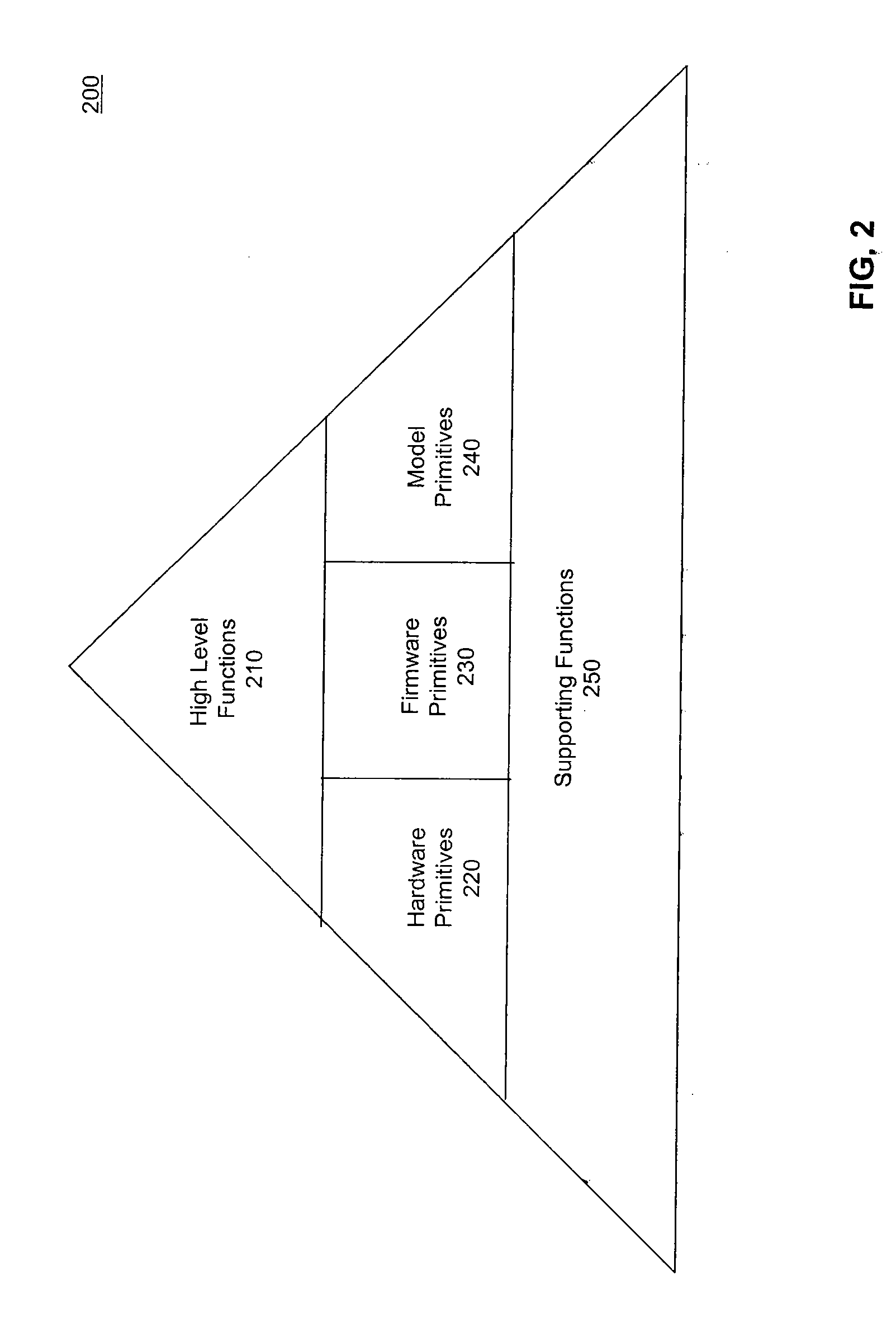
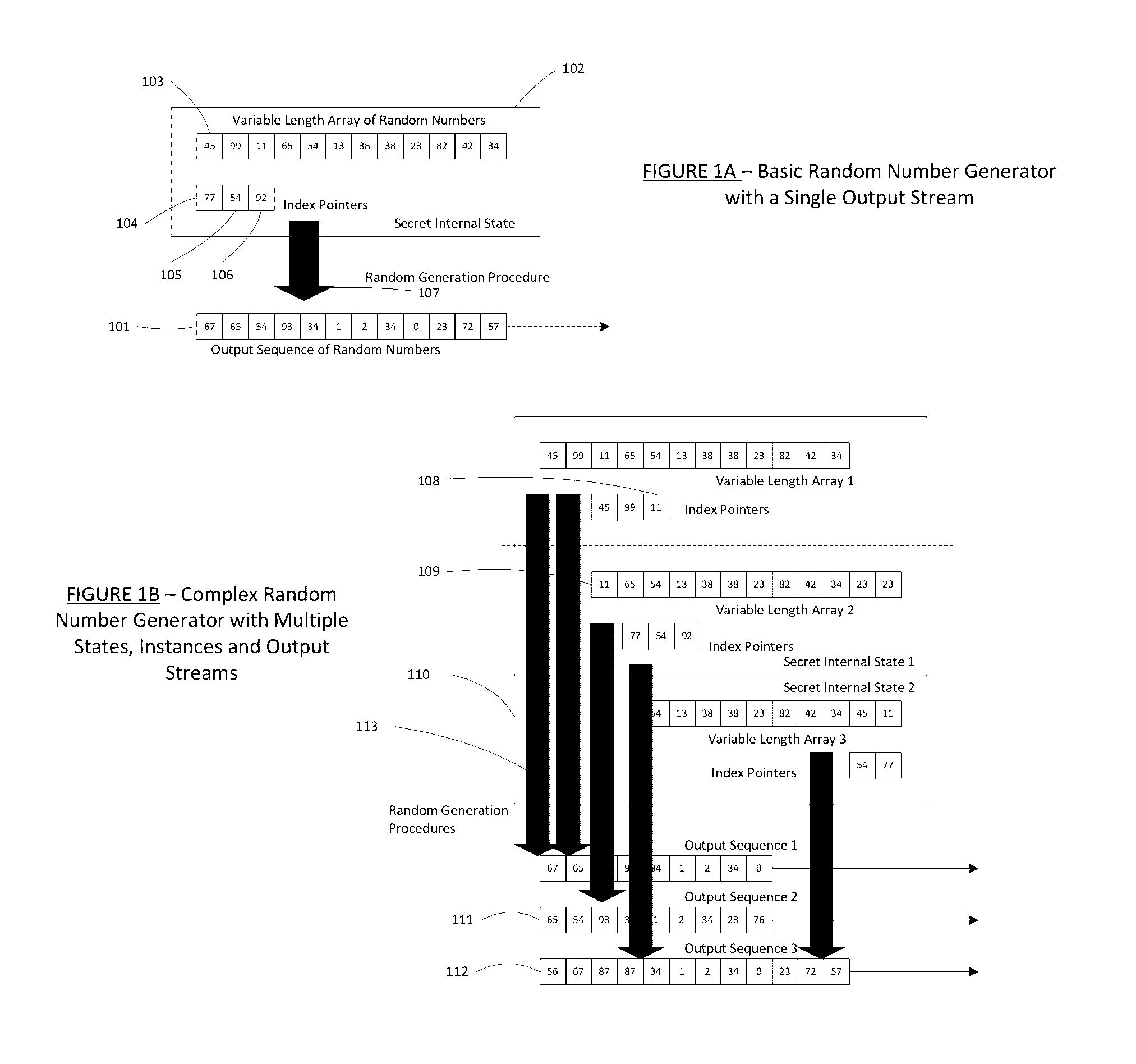
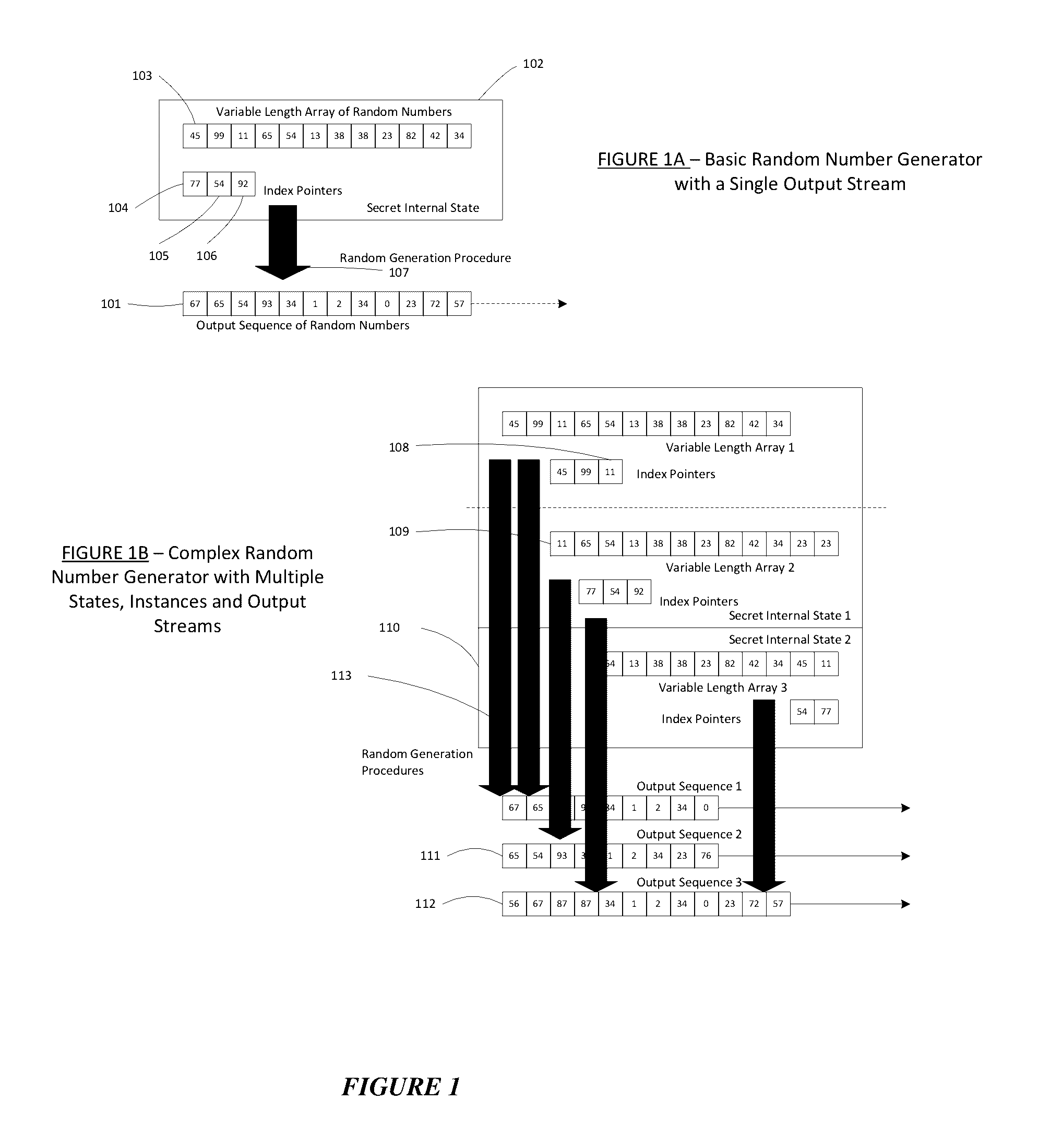
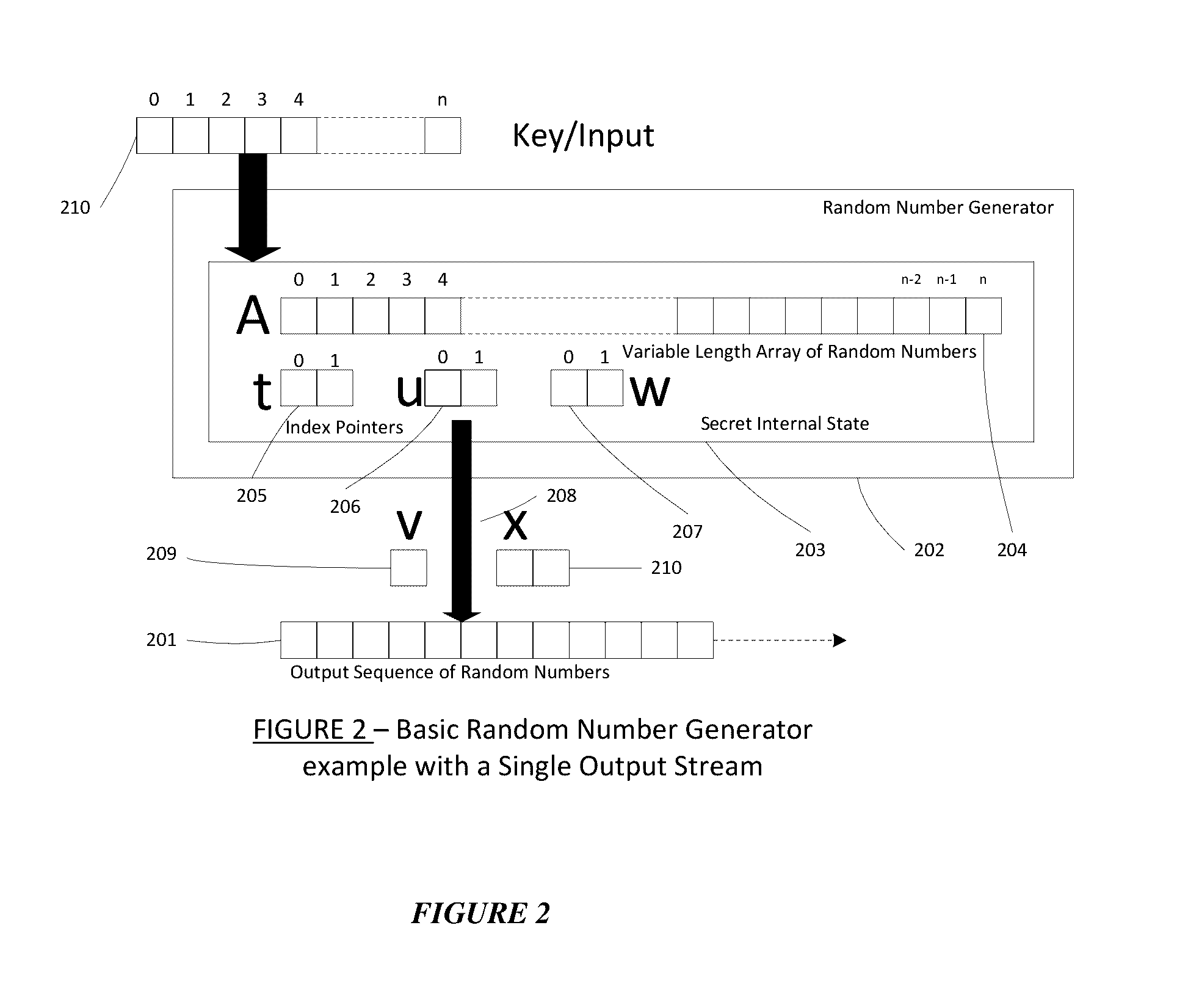
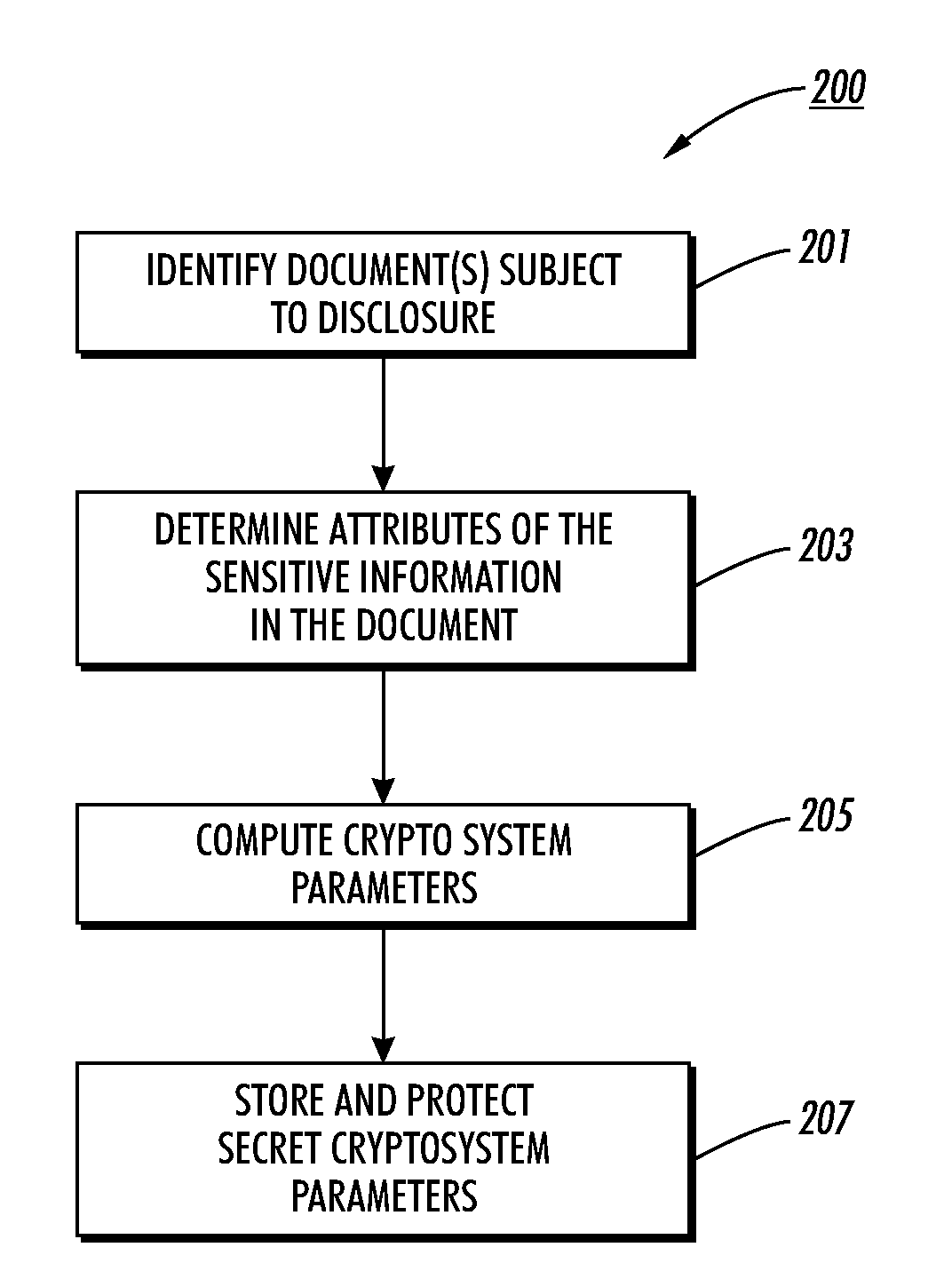
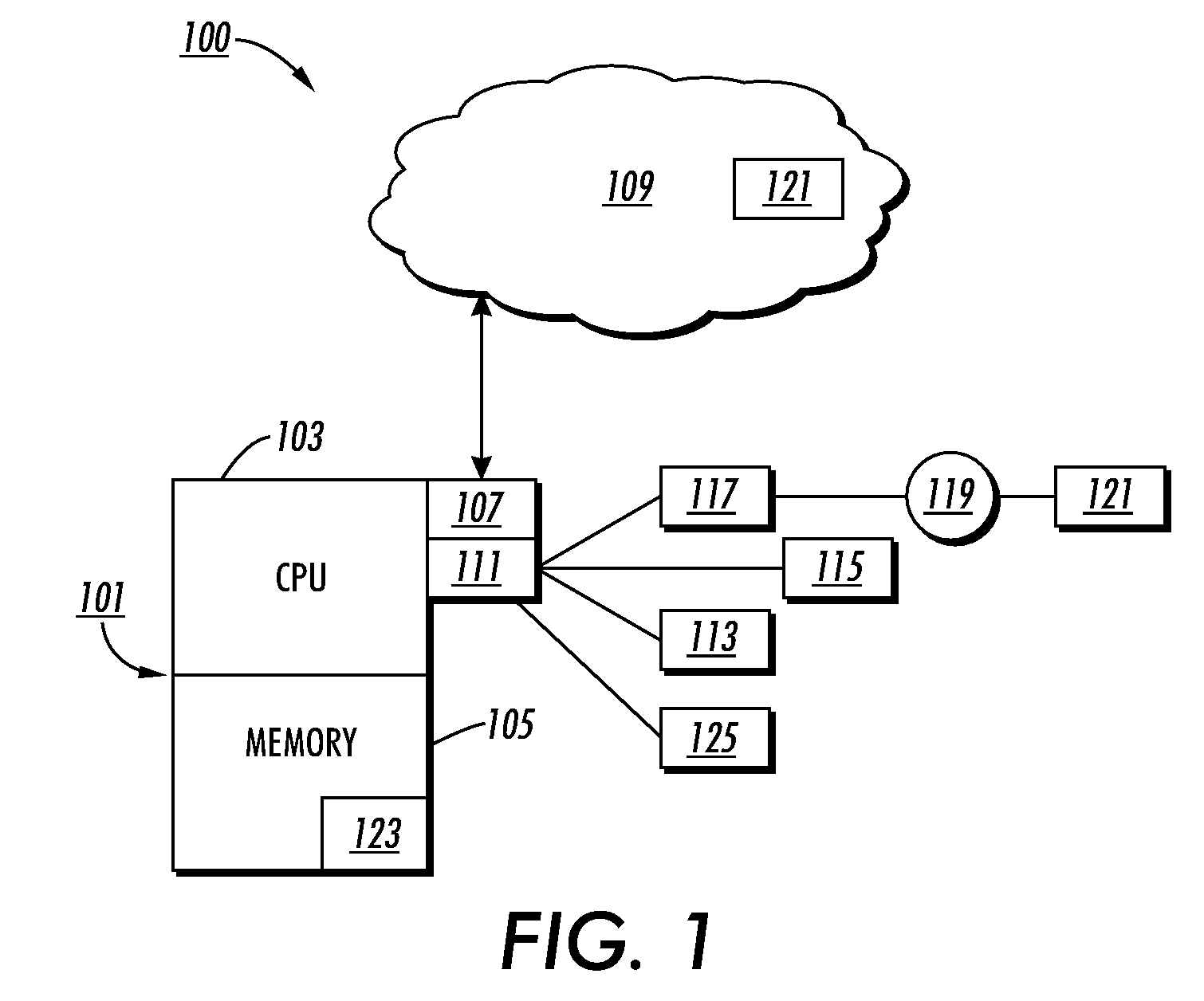
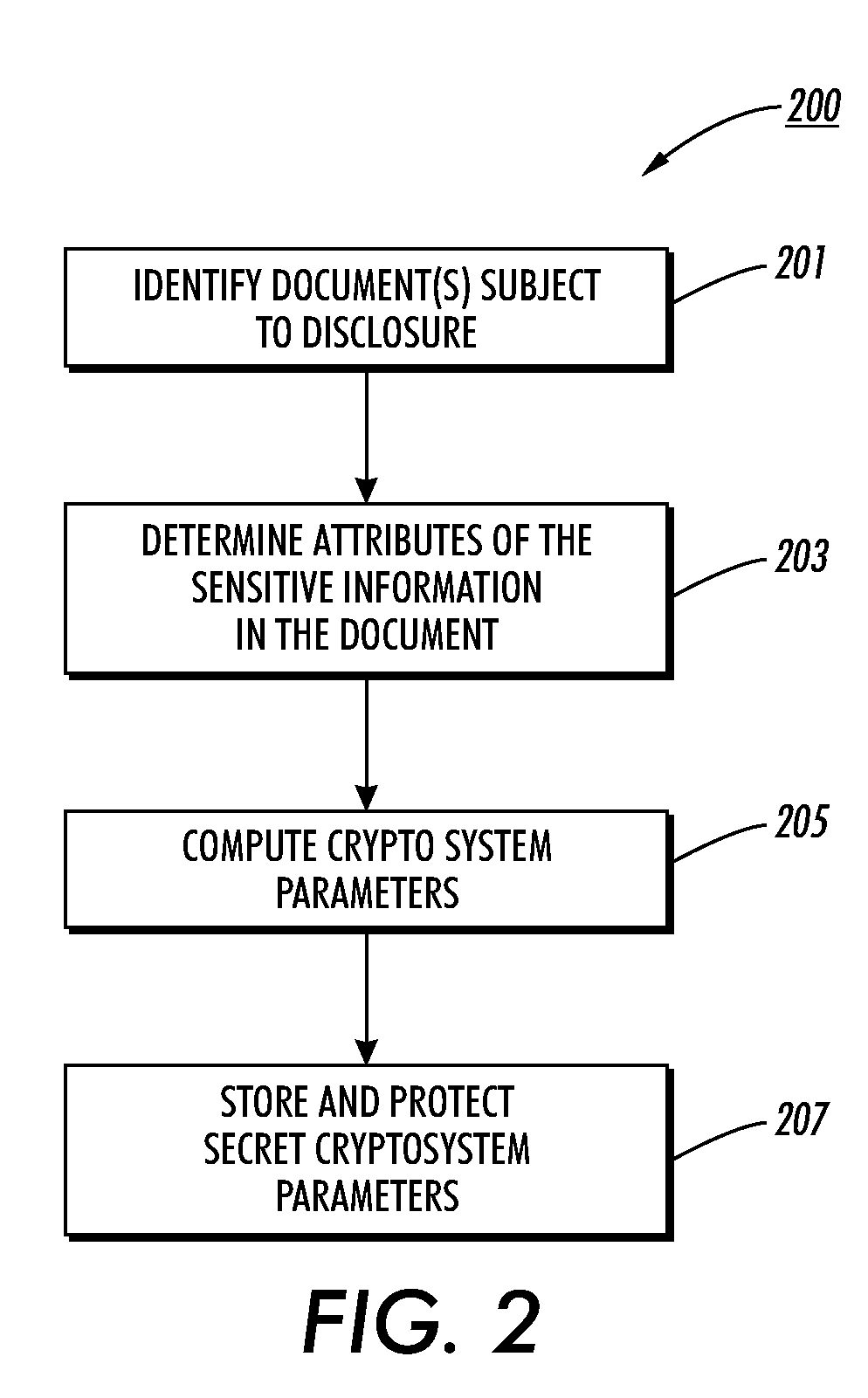
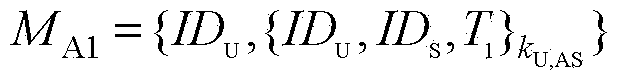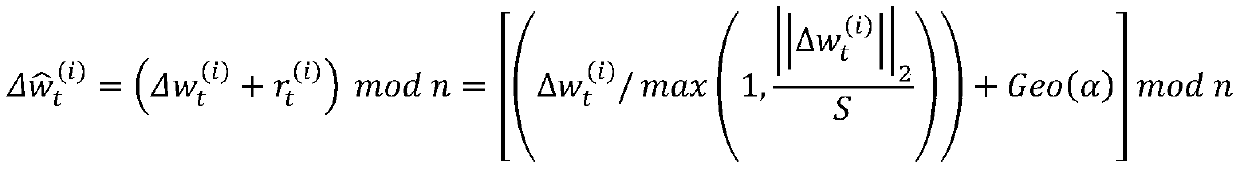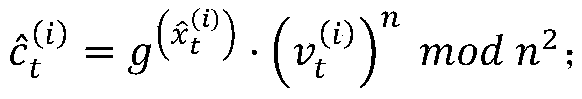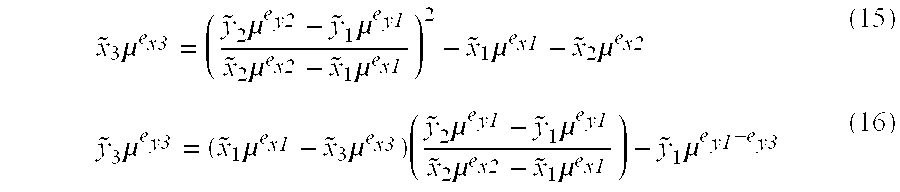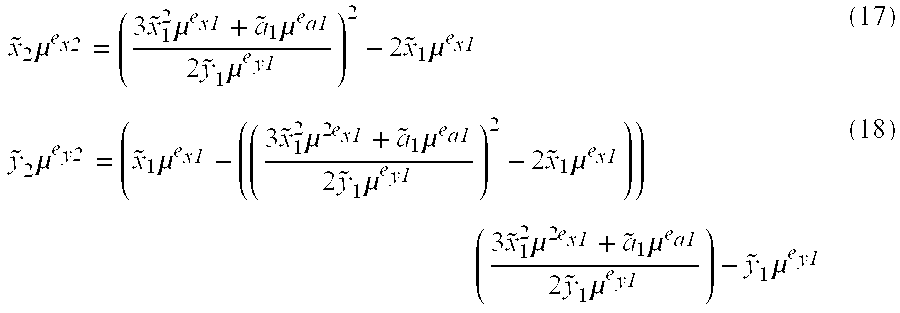Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
424 results about "Cryptosystem" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
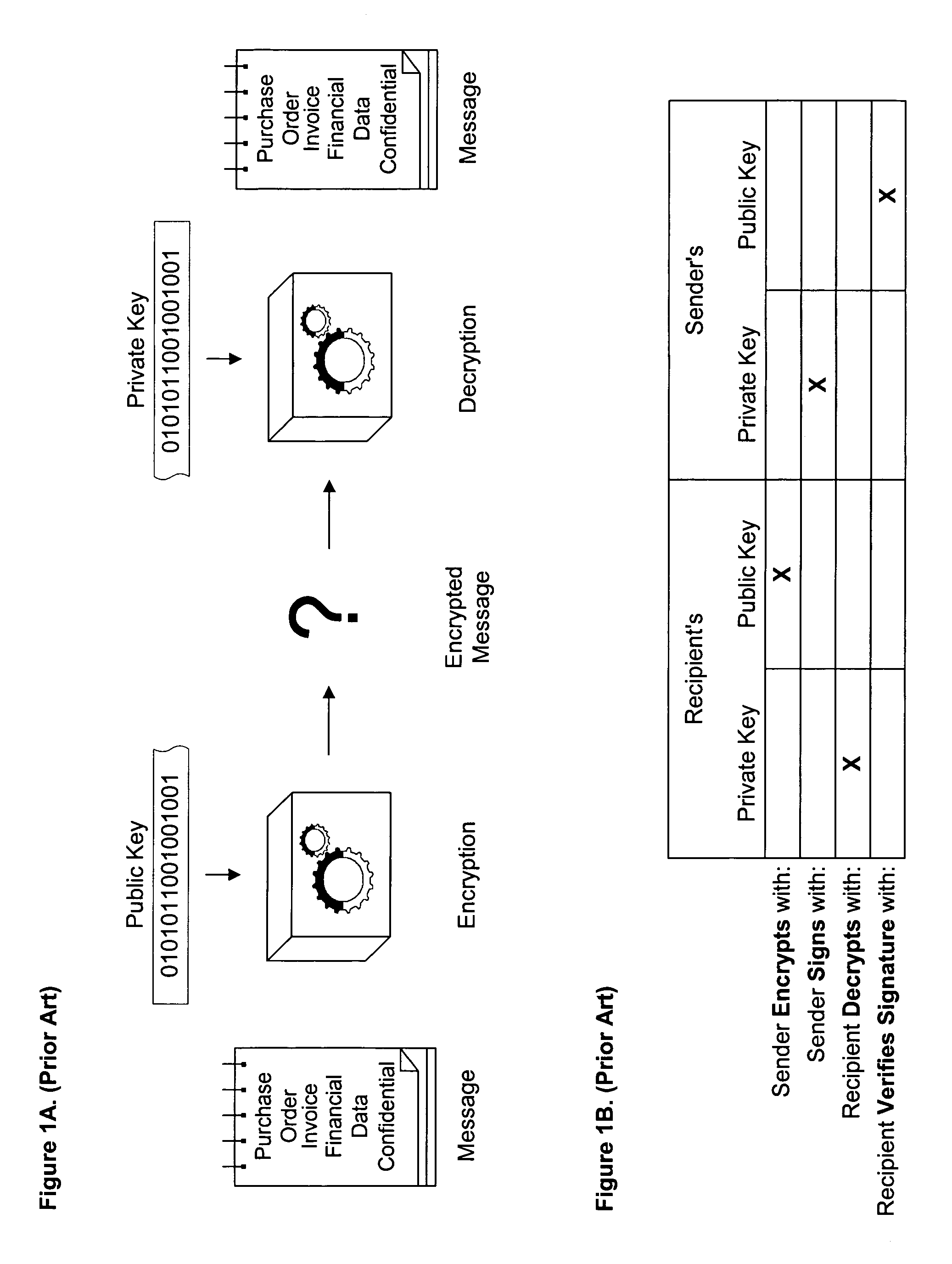
In cryptography, a cryptosystem is a suite of cryptographic algorithms needed to implement a particular security service, most commonly for achieving confidentiality (encryption). Typically, a cryptosystem consists of three algorithms: one for key generation, one for encryption, and one for decryption. The term cipher (sometimes cypher) is often used to refer to a pair of algorithms, one for encryption and one for decryption. Therefore, the term cryptosystem is most often used when the key generation algorithm is important. For this reason, the term cryptosystem is commonly used to refer to public key techniques; however both "cipher" and "cryptosystem" are used for symmetric key techniques.
