Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
80996results about "Digital storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
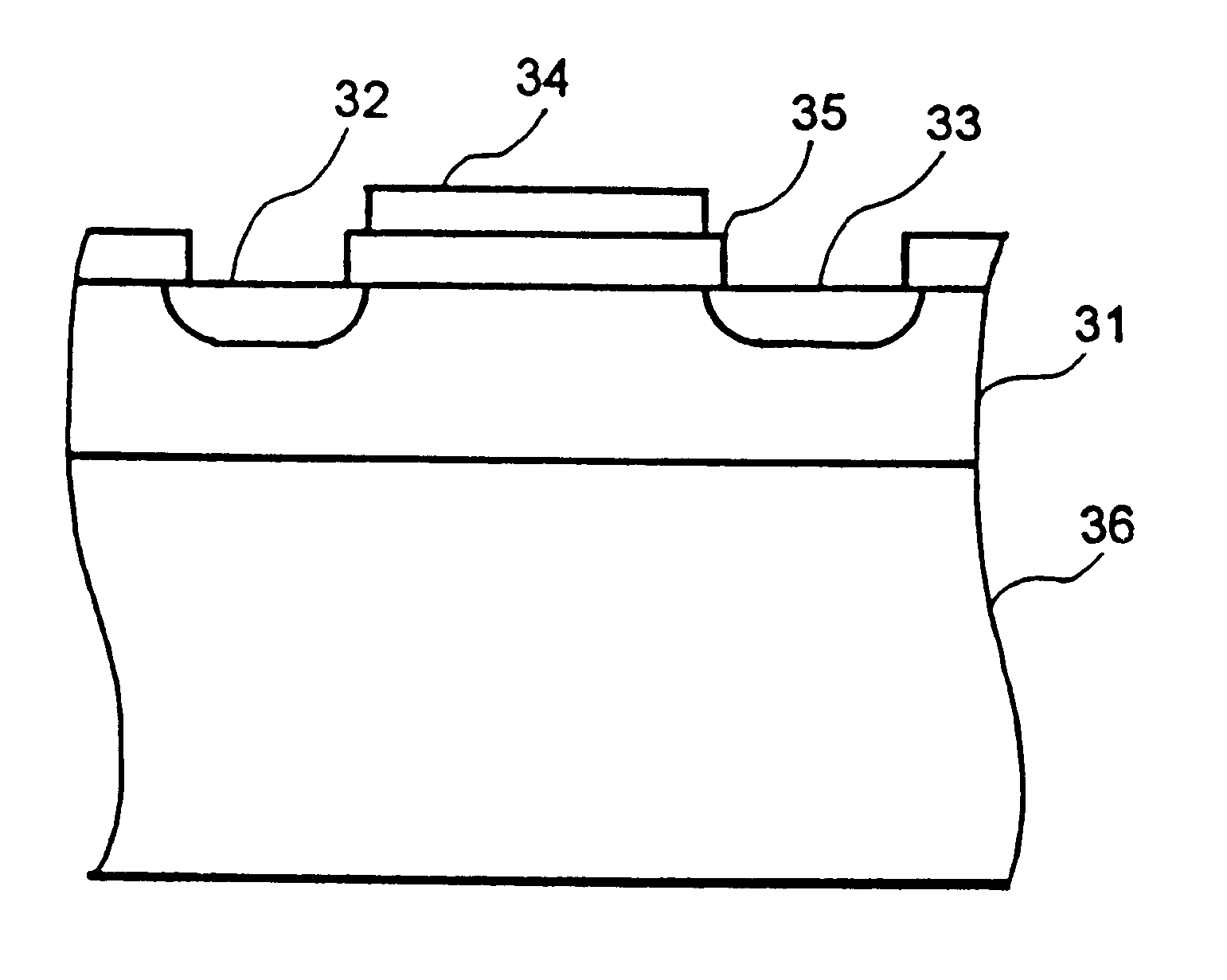
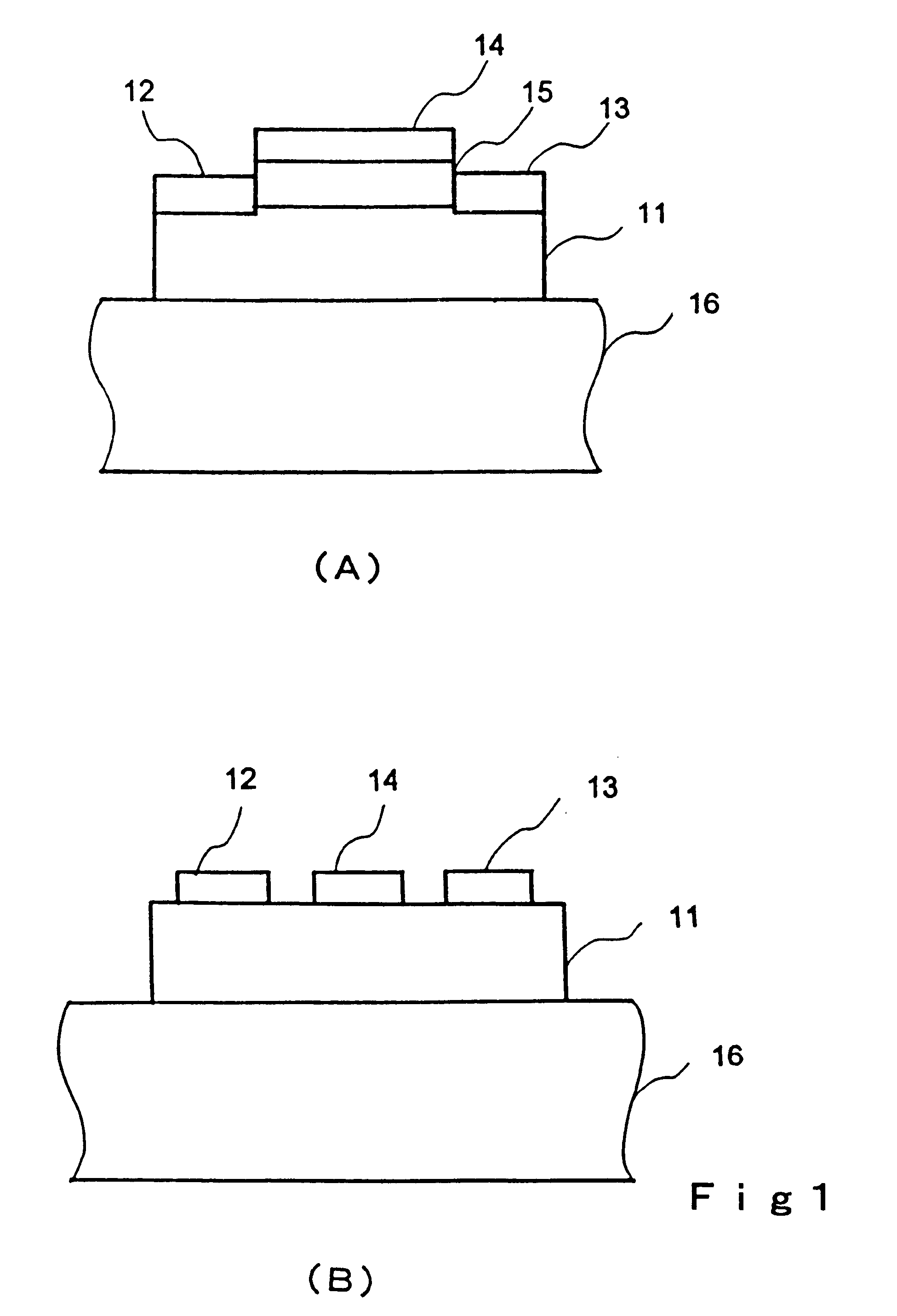
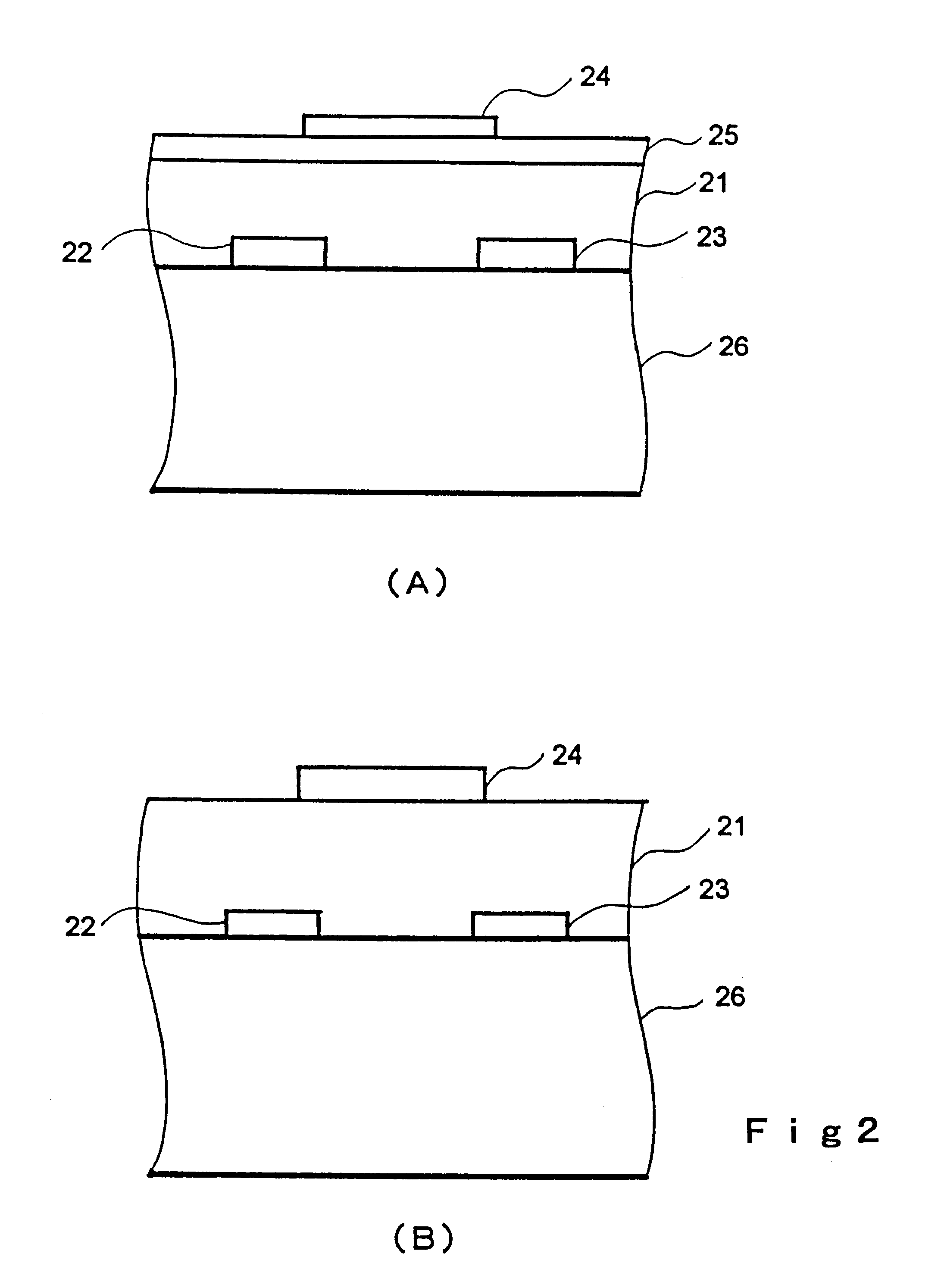
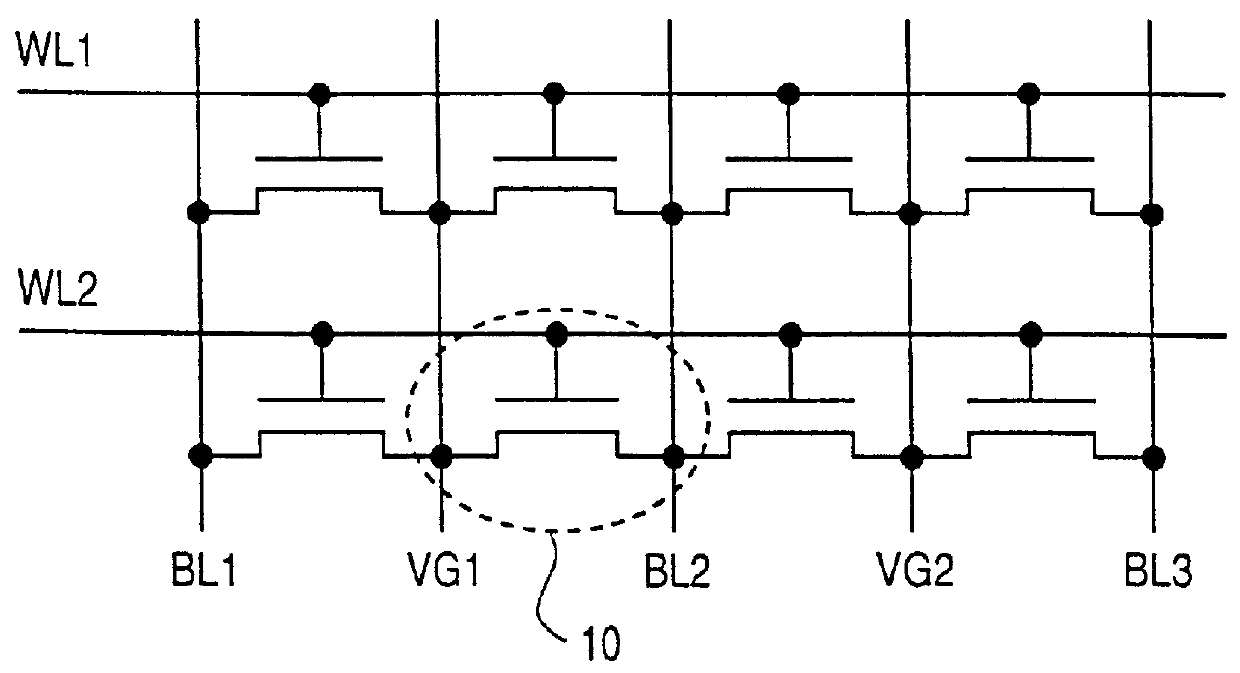
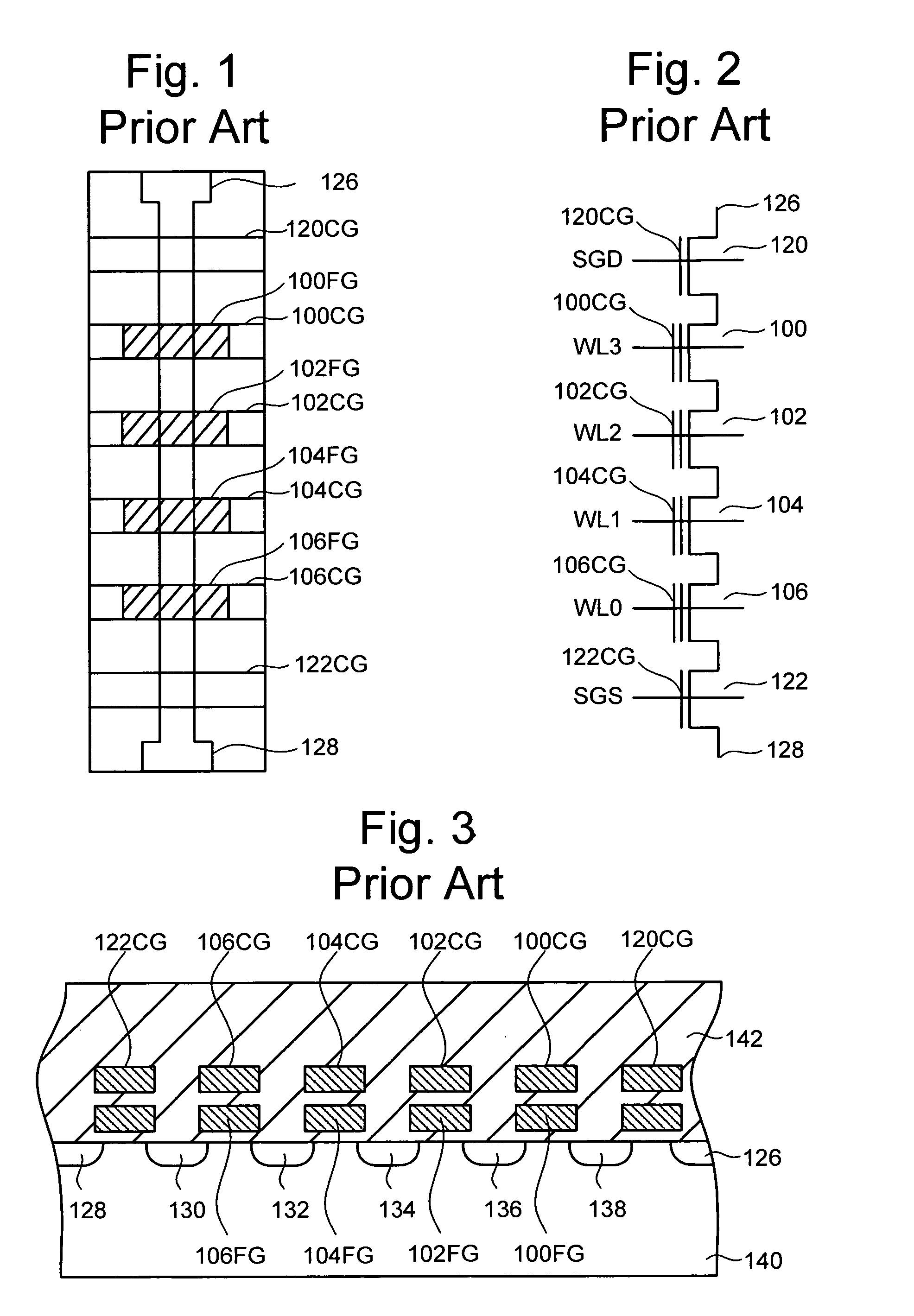
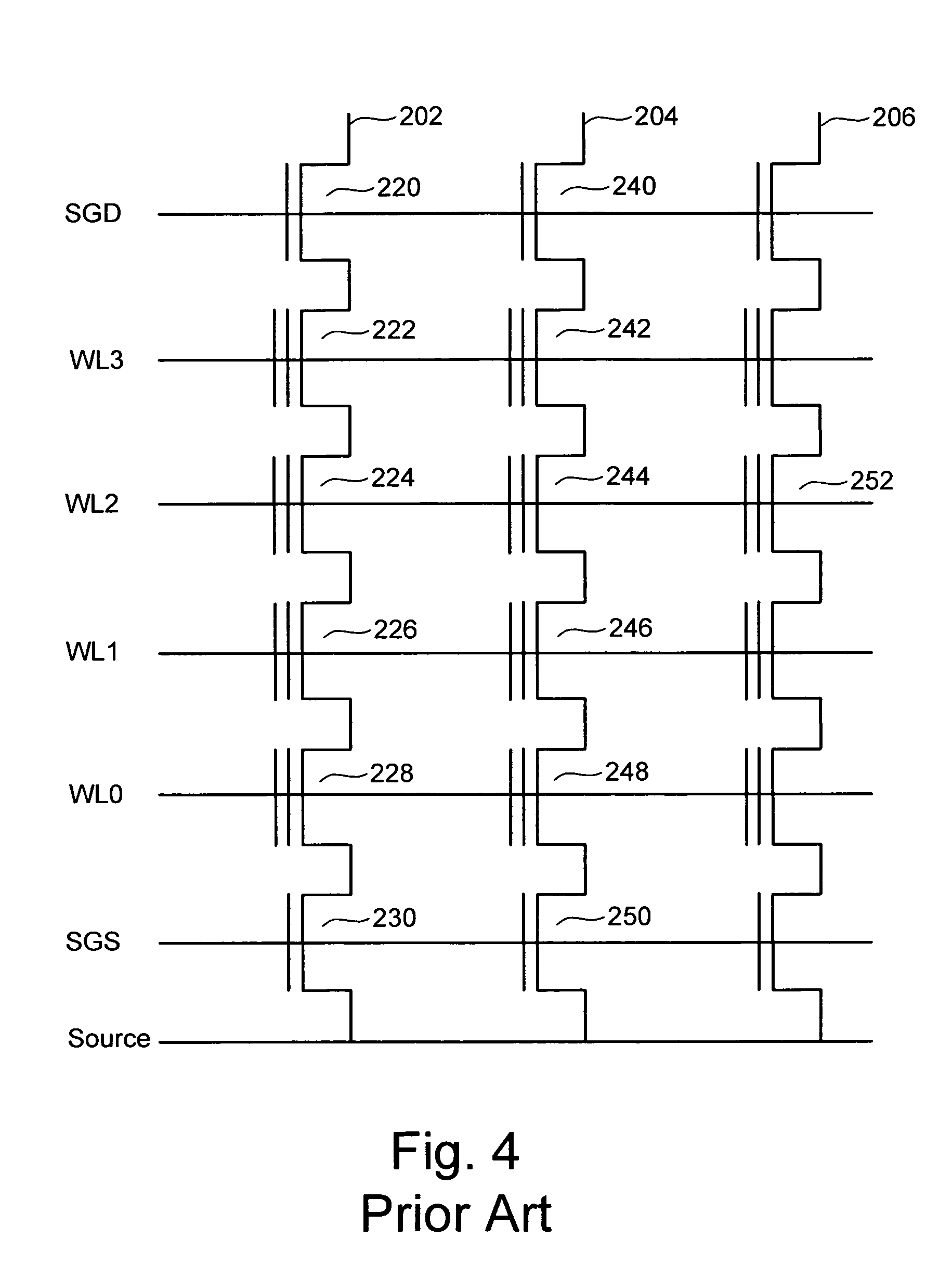
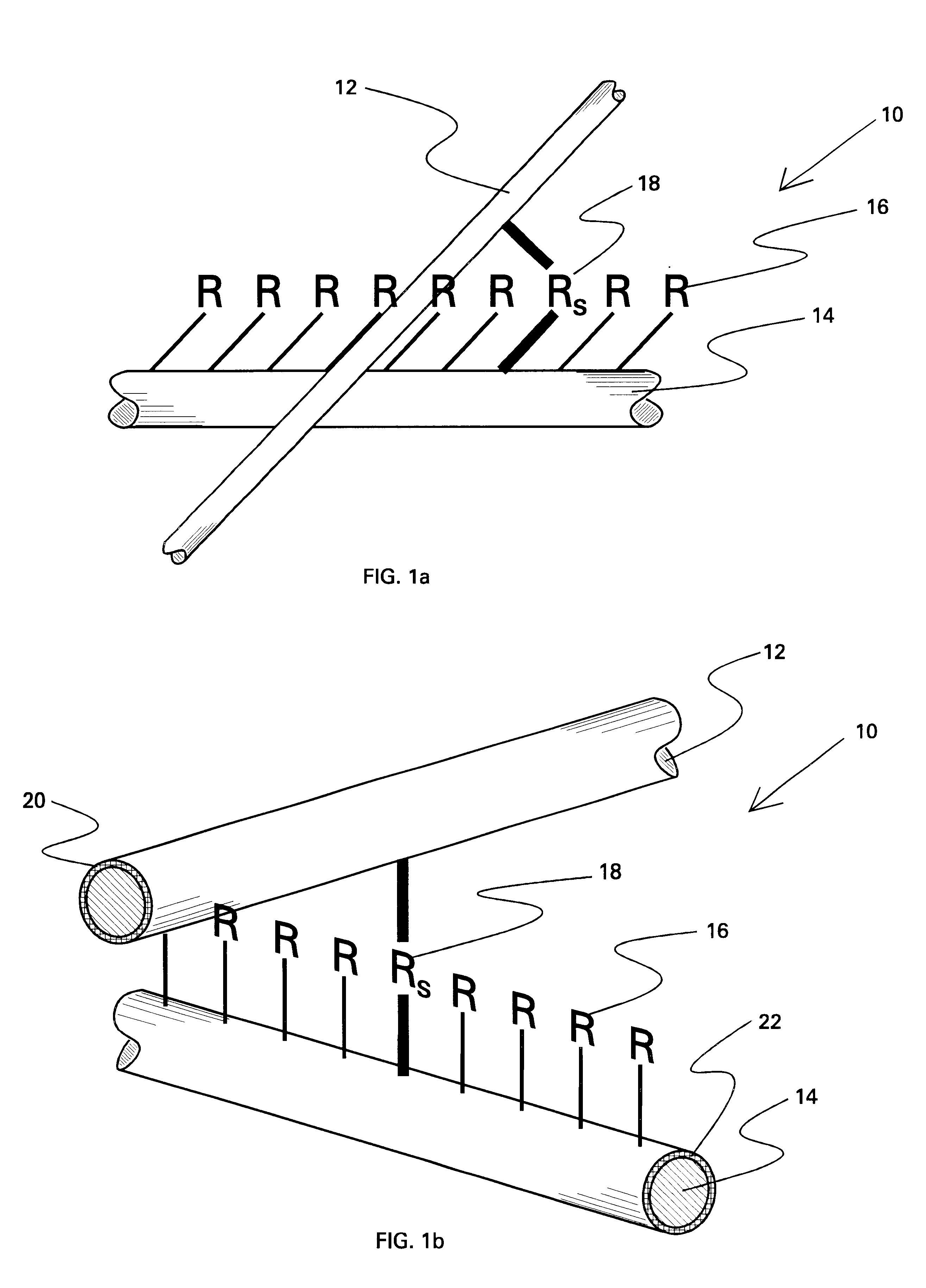
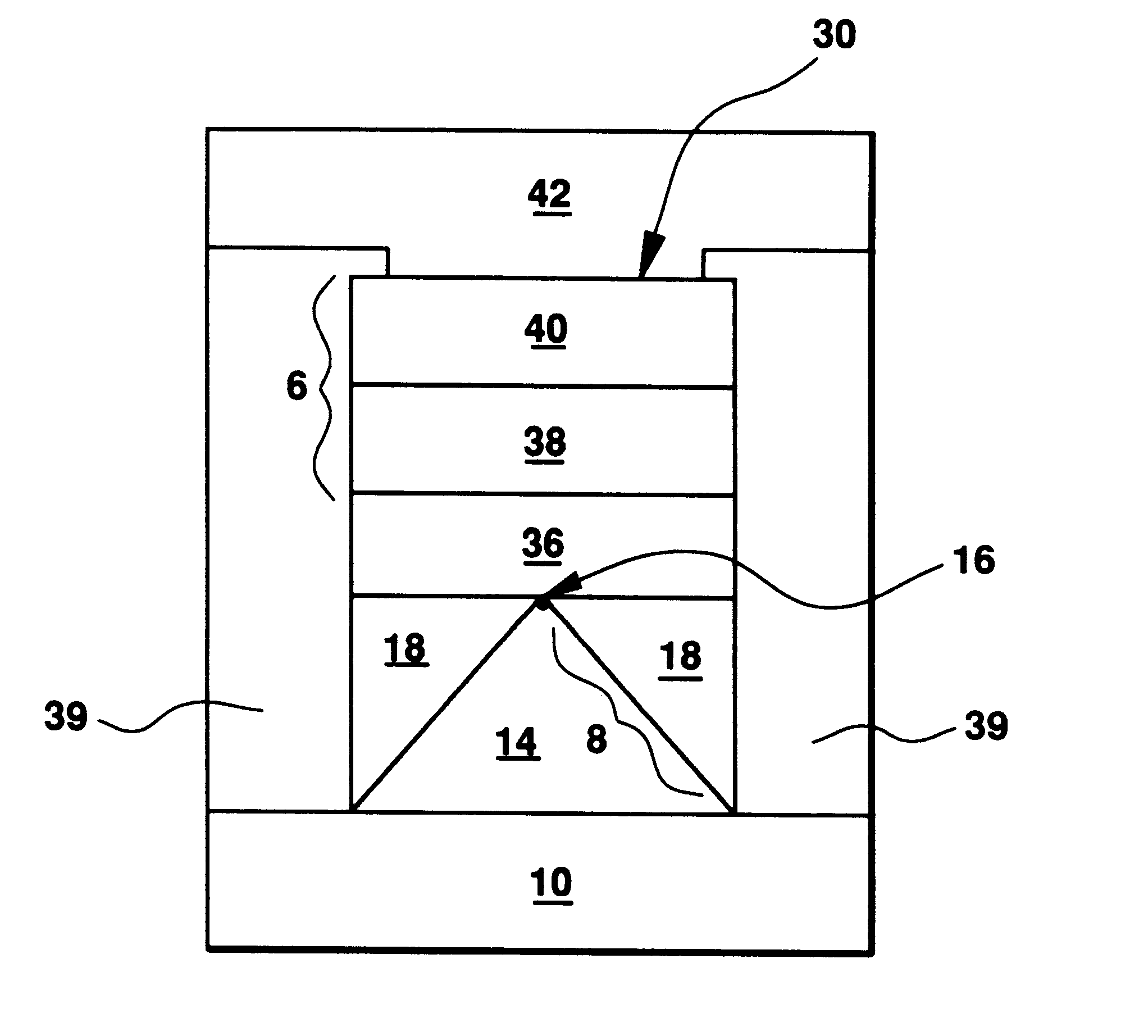
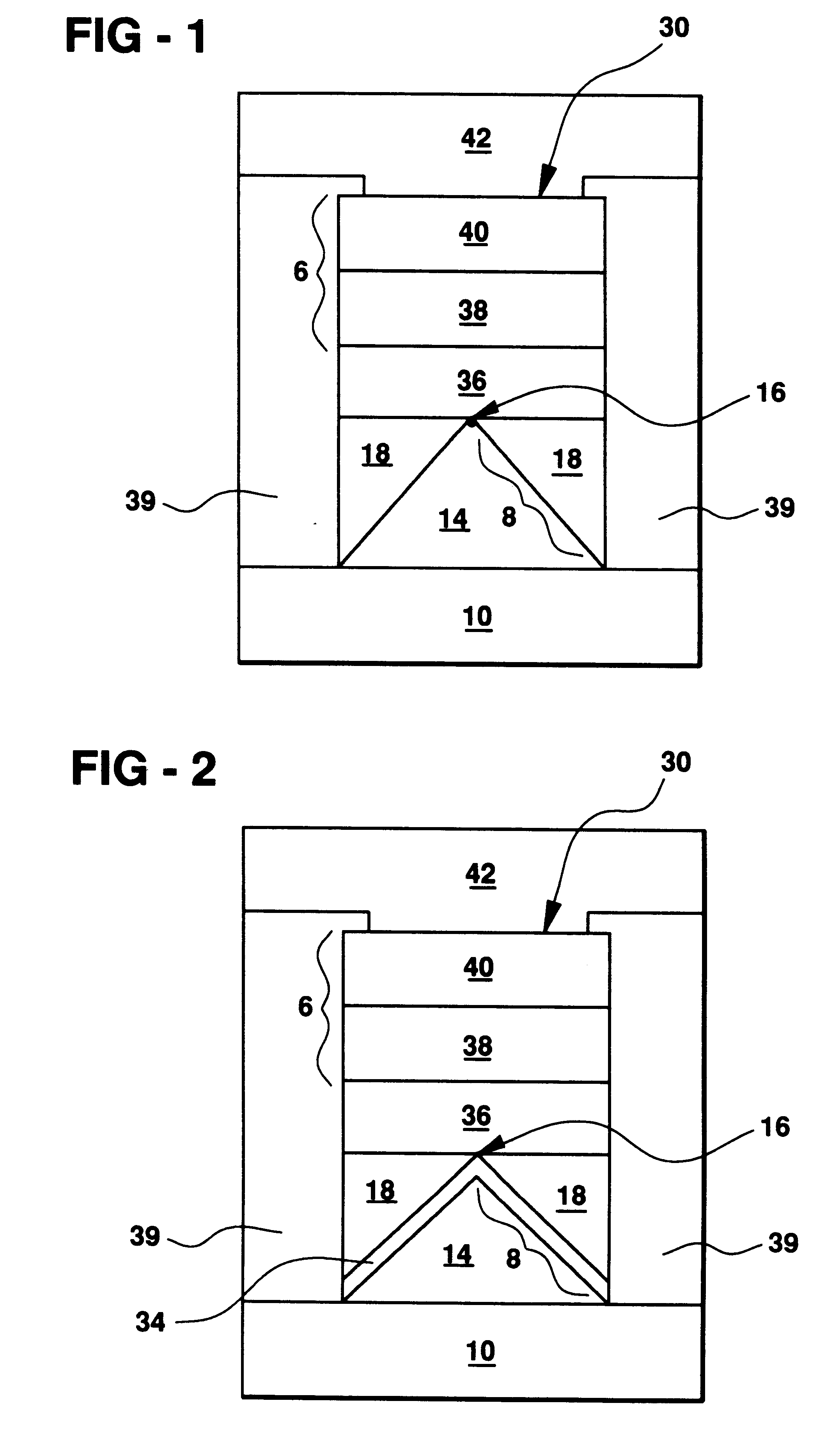
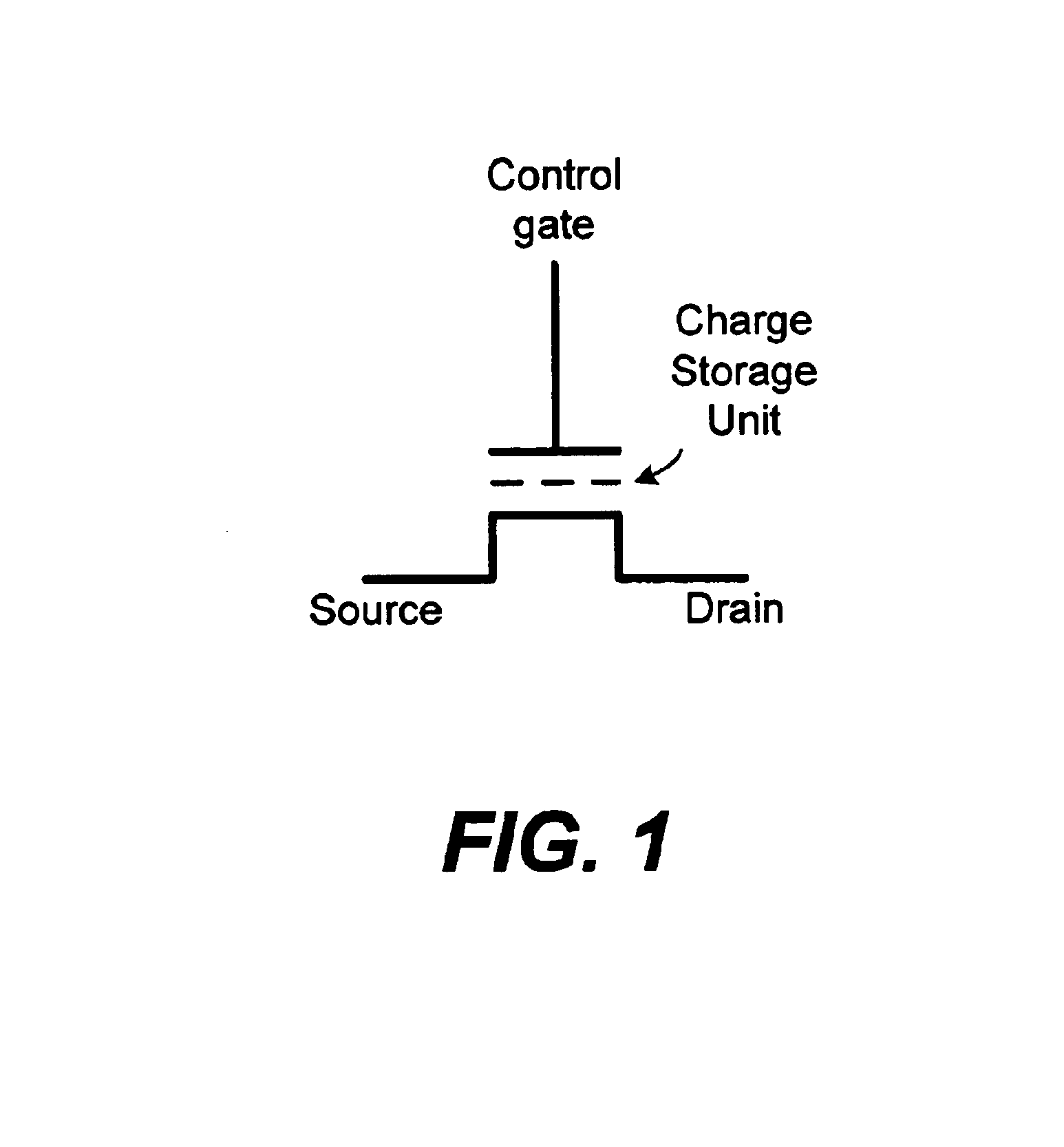
Transistor and semiconductor device
A transistor is provided, which is entirely and partially transparent by the use of a transparent channel layer made of zinc oxide or the like. A channel layer 11 formed of a transparent semiconductor such as zinc oxide ZnO. A transparent electrode is used for all of a source 12, a drain 13 and a gate 14, or a part of them. As the transparent electrode, a transparent conductive material such as conductive ZnO doped with, for example, group III elements is used. As a gate insulating layer 15, a transparent insulative material such as insulative ZnO doped with elements capable of taking a valence of one as a valence number or group V elements is used. If a substrate 16 must be transparent, for example, glass, sapphire, plastic or the like can be used as a transparent material.
