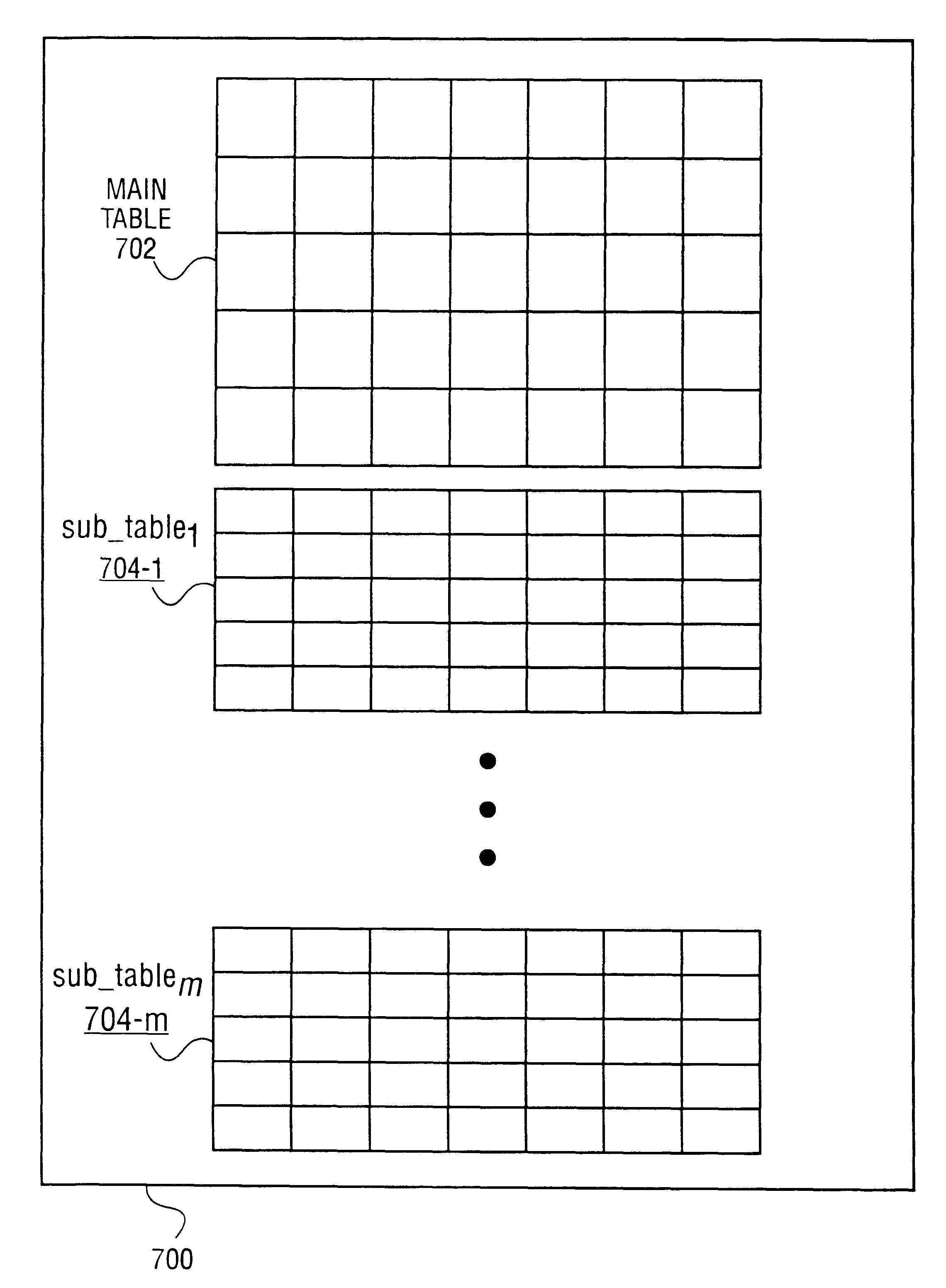
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
282476 results about "Computer engineering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computer engineering is a branch of engineering that integrates several fields of computer science and electronic engineering required to develop computer hardware and software. Computer engineers usually have training in electronic engineering (or electrical engineering), software design, and hardware-software integration instead of only software engineering or electronic engineering. Computer engineers are involved in many hardware and software aspects of computing, from the design of individual microcontrollers, microprocessors, personal computers, and supercomputers, to circuit design. This field of engineering not only focuses on how computer systems themselves work but also how they integrate into the larger picture.
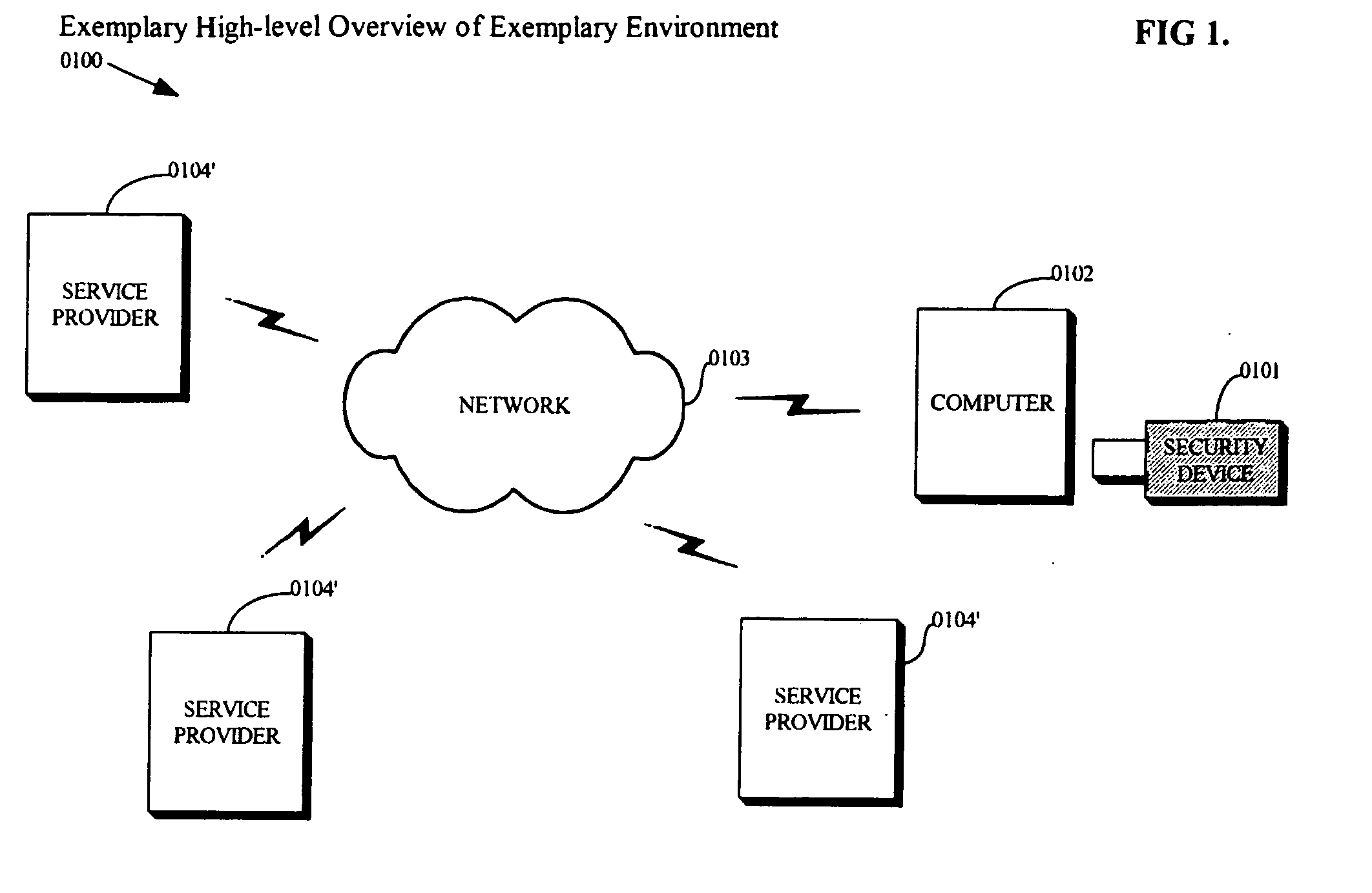
Methods and apparatus for interpreting user selections in the context of a relation distributed as a set of orthogonalized sub-relations
Owner:ORACLE INT CORP
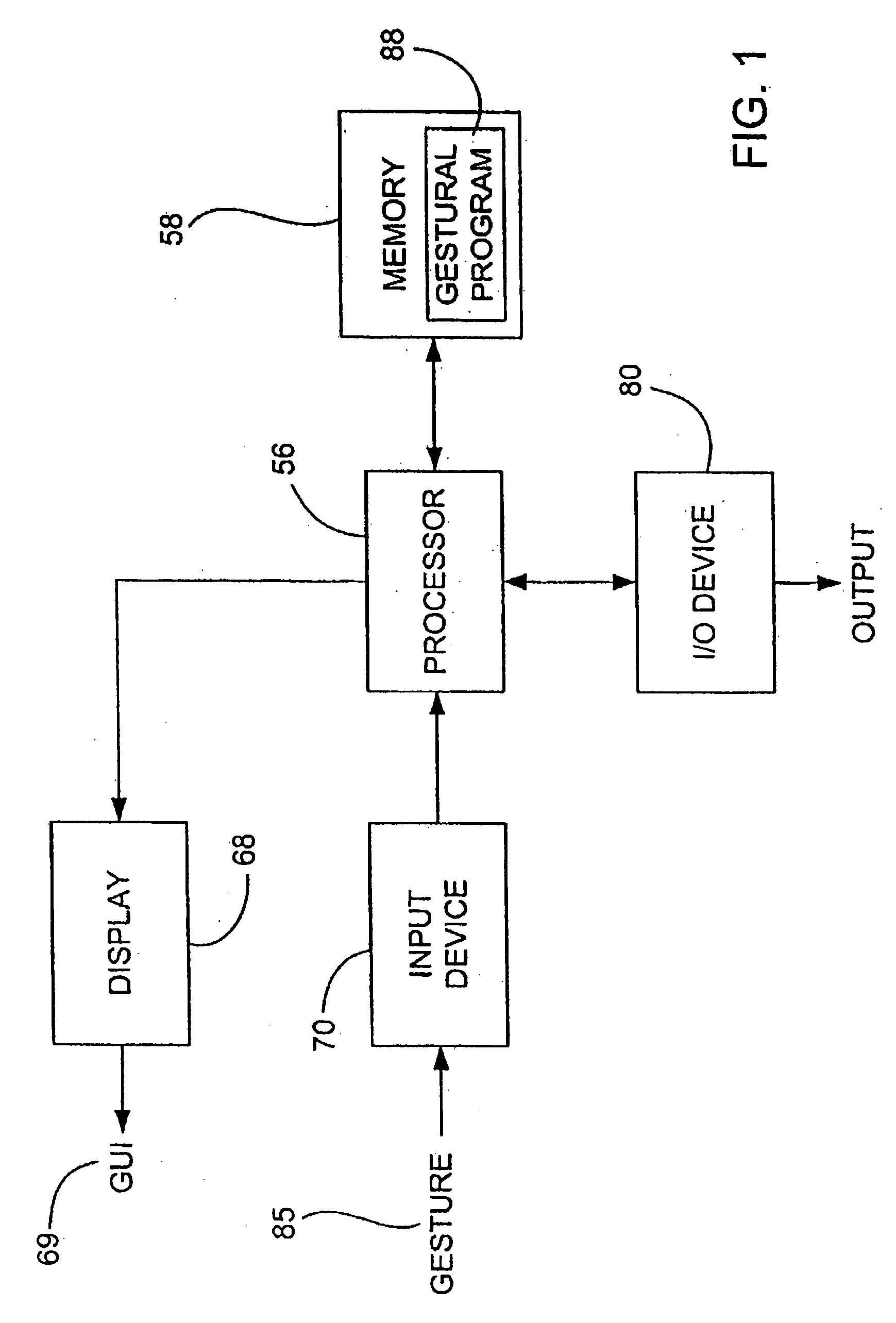
Gestures for controlling, manipulating, and editing of media files using touch sensitive devices
ActiveUS20080165141A1Electronic editing digitised analogue information signalsCarrier indicating arrangementsGraphicsSoftware
Embodiments of the invention are directed to a system, method, and software for implementing gestures with touch sensitive devices (such as a touch sensitive display) for managing and editing media files on a computing device or system. Specifically, gestural inputs of a human hand over a touch / proximity sensitive device can be used to control, edit, and manipulate files, such as media files including without limitation graphical files, photo files and video files.
Owner:APPLE INC
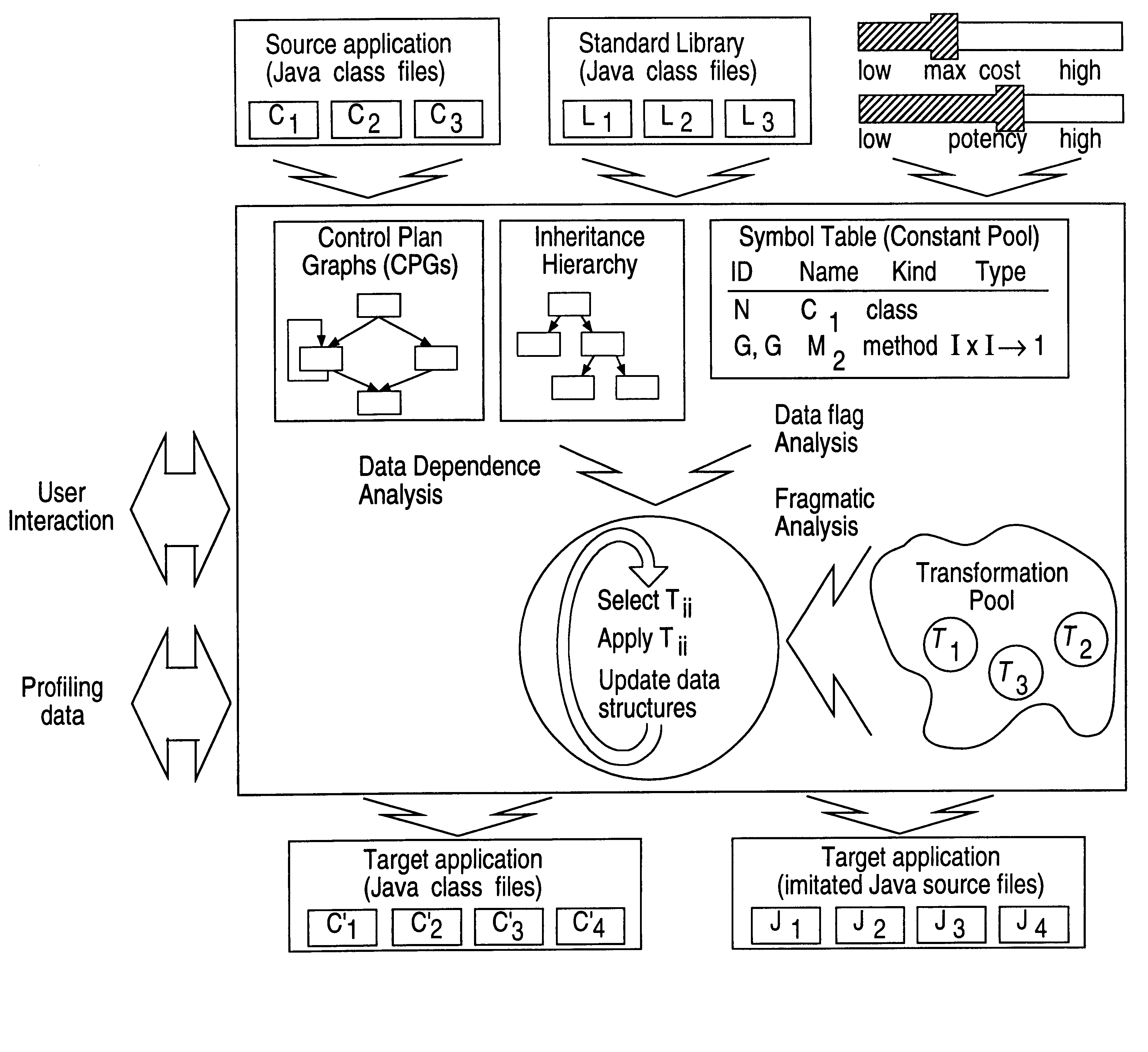
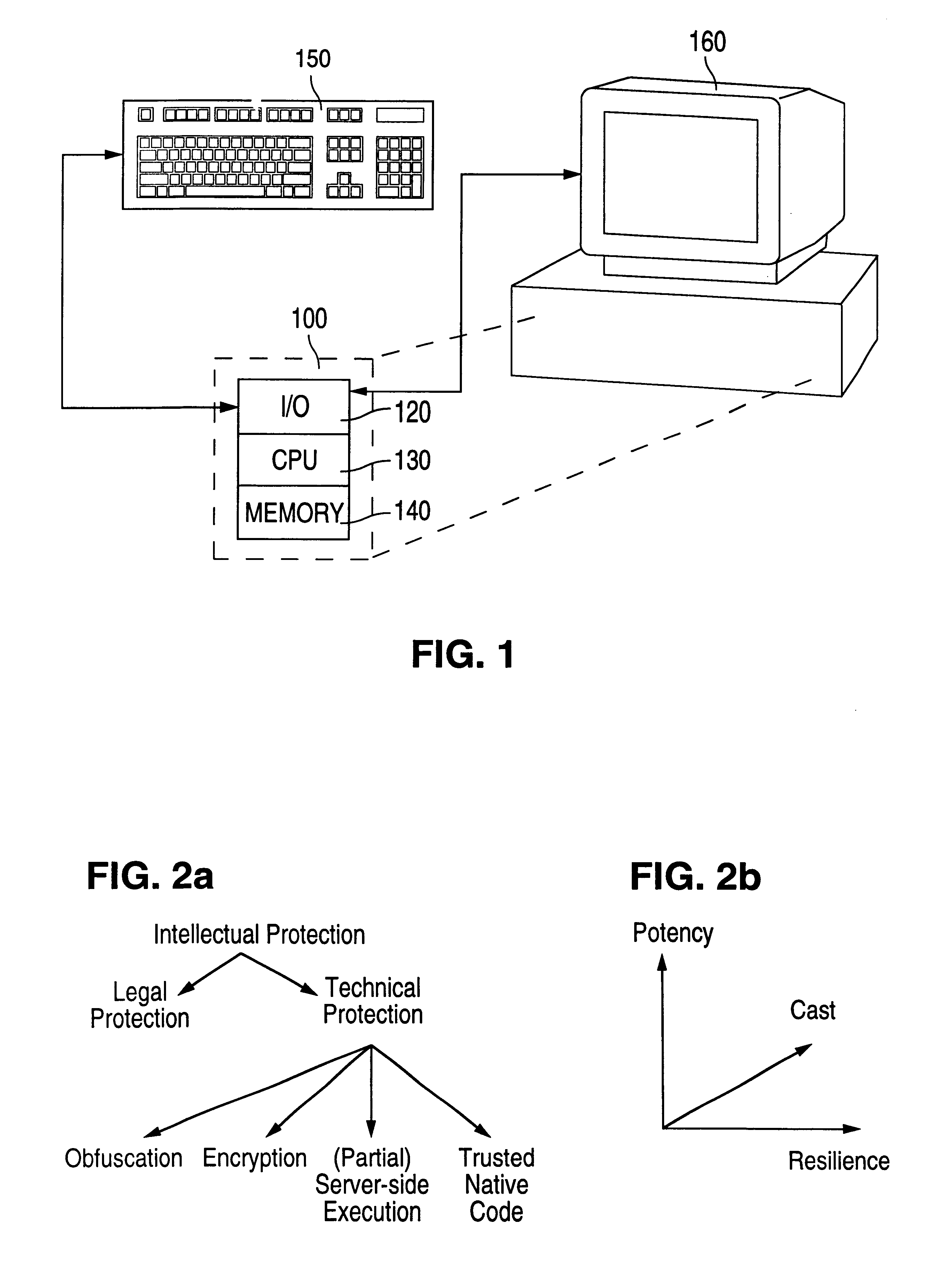
Obfuscation techniques for enhancing software security
InactiveUS6668325B1Guaranteed maximum utilizationDigital data processing detailsUnauthorized memory use protectionObfuscationTheoretical computer science
The present invention provides obfuscation techniques for enhancing software security. In one embodiment, a method for obfuscation techniques for enhancing software security includes selecting a subset of code (e.g., compiled source code of an application) to obfuscate, and obfuscating the selected subset of the code. The obfuscating includes applying an obfuscating transformation to the selected subset of the code. The transformed code can be weakly equivalent to the untransformed code. The applied transformation can be selected based on a desired level of security (e.g., resistance to reverse engineering). The applied transformation can include a control transformation that can be creating using opaque constructs, which can be constructed using aliasing and concurrency techniques. Accordingly, the code can be obfuscated for enhanced software security based on a desired level of obfuscation (e.g., based on a desired potency, resilience, and cost).
Owner:INTERTRUST TECH CORP
Variable programming of non-volatile memory
ActiveUS7020017B2Improve data retentionDecreased program disturbRead-only memoriesDigital storageReading levelNon-volatile memory
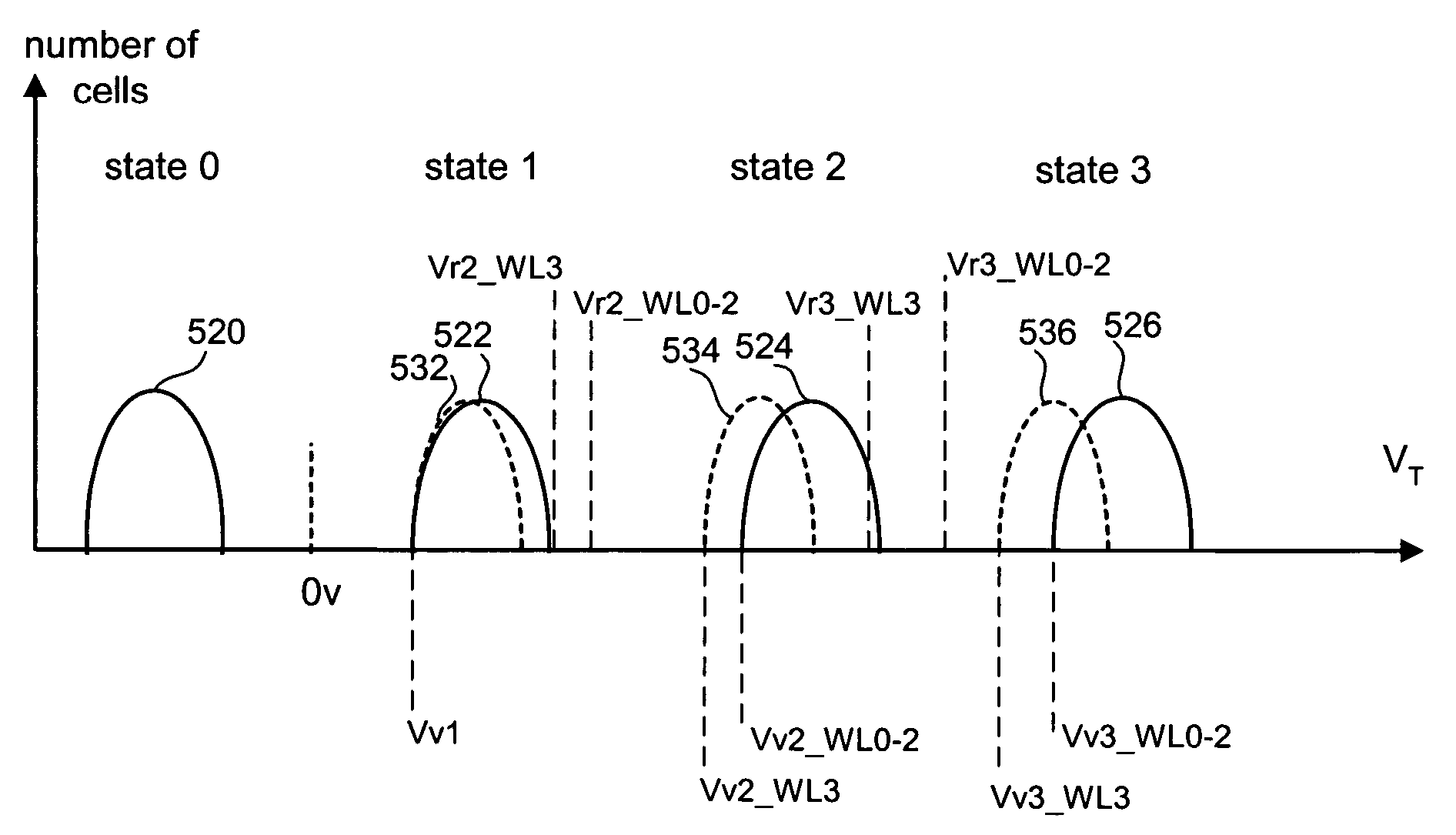
Systems and methods in accordance with various embodiments can provide for reduced program disturb in non-volatile semiconductor memory. In one embodiment, select memory cells such as those connected to a last word line of a NAND string are programmed using one or more program verify levels or voltages that are different than a corresponding level used to program other cells or word lines. One exemplary embodiment includes using a lower threshold voltage verify level for select physical states when programming the last word line to be programmed for a string during a program operation. Another embodiment includes applying a lower program voltage to program memory cells of the last word line to select physical states. Additional read levels are established for reading the states programmed using lower verify levels in some exemplary implementations. A second program voltage step size that is larger than a nominal step size is used in one embodiment when programming select memory cells or word lines, such as the last word line to be programmed for a NAND string.
Owner:SANDISK TECH LLC
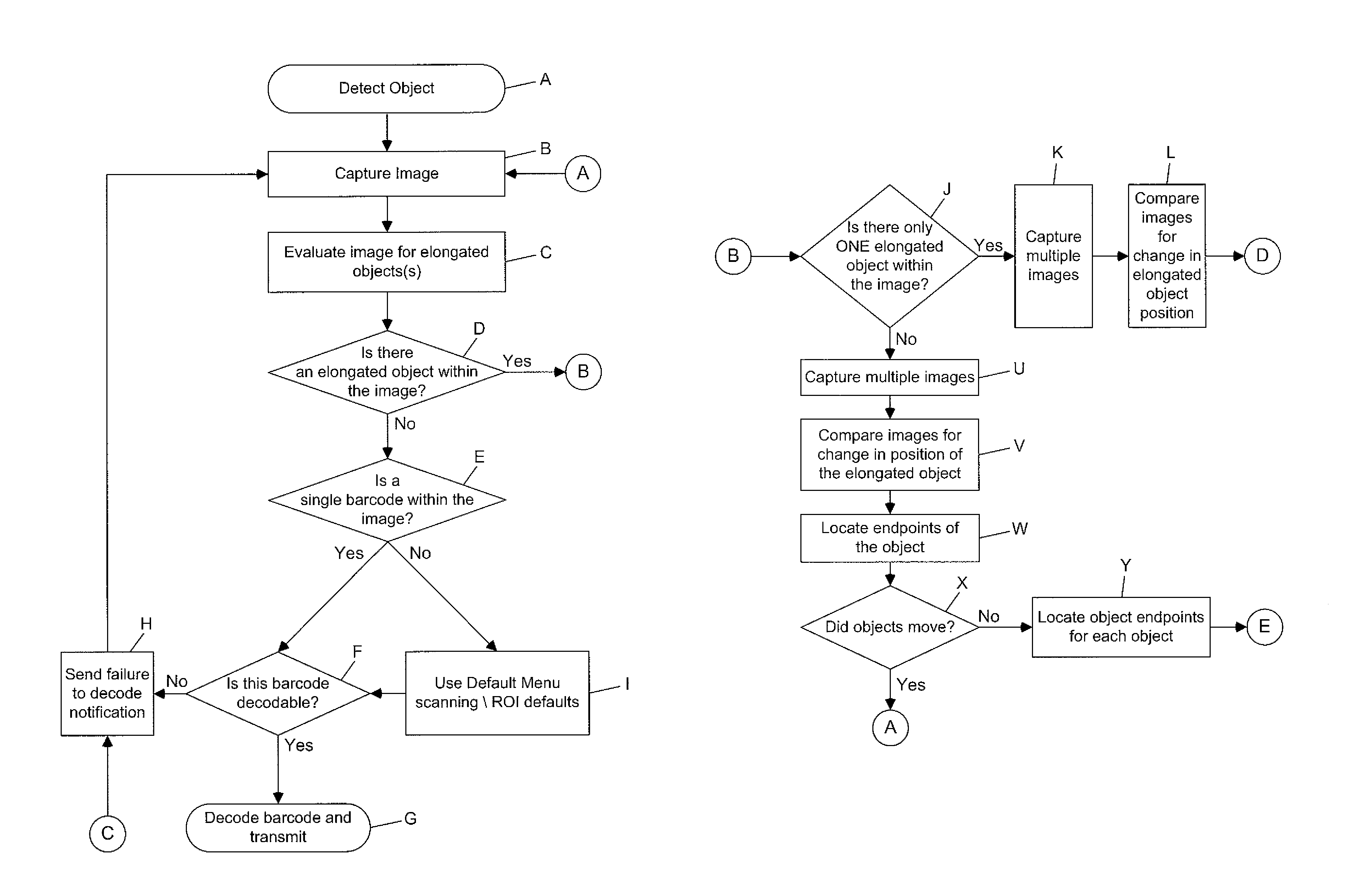
Digital-imaging based code symbol reading system having finger-pointing triggered mode of operation
ActiveUS8490877B2Character and pattern recognitionSensing by electromagnetic radiationComputer hardwareProgramming language
A digital-imaging based system for and method of reading graphical indicia, including code symbols, on objects such as, but not limited to, code symbol menus by the user simply pointing his or her finger at the particular code symbol on the code symbol menu to be read, while digital images of the code symbol menu and the pointing finger are automatically captured, buffered and processed.
