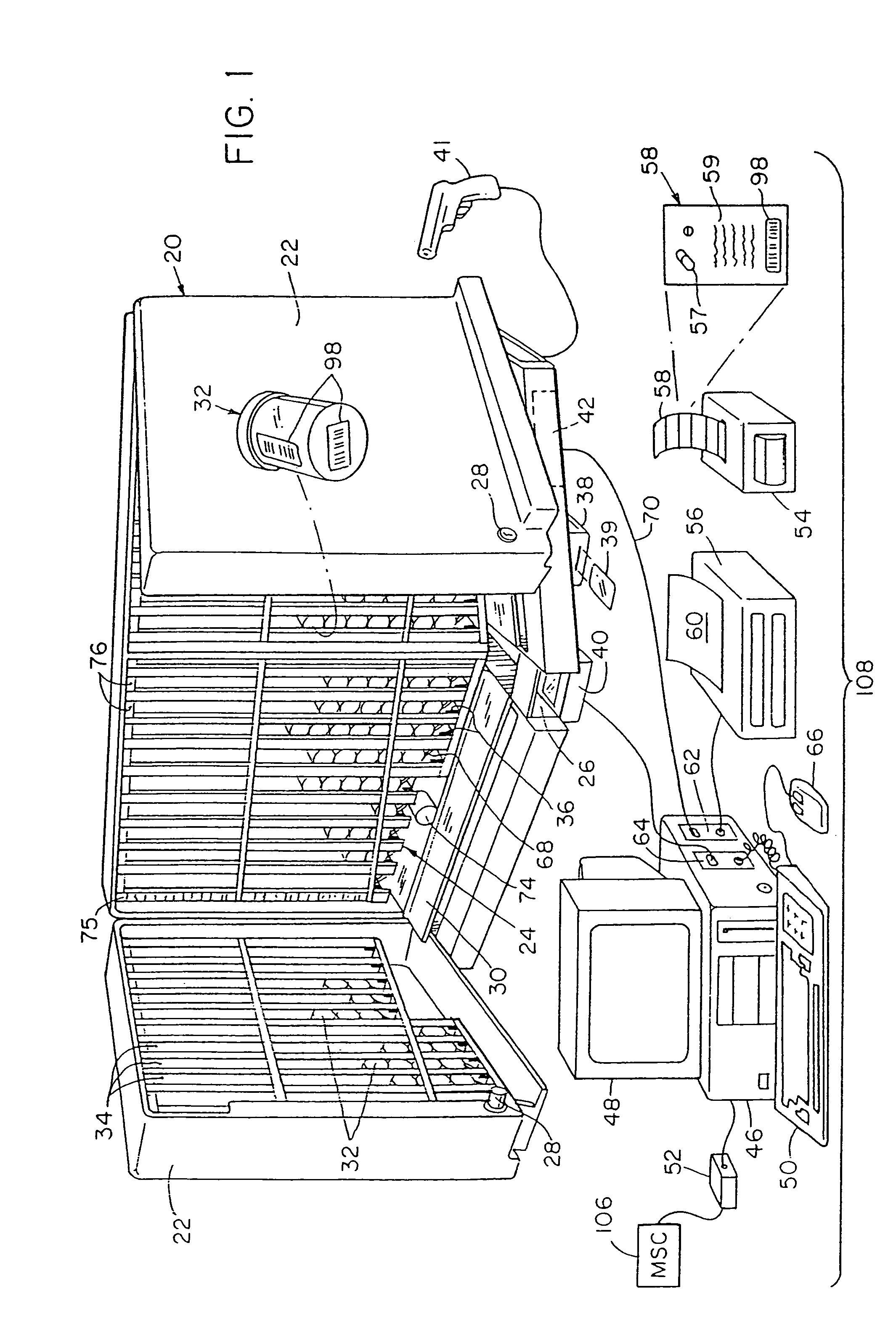
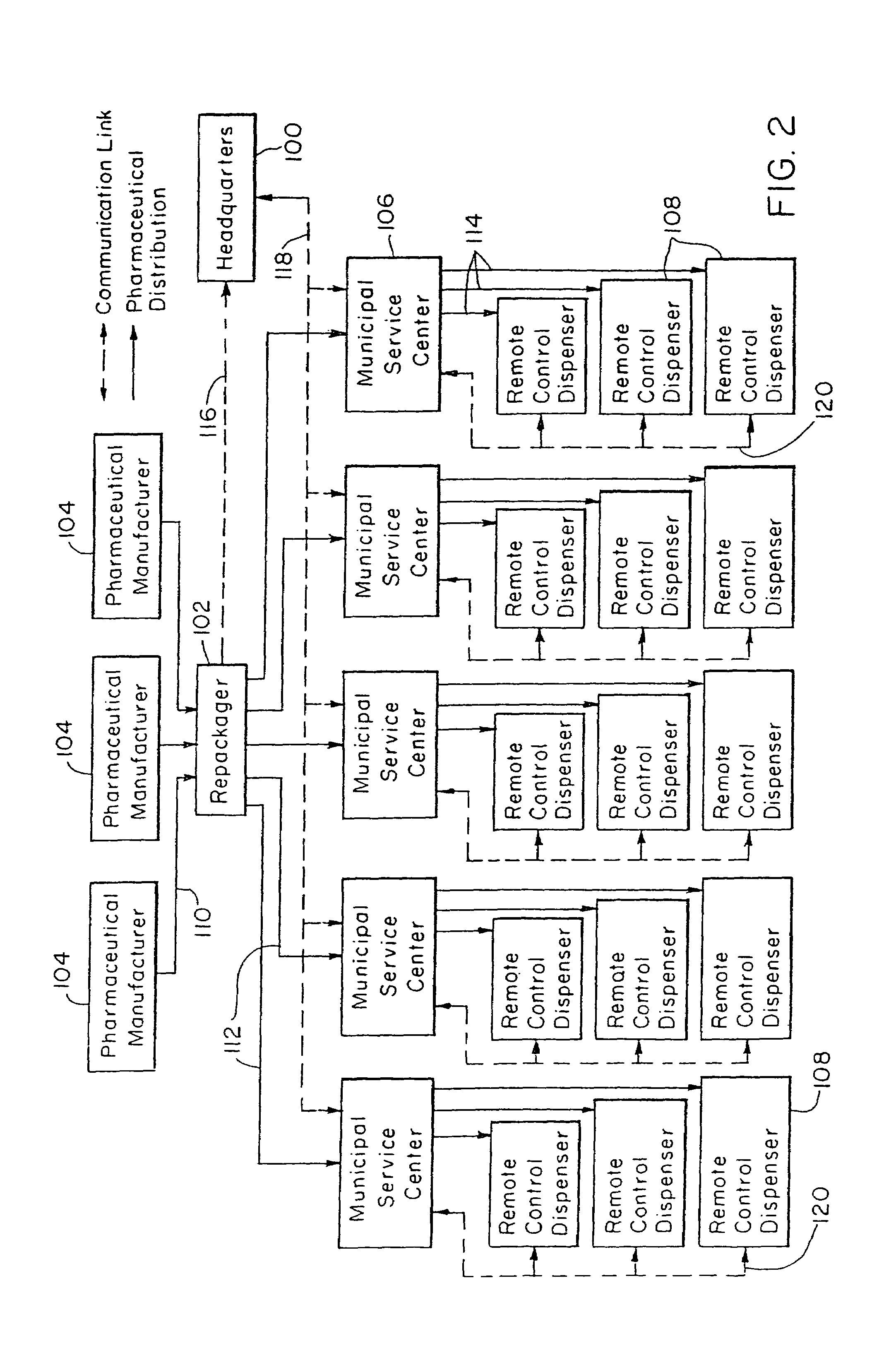
Pharmaceutical dispensing system
InactiveUS7151982B2Safe and convenientSafe and accurateDrug and medicationsComputer-assisted medicine prescription/deliveryDrug dispensingEngineering
An automated drug dispensing system includes a cabinet adapted to store a variety of prepackaged pharmaceuticals in a plurality of bins for filling patient prescriptions. Each bin stores a particular variety of packaged multiple-dose pharmaceutical. Each variety of pharmaceutical is associated with a particular code. A controller receives request signals and in response generates dispense signals. Each bin includes a dispenser coupled to the controller for dispensing the packaged pharmaceuticals therefrom in response to a dispense signal sent from the controller. After a package is dispensed, a code reader determines the code of the dispensed package and verifies whether the code on the dispensed package matches the code of the requested package.
Owner:ARXIUM INC
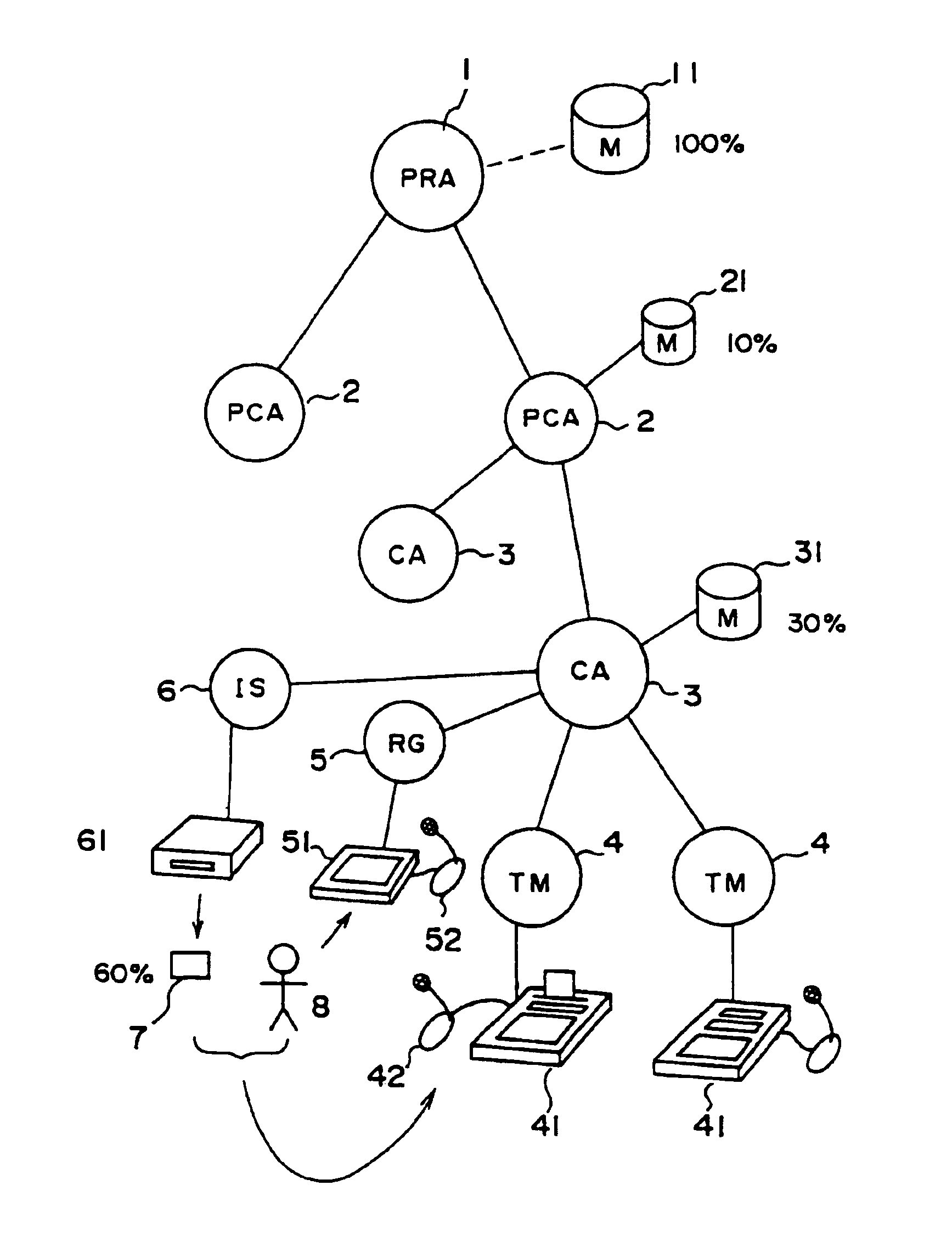
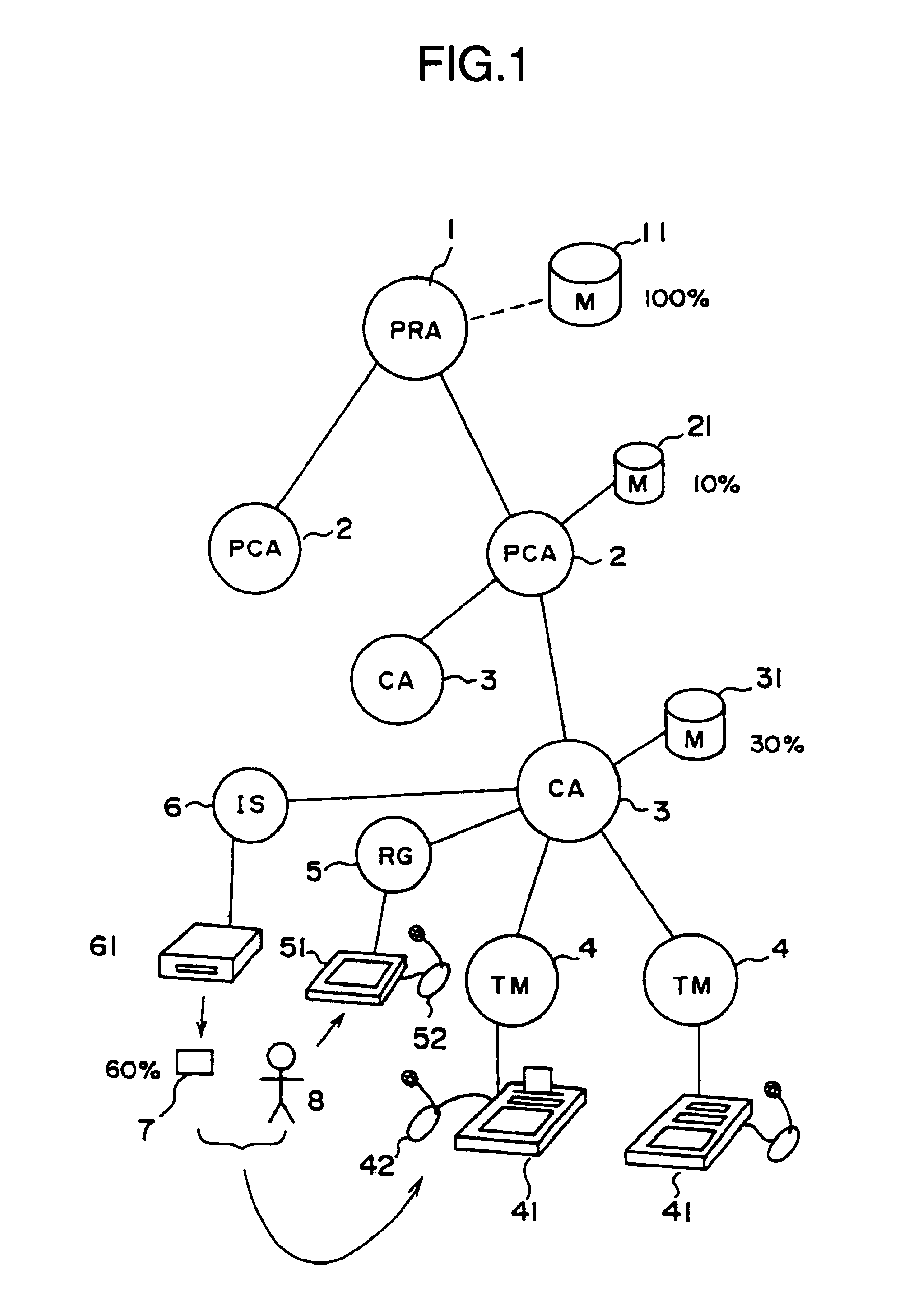
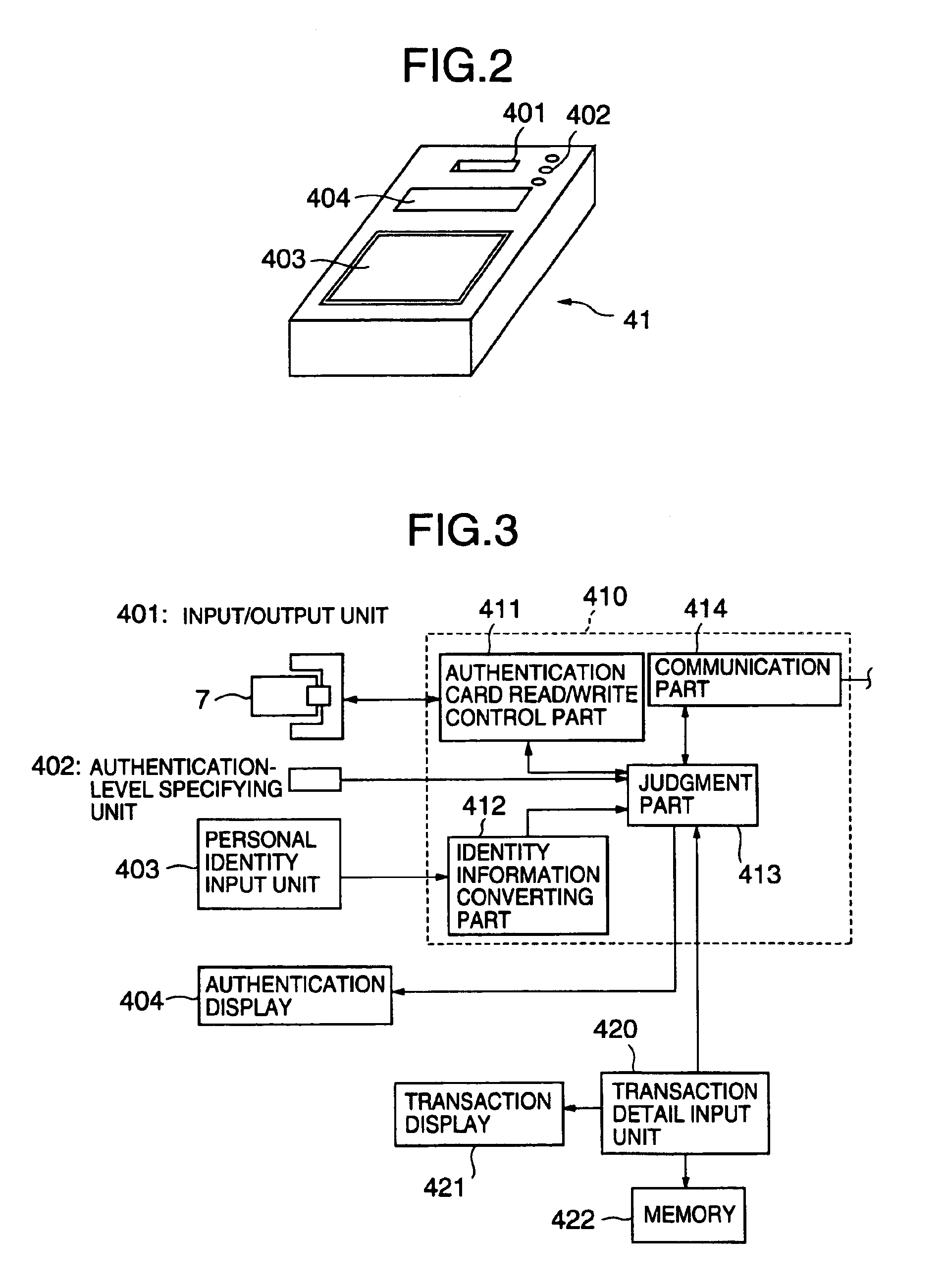
Authentication card system
InactiveUS6990588B1Recognizable more easily and securelyUser identity/authority verificationCo-operative working arrangementsComputer terminalUser authentication
Biological individuality data for use in distinguishing the individuality of a user (8) are picked up, and a user authentication card (7) with at least part of the biological individuality data recorded thereon is issued. The contents of the record in the user authentication card (7) are read out by an authentication-card reader (41), and compared with biological individuality data input by the user through an identity acquisition device. Such personal authentication is directly executed at an authentication access terminal (4). The system also includes certification authorities (2), (3), each of which records part of the biological individuality data so that the certification authorities can additionally authenticate personal identification in response to inquiry from the authentication access terminal (4), thus improving the reliability. The authentication IC card used in the system is provided with a CPU, an authentication file storing identity information, and an application file classified into files according to the depth of authentication.