Owner:JAPAN SCI & TECH CORP
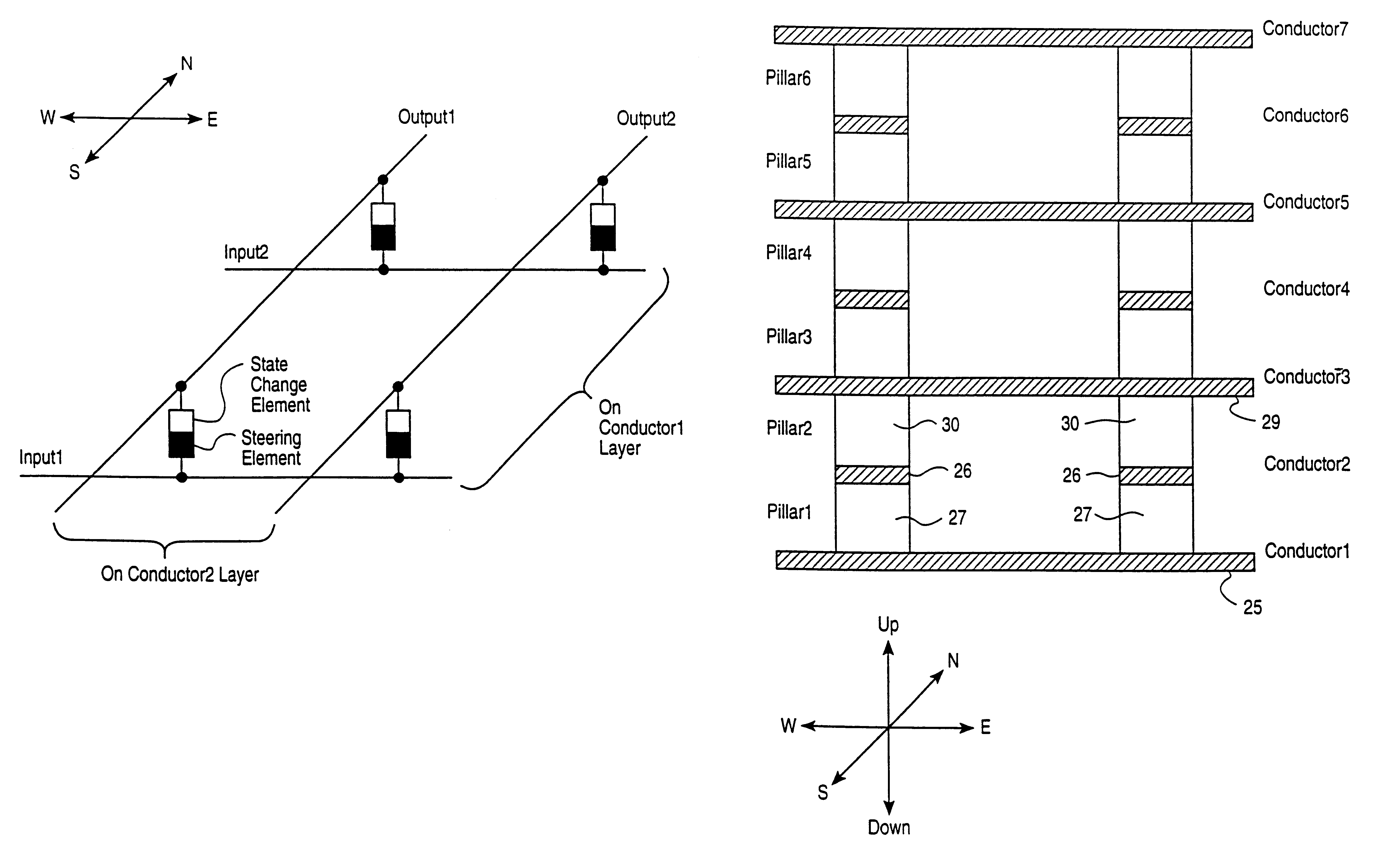
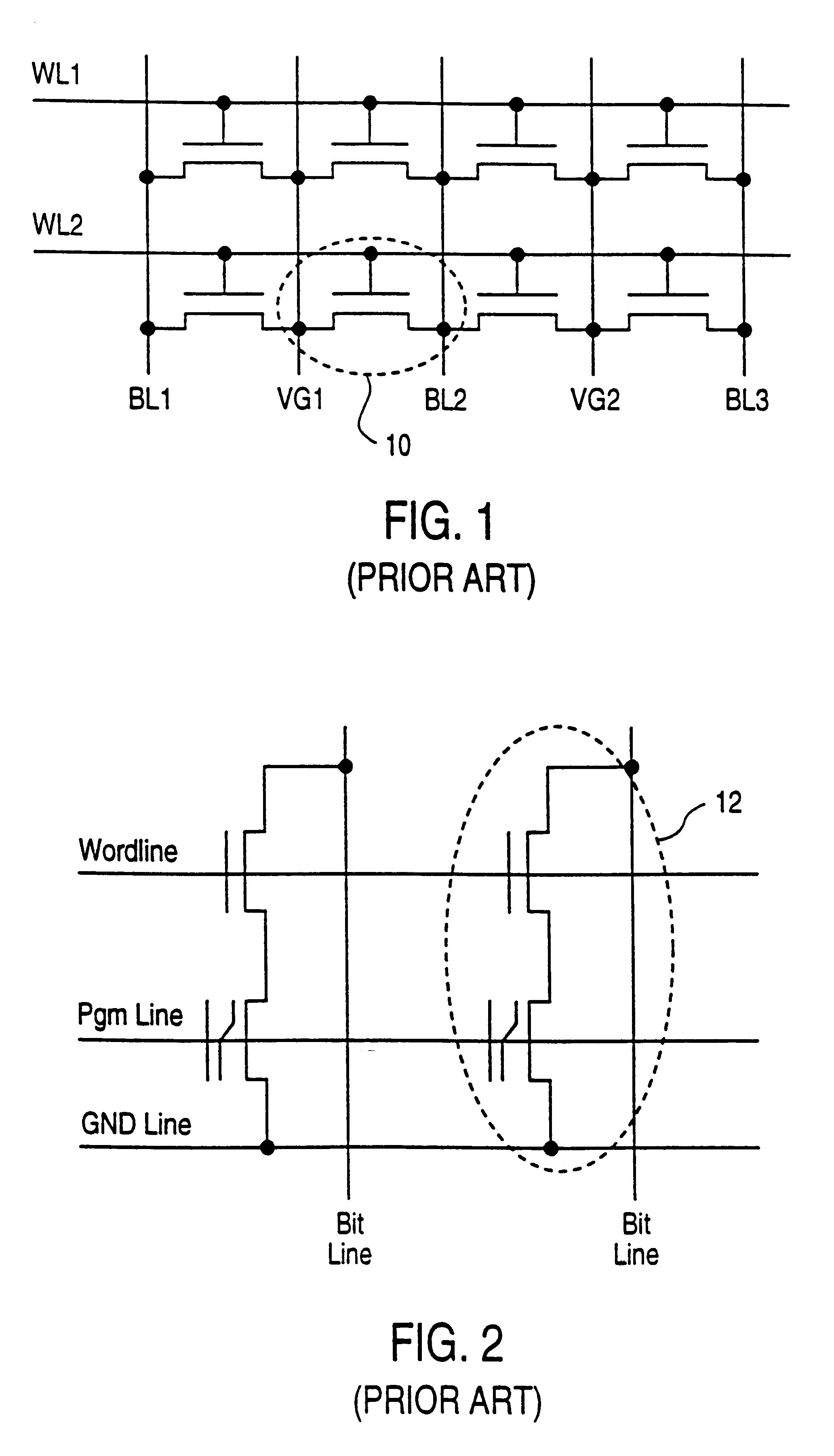
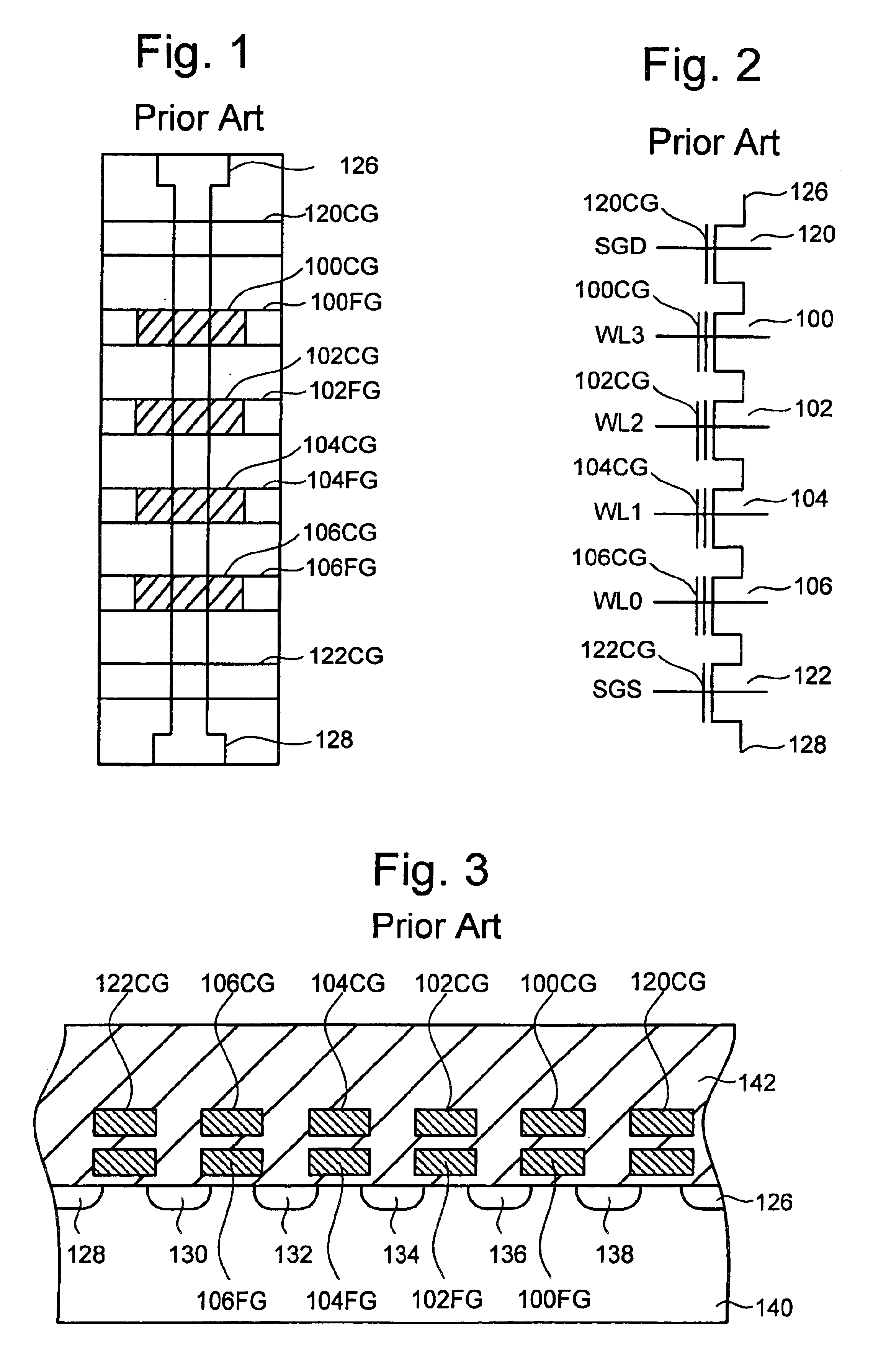
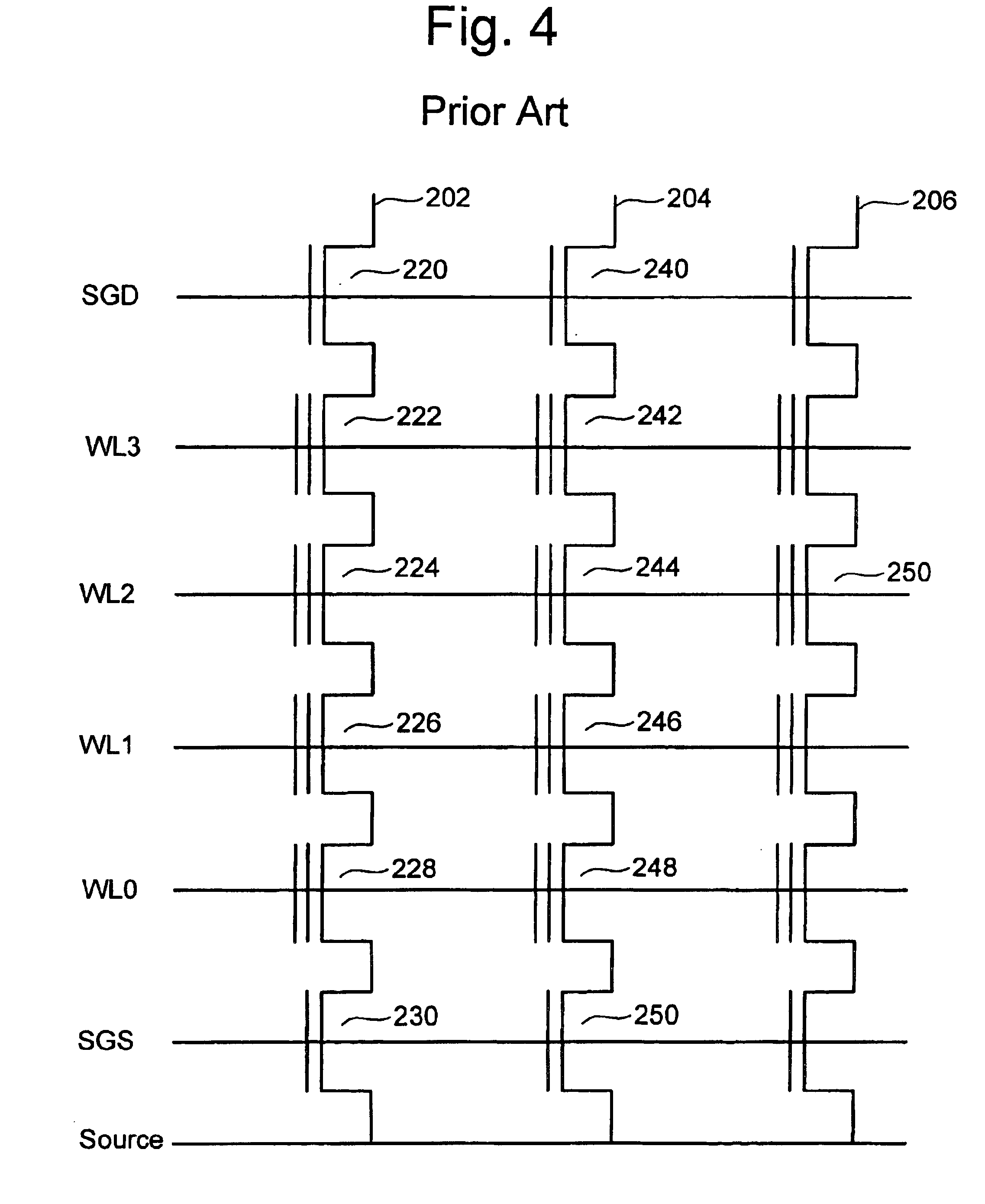
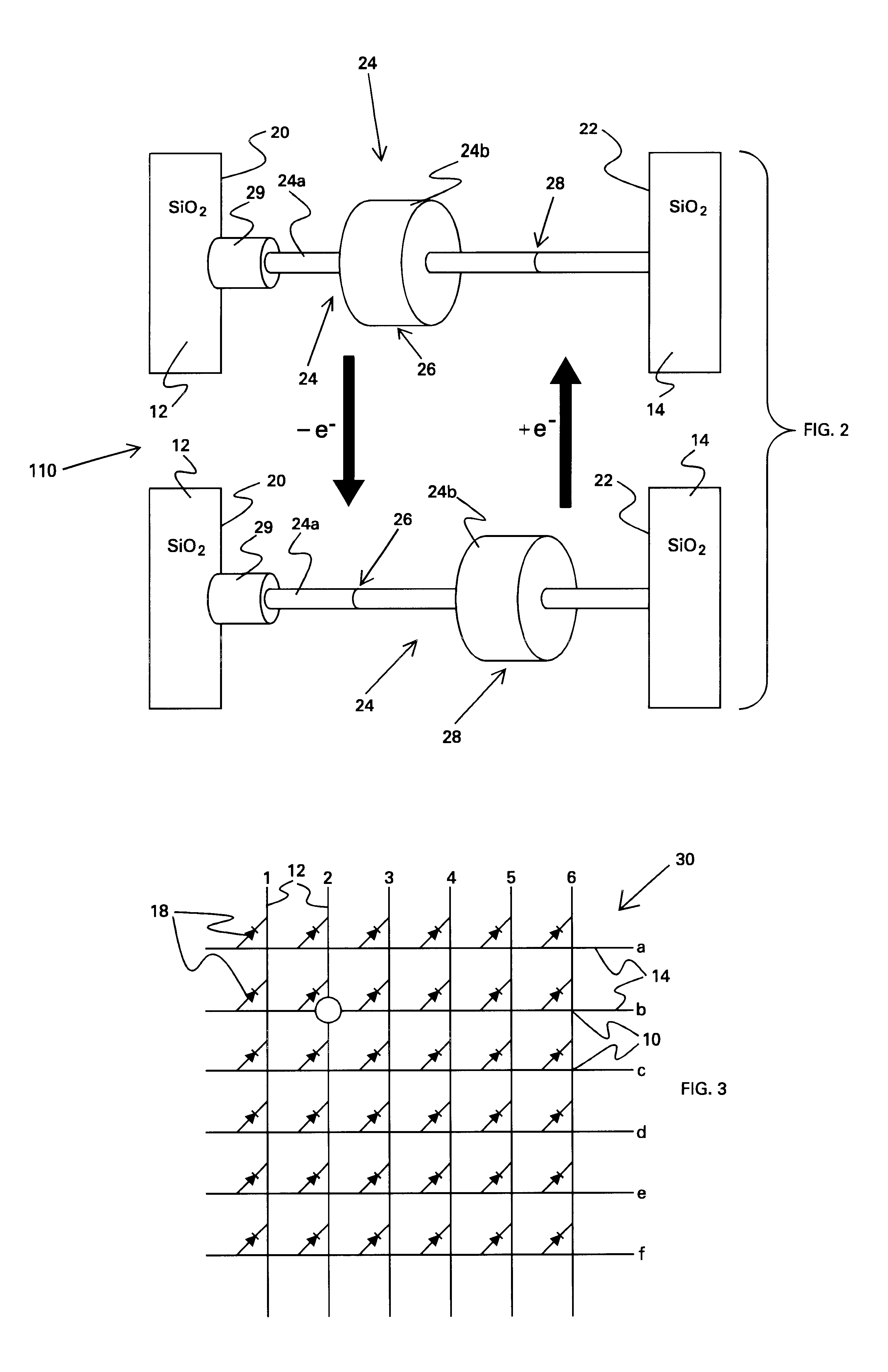
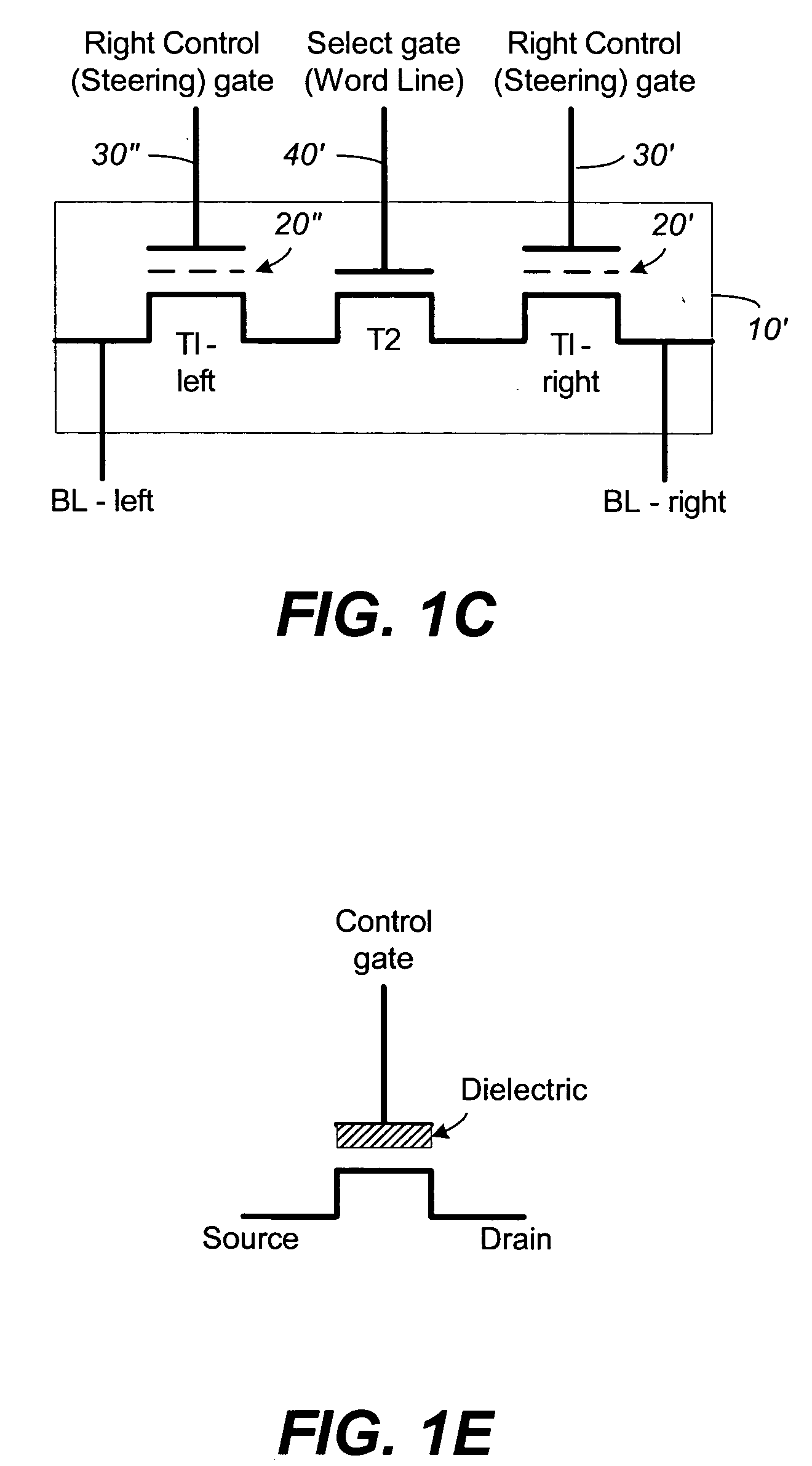
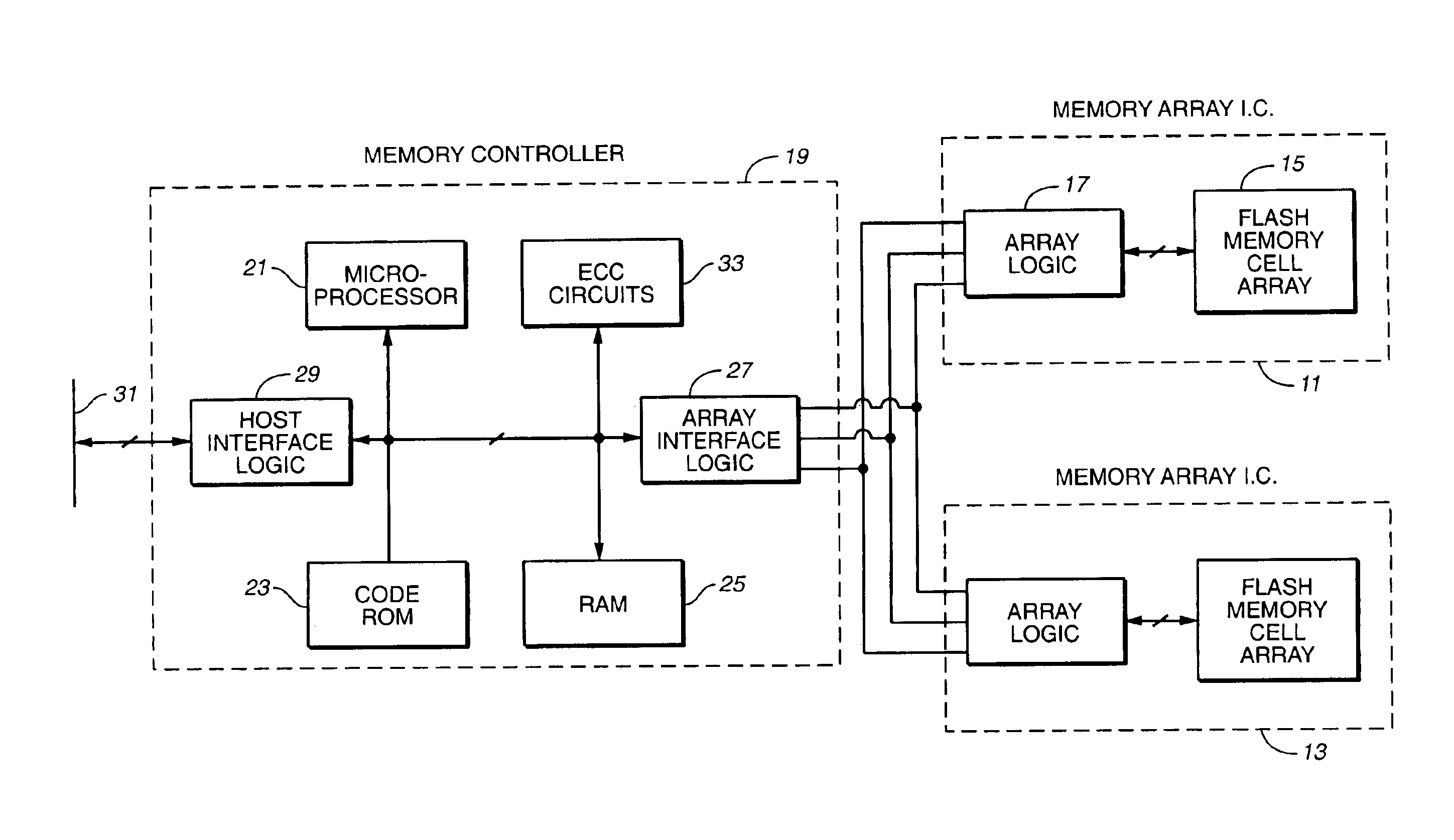
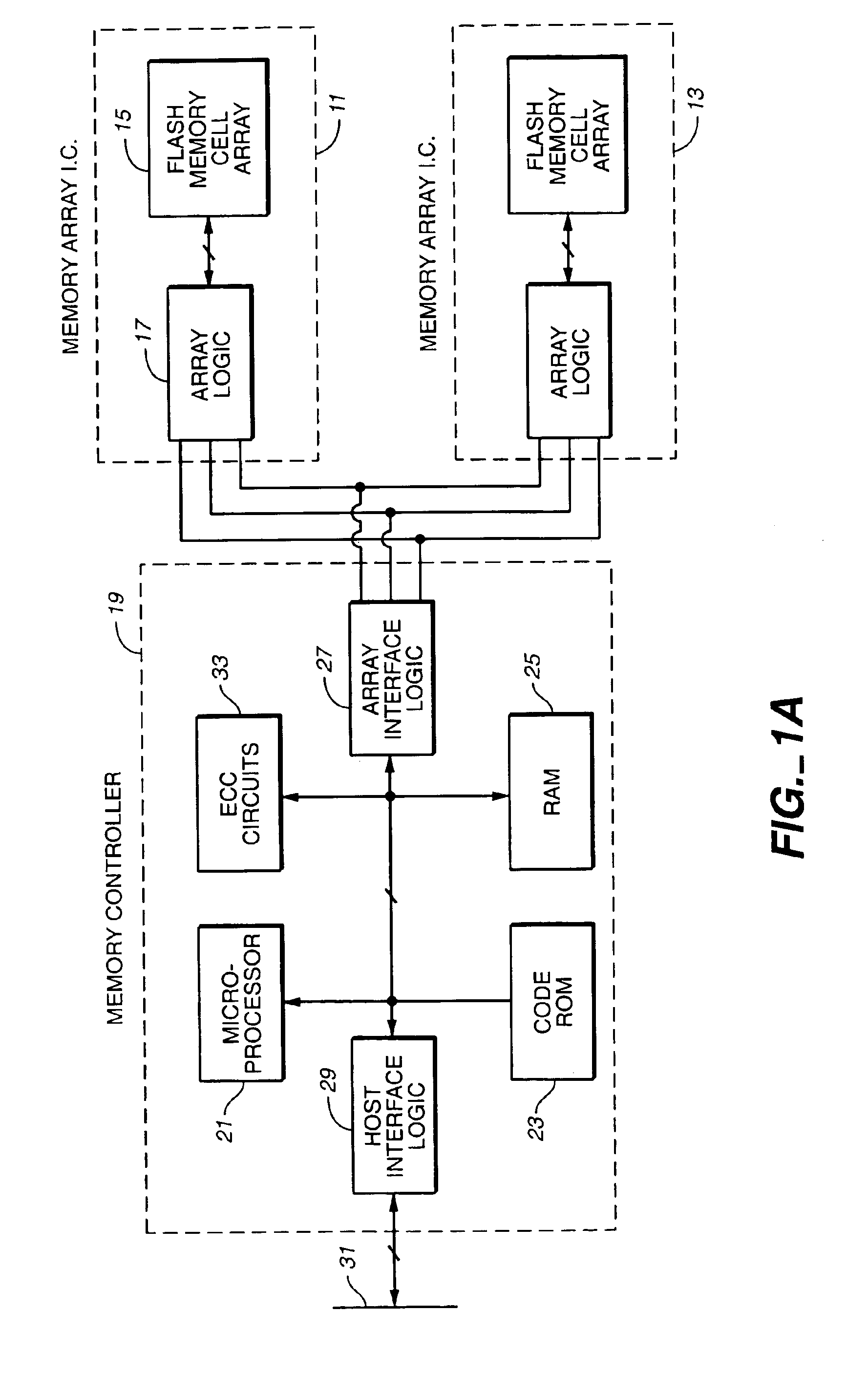
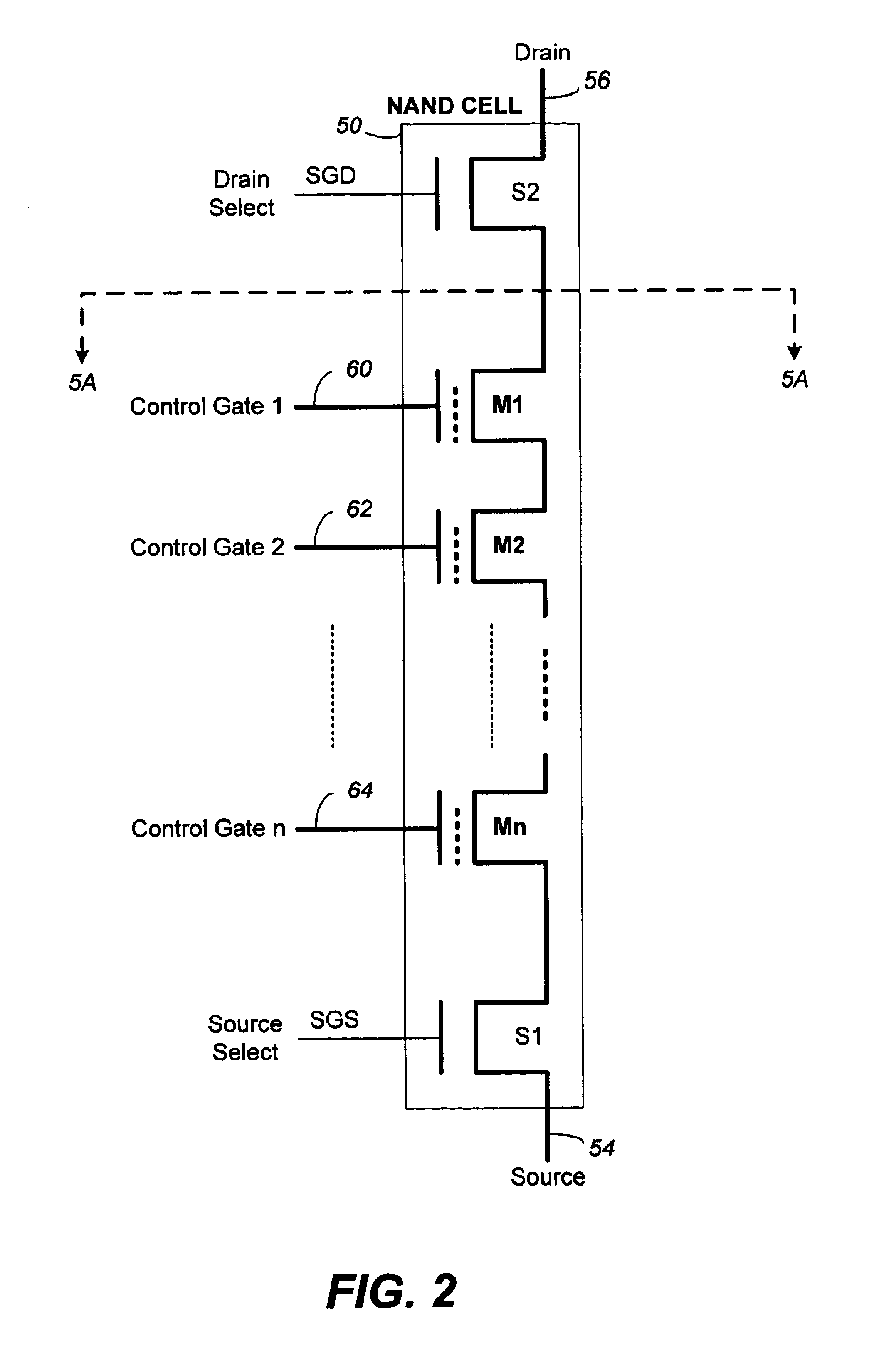
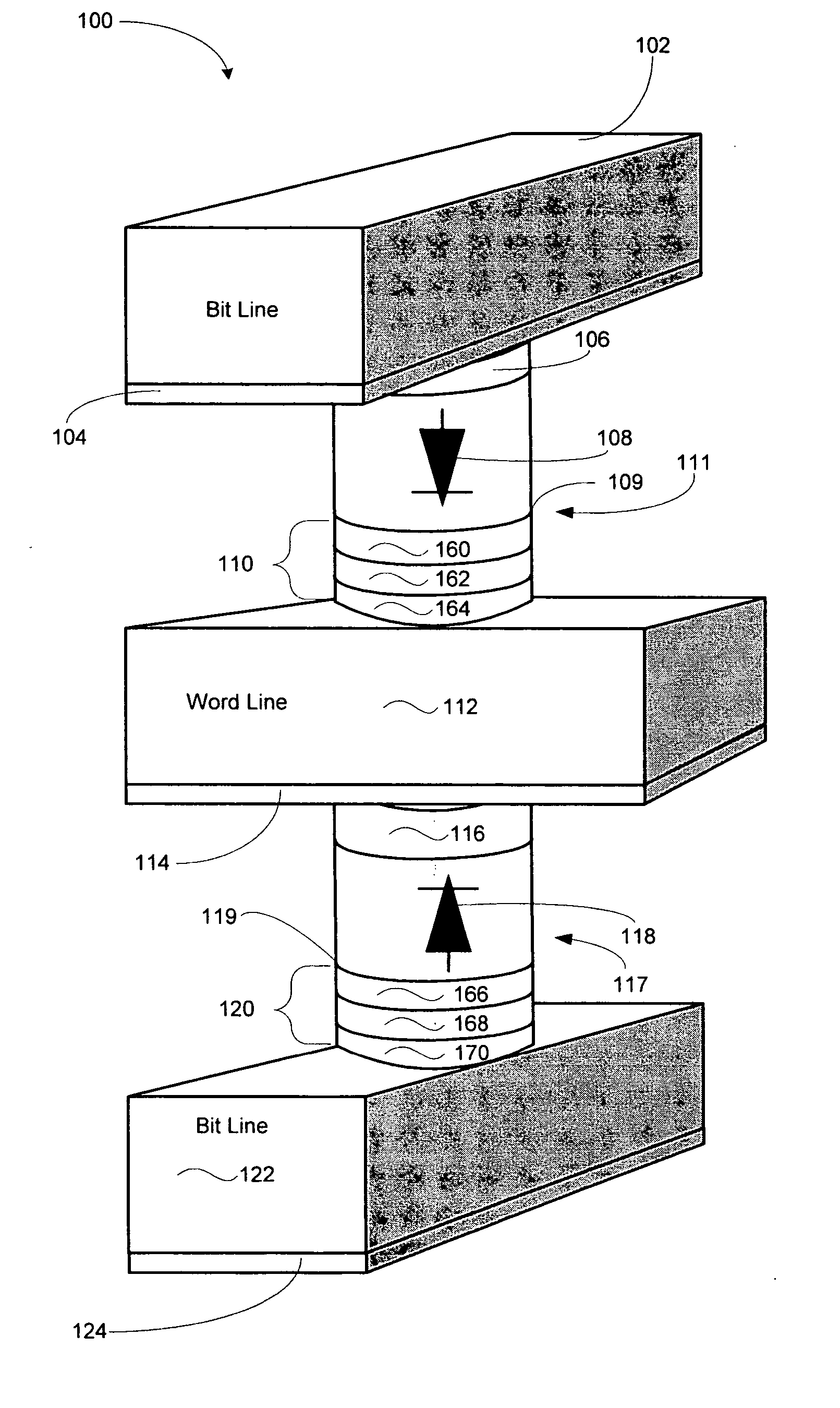
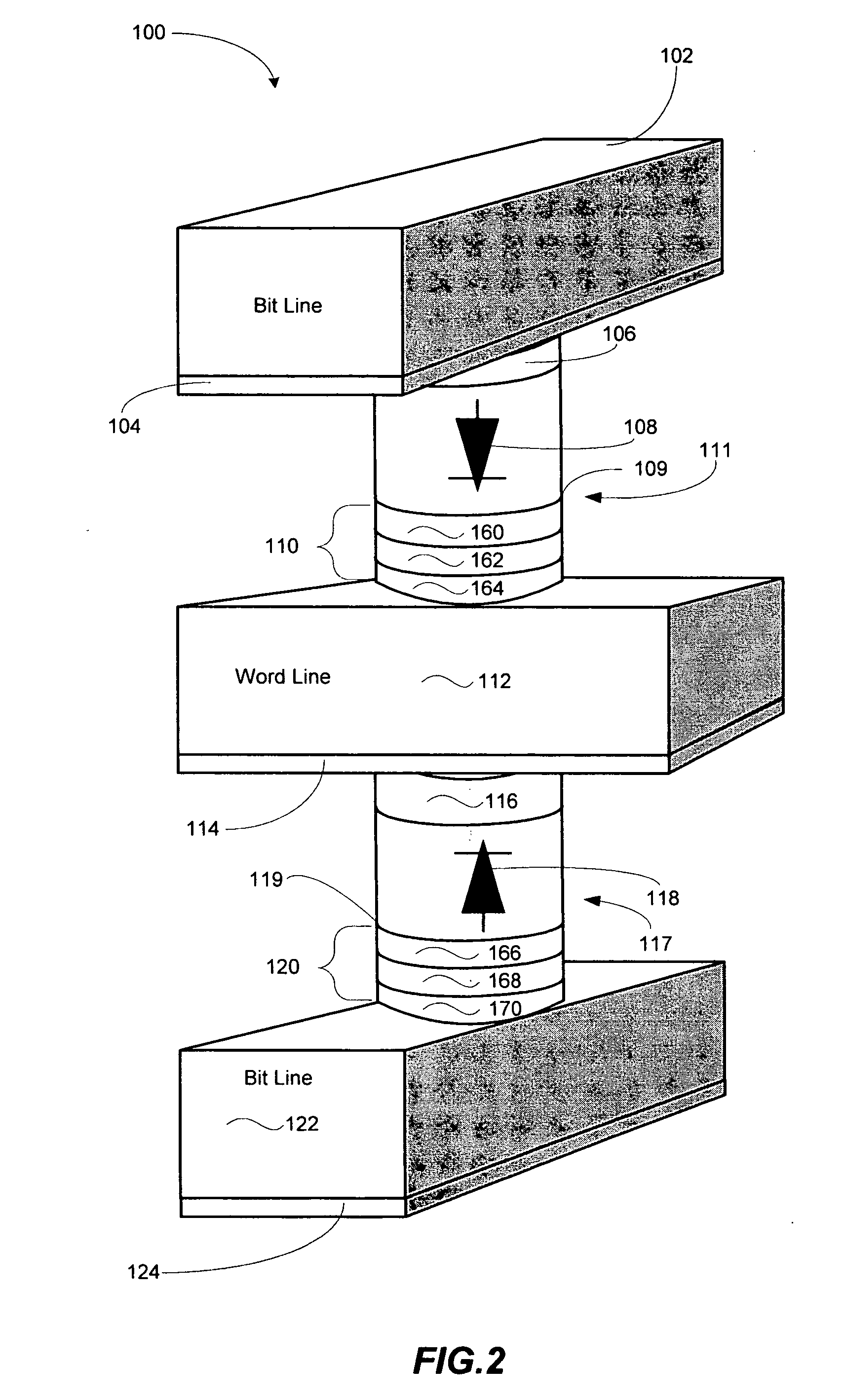
Vertically stacked field programmable nonvolatile memory and method of fabrication
A very high density field programmable memory is disclosed. An array is formed vertically above a substrate using several layers, each layer of which includes vertically fabricated memory cells. The cell in an N level array may be formed with N+1 masking steps plus masking steps needed for contacts. Maximum use of self alignment techniques minimizes photolithographic limitations. In one embodiment the peripheral circuits are formed in a silicon substrate and an N level array is fabricated above the substrate.
Owner:RHOMBUS
Vertically stacked field programmable nonvolatile memory and method of fabrication