Owner:METROLOGIC INSTR
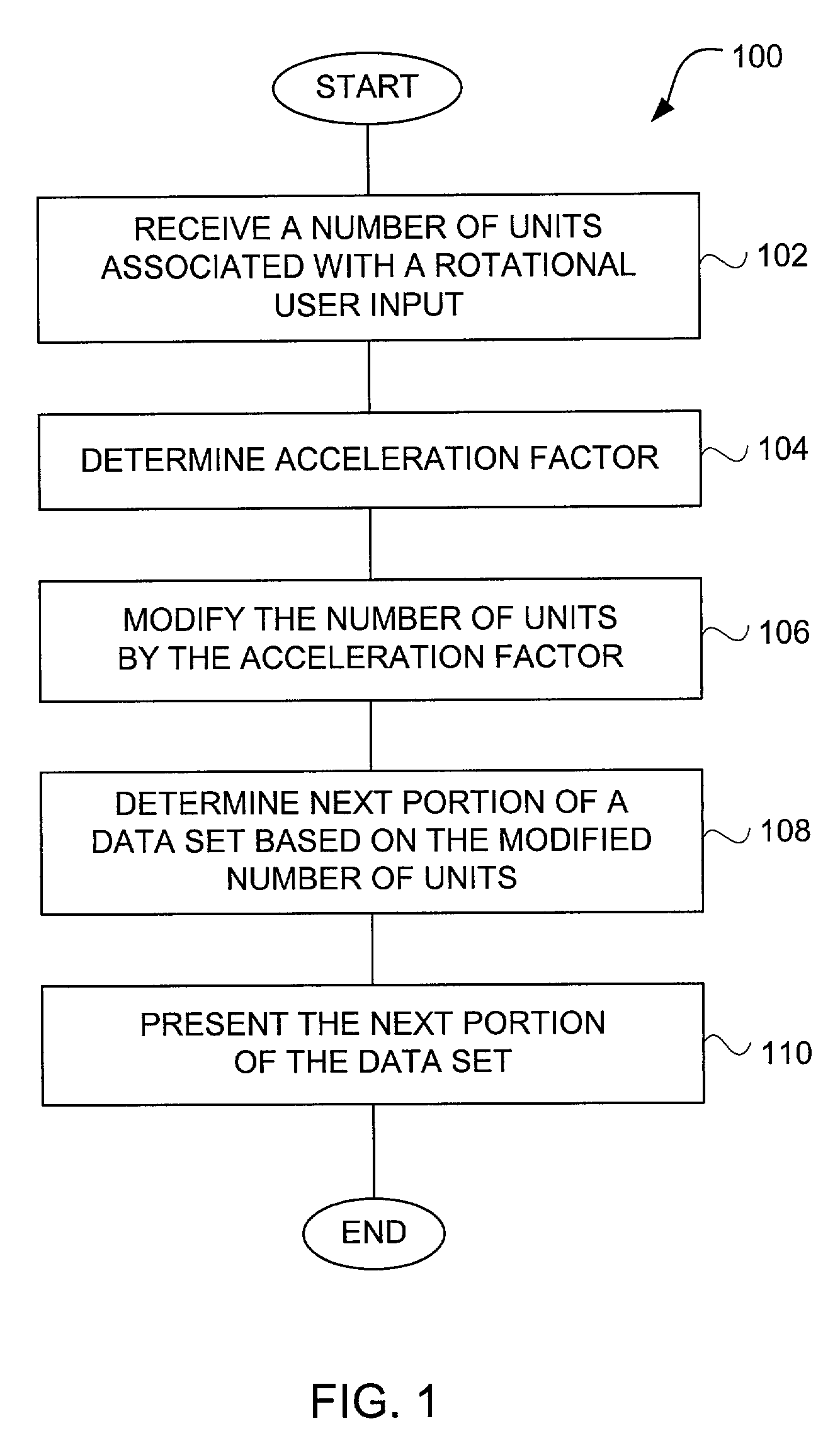
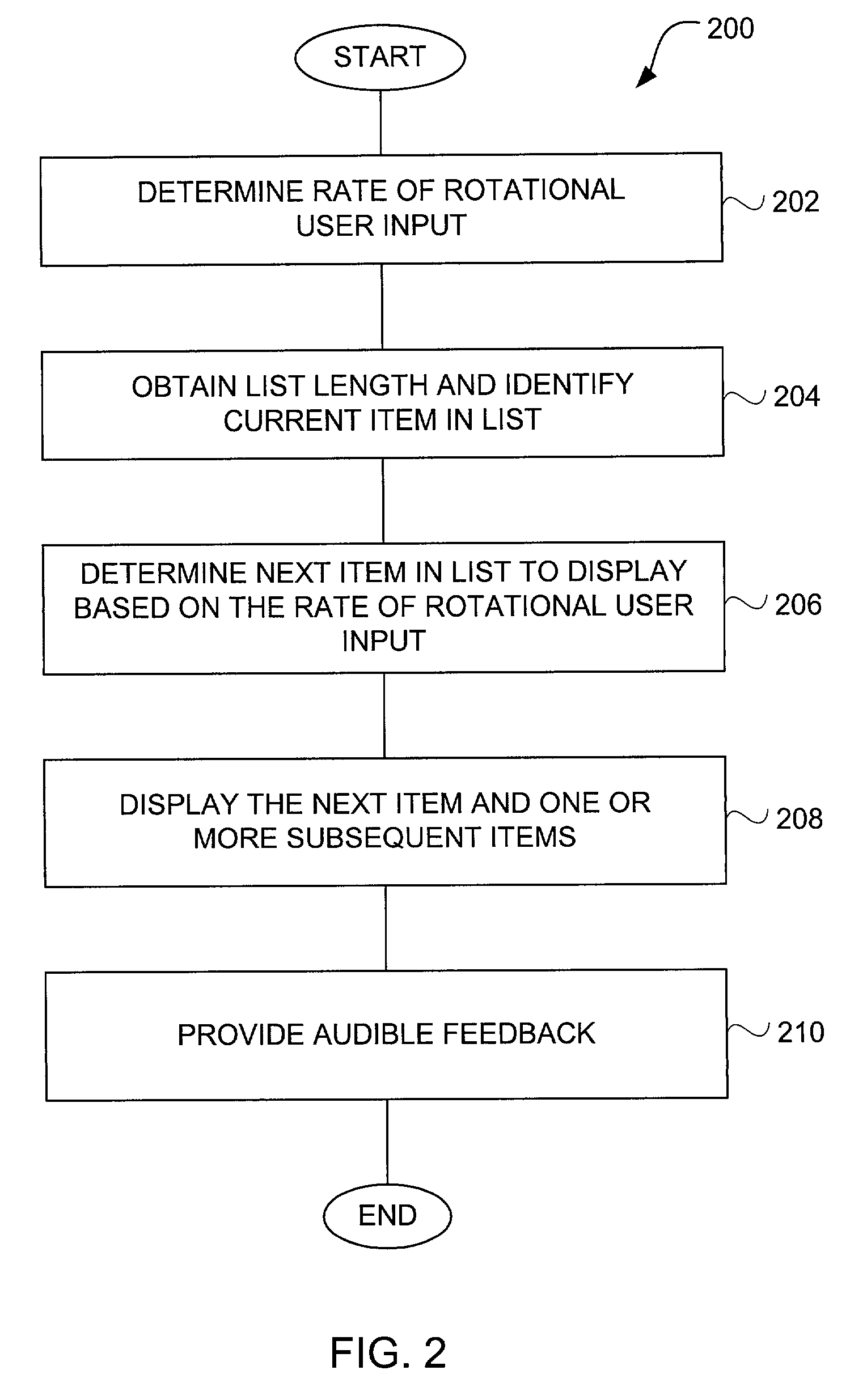
Method and apparatus for accelerated scrolling
InactiveUS7312785B2Increase scrollingFaster and with great easeInput/output for user-computer interactionCathode-ray tube indicatorsGraphicsData set
Improved approaches for users to with graphical user interfaces of computing devices are disclosed. A rotational user action supplied by a user via a user input device can provide accelerated scrolling. The accelerated nature of the scrolling enables users to scroll or traverse a lengthy data set (e.g., list of items) faster and with greater ease. The amount of acceleration provided can be performed in successive stages, and / or performed based on the speed of the rotational user action. In one embodiment, the rotational user action is transformed into linear action with respect to a graphical user interface. The resulting acceleration effect causes the linear action to be enhanced such that a lengthy data set is able to be rapidly traversed.
Owner:APPLE INC
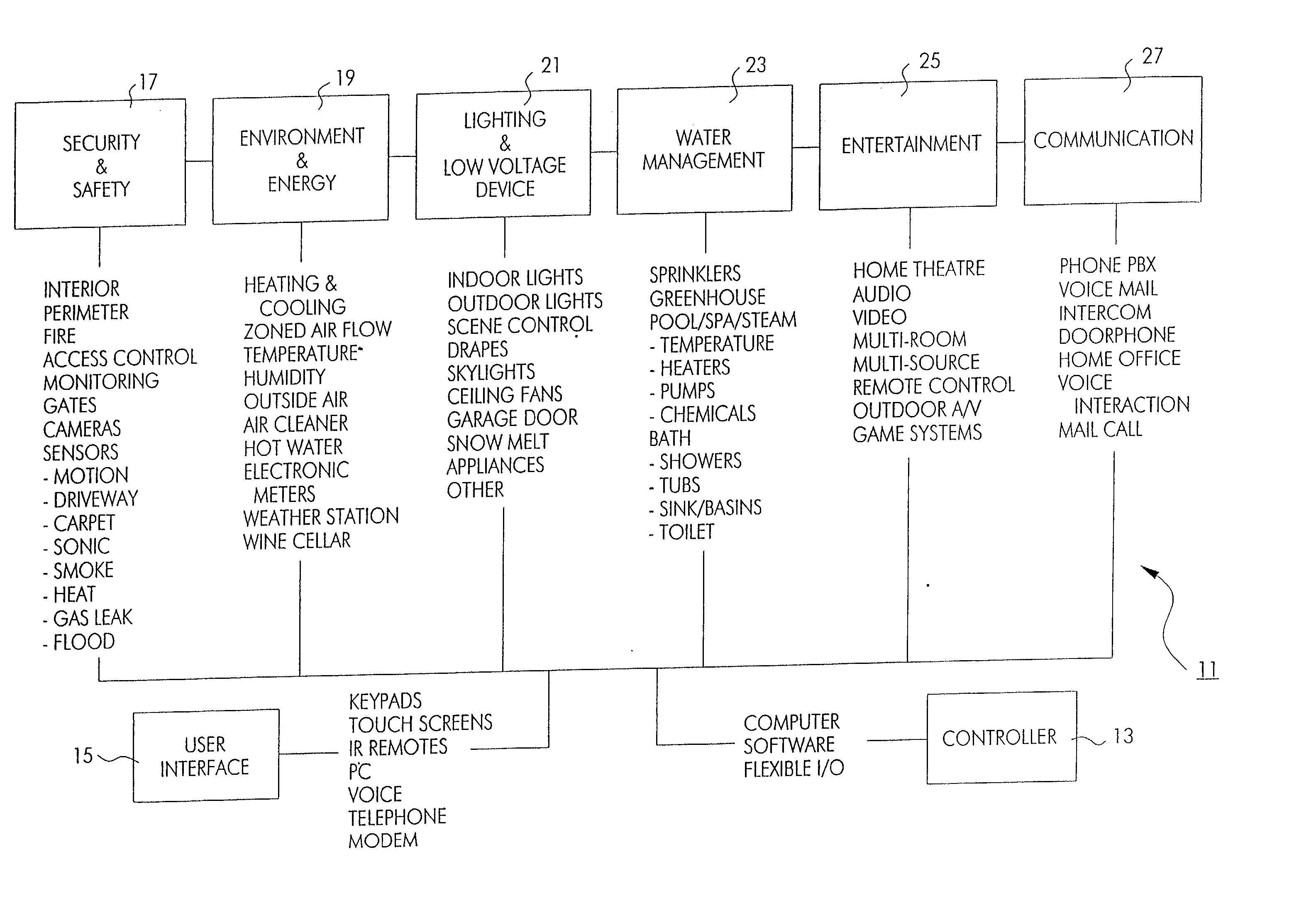
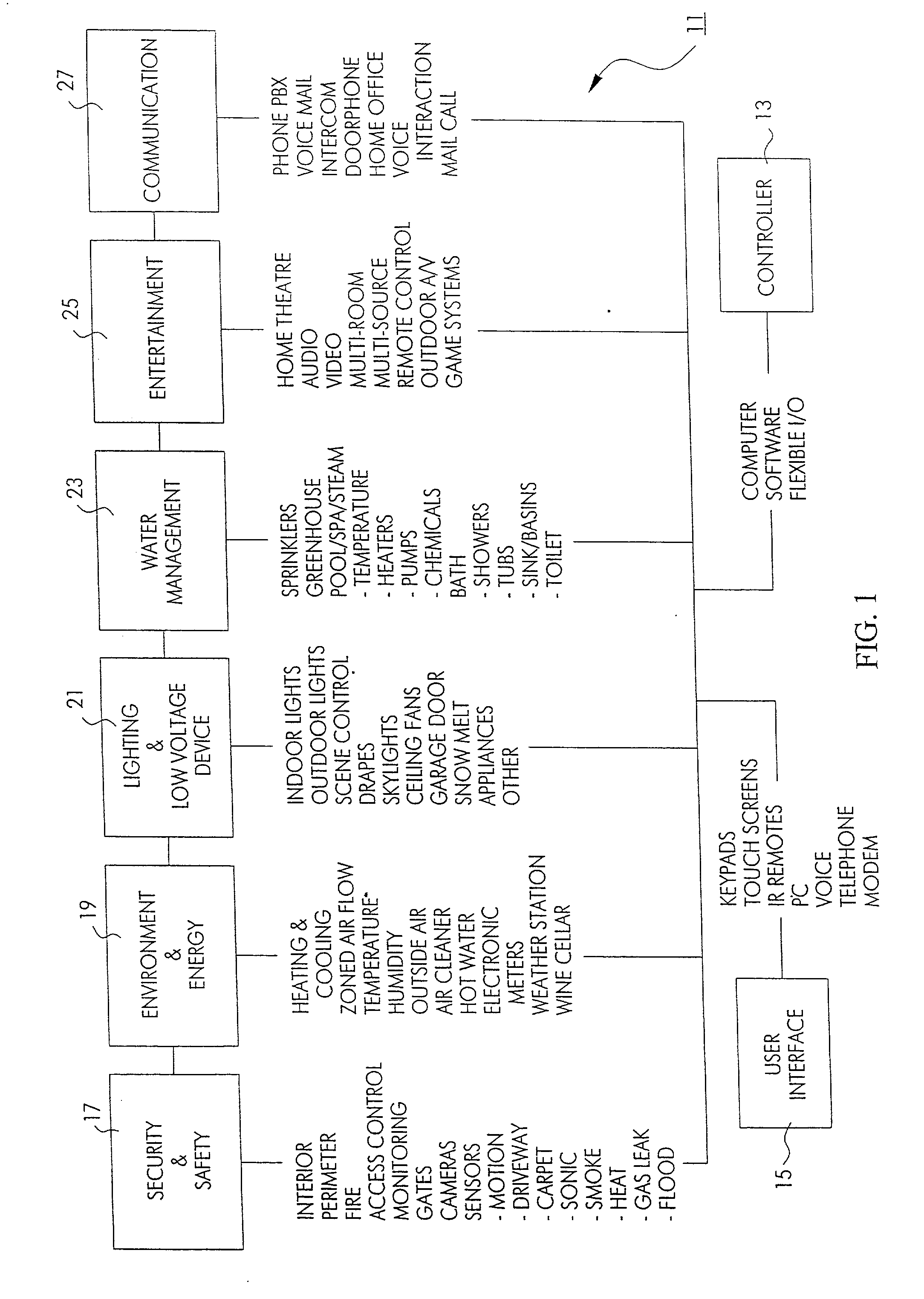
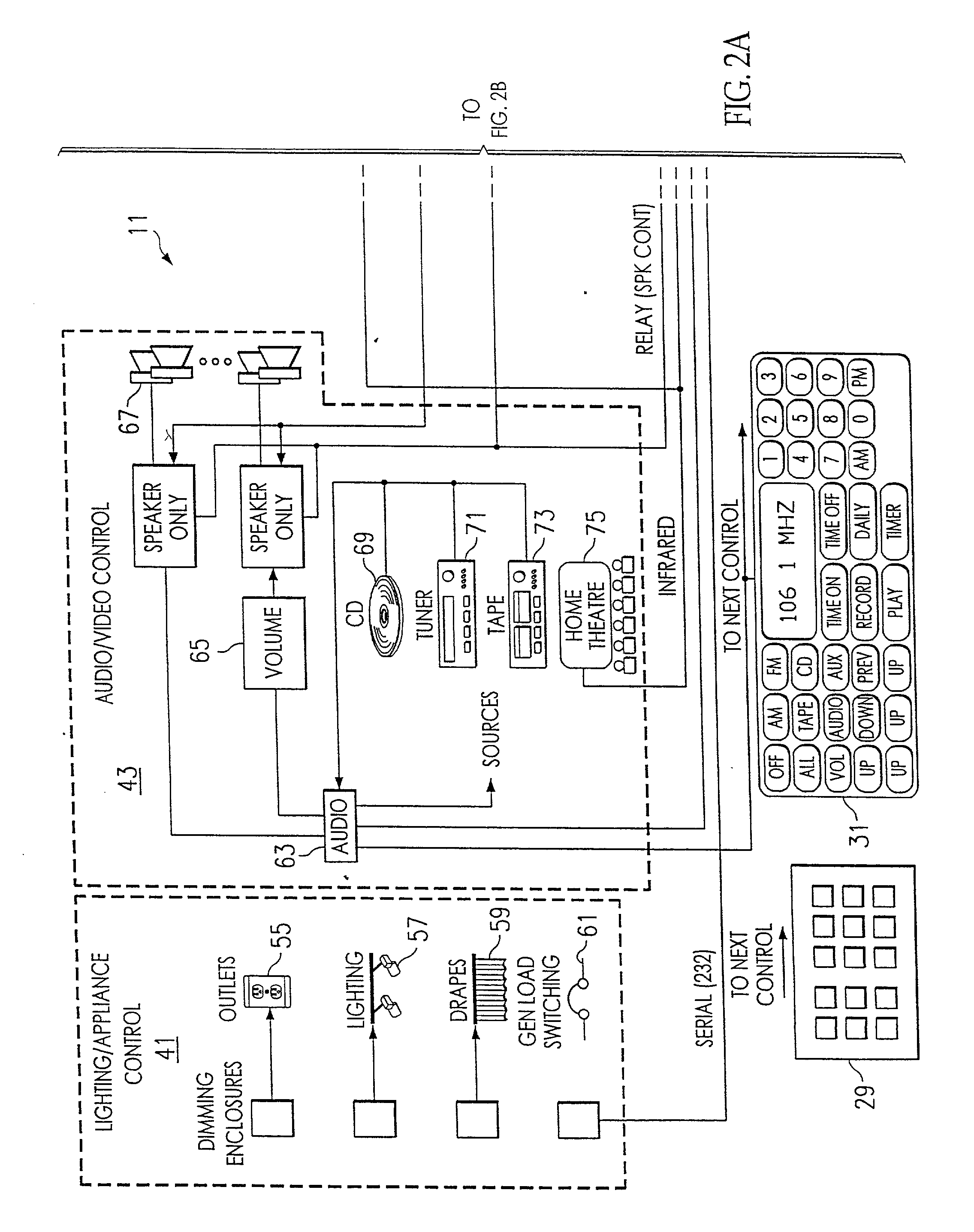
Method and apparatus for improved building automation
InactiveUS20020016639A1Large modularityCommunicationSampled-variable control systemsComputer controlModularityEngineering
The improved building automation system of the present invention is modular in the extreme. This diminishes the amount of custom programming required in order to affect control of a particular building. It allows for a relatively open architecture which can accommodate a variety of unique control applications which are scripted for a particular building. By modularizing many of the common processes utilized in the automation system, the custom programming required to control any particular building is minimized. This modularity in design allows for uniform and coordinated control over a plurality of automation subsystems which may be incompatible with one another at the device or machine level, but which can be controlled utilizing a relatively small and uniform set of "interprocess control commands" which define an interprocess control protocol which is utilized in relatively high level scripts and control applications which may be written for a particular building.
Owner:UNIDEN AMERICA
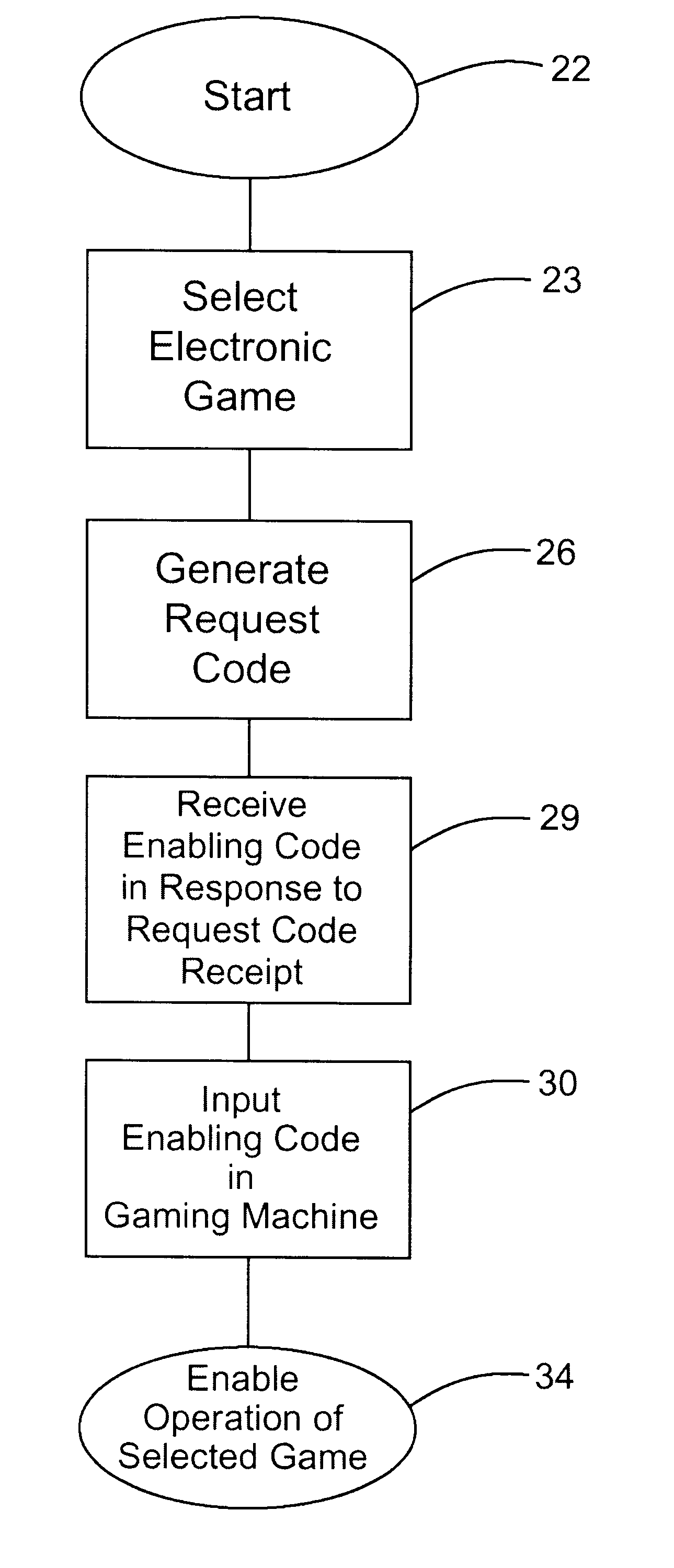
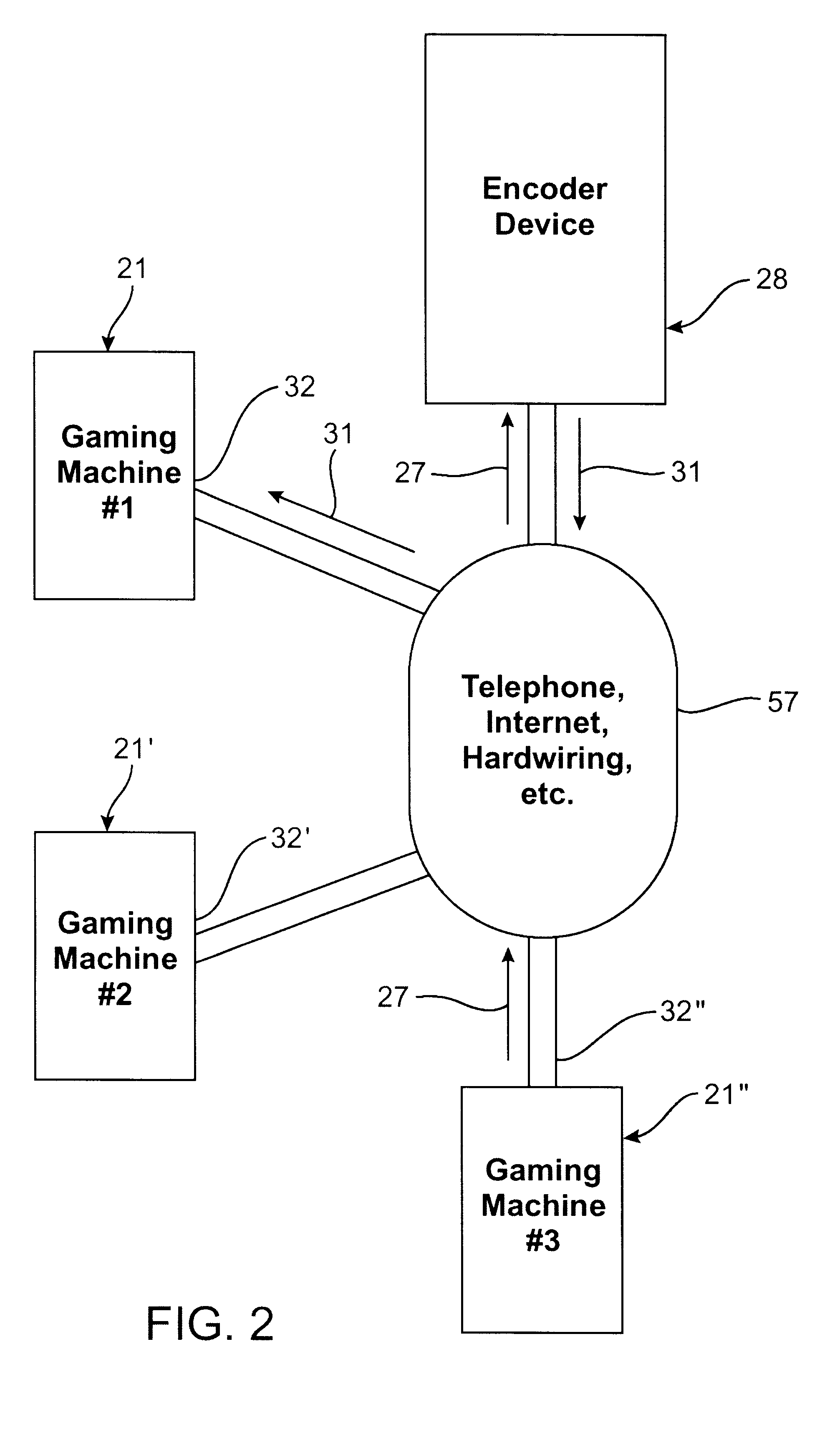
Electronic game licensing apparatus and method
InactiveUS6264561B1Board gamesApparatus for meter-controlled dispensingMultiple platformHuman–computer interaction
A use enabling method and mechanism to enable use of a disabled game resident on multiple platform gaming machines. When a gaming operator elects to enable a particular disabled game, an enabling device of generates an encrypted Request Code (27) having components identifying the specific gaming machine and the specific game to be enabled. This Request Code (27) is then communicated through a communication coupling (55) to a compatible, mating encoder device (28) operated by the licensing game vendor or game manufacture. In response, the encoder device (28) generates an encrypted Enabling Code (31) which enables use only for the selected game or games, and only in the gaming machine (21) upon which the corresponding Request Code originated. Upon inputting the corresponding Enabling Code (31) into the enabling device (32) incorporated on the particular gaming device, the selected disable game or games may be subsequently enabled for use.
