Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
225results about How to "Unauthorized use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
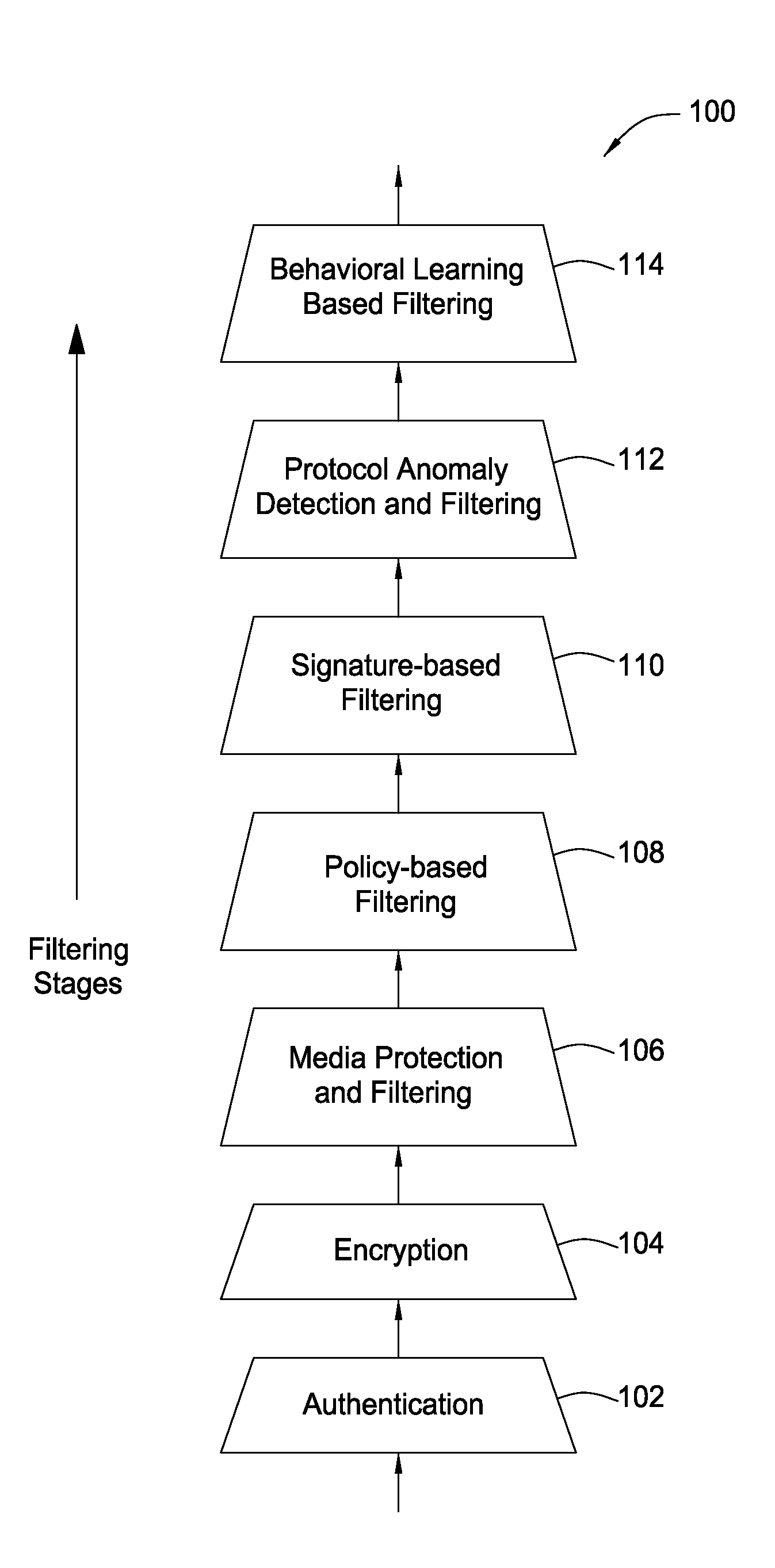
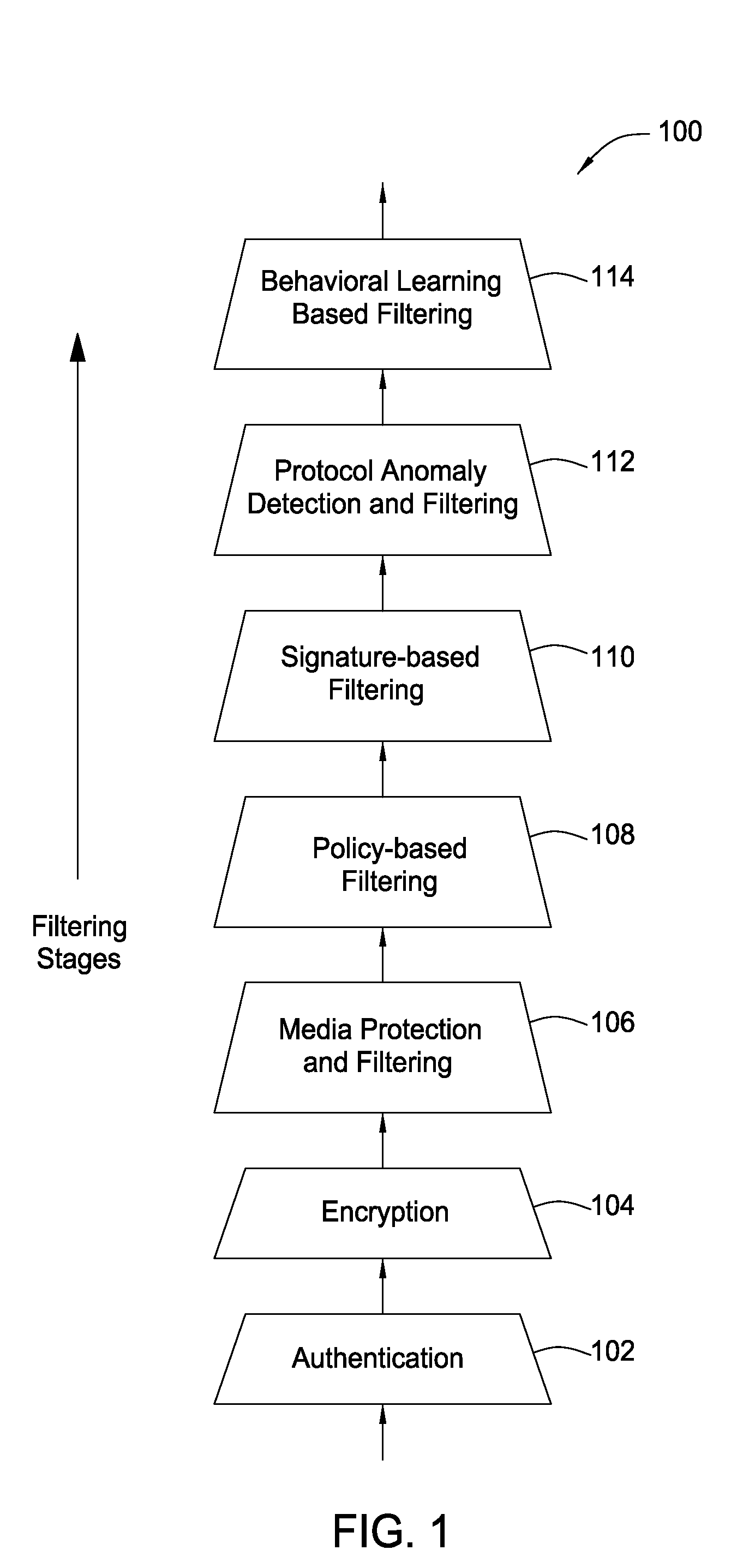
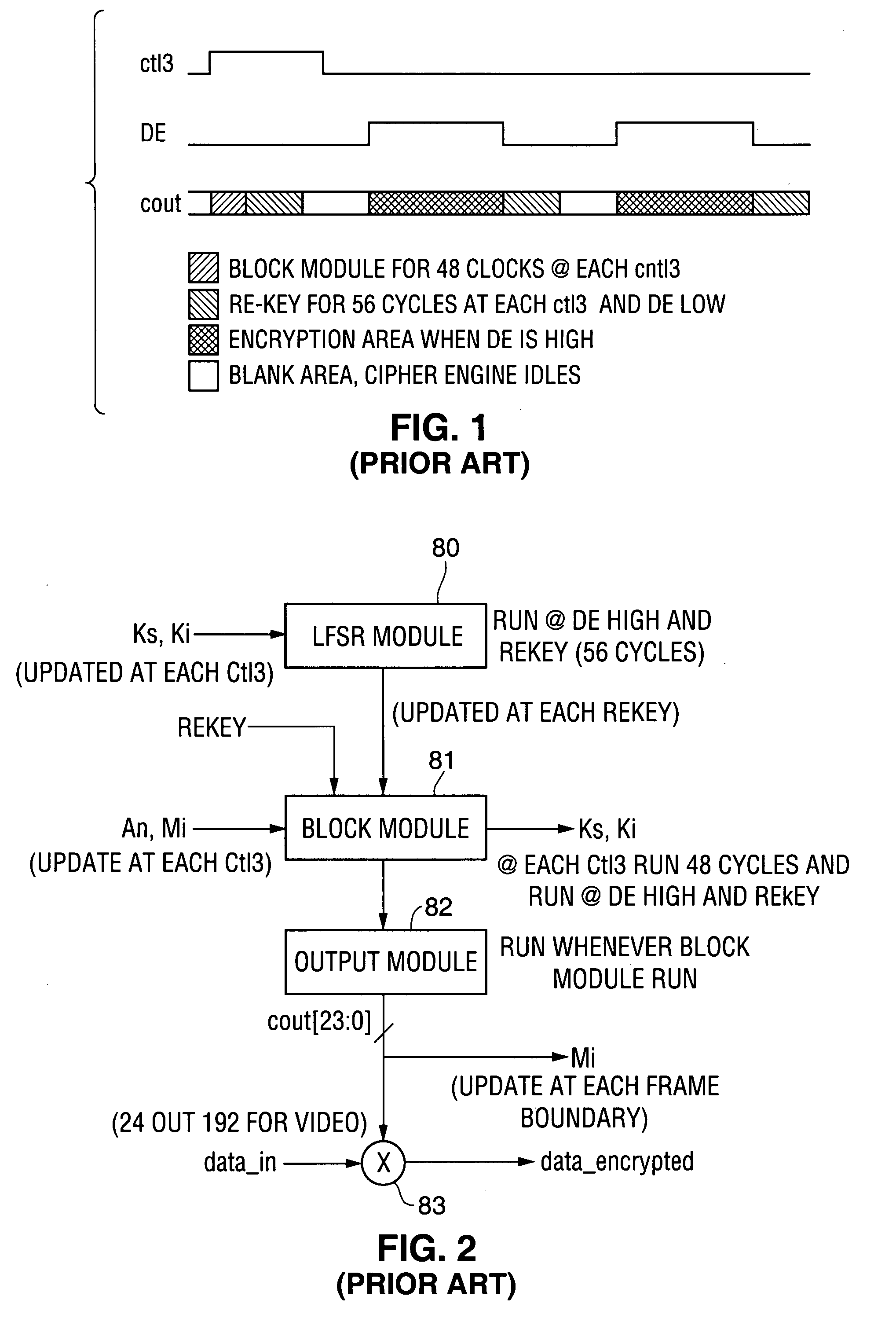
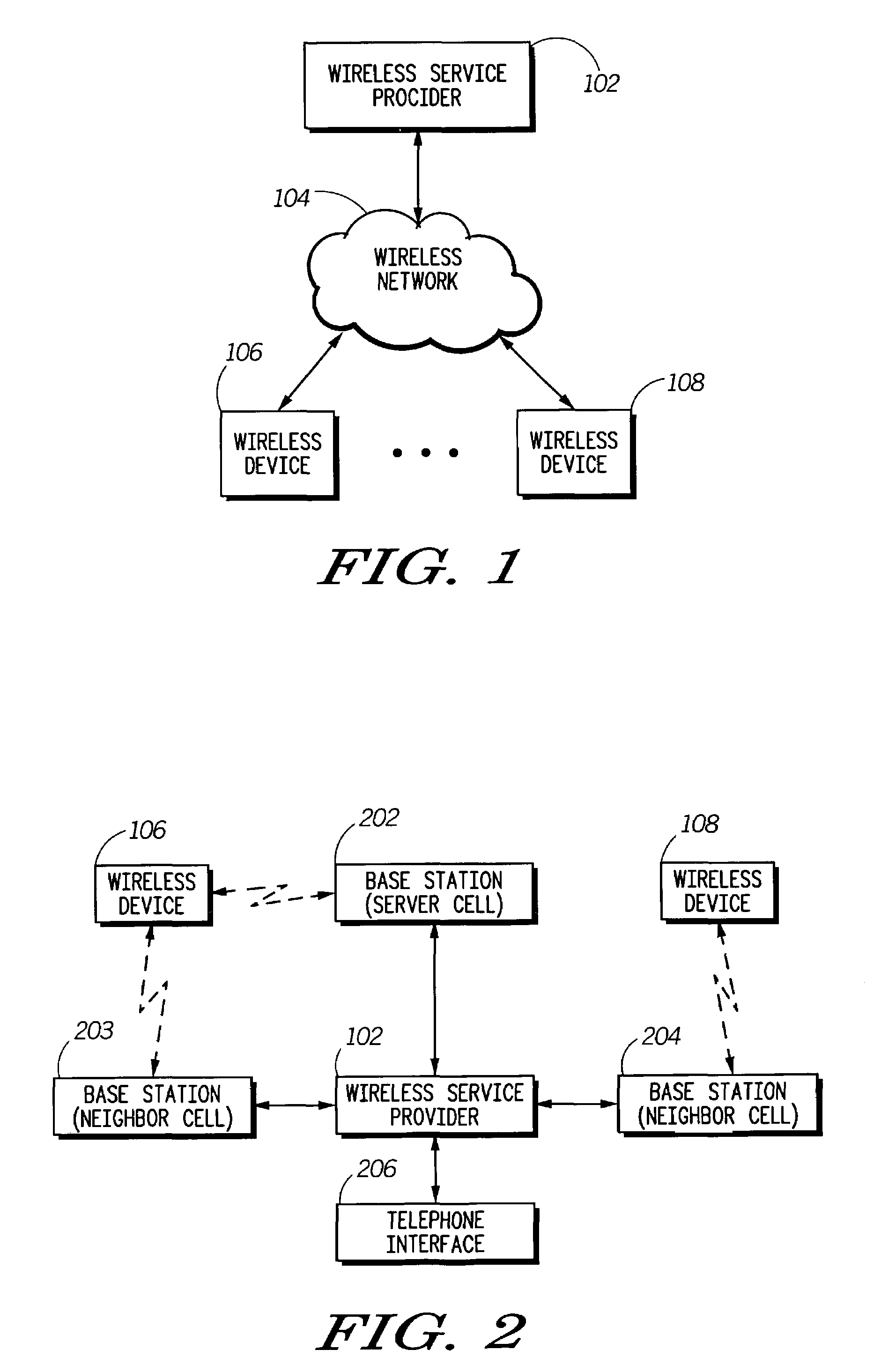
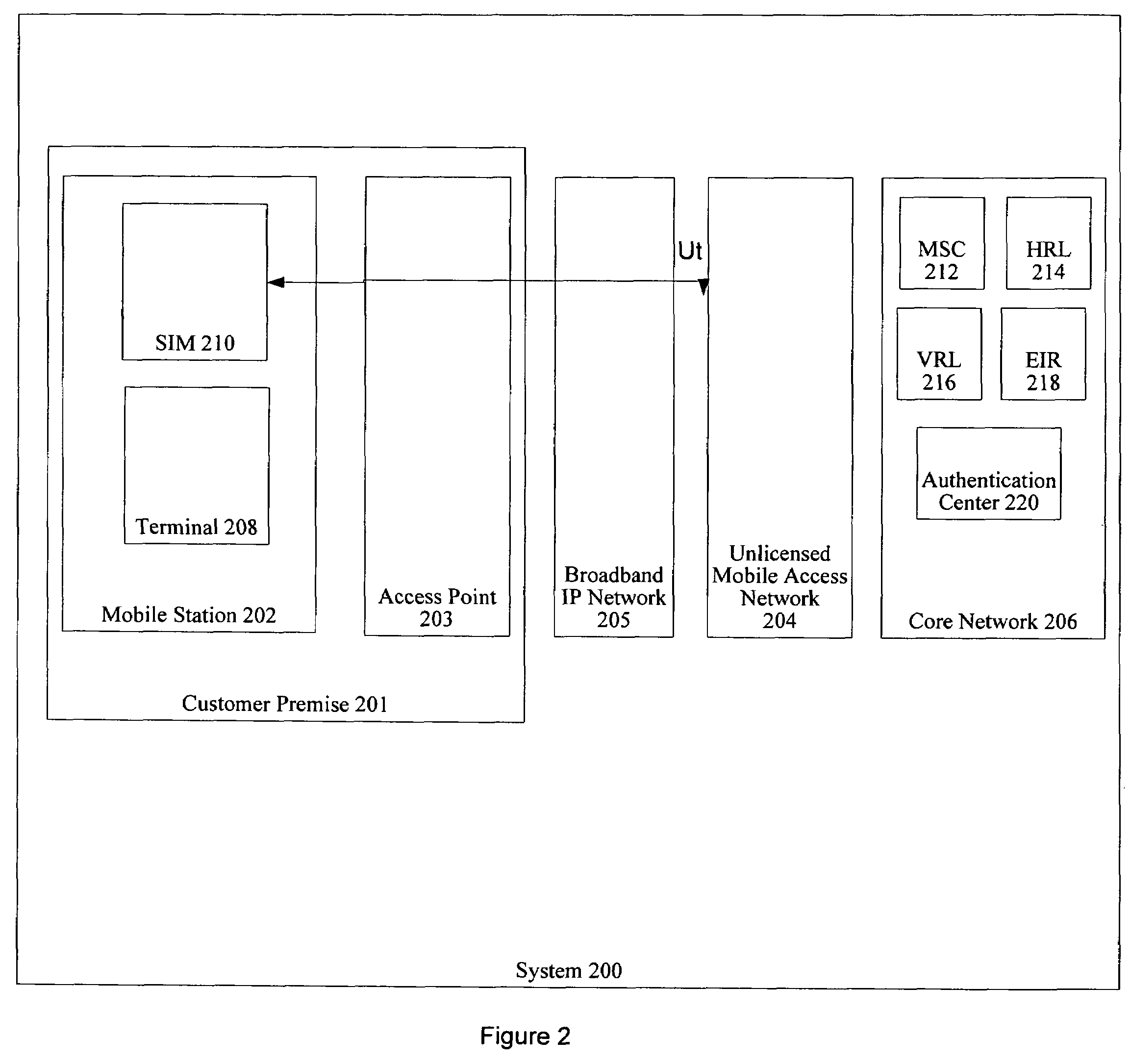
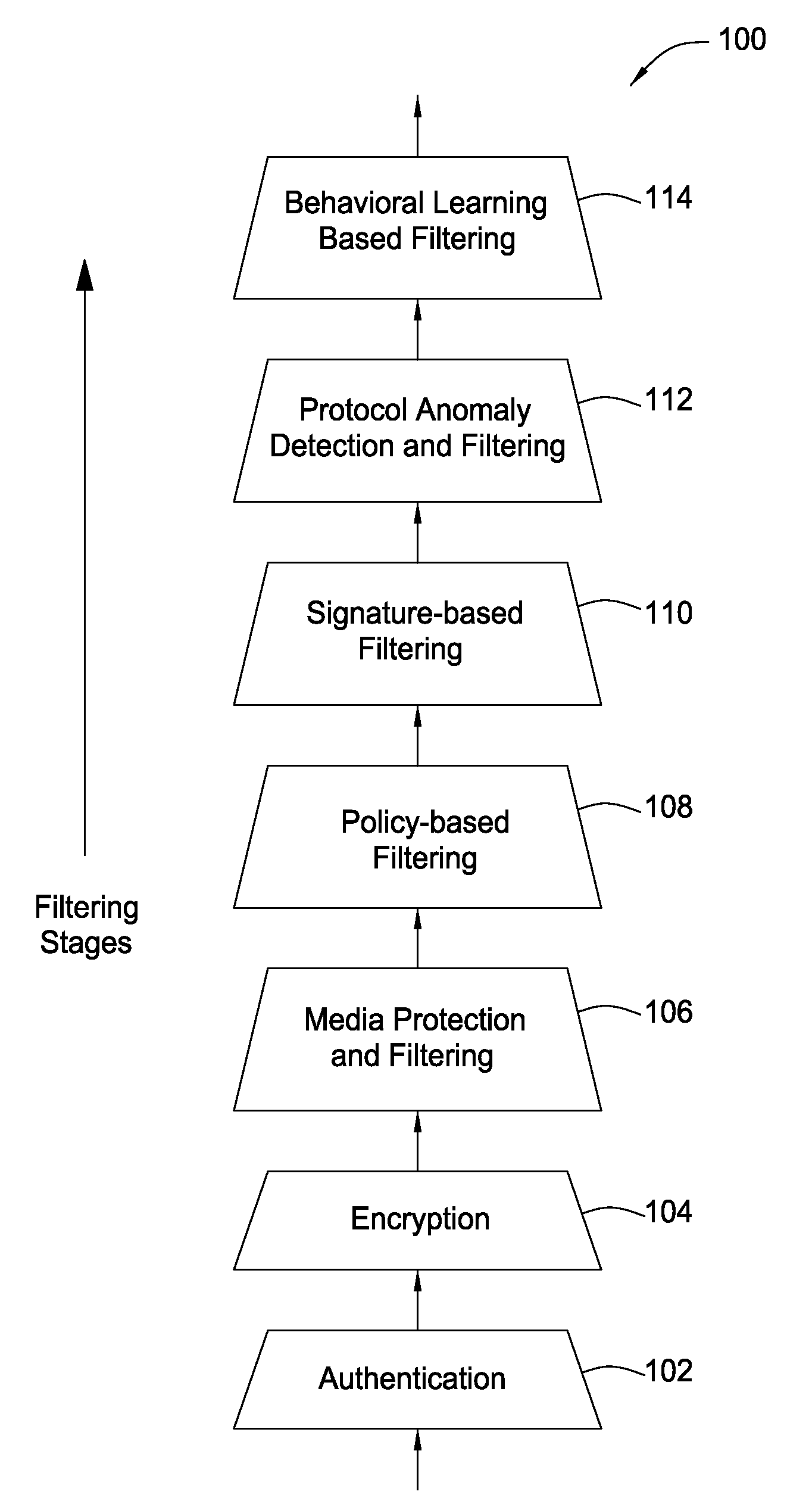
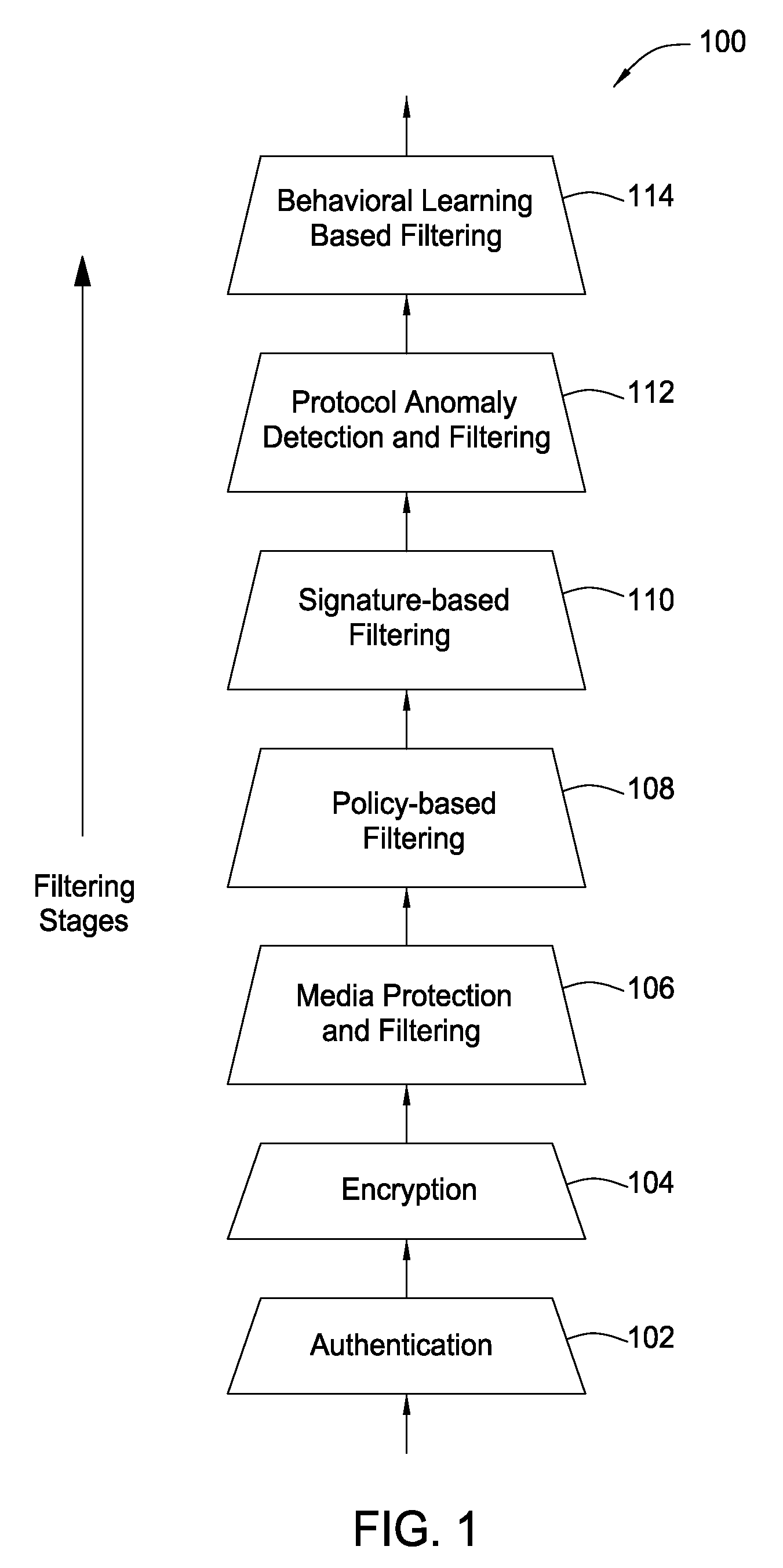
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS20070121596A1Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
The present invention provides a system, method and apparatus for providing network level and nodal level vulnerability protection in VoIP networks by receiving a communication, filtering the received communication using three or more stages selected from the group comprising a media protection and filtering plane, a policy based filtering plane, a signature based filtering plane, a protocol anomaly detection and filtering plane and a behavioral learning based filtering plane, and either allowing or denying the received communication based the filtering step. The stages are applicable to one or more protocols including SIP, IMS, UMA, H.248, H.323, RTP, CSTA / XML or a combination thereof. In addition, the stages can be implemented within a single device or are distributed across a network (e.g., SIP network, a UMA network, an IMS network or a combination thereof).
Owner:AVAYA INC
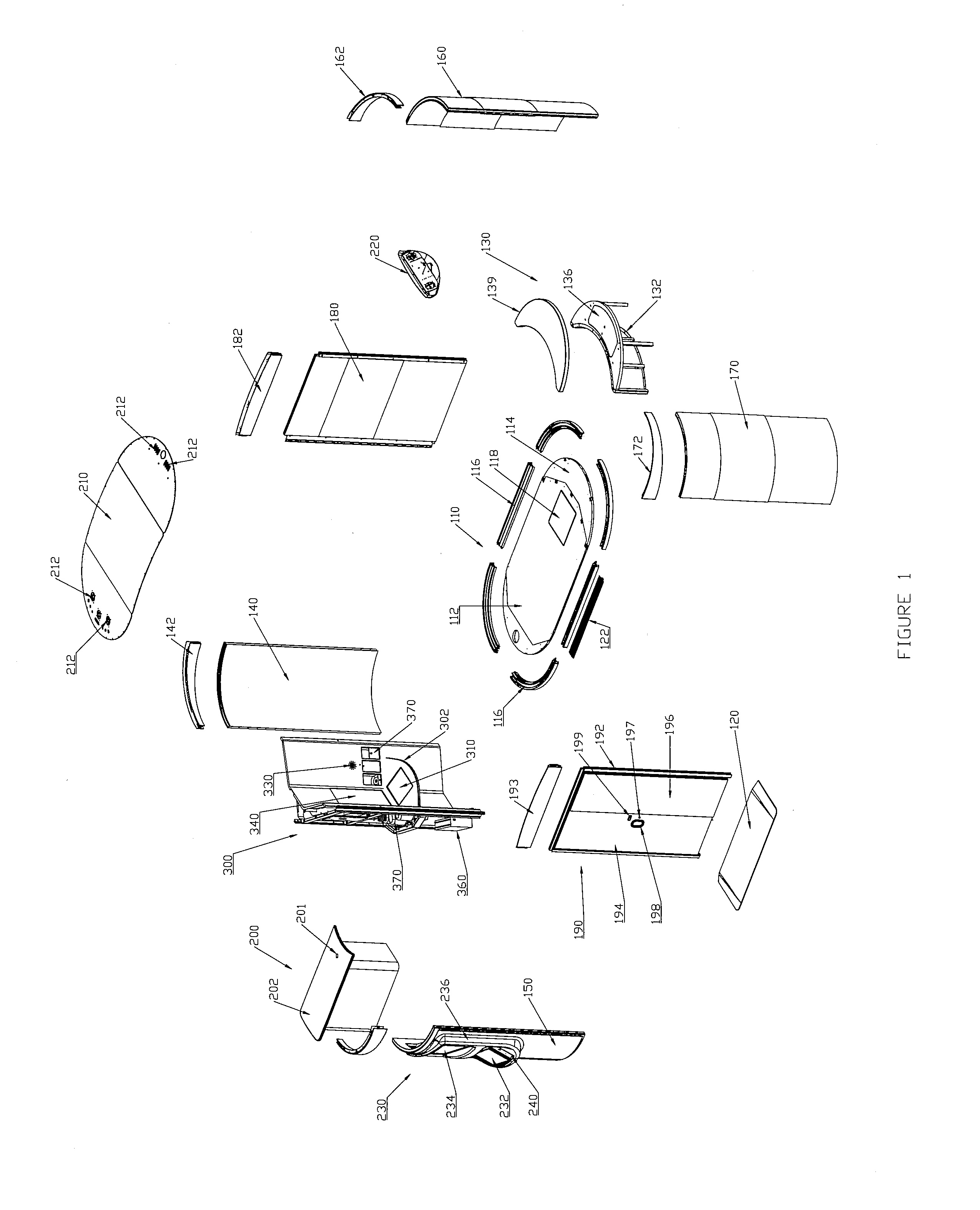
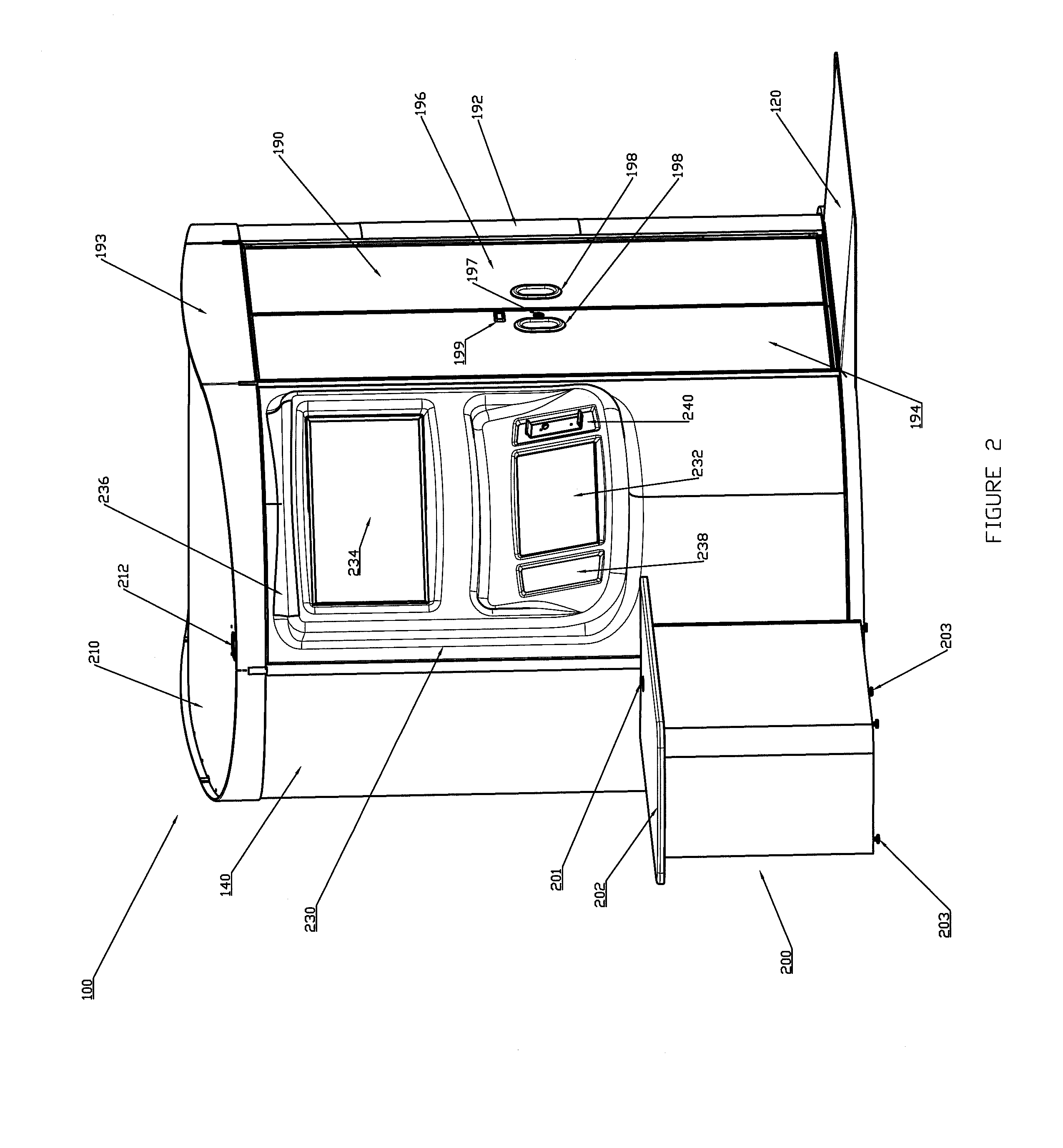
Medical Kiosk and Method of Use
InactiveUS20140330579A1Conveniently conveyed and usedUnauthorized useDrug and medicationsOffice automationMedical prescriptionTeleconference
A medical kiosk designed to provide tele-medicine services, check-in services, and / or prescription services for a user. The medical kiosk can include a user video conferencing system that is designed to enable the user to have a real-time or near real-time tele-conference with a medical provider located remotely from the medical kiosk.