A very high density field programmable memory is disclosed. An array is formed vertically above a substrate using several layers, each layer of which includes vertically fabricated memory cells. The cell in an N level array may be formed with N+1 masking steps plus masking steps needed for contacts. Maximum use of self alignment techniques minimizes photolithographic limitations. In one embodiment the peripheral circuits are formed in a silicon substrate and an N level array is fabricated above the substrate.
Owner:SANDISK TECH LLC
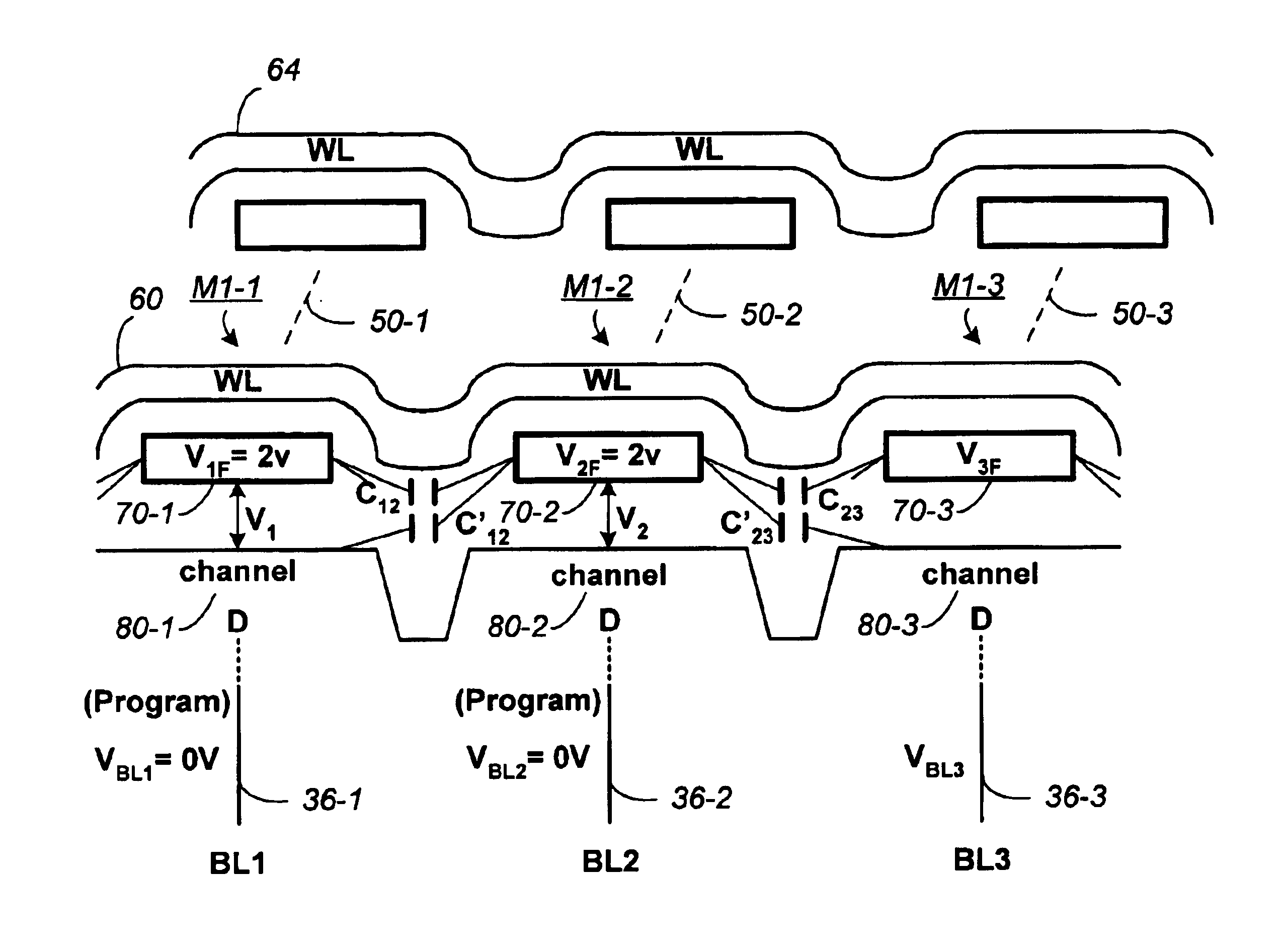
Compensating for coupling during read operations of non-volatile memory
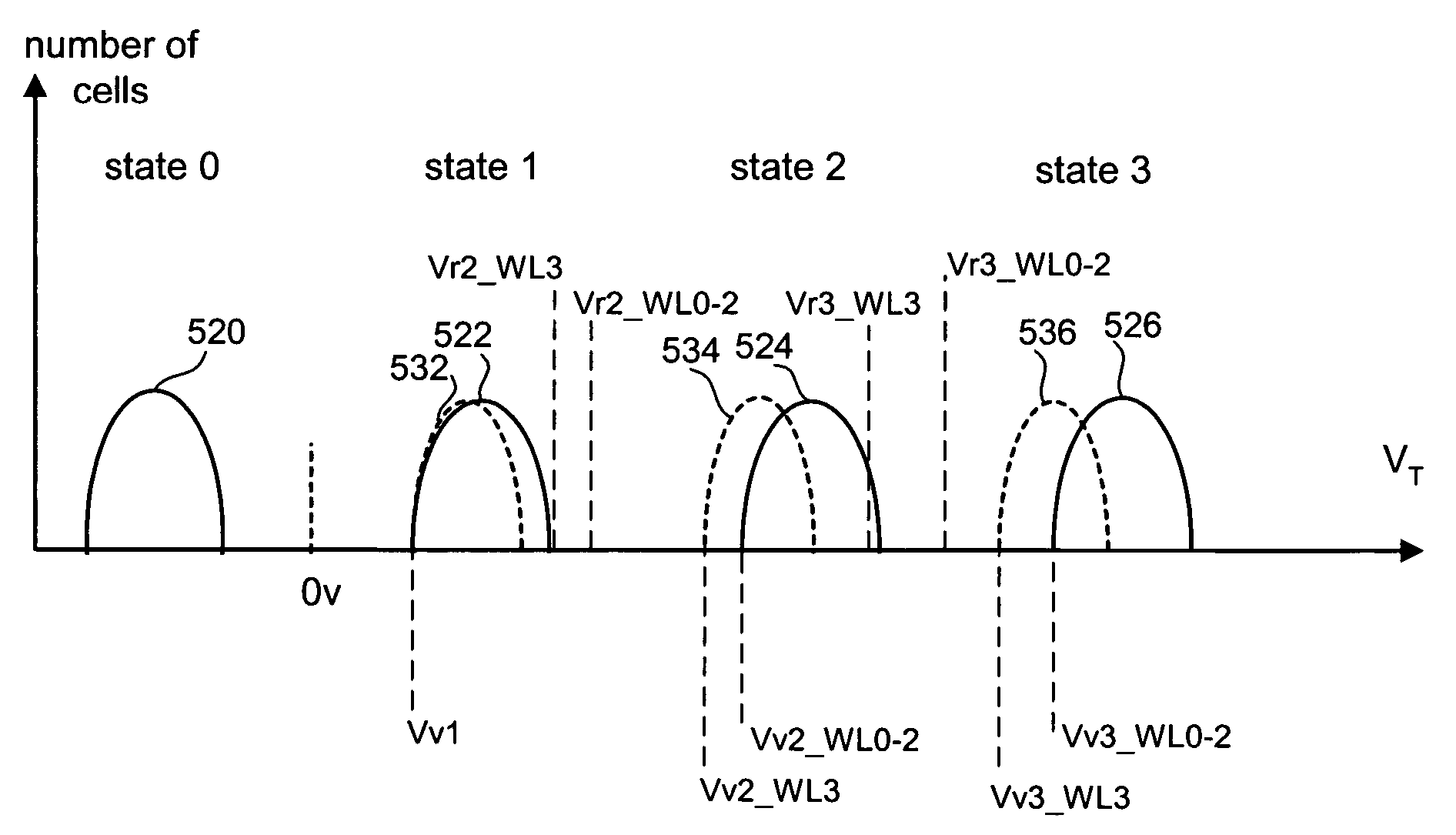
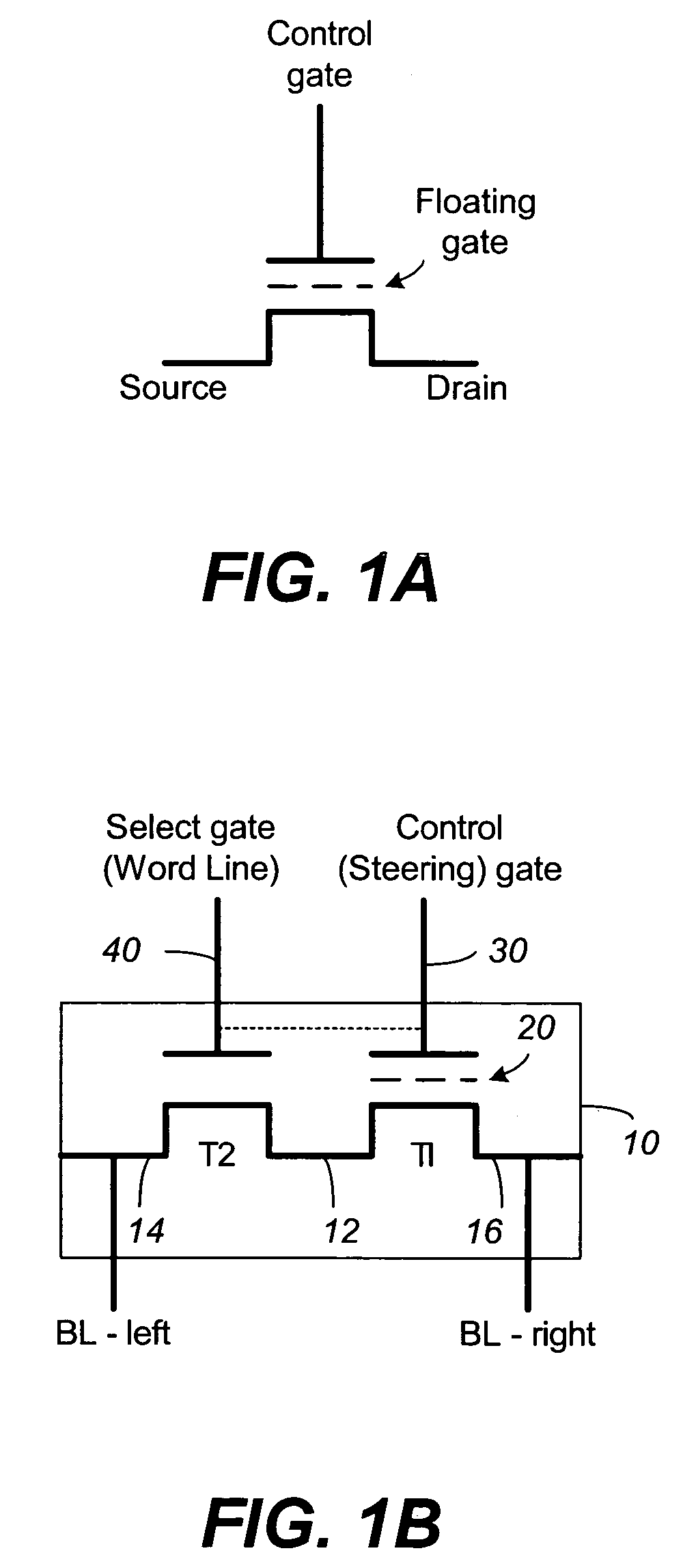
Shifts in the apparent charge stored on a floating gate (or other charge storing element) of a non-volatile memory cell can occur because of the coupling of an electric field based on the charge stored in adjacent floating gates (or other adjacent charge storing elements). The problem occurs most pronouncedly between sets of adjacent memory cells that have been programmed at different times. To compensate for this coupling, the read process for a given memory cell will take into account the programmed state of an adjacent memory cell.