Owner:IGT
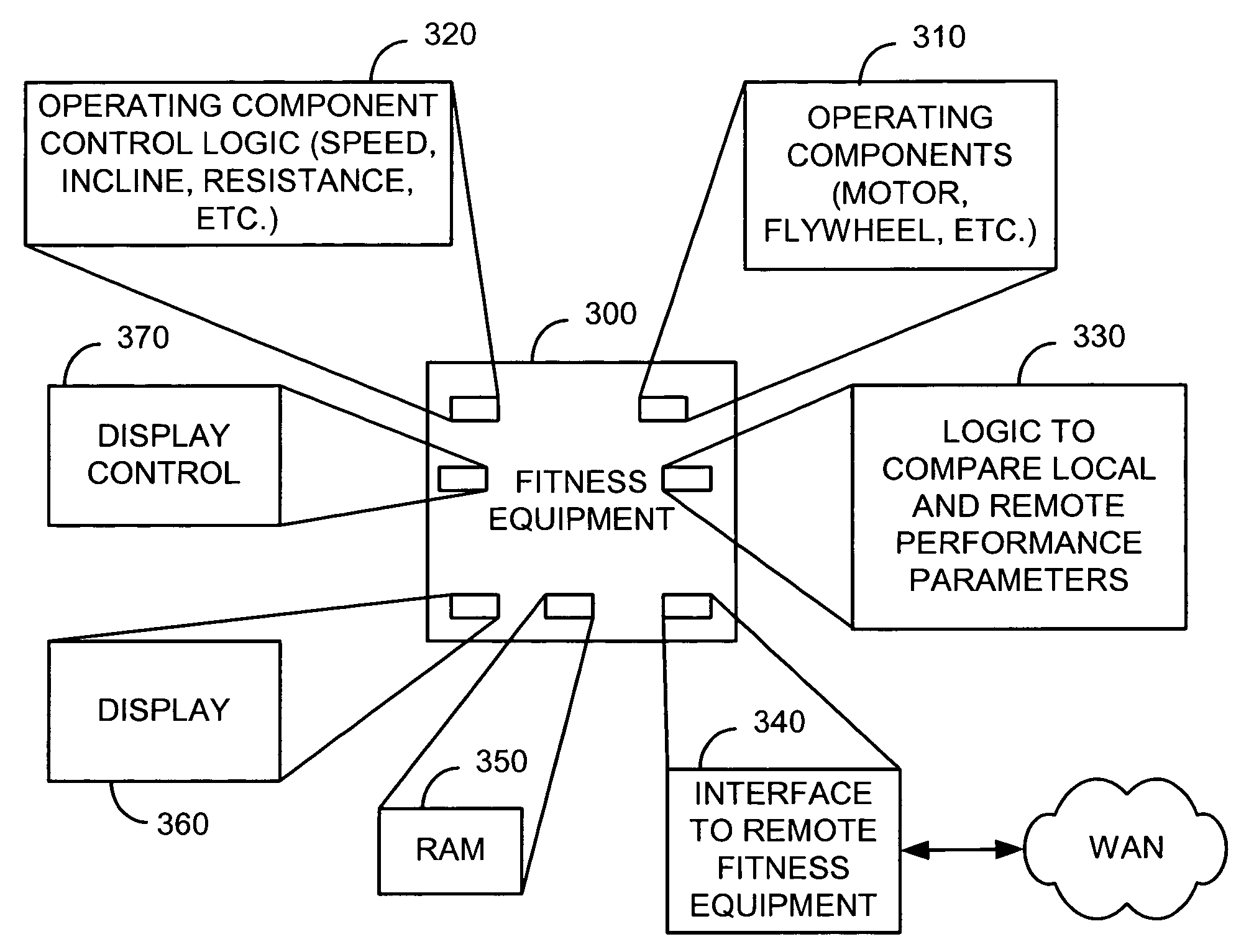
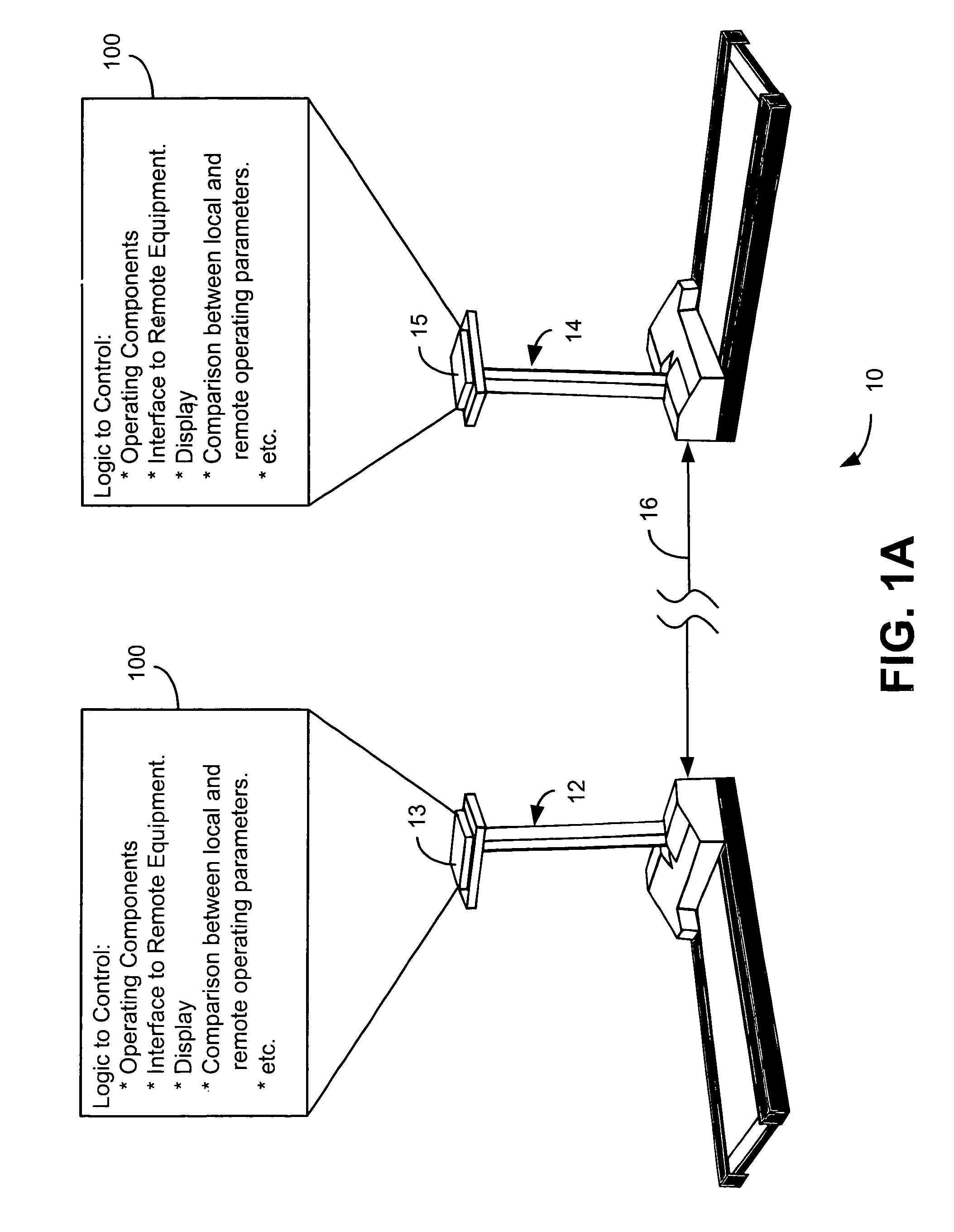
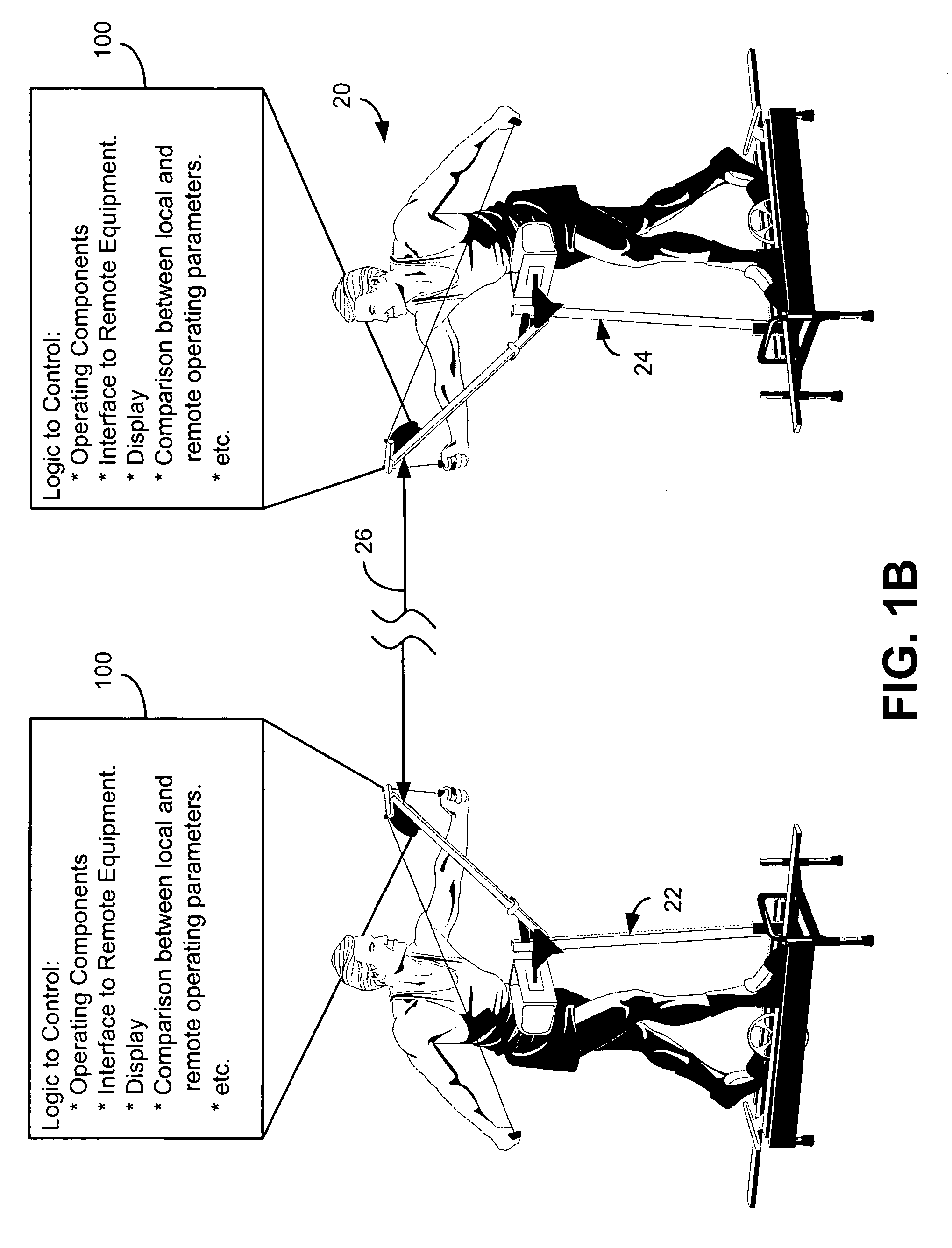
Interactive fitness equipment
InactiveUS6902513B1Therapy exerciseInput/output processes for data processingCommunication interfaceSimulation
The present invention is generally directed to a computerized fitness equipment that is designed to simulate, emulate, or implement actual race conditions with other users. An exemplar fitness equipment includes at least one operating component and sensors to monitor performance parameters of the at least one operating component (such as speed of movement). A display is also provided, along with logic to provide a visual display of a user's performance (as measured through the first performance parameters). In one embodiment, a communication interface is provided to communicate the first performance parameters to at least one remote, similarly-configured, fitness equipment. Performance parameters from the remote fitness equipment are also received through the communication interface. The fitness equipment includes logic to compare the first performance parameters with performance parameters received from remote fitness equipment and display the results in a comparative fashion to the user.
Owner:VR OPTICS LLC
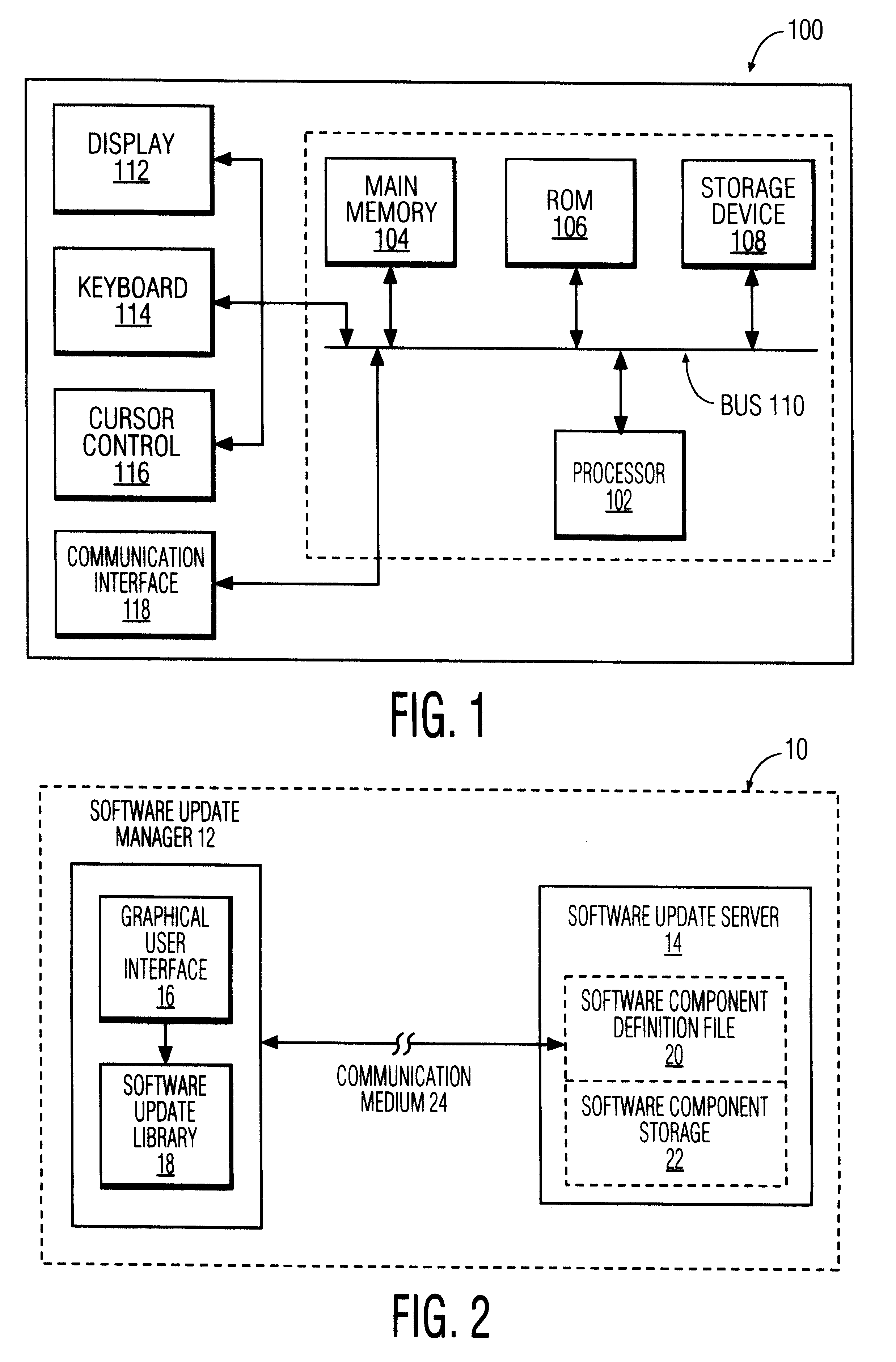
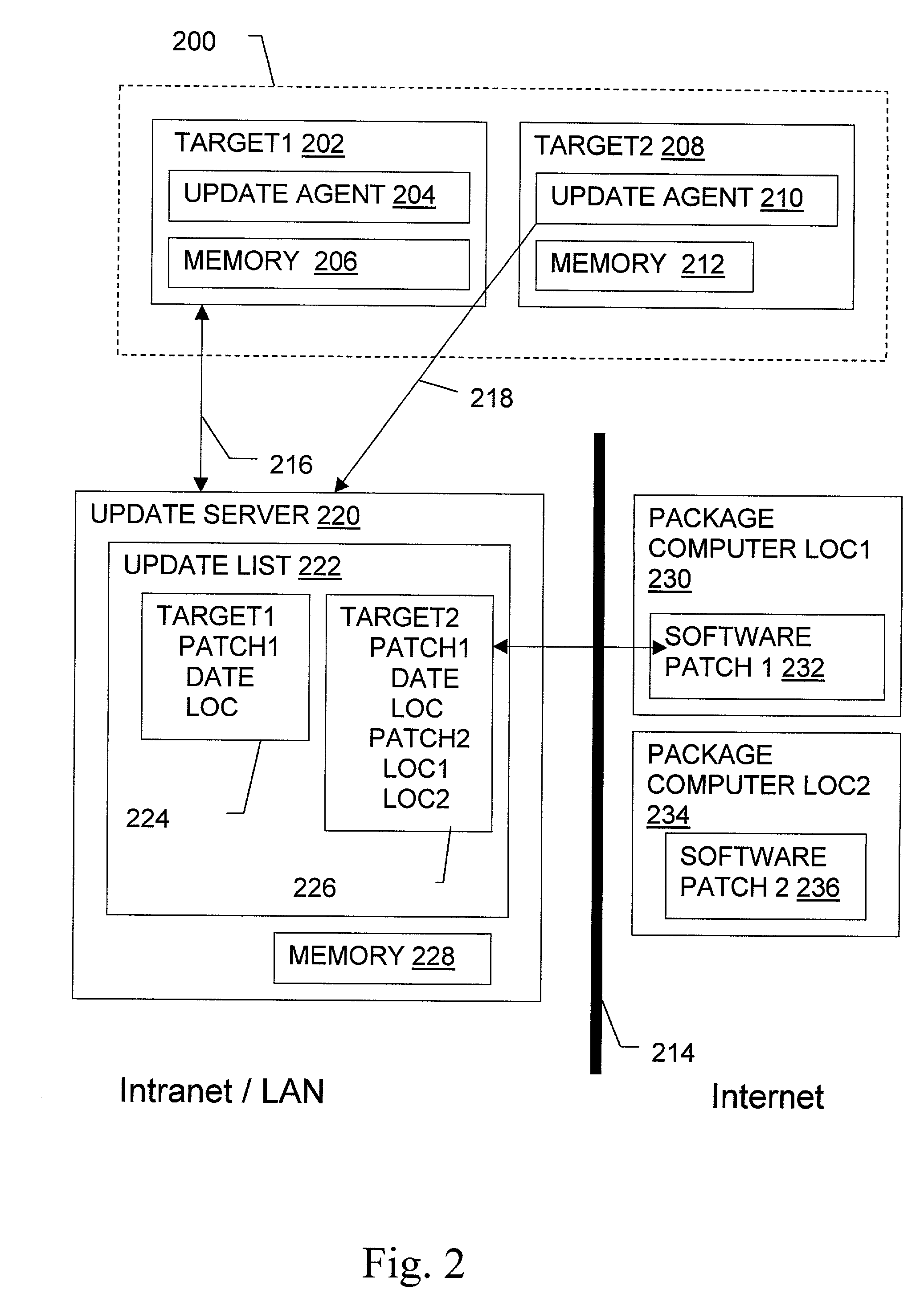
Software update manager
A method and apparatus for checking / updating existing software on a user's computer utilizes a graphical user interface (GUI). The GUI enables the user, without knowing what software exists on the computer, to download a text file from a remote server and check whether the software on the remote server is contained on the user's computer. The user can also download and automatically install a new or updated program via the GUI.
Owner:PHILIPS ELECTRONICS NORTH AMERICA
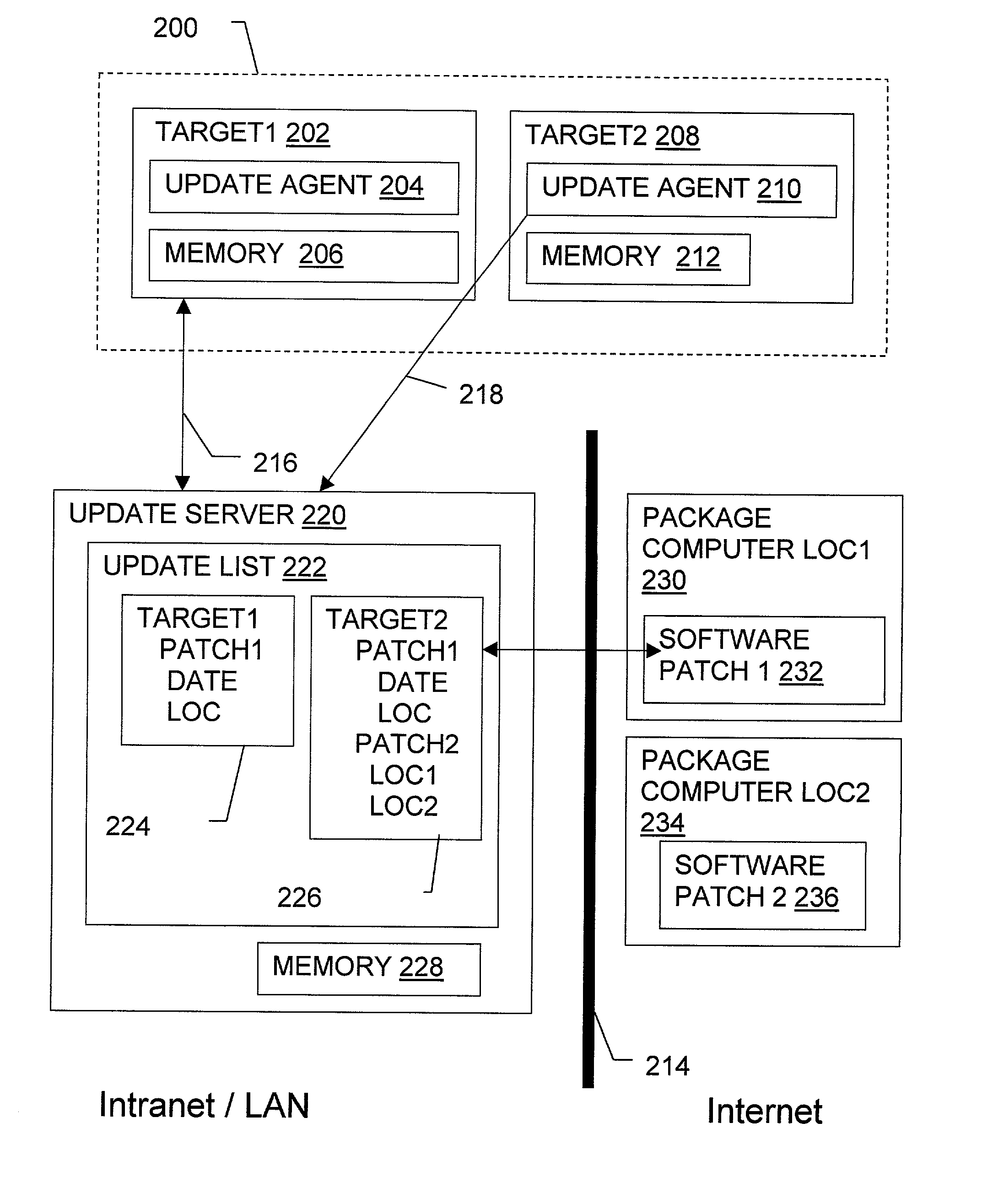
Non-invasive automatic offsite patch fingerprinting and updating system and method
InactiveUS20020100036A1Error detection/correctionDigital computer detailsSoftware updateNon invasive
Methods, systems, and configured storage media are provided for discovering software updates, discovering if a given computer can use the software update, and then updating the computers with the software as needed automatically across a network without storing the updates on an intermediate machine within the network. Furthermore, when a failure is detected, the rollout is stopped and the software can be automatically removed from those computers that already were updated. The software update can be stored originally at an address that is inaccessible through the network firewall by intermediately uploading the software update to an update computer which is not a part of the network but has access through the firewall, which is then used to distribute the update.