Owner:RITE AID HDQTRS CORP
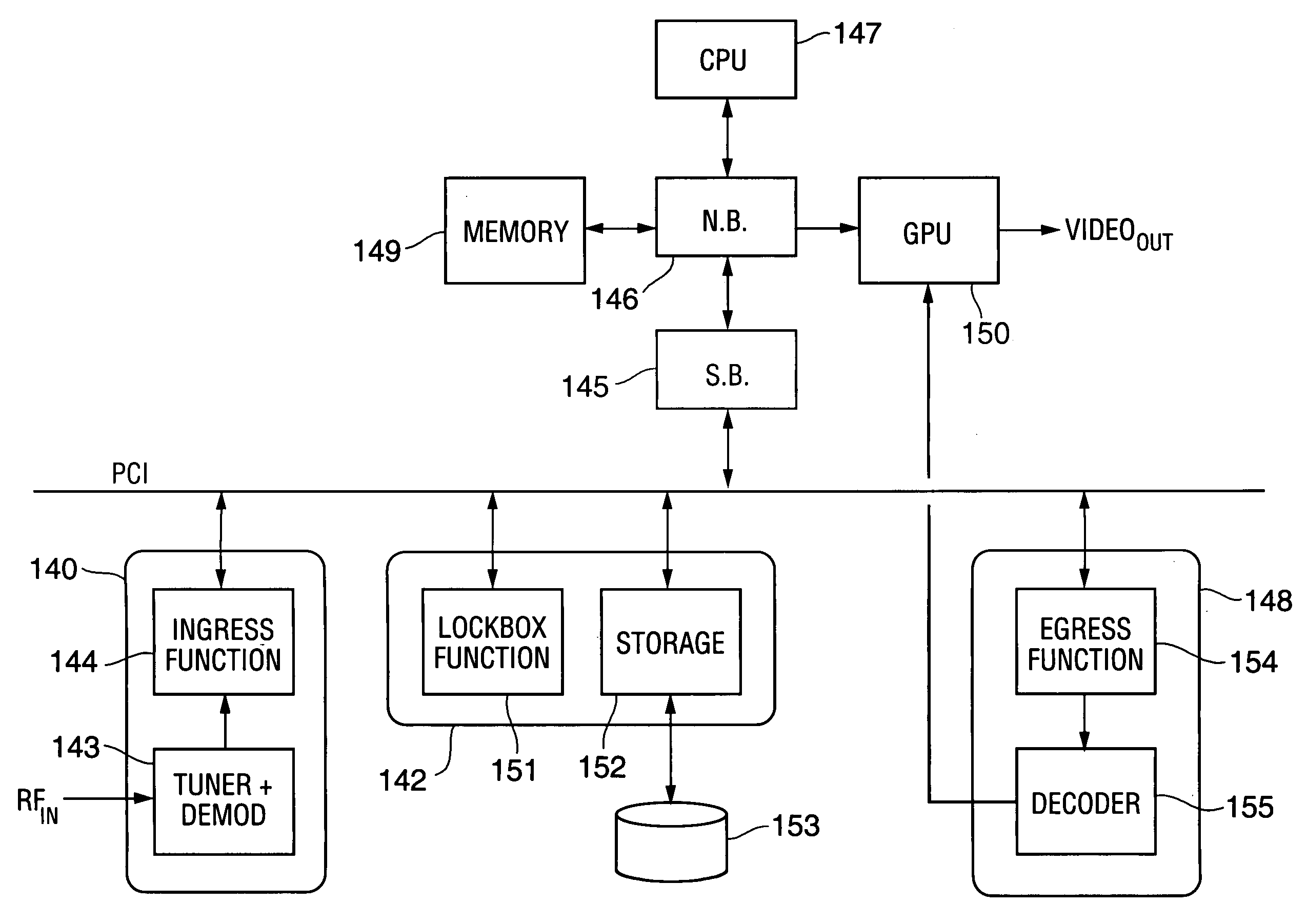
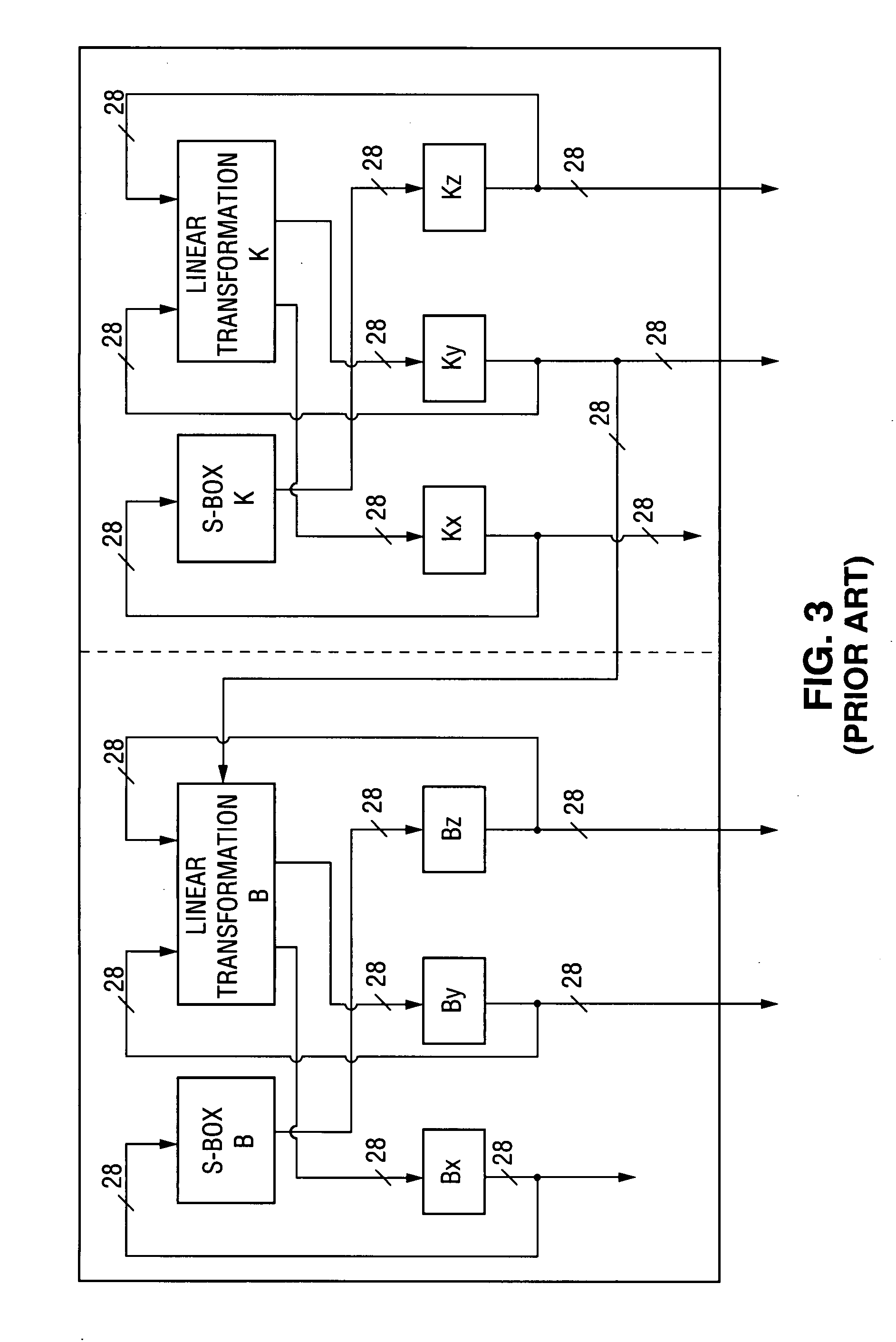
Method and apparatus for content protection in a personal digital network environment
InactiveUS20050144468A1Easy to disassembleReliable lockingTelevision system detailsUser identity/authority verificationGraphicsVideo processing
In some embodiments, the invention is a personal digital network (“PDN”) including hardware (sometimes referred to as Ingress circuitry) configured to transcrypt encrypted content that enters the PDN. Typically, the transcryption (decryption followed by re-encryption) is performed in hardware within the Ingress circuitry and the re-encryption occurs before the decrypted content is accessible by hardware or software external to the Ingress circuitry. Typically, transcrypted content that leaves the Ingress circuitry remains in re-encrypted form within the PDN whenever it is transferred between integrated circuits or is otherwise easily accessible by software, until it is decrypted within hardware (sometimes referred to as Egress circuitry) for display or playback or output from the PDN. Typically, the PDN is implemented so that no secret in Ingress or Egress circuitry (for use or transfer by the Ingress or Egress circuitry) is accessible in unencrypted form to software or firmware within the PDN or to any entity external to the PDN. Other aspects of the invention are methods for protecting content in a PDN (e.g., an open computing system) and devices (e.g., multimedia graphics cards, set top boxes, or video processors) for use in a PDN.
Owner:OPTIMUM CONTENT PROTECTION
Point Of Sale Transaction Device With Magnetic Stripe Emulator And Biometric Authentication
InactiveUS20080126260A1Cost effectiveImprove security levelAcutation objectsPoint-of-sale network systemsData setComputer science
A handheld unit which is capable of emulating a plurality of smartcards or magnetic stripe cards. The unit has the capability of storing a plurality of data sets representing a plurality of accounts. The unit is equipped with an RF interface that can emulate a smartcard interface that is capable of communicating with smartcard readers at POS or ATM terminals, or anywhere else a smartcard may be utilized. The unit is also equipped with a programmable magnetic strip such that it can be used anywhere a magnetic stripe card can be swiped or inserted. The unit is equipped with a biometric sensor to positively verify an authenticated user.
Owner:X CARD HLDG
Programmable key for a security system for protecting merchandise
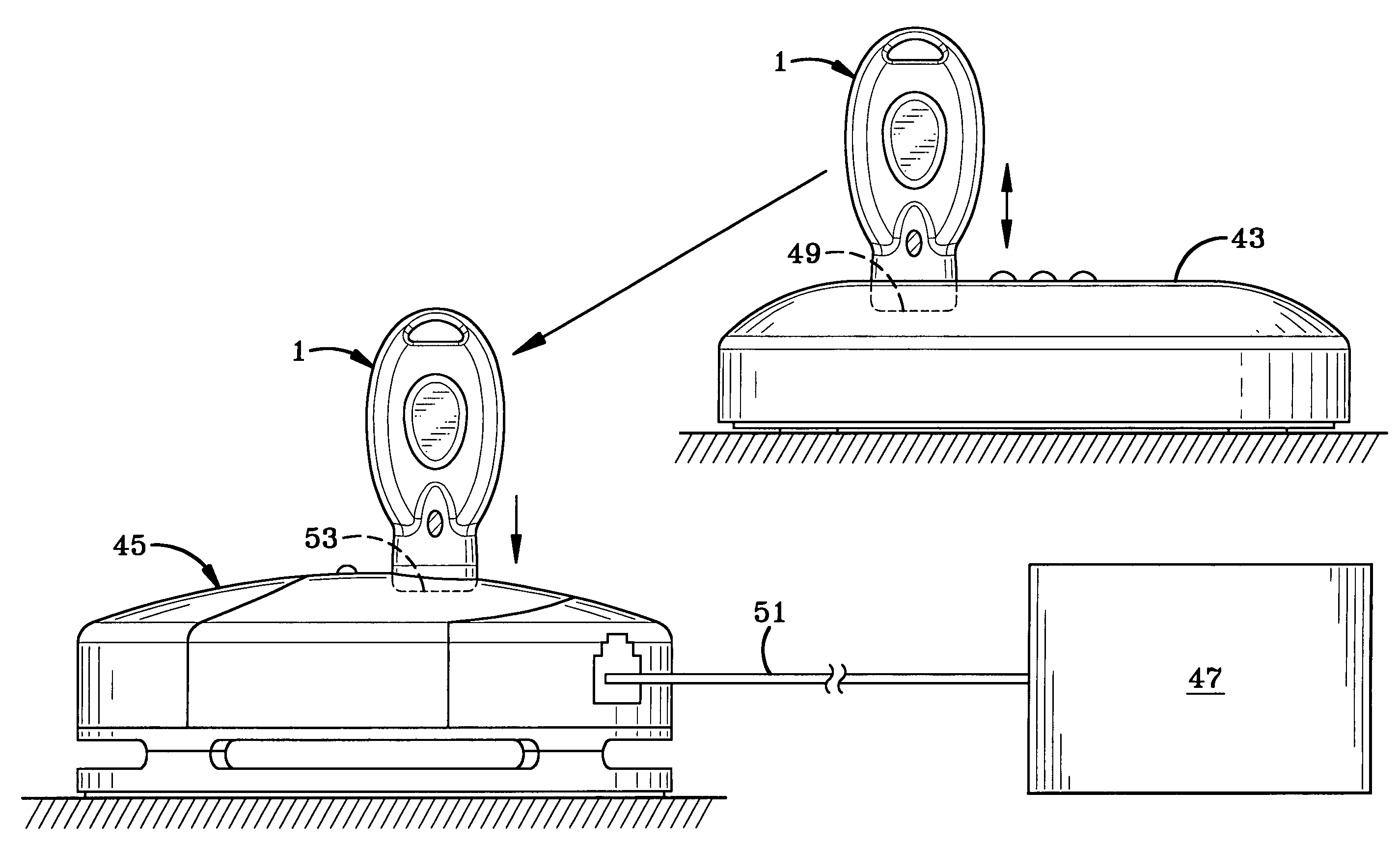
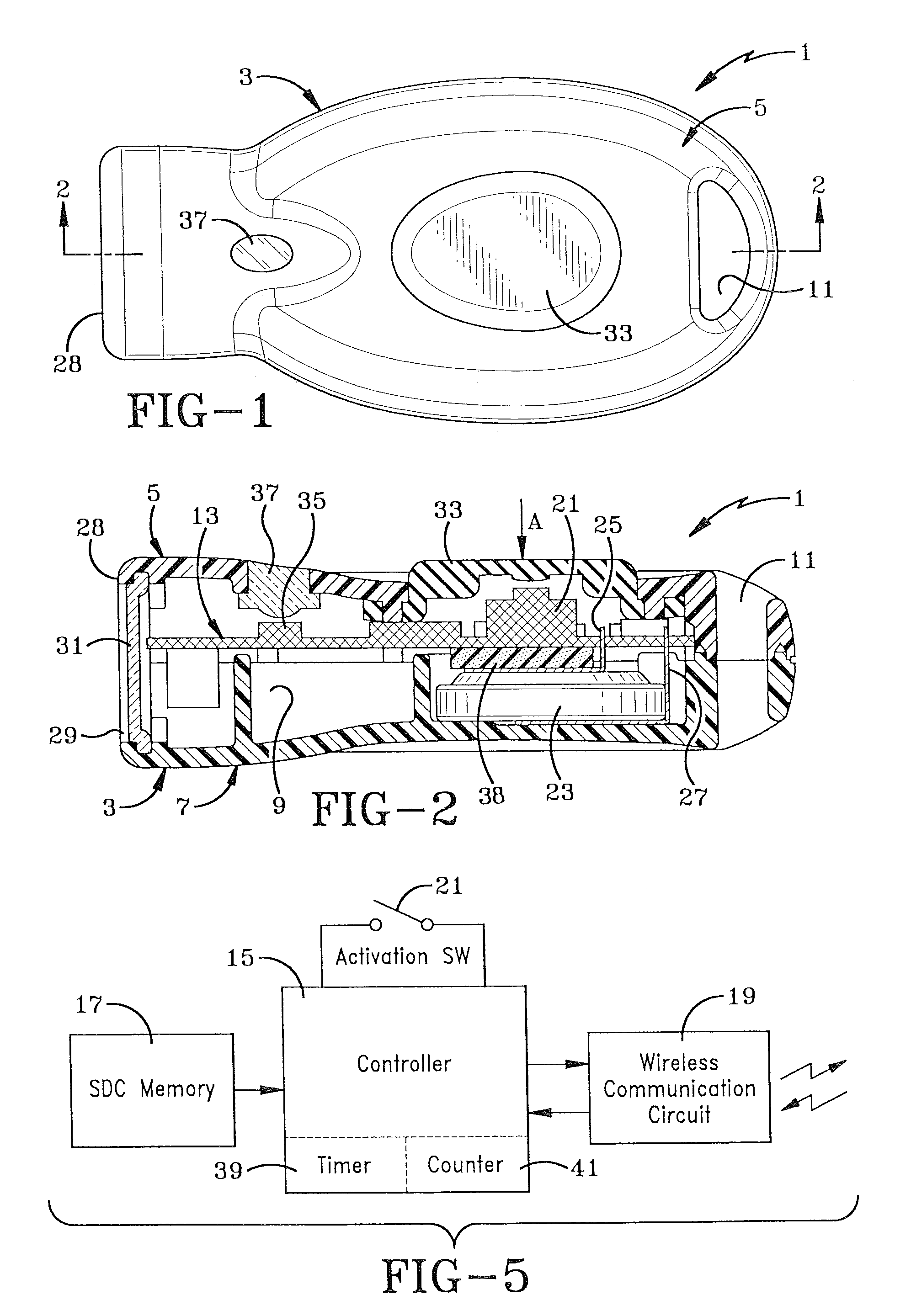
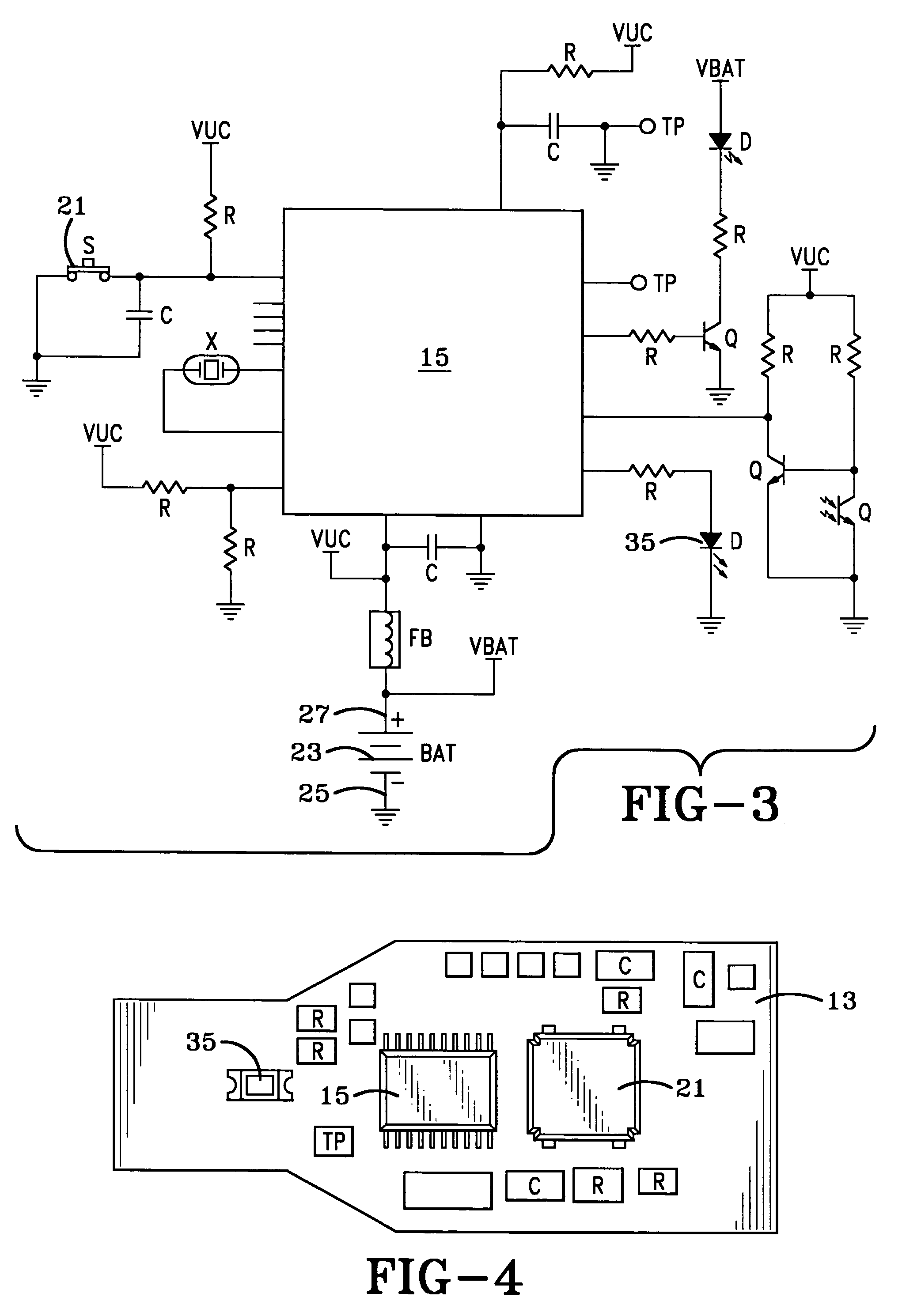
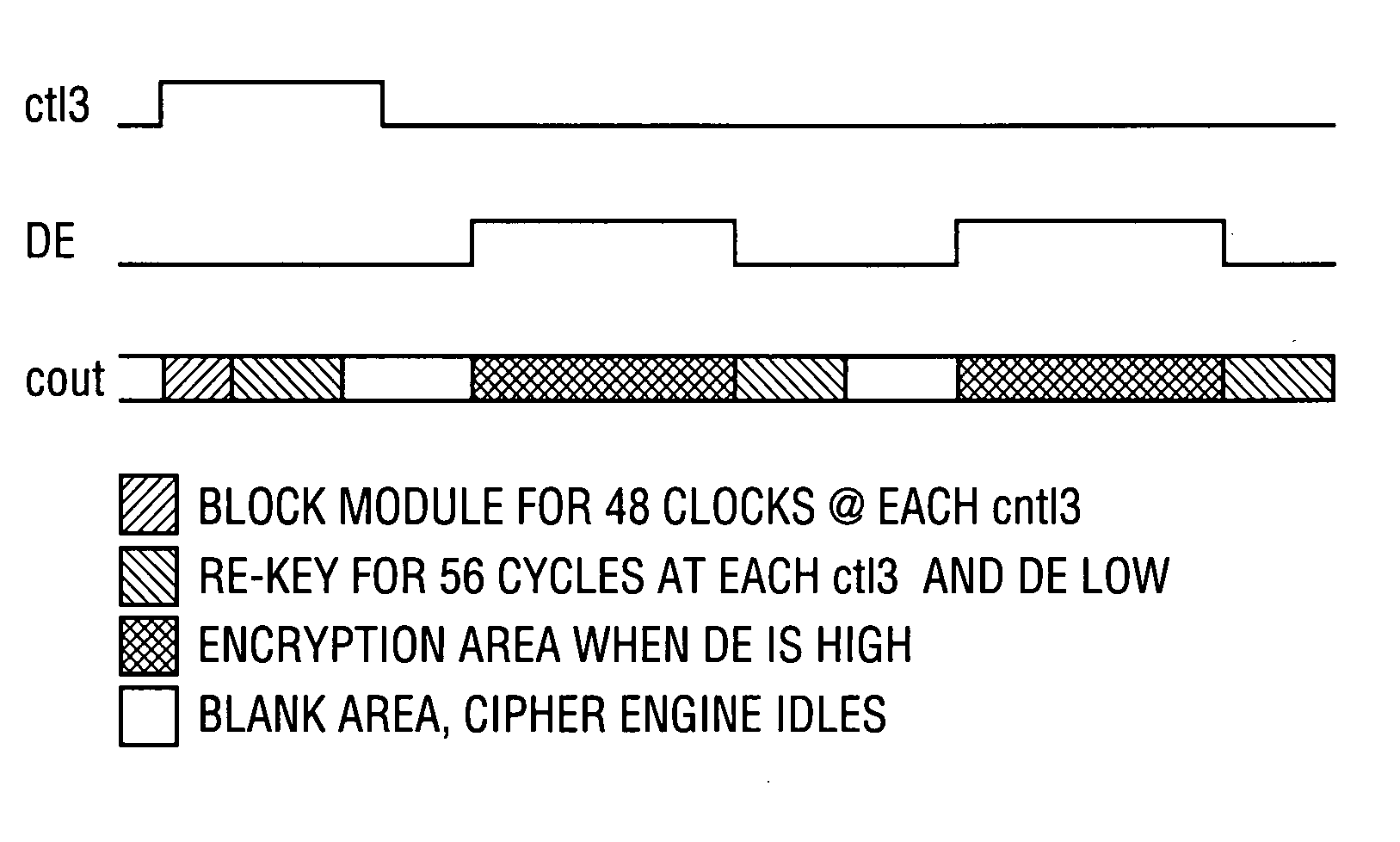
ActiveUS7737845B2Unauthorized useSufficient powerElectric signal transmission systemsMultiple keys/algorithms usageTime limitEngineering
Owner:INVUE SECURITY PROD INC
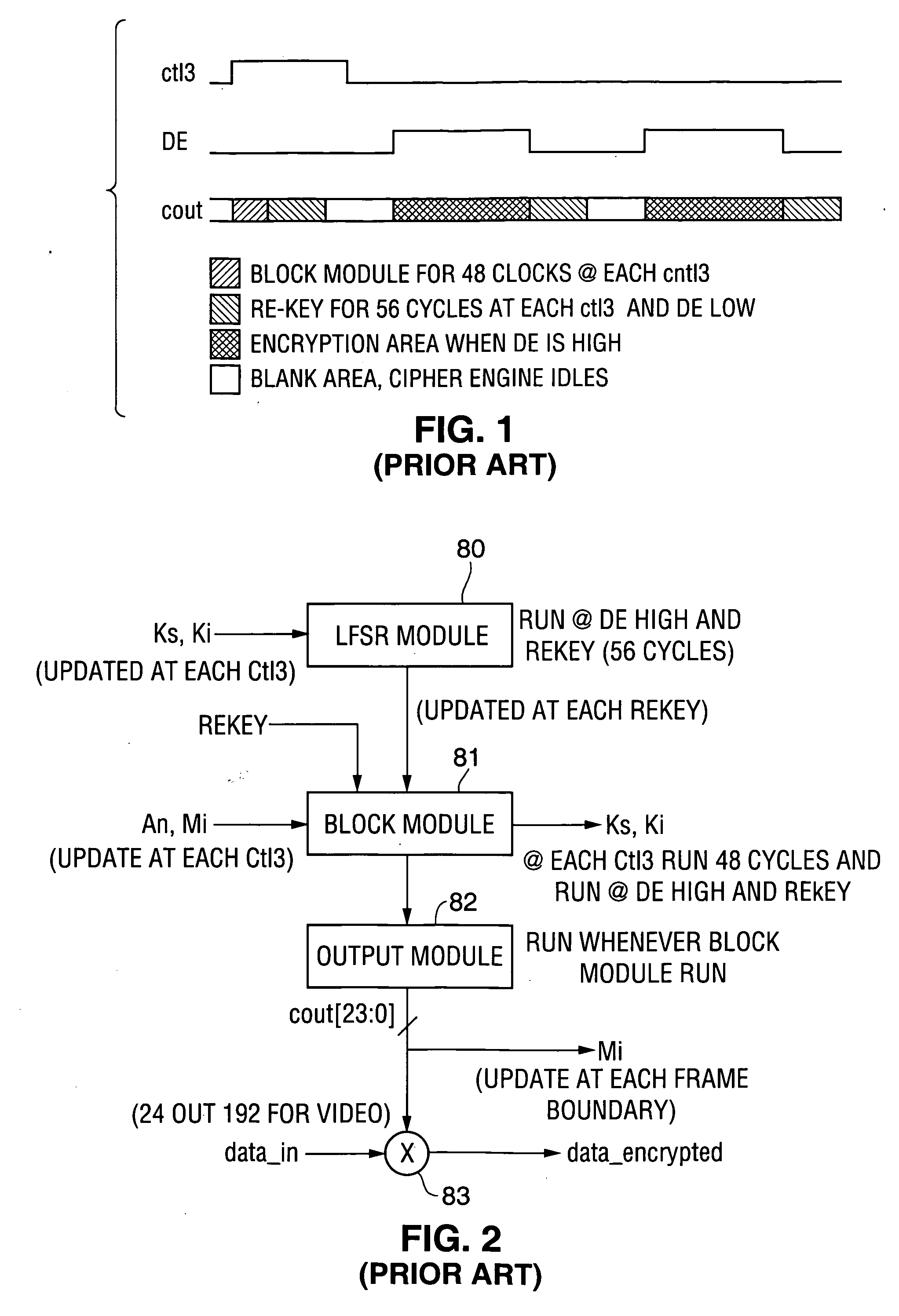
Method and apparatus for content protection in a personal digital network environment
InactiveUS20070220279A1Reduce sensitivityLimit key re-useUnauthorized memory use protectionHardware monitoringGraphicsVideo processing
Owner:OPTIMUM CONTENT PROTECTION
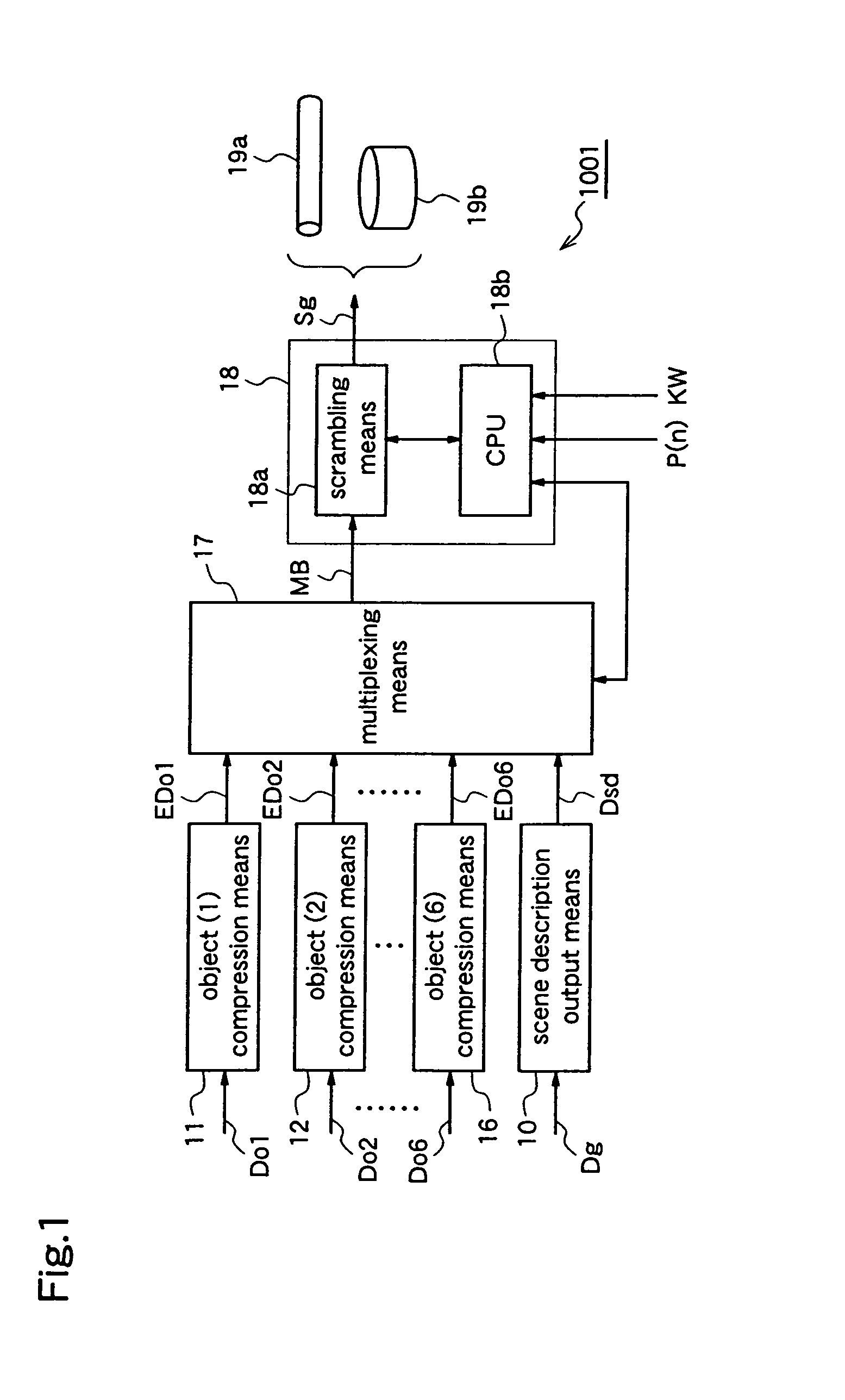
Image object recording, compression, and encryption method and system
InactiveUS6931531B1Satisfactorily preventedUnauthorized useTelevision system detailsAnalogue secracy/subscription systemsComputer hardwareMultiplexing
Selective encryption for object data such that objects having copyrights to-be-protected are encrypted. There are provided a plurality of data compression devices for compressing respective object data respectively corresponding to a plurality of objects which compose a scene, a multiplexor for multiplexing scene description data and compressed object data to produce a multiplexed bit stream MB, a scrambler for encrypting (scrambling) individual streams corresponding to the objects having copyrights to-be-protected in the multiplexed bit stream MB, to produce an encrypted bit stream SB, for outputting the encrypted bit stream SB to a data storage medium or a data transmission medium.