Owner:SANDISK TECH LLC
Variable programming of non-volatile memory
ActiveUS7020017B2Improve data retentionDecreased program disturbRead-only memoriesDigital storageReading levelNon-volatile memory
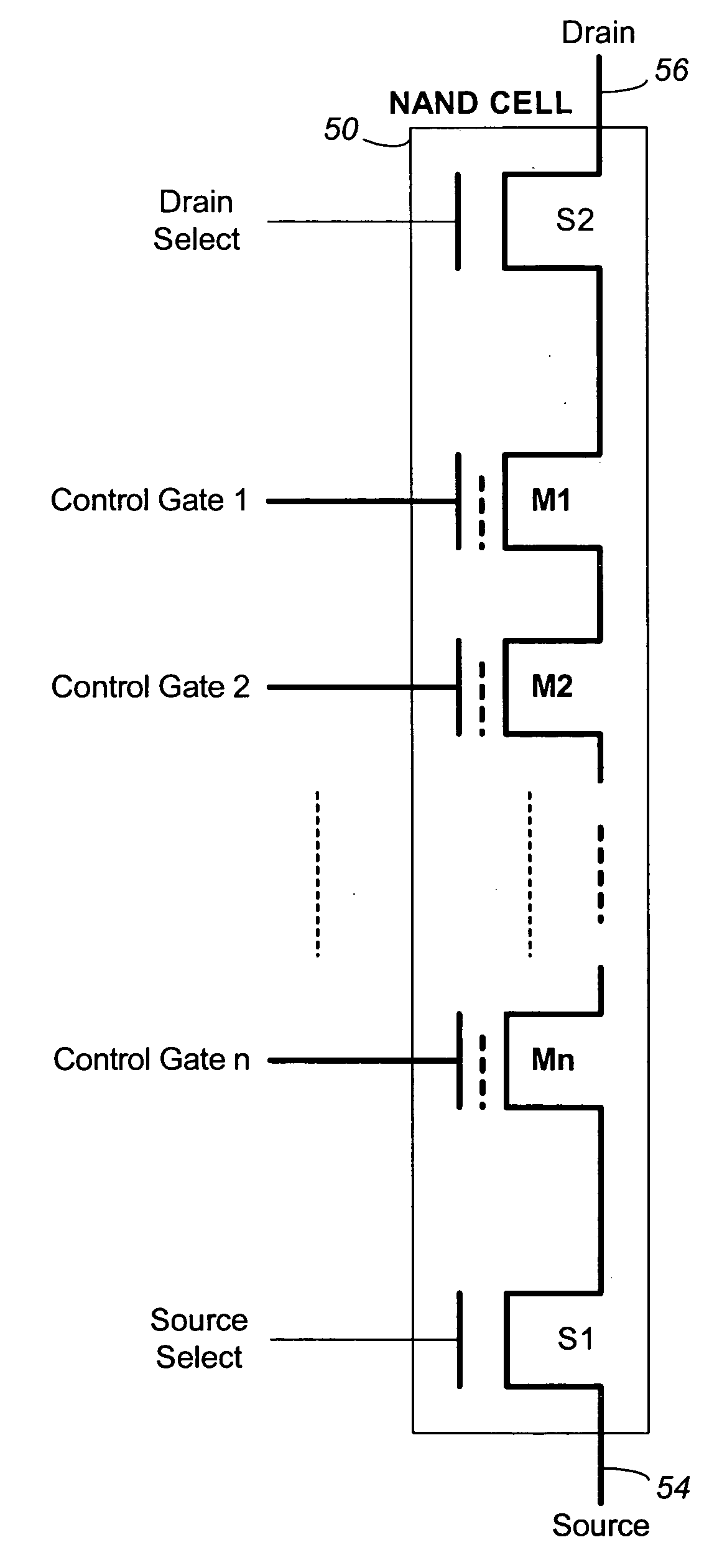
Systems and methods in accordance with various embodiments can provide for reduced program disturb in non-volatile semiconductor memory. In one embodiment, select memory cells such as those connected to a last word line of a NAND string are programmed using one or more program verify levels or voltages that are different than a corresponding level used to program other cells or word lines. One exemplary embodiment includes using a lower threshold voltage verify level for select physical states when programming the last word line to be programmed for a string during a program operation. Another embodiment includes applying a lower program voltage to program memory cells of the last word line to select physical states. Additional read levels are established for reading the states programmed using lower verify levels in some exemplary implementations. A second program voltage step size that is larger than a nominal step size is used in one embodiment when programming select memory cells or word lines, such as the last word line to be programmed for a NAND string.
Owner:SANDISK TECH LLC
Source side self boosting technique for non-volatile memory
InactiveUS6859397B2Improve performanceMinimize program disturbRead-only memoriesDigital storagePre-chargeProgramming process
A non-volatile semiconductor memory system (or other type of memory system) is programmed in a manner that avoids program disturb. In one embodiment that includes a flash memory system using a NAND architecture, program disturb is avoided by increasing the channel potential of the source side of the NAND string during the programming process. One exemplar implementation includes applying a voltage (e.g. Vdd) to the source contact and turning on the source side select transistor for the NAND sting corresponding to the cell being inhibited. Another implementation includes applying a pre-charging voltage to the unselected word lines of the NAND string corresponding to the cell being inhibited prior to applying the program voltage.
Owner:SANDISK TECH LLC
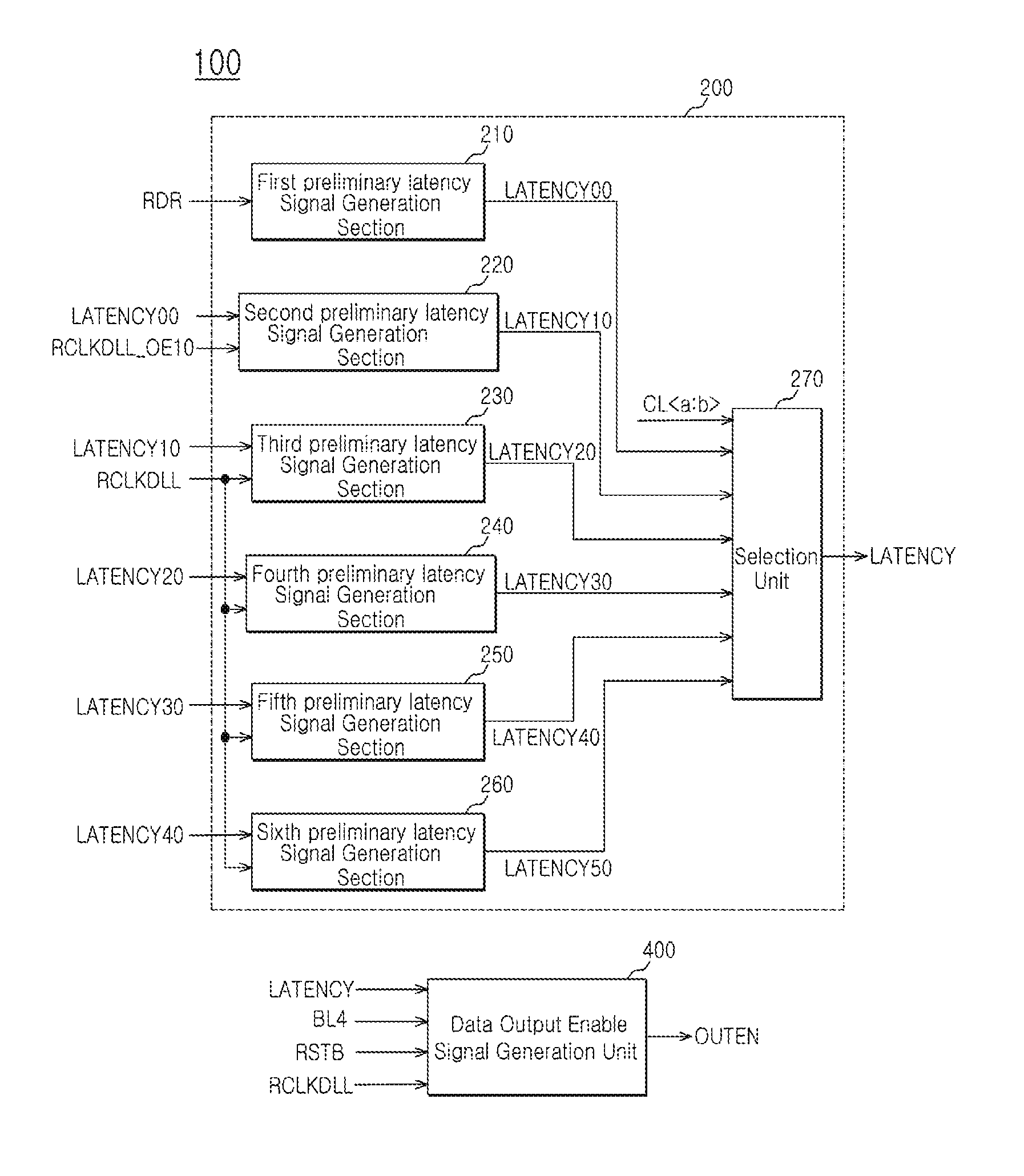
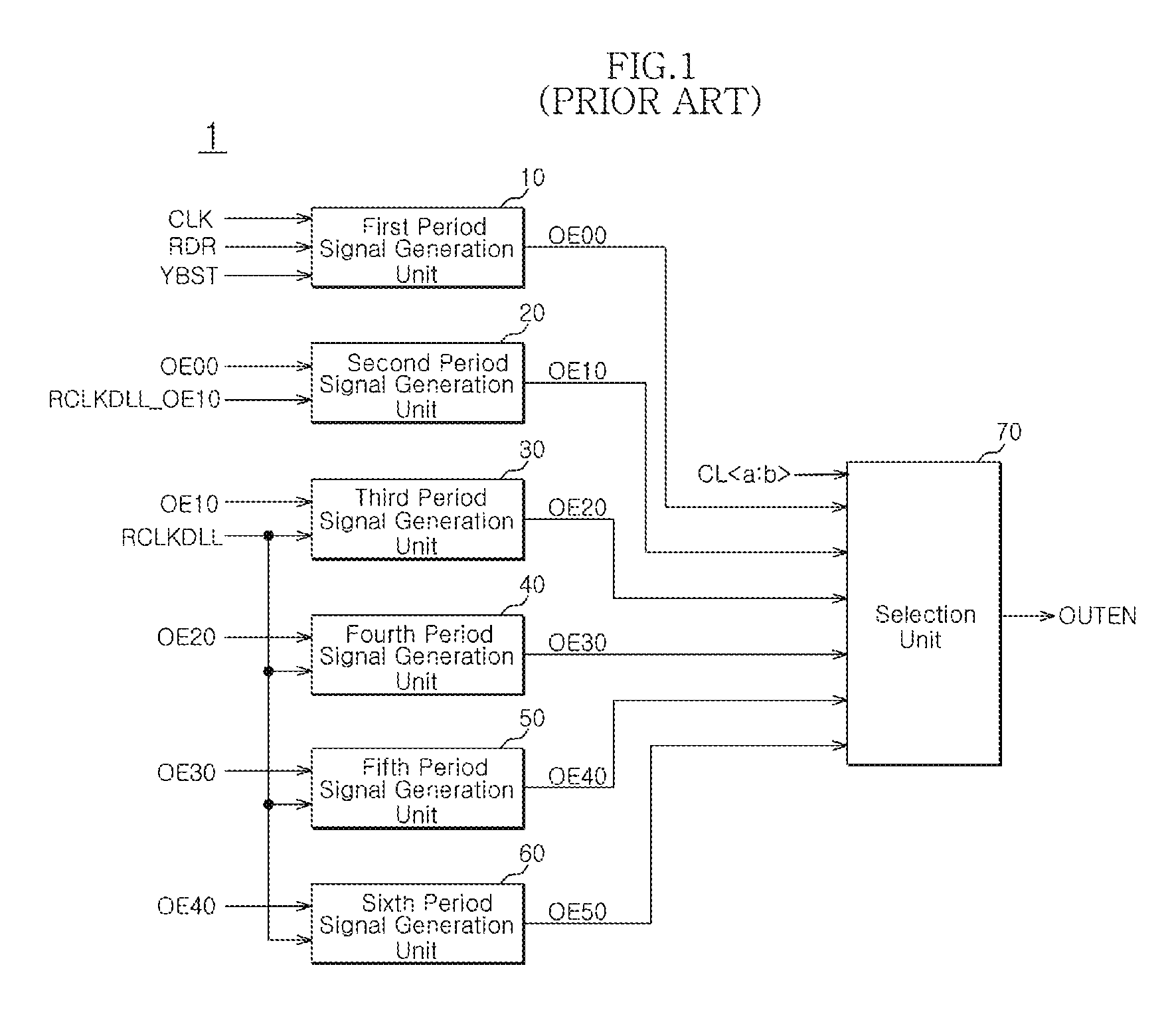
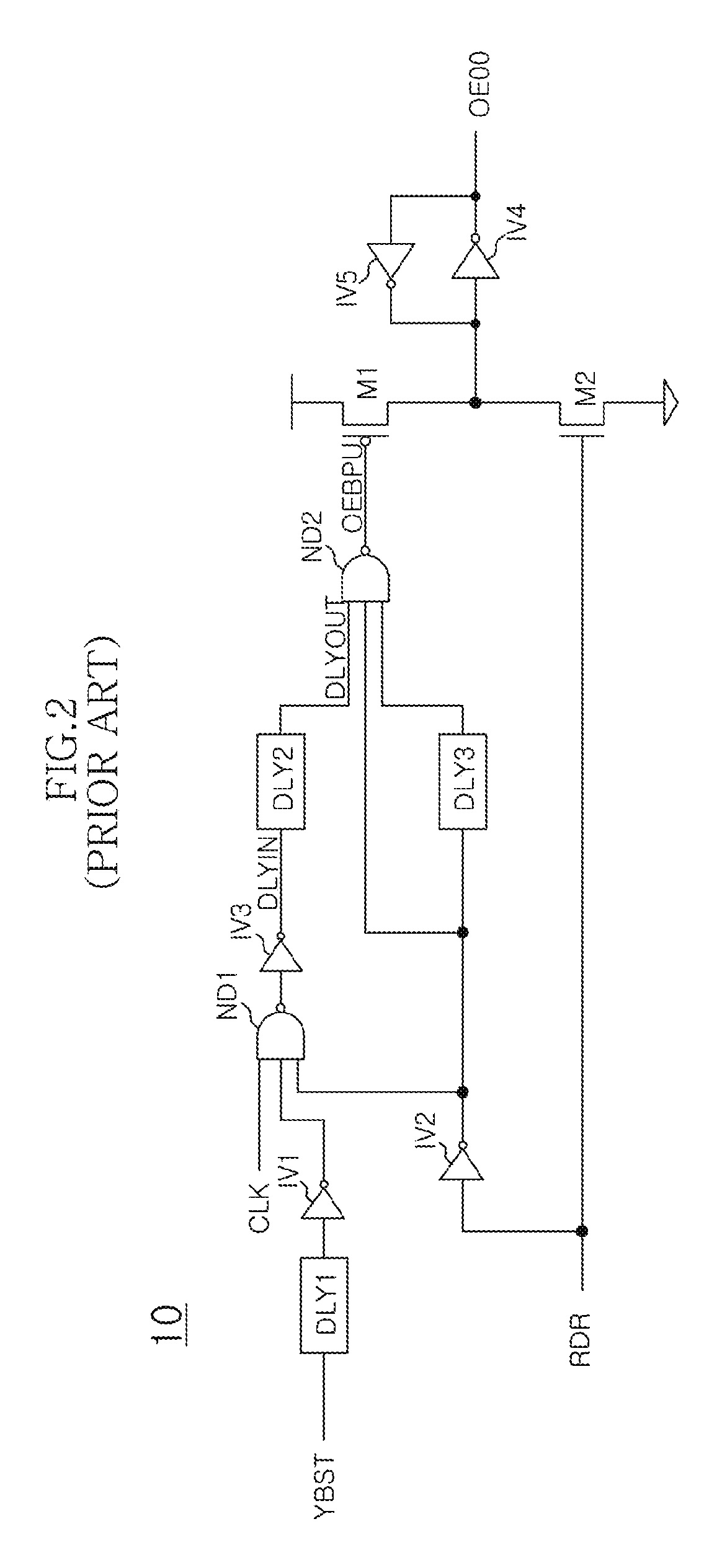
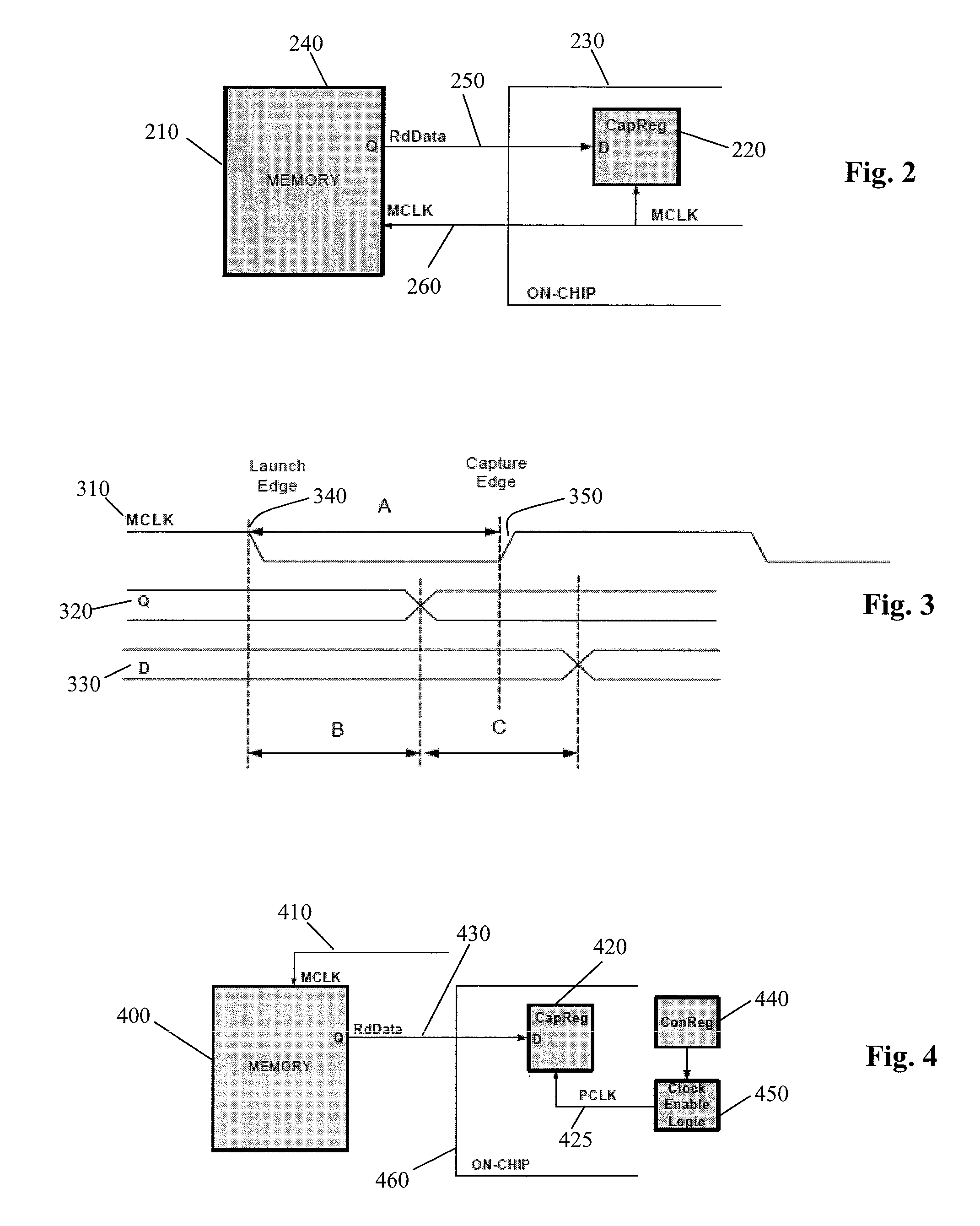
Output enable signal generation circuit of semiconductor memory
An output enable signal generation circuit of a semiconductor memory includes: a latency signal generation unit configured to generate a latency signal for designating activation timing of a data output enable signal in response to a read signal and a CAS latency signal; and a data output enable signal generation unit configured to control the activation timing and deactivation timing of the data output enable signal in response to the latency signal and a signal generated by shifting the latency signal based on a burst length (BL).
Owner:SK HYNIX INC
Location-based feature enablement for mobile terminals
ActiveUS8583924B2Digital data processing detailsUser identity/authority verificationComputer terminalComputer science
Owner:HAND HELD PRODS
Video-Based Privacy Supporting System
ActiveUS20100205667A1Improve securityPrivacy protectionDigital data processing detailsUnauthorized memory use protectionDisplay deviceOutput device
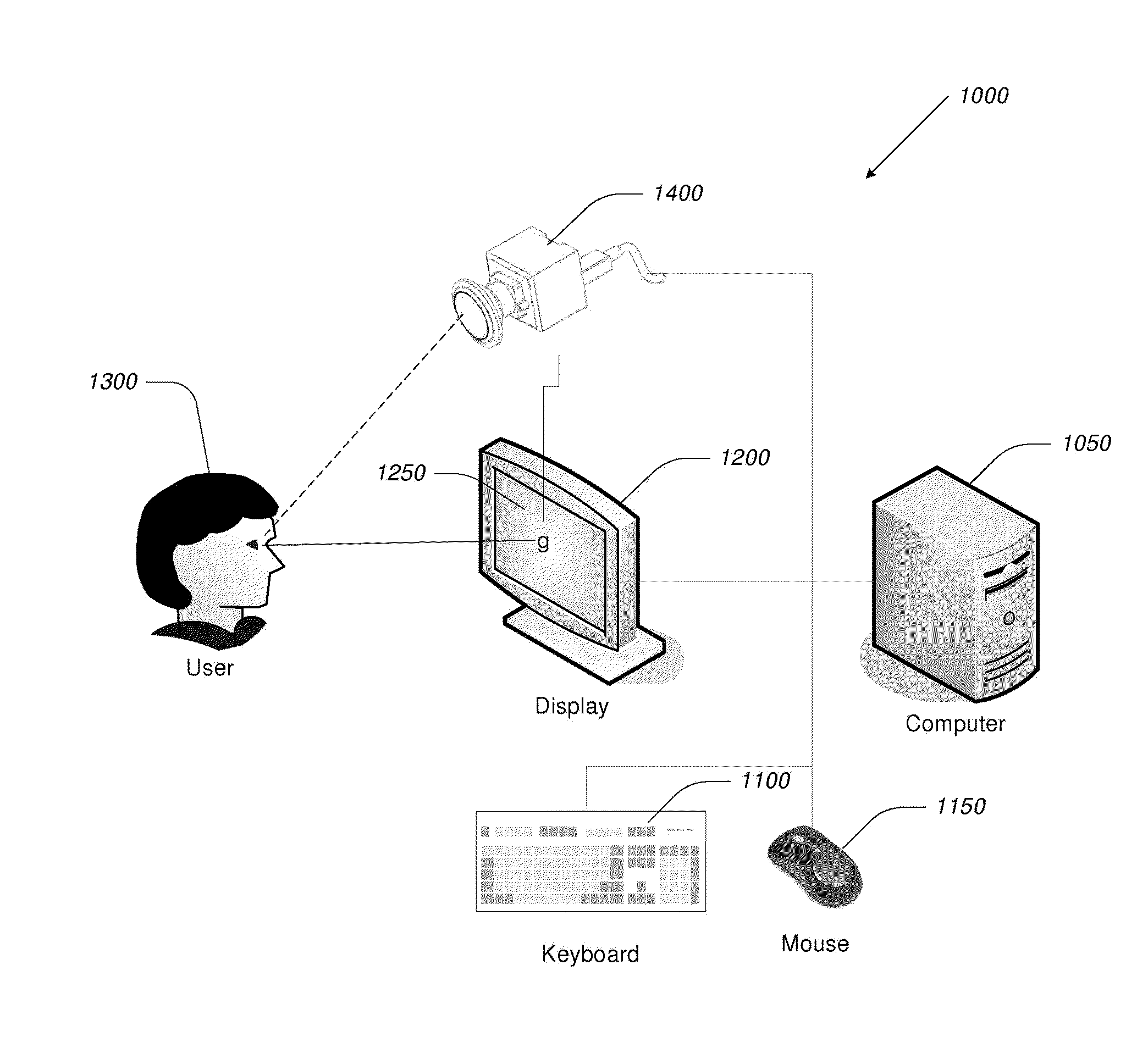
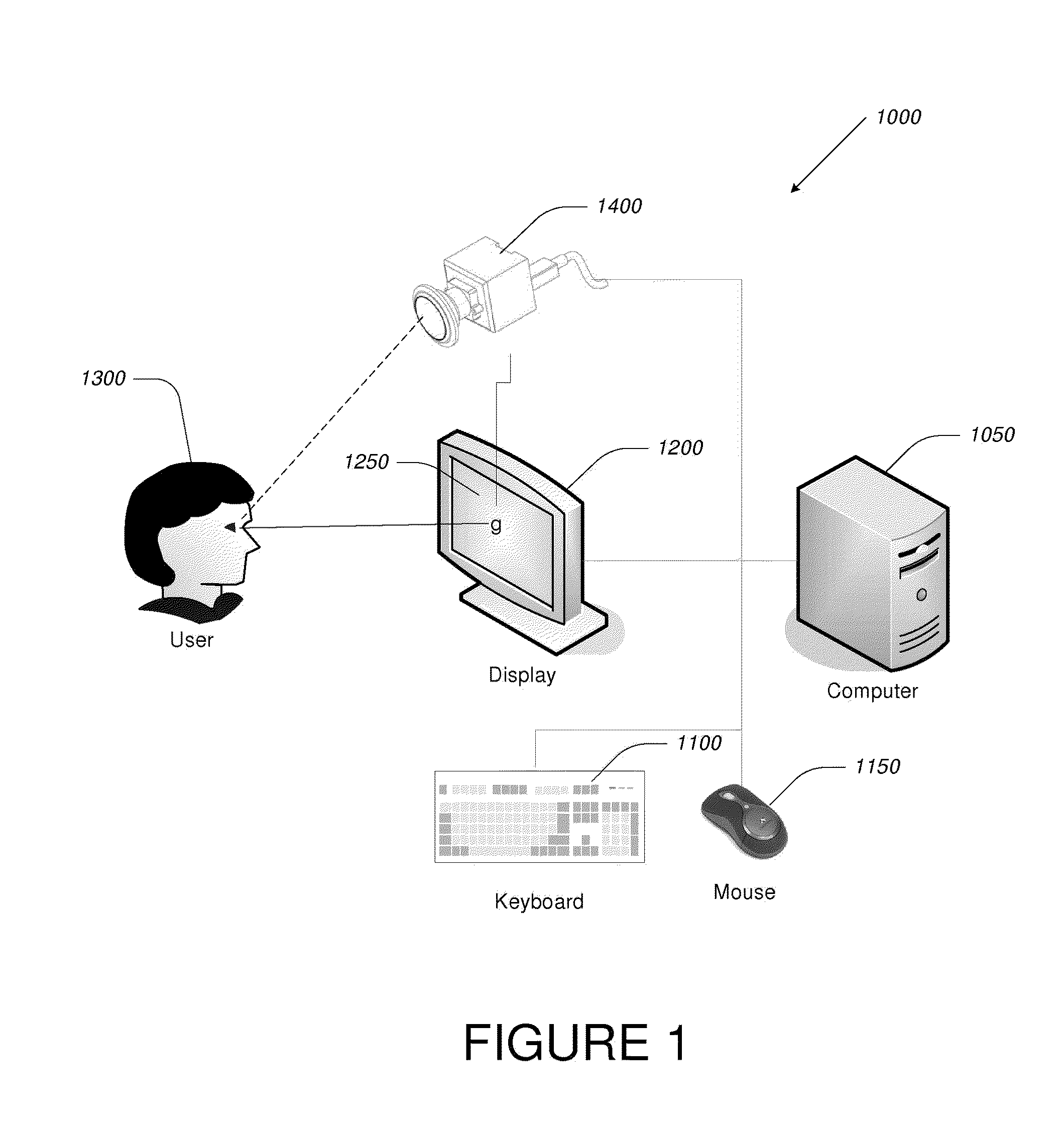
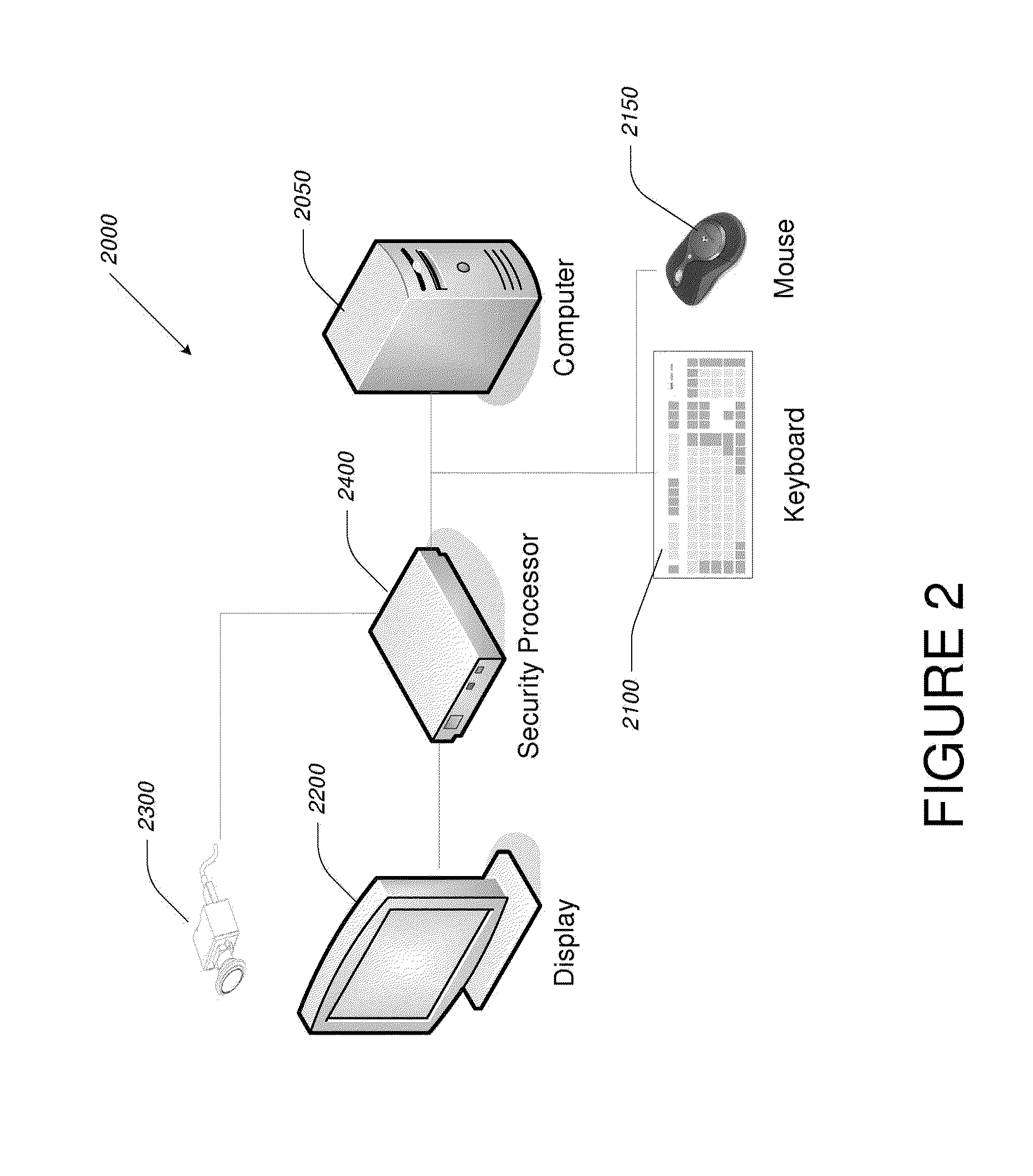
Computer display privacy and security for computer systems. In one aspect, the invention provides a computer-controlled system for regulating the interaction between a computer and a user of the computer based on the environment of the computer and the user. For example, the computer-controlled system provided by the invention comprises an input-output device including an image sensor configured to collect facial recognition data proximate to the computer. The system also includes a user security parameter database encoding security parameters associated with the user; the database is also configured to communicate with the security processor. The security processor is configured to receive the facial recognition data and the security parameters associated with the user, and is further configured to at least partially control the operation of the data input device and the data output device in response to the facial recognition data and the security parameters associated with the user.