Owner:HEAT SOFTWARE USA
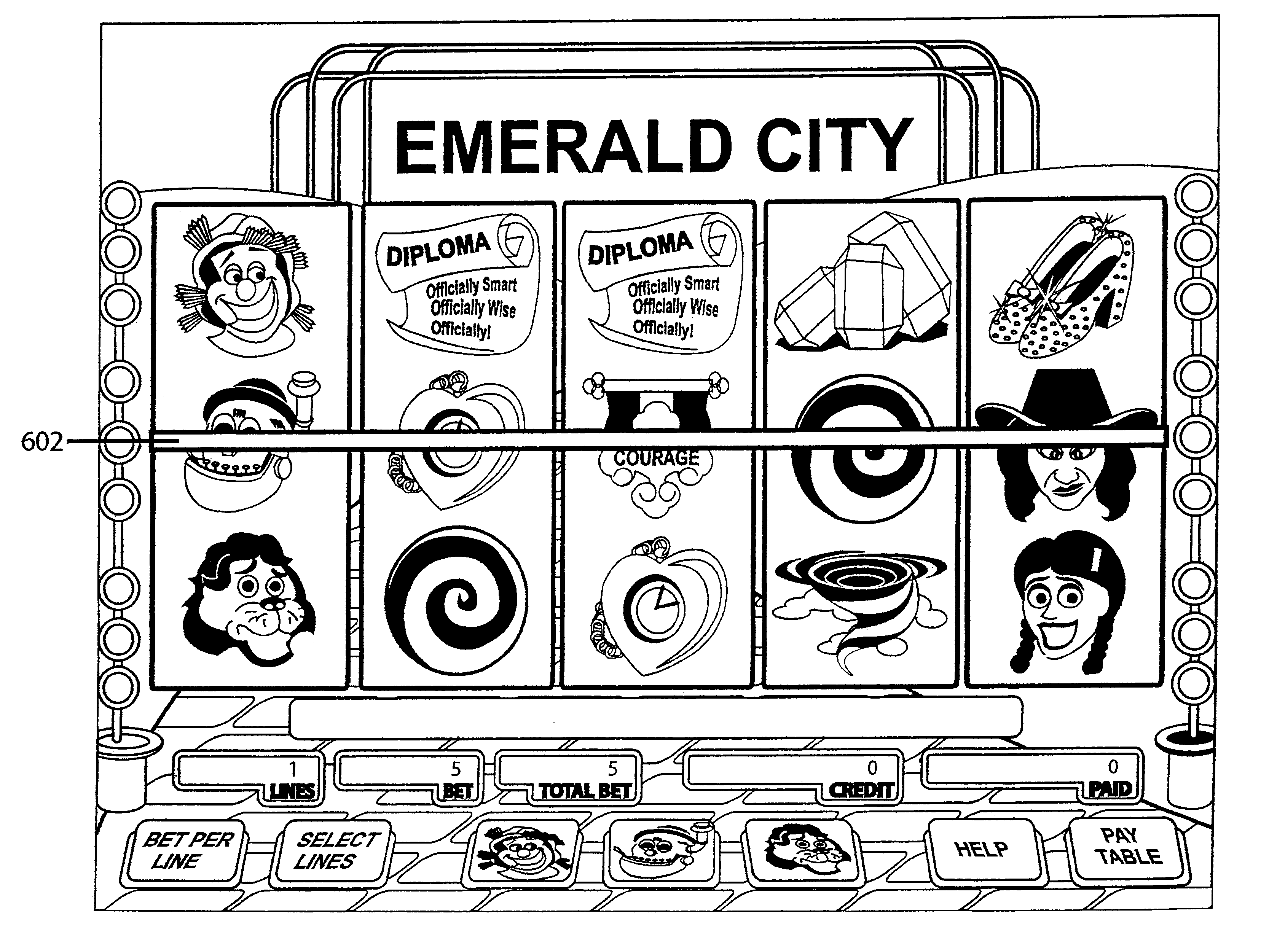
Slot machine game having a plurality of ways to designate one or more wild symbols (select-a-wild)
InactiveUS6604740B1Card gamesApparatus for meter-controlled dispensingAlgorithmComputer graphics (images)
A slot machine enables a player to select one or more symbols as wild symbols ("Select-A-Wild"). In one embodiment, the game displays three spin buttons. Each spin button is permanently associated with a symbol. All of the associated symbols have matching symbols on the reel strips. Each of the associated symbols have the same probability of appearing on the reel strips. The player selects a wild symbol by pressing a spin button. The symbol associated with the pressed spin button acts as a wild symbol for that spin. After each spin, the player receives awards for all winning combinations.
Owner:IGT
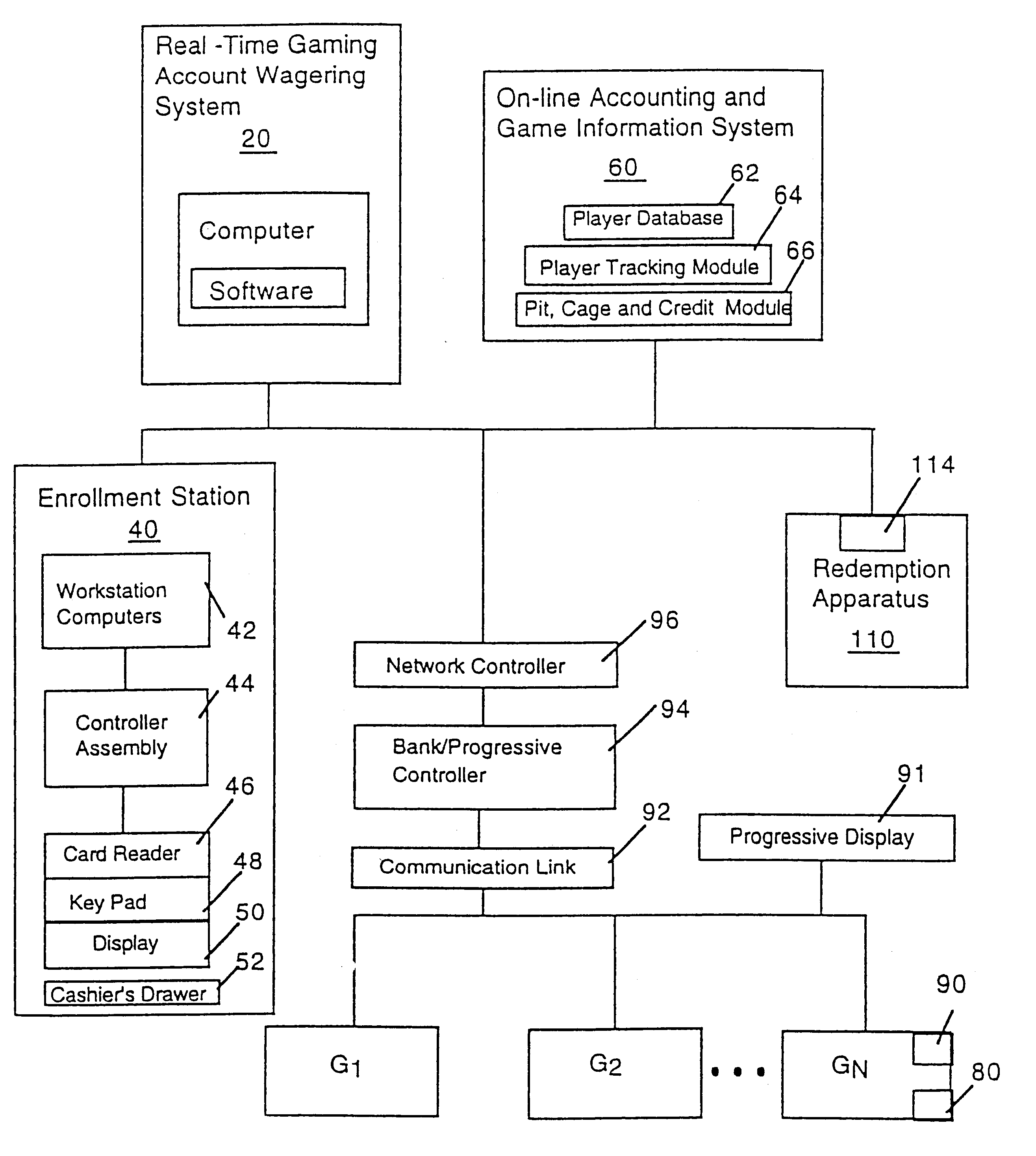
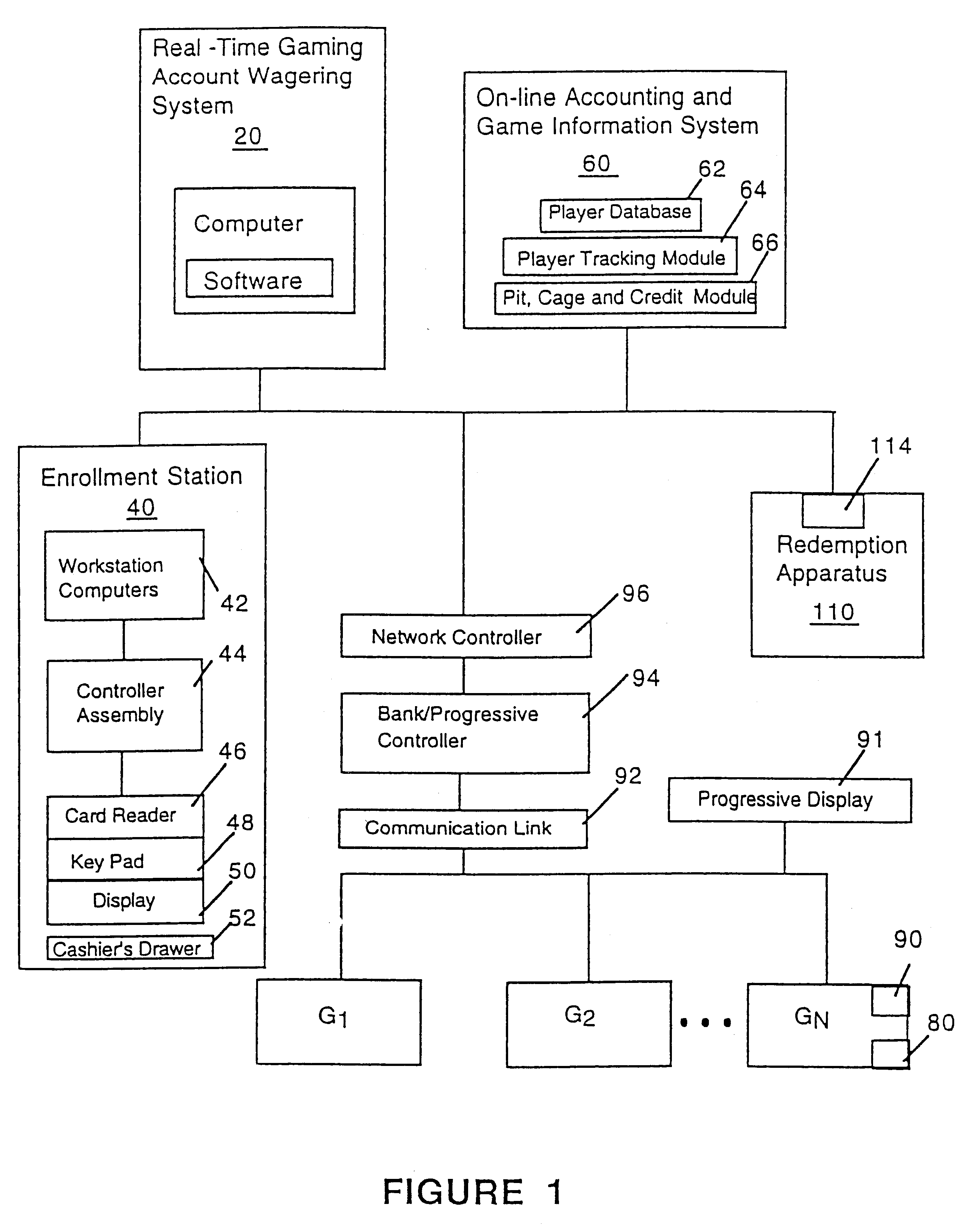
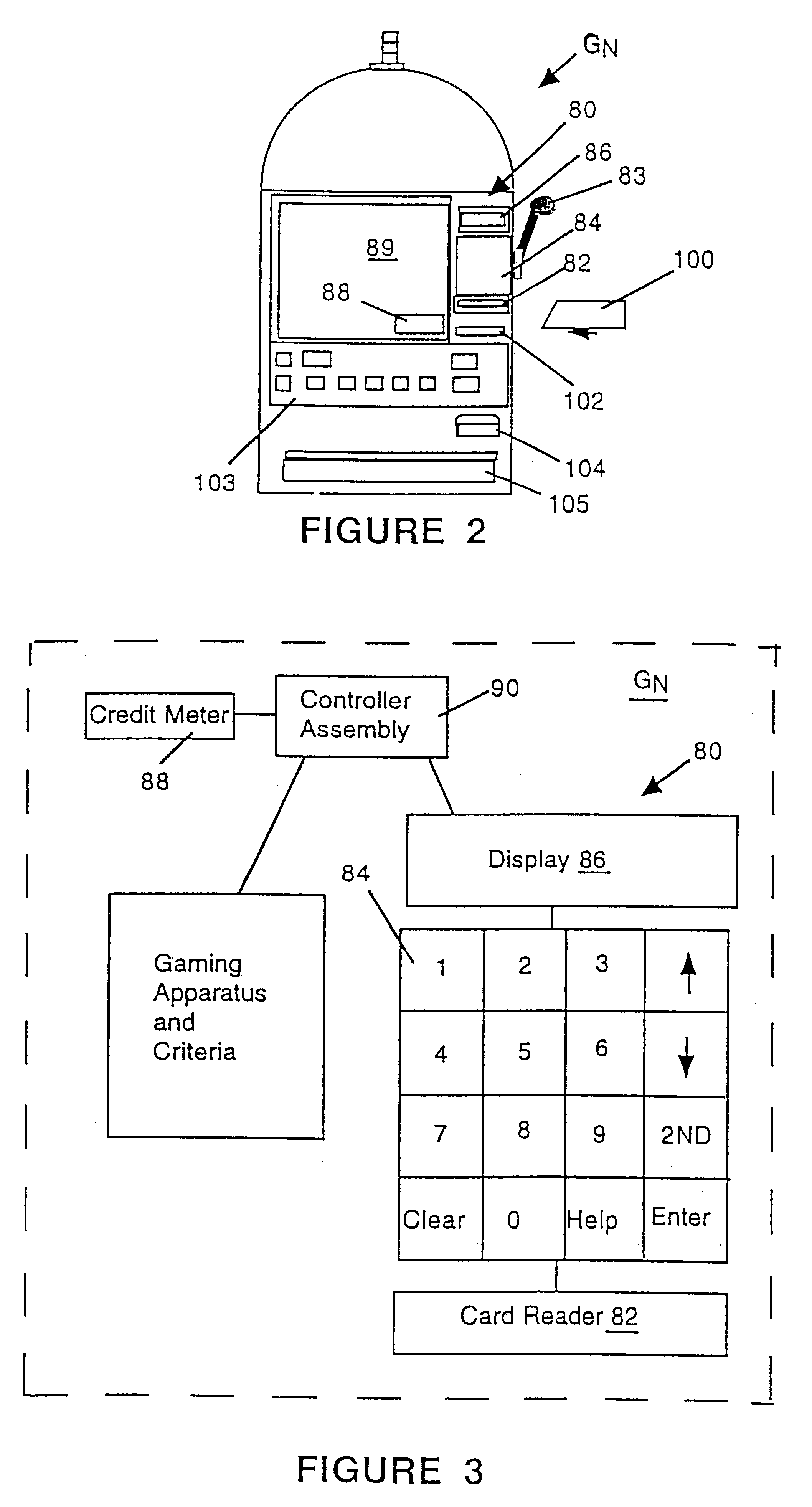
Cashless gaming system: apparatus and method
InactiveUS6511377B1Direct accessTake substantial amountApparatus for meter-controlled dispensingVideo gamesOperating systemComputer engineering
An apparatus and method for cashless gaming wherein a player can access credits via a pin activated keypad located on the gaming machine. Real-time accounting allows the player to redeem credits and secure perquisites as a function of patronage.
Owner:CASINO DATA SYST
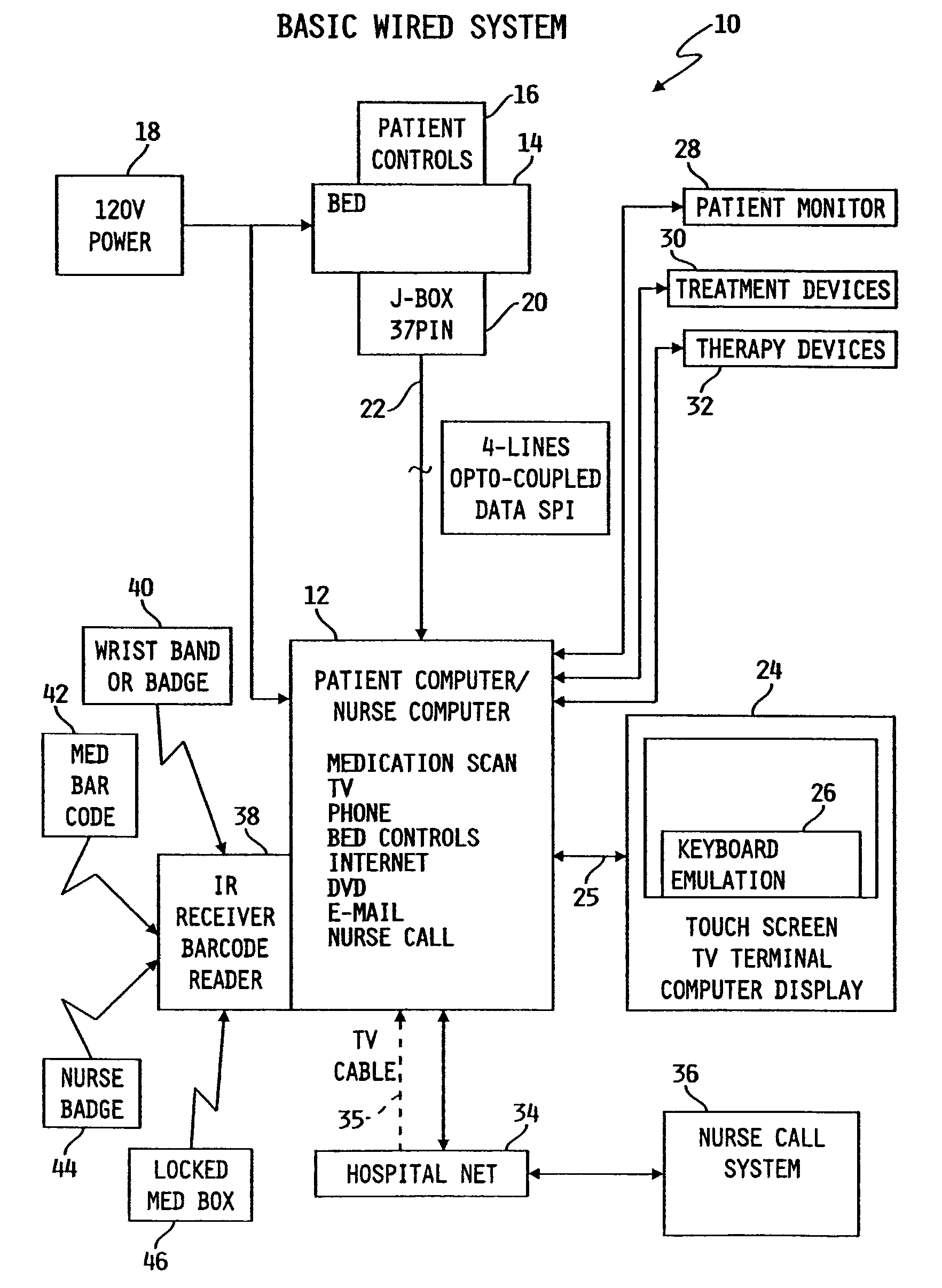
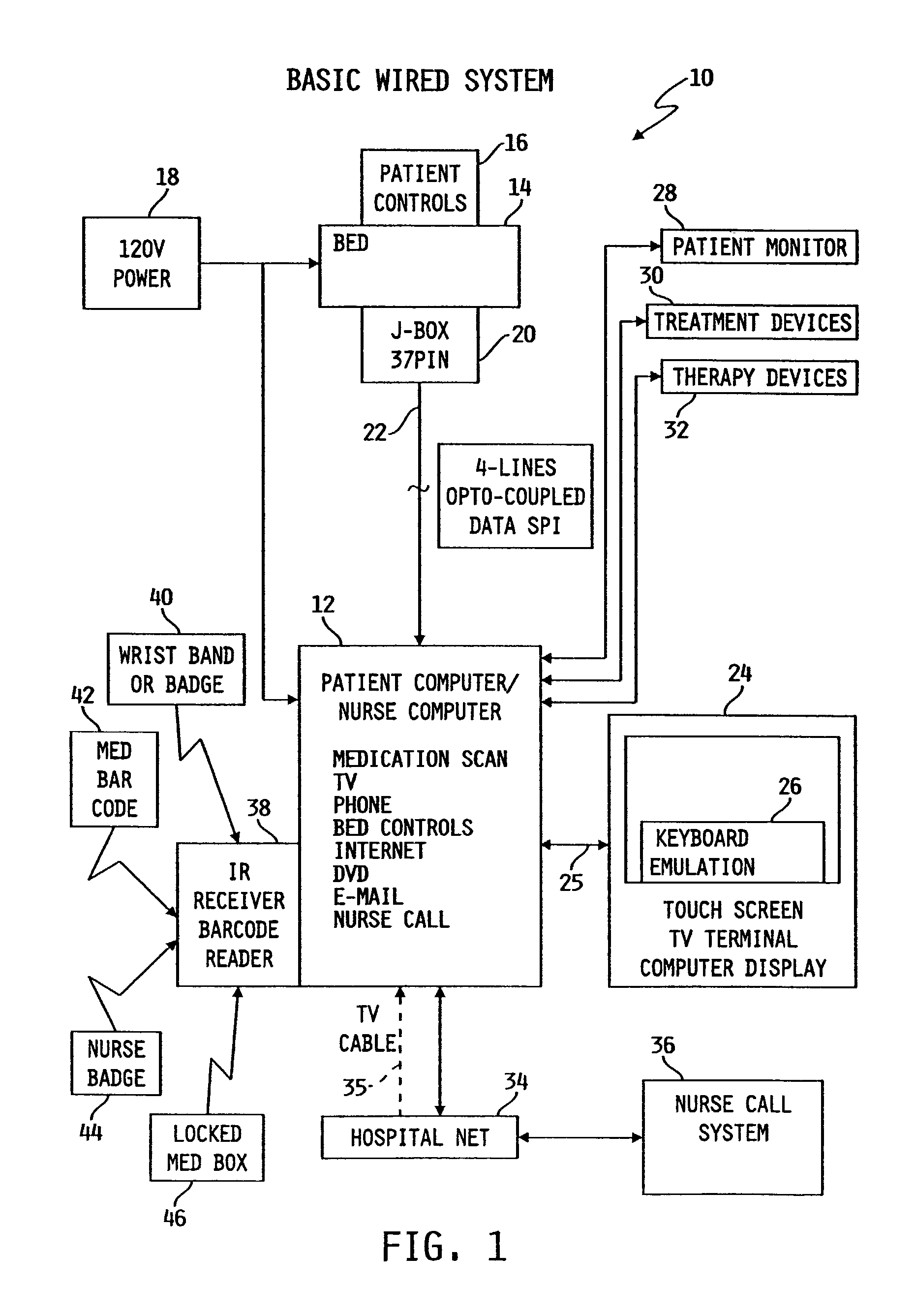
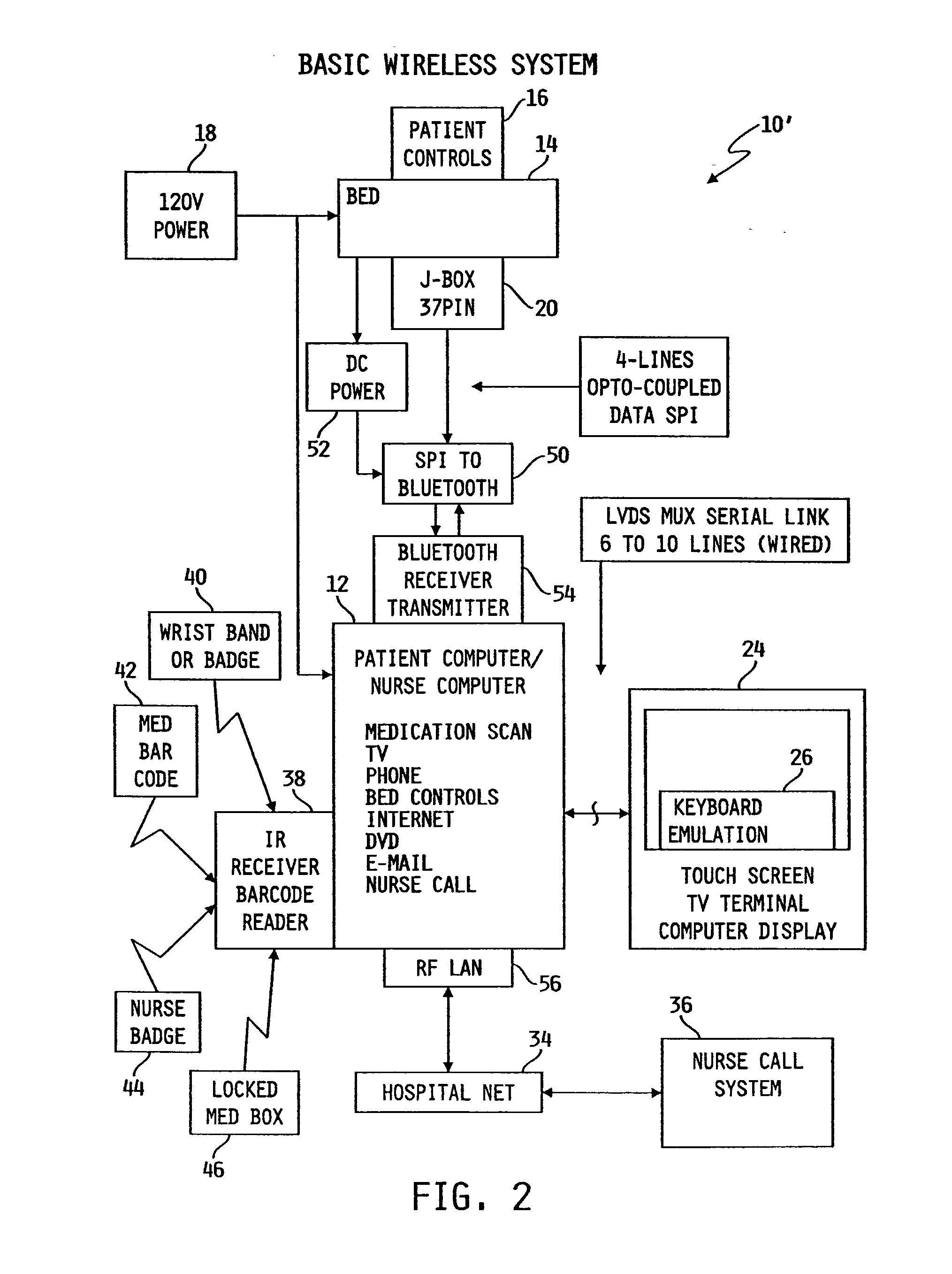
Patient point-of-care computer system
InactiveUS7154397B2Easy inputConvenient careTelevision system detailsDigital data processing detailsPoint of careDisplay device
A point-of-care computer system includes a display positioned in a point-of-care location, a computer coupled to the display, and a network coupled to the computer to enable the computer to access information stored in a remote location.