Owner:PANASONIC CORP
System and method for preventing use of a wireless device
ActiveUS7496957B2Unauthorized useMultiple digital computer combinationsProgram controlComputer hardwareCryptographic protocol
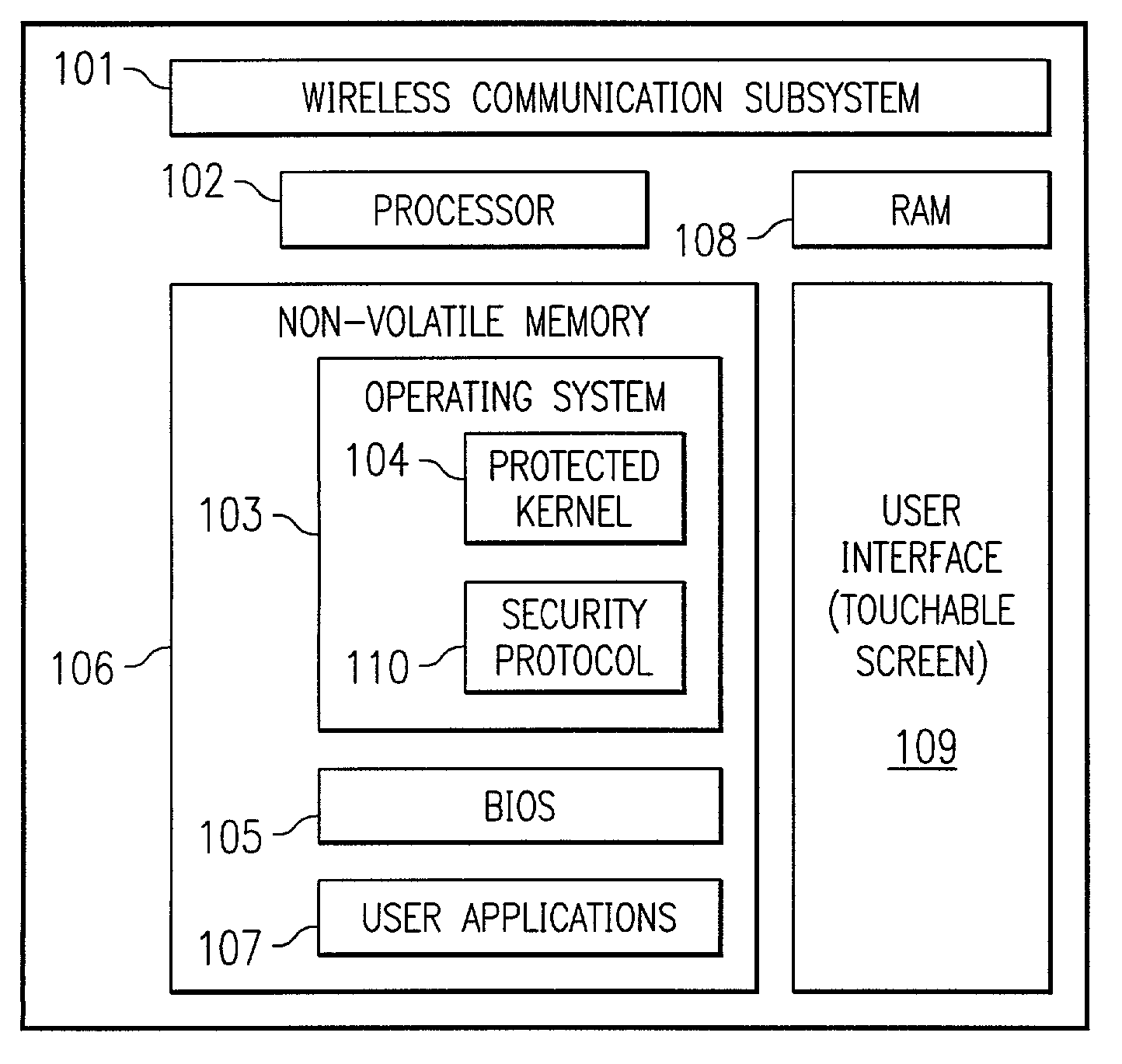
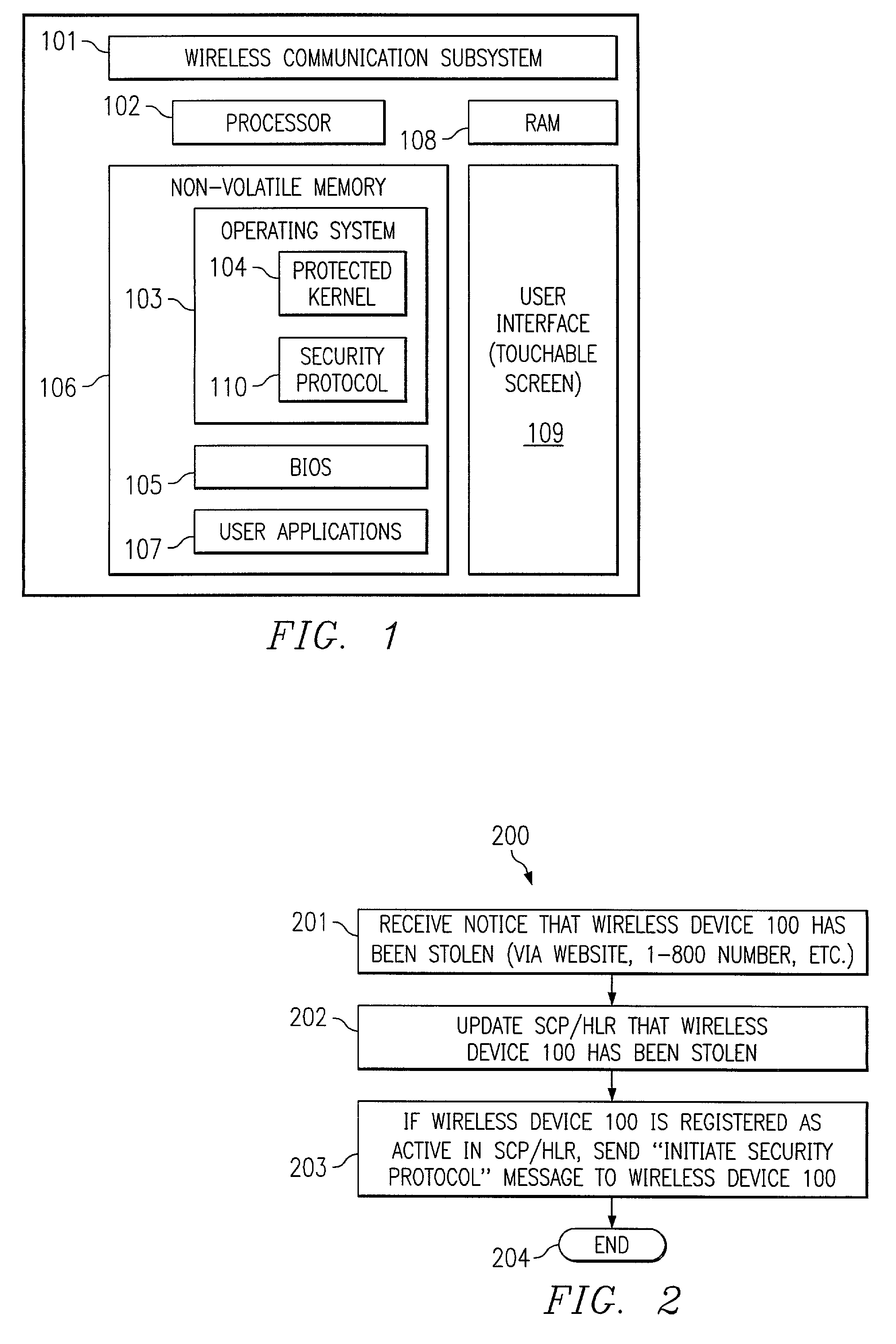
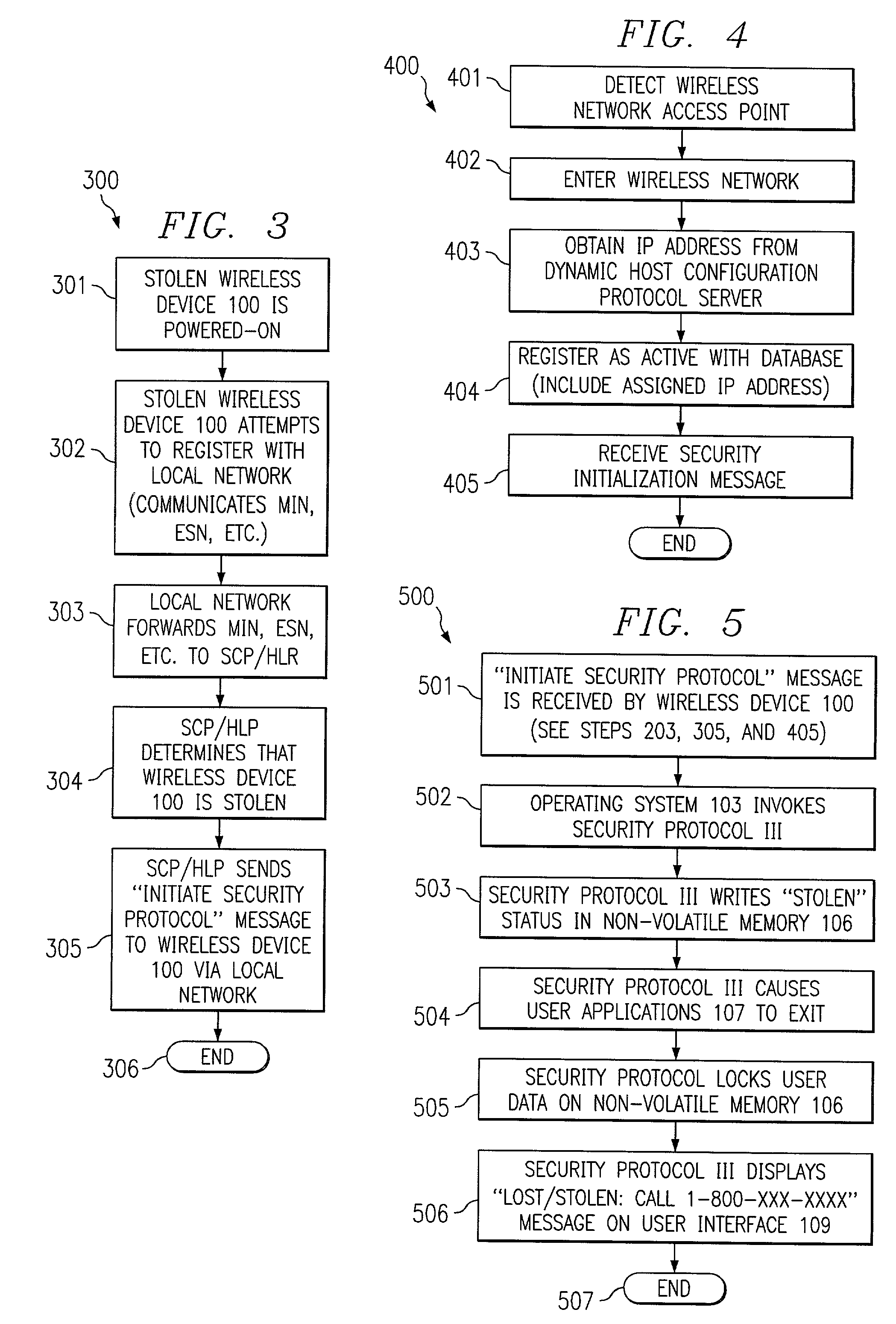
In one embodiment, the present invention is directed to a processor-based device that prevents unauthorized use, comprising a processor for executing software instructions, software instructions defining at least one user application, a wireless communication subsystem that is operable to transmit and receive data utilizing a wireless protocol, and software instructions defining a security protocol process that is operable to prevent execution of the software instructions defining the at least one user application by the processor when a message is received via the wireless communication subsystem, wherein the message indicates that the processor-based device is not in possession of a rightful user.
Owner:QUALCOMM INC
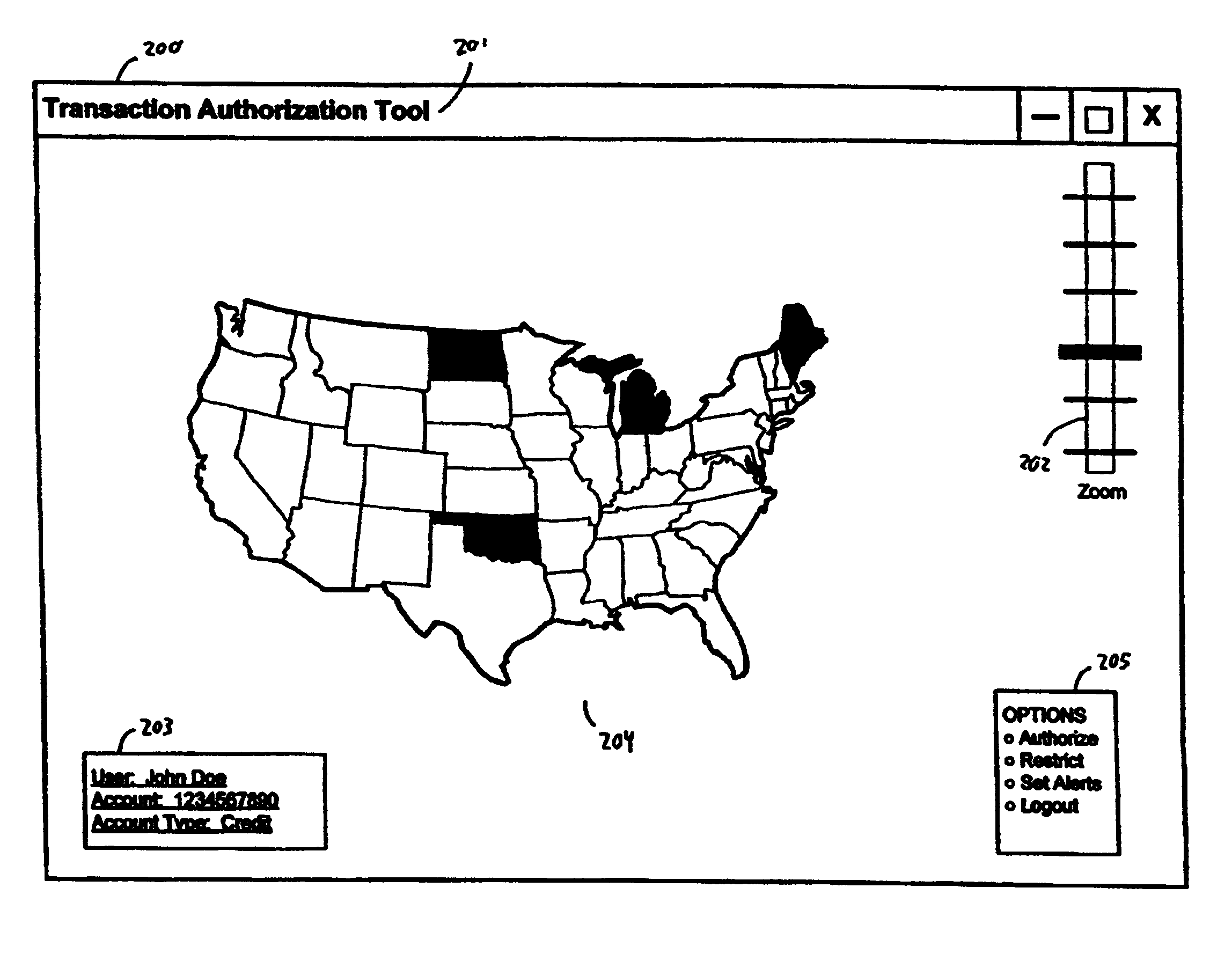
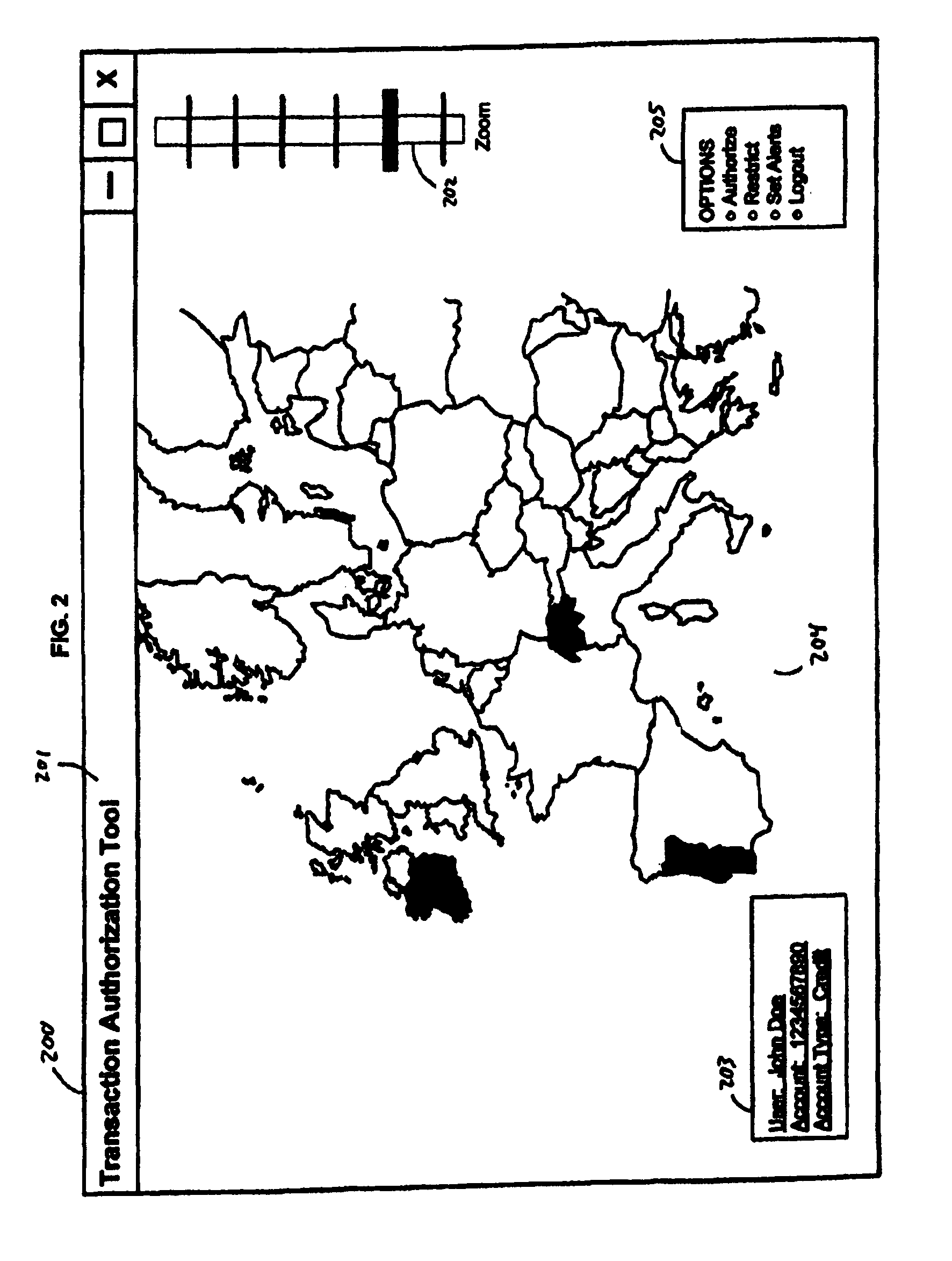
Method and system for authorizing card account transactions by geographic region
ActiveUS7857212B1Improve the level ofAvoid makingReservationsPoint-of-sale network systemsGeographic regionsAuthorization
A method and system for authorizing card account transactions by geographic region by providing data for a user interface displaying geographic regions and merchant locations each corresponding to the location of a merchant where a transaction using a card account may be initiated, receiving a user interface selection representing a request to authorize or restrict card account transactions, receiving authorization requests for desired transactions, and authorizing or restricting the transactions in accordance with the request.
Owner:CAPITAL ONE SERVICES
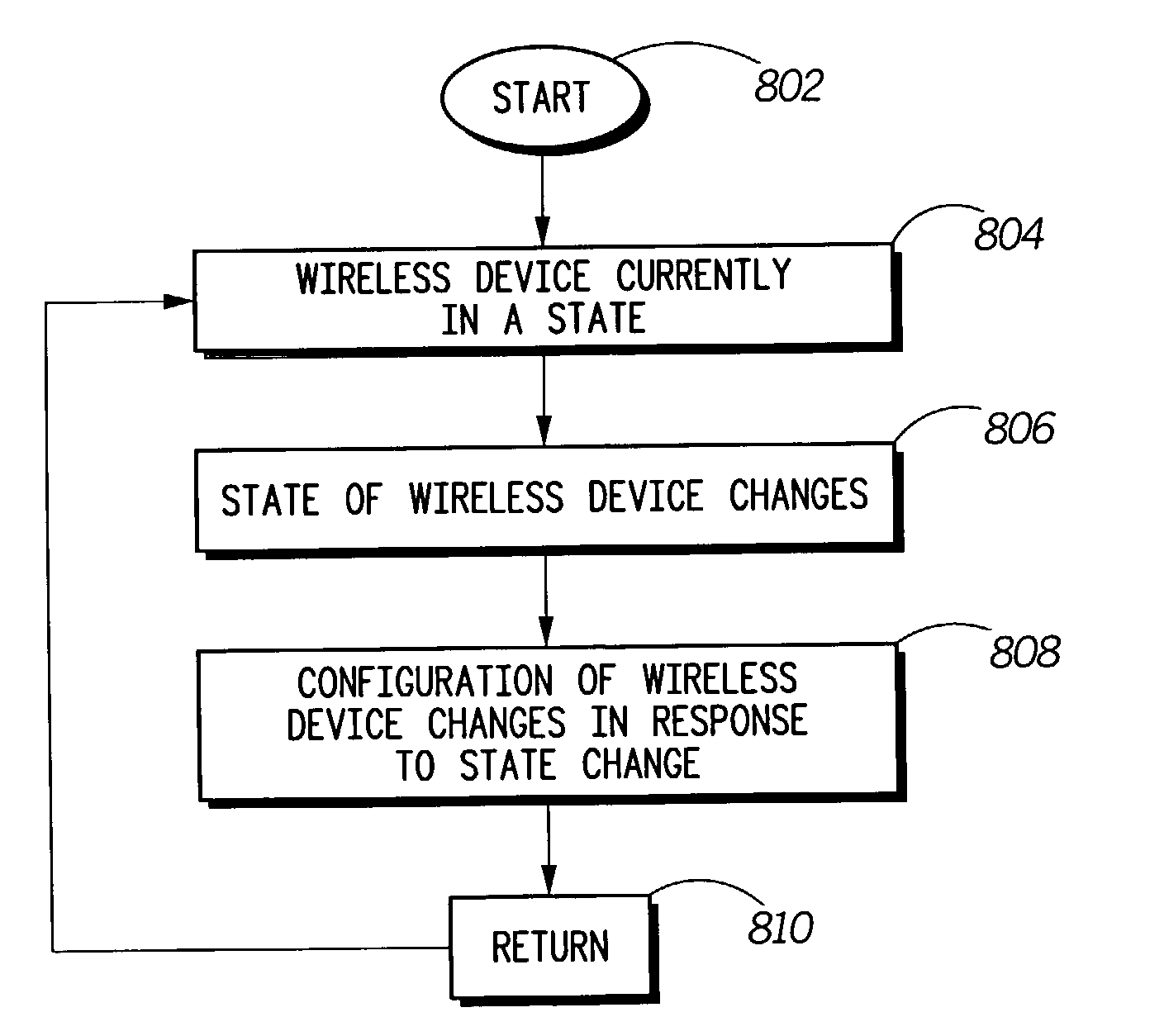
Wireless device allowing for configuration of settings and method therefor
InactiveUS6983169B2Avoid loud and disruptive ringingOptimizationDevices with sensorSubstation equipmentComputer network
Disclosed is a system, method and computer readable medium for configuring settings of a wireless device. The system on a wireless device includes means for detecting a user action indicating a particular mode for the wireless device. The means for detecting includes any one of means for detecting the proximity of a holster for holding the wireless device and means for detecting an on-call status and / or an off-call status of the wireless device. The system on a wireless device further includes a processor in the wireless device for configuring settings of the wireless device in response to the user action. The configuring of settings is performed any one of manually and automatically. The settings of the wireless device include at least one of a ring setting, a battery setting, an input pad setting and a device use setting.
Owner:GOOGLE TECH HLDG LLC
Information recording device, information playback device, information recording method, information playback method, and information recording medium and program providing medium used therewith
InactiveUS7319752B2Raise security concernsUnauthorized useTelevision system detailsKey distribution for secure communicationComputer hardwareCryptosystem
An information recording / playback device stores beforehand, on a recording medium, secret information in which a writing / reading method thereof cannot be analyzed and which can be read only by a special reading method. The secret information is applied to a key for content encryption or decryption when performing recording or playback of contents on the recording medium, such as music data and image data. The secret information is, for example, a stamper ID. By using the stamper ID as secret information, and a master key and a media key which are distributed in a tree-structure key-distribution system, a content-cryptosystem key is generated. Accordingly, each content is allowed to be used in only an appropriate device in which the special reading method for the secret information can be executed and to which the key is distributed by the tree-structure key-distribution system.