Owner:YASUKURA YUTAKA
Automated transaction machine and method
InactiveUS20010014881A1Firmly connectedExtension of timeComplete banking machinesFinanceTransaction serviceCard reader
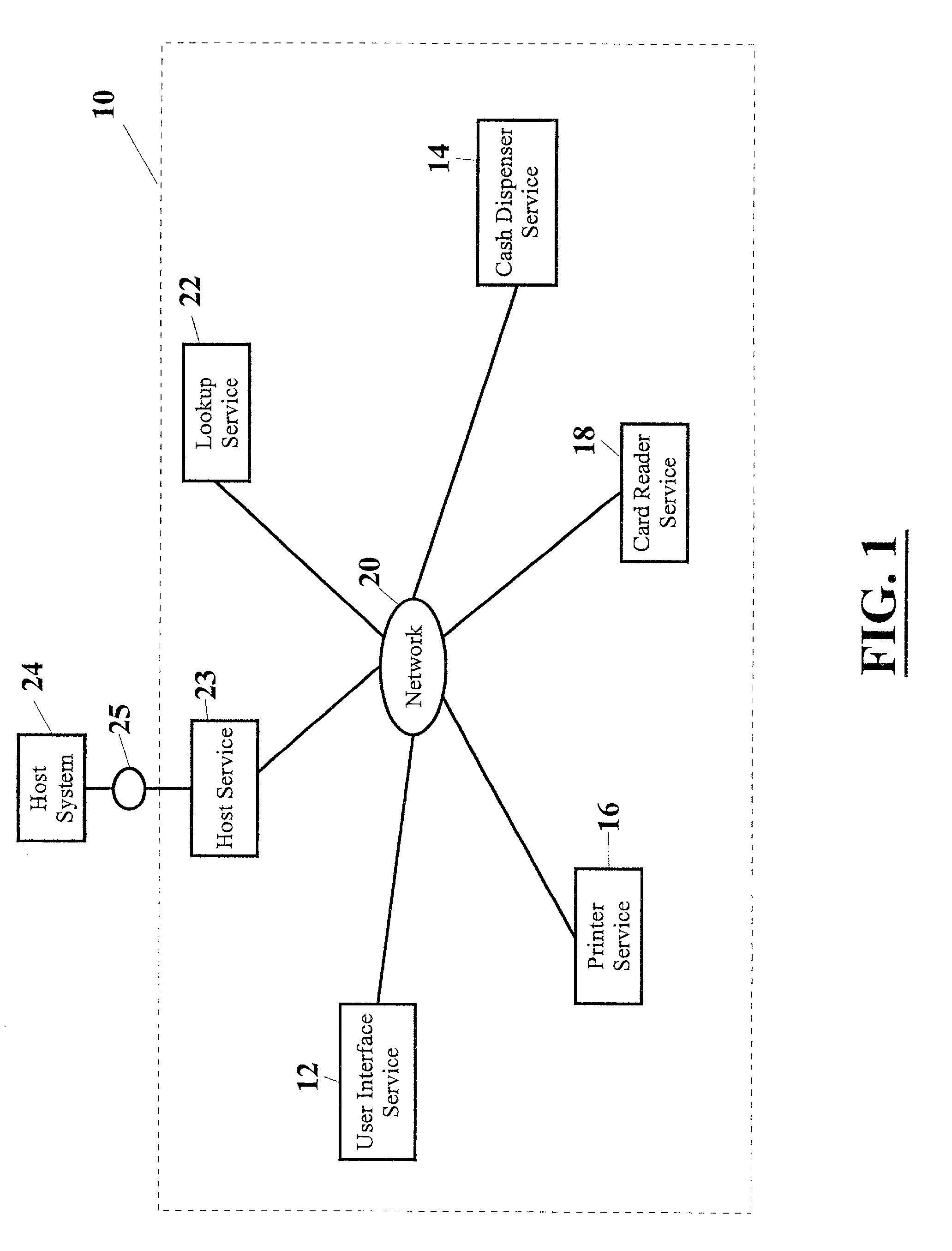
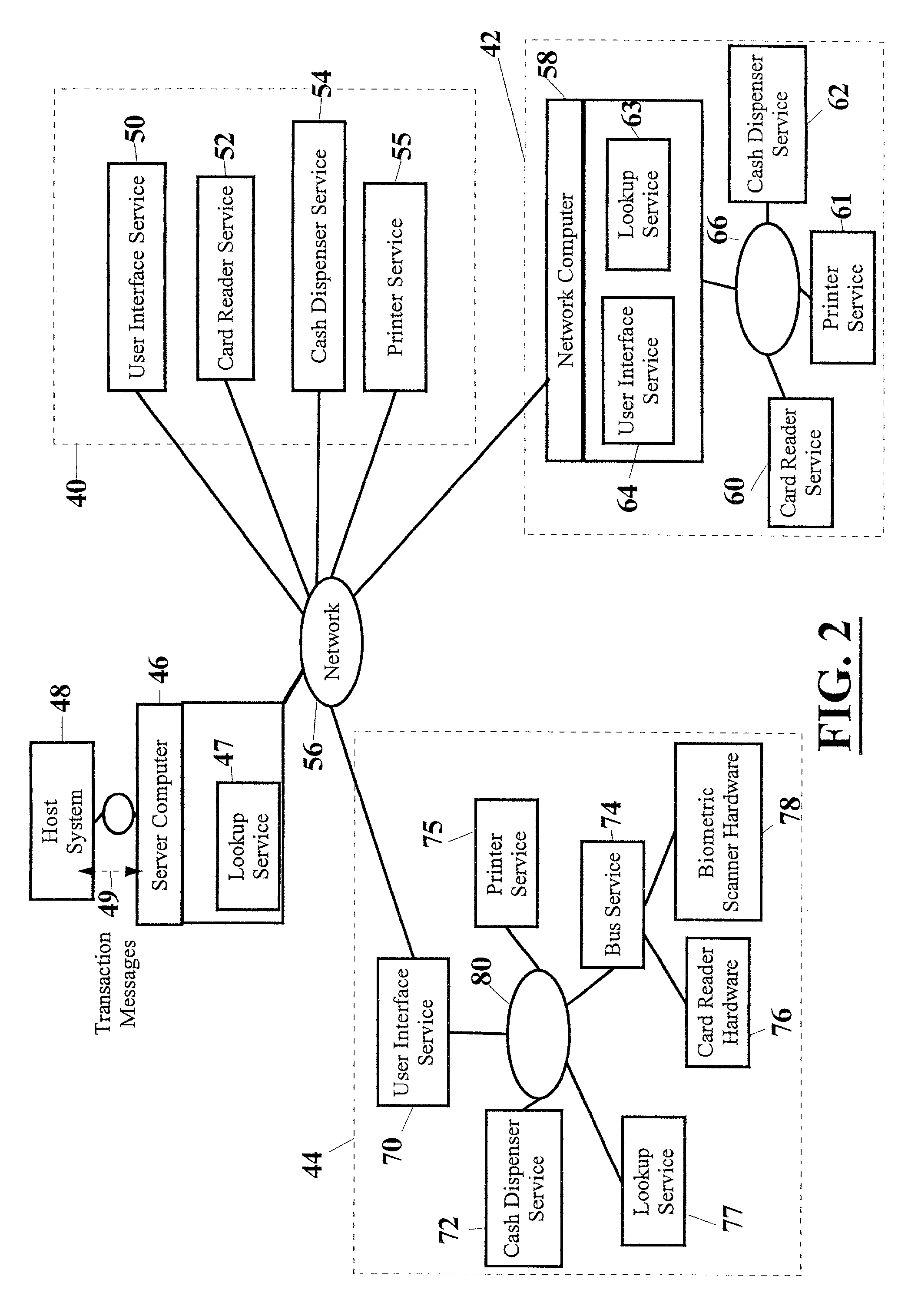
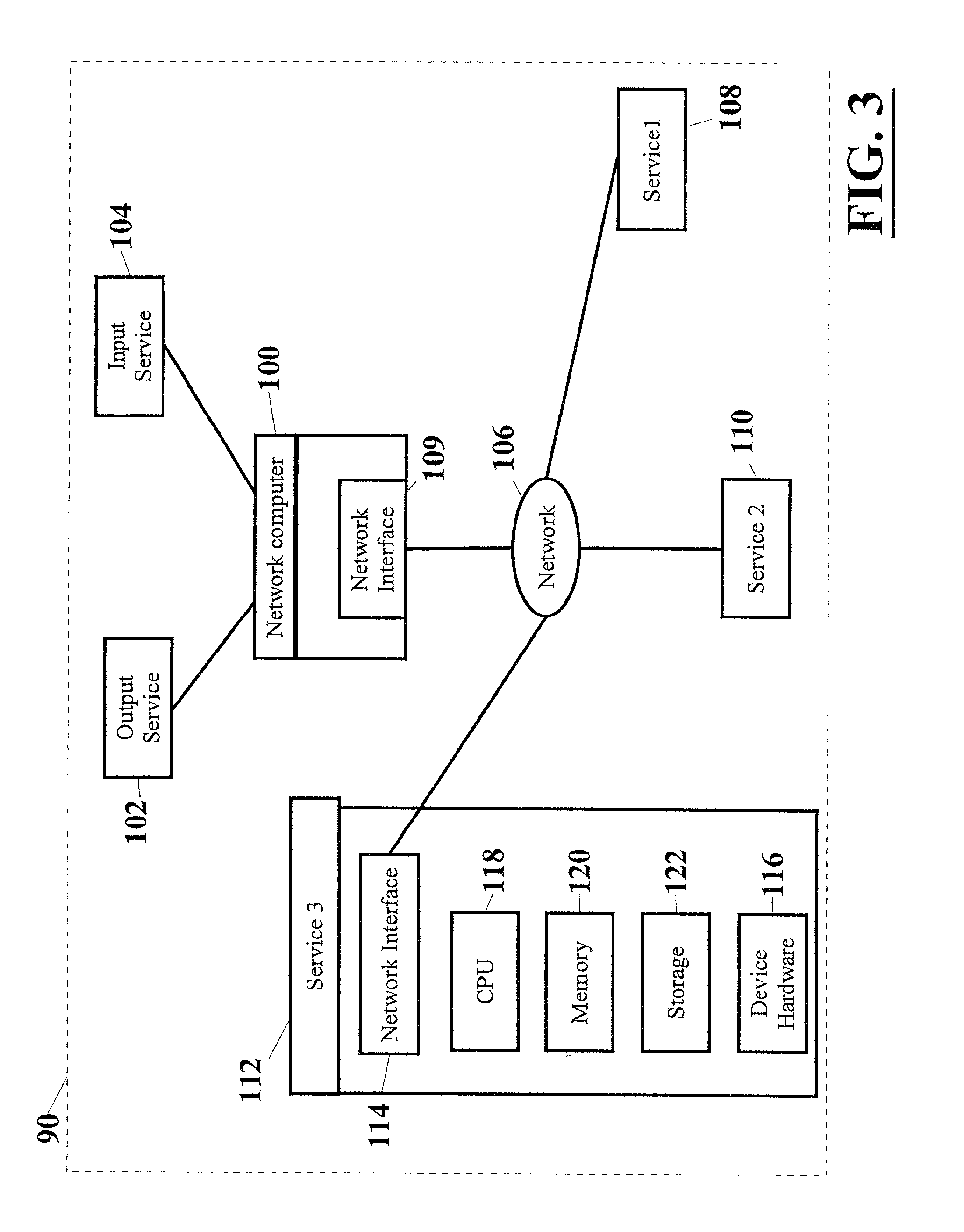
A system for connecting transaction services to an ATM (10, 500) that includes a network (20). A user interface service (12) and a lookup service (22) are in operative connection with the network. Transaction services such as a printer service (16), card reader service (18), and cash dispenser service (14) are also in operative connection with the network. These transaction services are operative to register with the lookup service and to upload a service proxy to the lookup service. The user interface service is operative to locate transaction services on the network by invoking a remote lookup method on the lookup service. The lookup service is operative to return service proxies that match the type of service that is required. The user interface service is further operative to invoke methods of the service proxies that remotely control the functionality of the transaction services on the network. The user interface service is further operative to register events with the service proxies for notification when certain events on the services occur.