Owner:TOBII TECH AB
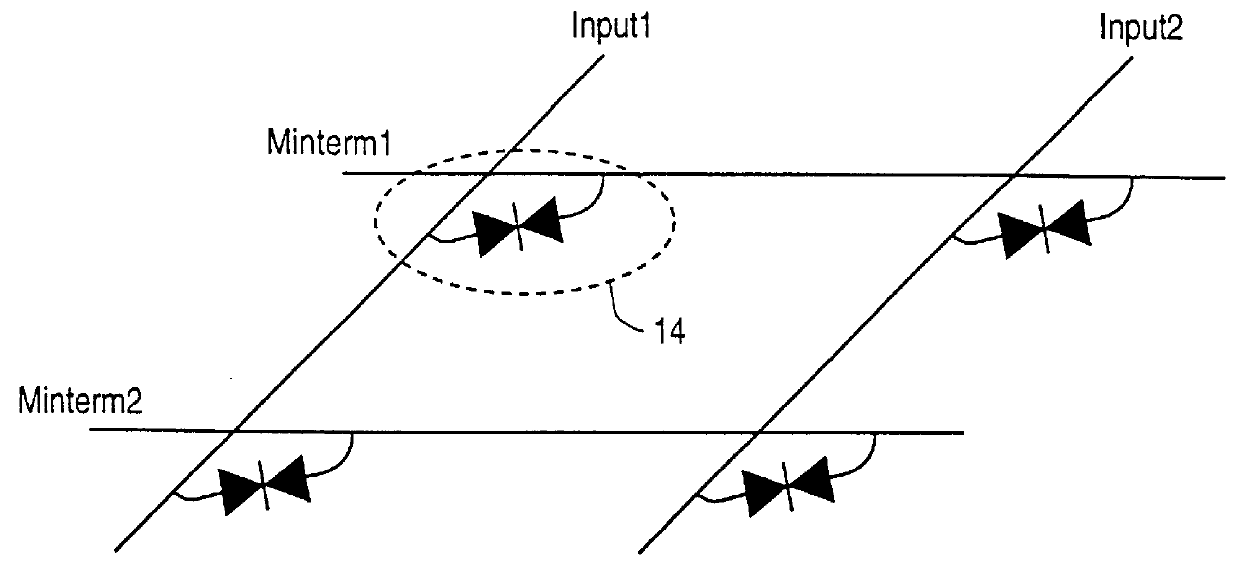
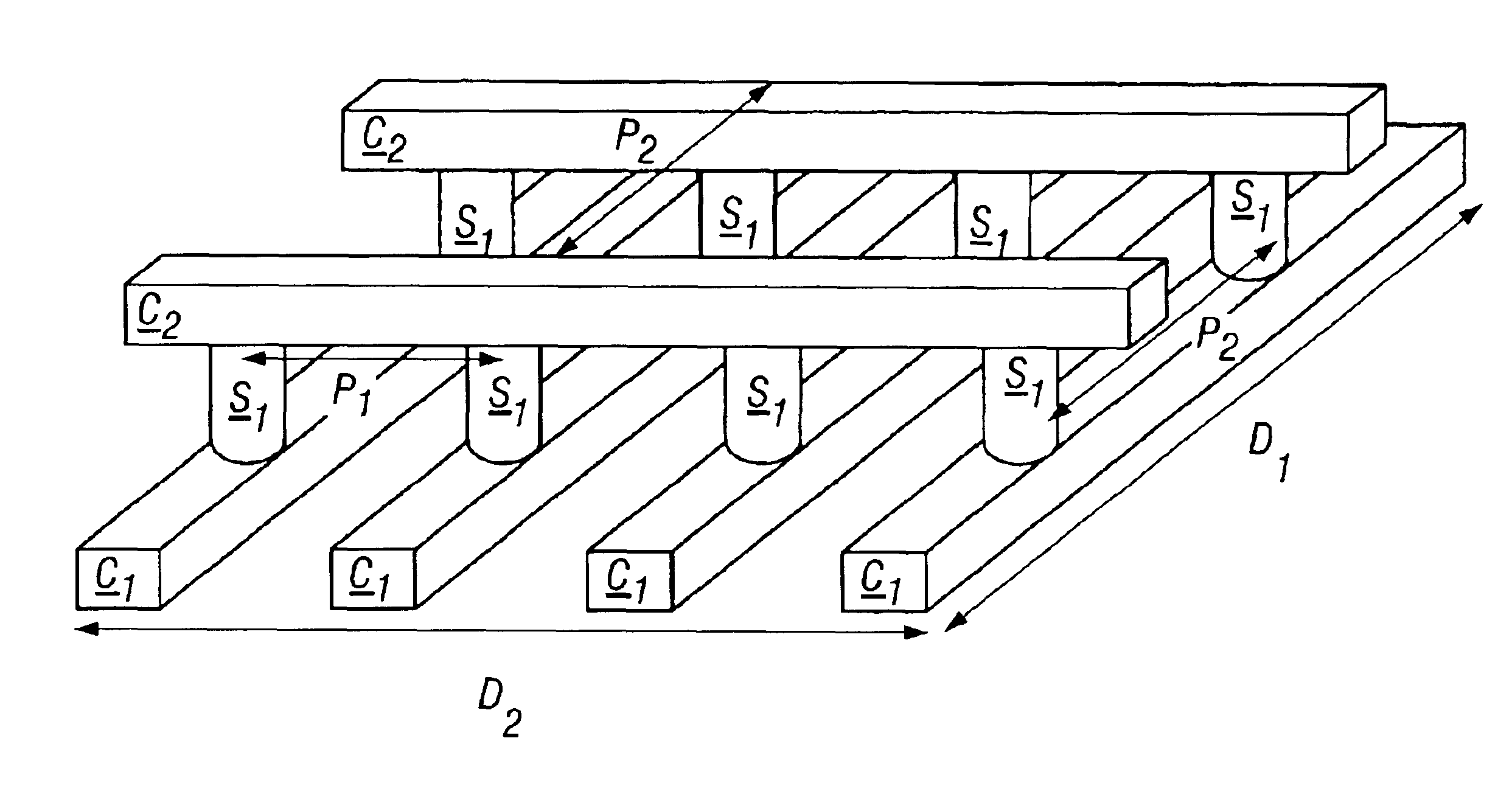
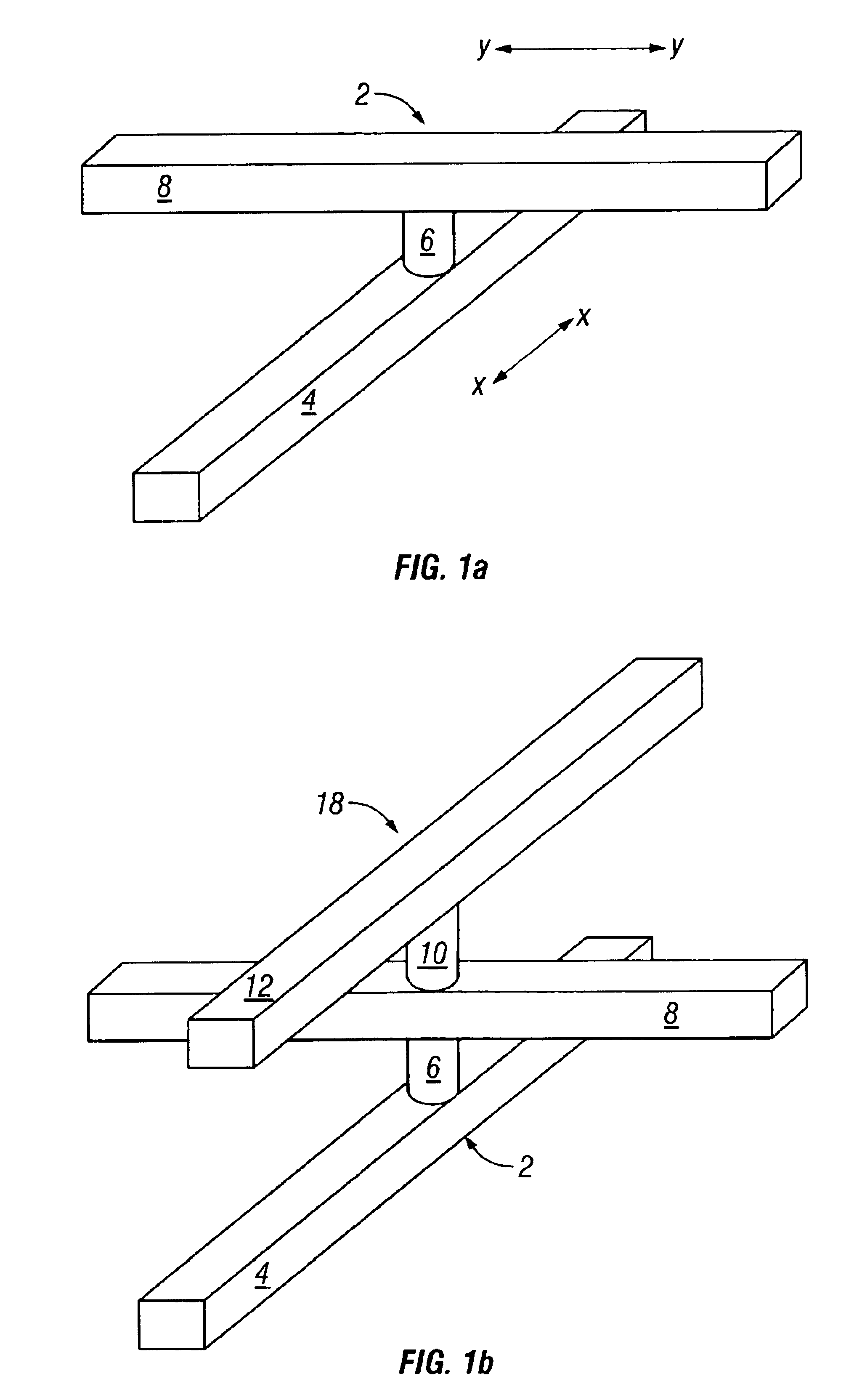
Demultiplexer for a molecular wire crossbar network (MWCN DEMUX)
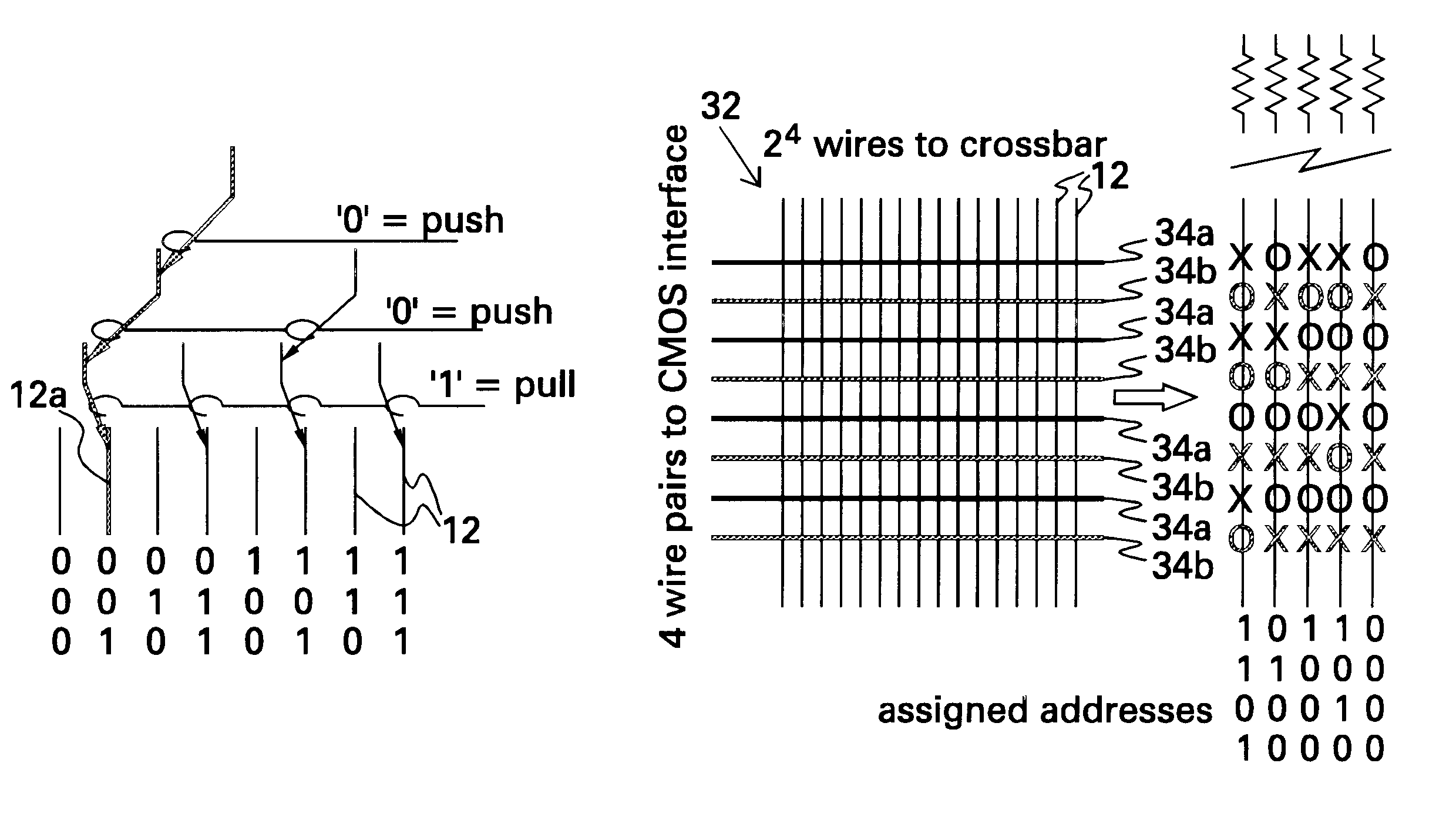
A demultiplexer for a two-dimensional array of a plurality of nanometer-scale switches (molecular wire crossbar network) is disclosed. Each switch comprises a pair of crossed wires which form a junction where one wire crosses another and at least one connector species connecting said pair of crossed wires in said junction. The connector species comprises a bi-stable molecule. The demultiplexer comprises a plurality of address lines accessed by a first set of wires in the two-dimensional array by randomly forming contacts between each wire in the first set of wires to at least one of the address lines. The first set of wires crosses a second set of wires to form the junctions. The demultiplexer solves both the problems of data input and output to a molecular electronic system and also bridges the size gap between CMOS and molecules with an architecture that can scale up to extraordinarily large numbers of molecular devices. Further, the demultiplexer is very defect tolerant, and can work despite a large number of defects in the system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
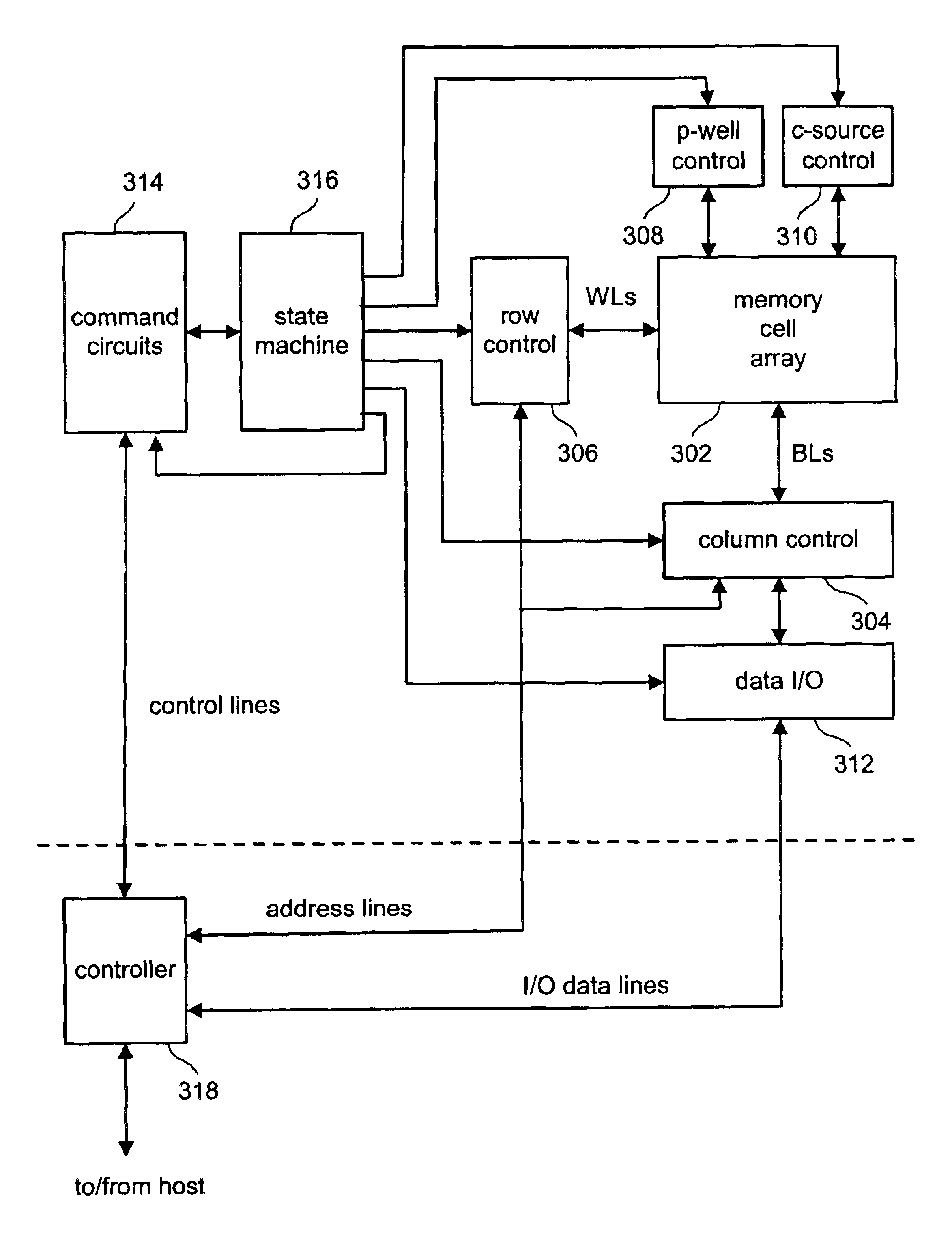
Non-volatile memory and method with shared processing for an aggregate of read/write circuits
InactiveUS20060140007A1Maximum versatilityMinimal componentRead-only memoriesDigital storageAudio power amplifierAssociative processor
A non-volatile memory device capable of reading and writing a large number of memory cells with multiple read / write circuits in parallel has an architecture that reduces redundancy in the multiple read / write circuits to a minimum. The multiple read / write circuits are organized into a bank of similar stacks of components. Redundant circuits such as a processor for processing data among stacks each associated with multiple memory cells are factored out. The processor is implemented with an input logic, a latch and an output logic. The input logic can transform the data received from either the sense amplifier or the data latches. The output logic further processes the transformed data to send to either the sense amplifier or the data latches or to a controller. This provides an infrastructure with maximum versatility and a minimum of components for sophisticated processing of the data sensed and the data to be input or output.
Owner:SANDISK TECH LLC
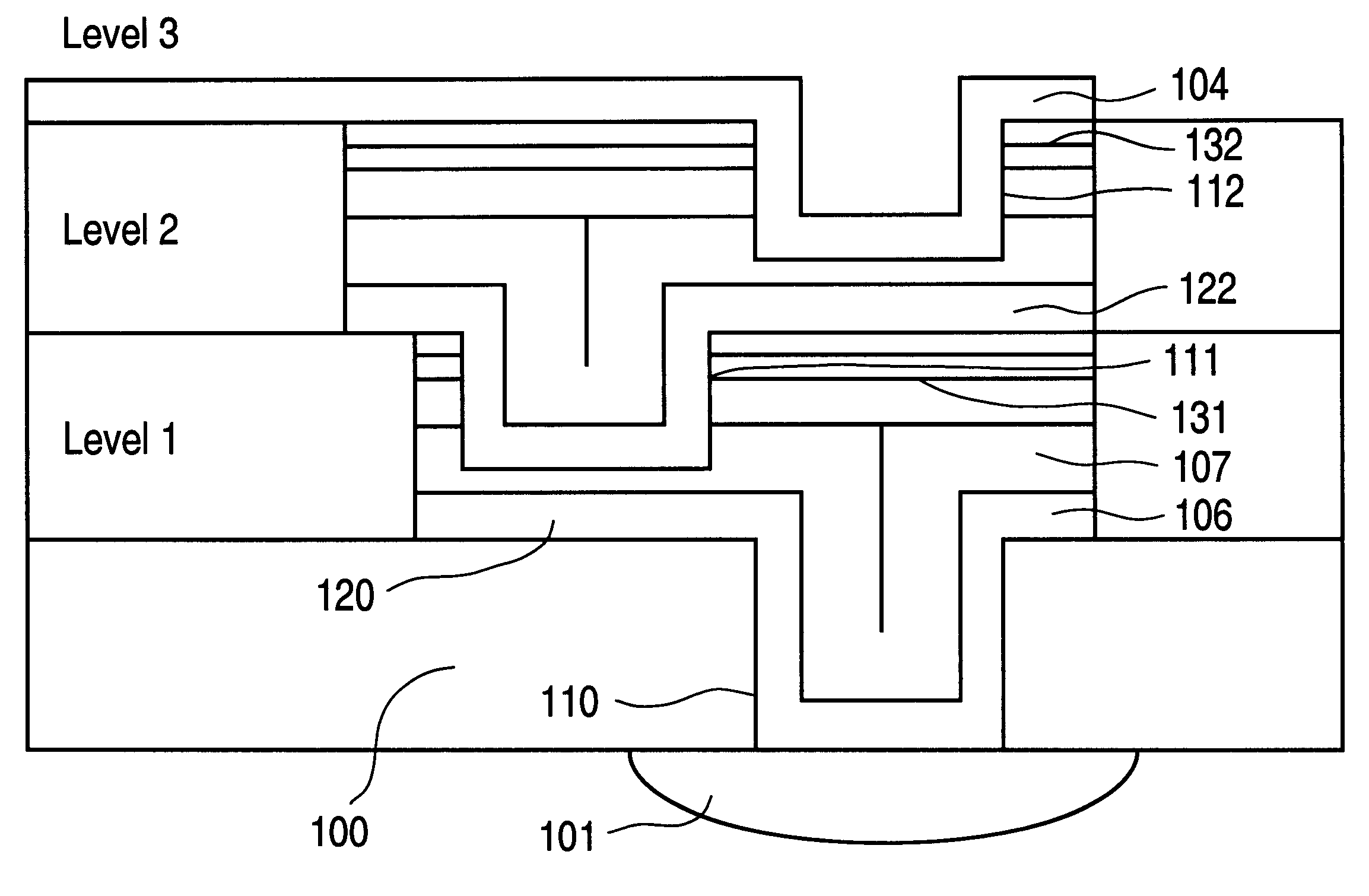
High-density three-dimensional memory cell
InactiveUS6952030B2High densityReduce the overall heightTransistorSemiconductor/solid-state device detailsElectrical conductorHigh density
A three dimensional monolithic memory comprising a memory cell allowing for increased density is disclosed. In the memory cell of the present invention, a bottom conductor preferably comprising tungsten is formed. Above the bottom conductor a semiconductor element preferably comprises two diode portions and an antifuse. Above the semiconductor element are additional conductors and semiconductor elements in multiple stones of memories. The arrangement of processing steps and the choice of materials decreases aspect ratio of each memory cell, improving the reliability of gap fill and preventing etch undercut.