Owner:SONY CORP
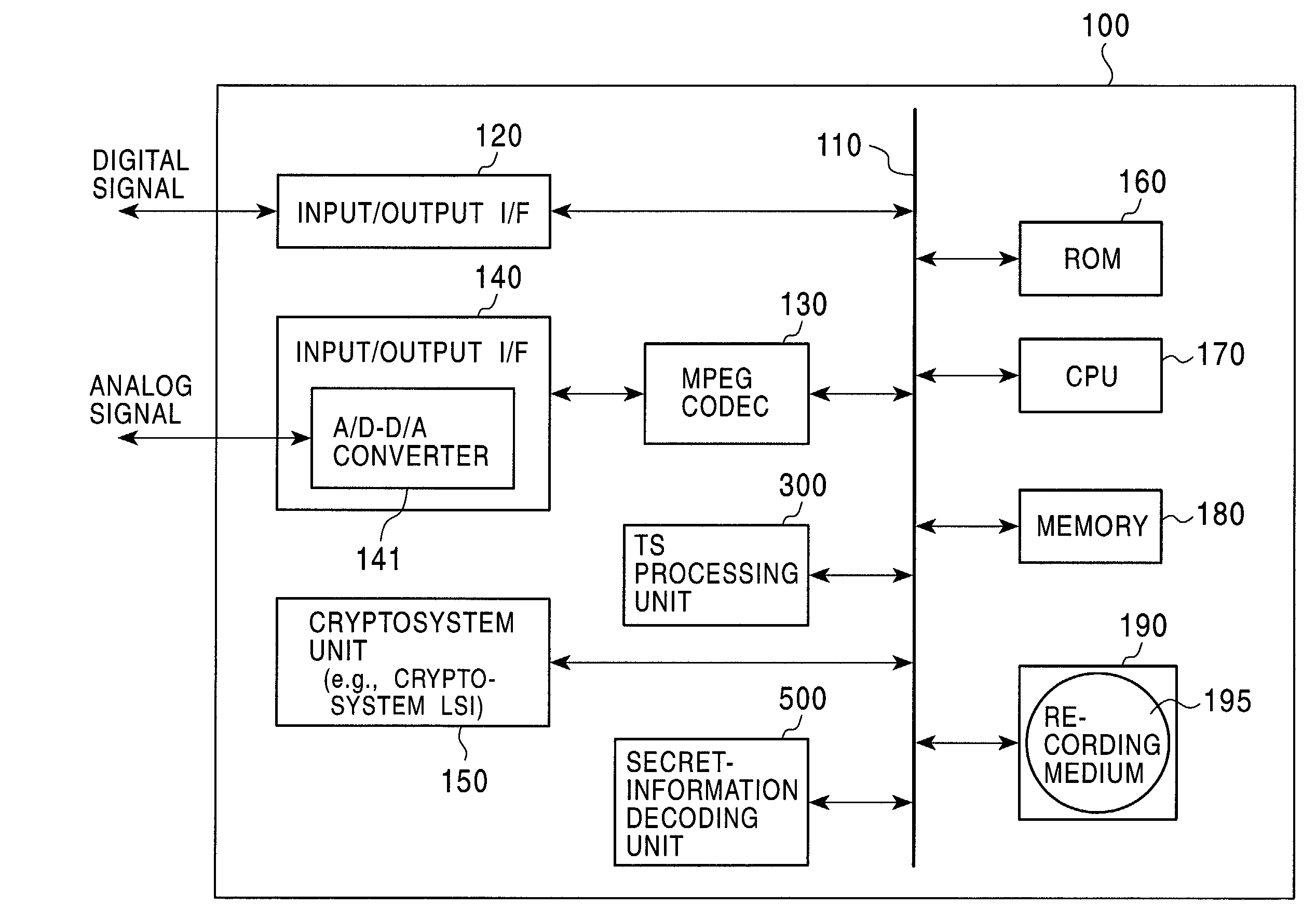
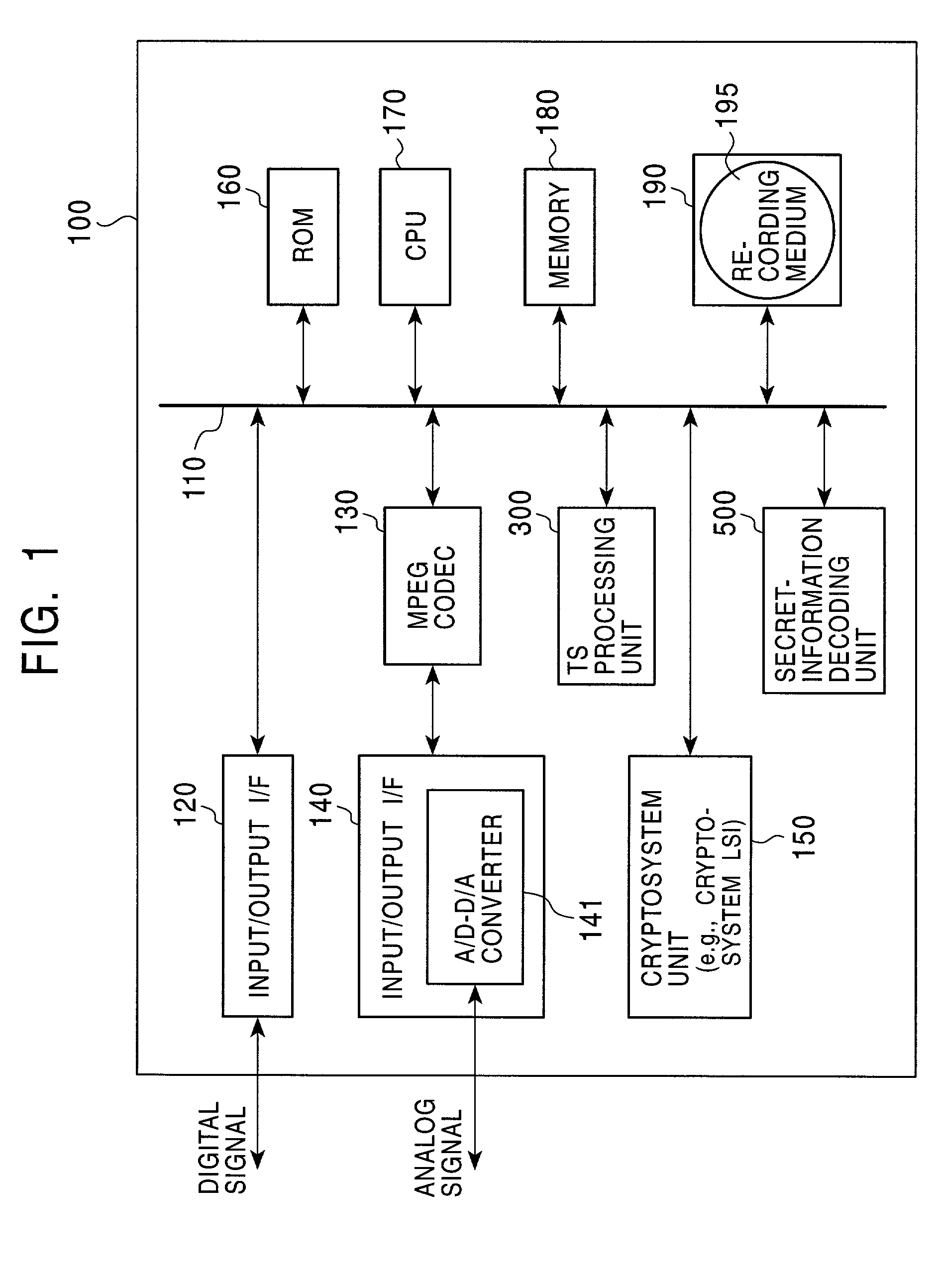
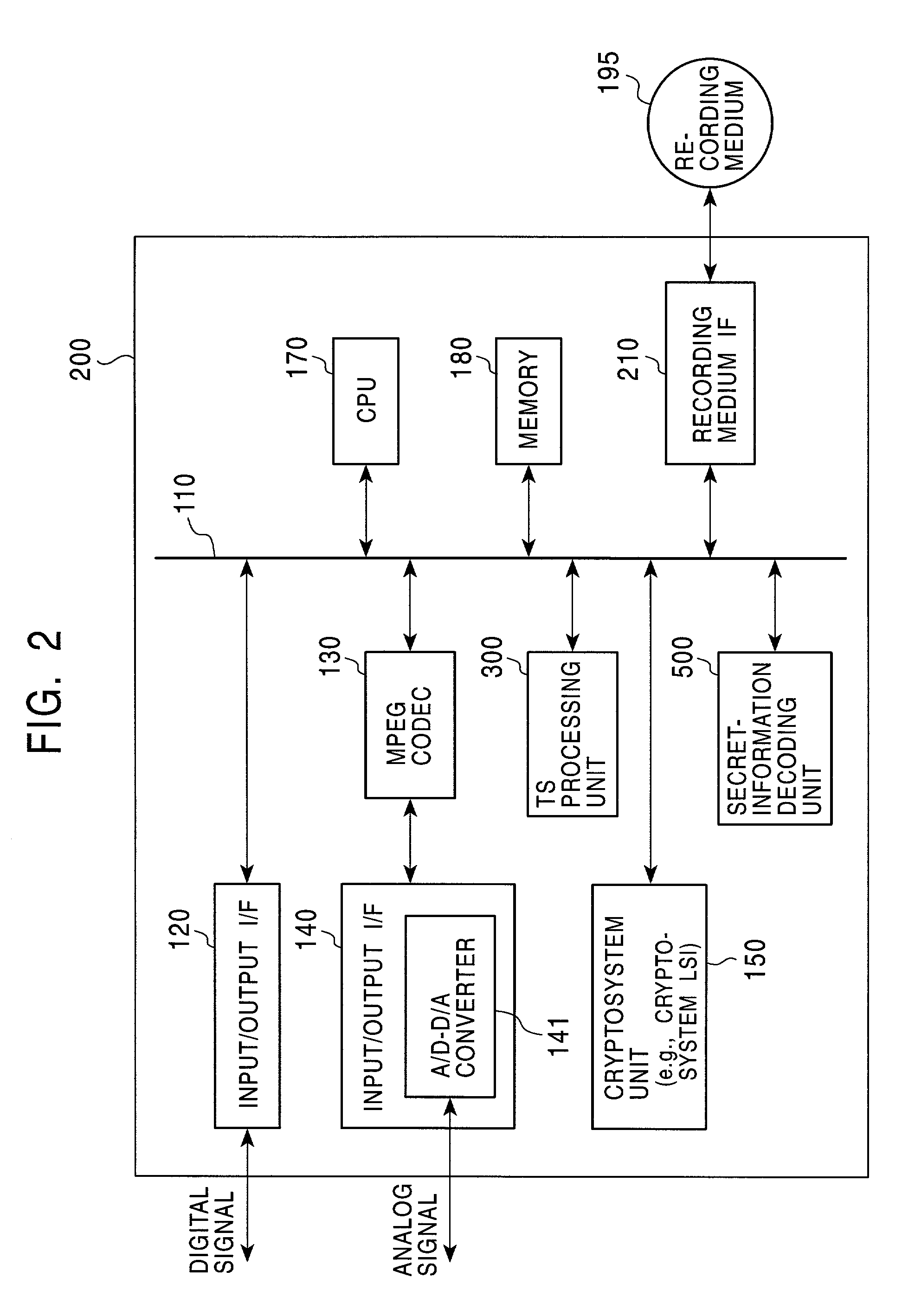
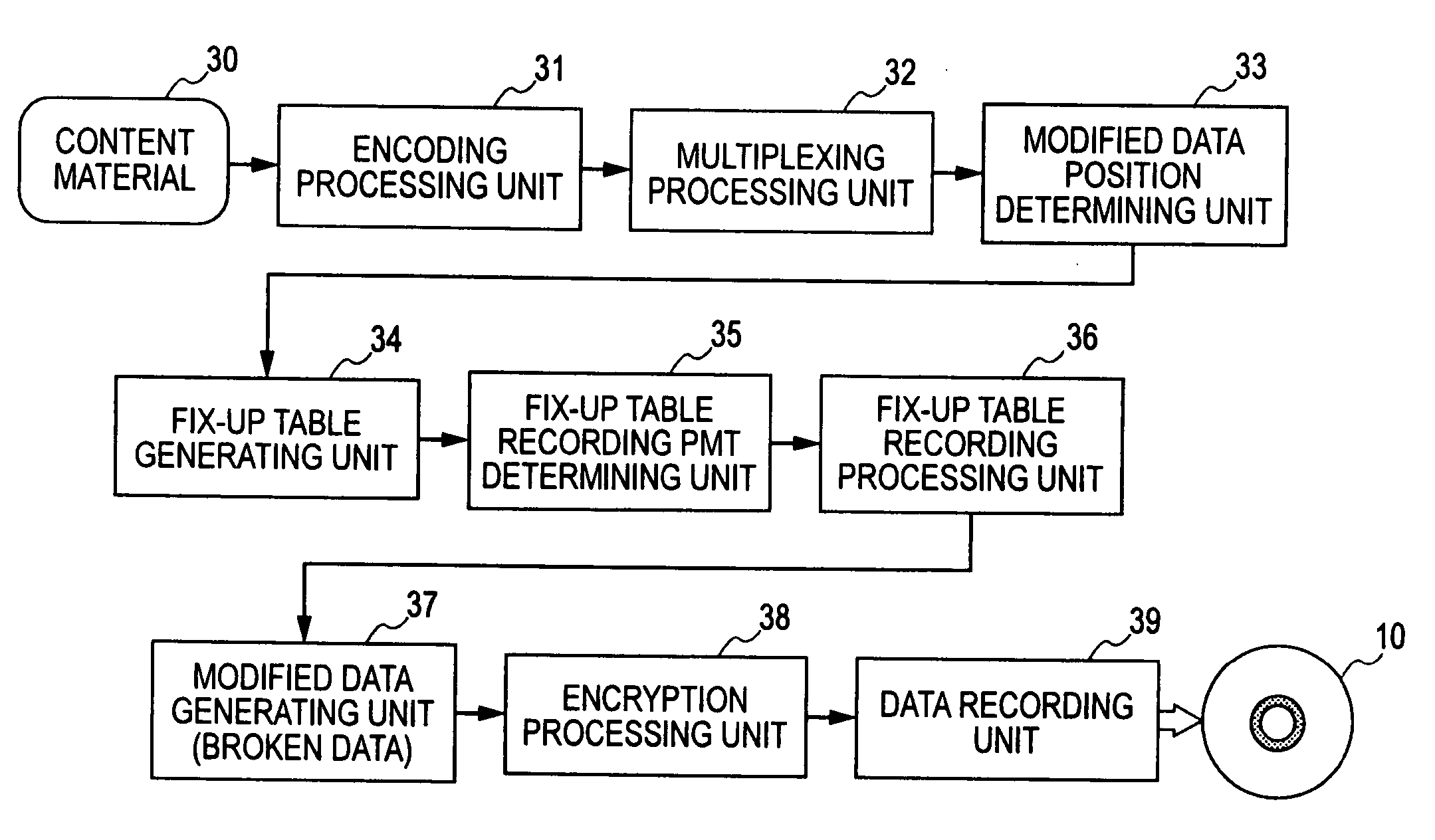
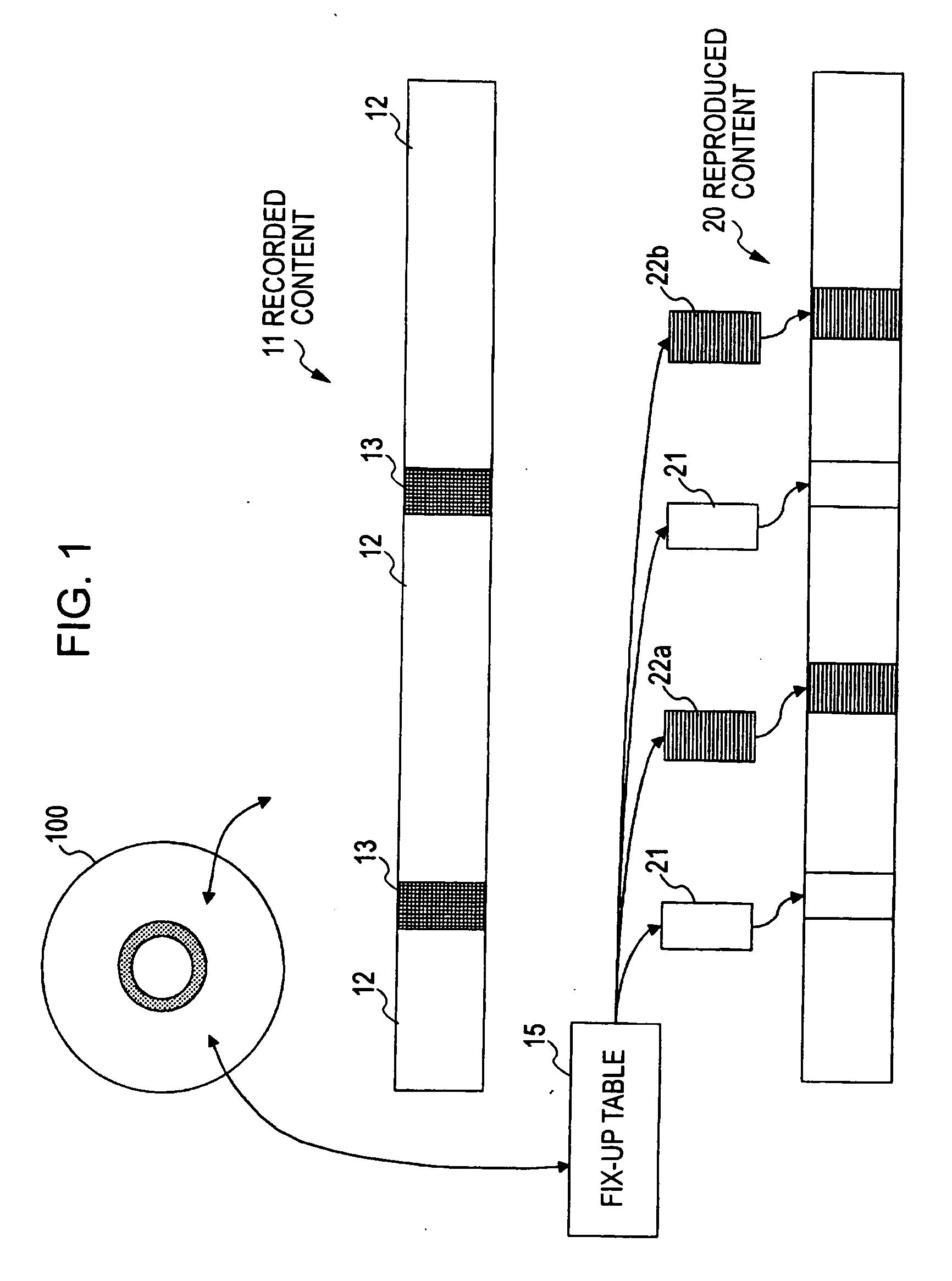
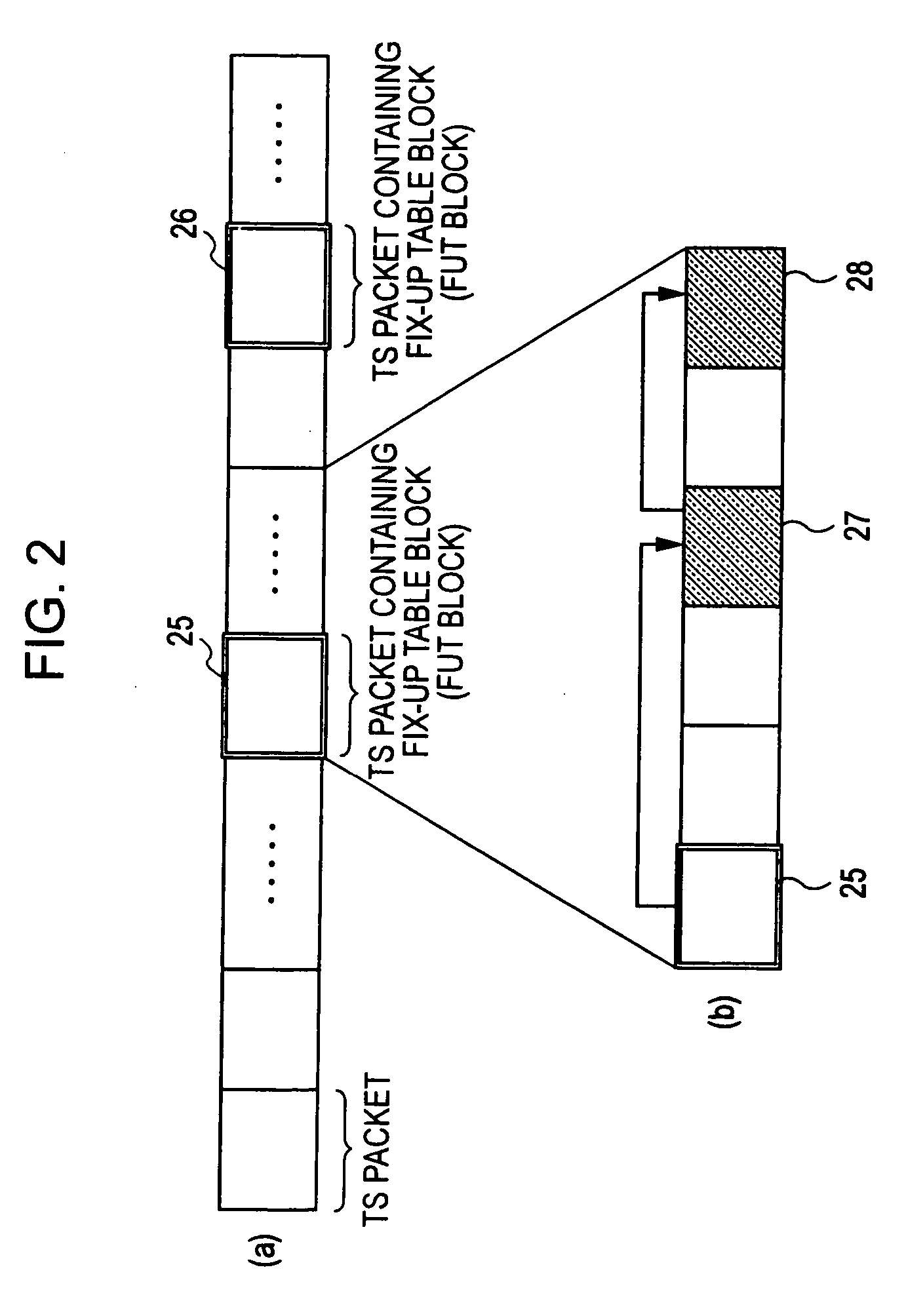
Information processing device, information recording medium manufacturing device, information recording medium, methods thereof, and computer program
InactiveUS20070047645A1Reduce the impactUnauthorized useTelevision system detailsPicture reproducers using cathode ray tubesInformation processingProcessing element
An information processing device includes: a modified data generating unit for generating modified data obtained by modifying content configuration data; a fix-up table generating unit for generating a fix-up table in which transformation data serving as an object to be replaced with the modified data is registered; and a data recording unit for recording content including the modified data and the fix-up table in an information recording medium; wherein the modified data generating unit is configured so as to execute data modification processing with the configuration units of MPEG encoded data included in a TS packet making up content as data modification processing units.
Owner:SONY CORP
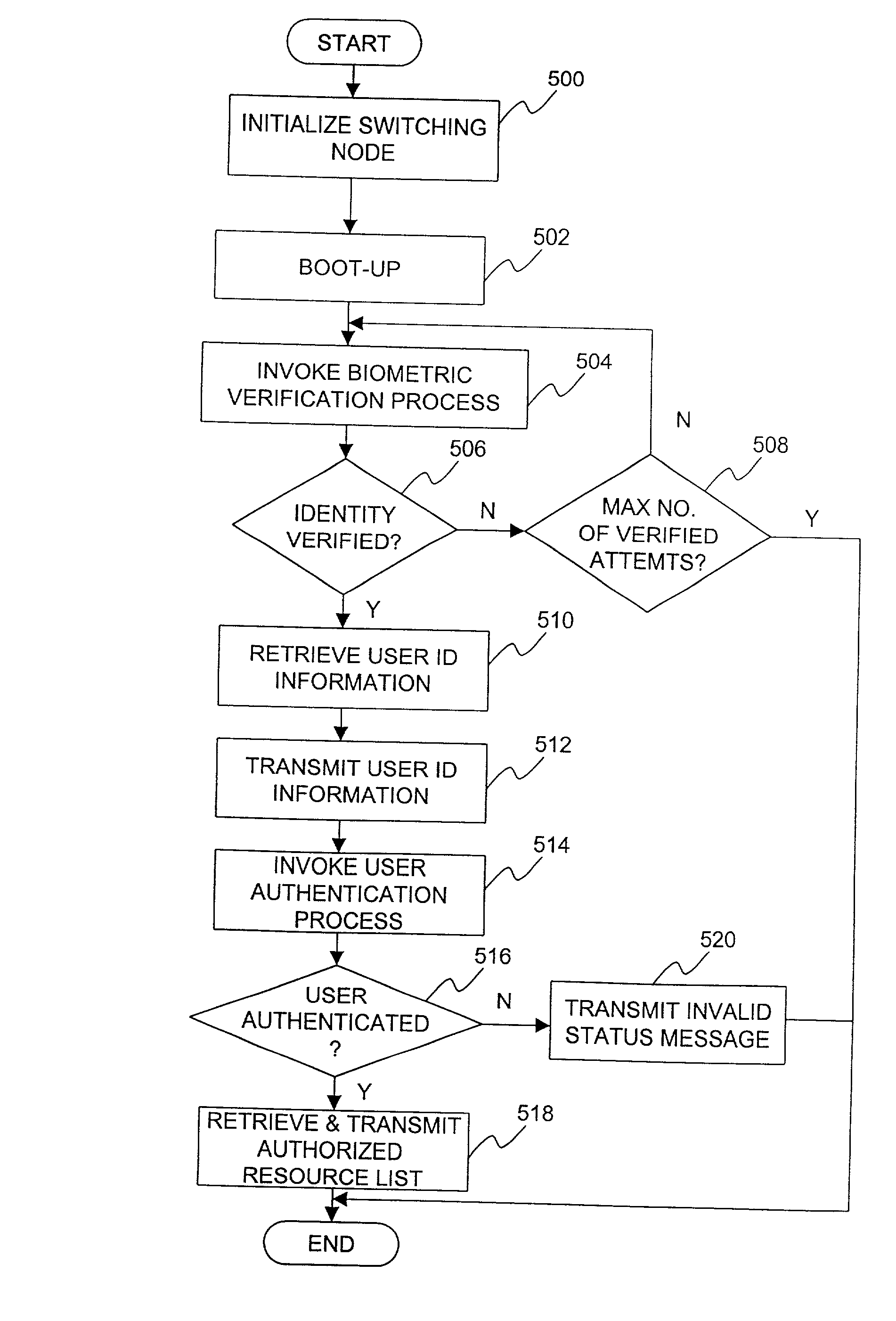
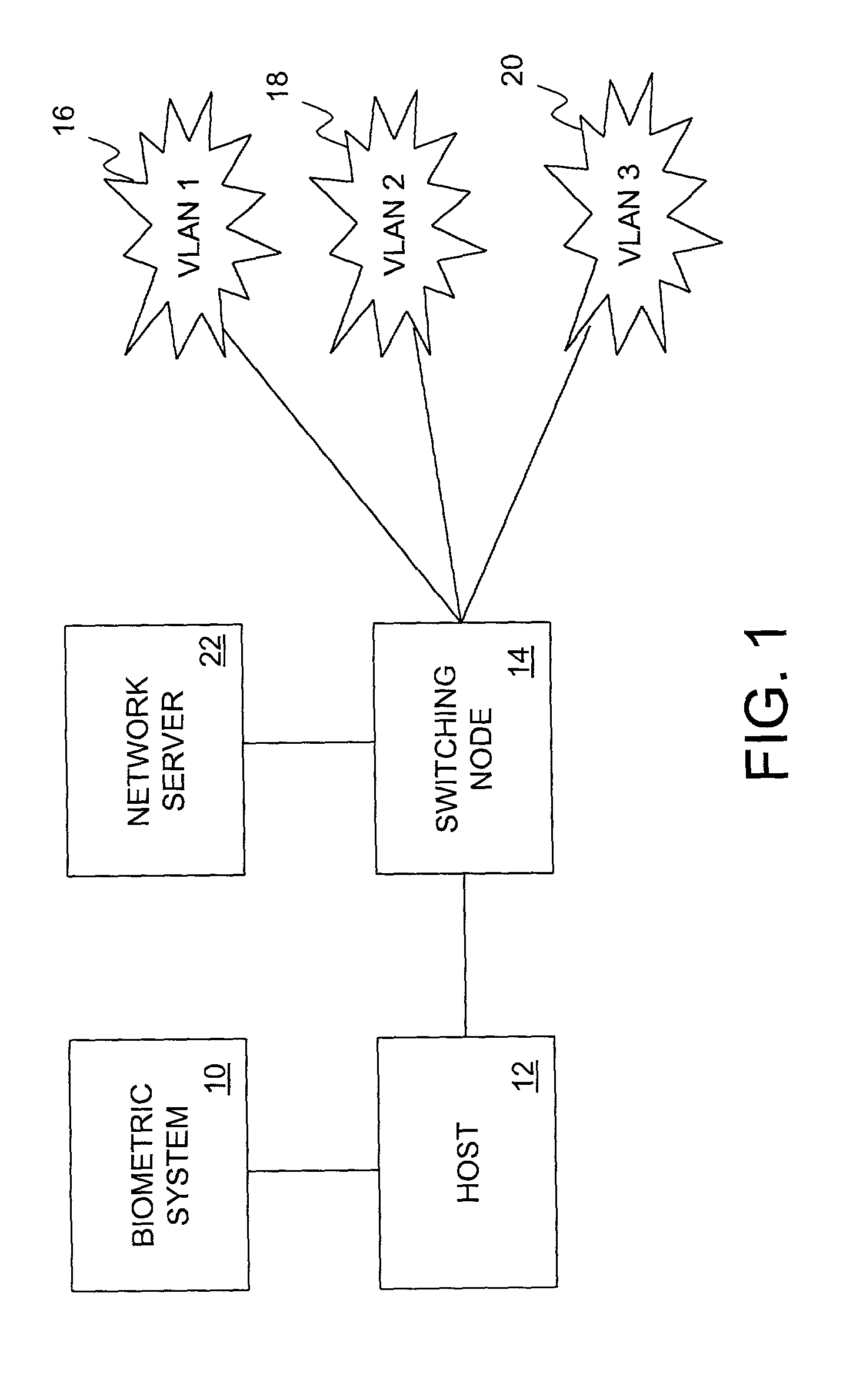
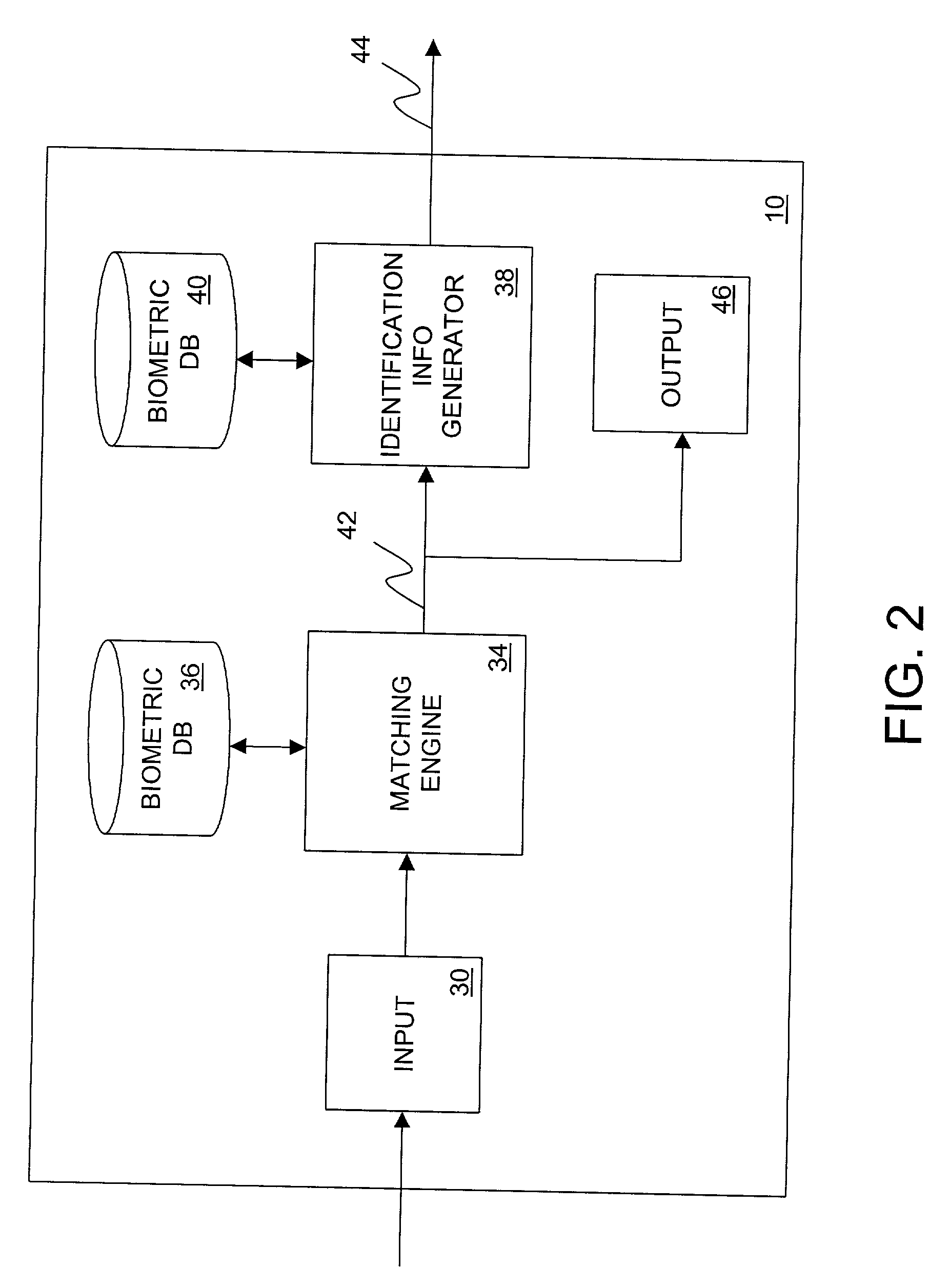
Biometric authenticated VLAN
InactiveUS20020129285A1Prevent illegal useUnauthorized useDigital data processing detailsUser identity/authority verificationInternet privacyUser authentication
A user authentication system and method for a data communication network that helps ensure that a user accessing the network resources is indeed the person having a claimed identity. The user's identity is verified by a biometric system by examining the user's physiological or behavioral characteristic. User identification information needed for accessing the network resources is stored in the biometric system and not released until the user's identity is verified. Upon verification of the user's identity, the user identification data is provided to a switching node for determining the VLANs that the user may access.