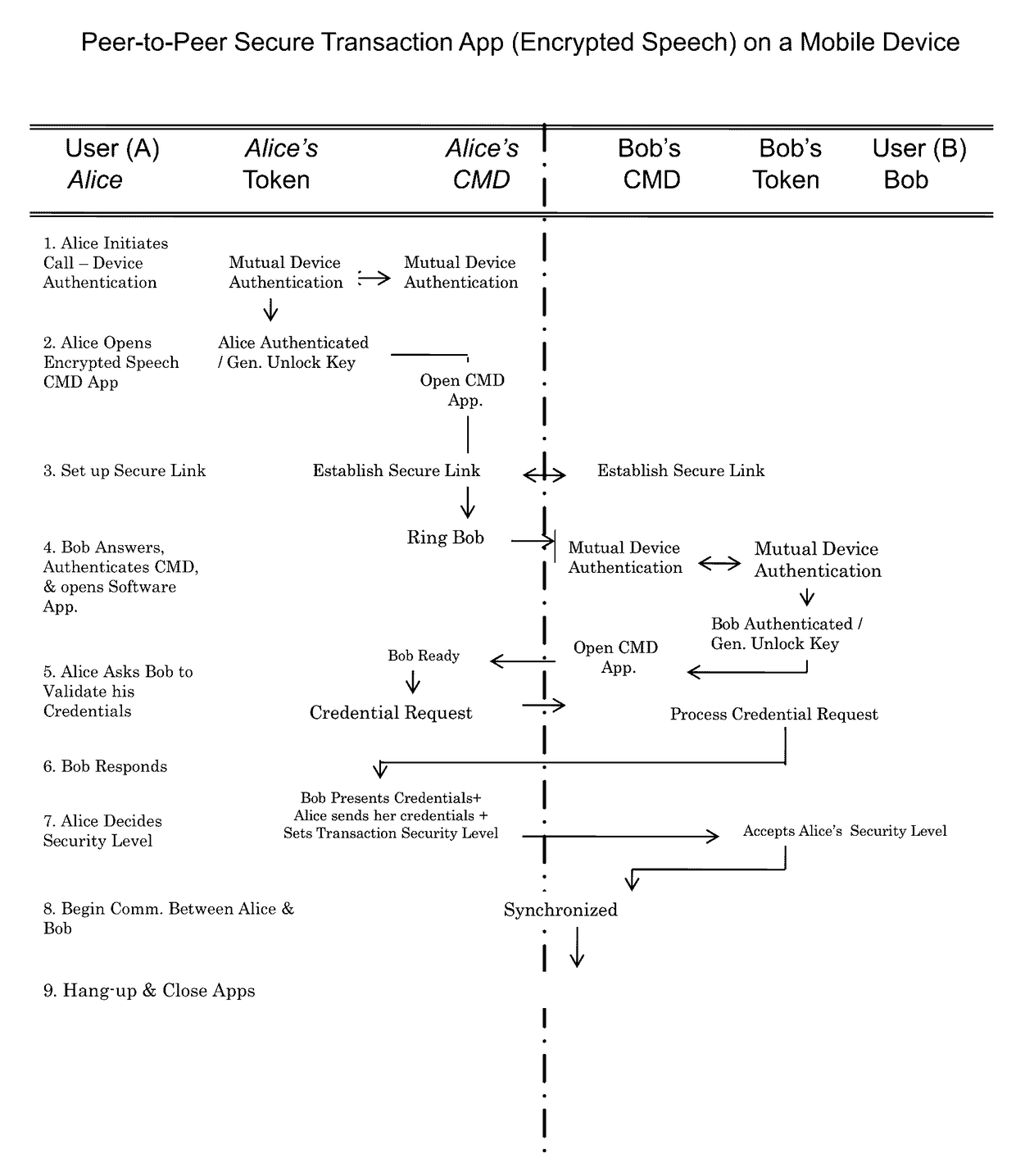
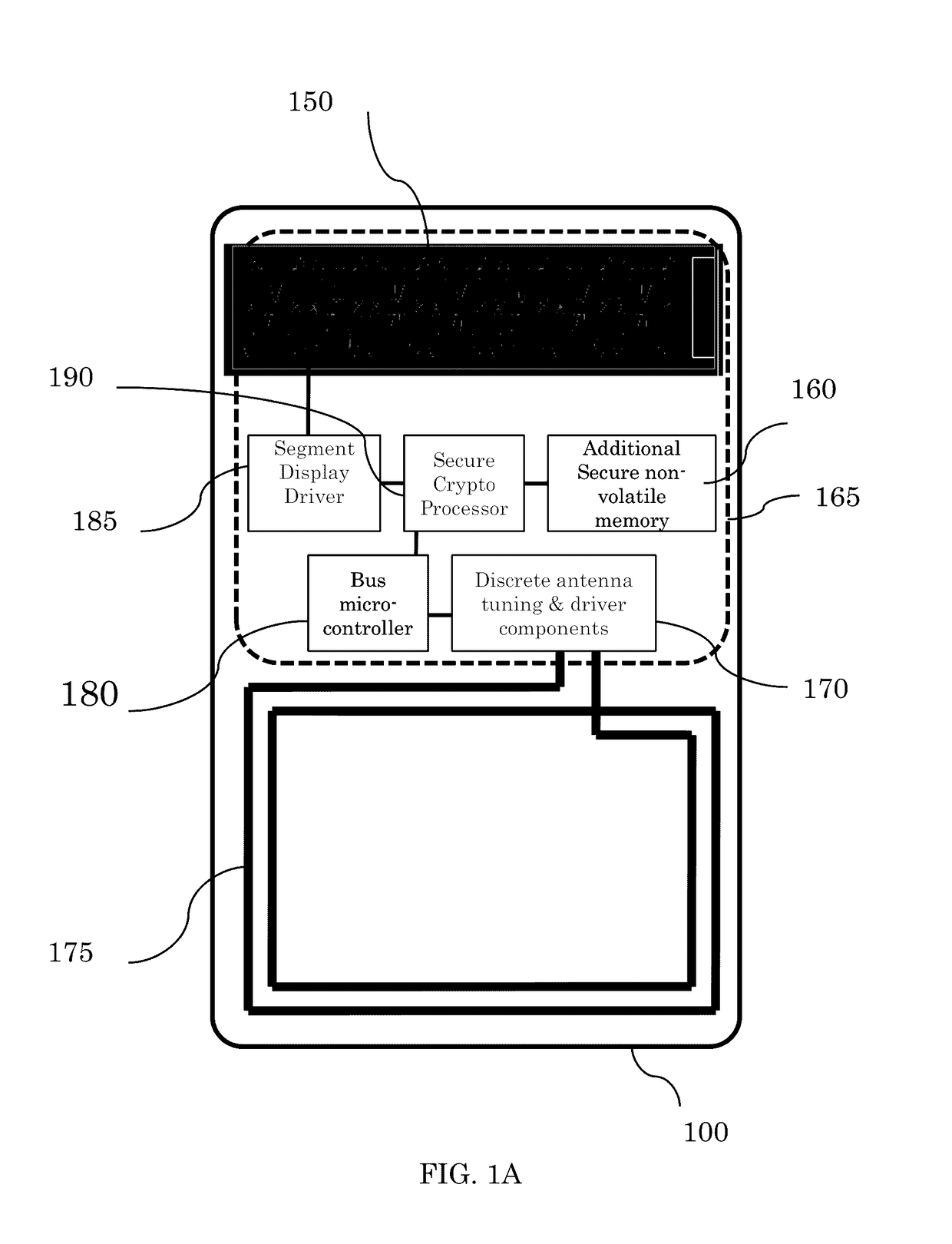
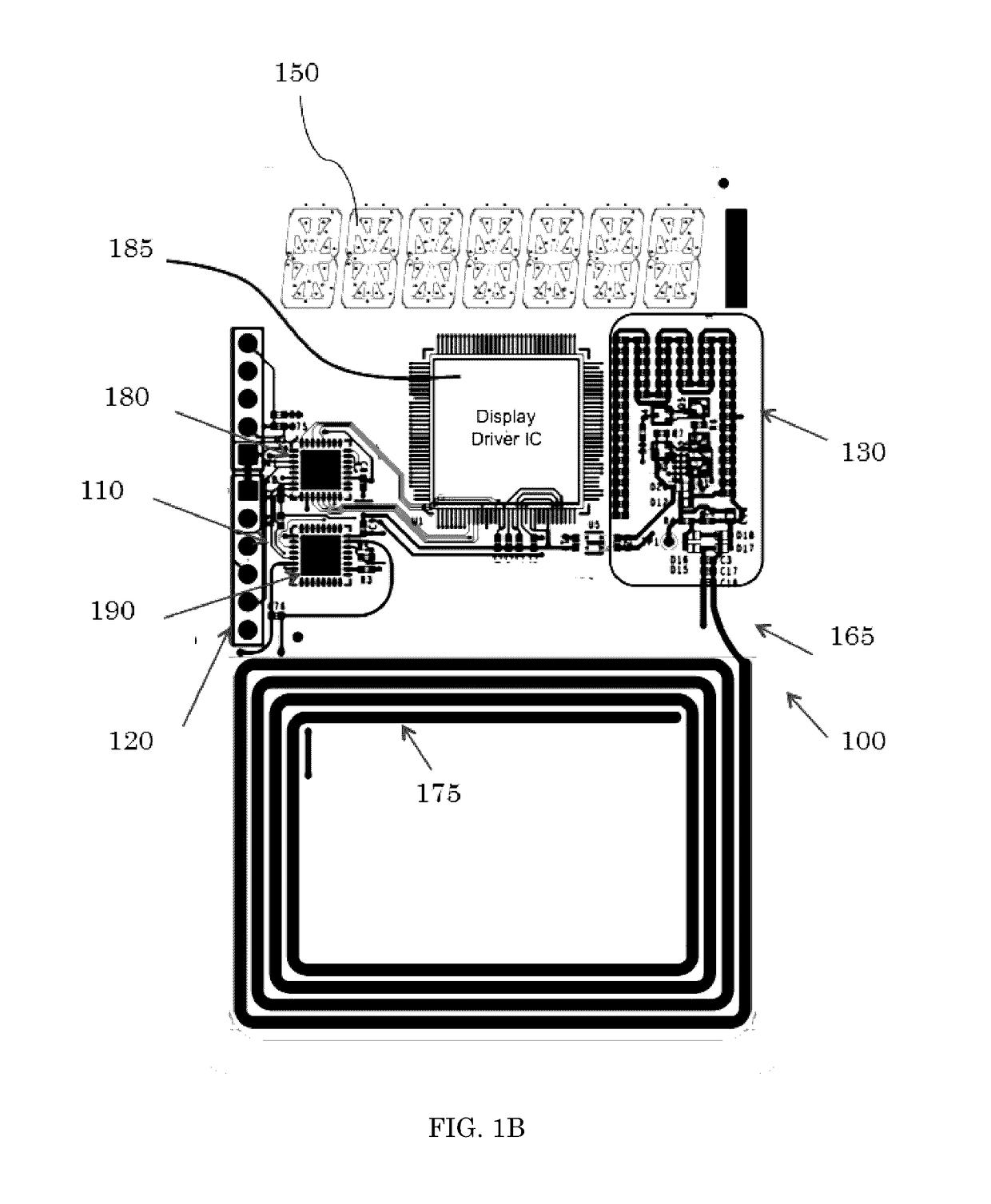
Method and system for secure peer-to-peer mobile communications
ActiveUS9674705B2Big advantageSecure and scalableUser identity/authority verificationNear-field for read/write/interrrogation/identification systemsComputer hardwareCryptosystem
A system and method for secure peer-to-peer mobile communications using cryptographic mobile unlock tokens (“CK tokens”) in conjunction with mobile devices. Each CK token integrates an entire cryptosystem. Executing these cryptographic based functions entirely in the token have significant operational advantages over the typically memory-only tokens. A more secure, scalable, and lower overall system cost are just a few advantages of the CK token over executing these functions within the smartphone. Of the many uses discussed for the CK token, mobile phone enabling, stored value and medical applications, most have centered on the use of the card in conjunction with a smartphone as the touch point in the transaction.
Owner:TOCREO LABS L L C
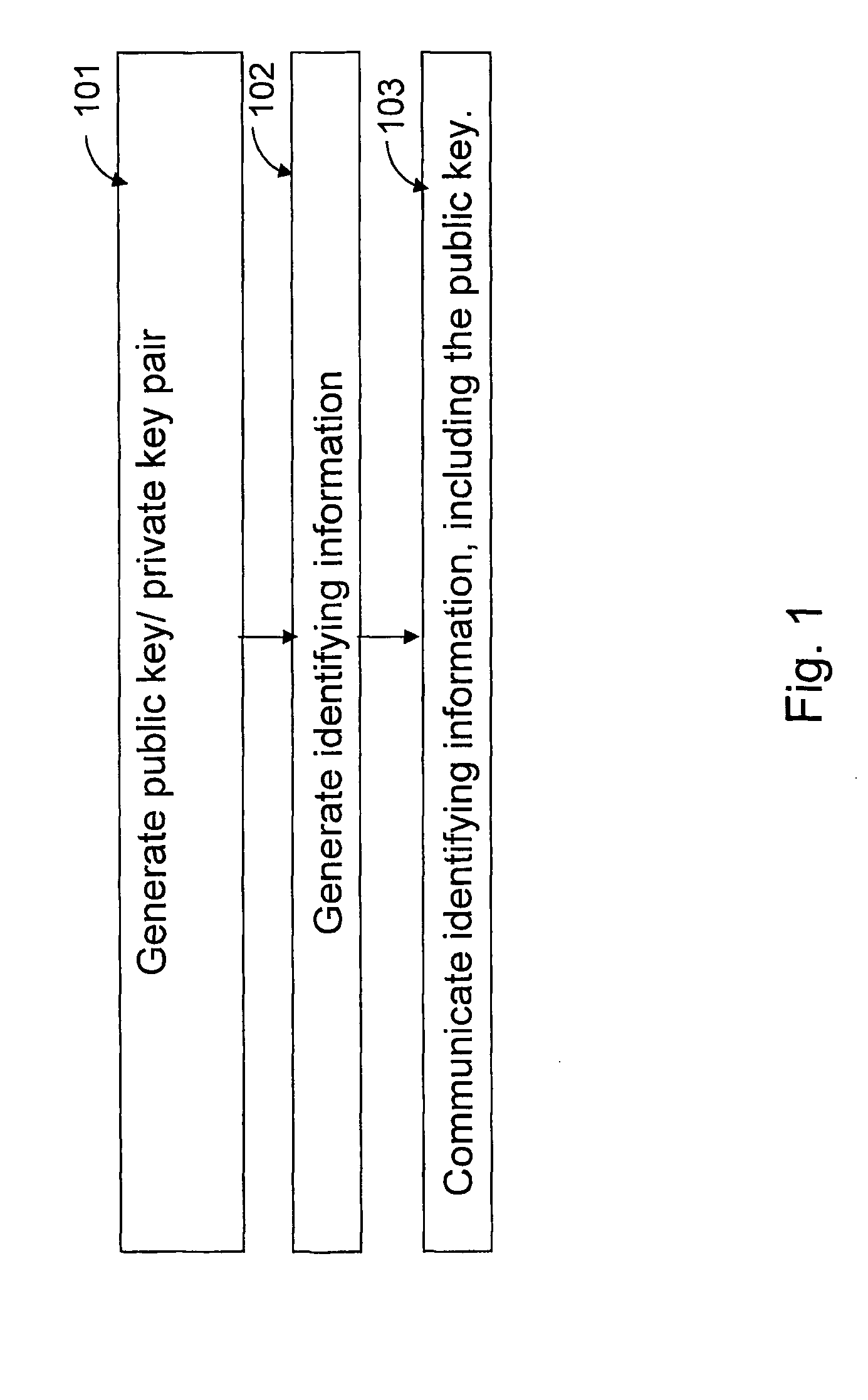
Certificate-based encryption and public key infrastructure
InactiveUS20050246533A1Key distribution for secure communicationPublic key for secure communicationCryptosystemSingle entity
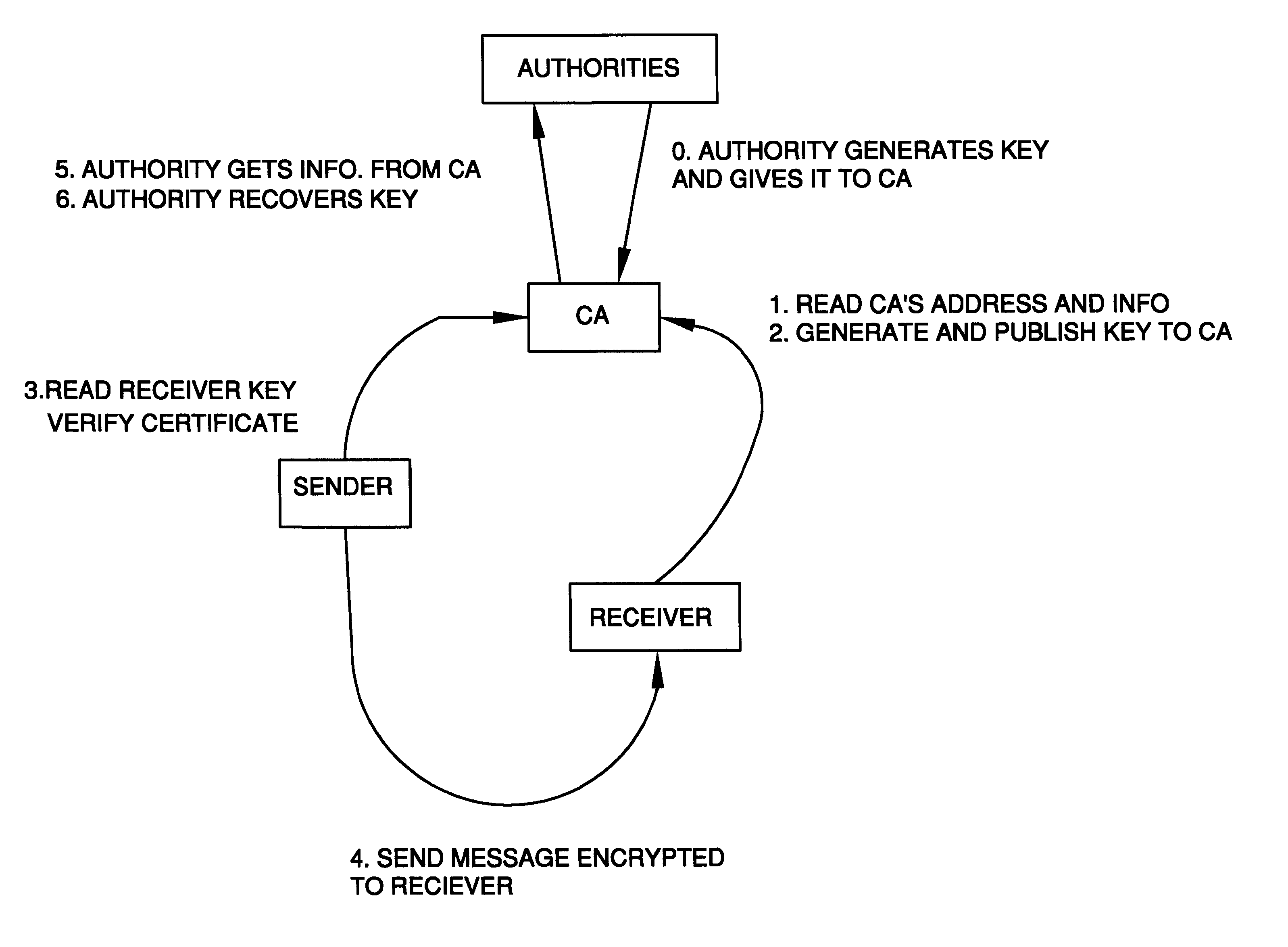
The present invention provides methods for sending a digital message from a sender (606) to a recipient (608) in a public-key based cryptosystem comprising an authorizer (606). The authorizer can be a single entity (606) or comprise a hierarchical or distributed entity (602, 604a-604b). The present invention allows communication of messages by an efficient protocol, not involving key status queries or key escrow, where a message recipient (608) can decrypt a message from a message sender (606) only if the recipient (608) possesses up-to-date authority from the authorizer. The invention allows such communication in a system comprising a large number (e.g. millions) of users.