Owner:DIEBOLD NIXDORF
Cashless payment system
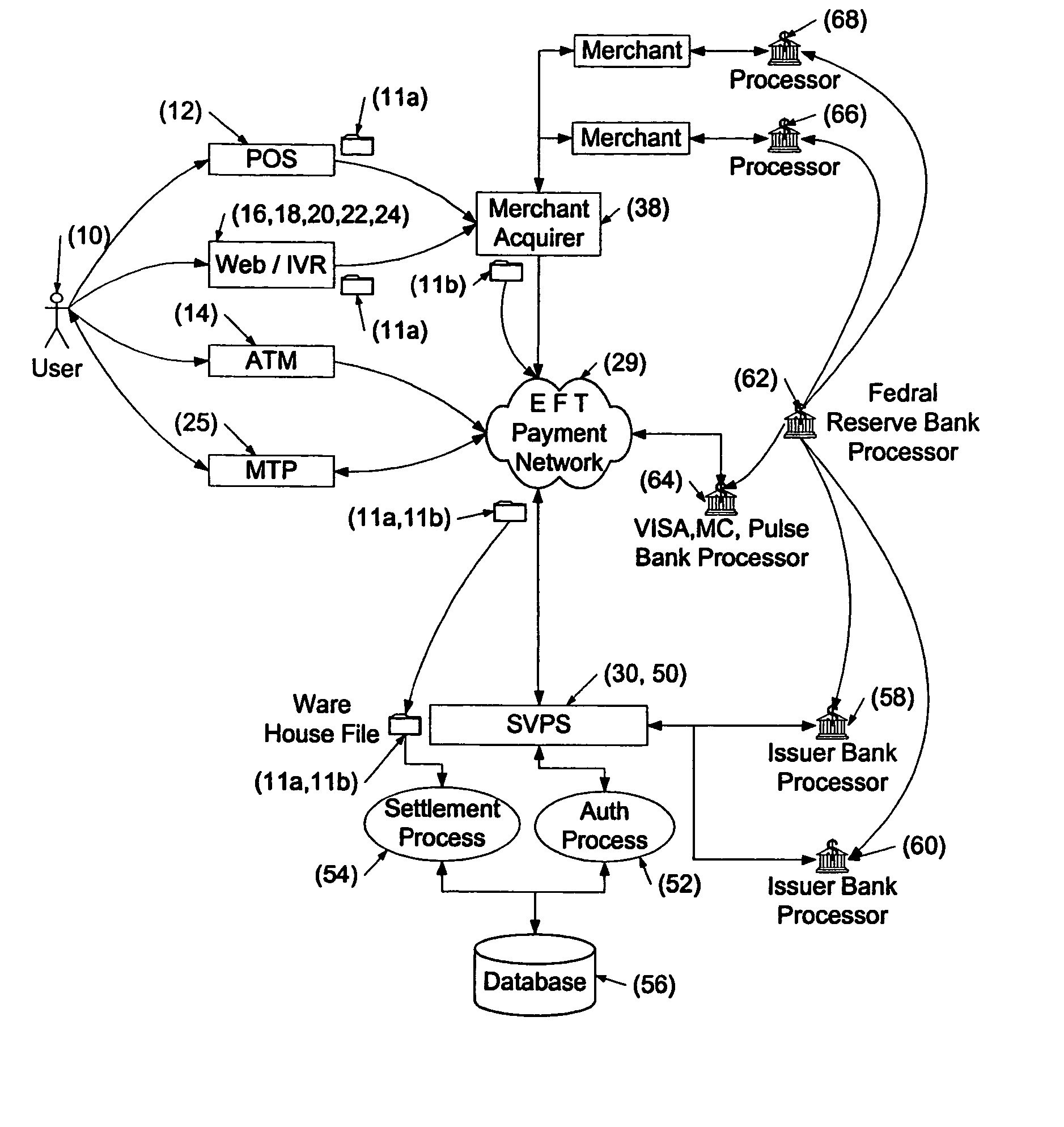
InactiveUS20050015332A1Without any loss of transaction processing flexibilityWidespread acceptanceFinanceBuying/selling/leasing transactionsComputer networkEngineering
A payment system that does not rely on credit or debit cards, does not require the merchant and purchaser to have compatible memberships to complete a transaction, and does not limit single transactions to a single account provides a wide range of flexibility permitting debit, credit, pre-paid and payroll cards to be accommodated in a seamless and invisible manner to the electronic transaction network. The transaction may be verified and approved at the point-of-sale whether or not the merchant is a member of a specific financial transaction system. Specifically, the point-of-sale transaction system permits an identified customer to use any of a variety of payment options to complete the transaction without requiring the merchant to pre-approve the type of payment selected by the customer. In one configuration, and in order to take advantage of the widespread use of the ATM / POS network, the invention uses a typical credit / debit card format to provide the identifying information in a stored value card. When a transaction is to be completed, the user enters the identifying information carried on the card at the point-of-sale. This can be a merchant or other service provider at a retail establishment, or on-line while the user is logged onto a web site, or other location. The information can be swiped by a card reader, or manually entered via a keyboard or other input device. The system supports a wide range of flexibility, permitting issuing systems such as parents and state welfare agencies to restrict the types of authorized uses, and permitting users to access accounts in a prioritized manner. Further, the accepting merchant is not required to be a member because settlement with the merchant may be made via the Federal Reserve Automatic Clearing House (ACH) system by typical and standard electronic transfer. This permits the merchant to take advantage of the lower ACH transaction fees with even greater convenience and flexibility than the current ATM / POS system. The system supports numerous types of identification methods from typical credit card structures with magnetic data strips to various biometric systems such as finger prints, facial recognition and the like. Specifically, once the user is identified, the transaction is managed by his membership data on record with the transaction processing system.
Owner:ECOMMLINK
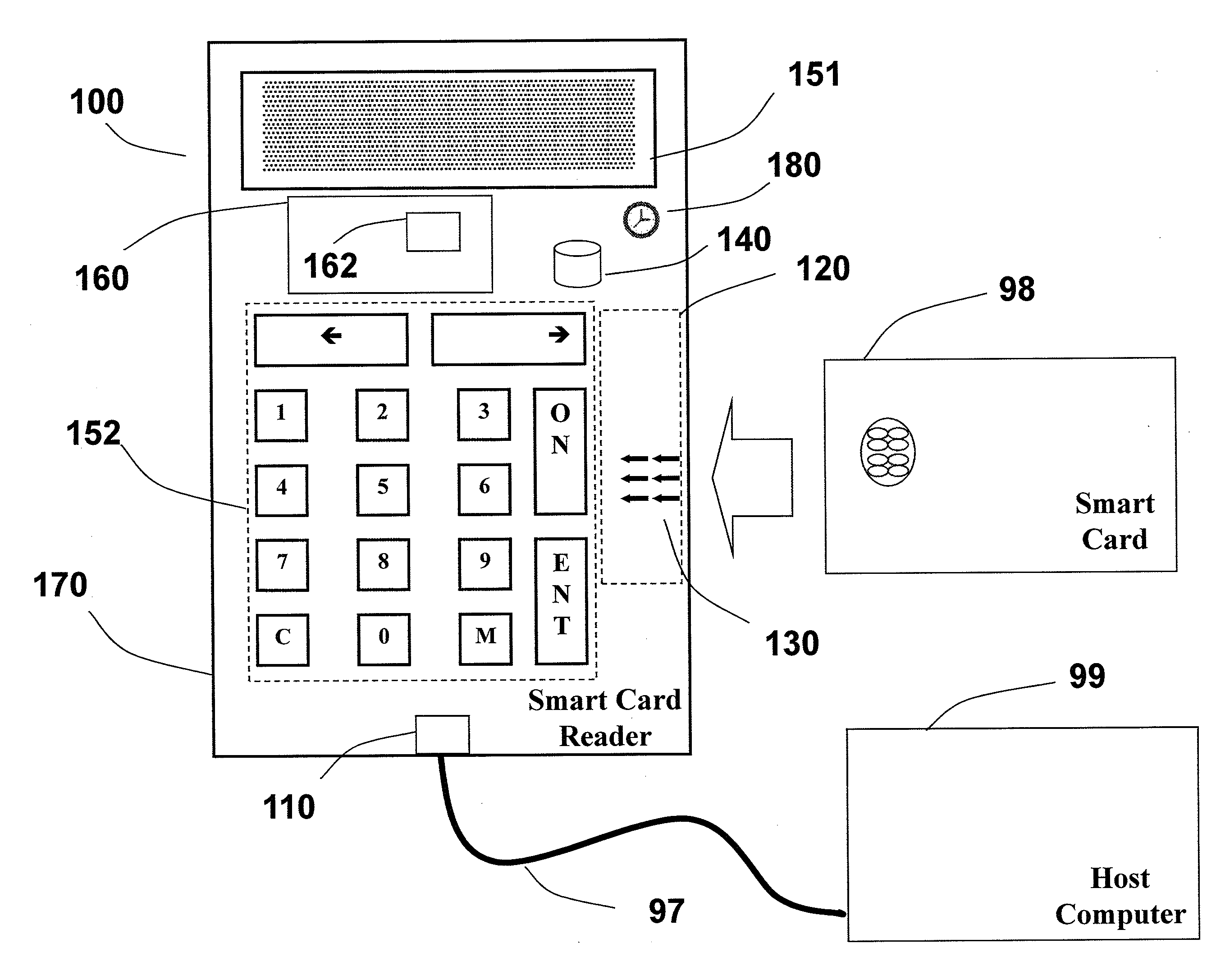
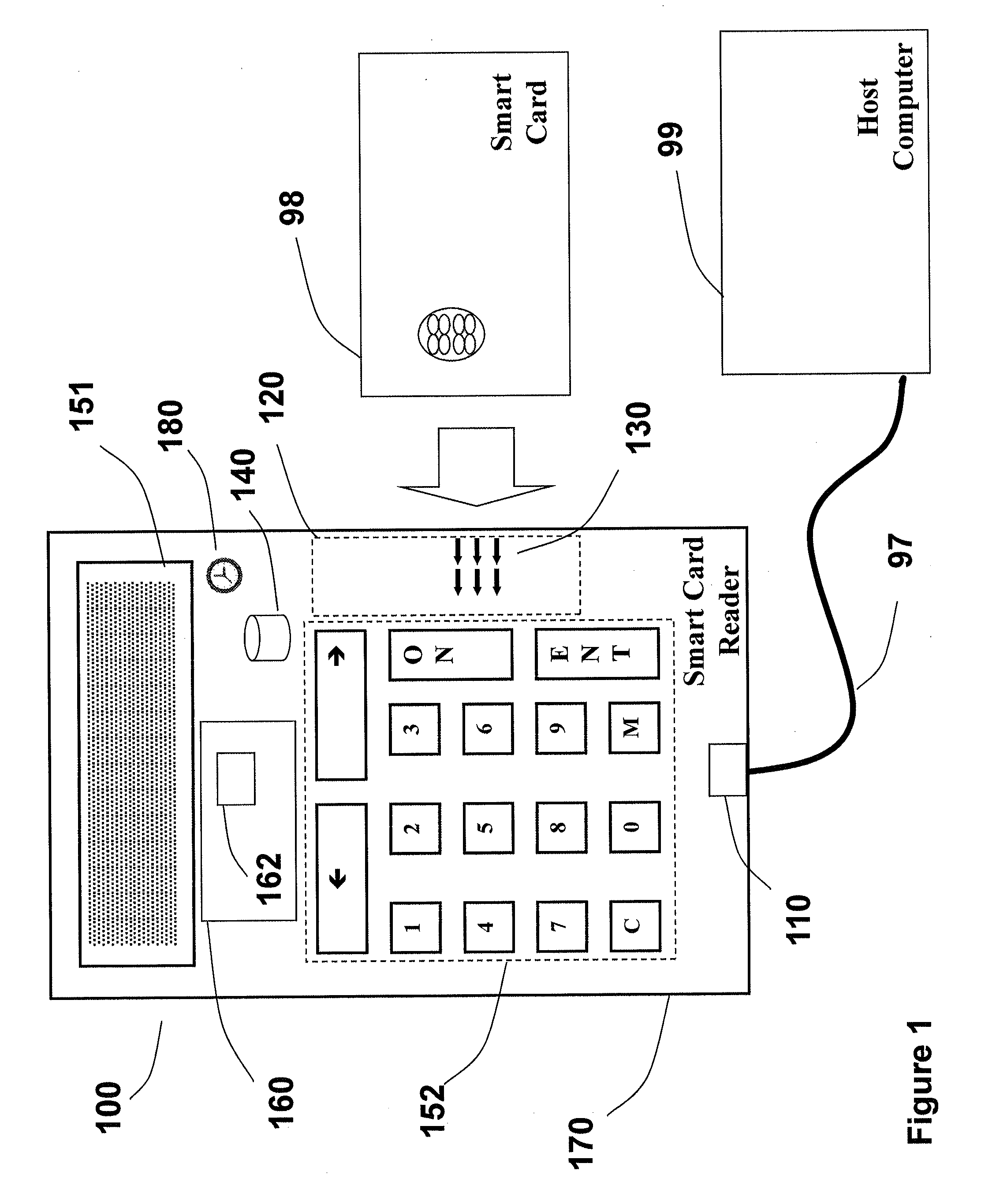
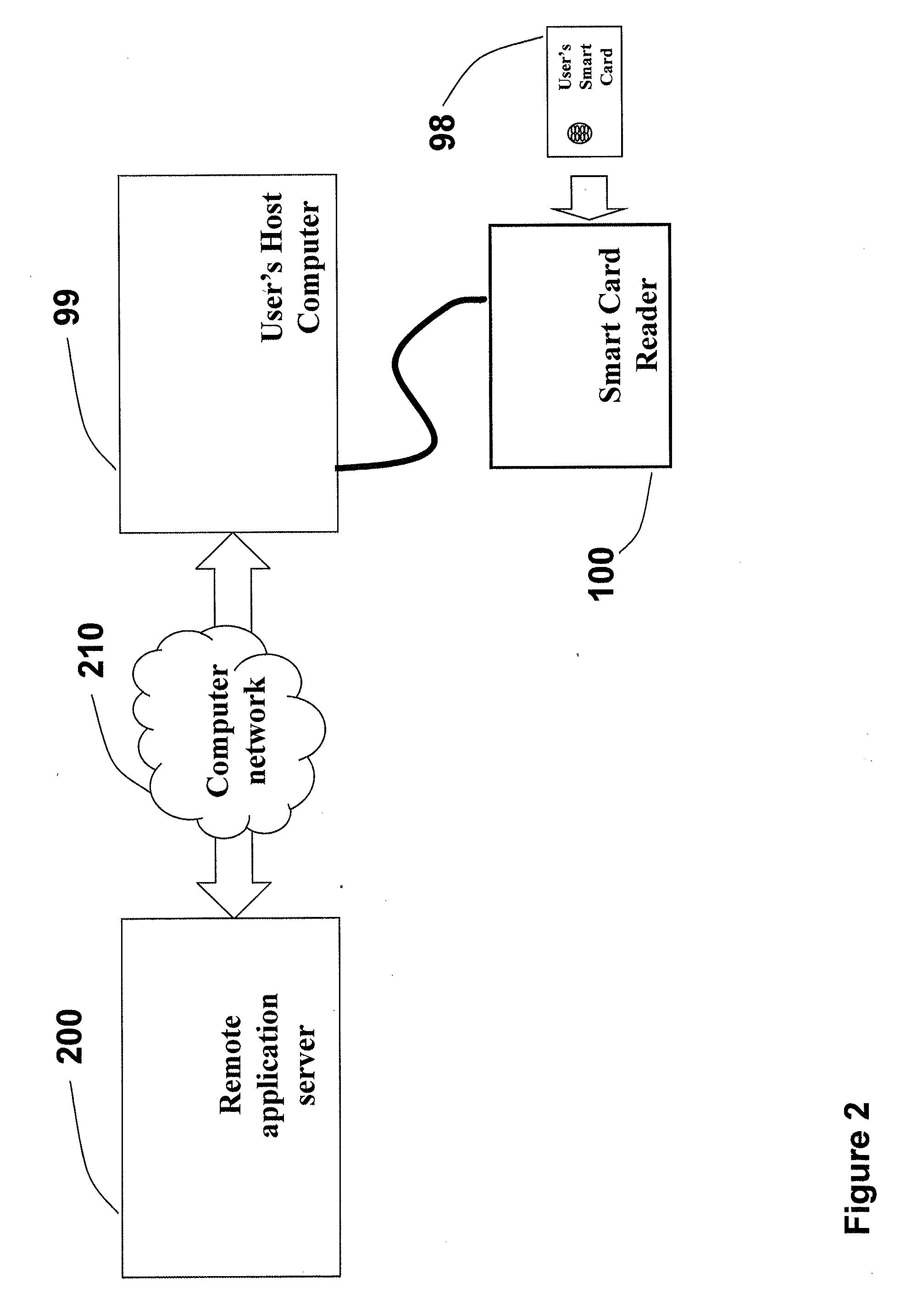
Smart card reader with a secure logging feature
A secure smart card reader is disclosed that is enabled to make reader signatures on data representative of events and actions which may be security related and which may include data representative of reader commands received from a host or remote application, smart card commands exchanged with an inserted smart card, data presented to a user for approval, and / or configuration parameters applied when dealing with any of the foregoing. The smart card reader may be adapted to maintain logs of events and actions which may include exchanging reader commands, exchanging smart card commands, and / or interactions with a user. The logs may include data representative of the reader commands received, the smart card commands exchanged, data presented to the user for approval, and / or configuration parameters applied when dealing with any of the foregoing. The secure smart card reader may be adapted to generate a reader signature over the logs.
Owner:ONESPAN NORTH AMERICA INC
Targeted marketing and purchase behavior monitoring system
A system for presenting customized special offers to customers, the special offers including targeted offers to a customer selected from a plurality of customers, and for collecting purchasing behavior information concerning the customers, the system comprising a computer including a database containing customer account information providing information specific to a particular customer account; the at computer also including a database containing special offers including a targeted offer which is to be made to selected customer accounts on the basis of targeted offer targeting parameters; a plurality of customer cards, each customer card having machine readable card information indicating at least identification of the card with a particular customer account; a customer interface in communication with the computer to transfer data therebetween; the customer interface having a card reader for reading machine readable card information from the customer card; the computer including means for generating a customized customer offer list available to that particular customer account which includes the special offer; an offer communicator for communicating the customer offer list to the customer for which it is generated; a check-out at which the customer presents purchased item information indicating items being purchased by the customer; the check-out including a card reader for reading the customer card; the computer including means for sending information from the customized customer offer list to the check-out; the computer further including means for collecting customer purchase information which is indicative of items being purchased by the customer via the check-out; the computer still further including means for editing the customer account information to reflect items purchased by the customer.