Owner:ALCATEL LUCENT SAS
RFID transponder and a method for fabricating the same
InactiveUS20120056002A1Easy to manufactureReduce usageRecord carriers used with machinesRadio frequencyElectric power
The present application provides a radio frequency identification (RFID) transponder and a method for fabricating the same. The RFID transponder, comprising: a microchip which is arranged to communicating with a reader; a battery which is arranged to provide an electrical power for operating the transponder, and is attached to the microchip by means of a conductive path; an antenna which is arranged to receive and backscatter radio frequency interrogation radiation; and a substrate, on which the microchip, the battery and the antenna are arranged.
Owner:CONFIDEX OY
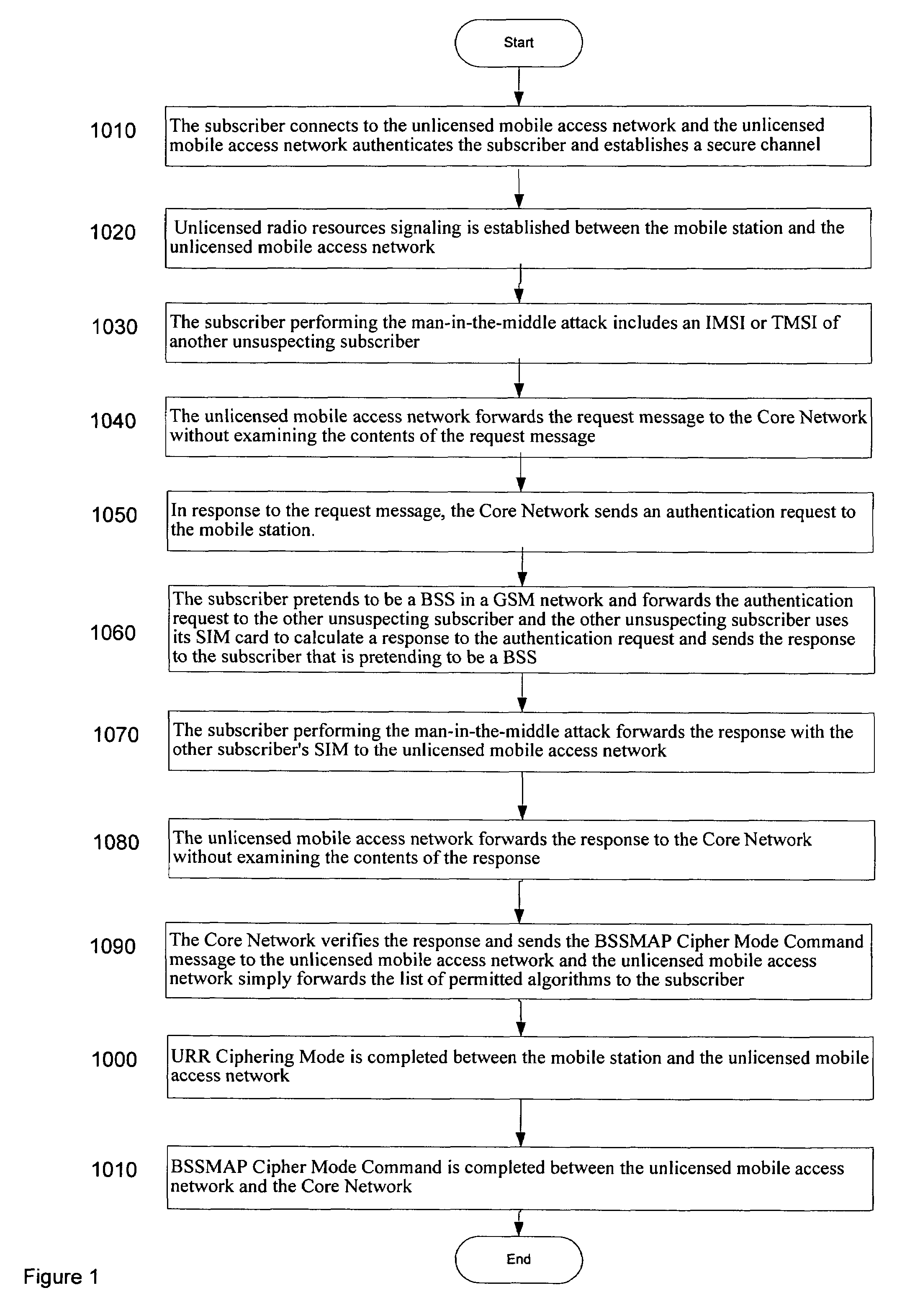
Subscriber authentication for unlicensed mobile access signaling
ActiveUS7200383B2Unauthorized useUnauthorised/fraudulent call preventionEavesdropping prevention circuitsAccess networkMobile station
Owner:NOKIA TECH OY
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS8582567B2Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
Owner:AVAYA INC
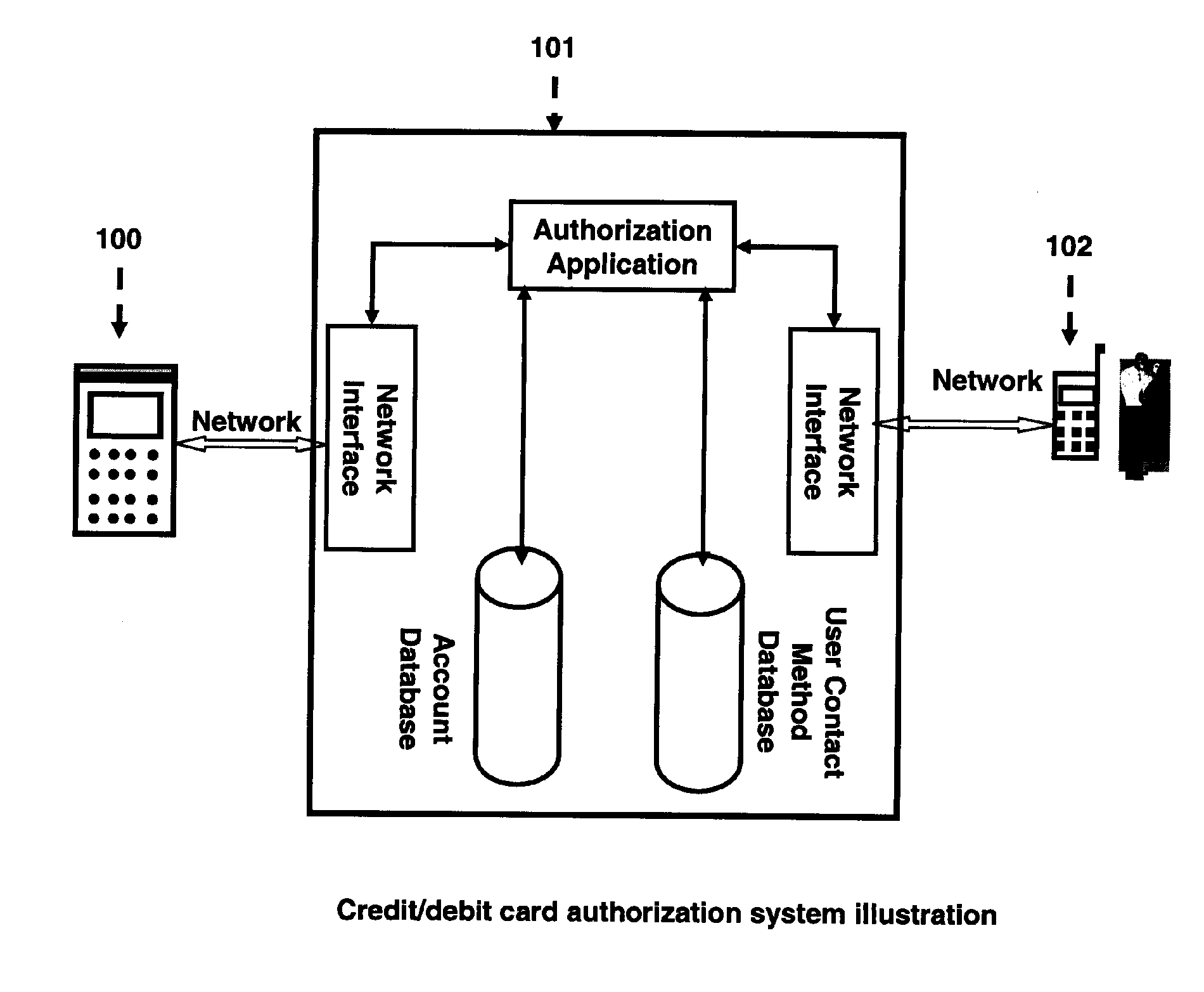
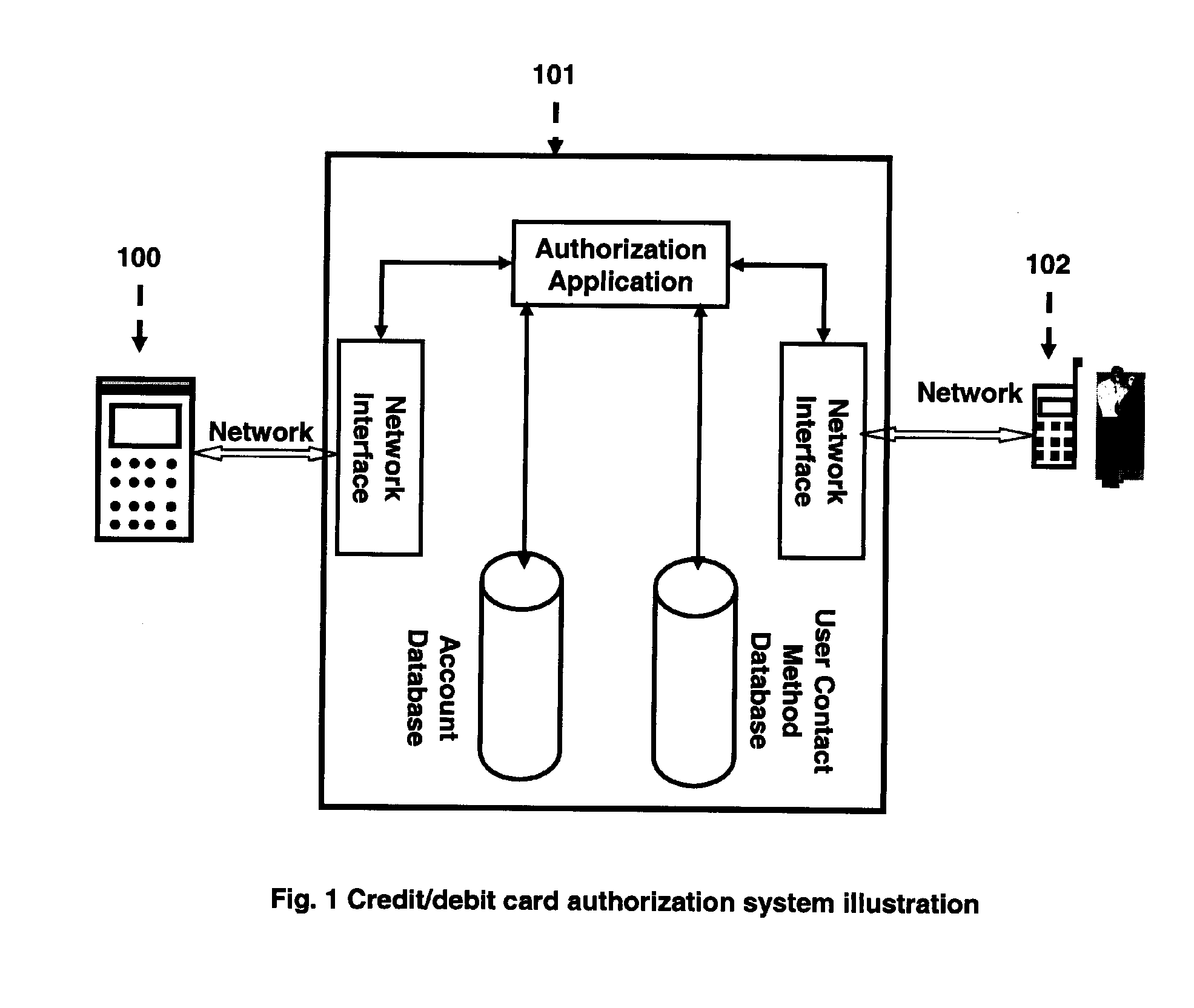
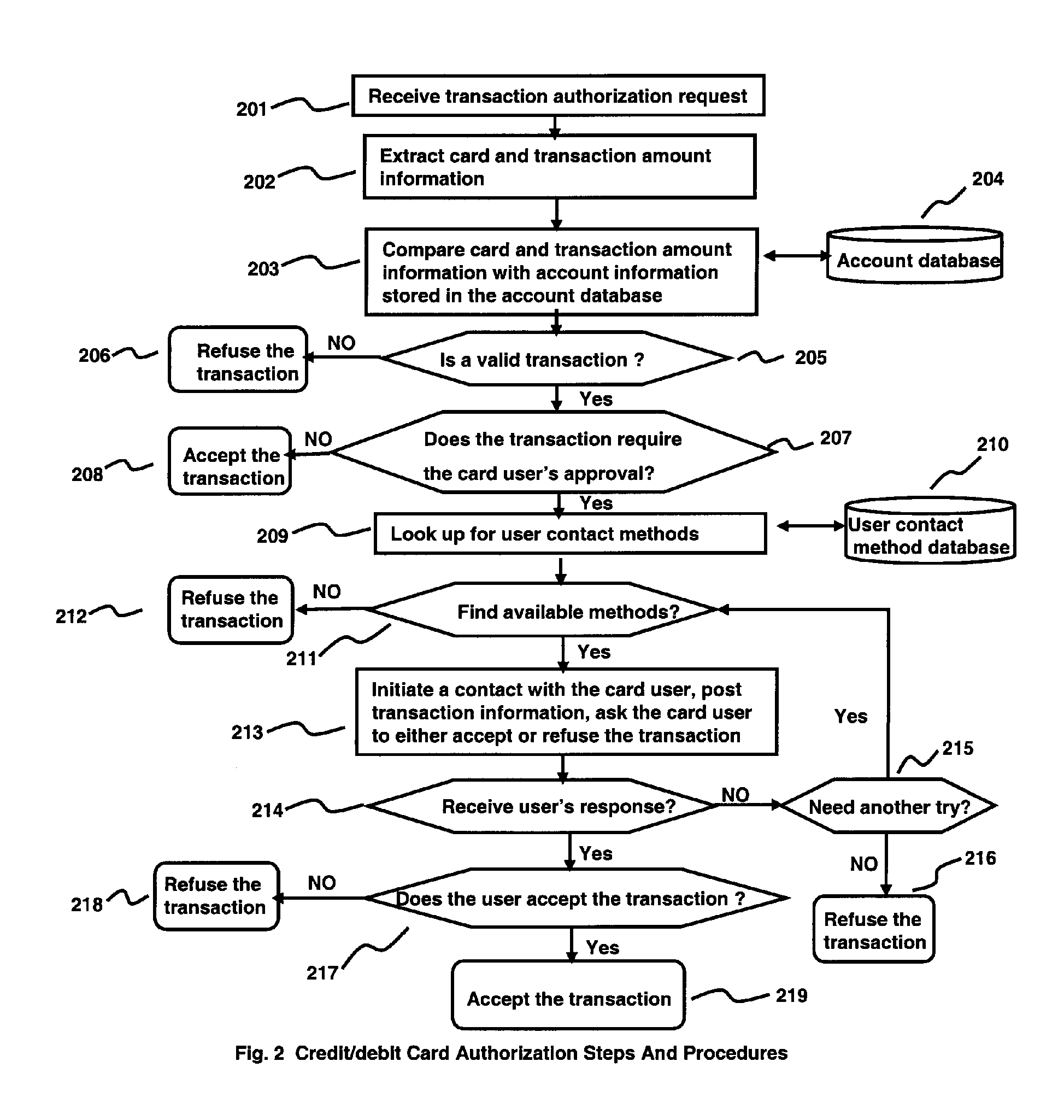
Anti-Fraud Credit/Debit Card Authorization System and Method
InactiveUS20070262136A1Unauthorized useMinimize impactPayment circuitsVerifying markings correctnessContact methodTwo step
The invention provides a credit / debit authorization system and method which aim at stopping unauthorized use of credit / debit cards. The authorization system and method takes a two-step authorization approach. When a credit / debit card transaction authorization request is routed to the authorization system, the authorization system first validates the transaction by comparing card and transaction amount information extracted from the transaction to the account information stored in an account database. If the transaction is invalid, the authorization system refuses the transaction. If the transaction is valid, the authorization system then determines if the transaction requires the card user's approval. If it does, the authorization system would look up for user contact methods in a user contact database for that card with a pending transaction, establish a communication channel with the card user on his / her personal communication device, inform the user of a pending transaction with transaction related information, ask the user to take appropriate actions to either approve or refuse the transaction and process the user's response. If the user approves the transaction, the authorization system sends an approval code back to the device / system which started the transaction authorization request. If the user refuses the transaction, the authorization system sends a refusal code back to the device / system which started the transaction authorization request. In this way, unauthorized use of credit / debit cards can be stopped.
Owner:OU XIAOFENG
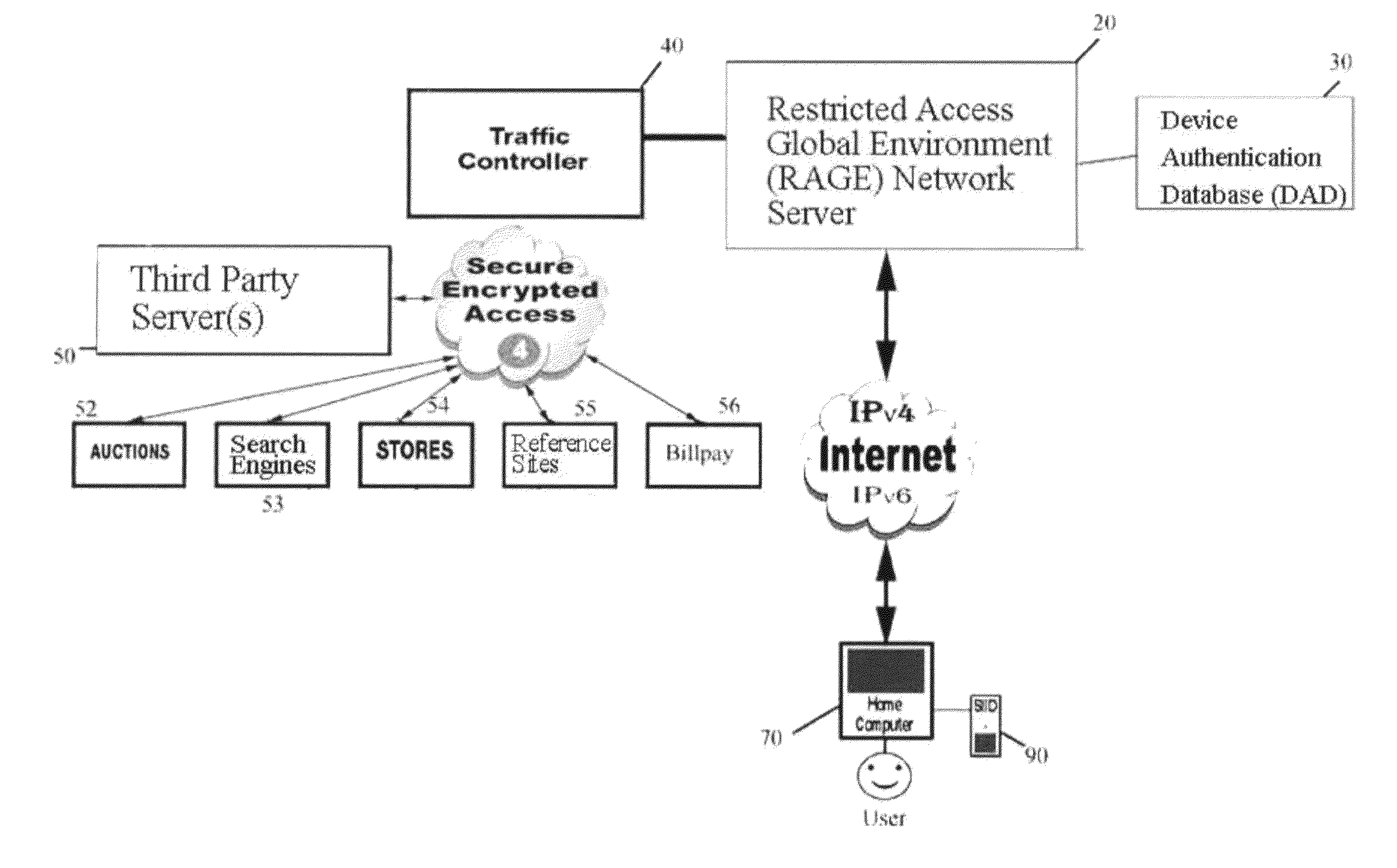
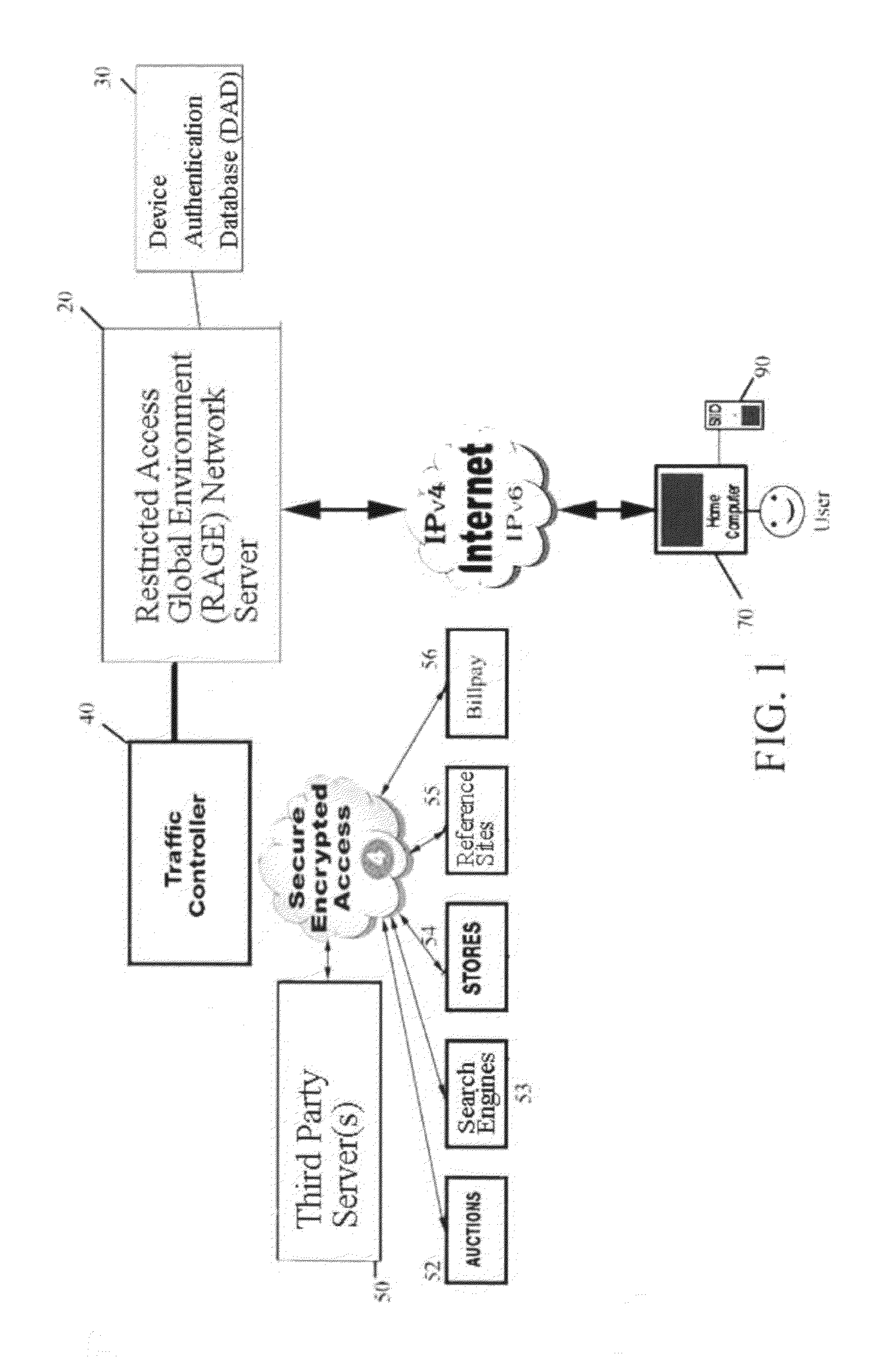
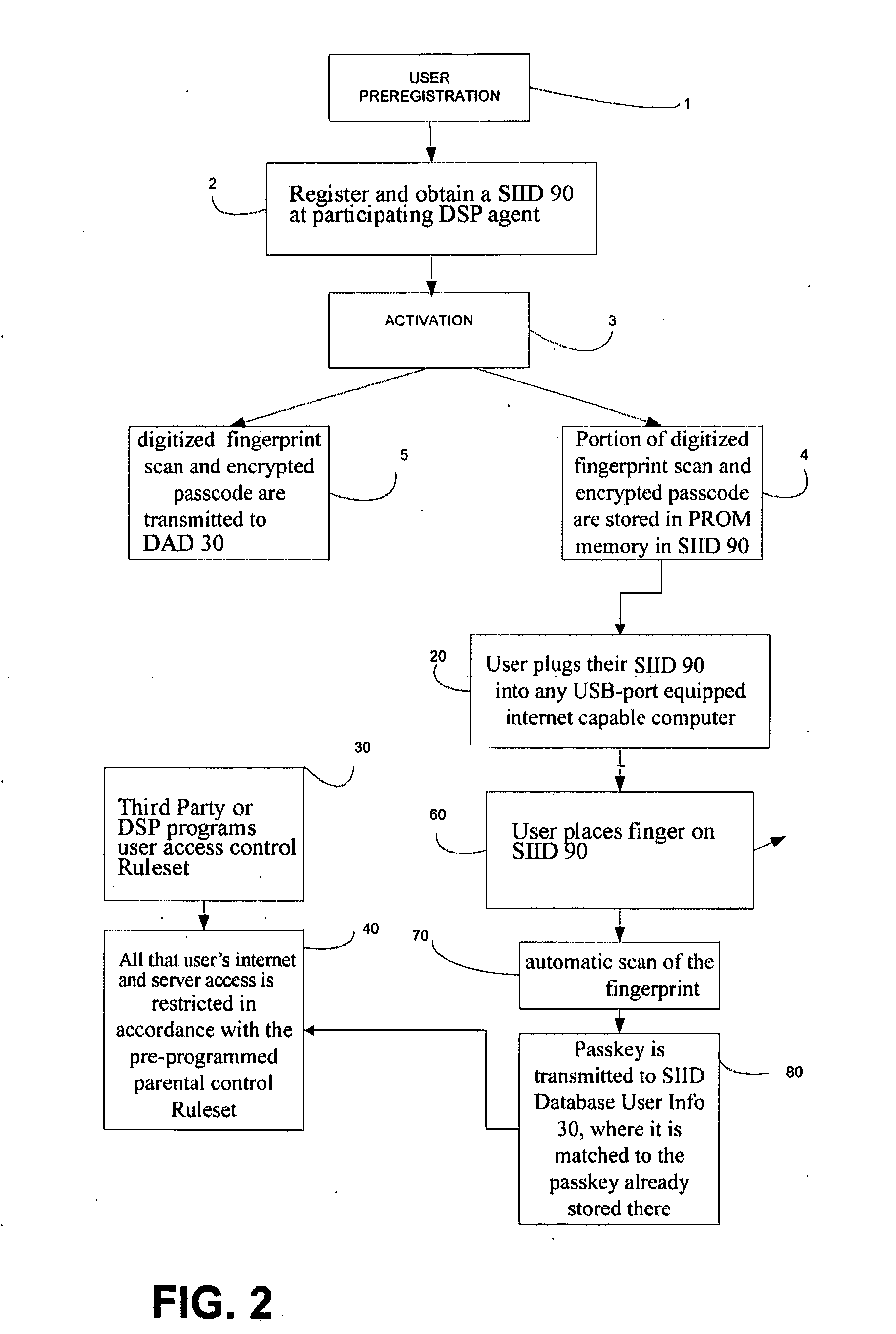
System for restricted biometric access for a secure global online and electronic environment
InactiveUS20120032782A1Easy to useFraudulent useElectric signal transmission systemsImage analysisIdentification deviceBiological activation
A method and system for biometric-secure settings that also simplifies the checkout process and eliminates fraudulent transactions. The system relies on an exchange service provider (RAGE) that hosts multiple servers: one implementing a web portal for secure online banking, auctions and other exchange opportunities, another being a biometric fingerprint device authenticating database, and yet another being a transaction traffic manager. Participating banks and supporting institutions distribute and activate Secure Individual Identity Devices (SIIDs) to registered users, each SIID being a portable biometric activated identification device that locally stores a fraction of the enrolled users fingerprint (minutia) along with an encrypted code that is used to verify and authenticate the user, eliminating the use of personal or financial information for this purpose. The SiiD becomes the user's own personal key for completing secure online transactions. The user simply plugs their SiiD into any equipped device for activation and scans their own fingerprint for each transaction. The encrypted codes are authenticated in the DSP database and the transaction is processed to the appropriate financial institutions.
Owner:COLELLA BRIAN A
Medical kiosk and method of use
InactiveUS20180158555A1Conveniently conveyed and usedUnauthorized useMedical communicationDrug and medicationsMedical prescriptionTeleconference
A medical kiosk designed to provide tele-medicine services, check-in services, and / or prescription services for a user. The medical kiosk can include a user video conferencing system that is designed to enable the user to have a real-time or near real-time tele-conference with a medical provider located remotely from the medical kiosk.