Owner:SANDISK TECH LLC
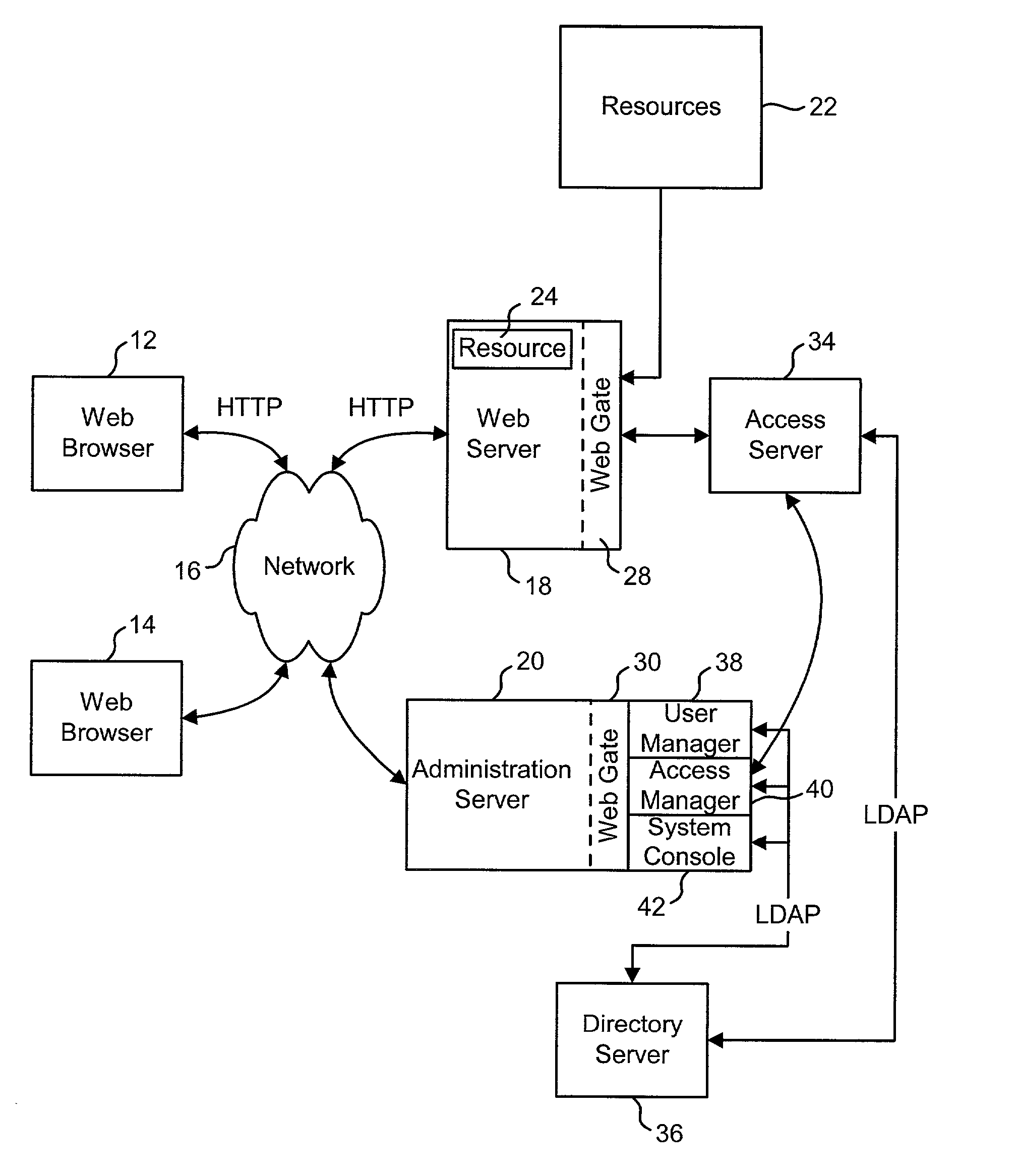
Methods and apparatus for controlling access to a resource
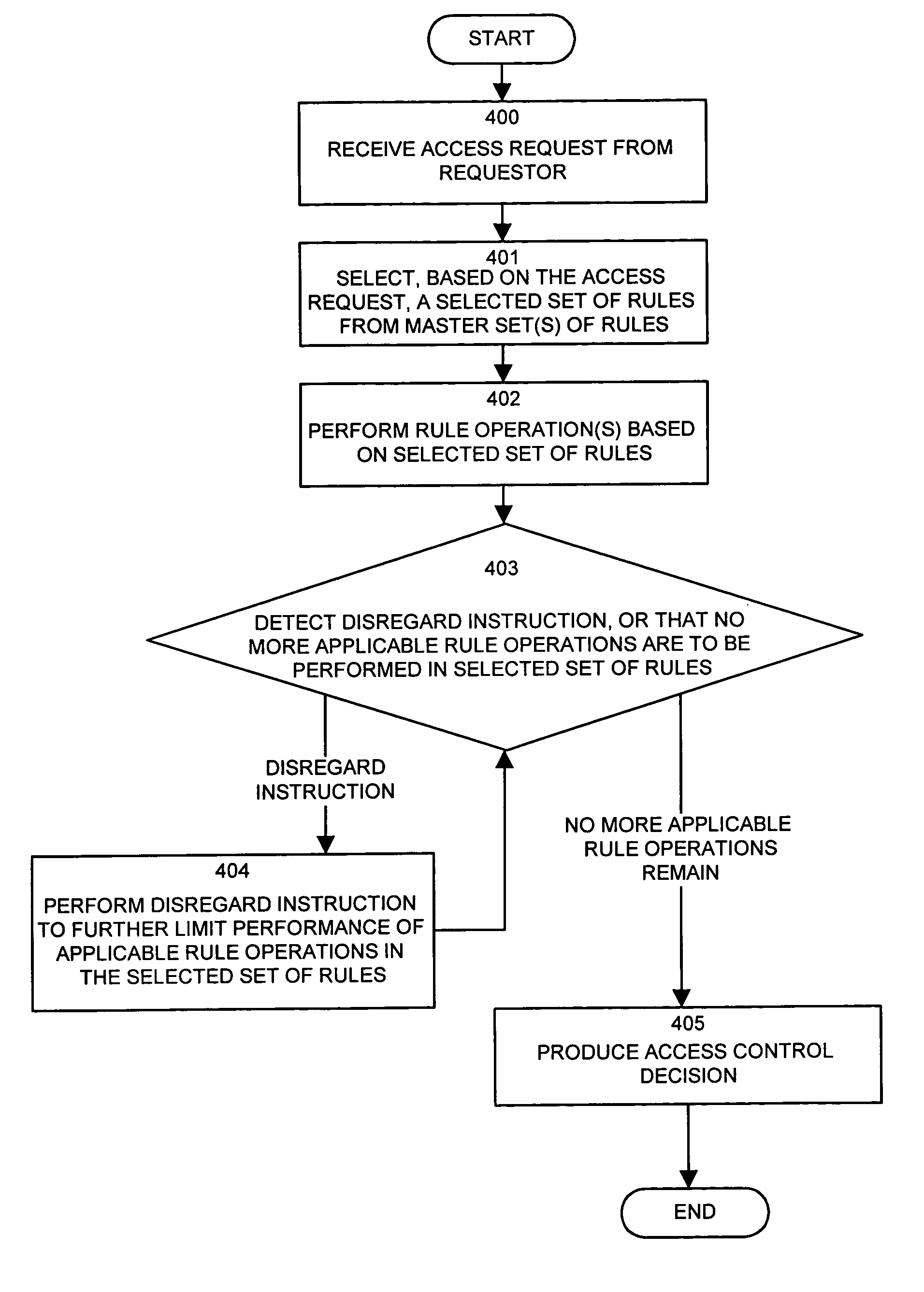
InactiveUS7185192B1Limit staff employee accessVerification of the security policy more straightforwardData processing applicationsDigital data processing detailsProgramming languageDecision taking
An input / output interface receives an access request from a requester. A processor associated with the input / output interface applies a filter operation to select a subset of rules from a master set of rules maintained within an authorization database. Rules can be selected in this manner using filter operations so that all rules in the rule set need not be processed. A rule may include a disregard instruction. The processor further performs at least one rule operation based on the subset of rules to produce an access control decision in the memory system until either a rule operation including a disregard instruction is performed to limit performance of rule operations in the selected set of rules or until all rule operations in the selected set of rules that are applicable to the access control decision are performed.
Owner:EMC IP HLDG CO LLC
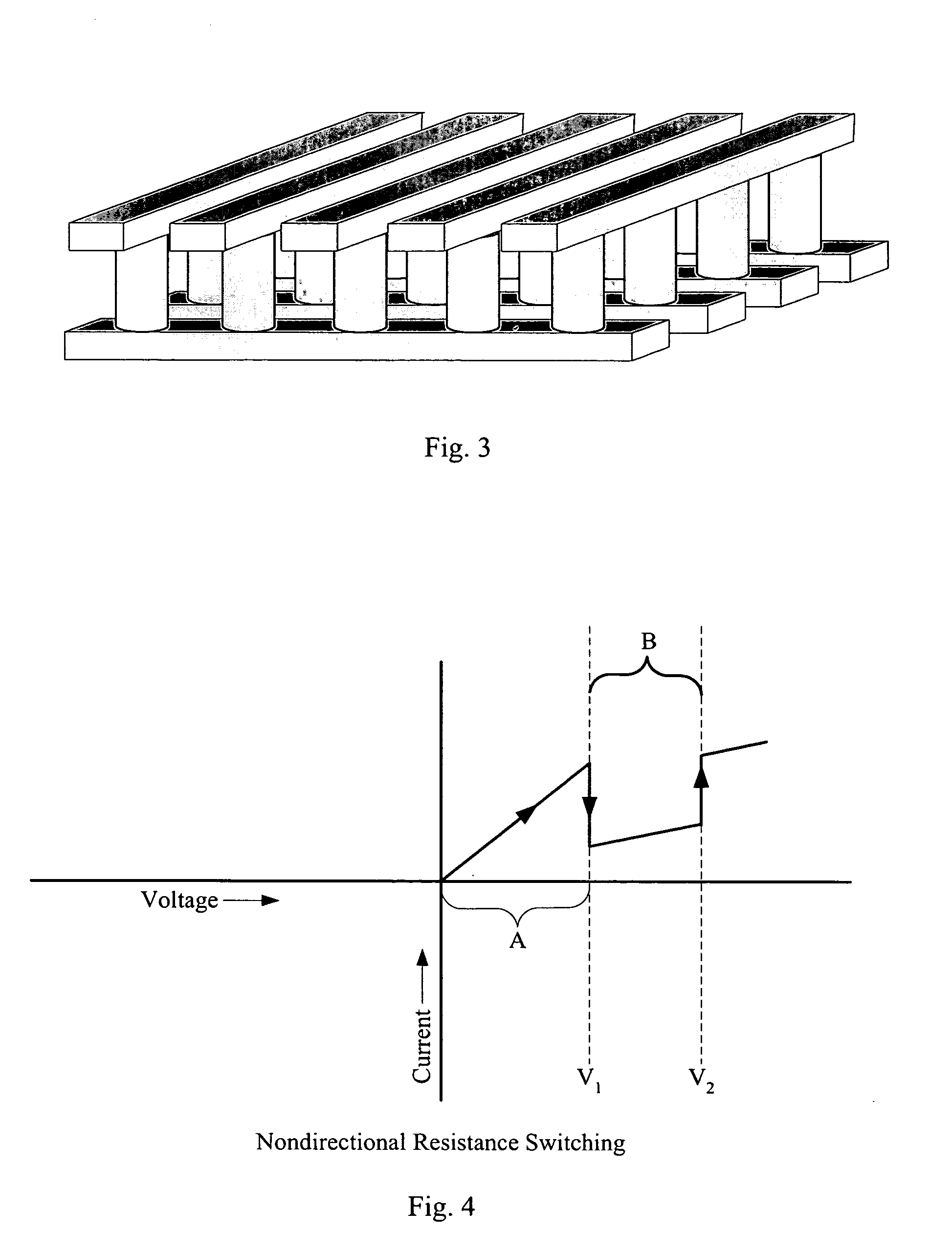
Rewriteable memory cell comprising a diode and a resistance-switching material
In a novel rewriteable nonvolatile memory cell formed above a substrate, a diode is paired with a reversible resistance-switching material, preferably a metal oxide or nitride such as, for example, NiO, Nb2O5, TiO2, HfO2, Al2O3, MgOx, CrO2, VO, BN, and AlN. In preferred embodiments, the diode is formed as a vertical pillar disposed between conductors. Multiple memory levels can be stacked to form a monolithic three dimensional memory array. In some embodiments, the diode comprises germanium or a germanium alloy, which can be deposited and crystallized at relatively low temperatures, allowing use of aluminum or copper in the conductors.
Owner:SANDISK TECH LLC
Method and system to reduce system boot loader download time for spi based flash memories
InactiveUS20140115229A1High frequencyMemory adressing/allocation/relocationDigital storageLoad timePeripheral
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Multibit single cell memory element having tapered contact
InactiveUSRE37259E1Large electric resistance valueSolid-state devicesRead-only memoriesPeak valueEngineering
An electrically operated, directly overwritable, multibit, single-cell chalcogenide memory element with multibit storage capabilities and having at least one contact for supplying electrical input signals to set the memory element to a selected resistance value, the second contact tapering to a peak adjacent to the memory element. In this manner the tapered contact helps define the size and position of a conduction path through the memory element.
Owner:OVONYX MEMORY TECH LLC
Current-induced magnetic switching device and memory including the same
InactiveUS6256223B1High bulk densitySimpler driving circuitsNanomagnetismMagnetic-field-controlled resistorsNanoparticleConduction band
A magnetic switching device, includes a first electrode, a second electrode, and a nanoparticle having a magnetic moment and being disposed between the first and second electrodes. At least one of the first electrode and the second electrode includes a magnetic material which has a net spin polarization in its conduction band for injecting, into the nanoparticle, an electrical current including a net spin polarization for overcoming the magnetic moment of the nanoparticle upon selection of a predetermined magnitude for the electrical current.
Owner:INT BUSINESS MASCH CORP
Agent based instruction system and method
InactiveUS6201948B1Highly configurableEffectively guide and engageData processing applicationsDigital data processing detailsPersonalizationInterface standard
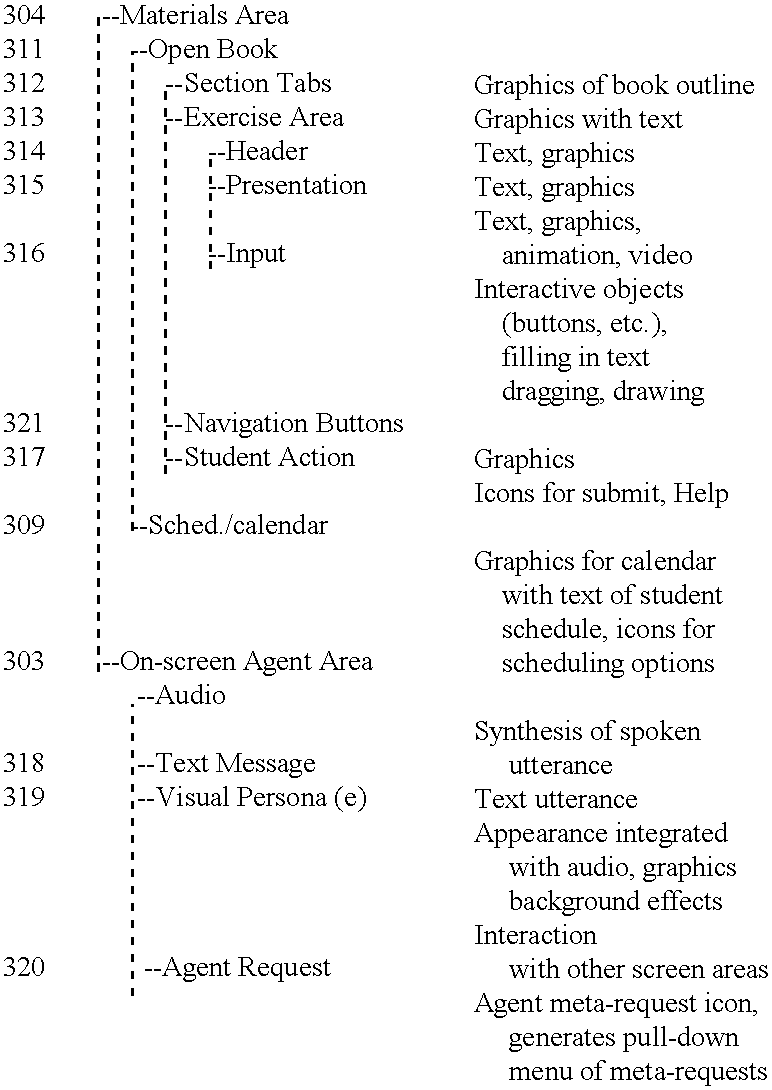
This invention relates to a system and method for interactive, adaptive, and individualized computer-assisted instruction. This invention includes an agent for each student which adapts to its student and provides individualized guidance to the student and controls to the augmented computer-assisted instructional materials. The instructional materials of this invention are augmented to communicate the student's performance and the material's pedagogical characteristics to the agent and to receive control from the agent. Preferably, the content of the communication between the agent and the materials conforms to specified interface standards so that the agent acts independently of the content of the particular materials. Also preferably, the agent can project using various I / O modalities integrated, engaging, life-like display persona(e) appropriate to the preferences of its student and appear as a virtual tutor to the student. Finally, preferably this invention is implemented on computers interconnected by a network so that instruction can be delivered to geographically distributed students from geographically distributed servers. An important application of this invention is delivering interactive, adaptive, and individualized homework to students in their homes and other locations.
Owner:CONVERGYS CUSTOMER MANAGEMENT GROUP
Doped elongated semiconductors, growing such semiconductors, devices including such semiconductors and fabricating such devices
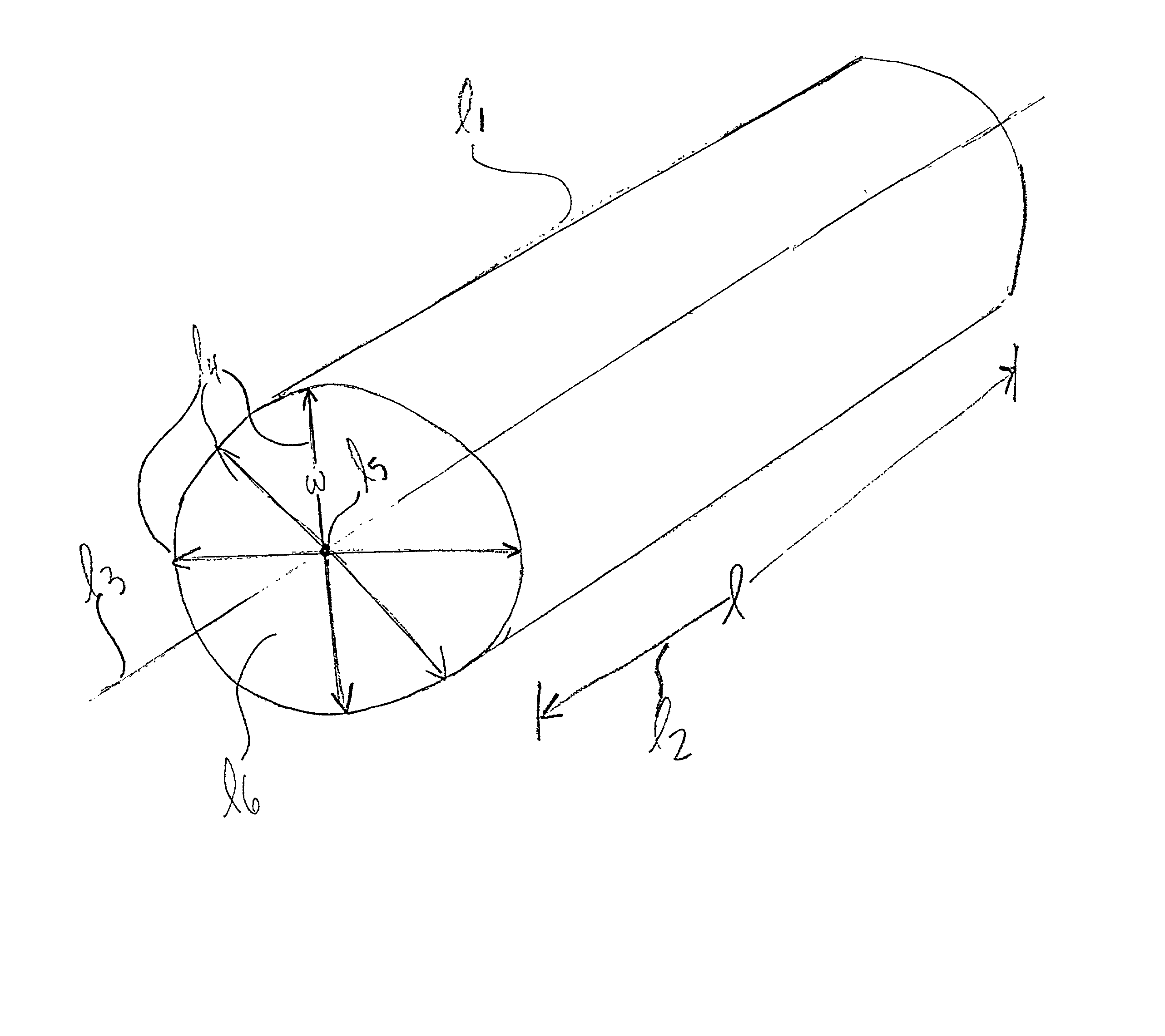
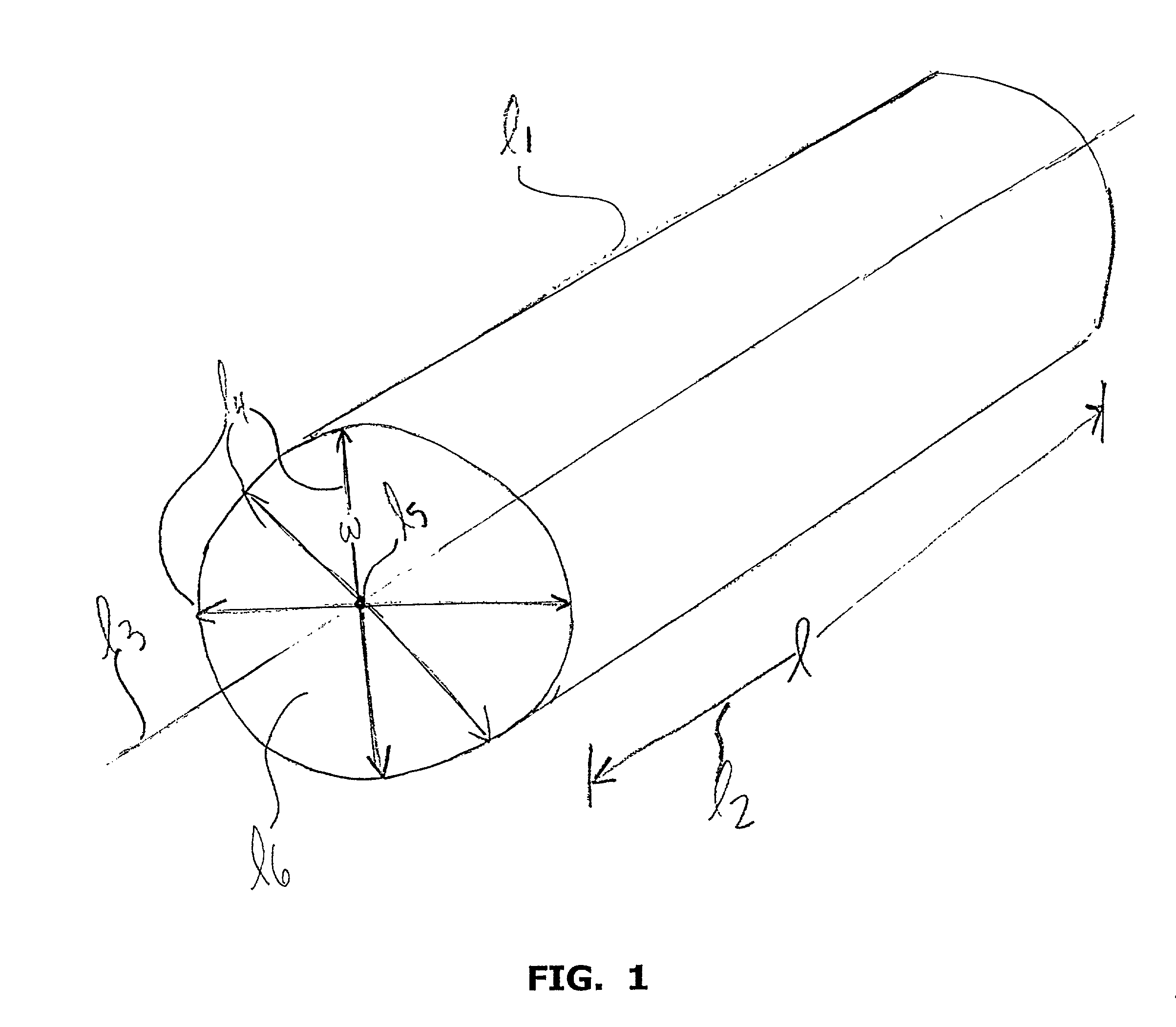
A bulk-doped semiconductor that is at least one of the following: a single crystal, an elongated and bulk-doped semiconductor that, at any point along its longitudinal axis, has a largest cross-sectional dimension less than 500 nanometers, and a free-standing and bulk-doped semiconductor with at least one portion having a smallest width of less than 500 nanometers. Such a semiconductor may comprise an interior core comprising a first semiconductor; and an exterior shell comprising a different material than the first semiconductor. Such a semiconductor may be elongated and my have, at any point along a longitudinal section of such a semiconductor, a ratio of the length of the section to a longest width is greater than 4:1, or greater than 10:1, or greater than 100:1, or even greater than 1000:1. At least one portion of such a semiconductor may a smallest width of less than 200 nanometers, or less than 150 nanometers, or less than 100 nanometers, or less than 80 nanometers, or less than 70 nanometers, or less than 60 nanometers, or less than 40 nanometers, or less than 20 nanometers, or less than 10 nanometers, or even less than 5 nanometers. Such a semiconductor may be a single crystal and may be free-standing. Such a semiconductor may be either lightly n-doped, heavily n-doped, lightly p-doped or heavily p-doped. Such a semiconductor may be doped during growth. Such a semiconductor may be part of a device, which may include any of a variety of devices and combinations thereof, and, and a variety of assembling techniques may be used to fabricate devices from such a semiconductor. Two or more of such a semiconductors, including an array of such semiconductors, may be combined to form devices, for example, to form a crossed p-n junction of a device. Such devices at certain sizes may exhibit quantum confinement and other quantum phenomena, and the wavelength of light emitted from one or more of such semiconductors may be controlled by selecting a width of such semiconductors. Such semiconductors and device made therefrom may be used for a variety of applications.
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE
Flash memory data correction and scrub techniques
ActiveUS7012835B2Data disturbanceReduce storage dataMemory loss protectionRead-only memoriesData integrityData storing
In order to maintain the integrity of data stored in a flash memory that are susceptible to being disturbed by operations in adjacent regions of the memory, disturb events cause the data to be read, corrected and re-written before becoming so corrupted that valid data cannot be recovered. The sometimes conflicting needs to maintain data integrity and system performance are balanced by deferring execution of some of the corrective action when the memory system has other high priority operations to perform. In a memory system utilizing very large units of erase, the corrective process is executed in a manner that is consistent with efficiently rewriting an amount of data much less than the capacity of a unit of erase.
Owner:SANDISK TECH LLC
Non-volatile memory and method with bit line compensation dependent on neighboring operating modes
ActiveUS6956770B2Large capacityImprove performanceRead-only memoriesDigital storageBit lineHigh density
When programming a contiguous page of memory storage units, every time a memory storage unit has reached its targeted state and is program-inhibited or locked out from further programming, it creates a perturbation on an adjacent memory storage unit still under programming. The present invention provides as part of a programming circuit and method in which an offset to the perturbation is added to the adjacent memory storage unit still under programming. The offset is added as voltage offset to a bit line of a storage unit under programming. The voltage offset is a predetermined function of whether none or one or both of its neighbors are in a mode that creates perturbation, such as in a program inhibit mode. In this way, an error inherent in programming in parallel high-density memory storage units is eliminated or minimized.
Owner:SANDISK TECH LLC
Vertically stacked field programmable nonvolatile memory and method of fabrication
A very high density field programmable memory is disclosed. An array is formed vertically above a substrate using several layers, each layer of which includes vertically fabricated memory cells. The cell in an N level array may be formed with N+1 masking steps plus masking steps needed for contacts. Maximum use of self alignment techniques minimizes photolithographic limitations. In one embodiment the peripheral circuits are formed in a silicon substrate and an N level array is fabricated above the substrate.
Owner:SANDISK TECH LLC
Read operation for non-volatile storage that includes compensation for coupling
Shifts in the apparent charge stored on a floating gate (or other charge storing element) of a non-volatile memory cell can occur because of the coupling of an electric field based on the charge stored in adjacent floating gates (or other adjacent charge storing elements). The problem occurs most pronouncedly between sets of adjacent memory cells that have been programmed at different times. To compensate for this coupling, the read process for a given memory cell will take into account the programmed state of an adjacent memory cell.
Owner:SANDISK TECH LLC
Unipolar resistance random access memory (RRAM) device and vertically stacked architecture
InactiveUS20070132049A1Improve performanceGalvano-magnetic devicesSolid-state devicesRandom access memoryEngineering
One embodiment of the present invention includes a low-cost unipolar rewritable variable-resistance memory device, made of cross-point arrays of memory cells, vertically stacked on top of one another and compatible with a polycrystalline silicon diode.