Owner:NTT DOCOMO INC
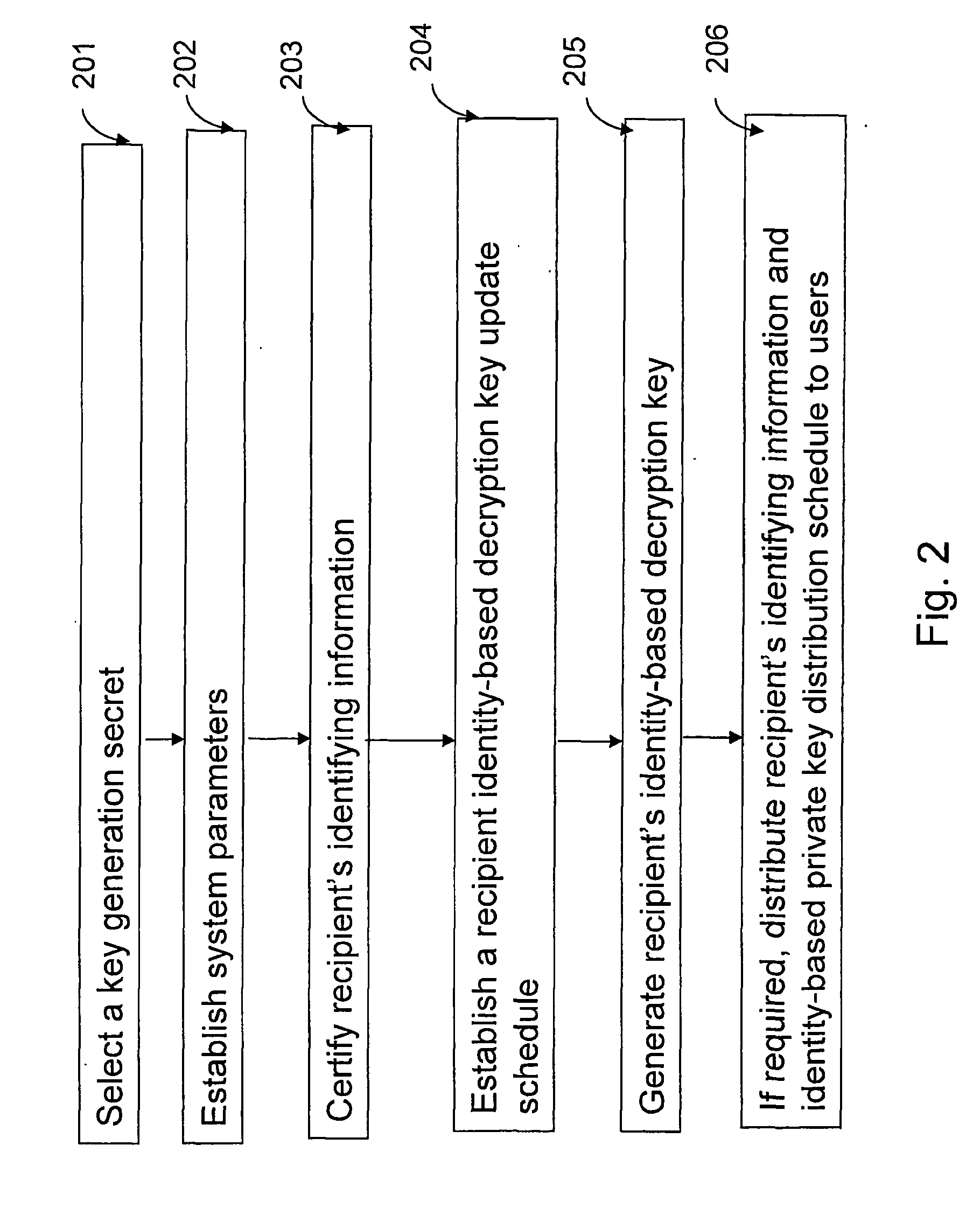
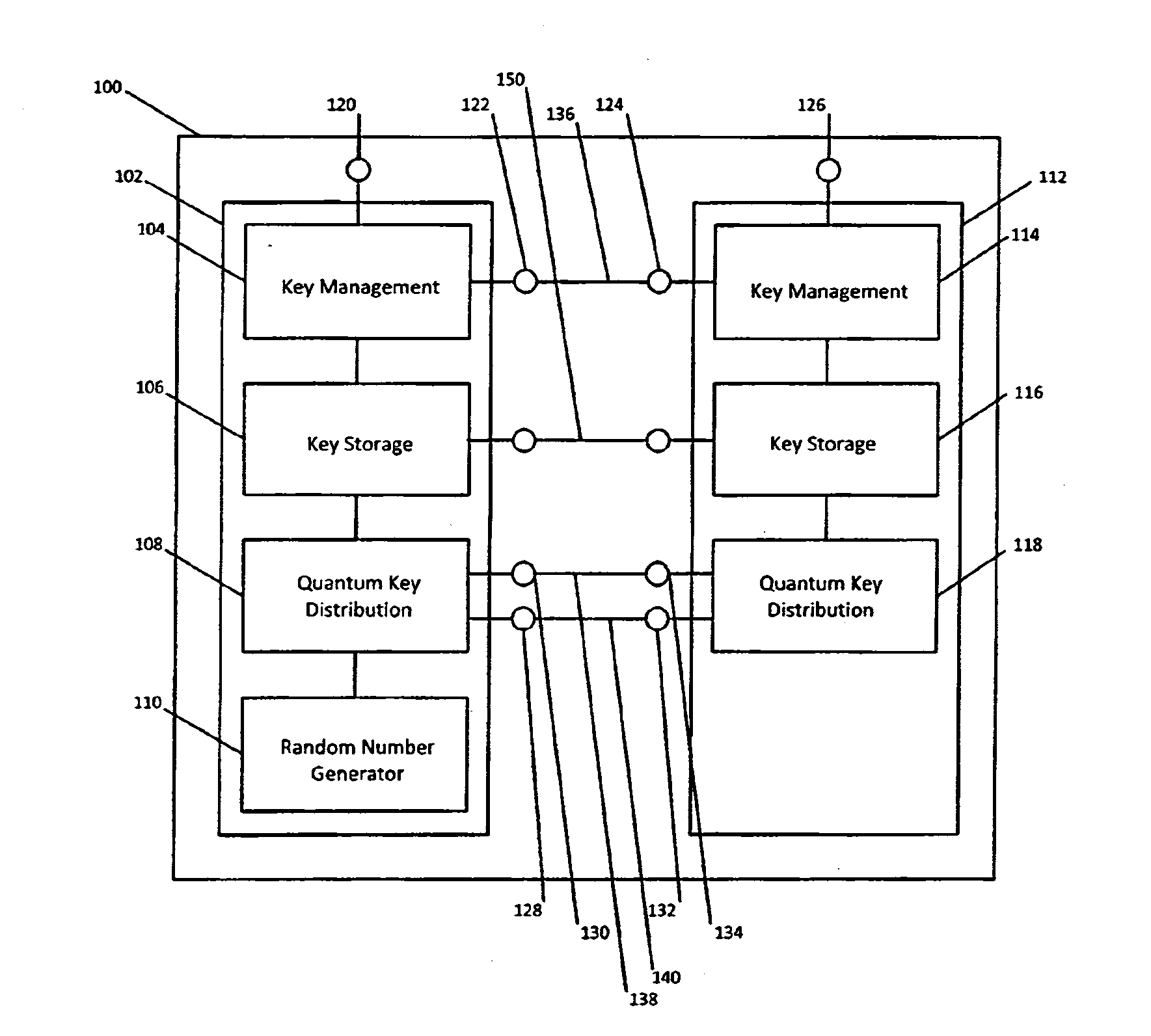
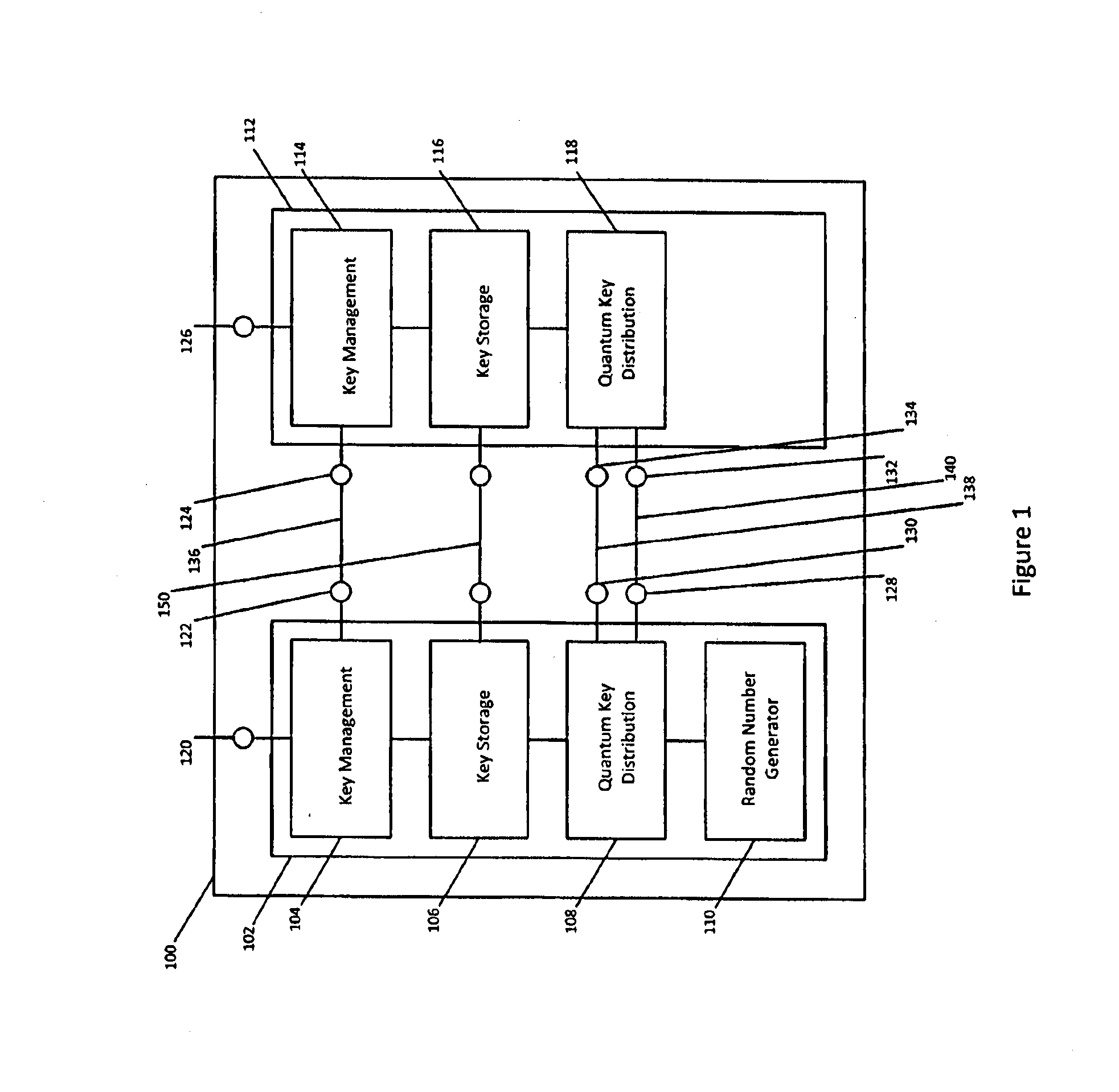
Qkd key management system
ActiveUS20140331050A1Enabling detectionEfficient management and deliveryKey distribution for secure communicationUser identity/authority verificationCryptosystemQuantum channel
Owner:QUINTESSENCELABS
Secure Distribution of Content
InactiveUS20140310527A1Avoid attackKey distribution for secure communicationData stream serial/continuous modificationCryptosystemComputer science
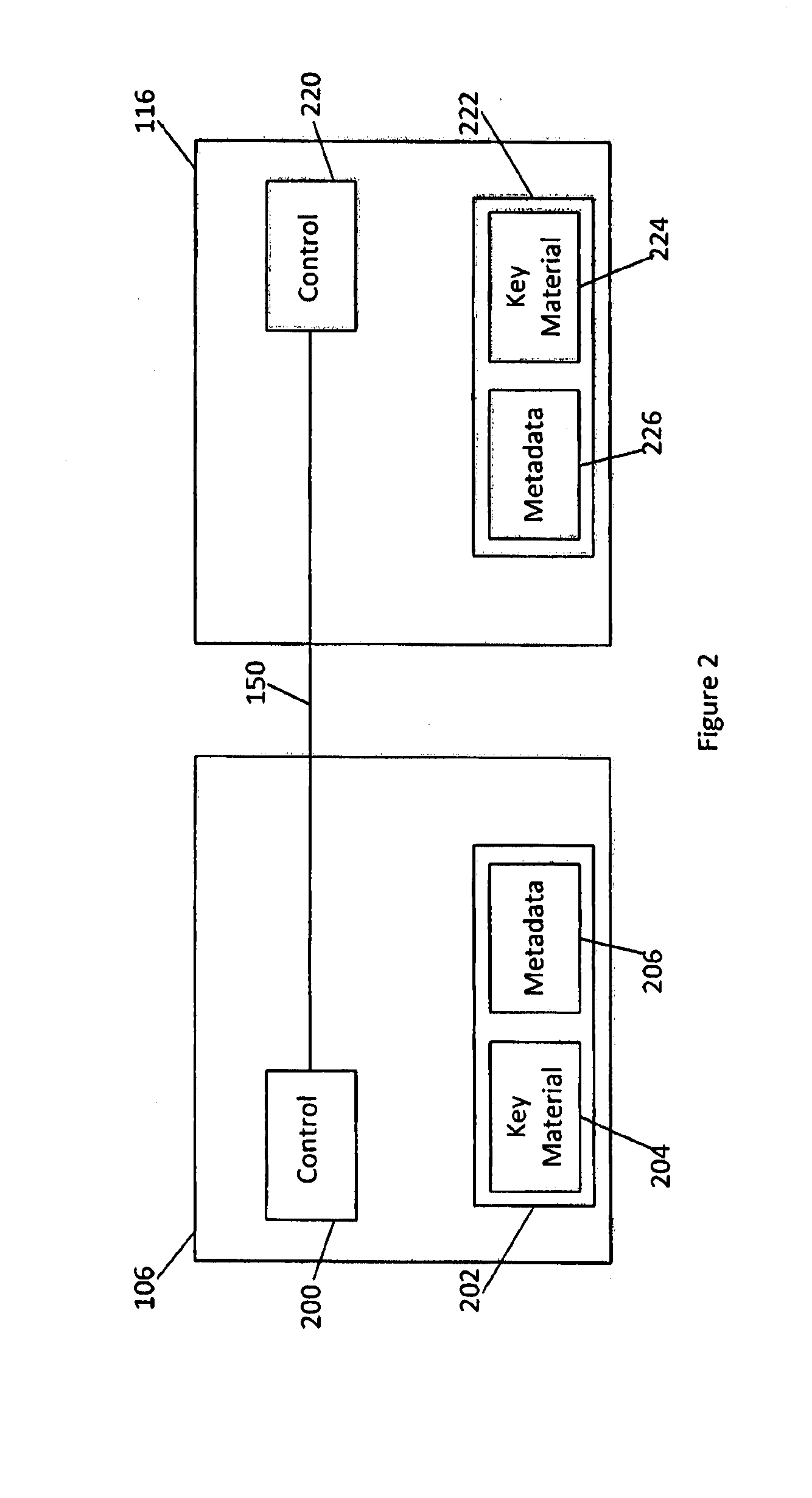
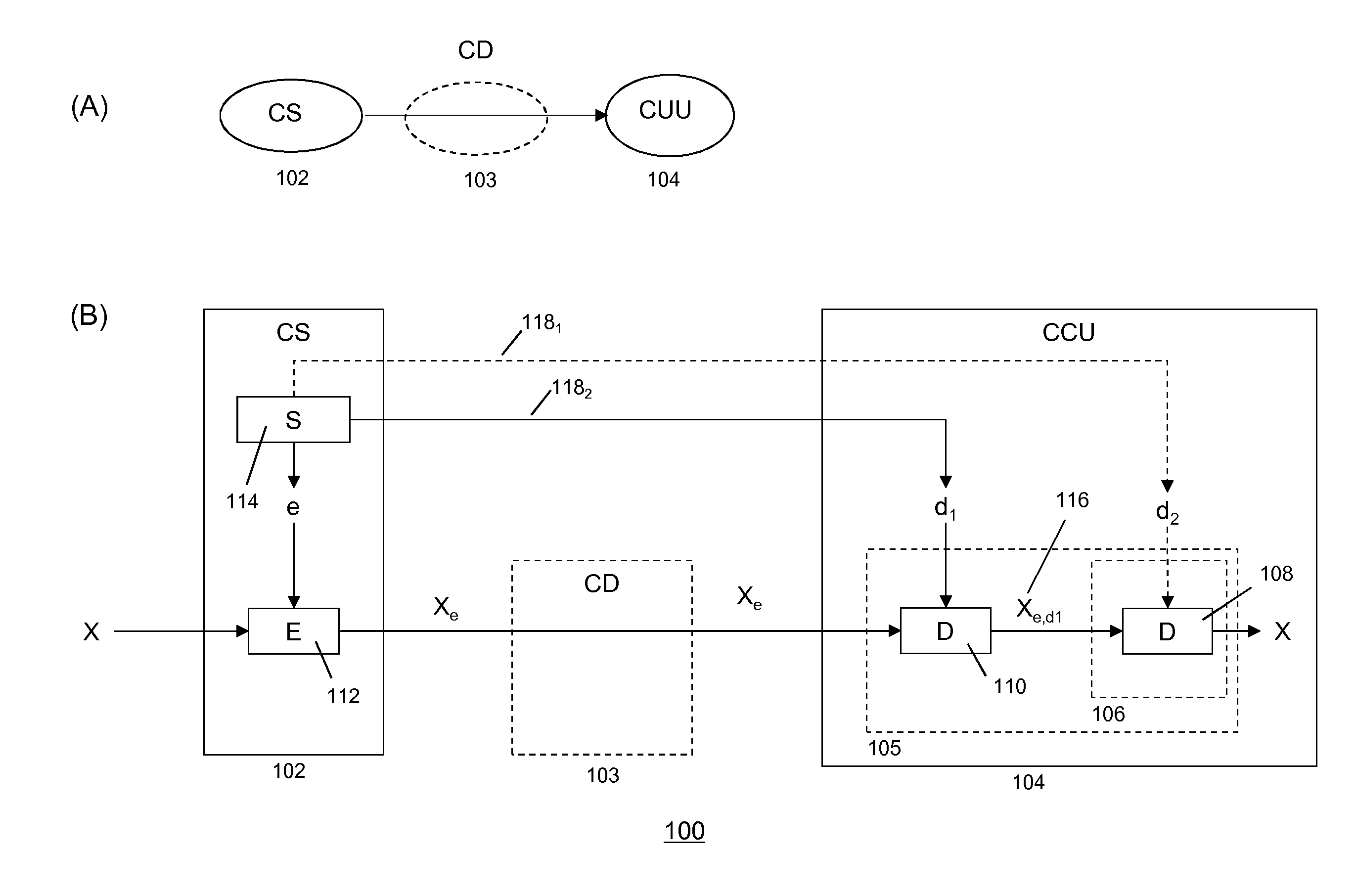
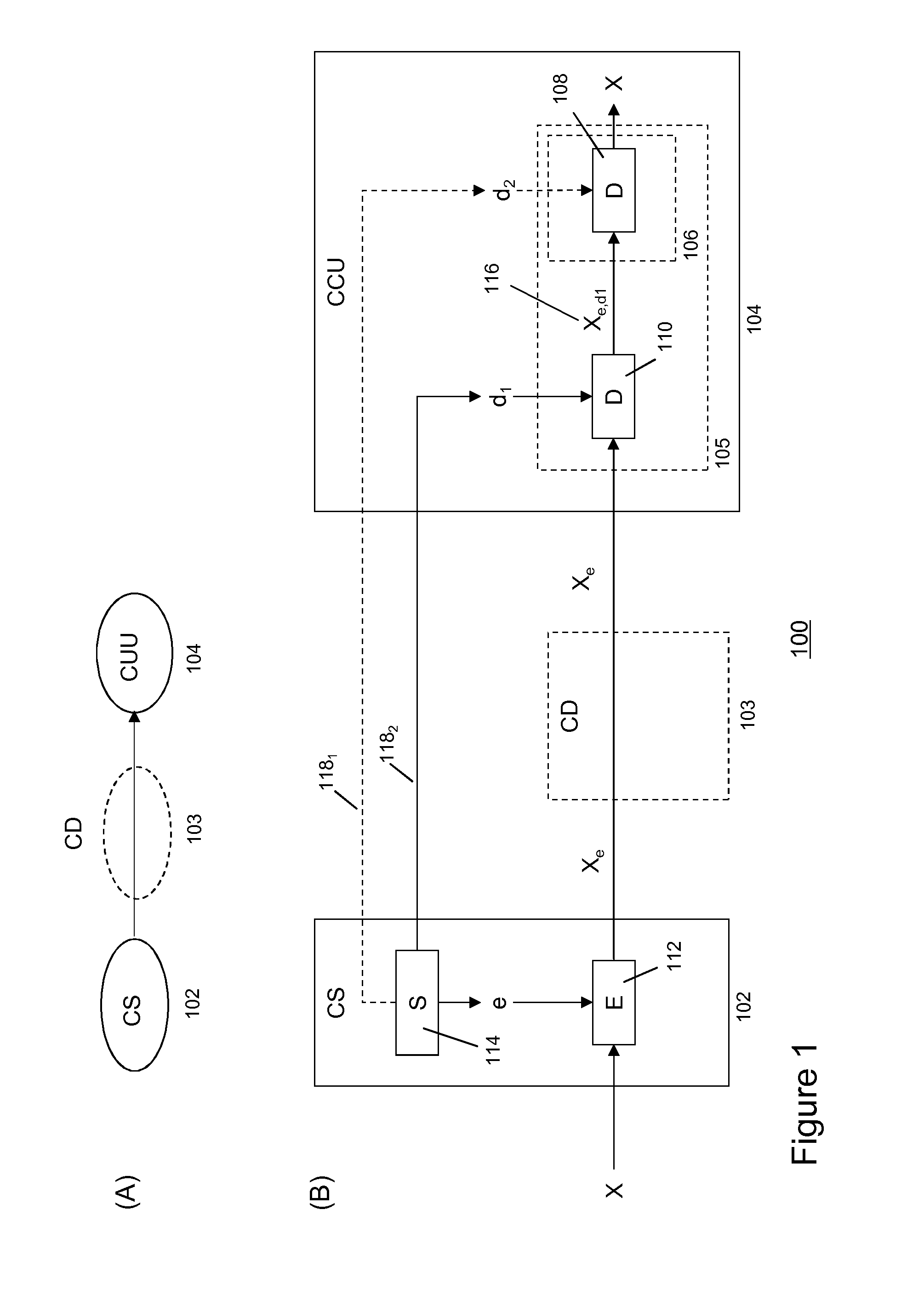
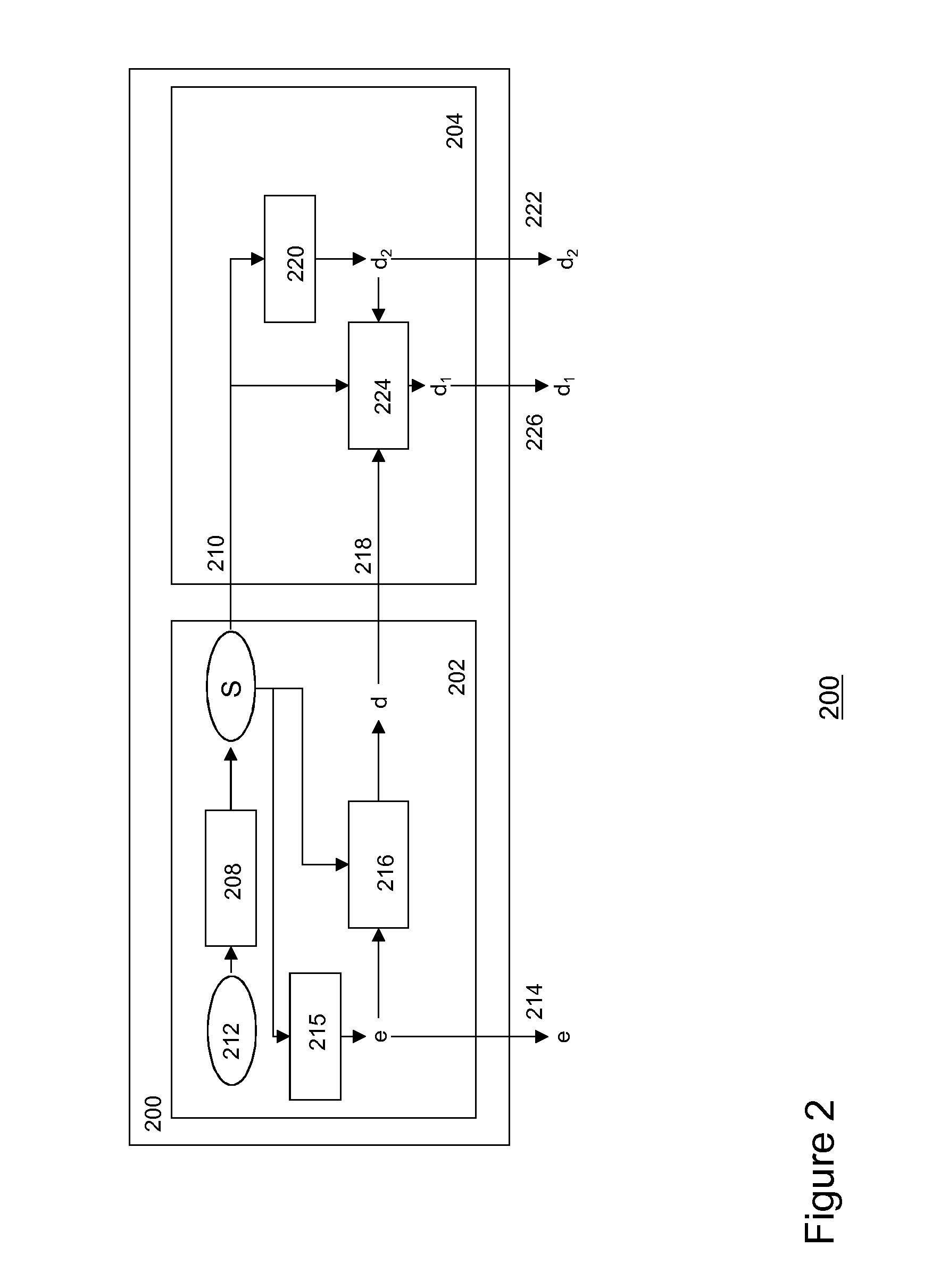
Methods and systems are described for enabling secure delivery of a content item from a content source to a content receiving device associated with a decryption module configured for use with a split-key cryptosystem comprising encryption and decryption algorithms E and D, a cipher algorithm for generating encryption and decryption keys e,d on the basis of secret information S and a split-key algorithm for splitting e and / or d into i different split-encryption keys e1, e2, . . . , ei and / or k different split-decryption keys d1, d2, . . . , dk respectively, such that Ddk(Ddk-1( . . . (Dd2(Dd1(Eei(Eei-1( . . . (Ee2(Ee1(X)) . . . ))=Ddk(Ddk-1( . . . (Dd2(Dd1(Xe1, e2, . . . , ei))=X wherein i,k≧1 and i+k>2, wherein the method comprises: provisioning said decryption module with first split-key information comprising at least a first split-key; generating second split-key information comprising at least a second split-key on the basis of said first split-key information, said decryption key d and, optionally, said secret information S; and, provisioning said decryption module with said at least second split-key 1 information for decrypting an encrypted content item Xe on the basis of said first and second split-key information and decryption algorithm D in said decryption module.
Owner:KONINK KPN NV +1
Information recording device, information playback device, information recording method, information playback method, and information recording medium and program providing medium used therewith
InactiveUS7319752B2Raise security concernsUnauthorized useTelevision system detailsKey distribution for secure communicationComputer hardwareCryptosystem
An information recording / playback device stores beforehand, on a recording medium, secret information in which a writing / reading method thereof cannot be analyzed and which can be read only by a special reading method. The secret information is applied to a key for content encryption or decryption when performing recording or playback of contents on the recording medium, such as music data and image data. The secret information is, for example, a stamper ID. By using the stamper ID as secret information, and a master key and a media key which are distributed in a tree-structure key-distribution system, a content-cryptosystem key is generated. Accordingly, each content is allowed to be used in only an appropriate device in which the special reading method for the secret information can be executed and to which the key is distributed by the tree-structure key-distribution system.
Owner:SONY CORP
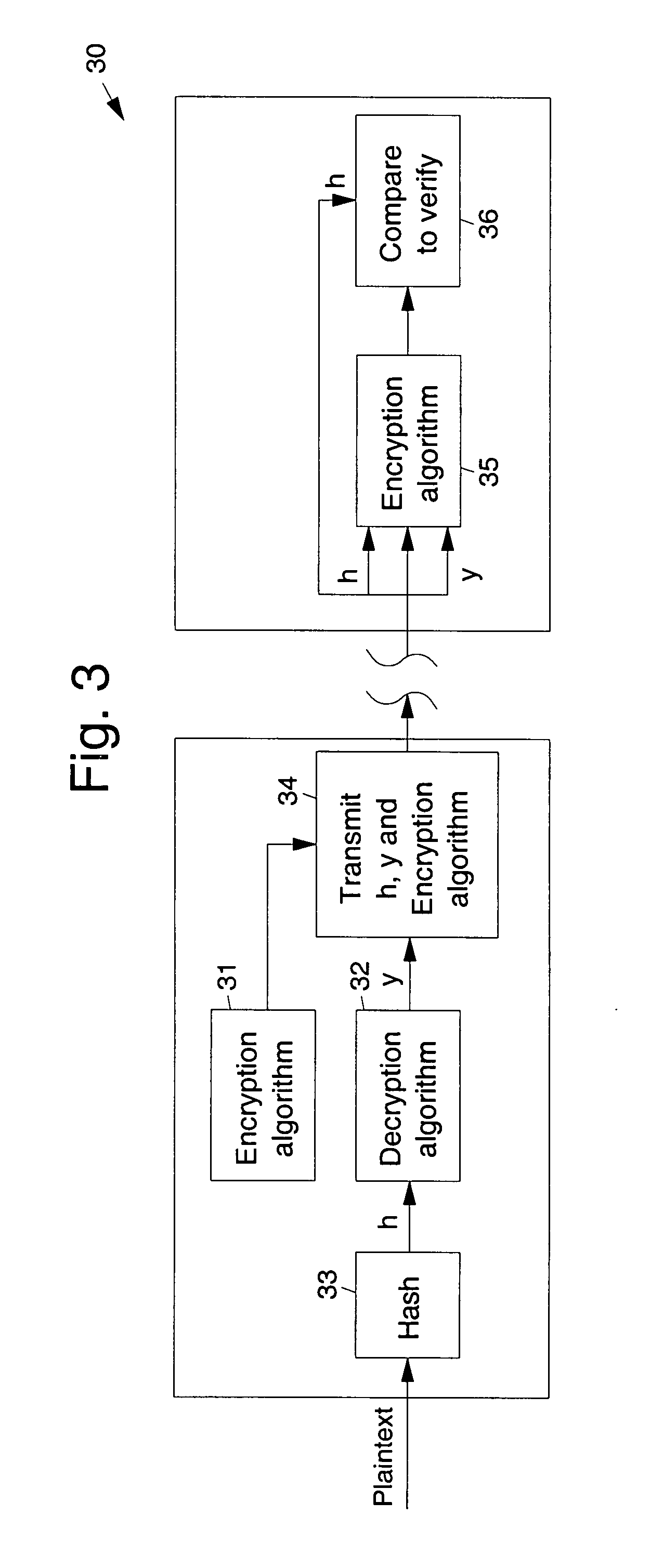
Cryptographic system with methods for user-controlled message recovery
InactiveUS7139399B1Storage requirement increaseKey distribution for secure communicationS/KEYCryptosystem
A cryptosystem is described which automatically provides an extra “message recovery” recipient(s) when an encrypted message is generated in the system. The system is typically configured such that the extra recipient or “message recovery agent” (MRA)—an entity which itself has a public key (i.e., a MRA public key)—is automatically added, under appropriate circumstances, as a valid recipient for an encrypted message created by a user. In a corporate setting, for example, the message recovery agent is the “corporate” message recovery agent designated for that company (firm, organization, or other group) and the user is an employee (or member) of that company (or group). In operation, the system embeds a pointer (or other reference mechanism) to the MRA public key into the public key of the user or employee, so that encrypted messages sent to the company's employees from outside users (e.g., those individuals who are not employees of the company) can nevertheless still be recovered by the company. Alternatively, the MRA public key itself can be embedded within the public key of the employee or user (i.e., a key within a key), but typically at the cost of increasing the storage requirement of the user's key. By including in the user's key (e.g., an employee) a pointer to a message recovery agent's key (or the MRA key itself), the system provides a mechanism for assisting a user outside a group (e.g., a user who is outside a particular company) with the task of including in an automatic and non-intrusive manner the key of an additional recipient, such as one intended for message recovery.