Owner:RITE AID HDQTRS CORP
Protecting electronic devices from extended unauthorized use
ActiveUS20070138999A1Hindering normal use and enjoymentReduce crimeCircuit authenticationUnauthorised/fraudulent call preventionMusic playerEngineering
Owner:APPLE INC
Electronic credit card with fraud protection
InactiveUS20110302089A1Unauthorized useFinanceUser identity/authority verificationCredit cardInternet privacy
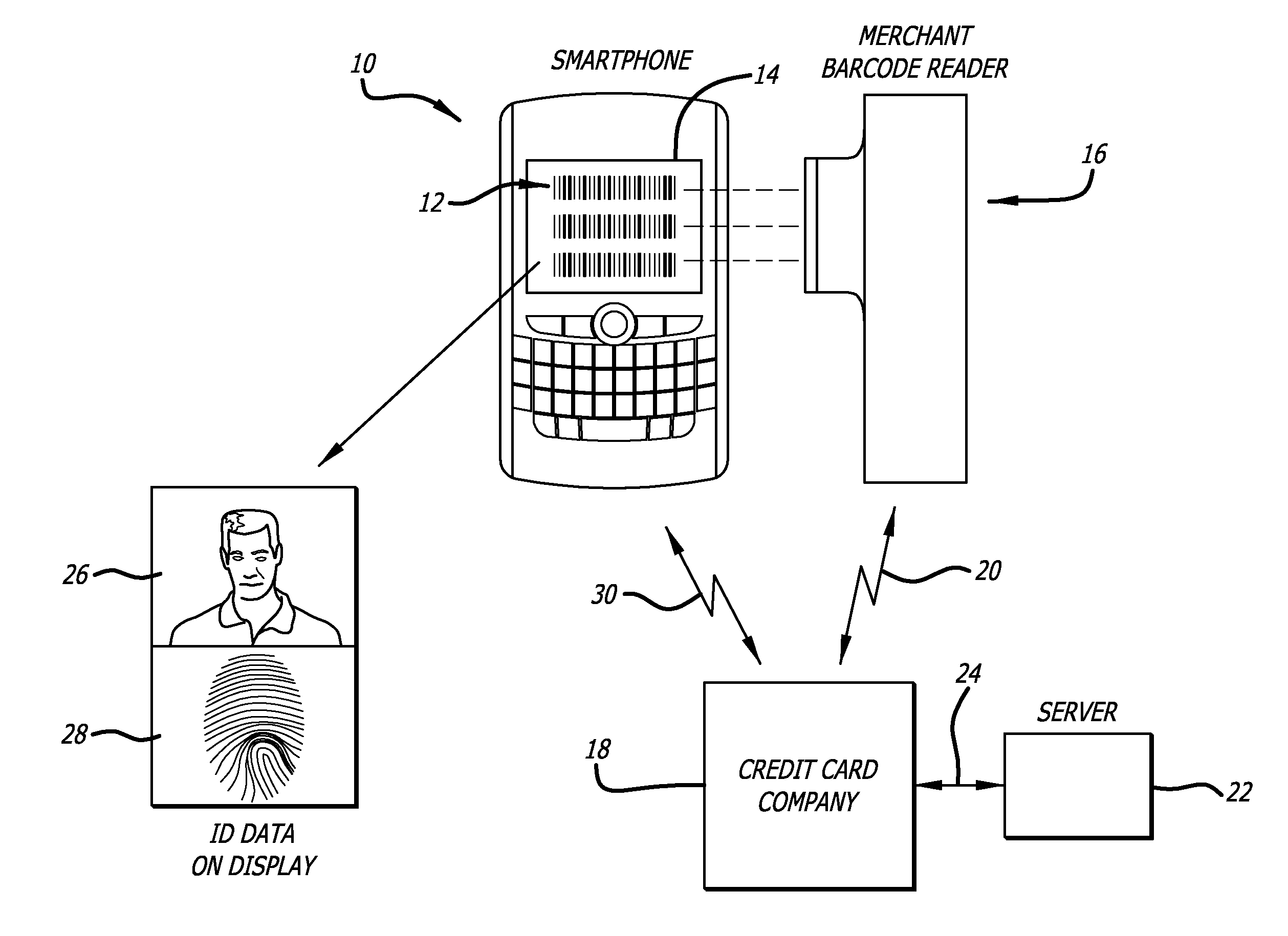
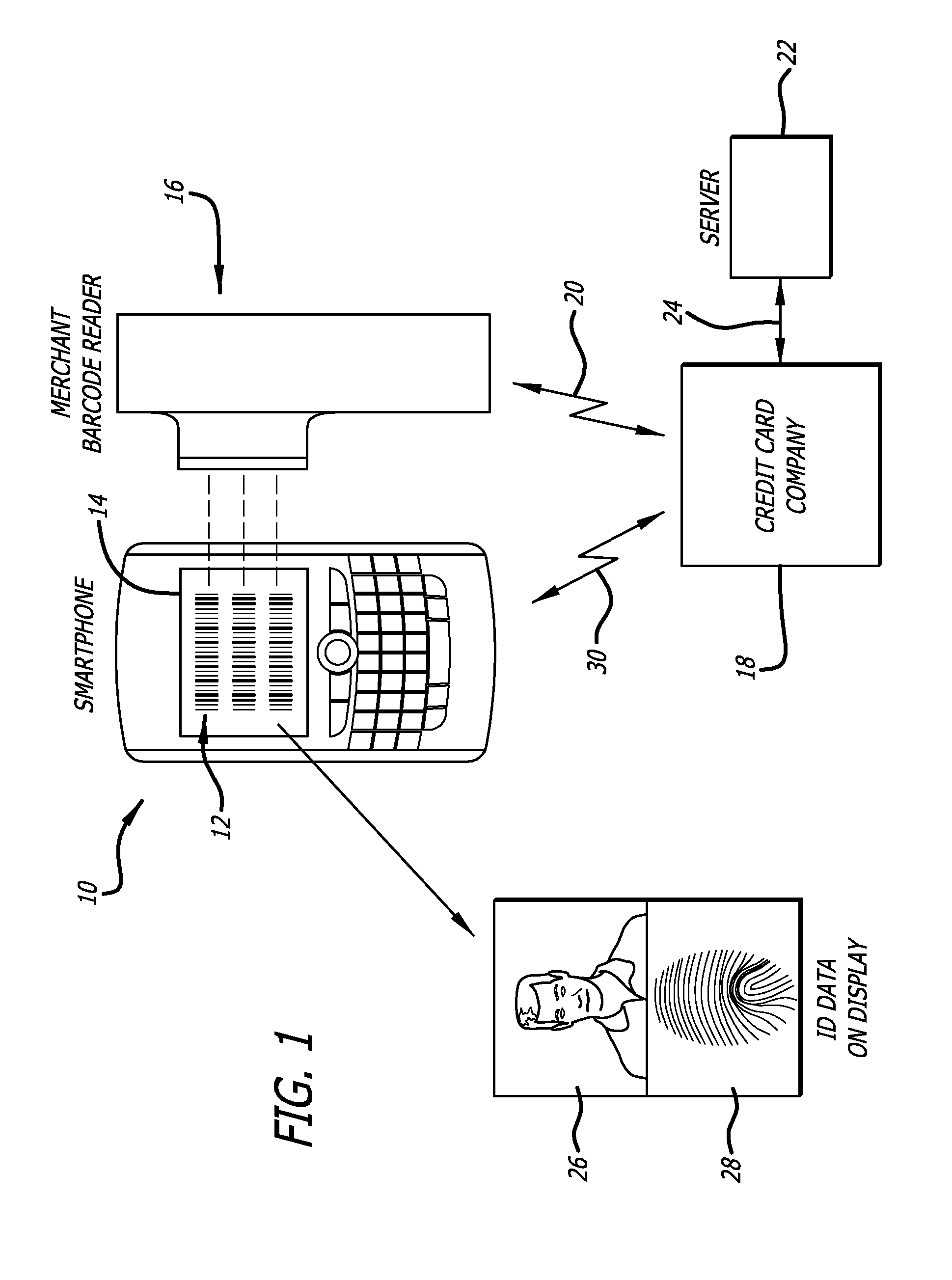
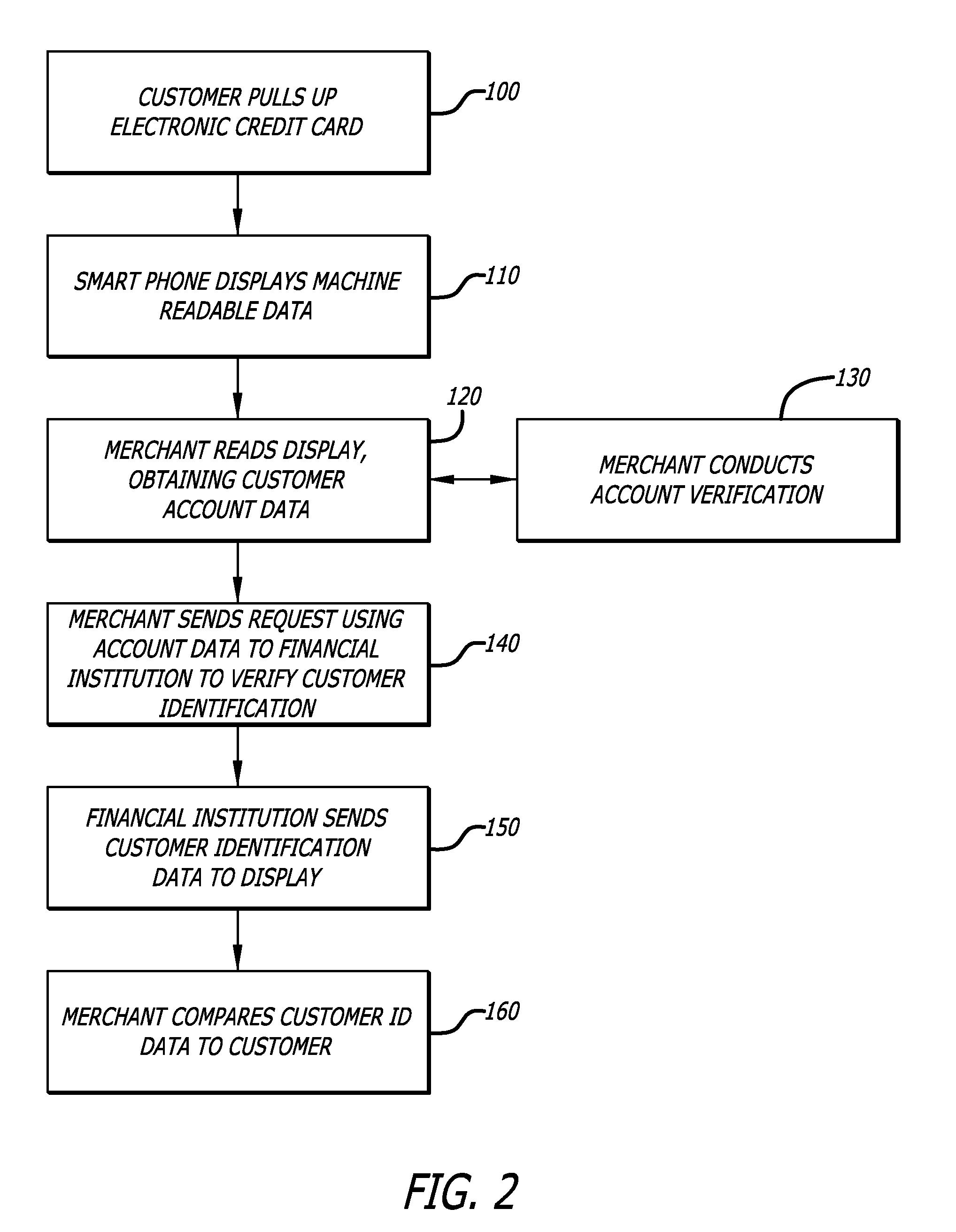
A method for verifying permission to use a payment system such as an electronic credit card, using a hand held communication device such as a smart phone, where the customer presents the communication device to a merchant who extracts account information from the hand held device, and the merchant sends a request for identification verification information to be sent to the hand held communication device directly or to an alternate display. The verification information can be in the form of a photograph, fingerprint, or the like. The merchant can then compare the identification verification data to the customer to determine if the customer is authorized to used the account according to the request.
Owner:MCKENZIE CRAIG
Car parking administration system
InactiveUS20110227533A1Improve mobilityBuying parking timeBatteries circuit arrangementsIndication of parksing free spacesMobile vehicleTelecommunications link
A car parking system for charging motor vehicles with electrical energy, with at least one charging station which is capable of being coupled electrically to a motor vehicle in order to charge a charge storage unit of this motor vehicle, wherein this charging station has associated with it at least one parking space for temporarily parking the motor vehicle to be charged. According to the invention the car parking system has at least one central processing unit which is separate from the charging station and which communicates in terms of data with the charging station, wherein data characteristic of the motor vehicle are capable of being transferred by way of a communication link existing at least temporarily between the central processing unit and the charging station.
Owner:WOLFIEN PATRICK
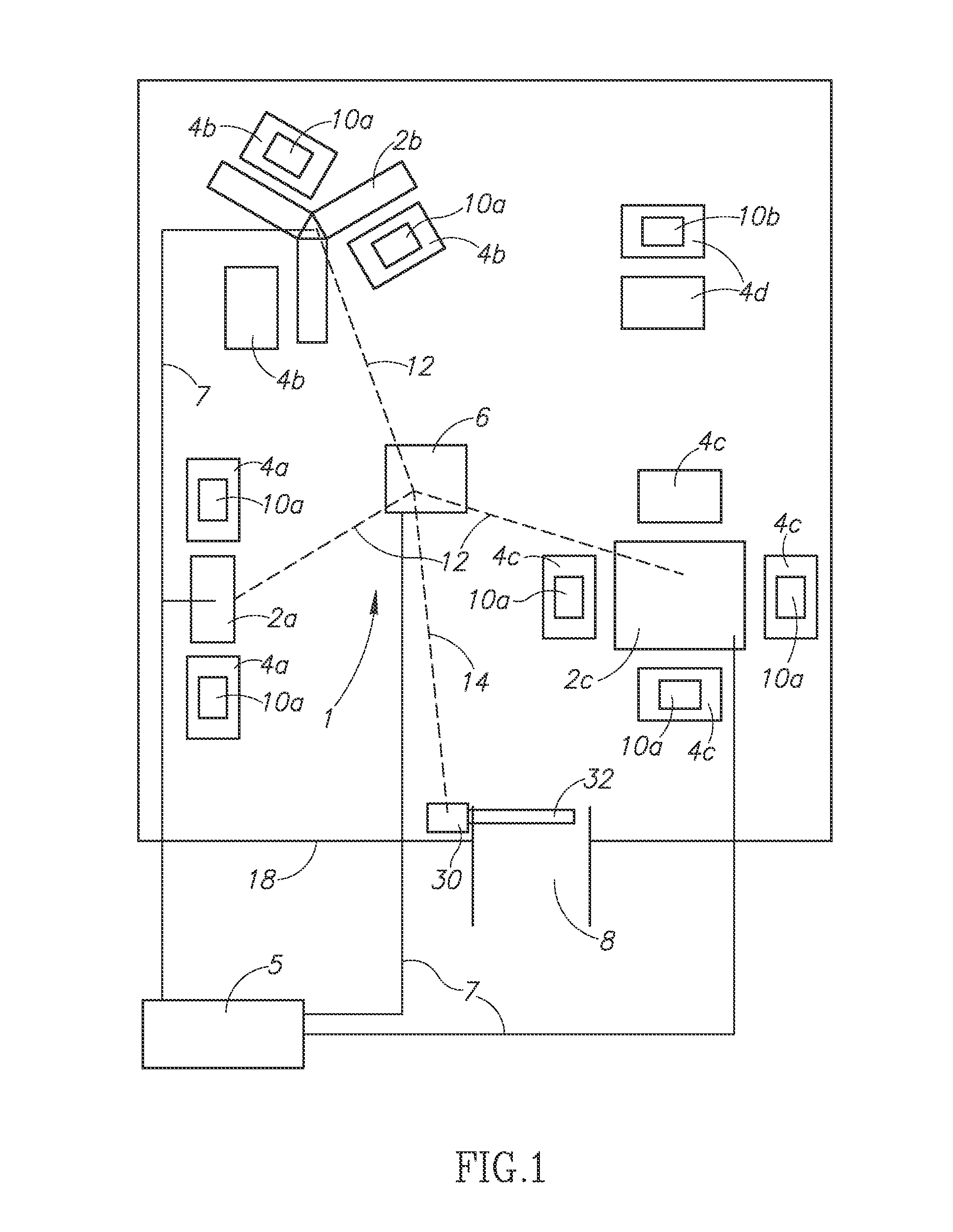
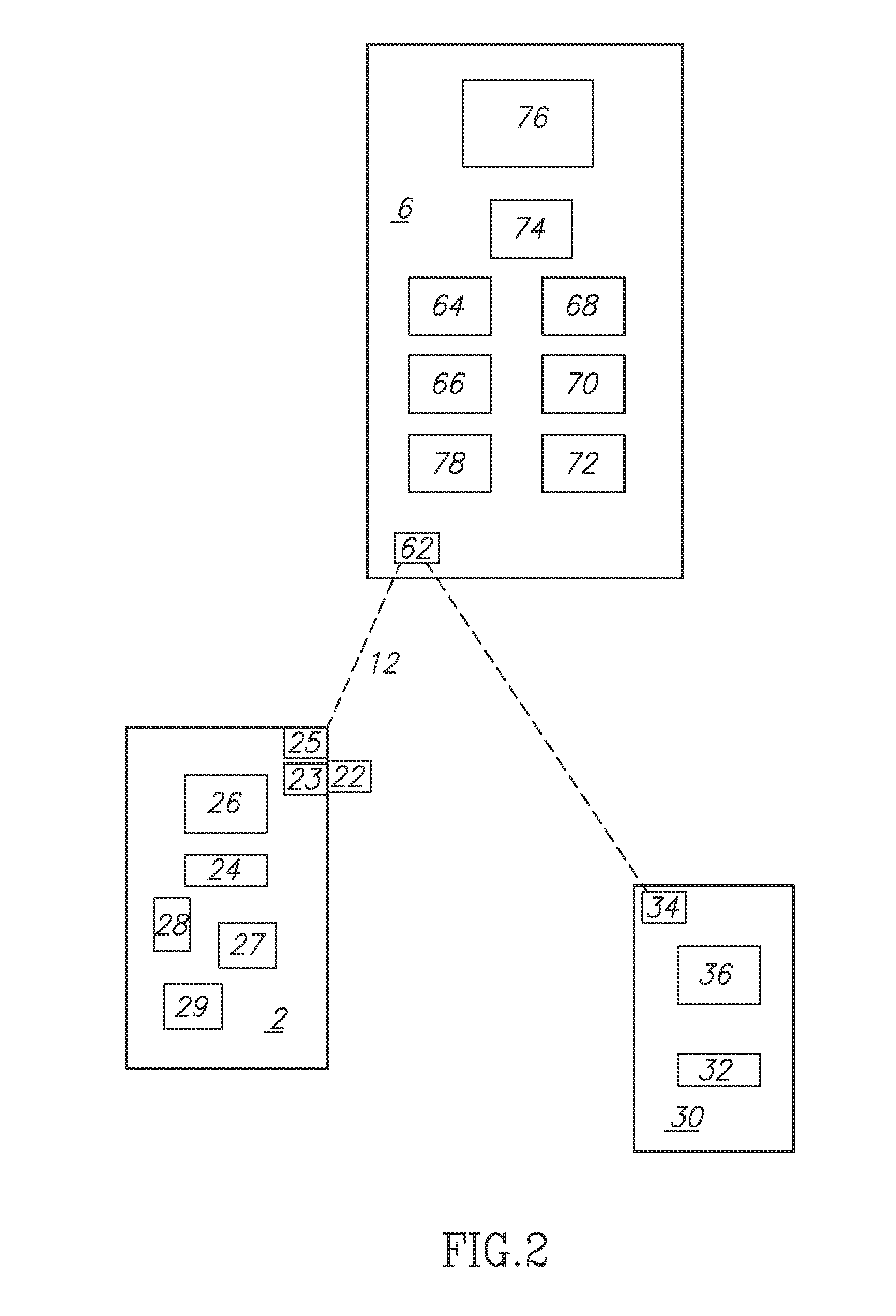
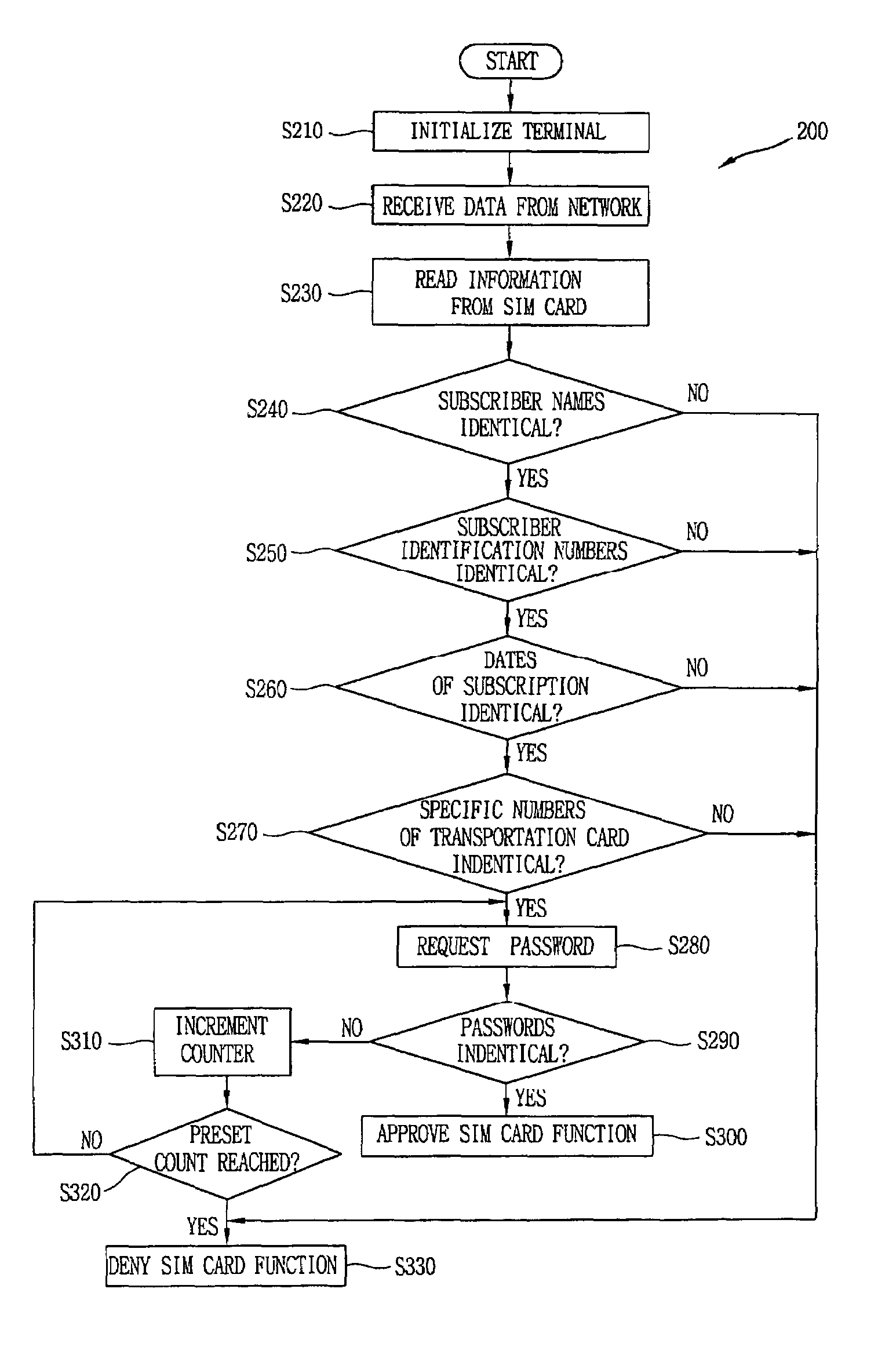
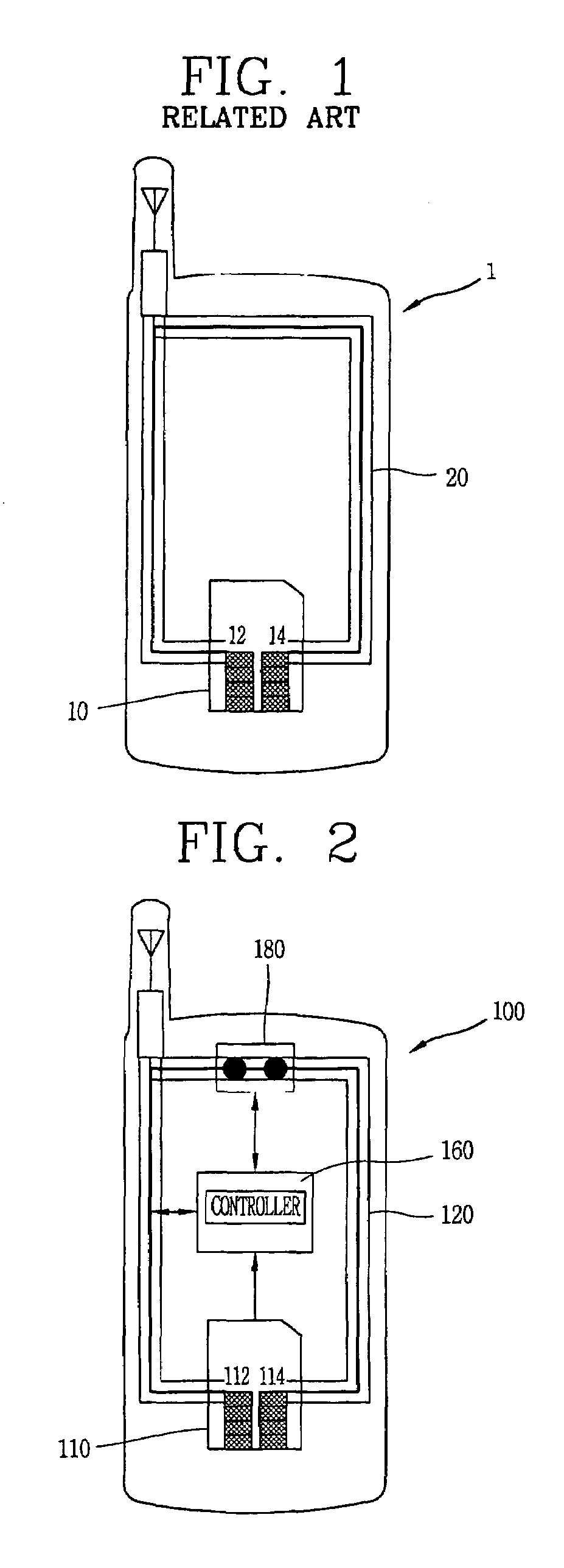
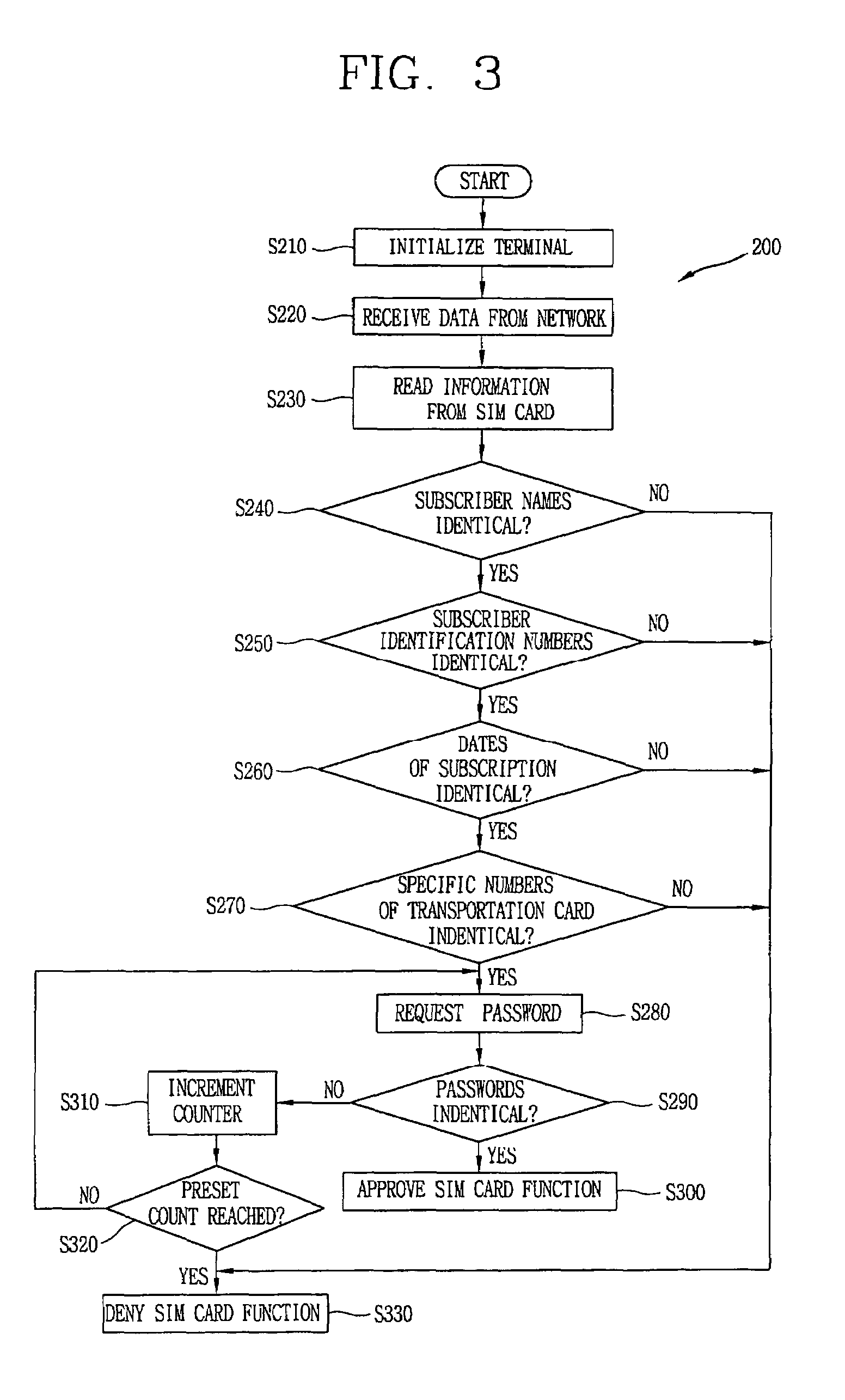
Apparatus and method for controlling use of a SIM card of a mobile terminal
InactiveUS7689251B2Unauthorized use can be preventedUnauthorized useCo-operative working arrangementsNear-field systems using receiversControl signalComputer terminal
An apparatus and a method for controlling the use of a SIM card mounted in a mobile terminal by employing a fraud technology includes comparing data related to the SIM card received from a network to information read from the SIM card in the terminal as part of a terminal initialization process and generating a control signal to cause an RF antenna switch to open or close an RF antenna loop structure in order to disable or enable a requested SIM card function. The data received form the network and the information read from the SIM card in the terminal include subscriber information and transportation card information that allow a determination of whether a user requesting a SIM card function is the subscriber entitled to access the function. If the data received form the network and the information read from the SIM card are identical, the requested SIM card function is approved. If the data received from the network and the information read form the SIM card are not identical, the requested SIM card function is not approved. Optional password protection of SIM card functions may also be provided.
