User identity authentication system and method
An identity authentication and user-side technology, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as low security, undisclosed keys, and large demand for keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
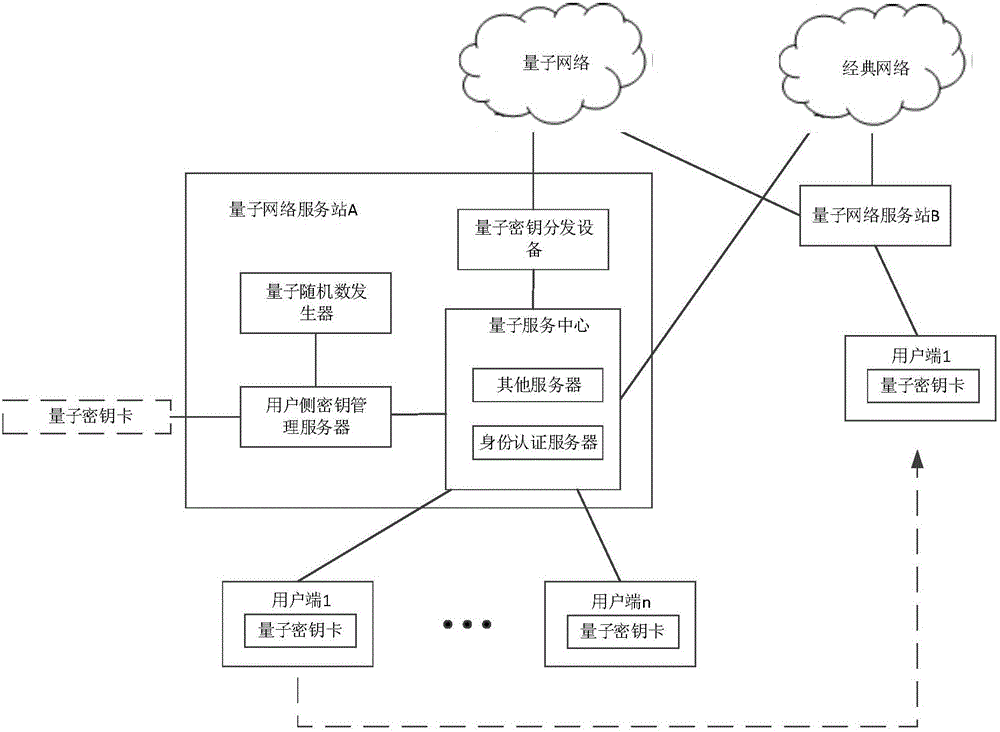
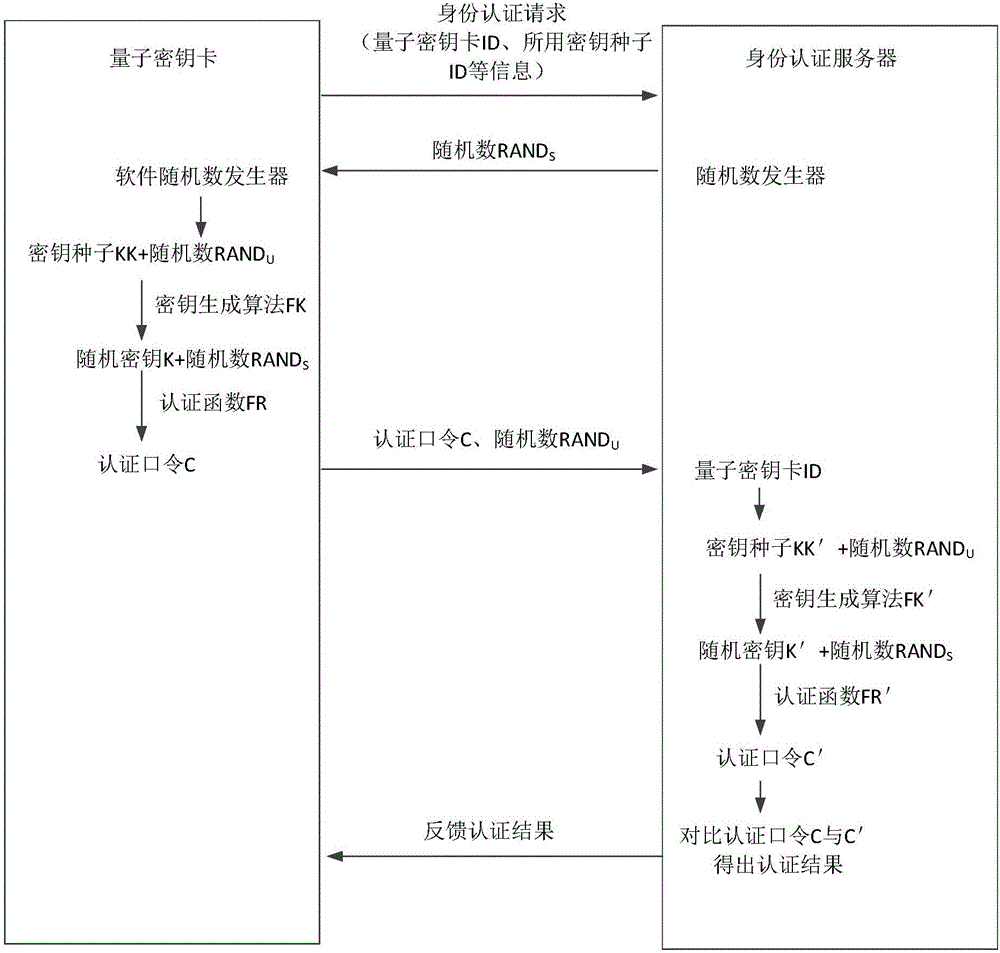
[0091] Such as figure 2 As shown, the identity authentication method between the client terminal and the quantum network service station in the local area network, wherein the quantum key card involved is registered and issued at the local quantum network service station, and the identity authentication method includes:
[0092] a. Authentication initiation: the client submits an authentication application to the identity authentication server of the current quantum network service station, and the authentication application includes at least the quantum key card ID and the key seed ID of the key seed that will be used in this identity authentication. After submitting the authentication application, the identity authentication server sends a random number RANDS (equivalent to the first random number) to the client.
[0093] b. User authentication key generation: After the quantum key card matched by the user end obtains the random number RANDS, the quantum key card uses the s...
Embodiment 2
[0107] The identity authentication method between the user terminal and the quantum network service station in the wide area network includes:
[0108] a. Authentication initiation: the client submits an authentication application to the identity authentication server of the current quantum network service station, and the authentication application includes at least the quantum key card ID and the key seed ID of the key seed that will be used in this identity authentication. After submitting the authentication application, the identity authentication server sends a random number RANDS (equivalent to the first random number) to the client.
[0109] b. User authentication key generation: After the quantum key card matched by the user end obtains the random number RANDS, the quantum key card uses the software random number generator inside the card to generate a random number RANDU (equivalent to the second random number).
[0110] Using the key generation algorithm FK and the r...
Embodiment 3
[0120] Another identity authentication method between the client and the quantum network service station in the WAN, including:
[0121] a. Authentication initiation: the client submits an authentication application to the identity authentication server of the current quantum network service station, and the authentication application includes at least the quantum key card ID and the key seed ID of the key seed that will be used in this identity authentication. After submitting the authentication application, the identity authentication server requests the quantum network service station pointed to by it to generate and send the random number RANDS (equivalent to the first random number) to the client according to the key seed ID.
[0122] b. User authentication key generation: After the quantum key card matched by the user end obtains the random number RANDS, the quantum key card uses the software random number generator inside the card to generate a random number RANDU (equiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com