Owner:CA TECH INC
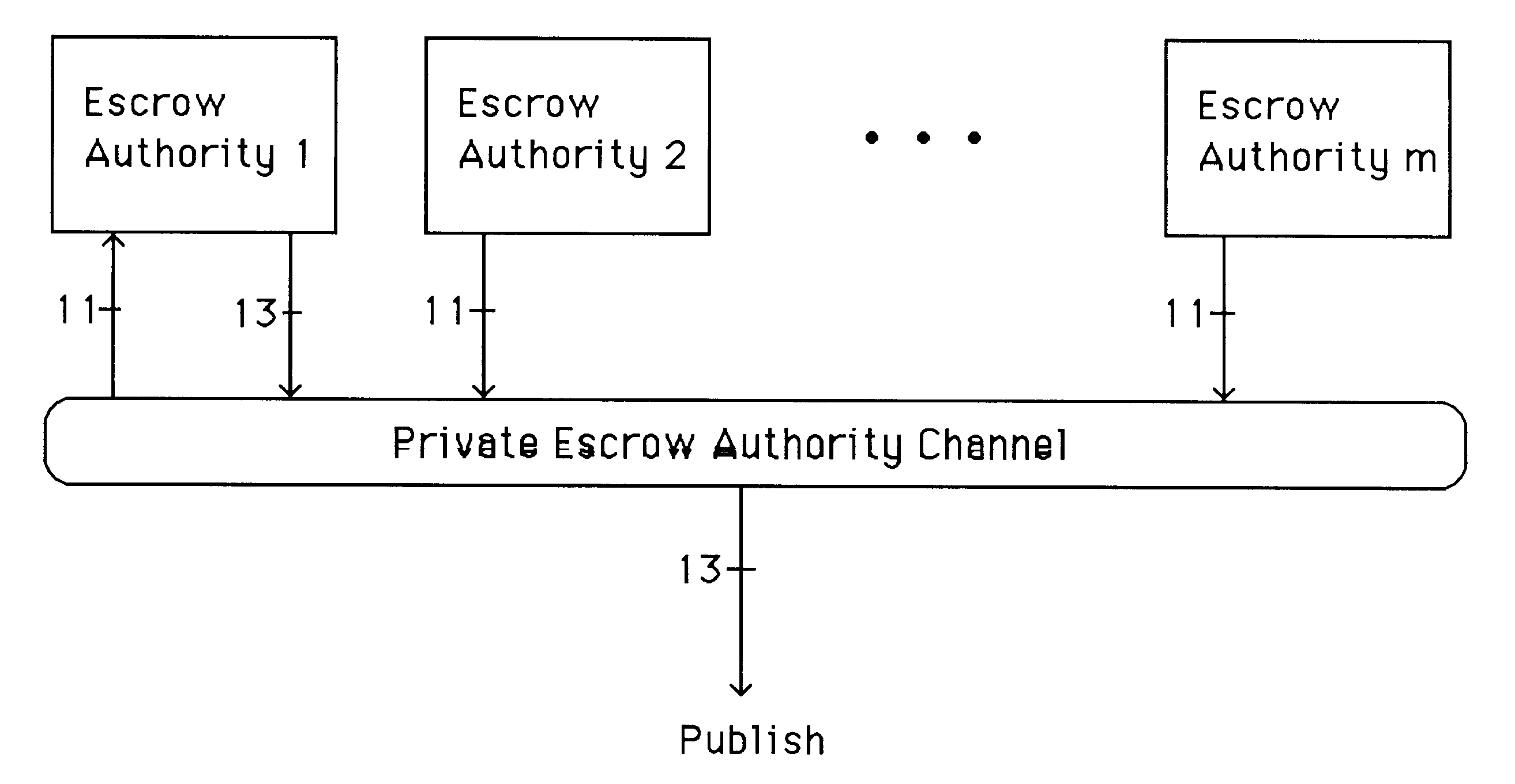
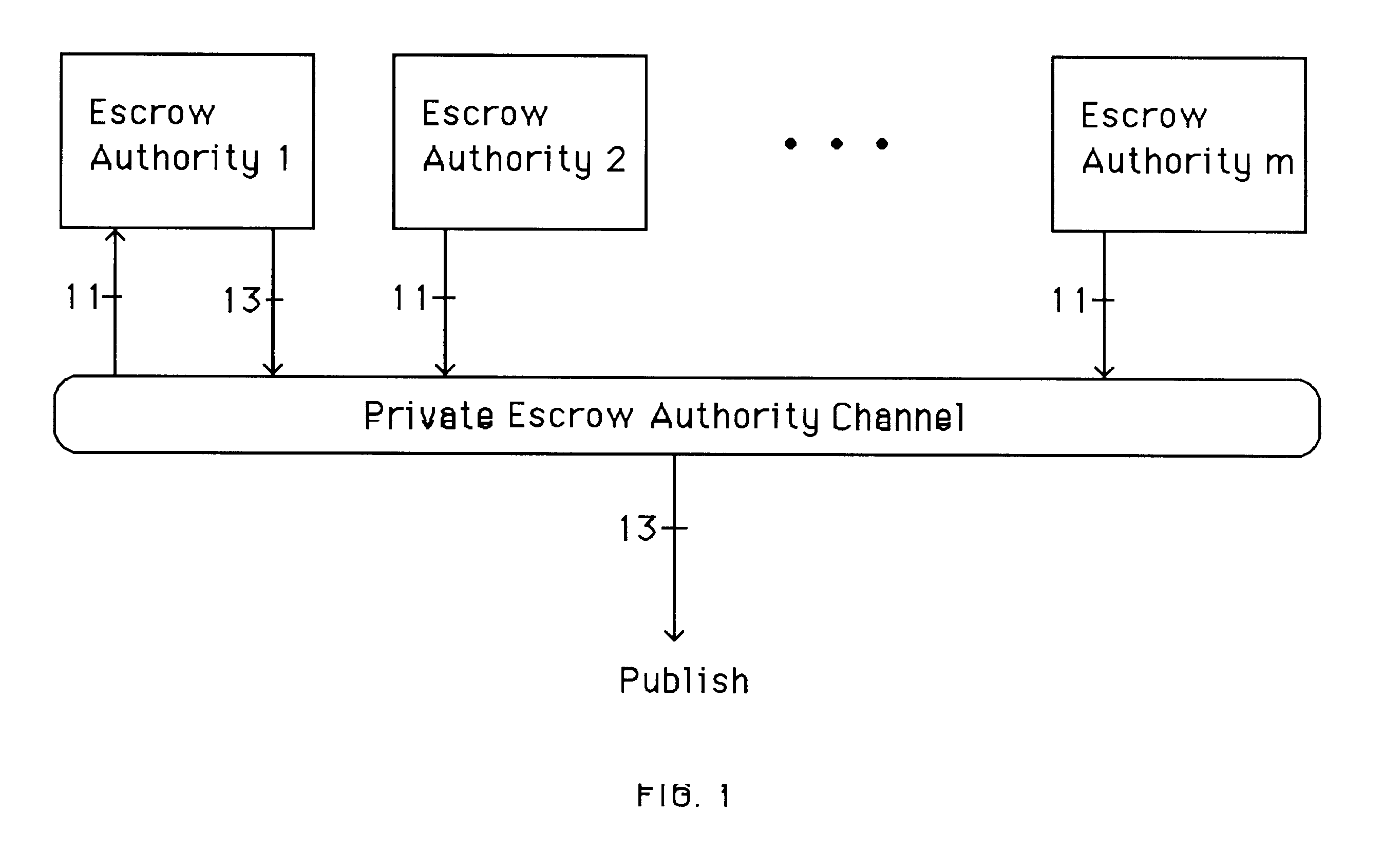
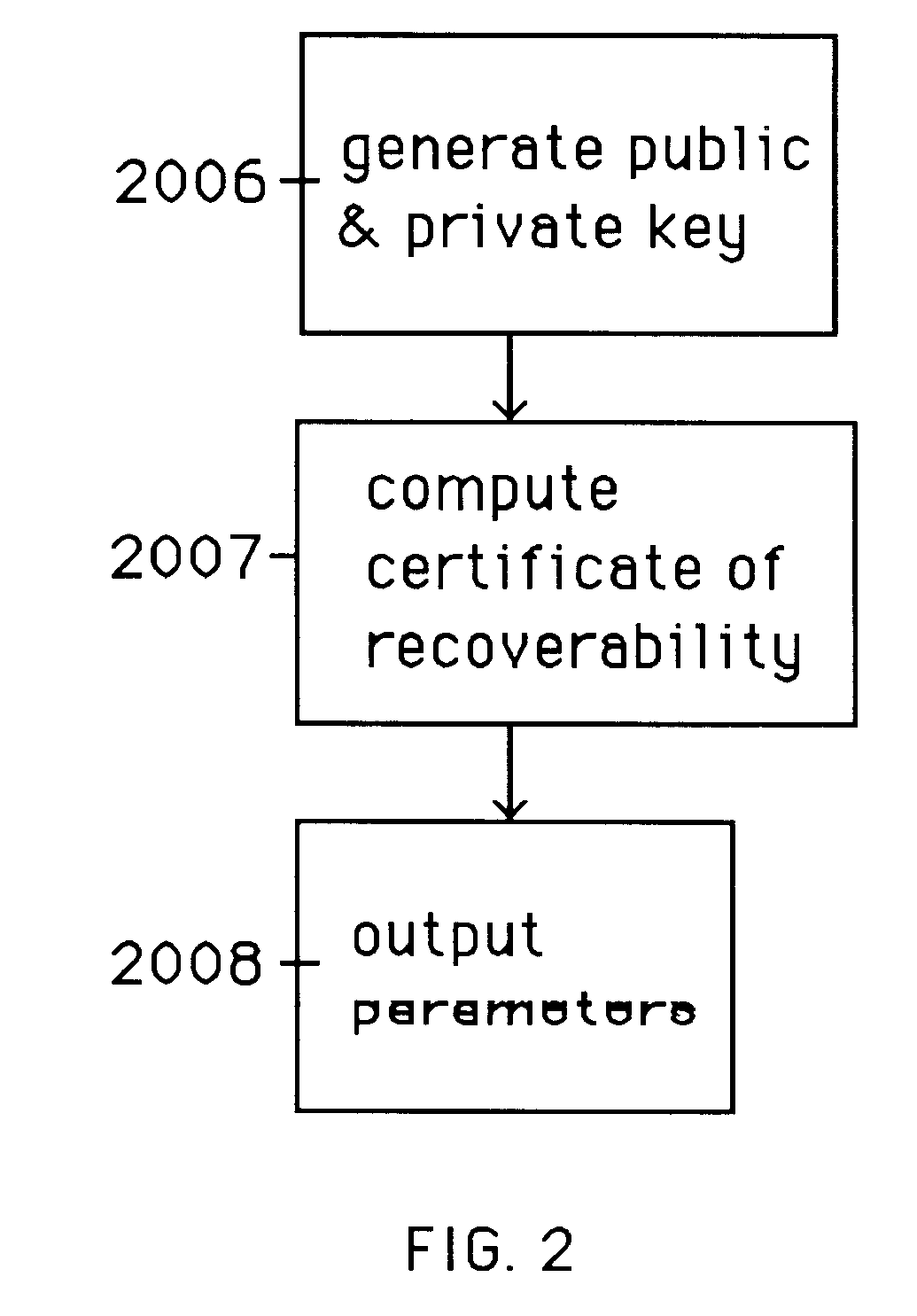
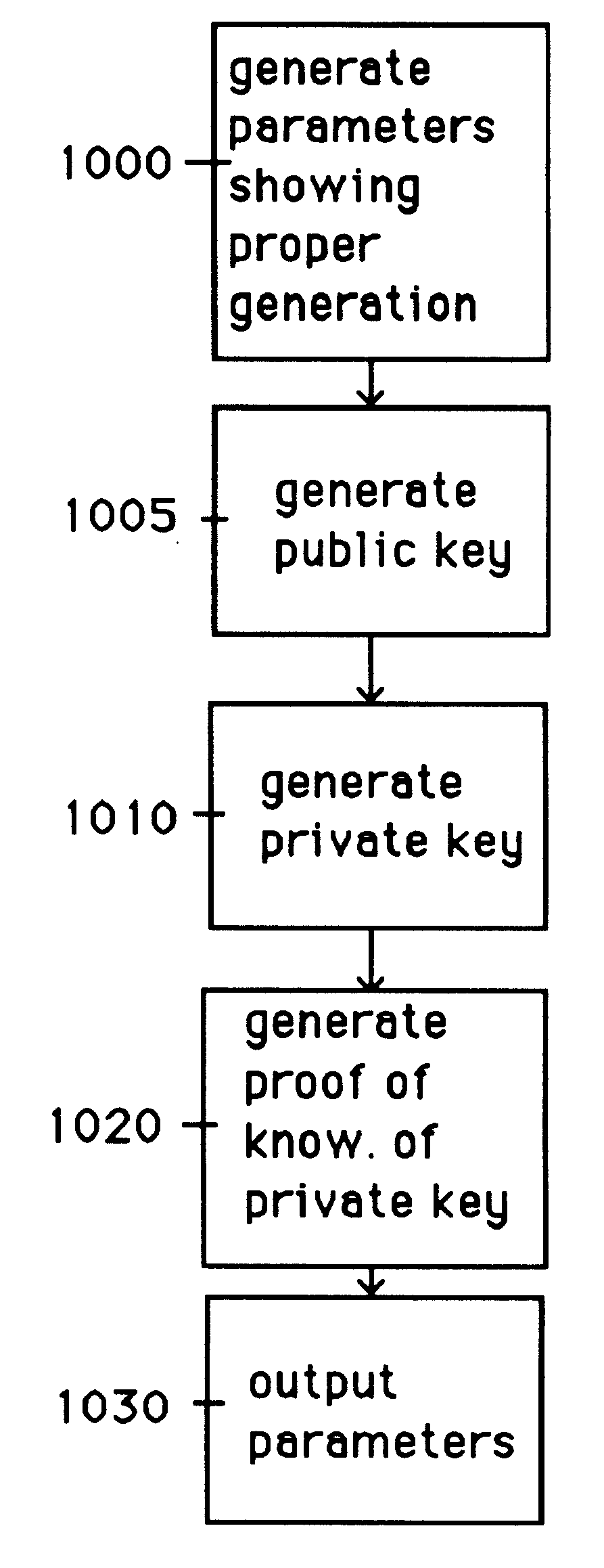
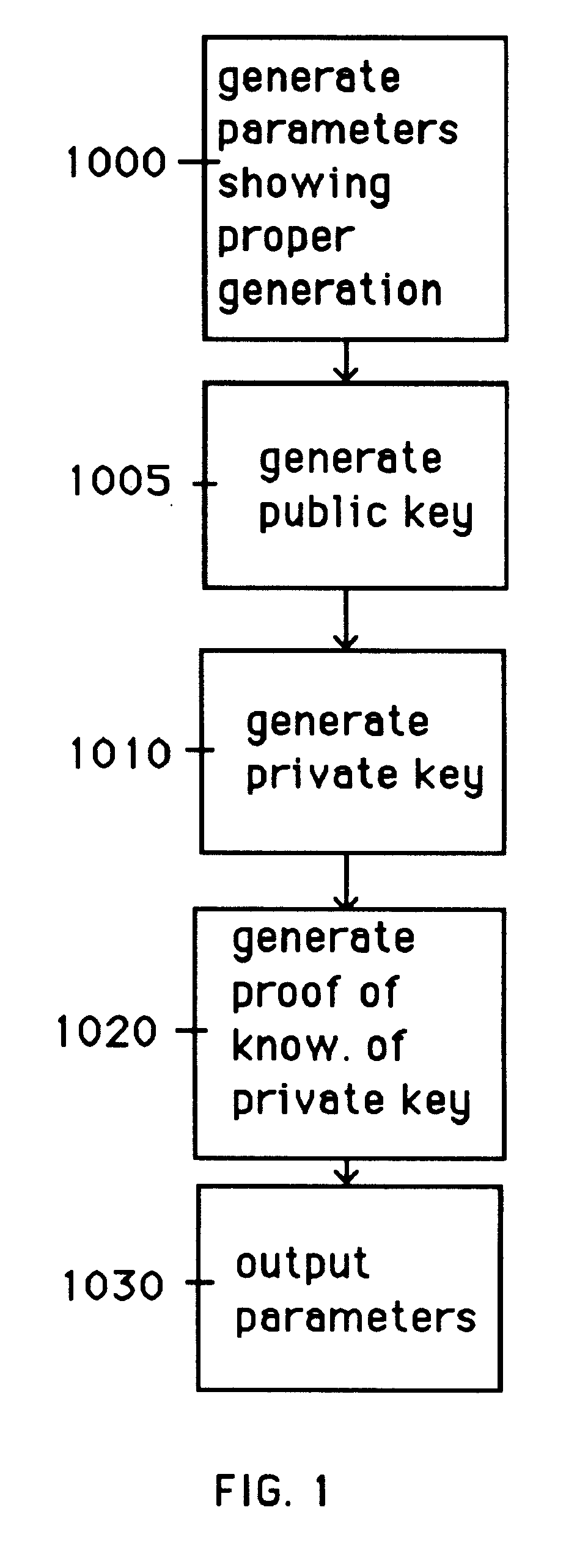
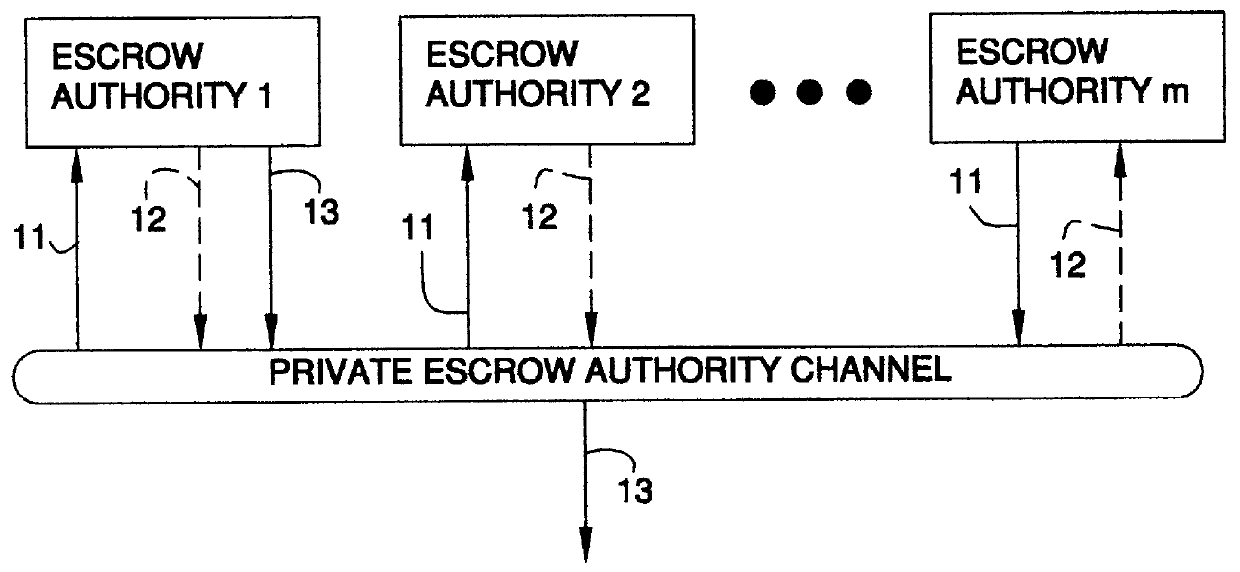
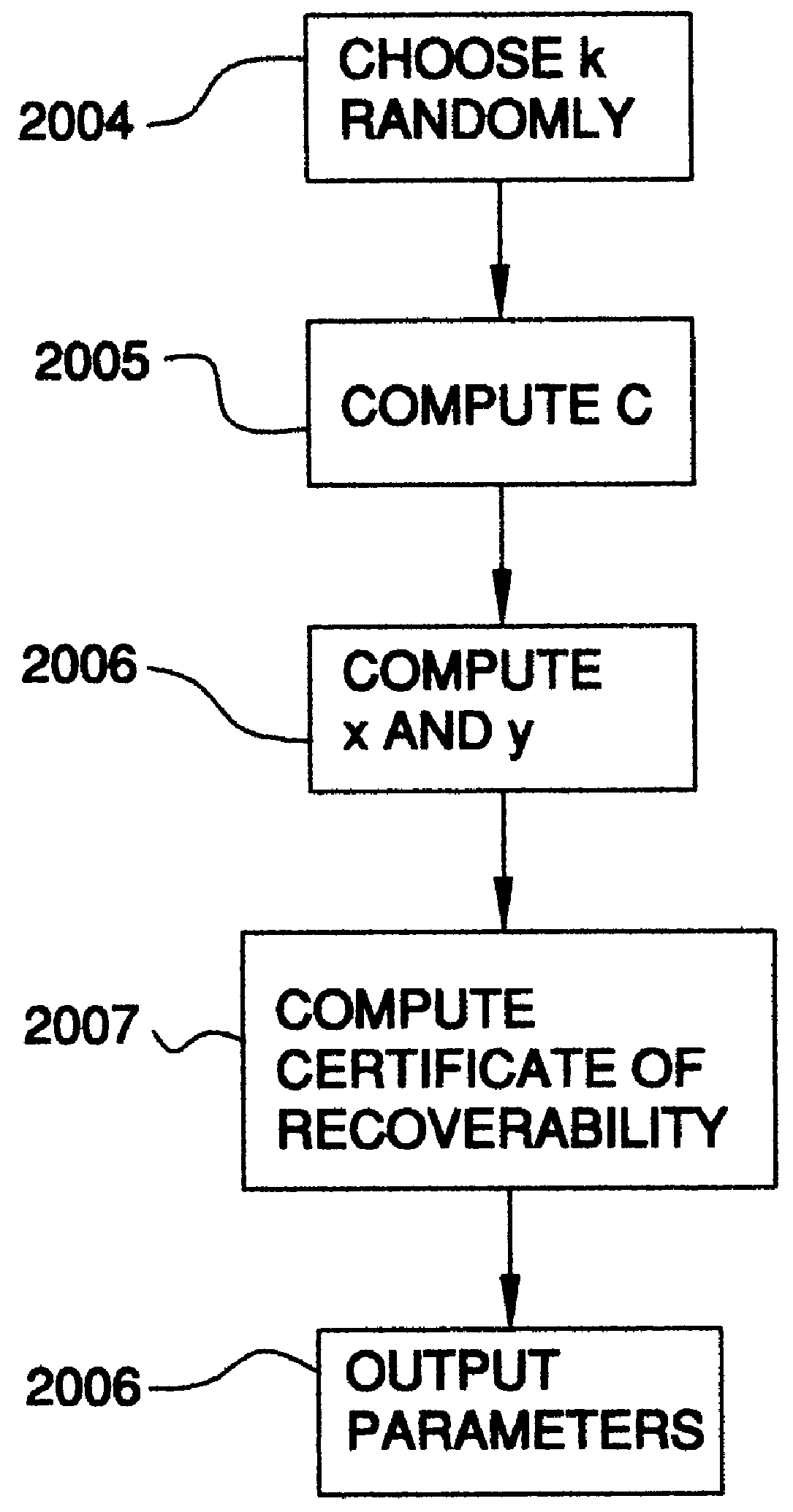
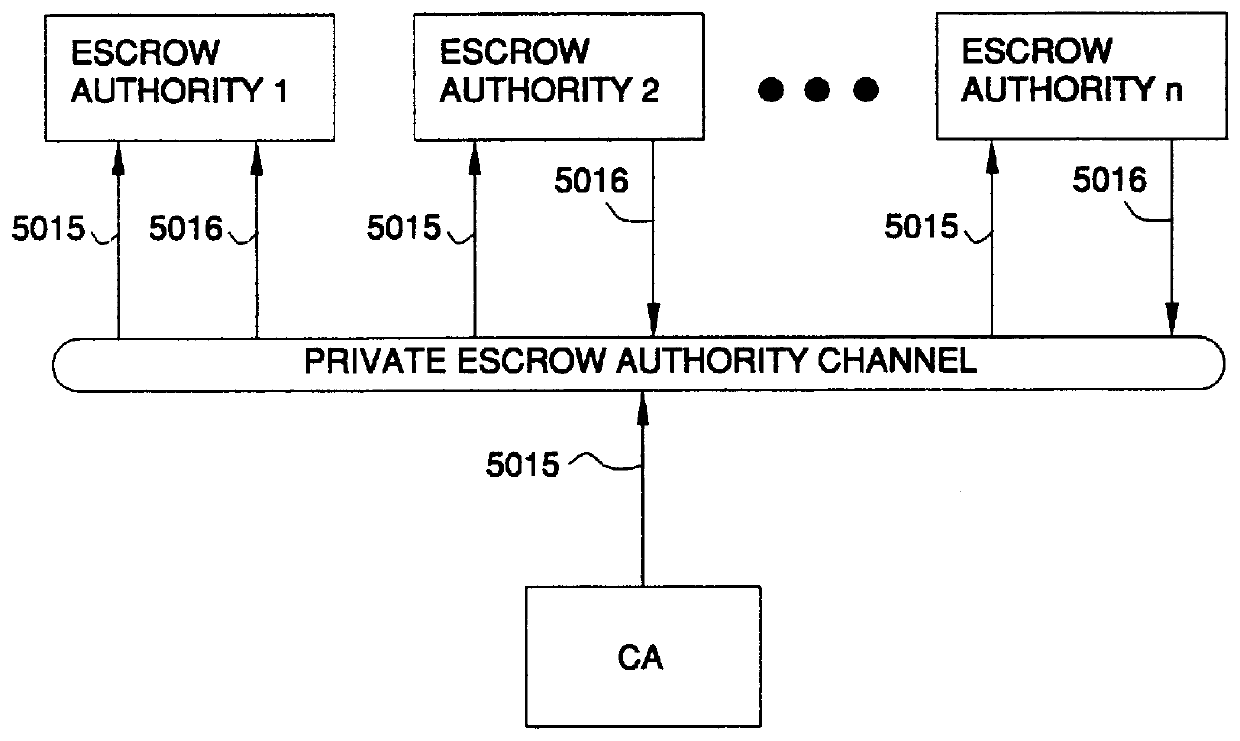
Auto-recoverable and auto-certifiable cryptostem using zero-knowledge proofs for key escrow in general exponential ciphers
InactiveUS6282295B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityValidation methods
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The proof and verification method involves one party proving to a second party that a third party can gain access to an encrypted value. In addition, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or ElGamal cryptosystem. The system is applicable for lawenforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. The system security relies solely on the security of cipher systems involved whose security has been extensively studied in the past.
Owner:CRYPTOPEAK SECURITY LLC
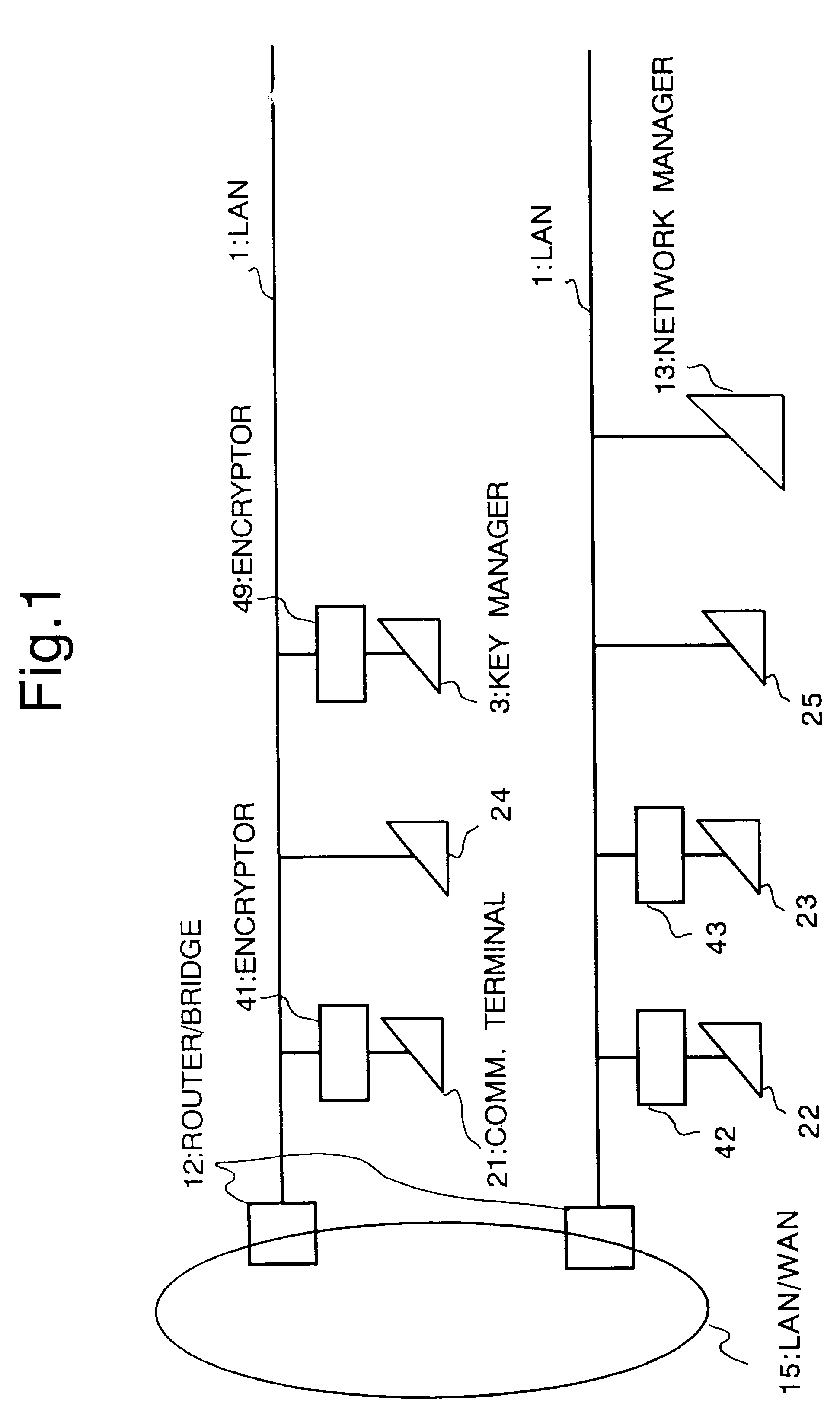
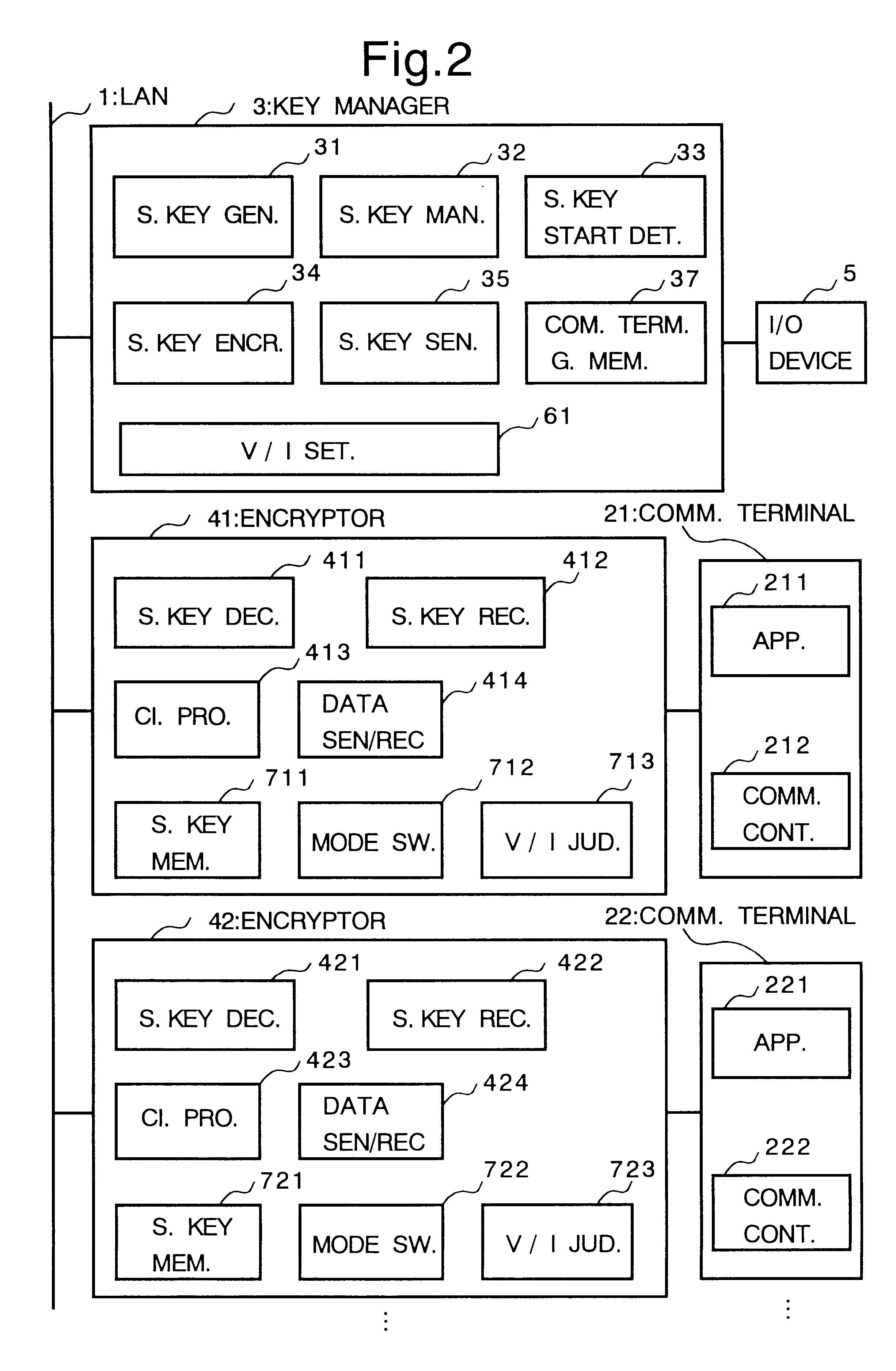
Cryptosystem
InactiveUS6178244B1Key distribution for secure communicationUser identity/authority verificationCryptosystemComputer security
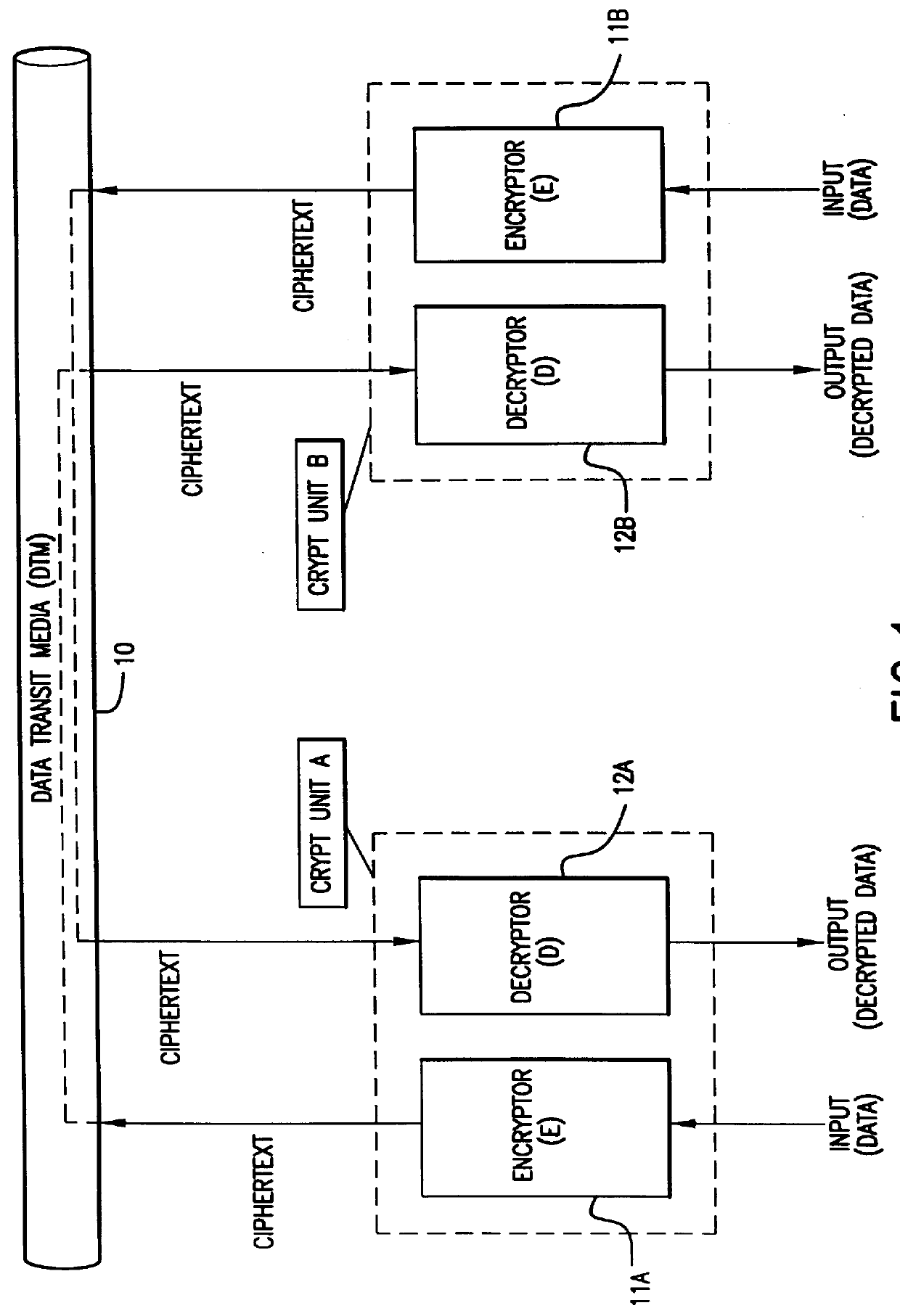
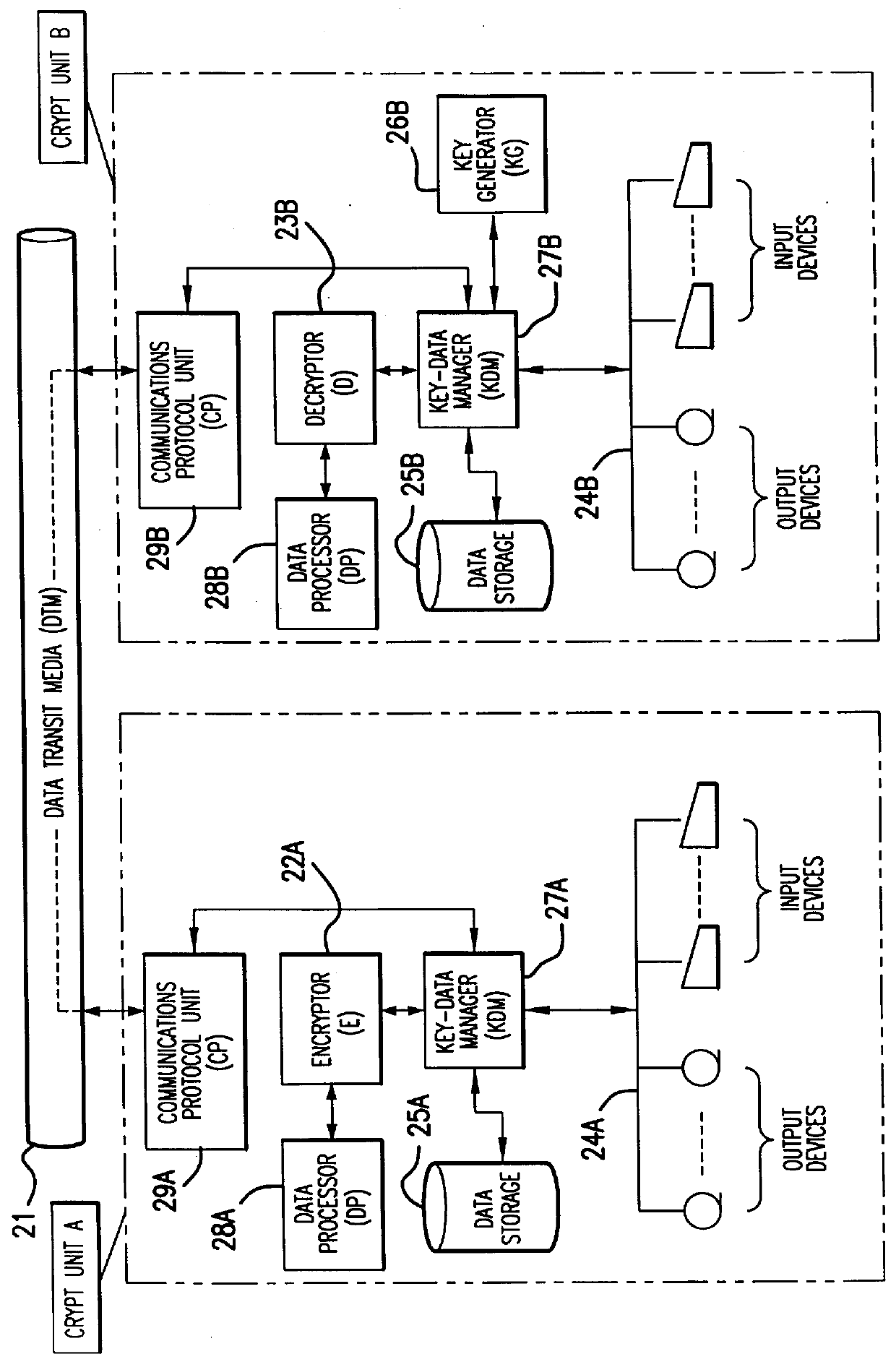
In a cryptosystem, communication terminals and encryptors can be grouped physically and logically. The communication mode can be switched by the encryptor between ciphertext communication and plaintext communication. The encryptor includes the session key memorizing unit for memorizing the session key and the mode switch for switching the communication mode between ciphertext communication and plaintext communication. The key manager distributes the session key generated by the session key generating unit and the valid / invalid information set by the valid / invalid setting unit to each encryptor. The valid / invalid judging unit judges whether the communication data should be sent in ciphertext or plaintext using the mode switch and the valid / invalid information.