Owner:CATALINA MARKETING CORP
Universal, biometric, self-authenticating identity computer having multiple communication ports
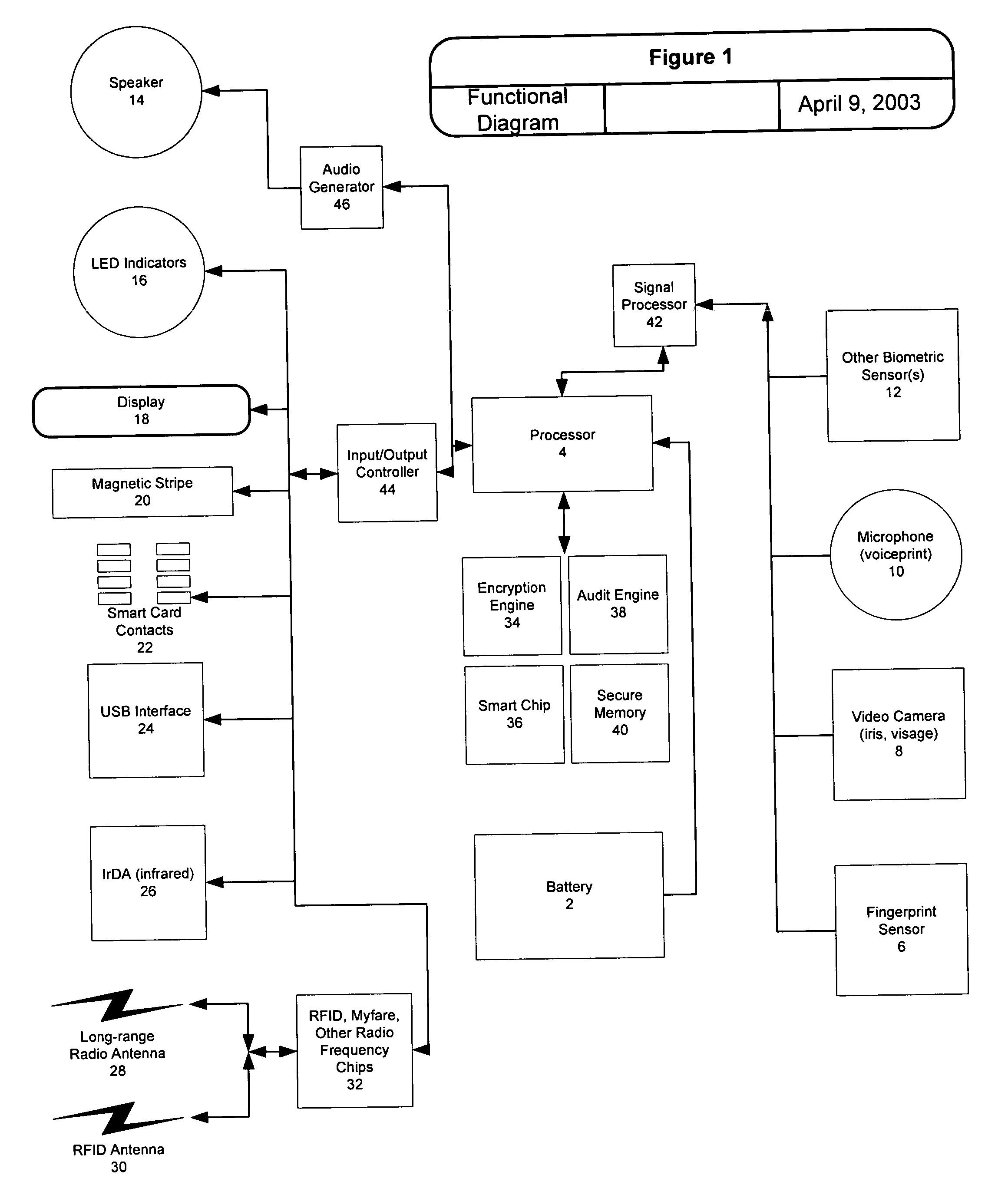
InactiveUS20050039027A1Limited accessIncrease profitDigital data authenticationSecret communicationUser inputSmart card
An improved device for use in authorizing transactions and performing applications is provided by the present invention. The device uses a local processor and secure data storage in conjunction with a variety of sensors to perform authentication processes that establish an individual's identity and provide authority to perform a desired transaction. The sensors allow the device to directly scan biometric identifying information from an individual. A card swipe interface and a proximity antenna are provided to facilitate communication between the device and remote interface devices such as magnetic swipe card readers, smart card readers, infrared communications ports and proximity and long range radio scanners. In addition, the local processor, memory, display and user inputs allow the device to run applications such as those performed by a traditional computer, gaming device or personal data assistant.
Owner:SECURE BIOMETRIC
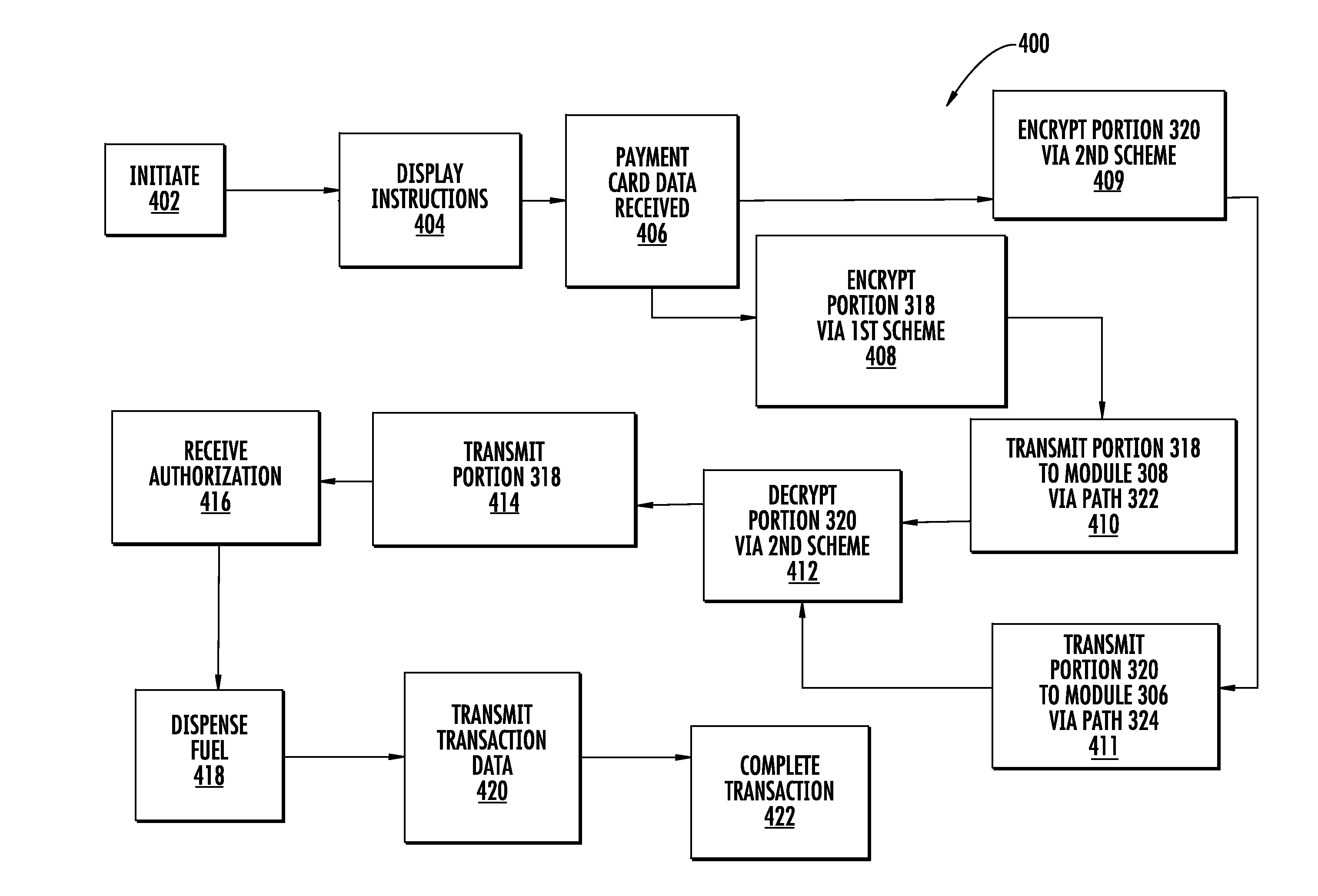
Fuel dispenser payment system and method
A system and method for effecting payment transactions comprising a card reader configured to encrypt a first portion of payment card data received by the card reader from a payment card according to a first encryption scheme associated with the financial institution responsible for an account associated with the payment card and to encrypt a second portion of the payment card data according to a second encryption scheme, where the first portion is sufficient to identify the payment card or account number and to effect a payment transaction involving the payment card or account and where the second portion is sufficient to identify the financial institution but insufficient to identify the payment card or account number.
Owner:GILBARCO
Identity verification system with self-authenticating card
InactiveUS20050212657A1Easy to compareImprove accuracyElectric signal transmission systemsDigital data processing detailsData matchingCard reader
An identity verification system that includes a self-authenticating identity card and a card reader. The self-authenticating card has a programmable microchip with data pertaining to the authorized card bearer, including data for a stored biometric feature, such as a fingerprint, a retinal scan, a voice print, a DNA sequence, etc. The card also includes a biometric sensor that senses an applied biometric feature and a data lock that releases data upon determinination of a match between the stored and the applied biometric features. In order to self-authenticate the card, the card bearer must provide the applied biometric feature. For example, the card bearer applies a finger tip to the sensor, if the applied biometric feature is a fingerprint. If the data match, the data lock transmits data stored on the card to the card reader for processing.
Owner:SIMON RUDY