Owner:HILL ROM SERVICES
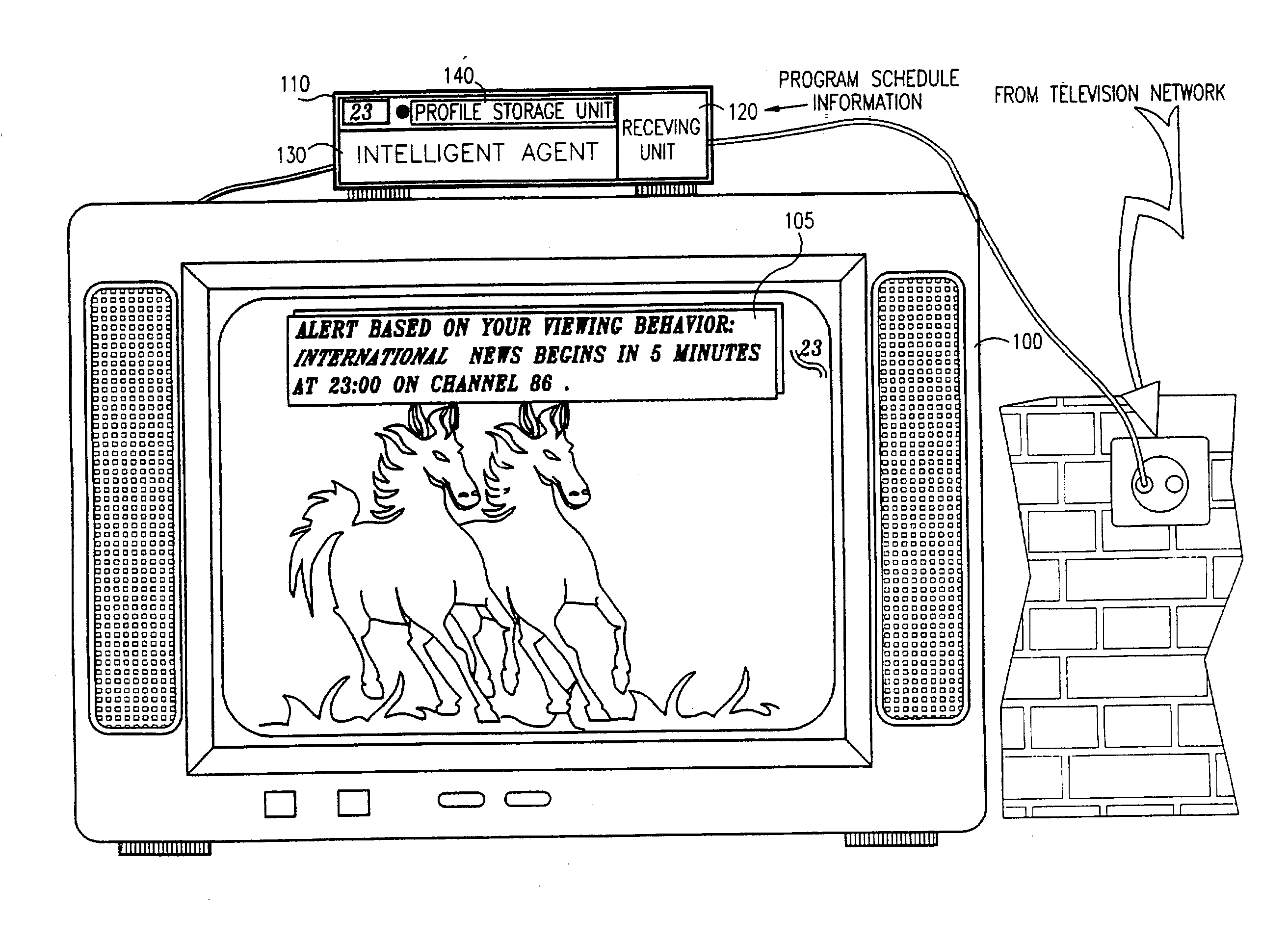
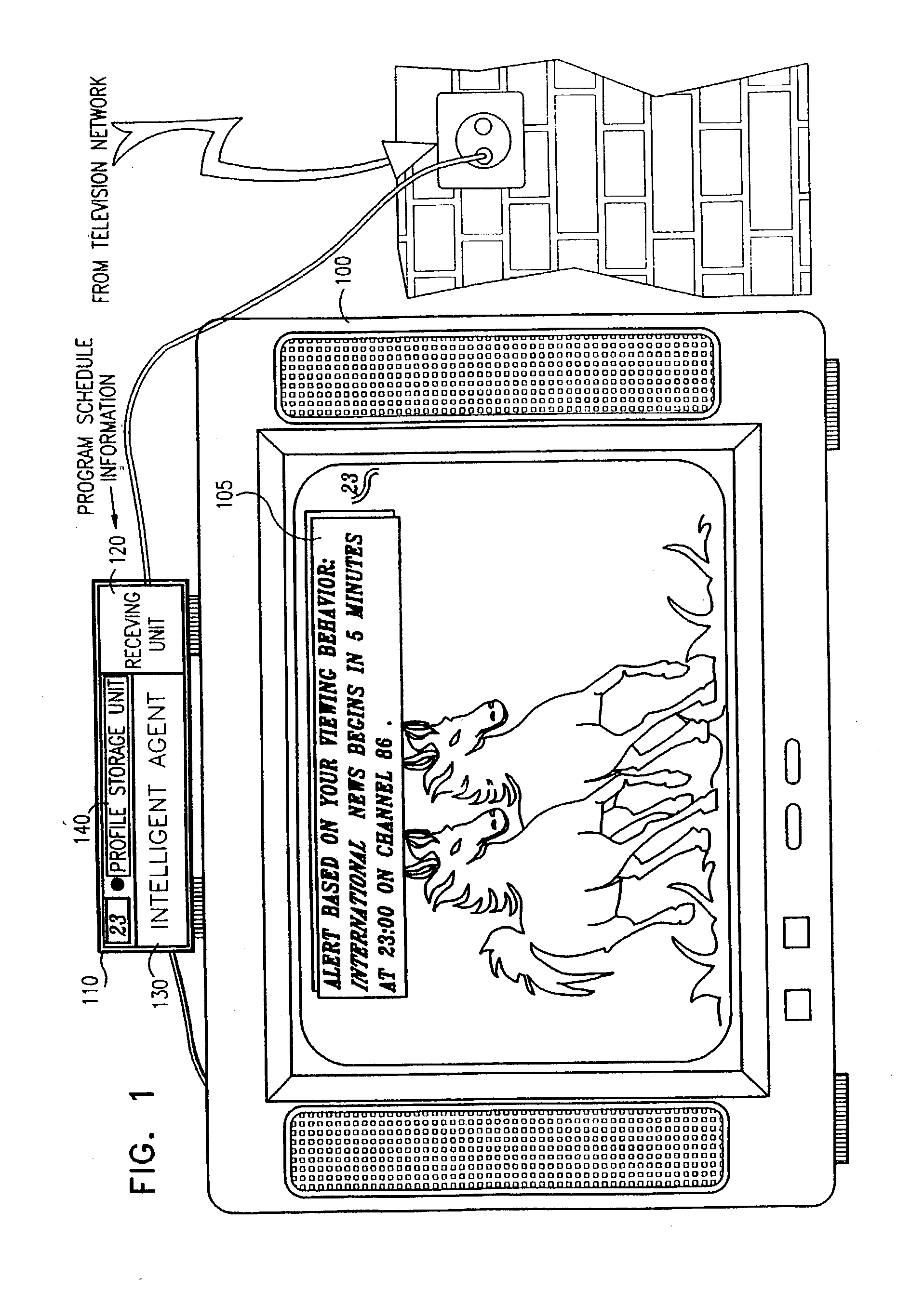
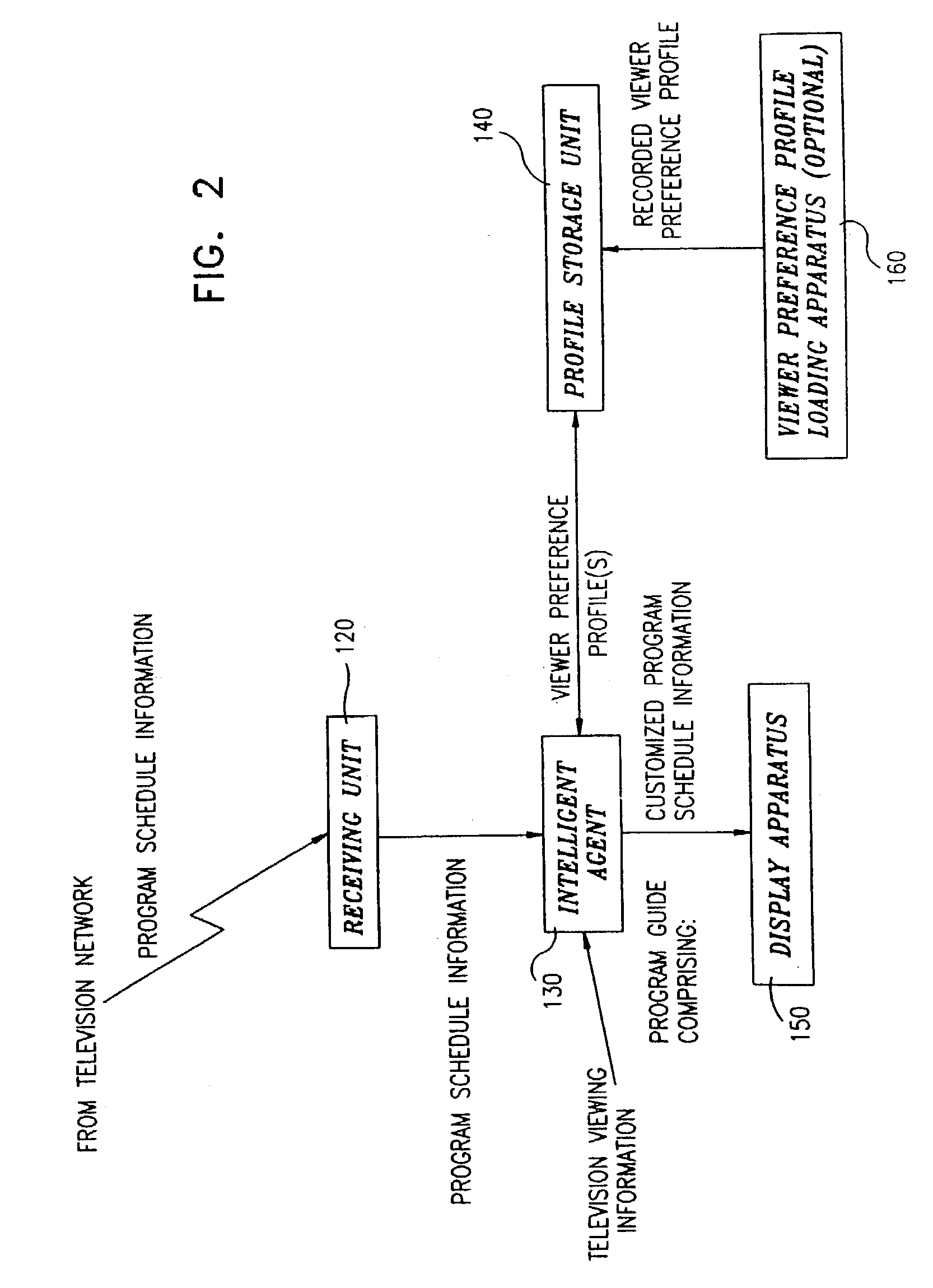
Advanced television system
InactiveUS20030088872A1Easy to switchSimplified user interfaceTelevision system detailsAnalogue secracy/subscription systemsTelevision systemComputer hardware
In a digital television recording method, programs are selected for recording based on analysis of program schedule information, user preferences, and the priority of previously recorded programs if there is insufficient memory.
Owner:CISCO TECH INC
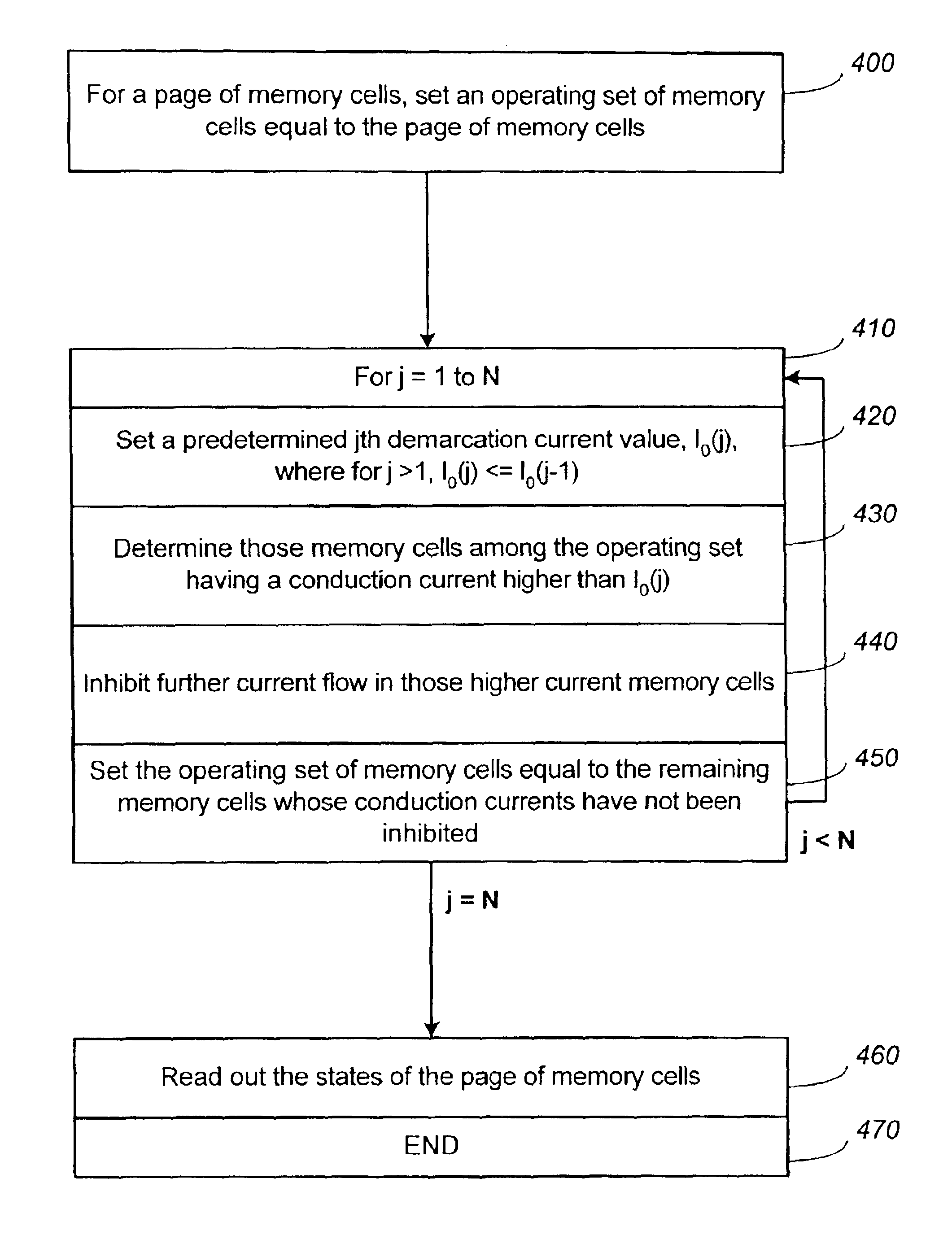
Non-volatile memory and method with reduced neighboring field errors
InactiveUS6987693B2Large capacityImprove performanceRead-only memoriesDigital storageNon-volatile memoryParallel programing
A memory device and a method thereof allow programming and sensing a plurality of memory cells in parallel in order to minimize errors caused by coupling from fields of neighboring cells and to improve performance. The memory device and method have the plurality of memory cells linked by the same word line and a read / write circuit is coupled to each memory cells in a contiguous manner. Thus, a memory cell and its neighbors are programmed together and the field environment for each memory cell relative to its neighbors during programming and subsequent reading is less varying. This improves performance and reduces errors caused by coupling from fields of neighboring cells, as compared to conventional architectures and methods in which cells on even columns are programmed independently of cells in odd columns.
Owner:SANDISK TECH LLC
System and method for securing sensitive data
ActiveUS20140344943A1Digital data processing detailsUser identity/authority verificationSoftware engineeringOperating system
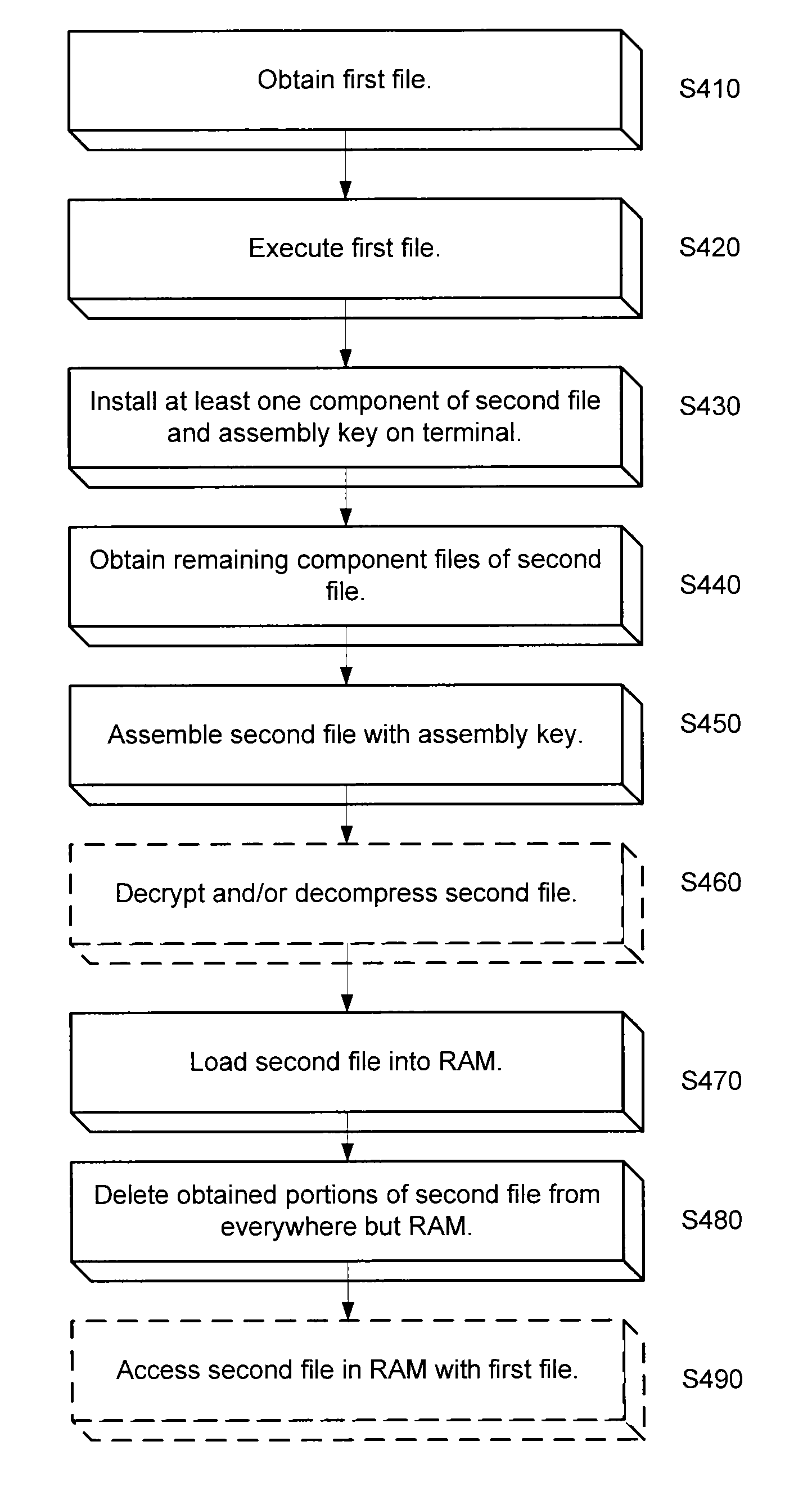
An approach is provided for securing data in a technical environment. In one embodiment, a processor obtains a first file, which when executed installs a first portion of a second file and an assembly key to assemble the second file. The processor executes this first file and then obtains the second portion of the second file. The processor assembles the second file using the first portion, the second portion, and the assembly key.
Owner:HAND HELD PRODS
Practical platform for high risk applications
InactiveUS20070180509A1Safe and reliable and easy to use practicalIncrease system complexityDigital data processing detailsUser identity/authority verificationSystem integrationComputer hardware
The present invention is a portable device that a computer can boot from, containing a prefabricated independent operating system environment which is engineered from the ground up to prioritize security while maximizing usability, in order to provide a safe, reliable and easy to use practical platform for high risk applications. An embodiment of the present invention may temporarily transform an ordinary computer into a naturally inexpensive logical appliance which encapsulates a turn-key functional solution within the digital equivalent of a military grade security fortress. This allows existing hardware to be conveniently leveraged to provide a self contained system which does not depend on the on-site labor of rare and expensive system integration and security experts.
Owner:SWARTZ ALON R +1
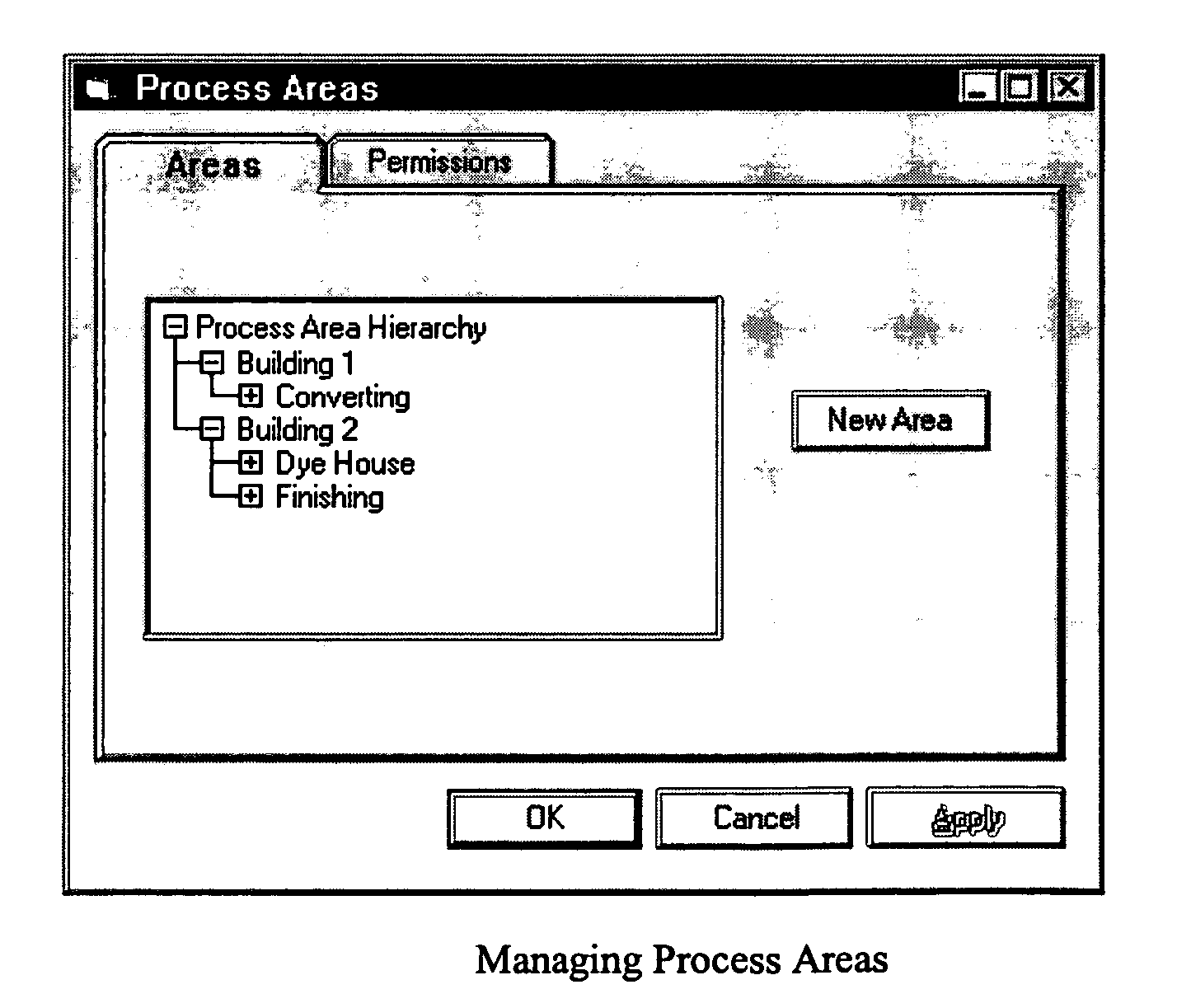
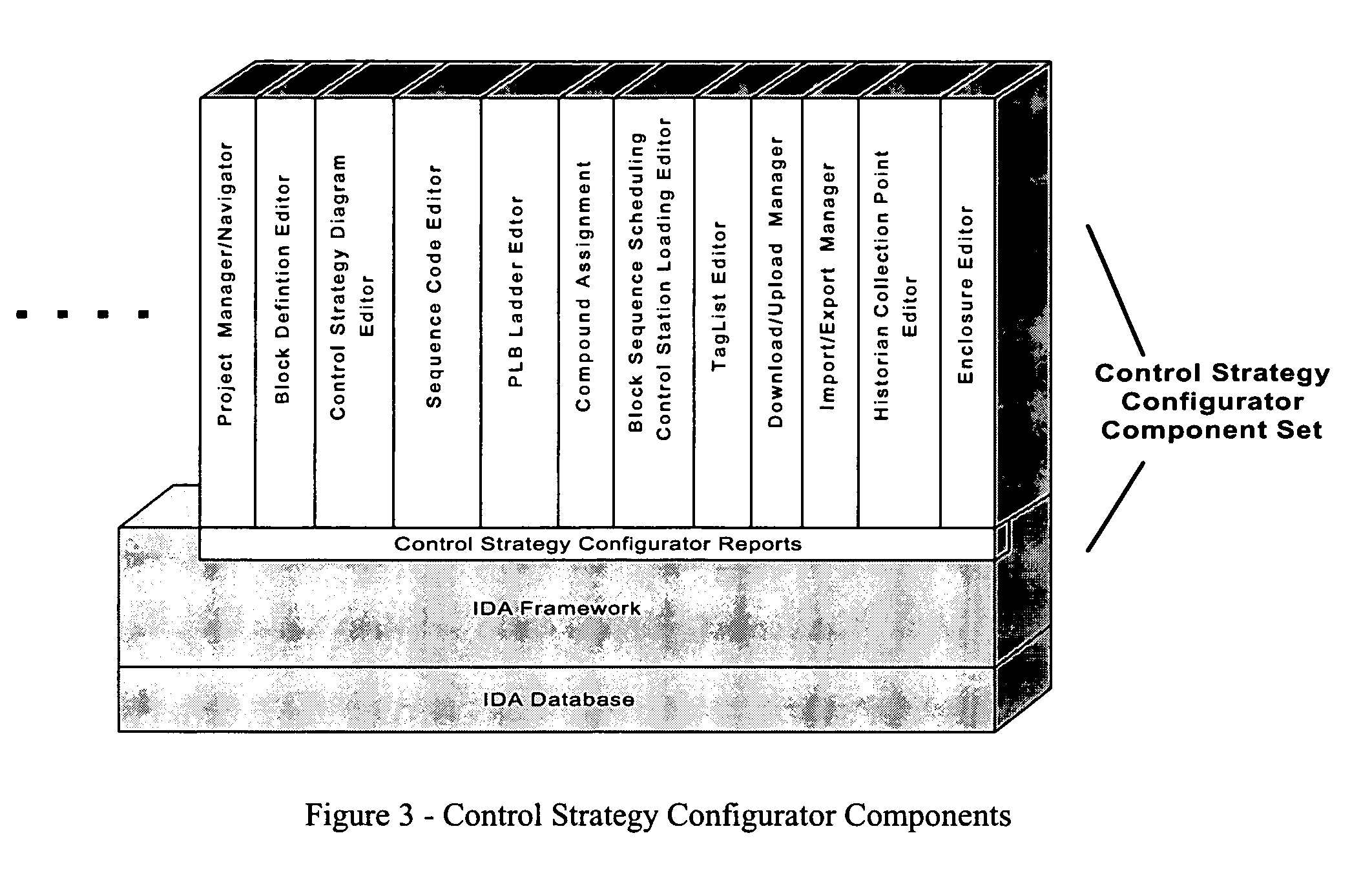
Methods and apparatus for control configuration with versioning, security, composite blocks, edit selection, object swapping, formulaic values and other aspects
InactiveUS7272815B1OptimizationOptimize system configurationData processing applicationsDigital data processing detailsGraphical user interfaceComposite object
Methods and apparatus for configuring process, environmental, industrial and other control systems generate and / or utilize models representing configurations of control systems and / or the systems controlled by them. Records of changes to the models or the configurations represented by them are maintained, thereby, for example, providing bases for determining current states, prior states and histories of changes. Objects in the model have characteristics, such as an object type characteristic and an area characteristic. Users can have corresponding permissions. A security mechanism apparatus controls access by users to the objects. Composite objects are defined by definition objects and are displayed in encapsulated or expanded formats. Objects can include an edit control type identifier that determines how they are presented for editing. Functionality responds to user commands by transferring characteristics of a first object depicted by the graphical user interface to a second object. Configuration-time formulas contained objects are evaluated to constants prior to downloading to the control system.