Owner:MITSUBISHI ELECTRIC CORP
User identity authentication system and method
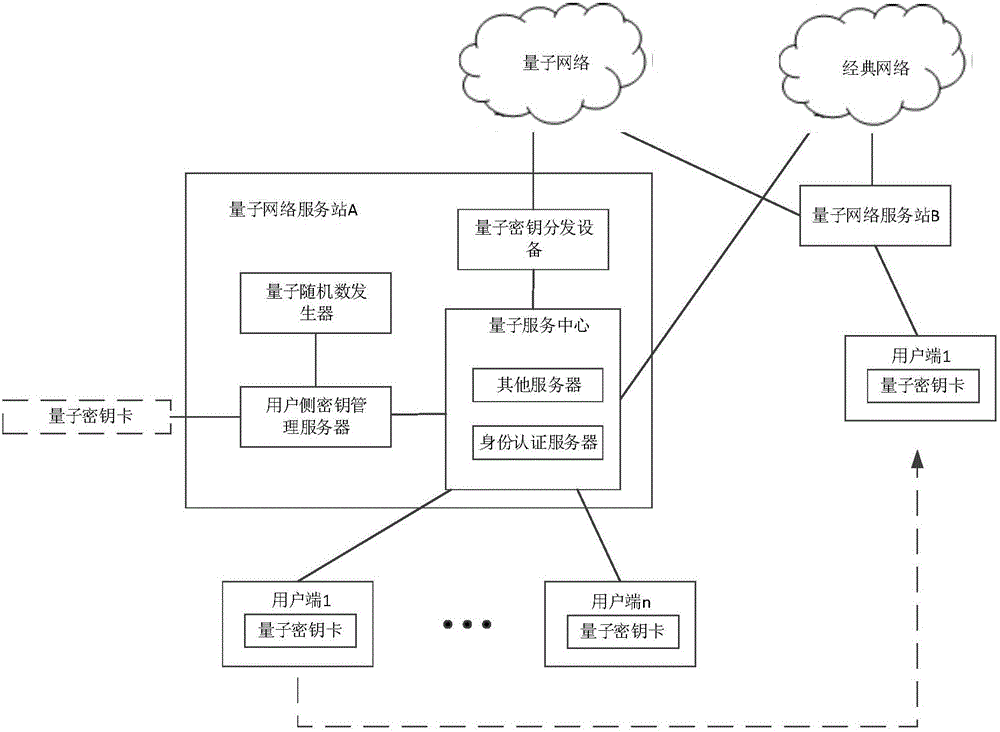
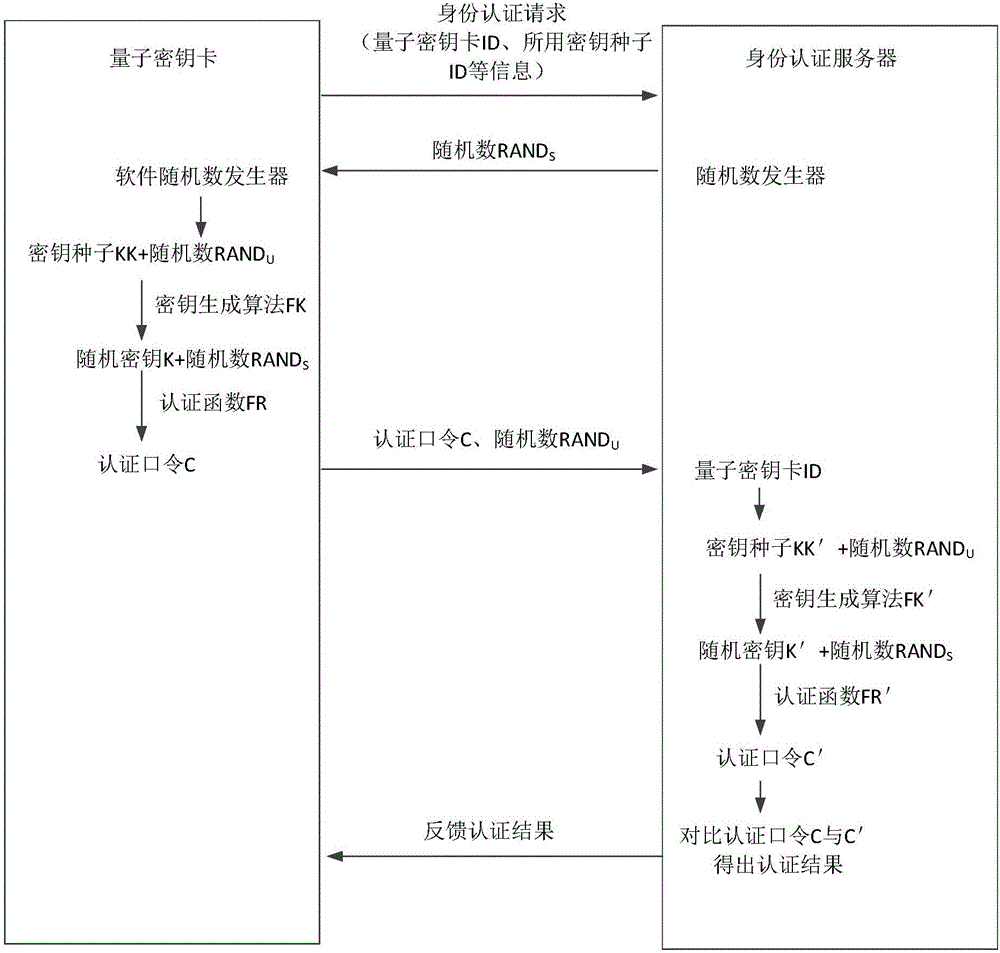
The invention discloses a user identity authentication system and a user identity authentication method. The user identity authentication system comprises quantum network service stations disposed on a network side and user ends disposed on a user side, and further comprises a quantum key card, wherein the network side generates true random numbers which are respectively stored on the quantum key card and the network side so as to generate corresponding user side secret keys, and the user side secret keys on the quantum key card and the network side are respectively used for generating authentication commands so as to perform comparison authentication. The true random numbers are generated by a certain quantum network service station on the network side, and the quantum key card and the certain quantum network service station respectively store the true random numbers so as to generate the corresponding user side secret keys. The user identity authentication method is an identity authentication method of a symmetric cryptographic system, uses the safety random keys generated by a quantum true random number generator as secret key seeds based on a mobile secret key device, is repeatedly used in identity authentication, and considers both secret key quantity and safety problems.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
System and Methods for Side-Channel Attack Prevention
InactiveUS20090010424A1Internal/peripheral component protectionSecret communicationProcessor registerCryptosystem
A side channel attack utilizes information gained from the physical implementation of a cryptosystem. Software and hardware-based systems and methods for preventing side channel attacks are presented. Cryptographic hardware may introduce dummy operations to compensate for conditional math operations in certain functions such as modular exponentiation. Cryptographic hardware may also introduce random stalls of the data path to introduce alterations in the power profile for the operation. A cryptographic function may be mapped to a micro code sequence having a plurality of instructions. Firmware in the cryptosystem may alter the micro code sequence by altering the order of instructions, add dummy operations in the micro code sequence, break the micro code sequence into multiple sub micro code sequences and / or change the register location for source and destination operands used in the sequence. These alterations are designed to randomly change the timing and power profile of the requested function.
Owner:AVAGO TECH INT SALES PTE LTD
Method for a Dynamic Perpetual Encryption Cryptosystem
A dynamic computer communication security encryption method or system using an initial seed key and multiple random number generators of a specific design, whereby a sequence of independent random entropy values is produced by one set of random number generators and encrypted along with the message stream using the initial seed key, or the output of a second set of random number generators initialized with the initial seed key, and following the subsequent transmission of the variable encrypted entropy / message block, the entropy values are used to symmetrically or identically augment or increase the current uncertainty or entropy of the cryptosystem at both the sender and the receiver, prior to the next encryption block operation. The encryption process effectively entailing the use of multiple encryption ciphers, and the entropy augmentation process entailing the encryption or application of various logical mathematical operations on the already dynamic but deterministic internal state values of the second set of random number generators, effectively altering their deterministic outputs in a random probabilistic manner.Random length message value sequences from one or more data sources is combined with one or more random length entropy value sequences from an independent source, following which the entropy “updates” may also be used to alter, or change any cryptosystem variable, value or component in a randomly determined manner. In addition, whilst ensuring synchronization, the random entropy sequences also serve to “pollute” the cipher-stream and thereby hinder most current forms of cryptanalysis, whilst simultaneously injecting additional entropy into the cryptographic system and allowing for its propagation to affect any connected system nodes, and thereby introducing unpredictable entropy into the system pseudorandom number generator outputs, and thereby ensuring the perpetual generation of unpredictable random numbers.Super-encryption mechanics are independent of the user data, simple, fast and efficient, and can incorporate compression, error correction and asymmetric encryption authentication routines. But most importantly, super-encryption ensures resistance to brute force attacks (not possible to verify if a message was even sent), an ability to exceed “perfect secrecy” requirements, and an improvement on previous super-encipherment design, since overhead can be dramatically reduced from 100% overhead.Communication links previously established by system nodes with central authorities may be used for secure node authentication and registration, whilst allowing the central authority to broker and synchronize communication channels and providing mutual authentication and other security functions between the system nodes.
Owner:FIGUEIRA HELDER SILVESTRE PAIVA
Auto-escrowable and auto-certifiable cryptosystems
InactiveUS6202150B1Fast and easy disseminationEasy to handleKey distribution for secure communicationUser identity/authority verificationTrusted authorityTamper proof hardware
A method is provided for an escrow cryptosystem that is overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The key generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key was generated according to the algorithm. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The cryptosystem is overhead free since there is no additional protocol interaction between the user who generates his or her own key, and the certification authority or the escrow authorities, in comparison to what is required to submit the public key itself in regular certified public key systems. Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware.
Owner:CRYPTOPEAK SECURITY LLC
Distributed access authentication management method in LEO satellite network
ActiveCN107147489AEasy to submitImprove scalabilityKey distribution for secure communicationMultiple keys/algorithms usageCryptosystemBlockchain
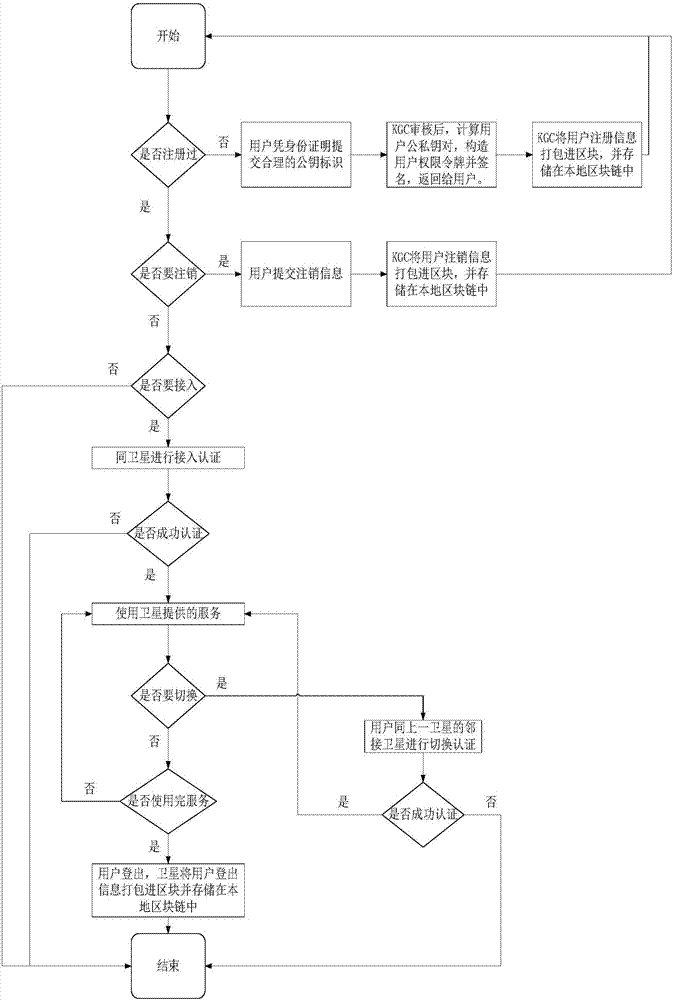
The invention discloses a distributed access authentication management method in an LEO satellite network. By adoption of an identity-based cryptosystem, the public and private key pair of a user and a satellite node is rapidly generated by utilization of the private key of a key generation centre; furthermore, identity information is appointed in an identification field, so that role differentiation in a system is realized; simultaneously, on the basis of a chain distributed storage technology of a blockchain, a trusted chain taking the key generation centre and a satellite as trust main bodies is constructed; the identity authentication function for rapid access authentication and inter-satellite rapid switching of users can be realized; the method is suitable for dynamic topology and frequent switching of a satellite-to-earth link in the LEO satellite network; on the other hand, the distributed storage technology of the blockchain is adopted in the method; the trusted chain is used as a consensus mechanism; related information, such as user registration, cancel, login, logout and switching, can be recorded; the accuracy, the integrity, the consistency, the retrospective property and the non-tampering property of user logs can be ensured; and thus, bottleneck restriction of centre nodes on the access function and the authentication property can be avoided.
Owner:NANJING UNIV OF SCI & TECH
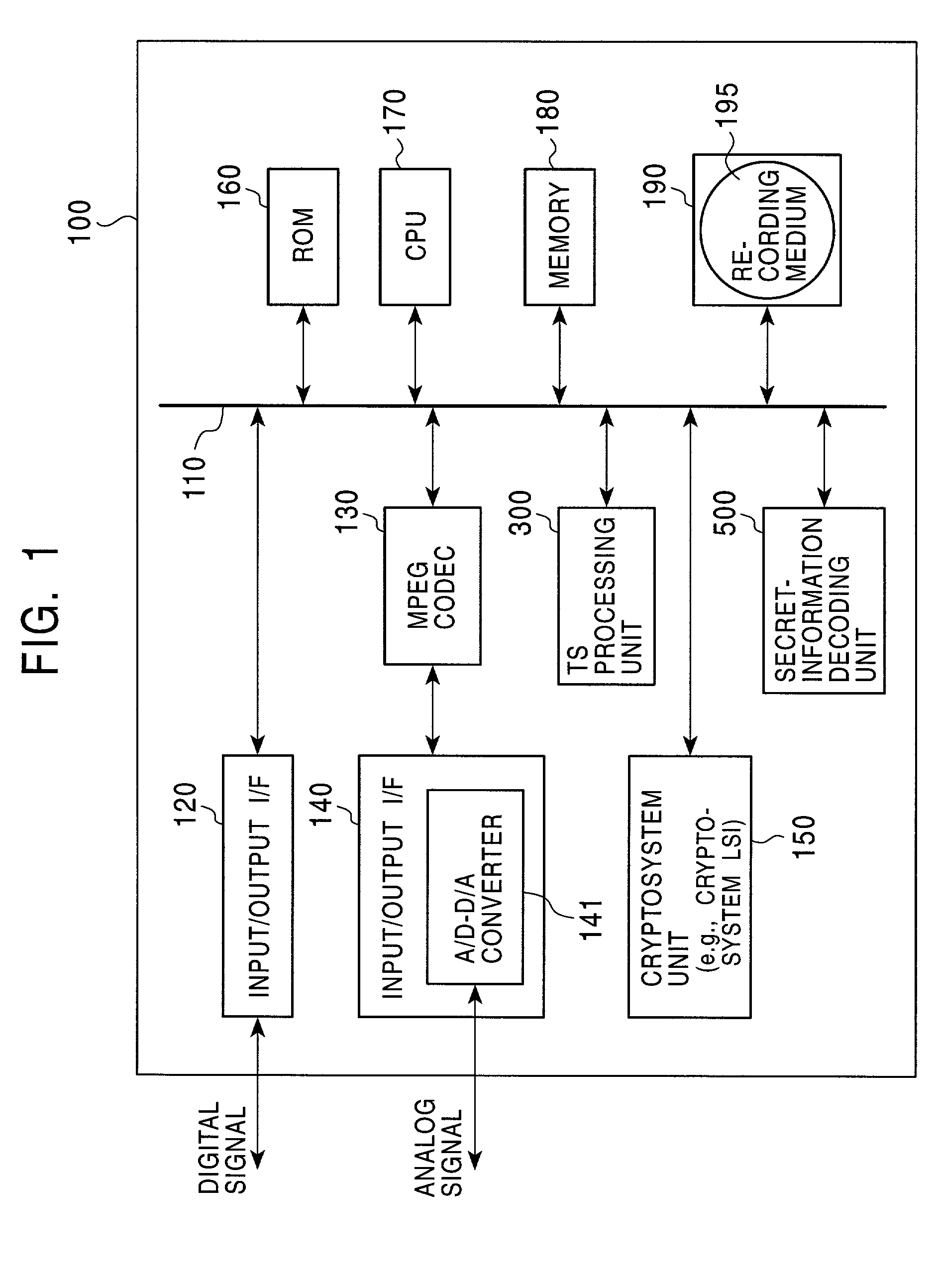
Information security device
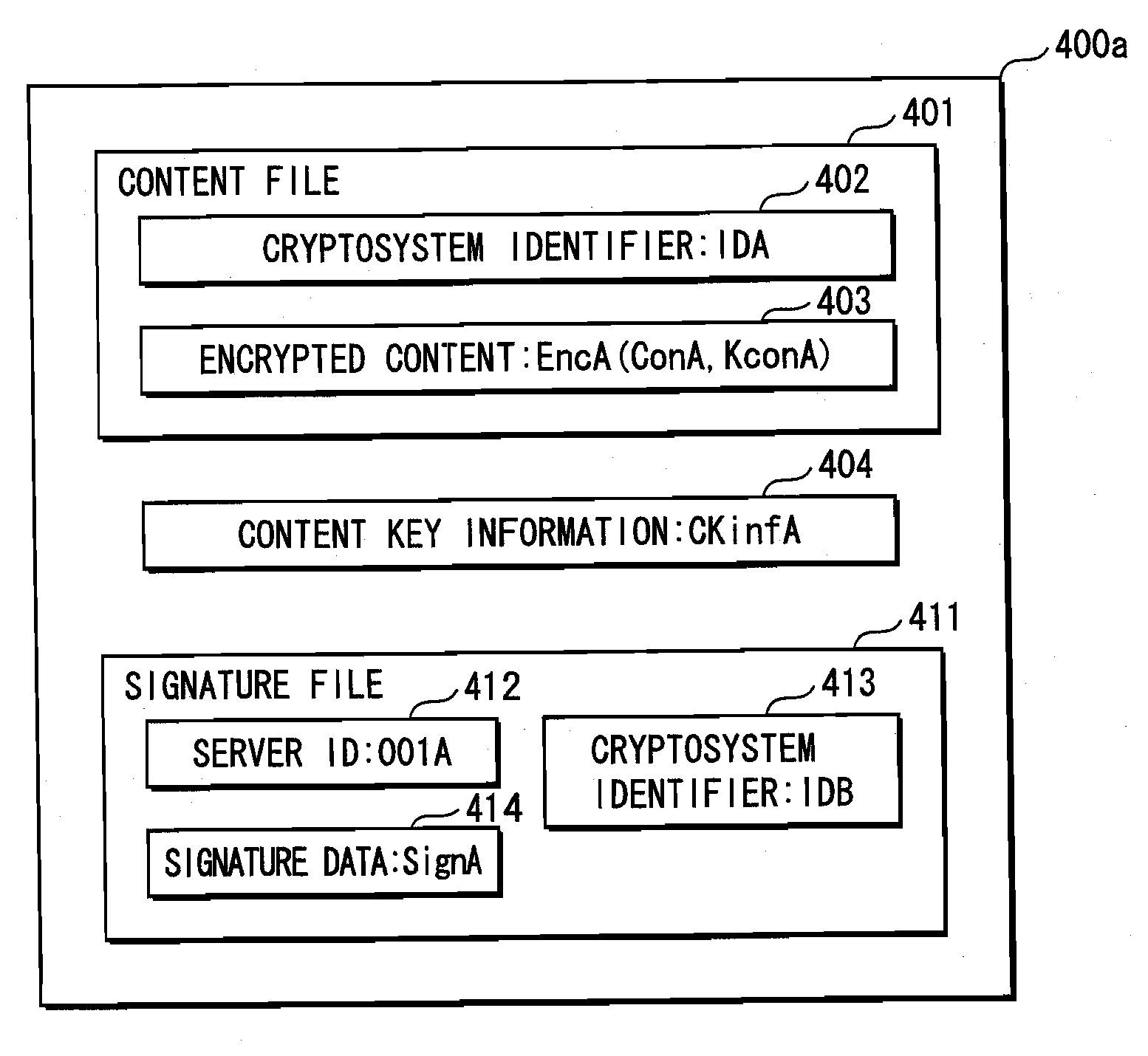
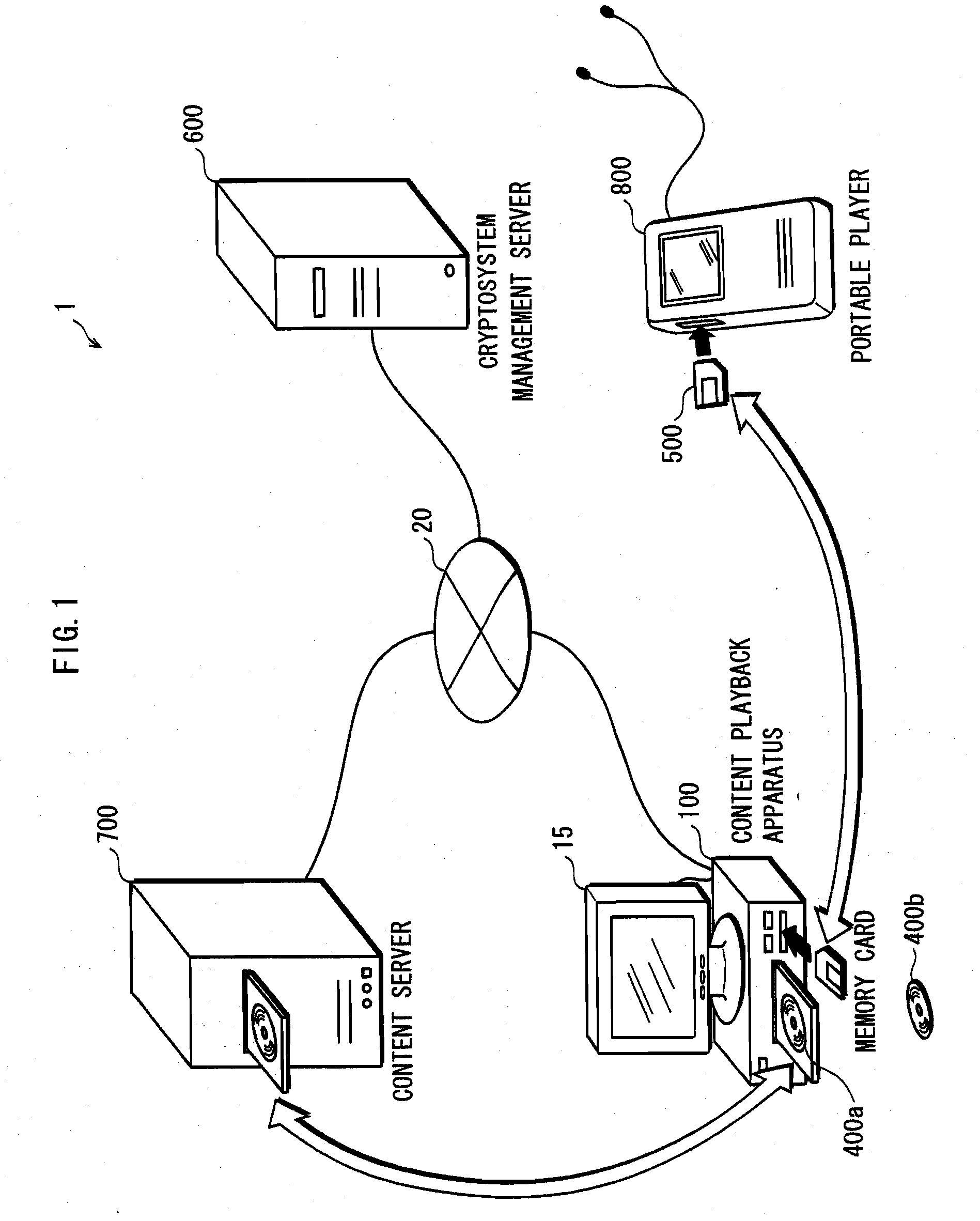
ActiveUS7958353B2Key distribution for secure communicationError detection/correctionComputer hardwareCryptosystem
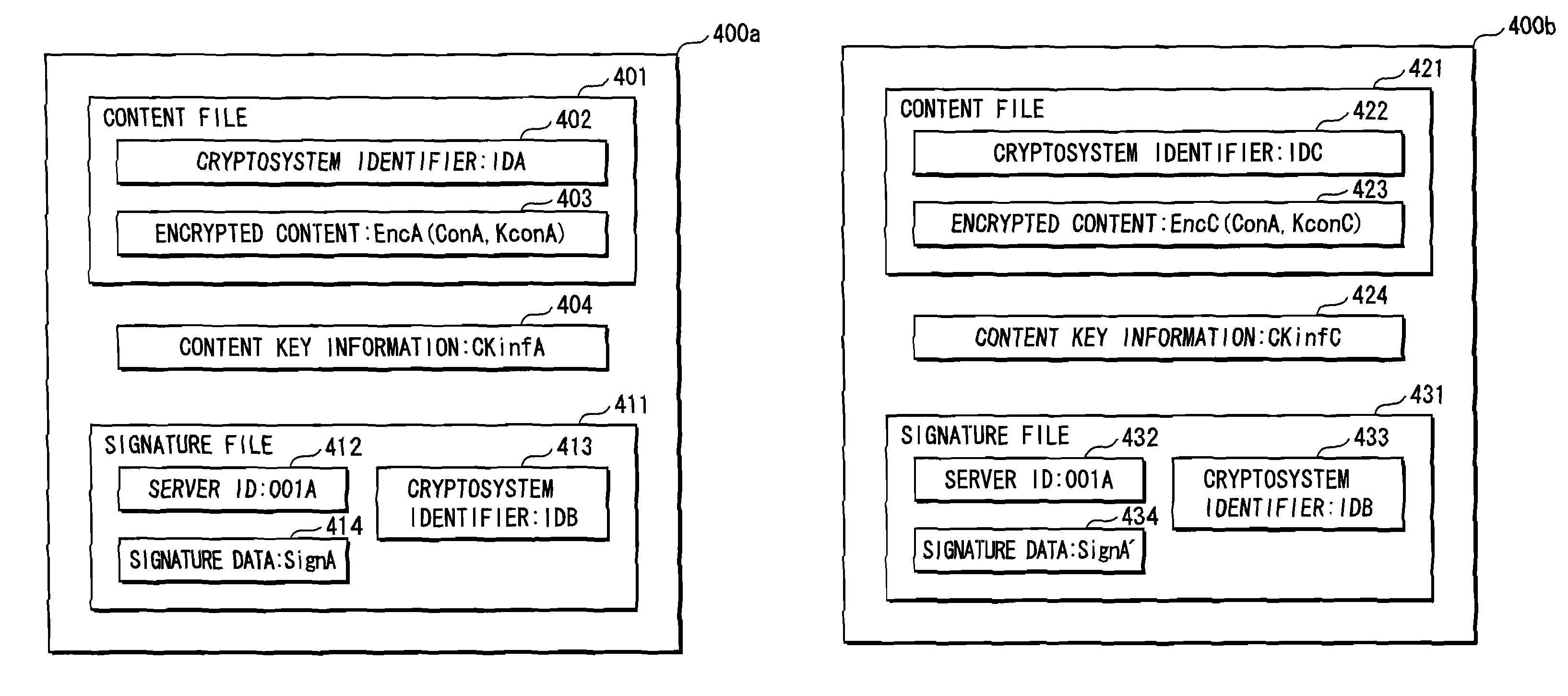
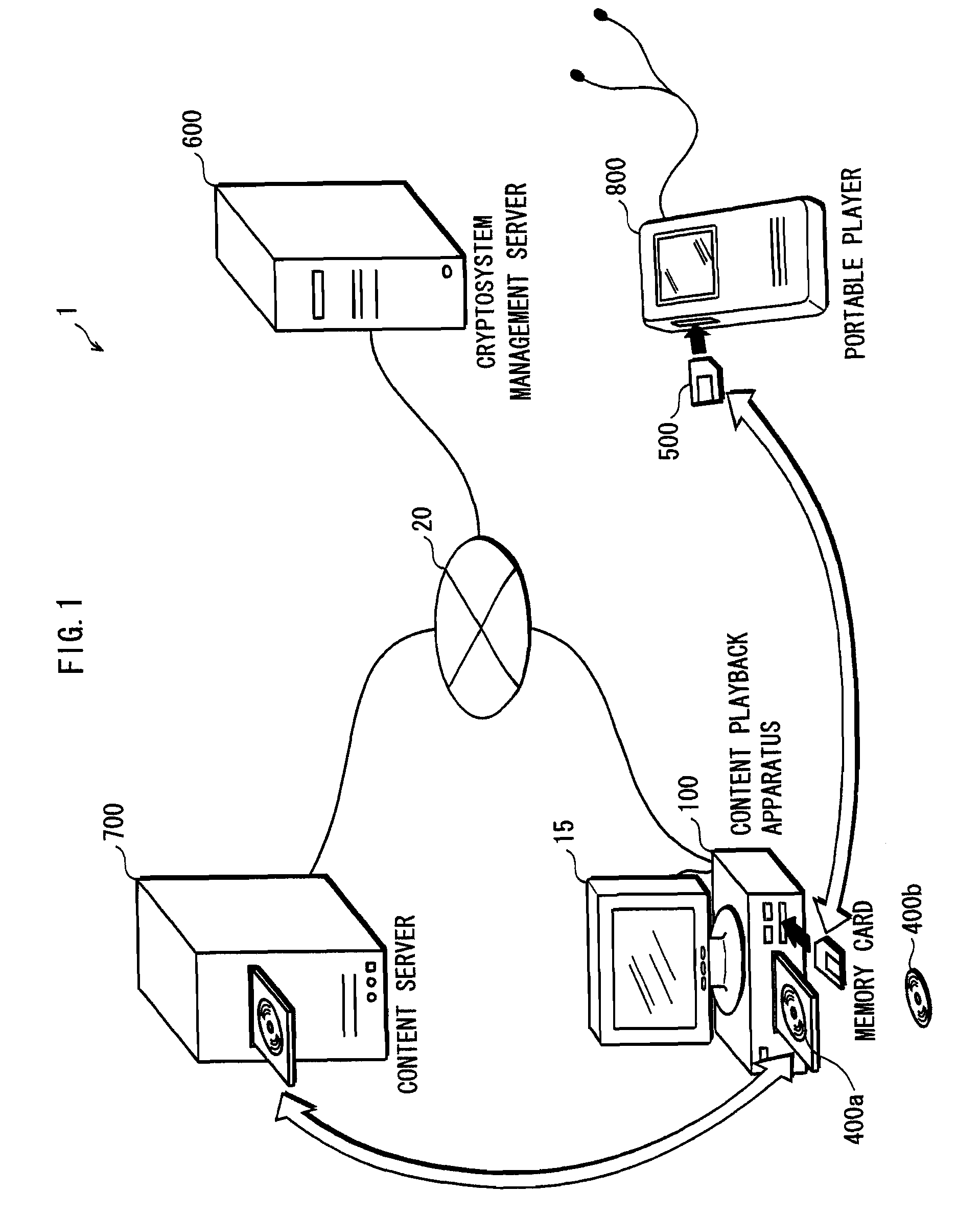
The present invention provides an apparatus for securely acquire a circuit configuration information set corresponding to a new cryptosystem without increasing the number of reconfigurable circuits. A content playback apparatus 100 includes an FPGA 122 that is reconfigurable. The content playback apparatus 100 stores a decryption circuit program that shows the structure of a decryption circuit that executes decryption in accordance with a prescribed cryptosystem. The FPGA is reconfigured in accordance with the program to configure the decryption circuit. The playback apparatus 100 acquires, from outside, an encrypted file that has been generated by encrypting a file including a decryption circuit program corresponding to the new cryptosystem in accordance with the prescribed cryptosystem, and decrypts the encrypted file by the decryption circuit.