Owner:LG ELECTRONICS INC
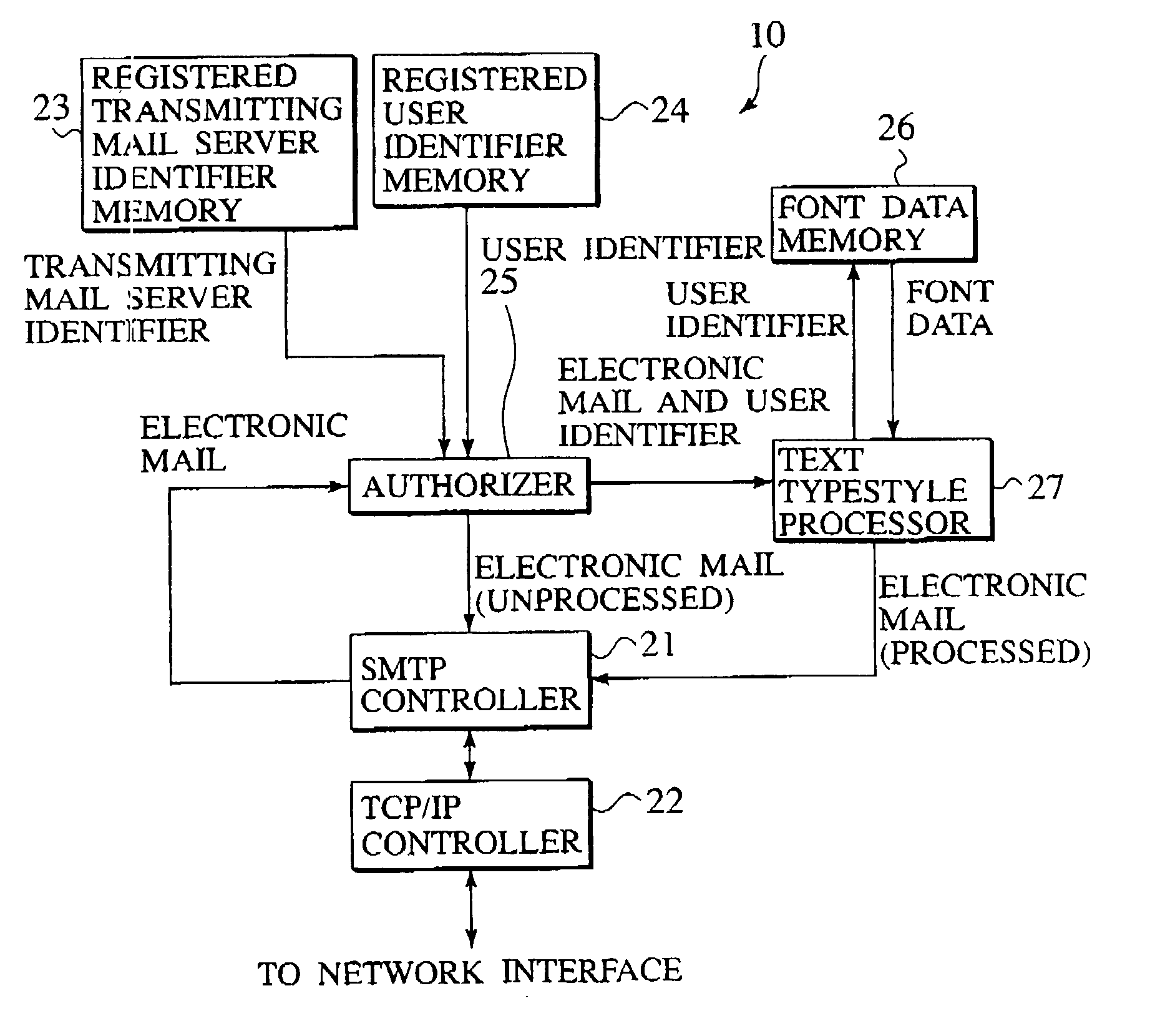
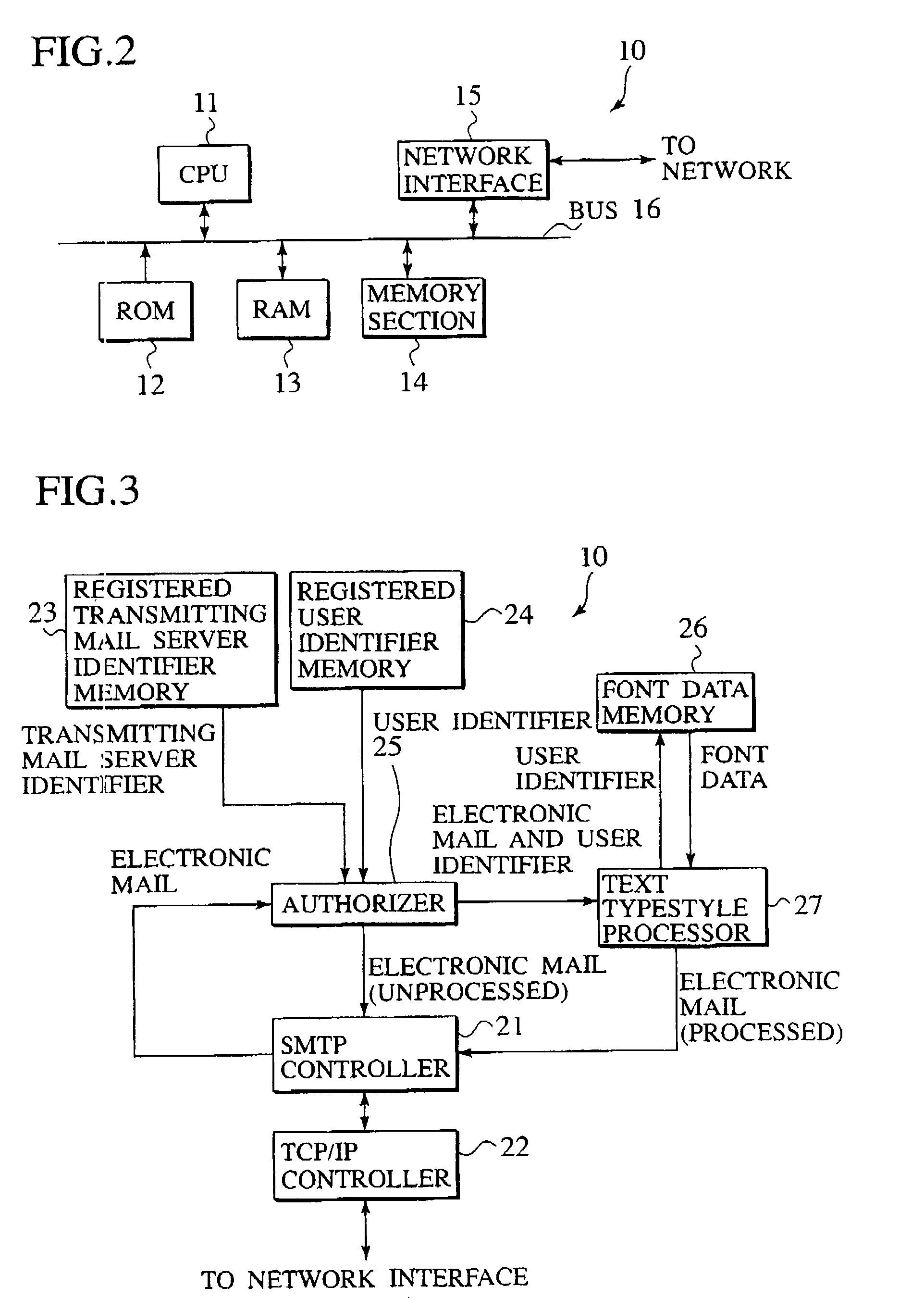
Electronic mail typestyle processing device
InactiveUS20020174186A1Easy to operateUnauthorized useNatural language data processingMultiple digital computer combinationsData memoryAuthorization
A user typestyle font reflecting personality of a registered user is stored in a font data memory in advance. When an electronic mail from the registered user is received, an authorizer performs authorization processing and then a typestyle of text of the electronic mail is processed by a text typestyle processor by use of the user typestyle font. The electronic mail is transmitted to a receiver of the electronic mail thereafter.
Owner:RISO KAGAKU CORP
Information processing unit with information division recording function
InactiveUS20070245108A1Unauthorized usePrevent falsificationUnauthorized memory use protectionDigital data protectionMain processing unitInformation processing
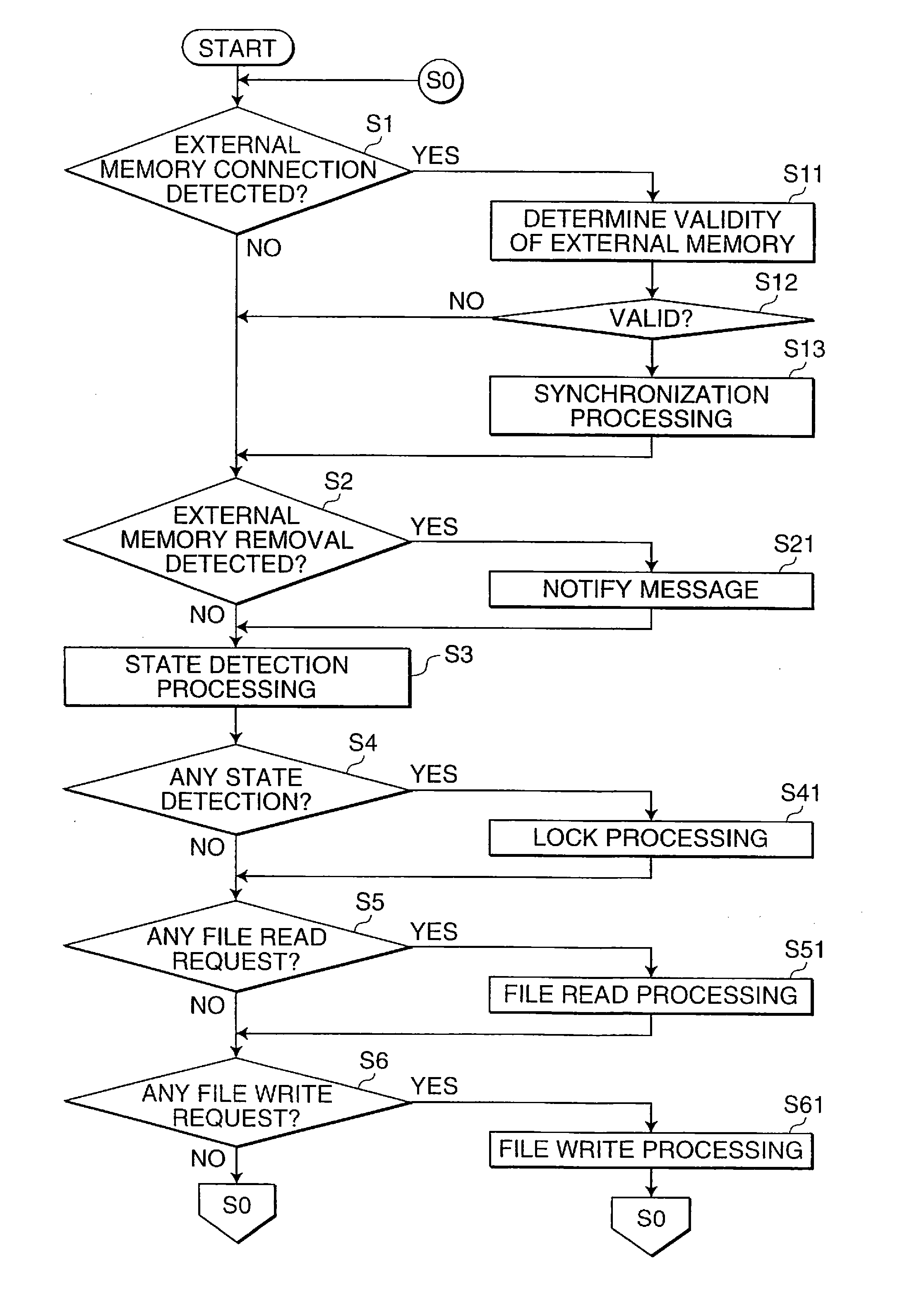
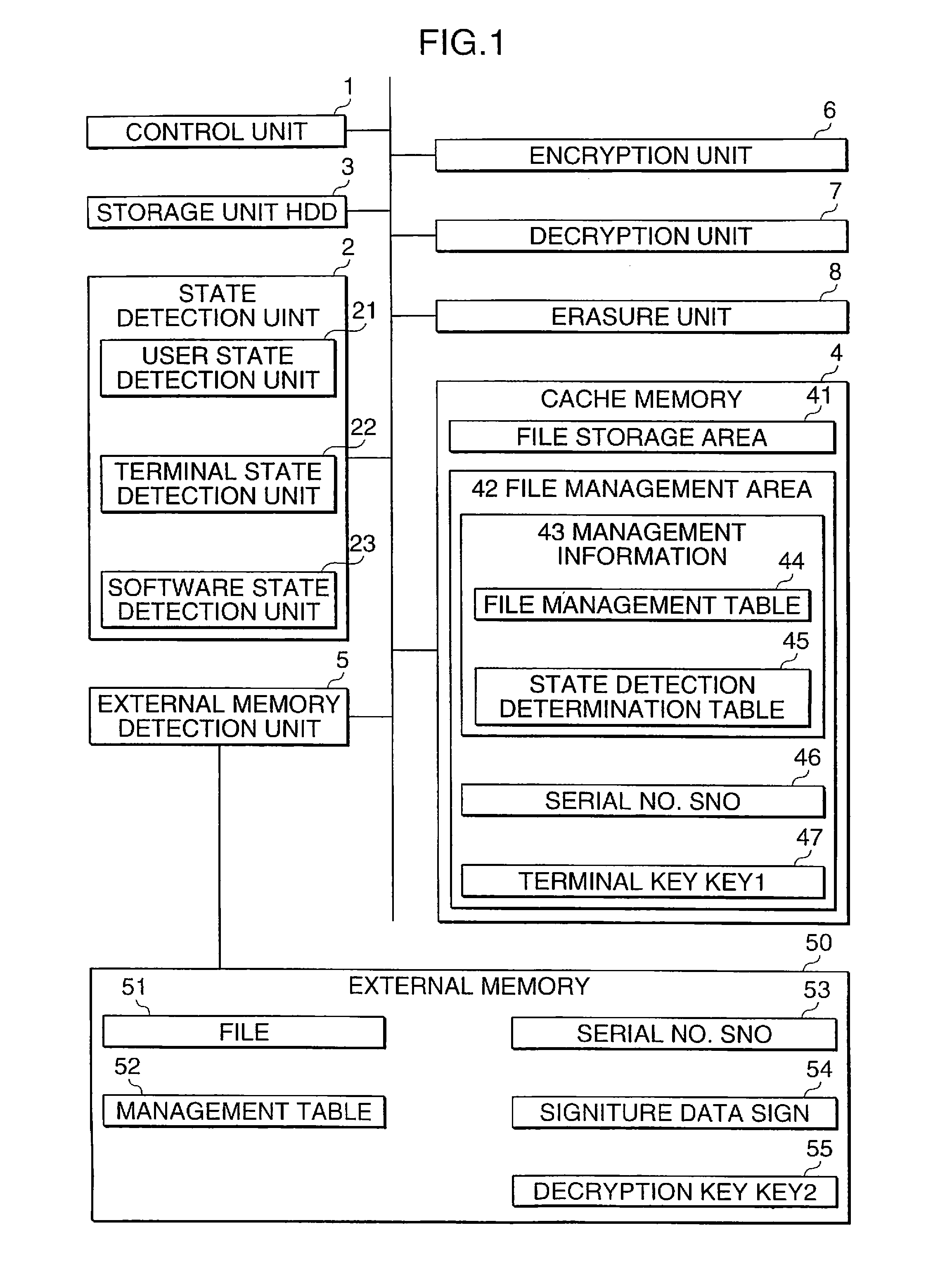
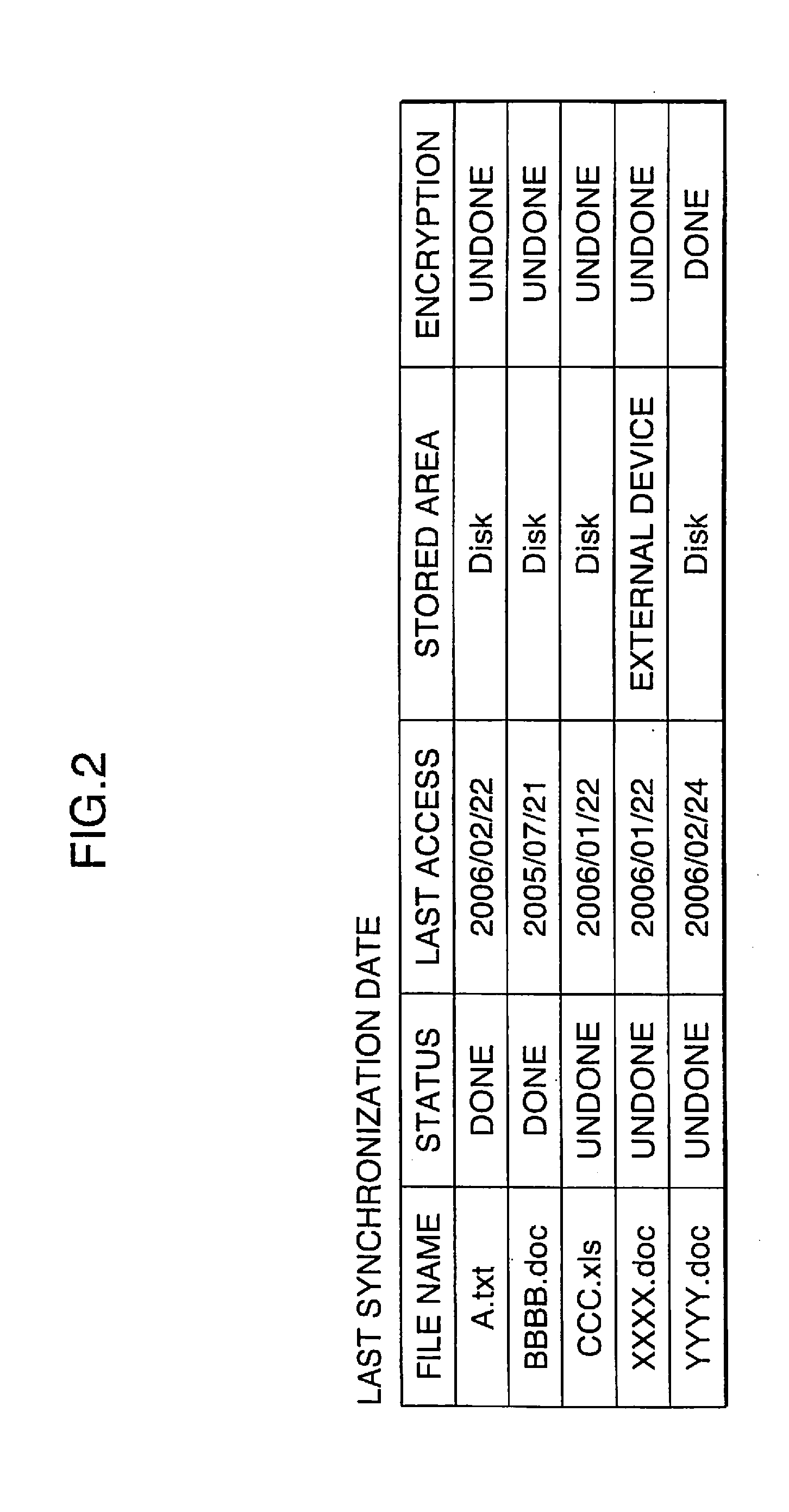
An information processing unit is an unit which has an information division recording function in which a file is divided and stored. The information processing unit includes a first storage section for storing a first partial file of a file divided, a second storage section for storing a second partial file, a state detection section for checking an operating state of the information processing unit and detecting that the operating state has changed in a specific manner, and a control section for performing a lock processing in accordance with the state detected to the second partial file stored on the second storage section when the state detected by the state detection section is determined as a risky state in which unauthorized access can be performed.
Owner:FUJITSU LTD
System and method for testing telematics software
ActiveUS7146307B2Unauthorized useVehicle testingRegistering/indicating working of vehiclesApplication softwareComputer science
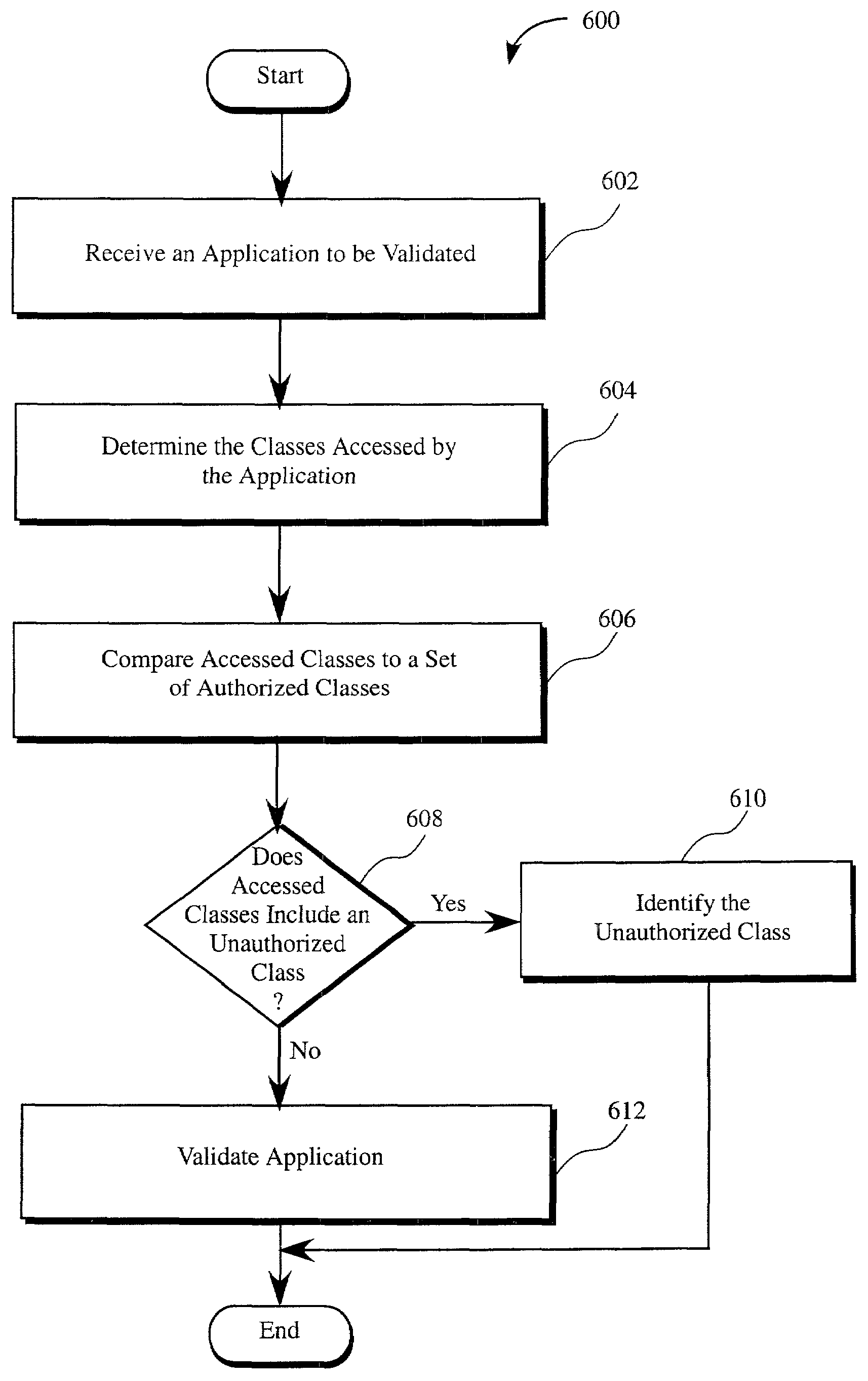
A system and method of validating an application includes receiving the application and determining a set of accessed classes that are accessed by the application. The set of accessed classes are compared to a set of authorized classes to determine if one or more unauthorized classes are included in the set of accessed classes. And, validating only the applications that do not access unauthorized classes.
Owner:ORACLE INT CORP
RFID transponder and a method for fabricating the same
InactiveUS9076092B2Reduce usageUnauthorized useRecord carriers used with machinesRadio frequencyElectric power
The present application provides a radio frequency identification (RFID) transponder and a method for fabricating the same. The RFID transponder, comprising: a microchip which is arranged to communicating with a reader; a battery which is arranged to provide an electrical power for operating the transponder, and is attached to the microchip by means of a conductive path; an antenna which is arranged to receive and backscatter radio frequency interrogation radiation; and a substrate, on which the microchip, the battery and the antenna are arranged.
Owner:CONFIDEX OY
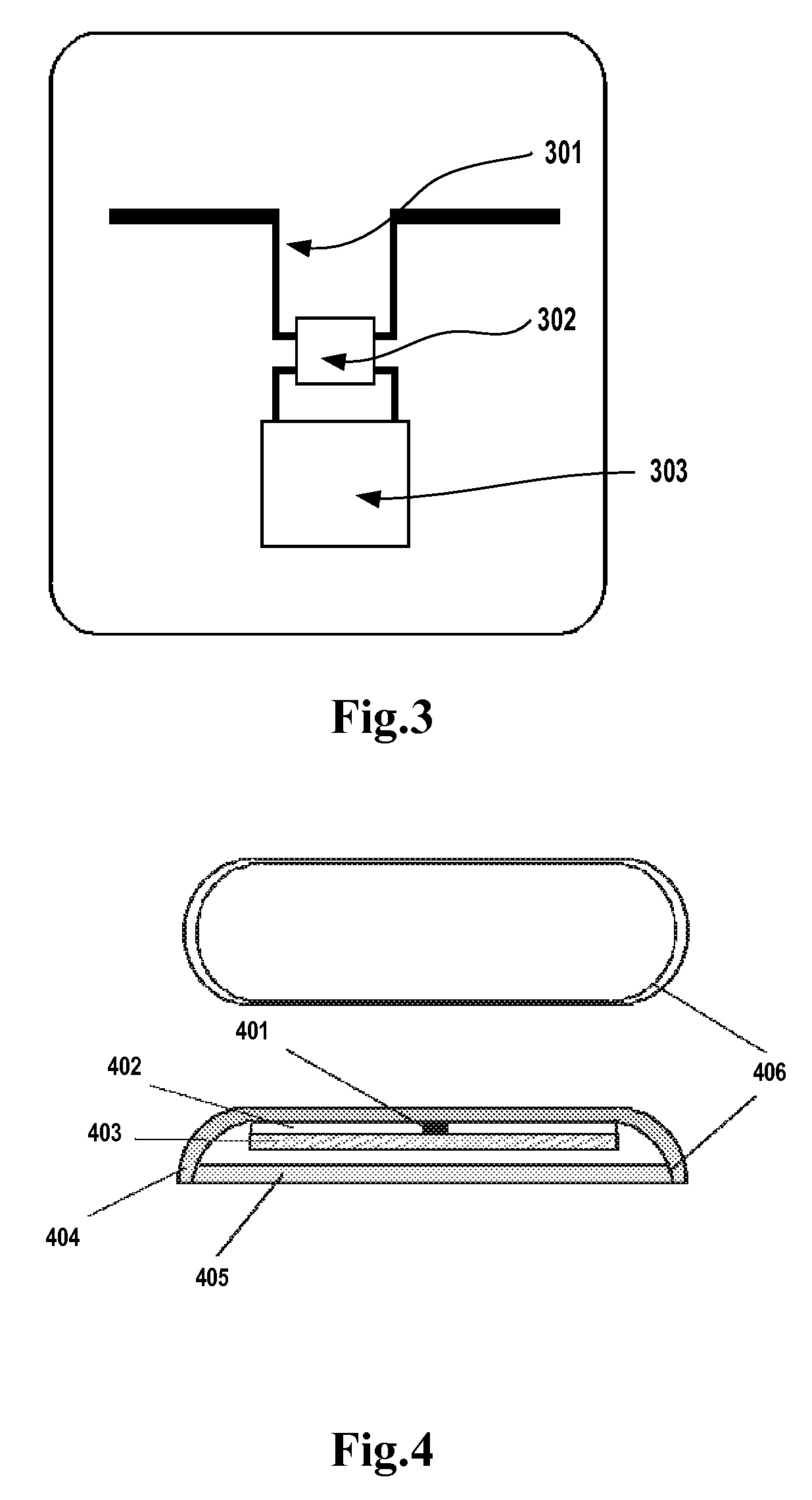
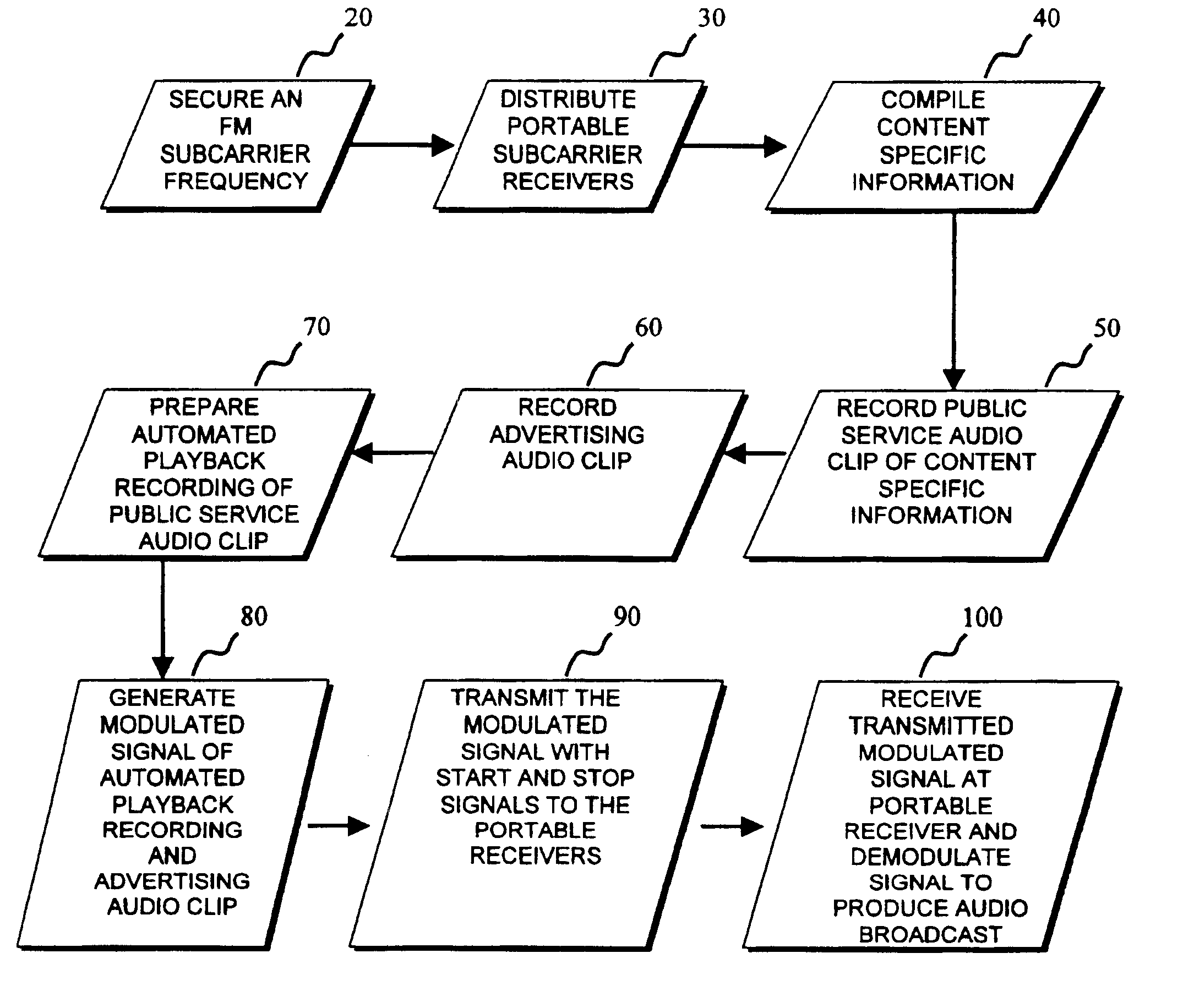
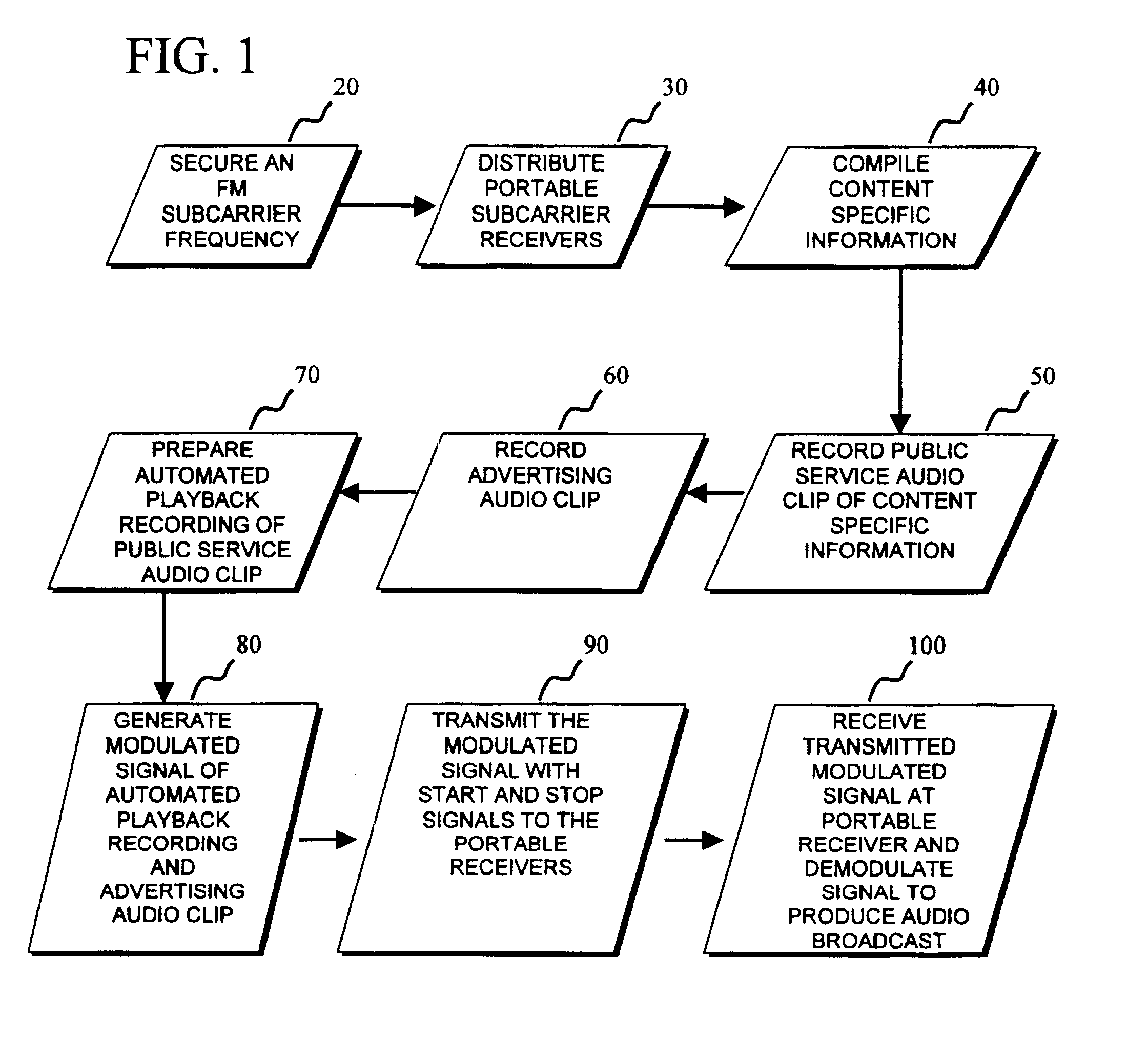
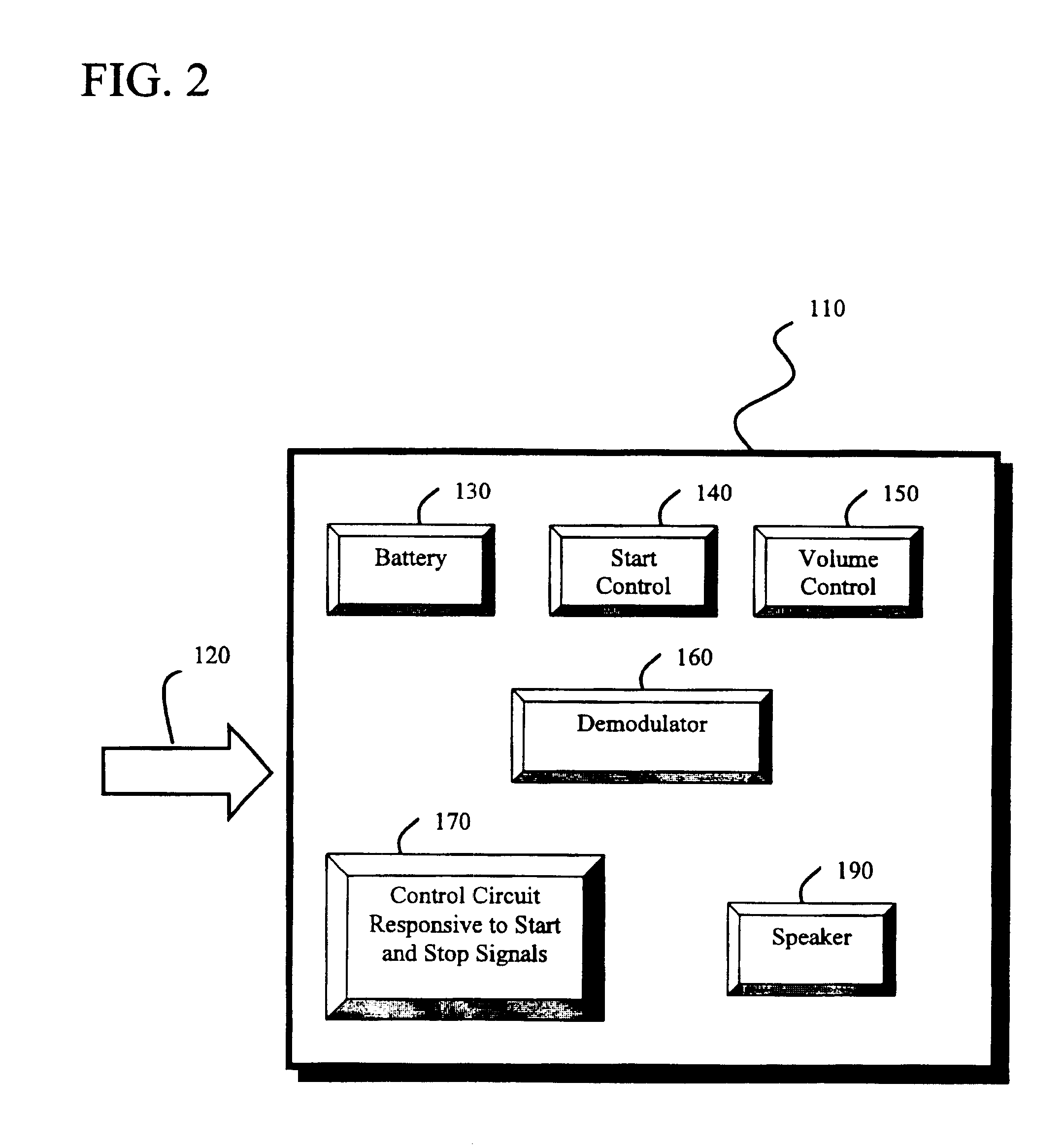
Revenue generating method of broadcasting on FM subcarrier
InactiveUS6915107B1Unauthorized useBroadcast specific applicationsBroadcast services for monitoring/identification/recognitionStart signalSubcarrier
A method of generating advertising revenue by securing an FM subcarrier frequency through an FM broadcasting station and distributing portable receivers to end users tailored to play the audio signals broadcast over the FM subcarrier frequency, on demand. Public service audio clips and advertising audio clips are broadcast to the portable receivers with the intention that a listener will be exposed to both the public service audio clip and the advertising audio clip during the period of the broadcast. The public service audio clips and advertising audio clips are broadcast in a continuous loop and are coded with start and stop signals to indicate the beginning and end of the broadcast. Through this method, an individual requesting the broadcast will hear a signal loop of the audio, starting with the detection of the start signal and ending when the detection of the stop signal.