Owner:SCHNEIDER ELECTRIC SYST USA INC
Extensible information system
InactiveUS20020184401A1Determining correlationEasy to determineDatabase management systemsInterprogram communicationInformation systemApplication software
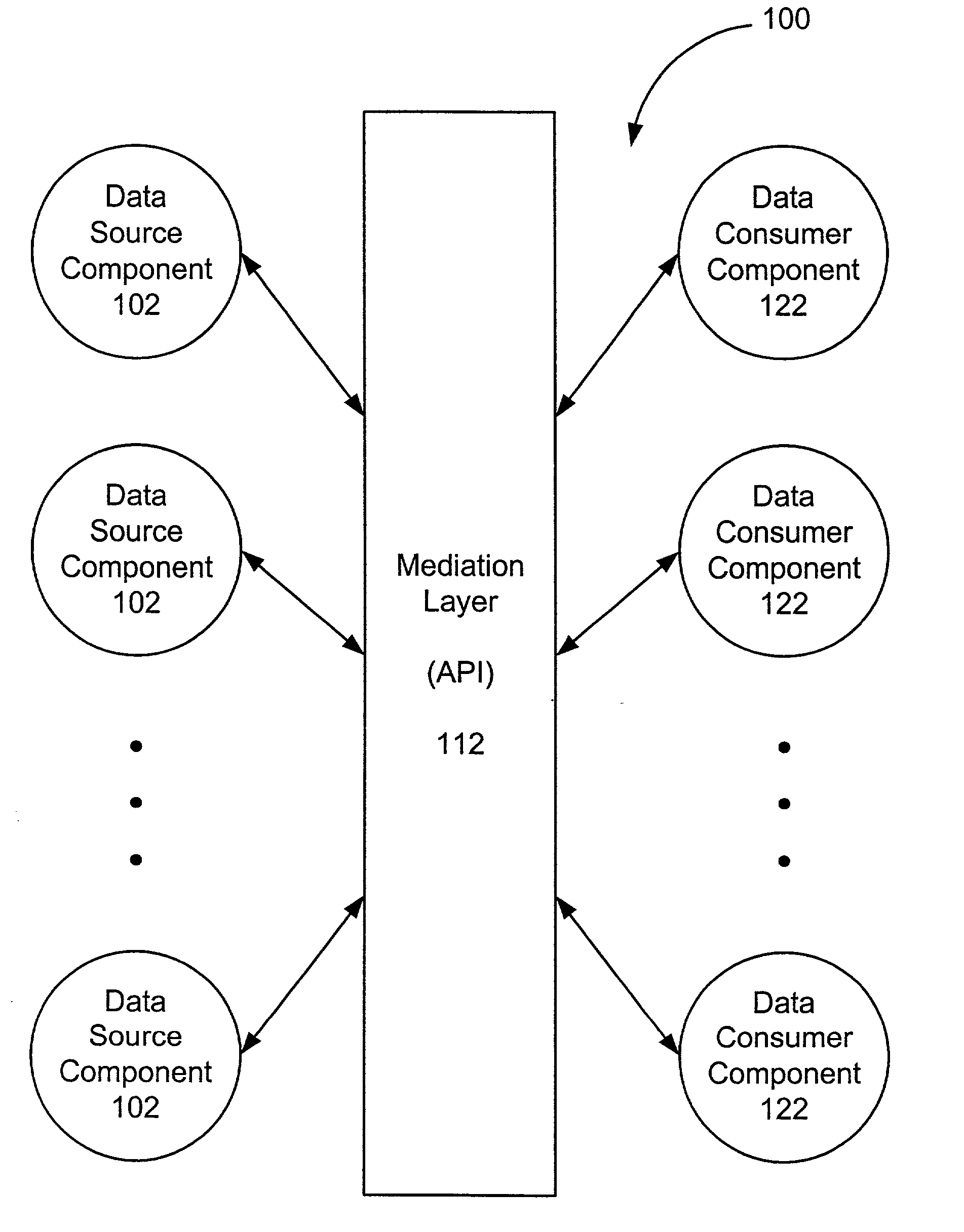
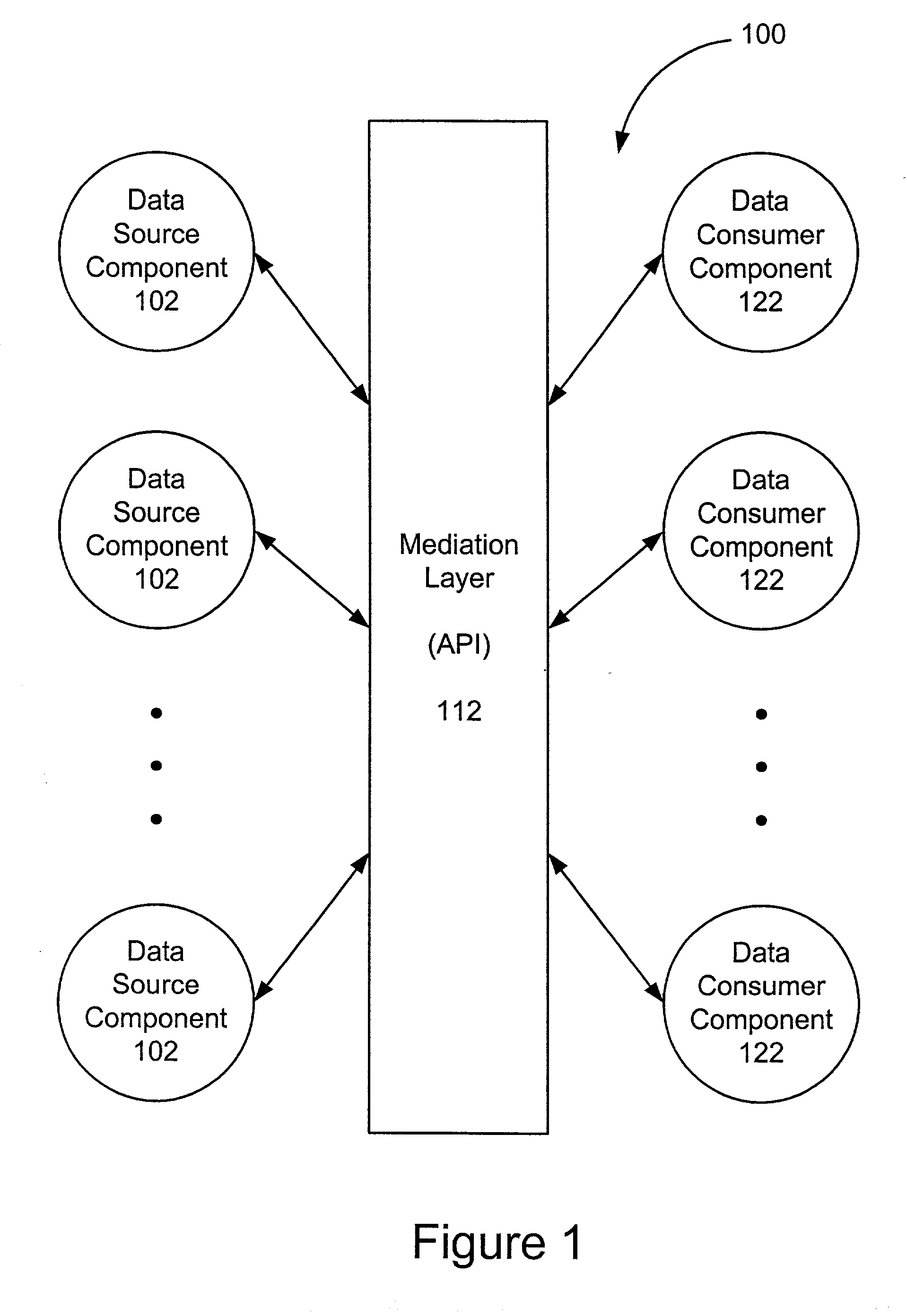
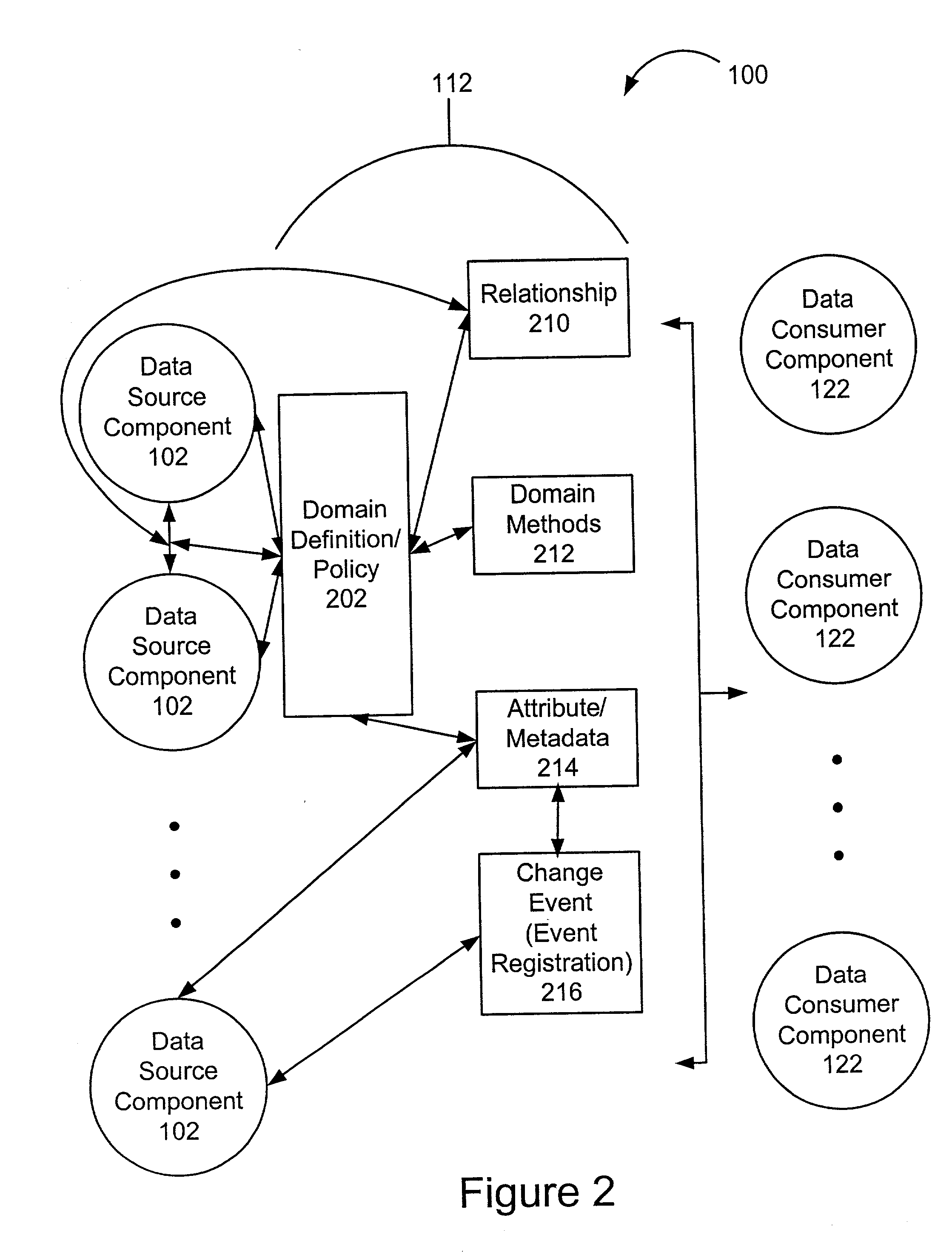
A framework enables data source components to be developed independently of data consumer components. A mediation layer, typically implemented as a group of APIs (application programming interface), handles and defines the mediation and interface between the source and data components. The framework, called XIS (extensible information system), is especially suited for development of information-handling systems and applications. Data source components and data consumer components are typically designed to communicate with each other via several interfaces. Domain, relationship, attribute / metadata, and change event interfaces are defined within the mediation layer. Other interfaces may also be defined. Data source components that are written for non-XIS aware environments or frameworks may still be used with XIS by "wrapping" such source components with code to conform to the interface requirements. Java objects are examples of data source components. Data consumer components thus are able to use or consume various source components regardless of the data types and the data source. Thus, once a data consumer component is developed within the XIS framework, any data source components within the XIS framework may be consumed by a data consumer component.
Owner:POLEXIS
System and method for configuring computer applications and devices using inheritance
InactiveUS20020091819A1Multiple digital computer combinationsData switching networksStructure of Management InformationNetwork topology
A system and method using inheritance for the configuration, management, and / or monitoring of computer applications and devices via a computer network are disclosed. The method generally comprises determining a hierarchical tree structure based upon locations of devices in a network topology, each device being a node in the hierarchical tree structure, determining policies for each node in the hierarchical tree structure to be enforced by an agent corresponding to each node, the agent being in communication with the device and the resources corresponding to the device, and communicating the policy to the corresponding agent, wherein the policies corresponding to the resources of each device are selectively inherited along the hierarchical tree structure of the network directory.
Owner:MCAFEE INC
Software update method, apparatus and system
A system for remotely updating software on at least one electronic device connected to a network. The electronic devices have a non-volatile rewritable storage unit divided into at least two partitions, one of which will contain core firmware and the other of which will contain auxiliary software. When an update is received at the device, the updated core firmware is written to overwrite the partition in the rewritable storage unit that contained the auxiliary software. When this is completed and verified, the previous version of the core firmware stored in the storage unit is disabled from execution by the device. Next, the updated auxiliary software is written to overwrite the old version of the core firmware. When this write is complete, the device determines a suitable time for it to be rebooted to execute the updated software. In another embodiment, the present core firmware in the device is copied from the partition it is in to the other partition, overwriting the auxiliary software stored there. The new core firmware received to update the device is overwritten into the first partition, the old copied core firmware being present in case of an upgrade failure, and upon a successful update of the first partition, the auxiliary software is written to the second partition, overwriting the copied old core firmware. In this manner, the position of the core firmware and auxiliary software within the partitions is preserved during normal operation of the device.
Owner:WI LAN INC
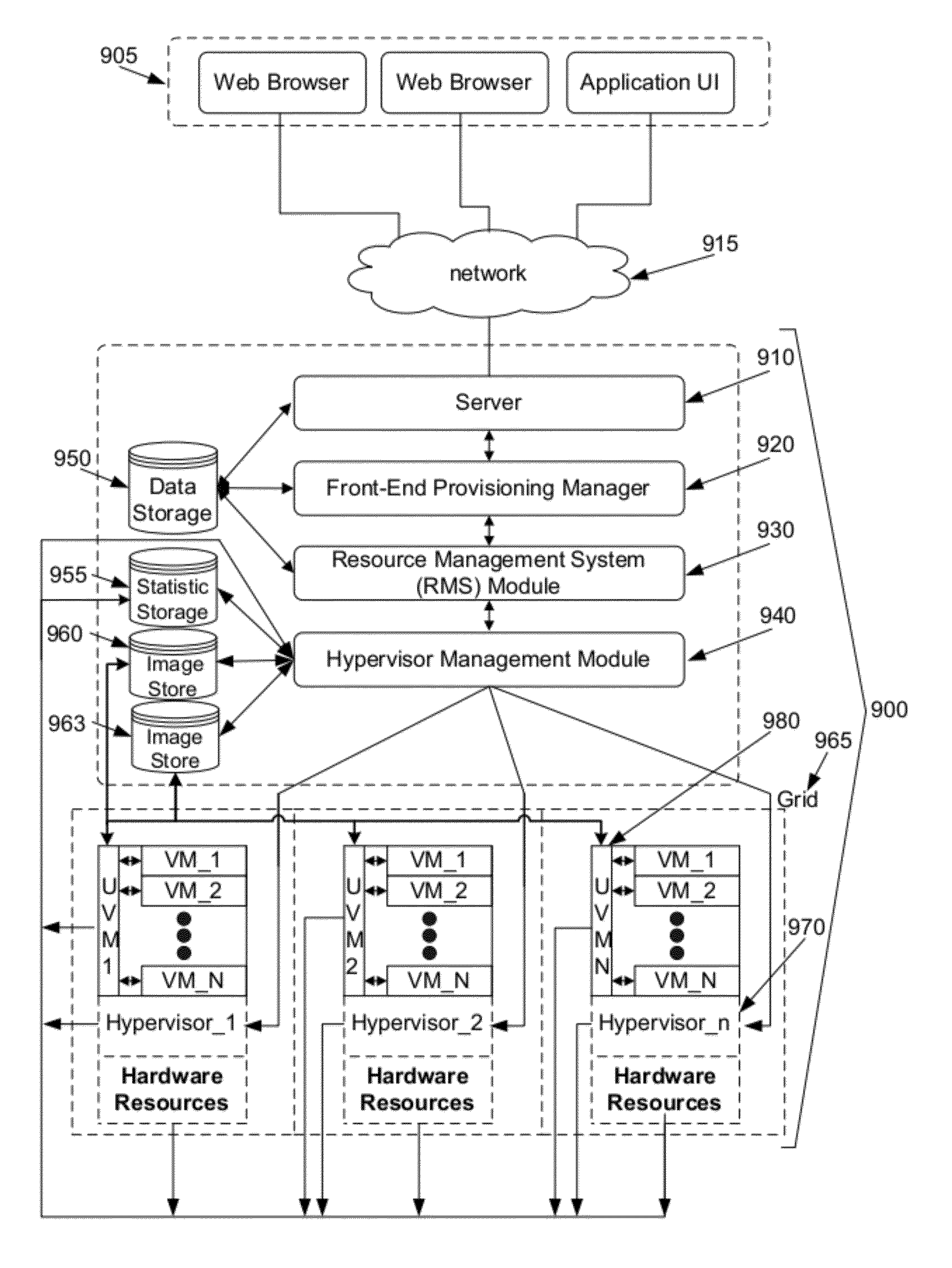
System and method for automated configuration of hosting resources
ActiveUS8352608B1Facilitate efficient deploymentMaximize useDigital computer detailsProgram controlAuto-configurationFile system
Some embodiments provide a method for automated configuration of a set of resources for hosting a virtual machine at a particular node in a hosting system. The hosting system includes several nodes for hosting several virtual machines. The method, at a first virtual machine operating using a first set of resources of the particular node, receives a configuration for a second virtual machine to be hosted on a second set of resources of the particular node. The method, from the first virtual machine, accesses the second set of resources to partition a file system for storing the second virtual machine. The method modifies the file system to configure the second virtual machine as specified by the configuration.
Owner:GOOGLE LLC
Apparatus, method and system for rapid delivery of distributed applications
ActiveUS20070078988A1Virtualized networkFirmly connectedEnergy efficient ICTMultiple digital computer combinationsVirtualizationVirtual device
An apparatus, method and system are disclosed for visually constructing and rapidly delivering distributed applications. The system includes a virtual appliance apparatus and a composite appliance apparatus, as well as a system for virtualizing hardware resources and for provisioning, executing and scaling distributed applications.