Payment cards and devices operable to receive point-of-sale actions before point-of-sale and forward actions at point-of-sale
PendingUS20090159663A1Shorten the timeEasy to changeImage enhancementImage analysisWaiters/waitressesUser input
A payment card or other device (e.g., mobile telephone) is provided with a magnetic emulator operable to communicate data to a magnetic stripe read-head. A user can utilize buttons located on the card to perform activities that would otherwise be performed at an ATM, payment card reader, or by a waitress. A user can provide instructions on a card to accelerate a transaction. The information a user enters can be communicated to a point-of-sale device. For example, a user can enter into his / her card that the user desires $100 withdrawal from a checking account. The user can also enter his / her PIN into the card. The user can swipe his / her card into an ATM and instantly be provided with the desired $100.
Owner:DYNAMICS
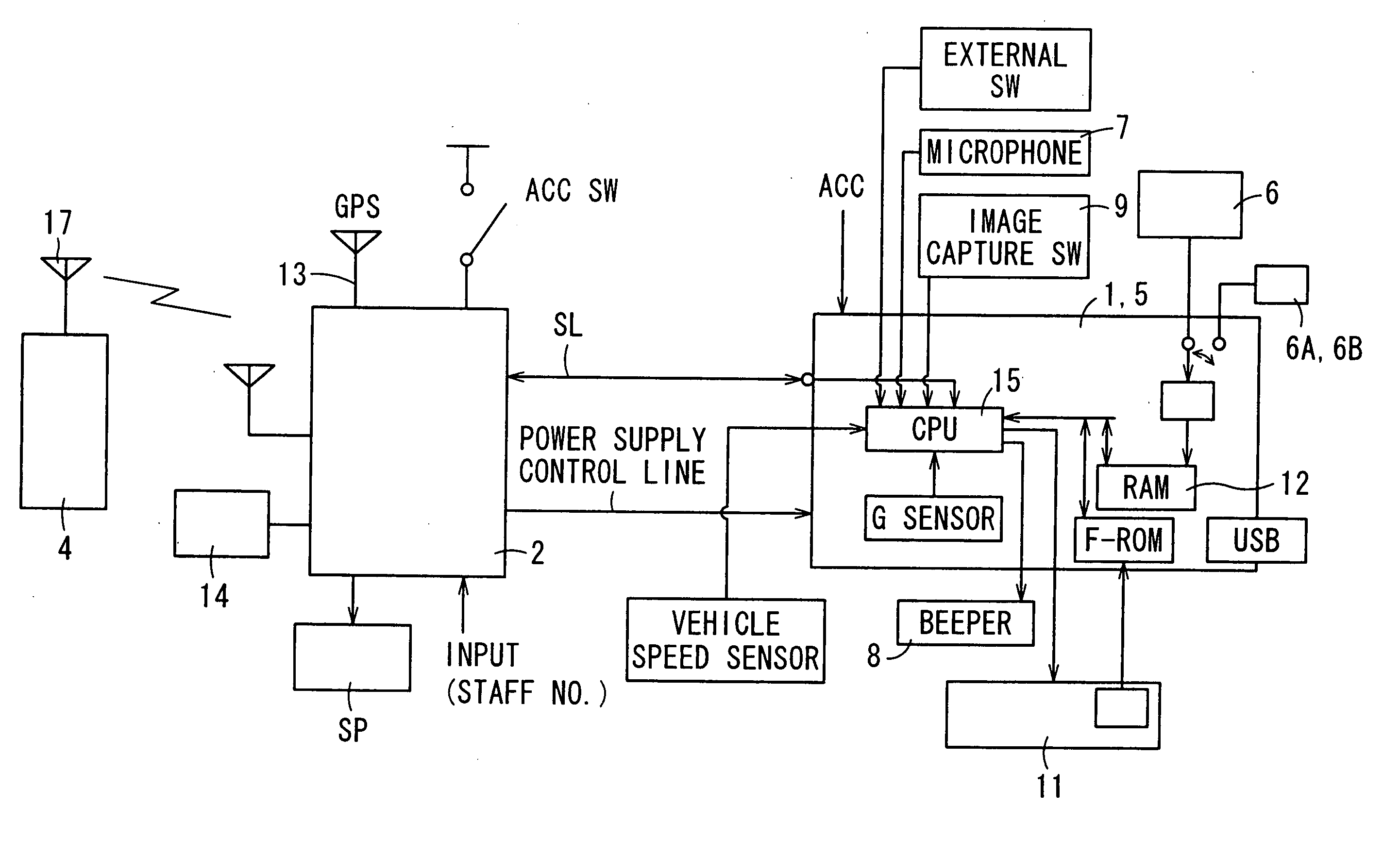
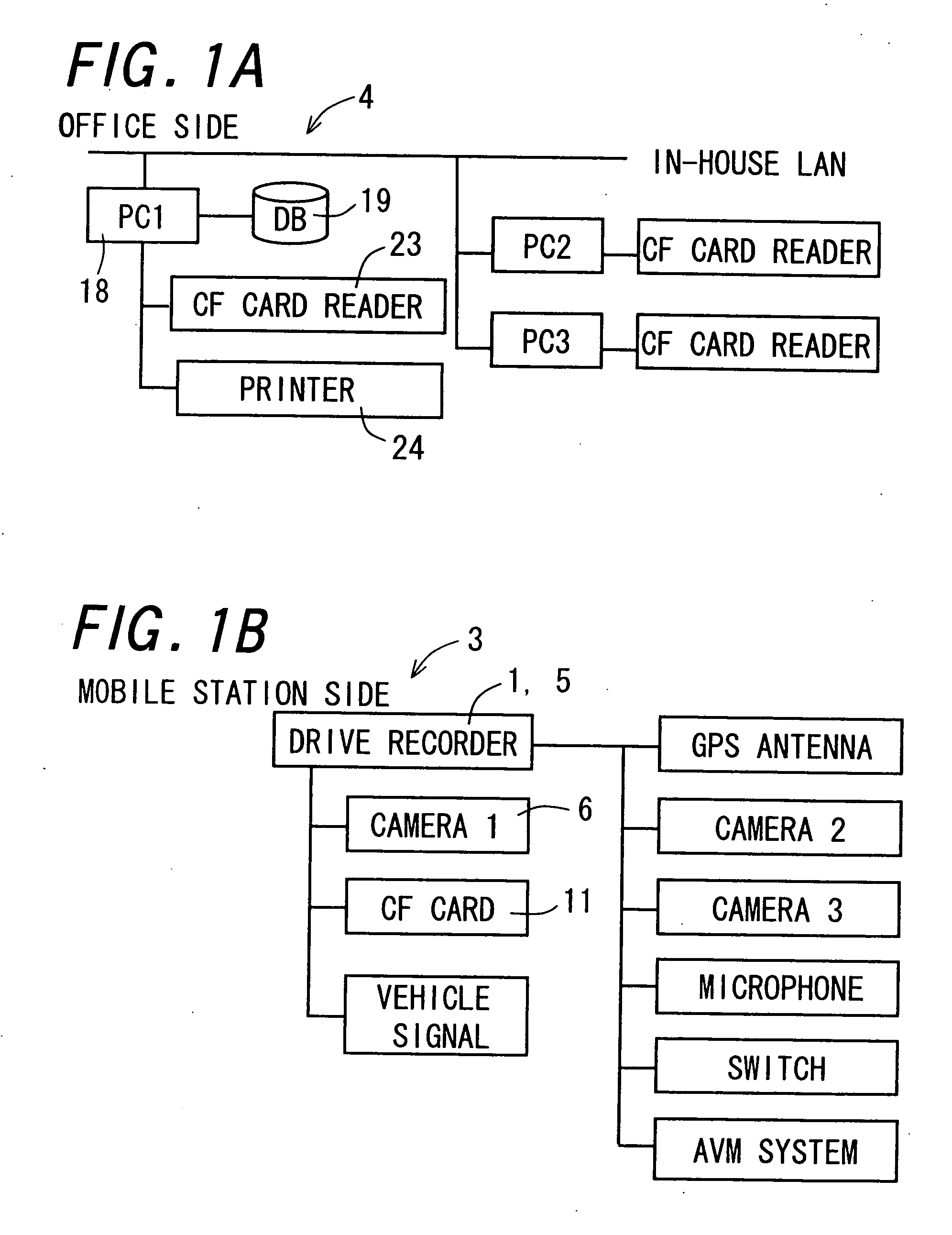
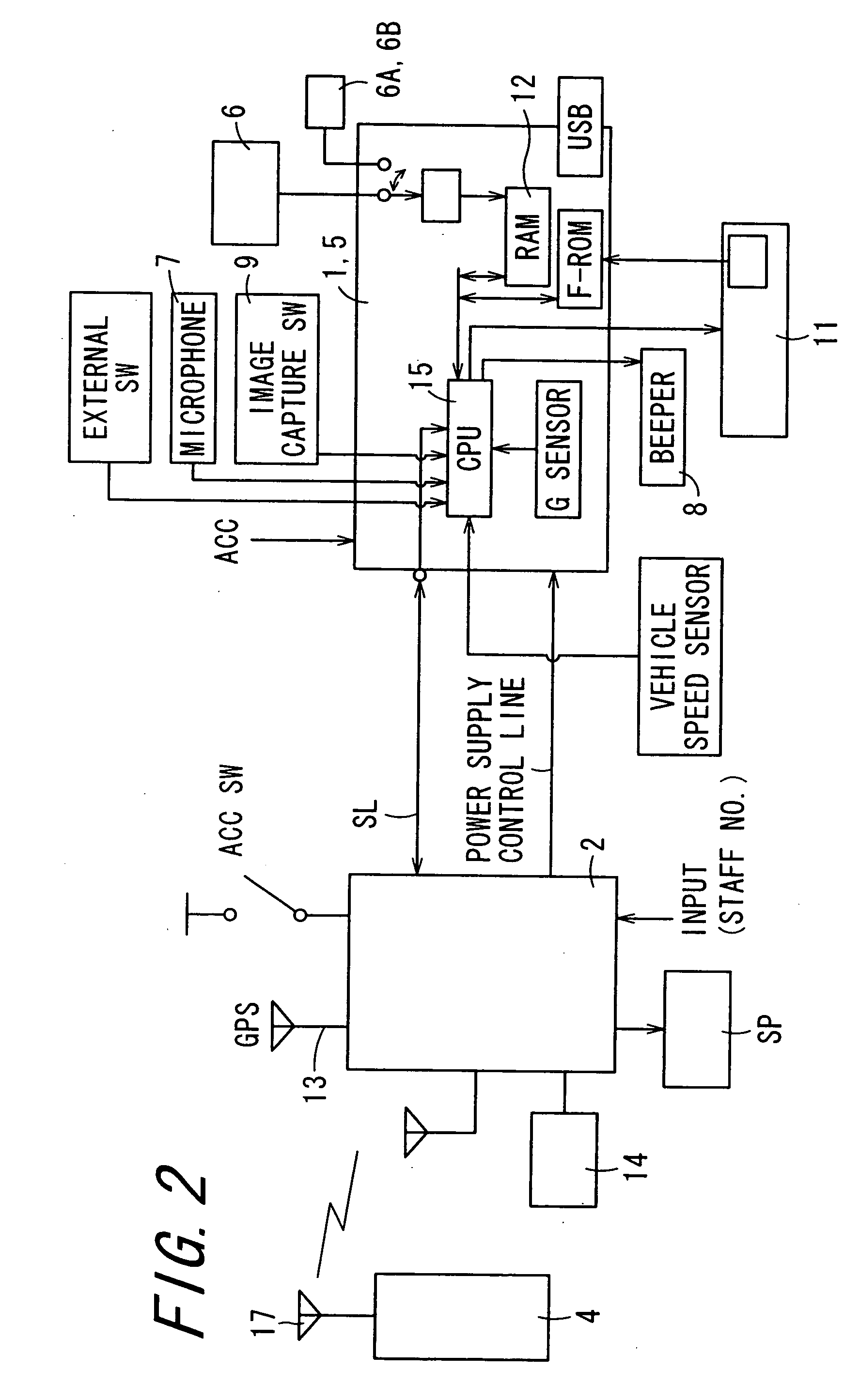
Driving information analysis apparatus and driving information analysis system
InactiveUS20070122771A1Cosmonautic condition simulationsRegistering/indicating working of vehiclesInformation analysisDriver/operator
A driving information analysis apparatus which serves well to assist drivers' safe driving with the ease of checking analysis results is provided. Based on driving information read by a CF card reader, a vehicle mark is displayed on a map to indicate position information of a vehicle when an event occurs. Simultaneously with the vehicle mark, a surrounding image of the vehicle corresponding to the position information is displayed on a display section. Such displays favorably help analyze what situation occurs where.
Owner:FUJITSU GENERAL LTD
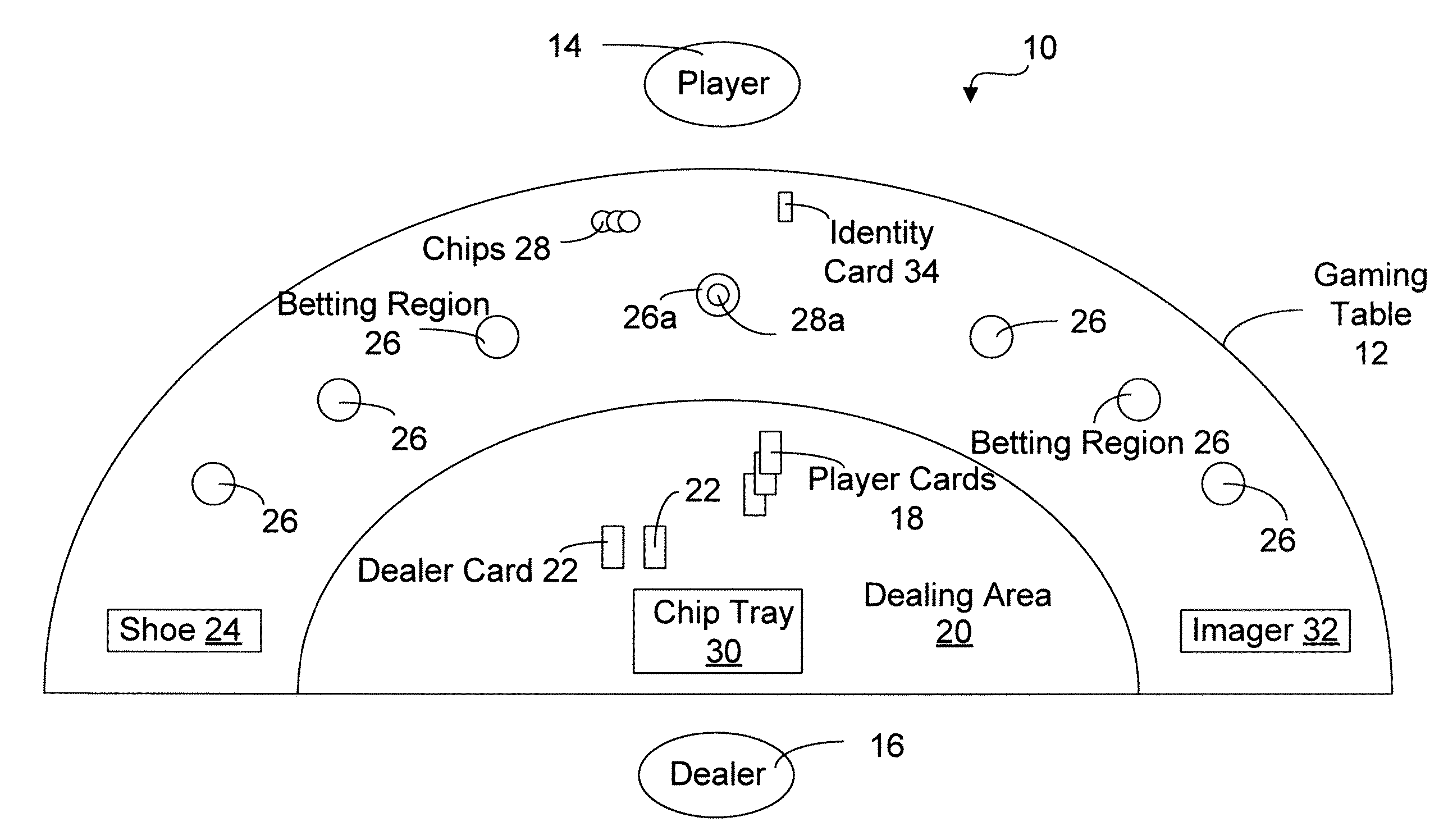
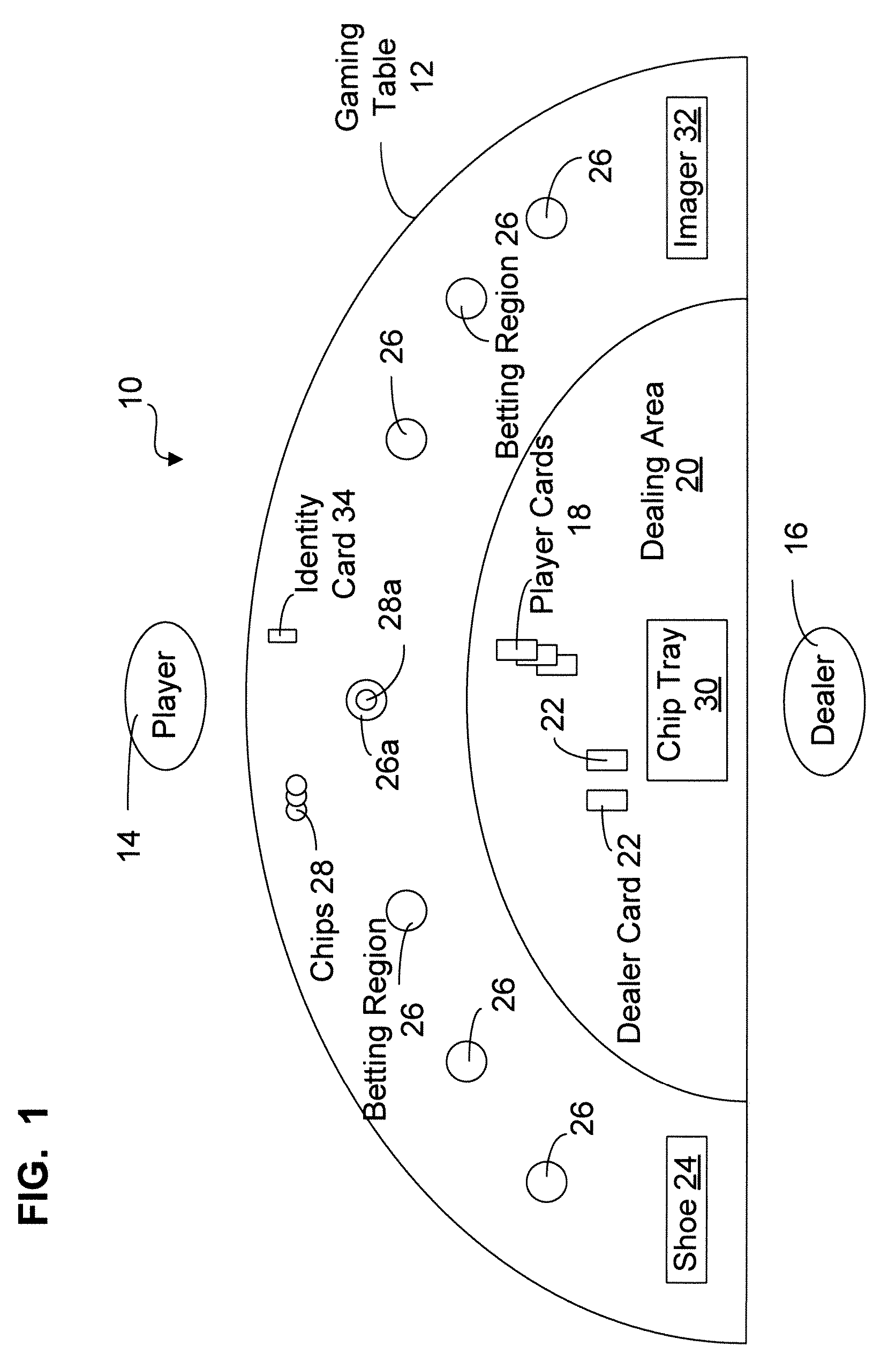
Gaming object recognition
InactiveUS20070077987A1Accurate and efficientApparatus for meter-controlled dispensingVideo gamesFeature extractionPlaying card
The present invention relates to a system and method for identifying and tracking gaming objects. The system comprises an overhead camera for capturing an image the table, a detection module for detecting a feature of the object on the image, a search module for extracting a region of interest of the image that describes the object from the feature, a search module for extracting a region of interest of the image that describes the object from the feature, a feature space module for transforming a feature space of the region of interest to obtain a transformed region of interest, and an identity module comprising a statistical classifier trained to recognize the object from the transformed region. The search module is able to extract a region of interest of an image from any detected feature indicative of its position. The system may be operated in conjunction with a card reader to provide two different sets of playing card data to a tracking module, which may reconcile the provided data in order to detect inconsistencies with respect to playing cards dealt on the table.