Owner:PANASONIC CORP
Method and apparatus for a robust high-speed cryptosystem
InactiveUS6154541AAccurate identificationMultiple keys/algorithms usagePublic key for secure communicationCommunications systemCiphertext
A cryptographic information and communication system of the knapsack type characterized by secret logical segregation of the key sets into sections by different construction methods, where different transformations are applied to different sections, and characterized by non-constant number of subset sum solutions to ciphertext, where resolution protocols are employed when necessary to resolve non-unique subset sum solutions at the decryptor.
Owner:ZHANG JINGLONG F
Auto-recoverable auto-certifiable cryptosystems with unescrowed signature-only keys
InactiveUS6473508B1Key distribution for secure communicationPublic key for secure communicationConfidentialityCryptosystem
A method is provided for digital signature infrastructure that provides public keys which are effective only for verifying digital signatures, and are not effective for encrypting information in a way that is unrecoverable by law-enforcement entities. The method can be implemented in software, thus avoiding the need for tamper-proof hardware. The method has the property that signing private keys are not escrowed, since the corresponding public keys cannot be used effectively for criminal communications. As a result no one can impersonate the user; alternatively users can prove impersonations. Furthermore, the system is shadow public key resistant. A shadow public key is a public key which is not escrowed and which can be used for untappable communications. Therefore, the method presented here cannot be used to publish public keys which are not escrowed. All information displayed by the certificate authorities, and even the digital signatures of users, are shadow public key resistant. The present invention is usefull for any application that requires that messages be verifiably authentic, and is particularly applicable to being used in a national public key infrastructure (PKI), since it is very scalable. It can be combined with Auto Recoverable auto certifiable systems to give a complete solution to encryption (confidentiality) and signature (authentication) in the context of escrow key systems.
Owner:CRYPTOPEAK SECURITY LLC
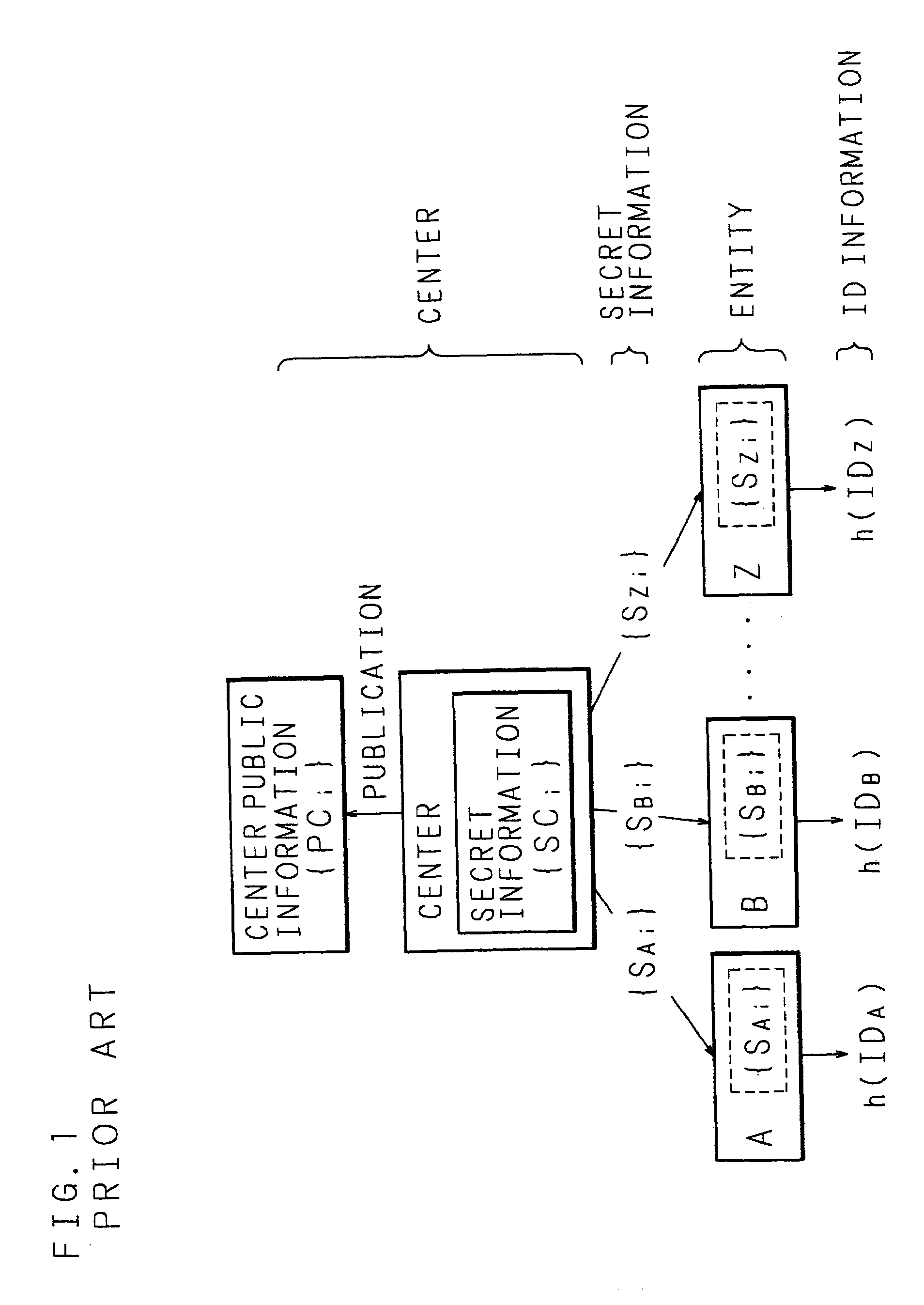
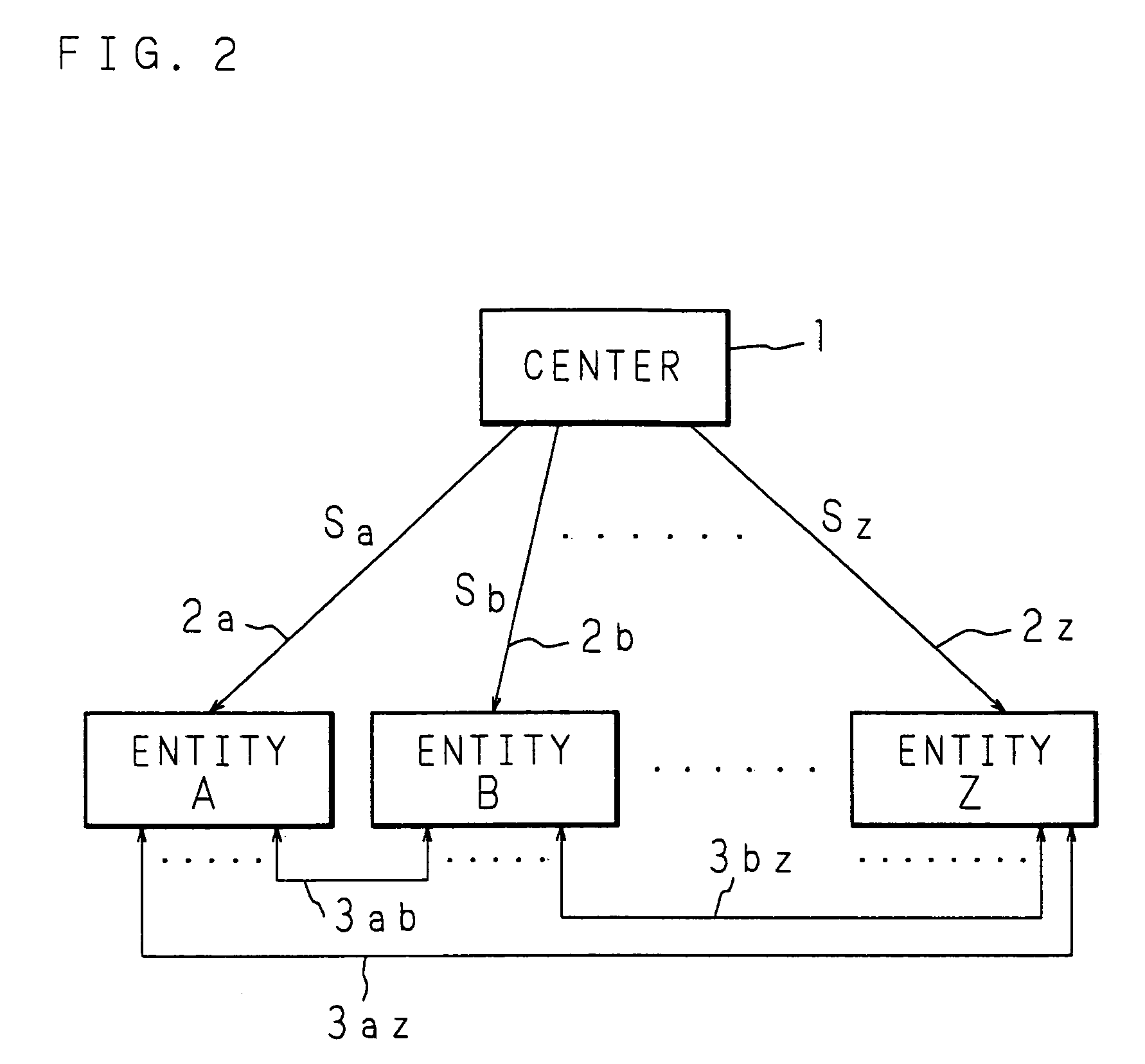
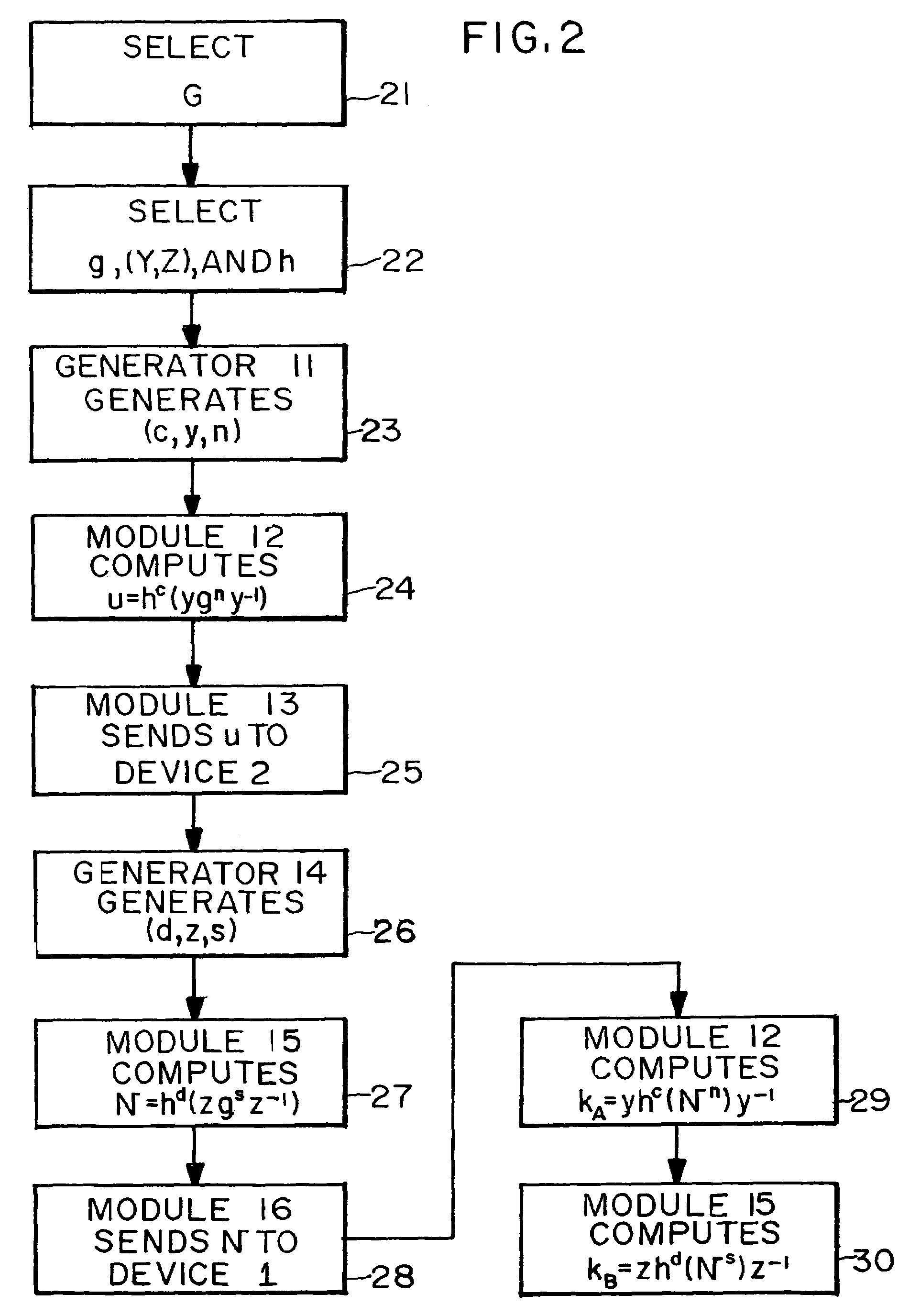
Key sharing method, secret key generating method, common key generating method and cryptographic communication method in ID-NIKS cryptosystem
InactiveUS7239701B1Easy to shareImprove securityKey distribution for secure communicationSecret communicationCryptosystemKey generation
Mapping is carried out at a point on an elliptic curve to be utilized for elliptic encryption based on identity information (ID information) of each entity and a mapping value is set to be a public key of the entity. By using the mapping value and secret information, a secret key of each entity is generated. The entity generates a common key to be used for an encrypting process and a decrypting process by utilizing the self-secret key and the public key to be the mapping value obtained by mapping at a point on the elliptic curve based on ID information of a communication participate. In this case, pairing on the elliptic curve is utilized.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Method, apparatus, and program product for enabling access to flexibly redacted content
InactiveUS20080016341A1Shorten the timeFacilitate content indexingDigital data processing detailsUser identity/authority verificationCryptosystemComputer security
A capability key is generated that provides access to sensitive information within a selectively encrypted data unit created from an unencrypted data unit. A user specifies access rights as a monotone boolean relationship between a selection of a list of attributes related to the unencrypted data unit. This relationship is used to compute a key descriptor. Next one or more shares of a master secret is generated responsive to the monotone boolean relationship and a random number. Next a unique capability key is computed from one or more cryptosystem parameters, the one or more shares and the random number. The unique capability key and the key descriptor together enable decryption of sensitive information within a selectively encrypted data unit created from an unencrypted data unit. Finally, the unique capability key and the key descriptor are provided to allow decryption of sensitive information within the selectively encrypted data unit.
Owner:MAJANDRO LLC
Method for cross-isomerism domain identity authentication and session key negotiation based on access authorization ticket
ActiveCN103780618AHigh security requirementsStrong computing powerUser identity/authority verificationPublic key authenticationKey-agreement protocol
The invention provides a method for cross-isomerism domain identity authentication and session key negotiation based on an access authorization ticket. The method mainly comprises the steps that firstly, a first-level trust relationship is established between a CA of a PKI domain and an AS of a Kerberos domain through a distributed trust model based on a public key authentication mechanism; on the basis, the authorization ticket allowing an outer-domain user to have access to resources of the domain is generated and distributed by the CA or the AS united with a TGS, and through design of a two-way cross-domain authentication and key negotiation protocol based on a symmetric key cryptosystem, a second-level trust relationship allowing the outer-domain user to have access to the resources of the domain is established. On the premise that the requirements for safety of the levels are satisfied, the calculated amount and the communication traffic of a terminal are effectively reduced, public key encryption and decryption operations of a Kerberos domain terminal can be completely avoided, and the implementation is good in the cross-isomerism domain identity authentication process of a dynamic distributed type system, session key negotiation is completed when identity authentication is conducted, and the protocol efficiency is high.
Owner:四川华创智能科技有限公司
Enhanced encryption method and system for ultra secure applications
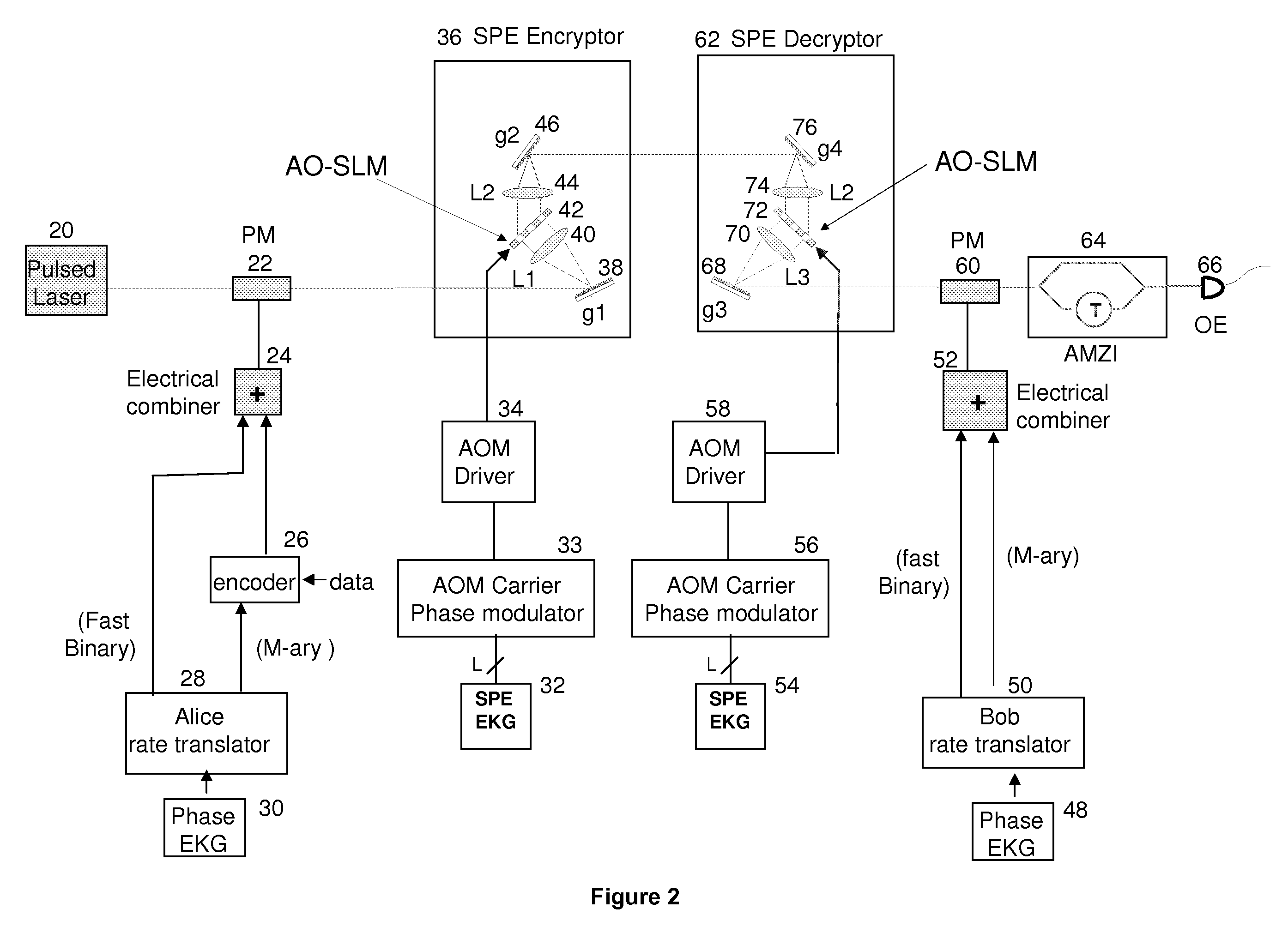
InactiveUS7831049B1Improve securityIncrease ratingsError detection/correctionData resettingSpatial light modulatorAlgorithm
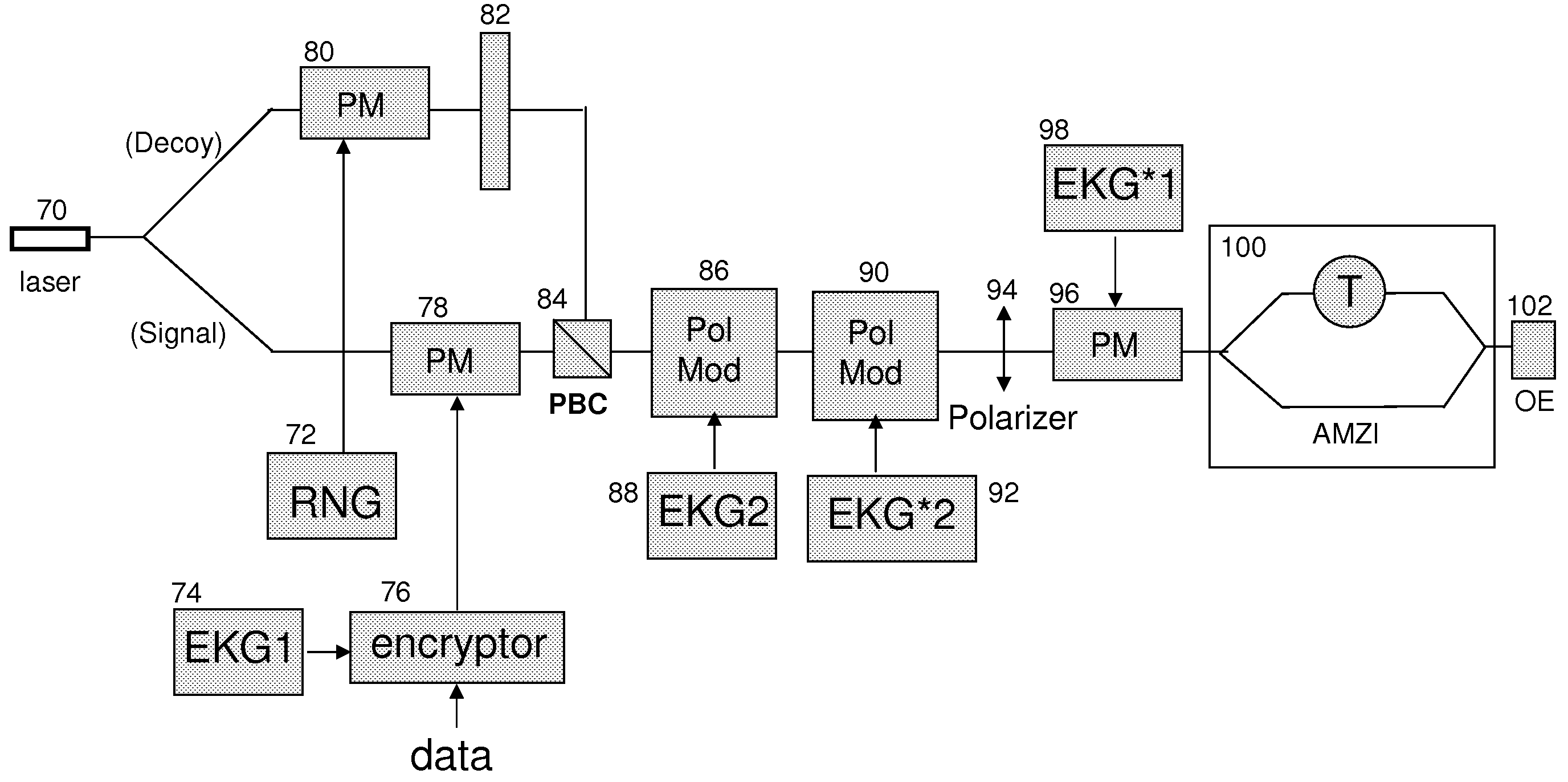
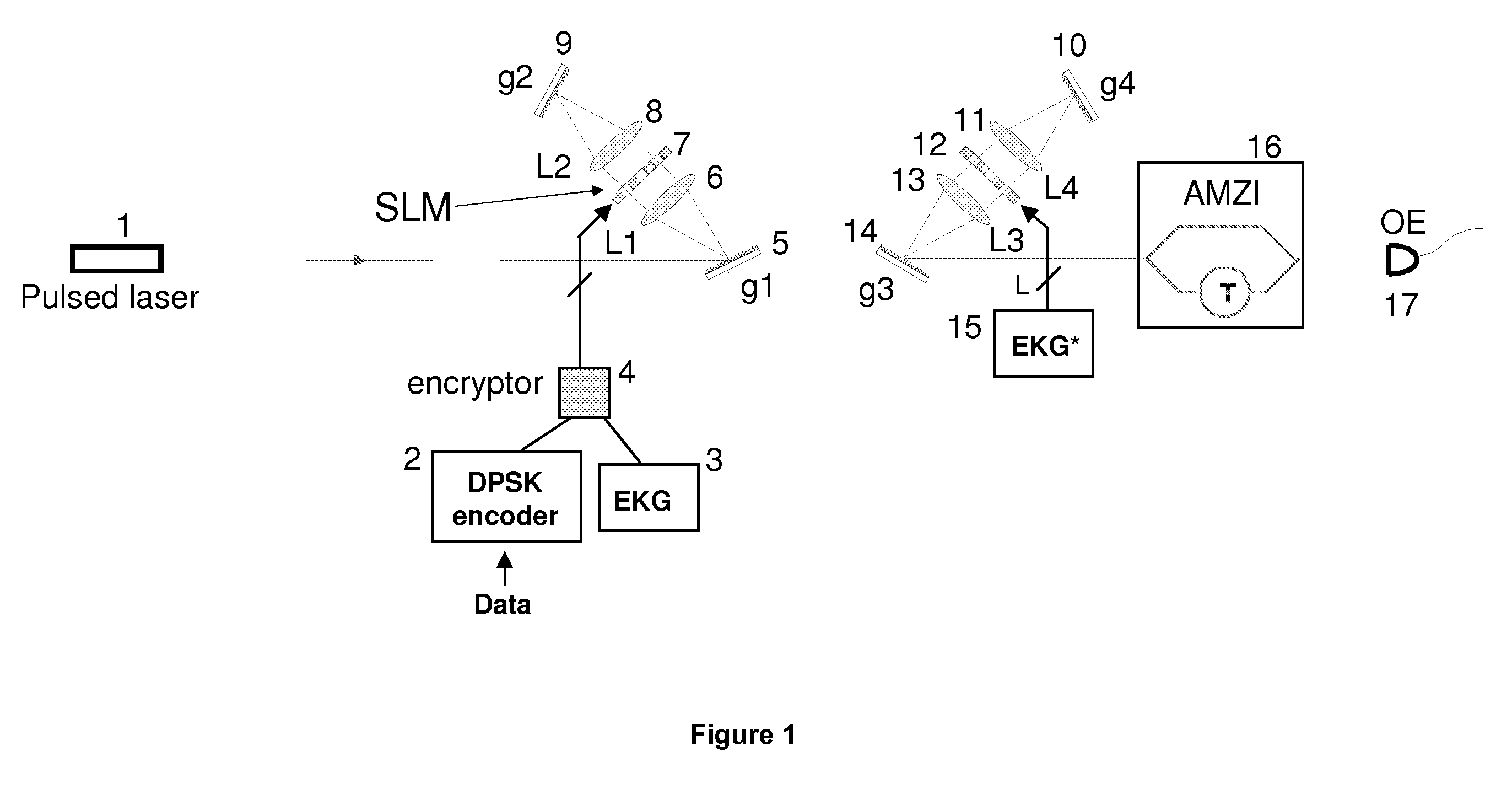
Techniques to bolster the security of an AlphaEta cryptosystem using spectral phase encoding. In one aspect, a spatial light modulator (SLM) is used to change the spectral code (spectral phase) of each optical bit in response to the output of an extended key generator based on a cryptographic algorithm. In other aspects, additional time and polarization modulations are used to maintain high security levels as well as good performance levels. Such methods are combined with traditional key generation methods such as key-distribution centers or one-way mathematical algorithms to bolster the security of traditional key generation as well.