Owner:HITACHI GLOBAL STORAGE TECH NETHERLANDS BV
Access system interface
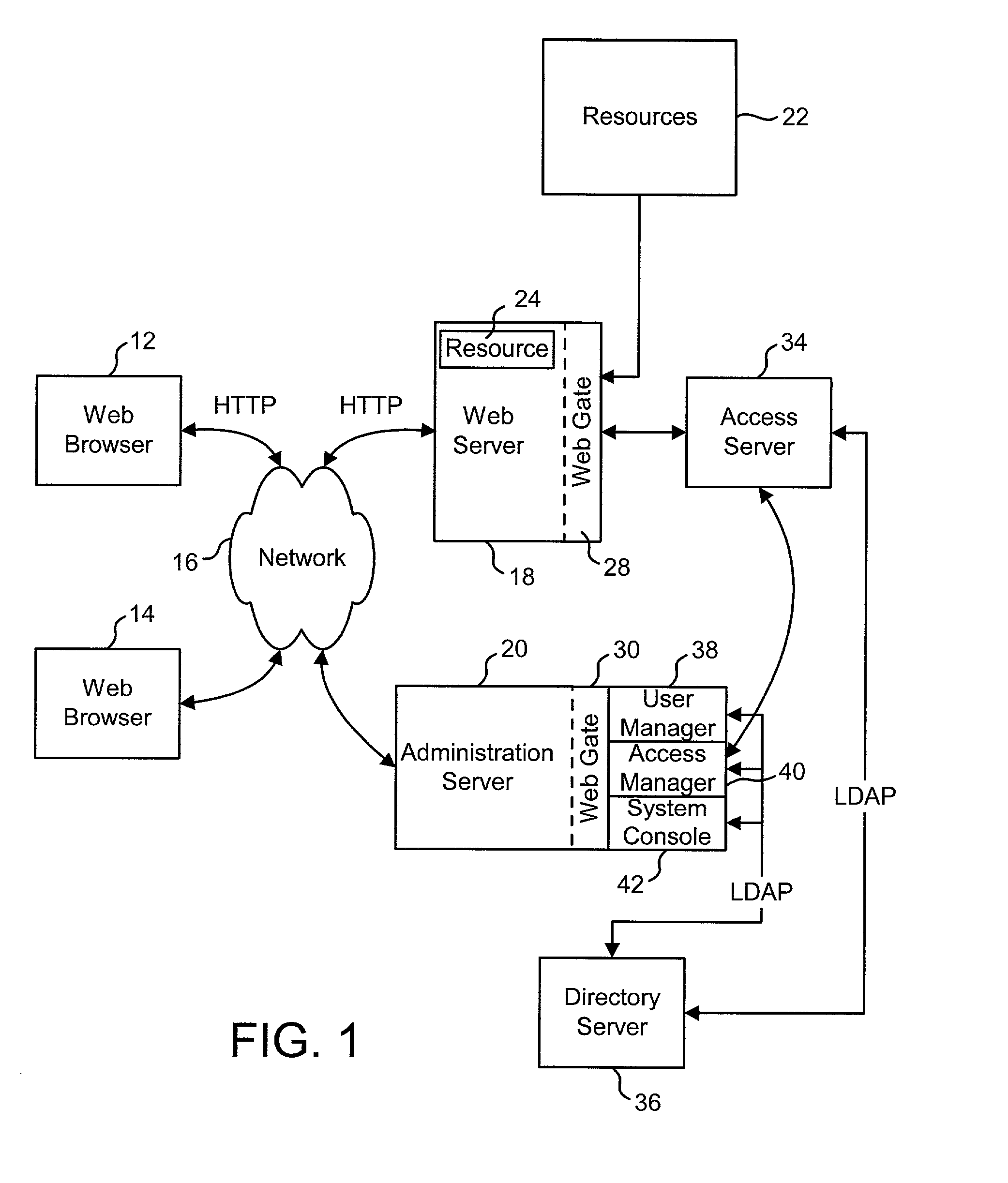
InactiveUS20030074580A1Easy mappingEasy to useDigital data processing detailsUser identity/authority verificationWeb serviceApplication software
An access system provides identity management and / or access management services for a network An application program interface for the access system enables an application without a web agent front end to read and use contents of an existing encrypted cookie to bypass authentication and proceed to authorization. A web agent is a component (usually software, but can be hardware or a combination of hardware and software) that plugs into (or otherwise integrates with) a web server (or equivalent) in order to participate in providing access services.
Owner:ORACLE INT CORP
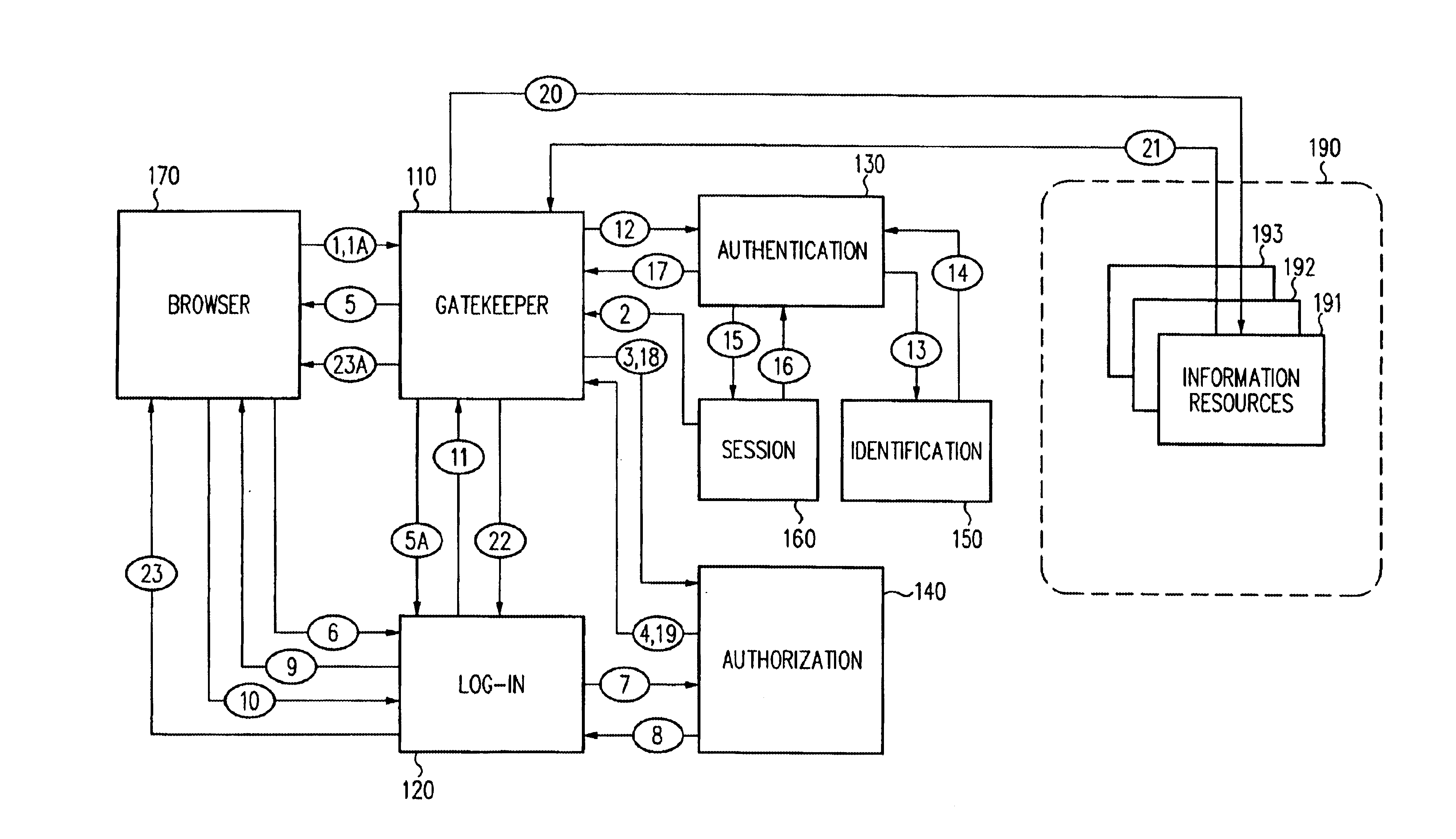
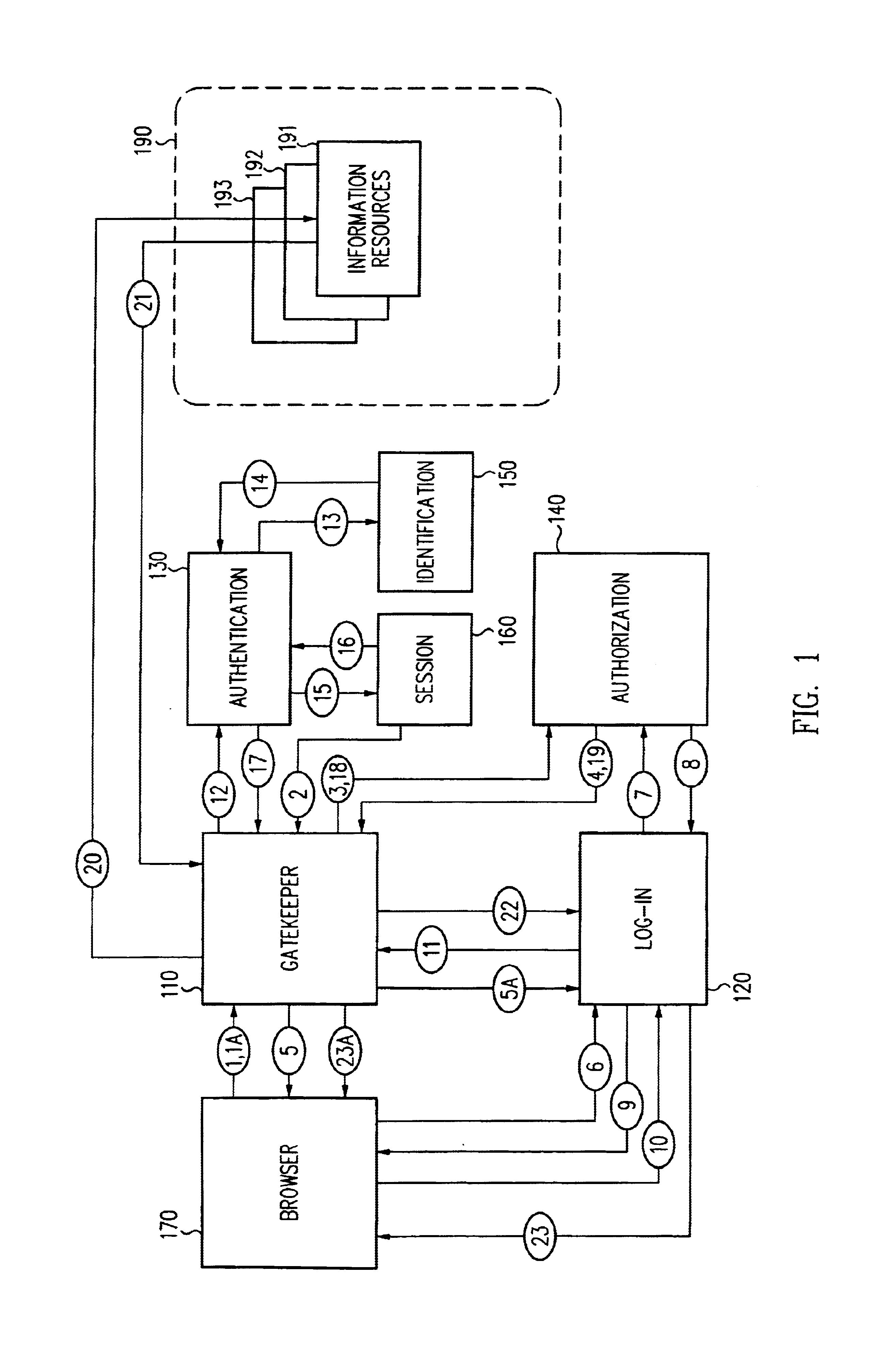
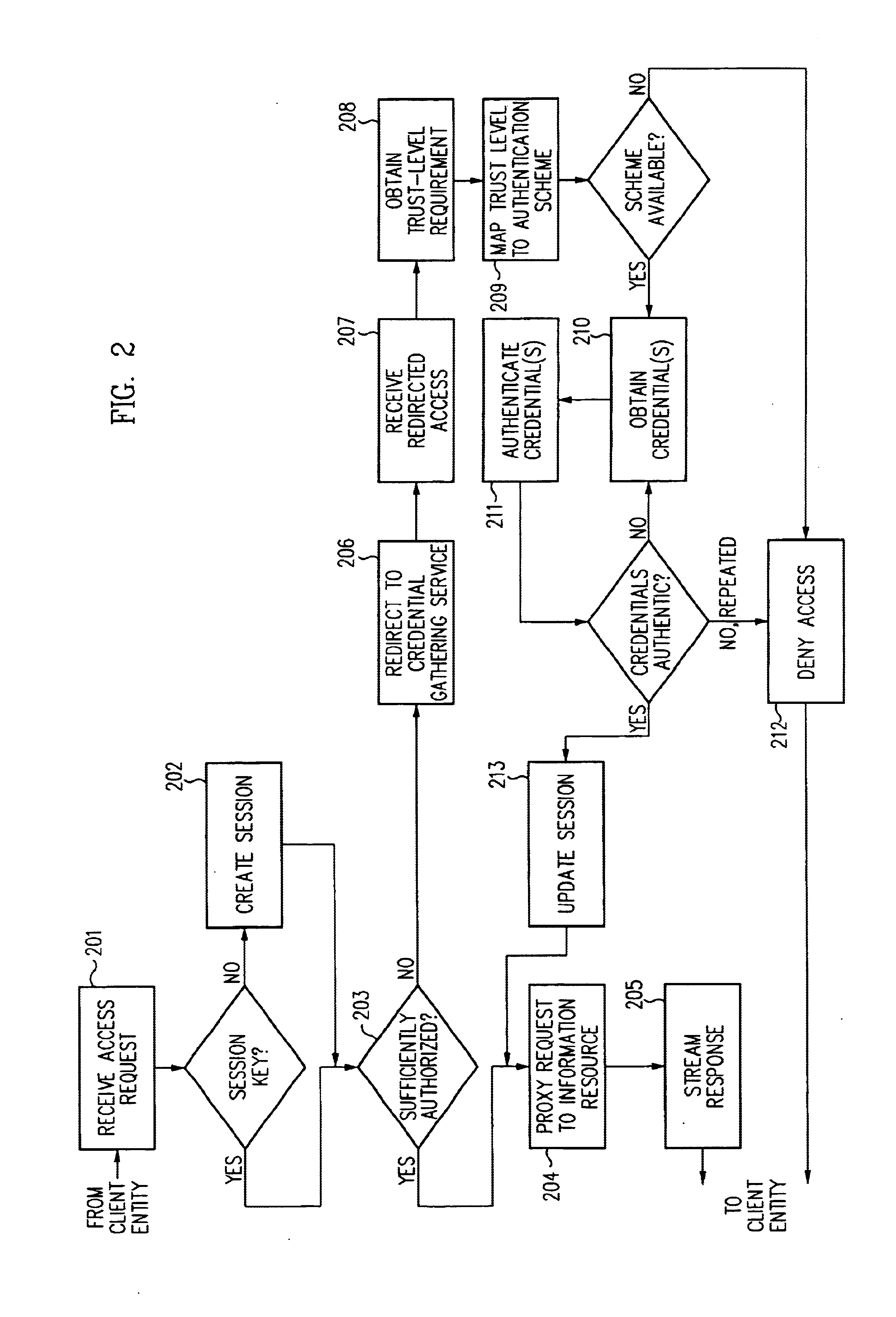
Security architecture with environment sensitive credential sufficiency evaluation
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
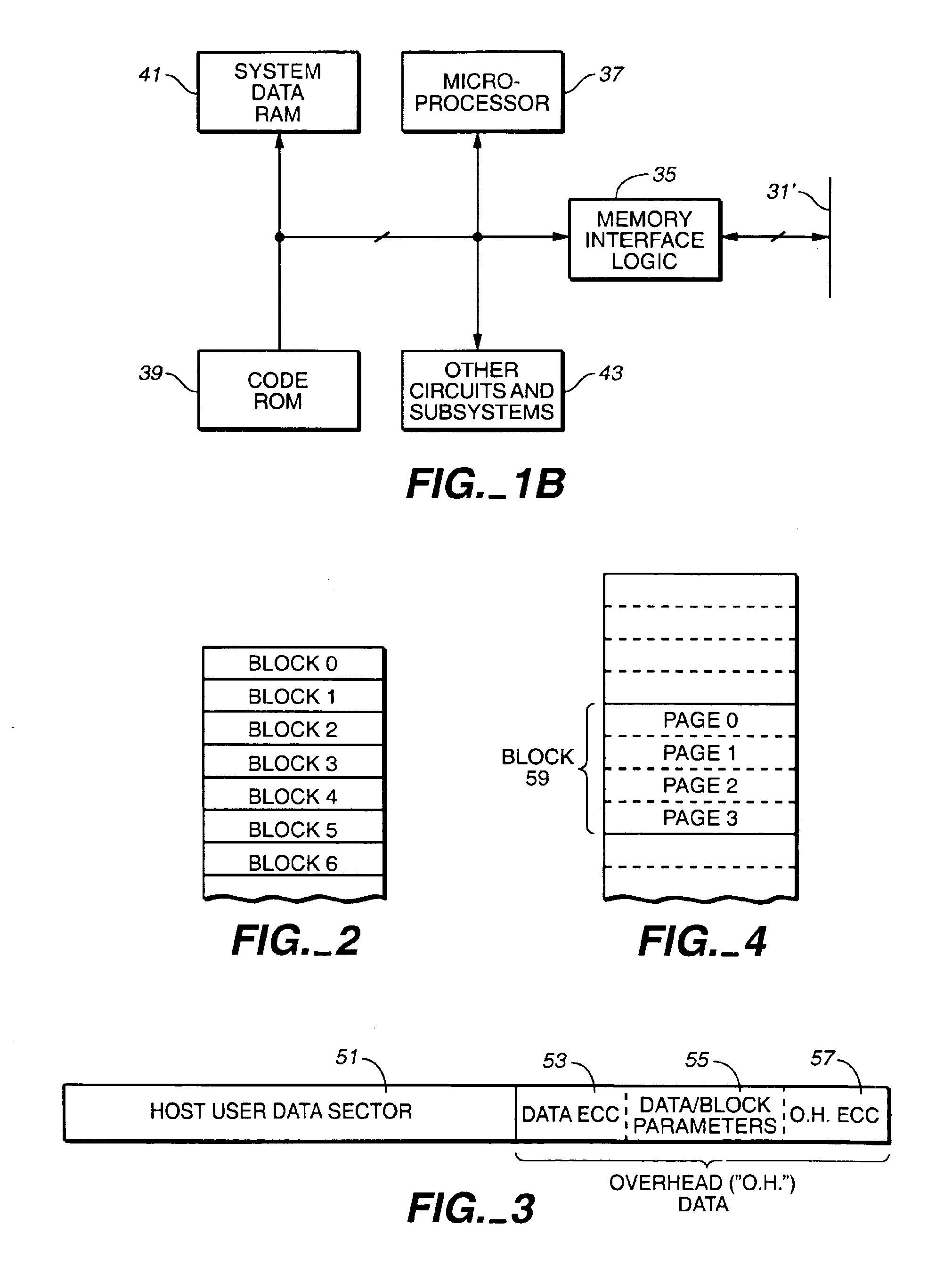
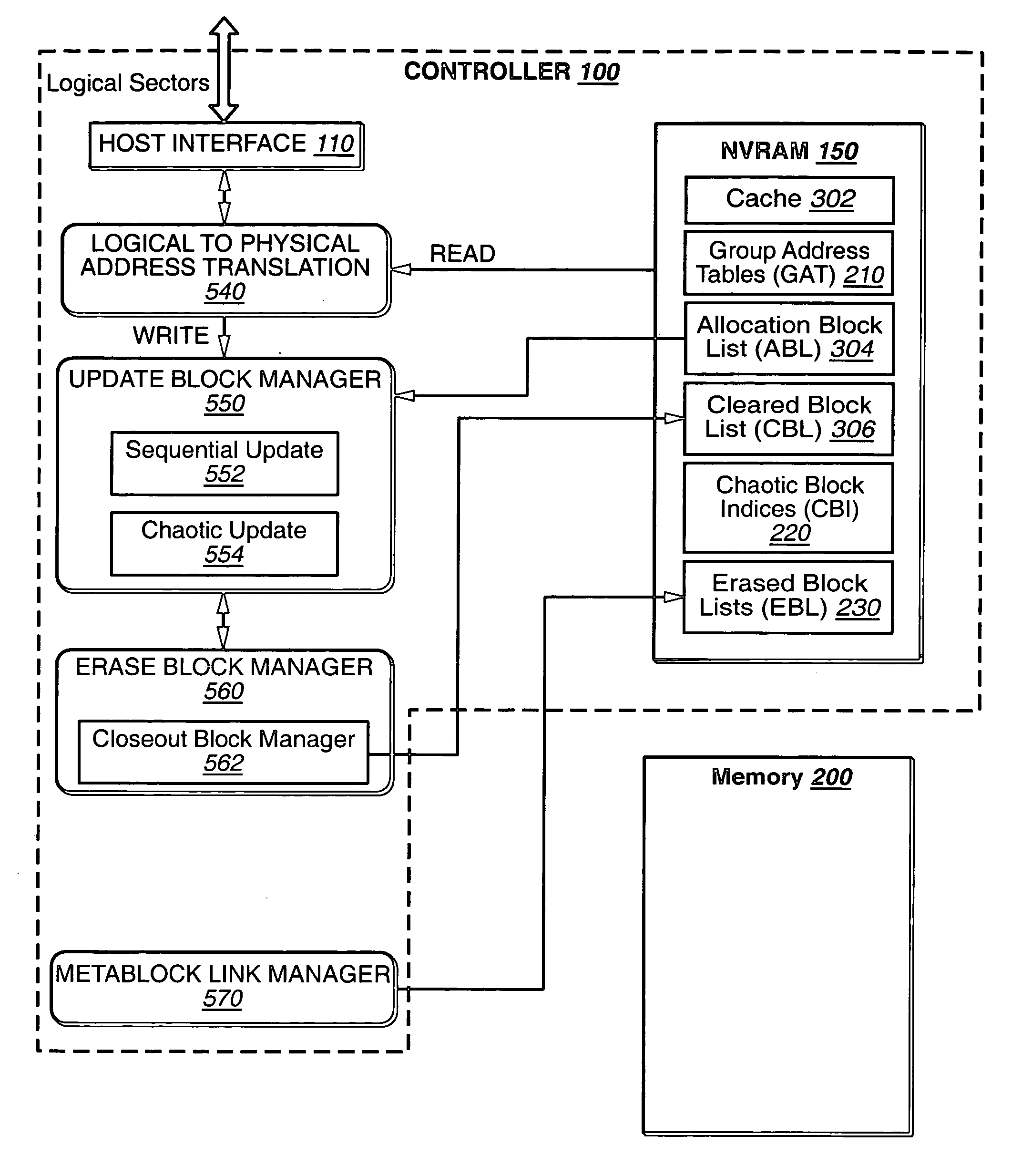
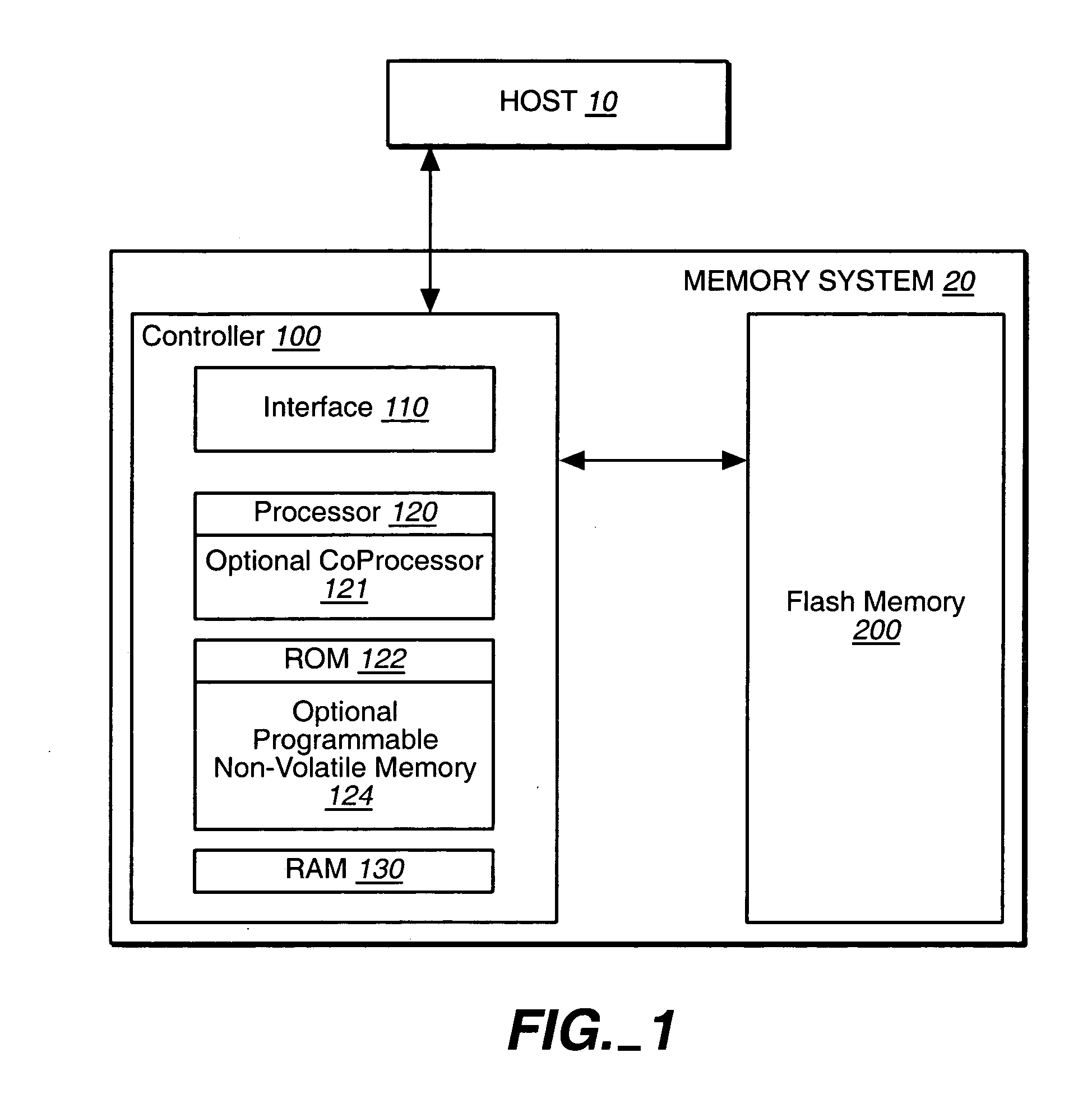
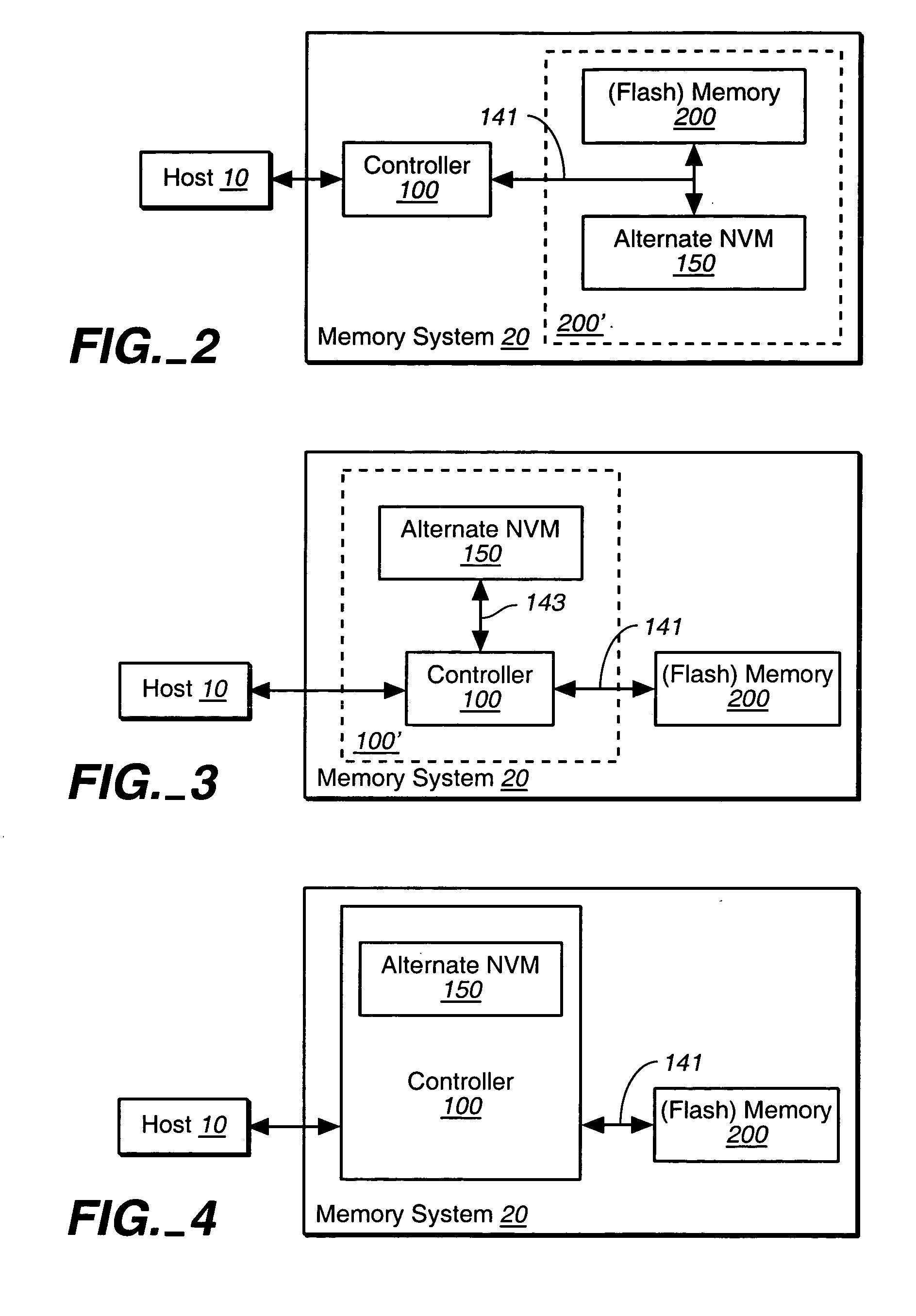
Hybrid non-volatile memory system
InactiveUS20050251617A1Easy accessMemory architecture accessing/allocationInput/output to record carriersData controlControl data
The present invention presents a hybrid non-volatile system that uses non-volatile memories based on two or more different non-volatile memory technologies in order to exploit the relative advantages of each these technology with respect to the others. In an exemplary embodiment, the memory system includes a controller and a flash memory, where the controller has a non-volatile RAM based on an alternate technology such as FeRAM. The flash memory is used for the storage of user data and the non-volatile RAM in the controller is used for system control data used by the control to manage the storage of host data in the flash memory. The use of an alternate non-volatile memory technology in the controller allows for a non-volatile copy of the most recent control data to be accessed more quickly as it can be updated on a bit by bit basis. In another exemplary embodiment, the alternate non-volatile memory is used as a cache where data can safely be staged prior to its being written to the to the memory or read back to the host.