Owner:TANGAM GAMING TECH
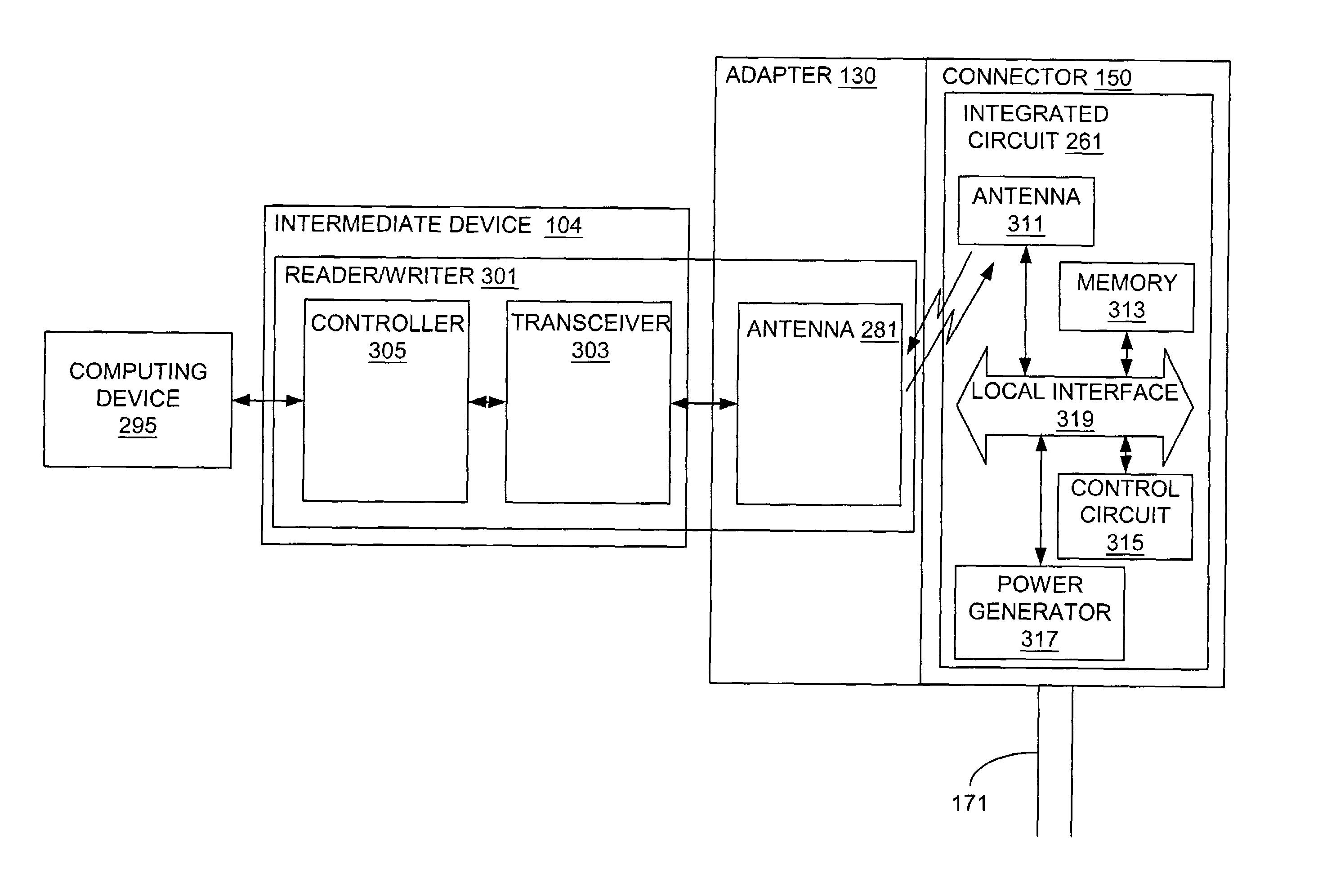
Self-registration systems and methods for dynamically updating information related to a network
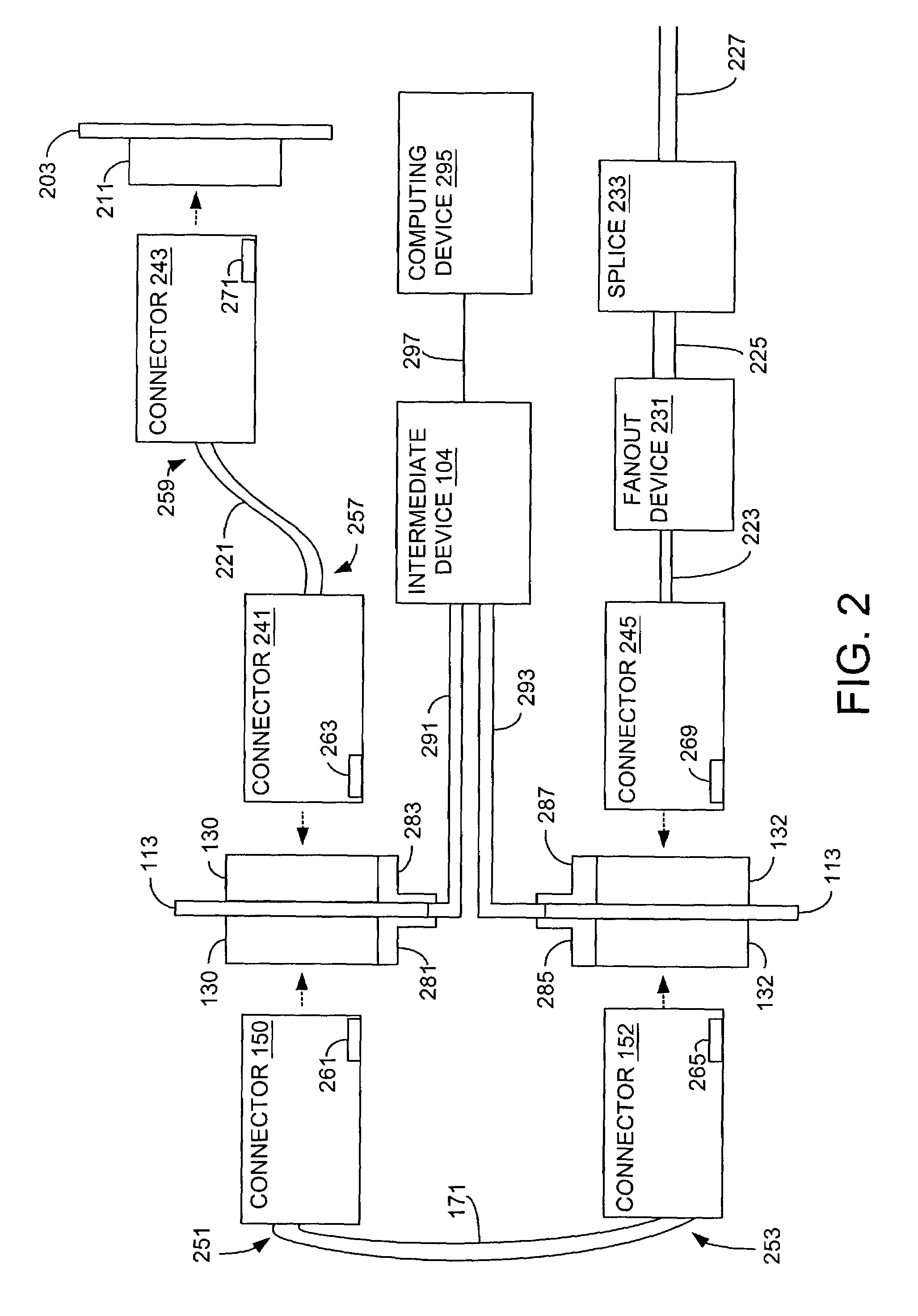
ActiveUS7081808B2Digital computer detailsData switching by path configurationCard readerRegistration system
Self-registration systems and methods for dynamically updating information related to a network, are provided. A self-registration system for dynamically updating information related to a network, comprises: a connector comprising an integrated circuit that stores a first block of information; an adapter coupled to the connector; a reader that receives the first block of information from the integrated circuit via the adapter; and a communication line coupled to the adapter via the connector, where the first block of information comprises a first block of information about network elements associated with the integrated circuit, and where the first block of information about network elements associated with the integrated circuit comprises information other than information identifying the connector, the adapter, the communication line and the integrated circuit.
Owner:FURAKAWA ELECTRIC NORTH AMERICA INC
Door Lock, System and Method for Remotely Controlled Access
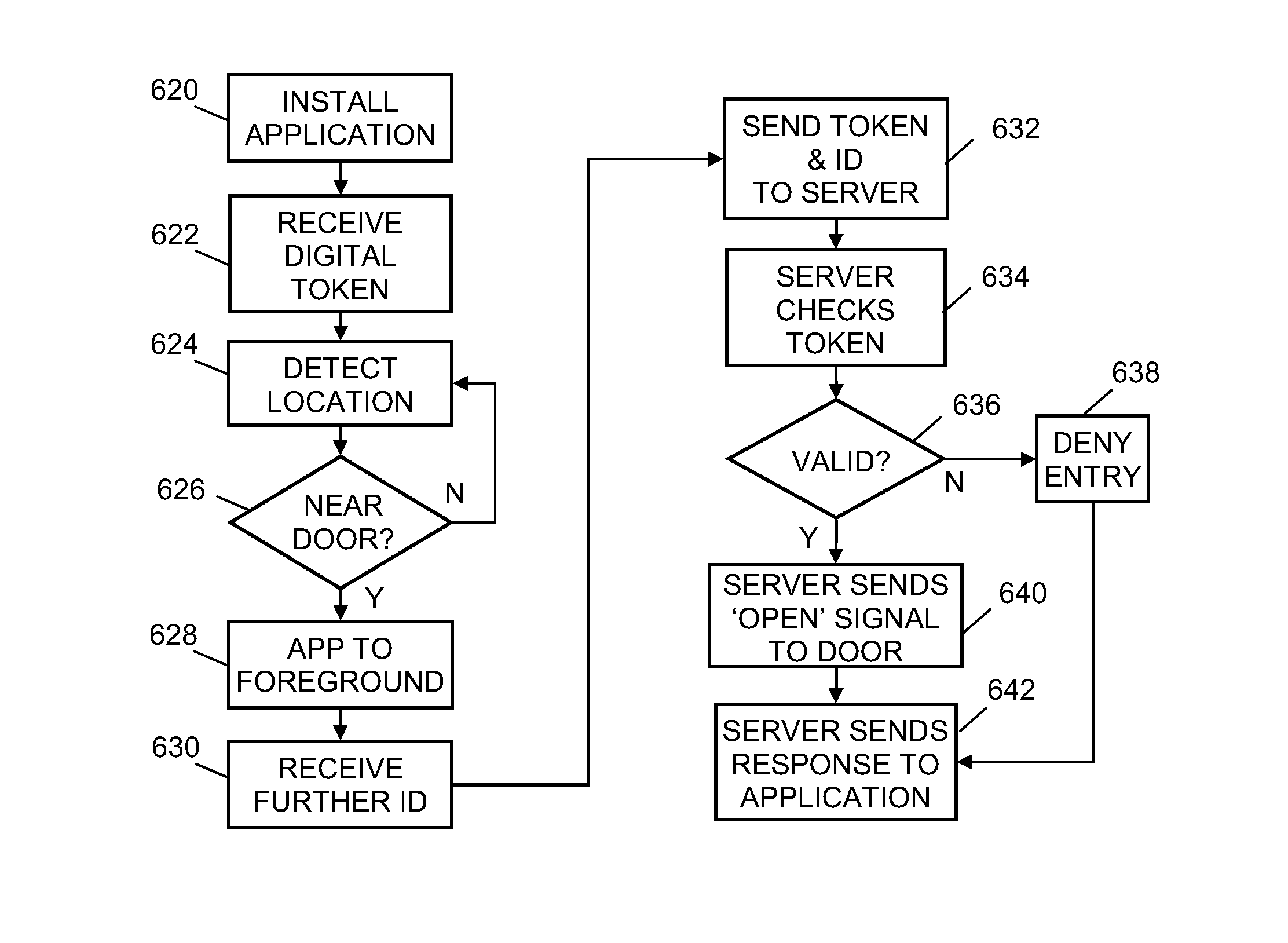
InactiveUS20140002236A1Electric signal transmission systemsDigital data processing detailsCard readerEmbedded system
Secure door entry without a traditional card reader is made possible by tagging the door with an unpowered, unique token which can be read by a user's personal mobile electronic device. The user's device transmits both door and user identification to a remote server, where the decision is made whether to open the door. If so, the server sends an open door signal using the IP suite of protocols to a processor in a powered door lock, opening the door. Another signal may be used indicate whether access is denied or granted. Multiple personal mobile electronic devices may be configured to operate the same door, and users may control access by others.
Owner:VISCOUNT SECURITY SYST
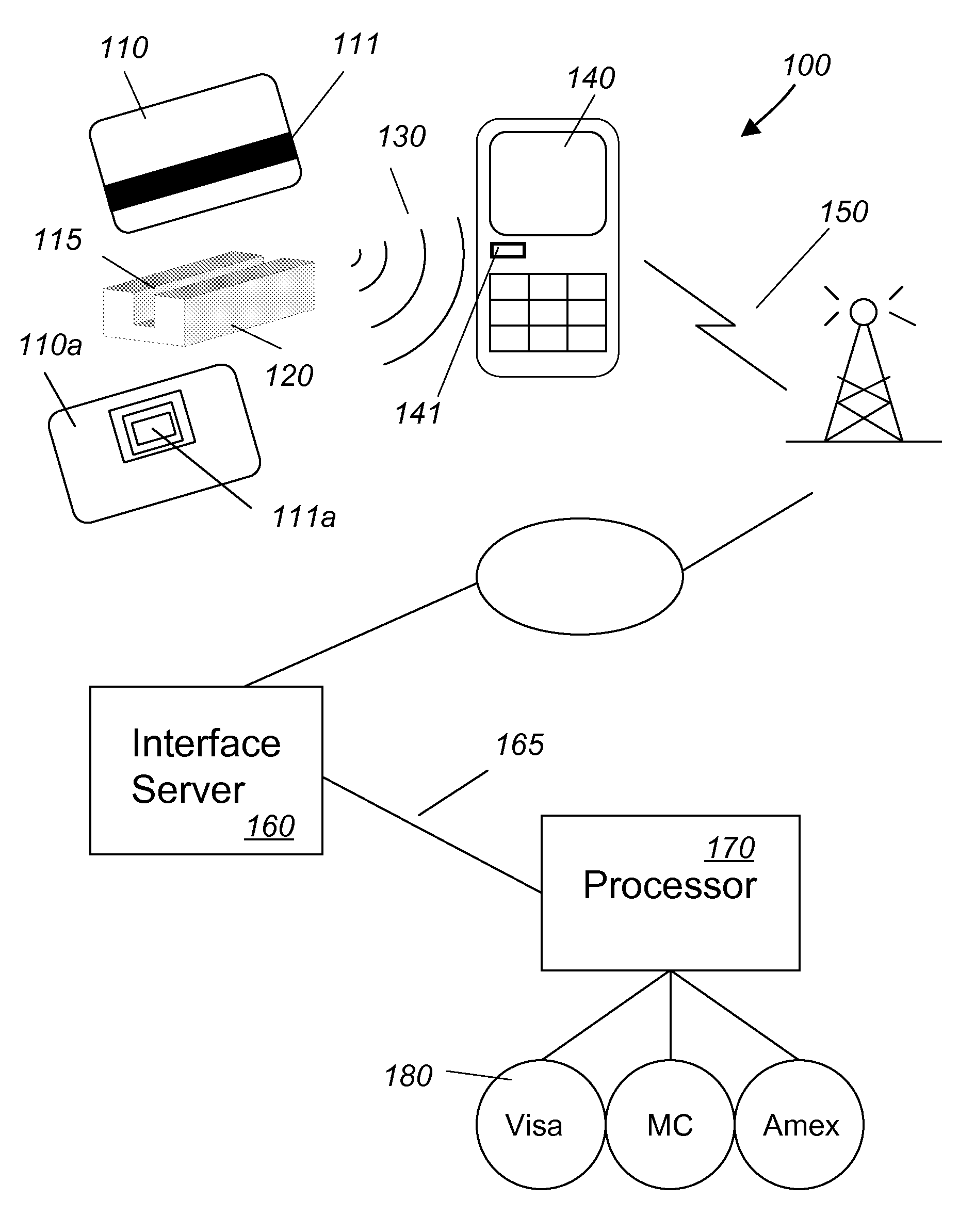
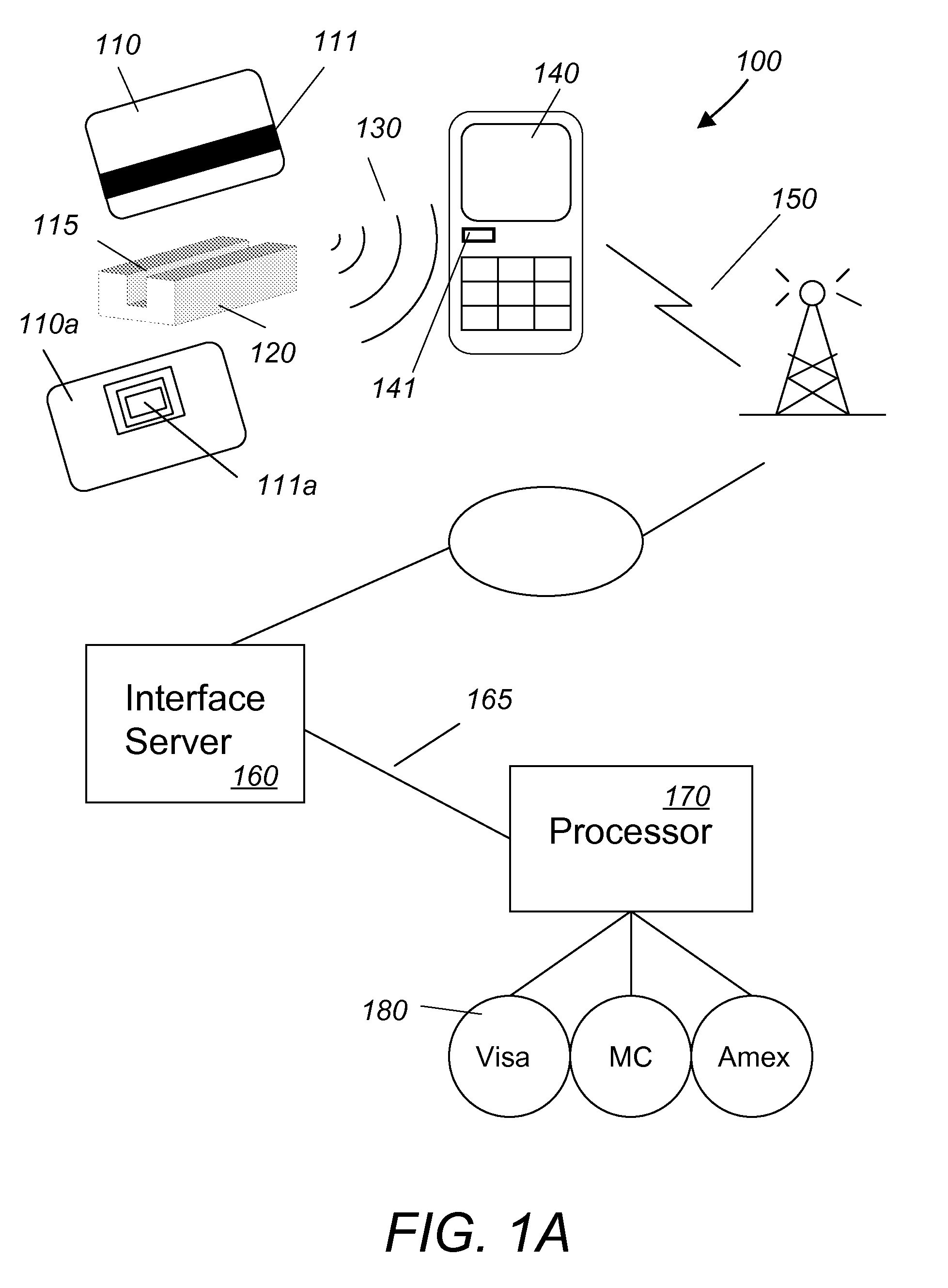
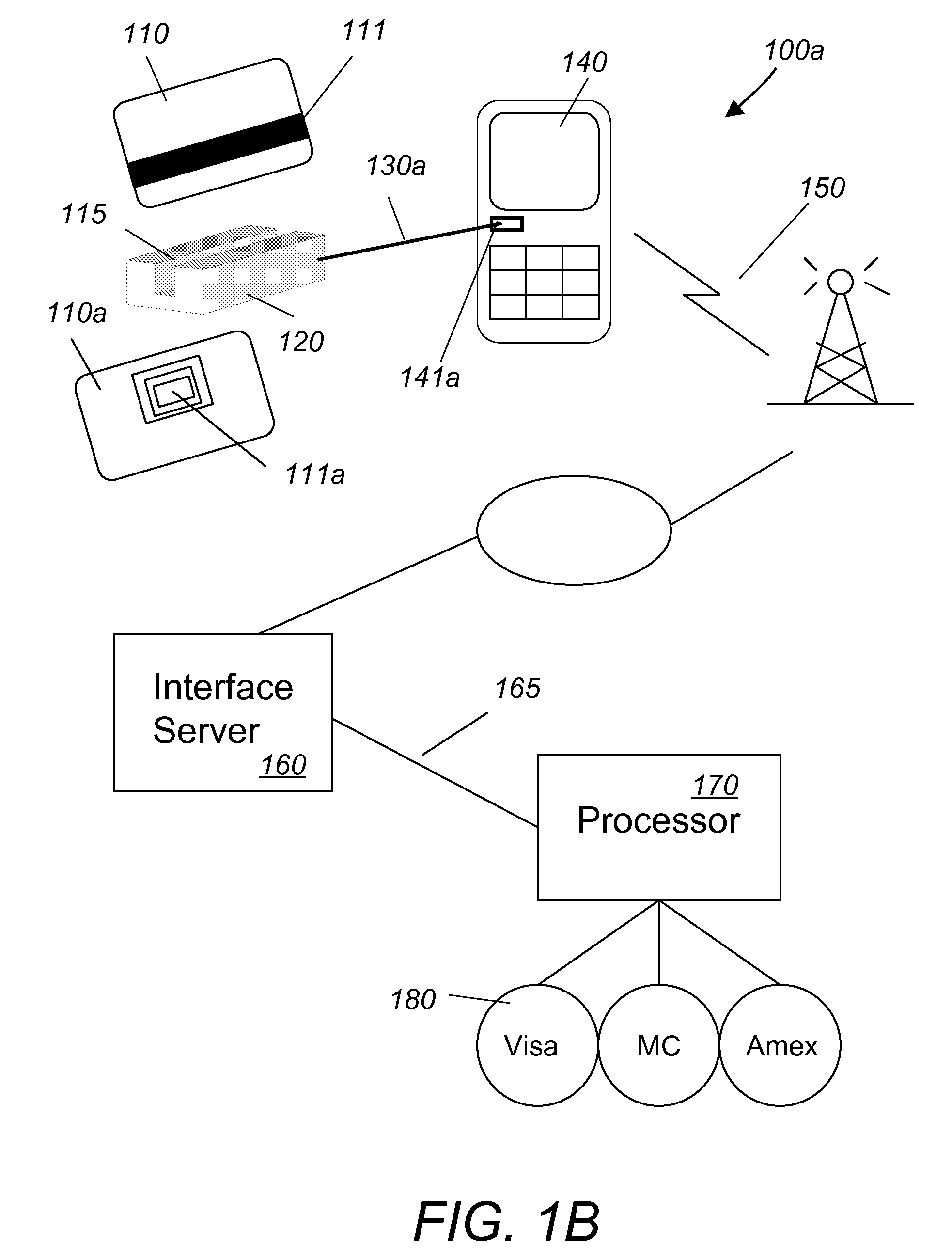
Audio/acoustically coupled card reader
InactiveUS20100243732A1Firmly connectedOvercome difficultiesSpecial service for subscribersPayment architectureNetwork connectionCard reader
A system for performing mobile payment transactions includes an audio / acoustically coupled card reader, a mobile communication device, an interface server and a payment card processor. The audio / acoustically coupled card reader includes means for reading payment card data from a payment card, means for generating a stream of audio / acoustical signals comprising the payment card data and means for transmitting the stream of audio / acoustical signals. The mobile communication device includes means for receiving the stream of audio / acoustical signals, means for generating an electrical signal comprising data contained in the stream of audio / acoustical signals and means for transmitting the electrical signal. The interface server includes means for extracting the payment card data from the electrical signal and means for transmitting the payment card data. The mobile communication device connects to the interface server device via a first network and transmits the electrical signal to the interface server. The interface server connects to the payment card processor via a second network and transmits the payment card data to the payment card processor for payment processing. The payment card processor processes payments via payment card companies.