Owner:NUCRYPT
Edge computing privacy protection system and method based on joint learning
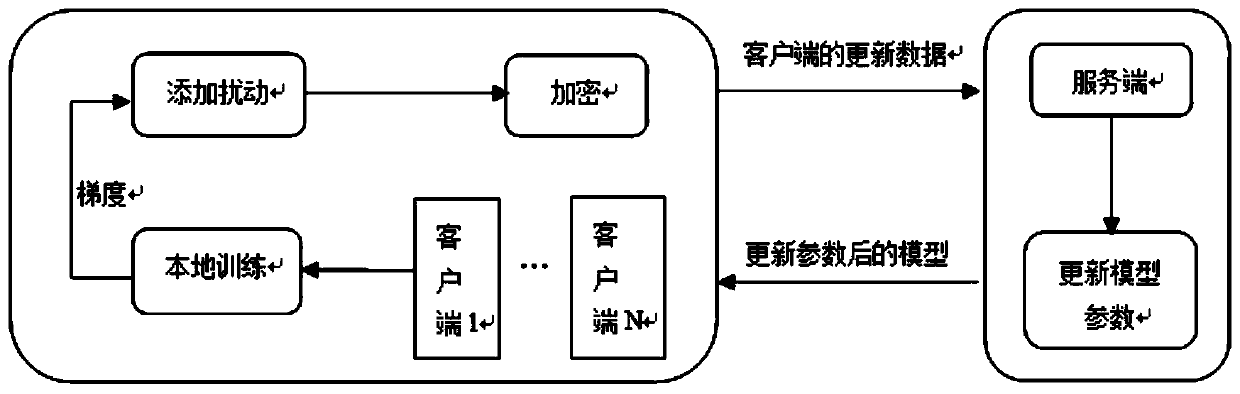
ActiveCN110719158AGuarantee authenticitySolve protection problemsDigital data protectionNeural learning methodsEdge computingPrivacy protection
The invention discloses an edge computing privacy protection system and method based on joint learning. The system comprises a client and a server, the client is used for local training, adding disturbance to updated parameters, encrypting the updated parameters and sending the encrypted parameters to the server, and the server receives encrypted data sent by the client, decrypts the encrypted data and updates local parameters to update a deep learning model; the protection method comprises the following steps: step 1, adding disturbance to parameters at a client; step 2, encrypting the data at a client; and step 3, decrypting the data at the server. According to the method, each participant can safely submit data on the premise of not needing any trusted aggregator; noise disturbance is added to local updating in a distributed mode, updating of the disturbance is encrypted through a Paillier homomorphic cryptosystem, safety and performance analysis shows that the PPFL protocol can guarantee privacy of client data and learning accuracy at the same time, and the conflict problem of privacy protection and learning accuracy is solved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
System and method for crypto-key generation and use in cryptosystem
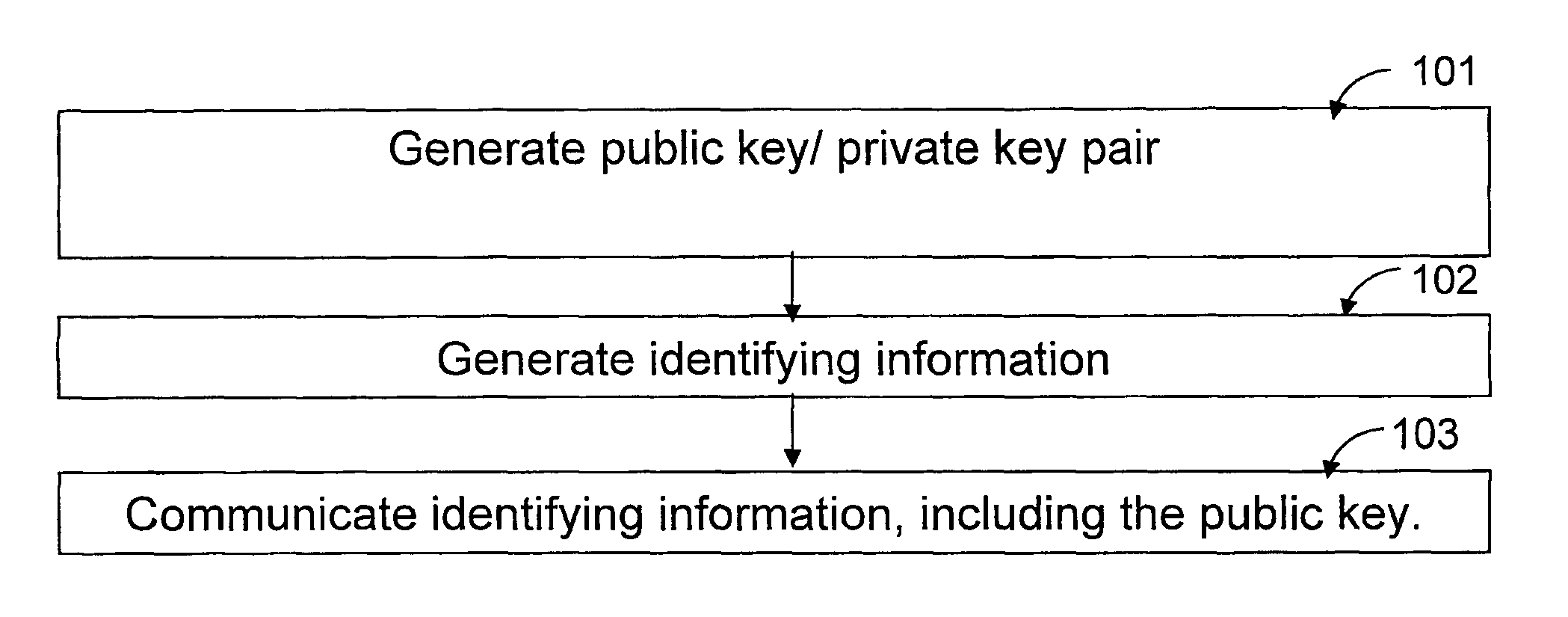
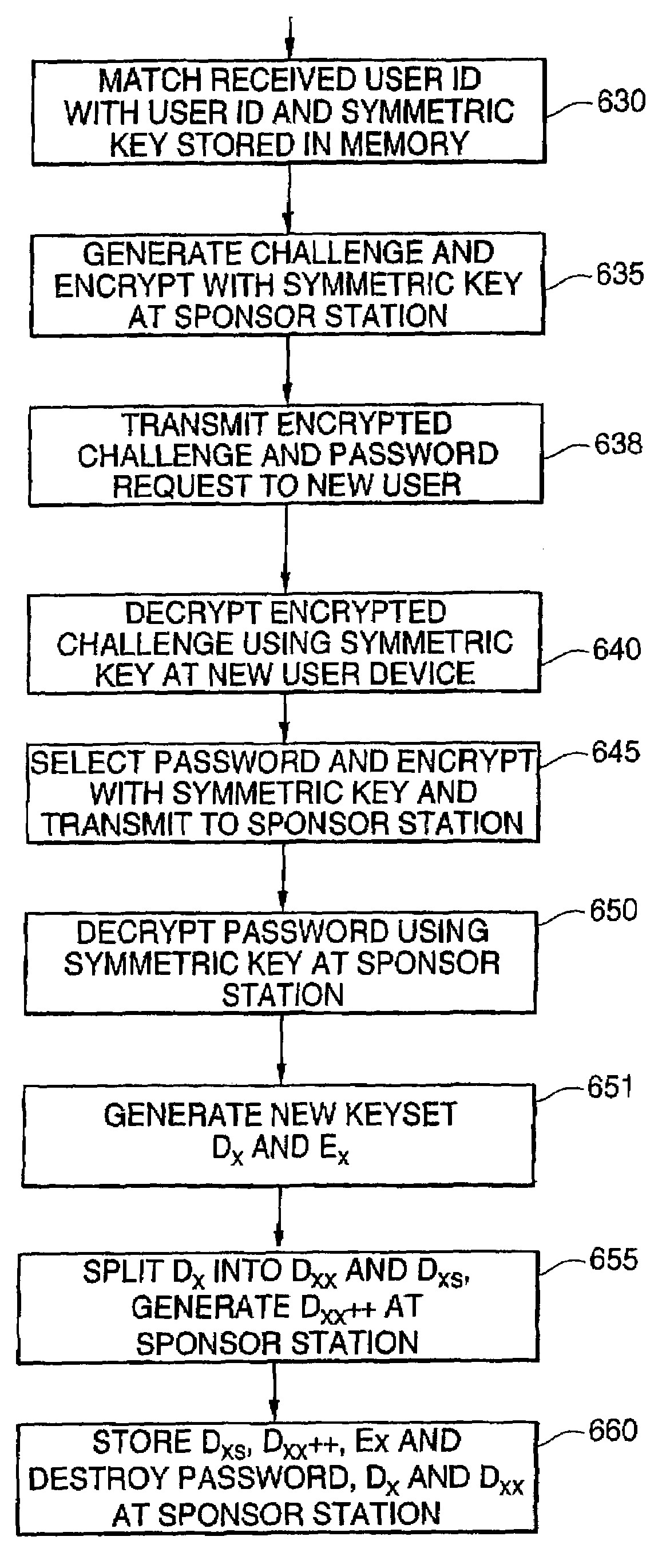
InactiveUS6970562B2Improve security levelShort passwordKey distribution for secure communicationPublic key for secure communicationCryptographic key generationPassword
A first processor generates a private crypto-key and a public crypto-key. The first processor divides the private crypto-key into two portions, a first private key portion, based upon a user's password, and a second private key portion. The private crypto-key and the first private key portion are then destroyed. The remaining portion, second private key portion, and the public crypto-key are stored in a memory. A second processor generates the first private key portion based upon the user's password and responsive to receiving the user's password. The second processor then destroys the generated first private key portion with out storing the generated first private key portion.
Owner:VMWARE INC
Cryptosystems using commuting pairs in a monoid
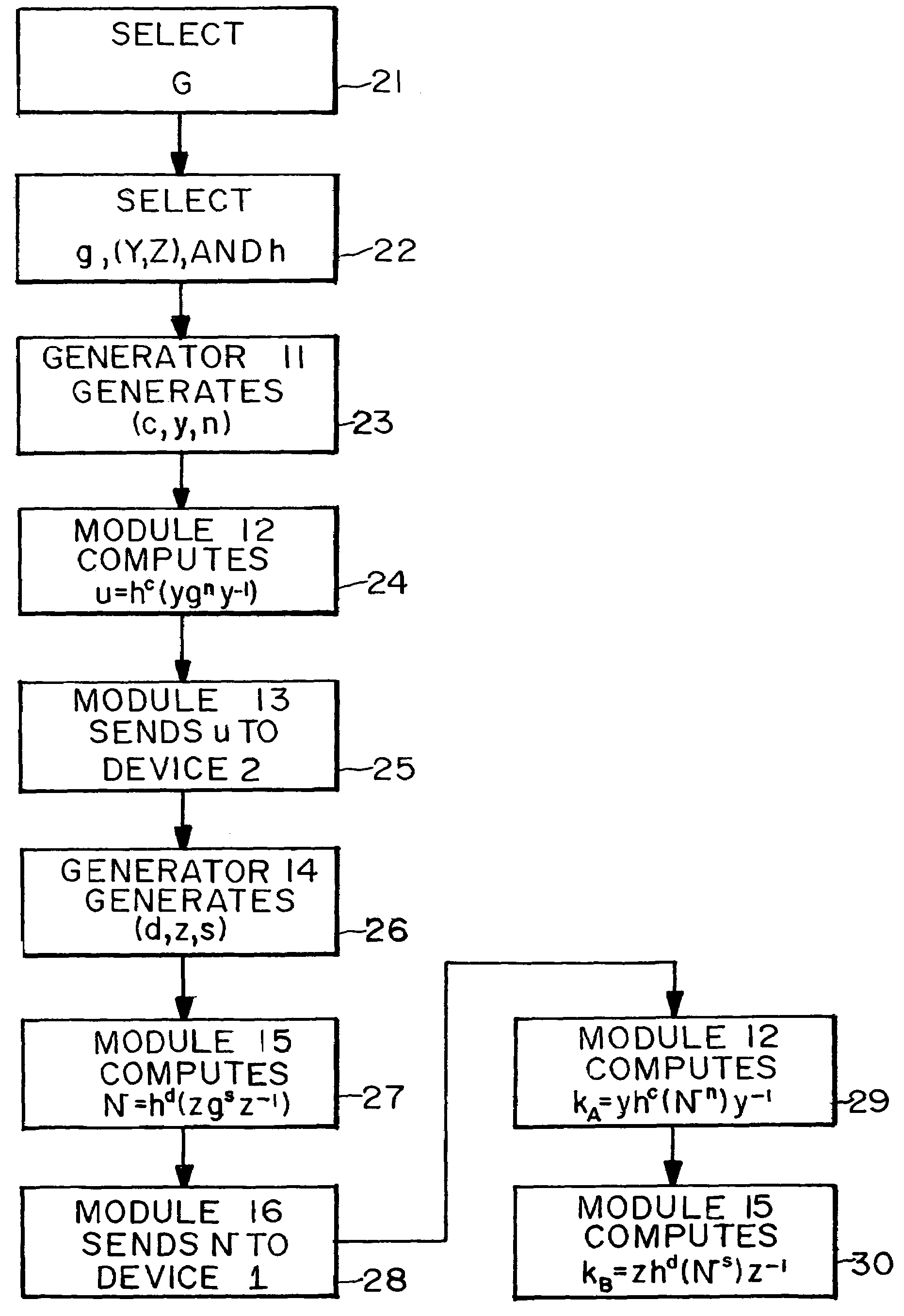
Apparati, methods, and computer readable media for enabling two parties (1,2) to exchange encrypted messages, exchange symmetric cryptographic keys, and perform functions of public key cryptography. First and second key exchange algorithms use commuting pairs of subsets of a monoid. The first key exchange algorithm has four principal embodiments. In three of the embodiments, a set of matrices over a hyperbolic ring is used as the monoid. In the fourth embodiment, a braid group is used as the monoid. The second key exchange algorithm has five principal embodiments. In four of the embodiments, a set of matrices over a hyperbolic ring is used as the monoid. In the fifth embodiment, a braid group is used as the monoid.
Owner:LATTICE SEMICON CORP
Asymmetric key cryptosystem based on shared knowledge
InactiveUS20060153364A1Facilitating adoption and usePublic key for secure communicationSecret communicationDigital signatureTheoretical computer science
An asymmetric key cryptosystem is provided using a private key of a public-private key pair by: identifying domain parameters of a finite cyclic group, the domain parameters including an initial generating point; transforming the initial generating point into a new generating point as a deterministic function; generating the public key as a deterministic function of the private key and the domain parameters, in which the new generating point is substituted for the initial generating point; and generating the digital signature as a deterministic function of the private key and the domain parameters, in which the new generating point is substituted for the initial generating point.
Owner:FIRST DATA
Method for communicating securely over an insecure communication channel
InactiveUS20060098814A1Improve securityMemory loss protectionDigital data processing detailsSecure communicationObject based
A method for enhancing the security of cryptographic systems against side channel attacks and cryptanalysis is based on the concept of object hopping or dynamic transformation of elements between objects that share the same category and / or floating objects which facilitate object hopping. The use of floating objects and floating finite fields to facilitate field hopping is also disclosed. Further, the use of curve hopping and floating elliptic curves to facilitate curve hopping and / or key floating when keys used in cryptosystems are floated through floating fields are also used for enhancing the security of cryptographic systems.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
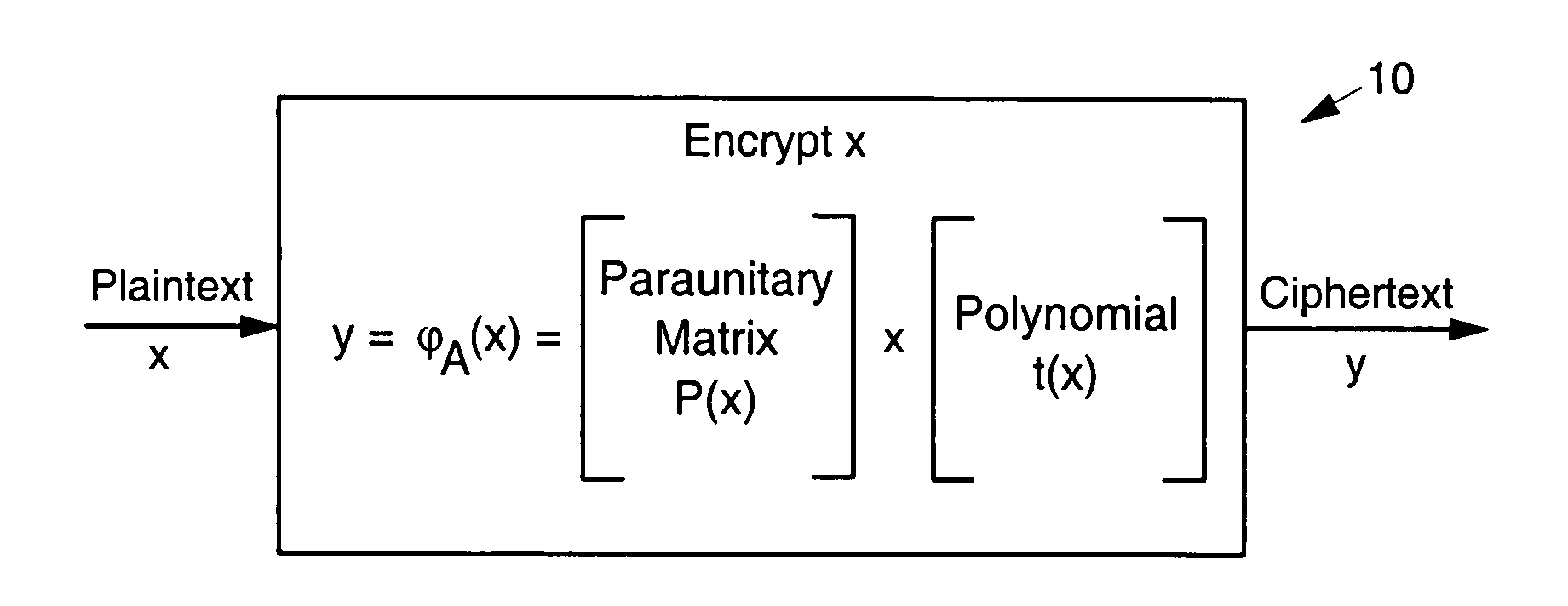
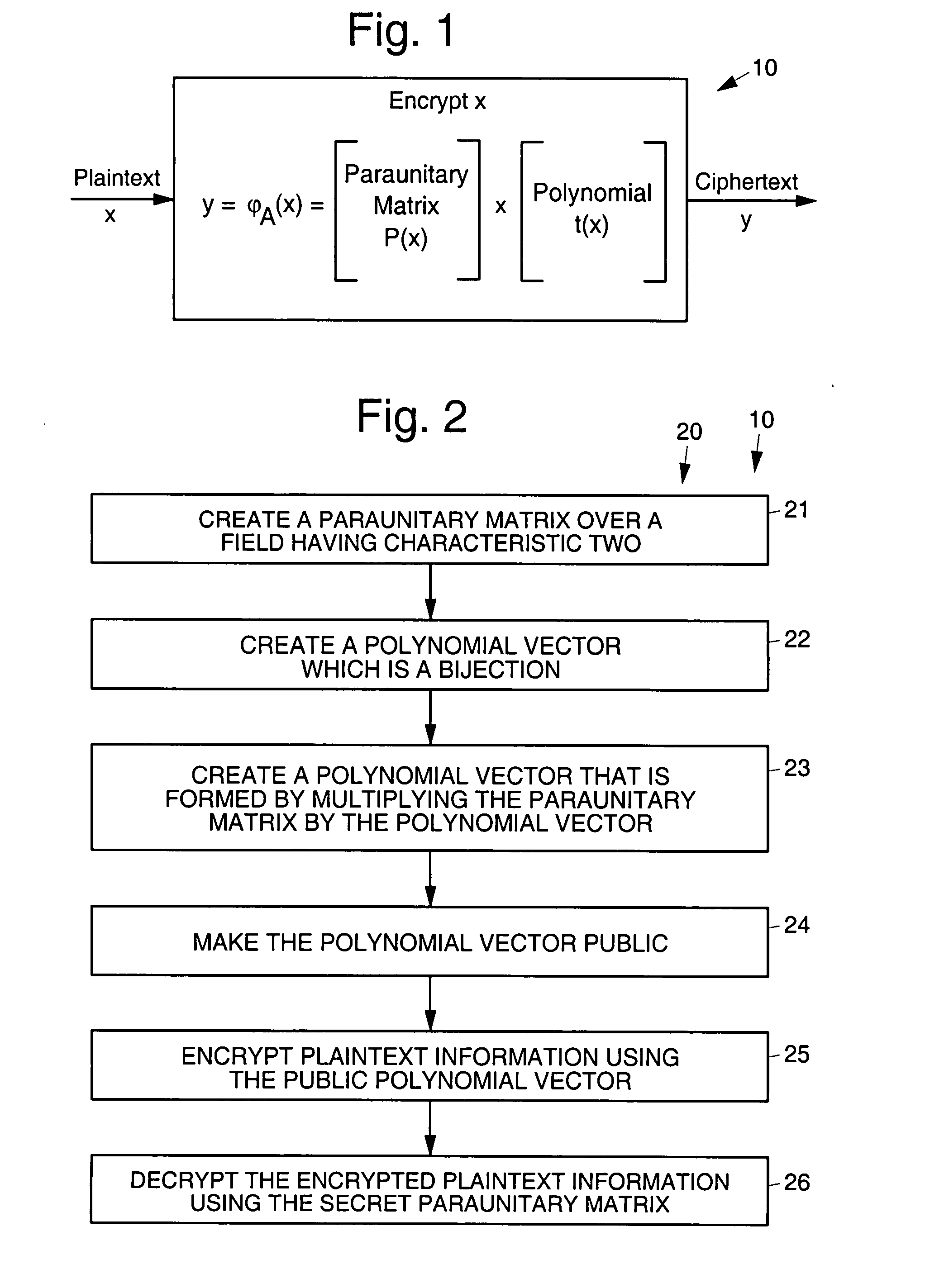
Asymmetric cryptosystem employing paraunitary matrices
InactiveUS20090010428A1Public key for secure communicationSecret communicationNon symmetricCiphertext
Disclosed are multivariate paraunitary asymmetric cryptographic systems and methods that are based on paraunitary matrices. An algebraic approach is employed in designing the multivariate cryptographic systems and methods. The cryptographic systems and methods are based on formulating a general system of multivariate polynomial equations by paraunitary matrices. These matrices are a family of invertible polynomial matrices that can be completely parameterized and efficiently generated by primitive building blocks. Using a general formulation that involves paraunitary matrices, a one-way function is designed that operates over the fields of characteristic two. To include a trapdoor, approximations are made to the paraunitary matrix. The result is a trapdoor one-way function that is efficient to evaluate, but hard to invert unless secret information about the trapdoor is known. An exemplary implementation operates on the finite field GF(256). In this example, the message block includes 16 to 32 symbols from GF(256), i.e., the block size n is an integer between 16 and 32. The ciphertext block takes its elements from the same field and has at least 10 extra symbols.
Owner:GEORGIA TECH RES CORP
Auto-recoverable and auto-certifiable cryptosystem with unescrowed signing keys
InactiveUS6122742AFast and easy disseminationEffective wayKey distribution for secure communicationDigital data processing detailsCryptosystemKey generation
A method is provided for an escrow cryptosystem combined with an unescrowed digital signature scheme that uses a single public key per user. This system is overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), and is publicly verifiable. The system cannot be used subliminally to enable a shadow public key system. Namely, an unescrowed public key system that is publicly displayed in a covert fashion. The cryptosystem contains a key generation mechanism that outputs a key triplet, and a certificate of proof that the keys were generated according to the algorithm. The key triplet consists of a public key, a private decryption key, and a private signing key. Using the public key and the certificate, the triplet can be verified efficiently by anyone to have the following properties: (1) the private signing key is known to the user, and (2) the private decryption key is recoverable by the escrow authorities. The system assures that the escrow authorities are not able to forge signatures or get the private signing key. The system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form).