Owner:CA TECH INC
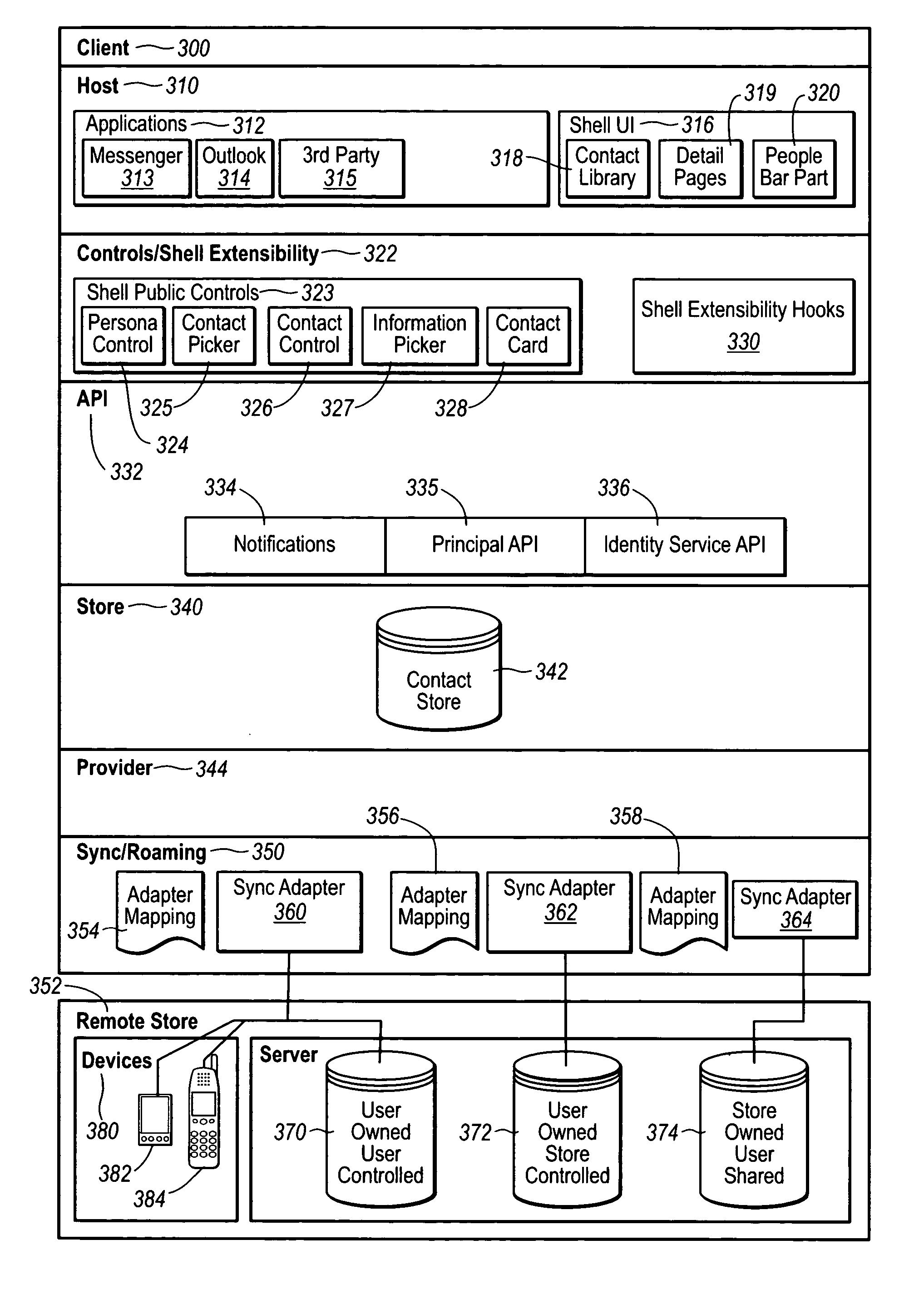
Contact management
InactiveUS20050091272A1Effective synchronizationCentralized storageDigital data processing detailsSubstation equipmentSoftware engineeringMechanical engineering
Owner:MICROSOFT TECH LICENSING LLC
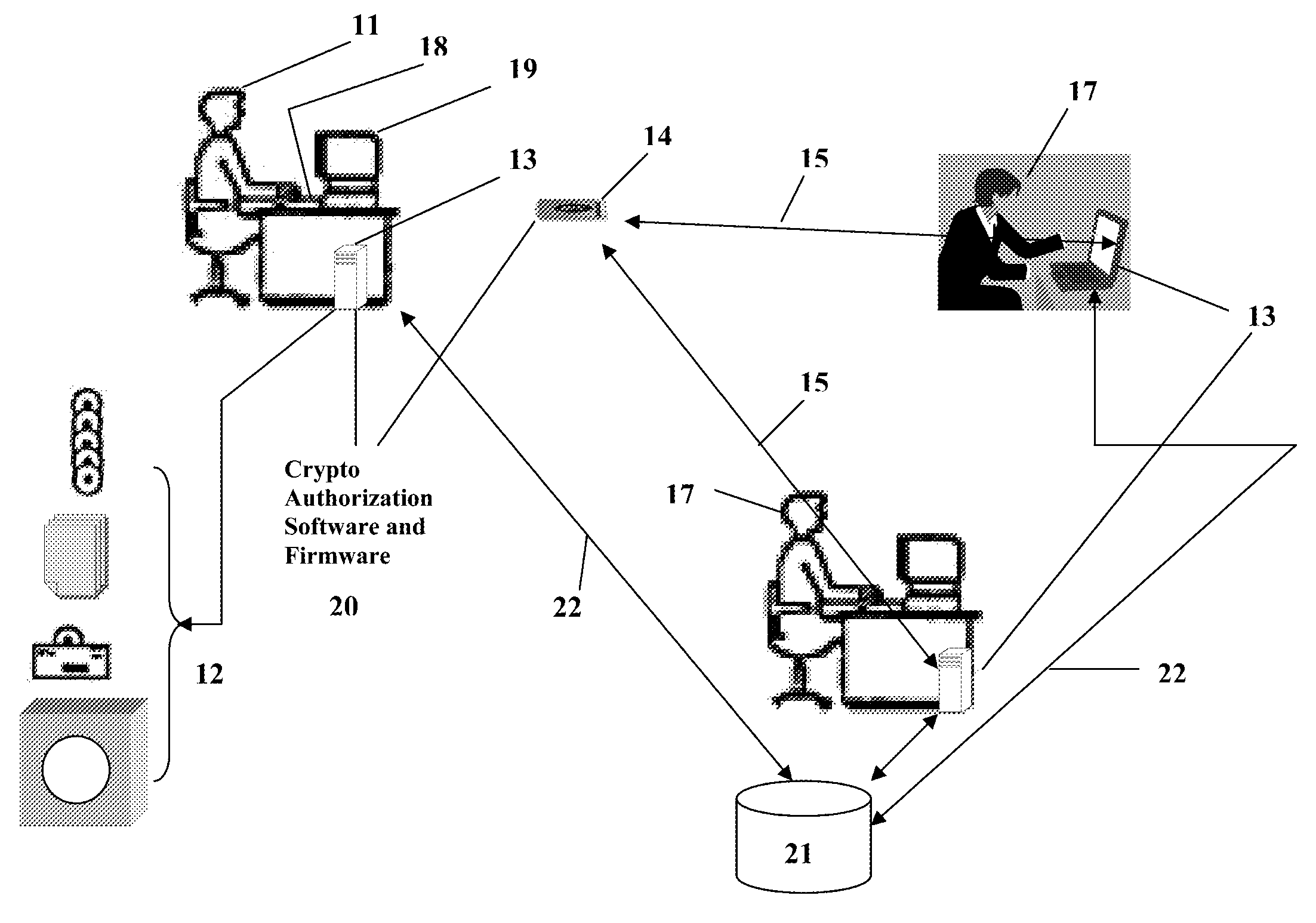
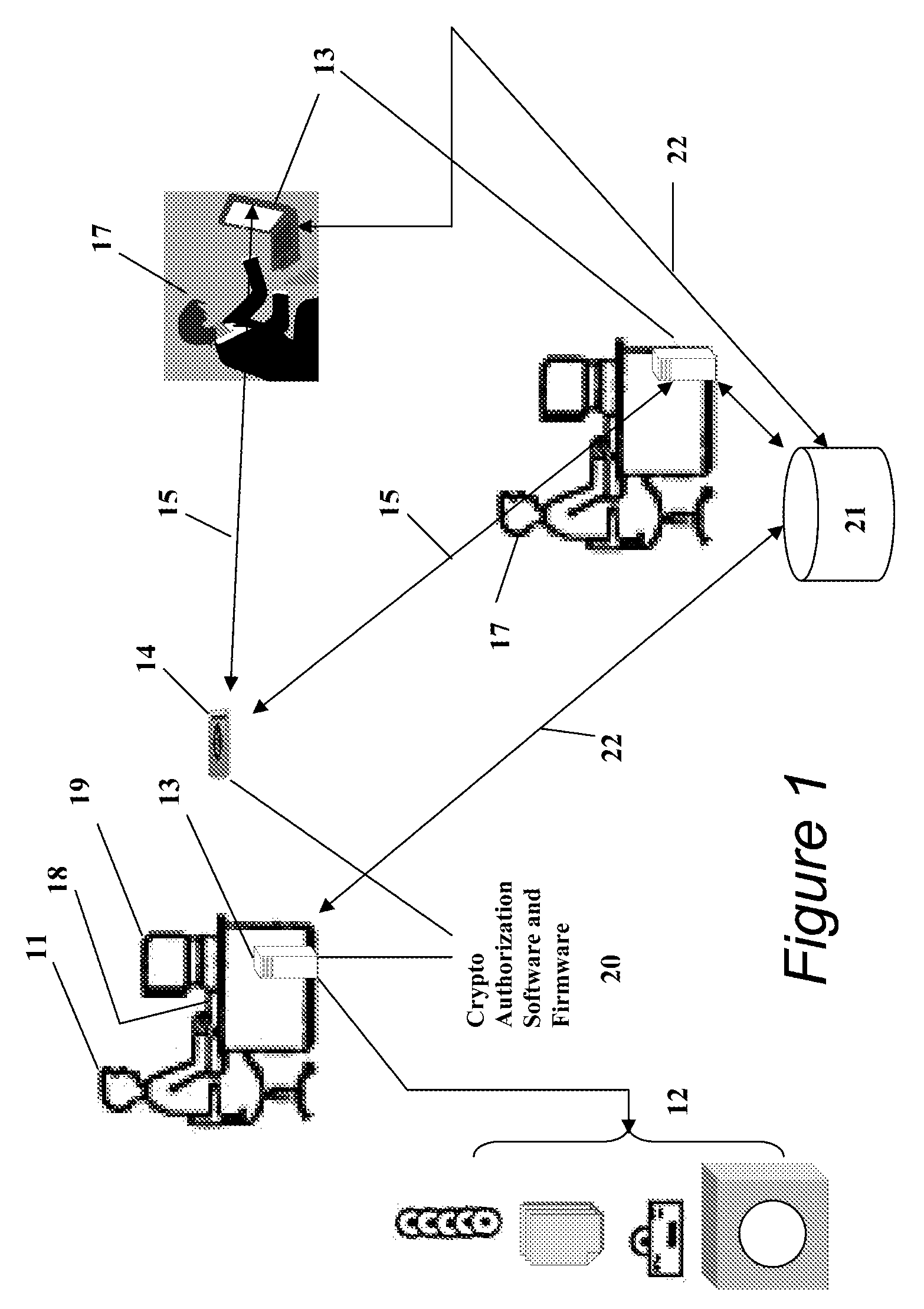
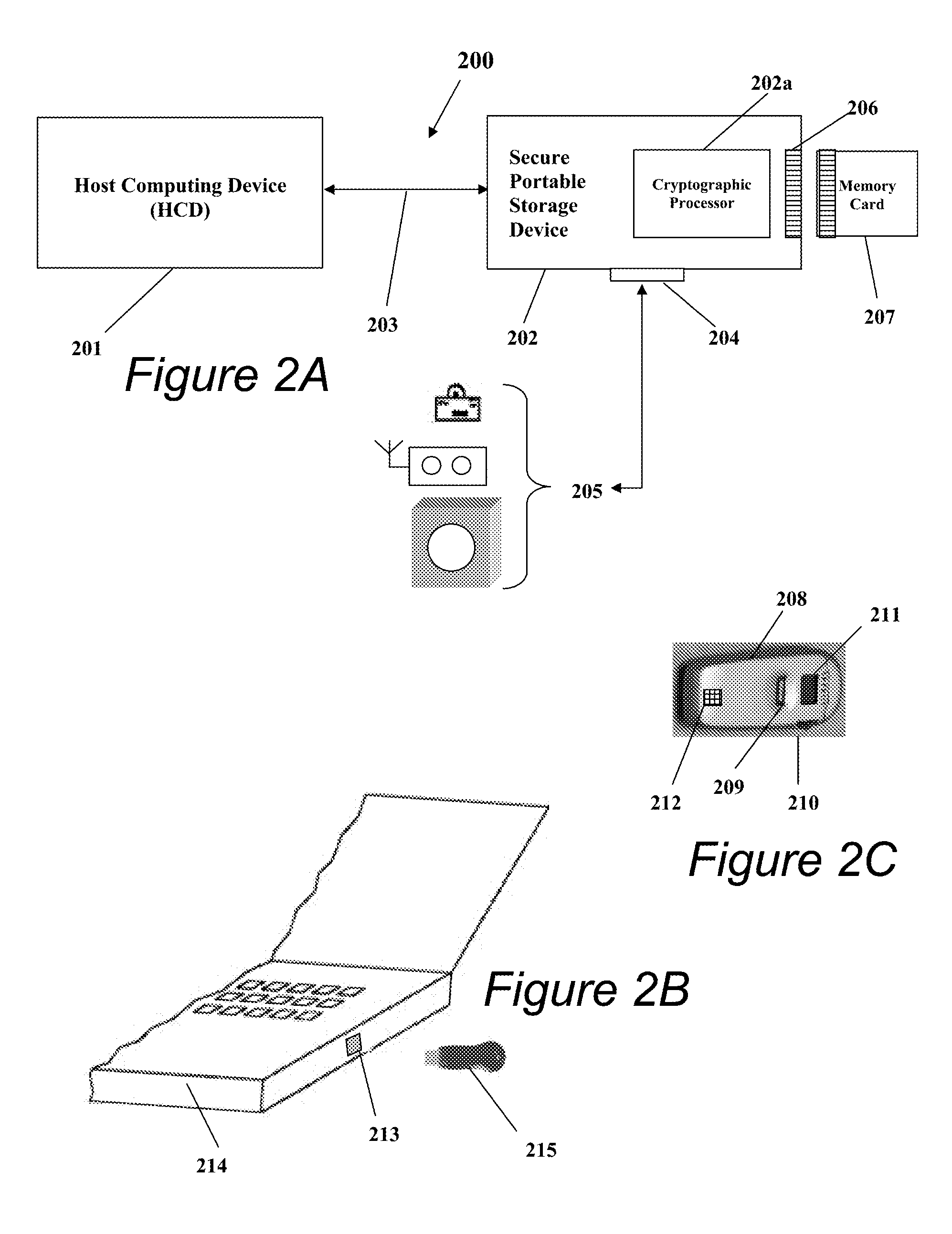
Portable Data Encryption Device with Configurable Security Functionality and Method for File Encryption
InactiveUS20080263363A1Mitigates and eliminates vulnerabilityUser identity/authority verificationInternal/peripheral component protectionComputer hardwarePlaintext
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
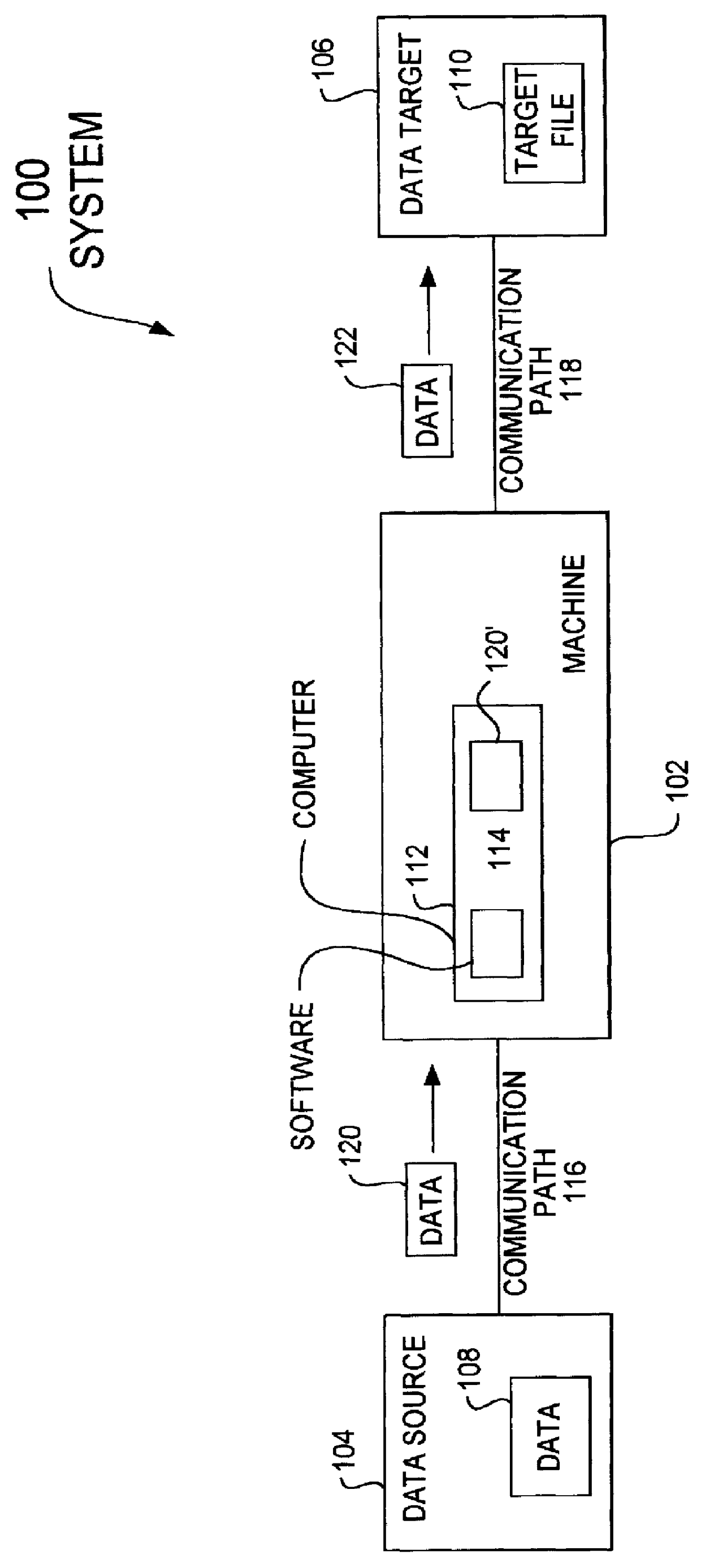
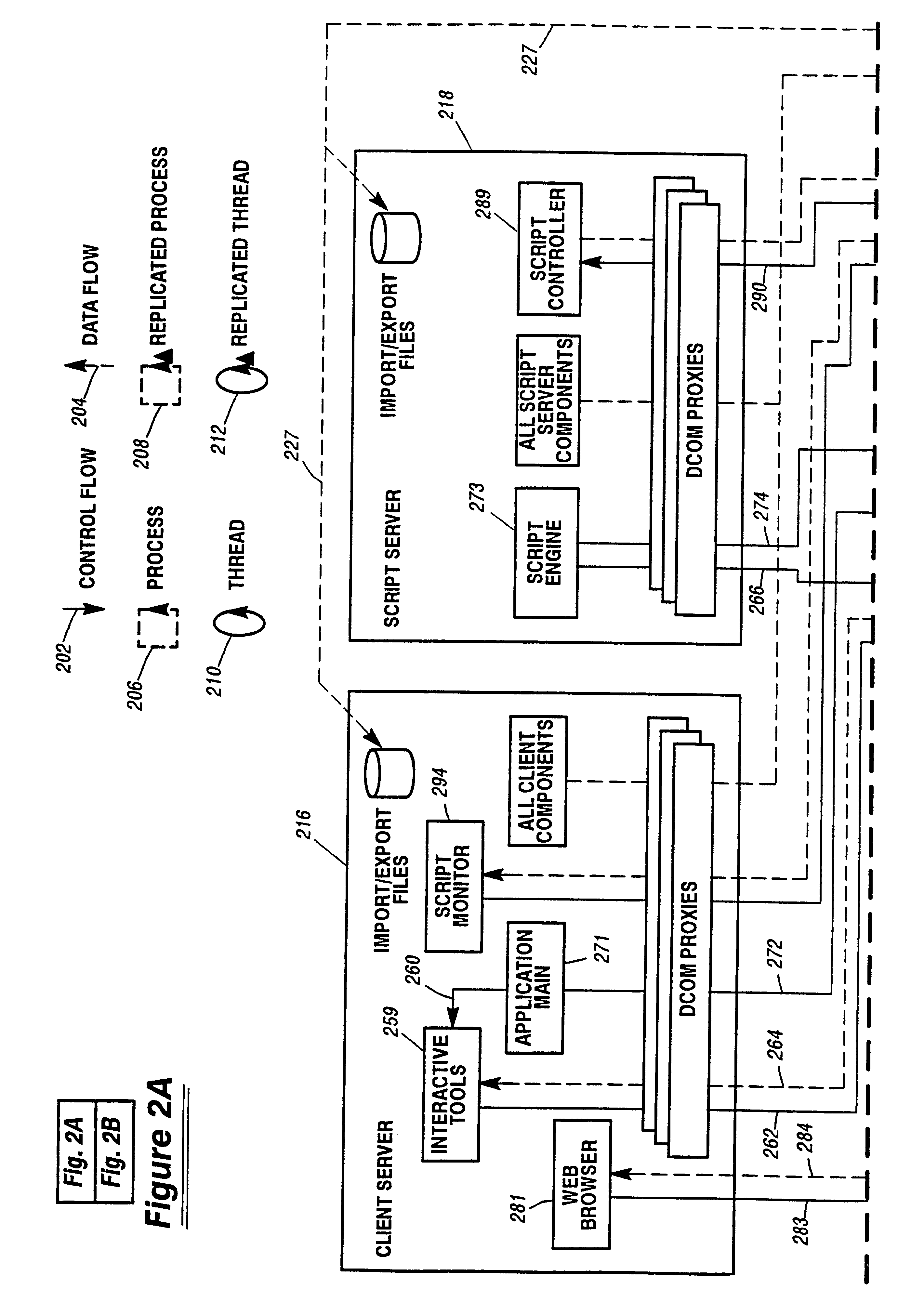
Method and apparatus for data communication
InactiveUS6094684AInterprogram communicationMultiple digital computer combinationsGraphicsGraphical user interface
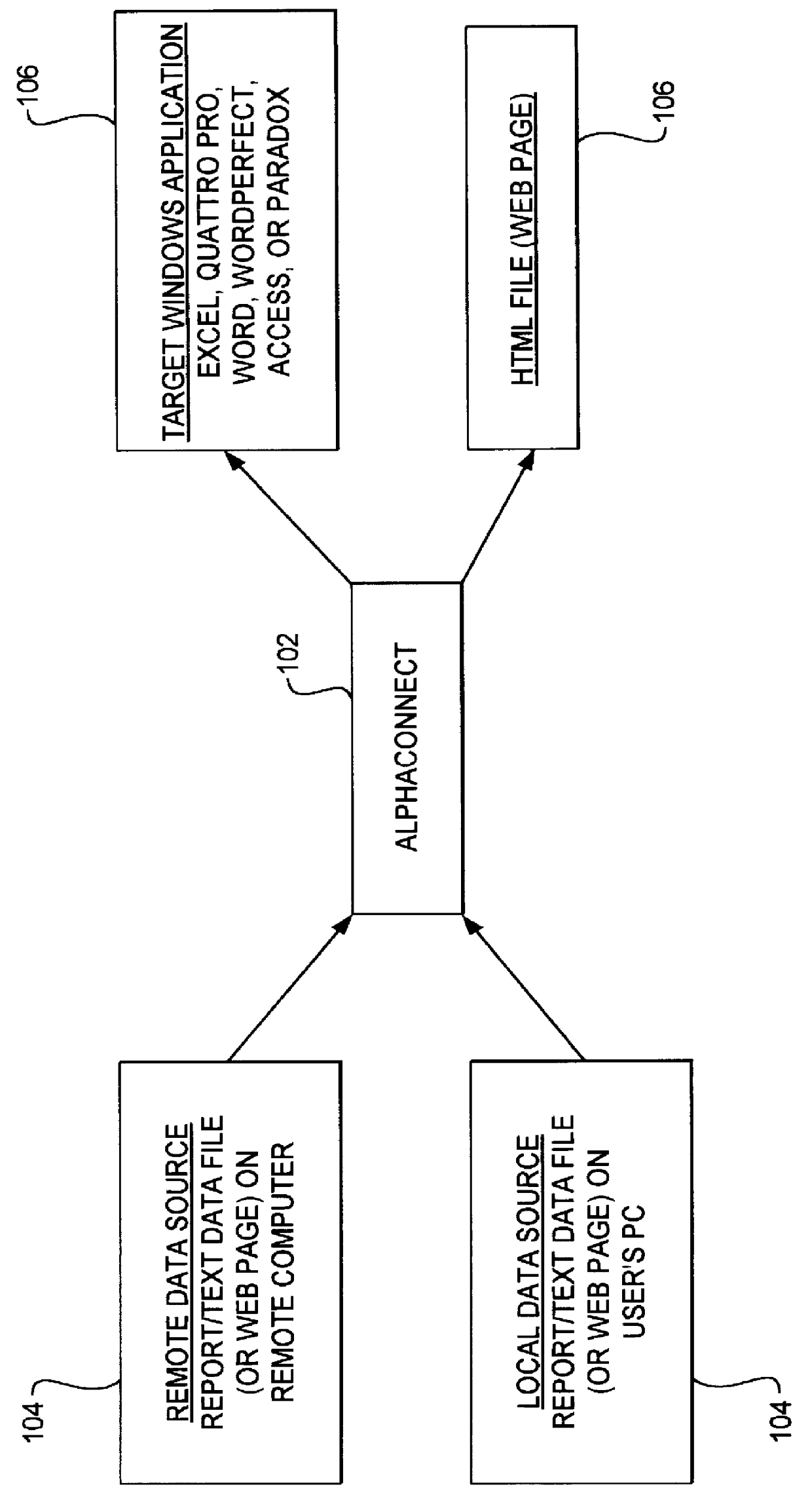
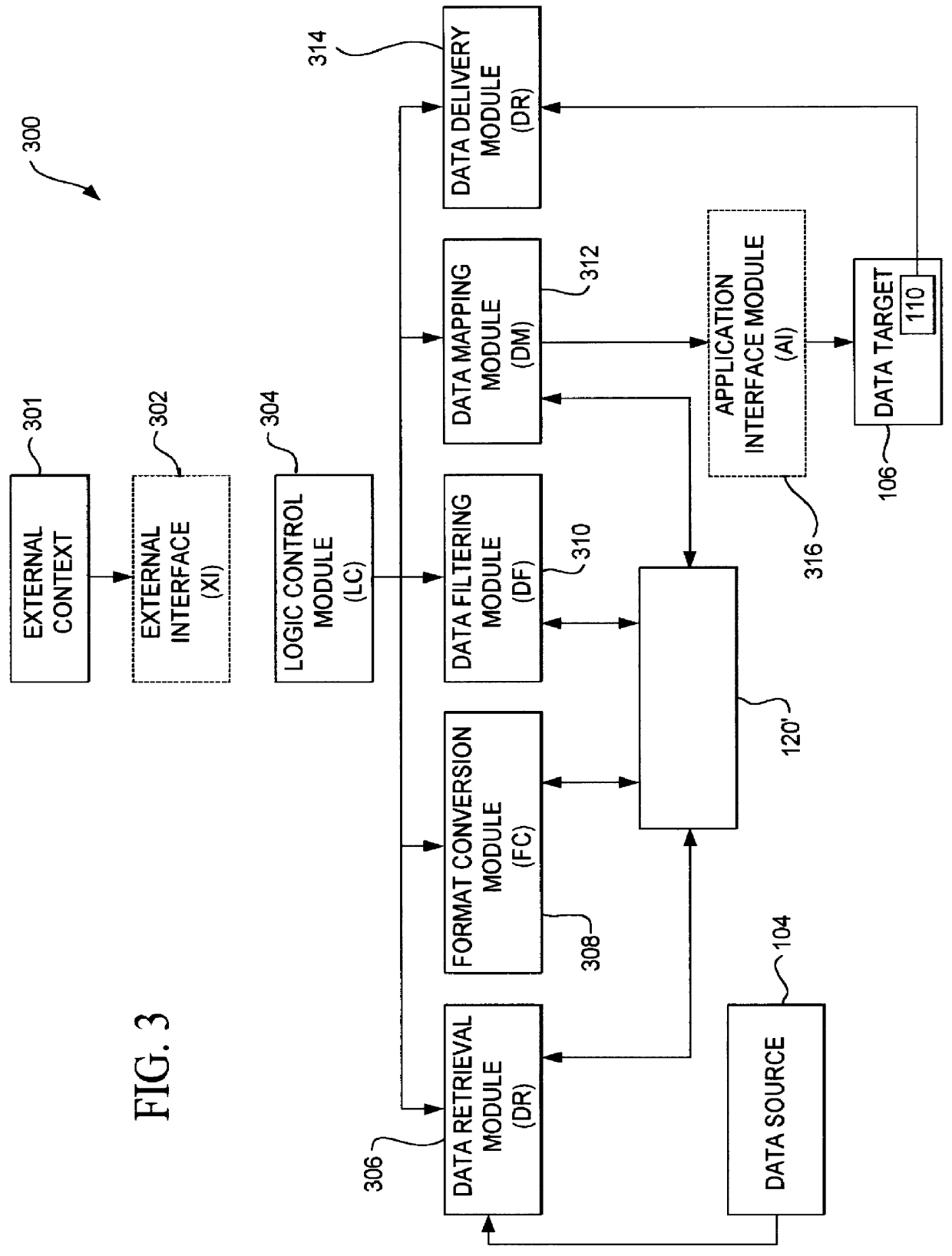
A data acquisition and delivery system for performing data delivery tasks is disclosed. This system uses a computer running software to acquire source data from a selected data source, to process (e.g. filter, format convert) the data, if desired, and to deliver the resulting delivered data to a data target. The system is designed to access remote and / or local data sources and to deliver data to remote and / or local data targets. The data target might be an application program that delivers the data to a file or the data target may simply be a file, for example. To obtain the delivered data, the software performs processing of the source data as appropriate for the particular type of data being retrieved, for the particular data target and as specified by a user, for example. The system can communicate directly with a target application program, telling the target application to place the delivered data in a particular location in a particular file. The system provides an external interface to an external context. If the external context is a human, the external interface may be a graphical user interface, for example. If the external context is another software application, the external interface may be an OLE interface, for example. Using the external interface, the external context is able to vary a variety of parameters to define data delivery tasks as desired. The system uses a unique notation that includes a plurality of predefined parameters to define the data delivery tasks and to communicate them to the software.