Owner:WALLNER GEORGE
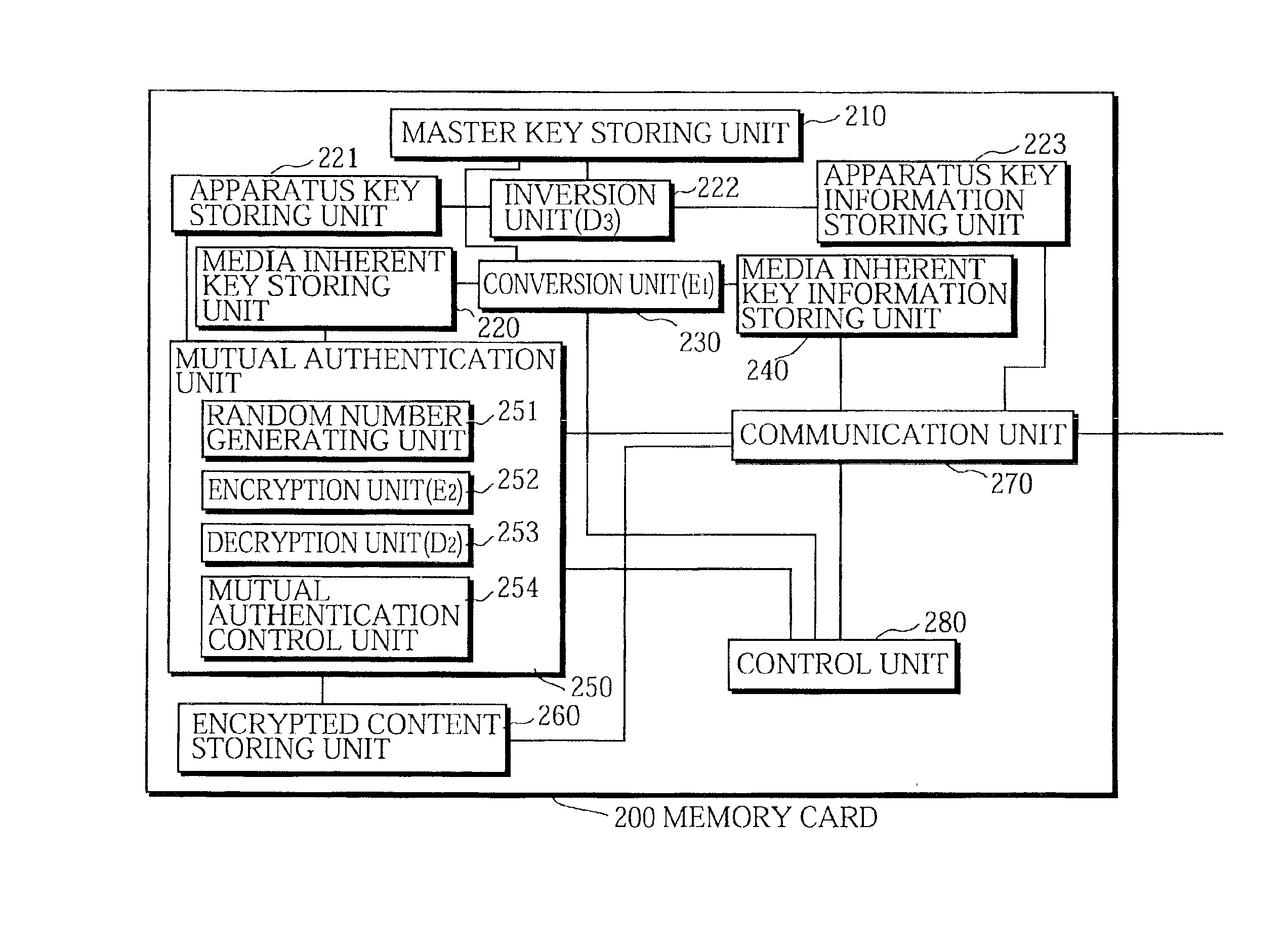
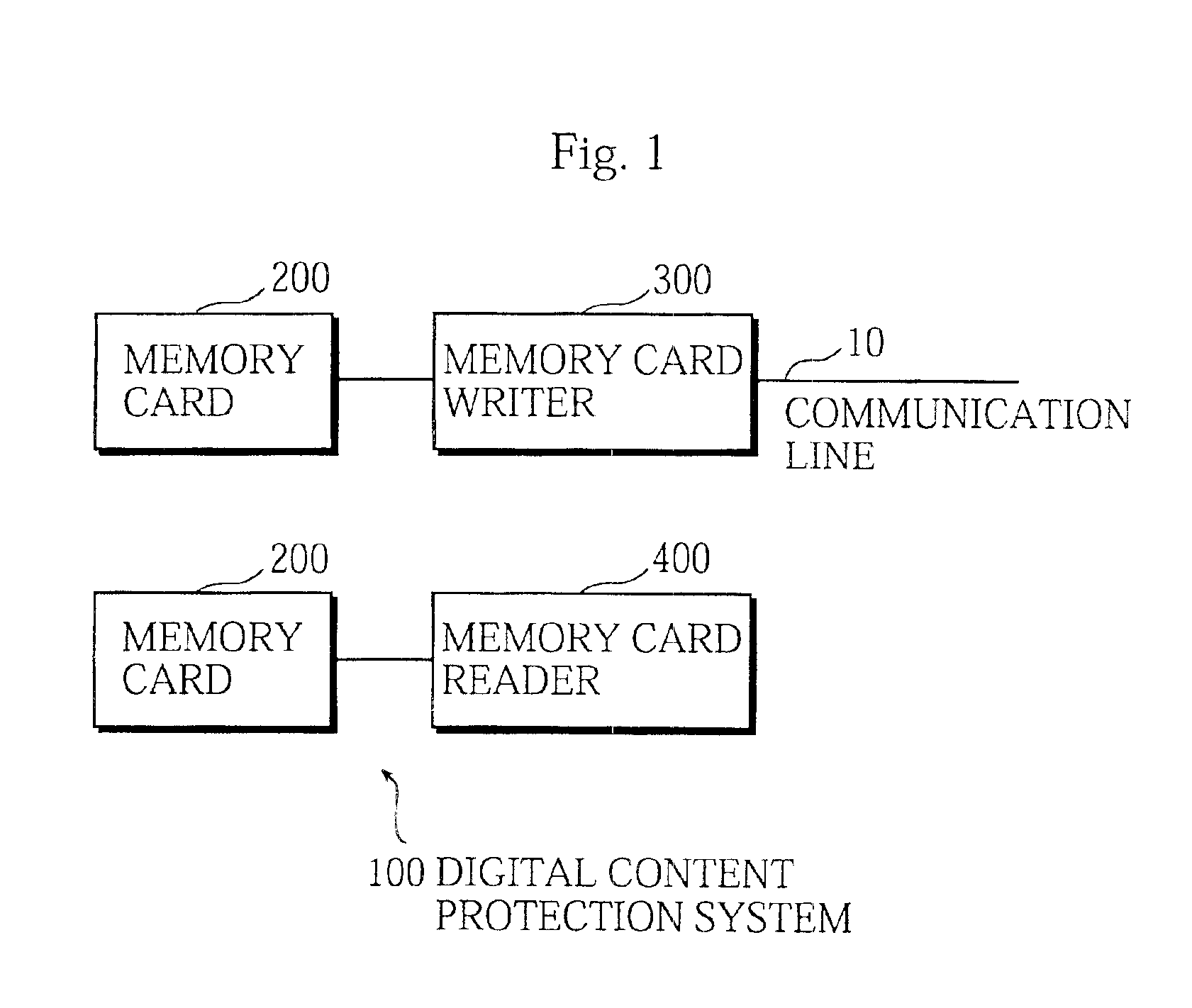
Digital content protection system
InactiveUS6859535B1Reduce scaleDigital data processing detailsUser identity/authority verificationDigital contentMediaFLO
The media inherent key storing unit 220 prestores an inherent key Ki, the conversion unit 230 generates an encrypted inherent key Ji from the inherent key read from the media inherent key storing unit 220, the random number generating unit 331 generates a random number R1, the encryption unit 252 generates an encrypted random number S1, the decryption unit 333 generates a random number R′1 from the encrypted random number R1, and the mutual authentication control unit 334 compares the random number R′1 with the random number R1 and, if the random number R′1 matches the random number R1, judges that the memory card 200 is an authorized device. If the memory card 200 and the memory card writer have successfully authenticated each other, the memory card writer encrypts a content using a decrypted inherent key. If the memory card 200 and the memory card reader have successfully authenticated each other, the memory card reader decrypts an encrypted content using the decrypted inherent key.