Owner:FLORIDA DIGITAL TECH
Methods and systems for detecting, verifying, preventing and correcting or resolving unauthorized use of electronic media content
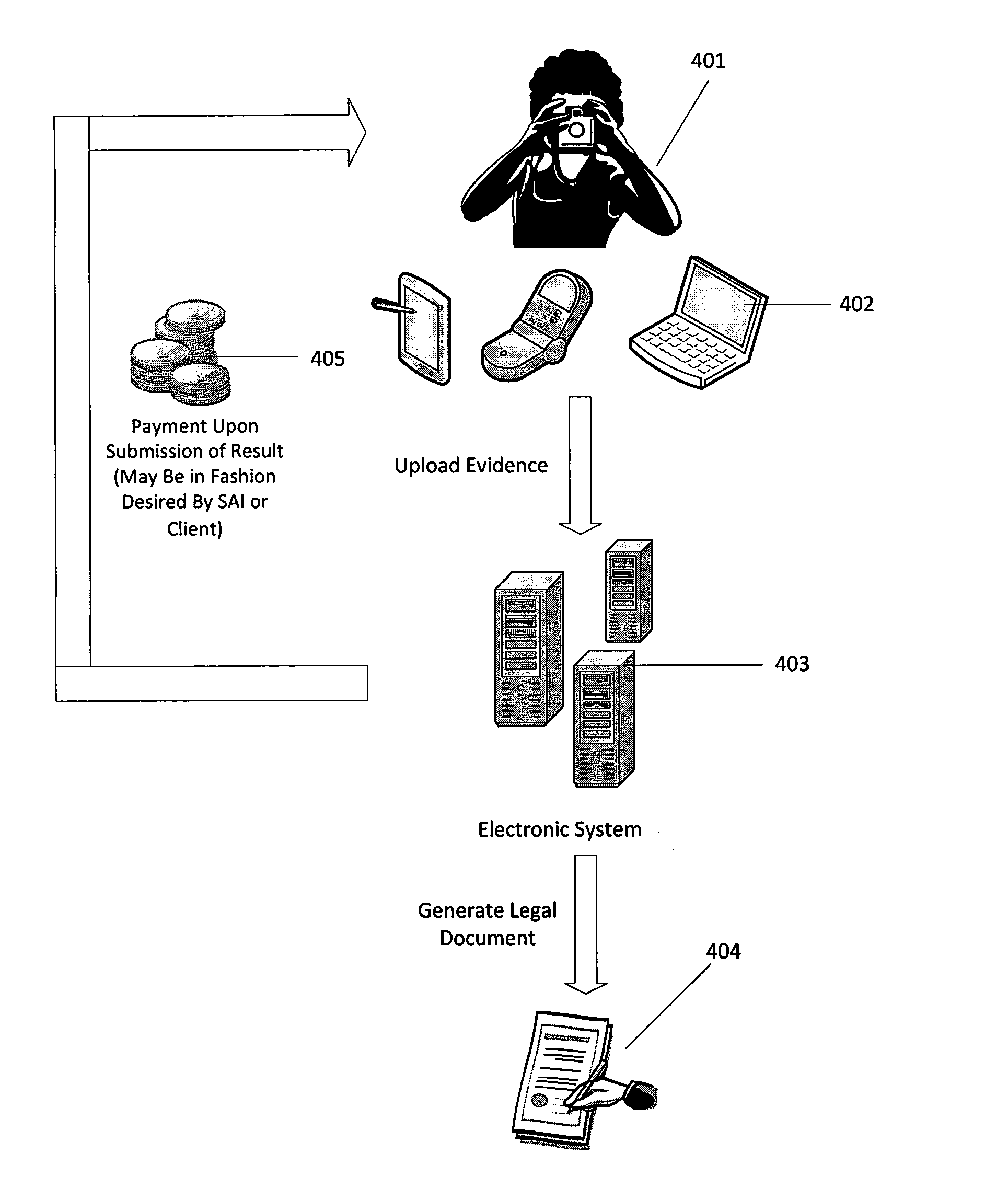
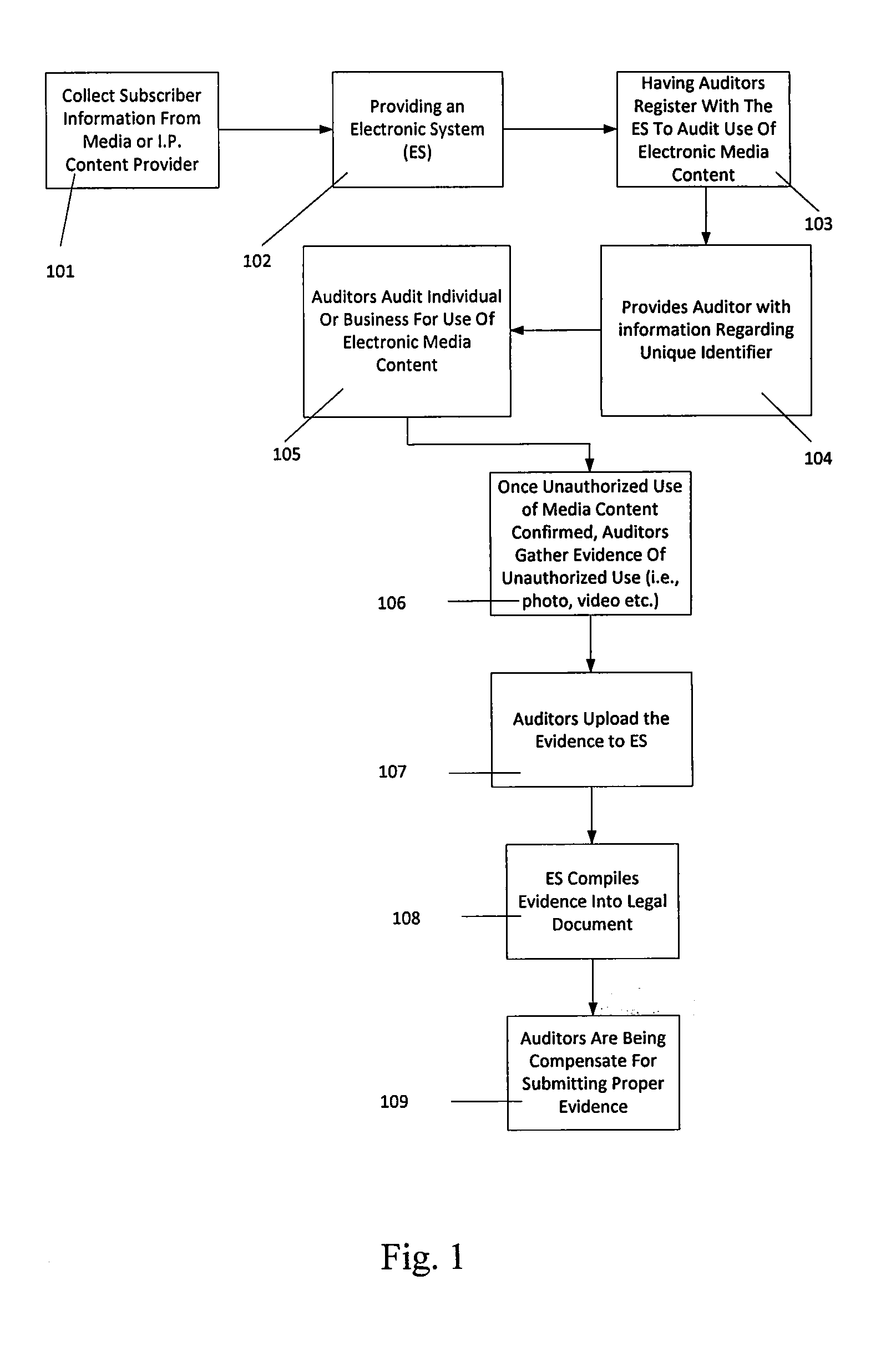
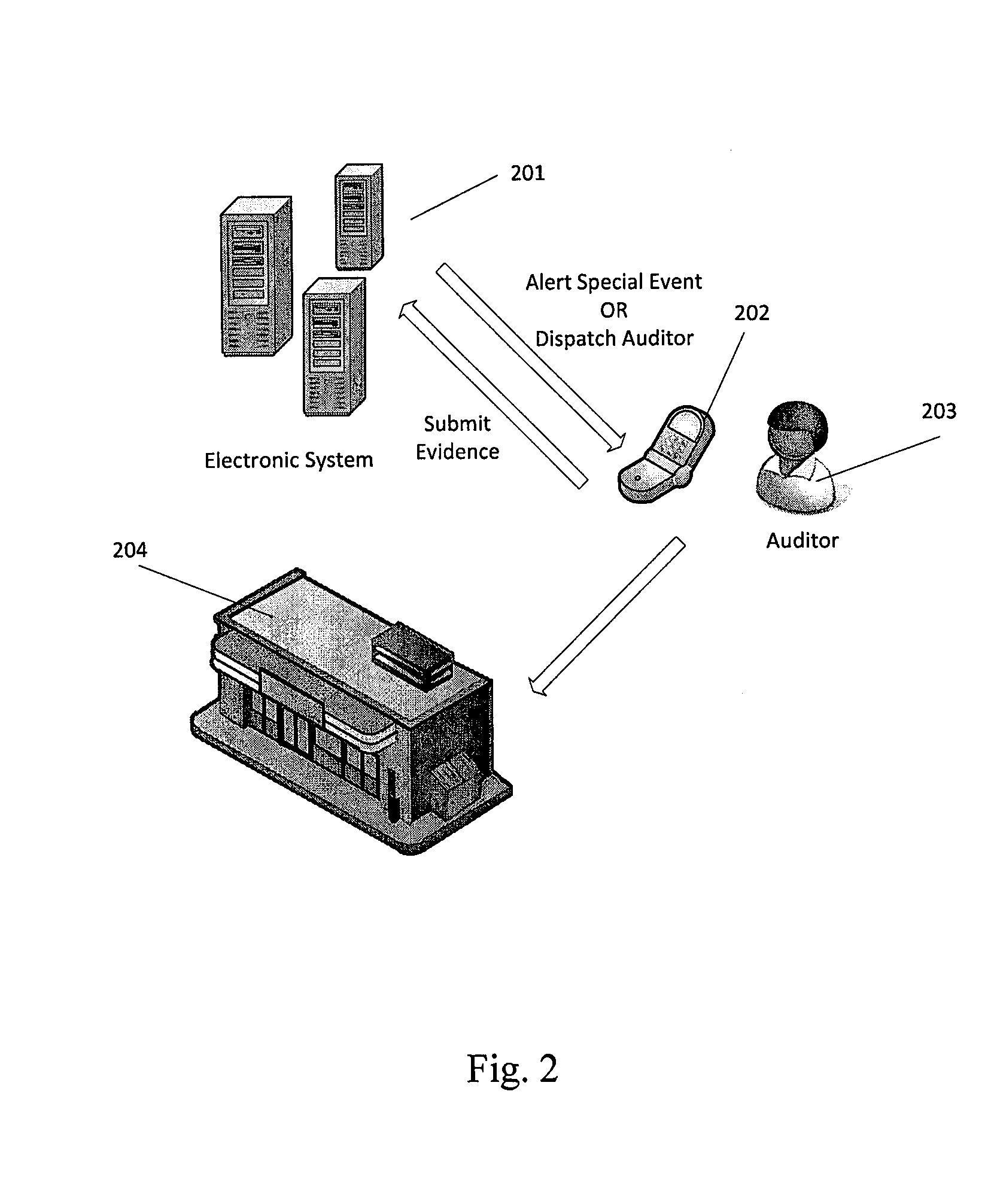
ActiveUS20140283123A1Efficient discoveryUnauthorized useData processing applicationsDigital data processing detailsElectronic systemsIntellectual property
A method of detecting, verifying, preventing and correcting or resolving unauthorized use of electronic media content. In one embodiment, the method comprises providing an electronic system that allows auditors to register to audit the use of electronic media content, providing the auditors with information through the electronic system regarding a unique identifier that identifies one or more items of electronic media content, owners of electronic media content or other intellectual property or users who have subscribed to the use of electronic media content, obtaining information from auditors through the electronic system regarding unauthorized use of the electronic media content and verifying that the information received from auditors is complete.
Owner:LONSTEIN WAYNE D +1
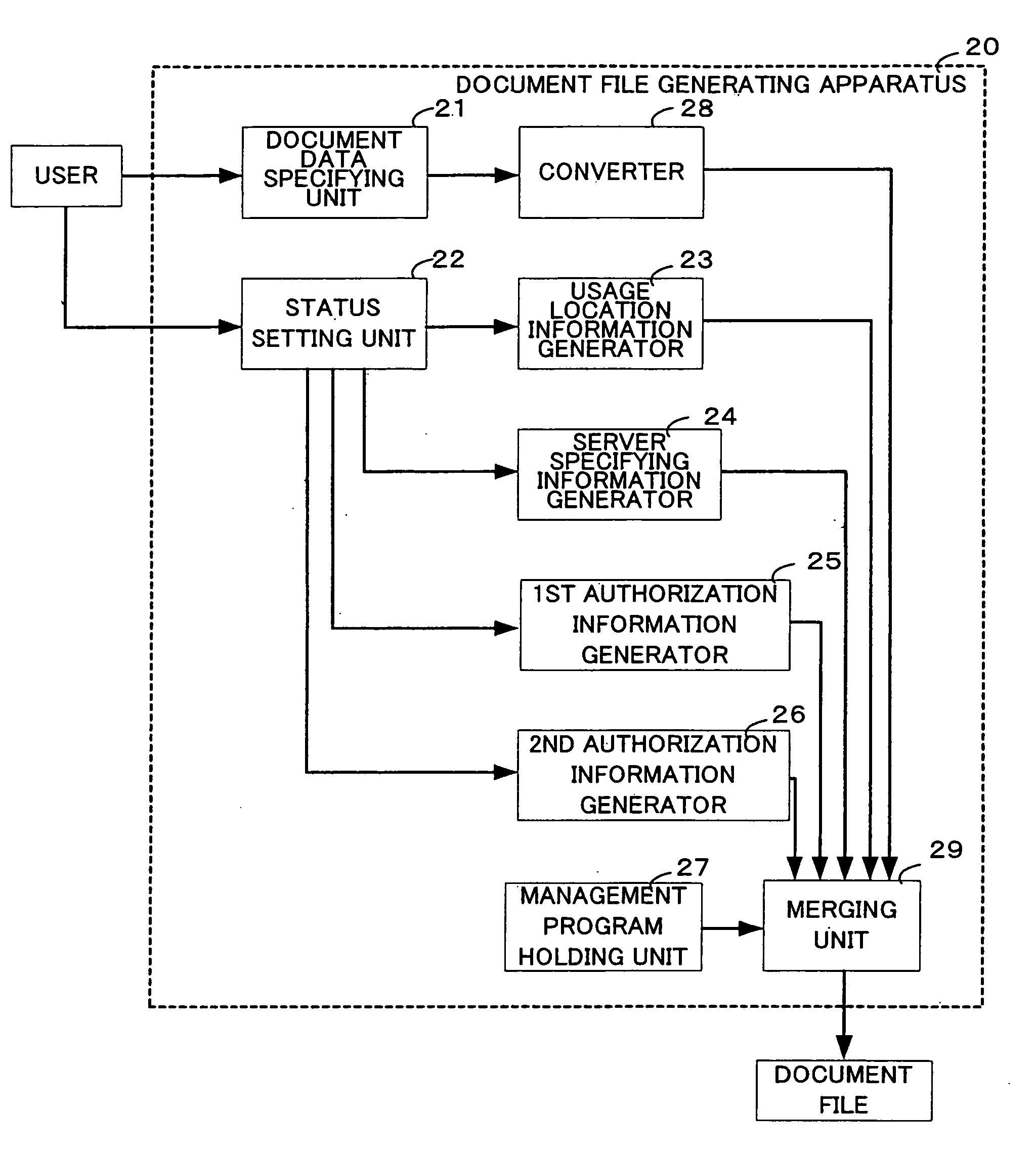
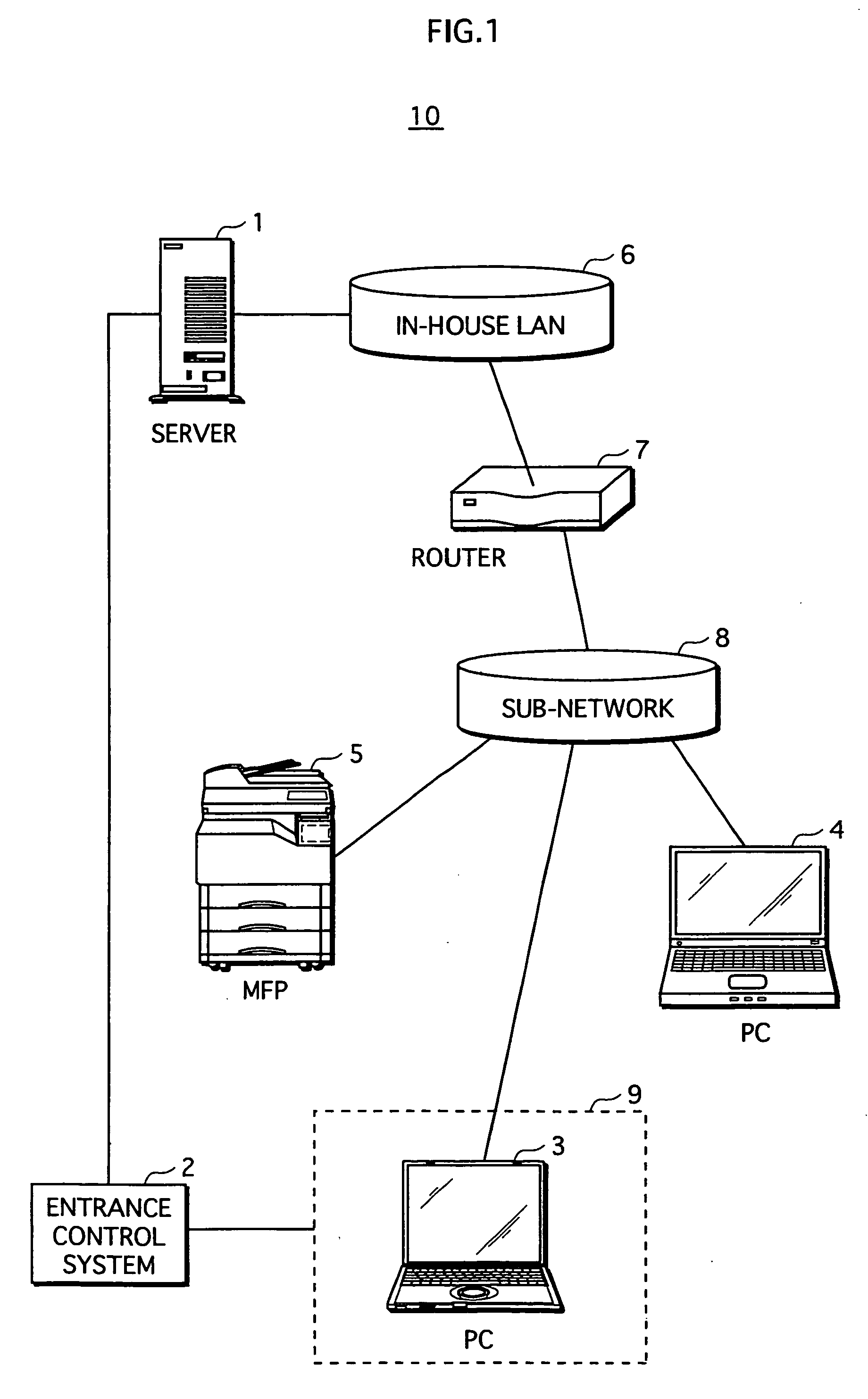
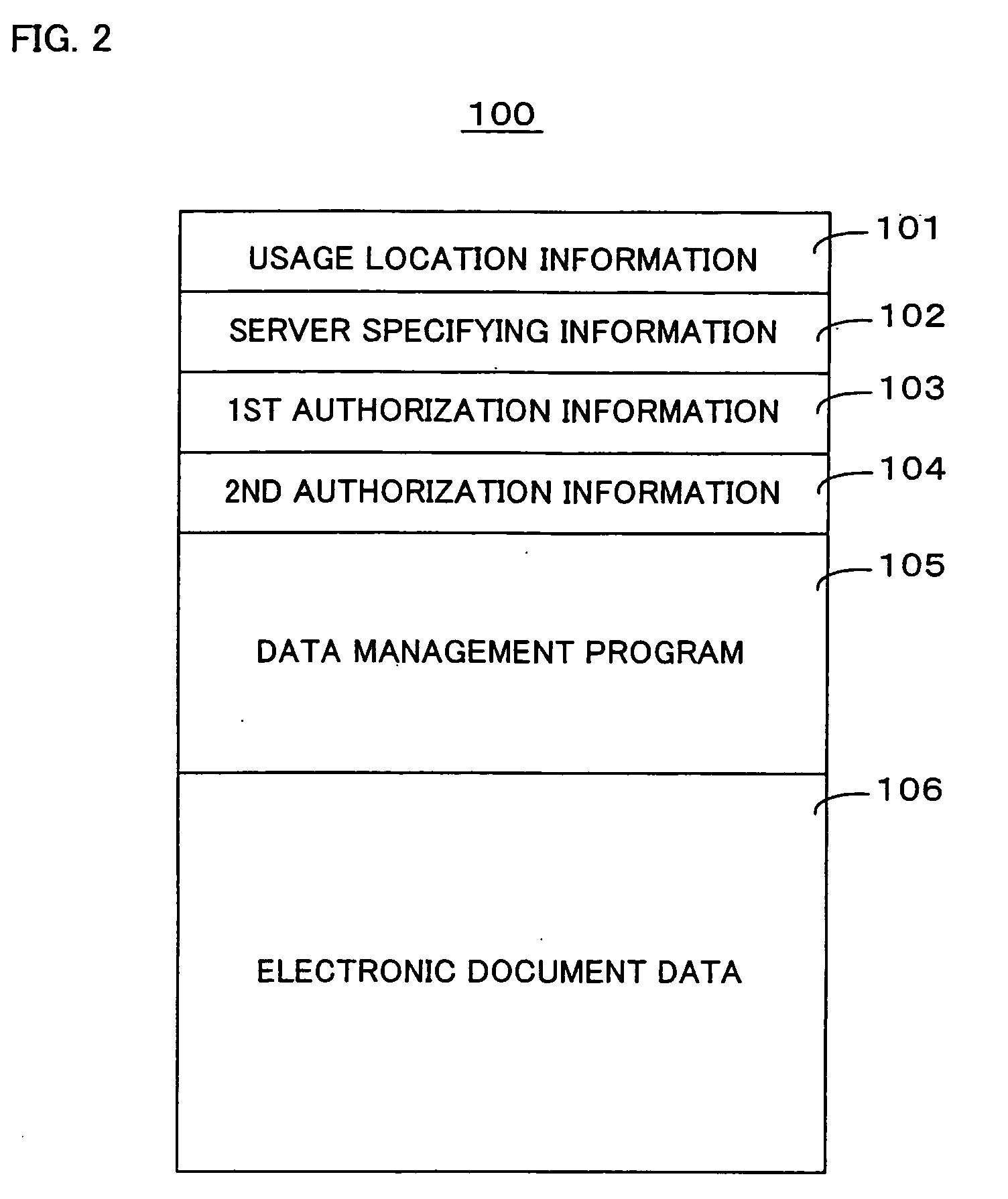
Document file, document file generating apparatus, and document file usage method
ActiveUS20080201783A1Reduce riskUnauthorized useDigital data processing detailsUser identity/authority verificationElectronic documentData management
A document file is configured to restrict, without a costly special-purpose terminal or the like, use of document data contained therein, if the document data is taken out of a predetermined location. A document file contains (i) electronic document data, (ii) usage location information indicating one or more usage locations in which use of the electronic document data is less restricted, and (ii) a data management program that causes, when a user requests use of the electronic document data, a computer to request for user location information indicating the current location of the user. Under control of the data management program, use of the electronic document data is permitted within a first usage pattern, if the user location is included in the usage locations. If not, use of the electronic document data is prohibited or permitted within a second usage pattern which is more restricted than the first usage pattern.
Owner:KONICA MINOLTA BUSINESS TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com