Owner:E BOTZ COM INC A DELAWARE +2
Semiconductor memory device and method for writing data into flash memory
ActiveUS7107389B2Small sizeReduce waiting timeMemory architecture accessing/allocationMemory adressing/allocation/relocationHome pageDatabase
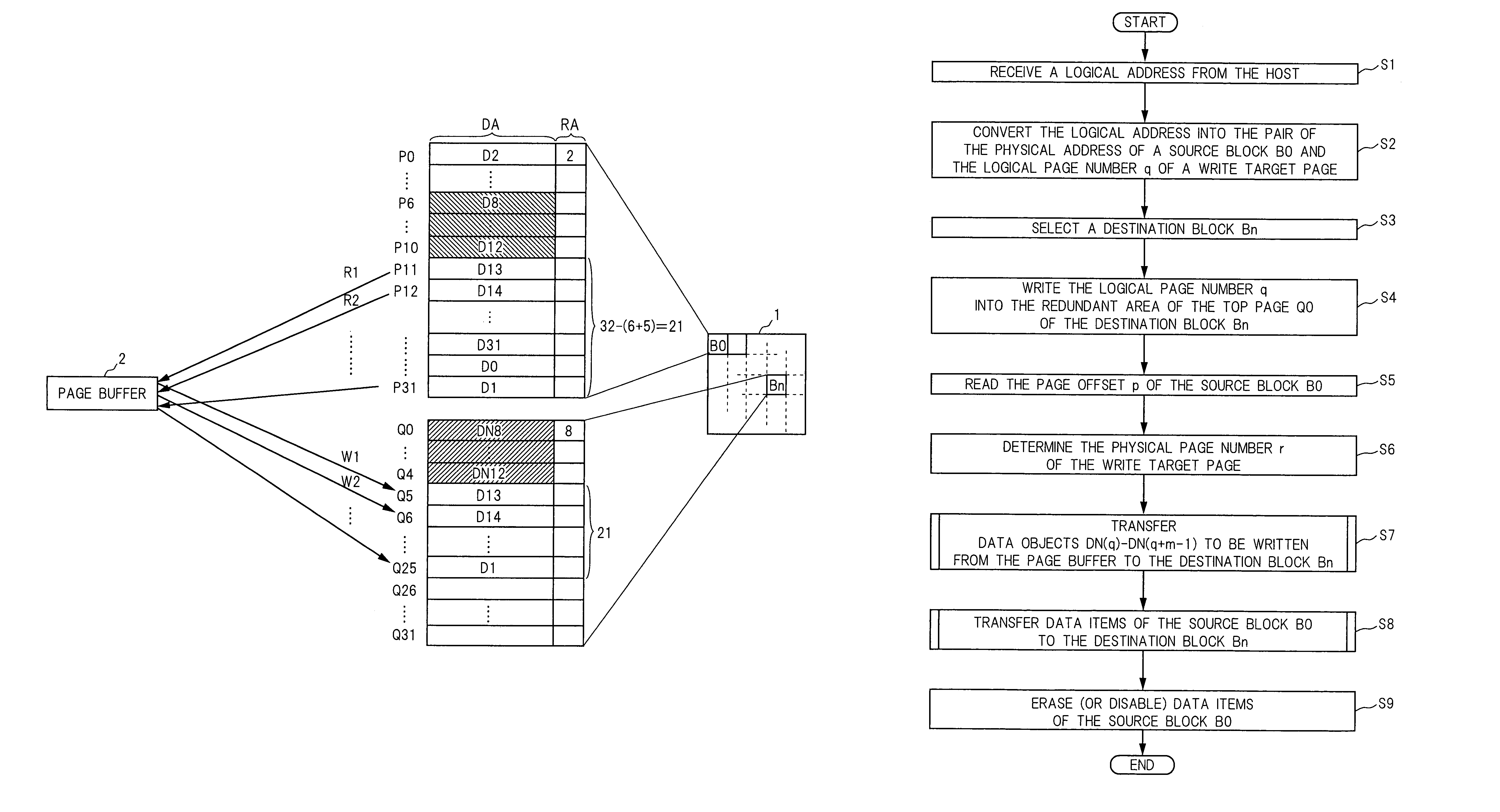
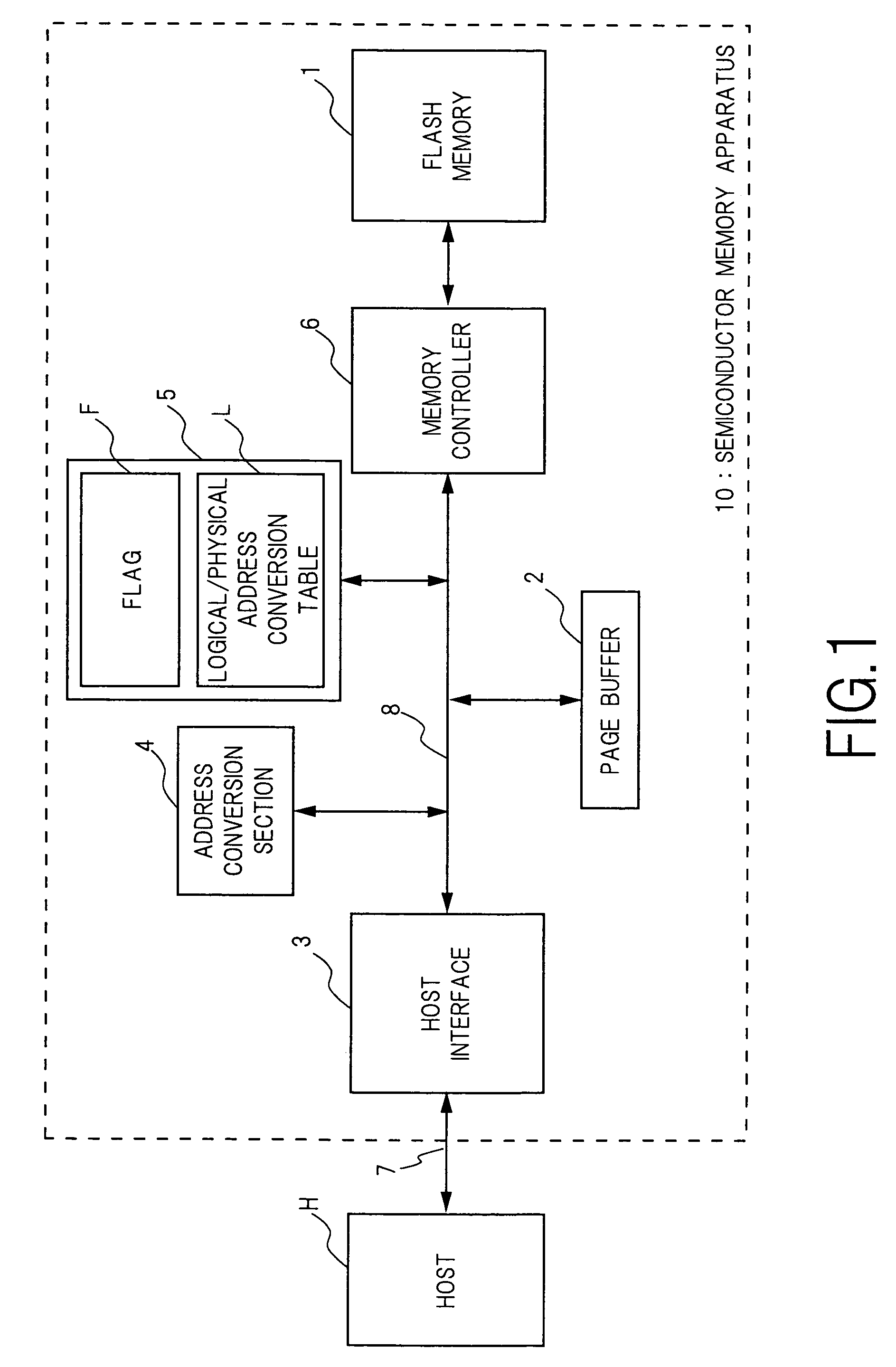
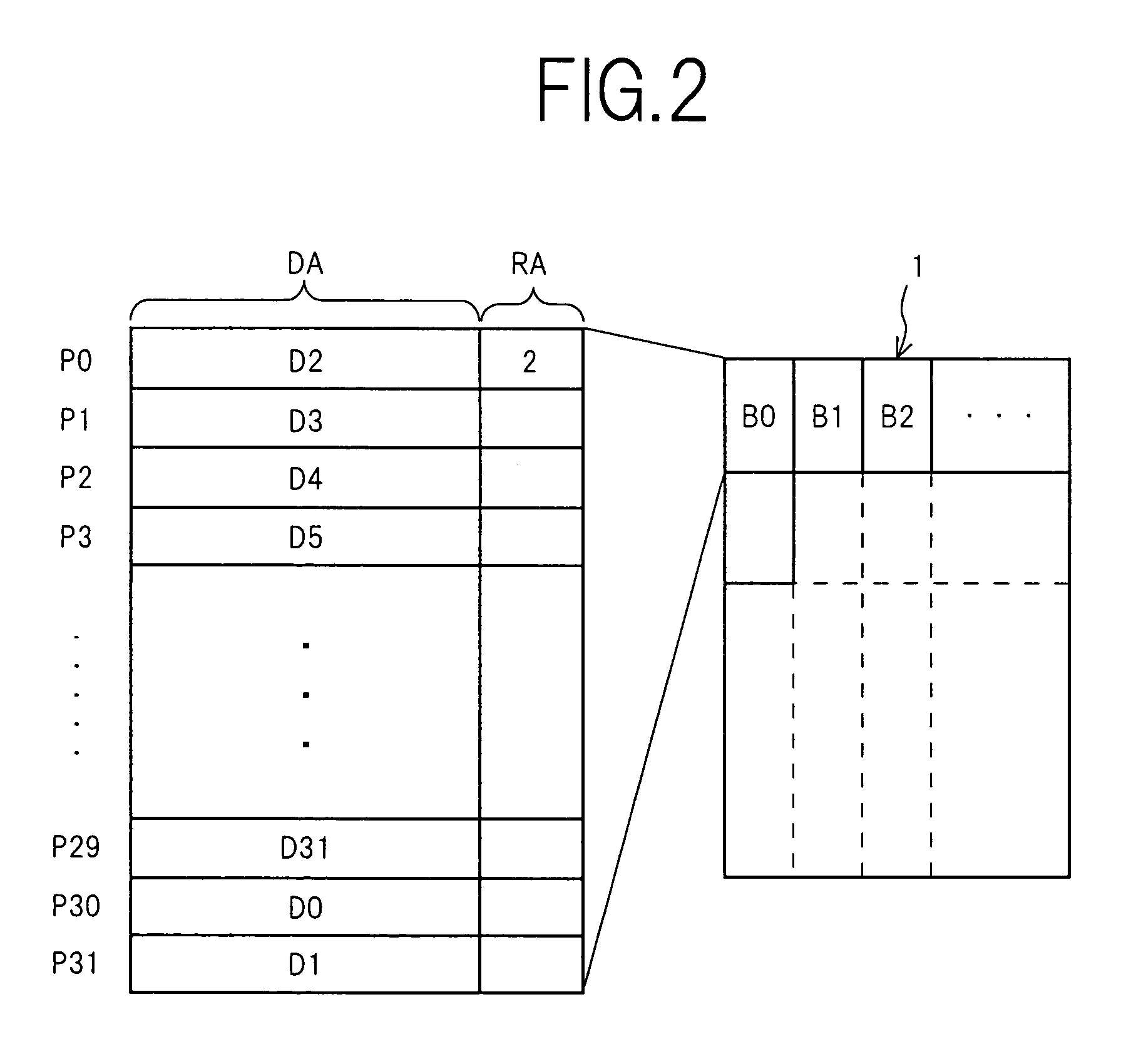
A source block (B0) and the logical page number (“8”) of a write target page are identified from the logical address of the write target page. Data objects (DN8, DN9, . . . , DN12) to be written, which a host stores in a page buffer (2), are written into the data areas (DA) of the pages (Q0, Q1, . . . , Q4) of a destination block (Bn), starting from the top page (Q0) in sequence. The logical page number (“8”) of the write target page is written into the redundant area (RA) of the top page (Q0). The physical page number (“6=8−2”) of the write target page is identified, based on the logical page number (“8”) of the write target page and the page offset (“2”) of the source block (B0). When notified by the host of the end of the sending of the data objects (DN8, . . . , DN12), the data items (D13, . . . , D31, D0, D1, . . . , D7) in the source block (B0) are transferred to the pages (Q5, Q6, . . . , Q31) in the destination block (Bn) via the page buffer (2) sequentially and cyclically, starting from the page (P11) situated cyclically behind the write target page (P6) by the number (“5”) of pages of the data objects (DN8, . . . , DN12).
Owner:PANASONIC CORP
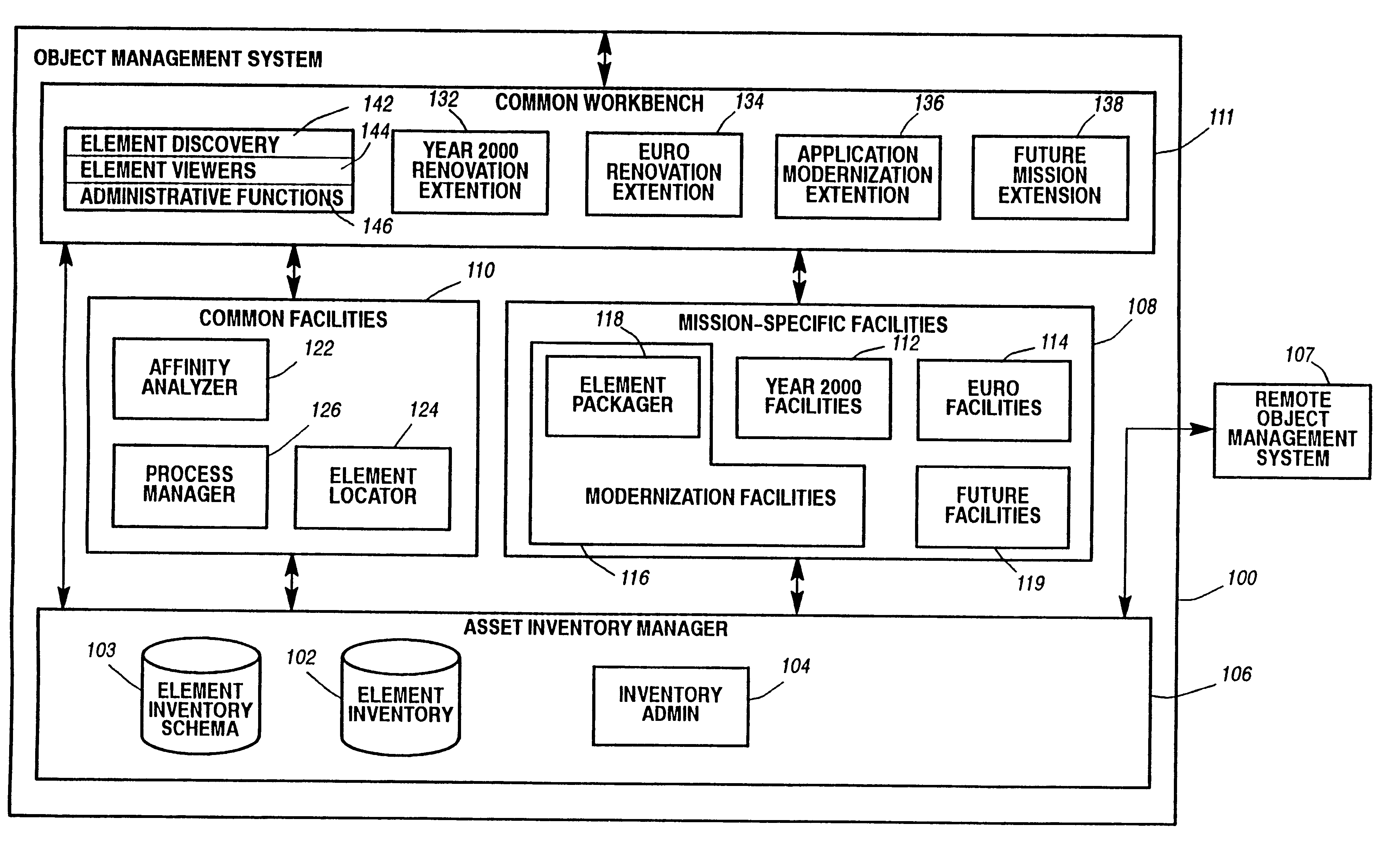
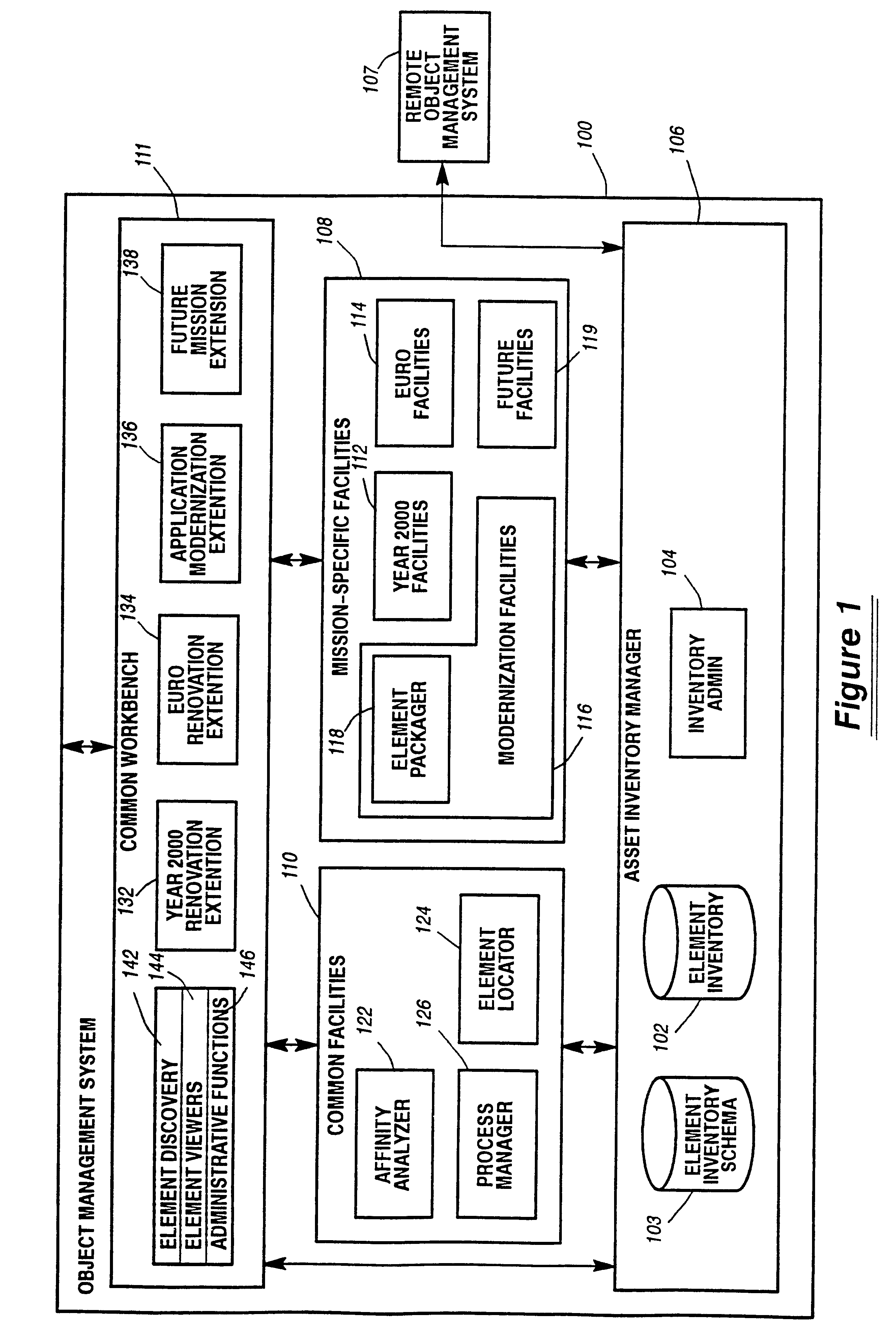
System and method for defining and managing reusable groups software constructs within an object management system
InactiveUS6427230B1Sure easyEasy to understandSoftware reuseSpecific program execution arrangementsManagement systemSoftware
A system for maintaining an object repository within an object management system where the objects are software constructs and the system provides a set of tools for creating packages of the objects that can be reused as well as monitored as they are changed or recombined. The packages themselves become new objects for the repository to store. The set of relationships within a package is also stored as are any relationships between any of the objects within the object management system object repository.
Owner:UNISYS CORP
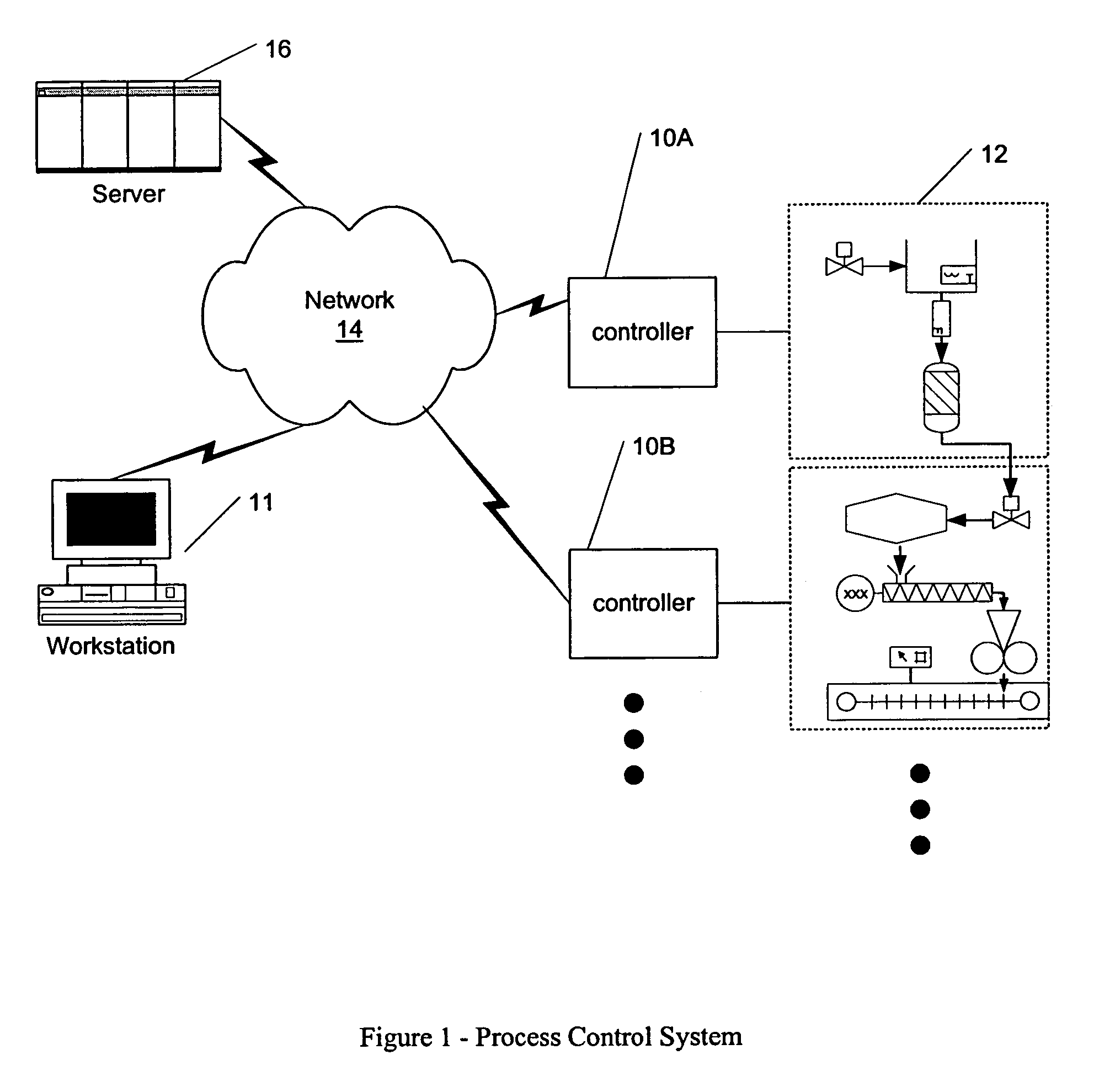
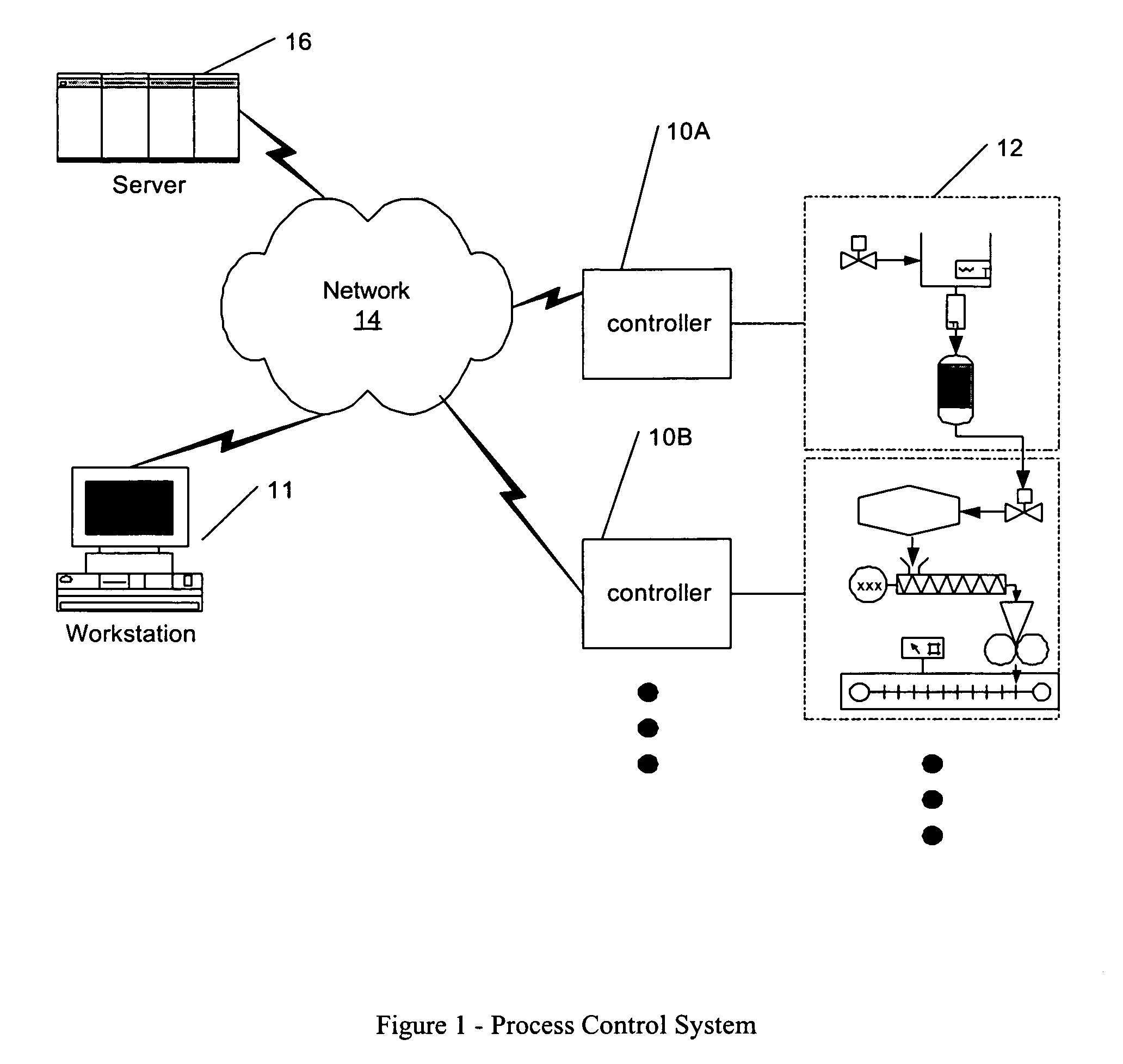
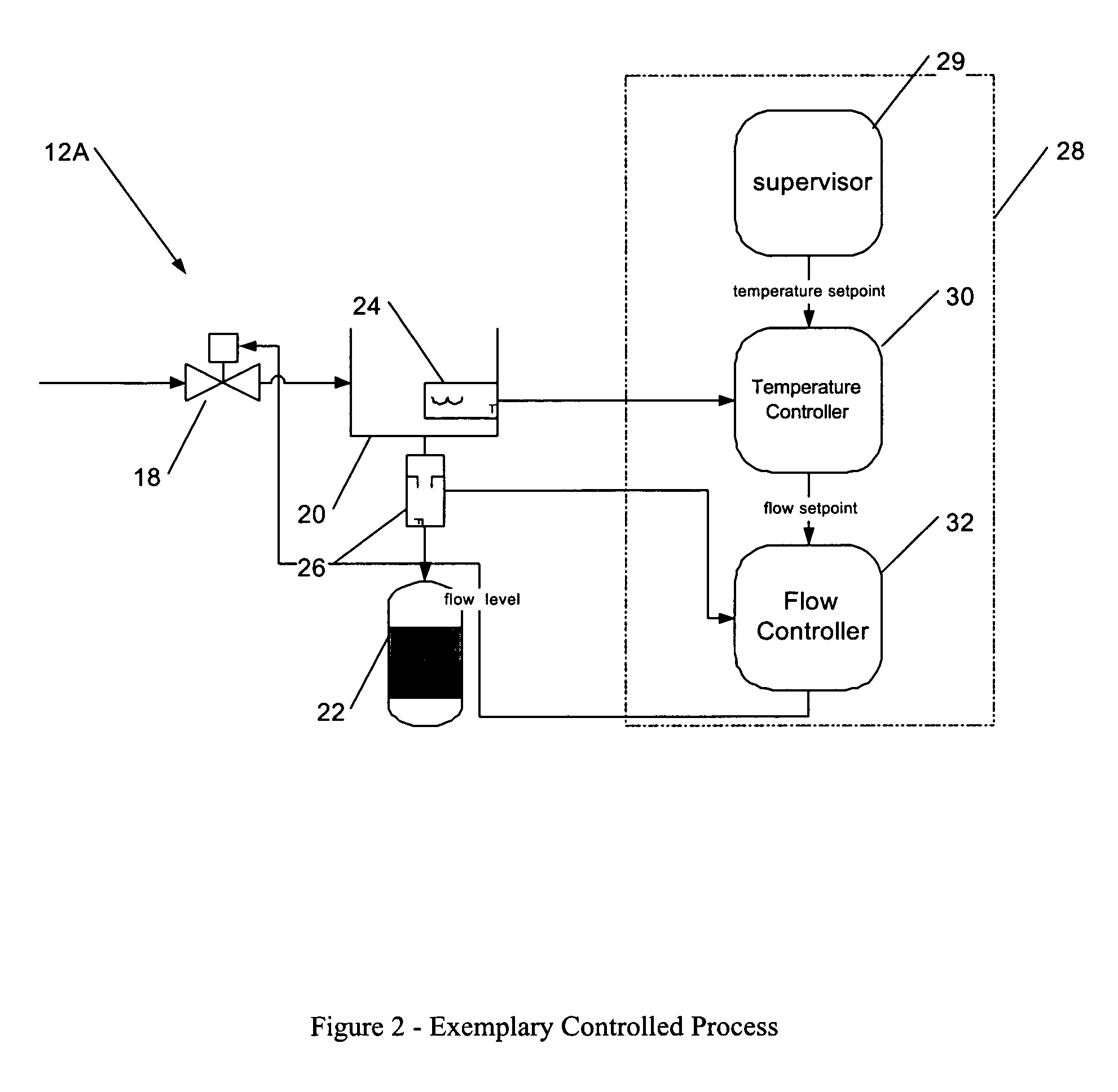
Process control configuration system with connection validation and configuration
Connection objects or other such data structures facilitate establishing and configuring connections between objects that model components in a process control system. A first set of data structures (e.g. the object connection type structures) identify valid types for component-to-component pairings and the respective roles of each component in the pairing (e.g., parent or child, source or sink). A second set of data structures (e.g., the parameter connection type structures) supply similar information for parameter-to-parameter connections. Together, these data structures can be used, for example, to validate component-to-component connections suggested by the user and to automatically configure parameter-to-parameter connections. Actual connections, both at the component or parameter level, are reflected using parameter overrides within the parameterized object model—with which the connection objects are constructed.
Owner:SCHNEIDER ELECTRIC SYST USA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com