Owner:PANASONIC CORP
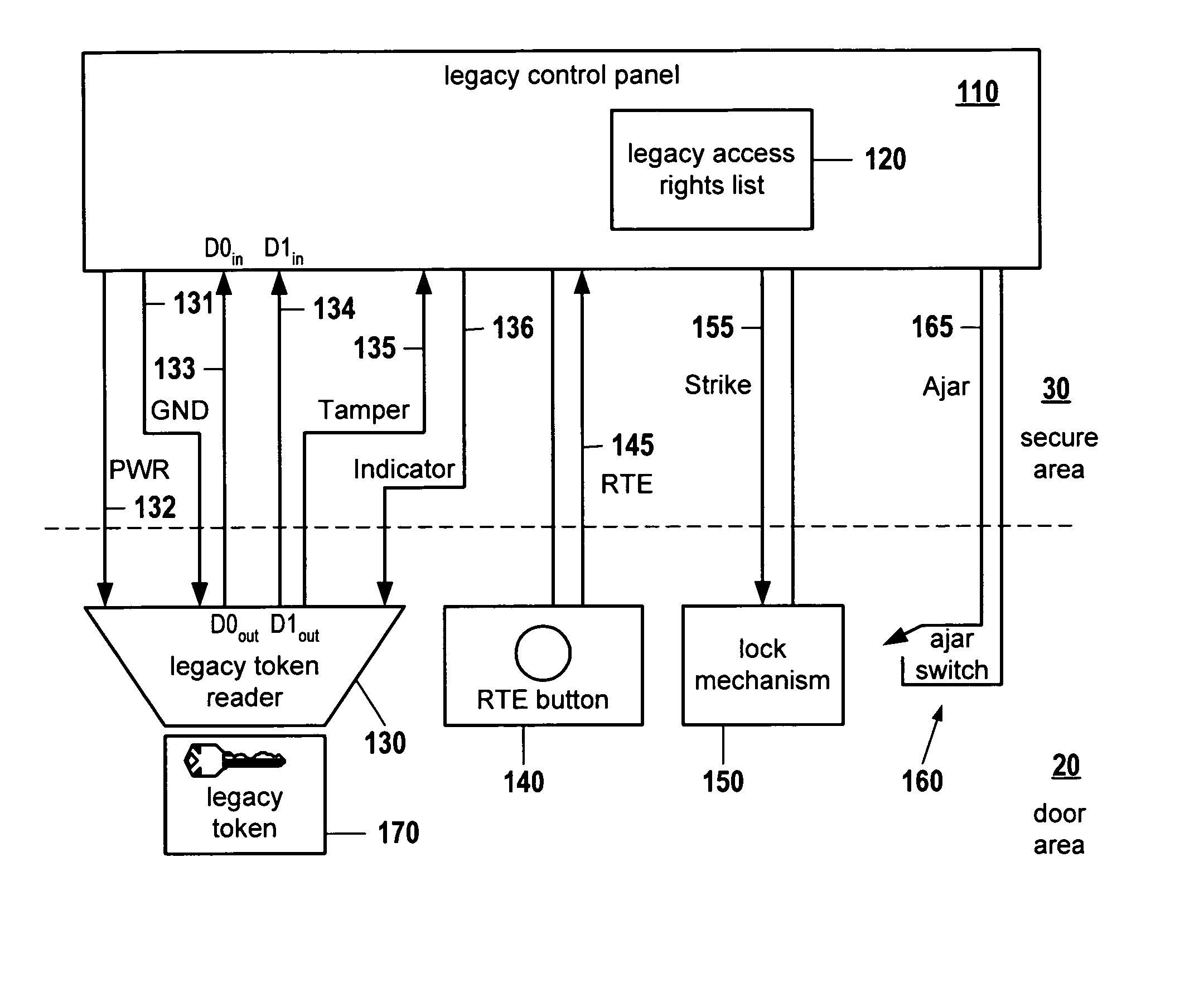
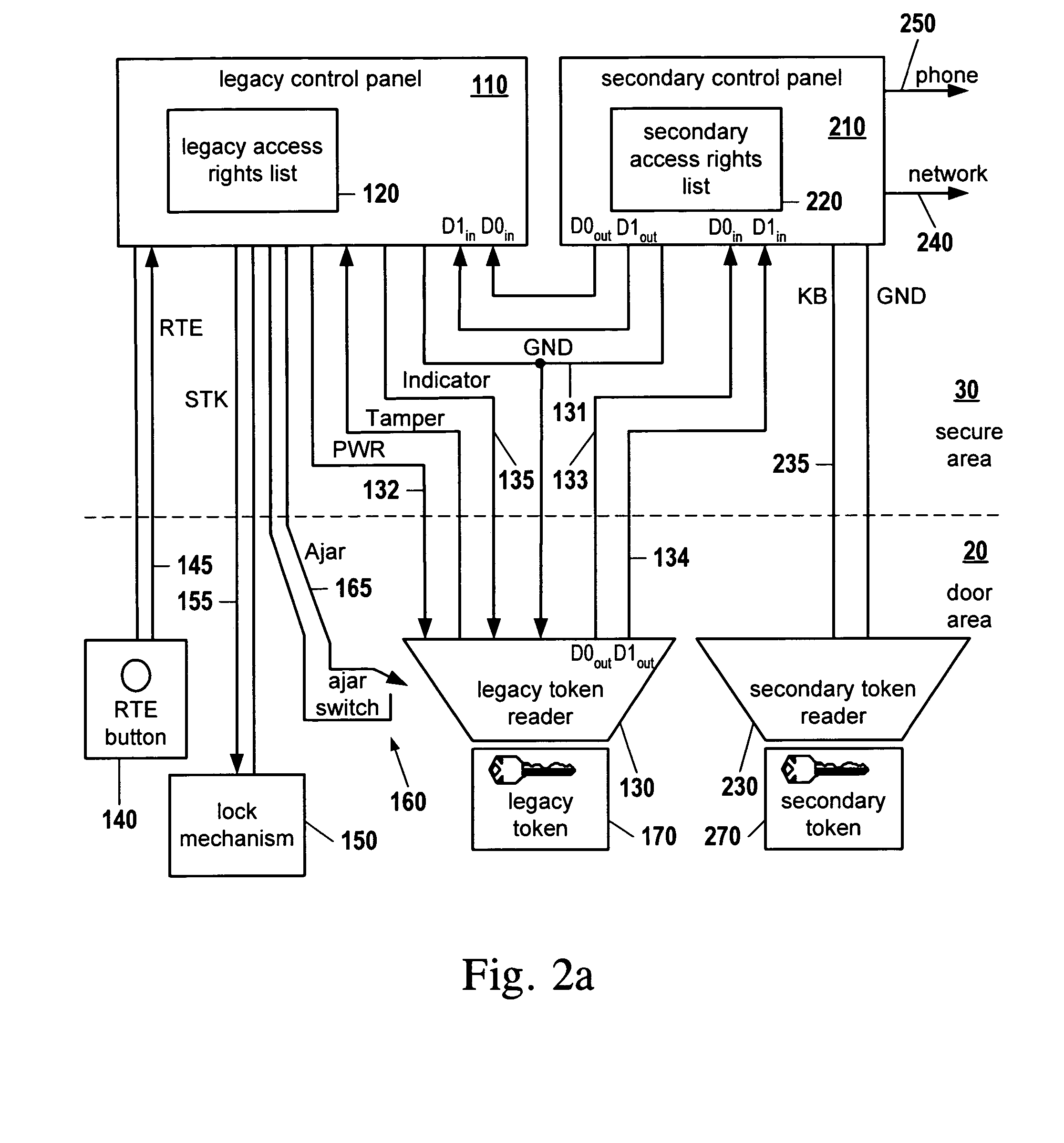
Legacy access control security system modernization apparatus
ActiveUS20070043954A1Solve insufficient capacityQuick installationUser identity/authority verificationDigital data authenticationLegacy systemCard reader
A system is provided for upgrading a legacy security system having a legacy control panel and a legacy card reader, without interfering with legacy system operation. A new control panel is installed between the legacy card reader and the legacy control panel. Also, a new token reader is installed next to the legacy card reader and connected to the new control panel. The new control panel passes credentials it receives from the legacy card reader to the legacy control panel, avoiding interference with legacy system operation. When the new control panel receives credentials from the new token reader, it evaluates them against an access rights list administered independently of the legacy access rights list. When the new control panel determines that an access request should be granted, it sends a memorized legacy credential associated with full access rights to the legacy control panel, causing it to open the door.
Owner:COMMON CREDENTIAL SYST
Method and apparatus for interfacing multiple peripheral devices to a host computer
InactiveUS6263392B1Discourage and prevent useUnauthorized useProgram loading/initiatingVideo gamesCredit cardJoystick
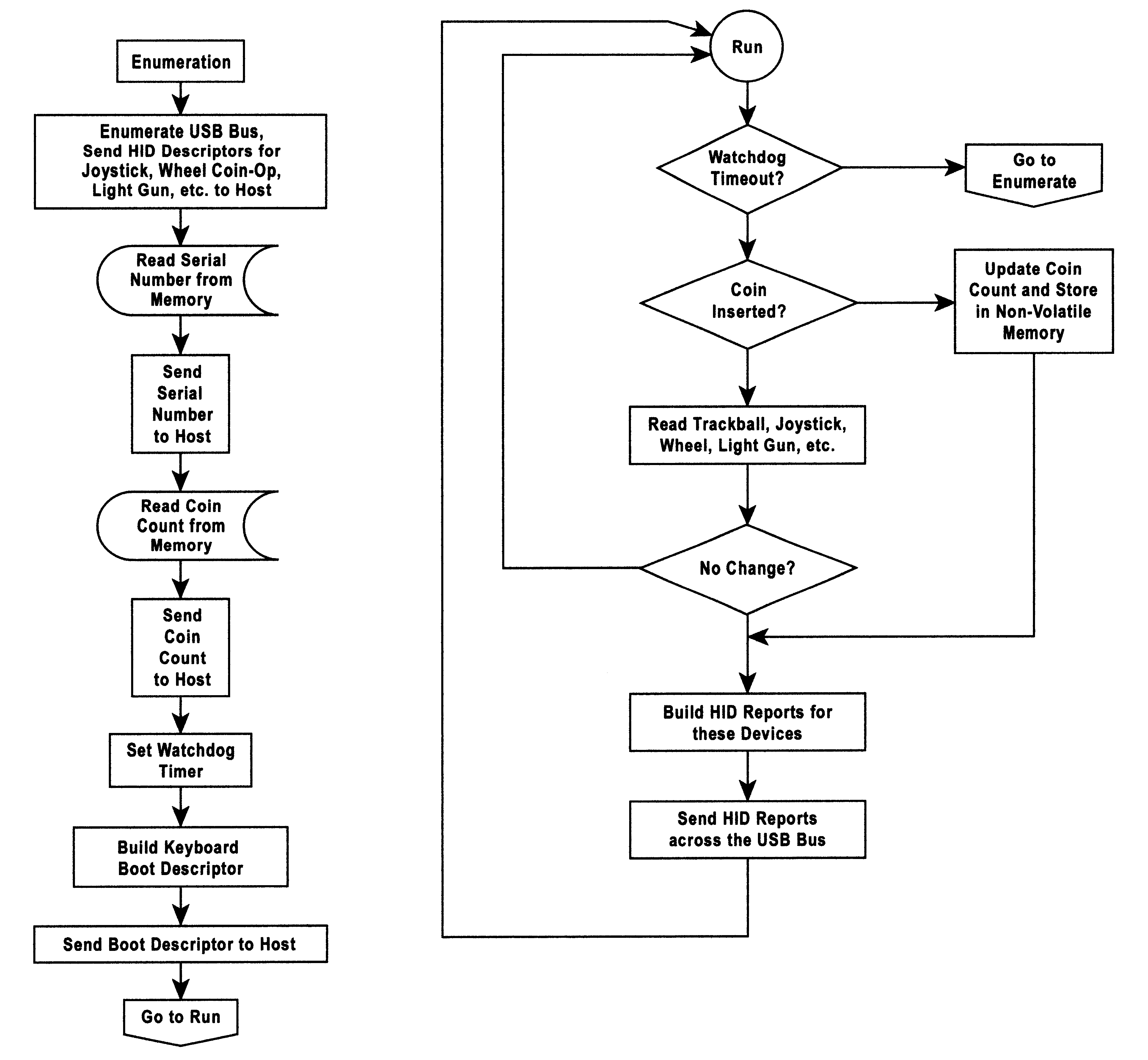
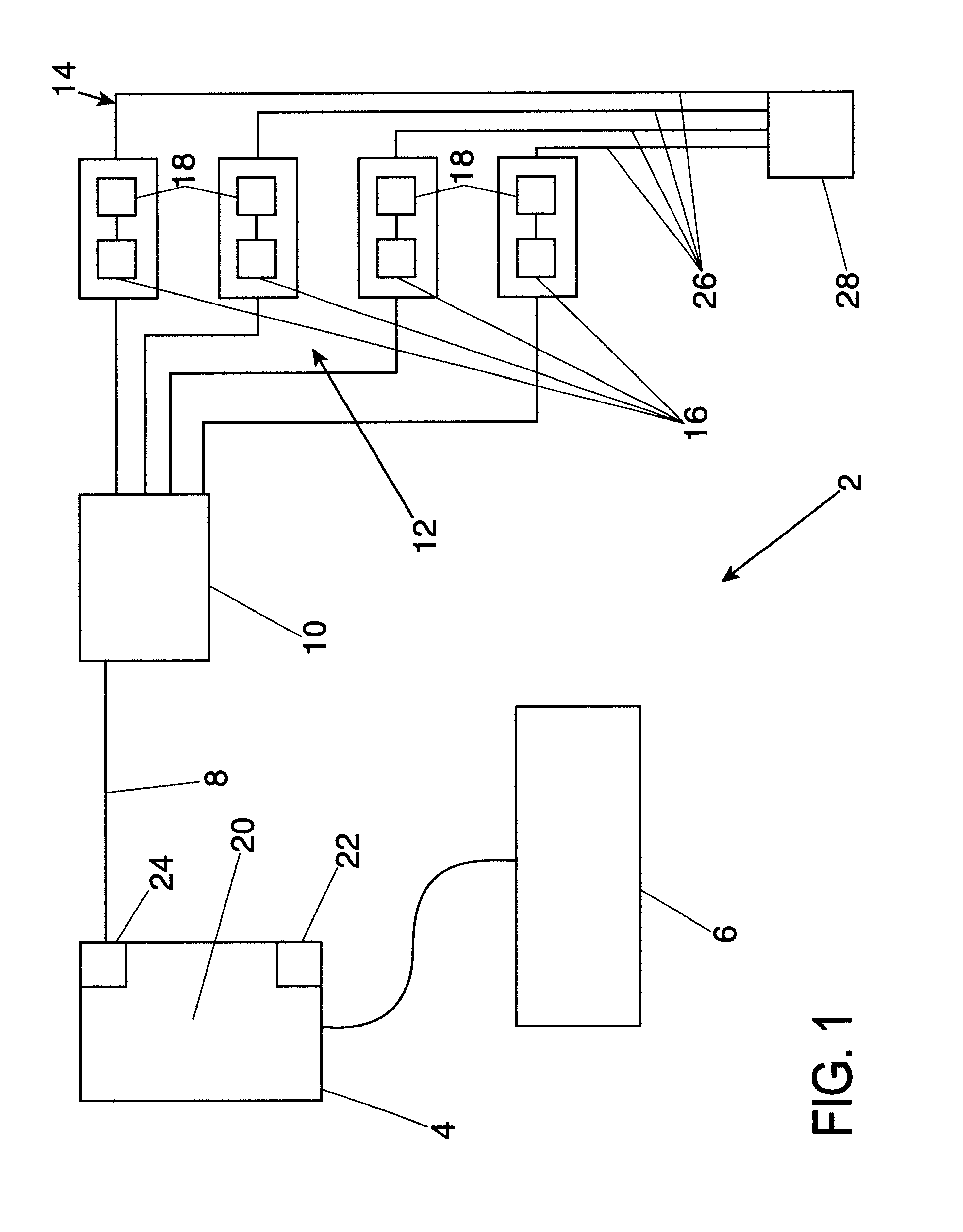
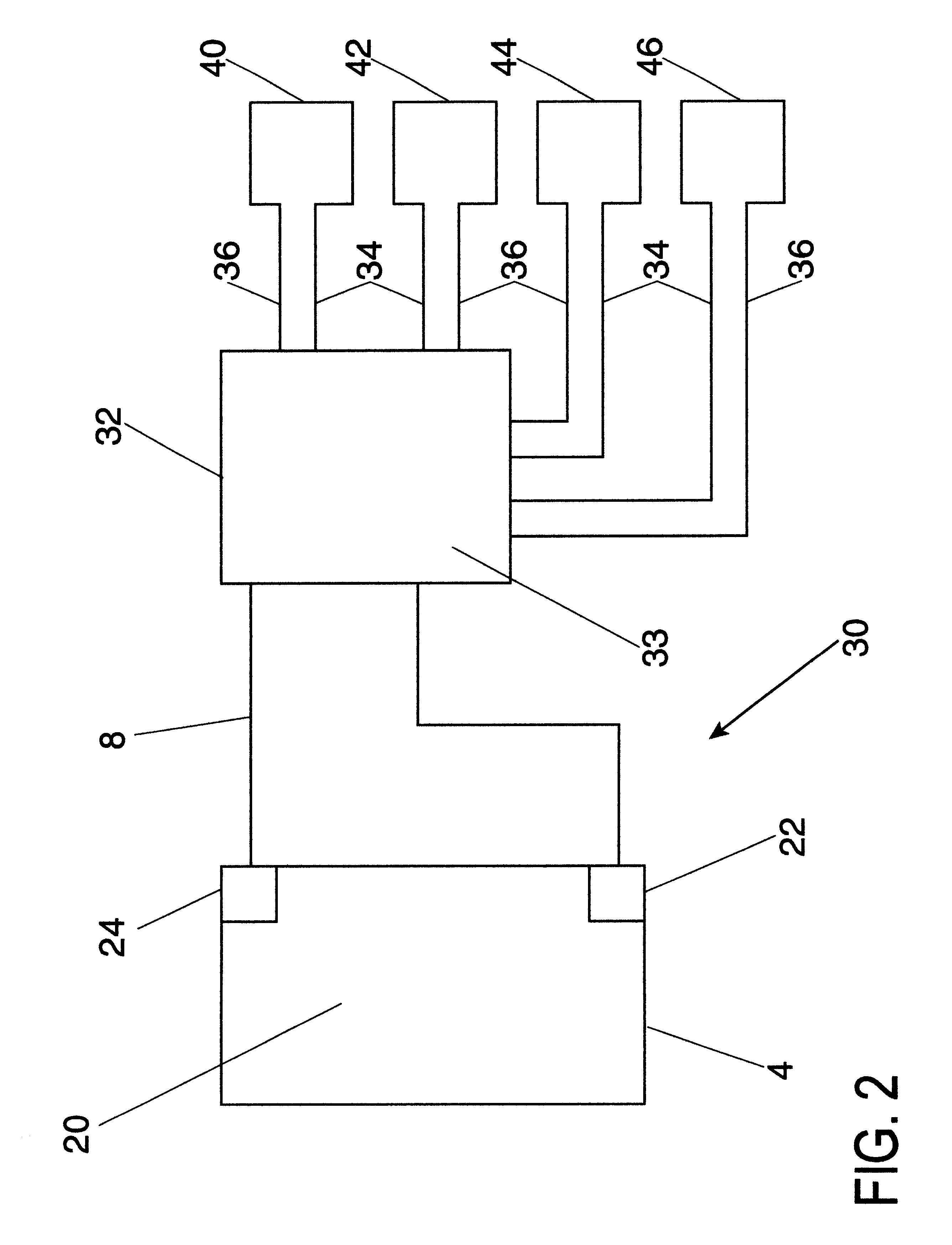
A method and an apparatus to interface multiple peripheral devices to a host computer is provided. An interface control module located in a multi-user computer game arcade system interfaces a host computer via a Universal Serial Bus (USB) to one or more joysticks, steering wheels, trackballs, coin op / bill counters, credit card readers and / or optical guns. A set of connectors allows the game builder or player to interface a variety of input peripherals to the interface control module. The interface control module recognizes the HID type of the input peripheral by the type of the selected connector, and then provides HD reports that describe each input device to the HID compliant software system of the host computer. The interface control module may support 127 HID peripherals. A watchdog function of the interface control module detects host computer malfunctions and crashes, and boots the host computer while retaining coin credit input data received proximate to and during the malfunction and recovery.
Owner:ACTIVISION PUBLISHING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com