Owner:SANDISK TECH LLC
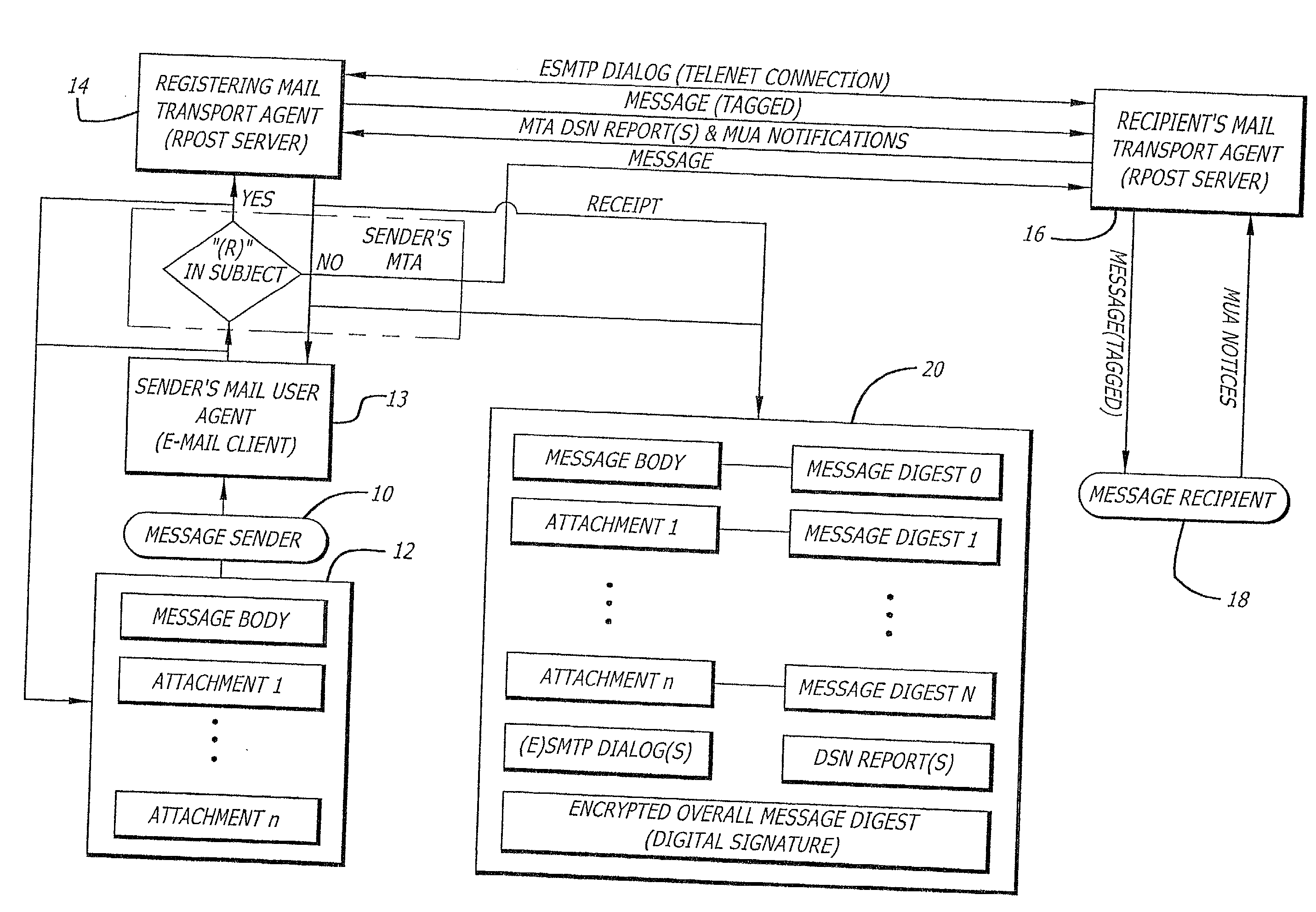
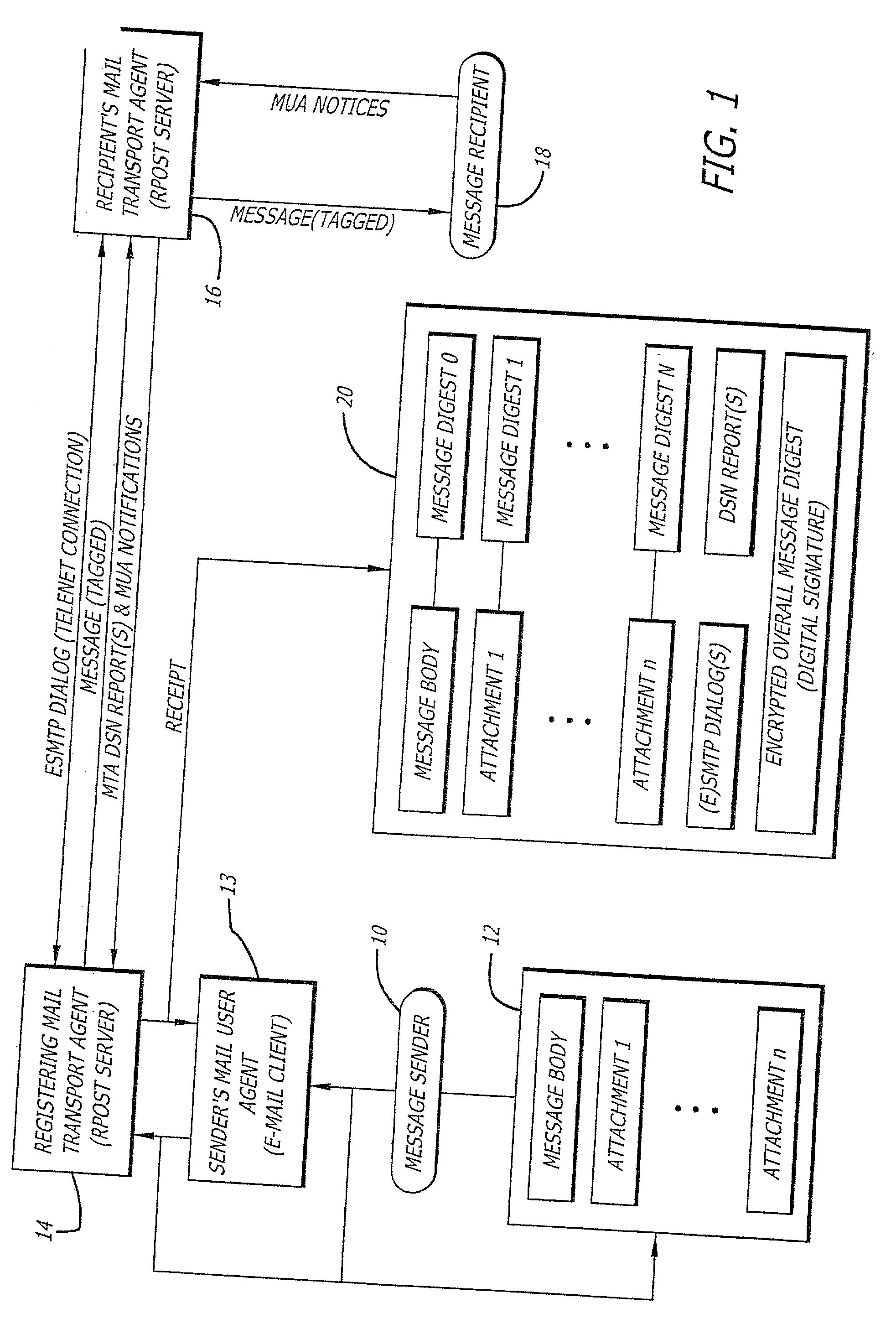
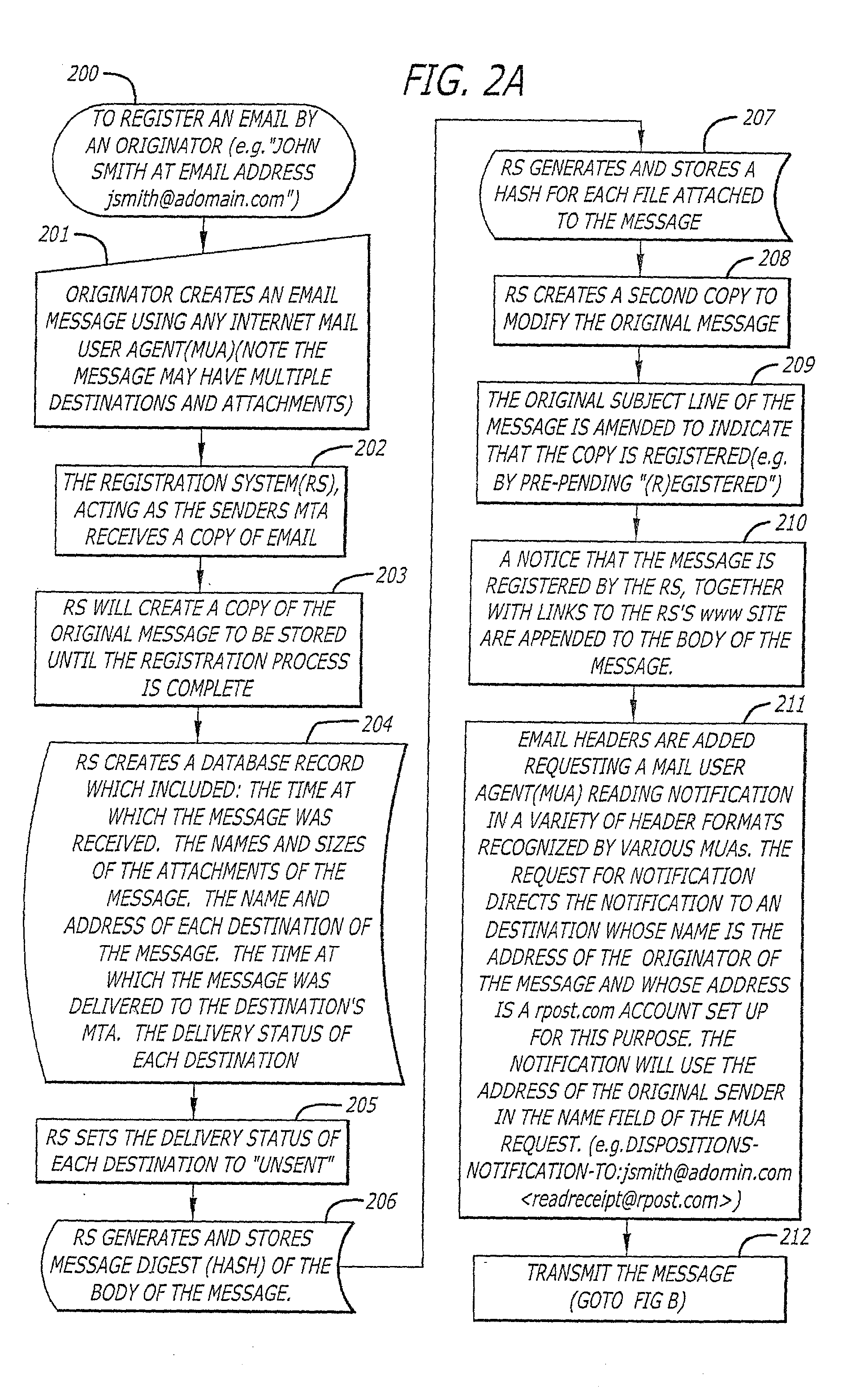
System and method for verifying delivery and integrity of electronic messages
InactiveUS20020144154A1Key distribution for secure communicationDigital data processing detailsDigital signatureThe Internet
A server receives a message from a sender and transmits the message through the Internet to a recipient. The server normally transmits the message in a first path through the Internet to the recipient. When the sender indicates at a particular position in the message that the message is registered, the server transmits the message in a second path through the Internet to the recipient. The sender can also provide additional indications in the message to have the server handle the message in other special ways not normally provided by the server. After learning from the receipt or the recipient's agent through the Internet that the message was successfully received, the server creates, and forwards to the sender, an electronic receipt. The receipt includes at least one, and preferably all: the message and any attachments, a delivery success / failure table listing the receipts, and the receipt times, of the message by the recipient's specific agents, and the failure of other agents of the recipient to receive the message and a digital signature of the message and attachments subsequently. By verifying that the digital signature on the sender's receipt matches the digital receipt at the server, the server can verify, without retaining the message, that the receipt is genuine and that the message is accurate.
Owner:RPOST COMM
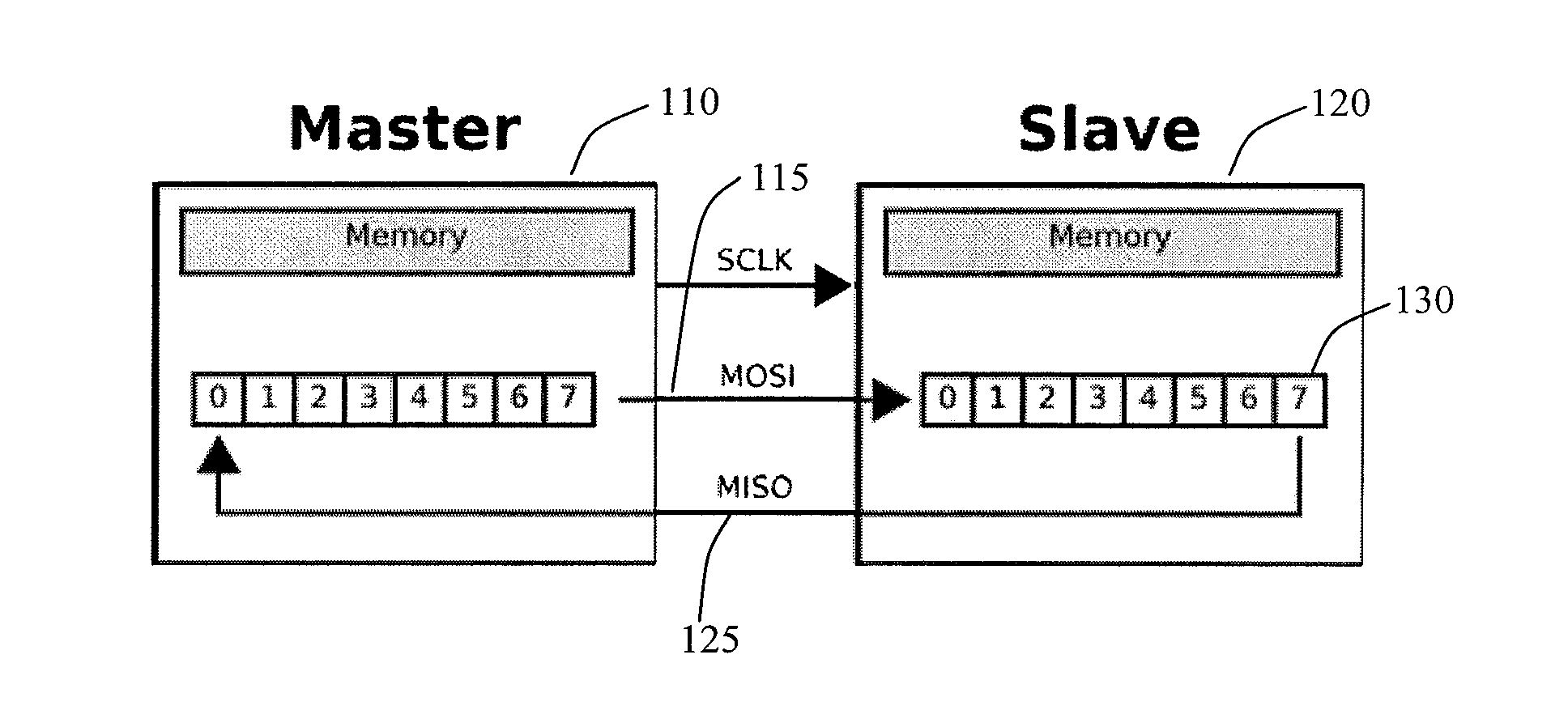
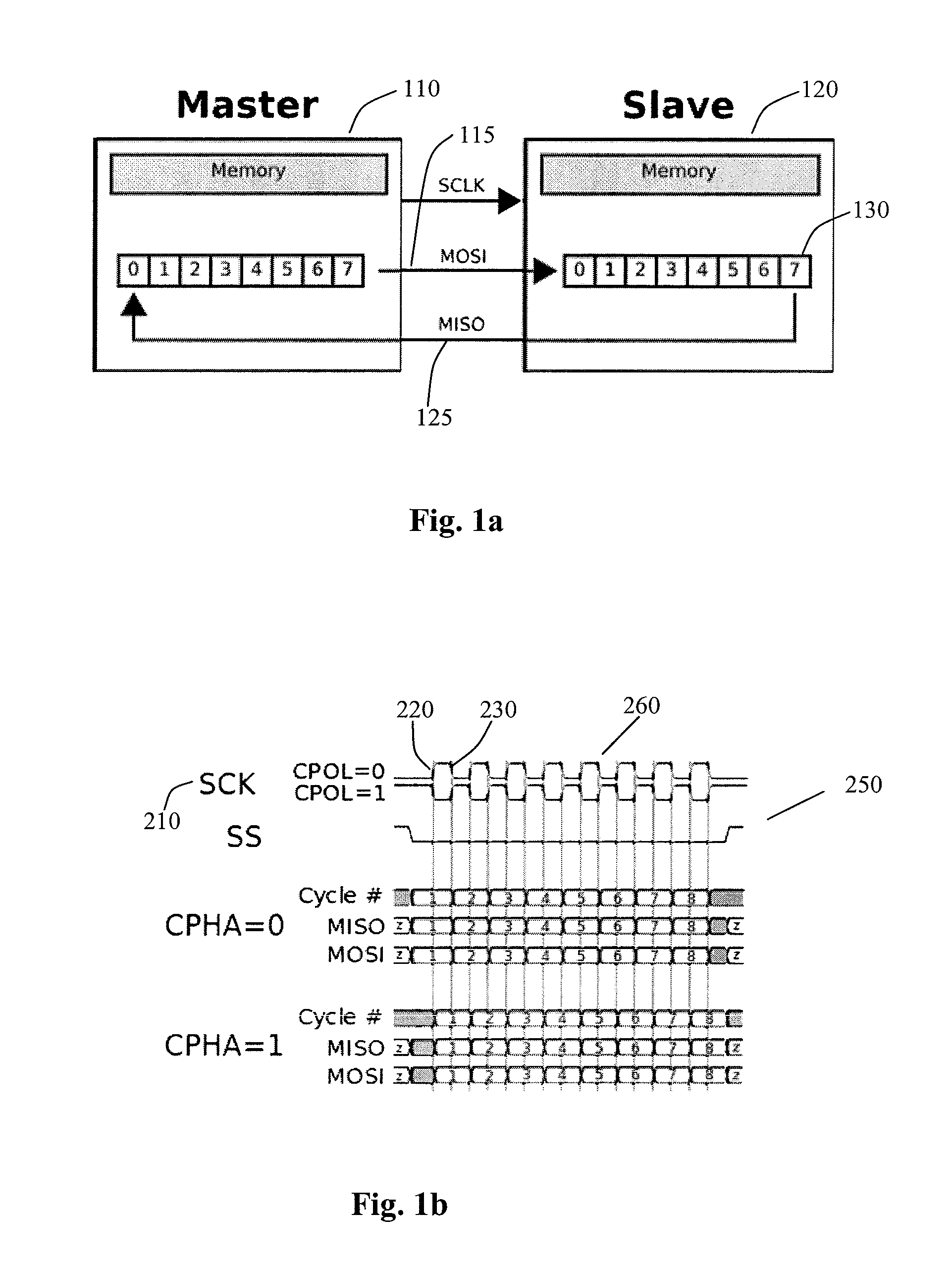
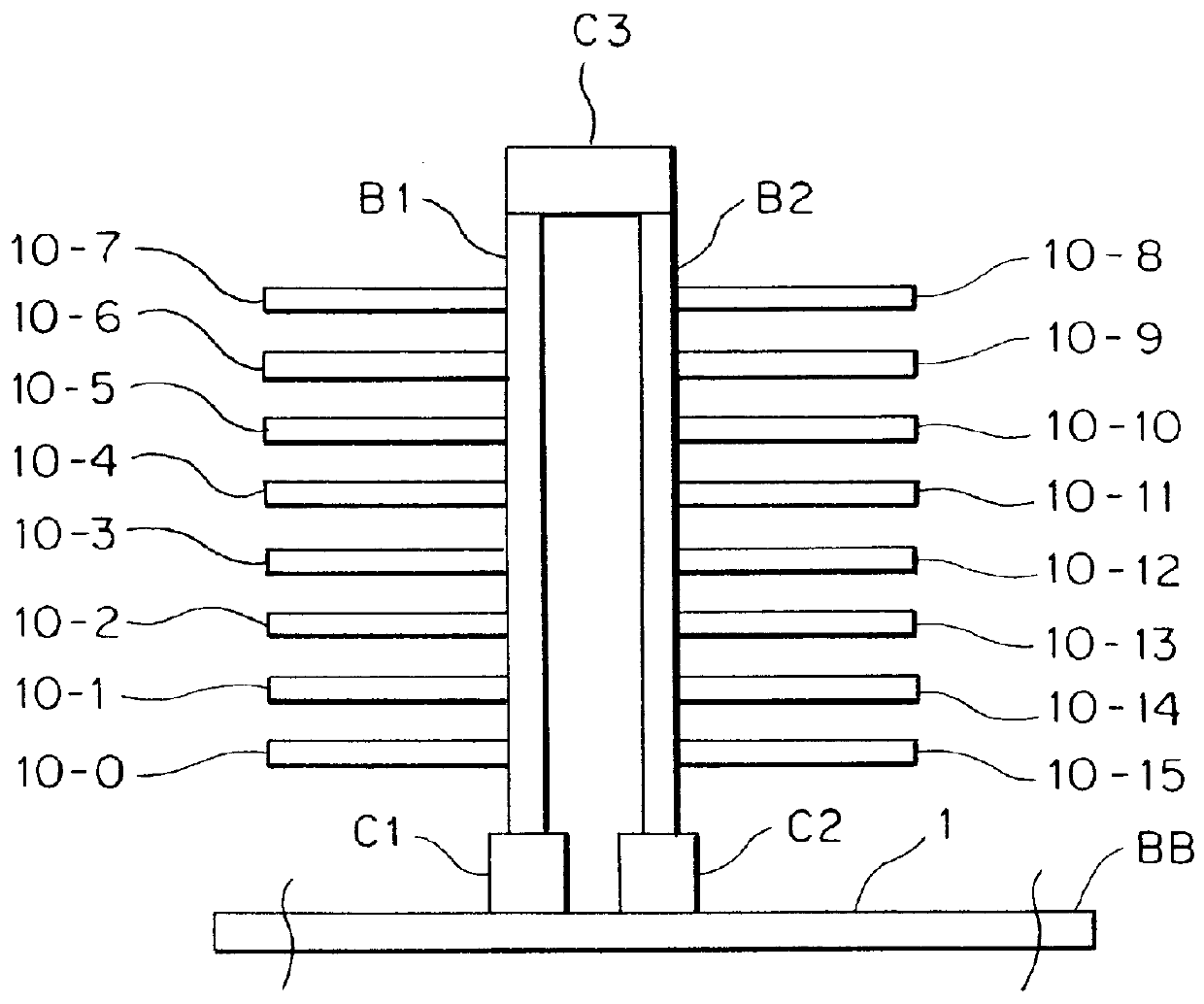
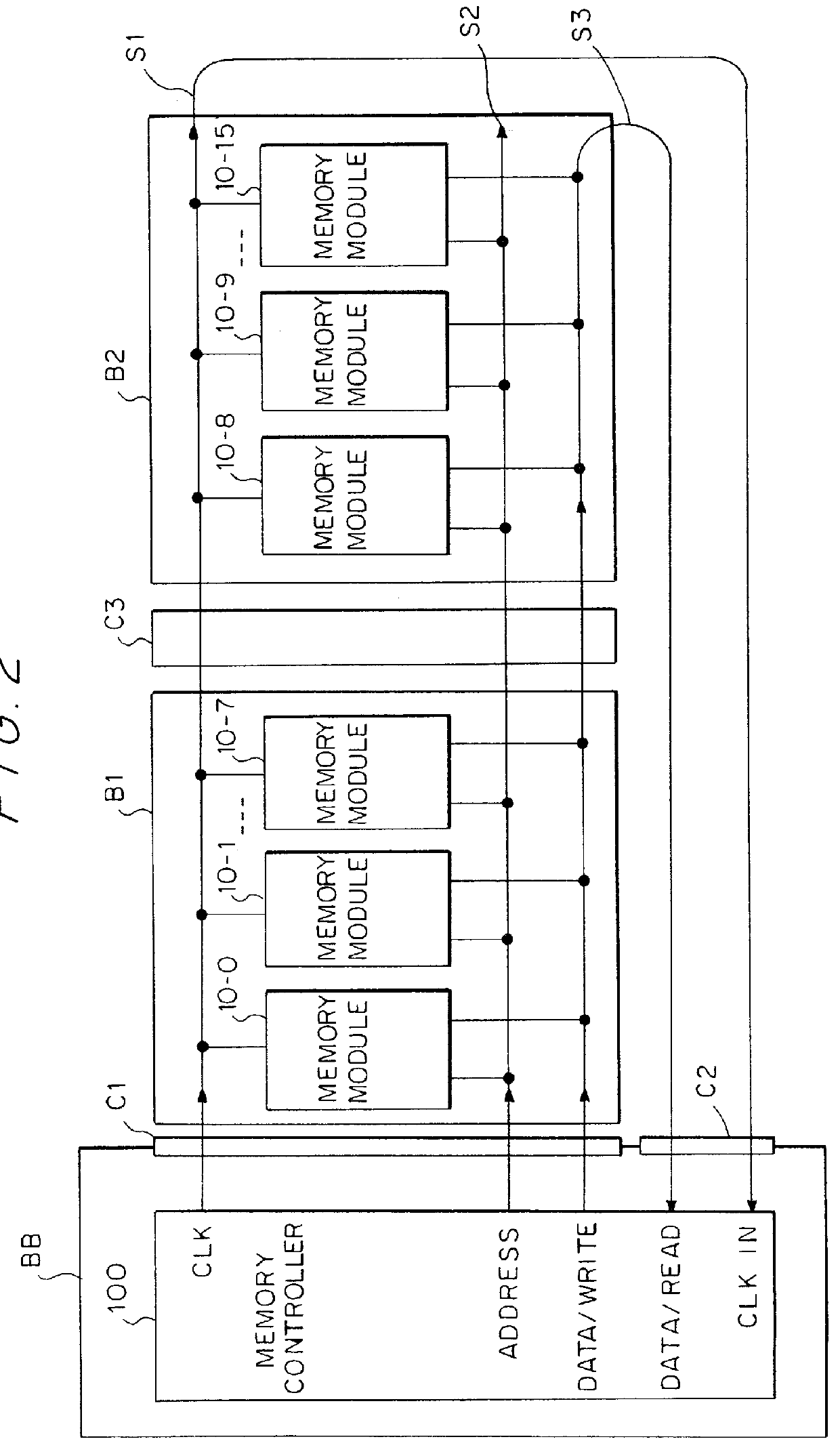
Source-clock-synchronized memory system and memory unit
InactiveUS6034878ALarge data storage capacity per memoryImprove installation densityMemory adressing/allocation/relocationDigital storageMemory bankComputer module
A source-clock-synchronized memory system having a large data storage capacity per memory bank and a high mounting density. The invention includes a memory unit having a first memory riser board B1 mounted on a base board through a first connector C1 and a second memory riser board B2 mounted on the base board BB through a second connector C2. The first memory riser board has a plurality of first memory modules mounted on the front surface thereof and the second memory riser board has a plurality of second memory modules mounted on the front surface thereof. The first and second memory riser boards are arranged in such a way that the back surface of the first memory riser board faces the back surface of the second memory riser board. The invention further includes a board linking connector for connecting signal lines on the first memory riser board to corresponding signal lines on the second memory riser board.
Owner:DELTA KOGYO CO LTD +1
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com