Owner:YOUNG ADAM LUCAS +1
Method for confidentially querying a location-based service by homomorphing cryptography
ActiveUS20180267981A1Instruments for road network navigationDigital data information retrievalCryptosystemDatabase
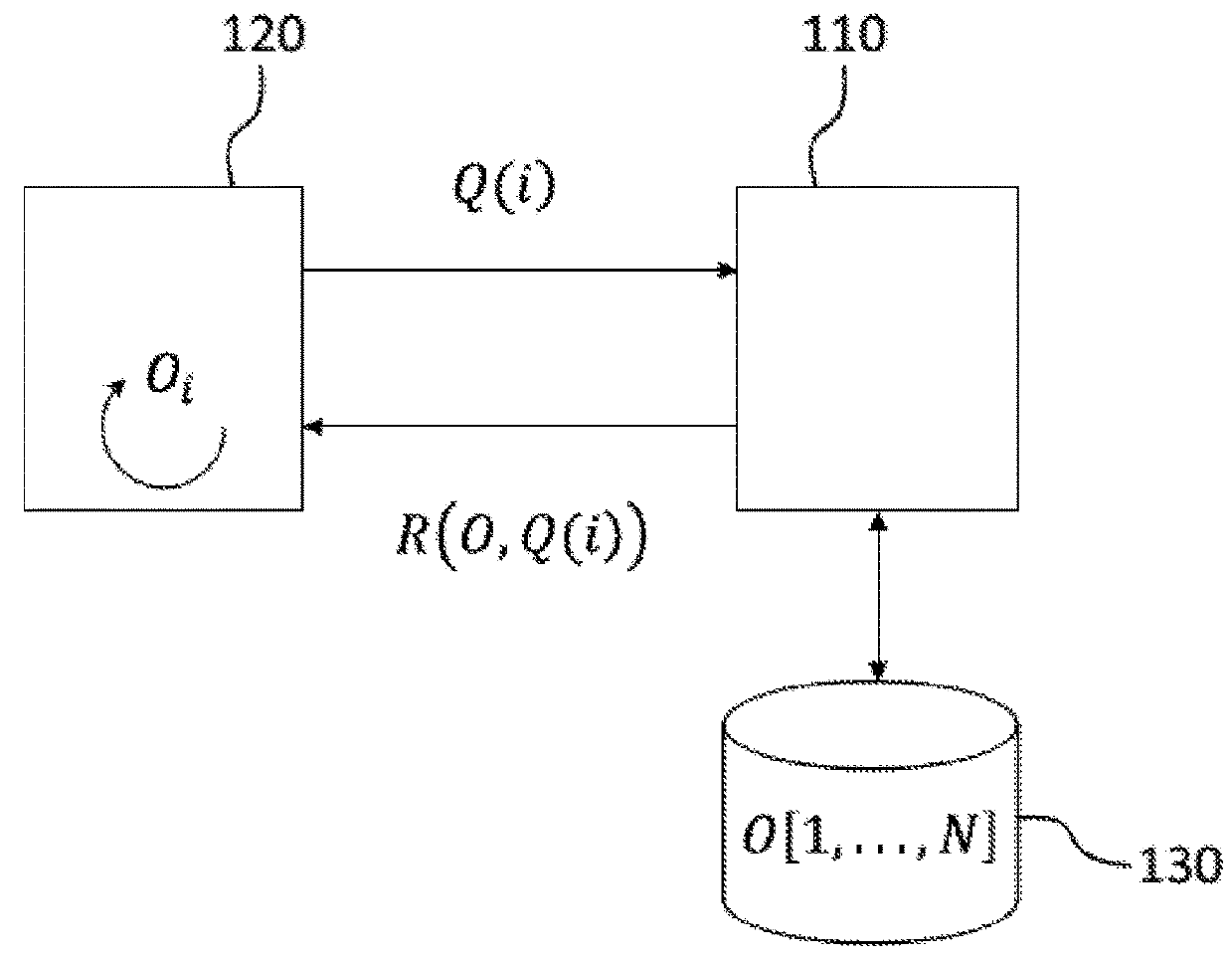
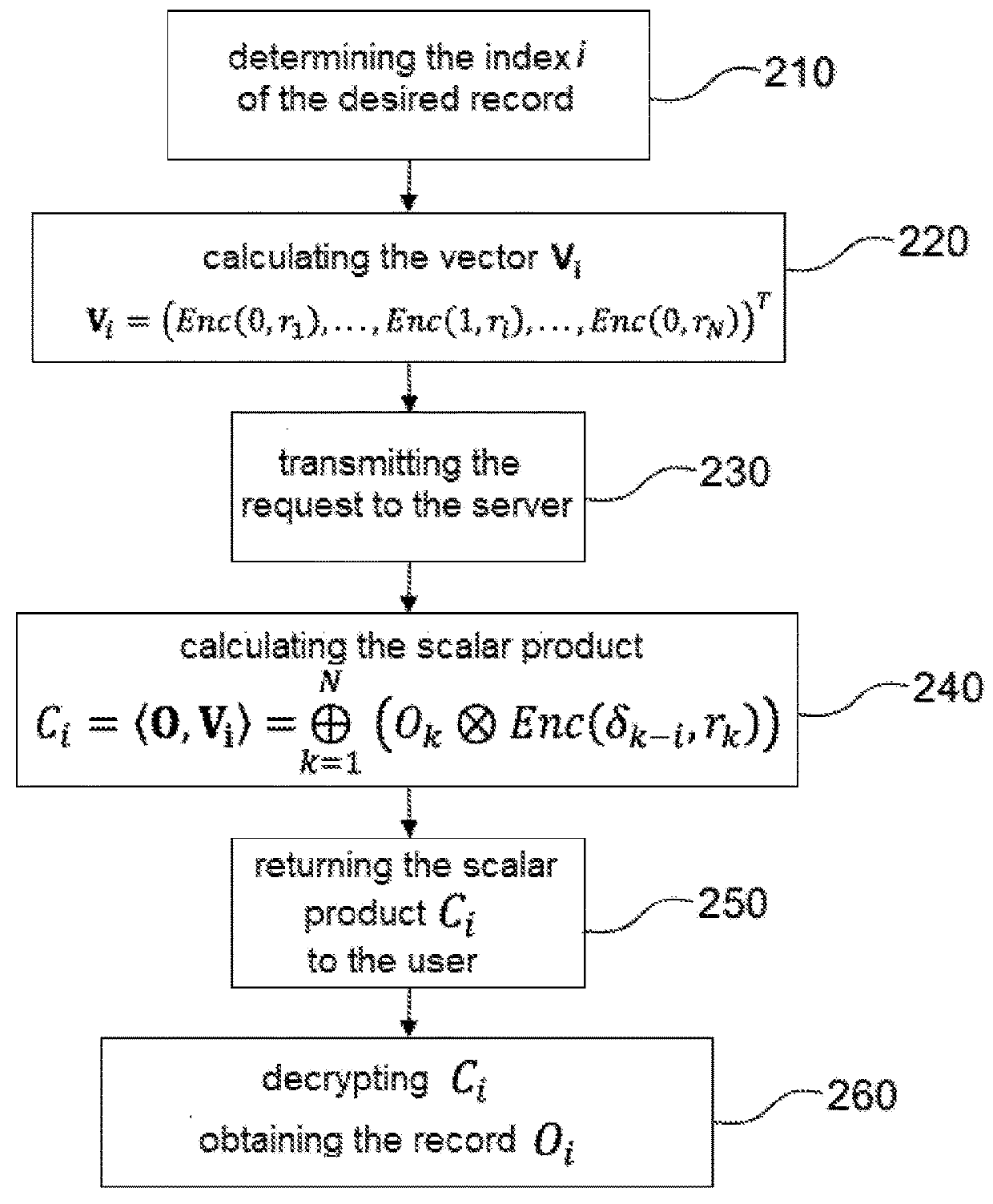
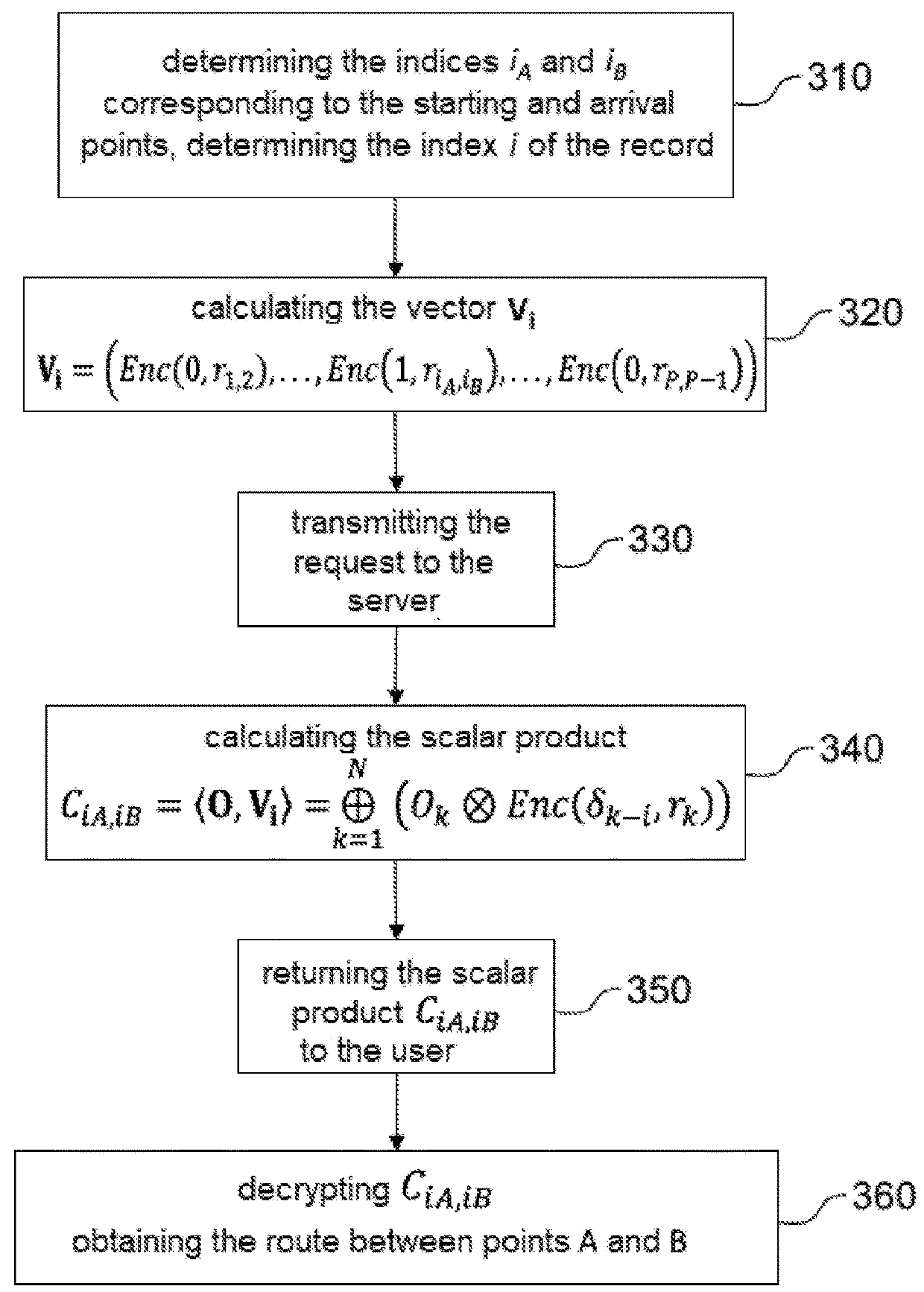
A method allowing a user confidentially to query a server including a database. The user builds, from an index of a desired entry, a vector encrypted by a homomorphic probabilistic cryptosystem, and transmits a request having the vector as an argument to the server. The server performs a scalar product between the vector of entries of the database and returns the result to the user. The user decrypts the scalar product to obtain the desired entry. The method can be used for example for querying a location-based service and for navigation by concealed routes.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
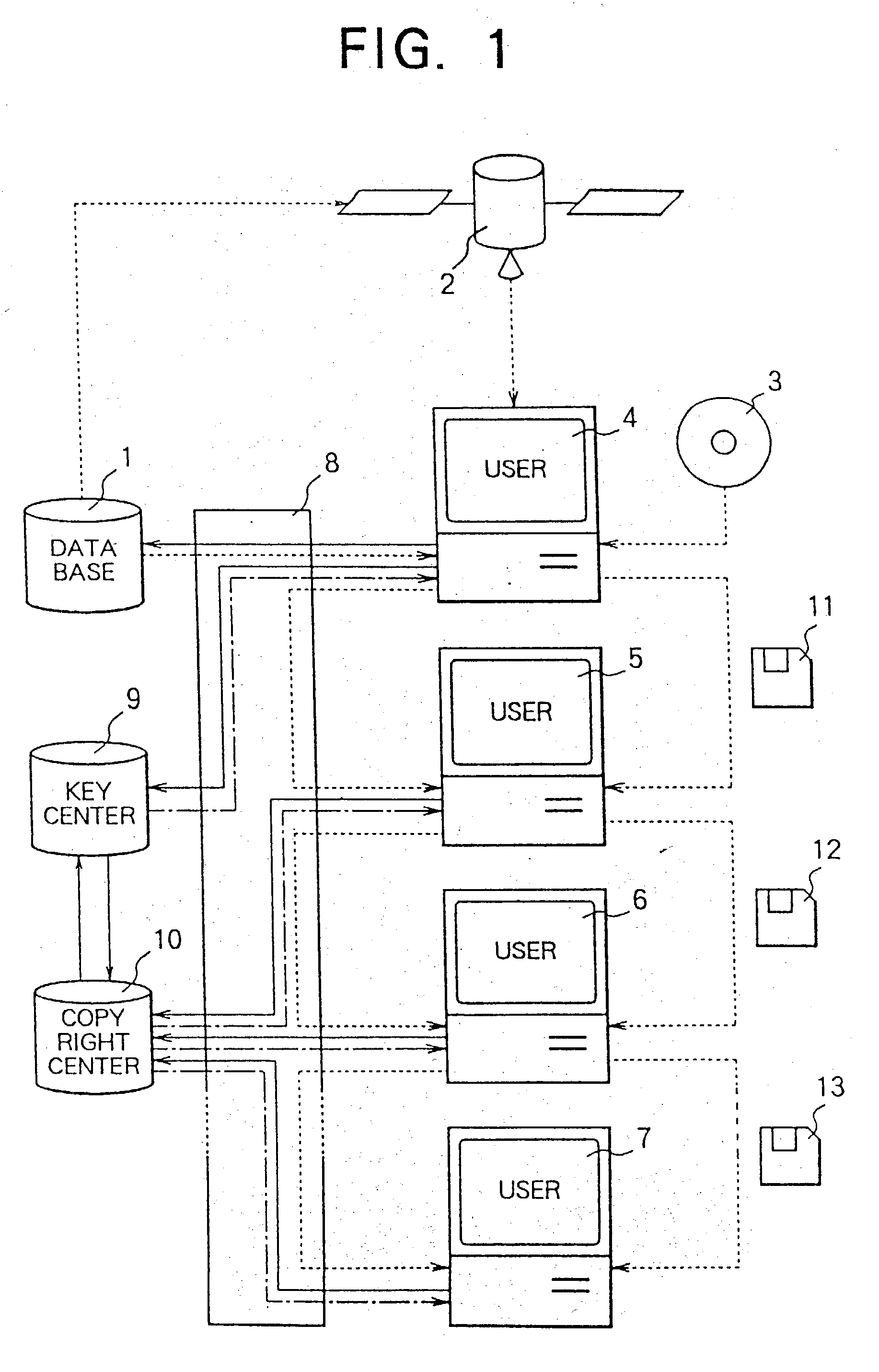
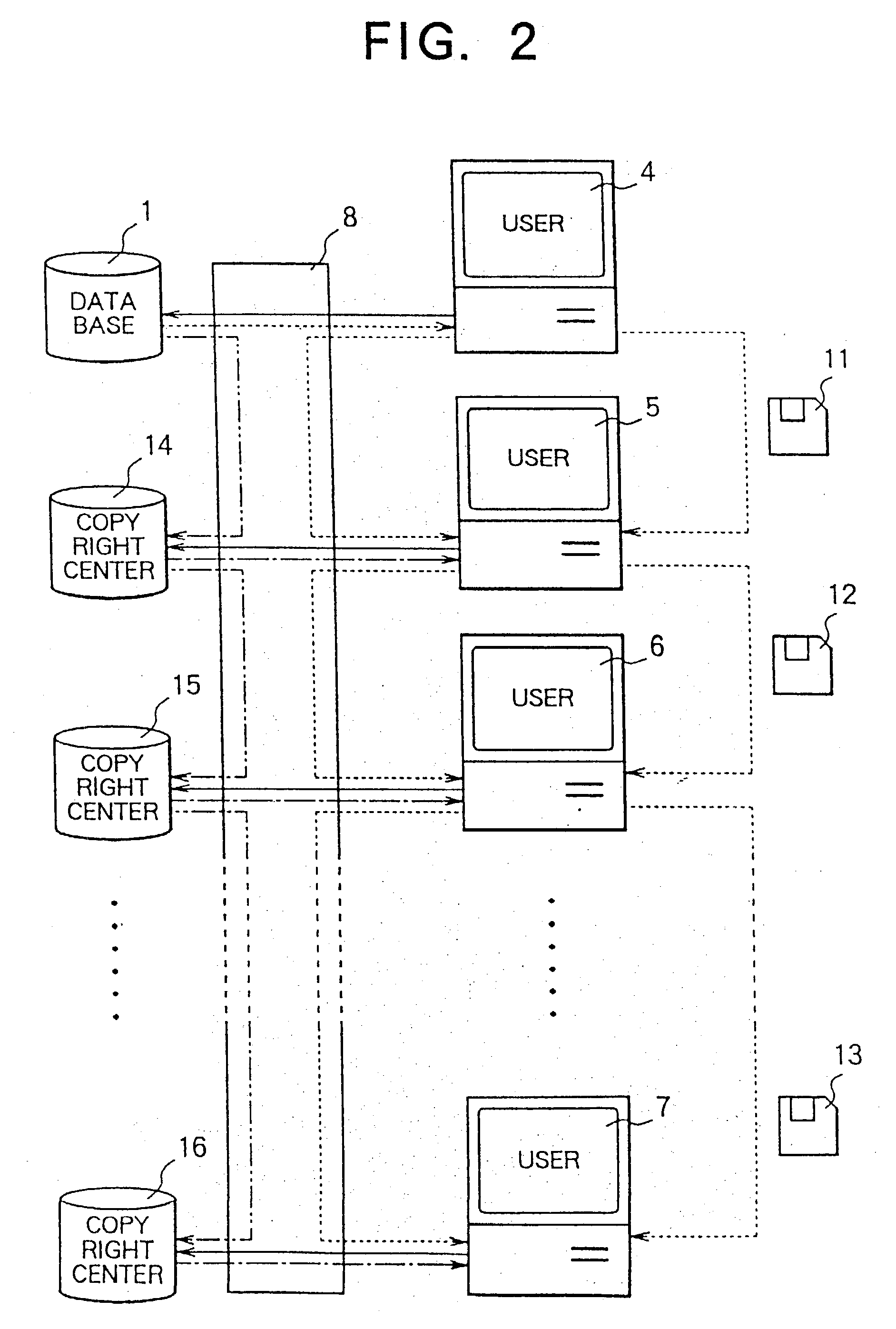
Data copyright management system
InactiveUS20030144963A1Key distribution for secure communicationPublic key for secure communicationOriginal dataControl data
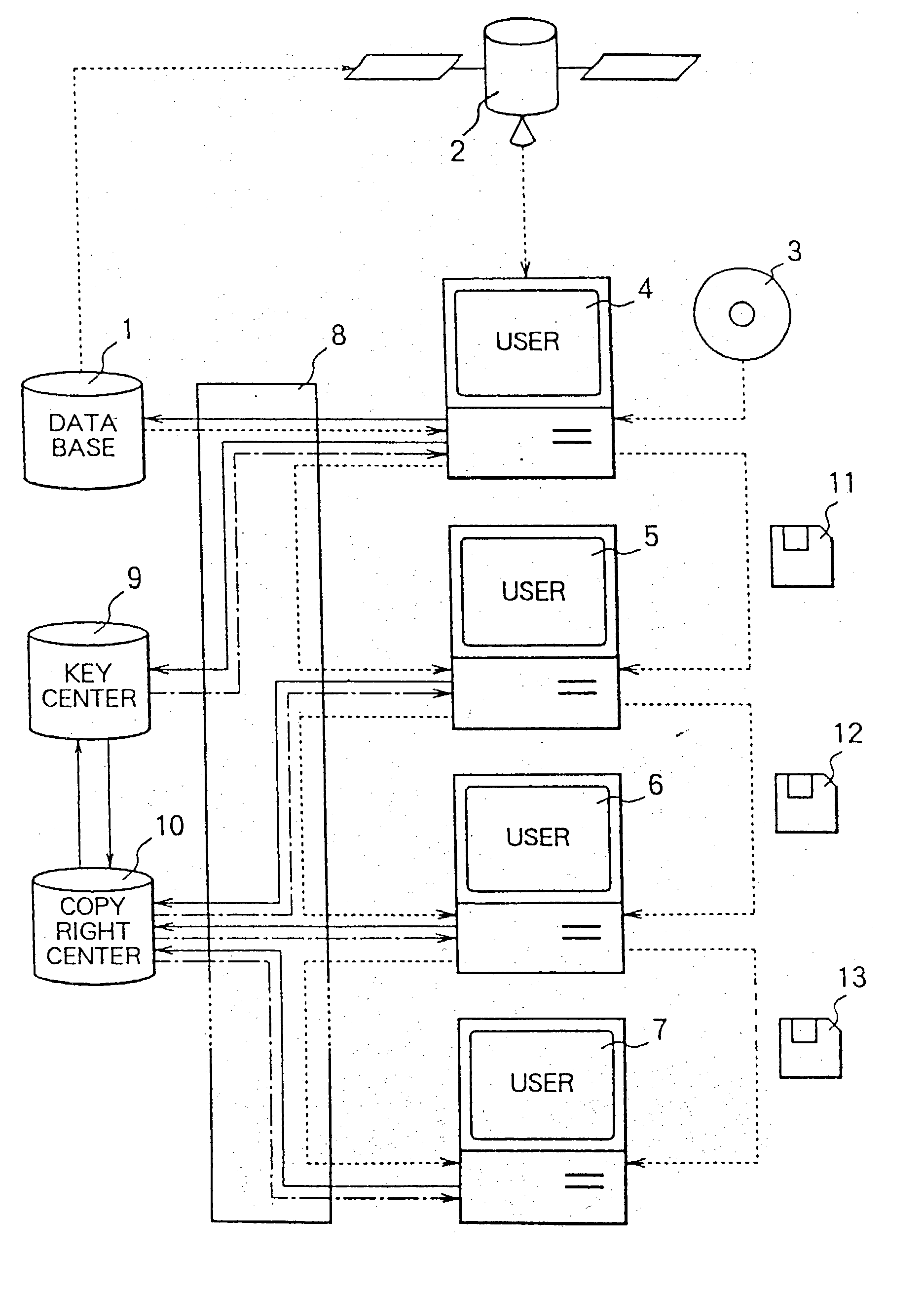
A data copyright management system comprises a database for storing original data, a key control center for managing crypt keys, copyright management center for managing data copyrights, and a communication network for connecting these sections. Data supplied from the database to users is encrypted and distributed. The users decrypts the encrypted data by crypt keys obtained from the key control center or copyright management center. To supply data to users, there are the following two methods: a one way supplying of encrypted data to users by means of broadcasting or the like; and two-way supplying of encrypted data to users corresponding to users' requests. A crypt key system used for encrypting data uses a secret-key cryptosystem, a public-key cryptosystem or a cryptosystem combining a secret-key and a public-key and further uses a copyright control program to control data copyrights. When a user stores, copies, or transfers data, the data is encrypted by a crypt key different from a crypt key used for supplying the data. The former crypt key is supplied from the key control center or from the copyright management center, or generated by the copyright control program. The present invention can be applied to a data copyright management system for using not only single data but also a plurality of data supplied from a single database or a plurality of data supplied from a plurality of databases. Further, an apparatus to be used by the user to perform data copyright management is proposed.
Owner:XYLON LLC +1
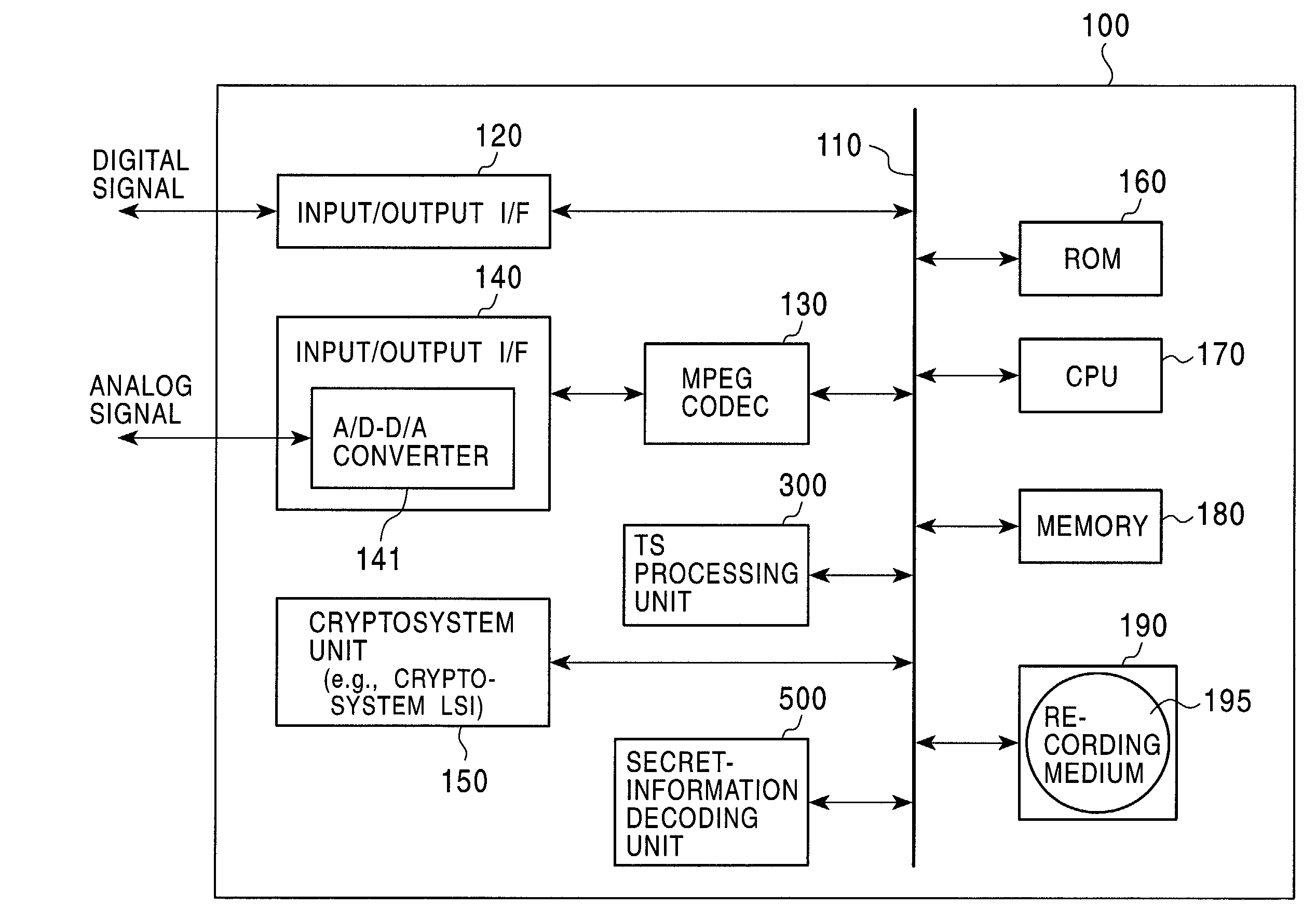
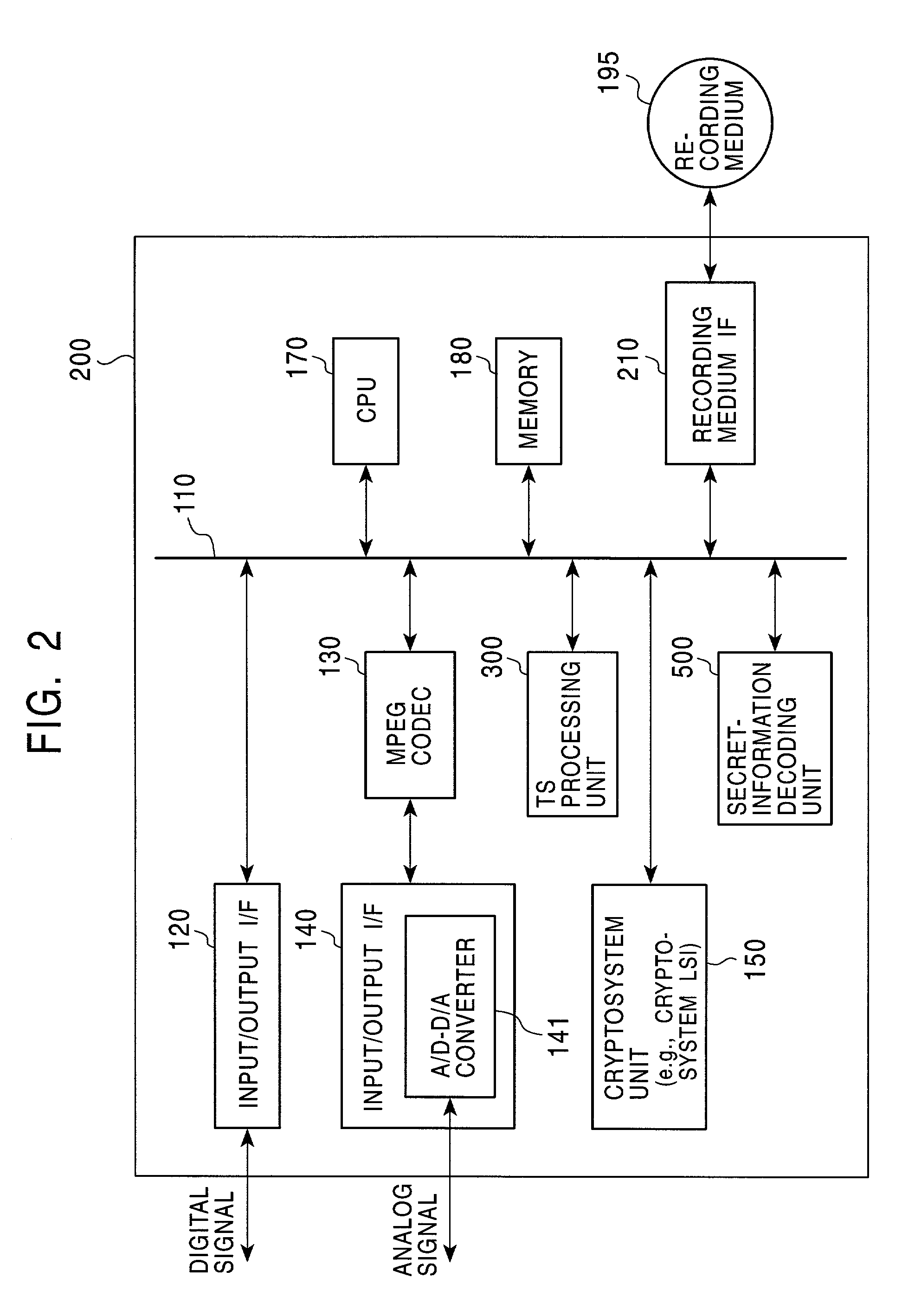
Information security device
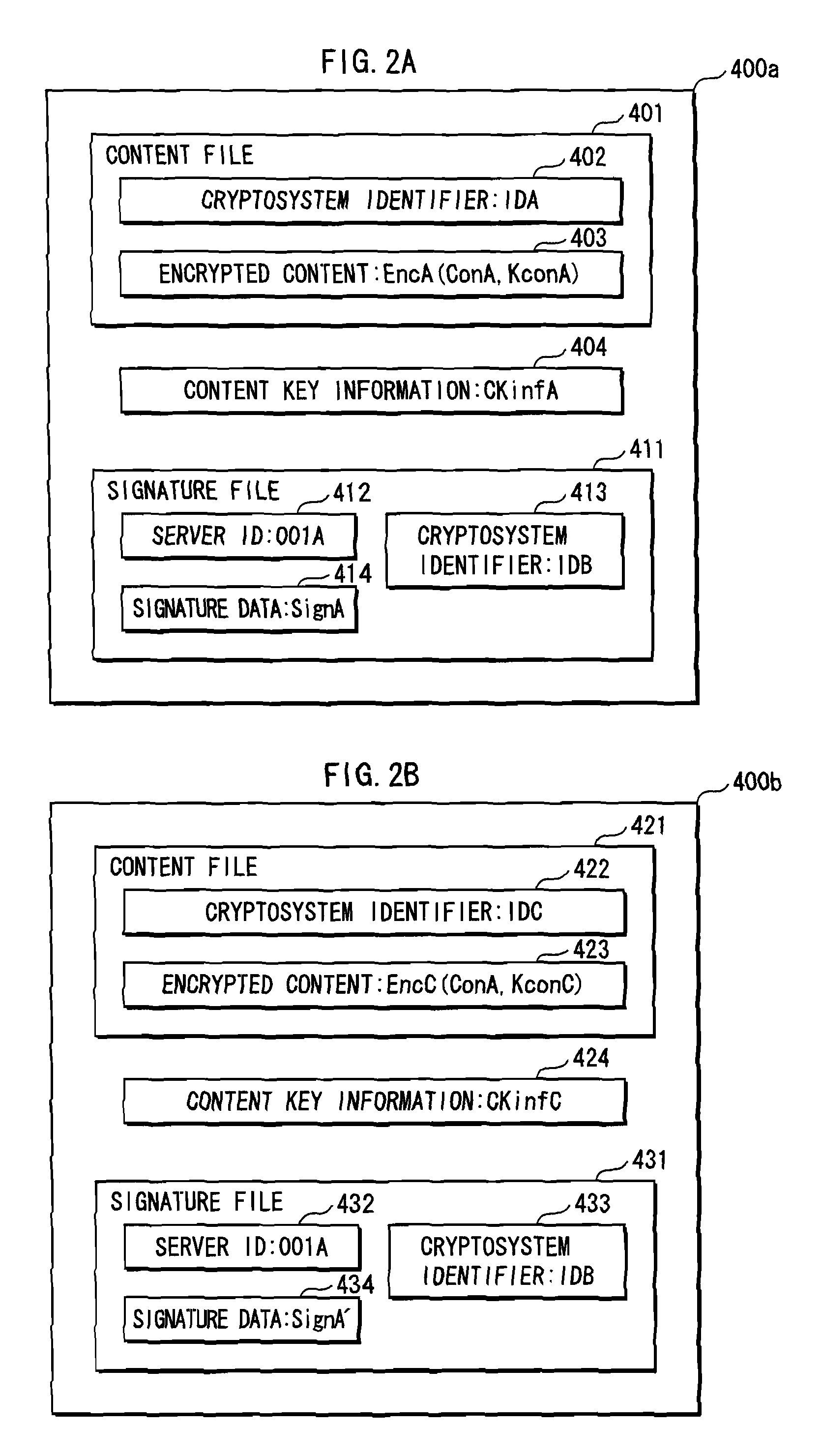
ActiveUS20090132821A1Appropriately processKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareCryptosystem
The present invention provides an apparatus for securely acquire a circuit configuration information set corresponding to a new cryptosystem without increasing the number of reconfigurable circuits. A content playback apparatus 100 includes an FPGA 122 that is reconfigurable. The content playback apparatus 100 stores a decryption circuit program that shows the structure of a decryption circuit that executes decryption in accordance with a prescribed cryptosystem. The FPGA is reconfigured in accordance with the program to configure the decryption circuit. The playback apparatus 100 acquires, from outside, an encrypted file that has been generated by encrypting a file including a decryption circuit program corresponding to the new cryptosystem in accordance with the prescribed cryptosystem, and decrypts the encrypted file by the decryption circuit.
Owner:PANASONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com